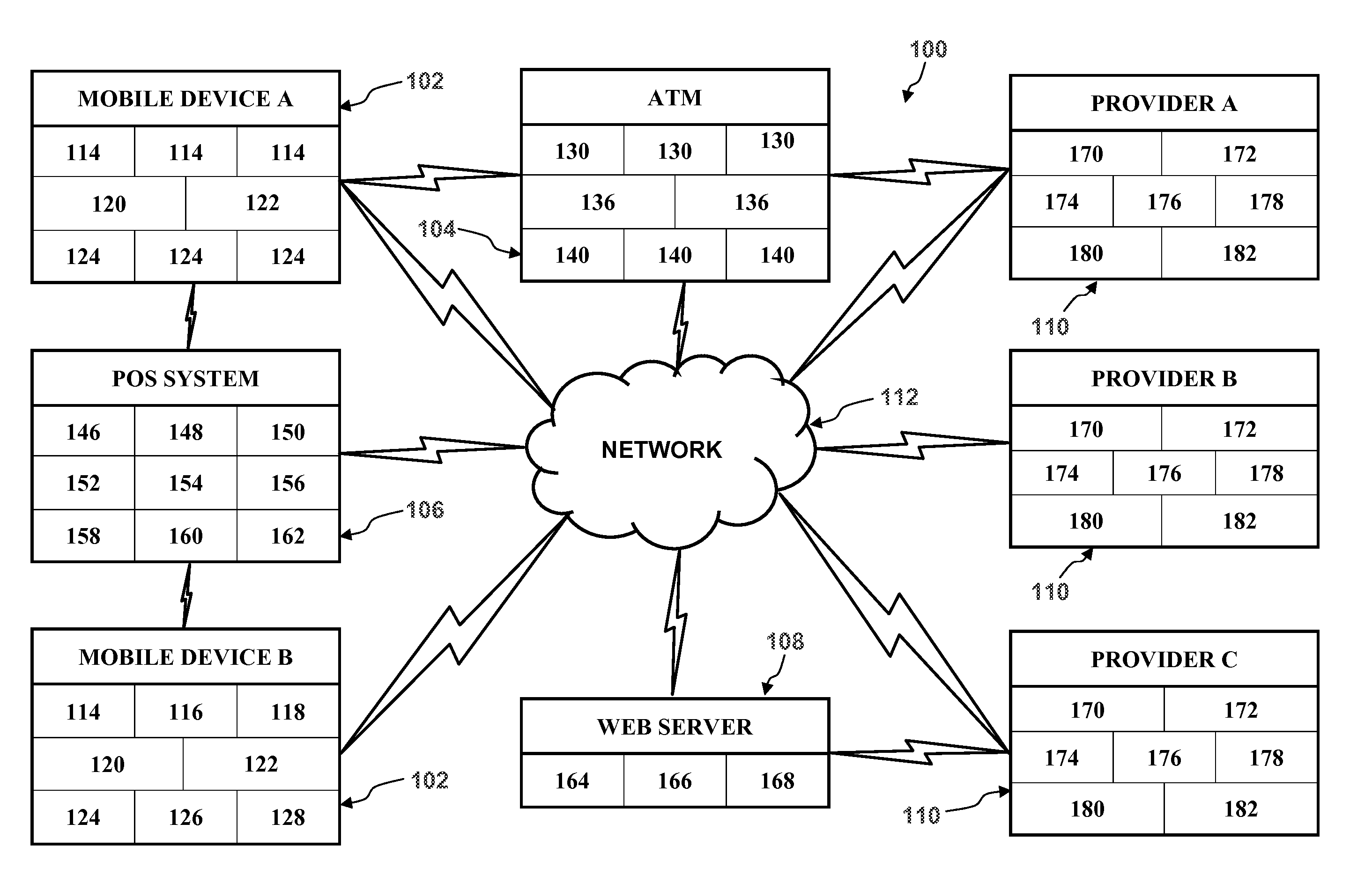
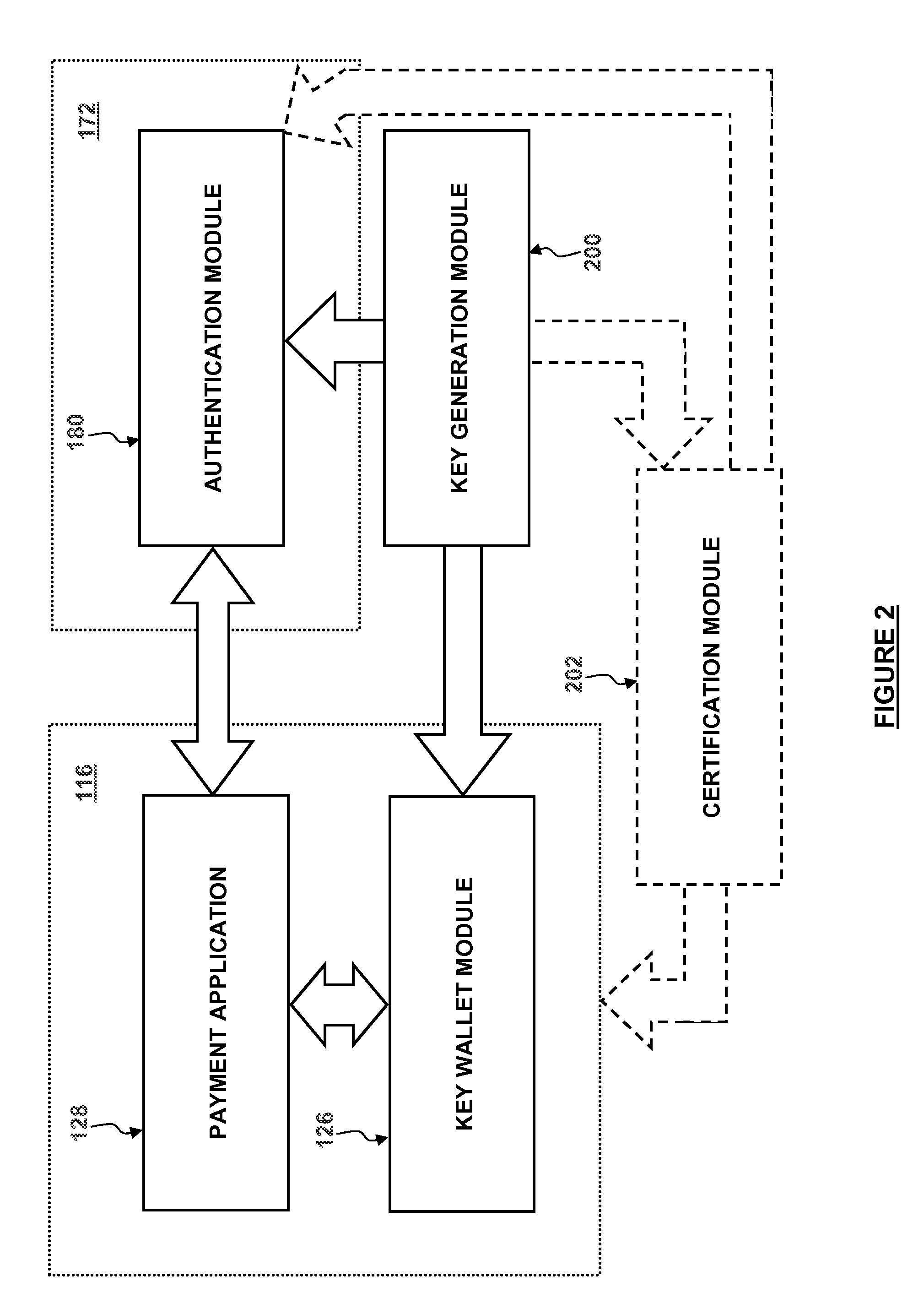
Patents
Literature
1010 results about "Trusted Computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
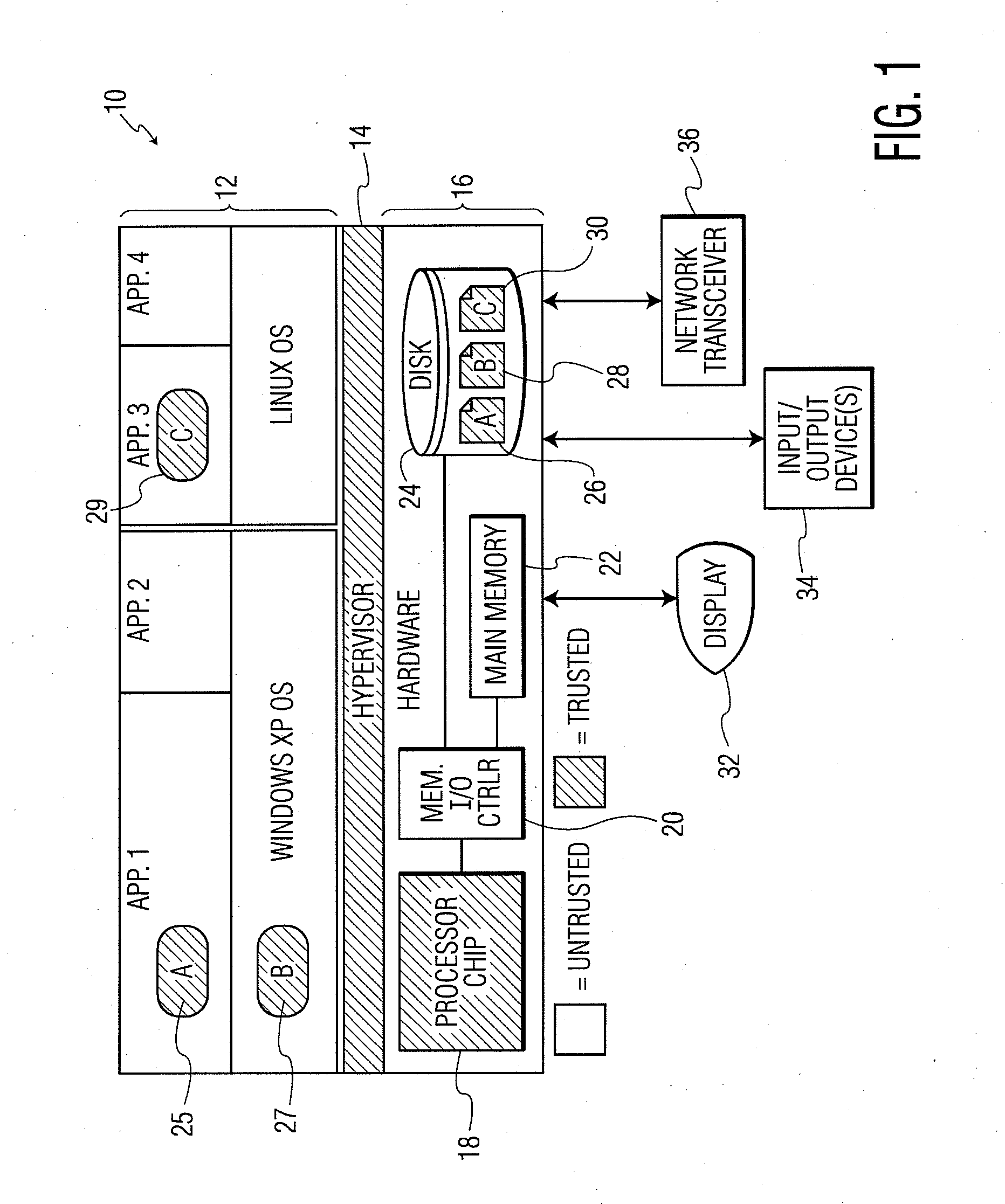
Trusted Computing (TC) is a technology developed and promoted by the Trusted Computing Group. The term is taken from the field of trusted systems and has a specialized meaning. With Trusted Computing, the computer will consistently behave in expected ways, and those behaviors will be enforced by computer hardware and software. Enforcing this behavior is achieved by loading the hardware with a unique encryption key inaccessible to the rest of the system.
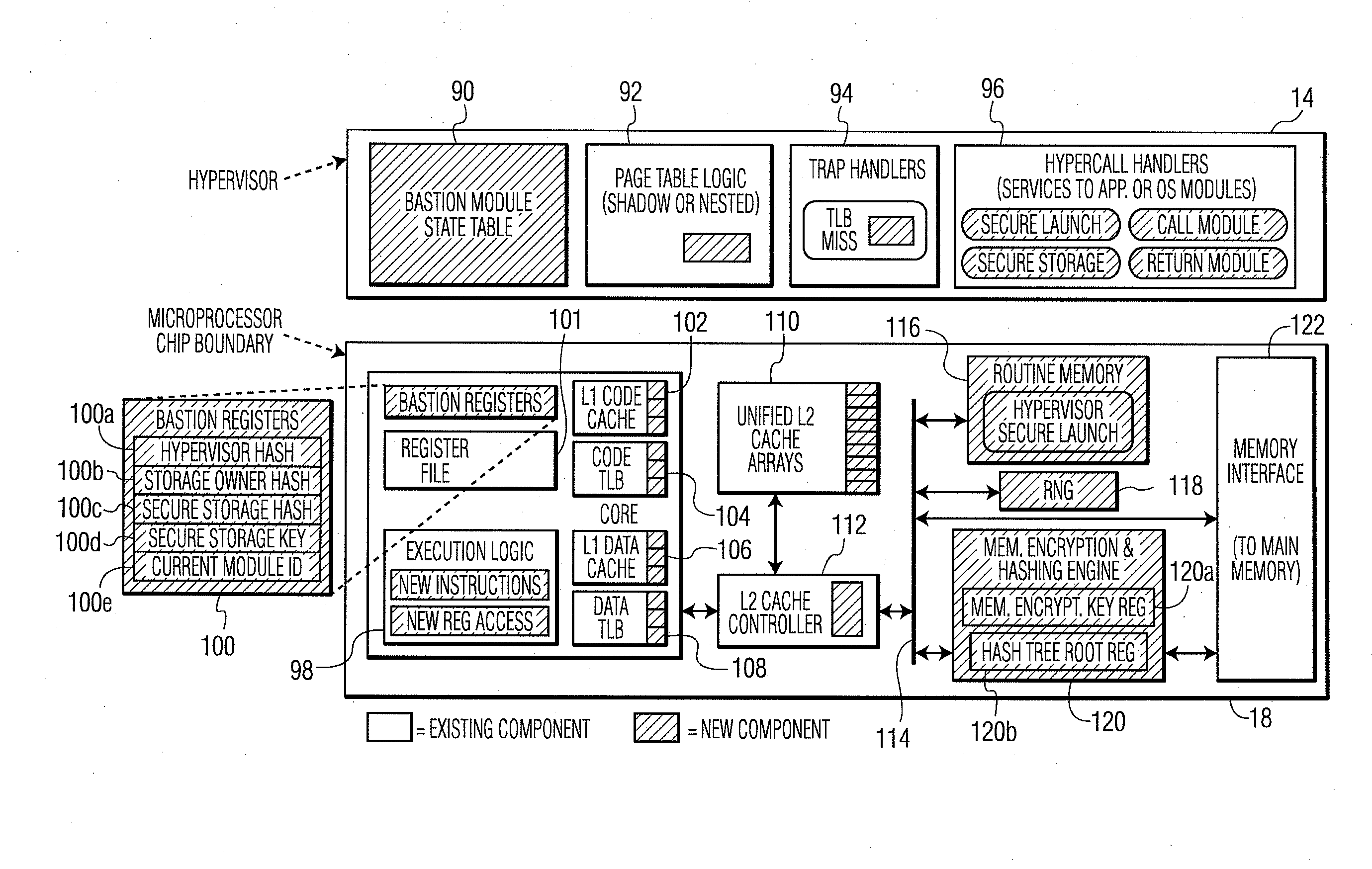
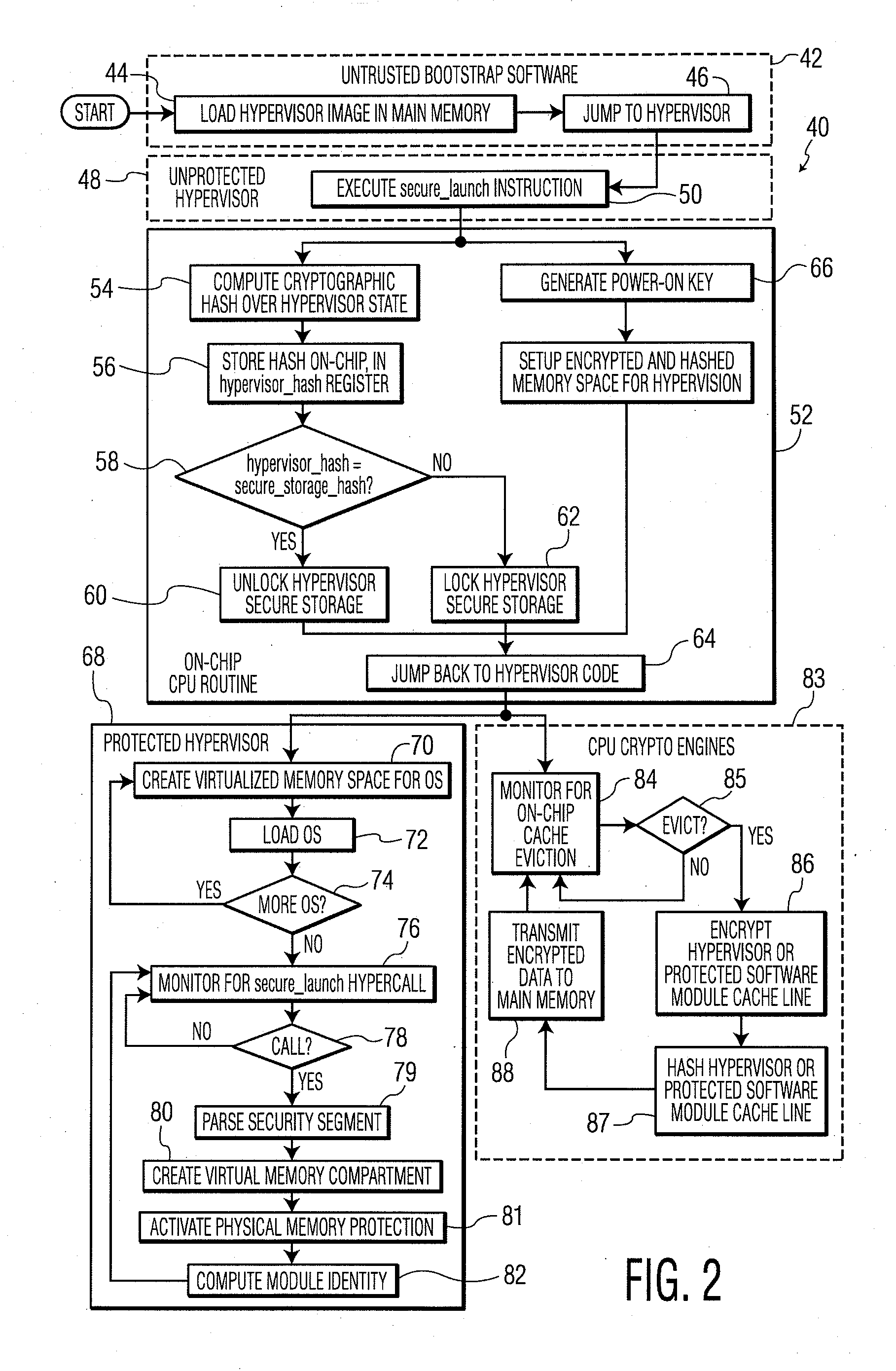
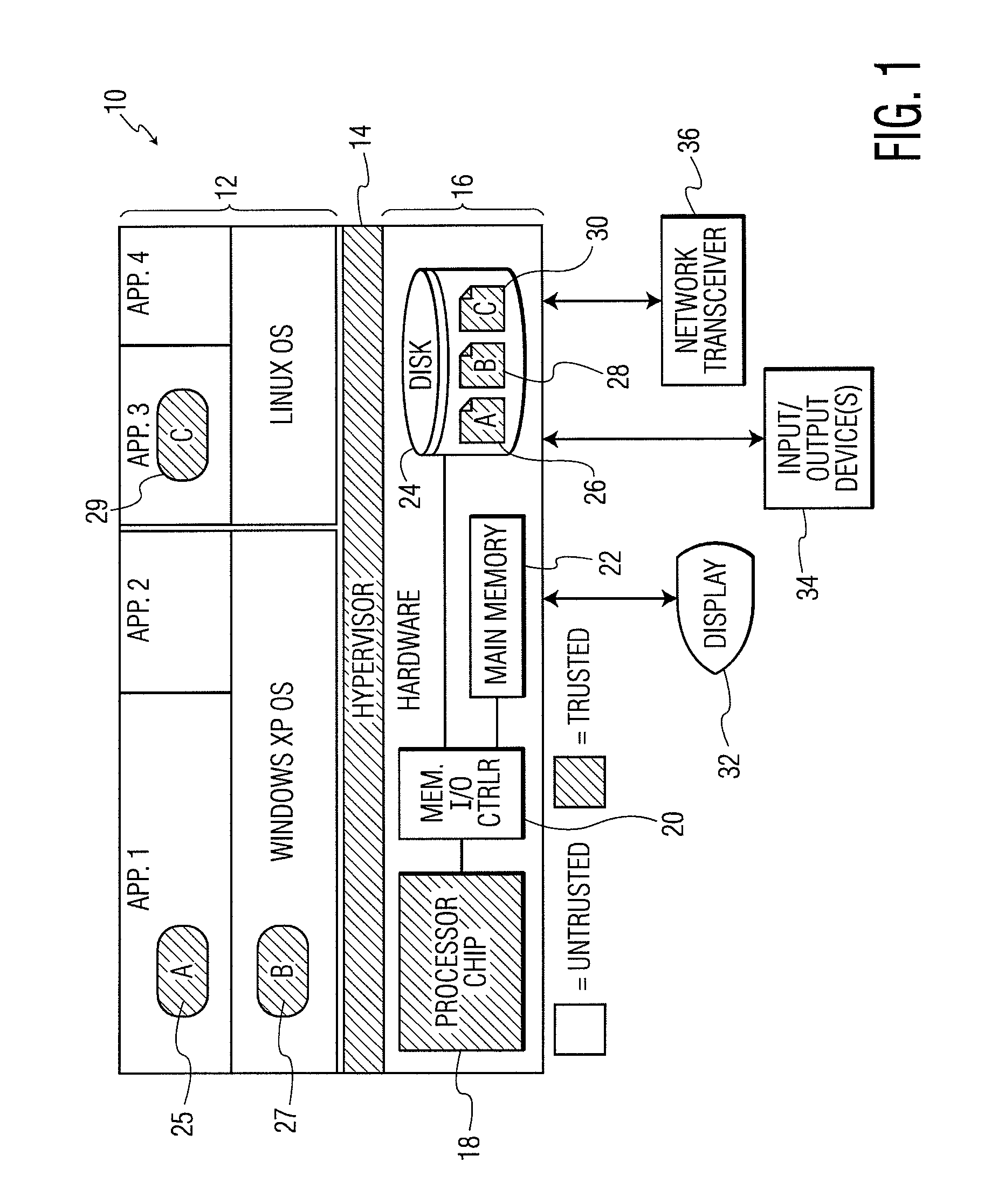
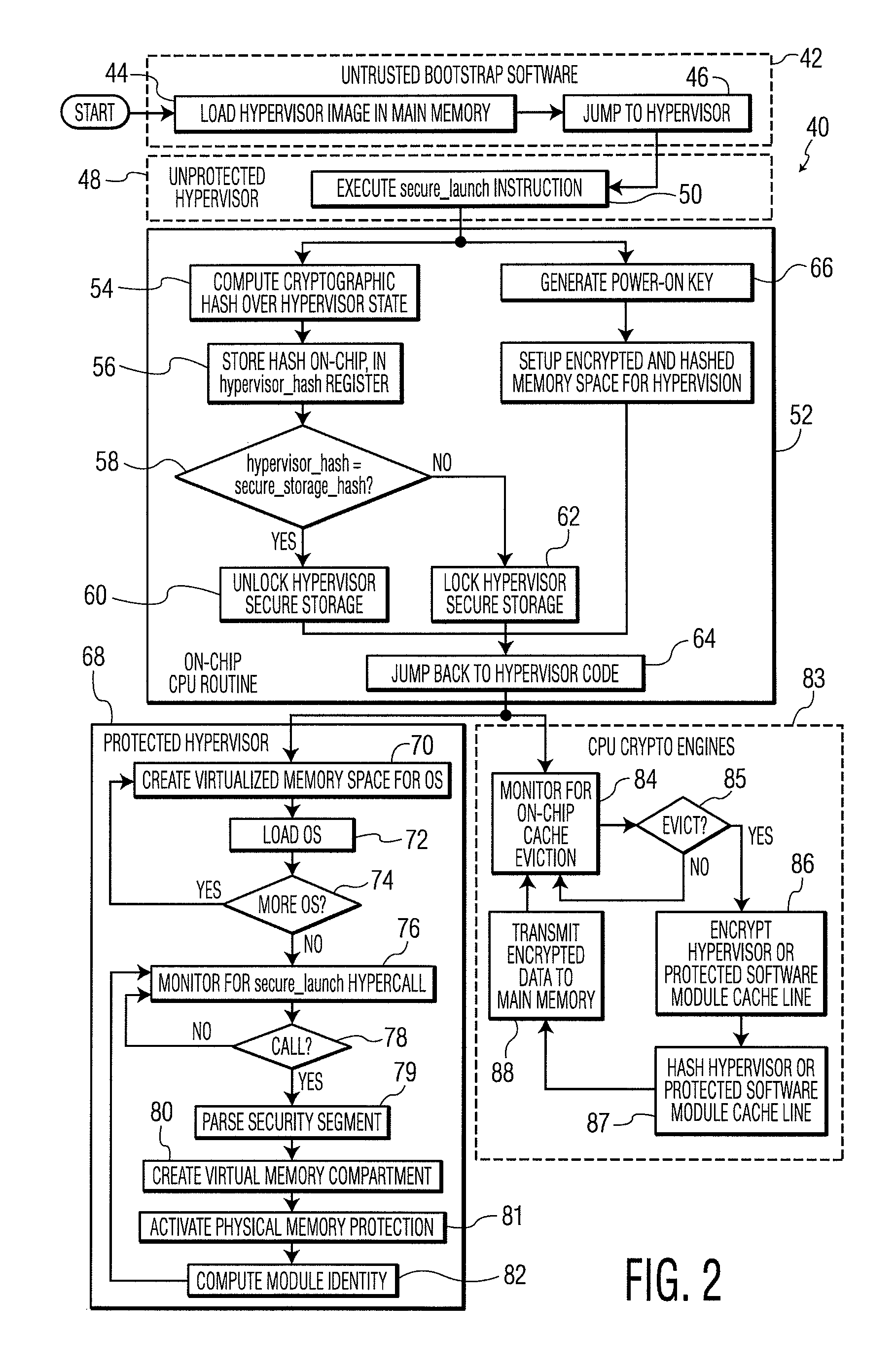
System and Method for Processor-Based Security
ActiveUS20100281273A1Avoid accessUnauthorized memory use protectionHardware monitoringExternal storageMemory interface
A system and method for processor-based security is provided, for on-chip security and trusted computing services for software applications. A processor is provided having a processor core, a cache memory, a plurality of registers for storing at least one hash value and at least one encryption key, a memory interface, and at least one on-chip instruction for creating a secure memory area in a memory external to the processor, and a hypervisor program executed by the processor. The hypervisor program instructs the processor to execute the at least one on-chip instruction to create a secure memory area for a software area for a software module, and the processor encrypts data written to, and decrypts data read from, the external memory using the at least one encryption key and the verifying data read from the external memory using the at least one hash value. Secure module interactions are provided, as well as the generation of a power-on key which can be used to protect memory in the event of a re-boot event. Lightweight, run-time attestation reports are generated which include selected information about software modules executed by the processors, for use in determining whether the processor is trusted to provide secure services.
