Patents
Literature
24159 results about "Ip address" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
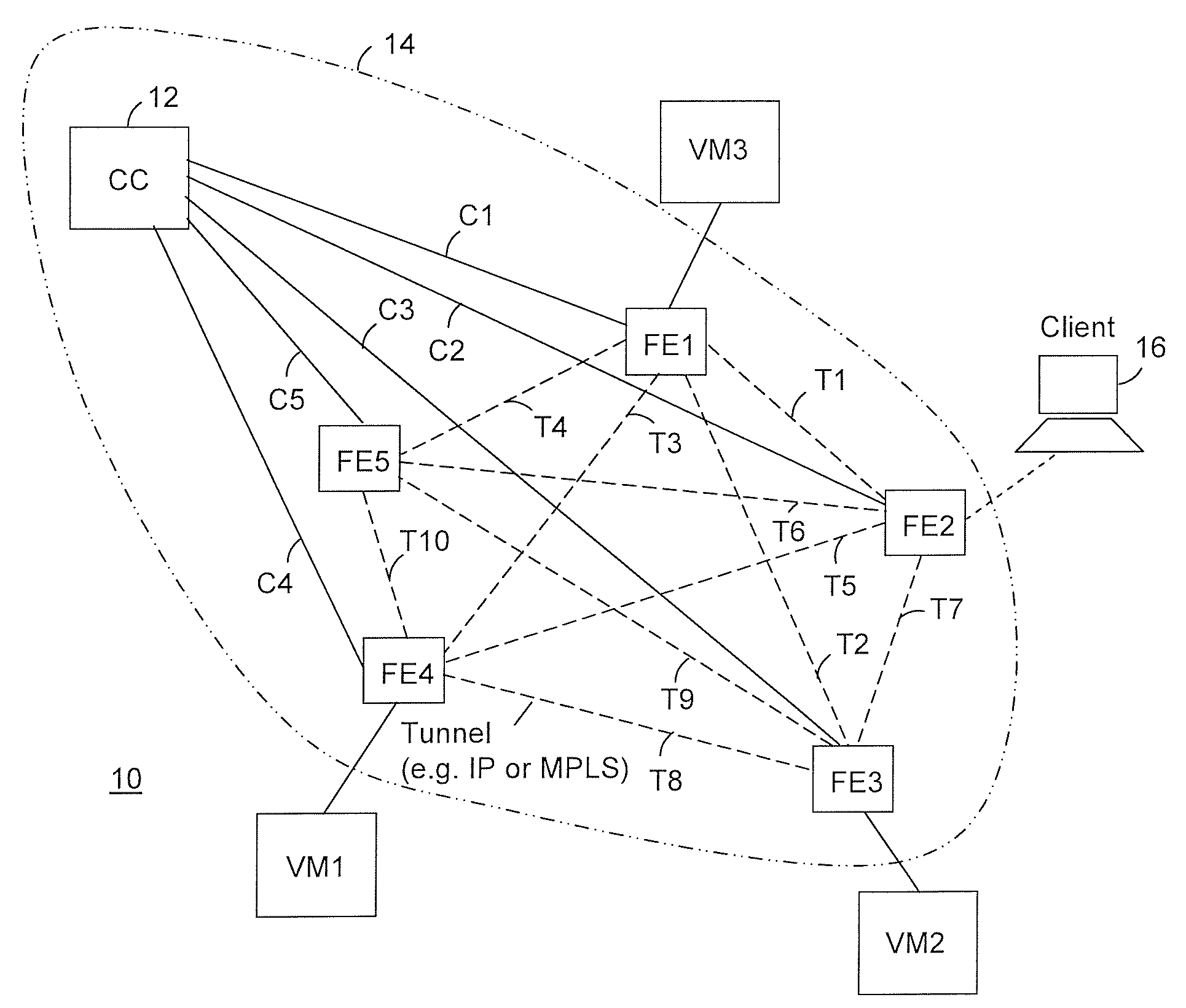
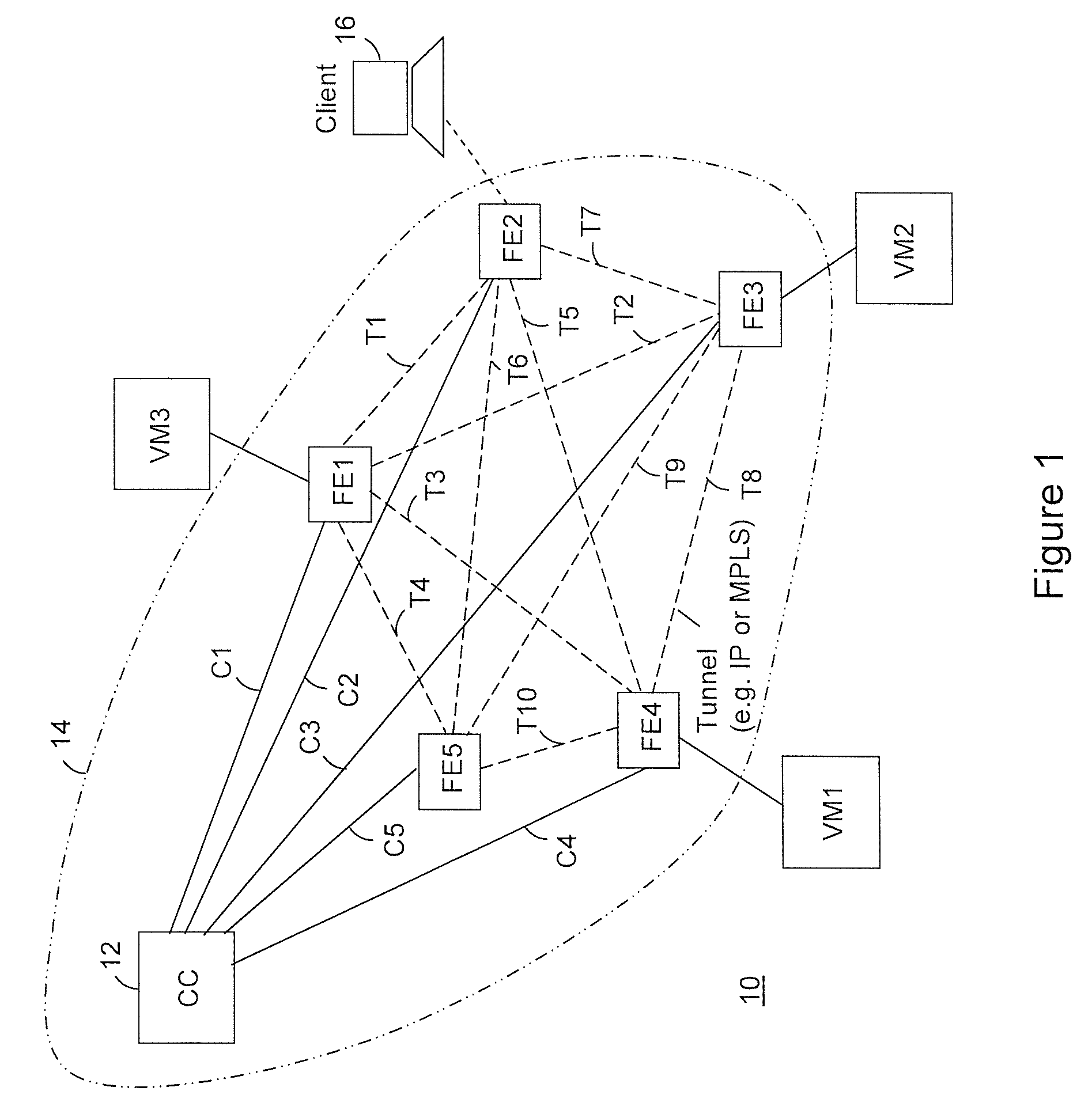
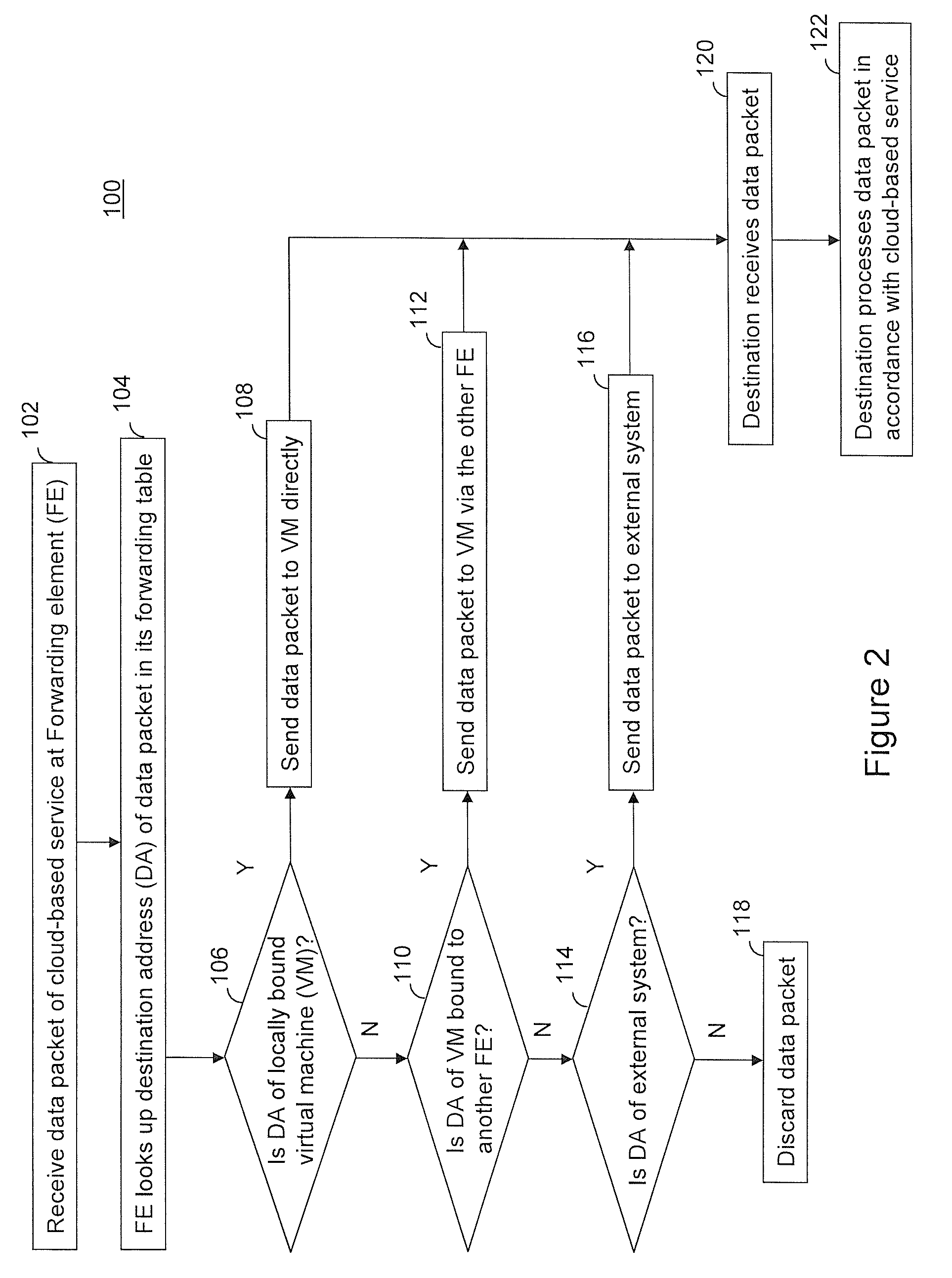
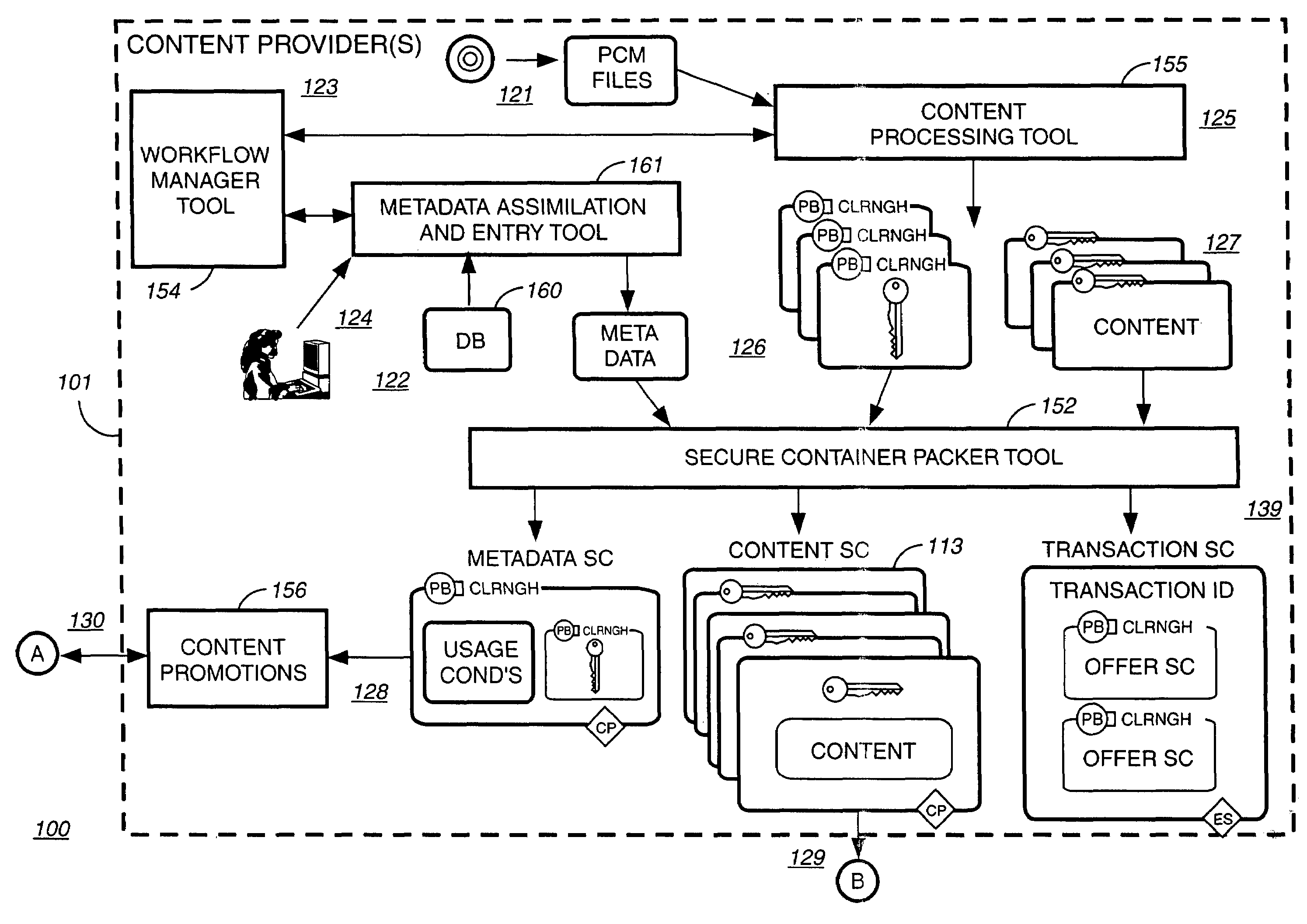
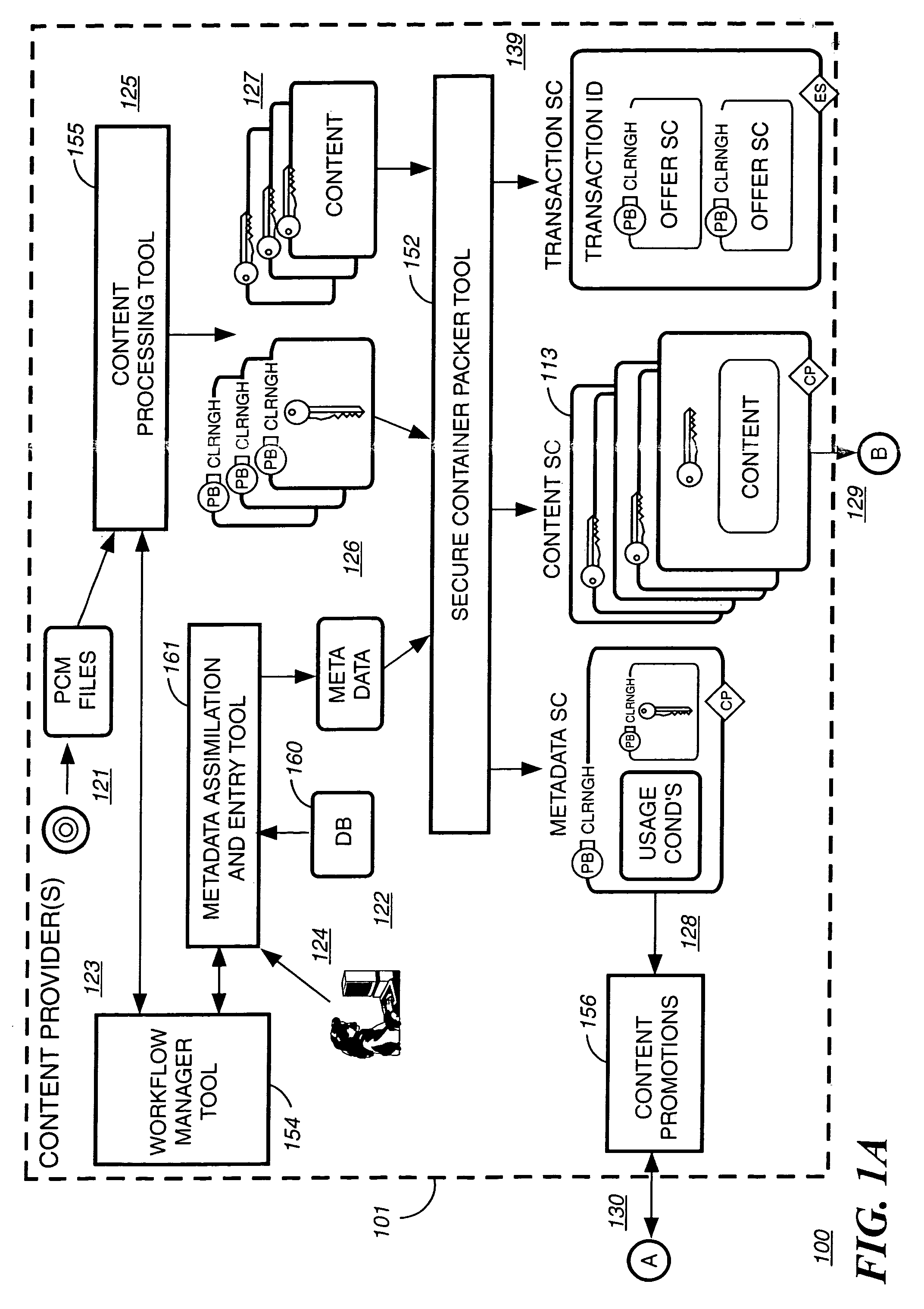
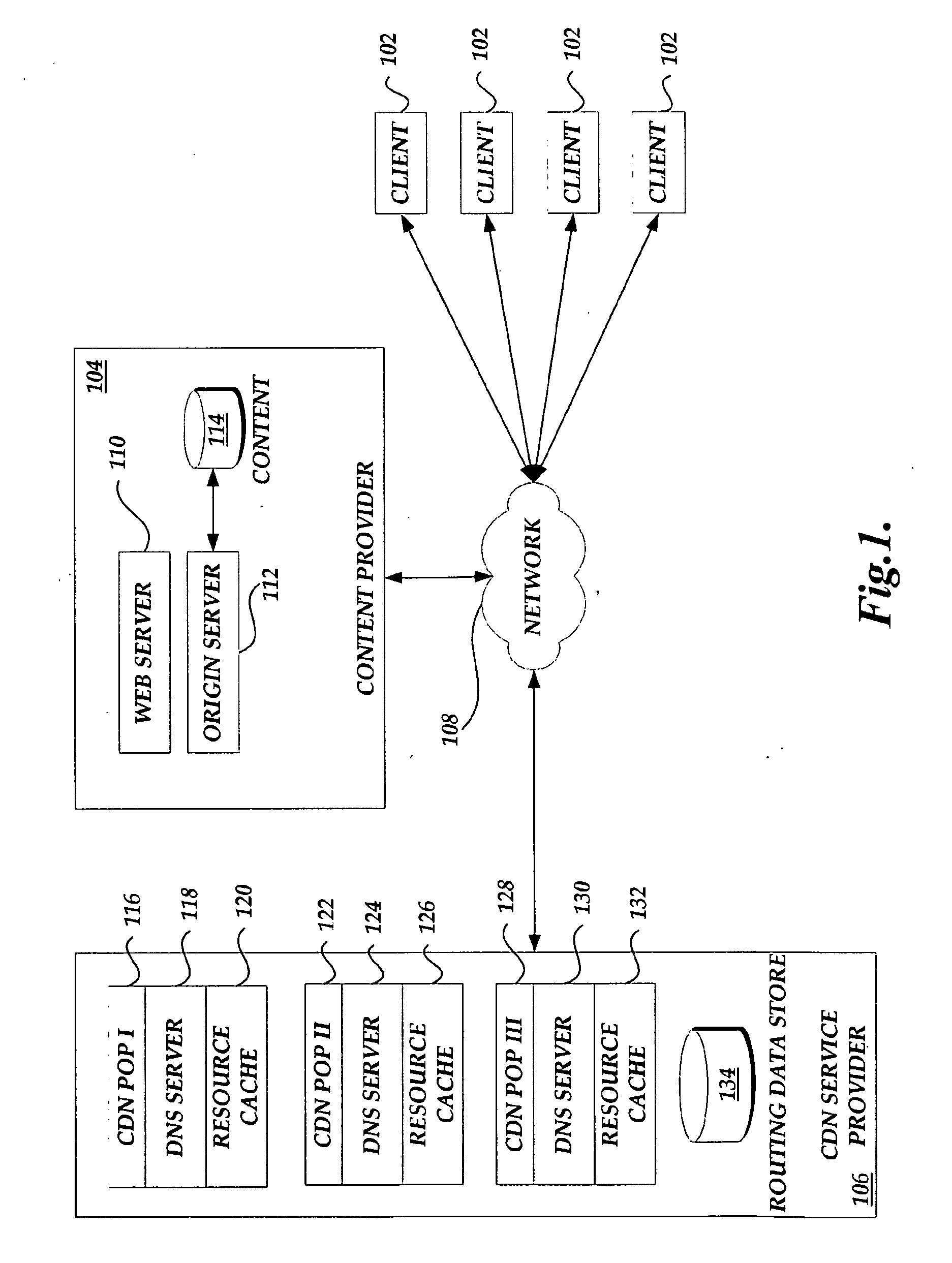
Providing cloud-based services using dynamic network virtualization
ActiveUS20100322255A1Network supportFaster service provisioningData switching by path configurationProgram controlCloud baseIp address
The invention is directed to providing cloud-based services using dynamic network virtualization. Embodiments of the invention provide a cloud-based service over a system that has a dynamic network virtualization architecture. The architecture includes a set of distributed forwarding elements with centralized control, and at least one virtual machine that is bound to one of the forwarding elements. These features enable the virtual machine to be migrated across a wide area network while maintaining its original IP address and service continuity.
Owner:ALCATEL LUCENT SAS
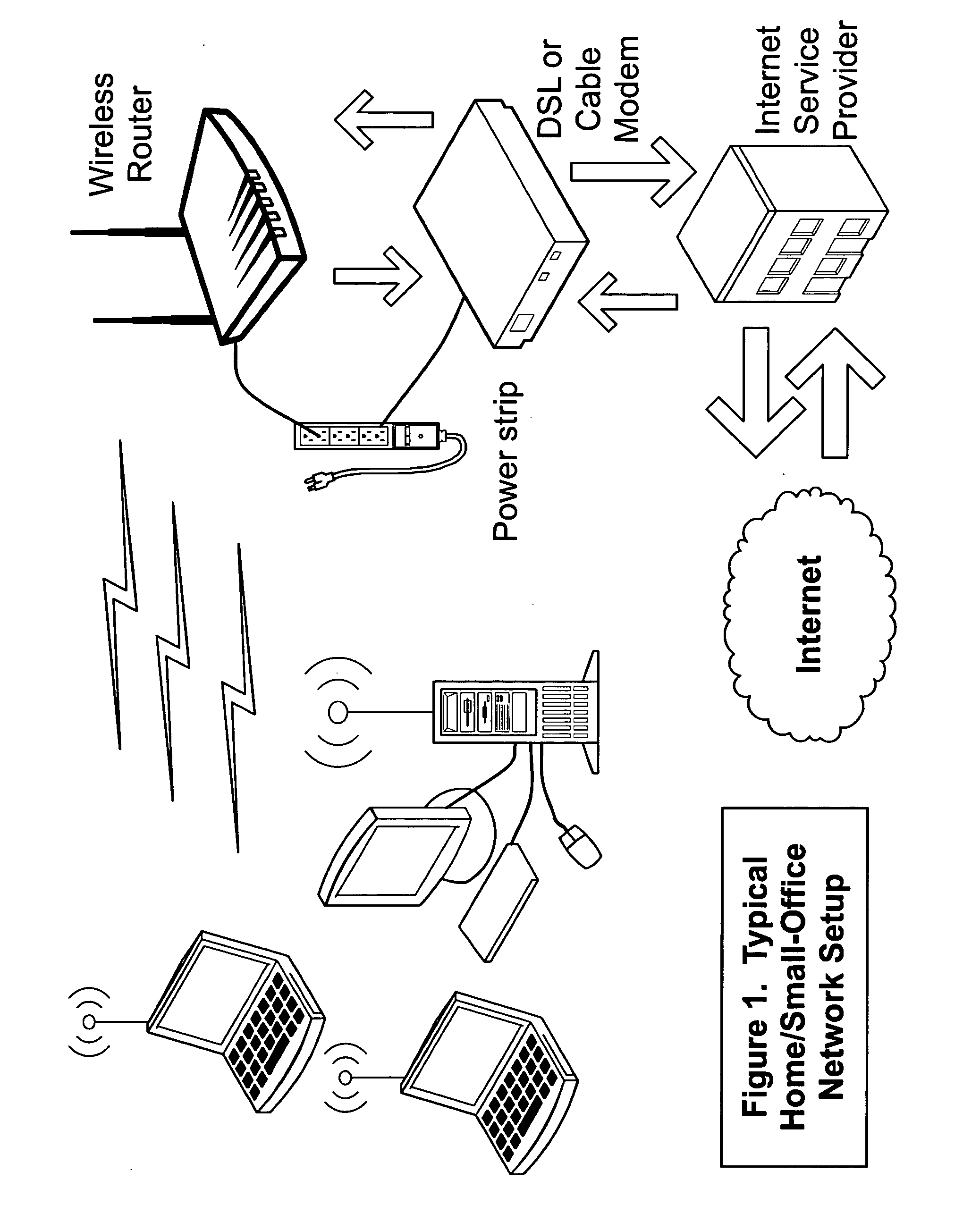
Systems, devices, agents and methods for monitoring and automatic reboot and restoration of computers, local area networks, wireless access points, modems and other hardware
ActiveUS20090013210A1Data switching networksRedundant operation error correctionDomain nameFully qualified domain name
An embodiment of the invention is a client on a local area network that periodically and automatically evaluates its physical connectivity with the local area network, exercises local-network services such as DHCP, and verifies Internet connectivity and function by pinging one or more numerically specified IP addresses and by pinging one or more IP addresses specified by an FQDN (Fully Qualified Domain Name) known to the assigned DNS servers. An embodiment of the invention may include a plurality of client elements monitoring one or more networks. Functionality according to embodiments of the invention can send notices, automatically initiate action, and otherwise assist in, among other things, remote monitoring and administration of networks, and particularly wireless networks.
Owner:SAND HLDG LLC
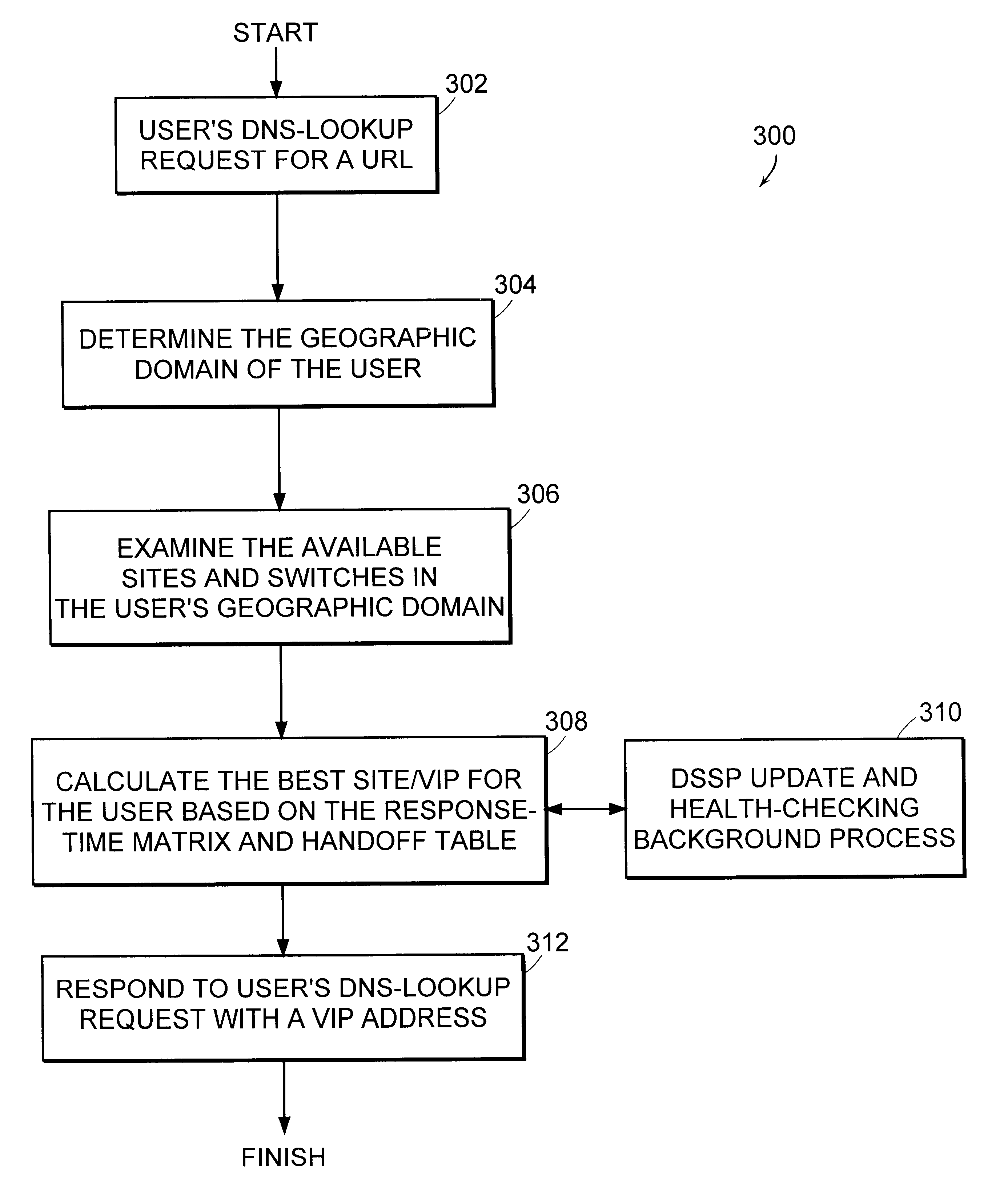
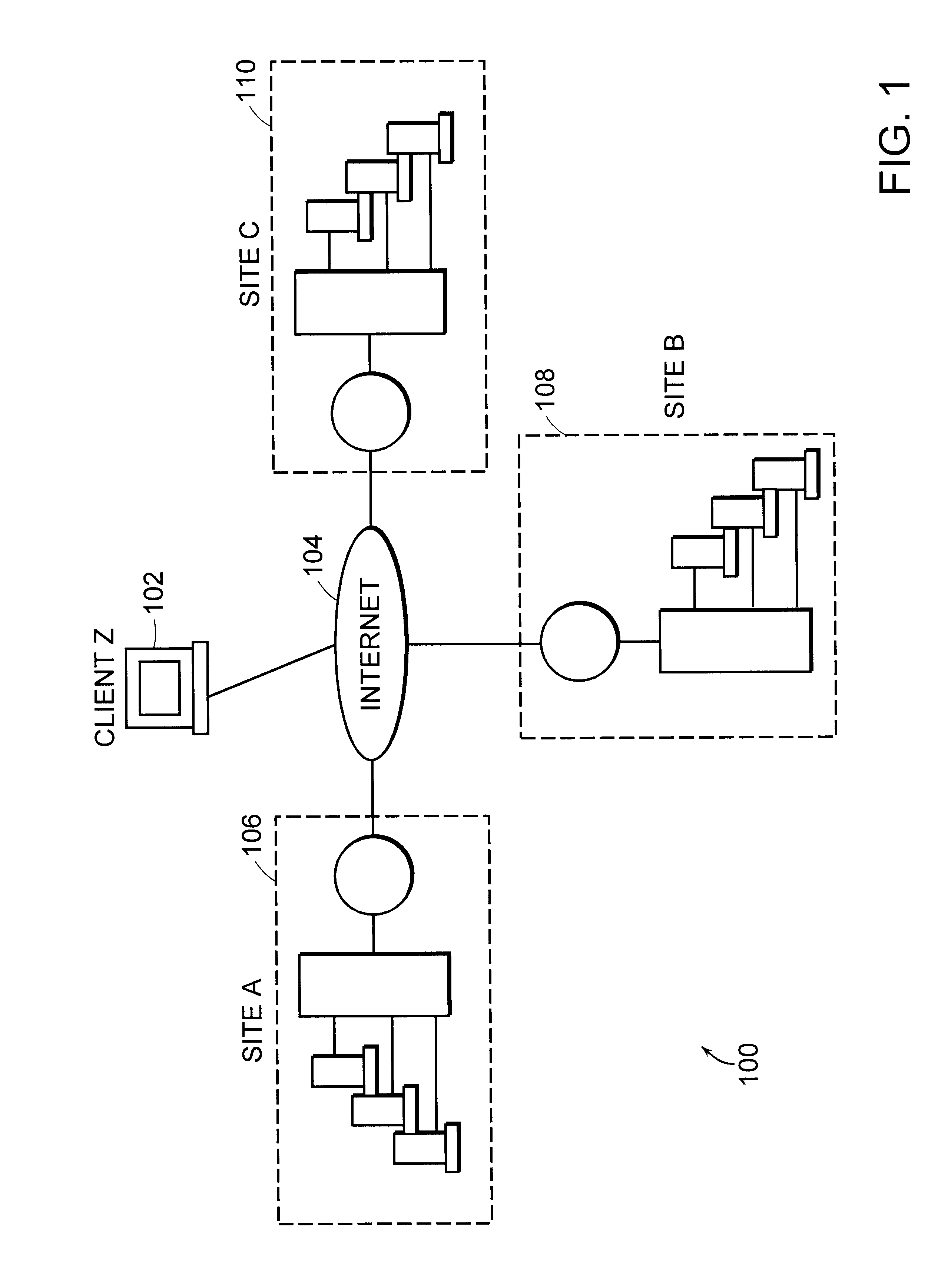
Distributed load-balancing internet servers
The actual site that serves the Web pages to a client in response to a URL domain name is automatically and transparently selected from a list of many switches each having identical data storage. In a peer hand-off process, a switch receives domain name server lookup request for a particular virtual Internet protocol (VIP) domain name. The switch examines the source IP-address for the domain name server request, examines the user's IP-address, and determines if there is server site that is geographically close to that user. The switch examines an ordered hand-off table corresponding to the domain. The switch chooses a next remote server (or its own VIP) in line based on, (a) the remote server location compared to domain name server request source, (b) the remote servers' weights, and (c) the remote server that experienced the previous hand-off. The switch then sends the domain name server response back to client domain name server with the IP-addresses in an ordered list.
