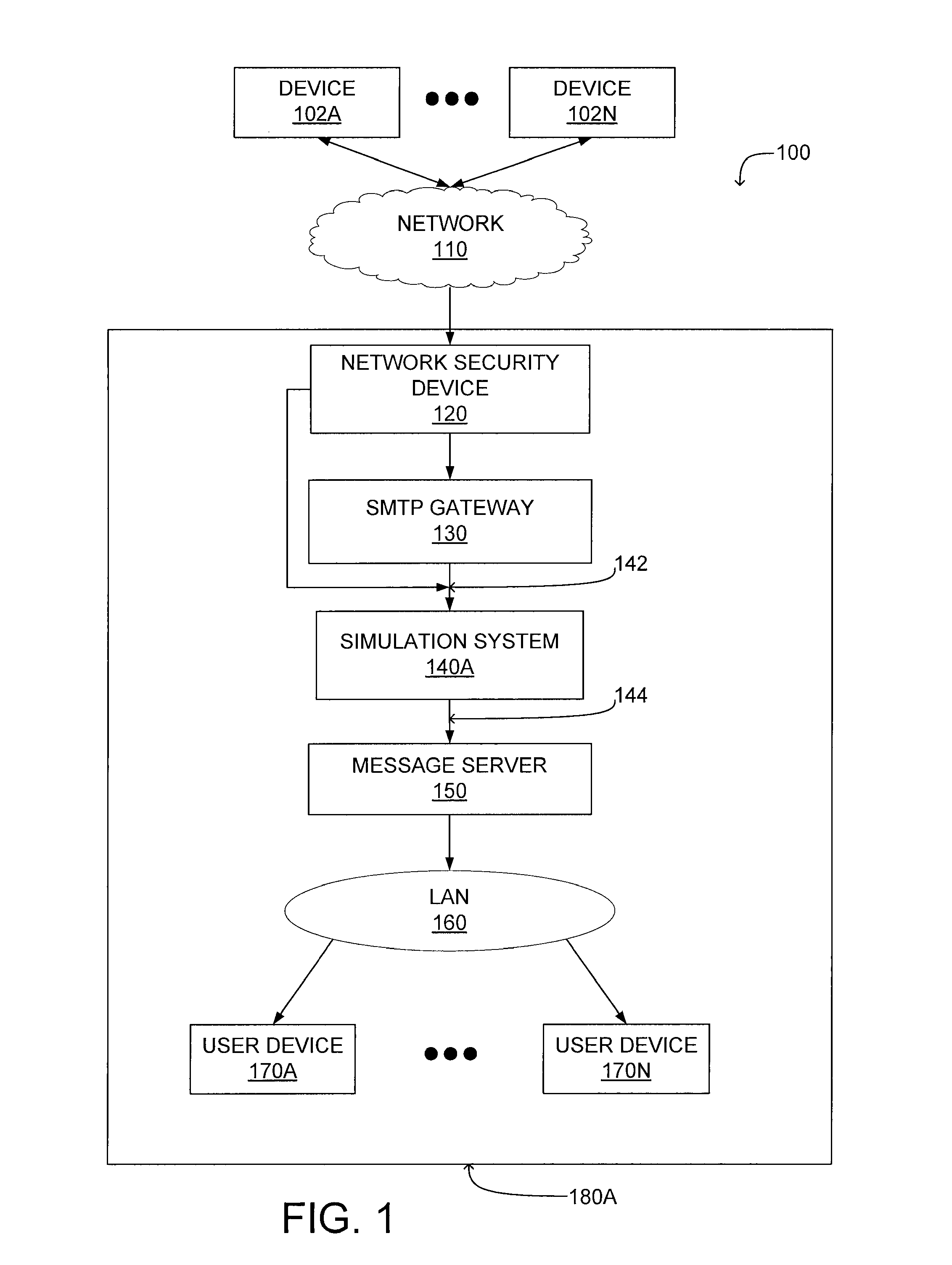
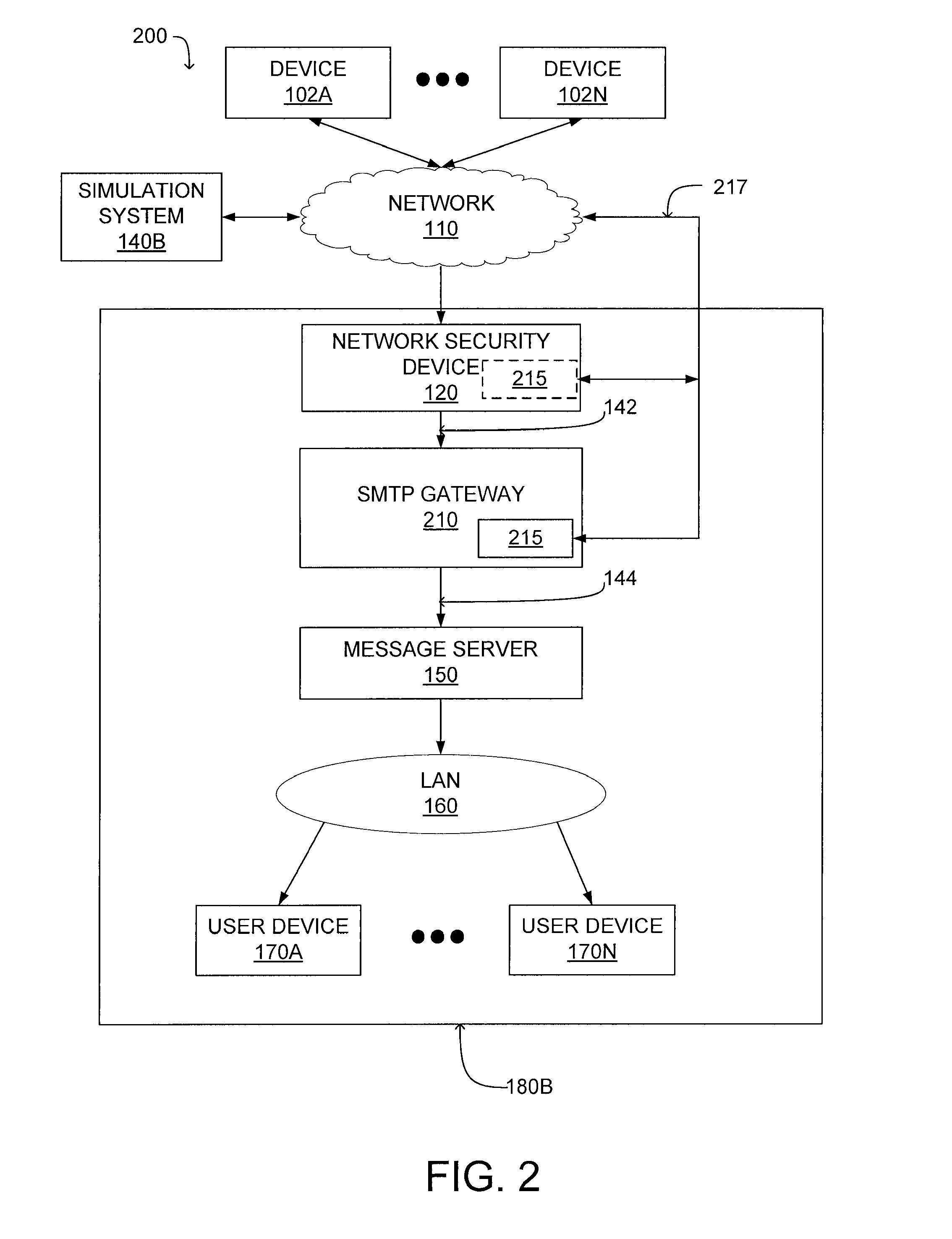
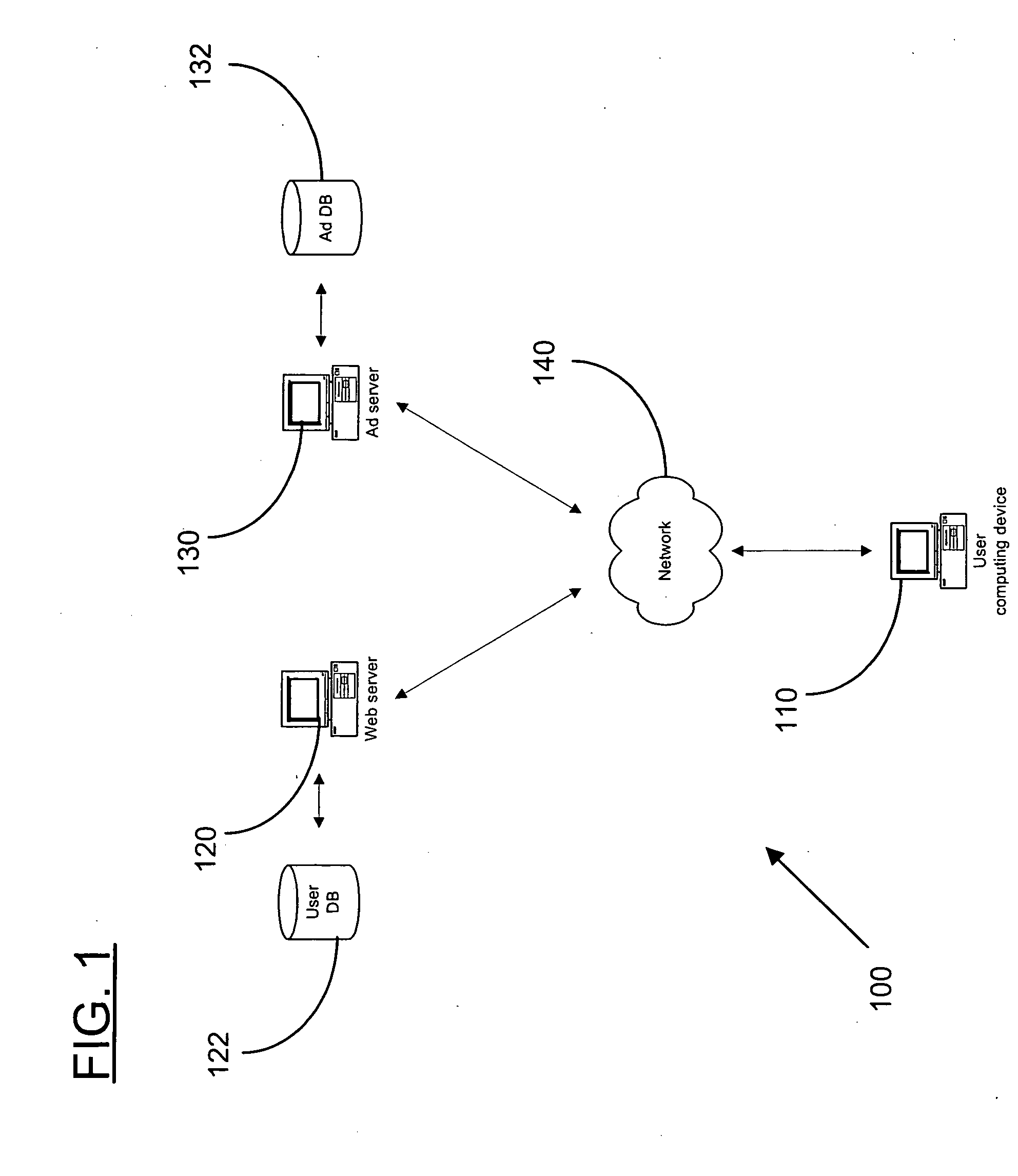
Patents
Literature
24901 results about "User information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
User information is information transferred across the functional interface between a source user and a telecommunications system for delivery to a destination user. In telecommunications systems, user information includes user overhead information.
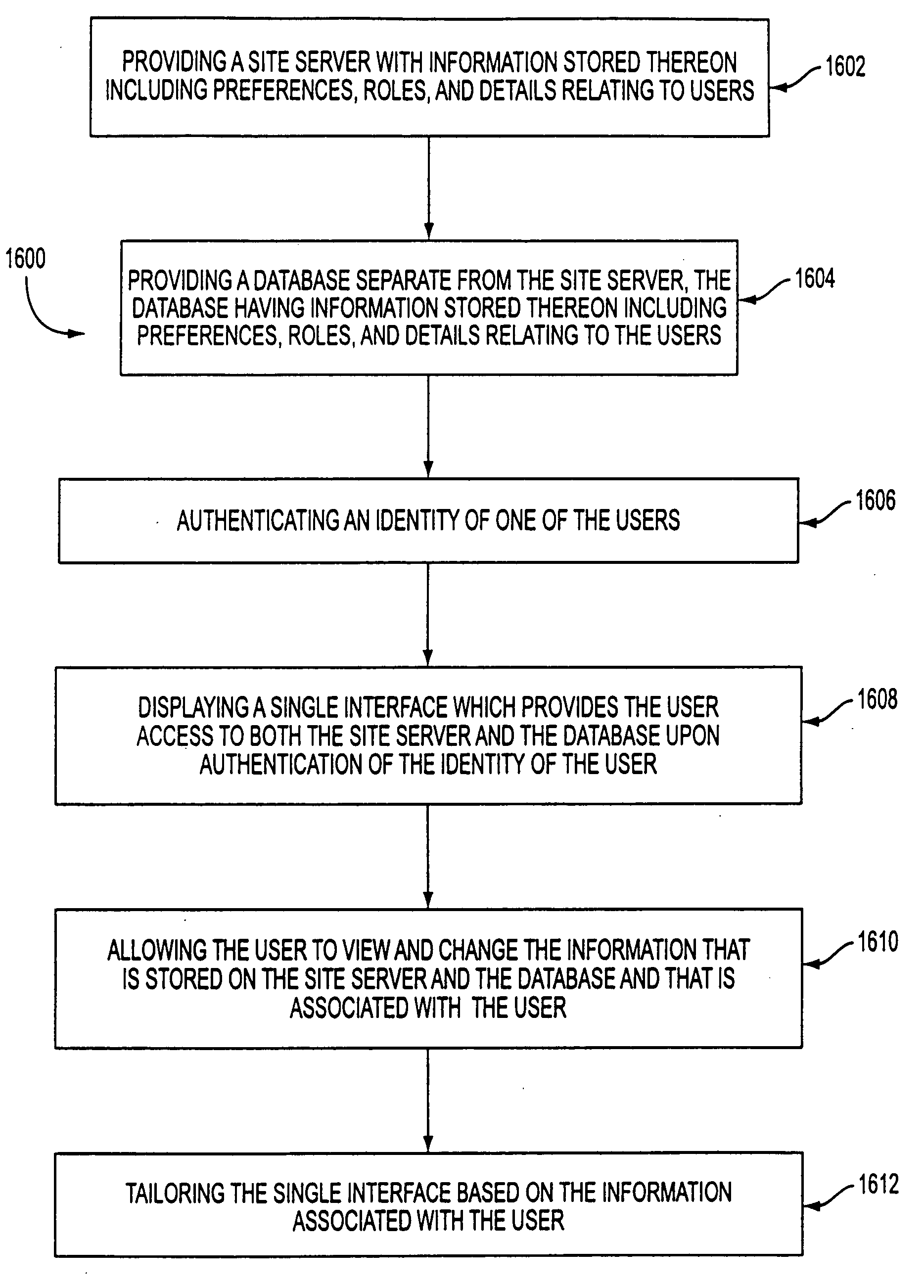
Managing user information on an e-commerce system
The present invention provides for the management of user information of both site server and regular web site users. A site server is provided with information stored thereon including preferences, roles, and details related to users. A database separate from the site server is also provided. The database has information stored thereon including preferences, roles, and details relating to the users. An identity of one of the users is authenticated. A single interface is displayed which provides the user access to both the site server and the database upon authentication of the identity of the user. The user is allowed to view and change the information that is stored on the site server and the database and that is associated with the user. The single interface is tailored based on the information associated with the user.
Owner:ACCENTURE GLOBAL SERVICES LTD
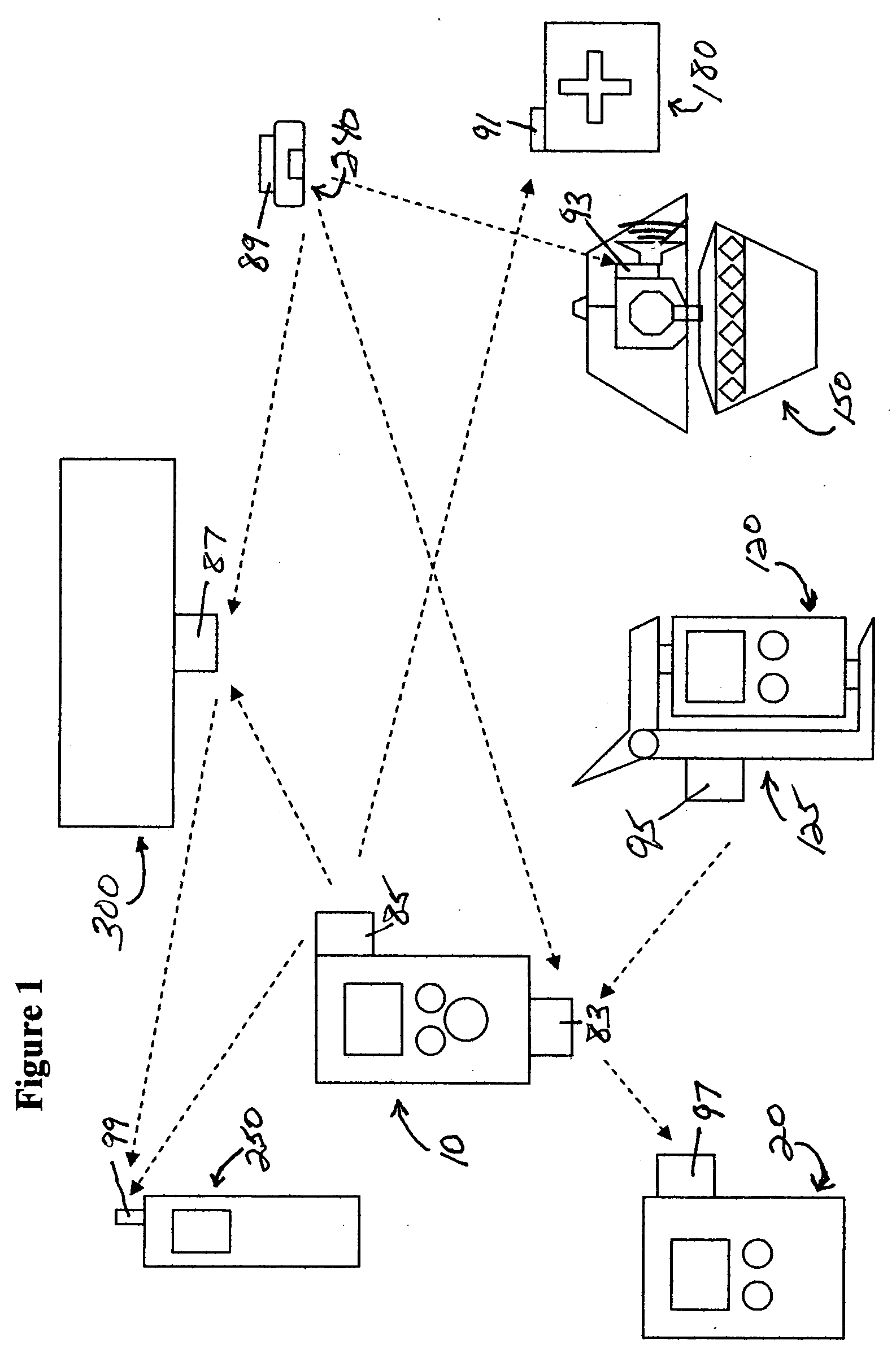
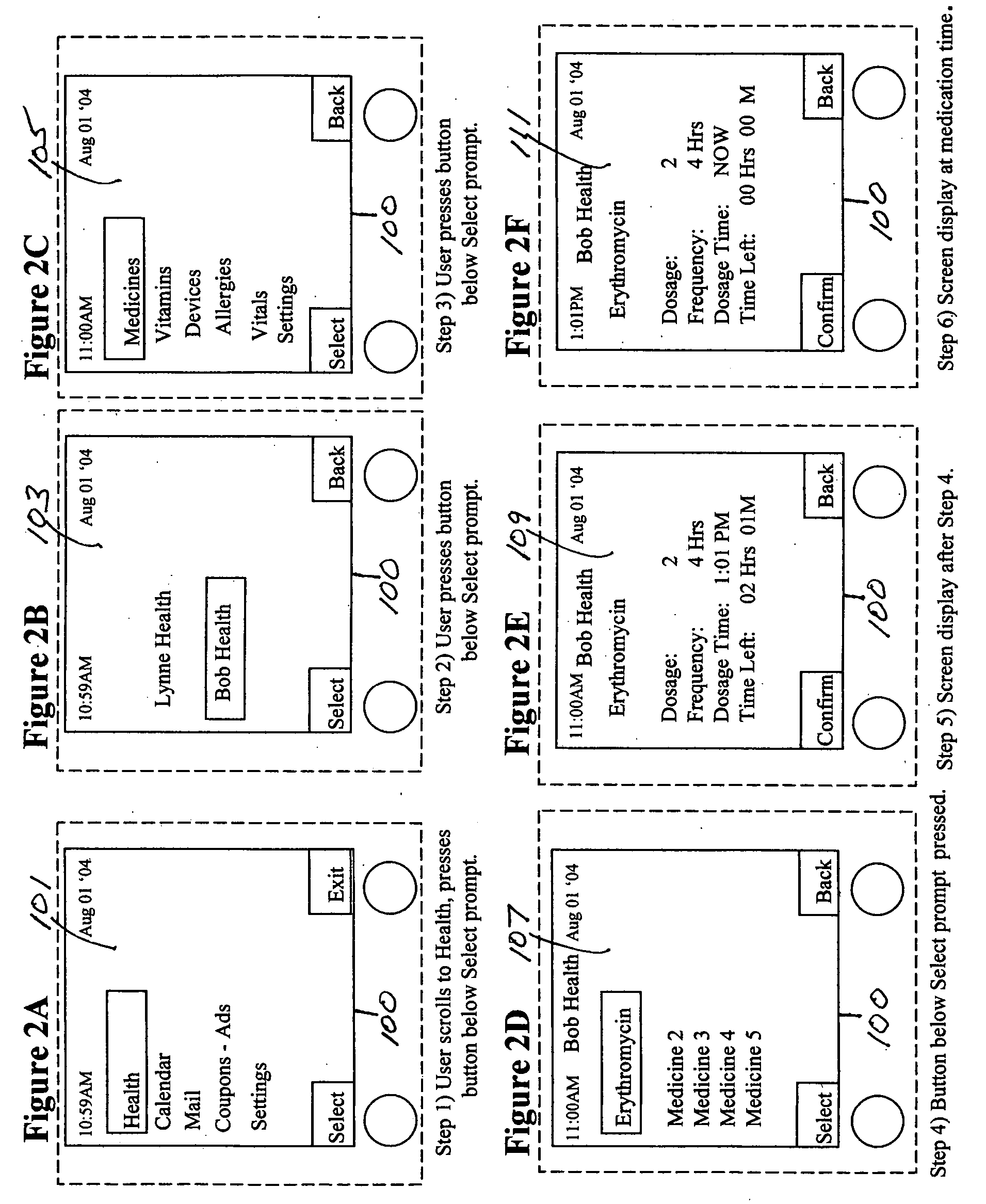
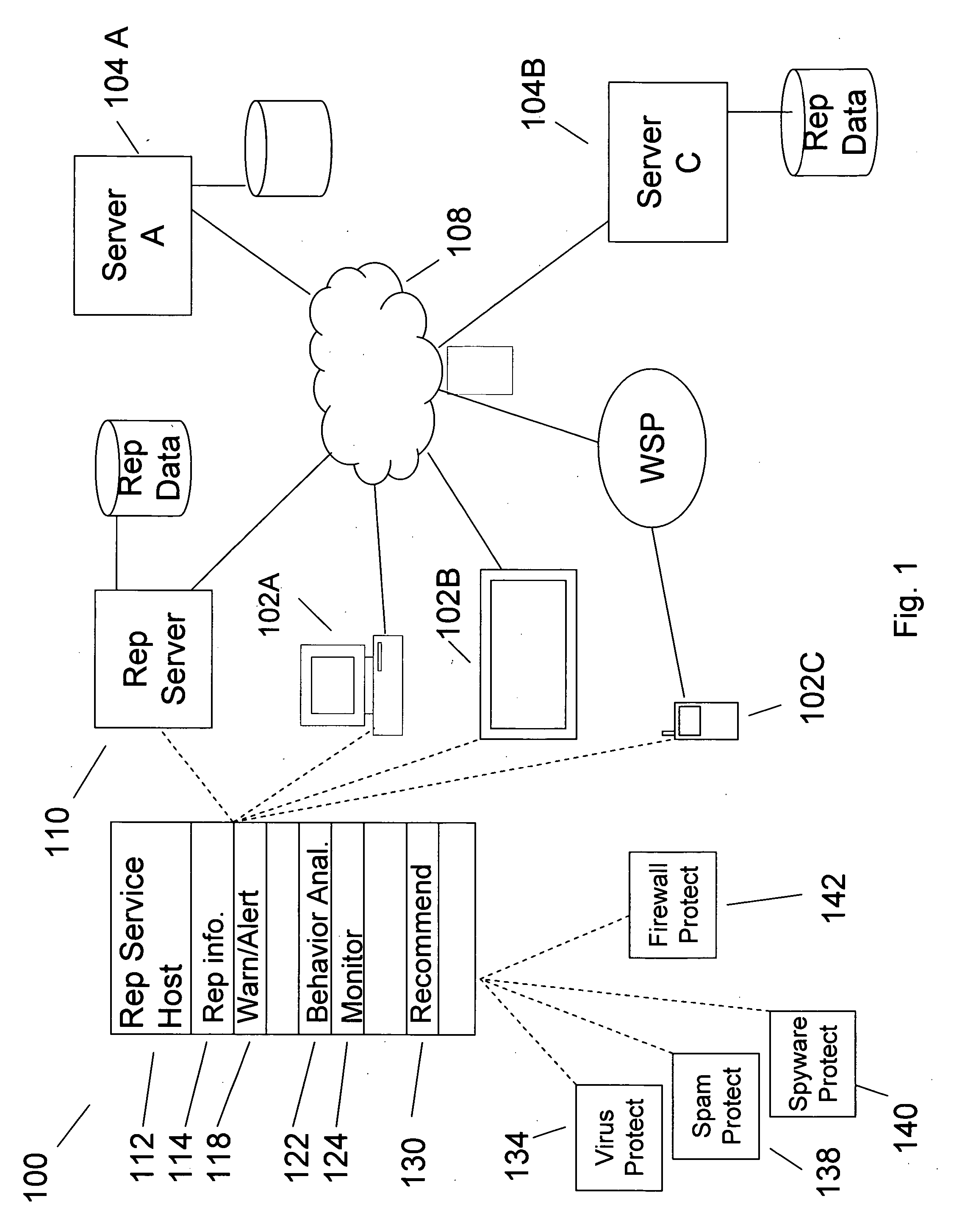
Medication & health, environmental, and security monitoring, alert, intervention, information and network system with associated and supporting apparatuses
InactiveUS20060154642A1Facilitate user and/or occupant well beingExtended stayDispersed particle filtrationDrug and medicationsNetworked systemHealth administration
Systems and apparatuses include devices, biosensors, environmental sensors, security related sensors, networked products, communications processors and components, alert and information components, processors, and software to support: 1) facilitating medication regimen and patient / user health administration, dosage control, tracking, compliance, information inquiry and presentation, reminder and notification; 2) providing monitoring, information, ordering, and intervention; 3) presenting the option of leveraging the preventative care, alert and notification components with other components to facilitate user or occupant well being, along with living, work area and dwelling environmental or security safety; and 4) enhancing the dwelling, living or work area with products that may be networked to support the widespread acceptance of these systems and apparatuses. The systems include a) processing, centralizing and communicating device commands and / or programs, e.g. a multifunctional device controller; b) device administration; c) patient / user information; d) dwelling environmental safety; e) security breach information; f) centralized and remote apparatus and system activations through primary component or at least one backup.
Owner:INSIGNIO TECH
Systems and Methods to Target Predictive Location Based Content and Track Conversions
ActiveUS20080248815A1Particular environment based servicesDevices with GPS signal receiverCommunications systemMobile device
Methods and systems that record the location of a user and transmit targeted content to a user based upon their current and past location information. A network is configured to include a server programmed with a database of targeted content, a database of location information, a database of user information, a database searching algorithm, and a wireless communication system capable of communicating with the user's mobile device. The location of the mobile device is ascertained and recorded. The location information is analyzed to determine the routes taken by the user, businesses visited by the user, and other behaviors of the user. Targeted content is sent to the mobile device of the user and whether the user visits the physical locations associated with the targeted content is monitored. Payment systems, phone exchange systems, and other features may also be integrated to provide detailed conversion tracking to producers of targeted content and business owners.