Owner:CORESECURE TECH LLC
Managing services in a cloud computing environment
What is provided are a system and method which enables an organization or user to manage computational services in a cloud computing network for security, compliance and governance. The management including creating a trusted virtual network including encrypted data storage, encrypted data transport, and trusted instances of servers all communicatively coupled together forming a trusted cloud computing environment that is associated with the organization. A web portal running on a web server provides a point of access to the cloud computing environment. A workflow is accessed to implement one or more policies in trusted computing environment to manage the trusted cloud computing environment, the workflow customized to the organization. The access control; and to the trusted cloud computing environment is used to ensure access by users authorized by the organization to ensure compliance with adopted standards.
Owner:CLOUDNEXA
Method And Apparatus For Trusted Federated Identity
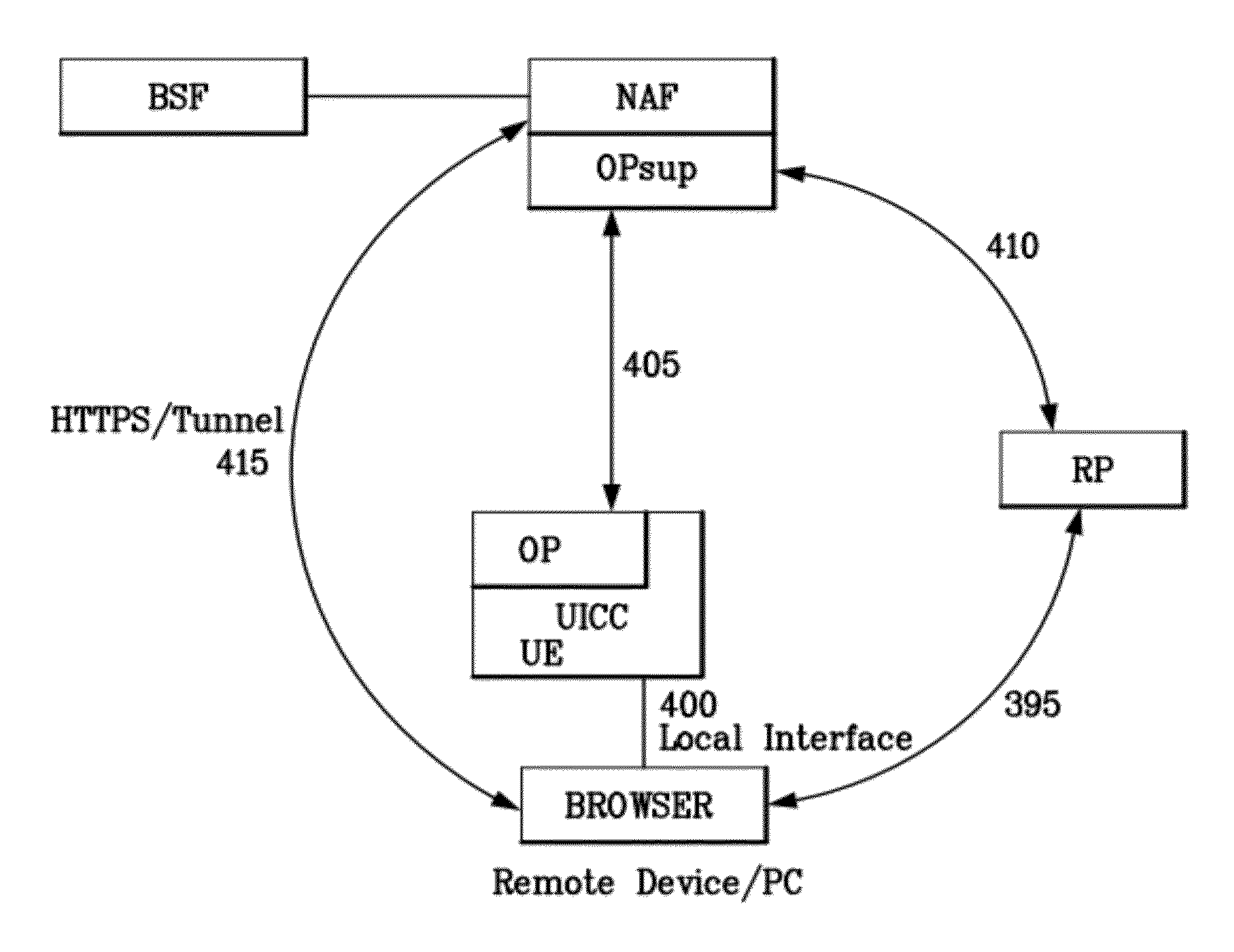
InactiveUS20120072979A1Well formedDigital data processing detailsUser identity/authority verificationTrusted ComputingFederated identity
A trusted computing environment, such as a smartcard, UICC, Java card, global platform, or the like may be used as a local host trust center and a proxy for a single-sign on (SSO) provider. This may be referred to as a local SSO provider (OP). This may be done, for example, to keep authentication traffic local and to prevent over the air communications, which may burden an operator network. To establish the OP proxy in the trusted environment, the trusted environment may bind to the SSO provider in a number of ways. For example, the SSO provider may interoperate with UICC-based UE authentication or GBA. In this way, user equipment may leverage the trusted environment in order to provide increased security and reduce over the air communications and authentication burden on the OP or operator network.
Owner:INTERDIGITAL PATENT HLDG INC
Remotely authenticated operation method
InactiveUS7509687B2Improvement effortsEfficient use ofDigital data processing detailsUser identity/authority verificationTrusted ComputingMedia server
The objective of this invention is to provide continuous remote authenticated operations for ensuring proper content processing and management in remote untrusted computing environment. The method is based on using a program that was hidden within the content protection program at the remote untrusted computing environment, e.g., an end station. The hidden program can be updated dynamically and it includes an inseparable and interlocked functionality for generating a pseudo random sequence of security signals. Only the media server that sends the content knows how the pseudo-random sequence of security signals were generated; therefore, the media server is able to check the validity of the security signals, and thereby, verify the authenticity of the programs used to process content at the remote untrusted computing environment. If the verification operation fails, the media server will stop the transmission of content to the remote untrusted computing environment.
Owner:ATTESTWAVE LLC
Secure and convenient mobile authentication techniques
ActiveUS20140040147A1User identity/authority verificationDigital data authenticationTrusted ComputingMobile authentication
Security and convenience are provided by a system, apparatus, method, and computer program product that stores two or more encryption keys that correspond to two or more levels of authentication. The encryption keys may be encrypted and decrypted utilizing an endorsement key and trusted computing techniques. Or the encryption keys may be stored in a secure manner utilizing key protection techniques, such as cryptographic camouflaging. A first encryption key is recovered automatically for the first level of authentication. And input is requested to recover the second encryption key for the second level of authentication.
Owner:CA TECH INC
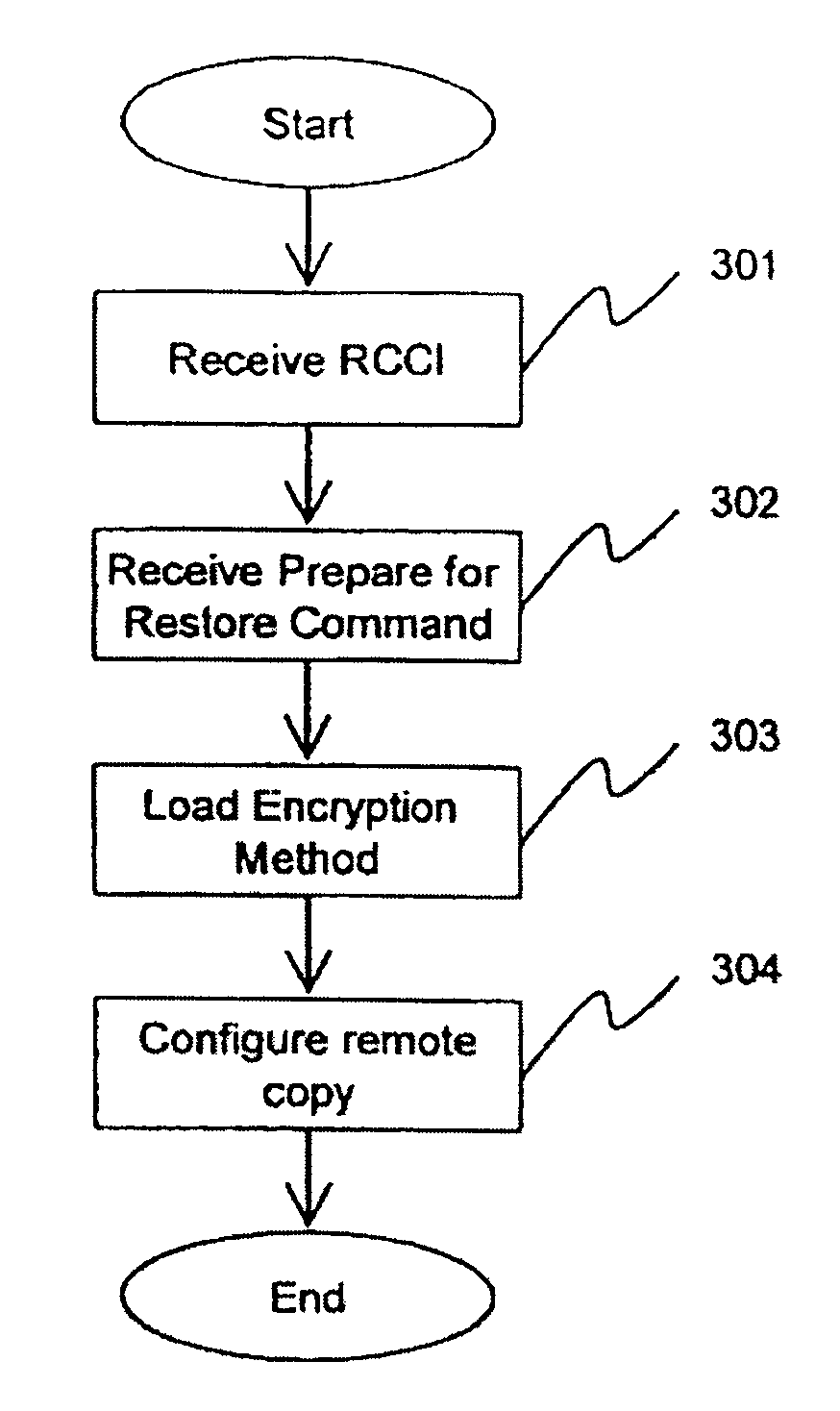
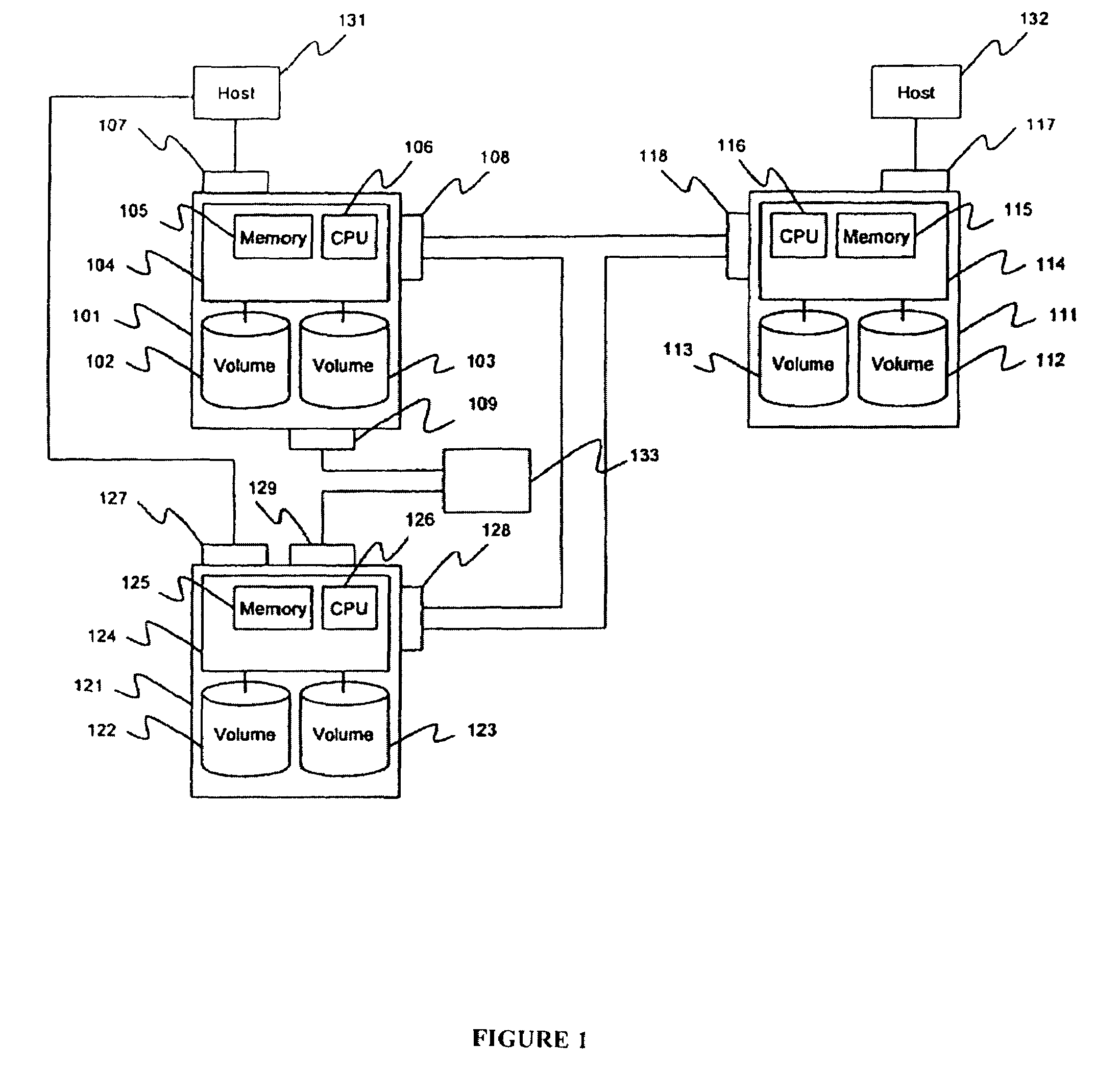
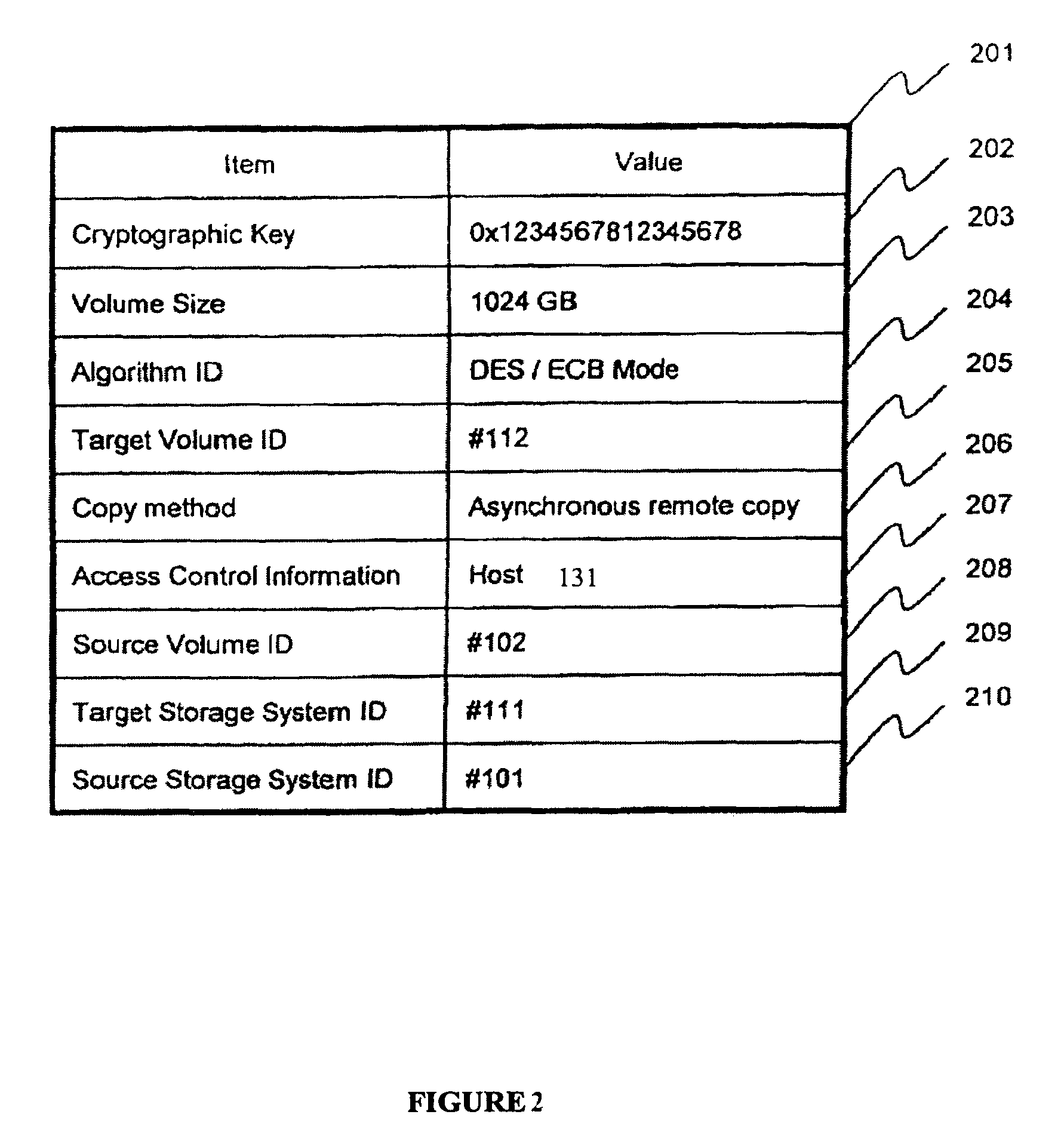
Method and apparatus for encrypted remote copy for secure data backup and restoration
InactiveUS7383462B2Digital data processing detailsUser identity/authority verificationThird partyTrusted Computing
Data at a primary storage system is encrypted and remote copied to a secondary storage system. A Remote Copy Configuration Information (RCCI) is created that identifies the encryption mechanism, keys, data source volume, and target volume for the remote copy. The RCCI is backed up on a trusted computer system. In one embodiment, the secondary storage system is an off-site data storage system managed by a third party. Upon detection of a failure in the primary storage system, the encrypted data and RCCI are transferred to a tertiary server, which is optionally created upon detection of the failure, and operations of the failed primary server are resumed by the tertiary server. In one embodiment, the failure is detected by loss of a heart beat signal transmitted from the primary storage system to a management server that initiates the transfers to the tertiary server.
Owner:HITACHI LTD
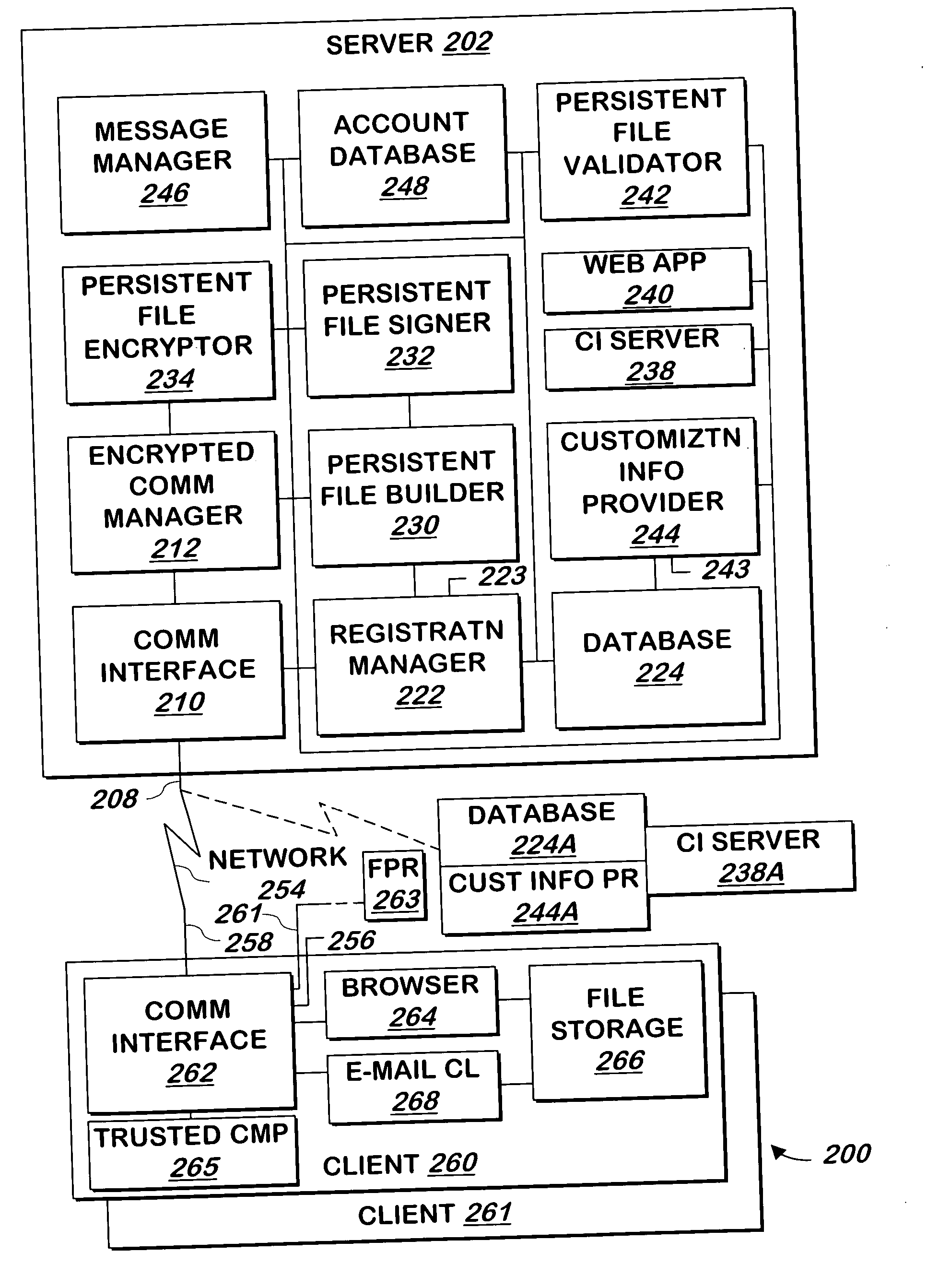
System and method for authentication of users and communications received from computer systems
InactiveUS20050177750A1Memory loss protectionDigital data processing detailsWeb siteInternet privacy
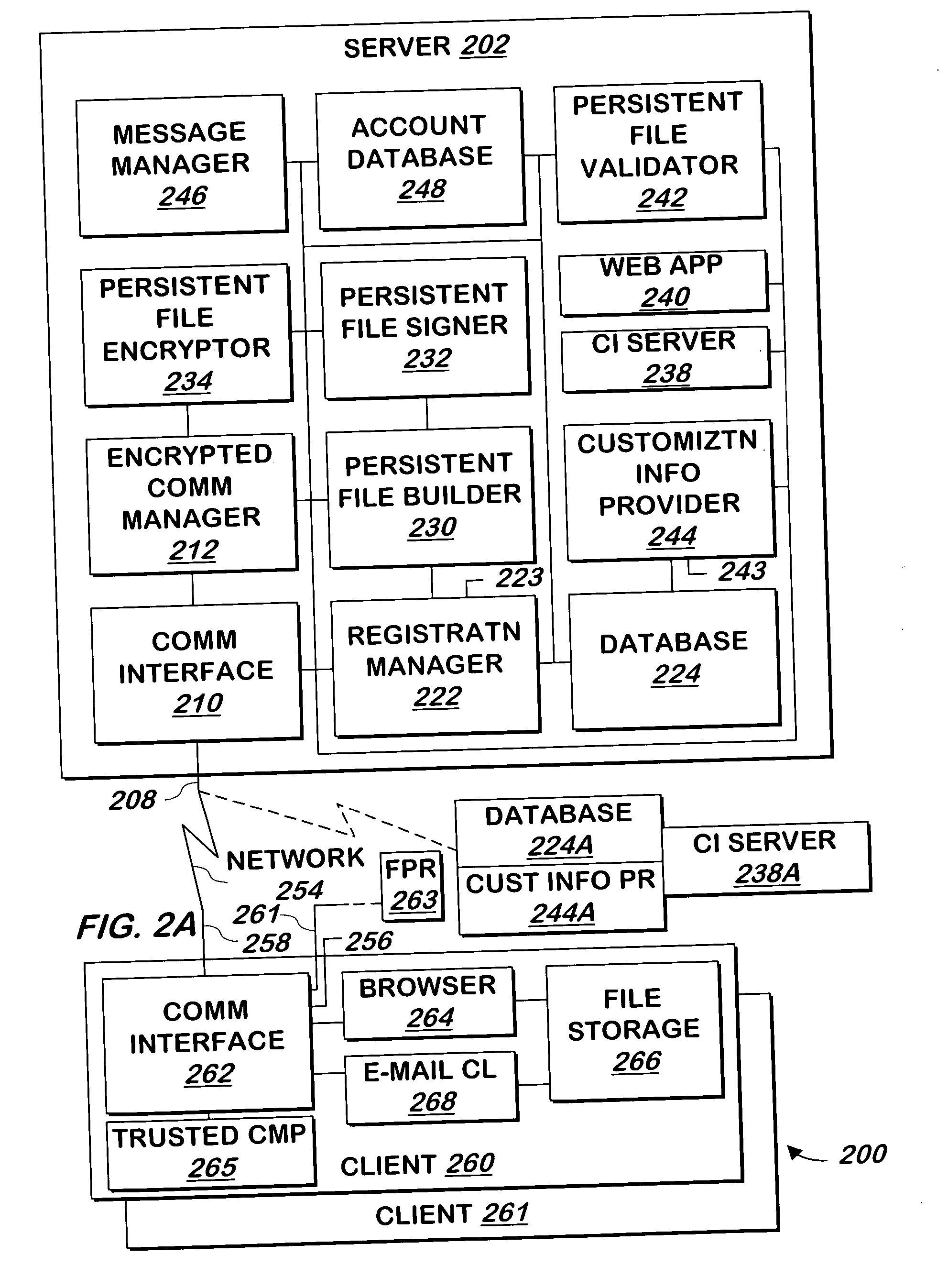
A system and method allows a user to authenticate a communication from a computer system, a computer system to authenticate a user, or both. When a user requests a web page from the web site, customization information that is recognizable to the user is provided to allow the user to authenticate the web site. A signed, encrypted persistent file stored on the user's computer system or installed on a different computer system, or a trusted computing subsystem allows the web site to authenticate the user. If the user is using a system that will not allow that user to be authenticated, the user may instruct the system to continue providing information without the user's customization information. The system and method may be used to allow the user to authenticate an e-mail message or its source, and Flash movies or other computer code may be used if the user's e-mail client does not employ cookies.
