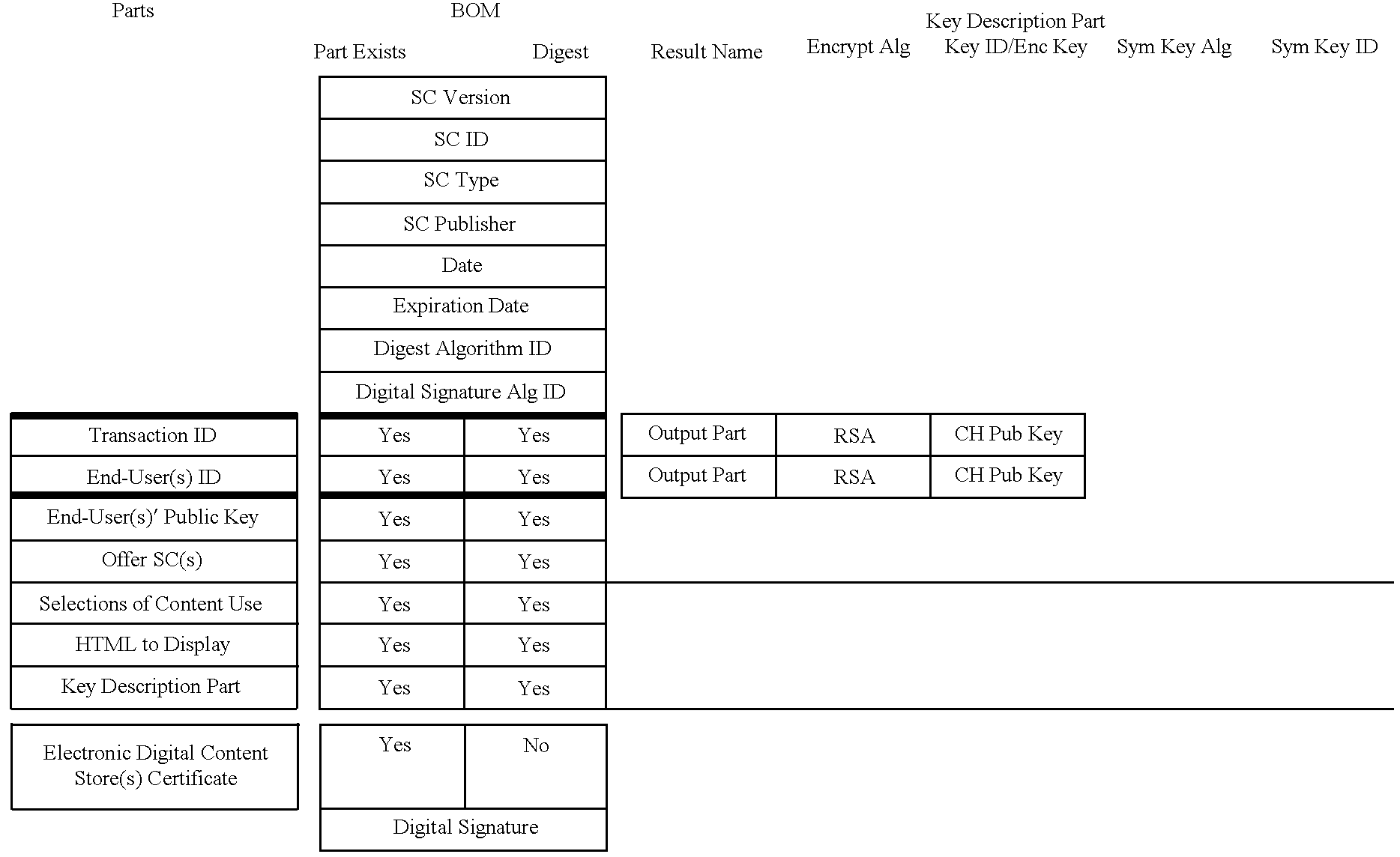
Patents
Literature
19395results about "Program/content distribution protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
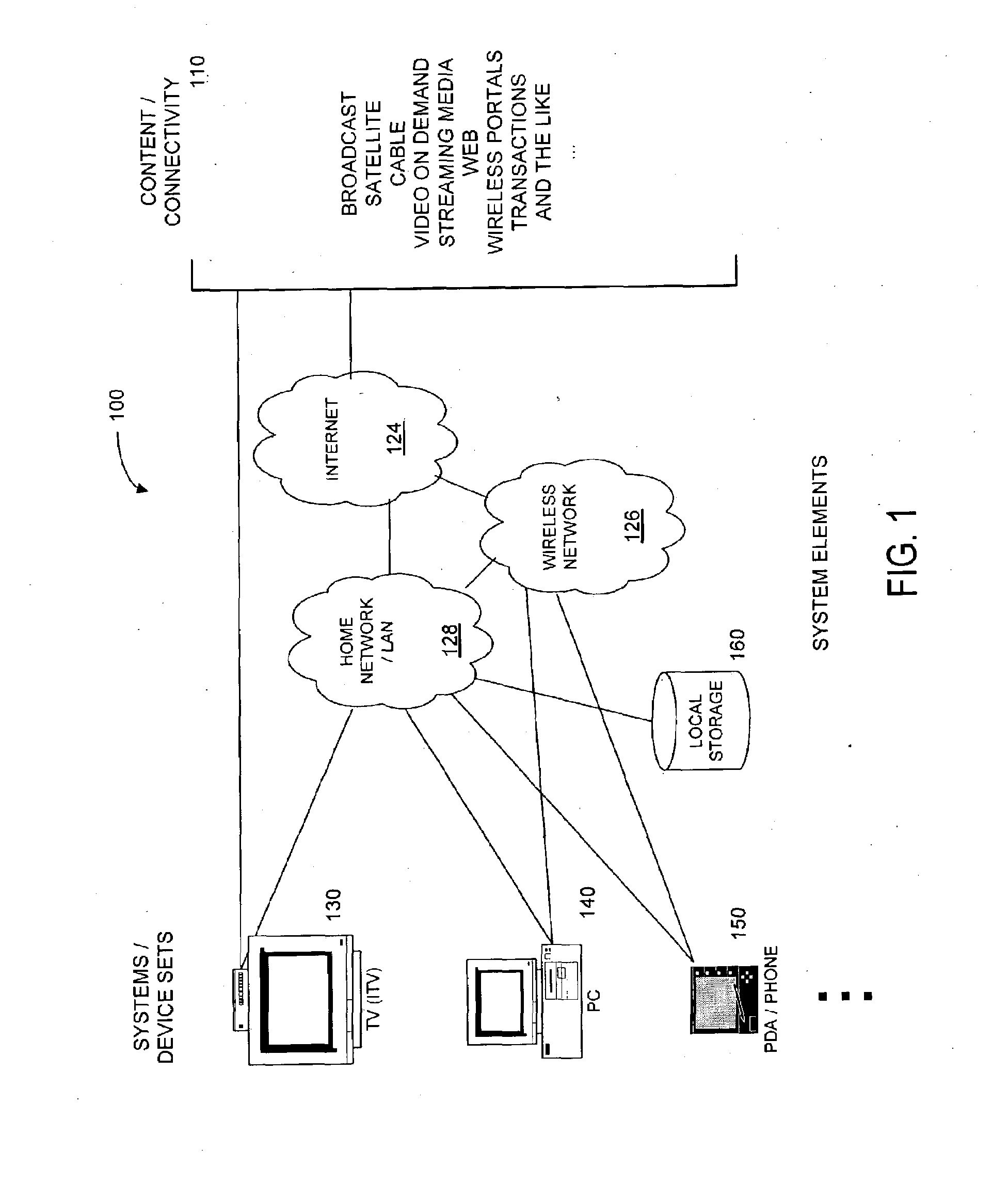
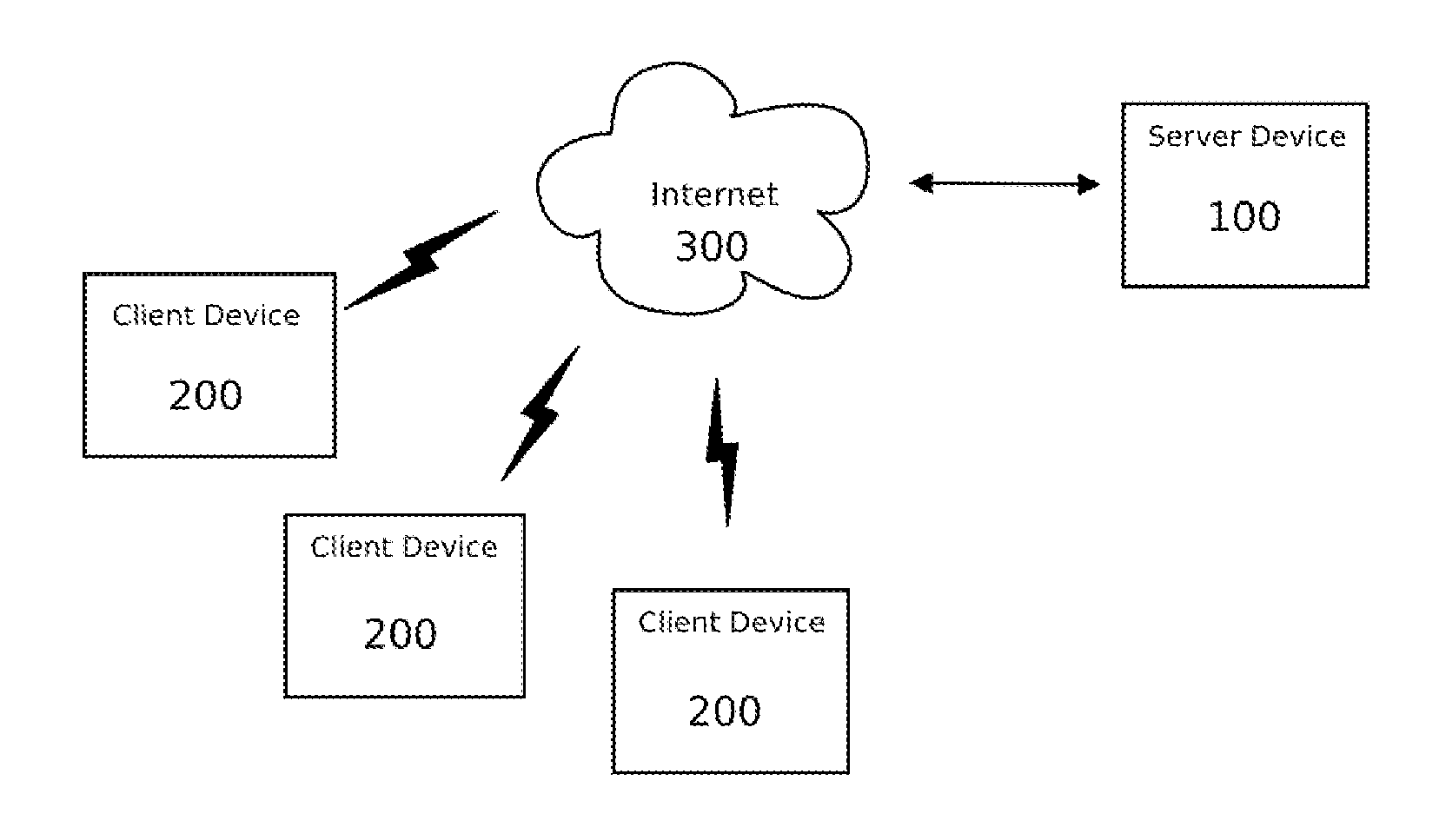
Electronic content delivery system
InactiveUS6226618B1Key distribution for secure communicationDigital data processing detailsDelivery systemSystem safety
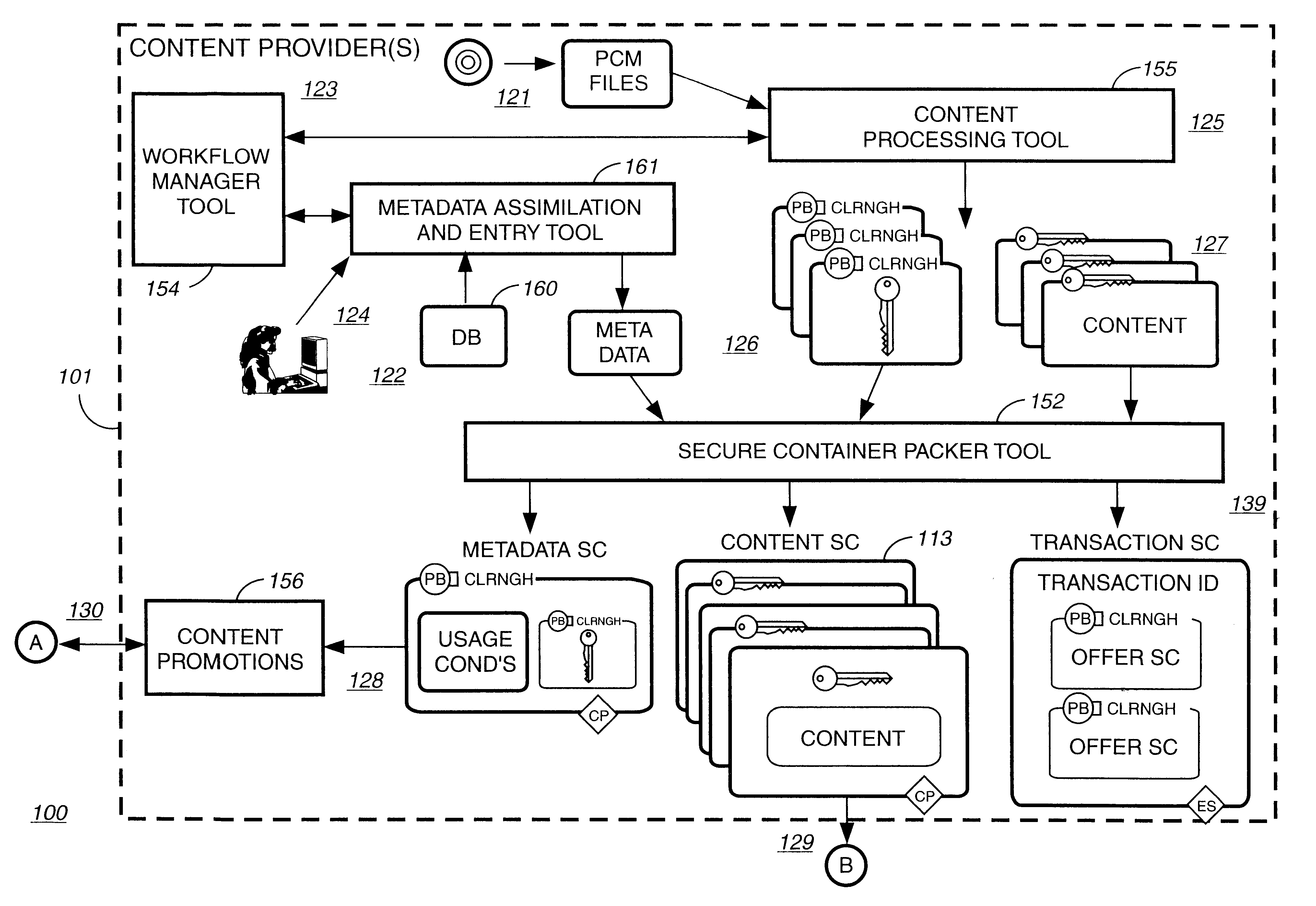
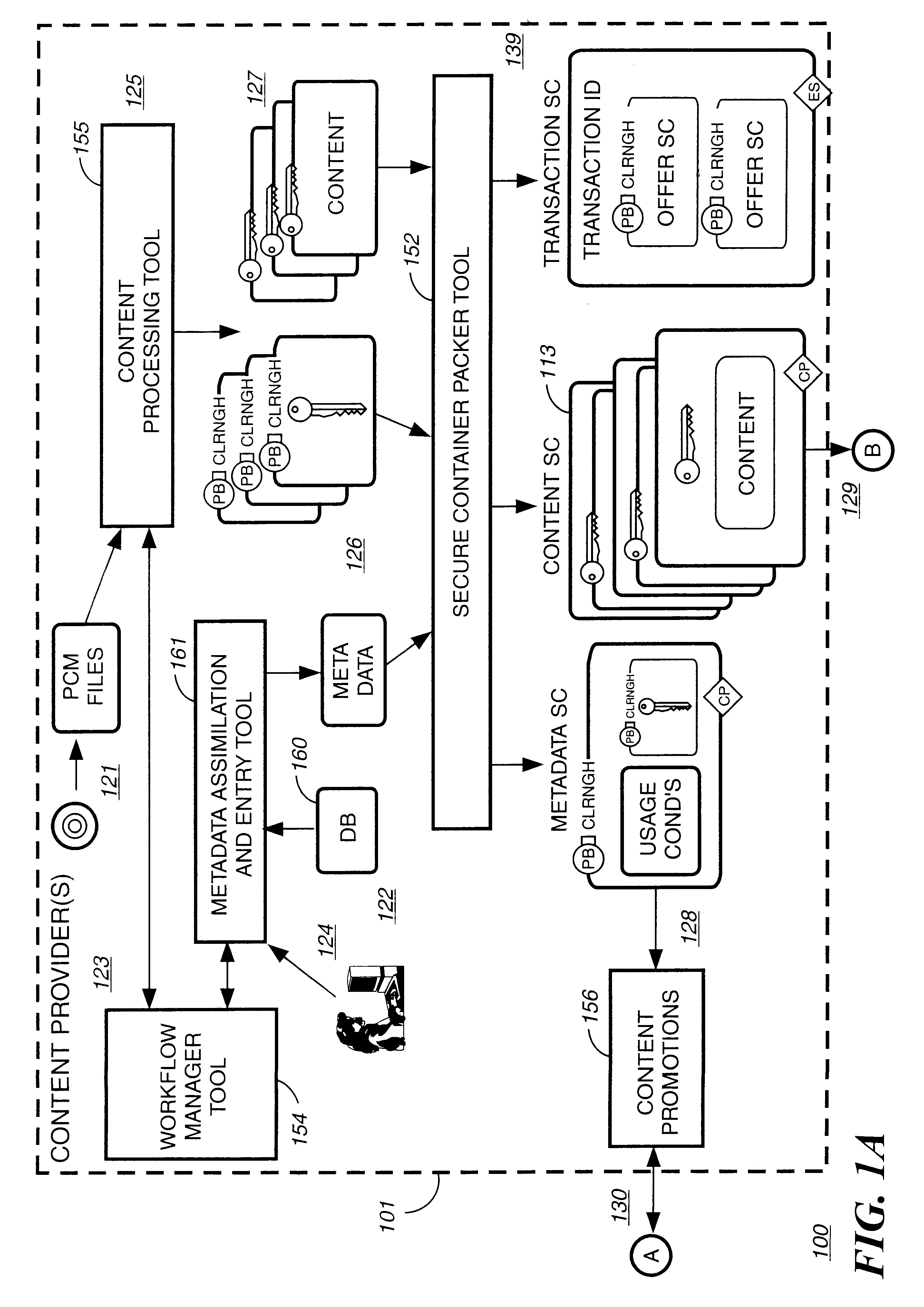
Disclosed is a method and apparatus of securely providing data to a user's system. The data is encrypted so as to only be decryptable by a data decrypting key, the data decrypting key being encrypted using a first public key, and the encrypted data being accessible to the user's system, the method comprising the steps of: transferring the encrypted data decrypting key to a clearing house that possesses a first private key, which corresponds to the first public key; decrypting the data decrypting key using the first private key; re-encrypting the data decrypting key using a second public key; transferring the re-encrypted data decrypting key to the user's system, the user's system possessing a second private key, which corresponds to the second public key; and decrypting the re-encrypted data decrypting key using the second private key.
Owner:LEVEL 3 COMM LLC
Systems and methods for matching, selecting, narrowcasting, and/or classifying based on rights management and/or other information
InactiveUS6112181AIncrease success rateCostly and inefficientUser identity/authority verificationSignalling system detailsRights managementUtility system
Rights management information is used at least in part in a matching, narrowcasting, classifying and / or selecting process. A matching and classification utility system comprising a kind of Commerce Utility System is used to perform the matching, narrowcasting, classifying and / or selecting. The matching and classification utility system may match, narrowcast, classify and / or select people and / or things, non-limiting examples of which include software objects. The Matching and Classification Utility system may use any pre-existing classification schemes, including at least some rights management information and / or other qualitative and / or parameter data indicating and / or defining classes, classification systems, class hierarchies, category schemes, class assignments, category assignments, and / or class membership. The Matching and Classification Utility may also use at least some rights management information together with any artificial intelligence, expert system, statistical, computational, manual, or any other means to define new classes, class hierarchies, classification systems, category schemes, and / or assign persons, things, and / or groups of persons and / or things to at least one class.
Owner:INTERTRUST TECH CORP
Audio visual player apparatus and system and method of content distribution using the same
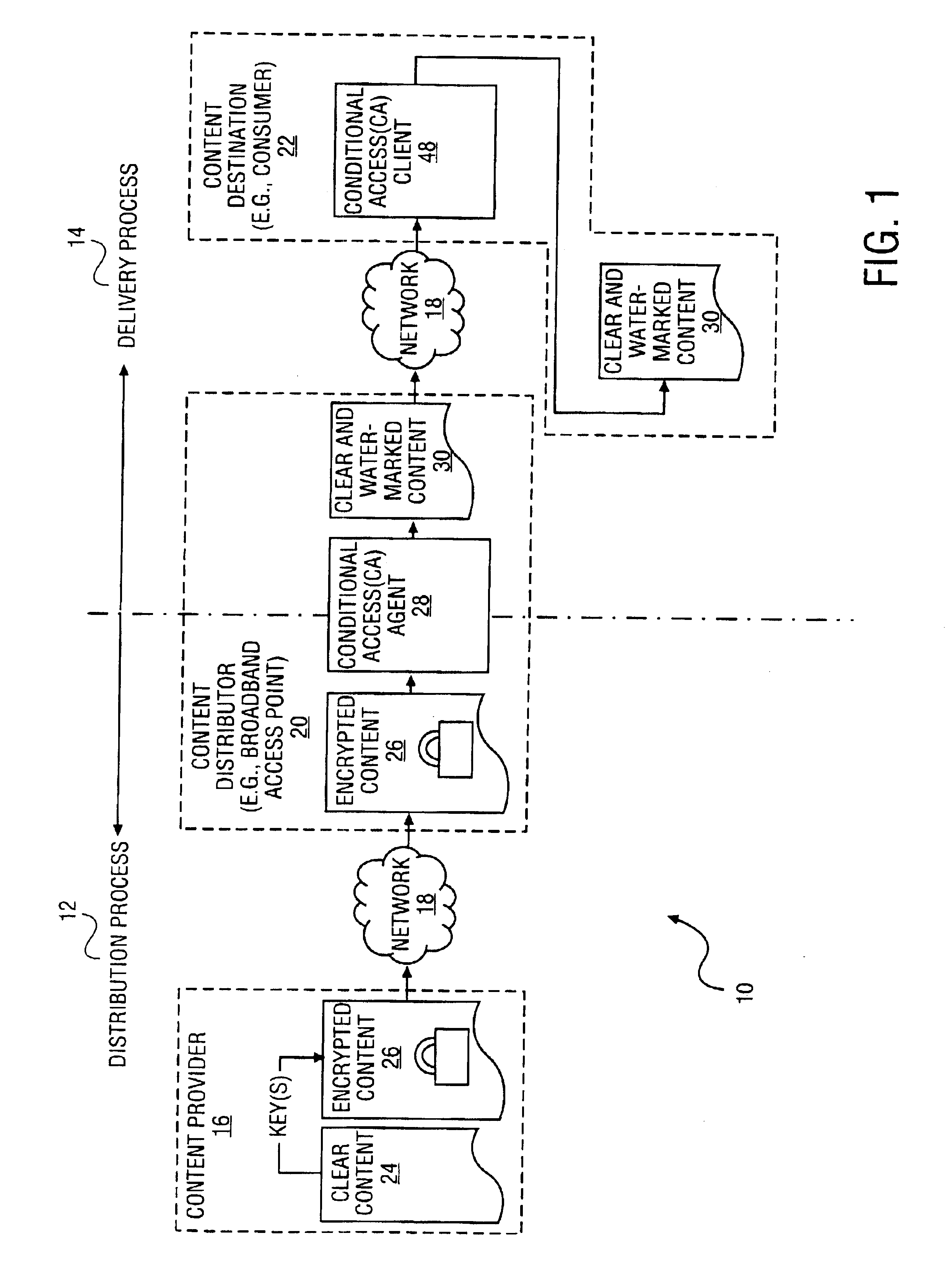
InactiveUS20060008256A1None of methods is secureTelevision system detailsColor television signals processingContent distributionVideo player
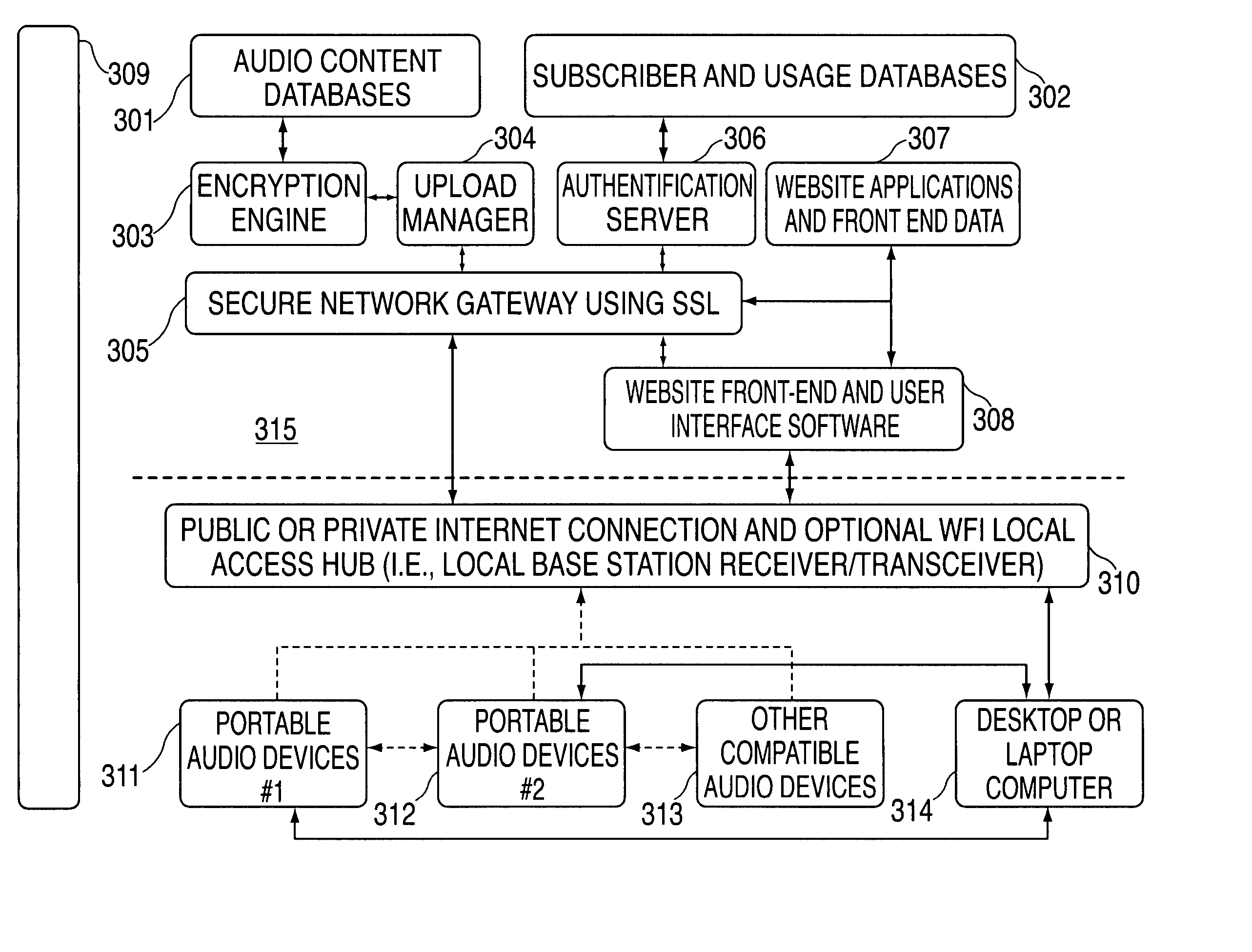
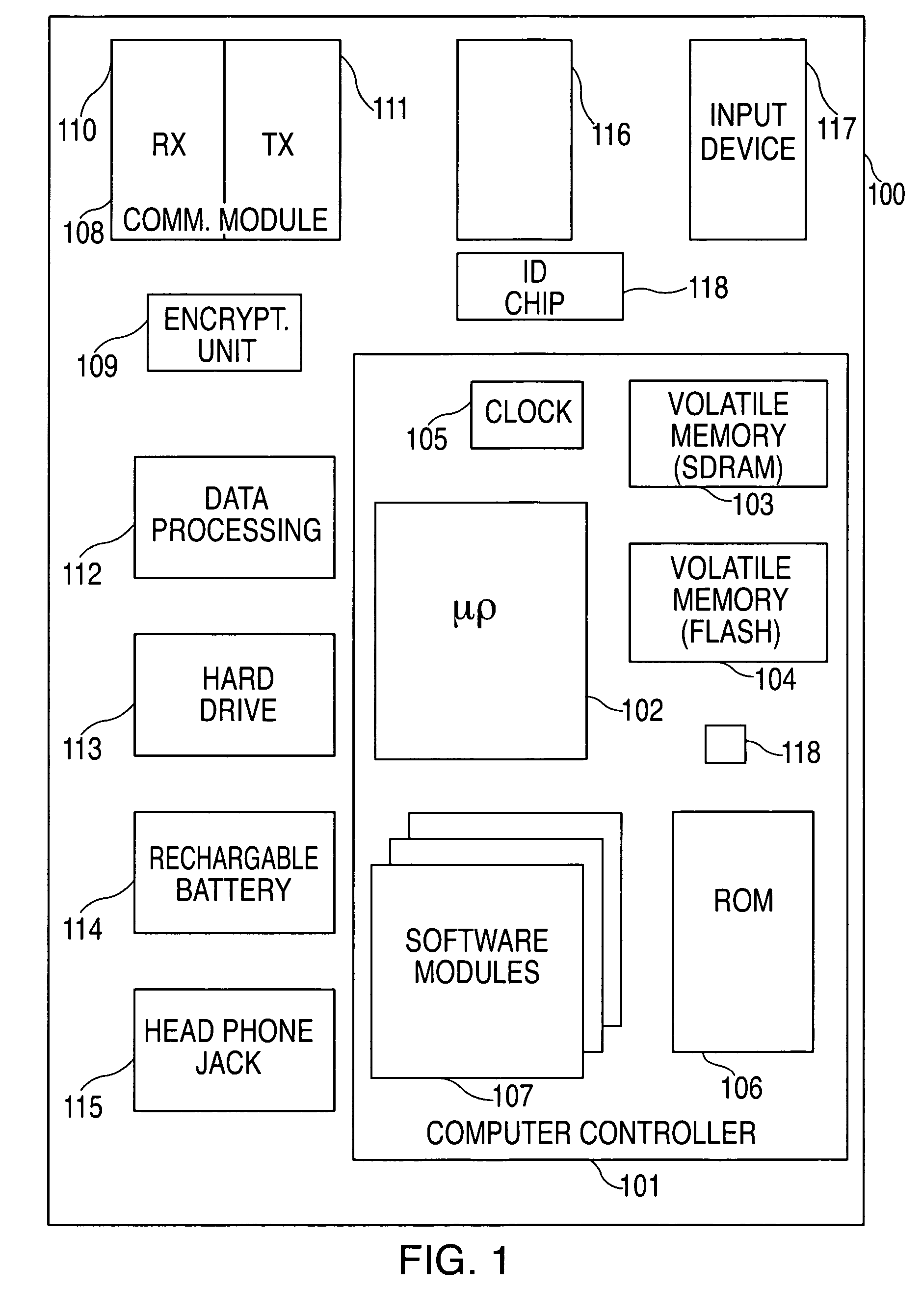
A portable wireless communications subscriber audio and / or video player apparatus and system and method for selecting, requesting, downloading, and playing audio and / or video data content files from an Internet-based database server. The wireless link is preferably implemented in accordance with the WiFi protocol, which allows connectivity to the Internet by being in proximity with a local base station or WiFi hotspot (i.e., publicly available local wireless access hub connected to the Internet). The portable wireless communications subscriber audio and / or video player apparatus and system preferably include a security means for monitoring and blocking unauthorized use of the player apparatus and system. The player apparatus further preferably has the capability to communicate with other neighboring player apparatus for the purpose of exchanging content data files, playlists and personal messages.