Owner:META PLATFORMS INC
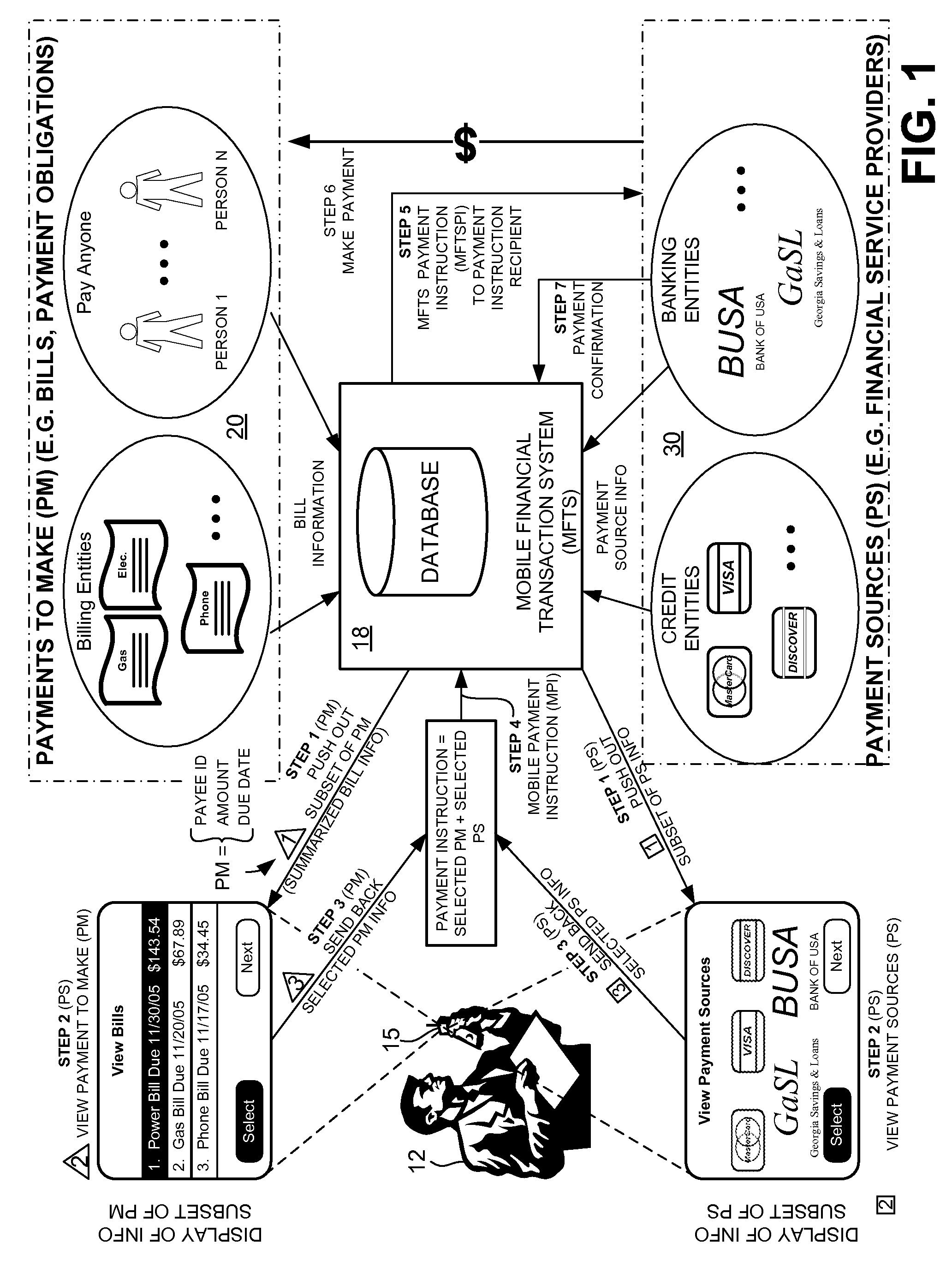
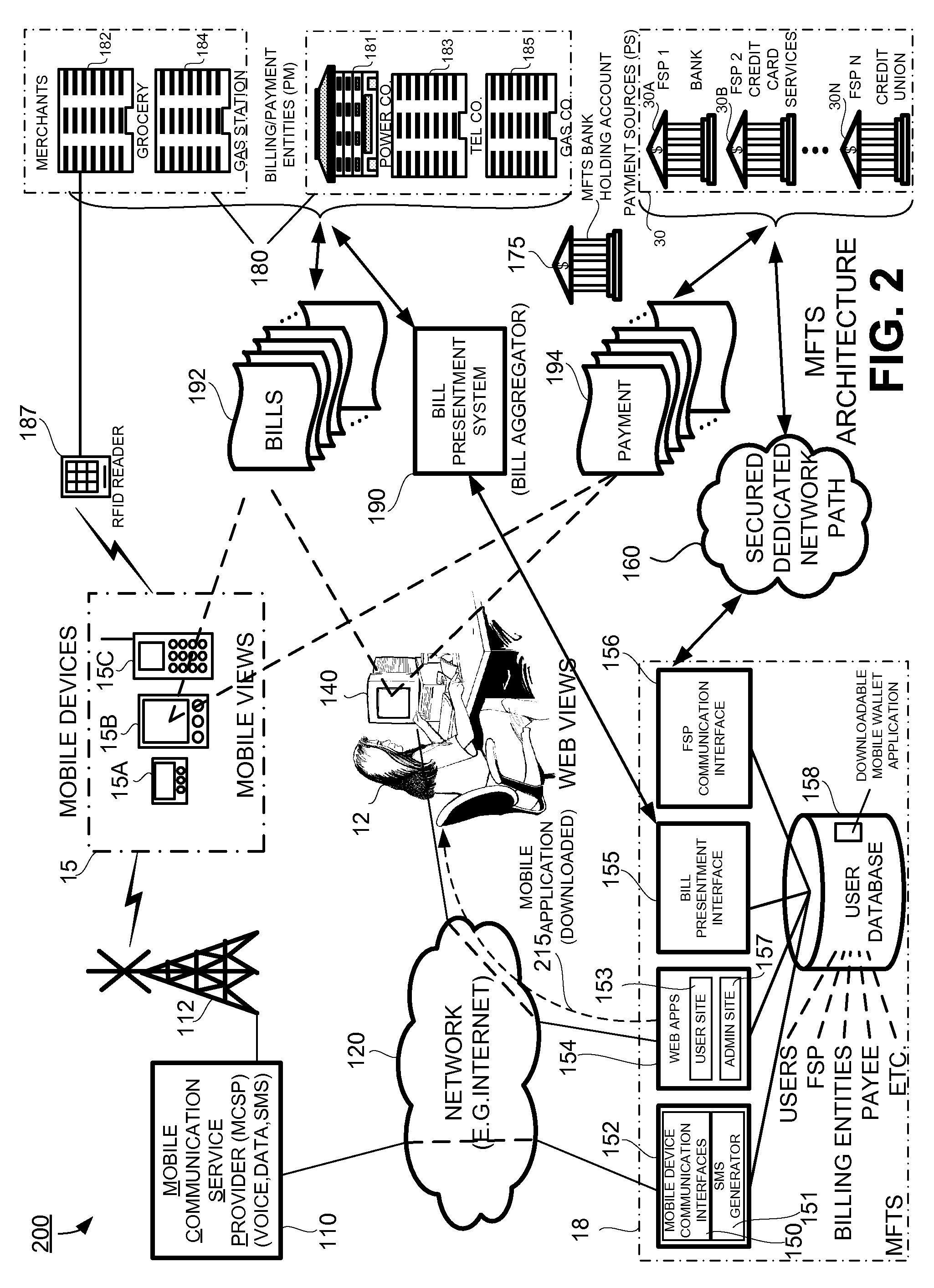
Methods and Systems For Making a Payment Via A Stored Value Card in a Mobile Environment
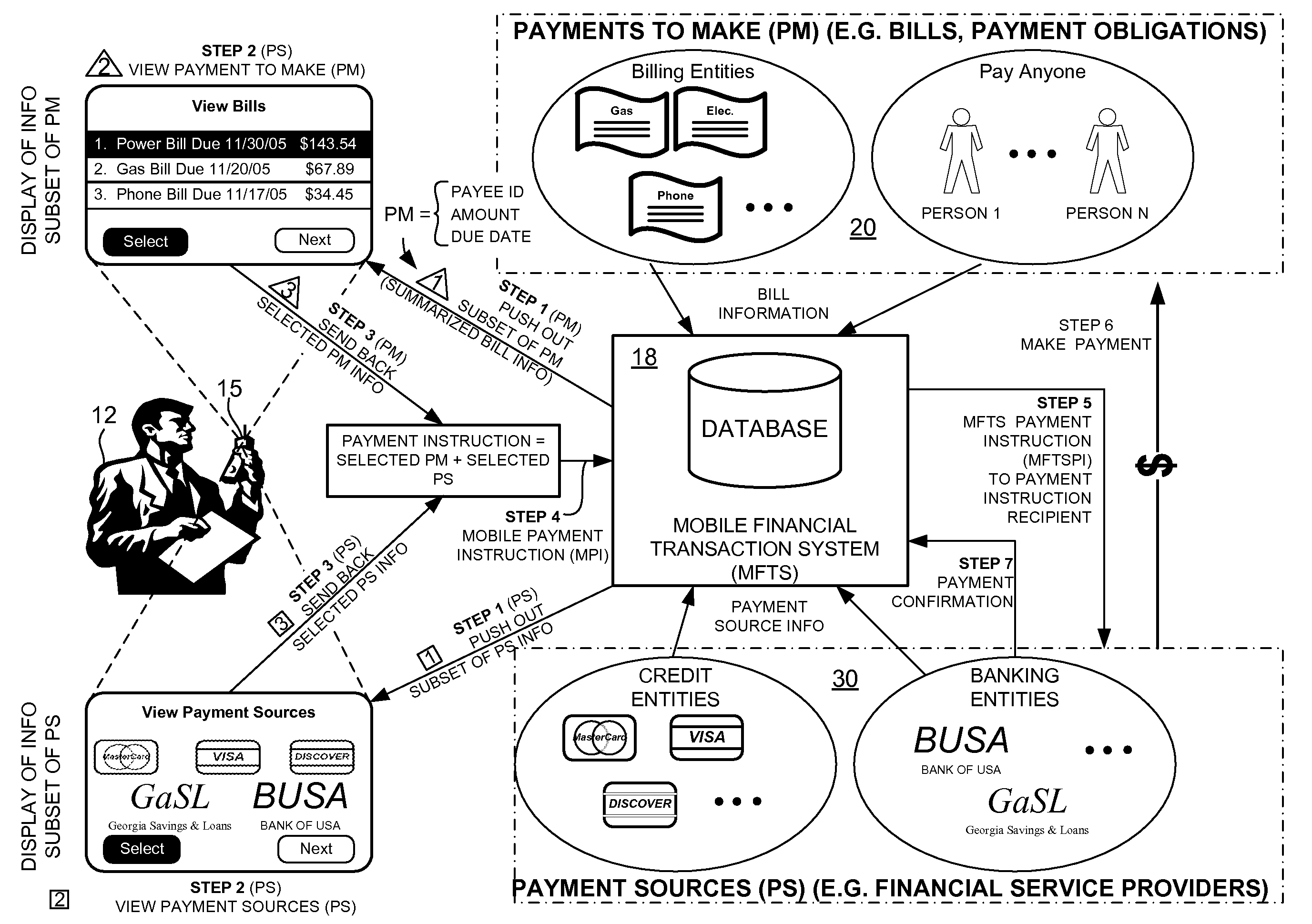
ActiveUS20080040265A1Unprecedented convenienceUnprecedented flexibilityFinanceBilling/invoicingFinancial transactionMobile context
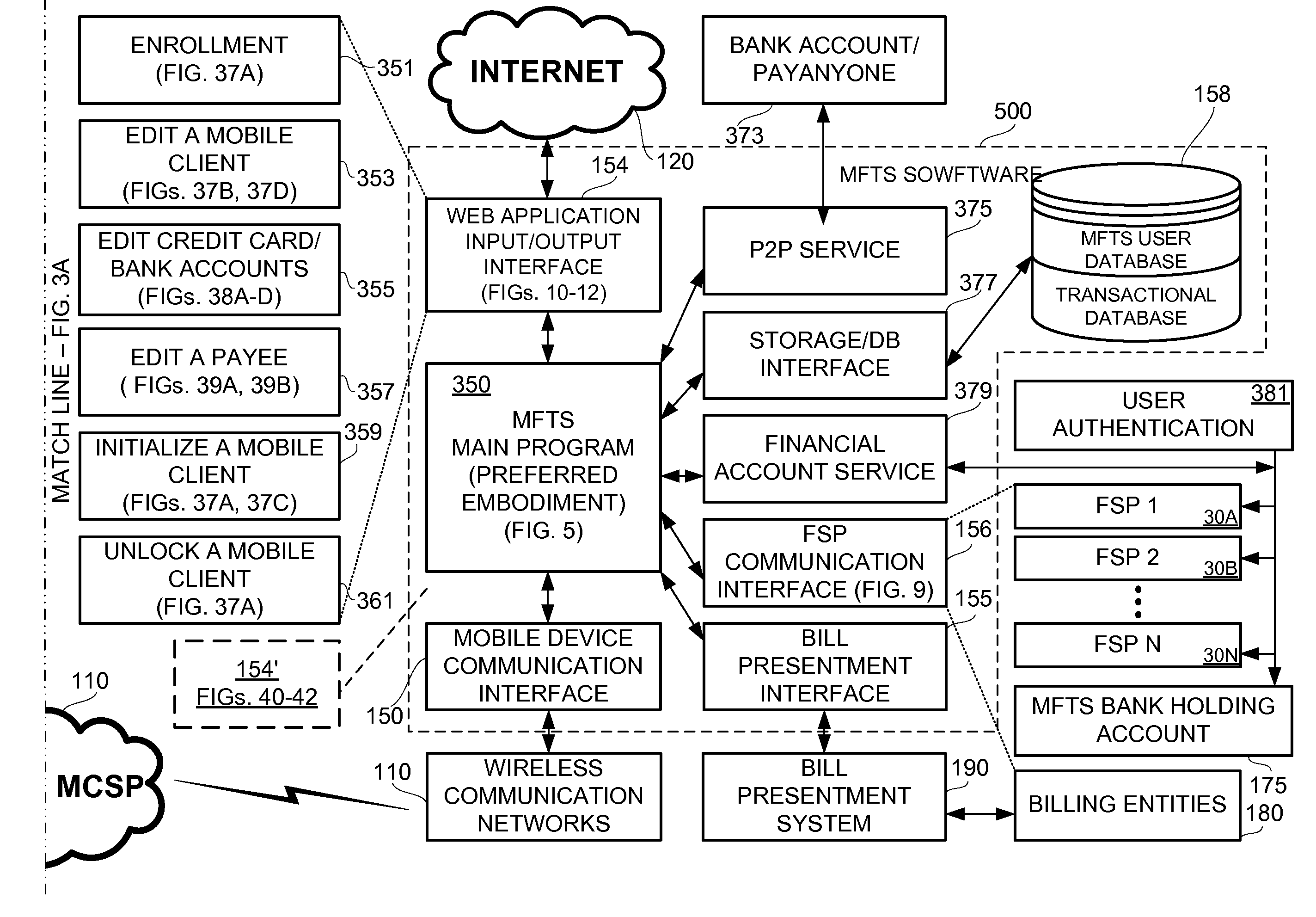
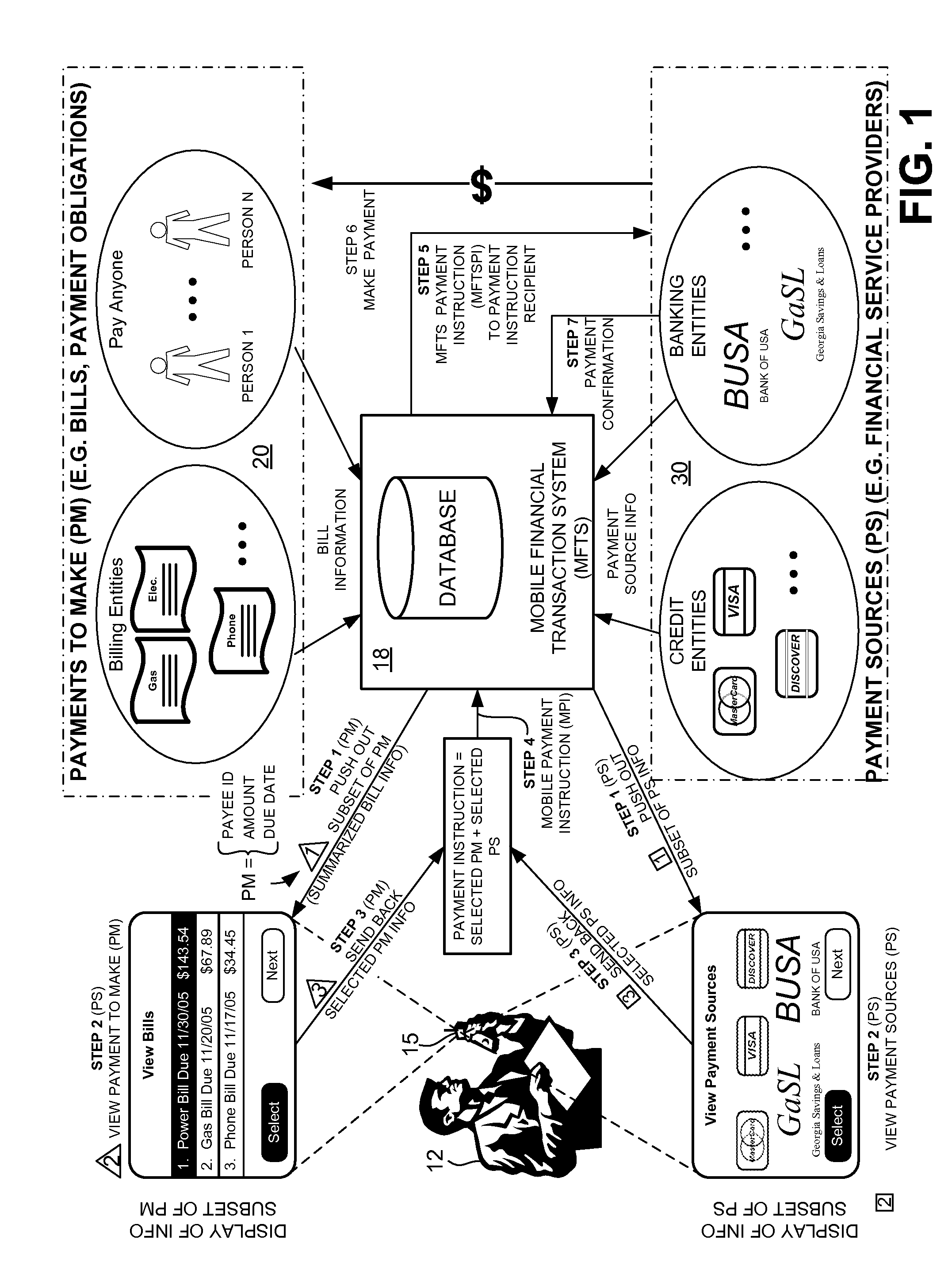
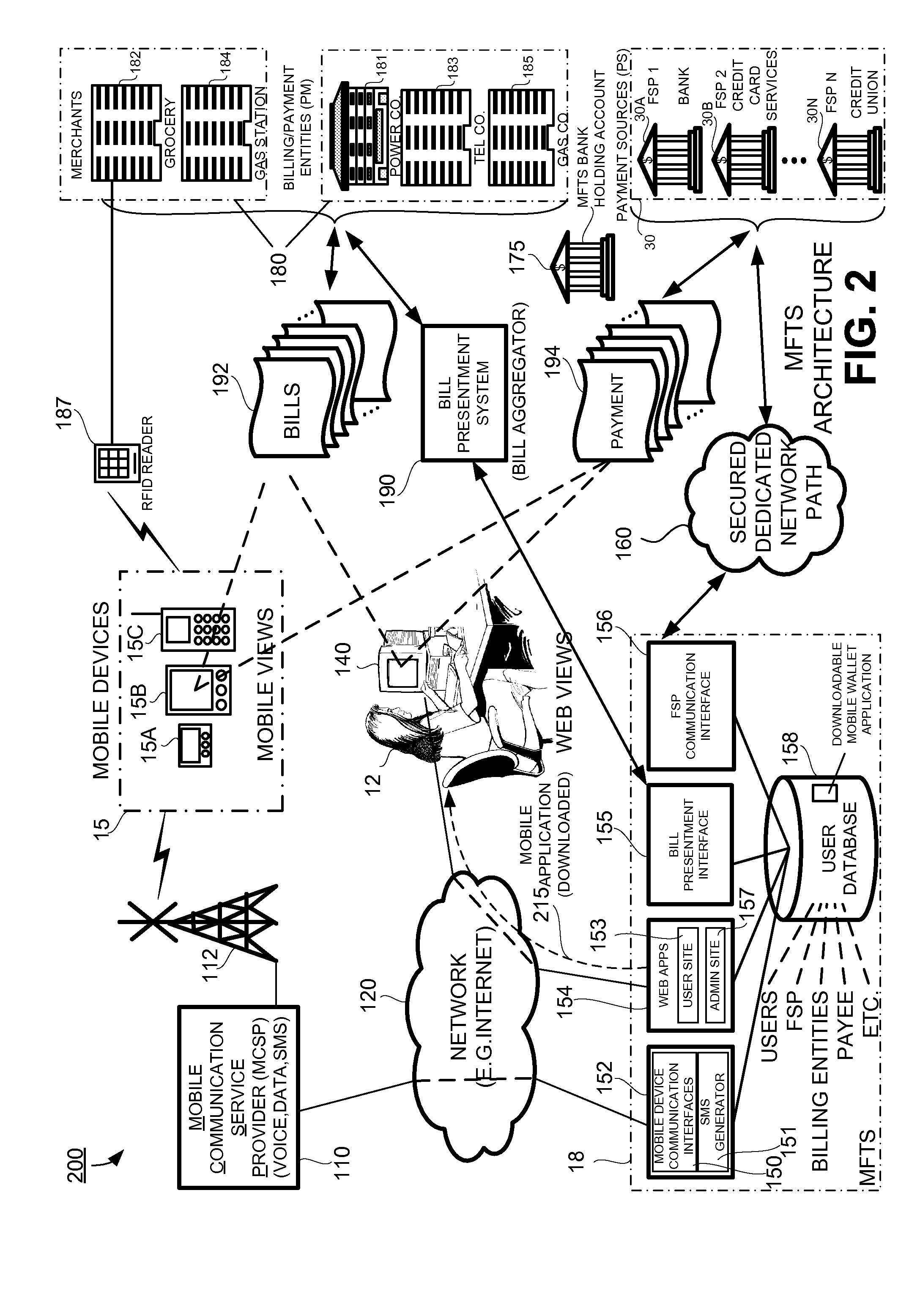
Methods and systems for making a financial payment to a payee via a stored value (SV) card utilizing a mobile device such as a mobile telephone (cellphone) or wireless connected personal digital assistant (PDA). The mobile device communicates wirelessly with a mobile financial transaction system (MFTS) that stores user information and transaction information. A user enters information via the mobile device identifying a payee and indicating a stored value card payment method. The mobile device generates a mobile payment instruction that includes information corresponding to the identified payee and indicating a stored value card payment method. The mobile payment instruction is wirelessly communicated to the MFTS. The MFTS generates an MFTS payment instruction to a payment instruction recipient that can issue a new stored value card and / or reload funds onto a pre-existing stored value card. The MFTS communicates the MFTS payment instruction to the payment instruction recipient, which arranges for payment to the identified payee by issuing a new stored value card or reloading funds onto a pre-existing stored value card.
Owner:QUALCOMM INC
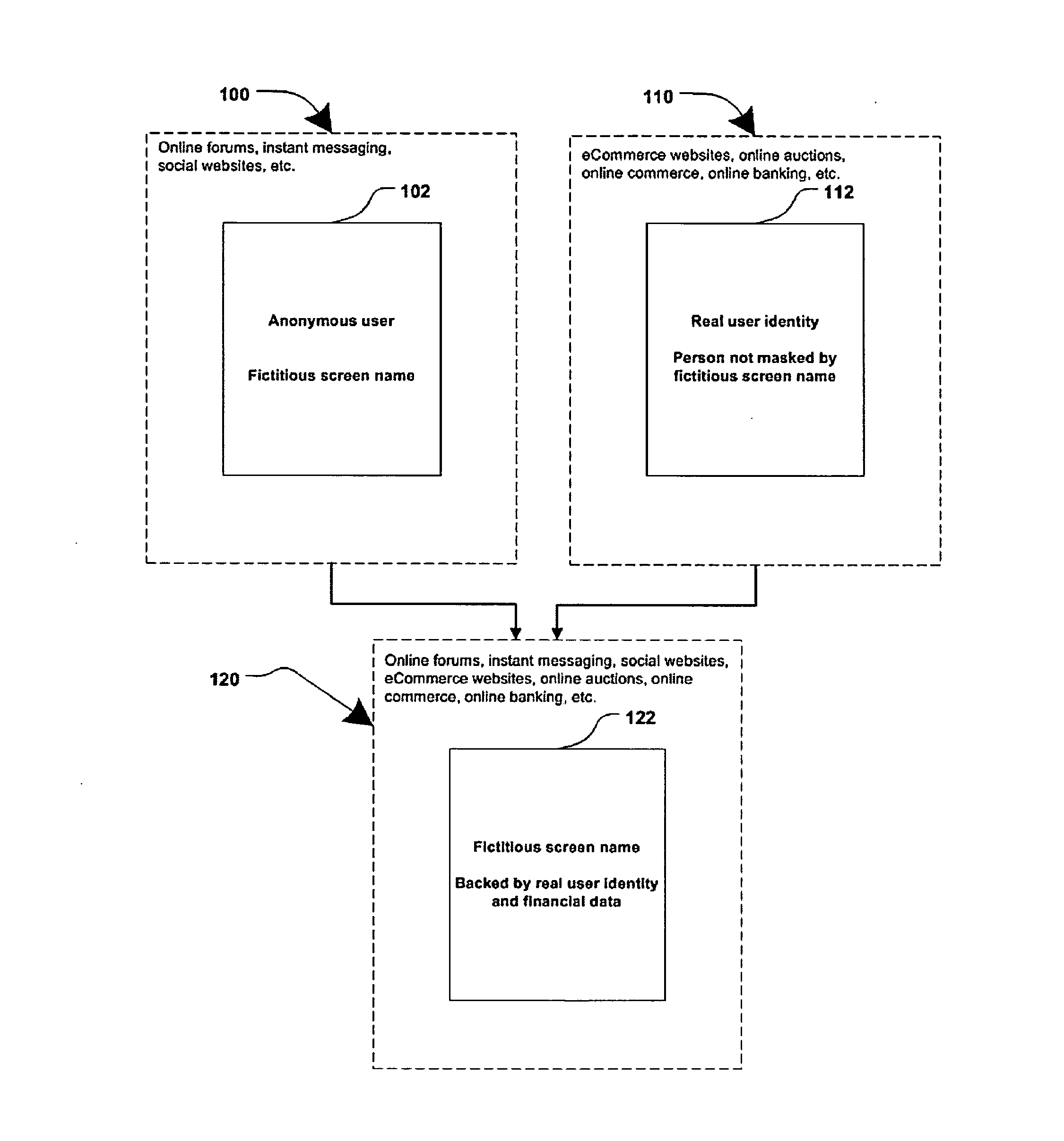
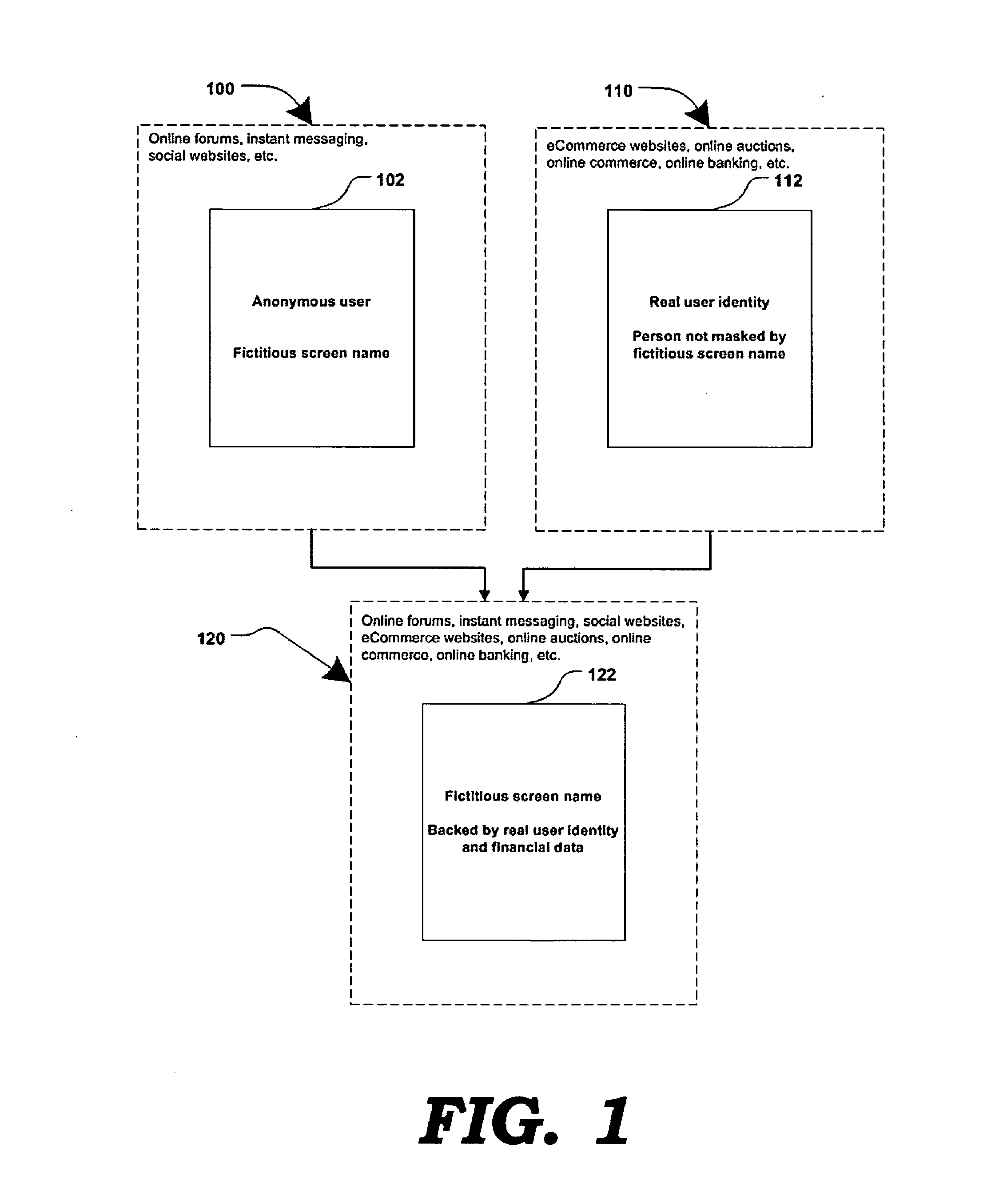
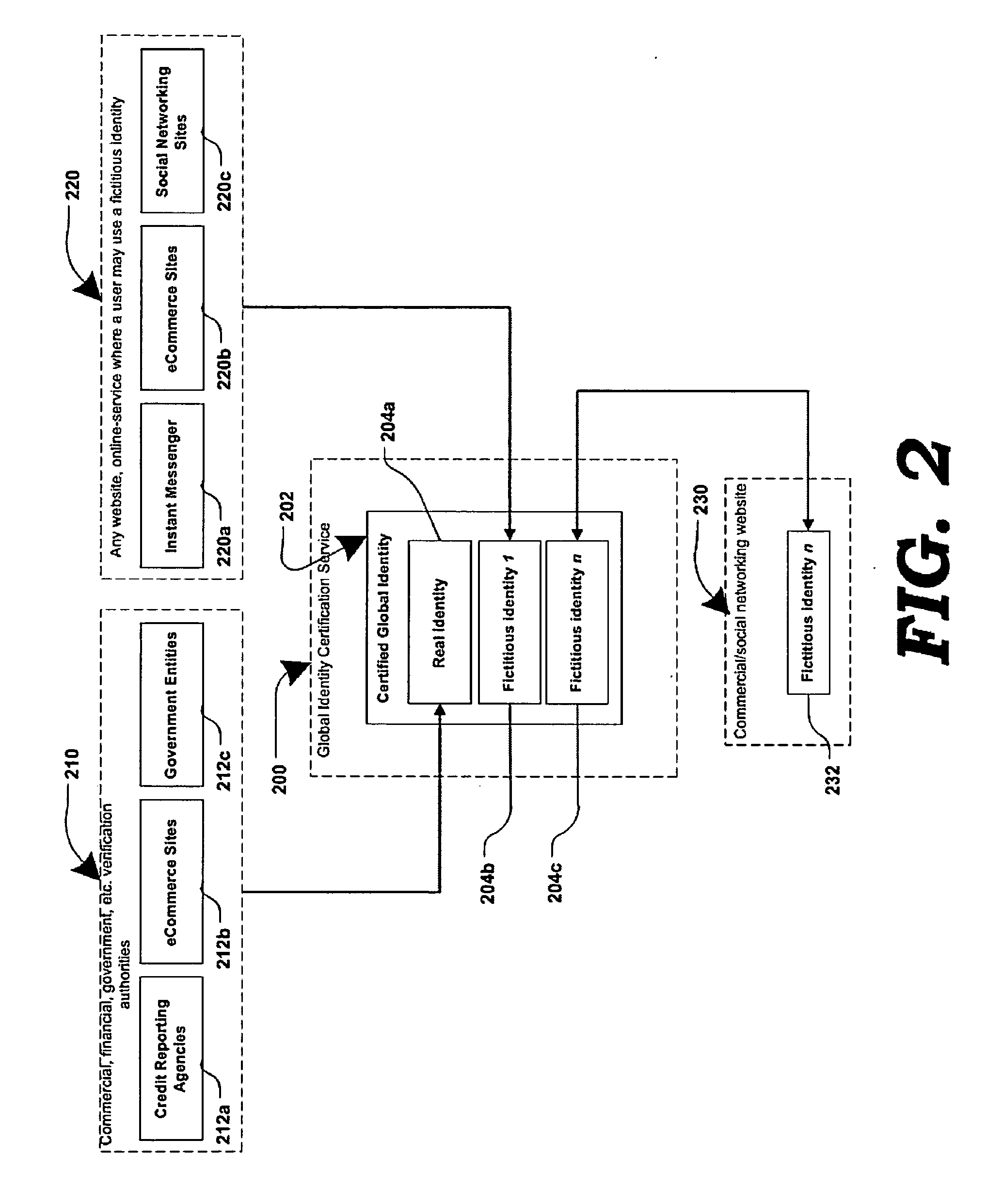
Method and systems for online advertising to users using fictitious user idetities
Various methods, systems and apparatus for associating fictitious user identities (e.g. screen names, user names, email addresses, handles, etc.) used in electronic communications (e.g. over the internet or mobile network via instant messenger, e-mail, social networks, ecommerce, auction websites, etc.) with real personal information (e.g. the true identity of an individual such as their name, address, credit score, driving record, mobile number, etc.) are disclosed. One such method may include discovering, verifying and storing real personal information, associated with fictitious user identities and email addresses. The method may further include allowing a remote user or service to submit a fictitious user identity and a query requesting real-user information associated with the submitted fictitious user identity. In one possible embodiment, a targeted-advertising service may utilize real user information, associated with a fictitious user name, to target advertisements at the user of the fictitious user name.
