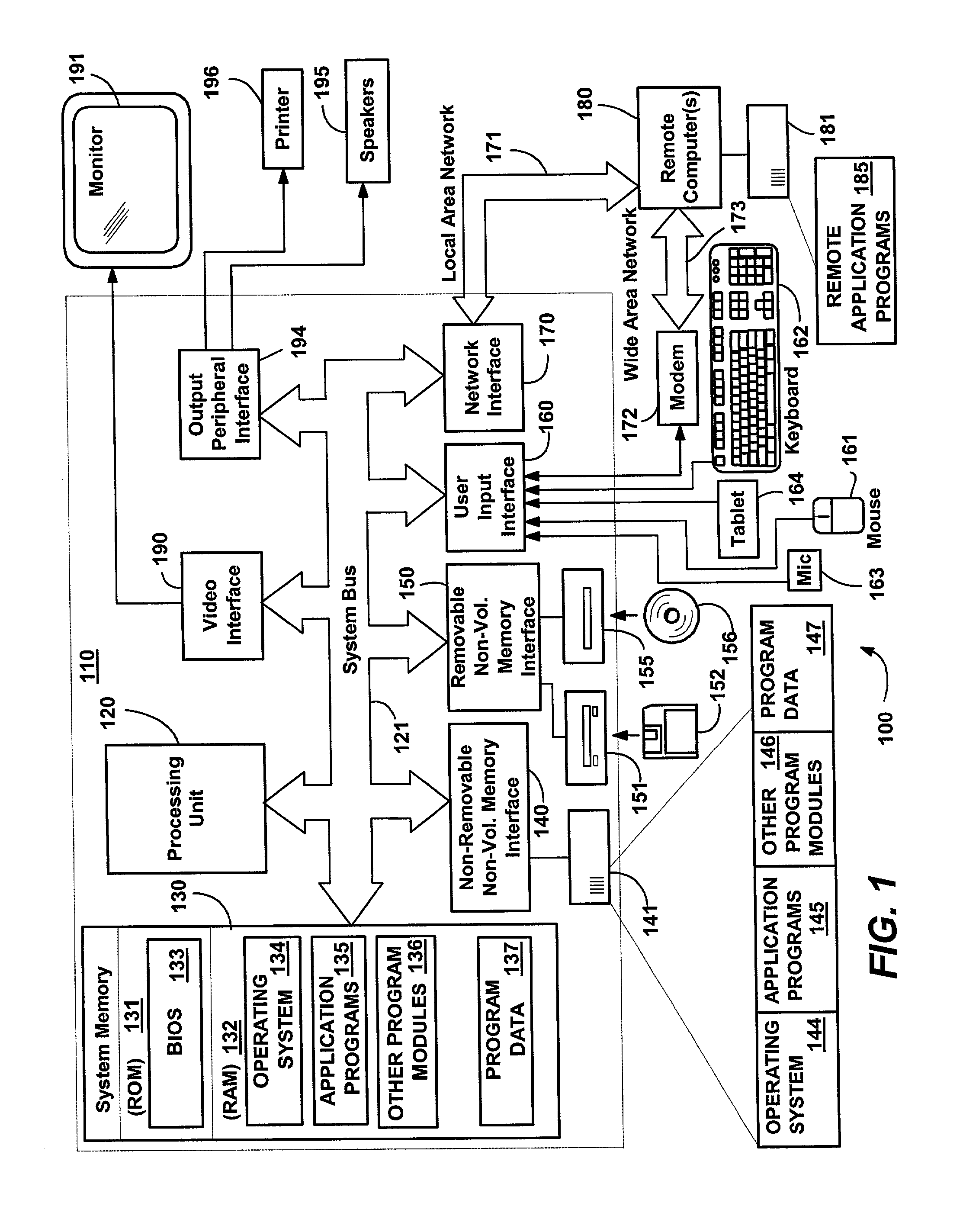
Patents
Literature
81 results about "Registry data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
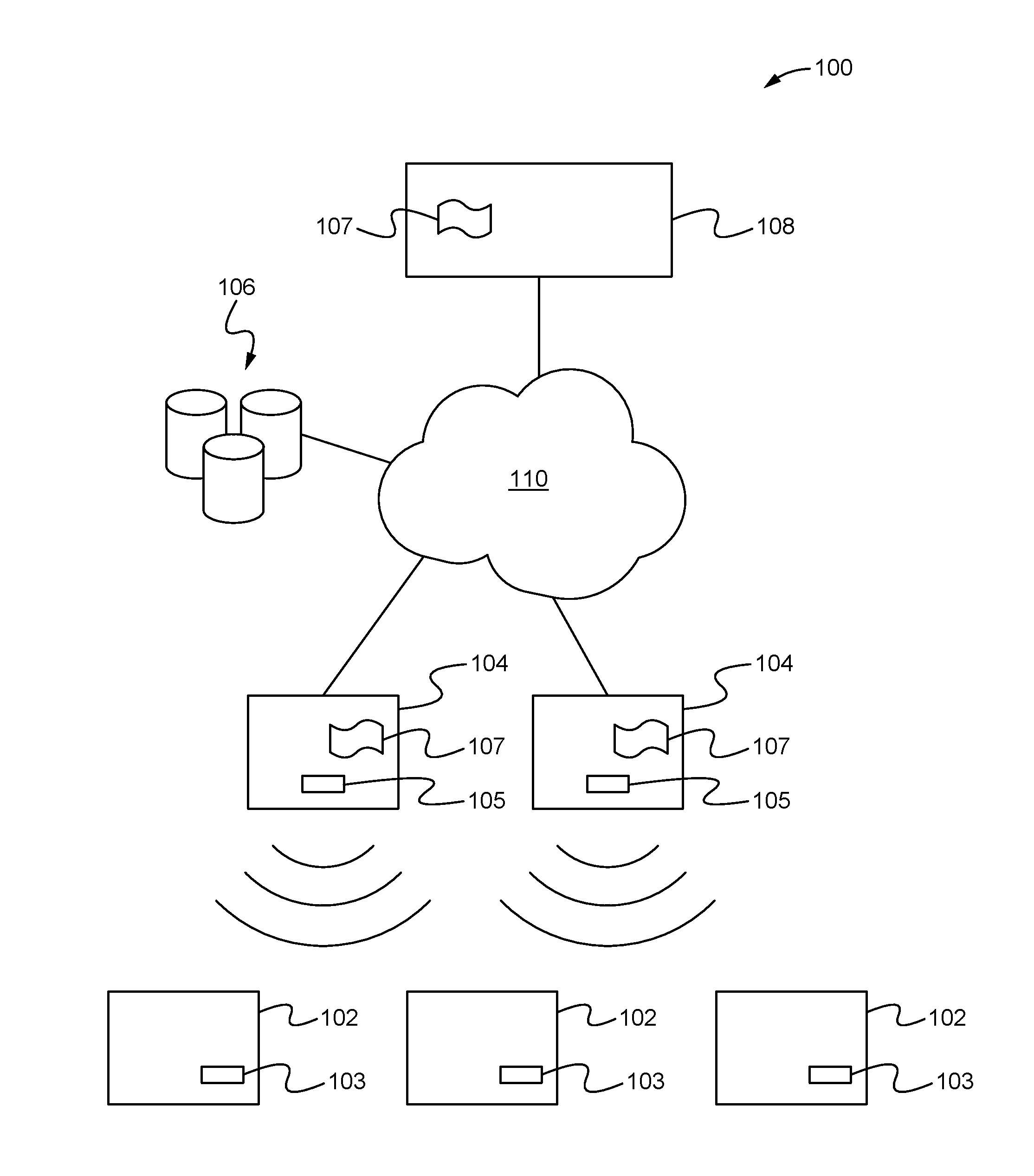
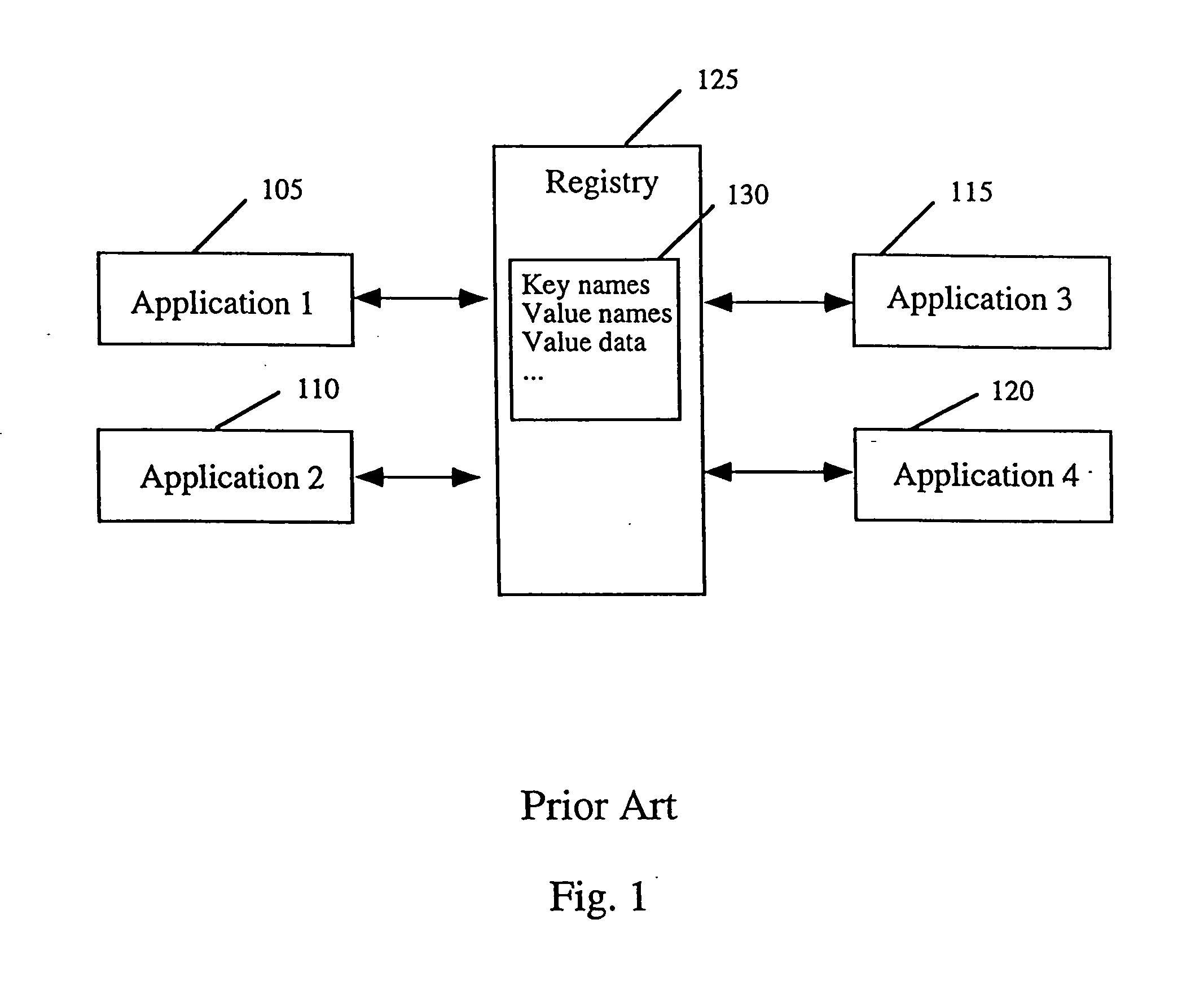
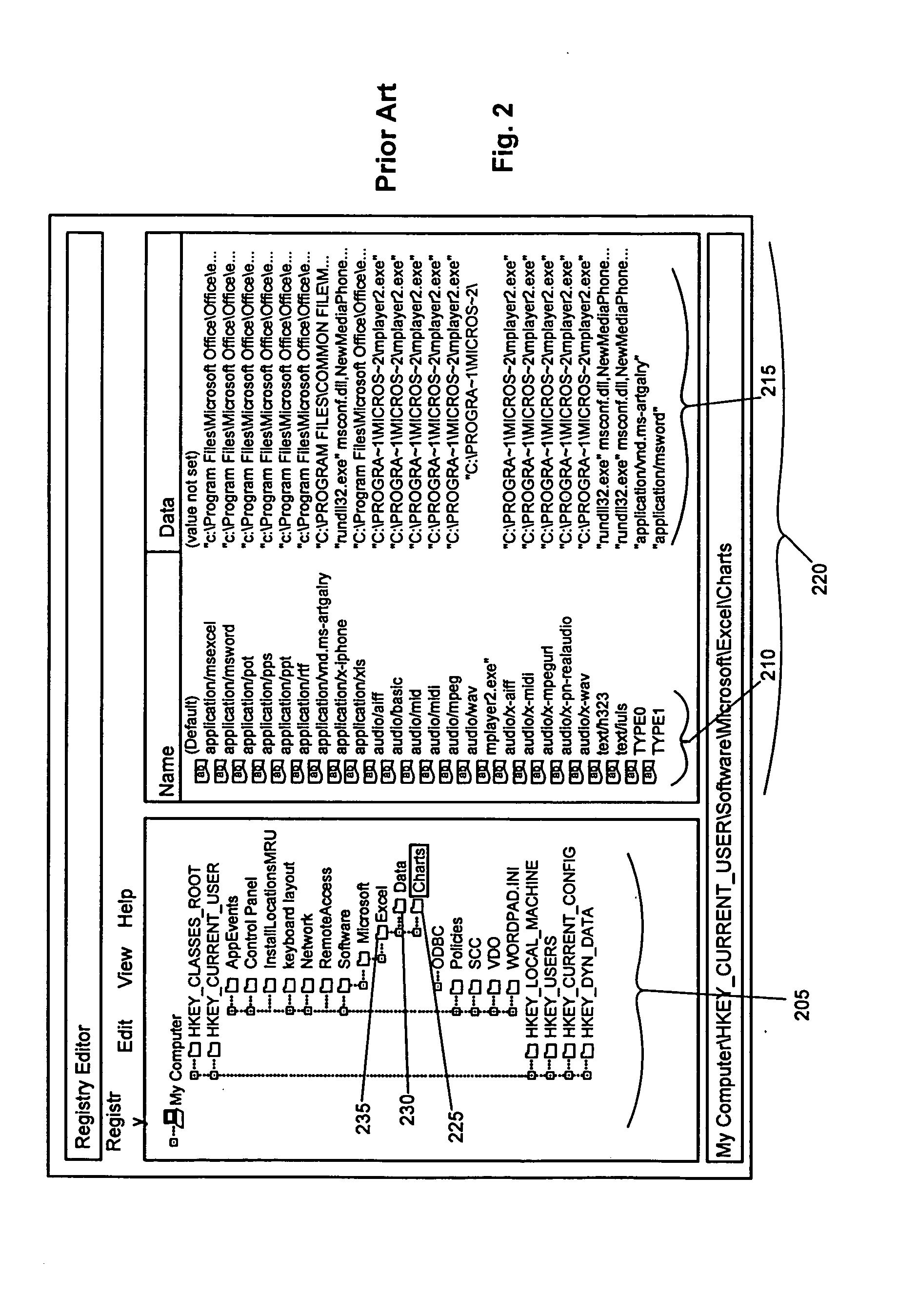
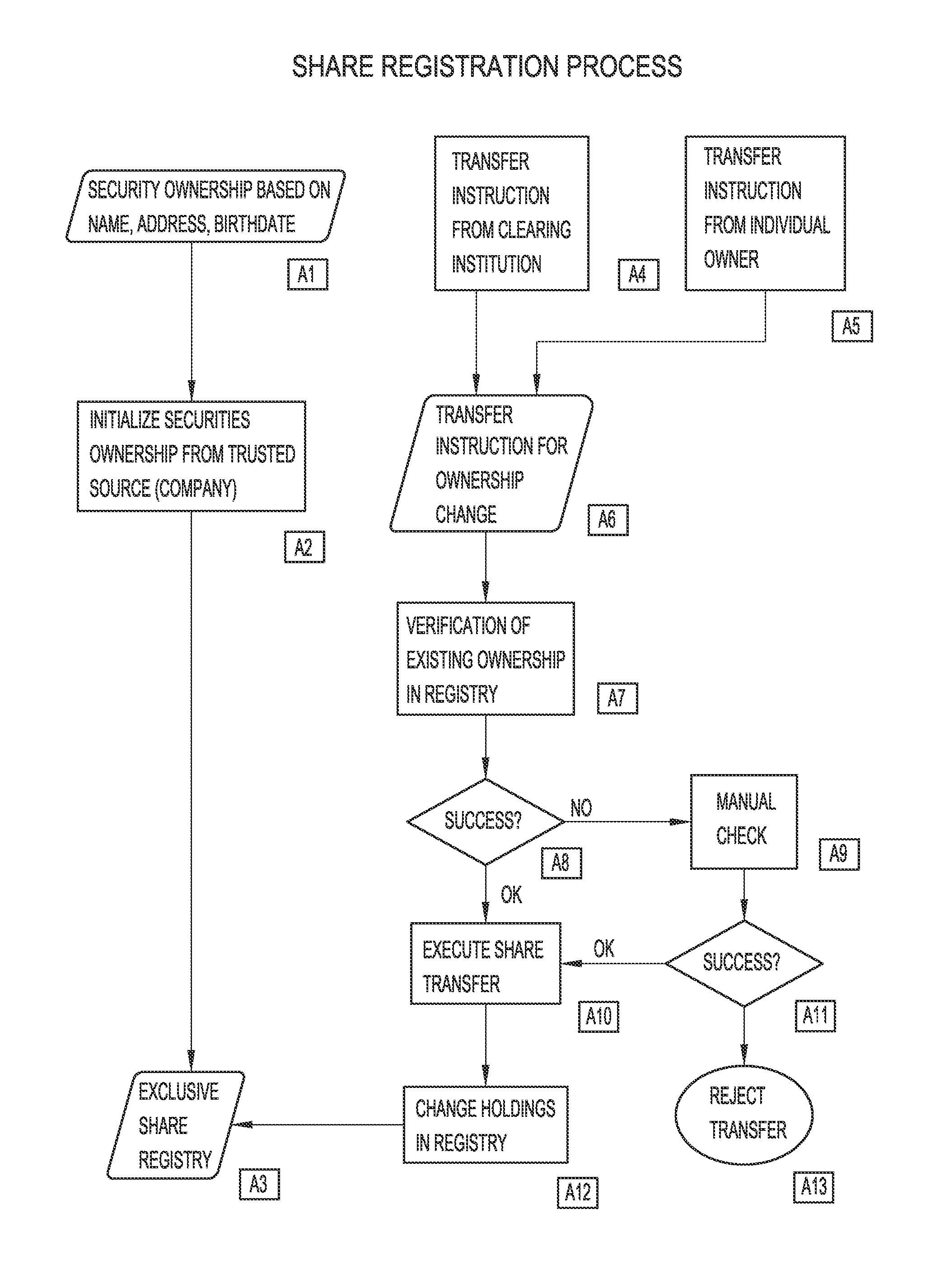
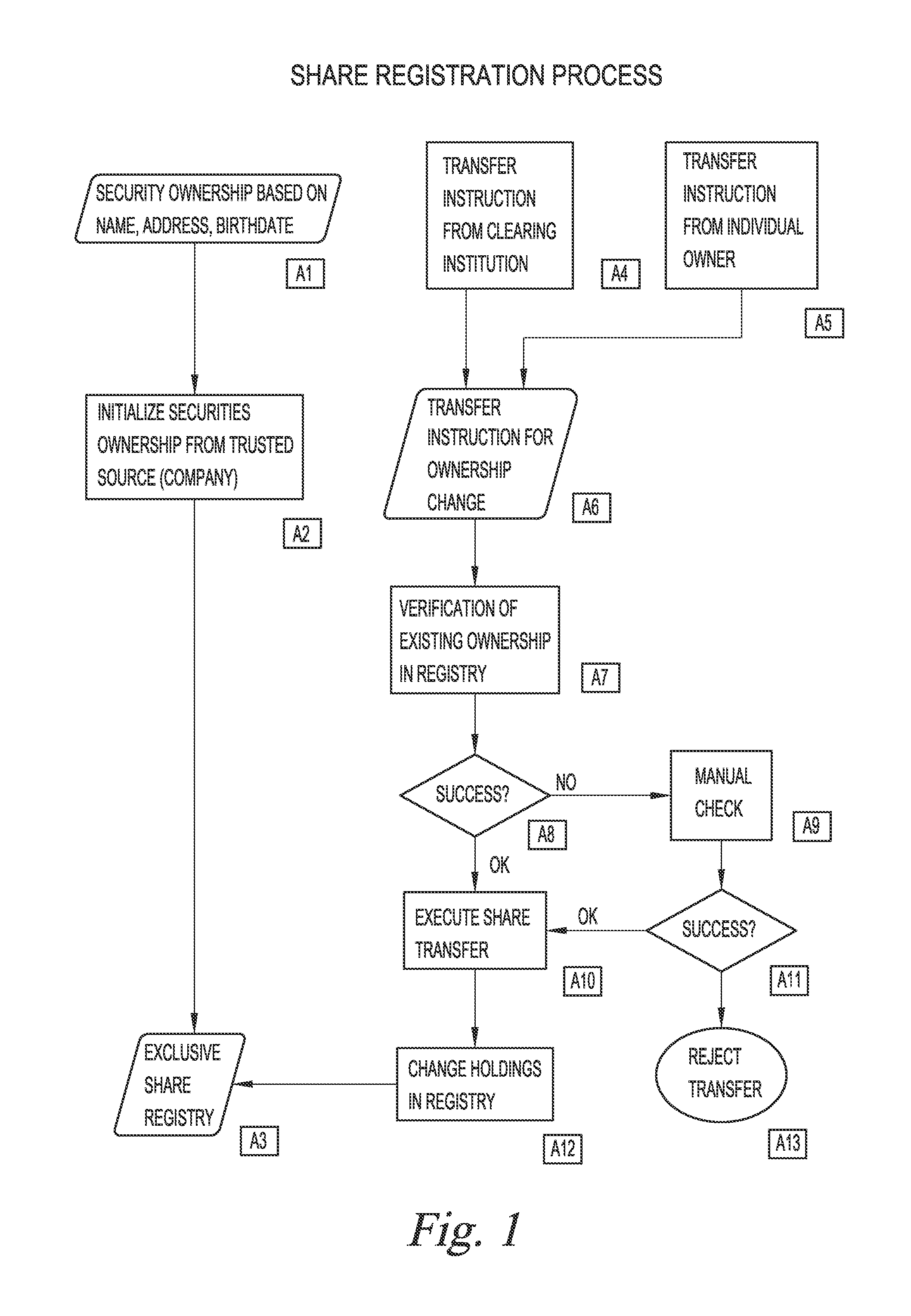
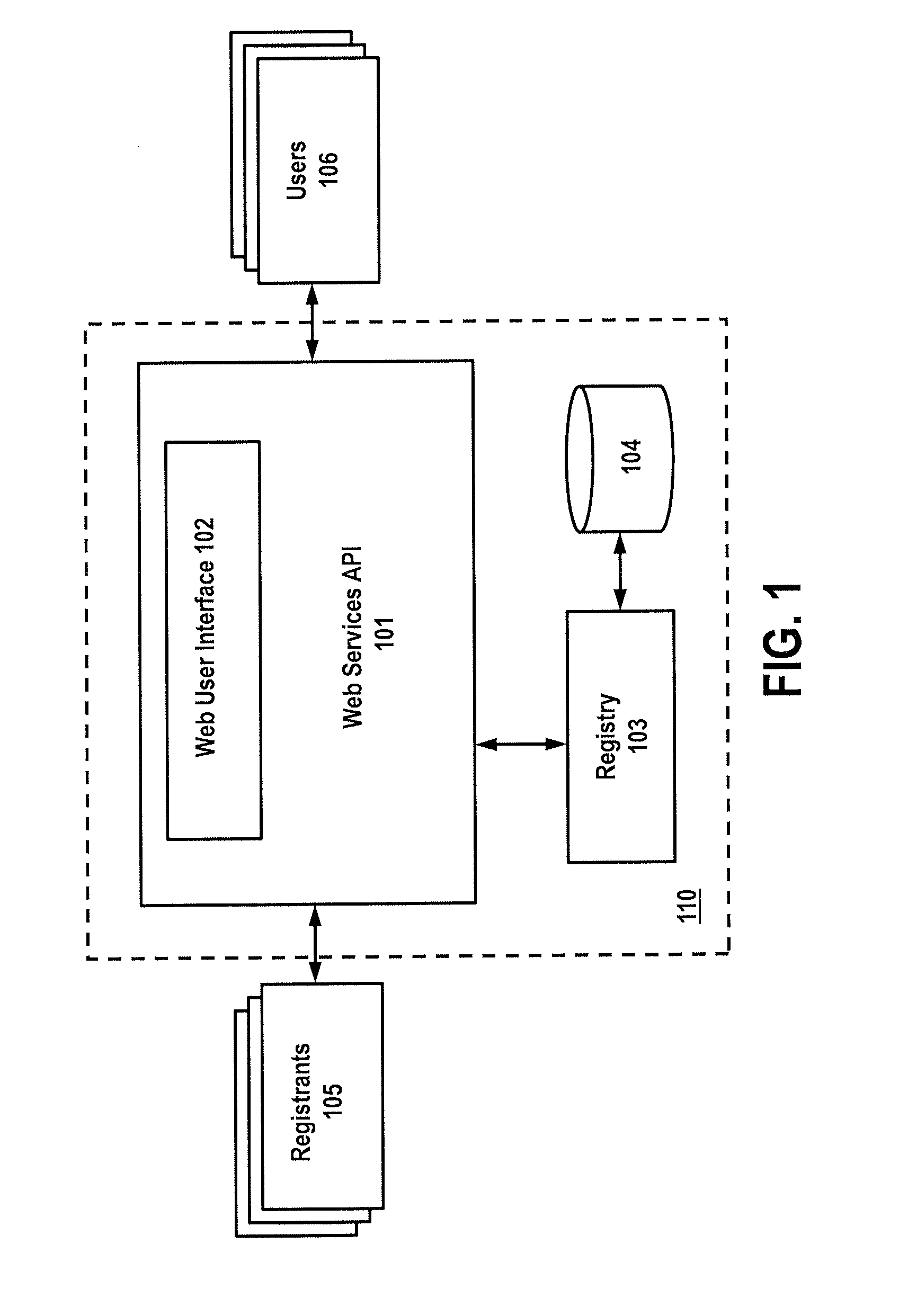
The Data Element Registry is a "storage container" that provides important information about environmental data that is called metadata.