Owner:SANDISK TECH LLC
Trusted and secure techniques, systems and methods for item delivery and execution
InactiveUS6185683B2Avoid deletionEasy to identifyTelevision system detailsPulse modulation television signal transmissionDocumentation procedureDocument preparation
Documents and other items can be delivered electronically from sender to recipient with a level of trustedness approaching or exceeding that provided by a personal document courier. A trusted electronic go-between can validate, witness and / or archive transactions while, in some cases, actively participating in or directing the transaction. Printed or imaged documents can be marked using handwritten signature images, seal images, electronic fingerprinting, watermarking, and / or steganography. Electronic commercial transactions and transmissions take place in a reliable, "trusted" virtual distribution environment that provides significant efficiency and cost savings benefits to users in addition to providing an extremely high degree of confidence and trustedness. The systems and techniques have many uses including but not limited to secure document delivery, execution of legal documents, and electronic data interchange (EDI).
Owner:INTERTRUST TECH CORP
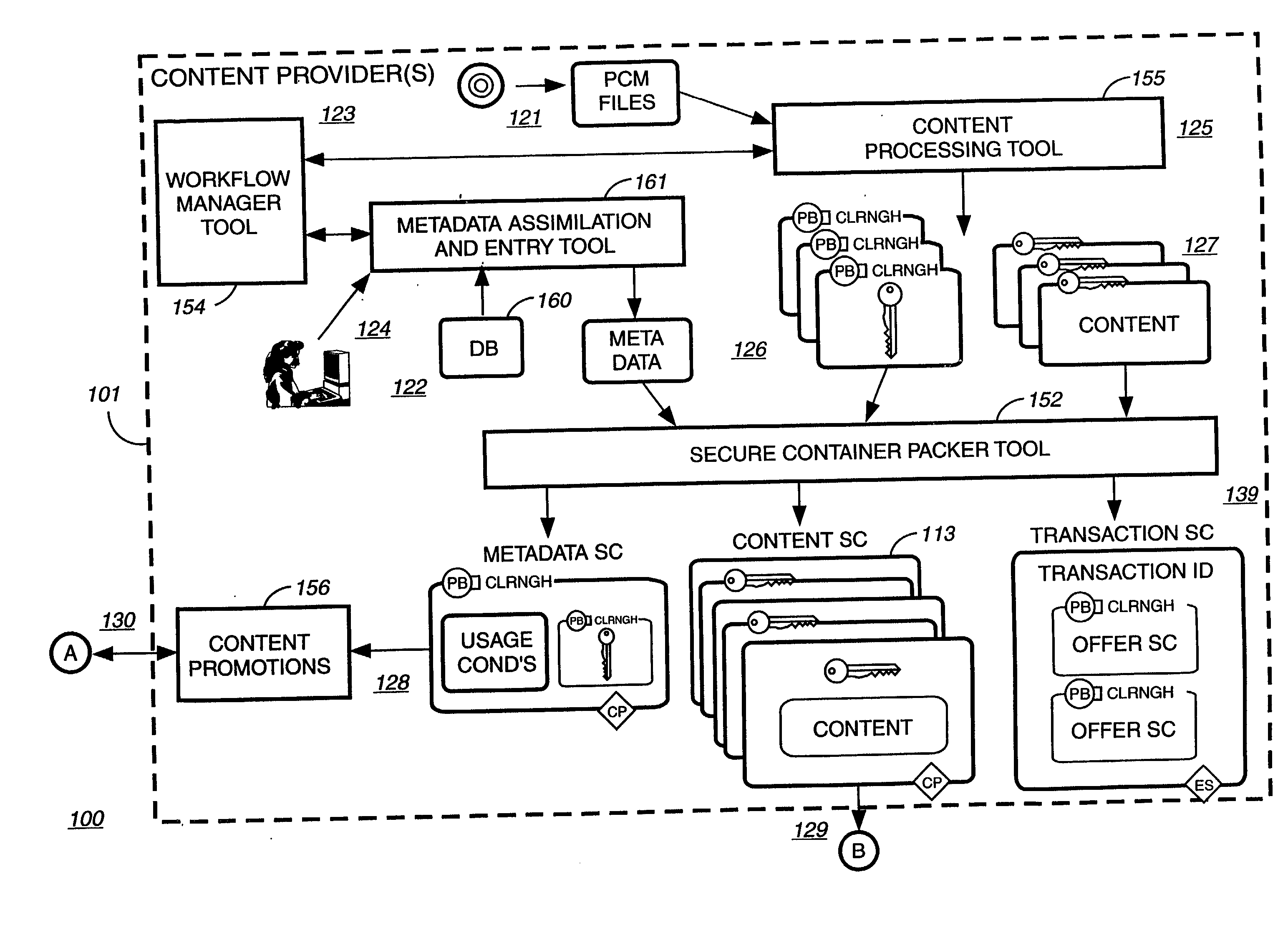
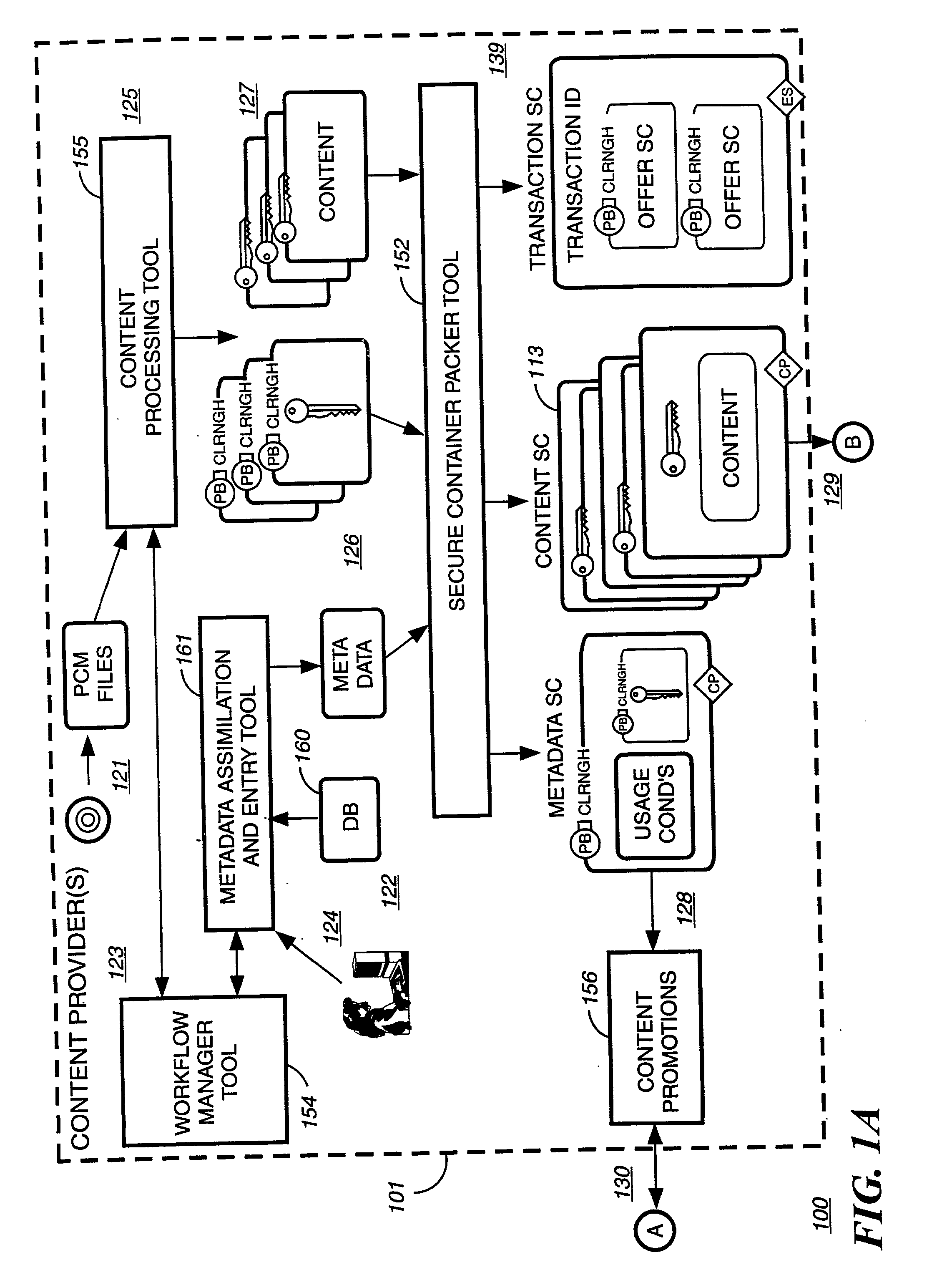
Automated method and apparatus to package digital content for electronic distribution using the identity of the source content
InactiveUS6345256B1Key distribution for secure communicationDigital data processing detailsDigital contentNumber content
A method to automatically retrieve data associated with content. An identifier is read that is stored on electronic readable medium storing content. The identifier is used to search a database for data associated with the content. Data that is associated with the content is retrieved as guided by the database. And the data retrieved is used to create a version of the content for electronic distribution. In accordance with another aspect of the invention, a computer readable medium is described to carry out the above method.
Owner:INT BUSINESS MASCH CORP
Digital rights management in a mobile environment
ActiveUS20110225417A1Facilitating access to contentOptimization of content deliveryOffice automationResourcesComputer hardwareDigital rights management
Embodiments provide a method that causes a plurality of virtual machine instructions to be interpreted for indications of a mobile device's hardware identification information, thus forming a plurality of hardware instruction interpretations. The embodiment also combines each of the plurality of hardware instruction interpretations and hashes the combination to form a quasi-hardware device identifier. An encryption process is based on the quasi-hardware encryption device identifier and the media is then encrypted using the encryption process. The encrypted media is transferred to the mobile device wherein the mobile device decrypts the media based at least in part on the mobile device's internal knowledge of the quasi-hardware device identification.
Owner:DIRECTV LLC
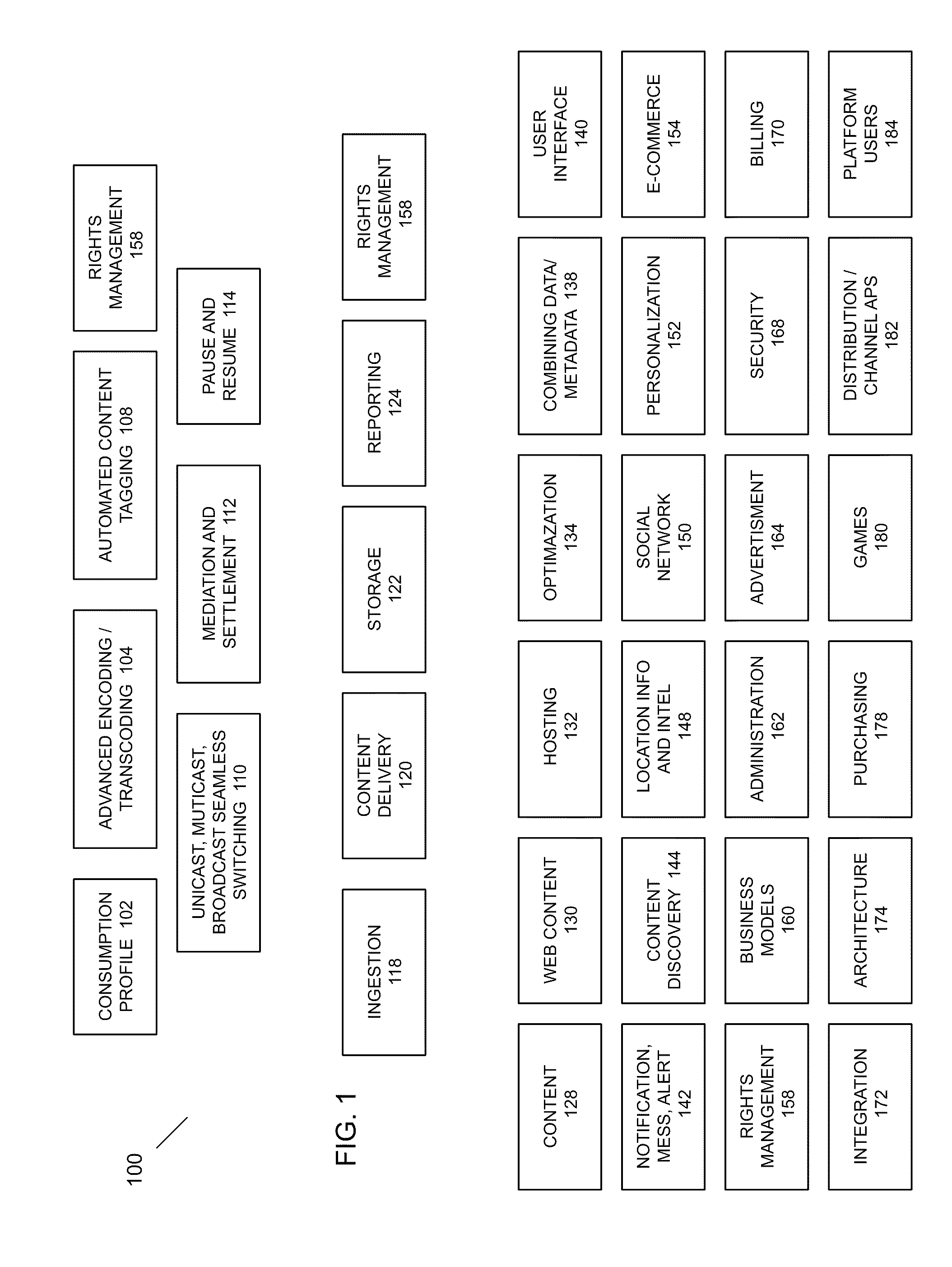
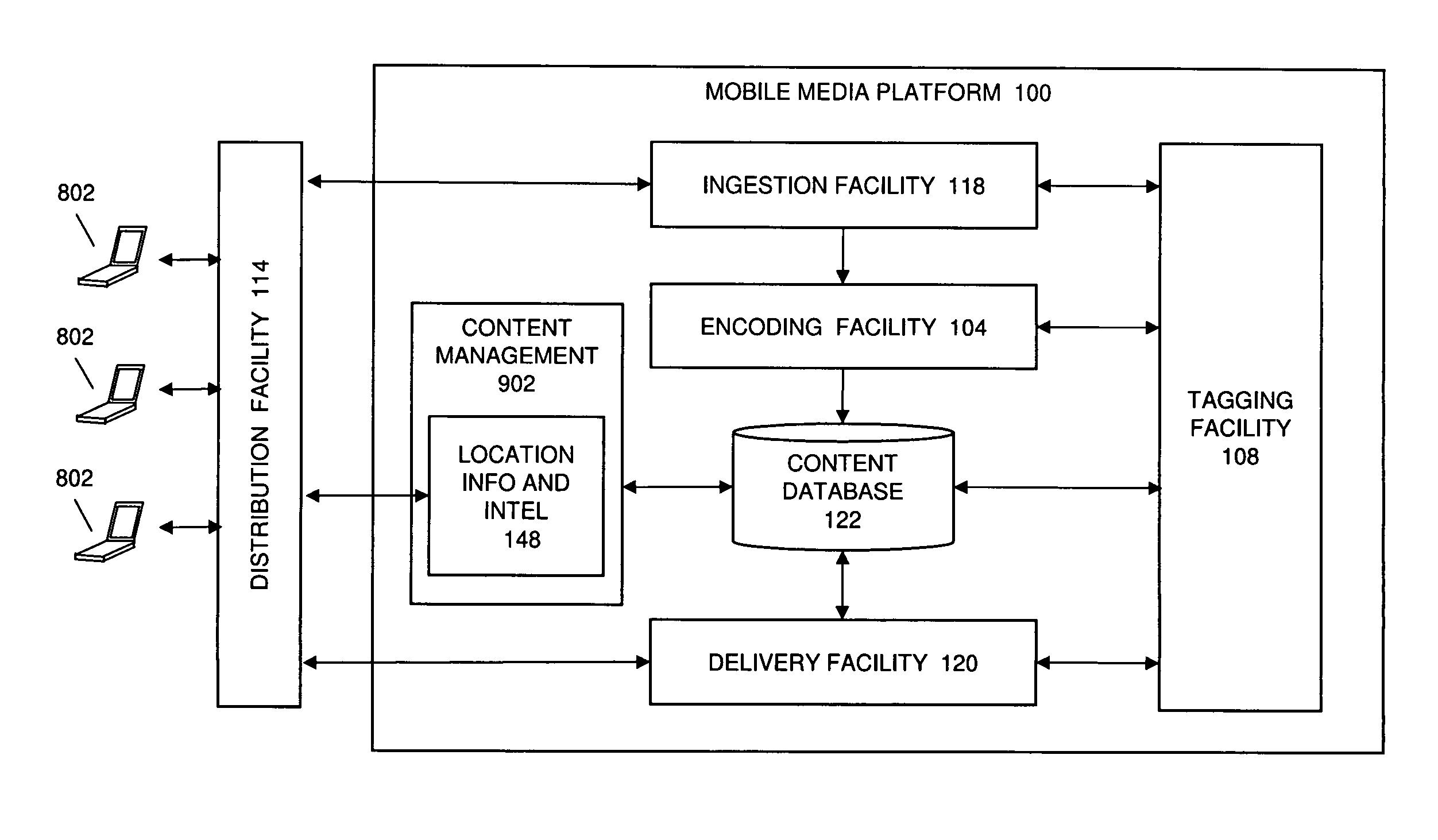
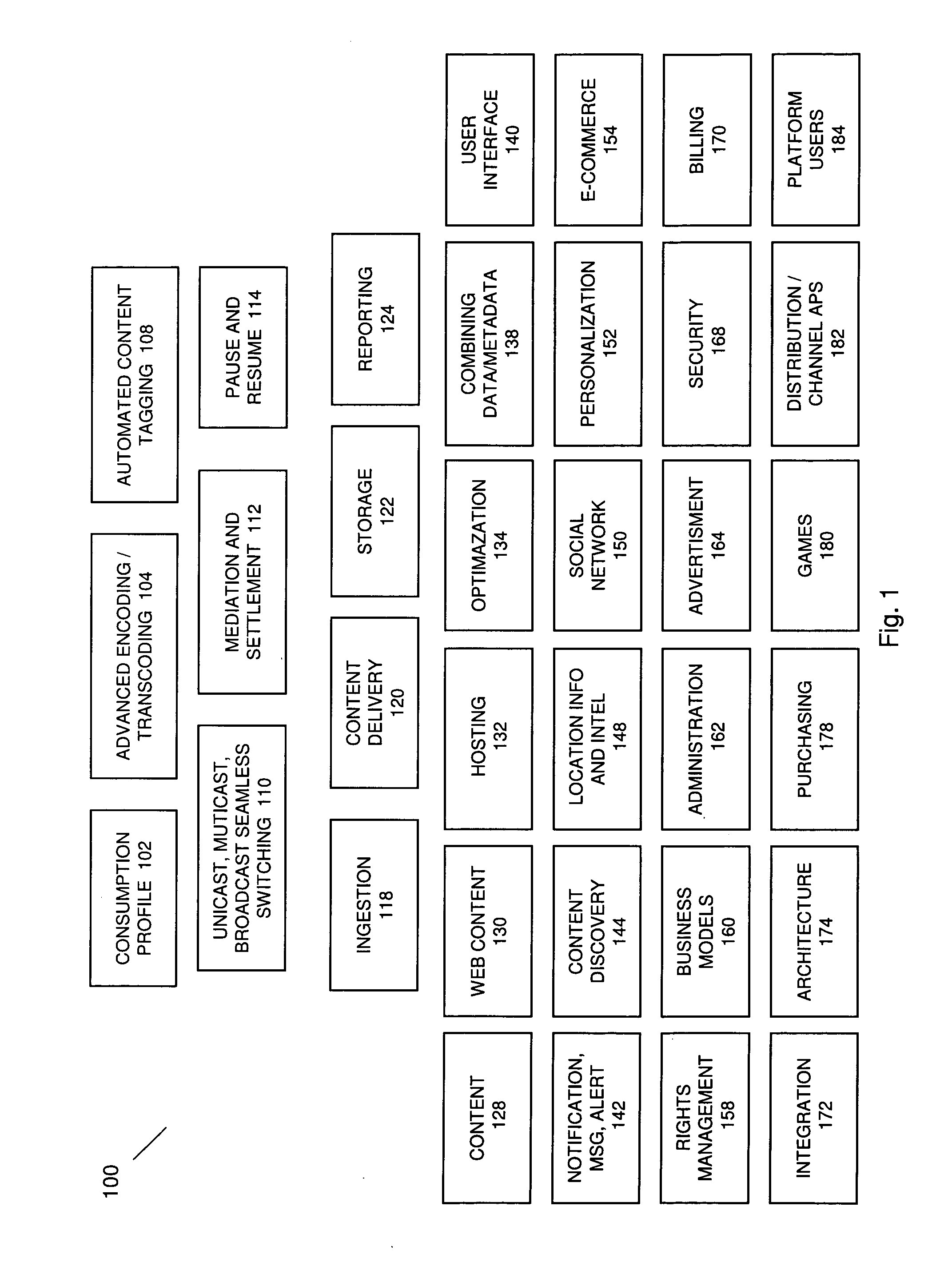
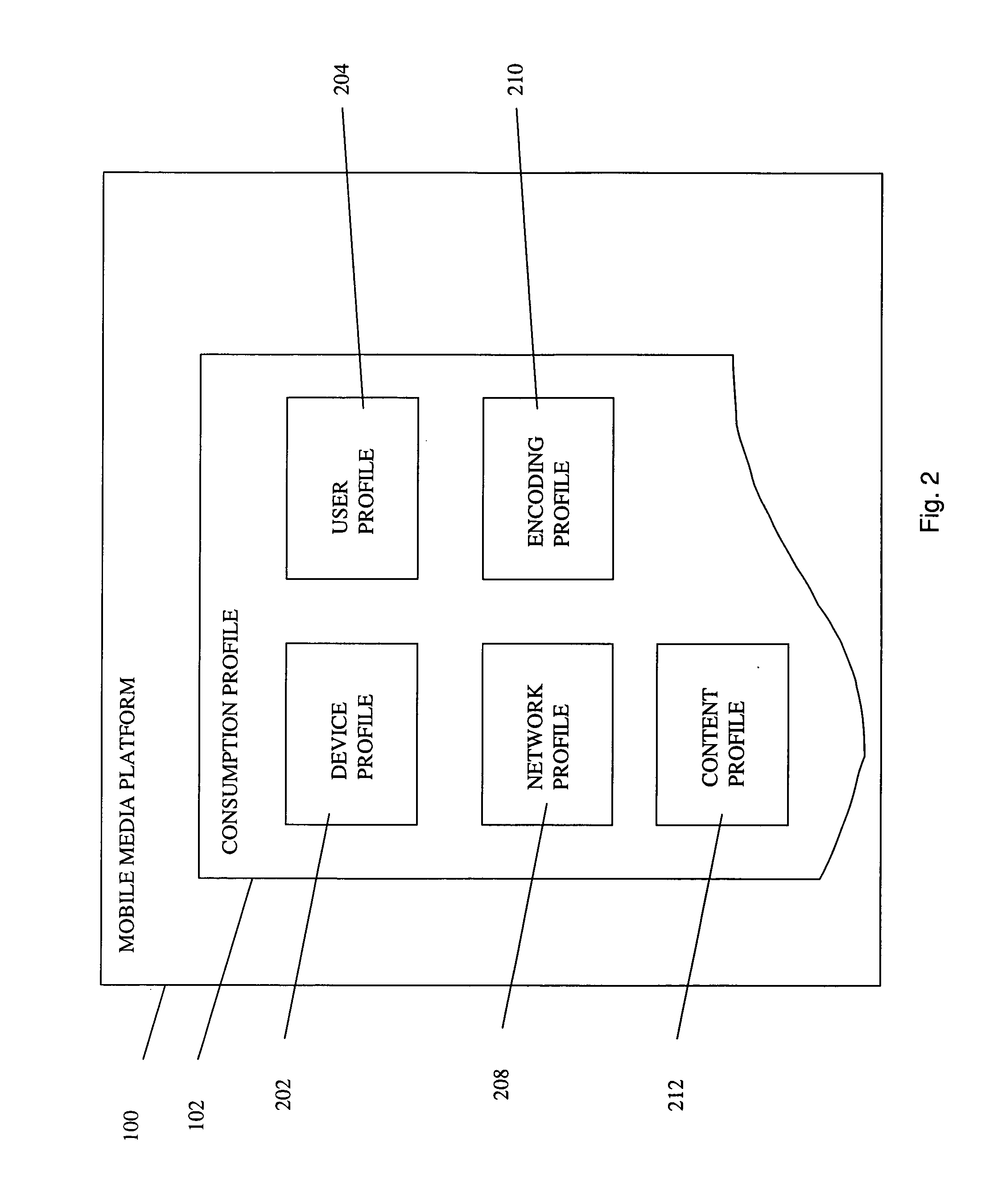
Automated Content Tag Processing for Mobile Media
InactiveUS20080195664A1Facilitating access to contentOptimization of content deliveryAdvertisementsDigital data processing detailsMobile deviceMobile media
In embodiments, the present invention provides a method and system for delivery of content on a mobile media platform, providing an automated tag processing facility, and delivering content to a mobile device, wherein content delivery is based at least in part on the automated tag processing.
