Patents
Literature
2834 results about "Malware" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
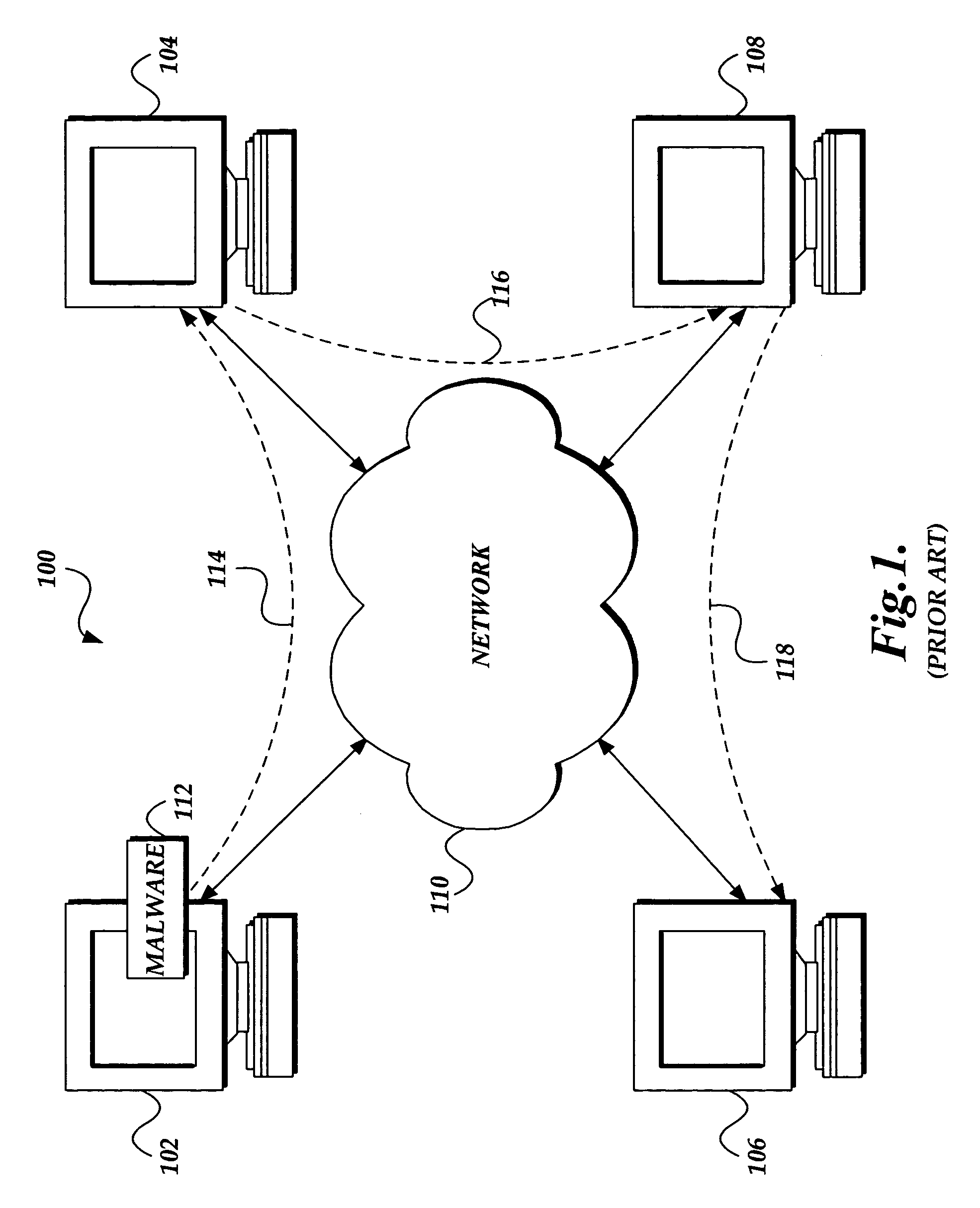
Malware (a portmanteau for malicious software) is any software intentionally designed to cause damage to a computer, server, client, or computer network. Malware does the damage after it is implanted or introduced in some way into a target's computer and can take the form of directly executable code, scripts, so-called "active content" (Microsoft Windows), and other forms of data. Some kinds of malware are largely referred to in the media as computer viruses, worms, Trojan horses, ransomware, spyware, adware, and scareware, among other terms. Malware has a malicious intent, acting against the interest of the computer user—and so does not include software that causes unintentional harm due to some deficiency, which is typically described as a software bug.
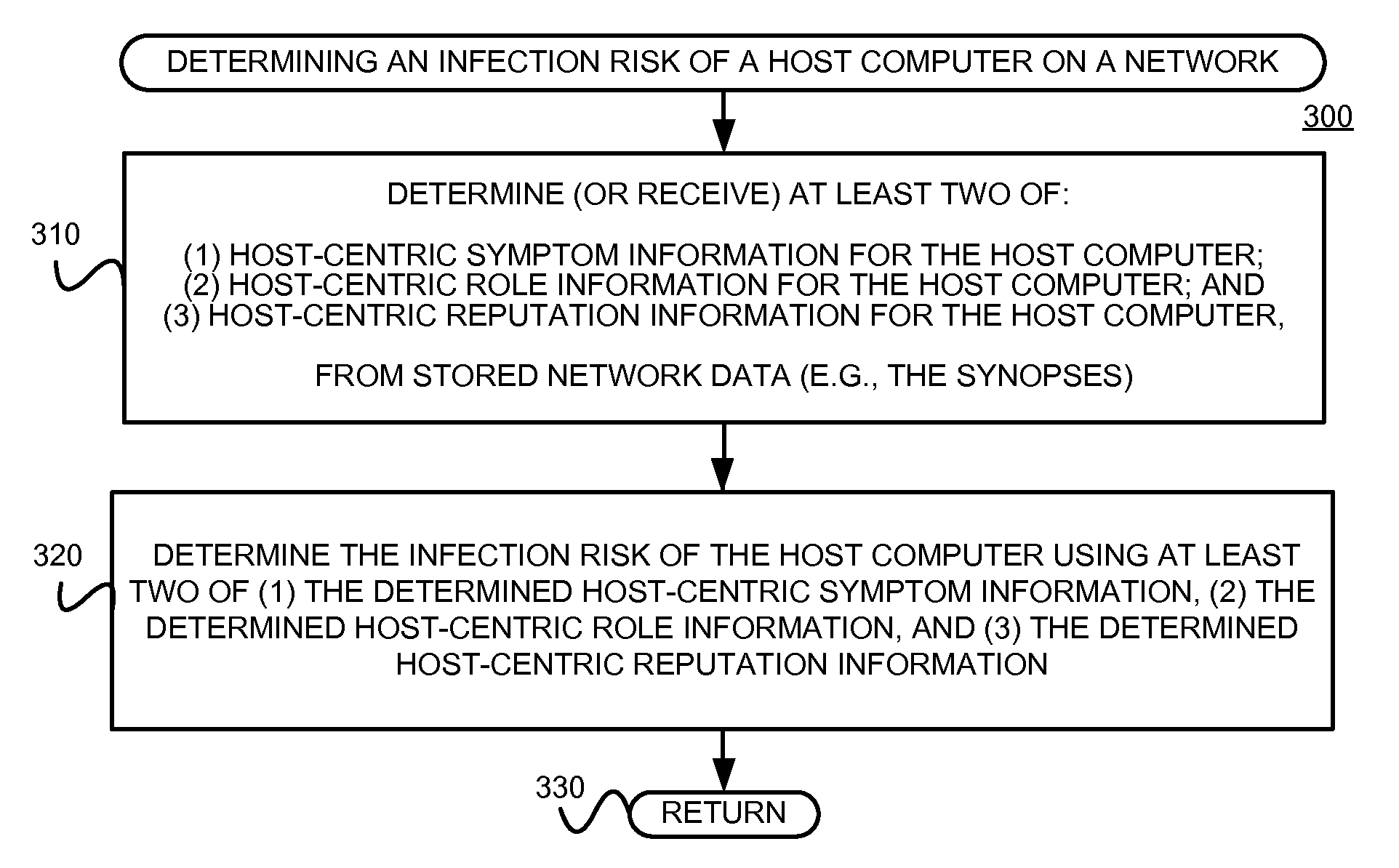
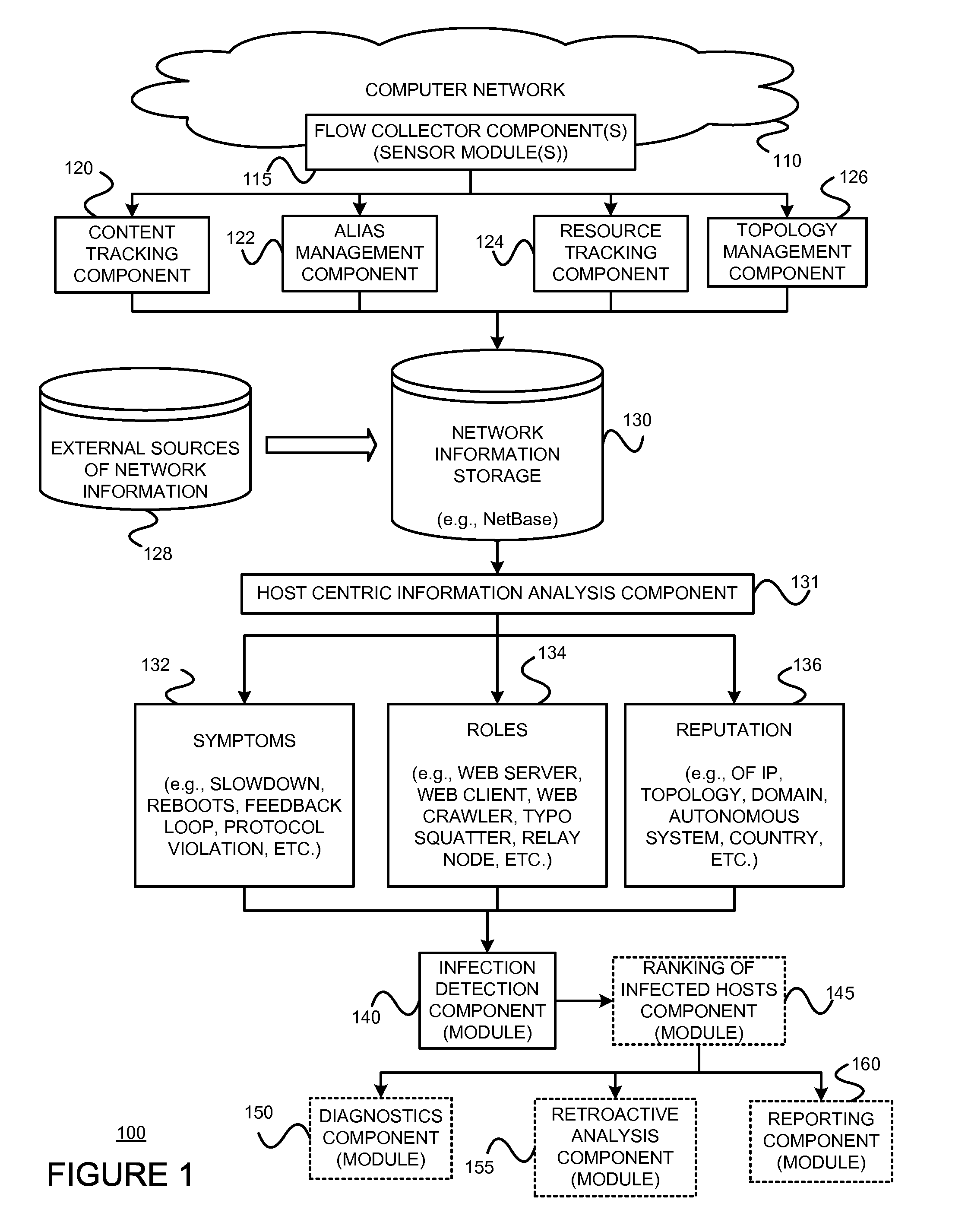
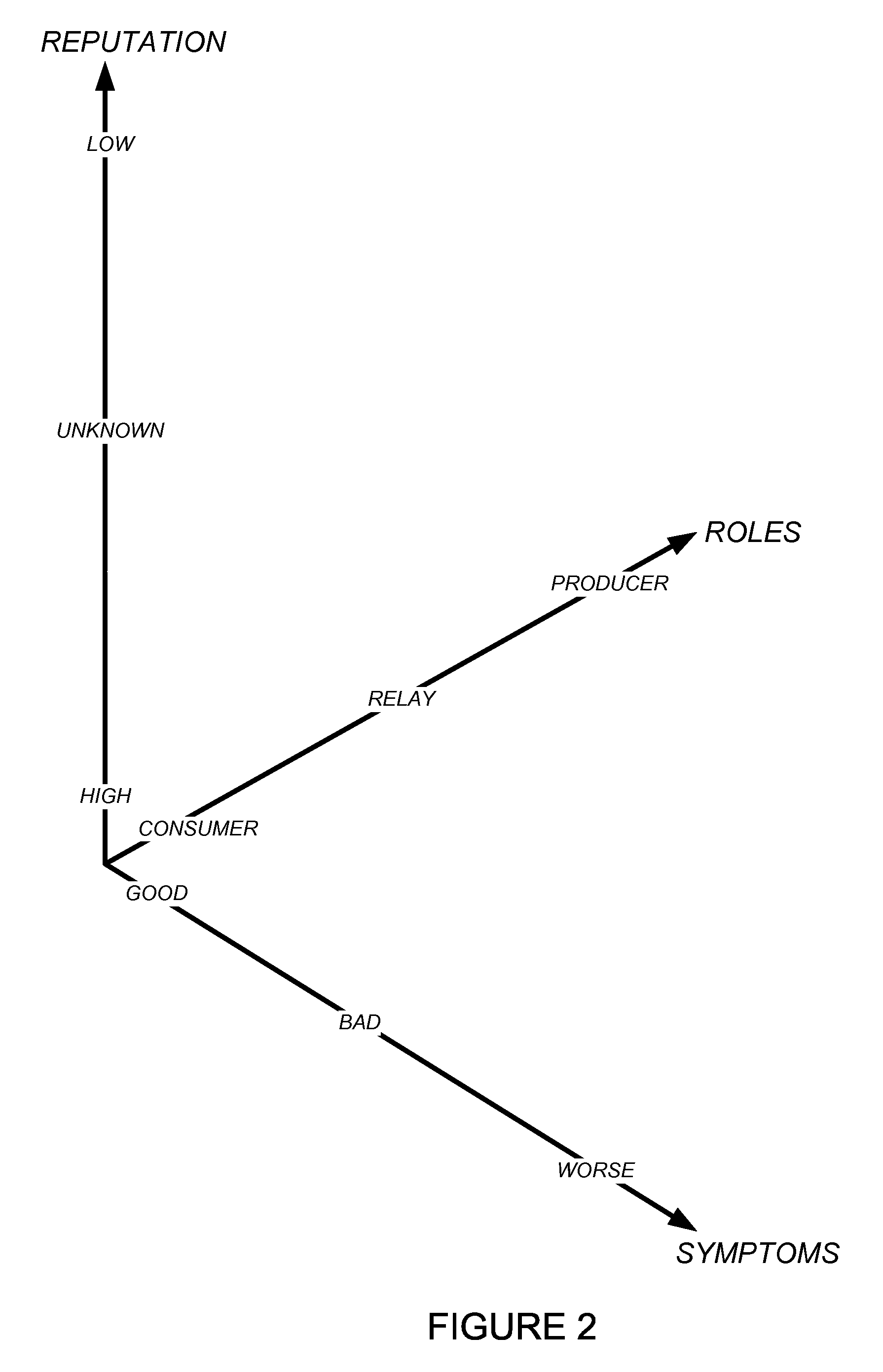
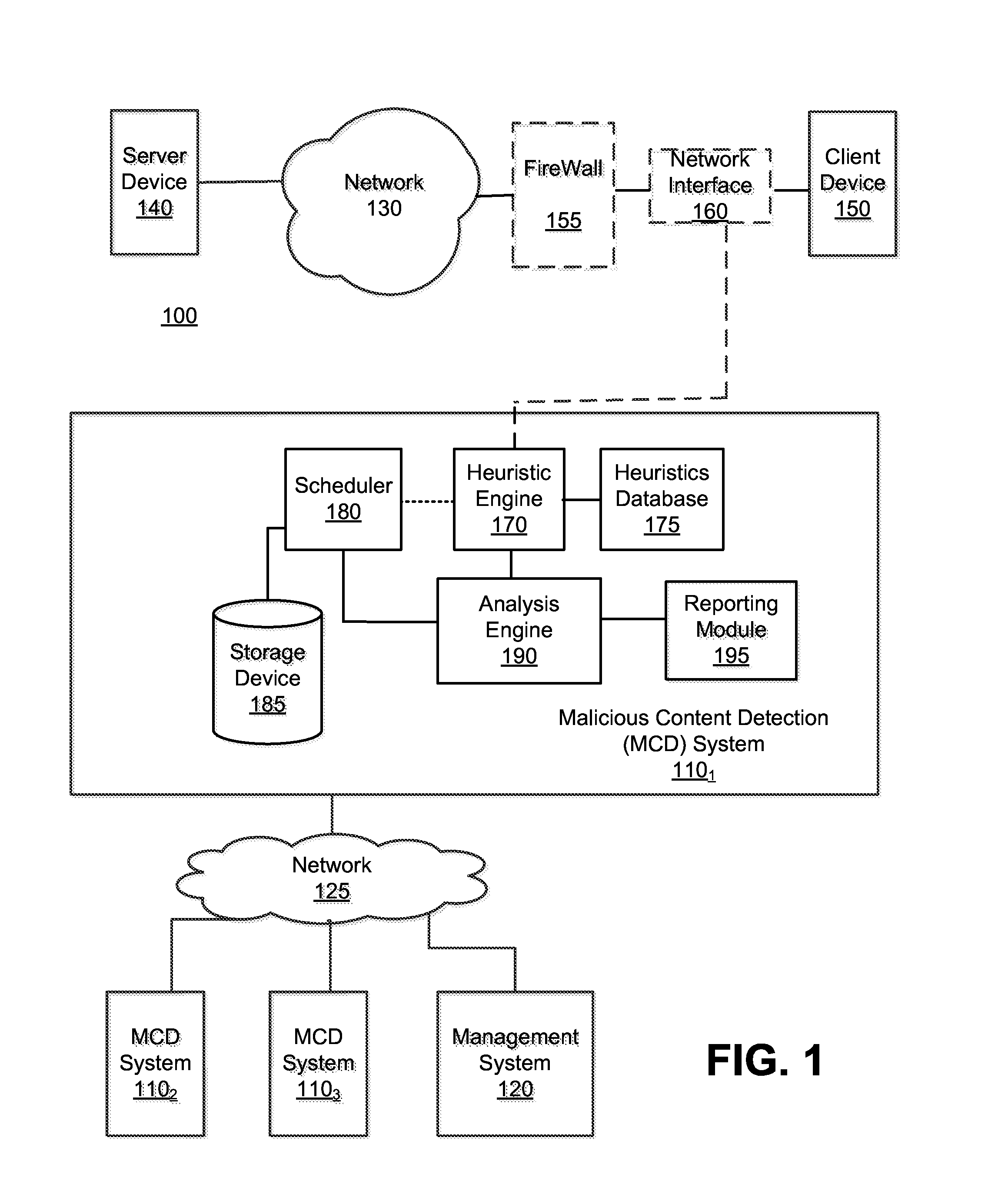
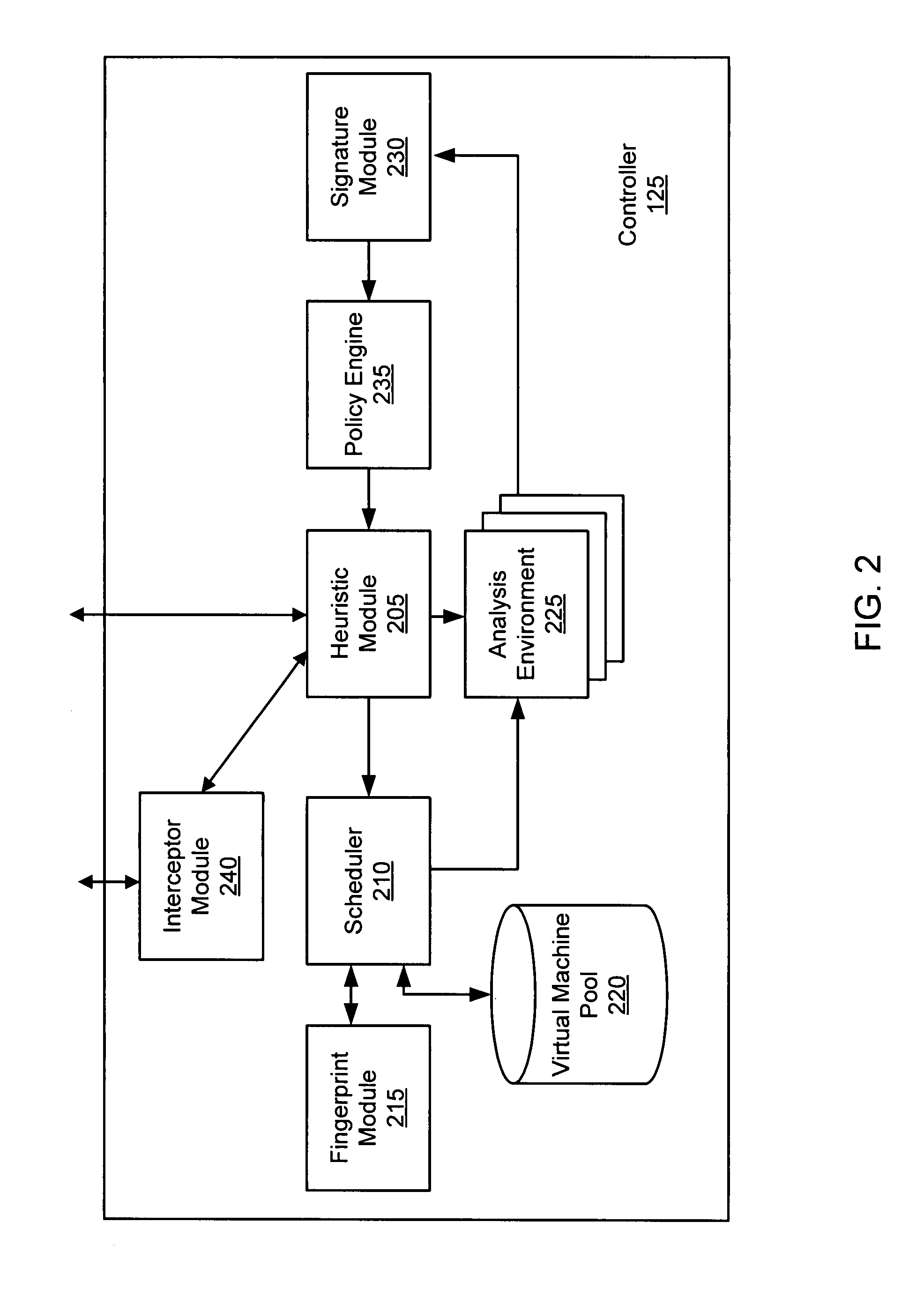
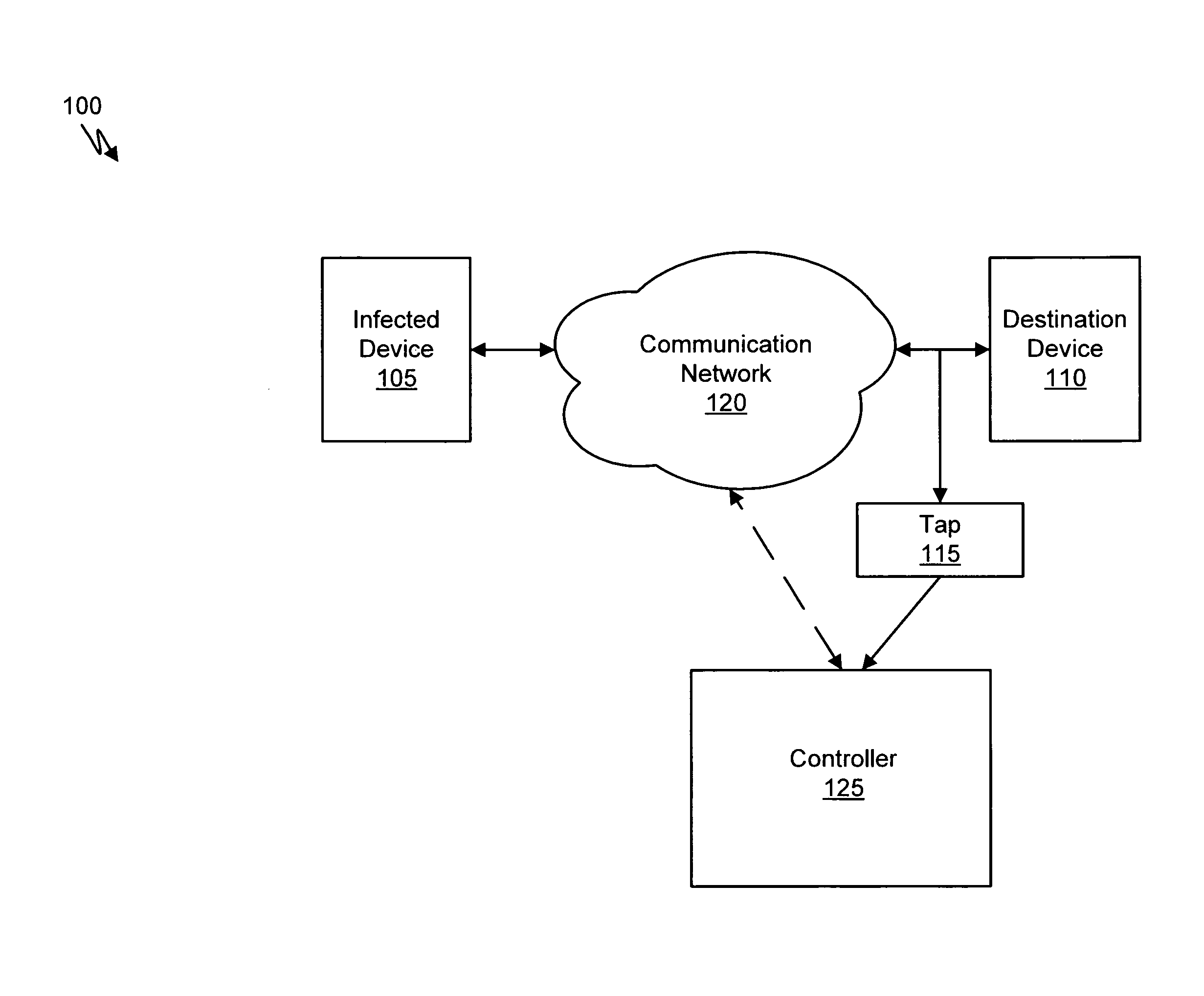
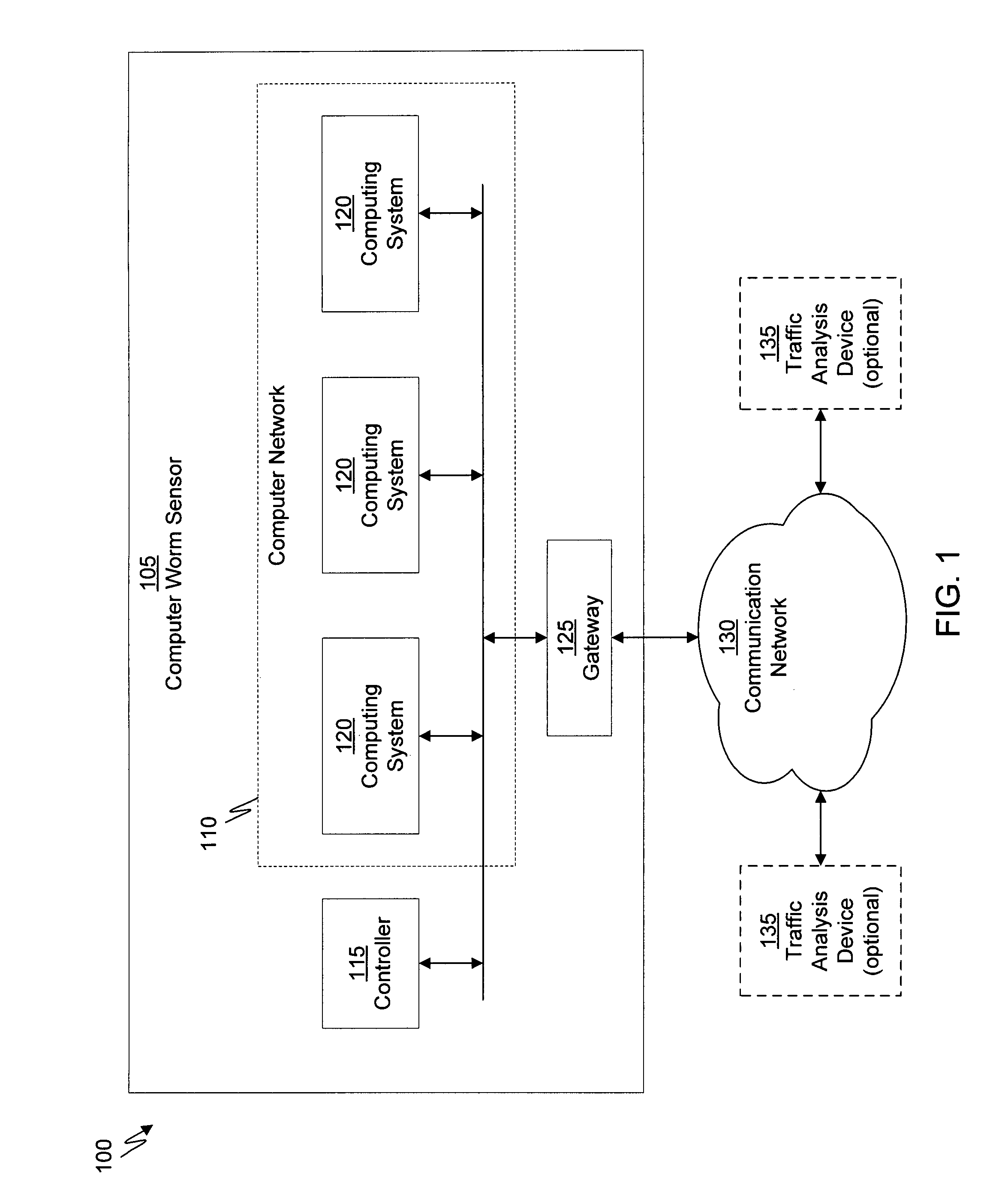
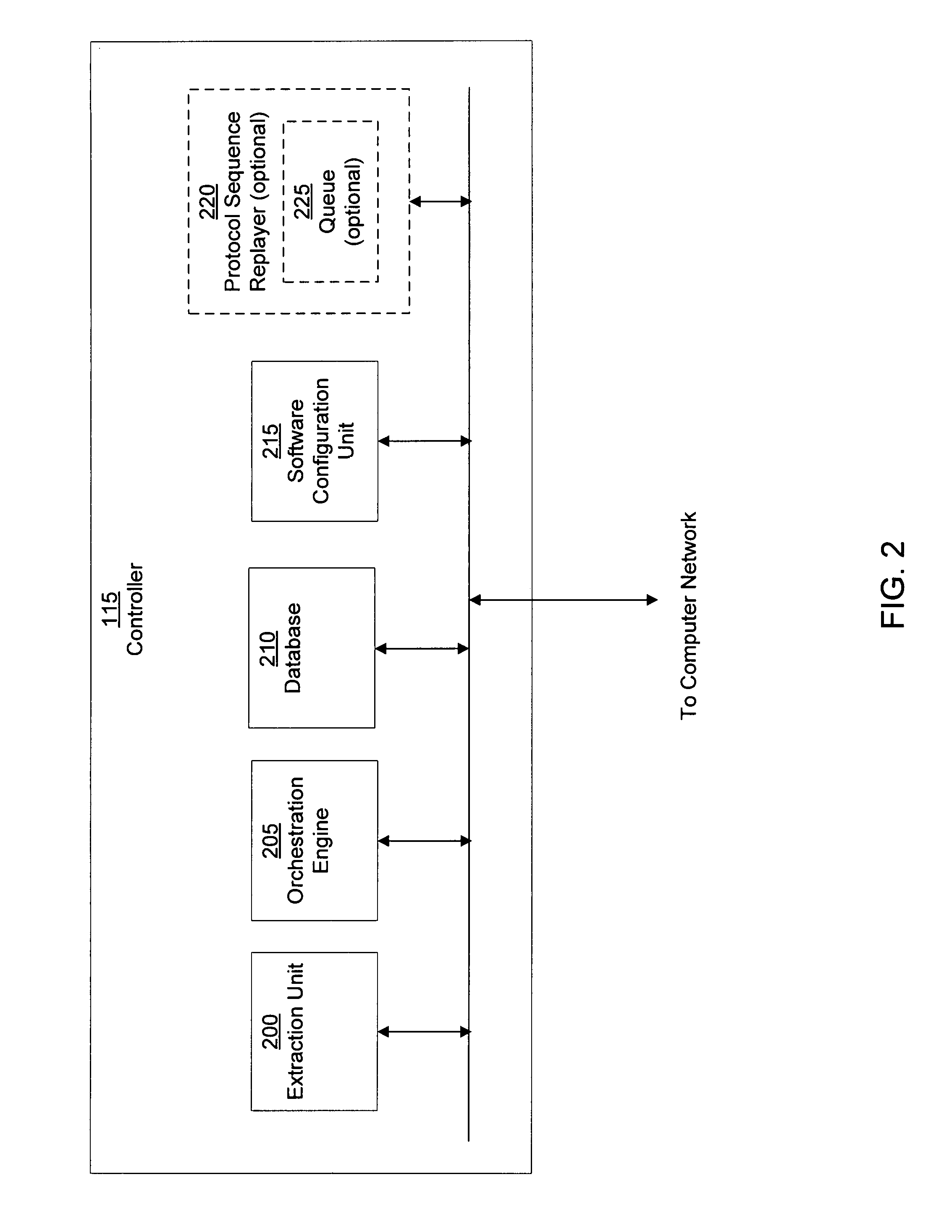
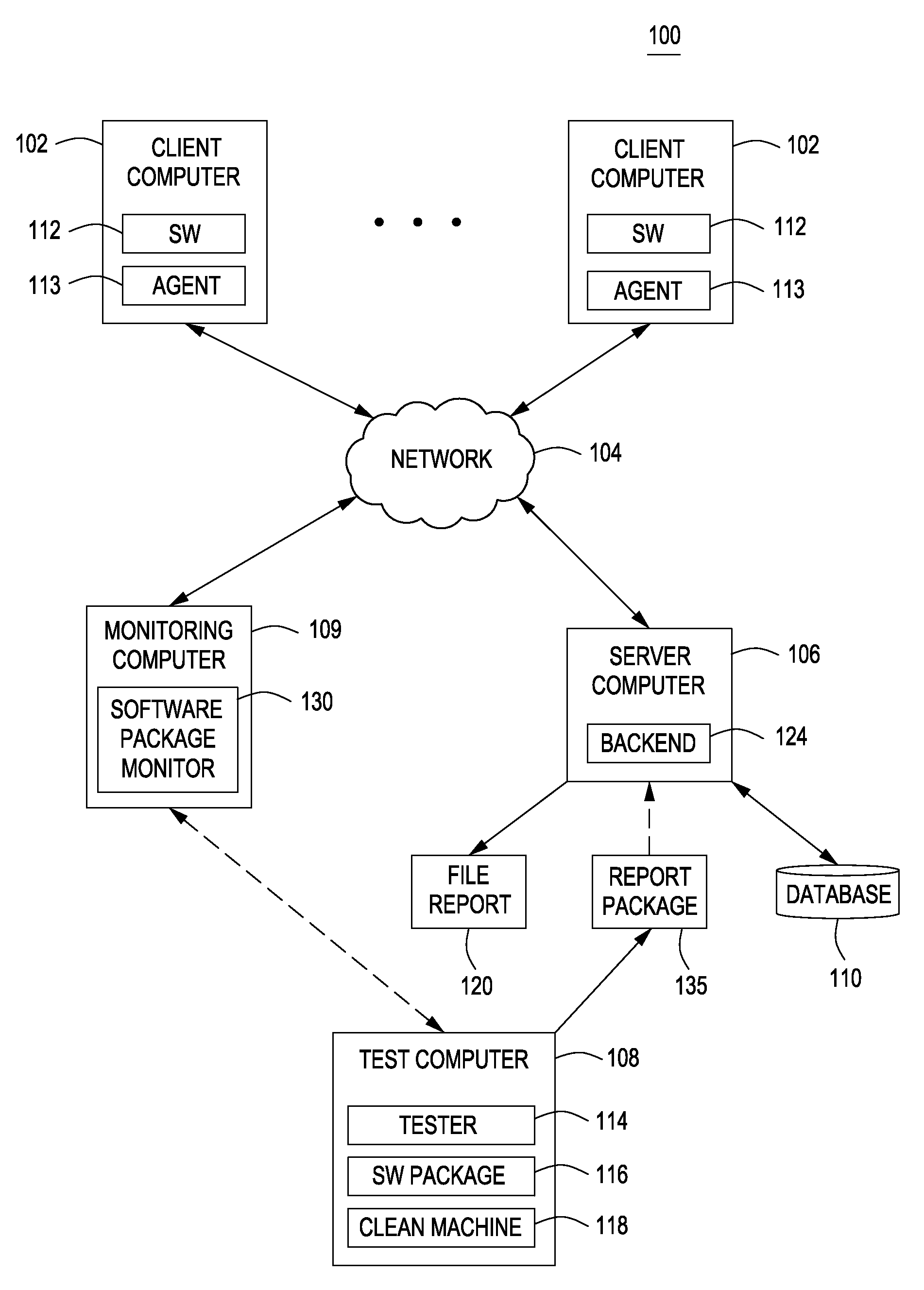
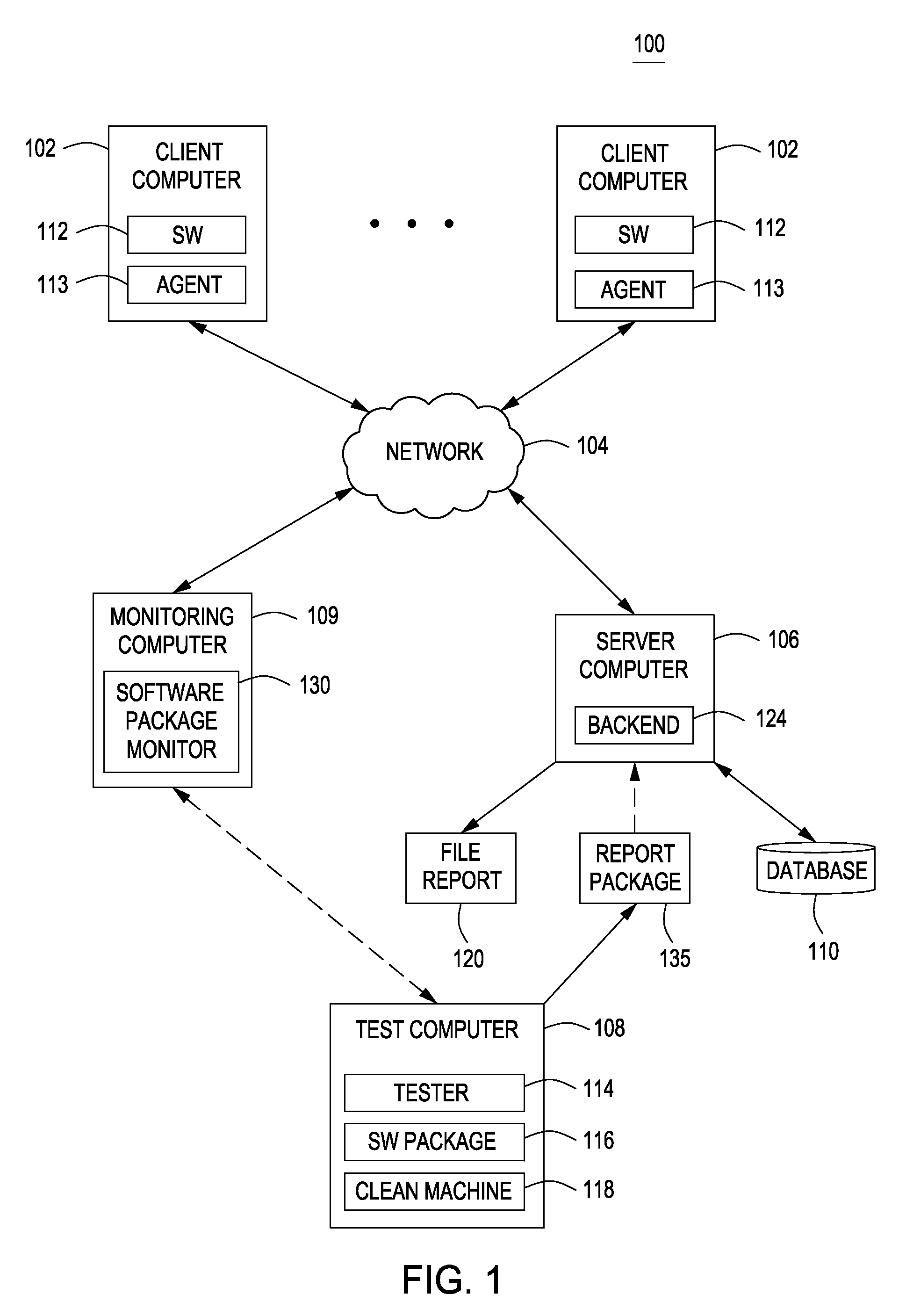
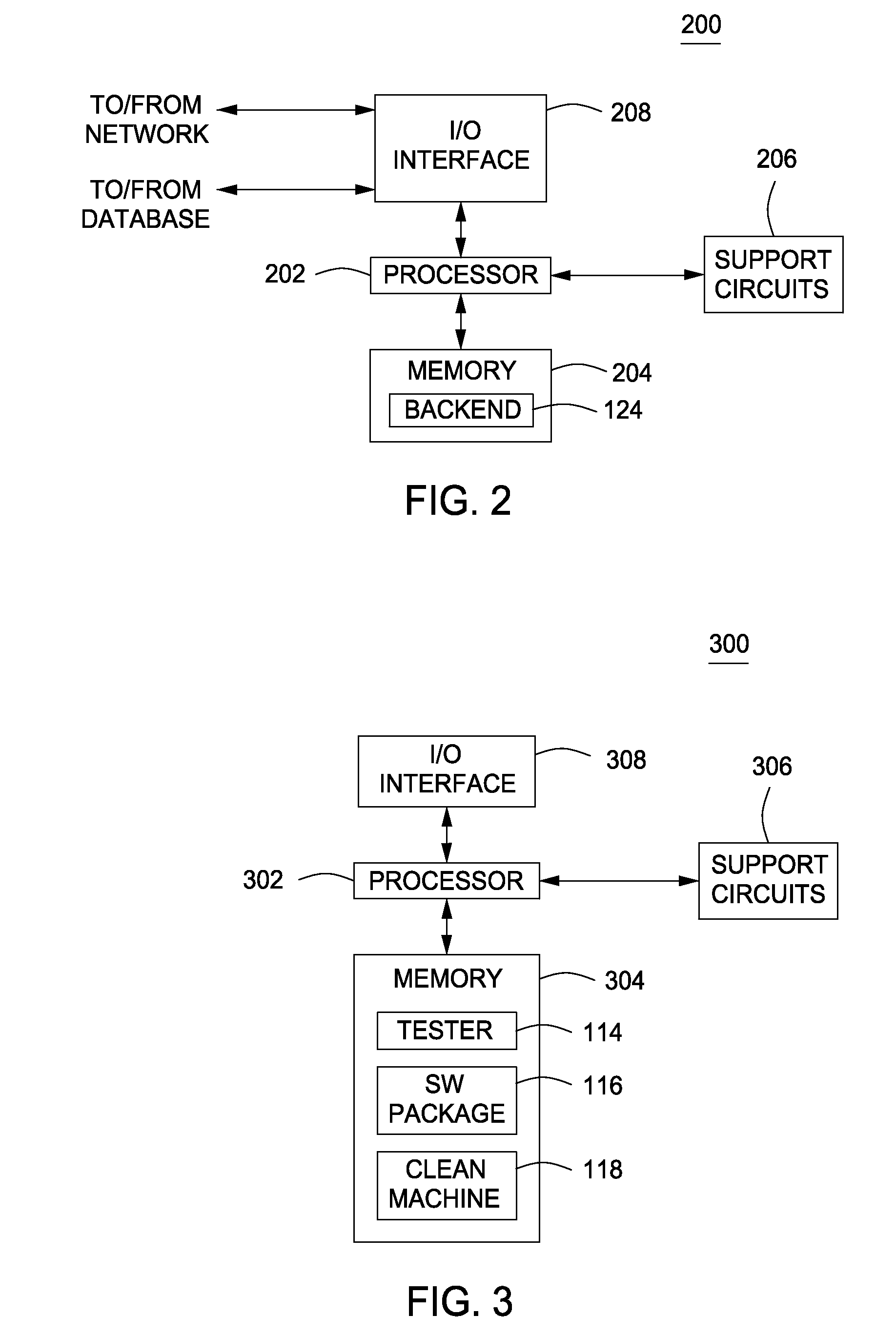
Using host symptoms, host roles, and/or host reputation for detection of host infection
InactiveUS20100235915A1Memory loss protectionError detection/correctionMalwareIntrusion prevention system
Detecting and mitigating threats to a computer network is important to the health of the network. Currently firewalls, intrusion detection systems, and intrusion prevention systems are used to detect and mitigate attacks. As the attackers get smarter and attack sophistication increases, it becomes difficult to detect attacks in real-time at the perimeter. Failure of perimeter defenses leaves networks with infected hosts. At least two of symptoms, roles, and reputations of hosts in (and even outside) a network are used to identify infected hosts. Virus or malware signatures are not required.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
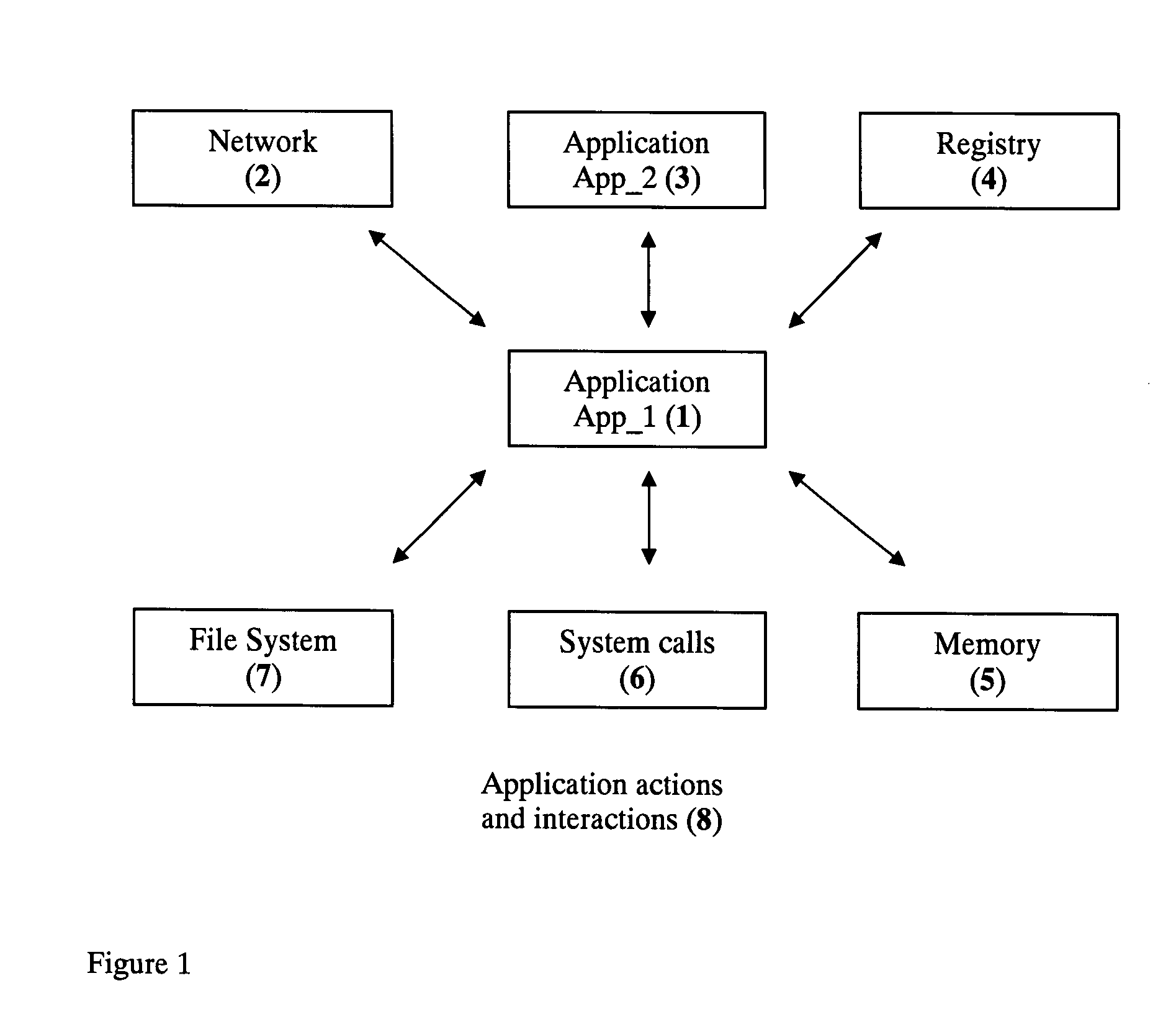
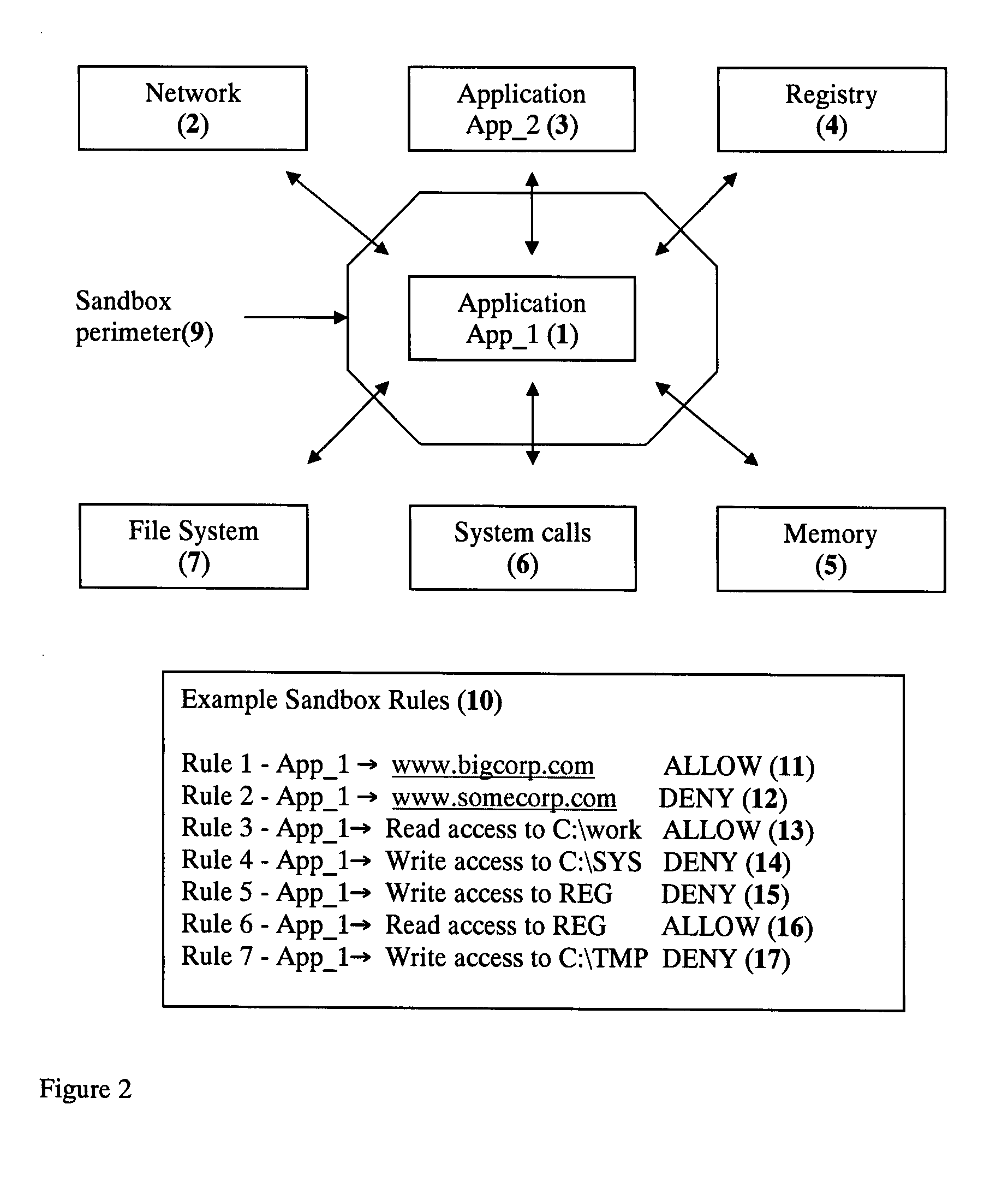
Application Sandbox to Detect, Remove, and Prevent Malware
InactiveUS20080016339A1Limit and eliminate attackRemove or neutralized malware on disk and in memoryPlatform integrity maintainanceSecuring communicationNetwork attackMalware