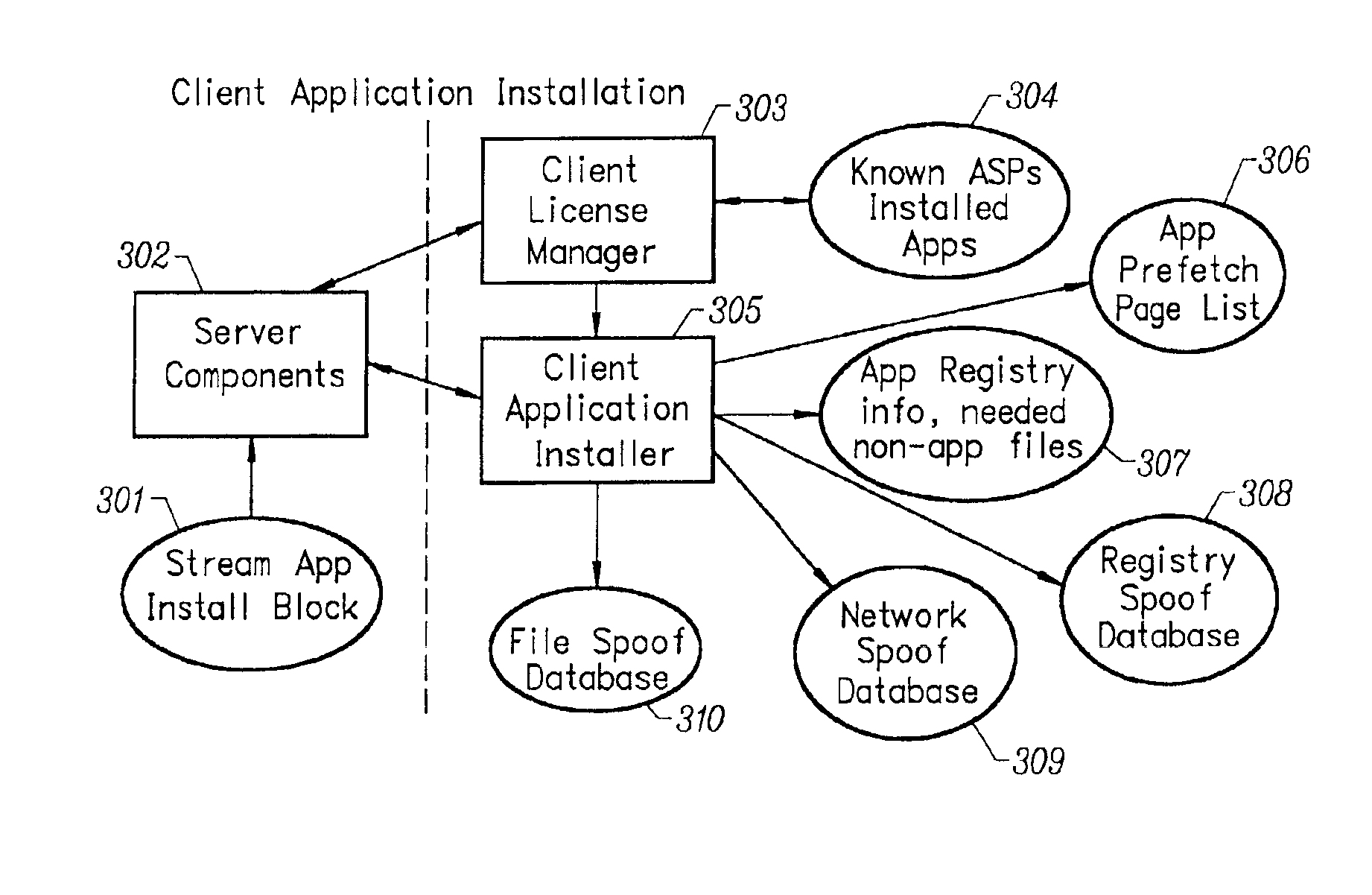
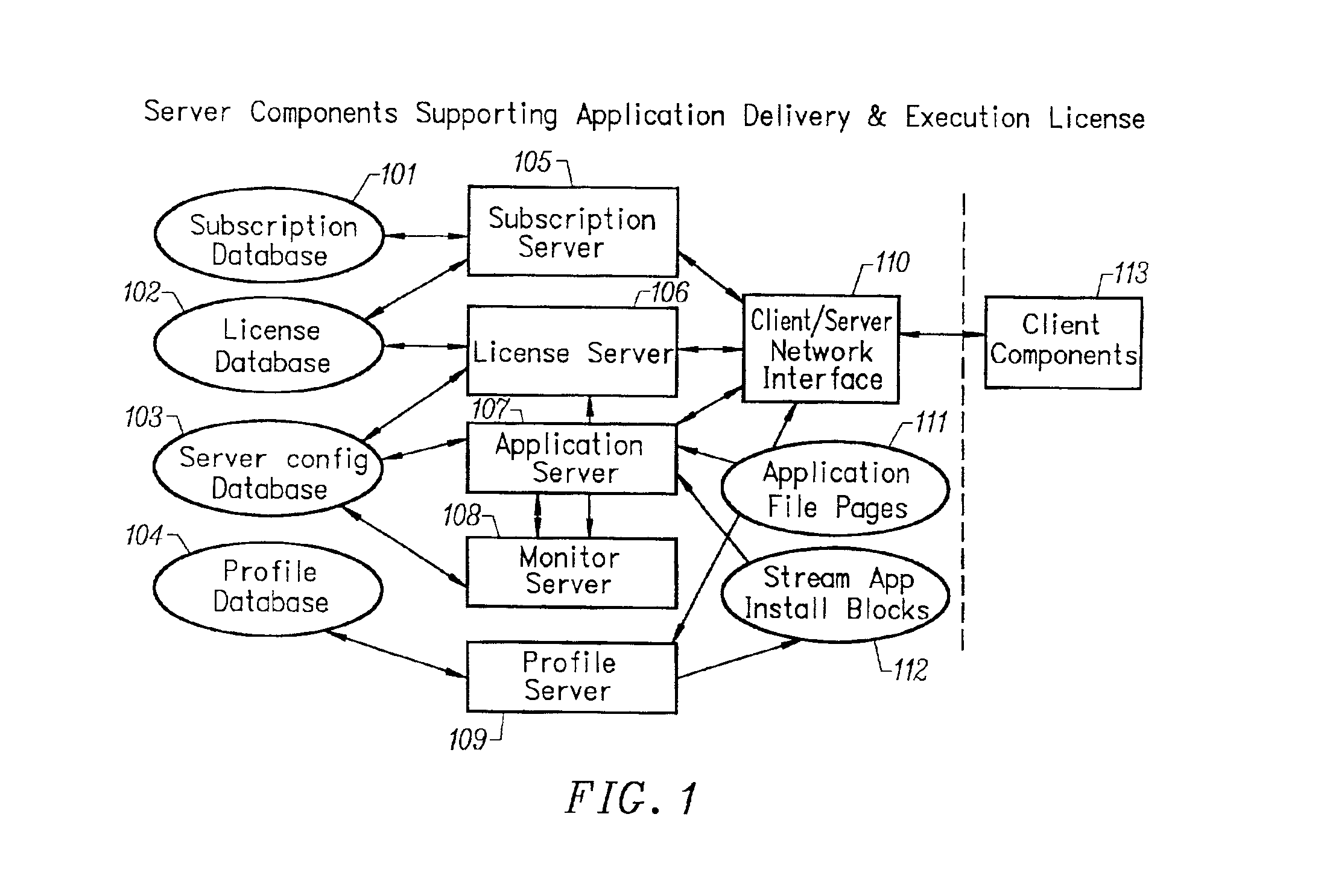
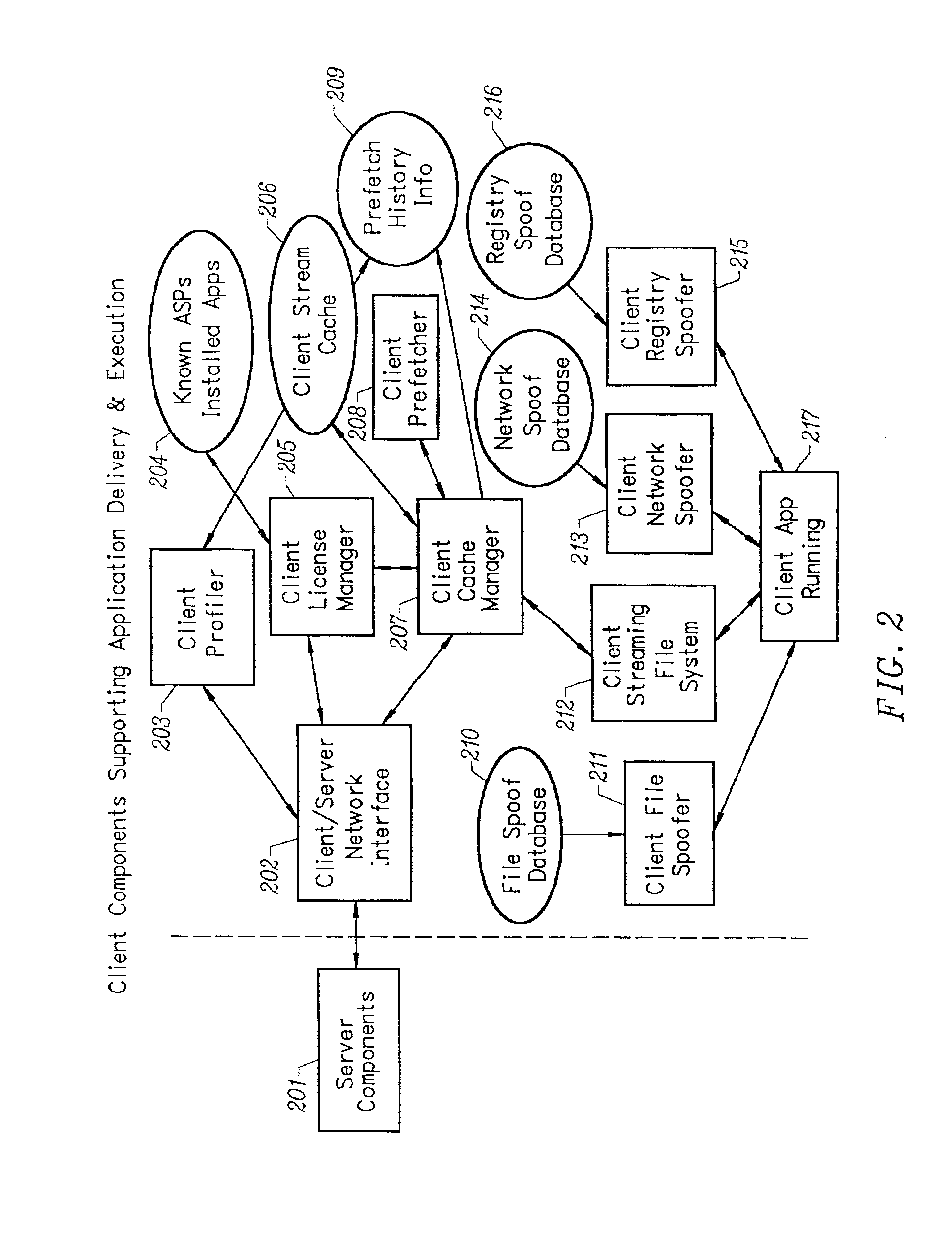
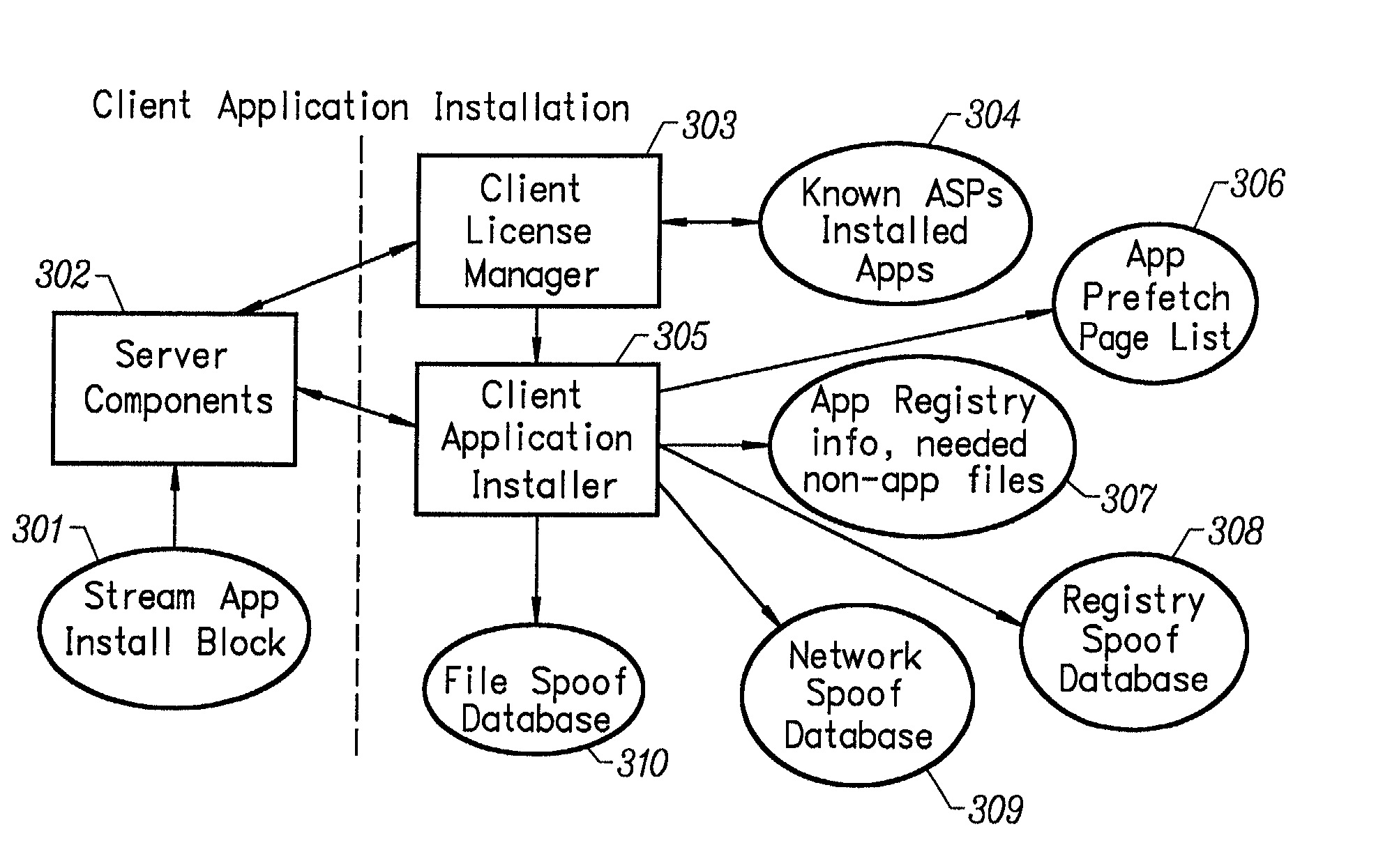
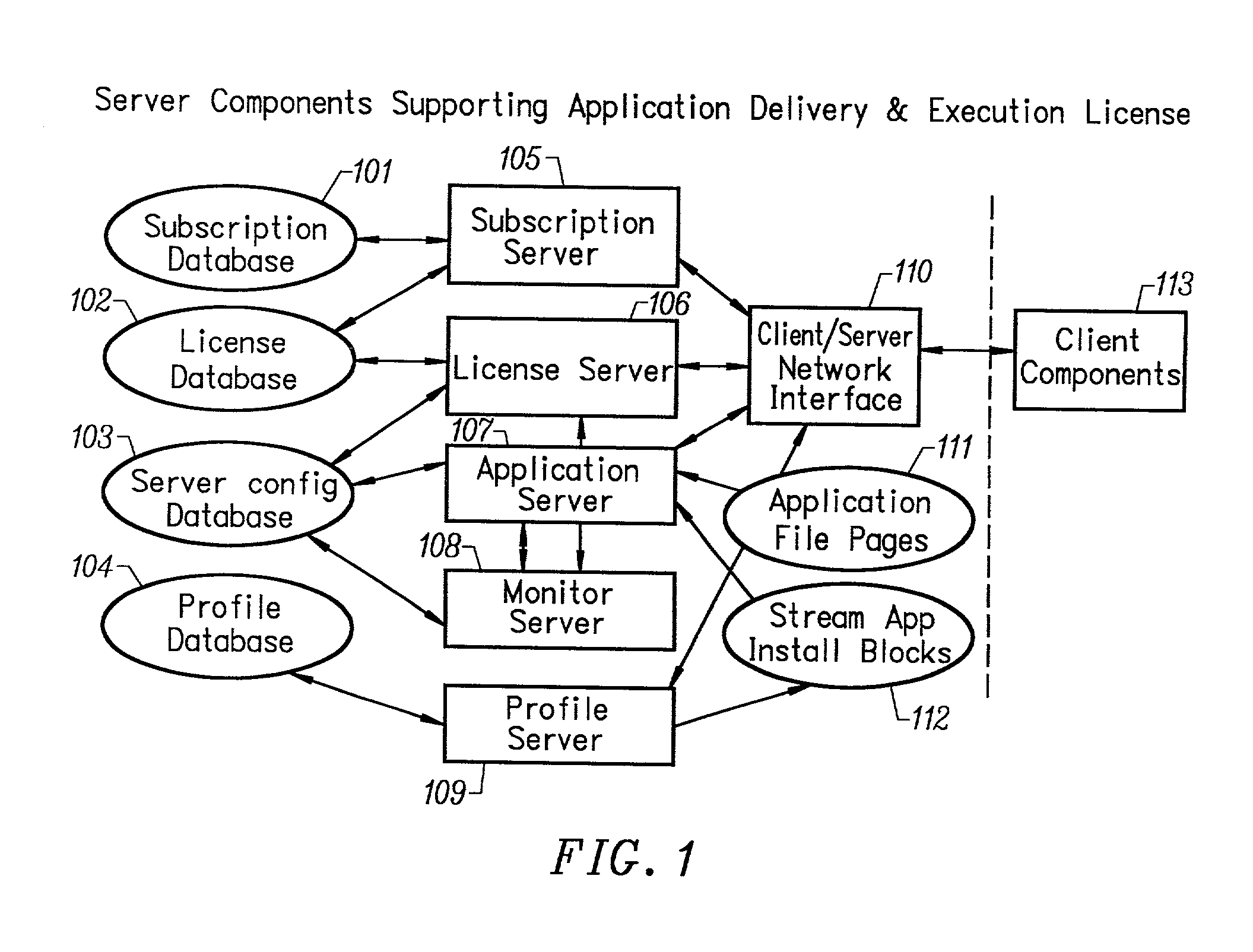
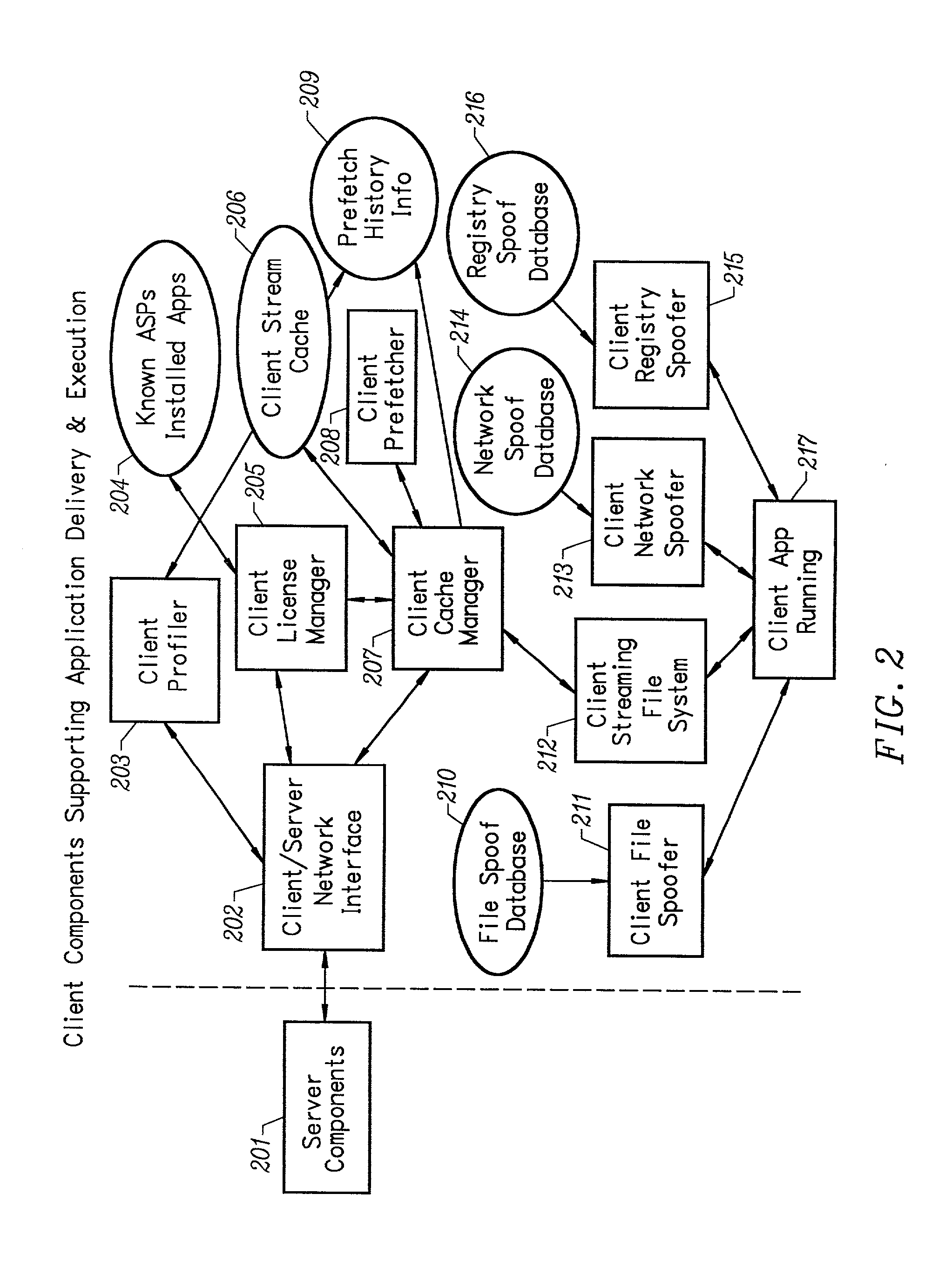
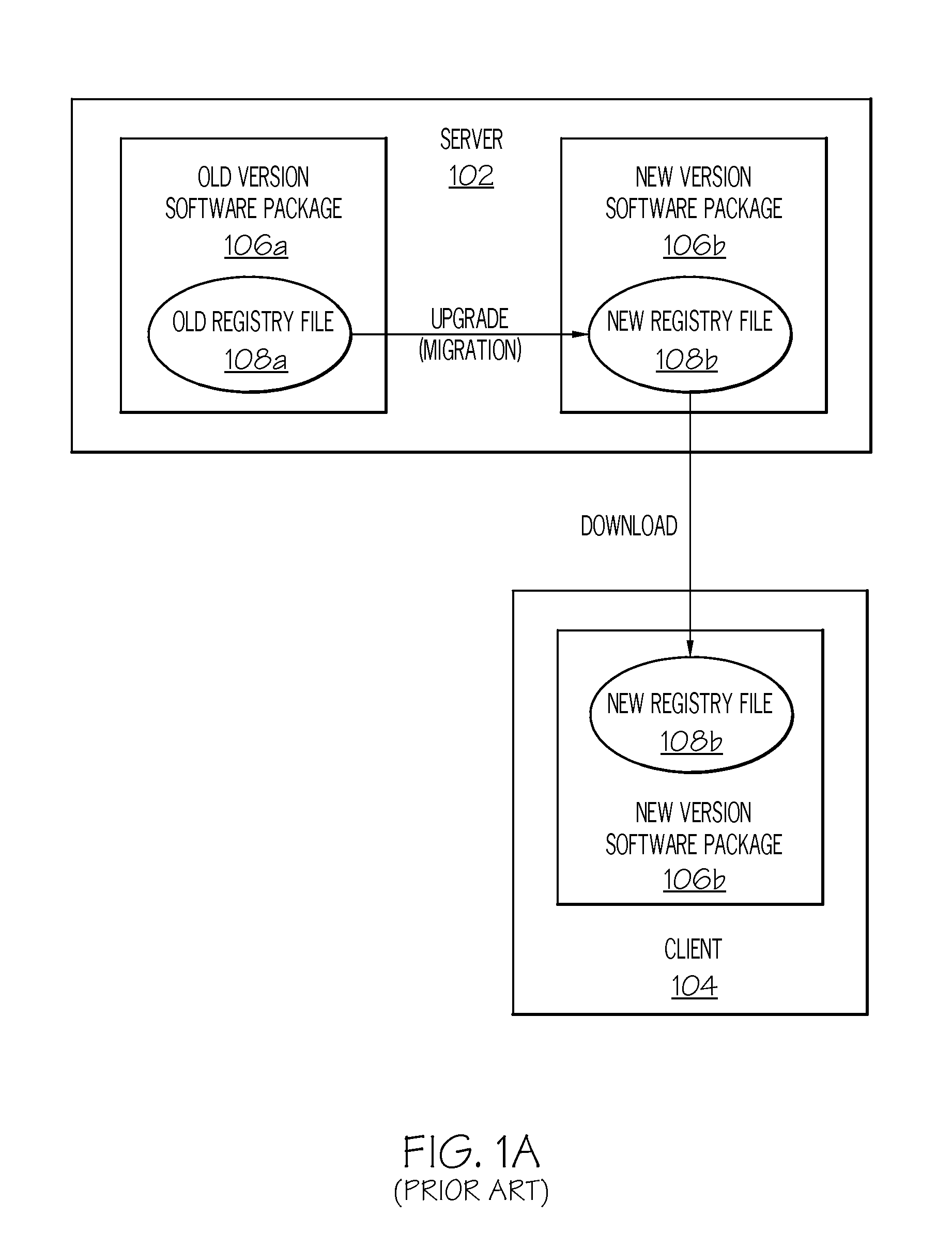
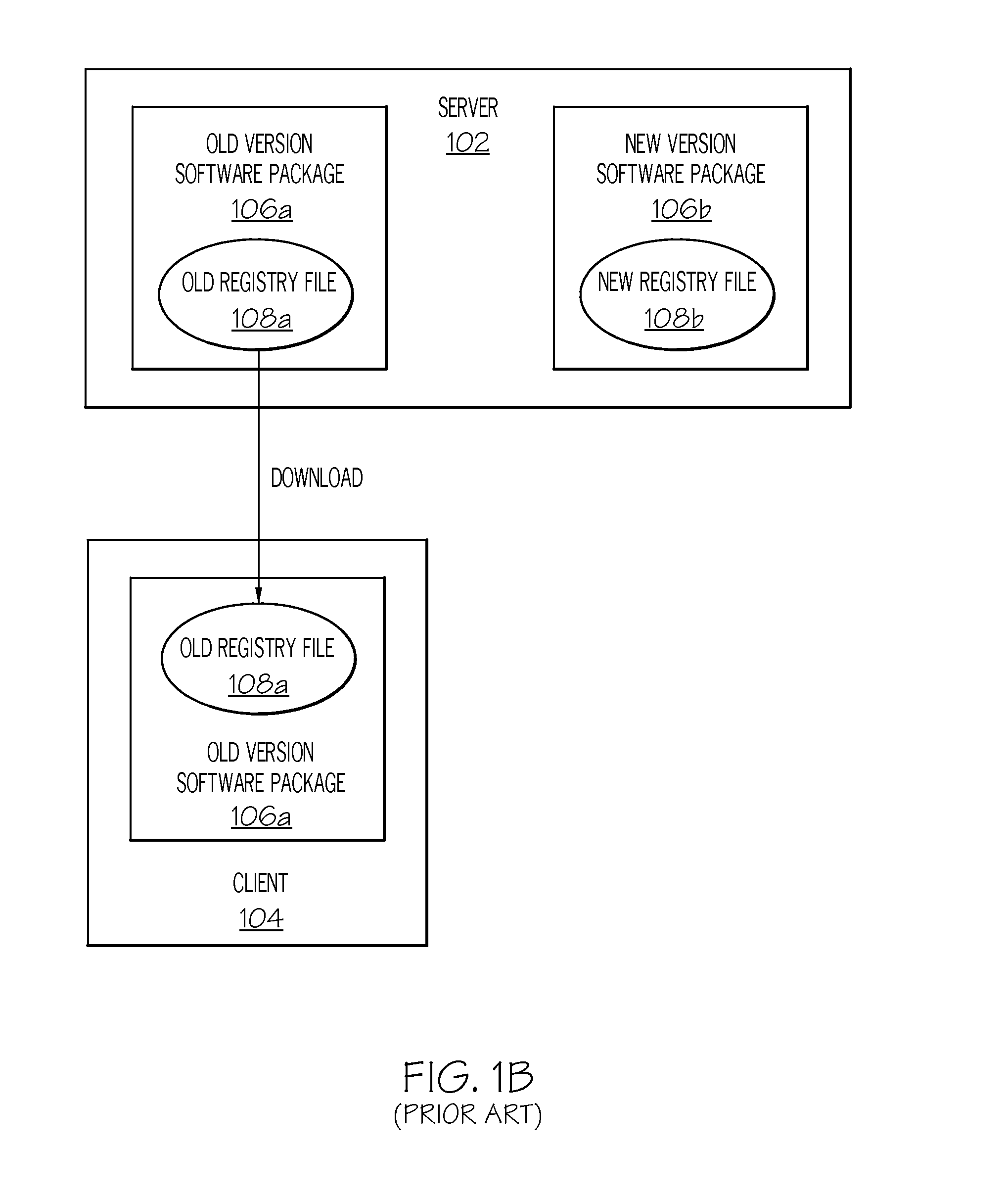
Client installation and execution system for streamed applications
InactiveUS6918113B2Multiple digital computer combinationsProgram loading/initiatingRegistry dataFile system
Owner:NUMECENT HLDG +1
Client installation and execution system for streamed applications
InactiveUS20020157089A1Multiple digital computer combinationsProgram loading/initiatingRegistry dataFile system
Owner:NUMECENT HLDG +1
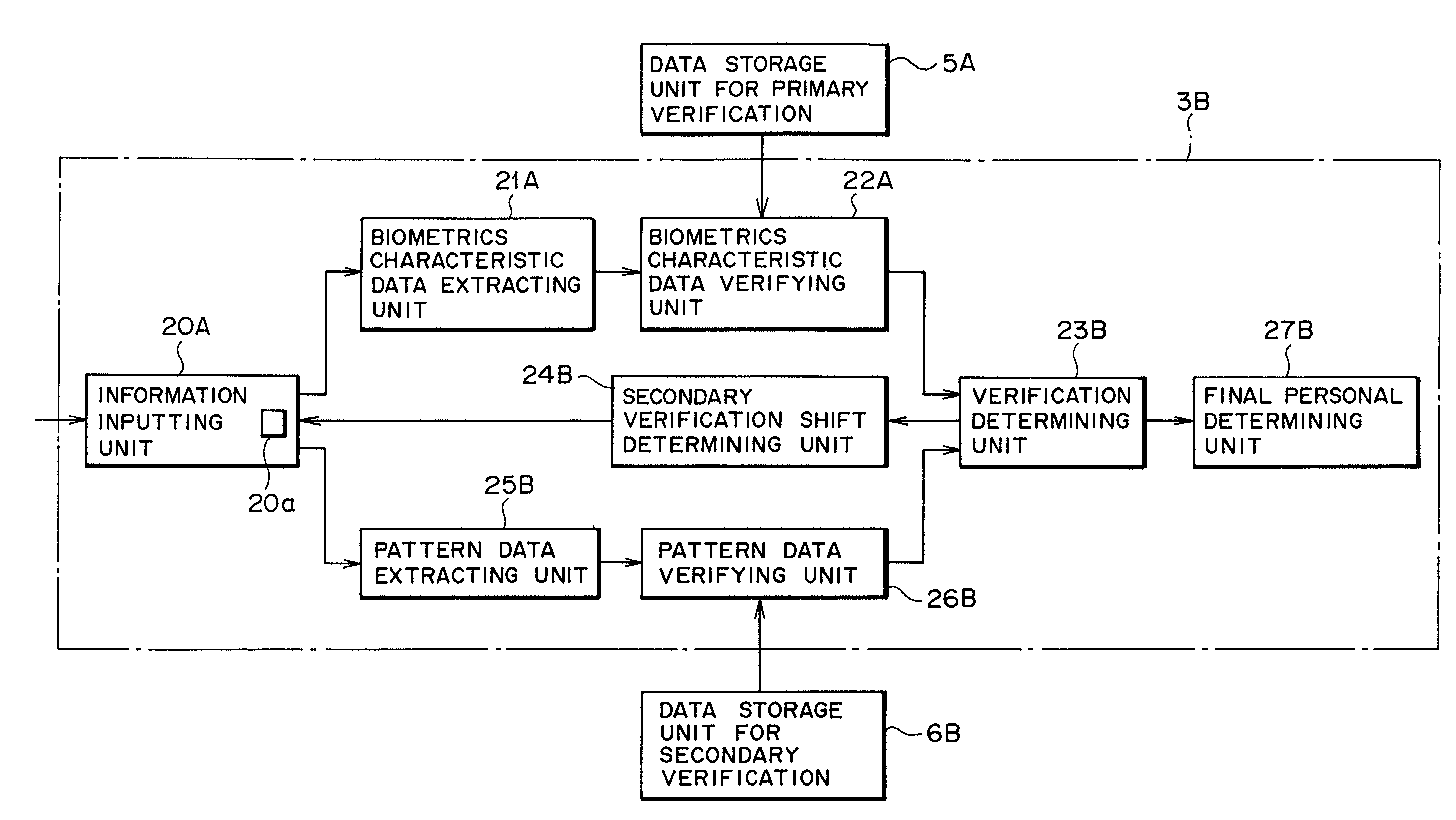
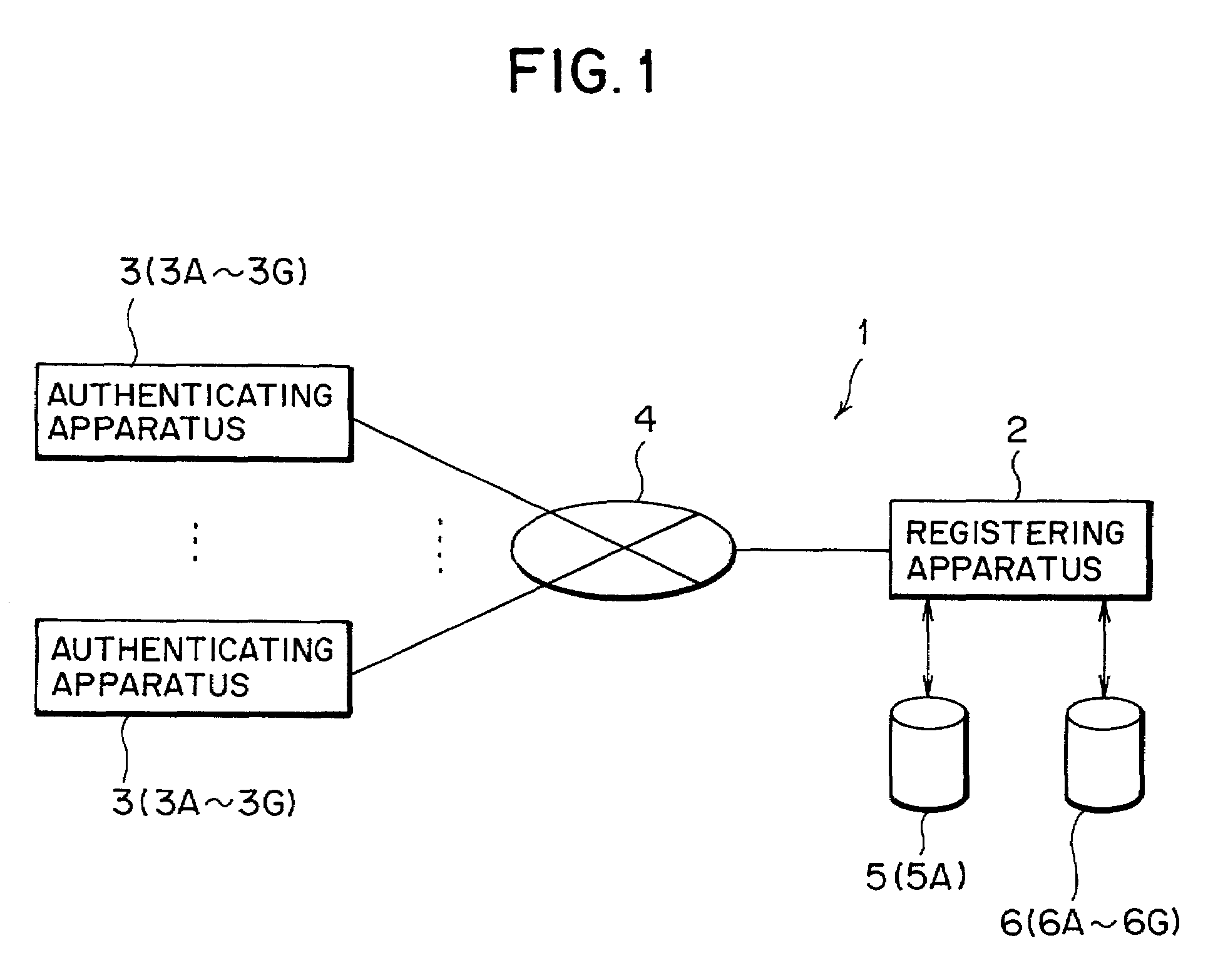
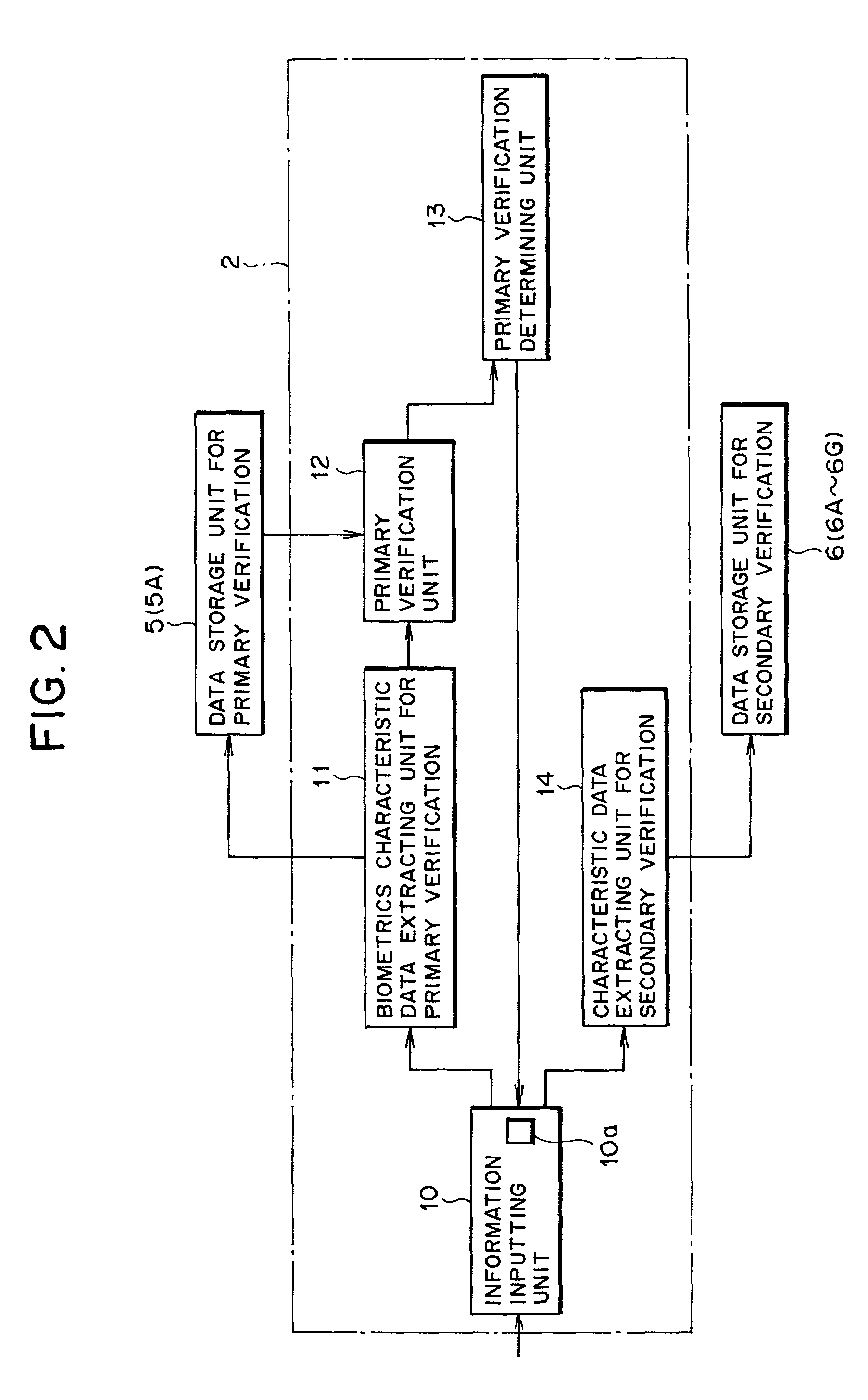
Personal authentication system and method using biometrics information, and registering apparatus, authenticating apparatus and pattern information input medium for the system
InactiveUS6983061B2Increase costElectric signal transmission systemsImage analysisRegistry dataPalm print
A system performing secondary verification using only existing apparatuses to accomplish a measure for relief in personal authentication without causing complexity or without increasing cost. The system has a registering apparatus for obtaining data for verification from information inputted using an inputting unit and registering the data. The registering apparatus has a first extracting unit for extracting biometrics characteristic data from the biometrics information obtained by the inputting unit, and registering the biometrics characteristic data as registry biometrics characteristic data for primary verification, and a second extracting unit for extracting data, which is different from the registry biometrics characteristic data, from information inputted using the inputting unit and registering the data as registry data for secondary verification. The system is used for personal authentication using biometrics information such as fingerprint, palm print, finger shape, palm shape, voice, retina, iris, face image, dynamic signature, blood vessel pattern, keystroke, or the like.