Owner:EMC IP HLDG CO LLC
Method and system for maintaining backup of portable storage devices
ActiveUS7240219B2Safe storageEasy to carryUser identity/authority verificationUnauthorized memory use protectionPasswordTrusted Computing
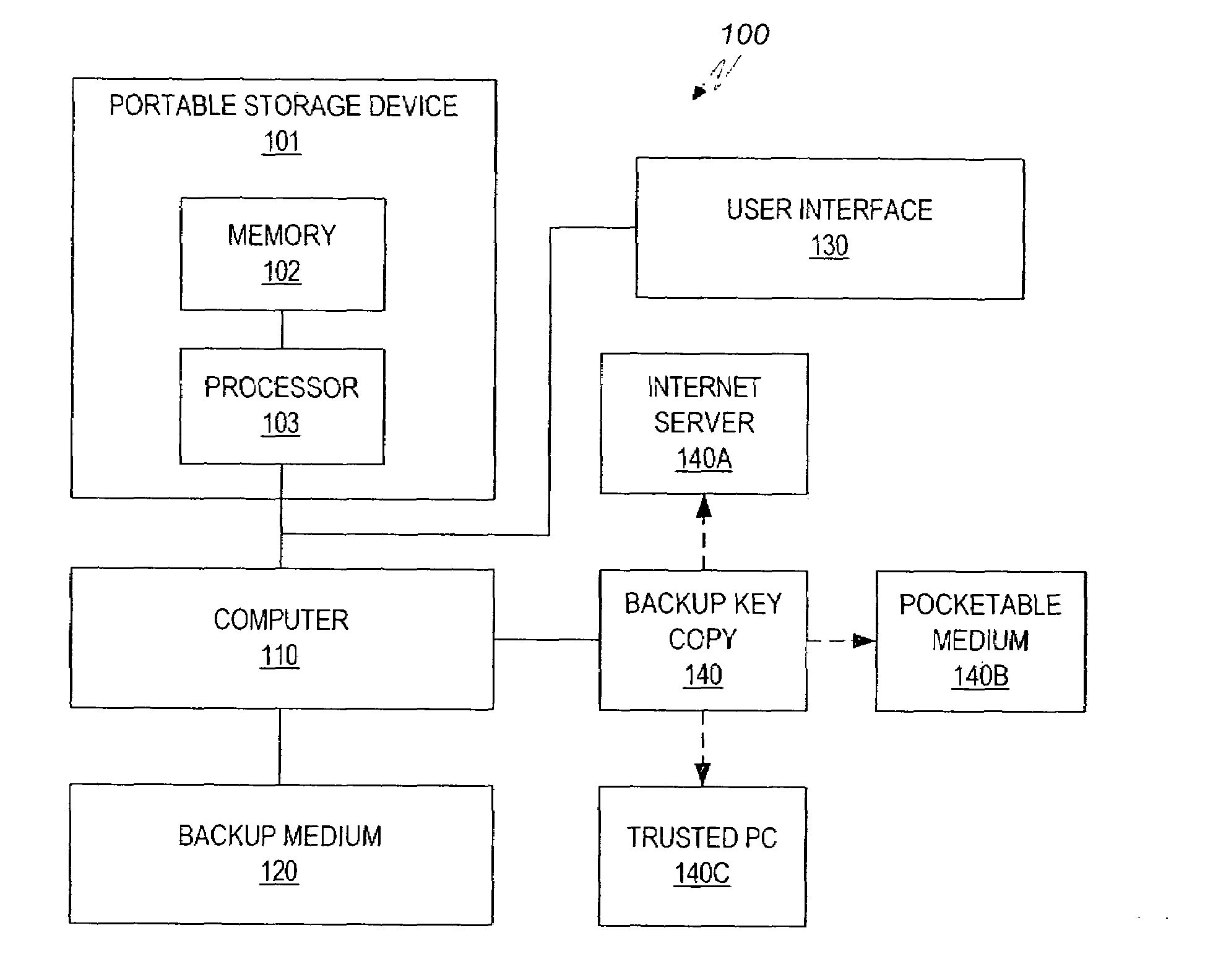
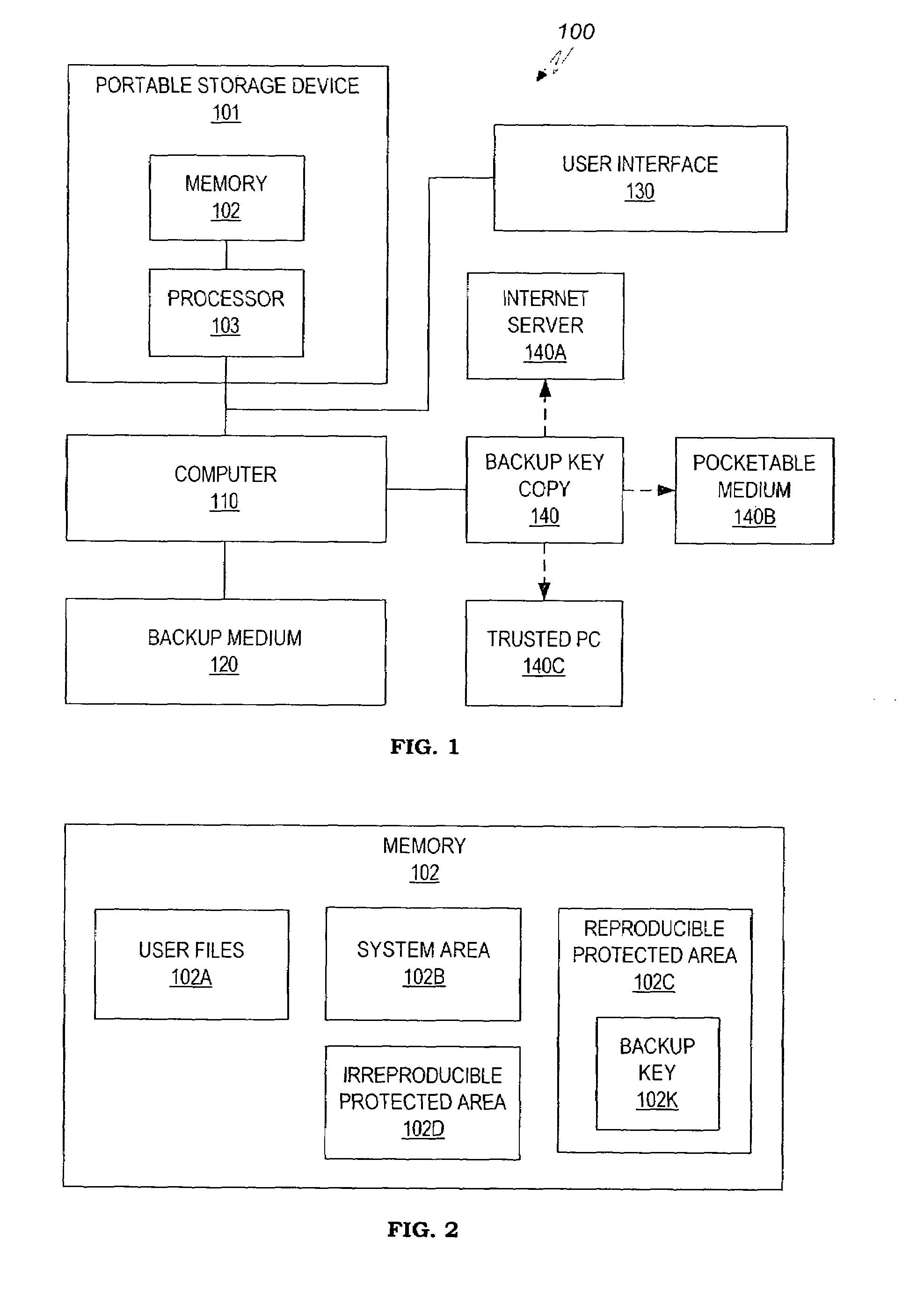
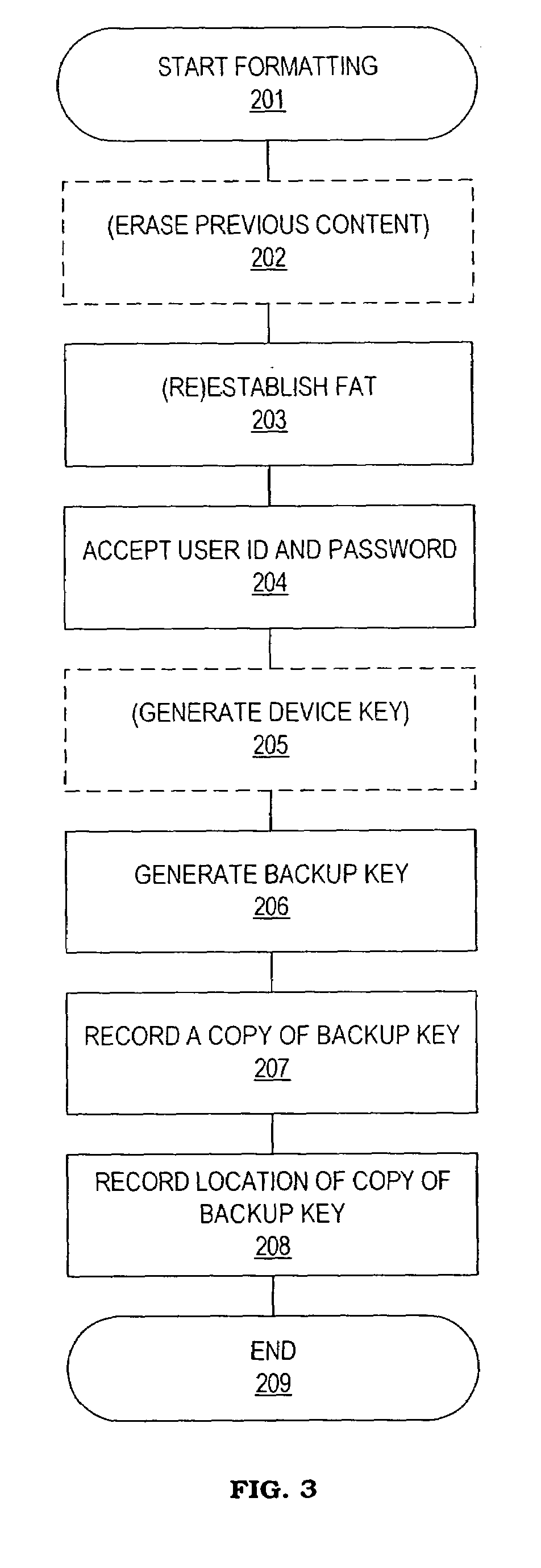
Data stored in a portable storage device are encrypted, for example by a processor of the portable storage device itself, using a backup key and stored in a backup medium. The backup key is protected by being stored in a backup key storage medium, such as an internet server, a pocketable medium or a trusted computer, preferably after being encrypted using a password. As needed, the backup key is retrieved and used to decrypt the data from the backup medium. The decrypted data are restored to the original portable storage device or to a different portable storage device.
Owner:WESTERN DIGITAL ISRAEL LTD
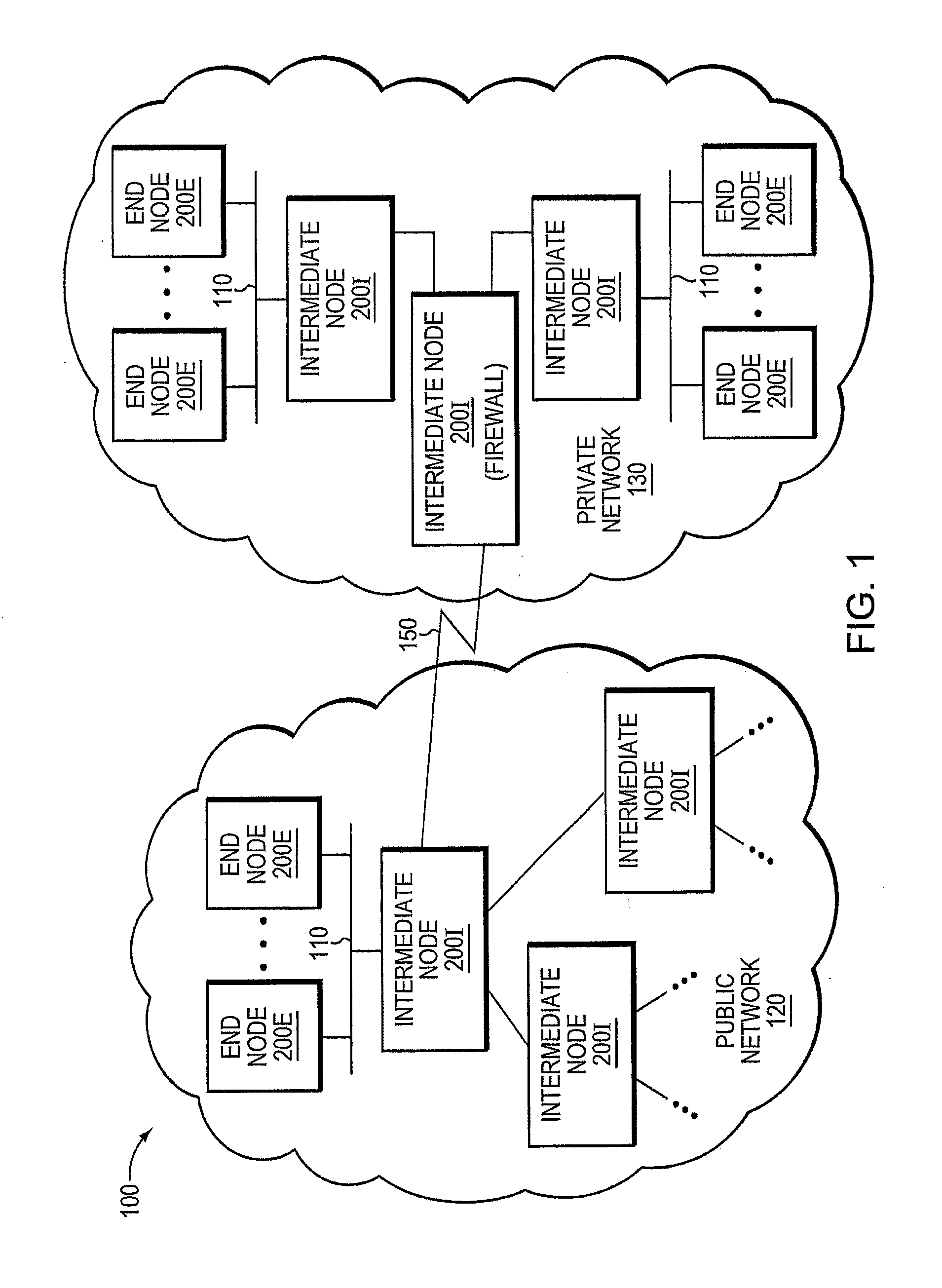
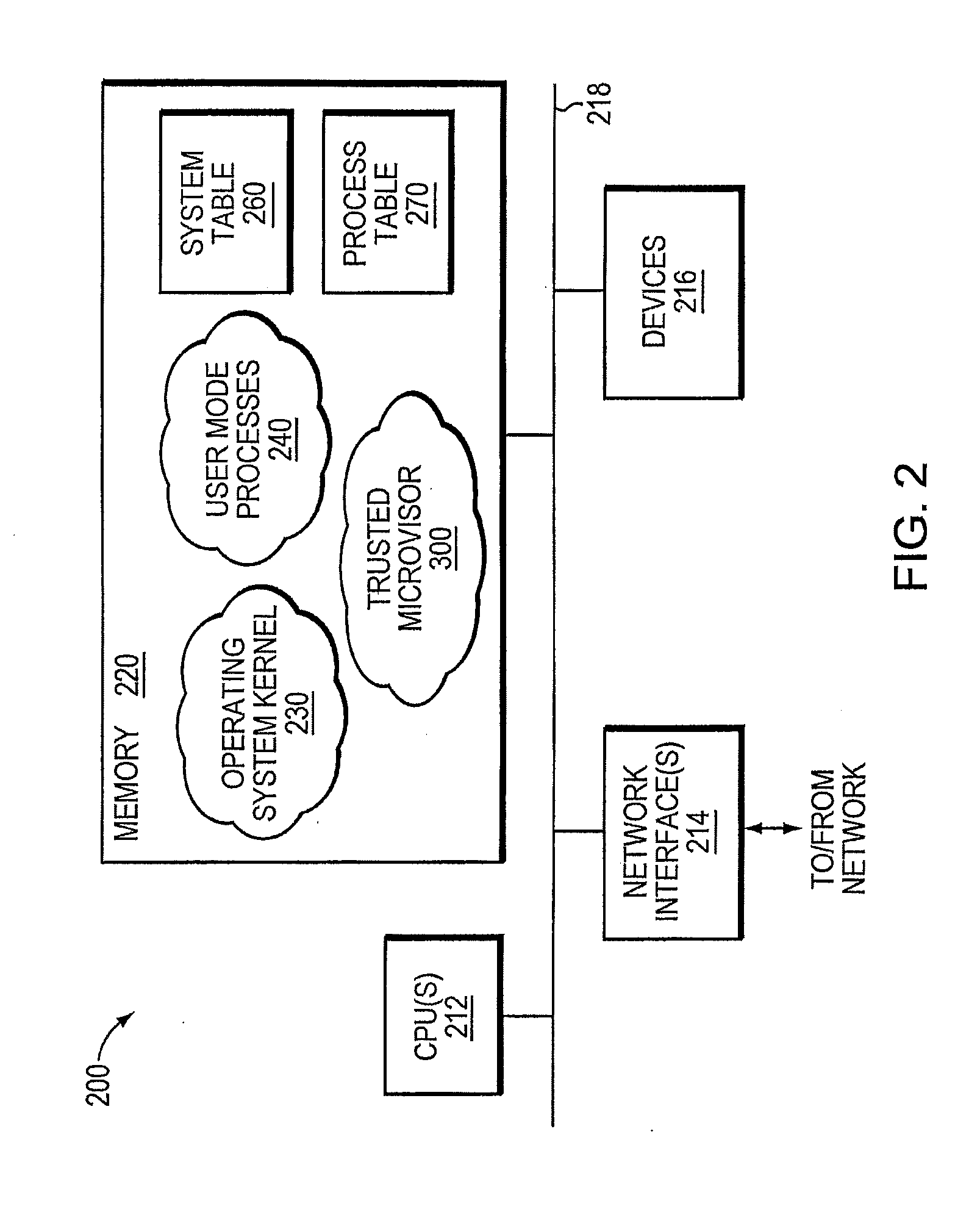
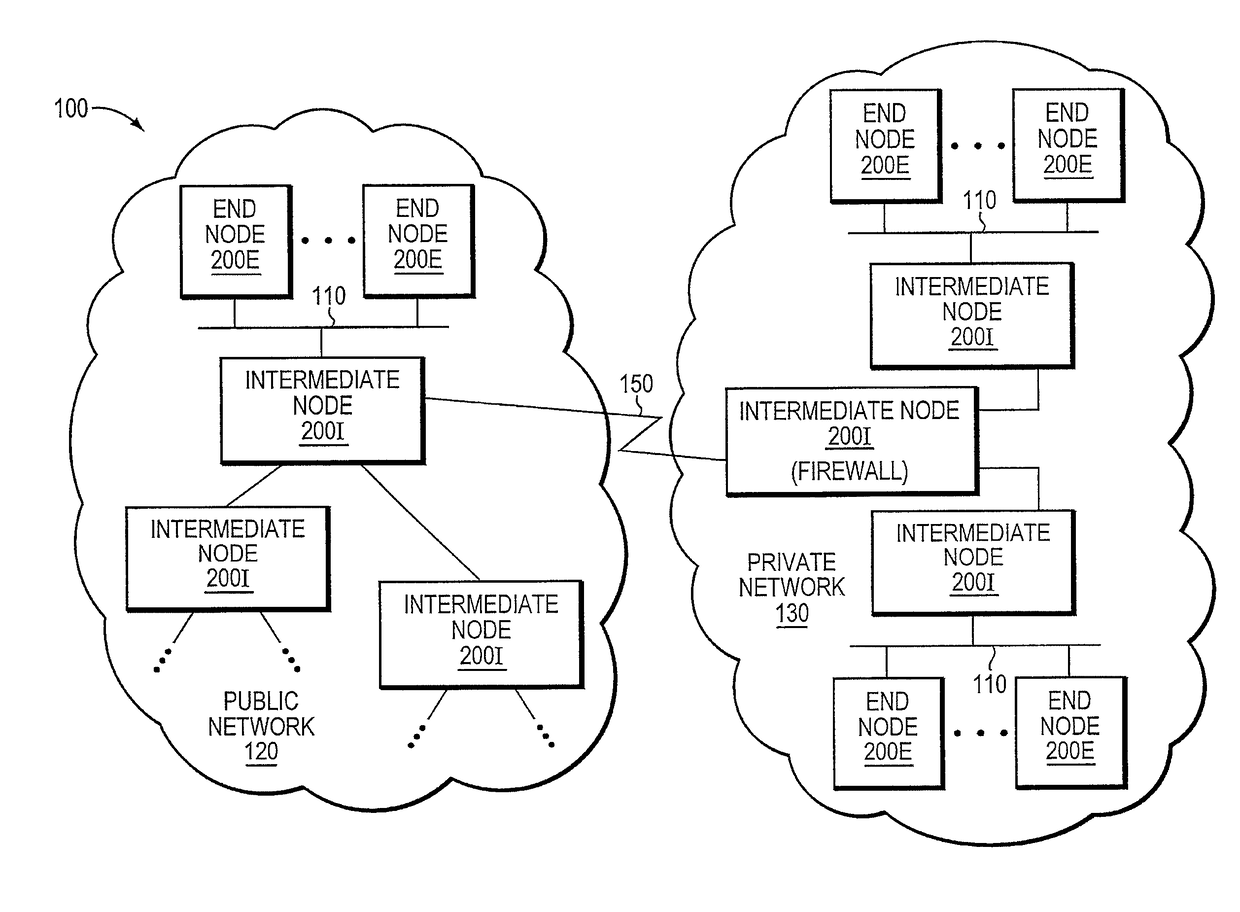
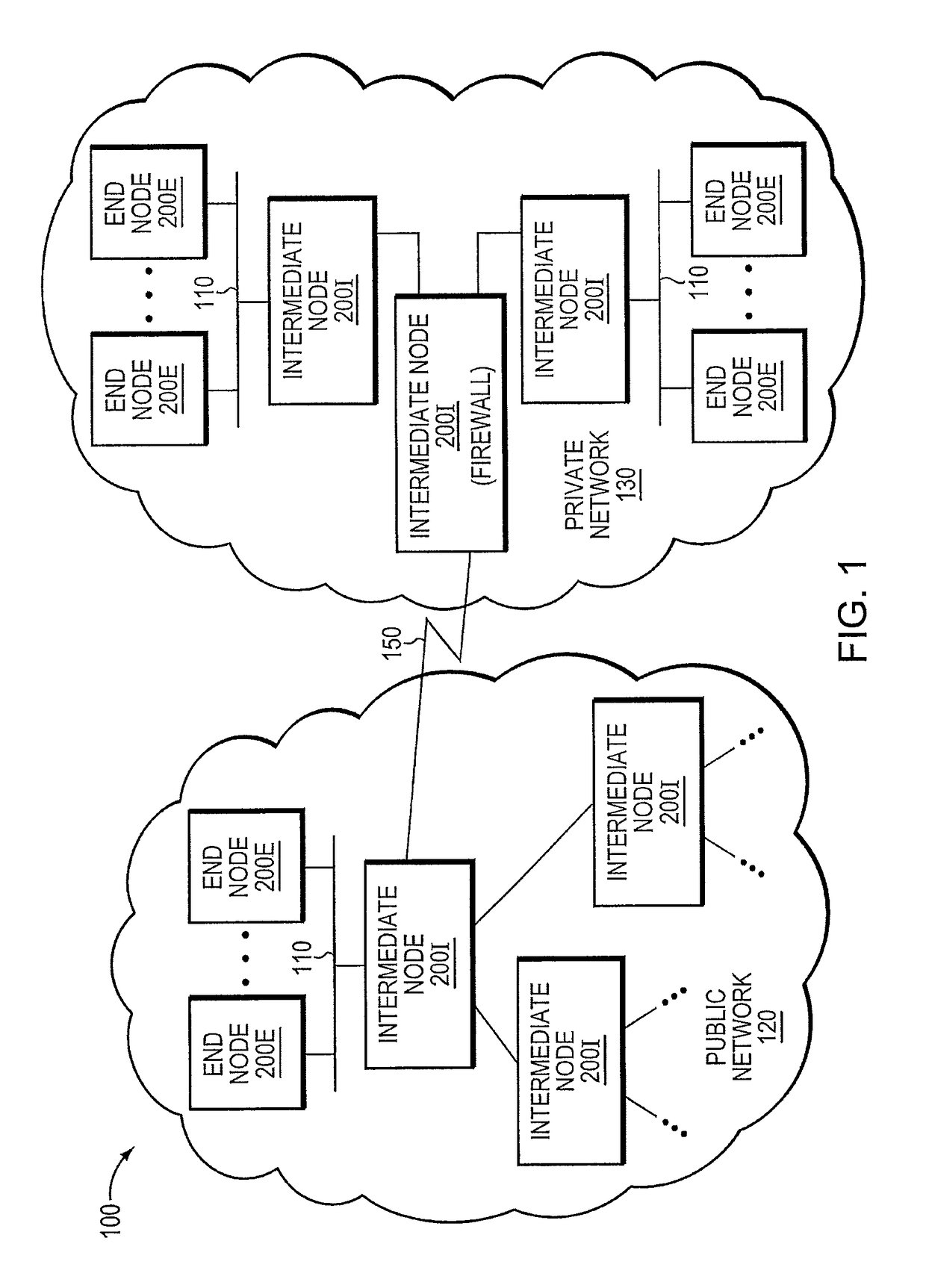
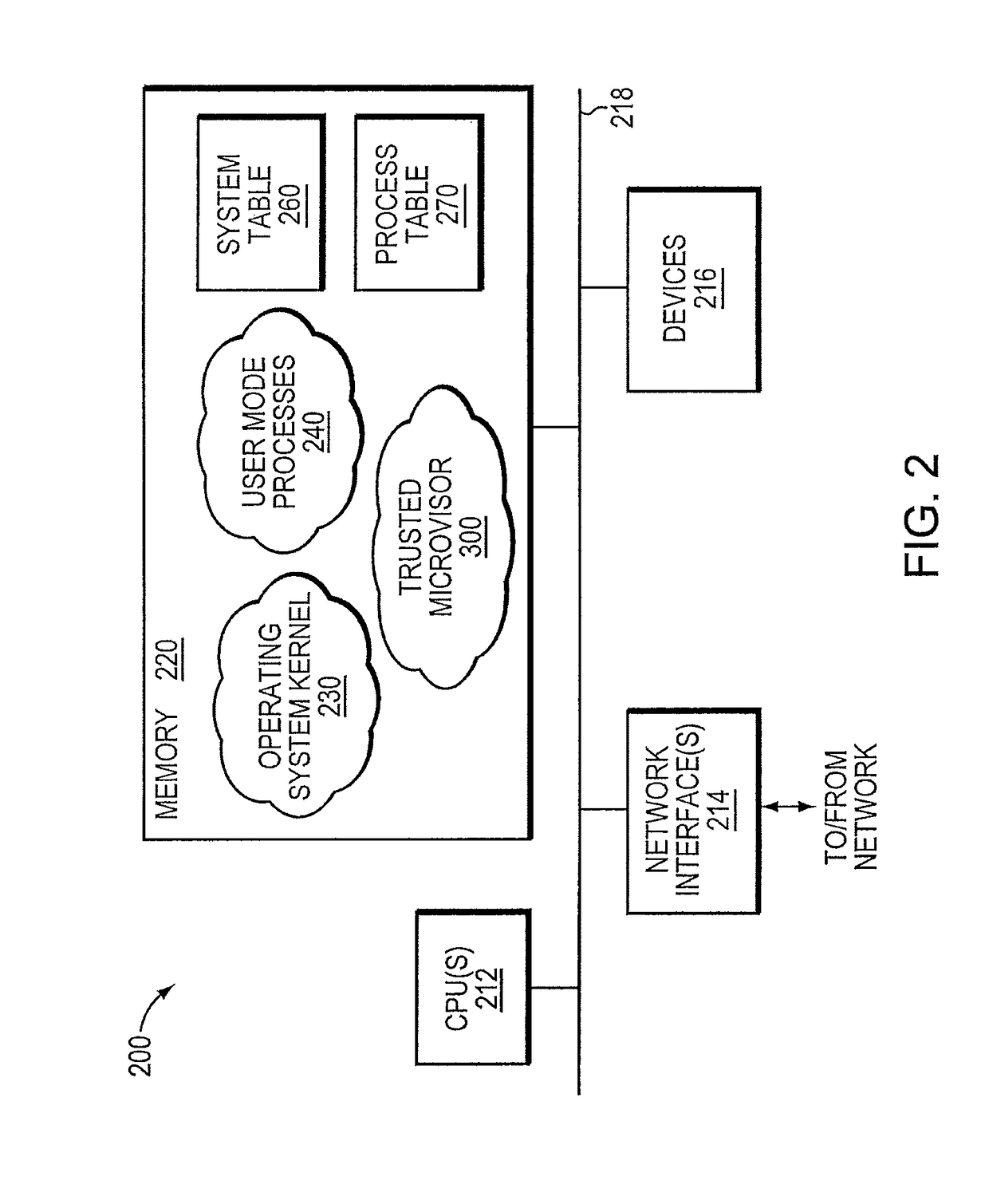
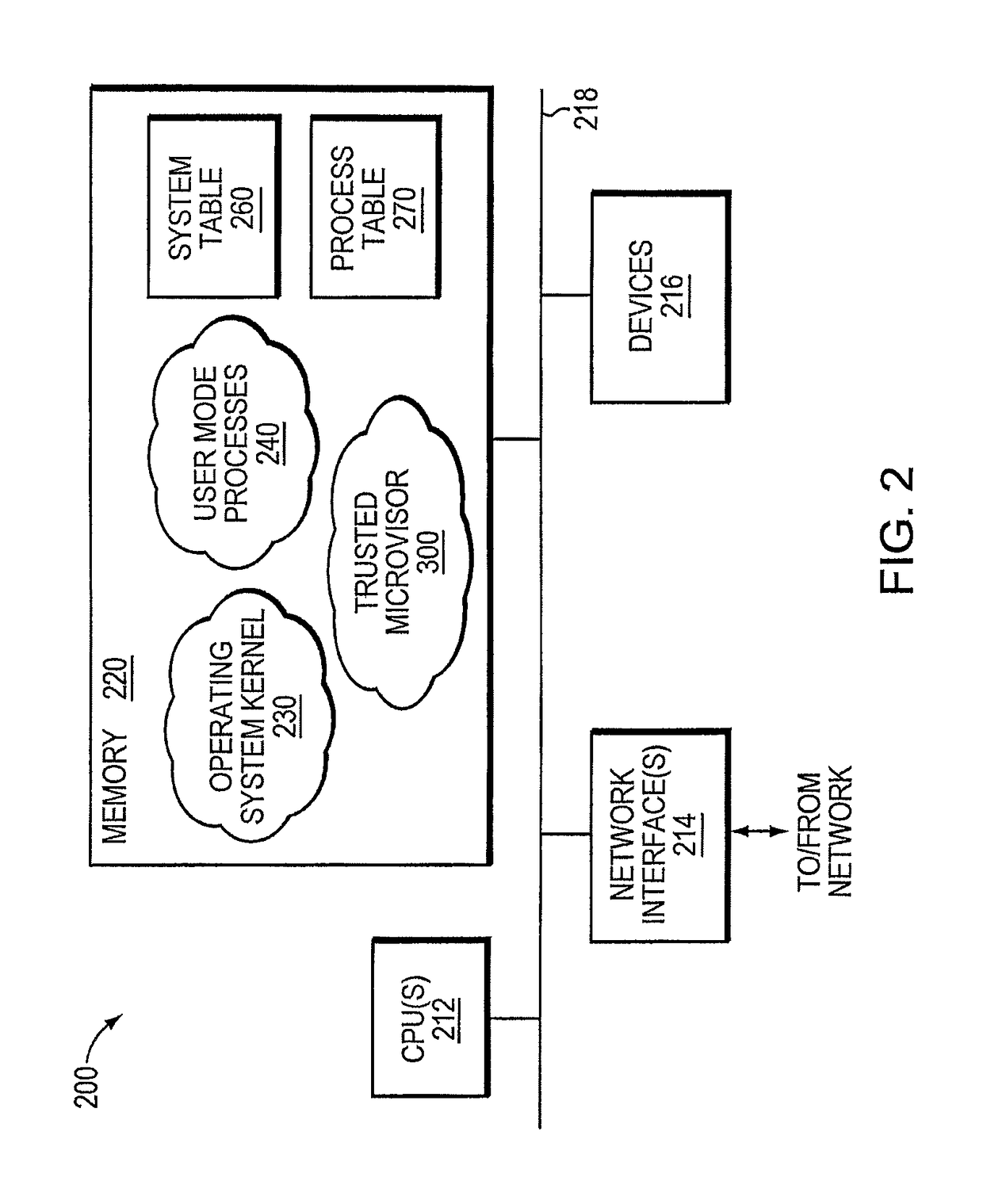
Trusted threat-aware microvisor
ActiveUS20160006756A1Memory loss protectionError detection/correctionTrusted ComputingSecurity properties
A trusted threat-aware microvisor may be deployed as a module of a trusted computing base (TCB) that also includes a root task module configured to cooperate with the microvisor to load and initialize one or more other modules executing on a node of a network environment. The root task may cooperate with the microvisor to allocate one or more kernel resources of the node to those other modules. As a trusted module of the TCB, the microvisor may be configured to enforce a security policy of the TCB that, e.g., prevents alteration of a state related to security of the microvisor by a module of or external to the TCB. The security policy of the TCB may be implemented by a plurality of security properties of the microvisor. Trusted (or trustedness) may therefore denote a predetermined level of confidence that the security property is demonstrated by the microvisor.
