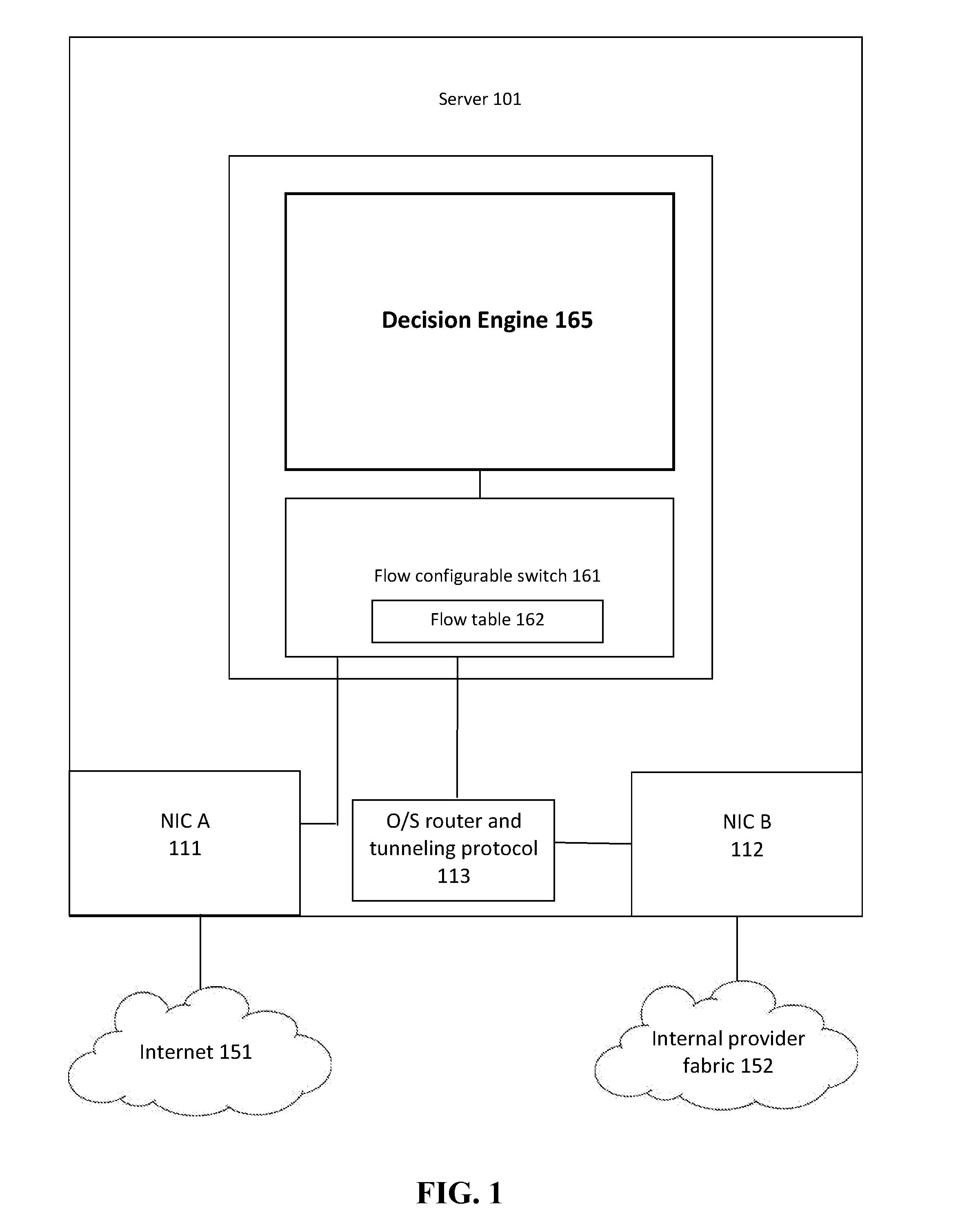
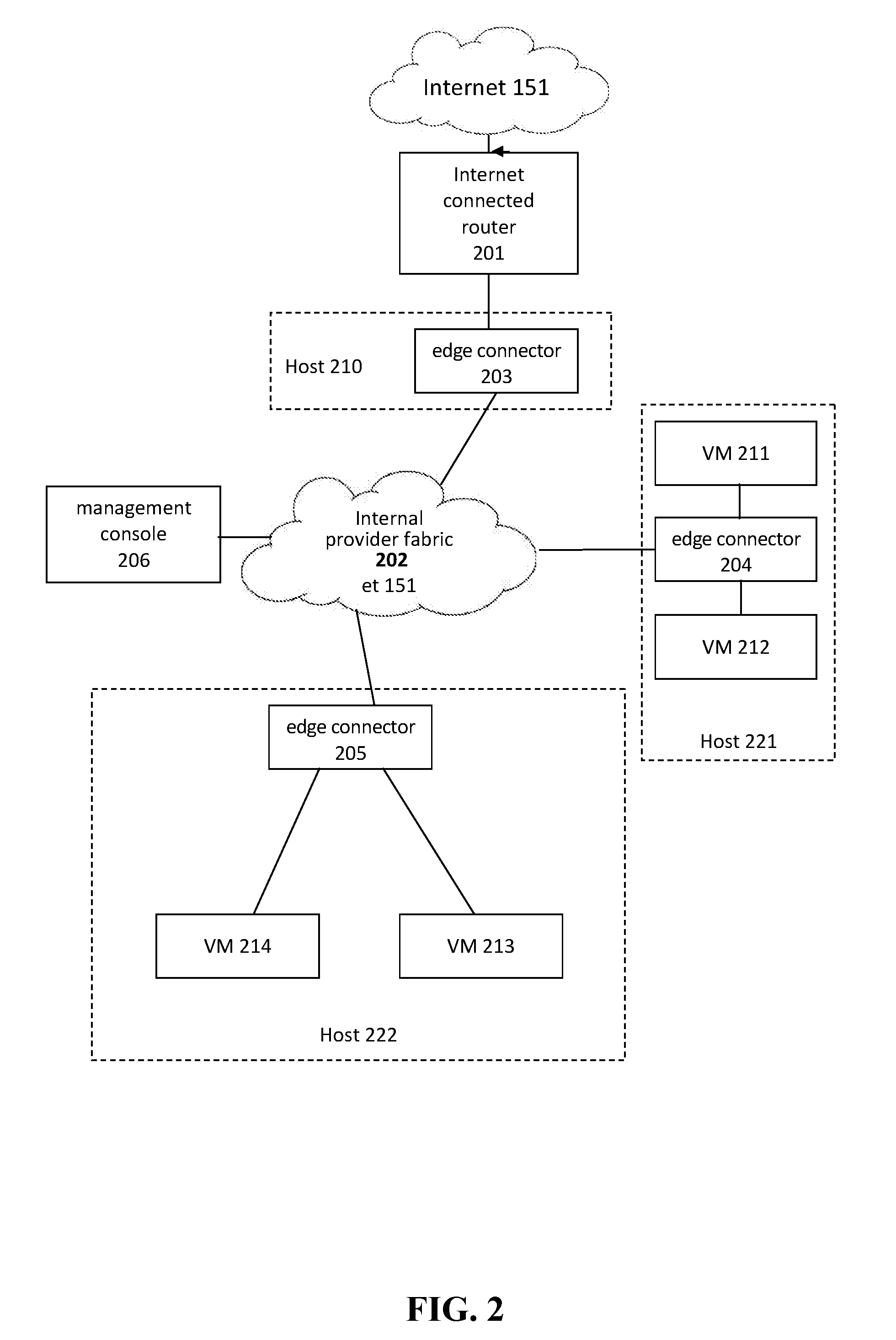
Patents
Literature
4407 results about "Virtual network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
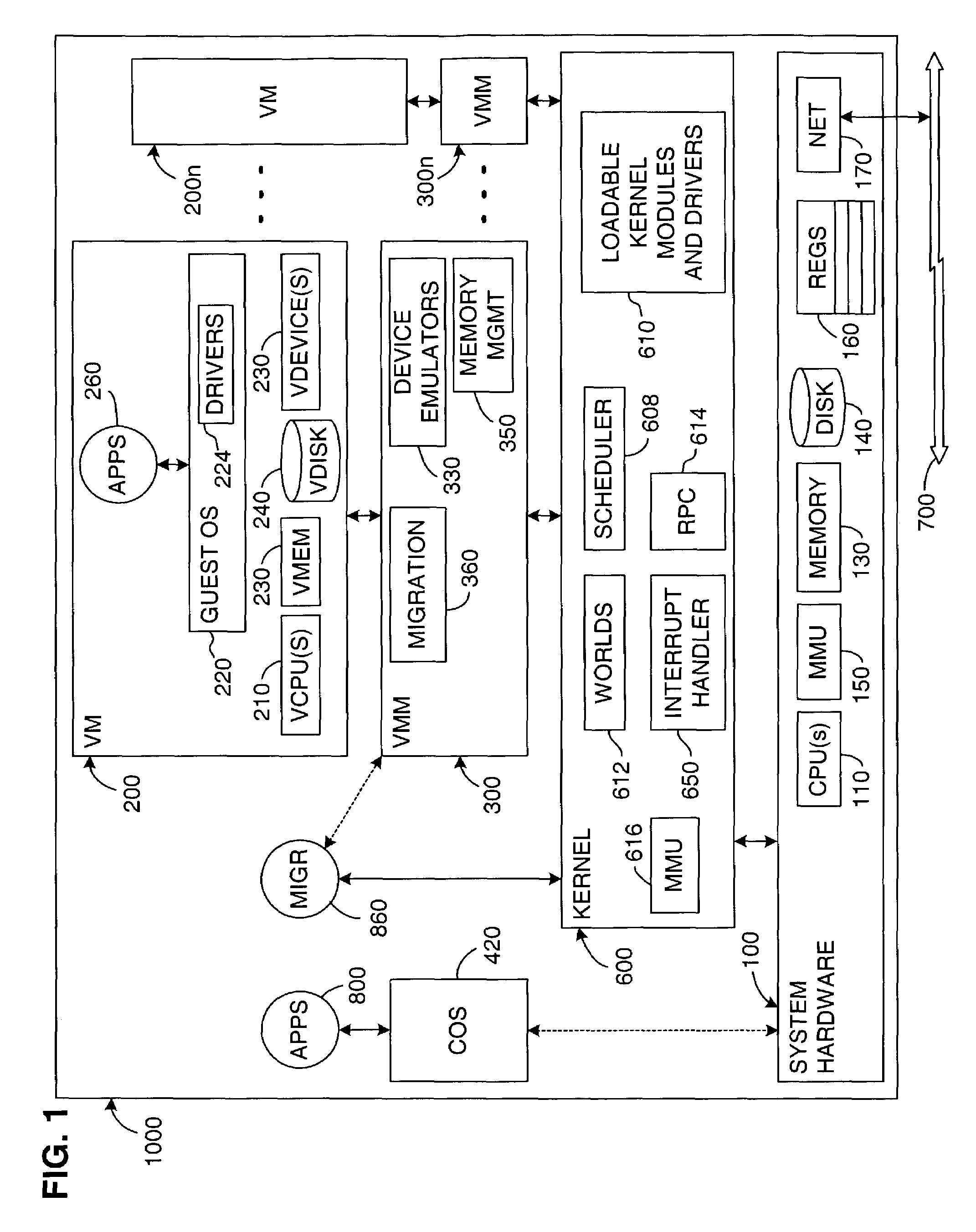
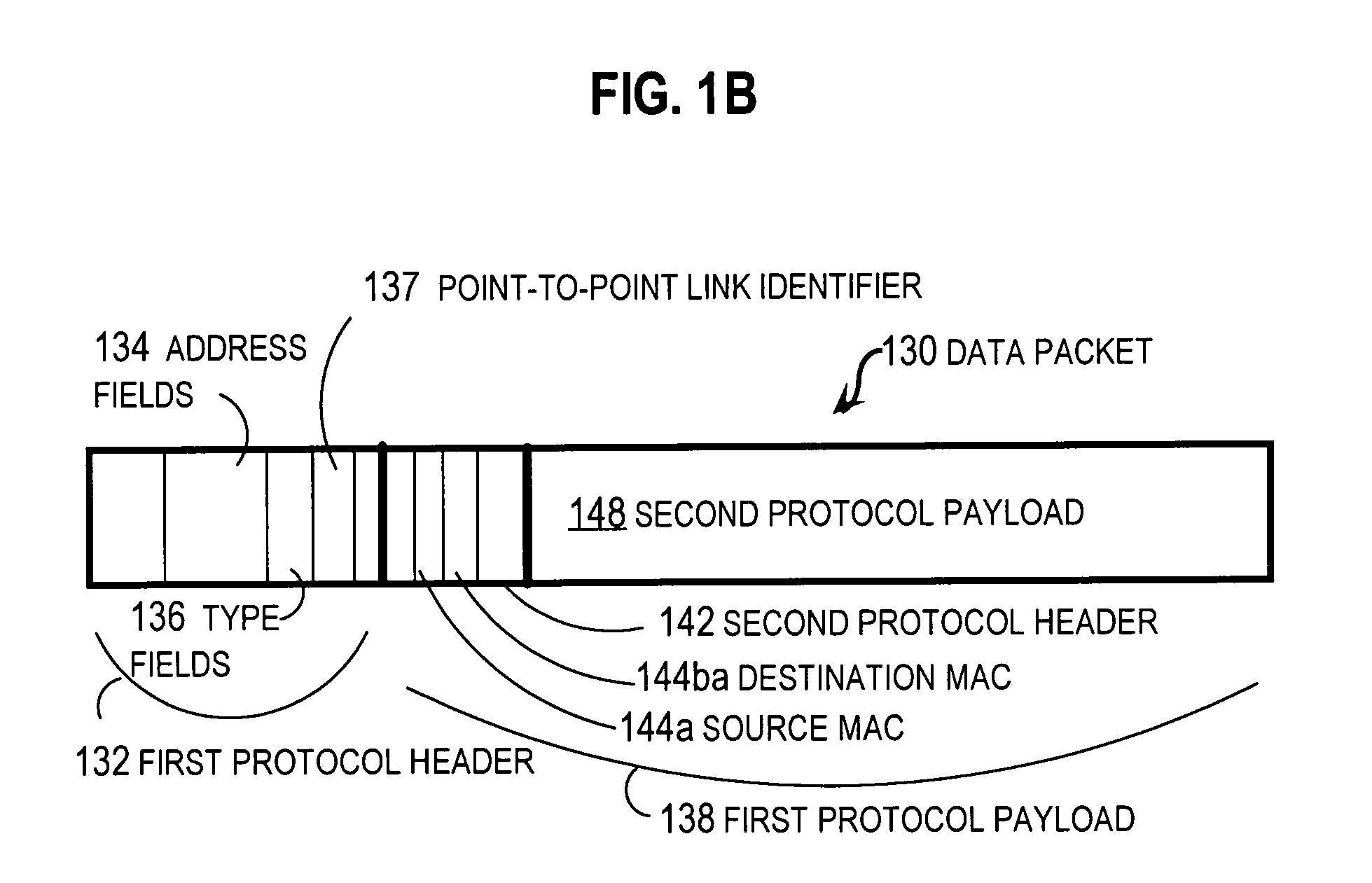
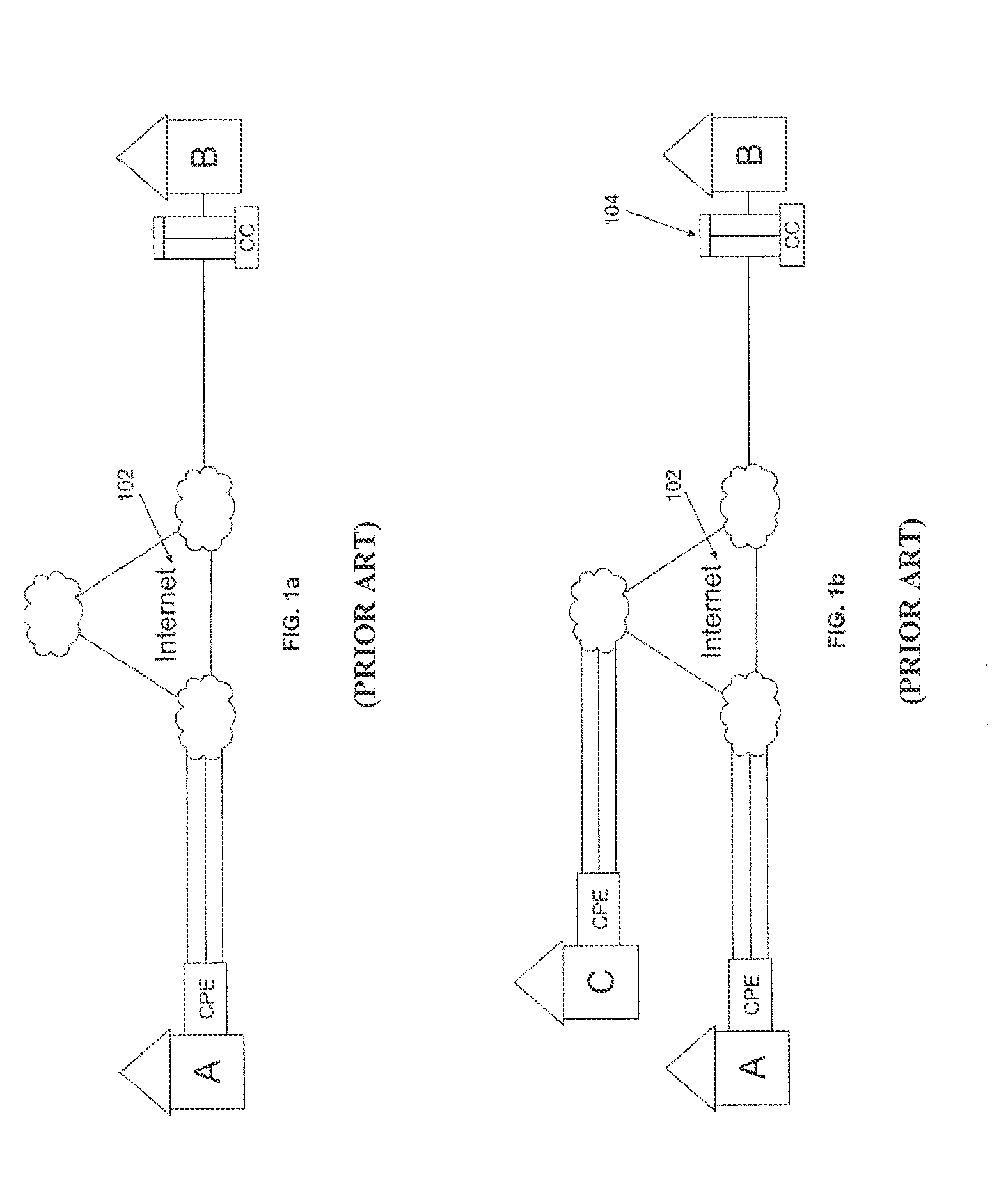
A virtual network is a computer network that consists, at least in part, of virtual network links. A virtual network link is a link that does not consist of a physical connection between two computing devices but is implemented using methods of network virtualization. The two most common forms of network virtualization are protocol-based virtual networks, and virtual networks that are based on virtual devices. In practice, both forms can be used in conjunction. Virtual LANs are logical local area networks based on physical LANs. A VLAN can be created by partitioning a physical LAN into multiple logical LANs using a VLAN ID. Alternatively, several physical LANs can function as a single logical LAN. The partitioned network can be on a single router, or multiple VLAN's can be on multiple routers just as multiple physical LAN's would be. A VLAN can be on a VPN. A virtual private network consists of multiple remote end-points joined by some sort of tunnel over another network, usually a third party network. Two such end points constitute a 'Point to Point Virtual Private Network'. Connecting more than two end points by putting in place a mesh of tunnels creates a 'Multipoint VPN'.
Network consolidation for virtualized servers
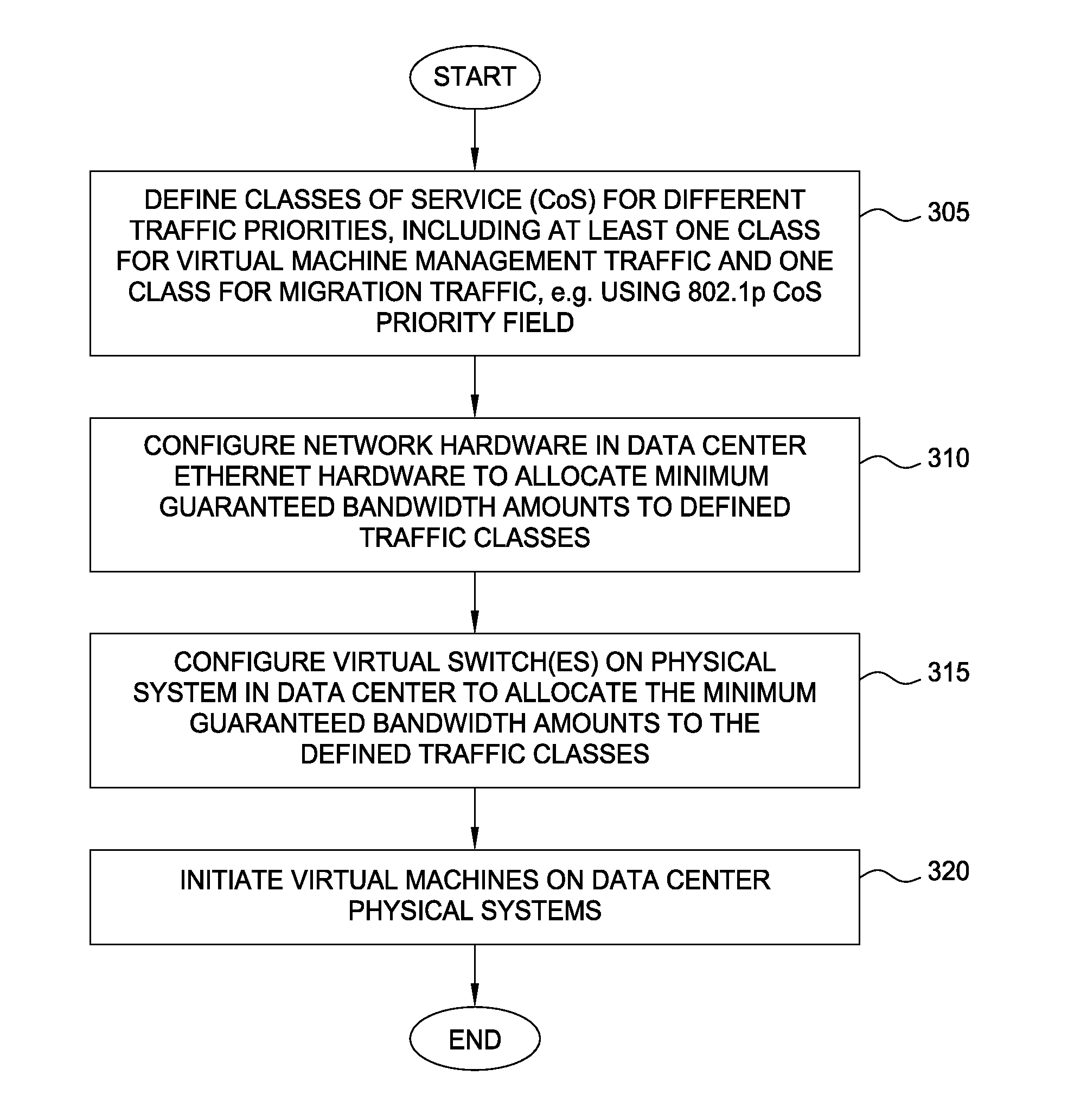
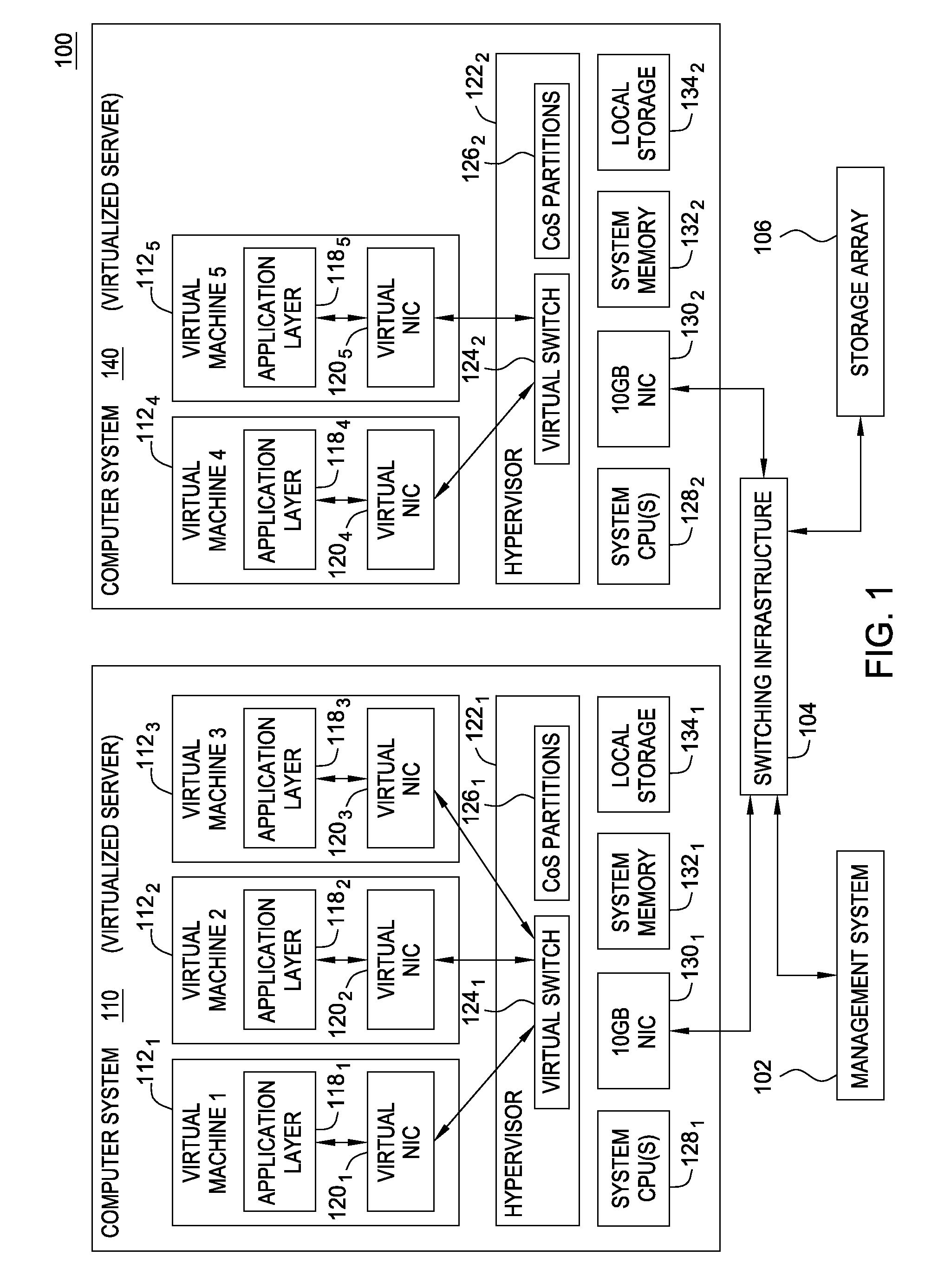
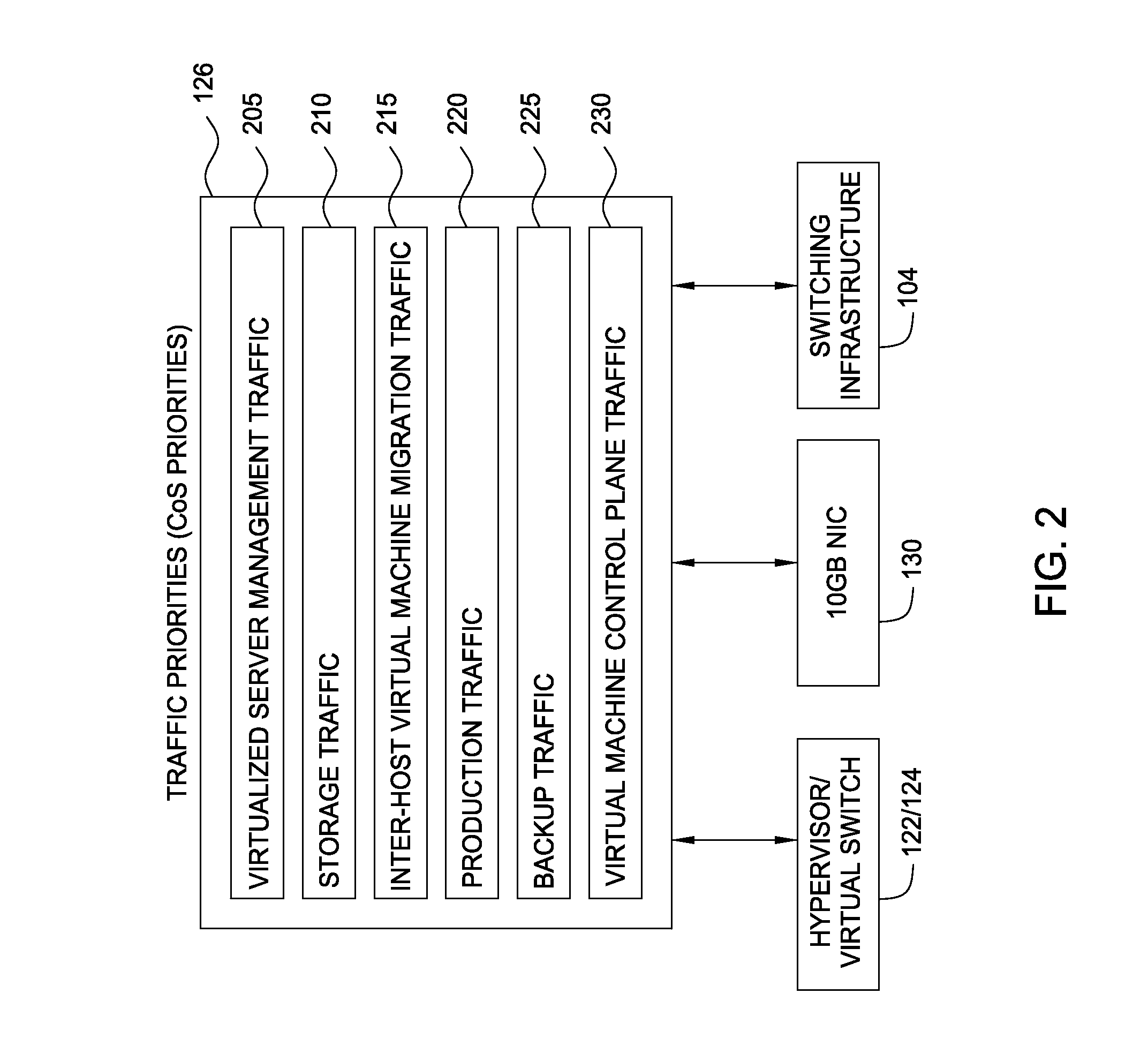
Techniques are disclosed for virtualized server kernel and virtual networks consolidation. The network consolidation allows a data center to migrate from an infrastructure that uses multiple dedicated gigabit Ethernet Network Adapters to manage system virtualization and migration to an infrastructure using consolidated, redundant, 10 gigabit Ethernet adapters. Different priority classes may be defined for different classes of network traffic such as hypervisor management traffic, inter-host virtual machine migration traffic, virtual machine production traffic, virtualized switching control plane traffic, etc. Further, an enhanced transmission standard may be used to specify a minimum bandwidth guarantee for certain traffic classes. Thus, the hypervisor management and inter-host virtual machine migration traffic may be transmitted, even the presence of congestion.