Owner:JAKOBSON GABRIEL +1
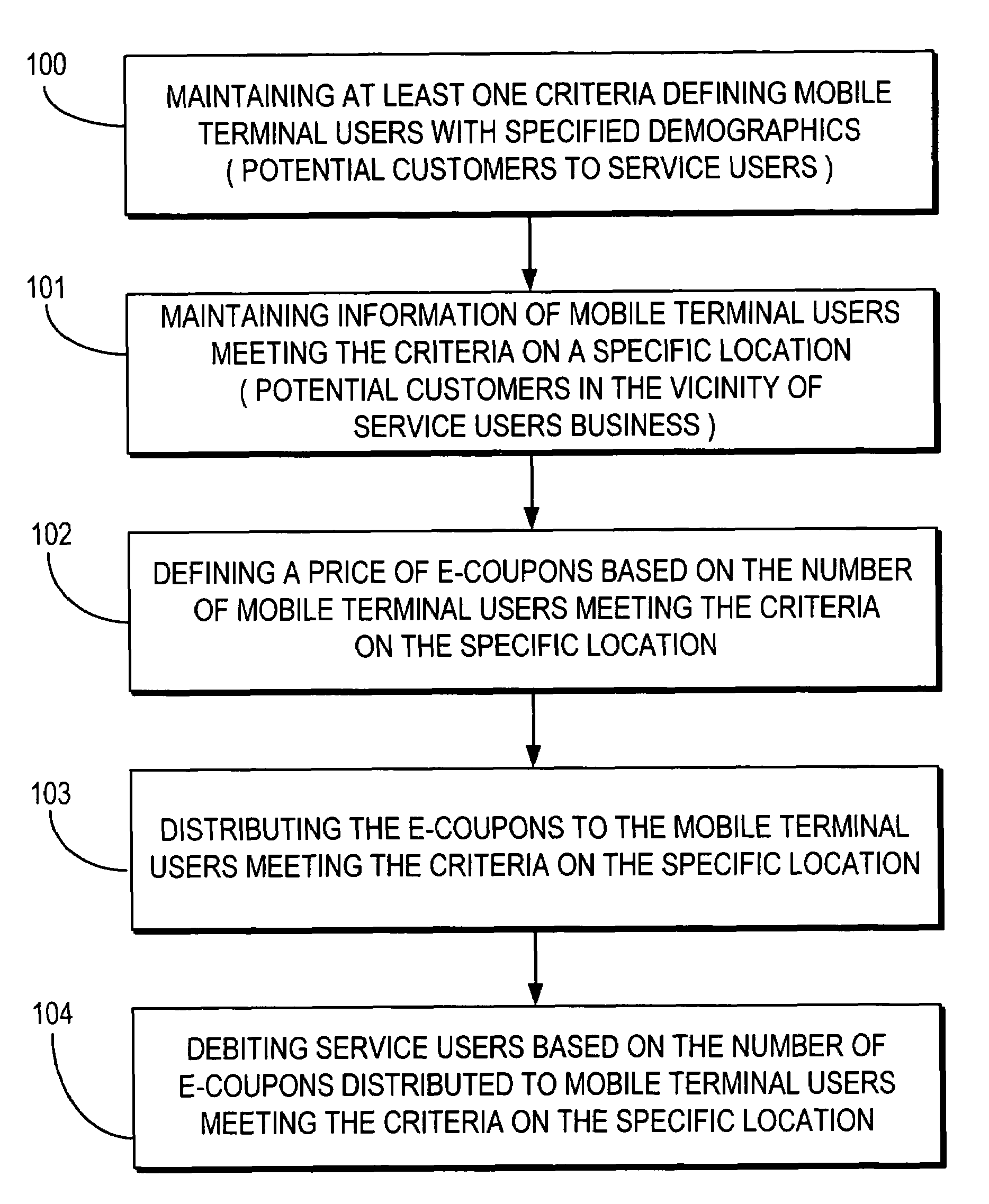
Real-time wireless e-coupon (promotion) definition based on available segment
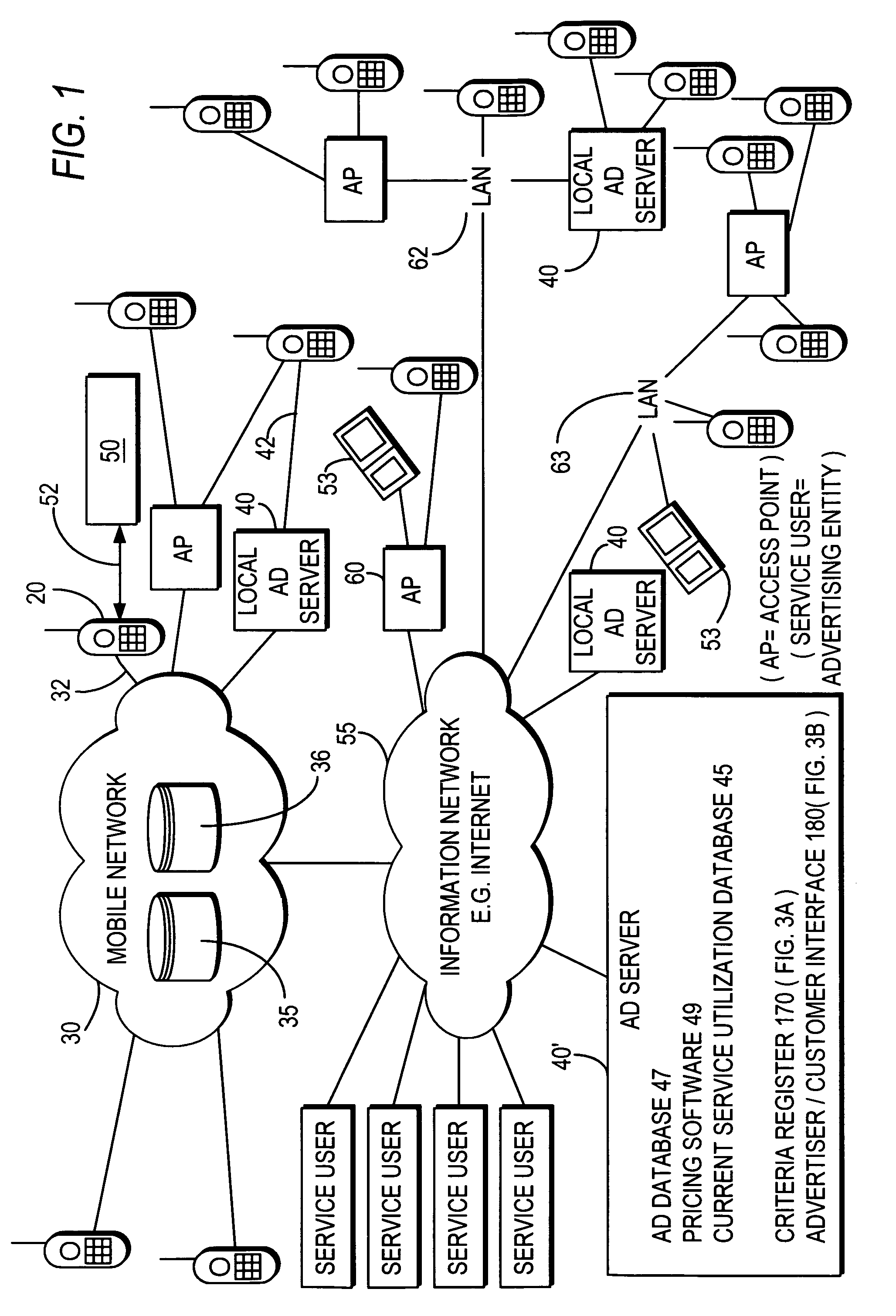
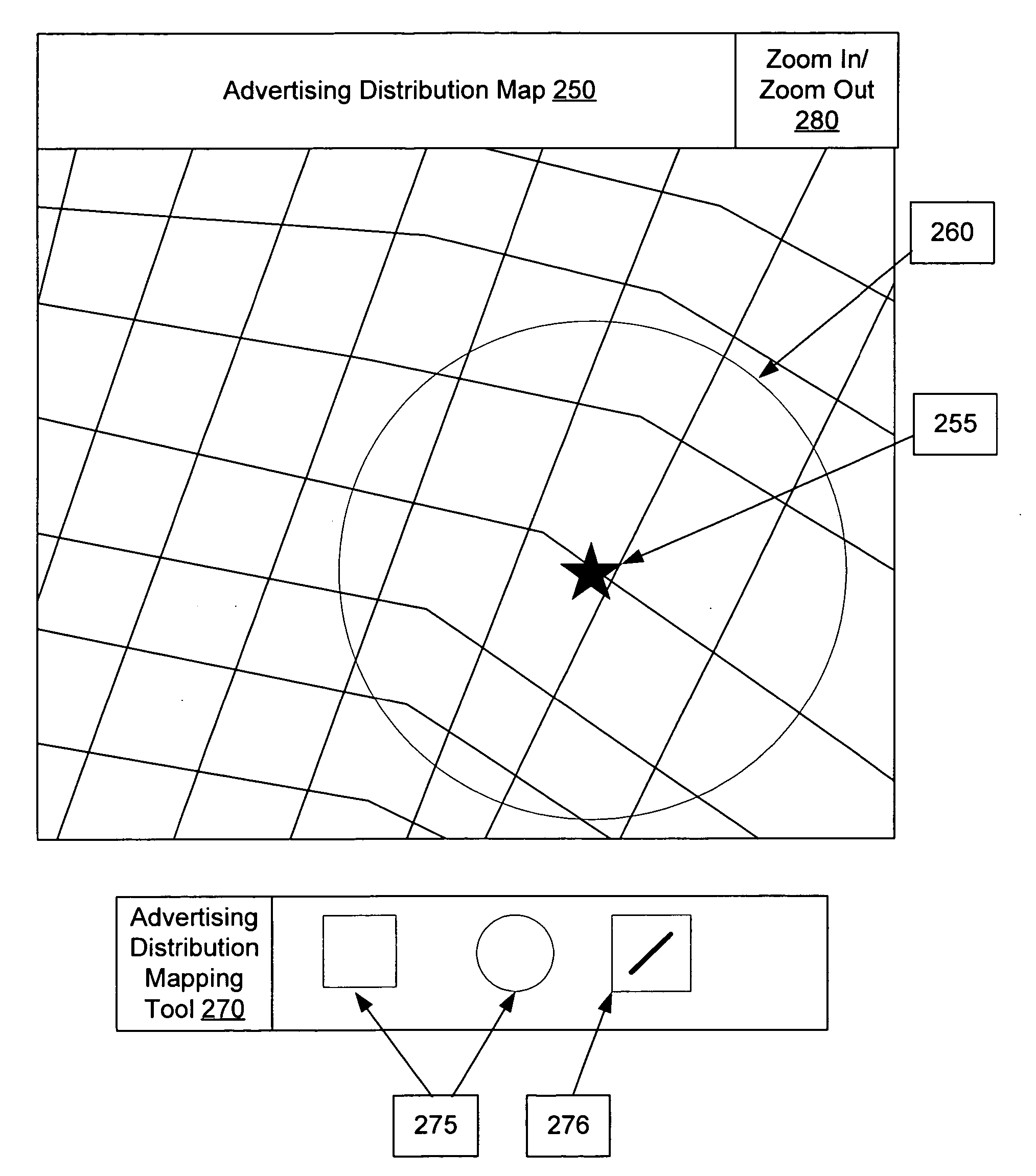
Advertising messages are provided to mobile terminals of those users identified by user information as meeting certain criteria, such as users fitting particular user profiles and / or users located in a particular desired location. The content of the advertising messages is dynamically generated based on the number of mobile terminals to whom the advertising message is to be sent and the advertising message is sent to the identified mobile terminals over a mobile network or a short range communication signal. In the latter case, location information may be sent to the mobile terminal along with an advertising message. Where the content of an advertising message comprises an electronic coupon, the value of the coupon depends on the number of mobile terminals to whom the advertising message is to be sent. A mobile terminal user can redeem an electronic coupon by transmitting it from his mobile terminal to a coupon redemption terminal.
Owner:NOKIA TECH OY
Screen icon manipulation by context and frequency of use
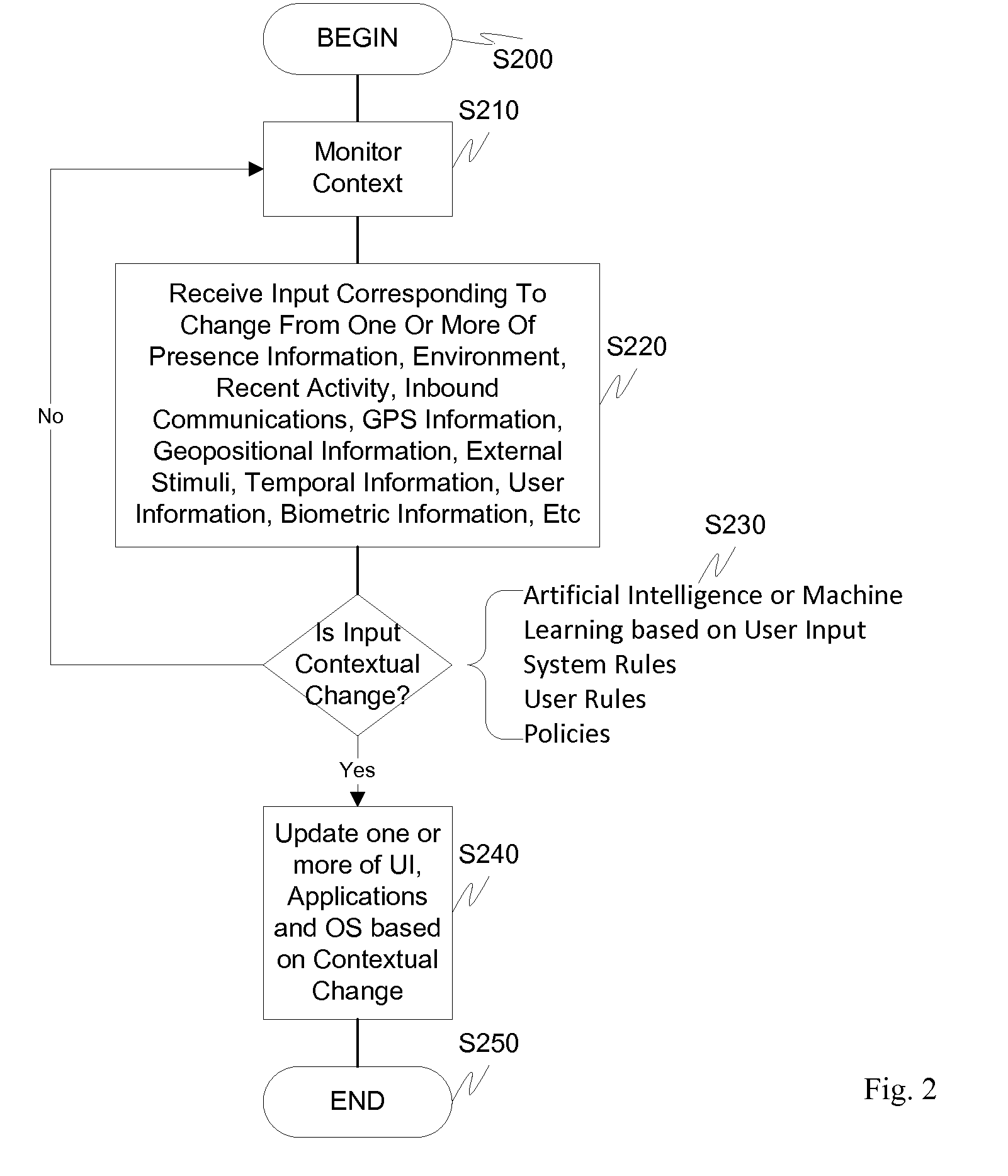
ActiveUS20110072492A1More user confidenceDigital data processing detailsMultiple digital computer combinationsTemporal informationOutbound communication
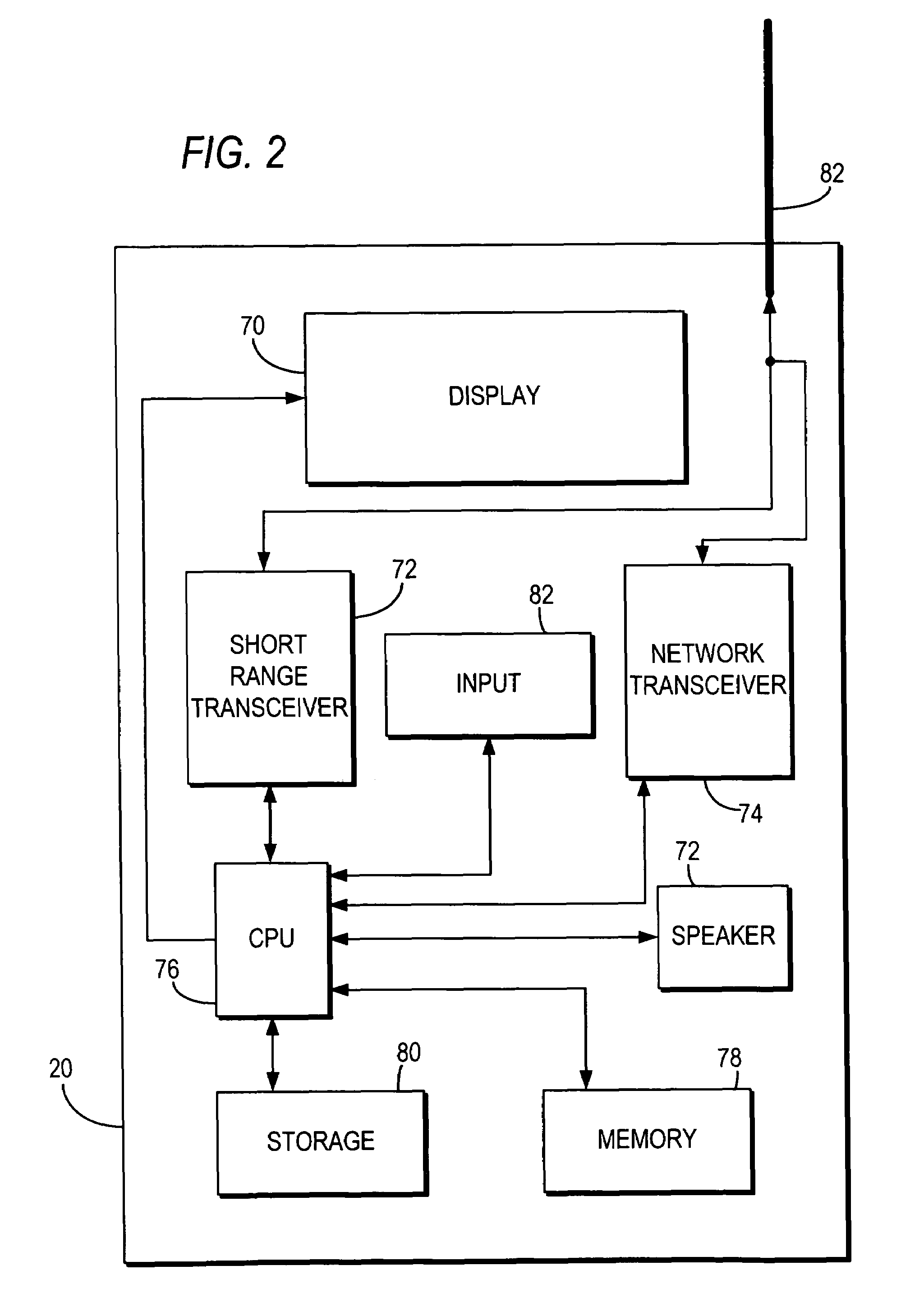
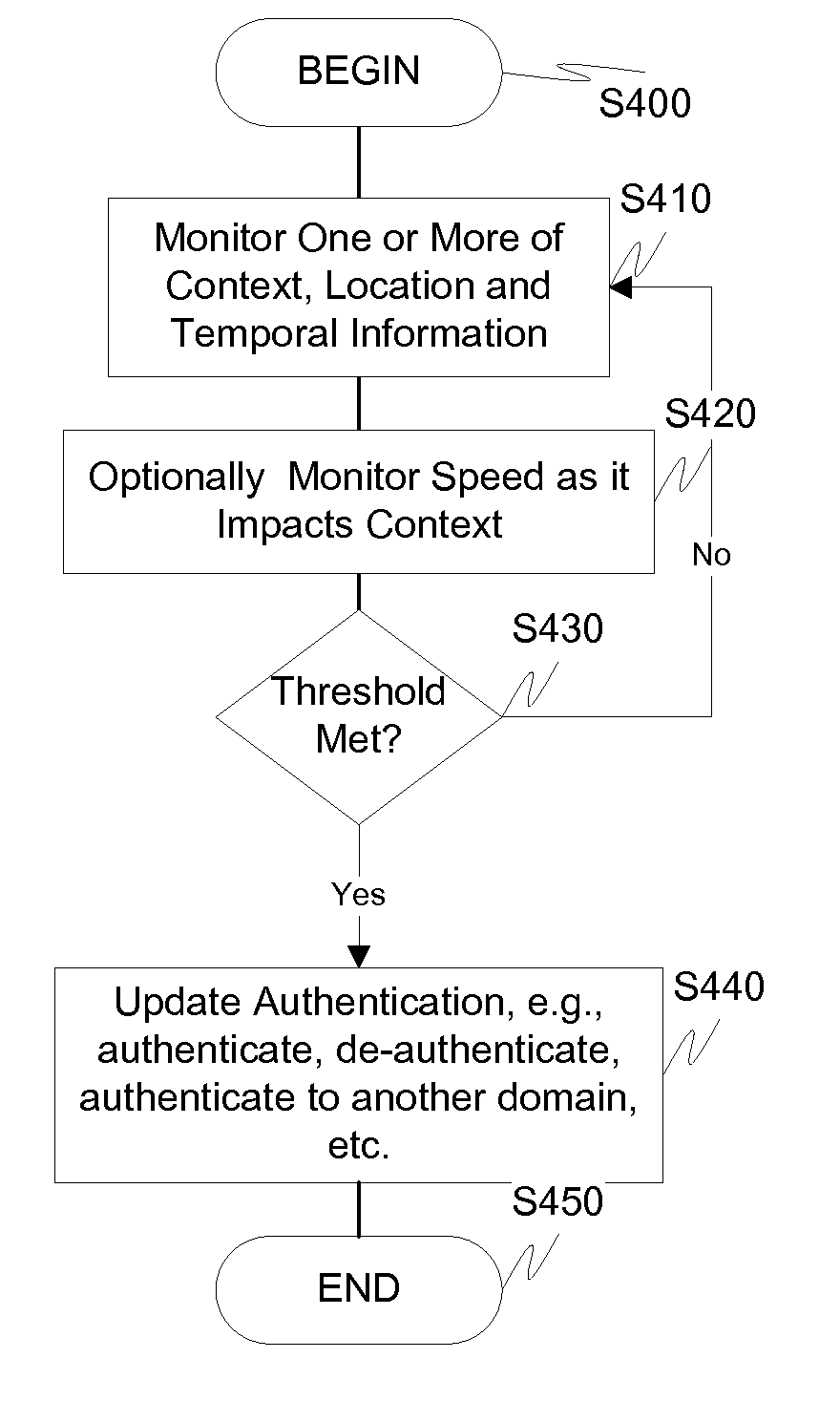
Dynamic device management is provided based on a change in context. The management can be for one or more of icons, application, operating system(s), preferences, display characteristics, and the like. Detection and / or monitoring of one or more of presence information, environmental information, user information, recent activity information, inbound / outbound communication information, external stimuli information, geopositional information, temporal information, calendar information, user information, biometric information, and security information can be used as inputs to determining a change in this context.
Owner:AVAYA INC
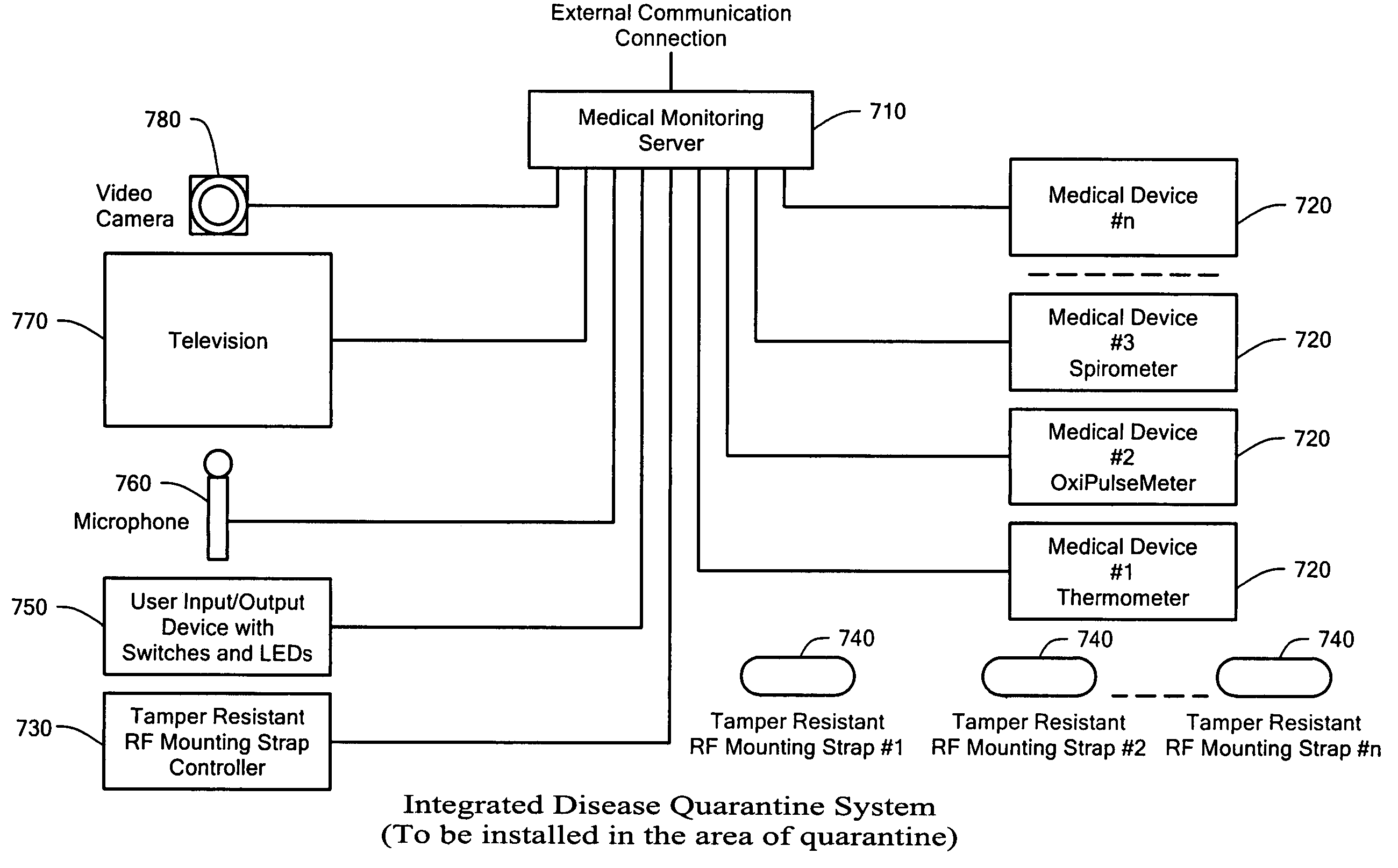
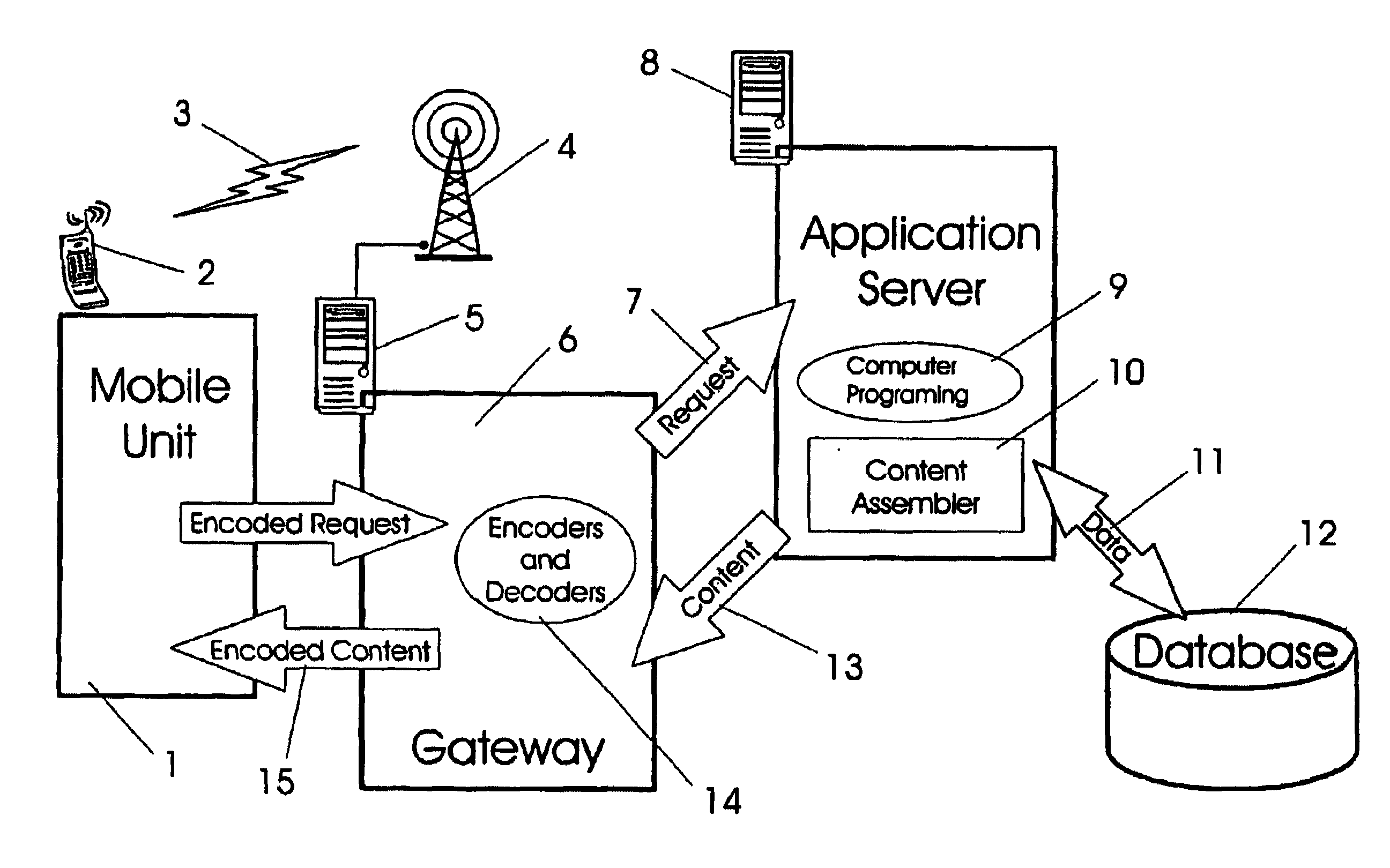
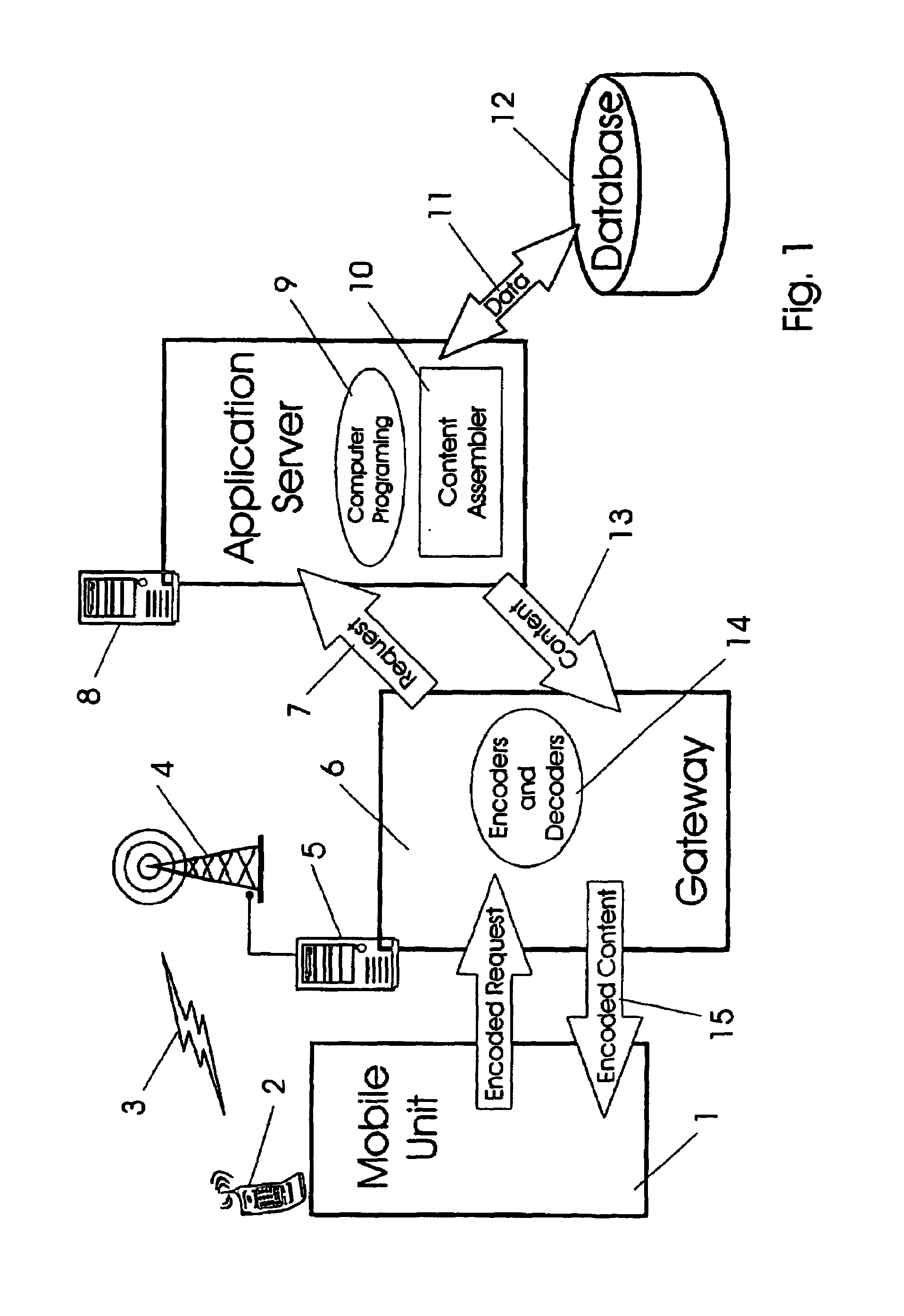
System, device, and method for remote monitoring and servicing
A system, device, and method for remote monitoring and servicing uses a gateway to collect user information, such as physiological, audio, video, and proximity information. The gateway processes the user information locally, and may send the user information or other information, such as alarms, to remote service providers through one or more head-end servers. The gateway also allows service provider information, such as audio and video information, to be conveyed from the service providers to the users. The gateway may output video information on a predetermined television channel, and may output audio information on the predetermined television channel or to a wireless remote controller with in-built speaker. The gateway may receive audio information from the user via a wireless remote controller with in-built microphone. The gateway provide for videoconferencing between the user and one or more remote service providers.
