Patents
Literature
182 results about "Computer usage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
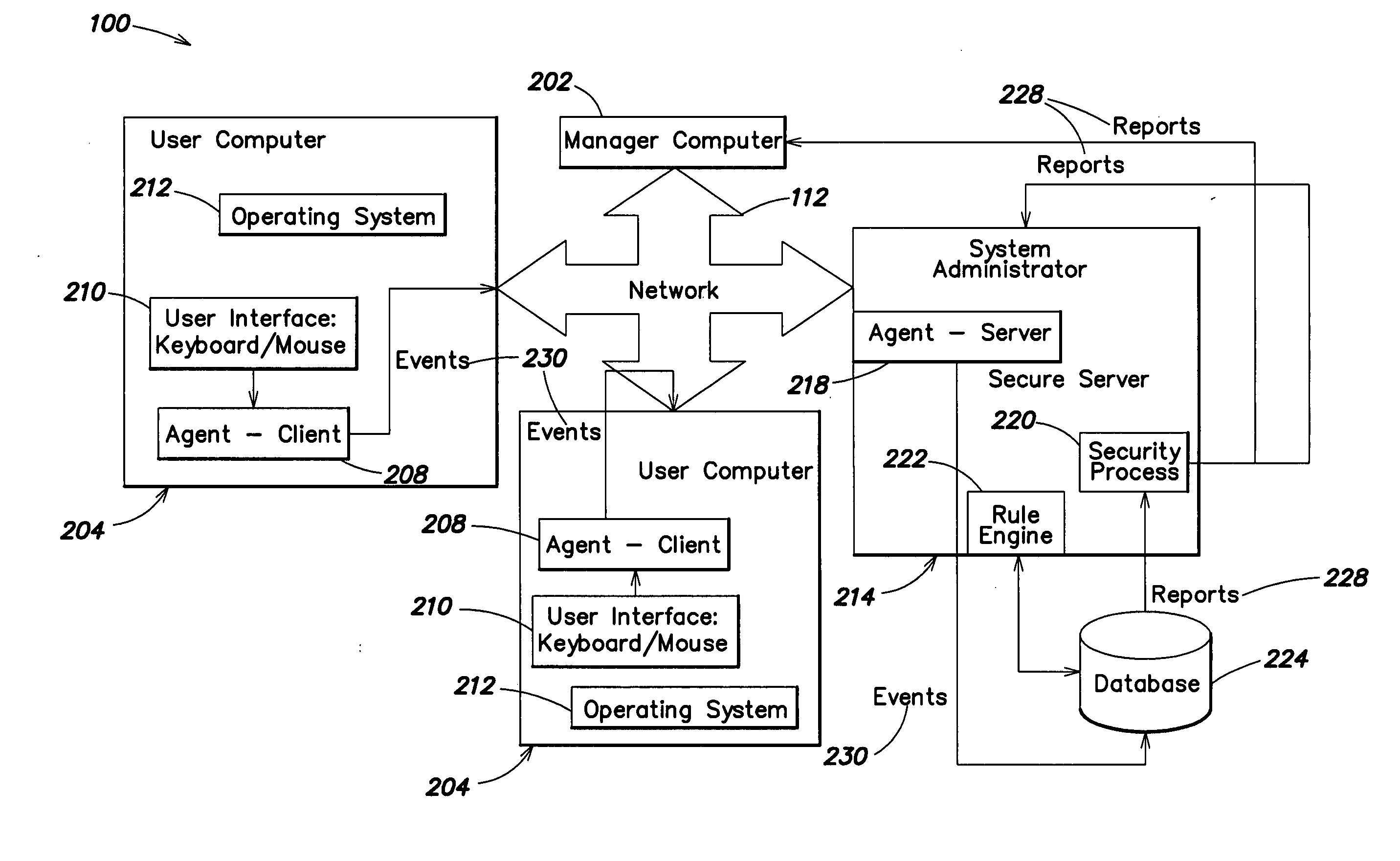
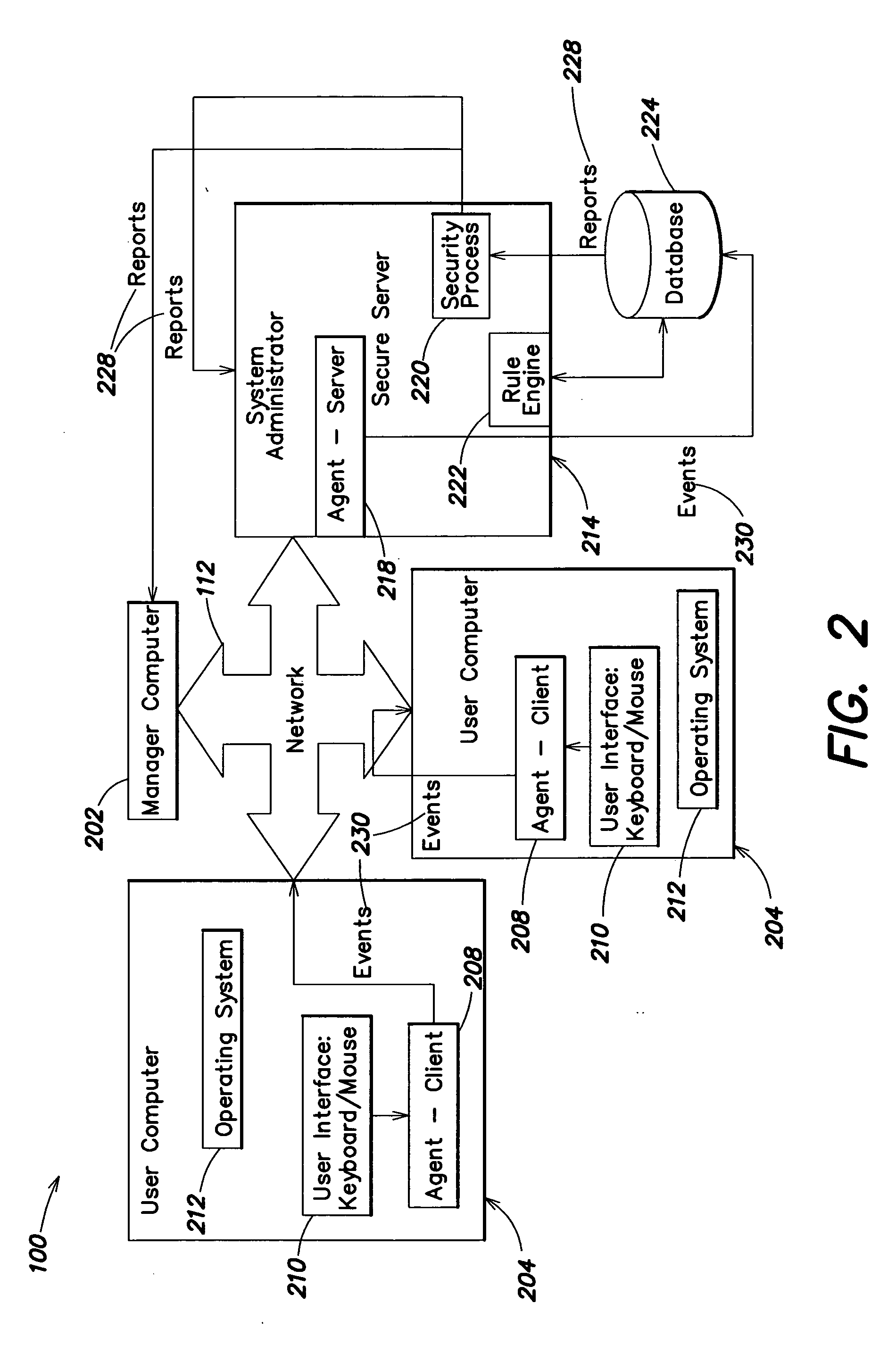
Methods and systems for monitoring user, application or device activity
InactiveUS20050183143A1Improve securityMemory loss protectionUnauthorized memory use protectionWorking environmentComputer usage
Methods and systems are provided for capturing usage data from a user computer, processing a subset of such data to form output, and offering access to selective views of such output, such as to assist a company's management in monitoring computer usage in a work environment. The output may be processed and viewed according to software application, device, or specified user. The output, or a report generated therefrom, may be accessible in differing degrees to individuals having appropriate levels of permission.
Owner:SERGEANT LAB
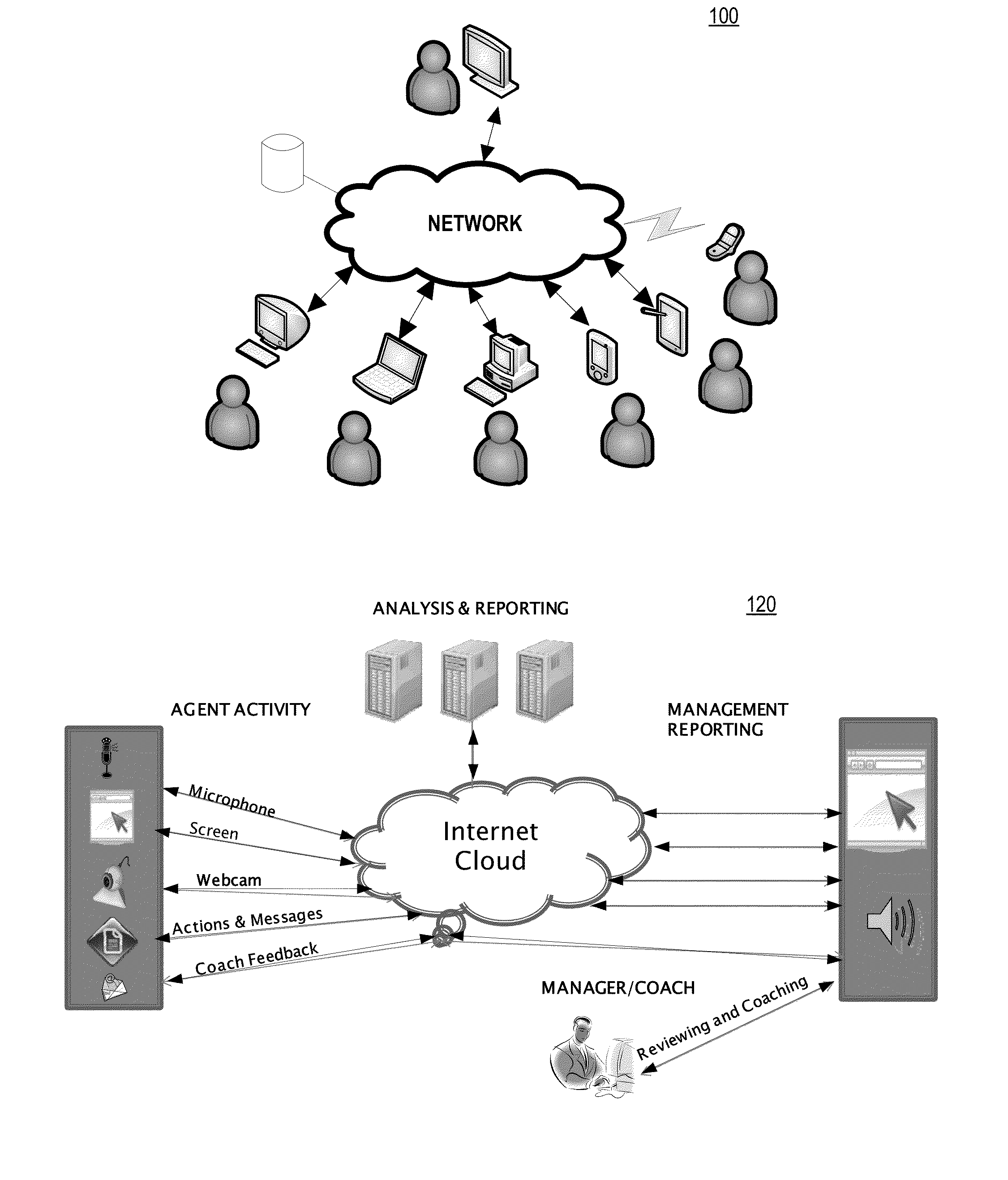
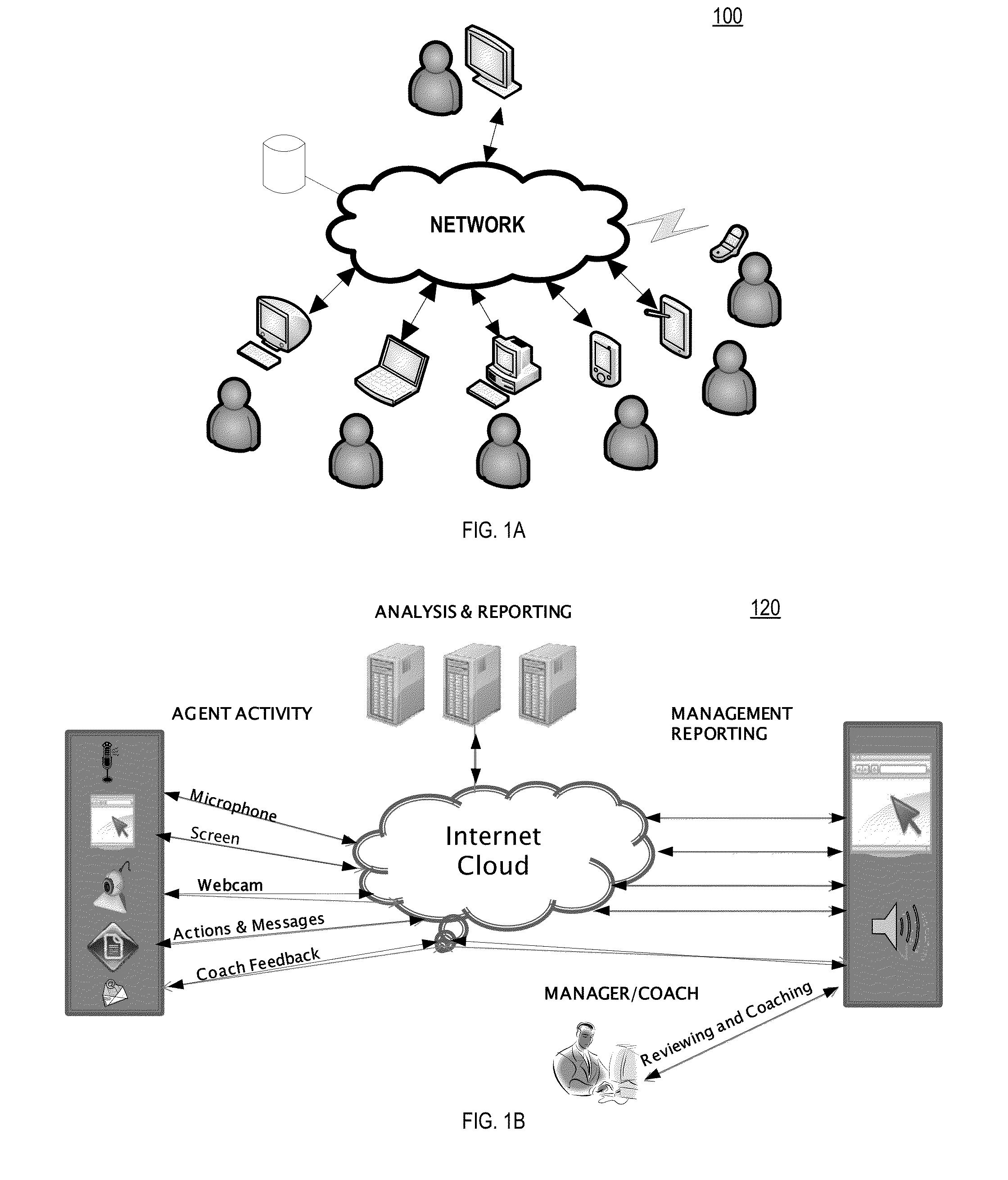
System, Method and Computer Program Product for Distributed User Activity Management
InactiveUS20130110565A1Effectively closedAutomatic exchangesResourcesElectronic communicationComputer usage
A system, method and computer program product for providing a user activity management system including recording activity which may include audio; video or image; screen capture; data from a sensor; location information; computer usage; electronic communications; or social networking activities; transmitting activity information to a network cloud; making available for analyzing, viewing, reporting, training, or alerting; attaching a user activity record to IT systems; or verifying user commitments. The system or method may optionally further include providing playback or supervisor review of recordings; incorporating feedback into an employee or user record; incorporating notes-to-self; or enabling selecting an activity as a best practice for training purposes.
Owner:TRANSPARENCY SCI
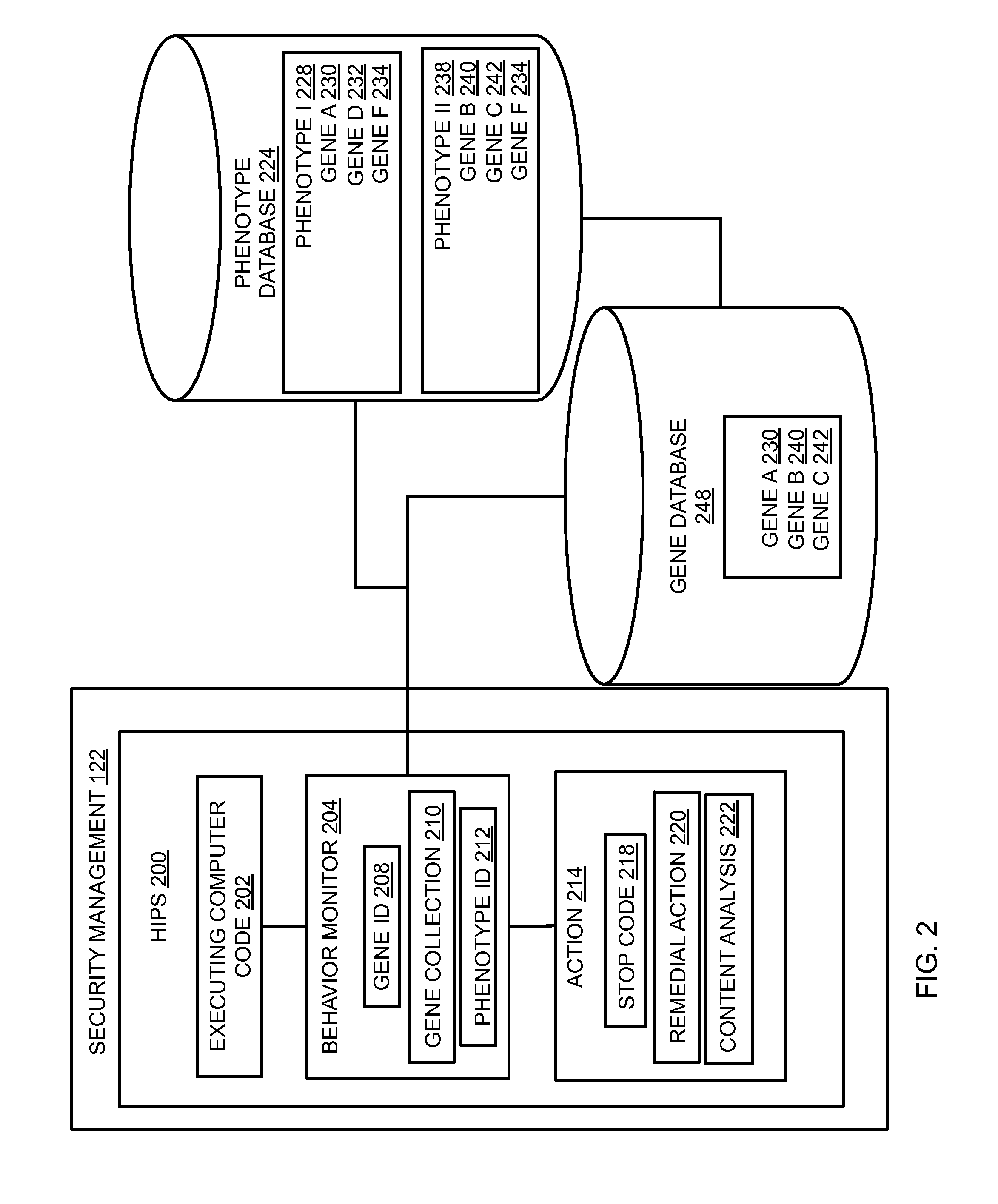
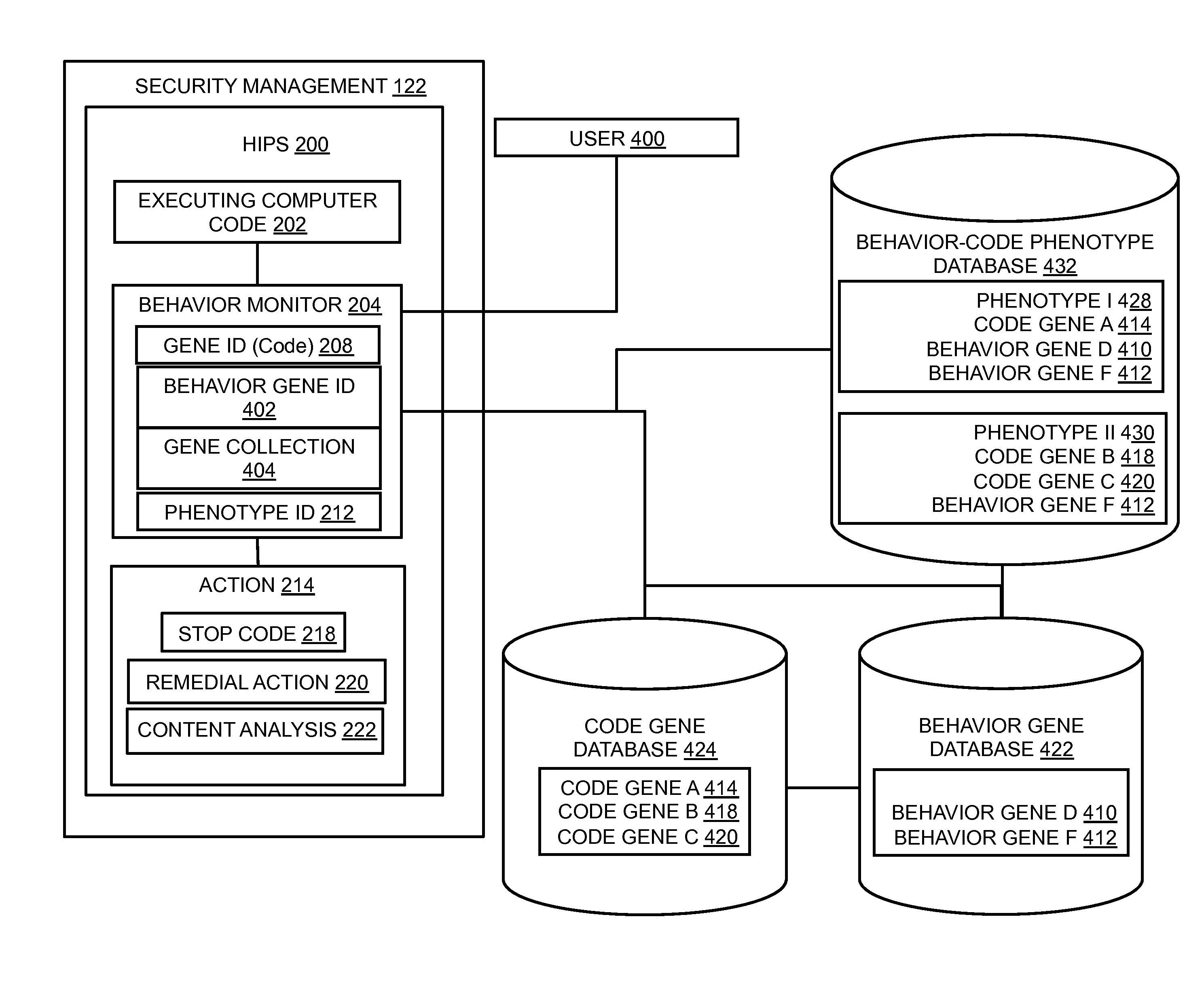
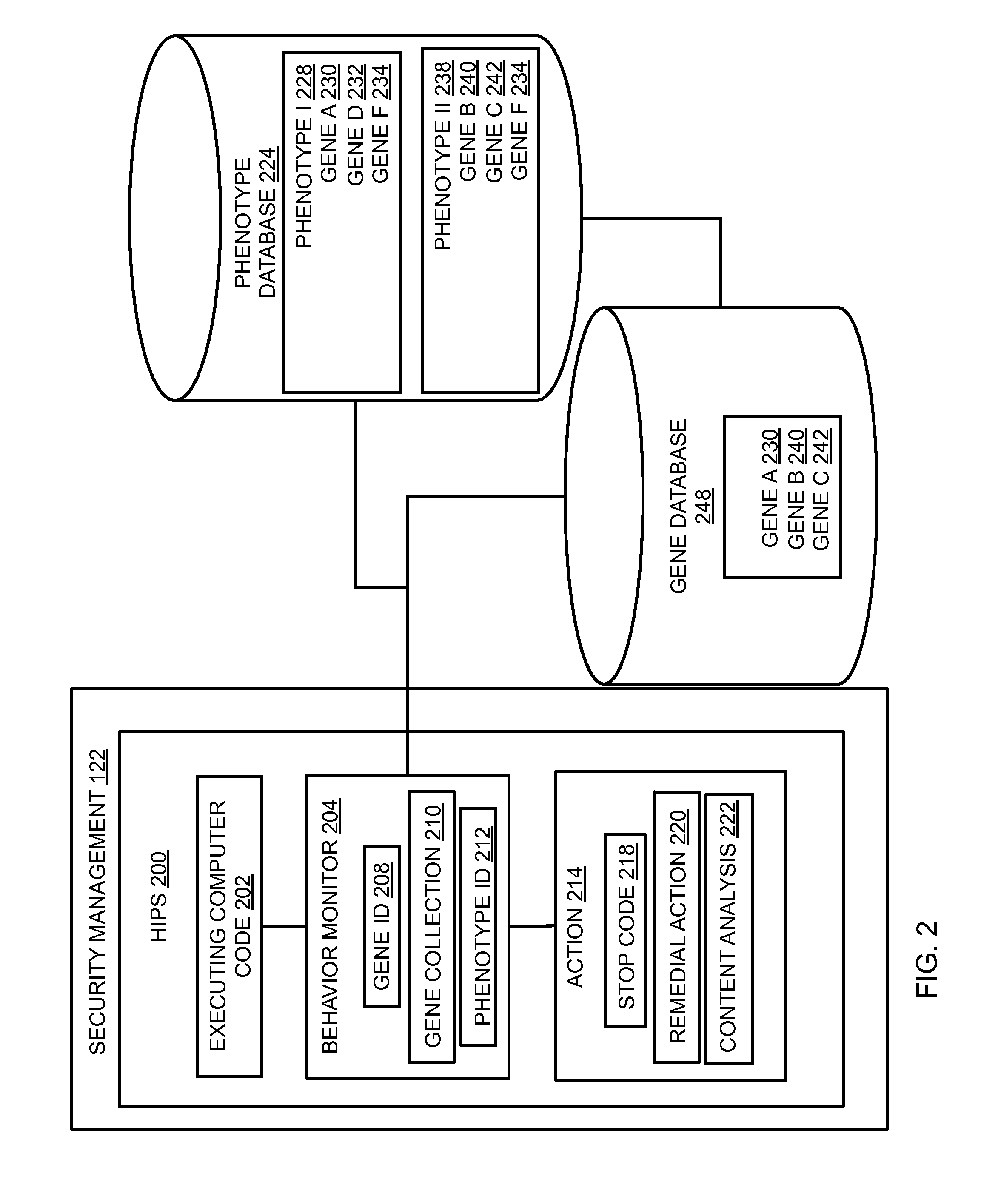
Host intrusion prevention system using software and user behavior analysis
ActiveUS20110023115A1Reduce processing stepsNetwork access restrictionMemory loss protectionError detection/correctionGraphicsGraphical user interface
In embodiments of the present invention improved capabilities are described for threat detection using a behavioral-based host-intrusion prevention method and system for monitoring a user interaction with a computer, software application, operating system, graphic user interface, or some other component or client of a computer network, and performing an action to protect the computer network based at least in part on the user interaction and a computer code process executing during or in association with a computer usage session.