The disclosed invention is a new method and apparatus for protecting applications from local and network attacks. This method also detects and removes malware and is based on creating a sandbox at application and kernel layer. By monitoring and controlling the behavior and access privileges of the application and only selectively granting access, any attacks that try to take advantage of the application vulnerabilities are thwarted.
Owner:SHUKLA JAYANT
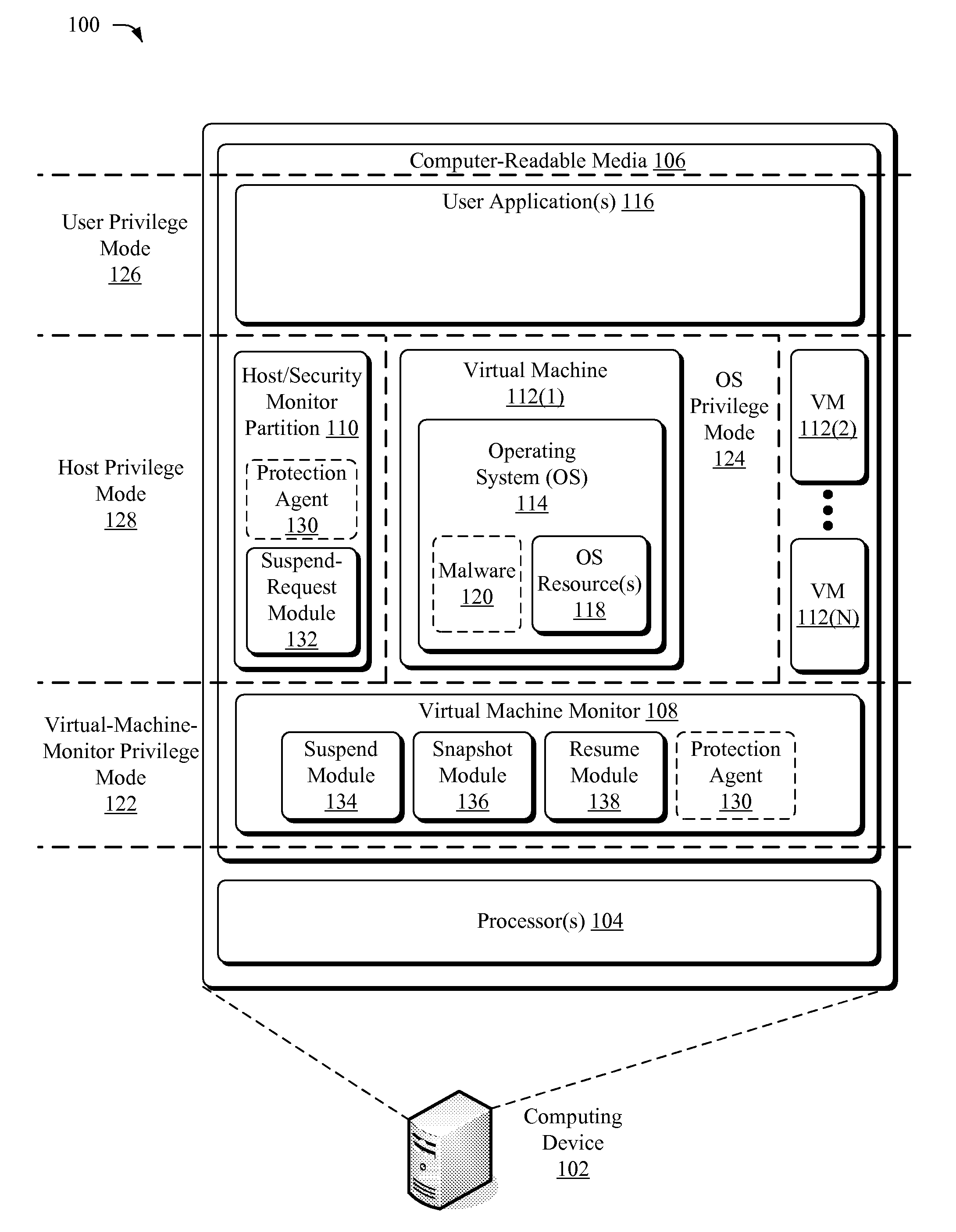
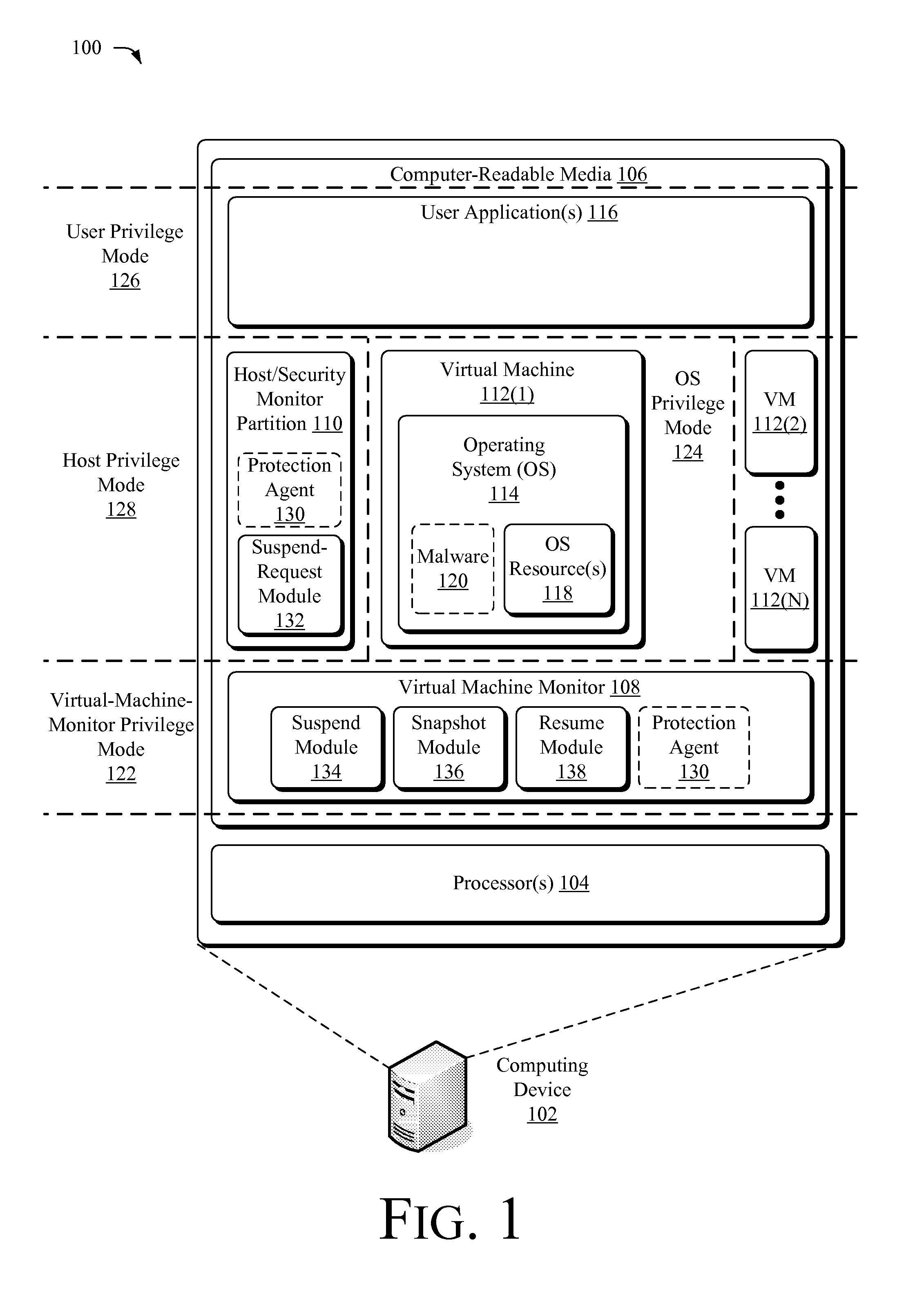
Suspending a Running Operating System to Enable Security Scanning
InactiveUS20090007100A1Well formedUser identity/authority verificationPlatform integrity maintainanceOperational systemRemedial action
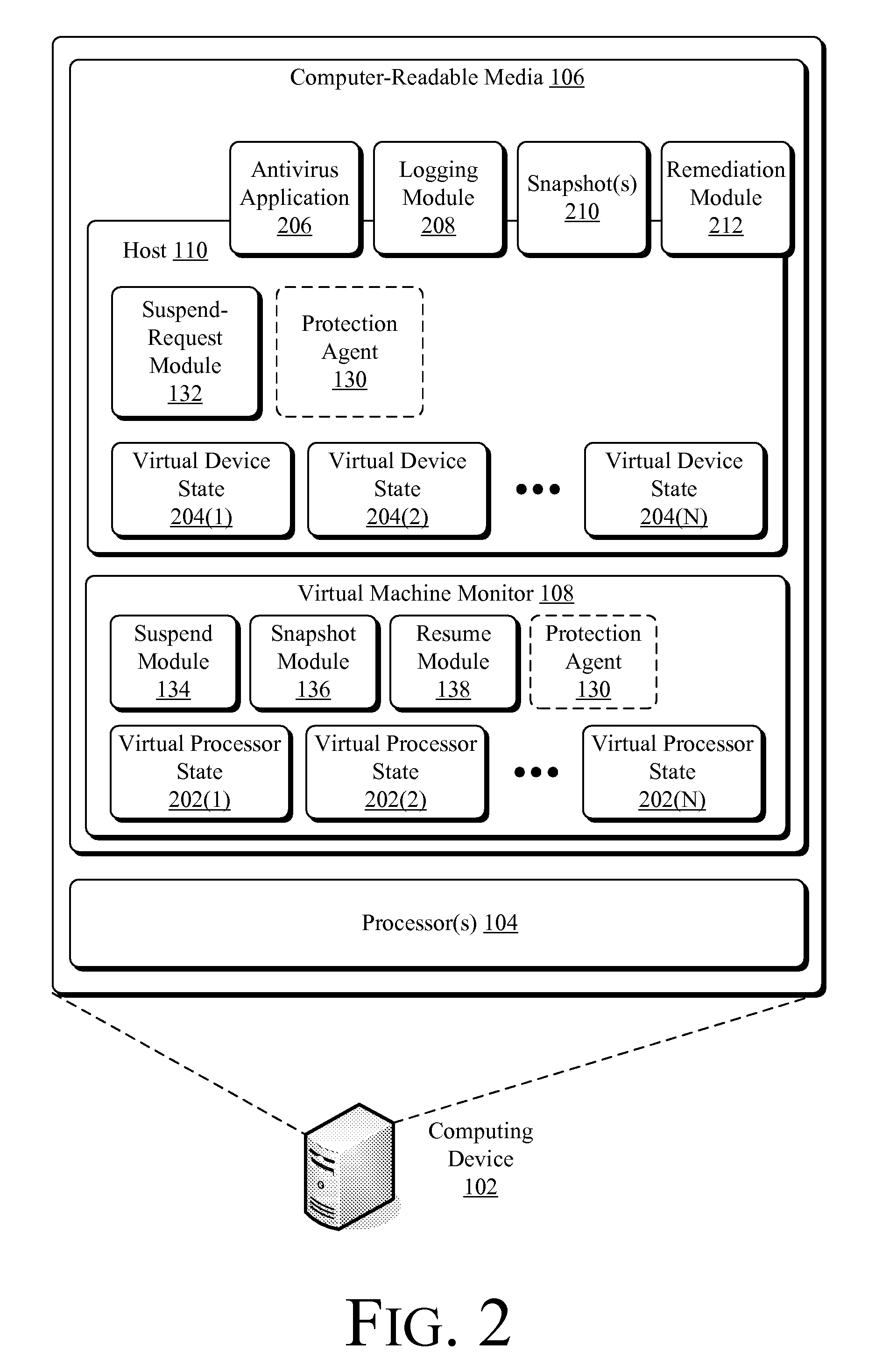
Techniques described herein enable virtualizing a processor into one or more virtual machines and suspending an operating system of one of the virtual machines from outside of the operating system environment. Once suspended, these techniques capture a snapshot of the virtual machine to determine a presence of malware. This snapshot may also be used to determine whether an unauthorized change has occurred within contents of the virtual machine. Remedial action may occur responsive to determining a presence of malware or an unauthorized change.
Owner:MICROSOFT TECH LICENSING LLC
Malware Detector
InactiveUS20080320594A1Memory loss protectionError detection/correctionVirtual memoryOperational system
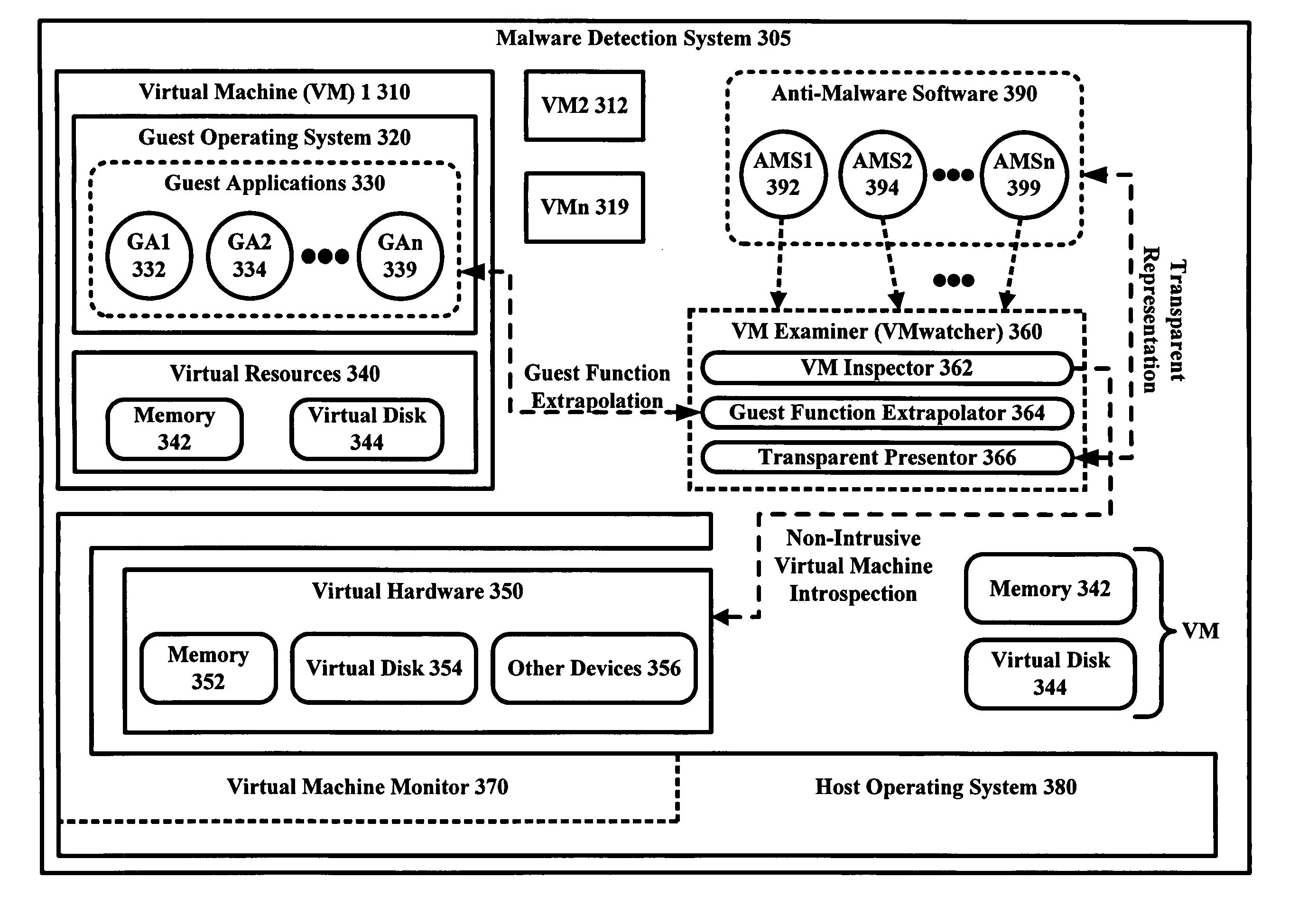
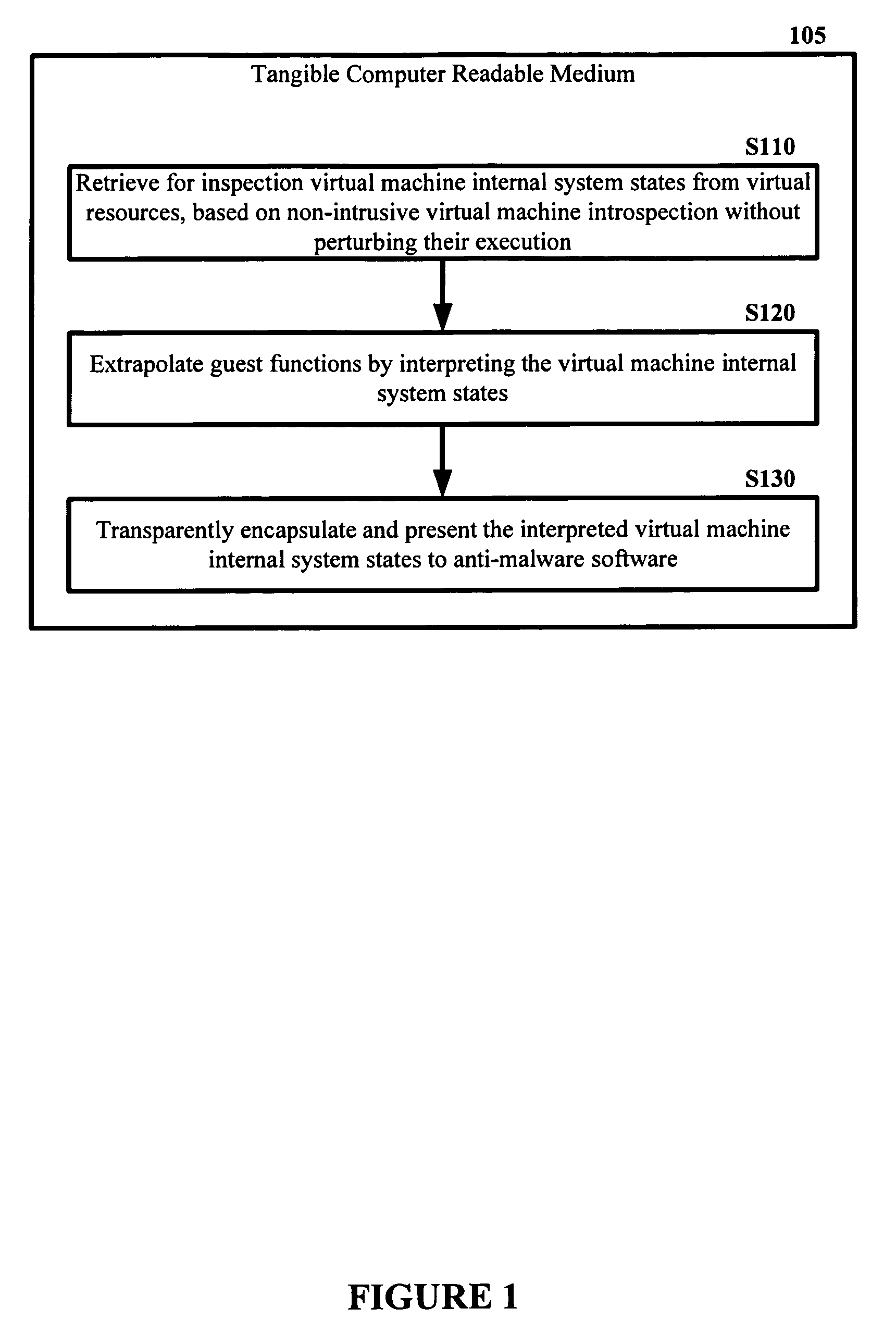
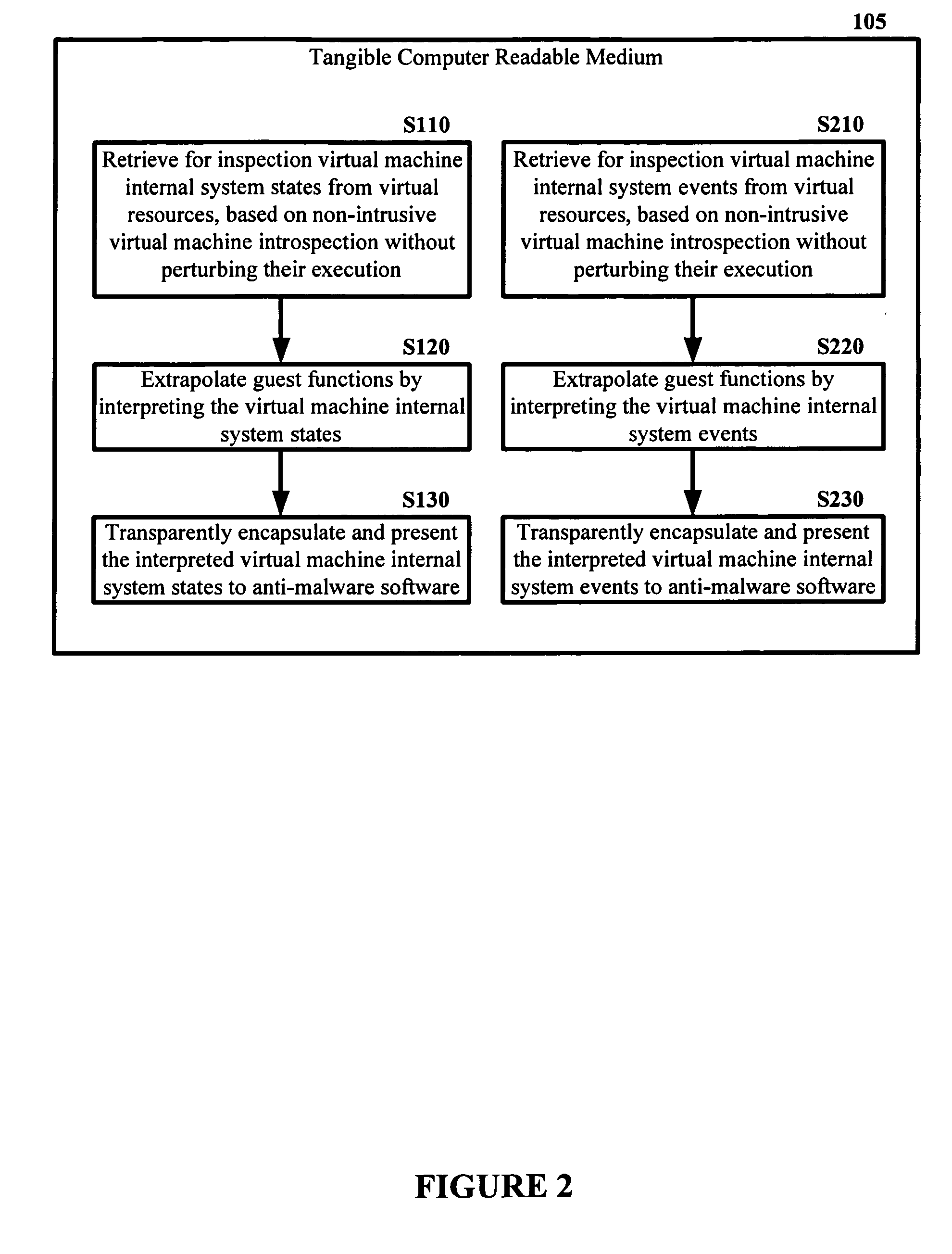
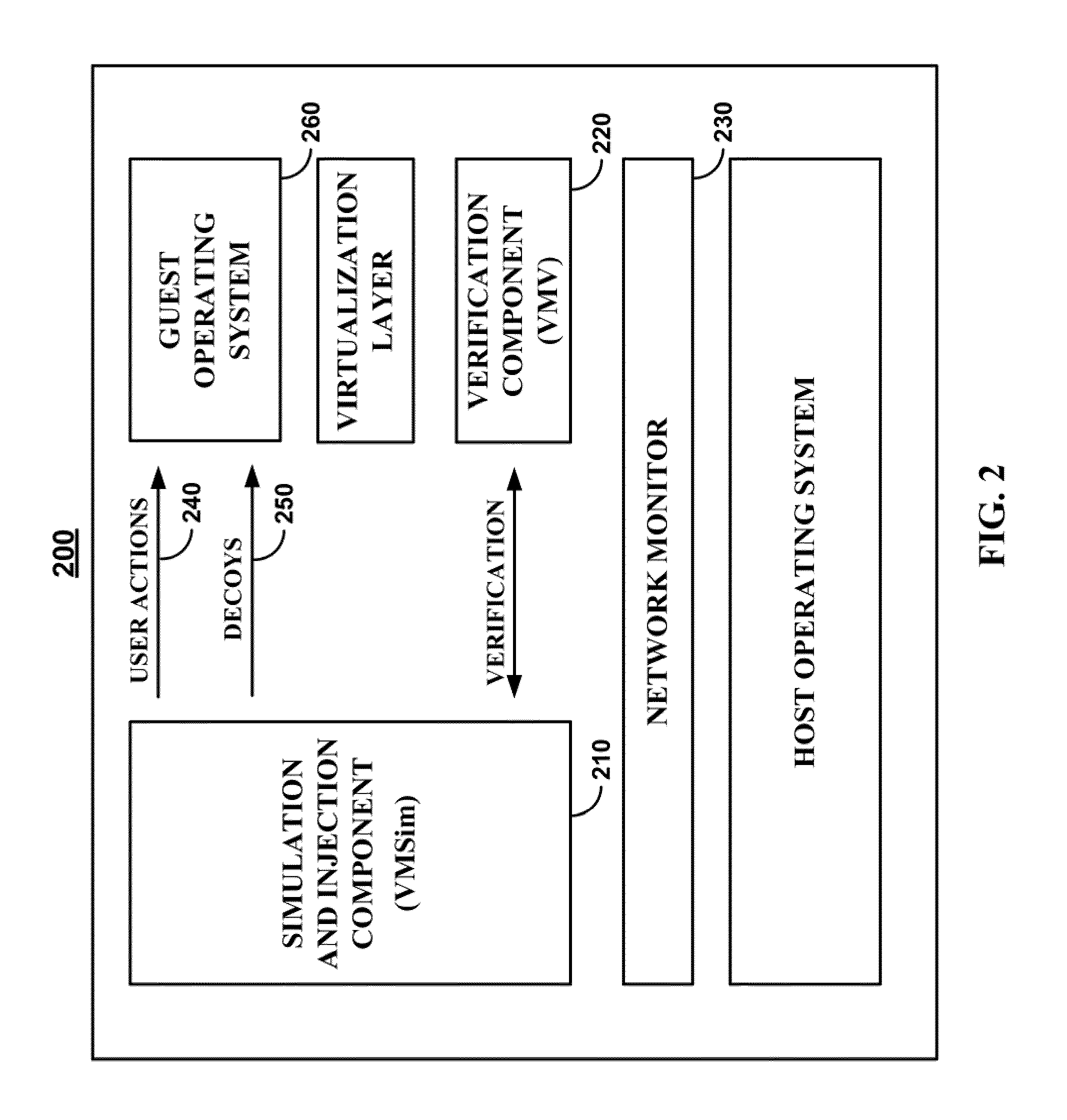
The malware detection system enables out-of-the box, tamper-resistant malware detection without losing the semantic view. This system comprises at least one guest operating system and at least one virtual machine, where the guest operating system runs on the virtual machine. Having virtual resources, the virtual machine resides on a host operating system. The virtual resources include virtual memory and at least one virtual disk. A virtual machine examiner is used to examine the virtual machine. With a virtual machine inspector, a guest function extrapolator, and a transparent presenter, the virtual machine examiner resides outside the virtual machine. The virtual machine inspector is configured to retrieve virtual machine internal system states and / or events. The guest function extrapolator is configured to interpret such states and / or events. The transparent presenter is configured to present the interpreted states and / or events to anti-malware software. The anti-malware software is configured to use the interpreted states and / or events to detect any system compromise.
