Patents
Literature
462 results about "Security properties" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
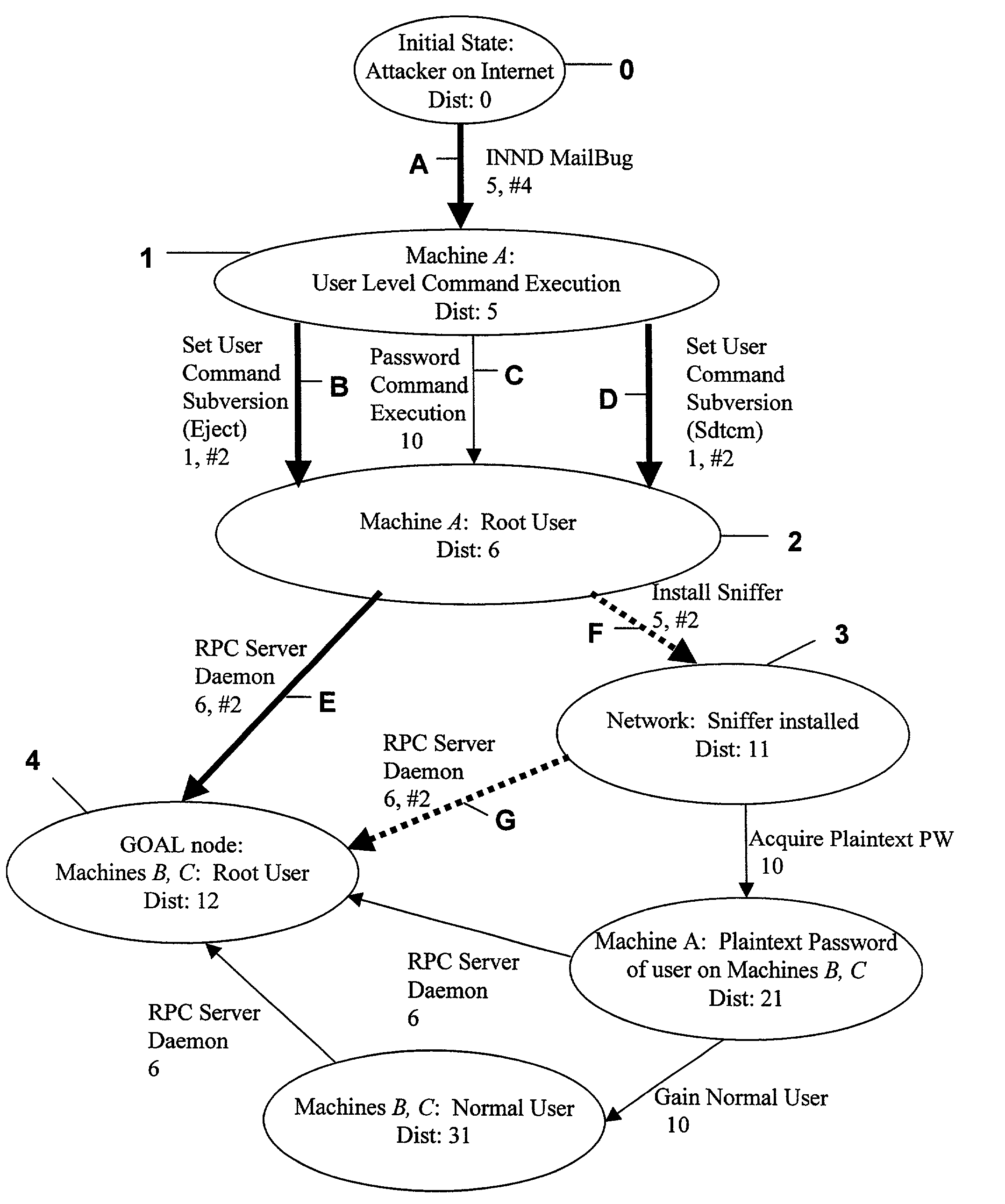
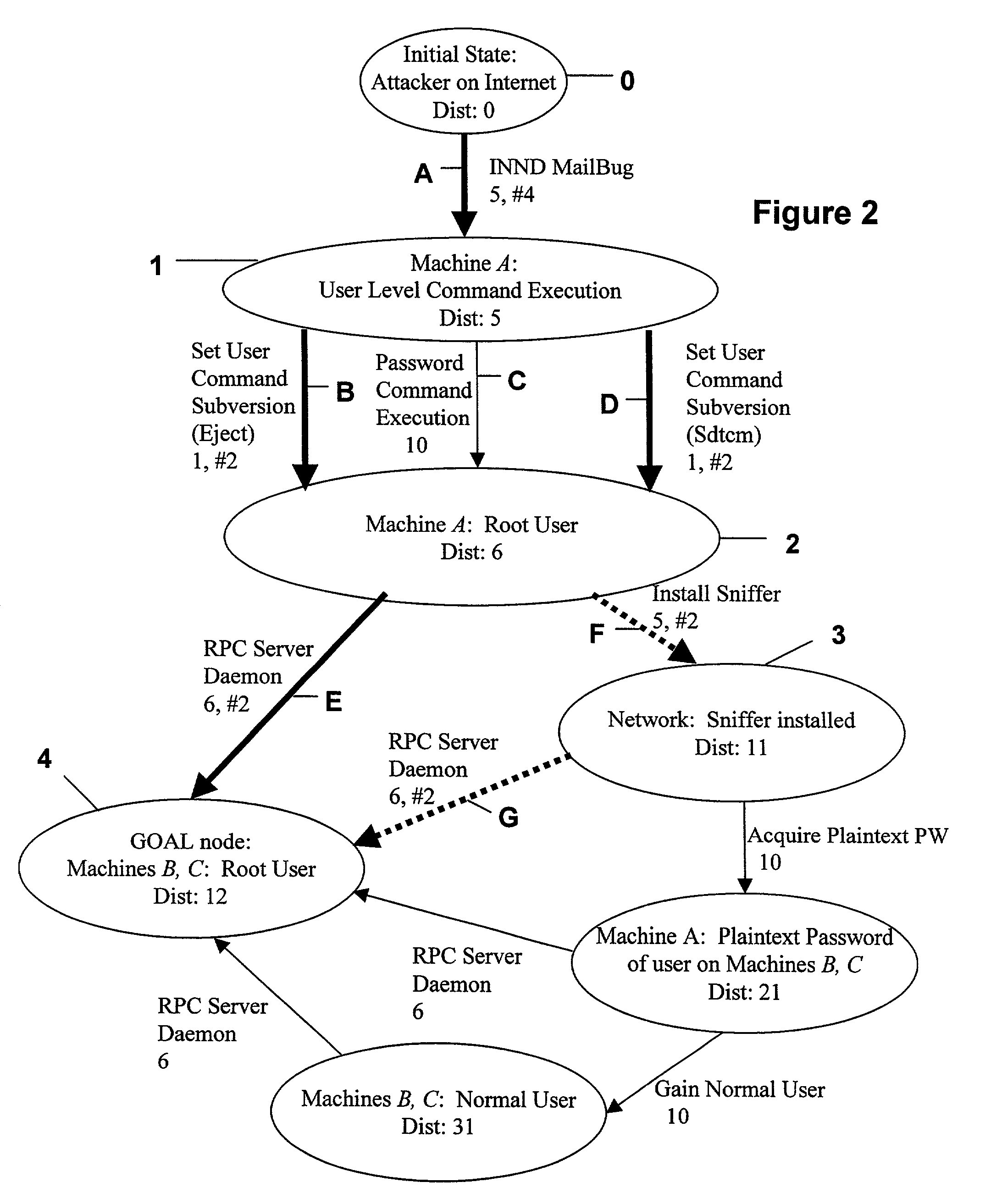
Method and tool for network vulnerability analysis
InactiveUS7013395B1Avoid low successLow “ effort ” costMemory loss protectionUnauthorized memory use protectionLimited resourcesCountermeasure
A computer system analysis tool and method that will allow for qualitative and quantitative assessment of security attributes and vulnerabilities in systems including computer networks. The invention is based on generation of attack graphs wherein each node represents a possible attack state and each edge represents a change in state caused by a single action taken by an attacker or unwitting assistant. Edges are weighted using metrics such as attacker effort, likelihood of attack success, or time to succeed. Generation of an attack graph is accomplished by matching information about attack requirements (specified in “attack templates”) to information about computer system configuration (contained in a configuration file that can be updated to reflect system changes occurring during the course of an attack) and assumed attacker capabilities (reflected in “attacker profiles”). High risk attack paths, which correspond to those considered suited to application of attack countermeasures given limited resources for applying countermeasures, are identified by finding “epsilon optimal paths.”
Owner:SANDIA NAT LAB
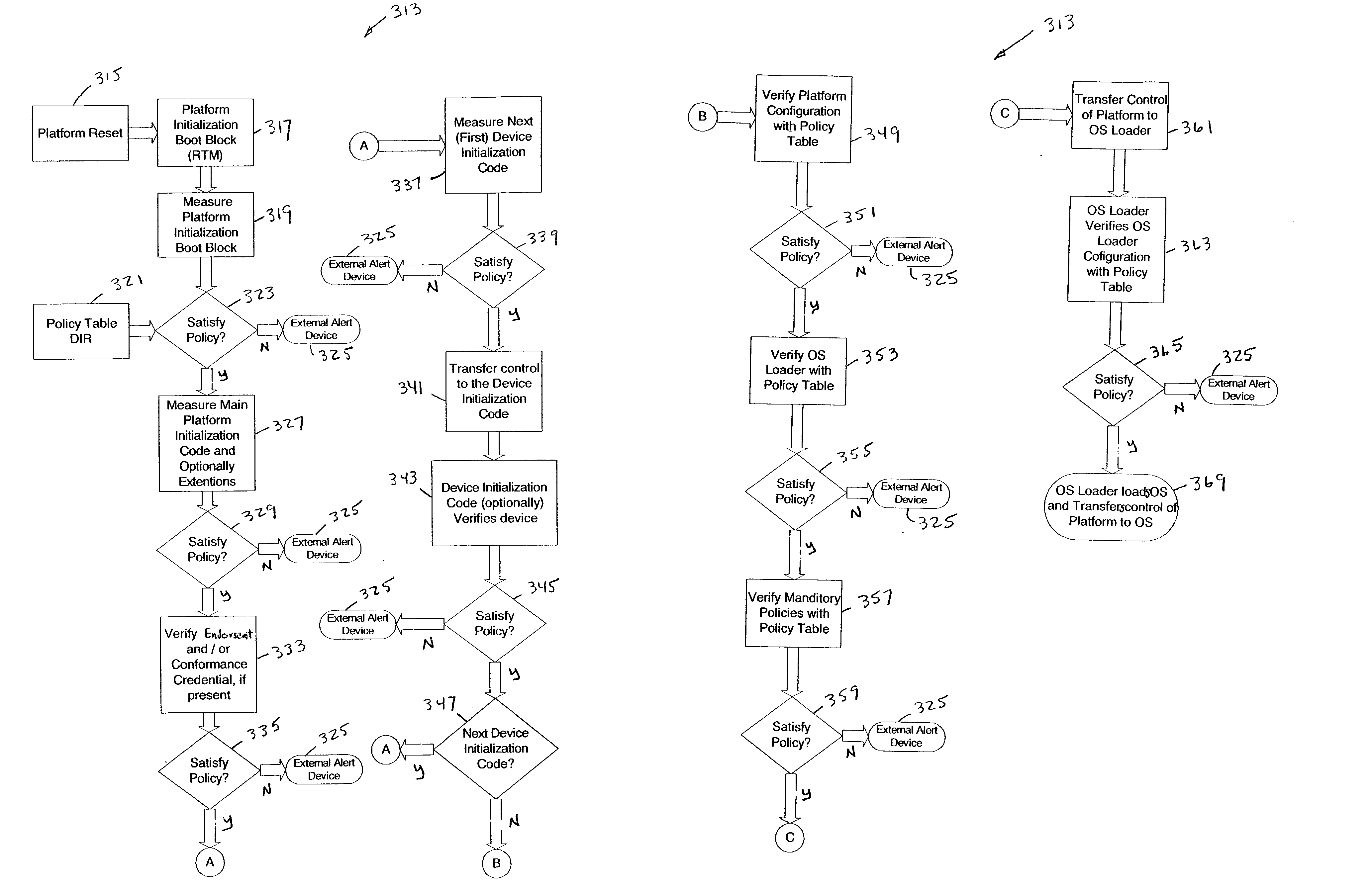
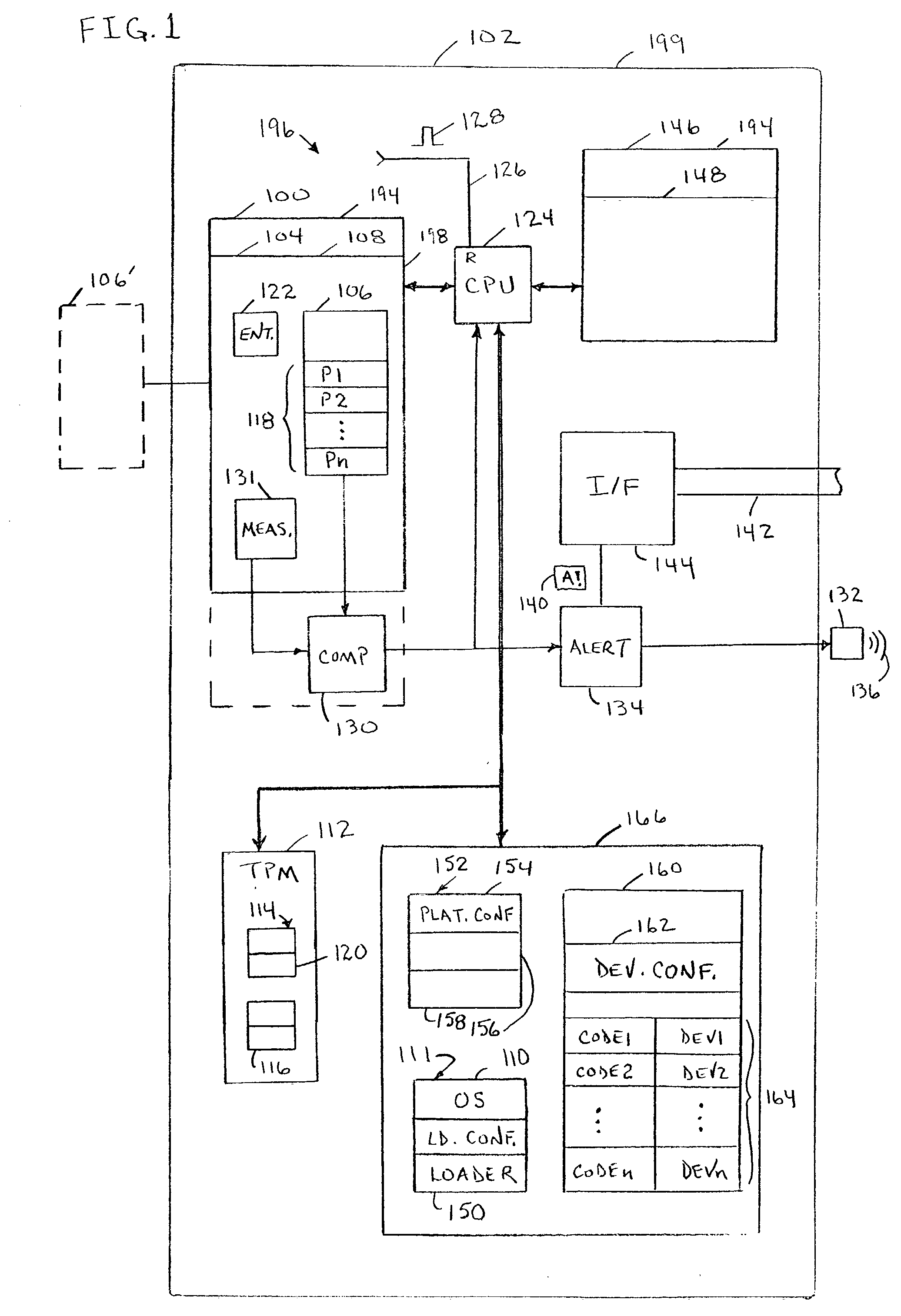
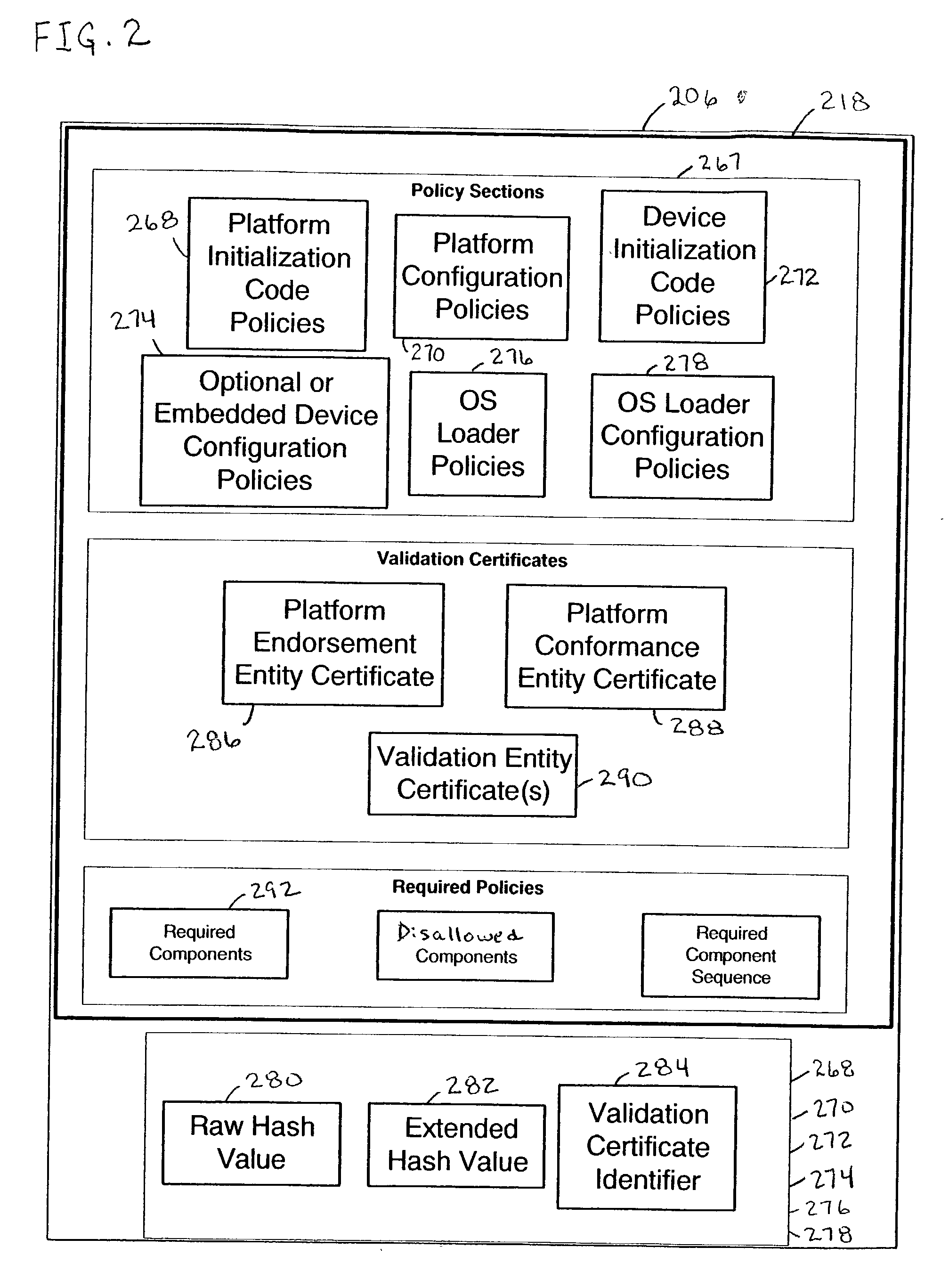
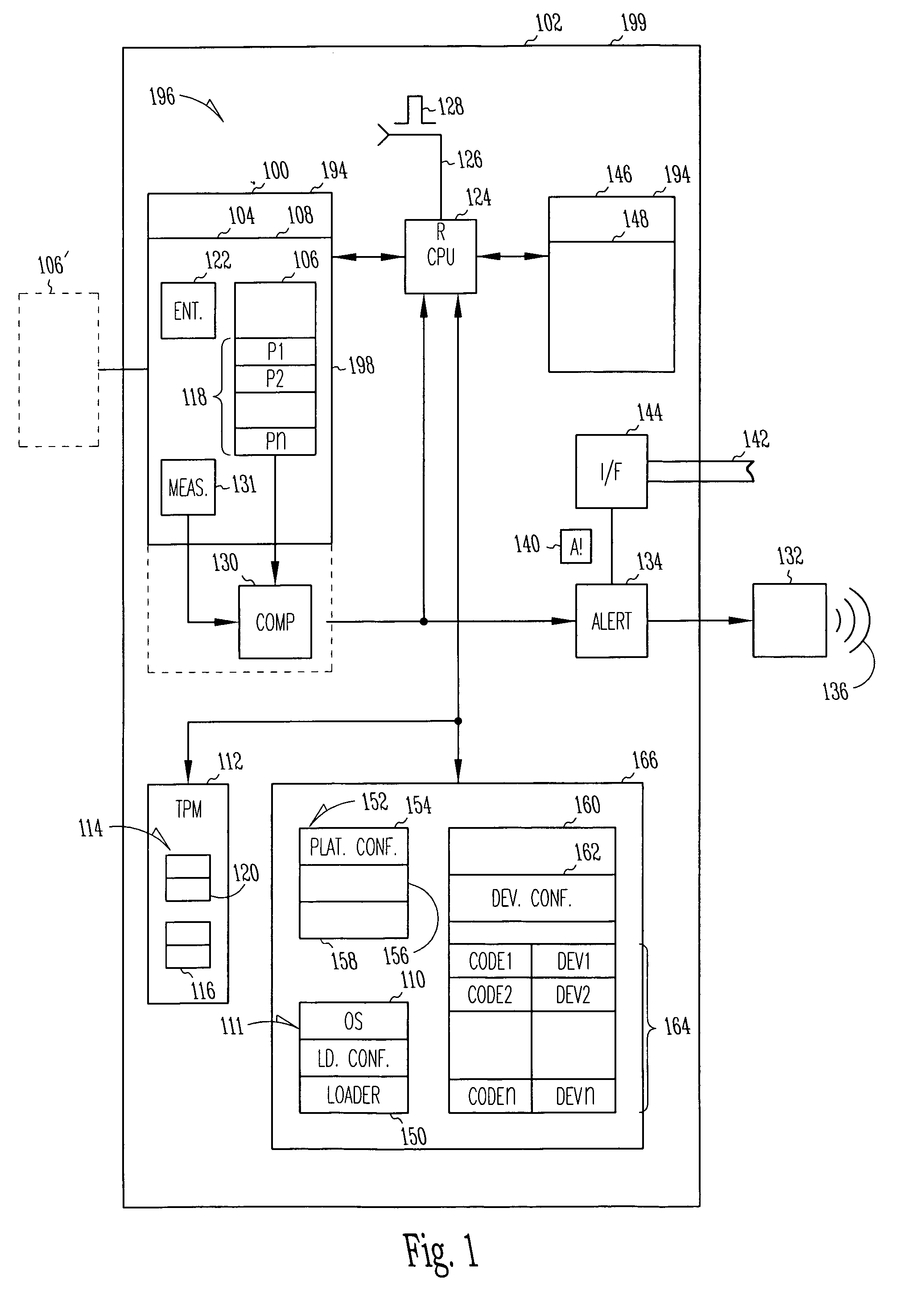
Trusted platform apparatus, system, and method
InactiveUS20040003288A1Volume/mass flow measurementDigital computer detailsOperational systemEntry point
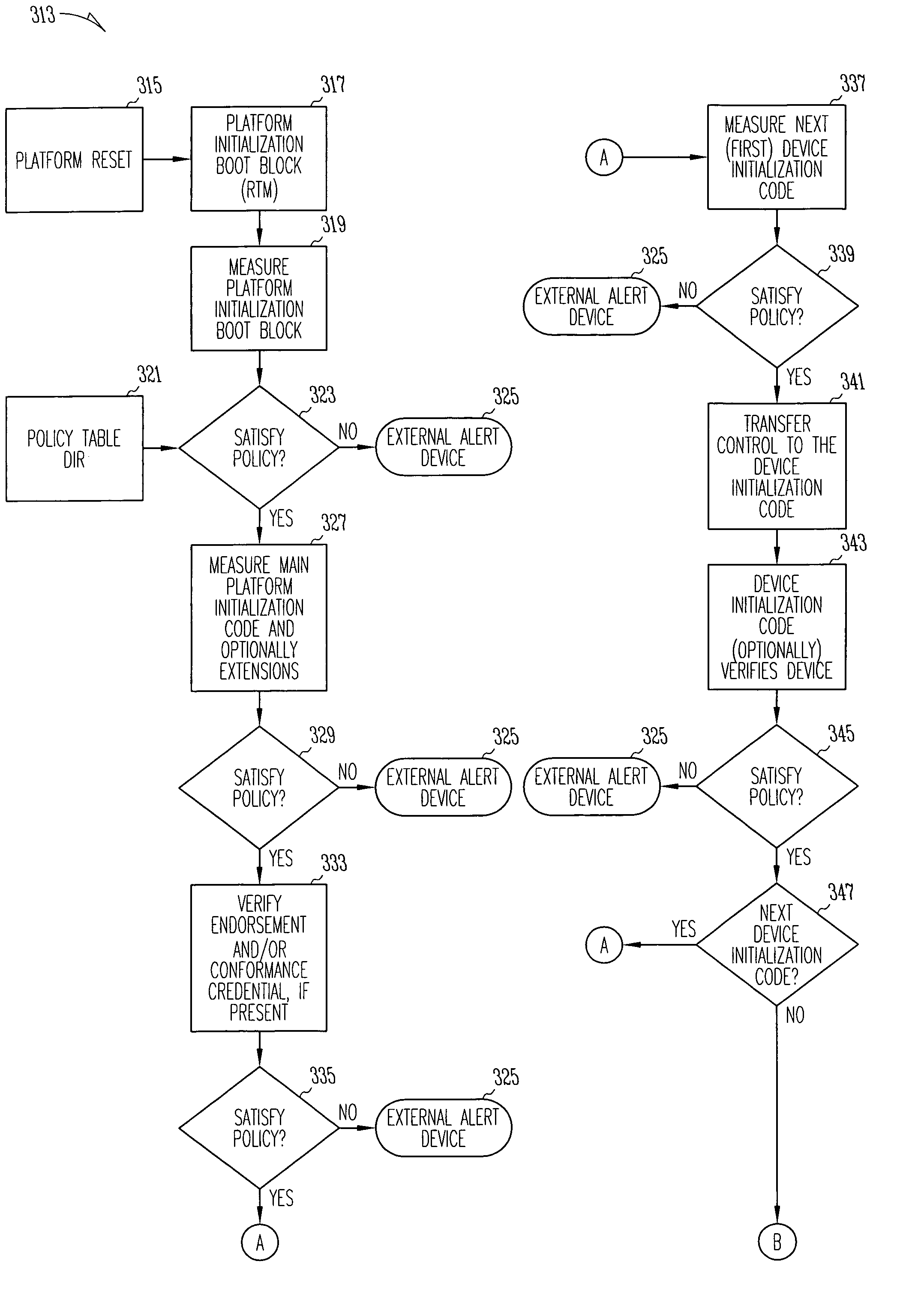
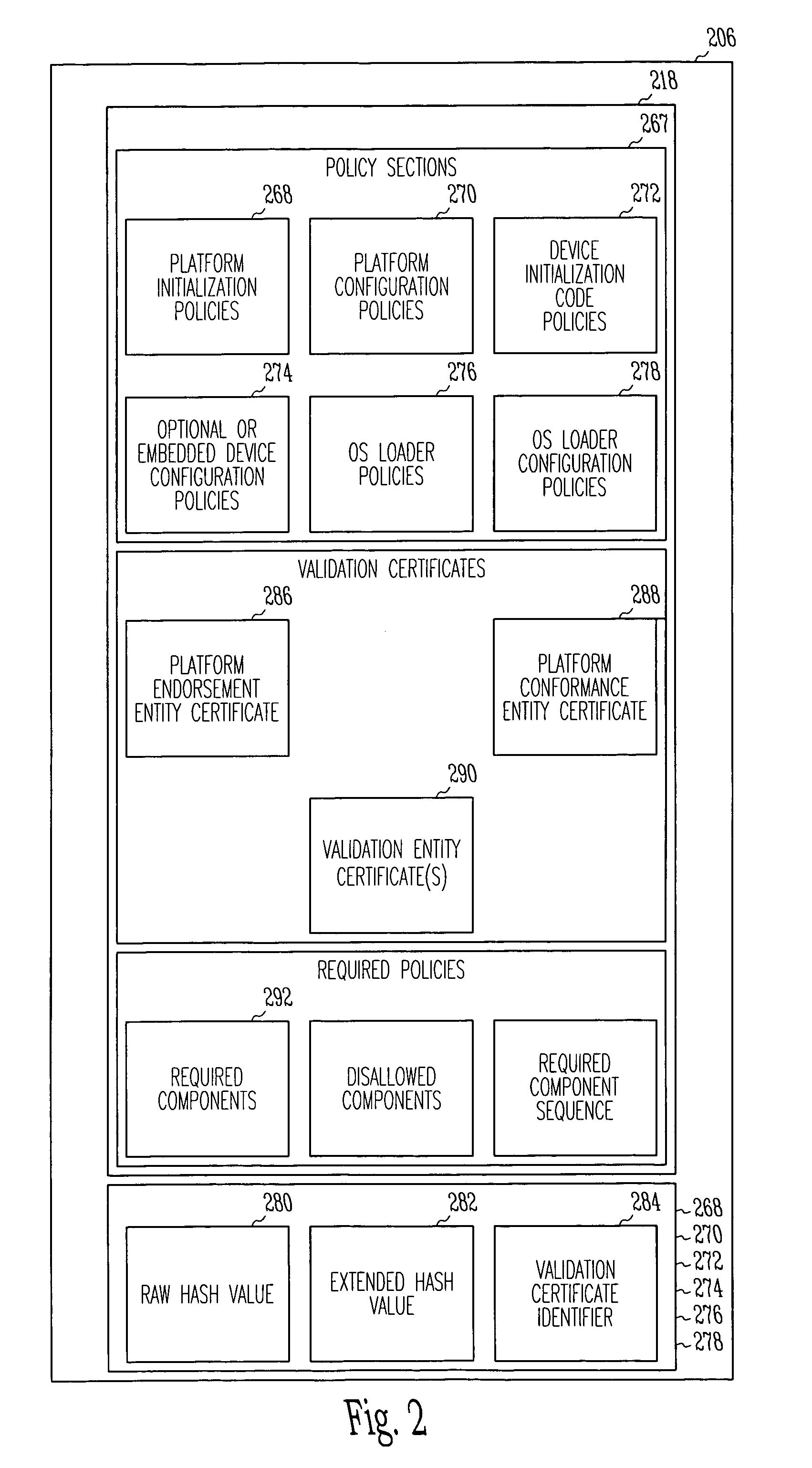
An apparatus may include a root of trust for measurement (RTM) module coupled to a verified platform security property policy module and a comparison module. The comparison module may operate to prevent transfer of control to an operating system (and / or halt the boot process) if a policy included in the platform security property policy module is violated. A system may include a memory coupled to a processor, a platform security property policy module, and a comparison module. The memory may include an RTM. A method may include beginning execution at an entry point within an RTM, determining that the RTM is trustworthy, determining that a main initialization code associated with a platform is trustworthy and transferring control to the main initialization code, and otherwise, refraining from transferring control to the main initialization code.