Owner:SOPHOS
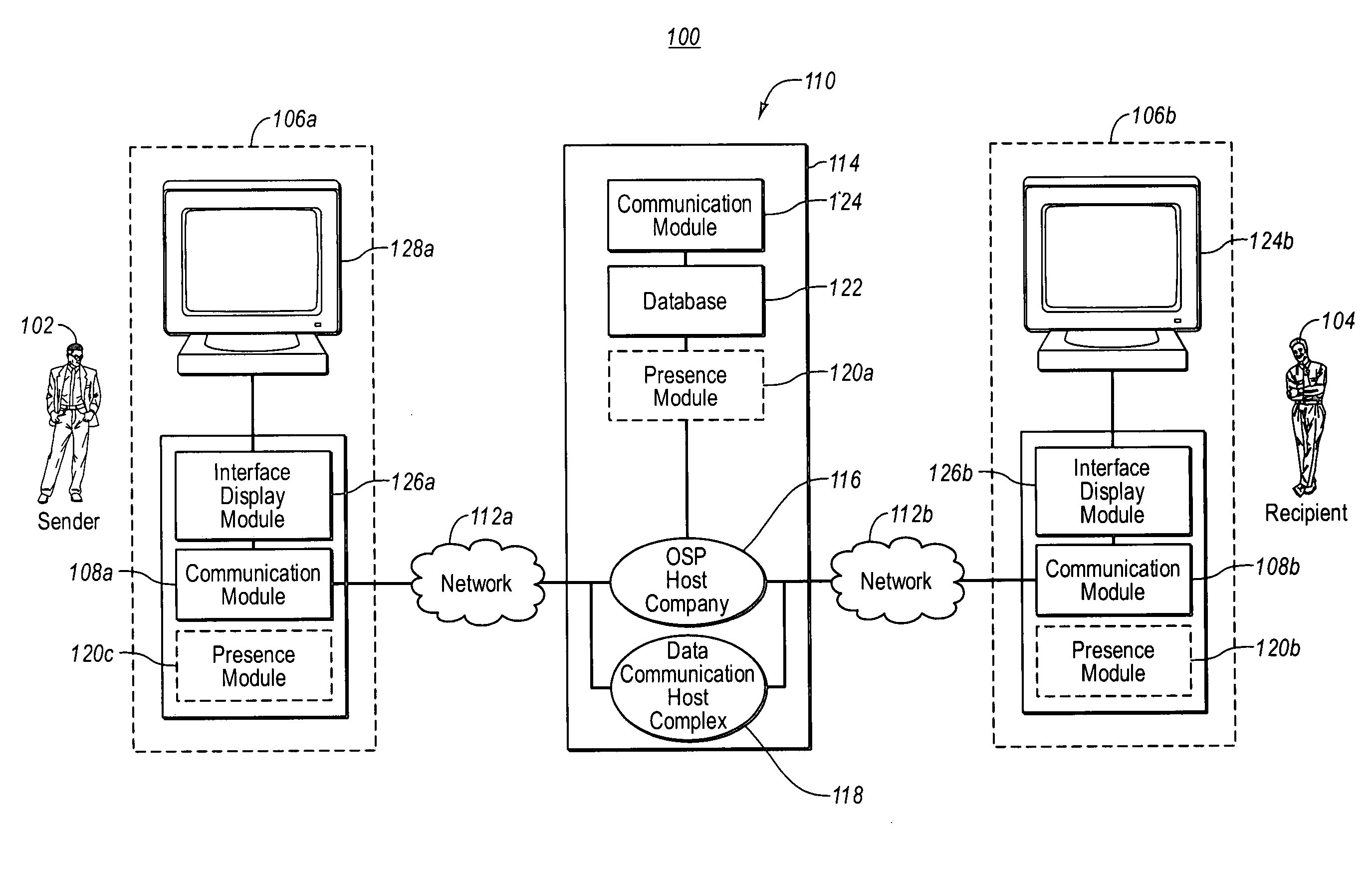
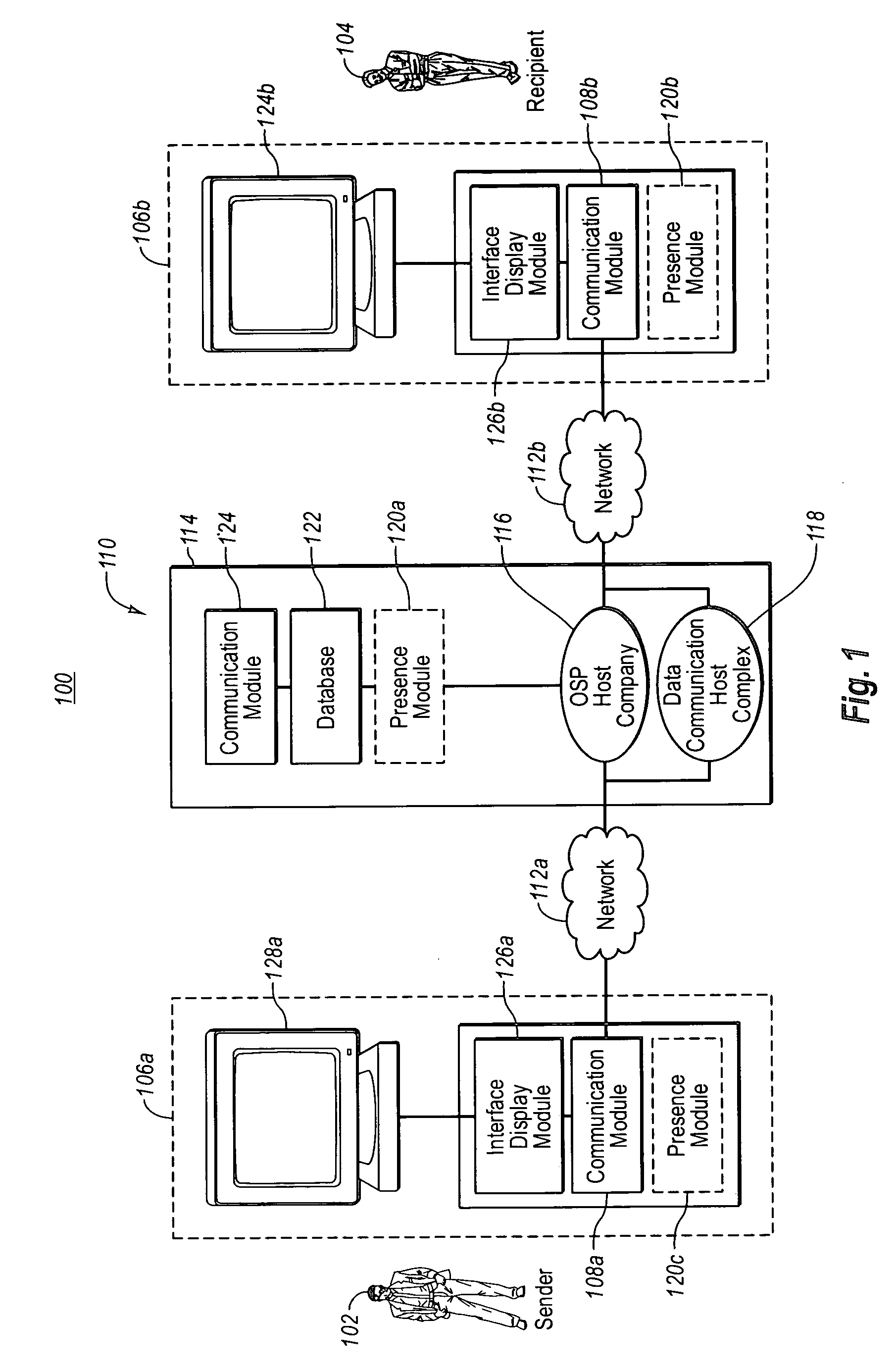
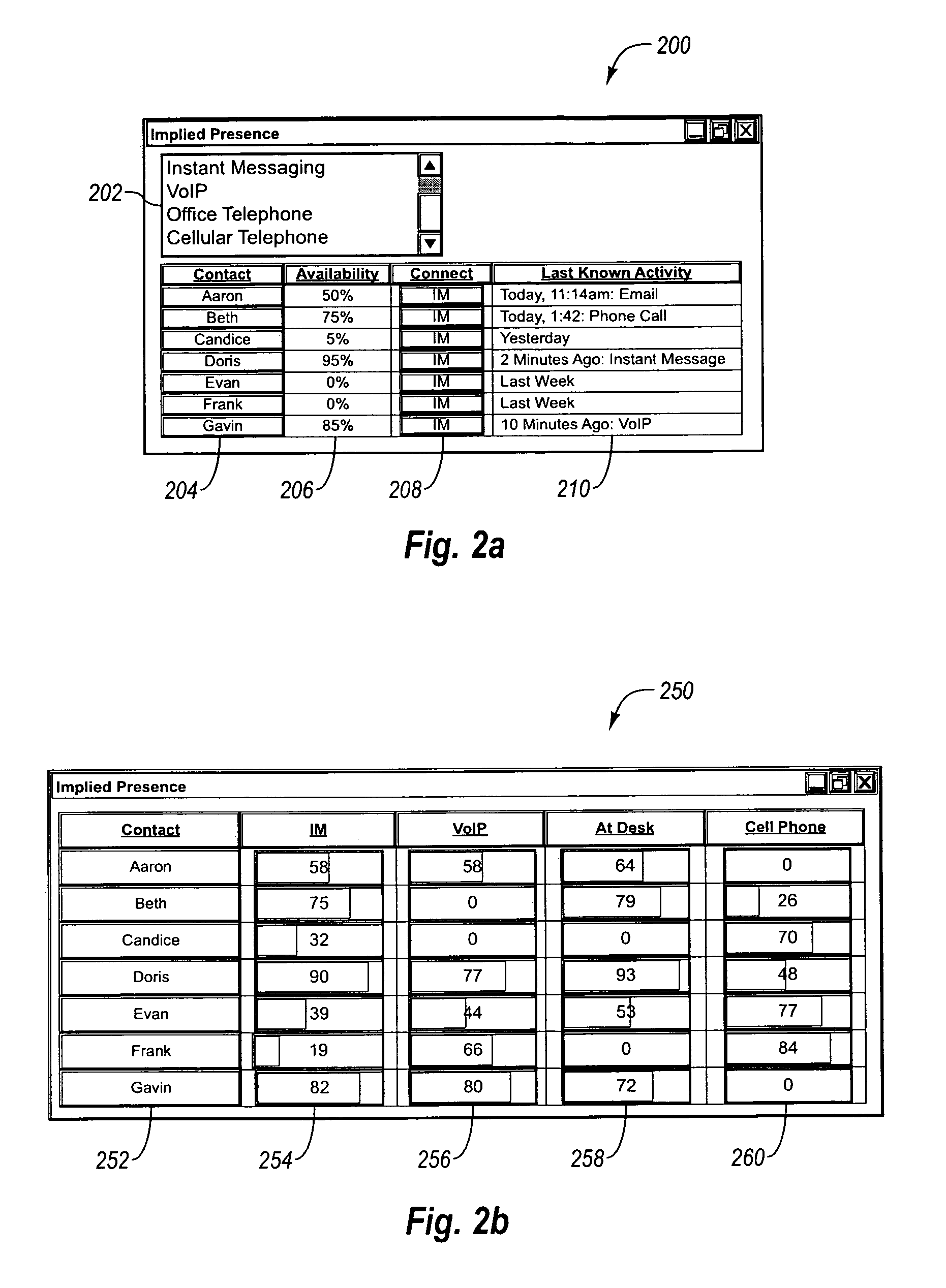
Implied presence detection in a communication system
The present invention provides for systems and methods for determining the likelihood that an intended recipient is currently available to communicate via at least one communication mechanism. A presence module monitors the computer usage activity of the intended recipient. The data relating to the computer usage activity of the intended recipient is stored in a database, and is later utilized by a processing module for determining the likelihood that the intended recipient is currently available to communicate via the at least one communication mechanism. The likelihood that the intended recipient is currently available to communicate via the at least one communication mechanism is displayed to at least one other user by an interface module. A communication module is configured to send a message to the intended recipient via the at least one communication mechanism.
Owner:AOL LLC A DELAWARE LLC
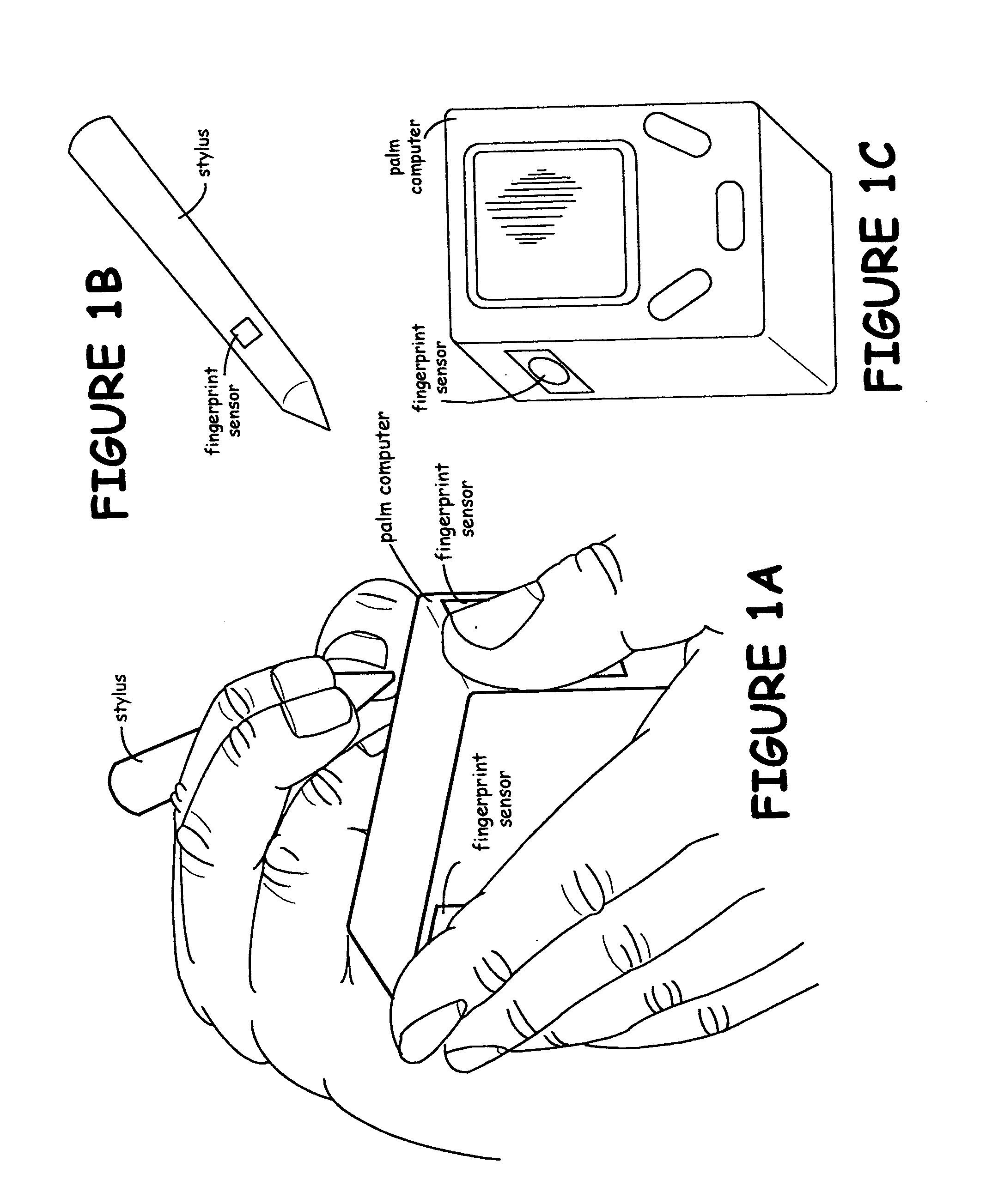
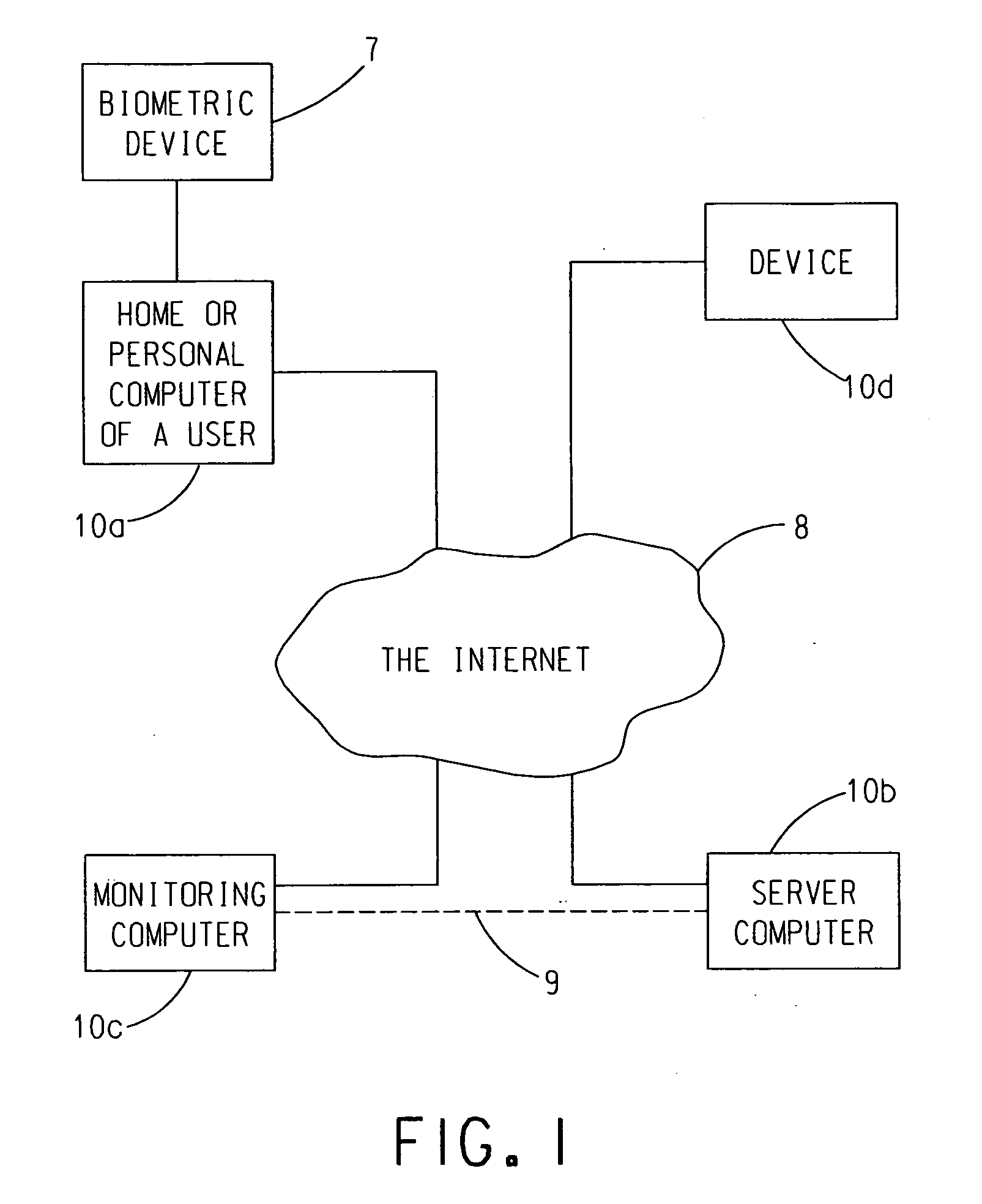
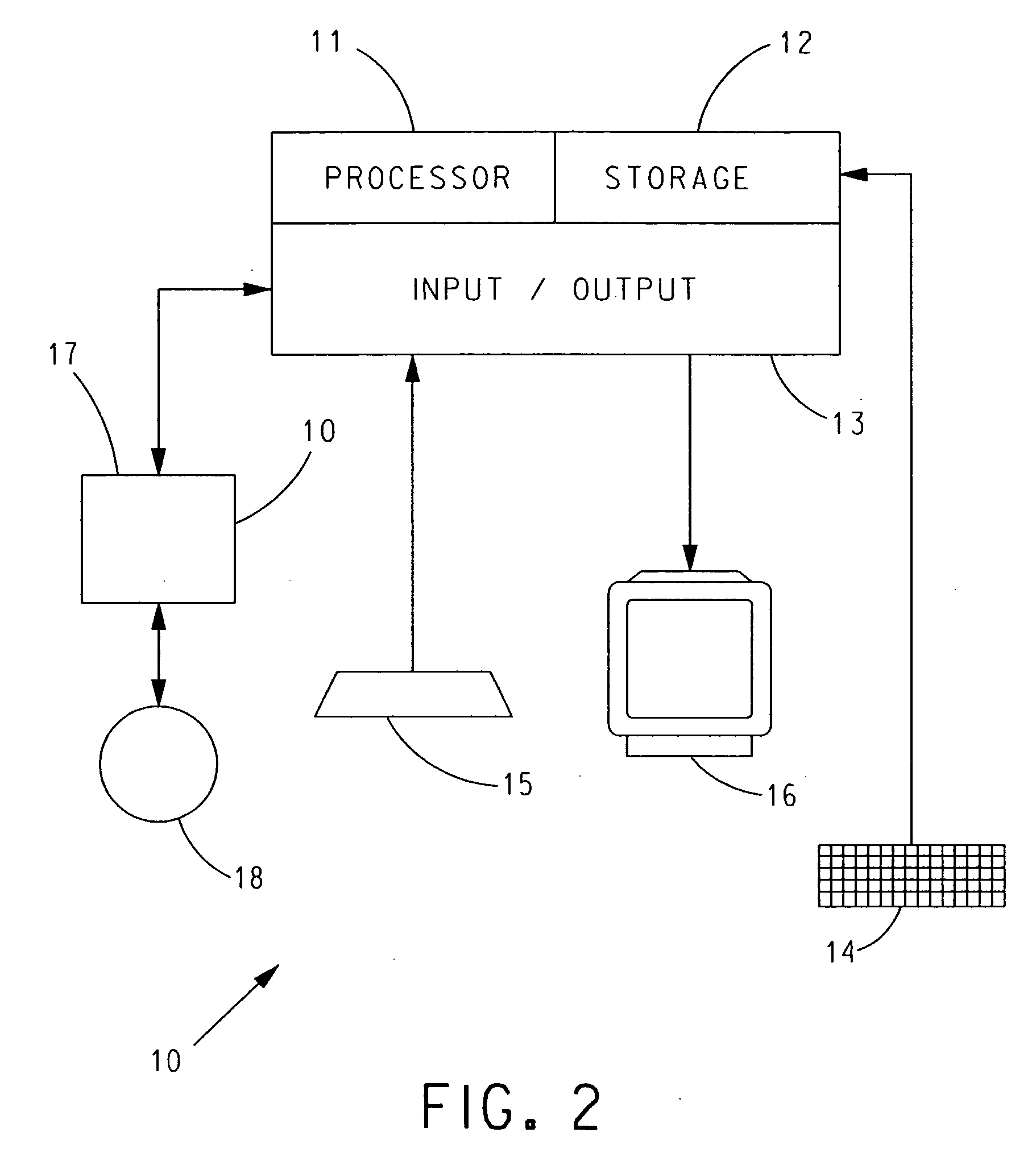
Data security system
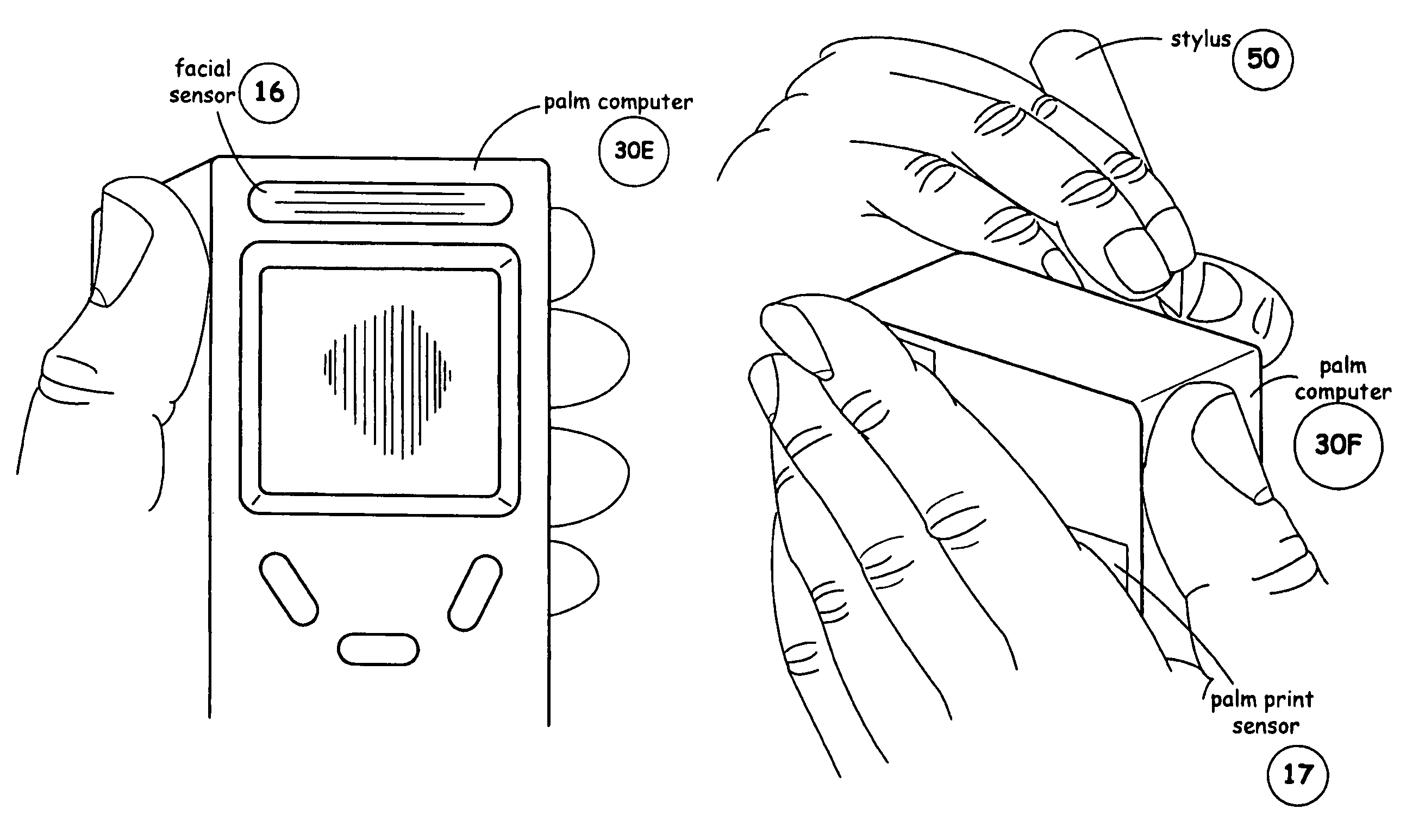
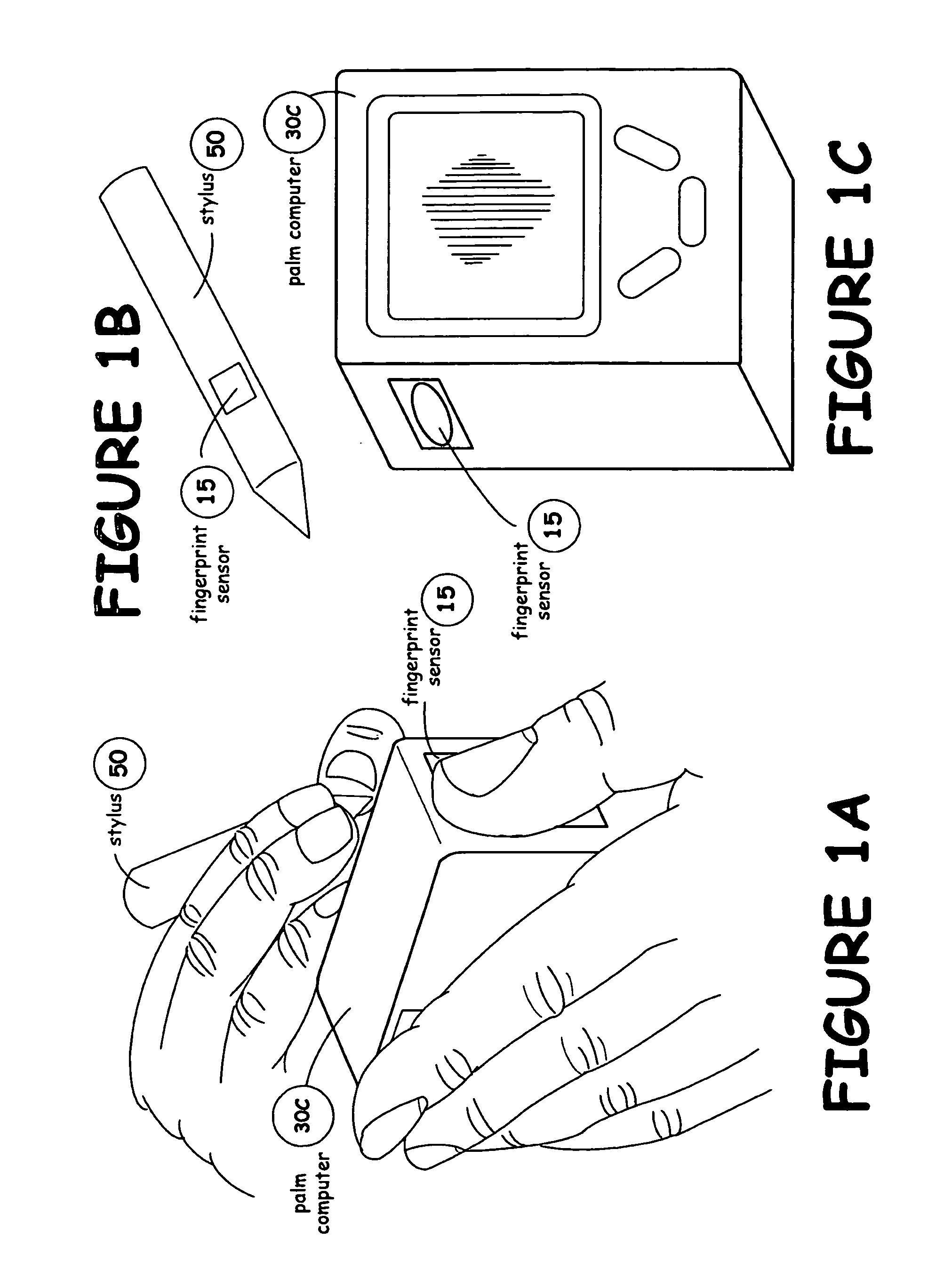
InactiveUS7047419B2Easy accessNeed can be addressedDigital data processing detailsInternal/peripheral component protectionComputer usageData access
A data security system comprises a host processor, and a plurality of remote computers. Each remote computer provides biometric authentication of a user prior to responding to the user request for data access. The remote computers are handheld when in operational mode. A sensor in the handheld computer captures a biometric image while the remote computer is being used. The biometric sensor is positioned in such a way that the sensor enables the capture of the biometric image continually during computer usage with each request for access to secure data. The biometric authentication occurs in a seamless manner and is incidental to the data request enabling user identity authentication with each request to access secure data.
Owner:UNITED STATES CP LLC
Data security system
InactiveUS20060005042A1Easy accessNeed can be addressedDigital data processing detailsChecking apparatusData accessComputer usage
A data security system comprises a host processor, and a plurality of remote computers. Each remote computer provides biometric authentication of a user prior to responding to the user request for data access. The remote computers are handheld when in operational mode. A sensor in the handheld computer captures a biometric image while the remote computer is being used. The biometric sensor is positioned in such a way that the sensor enables the capture of the biometric image continually during computer usage with each request for access to secure data. The biometric authentication occurs in a seamless manner and is incidental to the data request enabling user identity authentication with each request to access secure data.
Owner:UNITED STATES CP LLC
Host intrusion prevention system using software and user behavior analysis
In embodiments of the present invention improved capabilities are described for threat detection using a behavioral-based host-intrusion prevention method and system for monitoring a user interaction with a computer, software application, operating system, graphic user interface, or some other component or client of a computer network, and performing an action to protect the computer network based at least in part on the user interaction and a computer code process executing during or in association with a computer usage session.