Owner:CISCO TECH INC
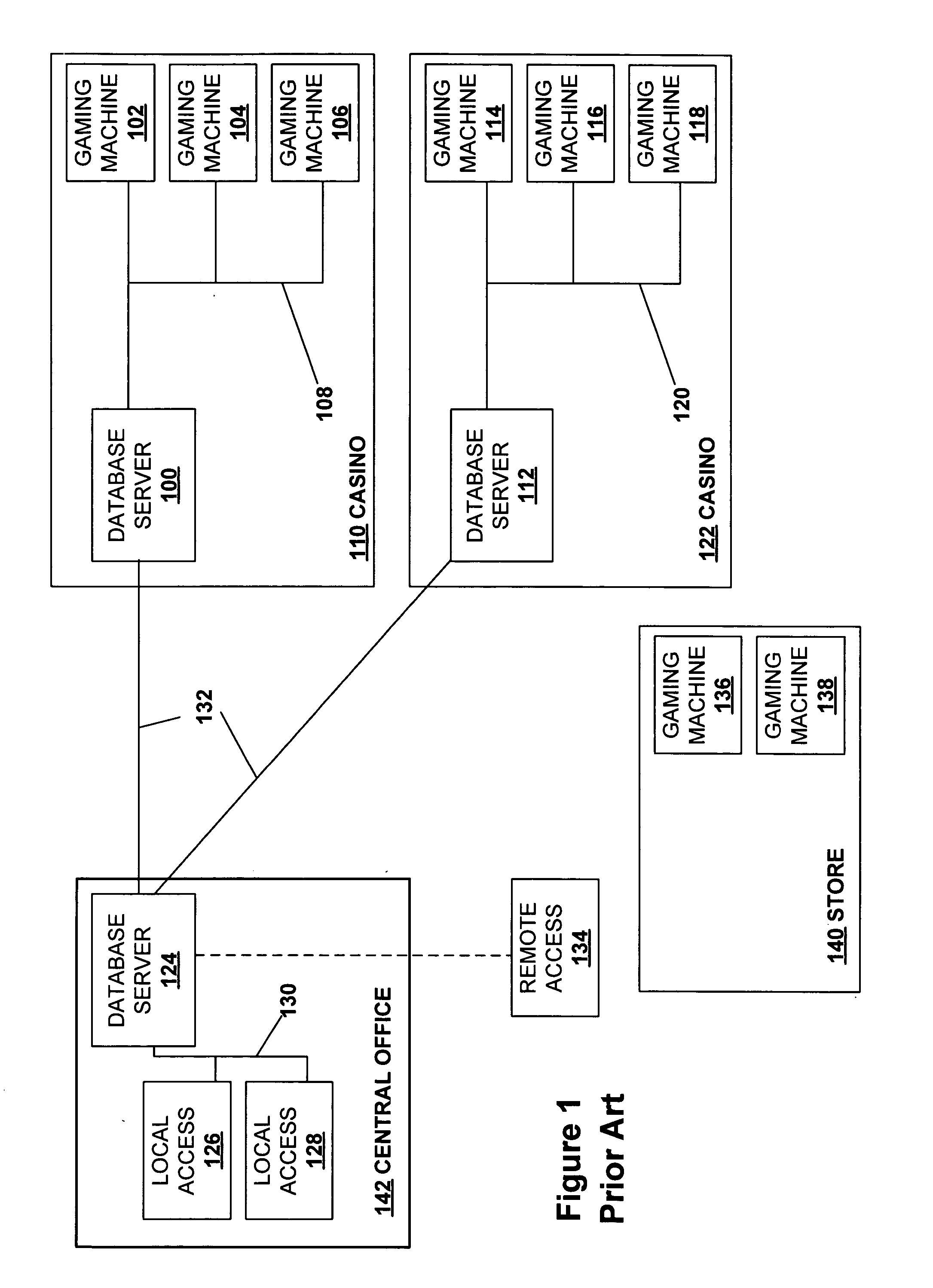
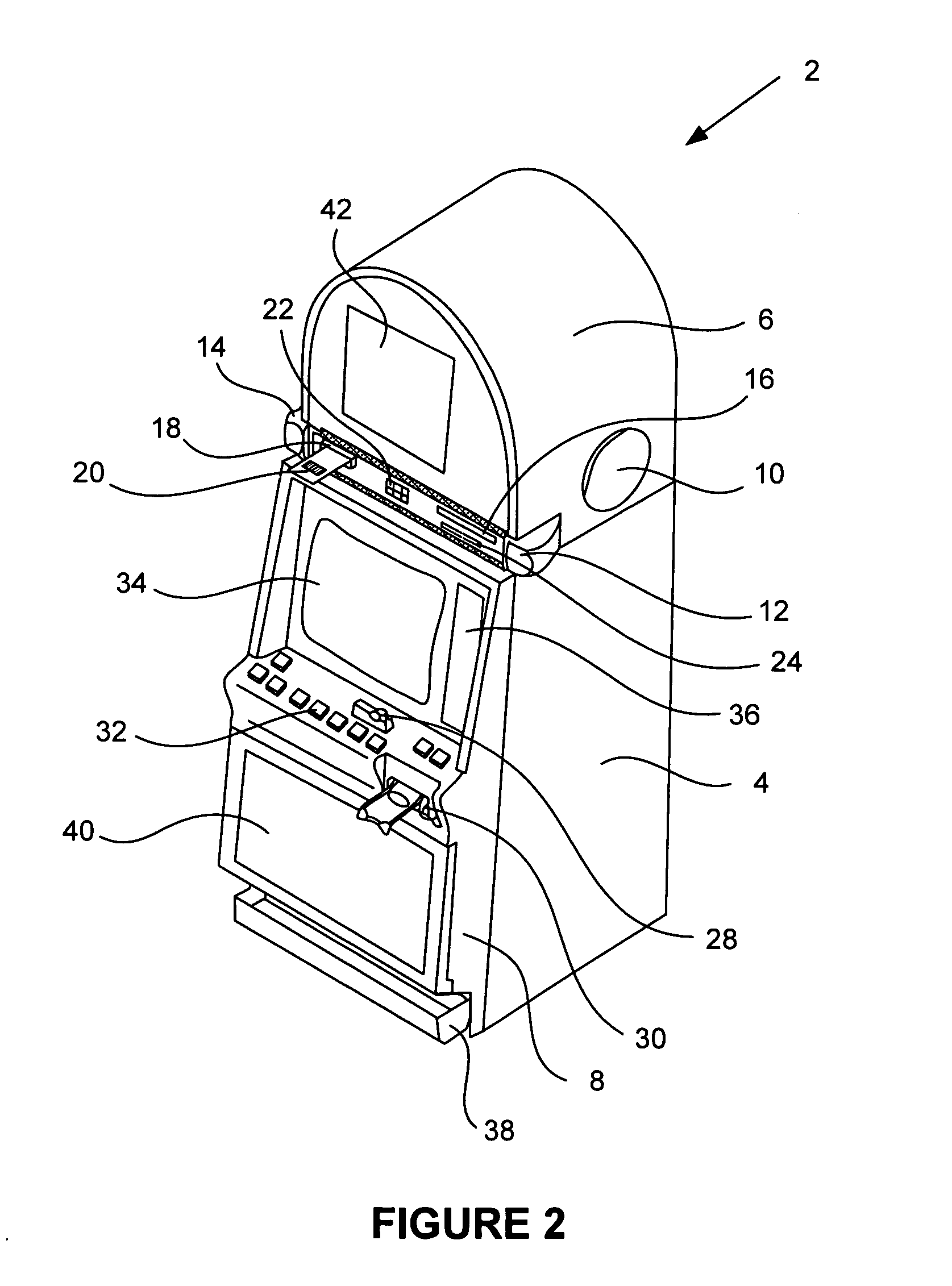
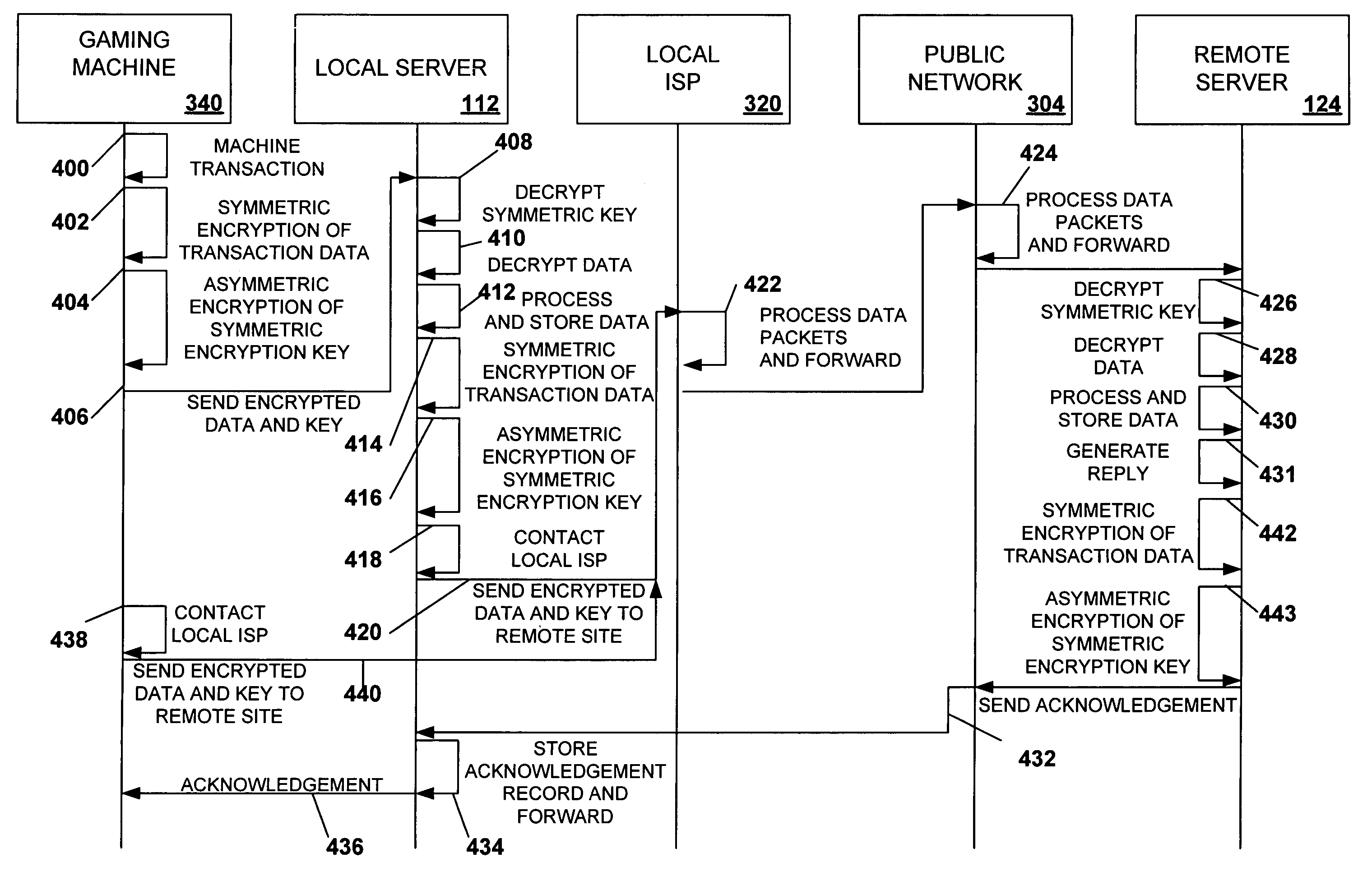
Secured virtual network in a gaming environment
InactiveUS20050192099A1Key distribution for secure communicationApparatus for meter-controlled dispensingSecure communicationThe Internet
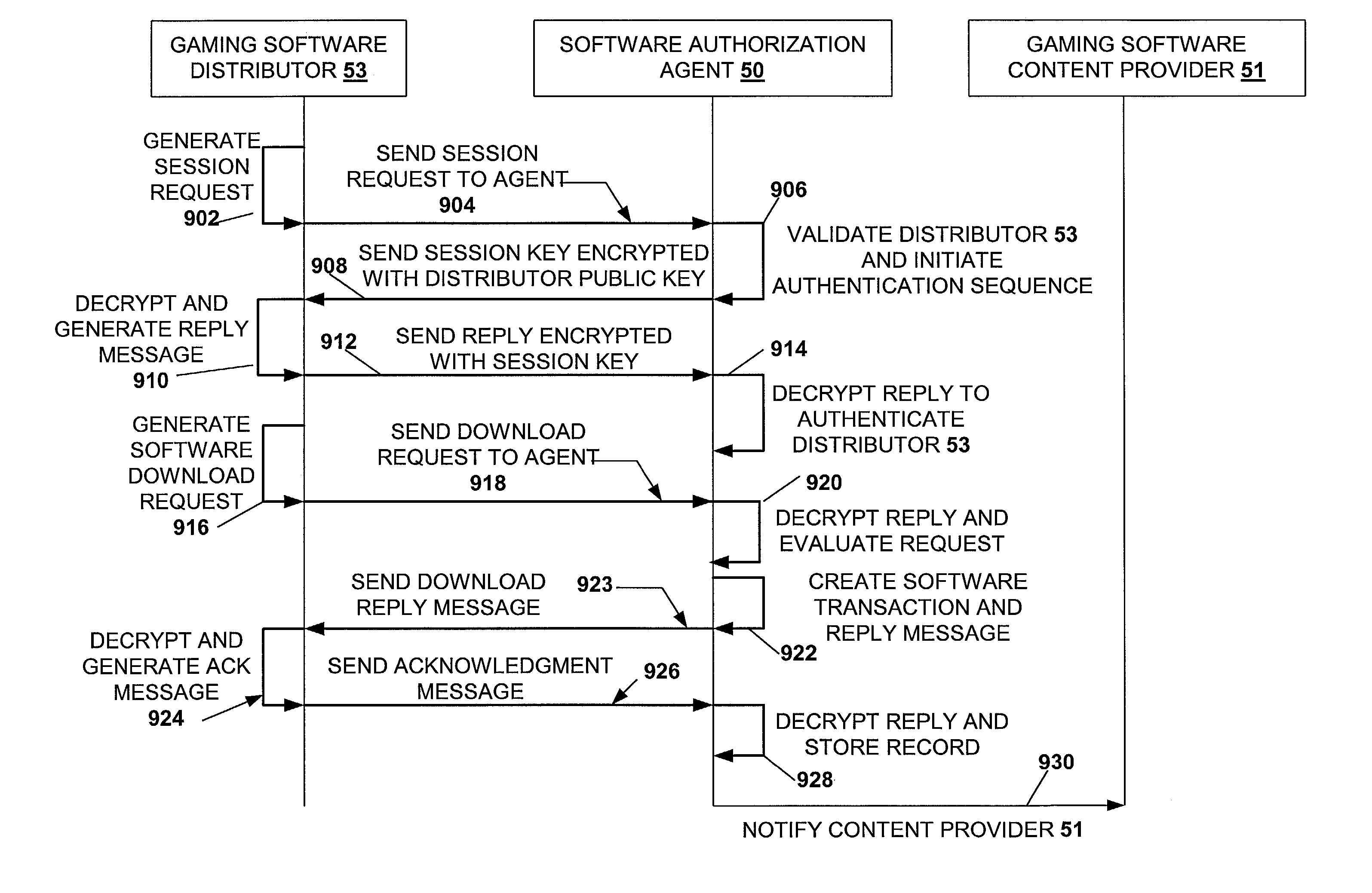
A disclosed gaming machine may securely communicate with devices over a public network such as the Internet. The gaming machine utilizes a combination of symmetric and asymmetric encryption that allows a single gaming machine to securely communicate with a remote server using a public network. The secure communication methods may be used to transfer gaming software and gaming information between two gaming devices, such as between a game server and a gaming machine. For regulatory and tracking purposes, the transfer of gaming software between the two gaming devices may be authorized and monitored by a software authorization agent.
Owner:IGT
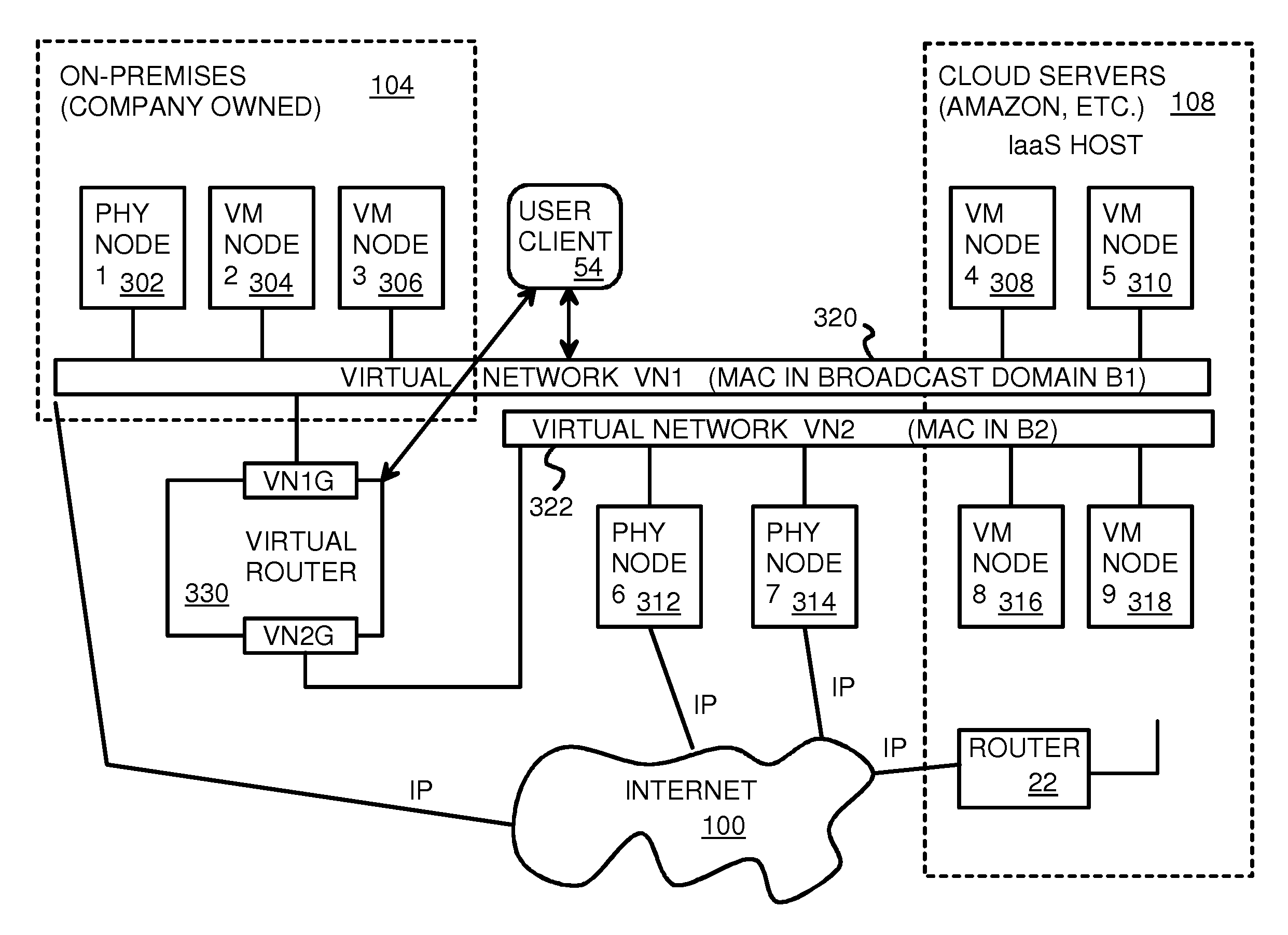
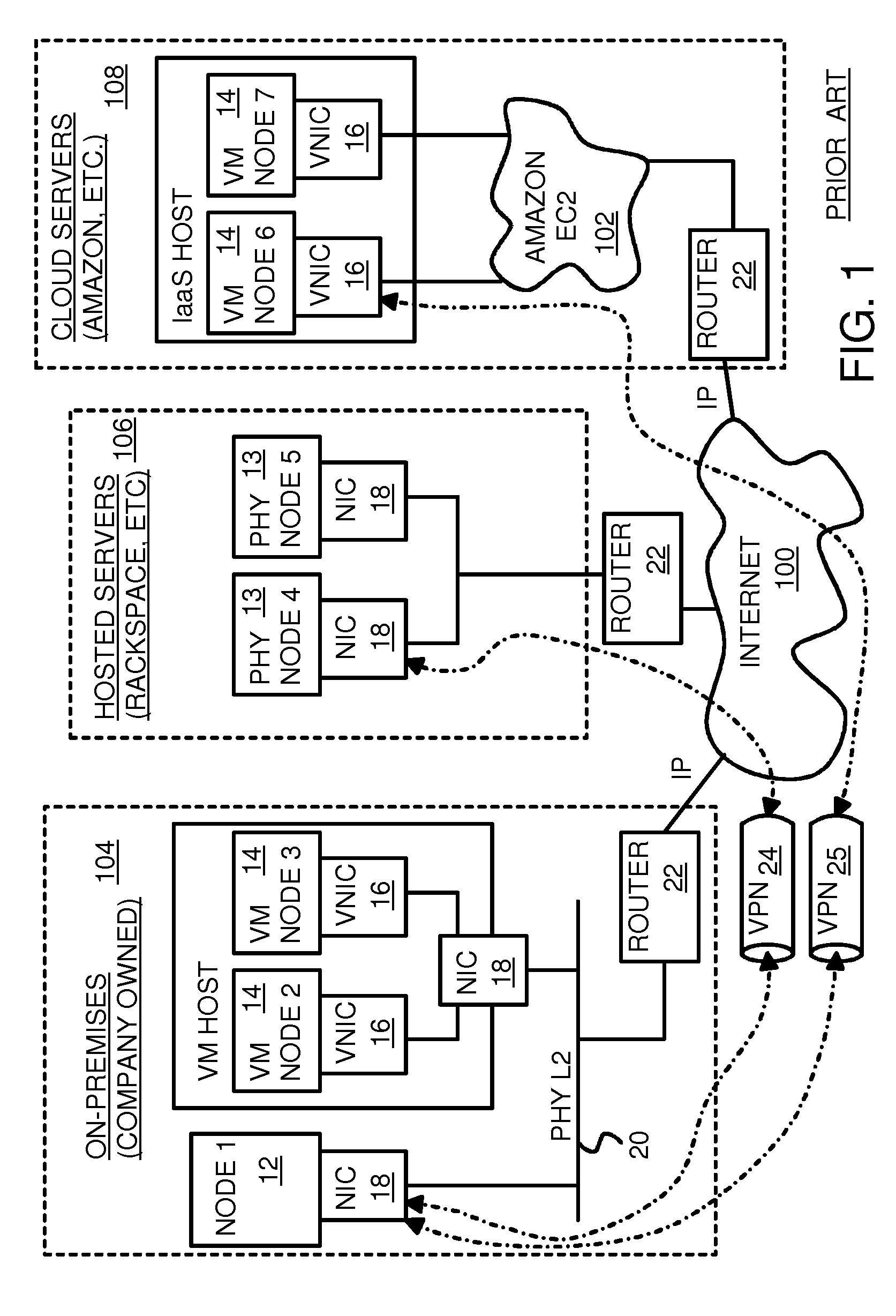
Fully distributed routing over a user-configured on-demand virtual network for infrastructure-as-a-service (IaaS) on hybrid cloud networks
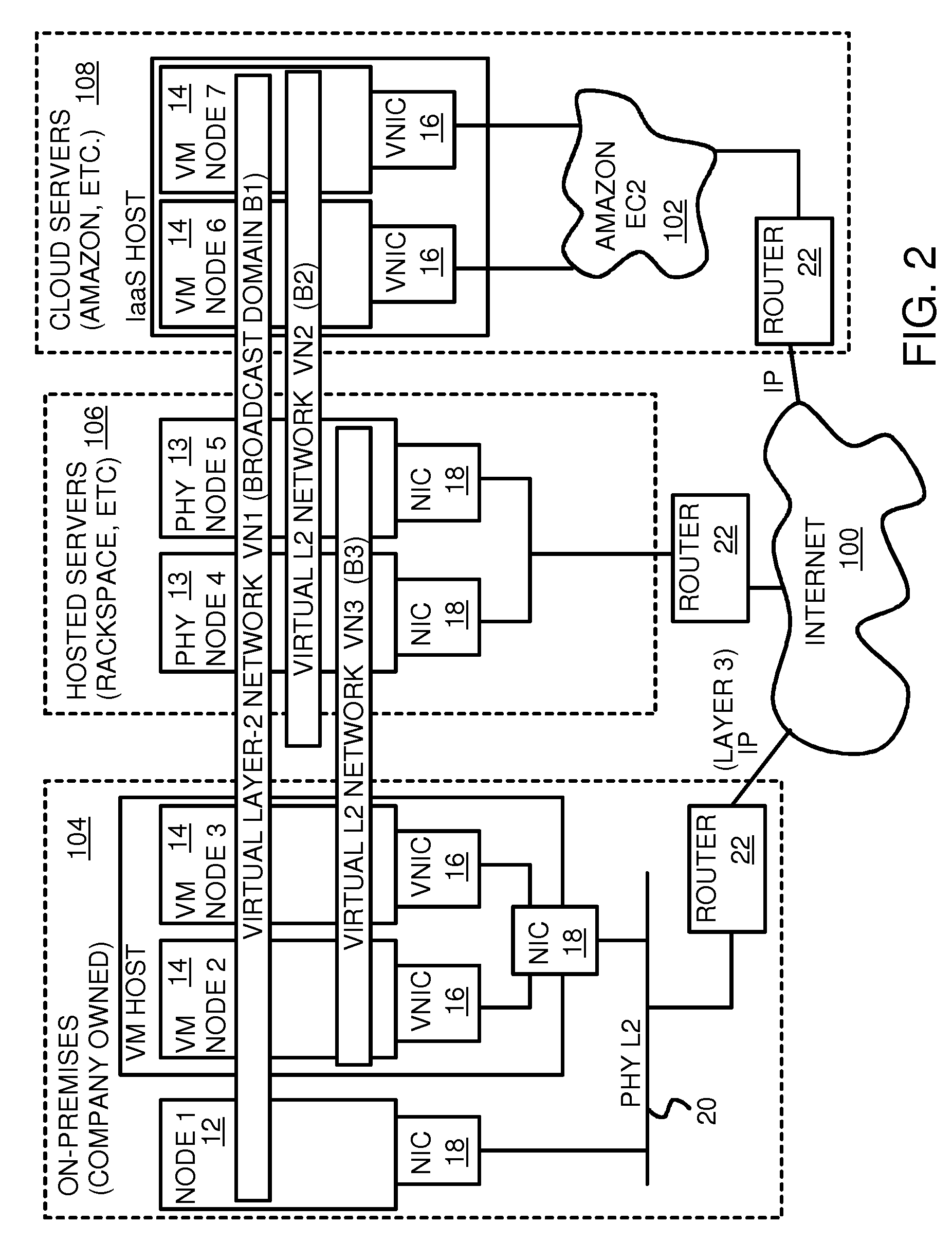
A layer-3 virtual router connects two or more virtual networks. Virtual networks are overlaid upon physical networks. Each virtual network (VN) is a layer-2 network that appears to expand an organization's LAN using virtual MAC addresses. The network stack forms a virtual-network packet with a virtual gateway MAC address of the virtual router to reach a remote virtual network. A VN device driver shim intercepts packets and their virtual MAC and IP addresses and encapsulates them with physical packets sent over the Internet. A VN switch table is expanded to include entries for nodes on the remote virtual network so that all nodes on both virtual networks are accessible. A copy of the VN switch table is stored on each node by a virtual network management daemon on the node. A Time-To-Live field in the virtual-network packet is decremented for each virtual hop and a checksum recalculated.