Owner:FUJITSU LTD
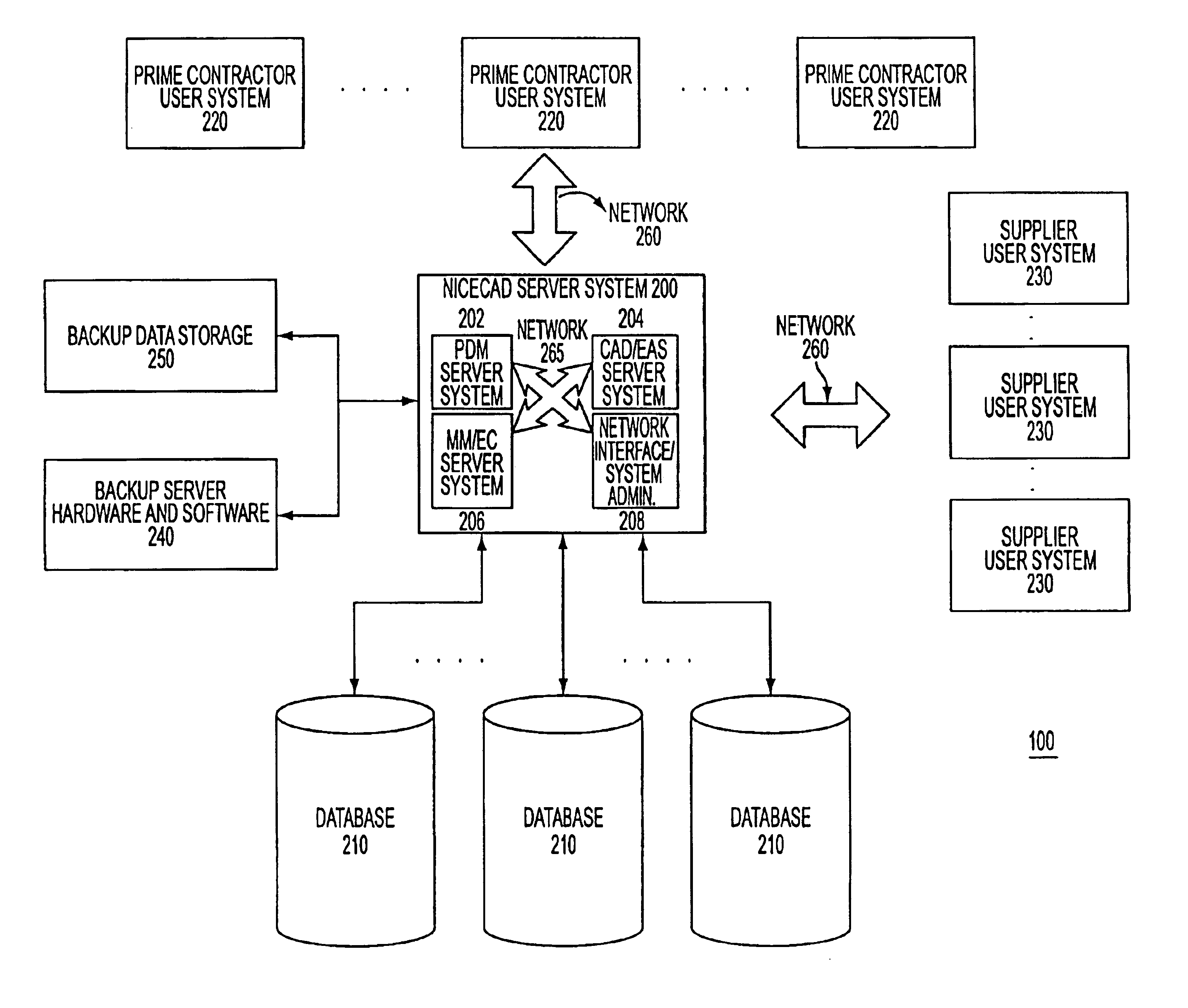
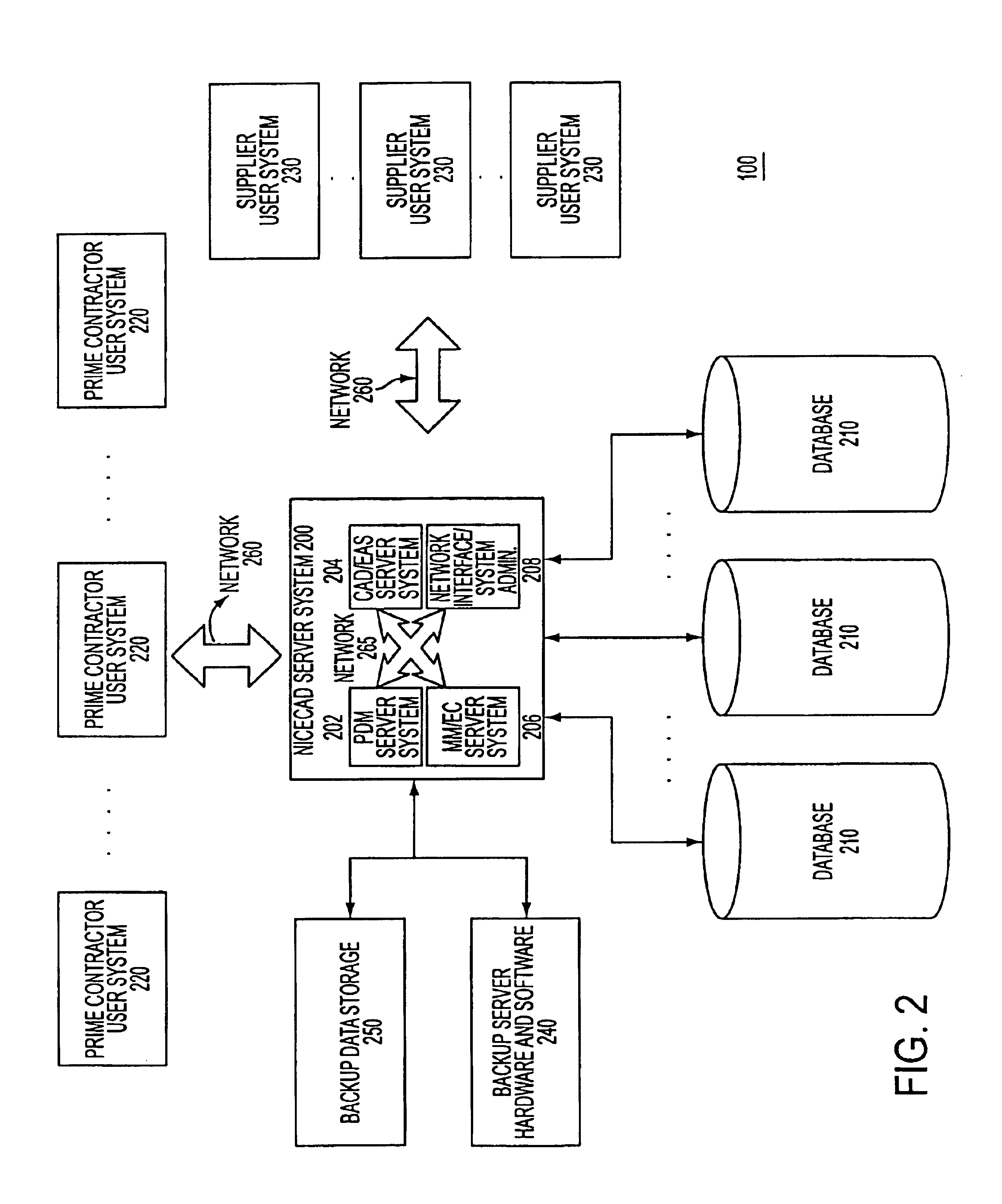
Network-based system for the manufacture of parts with a virtual collaborative environment for design, development and fabricator selection
InactiveUS6928396B2Reduce processing burdenReduce needProgramme controlComputer controlGraphicsRegistry data
The invention relates generally to a comprehensive, integrated computer-based system and method for undertaking an engineering design and development effort in a virtual collaborative environment, identifying qualified fabricators for manufacturing a part design based on fabricator capability information stored in a global registry database substantially maintained by the fabricators themselves, and conducting a virtual bidding process whereby electronic representations of three dimensional model and specification data are provided by a central server. The central server further supports the bidding process by providing quasi-real time audio, video and graphics, and the contracts negotiation and formalization steps.
Owner:CHEMTRON RES
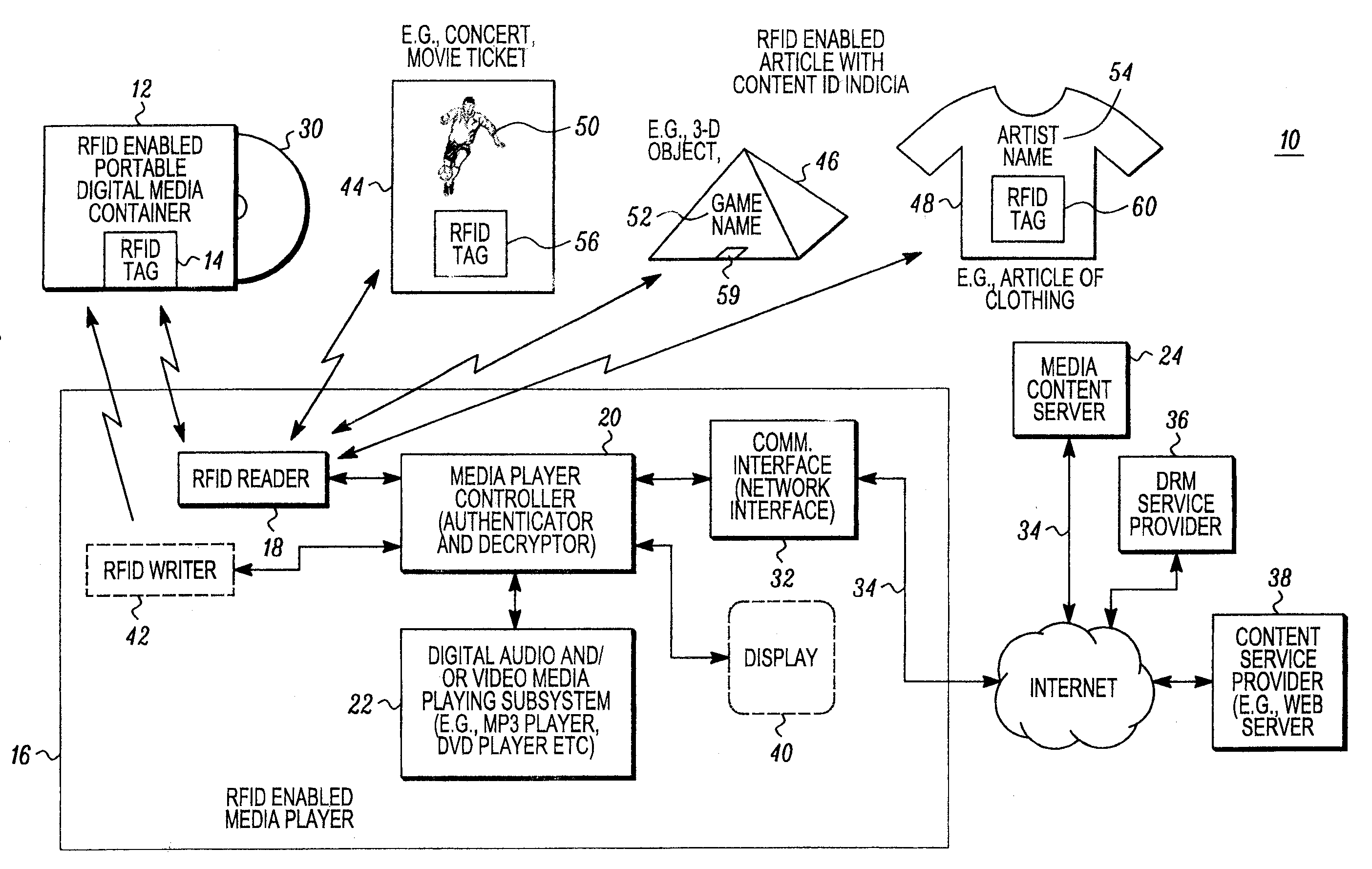
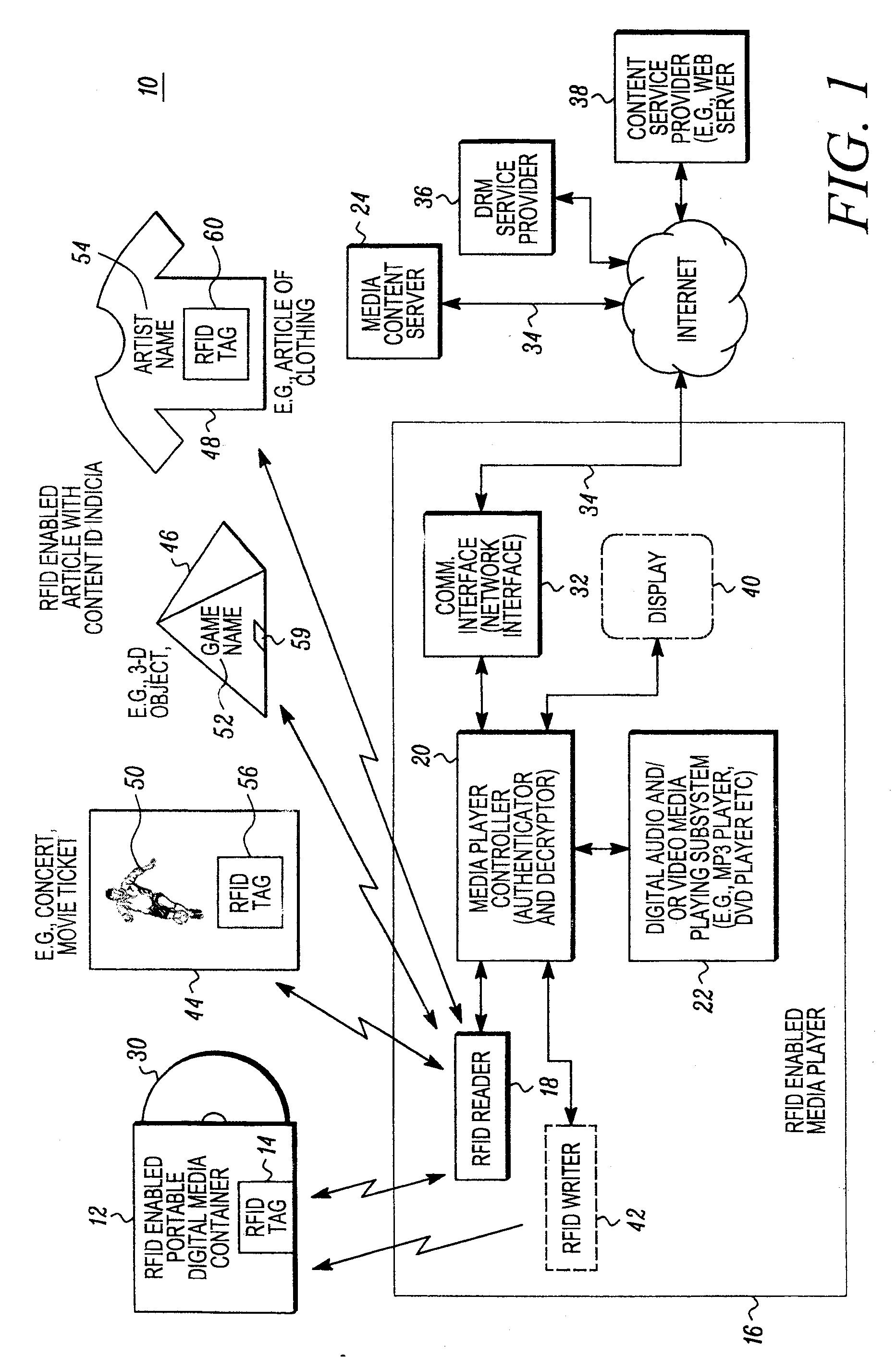
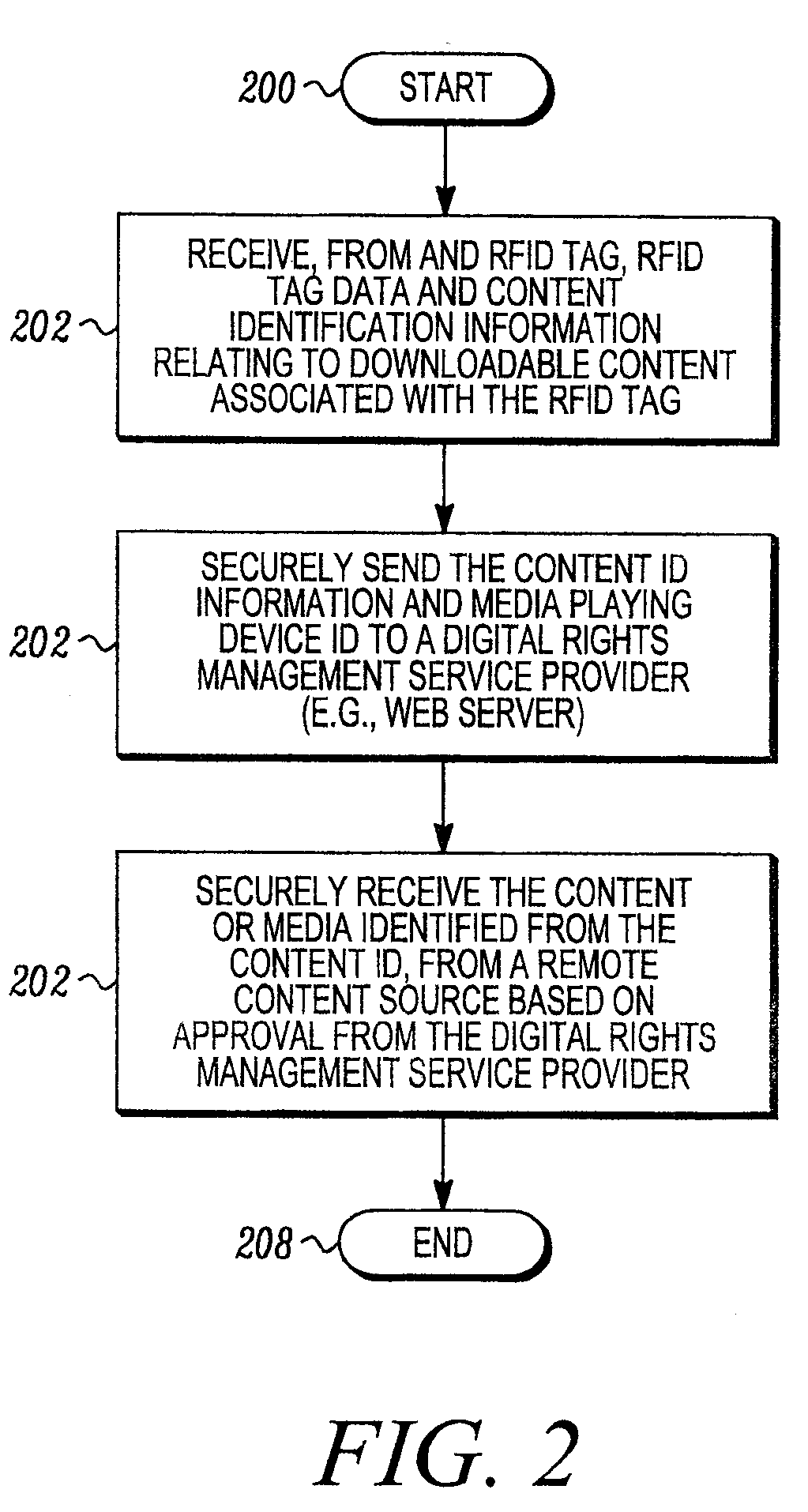
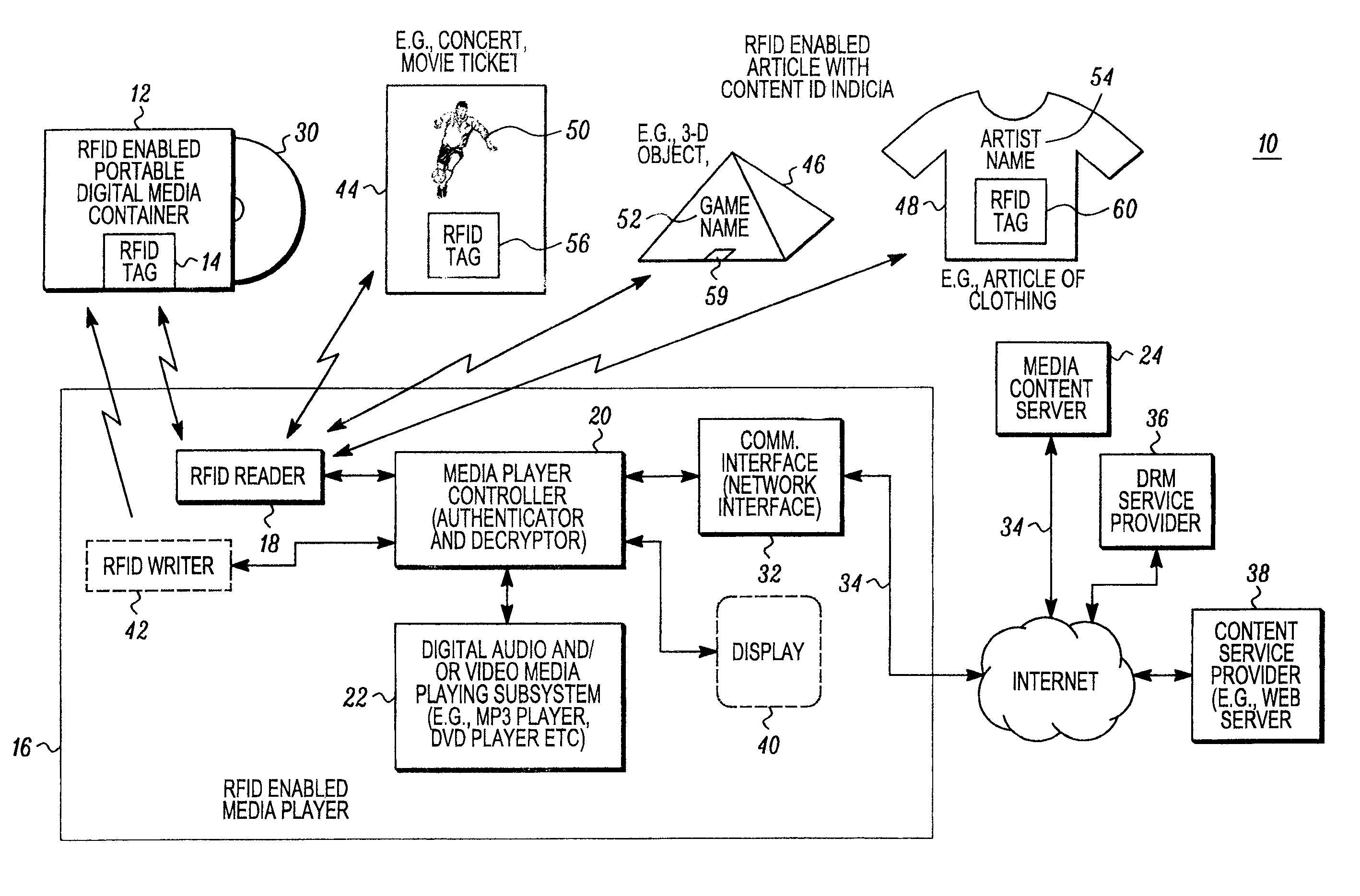
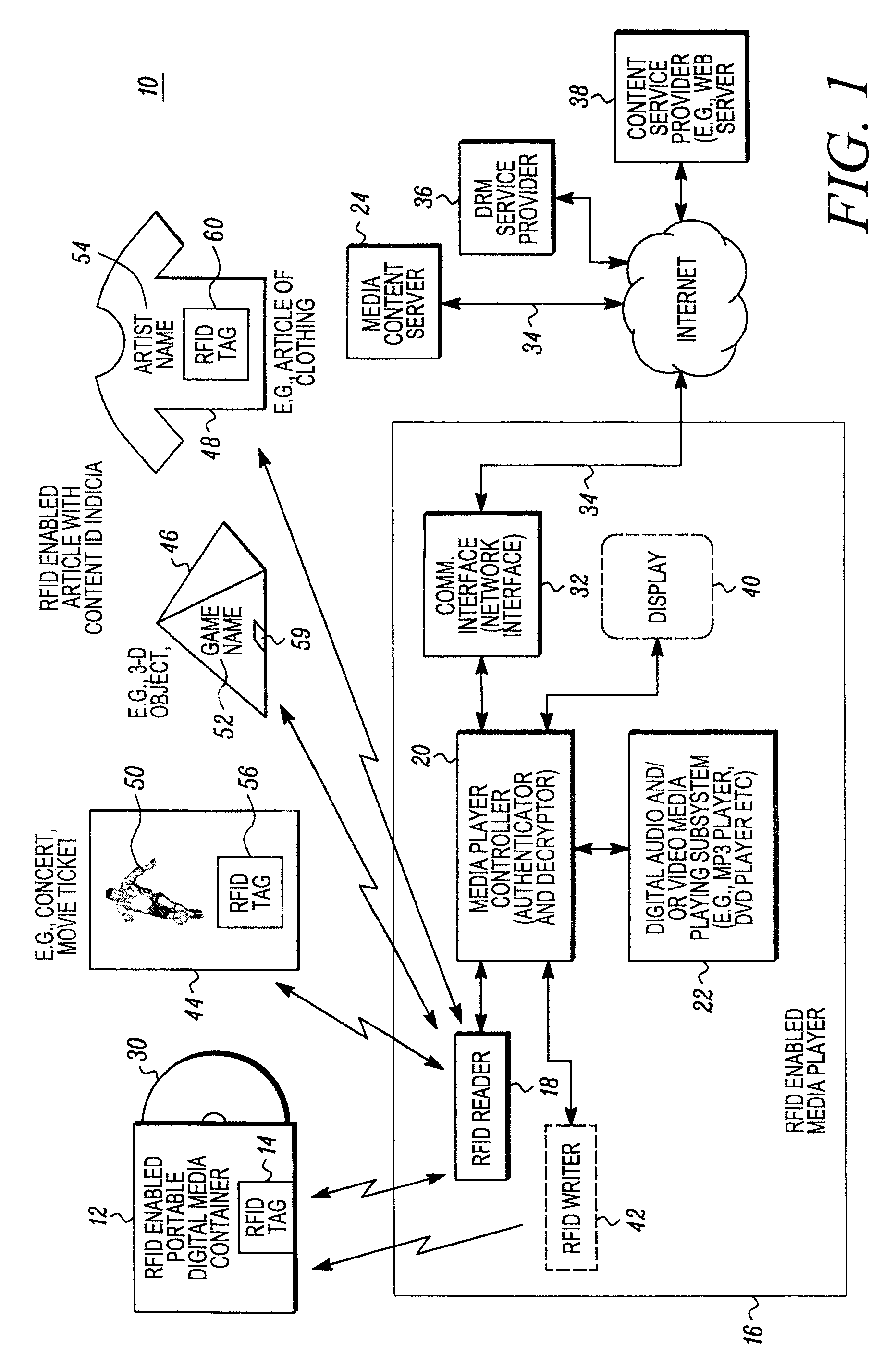
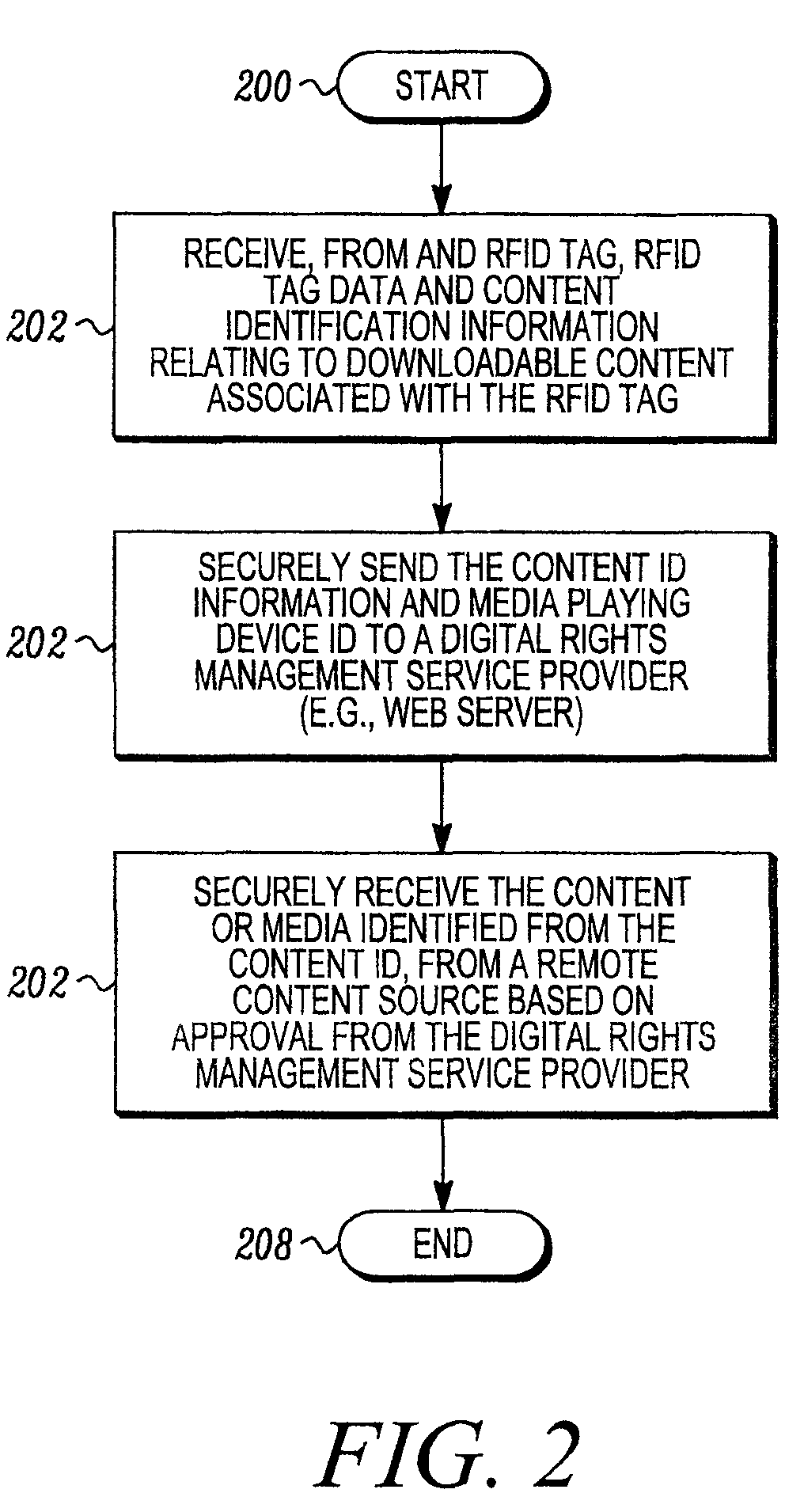
RFID enabled media system and method that provides dynamic downloadable media content
ActiveUS20090085724A1Easy to identifyShort timeDigital data processing detailsSubscribers indirect connectionRegistry dataComputer network
An audio and / or video media content providing device includes a controller, such as a server, that is responsive to RFID tag based information obtained from a remote RFID enabled media object. The controller is operative to facilitate access to media content associated with a stored periodically changing media content list. For example, a content registry database may be periodically updated through a suitable user