Owner:RADWARE
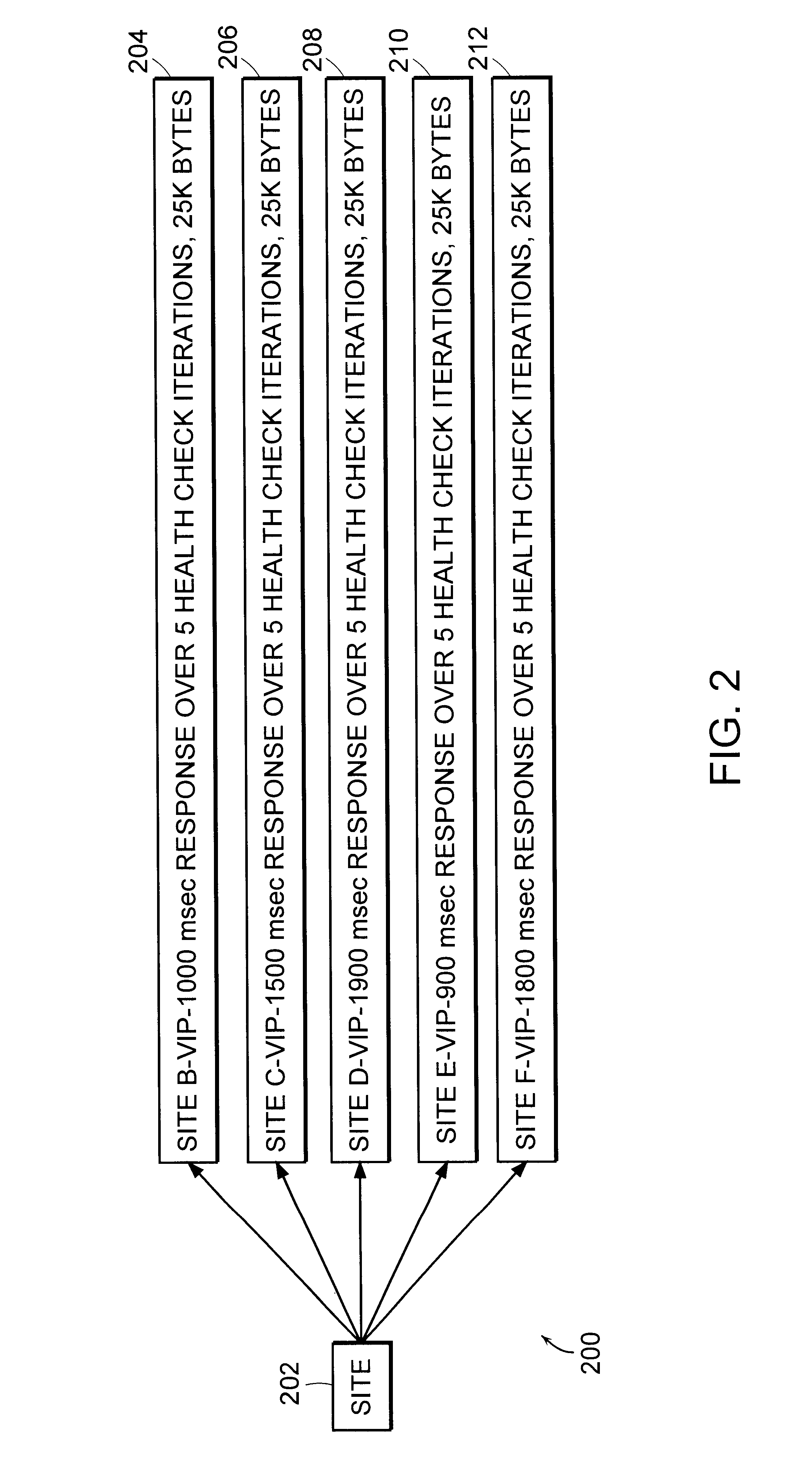
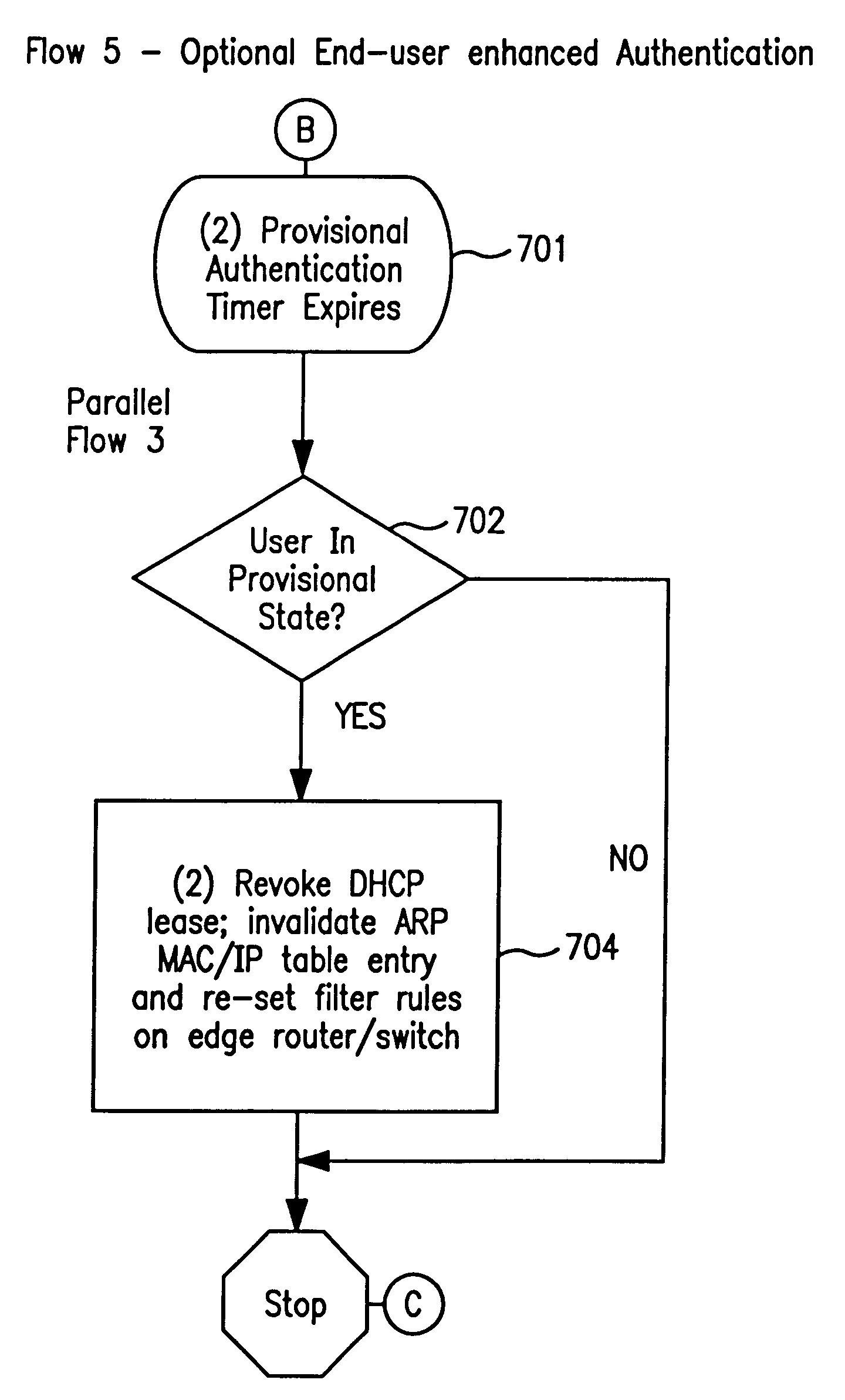
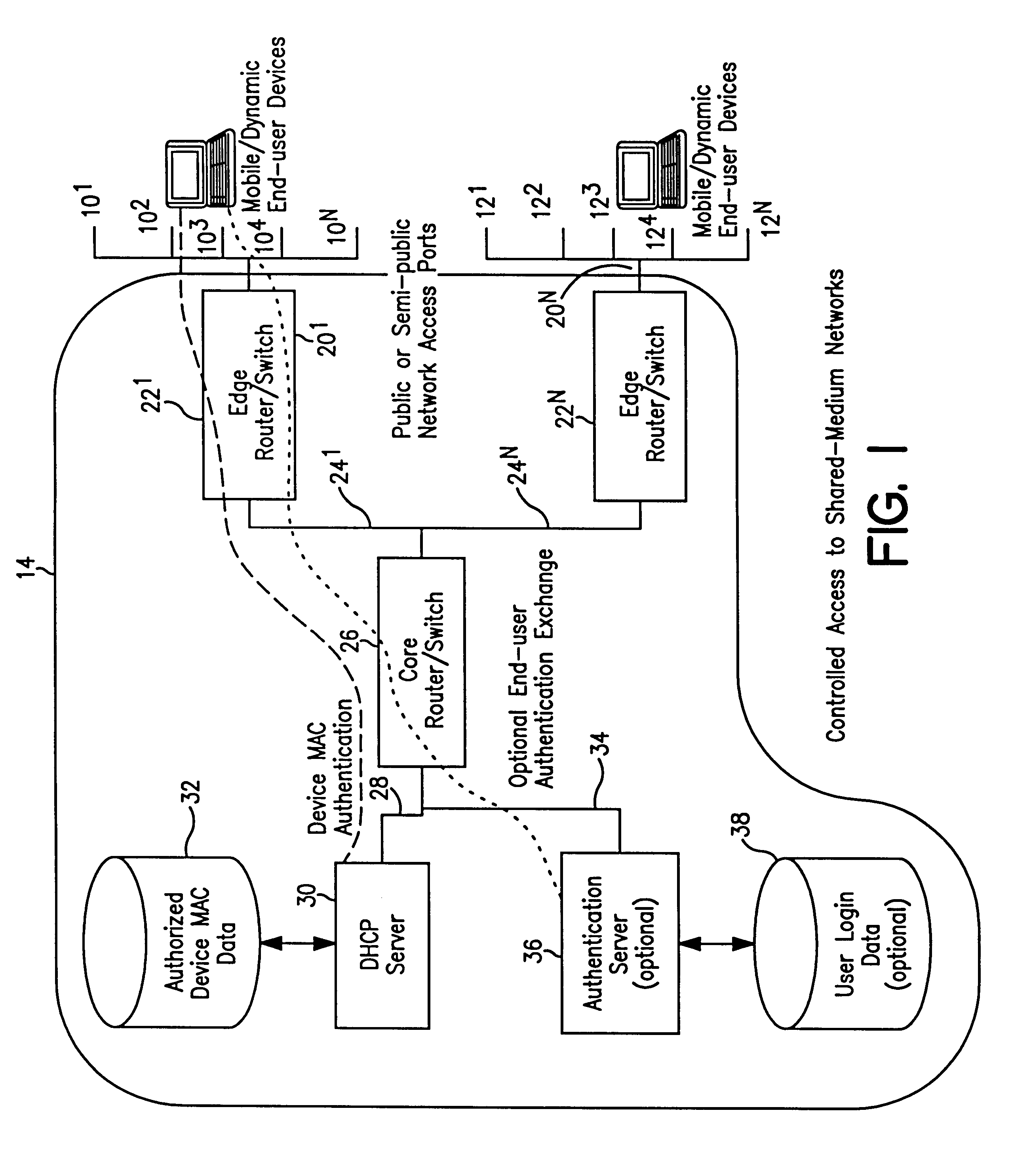
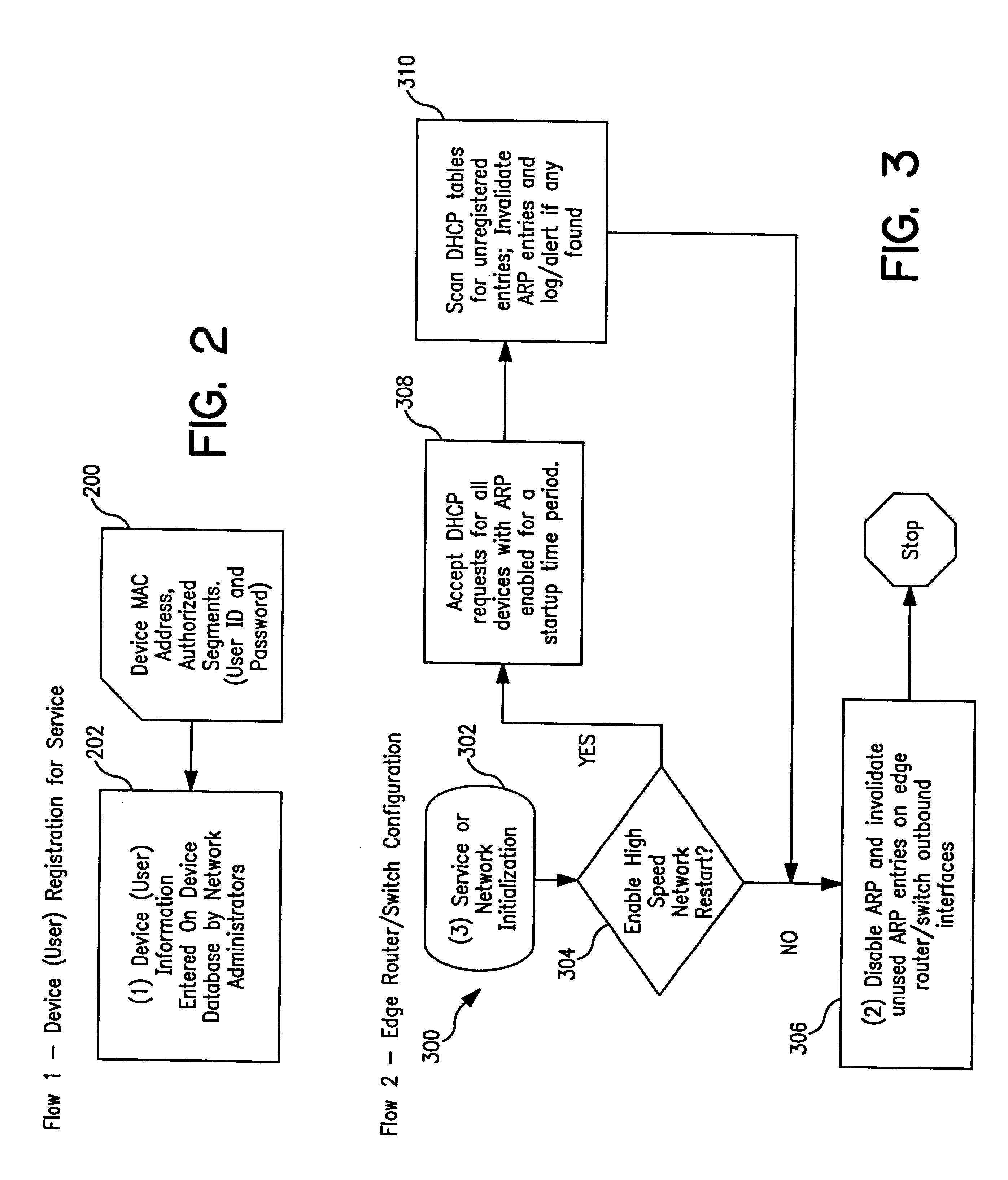
System and method for controlled access to shared-medium public and semi-public internet protocol (IP) networks
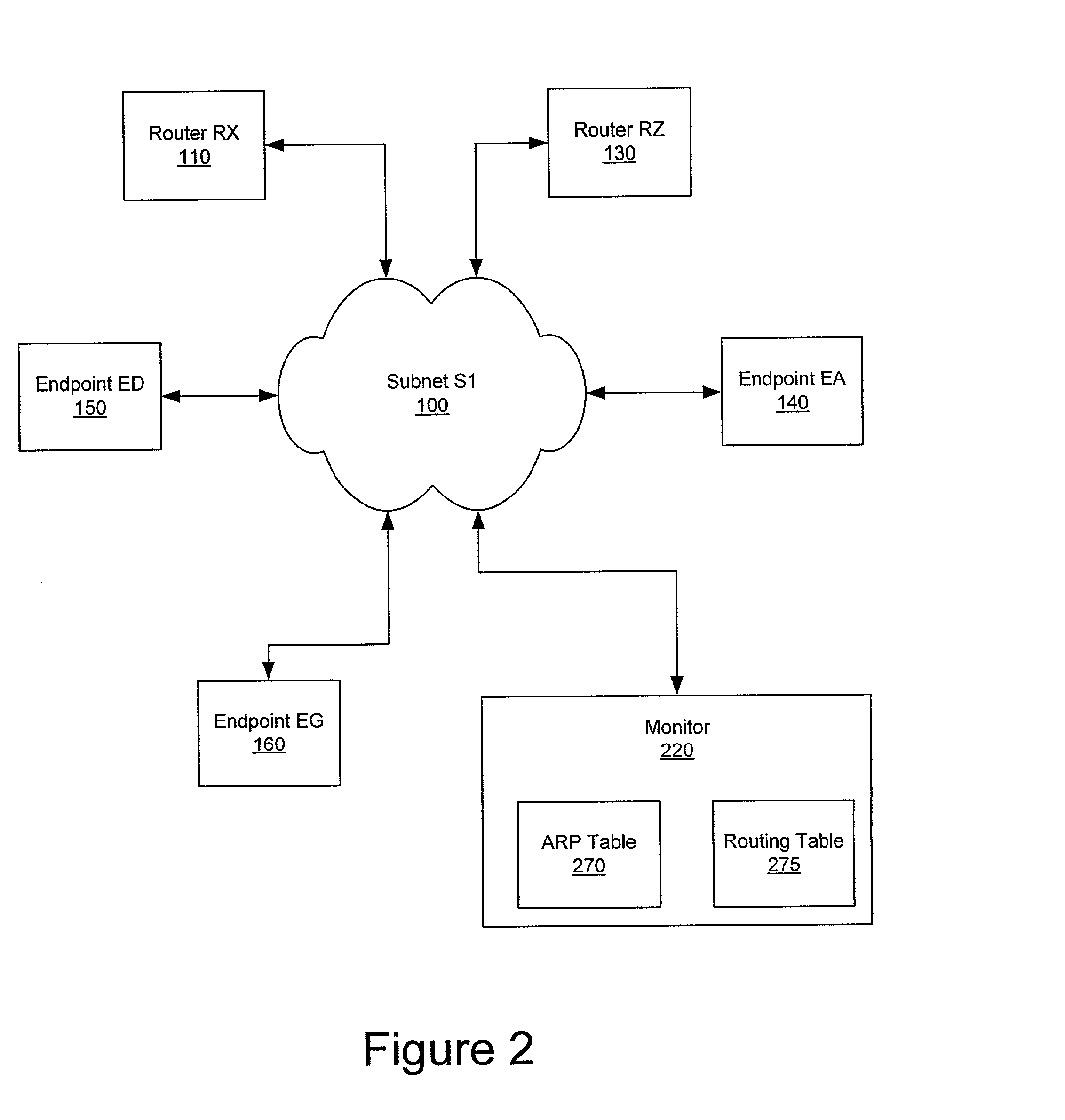
InactiveUS6393484B1Multiple digital computer combinationsTransmissionAddress Resolution ProtocolDevice register
A system and method prevent unauthorized users and devices, in a dynamic user / device environment, from obtaining access to shared-medium public and semi-public IP networks. A network includes a layered communication system and routers / switches for coupling users and devices to a Dynamic Host Control Protocol (DHCP) server and an authentication server. Databases support the servers. The network incorporates Address Resolution Protocol (ARP). Authorized users and devices register for service by providing the DHCP with user identification for log-in, passwords, MAC addresses, etc. When users connect to the network access point, a DHCP exchange is initiated to obtain a valid IP address and other associated parameters. The DHCP client initiates a MAC broadcast for IP addresses which contain in the request the end user's device MAC address. The associated router switch will pick up and forward to a DHCP server the end user's device request. The DHCP server will process the end user's request and extract the end user's device MAC address. With the end user's MAC address, the DHCP server accesses its device and / or user information in the database. If the MAC address is not registered, the DHCP server refuses to handle the request and logs the attempt, potentially alerting network operators of a security breach. If the MAC address is registered, a DHCP server selects an appropriate IP address and associated parameters to be returned to the requesting end user and connects via programming or command interface to the router switch that is forwarding the DHCP request on behalf of the end user device. The server adds an ARP IP to the MAC address table entry with the selected IP address and end user's MAC address. End user device authentication and IP lease are marked as provisional. A timer is started for a suggested duration. Optionally, the DHCP dynamically sets up filter rules in the router switch limiting access to a subset of IP addresses such as the address of a log-in server. Initial DHCP processing is completed and an IP address is assigned to the requesting end user's device by DHCP. When the timer expires, if the DHCP server finds the authenticating user state is provisional, it will revoke the IP lease, invalidate the corresponding ARP to MAC table entry in the associated router switch, and reset any IP-permissive filtering for that device. If the user is in the full authenticated state, it will simply remove the restrictive filtering.
Owner:IBM CORP
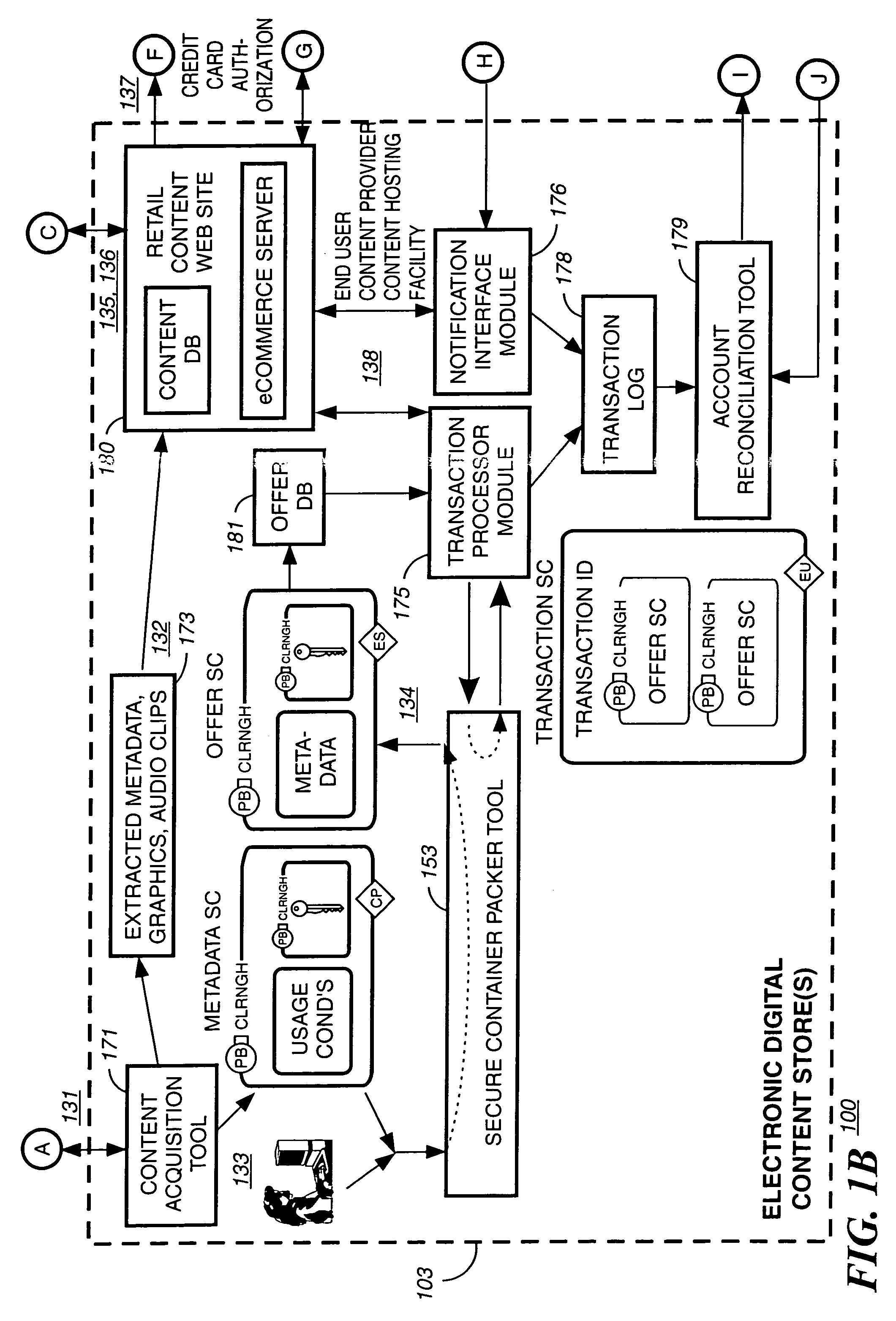
Method and system for delivering encrypted content with associated geographical-based advertisements
A method, a system and computer readable medium at an electronic digital content store, such as a web site, for associating advertisement with digital content. The geographic location of the end user device receiving the encrypted digital content is determined using an address verification system. Advertisement is selected to be associated with the delivery of encrypted digital content if the address verification system returns an address in a predetermined geographic region. The address verification system includes the IP address of the end user device, the country codes found in the trace routes to the IP address, and the billing address.
Owner:LEVEL 3 COMM LLC
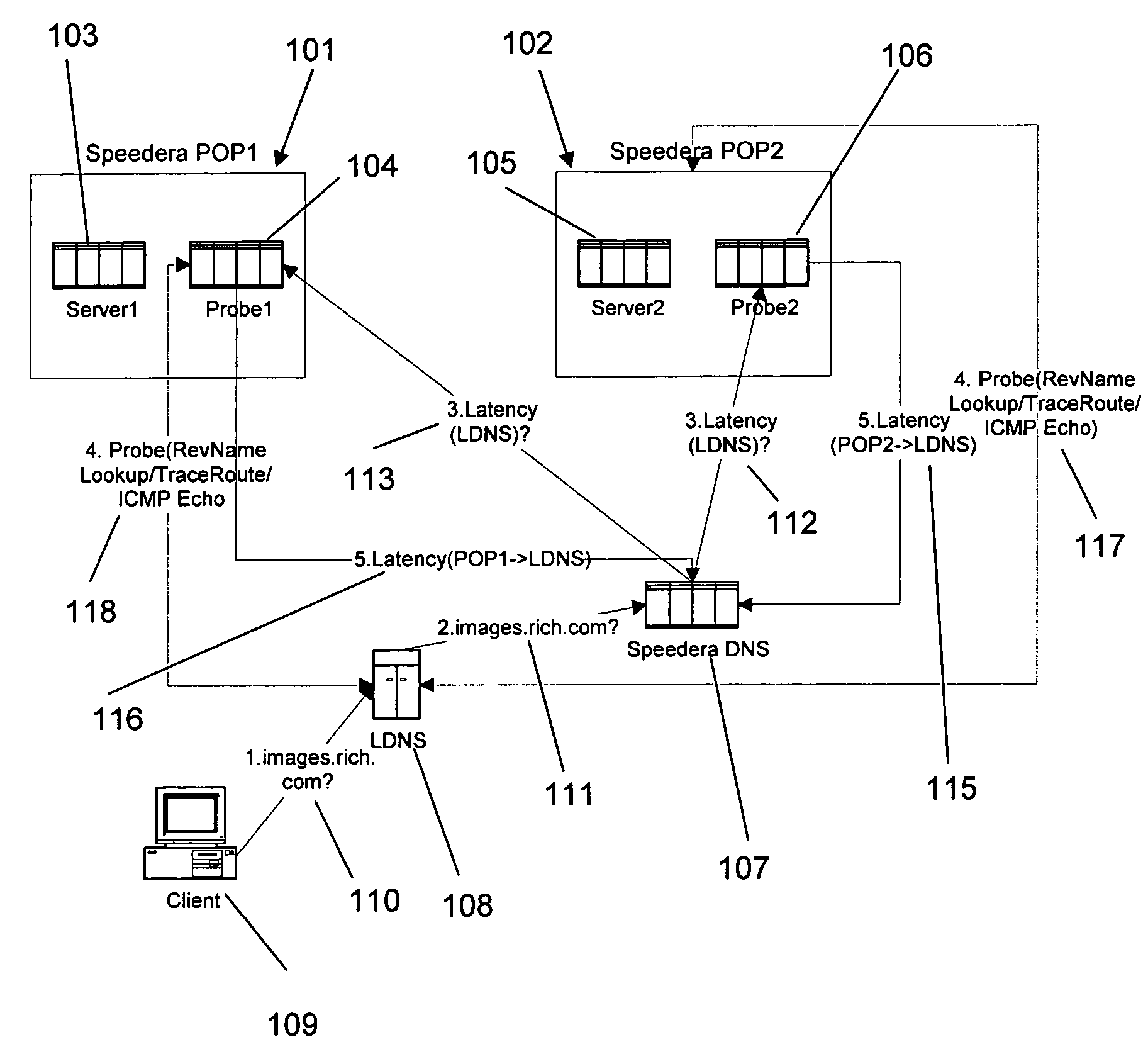
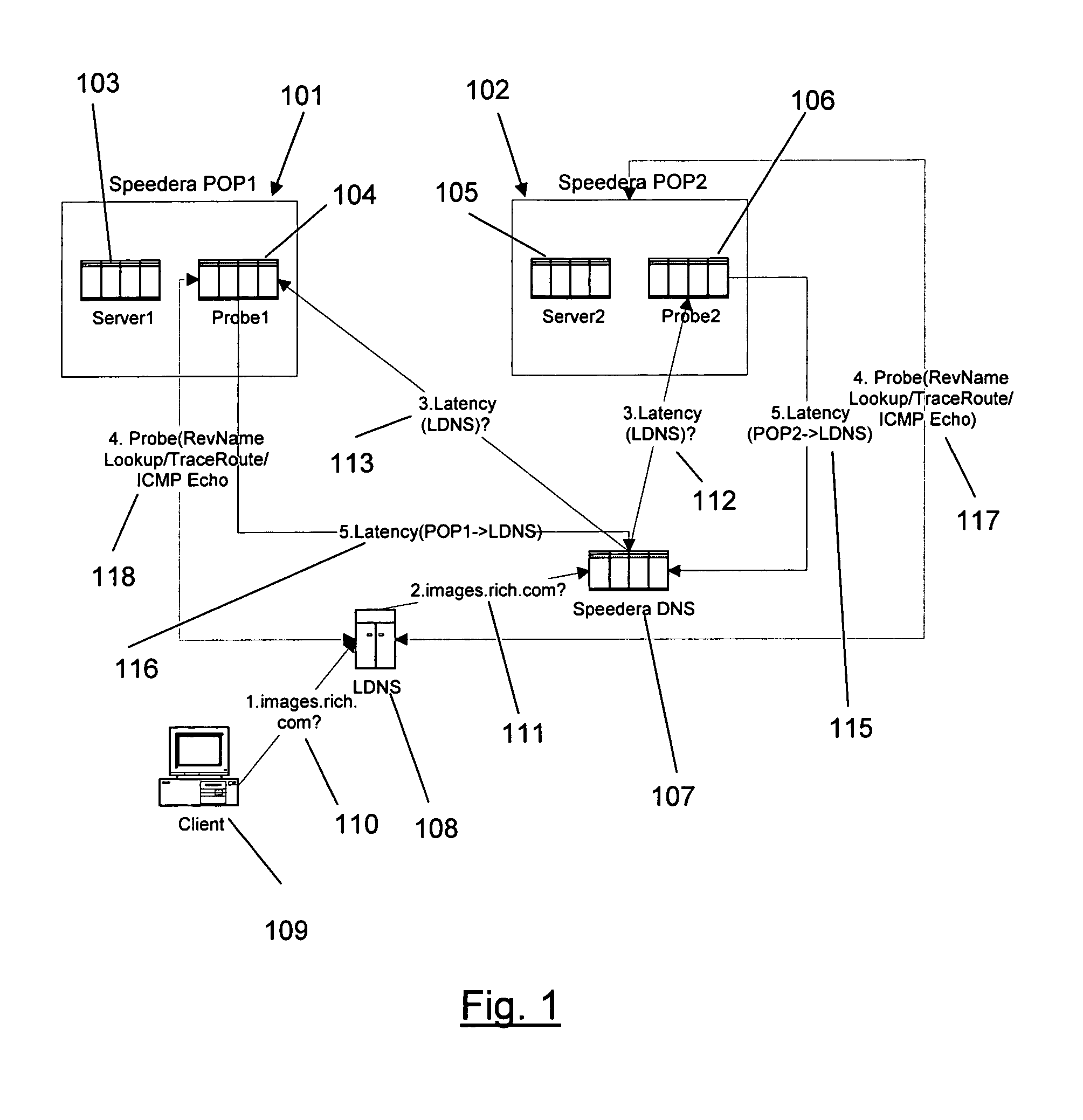
Method and apparatus for determining latency between multiple servers and a client
InactiveUS7058706B1Reduce network trafficAccurately determineDigital computer detailsData switching networksTraffic capacityName server
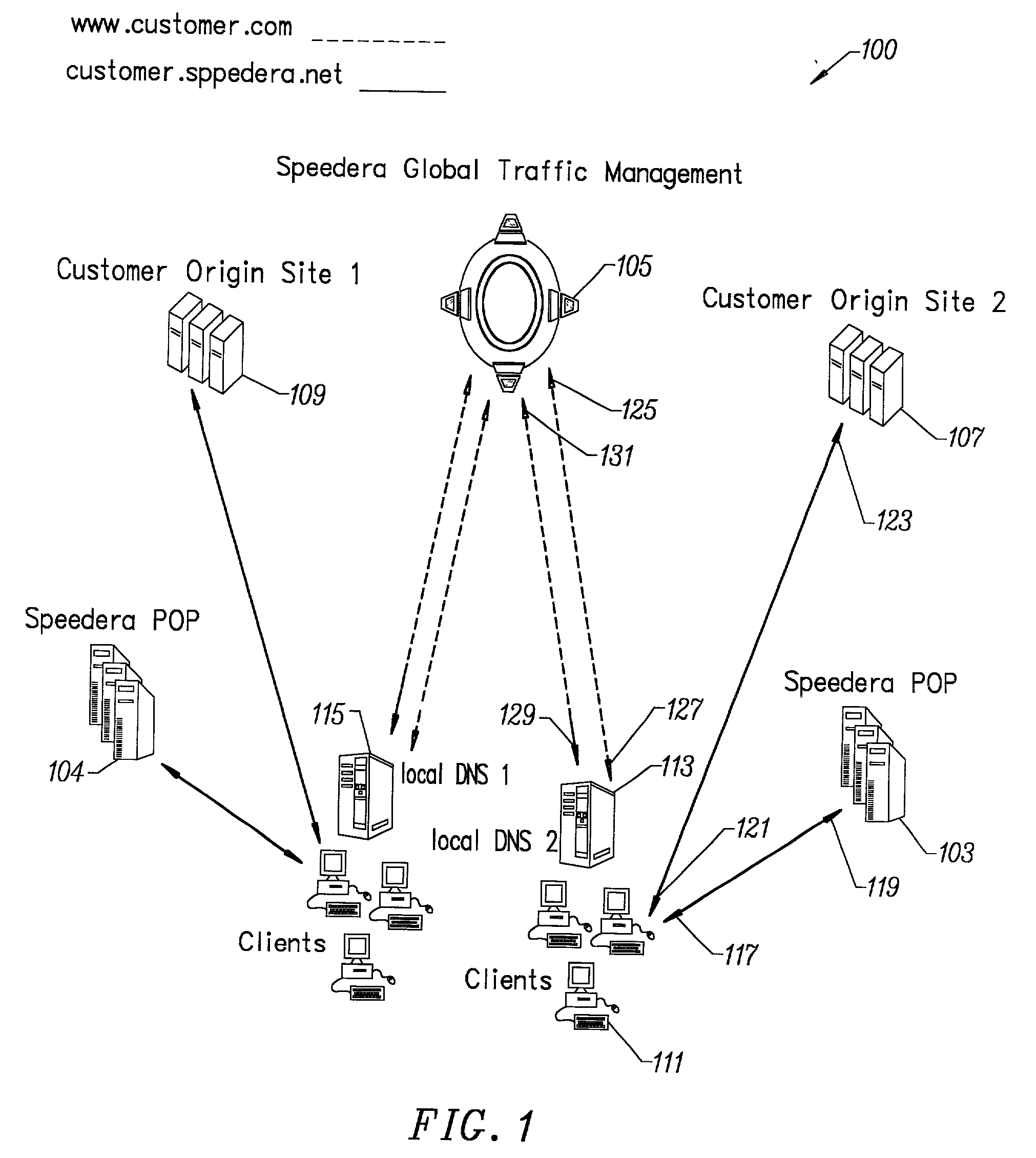
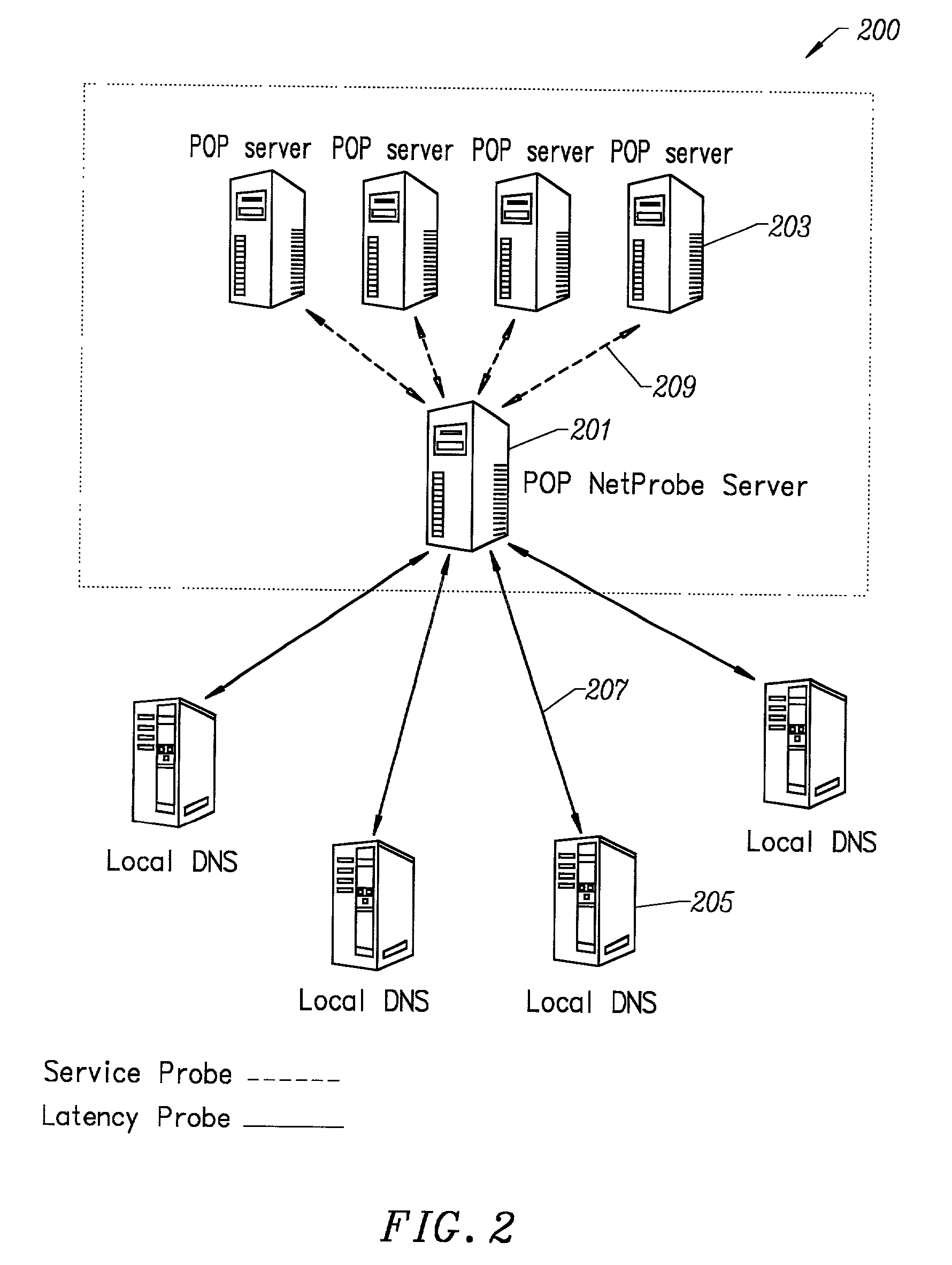
A method and apparatus for determining latency between multiple servers and a client receives requests for content server addresses from local domain names servers (LDNS). POPs that can serve the content are determined and sent latency metric requests. The content server receives the request for latency metrics and looks up the latency metric for the requesting client. Periodic latency probes are sent to the IP addresses in a Latency Management Table. The IP addresses of clients are masked so the latency probes are sent to higher level servers to reduce traffic across the network. The hop count and latency data in the packets sent in response to the latency probes are stored in the Latency Management Table and is used to determine the latency metric from the resident POP to the requesting client before sending the latency metric to the requesting server. The BGP hop count in the Latency Management Table is used for the latency metric upon the first request for an IP address. The latency metric is calculated for subsequent requests of IP addresses using the hop count and RTT data in the Latency Management Table. Latency metrics from POPs are collected and the inverse relationship of the hop counts in a weighted combination with the RTT are used to determine which latency metric indicates the optimal POP. The address of the optimal POP is then sent to the requesting LDNS.