Owner:INTEL CORP
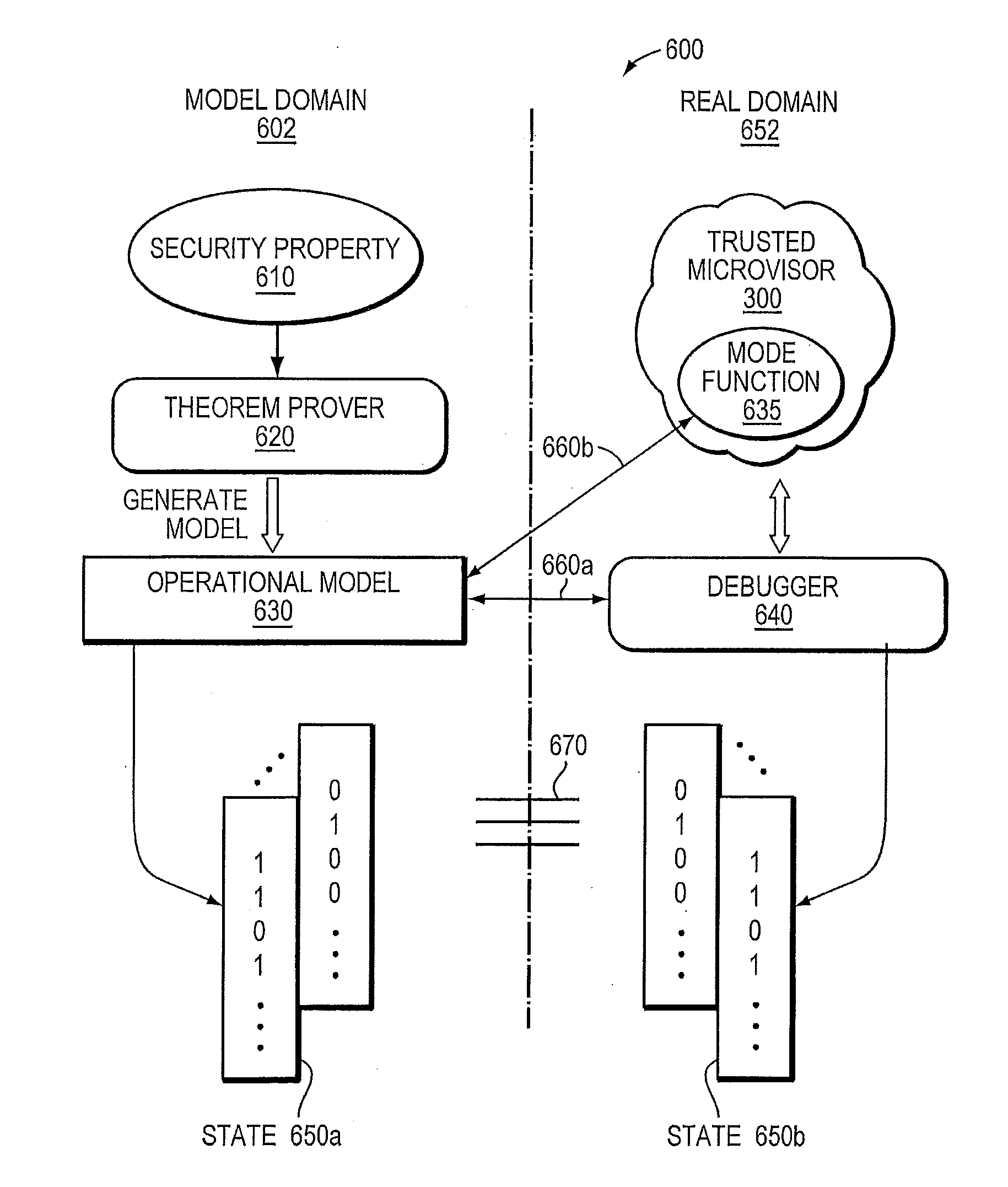
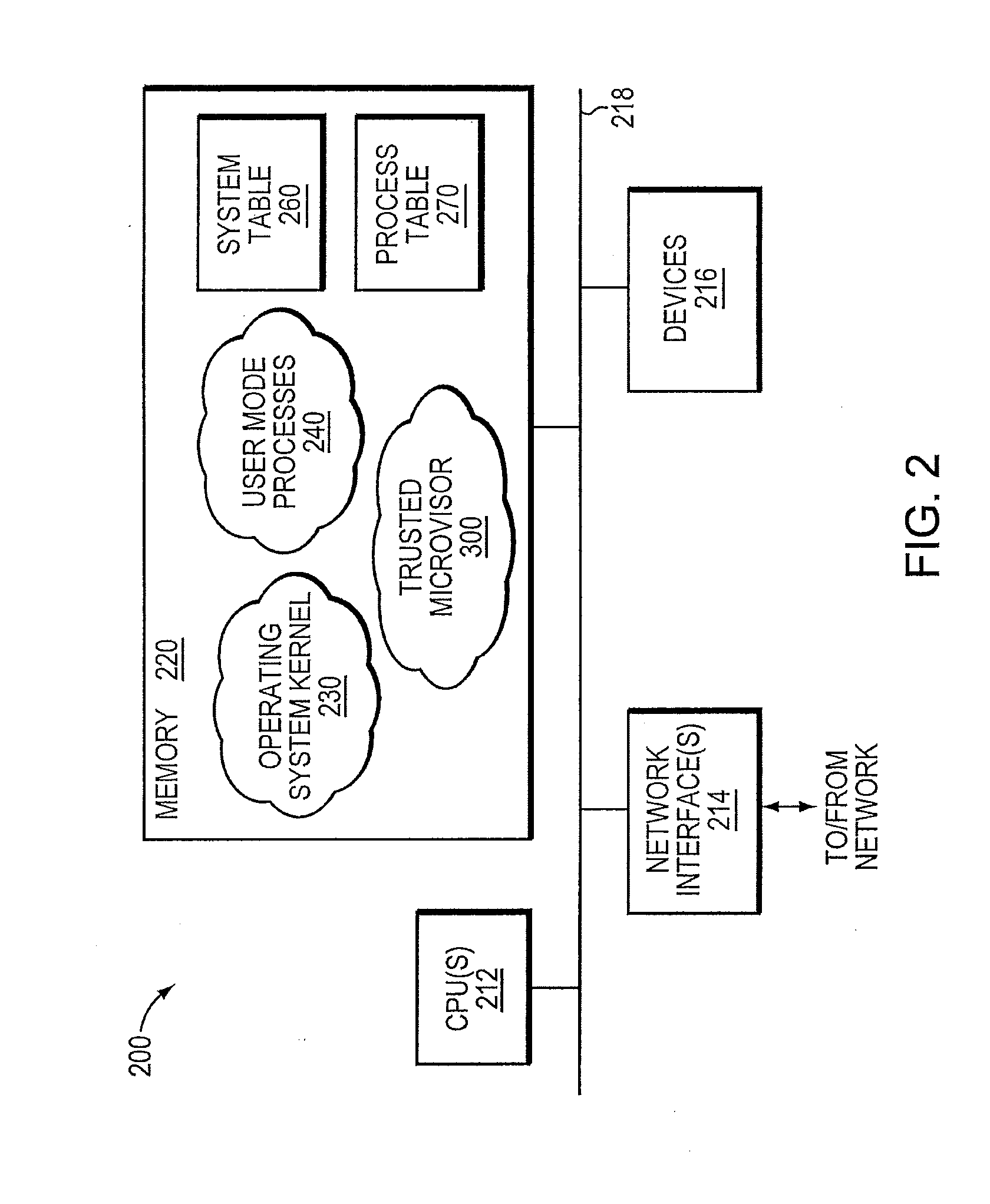
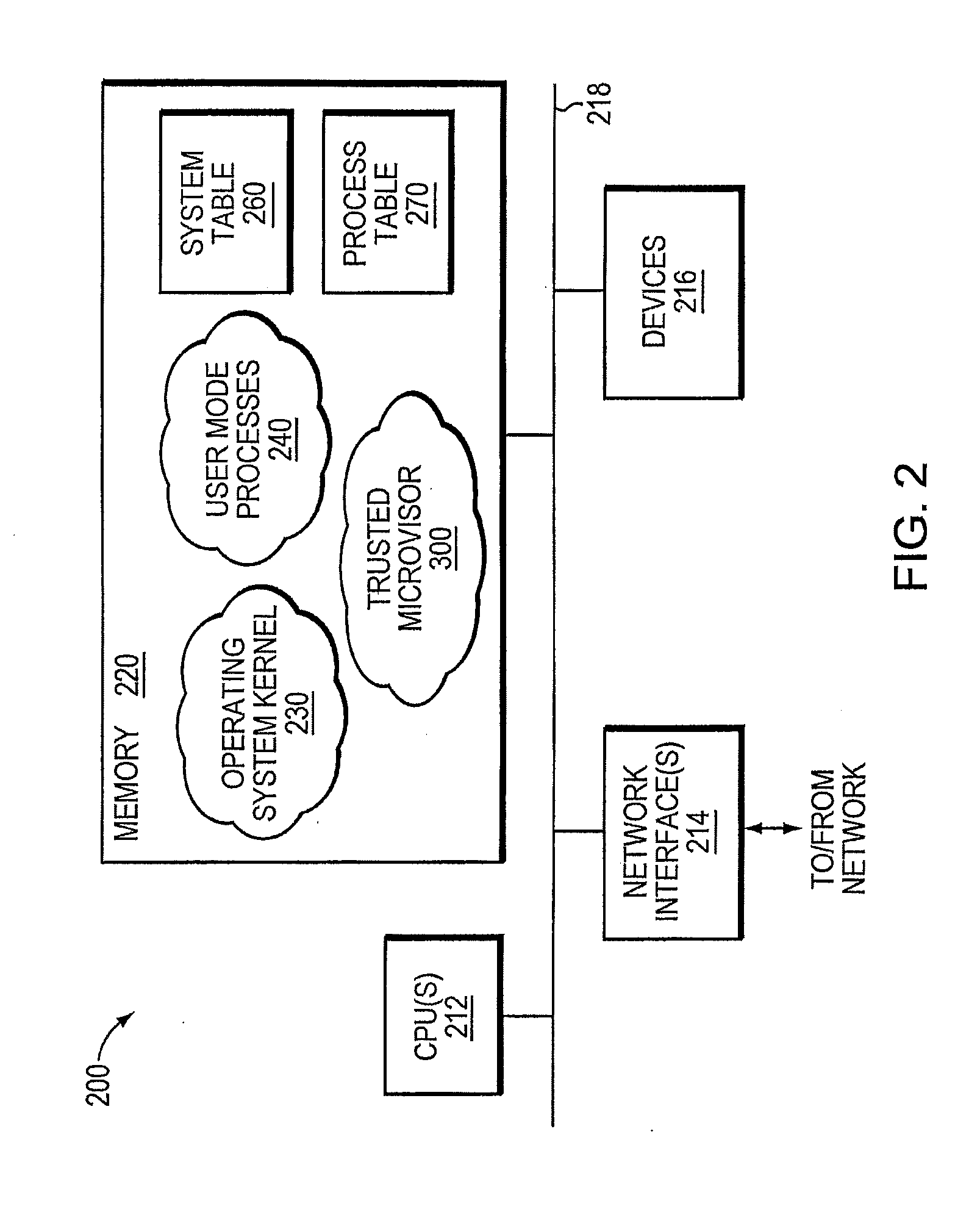
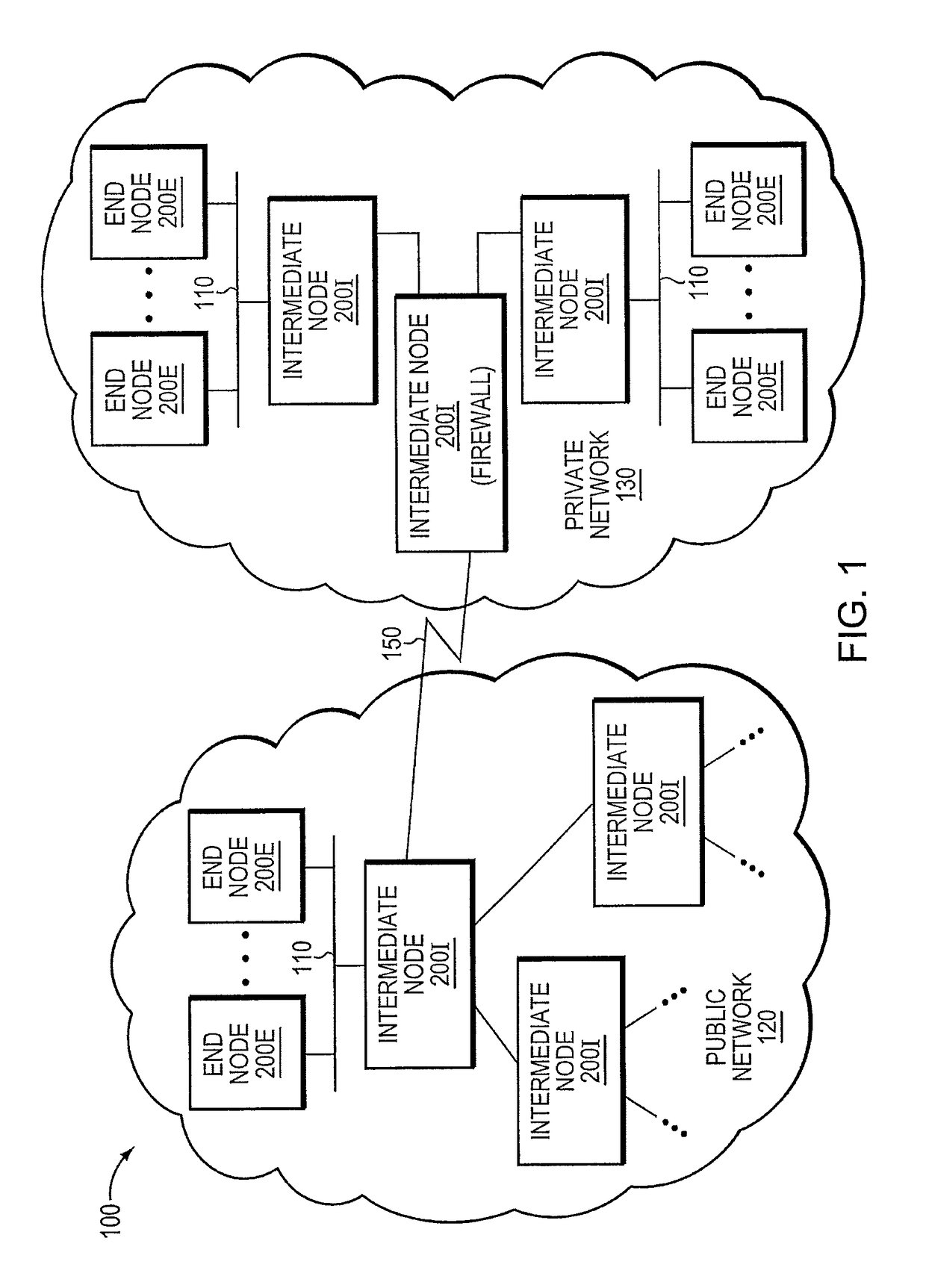
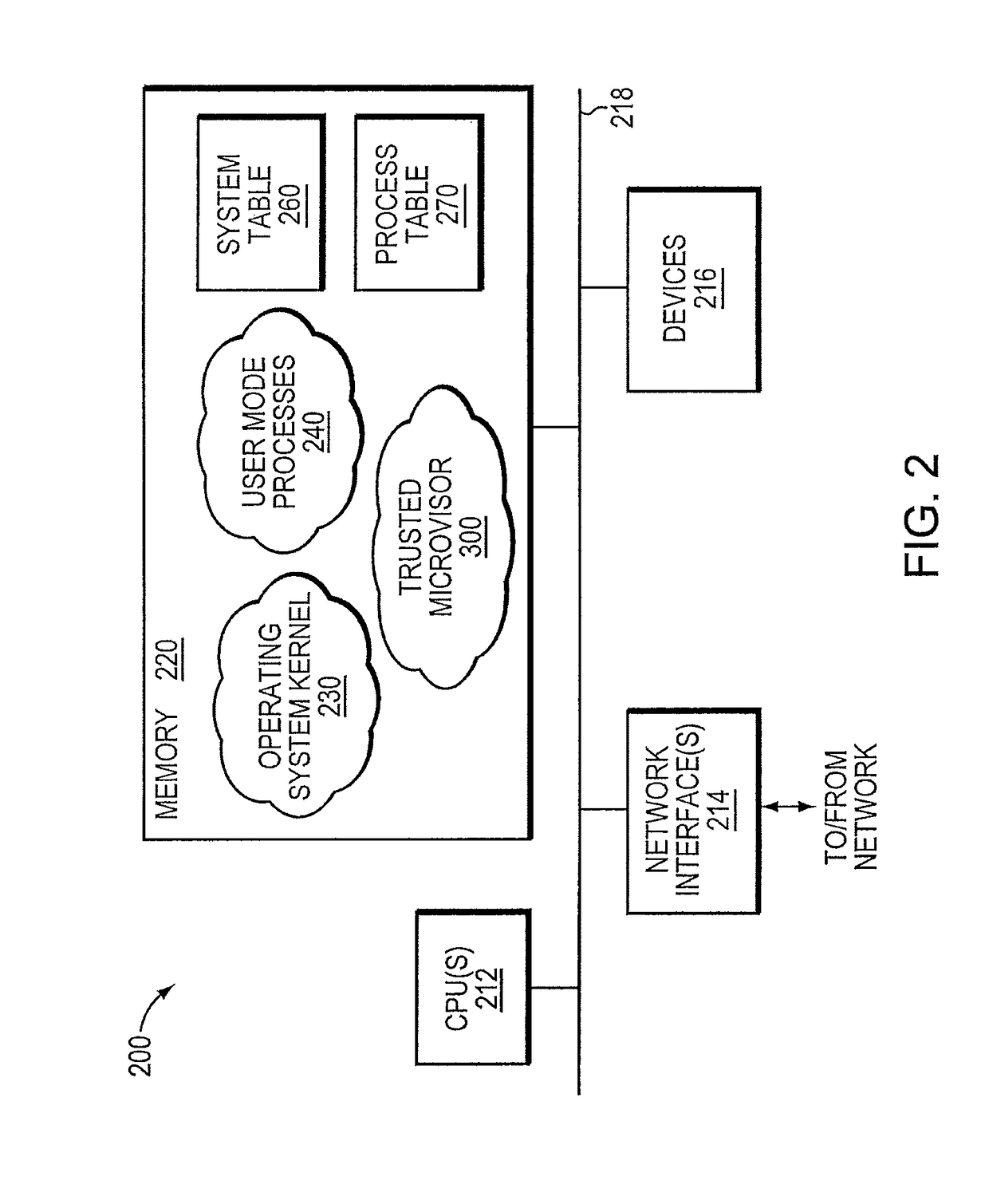
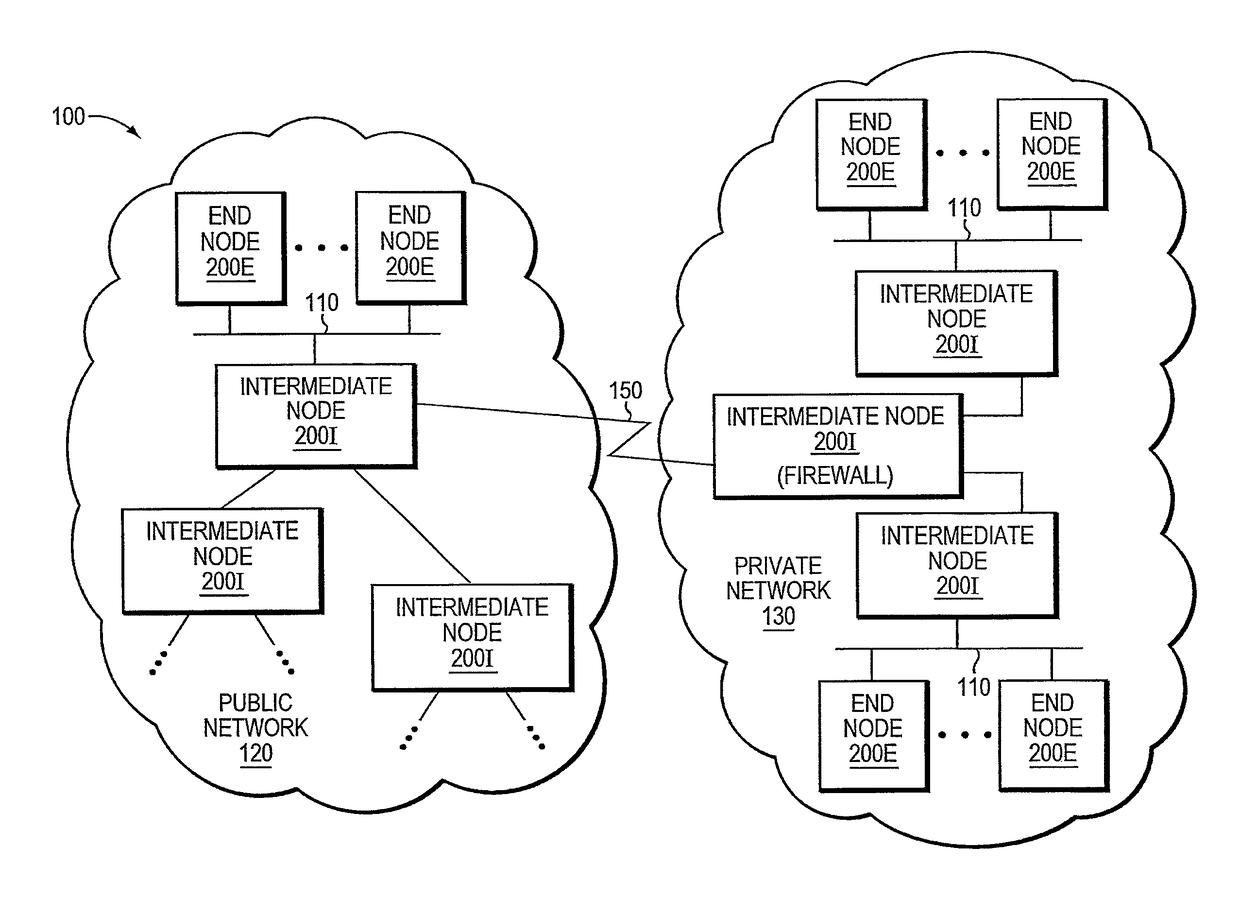
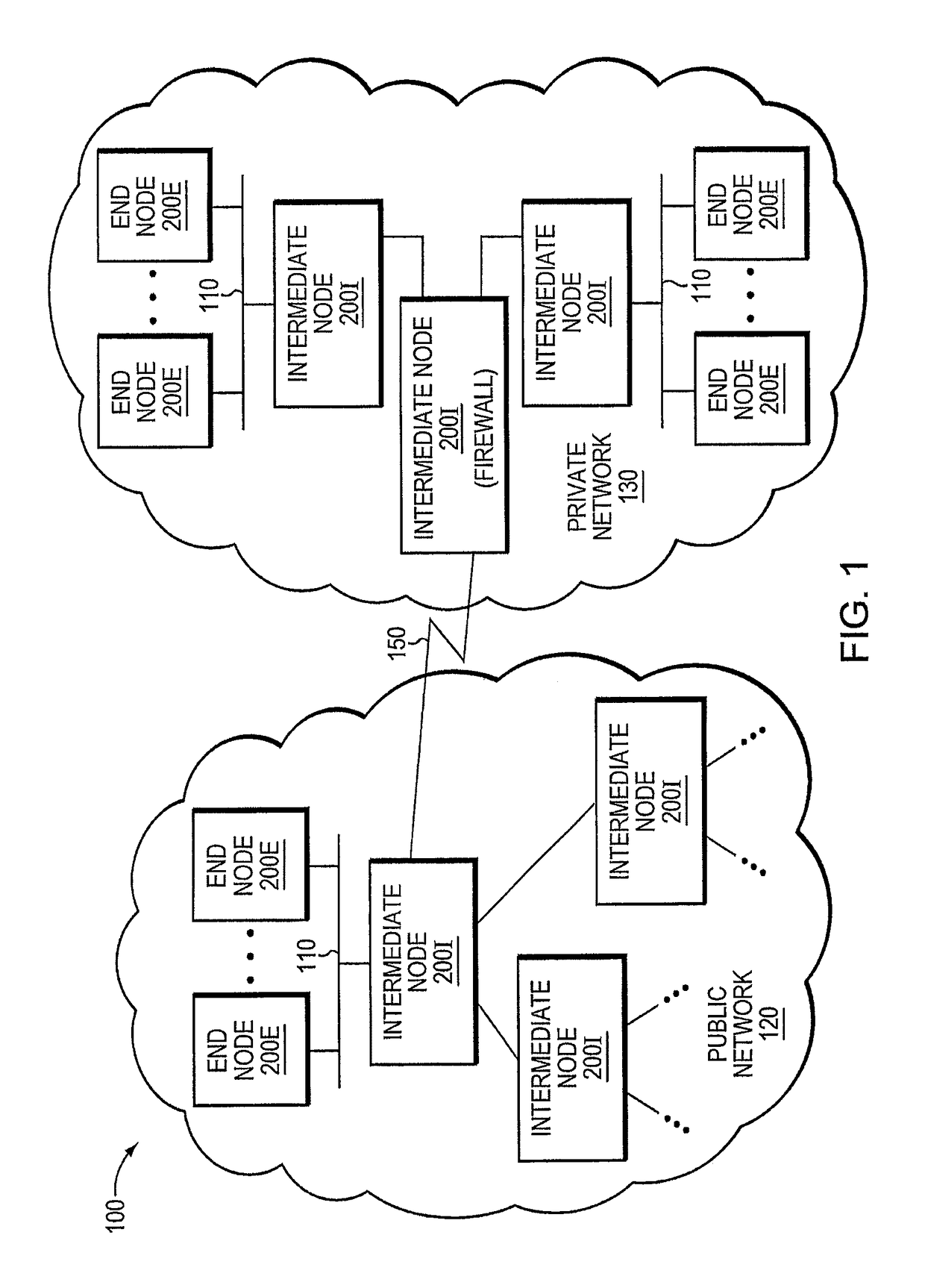
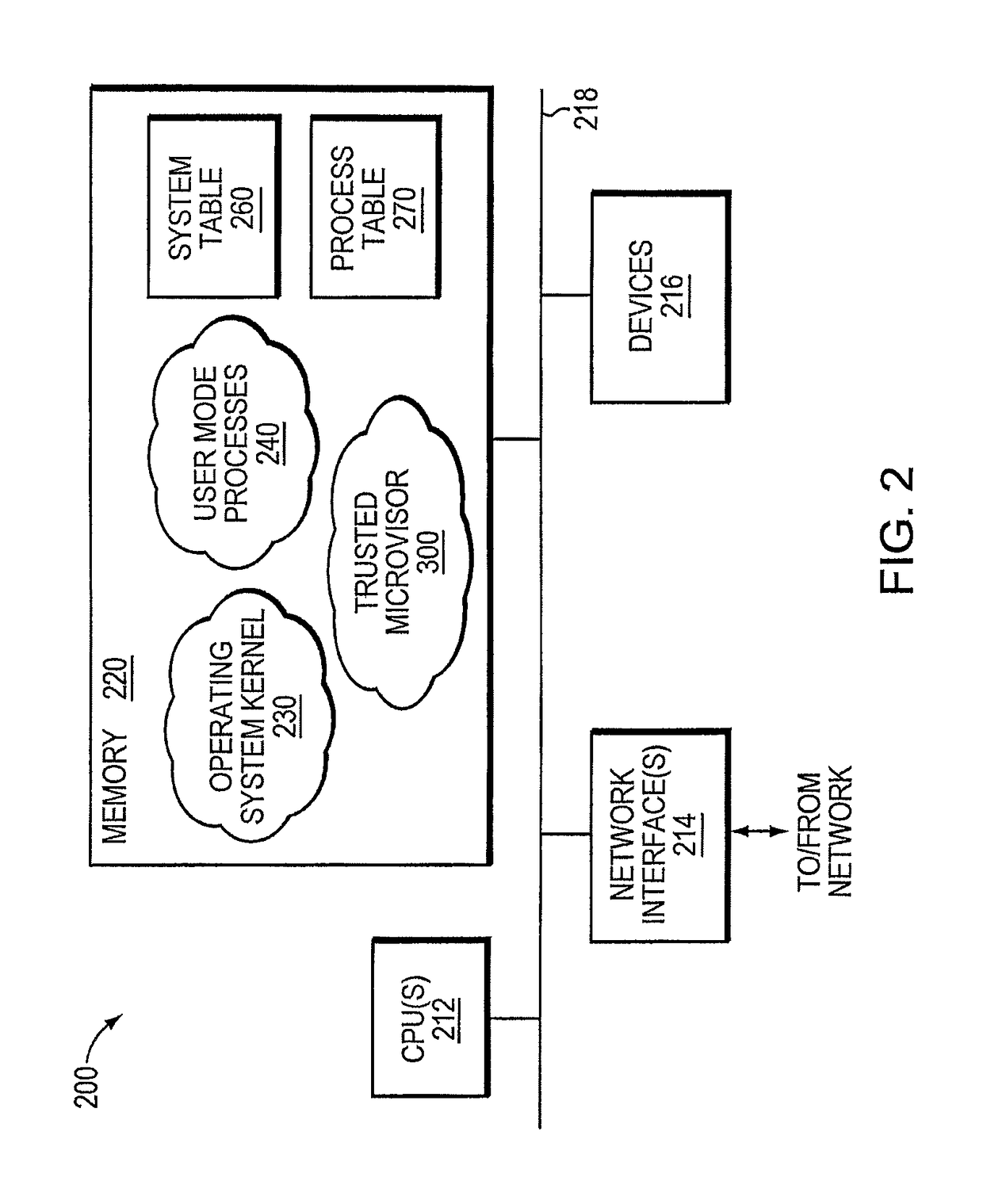
Trusted threat-aware microvisor
ActiveUS20160006756A1Memory loss protectionError detection/correctionTrusted ComputingSecurity properties
A trusted threat-aware microvisor may be deployed as a module of a trusted computing base (TCB) that also includes a root task module configured to cooperate with the microvisor to load and initialize one or more other modules executing on a node of a network environment. The root task may cooperate with the microvisor to allocate one or more kernel resources of the node to those other modules. As a trusted module of the TCB, the microvisor may be configured to enforce a security policy of the TCB that, e.g., prevents alteration of a state related to security of the microvisor by a module of or external to the TCB. The security policy of the TCB may be implemented by a plurality of security properties of the microvisor. Trusted (or trustedness) may therefore denote a predetermined level of confidence that the security property is demonstrated by the microvisor.
Owner:FIREEYE SECURITY HLDG US LLC
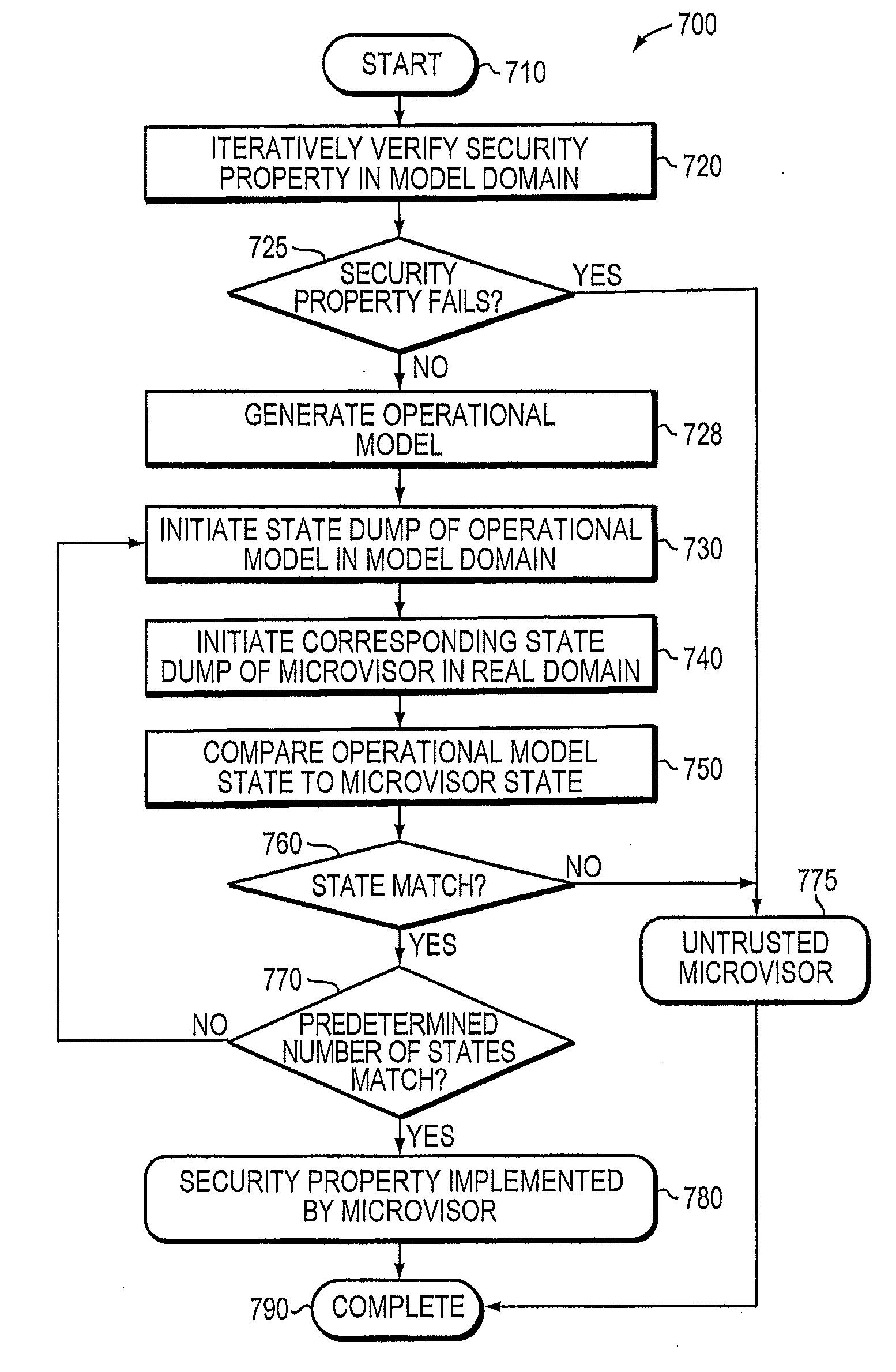
Verification of trusted threat-aware microvisor
A trusted threat-aware microvisor may be deployed as a module of a trusted computing base (TCB). The microvisor is illustratively configured to enforce a security policy of the TCB, which may be implemented as a security property of the microvisor. The microvisor may manifest (i.e., demonstrate) the security property in a manner that enforces the security policy. Trustedness denotes a predetermined level of confidence that the security property is demonstrated by the microvisor. The predetermined level of confidence is based on an assurance (i.e., grounds) that the microvisor demonstrates the security property. Trustedness of the microvisor may be verified by subjecting the TCB to enhanced verification analysis configured to ensure that the TCB conforms to an operational model with an appropriate level of confidence over an appropriate range of activity. The operational model may then be configured to analyze conformance of the microvisor to the security property. A combination of conformance by the microvisor to the operational model and to the security property provides assurance (i.e., grounds) for the level of confidence and, thus, verifies trustedness.