interface to change a link between content identification information read from a remote RFID enabled media object, with media application information so that the same RFID tag may allow the downloading of different media. The link between the content ID and the media ID may be dynamically changed through the controller. This may be advantageous, to provide for example, a Top 10 song card or other RFID enabled object that stays the same but can be used to securely download different media over time.
Owner:ACCENTURE GLOBAL SERVICES LTD
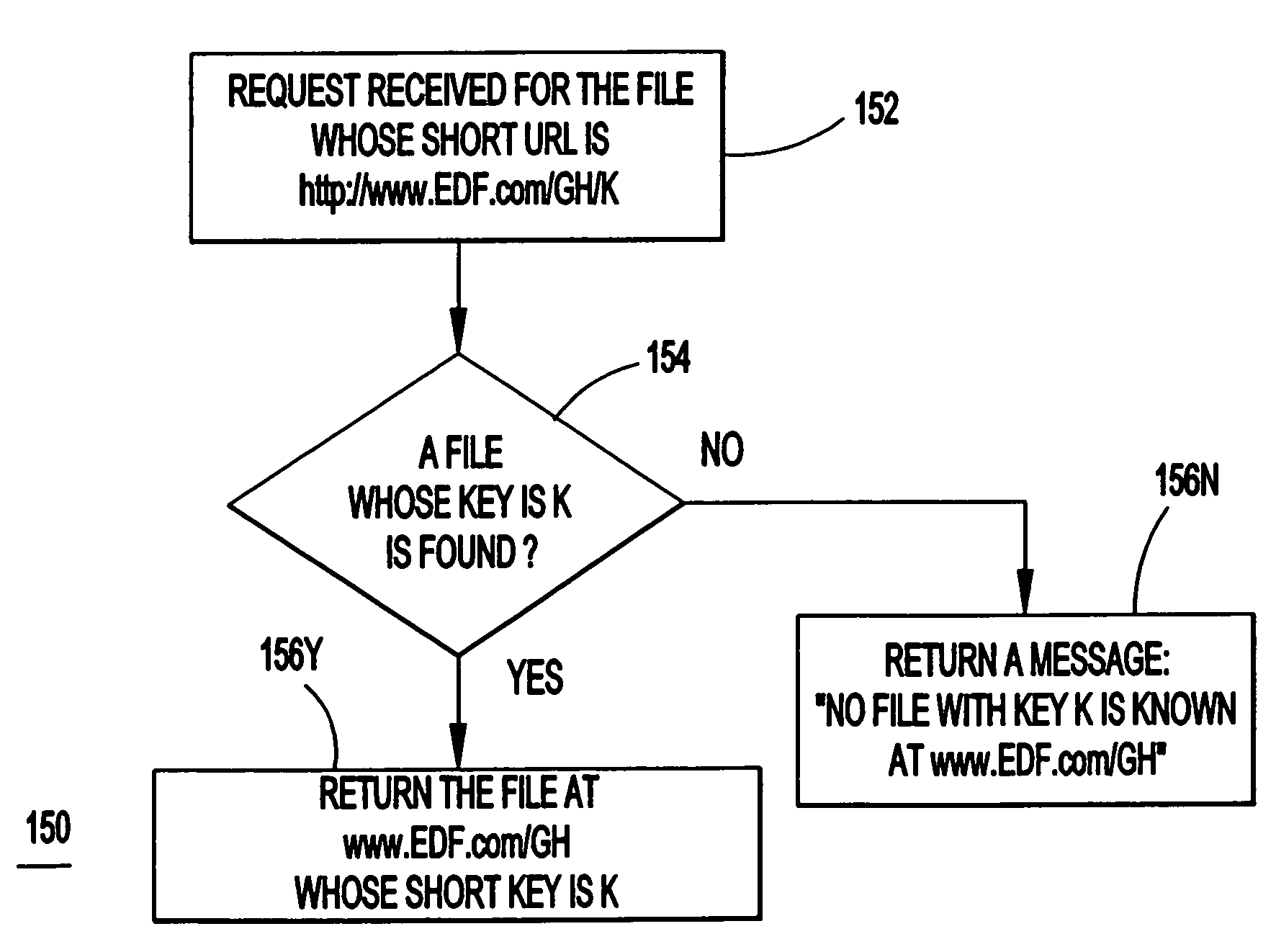
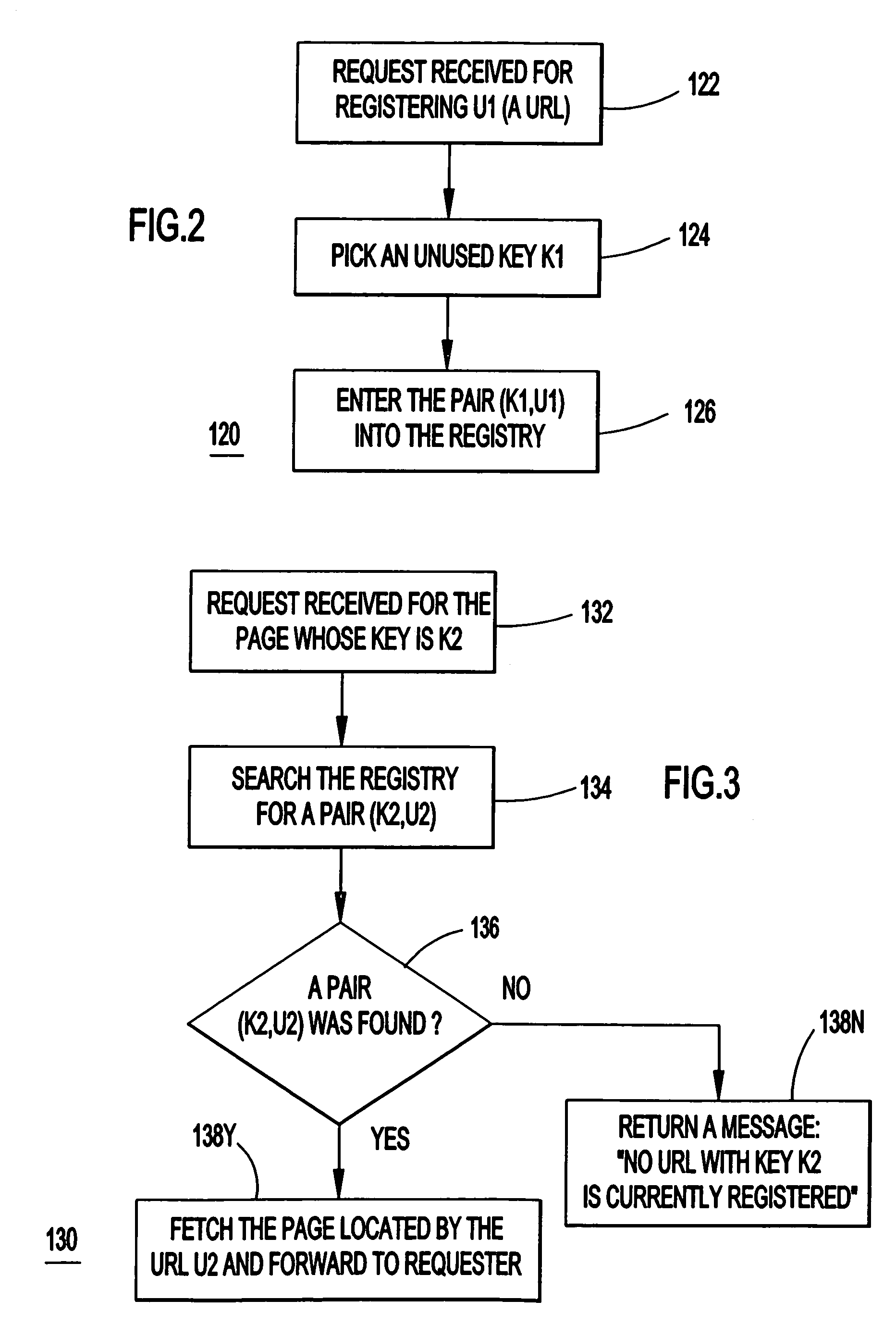
Efficient retrieval of uniform resource locators
InactiveUS6957224B1Small sizeReduce loadData processing applicationsTransmissionRegistry dataUniform resource locator
A system, method and computer program product for providing links to remotely located information in a network of remotely connected computers. The system may or may not include a server providing an interface between shorthand codes and corresponding original files. If the server is included, a uniform resource locator (URL) is registered with a server. A shorthand link is associate with the registered URL. The associated shorthand link and URL are logged in a registry database. When a request is received for a shorthand link, the registry database is searched for an associated URL. If the shorthand link is found to be associated with an URL, the URL is fetched, otherwise an error message is returned. If the server is not included, all URLs located at a root page may be listed and associated with shorthand keys or links. Associated files and keys are indexed in an index file. The shorthand codes or keys are combined with the root page to form shorthand URLs. Requests are made for the shorthand URLs and the index file is searched for the requested shorthand URL. If the requested shorthand URL is encountered, the corresponding file is returned; otherwise, an error message is returned.