Owner:AKAMAI TECH INC
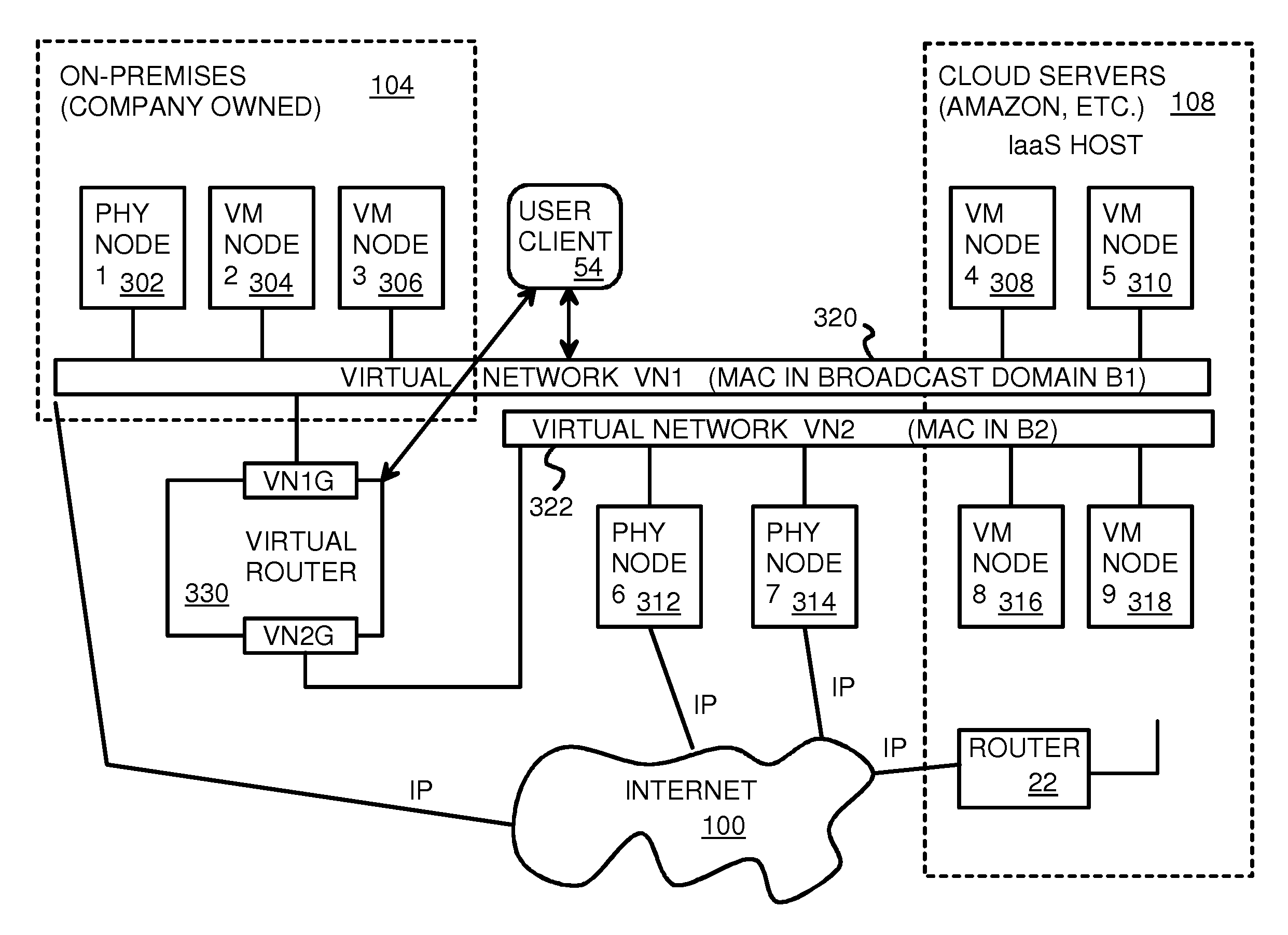
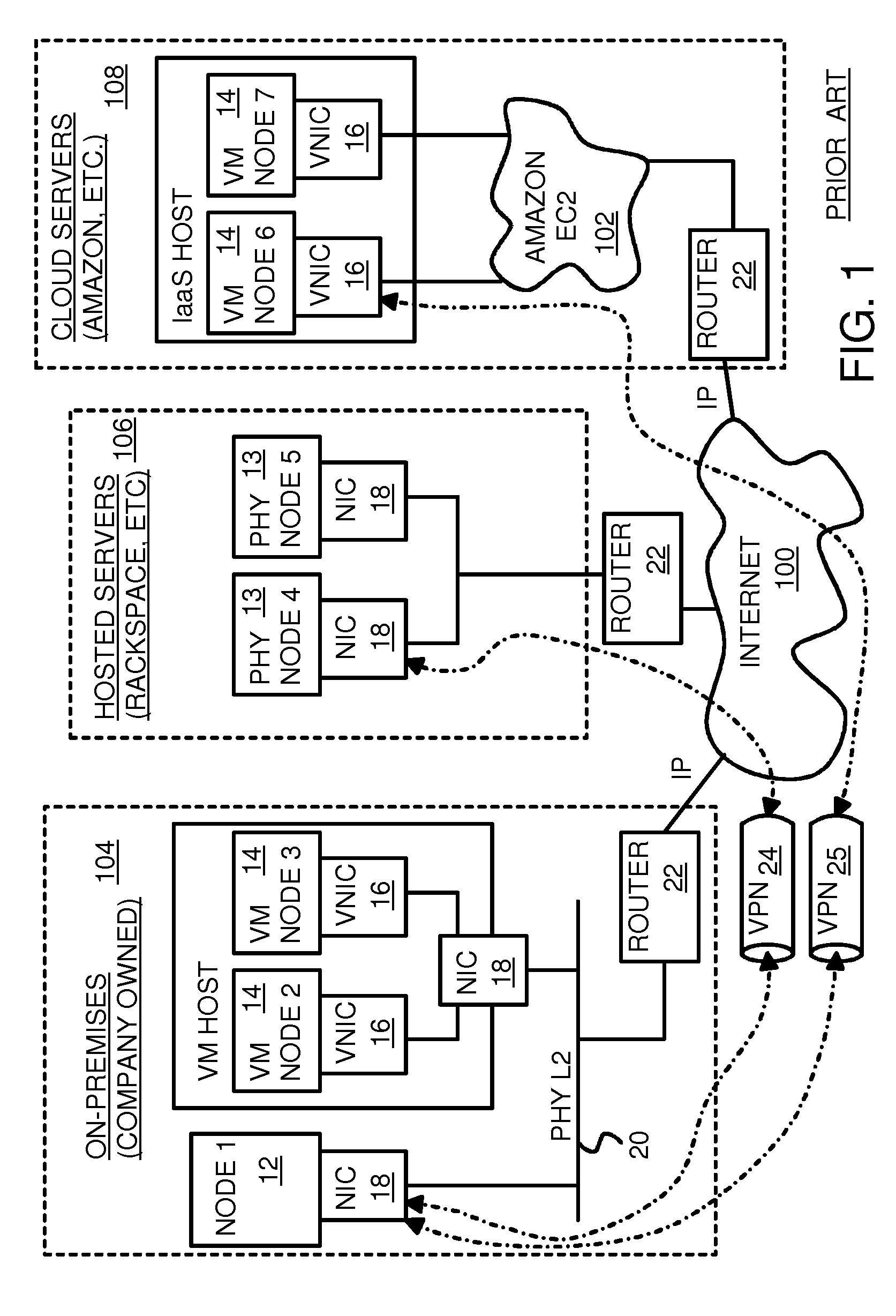
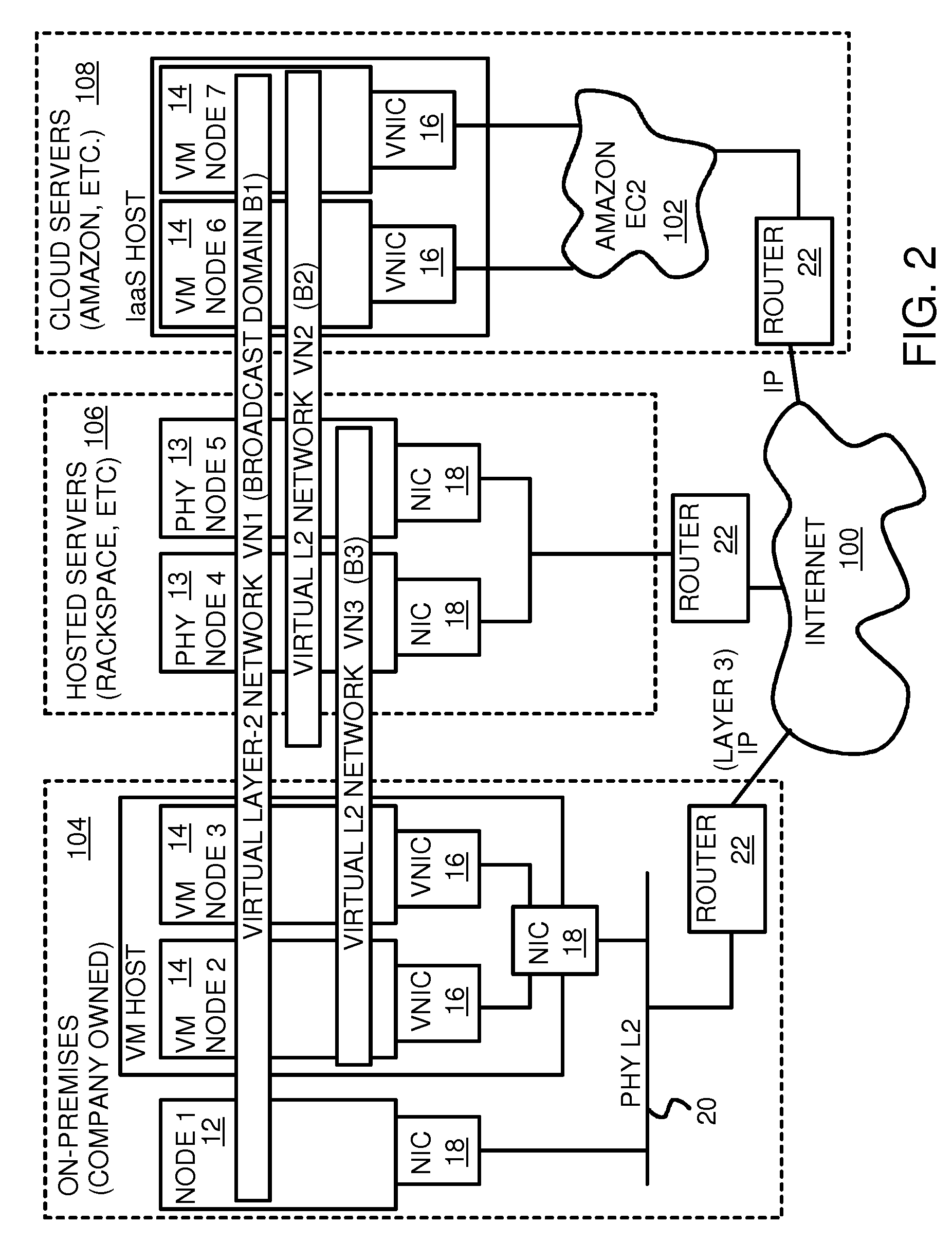
Fully distributed routing over a user-configured on-demand virtual network for infrastructure-as-a-service (IaaS) on hybrid cloud networks
A layer-3 virtual router connects two or more virtual networks. Virtual networks are overlaid upon physical networks. Each virtual network (VN) is a layer-2 network that appears to expand an organization's LAN using virtual MAC addresses. The network stack forms a virtual-network packet with a virtual gateway MAC address of the virtual router to reach a remote virtual network. A VN device driver shim intercepts packets and their virtual MAC and IP addresses and encapsulates them with physical packets sent over the Internet. A VN switch table is expanded to include entries for nodes on the remote virtual network so that all nodes on both virtual networks are accessible. A copy of the VN switch table is stored on each node by a virtual network management daemon on the node. A Time-To-Live field in the virtual-network packet is decremented for each virtual hop and a checksum recalculated.
Owner:CISCO TECH INC
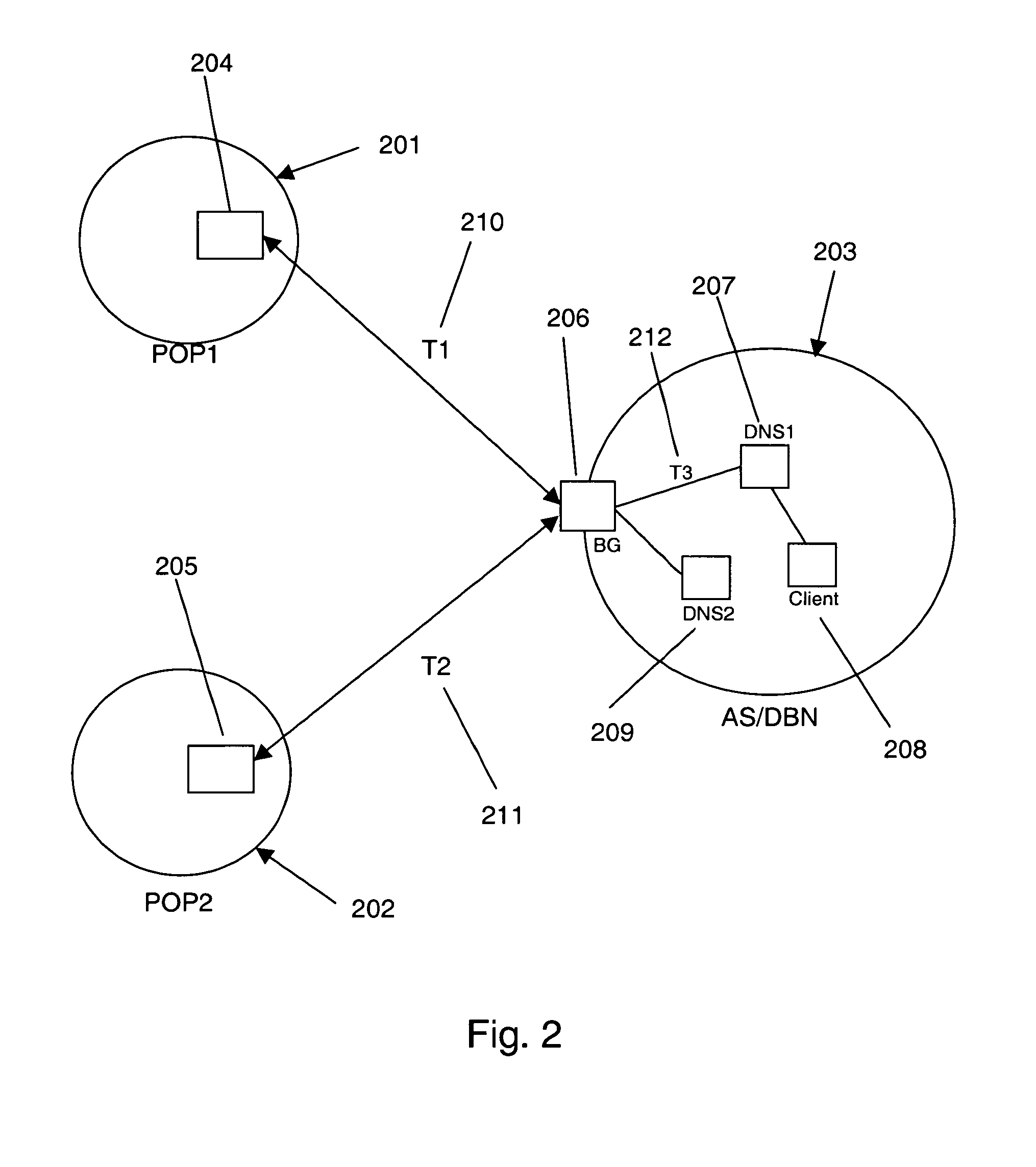
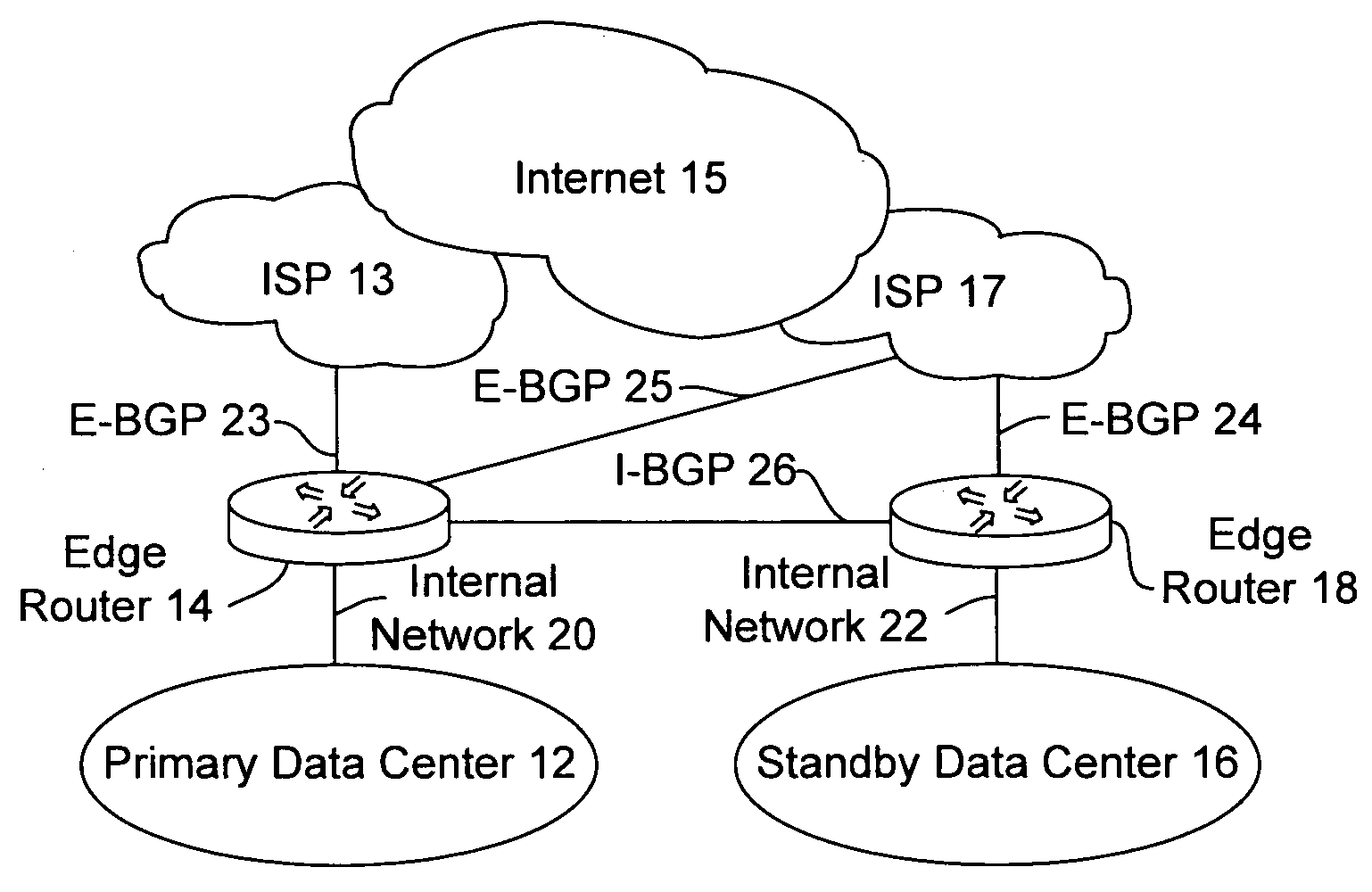
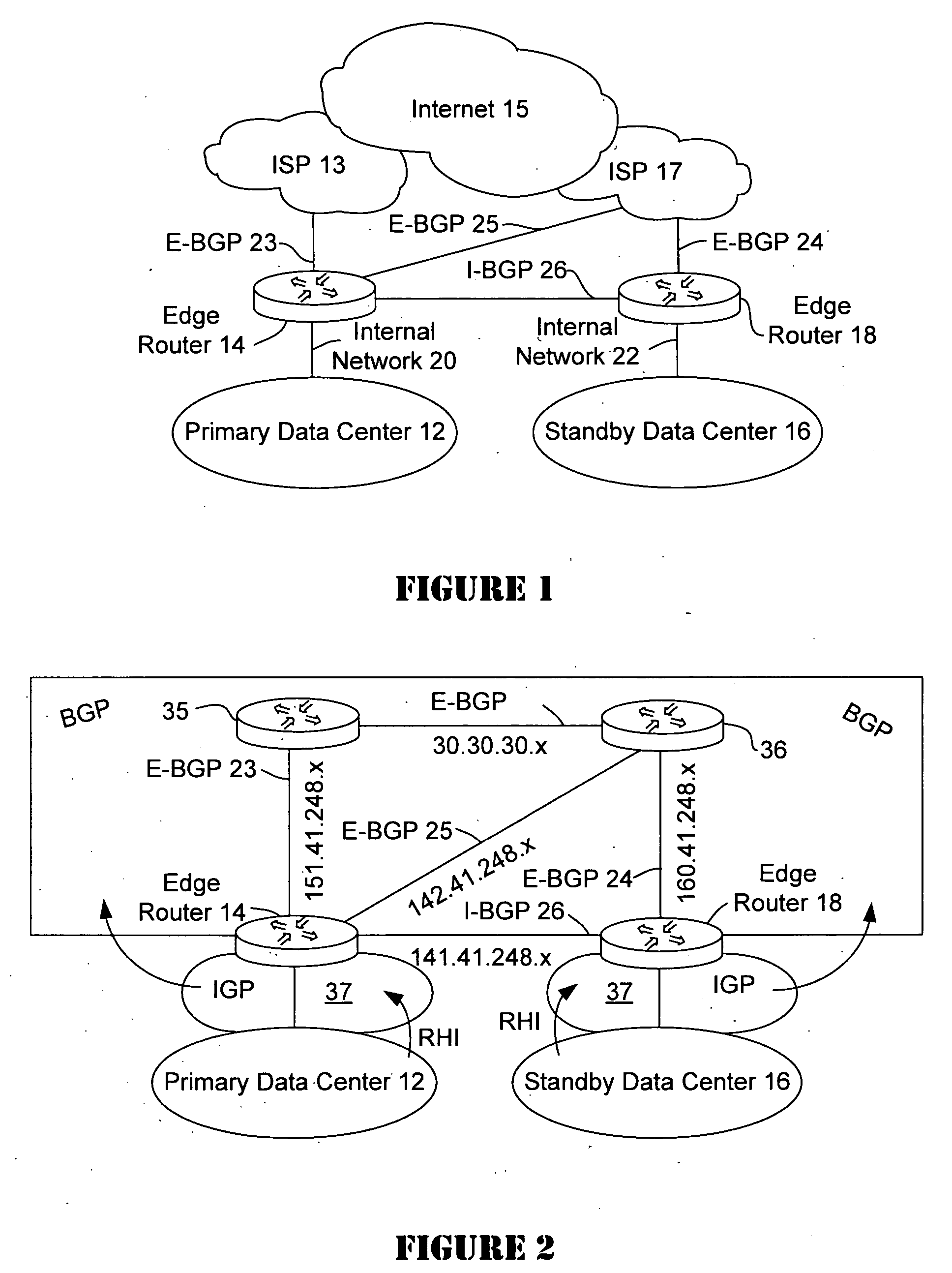
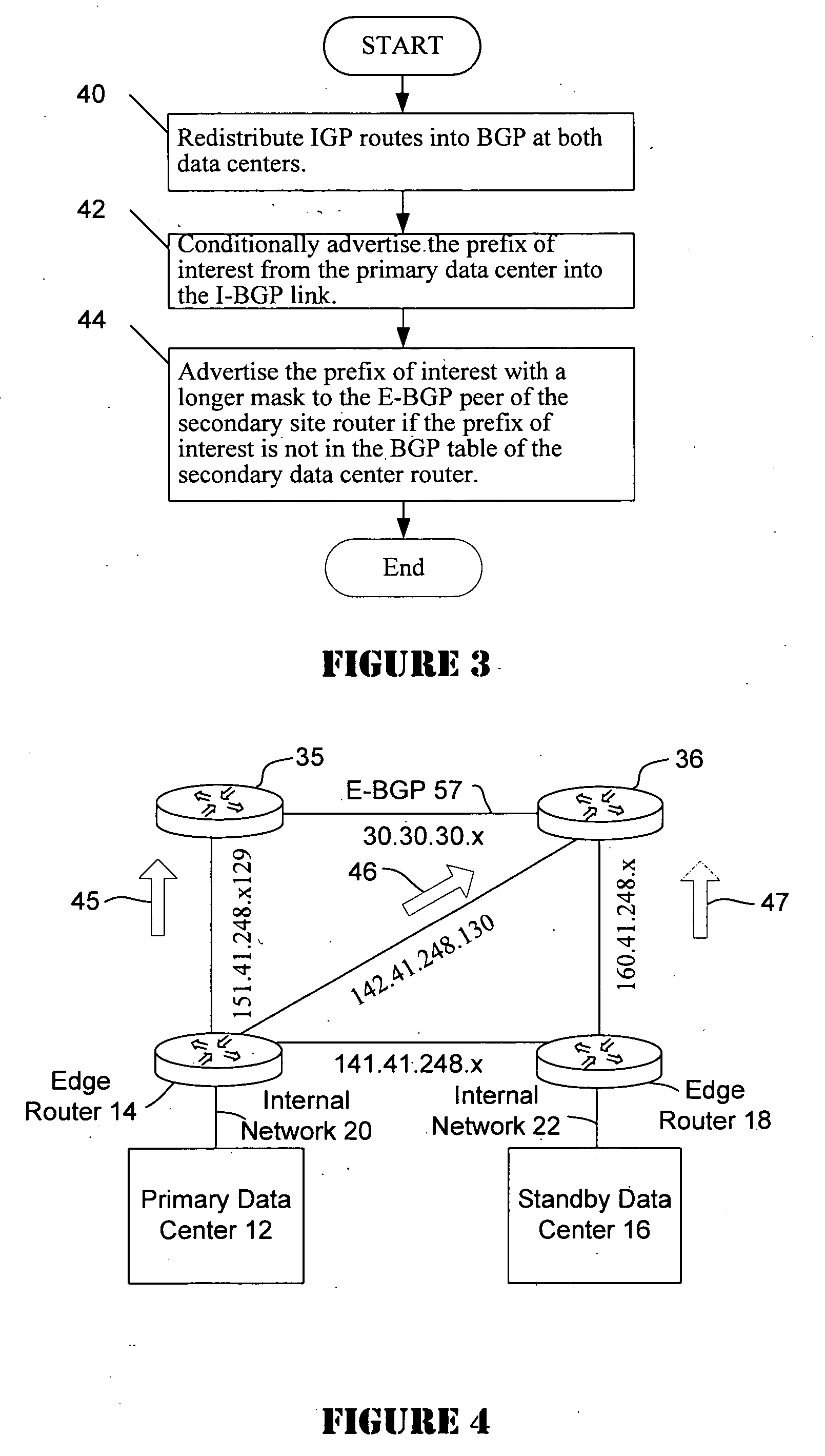
Disaster recovery for active-standby data center using route health and BGP
The present invention provides an active / standby data center that avoids the delay associated with a cached DNS entry to switch from the active data center to the standby data center. When the active data center becomes unavailable, the standby data center advertises the same address as the primary data center so the change over occurs quickly. When the IP address of the primary data center is no longer visible to the standby data center, the standby data center begins to advertise.
Owner:CISCO TECH INC
Systems and methods for dynamic protection from electronic attacks
InactiveUS8726379B1Reduce security risksMemory loss protectionError detection/correctionIp addressComputer security
Systems and methods for gathering, classifying, and evaluating real time security intelligence data concerning security threats presented by an IP address, and reporting in real time the degree and character of such security threats.