Owner:CISCO TECH INC
Secured virtual network in a gaming environment
InactiveUS7168089B2Digital data processing detailsUser identity/authority verificationSecure communicationThe Internet
A disclosed gaming machine may securely communicate with devices over a public network such as the Internet. The gaming machine utilizes a combination of symmetric and asymmetric encryption that allows a single gaming machine to securely communicate with a remote server using a public network. The secure communication methods may be used to transfer gaming software and gaming information between two gaming devices, such as between a game server and a gaming machine. For regulatory and tracking purposes, the transfer of gaming software between the two gaming devices may be authorized and monitored by a software authorization agent.
Owner:IGT
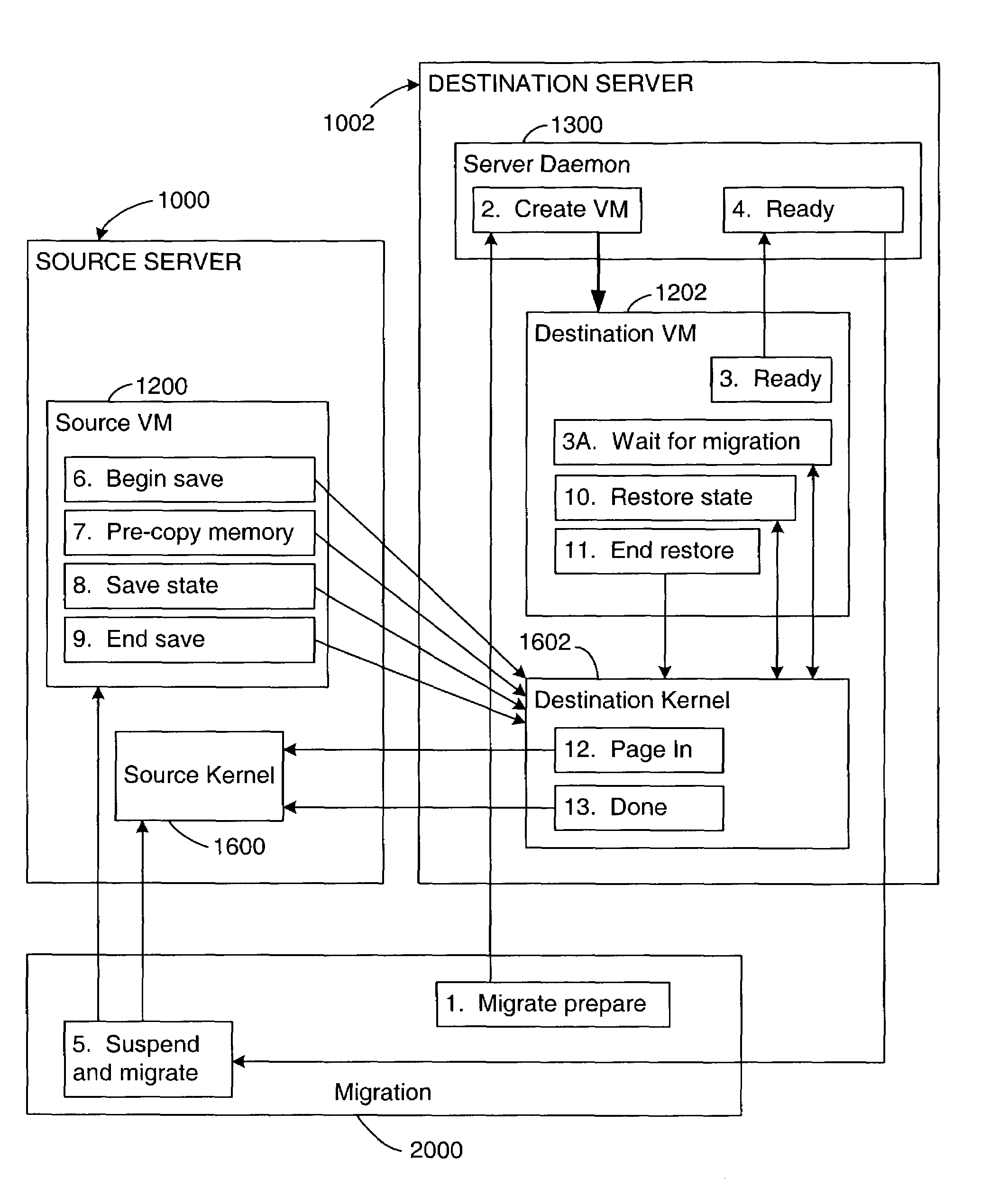
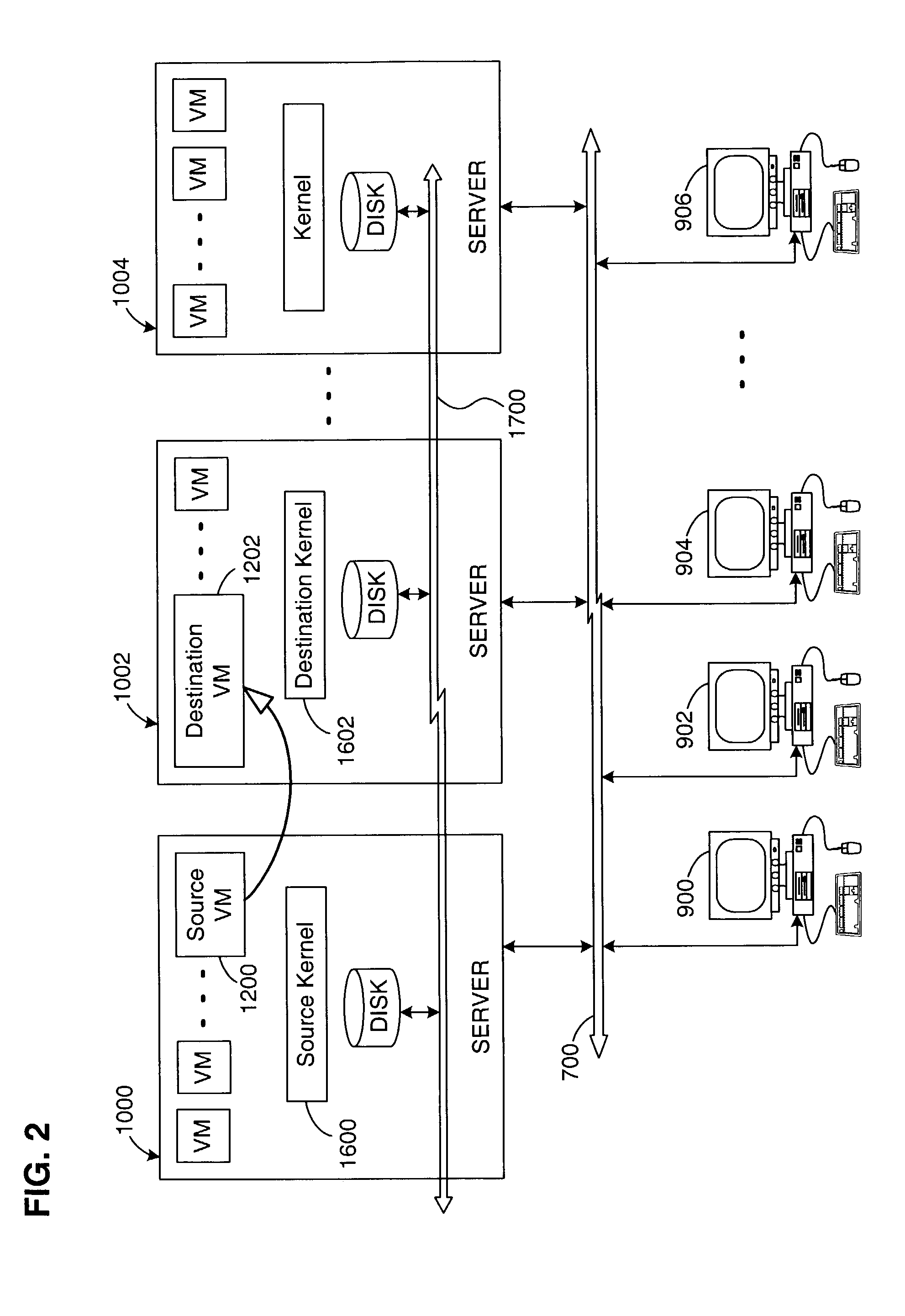
Virtual machine migration
A source virtual machine (VM) hosted on a source server is migrated to a destination VM on a destination server without first powering down the source VM. After optional pre-copying of the source VM's memory to the destination VM, the source VM is suspended and its non-memory state is transferred to the destination VM; the destination VM is then resumed from the transferred state. The source VM memory is either paged in to the destination VM on demand, or is transferred asynchronously by pre-copying and write-protecting the source VM memory, and then later transferring only the modified pages after the destination VM is resumed. The source and destination servers preferably share common storage, in which the source VM's virtual disk is stored; this avoids the need to transfer the virtual disk contents. Network connectivity is preferably also made transparent to the user by arranging the servers on a common subnet, with virtual network connection addresses generated from a common name space of physical addresses.
Owner:VMWARE INC
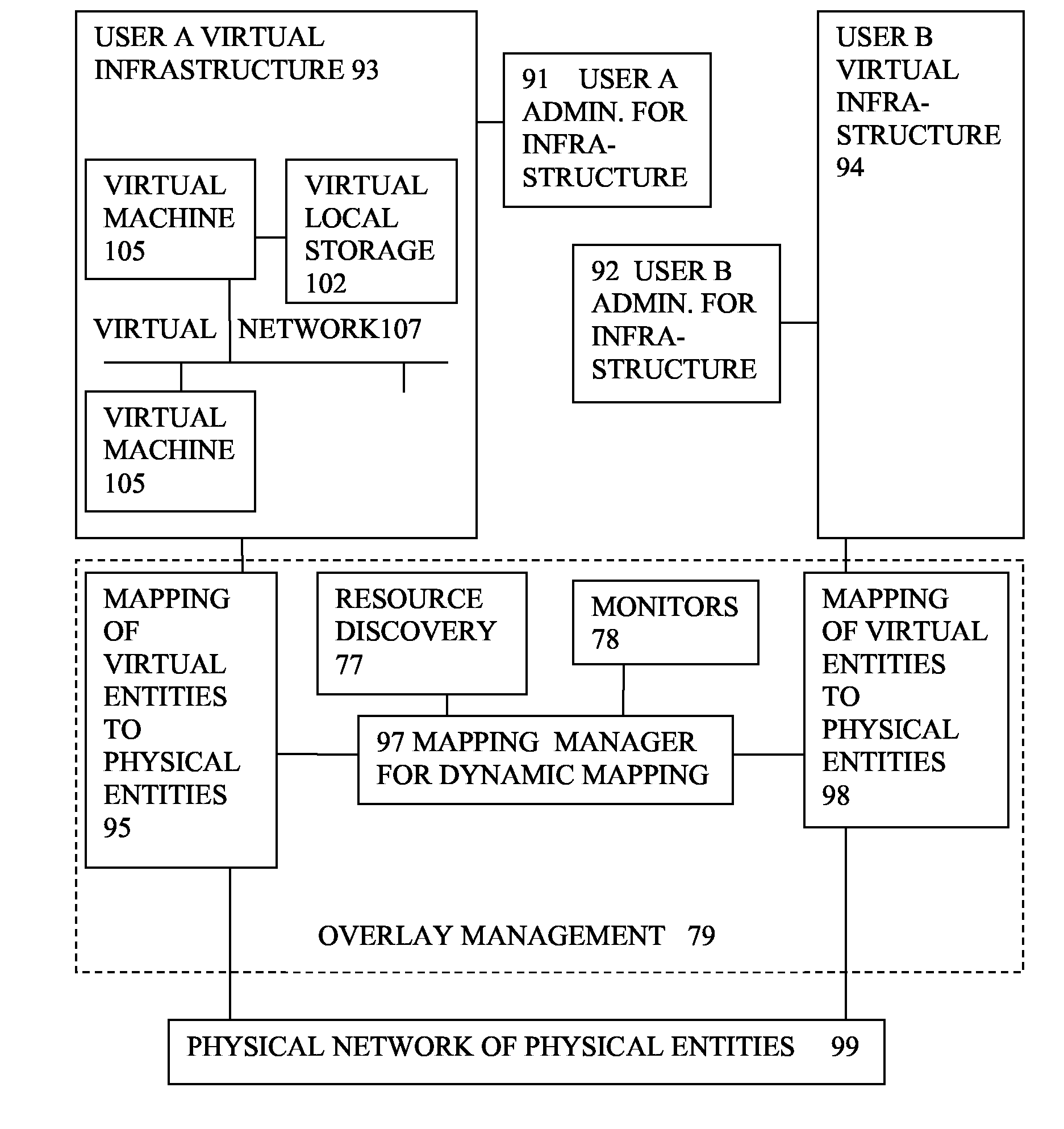
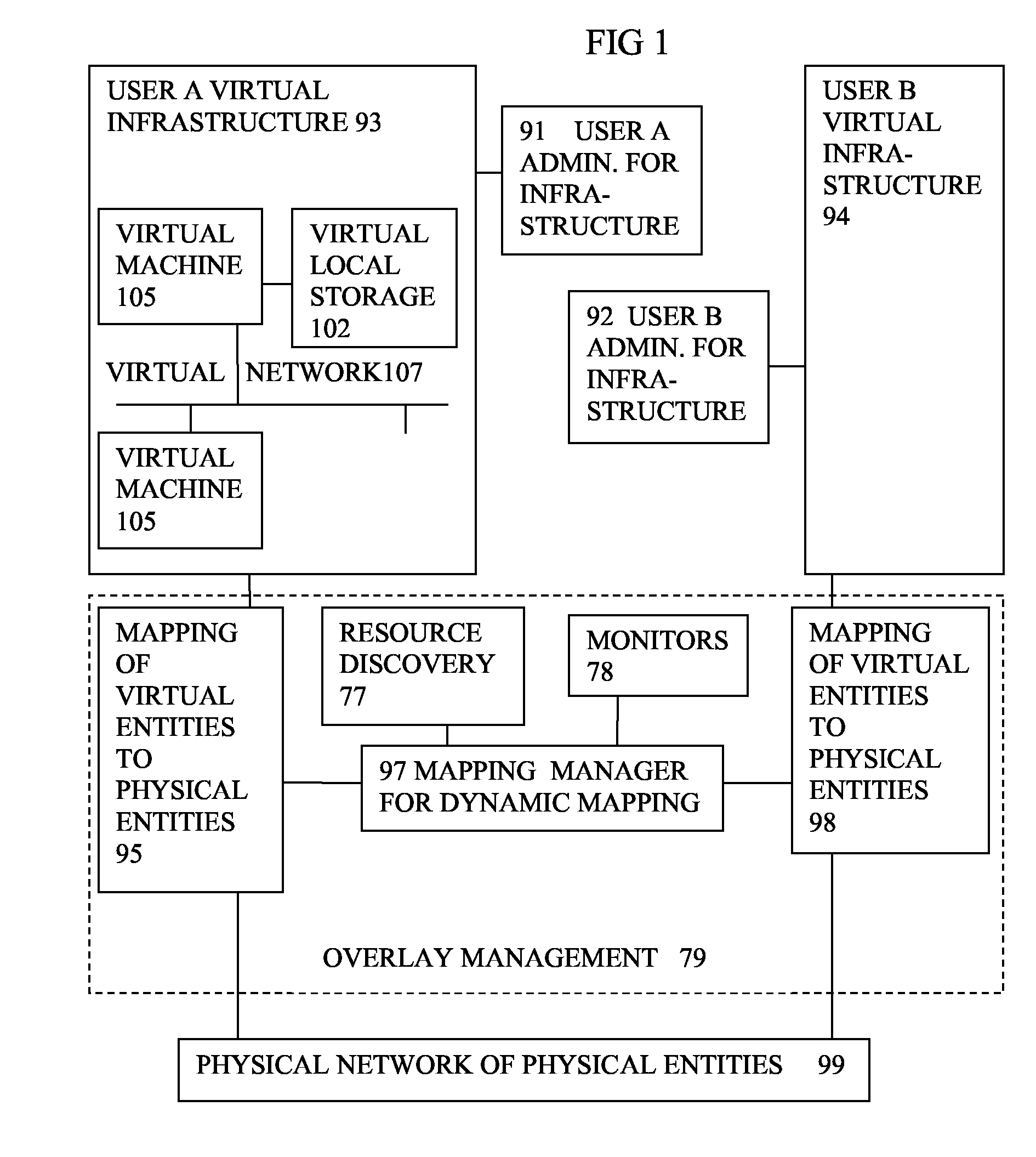
Virtual computing infrastructure
ActiveUS20110119748A1More separatedReduce hardware costsResource allocationComputer security arrangementsNetwork communicationApplication software
A system has a virtual overlay infrastructure mapped onto physical resources for processing, storage and network communications, the virtual infrastructure having virtual entities for processing, storage and network communications. Virtual infrastructures of different users share physical resources but are isolated and have their own management entities. An interface between infrastructures allows controlled relaxation of the isolation, using a gateway between virtual nets, or shared virtual storage devices. This can allow businesses to share data or applications, while maintaining control of security.
Owner:RED HAT +1
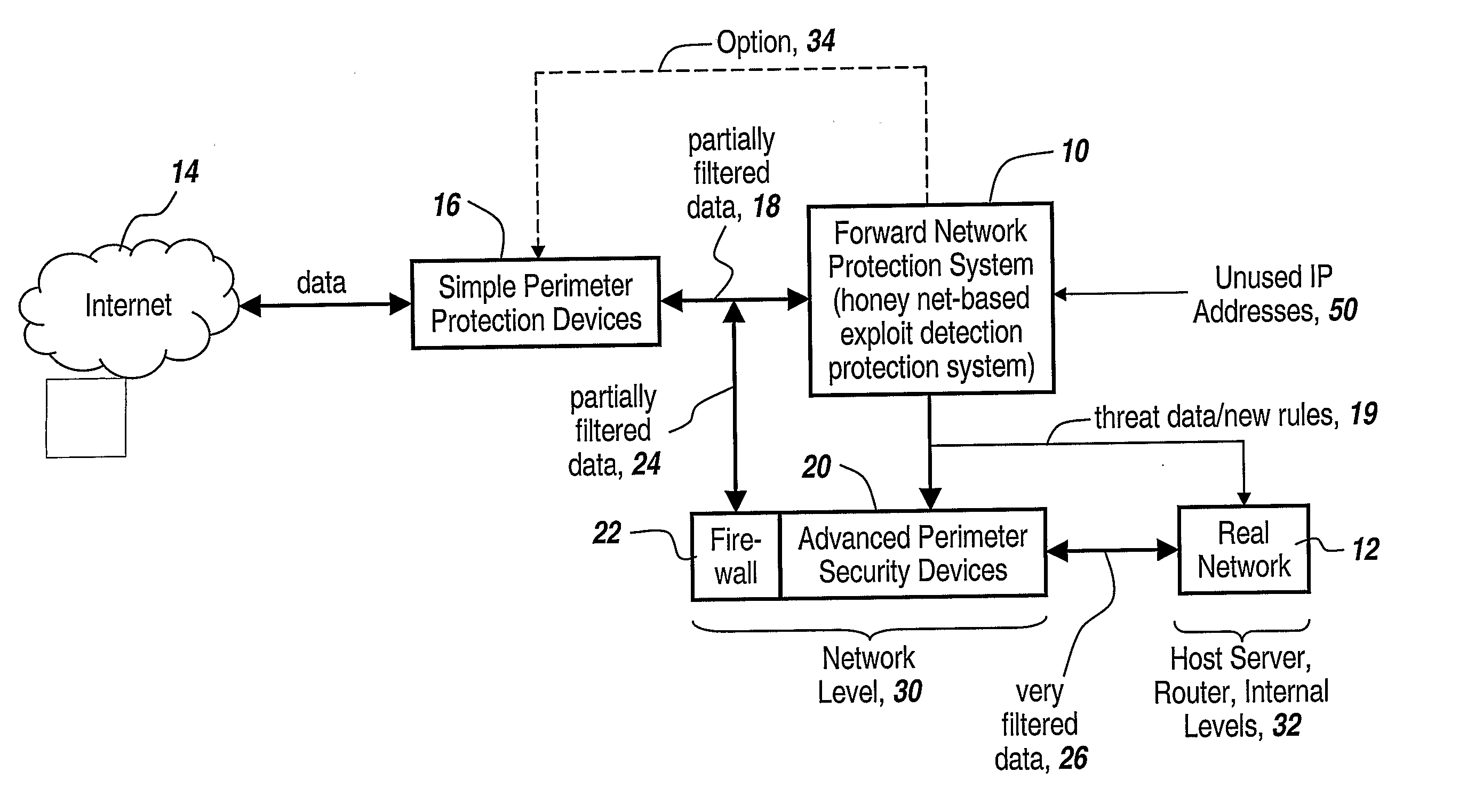
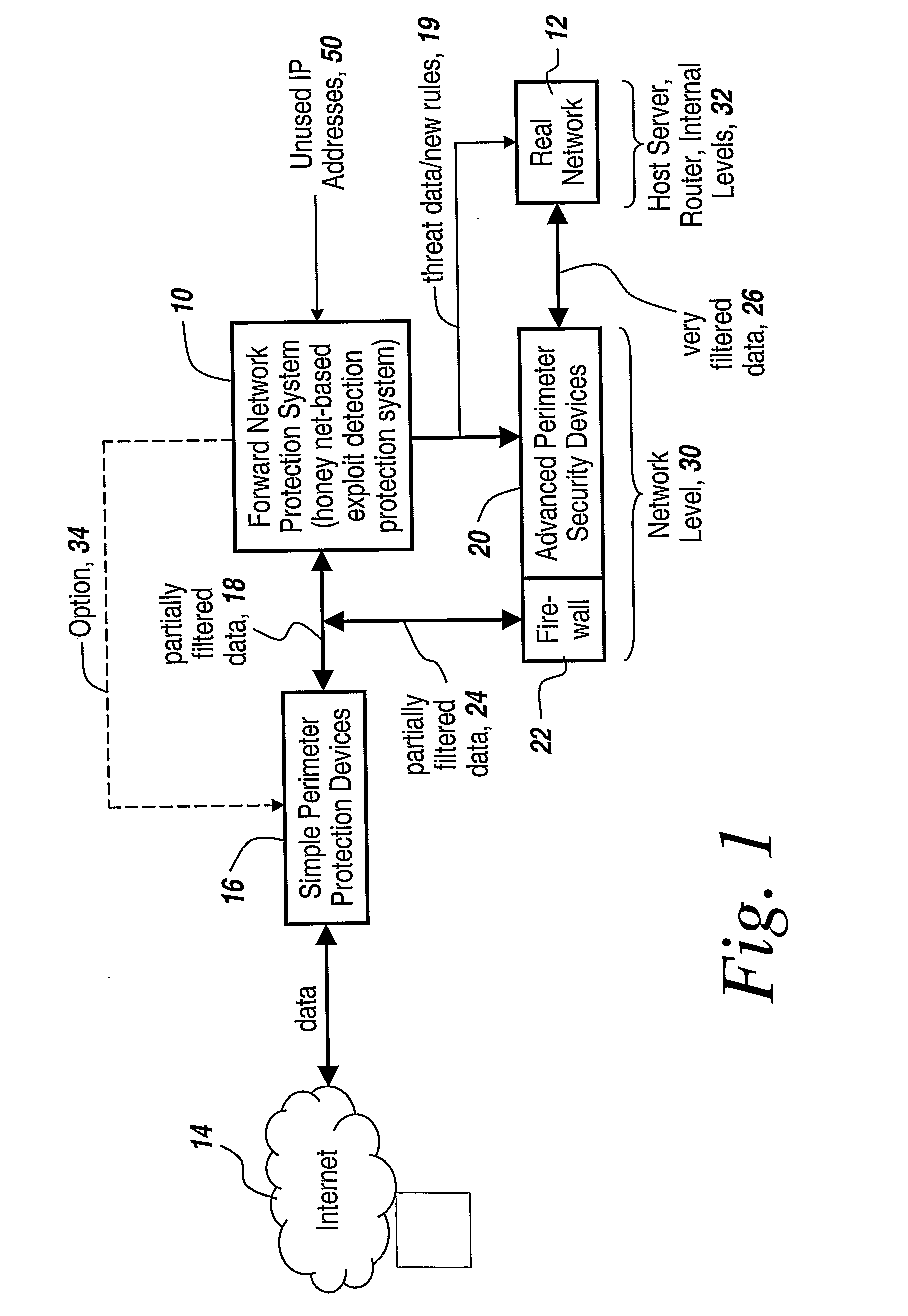
Method and Apparatus for Defending Against Zero-Day Worm-Based Attacks
InactiveUS20080098476A1Curb workloadEliminate usual spam and other simple attackMemory loss protectionError detection/correctionData packOperational system
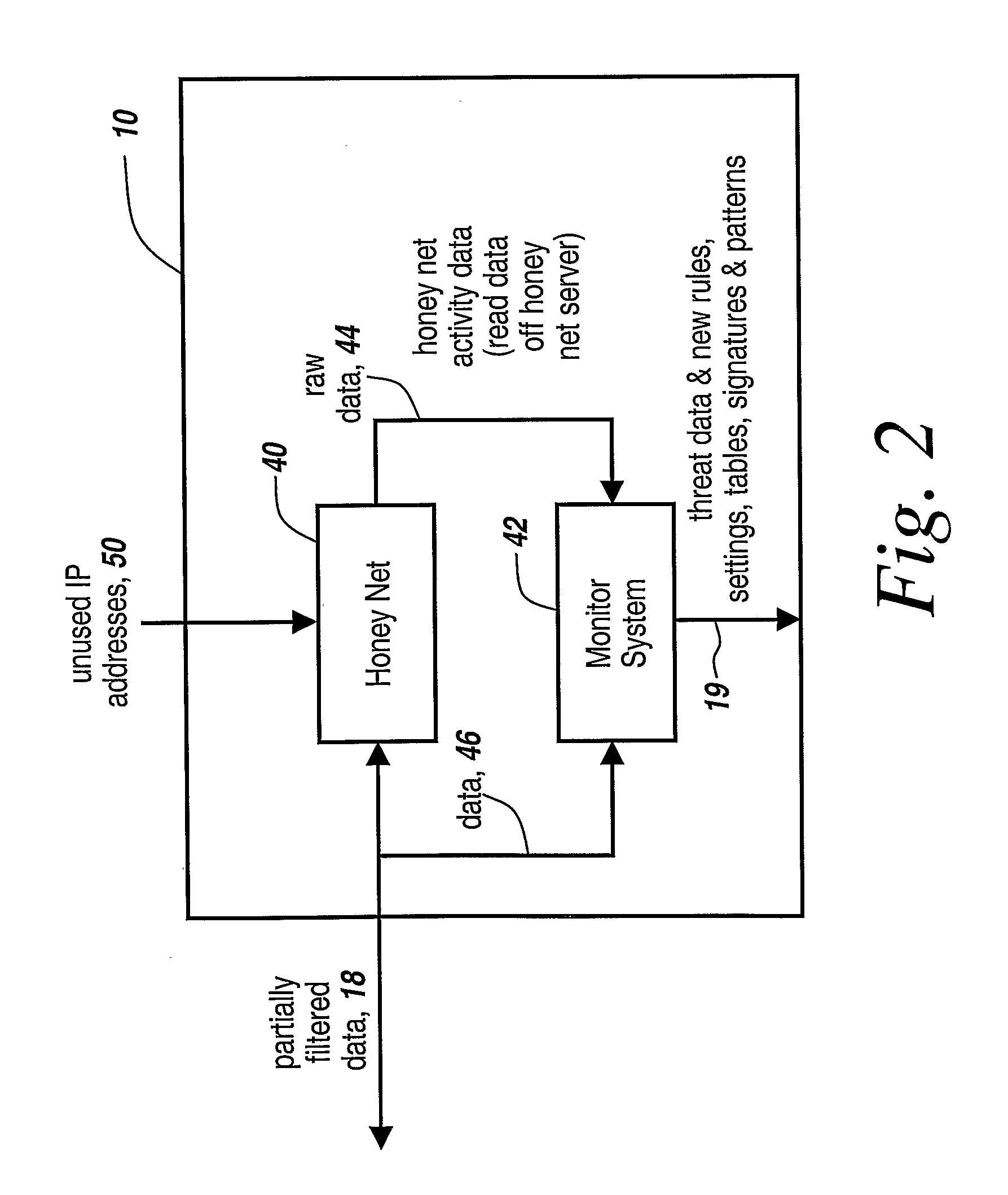