Owner:GEORGE MASON INTPROP INC
Methods, systems, and media for detecting covert malware
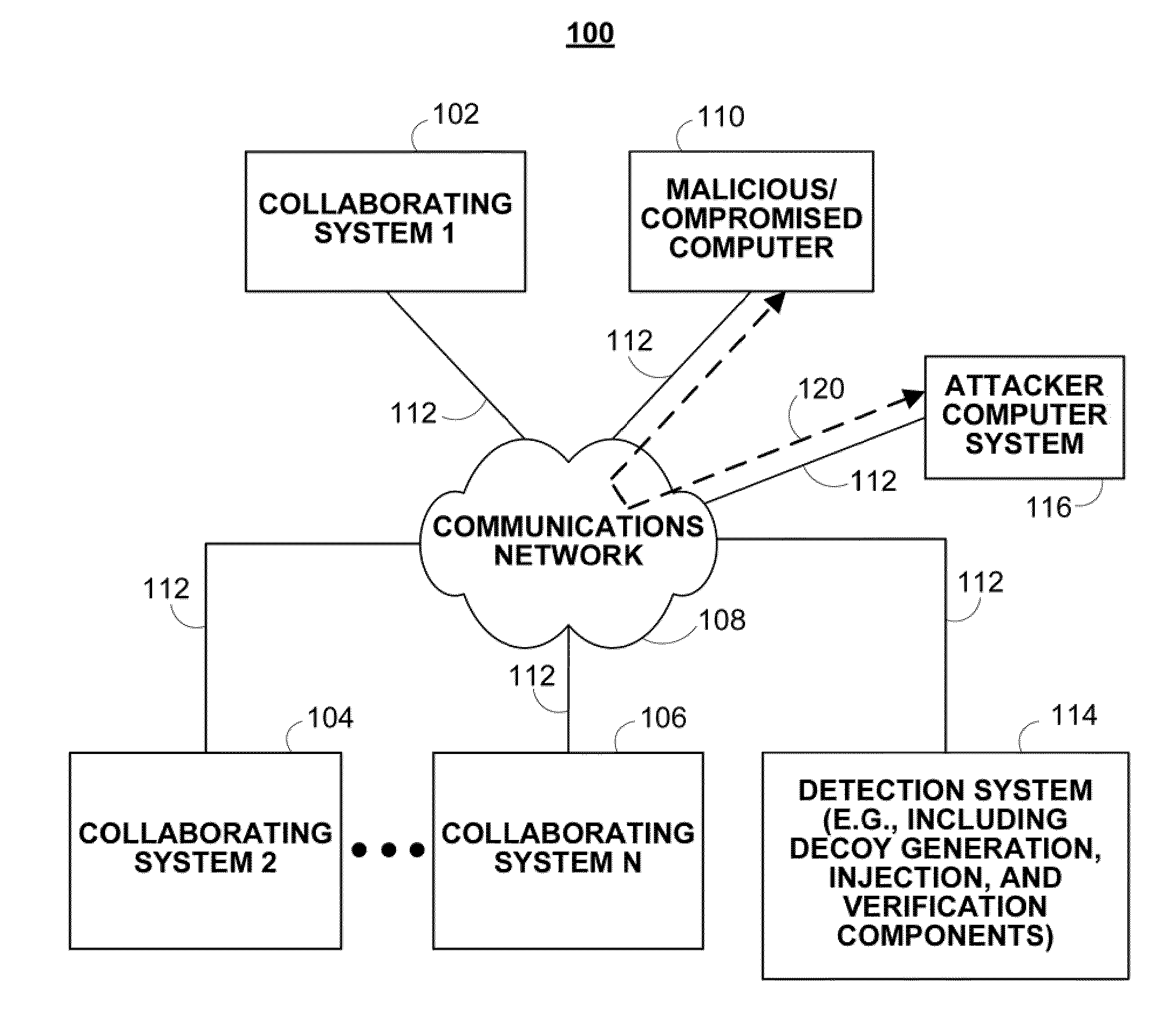
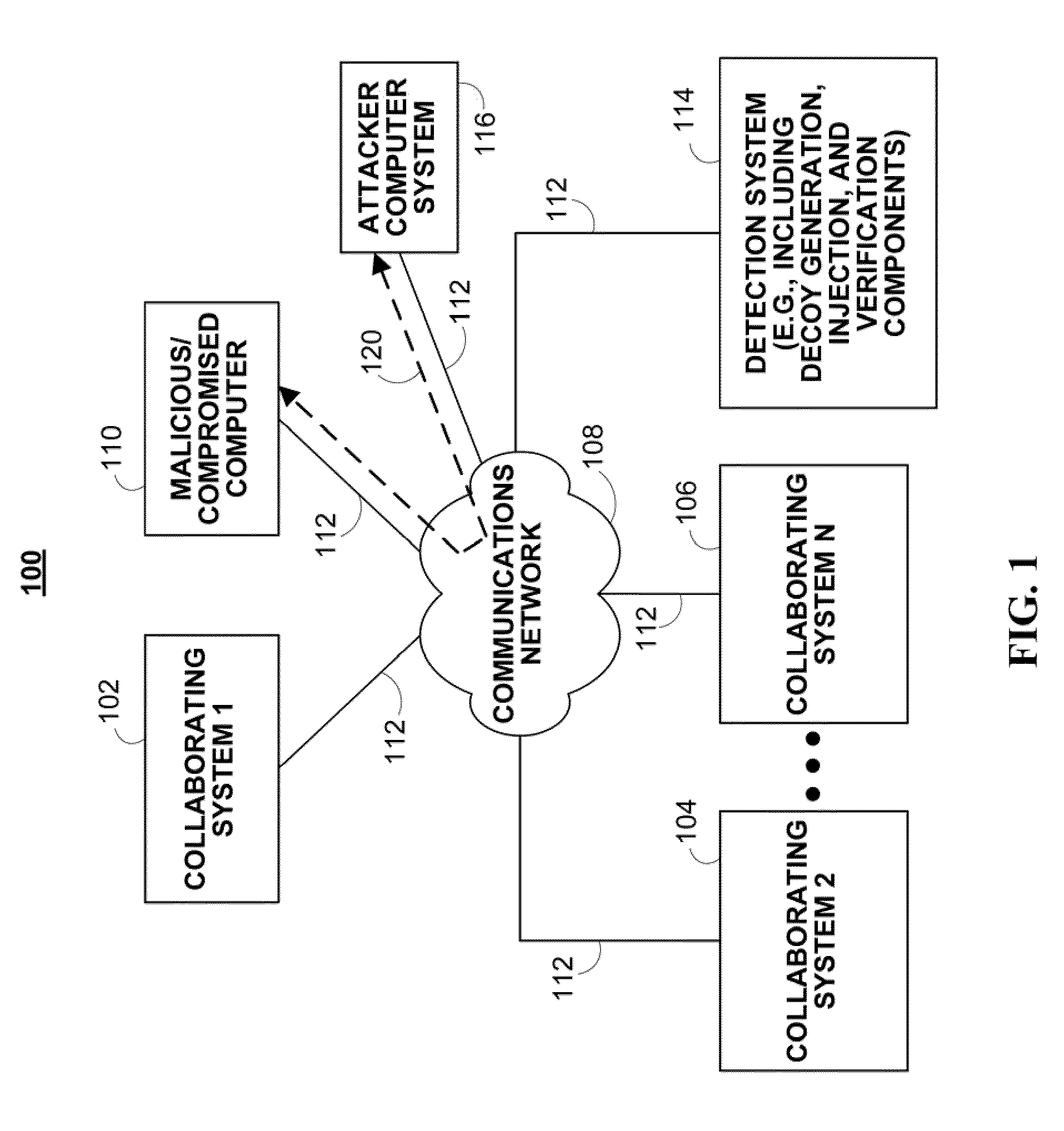
ActiveUS20110167494A1Reduce level of system knowledgeMemory loss protectionError detection/correctionDecoyApplication software
Methods, systems, and media for detecting covert malware are provided. In accordance with some embodiments, a method for detecting covert malware in a computing environment is provided, the method comprising: generating simulated user activity outside of the computing environment; conveying the simulated user activity to an application inside the computing environment; and determining whether a decoy corresponding to the simulated user activity has been accessed by an unauthorized entity.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
Malware Modeling Detection System And Method for Mobile Platforms
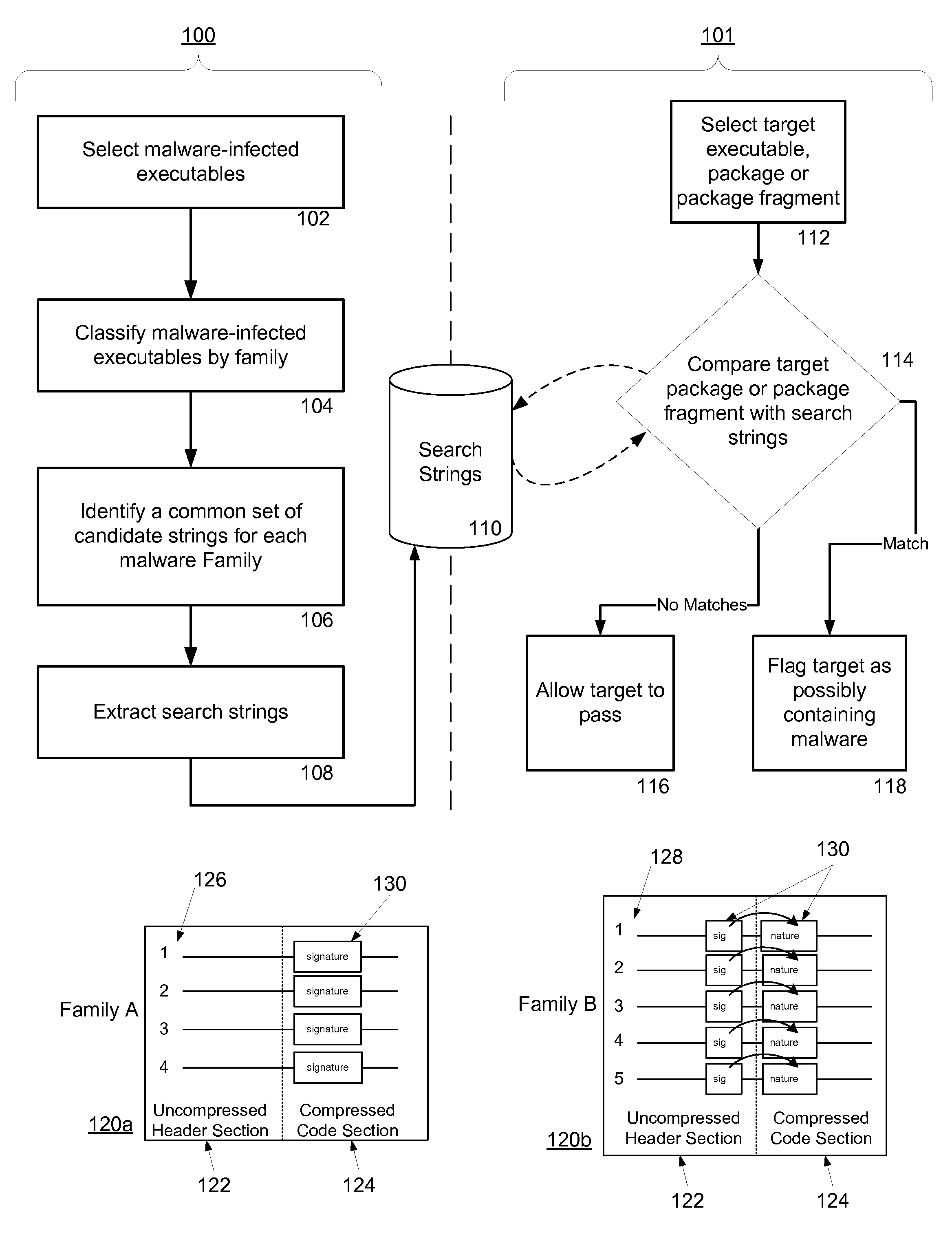
ActiveUS20070240217A1Suitable for useReliable detectionMemory loss protectionUser identity/authority verificationFeature setAlgorithm
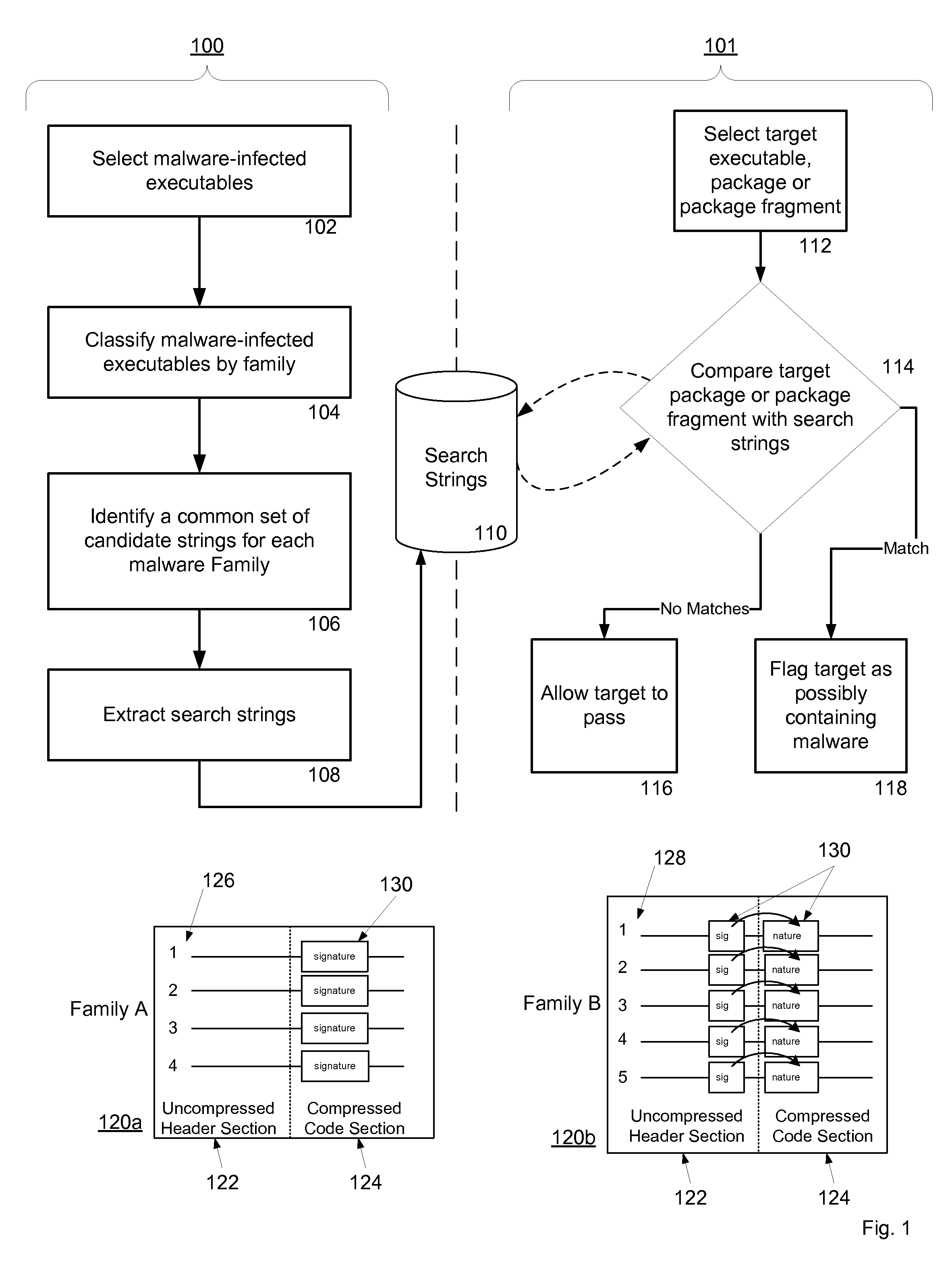
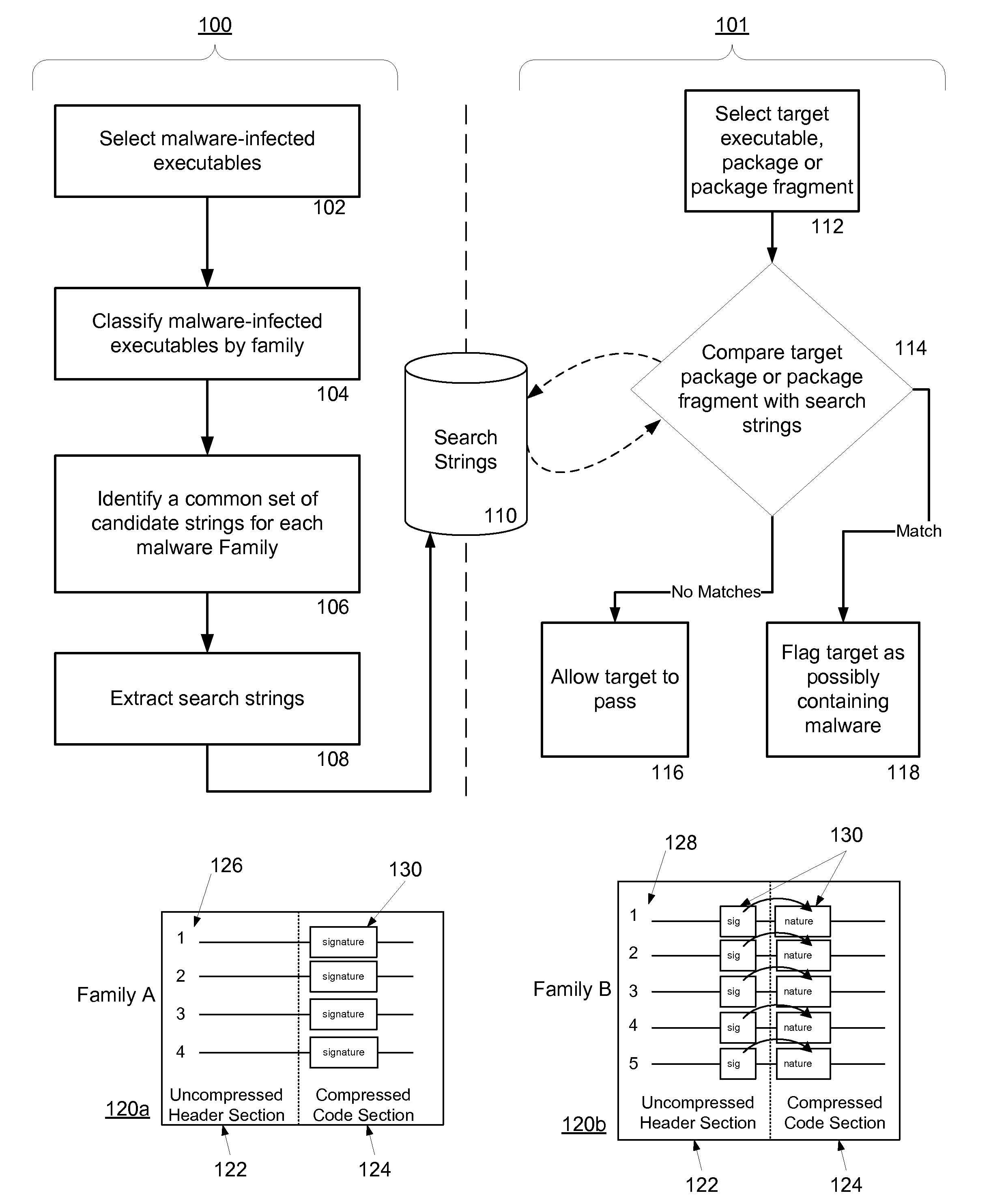
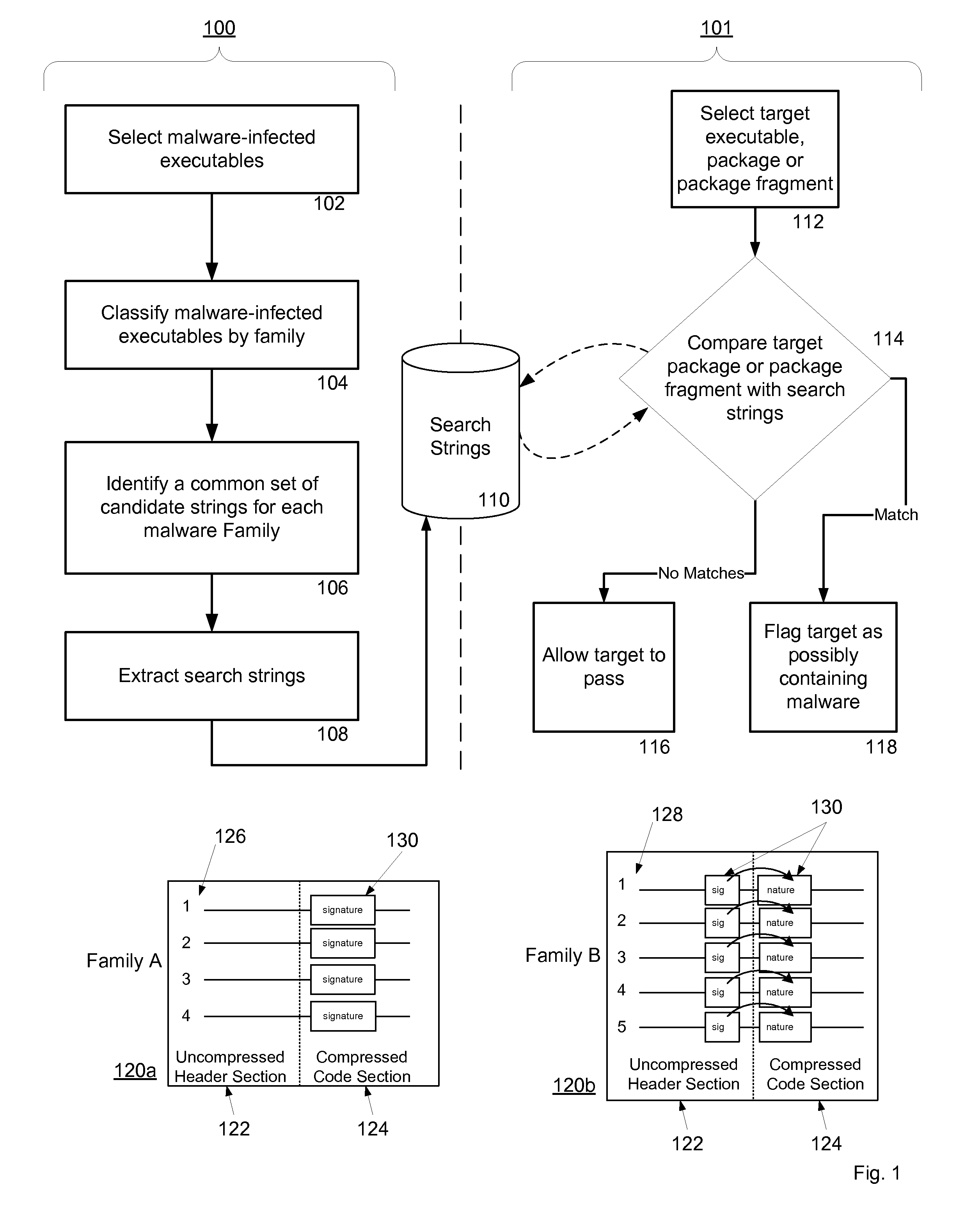
A system and method for detecting malware by modeling the behavior of malware and comparing a suspect executable with the model. The system and method extracts feature elements from malware-infected applications, groups the feature elements into feature sets, and develops rules describing a malicious probability relationship between the feature elements. Using malware-free and malware-infected applications as training data, the system and method heuristically trains the rules and creates a probability model for identifying malware. To detect malware, the system and method scans the suspect executable for feature sets and applies the results to the probability model to determine the probability that the suspect executable is malware-infected.
Owner:PULSE SECURE
Method and apparatus for detecting malware infection
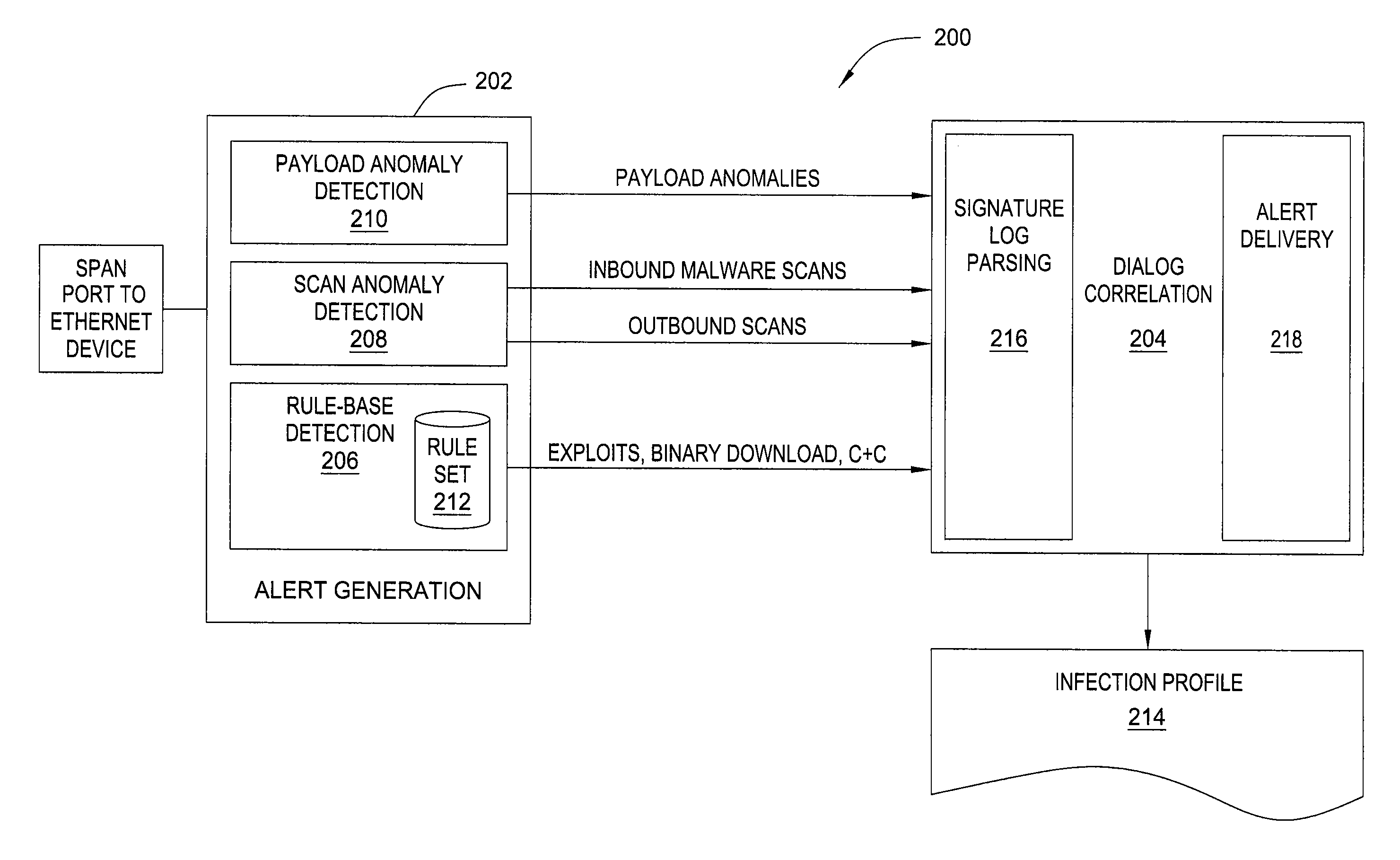
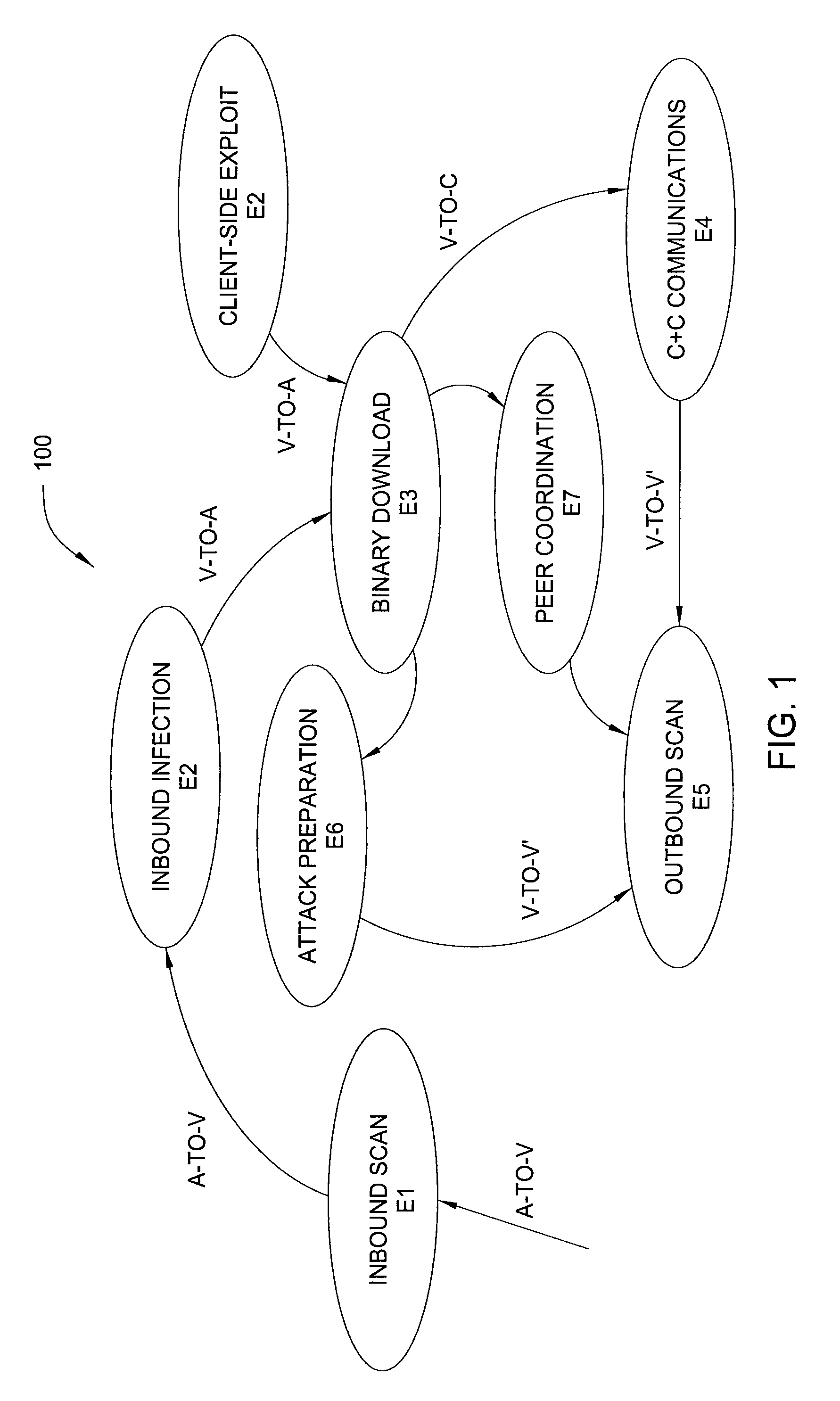
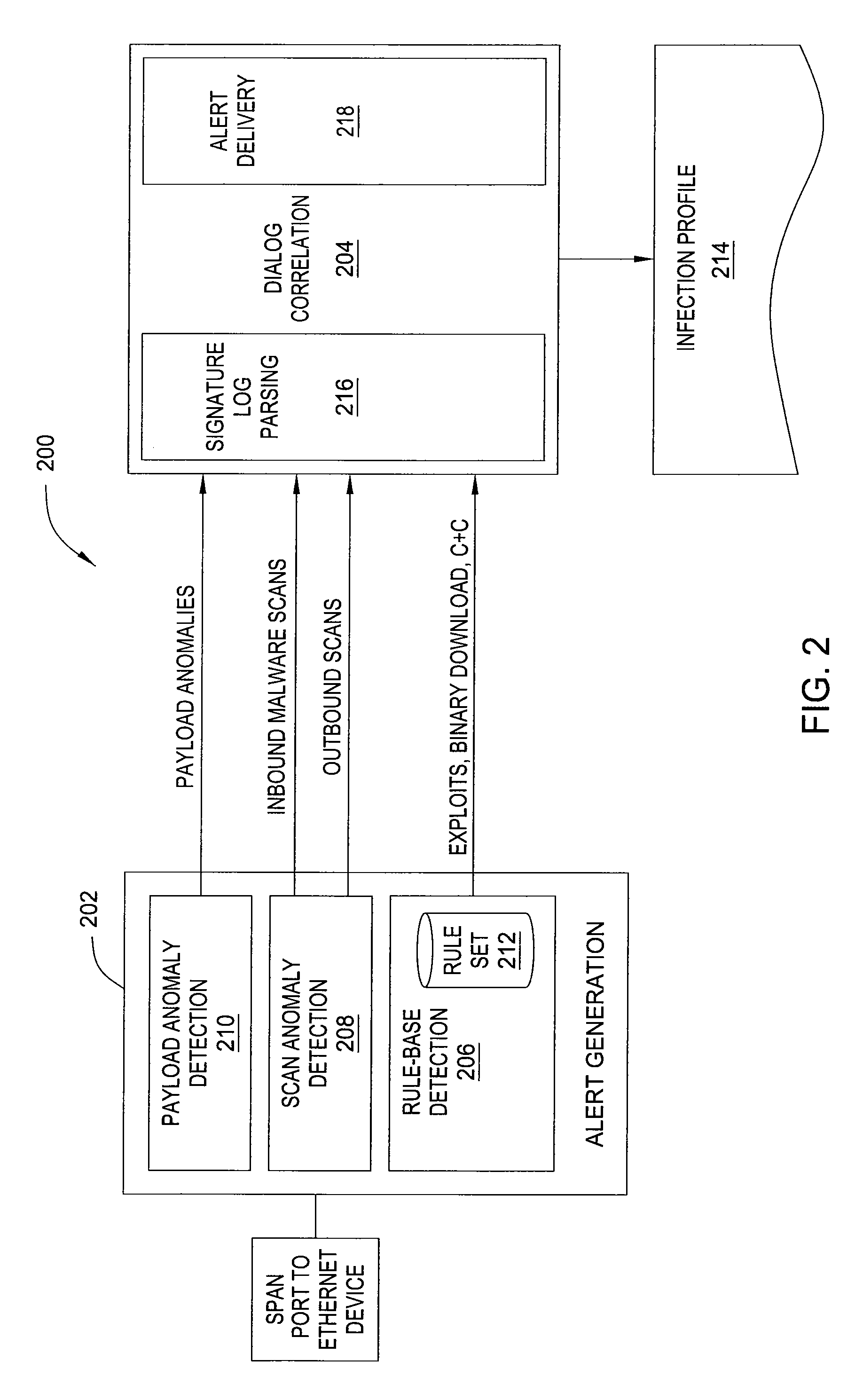
In one embodiment, the present invention is a method and apparatus for detecting malware infection. One embodiment of a method for detecting a malware infection at a local host in a network, includes monitoring communications between the local host and one or more entities external to the network, generating a dialog warning if the communications include a transaction indicative of a malware infection, declaring a malware infection if, within a predefined period of time, the dialog warnings includes at least one dialog warning indicating a transaction initiated at the local host and at least one dialog warning indicating an additional transaction indicative of a malware infection, and outputting an infection profile for the local host.
Owner:SRI INTERNATIONAL
System and method for managing malware protection on mobile devices
ActiveUS20070240220A1Suitable for useReliable detectionMemory loss protectionError detection/correctionLimited accessFeature set
A system and method for detecting malware on a limited access mobile platform in a mobile network. The system and method uses one or more feature sets that describe various non-executable portions of malware-infected and malware-free applications, and compares a application on the limited access mobile platform to the features sets. A match of the features in a suspect application to one of the feature sets provides an indication as to whether the suspect application is malware-infected or malware-free.