Owner:FIREEYE SECURITY HLDG US LLC
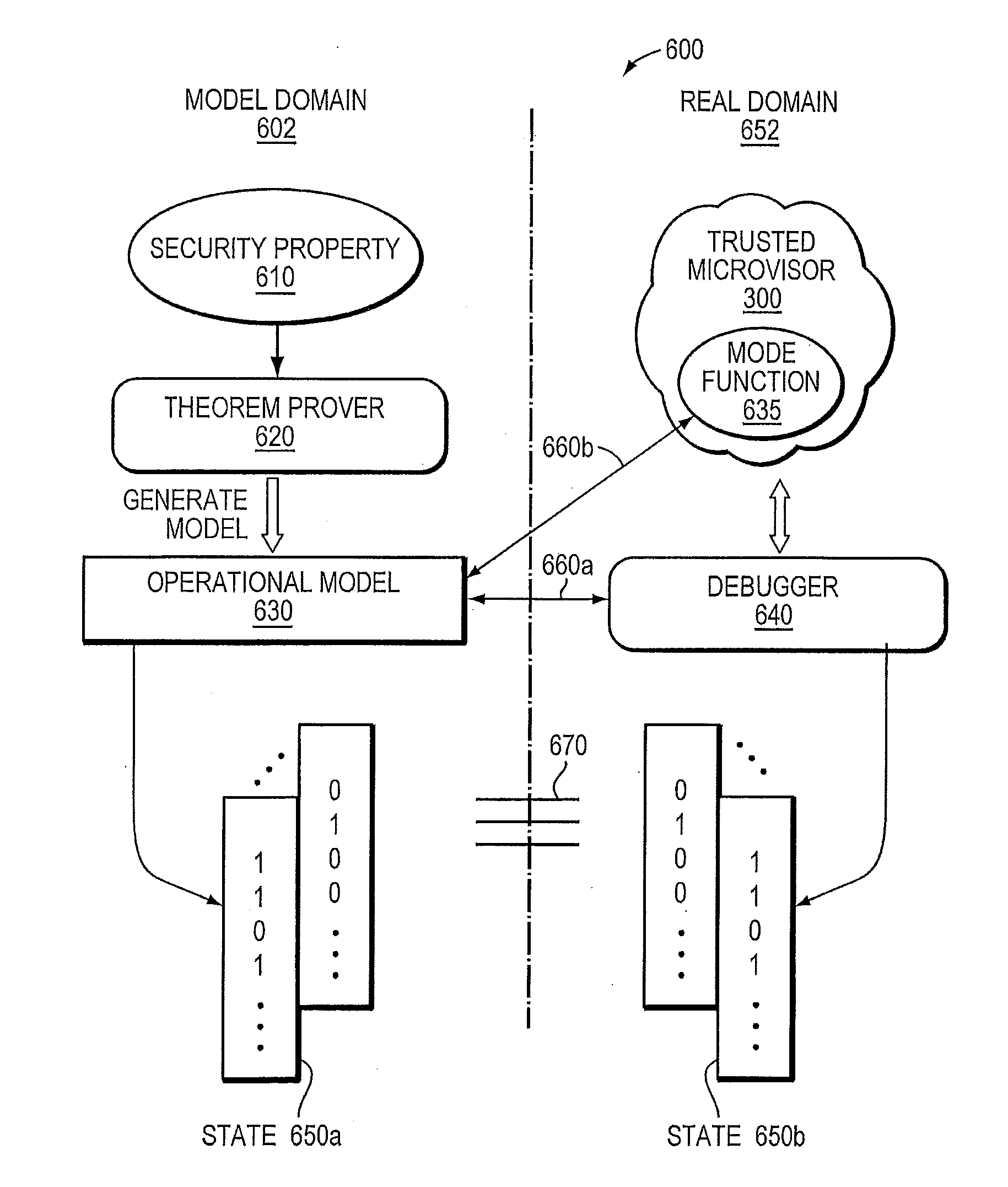
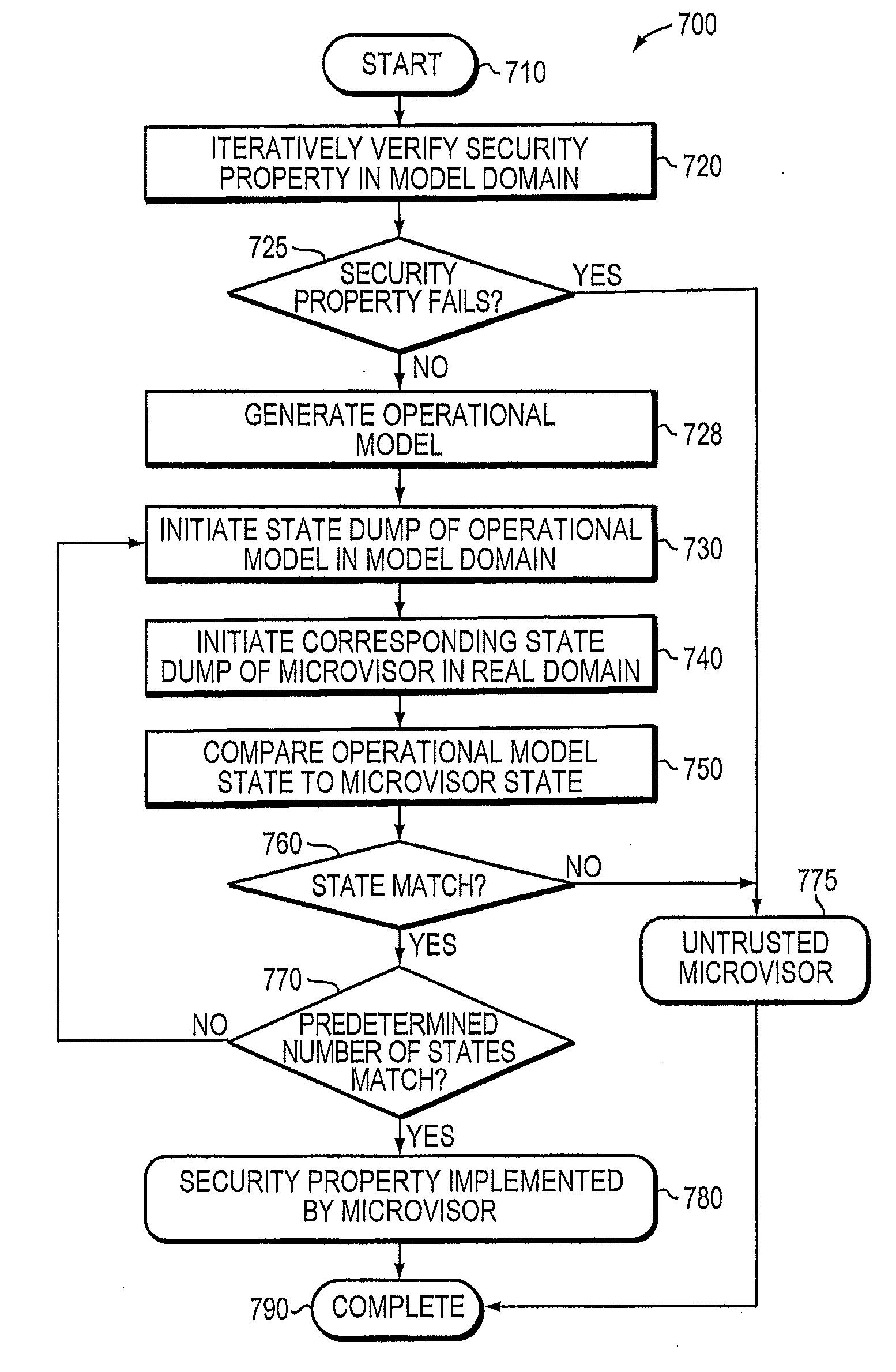
Verification of trusted threat-aware microvisor
A trusted threat-aware microvisor may be deployed as a module of a trusted computing base (TCB). The microvisor is illustratively configured to enforce a security policy of the TCB, which may be implemented as a security property of the microvisor. The microvisor may manifest (i.e., demonstrate) the security property in a manner that enforces the security policy. Trustedness denotes a predetermined level of confidence that the security property is demonstrated by the microvisor. The predetermined level of confidence is based on an assurance (i.e., grounds) that the microvisor demonstrates the security property. Trustedness of the microvisor may be verified by subjecting the TCB to enhanced verification analysis configured to ensure that the TCB conforms to an operational model with an appropriate level of confidence over an appropriate range of activity. The operational model may then be configured to analyze conformance of the microvisor to the security property. A combination of conformance by the microvisor to the operational model and to the security property provides assurance (i.e., grounds) for the level of confidence and, thus, verifies trustedness.
Owner:FIREEYE SECURITY HLDG US LLC
Trusted threat-aware microvisor
ActiveUS9680862B2Digital data protectionPlatform integrity maintainanceTrusted ComputingSecurity properties
A trusted threat-aware microvisor may be deployed as a module of a trusted computing base (TCB) that also includes a root task module configured to cooperate with the microvisor to load and initialize one or more other modules executing on a node of a network environment. The root task may cooperate with the microvisor to allocate one or more kernel resources of the node to those other modules. As a trusted module of the TCB, the microvisor may be configured to enforce a security policy of the TCB that, e.g., prevents alteration of a state related to security of the microvisor by a module of or external to the TCB. The security policy of the TCB may be implemented by a plurality of security properties of the microvisor. Trusted (or trustedness) may therefore denote a predetermined level of confidence that the security property is demonstrated by the microvisor.
Owner:FIREEYE SECURITY HLDG US LLC
Verification of trusted threat-aware microvisor
Owner:FIREEYE SECURITY HLDG US LLC
Verifying integrity and guaranteeing execution of code on untrusted computer platform
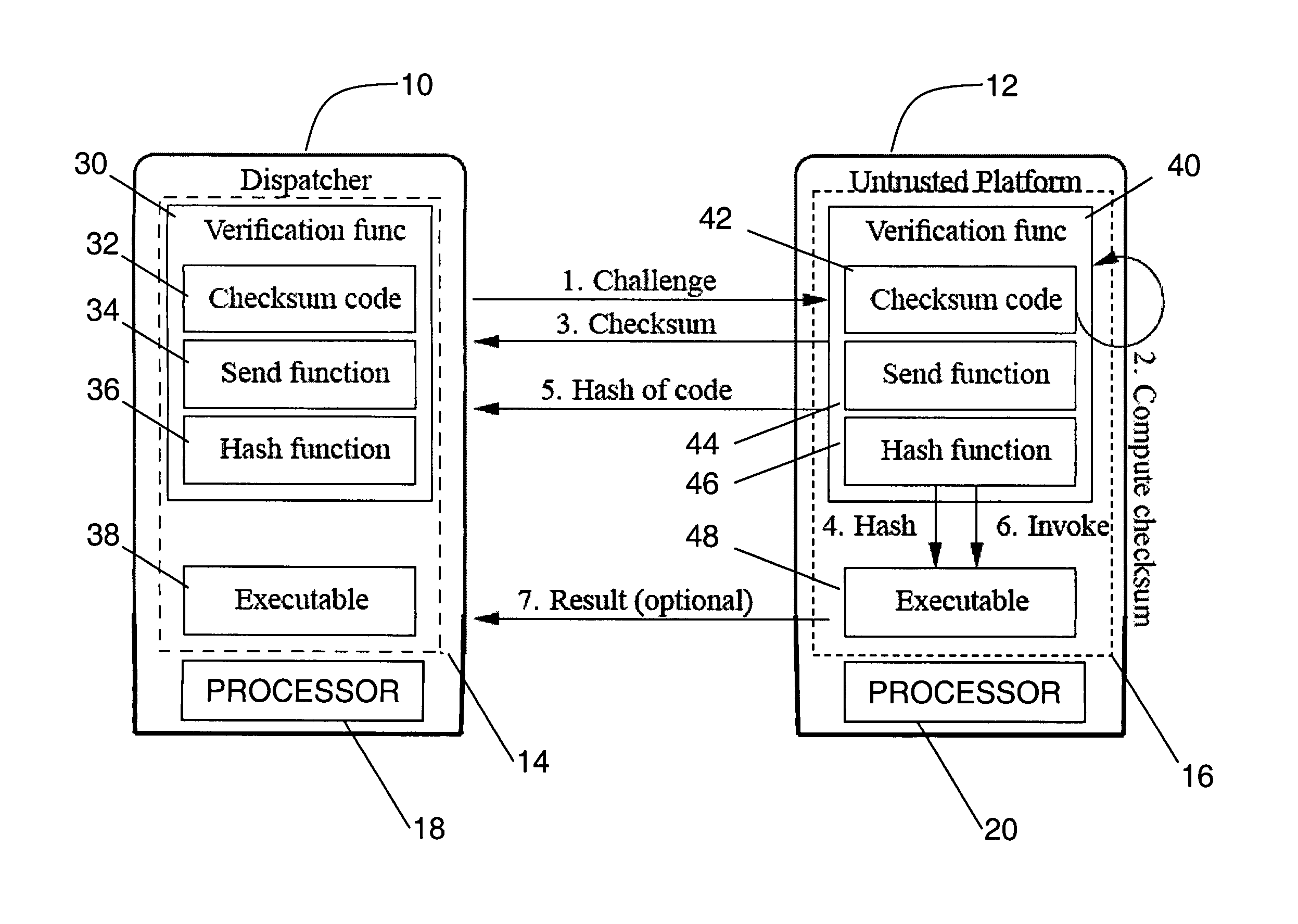
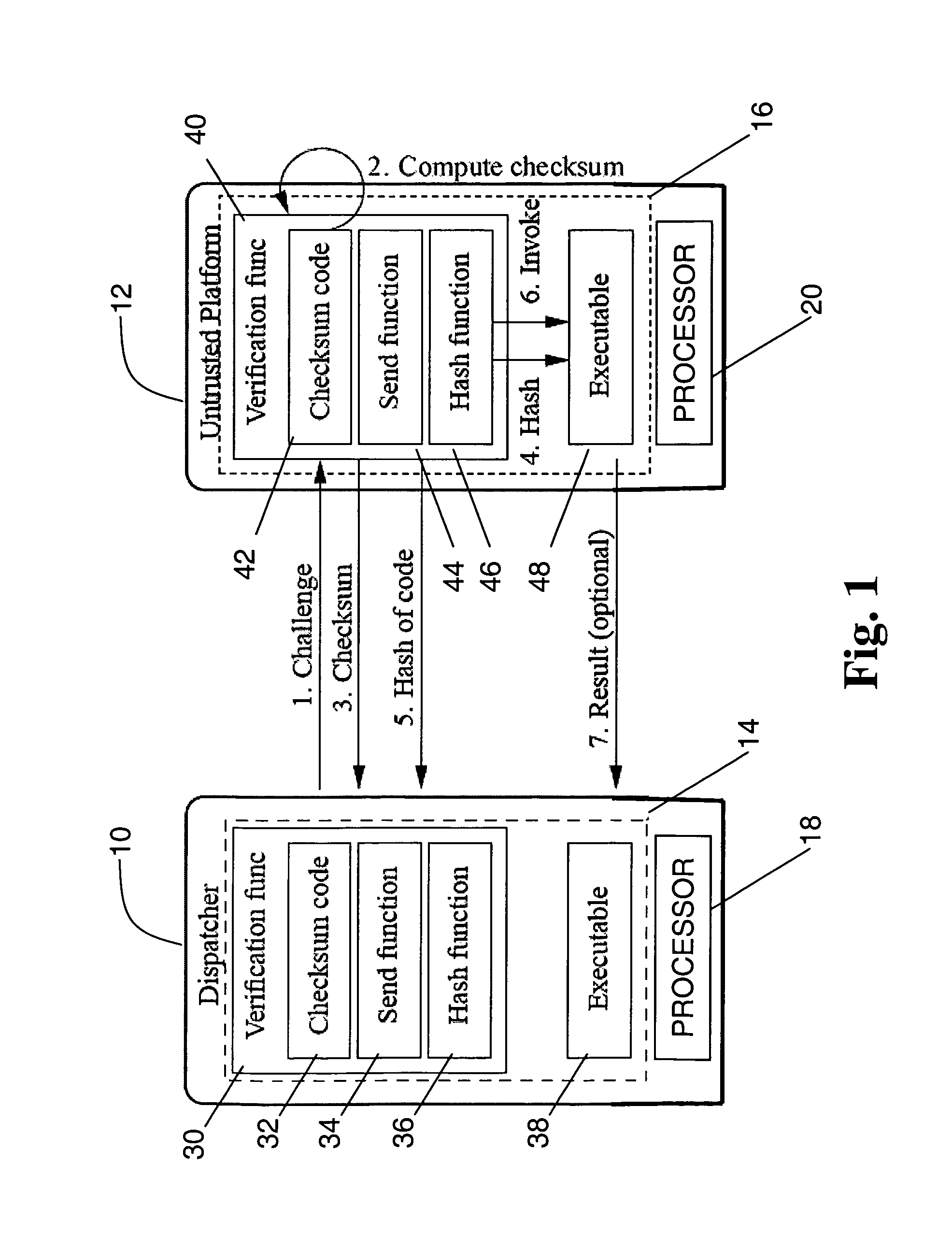
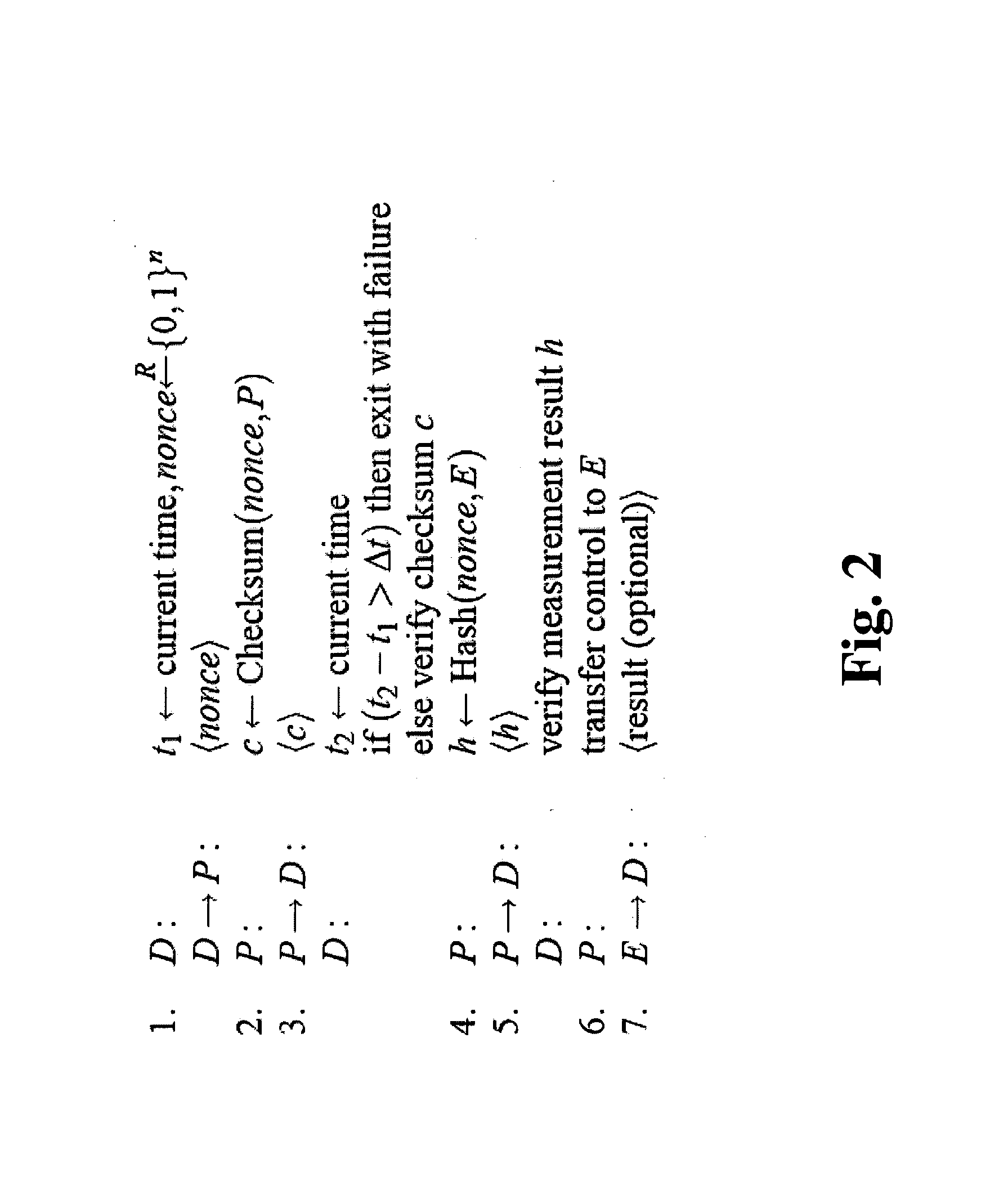
A method, system, and apparatus for verifying integrity and execution state of an untrusted computer. In one embodiment, the method includes placing a verification function in memory on the untrusted computer; invoking the verification function from a trusted computer; determining a checksum value over memory containing both the verification function and the execution state of a processor and hardware on the untrusted computer; sending the checksum value to the trusted computer; determining at the trusted computer whether the checksum value is correct; and determining at the trusted computer whether the checksum value is received within an expected time period.