Honey pots are used to attract computer attacks to a virtual operating system that is a virtual instantiation of a typical deployed operational system. Honey nets are a collection of these virtual systems assembled to create a virtual network. The subject system uses a forward deployed honey net combined with a parallel monitoring system collecting data into and from the honey net, leveraging the controlled environment to identify malicious behavior and new attacks. This honey net / monitoring pair is placed ahead of the real deployed operational network and the data it uncovers is used to reconfigure network protective devices in real time to prevent zero-day based attacks from entering the real network. The forward network protection system analyzes the data gathered by the honey pots and generates signatures and new rules for protection that are coupled to both advanced perimeter network security devices and to the real network itself so that these devices can be reconfigured with threat data and new rules to prevent infected packets from entering the real network and from propagating to other machines. Note the subject system applies to both zero-day exploit-based worms and also manual attacks conducted by an individual who is leveraging novel attack methods.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
Virtual network in server farm
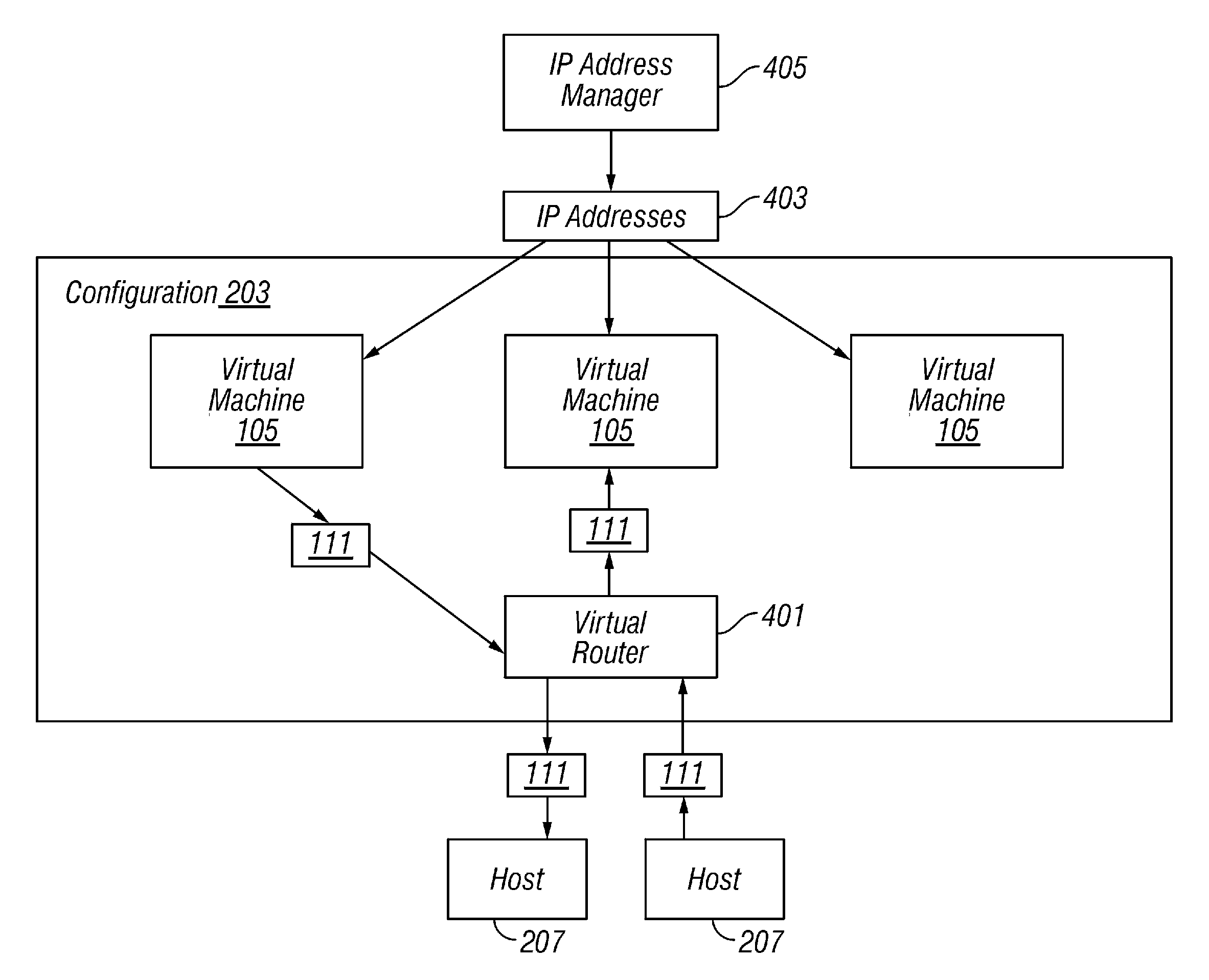
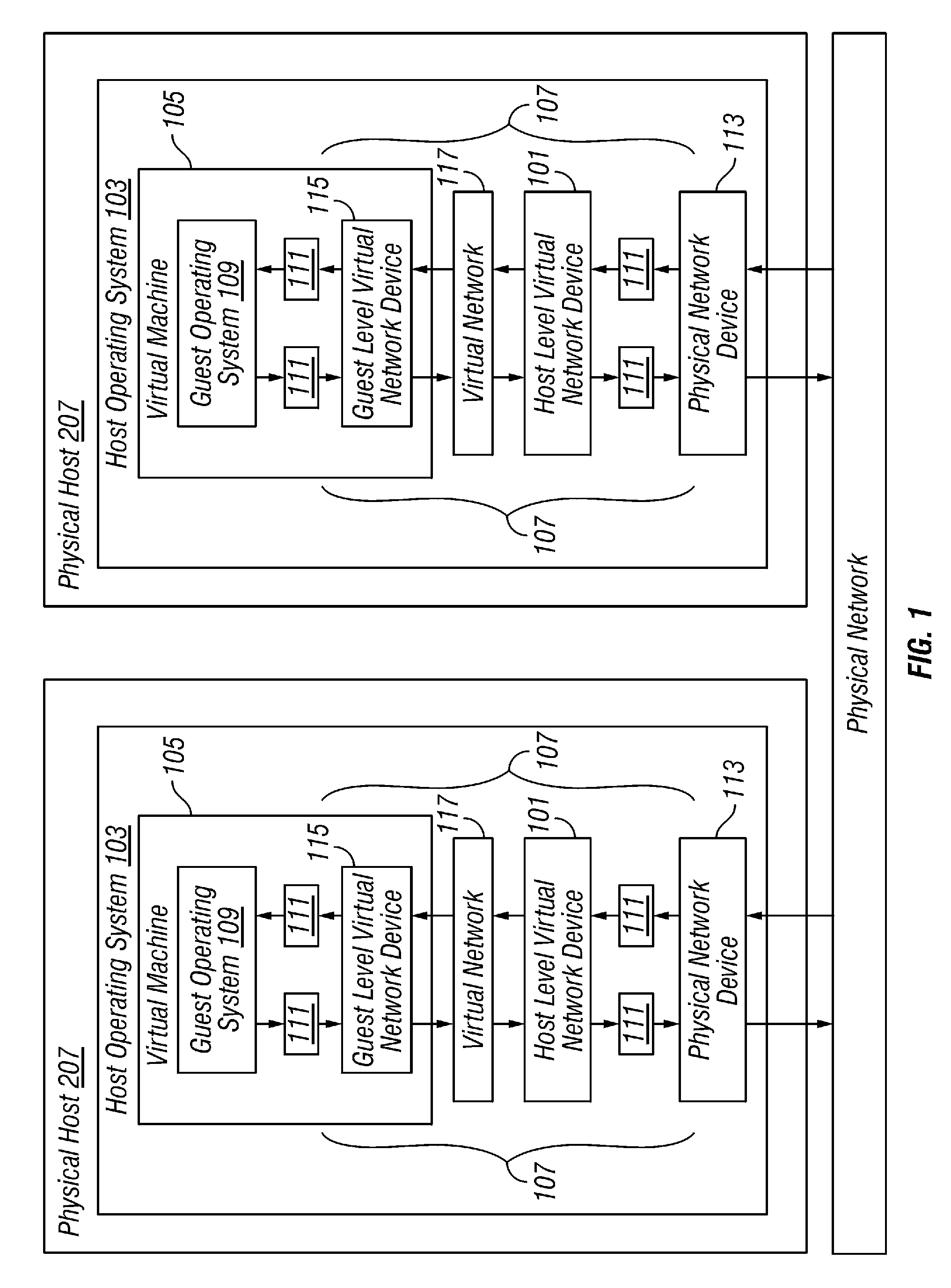
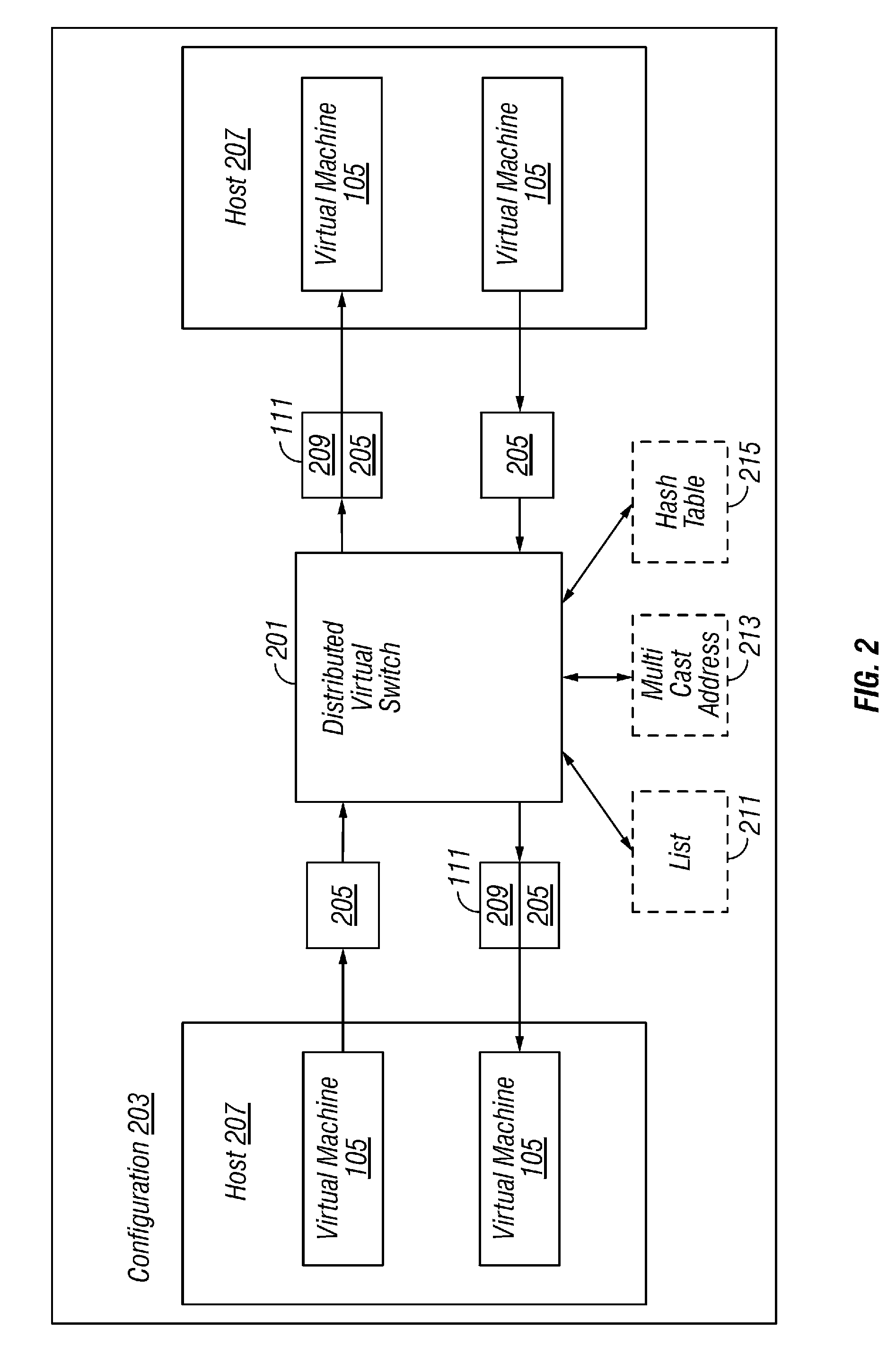
ActiveUS7802000B1Telephonic communicationUnauthorized memory use protectionTraffic capacityVirtual switch
A plurality of virtual machines execute on a network of physical computers. The virtual machines are deployed in fenced and unfenced configurations across multiple physical computers. Host level virtual network devices execute on the physical computers, and intercept the virtual machine network traffic. For each fenced configuration of virtual machines, a distributed virtual switch transmits network traffic between the virtual machines deployed in that fenced configuration, and a virtual router routes network traffic between virtual machines deployed in that fenced configuration and external components.
Owner:VMWARE INC
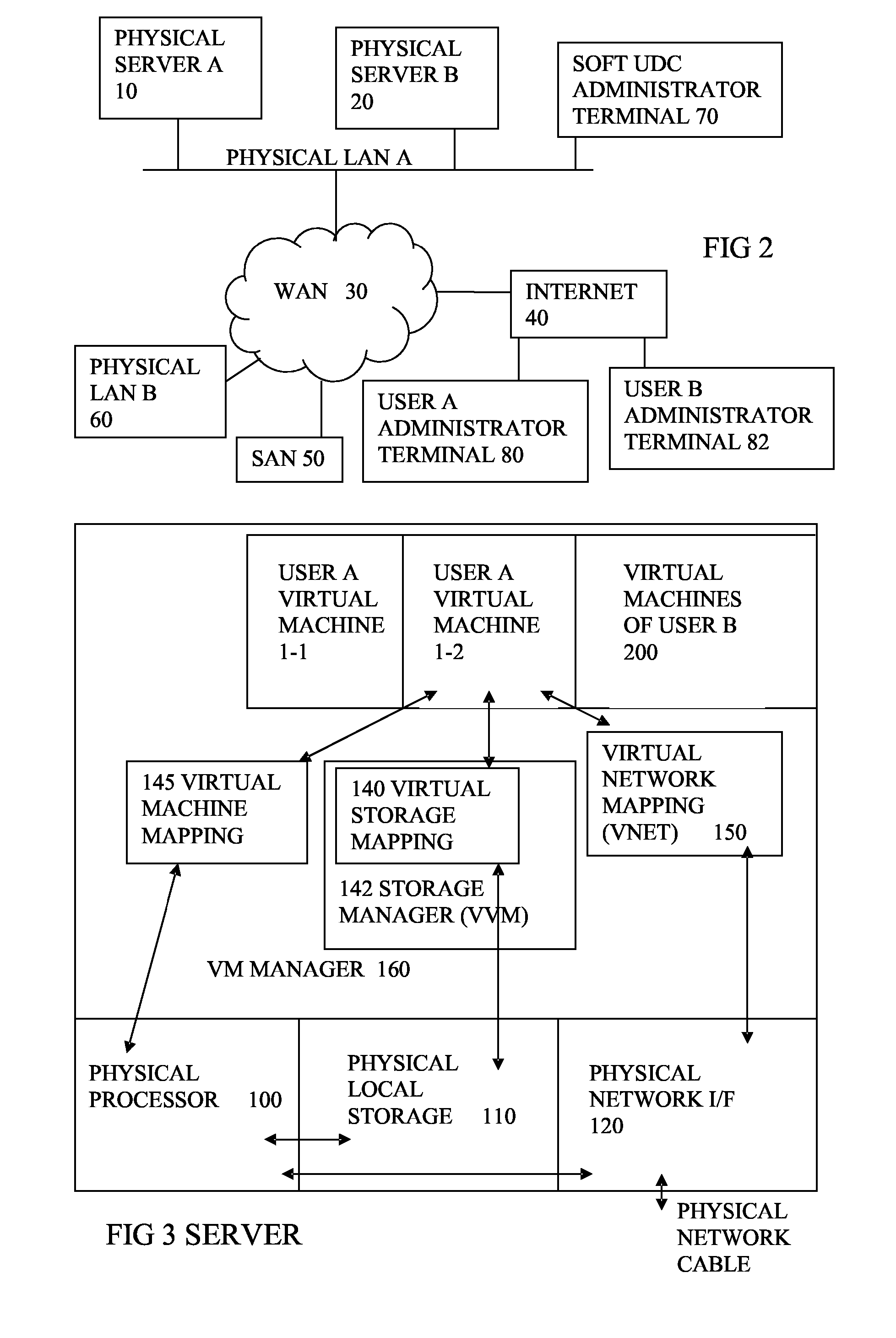
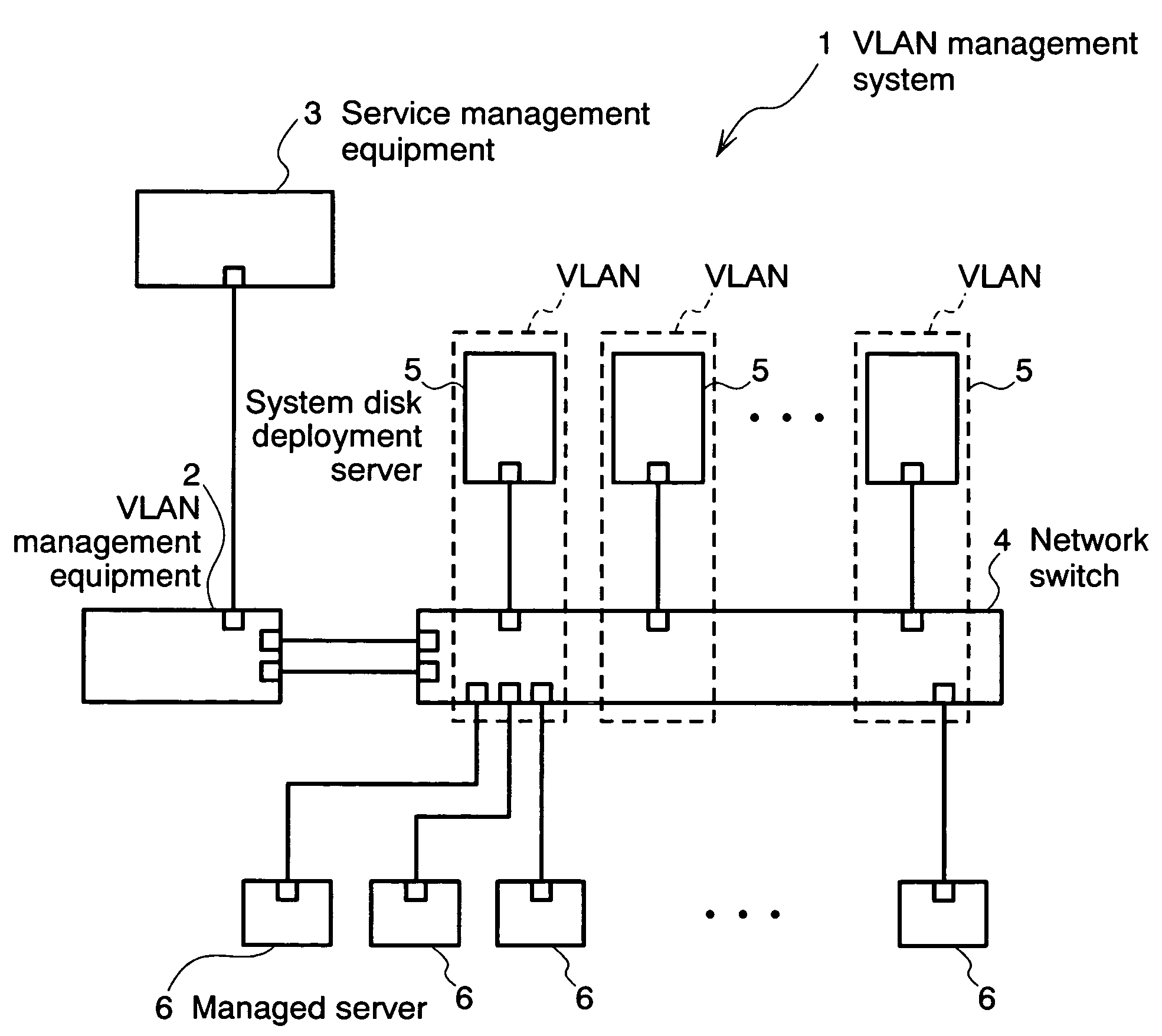
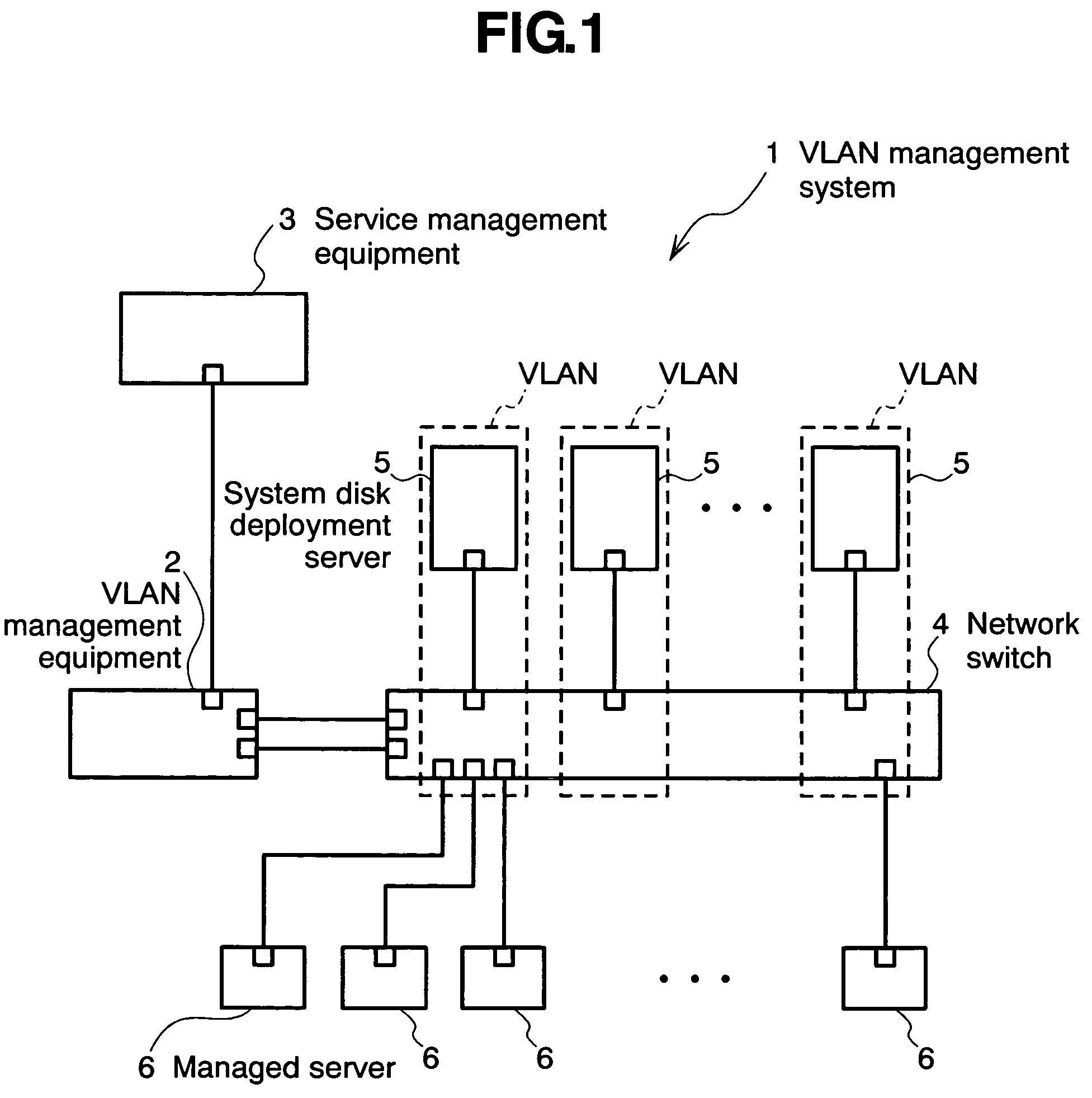
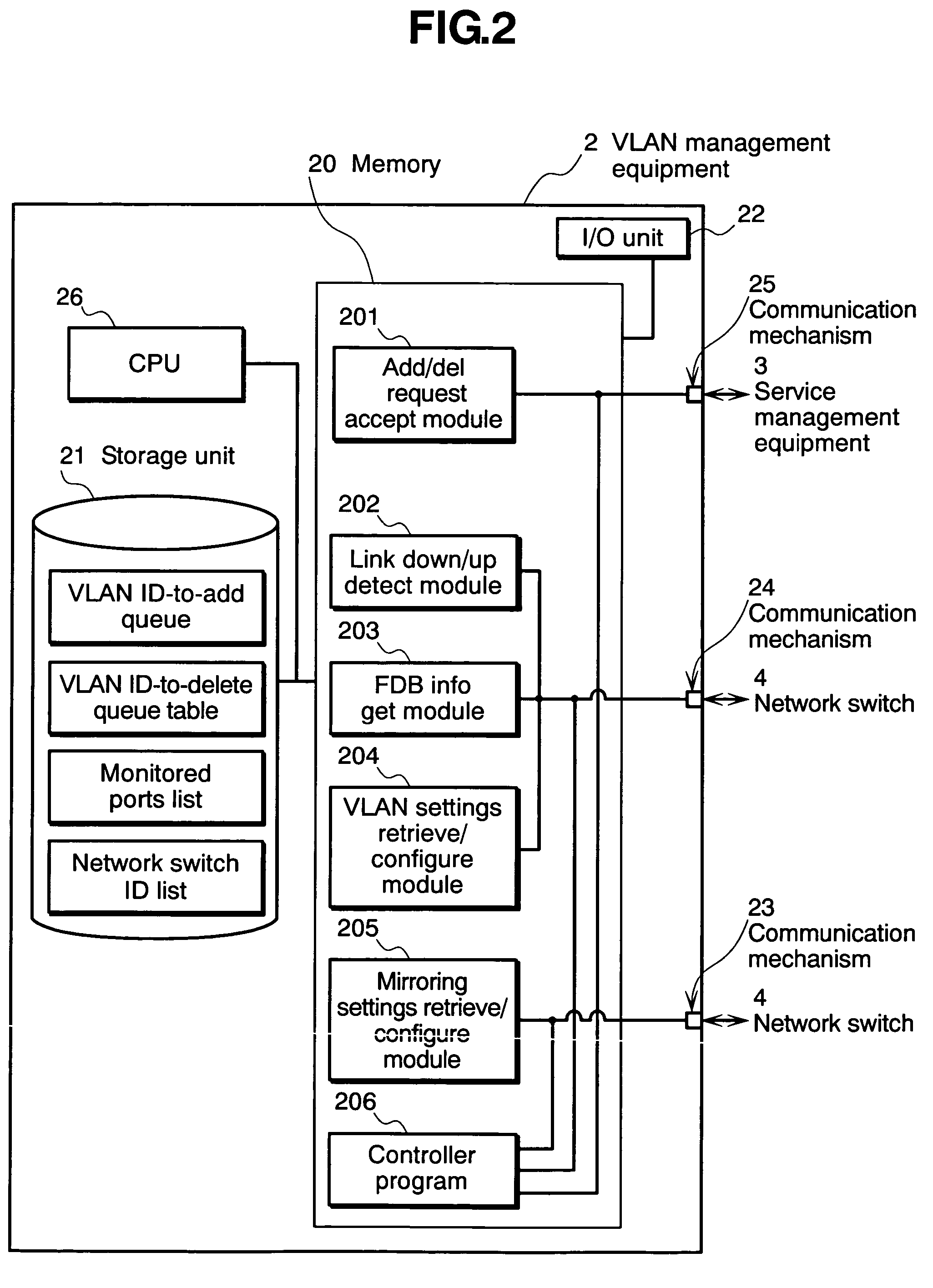
Virtual network management method, virtual network management program, virtual network management system, and virtual network means
InactiveUS7649851B2Lighten the taskDigital computer detailsData switching by path configurationManagement information baseNetwork management
The invention relates to a network management method wherein: a service management equipment holds the mapping of services and virtual networks as management information; a managed server sends an advice to a VLAN management equipment when its status changes; and the VLAN management equipment receives the advice and refers to the information contained in the advice to thereby identify the managed server and the connection port of a network switch, and configures a virtual network belonging to the identified port of the network switch. The method alleviates the task of reconfiguration associated with the adding or deleting of servers.