Owner:FIREEYE SECURITY HLDG US LLC
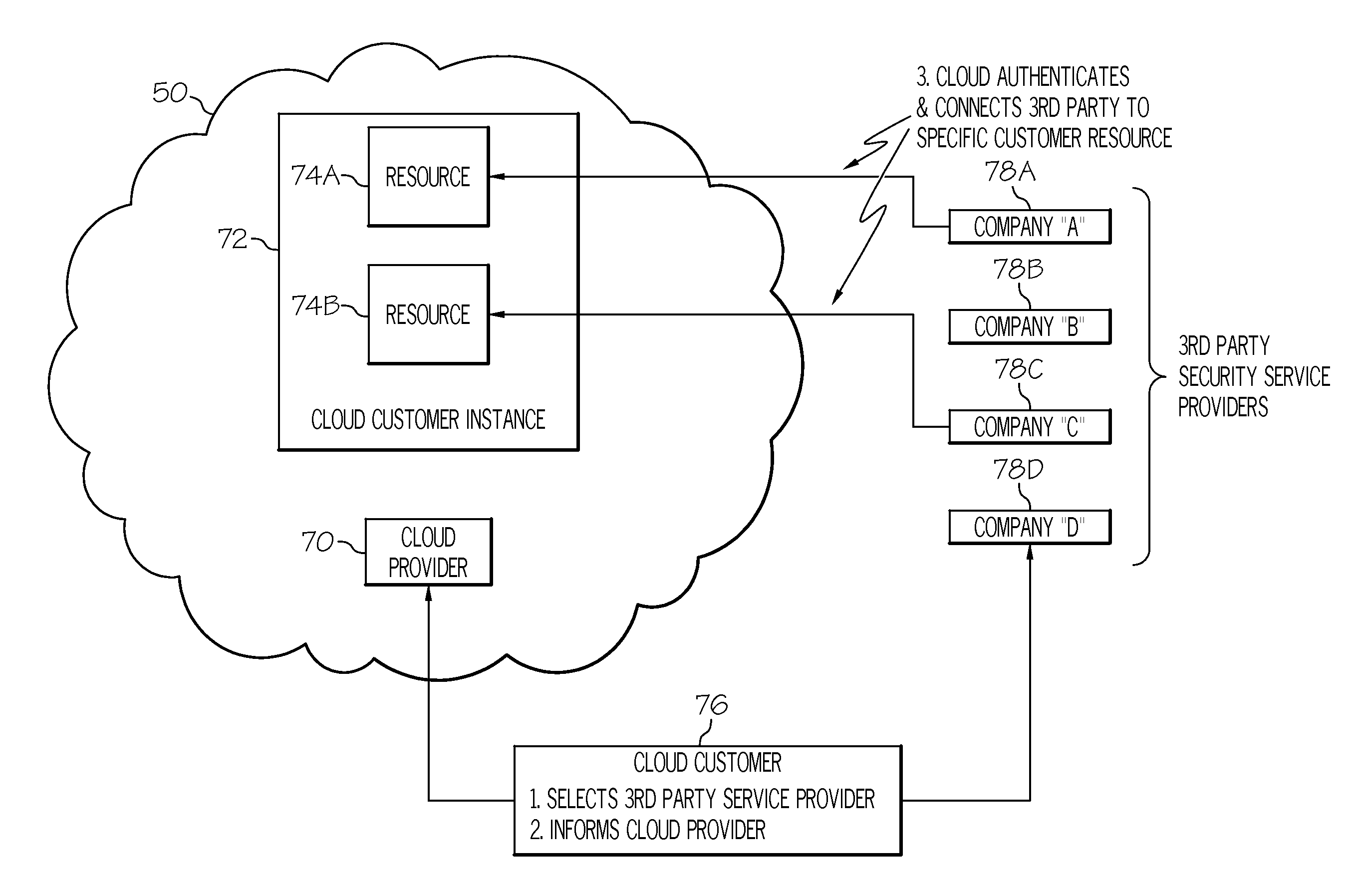
Providing security services within a cloud computing environment
InactiveUS20110219434A1Digital data processing detailsUser identity/authority verificationThird partySecurity properties
Embodiments of the present invention allow for the provisioning of security services within a Cloud computing environment by third parties. Specifically, under the present invention, a Cloud provider will publish a set of potential security attributes (e.g., a list), which can be monitored, to the Cloud customer. The Cloud customer will designate / select one or more of those attributes that the Cloud customer wishes to have monitored for one or more Cloud resources that it is using. The Cloud provider will then provide to the Cloud customer a set of third party security service providers capable of monitoring the attributes the Cloud customer designated. The Cloud customer will then select one or more third party providers from the provided set, and the Cloud provider will associate the given Cloud resources with the respective third party providers. Once third party providers have been associated with Cloud resources, a secure relationship between the third party provider(s) and the Cloud providers will be established.
Owner:KYNDRYL INC
Trusted threat-aware microvisor
ActiveUS9680862B2Digital data protectionPlatform integrity maintainanceTrusted ComputingSecurity properties
A trusted threat-aware microvisor may be deployed as a module of a trusted computing base (TCB) that also includes a root task module configured to cooperate with the microvisor to load and initialize one or more other modules executing on a node of a network environment. The root task may cooperate with the microvisor to allocate one or more kernel resources of the node to those other modules. As a trusted module of the TCB, the microvisor may be configured to enforce a security policy of the TCB that, e.g., prevents alteration of a state related to security of the microvisor by a module of or external to the TCB. The security policy of the TCB may be implemented by a plurality of security properties of the microvisor. Trusted (or trustedness) may therefore denote a predetermined level of confidence that the security property is demonstrated by the microvisor.
Owner:FIREEYE SECURITY HLDG US LLC
Verification of trusted threat-aware microvisor
Owner:FIREEYE SECURITY HLDG US LLC
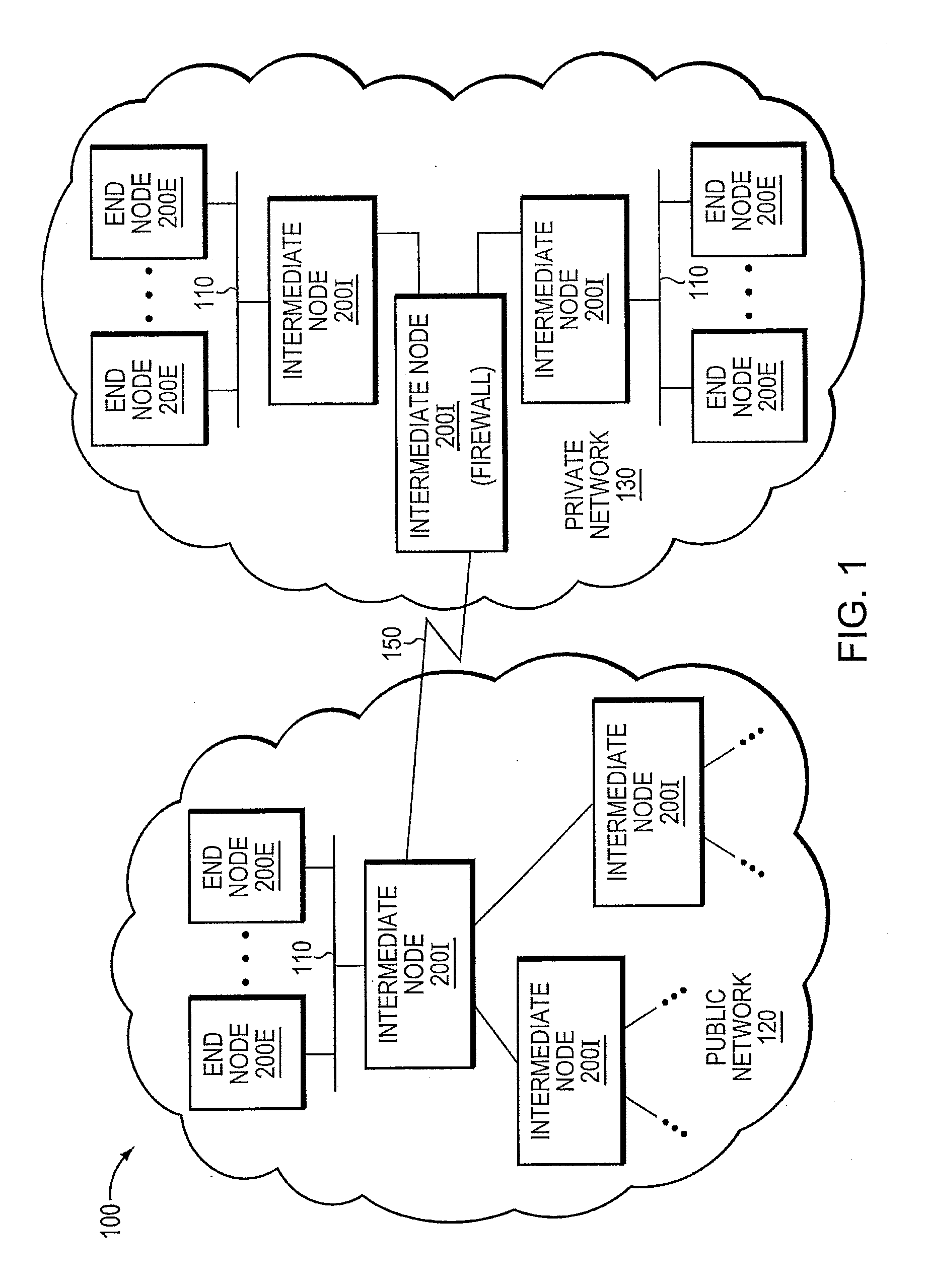
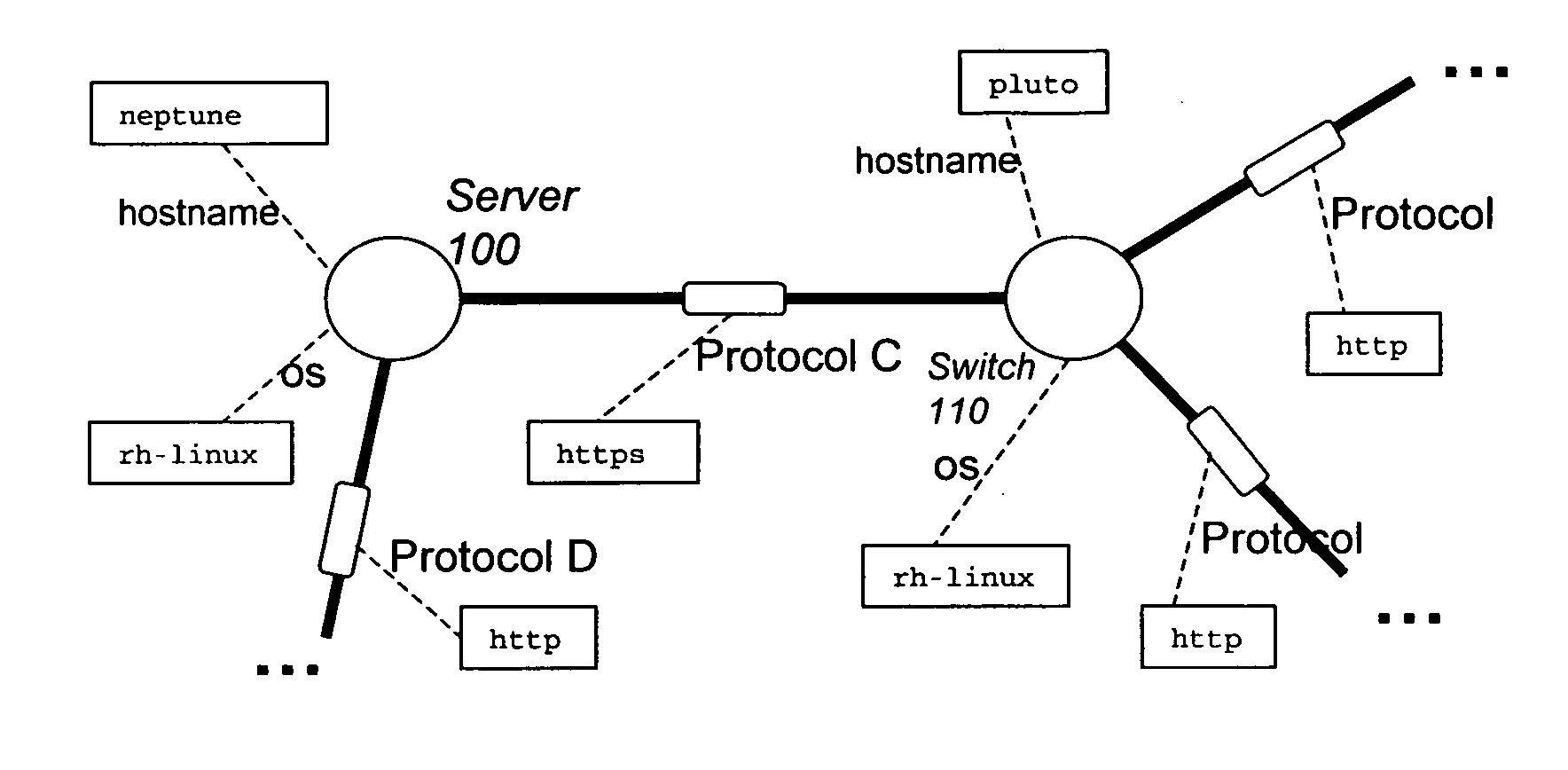
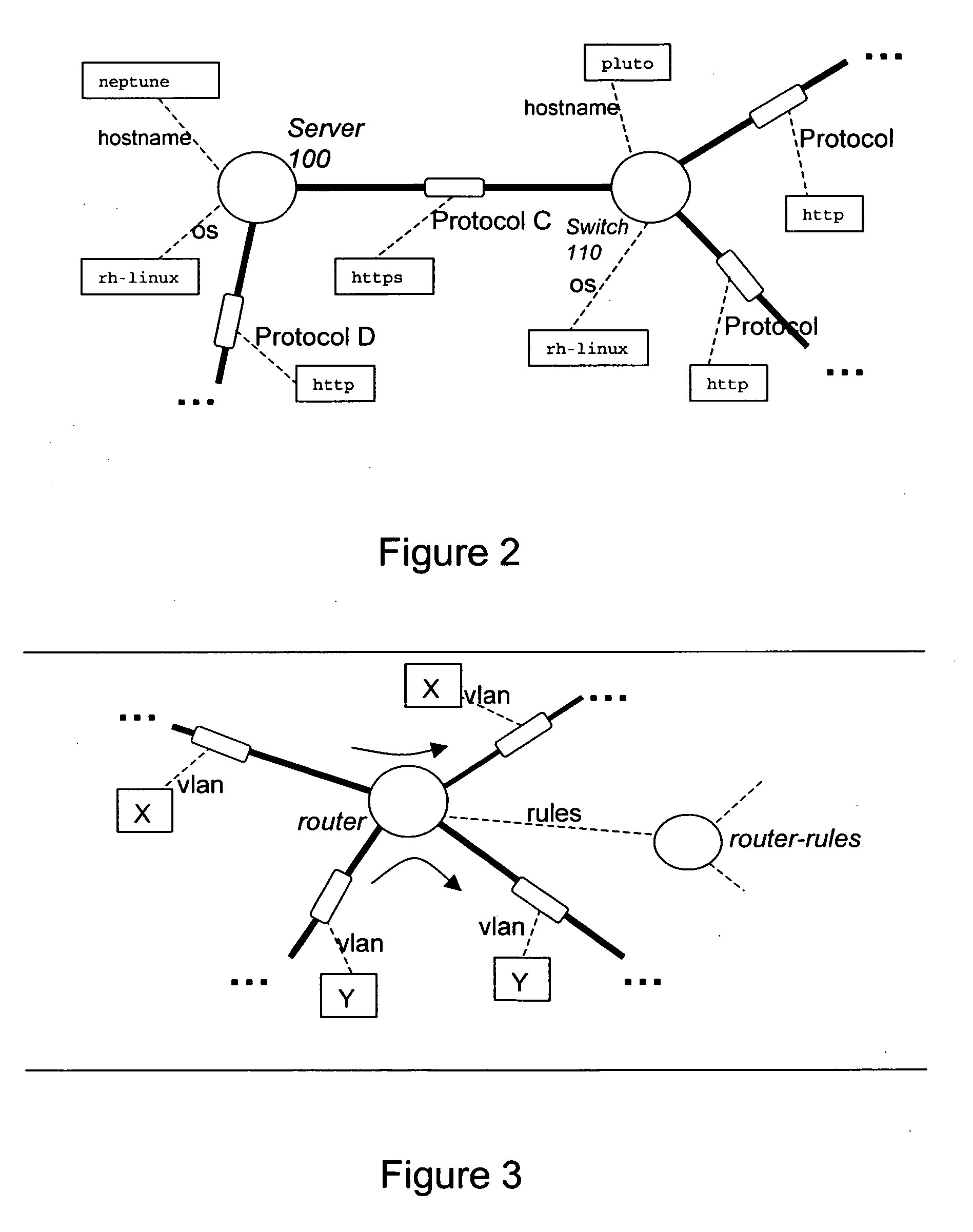
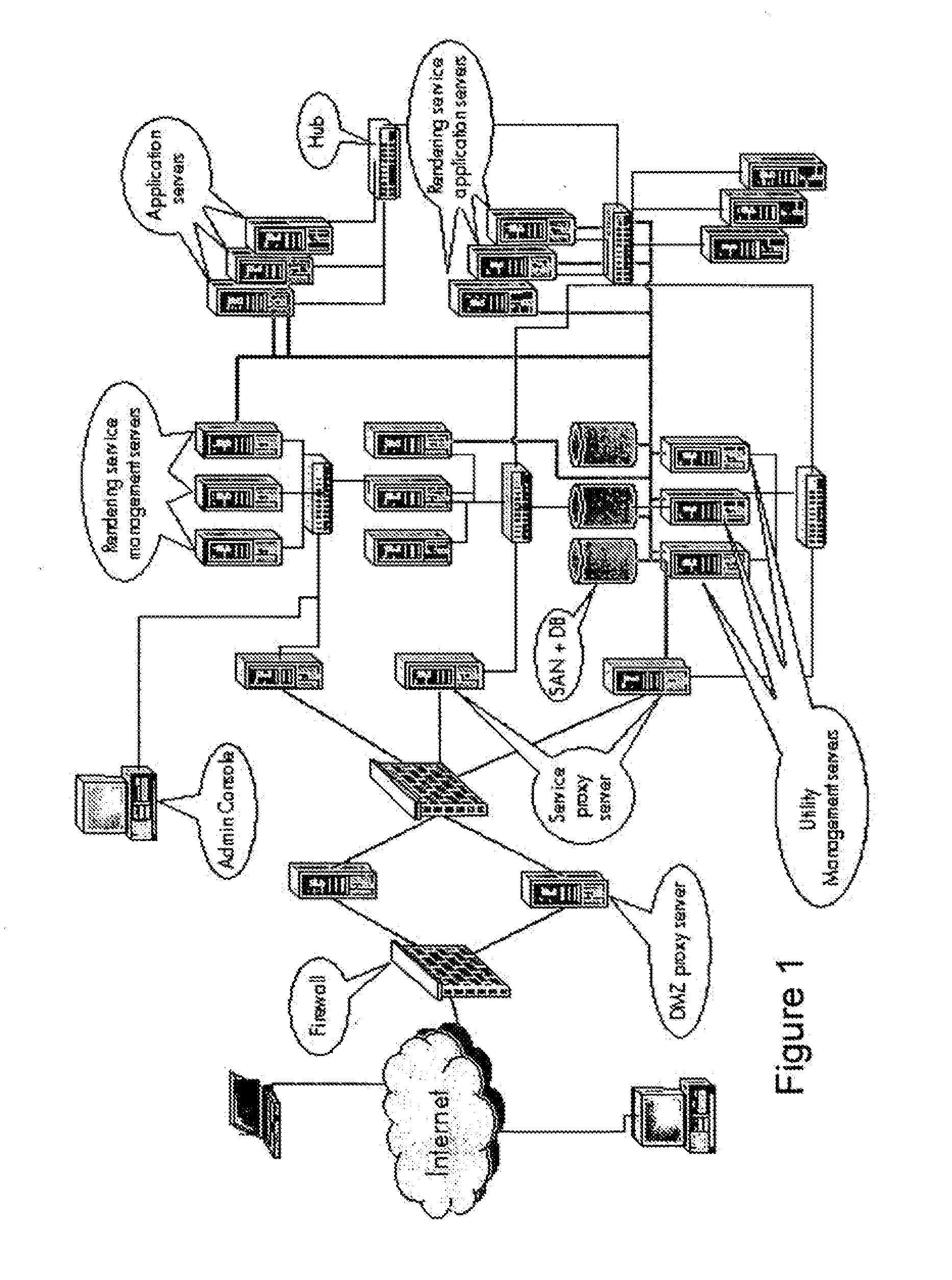
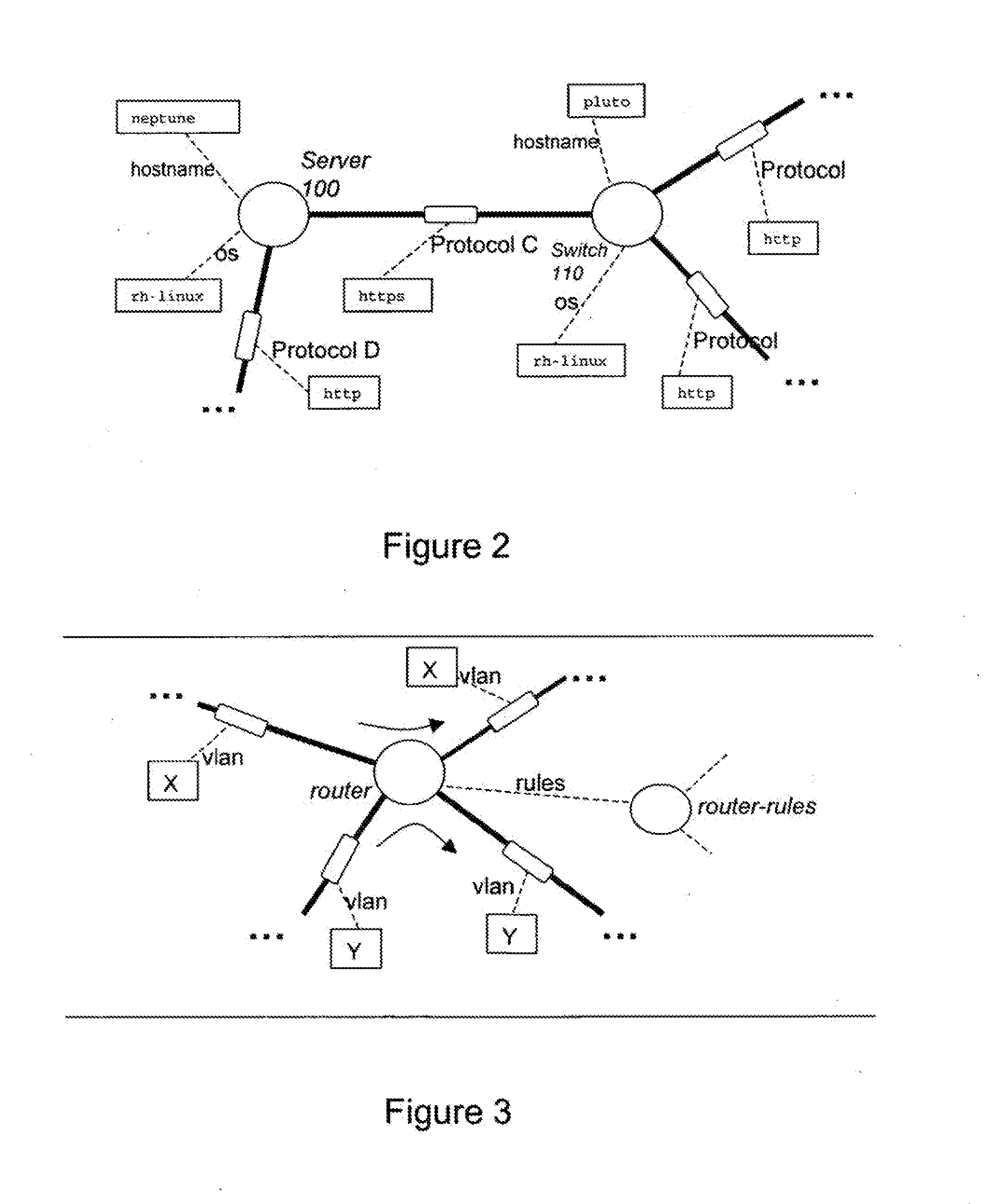
Modelling network to assess security properties
ActiveUS20070136788A1Random number generatorsUser identity/authority verificationRich modelReachability
A method of assessing a network uses a model (450) having nodes (100, 110) to represent parts of the network infrastructure and the application services, and having links to represent how the nodes influence each other. Dependencies or effects of the application services are found by determining paths through the nodes and links of the model (530). Such assessment can be useful for design, test, operations, and diagnosis, and for assessment of which parts of the infrastructure are critical to given services, or which services are dependent on, or could have an effect on a given part of the infrastructure. The dependencies or effects can encompass reachability information. The use of a model having links and nodes can enable more efficient processing, to enable larger or richer models. What changes in the dependencies or effects result from a given change in the network can be determined (830).
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
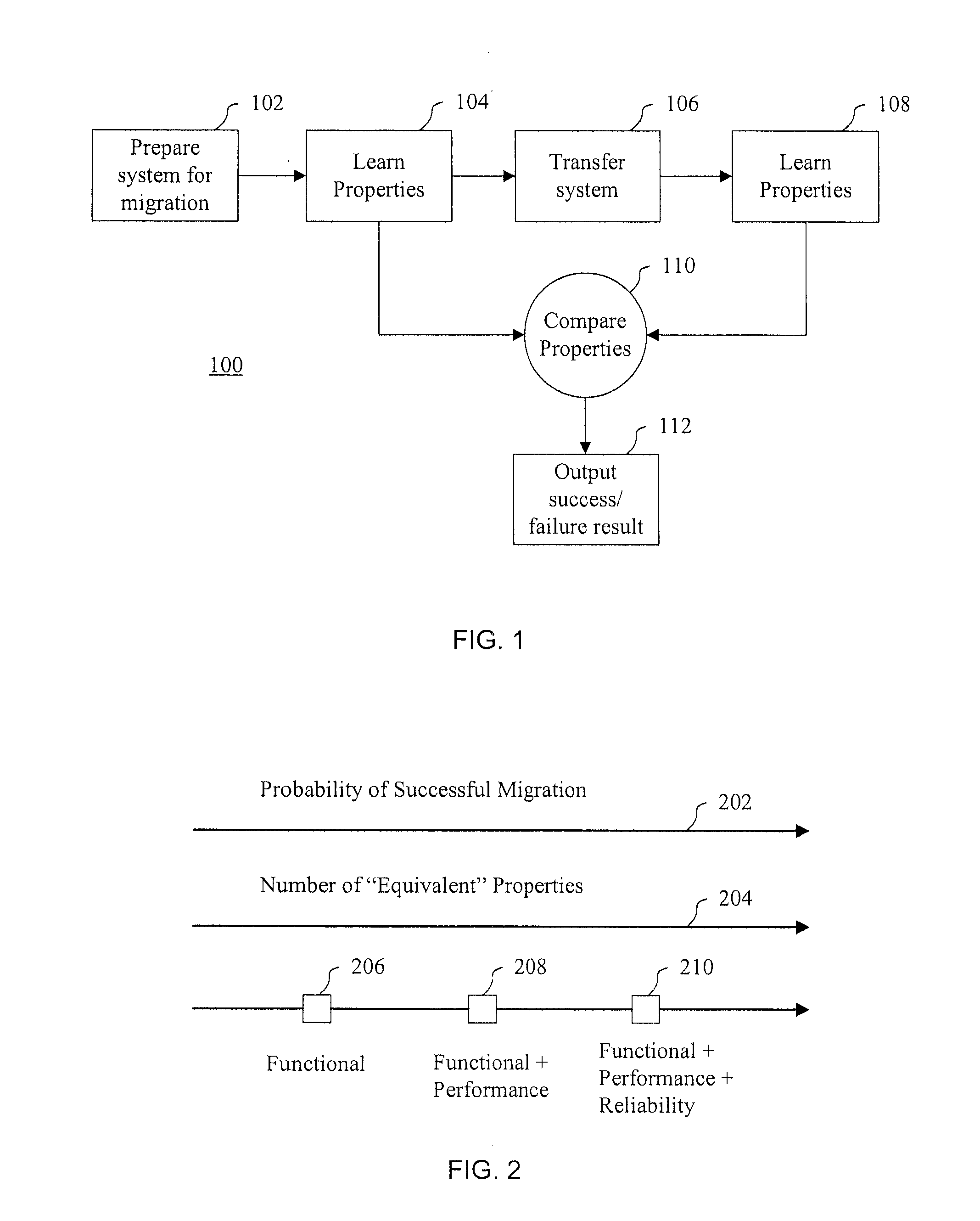
Methods and systems for migrating networked systems across administrative domains
ActiveUS20110276675A1Multiple digital computer combinationsProgram controlTransfer systemAdministrative domain
Systems and methods for determining whether networked system migrations are successful are disclosed. In accordance with one method, a first set of properties of the networked system on a source platform in a first administrative domain is determined. Further, the method includes transferring the networked system to a destination platform in a second administrative domain. In addition, a second set of properties of the transferred system on the destination platform is determined, where the first and second sets of properties include functional properties and at least one of: performance properties, security properties or reliability properties. The method also includes outputting an indication that the transfer of the system to the destination platform is successful in response to determining that one or more of the properties of the second set are equivalent to corresponding properties of the first set.