Owner:SOPHOS
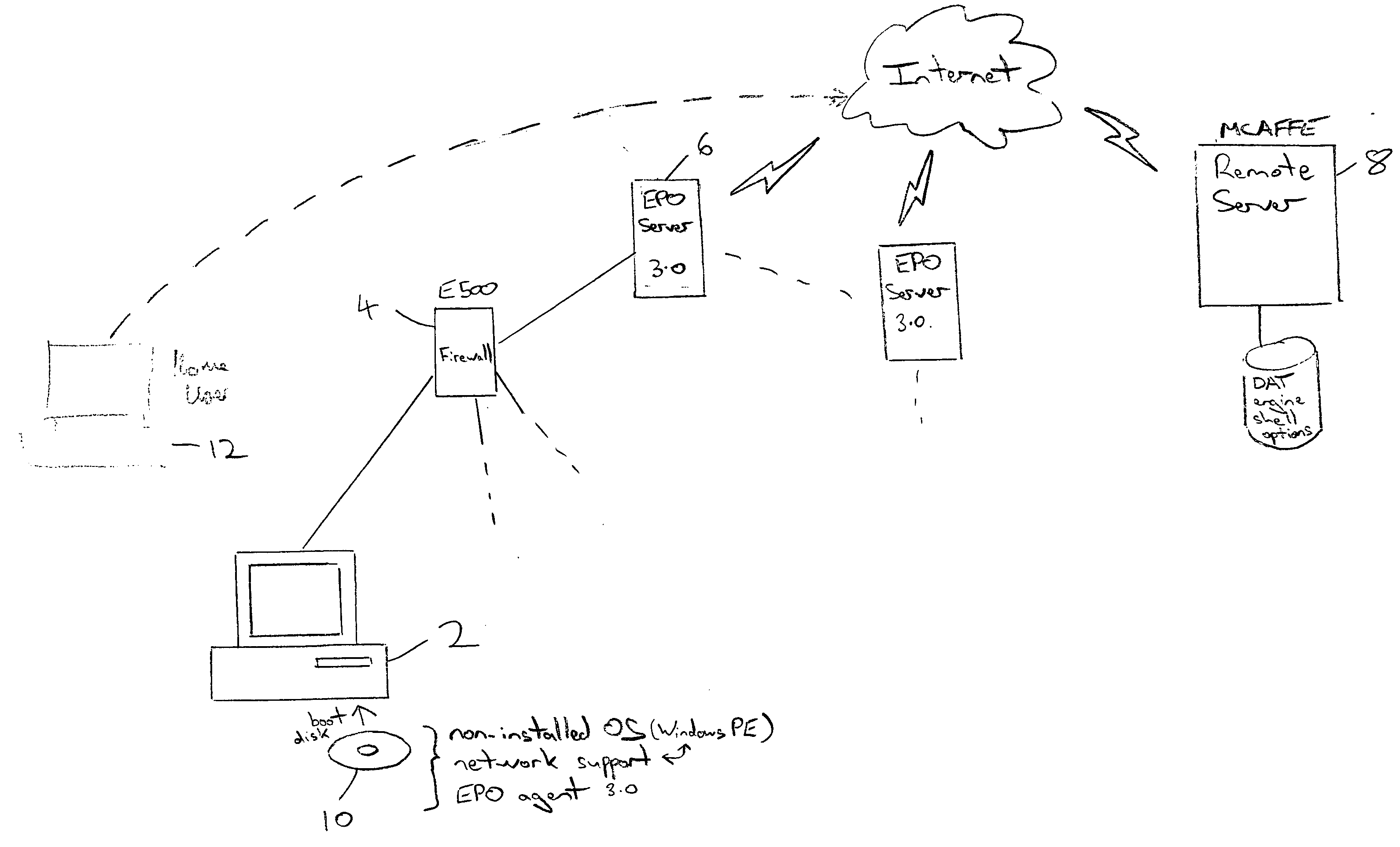
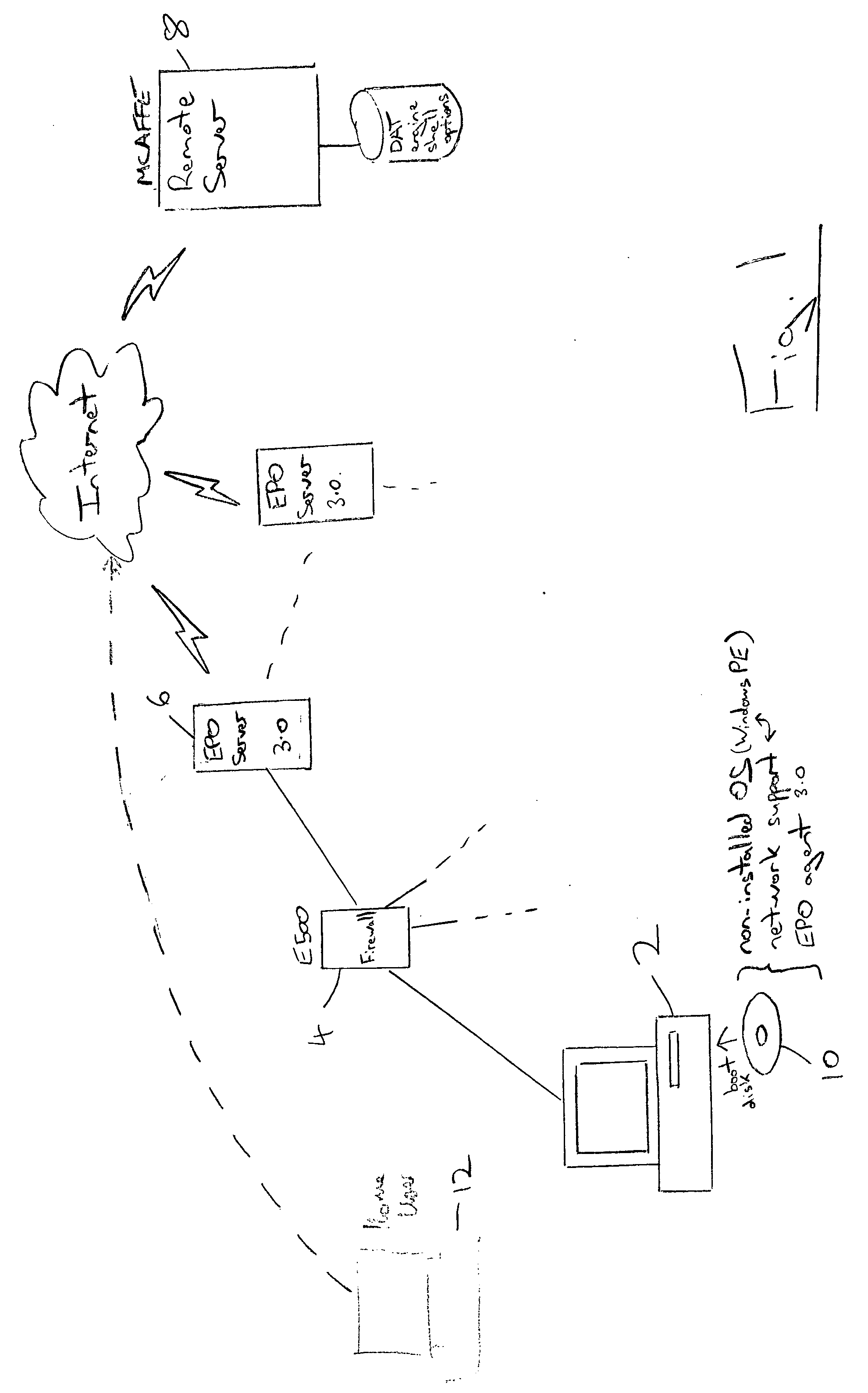
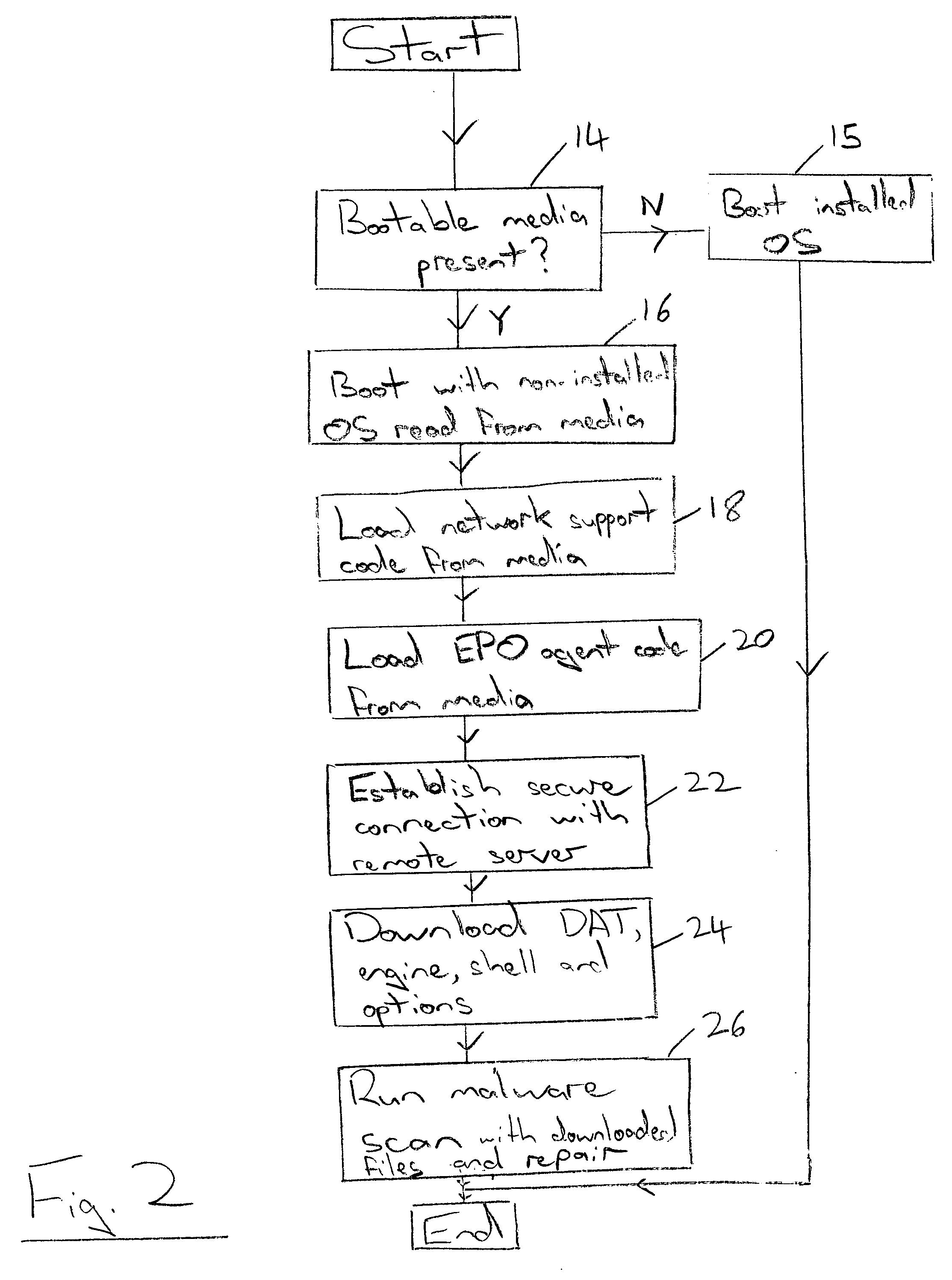
Malware scanning using a boot with a non-installed operating system and download of malware detection files
InactiveUS20050015606A1Efficient downloadEasy to detectUser identity/authority verificationUnauthorized memory use protectionOperational systemComputer usage
A computer 2 is booted with a removable physical media 10 which bears a clean non-installed operating system. Network support code is also loaded from the removable physical media 10 and used to establish a connection with a remote computer 6, 8. Malware detection files are then downloaded from the remote computer 6, 8 and used to perform a malware detection operation upon the computer 2. Thus, the removable physical media 10 necessary to perform the clean boot may be distributed in advance of a malware outbreak whilst the downloading from a remote computer 6, 8 of the malware detection files ensures that the most up-to-date versions of these files will be used when the removable physical media 10 is employed to conduct a clean boot and trigger a malware detection operation in a malware outbreak situation.
Owner:MCAFEE INC
Method and apparatus for extracting relevant content based on user preferences indicated by user actions
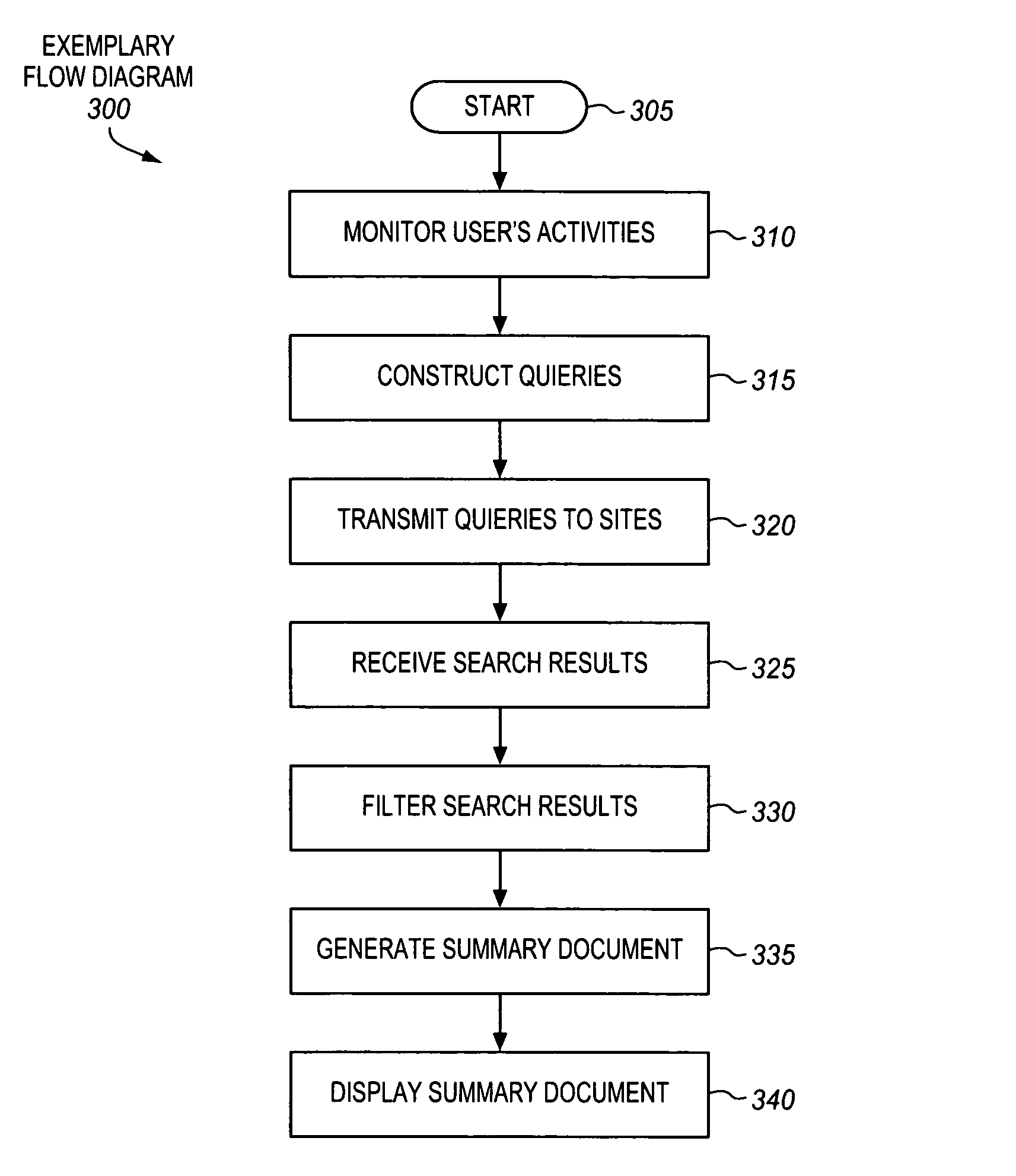
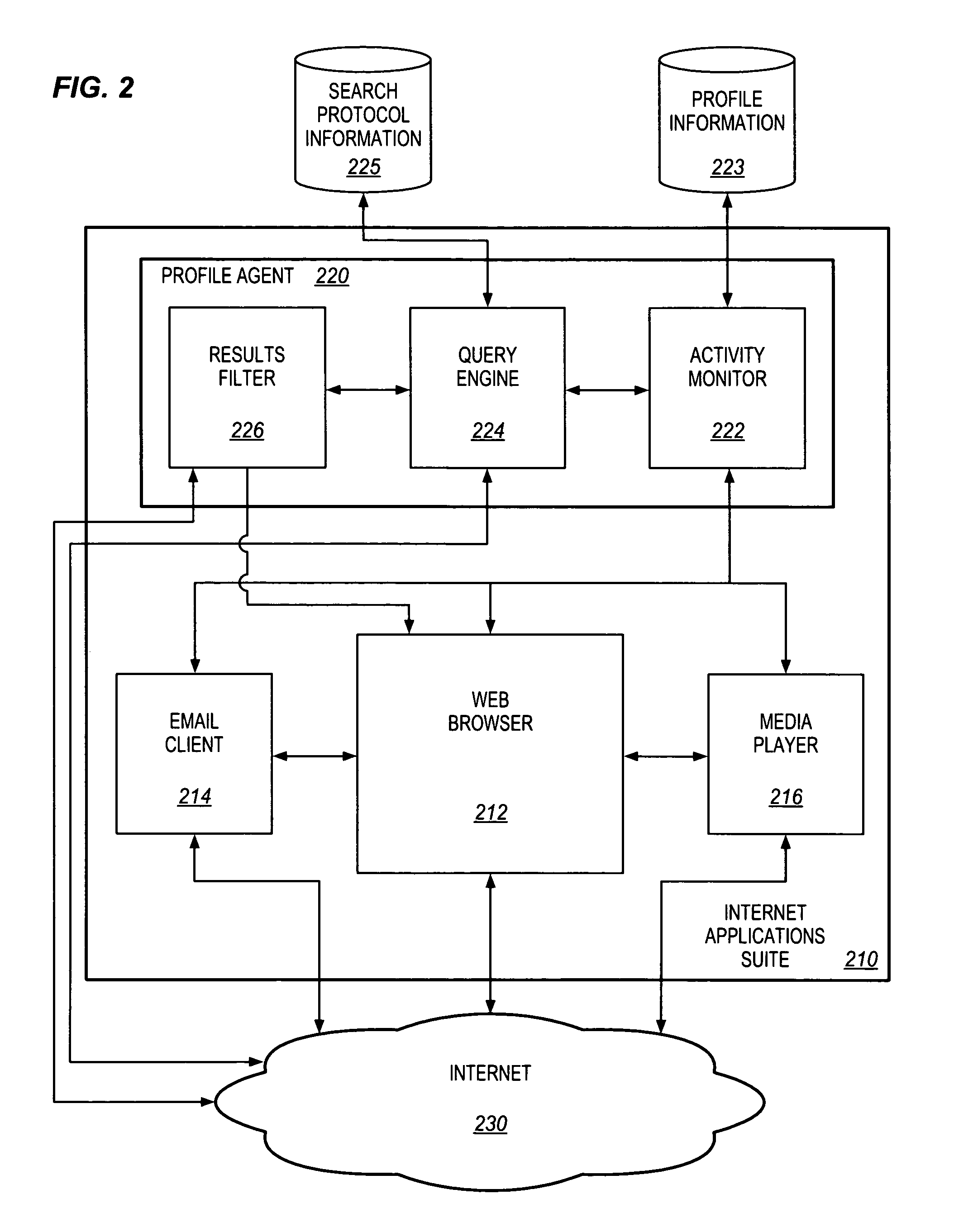
InactiveUS7444319B1Data processing applicationsDigital data information retrievalWeb siteComputer users
A method and apparatus are described for facilitating efficient retrieval and display of information to a computer user from sites on a network. An agent is described that monitors computer usage to determine the purpose or intent of a particular session. The agent analyzes information gathered during the monitoring to determine the user's purpose, and subsequently generates queries to search a plurality of network sites that may have information useful to the user related to the purpose. The queries are sent to the sites and when the search results are returned to the computer, the agent filters the search result entries to determine their relevance to the purpose. A summary document comprising the search result entries relevant to the users purpose is prepared and displayed to the user.
Owner:INTEL CORP
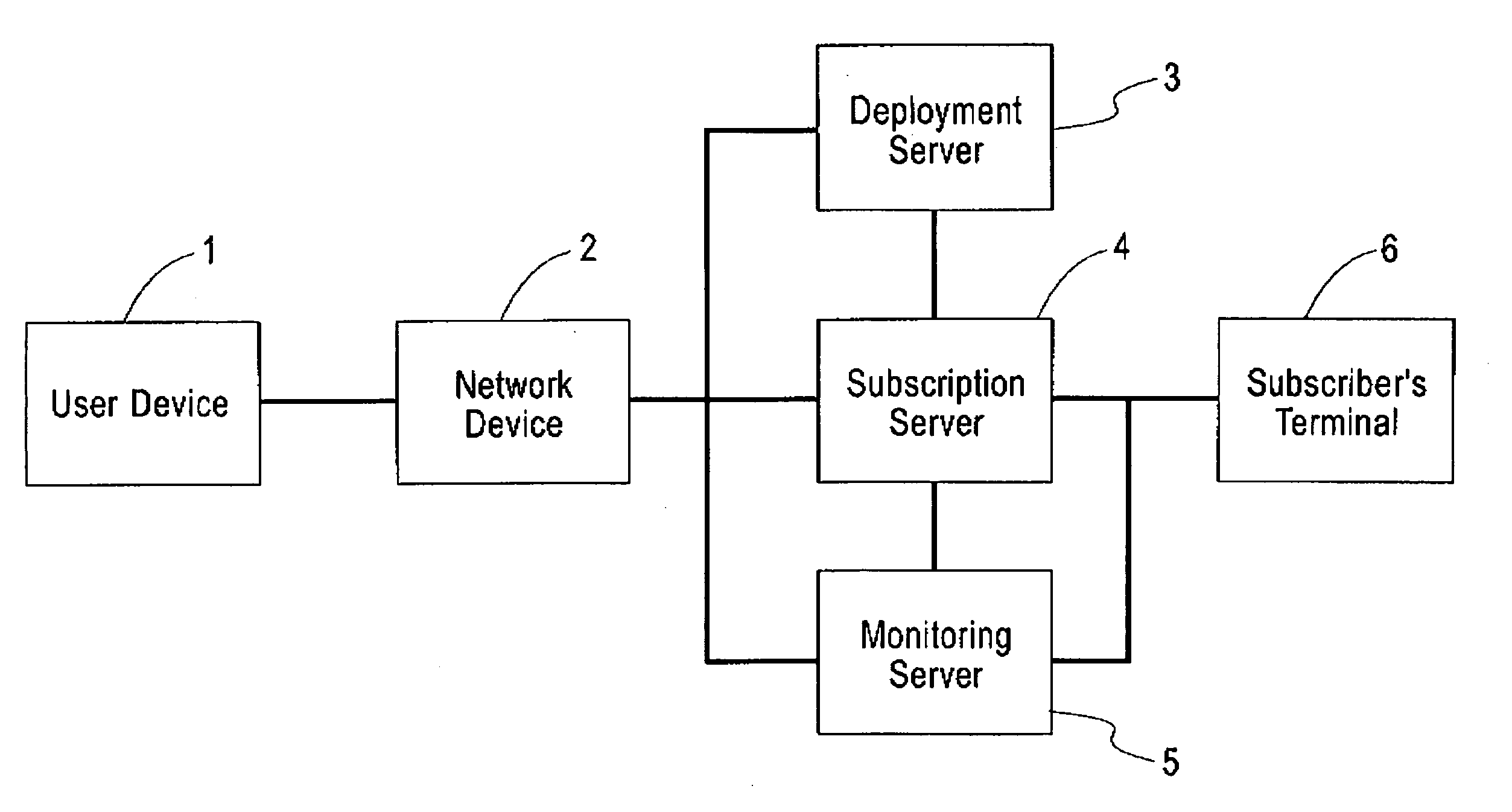
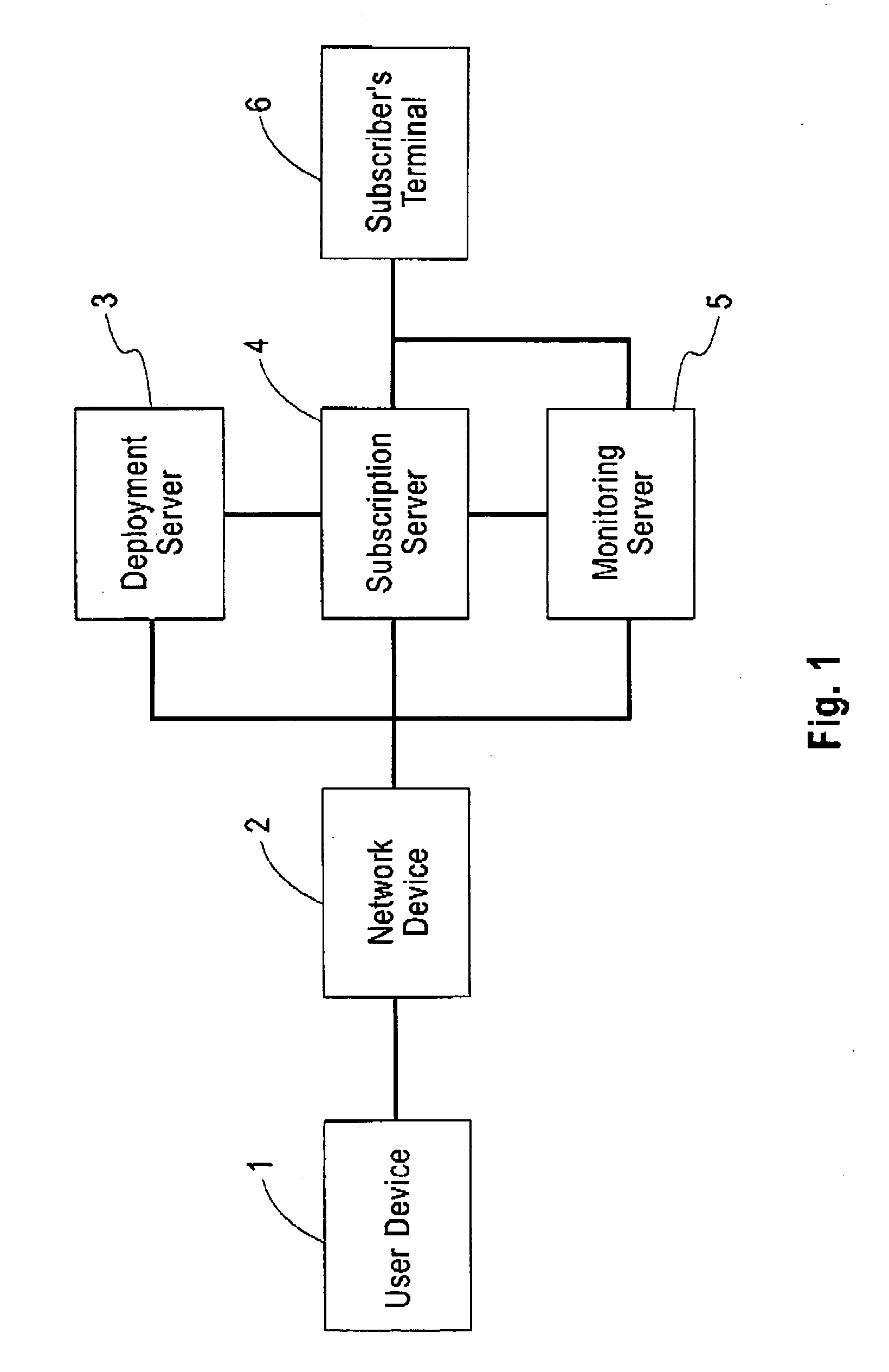
Remote User Computer Control And Monitoring
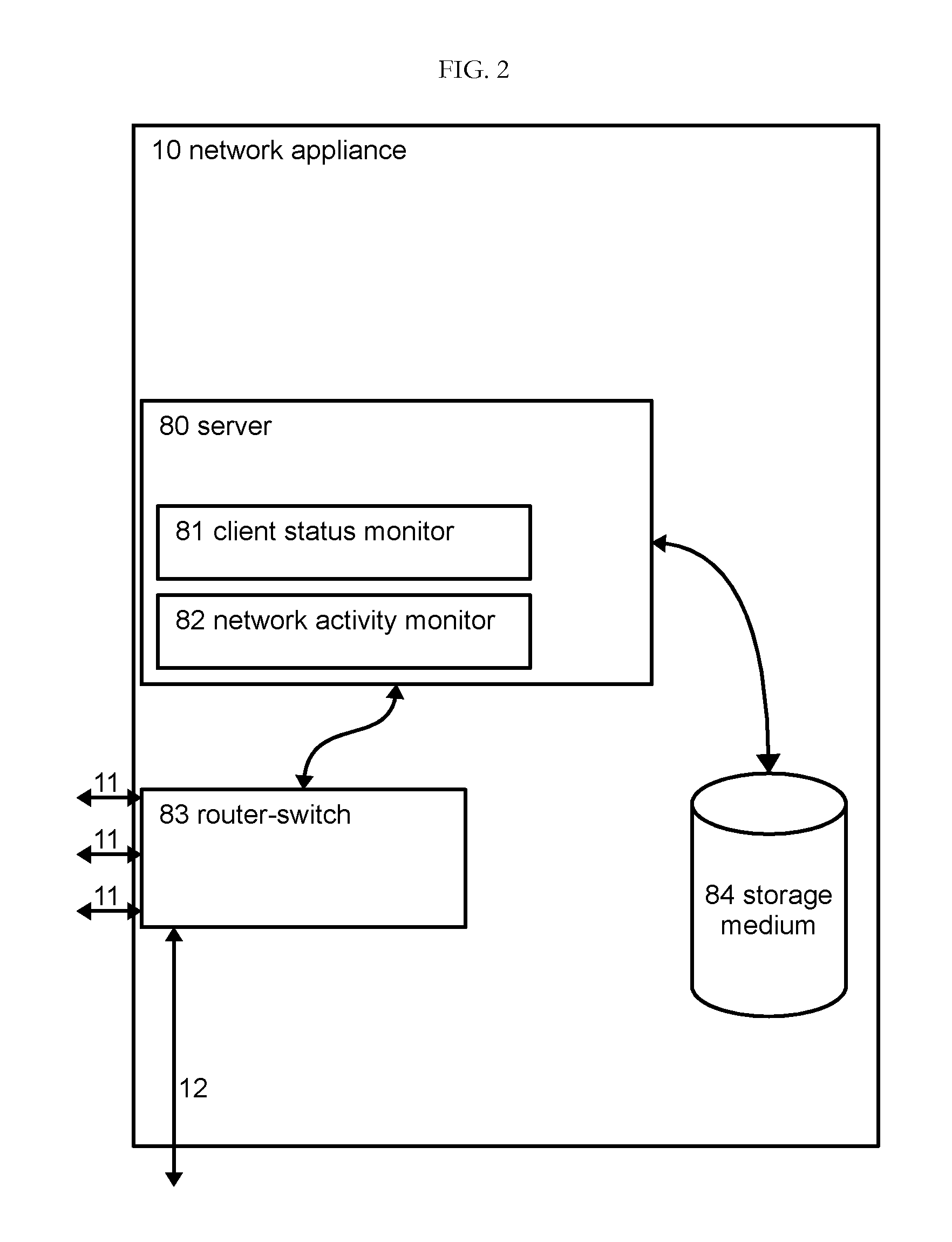
ActiveUS20080215722A1Not compromise effectivenessApproach is limitedDigital data processing detailsMultiple digital computer combinationsComputer monitorComputer usage
Owner:INTERNET PROBATION & PAROLE CONTROL
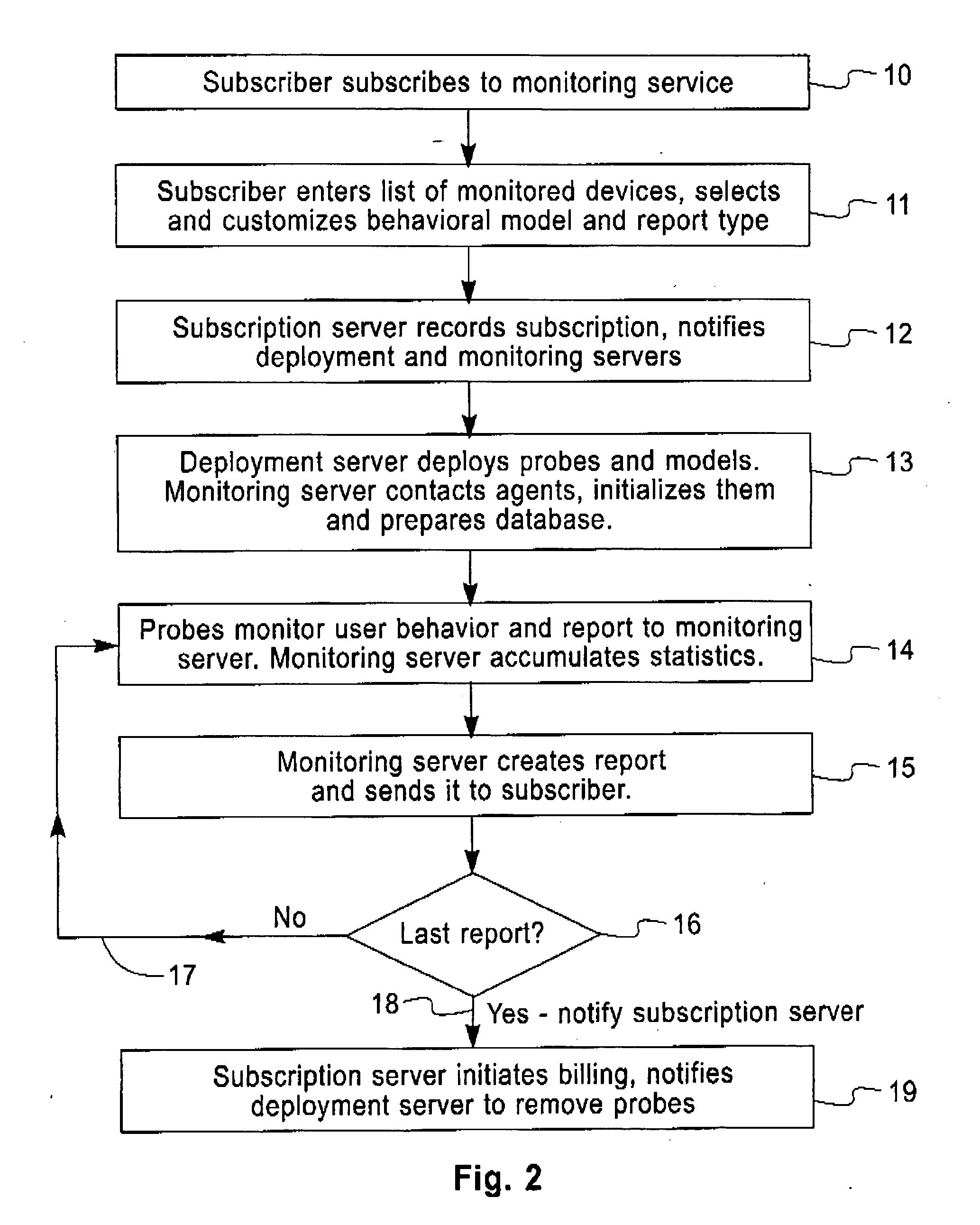
Services for capturing and modeling computer usage
InactiveUS20050246434A1Easy and generally less-expensive to captureSufficient supplyDigital computer detailsComputation using non-denominational number representationComputer usageReal-time computing
A subscriber to a service that monitors user behavior first registers with that service and selects a model of user behavior. The service then transmits that model to an agent, situated capable of monitoring user behavior and relating it to the model. After the monitoring interval the agent transmits data from the model to a server, where that data is summarized and reports created. These reports can then be sent to the subscriber in satisfaction of their needs for behavioral information.