Owner:NORSE NETWORKS INC
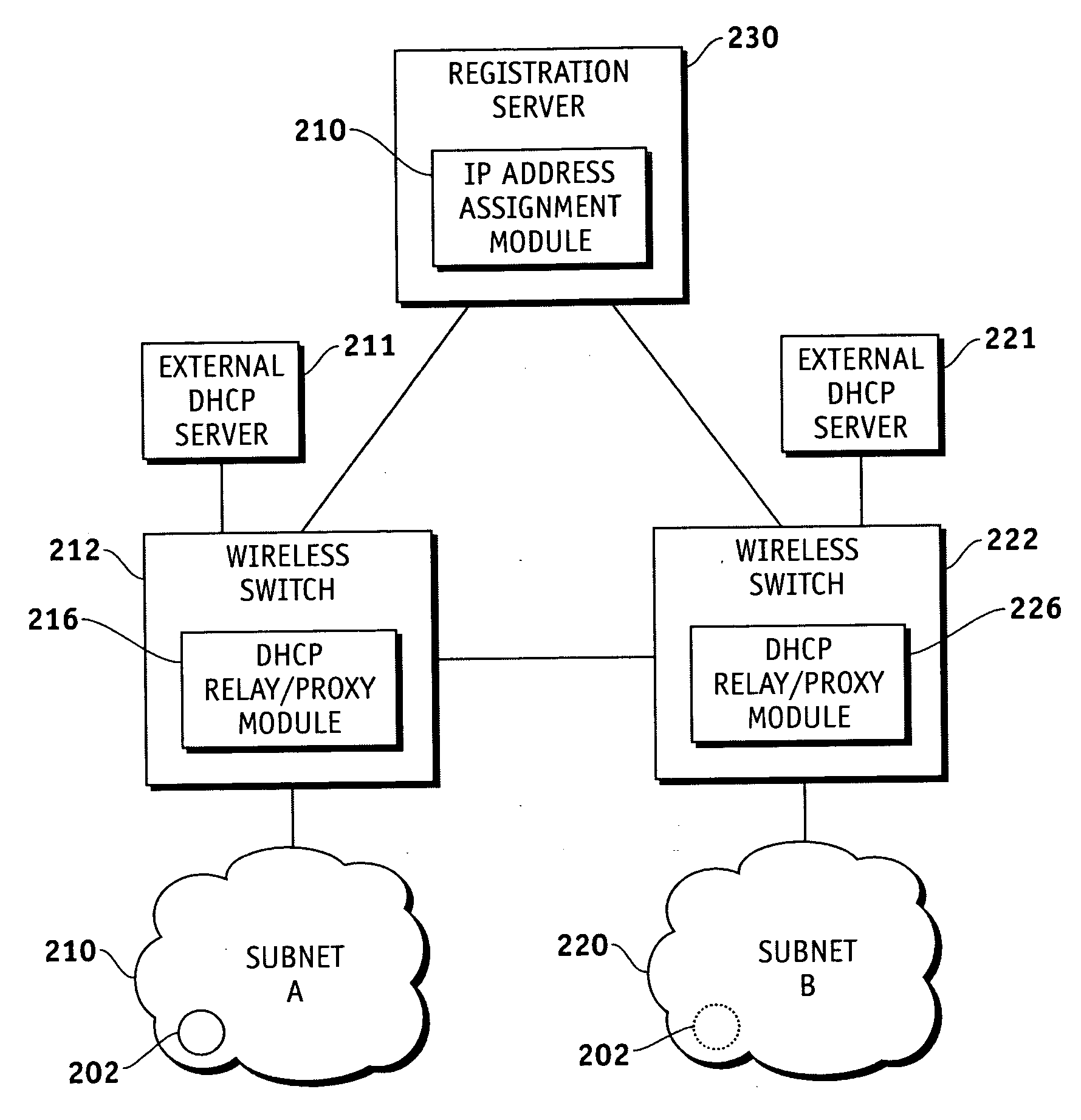
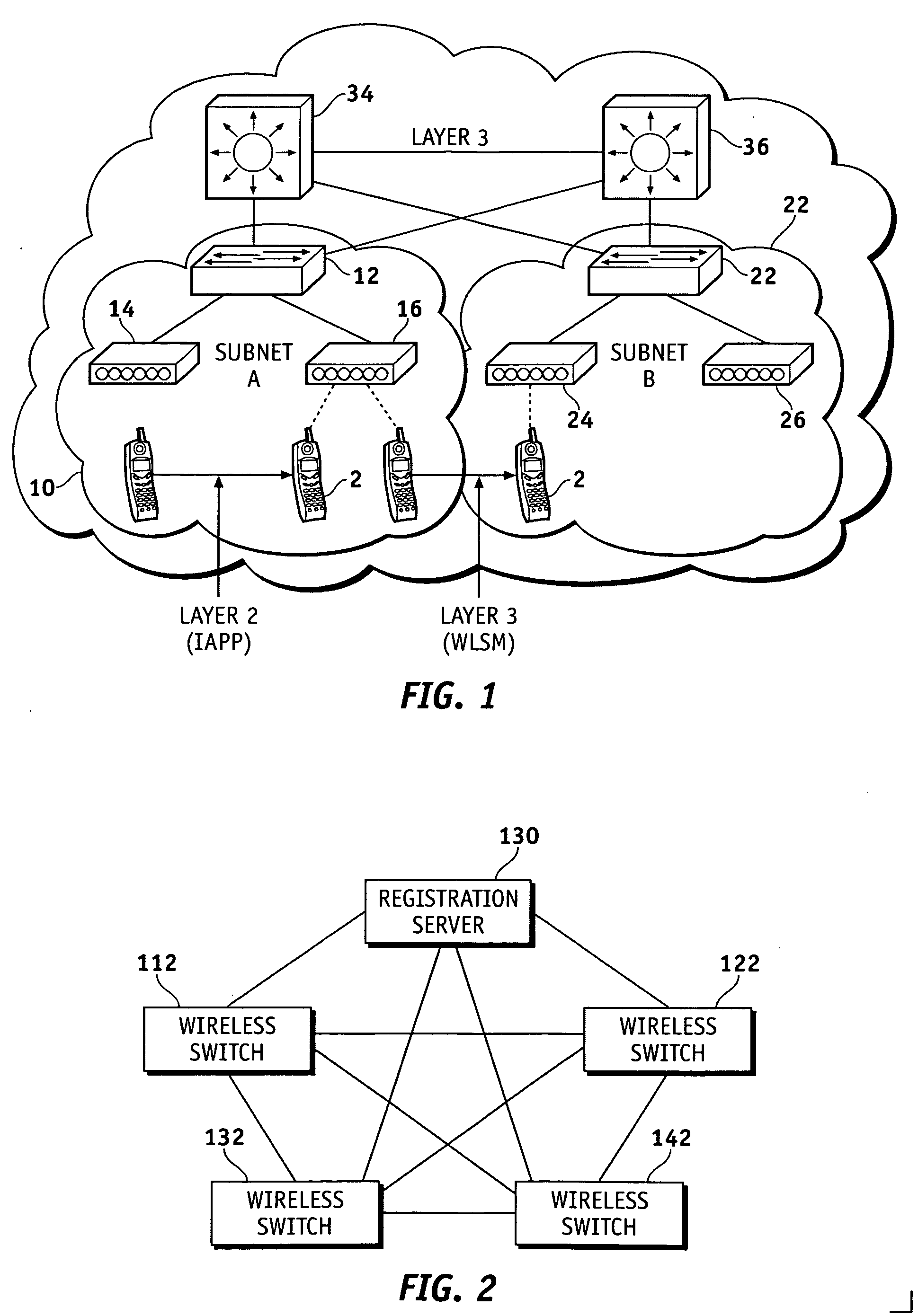
Method, system and apparatus for assigning and managing IP addresses for wireless clients in wireless local area networks (WLANs)
Techniques are provided IP address assignment and management in a wireless network. Such a wireless network can comprise a plurality of wireless clients, a registration server, a plurality of wireless switches each being configured to support a particular subnet. Each wireless client can generate a Dynamic Host Configuration Protocol (DHCP) request for an Internet Protocol (IP) address when the client either powers up in of moves to a new subnet, 802.11 authenticates and associates and 802.1x authenticates. The wireless switches can communicate with the registration server over an IP tunnel. For example, each wireless switch can receive the DHCP requests from wireless clients associated with the subnet of the wireless switch, and forward the DHCP requests to the registration server. The registration server can receive the forwarded DHCP requests, and assign IP addresses to the wireless clients based on the forwarded DHCP requests.
Owner:SYMBOL TECH INC
Method and system for balancing load distribution on a wide area network
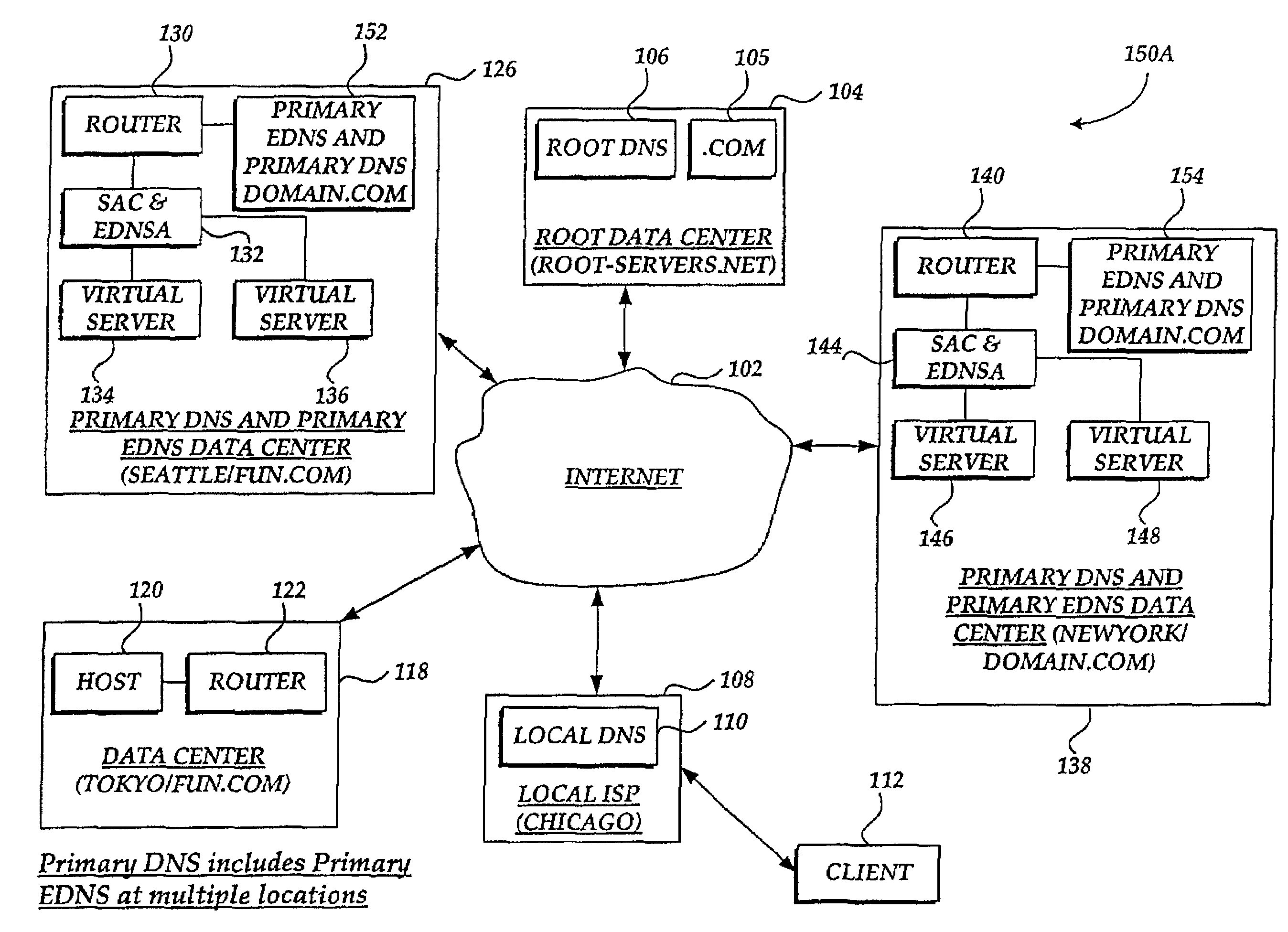
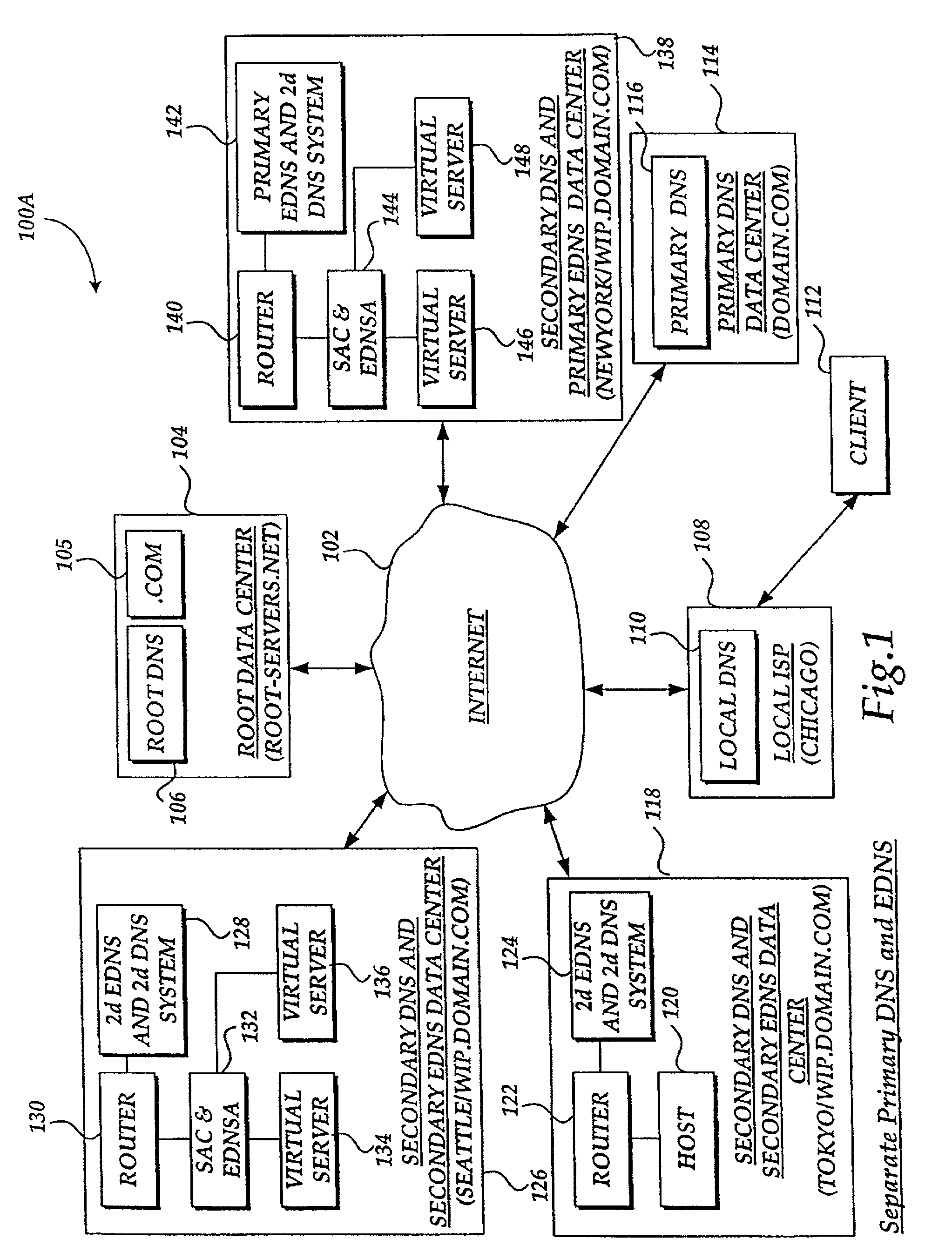
InactiveUS7441045B2Close contactResource allocationMultiple digital computer combinationsDomain nameIp address
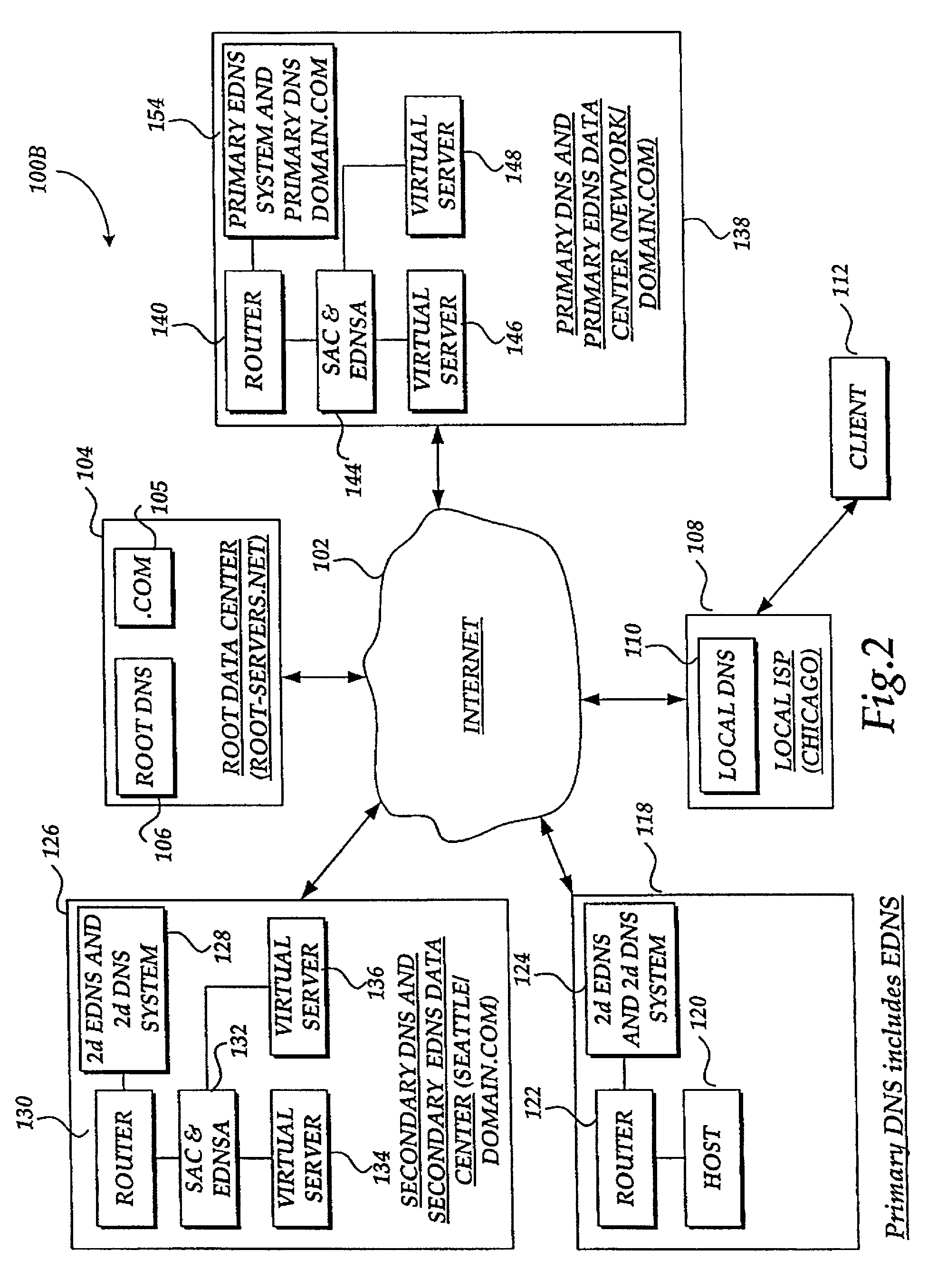
A system and method for balancing the load on virtual servers managed by server array controllers at separate data centers that are geographically distributed on a wide area network such as the Internet is described. The virtual servers provide access to resources associated with a domain name request by a client program. When a Primary Domain Name System (DNS) determined the requested domain name is delegated to a EDNS, the EDNS employs metric information and statistics to resolve an IP address for a virtual server that is selected by the EDNS to optimally balance the load and provide access to resources associated with the domain name. The EDNS may load balance name servers. Additionally, the name server load balancing system may bridge disparate content delivery networks. Internet addresses are divided into geographical information that is used to delegate traffic. Also, metric information is collected and analyzed to help distribute the traffic.
Owner:F5 NETWORKS INC
Content delivery and global traffic management network system
InactiveUS20020052942A1Meet cutting requirementsReduce trafficMetering/charging/biilling arrangementsError preventionWeb serviceCache server
Owner:AKAMAI TECH INC
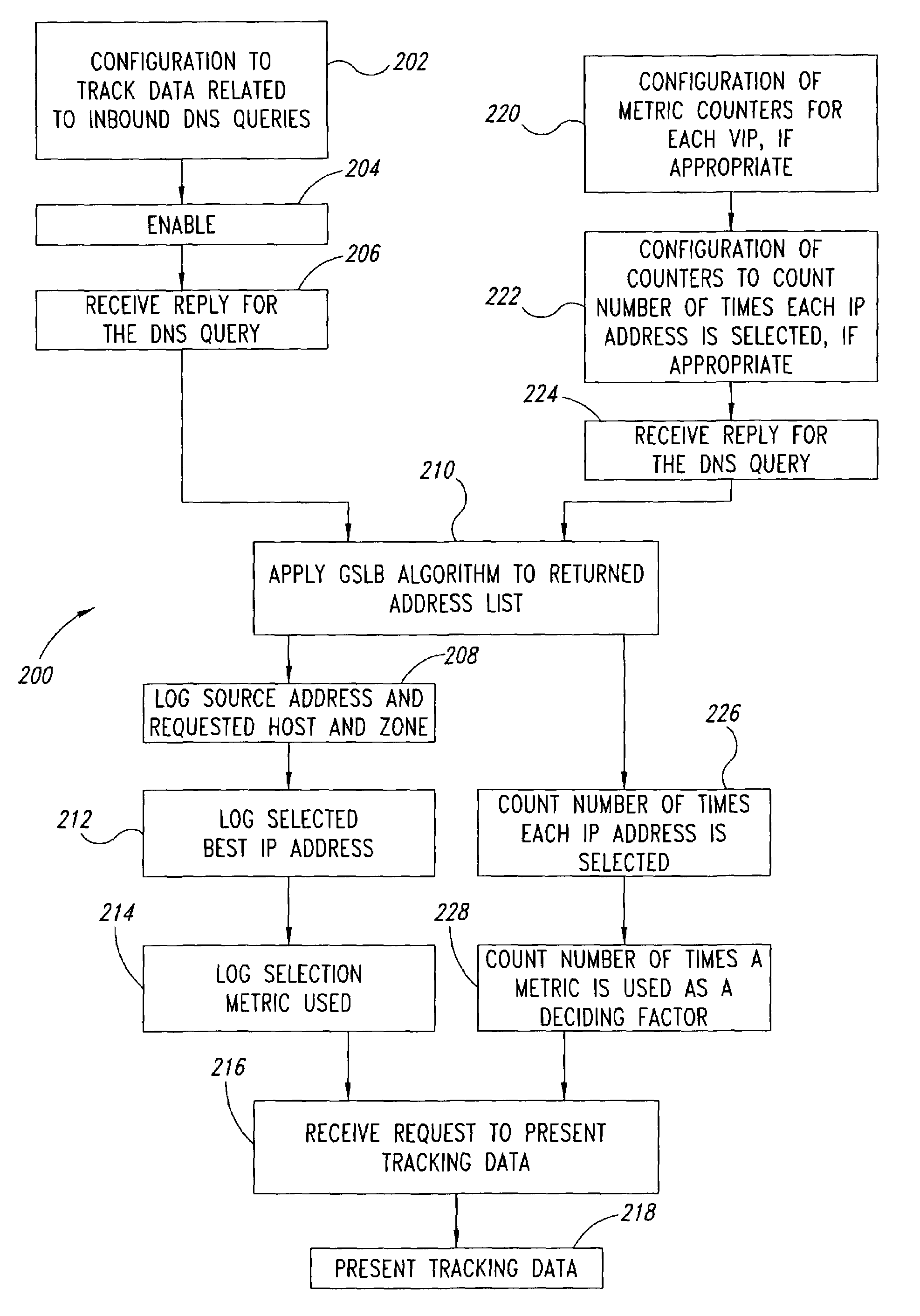
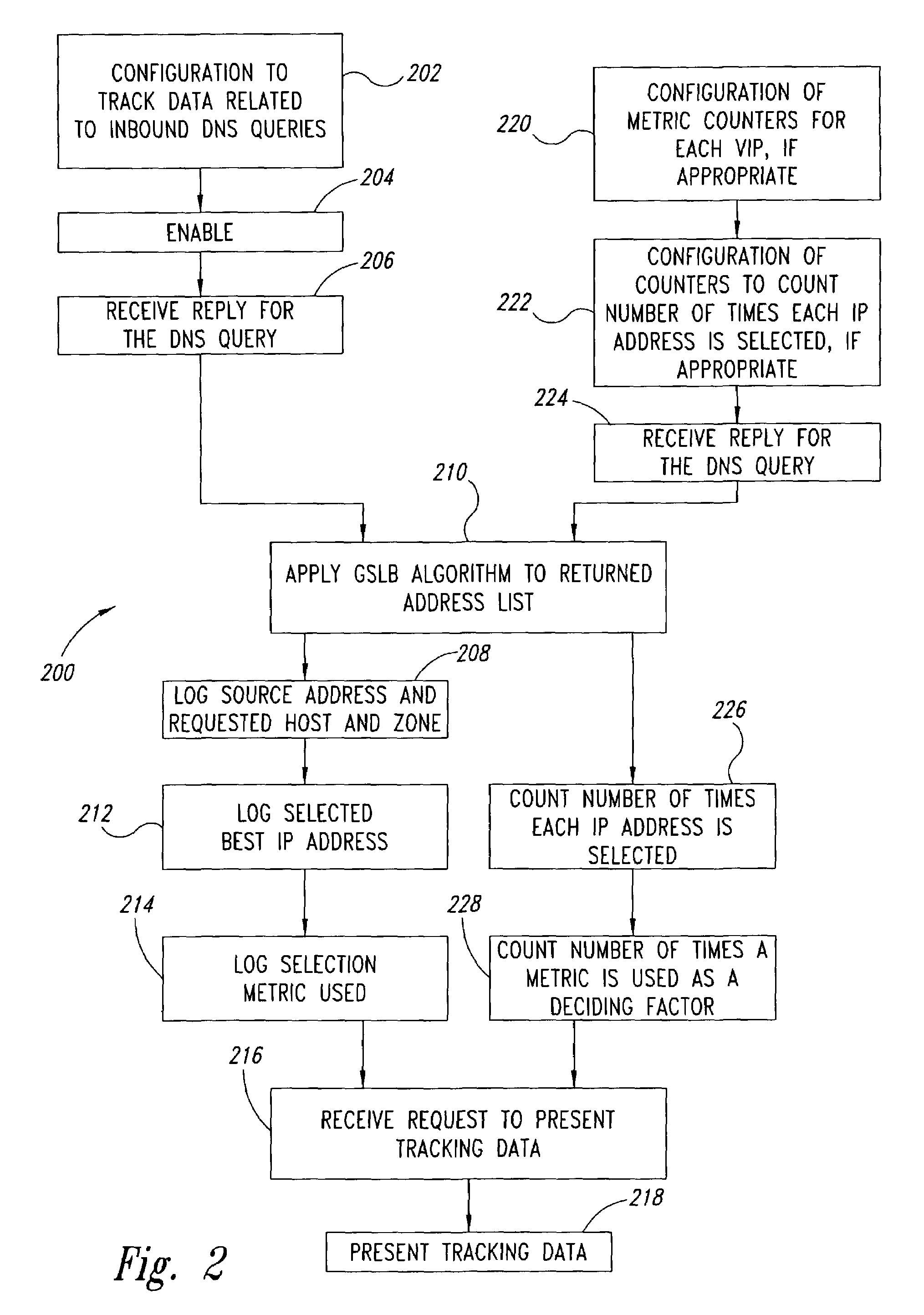
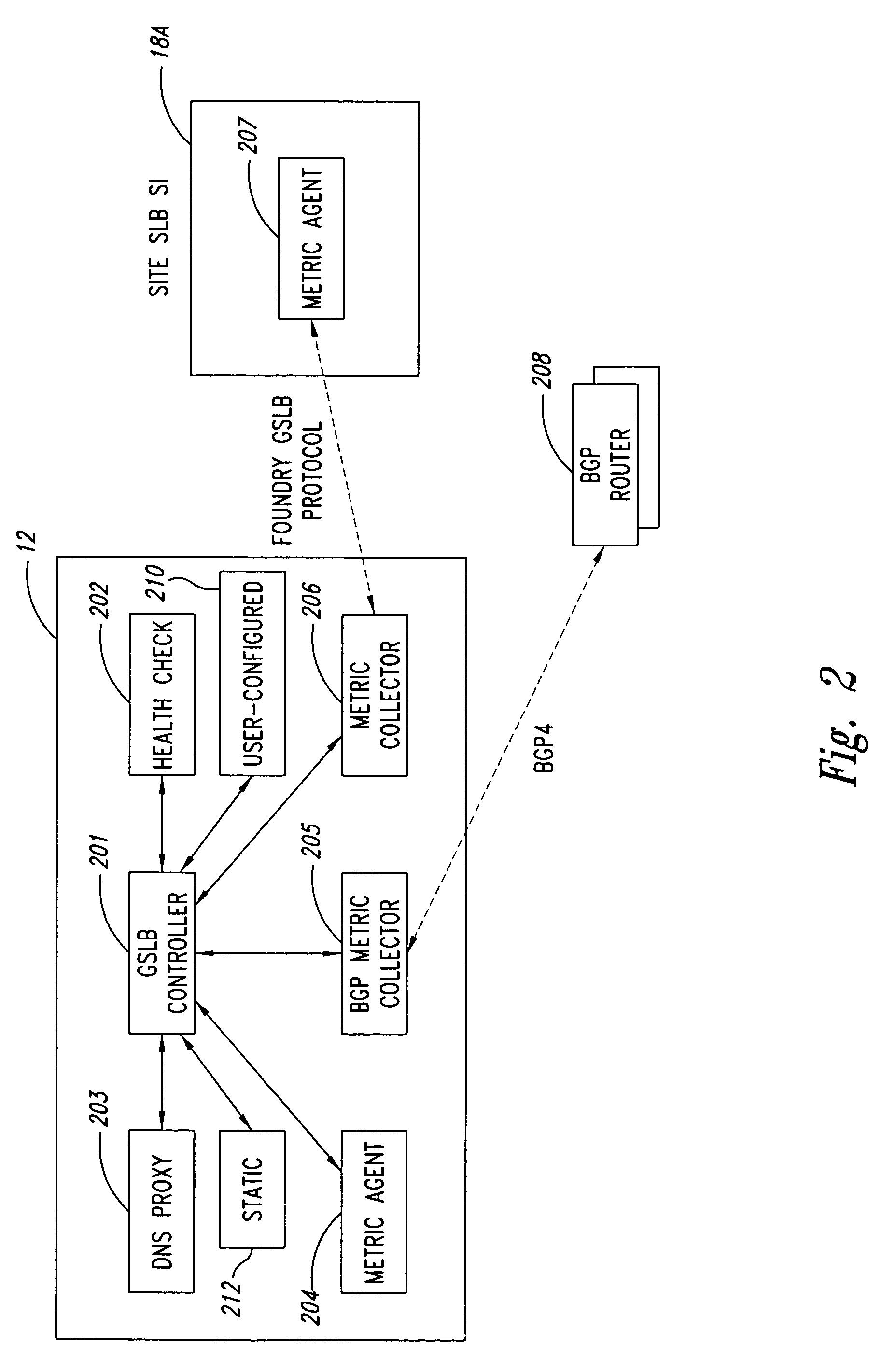
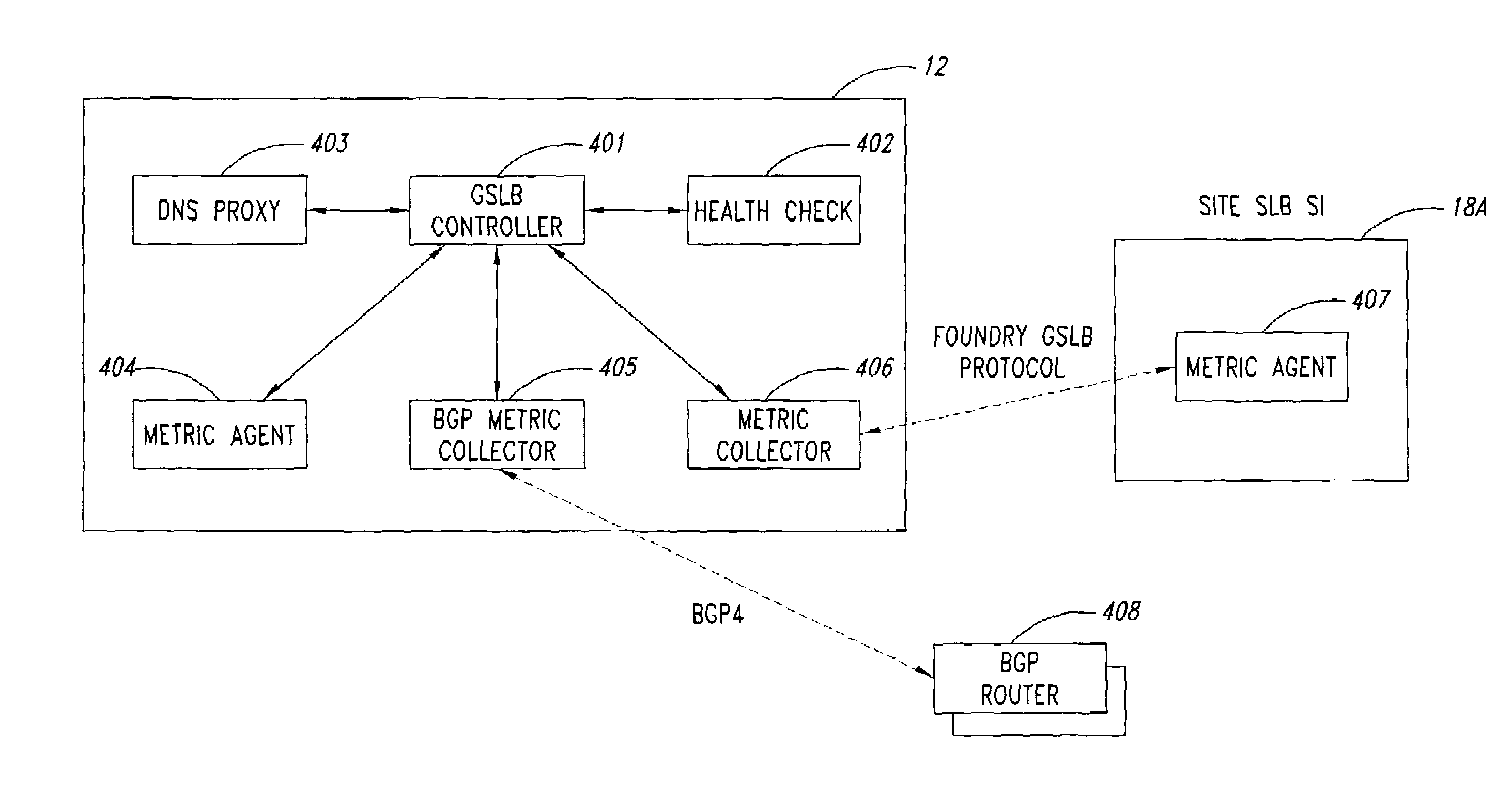
Statistical tracking of global server load balancing for selecting the best network address from ordered list of network addresses based on a set of performance metrics
ActiveUS7086061B1Multiprogramming arrangementsMultiple digital computer combinationsPolicy decisionIp address
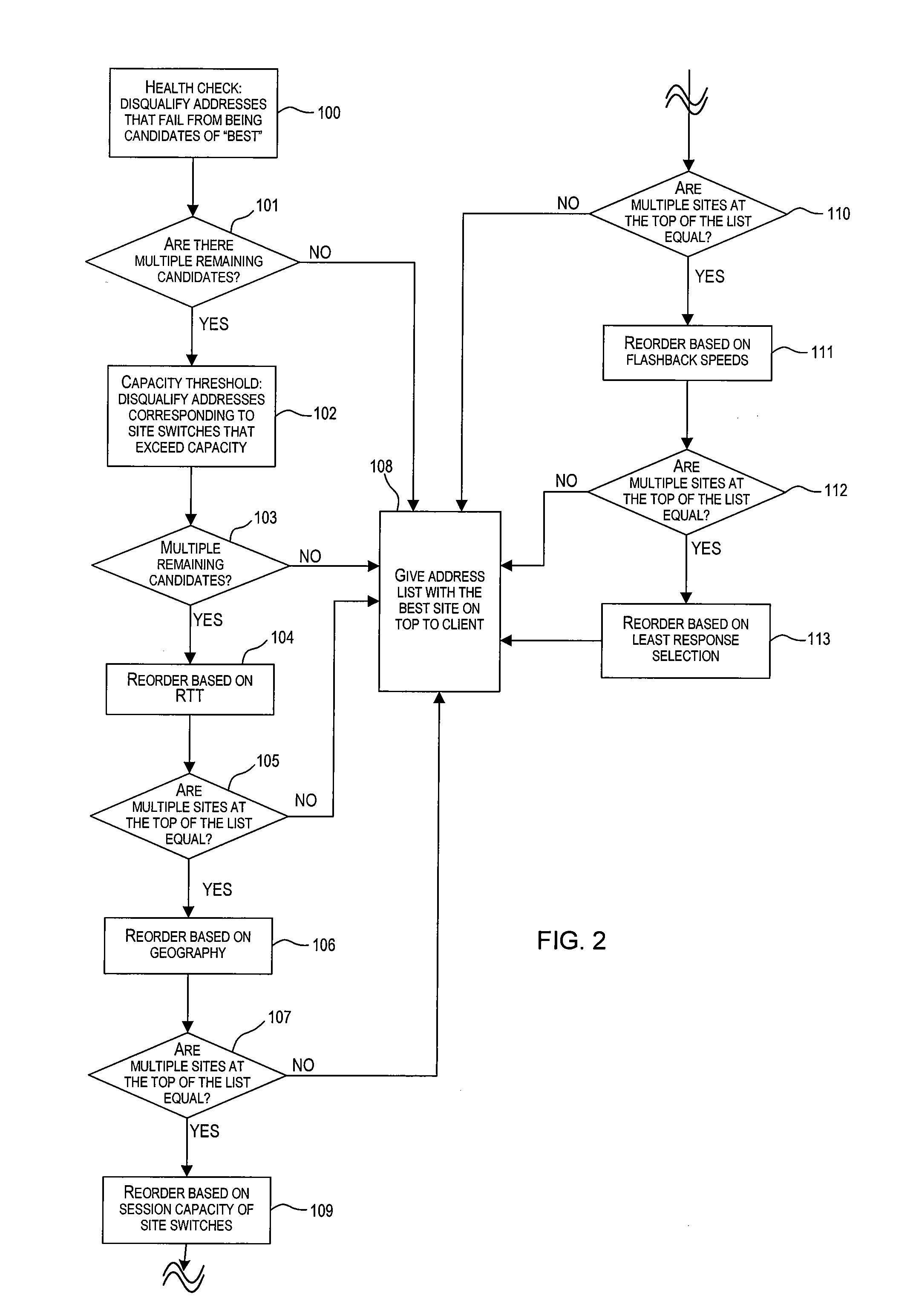
Server load-balancing operation-related data, such as data associated with a system configured for global server load balancing (GSLB) that orders IP addresses into a list based on a set of performance metrics, is tracked. Such operation-related data includes inbound source IP addresses (e.g., the address of the originator of a DNS request), the requested host and zone, identification of the selected “best” IP addresses resulting from application of a GSLB algorithm and the selection metric used to decide on an IP address as the “best” one. Furthermore, the data includes a count of the selected “best” IP addresses selected via application of the GSLB algorithm, and for each of these IP addresses, the list of deciding performance metrics, along with a count of the number of times each of these metrics in the list was used as a deciding factor in selection of this IP address as the best one. This tracking feature allows better understanding of GSLB policy decisions (such as those associated with performance, maintenance, and troubleshooting) and intelligent deployment of large-scale resilient GSLB networks.