Owner:MATHUR MICHAEL
Computer services for assisting users in locating and evaluating items in an electronic catalog based on actions performed by members of specific user communities
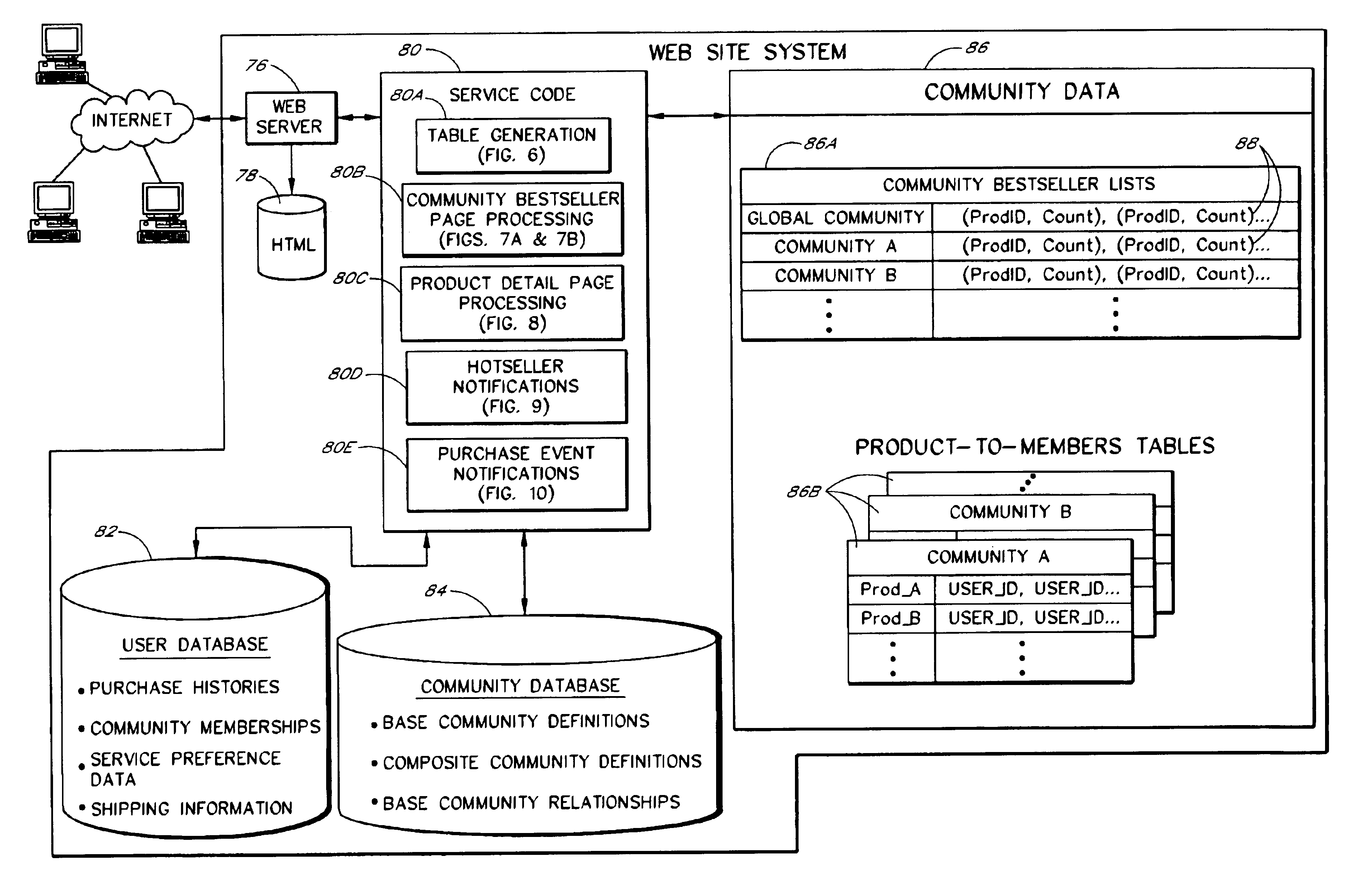
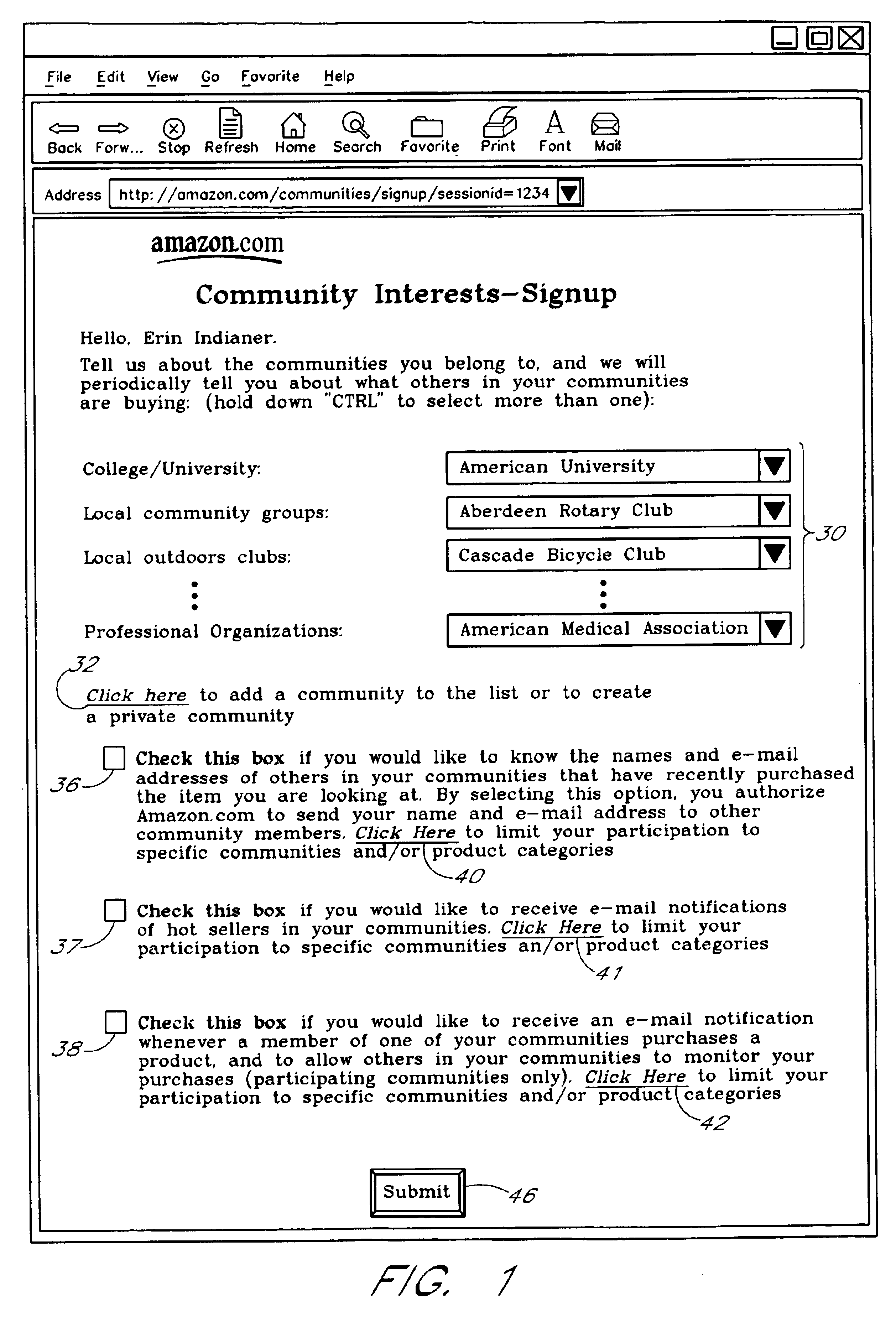
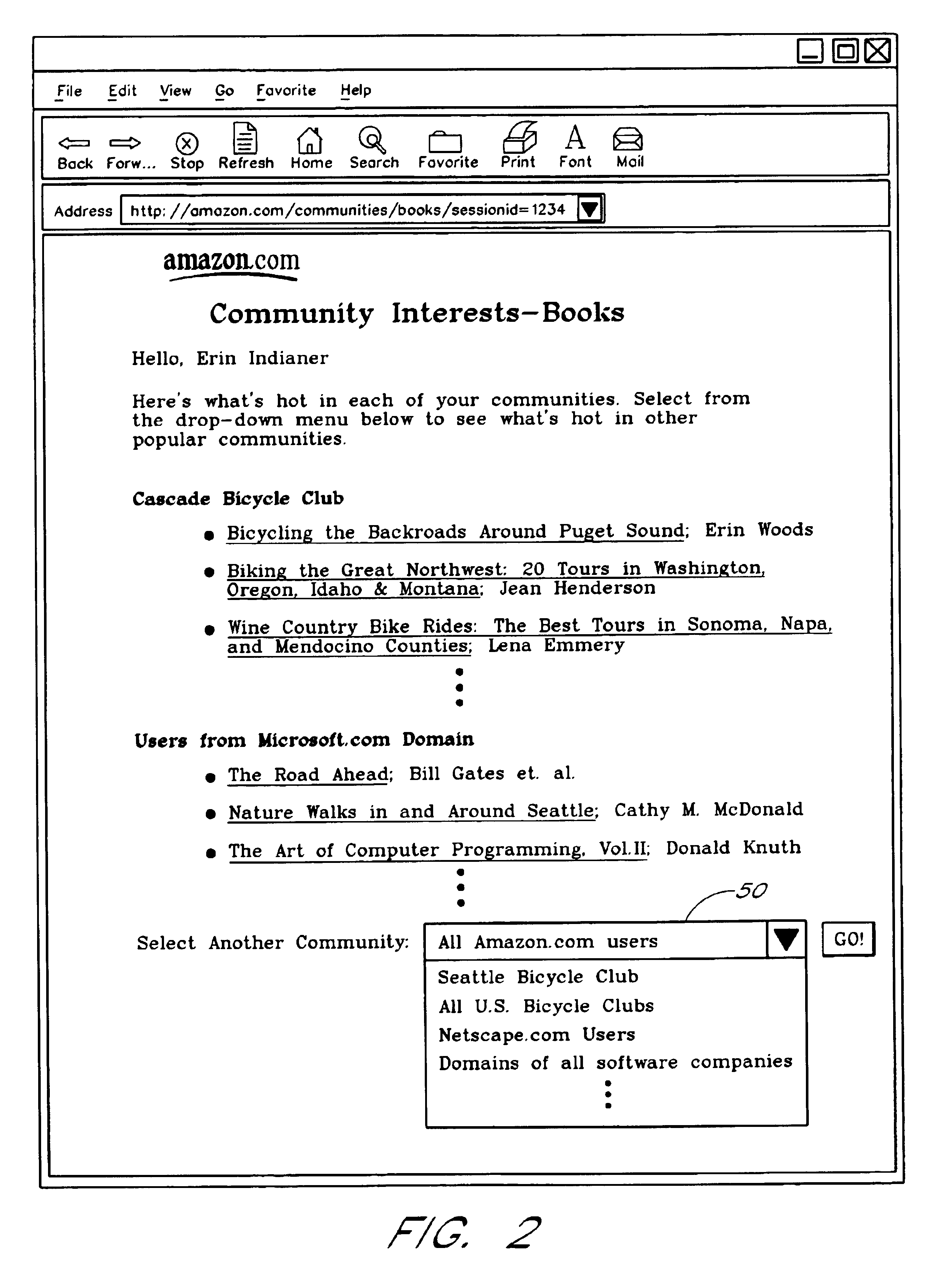
A Web based system provides informational services for assisting customers in selecting products or other types of items from an electronic catalog of a merchant. Users of the system can create and join user communities, such as communities based on user hobbies, localities, professions, and organizations. The system also supports implicit membership communities that are based on email addresses (e.g., all users having a “nasa.com” email address), shipping / billing addresses, and other known user information. Using purchase history data collected for online users, the system automatically identifies and generates lists of the most popular items (and / or items that are becoming popular) within particular communities, and makes such information available to users for viewing. For example, in the context of an online book store users of the nasa.com community may automatically be presented a Web page which lists the bestselling book titles among nasa.com users, or may be sent email notifications of purchase events or hotselling books within the community. Another feature involves automatically notifying users interested in particular products of other users (preferably other members of the same community) that have purchased the same or similar products. For example, in one embodiment, when a user accesses a book detail page, the detail page is customized to include the names and email addresses of other members of the user's community that recently purchased the same book.
Owner:AMAZON TECH INC
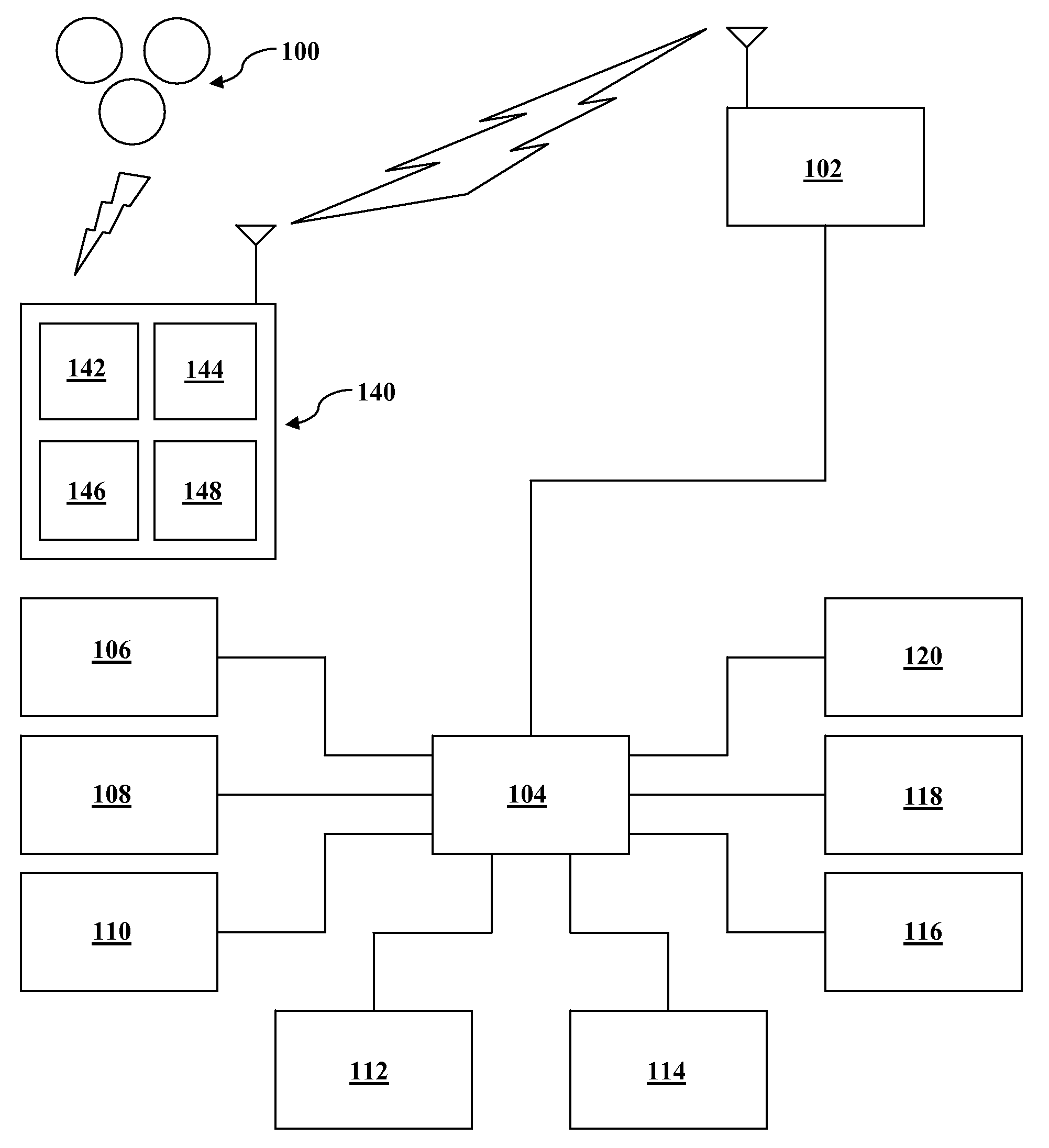
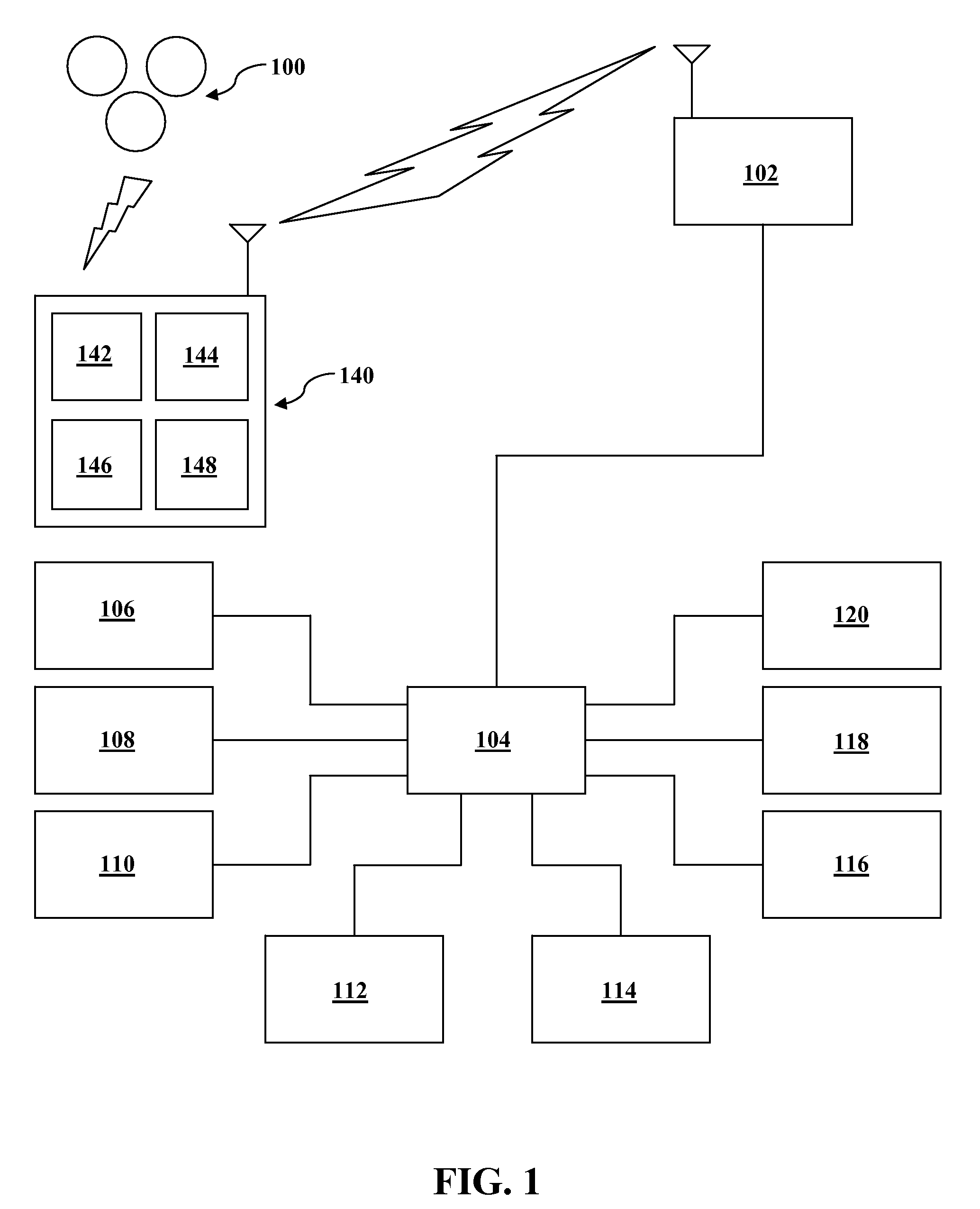
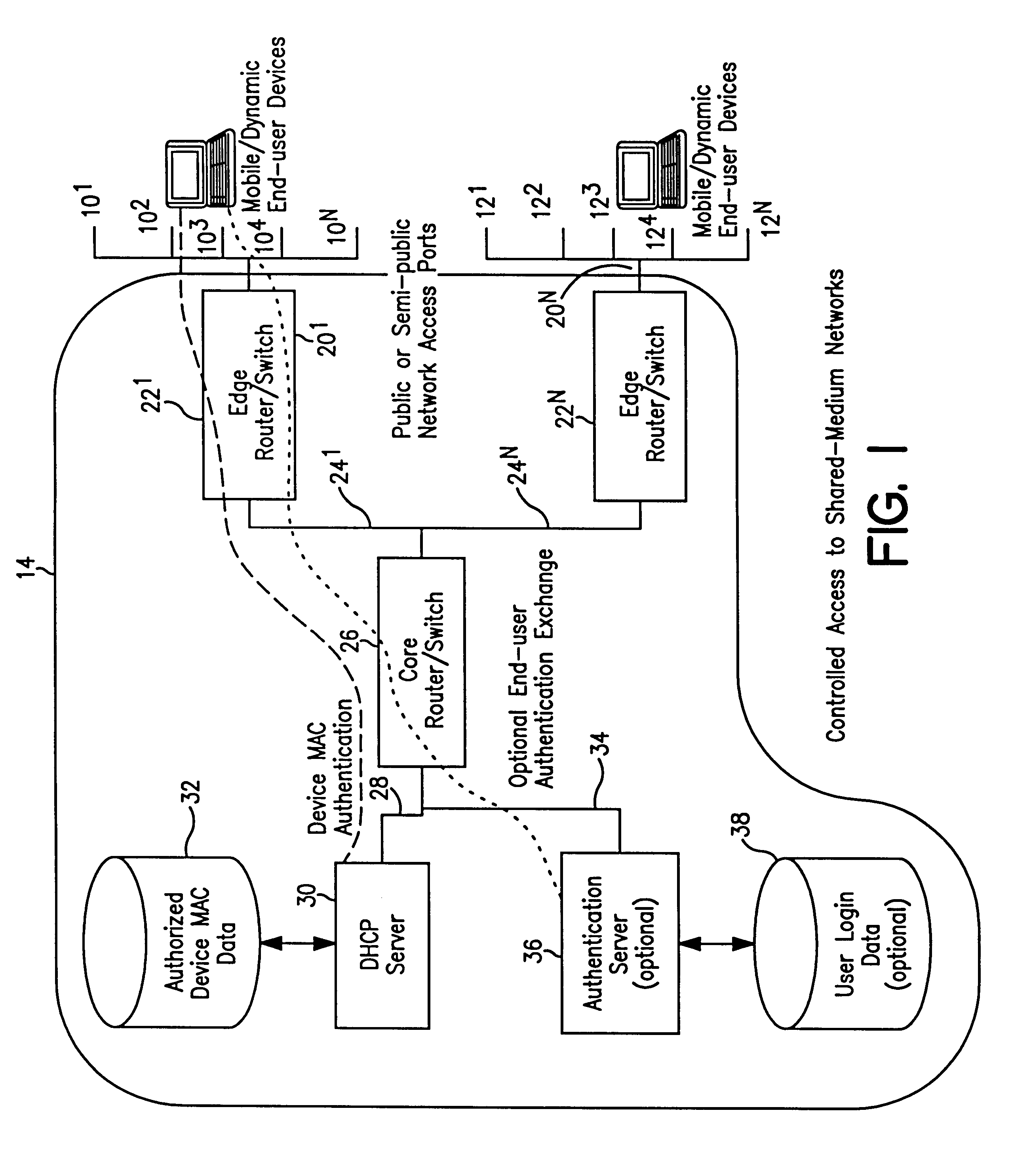
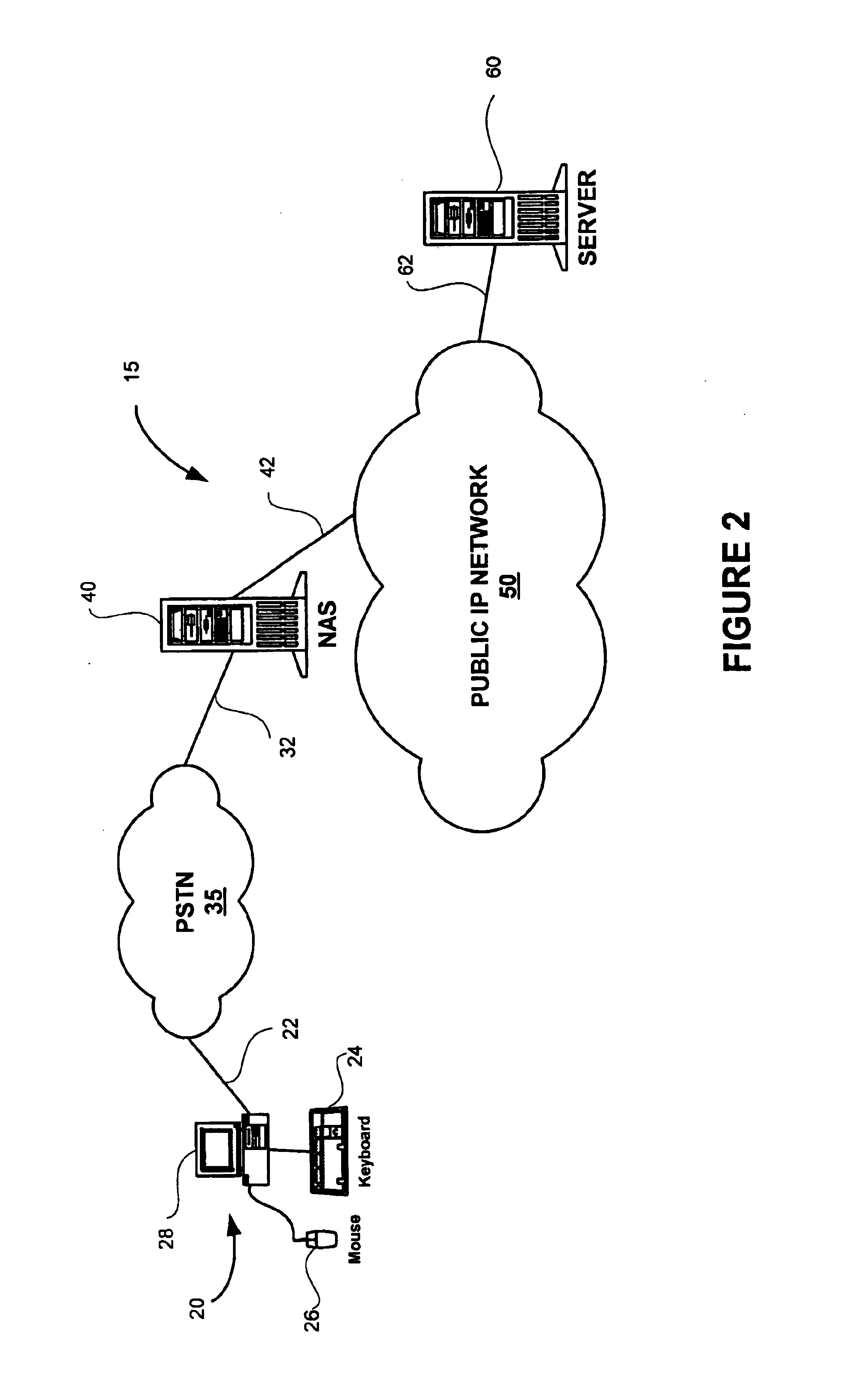
System and method for controlled access to shared-medium public and semi-public internet protocol (IP) networks
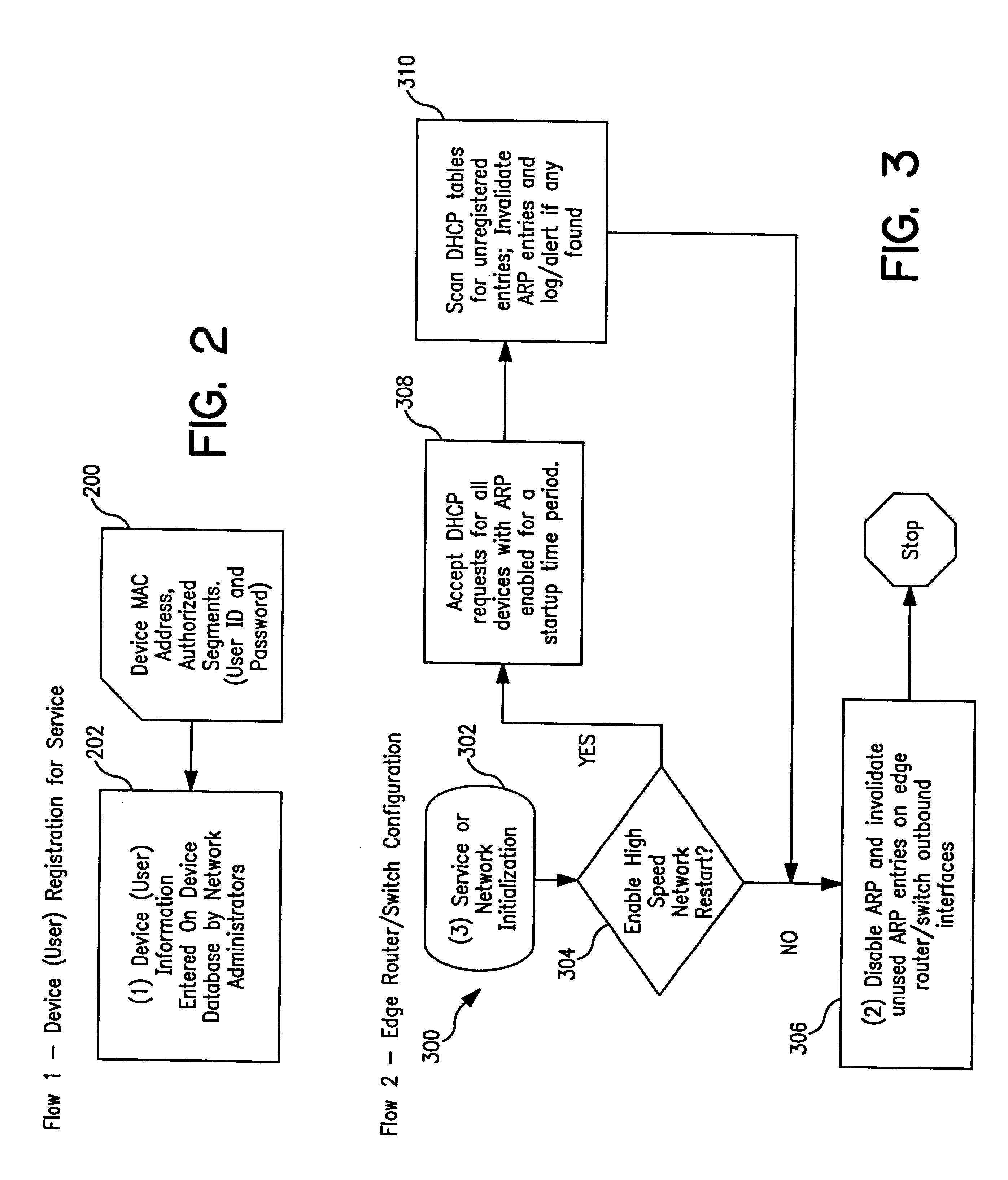
InactiveUS6393484B1Multiple digital computer combinationsTransmissionAddress Resolution ProtocolDevice register
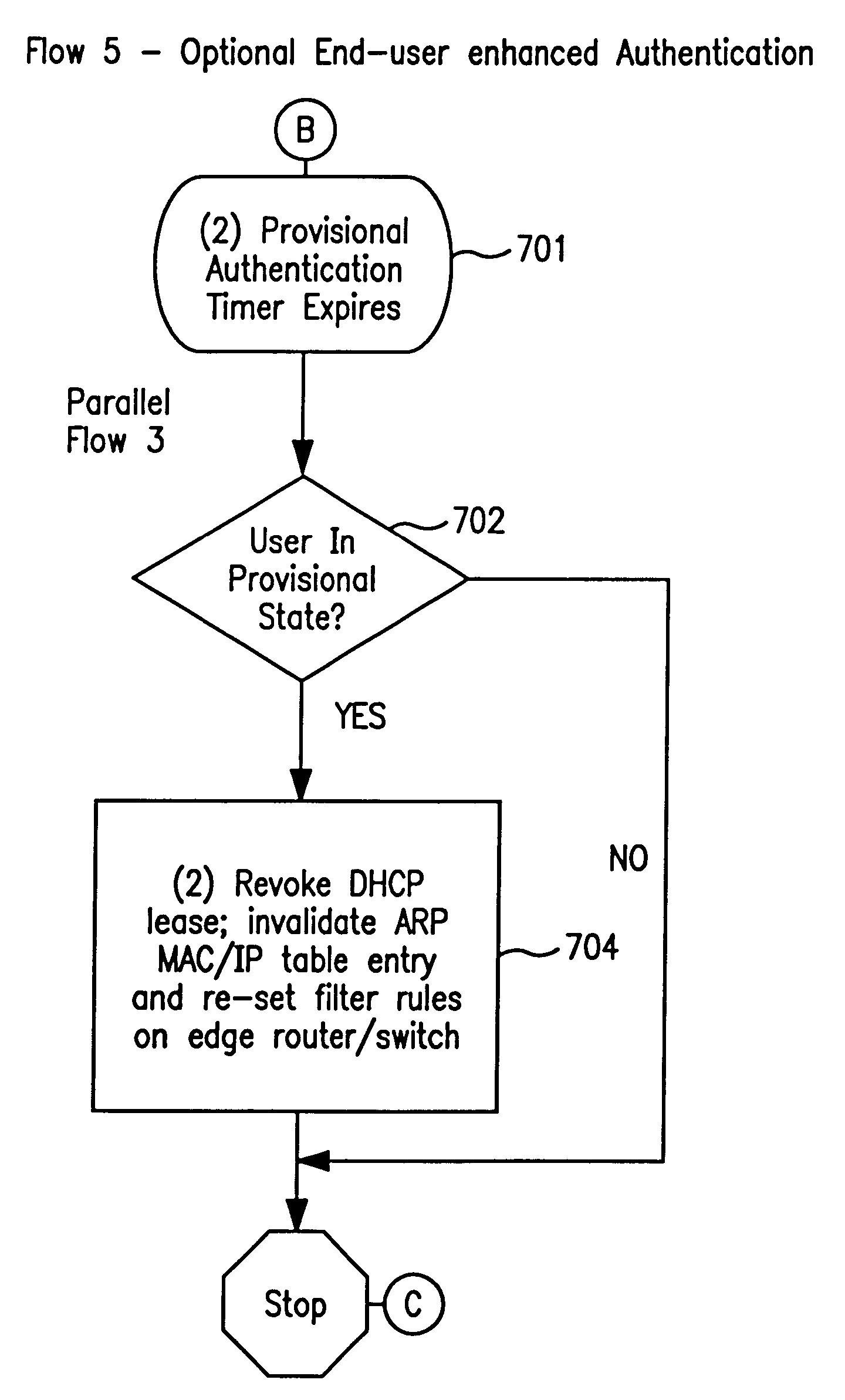
A system and method prevent unauthorized users and devices, in a dynamic user / device environment, from obtaining access to shared-medium public and semi-public IP networks. A network includes a layered communication system and routers / switches for coupling users and devices to a Dynamic Host Control Protocol (DHCP) server and an authentication server. Databases support the servers. The network incorporates Address Resolution Protocol (ARP). Authorized users and devices register for service by providing the DHCP with user identification for log-in, passwords, MAC addresses, etc. When users connect to the network access point, a DHCP exchange is initiated to obtain a valid IP address and other associated parameters. The DHCP client initiates a MAC broadcast for IP addresses which contain in the request the end user's device MAC address. The associated router switch will pick up and forward to a DHCP server the end user's device request. The DHCP server will process the end user's request and extract the end user's device MAC address. With the end user's MAC address, the DHCP server accesses its device and / or user information in the database. If the MAC address is not registered, the DHCP server refuses to handle the request and logs the attempt, potentially alerting network operators of a security breach. If the MAC address is registered, a DHCP server selects an appropriate IP address and associated parameters to be returned to the requesting end user and connects via programming or command interface to the router switch that is forwarding the DHCP request on behalf of the end user device. The server adds an ARP IP to the MAC address table entry with the selected IP address and end user's MAC address. End user device authentication and IP lease are marked as provisional. A timer is started for a suggested duration. Optionally, the DHCP dynamically sets up filter rules in the router switch limiting access to a subset of IP addresses such as the address of a log-in server. Initial DHCP processing is completed and an IP address is assigned to the requesting end user's device by DHCP. When the timer expires, if the DHCP server finds the authenticating user state is provisional, it will revoke the IP lease, invalidate the corresponding ARP to MAC table entry in the associated router switch, and reset any IP-permissive filtering for that device. If the user is in the full authenticated state, it will simply remove the restrictive filtering.