Owner:PULSE SECURE
Malware detection method, system and computer program product
InactiveUS20110219449A1Easy to detectMemory loss protectionError detection/correctionMalwareSoftware
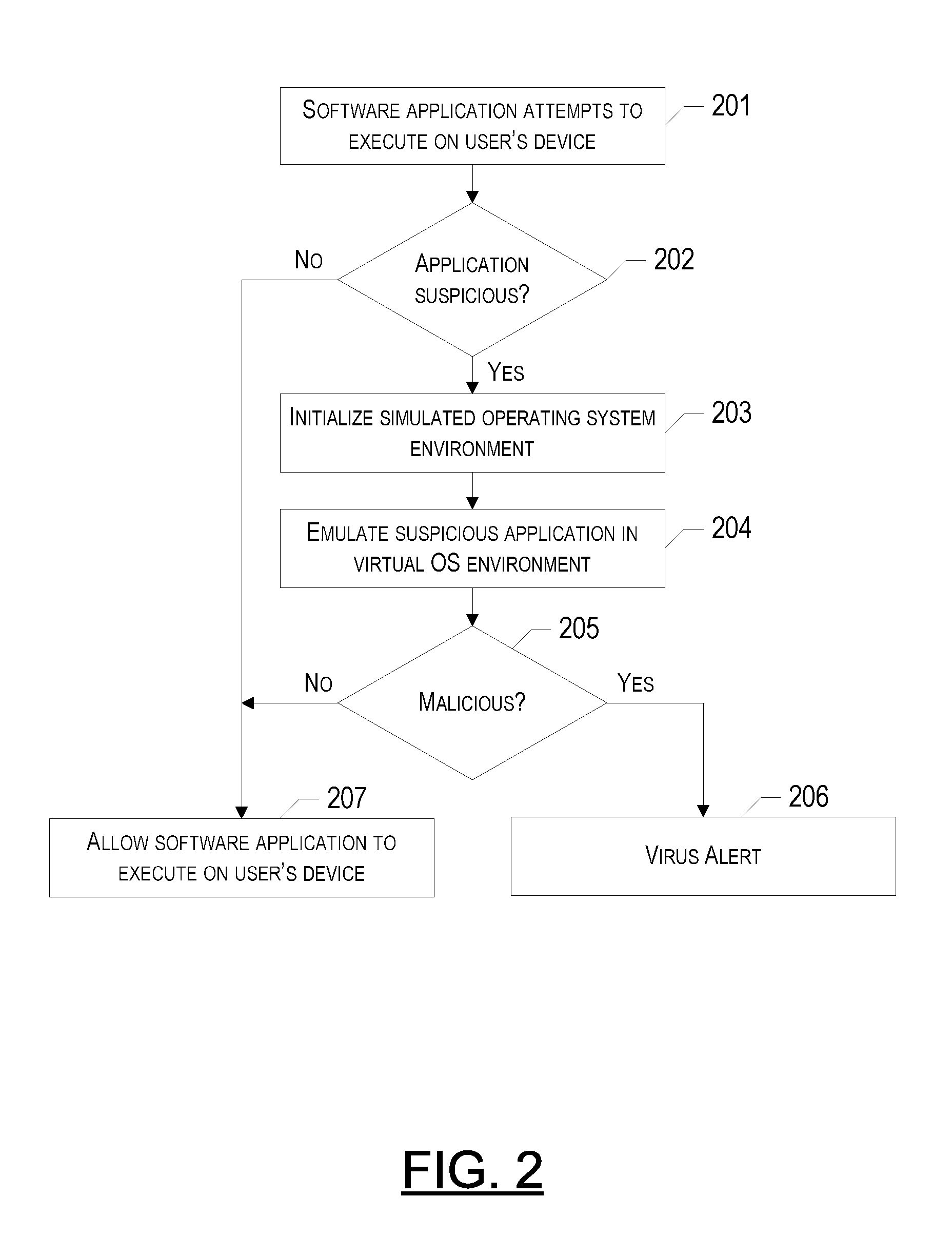
A method, electronic device and computer program product for real-time detection of malicious software (“malware”) are provided. In particular, execution of a suspicious software application attempting to execute on a user's device may be emulated in a virtual operating system environment in order to observe the behavior characteristics of the suspicious application. If after observing the behavior of the suspicious application in the virtual environment, it is determined that the application is malicious, the application may not be permitted to execute on the user's actual device. The suspicious application may be identified as malicious if an isolated data string of the application matches a “blacklisted” data string, a certain behavior of the application matches a behavior that is known to be malicious, and / or the overall behavior of the application is substantially the same or similar to a known family of malware.
Owner:SUNBELT SOFTWARE
System and method for malicious software detection in multiple protocols
ActiveUS8321936B1Overcome limitationsEasy to detectMemory loss protectionError detection/correctionTransport systemSystem configuration
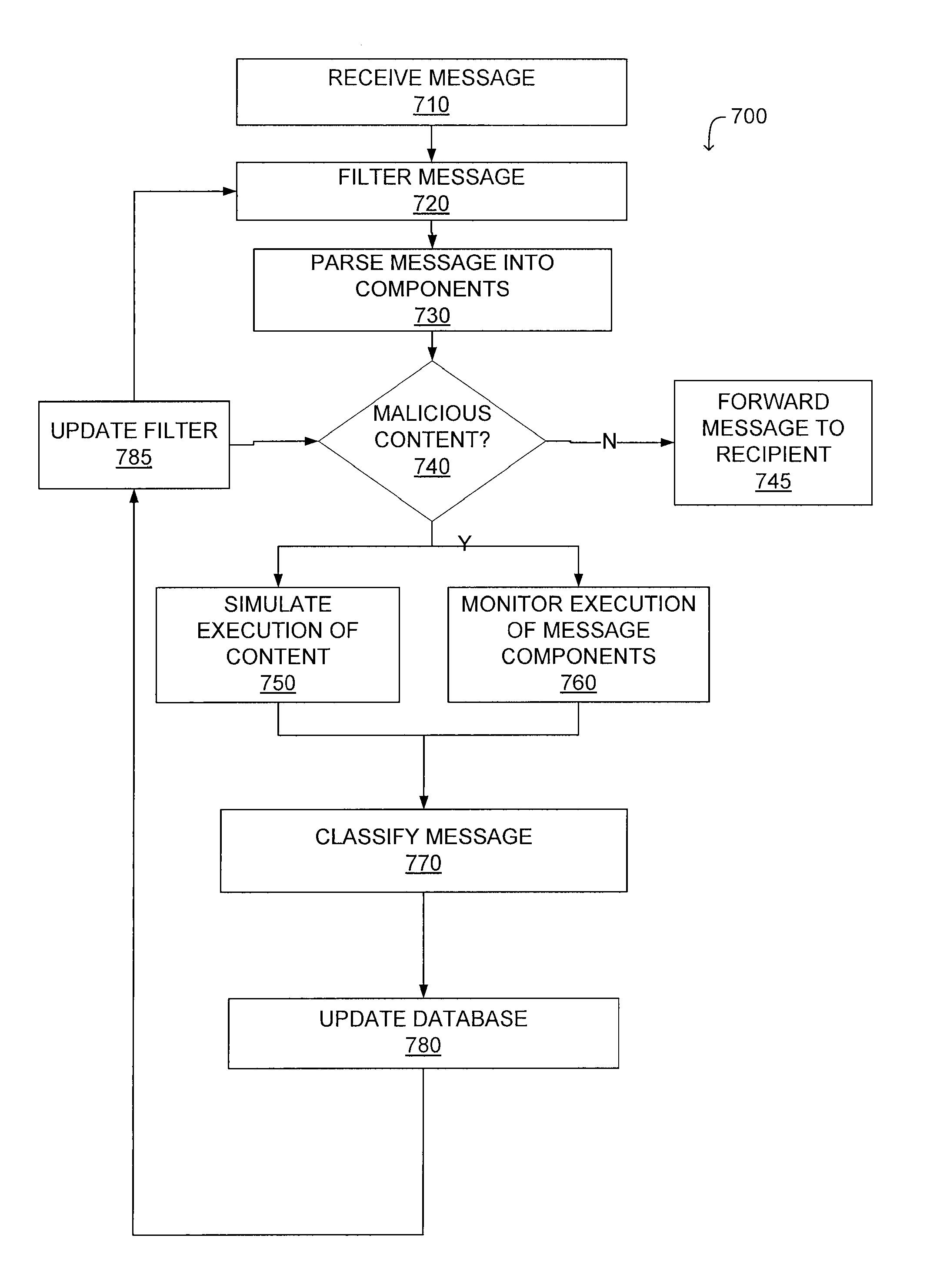
A system and a method for detecting malicious content associated with an electronic message are described. An electronic message, such as an e-mail, a chat request, a torrent file or a text message is initially received. The electronic message can then be compared to known viruses using pattern or signature matching techniques. The electronic message is then transmitted to a virtual machine which executes the electronic message in an environment simulating the destination computing system of the electronic message. The virtual machine monitors execution of the electronic message to identify one or more malicious actions and classifies the electronic message accordingly. For example, message component execution is monitored for attempts to access system files, attempts to access user information, attempts to transmit system configuration data or attempts to transmit user information.
Owner:AVINTI CORP
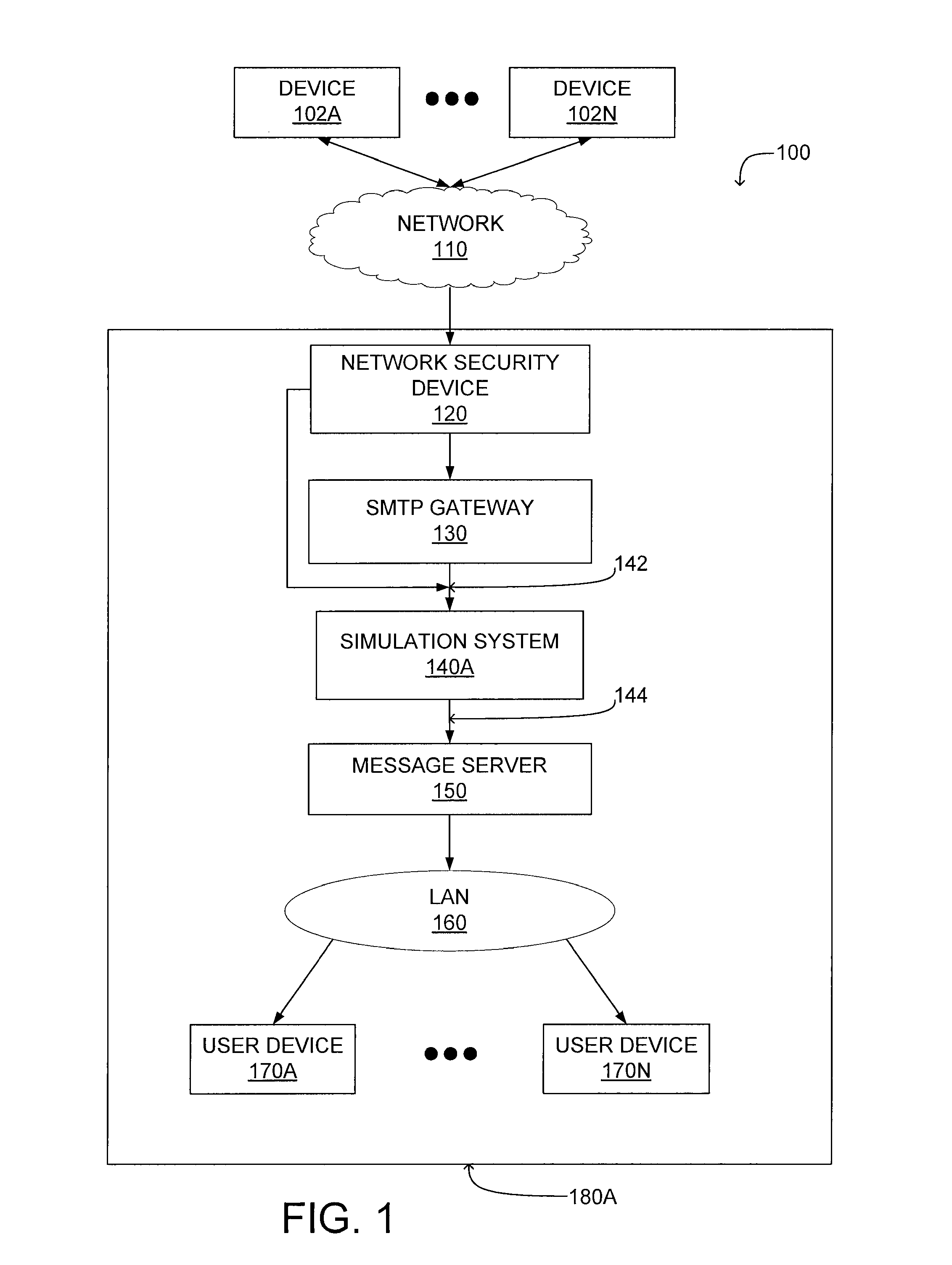
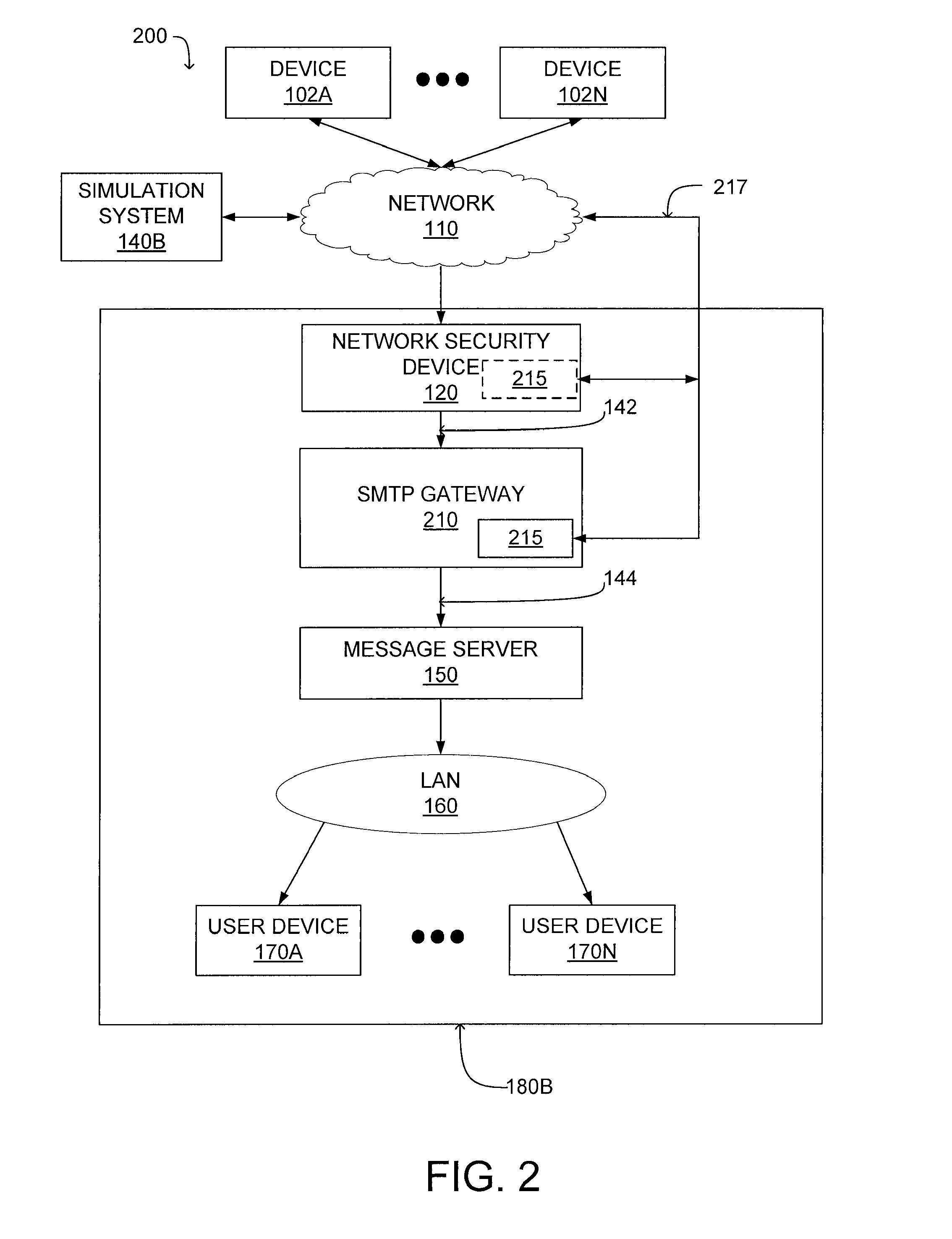
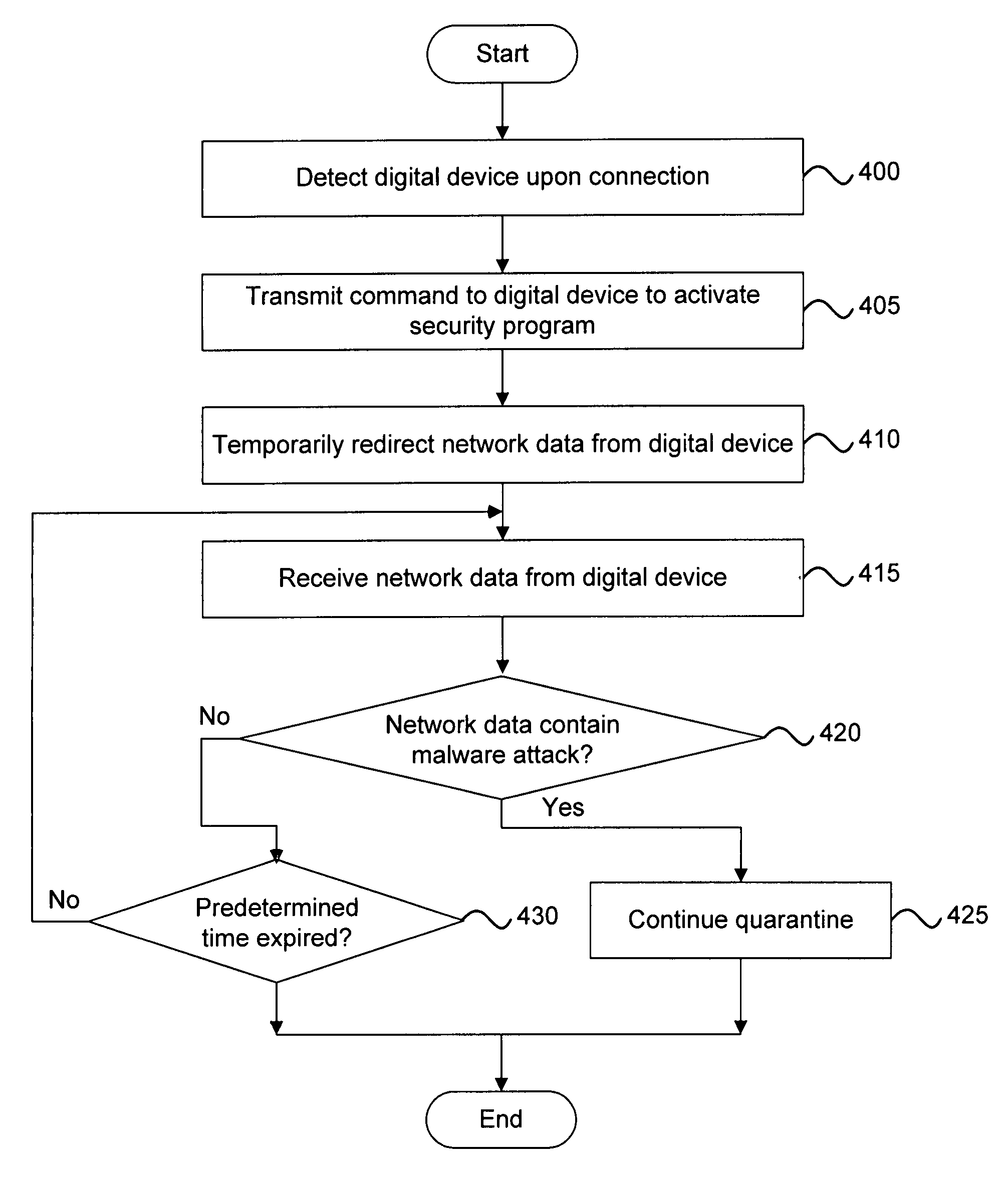
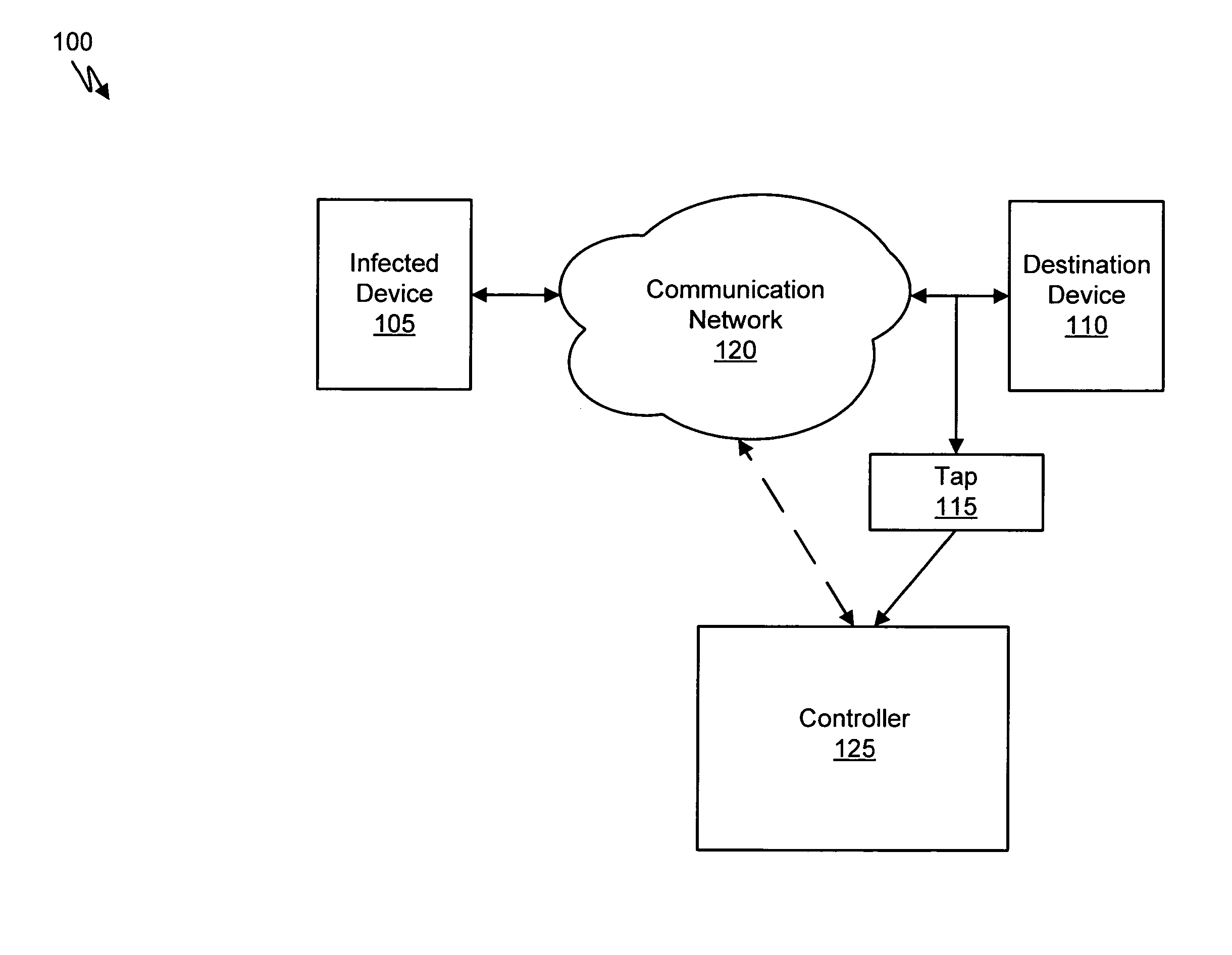
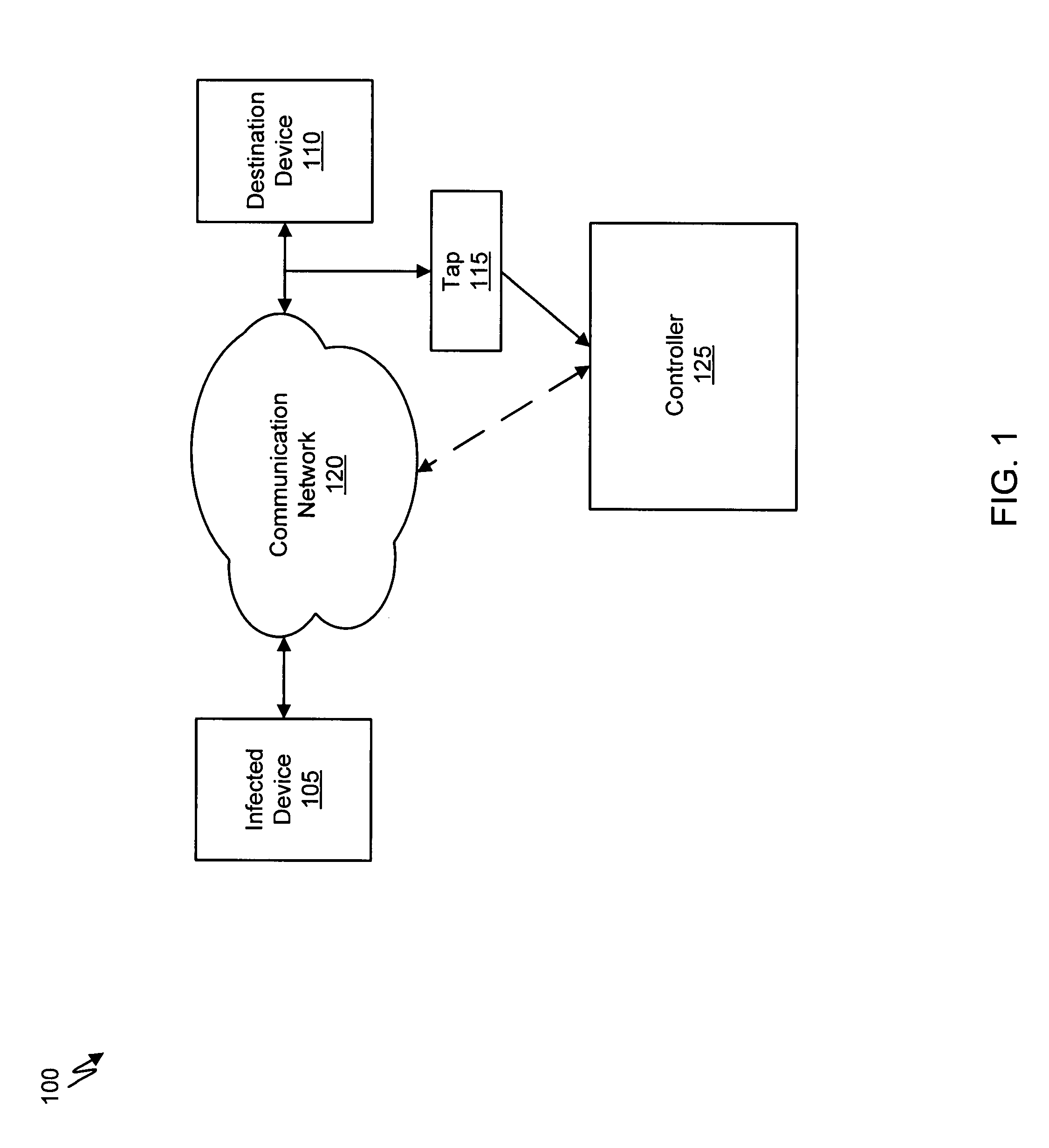
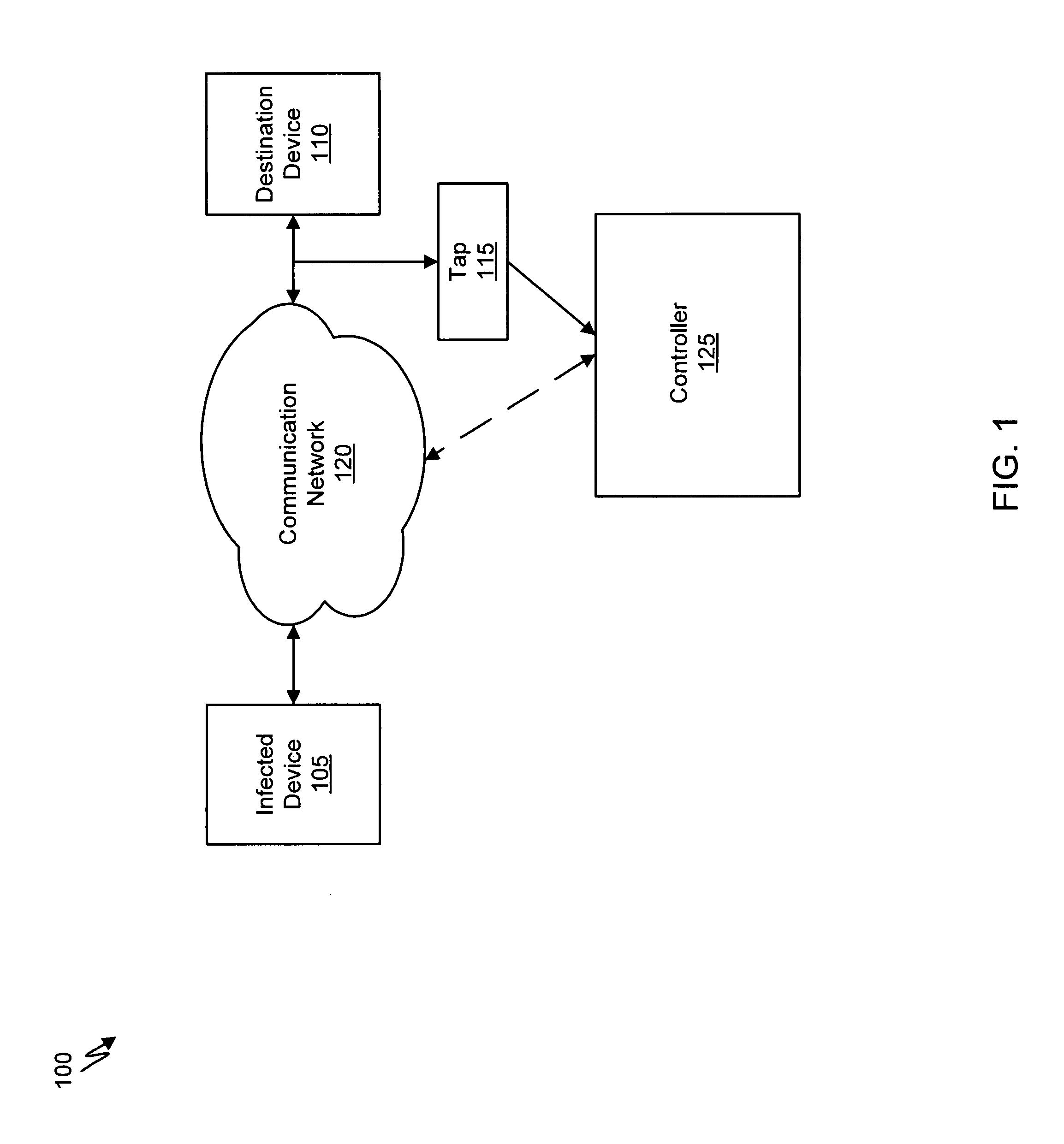
Malware containment and security analysis on connection
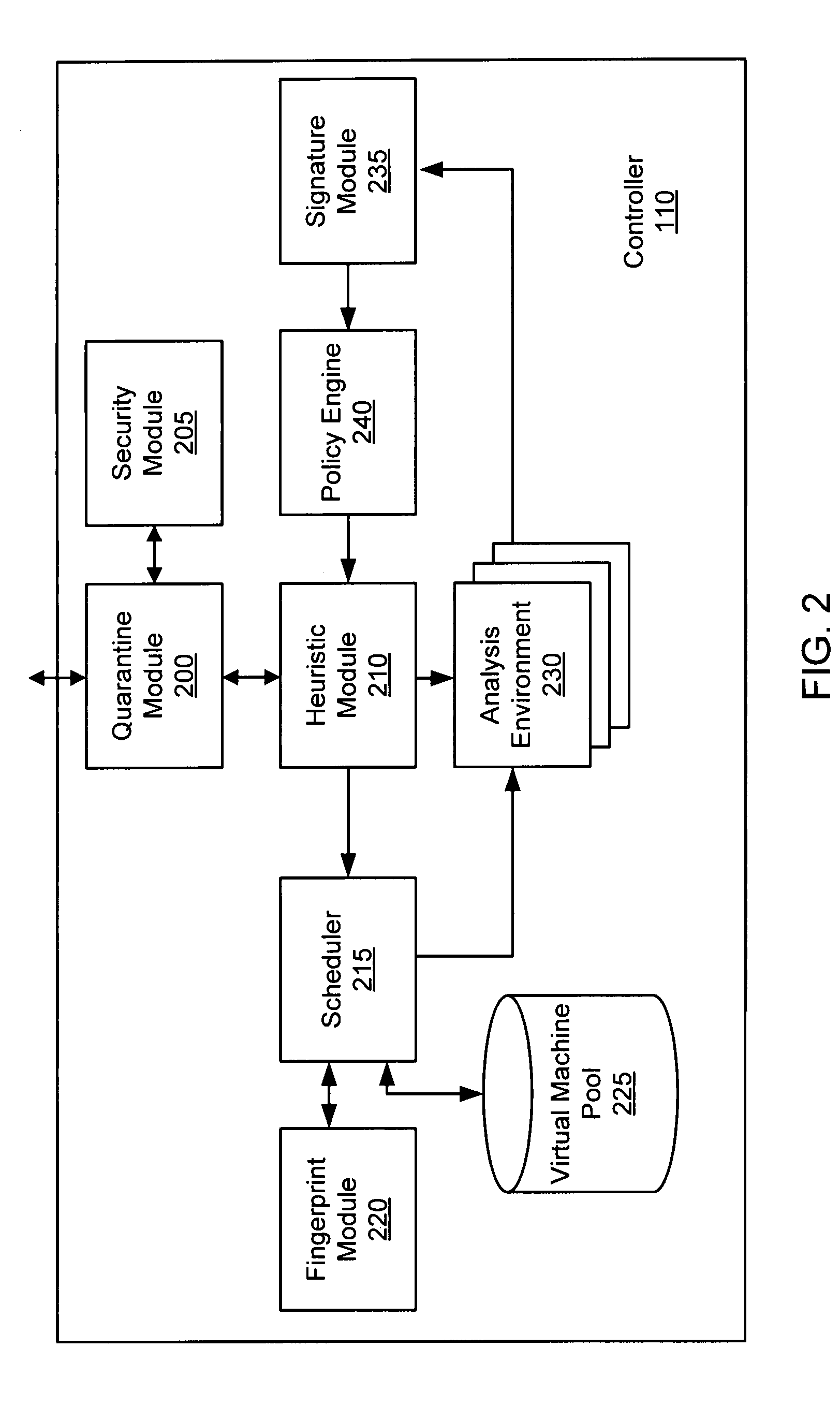
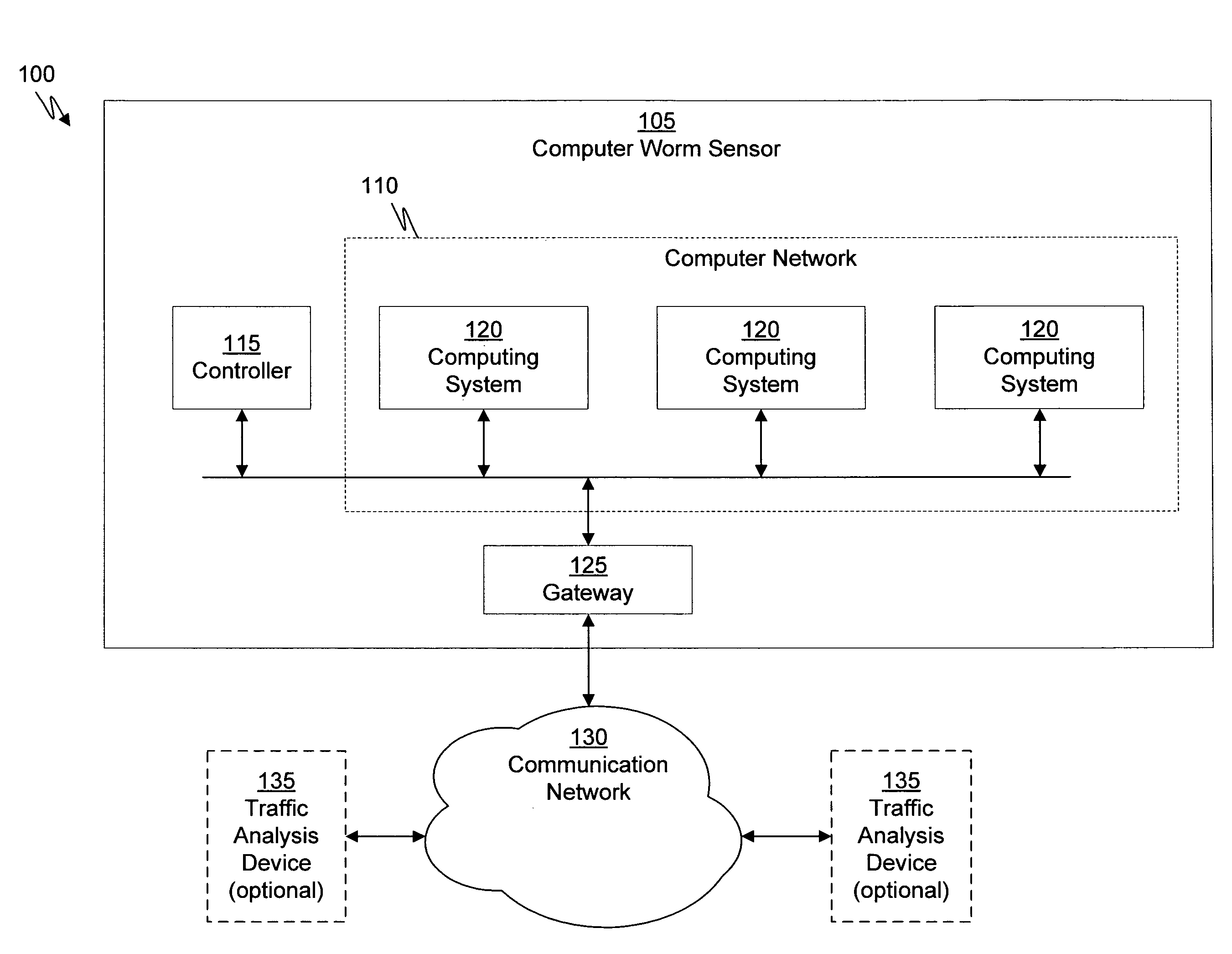
Systems and methods for malware containment and security analysis on connection are provided. Digital devices are quarantined for a predetermined period of time upon connection to the communication network. When a digital device is quarantined, all network data transmitted by the digital device is directed to a controller which then analyzes the network data to identify unauthorized activity and / or malware within the newly connected digital device. An exemplary method to contain malware includes detecting a digital device upon connection with a communication network, quarantining network data from the digital device for a predetermined period of time, transmitting a command to the digital device to activate a security program to identify security risks, and analyzing the network data to identify malware within the digital device.