Owner:HITACHI LTD
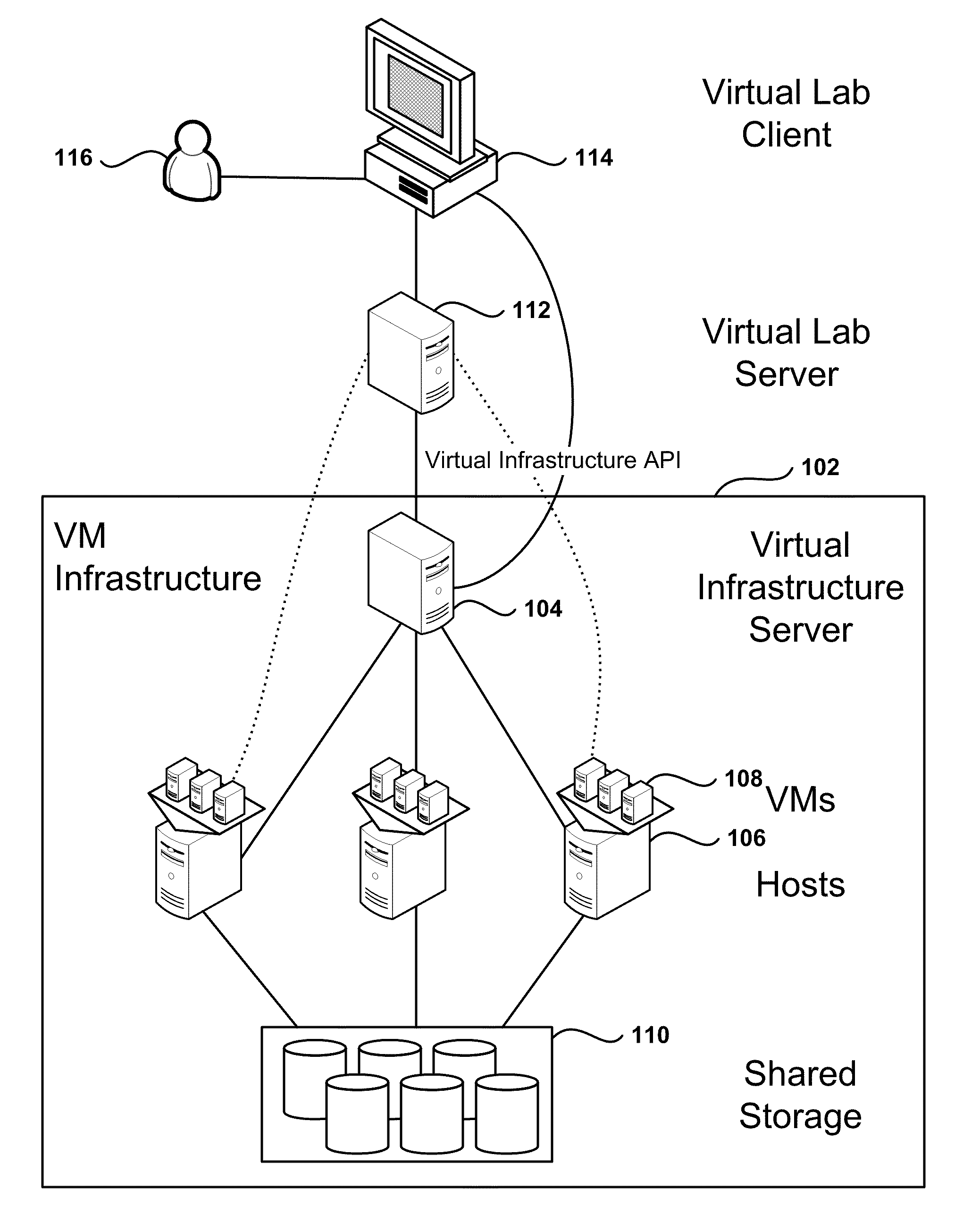
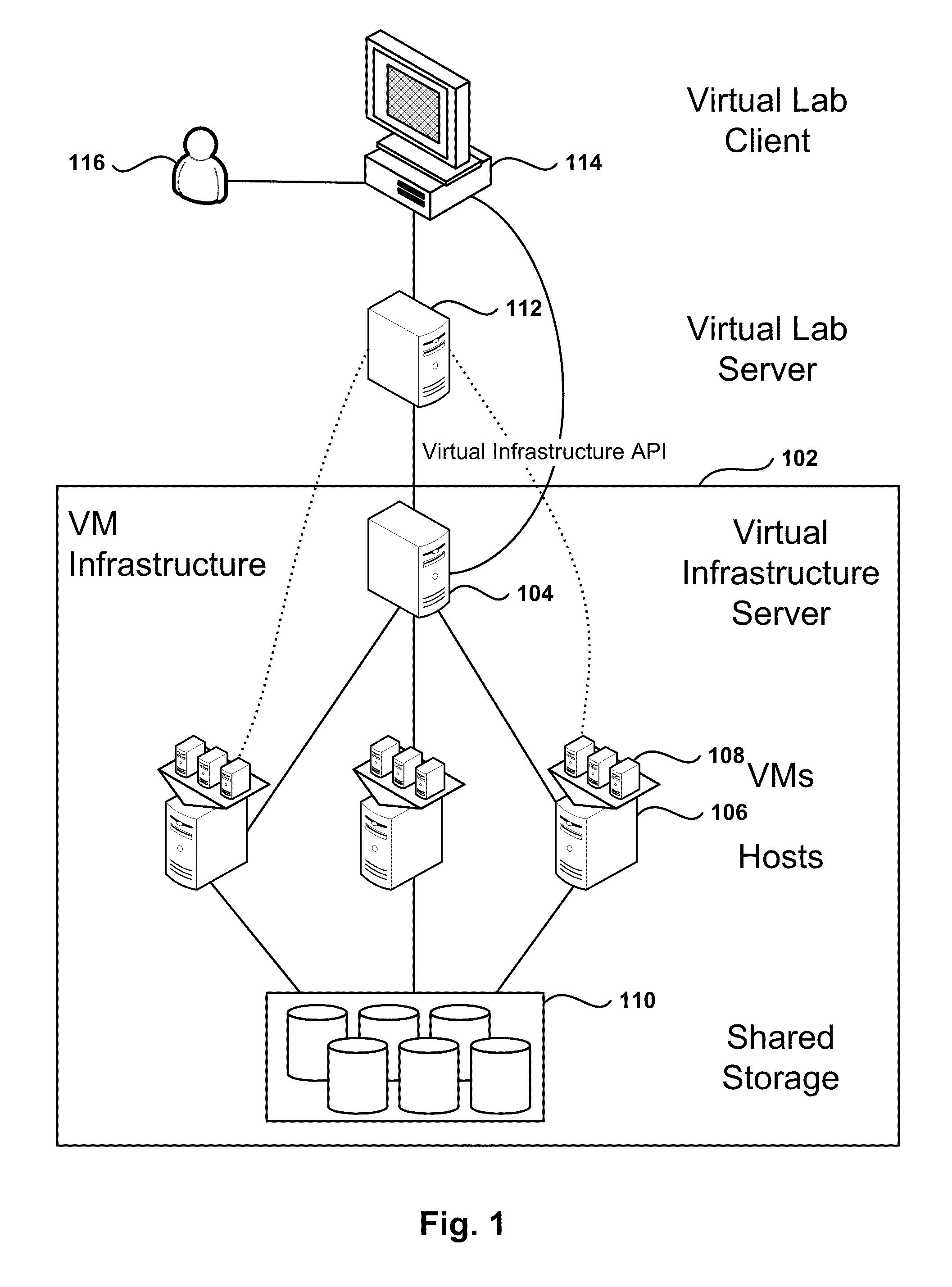
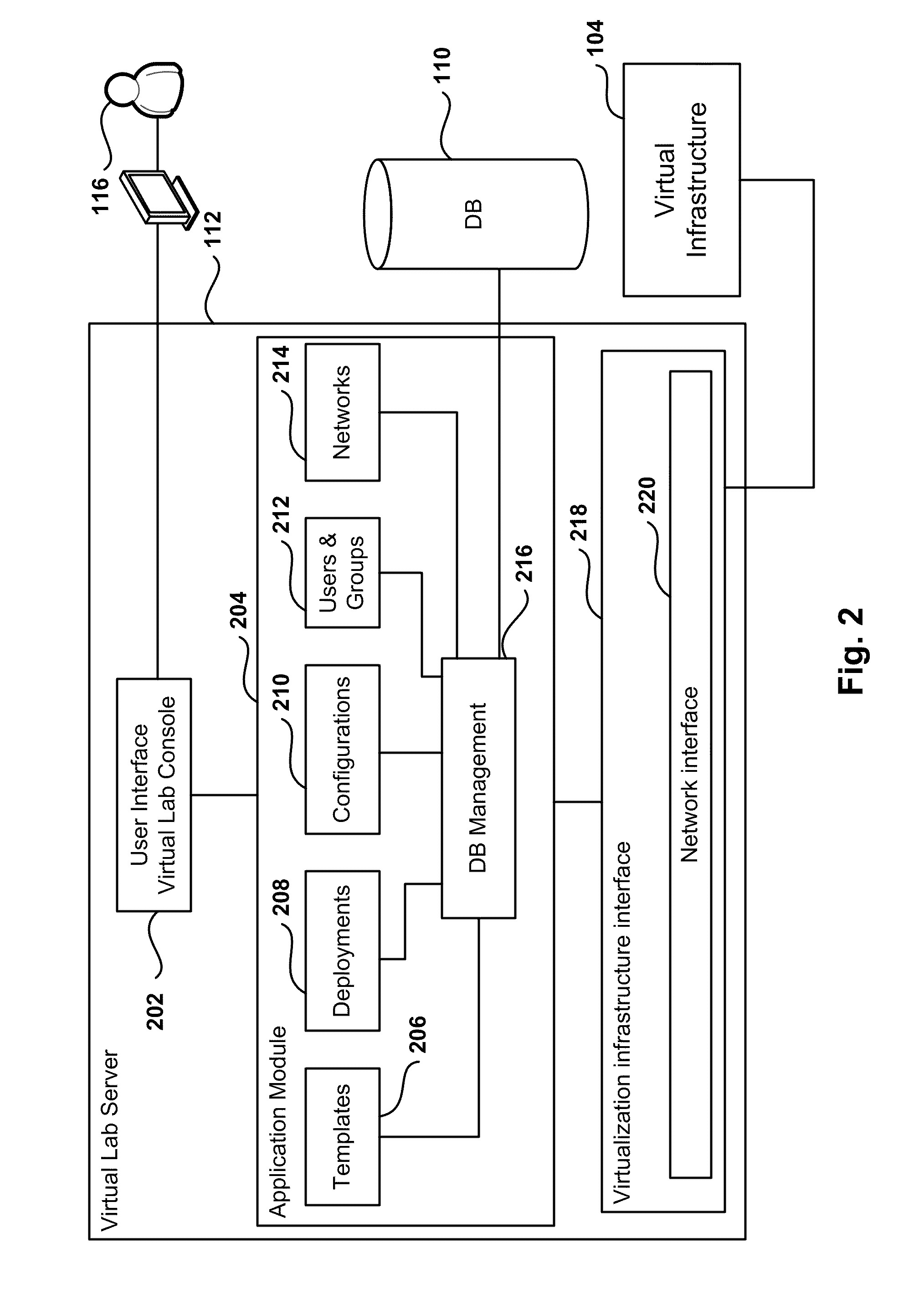
Automated Network Configuration of Virtual Machines in a Virtual Lab Environment
Methods, systems, and computer programs for creating virtual machines (VM) and associated networks in a virtual infrastructure are presented. The method defines virtual network templates in a database, where each virtual network template includes network specifications. A configuration of a virtual system is created, which includes VMs, virtual lab networks associated with virtual network templates, and connections from the VMs to the virtual lab networks. Further, the configuration is deployed in the virtual infrastructure resulting in a deployed configuration. The deployment of the configuration includes instantiating in the virtual infrastructure the VMs of the configuration, instantiating in the virtual infrastructure the virtual lab networks, retrieving information from the database, and creating and executing programming instructions for the VMs. The database information includes the network specifications from the virtual network templates associated with the virtual lab networks, and network resources for the virtual lab networks from a pool of available network resources. The programming instructions are created for the particular Guest Operating System (GOS) running in each VM based on the GOS and on the retrieved database information. When executed in the corresponding VM GOS, the programming instructions configure the VMs network interfaces with the corresponding network specifications.
Owner:NICIRA
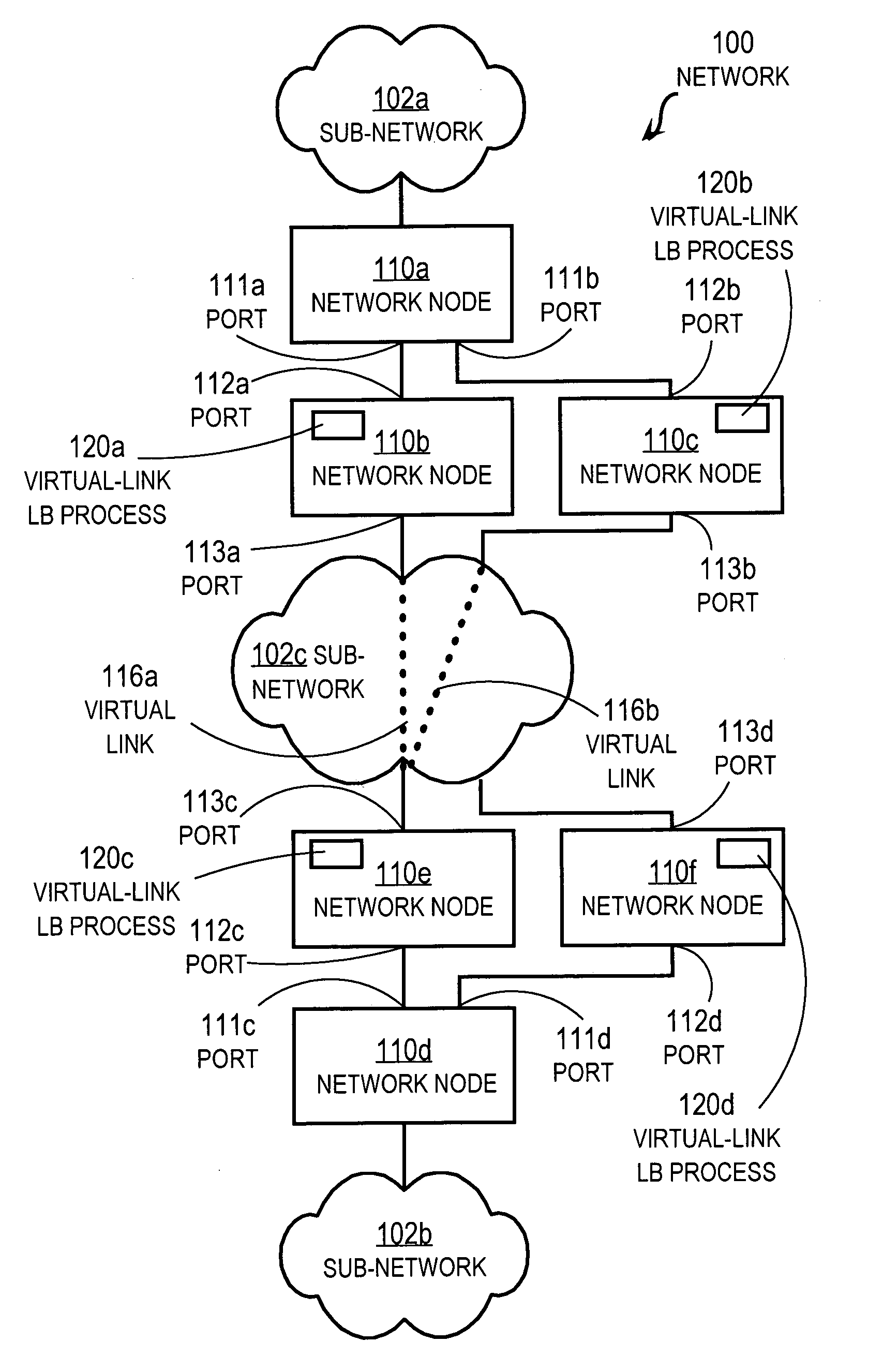
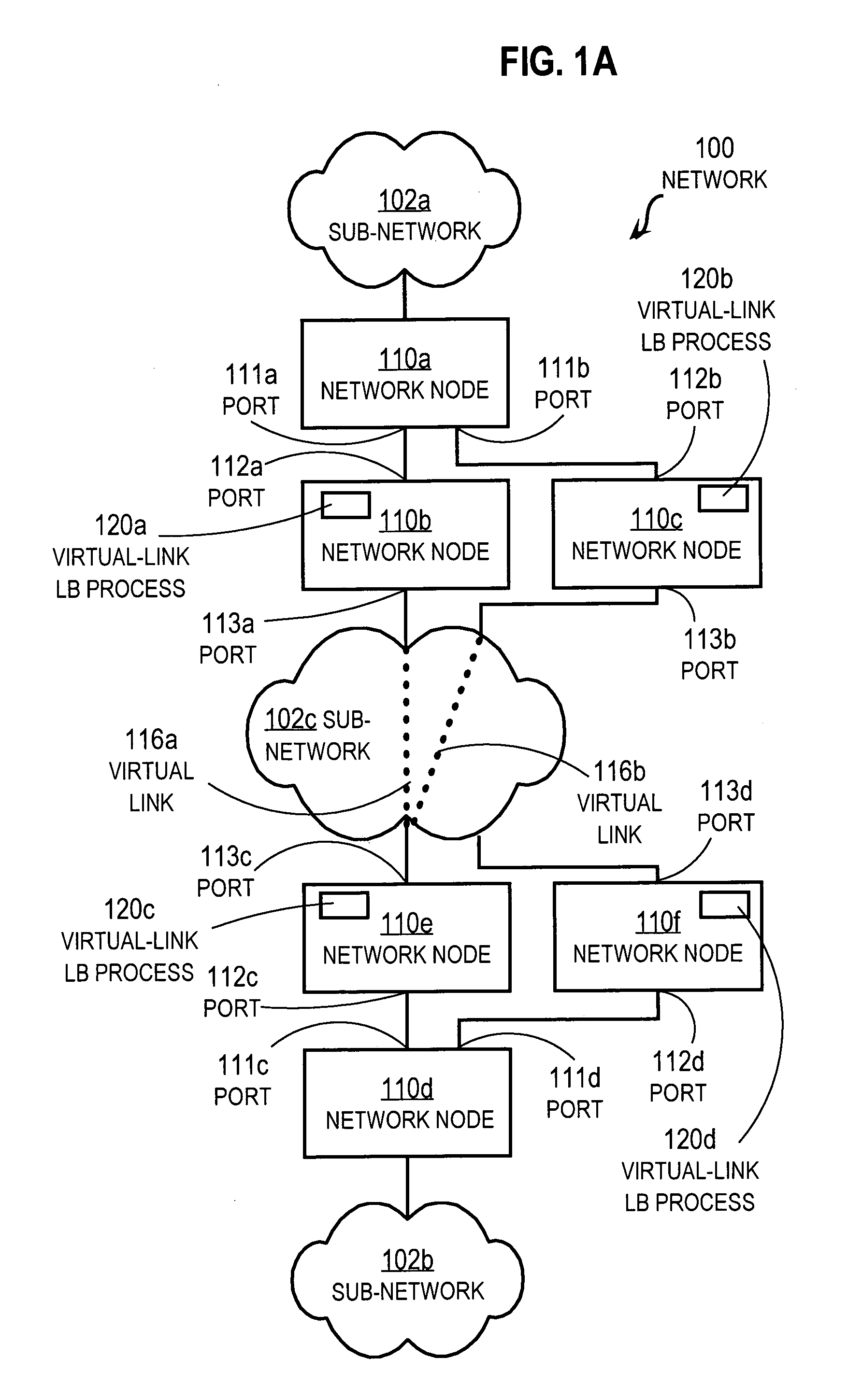
Method and apparatus for load balancing over virtual network links
Techniques for load balancing network traffic over virtual point-to-point data links at a data-link layer include determining a particular group of virtual point-to-point data links that reach a particular local area network of one or more network nodes. A particular data-link address for a particular node of the particular local area network is associated with each virtual point-to-point data link of the particular group. When a data packet is received that includes data that indicates the particular data-link address as a destination; one virtual point-to-point data link of the group is determined to balance traffic among the group. The data packet is sent only over the one virtual point-to-point data link. These techniques enable virtual point-to-point data links through two or more intermediate network nodes, such as a pair of provider edge nodes, to be bundled for load balancing purposes.
Owner:CISCO TECH INC
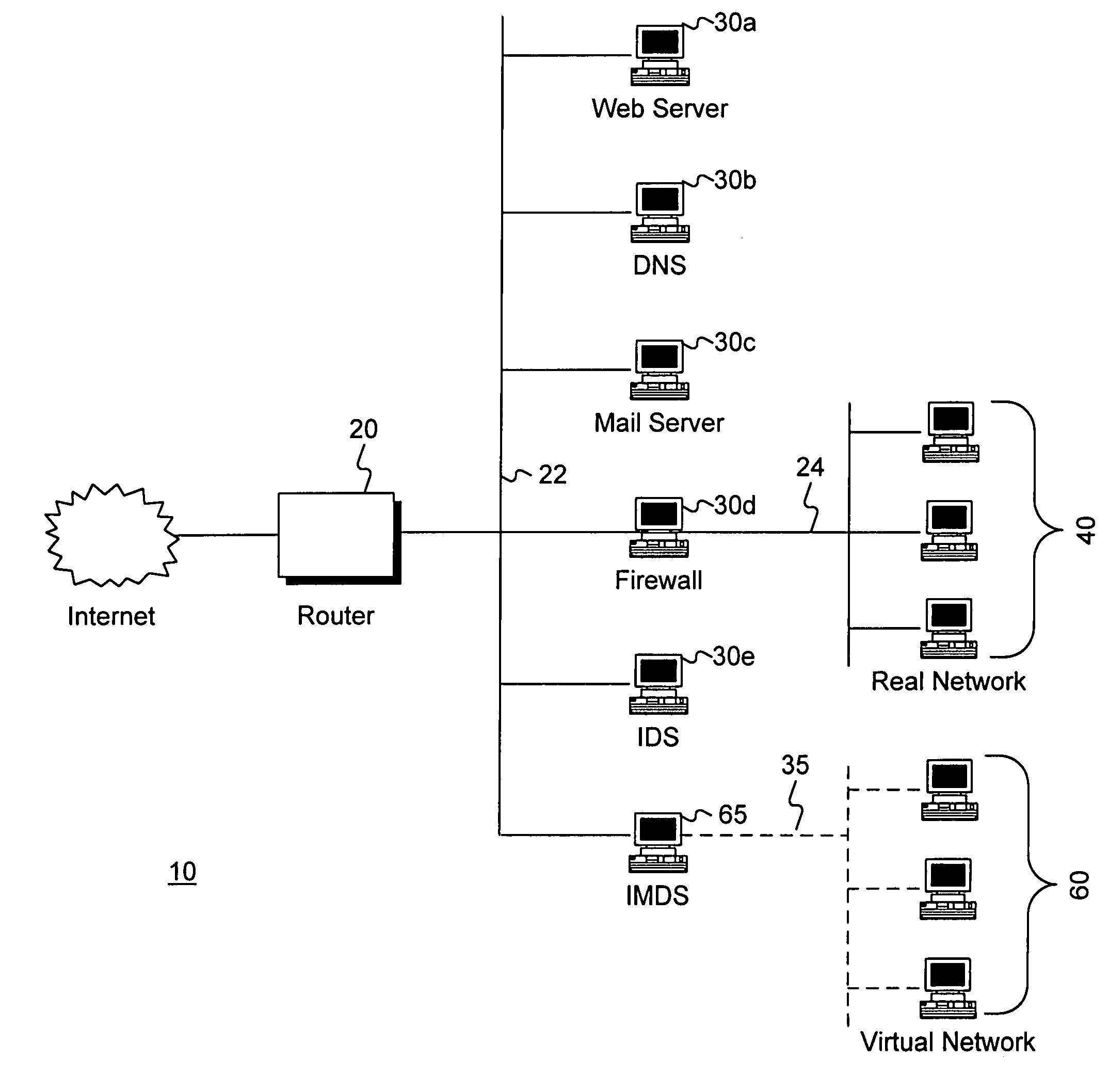
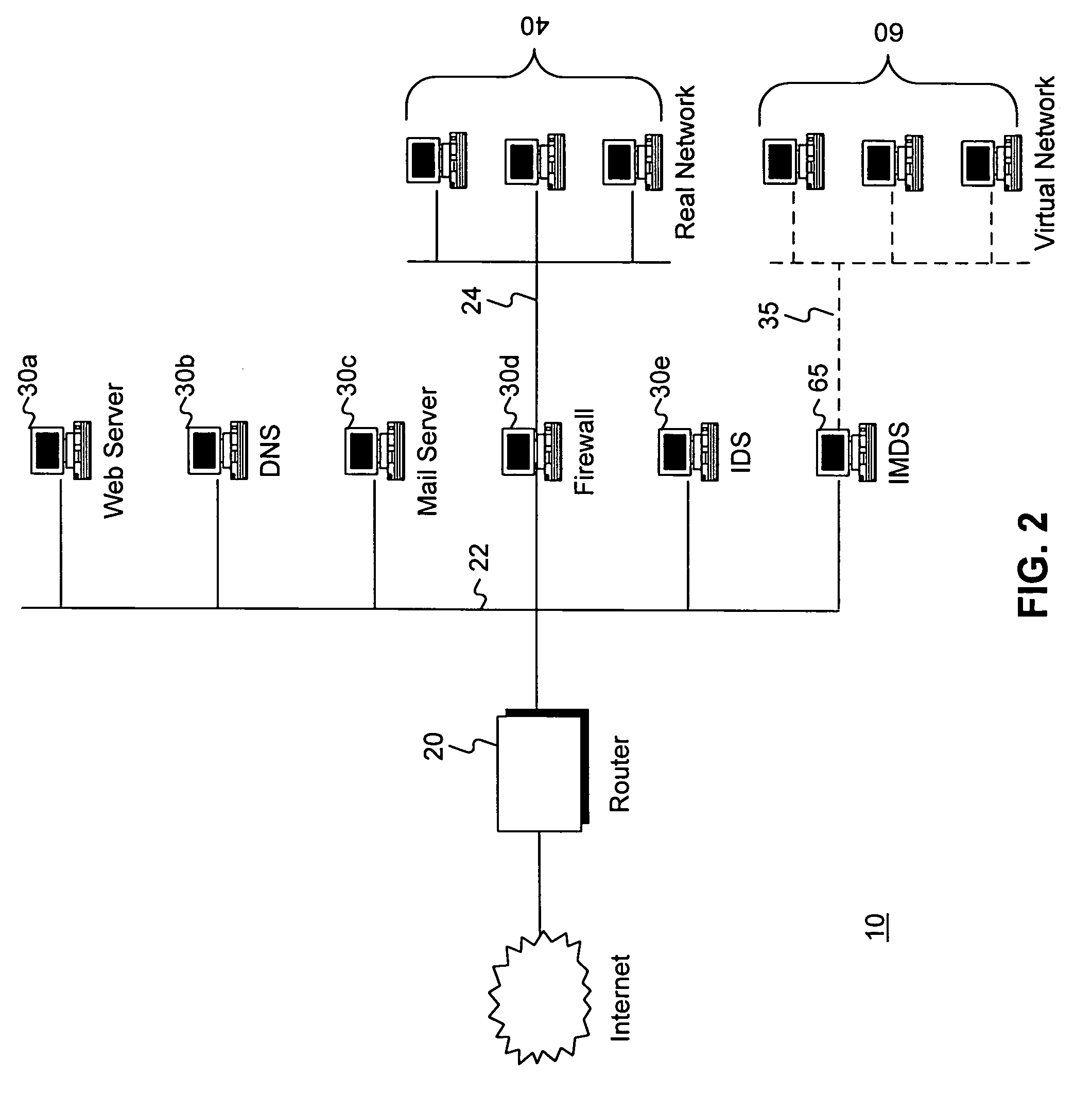
Intrusion and misuse deterrence system employing a virtual network
InactiveUS7240368B1Improve securityEasy to implementMemory loss protectionError detection/correctionIp addressBandwidth limitation
A method and apparatus is disclosed for increasing the security of computer networks through the use of an Intrusion and Misuse Deterrence System (IMDS) operating on the network. The IMDS is a system that creates a synthetic network complete with synthetic hosts and routers. It is comprised of a network server with associated application software that appears to be a legitimate portion of a real network to a network intruder. The IMDS consequently invites inquiry and entices the intruder away from the real network. Simulated services are configured to appear to be running on virtual clients with globally unique, class “C” IP addresses. Since there are no legitimate users of the virtual network simulated by the IMDS, all such activity must be inappropriate and can be treated as such. Consequently, the entire set of transactions by an intruder can be collected and identified rather than just those transactions that meet a predefined attack profile. Also, new exploits and attacks are handled just as effectively as known attacks, resulting in better identification of attack methodologies as well as the identification and analysis of new attack types. Since the IMDS only has to be concerned with the traffic going to its simulated hosts it additionally eliminates the bandwidth limitation that plagues a traditional intrusion detection system (IDS).
Owner:VERIZON SERVICES GROUP +2
Secured virtual network in a gaming environment
InactiveUS7515718B2Mosaic printer telegraph systemKey distribution for secure communicationSecure communicationThe Internet
A disclosed gaming machine may securely communicate with devices over a public network such as the Internet. The gaming machine utilizes a combination of symmetric and asymmetric encryption that allows a single gaming machine to securely communicate with a remote server using a public network. The secure communication methods may be used to transfer gaming software and gaming information between two gaming devices, such as between a game server and a gaming machine. For regulatory and tracking purposes, the transfer of gaming software between the two gaming devices may be authorized and monitored by a software authorization agent.
Owner:IGT
Managing services in a cloud computing environment
What is provided are a system and method which enables an organization or user to manage computational services in a cloud computing network for security, compliance and governance. The management including creating a trusted virtual network including encrypted data storage, encrypted data transport, and trusted instances of servers all communicatively coupled together forming a trusted cloud computing environment that is associated with the organization. A web portal running on a web server provides a point of access to the cloud computing environment. A workflow is accessed to implement one or more policies in trusted computing environment to manage the trusted cloud computing environment, the workflow customized to the organization. The access control; and to the trusted cloud computing environment is used to ensure access by users authorized by the organization to ensure compliance with adopted standards.