Owner:AVAGO TECH INT SALES PTE LTD
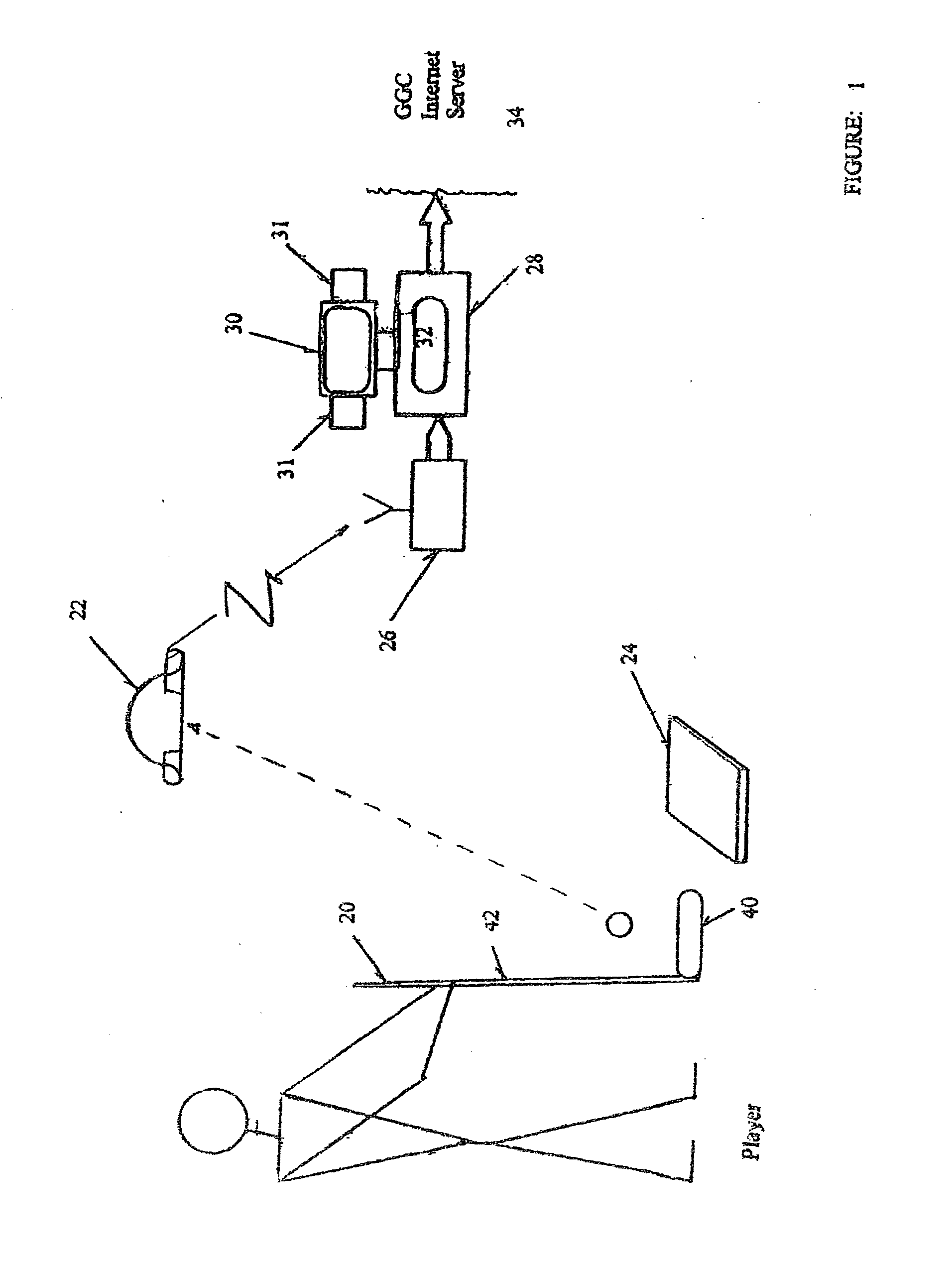
Computerized smart gaming tournament system for the internet
Owner:MURDOCK WILBERT Q +1
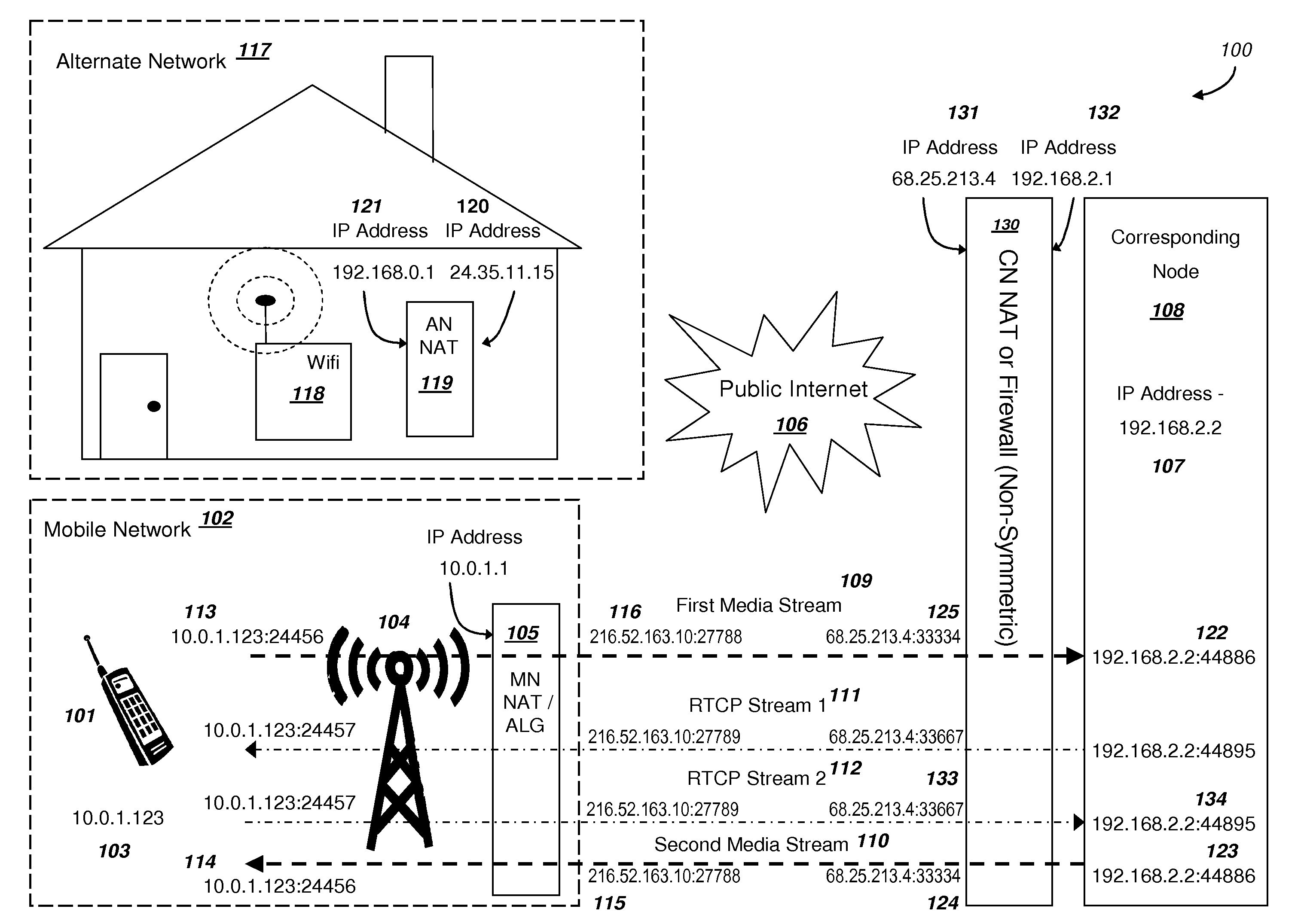
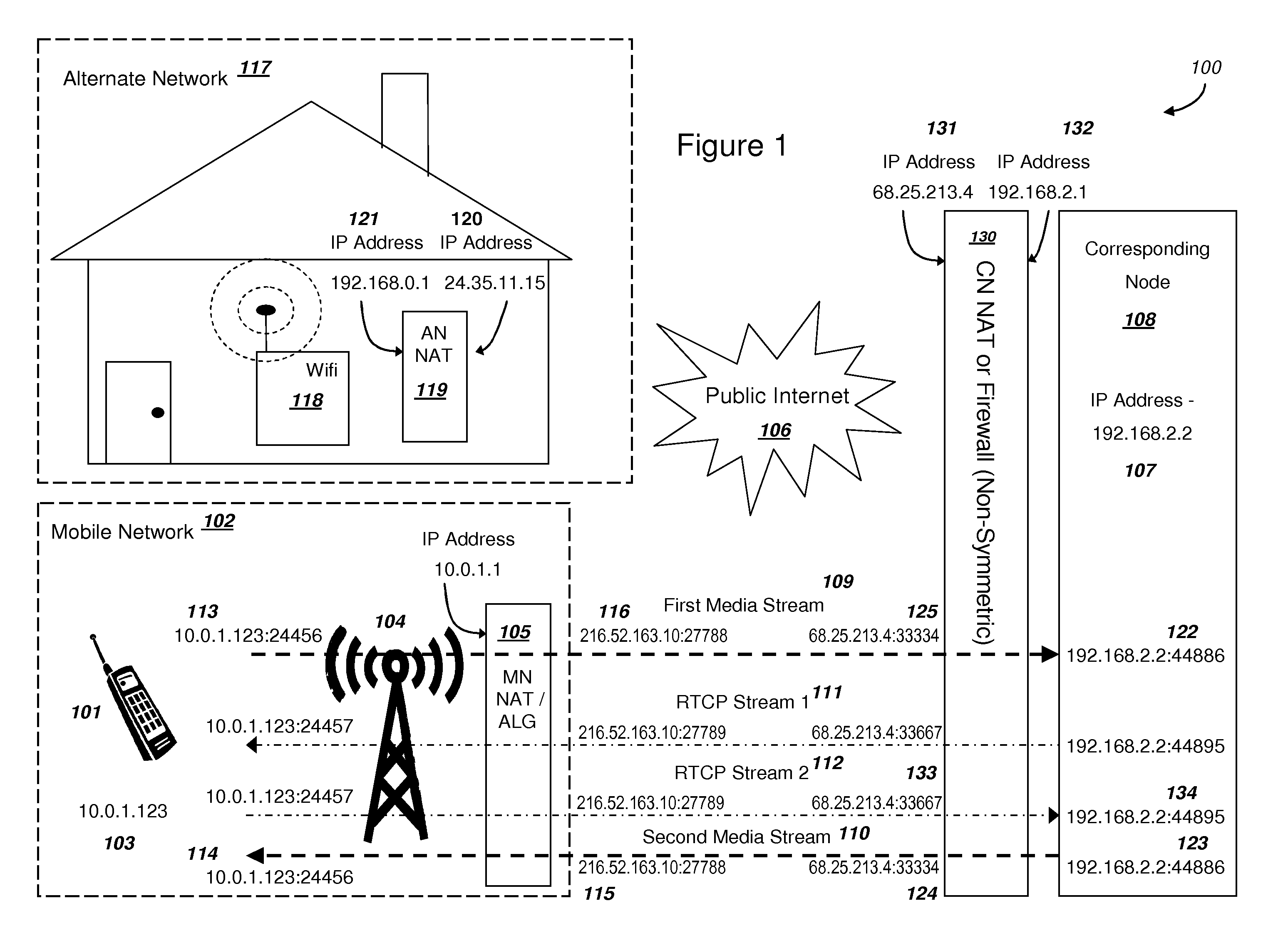
Efficient Handover of Media Communications in Heterogeneous IP Networks using LAN Profiles and Network Handover Rules
ActiveUS20090323632A1Reduce complexityImprove efficiencyWireless network protocolsRadio/inductive link selection arrangementsMedia controlsData pack
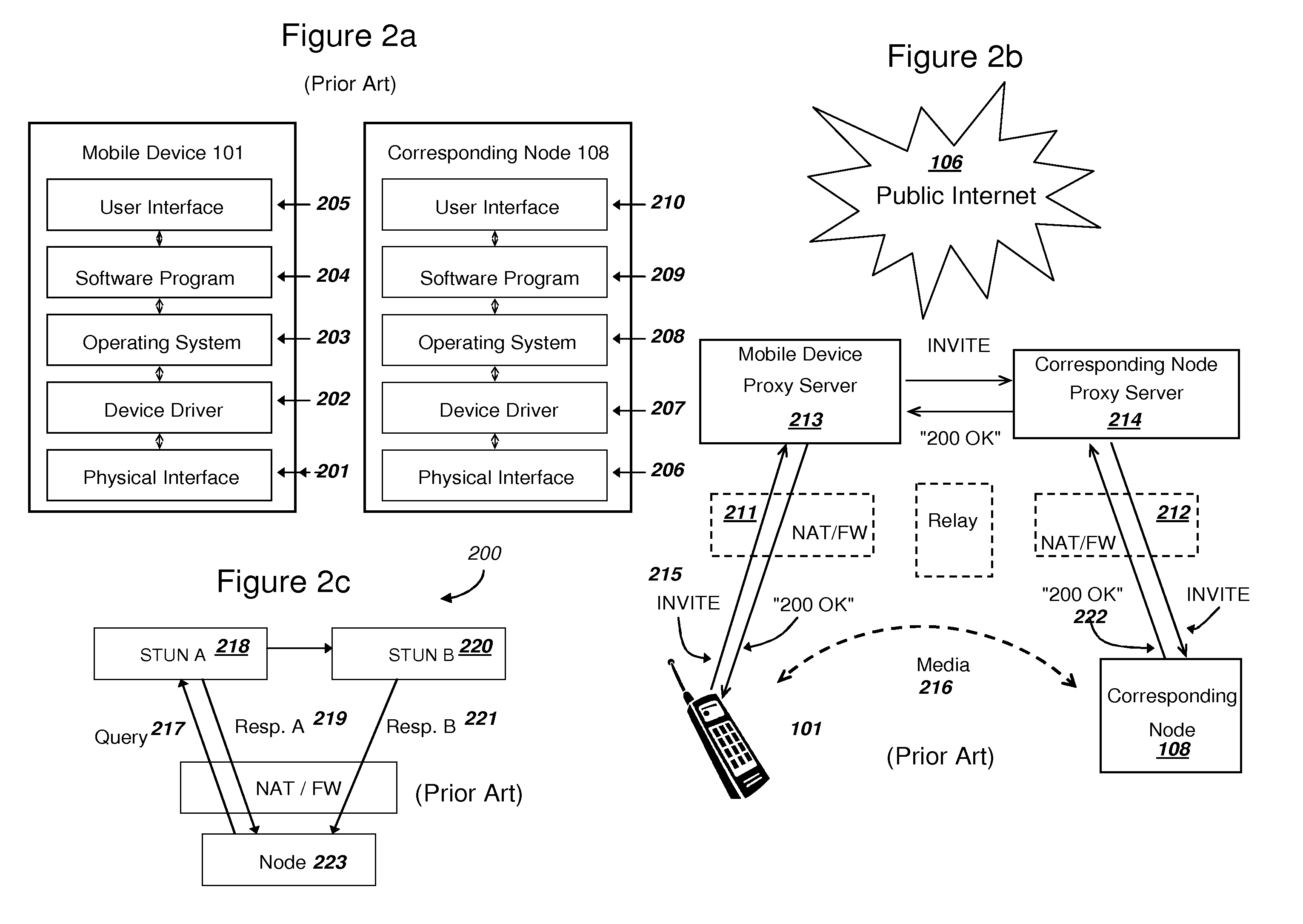
Methods and systems are provided for efficient handover of a media session between heterogeneous IP networks. A mobile device with Internet access can operate a software program to communicate with a corresponding node. The corresponding node may access the Internet through either a NAT router or a firewall. The mobile device establishes a media session with a corresponding node via the transmission of a first media stream and receipt of a second media stream, and a media control channel can optionally be implemented. The mobile device can acquire Internet access through a second IP address, and packets routed between the second IP address and the Internet may traverse a NAT router. The mobile device can evaluate the type of NAT at the second IP address from a stored LAN profile. A software routine can determine that handover of the media session from the first IP address to the second IP address is preferred. A software routine can determine efficient handover procedures according to Network handover rules. The mobile device may begin transmitting a third media stream to the corresponding node and the corresponding node can transmit a fourth media stream to the second IP address. A media control channel is optionally supported.
Owner:GOOGLE LLC
System and method for performing client-centric load balancing of multiple globally-dispersed servers
InactiveUS7653700B1Improve performanceLittle latencyMultiple digital computer combinationsData switching networksDomain nameIp address
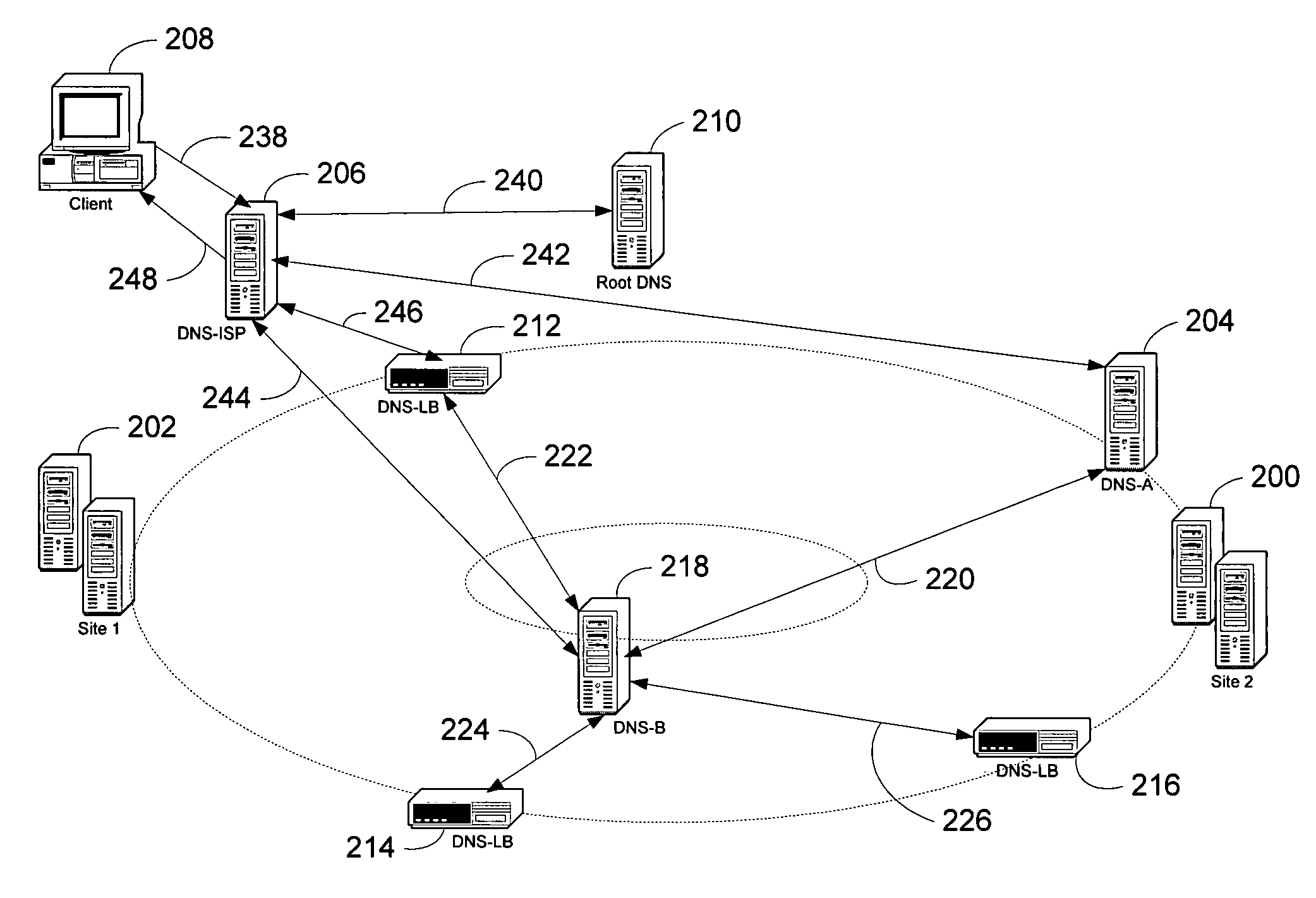
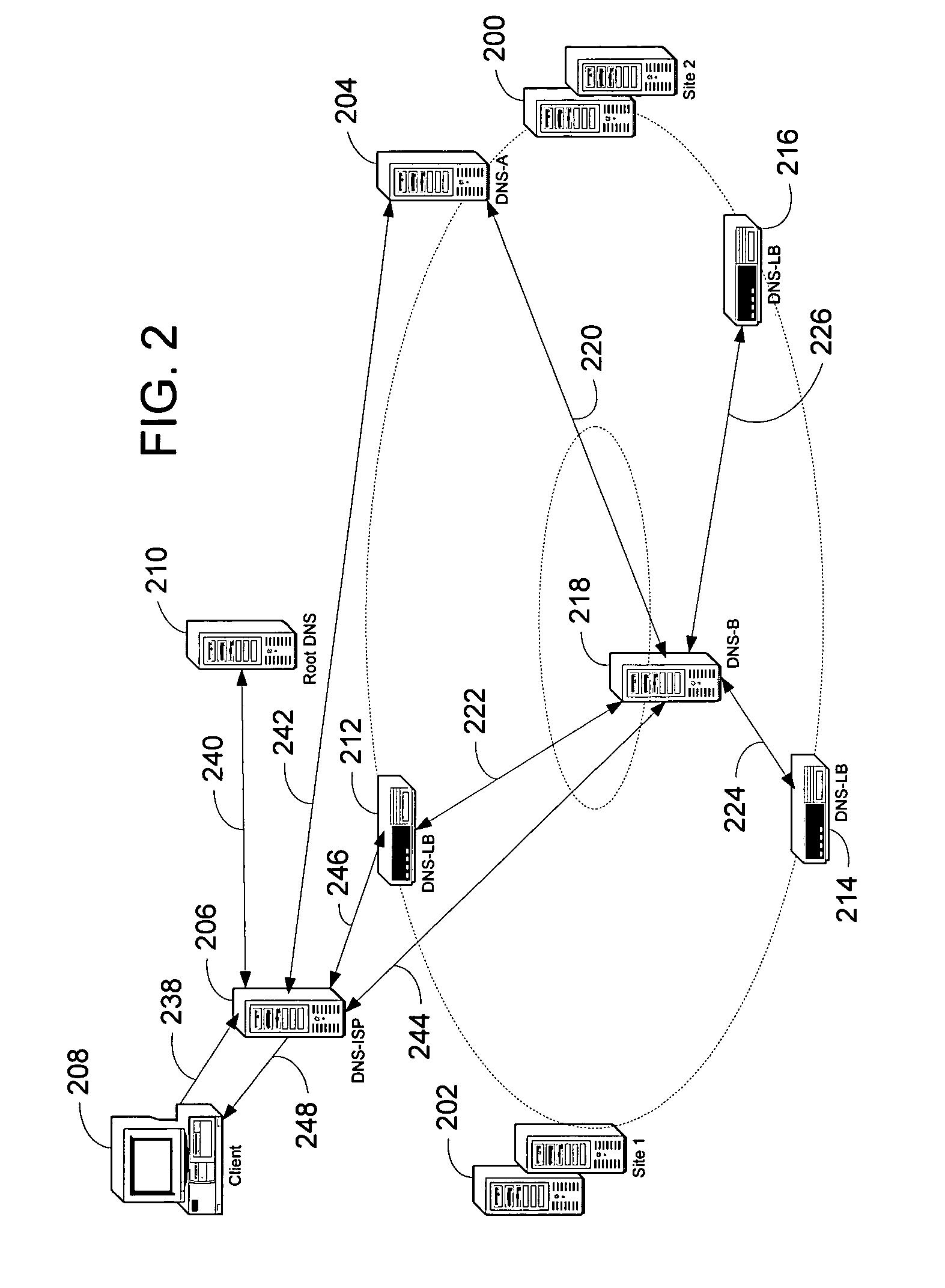
Presented is a system and a method for load balancing multiple globally-dispersed servers based on client-centric performance criteria. The infrastructure of the system includes load balancing domain name servers (DNS-LBs) deployed in close physical proximity to the Internet service providers' points of presence. The DNS-LBs are then able to monitor the performance of the servers from a location close to the clients, which allows the DNS-LBs to select a server that will yield the best performance from that location for the client. A second level of the infrastructure utilizes domain name servers (DNS-Bs) that are deployed on the Internet backbones and regional provides. The authoritative domain name servers (DNS-As) for the servers to be load balanced refer all name queries to these DNS-Bs. The DNS-Bs then refer the queries to one of the DNS-LBs based on a mapping of the DNS-ISP address to its physically proximate DNS-LB. The DNS-LB then returns the IP address of the server that will provide the best performance from that location.
Owner:MICROSOFT TECH LICENSING LLC
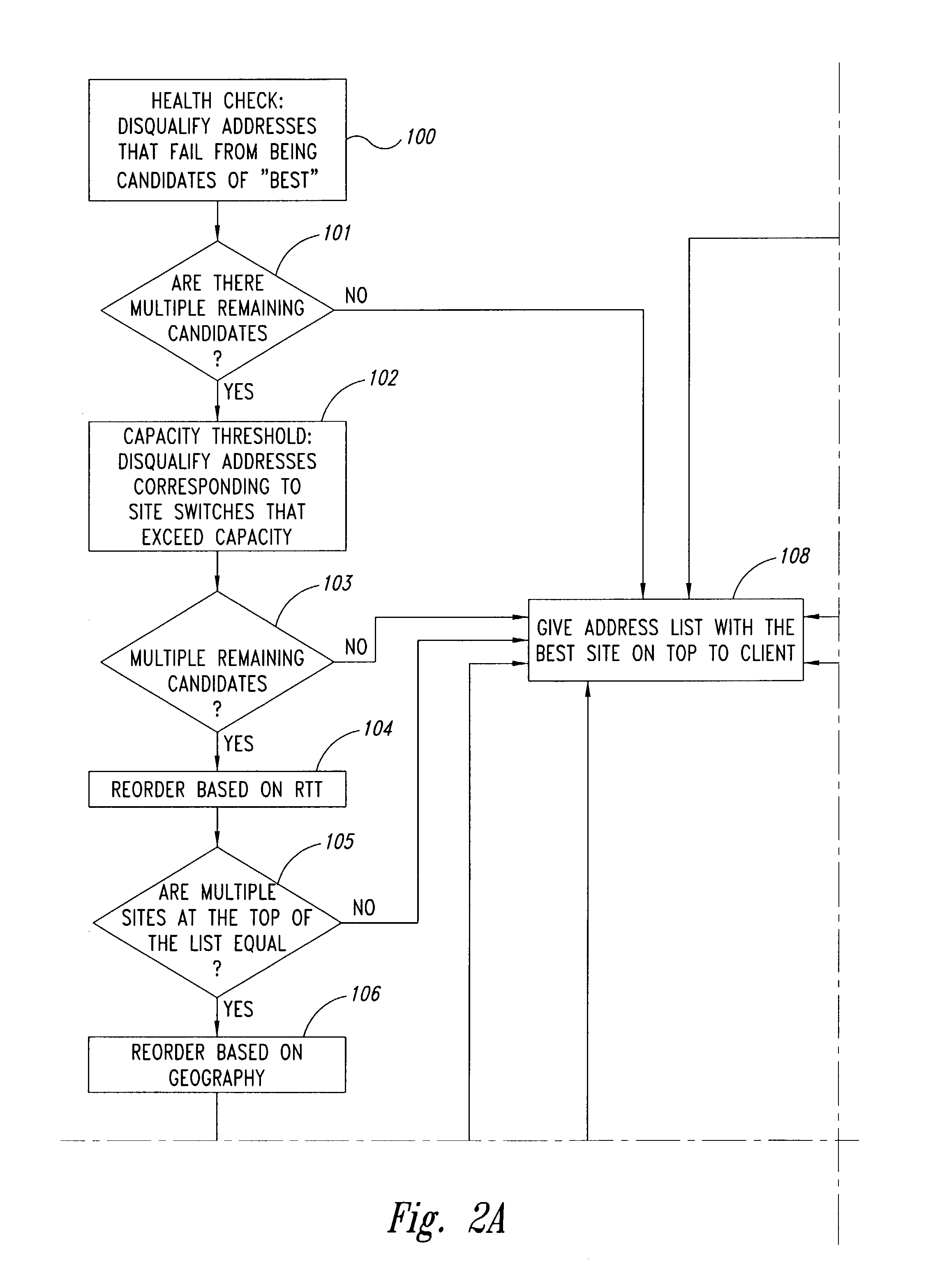
Configurable geographic prefixes for global server load balancing
ActiveUS7496651B1Traffic loadMultiprogramming arrangementsMultiple digital computer combinationsGeographic regionsIp address
In a load balancing system, user-configurable geographic prefixes are provided. IP address prefix allocations provided by the Internet Assigned Numbers Authority (IANA) and associated geographic locations are stored in a first, static database in a load balancing switch, along with other possible default geographic location settings. A second, non-static database stores user-configured geographic settings. In particular, the second database stores Internet Protocol (IP) address prefixes and user-specified geographic regions for those prefixes. The specified geographic region can be continent, country, state, city, or other user-defined region. The geographic settings in the second database can override the information in the first database. These geographic entries help determine the geographic location of a client and host IP addresses, and aid in directing the client to a host server that is geographically the closest to that client.
Owner:AVAGO TECH INT SALES PTE LTD
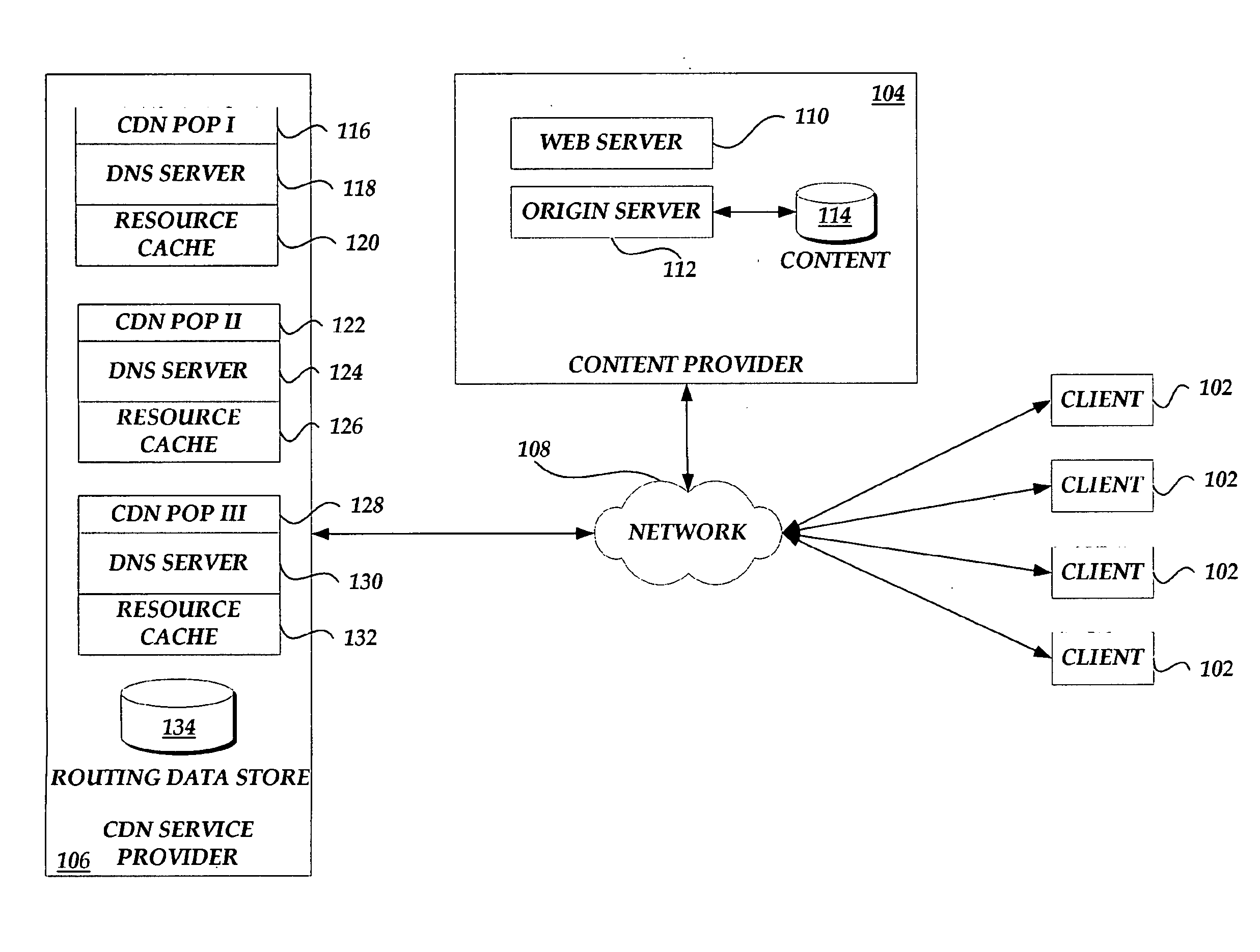
Updating routing information based on client location
ActiveUS20100125675A1Digital computer detailsLocation information based serviceIp addressClient-side
A system, method, and computer-readable medium for updating request routing information associated with client location information are provided. A content delivery network service provider receives a DNS query from a client computing device. The DNS query corresponds to a resource identifier for requested content from the client computing device. The content delivery network service provider obtains a query IP address corresponding to the client computing device. Based on routing information associated with the query IP address, the content delivery network service provider routes the DNS query. The process further includes monitoring performance data associated with the transmission of the requested resource and updating routing information associated with the query IP address based on the performance data for use in processing subsequent requests form the client computing device.