Owner:THE DIRECTV GROUP
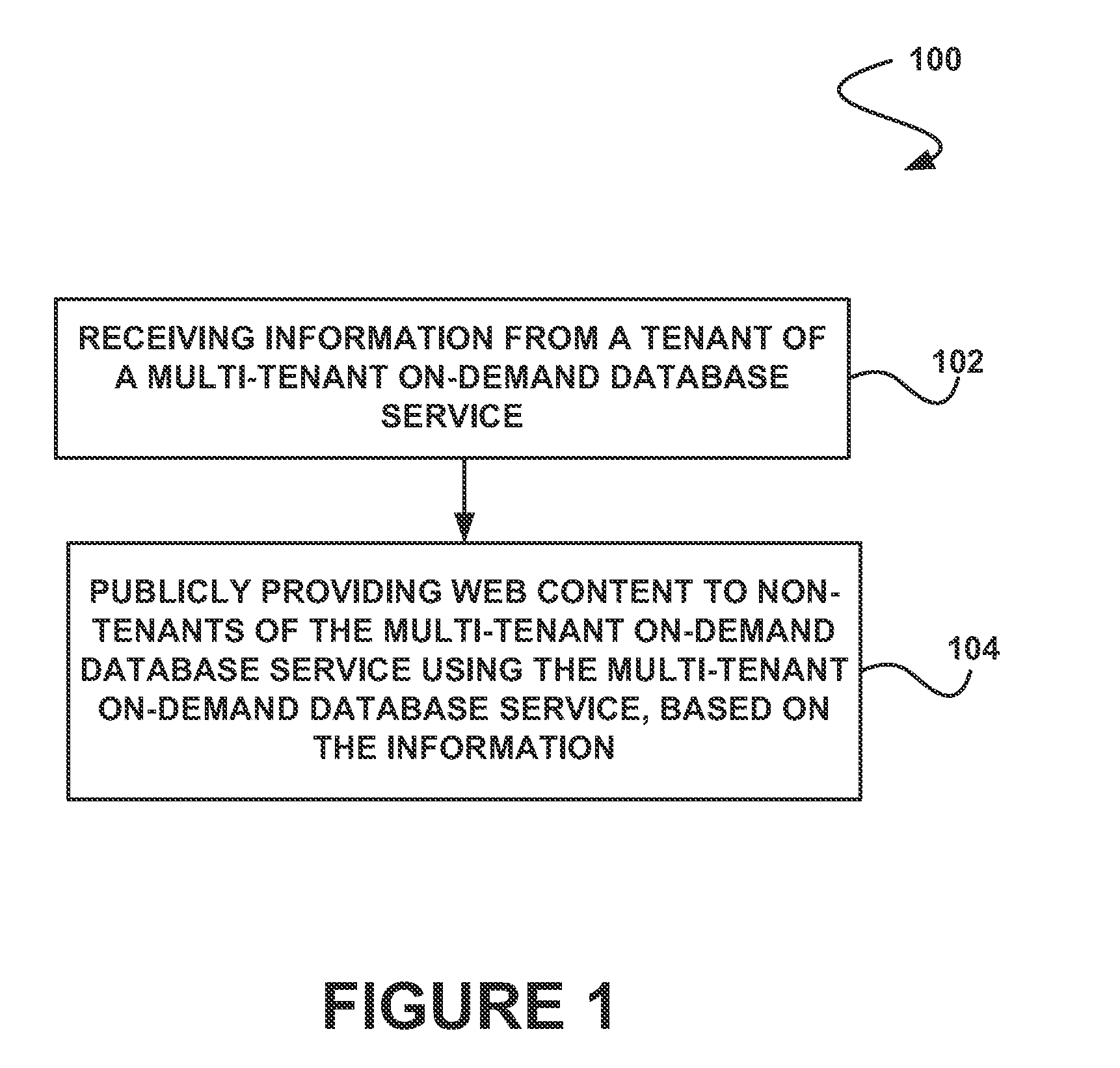
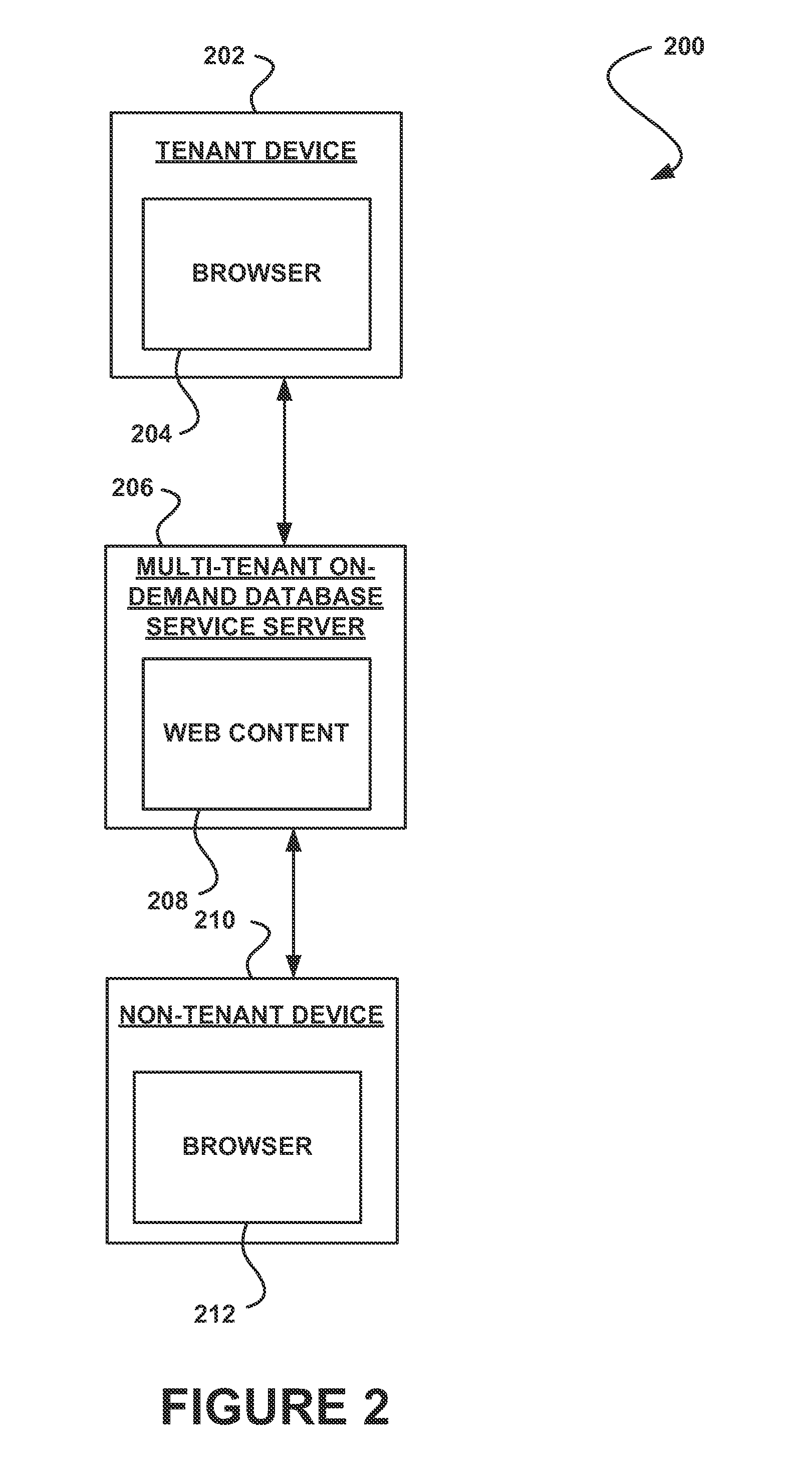
System, method and computer program product for publicly providing web content of a tenant using a multi-tenant on-demand database service
In accordance with embodiments, there are provided mechanisms and methods for publicly providing web content of a tenant using a multi-tenant on-demand database service. These mechanisms and methods for publicly providing web content of a tenant using a multi-tenant on-demand database service can allow the web content to be published by a tenant using the multi-tenant on-demand database service for use by non-tenants of the multi-tenant on-demand database service.
Owner:SALESFORCE COM INC
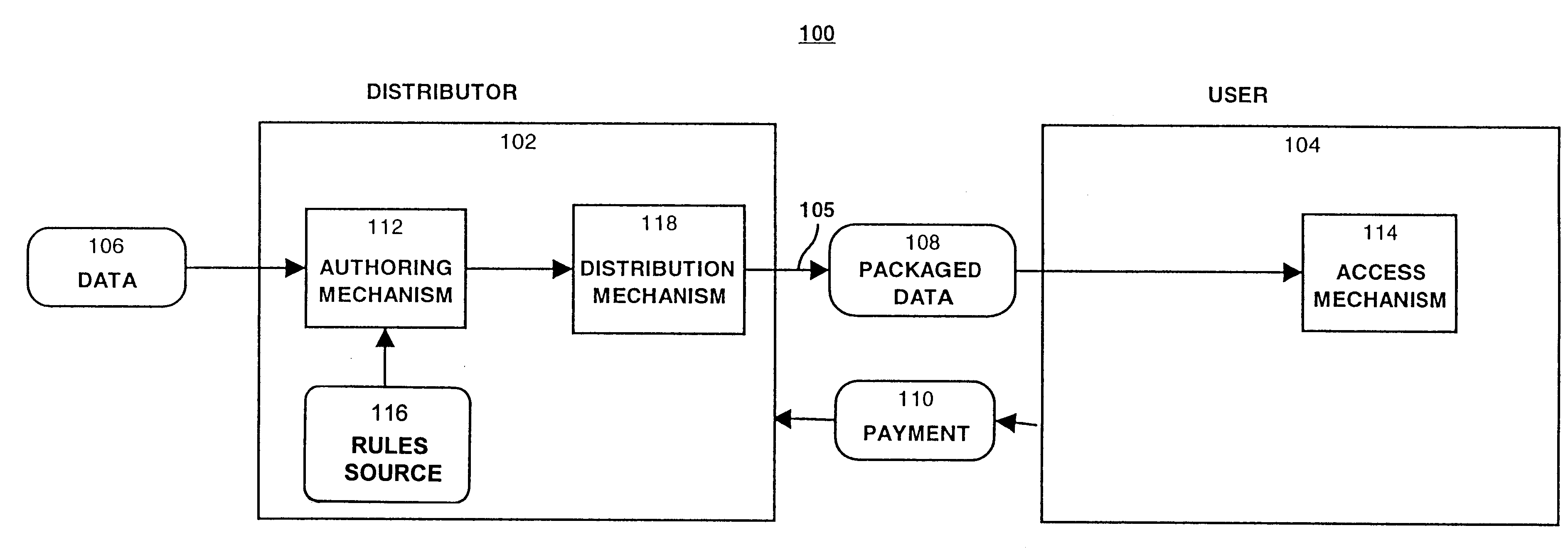
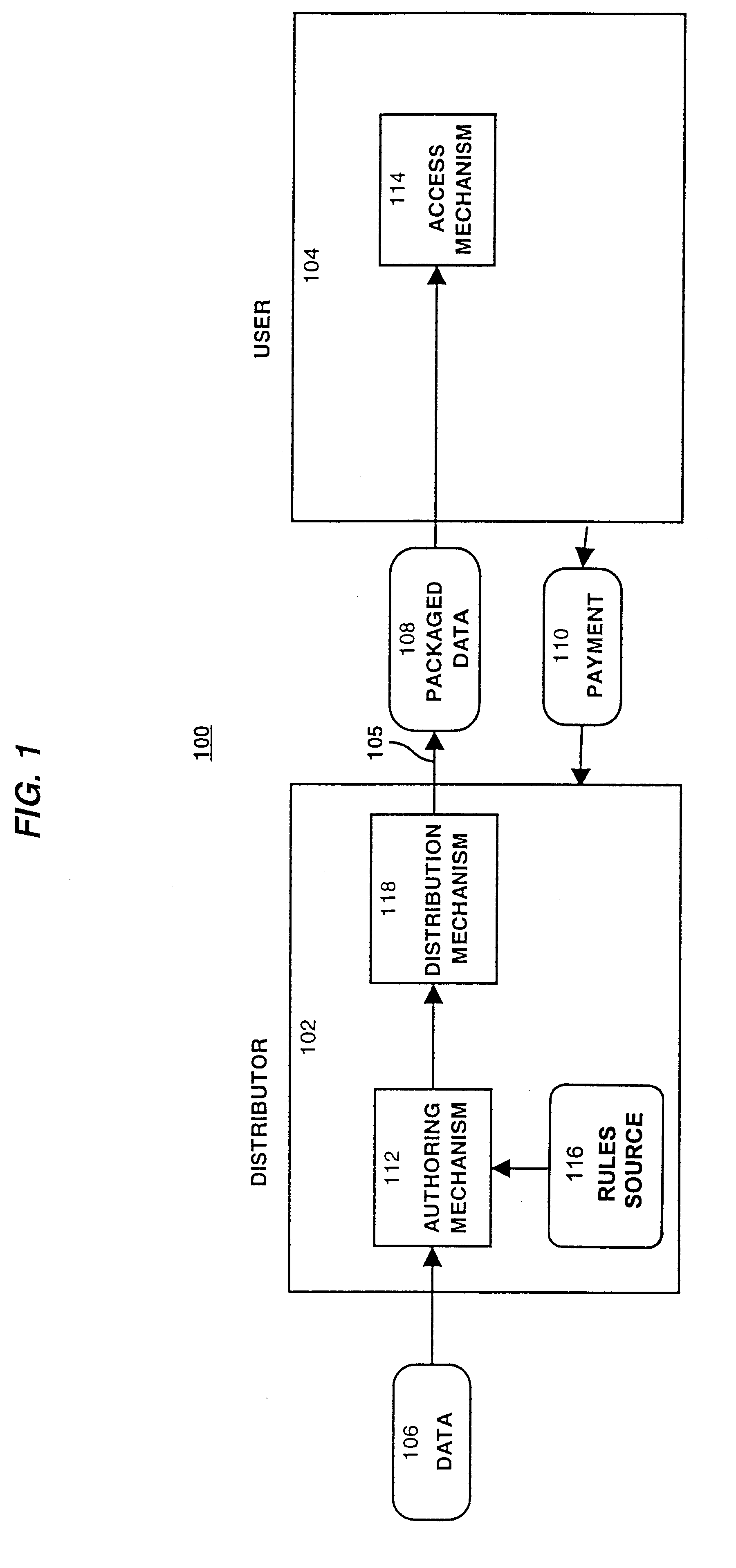
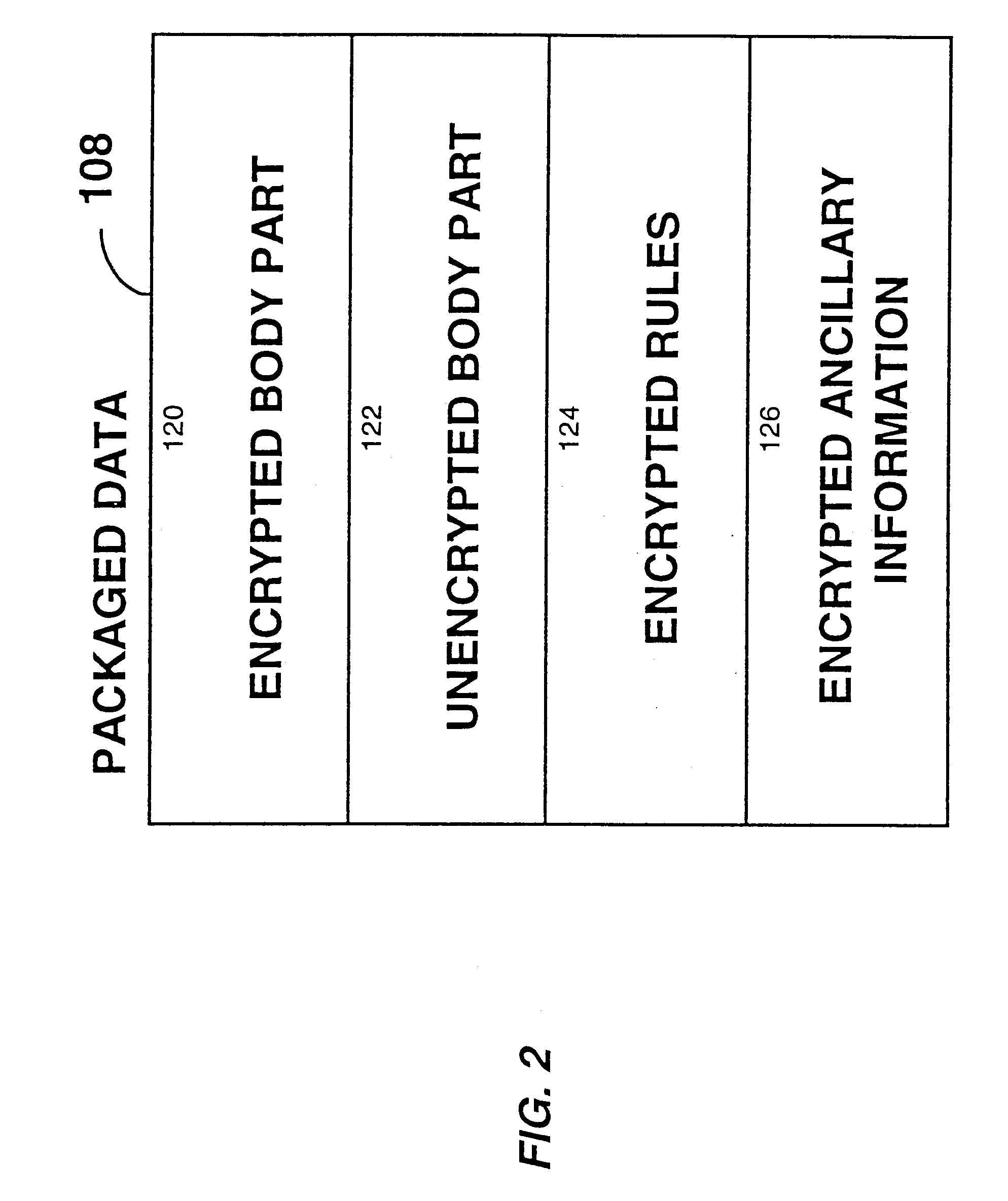
System for controlling access and distribution of digital property
InactiveUS6314409B2Key distribution for secure communicationMultiple keys/algorithms usageTamper resistanceData access
A method and device are provided for controlling access to data. Portions of the data are protected and rules concerning access rights to the data are determined. Access to the protected portions of the data is prevented, other than in a non-useable form; and users are provided access to the data only in accordance with the rules as enforced by a mechanism protected by tamper detection. A method is also provided for distributing data for subsequent controlled use of those data. The method includes protecting portions of the data; preventing access to the protected portions of the data other than in a non-useable form; determining rules concerning access rights to the data; protecting the rules; and providing a package including: the protected portions of the data and the protected rules. A user is provided controlled access to the distributed data only in accordance with the rules as enforced by a mechanism protected by tamper protection. A device is provided for controlling access to data having protected data portions and rules concerning access rights to the data. The device includes means for storing the rules; and means for accessing the protected data portions only in accordance with the rules, whereby user access to the protected data portions is permitted only if the rules indicate that the user is allowed to access the portions of the data.
Owner:HANGER SOLUTIONS LLC
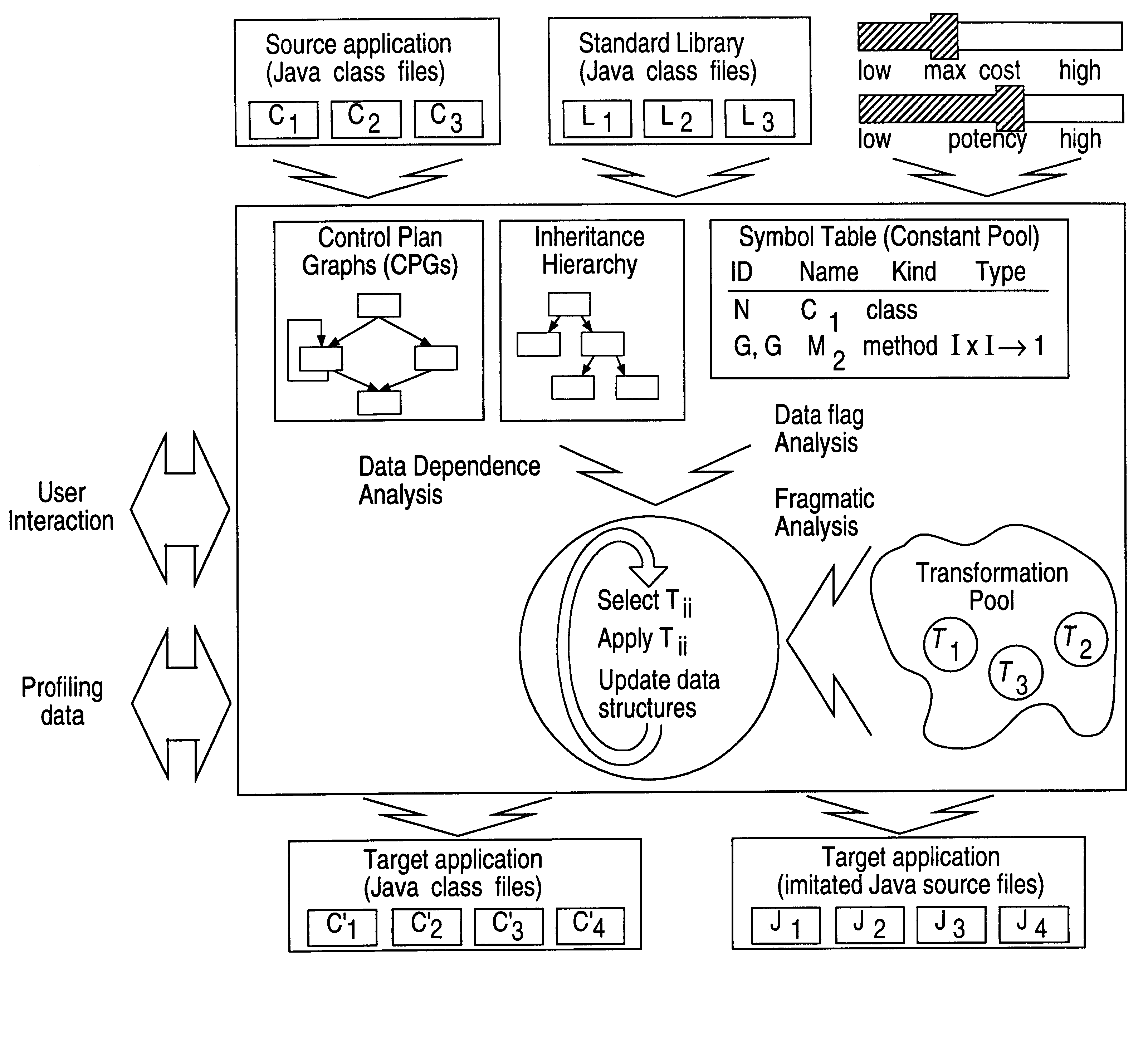
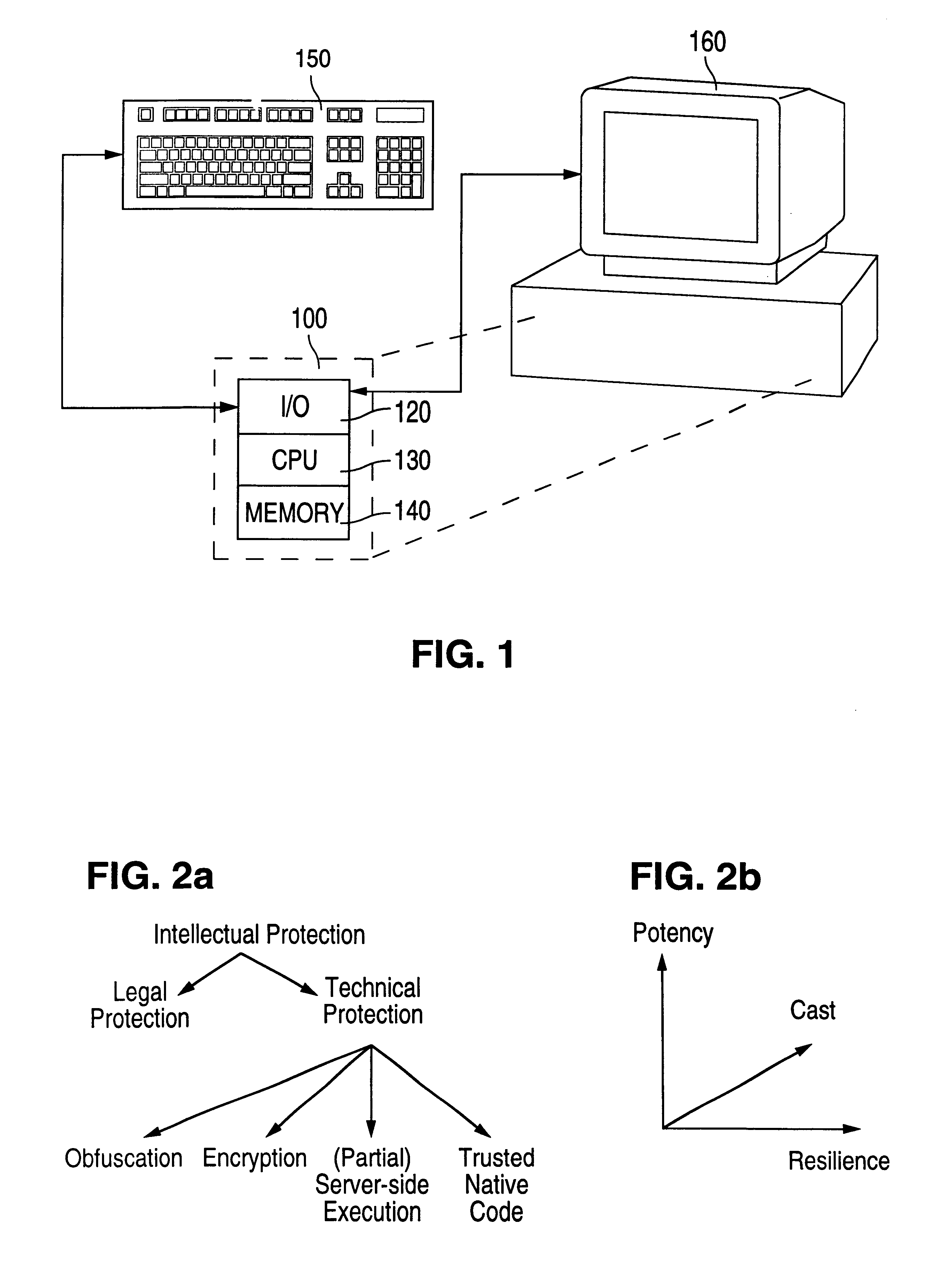
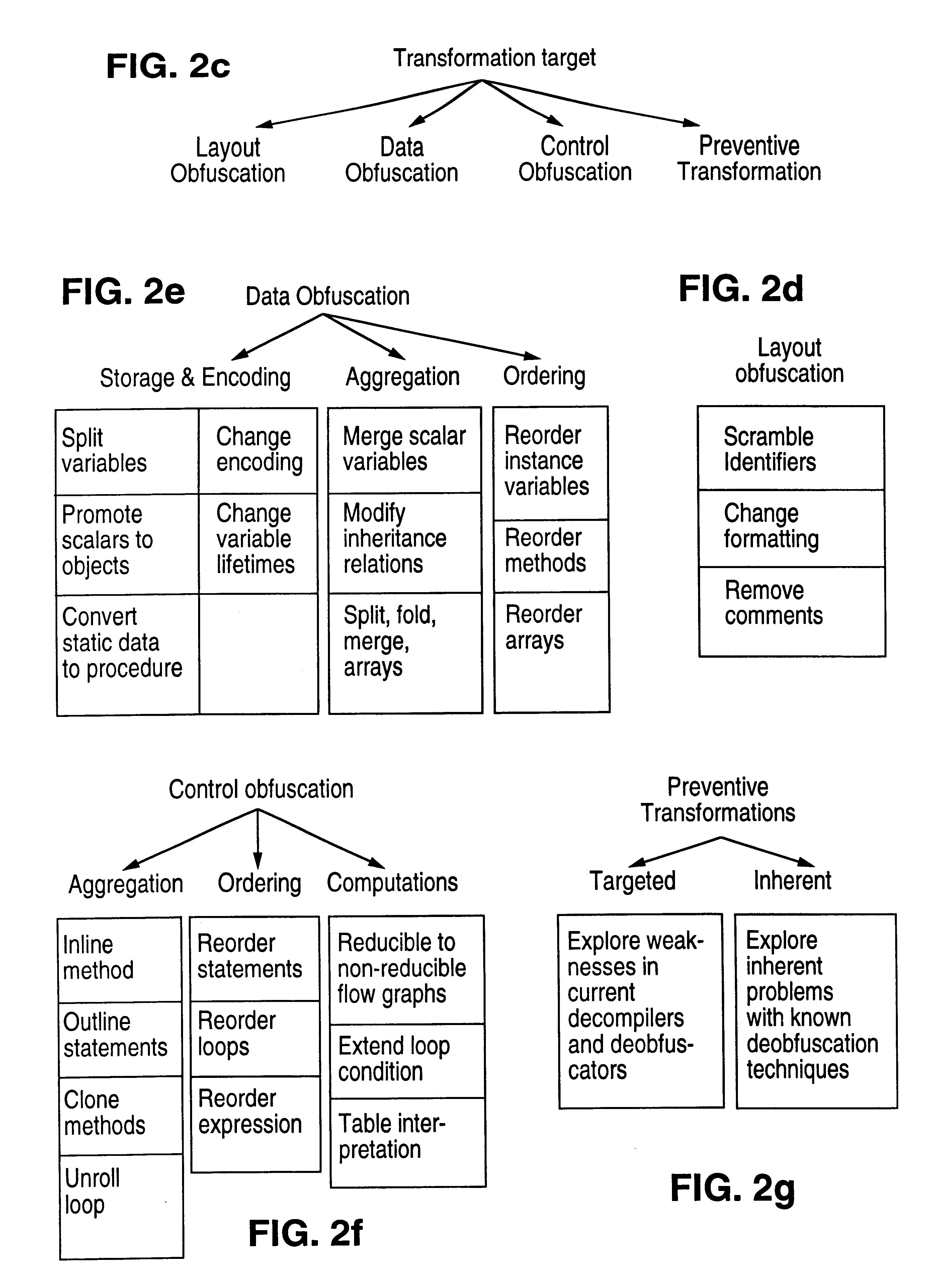
Obfuscation techniques for enhancing software security
InactiveUS6668325B1Guaranteed maximum utilizationDigital data processing detailsUnauthorized memory use protectionObfuscationTheoretical computer science
The present invention provides obfuscation techniques for enhancing software security. In one embodiment, a method for obfuscation techniques for enhancing software security includes selecting a subset of code (e.g., compiled source code of an application) to obfuscate, and obfuscating the selected subset of the code. The obfuscating includes applying an obfuscating transformation to the selected subset of the code. The transformed code can be weakly equivalent to the untransformed code. The applied transformation can be selected based on a desired level of security (e.g., resistance to reverse engineering). The applied transformation can include a control transformation that can be creating using opaque constructs, which can be constructed using aliasing and concurrency techniques. Accordingly, the code can be obfuscated for enhanced software security based on a desired level of obfuscation (e.g., based on a desired potency, resilience, and cost).