Owner:FIREEYE SECURITY HLDG US LLC
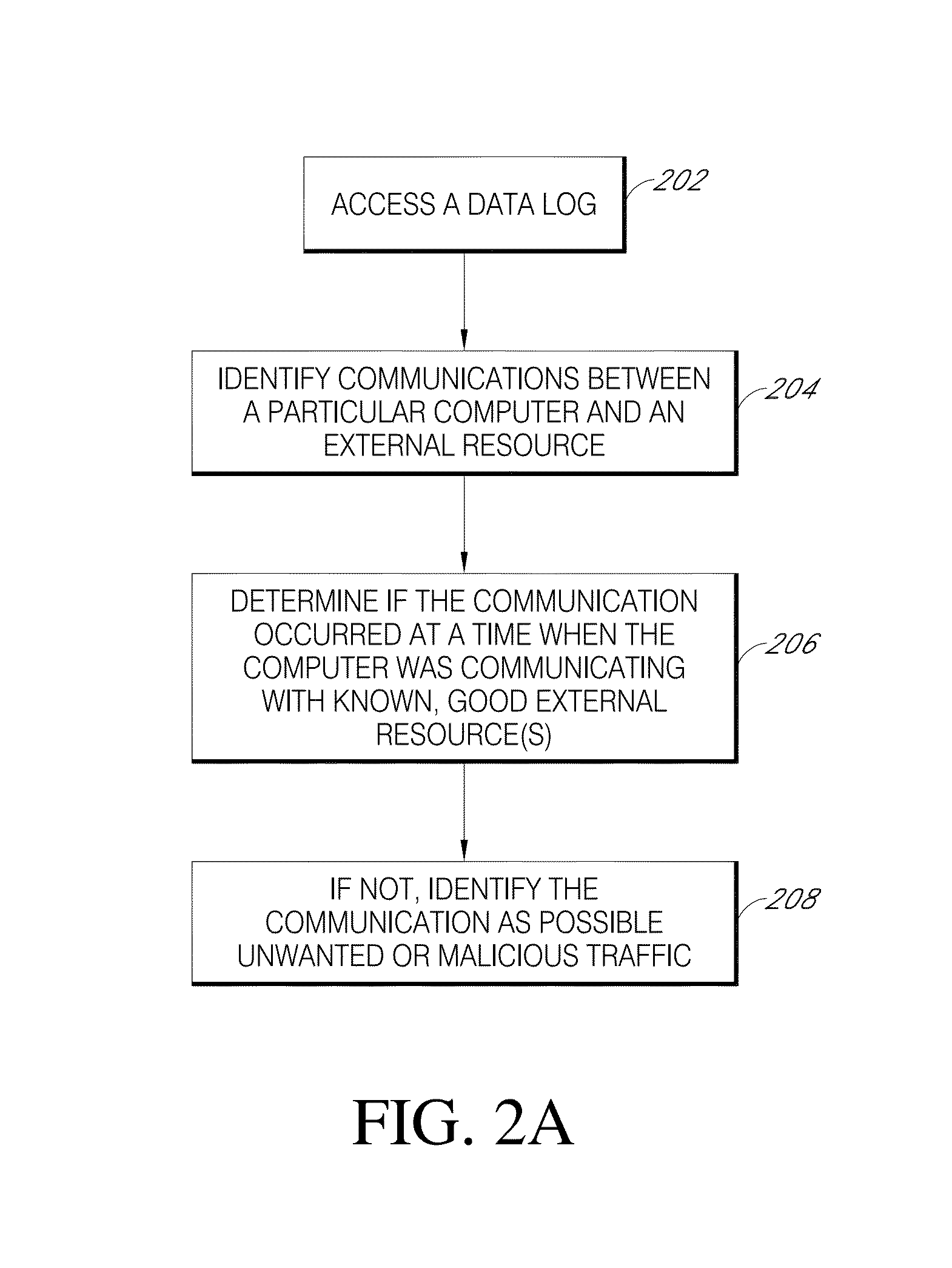
System and method of identifying the source of an attack on a computer network
The present invention provides a system and method of tracing the spread of computer malware in a communication network. One aspect of the present invention is a method that traces the spread of computer malware in a communication network. When suspicious data characteristic of malware is identified in a computing device connected to the communication network, the method causes data that describes the state of the computing device to be stored in a database. After a specific attack against the communication network is confirmed, computing devices that are infected with the malware are identified. Then, the spread of the malware between computing devices in the communication network is traced back to a source.
Owner:MICROSOFT TECH LICENSING LLC
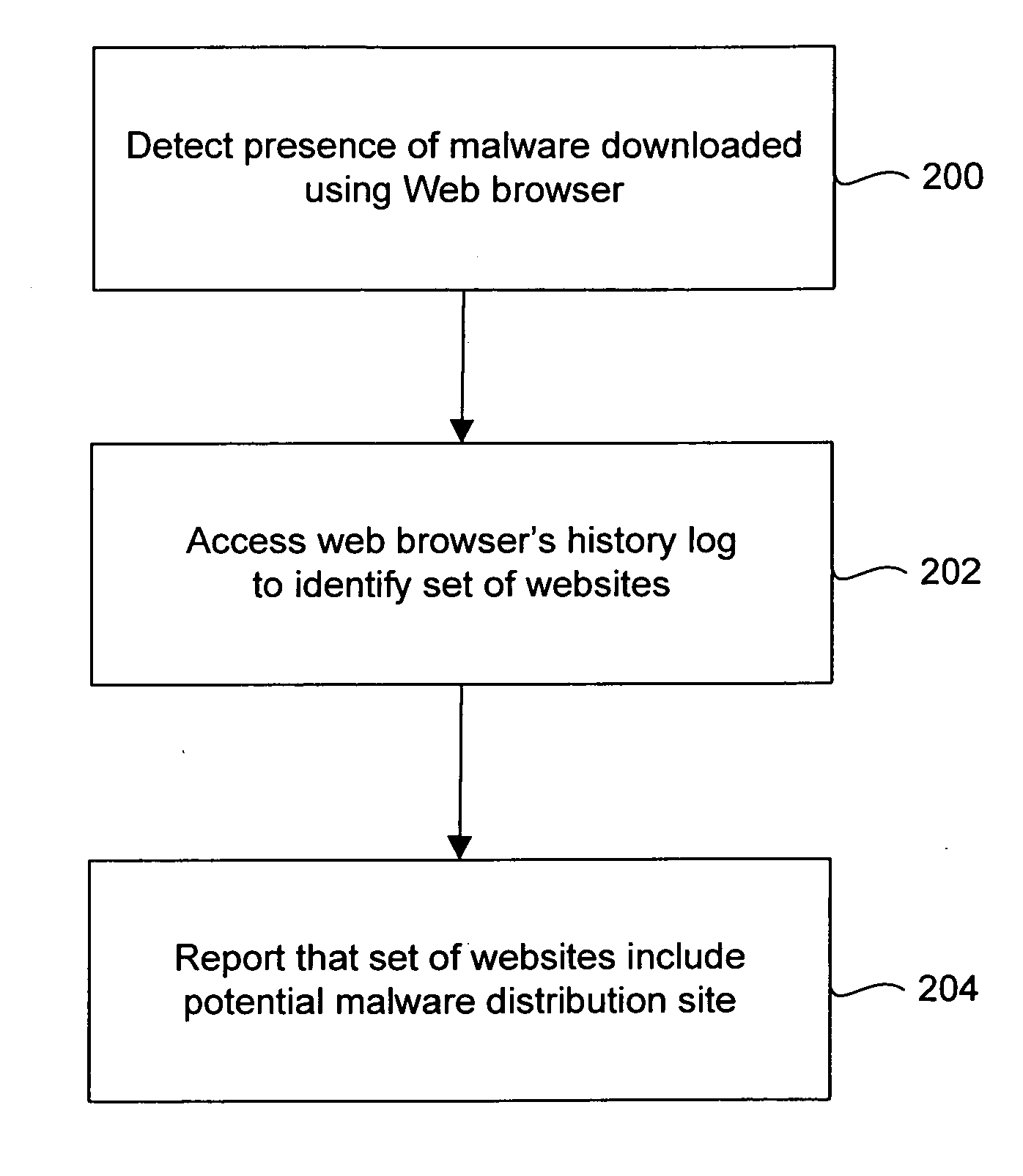
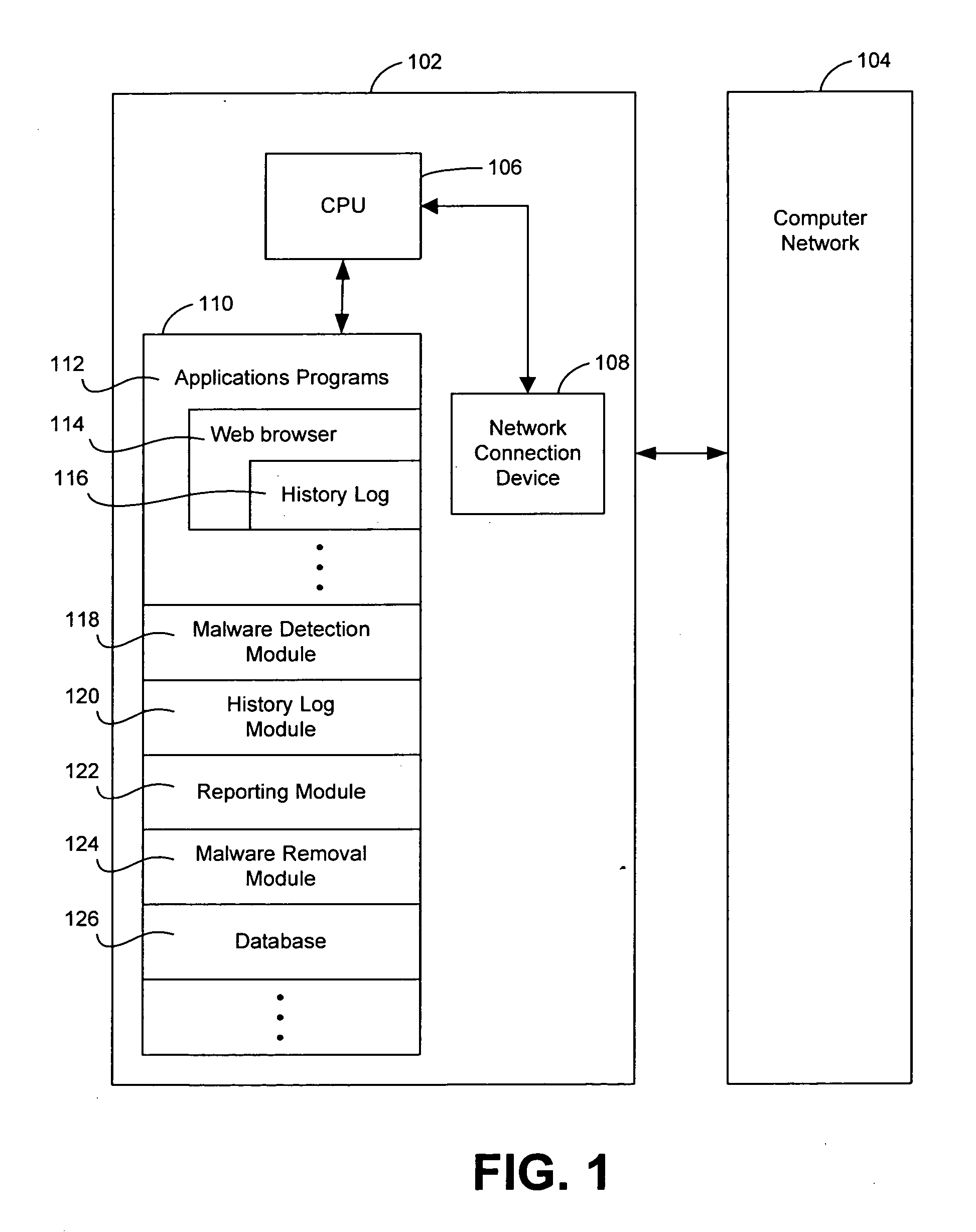
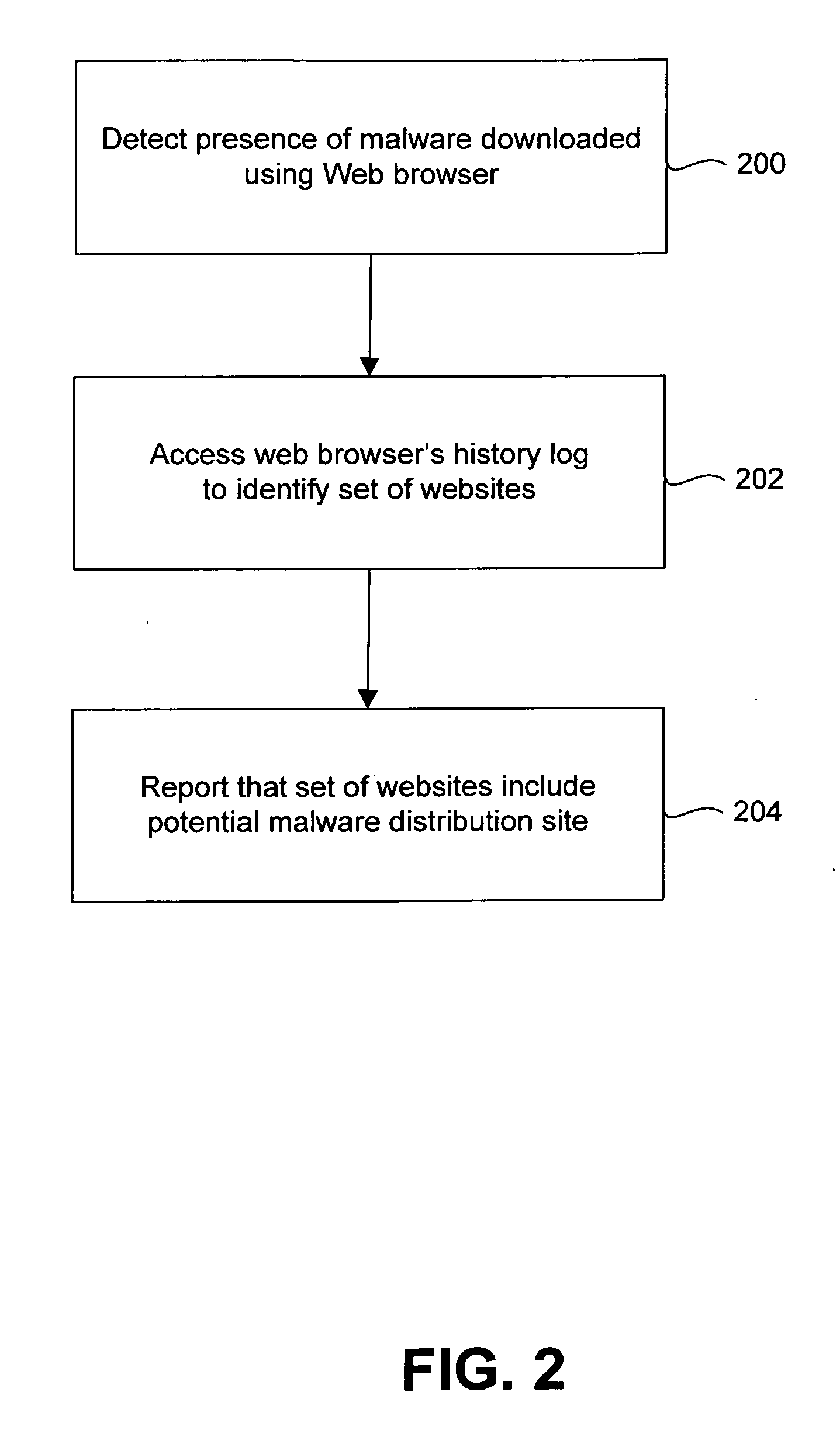
Systems and methods for identifying sources of malware
Systems and methods for identifying sources of malware are described. In one embodiment, a system includes a malware detection module configured to determine that a protected computer includes malware. The system also includes a history log module configured to access a history log of the protected computer to identify a set of potential sources of the malware.
Owner:WEBROOT SOFTWARE INCORPORATED
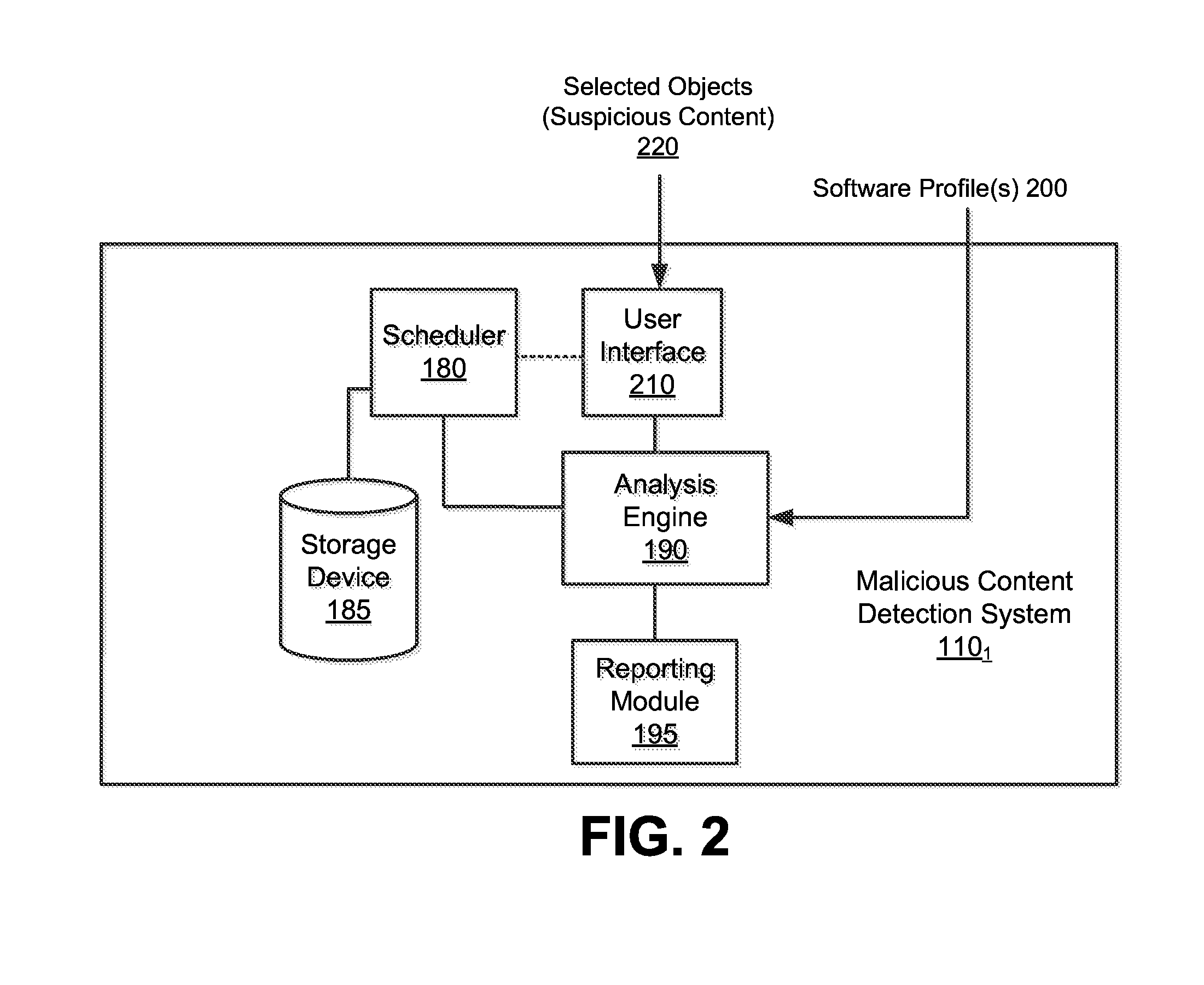
Optimized resource allocation for virtual machines within a malware content detection system
According to one embodiment, a computerized method comprises operations of instantiating a first virtual machine instance and a second virtual machine instance to run concurrently with the first virtual machine instance. The first virtual machine instance provides a first virtual operating environment while the second virtual machine instance is adapted to share the resources allocated to the first virtual machine instance. The second virtual machine instance is further adapted to allocate additional resources upon conducting a Copy-On Write operation.
Owner:FIREEYE SECURITY HLDG US LLC
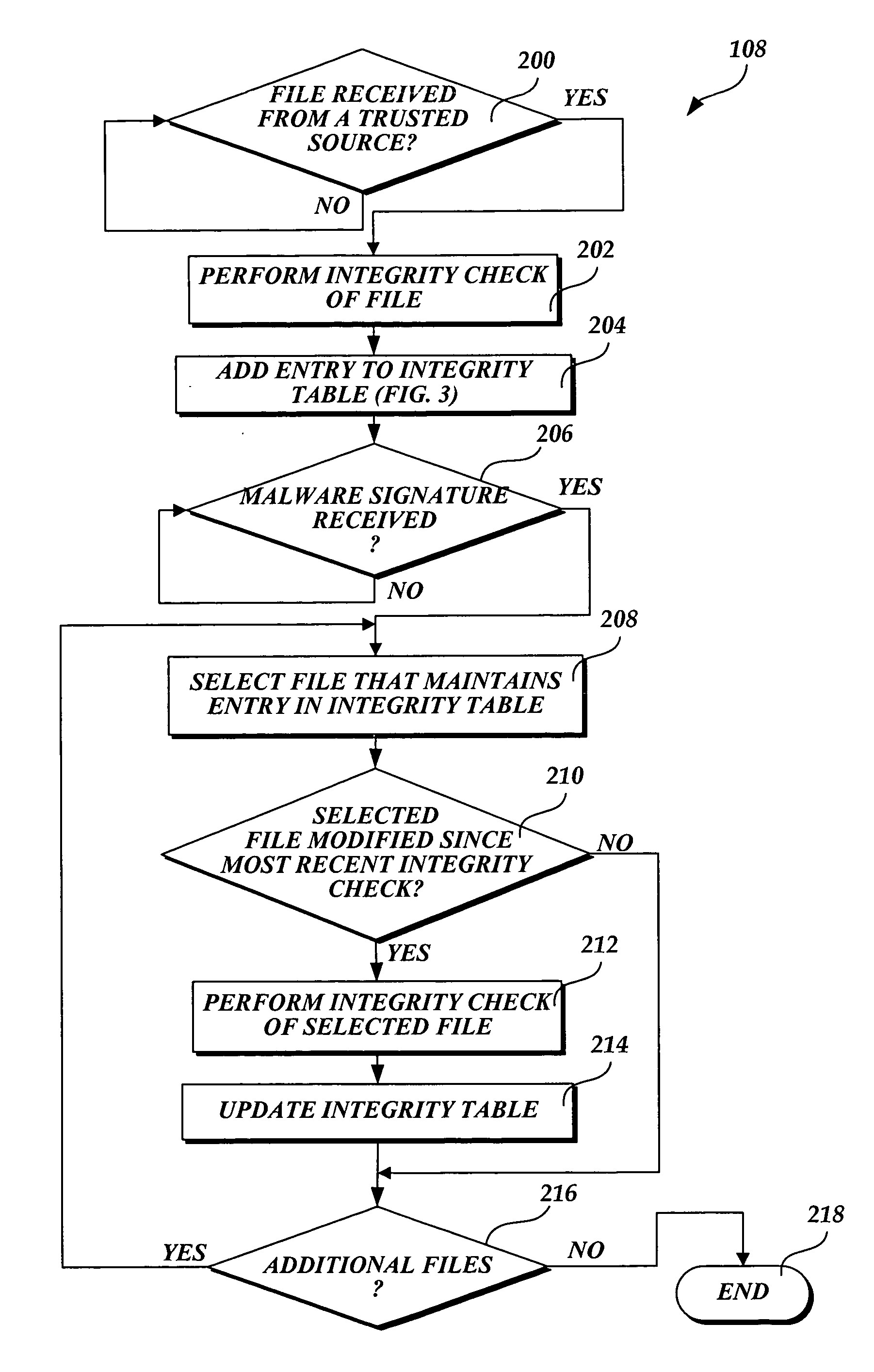
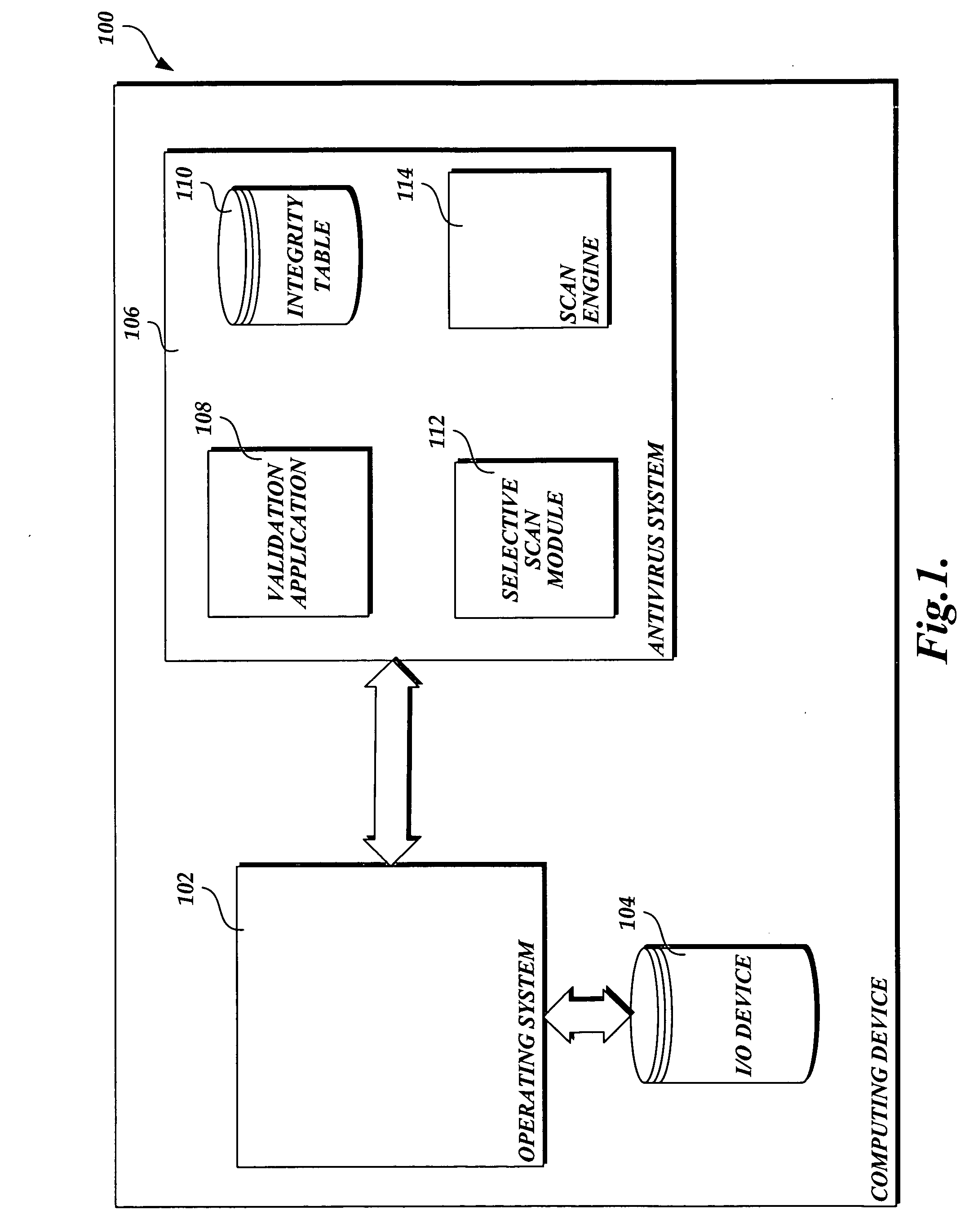
System and method of selectively scanning a file on a computing device for malware
ActiveUS20060218637A1Improve computing powerMemory loss protectionDigital data processing detailsOperational systemHash function
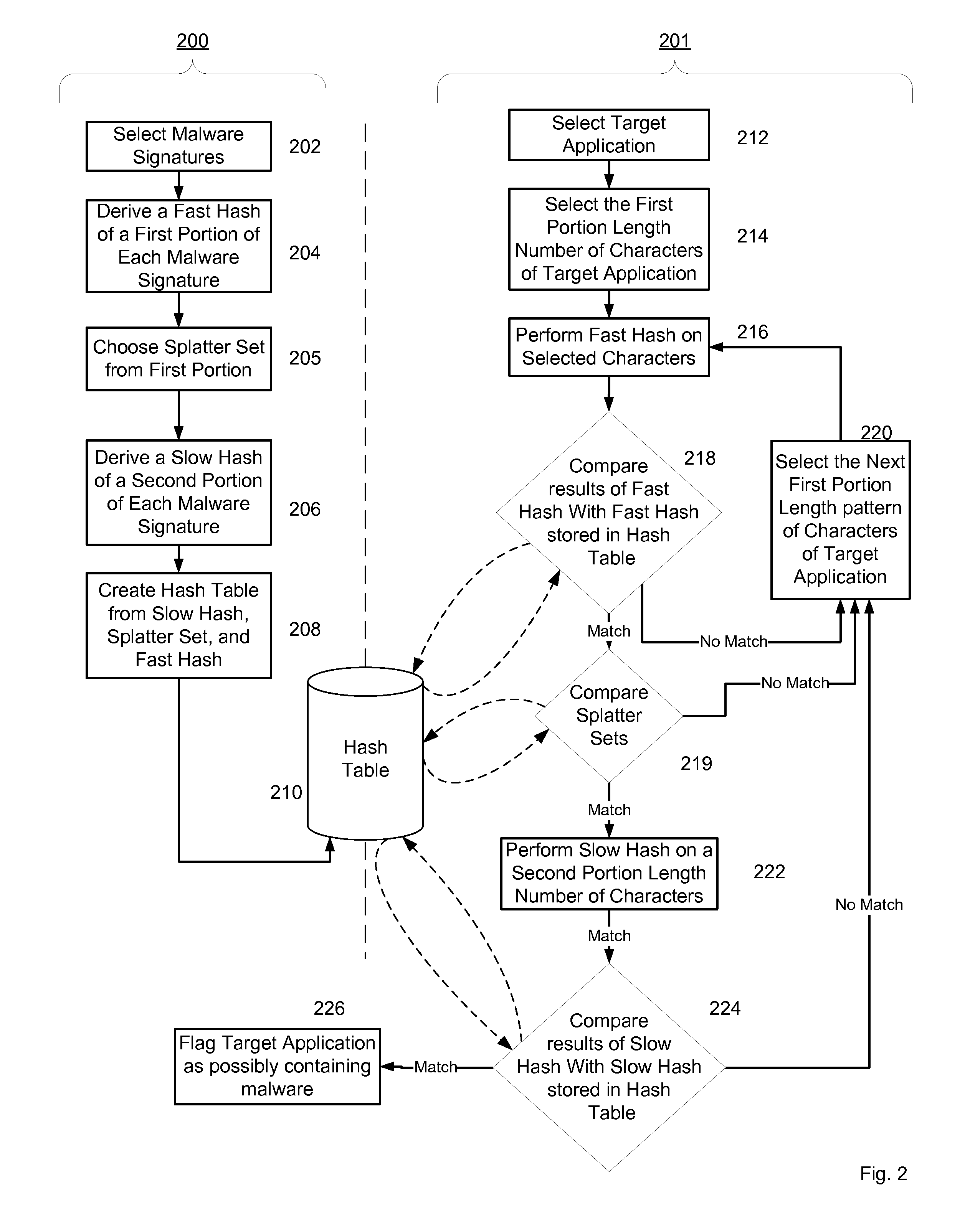
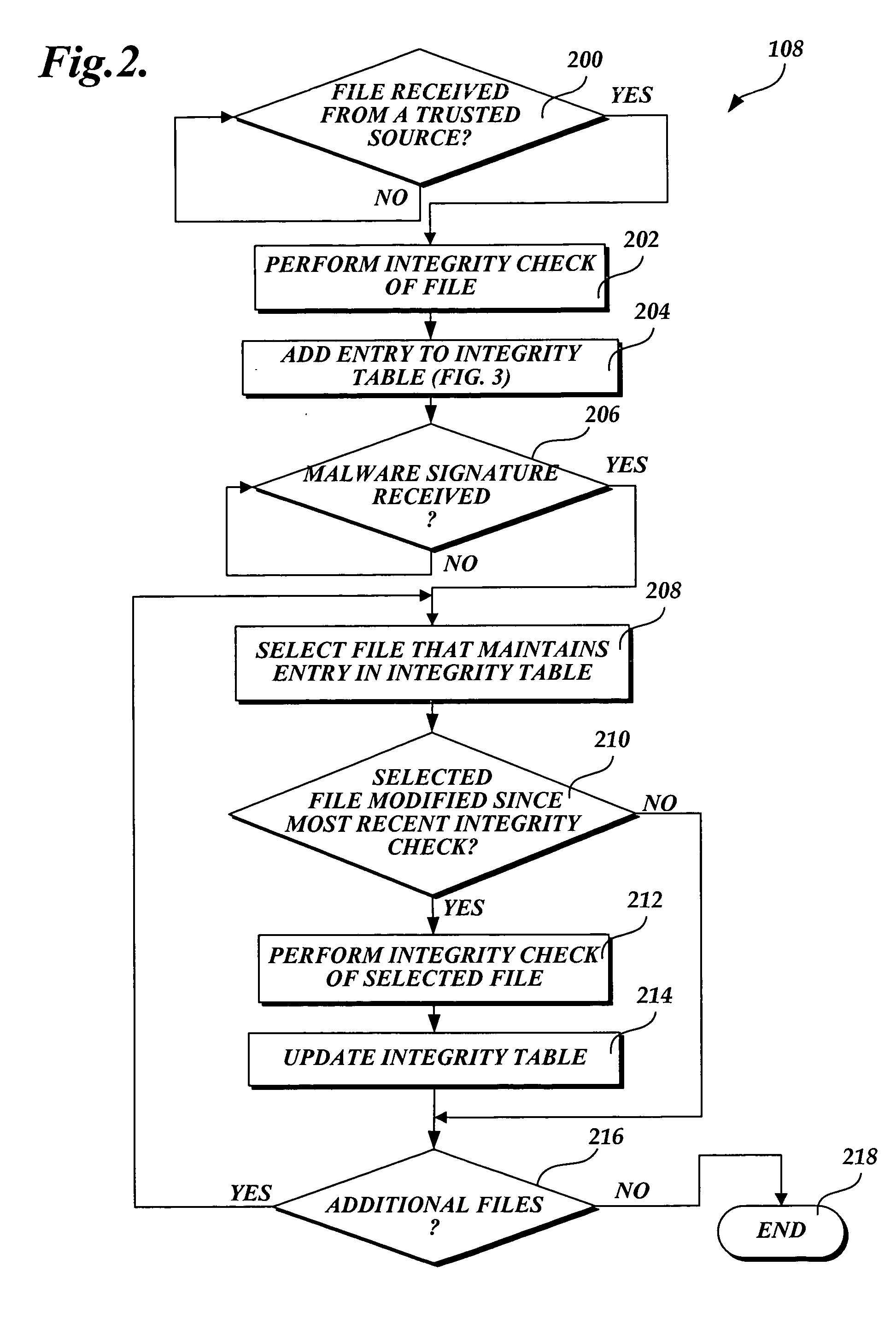
In accordance with this invention, a system, method, and computer-readable medium that selectively scans files stored on a computing device for malware is provided. One or more files may be sent from a trusted source to a computing device that implements the present invention. The integrity of the files that originate from a trusted source is validated using a signature-based hashing function. Any modifications made to files stored on the computing device are tracked by a component of the operating system. In instances when the file is not modified after being validated, an aspect of the present invention prevents the file from being scanned for malware when a scanning event is directed to the file. As a result, the performance of the computing device is improved as static files from trusted sources are not repeatedly scanned for malware.
Owner:MICROSOFT TECH LICENSING LLC
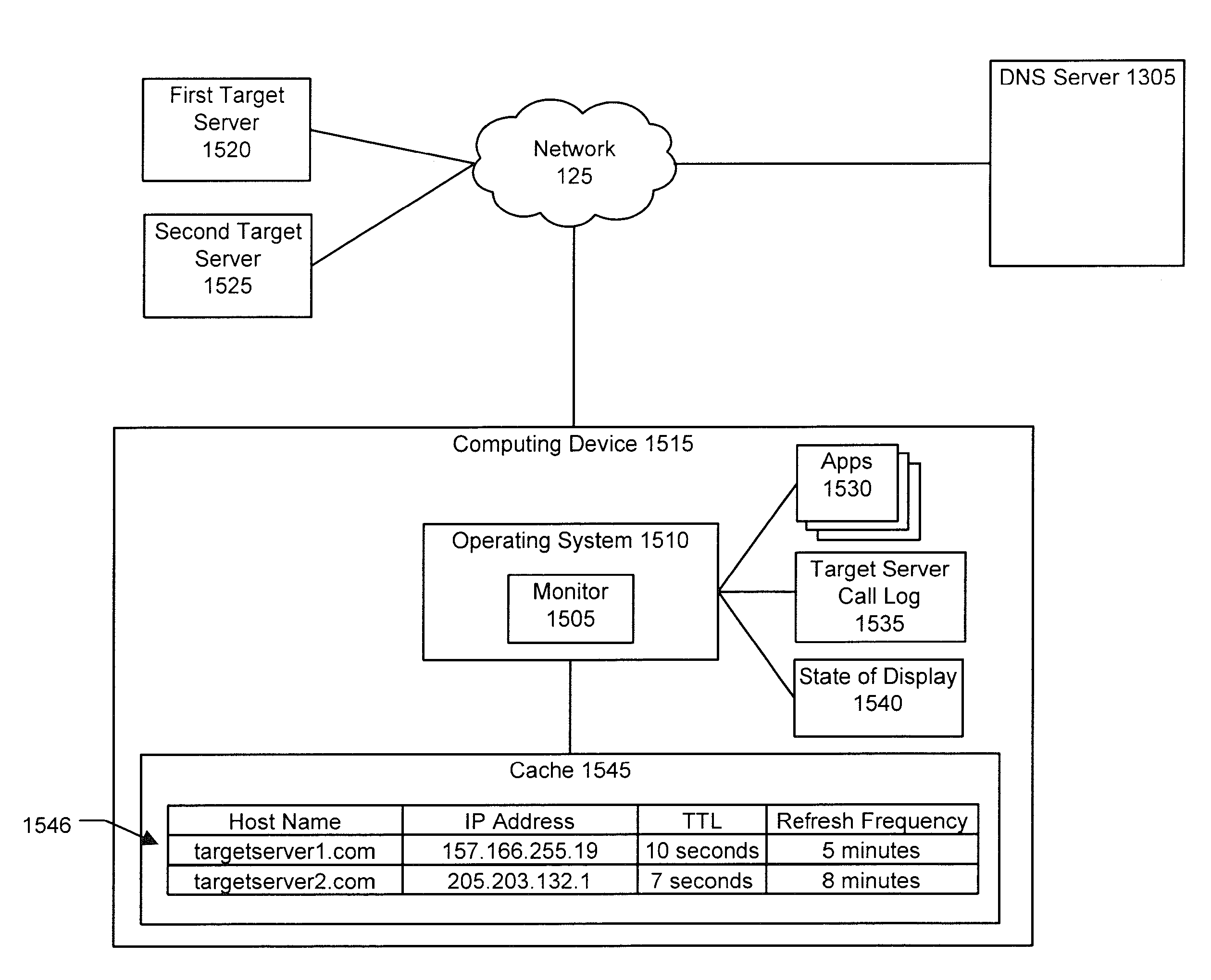
Method and System for Mobile Network Security, Related Network and Computer Program Product
ActiveUS20090144823A1Easy to scanReduce overheadMemory loss protectionUnauthorized memory use protectionUser deviceDevice status
A honeypot system for protecting a mobile communication network against malware includes one or more user-less mobile devices including a monitoring module for monitoring the events conveying software applications in the associated mobile device as well as a controller client module that emulates human-like interaction with the user-less devices as a function of the events monitored. The system controllably performs, for the applications conveyed by the events monitored, one or more of the following steps: i) installing the application on the device; ii) executing the application installed on the device; and iii) de-installing the application from the- device. After any of these steps, the state of the device is checked in order to detect if any anomalous variation has occurred in the state of the device indicative of the device being exposed to the risk of malware. If any anomalous variation is detected, the system issues a malware alert message.