Owner:NEC CORP
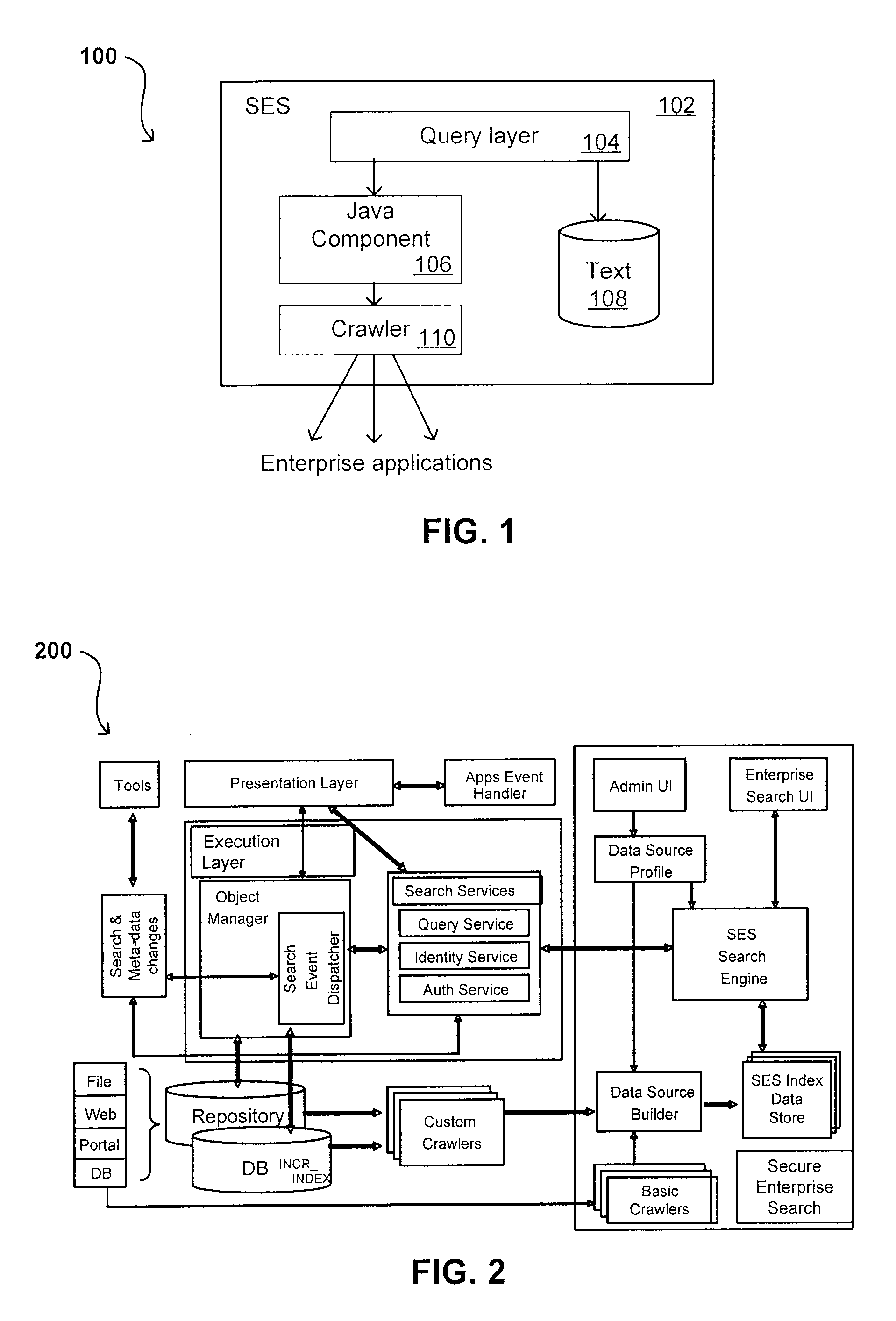
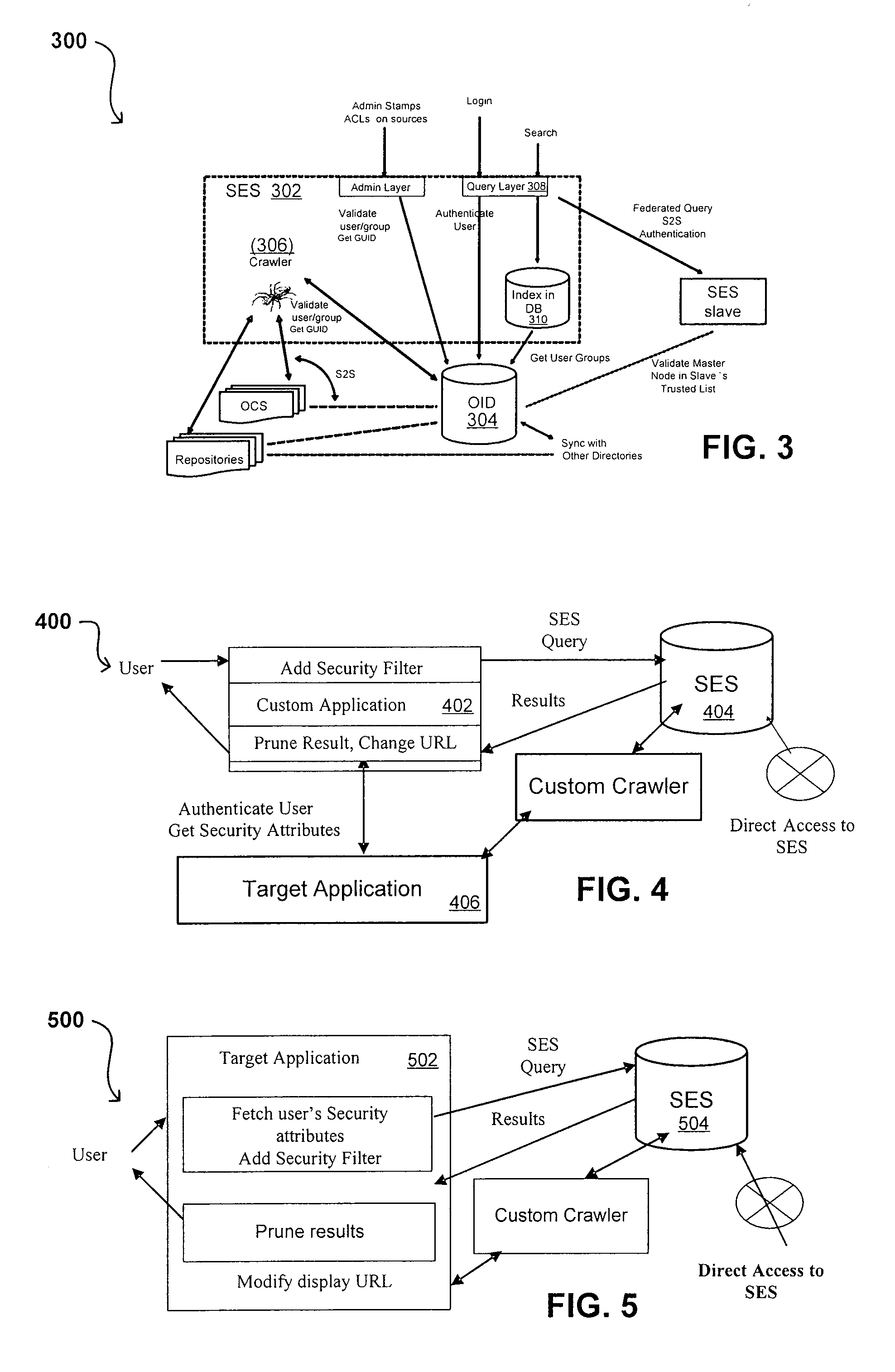
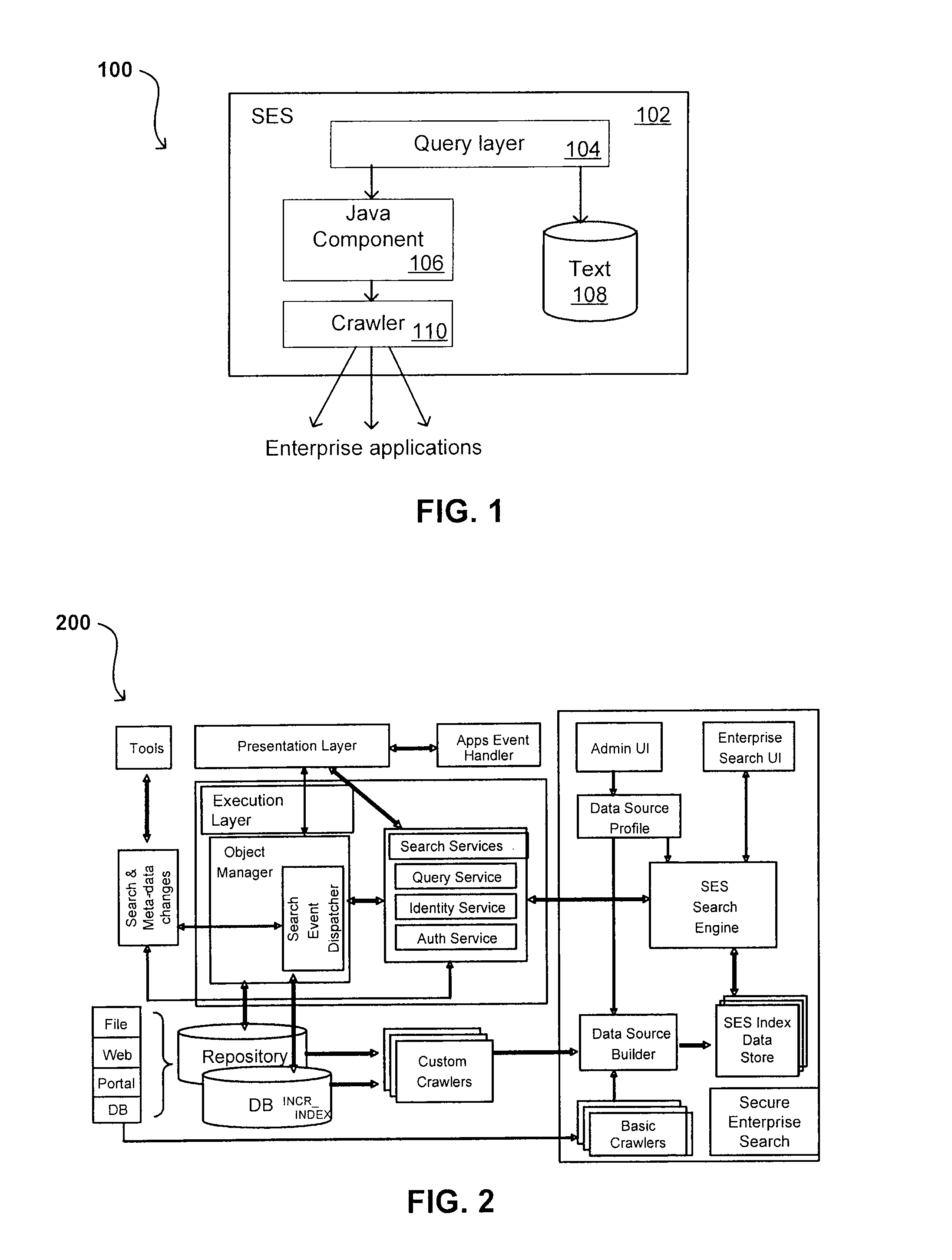
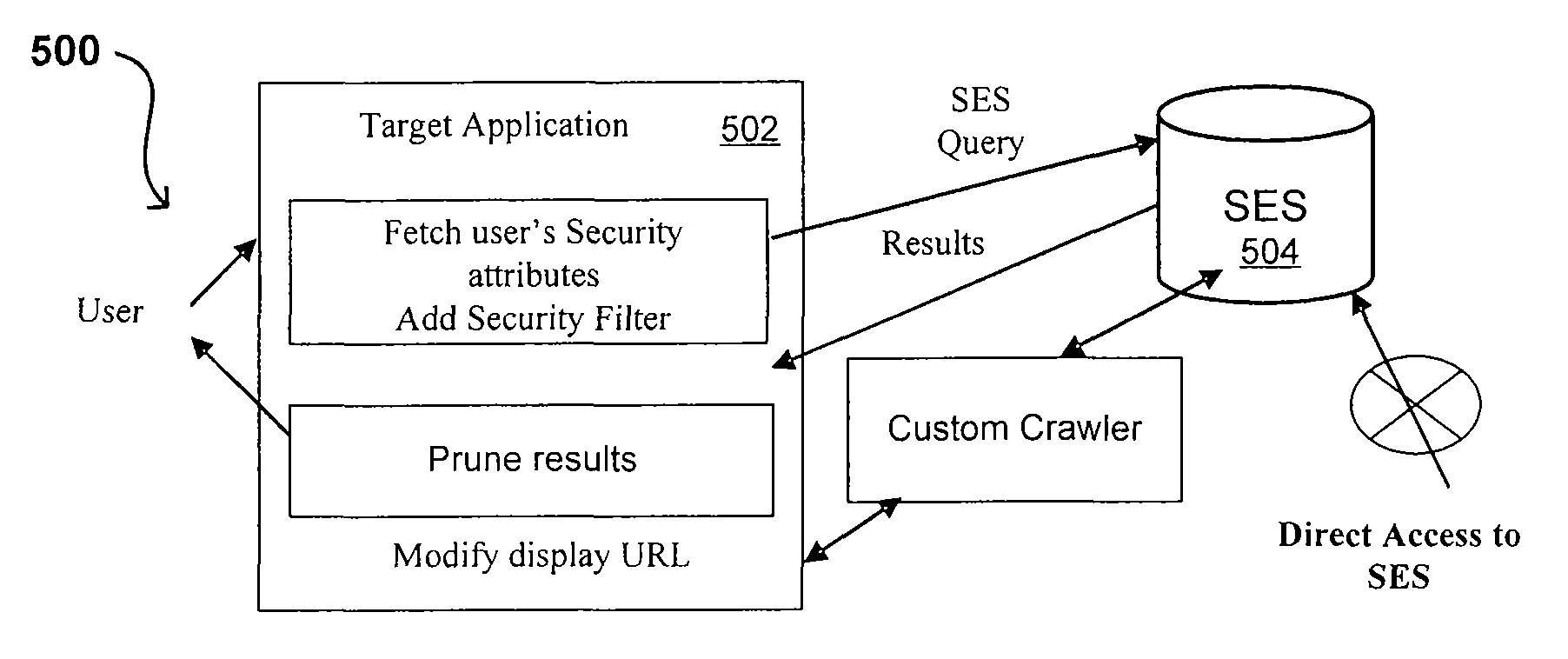
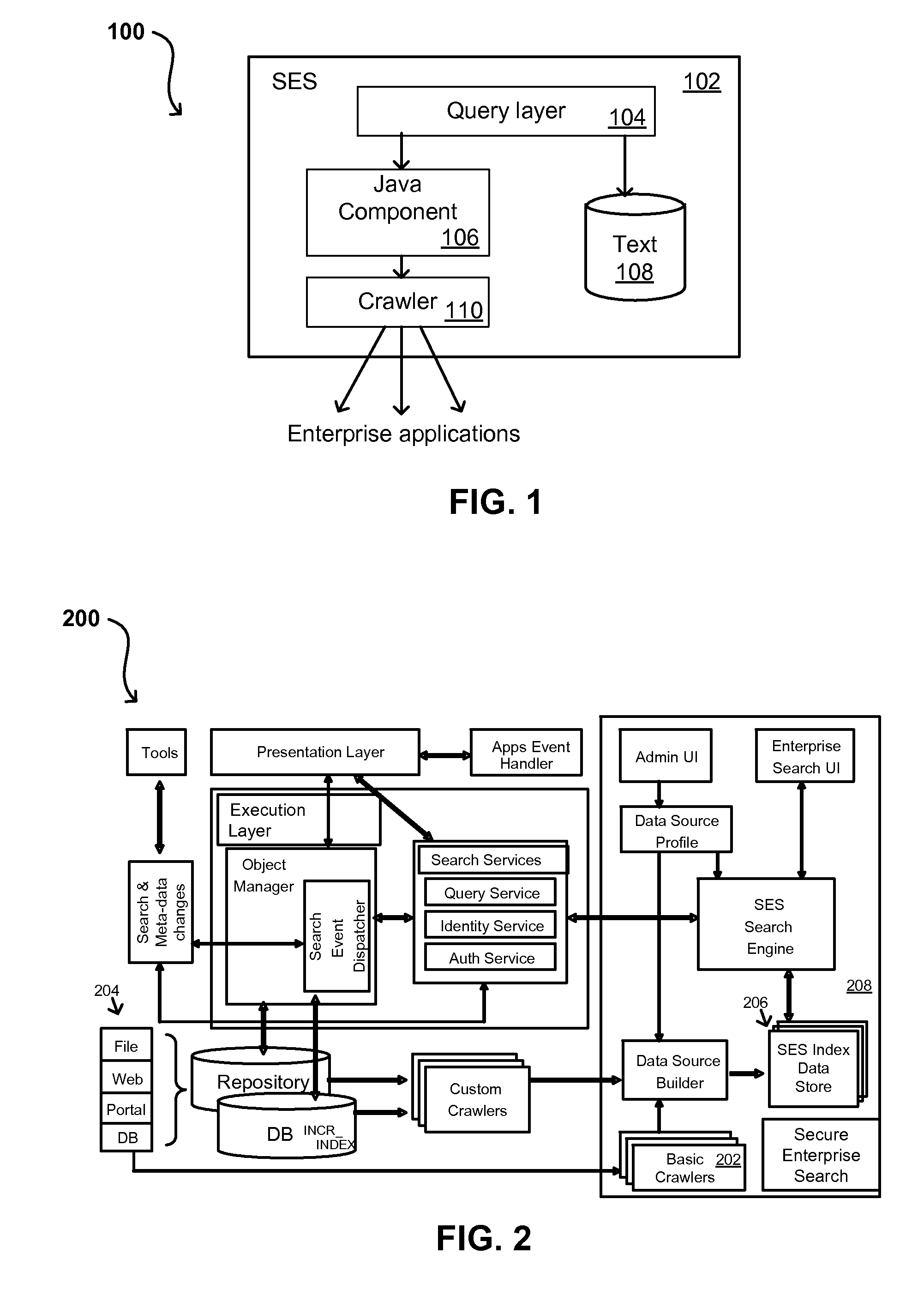
Propagating User Identities In A Secure Federated Search System
ActiveUS20070220268A1Limited lifetimeImprove performanceDigital data information retrievalDigital data processing detailsThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
Memory management system and method providing increased memory access security
Owner:GLOBALFOUNDRIES INC
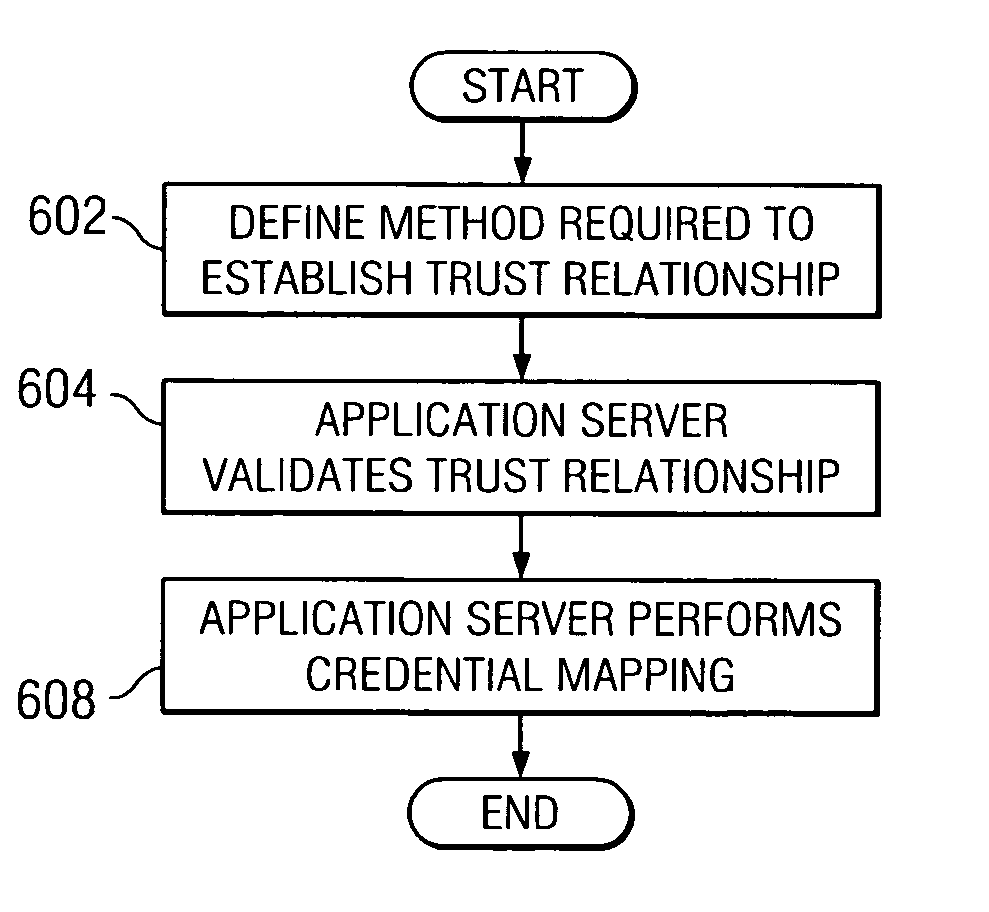
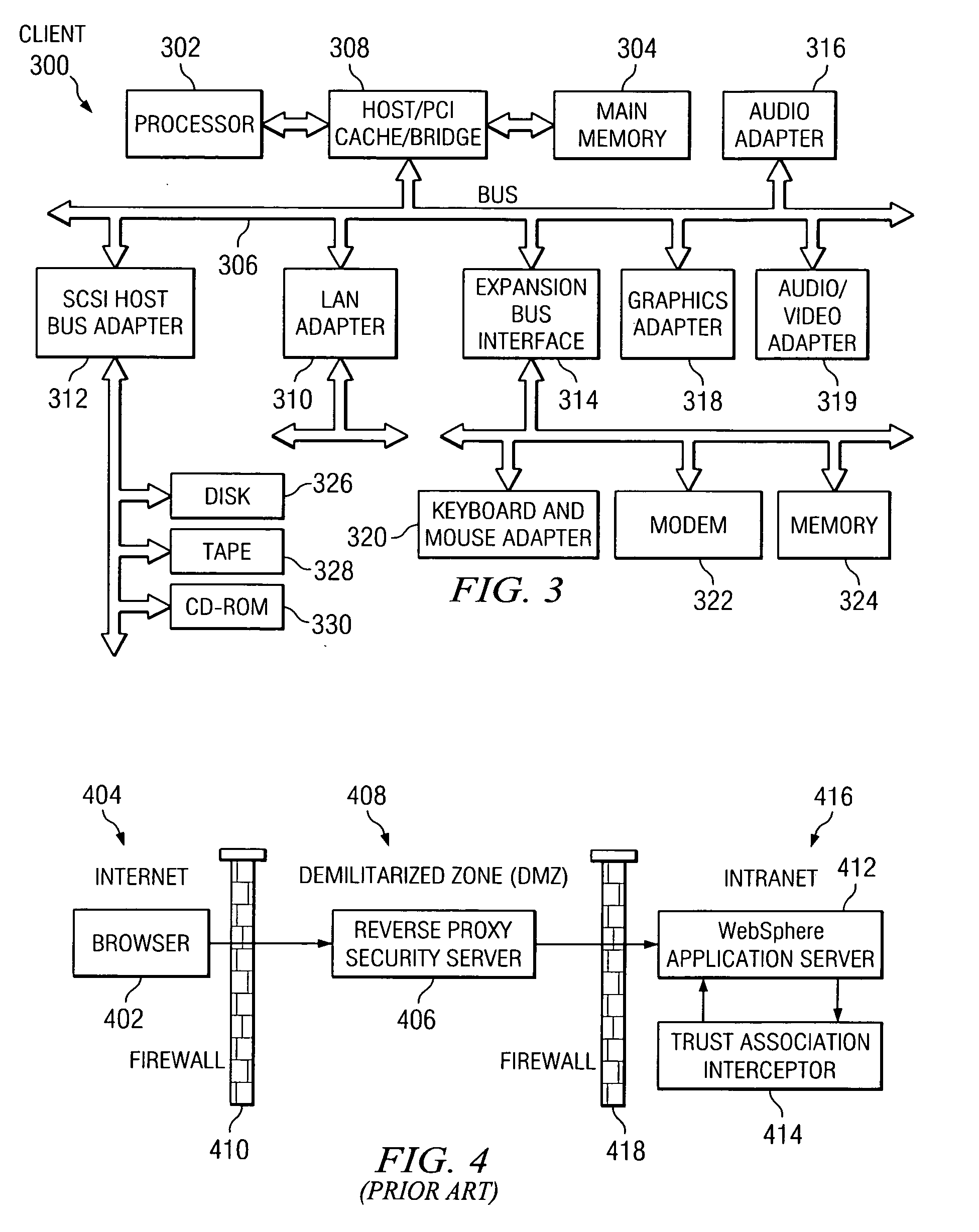
Declarative trust model between reverse proxy server and websphere application server
A method and system for providing a declarative trust association model that formalizes the way trust is established and requires corresponding authentication information to be presented in a standard format. Consequently, the application server may provide a guaranteed level of protection. The mechanism of the present invention provides a framework that allows an application server to enforce a trust evaluation and allows reverse proxy security server to assert a client's security identity, as well as other client security credential information. A known trust association interceptor model is extended to allow the reverse proxy security server to assert the authenticated user's security attributes. Such security attributes include, for example, group information, authentication strength, and location (i.e., where does the user enter the request, intranet vs. internet, IP address, etc.,). The security attributes can be used in making authorization decisions.
Owner:IBM CORP
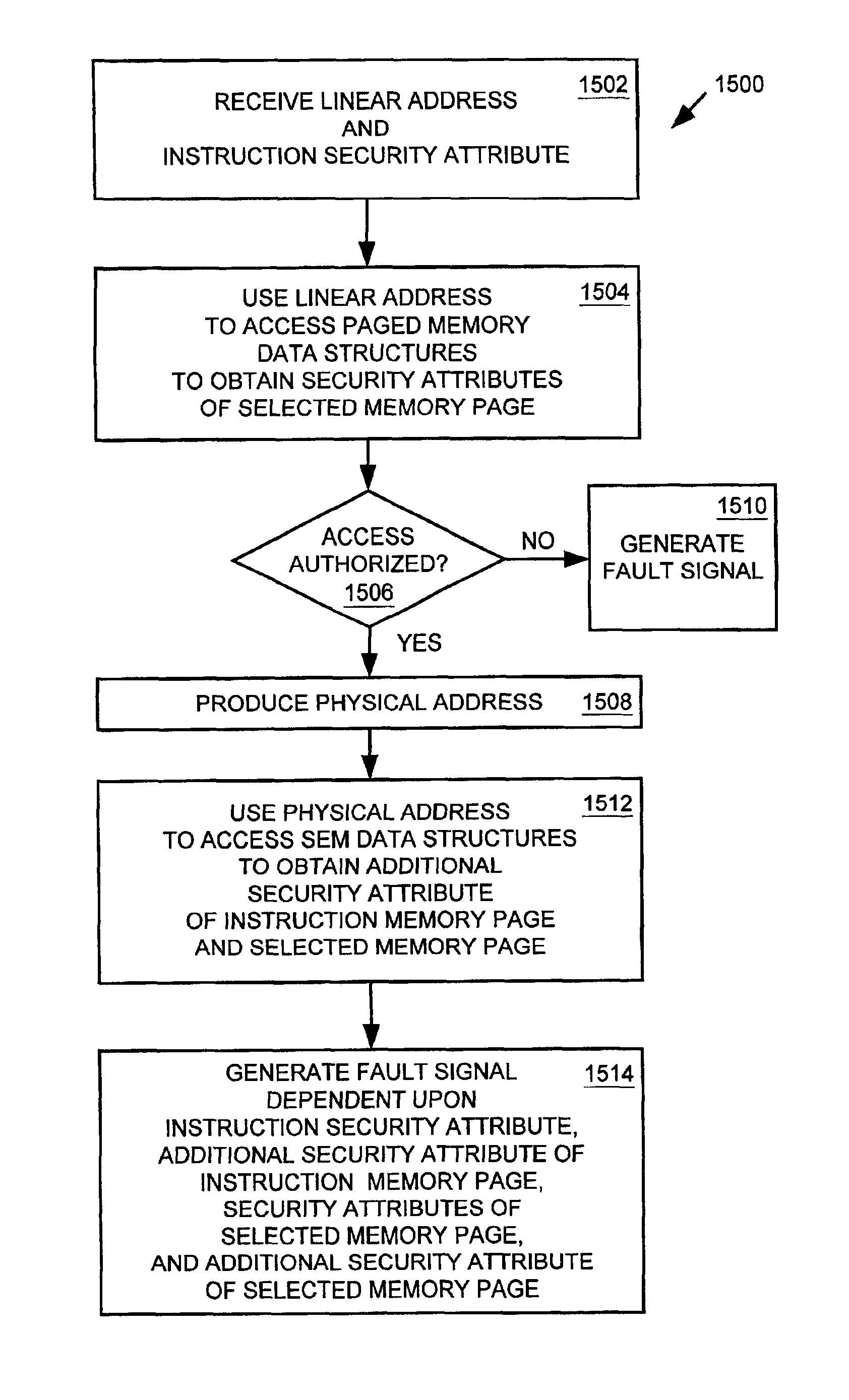
Memory management system and method for providing physical address based memory access security
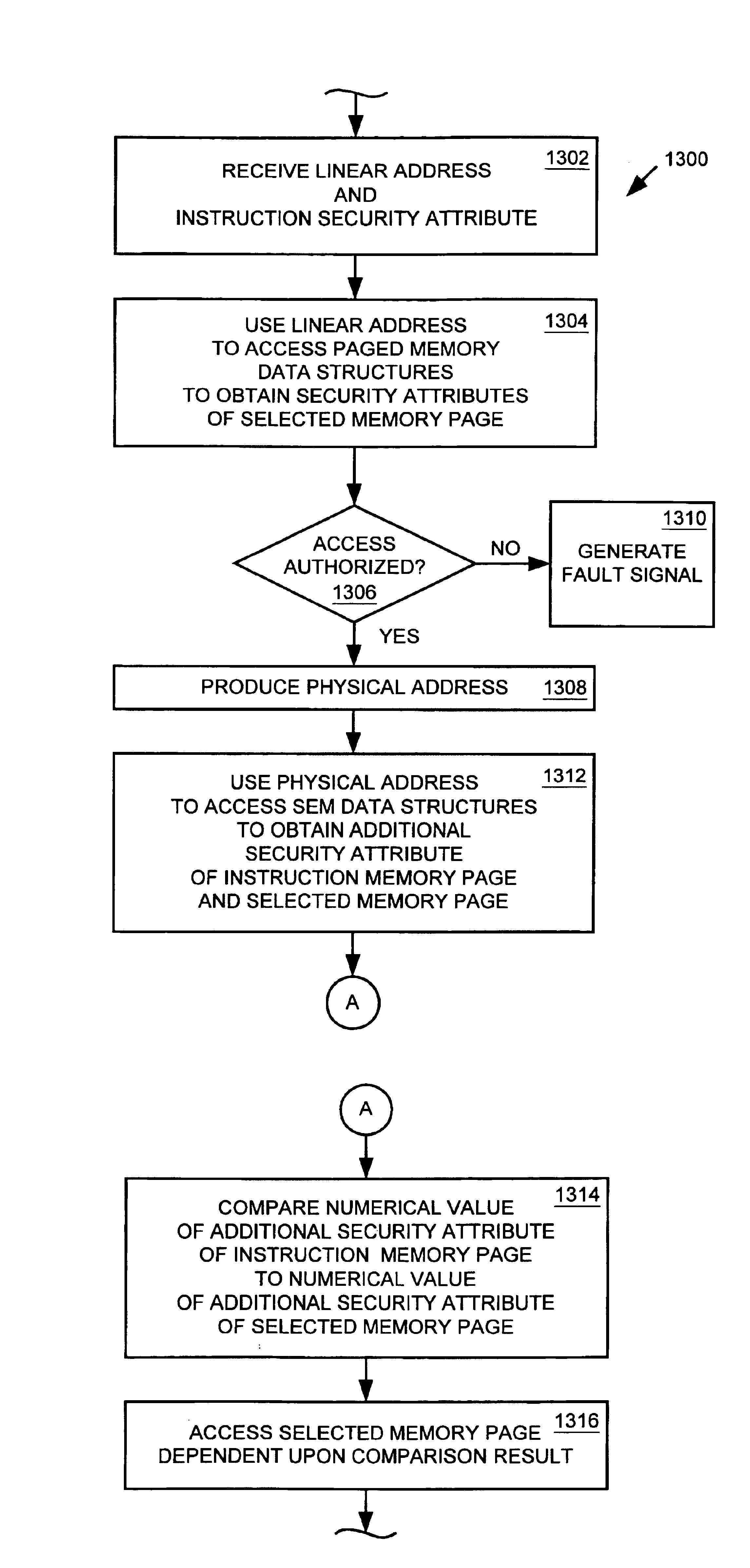
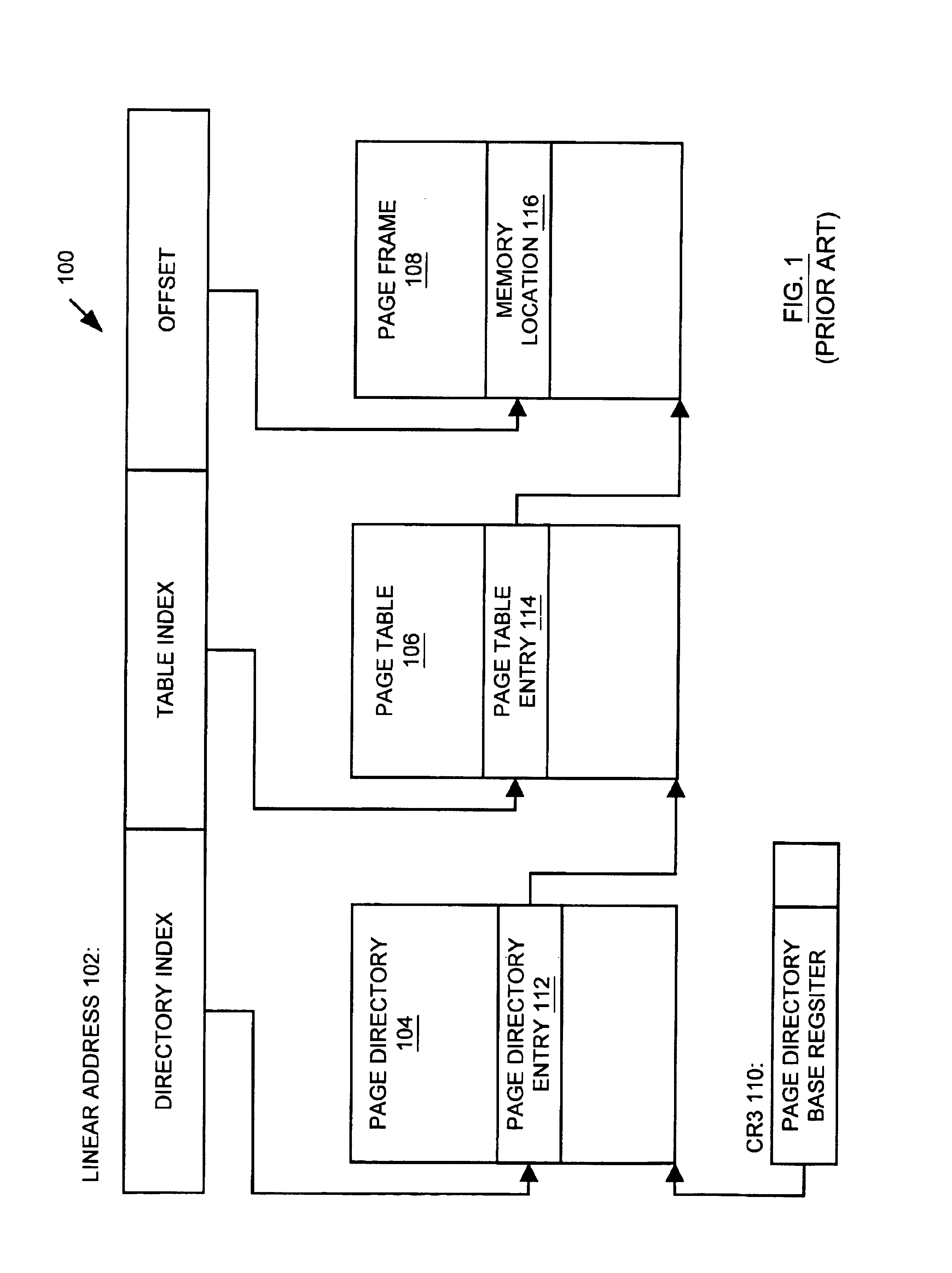
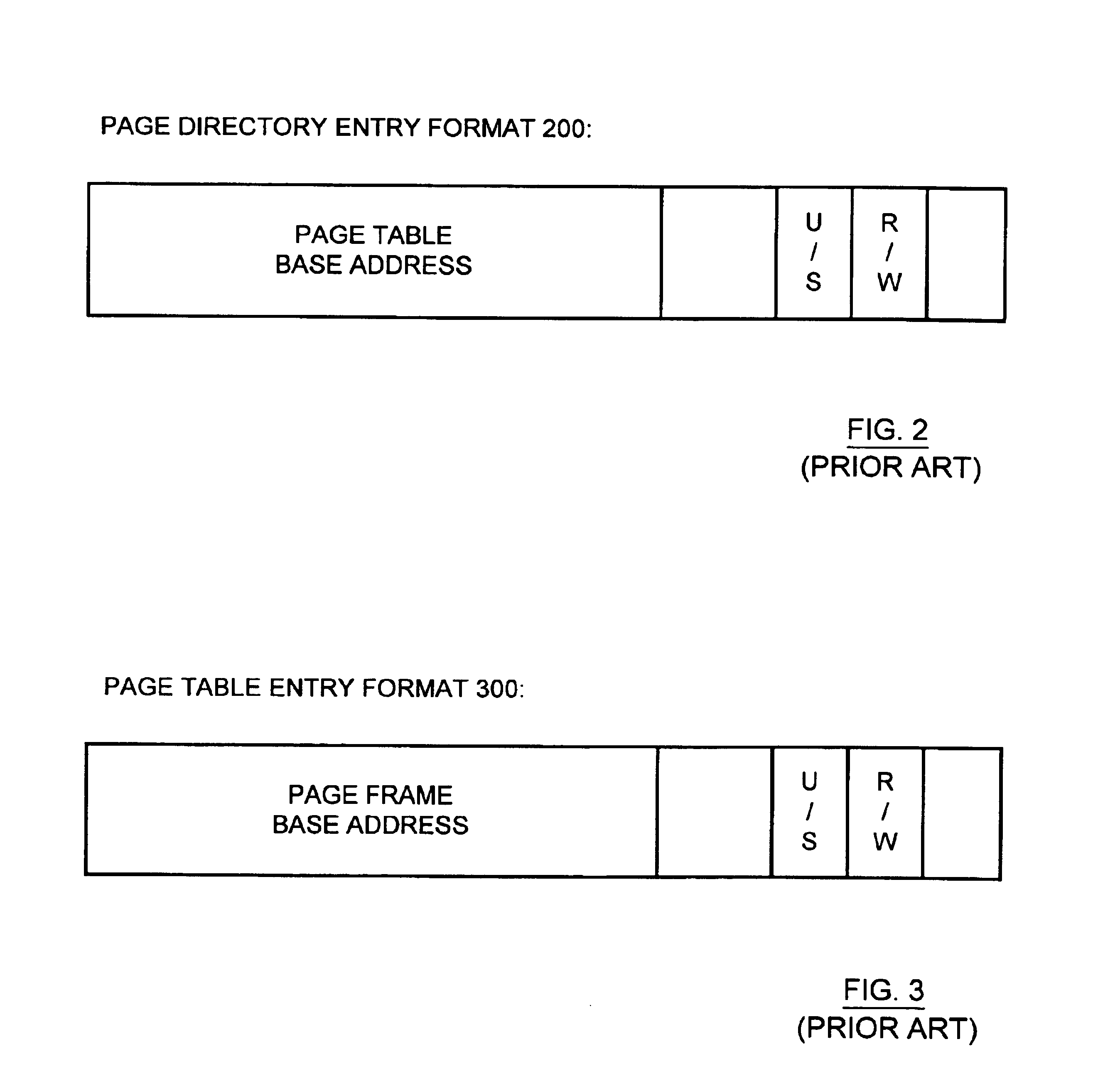
InactiveUS6823433B1Memory adressing/allocation/relocationUnauthorized memory use protectionManagement unitComputerized system
A memory management unit (MMU) is disclosed for managing a memory storing data arranged within a plurality of memory pages. The MMU includes a security check unit (SCU) receiving a physical address generated during execution of a current instruction. The physical address resides within a selected memory page. The SCU uses the physical address to access one or more security attribute data structures located in the memory to obtain a security attribute of the selected memory page, compares a numerical value conveyed by a security attribute of the current instruction to a numerical value conveyed by the security attribute of the selected memory page, and produces an output signal dependent upon a result of the comparison. The MMU accesses the selected memory page dependent upon the output signal. The security attribute of the selected memory page may include a security context identification (SCID) value indicating a security context level of the selected memory page. The security attribute of the current instruction may include an SCID value indicating a security context level of a memory page containing the current instruction. A central processing unit (CPU) is described including an execution unit and the MMU. A computer system is described including the memory, the CPU, and the MMU. A method is described for providing access security for a memory used to store data arranged within a plurality of memory pages. The method may be embodied within the MMU.