Owner:AMAZON TECH INC
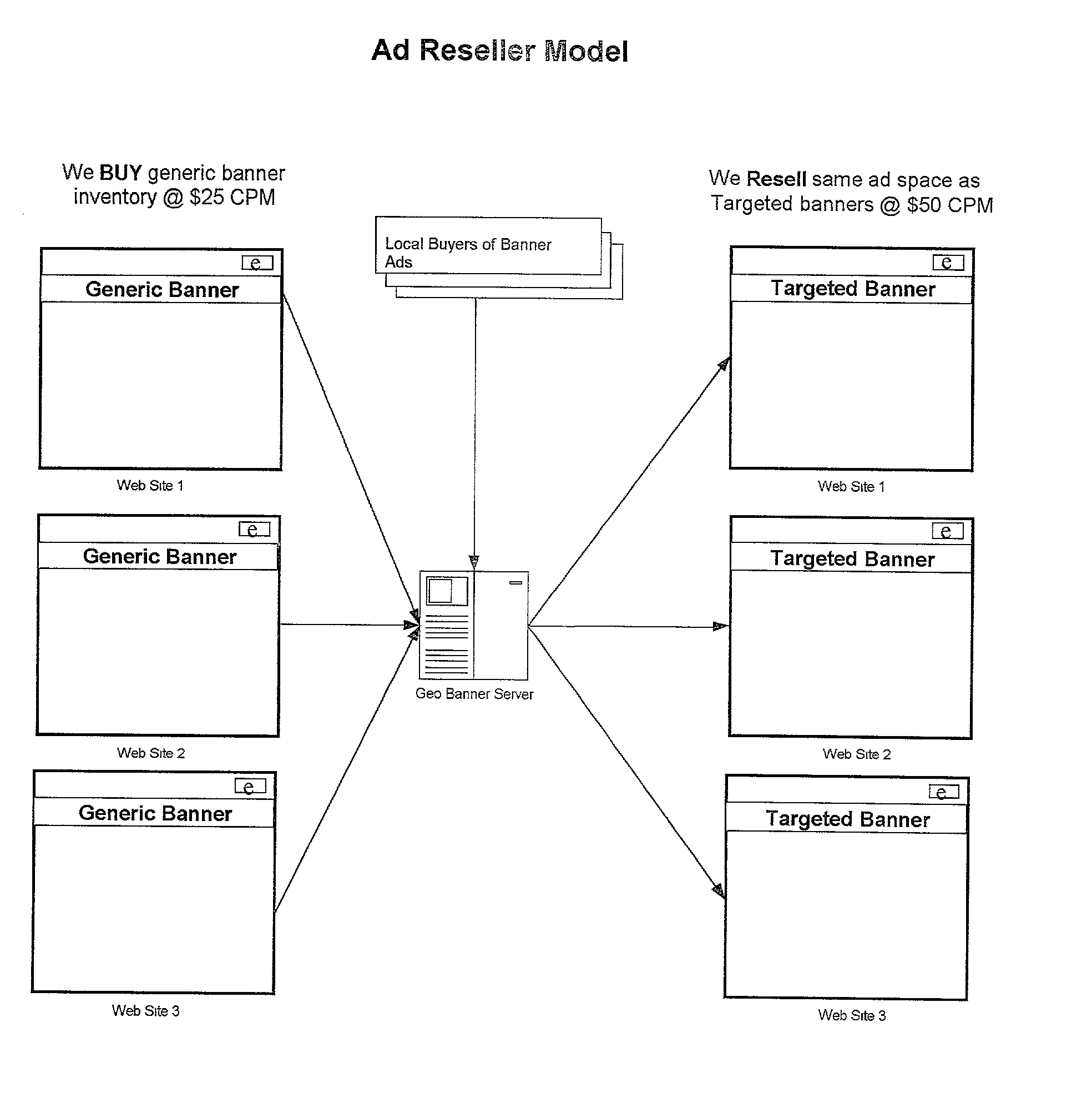
Method and system for targeting internet advertisements and messages by geographic location
A method and system of targeting an Internet messaged to an Internet client based on geographic information of the Internet client is disclosed. The present invention first obtains IP addresses of Internet clients as they visit their web sites. The present invention then obtains addresses from the Internet clients and transforming the addresses to latitude / longitude coordinates for each of the Internet clients. A lookup table can thus be generated by correlating the IP addresses with the addresses and latitude / longitude coordinates. The information can be mined to resolve multiple entry conflicts to extract most likely position of a particular address. When an Internet client visits a web server, the IP address is collected from the Internet client to be targeted. The location of the Internet client can then be approximated by comparing the client's IP address with the lookup table. Upon approximation, a commercial message is transmitted to the Internet client, wherein the commercial message is related to the geographical location of the Internet client.
Owner:GEOMICRO
Enhanced E911 location information using voice over internet protocol (VoIP)
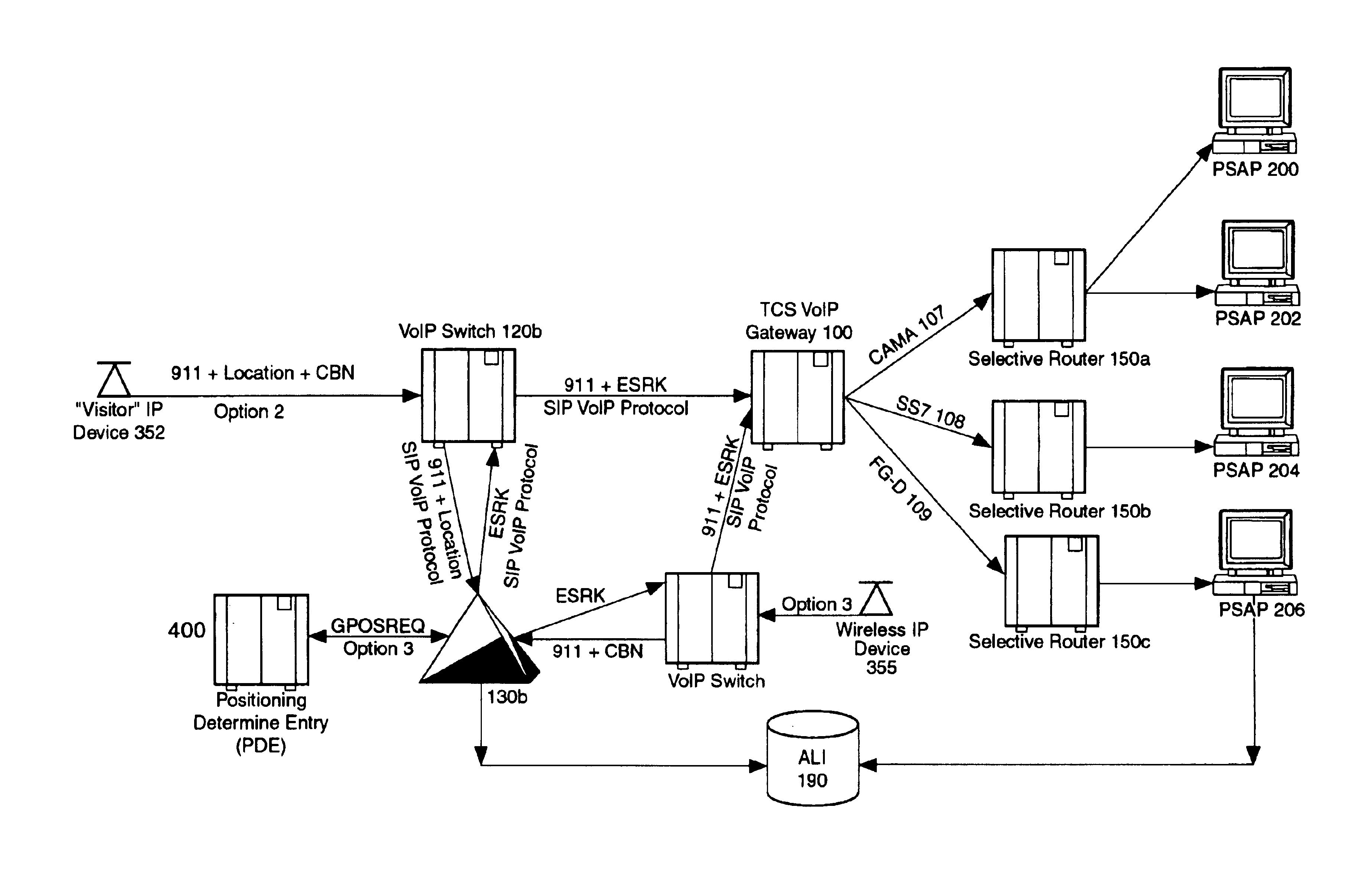
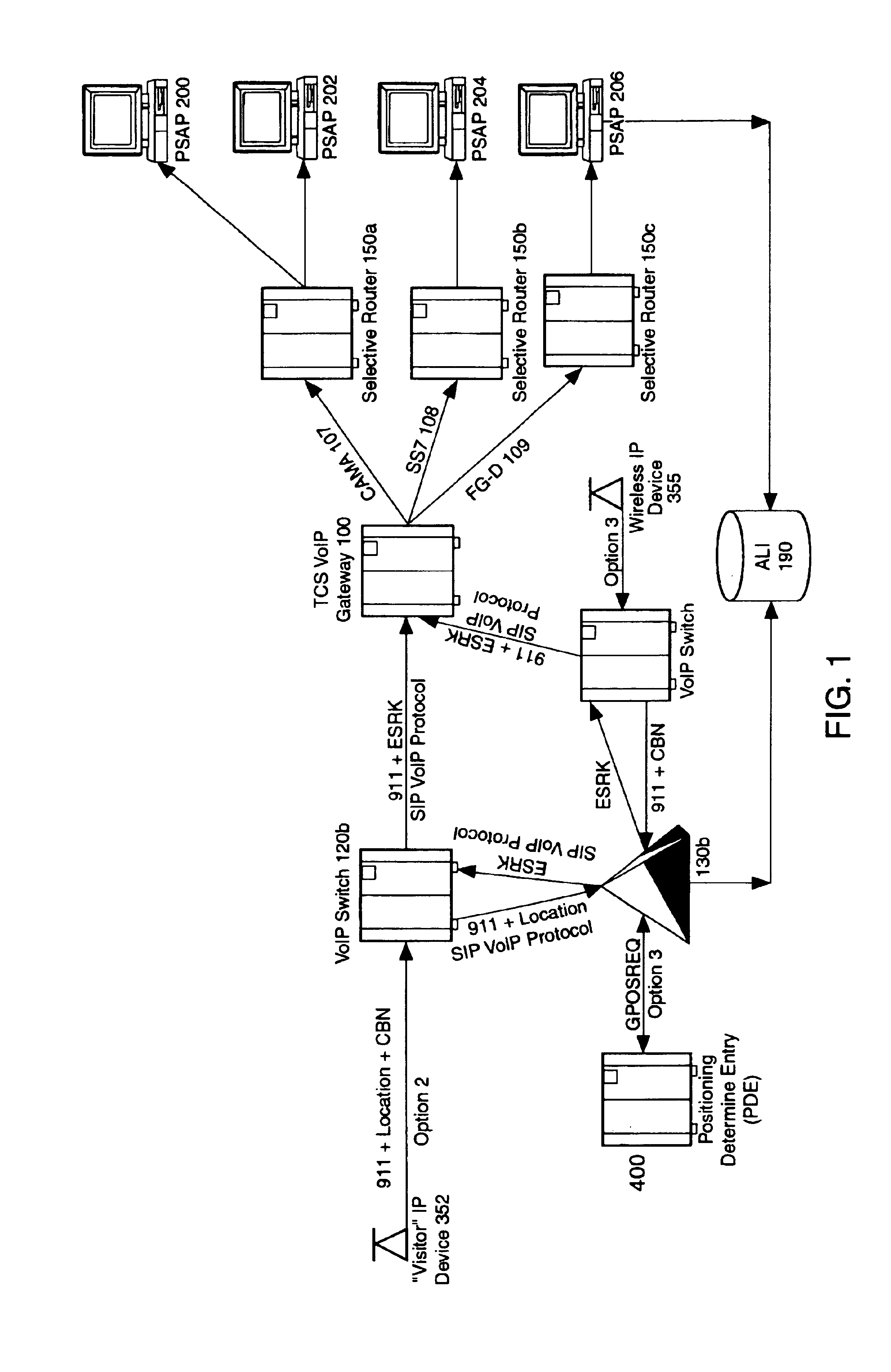
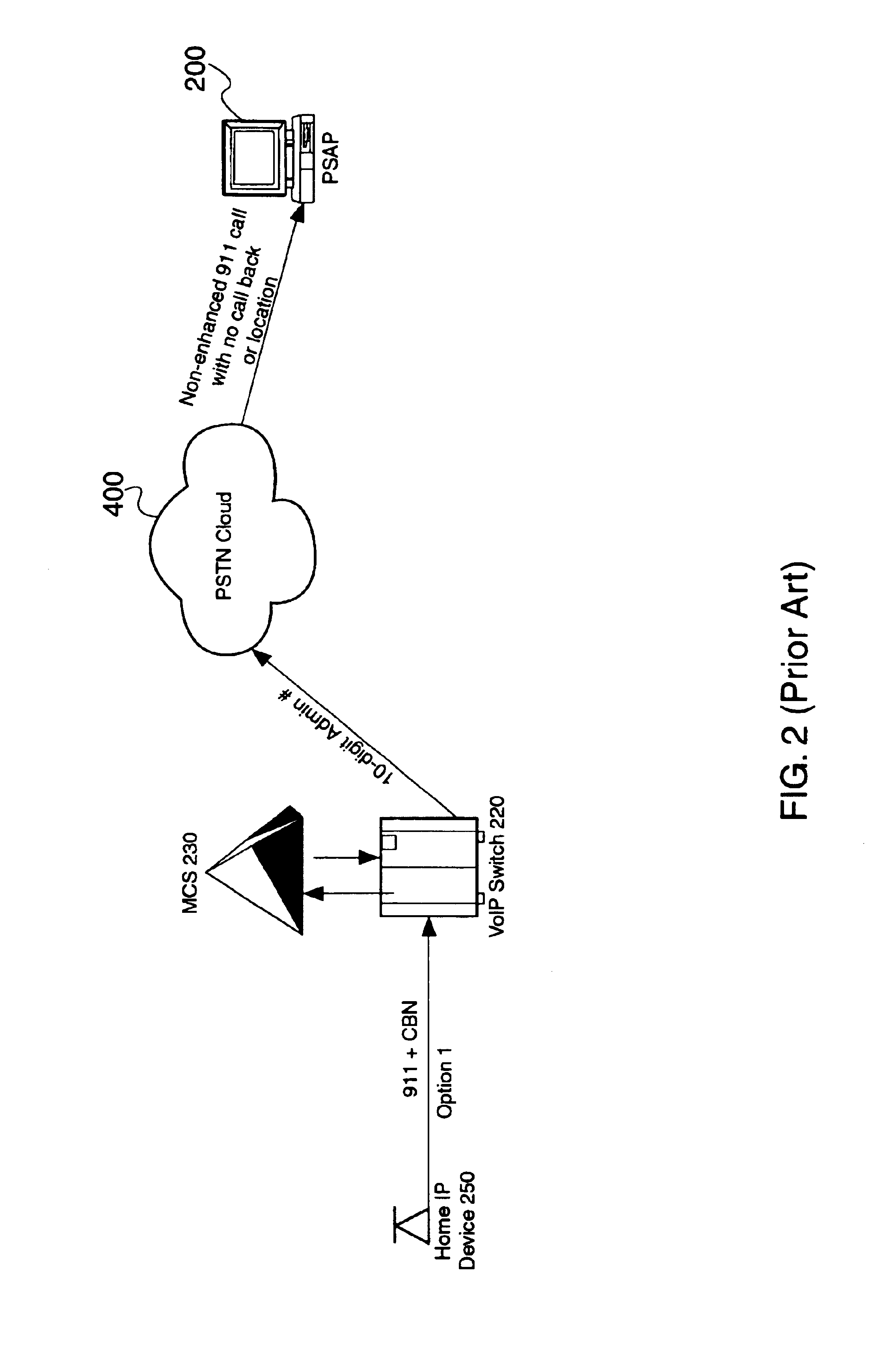
An E-9-1-1 voice-over-IP (VoIP) solution is provided wherein a 911 call from a wireless VoIP device is routed directly to the correct Public Safety Answer Point (PSAP) via dedicated trunks, together with correct location information and call-back number. VoIP gateways are implemented locally, at least one per LATA, and accept VoIP packetized data inbound, and convert it to standard wireline voice calls. Calls are routed to an IP address at the VoIP gateway, which then egresses the call to a voice port at a selective router. Dedicated voice trunks (CAMA, SS7, FG-D) are installed between each local VoIP gateway and appropriate selective routers. An Automatic Location Identification (ALI) database is provisioned with ESRKs dedicated for VoIP use. TCP / IP circuits may be established between some or all of the various local VoIP gateways.
Owner:TELECOMM SYST INC
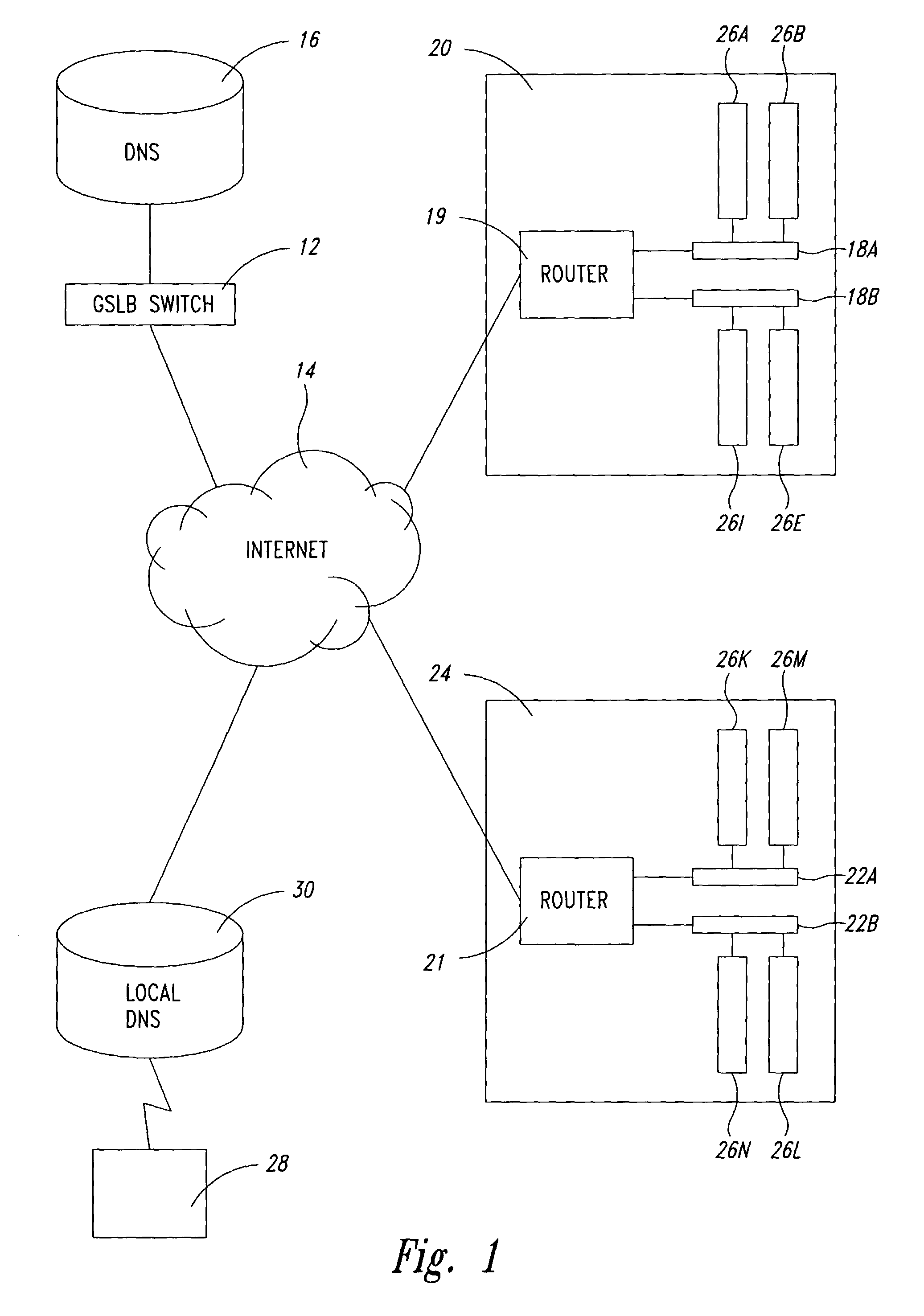
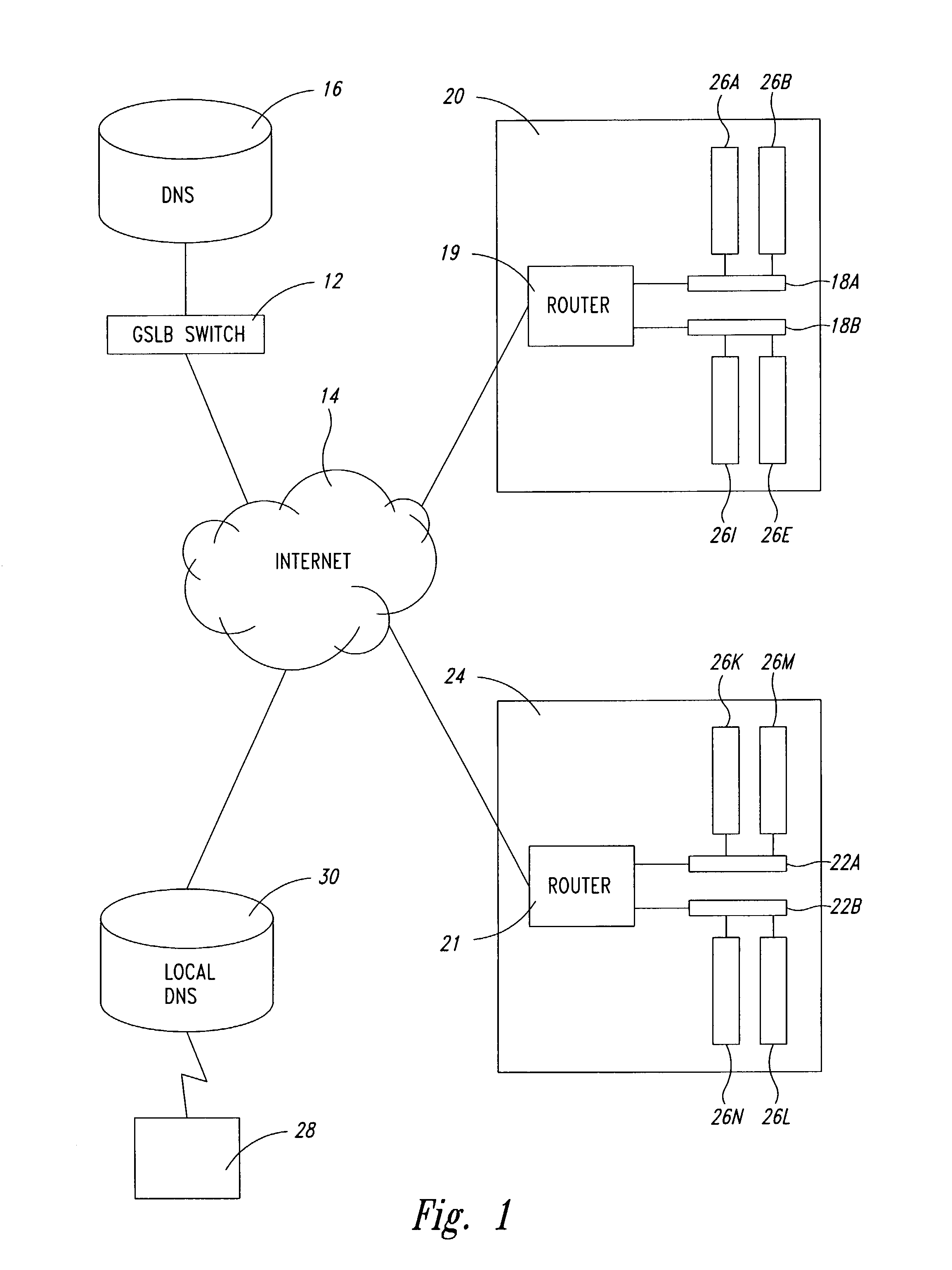
Global server load balancing
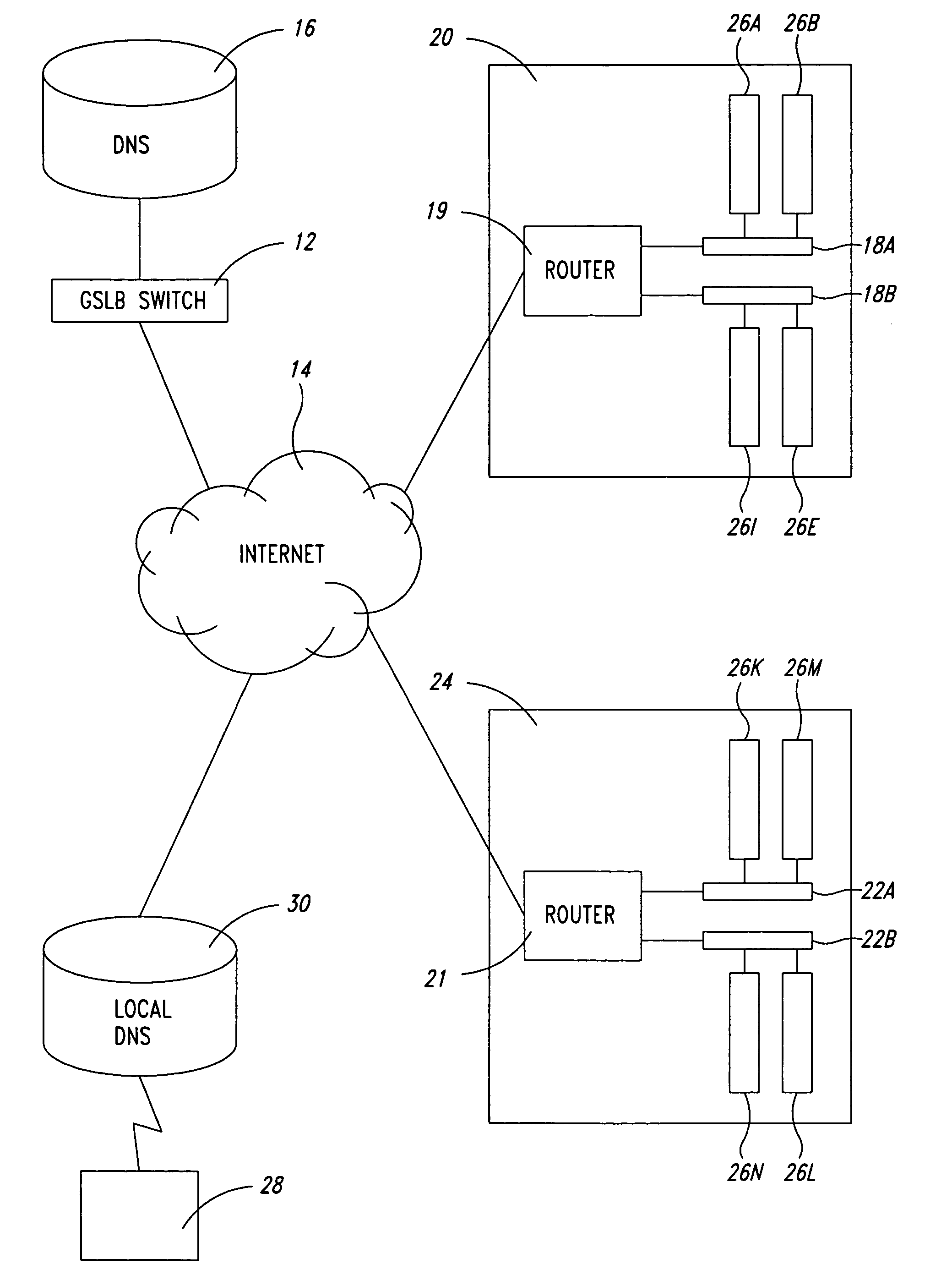
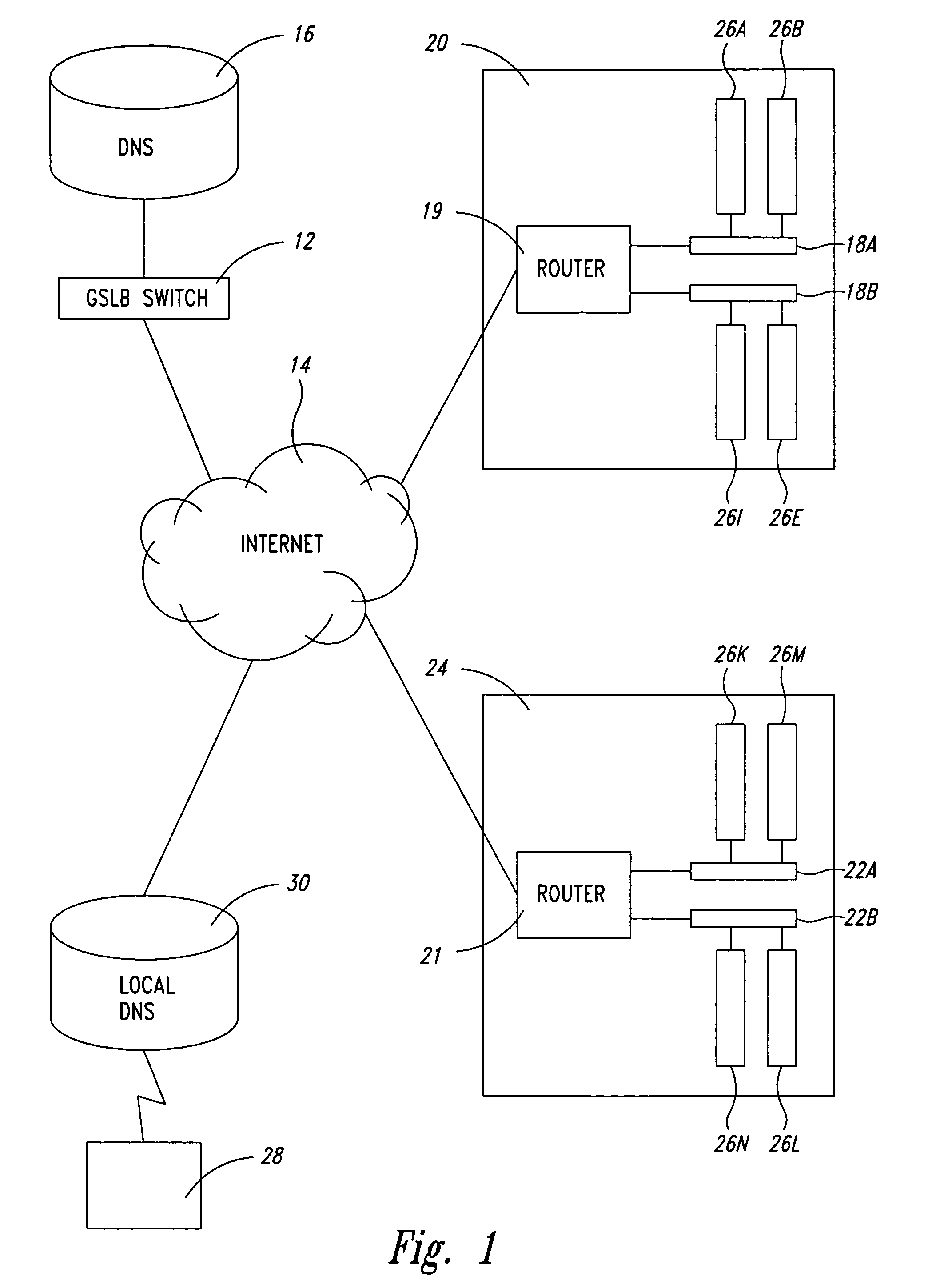
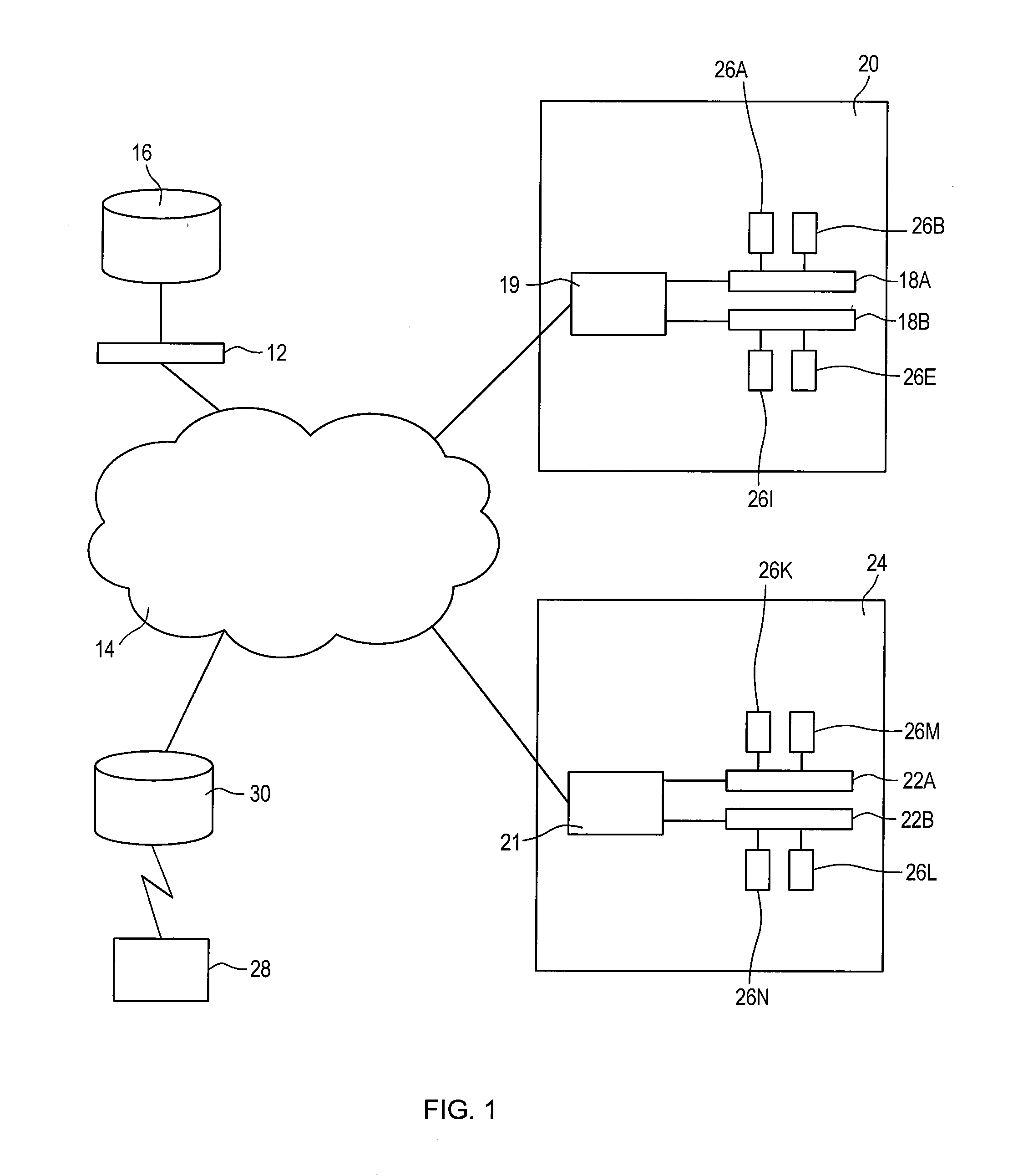
A global server load-balancing (GSLB) switch serves as a proxy to an authoritative DNS and communicates with numerous site switches that are coupled to host servers serving specific applications. The GSLB switch receives from site switches operational information regarding host servers within the site switches neighborhood. When a client program requests a resolution of a host name, the GSLB switch, acting as a proxy of an authoritative DNS, returns one or more ordered IP addresses for the host name. The IP addresses are ordered using metrics that include the information collected from the site switches. In one instance, the GSLB switch places the address that is deemed “best” at the top of the list.