Owner:IBM CORP
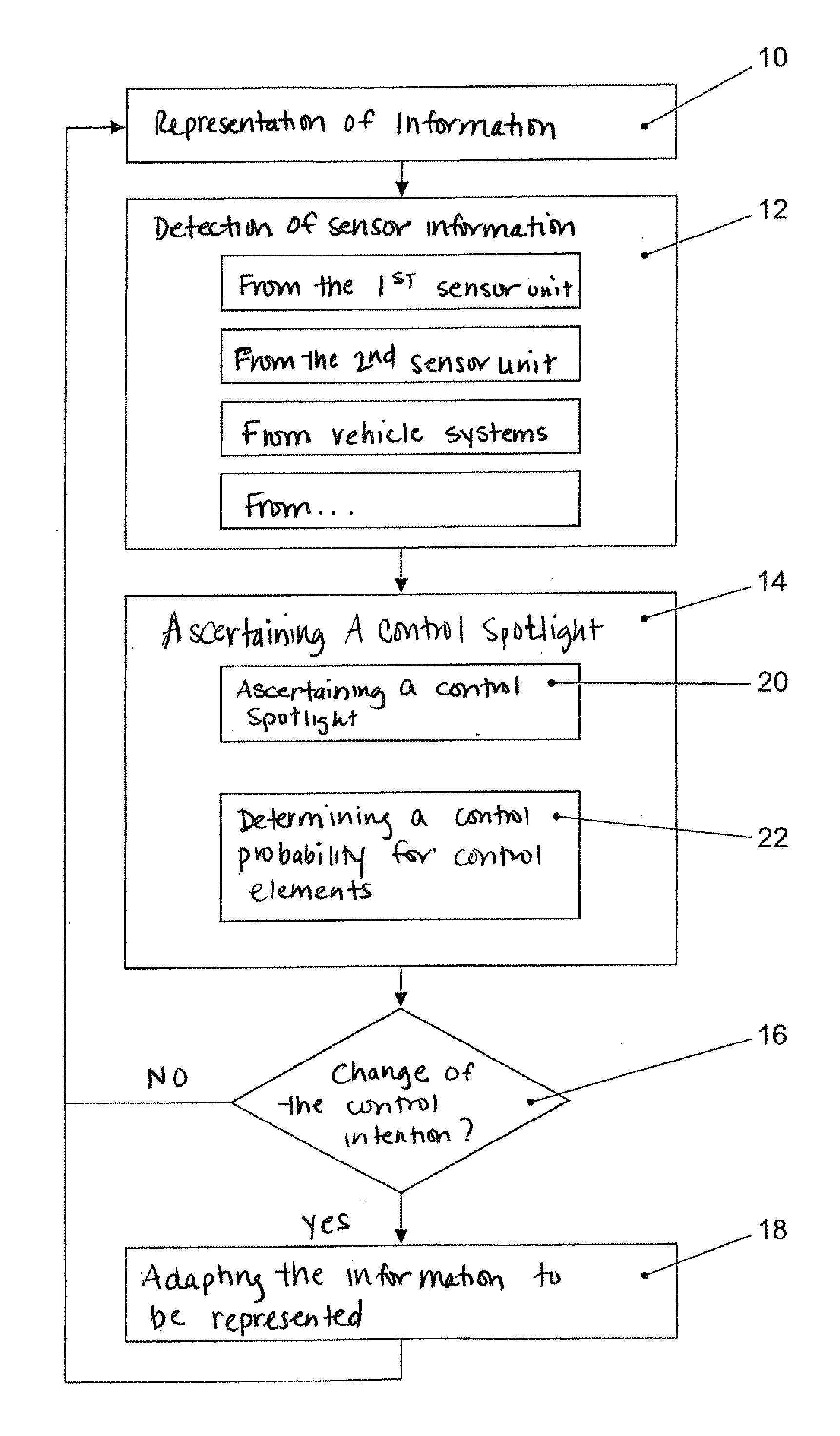
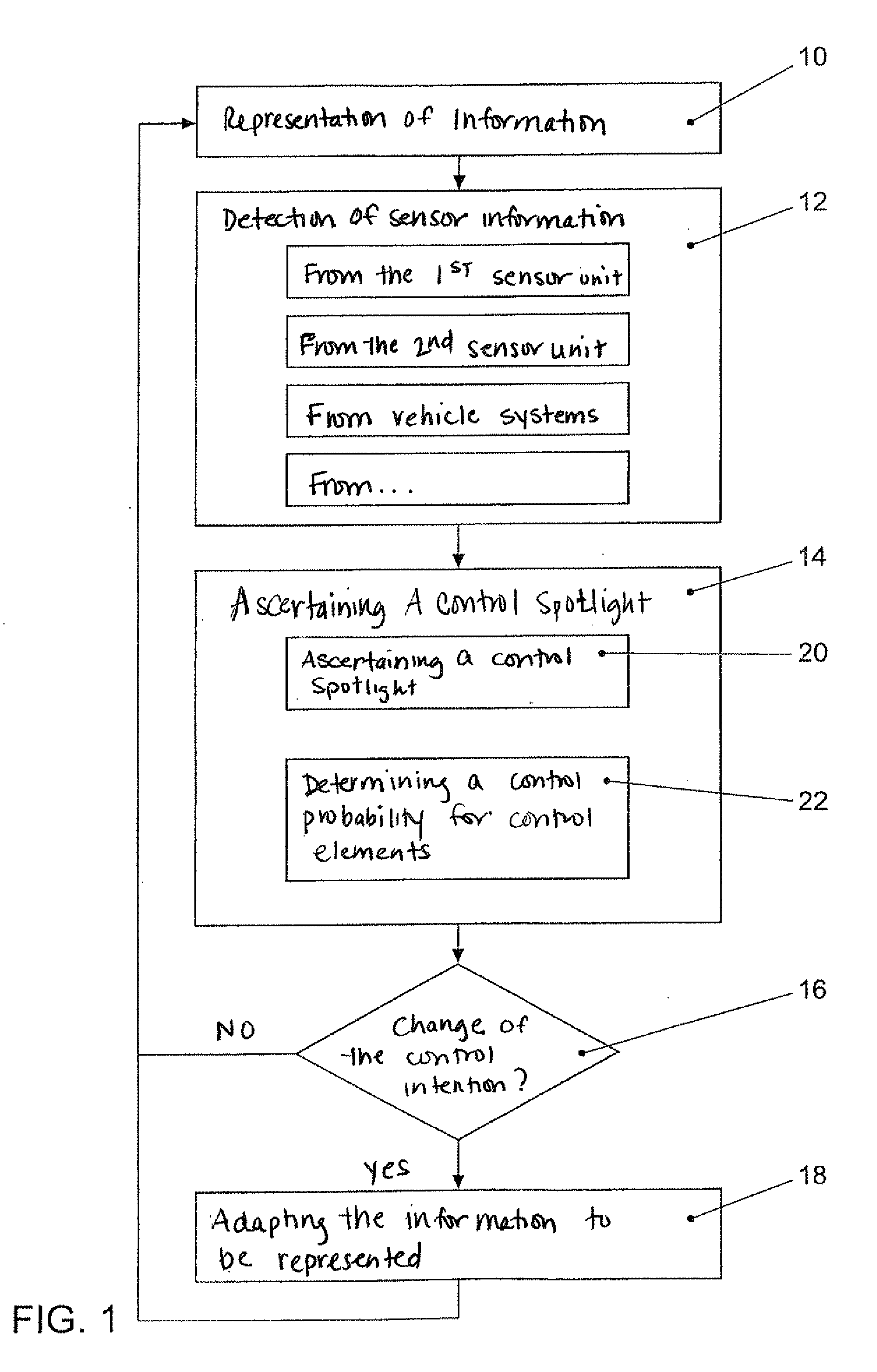
Interactive control device and method for operating the interactive control device
ActiveUS20090327977A1Optimal communication of informationComfortable activationDashboard fitting arrangementsInstrument arrangements/adaptationsGraphicsDisplay device
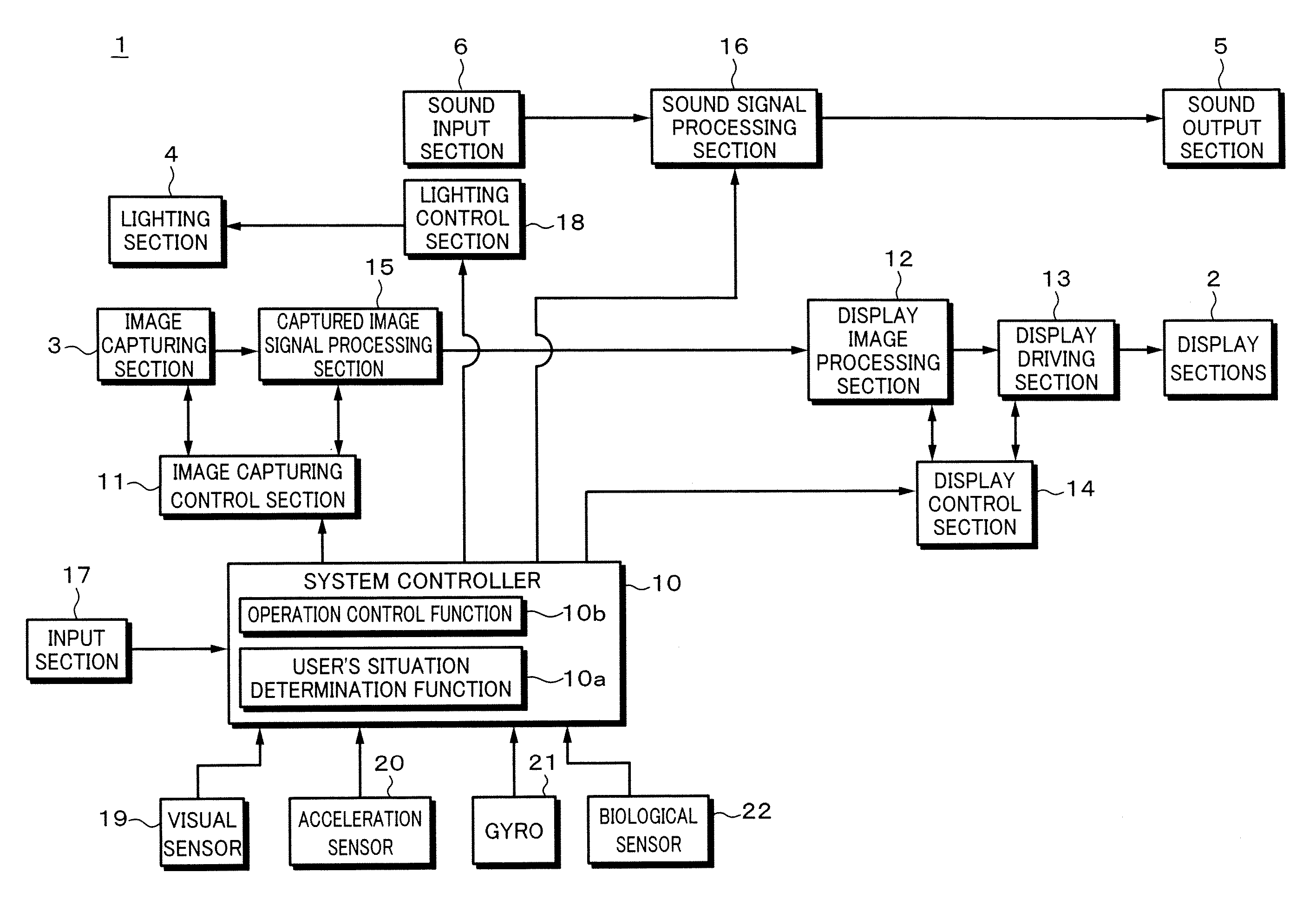
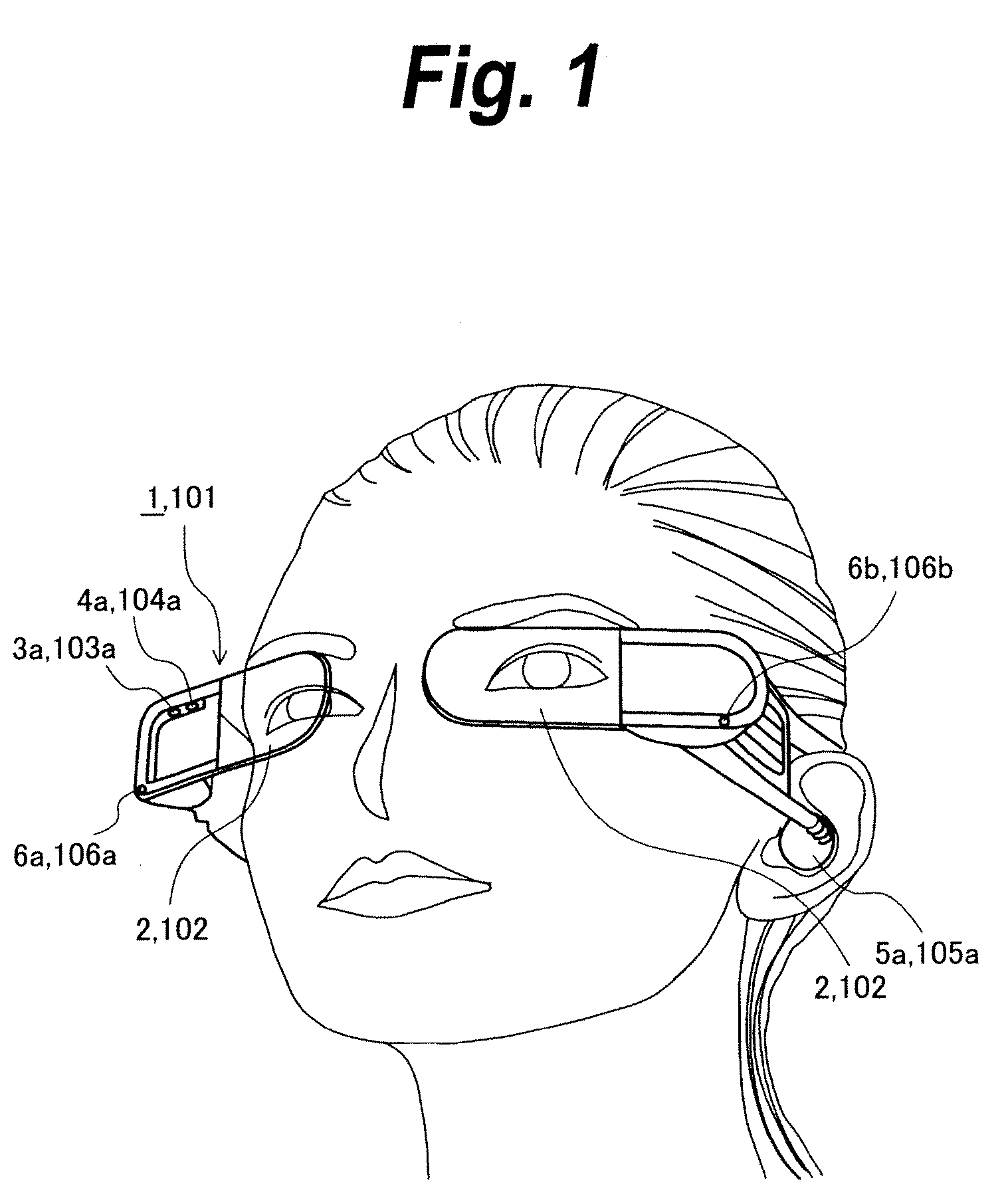
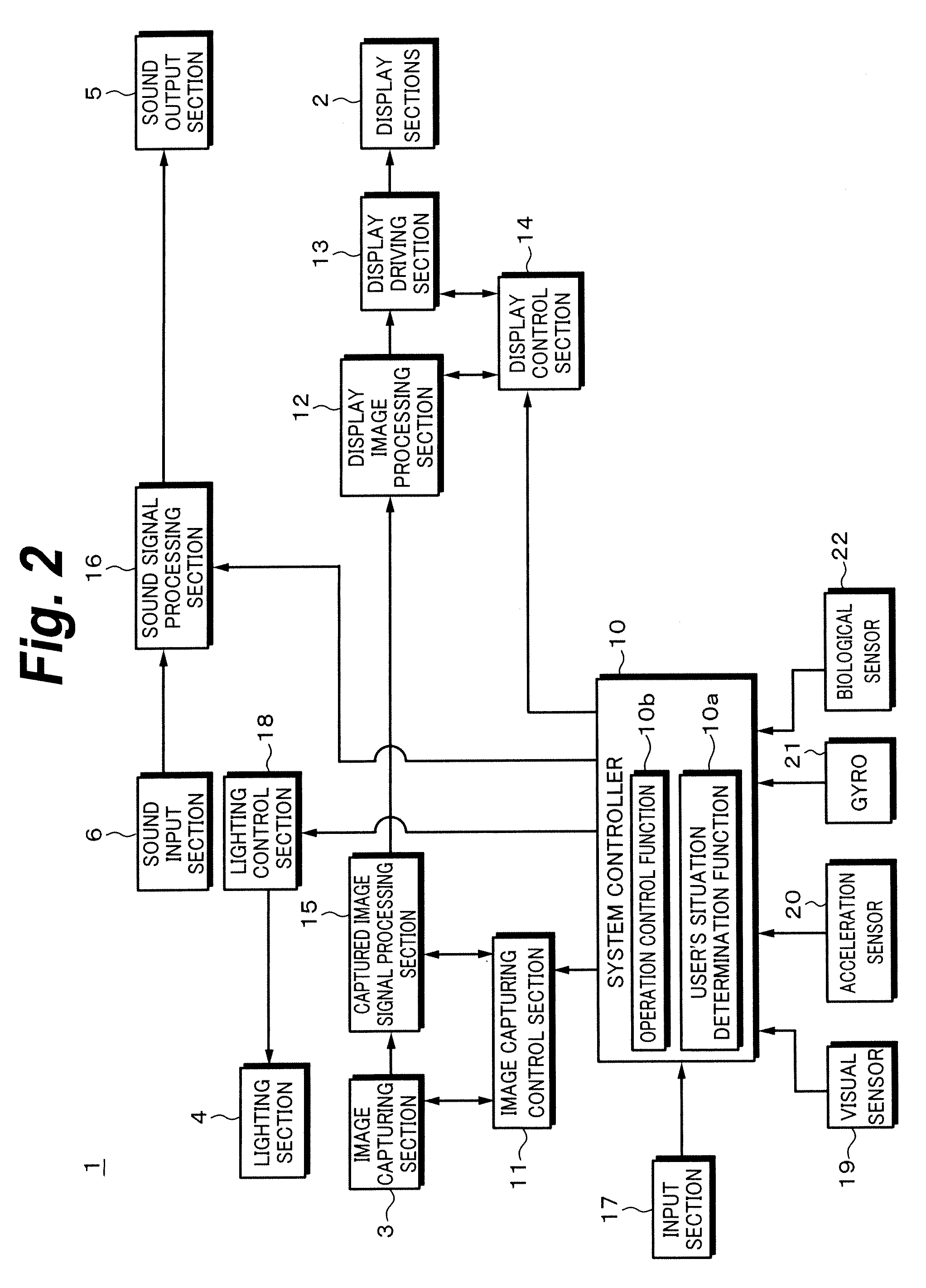
An interactive control device includes a display device, and a method is for operating the interactive control device. The method includes: displaying graphical information on the display device; receiving sensor information; activating a control action if on the basis of the sensor information it is ascertained that a body part of a user is located within an activation region that is spatially defined relative to a display region of a control element on the display device with which the control action is associated; the received sensor information including user information that is evaluated prior to an activation of the control action in order to ascertain a control intention for the at least one control element; and the information represented on the display device being adapted as a function of the ascertained control intention such that the at least one control element is represented in a manner optimized for the activation of the control action associated with the control element. The control device may be arranged as a component of a motor vehicle console so as to be able to implement the control method.
Owner:VOLKSWAGEN AG
Pointing systems for addressing objects
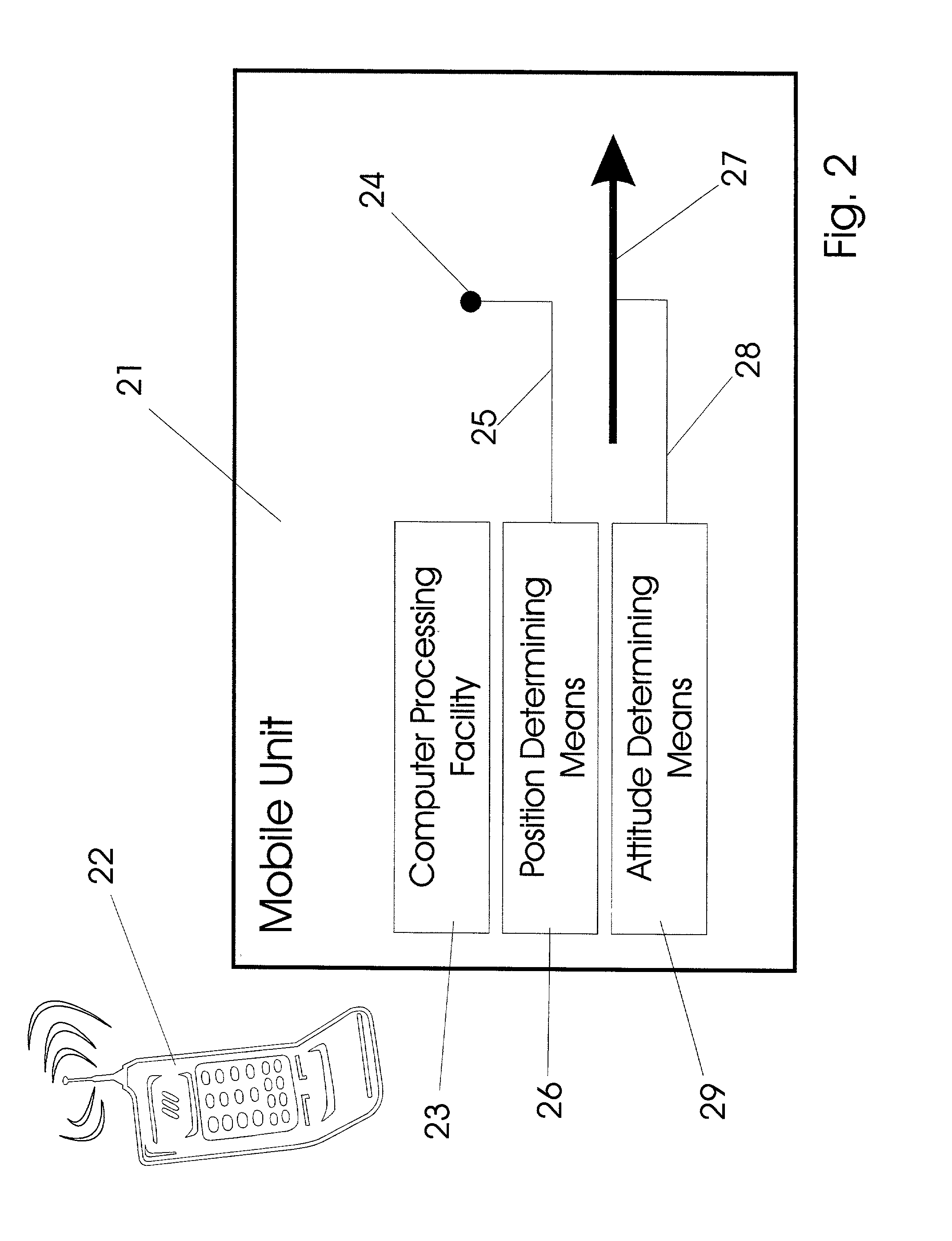
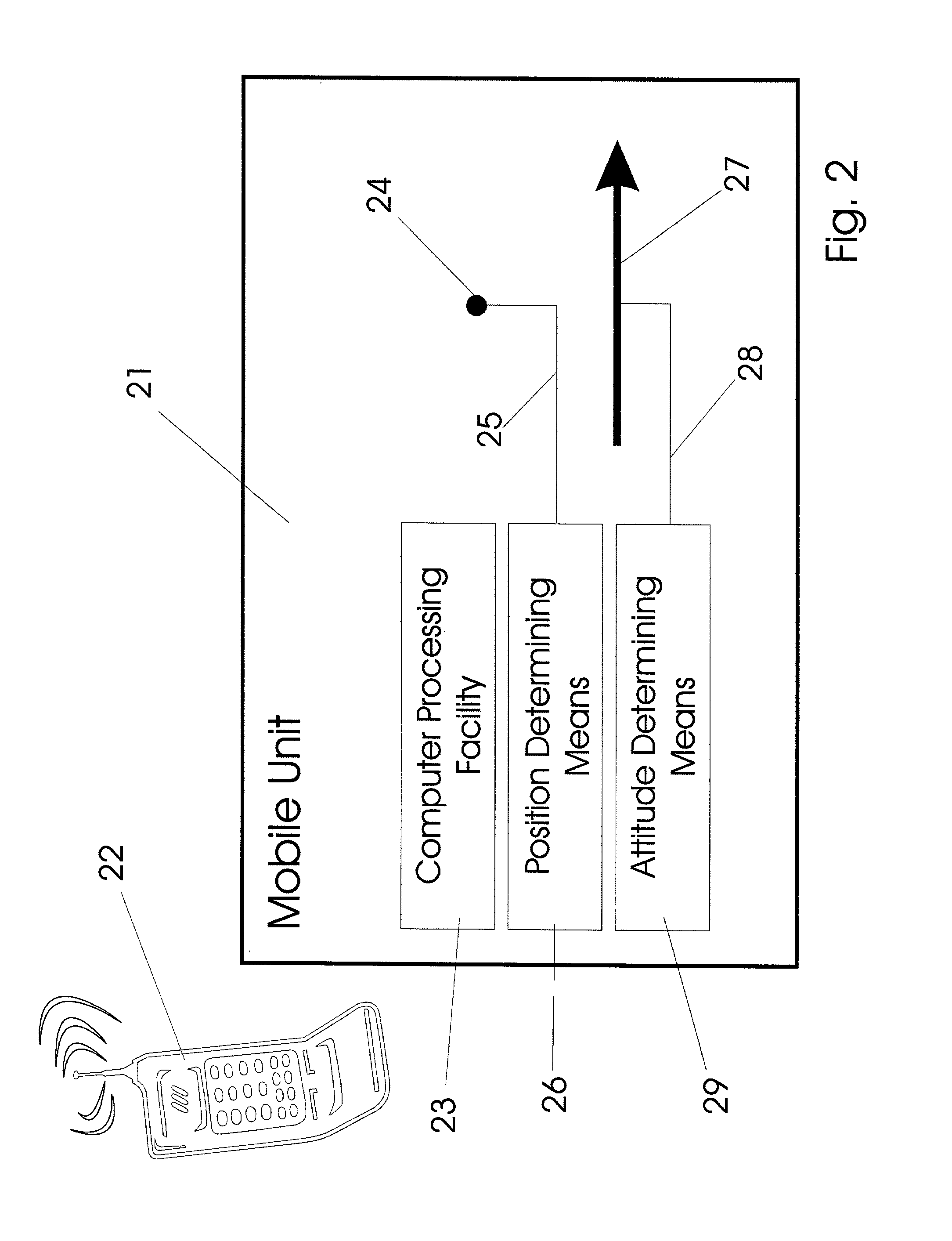
InactiveUS7031875B2Navigational calculation instrumentsDigital data processing detailsHand heldHand held devices
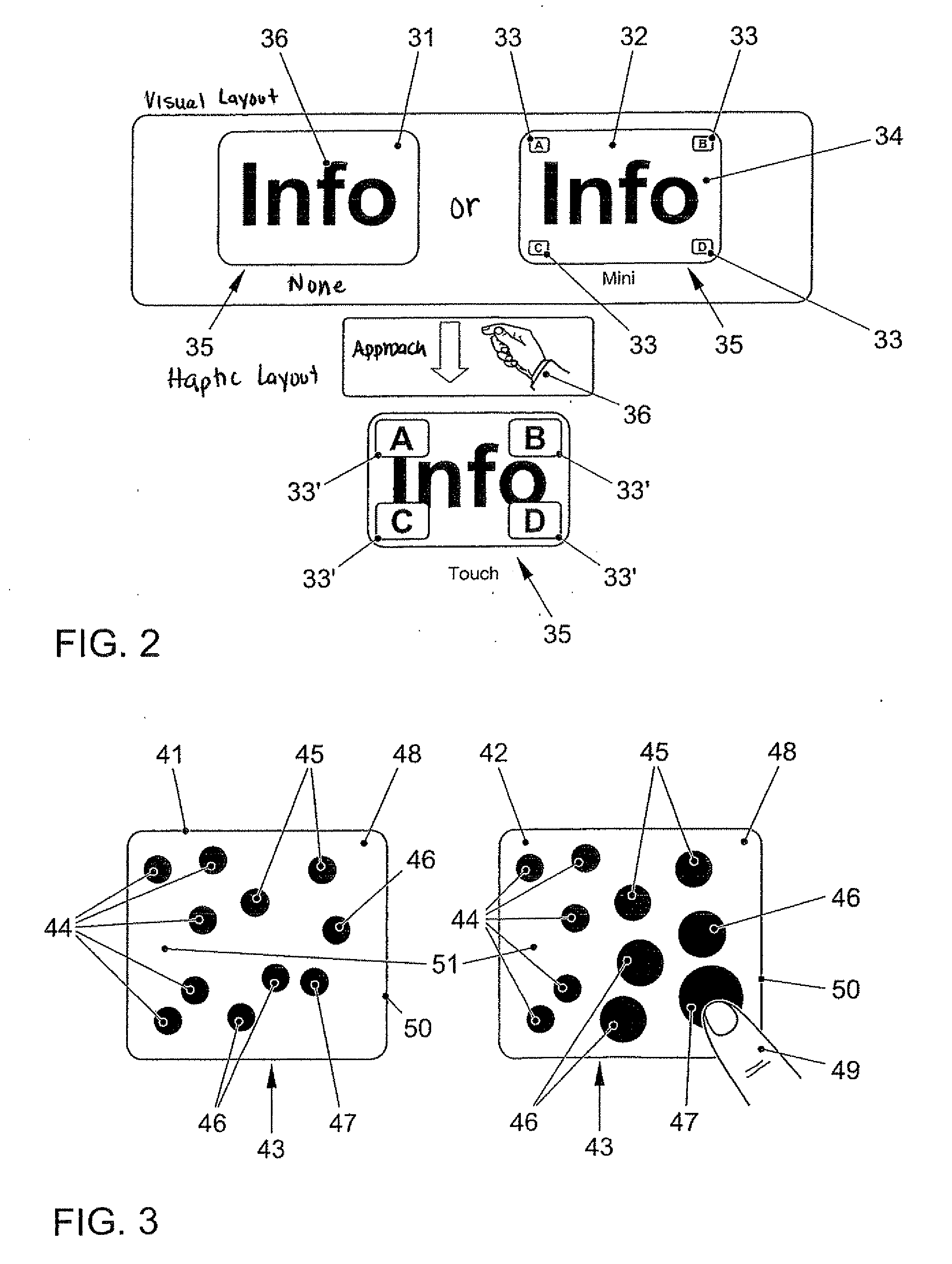
Systems are arranged to provide a user information which relates to objects of interest. A user may point a hand held device toward an object to address it. The device determines which objects are being addressed by making position and attitude measurements and further a reference and search of a database containing preprogrammed information relating to objects. Information relating to objects determined as objects presently being addressed is thereafter presented at a user interface. Devices of these systems include a point reference, a direction reference, a position determining support, attitude determining support, a computer processor and database, and a user interface. Methods of systems include the steps of addressing an object, determining position and attitude, searching a database, and presenting information to a user.