Owner:LENOVO (SINGAPORE) PTE LTD
Method and apparatus for controlling child's internet use
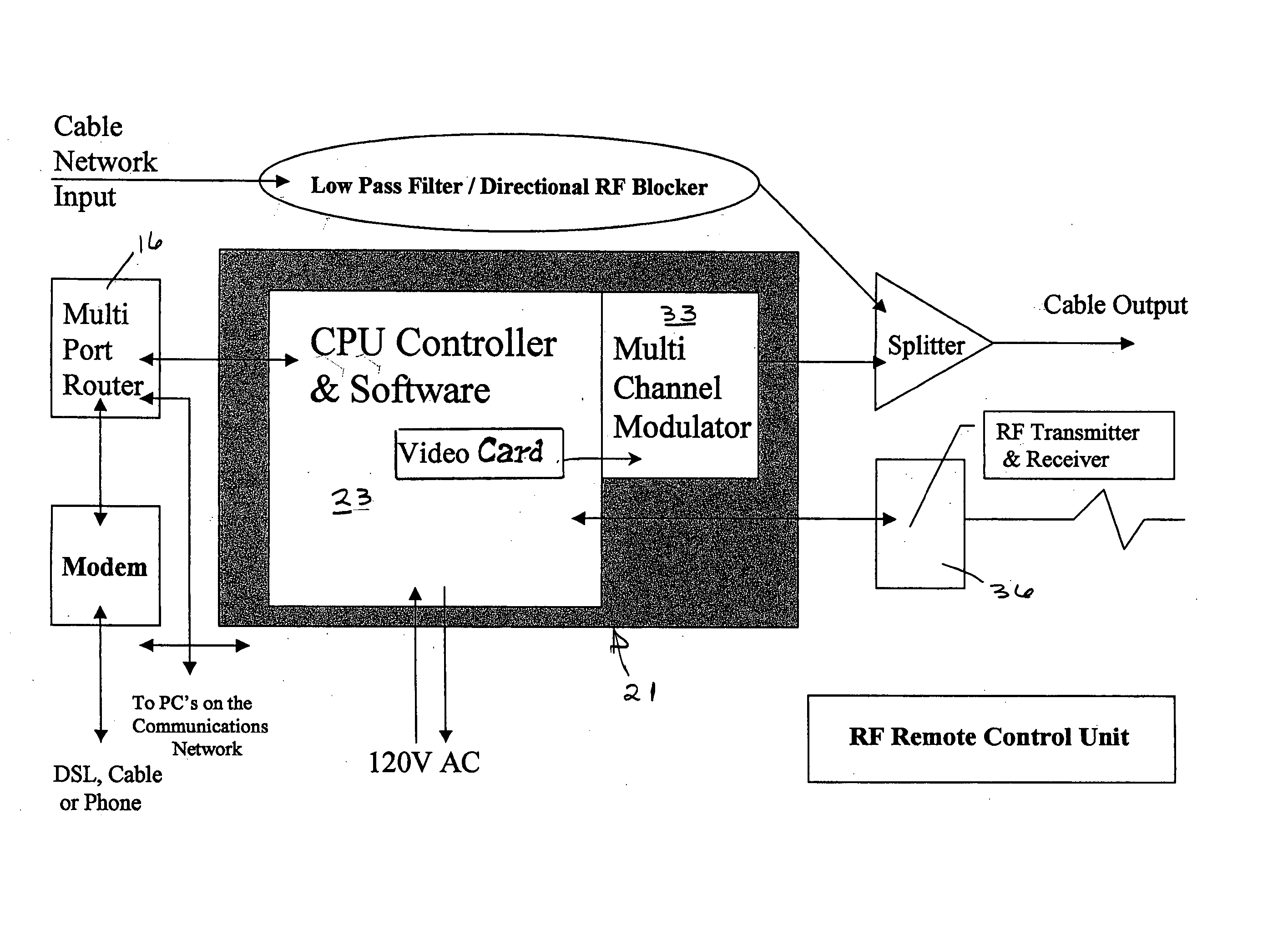
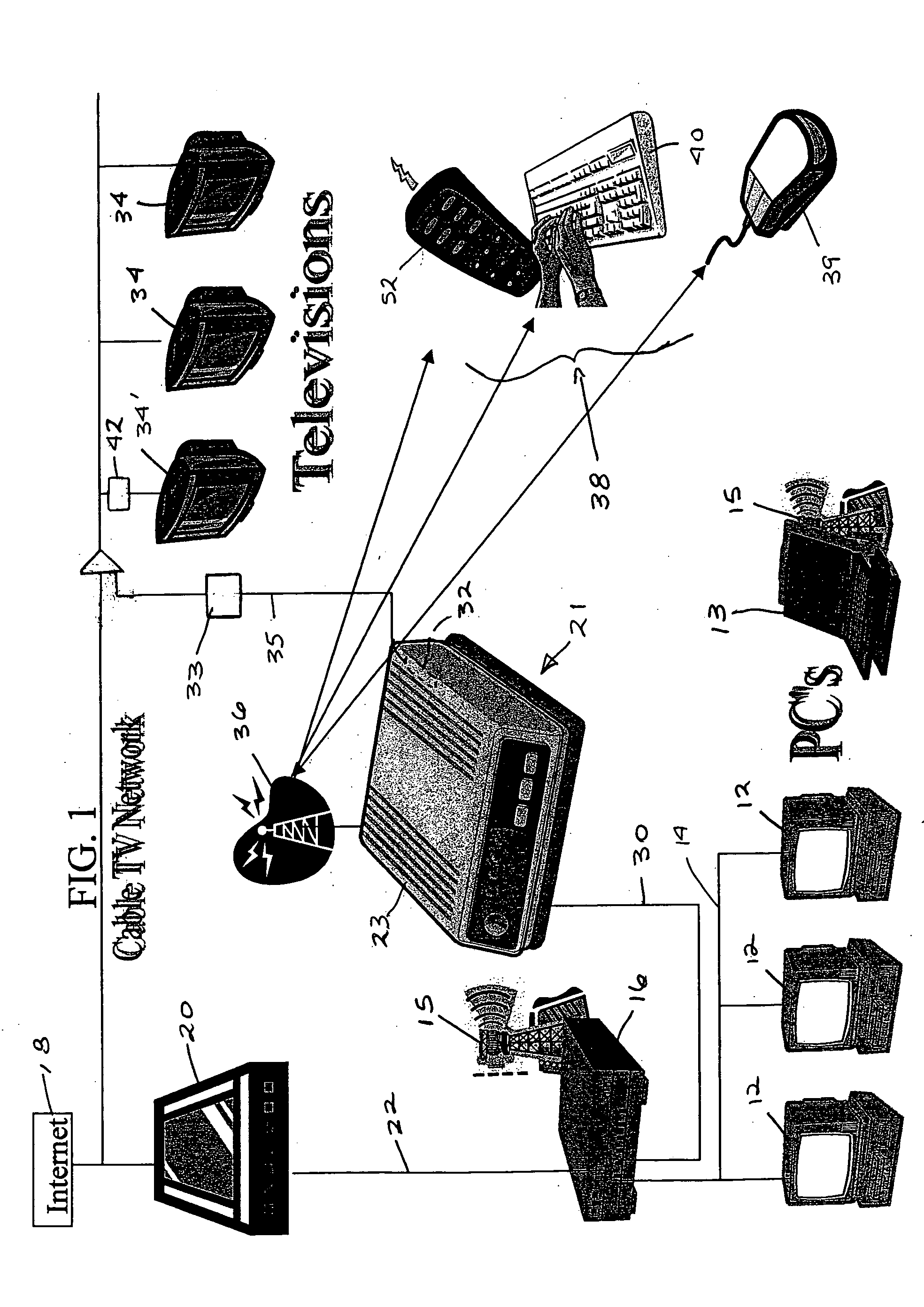
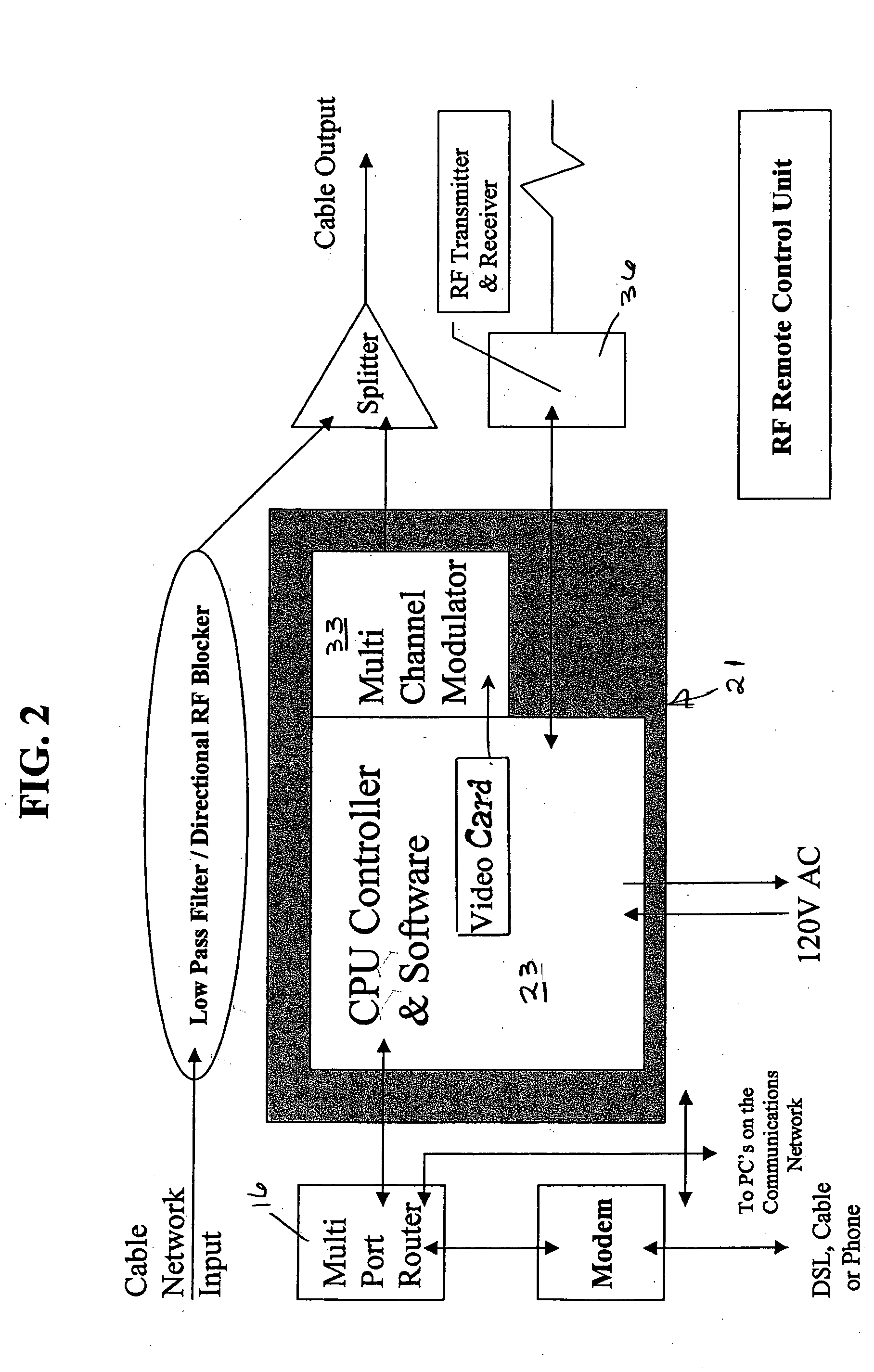
InactiveUS20050240960A1Digital data information retrievalDigital data processing detailsRemote controlComputer usage
A method and apparatus for inducing children to select appropriate programming over the Internet comprises providing a parent or other supervisor with equipment and software for monitoring Internet usage by the child's computer on a remote television set and providing the supervisor with a remote control device for disconnecting the child's computer from the Internet or disabling the child's computer completely if undesirable content is detected. The child's computer usage can be recorded and stored for later viewing. A controller can be set to permit time periods during which Internet usage is permitted.
Owner:NAGTZAAM MARTINUS
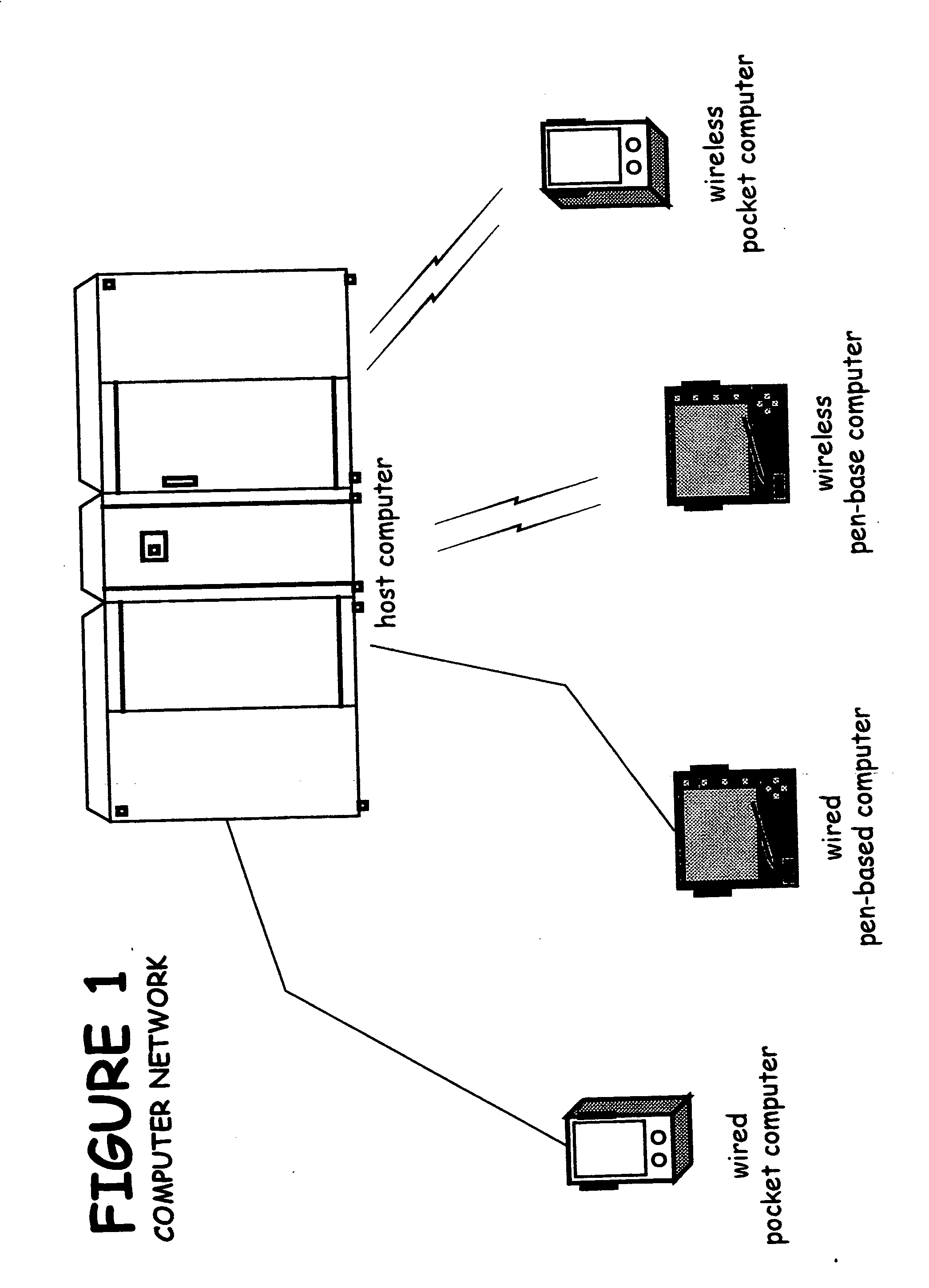
Multifunction personal computer/mobile phone
InactiveUS20050026658A1Easy to operateAdequate space for arrangementDetails for portable computersAutomatic exchangesDisplay deviceComputer usage
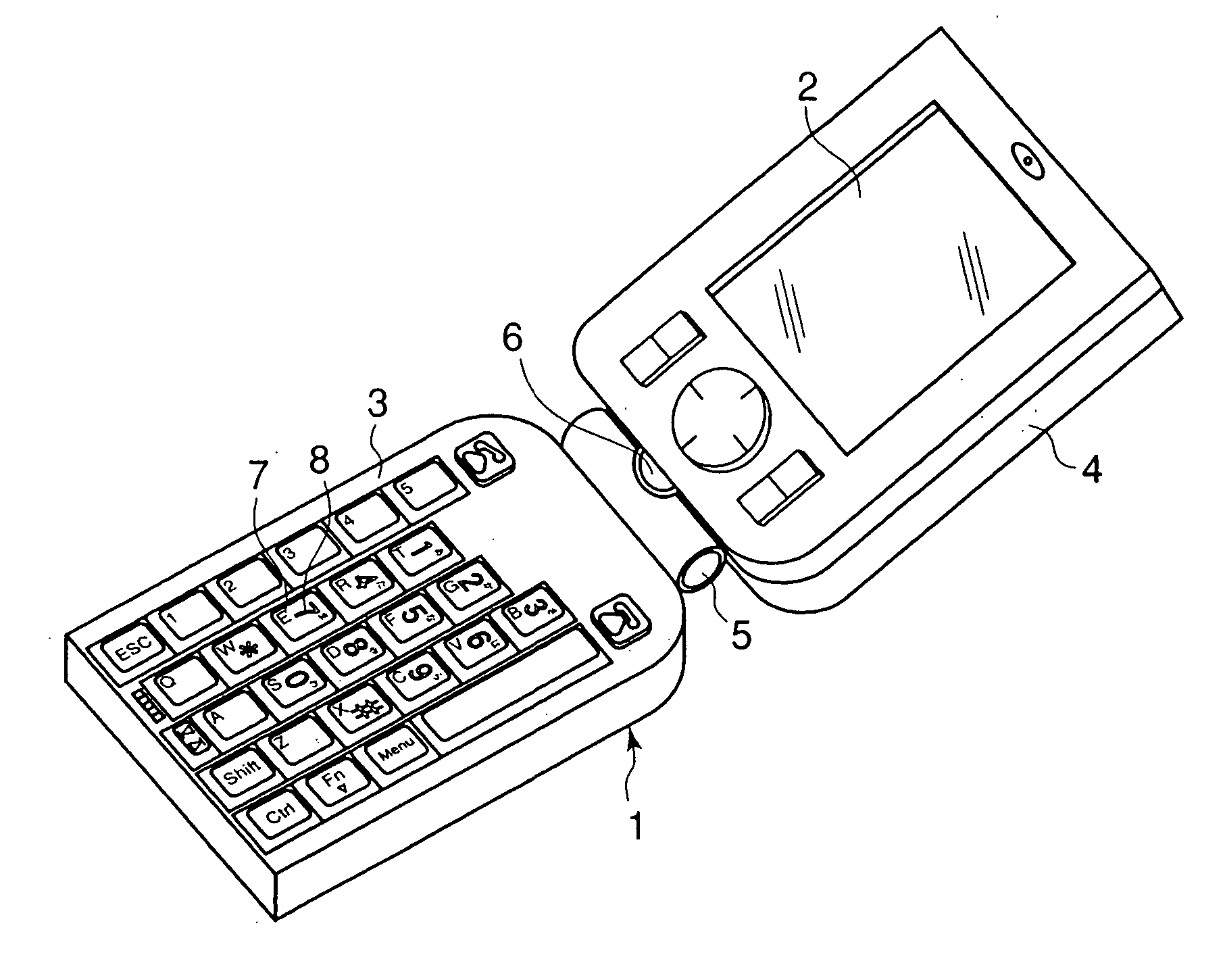
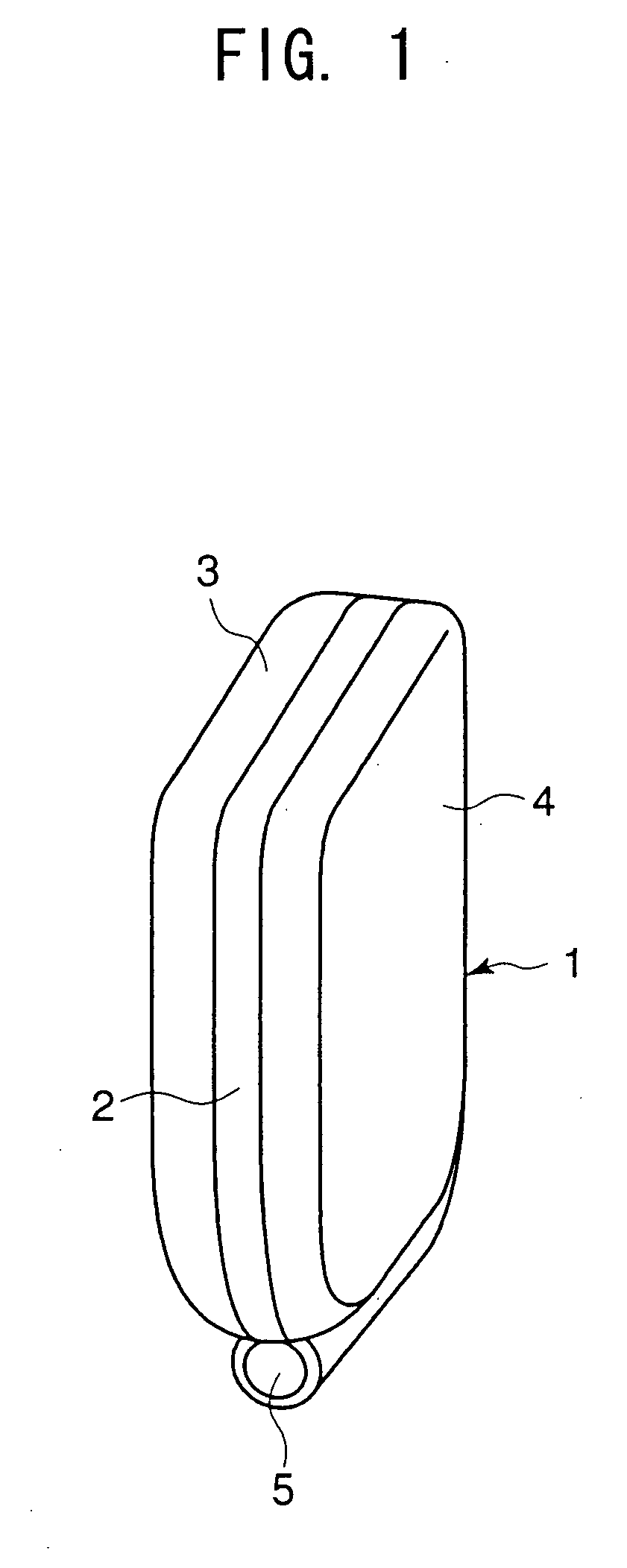
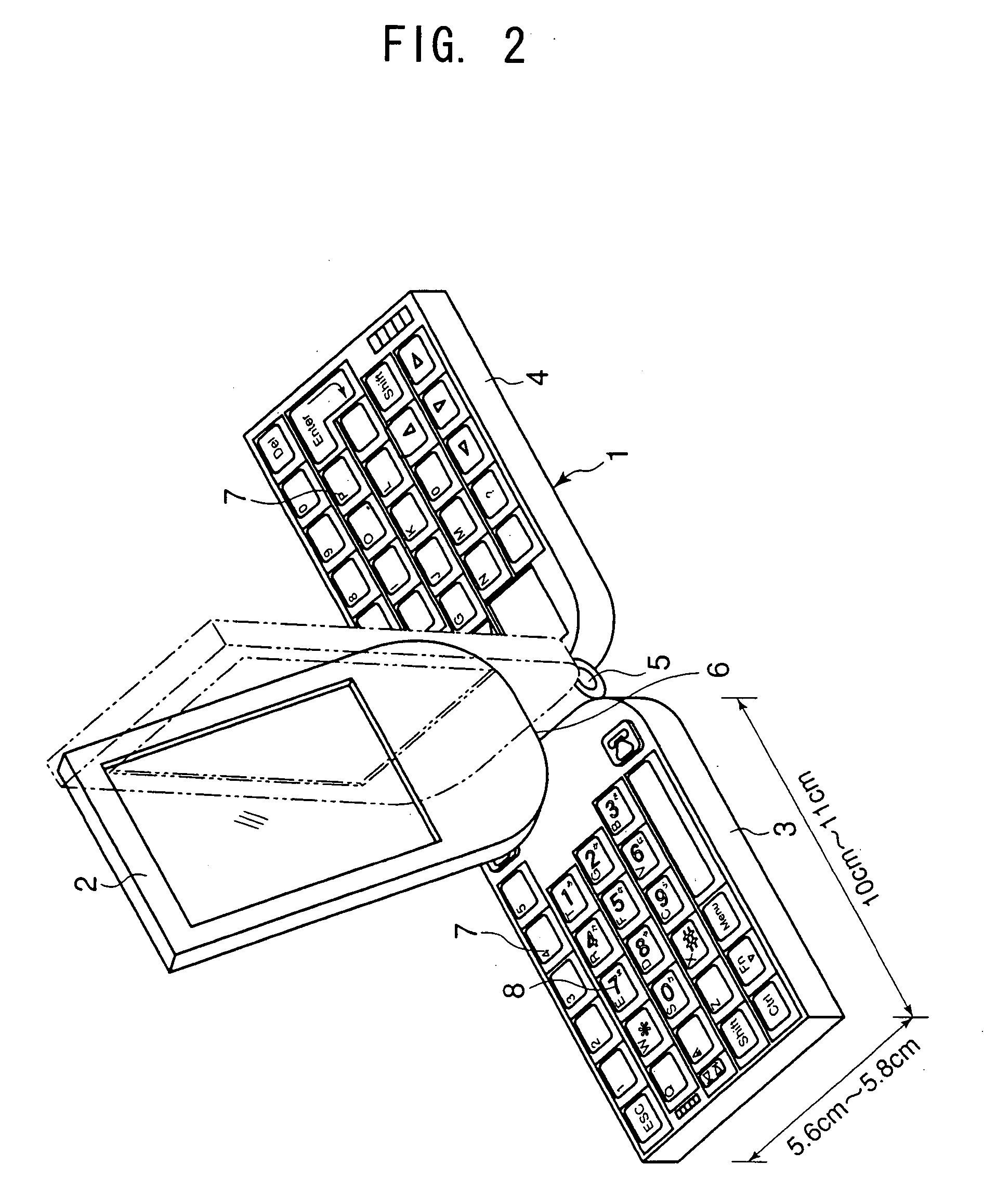
The invention aims to provide a multifunction personal computer / mobile phone capable of being used both as a mobile phone and as a mobile personal computer, to improve input operability when used as a mobile phone as well as a personal computer, and to retain a compact form when it is not used. A multifunction personal computer / mobile phone is so configured that a left keyboard, a display and a right keyboard are mounted on a hinge so that they are folded and unfolded freely, wherein on the left and right keyboards, key indications for digits, characters, symbols or the like for personal computer use are arranged, and on either of the keyboards, key indications for digits, characters, symbols or the like for mobile phone use are arranged so that the hinge is at the far end from a user, wherein the display is formed rotatably with respect to the keyboard, and the left and right keyboards are spread to a position where the surfaces of the keyboards are horizontal.