Owner:INTERTRUST TECH CORP
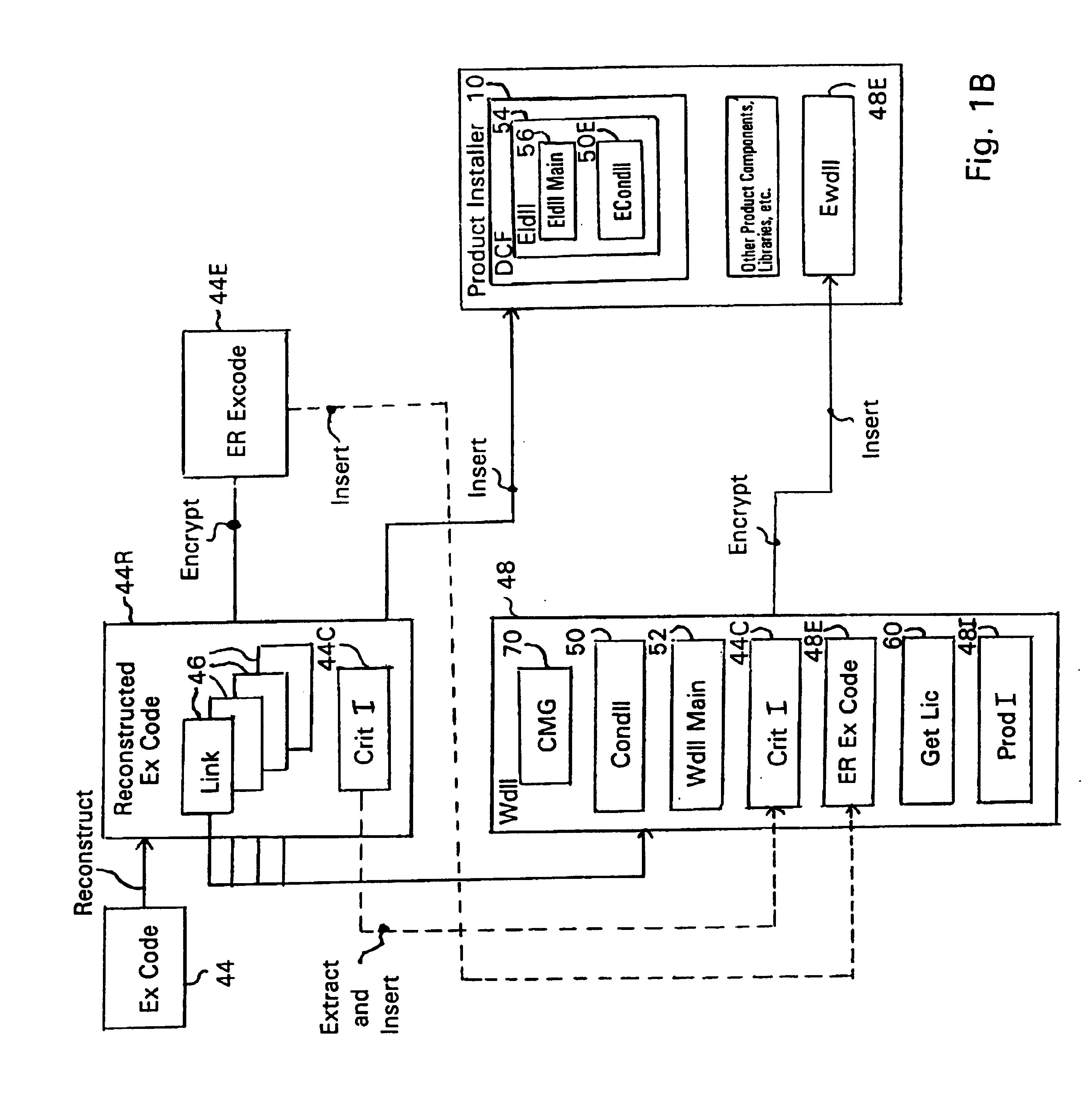
Secure electronic content distribution on CDS and DVDs
InactiveUS6611812B2Key distribution for secure communicationDigital data processing detailsDigital contentComputer terminal
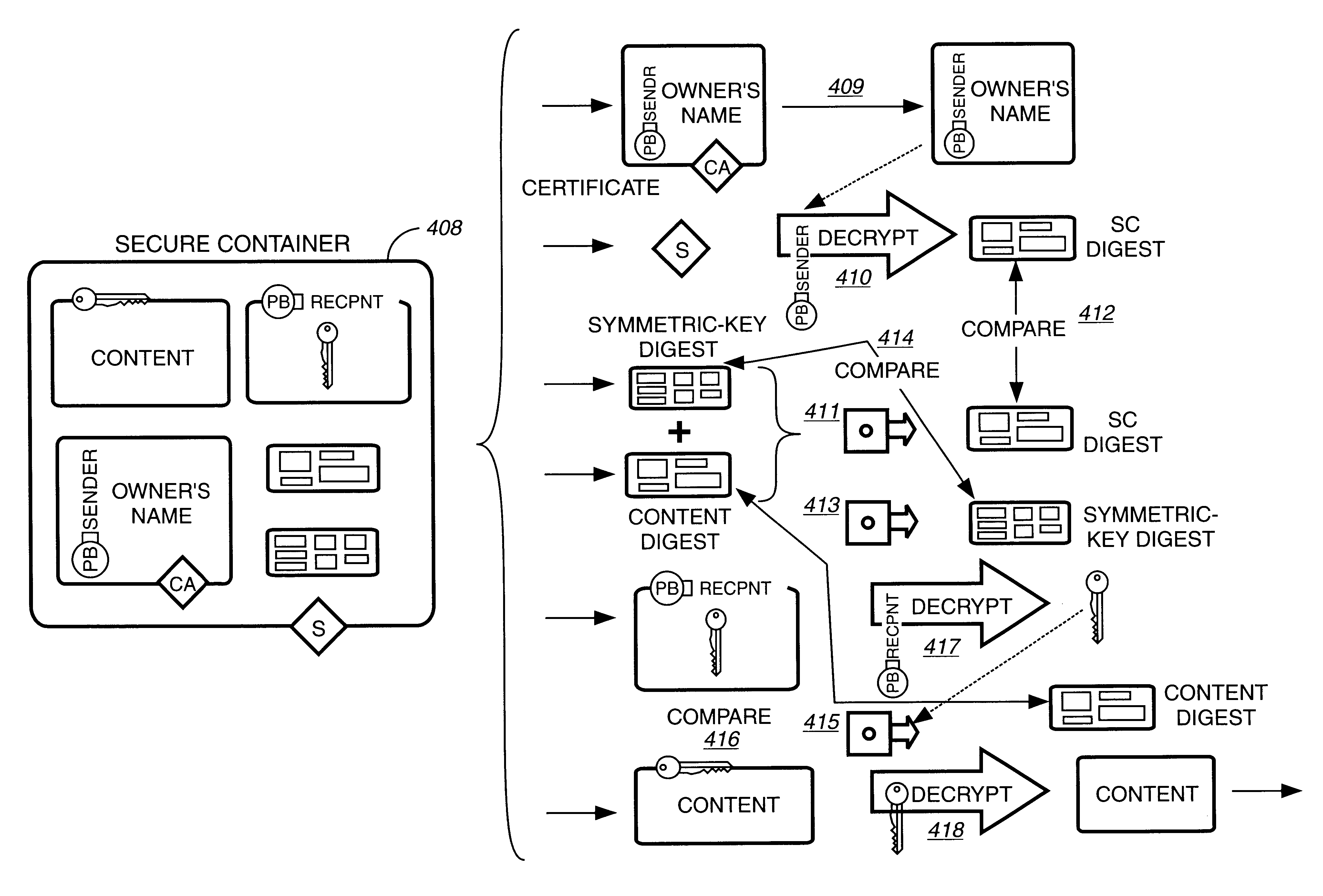
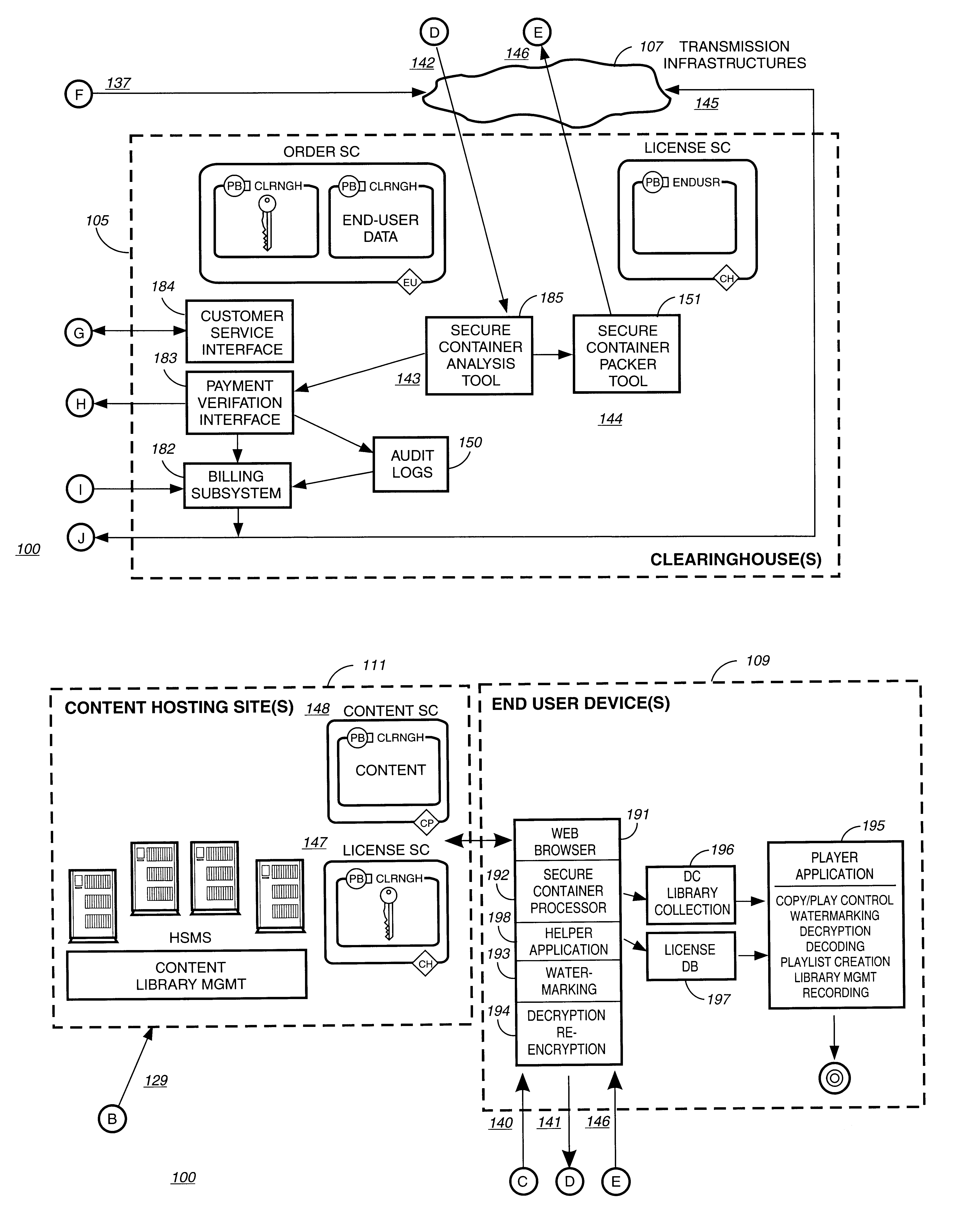
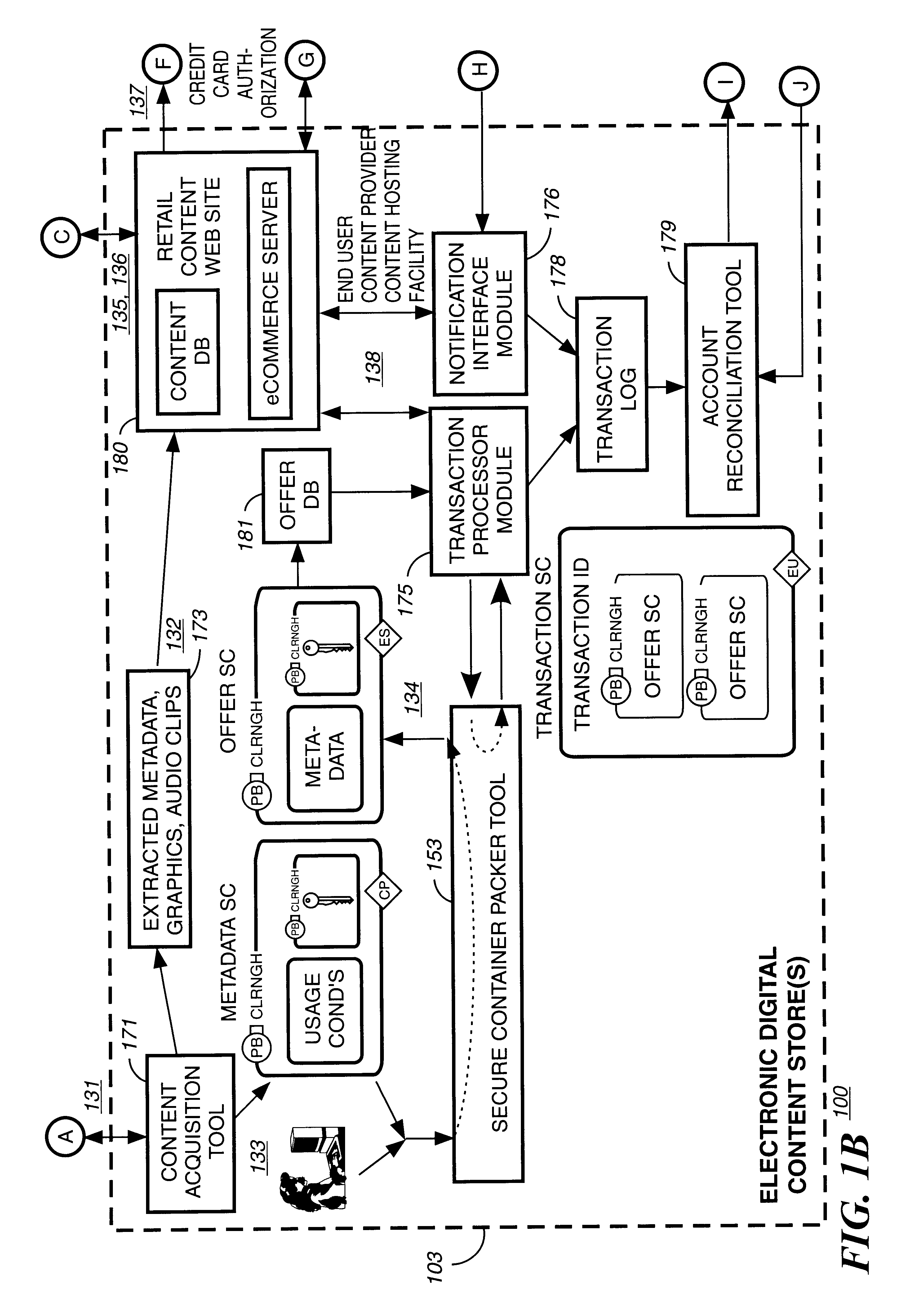
A method to delivery encrypted digital content to a end user system for playing the content comprising the steps of: reading from a computer readable medium metadata which has previously associated with the content. A user selects from the metadata associated content to decrypt and the end user system establishes a secure connection with an authorization authority for decrypting the content. The end user system receives a secure container containing the decrypting key for decrypting at least part of the previously encrypted content as permitted. The system creates a secure container using the encrypting key from a clearing house, wherein the secure container has an encrypting key therein from the end user system; transferring the secure container to the clearing house for authentication of permission to decrypt the content. The system receives from the clearing house, a secure container encrypted using the encrypting key of the end user system containing the decrypting key for decrypting at least part of the previously encrypted content stored on the computer readable medium as permitted; and playing at least part of the previously encrypted content by decrypting the secure container using the encrypting key of the end user system to access the decrypting key for decrypting at least part of the encrypted content.
Owner:WISTRON CORP
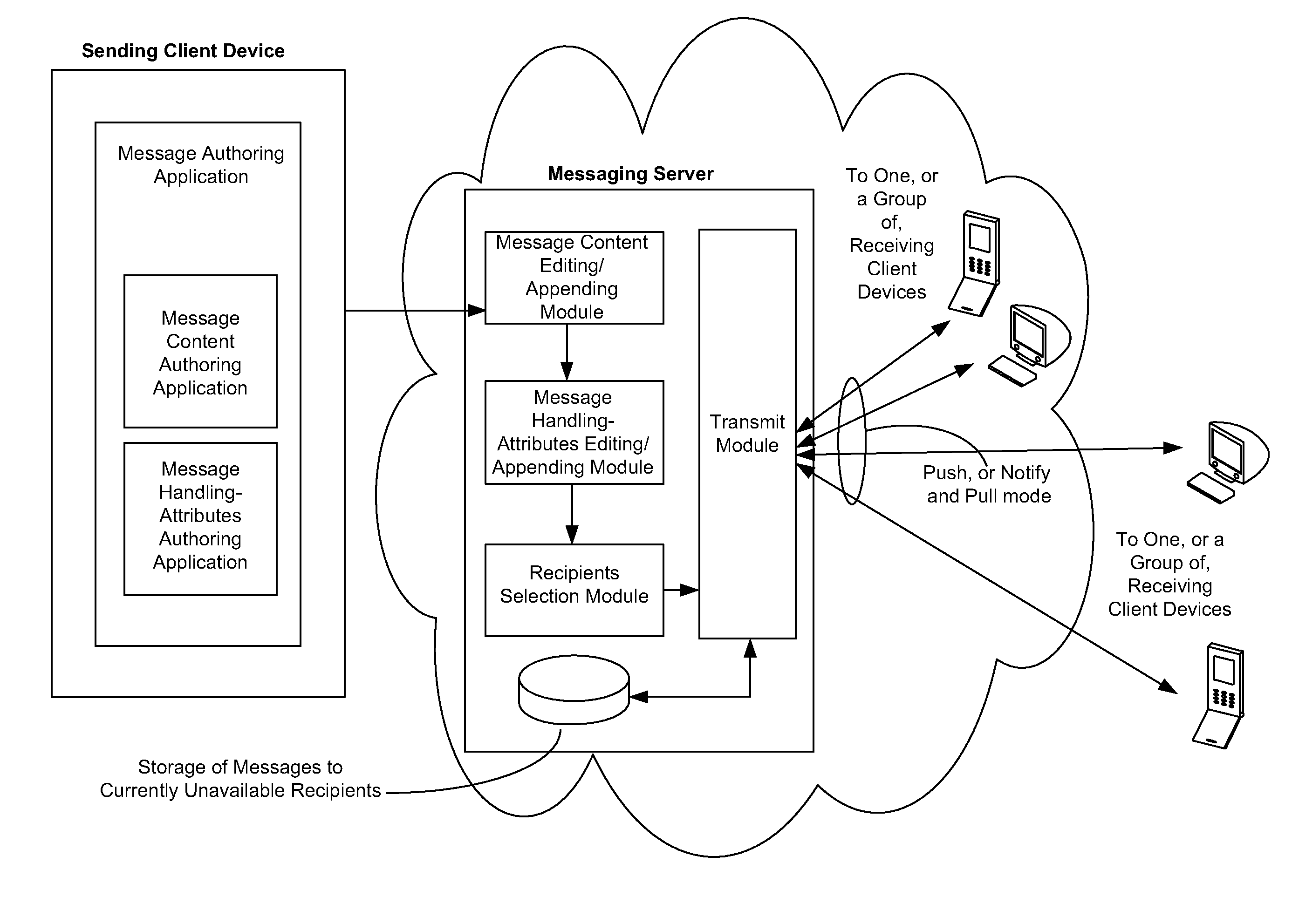
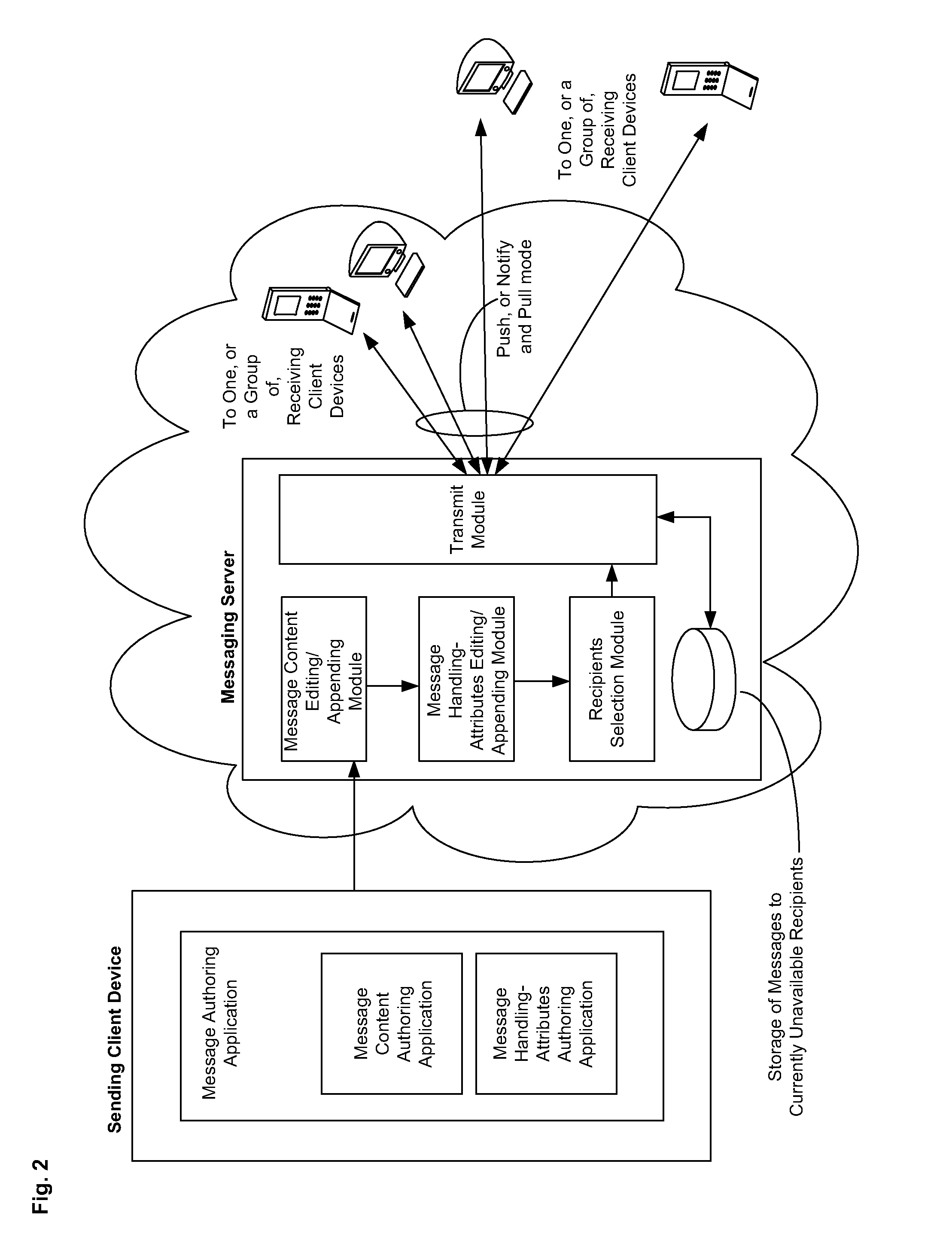
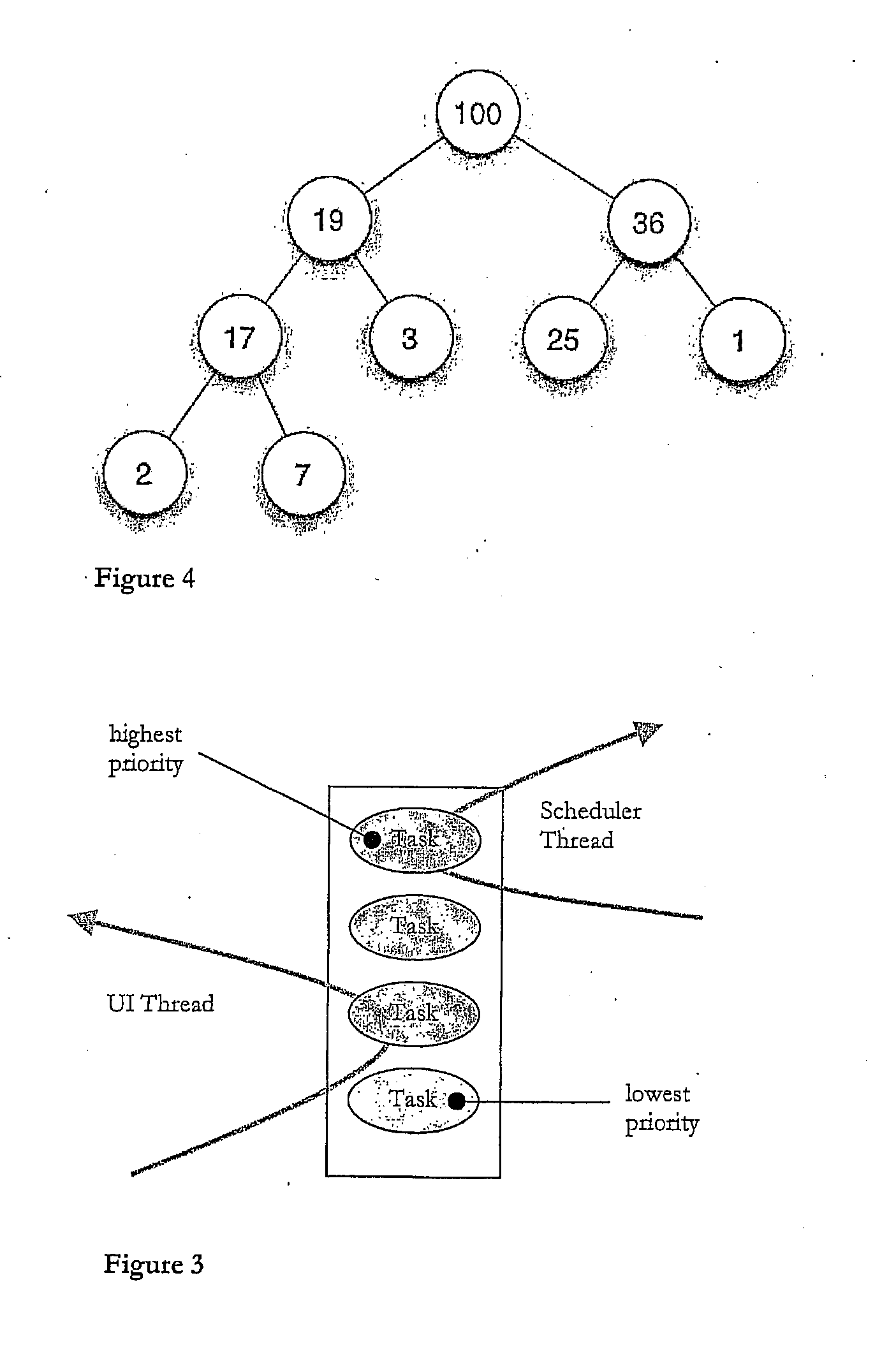
Messaging System Apparatuses Circuits and Methods of Operation Thereof
ActiveUS20120209924A1Multiple digital computer combinationsMessaging/mailboxes/announcementsClient-sideMessage passing system
Owner:TIGERCONNECT INC
Location-based feature enablement for mobile terminals
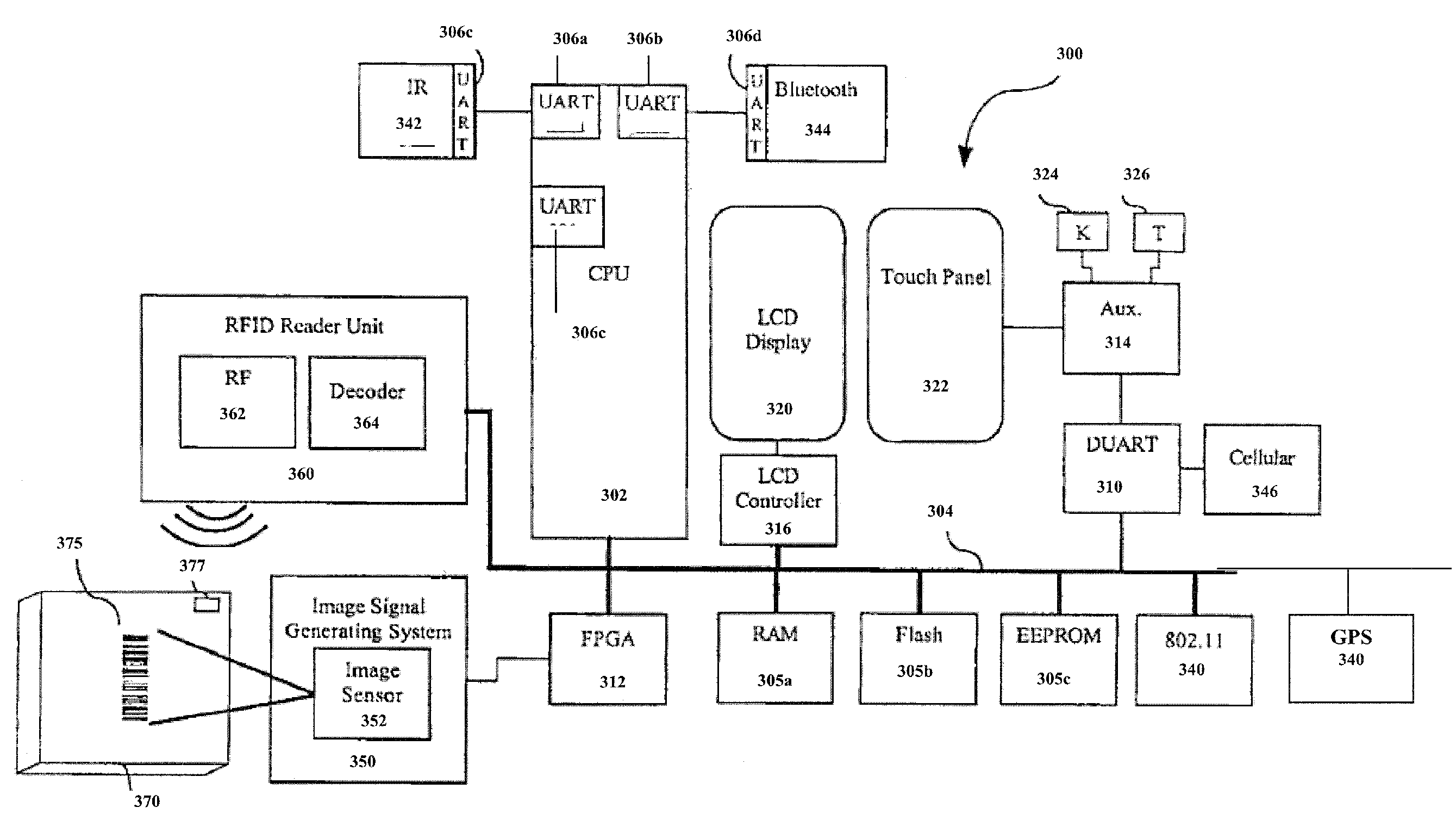
ActiveUS8583924B2Digital data processing detailsUser identity/authority verificationComputer terminalComputer science
Owner:HAND HELD PRODS
Method and apparatus for the free licensing of digital media content
ActiveUS20040003398A1Improve securityReduce partAnalogue secracy/subscription systemsTwo-way working systemsDigital contentControl signal
A system and method for displaying digital media files with compulsory advertisement files is disclosed. In one embodiment, the system includes a user interface, a media file decryptor, an ad manager, an intersplicer, and a media player. The user interface receives input from a user indicating the selection of media files to be presented. The media file decryptor receives and decrypts the selected media files. The ad manager receives and manages ad files from an ad file source. The intersplicer combines the media files with the ad files by providing control signals to the media player, causing the media player to present the ad files with the selected media files. Various embodiments of the invention facilitate the wide distribution of media content in a way that allows the free use of media properties, on demand, with direct consumer exchange capabilities, while at the same time enabling compensation to copyright holders.