Owner:IBM CORP +1
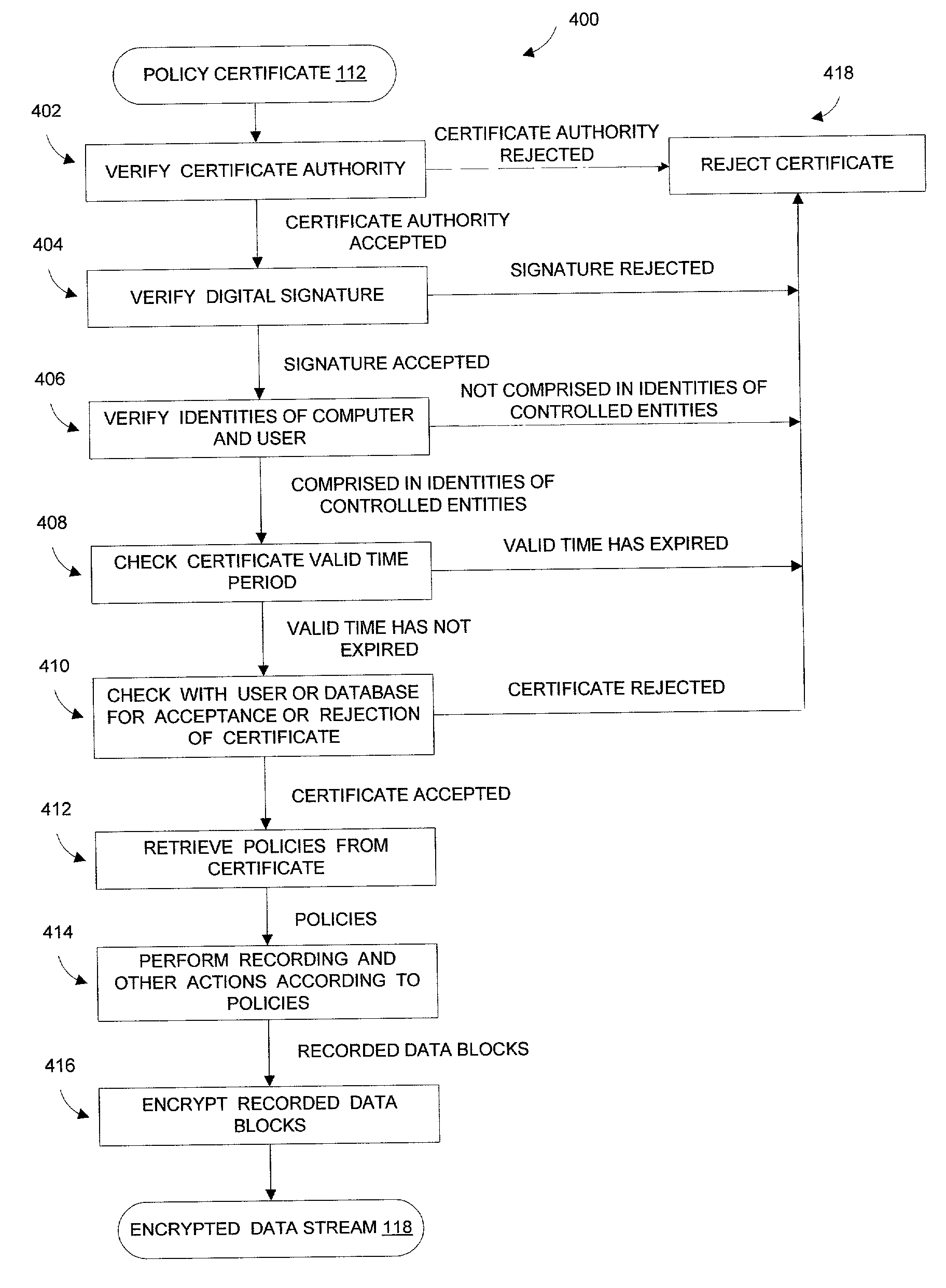
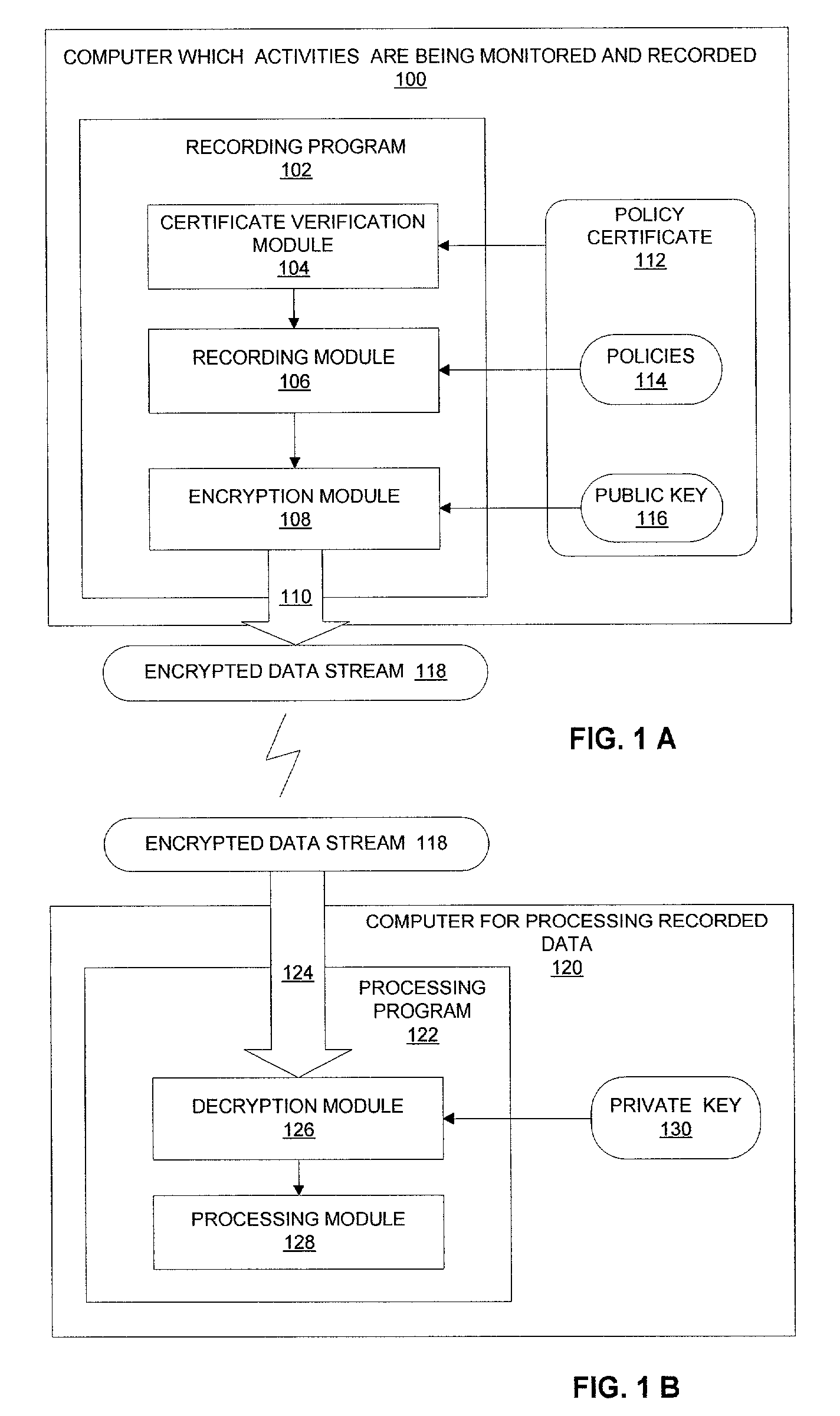
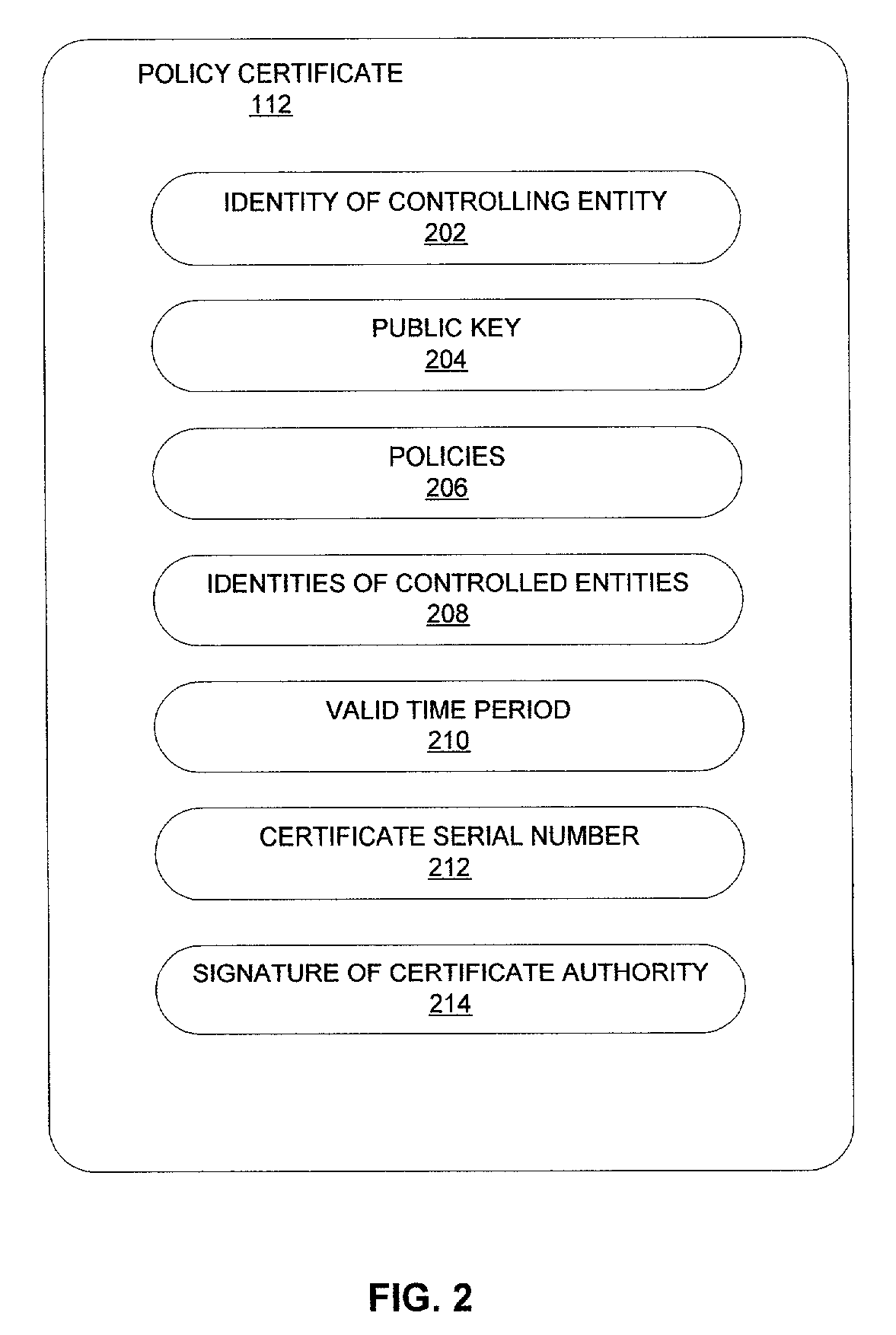
Trusted computer activity monitoring and recording system and method
InactiveUS20060041760A1Overcomes drawbackEnsure trustUnauthorized memory use protectionHardware monitoringComputer usersDigital signature
A trusted computer activity monitoring and recording system and method provides trust between the computer or the computer user which activities are being recorded and the supervisor who governs the monitoring and recording system by using a digital certificate comprising a plurality of policies and the public key of the supervisor. Computer activities are recorded and actions are performed according to the policies comprised in the certificate, and recorded data are encrypted using the public key comprised in the certificate. Recorded data may be further signed by digital signatures created with the private key of the computer or the computer user.
Owner:HUANG ZEZHEN
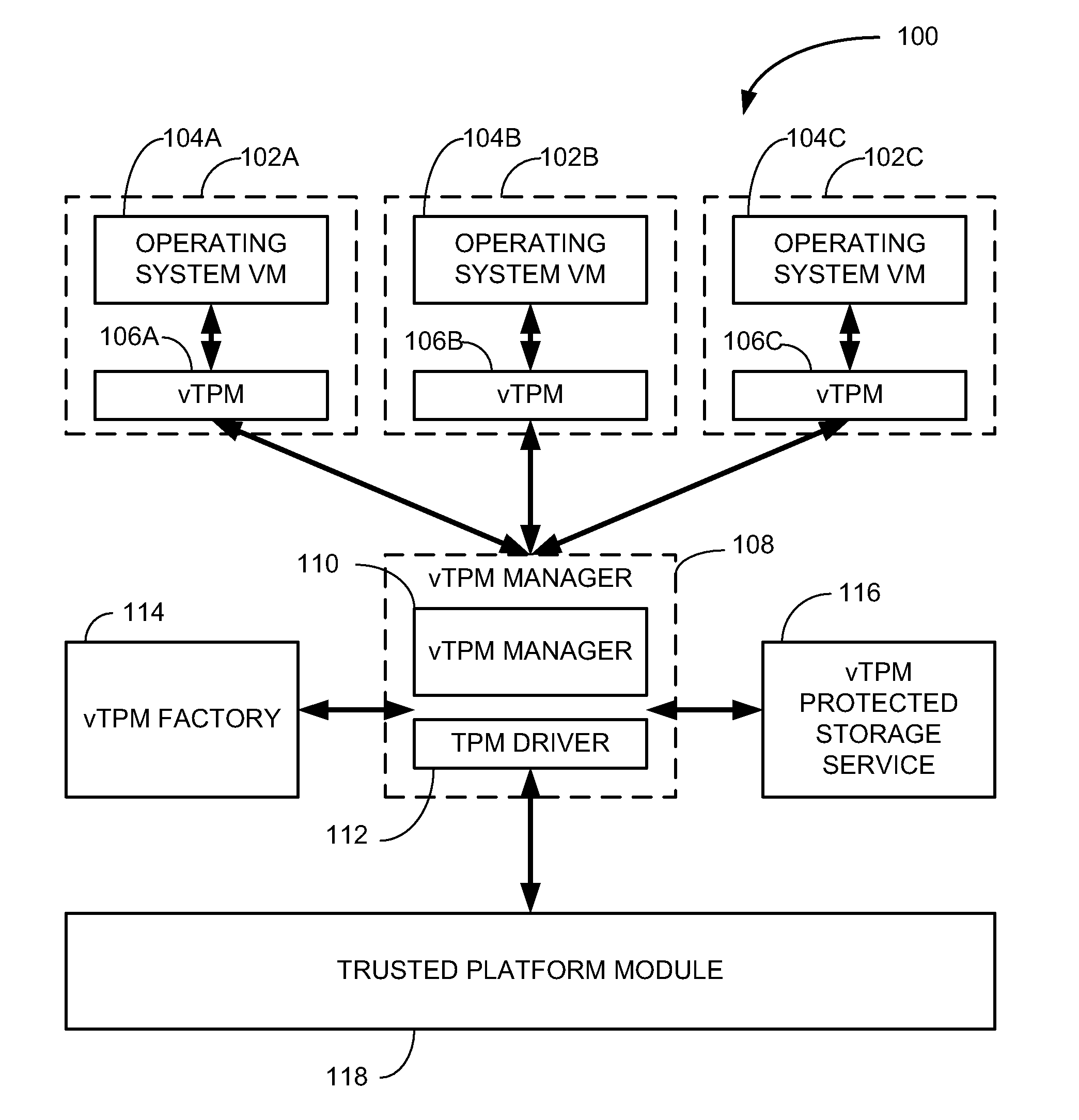
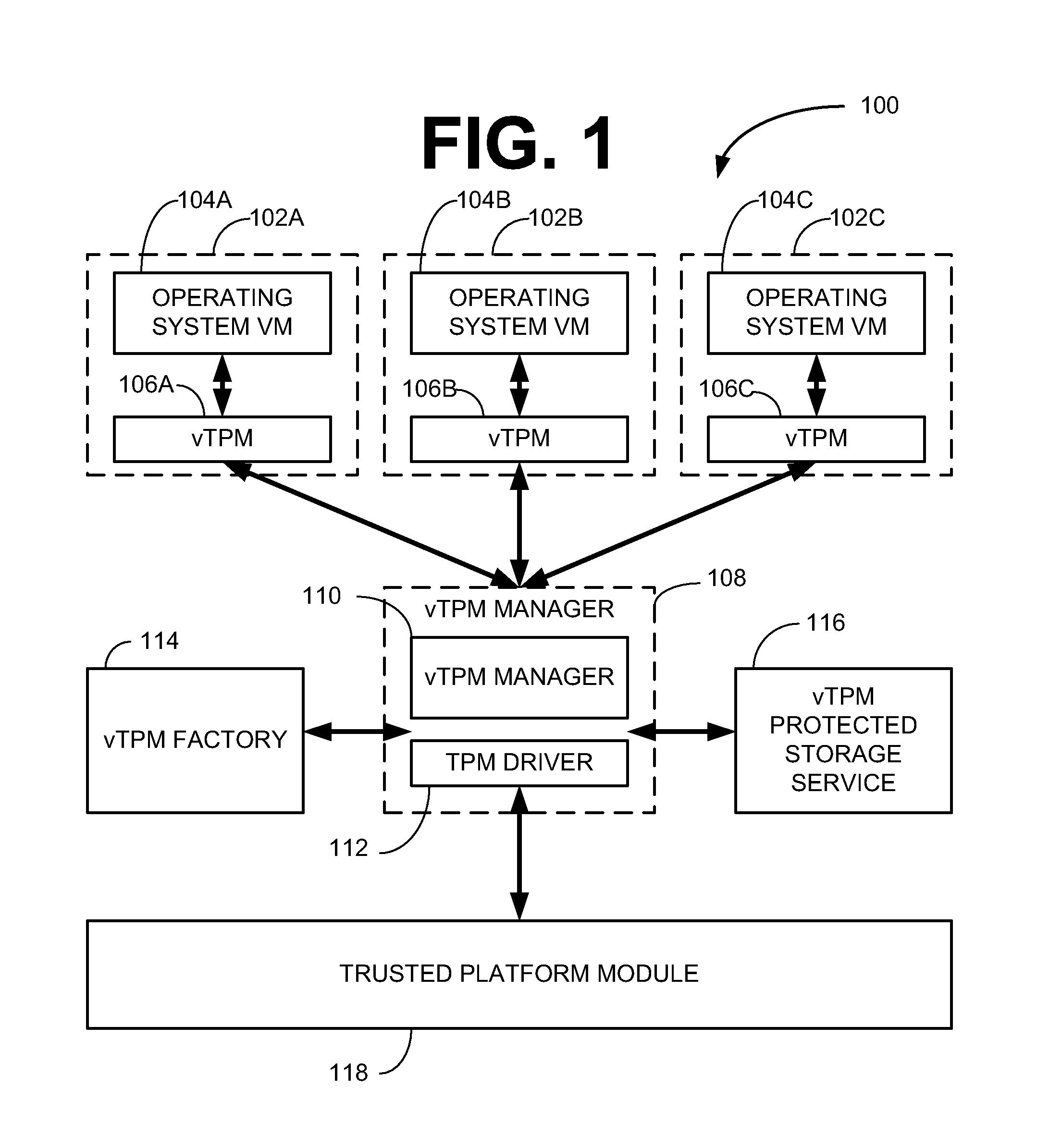
Virtual tpm key migration using hardware keys
ActiveUS20090169012A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesVirtualizationComputer hardware
The present subject matter is related to trusted computing, and more particularly to migration of virtual trusted platform module keys that are rooted in a hardware trusted platform module. Some embodiments include a trusted platform virtualization module that may perform one or more of inbound and outbound trusted platform module key migrations. Such migrations may be performed between a virtual trusted platform module and either a hardware or a virtual trusted platform module.
Owner:INTEL CORP
Method and computer system for controlling access by applications to this and other computer systems
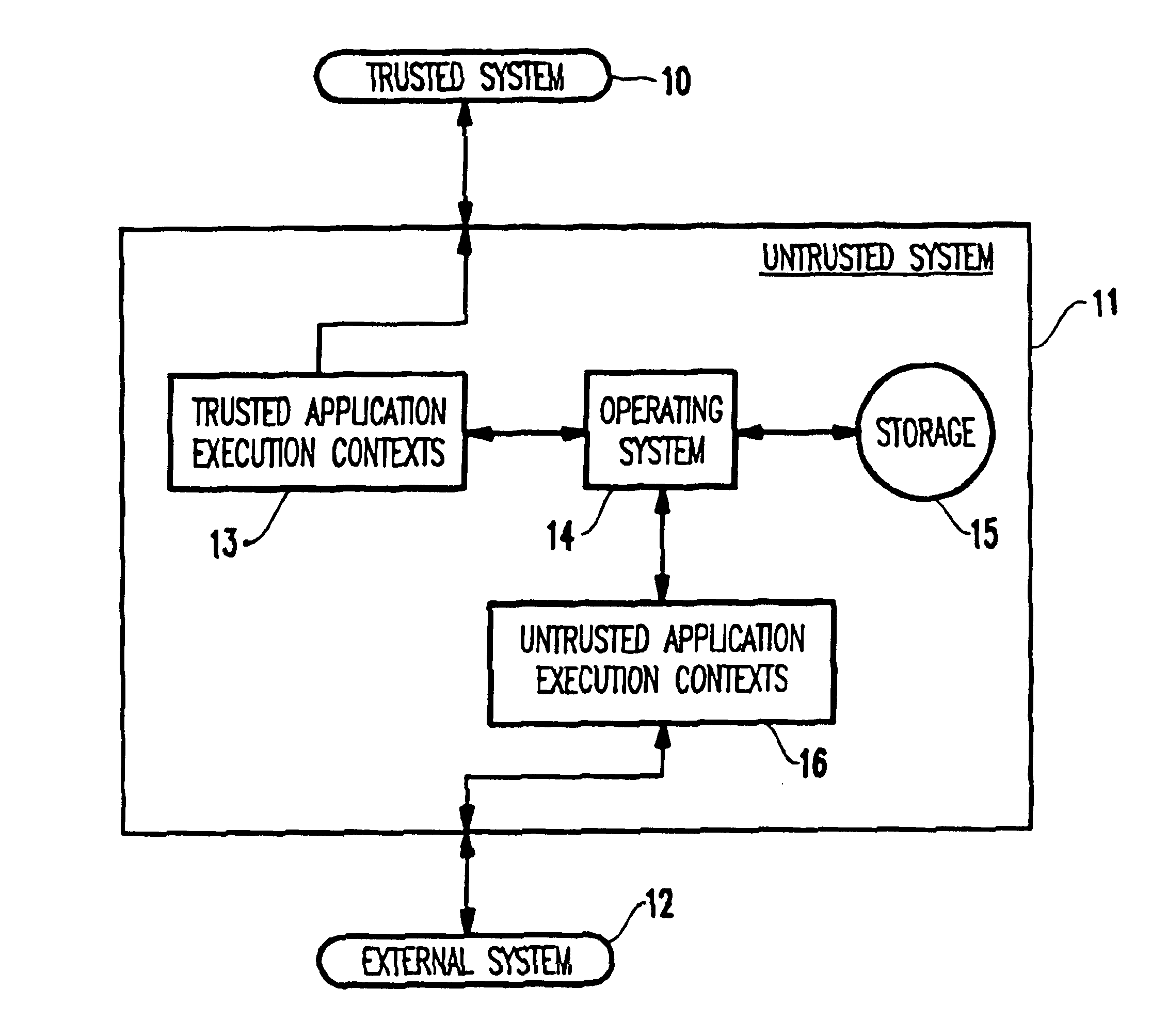
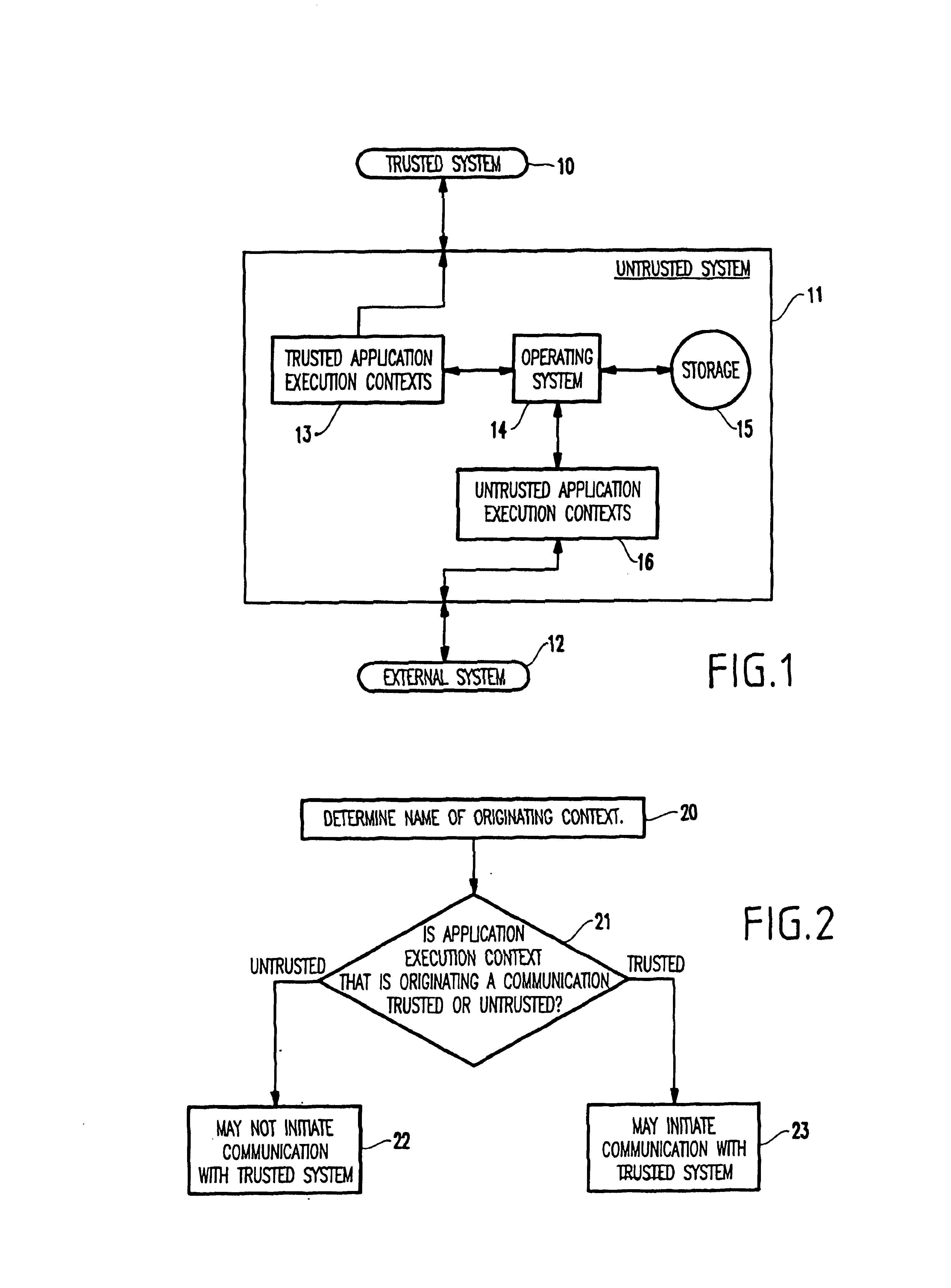
InactiveUS6883098B1Digital data processing detailsMultiple digital computer combinationsOperational systemComputerized system
Application execution contexts within an untrusted computer system are classified as trusted or untrusted based on respective names assigned to the execution contexts. If an application runs in an untrusted execution context, an operating system within the untrusted computer system prevents the application from initiating a connection with a trusted computer system and accessing sensitive parts of the untrusted computer system. If the application runs in a trusted execution context, the operating system permits the application to initiate a connection with the trusted computer system.