Owner:CLOUDNEXA
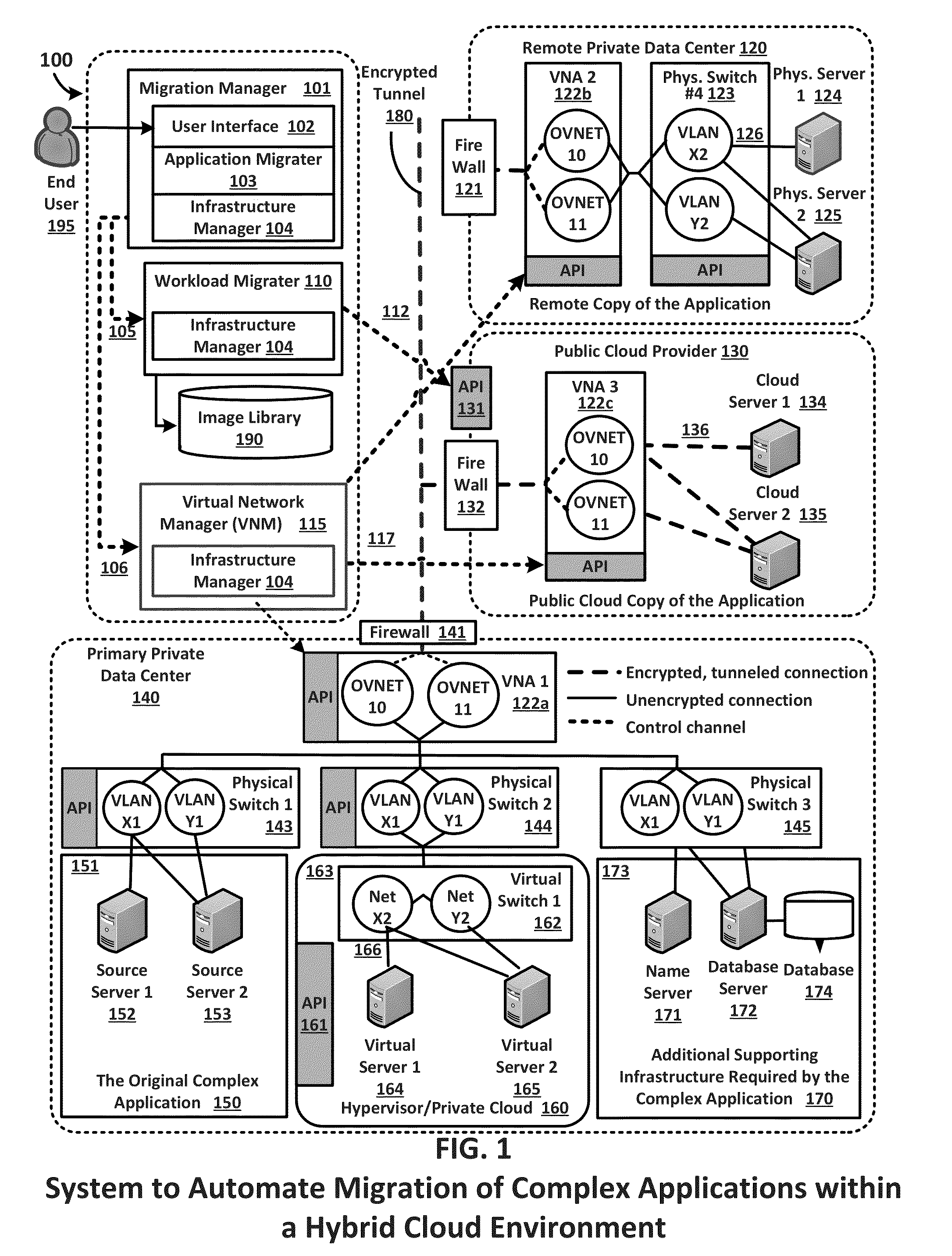
Migration of complex applications within a hybrid cloud environment
ActiveUS20150096011A1Increase the number ofFully automatedMultiple digital computer combinationsProgram controlResource poolData center
A system and methods for the migration of complex computer applications and the workloads comprising them between physical, virtual, and cloud servers that span a hybrid cloud environment comprising private local and remote customer data centers and public cloud data centers, without modification to the applications, their operational environments, or user access procedures. A virtual network manager securely extends the subnets and VLANS within the customer's various data center across the distributed, hybrid environment using overlay networks implemented with virtual network appliances at nodes of the overlay network. A server migrater migrates individual workloads of servers used by the complex application from one pool of server resources to another. A migration manager application provides a control interface, and also maps and manages the resources of the complex application, the hybrid environment, and the virtual network spanning the hybrid cloud environment.
Owner:RACEMI
Methods and systems for automatic inference and adaptation of virtualized computing environments
ActiveUS20080155537A1Multiprogramming arrangementsMultiple digital computer combinationsTraffic capacityVirtualization
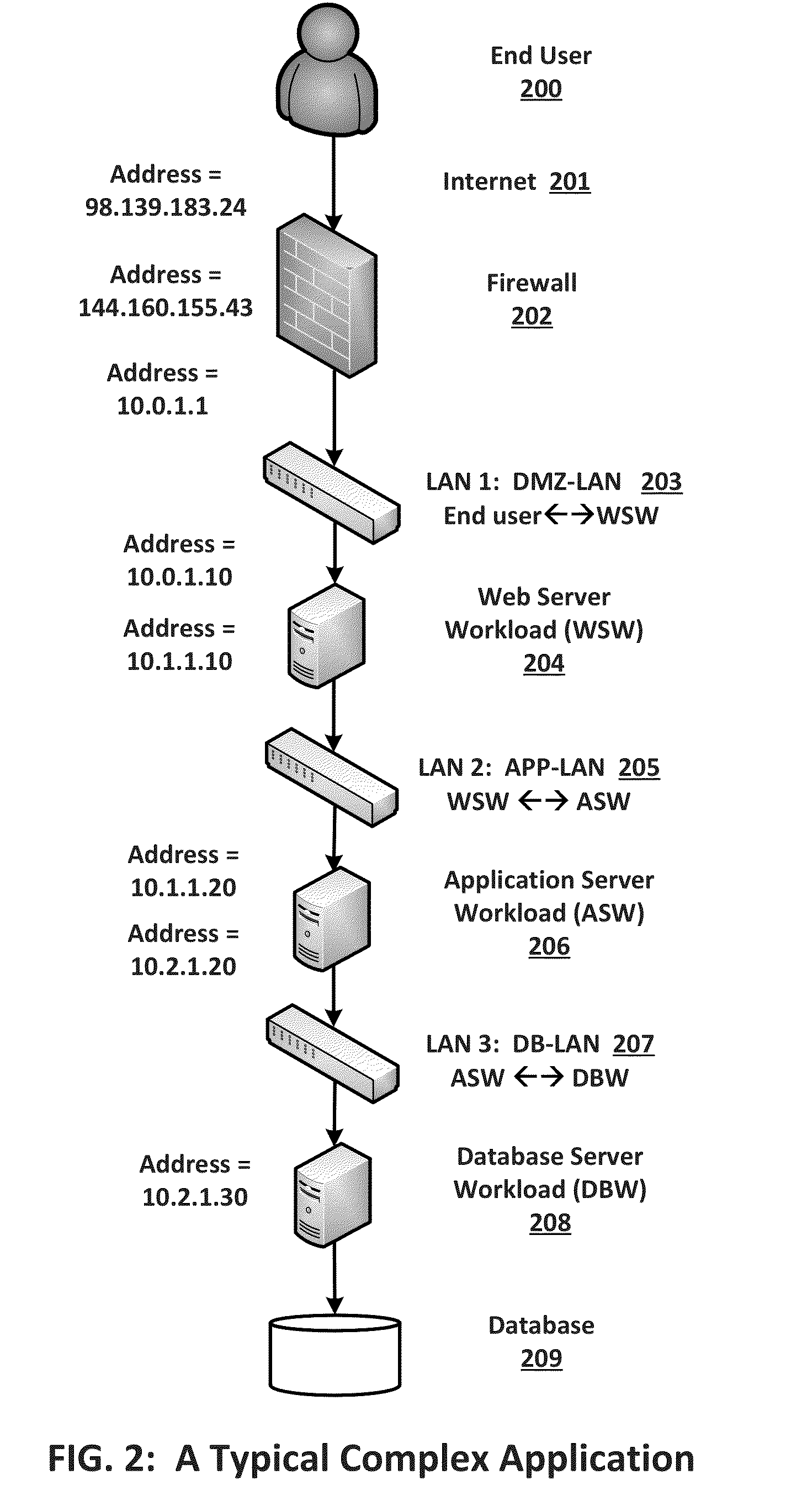
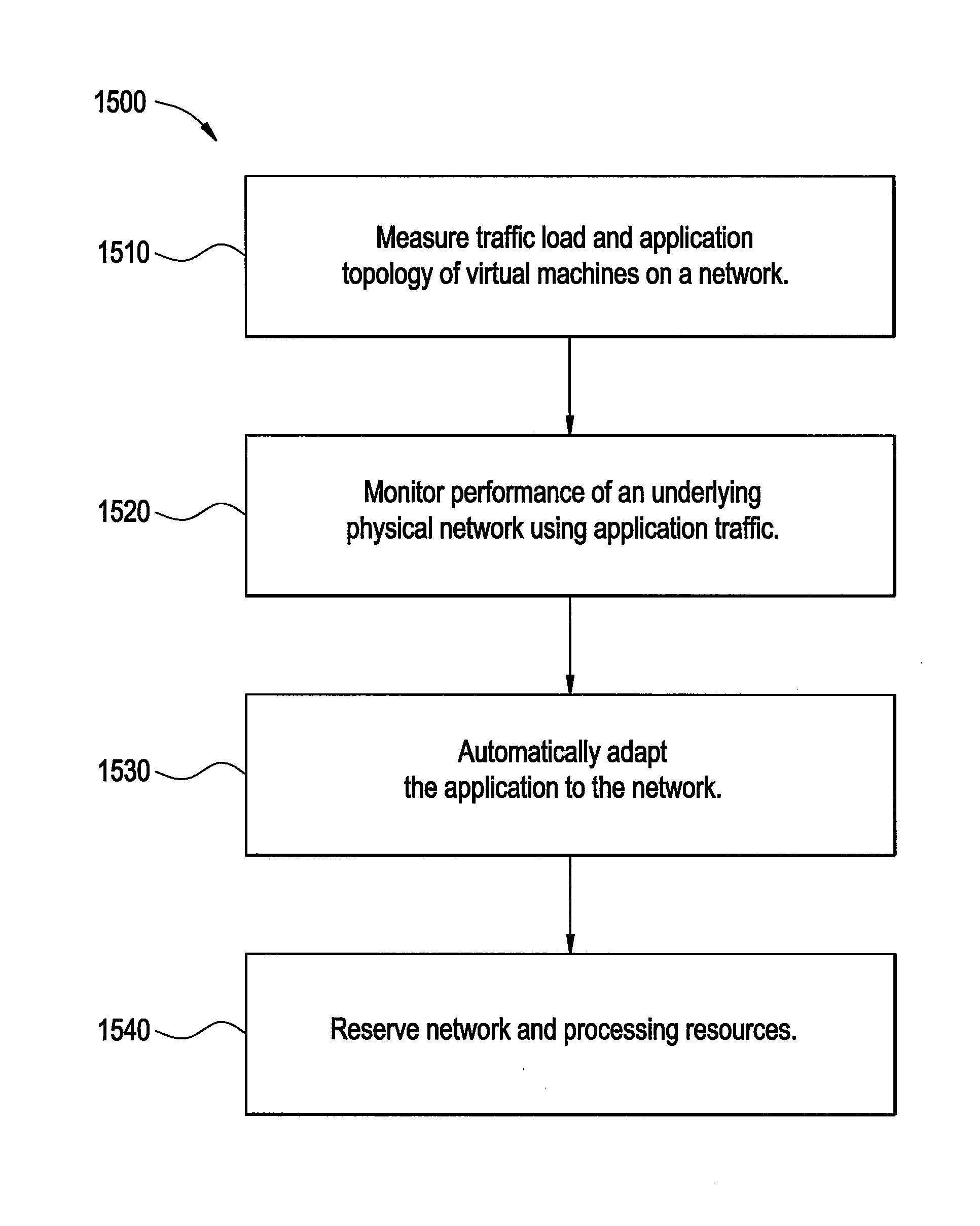
Certain embodiments of the present invention provide systems and method for automatic inference and adaptation of a virtualized computer environment. Certain embodiments of a system include a virtual topology and traffic inference framework tool adapted to monitor traffic for an application on a virtual network to produce a view of network demands for the application. The system also includes a monitoring tool adapted to monitor performance of an underlying physical network associated with the virtual network using traffic for the application. Further, the system includes an adaptation component adapted to automatically adapt the application to the virtual network based on the measured application traffic, the monitored network performance, and one or more adaptation control algorithms.
Owner:NORTHWESTERN UNIV
Secure virtual network platform for enterprise hybrid cloud computing environments
ActiveUS20140244851A1Broaden applicationEasy to deployMultiple digital computer combinationsData switching networksVirtual platformCloud computing
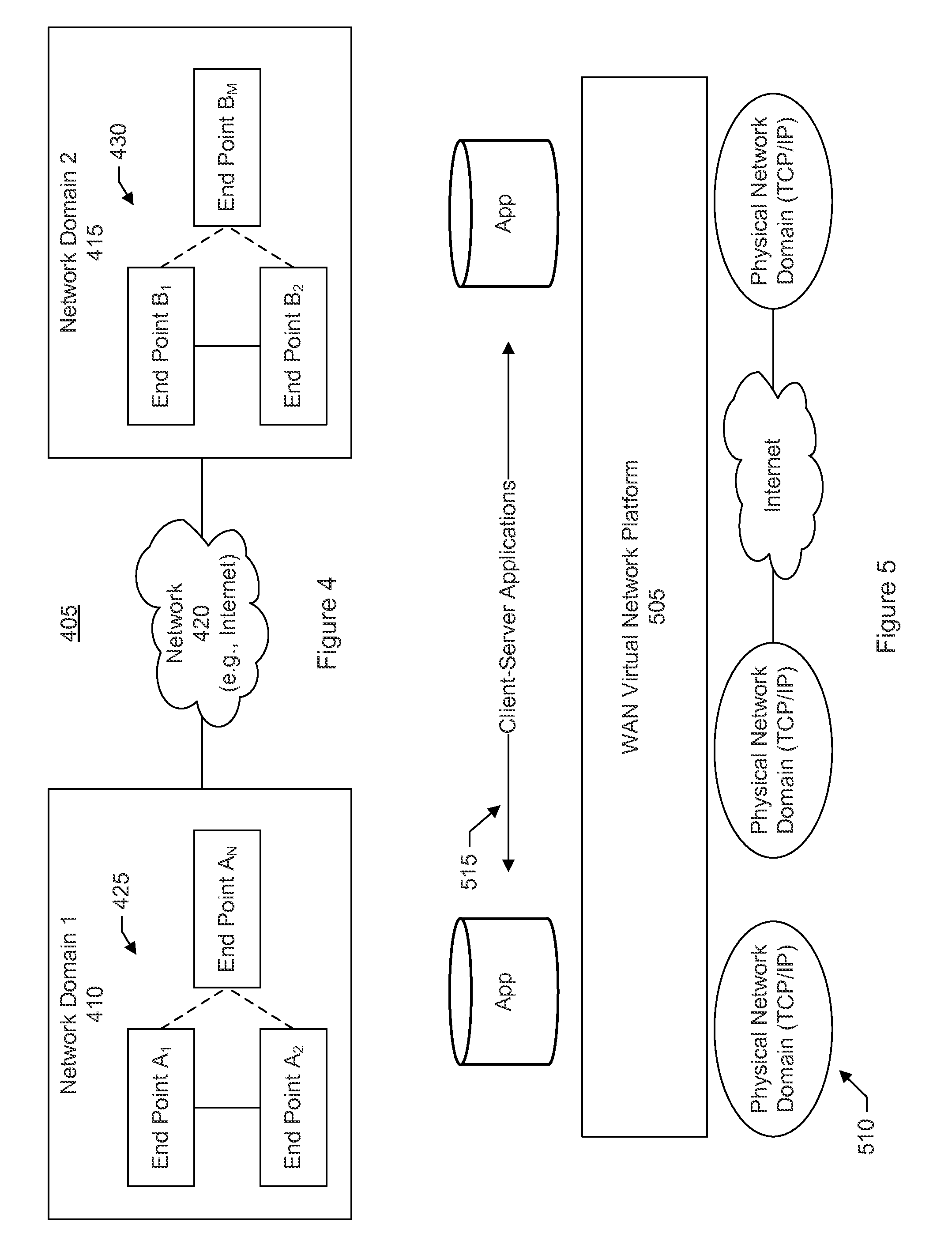
A secure virtual network platform connects two or more different or separate network domains. When a data packet is received at an end point in one network domain, a determination is made as to whether the data packet should be forwarded outside the virtual network platform, or transmitted via the virtual network to a destination in another network domain connected by the virtual network platform.
Owner:ZENTERA SYST
System, apparatus and method for providing a virtual network edge and overlay with virtual control plane
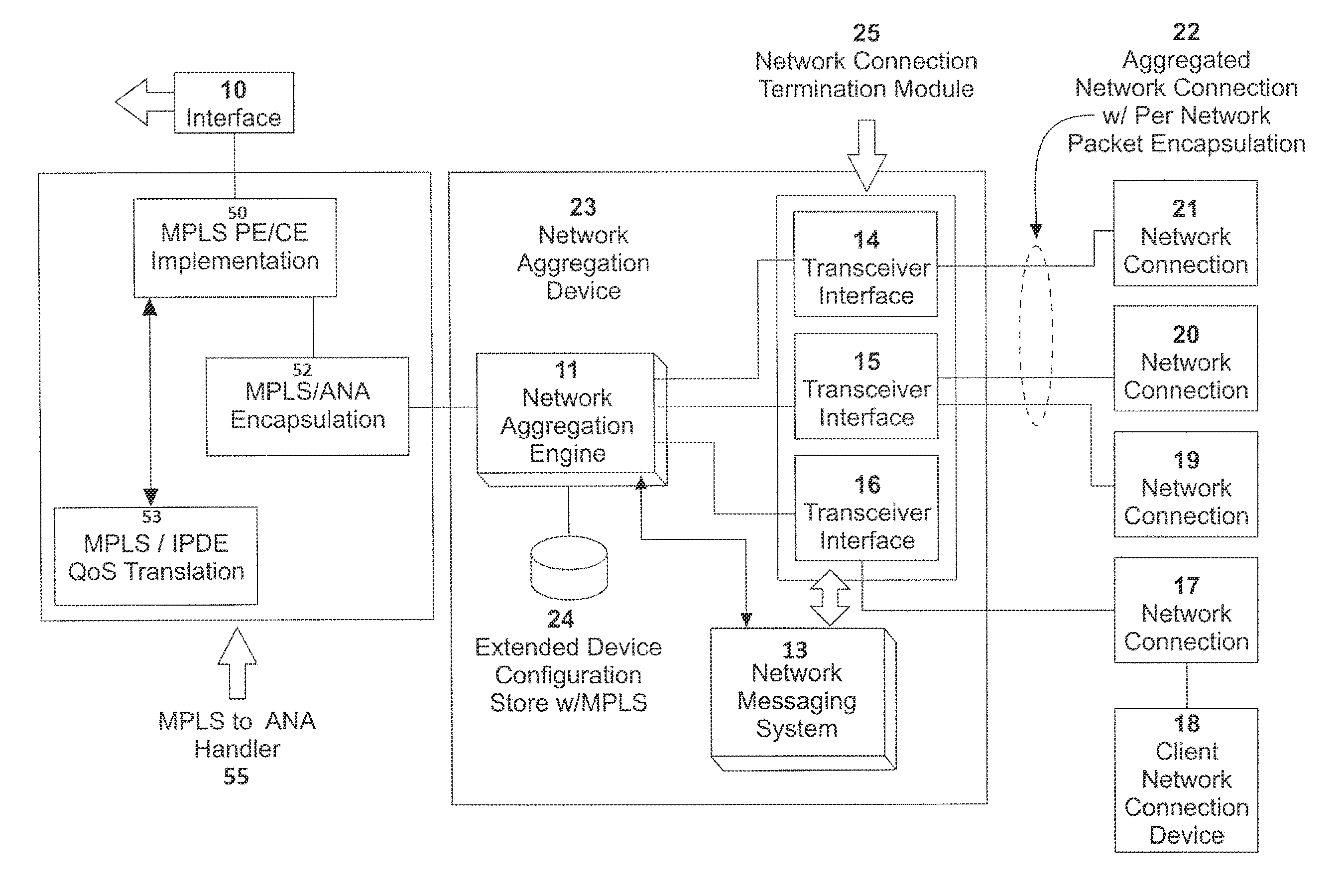
ActiveUS20160072669A1Improve communication performanceImprove throughputDigital computer detailsNetworks interconnectionTraffic capacityNetwork connection
A network system is provided between at least a first client site and a second client site. A client site network component is implemented at least at the first client site, the client site network component aggregating one or more diverse network connections so as to configure an aggregated connection that has increased throughput. At least one network server component may be configured to connect to the client site network component using the aggregated connection. A cloud network controller may be configured to manage the data traffic and a virtual edge providing transparent lower-link encryption for the aggregated connection between the client site network component and the network server component. The network server component includes a virtual control plane interface configured to establish a unicast path between the network server component and each of a plurality of remote network server components.
Owner:ADAPTIV NETWORKS INC
Method, computer program, and algorithm for computing network service value pricing based on communication service experiences delivered to consumers and merchants over a smart multi-services (SMS) communication network
ActiveUS20110243553A1Low costIncrease statistical probabilityInterconnection arrangementsMetering/charging/biilling arrangementsService experienceComputer terminal
A system and method for providing multi-services within a communication network according to various exemplary embodiments can include storing, in a database of a computer, user-defined sets of rules and instructions for providing multi-services to end user devices connected to a communication network comprising a Hybrid Fiber-Wireless (HFW) network having policy management capabilities. The system and method can receive, at one or more processors, the user-defined sets of rules and instructions from a plurality of end users via a plurality of end user devices. The system and method can configure a virtual network for each end user within the communication network using the policy management capabilities based on the user-defined sets of rules and instructions provided by each end user. The user-defined sets of rules and instructions define provisioning and delivery of resources and services provided by the communication network to the end user.
Owner:INCNETWORKS
Virtual machine based network carriers
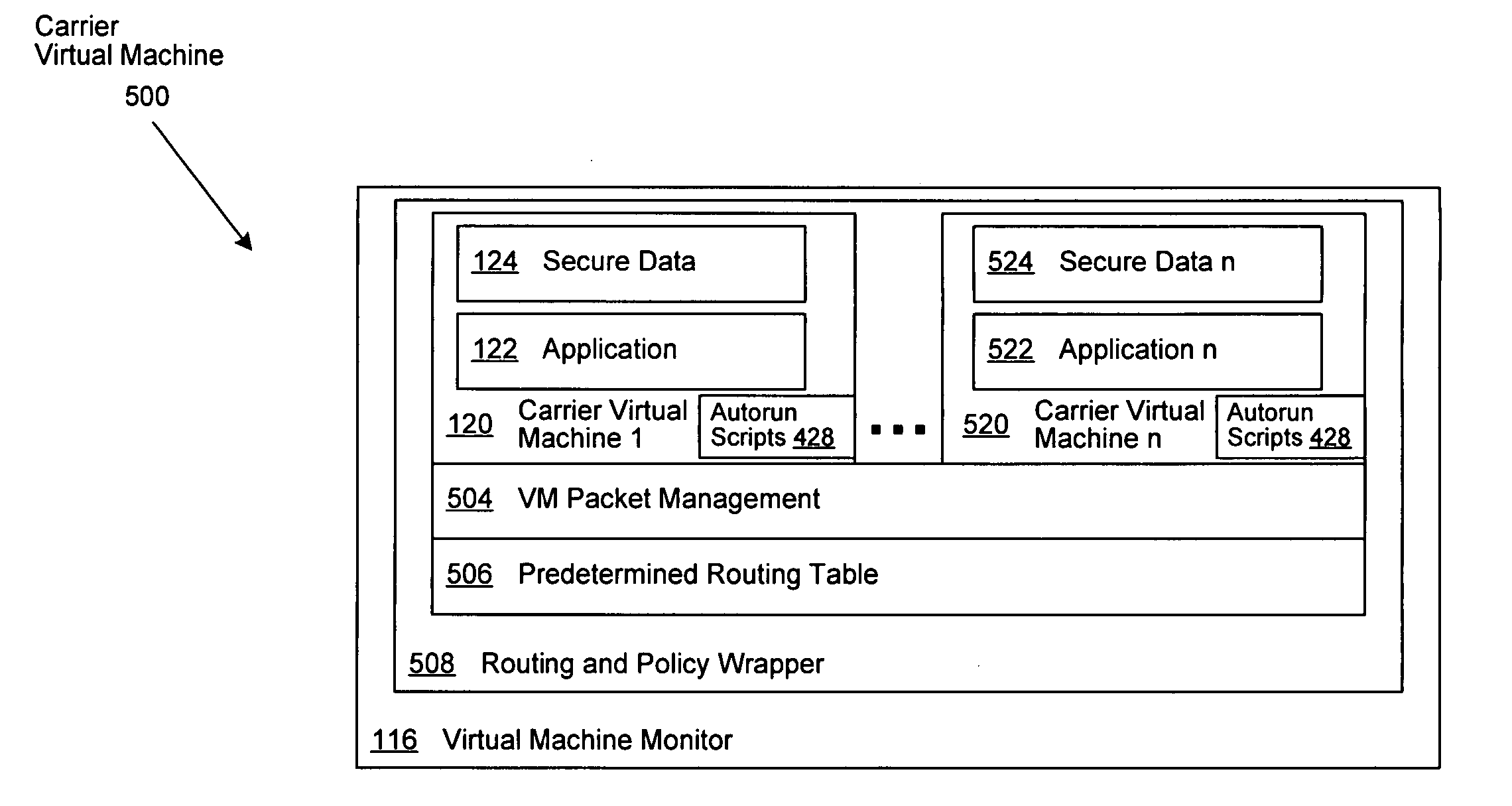
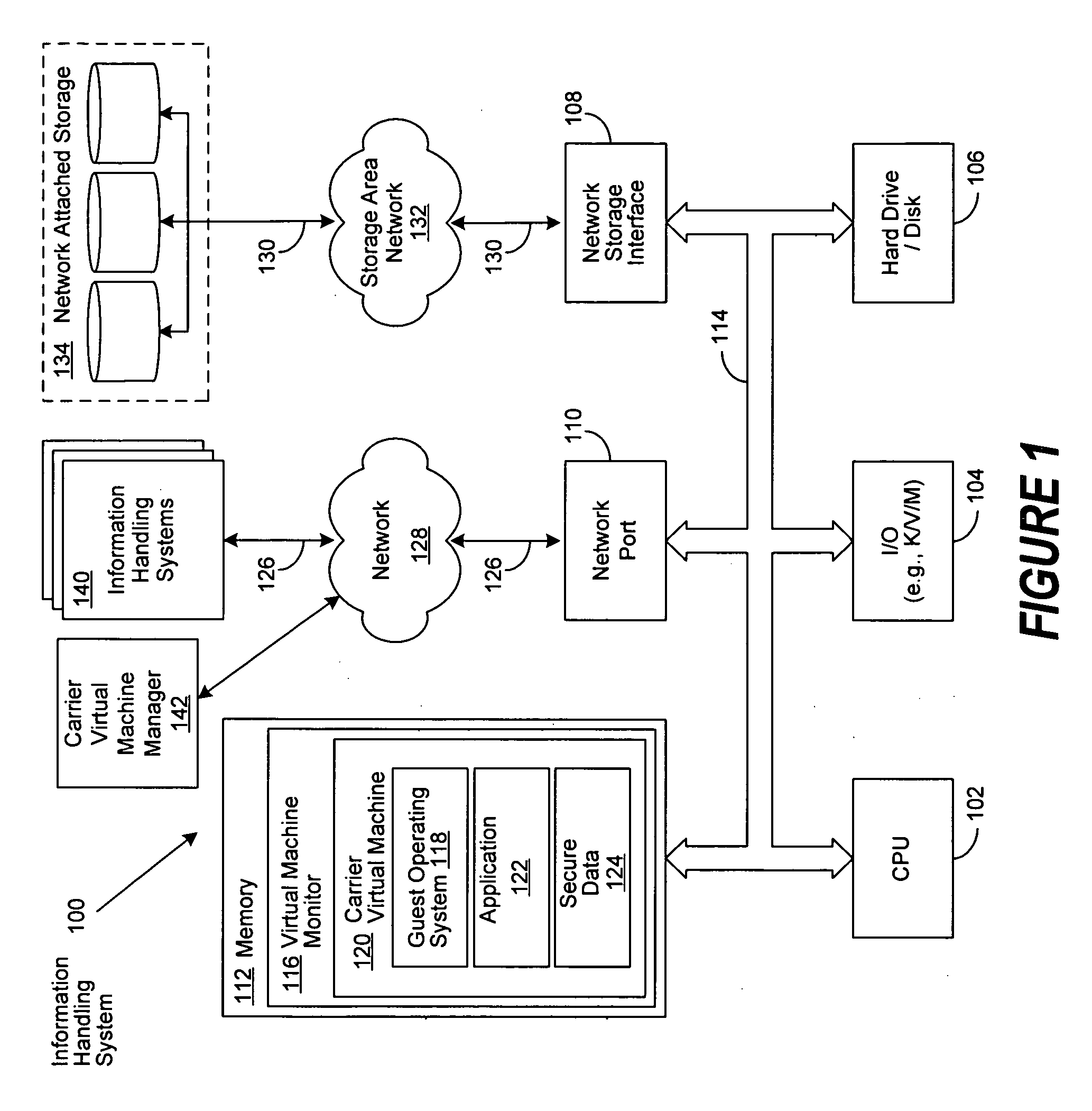
InactiveUS20070079307A1Environment safetyTransmissionSoftware simulation/interpretation/emulationData packData set
A system and method is disclosed for the secure transfer of data by carrier virtual machines between participating physical hosts through a virtual network (VNET) implemented on one or more internal and / or external networks. The method of the invention can provide additional security controls, comprising parameters that may include, but are not limited to, time-to-live (TTL), access control lists (ACLs), usage policies, directory roles, etc. Additionally, access to one or more of a plurality of carrier virtual machine payloads by security groups, individual access, subdivided individual access, and MIME-like subdivision of a VM-encapsulated payload may be controlled, thereby providing the carrier VM the ability to carry many secured payloads. In addition, VM packets, a group of packets, a single VM, or subpackets within a VM between network endpoints, or at a predetermined intermediary network point, may be quarantined to realize further security. Individual or combinations of these functionalities on carrier virtual machines, and by extension, application and / or one or more sets of secure data may be implemented.