Owner:PIRANHA MEDIA DISTRIBUTION LLC
Method and apparatus to create encoded digital content
InactiveUS6263313B1Electrophonic musical instrumentsKey distribution for secure communicationDigital contentNumber content
Owner:LEVEL 3 COMM LLC
Messaging System Apparatuses Circuits and Methods of Operation Thereof
ActiveUS20110202598A1Multiple digital computer combinationsMessaging/mailboxes/announcementsClient-sideMessage passing
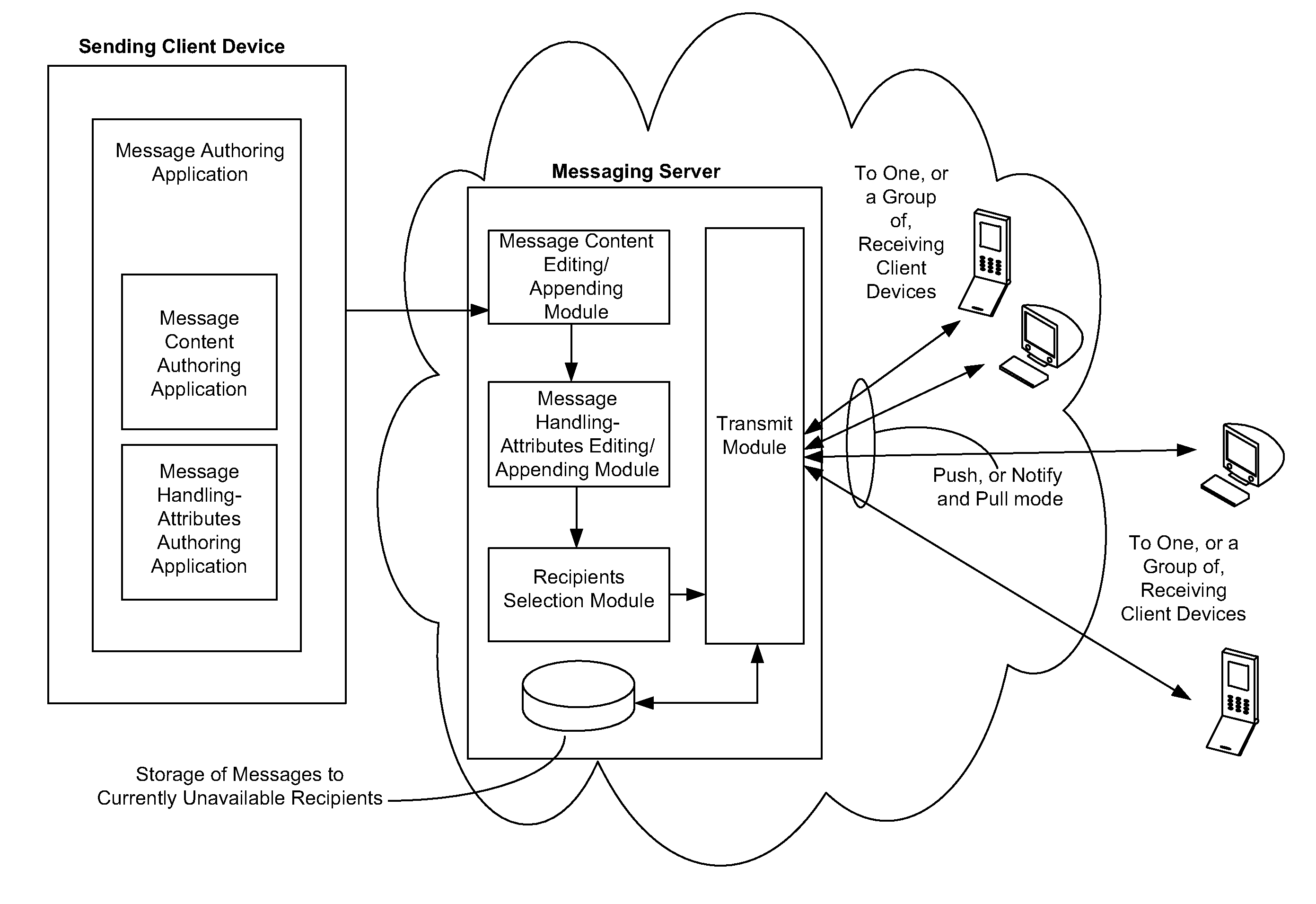
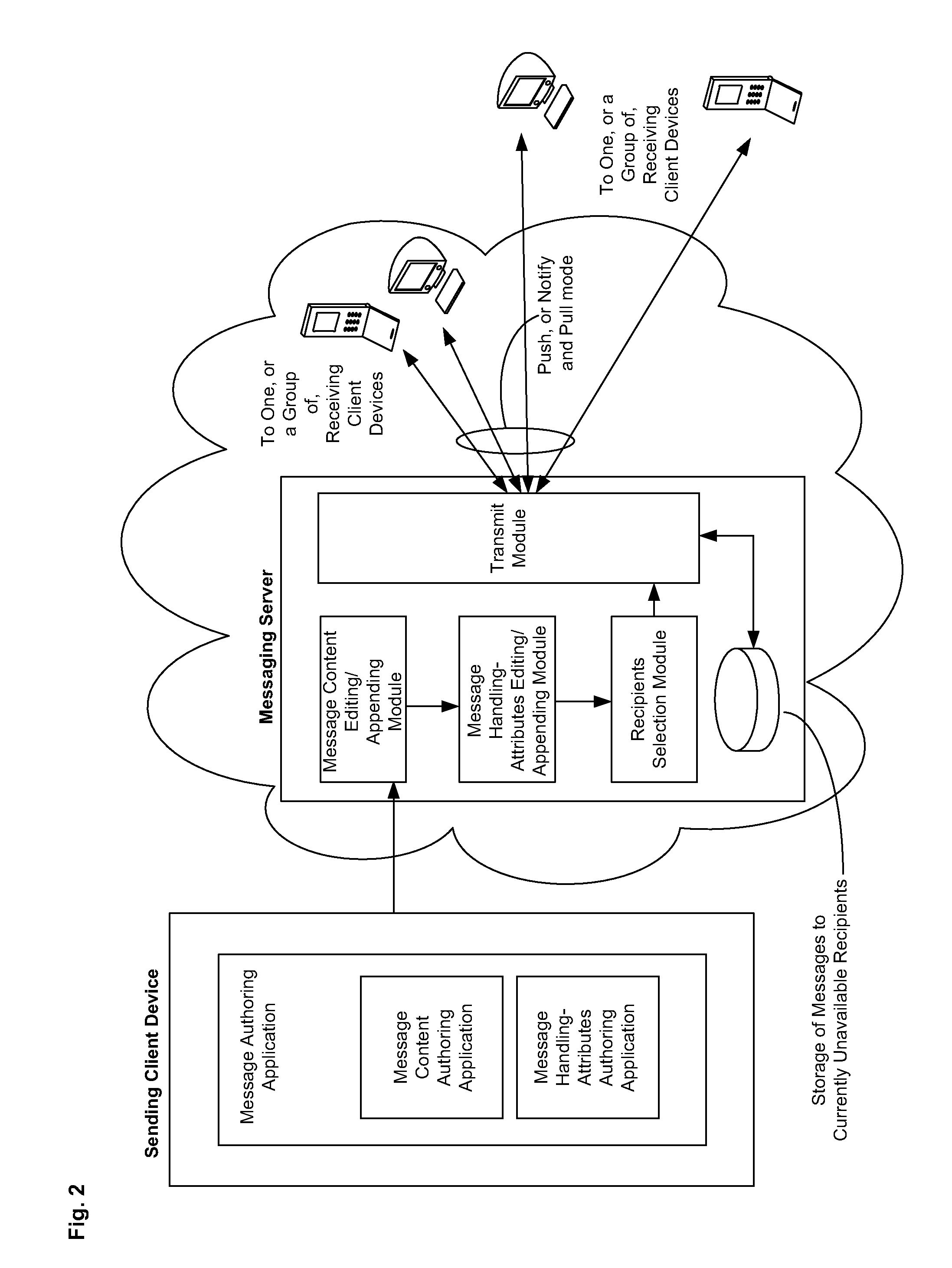
Disclosed are a messaging system, apparatuses circuits and methods of operation thereof. A messaging client device is adapted to receive an impermanent message and to manage the received message in accordance with a message management policy associated with the message. An impermanent messaging server is adapted to validate said messaging client device as complying with message management policies prior to authorizing transmission of the message to said messaging client device.
Owner:TIGERCONNECT INC
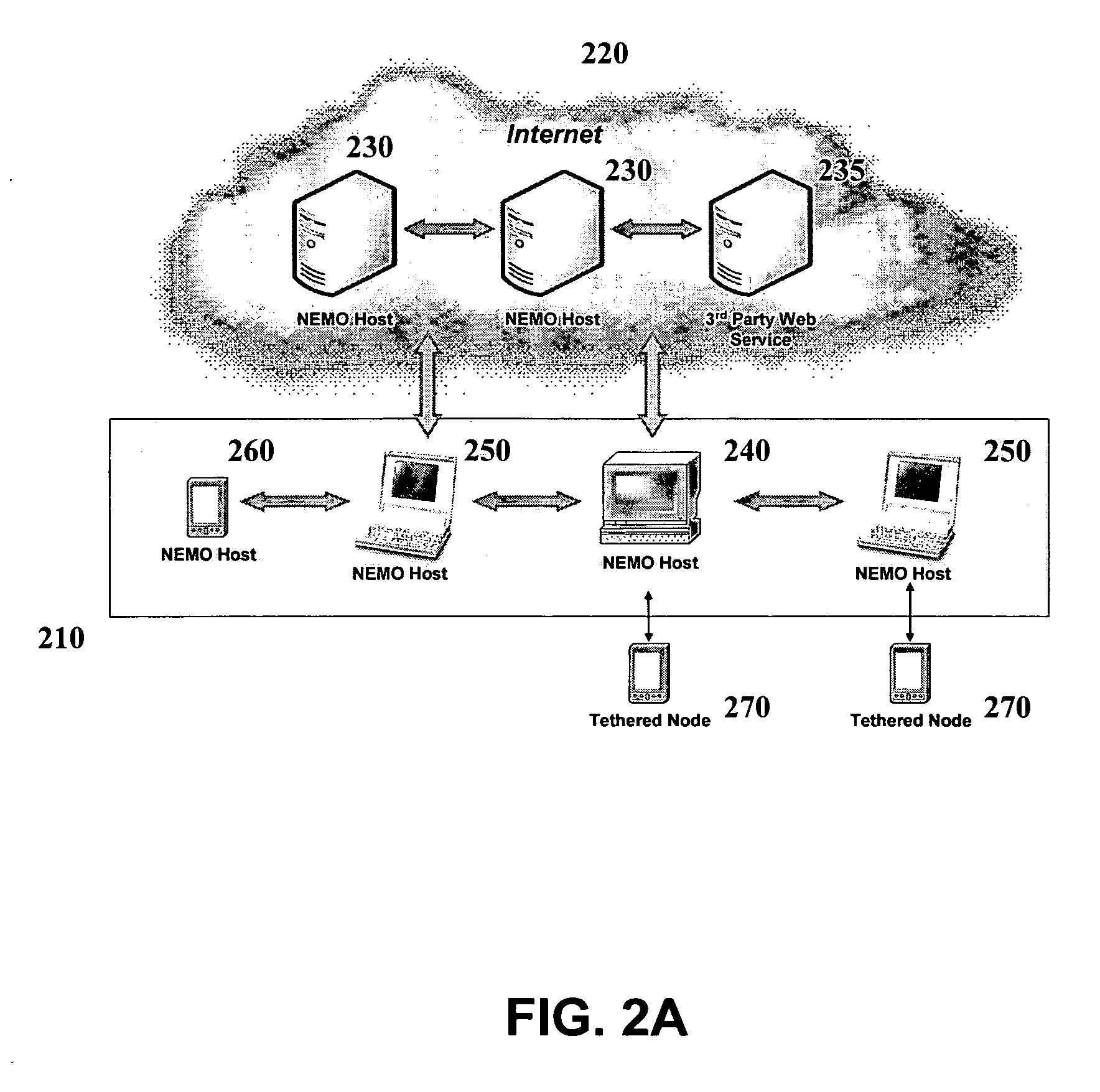
Interoperable systems and methods for peer-to-peer service orchestration
InactiveUS20050027871A1Facilitating commercial exchangeIncrease flexibilityWeb data indexingCryptography processingOperational systemWeb service
Systems and methods are described for performing policy-managed, peer-to-peer service orchestration in a manner that supports the formation of self-organizing service networks that enable rich media experiences. In one embodiment, services are distributed across peer-to-peer communicating nodes, and each node provides message routing and orchestration using a message pump and workflow collator. Distributed policy management of service interfaces helps to provide trust and security, supporting commercial exchange of value. Peer-to-peer messaging and workflow collation allow services to be dynamically created from a heterogeneous set of primitive services. The shared resources are services of many different types, using different service interface bindings beyond those typically supported in a web service deployments built on UDDI, SOAP, and WSDL. In a preferred embodiment, a media services framework is provided that enables nodes to find one another, interact, exchange value, and cooperate across tiers of networks from WANs to PANs.
Owner:INTERTRUST TECH CORP
Screen icon manipulation by context and frequency of use
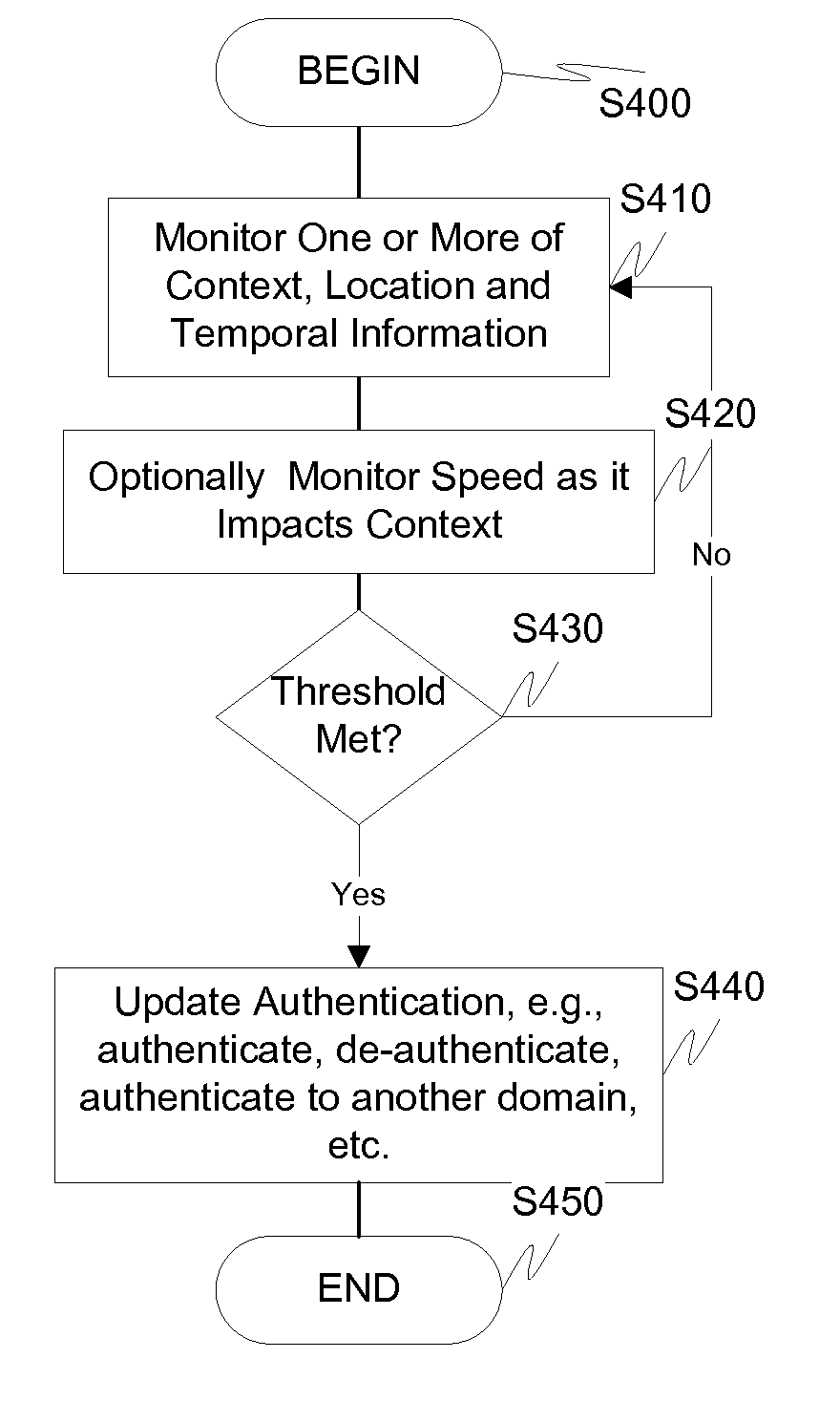
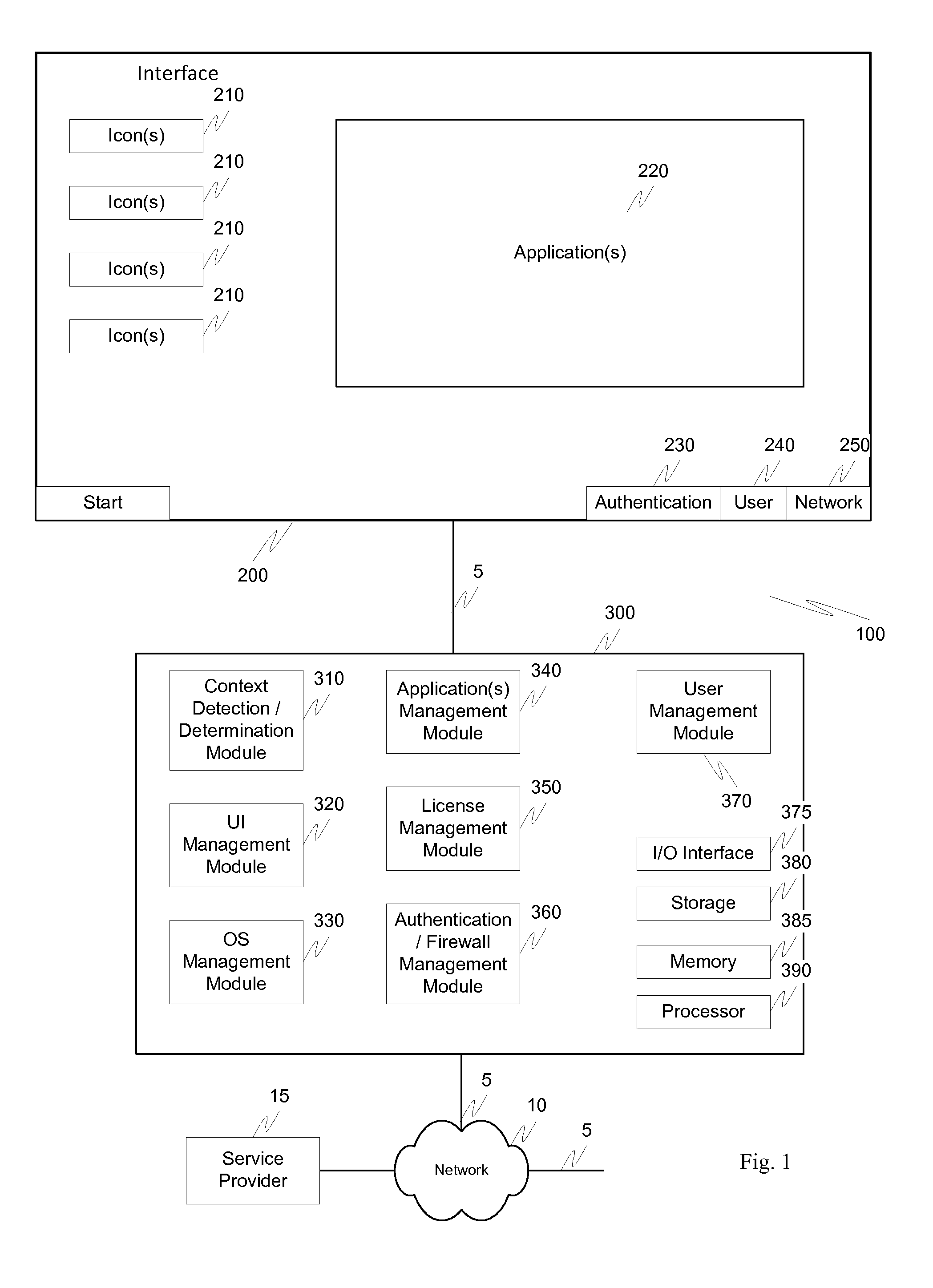
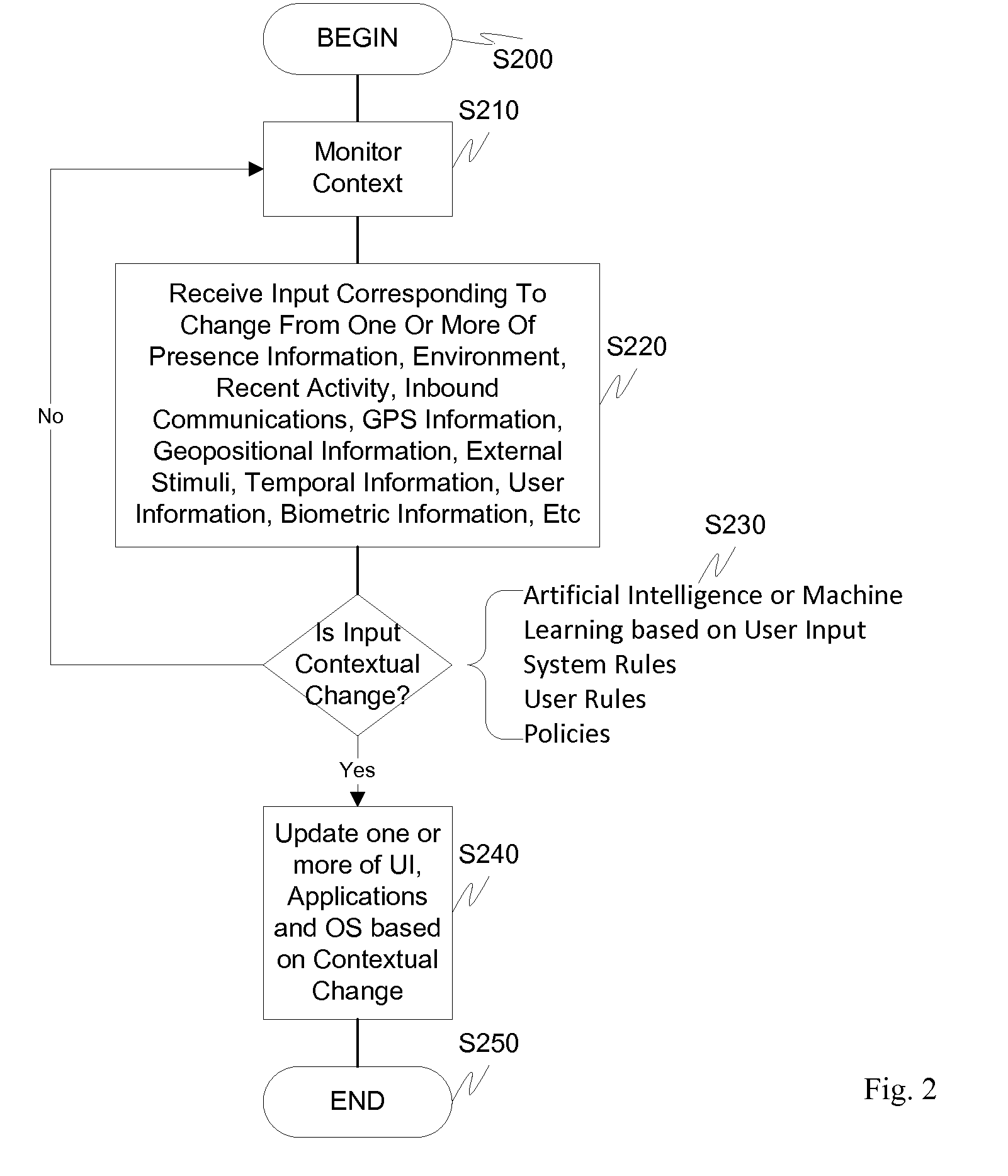
ActiveUS20110072492A1More user confidenceDigital data processing detailsMultiple digital computer combinationsTemporal informationOutbound communication
Dynamic device management is provided based on a change in context. The management can be for one or more of icons, application, operating system(s), preferences, display characteristics, and the like. Detection and / or monitoring of one or more of presence information, environmental information, user information, recent activity information, inbound / outbound communication information, external stimuli information, geopositional information, temporal information, calendar information, user information, biometric information, and security information can be used as inputs to determining a change in this context.
Owner:AVAYA INC
Digital rights management in a mobile communications environment
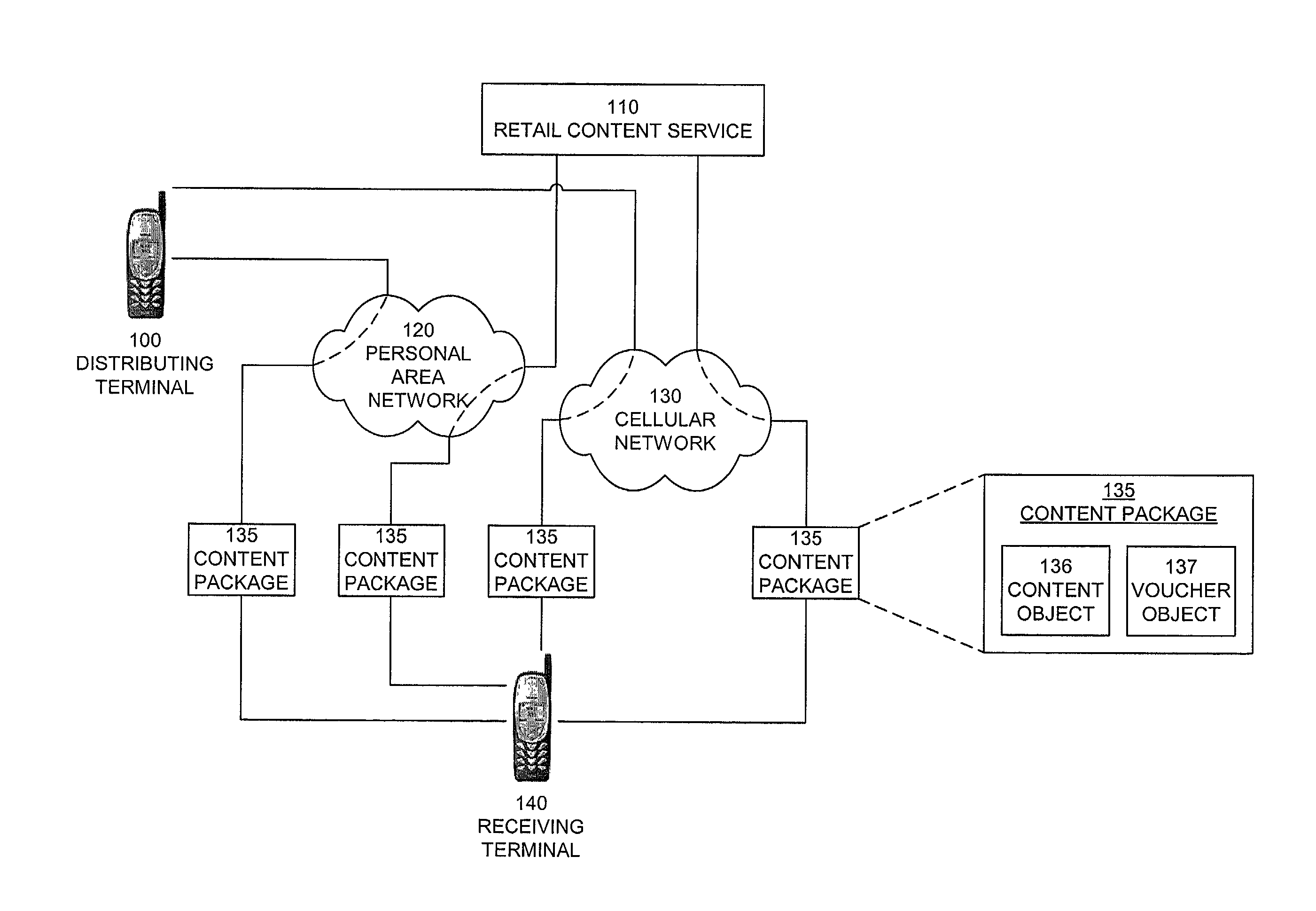
InactiveUS20050004875A1Payment architectureProgram/content distribution protectionVoucherDigital rights management
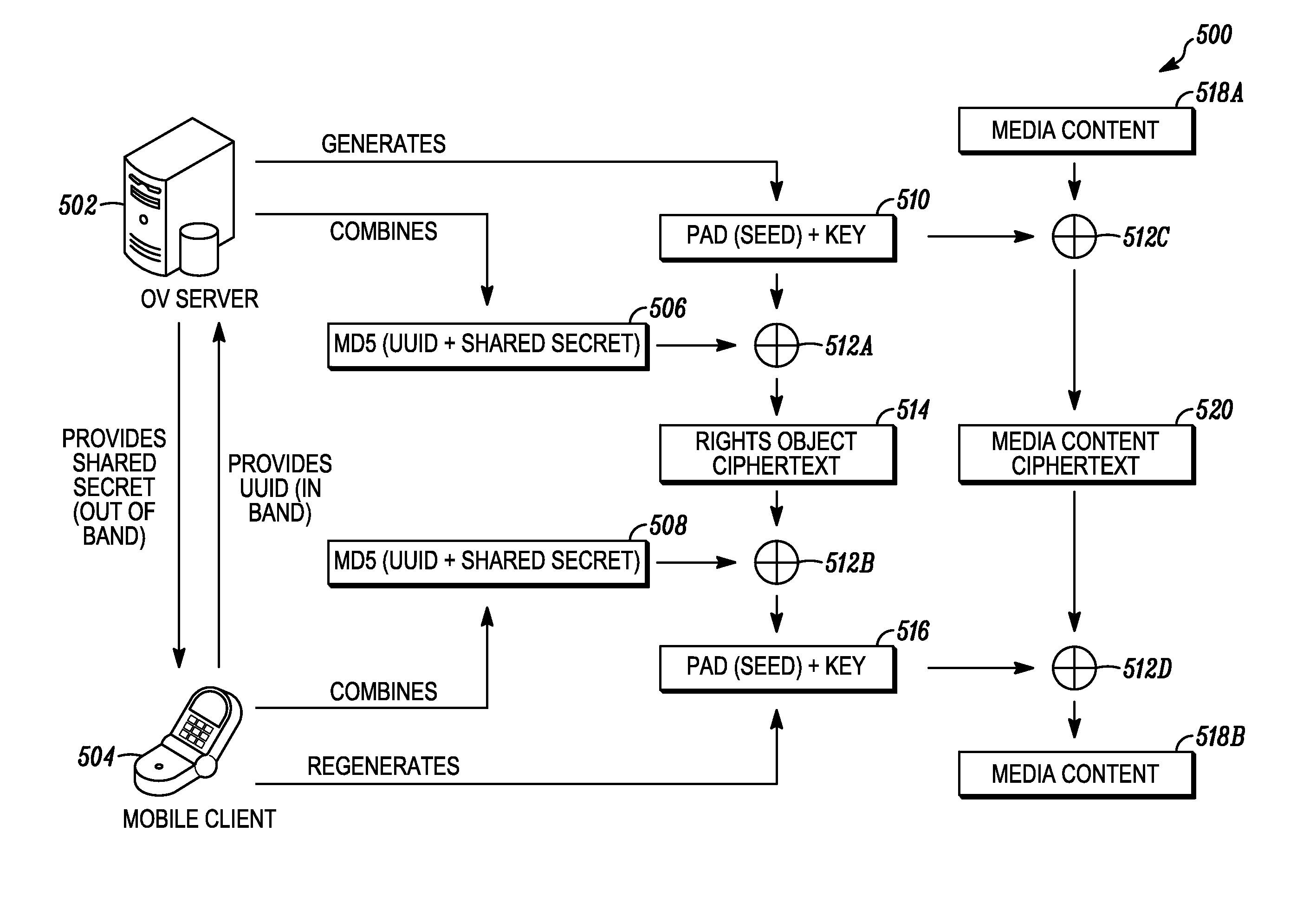
A method, system, and computer program product for enabling a wireless device in a mobile communication environment to obtain rights to protected content of a digital asset. The digital asset is downloaded to the wireless device from any one of a plurality of content servers or other wireless devices. The digital asset comprising a content ID, content encrypted with a content key, and information on obtaining rights to the content being expressed in a voucher generated by a voucher server in the network. The method, system, and computer program product also creates the digital asset for downloading to a wireless device from one of a plurality of content servers in a network and generates a voucher at the voucher server.