Owner:TELECOM ITALIA SPA
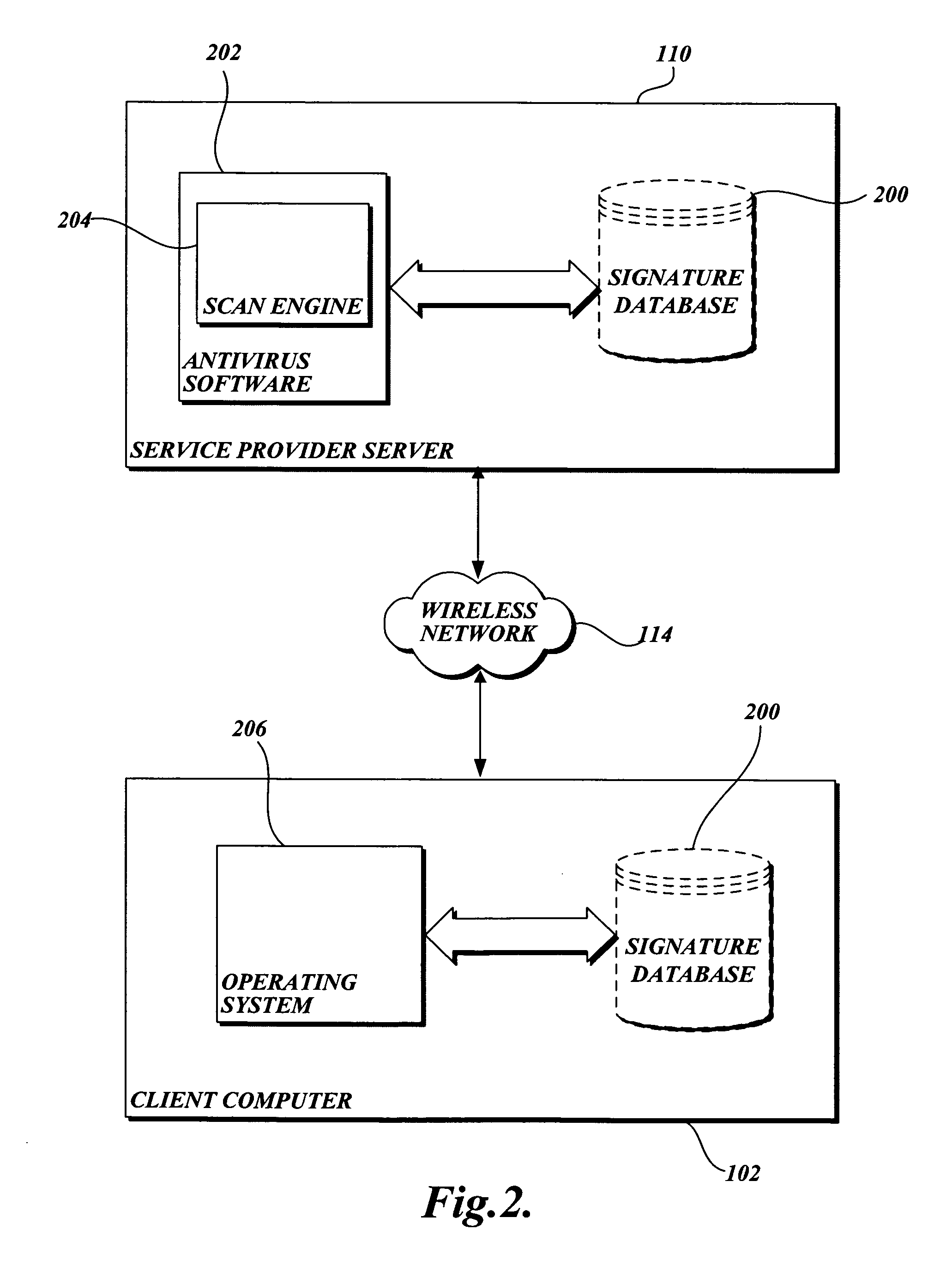
System and method for protecting a limited resource computer from malware
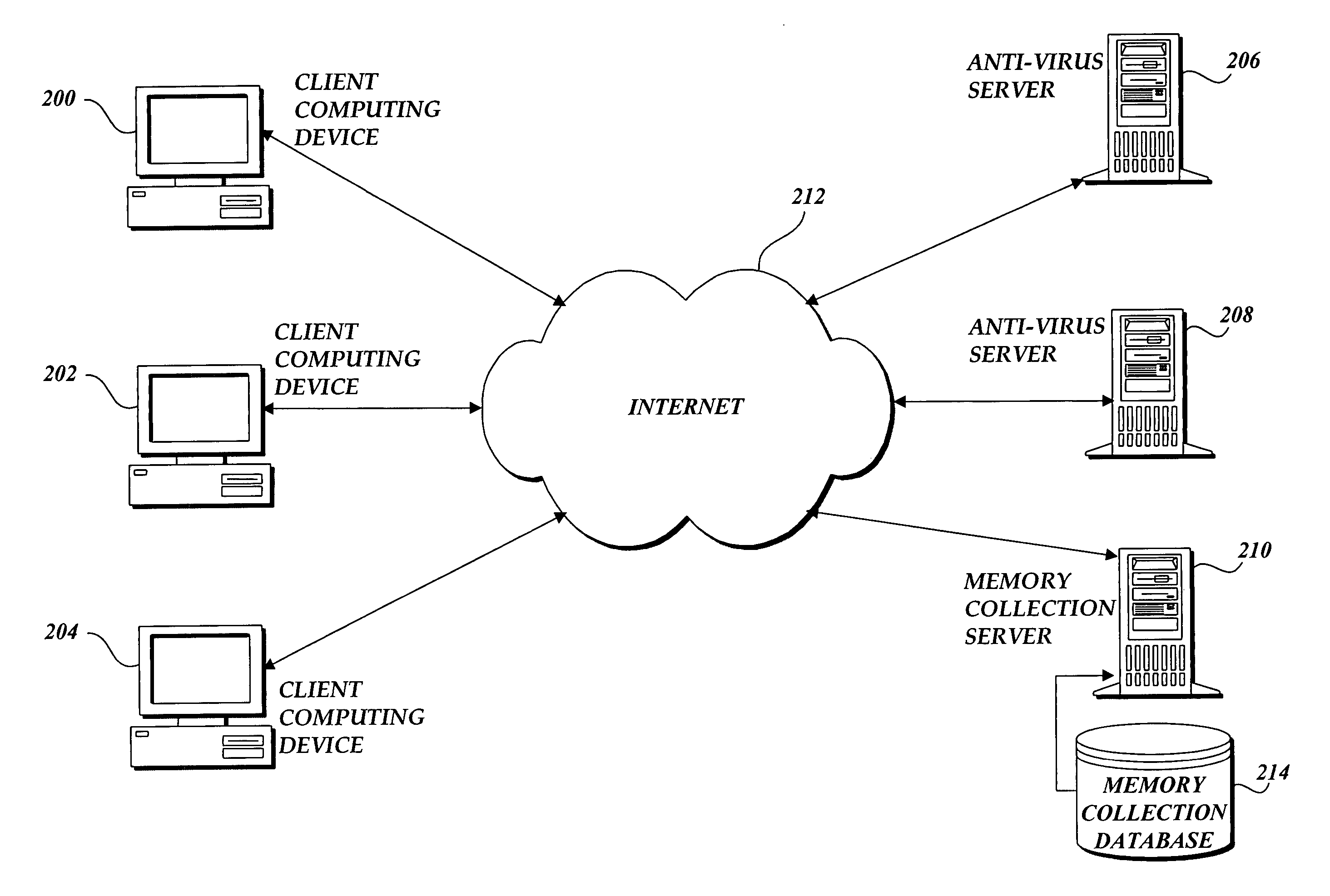
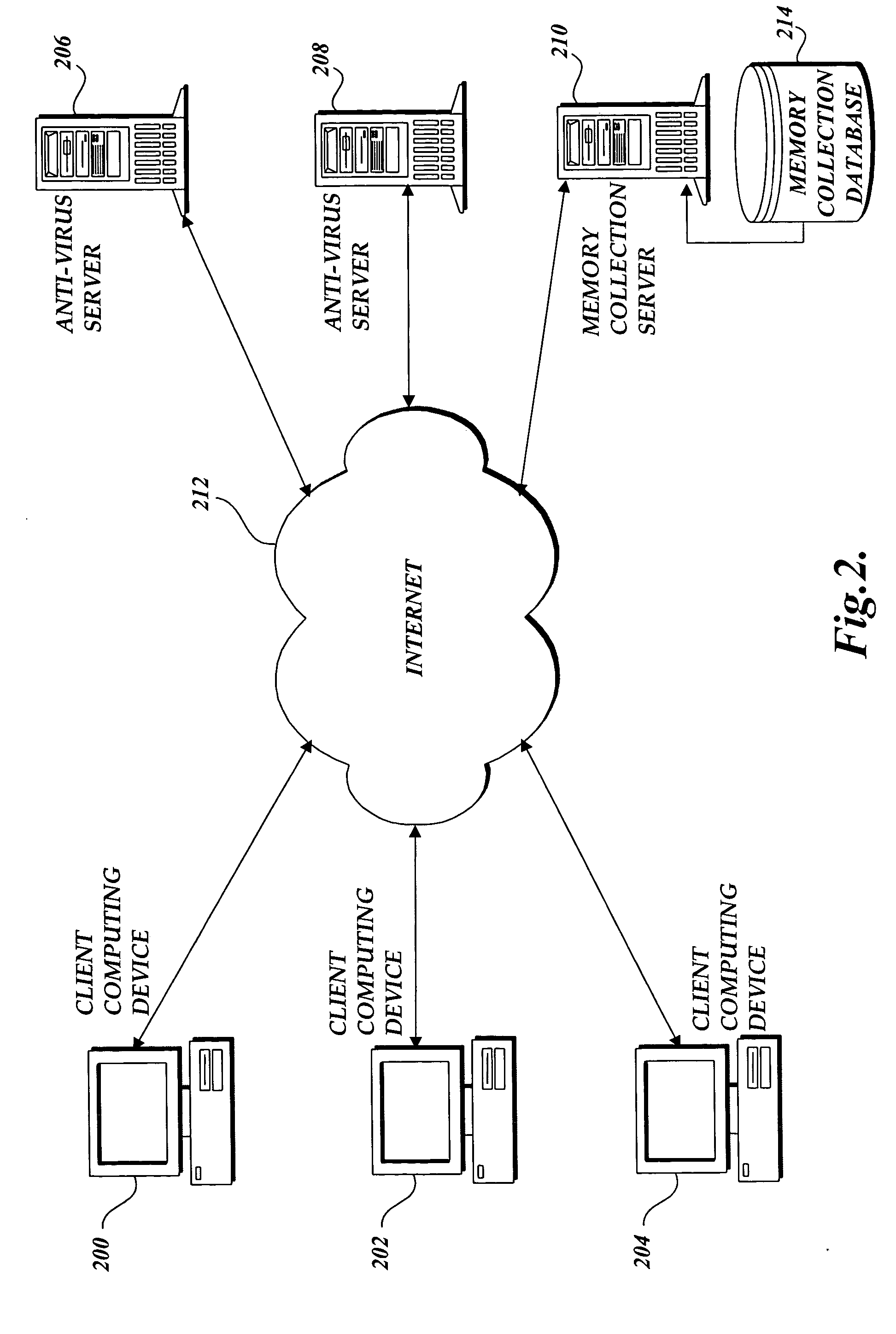
ActiveUS20060236393A1Prevent malwareMemory loss protectionError detection/correctionLimited resourcesSoftware update
The present invention is directed to a system and methods for protecting a limited resource computer from malware. Aspects of the present invention use antivirus software on a general purpose computer to prevent malware from infecting a limited resource computer. Typically, antivirus software on the general purpose computer is kept “up-to-date” with the most recent software updates. When a connection is established between the limited resource computer and the general purpose computer, a signature of each application installed on the limited resource computer is transmitted to the general purpose computer. Then antivirus software on the general purpose computer compares the received signatures to known malware. Finally, the results of the scan are reported to the limited resource computer.
Owner:MICROSOFT TECH LICENSING LLC
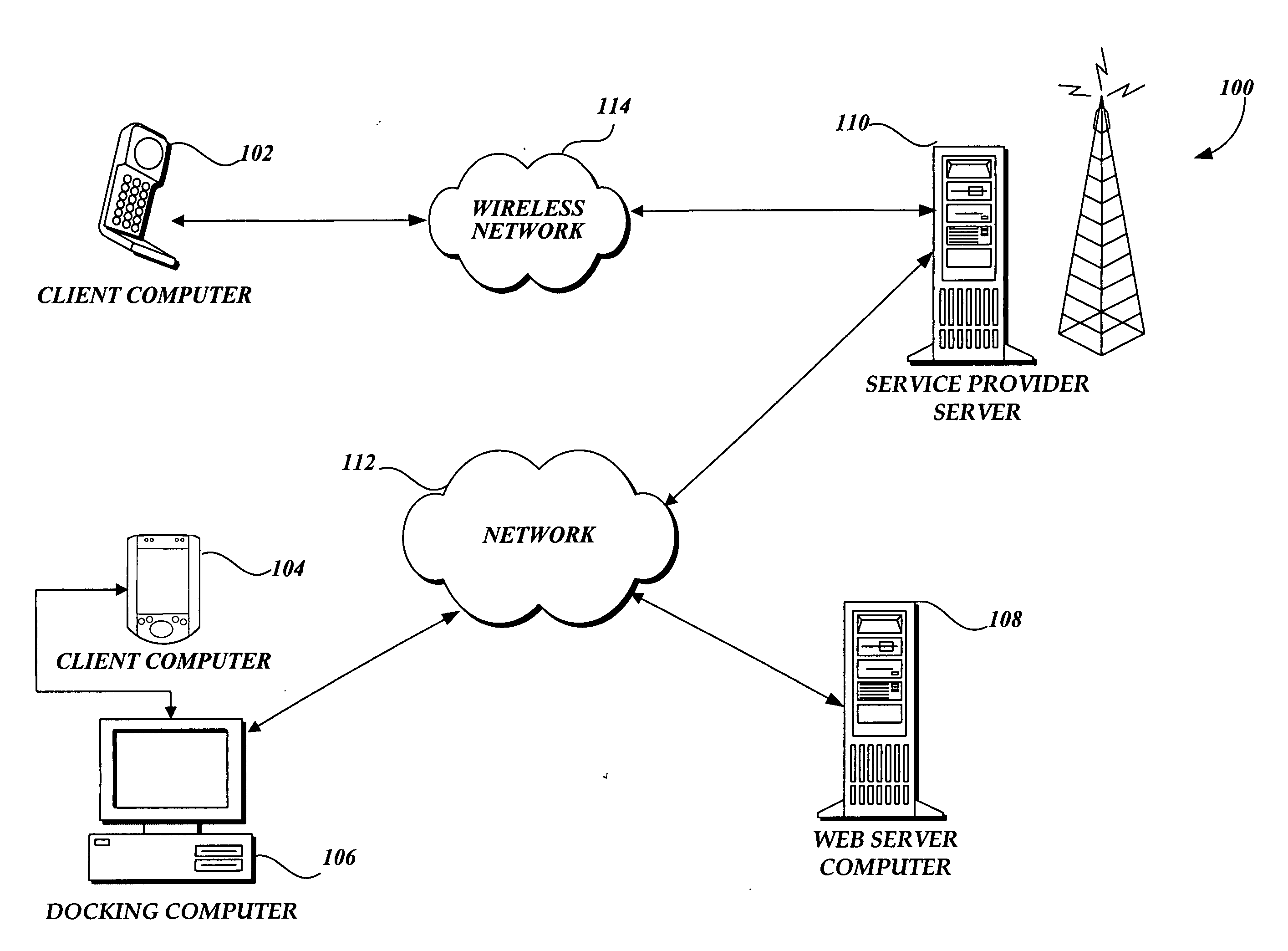
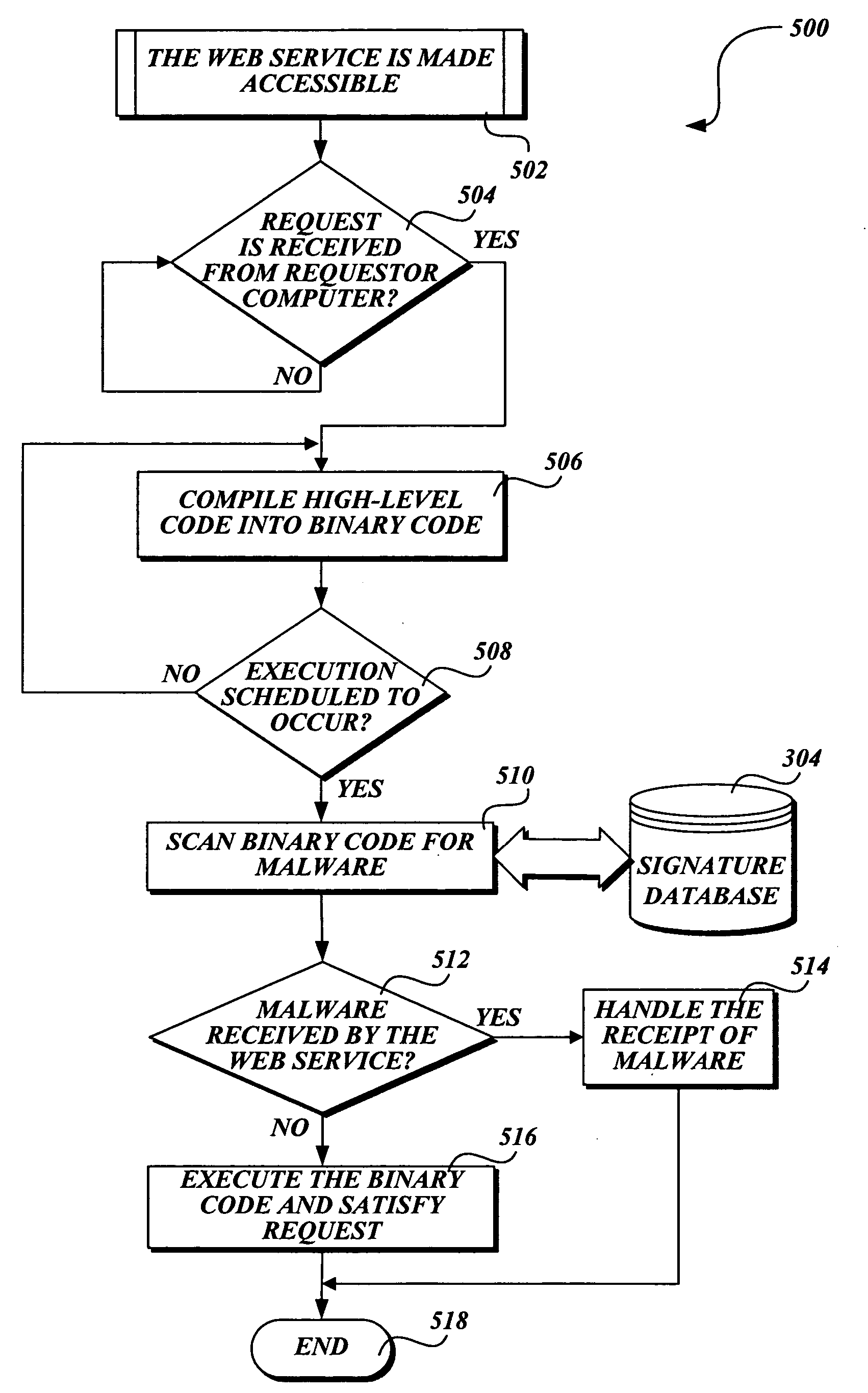
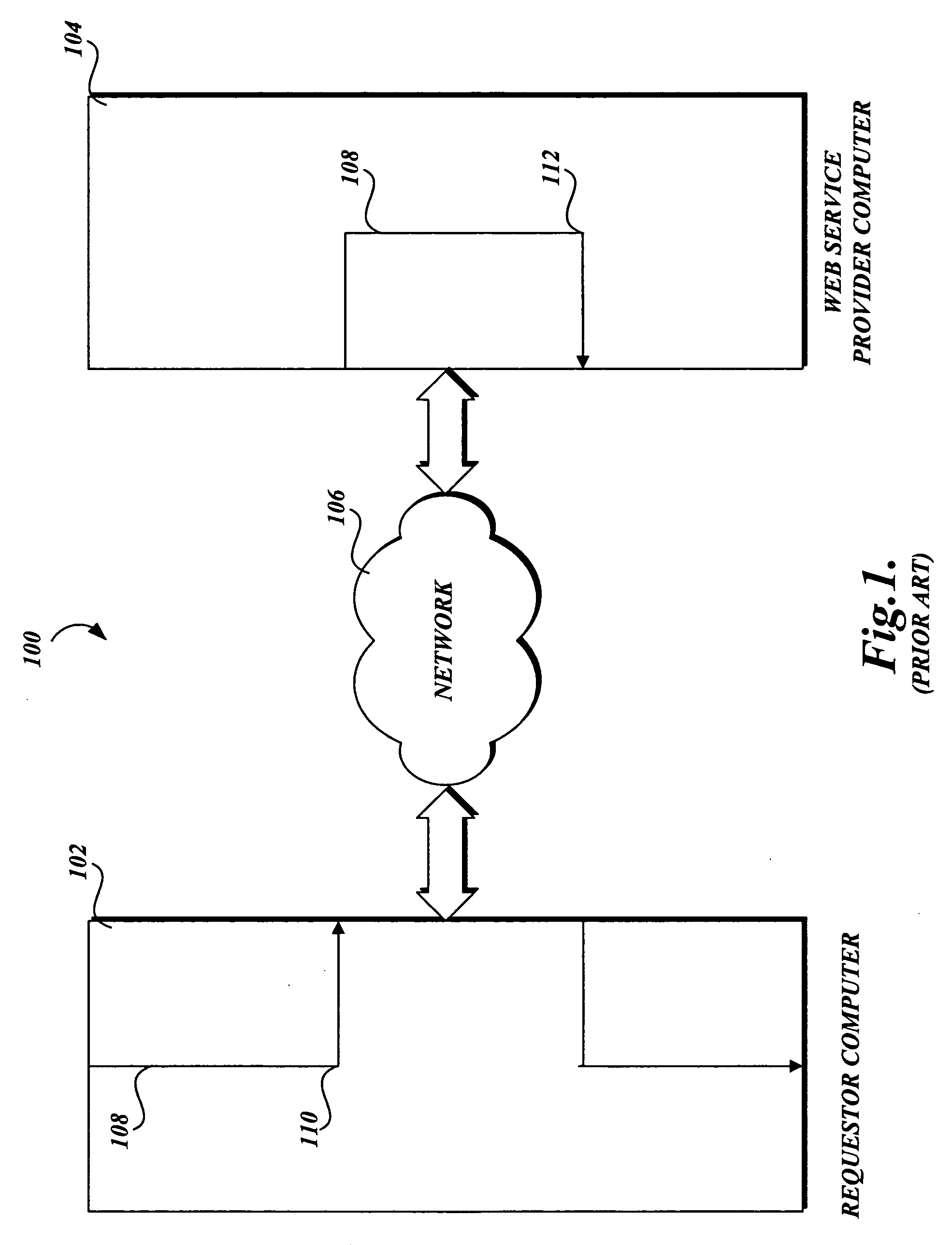
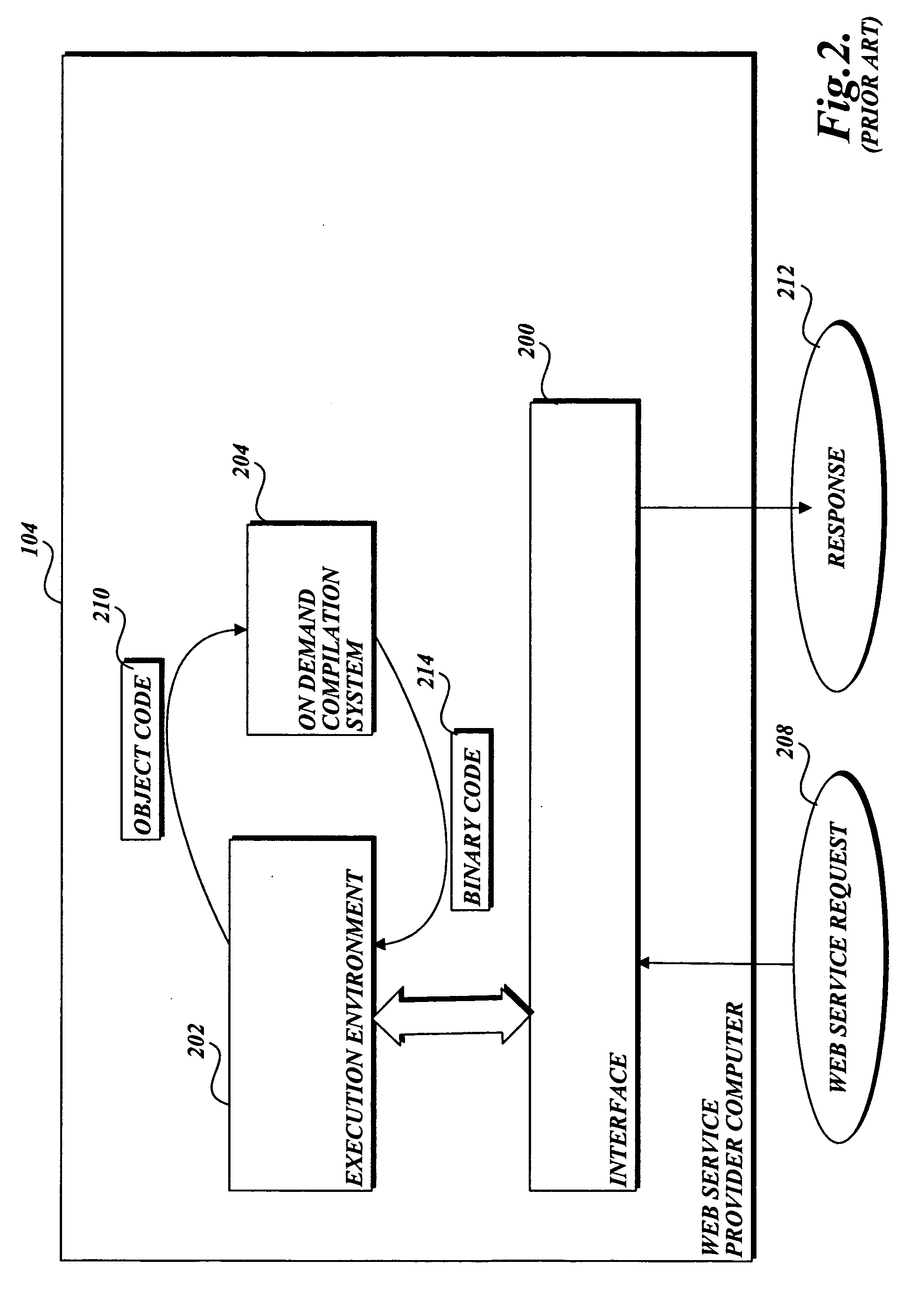
Protecting a computer that provides a Web service from malware
InactiveUS20060242709A1Preventing executionMemory loss protectionError detection/correctionWeb serviceSoftware design
In accordance with the present invention, a system, method, and computer-readable medium for identifying malware in a request to a Web service is provided. One aspect of the present invention is a computer-implemented method for protecting a computer that provides a Web service from malware made in a Web request. When a request is received, an on-demand compilation system compiles high-level code associated with the request into binary code that may be executed. However, before the code is executed, antivirus software designed to identify malware scans the binary code for malware. If malware is identified, the antivirus software prevents the binary code associated with the request from being executed.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for malware attack prevention
Systems and methods for malware attack prevention are provided. Network data is copied from a communication network. It is then determined if a possible malware attack is within the copied network data. The network data is intercepted based on the determination. The network data is then analyzed to identify a malware attack.
Owner:FIREEYE SECURITY HLDG US LLC
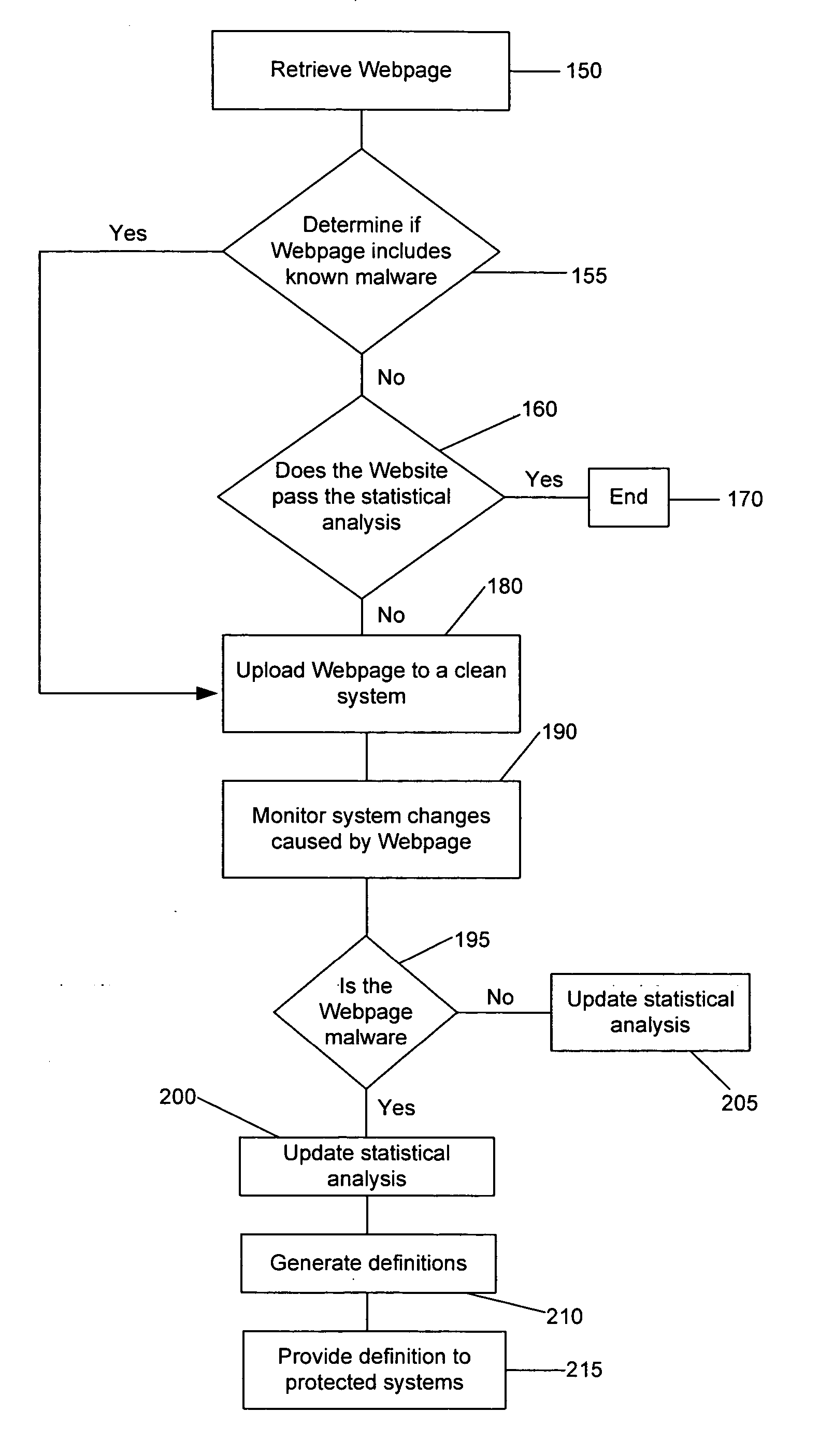
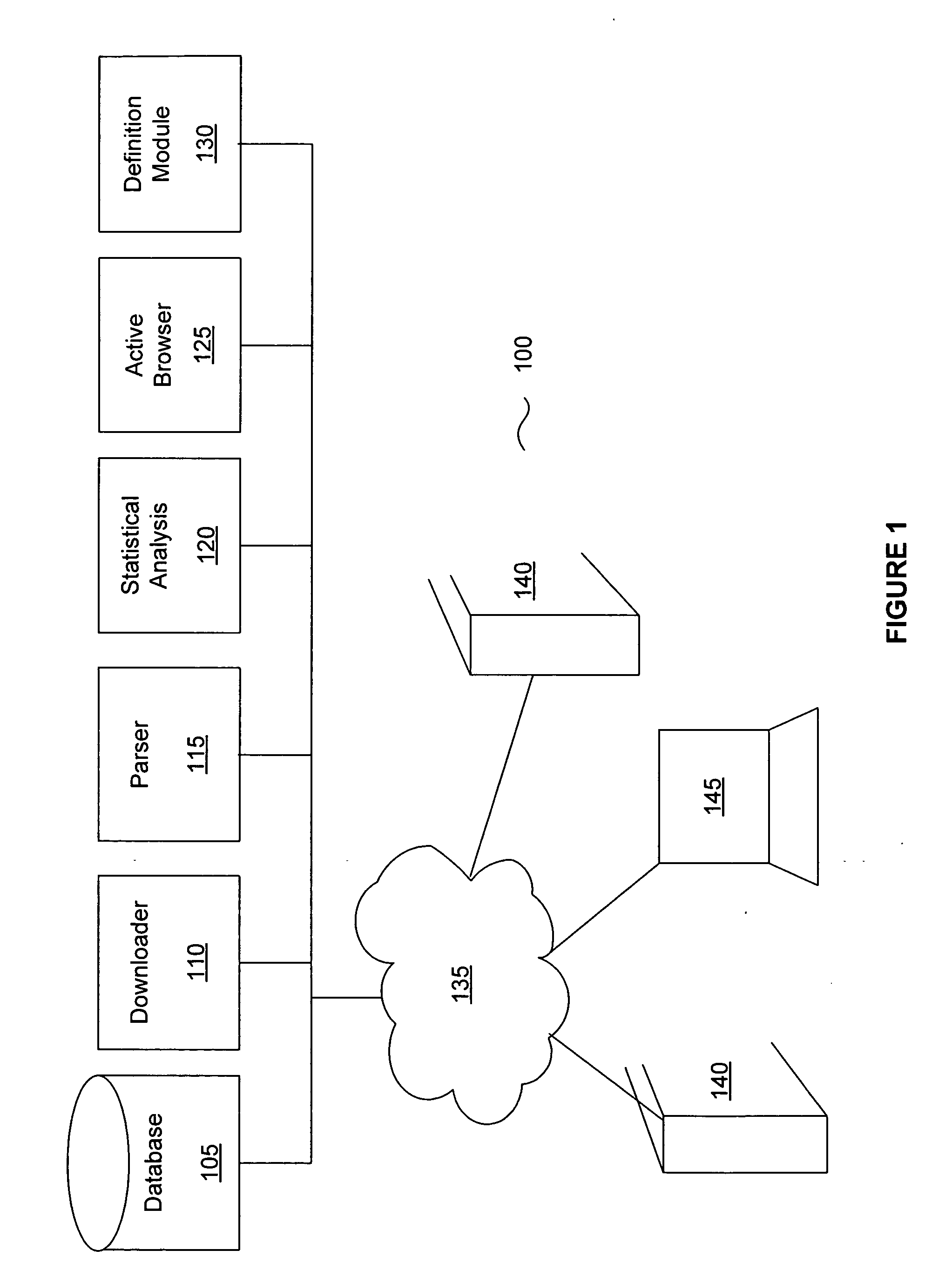
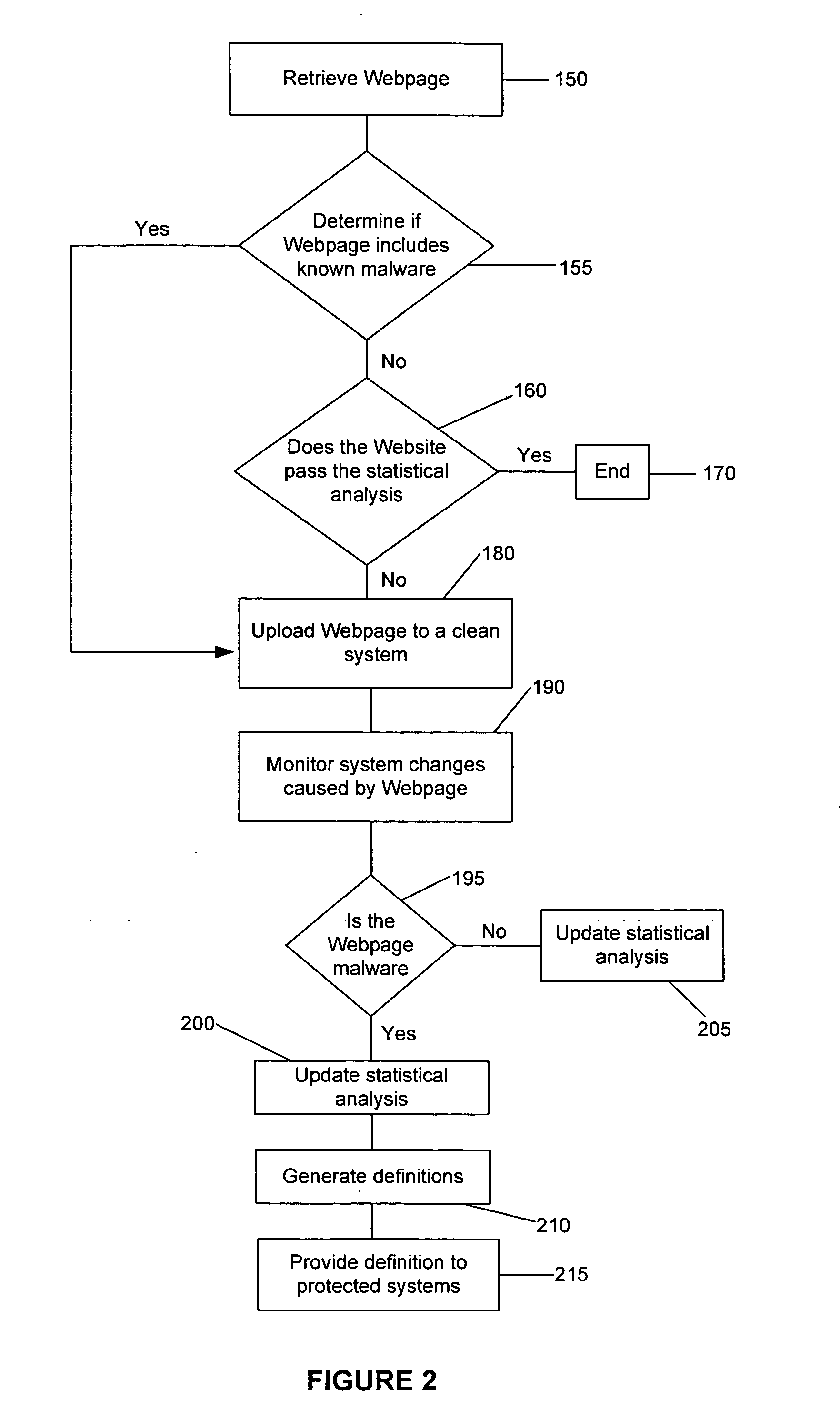
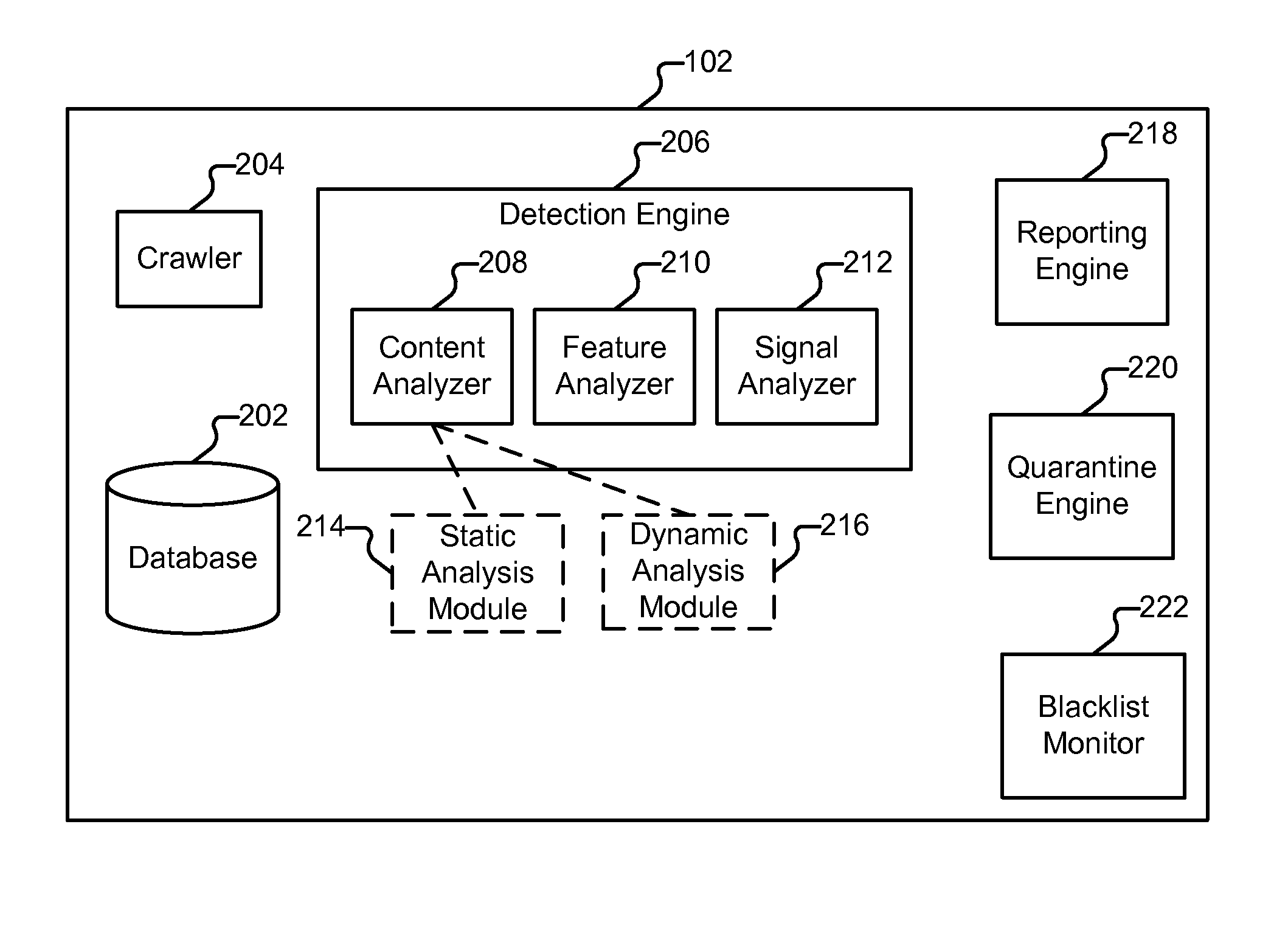
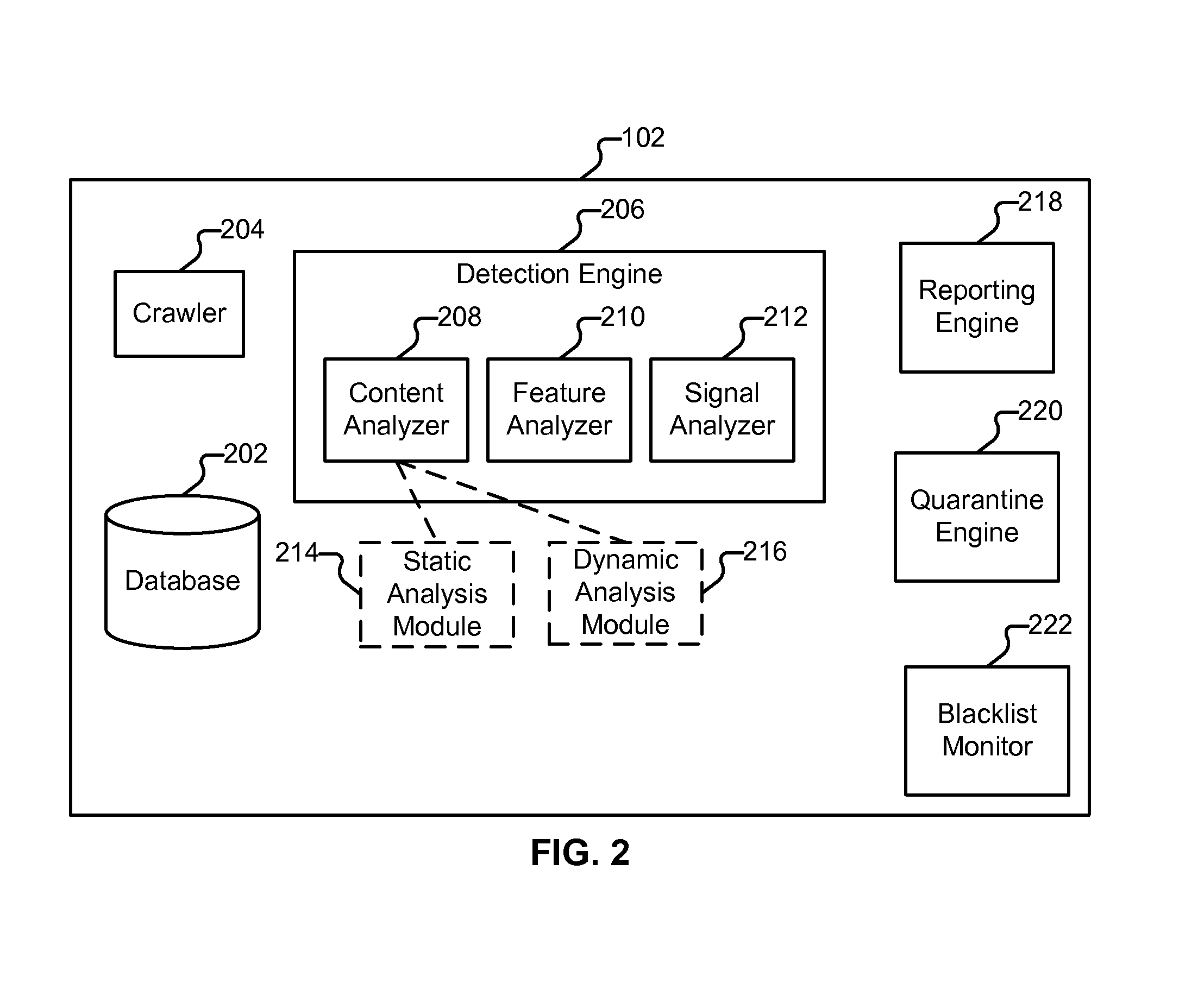
Method and system for analyzing data for potential malware
A system and method for generating a definition for malware and / or detecting malware. is described. One exemplary embodiment includes a downloader for downloading a portion of a Web site; a parser for parsing the downloaded portion of the Web site; a statistical analysis engine for determining if the downloaded portions of the Web site should be evaluated by the active browser; an active browser for identifying changes to the known configuration of the active browser, wherein the changes are caused by the downloaded portion of the Web site; and a definition module for generating a definition for the potential malware based on the changes to the known configuration.