Owner:AVAGO TECH INT SALES PTE LTD
Systems and Methods for Dynamic Protection from Electronic Attacks
InactiveUS20140366132A1Reduce security risksMemory loss protectionError detection/correctionIp addressComputer security
Systems and methods for gathering, classifying, and evaluating real time security intelligence data concerning security threats presented by an IP address, and reporting in real time the degree and character of such security threats.
Owner:NORSE NETWORKS INC
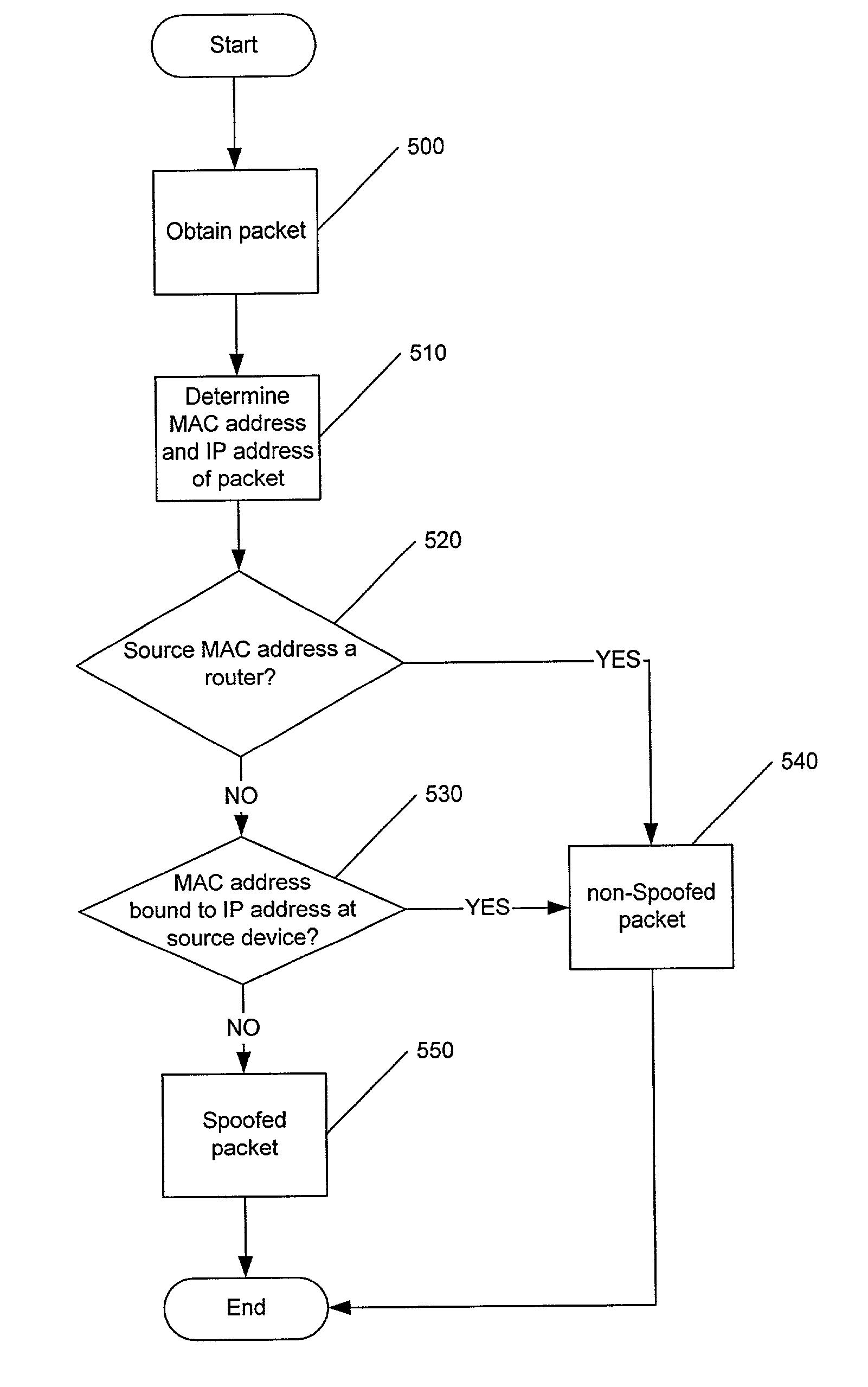
Methods, systems and computer program products for detecting a spoofed source address in IP datagrams
InactiveUS7134012B2Improve usabilityFrequency-division multiplexData switching by path configurationIp addressMedia access control
Methods, systems and computer program products are provided for determining if a packet has a spoofed source Internet Protocol (IP) address. A source media access control (MAC) address of the packet and the source IP address are evaluated to determine if the source IP address of the packet has been bound to the source MAC address at a source device of the packet. The packet is determined to have a spoofed source IP address if the evaluation indicates that the source IP address is not bound to the source MAC address. Such an evaluation may be made for packets having a subnet of the source IP address which matches a subnet from which the packet originated.
Owner:IBM CORP
Method and system for distributed network address translation with network security features
InactiveUS7032242B1Digital data processing detailsUser identity/authority verificationSecurity associationIp address
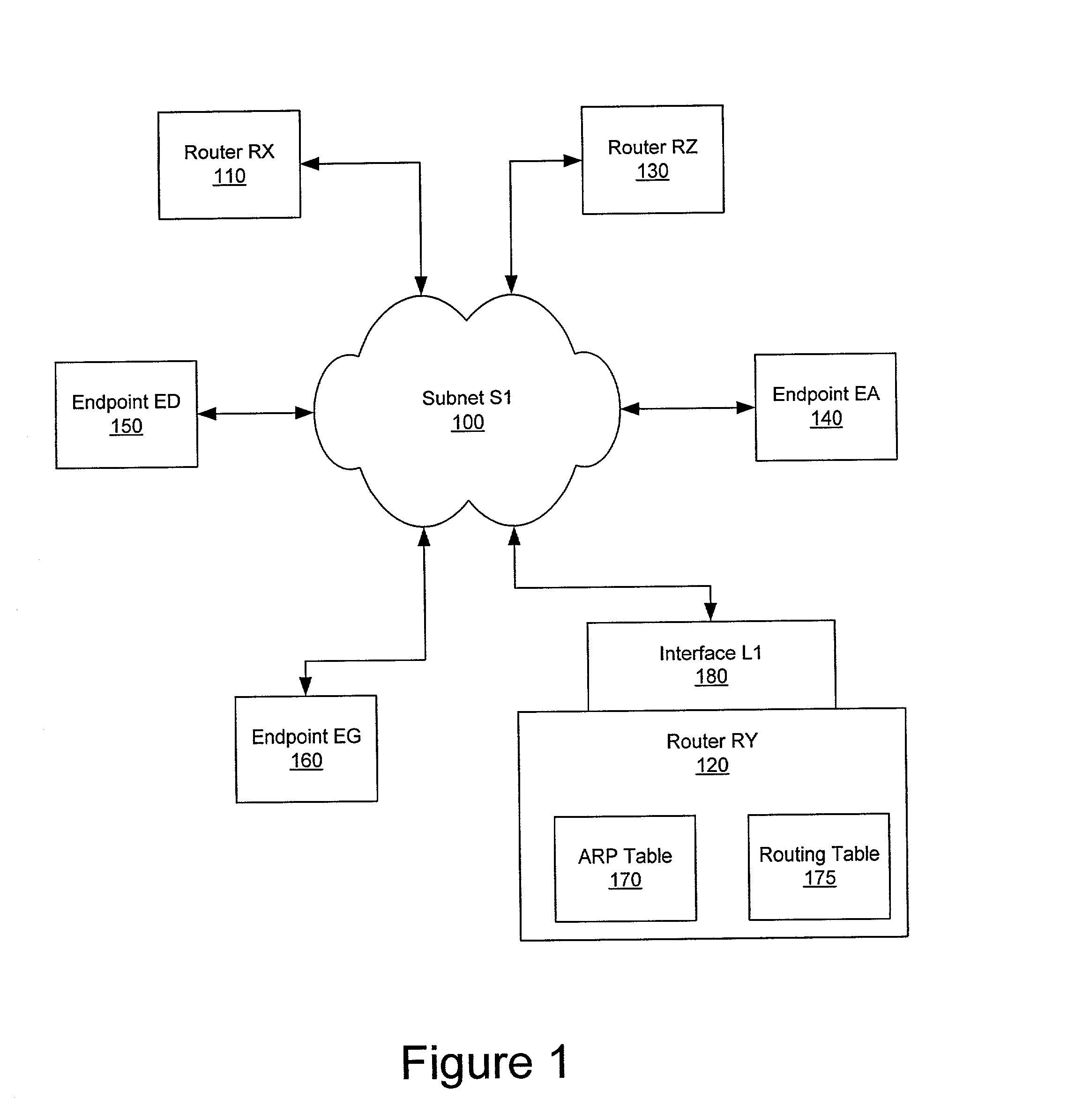
A method and system for distributed network address translation with security features. The method and system allow Internet Protocol security protocol (“IPsec”) to be used with distributed network address translation. The distributed network address translation is accomplished with IPsec by mapping a local Internet Protocol (“IP”) address of a given local network device and a IPsec Security Parameter Index (“SPI”) associated with an inbound IPsec Security Association (“SA”) that terminates at the local network device. A router allocates locally unique security values that are used as the IPsec SPIs. A router used for distributed network address translation is used as a local certificate authority that may vouch for identities of local network devices, allowing local network devices to bind a public key to a security name space that combines a global IP address for the router with a set of locally unique port numbers used for distributed network address translation. The router issues security certificates and may itself be authenticated by a higher certificate authority. Using a security certificate, a local network device may initiate and be a termination point of an IPsec security association to virtually any other network device on an IP network like the Internet or an intranet. The method and system may also allow distributed network address translation with security features to be used with Mobile IP or other protocols in the Internet Protocol suite.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
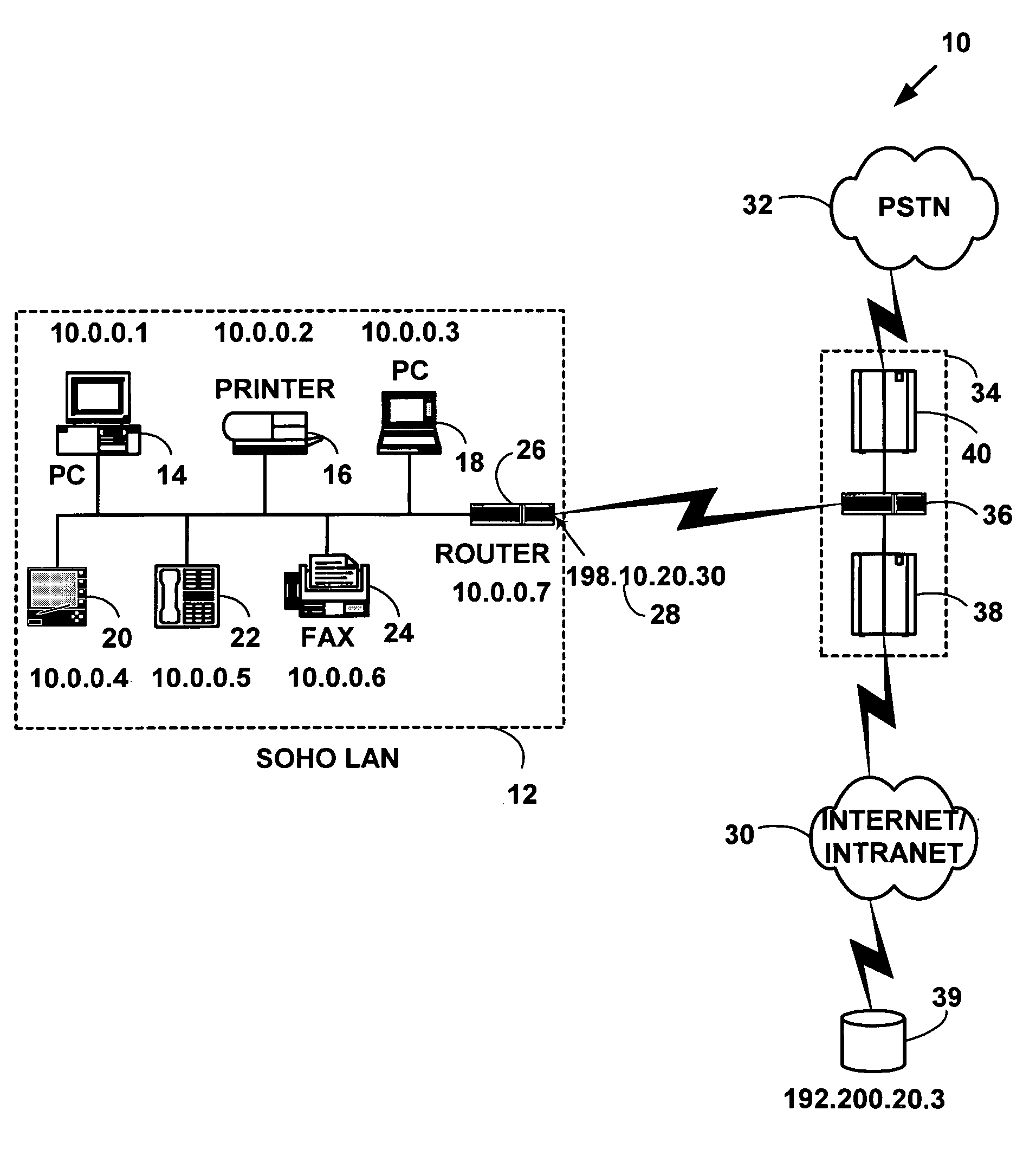
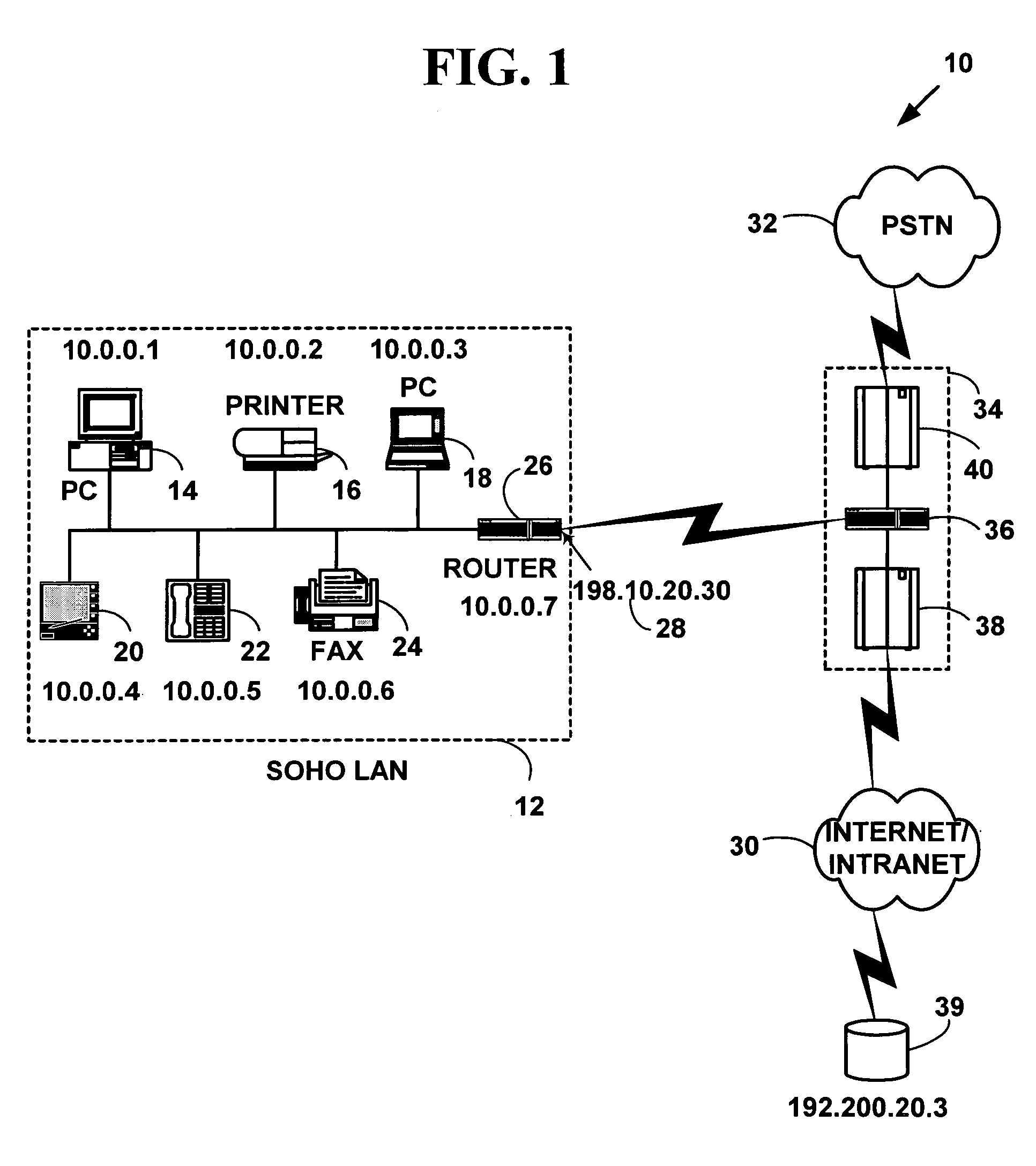
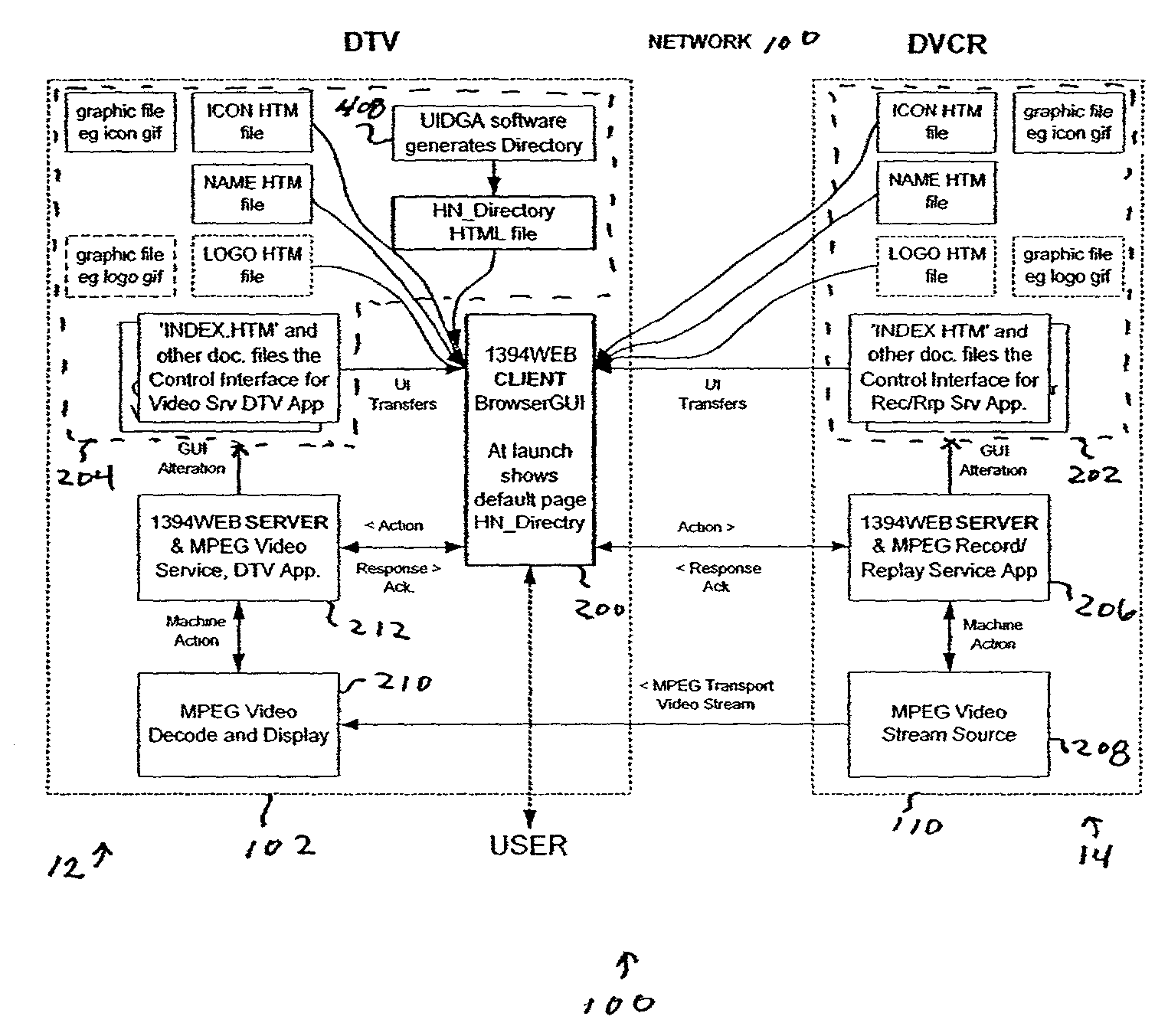
Architecture for home network on world wide web with private-public IP address/URL mapping
InactiveUS7349967B2Special service provision for substationTelevision system detailsIp addressNetwork on
A method for providing user interfaces in a first network to a remote access device, the first network including interconnected first devices and at least one interface device for connecting the first network to a second network. The remote access device establishes communication with the second network and sends a request to the interface device for accessing the first network; at least one of the first devices obtains information from one or more of the first devices, and generates a user interface description including at least one reference associated with the device information, the reference including an external address such that the device is accessible from the remote access device; the interface device sends the user interface description to the remote access device; and the remote access device displays a user interface based on the user interface description.
Owner:SAMSUNG ELECTRONICS CO LTD
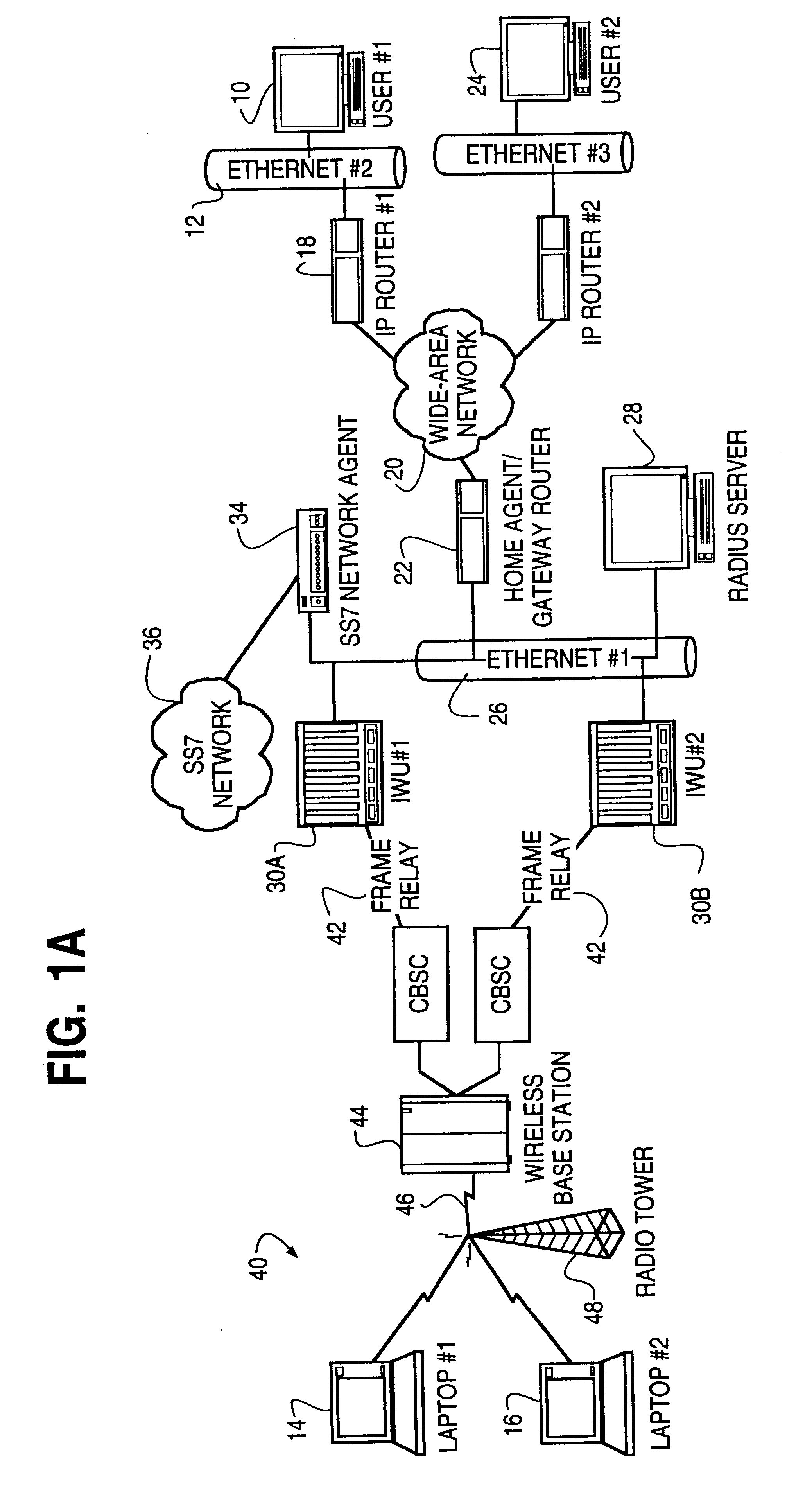
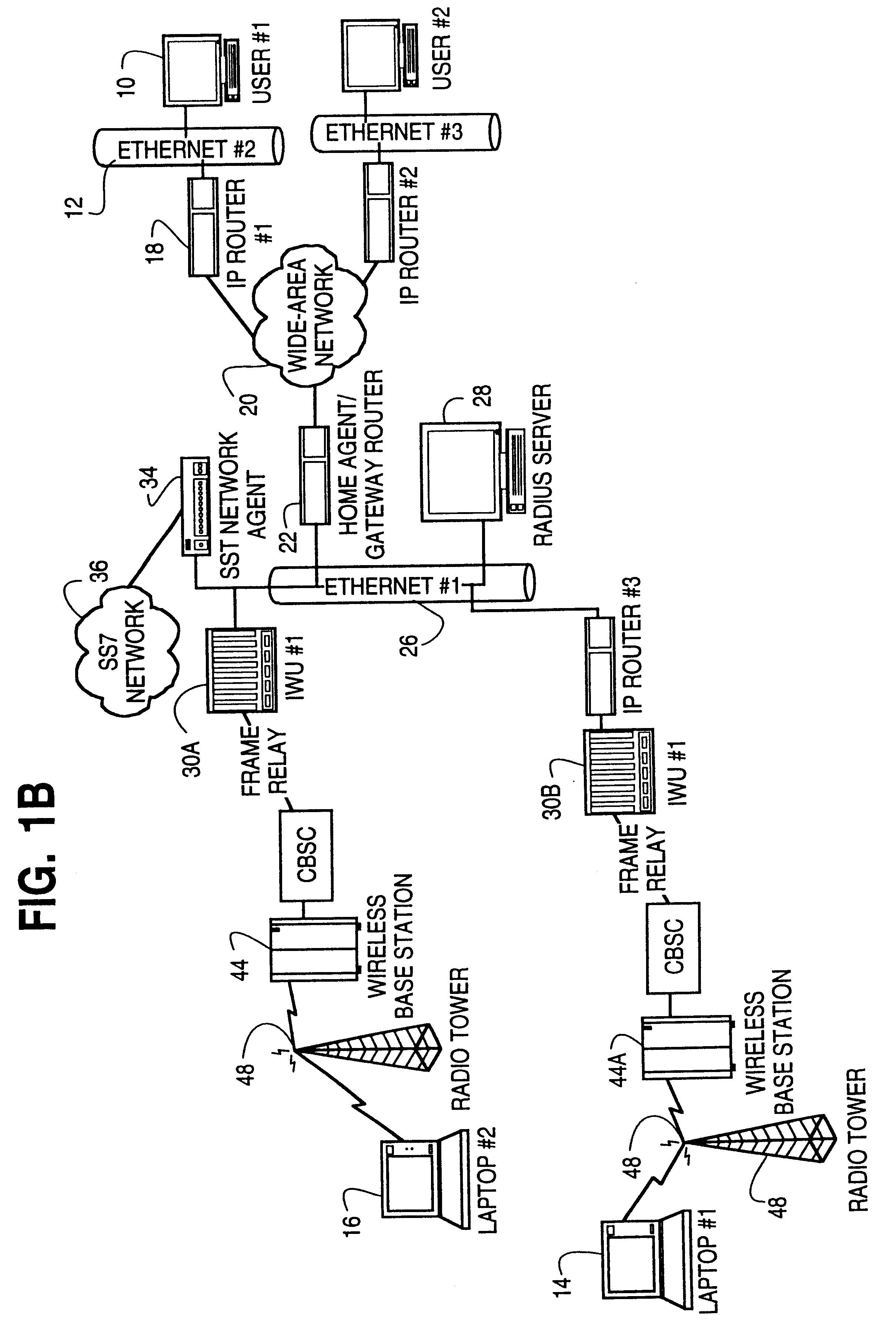
Dynamic allocation of wireless mobile nodes over an internet protocol (IP) network
InactiveUS6272129B1Data switching by path configurationWireless network protocolsTTEthernetIp address
A method is described of automatically locating and connecting a mobile wireless communications device to a packet-switched network such as the Internet. An Internet Protocol (IP) packet from a terminal on the network, destined for receipt by the mobile device, is received at a home agent acting as a gateway or router linking the packet switched network to a second network, such as LAN, coupled to a wireless communications network. The home agent transmits an access-request message to an authentication server. The access-request message includes a destination IP address associated with the mobile device found in the IP packet. The authentication server responsively issues an access-accept message to the home agent if the mobile device is authorized to receive the IP packet. The access-accept message comprises (a) information uniquely identifying said device, such as the IMSI / ESN number for the device, and (b) information identifying a network to use to locate said device. The home agent issues a message containing the information uniquely identifying the device to a mobile node location server. The mobile node location server maintains a table mapping IP addresses for a plurality of mobile communication devices to information uniquely identifying the devices. In the event that the mobile node location server does not find an IP address for the device in the table, the device is paged via the wireless communications network. In response to the page, the mobile device dials into the wireless communications network and second network and initiates a connection to the packet switched network whereby the IP packet is transmitted to the device.