Owner:UME INSURANCE
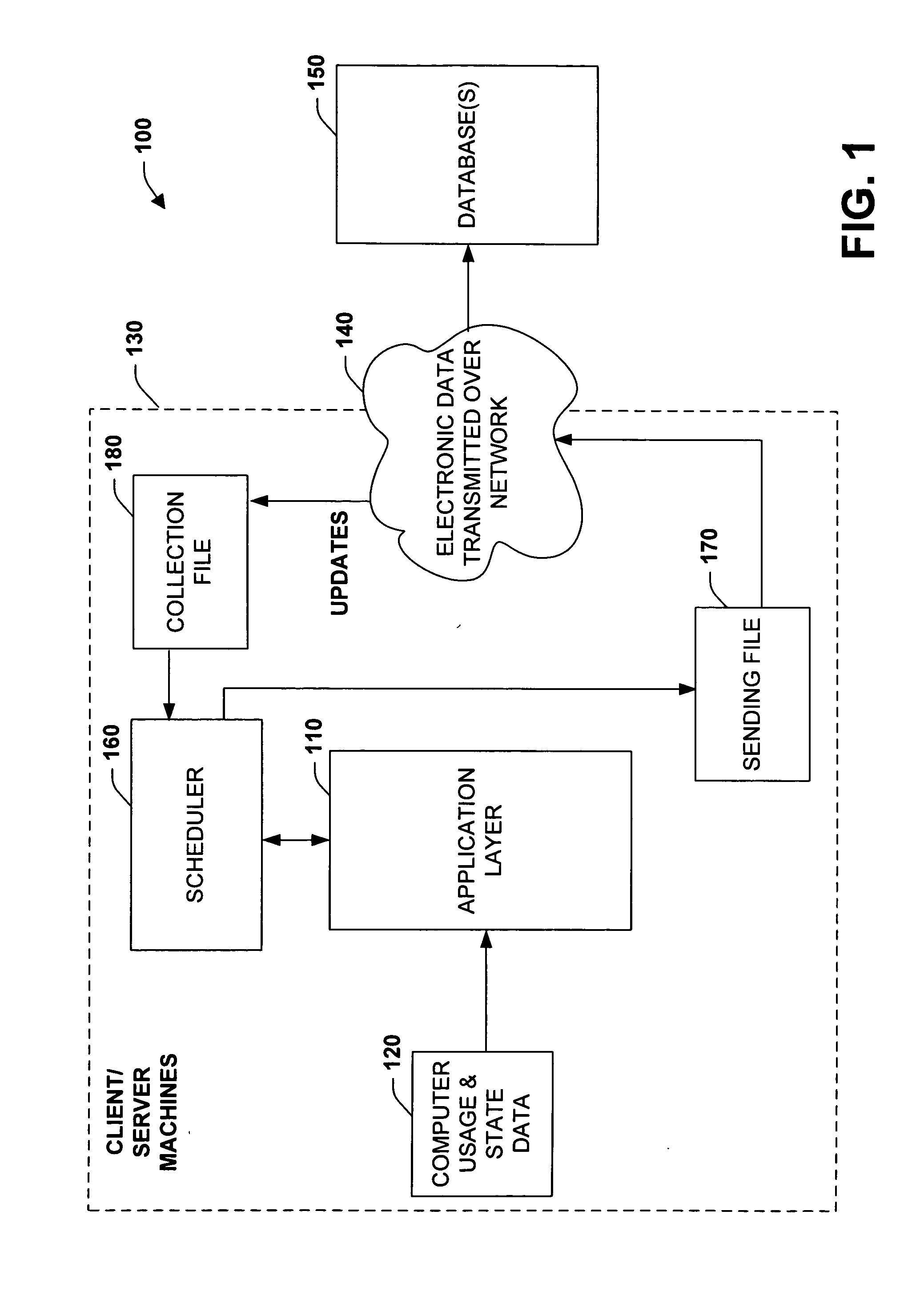
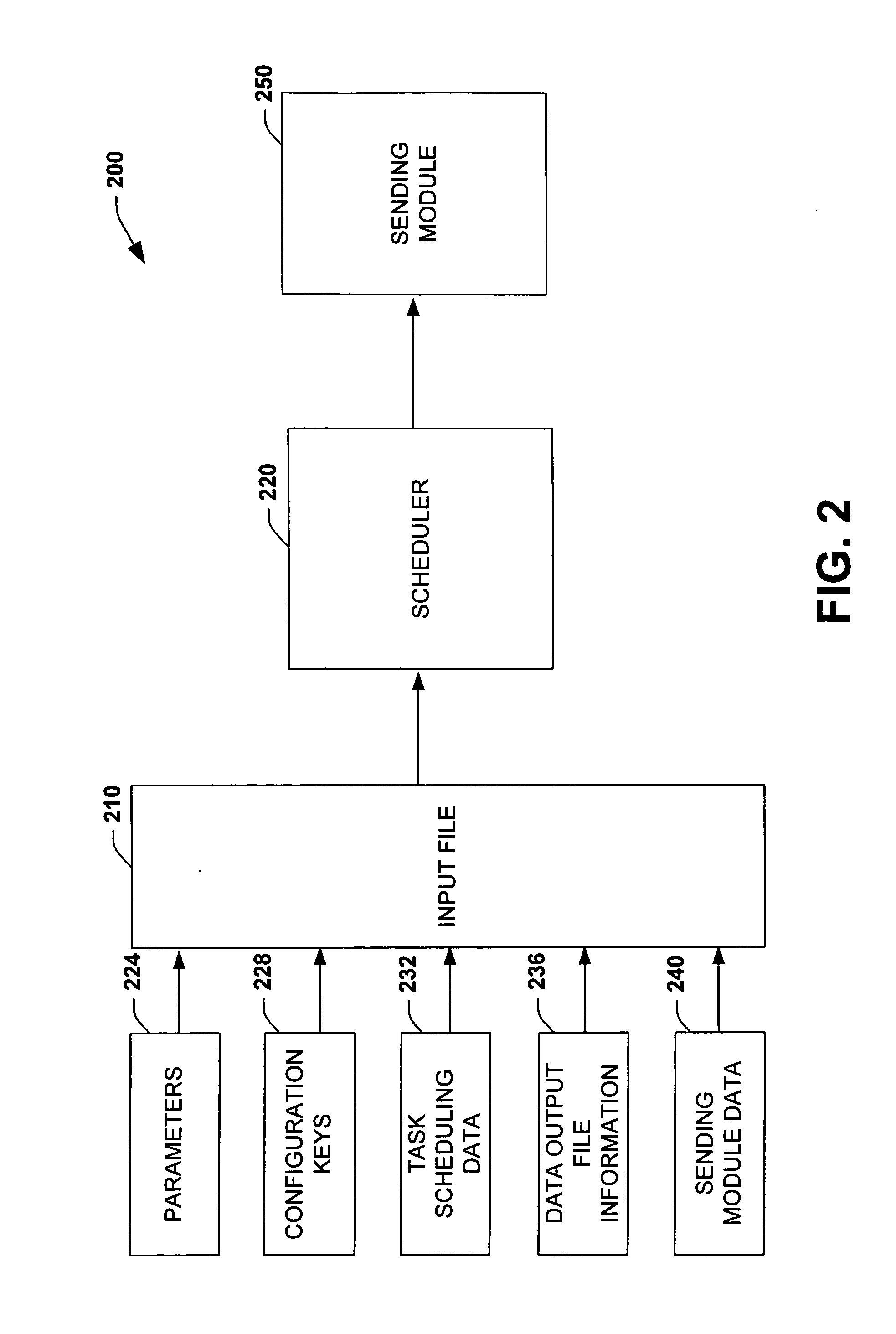
Systems and methods for collecting, representing, transmitting, and interpreting usage and state data for software
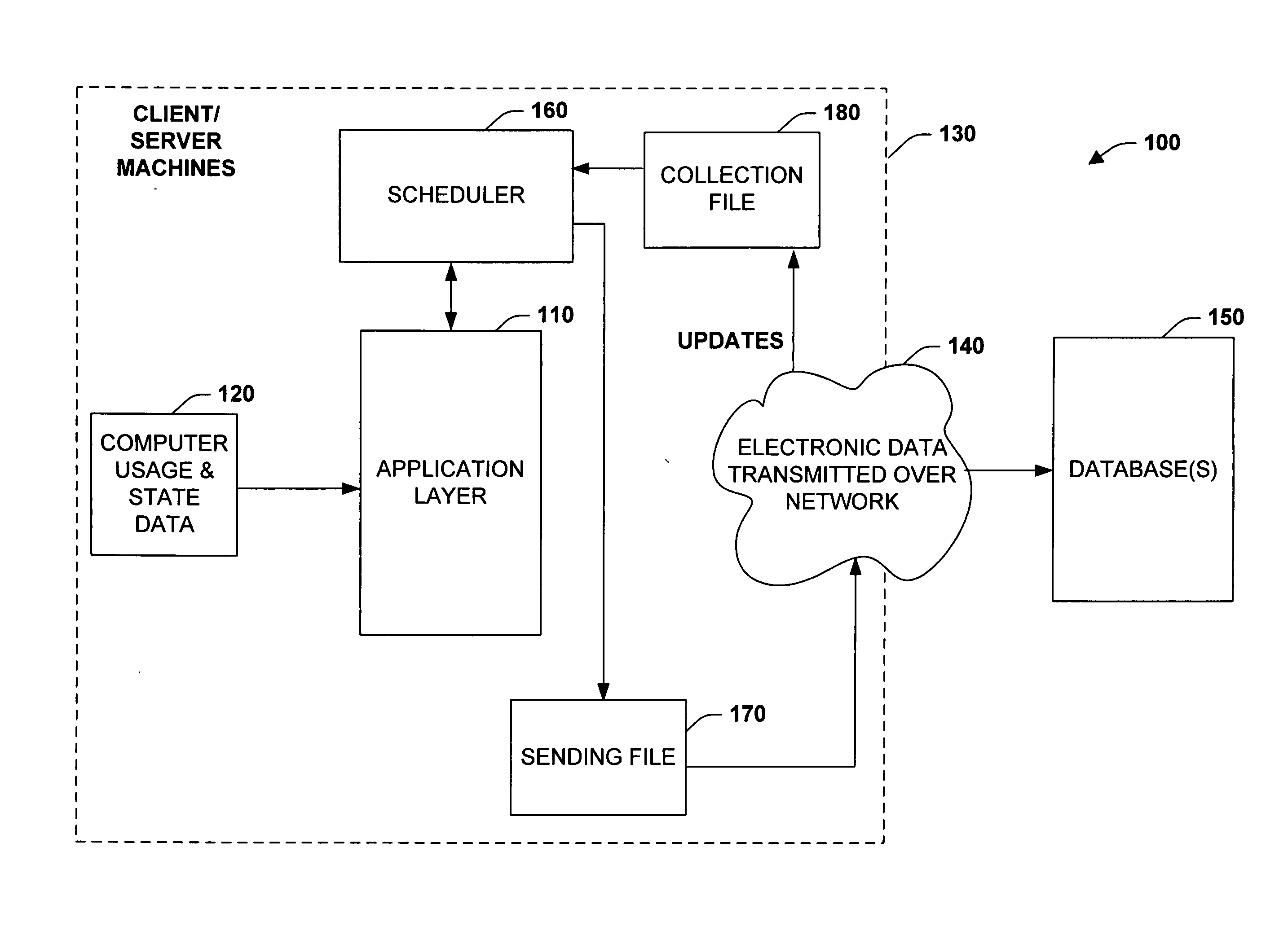
InactiveUS20060004767A1Increased data gathering scalabilityImprove rendering capabilitiesError detection/correctionSpecial data processing applicationsOperational systemComputer usage
The present invention provides systems and methods for automatically gathering computer data from a plurality of networked computer systems. In one aspect, a system is provided for automatically generating computer usage and state data. The system includes an application layer associated with an operating system to gather data from one or more computer components, wherein a collection file specifies the data to gather. The collection file includes query information for directing the application layer with respect to what type of information to gather from various components or modules in the computer system. An automated task scheduler operates with the collection file to transmit gathered data to a centralized collection agency for further analysis.
Owner:MICROSOFT TECH LICENSING LLC
Multi-band antenna and notebook computer with built-in multi-band antenna
InactiveUS7072690B2Facilitate communicationAvoid damageAntenna arraysAntenna supports/mountingsMulti bandFit frequency
A multi-band antenna and a notebook computer with a built-in multi-band antenna are disclosed. Since the multi-band antenna is installed at the inner side of a upper and a lower case, it is much favored for a radio communication when a computer is in use by standing up a display device. The multi-band antenna includes at least two transmitting and receiving parts formed with different lengths to fit frequency bands, so that a remote communication of at least two or more bands can be made. The multi-band antenna is positioned between liquid crystal and a side wall of the lower case, and a grounding unit is installed to contact a liquid crystal frame. That is, since the grounding unit is grounded to the liquid crystal frame and the bracket, substantially, the liquid crystal frame and the bracket are wholly grounded to ensure a stable radio frequency communication.
Owner:LG ELECTRONICS INC
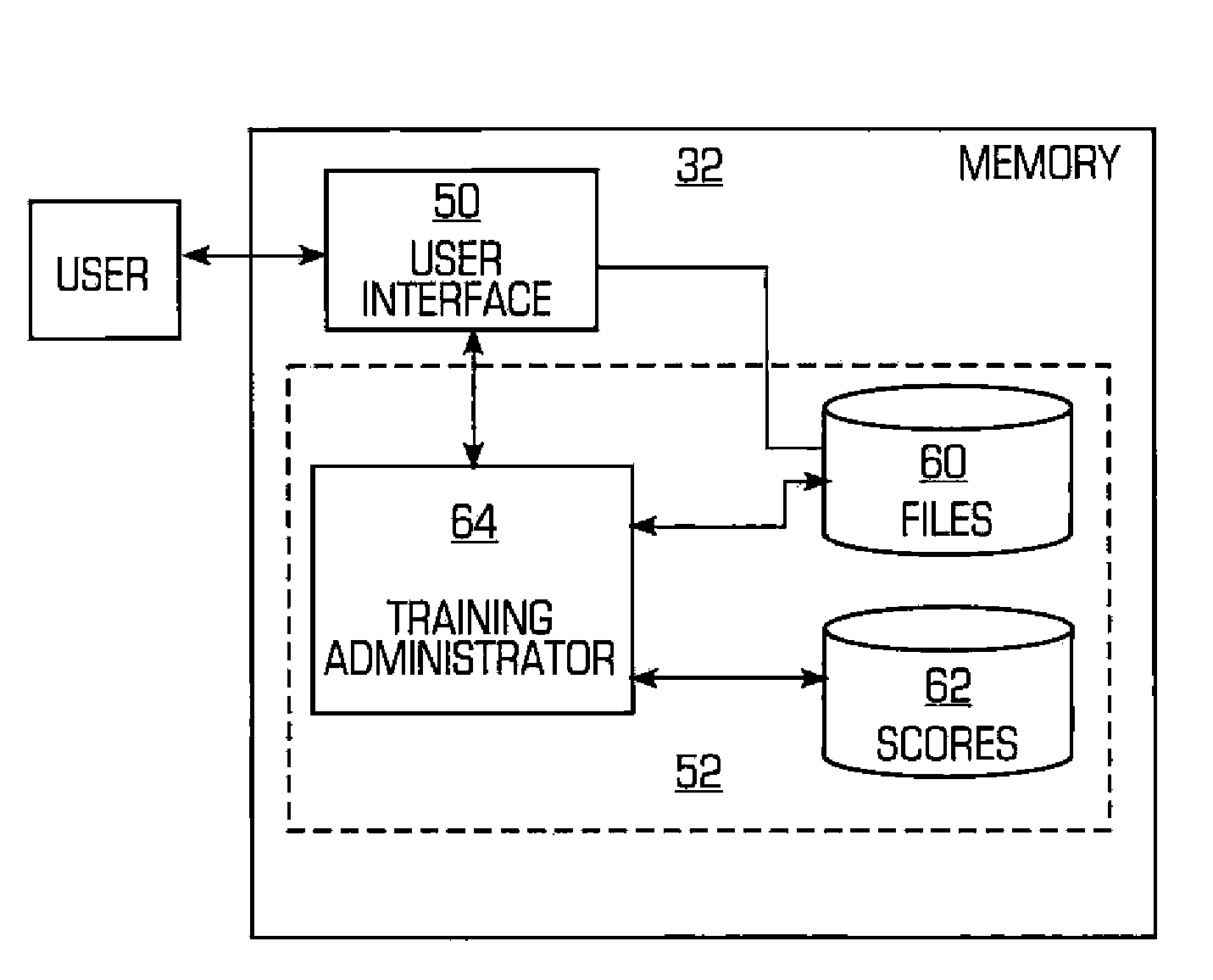
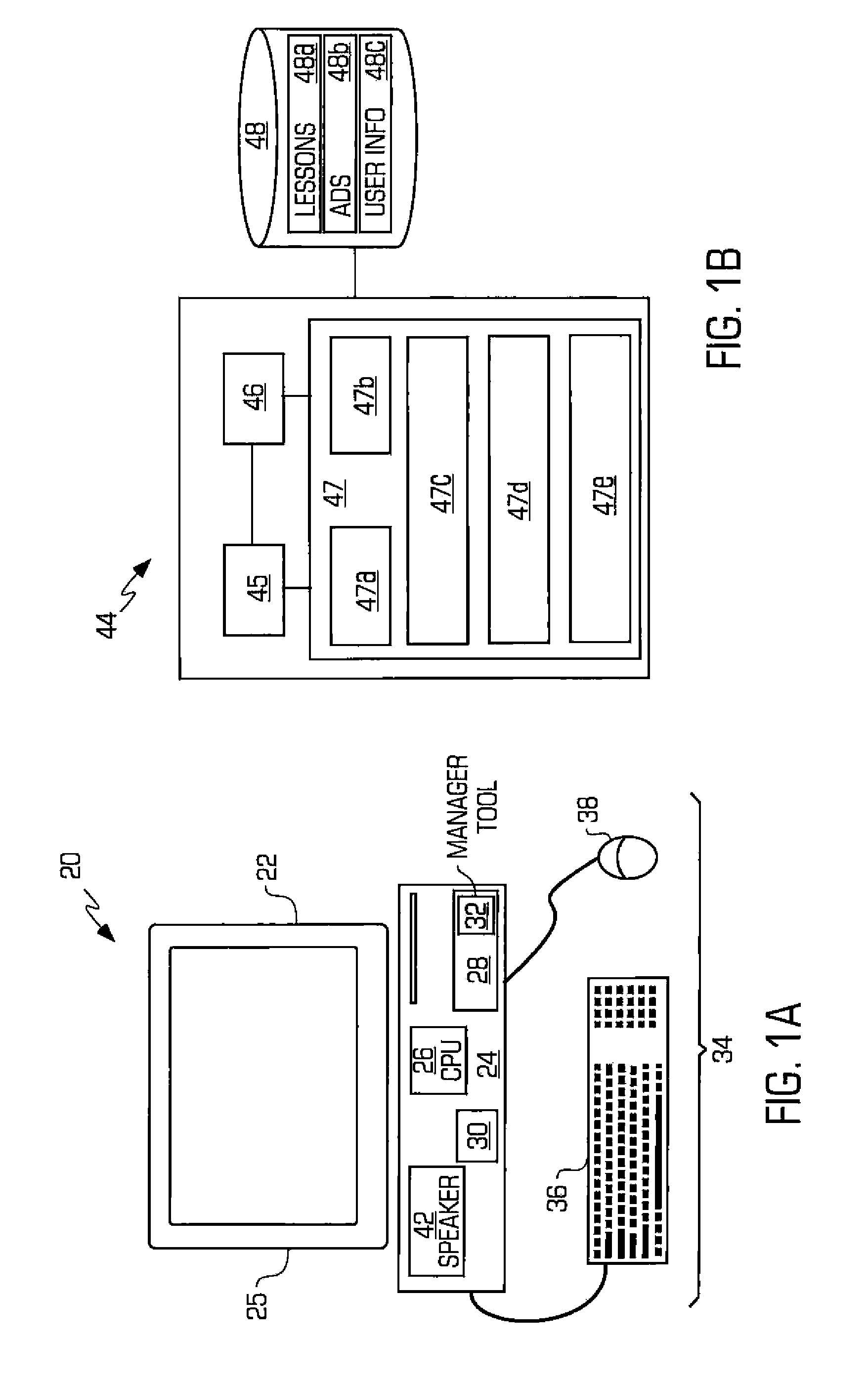
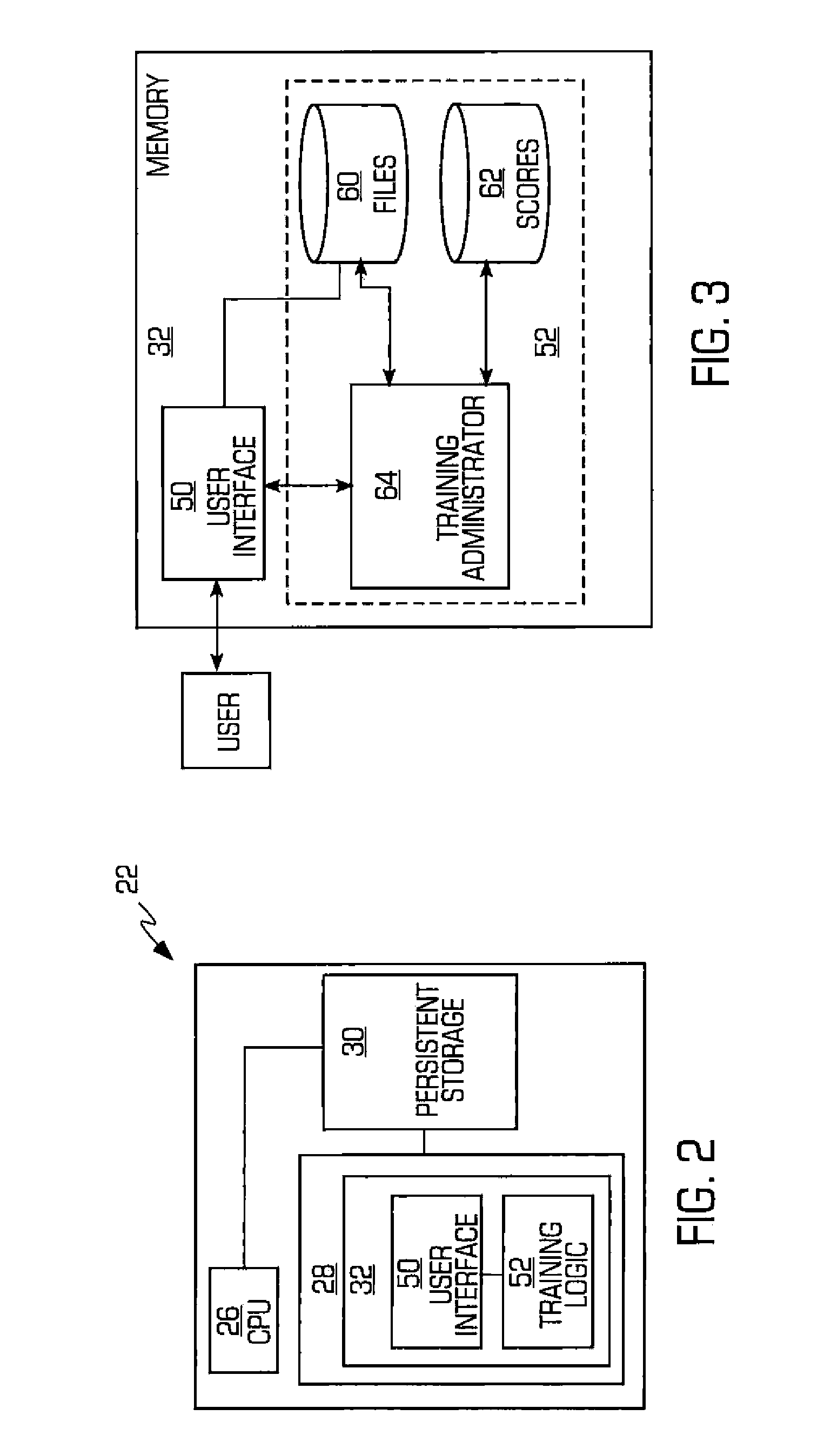
Computer usage management system and method
InactiveUS20080155538A1Reduce usageError detection/correctionMultiprogramming arrangementsComputer usageComputerized system
A manager tool system and method are provided wherein the use of the computer system by a user is controlled and monitored. The system also requires the user to engage in a learning process during the use of the computer system in order to be able to continue using the computer system. In a preferred embodiment, the learning process may be a series of questions that must be correctly answered before any further use of the computer system is permitted.
Owner:PAPPAS MATTHEW S
System and method of monitoring computer usage
InactiveUS20090193360A1Determine efficiencyError detection/correctionDigital computer detailsWeb siteComputer usage
The present invention provides a system and method of monitoring a person's use of a computer. The method includes the steps of providing a website for monitoring the person's use of the computer, identifying an application or site the person is using, detecting when the person begins use of the application or site, and detecting when the person stops use of the application or site. The difference between when the person stops use of the application or the site and when the person begins use of the application or the site is used to determine an amount of time the person used the application or the site.
Owner:WI TECH DE C V
Method and apparatus for frequency independent processor utilization recording register in a simultaneously multi-threaded processor
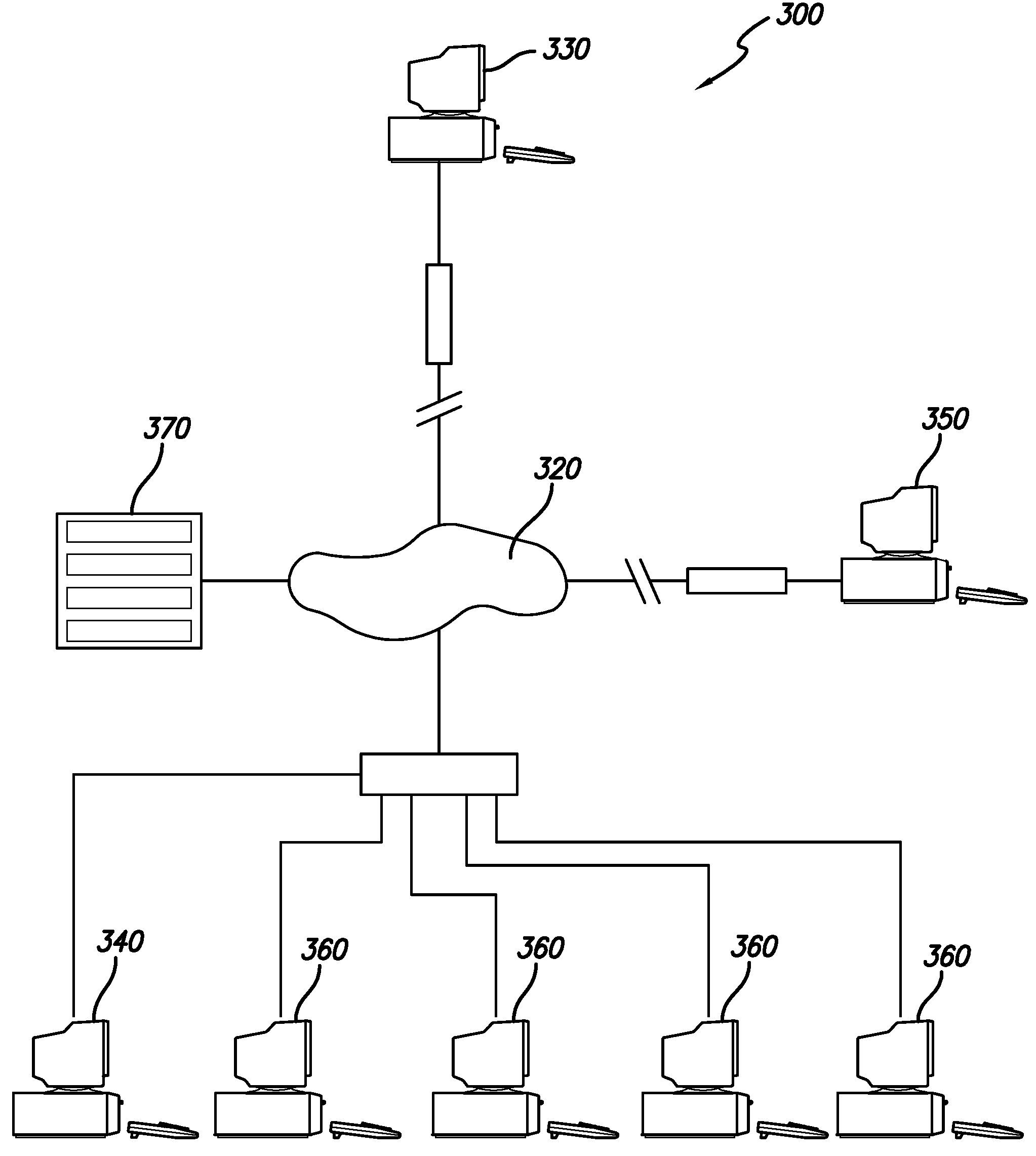
InactiveUS20080086395A1Accurate chargesComplete banking machinesTelephonic communicationComputer resourcesComputer usage
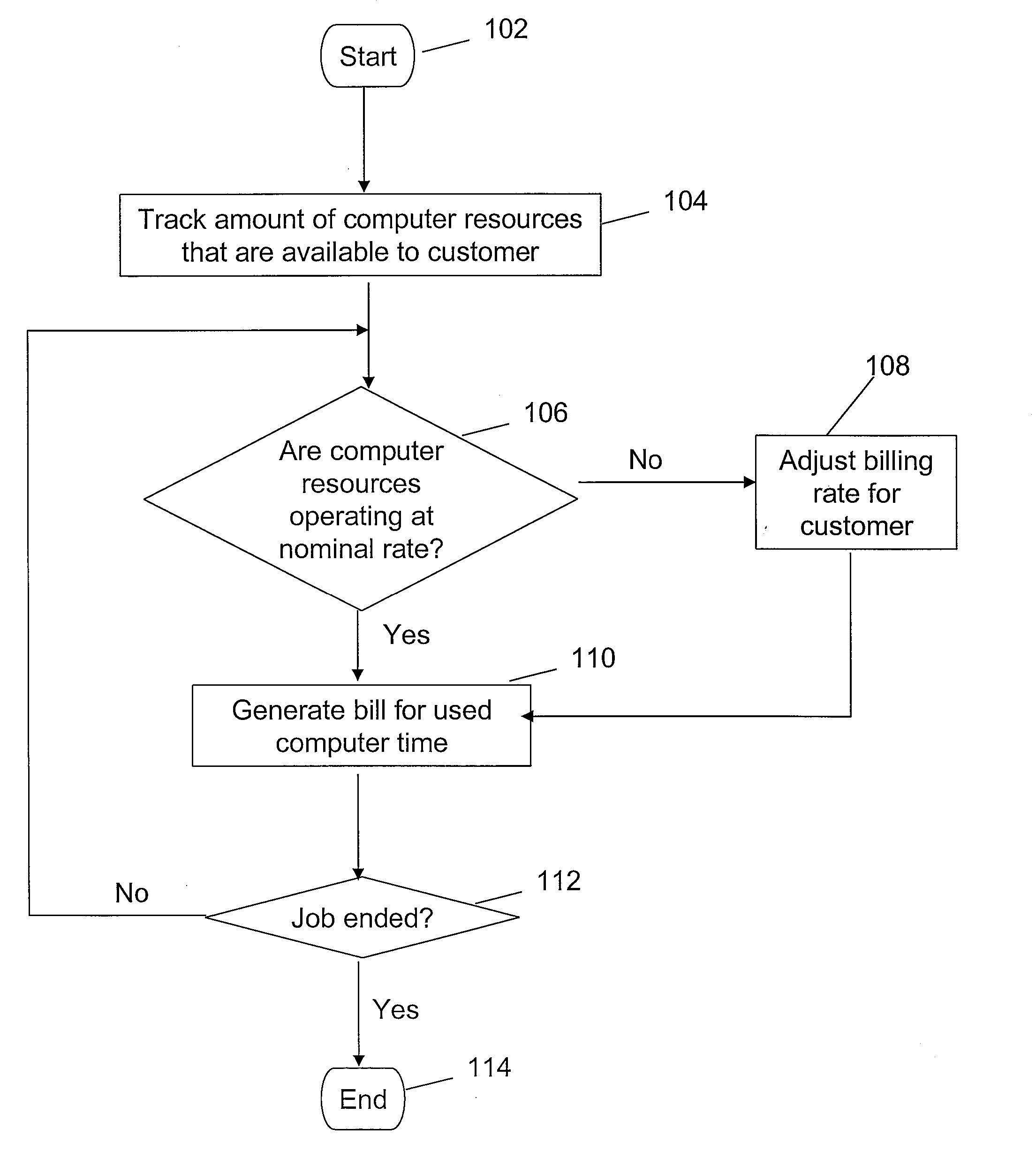
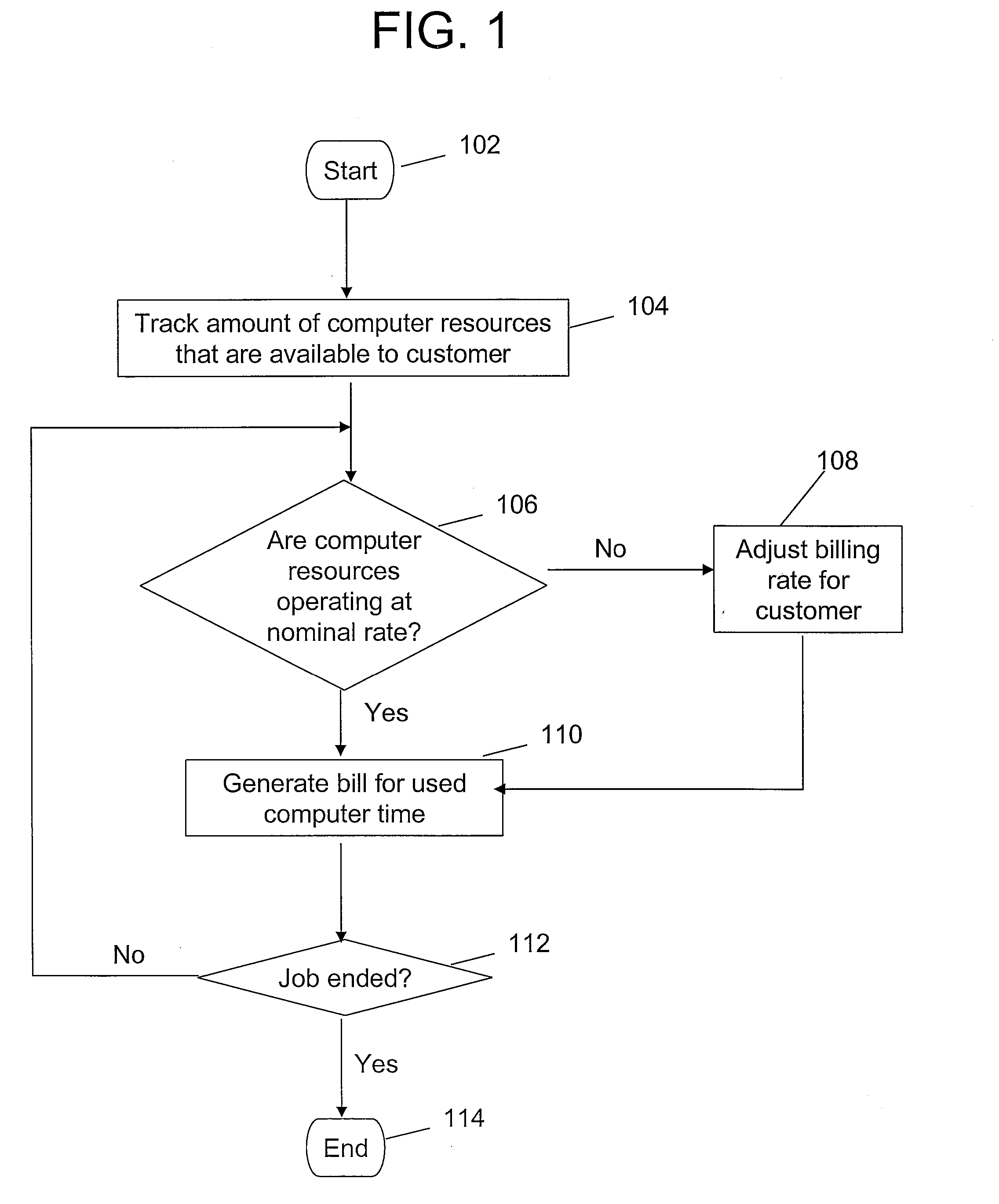
The present invention thus provides for a method, system, and computer-usable medium that afford an equitably charging of a customer for computer usage time. In a preferred embodiment, the method includes the steps of: tracking an amount of computer resources in a Simultaneous Multithreading (SMT) computer that are available to a customer for a specified period of time; determining if the computer resources in the SMT computer are operating at a nominal rate; and in response to determining that the computer resources are operating at a non-nominal rate, adjusting a billing charge to the customer, wherein the billing charge reflects that the customer has available computer resources, in the SMT computer, that are not operating at the nominal rate during the specified period of time.