Owner:TWITTER INC
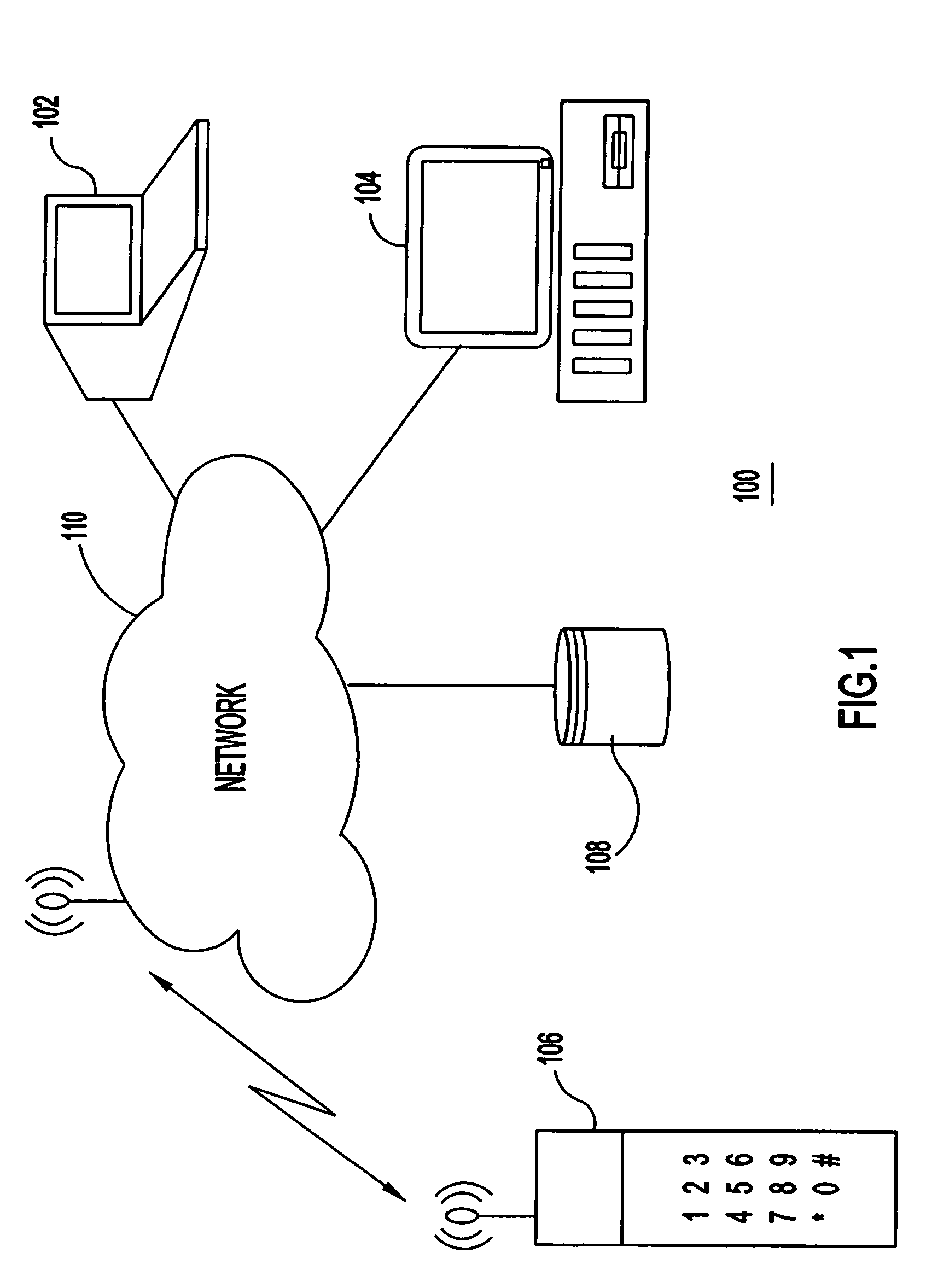
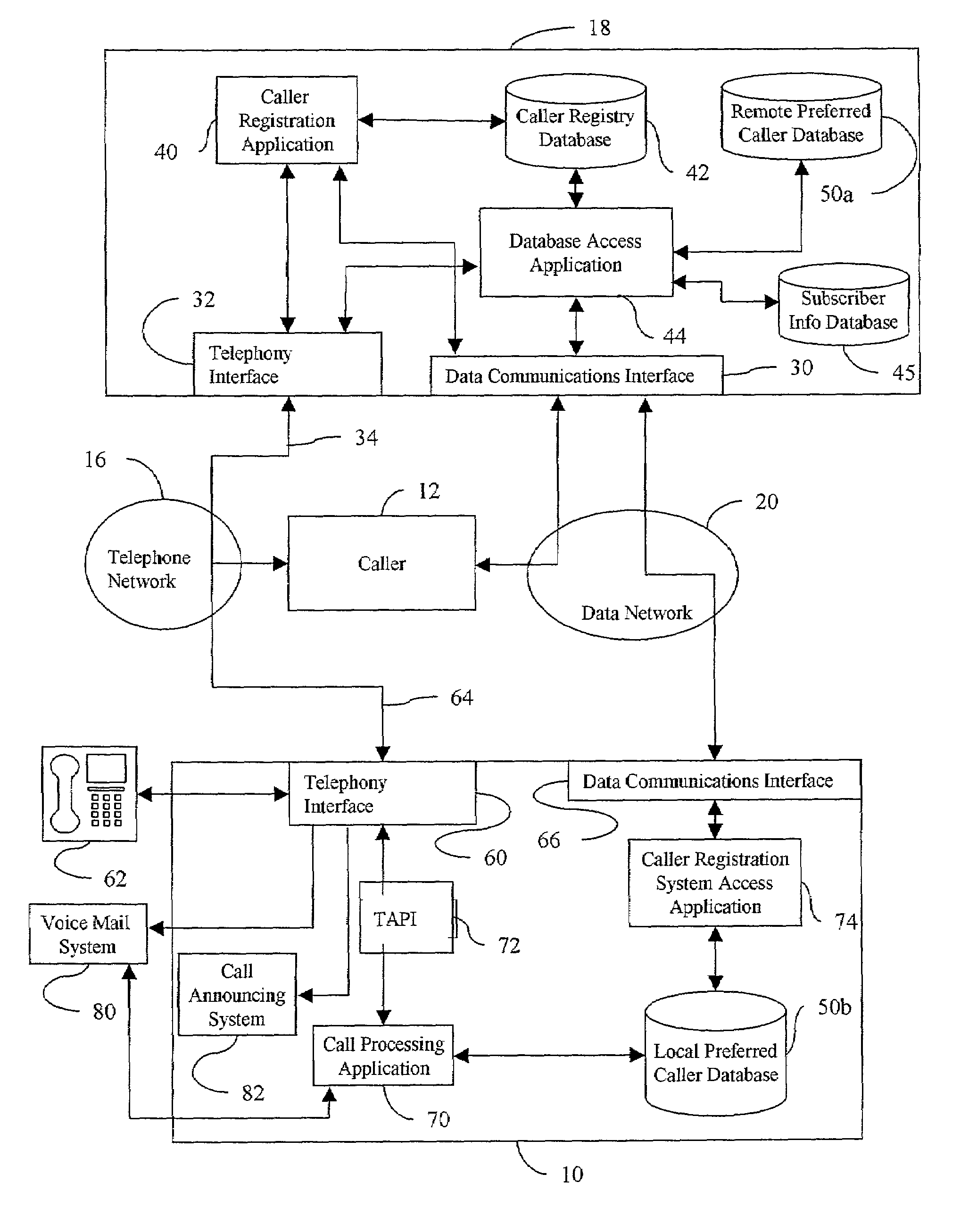
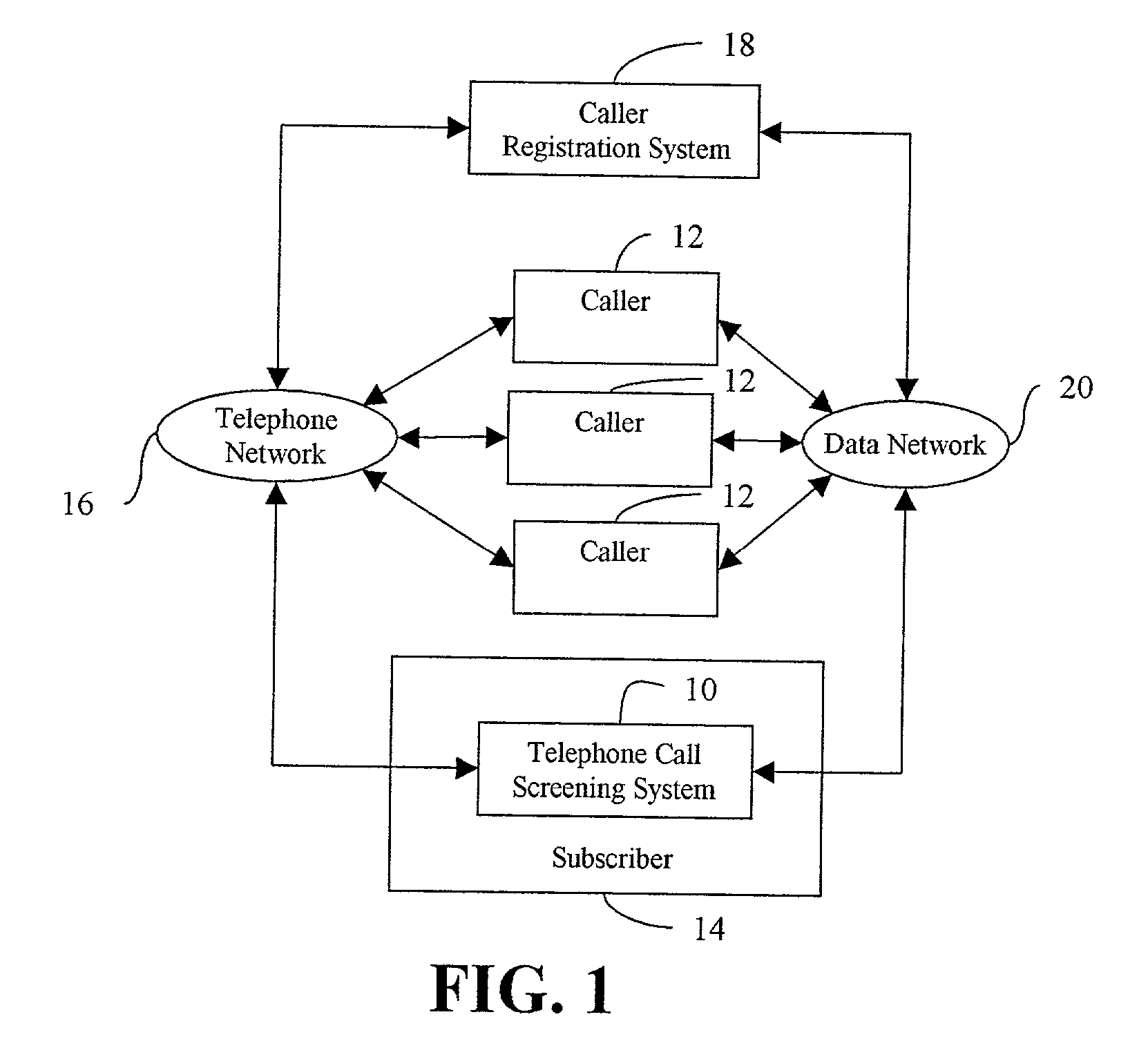
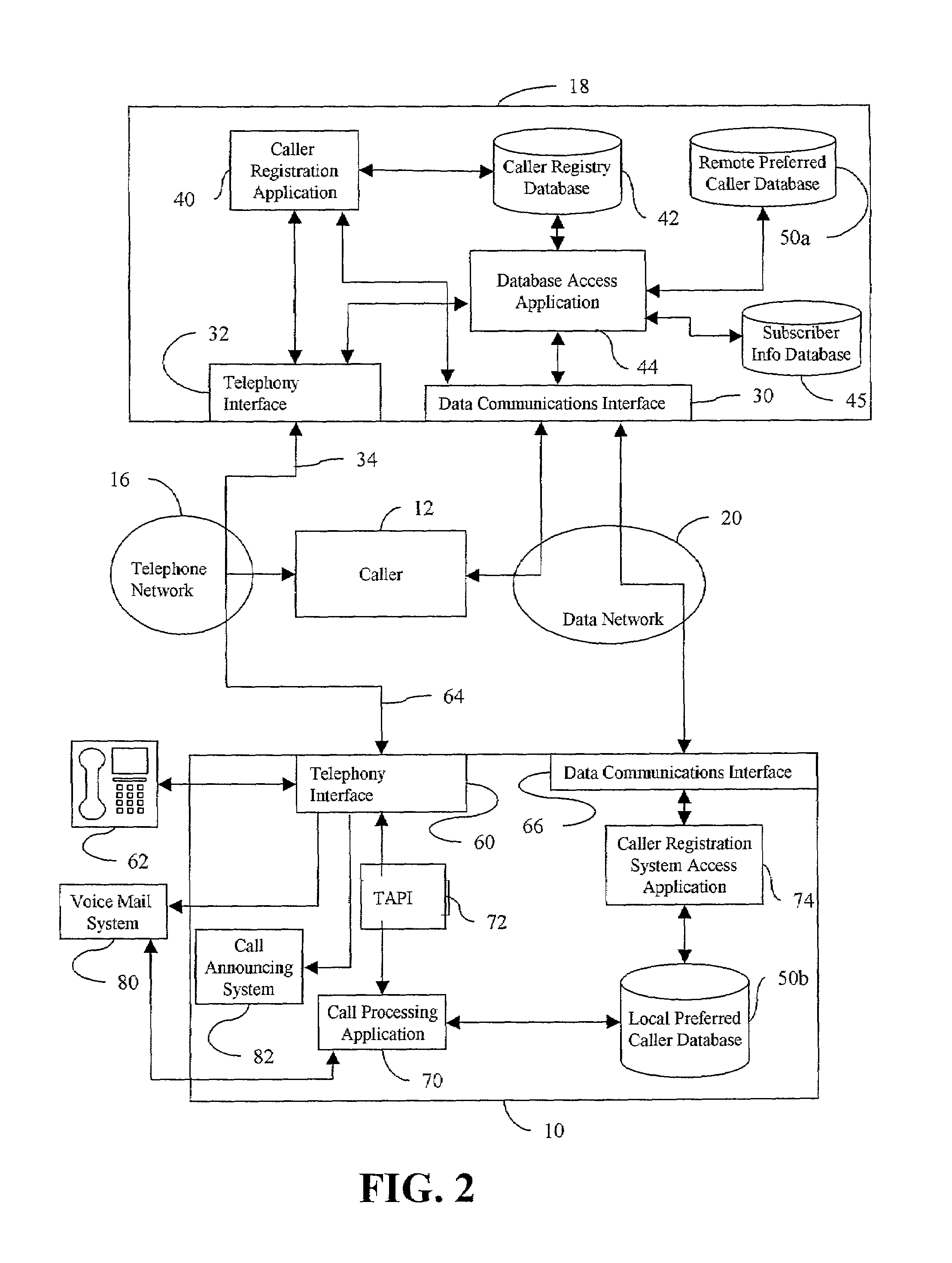
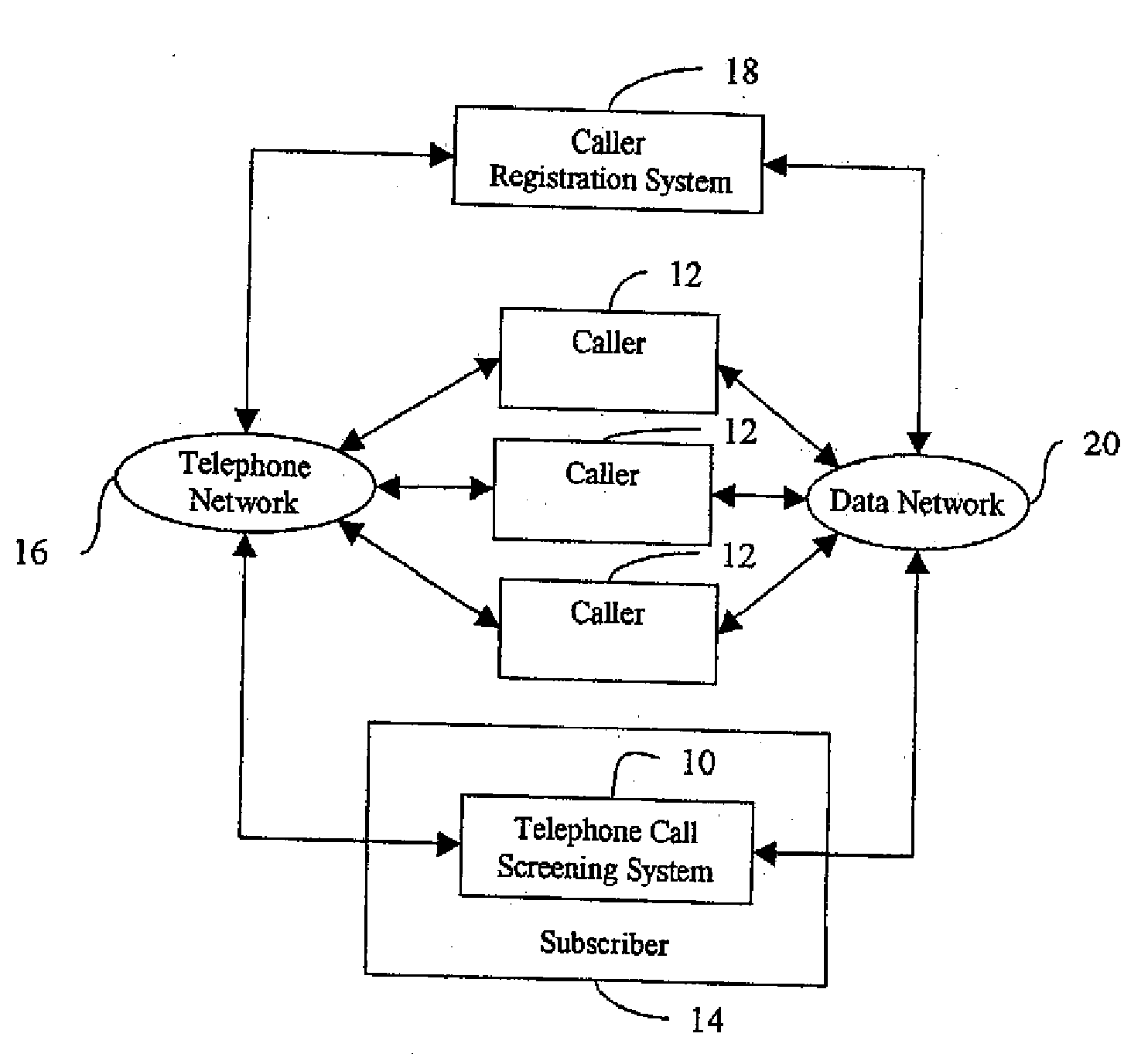
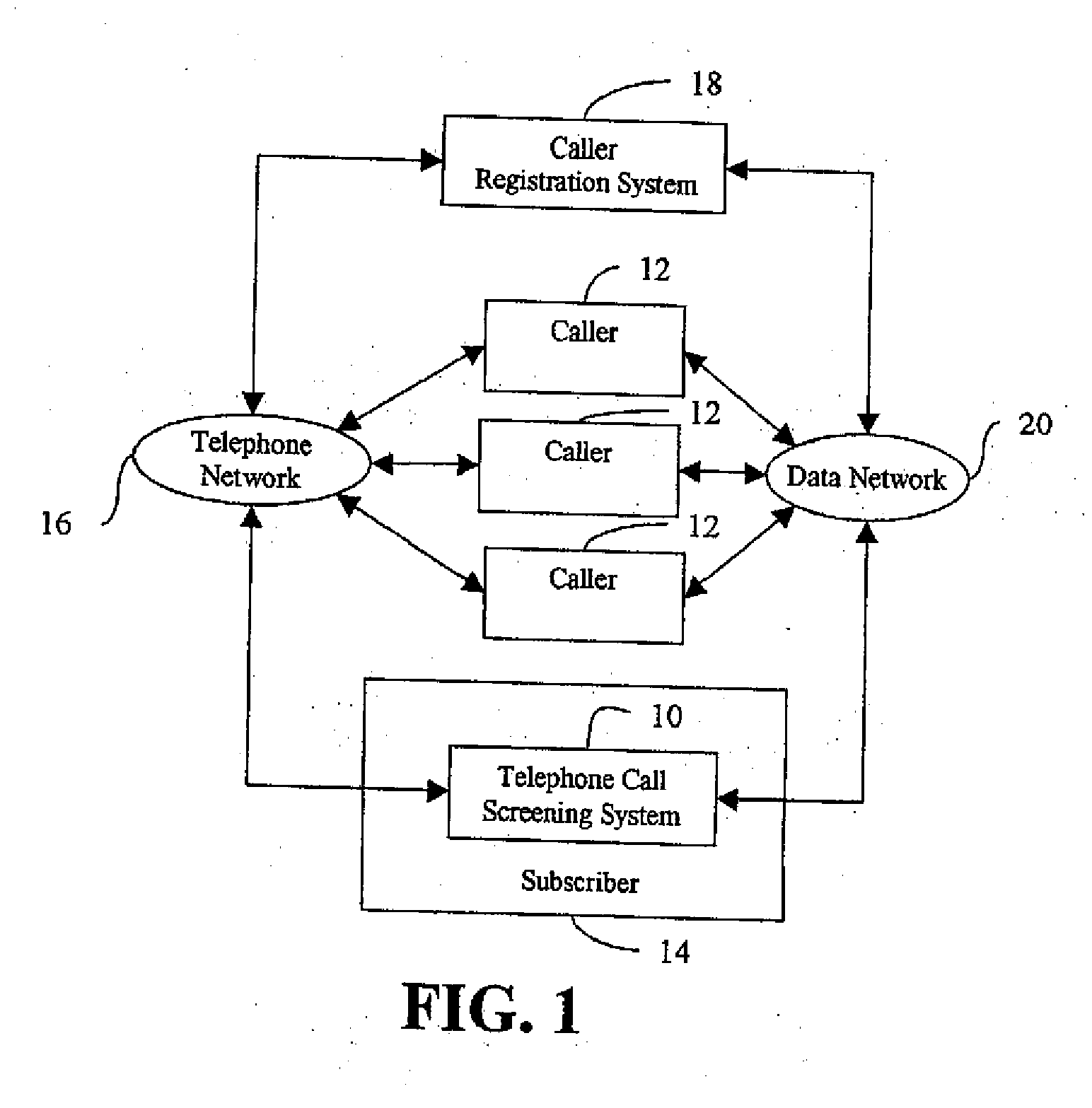
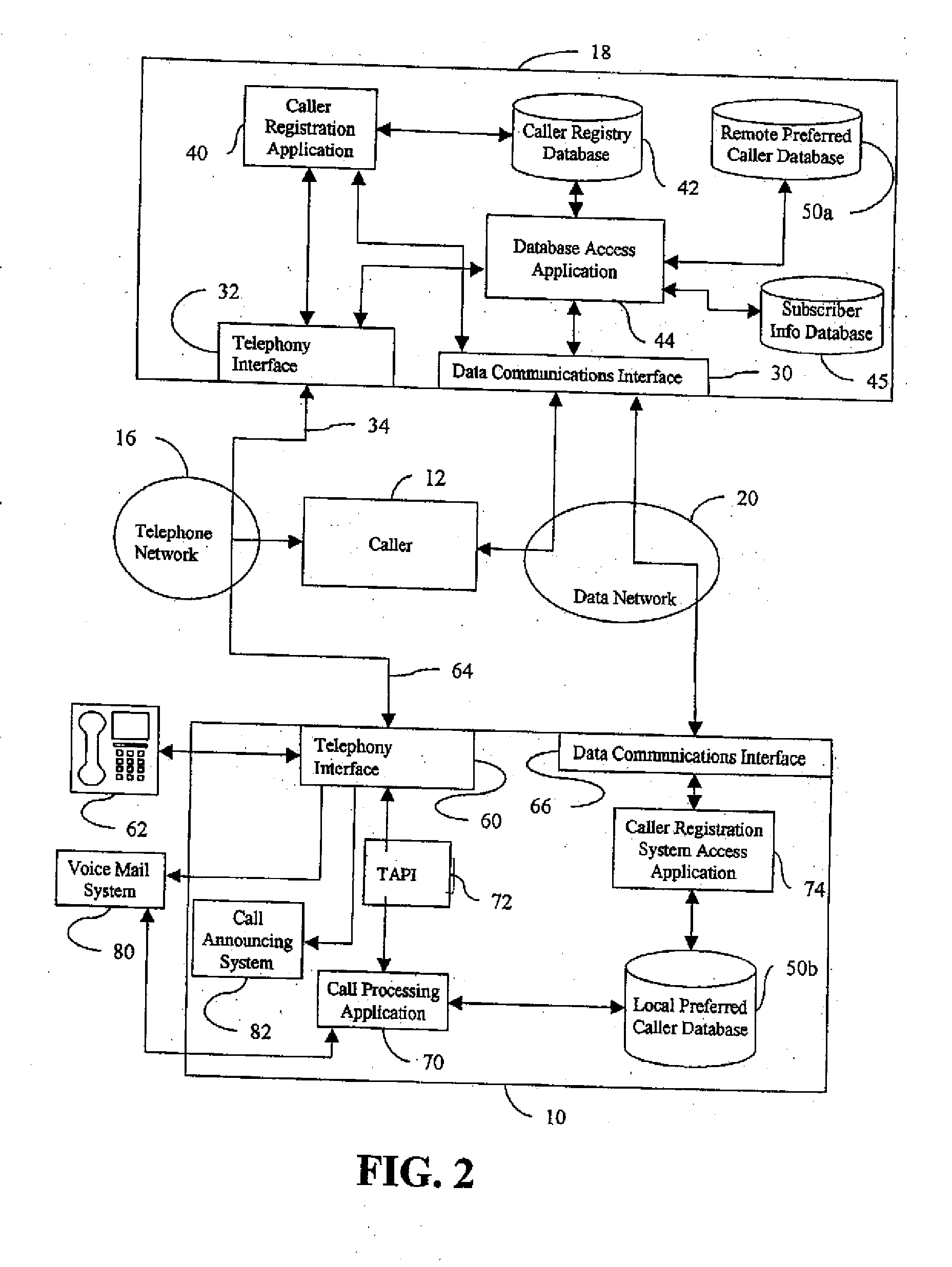
Telephone call screening system and method and caller registration system and method for use therewith
InactiveUS7027569B2Automatic call-answering/message-recording/conversation-recordingSpecial service for subscribersRegistry dataRegistration system
A telephone call screening system screens telephone calls placed to a subscriber based upon a preferred caller database established by the subscriber from a networked caller registry database. A caller registration system allows callers to select a private identifier unique to the caller and registers the callers in a caller registry database. The subscriber establishes the preferred caller database by connecting to the caller registration system and selecting the preferred callers. The private identifiers associated with the selected preferred callers are then stored in the preferred caller database. When a caller calls the subscriber, the caller is asked to enter the caller's private identifier. A caller disposition process is initiated based on whether the private identifier is in the preferred caller database.
Owner:PROLOGUE COMM
DNSSEC inline signing
Systems and methods of performing incremental DNSSEC signing at a registry are described in which digital signature operations may be performed as part of a single transaction including DNS add, update, and / or delete operations and the like. Exemplary methods may include receiving a domain command from a requester, the domain command including an identifier of a domain. The received domain command may be executed with respect to data stored by the registry for the domain. As part of an individual transaction including the execution of the domain command, the registry may also sign DNSSEC records for the domain using a private key of an authoritative server. After the DNSSEC records have been signed, the registry may incrementally publish the signed DNSSEC records to a separate server. Exemplary methods may also include “took-aside” operations in which, for example, add, update, and / or delete operations may be executed on data stored in a registry database and reported to a requester, prior to applying digital-signatures to the DNSSEC data. After reporting that the instructions have been executed, the registry may generate a digital signature based on the add, update, and / or delete changes, and commit the digital signature to a registry resolution database.