Owner:NOKIA TECHNOLOGLES OY
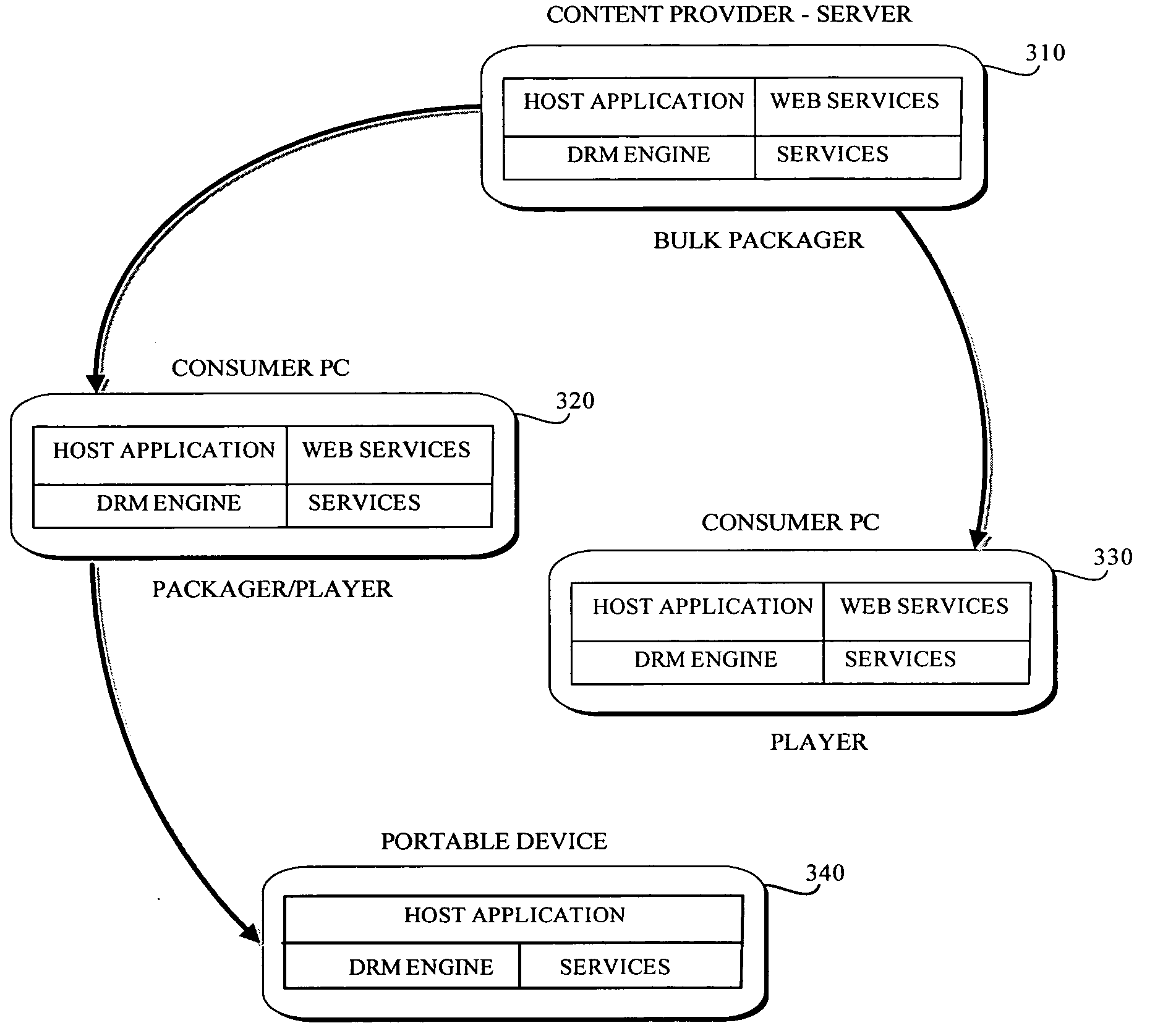
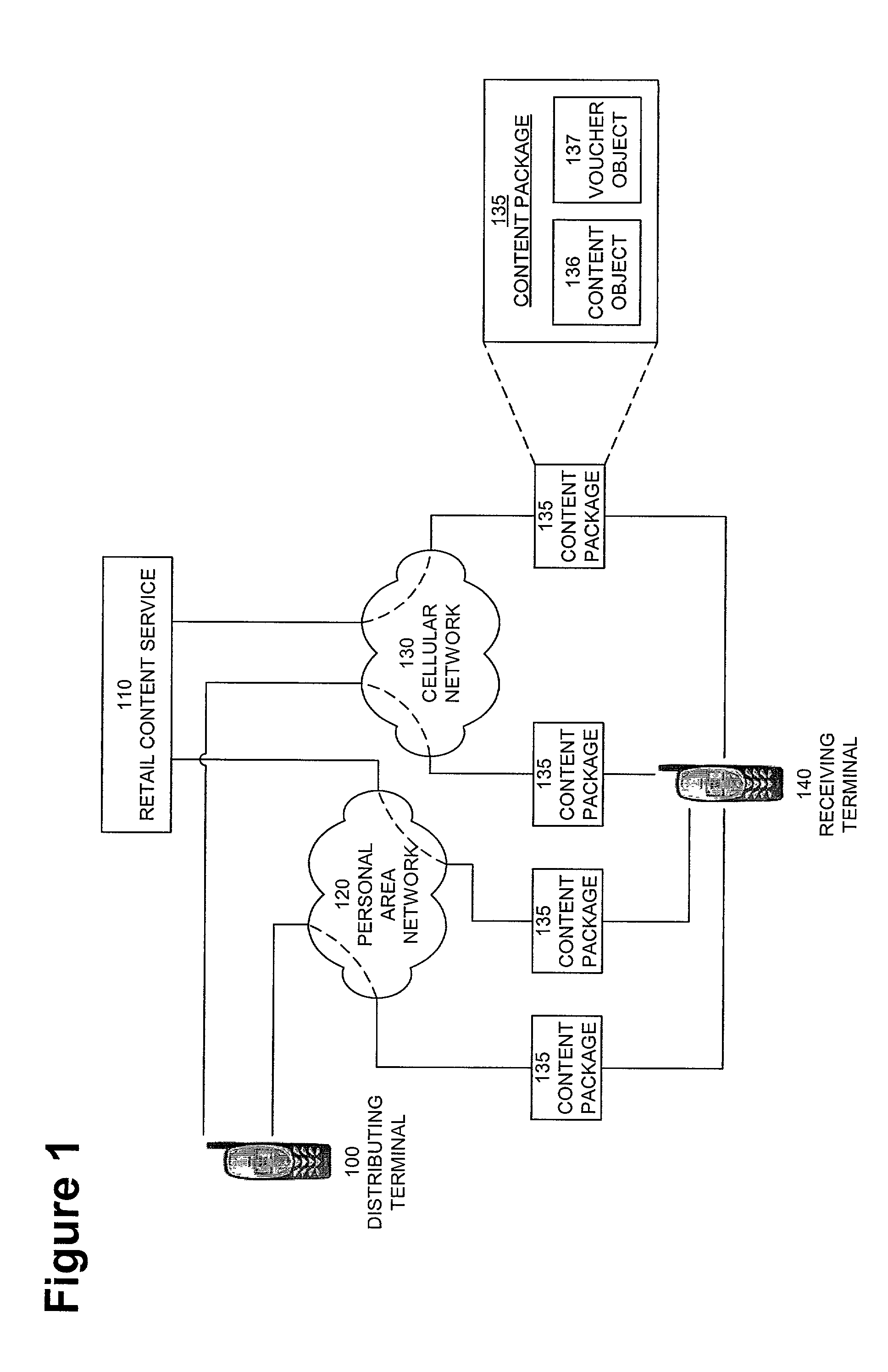
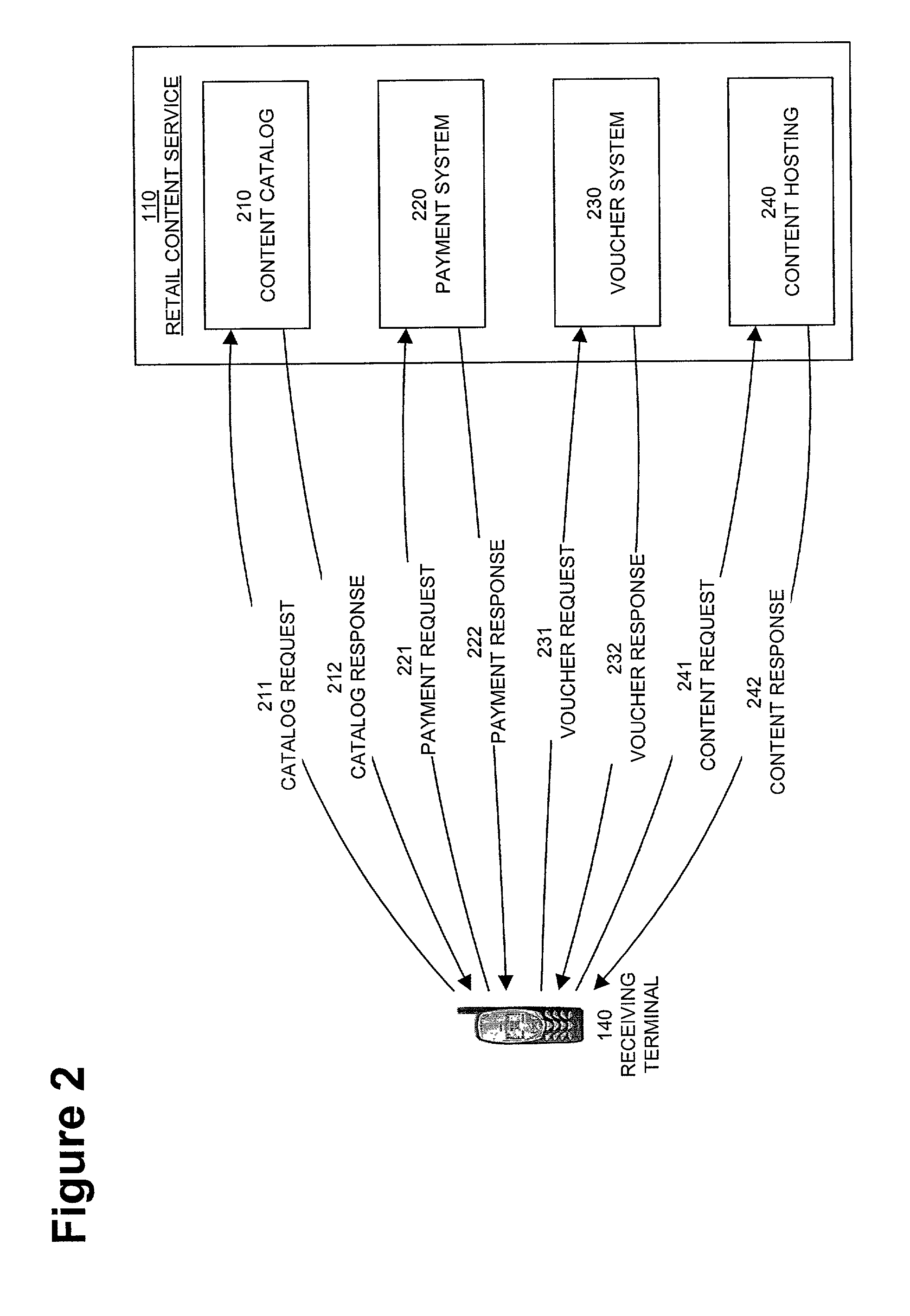
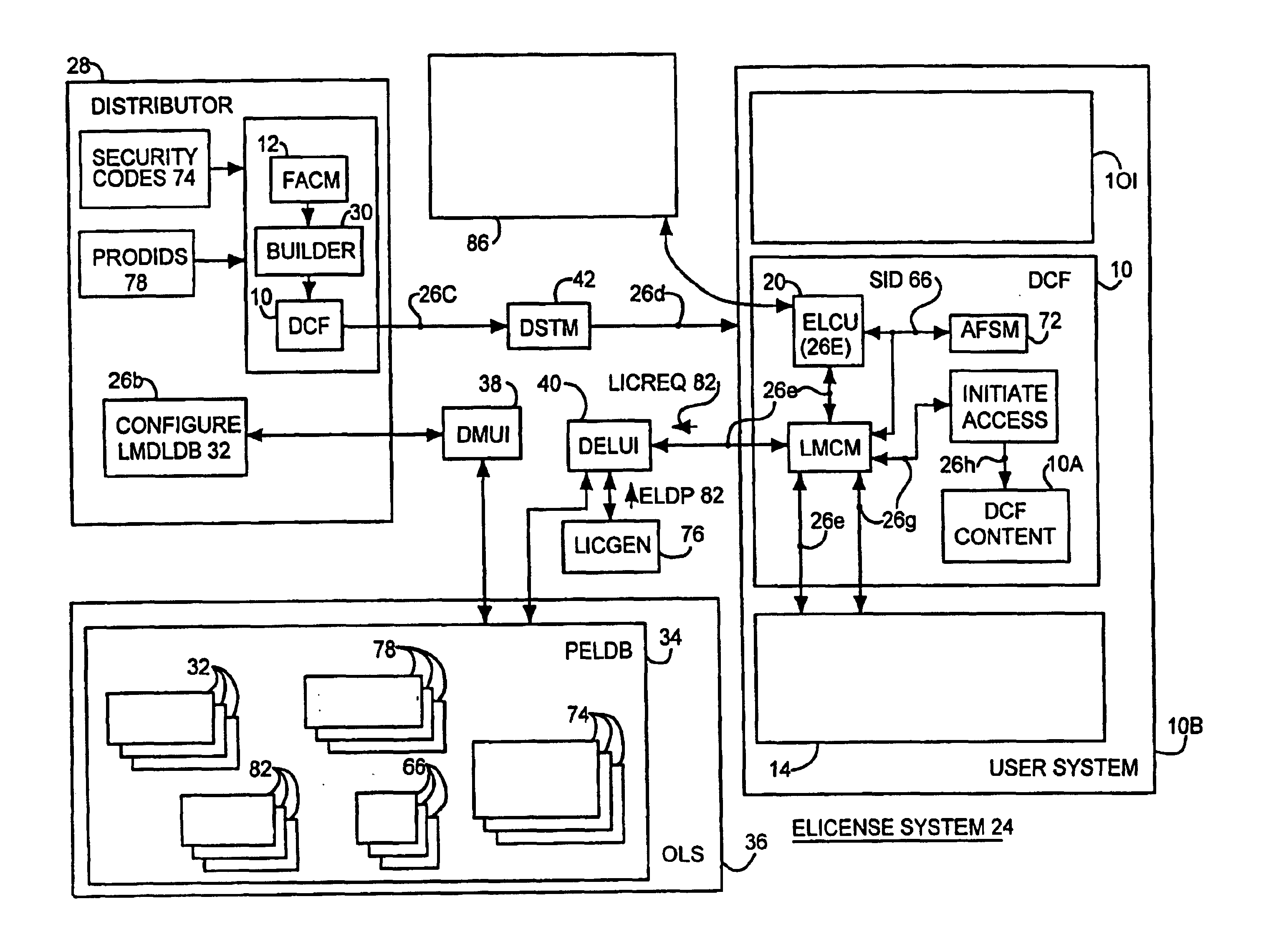
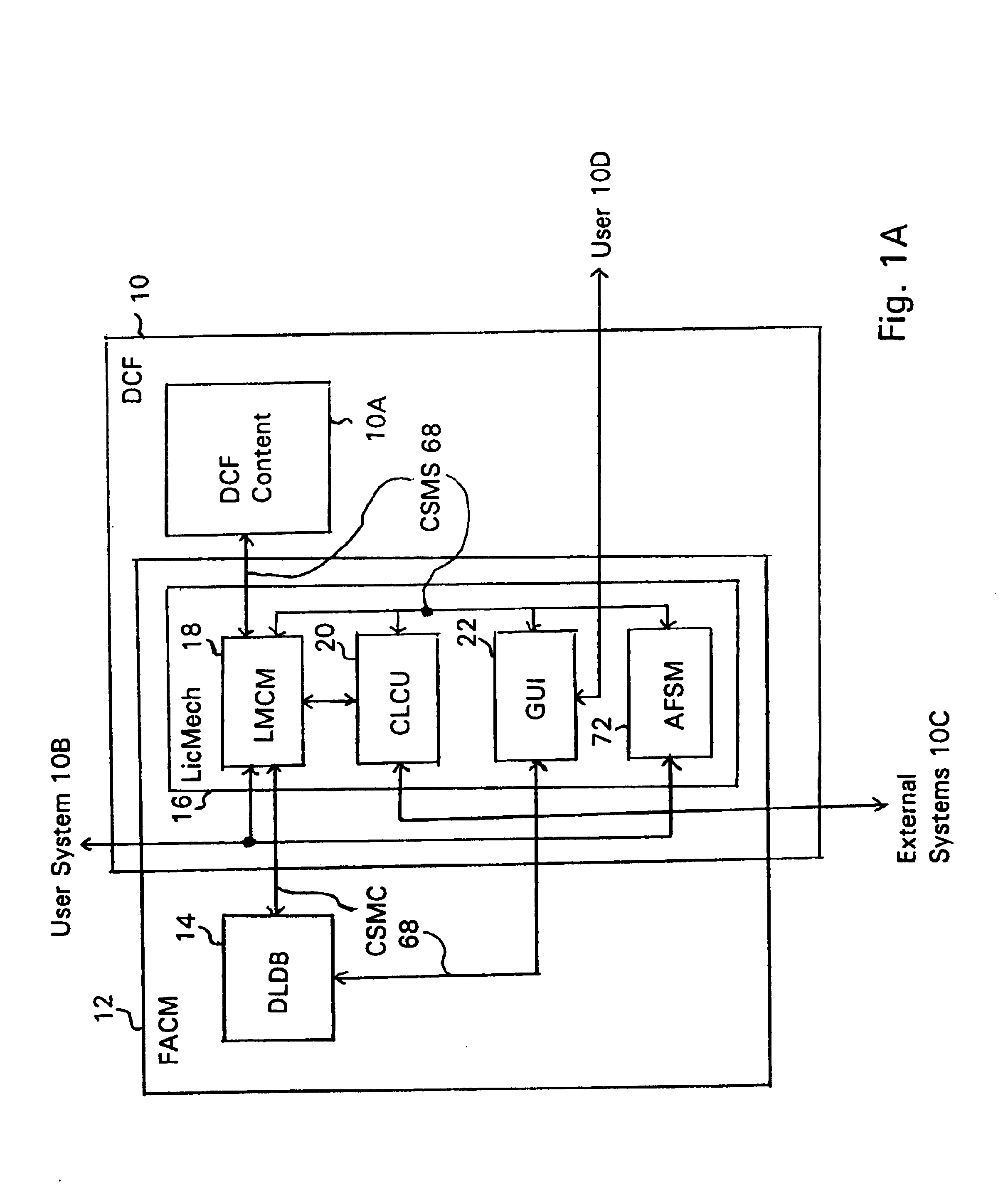
System and embedded license control mechanism for the creation and distribution of digital content files and enforcement of licensed use of the digital content files
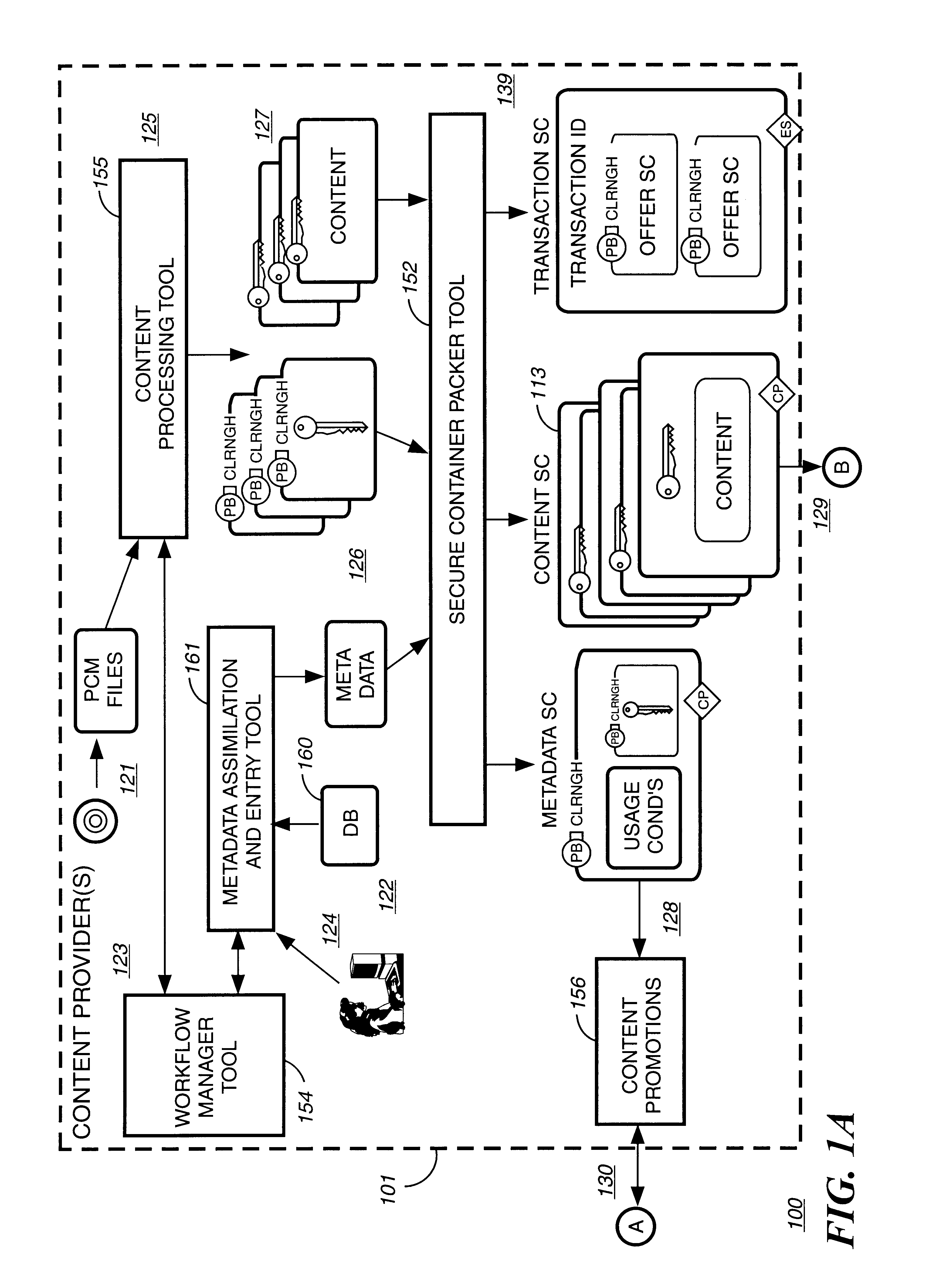
A digital content file including a license control mechanism controlling the licensed use of digital content and a system and method for distributing licensable digital content files and licenses. A digital content file includes a digital content, which may be executable code or data, an embedded file access control mechanism and a dynamic license database associated with the file access mechanism for storing license information used by the file access control mechanism in controlling use of the digital content. The file access control mechanism includes a license monitor and control mechanism communicating with the dynamic license database and controlling use of the digital content and a license control utility providing communications between a user system and an external system to communicate license definition information and includes a graphical user interface. License information may be stored initially in the dynamic license database or provided from an external system. The system allows the distribution of digital content files and the acquisition of licenses with seamless transaction processing through an order processing system generating an order identification and authorization for a license and a product configuration and order database containing license management databases associated with the digital content files and containing license information to be transmitted to a user system upon receipt of an order identifier. The product configuration and order database also generates a license record for each transaction.
Owner:VIATECH TECH
Digital content distribution using web broadcasting services
InactiveUS20030135464A1Website content managementElectronic credentialsBroadcast channelsDigital content
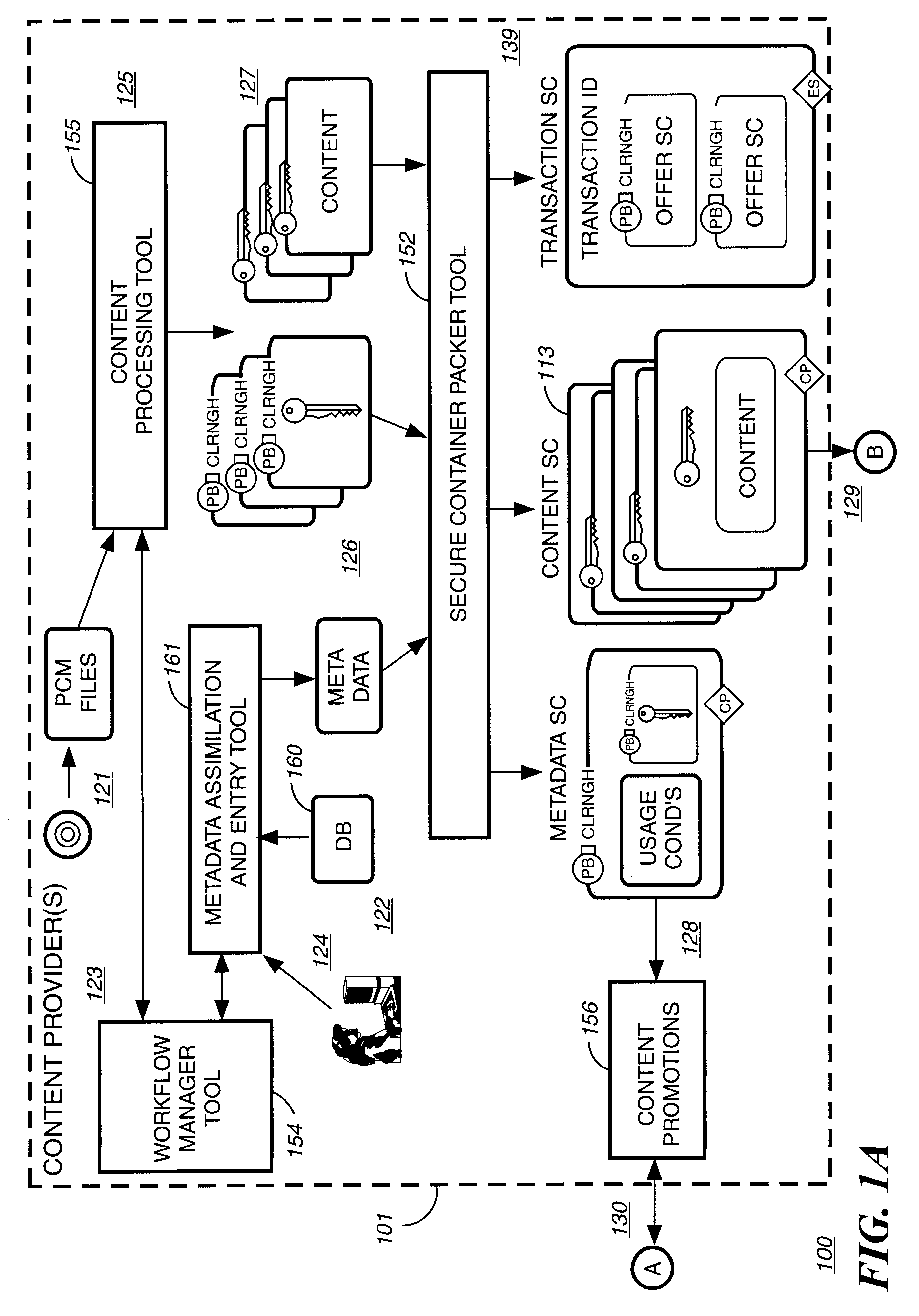
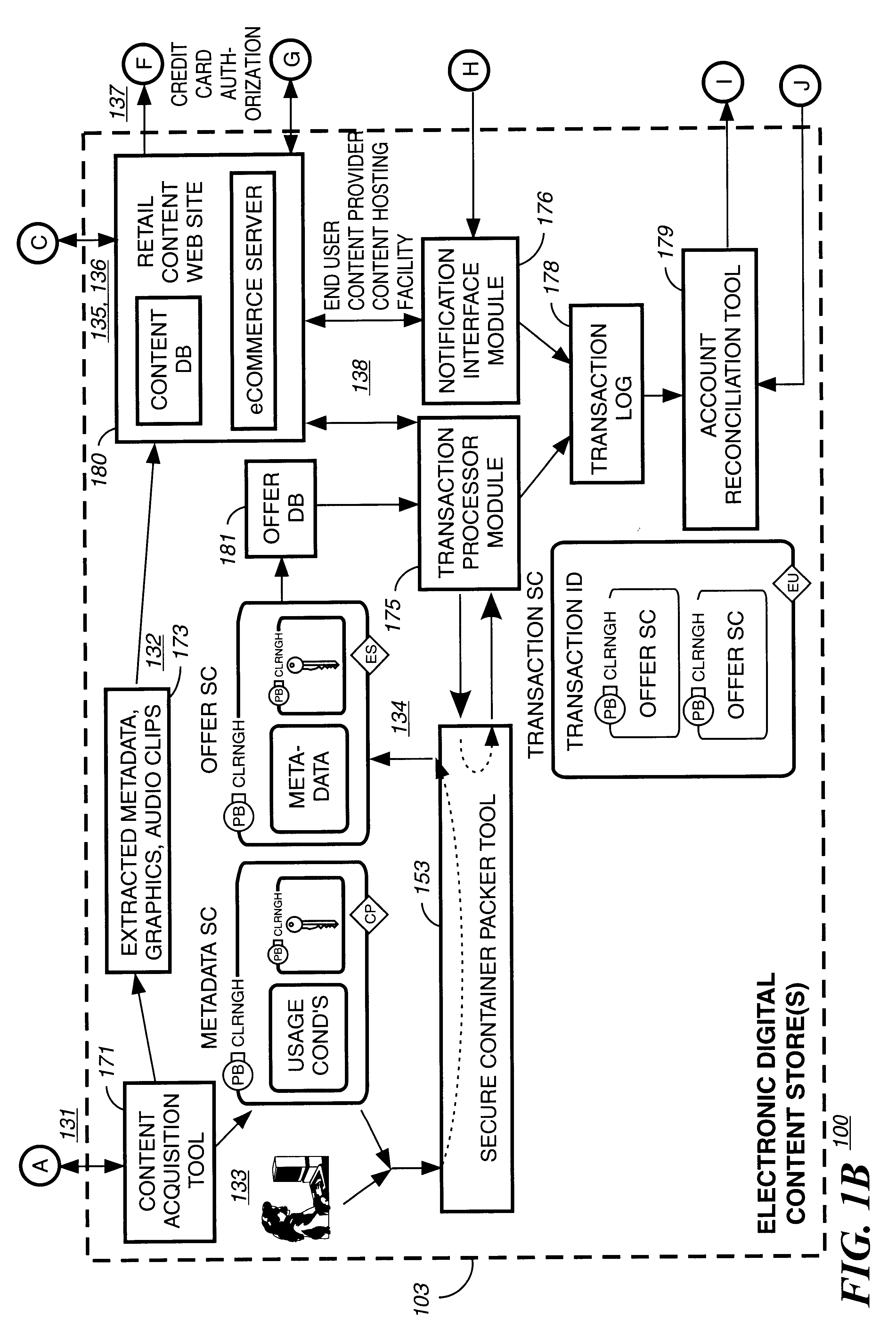
A method of securely receiving data on a user's system from a web broadcast infrastructure with a plurality of channels. The method comprising the steps of: receiving promotional metadata from a first web broadcast channel, the promotional metadata related to data available for reception; assembling at least part of the promotional metadata into a promotional offering for review by a user; selecting by a user, data to be received related to the promotional metadata; receiving data from a second web broadcast channel, the data selected from the promotional metadata, and wherein the data has been previously encrypted using a first encrypting key; and receiving the first decrypting key via a computer readable medium, the first decrypting key for decrypting at least some of the data received via the second web broadcast channel. In another embodiment, a method and system to transmit data securely from a web broadcast center is disclosed.