Owner:IBM CORP
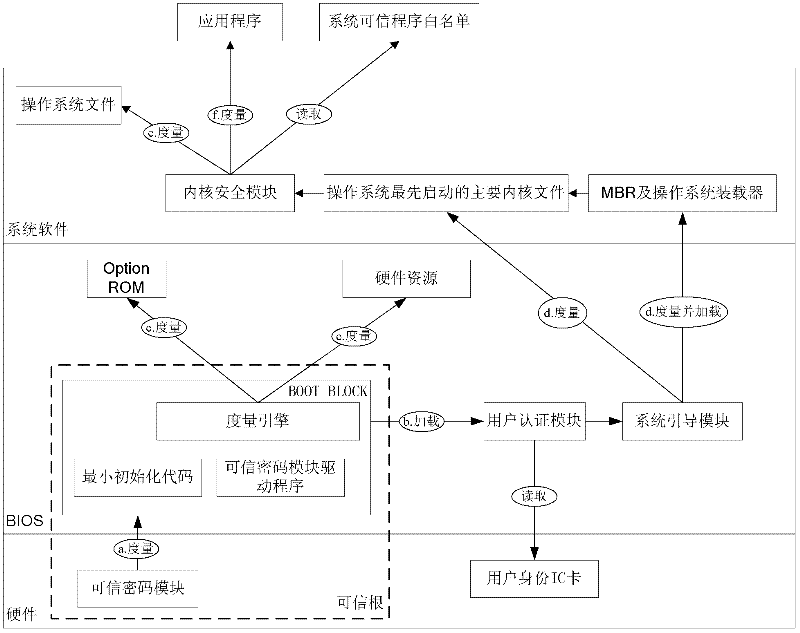
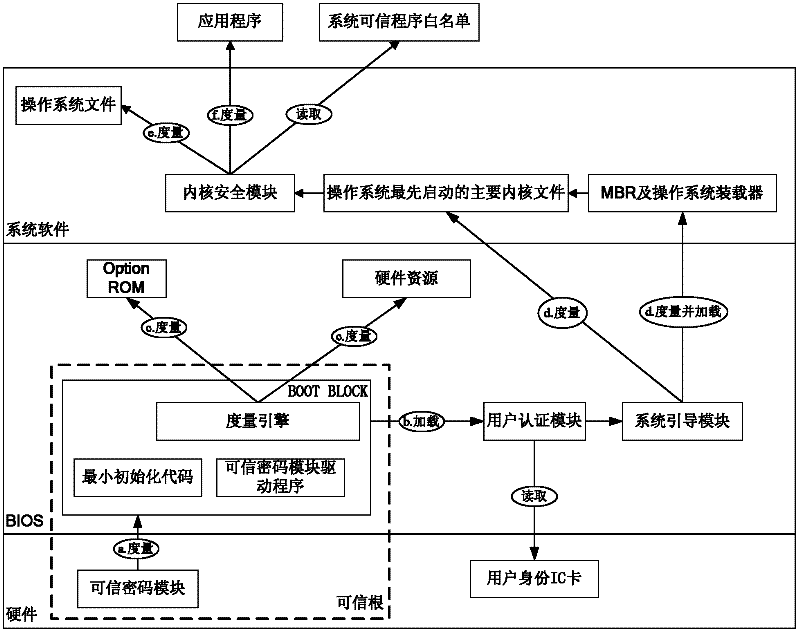
Trust chain transfer method for trusted computing platform
InactiveCN102332070ANot easy to tamper withNot easy to attackPlatform integrity maintainanceOperational systemTrusted Computing
The invention discloses a trust chain transfer method for a trusted computing platform. A trusted computing module (TCM) serving as a starting point of starting a trust chain is started and actively initiated at first to verify the trustiness of a BIOS (basic input output system) chip; after the trusted BIOS chip is started, a MAIN BLOCK of the BIOS chip performs concentrated integrity verification on key files of an MBR (master boot record), an operating system loader and an operating system kernel; in the starting process of an operating system, the starting and running of an unauthorized program are prevented in a way of combining the integrity verification based on a white list and running program control; and hashing operations for the integrity verification are finished by a hardware computing engine. When a user starts any executable program, a security module in the operating system kernel checks the integrity of the program and checks whether the program is in the trusted program white list or not, and only application programs which are in the trusted program white list of the system and have integrity measures consistent with an expected value are permitted to be run. High-efficiency and fine-grained trust chain transfer is realized, the damages of viruses to system files and program files can be prevented, and the execution of the unauthorized program can be prevented.
Owner:中国人民解放军海军计算技术研究所
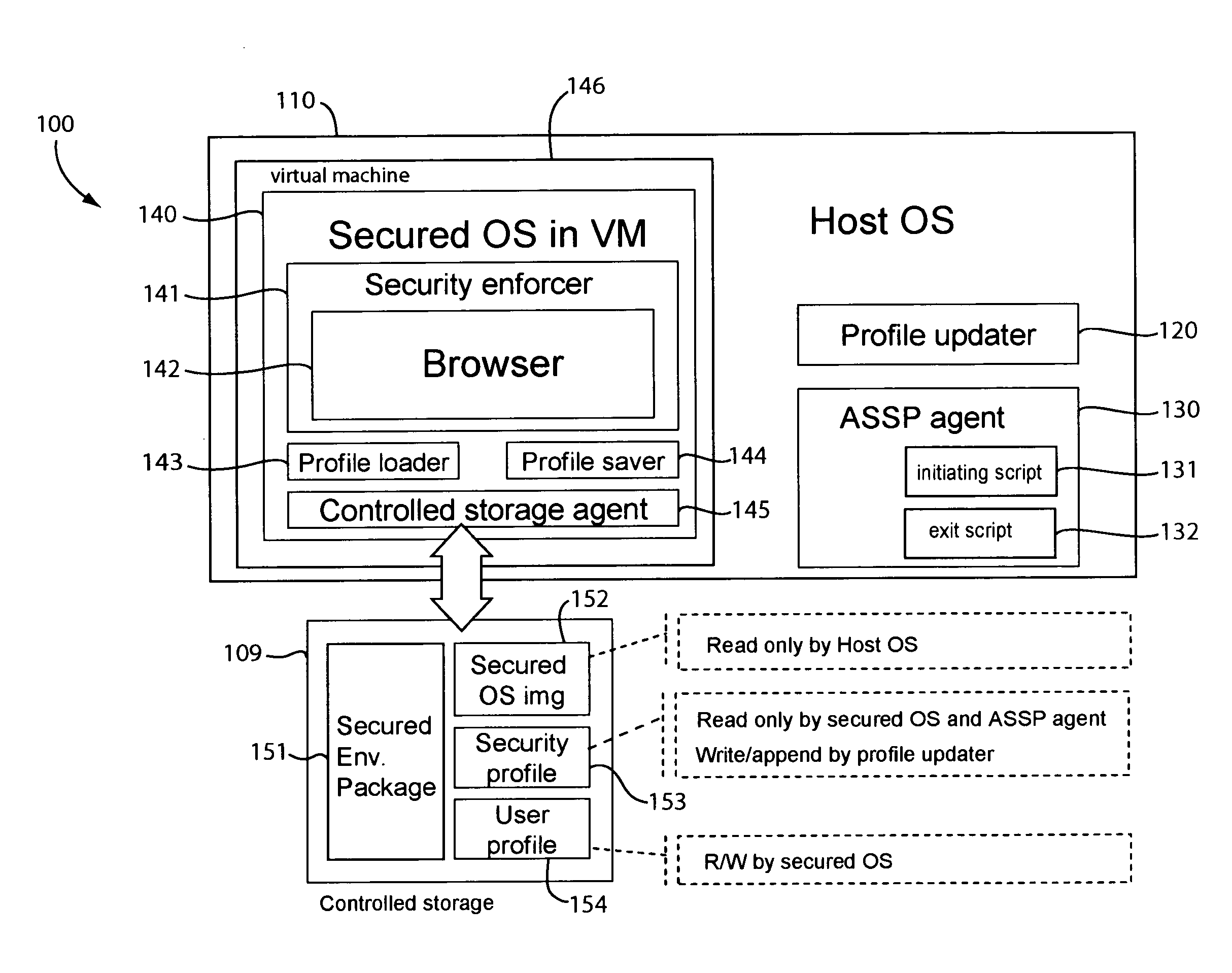
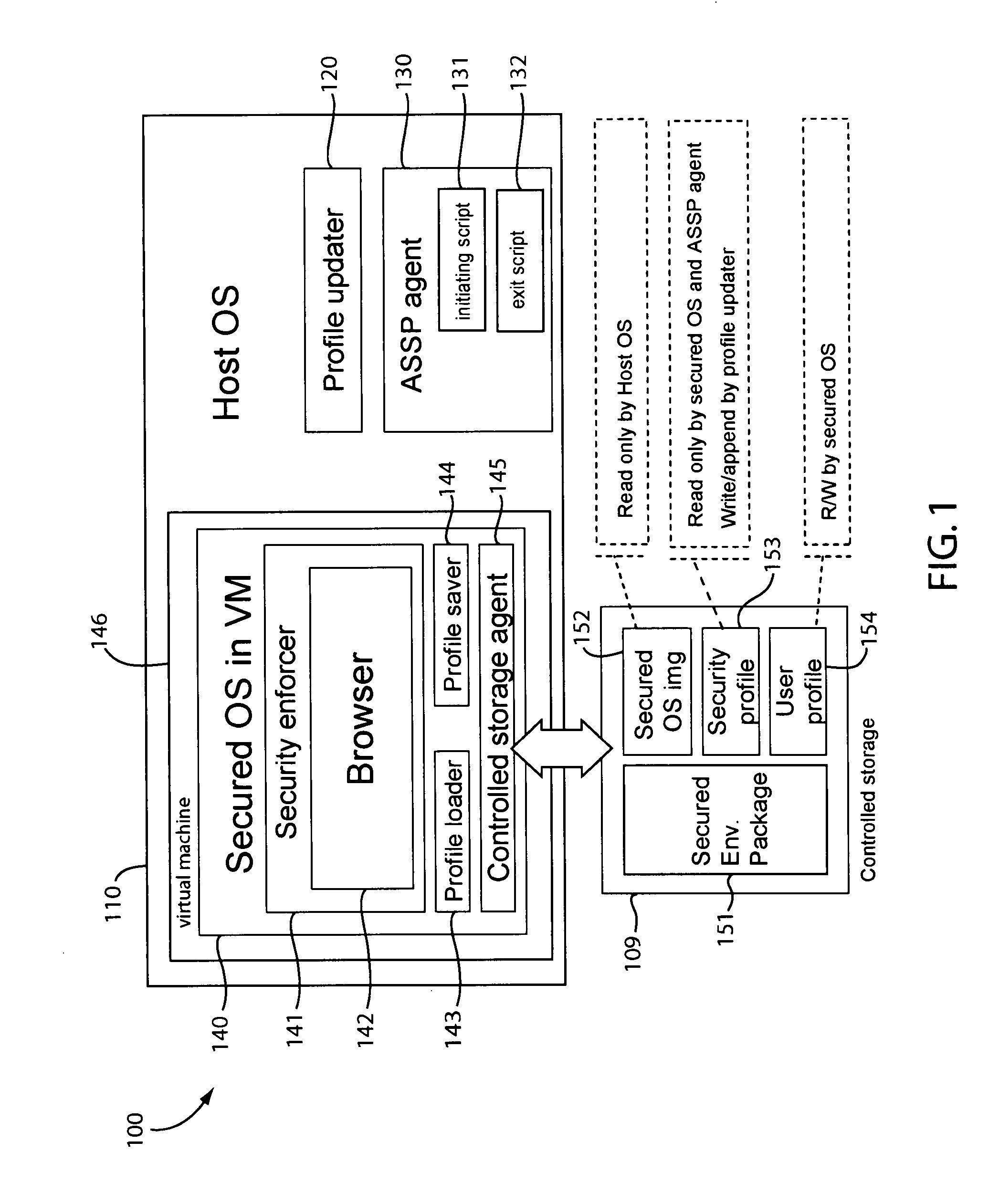
Portable secured computing environment for performing online confidential transactions in untrusted computers
ActiveUS20080256536A1Readily apparentMemory loss protectionDigital data processing detailsAccess networkOperational system
A portable secured computing environment for performing online confidential transactions in an untrusted host computer. The secured computing environment may be loaded from a portable storage device, such as a USB stick, plugged into a peripheral port of the host computer. The secured computing environment may include a virtual machine running under a host operating system of the host computer. A secured operating system may be running in the virtual machine. An online application, such as a web browser in communication with an online service, may be run under the secured operating system. Operation of the online application may be restricted by a security profile. For example, the online application may only access network addresses specifically indicated in a whitelist of the security profile.
Owner:TREND MICRO INC
System for providing secure and trusted computing environments
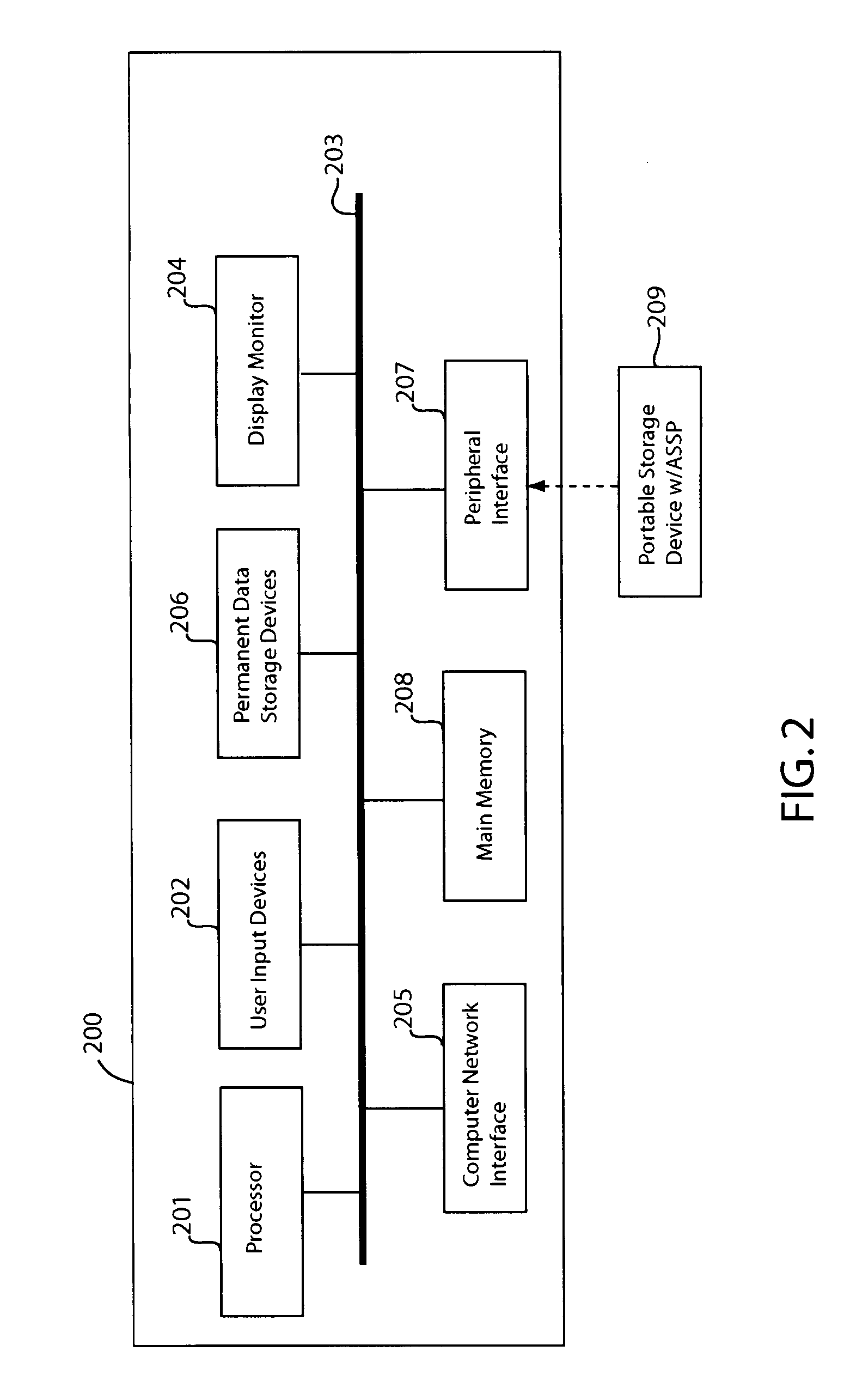
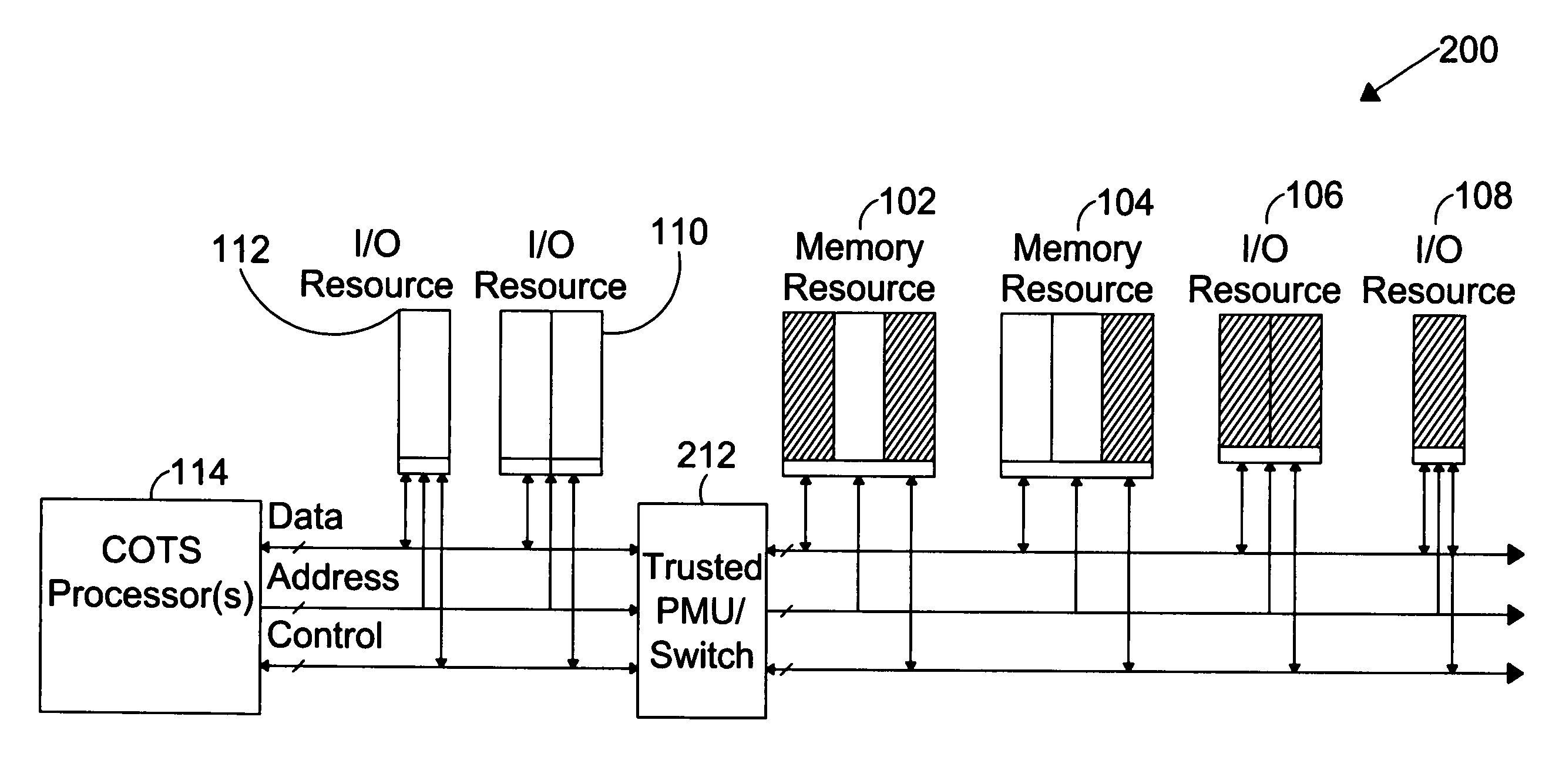
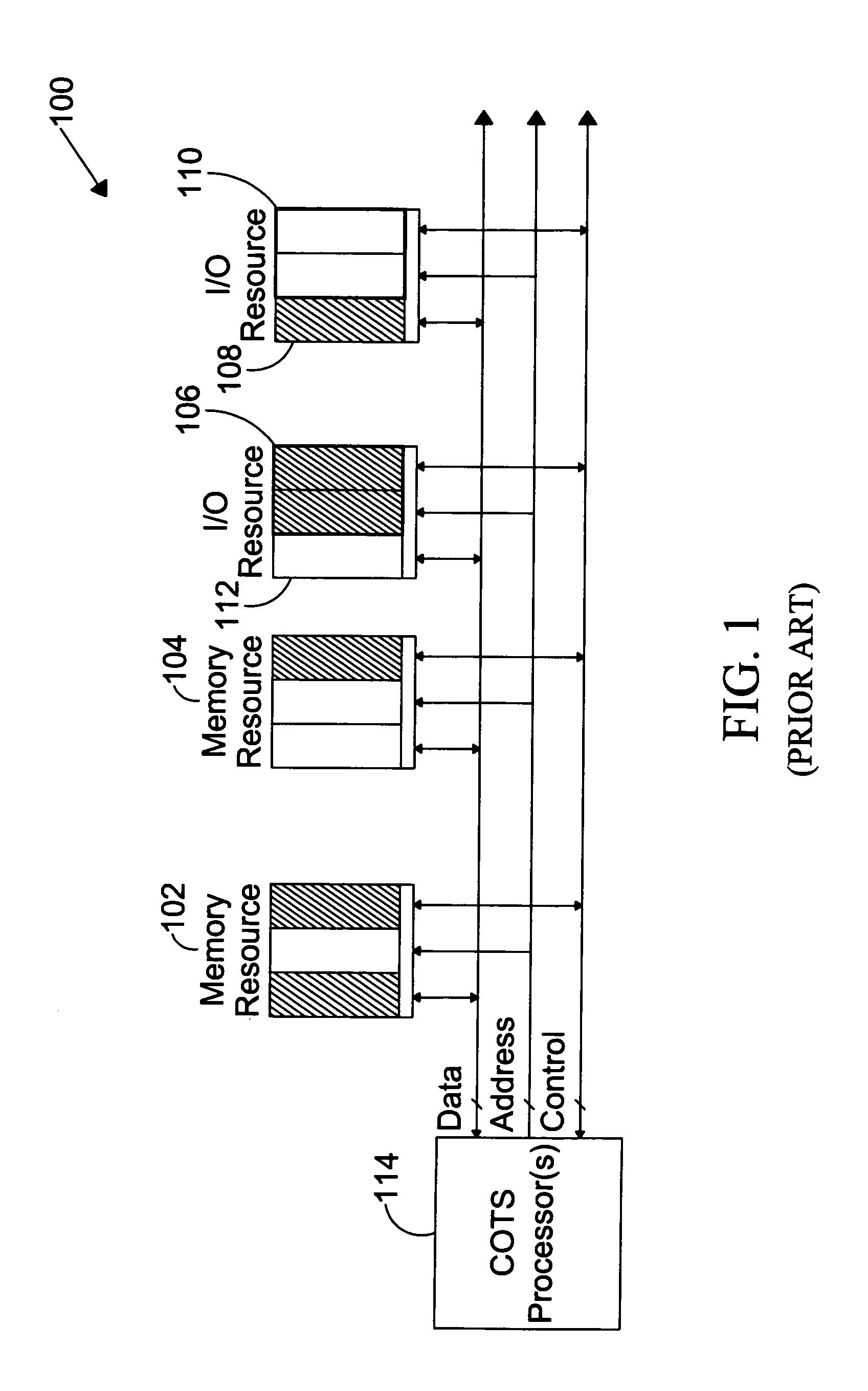
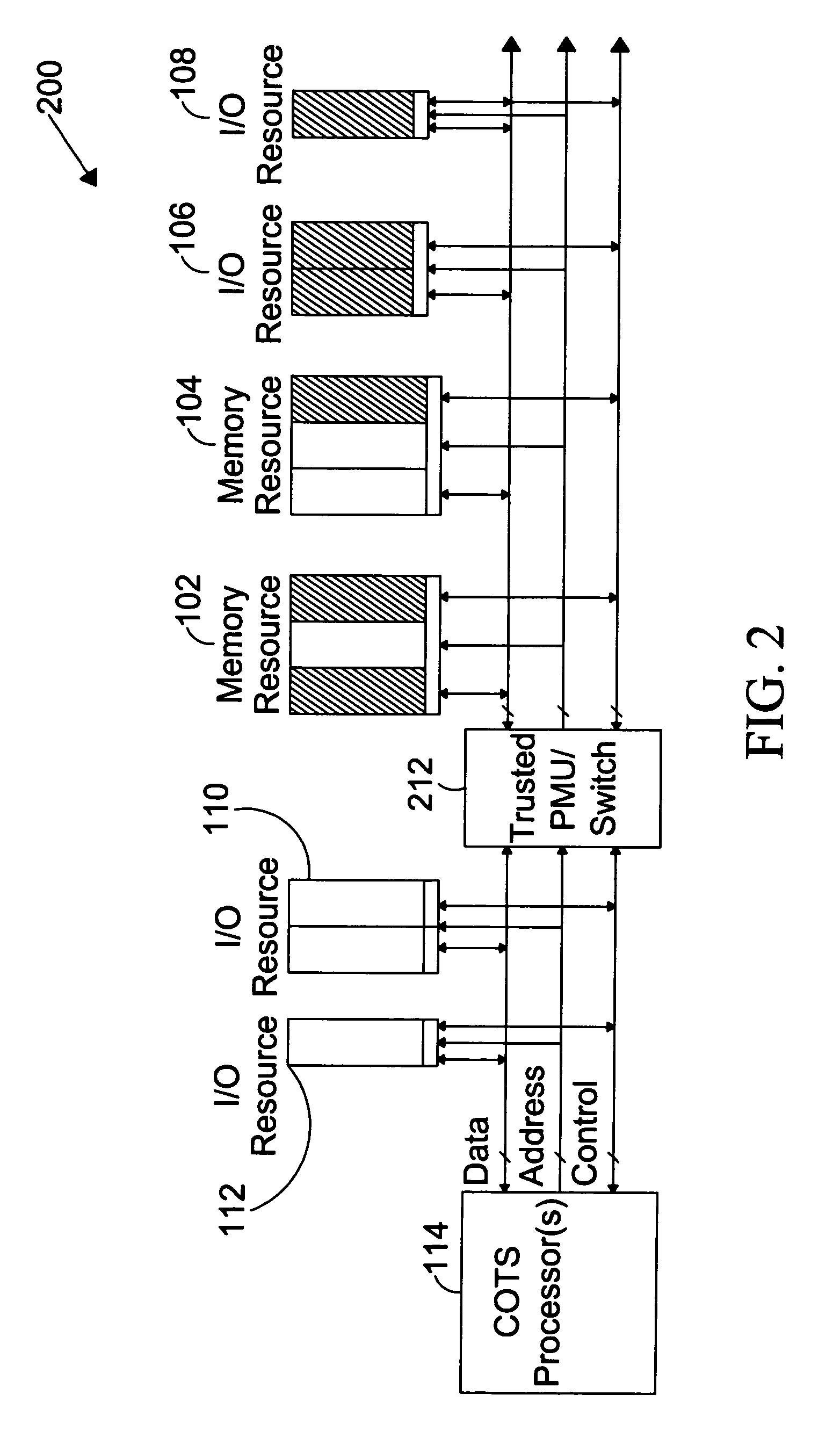
ActiveUS7716720B1Provide partEnvironment safetyDigital data processing detailsUser identity/authority verificationTrusted ComputingComputer module
The present invention is directed to a system for providing a trusted environment for untrusted computing systems. The system may include a HAC subsystem managing shared resources and a trusted bus switch for controlling a COTS processor to access the shared resources. The shared resources such as memory and several I / O resources reside on the trusted side of the trusted bus switch. Alternatively, the system may include a SCM as an add-on module to an untrusted host environment. Only authenticated applications including COTS OS execute on the SCM while untrusted applications execute on the untrusted host environment. The SCM may control secure resource access from the untrusted host through a plug-in module interface. All secure resources may be maintained on the trusted side of the plug-in module interface.