Owner:VERISIGN
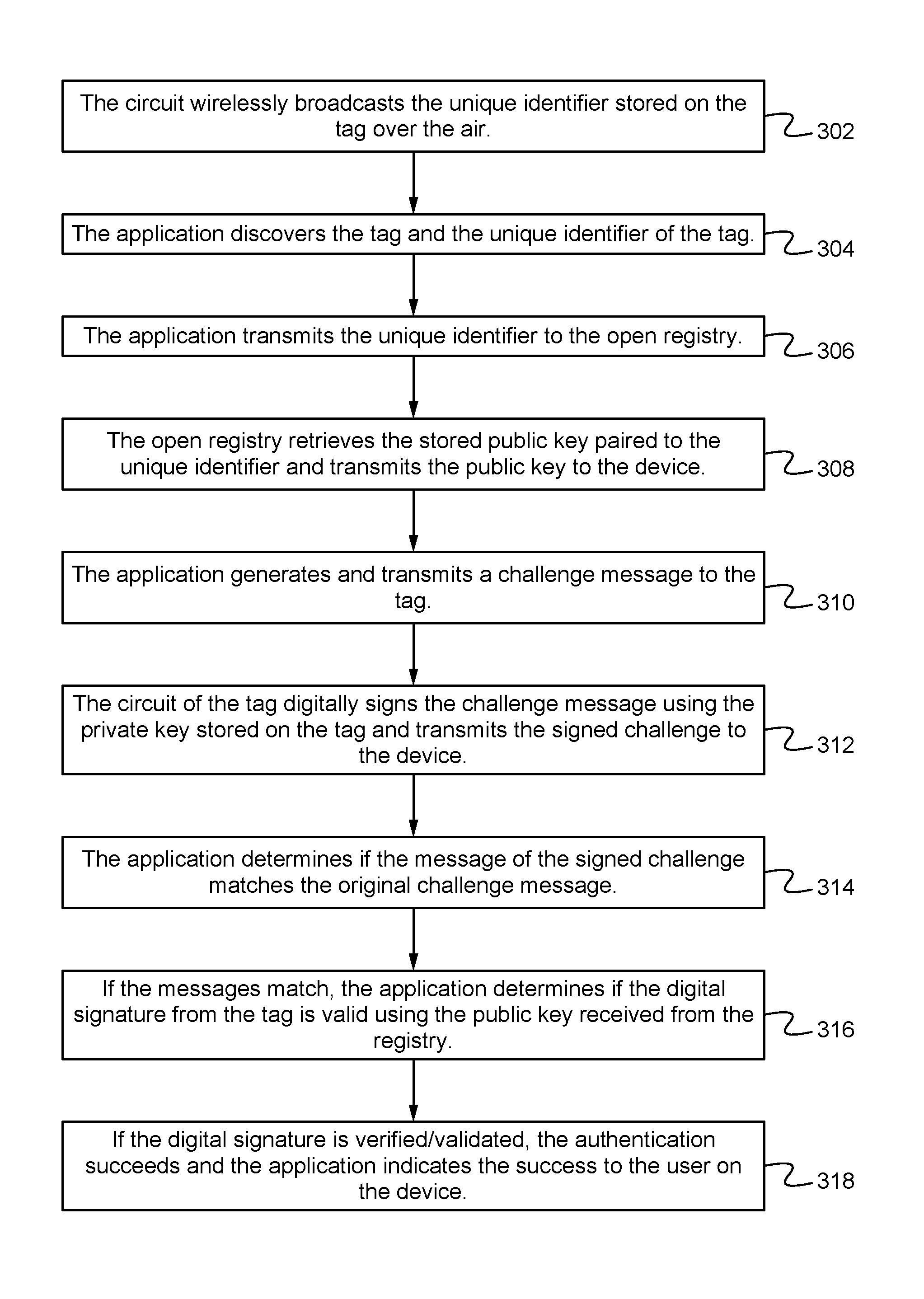
Open registry for identity of things
ActiveUS20160358186A1Avoid readingMultiple keys/algorithms usageCryptography processingThird partyRegistry data
An identity system for the Internet of Things (IOT) that enables users and machines to identify, authenticate and interact with products and collectibles without relying on a third-party-controlled authentication service. The system includes wireless tamperproof tags coupled to products and an open registry database where a chain of ownership of the items is able to be stored. The open registry enables public access to the item identity and data combined with item registration anonymity.
Owner:CHRONICLED INC
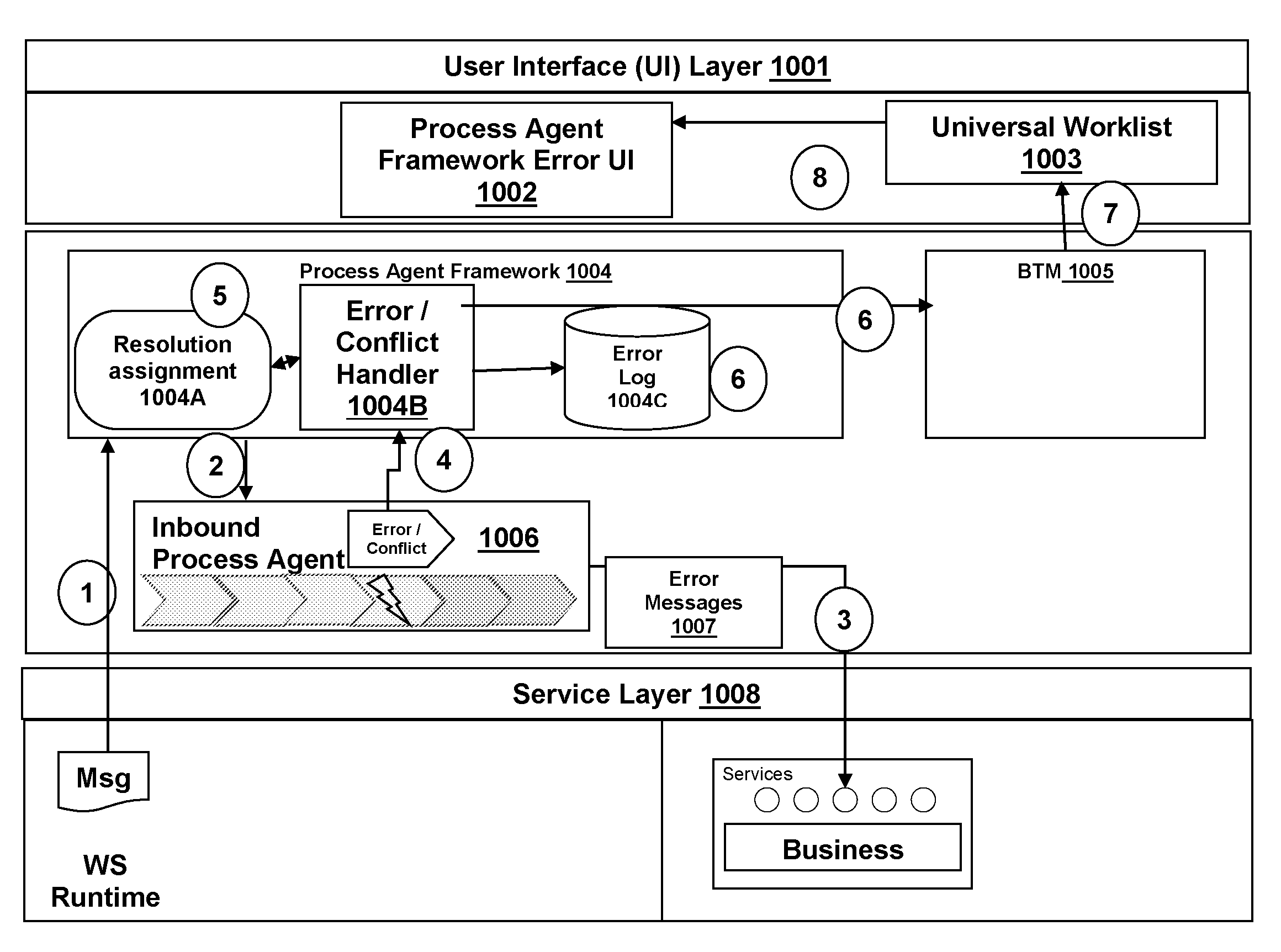
System and method for a message registry and message handling in a service -oriented business framework
InactiveUS20100001834A1Frequency-division multiplex detailsTime-division multiplexRegistry dataMessage handling
A system and method are provided for handling a notification message in an enterprise services framework, including in response to the saving of a transaction, sending a notification message to the enterprise system framework, the notification message containing an associated message class including information of message severity and message symptom. The framework includes a controller layer situated between a service management layer and a business object layer, the controller layer maintaining a message registry database which collects and stores the notification message and the information of message severity, message symptom, and message identification. A system and method is provided for the hierarchical handling of software objects, including providing software objects, each associated with a user interface message, hierarchically associating the user interface messages, and displaying those messages in a tree structure in association with each of the software objects.
Owner:SAP AG
System and method for secure machine-to-machine communications
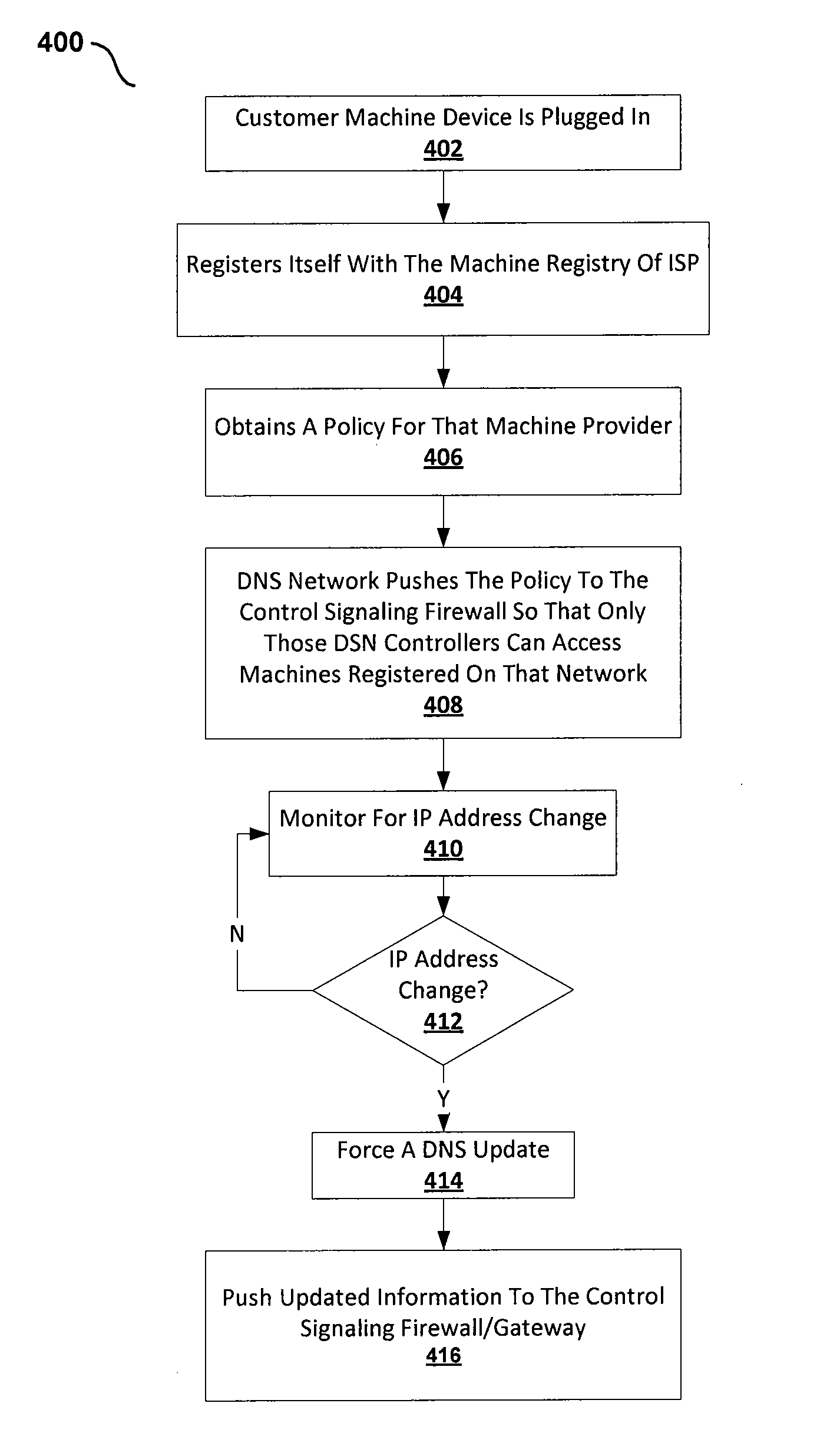
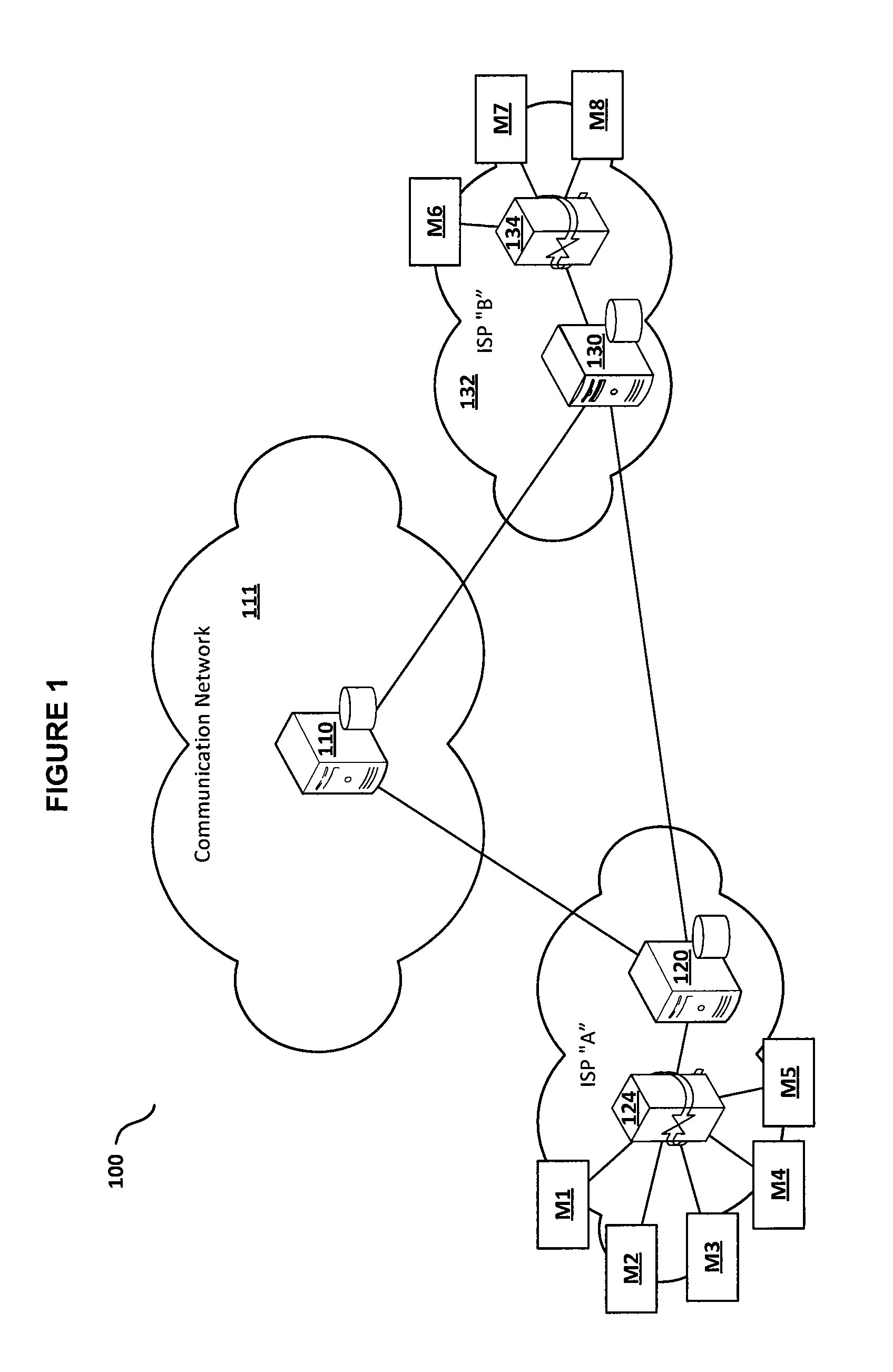
ActiveUS20130305345A1Eliminate riskFacilitate communicationMultiple digital computer combinationsProgram controlRegistry dataDomain name
Embodiments of the present invention include a method for providing a secure domain name system (DNS) for machine to machine communications. In one embodiment, the method includes storing policy information for machine to machine communications in a global DNS registry database server. The method further includes communicating the policy information for machine to machine communications from the global DNS registry database server to a machine DNS registry server located in an Internet service provider (ISP) network, wherein a control signaling gateway located in the ISP network is configured to utilize the policy information for machine to machine communications to allow only registered controllers associated with a machine to communicate with the machine.
Owner:CENTURYLINK INTPROP
DNSSEC Inline Signing
Systems and methods of performing incremental DNSSEC signing at a registry are described in which digital signature operations may be performed as part of a single transaction including DNS add, update, and / or delete operations and the like. Exemplary methods may include receiving a domain command from a requester, the domain command including an identifier of a domain. The received domain command may be executed with respect to data stored by the registry for the domain. As part of an individual transaction including the execution of the domain command, the registry may also sign DNSSEC records for the domain using a private key of an authoritative server. After the DNSSEC records have been signed, the registry may incrementally publish the signed DNSSEC records to a separate server. Exemplary methods may also include “took-aside” operations in which, for example, add, update, and / or delete operations may be executed on data stored in a registry database and reported to a requester, prior to applying digital-signatures to the DNSSEC data. After reporting that the instructions have been executed, the registry may generate a digital signature based on the add, update, and / or delete changes, and commit the digital signature to a registry resolution database.
Owner:VERISIGN
Open registry for identity of things including tamperproof tags
InactiveUS20160358184A1Avoid readingMultiple keys/algorithms usageCryptography processingRegistry dataThird party
An identity system for the Internet of Things (IOT) that enables users and machines to identify, authenticate and interact with products and collectibles without relying on a third-party-controlled authentication service. The system includes wireless tamperproof tags coupled to products and an open registry database where a chain of ownership of the items is able to be stored. The open registry enables public access to the item identity and data combined with item registration anonymity.
Owner:CHRONICLED INC
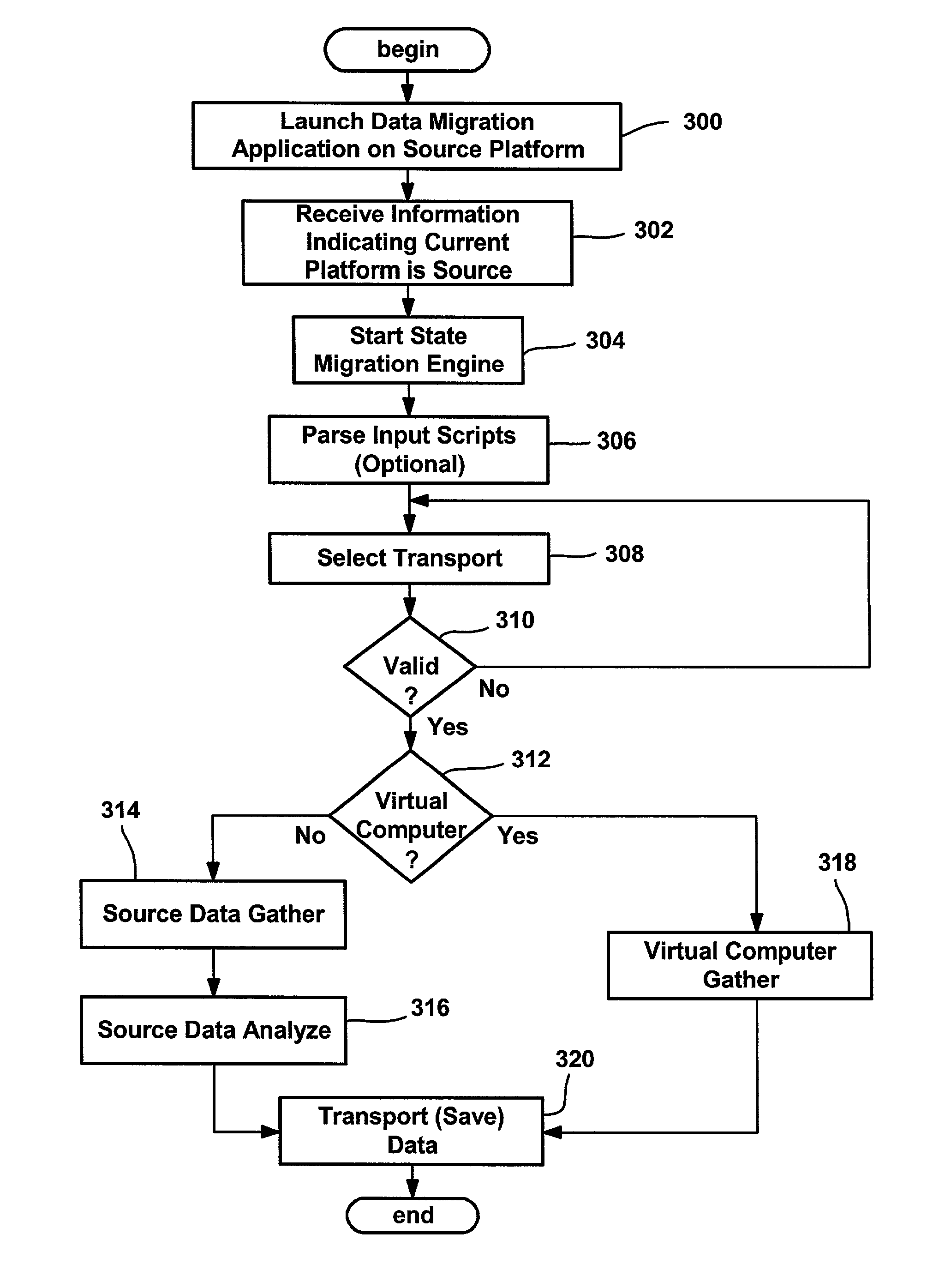
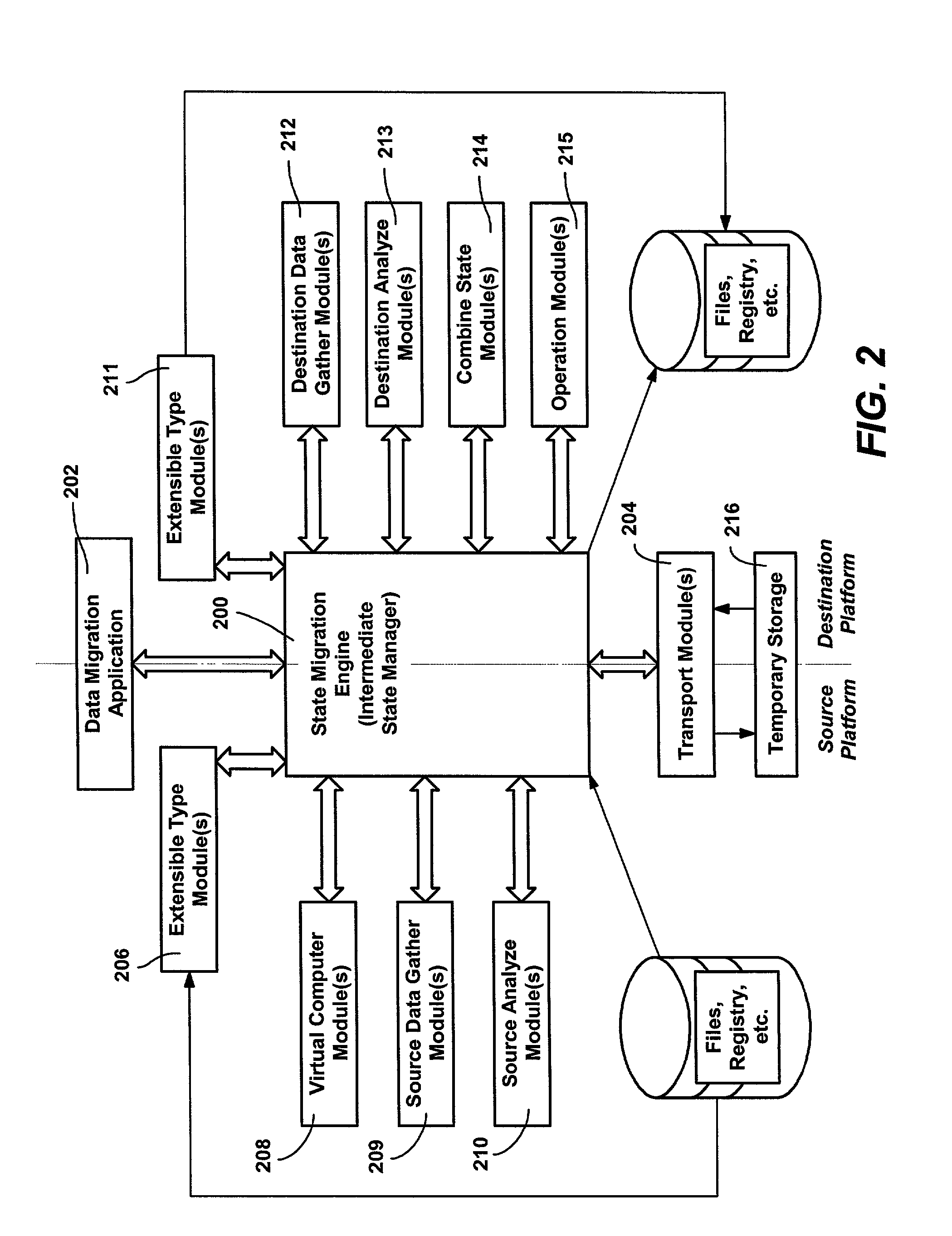
Method and system for migrating computer state
InactiveUS7210131B2Program loading/initiatingSoftware simulation/interpretation/emulationRegistry dataData transmission
A system and method for migrating state data from a source computing platform to a destination platform, such as for migrating state data from one computer to another computer. Pluggable modules collect state on a source platform and transport it to temporary storage as state objects that are independent of any particular destination platform. For example, a state object may contain the information that represents a file on a source machine, while another state object may contain a piece of registry data on that machine. At the source platform, modules provide state data gathering and analysis that collect the data into the state objects. A transport module transports the data to storage accessible to the destination. At the destination, the state objects are applied by pluggable modules to the destination platform. The object data can be adjusted, translated and / or merged with destination state data as appropriate for the destination platform.