Owner:IBM CORP
Supervised Access Computer Network Router
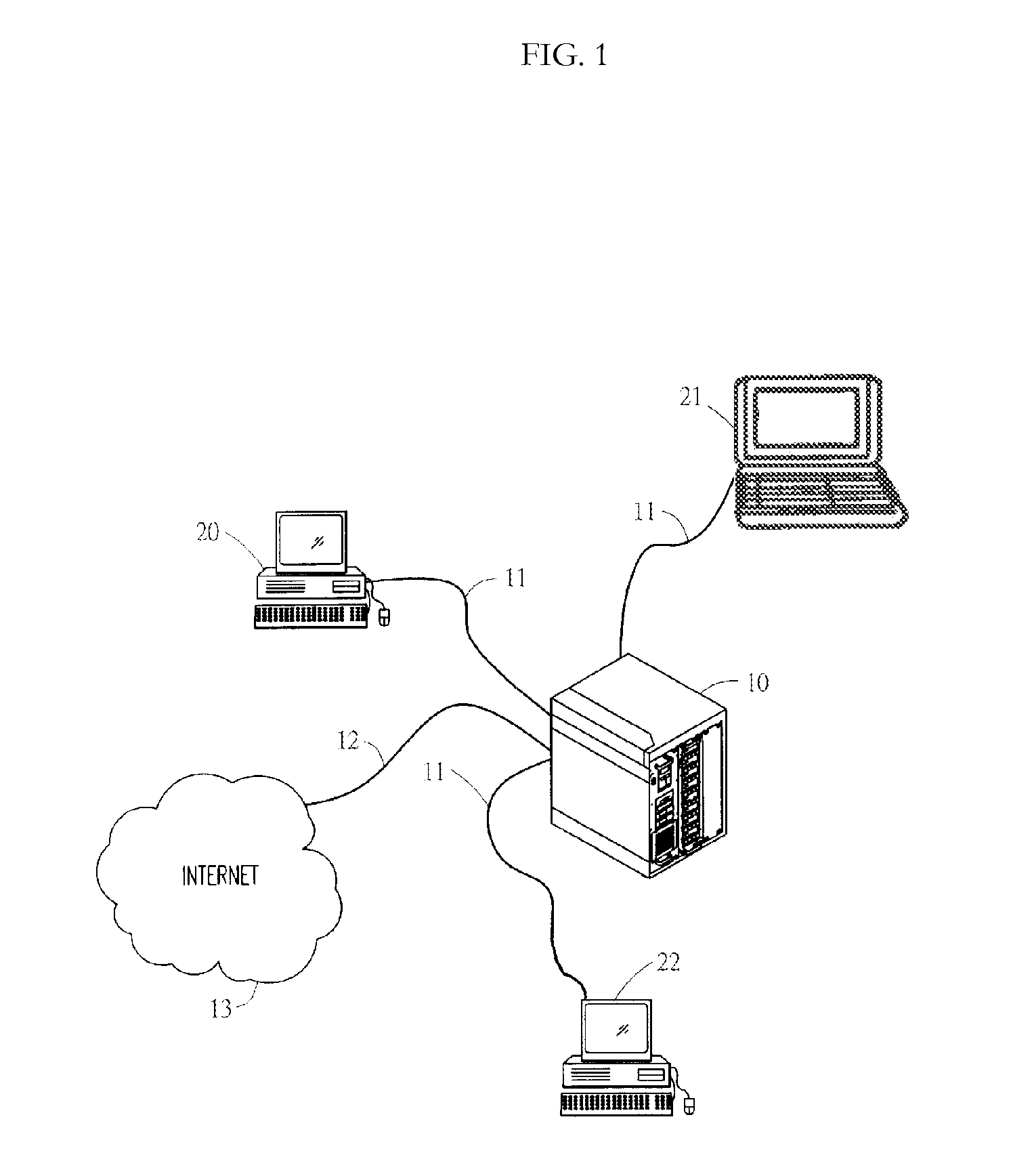
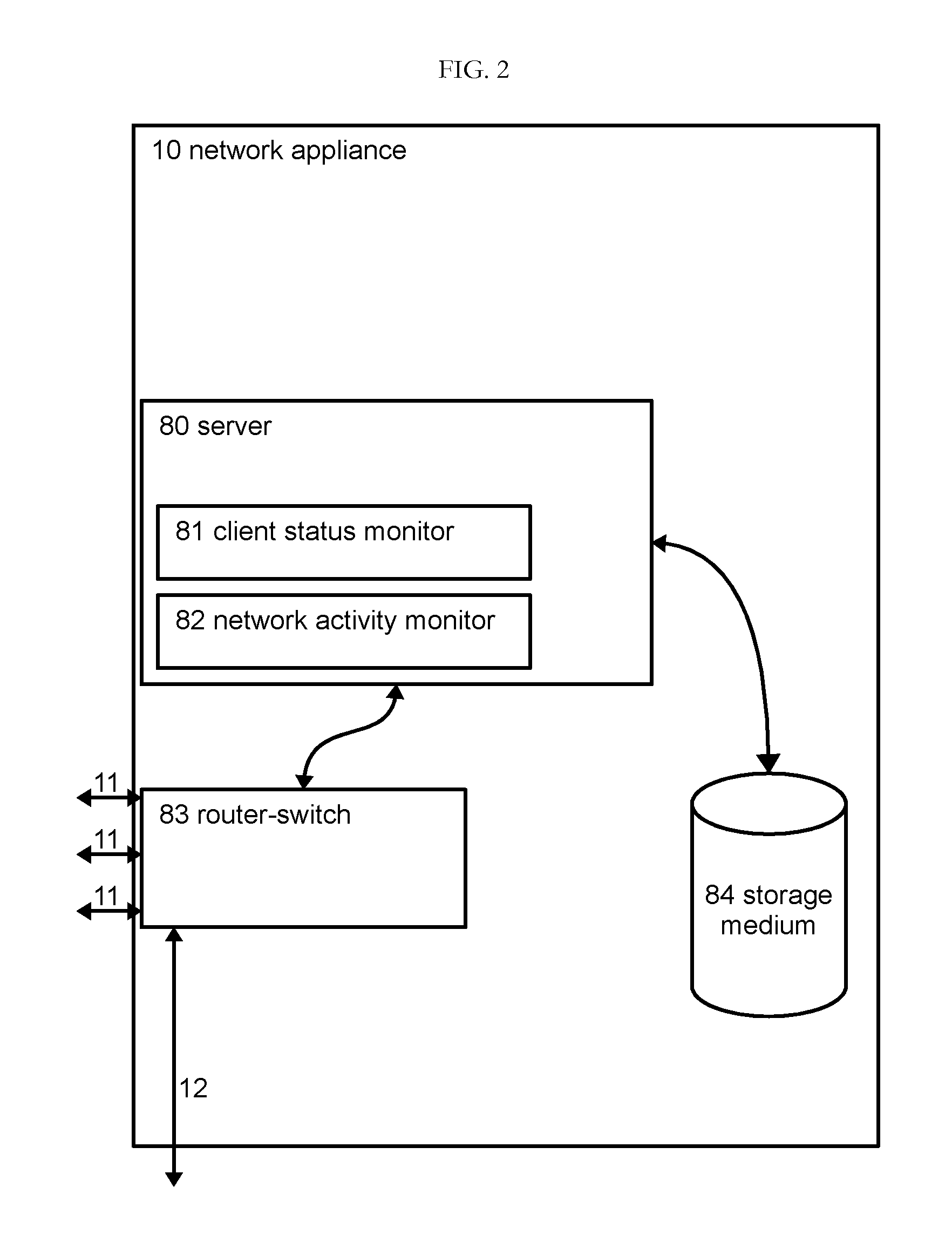
InactiveUS20100325259A1Good effectError detection/correctionMultiple digital computer combinationsComputer usageNetwork communication
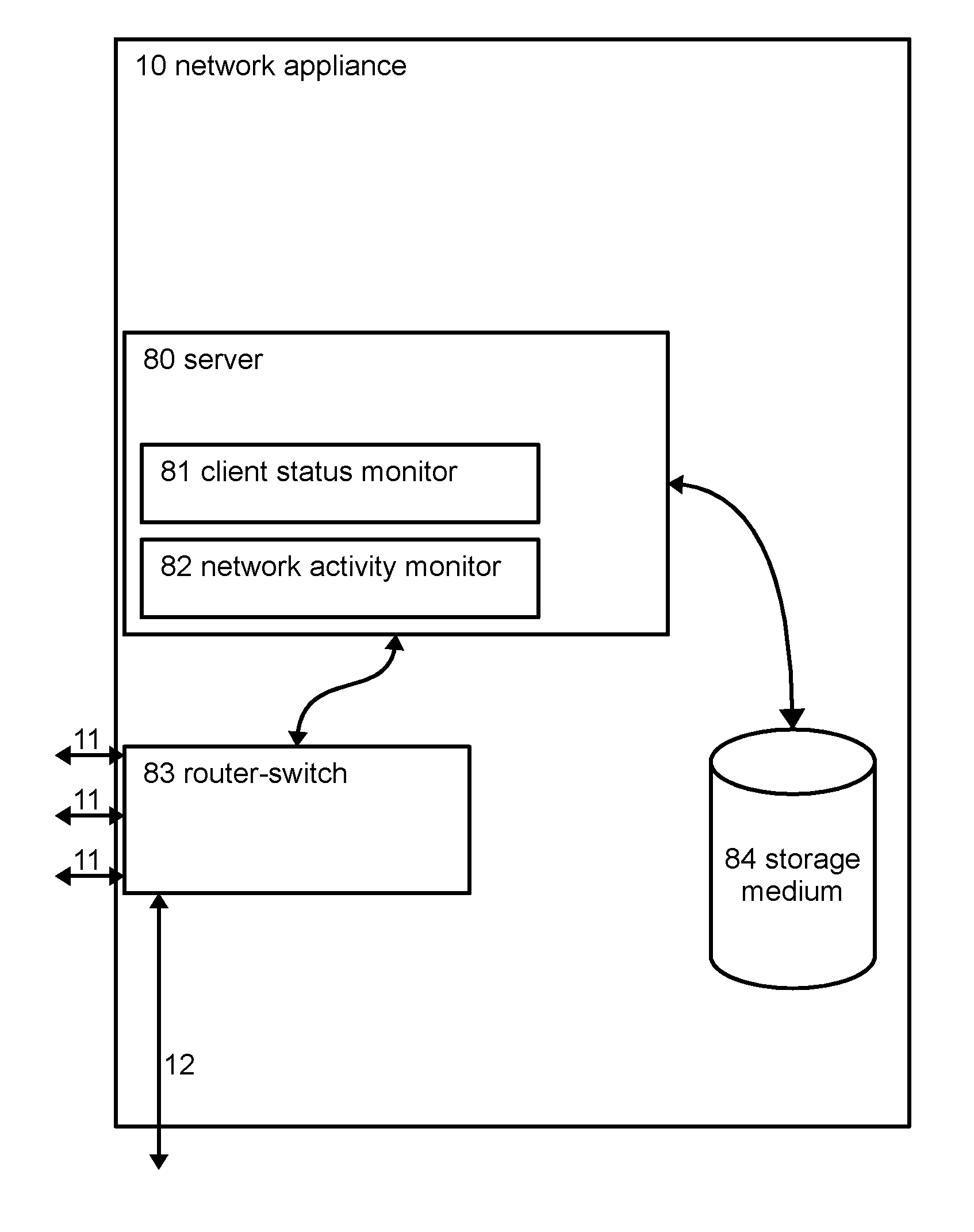
A system for monitoring and regulating computer usage on a local network is disclosed. Computers on a network are configured with a client activity monitoring module that collects activity information including screen captures, keyboard activity, and / or information relating to network communications and sends the collected activity information to a network activity monitor for storage and later retrieval. Each computer on the local network periodically verifies that its client activity monitor module is operable. If a computer fails to send such verification, the system restricts network access by that computer, thus enforcing compliance with the activity monitoring system. The system further provides means for automatically displaying the collected activity information, including through screen savers, automatically changing desktop background images, and pop-up or sidebar windows. The system thus enables review of computer activities for appropriateness by both supervisors or parents as well as by peer users without requiring the reviewer to take affirmative steps to retrieve the activity information.
Owner:VOLONICS CORP
Providing method and system for plug-in extension in browser
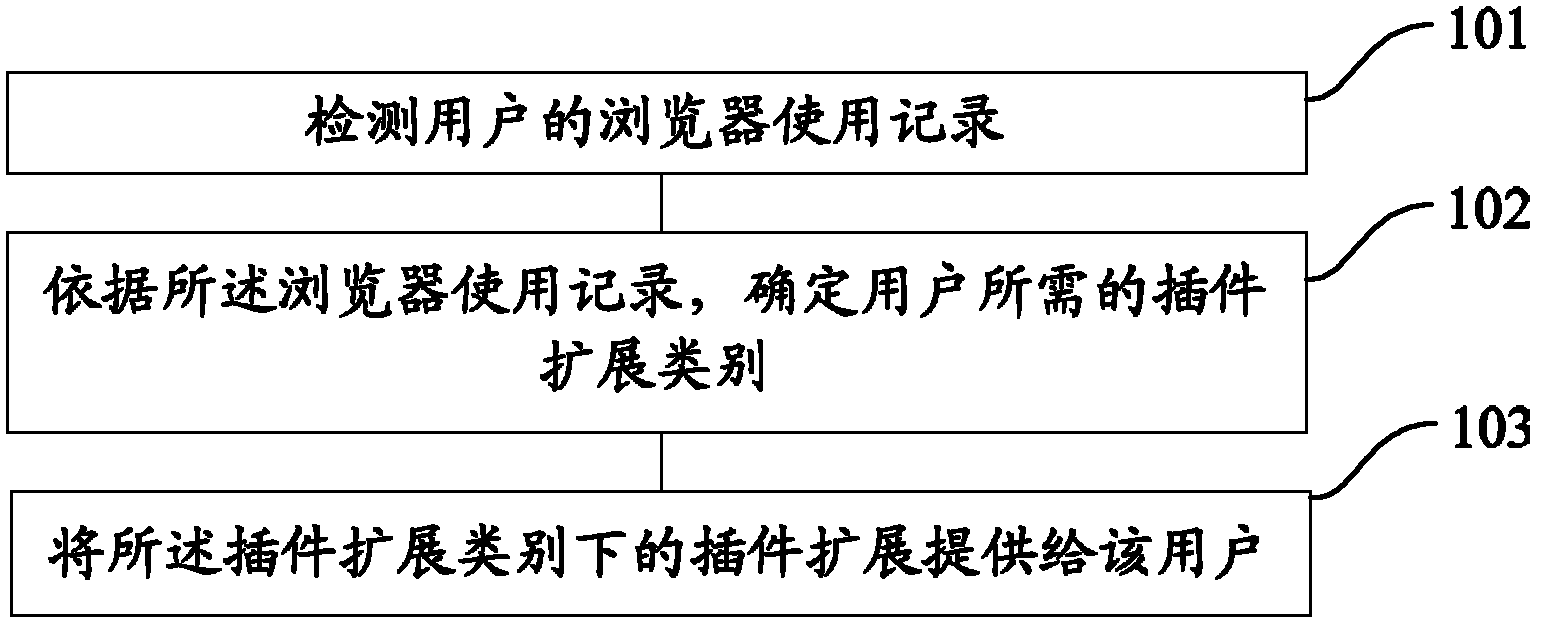
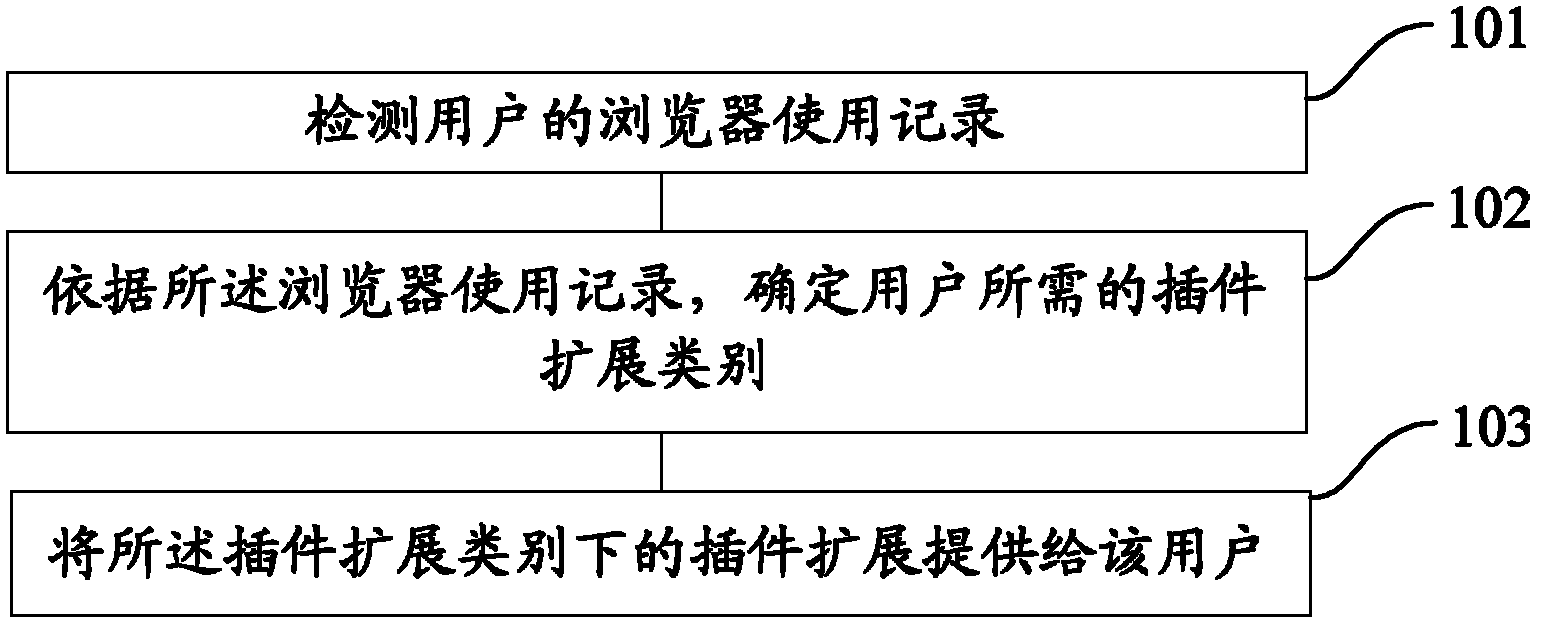
ActiveCN102222091ARealize individual needsAvoid bloatingProgram loading/initiatingSpecial data processing applicationsUser needsComputer usage
The invention provides a providing method and system for a plug-in extension in a browser. The providing method disclosed by the invention comprises such specific procedures as follows: detecting the browser usage record of a user; determining the plug-in extension type that the user needs by means of the browser usage record; providing the user with a plug-in extension belonging to the plug-in extension type. The invention is capable of providing a plug-in extension applicable to the user without asking the user for a high computer usage technique and complex operation.