Owner:ROCKWELL COLLINS INC
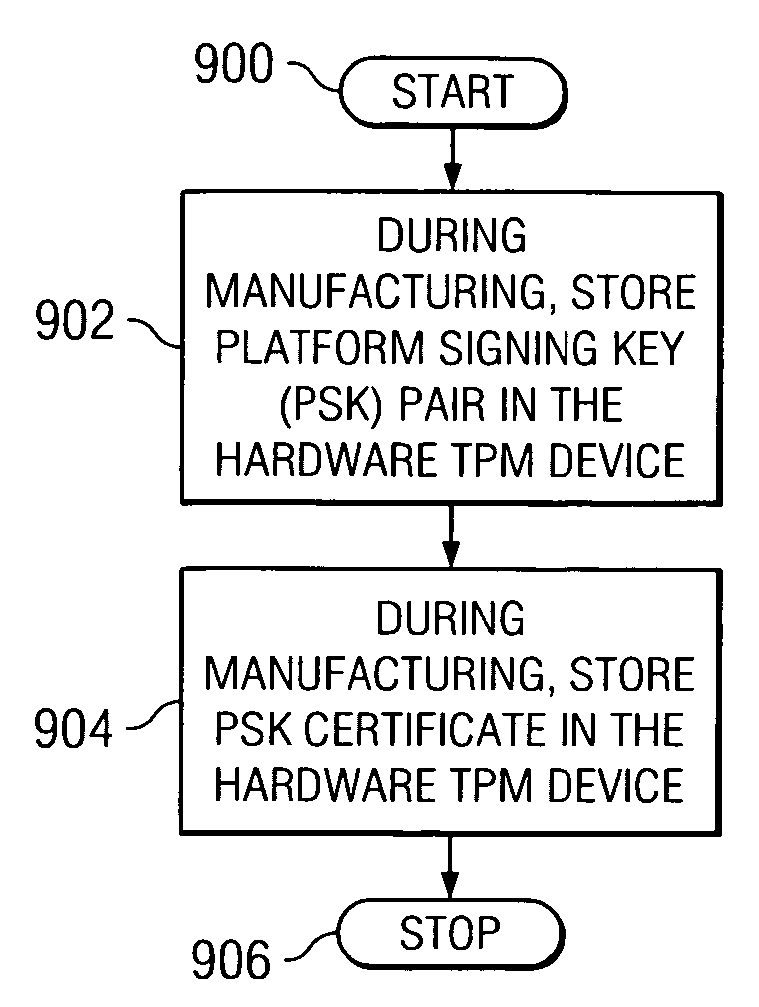
Method, apparatus, and product for establishing virtual endorsement credentials for dynamically generated endorsement keys in a trusted computing platform
ActiveUS20070016801A1User identity/authority verificationUnauthorized memory use protectionData processing systemThird party
A method, apparatus, and computer program product are disclosed in a data processing system for establishing virtual endorsement credentials. The data processing system includes a hardware trusted platform module (TPM). Logical partitions are generated in the system. A different virtual TPM is generated for each one of the logical partitions. For each one of the logical partitions, the virtual TPM that was generated for the logical partition then dynamically generates a virtual endorsement credential for use by the logical partition that includes the virtual TPM. The virtual endorsement credential is generated within the data processing system without the data processing system or its devices accessing a trusted third party that is external to the data processing system.
Owner:IBM CORP
System and method for processor-based security
ActiveUS8738932B2Avoid accessDigital data processing detailsUser identity/authority verificationExternal storageProcessor register
A system and method for processor-based security is provided, for on-chip security and trusted computing services for software applications. A processor is provided having a processor core, a cache memory, a plurality of registers for storing at least one hash value and at least one encryption key, a memory interface, and at least one on-chip instruction for creating a secure memory area in a memory external to the processor, and a hypervisor program executed by the processor. The hypervisor program instructs the processor to execute the at least one on-chip instruction to create a secure memory area for a software area for a software module, and the processor encrypts data written to, and decrypts data read from, the external memory using the at least one encryption key and the verifying data read from the external memory using the at least one hash value. Secure module interactions are provided, as well as the generation of a power-on key which can be used to protect memory in the event of a re-boot event. Lightweight, run-time attestation reports are generated which include selected information about software modules executed by the processors, for use in determining whether the processor is trusted to provide secure services.
Owner:CORESECURE TECH LLC
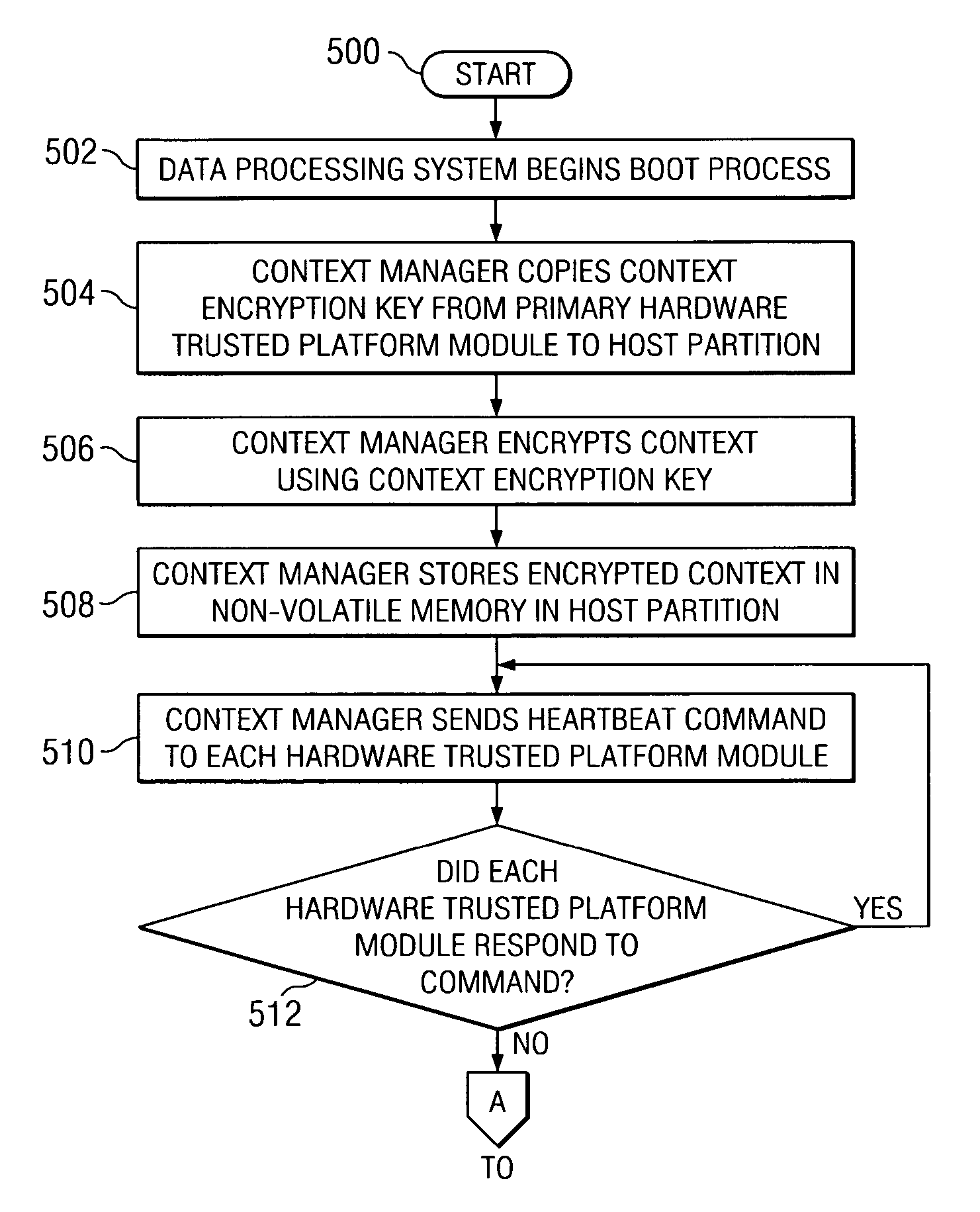
Method, apparatus, and product for providing a backup hardware trusted platform module in a hypervisor environment
A method, apparatus, and computer program product are described for implementing a trusted computing environment within a data processing system. The data processing system includes a primary hardware trusted platform module (TPM) and a secondary hardware backup TPM. The data processing system also includes multiple logical partitions. The primary hardware TPM is used to provide trusted computing services to the logical partitions. A determination is made as to whether the primary hardware TPM is malfunctioning. If a determination is made that the primary hardware TPM is malfunctioning, the secondary hardware TPM is designated as a new primary hardware TPM and is utilized instead of the primary TPM to provide trusted computing services to the logical partitions.
Owner:IBM CORP
Trusted computing platform for restricting use of data
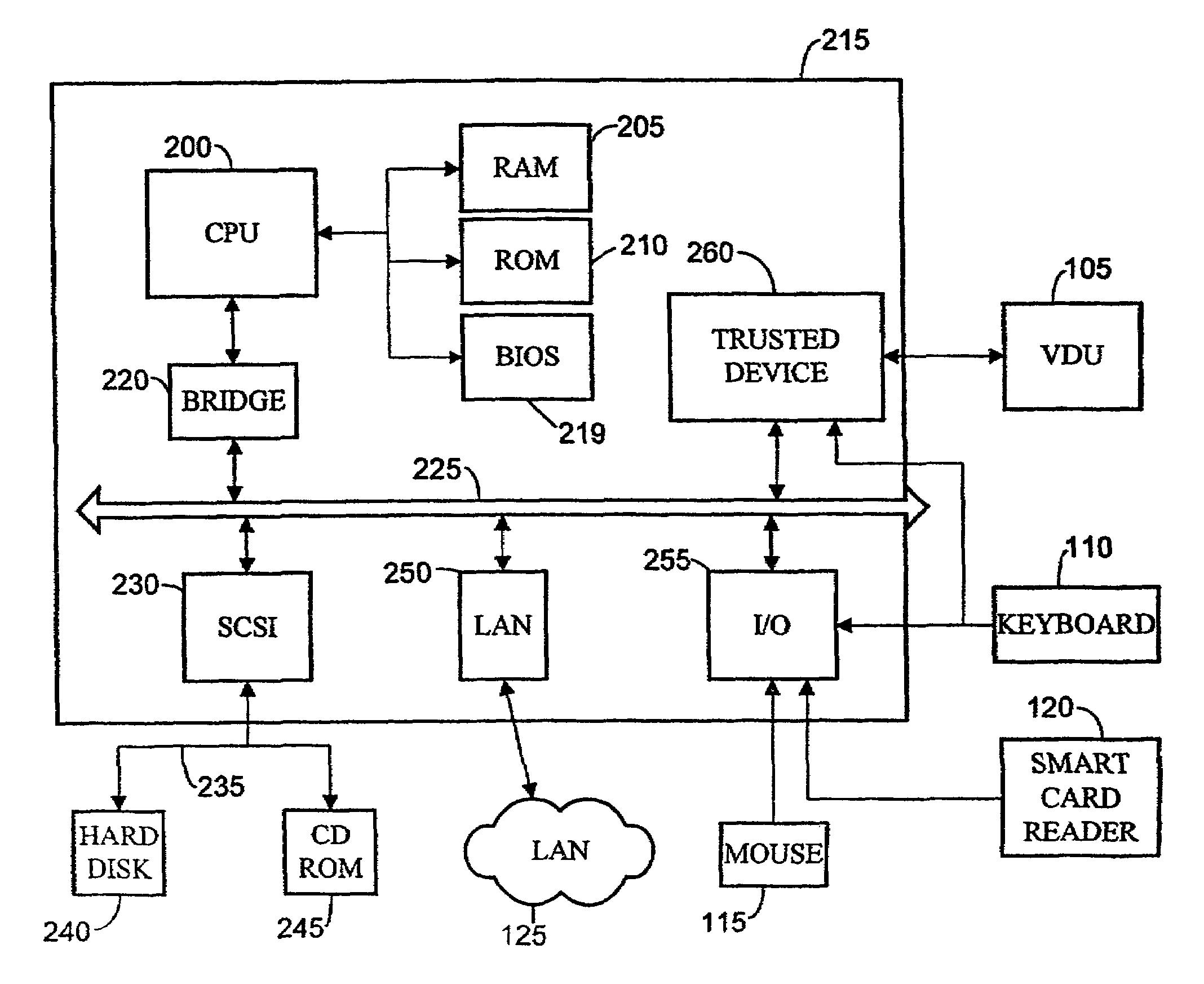
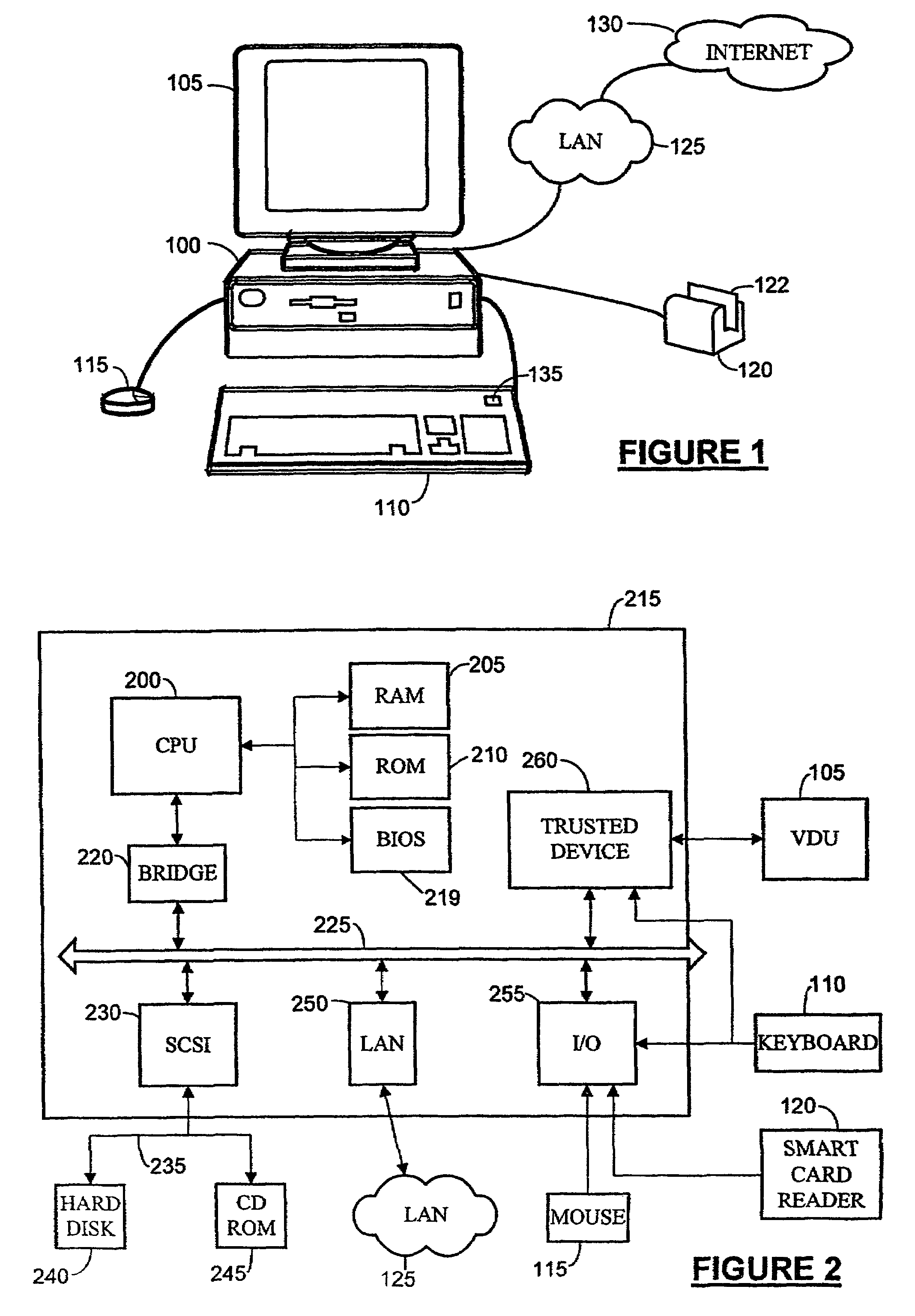
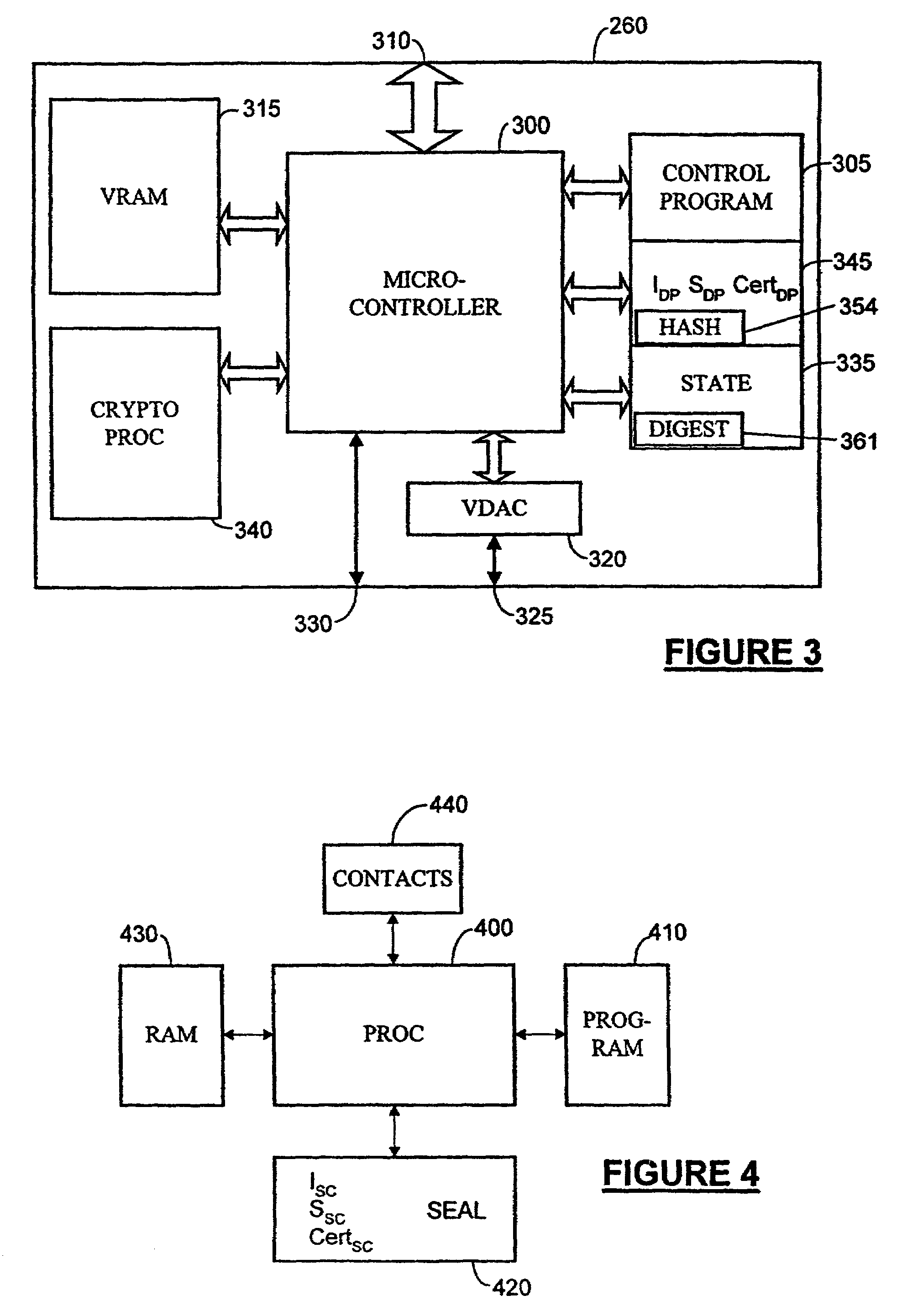
InactiveUS7526785B1Avoid misuseEffectively protected against attack confidentialityTelevision system detailsData processing applicationsSecure communicationService provision
A client / server system has a client platform adapted to provide restricted use of data provided by a serve. The client platform comprises a display, secure communications means, and a memory containing image receiving code for receiving data from a server by the secure communication means and for display of such data. The client platform is adapted such that the data received from a server is used for display of the data and not for an unauthorised purpose. A server adapted to provide data to a client platform for restricted use by the client platform comprises a memory containing image sending code for providing an image of data executed on the server, and secure communications means for secure communication of images of data to a client platform. The server is adapted to determine that a client platform is adapted to ensure restricted use of the data before it is sent by the image sending code.
Owner:HEWLETT PACKARD DEV CO LP
Method and apparatus for trusted federated identity
InactiveUS8533803B2Digital data processing detailsUser identity/authority verificationTrusted ComputingFederated identity
A trusted computing environment, such as a smartcard, UICC, Java card, global platform, or the like may be used as a local host trust center and a proxy for a single-sign on (SSO) provider. This may be referred to as a local SSO provider (OP). This may be done, for example, to keep authentication traffic local and to prevent over the air communications, which may burden an operator network. To establish the OP proxy in the trusted environment, the trusted environment may bind to the SSO provider in a number of ways. For example, the SSO provider may interoperate with UICC-based UE authentication or GBA. In this way, user equipment may leverage the trusted environment in order to provide increased security and reduce over the air communications and authentication burden on the OP or operator network.
Owner:INTERDIGITAL PATENT HLDG INC
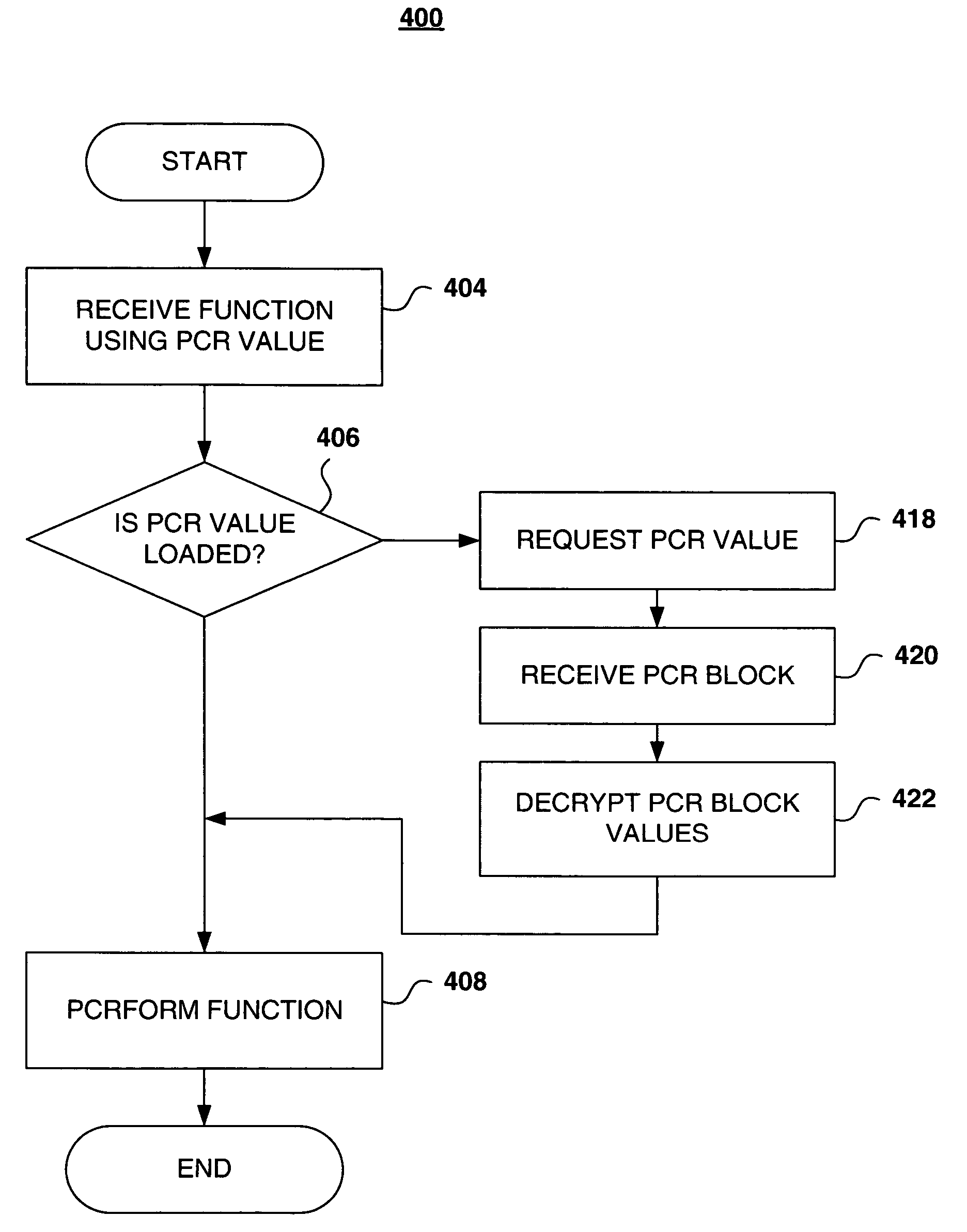
Scalable paging of platform configuration registers
ActiveUS20060075223A1Prevent breachUser identity/authority verificationDigital computer detailsComputer hardwareProcessor register
A method, computer program, and system for paging platform configuration registers in and out of a trusted platform module. In a trusted computing platform, an unlimited number of platform configuration registers can be obtained through paging. The trust platform module encrypts and decrypts platform configuration registers for storage outside the trusted platform module.