Owner:GEOVECTOR
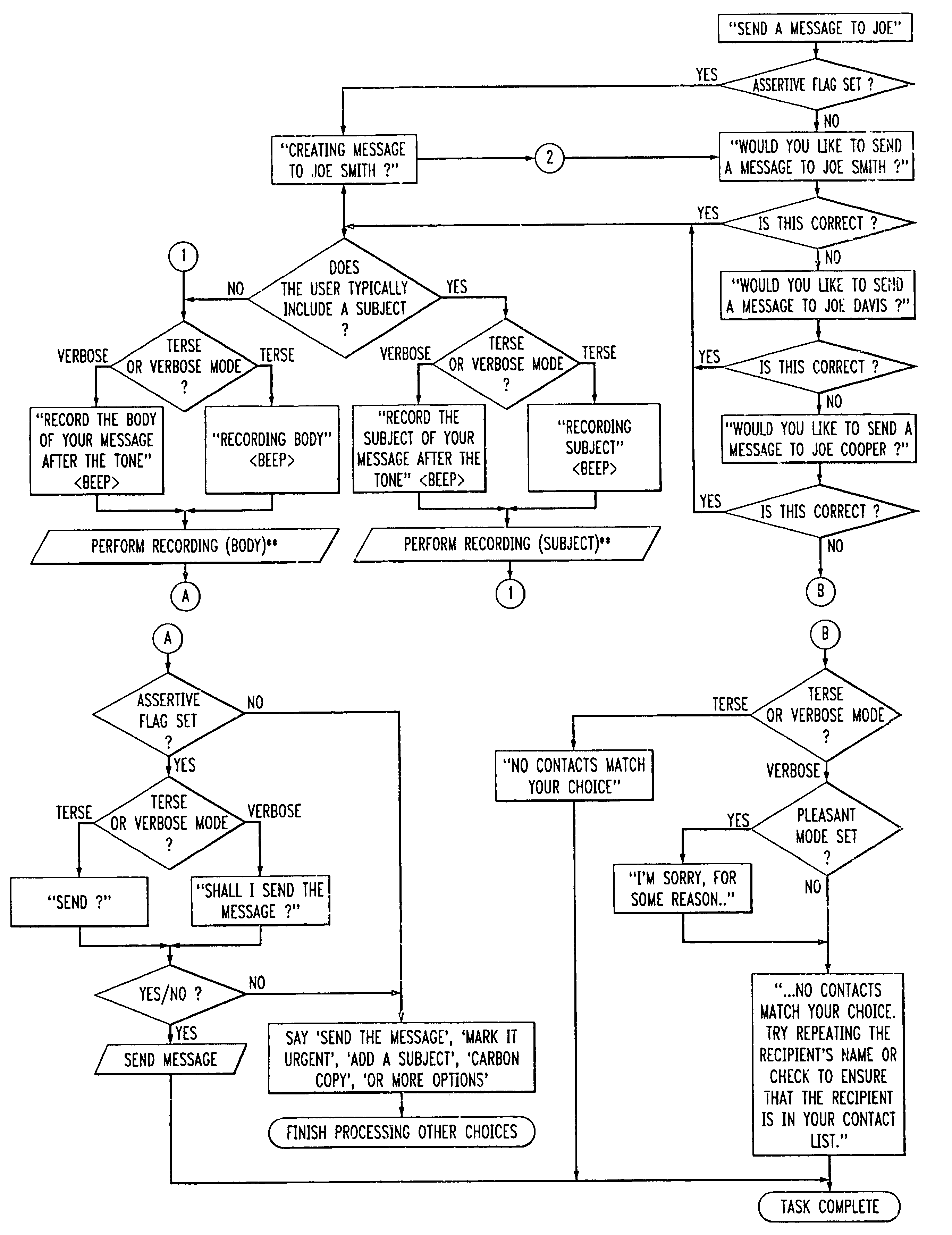
Personal virtual assistant
InactiveUS7415100B2Automatic call-answering/message-recording/conversation-recordingAutomatic exchangesUser inputZoom
A computer-based virtual assistant the behavior of which can be changed by the user, comprising a voice user interface for inputting information into and receiving information from the virtual assistant by speech, a communications network, a virtual assistant application running on a remote computer, the remote computer being electronically coupled to the user interface via the communications network, wherein the behavior of the virtual assistant changes responsive to user input. A computer-based virtual assistant that also automatically adapts its behavior is disclosed, comprising a voice user interface for inputting information into and receiving information from the virtual assistant by speech, a communications network, a virtual assistant application running on a remote computer, the remote computer being electronically coupled to the user interface via the communications network, wherein the remote computer is programmed to automatically change the behavior of the virtual assistant responsive to input received by the virtual assistant. As detailed below, the virtual assistant adapts to the user in many different ways based on the input the virtual assistant receives. Such input could be user information, such as information about the user's experience, the time between user sessions, the amount of time a user pauses when recording a message, the user's emotional state, whether the user uses words associated with polite discourse, and the amount of time since a user provided input to the virtual assistant during a session.
Owner:AVAYA TECH LLC
Context aware search service
InactiveUS20030135582A1Digital data information retrievalMultiple digital computer combinationsService provisionComputer science
A context-aware search service is provided to users requesting information. The context-aware search incorporates contextual information such as the context of the user making the request, the external context of the user or terminal that the user accesses, or the characteristics or context of the terminal. The contextualized request is processed through sets of analyses to customize the request including analyses to determine an exact nature of the request, analyses to limit a universe of reference to be examined to provide the result, and analyses to select the most appropriate content and format for presentation to the user once the result is obtained from separate service providers.
Owner:DOCOMO LAB USA
Systems and methods for detecting glucose level data patterns
Systems and methods for detecting and reporting patterns in analyte concentration data are provided. According to some implementations, an implantable device for continuous measurement of an analyte concentration is disclosed. The implantable device includes a sensor configured to generate a signal indicative of a concentration of an analyte in a host, a memory configured to store data corresponding at least one of the generated signal and user information, a processor configured to receive data from at least one of the memory and the sensor, wherein the processor is configured to generate pattern data based on the received information, and an output module configured to output the generated pattern data. The pattern data can be based on detecting frequency and severity of analyte data in clinically risky ranges.
Owner:DEXCOM
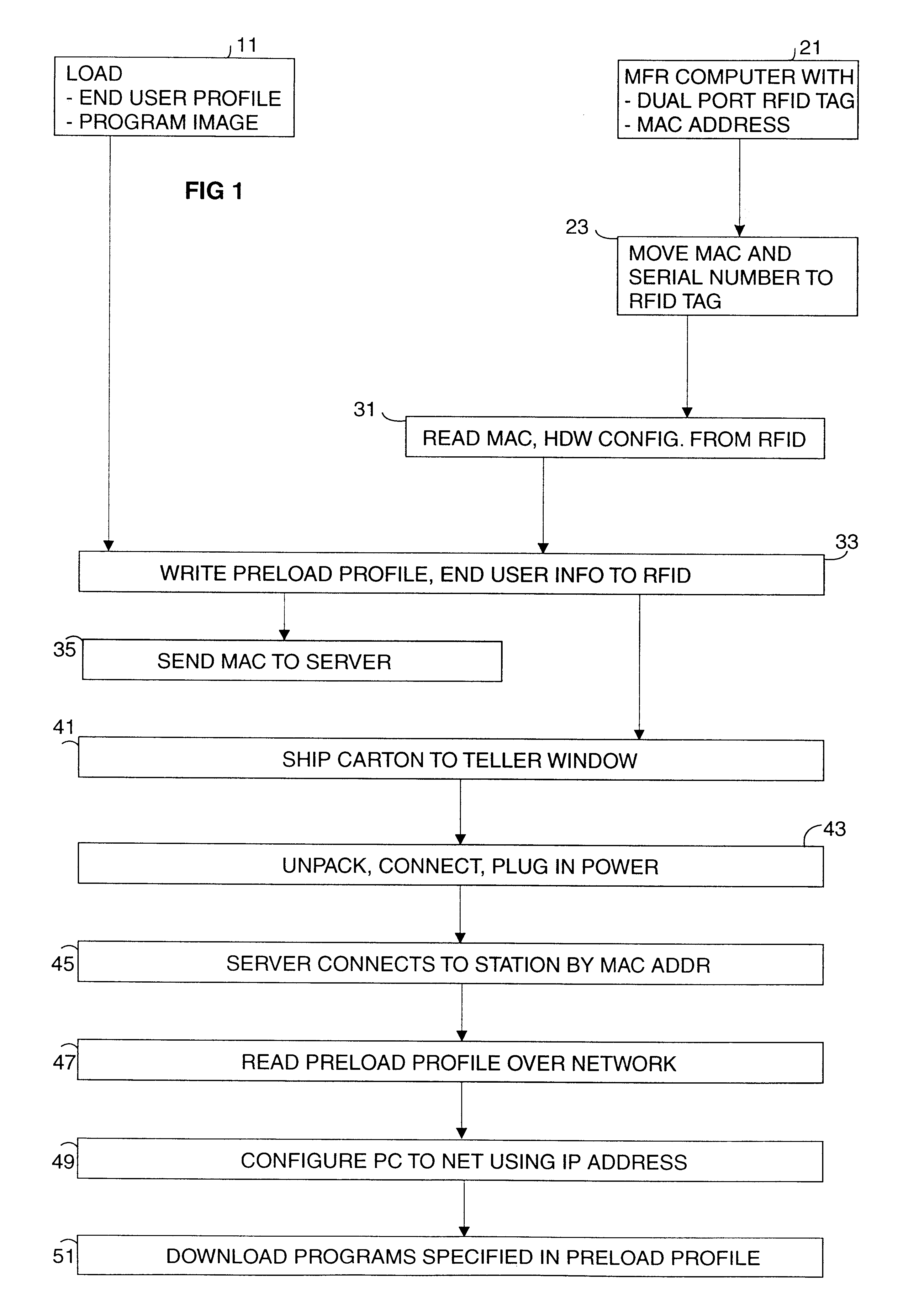
Method and economical direct connected apparatus for deploying and tracking computers
A method of asset control and workstation computer deployment that utilizes a dual port electronic memory identification RFID tag to hold serial number and hardware and software configuration profiles as well as user information. The RFID tag is mapped into the workstation computer memory space and can also be read and written by radio frequency signalling through a wired plug and access flap in a shipping carton. Serial numbers and MAC address is stored on the tag by the manufacturer. User information, workstation profile and software image information is stored onto the tag while the computer is being received for forwarding to the final workstation destination without the need to unpack and power up the computer. The information stored on the tag is used to allow automated system configuration and software downloading to the computer.
Owner:IBM CORP
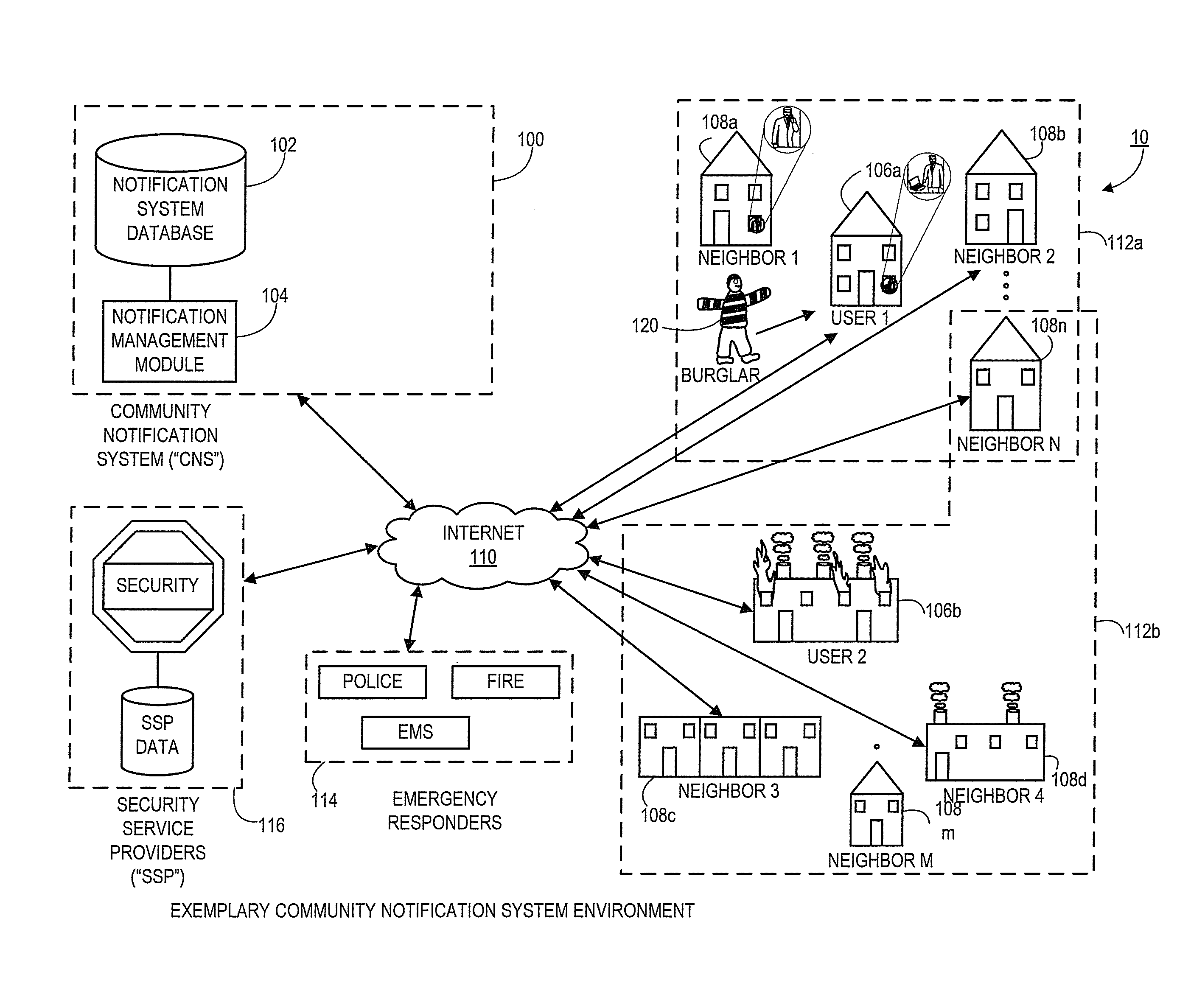
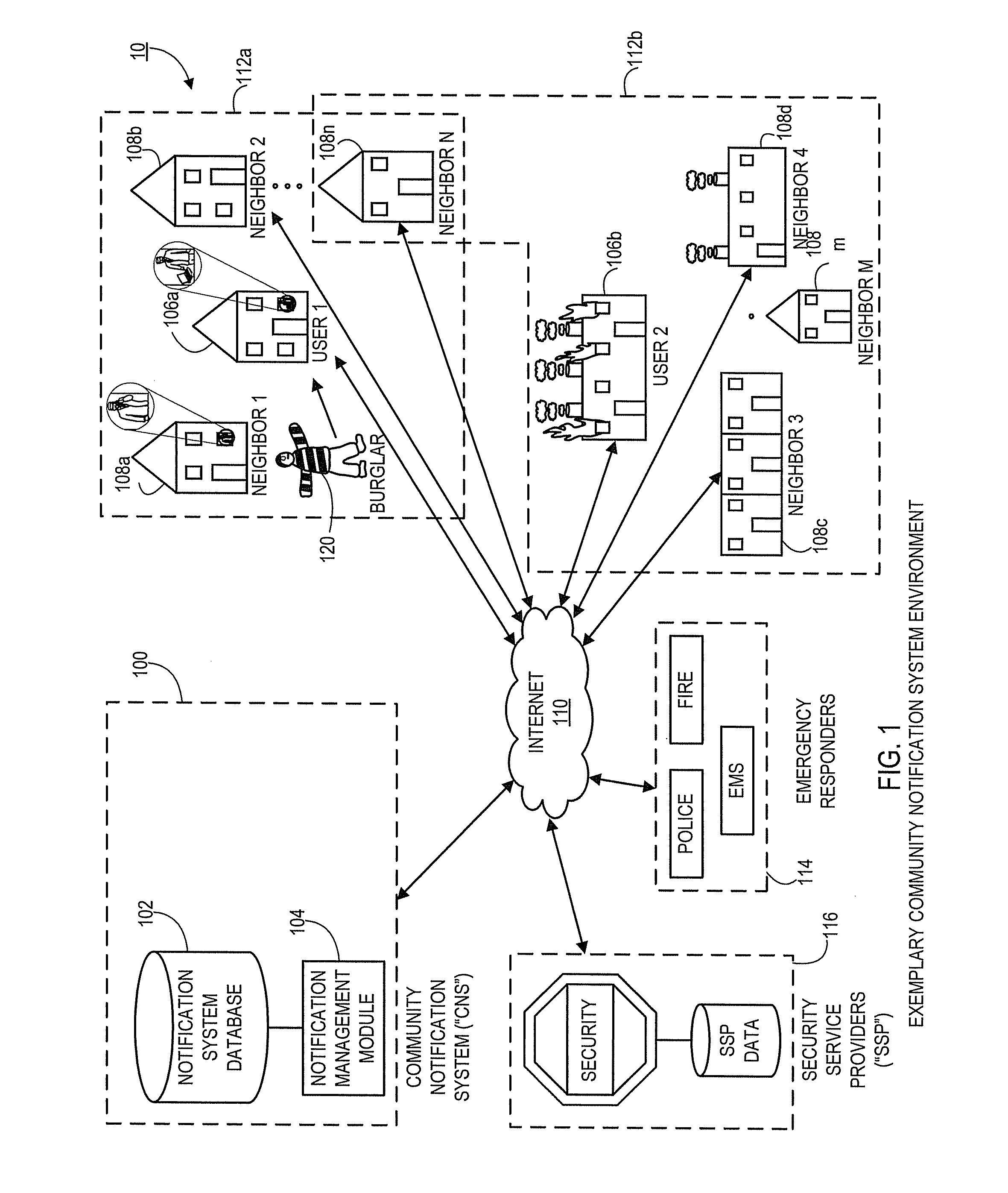
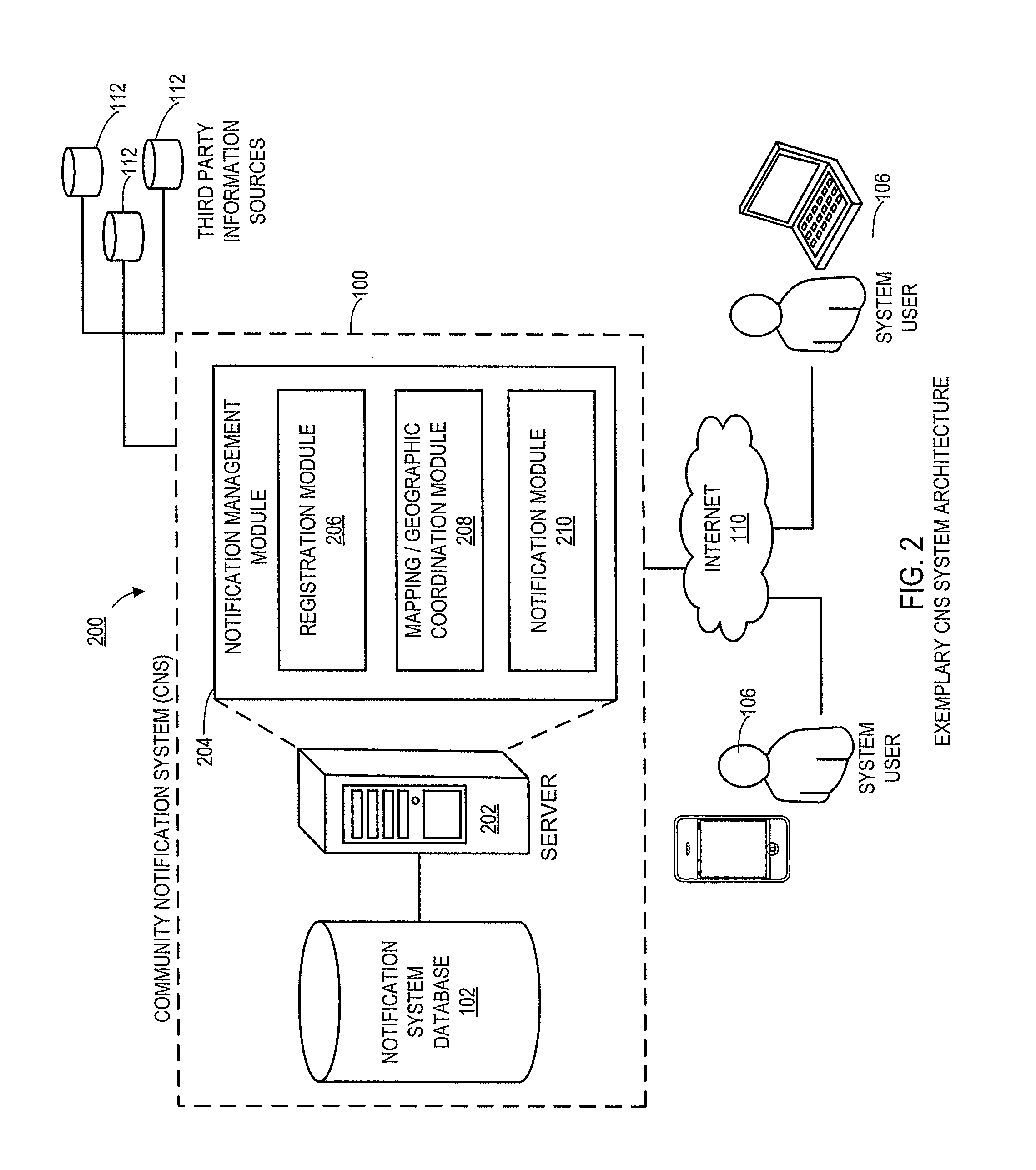
Systems and methods for notifying proximal community members of an emergency or event
Aspects of the present disclosure generally relate to systems and methods for an automated community notification system (“CNS”) that is configured to notify certain individuals with relevant information relating to occurrence of an event or emergency at a given geographical location. Generally, aspects of the system include operative connections to one or more security system providers (“SSPs”) to identify events / emergencies at properties. In alternate embodiments, system users provide event information to the CNS via users' electronic devices. According to one aspect, system users register with the CNS and provide user information, preferences, geographic information, etc., and the CNS subsequently utilizes that information (in connection with other third party information sources) to establish “neighborhood networks” for system users. Typically, members of in the same neighborhood network are notified and provided with relevant information when an emergency occurs at the property or geographic location of another user in the members' network.
Owner:CLIMOTE
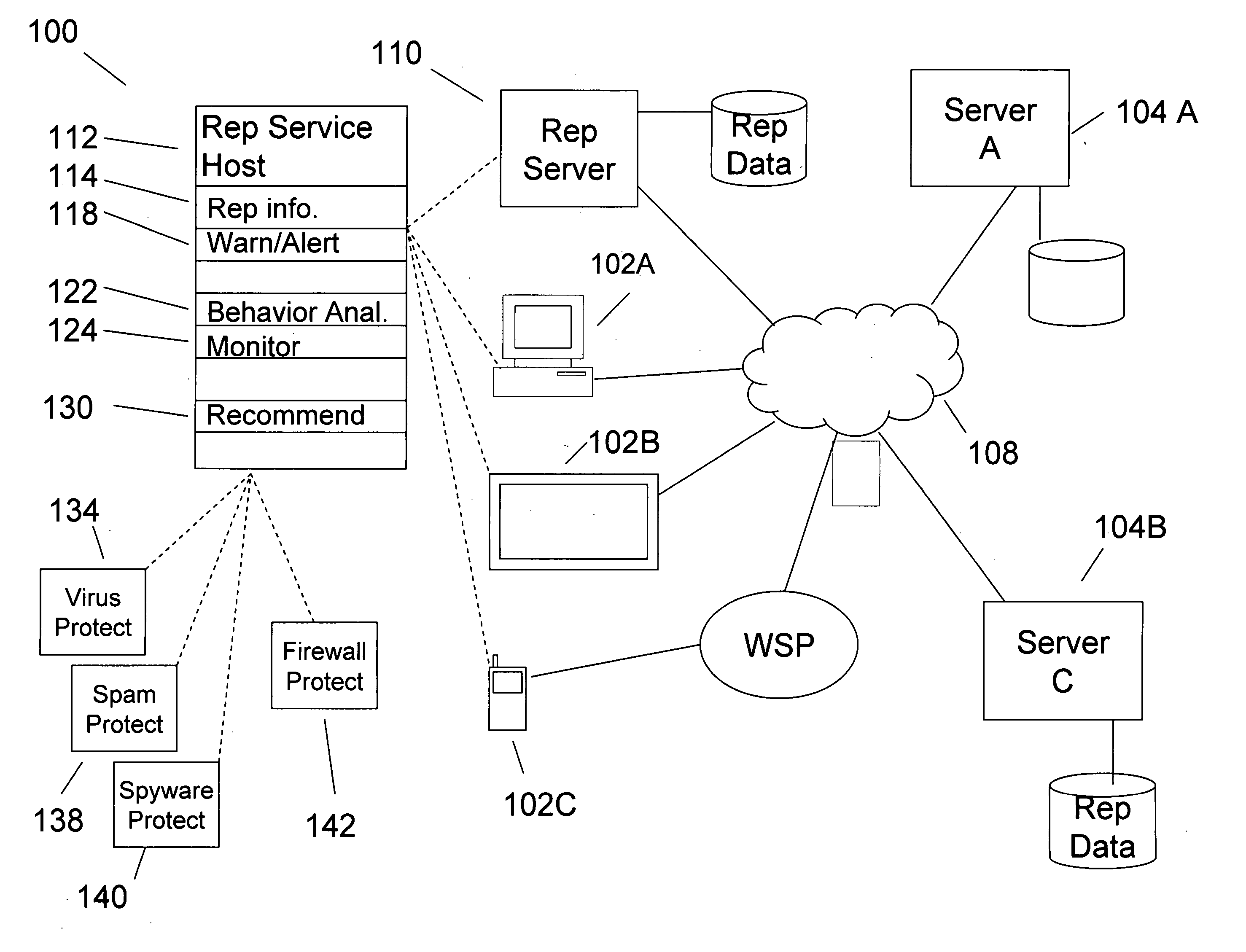
Indicating website reputations during website manipulation of user information
An aspect of the present invention relates to methods and systems involving receiving an indicator of an attempted interaction of a client computing facility with an item of content associated with a website and presenting an indicator of reputation to a client computing facility attempting to interact with the web content. The indicator of reputation may be based at least in part upon whether an entity associated with the web content seeks to manipulate a user in order to obtain information from the user.
Owner:MCAFEE LLC
Pointing systems for addressing objects
InactiveUS20020140745A1Quickly availableNavigational calculation instrumentsDigital data processing detailsHand heldHand held devices
Systems are arranged to provide a user information which relates to objects of interest. A user may point a hand held device toward an object to address it. The device determines which objects are being addressed by making position and attitude measurements and further a reference and search of a database containing preprogrammed information relating to objects. Information relating to objects determined as objects presently being addressed is thereafter presented at a user interface. Devices of these systems include a point reference, a direction reference, a position determining support, attitude determining support, a computer processor and database, and a user interface. Methods of systems include the steps of addressing an object, determining position and attitude, searching a database, and presenting information to a user.