Owner:GLOBALFOUNDRIES US INC +1
Trusted platform apparatus, system, and method
InactiveUS7216369B2Volume/mass flow measurementDetecting faulty computer hardwareOperational systemEntry point
An apparatus may include a root of trust for measurement (RTM) module coupled to a verified platform security property policy module and a comparison module. The comparison module may operate to prevent transfer of control to an operating system (and / or halt the boot process) if a policy included in the platform security property policy module is violated. A system may include a memory coupled to a processor, a platform security property policy module, and a comparison module. The memory may include an RTM. A method may include beginning execution at an entry point within an RTM, determining that the RTM is trustworthy, determining that a main initialization code associated with a platform is trustworthy and transferring control to the main initialization code, and otherwise, refraining from transferring control to the main initialization code.
Owner:INTEL CORP
Medical chitosan fibre and preparation method thereof
ActiveCN101250759AHigh molecular weightEnough aminoFilament manufactureArtificial filament washing/dryingAcetic acidBrute force
The invention relates to medical chitosan fiber in the textile processing field and a preparing method thereof, the method for preparing spinning fluid comprises the following steps: arranging the chitosan powder in glacial acetic acid water solution and slowly dissolving by stirring under the condition of controlling temperature and time, wherein the dissolution temperature is 10-30DEG C, the dissolution time is 10-48h, and the stirring speed is 60-180r / min, wherein the chitosan powder occupies 3%-10%, dissolvent glacial acetic acid occupies 1%-5% and the other is water in the spinning raw materials, the chitosan content is more than 99.9% in chitosan fiber, and the chitosan fiber has higher molecular weight, sufficient amido, steady fiber structure, and good antibacterial property, brute force and hygiene security property.
Owner:HISMER BIO TECH
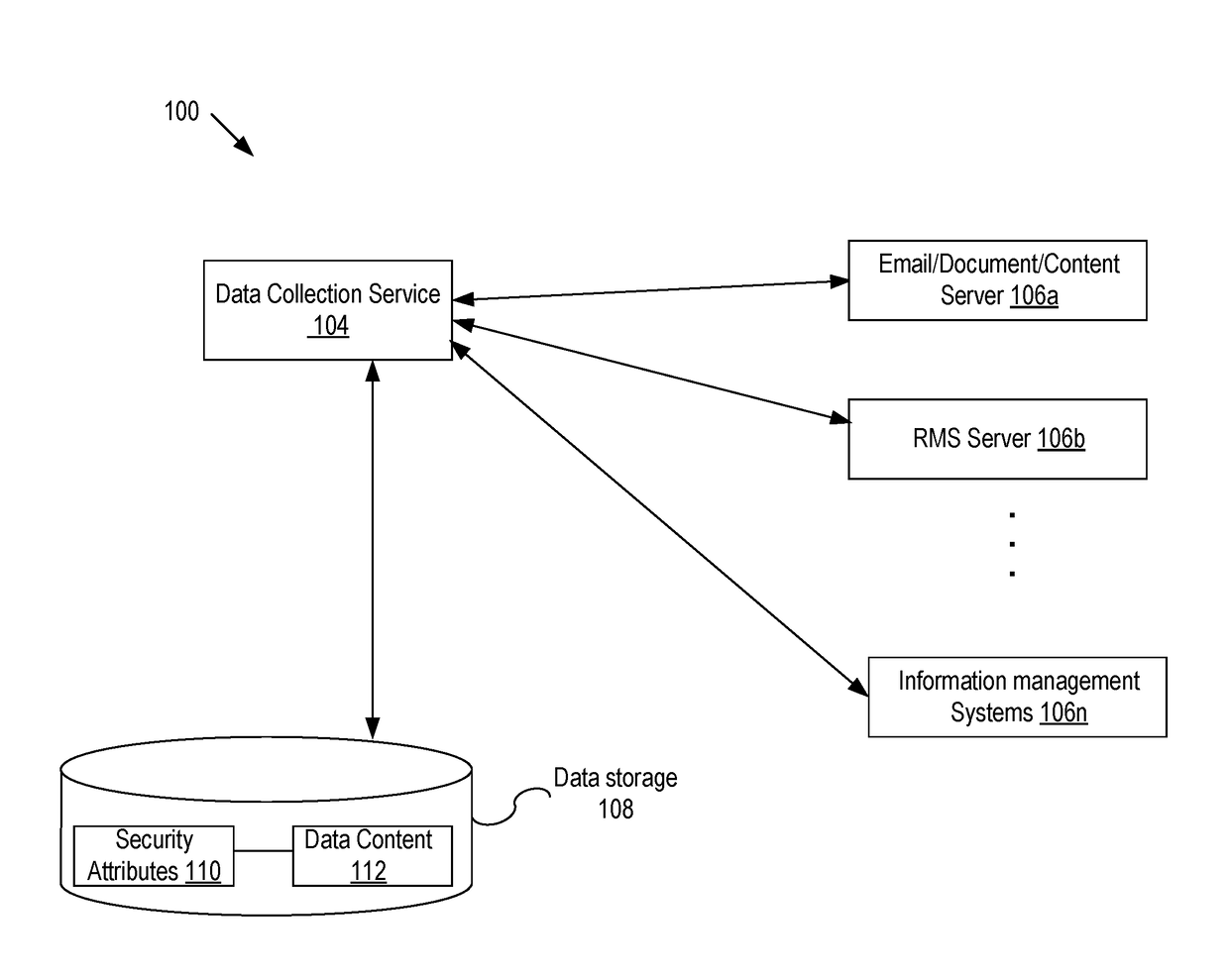
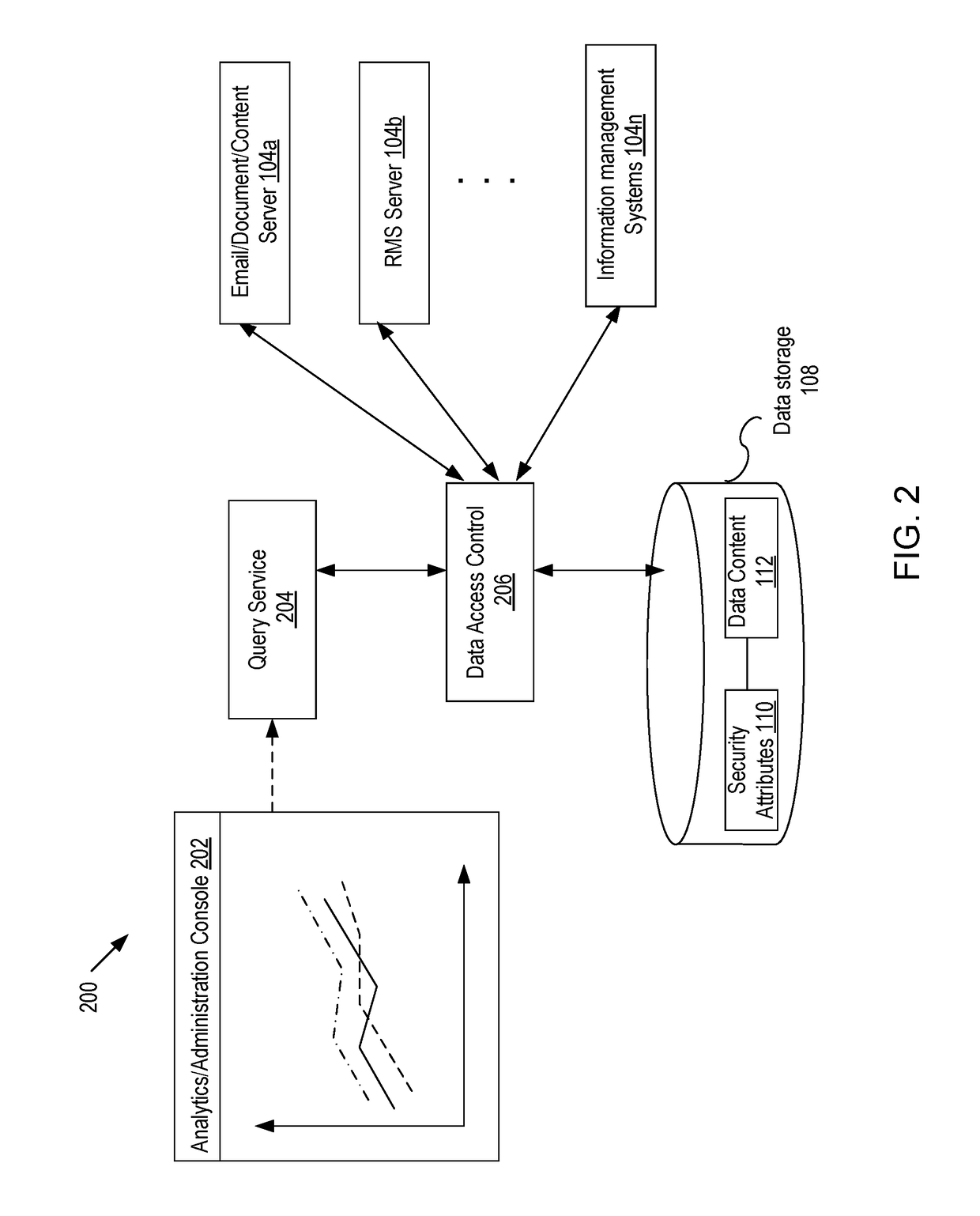
Preserving data protection and enabling secure content awareness in query services
ActiveUS20170300702A1Digital data information retrievalDigital data protectionInternet privacyData source
Embodiments of the present disclosure include systems and methods for providing query service of secured contents. A data collection service collects data and security context associated with the data from a data source and stores the data with the security attributes in a datastore, where the security attributes are derived from the security context and used to determine access to the data so that access to the data is consistent with the security context. Upon receiving a query and a user context of a requester making the query of the datastore, a set of query results is obtained. Based on the user context and security attributes, it is determined whether the requestor has a proper right to access the query results. If the requestor has a proper right to access the query results, access to the query results is granted.
Owner:QUEST SOFTWARE INC
Method for enforcing resource access control in computer systems
ActiveUS20120079590A1Digital data processing detailsUnauthorized memory use protectionSystems designComputerized system
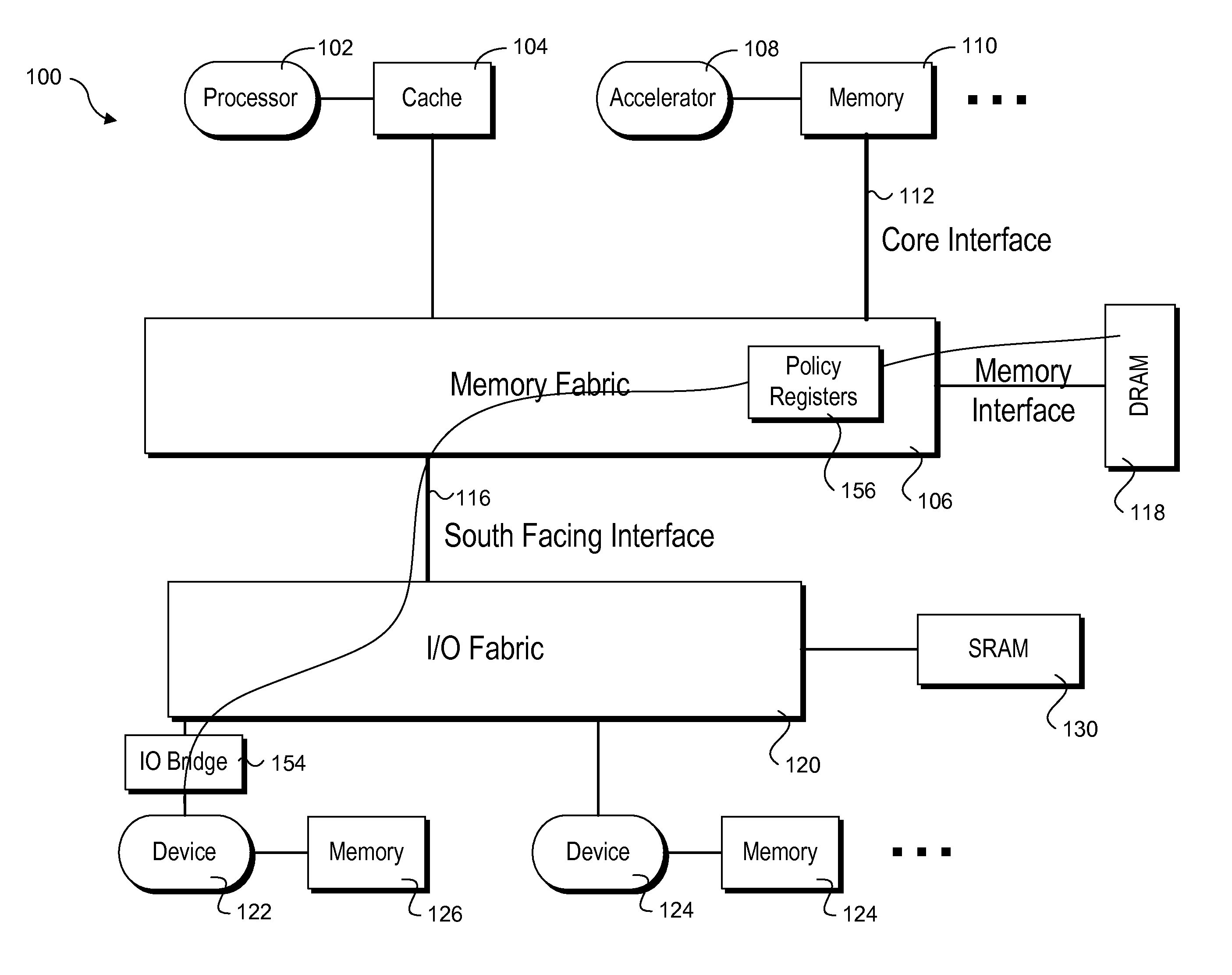
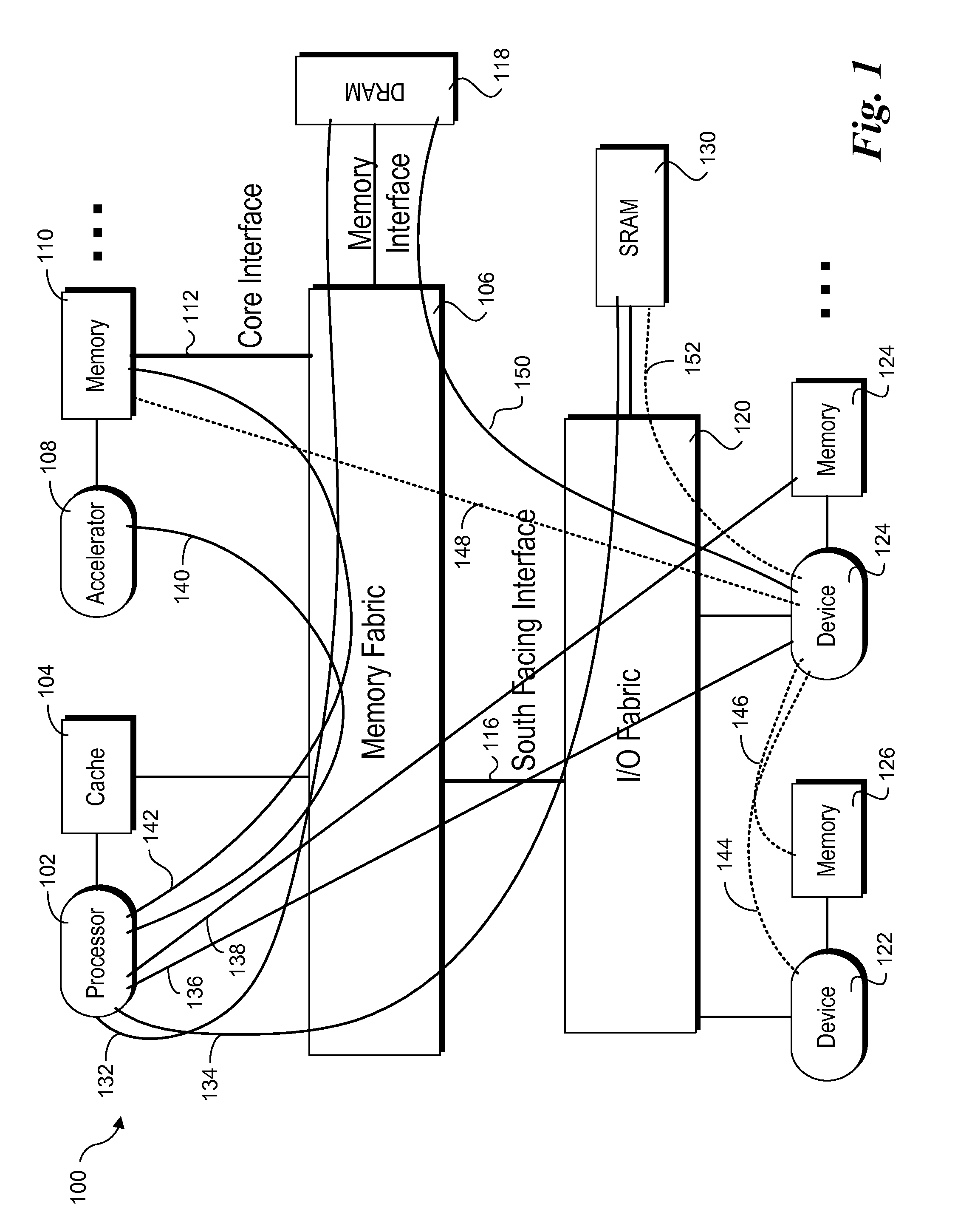
A method and system for enforcing access control to system resources and assets. Security attributes associated with devices that initiate transactions in the system are automatically generated and forwarded with transaction messages. The security attributes convey access privileges assigned to each initiator. One or more security enforcement mechanisms are implemented in the system to evaluate the security attributes against access policy requirements to access various system assets and resources, such as memory, registers, address ranges, etc. If the privileges identified by the security attributes indicate the access request is permitted, the transaction is allowed to proceed. The security attributes of the initiator scheme provides a modular, consistent secure access enforcement scheme across system designs.
Owner:TAHOE RES LTD
Security system
A security system for connecting a cable to consumer articles, such as cameras, and the like, to prevent unauthorized removal of the articles from a predetermined area while being displayed in retail establishments on open shelves. The system in its most basic form comprises a device including a security cable and a threaded fastener. The security cable is passed through the threaded fastener, and then the threaded fastener is attached into the body of the article. The threaded fastener head has a special configuration and cannot be removed without a special key, thereby preventing the unauthorized removal of the secured property. The threaded fastener also includes a circular borehole through the entire length of the threaded fastener to allow the cable to pass through the opening, and a step is provided inside the borehole to stop the cable from coming off the fastener. Optionally, a reel, an alarm, or a fastener cover can be added to the basic system to make more difficult the removal of the security cable from the article.