Owner:DELL PROD LP
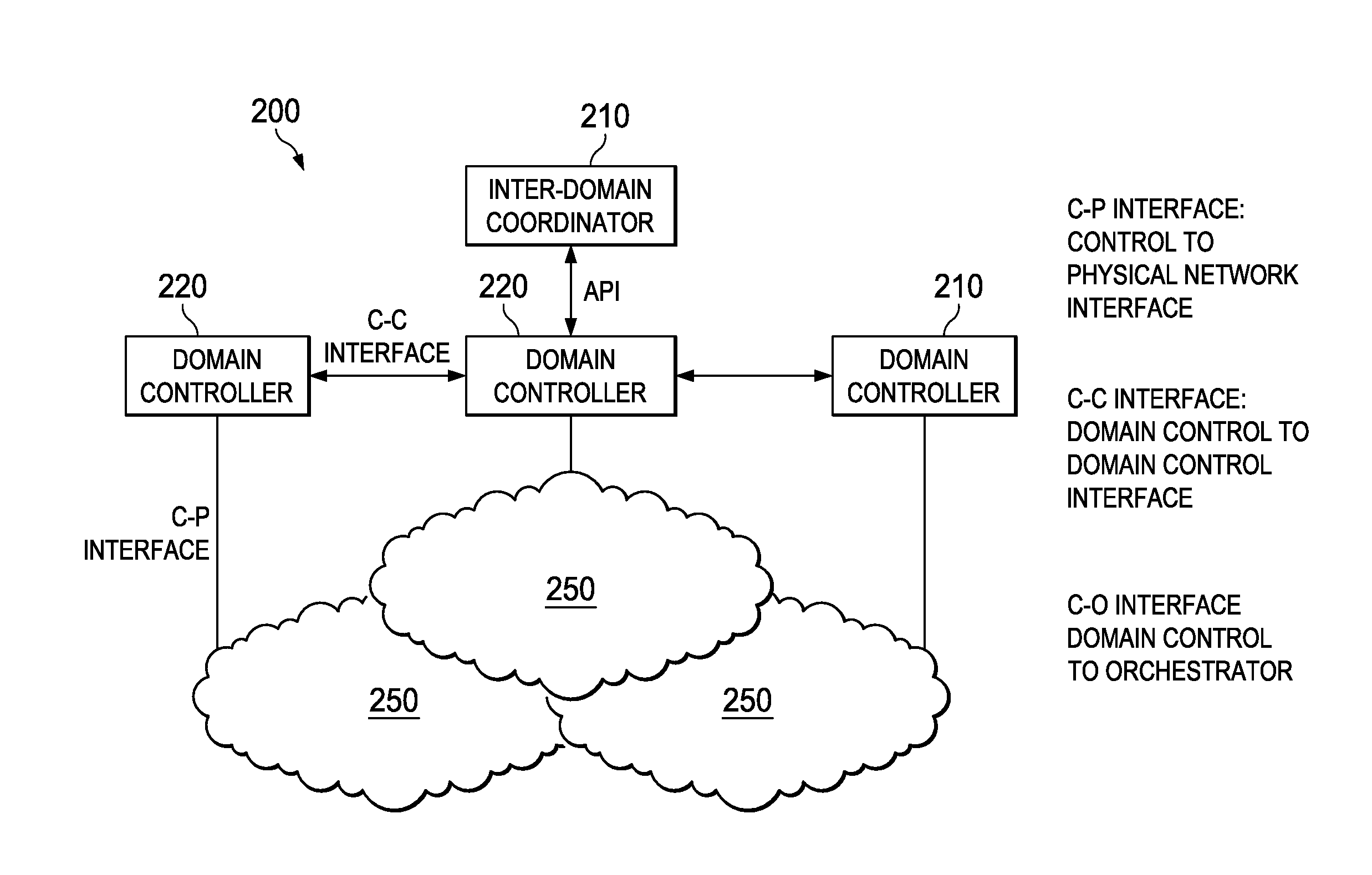
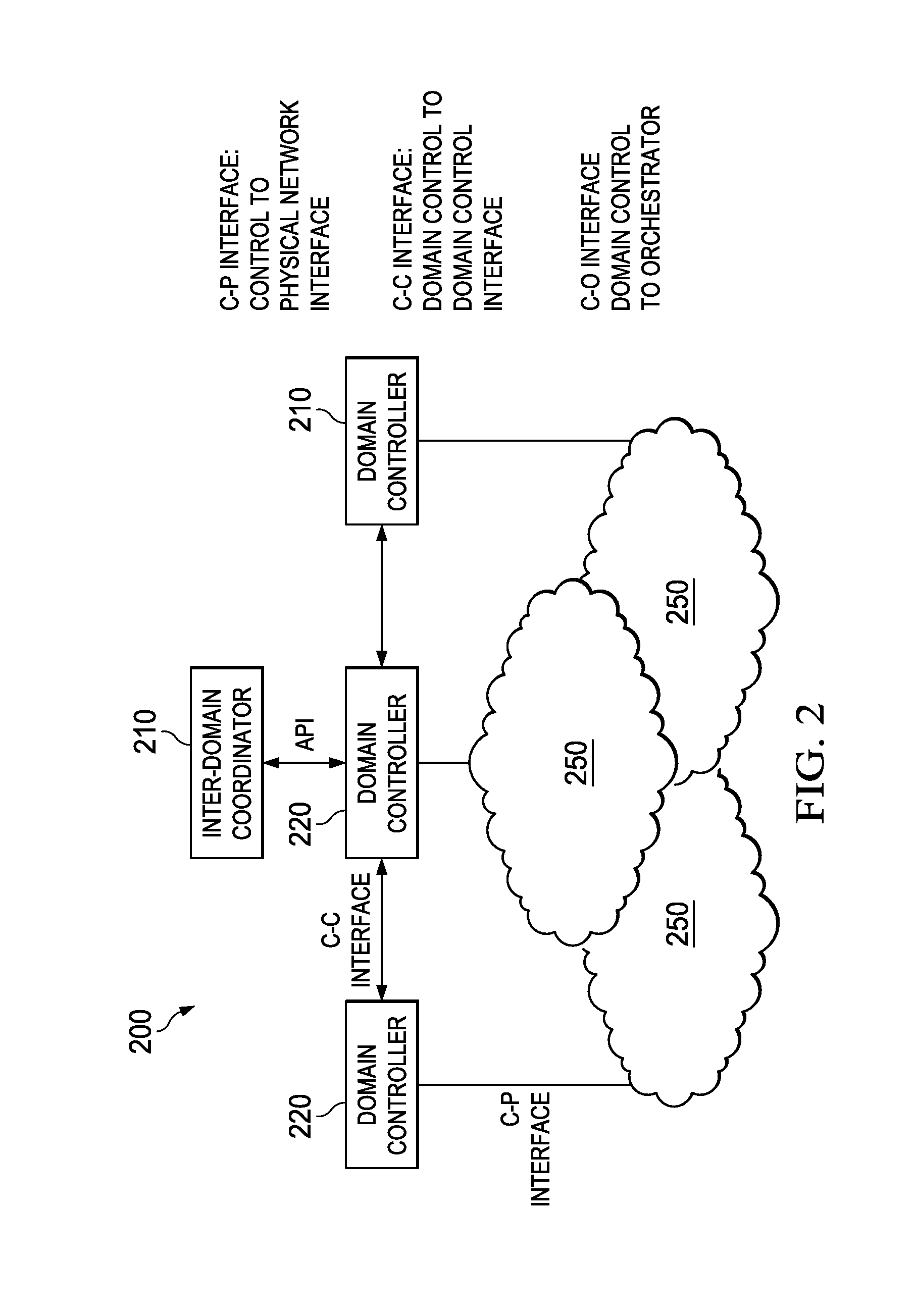
System and Method for a Control Plane Reference Model Framework
ActiveUS20140307556A1Quality improvementEasy to useError preventionFrequency-division multiplex detailsReference modelLogical topology
Embodiments are provided for implementing control plane functionality to configure a data plane at a plurality of network nodes. A software defined topology (SDT) component is configured to determine a data plane logical topology indicating a plurality of selected nodes and a logical architecture connecting the selected nodes. The data plane logical topology enables traffic delivery for a service or virtual network for an end-customer or operator. A software defined networking (SDN) component is configured to interact with the SDT component and map the data plane logical topology to a physical network. The mapping includes allocating network nodes including the selected nodes and network resources which enable communications for the service or virtual network and meet QoS requirement. A software defined protocol (SDP) component is configured to interact with the SDN and define data plane protocol and process functionality for the network nodes.
Owner:HUAWEI TECH CO LTD
Secure cloud fabric to connect subnets in different network domains
ActiveUS20140337500A1Digital computer detailsData switching networksStructure of Management InformationNetwork topology
A secure virtual network platform connects two or more subnets in different or separate network domains. The secure virtual network can use the under layer physical networks in various domains as an IP forwarding fabric without changing any existing firewalls, security settings, or network topology. A first type of connection across the virtual network involves connecting server groups. A second type of connection across the virtual network involves connecting a server group to a physical network. A third type of connection across the virtual network involves connecting a physical network to another physical network.
Owner:ZENTERA SYST
Method and apparatus for securing communication over public network
InactiveUS8458453B1Reduce packet-processing timeMultiple digital computer combinationsProgram controlSecure communicationPublic network
A system and method of providing secure communications between two or more hosts connected to a public network, where a secure virtual network (SVN) is established among the two or more hosts.
Owner:RPX CORP
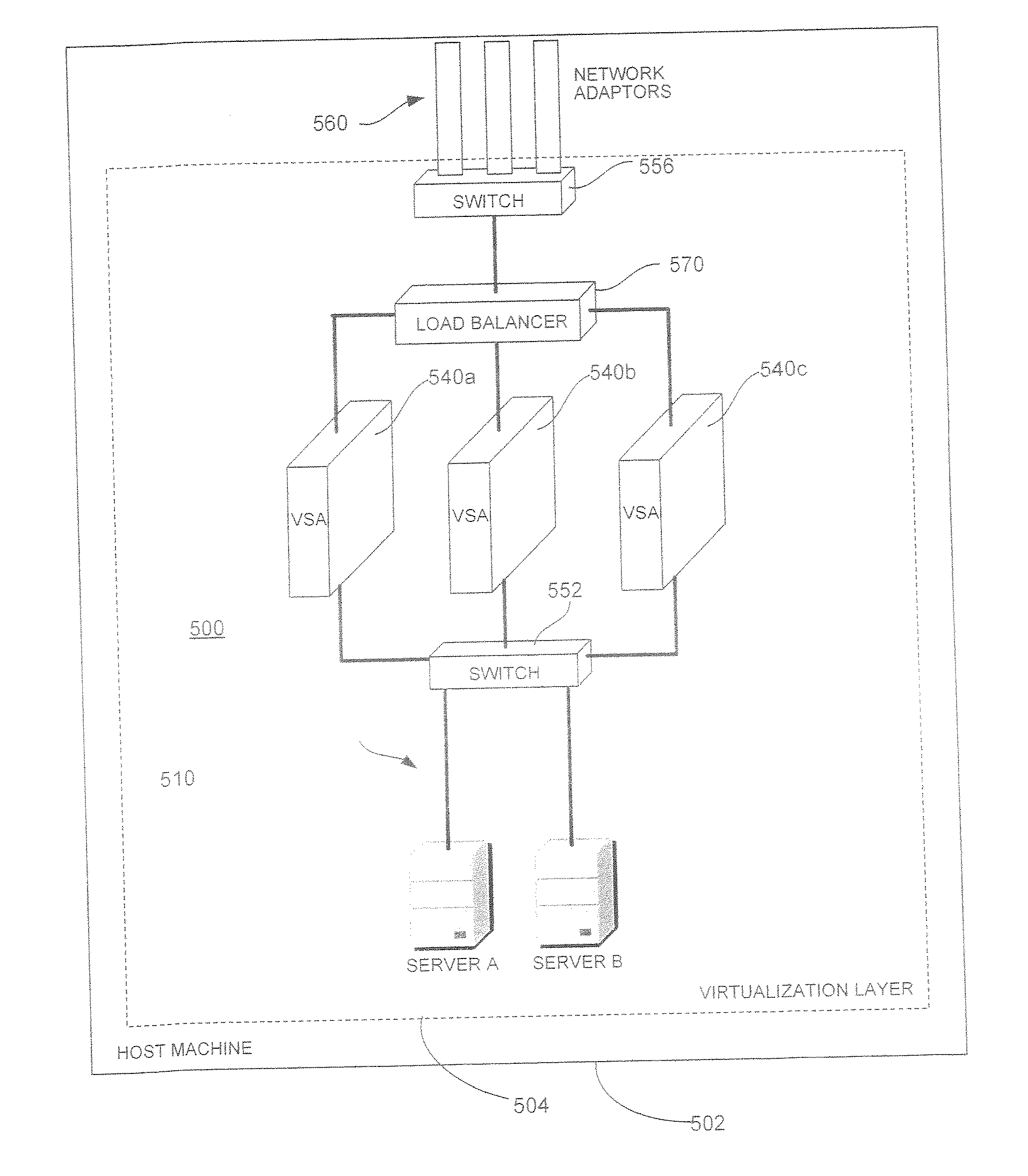
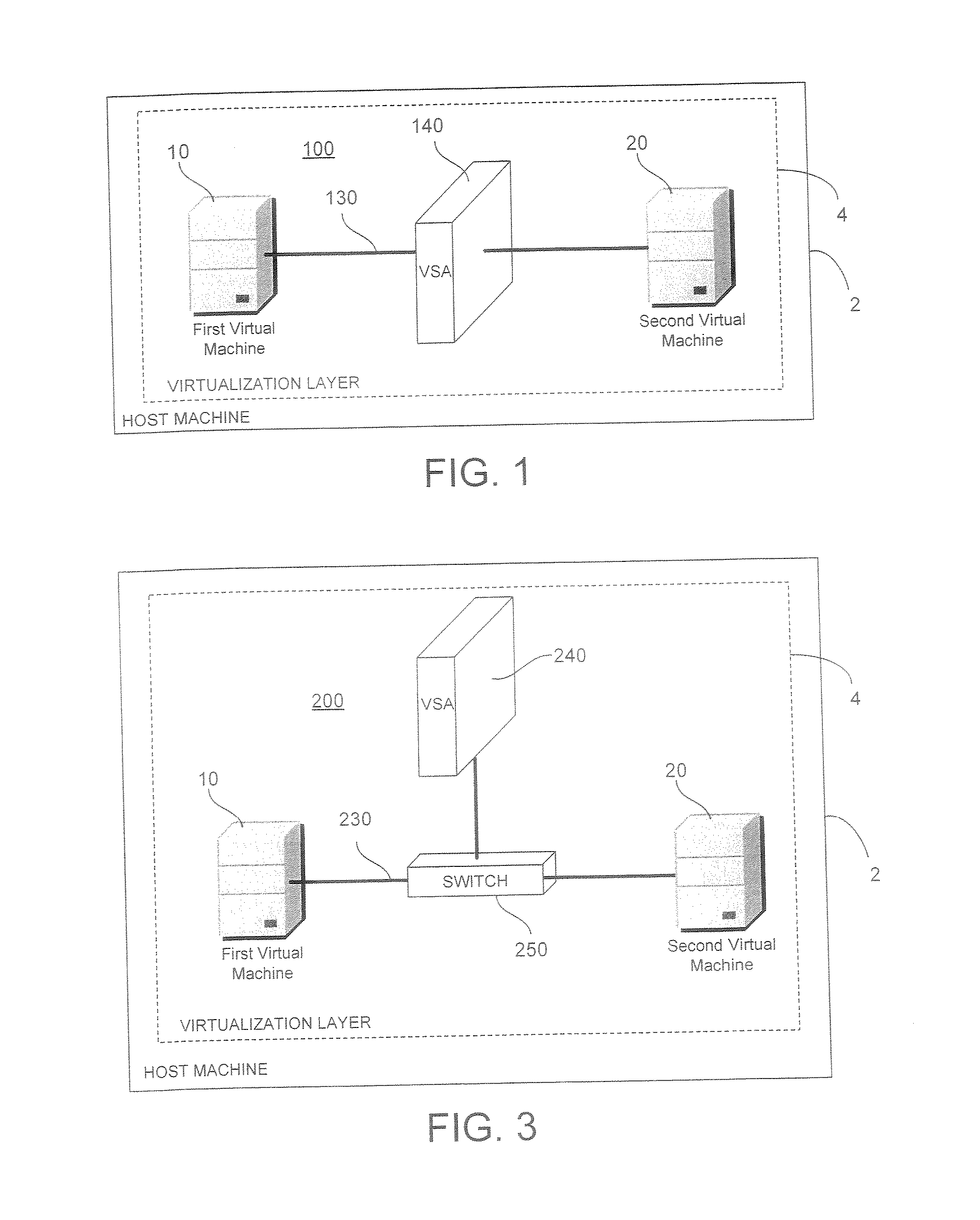
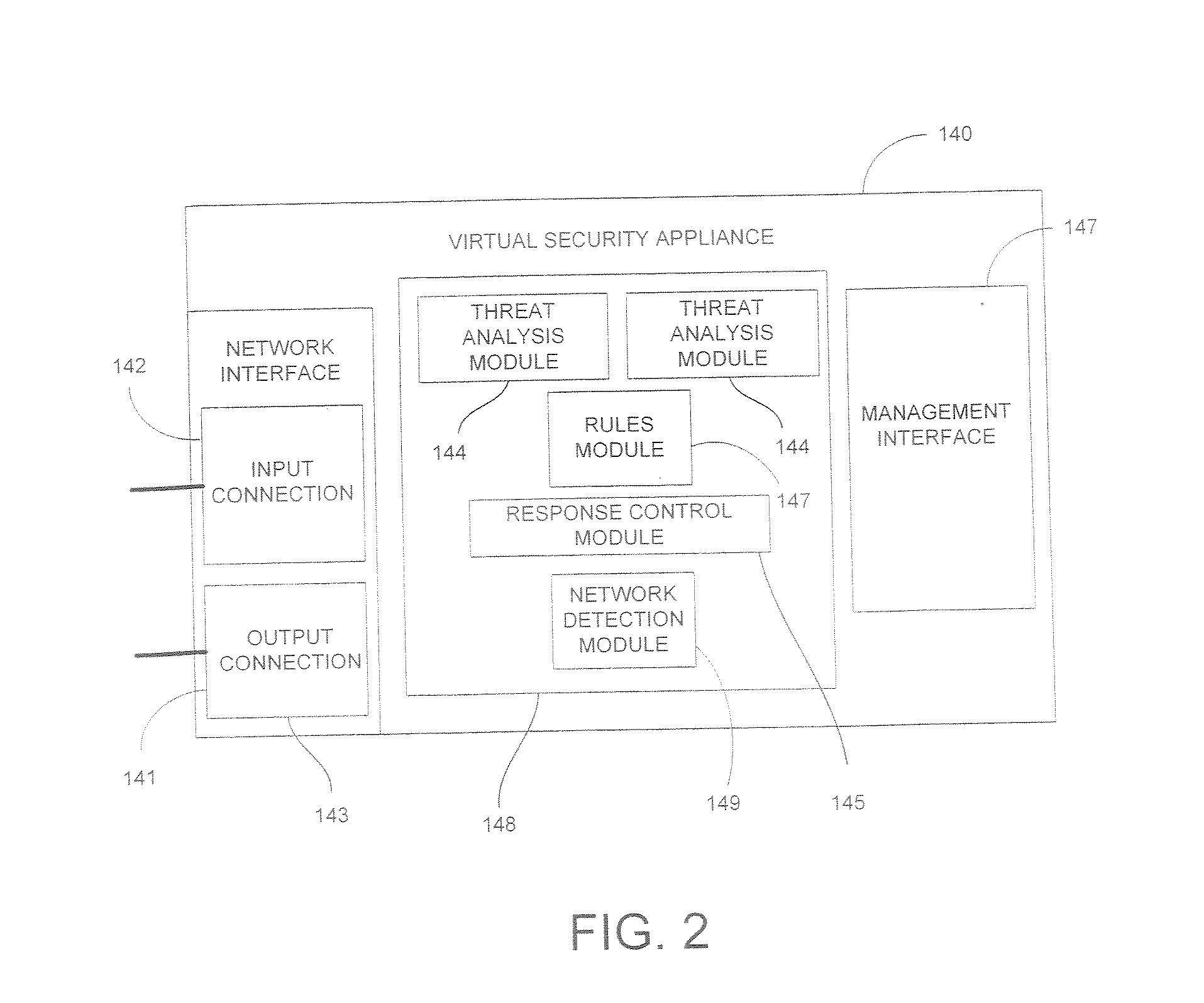
System and Method for Securing Information in a Virtual Computing Environment
InactiveUS20070266433A1Improve employee productivityIncrease the challengeMultiple digital computer combinationsPlatform integrity maintainanceVirtual computingHost machine
A virtual security appliance is provided for disposition in a virtual network having at least one other virtual network device, the virtual network residing on a host data processing machine. The virtual security appliance comprises an interface configured for receiving a data communication directed to the at least one other virtual network device and a security function module adapted for initiating a security function responsive to said data communication meeting predetermined criteria.
Owner:STRATACLOUD
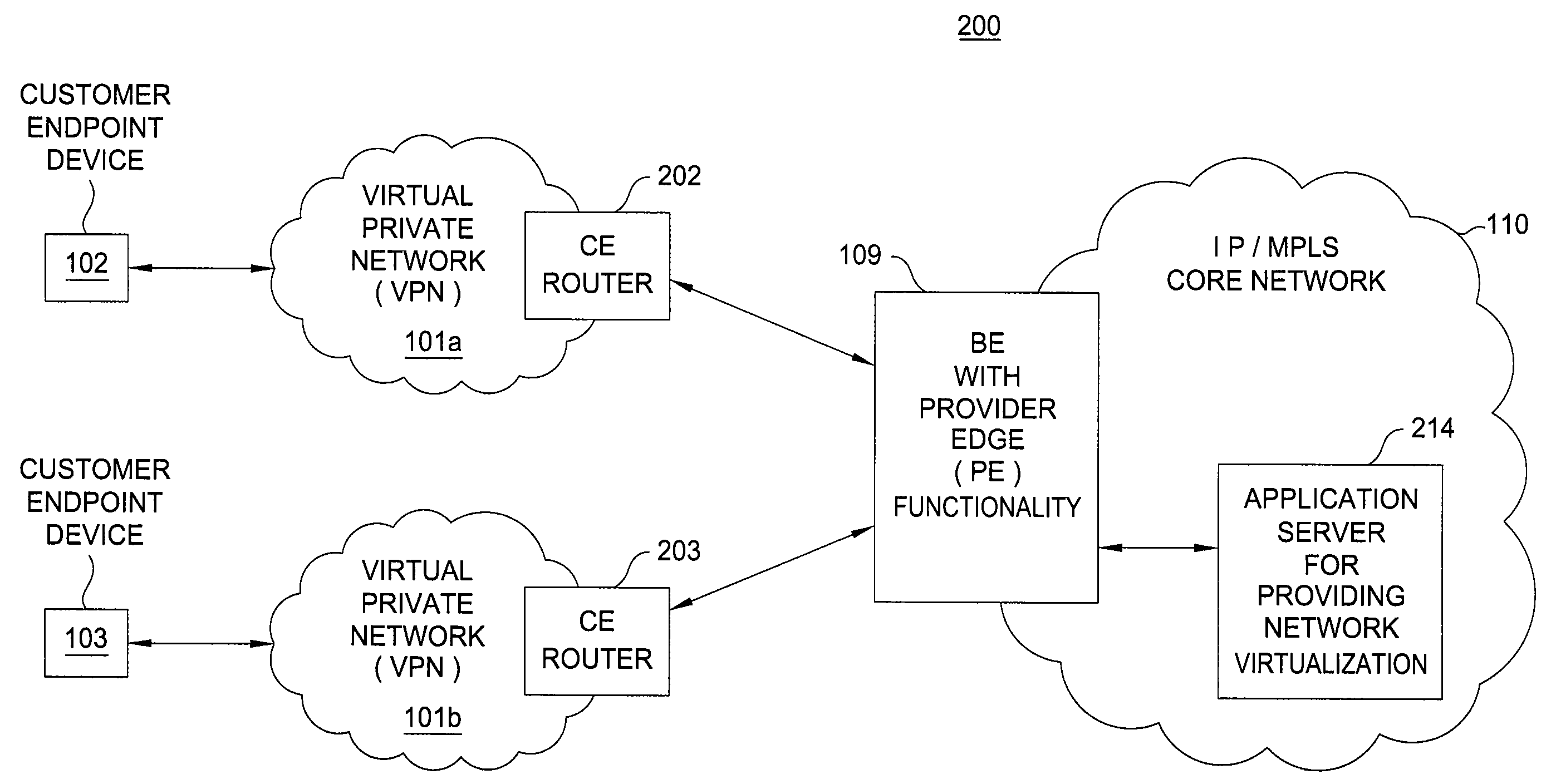
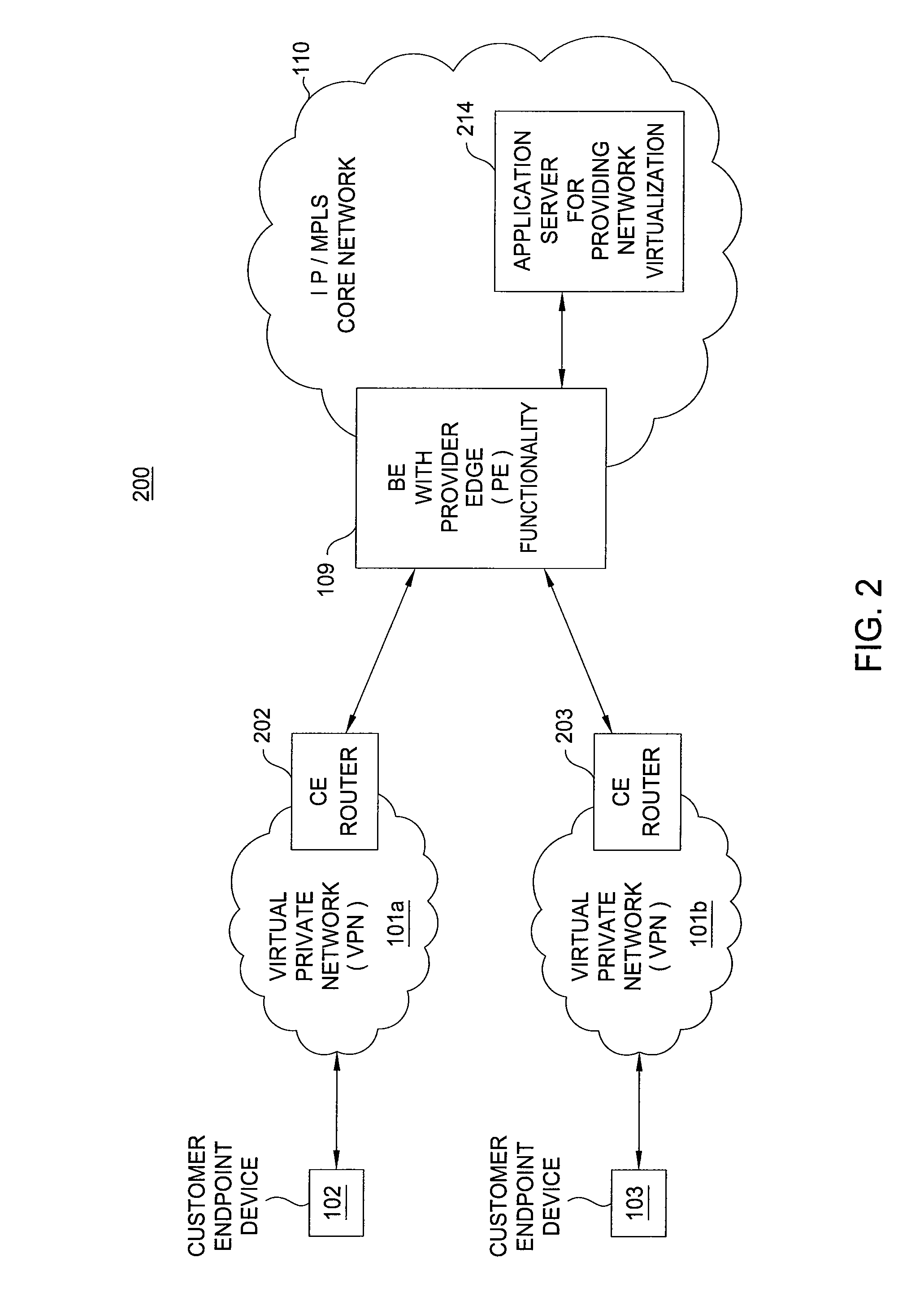
Method and apparatus for providing network virtualization
A method and apparatus for providing network virtualization on a packet network are disclosed. For example, the method receives a request from a user, wherein the request comprises at least one of: a feature of a network component or a network component for a virtual network. The method determines if the request can be instantiated over one or more real network resources, and then instantiates the request via the one or more real network resources, if it is determined that the request can be instantiated.