Owner:BEIJING QIHOO TECH CO LTD
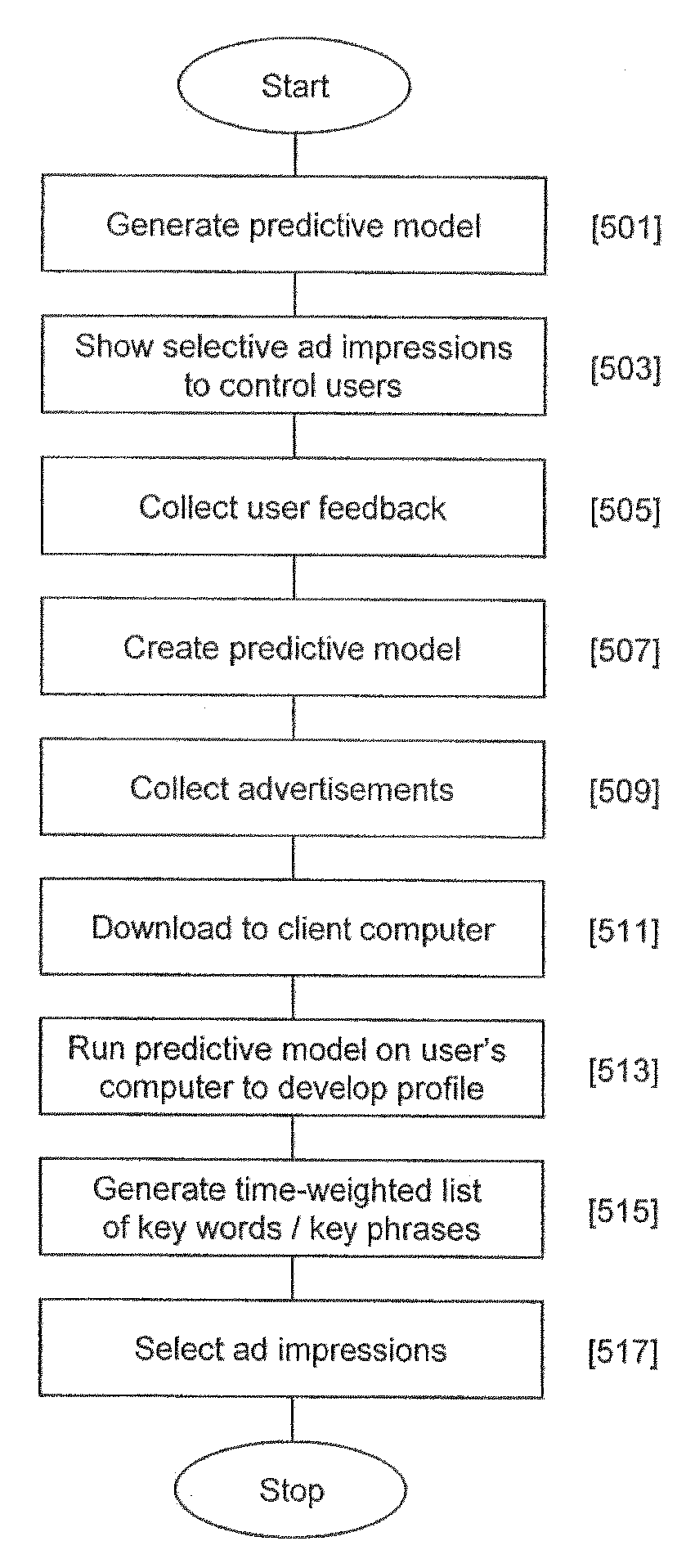
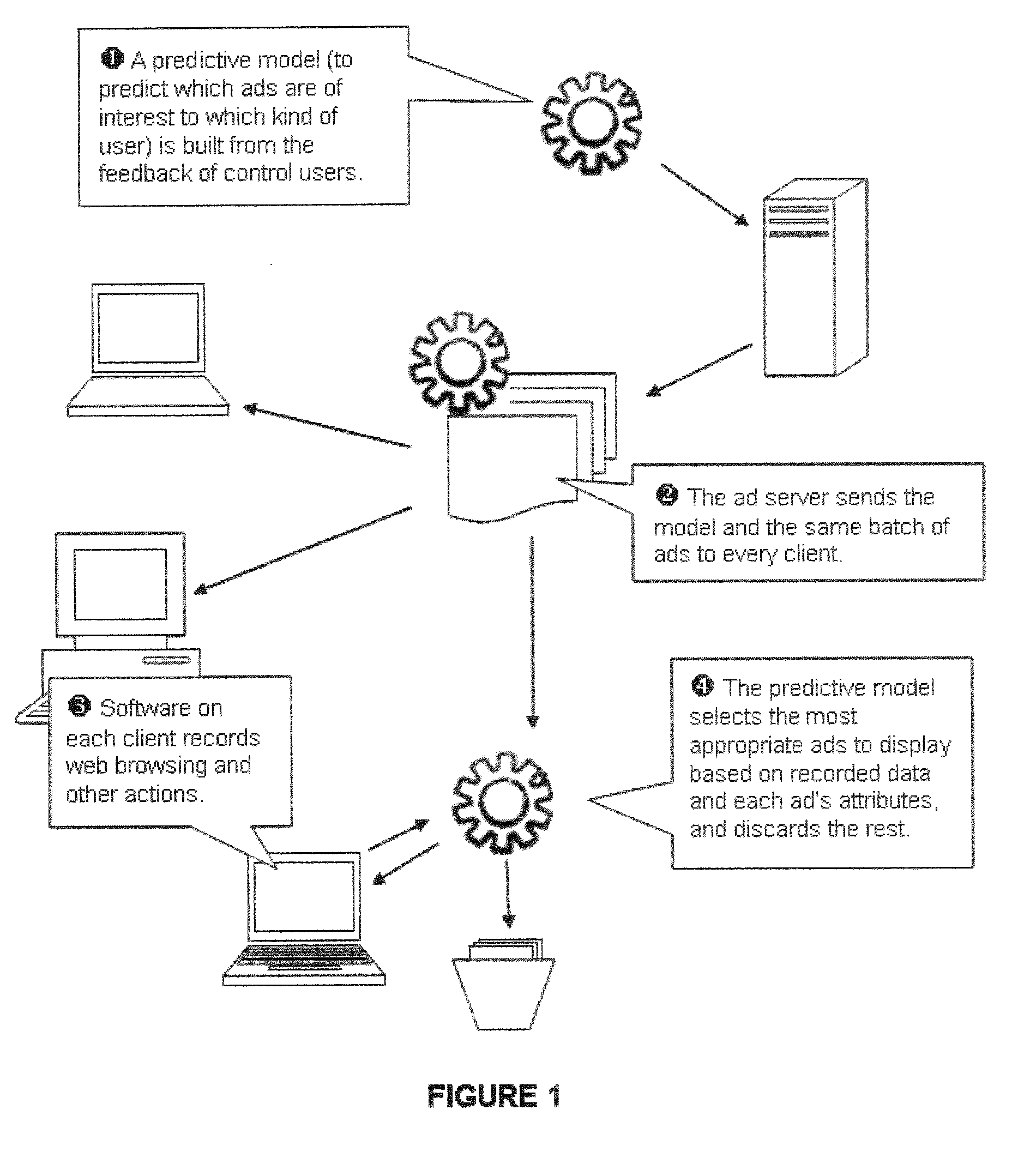
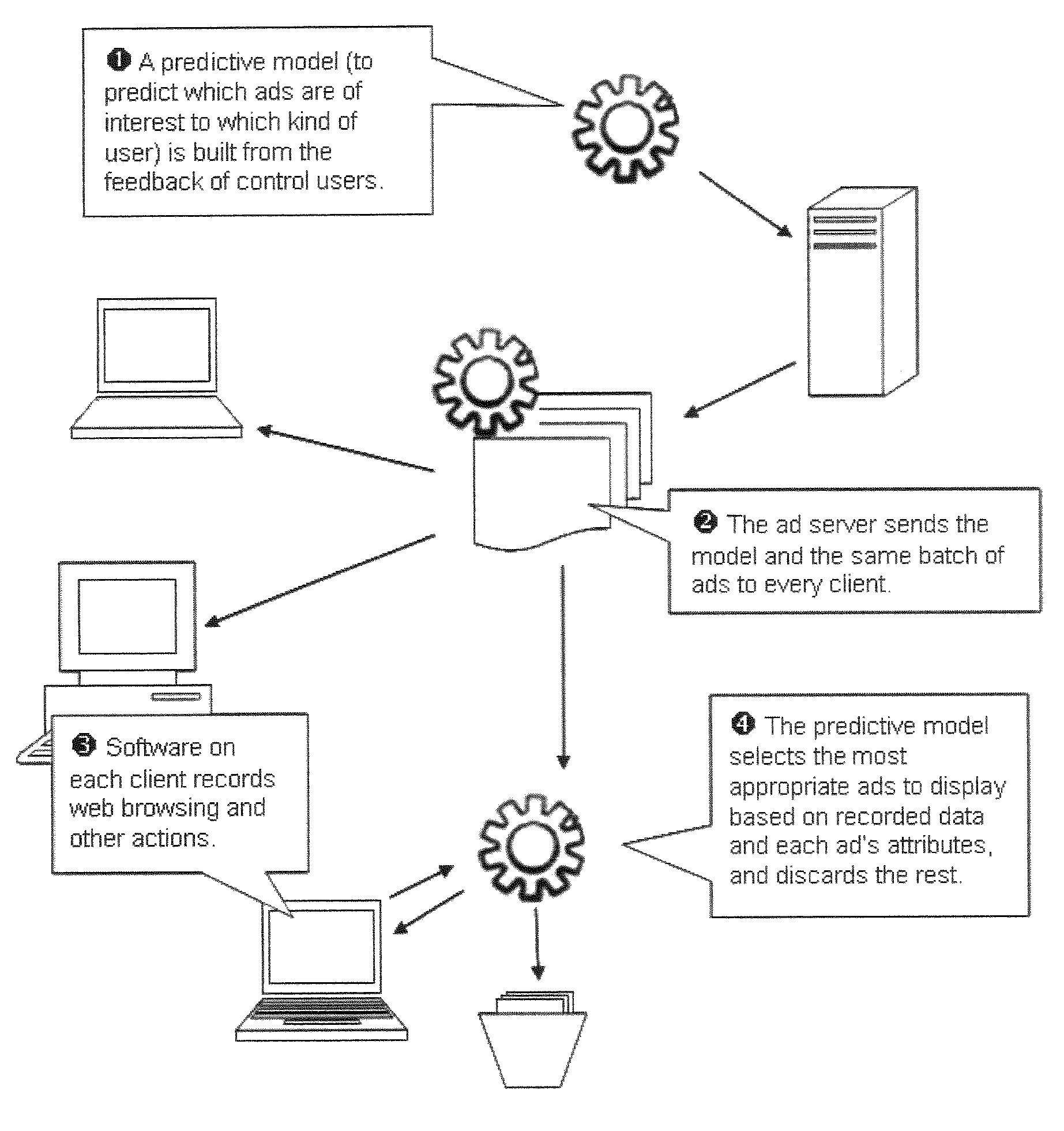
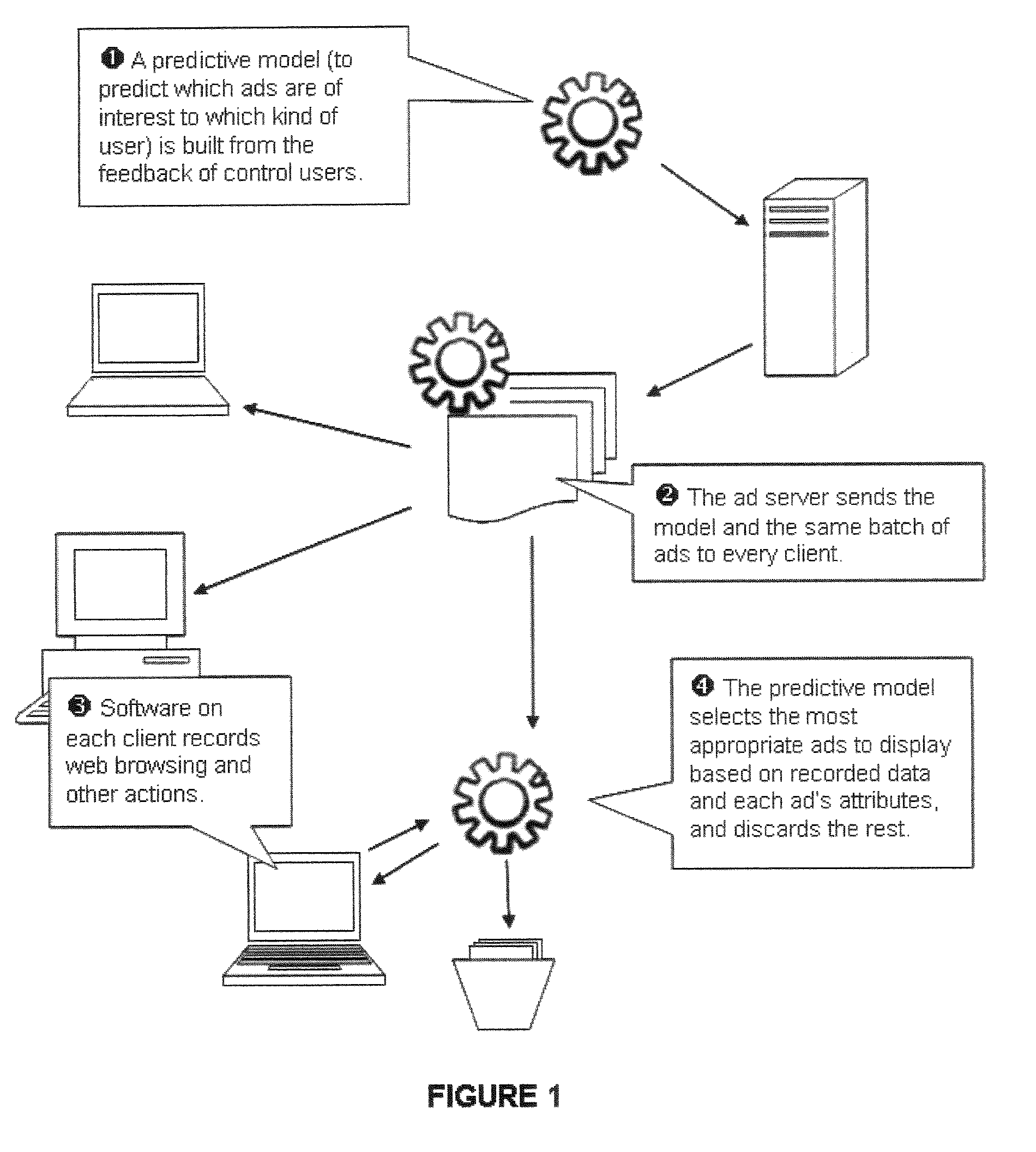
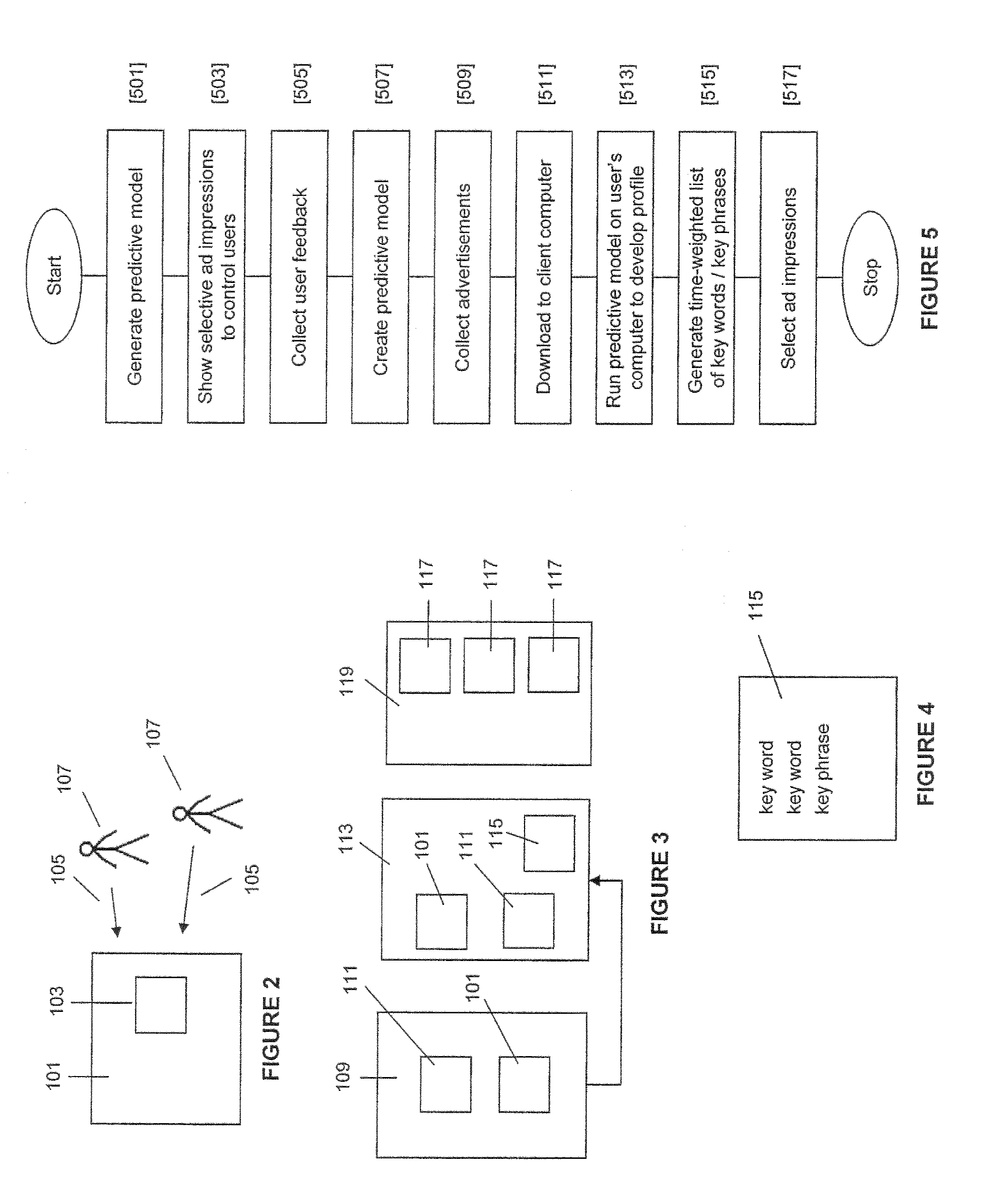
Method and System for Targeted Advertising
A method and system of displaying advertisements may include generating a predictive model to predict a type of user, collecting advertisements based upon the type of user, placing the predictive model and collected advertisements on a computer of a user, executing the predictive model on the computer of the user to determine the type of user, and selecting an advertisement to be displayed to the user based upon the execution of the predictive model. The predictive model may be generated based upon feedback from the control users, and the predictive model may be generated based upon the computer of the control users. The predictive model may be generated based upon Web browsing of the computer of the control users, and the predictive model may be generated based upon computer usage behavior of the control users.
Owner:PDI DEV CO LLC
Supervised access computer network router
InactiveUS8307068B2Good effectError detection/correctionMultiple digital computer combinationsNetwork activityComputer usage
A system for monitoring and regulating computer usage on a local network is disclosed. Computers on a network are configured with a client activity monitoring module that collects activity information including screen captures, keyboard activity, and / or information relating to network communications and sends the collected activity information to a network activity monitor for storage and later retrieval. Each computer on the local network periodically verifies that its client activity monitor module is operable. If a computer fails to send such verification, the system restricts network access by that computer, thus enforcing compliance with the activity monitoring system. The system further provides means for automatically displaying the collected activity information, including through screen savers, automatically changing desktop background images, and pop-up or sidebar windows. The system thus enables review of computer activities for appropriateness by both supervisors or parents as well as by peer users without requiring the reviewer to take affirmative steps to retrieve the activity information.
Owner:VOLONICS CORP
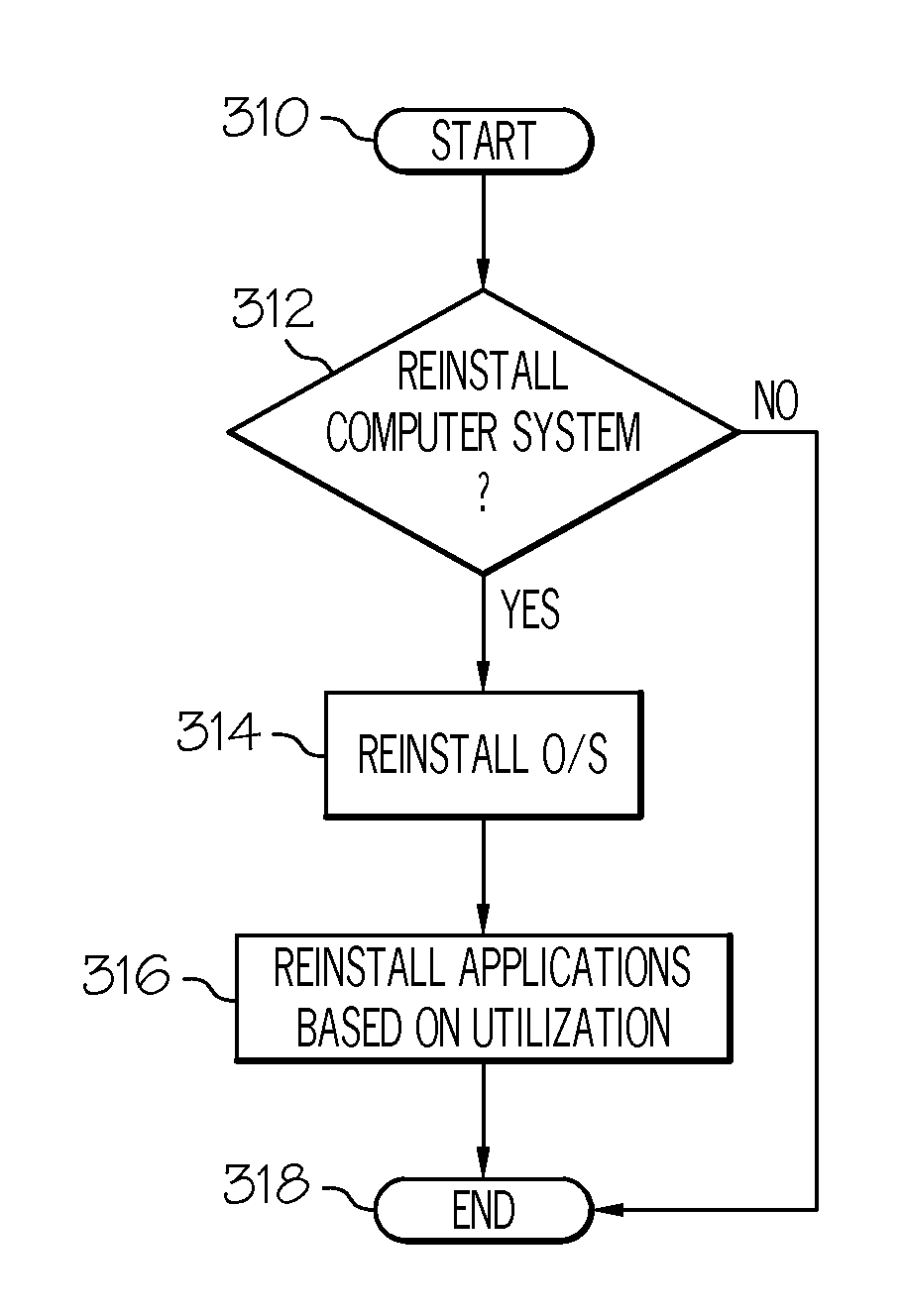
Method of reinstalling a computer based on frequency of application utilization
ActiveUS20090265702A1Efficiently reinstallingError detection/correctionProgram loading/initiatingComputer usersOperational system
A system and method for efficiently reinstalling computer software, which tracks frequency of utilization for each software application loaded onto the computer and reinstalls applications based on frequency of utilization, with the option to reinstall a computer operating system first or to reinstall computer applications along with libraries, so that computer users can resume working as soon as possible instead of waiting many hours for the entire reinstallation image to complete before a computer system reboot allows for continuation of computer usage.
Owner:IBM CORP
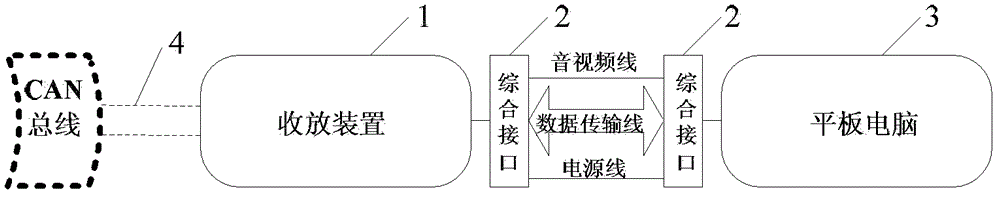
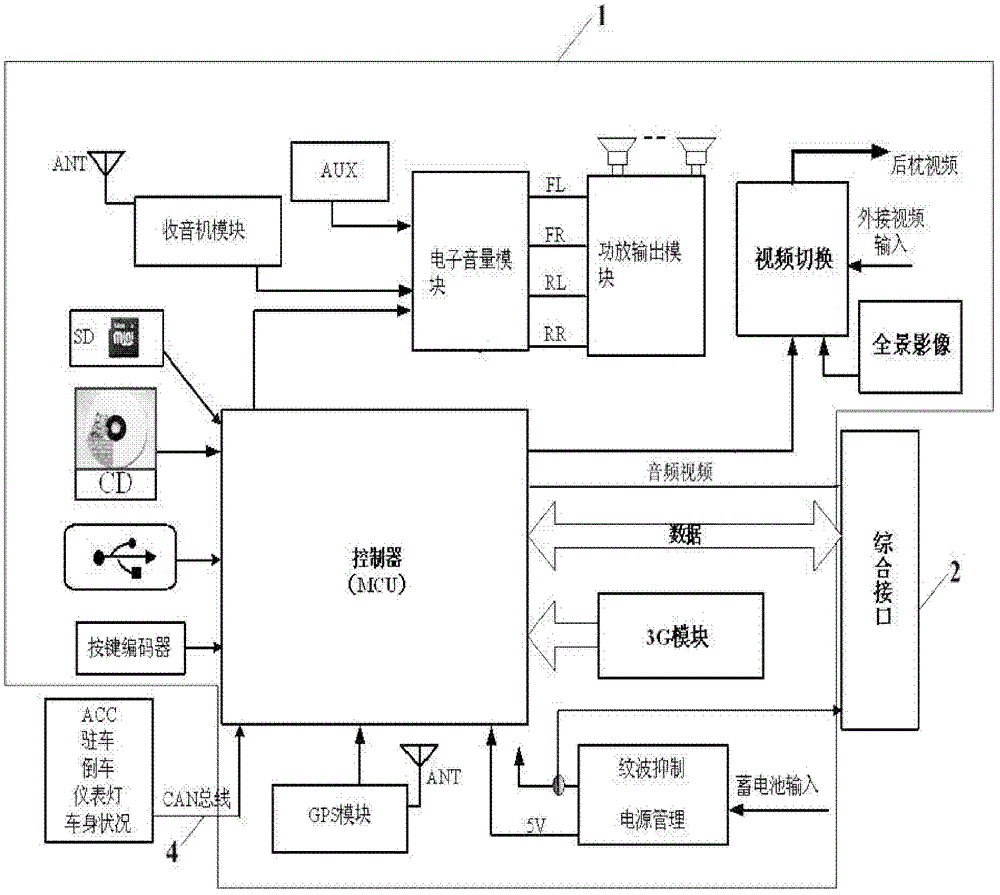
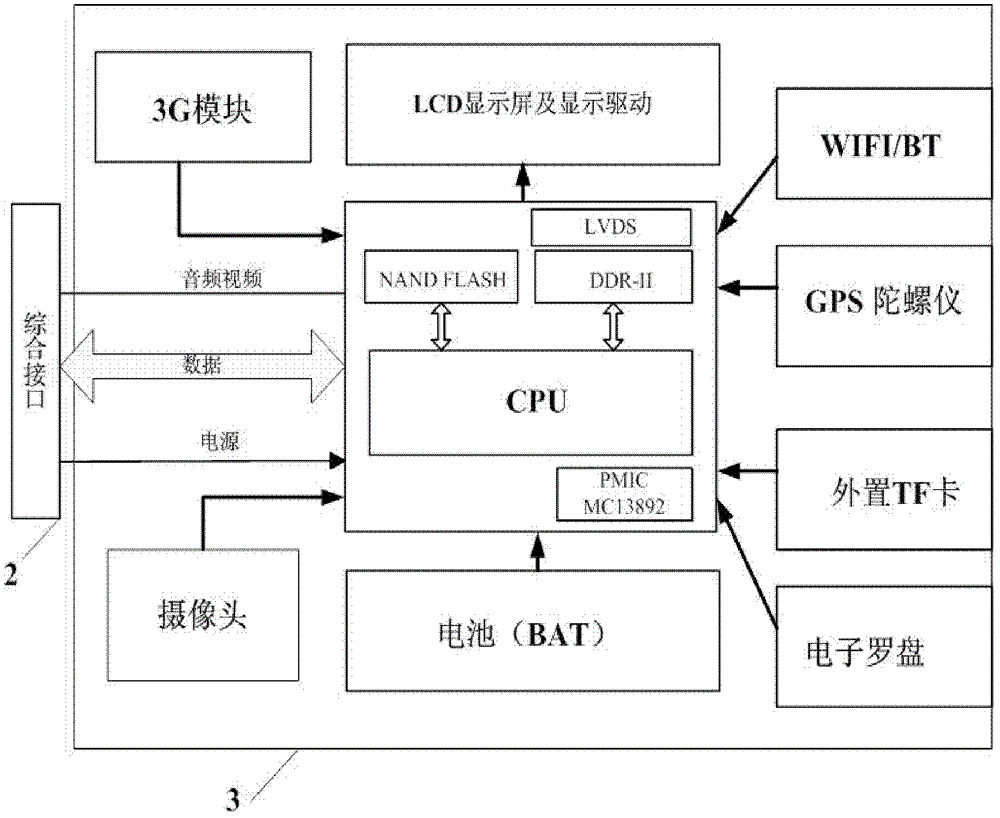
Split type portable vehicle-mounted computer system
InactiveCN102749967ADisassemble at any timeEasy to plug inDigital data processing detailsLiquid-crystal displayComputer usage
The invention discloses a split type portable vehicle-mounted computer system which is designed in a split mode and mainly formed by a vehicle-mounted retractable device and a vehicle-mounted computer. The vehicle-mounted retractable device and the vehicle-mounted computer have complete software and hardware processing capabilities and can independently achieve various functions of their own. When the vehicle-mounted retractable device and the vehicle-mounted computer are connected together, the vehicle-mounted computer can serve complete functions. The vehicle-mounted computer is detachable and serves as a tablet personal computer to be used after dismantling, device utilization rate is improved, and a liquid crystal display (LCD) at a consumption level and a capacitive touch screen are applied to the vehicle-mounted system very well.
Owner:ZHEJIANG ZHIHUI ELECTRIC ACCESSORY +1
Computer assembly
ActiveCN101685327AQuick dismantlingGuaranteed appearance integrityDigital processing power distributionComputer usagePersonal computer
The invention discloses a computer assembly, comprising a base, a panel personal computer and a back plate which is connected with the base by a rotating shaft; the panel personal computer comprises afirst assembly structure which is arranged at a first side edge of the panel personal computer, a second assembly structure which is arranged at a second side edge of the panel personal computer, andthe first side edge and the second side are opposite in parallel; the back plate comprises a first fixing structure which is arranged on a third side edge of the back plate, and the position of the first fixing structure corresponds to the first assembly structure; a second fixing structure which is arranged at a fourth side edge of the back plate, and the position of the second fixing structurecorresponds to the second assembly structure, the third side edge and the fourth side edge are opposite in parallel; by matching the first assembly structure and the first fixing structure and the second assembly structure and the second fixing structure, the panel personal computer is fixed in the back plate, by releasing the second assembly structure and the second fixing structure, the panel personal computer is separated from the inner part of the back plate. In the invention, the panel personal computer is fixed in the back plate for being used as a notebook PC, or is used independently by being detached from the inner part of the back plate.
Owner:LENOVO (BEIJING) CO LTD
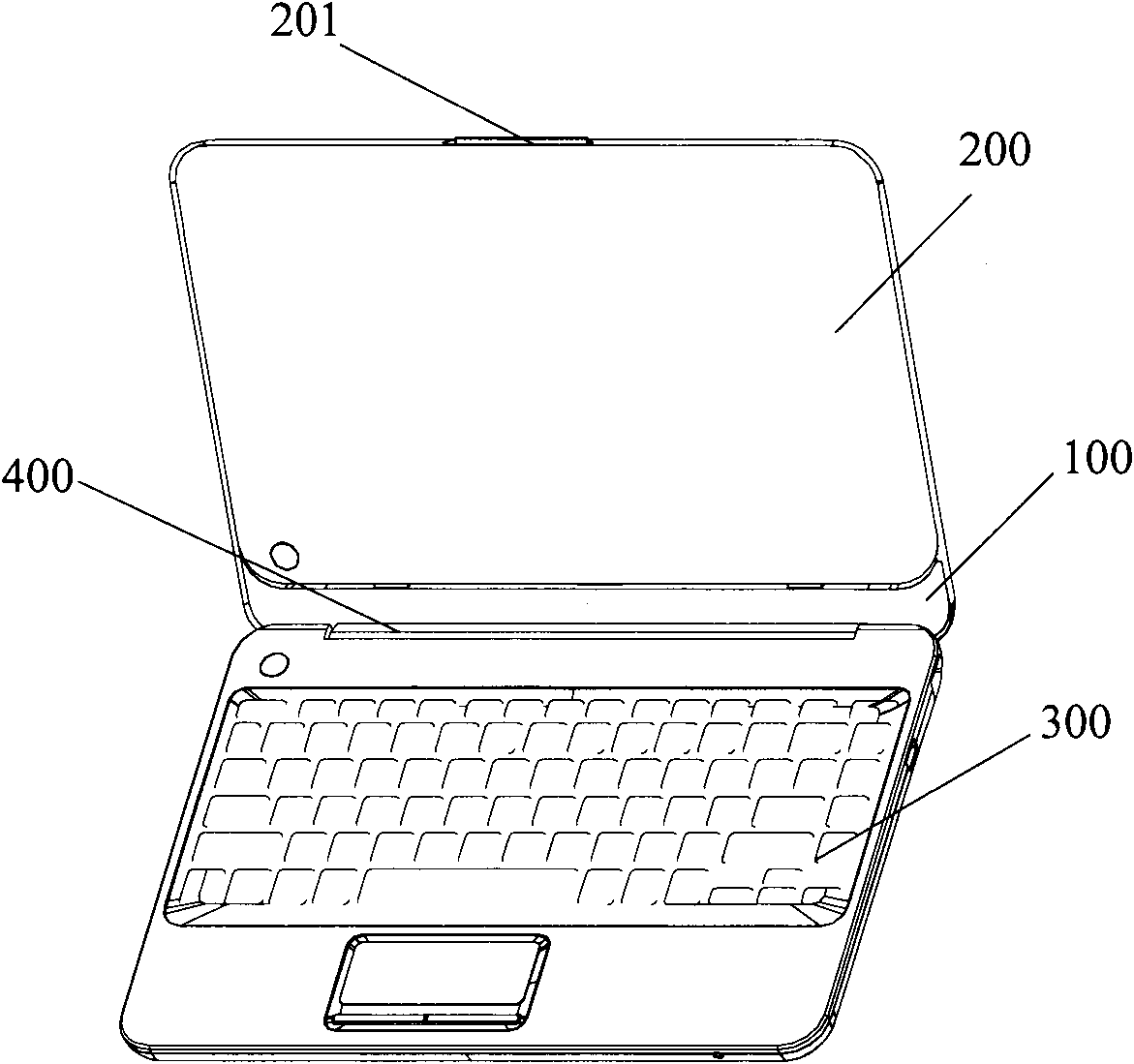
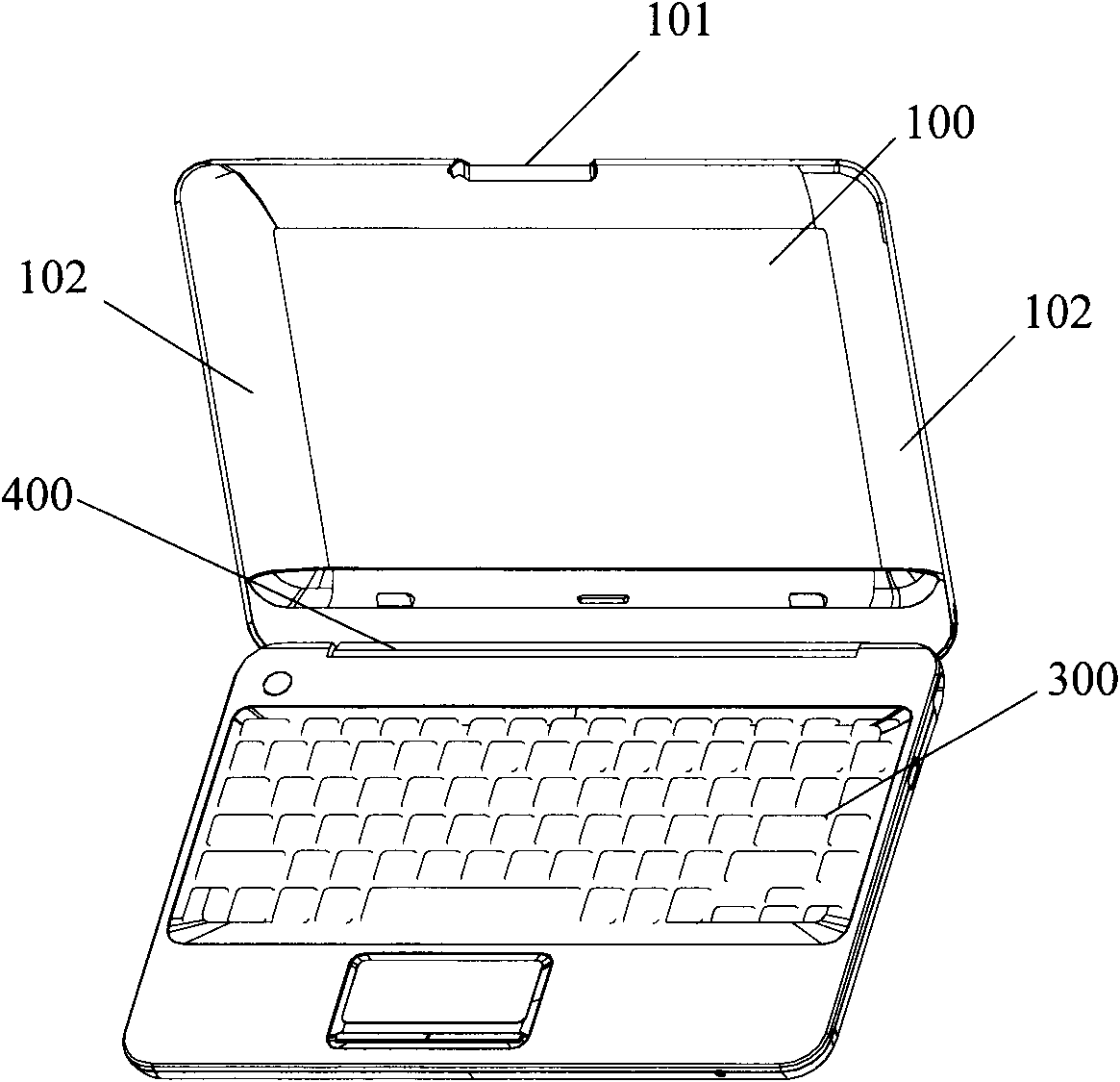
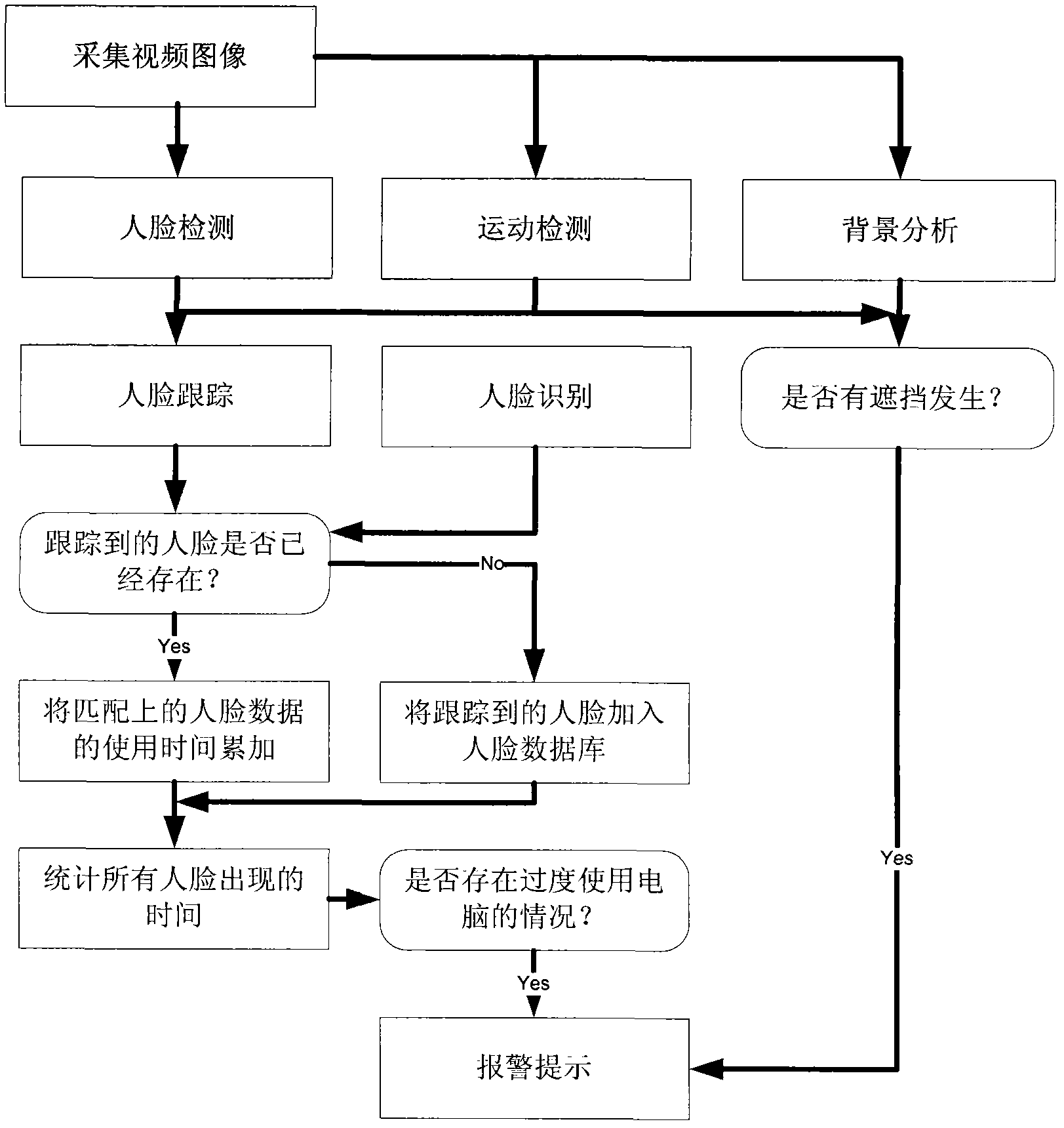
Computer using time prompting method and system based on intelligent video analysis
ActiveCN103164315AUse time controlHardware monitoringCharacter and pattern recognitionFace detectionPattern recognition
A computer using time prompting method based on intelligent video analysis includes the following steps: collecting a video image in front of a computer monitor, conducting face detection and tracking on the video image, counting the time of appearance a face when the face is detected, judging whether an owner of the face overuses a computer or not according to the counted time of appearance of the face, and sending an alarm prompting signal when the owner of the face overuses the computer.