Owner:WEBROOT SOFTWARE INCORPORATED
Prospective client identification using malware attack detection
Systems and methods for prospective client identification using malware attack detection are provided. A malware device is identified. The entity with the responsibility for the malware device or a potentially compromised device in communication with the malware device is determined. A message is communicated to the entity based on the determination. In various embodiments, the message comprises an offer for security related products and / or services.
Owner:FIREEYE SECURITY HLDG US LLC
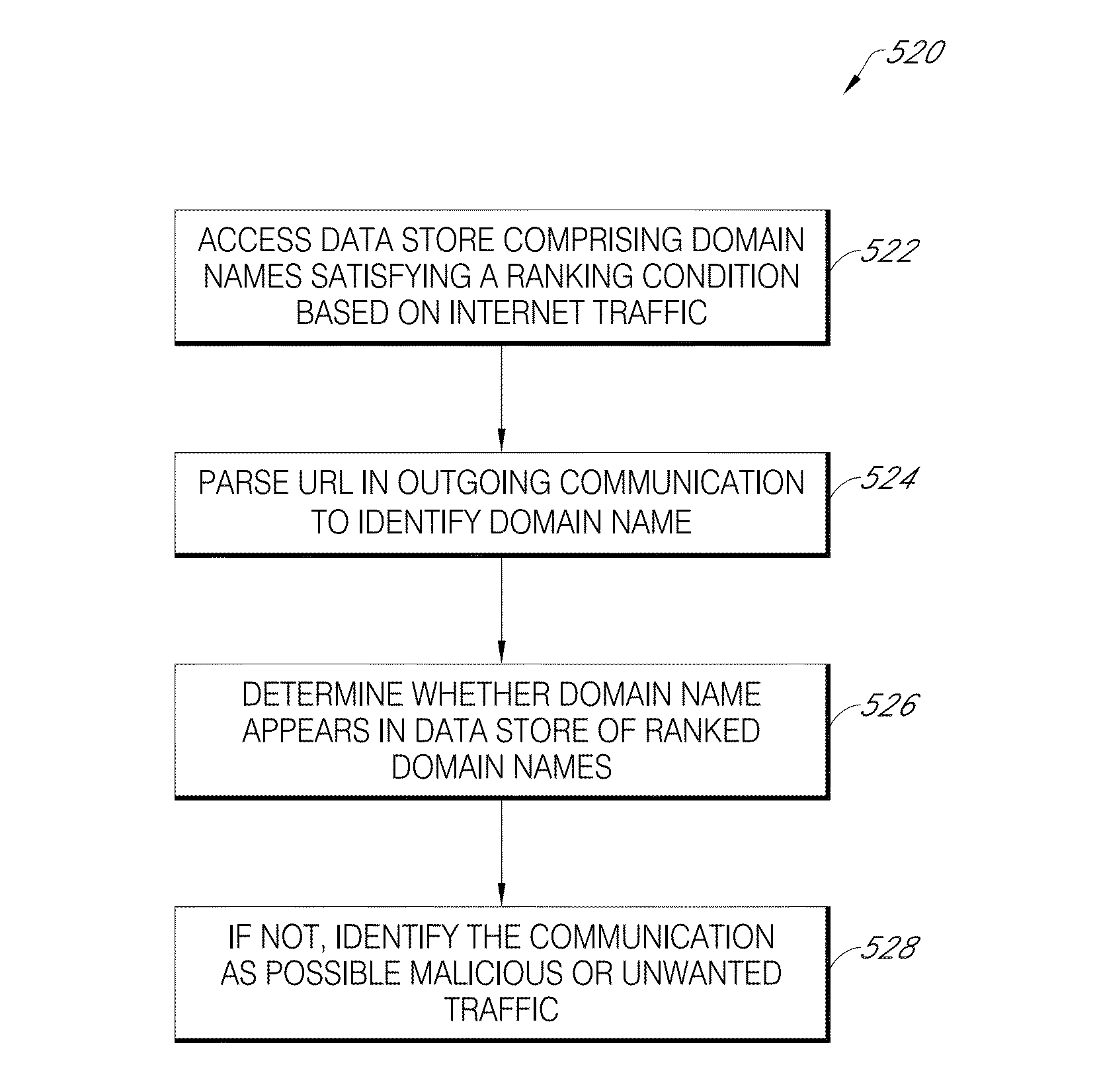
Malicious software detection in a computing system
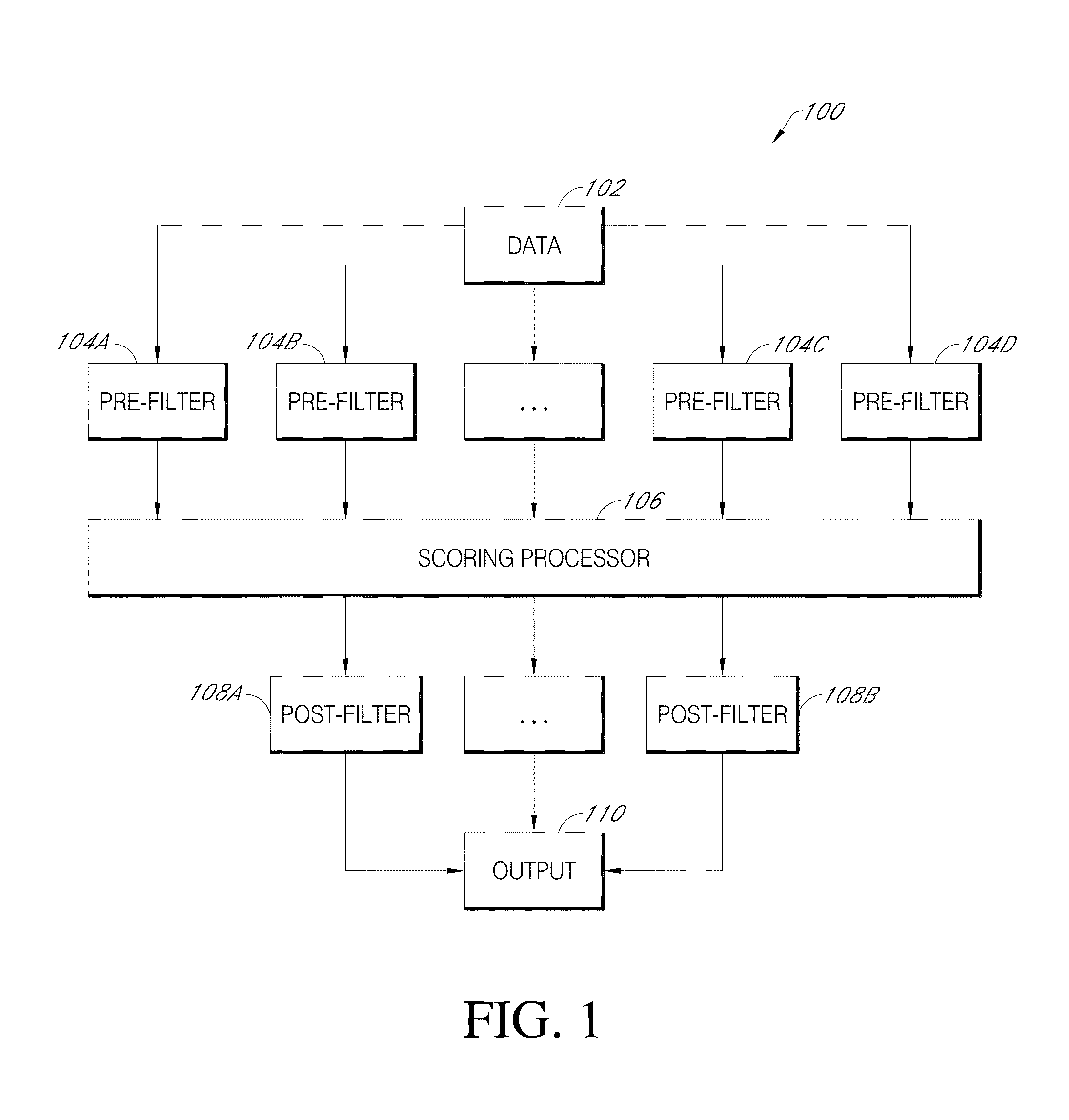
ActiveUS9043894B1Function increaseConsume significant storageComputer security arrangementsMultiple digital computer combinationsComputerized systemMalware
A computer system identifies malicious Uniform Resource Locator (URL) data items from a plurality of unscreened data items that have not been previously identified as associated with malicious URLs. The system can execute a number of pre-filters to identify a subset of URLs in the plurality of data items that are likely to be malicious. A scoring processor can score the subset of URLs based on a plurality of input vectors using a suitable machine learning model. Optionally, the system can execute one or more post-filters on the score data to identify data items of interest. Such data items can be fed back into the system to improve machine learning or can be used to provide a notification that a particular resource within a local network is infected with malicious software.
Owner:PALANTIR TECHNOLOGIES
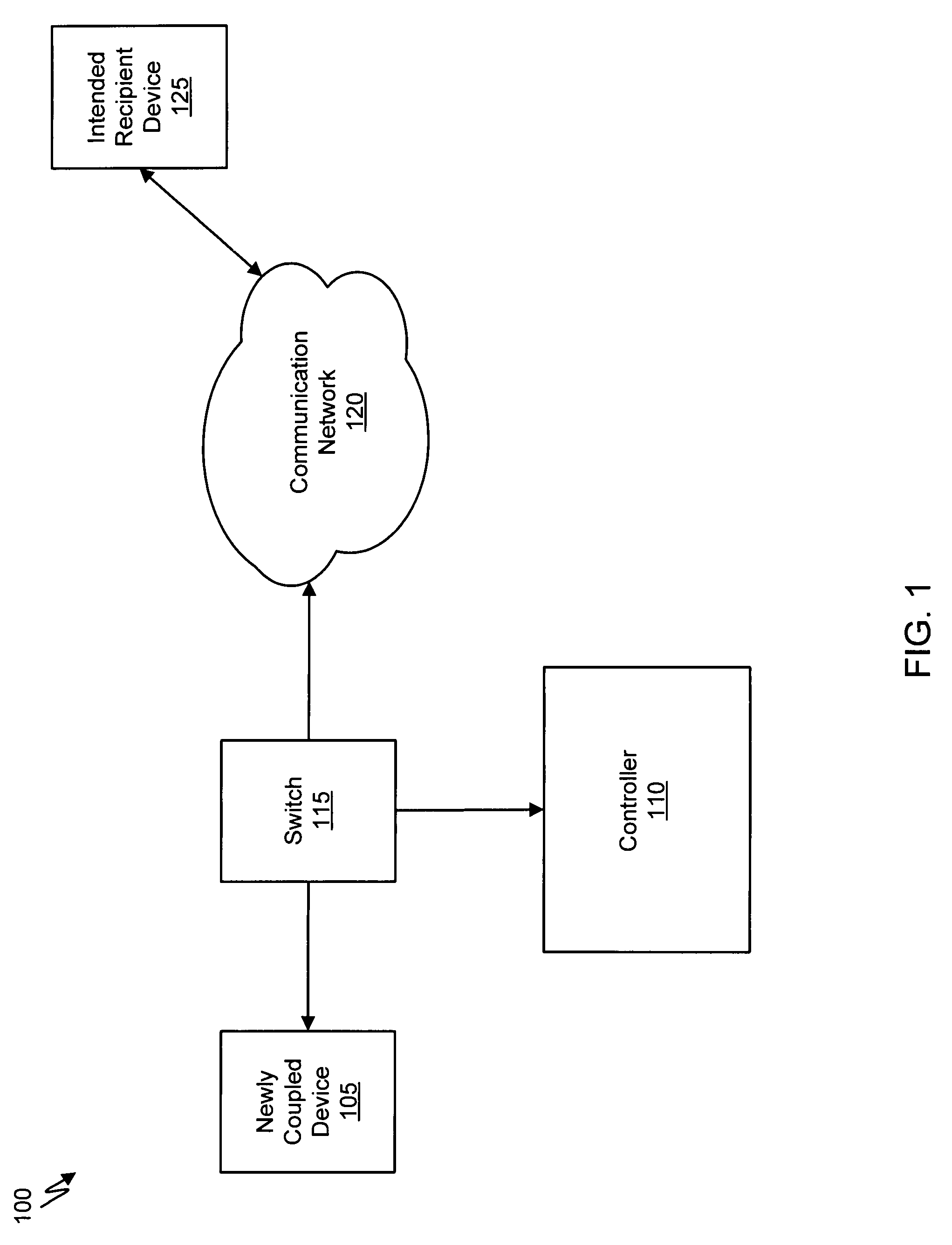
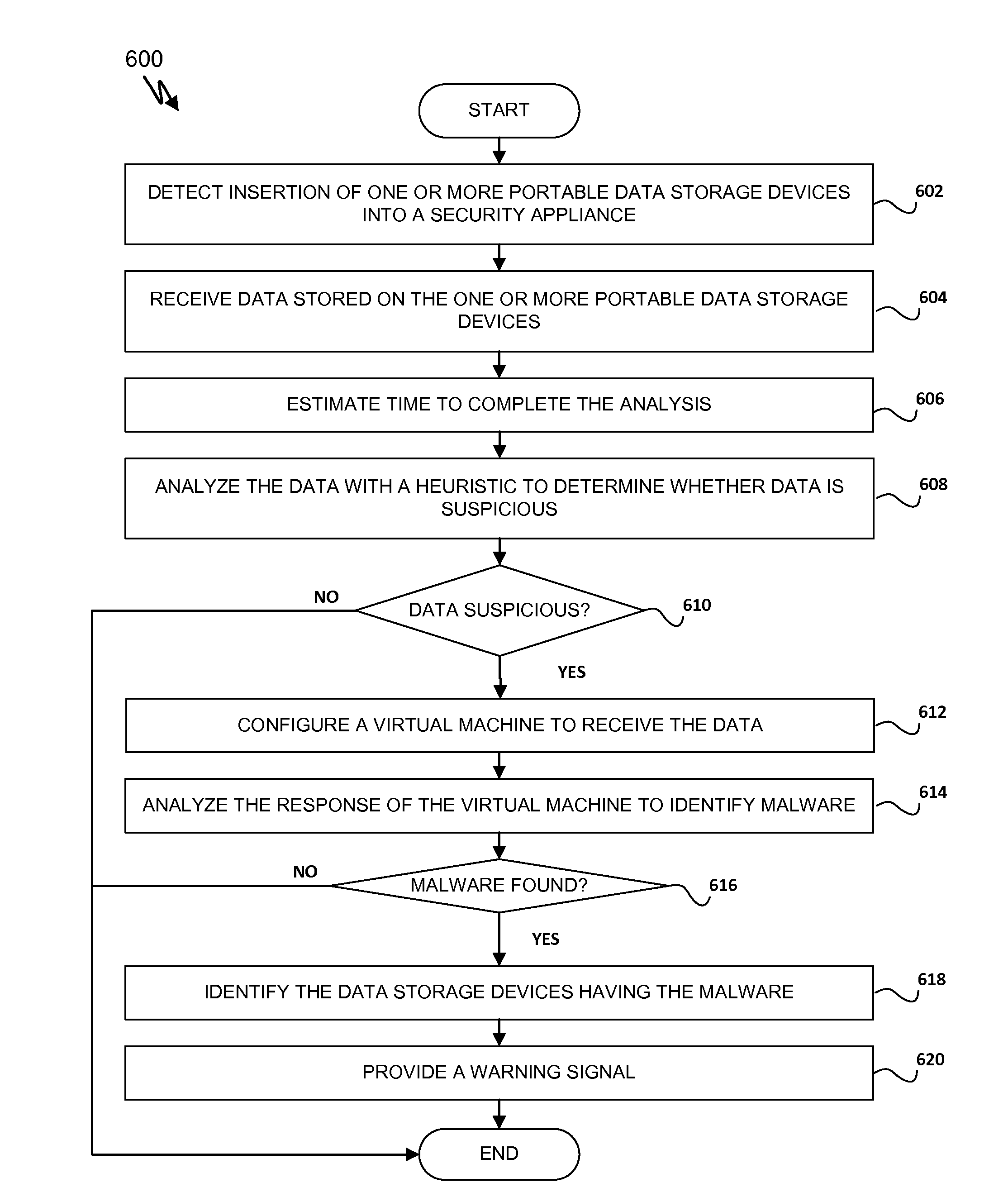
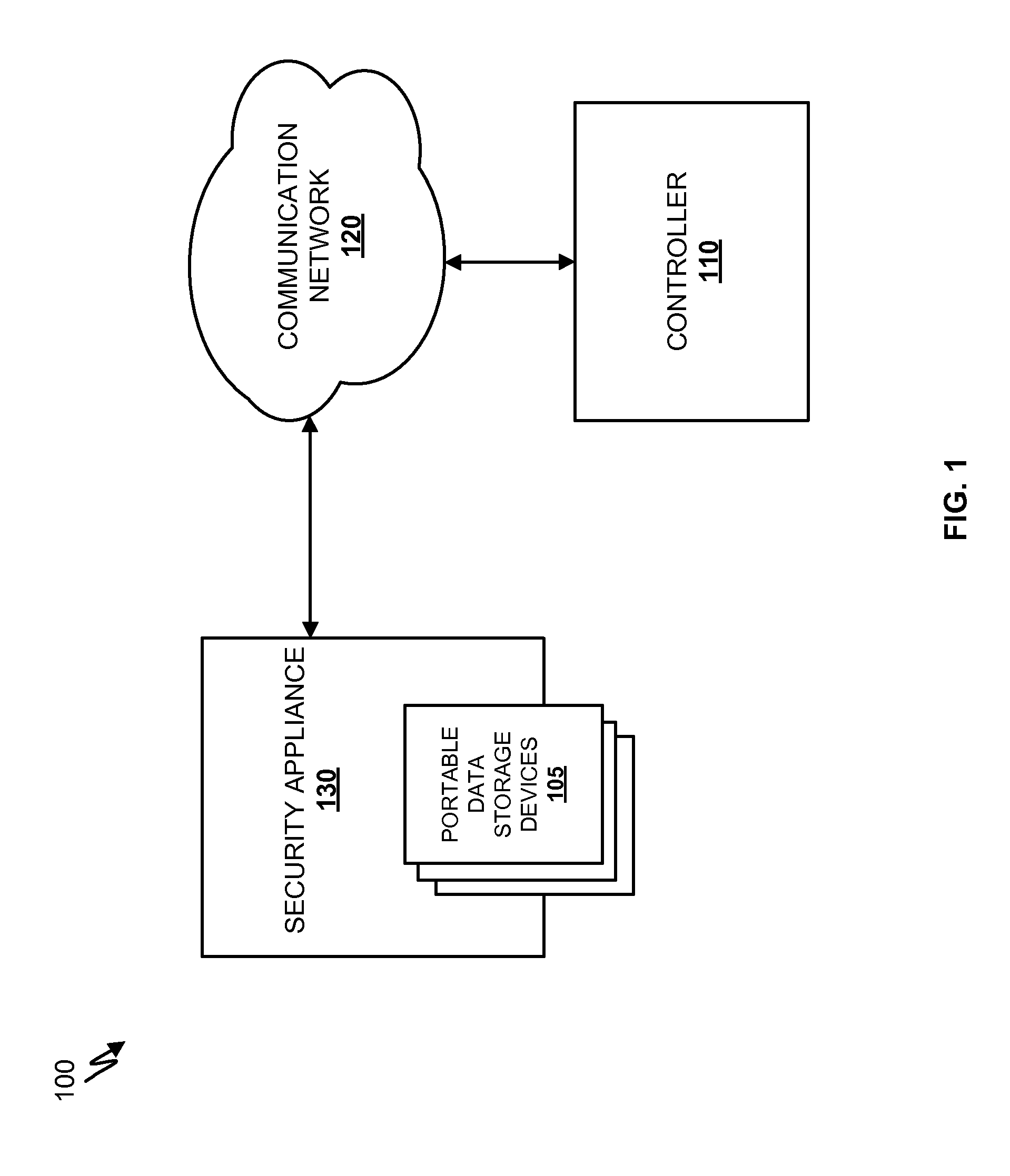
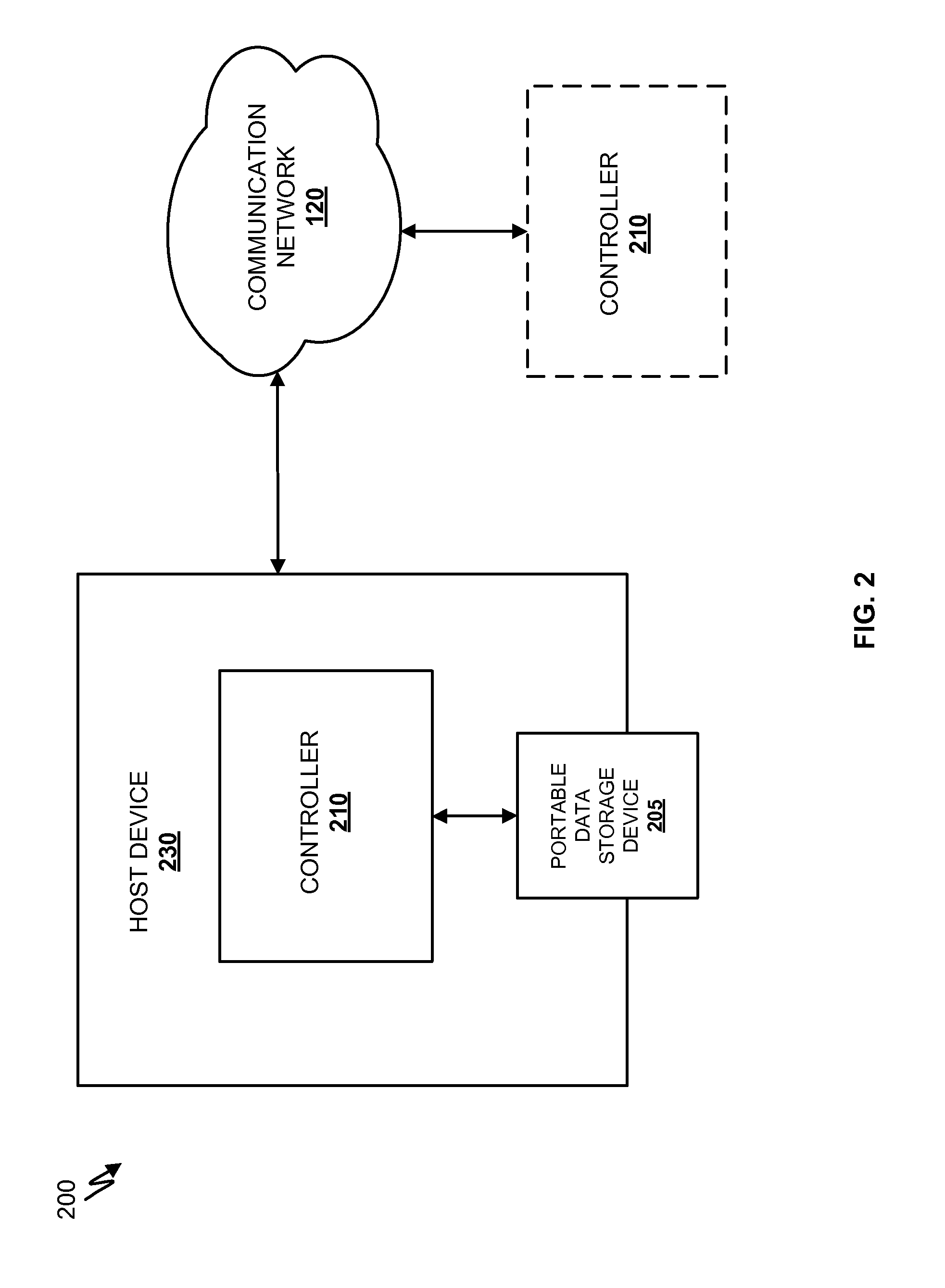
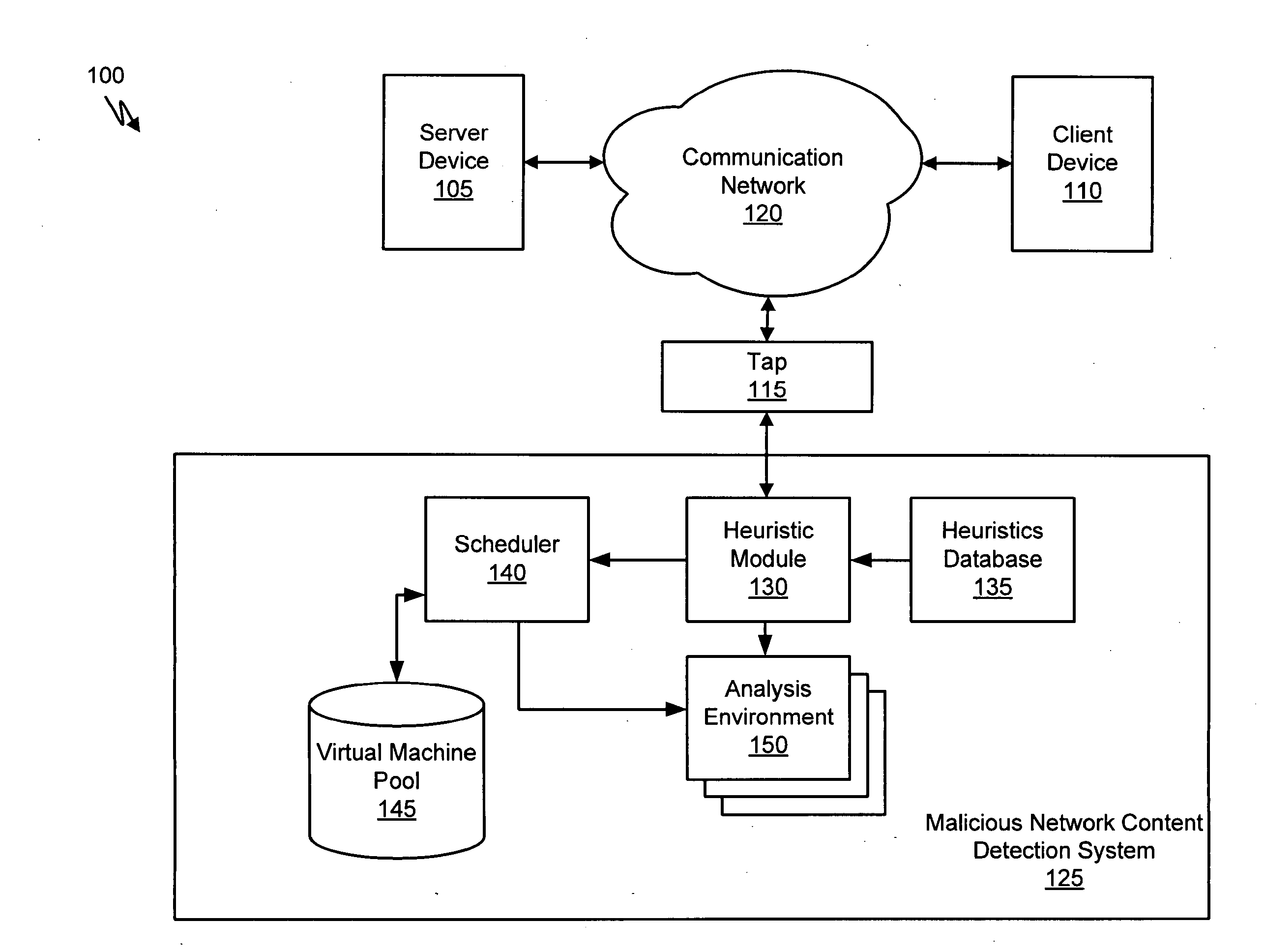
Detecting Malicious Network Content
Systems and methods for detecting malicious content on portable data storage devices or remote network servers are provided. In an exemplary embodiment, a system comprises a quarantine module configured to detect one or more portable data storage devices upon insertion of the devices into a security appliance, wherein the security appliance is configured to receive the portable data storage devices, a controller configured to receive from the security appliance, via a communication network, data associated with the portable data storage devices, an analysis module configured to analyze the data to determine whether the data includes malware, and a security module to selectively identify, based on the determination, the one or more portable data storage devices storing the malware.
Owner:FIREEYE SECURITY HLDG US LLC
Mitigating malware
Remediating a suspicious element in a web page is disclosed. An indication of a suspicious element is received. A quarantine instruction is sent to a server of the web page. One example of a quarantine instruction is an instruction to block the page from being served. Another example of a quarantine instruction in as instruction to block an element of the page from being served.