Owner:SENNCO SOLUTIONS INC
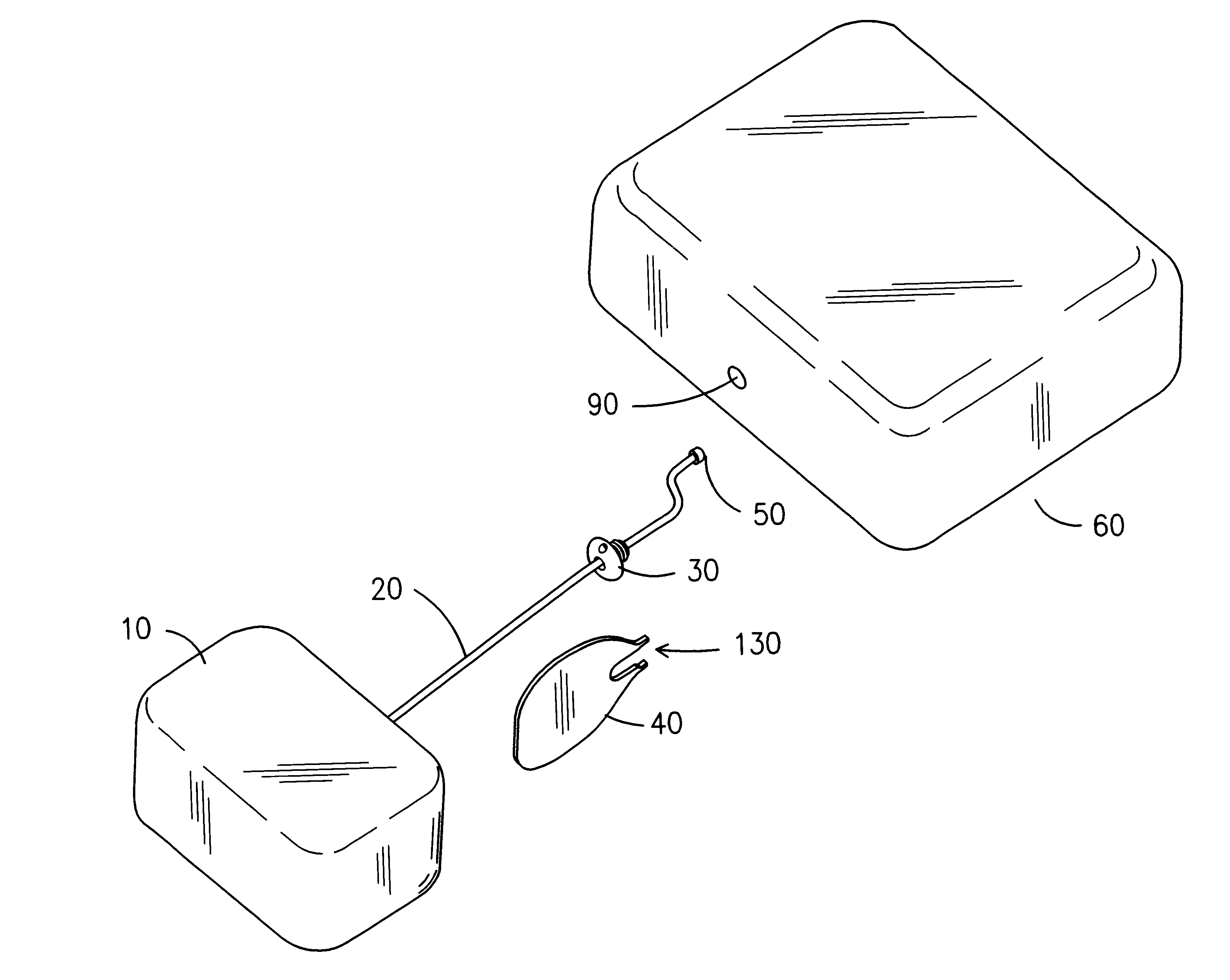
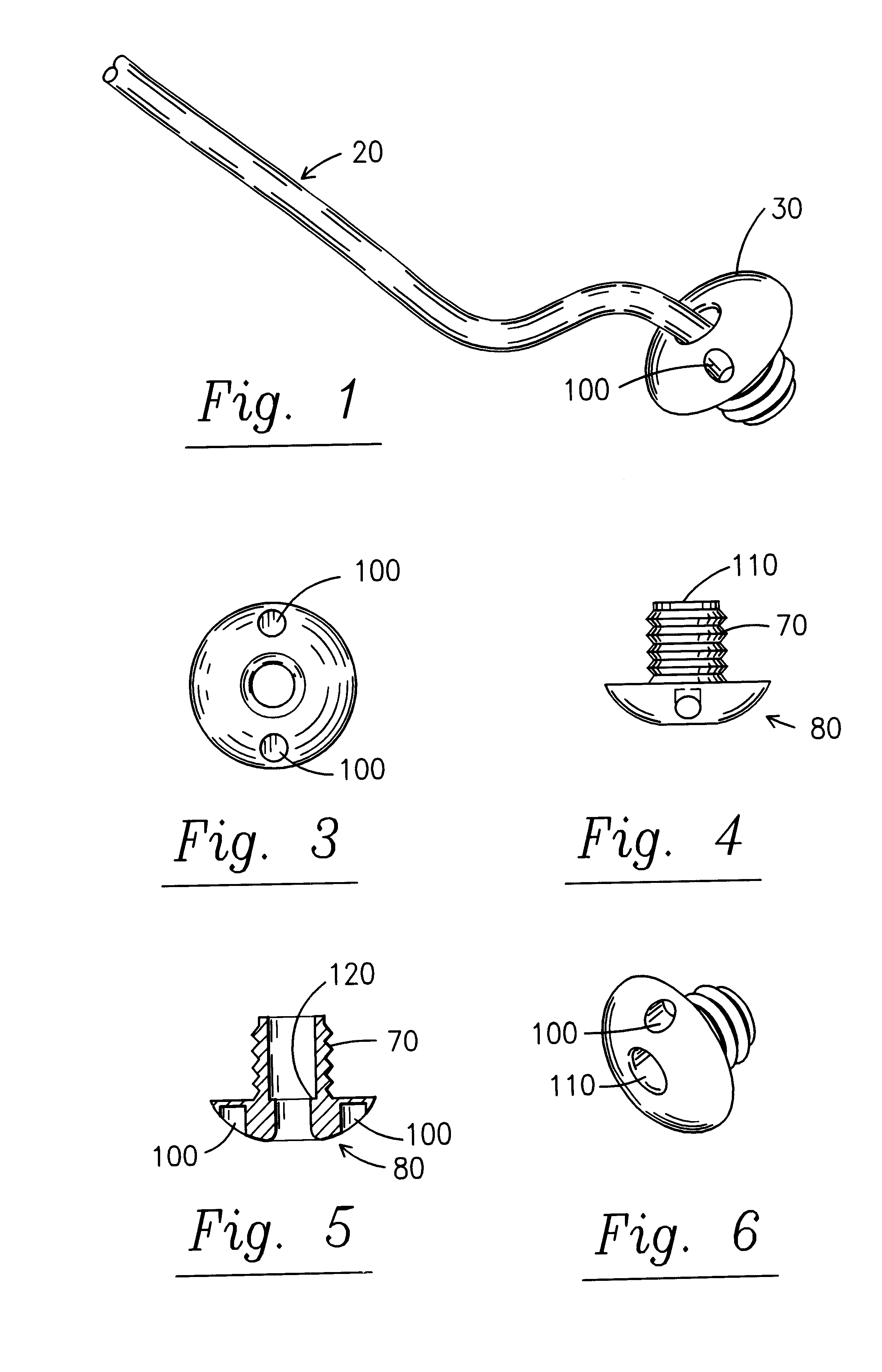
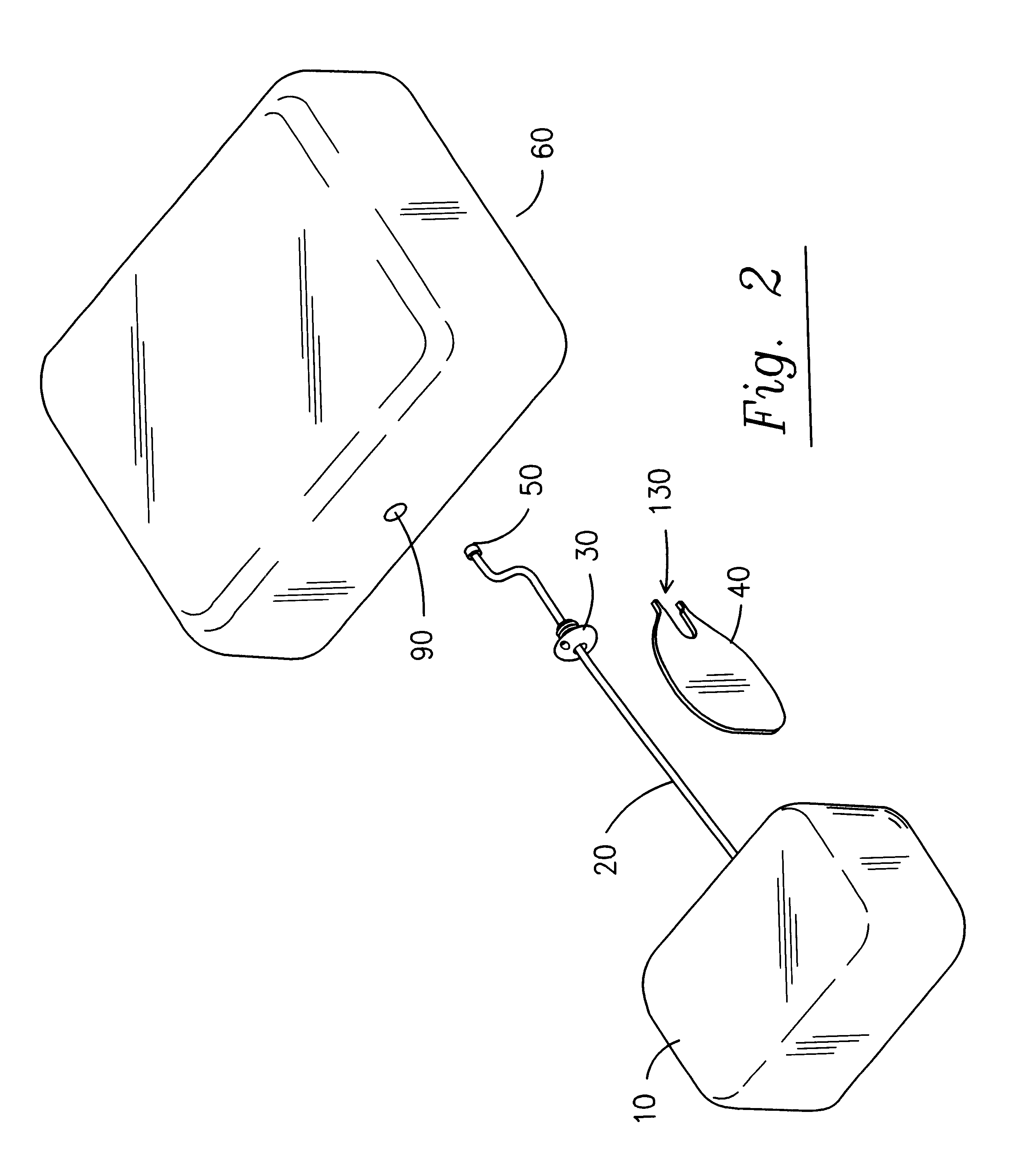
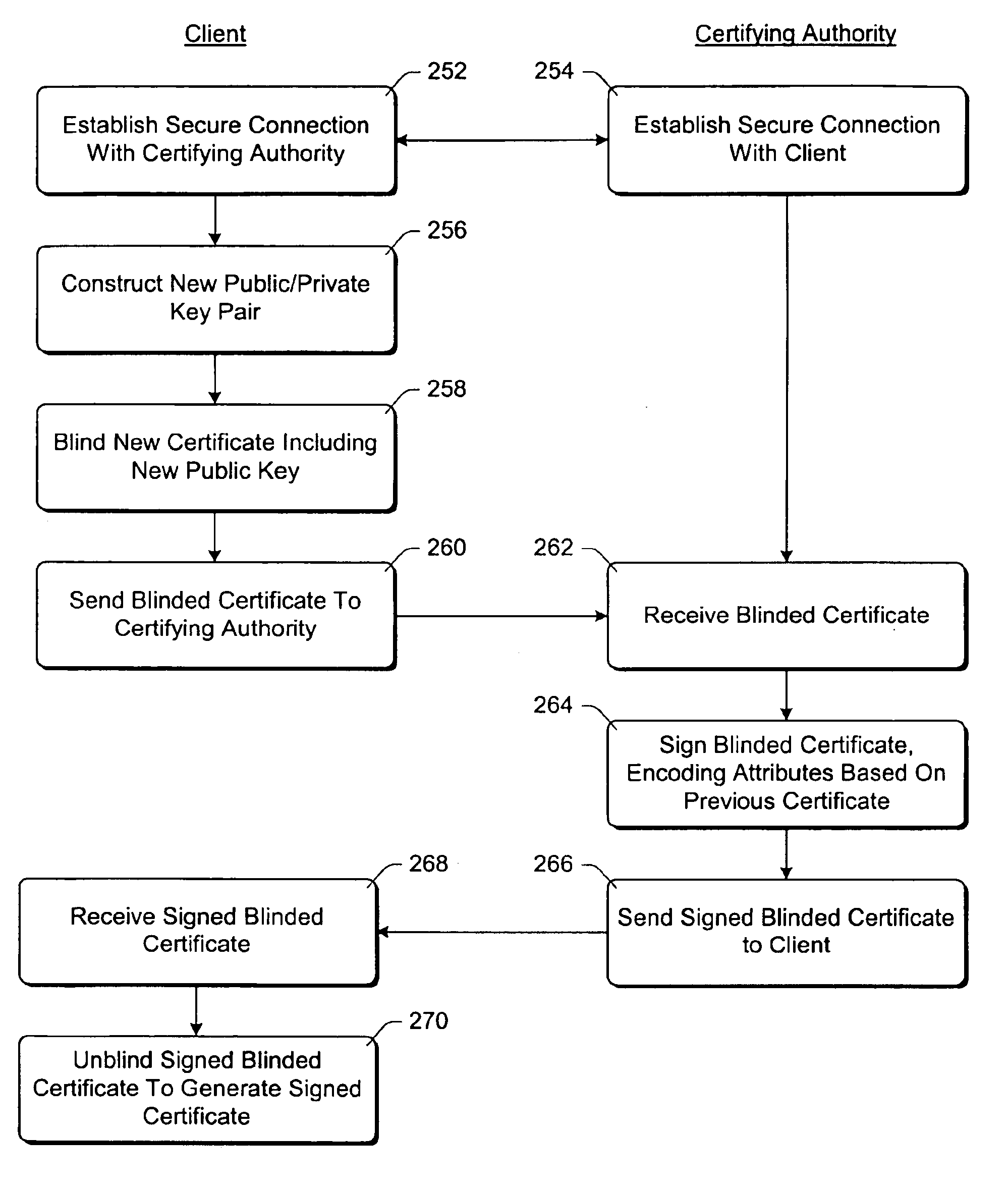
Controlled-content recoverable blinded certificates
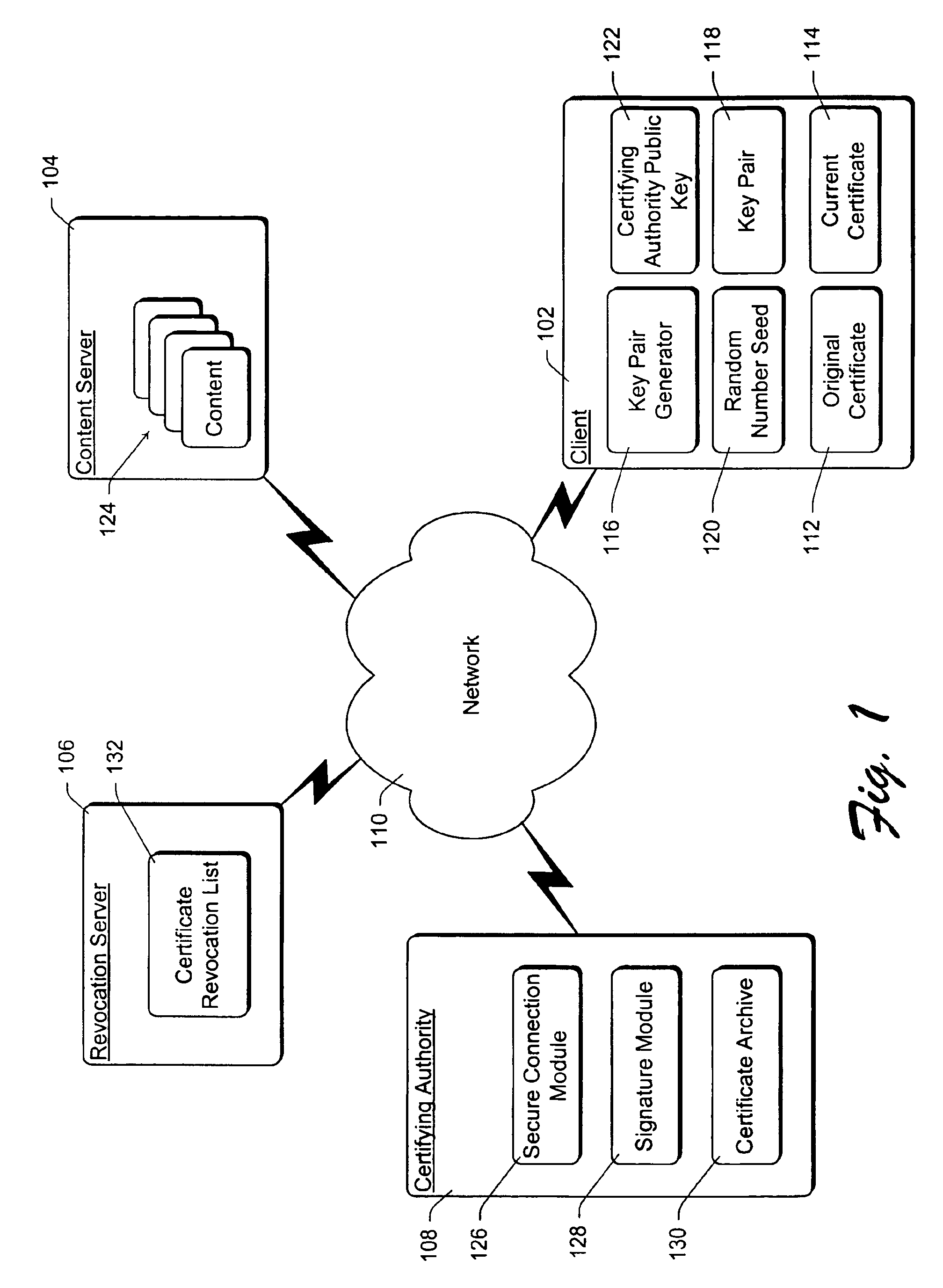
InactiveUS6871276B1Synchronising transmission/receiving encryption devicesPublic key for secure communicationSecurity propertiesClient-side
In a cryptographic system, a certificate is used to provide information regarding a client device. The certificate is blindly signed by a certifying authority to preserve the anonymity of the client device. However, information is encoded into the signature so that a content server can readily verify security attributes of the client device and make decisions regarding the delivery of electronic content to the client device based on those security attributes.
Owner:MICROSOFT TECH LICENSING LLC
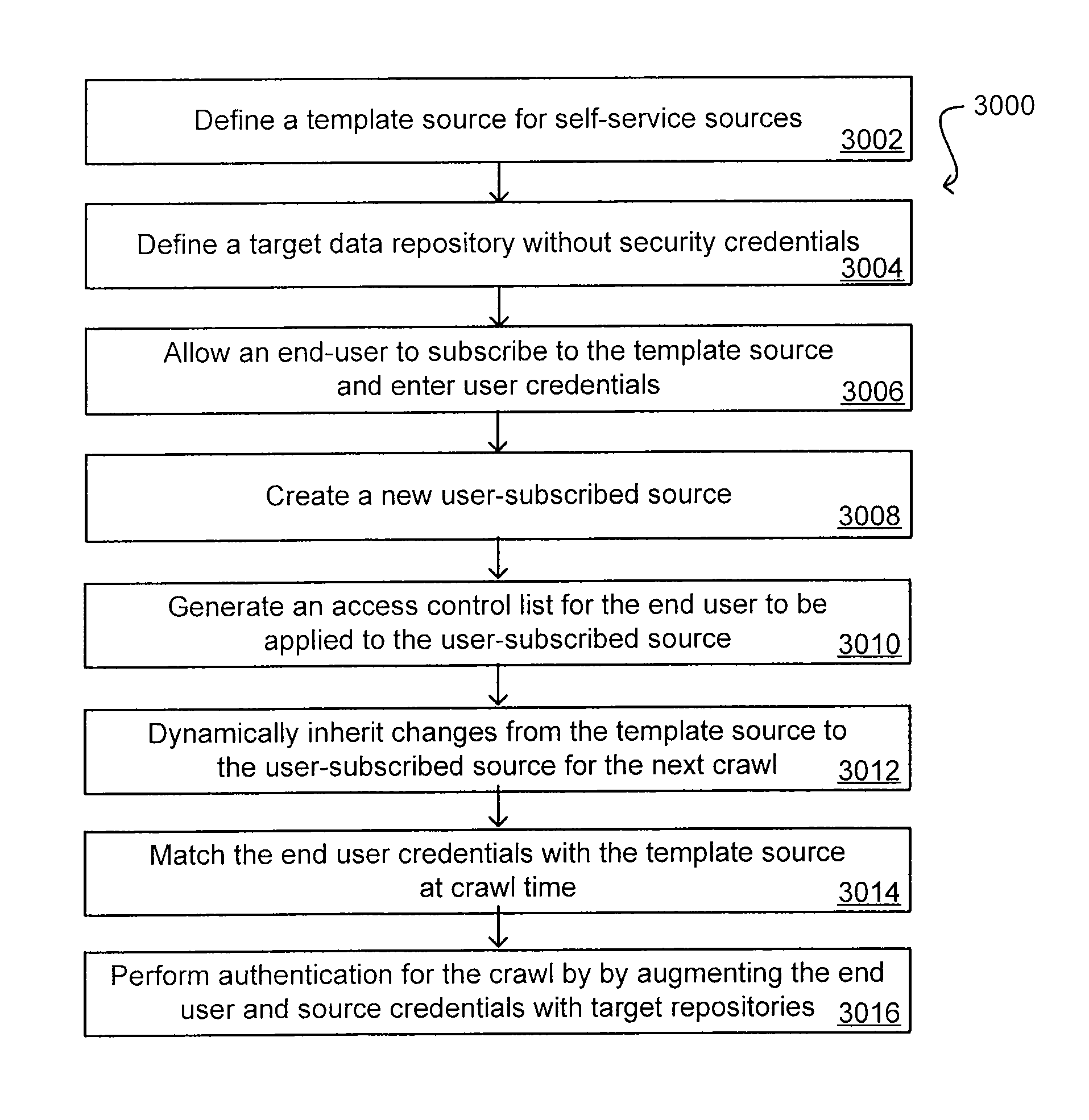
Self-Service Sources for Secure Search
ActiveUS20070208745A1Limited lifetimeImprove performanceDigital data processing detailsComputer security arrangementsExtensible architectureThe Internet
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
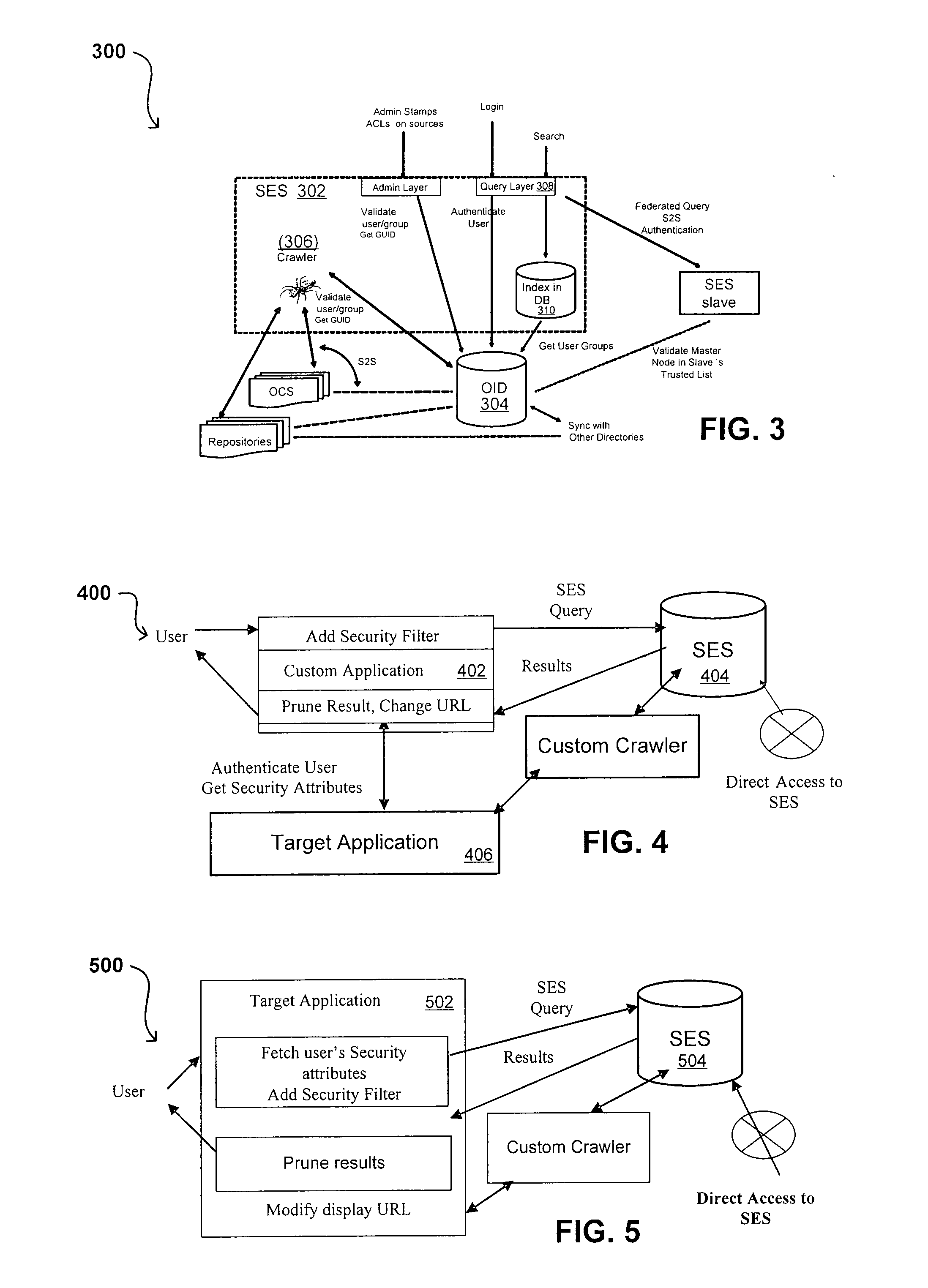
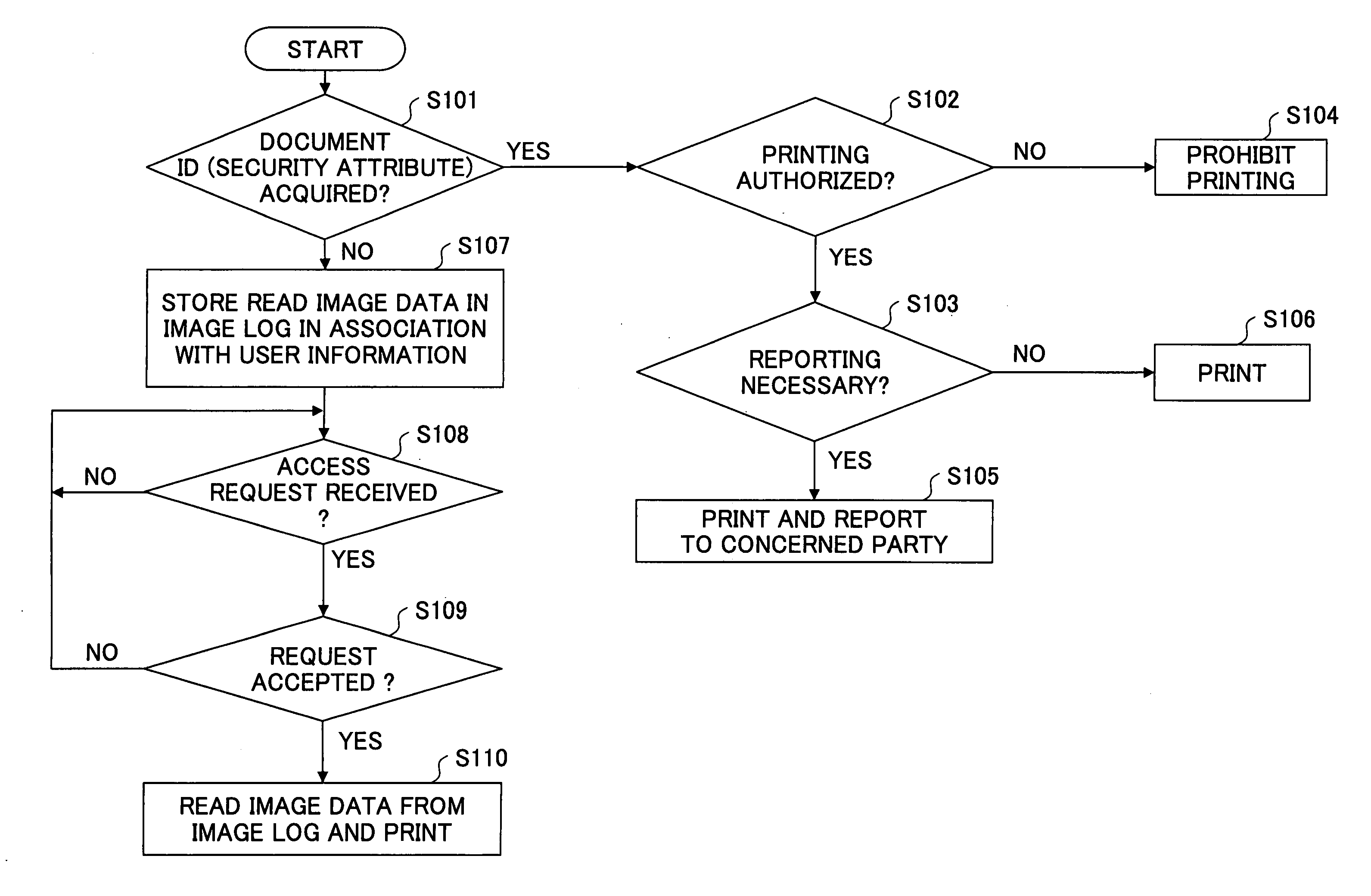
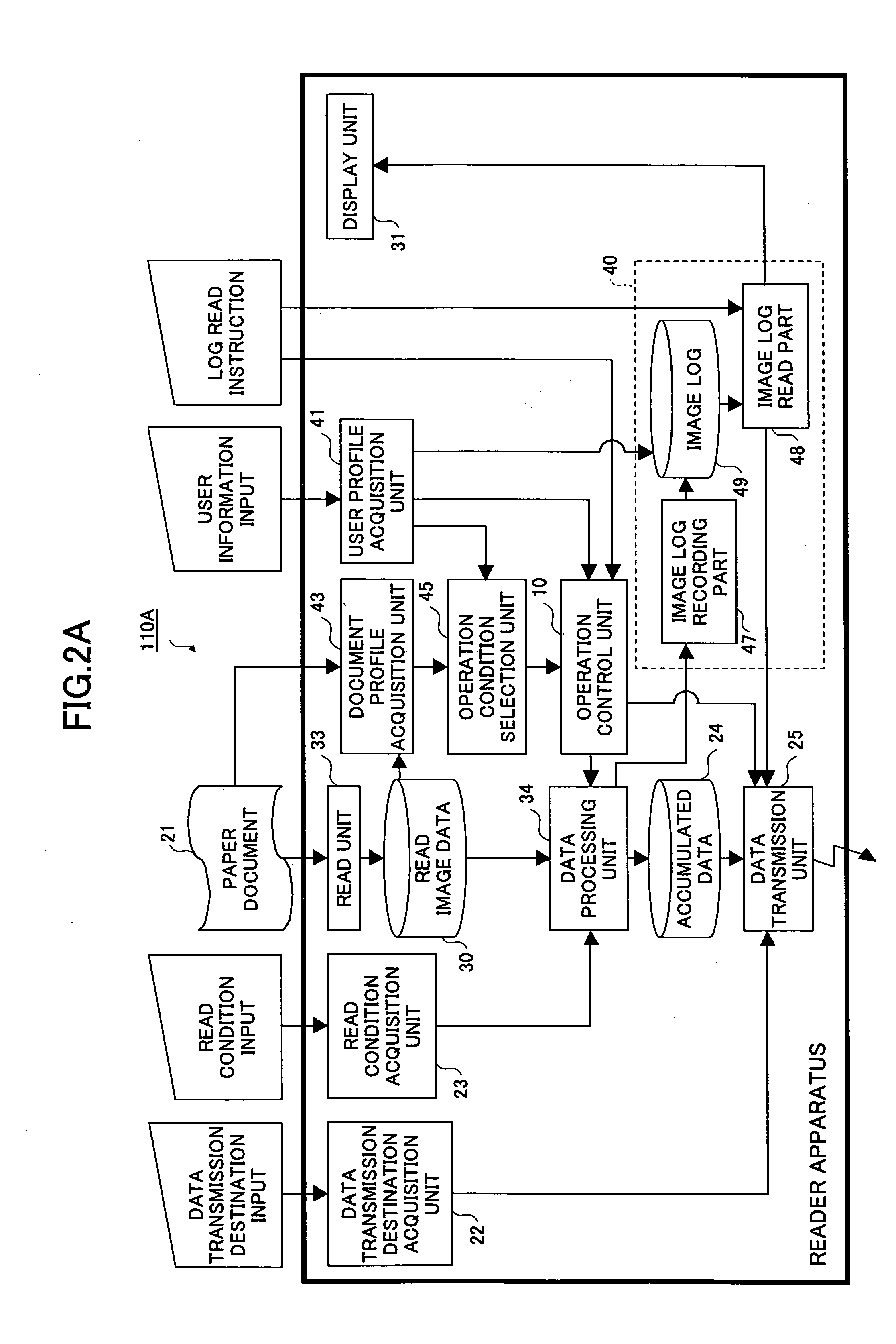
Imaging apparatus, imaging system, security management apparatus, and security management system
InactiveUS20050144469A1User identity/authority verificationUnauthorized memory use protectionSafety management systemsPaper document
An imaging apparatus is provided that is capable of maintaining document security control even in a case where document ID information cannot be identified from a physical document that is subject to an imaging operation. The imaging apparatus includes a read unit for reading image data from a physical document in response to an imaging request from a user, a user information acquisition unit for acquiring user information including a security attribute of the user, a document information acquisition unit for acquiring document information including a security attribute of the physical document, an operating condition selection unit for determining whether to authorize outputting of the image data read from the physical document based on the user information and the document information by referring to a predetermined rule, and a log management unit for storing the image data in association with the user information without allowing the image data to be output when the document information is not acquired at the document information acquisition unit.