Owner:WUXI ZGMICRO ELECTRONICS CO LTD
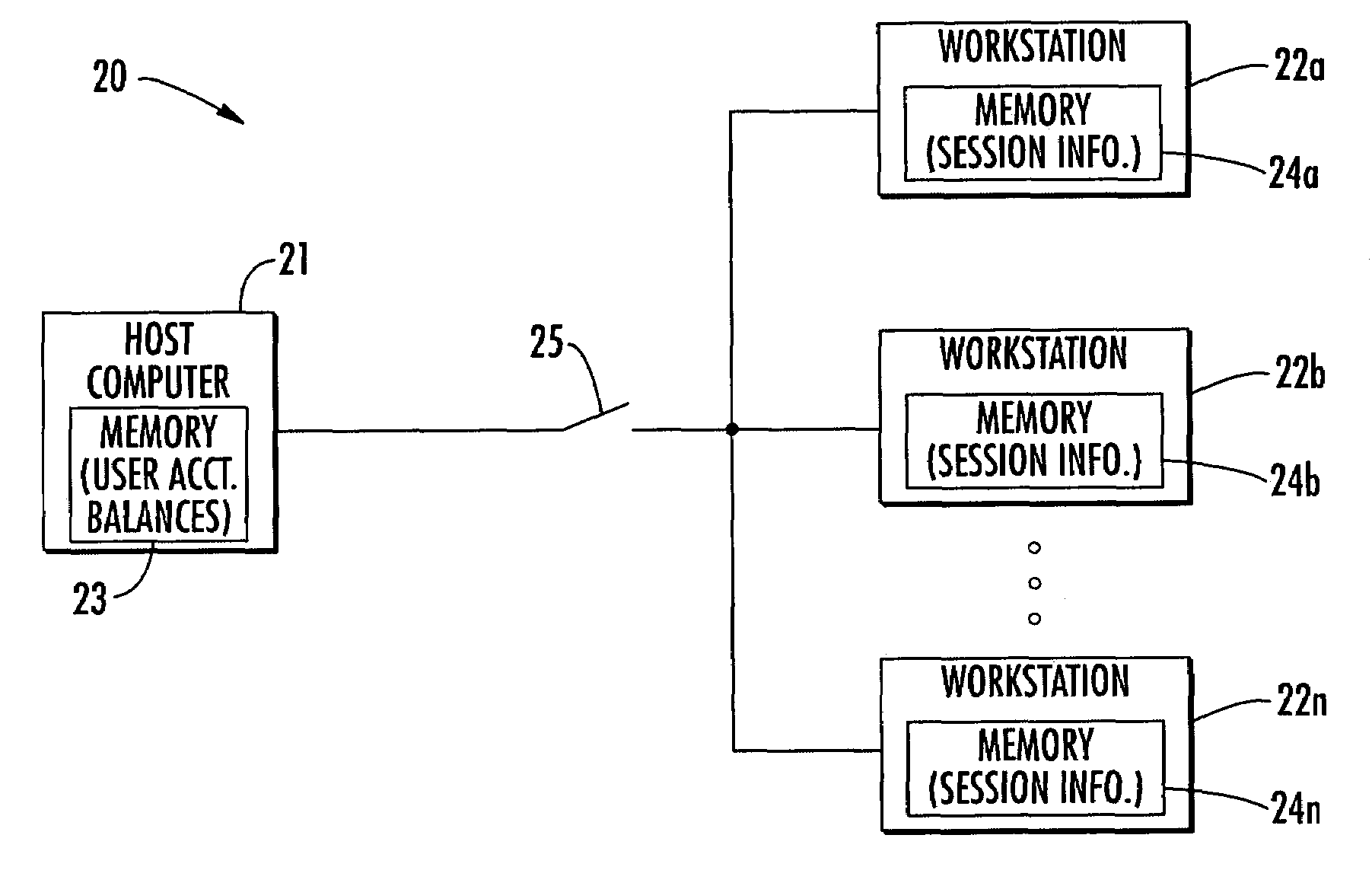
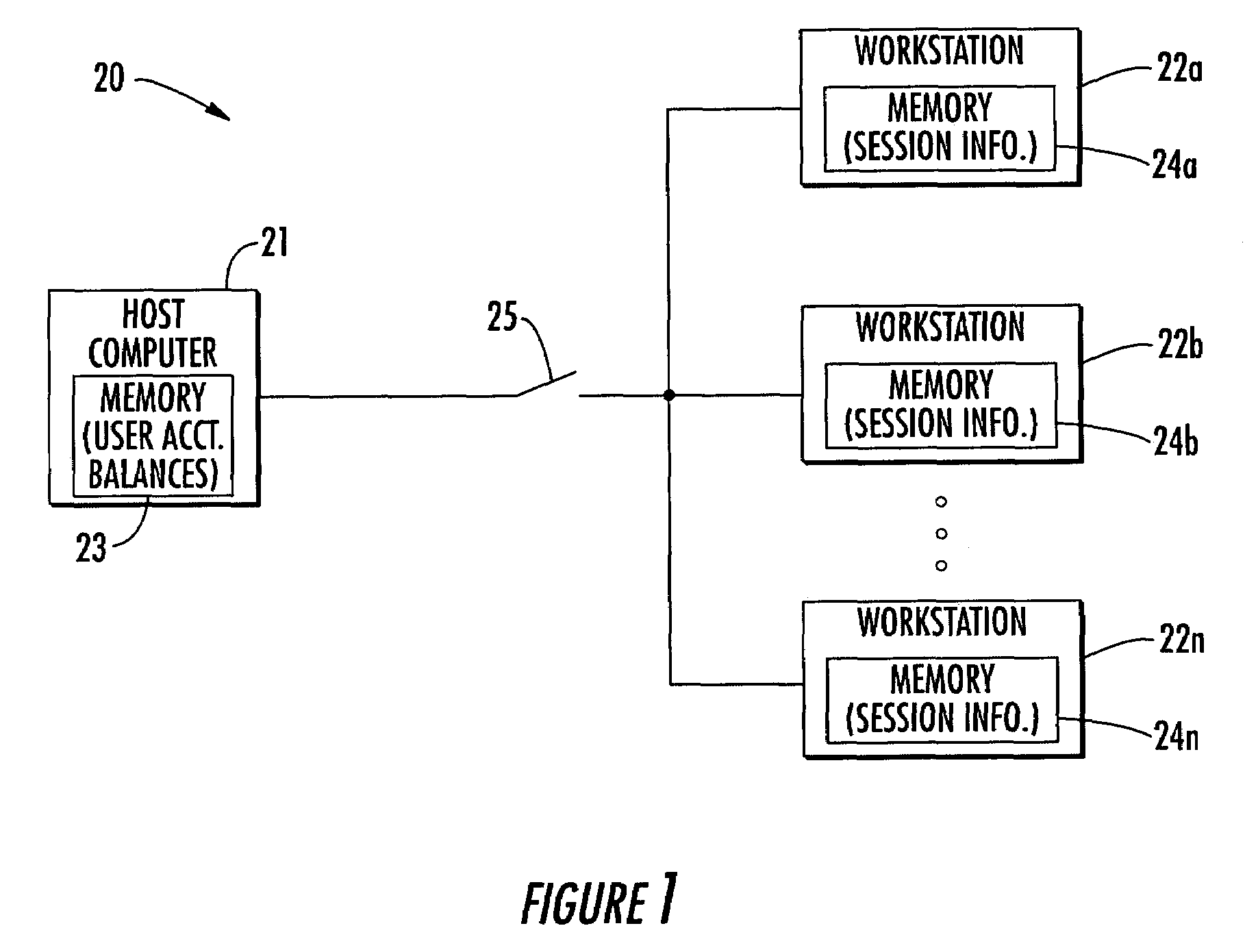
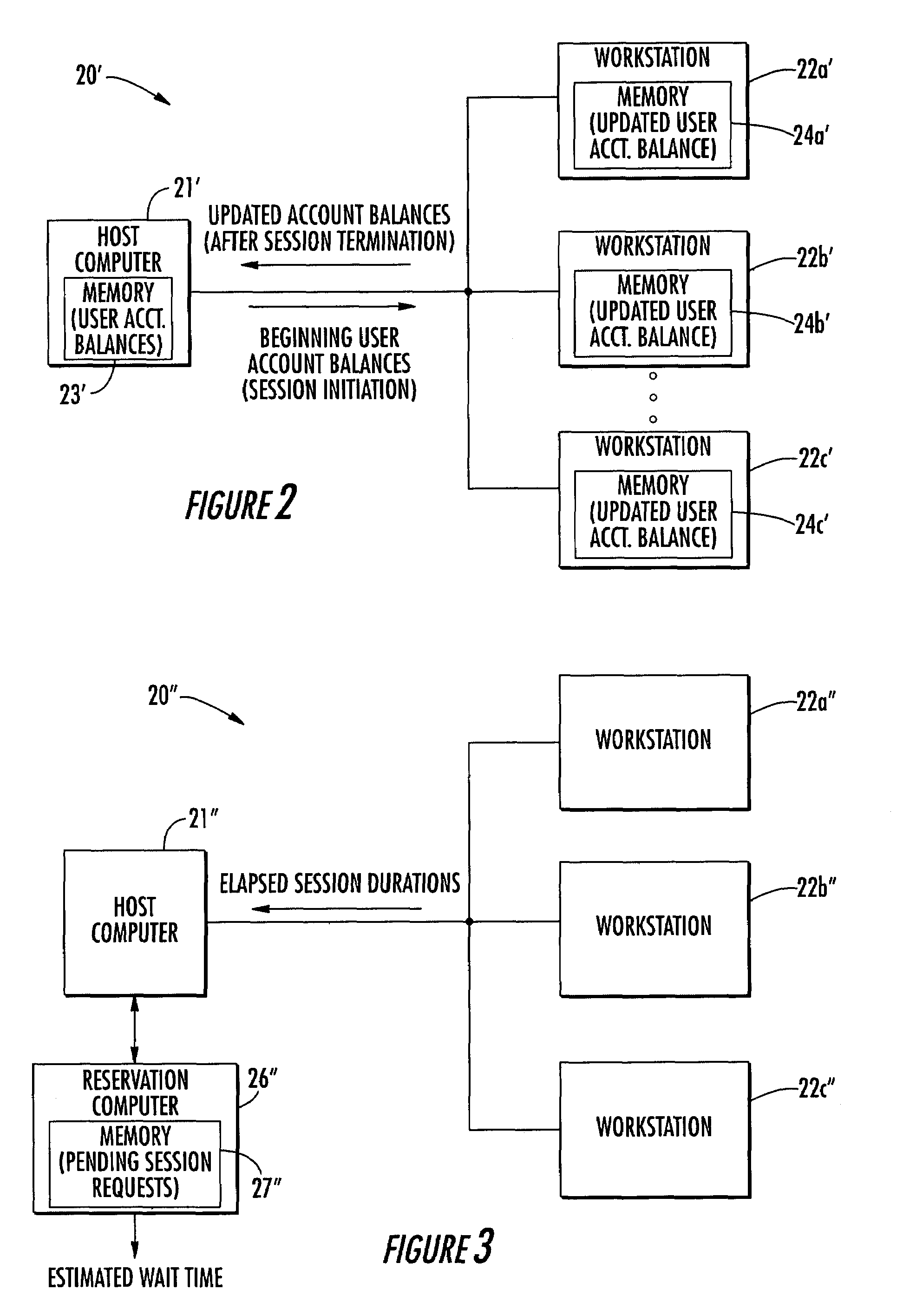
Computer reservation and usage monitoring system and related methods
A computer network may include a host computer and a plurality of computer workstations selectively connectable thereto at which user work sessions may be initiated. Each computer workstation when disconnected from the host computer (e.g., due to server outage, etc.) may advantageously initiate a user session responsive to a user request and store session information for updating the respective user account balance when reconnected with the host computer. Additionally, when the computer workstations are connected to the host computer they may copy respective user account balances from the host computer upon initiation of user sessions, and update the copied account balances based upon computer usage during the respective user sessions. The computer network may also include at least one reservation computer for cooperating with the host computer to schedule user session reservations and provide a requesting user an estimated time before a user session will be made available.
Owner:PHAROS SYST INT
Computer Usage Monitoring
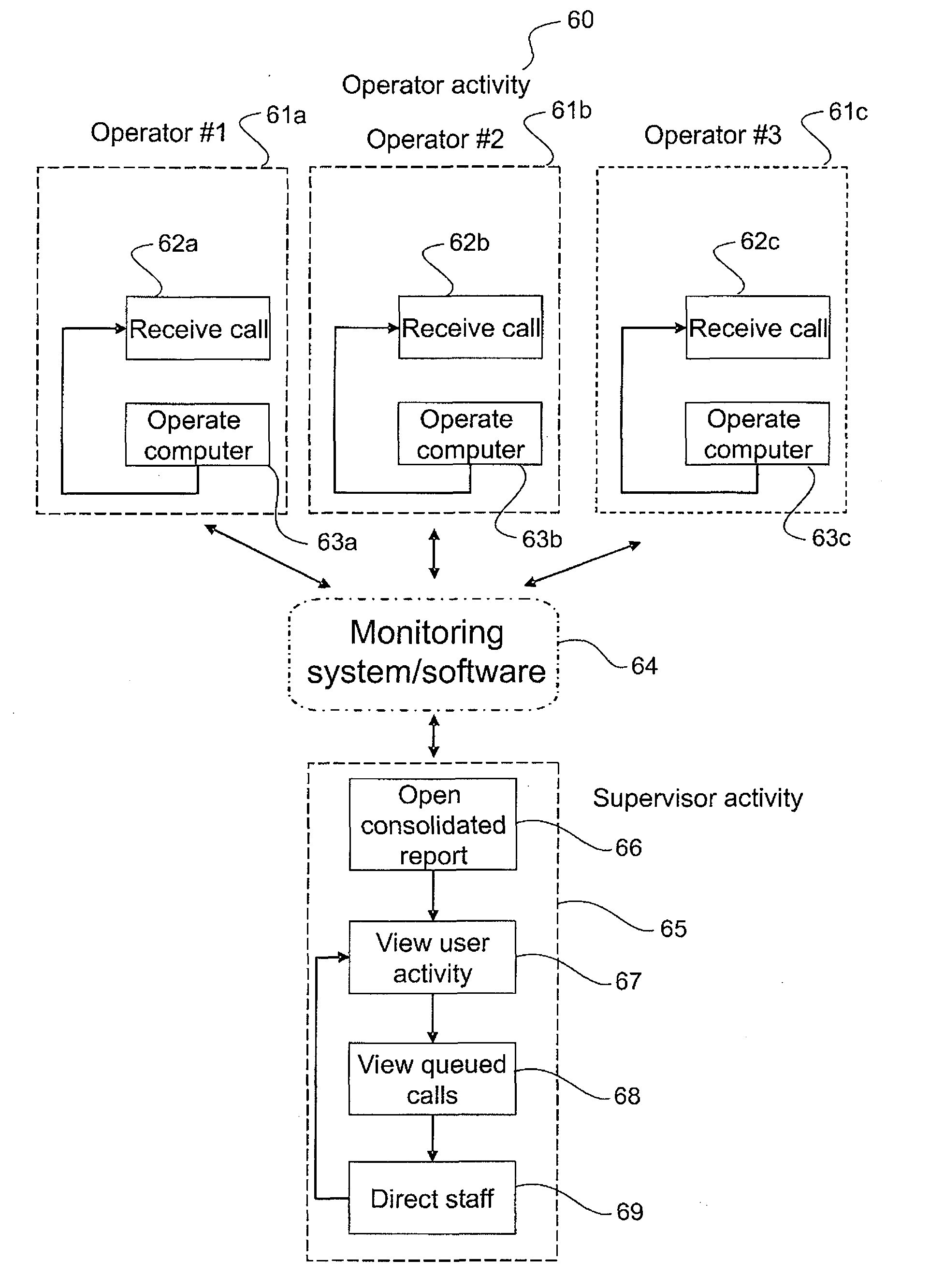
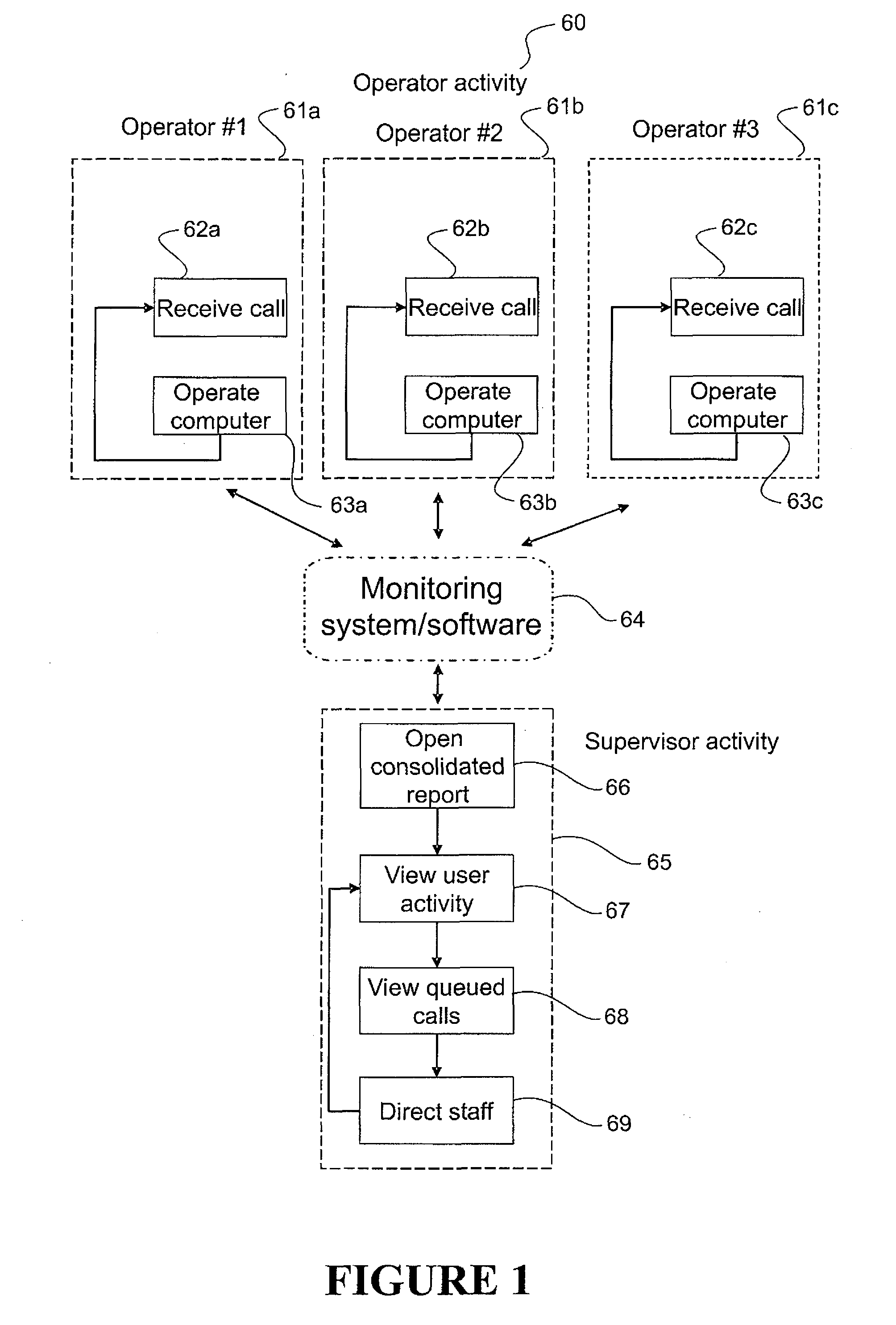
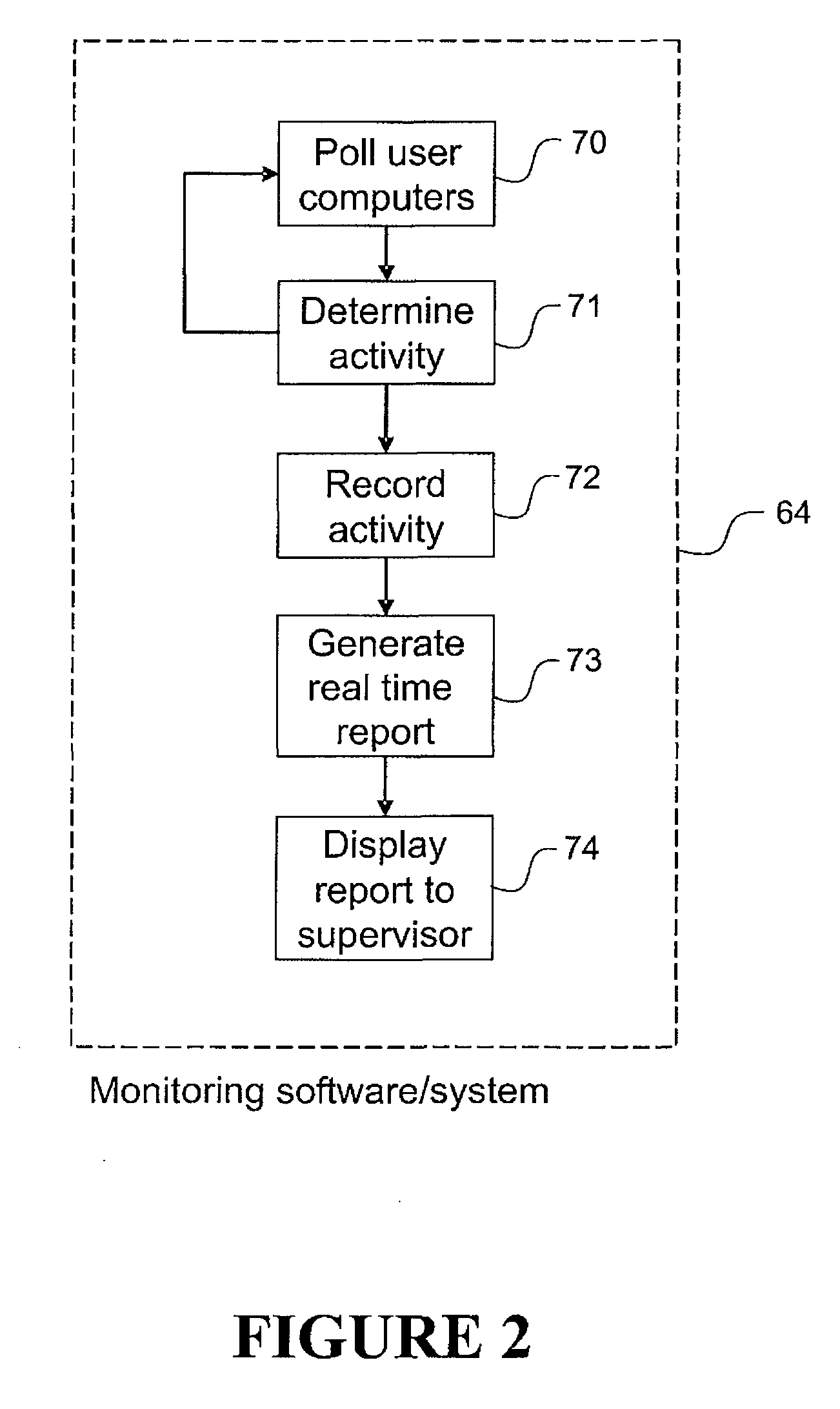
InactiveUS20080222286A1Improve productivityError detection/correctionDigital computer detailsComputer usageData science
The present invention relates to a method of monitoring worker activity in a work group, the work group comprising workers each using a computer on a computer network their method comprising displaying to a work group supervisor, in consolidated form, a label indicating each worker and information indicating the current activity and / or classification determined for each worker.
Owner:PLUMPTON KEVIN I
Method and system for targeted advertising
A method and system of displaying advertisements may include generating a predictive model to predict a type of user, collecting advertisements based upon the type of user, placing the predictive model and collected advertisements on a computer of a user, executing the predictive model on the computer of the user to determine the type of user, and selecting an advertisement to be displayed to the user based upon the execution of the predictive model. The predictive model may be generated based upon feedback from the control users, and the predictive model may be generated based upon the computer of the control users. The predictive model may be generated based upon Web browsing of the computer of the control users, and the predictive model may be generated based upon computer usage behavior of the control users.
Owner:PDI DEV CO LLC
Computer permission control method based on mobile dynamic password
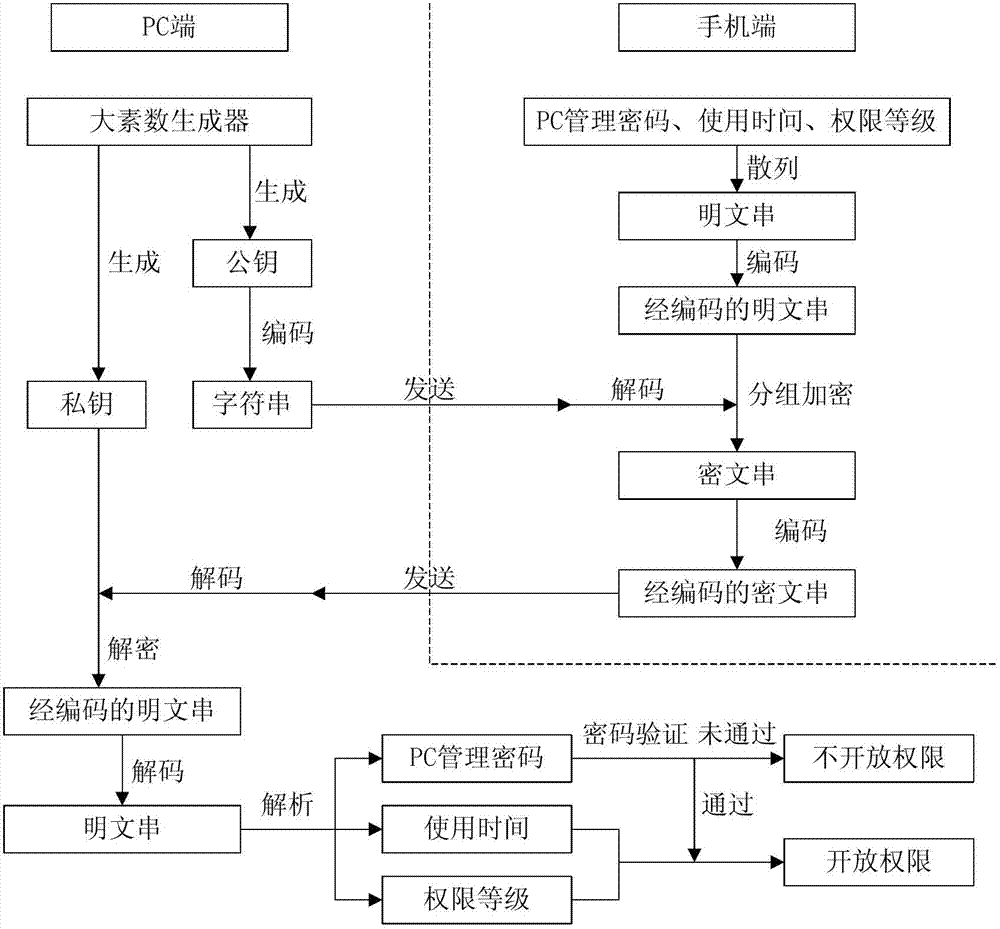
InactiveCN103036674AImprove resistance to attackLower requirementEncryption apparatus with shift registers/memoriesRemote controlCiphertext
The invention relates to a computer permission control method based on a mobile dynamic password. The computer permission control method based on the mobile dynamic password comprises the following steps: generating a private key and a public key by adopting encryption algorithm at an personal computer (PC) end and sending the public key to a mobile end; encrypting a PC management password, using time and permission level information which are stored at the mobile end in advance by adopting the public key after the mobile end receives the public key, generating a ciphertext string, and then sending the ciphertext string to the PC end; deciphering the ciphertext string by adopting the private key after the PC end receives the ciphertext string, getting the PC management password, the using time and the permission level information; and conducting a password authentication with the PC end by using the PC management password information. When the PC end passes the password authentication, computer permission is opened according to the using time and the permission level information. When the PC end does not pass the password authentication, the computer permission ends. Compared with the prior art, the computer permission control method based on the mobile dynamic password has the advantages of being capable of achieving a remote control of the using time and the permission of a computer by a mobile, convenient to use, good in safety and the like.
Owner:TONGJI UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com