Owner:DASIENT
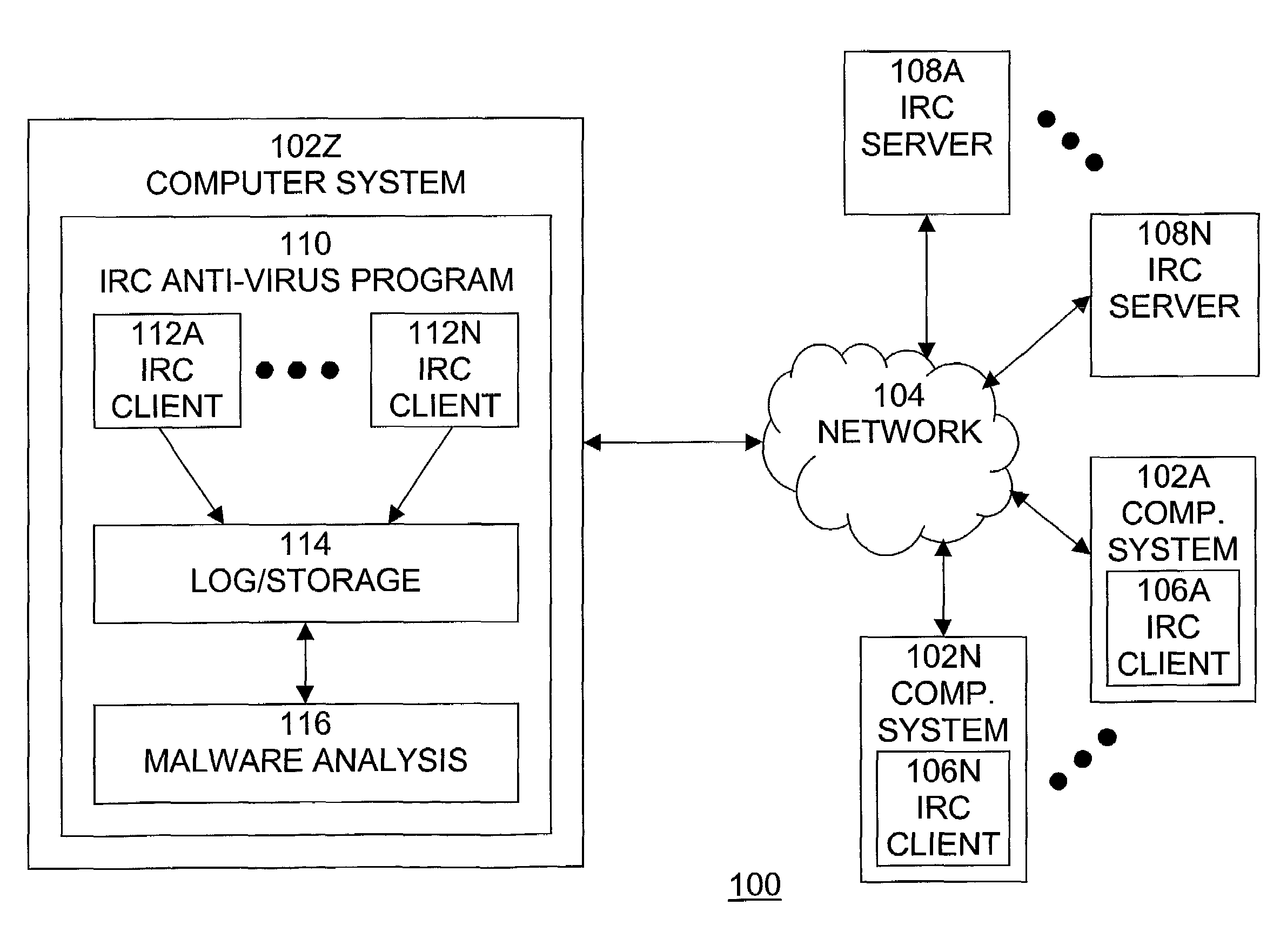
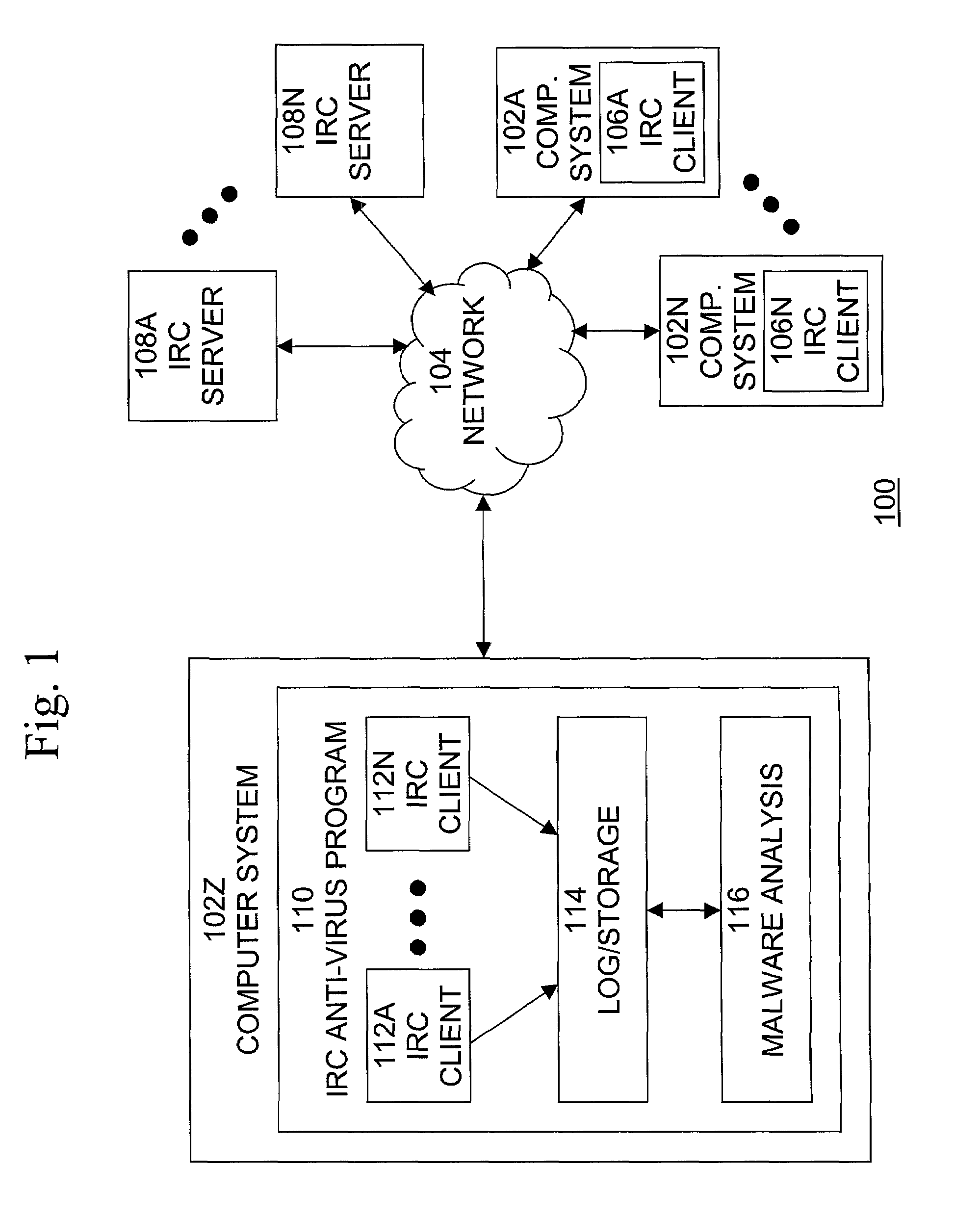
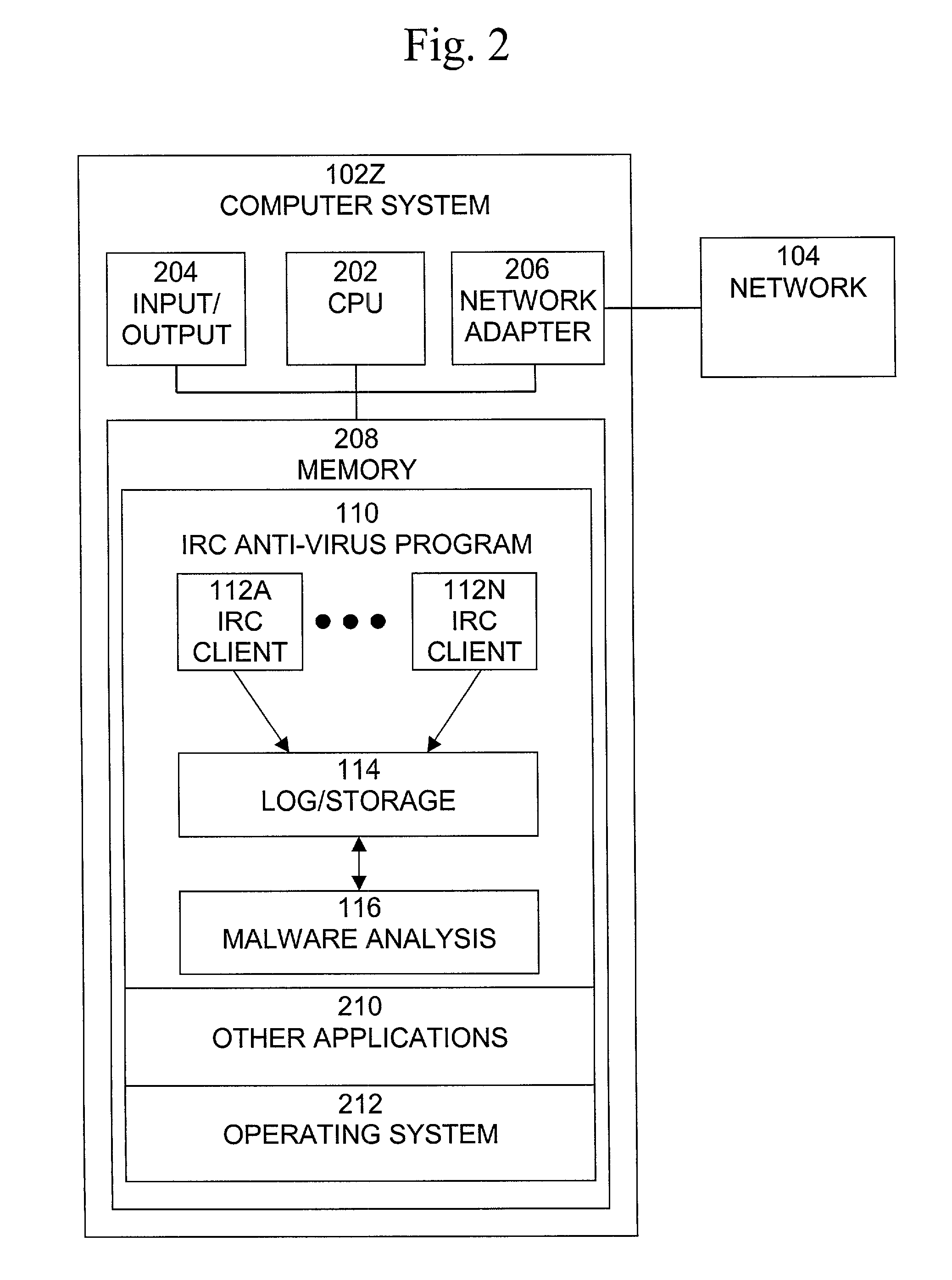
Automated Internet Relay Chat malware monitoring and interception
A method, system, and computer program product for providing monitoring and interception of malwares in Internet Relay Chat (IRC), which is secure, does not require significant system resources, and is capable of monitoring multiple IRC networks and servers. A method of detecting a computer malware comprises the steps of joining an Internet Relay Chat server, retrieving a list of channels of the Internet Relay Chat server, monitoring at least one channel in the list of retrieved channels, accepting data received from the monitored channel, and storing and logging the data received from the monitored channel.
Owner:MCAFEE LLC
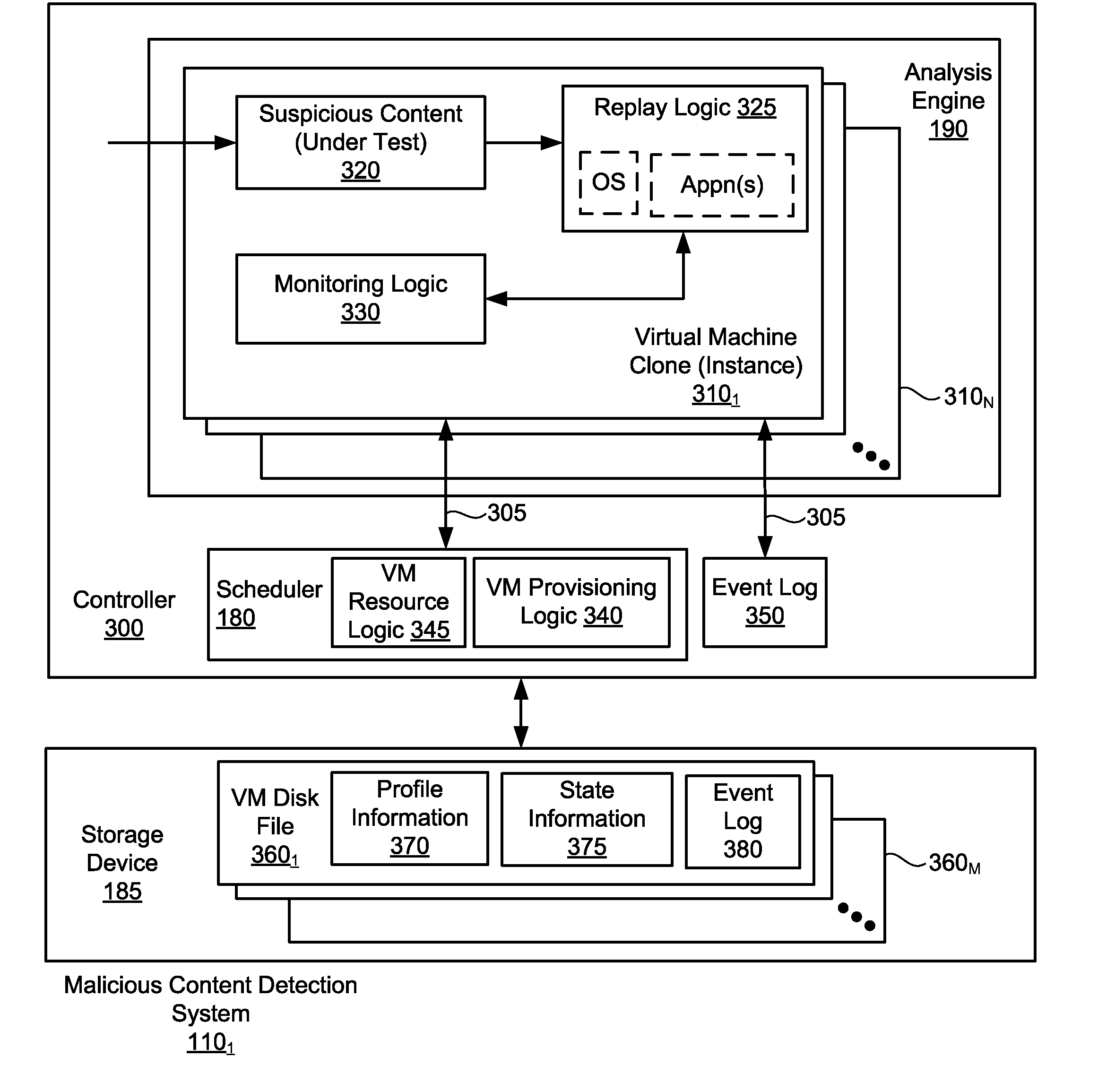
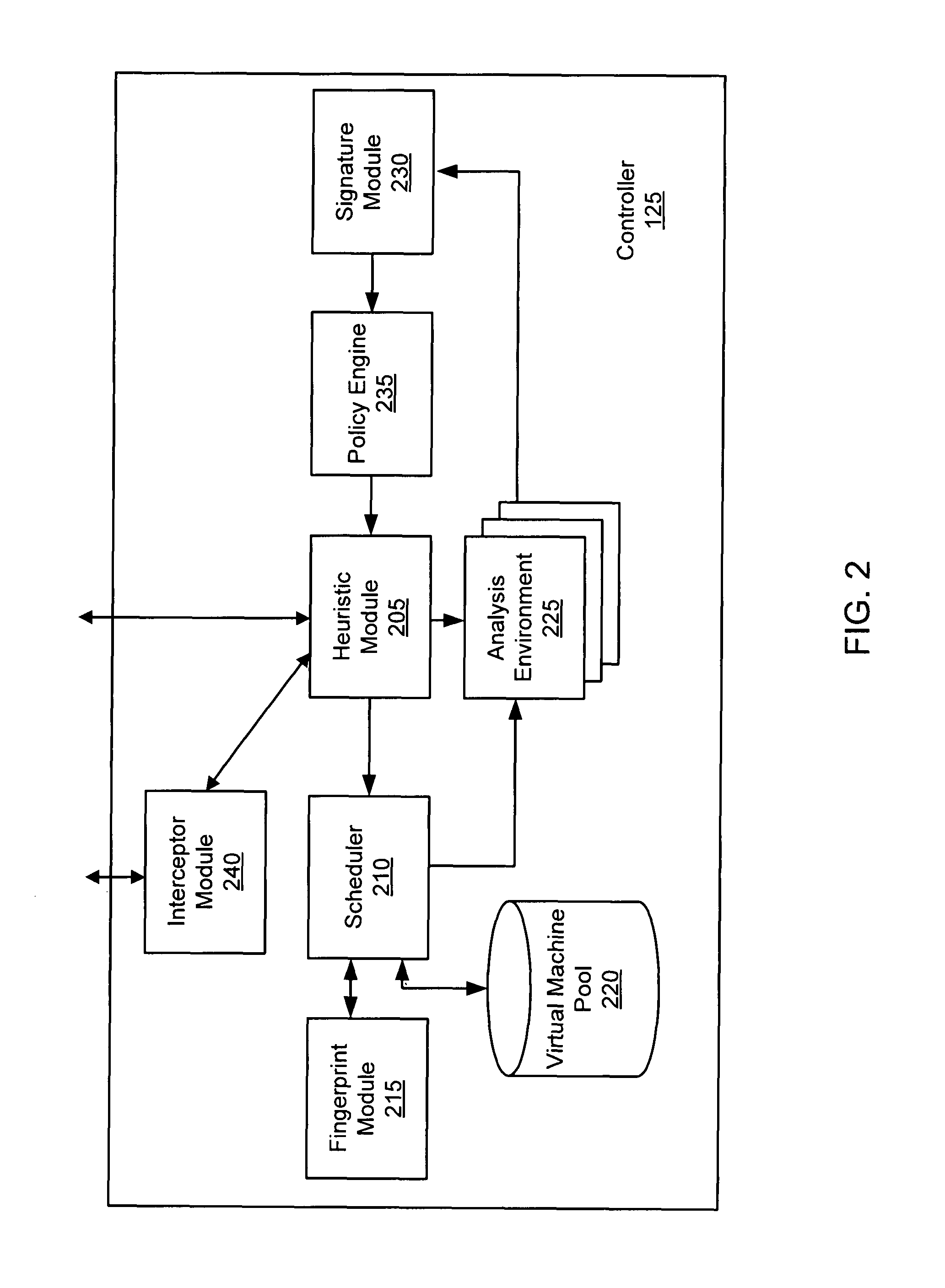
Systems and methods for malware attack detection and identification
Exemplary systems and methods for malware attack detection and identification are provided. A malware detection and identification system can comprise a controller. The controller can comprise an analysis environment configured to transmit network data to a virtual machine, flag input values associated with the network data from untrusted sources, monitor the flagged input values within the virtual machine, identify an outcome of one or more instructions that manipulate the flagged input values, and determine if the outcome of the one or more instructions comprise an unauthorized activity.
Owner:FIREEYE SECURITY HLDG US LLC
Mobile web protection
InactiveUS20120324568A1Computer security arrangementsMultiple digital computer combinationsEvaluation resultWeb browser
On a mobile communications device, visiting a link from a messaging application or web browser may result in an undesired action, such as visiting a phishing site, downloading malware, causing unwanted charges, using too much battery, or the device being exploited. In an implementation, a mobile application intercepts a request including an identifier associated with an action to be performed by another application on the device and evaluates the identifier to determine when the request should be permitted, blocked, or conditionally permitted. The client may use local data or make a request to a server to evaluate the identifier. In an implementation, server communications are optimized to minimize latency by caching evaluation results on the device, proactively priming the device's DNS cache, optimizing when DNS lookups are performed, and adapting evaluation policy based on factors such as the source of the request, and the currently active network connection.
Owner:LOOKOUT MOBILE SECURITY
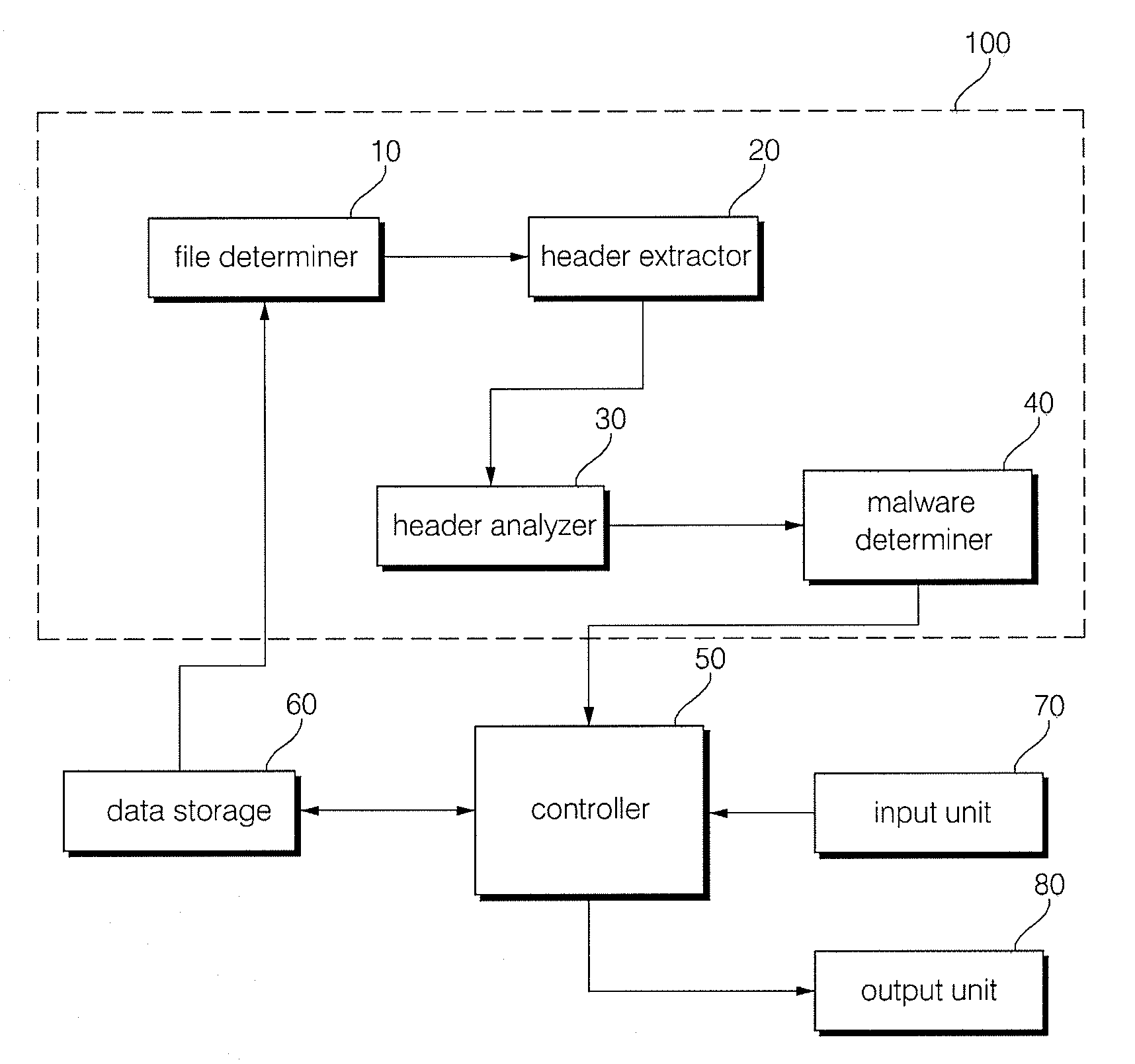
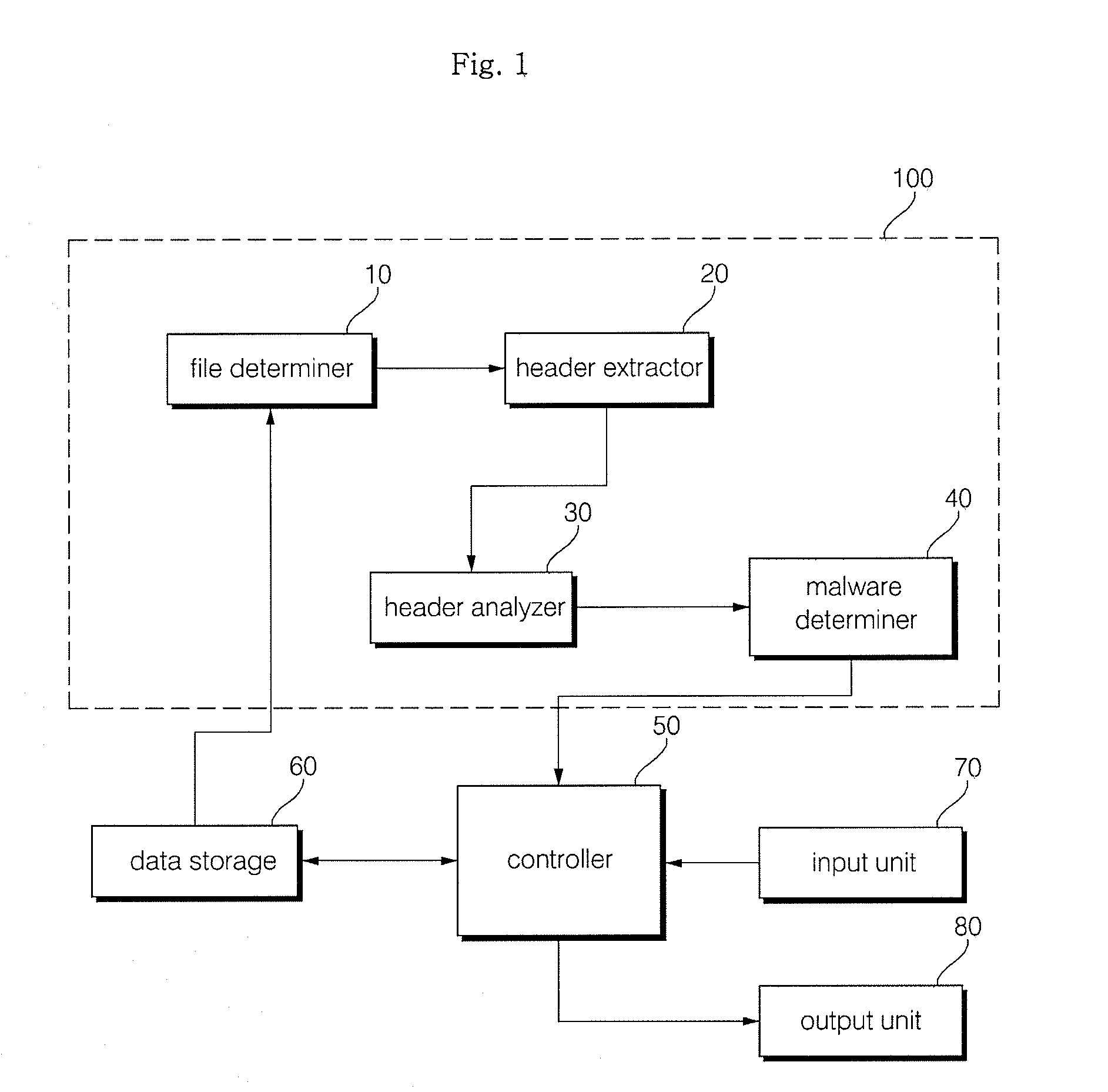
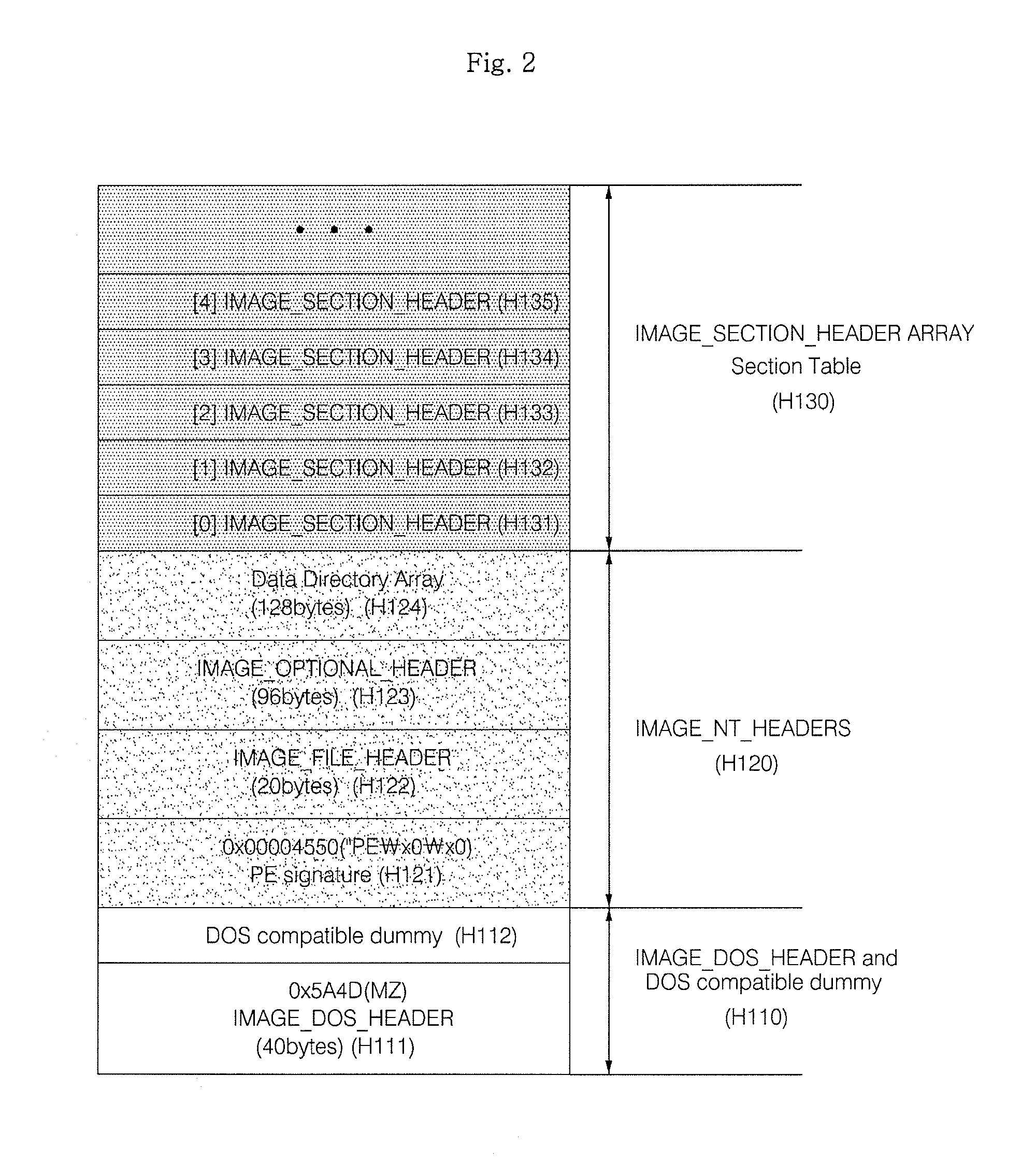
Method and apparatus for malware detection
InactiveUS20090133125A1Shorten detection timeImprove security levelMemory loss protectionUnauthorized memory use protectionMalwareProtection system
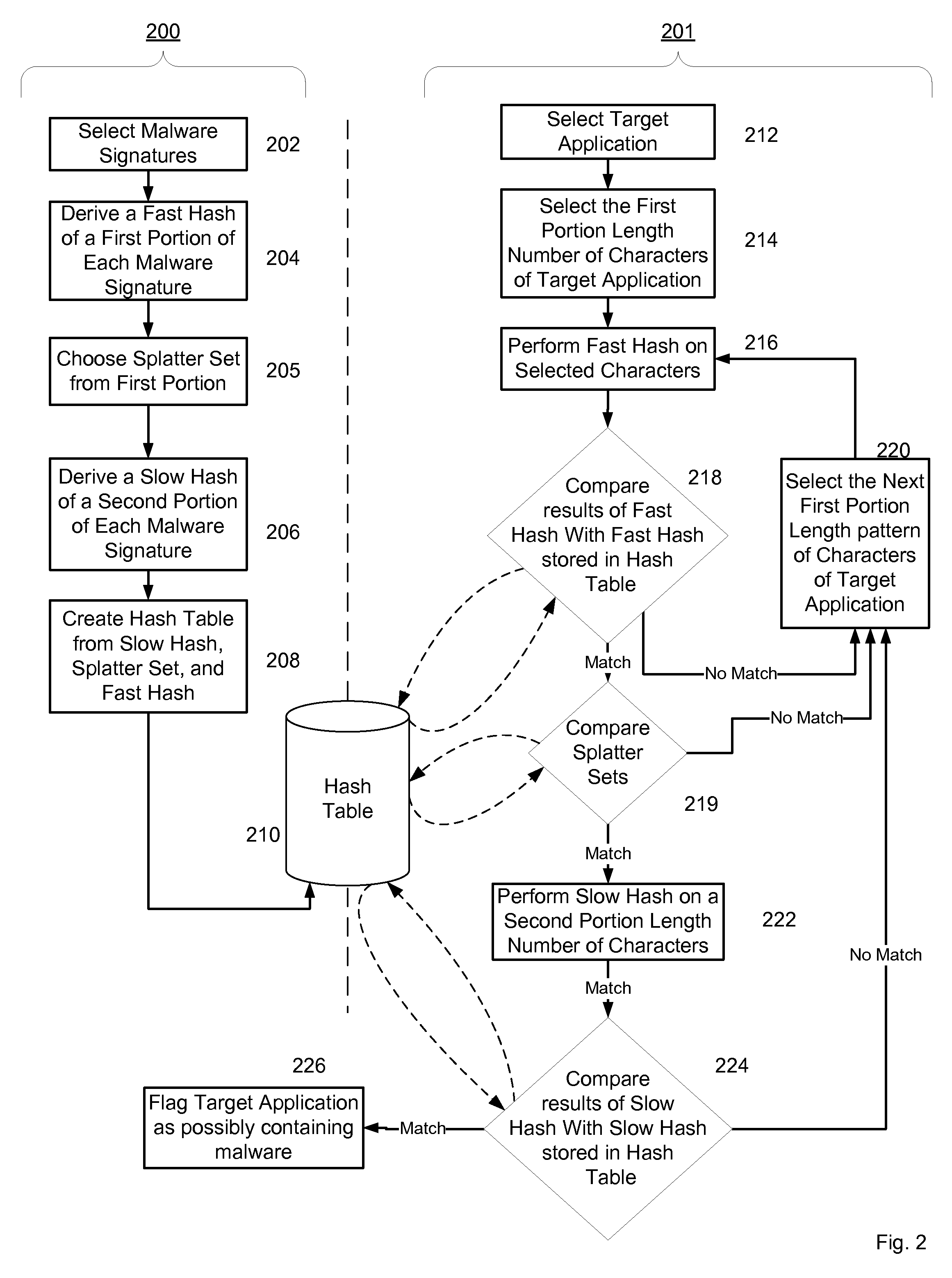
The present invention relates to an apparatus and method for detecting malware. The malware detection apparatus and method of the present invention determines whether a file is malware or not by analyzing the header of an executable file. Since the malware detection apparatus and method can quickly detect presence of malware, it can shorten detection time considerably. The malware detection apparatus and method can also detect even unknown malware as well as known malware to thereby estimate and determine presence of malware. Therefore, it is possible to cope with malware in advance, protect a system with a program, and increase security level remarkably.
Owner:ELECTRONICS & TELECOMM RES INST
Method and apparatus for reducing false positive detection of malware
Method and apparatus for detecting malware are described. In some examples, files of unknown trustworthiness are identified as potential threats on the computer. A trustworthiness level for each of the files is received from a backend. The trustworthiness level of each of the files is compared to a threshold level. Each of the files where the trustworthiness level thereof satisfies the threshold level is designated as a false positive threat. Each of the files where the trustworthiness level thereof does not satisfy the threshold level is designated as a true positive threat.
Owner:SYMANTEC CORP
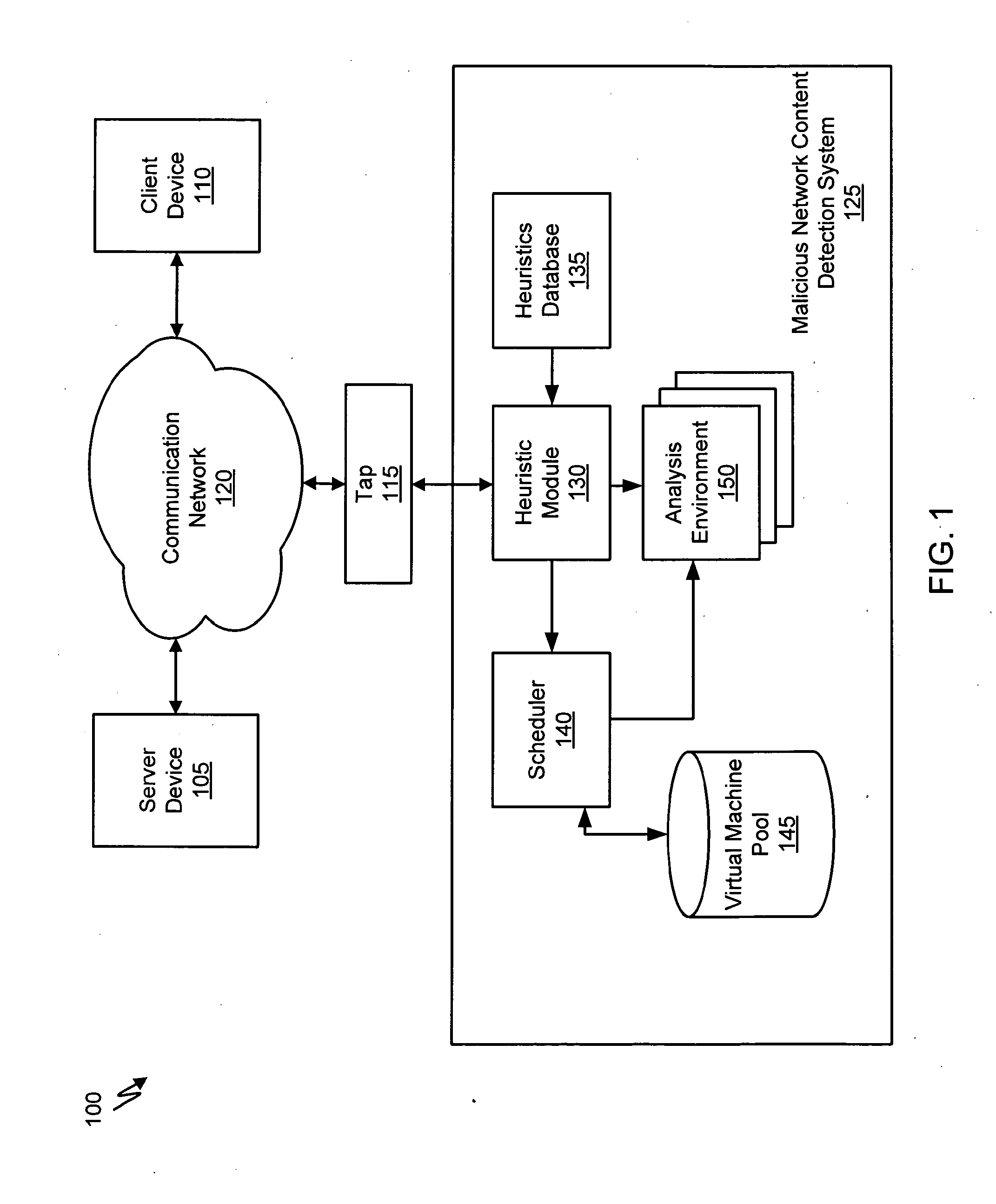
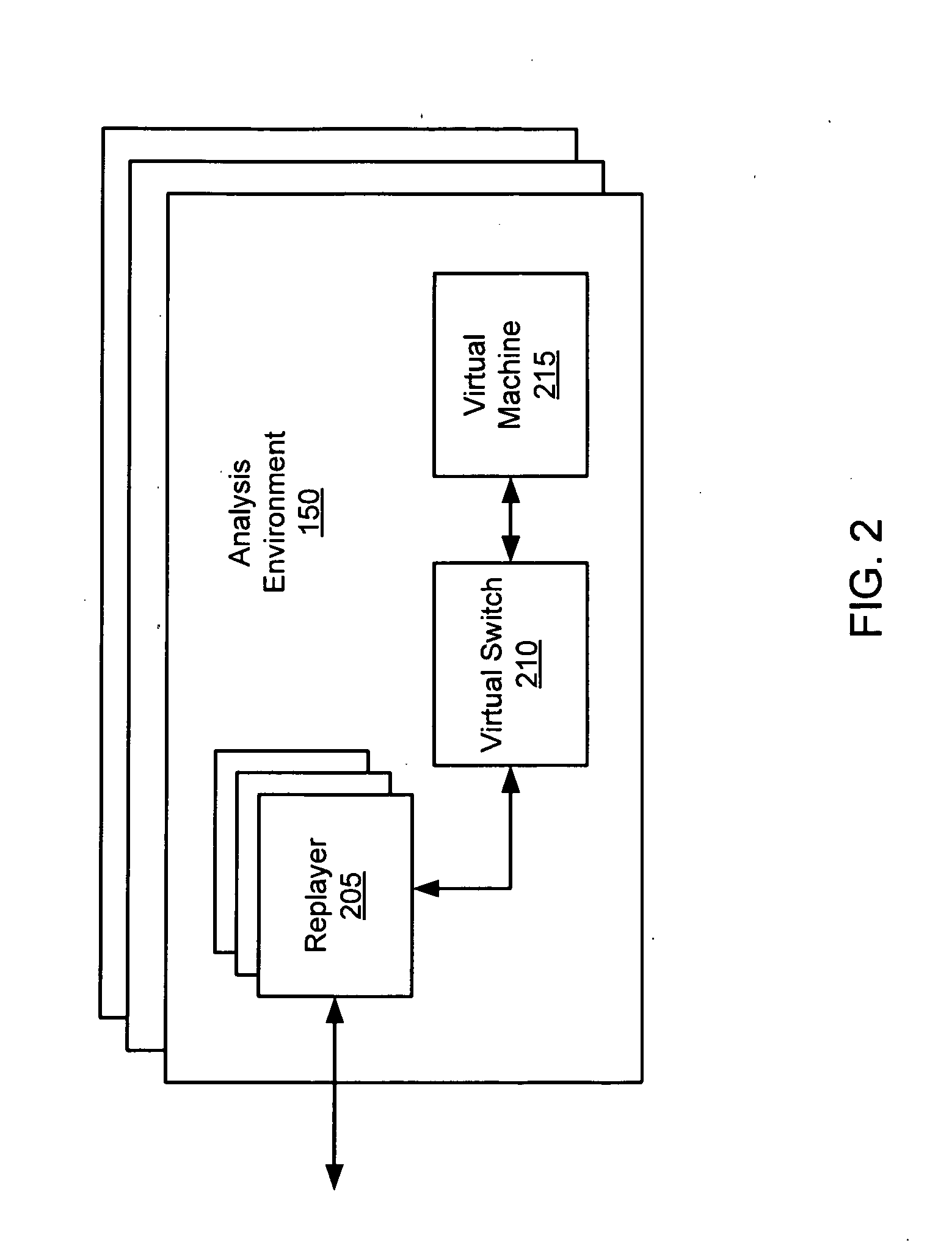
Systems and Methods for Scheduling Analysis of Network Content for Malware
A method for detecting malicious network content comprises inspecting one or more packets of network content, identifying a suspicious characteristic of the network content, determining a score related to a probability that the network content includes malicious network content based on at least the suspicious characteristic, identifying the network content as suspicious if the score satisfies a threshold value, executing a virtual machine to process the suspicious network content, and analyzing a response of the virtual machine to detect malicious network content.
Owner:FIREEYE SECURITY HLDG US LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com