Owner:GEOVECTOR
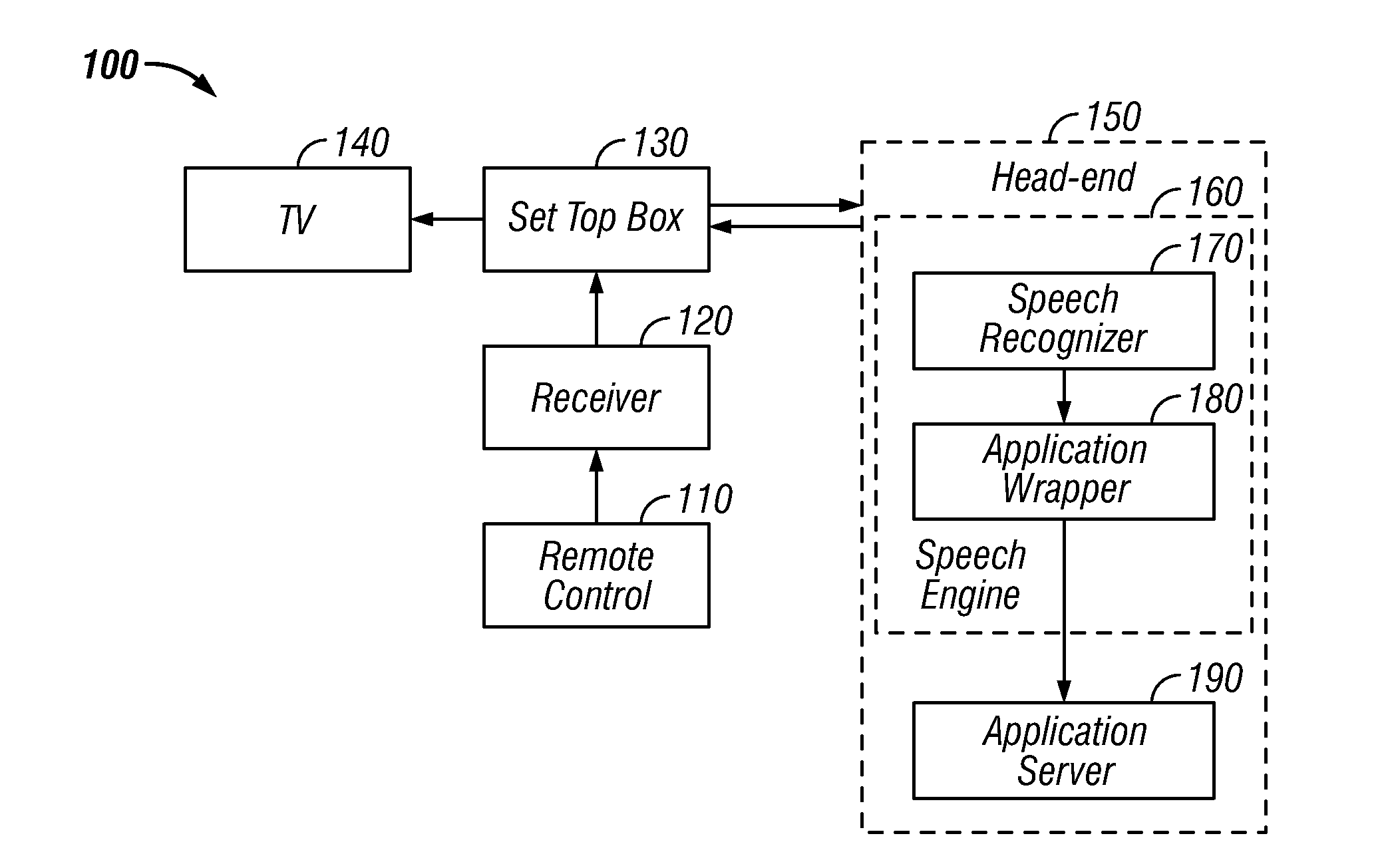
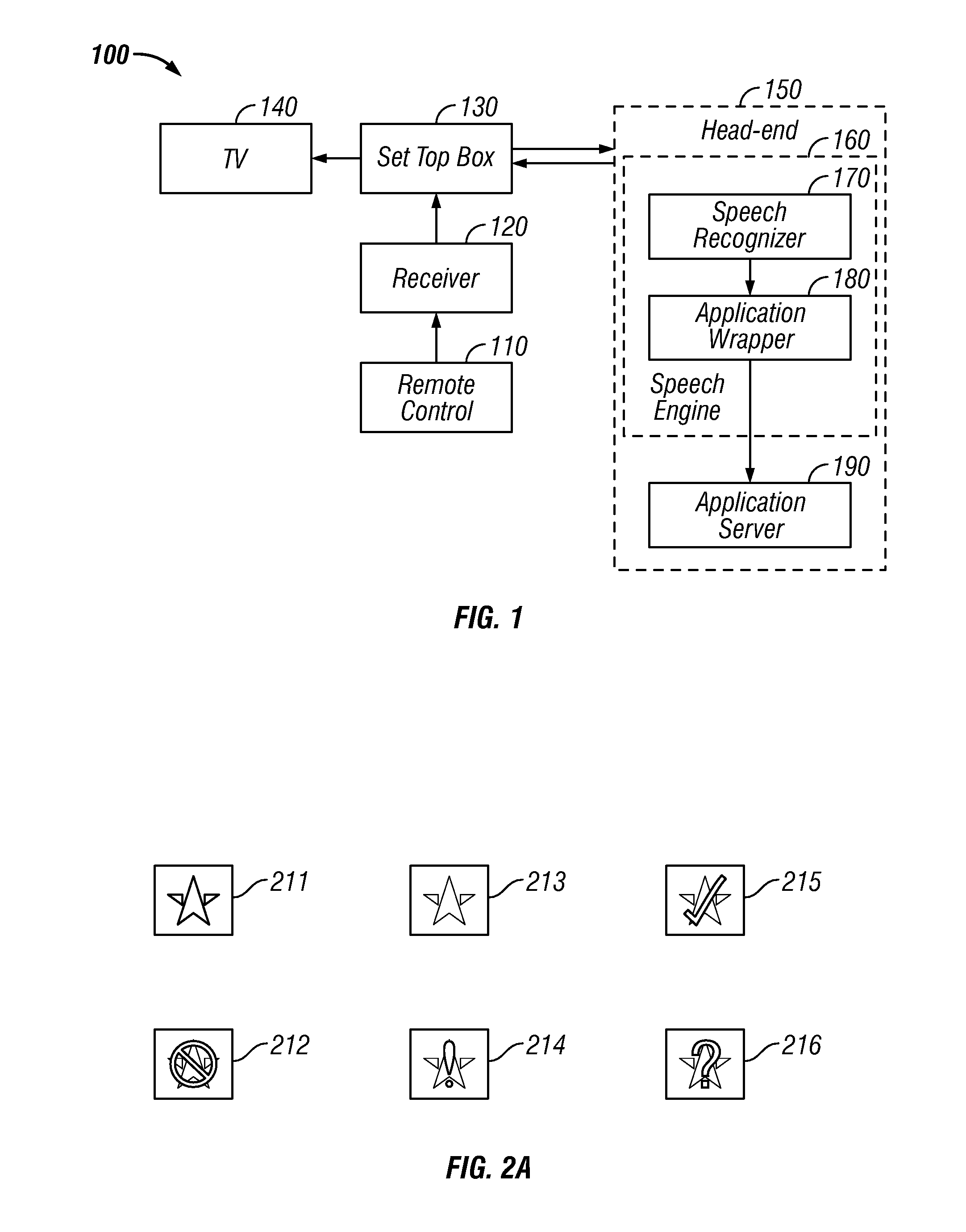
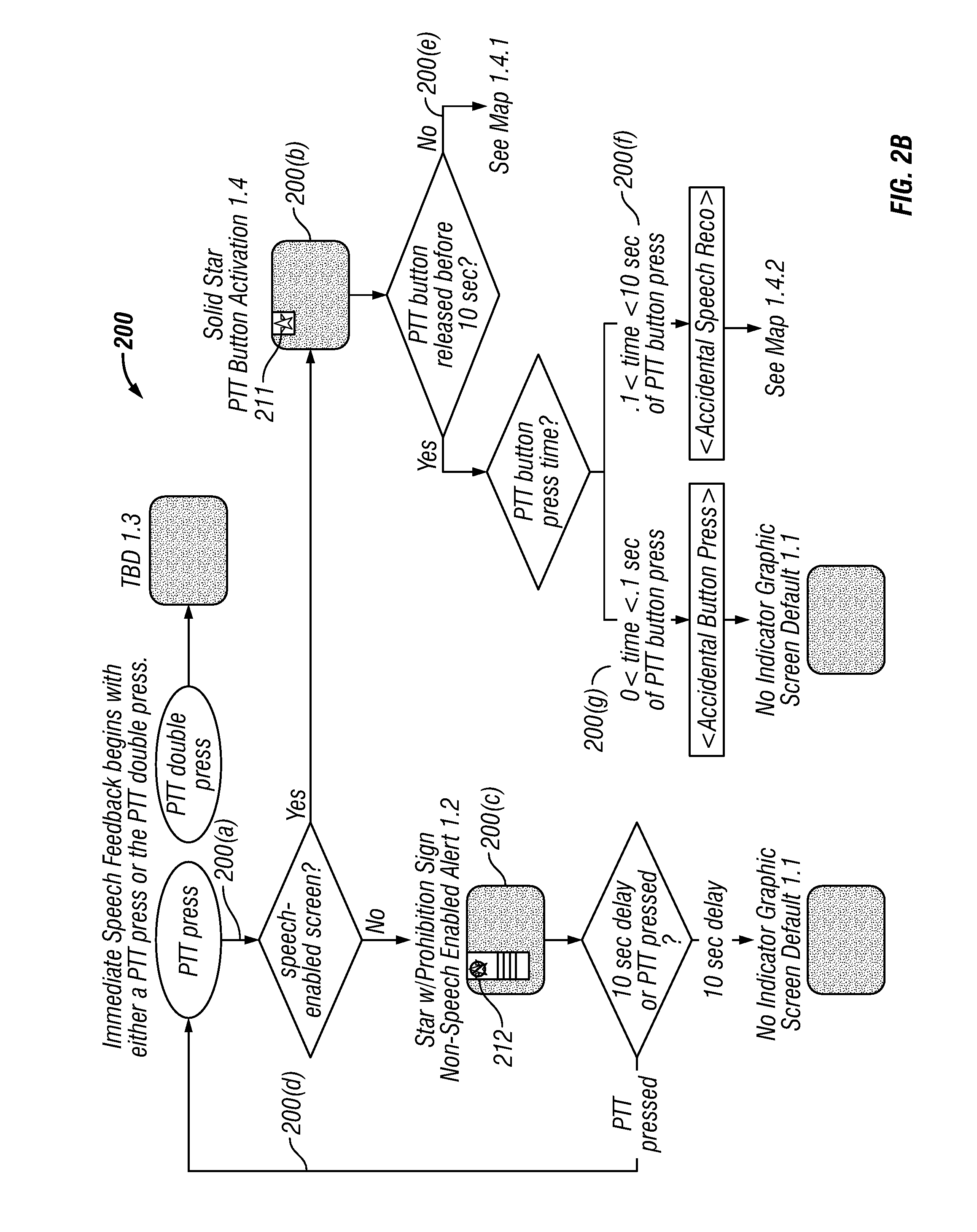
Global speech user interface
ActiveUS20080120112A1Good informationInput/output for user-computer interactionTelevision system detailsTelevision screenApplication software
A global speech user interface (GSUI) comprises an input system to receive a user's spoken command, a feedback system along with a set of feedback overlays to give the user information on the progress of his spoken requests, a set of visual cues on the television screen to help the user understand what he can say, a help system, and a model for navigation among applications. The interface is extensible to make it easy to add new applications.
Owner:PROMPTU SYST CORP
Wireless Power Supply System and Wireless Power Supply Method
ActiveUS20080122297A1Improve convenienceMeet needsElectrical testingLoop antennasElectric power systemComputer terminal
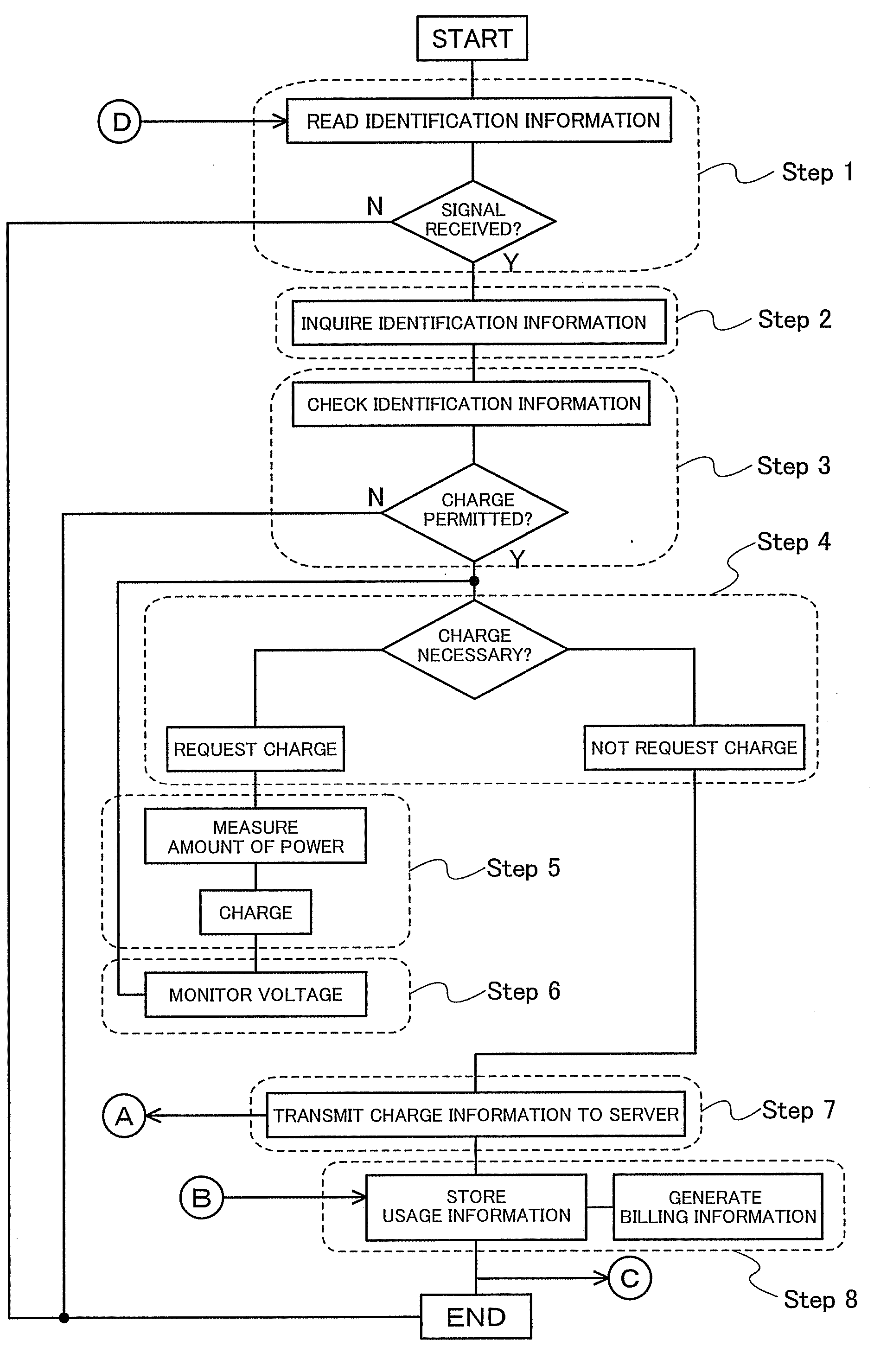
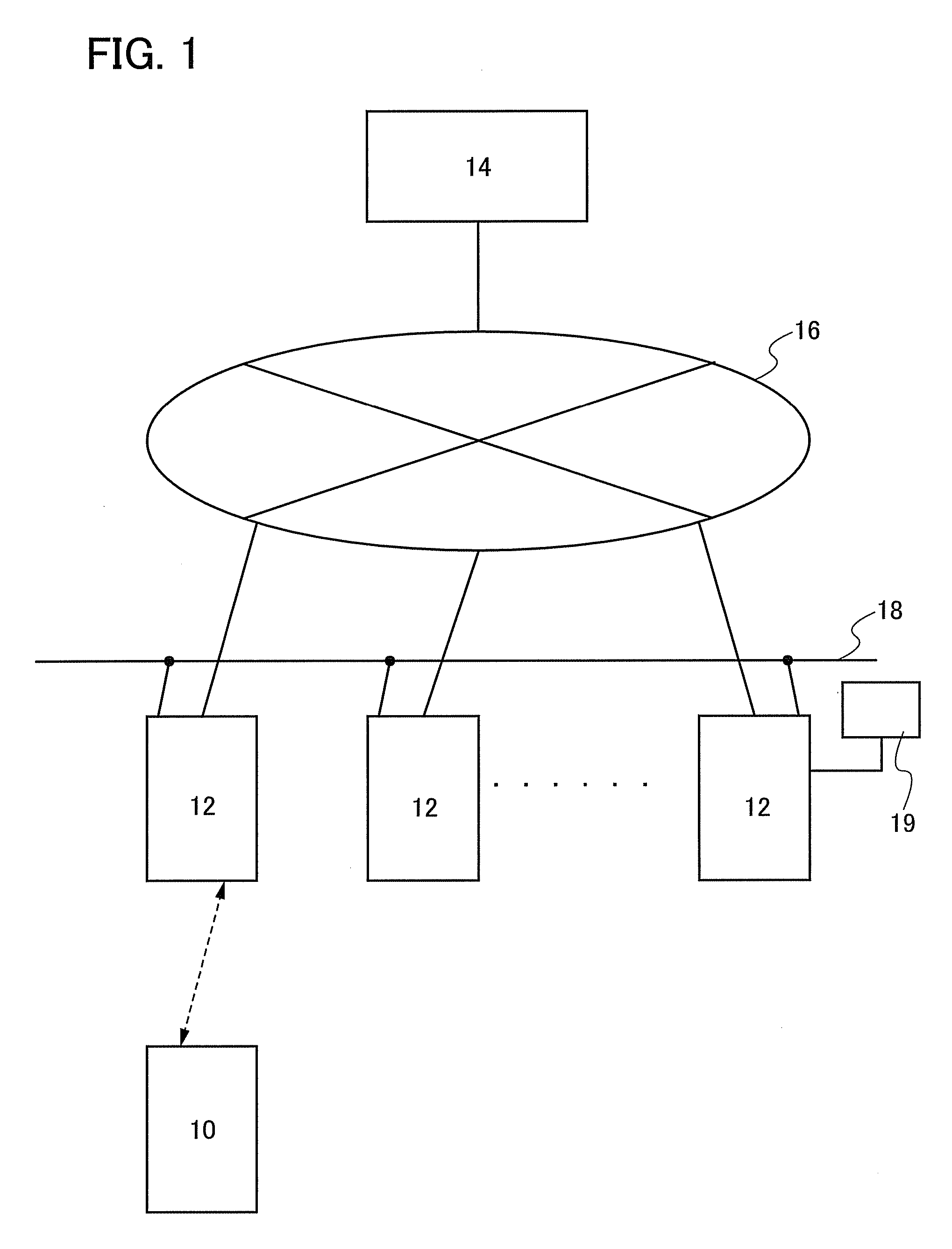
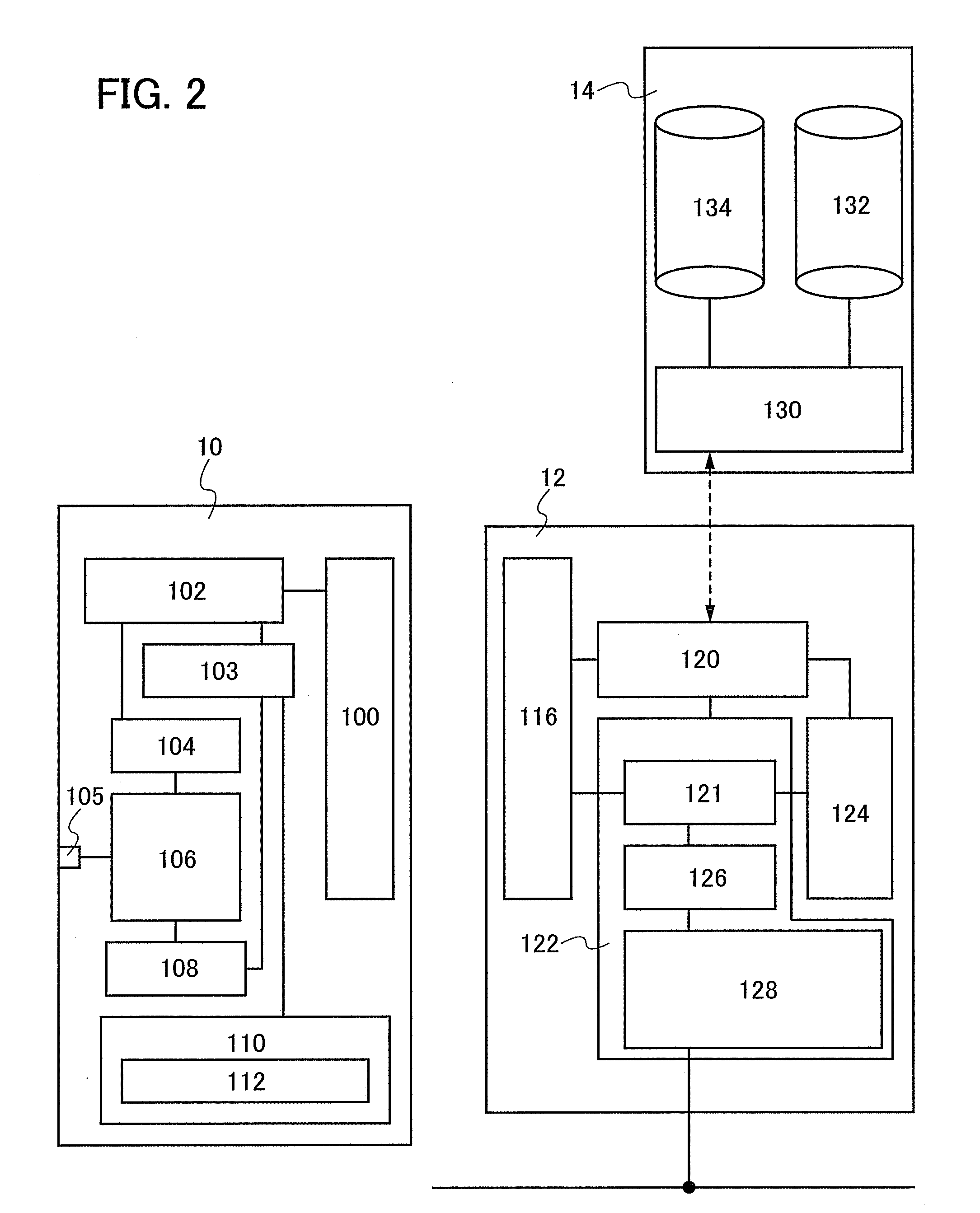
An object is to provide a system for improving convenience for users, by which a portable electronic device or the like can be charged even in a place where utility power is not available. Another object is to provide a system which allows a service provider to easily perform customer management. A wireless power supply system includes a power storage device having a power storage portion, a terminal charging device for wirelessly supplying electric power to the power storage device, and a management server having user information. Electric power can be supplied to specified users by intercommunication of user information between the power storage device and the terminal charging device and between the terminal charging device and the management server.
Owner:SEMICON ENERGY LAB CO LTD
System and method for malicious software detection in multiple protocols
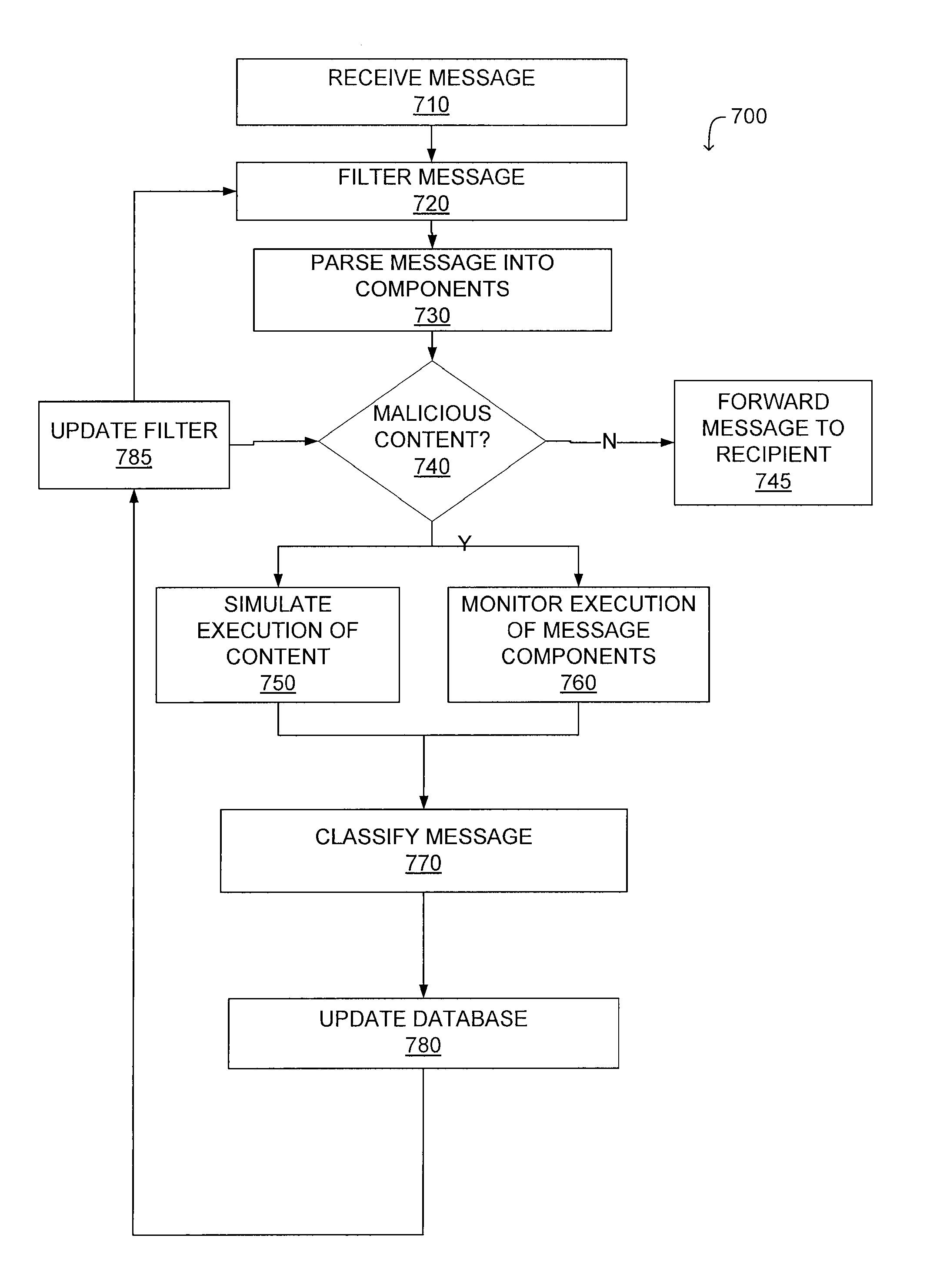
ActiveUS8321936B1Overcome limitationsEasy to detectMemory loss protectionError detection/correctionTransport systemSystem configuration
A system and a method for detecting malicious content associated with an electronic message are described. An electronic message, such as an e-mail, a chat request, a torrent file or a text message is initially received. The electronic message can then be compared to known viruses using pattern or signature matching techniques. The electronic message is then transmitted to a virtual machine which executes the electronic message in an environment simulating the destination computing system of the electronic message. The virtual machine monitors execution of the electronic message to identify one or more malicious actions and classifies the electronic message accordingly. For example, message component execution is monitored for attempts to access system files, attempts to access user information, attempts to transmit system configuration data or attempts to transmit user information.
Owner:AVINTI CORP
Method and system for serving advertisements
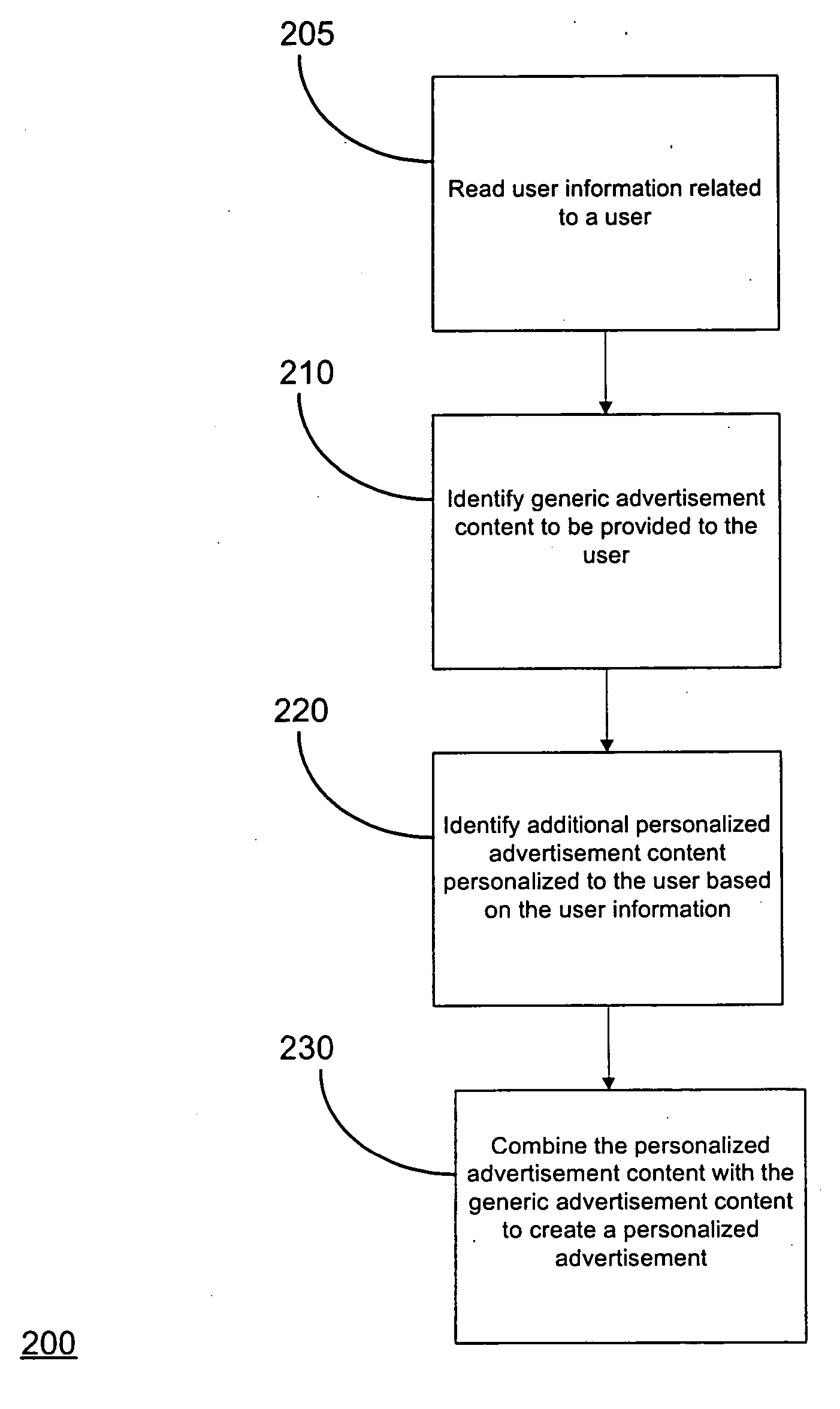
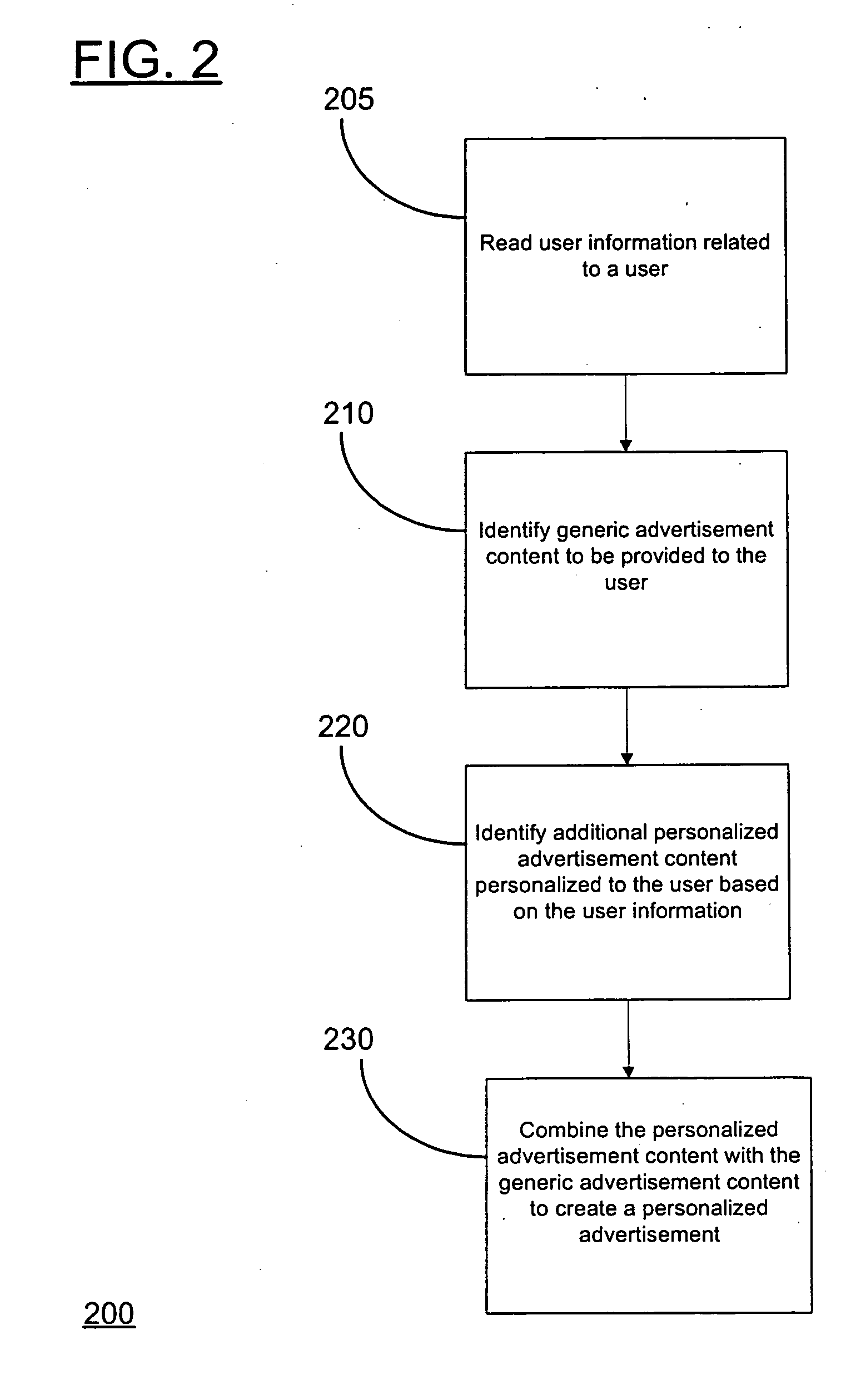
InactiveUS20050144073A1AdvertisementsSpecial data processing applicationsPersonalizationUser information
An embodiment comprises a method and system for serving an advertisement. The method comprises identifying generic advertisement content to be provided to the user, identifying additional personalized advertisement content which is personalized to the user based on user information, and combining the personalized advertisement content with the generic advertisement content to create a personalized advertisement.