Owner:LENOVO PC INT
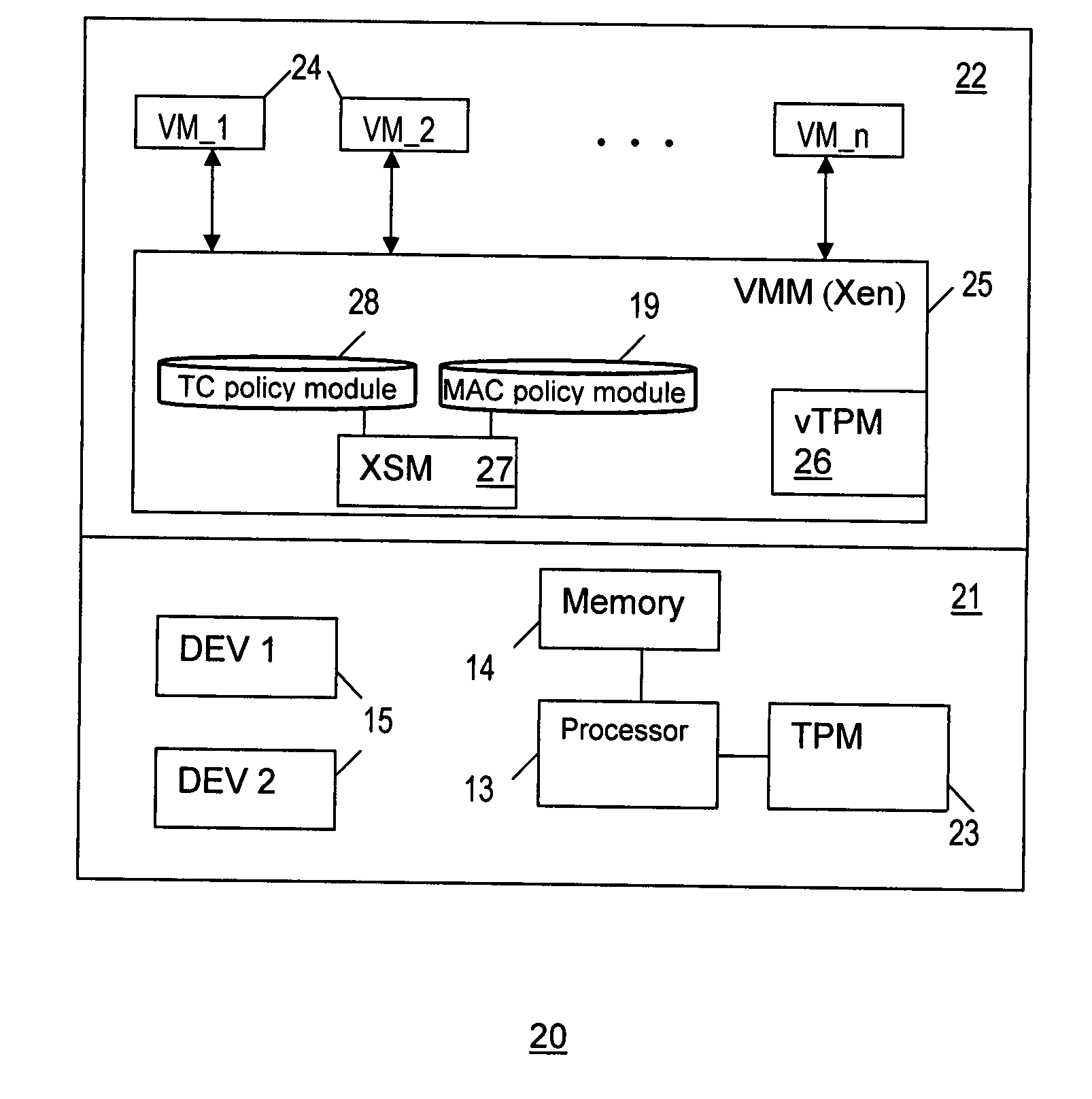
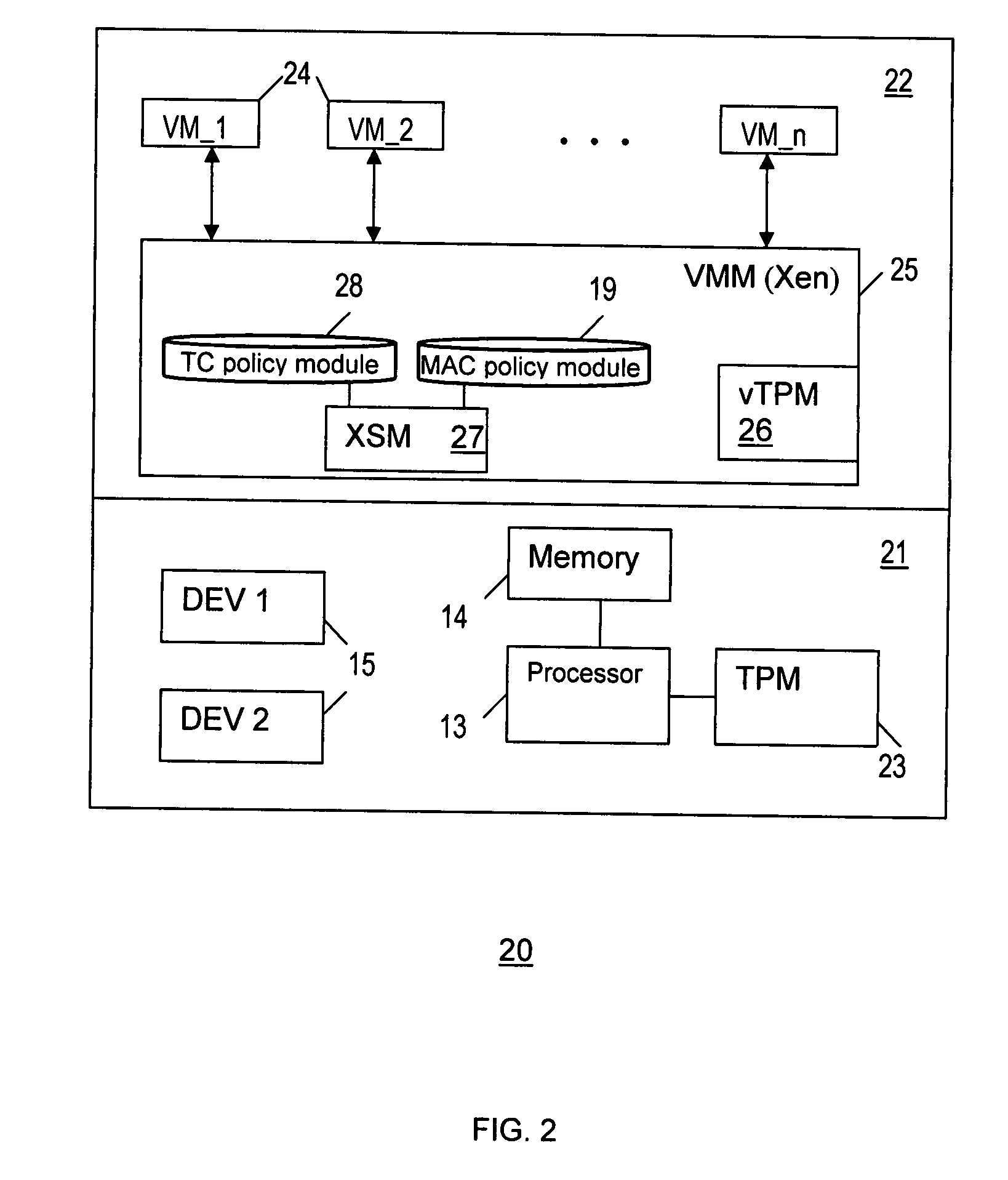
Method and system for enforcing trusted computing policies in a hypervisor security module architecture
InactiveUS20090125974A1Platform integrity maintainanceTransmissionObject basedTrusted Platform Module
A method and system for enforcing trusted computing (TC) policies in a security module architecture for a hypervisor. Upon receiving a request from a subject for access to an object, TC-related attribute values are obtained for the subject and the object based on a virtualized trusted platform module (vTPM). Access control decisions are the made based at least on the TC-related attribute values and TC-related policies.
Owner:SAMSUNG ELECTRONICS CO LTD
Data integrity monitoring in trusted computing entity
InactiveUS7457951B1Digital data processing detailsUnauthorized memory use protectionData integrityTrusted components
A method of security monitoring of data files in a computer platform is carried out by a trusted component having a processor and trusted memory area. The method comprises creating one or a plurality of data files in an untrusted memory area of said computing platform, for each created data file, periodically generating a digest data by applying a hash function to each data file, storing the digest data in a trusted memory area and for each file periodically comparing a current digest data of the file with a previously generated digest data of the file. Any differences between a previous and a current digest data indicate that a file in the untrusted memory area has been corrupted.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Safety and management of computing environments that may support unsafe components
InactiveUS20090265756A1Effectively guardEffective isolationMemory loss protectionError detection/correctionTrusted componentsTrusted Computing
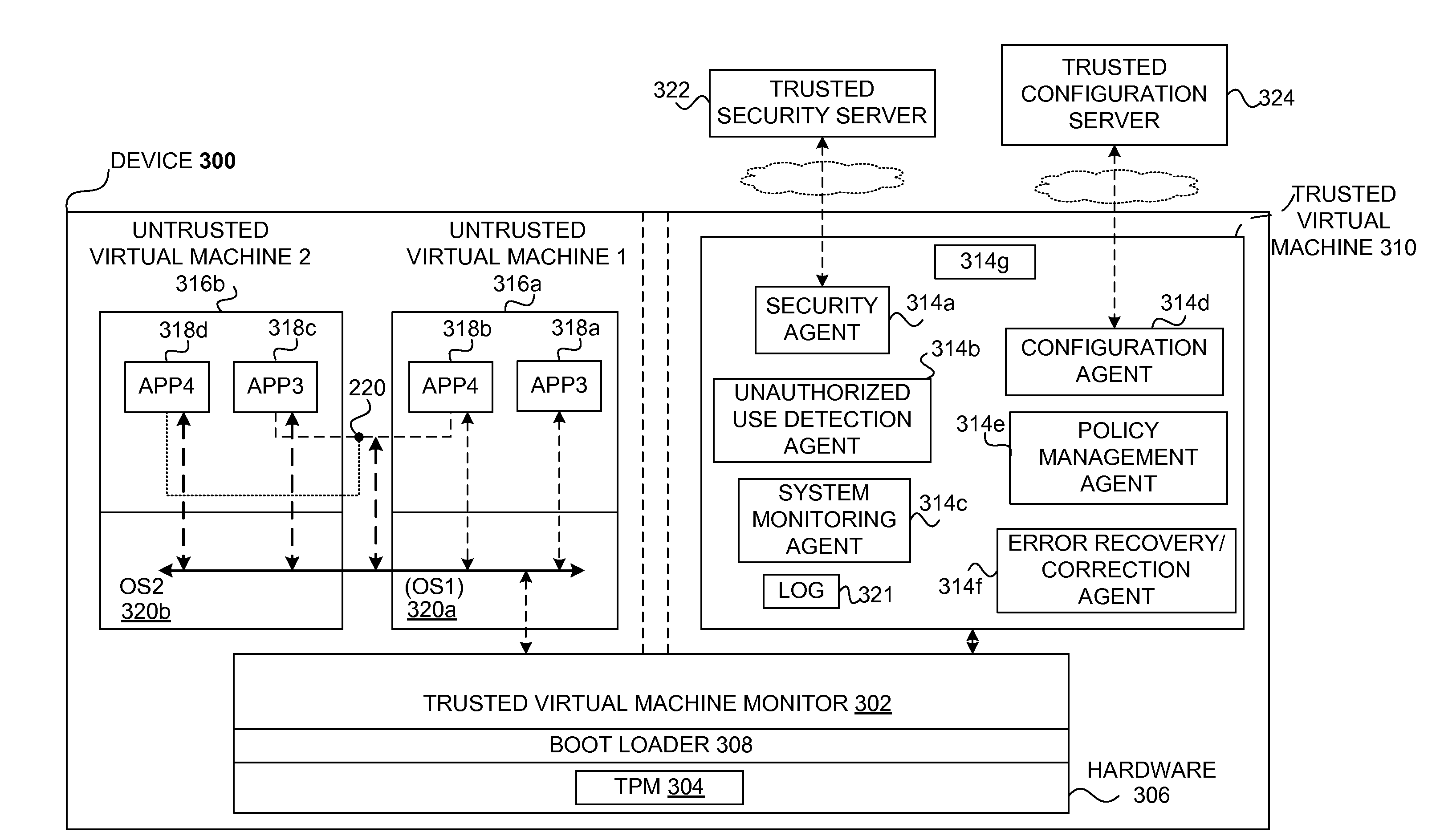
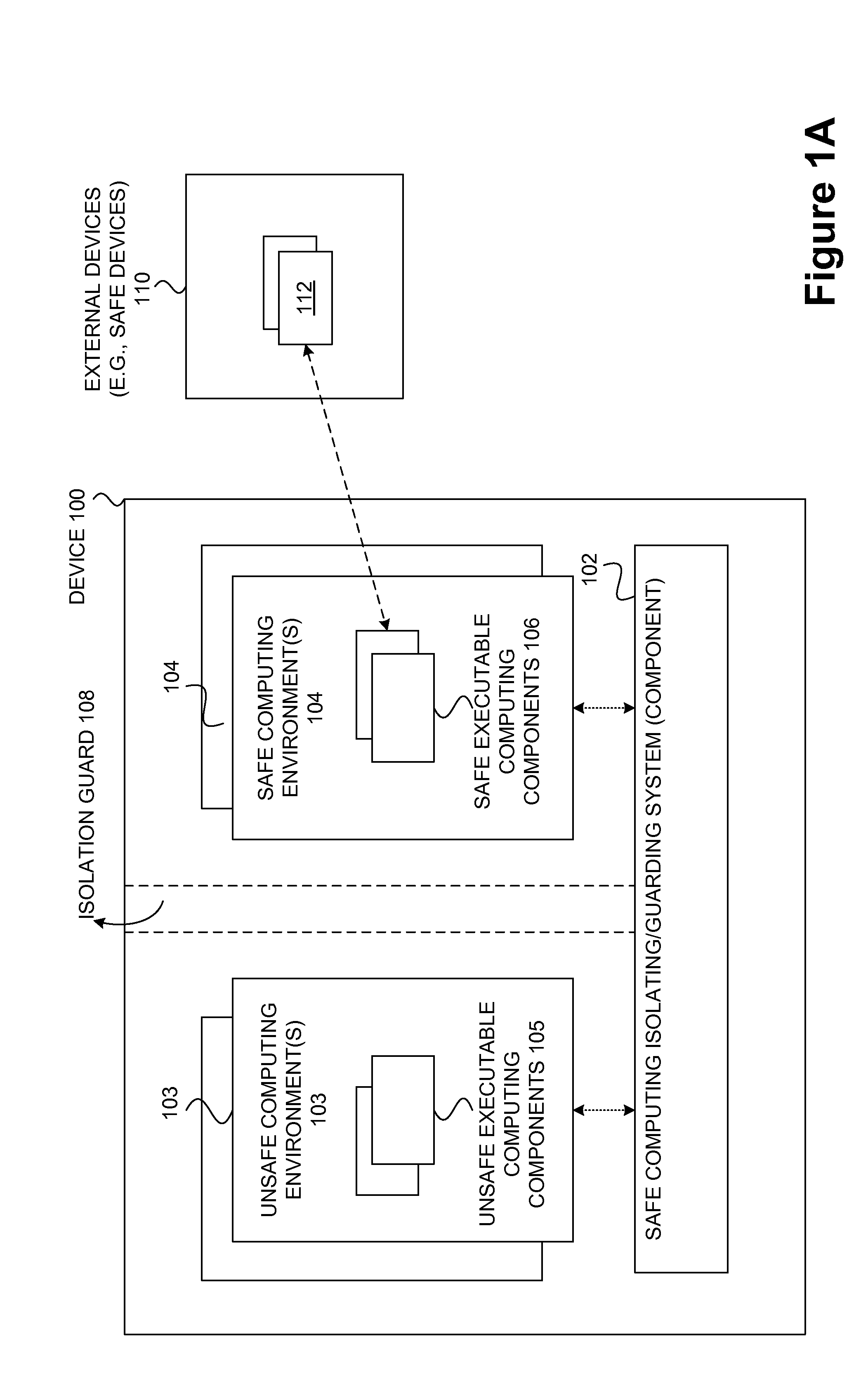
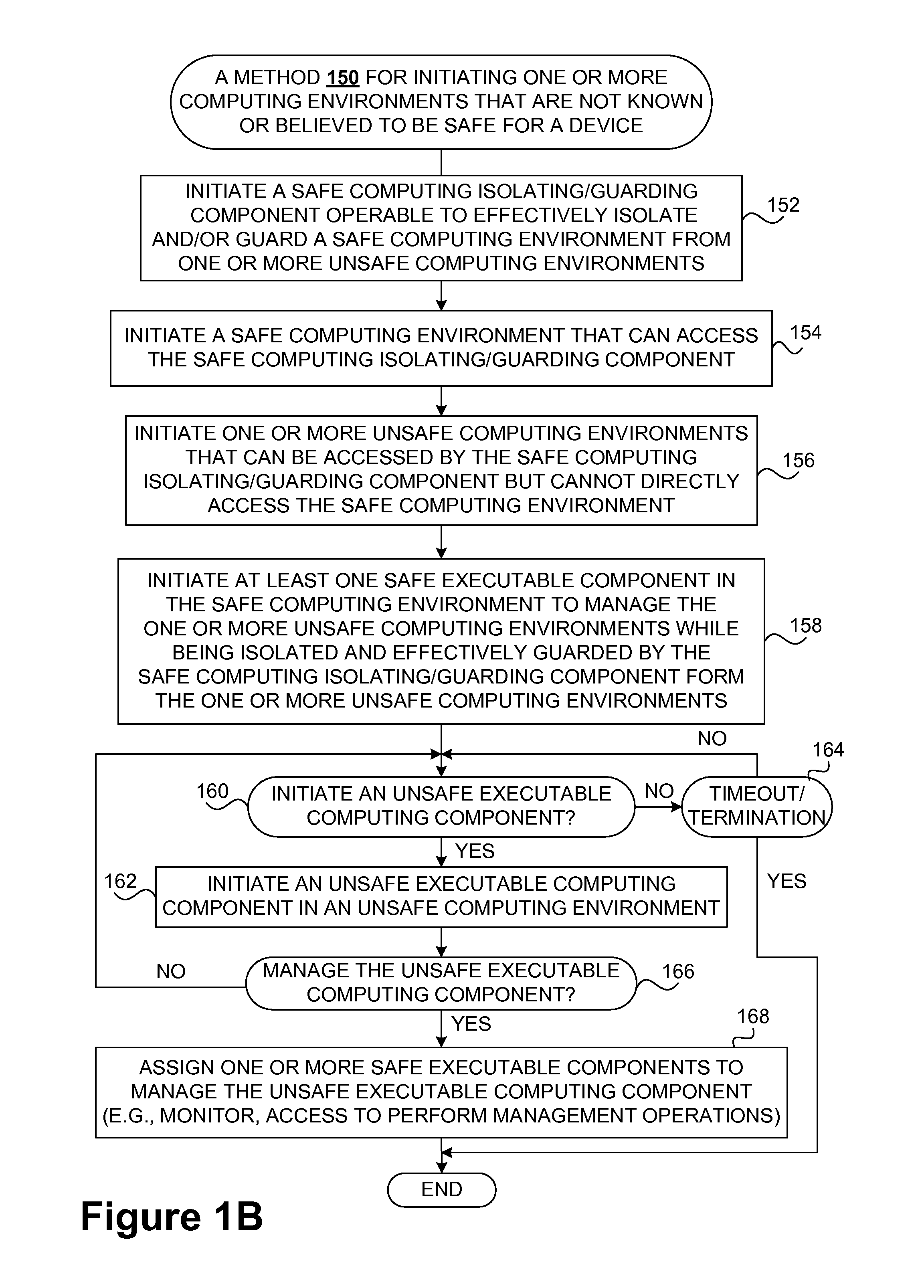
Techniques for managing and protecting computing environments are disclosed. A safe computing environment can be provided for ensuring the safety and / or management of a device. The safe computing environment can be secured by a safe component that isolates and protects it from unsafe computing environments which may also be operating. As a result, various security and management activities can be securely performed from a safe computing environment. A safe computing environment can, for example, be provided on a device as a safe virtual computing environment (e.g., a safe virtual machine) protected by a safe virtual computing monitor (e.g., a safe virtual machine monitor) from one or more other virtual computing environments that are not known or not believed to be safe for the device. It will also be appreciated that the safe components can, for example, be provided as trusted components for a device. As such, various trusted components (or agent) can operate in a trusted computing environment secured from interference by components that many not be trusted and perform various security and / or management tasks alone or in connection, for example, with other trusted components (e.g., trusted serves).
Owner:SAMSUNG ELECTRONICS CO LTD
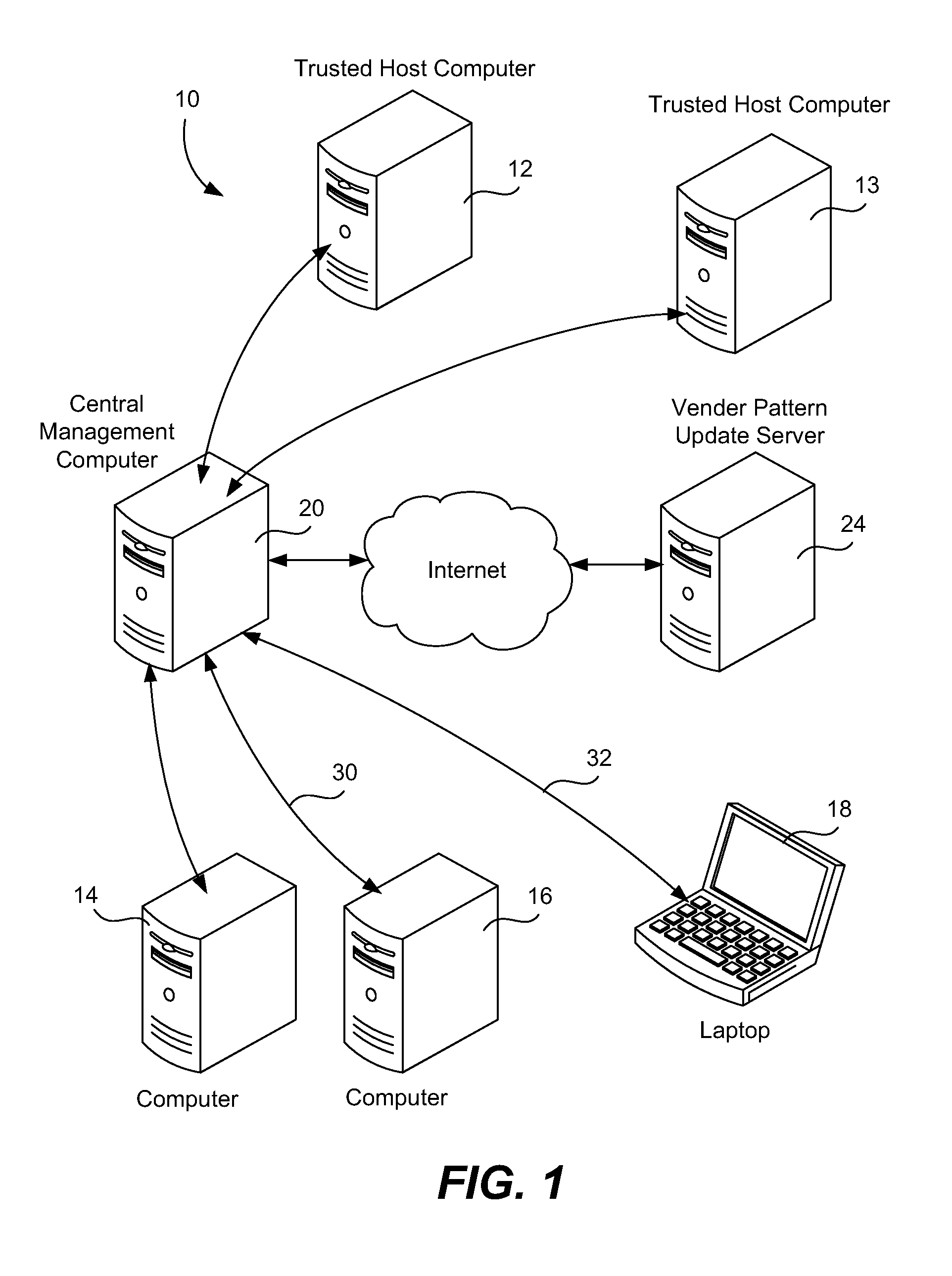
Early malware detection by cross-referencing host data
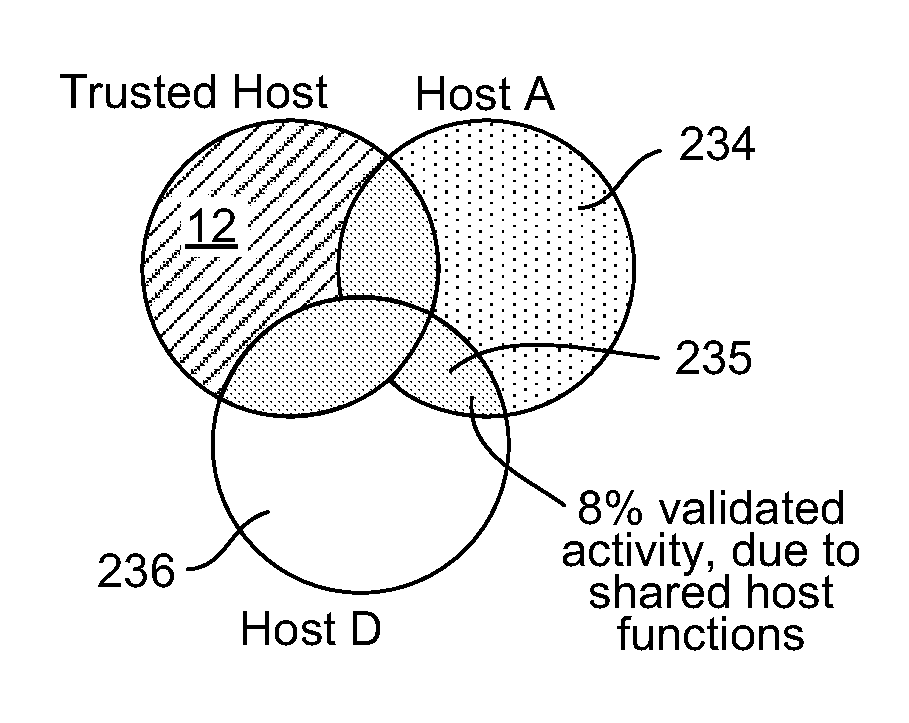
A computer network of an enterprise includes a central management computer linking at least one trusted host computer with at least one user computer. The trusted host computer is not used for normal day-to-day activities within the enterprise, and may also not be used for reading electronic mail nor for accessing the Internet and downloading Web site content. Antivirus software on the user computer screens for suspect activity or features and, if found, the suspect activity or features are compared to rules database. If a determination of malware cannot be made, then these unresolved activities or features are sent to the central management computer to be compared to the trusted, known activities and features of the trusted computer. The suspect activities may be deemed acceptable if activities are shared amongst a certain number of user computers all configured to perform the same function. A user computer may be compared against itself over time.
Owner:TREND MICRO INC
Method and apparatus for secure interaction with a computer service provider
InactiveUS20140282978A1Low costEasy to useDigital data processing detailsMultiple digital computer combinationsPasswordTrusted Computing
A method for secure interaction with a website server capable of an authentication operation with a login operation checking a username and a password, is described. Standard web browsing environments are generally insecure and private information, such as passwords, are prone to theft. The proposed solution comprises securing the password used for the authentication in a trusted computing environment, such as a separate computer, without the need of revealing the password to a browser running in an untrusted computing environment, and basing the browsing on authentication data obtained as result of the login operation, that can be confirmed by the user in the trusted environment, prior of being performed.
Owner:LERNER SERGIO DEMIAN +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com