Owner:RICOH KK
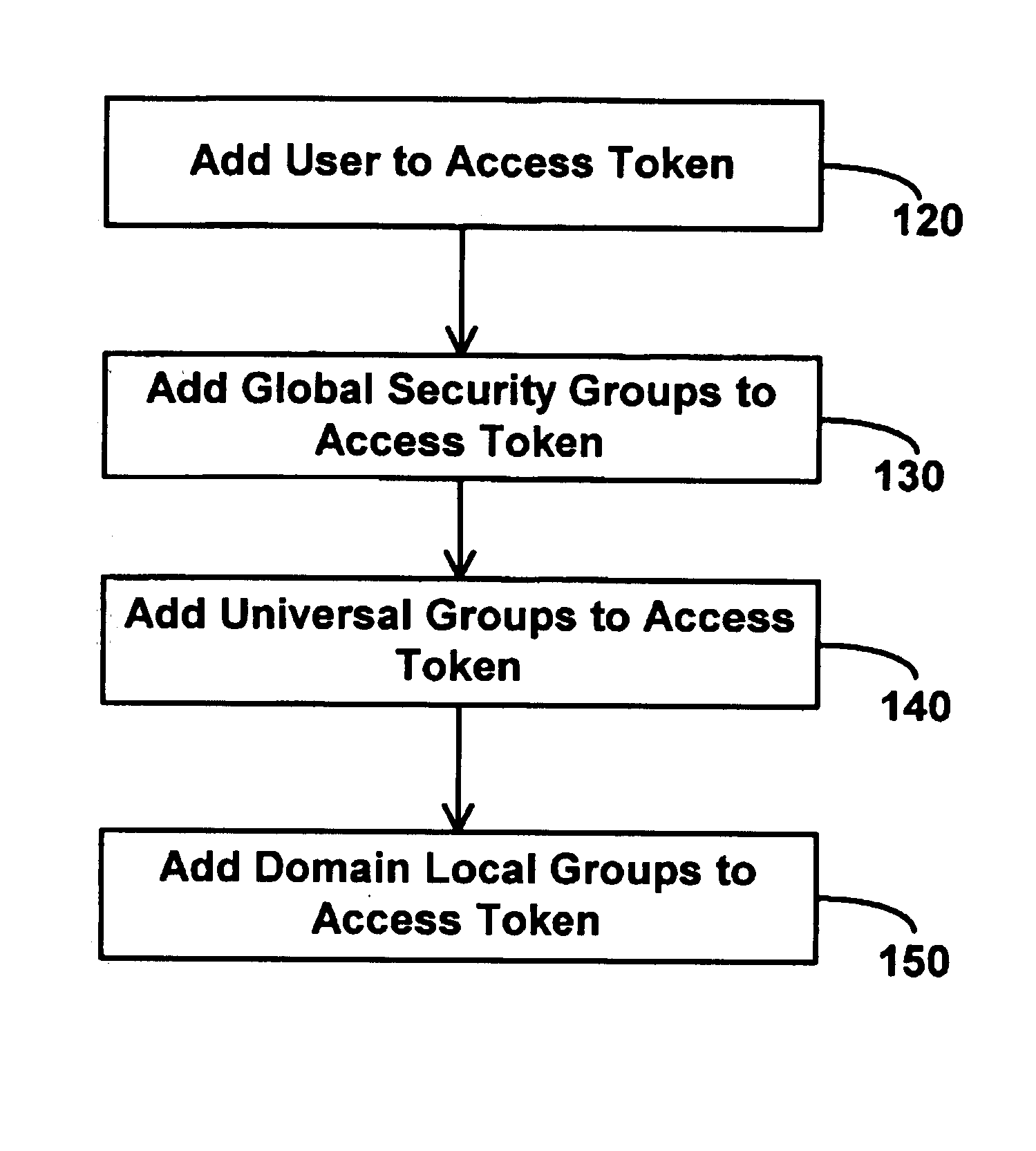
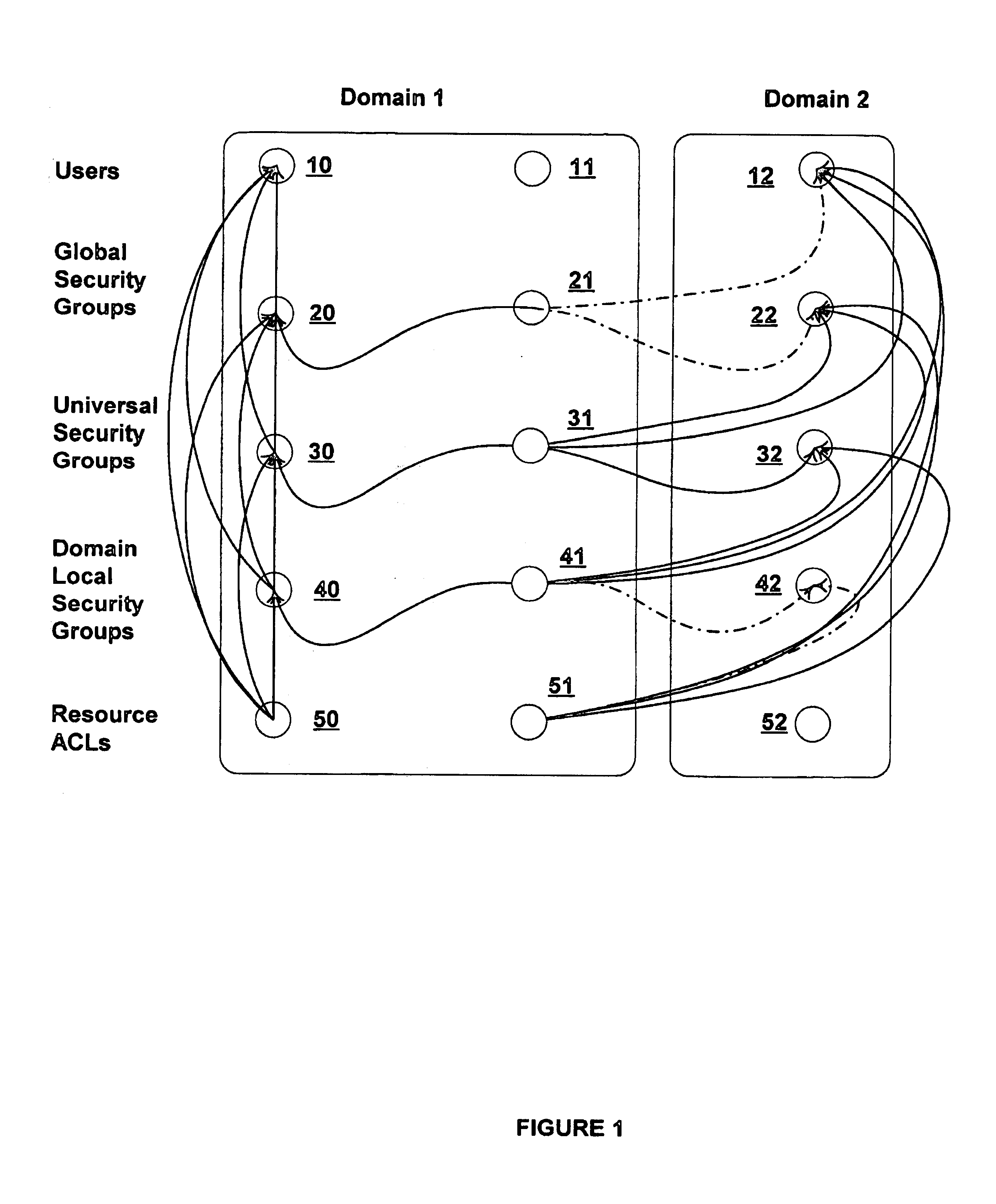
Group types for administration of networks
InactiveUS7103784B1AdministeringReduce overheadDigital data processing detailsComputer security arrangementsNetwork managementSecurity properties
An improved system and method for network management is presented which facilitates better administration with a more intuitive reflection of the organizational structure with integrated security concerns by introducing novel strategies for grouping users of a network. In particular, a new group, the Universal Group, is introduced to facilitate nested groups with members in more than one Domain. Members of a universal group may be allowed access to resources across Domain boundaries, where Domains reflect a security boundary in the Network. In addition, the nesting of groups, e.g., within Universal Groups, is enabled, subject to some restrictions, in order to reduce the overhead associated with discovering the groups to which a user belongs. Furthermore, allowing a group to include members without security clearance, but restricting the groups listed on an access token corresponding to a user to groups to which the user has security clearence / authorizarion allows flexible management of groups having similar memberships but different security attributes.
Owner:MICROSOFT TECH LICENSING LLC
Modelling network to assess security properties
A method of assessing a network uses a model (450) having nodes (100, 110) to represent parts of the network infrastructure and the application services, and having links to represent how the nodes influence each other. Dependencies or effects of the application services are found by determining paths through the nodes and links of the model (530). Such assessment can be useful for design, test, operations, and diagnosis, and for assessment of which parts of the infrastructure are critical to given services, or which services are dependent on, or could have an effect on a given part of the infrastructure. The dependencies or effects can encompass reachability information. The use of a model having links and nodes can enable more efficient processing, to enable larger or richer models. What changes in the dependencies or effects result from a given change in the network can be determined (830).
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Probabilistic signature scheme
InactiveUS6266771B1Reduce bandwidth requirementsUser identity/authority verificationHash functionAlgorithm
An RSA-based signing scheme that combines essentially optimal efficiency with attractive security properties. One preferred signing routine requires one RSA decryption plus some hashing, verifications requires one RSA encryption plus some hashing, and the size of the signature preferably is the size of the modulus. Given an ideal underlying hash function, the scheme is not only provably secure, but has security tightly related to the security of RSA. An alternative embodiment maintains all of the above features and, in addition, provides message recovery. The techniques can be extended to provide schemes for Rabin-based signatures or signatures using other trapdoor functions.
Owner:RGT UNIV OF CALIFORNIA
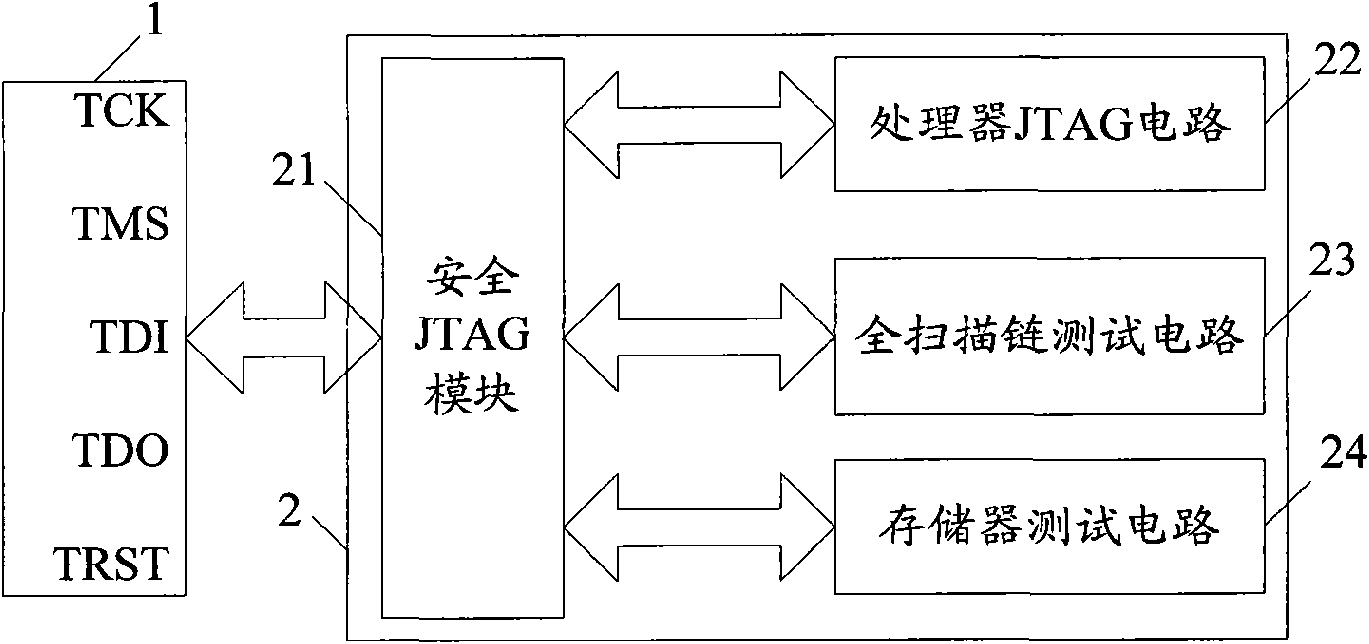
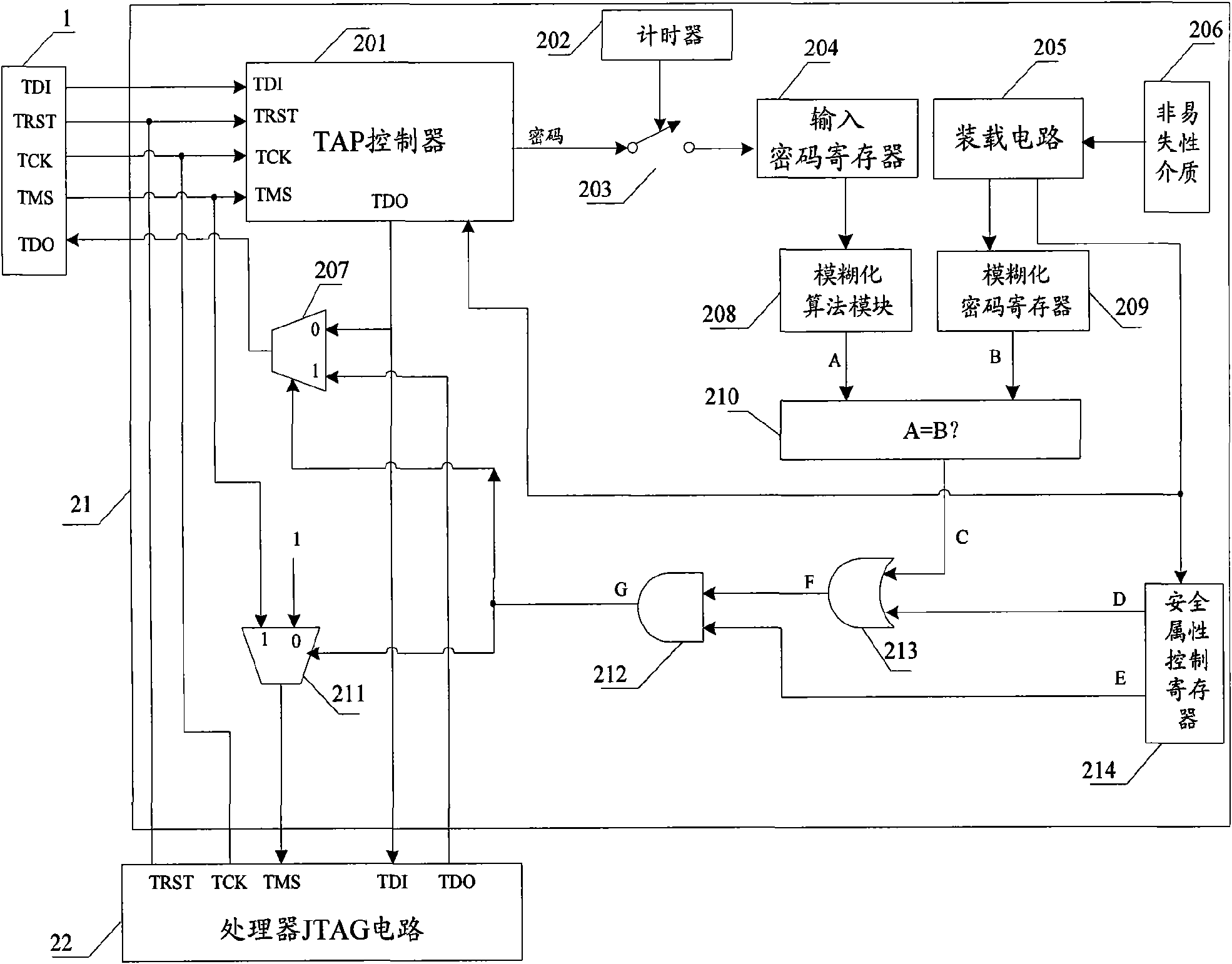
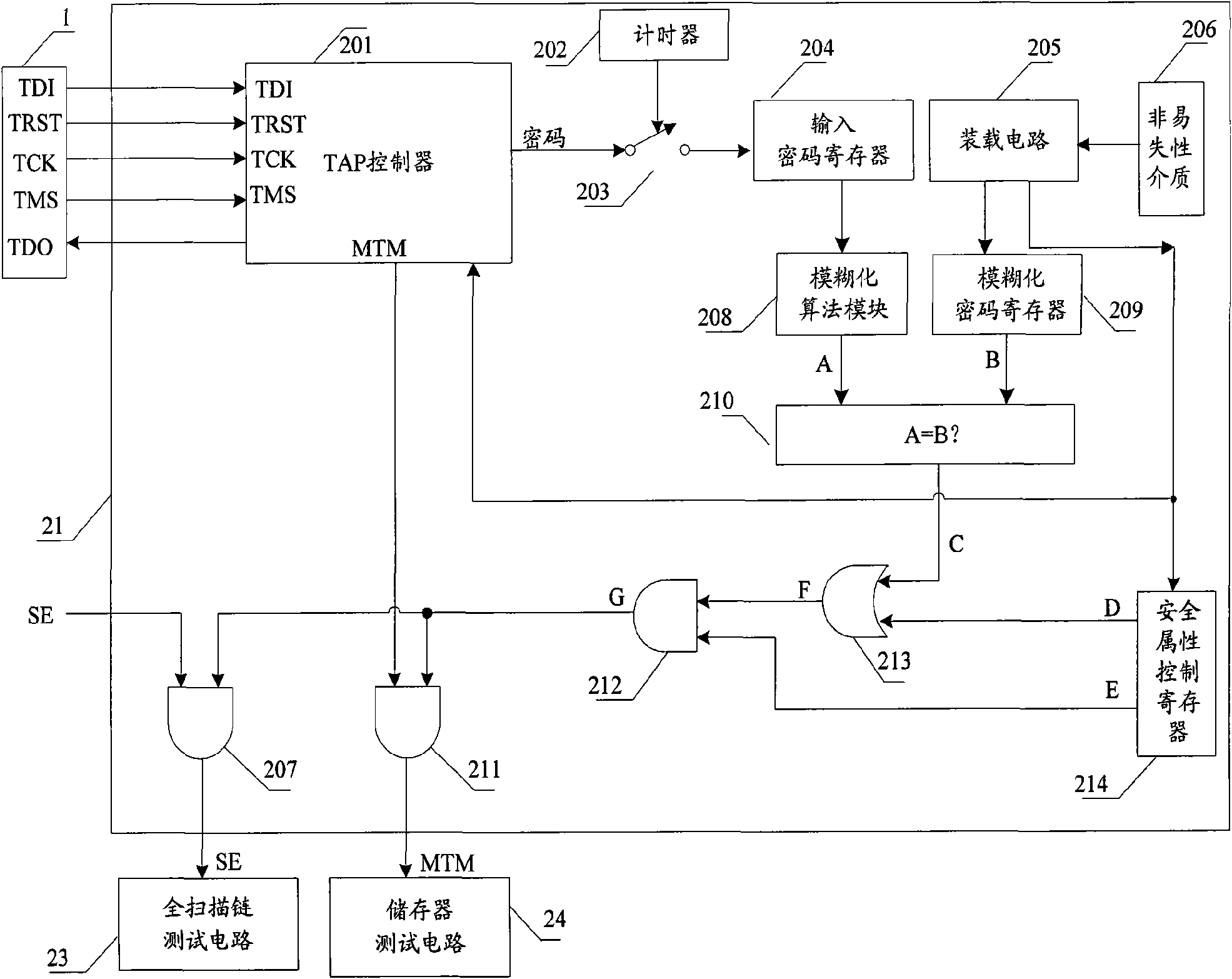
Safety JTAG module and method for protecting safety of information inside chip
InactiveCN101620656AReduce security risksImprove data security featuresInternal/peripheral component protectionProcessor registerPassword
The invention relates to a safety JTAG module and a method for protecting security of information inside a chip, wherein the safety JTAG module comprises a nonvolatile medium (206), a loading circuit (205), a security attribute control register (214), a TAP controller (201), two selectors (207 and 211), a switch (203), a password authentication module and a logic processing module; the TAP controller (201) and the two selectors (207 and 211) are connected between a JTAG port (1) and a protected object inside the chip; the switch (203) is switched by the control of a timer (202); the password authentication module is used for authenticating whether a clear-text password input by a user is accordant with a fuzzification password or not; and the logic processing module is used for logically processing an authentication result output by the password authentication module and an indication signal output by the security attribute control register (214) and outputting an enable signal to the two selectors (207 and 211) so as to control whether the JTAG port (1) is allowed to be connected with the protected object inside the chip through the TAP controller (201) or not. The invention ensures the security and the convenience of an SOC chip in testing and debugging processes, thereby protecting the security of data inside the chip.
Owner:SHENZHEN STATE MICRO TECH CO LTD
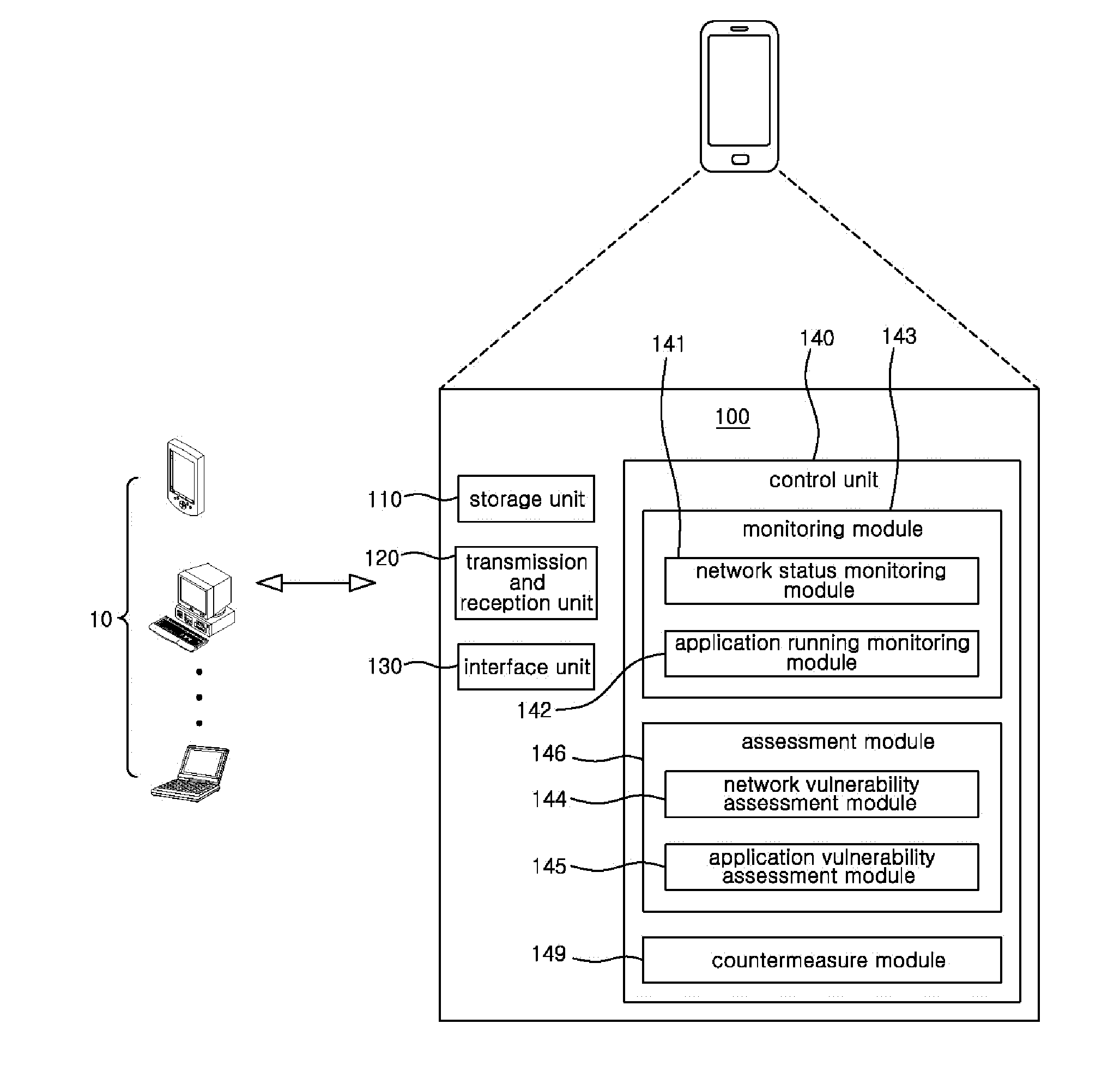
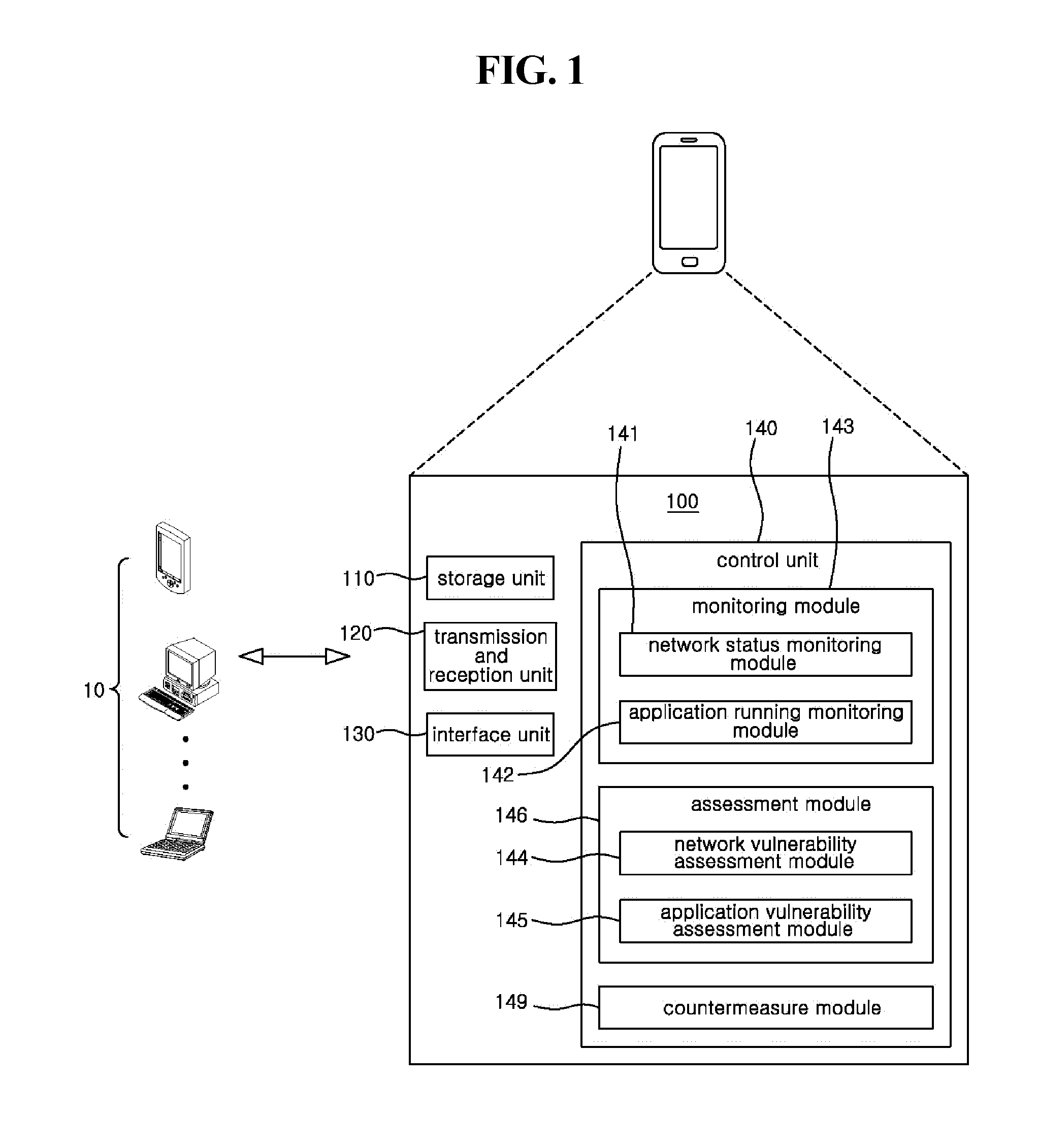
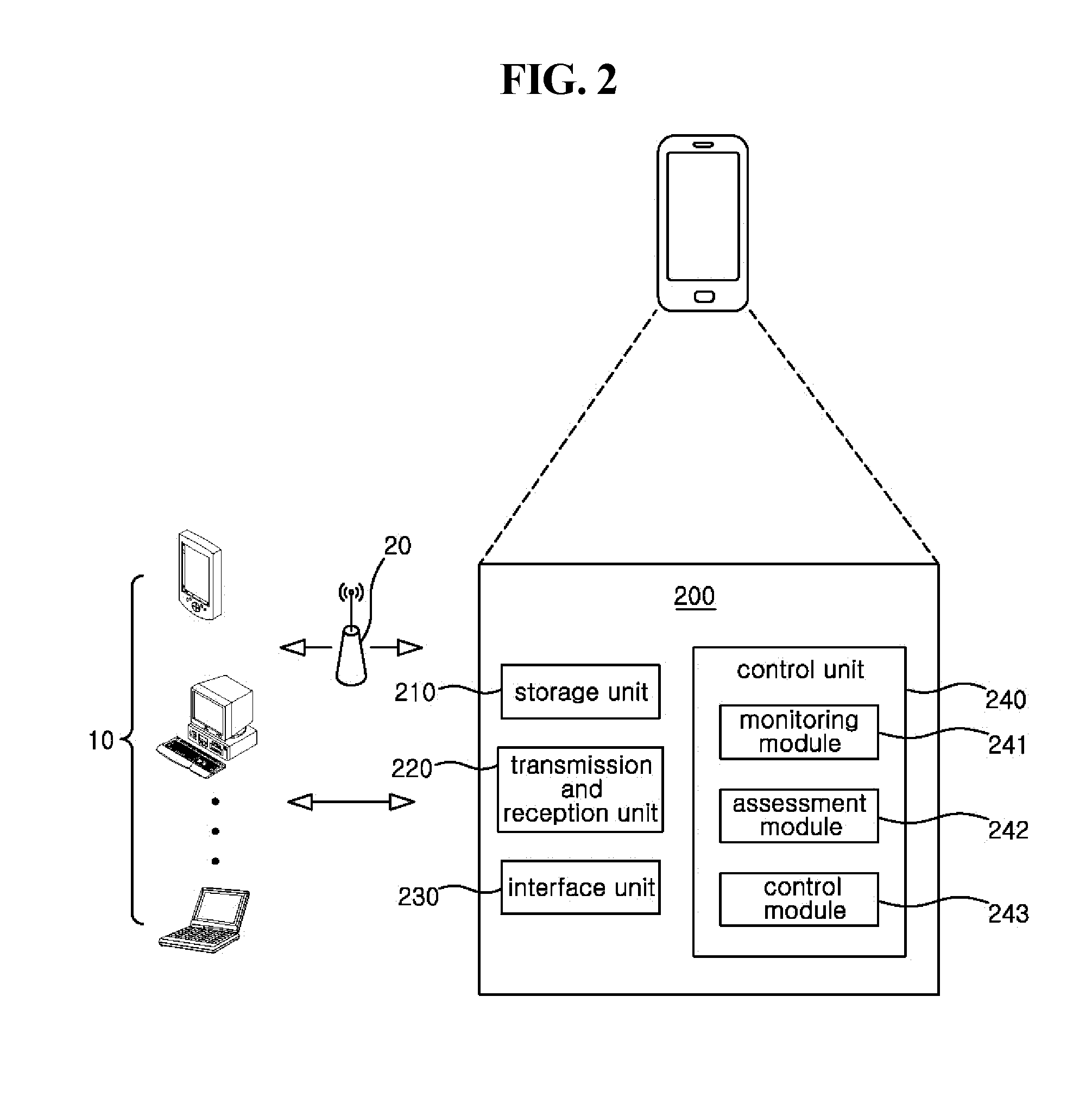
Mobile terminal with security functionality and method of implementing the same
InactiveUS20120137369A1Prevent leakageMemory loss protectionError detection/correctionCountermeasureSecurity properties
Disclosed herein is a mobile terminal with security functionality and a method of implementing the mobile terminal. The mobile terminal with security functionality includes a storage unit, a first module, a second module, and a third module. The storage unit stores a list of risky function combinations which may cause security risks. The first module monitors functions included in an application to be installed or running in the mobile terminal. The second module assesses security vulnerabilities based on whether a combination of the monitored functions corresponds to a risky function combination and / or security attributes of the mobile terminal. The third module takes countermeasures when a security vulnerability has been found based on the assessment.