Owner:YAHOO INC
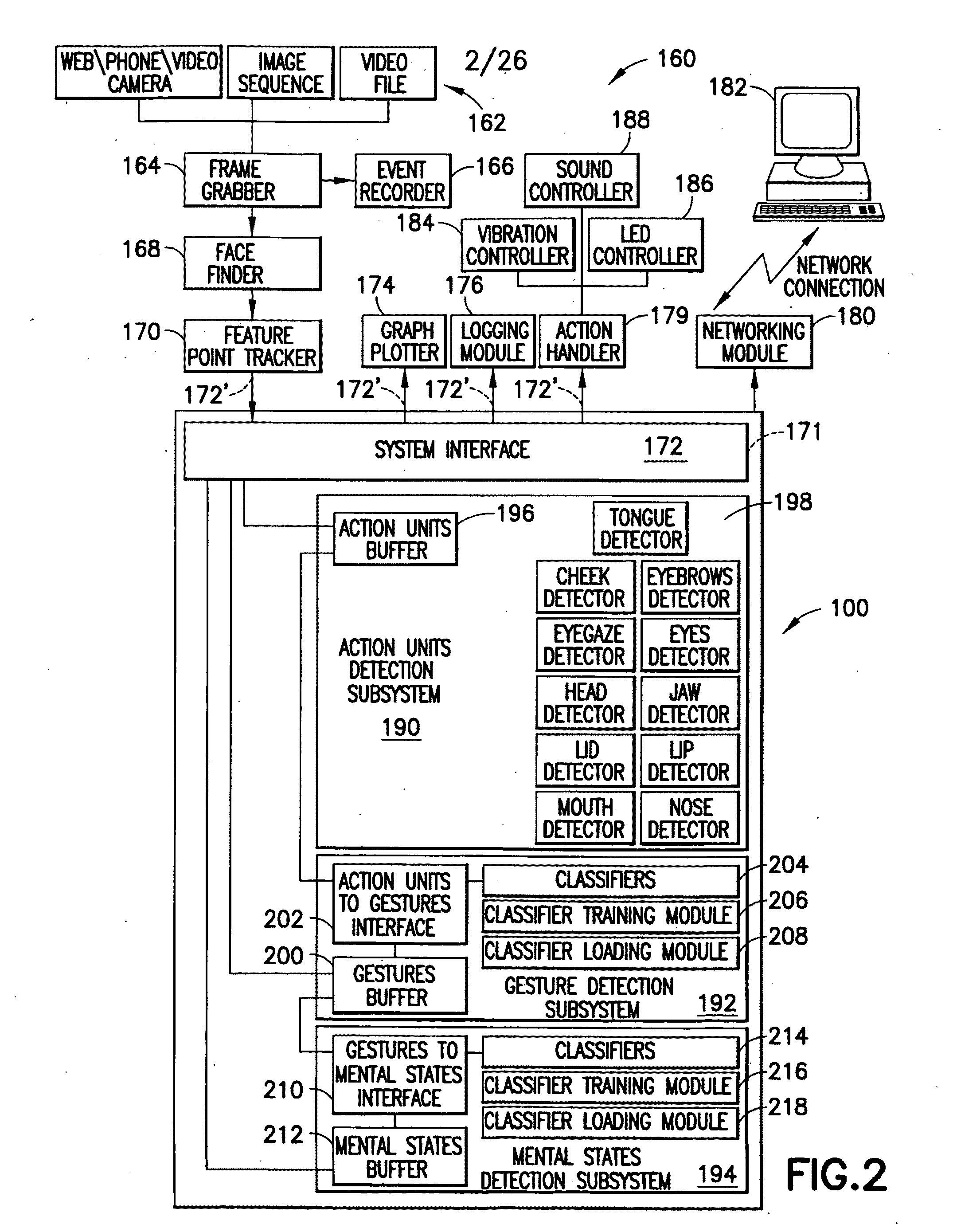
Method and system for real-time and offline analysis, inference, tagging of and responding to person(s) experiences
InactiveUS20110263946A1Medical data miningCharacter and pattern recognitionHead movementsMental state
A digital computer and method for processing data indicative of images of facial and head movements of a subject to recognize at least one of said movements and to determine at least one mental state of said subject is provided. The outputting instructions for providing to a user information relating to at least one said mental state. A further processing data reflective of input from a user, and based at least in part on said input, confirming or modifying said determination and generating with a transducer an output of humanly perceptible stimuli indicative of said at least one mental state.
Owner:MASSACHUSETTS INST OF TECH
Method, system and apparatus for location based advertising
InactiveUS20060155597A1Good curative effectOvercome deficienciesDiscounts/incentivesFile systemUser profile
The invention relates to a method, system and apparatus for managing a small business' advertising. More specifically, the system creates and administers a virtual online world accessible to users (players) within a virtual environment. A player interacts with various elements of the virtual environment and during those interactions the advertising is displayed to the user. To subscribe to the virtual environment, a player provides user information through a registration process to create a user profile. The system selects and displays advertisements that are correlated to a given user. The correlation between advertisement and user in one embodiment of the invention is based on a user's zip code. Further, in order to facilitate the quick adoption of the system among small business owners, a fundraising paradigm is implemented. More specifically, people volunteer to sell advertising opportunities within a virtual environment in exchange for a share of sales revenues.
Owner:GLEASON DAVID MARTIN
Methods and Systems For Making a Payment Via a Paper Check in a Mobile Environment
InactiveUS20080010204A1Unprecedented convenienceUnprecedented flexibilityAcutation objectsFinanceChequeFinancial transaction
Methods and systems for making a financial payment to a payee via a paper check utilizing a mobile device such as a mobile telephone (cellphone) or wireless connected personal digital assistant (PDA). The mobile device communicates wirelessly with a mobile financial transaction system (MFTS) that stores user information and transaction information. A user enters information via the mobile device identifying a payee and indicating a paper check payment method. The mobile device generates a mobile payment instruction that includes information corresponding to the identified payee and indicating a paper check payment method. The mobile payment instruction is wirelessly communicated to the MFTS. The MFTS generates an MFTS payment instruction to a payment instruction recipient that can issue a paper check. The MFTS communicates the MFTS payment instruction to the payment instruction recipient, which arranges for payment to the identified payee by printing and mailing of a paper check to the payee.
Owner:QUALCOMM INC
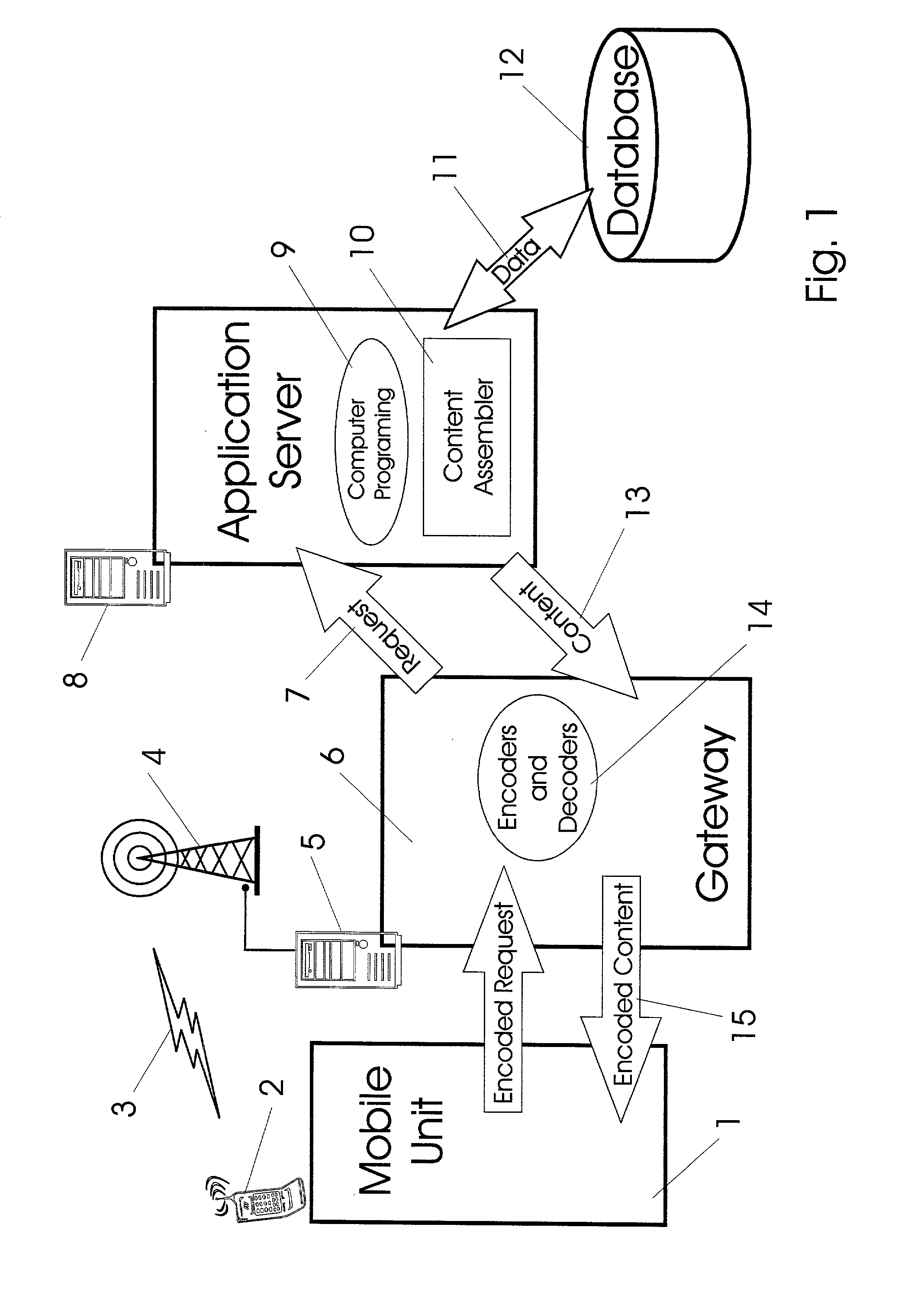
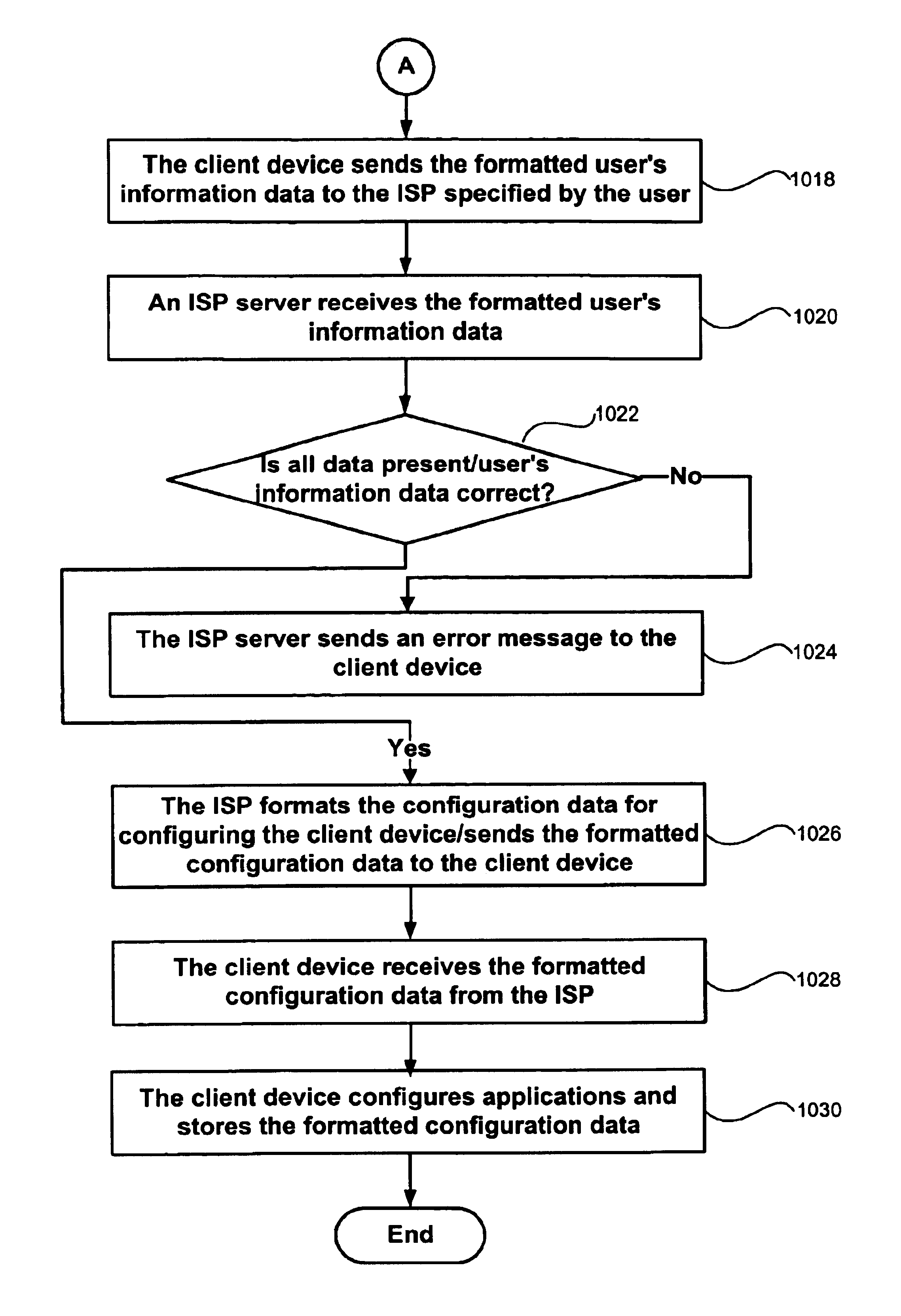
System and method for automatically configuring a client device
InactiveUS6938079B1Multiple digital computer combinationsProgram loading/initiatingAuto-configurationService provision
A user of a client device selects a service provider from a plurality of available service providers. The client device then queries the user for the user's information and formats the user's information into a predetermined data structure and format. The client device connects to the service provider and sends the formatted user's information to the service provider. The service provider responsively creates configuration data and provides it to the client device. The configuration data is used to configure a plurality of applications on the client device, allowing the user to establish future communication sessions with the service provider.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
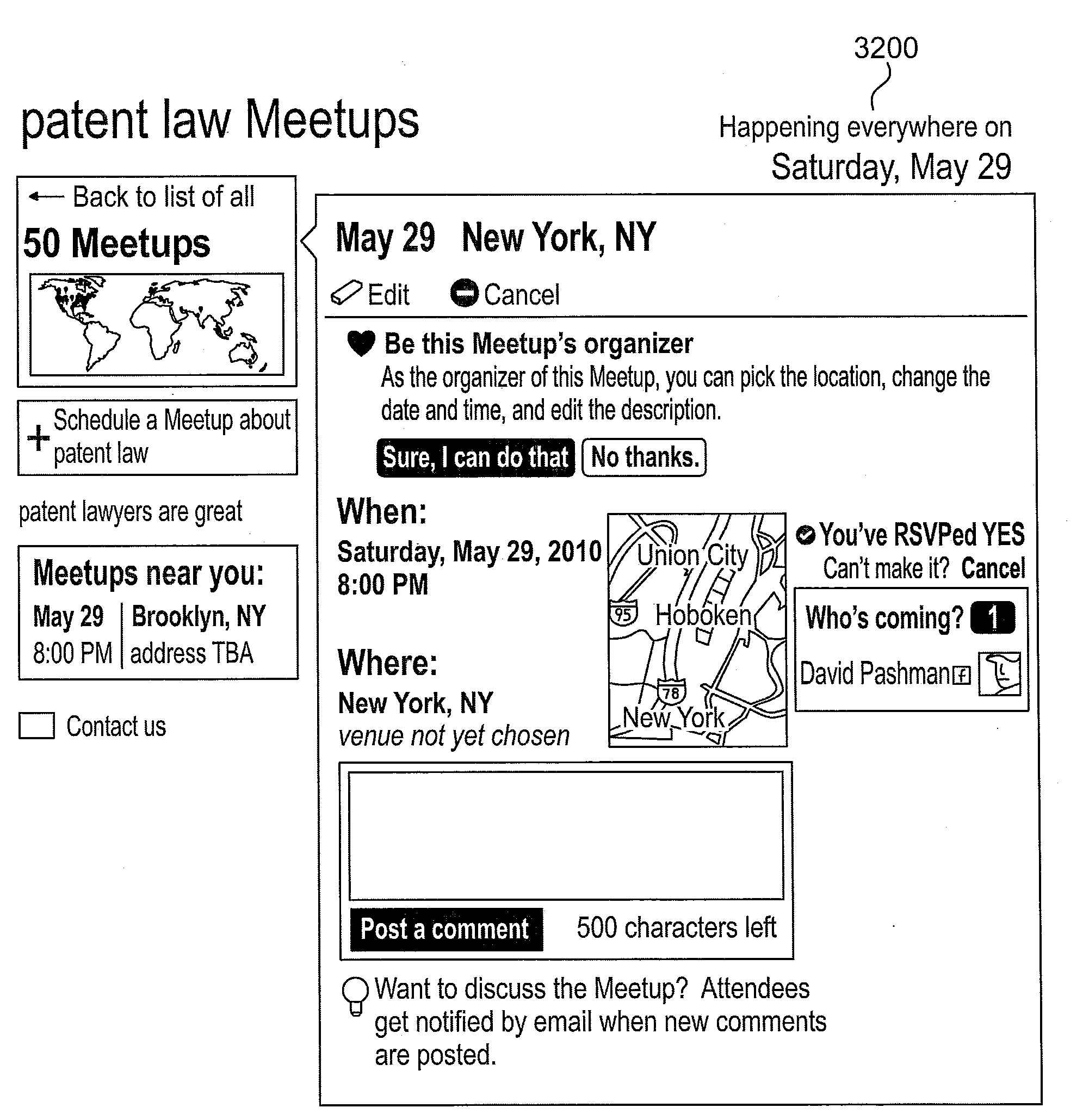
Web-Based Interactive Meeting Facility with Recommendations to Users
ActiveUS20110289433A1Overcome problemsServices signallingOffice automationComputer scienceSubject specific
A computer implemented method for providing recommendations for an in-person meeting group, the method comprising: collecting user information, wherein the user information provides information related to topical interests and location information for at least one of a plurality of users; comparing the user information with a topical listing of in-person meeting groups in the same geographical region as the at least one user, wherein the in-person meeting group is formed and maintained through a web-based meeting facility; and providing an in-person meeting group recommendation to the at least one user based on the comparison.
Owner:MEETUP
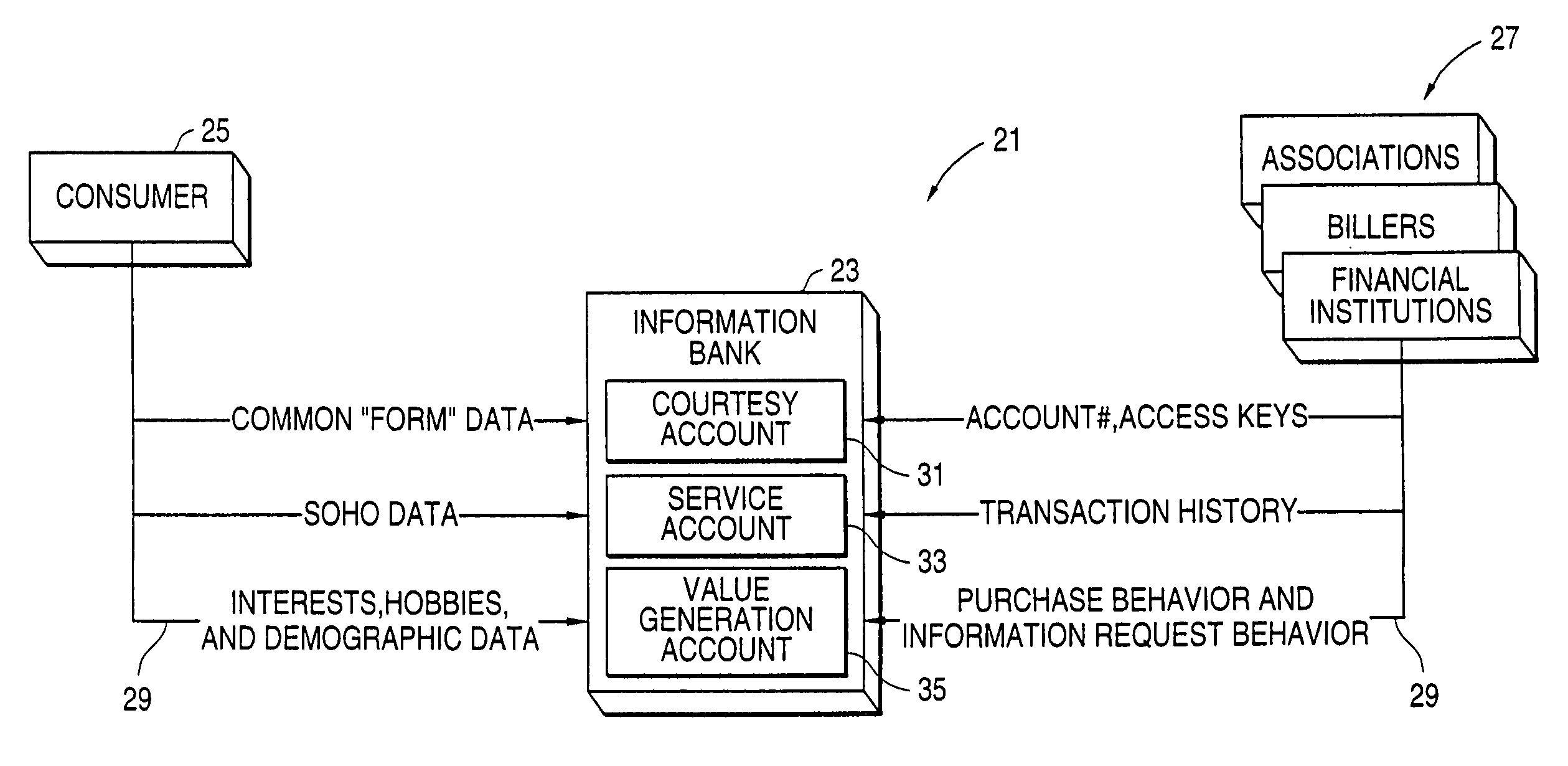
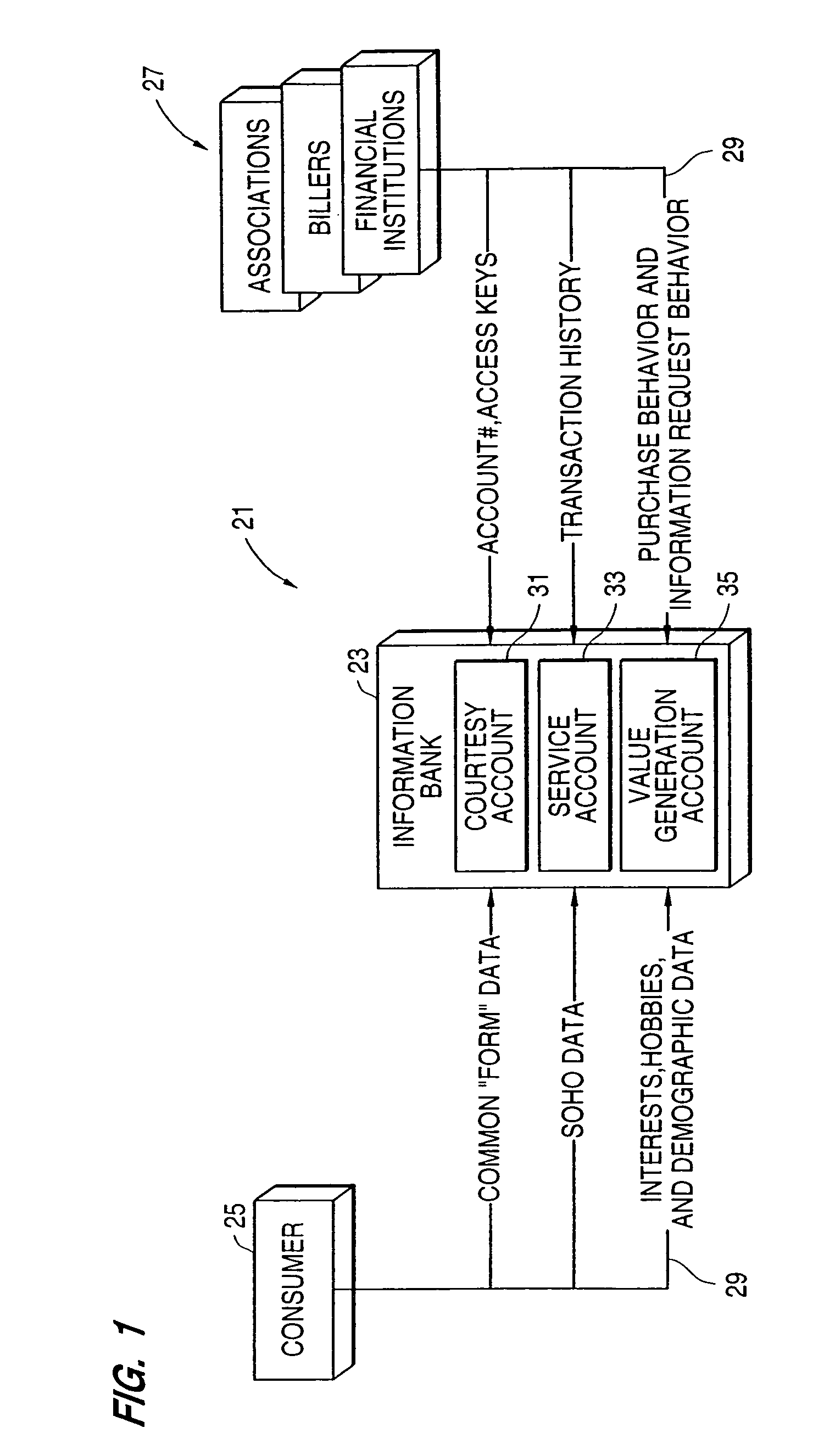
Method and system for anonymizing purchase data
InactiveUS7200578B2Easy accessEliminate needComplete banking machinesFinanceInternet privacyData storing
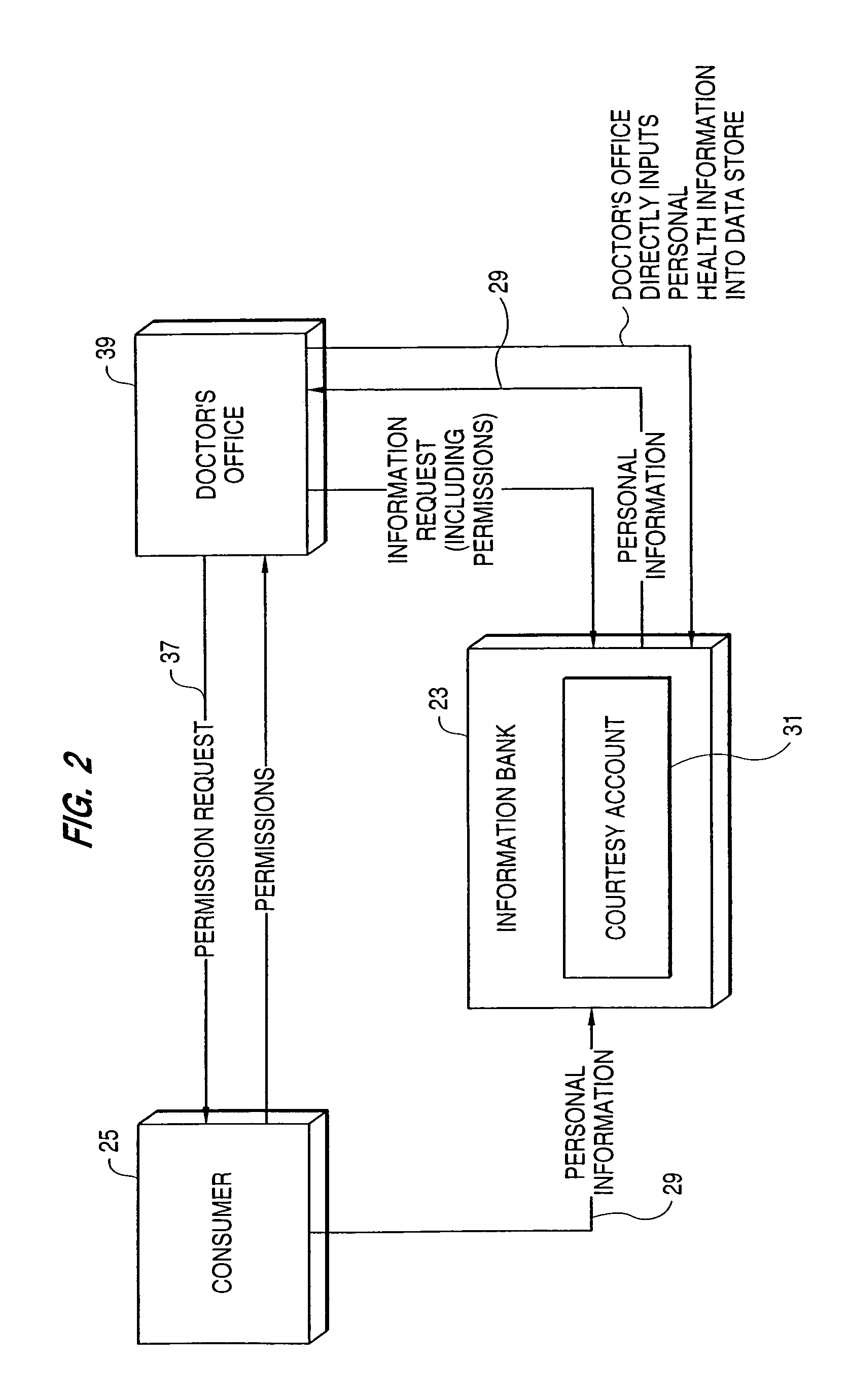
A system, in which information is the primary asset and in which investments may be made in information, includes multiple data stores for storing different types of a user's information. The safe, secure and properly authorized transfer of information while preserving individual privacy is provided. The system also provides for secure backup and storage, as well as for ubiquitous and nomadic access to information while maintaining the privacy of such information. A first data store includes static identification data about a user. A second data store includes moderately dynamic personal data about the user. A third data store includes dynamic demographic information data about the user. An electronic wallet can be used with the system to download selected portions of the data for use by the user. A method of use of the data includes using the data for billing out forms, providing services to the user and allowing merchants to selectively target users for sales while maintaining user anonymity.
Owner:CITICORP CREDIT SERVICES INC (USA)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com