Owner:IBM CORP
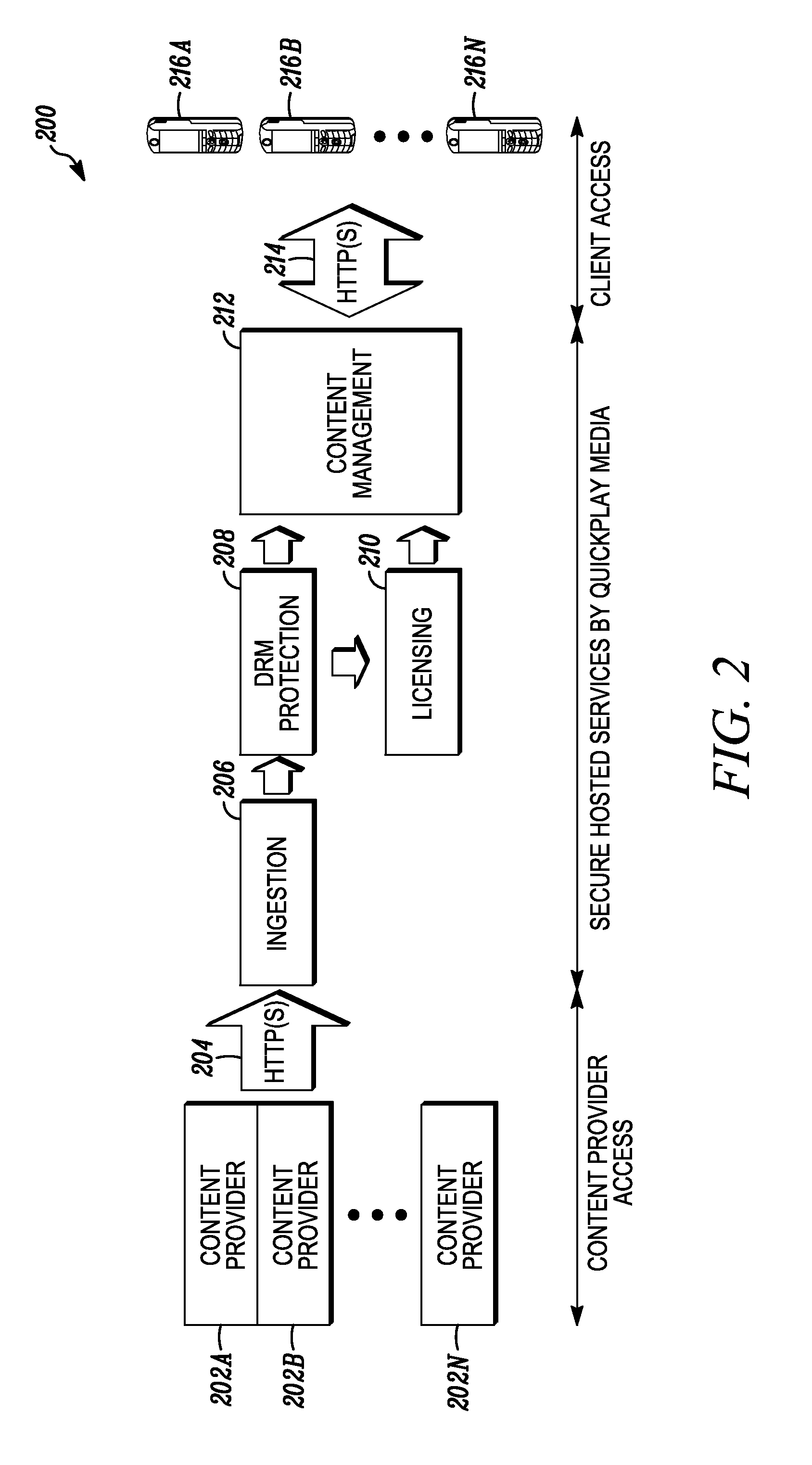
Method and apparatus for installation abstraction in a secure content delivery system
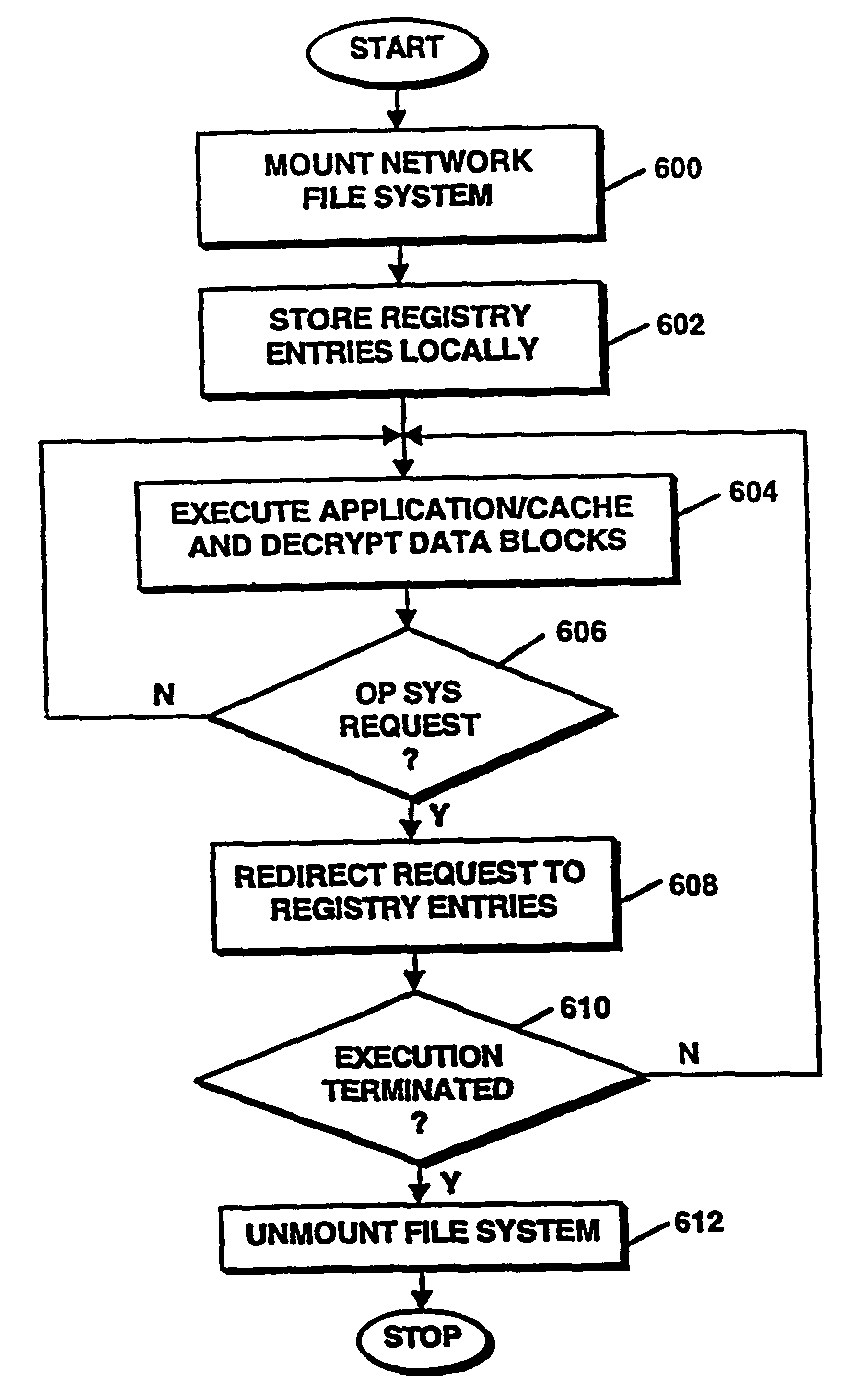
InactiveUS6374402B1Expand accessAvoid leverageTelevision system detailsBroadband local area networksOperational systemNetwork addressing
A system for secure delivery of on-demand content over broadband access networks includes a client application executing on a user's local computer system. The client application interacts with a content server on which a plurality of selectable titles are stored and further interacts with an access server which provides the network address of a title and keying data necessary for to the client process access and execute the title. The client process utilizes an installation abstraction which enables a title to be executed on the local computer system without ever being installed. The abstraction is achieved by mounting a network file system and storing a set of registry entries related to the title on the local computer system. Portions of the title are retrieved from the content server and executed by the local operating system. During title execution, requests from the local operating system are intercepted and redirected to the set of registry entries, as applicable. The times at which the client process may retrieve the title data from the content server are defined by the access server through use of an activator and token.
Owner:MICROSOFT TECH LICENSING LLC
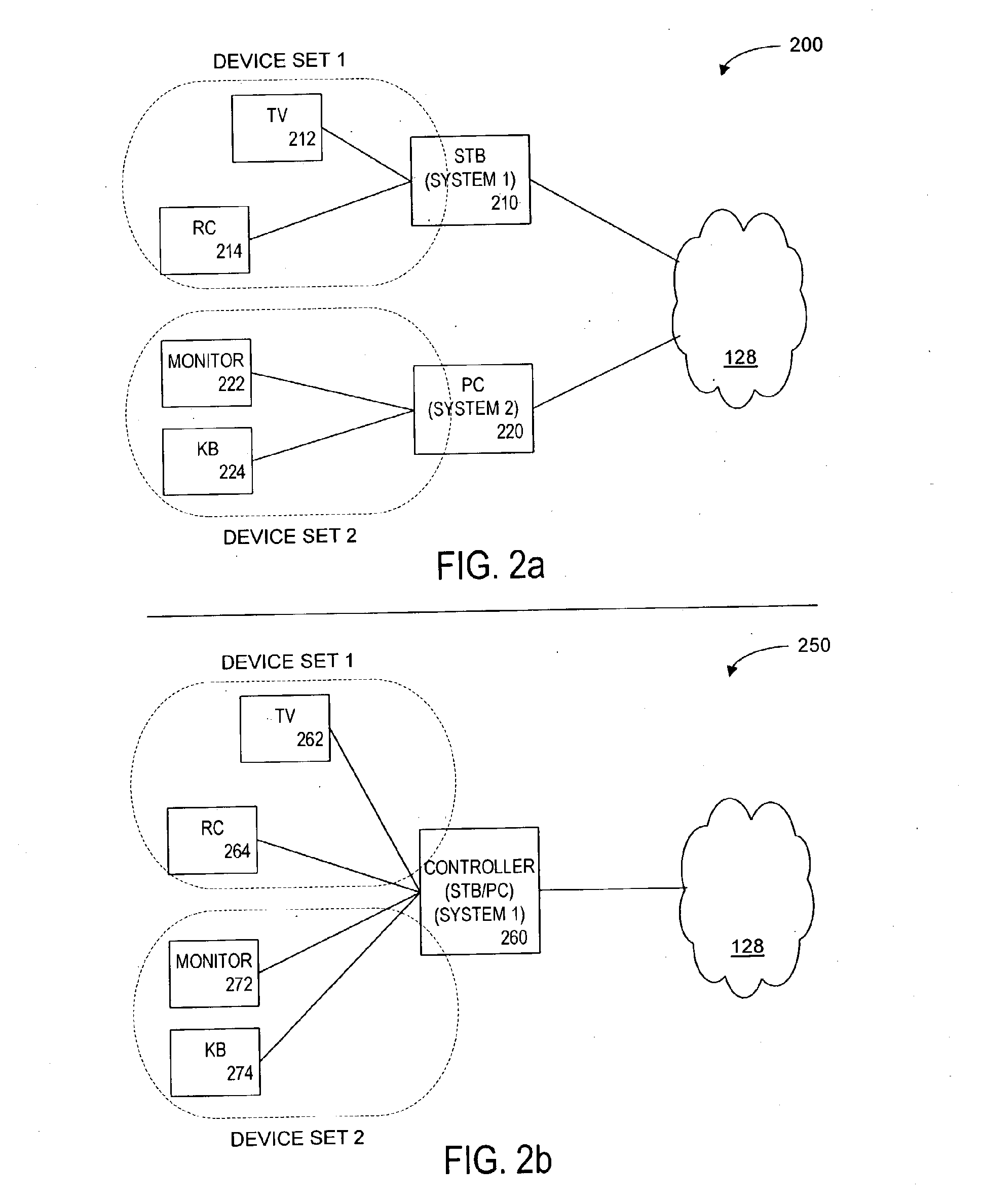
Method and Apparatus for Browsing Using Multiple Coordinated Device Sets
Systems and methods for navigating hypermedia using multiple coordinated input / output device sets. Disclosed systems and methods allow a user and / or an author to control what resources are presented on which device sets (whether they are integrated or not), and provide for coordinating browsing activities to enable such a user interface to be employed across multiple independent systems. Disclosed systems and methods also support new and enriched aspects and applications of hypermedia browsing and related business activities.
Owner:CONVERGENT MEDIA SOLUTIONS
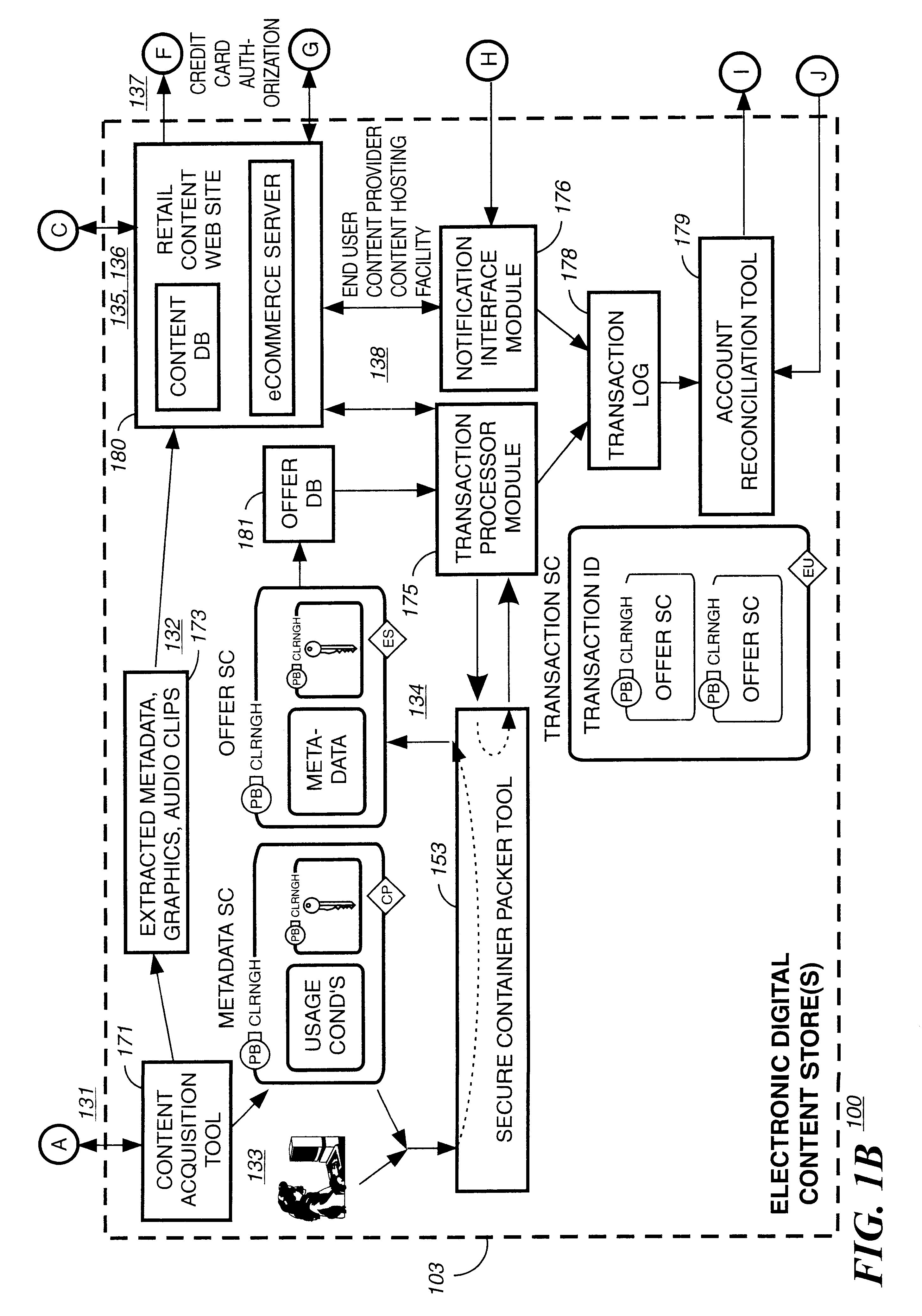
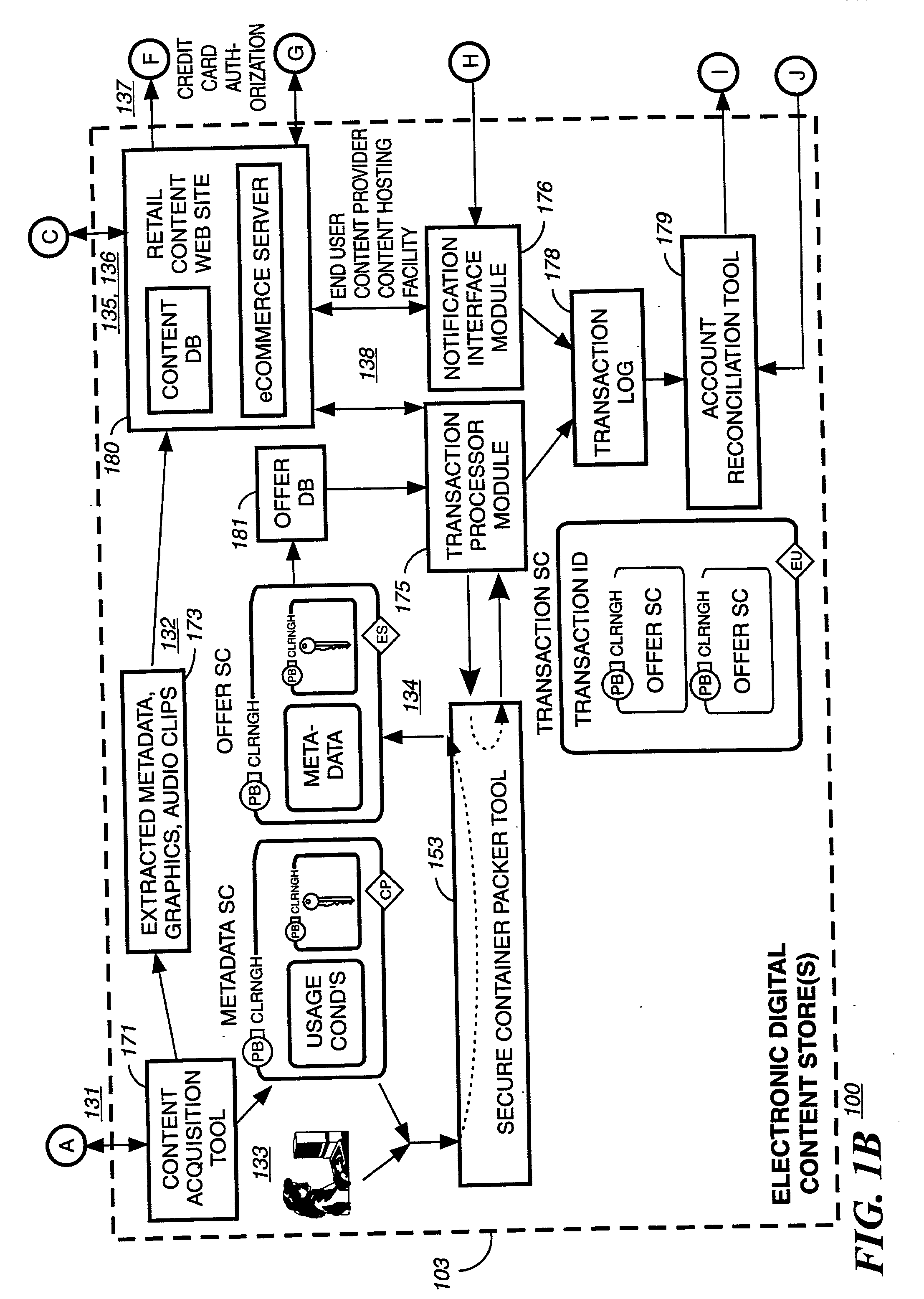
Method and apparatus for uniquely identifying a customer purchase in an electronic distribution system
InactiveUS6389403B1Key distribution for secure communicationDigital data processing detailsContent IdentifierUser device
A system for tracking usage of digital content on user devices. Content sites for distributing digital content over a computer readable medium to users. The content sites associate unique content identifier with the content associated. Electronic stores coupled to a network sell licenses to play digital content data to users. The licenses contain a unique transaction identifier for uniquely identifying the transaction, and the licenses contain a unique item identifier for uniquely identifying at least one item in the transaction. Content players, which receive from the network the licensed content data, are used to play the licensed content data. The content players produce a purchase identifier based upon the mathematical combination of the content identifier, the transaction identifier and the item identifier.
Owner:WISTRON CORP
Method and system to secure content for distribution via a network
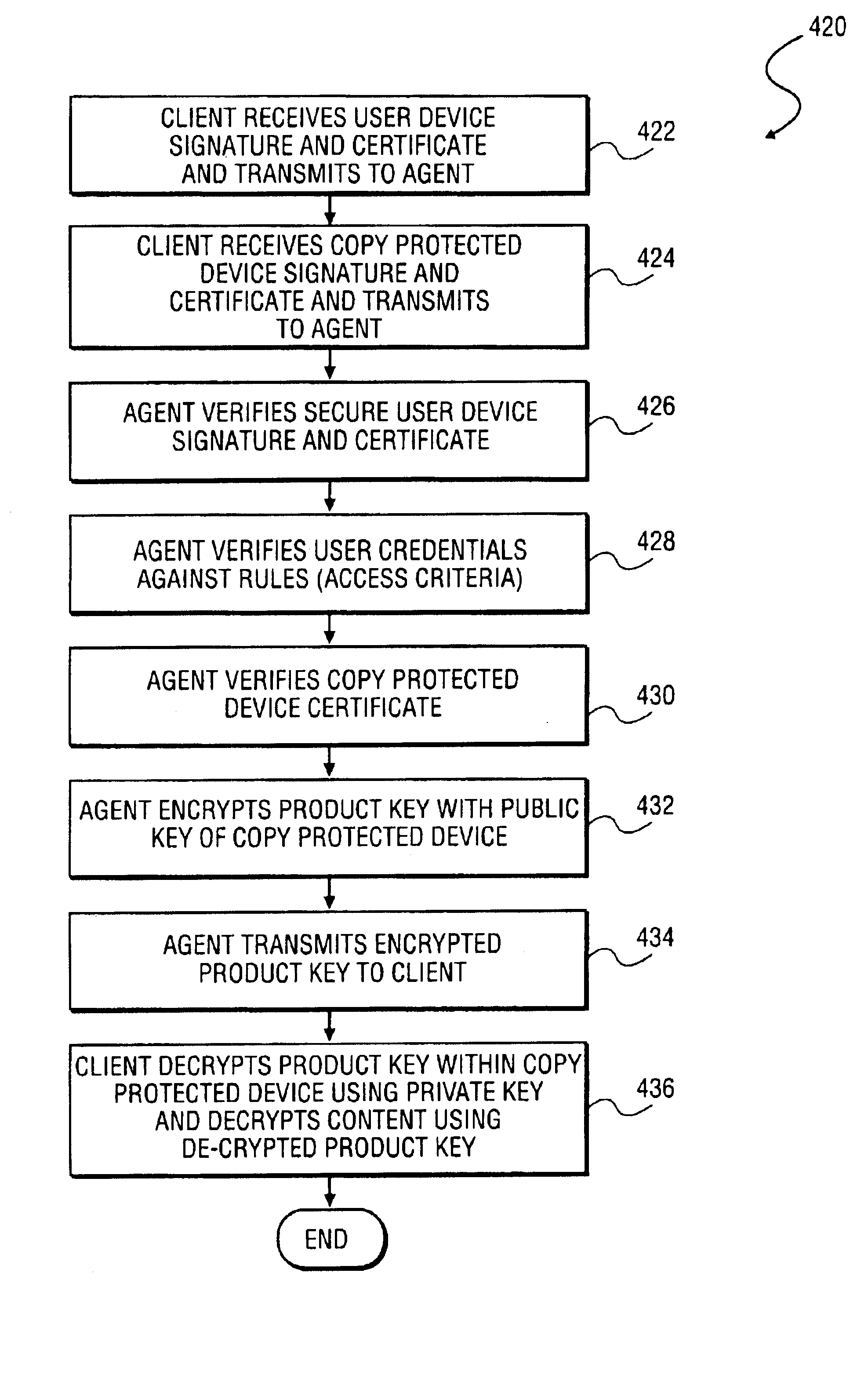
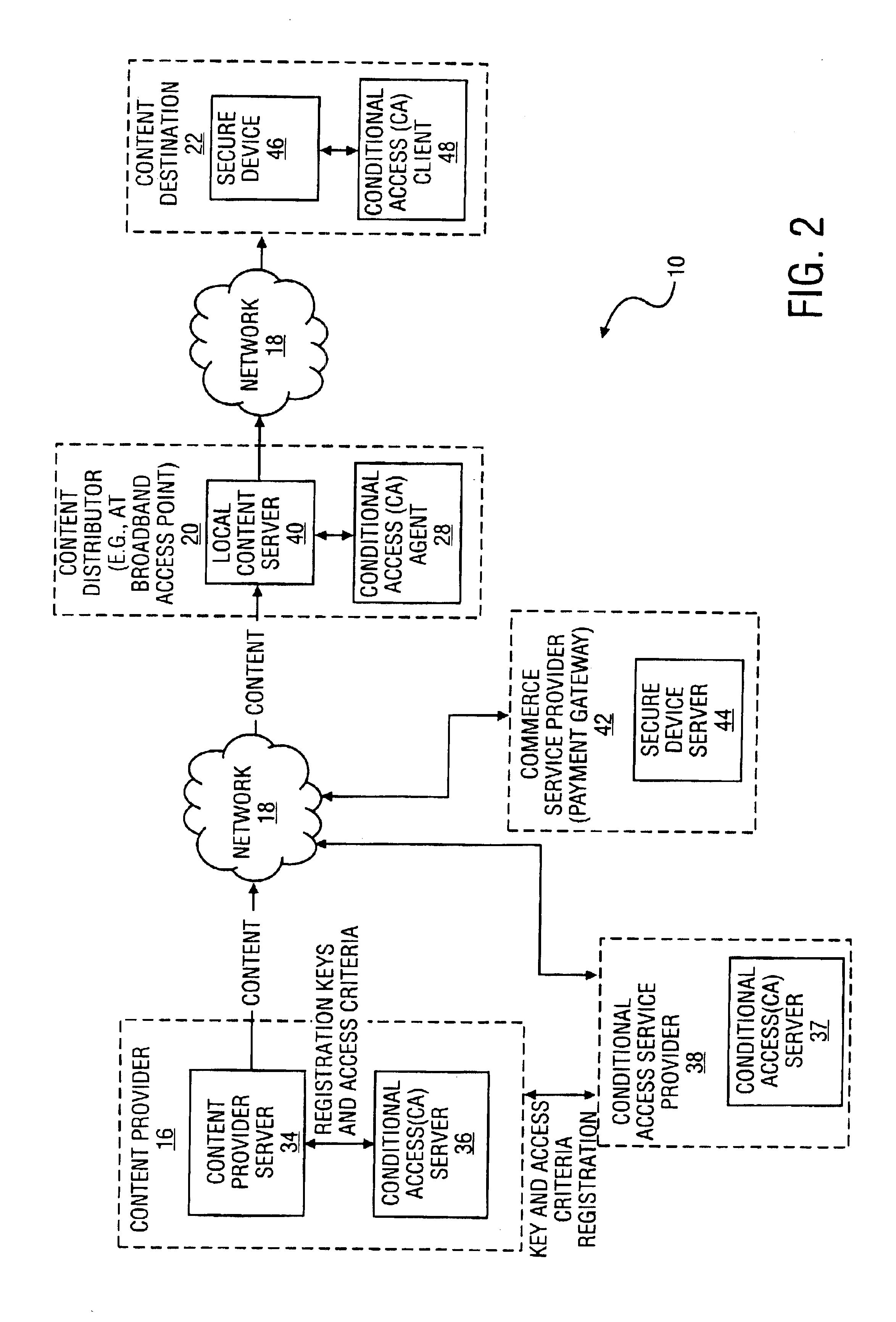
InactiveUS6961858B2Key distribution for secure communicationDigital data processing detailsUser deviceAuthentication
A method and system to secure content for distribution via a communications network commences when a user device authentication process is associated with content from a content provider. A copy-protected device authentication process is associated with the content. The user device authentication process and the copy-protected device authentication process are separate authentication processes to protect the content from unauthorized access.