Owner:RAKUTEN GRP INC
Method and apparatus for network virtualization
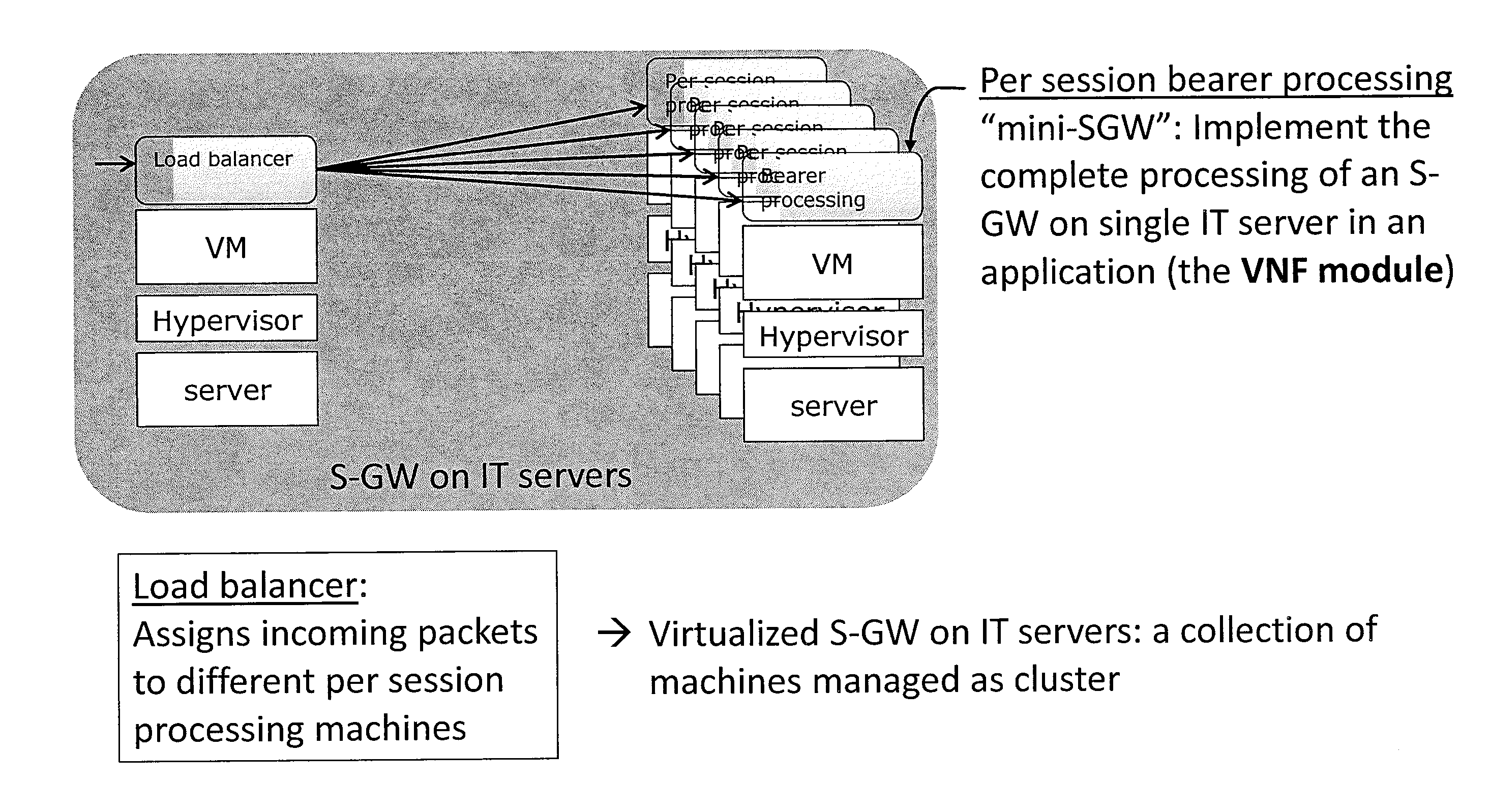
ActiveUS20150082308A1Avoid wasting resourcesFlexible implementationData switching networksSoftware simulation/interpretation/emulationExecution unitNetwork virtualization
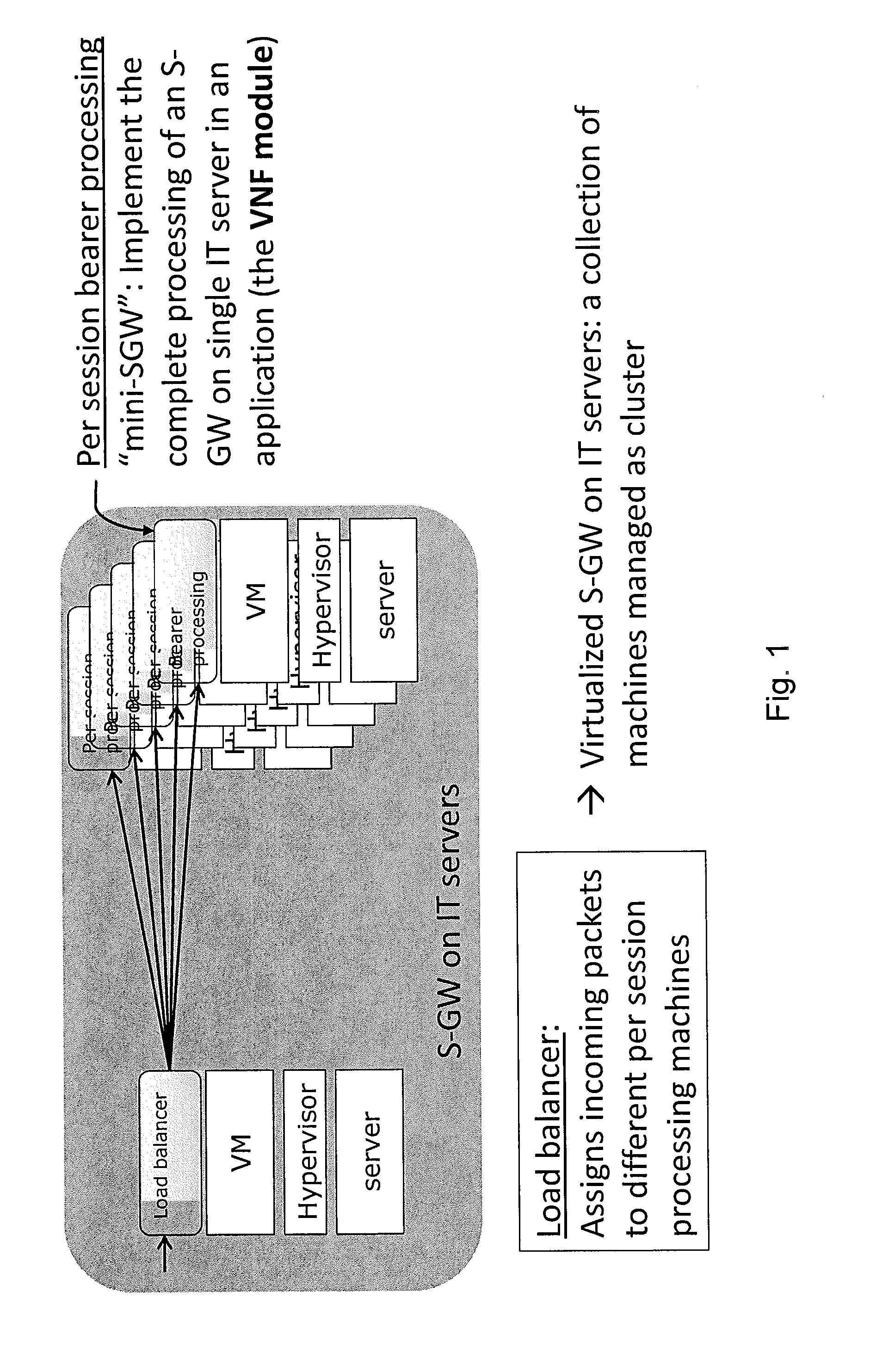
A method for implementing an entity of a network by virtualizing said network entity and implementing it on one or more servers each acting as an execution unit for executing thereon one or more applications running and / or one or more virtual machines running on said execution unit, each of said application programs or virtual machines running on a server and implementing at least a part of the functionality of said network entity being called a virtual network function VNF module, wherein a plurality of said VNF modules together implement said network entity to thereby form a virtual network function VNF, said method comprising the steps of: obtaining m key performance indicators (KPI) specifying the required overall performance of the VNF, obtaining n performance characteristics for available types of execution units, determining one or more possible deployment plans based on the obtained m KPI and n performance characteristics, each deployment plan specifying the number and types of execution units, such that the joint performance of VNF modules running on these execution units achieves the required overall performance of the VNF.
Owner:NTT DOCOMO INC
Method and apparatus for achieving dynamic capacity and high availability in multi-stage data networks using adaptive flow-based routing
ActiveUS20050091396A1Multiplex system selection arrangementsError preventionSystems managementHigh availability
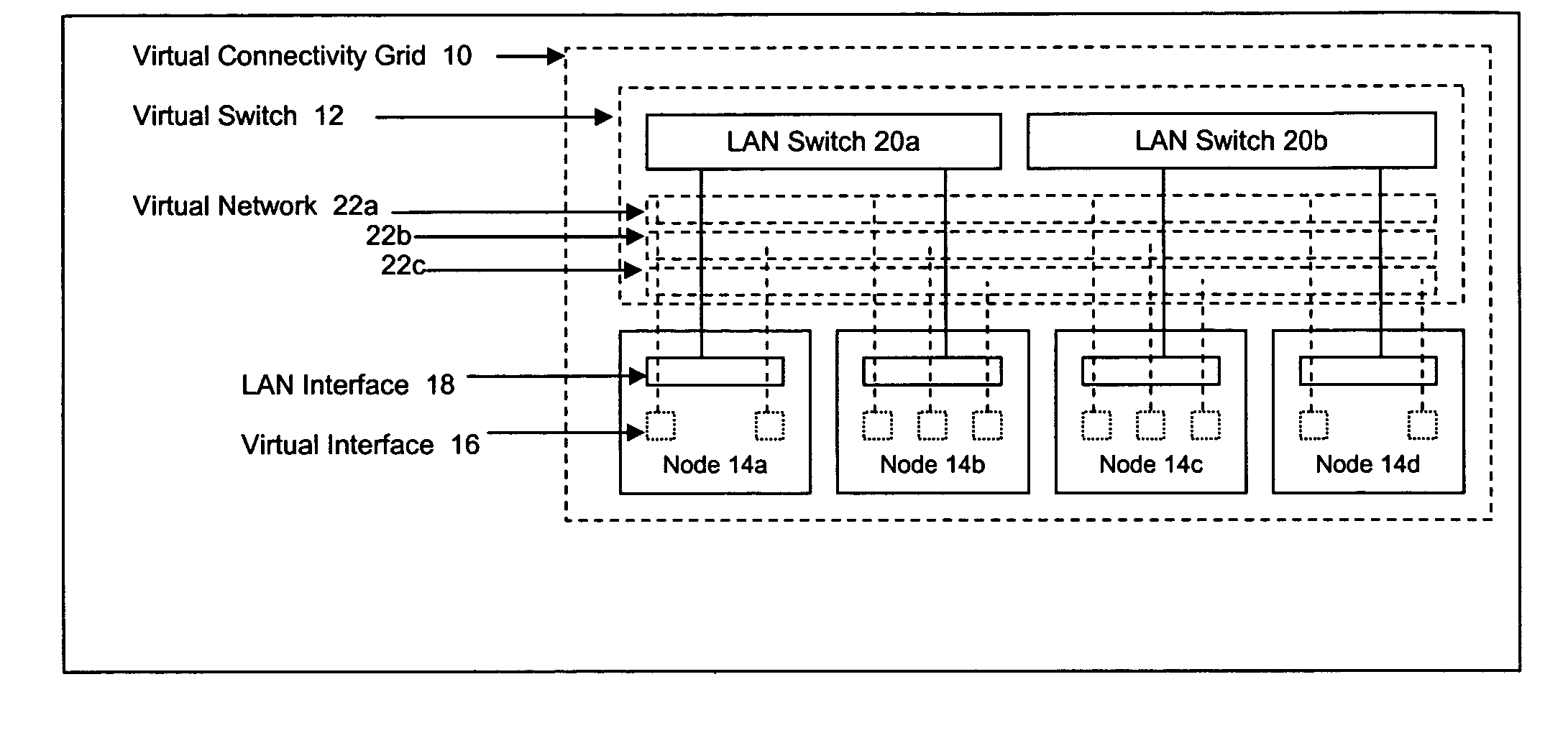
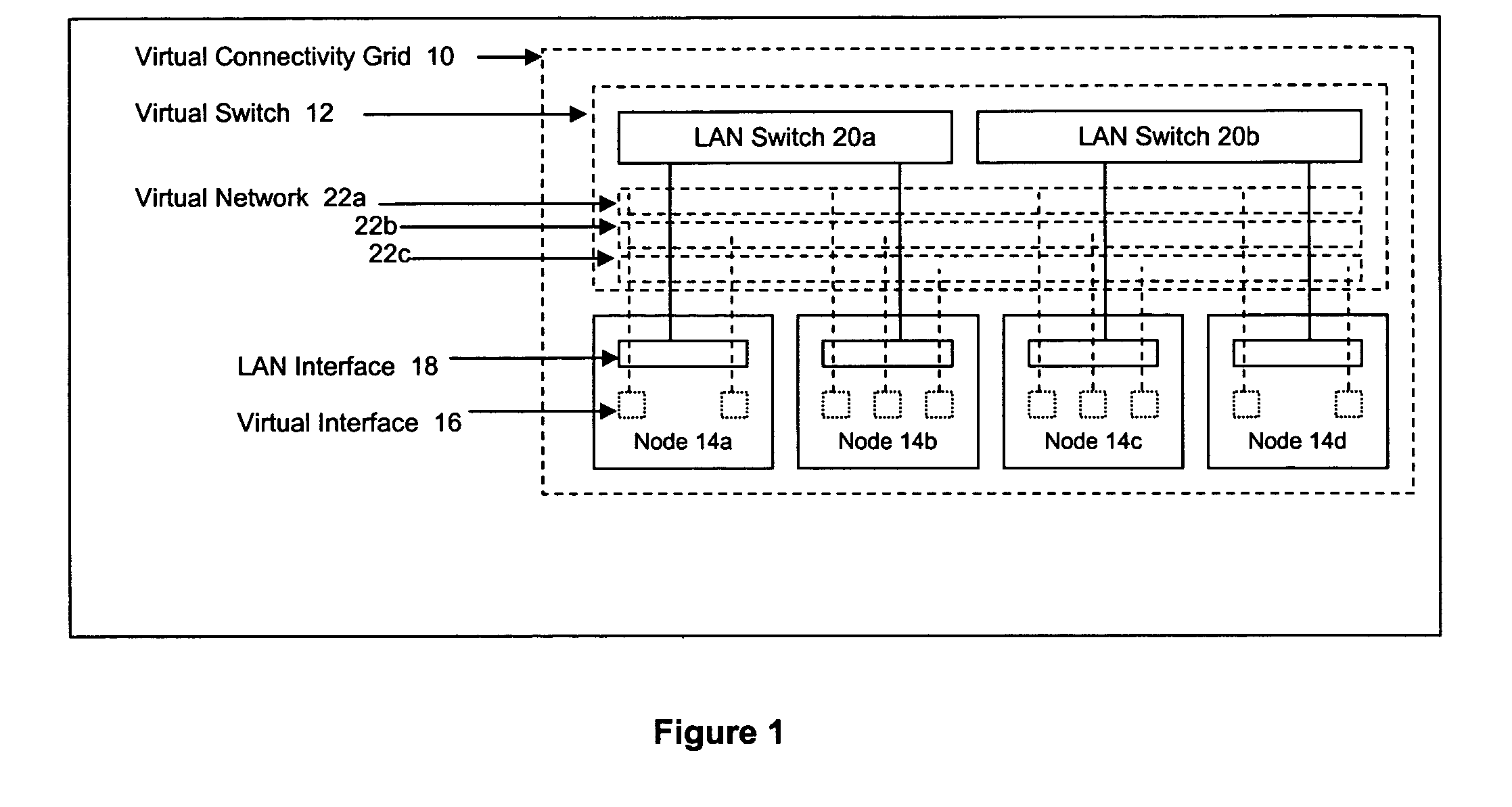
Methods and systems for determining paths for flows within a multi-stage network made up of clusters of processing nodes. The flow paths may be determined without knowledge of whether or not packets of a particular flow will actually traverse specific ones of the clusters within the multi-stage network. In various implementations, the nodes of the multi-stage network may be coupled to one or more physical network switches through respective physical interfaces and a virtual connectivity grid superimposed thereon and configured through the use of a flow routing framework and system management framework to group the nodes into a number of clusters. The nodes of each cluster are configured to perform similar packet processing functions and the clusters are interconnected through virtual networks to which the nodes are communicatively coupled via virtual interfaces overlaid on top of the physical network interfaces.
Owner:DELL PROD LP
Cloud-Based Middlebox Management System
ActiveUS20140068602A1Effectively scaledData switching networksSoftware simulation/interpretation/emulationApplication softwareMiddleware
A virtual network virtual machine may be implemented on a cloud computing facility to control communication among virtual machines executing applications and virtual machines executing middlebox functions. This virtual network virtual machine may provide for automatic scaling of middleboxes according to a heuristic algorithm that monitors the effectiveness of each middlebox on the network performance as application virtual machines are scaled. The virtual machine virtual network may also locate virtual machines in actual hardware to further optimize performance.
Owner:WISCONSIN ALUMNI RES FOUND
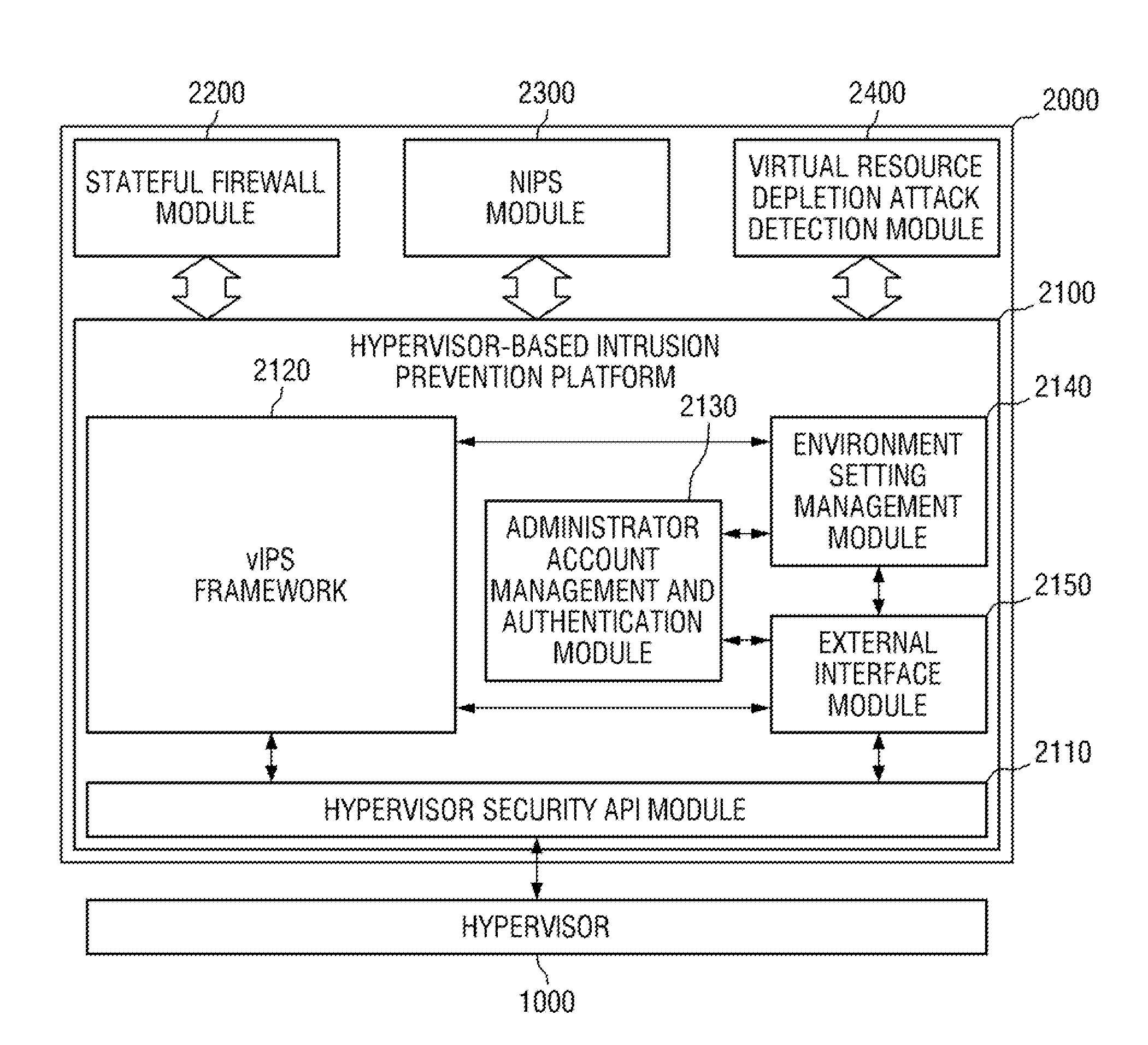
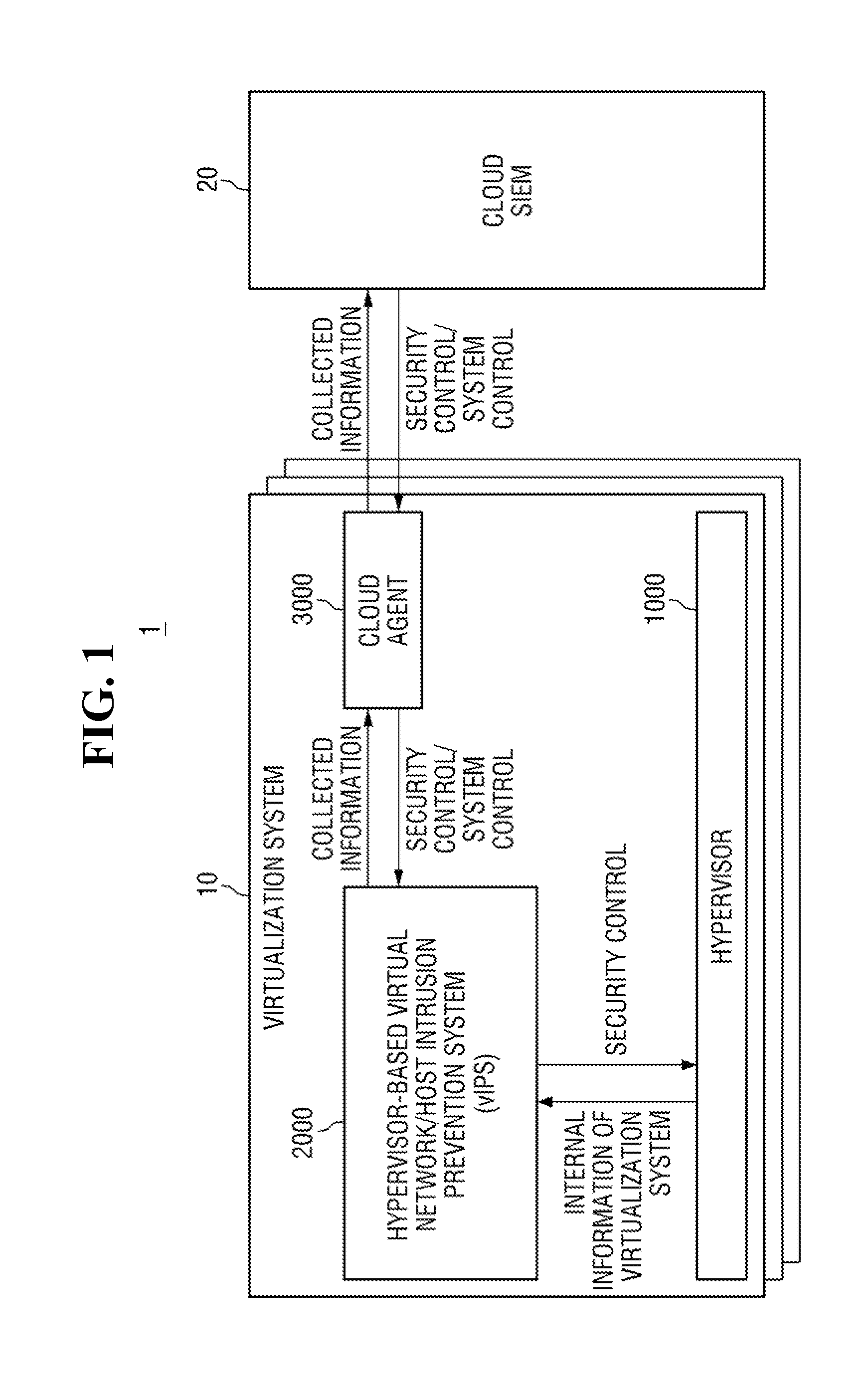
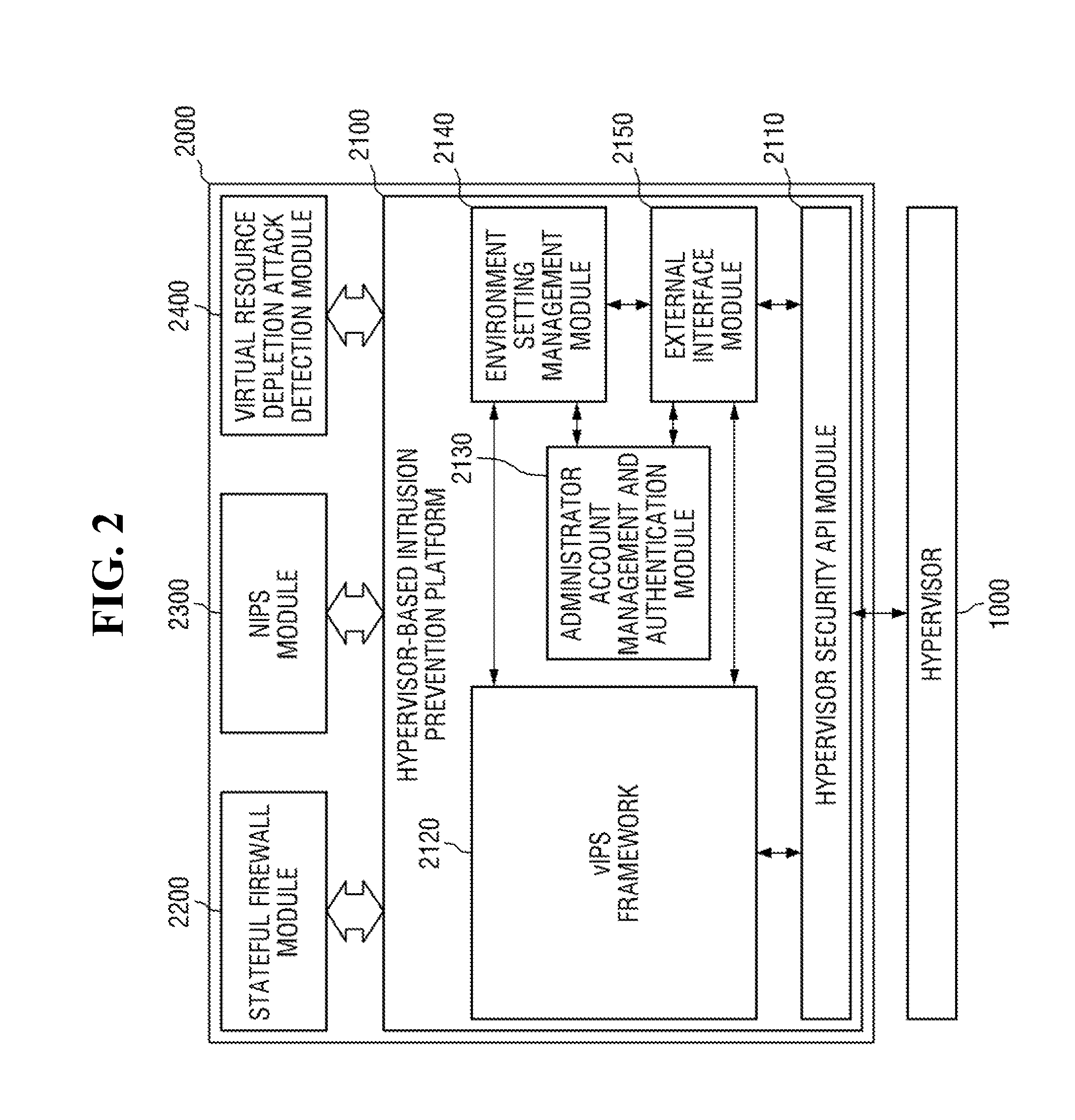
Hypervisor-based intrusion prevention platform and virtual network intrusion prevention system
InactiveUS20140317737A1Memory loss protectionData taking preventionApplication programming interfaceIntrusion prevention system
Hypervisor-based intrusion prevention platform is provided. The hypervisor-based intrusion prevention platform comprises a virtual network intrusion prevention system (vIPS) framework which obtains internal information of a virtualization system from a hypervisor and performs security control on the hypervisor in response to the result of intrusion detection carried out by using the internal information of the virtualization system, a hypervisor security application programming interface (API) module which provides an API used by the vIPS framework to access the hypervisor, an administrator account management and authentication module which manages an administrator account of a vIPS and authenticates the administrator account, an environment setting management module which manages environment setting values of modules within the vIPS, and an external interface module which provides an interface for system control and security control.
Owner:KOREA INTERNET & SECURITY AGENCY
System and method for distributed flow state p2p setup in virtual networks
ActiveUS20160105471A1Well formedMultiple digital computer combinationsNetworks interconnectionData interchangeData store
Systems and methods for virtual network implementation and management based on a peer-to-peer metadata exchange are disclosed. Metadata pertaining to a flow traversing a virtual network overlaying an underlying network is generated in accordance with actions executed to send data packets via the underlying network relative to the virtual network. The metadata is encapsulated in one or more control packets sent to a set of nodes of the underlying network. Each node of the set of nodes maintains a copy of the metadata received in the one or more control packets in a local data store. The metadata is accessed via the local data store when needed to process packets of the flow.
Owner:MIDO HLDG LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com