Owner:UTSTARCOM INC
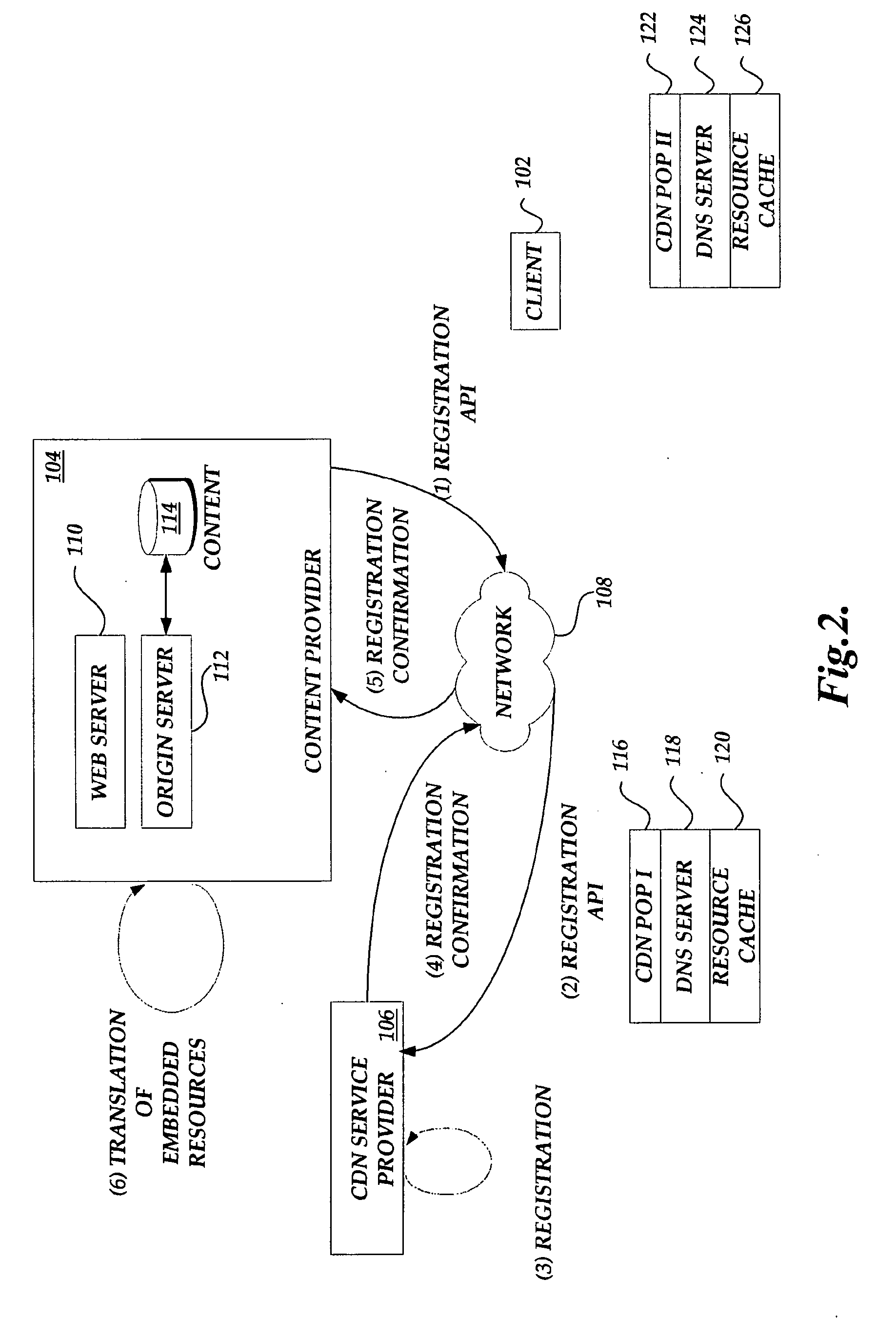
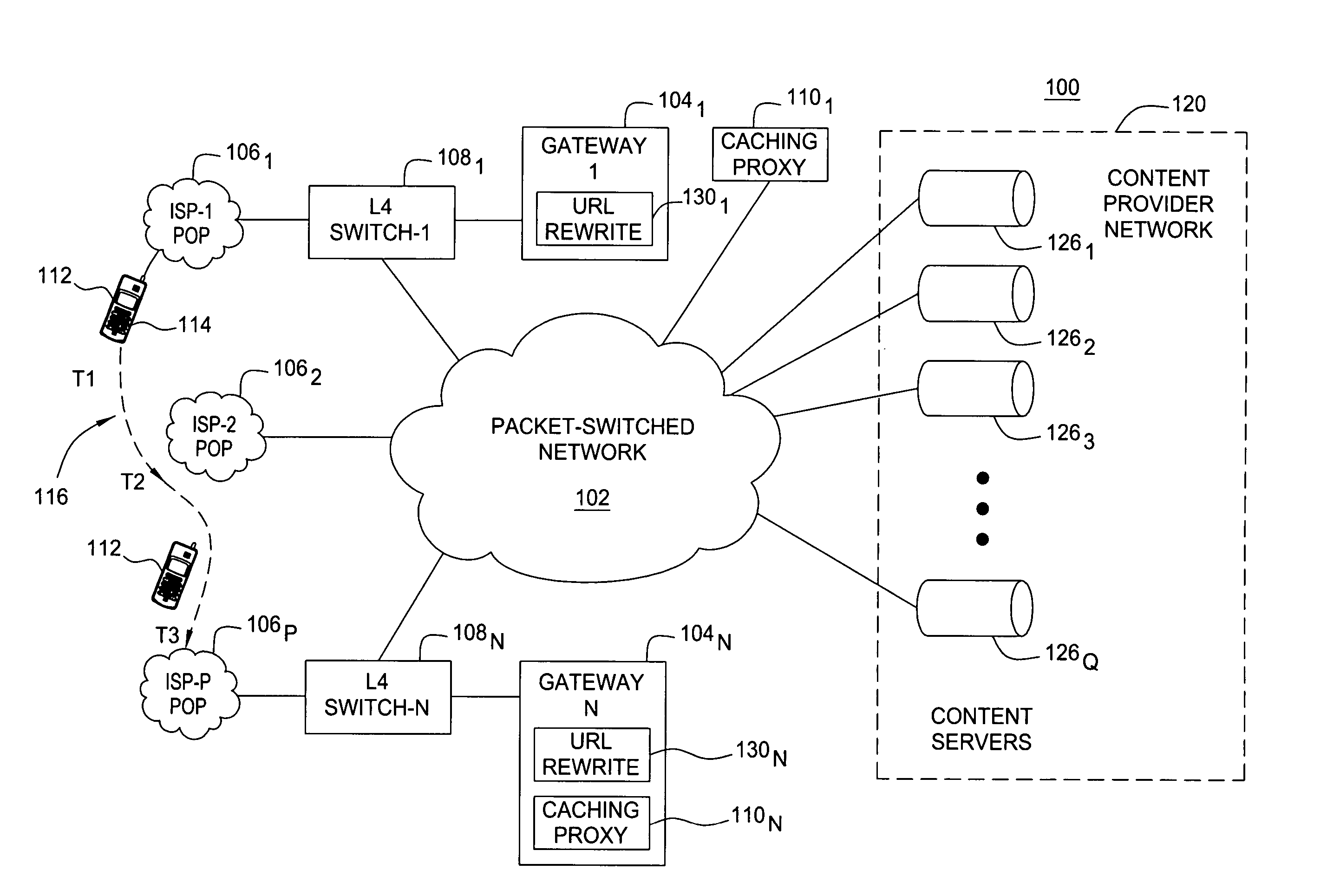
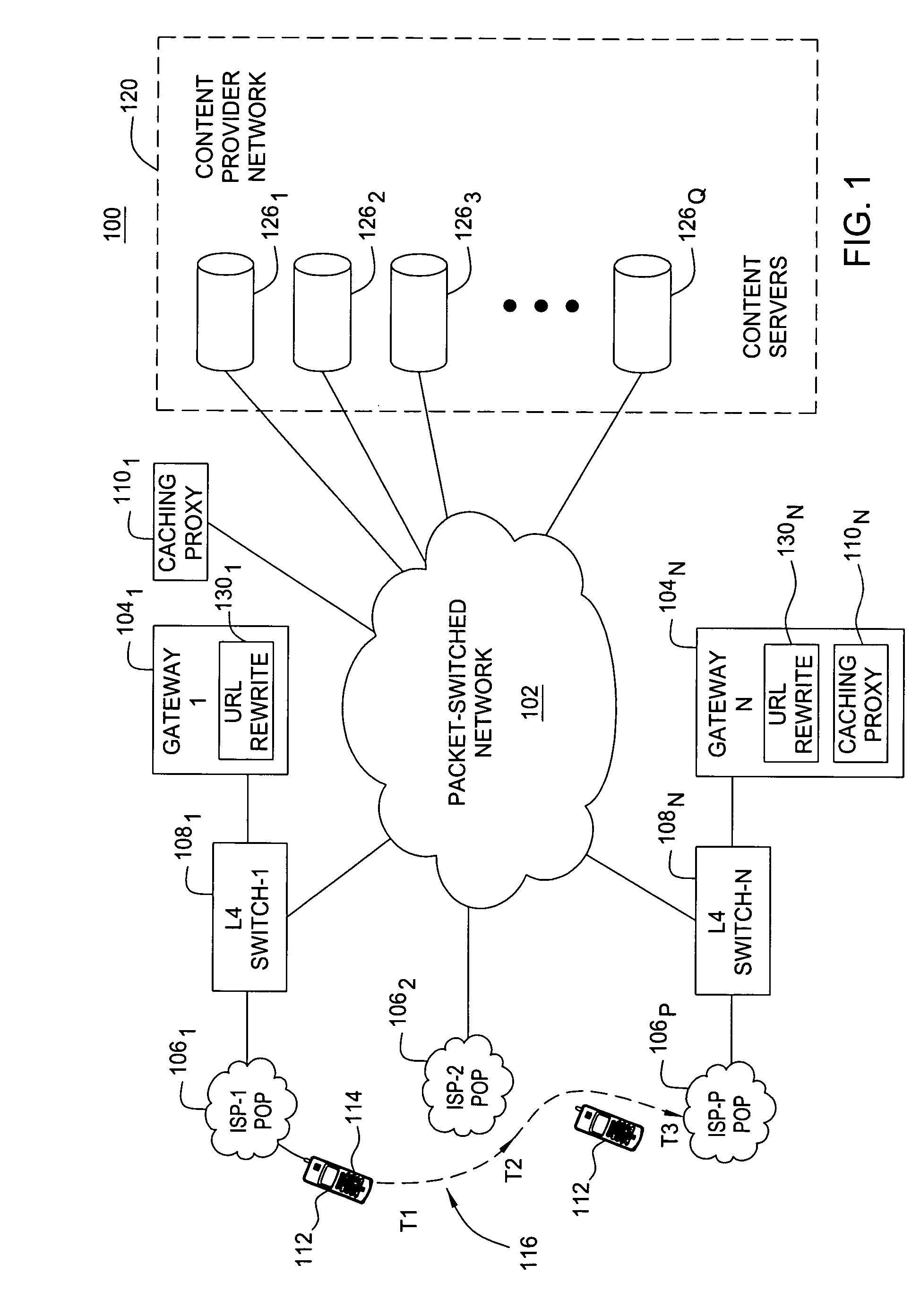
Session level technique for improving web browsing performance on low speed links
ActiveUS20060218304A1Digital data information retrievalSpecial service for subscribersLow speedIp address
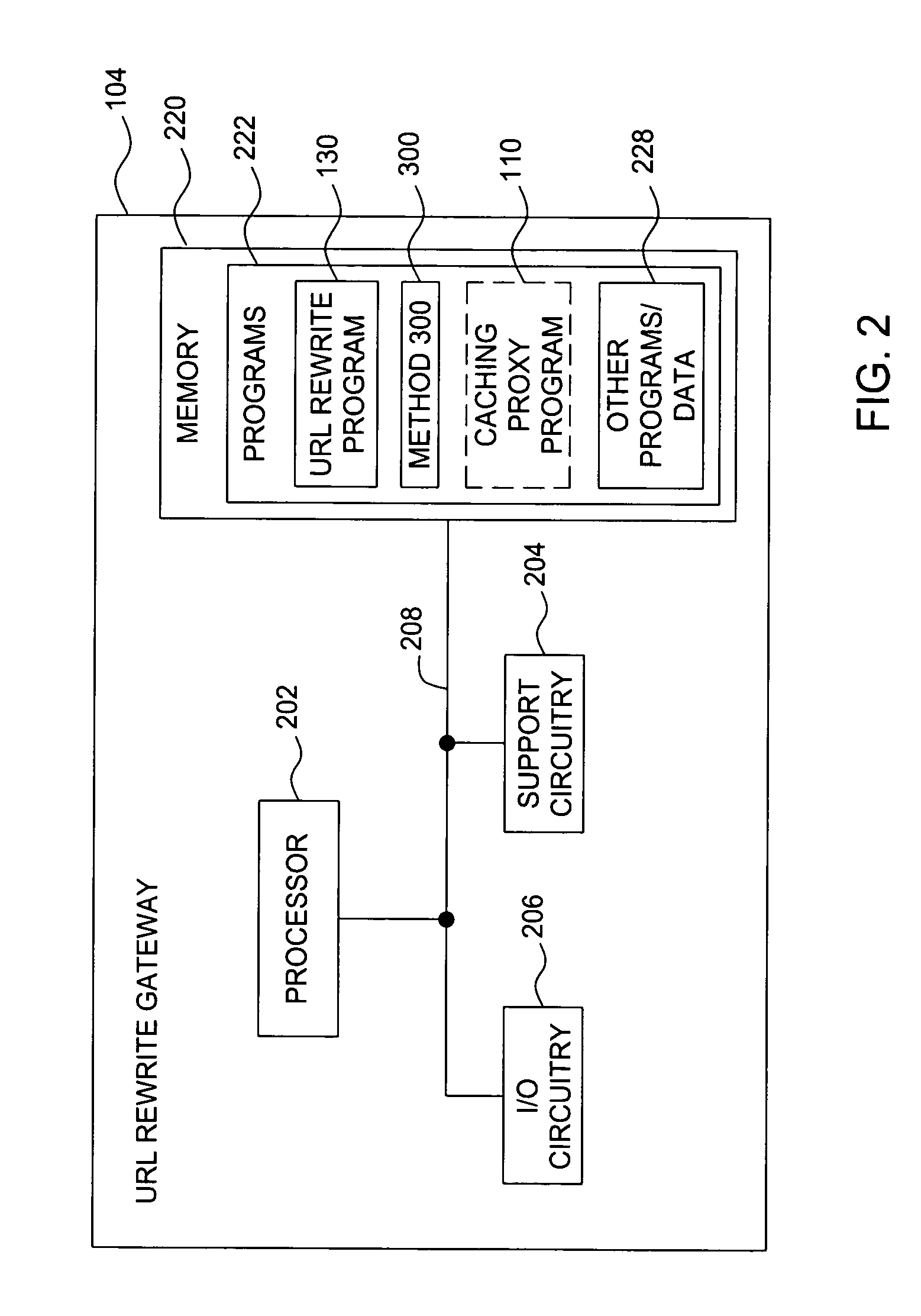
A method and apparatus for retrieving embedded objects of a web page across links. The method and apparatus include receiving, at a gateway, a requested top-level web page having at least one embedded uniform resource locator (URL) from at least one content server in response to a request for the web page from an end-user browser. The at least one embedded URL is modified with an IP address of a caching proxy. The caching proxy may be either co-located or separate from the gateway. The top-level web page and modified embedded URLs are sent to the end-user browser, wherein the caching proxy forwards the at least one embedded URL from the at least one content server to the end-user browser.
Owner:SOUND VIEW INNOVATIONS
Layer 2 seamless site extension of enterprises in cloud computing
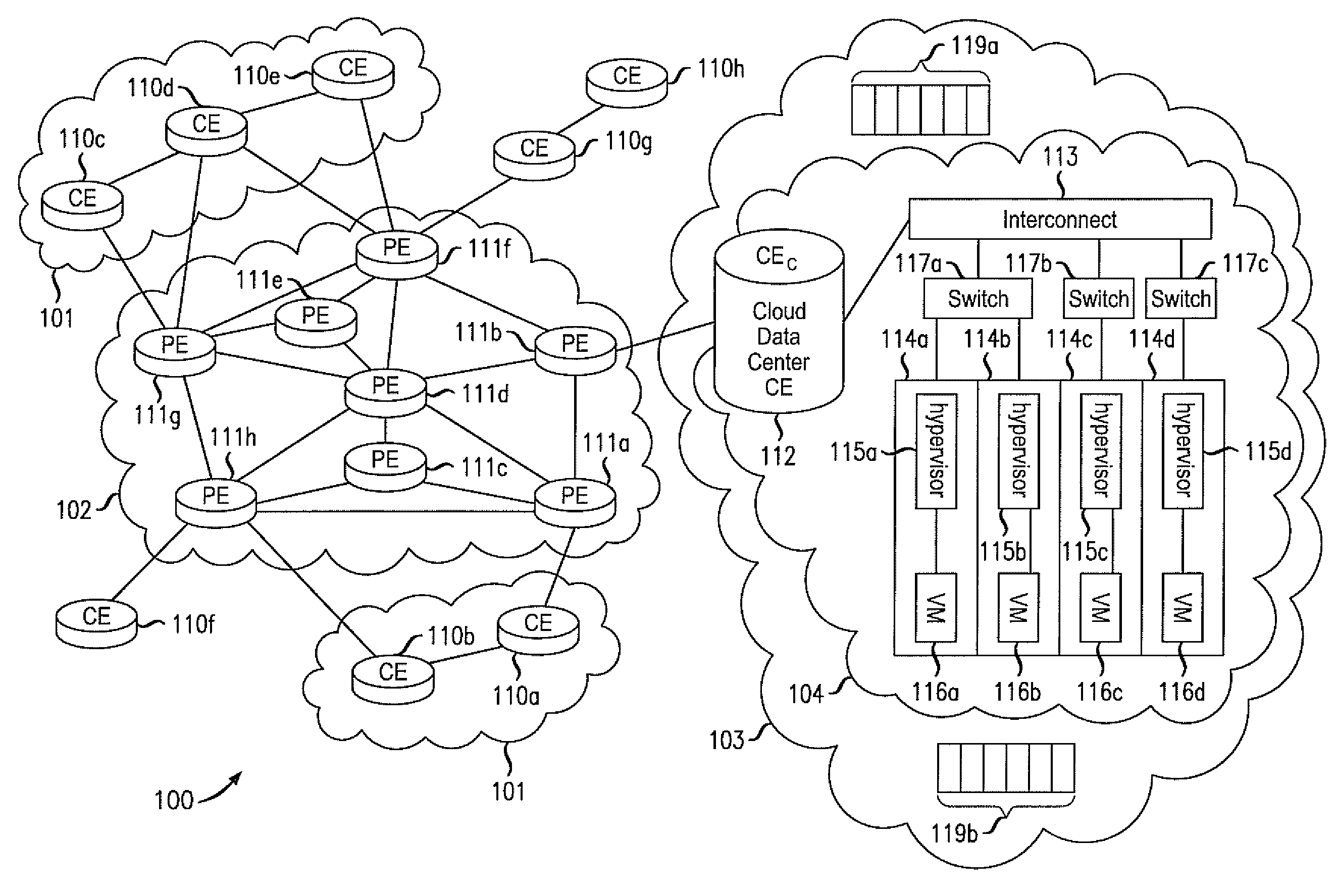
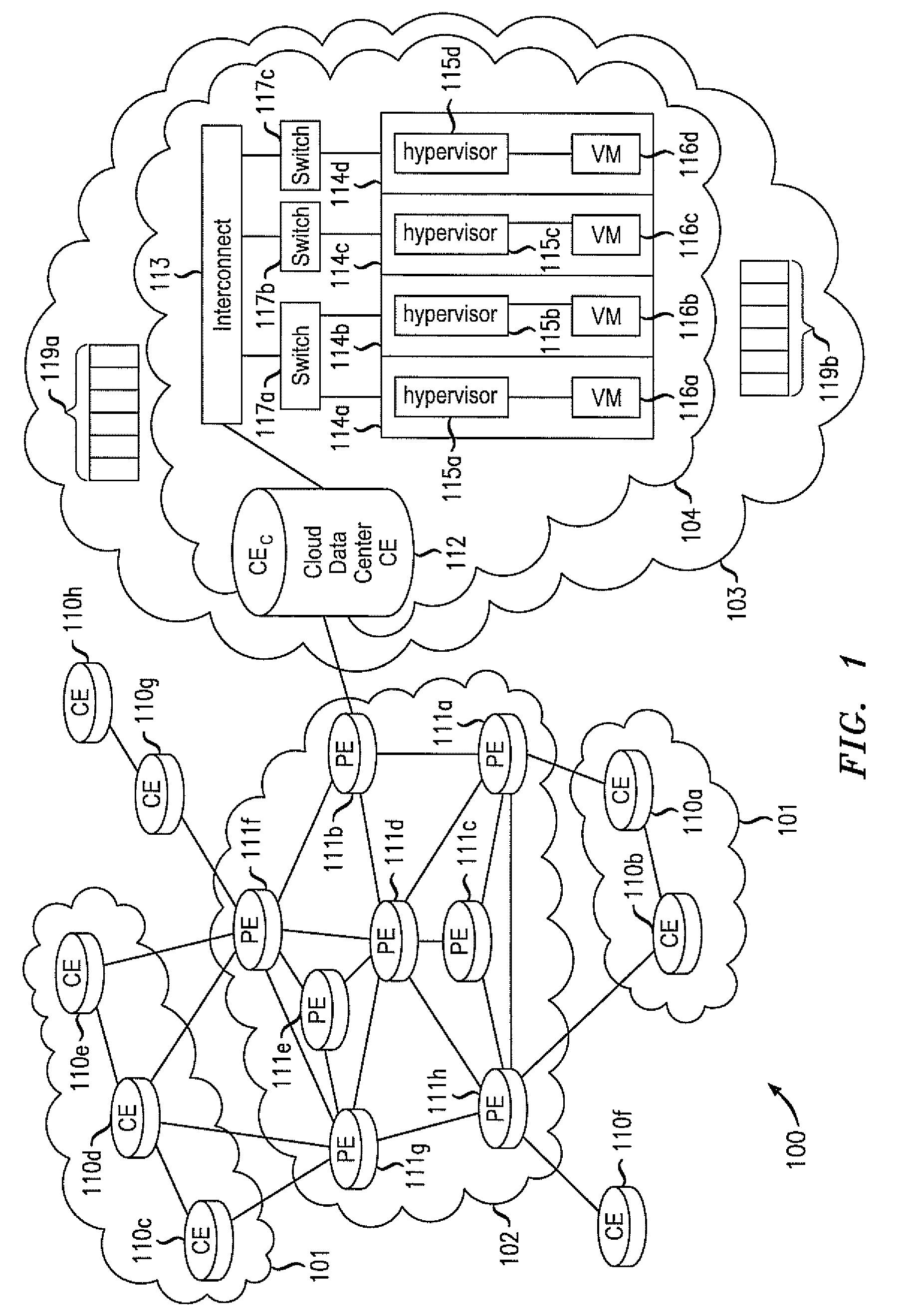
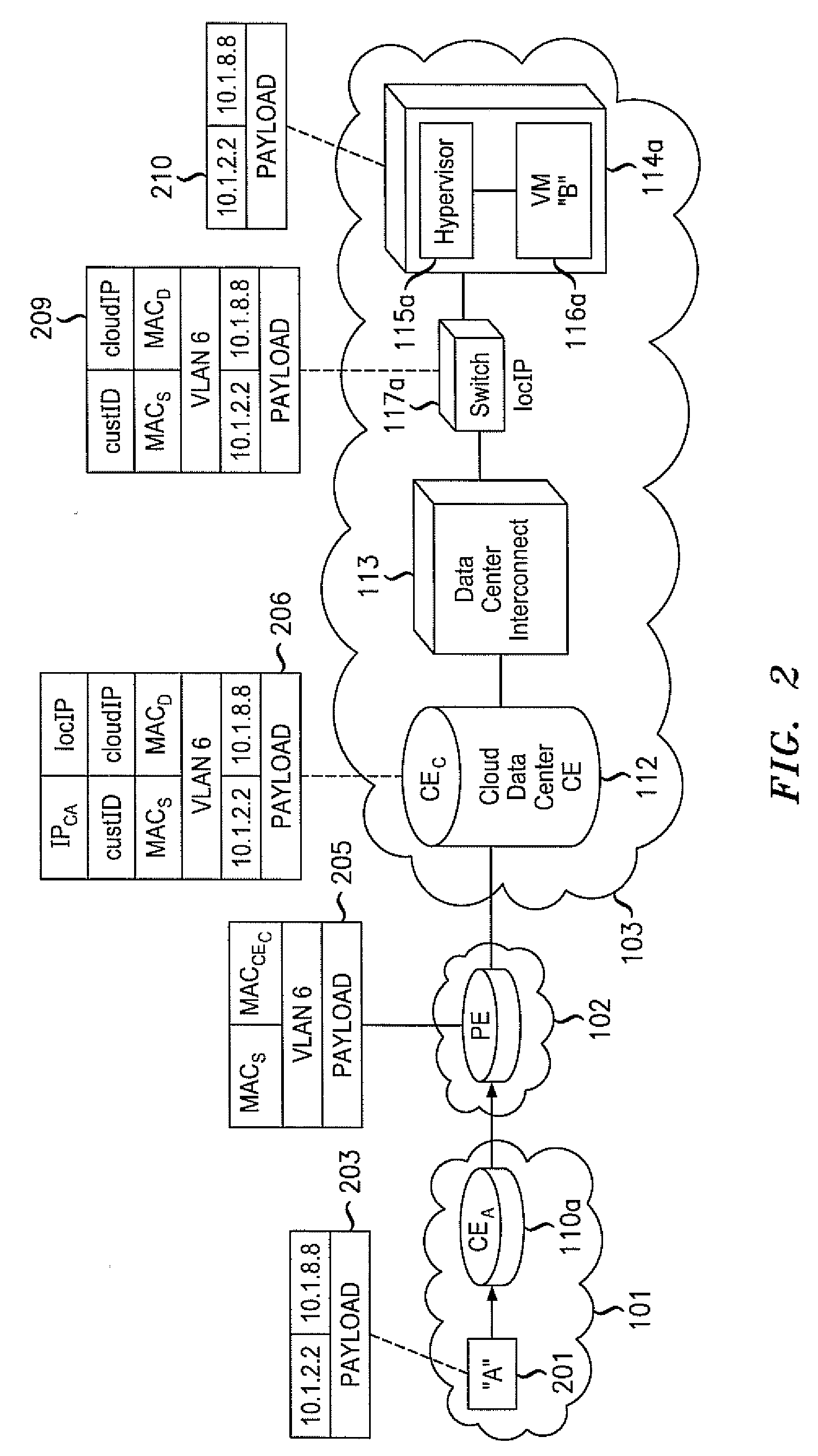
ActiveUS20110075667A1Ensure safetyHighly-dynamic scalability of cloud resourcesMultiple digital computer combinationsNetworks interconnectionNetwork packetIp address
Various embodiments relate to a Cloud Data Center, a system comprising the Cloud Data Center, and a related method. The Cloud Data Center may include a logical customer edge router to send packets between addresses in a private enterprise network and addresses in a logical network within a cloud network using Layer 2 protocol and MAC addressing. The logical network may have resources, known as virtual machines, allocated to the private enterprise network and may share a common IP address space with the private enterprise network. A directory at the Cloud Data Center may correlate the enterprise IP addresses of virtual machines with a MAC address, cloud IP address, and a location IP address within the logical network. The Cloud Data Center may double encapsulate packets with MAC, cloudIP, and locIP headers, when sending a packet to a destination in the logical network.
Owner:ALCATEL LUCENT SAS
Wide area network using internet with quality of service
InactiveUS7111163B1Reduces monthly costQuality improvementDigital data processing detailsMultiple digital computer combinationsQuality of serviceTTEthernet
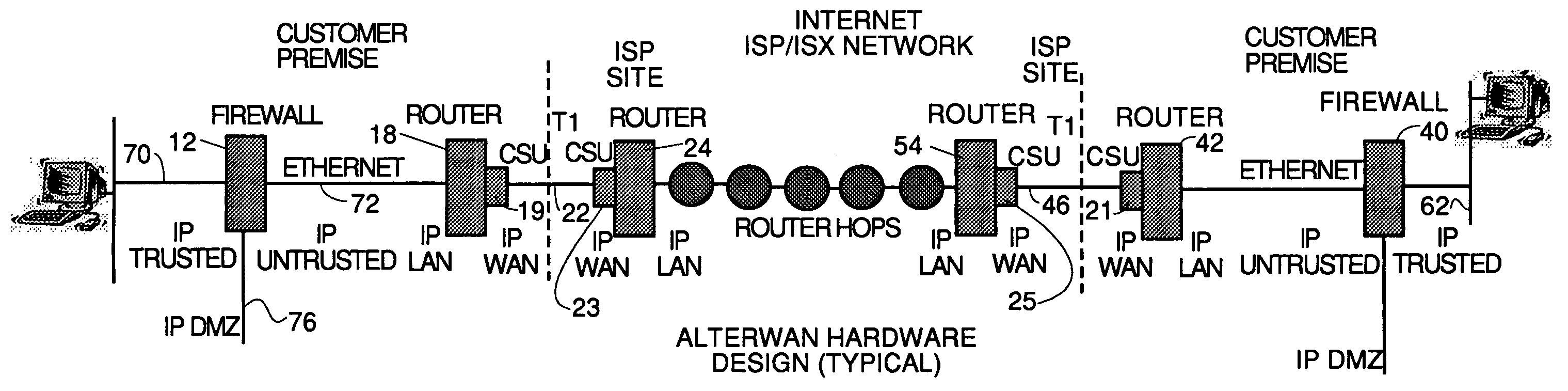
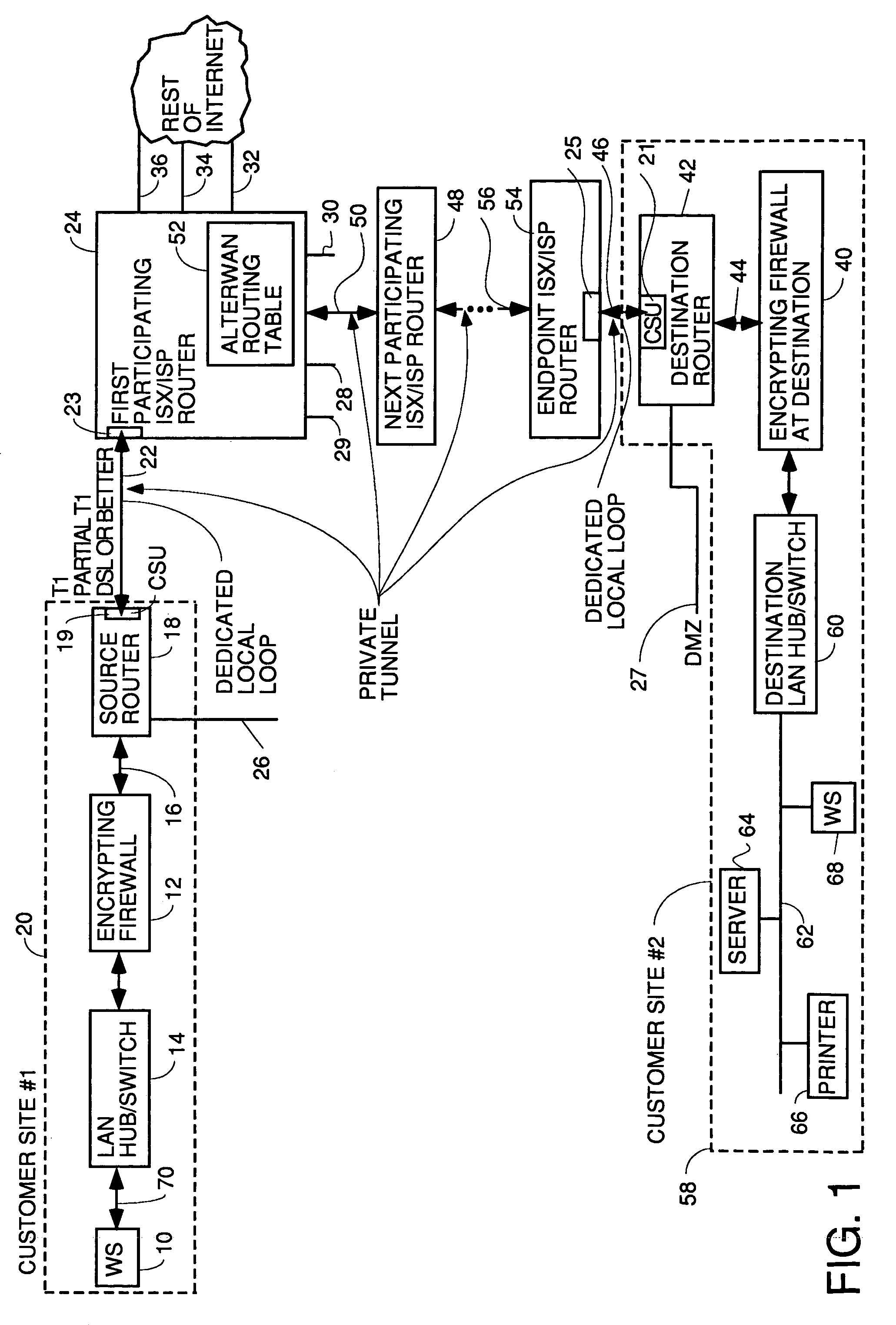
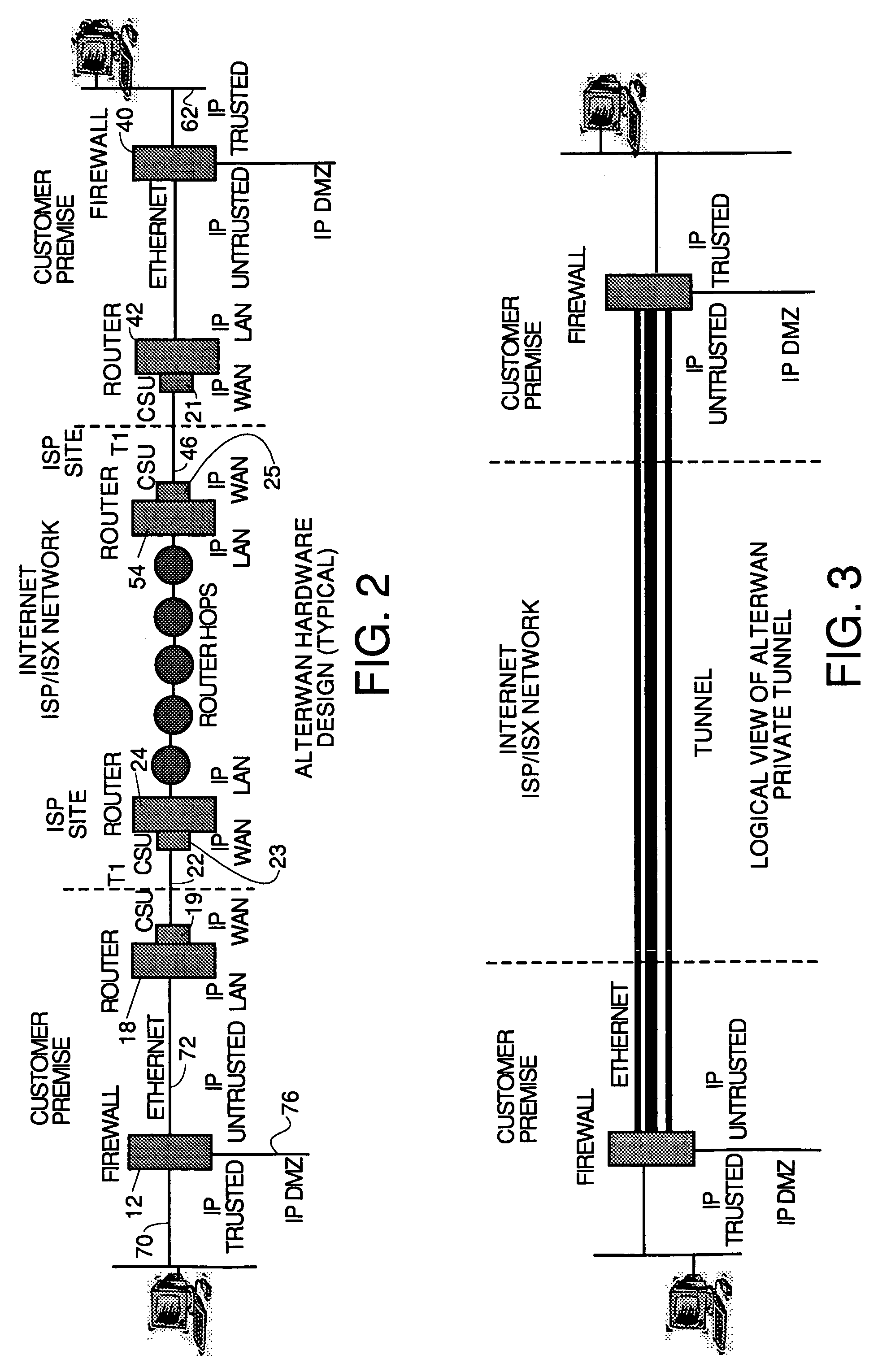
A wide area network using the internet as a backbone utilizing specially selected ISX / ISP providers whose routers route AlterWAN packets of said wide area network along private tunnels through the internet comprised of high bandwidth, low hop-count data paths. Firewalls are provided at each end of each private tunnel which recognize IP packets addressed to devices at the other end of the tunnel and encapsulate these packets in other IP packets which have a header which includes as the destination address, the IP address of the untrusted side of the firewall at the other end of the tunnel. The payload sections of these packets are the original IP packets and are encrypted and decrypted at both ends of the private tunnel using the same encryption algorithm using the same key or keys.
Owner:ALTERWAN
Global server load balancing
A global server load balancing (GSLB) switch serves as a proxy to an authoritative DNS communicates with numerous site switches which are coupled to host servers serving specific applications. The GSLB switch receives from site switches operational information regarding host servers within the site switches neighborhood. When a client program requests a resolution of a host name, the GSLB switch, acting as a proxy of an authoritative DNS, returns one or more ordered IP addresses for the host name. The IP addresses are ordered using metrics that include the information collected from the site switches. In one instance, the GSLB switch places the address that is deemed “best” at the top of the list.
Owner:AVAGO TECH INT SALES PTE LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com