Owner:SKINFOSEC CO LTD
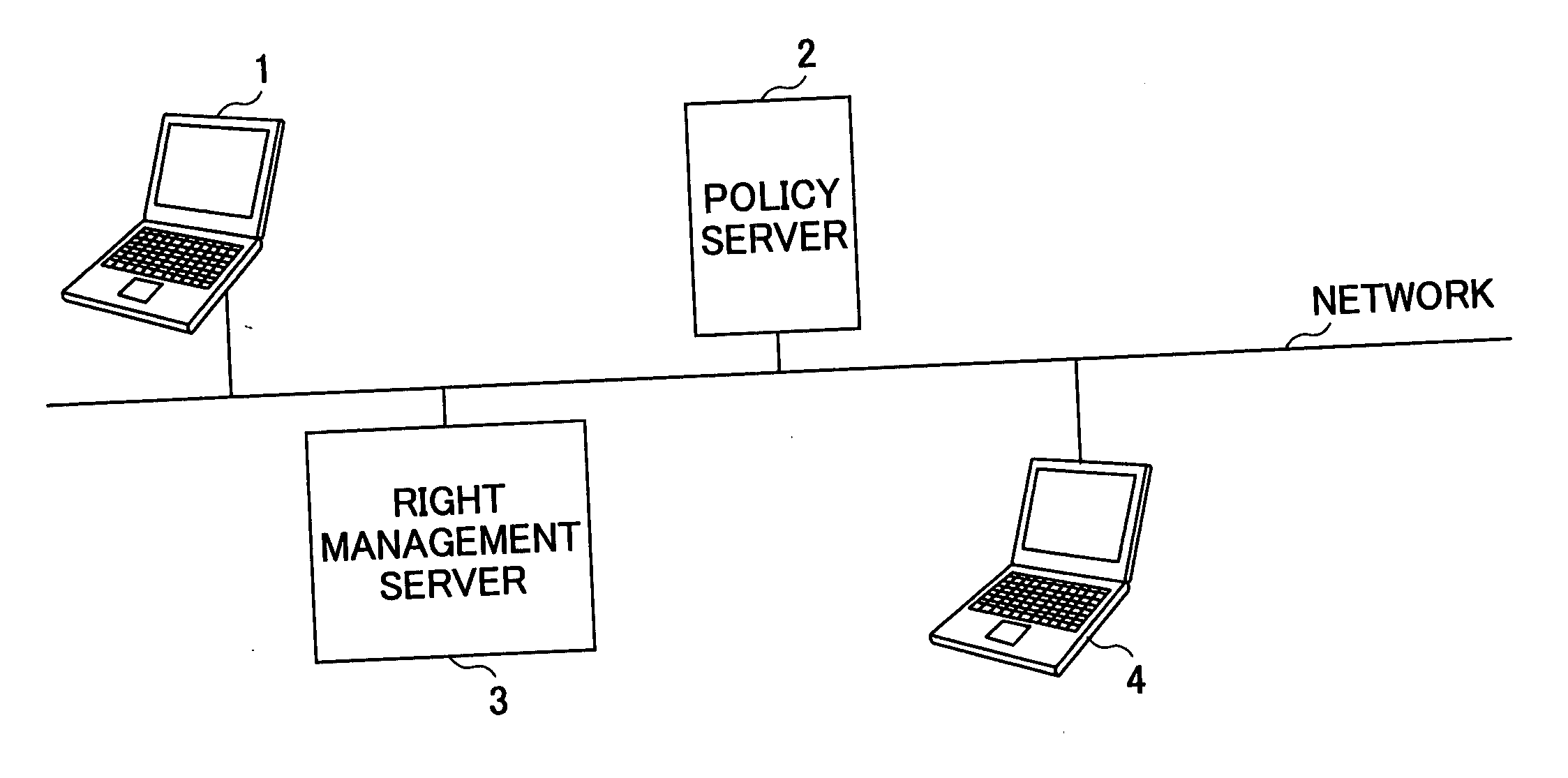
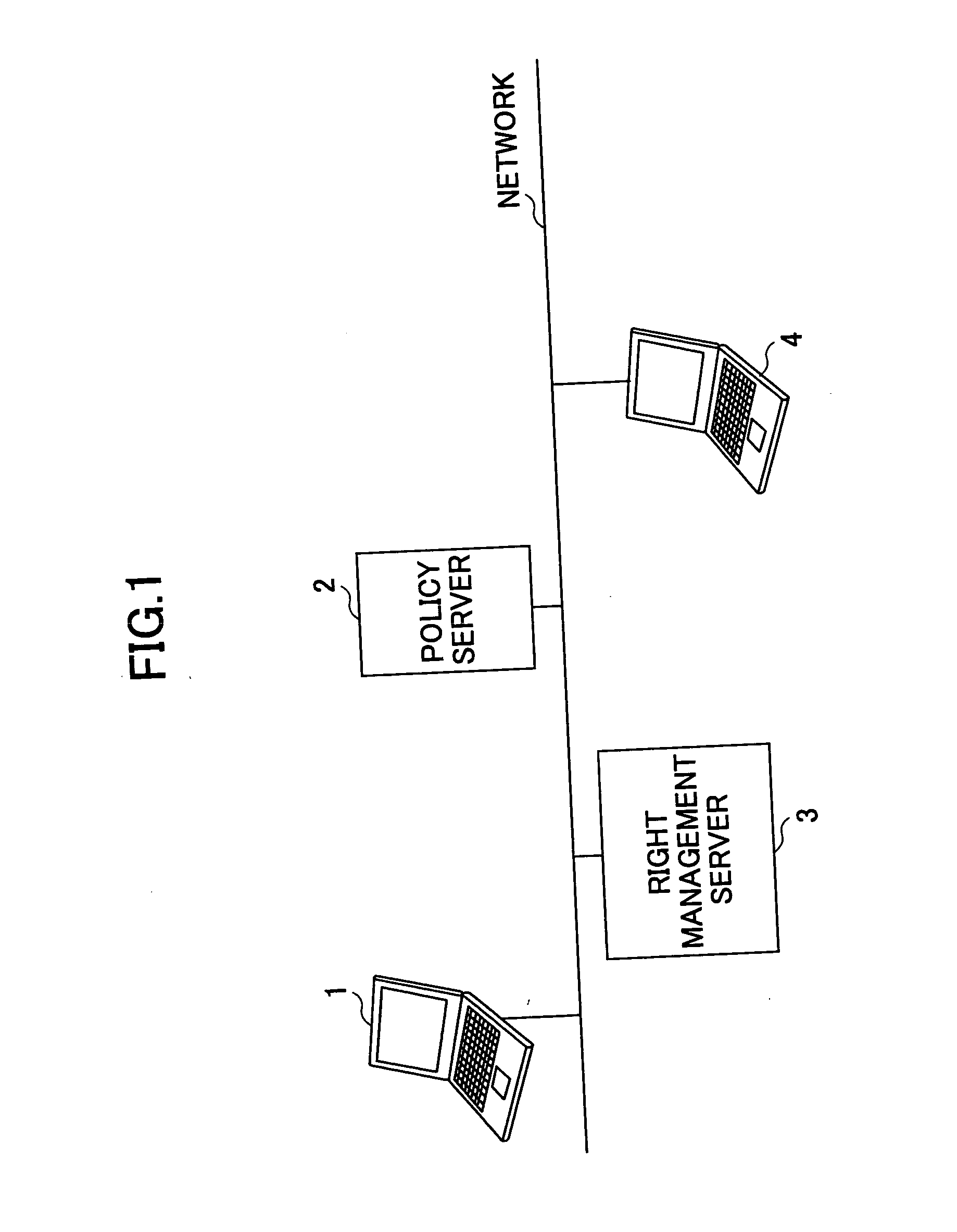
Access control list attaching system, original content creator terminal, policy server, original content data management server, program and computer readable information recording medium
InactiveUS20060031923A1Failure of attachmentDigital data protectionProgram/content distribution protectionNetwork connectionData management
An access control list attaching system in which an original content creator terminal for creating original content data, a policy server producing a security policy file concerning the original content data and holding it in a storage part and a right management server managing a right concerning the original content data are connected via a communication network. The policy server includes an access control list generating part generating an access control list concerning the original content data based on an attribute of the security concerning the original content data and the security policy file in which the security policy is described.
Owner:RICOH KK
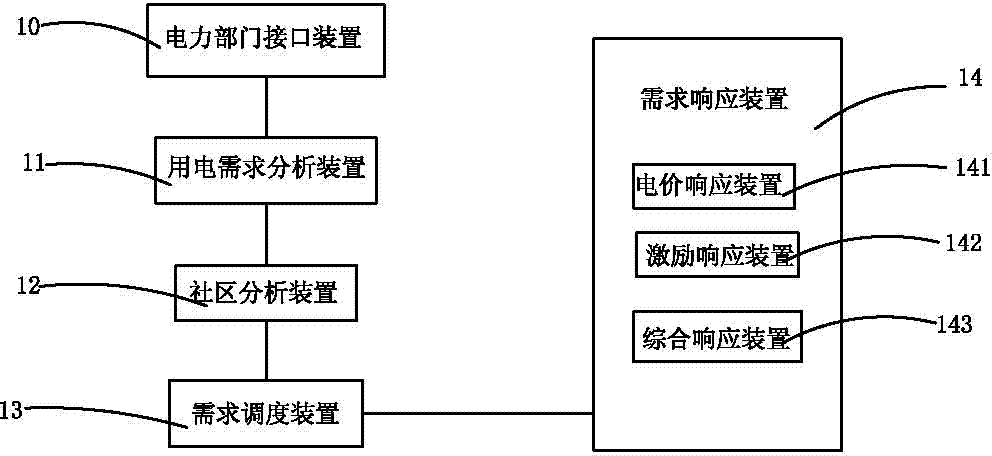
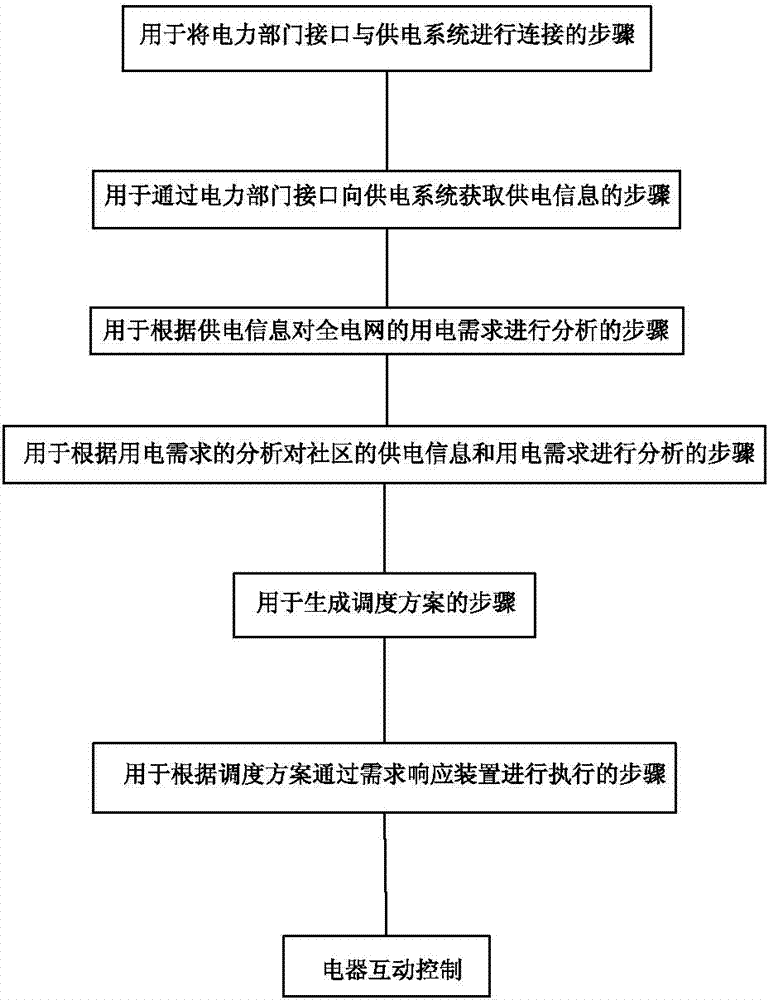
Power demand responding method and system
InactiveCN102738801AHigh transparencyImprove securityPower network operation systems integrationAc network voltage adjustmentPower gridSecurity properties
The invention provides a power demand responding method, comprising the following steps of: connecting a power department interface with a power supply system; obtaining power supply information from the power supply system through the power department interface; analyzing a power demand on an entire power grid according to the power supply information; analyzing the power supply information and a power demand of a community according to the analysis of the power demand; generating a scheduling scheme; and executing the scheduling scheme through a demand responding device. A system corresponding to the power demand responding method comprises a power department interface device, a power demand analyzing device, a community analyzing device, a demand scheduling device and the demand responding device. With the adoption of the responding method and the responding system, the load of the power grid can be balanced; the security property of the power grid is improved; the comprehensive electric charge of a user can be reduced; and the influence of power rationing on resident lives can be avoided.
Owner:SHENZHEN CLOU ELECTRONICS
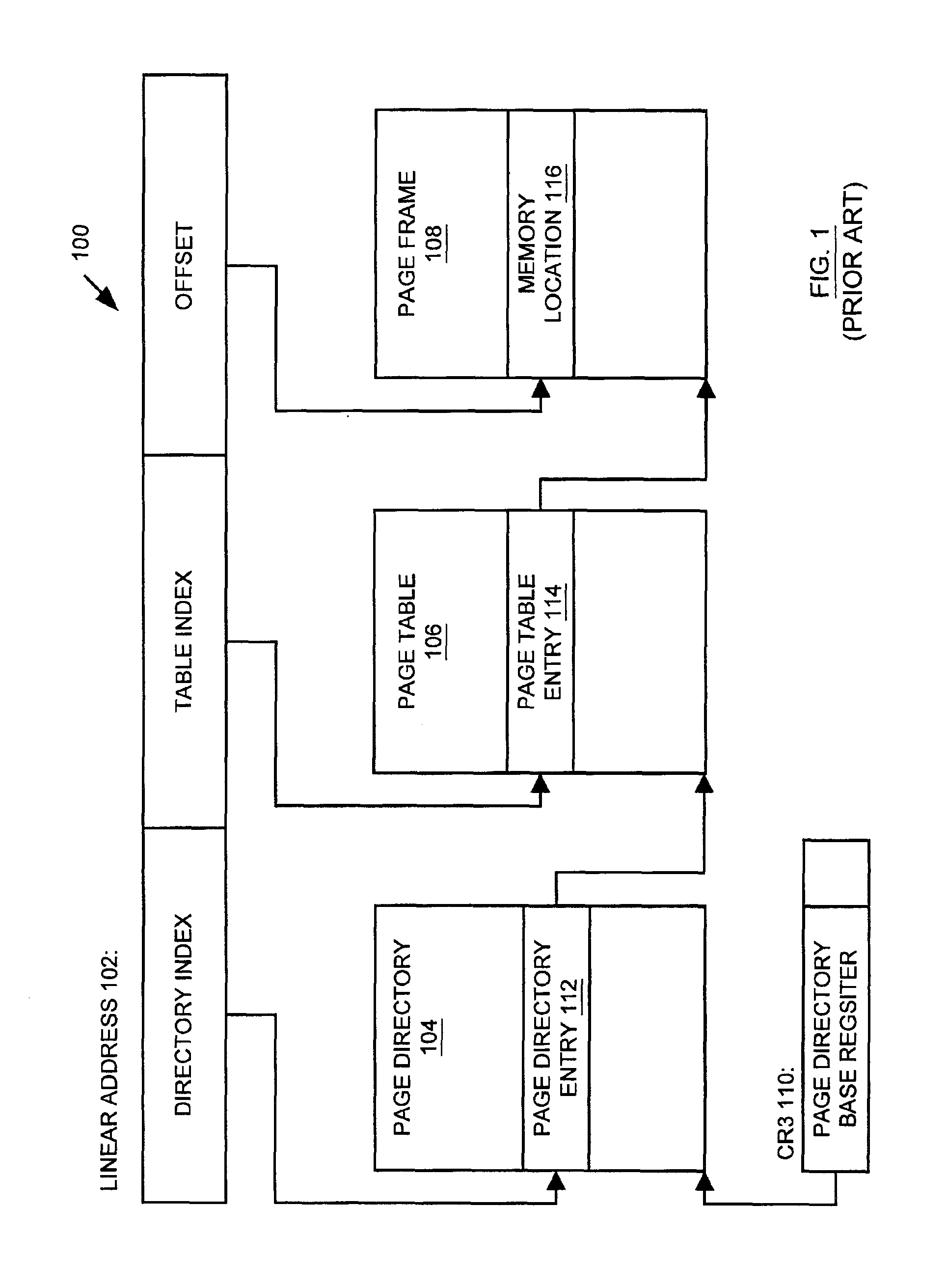
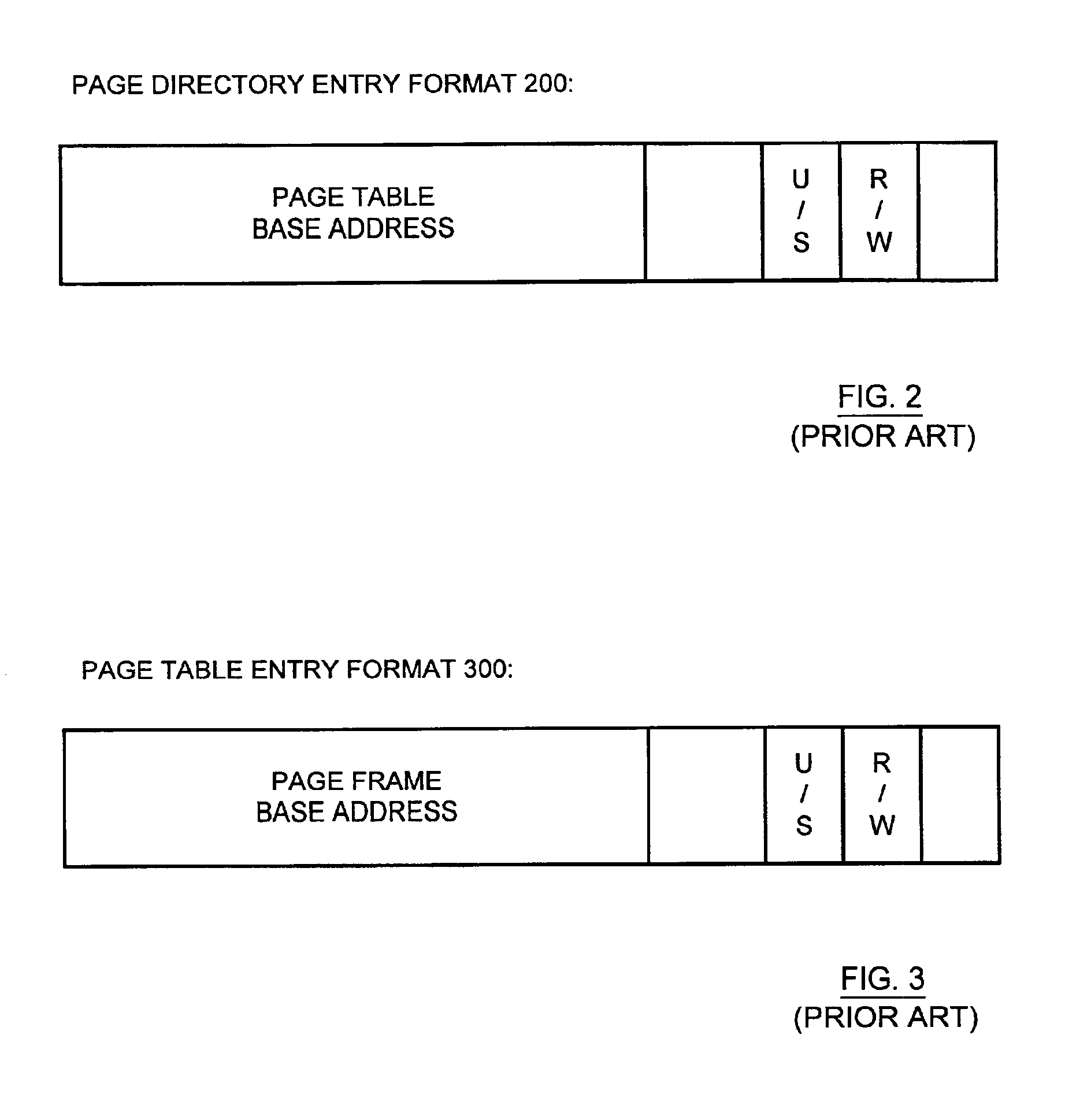
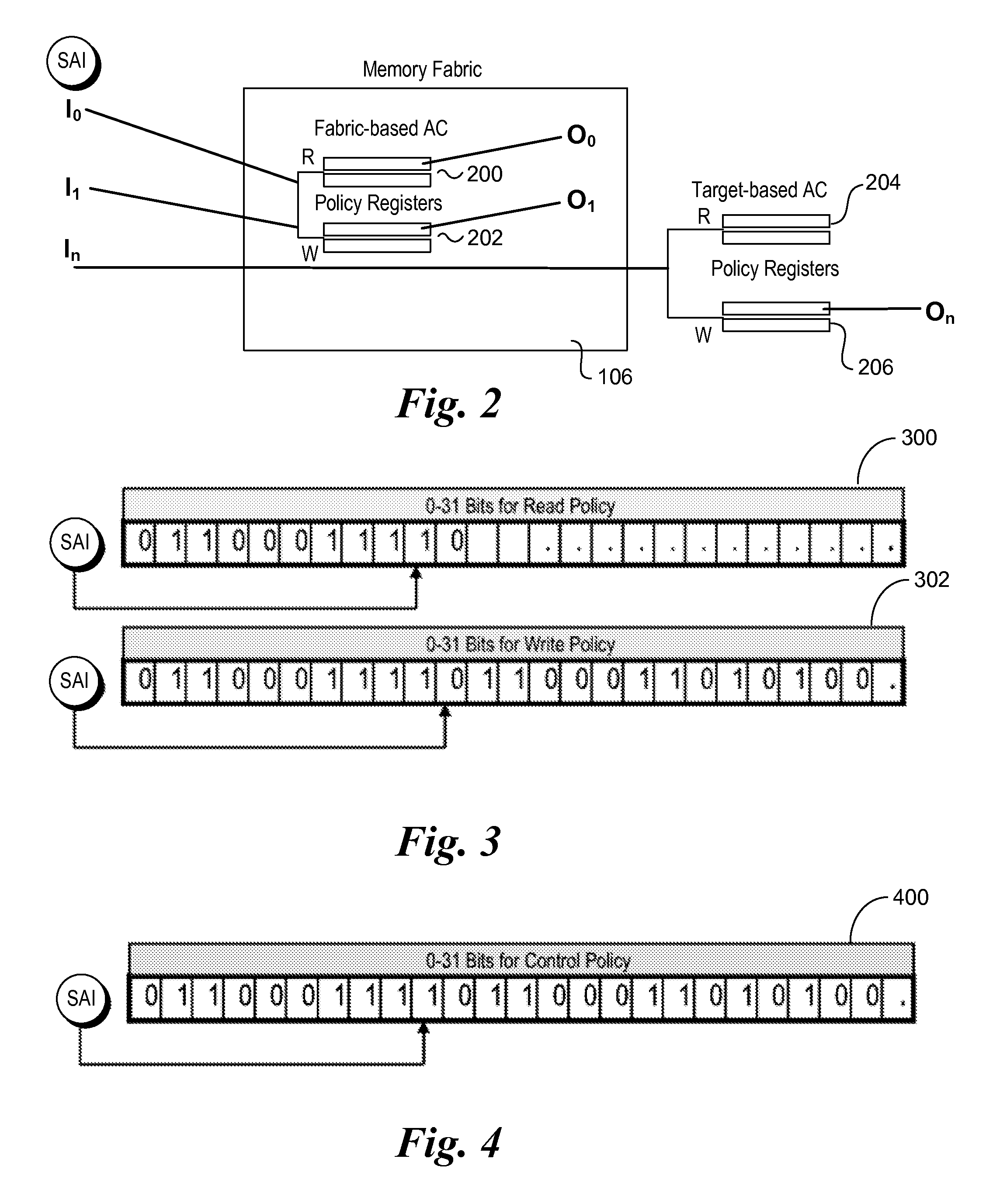
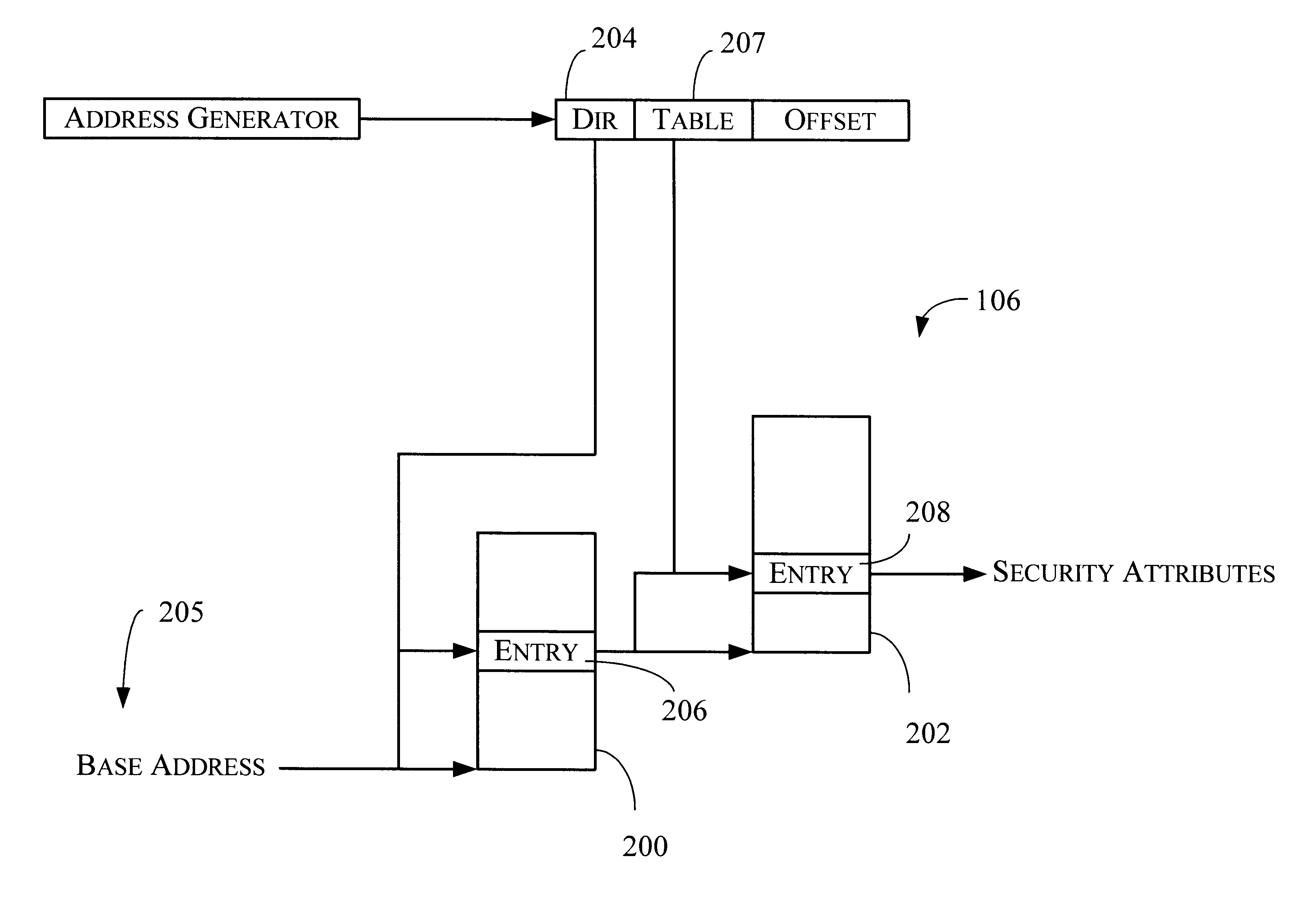
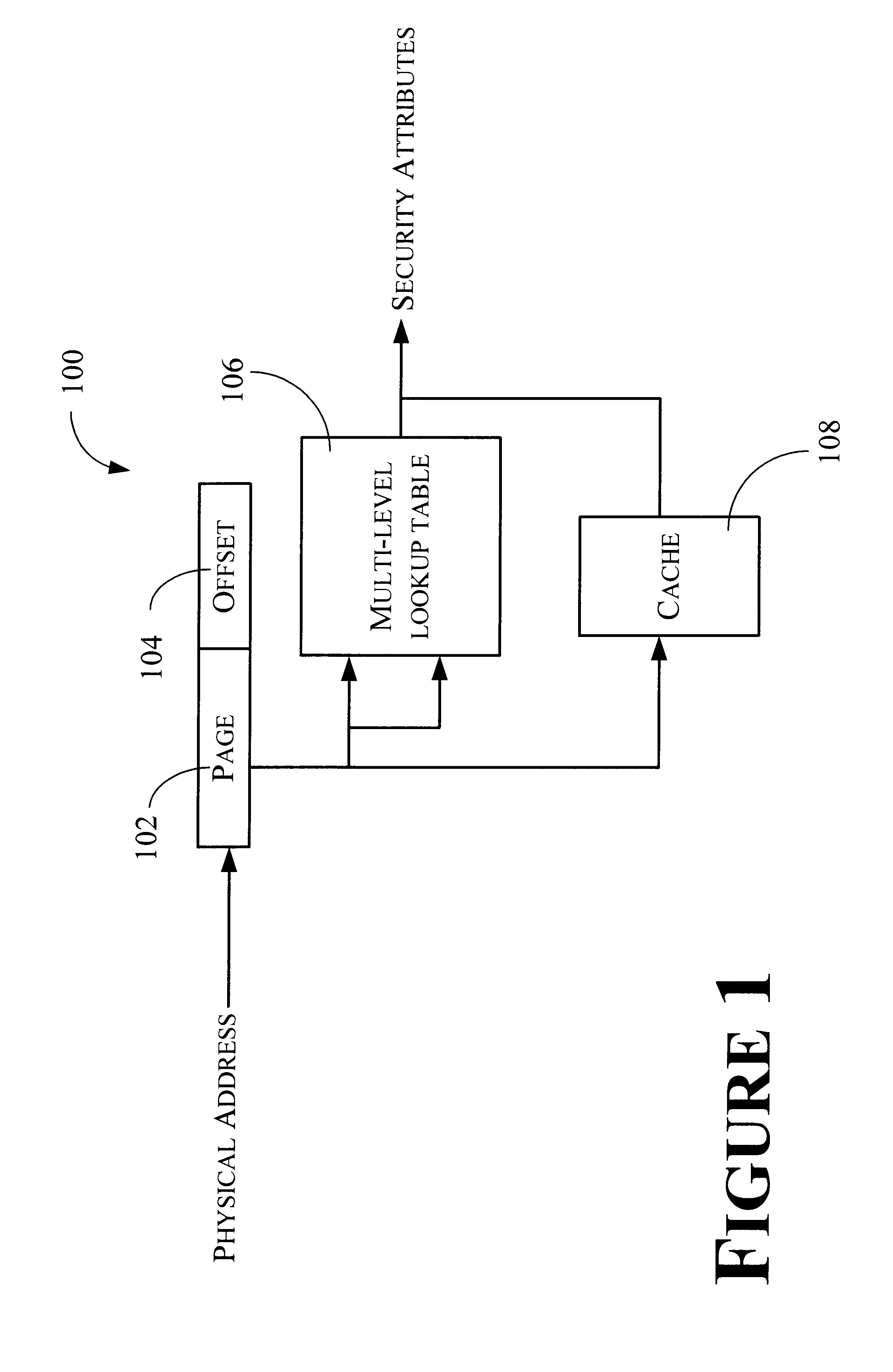
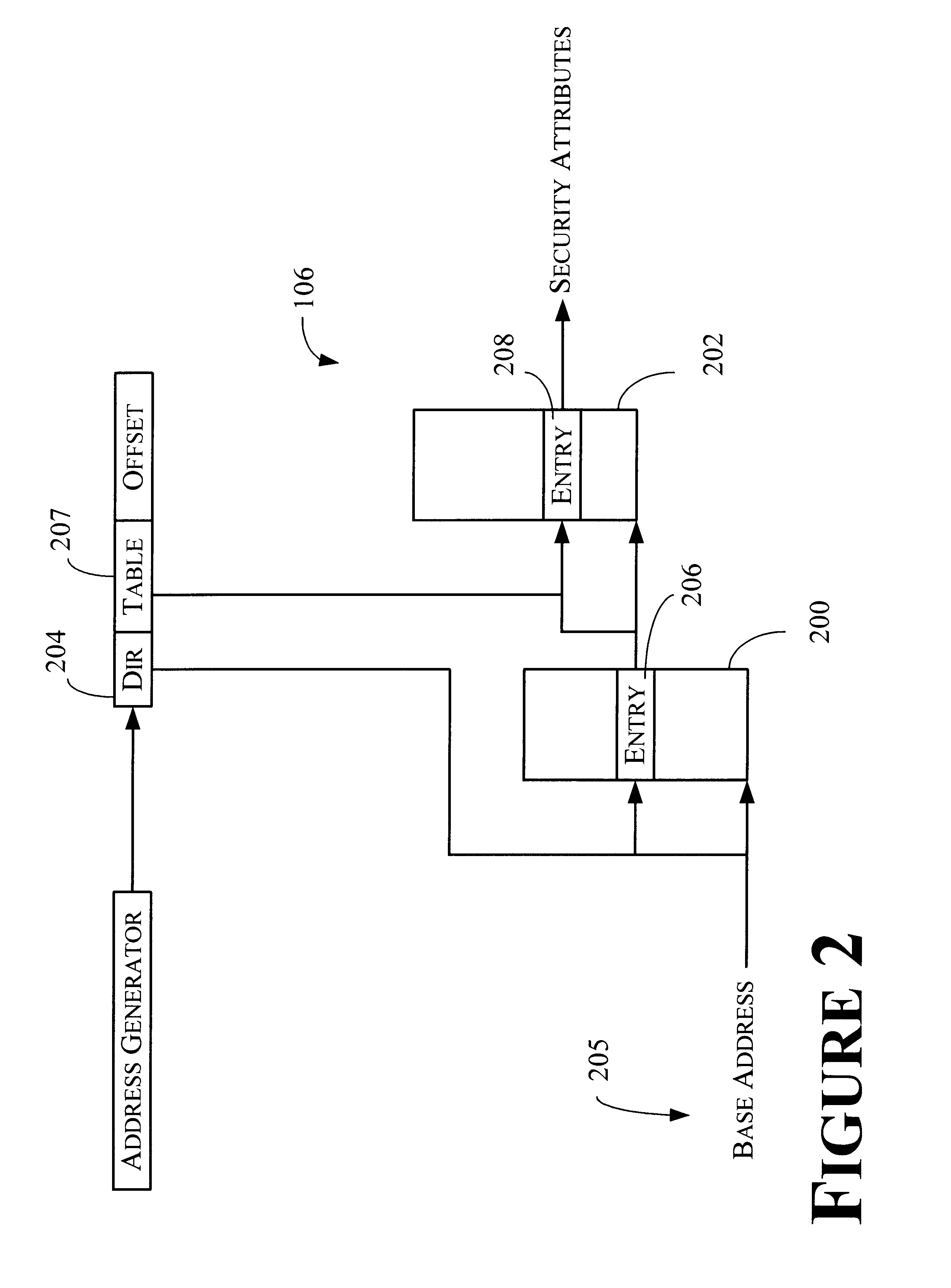
Method and apparatus for storing and retrieving security attributes
An apparatus is provided for providing security in a computer system. The apparatus comprises an address generator, a multi-level lookup table, and a cache. The address generator is adapted for producing an address associated with a memory location in the computer system. The multi-level lookup table is adapted for receiving at least a portion of said address and delivering security attributes stored therein associated with said address, wherein the security attributes are associated with each page of memory in the computer system. The cache is a high-speed memory that contains a subset of the information contained in the multi-level lookup table, and may be used to speed the overall retrieval of the requested security attributes when the requested information is present in the cache.
Owner:ADVANCED MICRO DEVICES INC
Self-service sources for secure search
ActiveUS8027982B2Limited lifetimeImprove performanceDigital data processing detailsComputer security arrangementsExtensible architectureThe Internet
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety of sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com