Owner:MIH TECH HLDG BV
System and method for securely transmiting sensitive information
InactiveUS20130194301A1Inhibitory contentSecure transmissionCathode-ray tube indicatorsDigital data protectionComputer hardwareClient-side
A system and method for securely transmitting information over a communications network comprises receiving a message notification that a recipient has a message on a recipient's client device from a processor based server upon receipt of the message from a sender's client device. The message from the sender's client device is stored in a storage device by the server. The recipient accesses the server to view the message using the recipient's client device. The message is rendered and displayed on the screen by the recipient's client device in accordance with a display method selected by the sender of the message to present only a portion of the message at any given time to the recipient. The prevents the message from being recorded or captured.
Owner:BURN NOTE
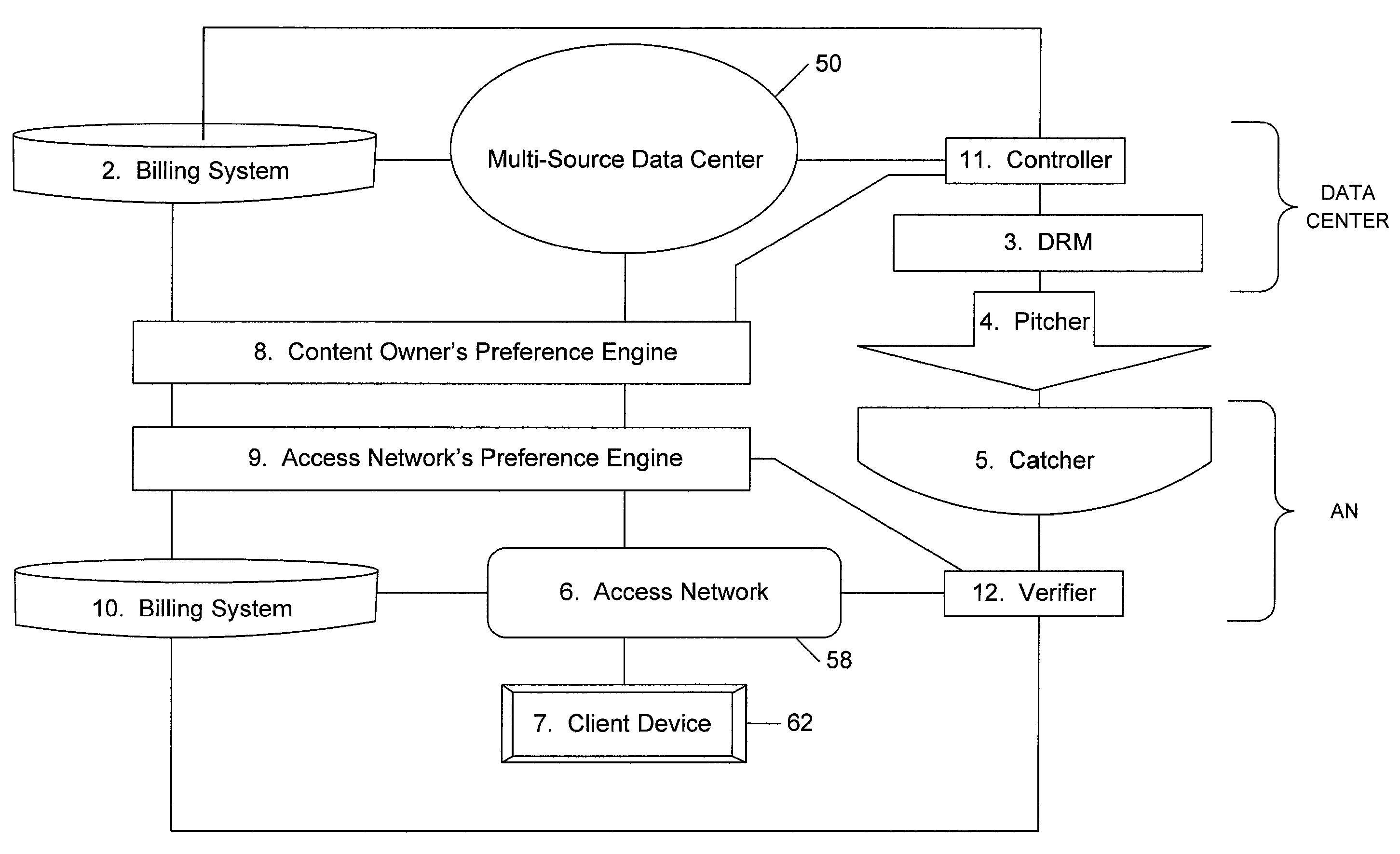
Multi-source bridge content distribution system and method
ActiveUS20080155614A1Appropriately sharedComplete banking machinesAdvertisementsContent distributionAccess network
A multi-source bridge content distribution system links multiple content owners with access network operators or content distribution providers leasing space on access networks so that multi-media content can be provided from multiple content owners to consumers through a multi-source bridge or data center. Content files and associated content owner preference settings are provided from a plurality of content sources or providers to the multi-source data center. Files stored at the data center or locally at an access network are provided to subscribers through the local access network Content files are provided if the content owner preference settings are a sufficient match with service provider access network preference settings set up by the service provider using the access network to provide content to subscribers.
Owner:VERIMATRIX INC
Method of Providing Digital Rights Management for Music Content by Means of a Flat-Rate Subscription
ActiveUS20100031366A1Reliable and goodEasy to manageMetering/charging/biilling arrangementsDigital data processing detailsOperational systemComputer network
The invention enables digital music content to be downloaded to and used on a portable wireless computing device. An application running on the wireless device has been automatically adapted to parameters associated with the wireless device without end-user input (e.g. the application has been configured in dependence on the device OS and firmware, related bugs, screen size, pixel number, security models, connection handling, memory etc. This application enables an end-user to browse and search music content on a remote server using a wireless network; to download music content from that remote server using the wireless network and to playback and manage that downloaded music content. The application also includes a digital rights management system that enables unlimited legal downloads of different music tracks to the device and also enables any of those tracks stored on the device to be played so long as a subscription service has not terminated.
Owner:TIKTOK PTE LTD
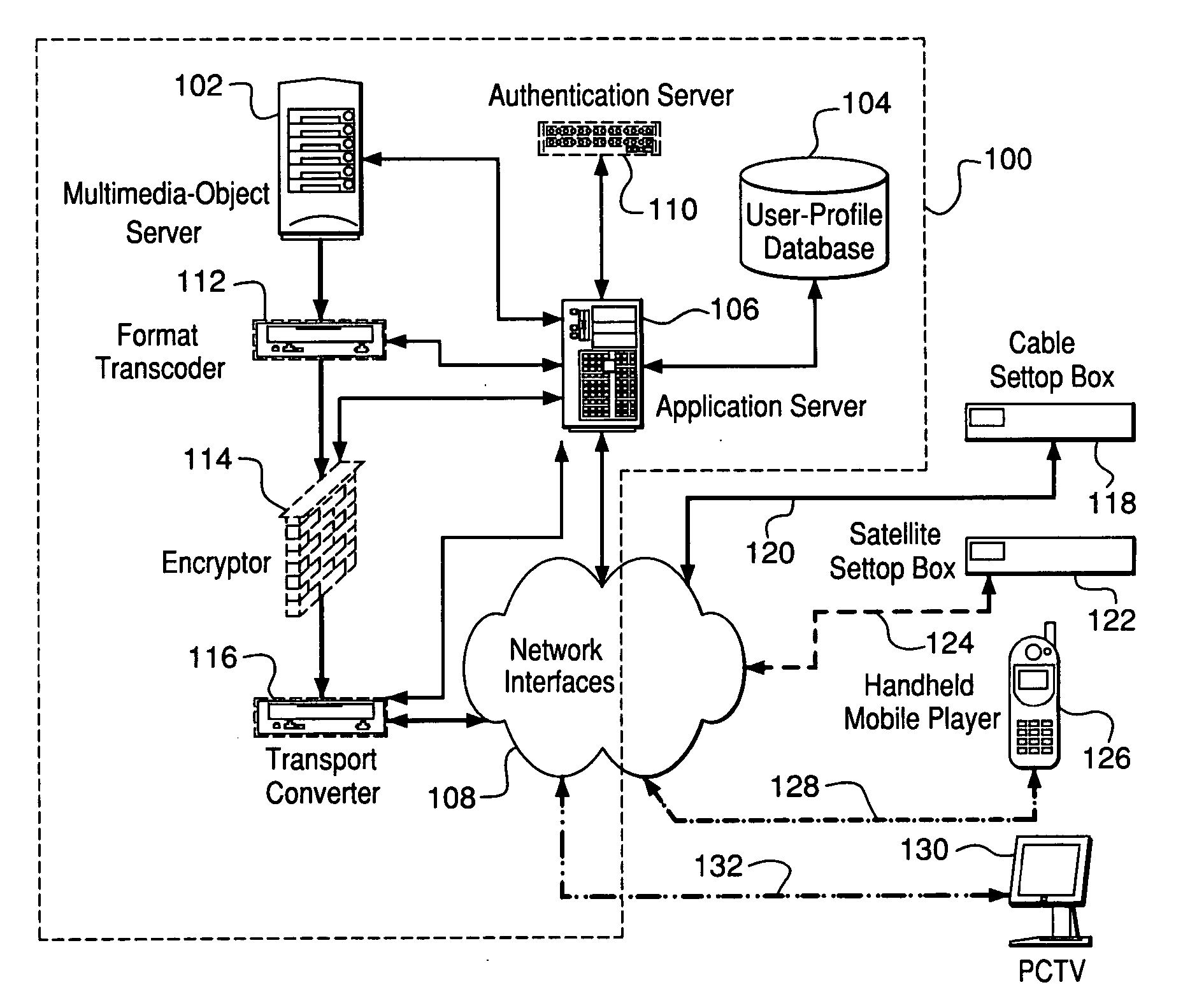
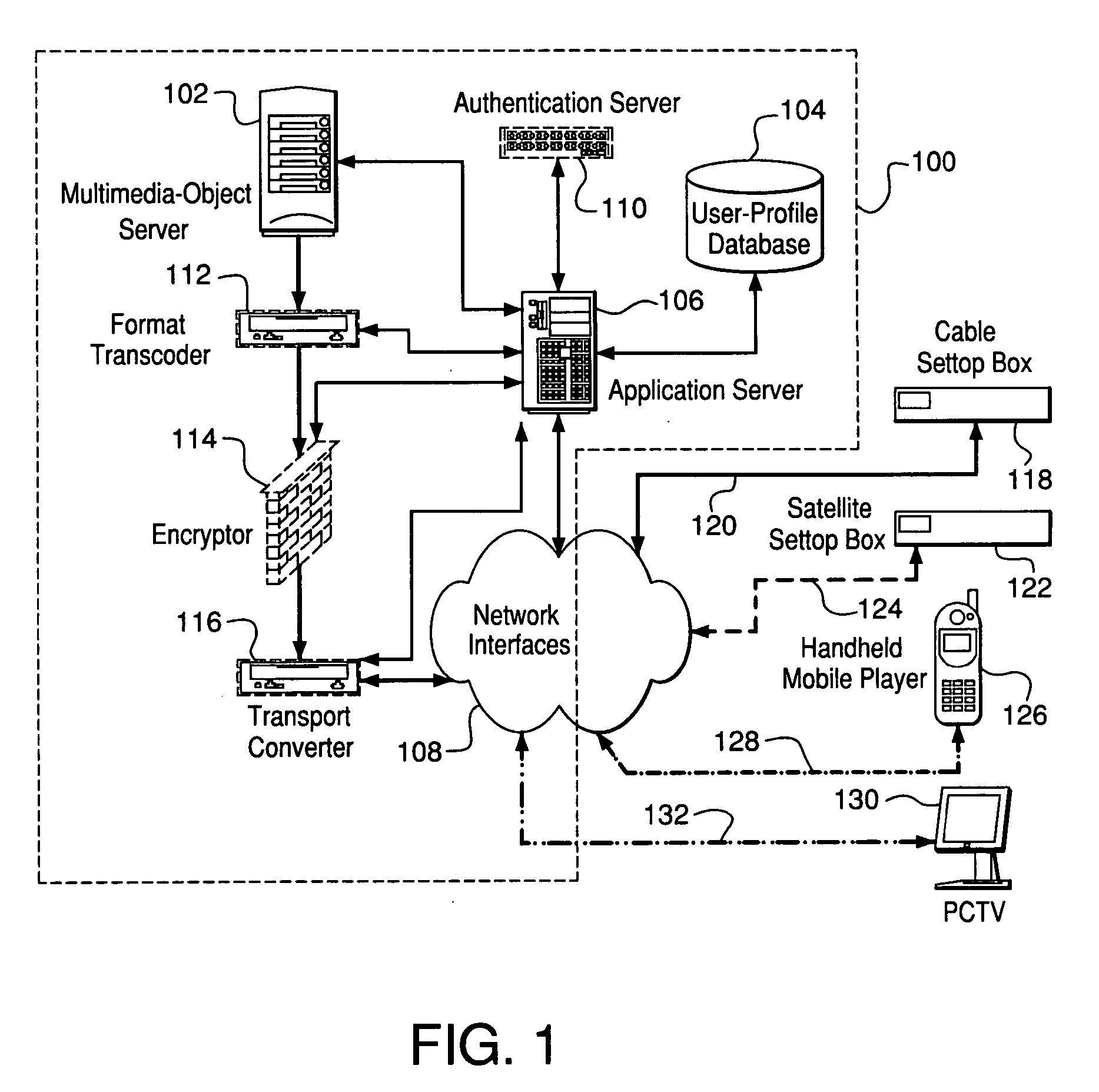
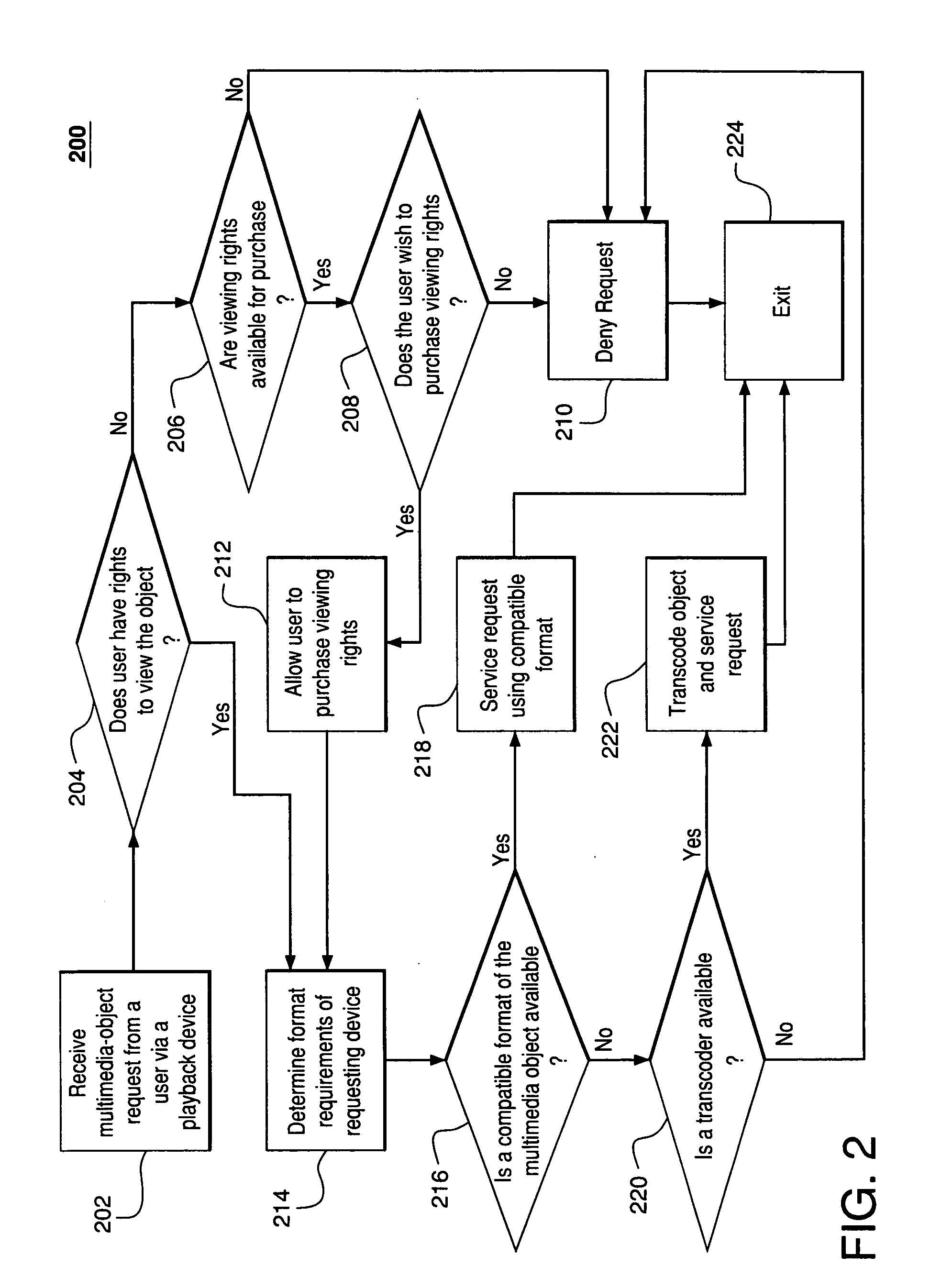
Multimedia content distribution
InactiveUS20060015580A1Multiple digital computer combinationsTelevision systemsContent distributionEnd user
A process and facility supports device-specific delivery of a multimedia object to an end user's device as a function of the device's capabilities, the transport interface to the device, and / or the viewing state and / or access privileges of the device's user with respect to the object or the user's relationship to an owner of the device and / or multimedia object.
Owner:HOME BOX OFFICE INC
Client installation and execution system for streamed applications
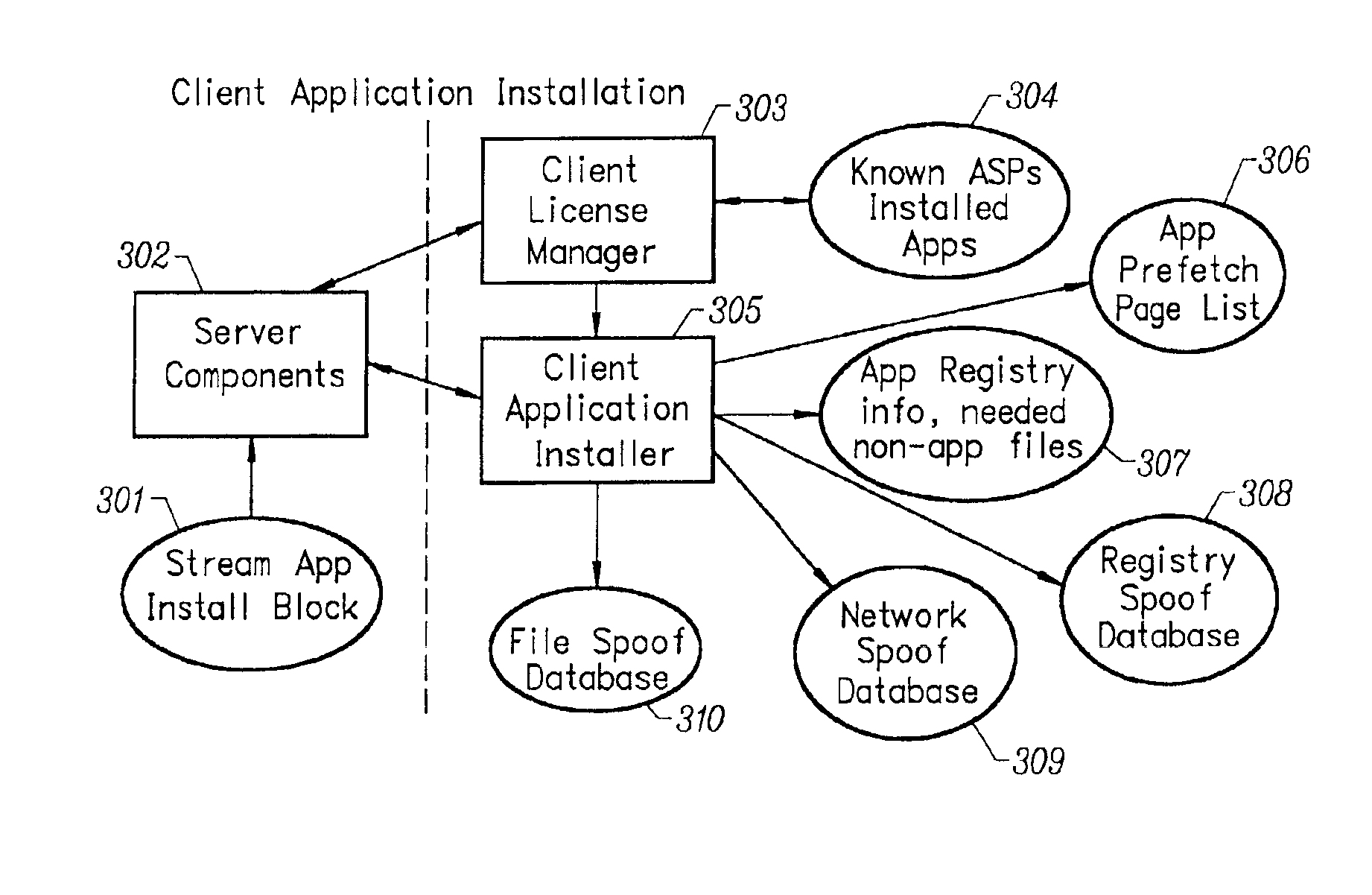
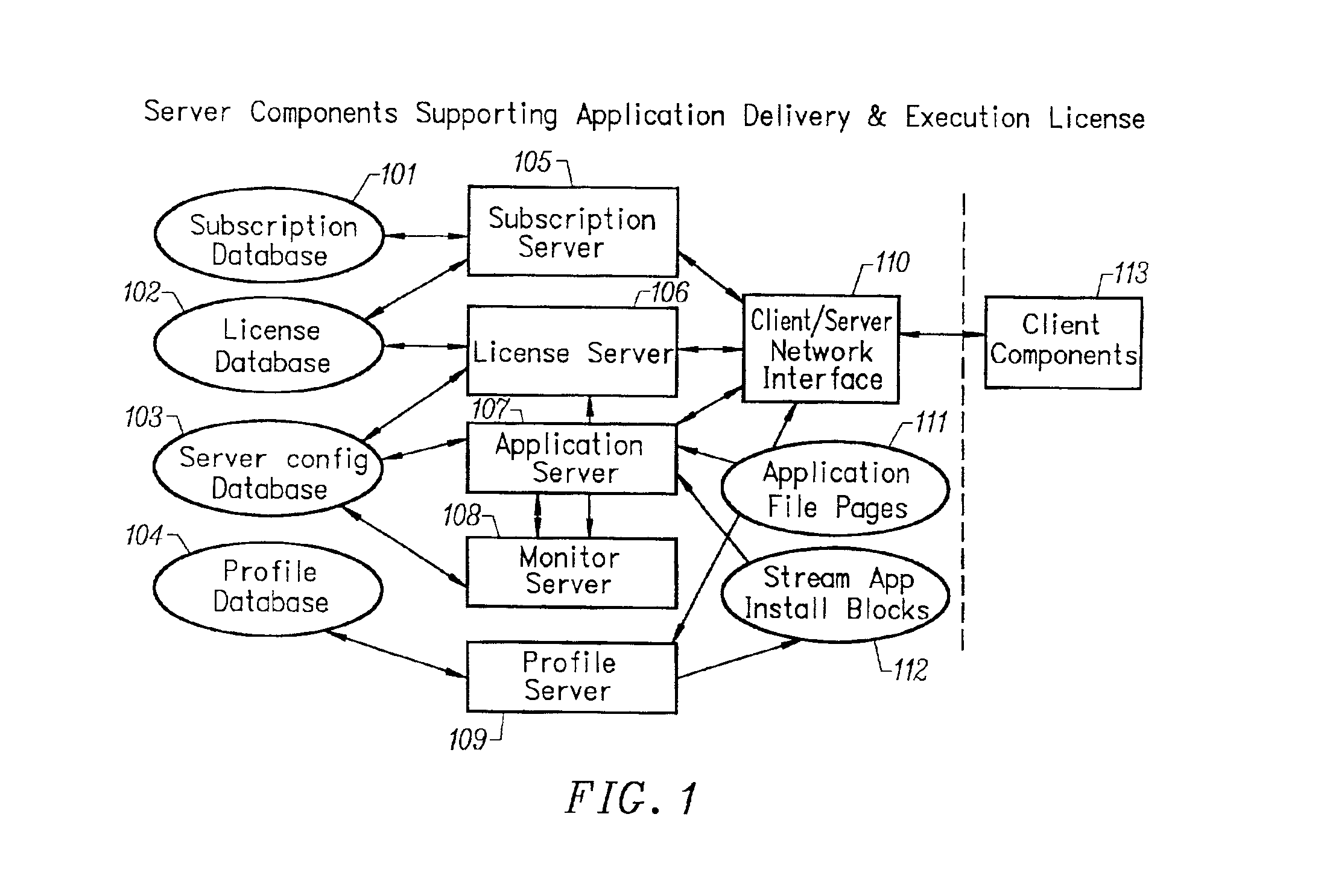
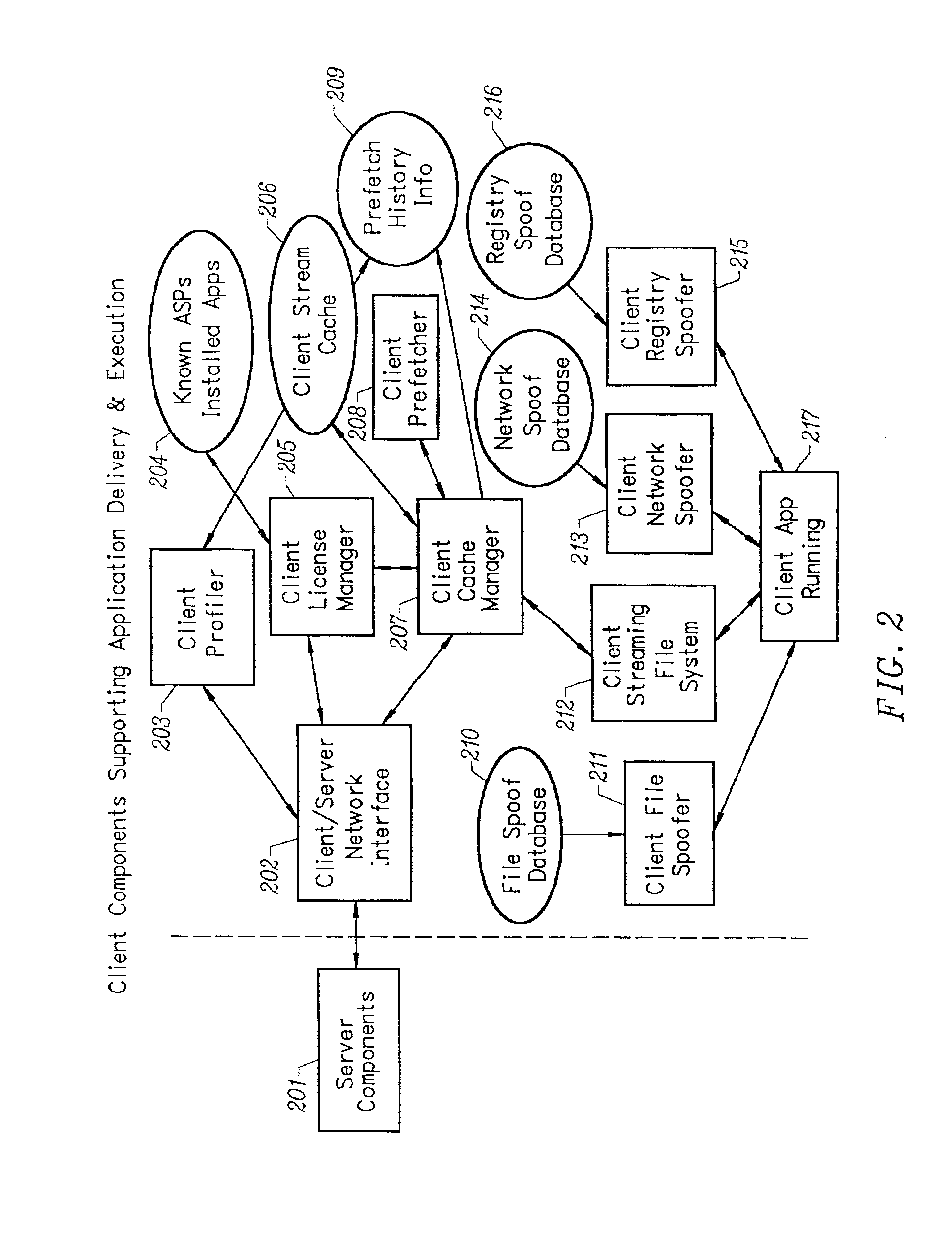
InactiveUS6918113B2Multiple digital computer combinationsProgram loading/initiatingRegistry dataFile system
Owner:NUMECENT HLDG +1
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com