Owner:MICROSOFT TECH LICENSING LLC
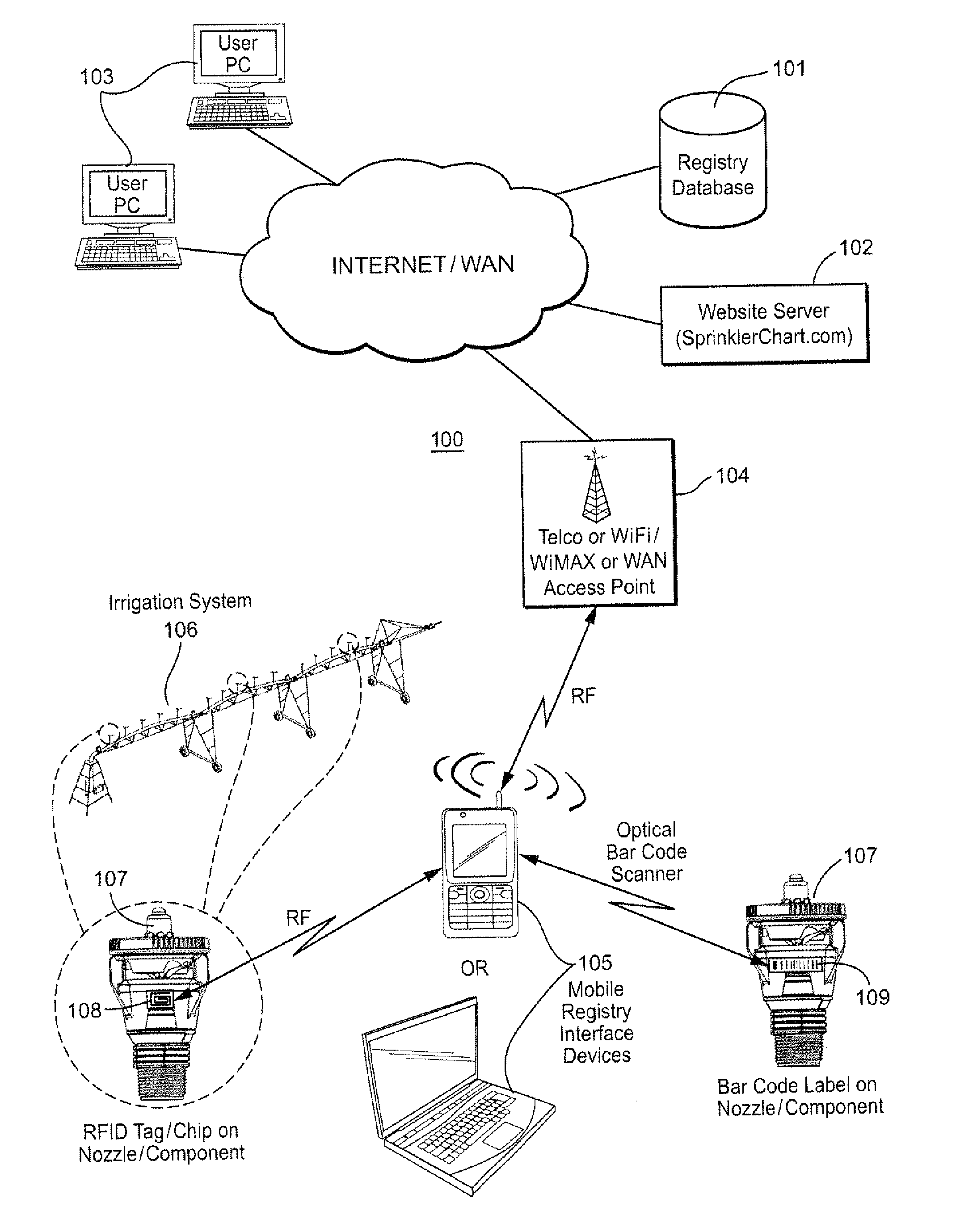
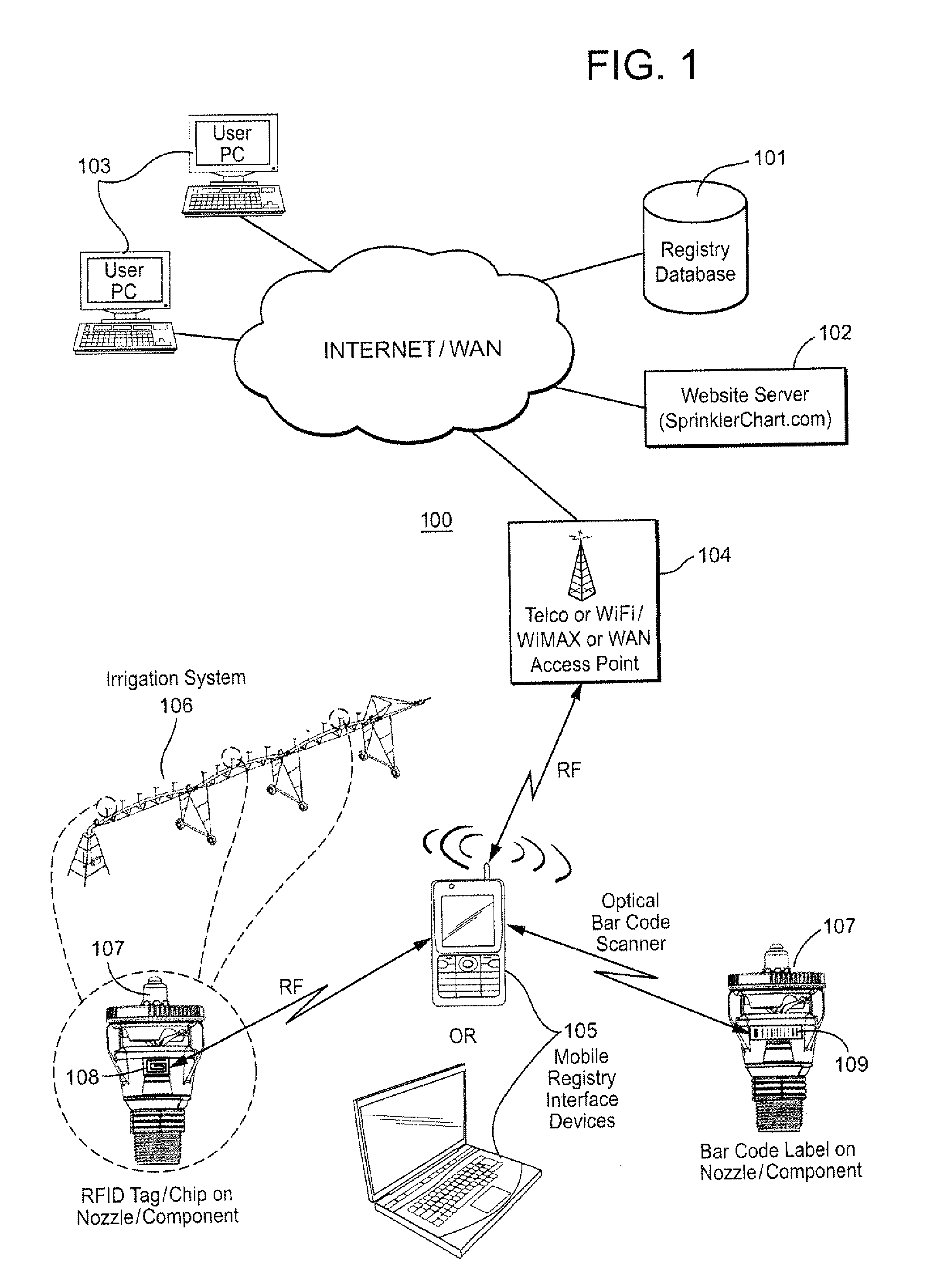
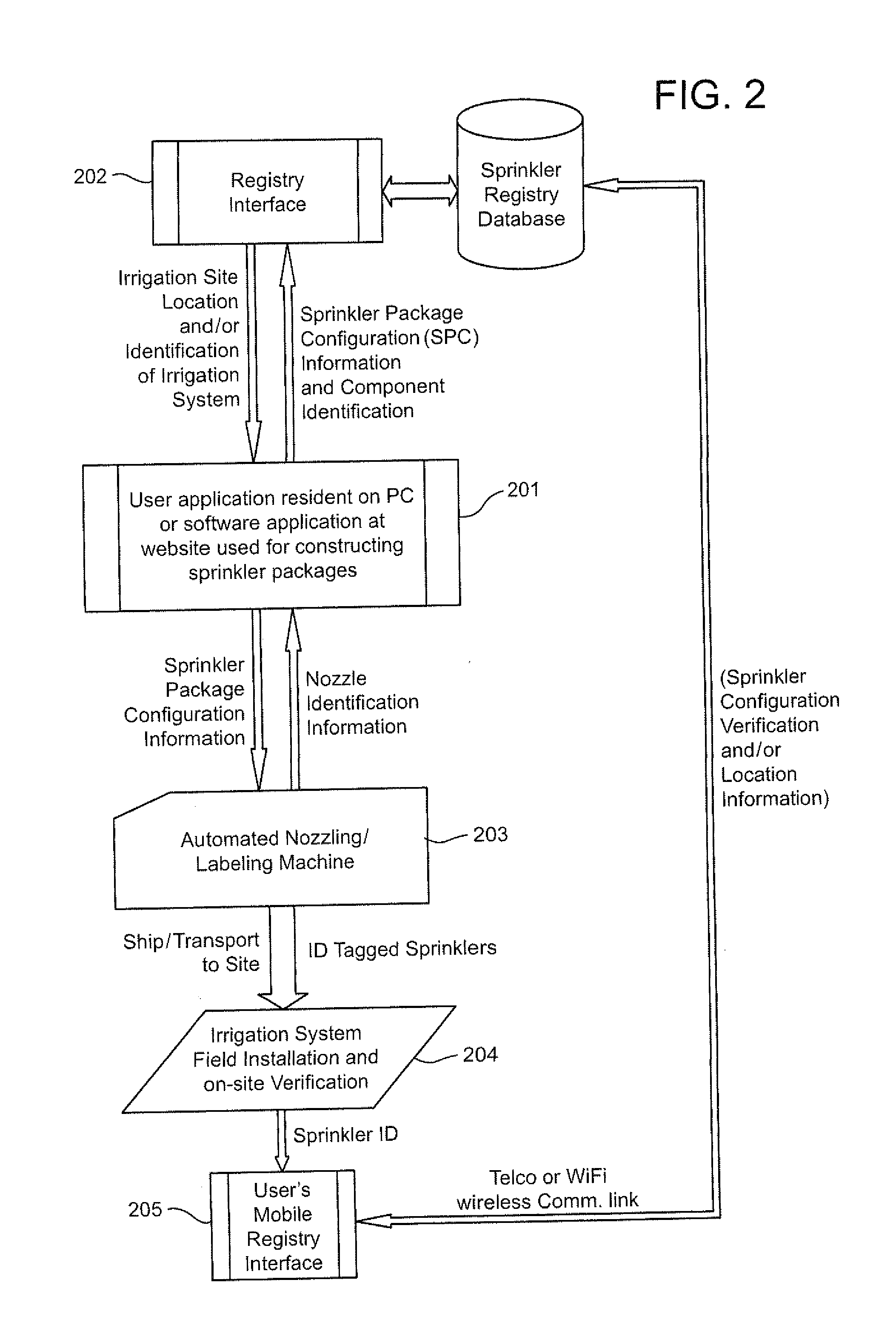
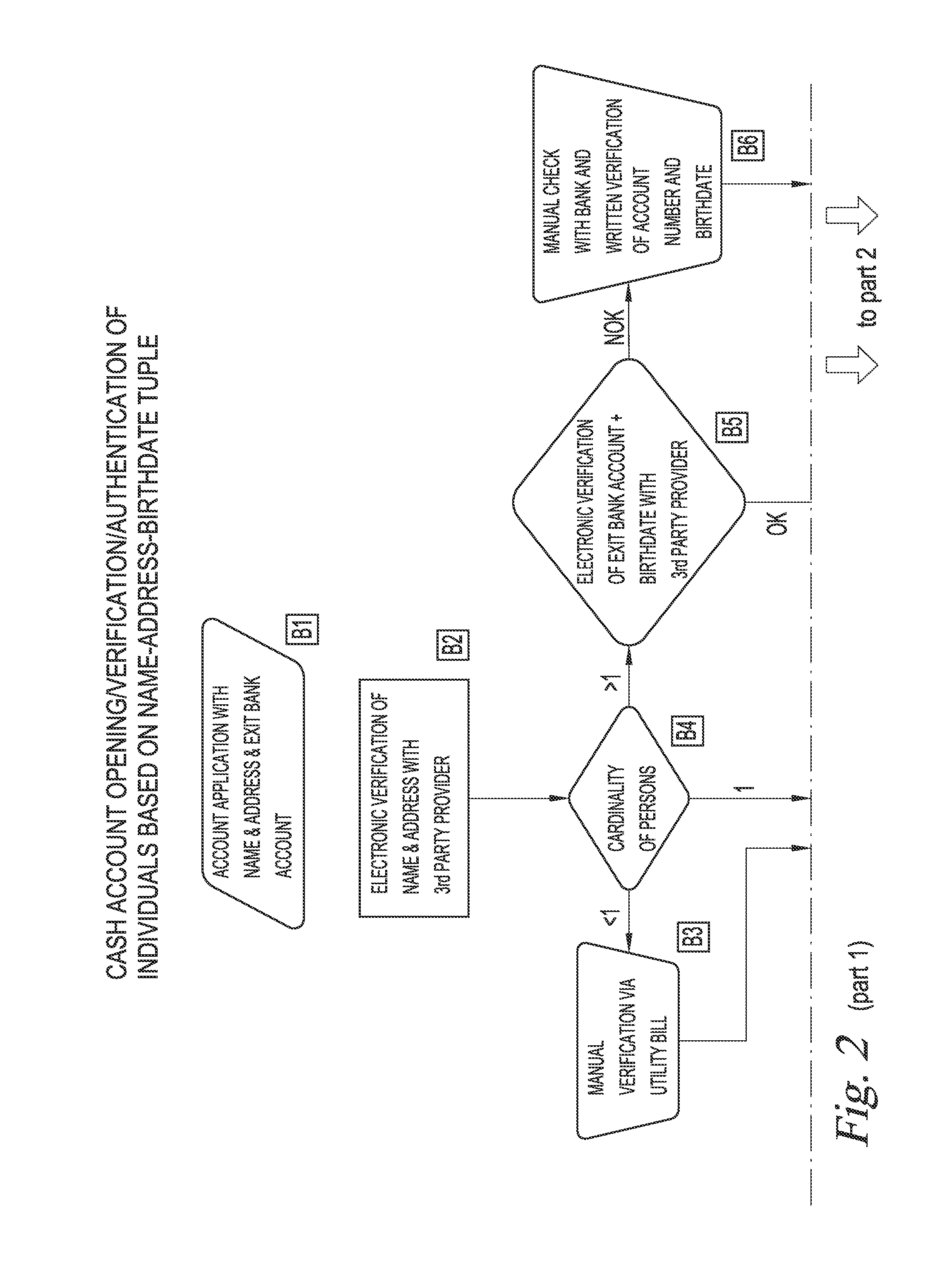
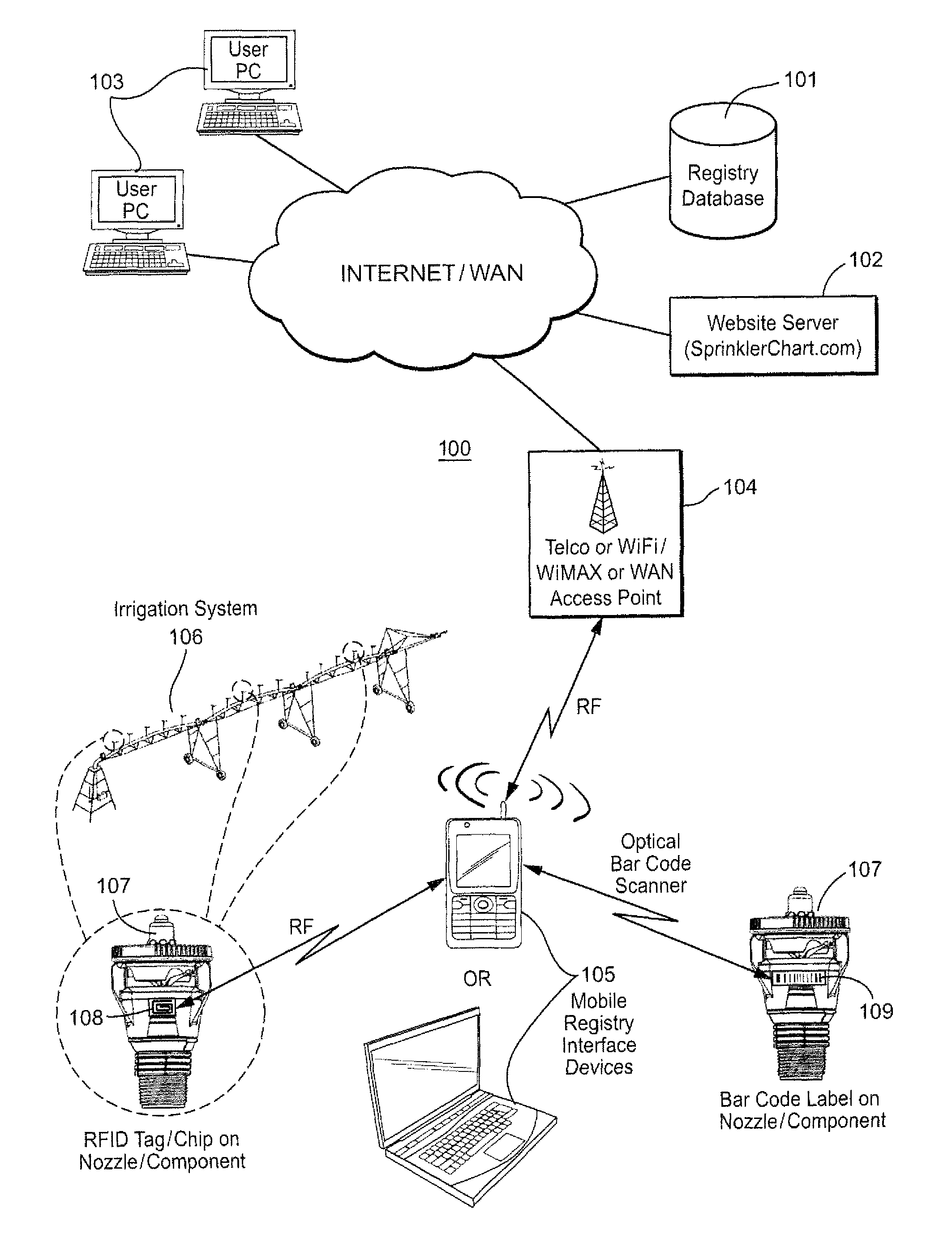
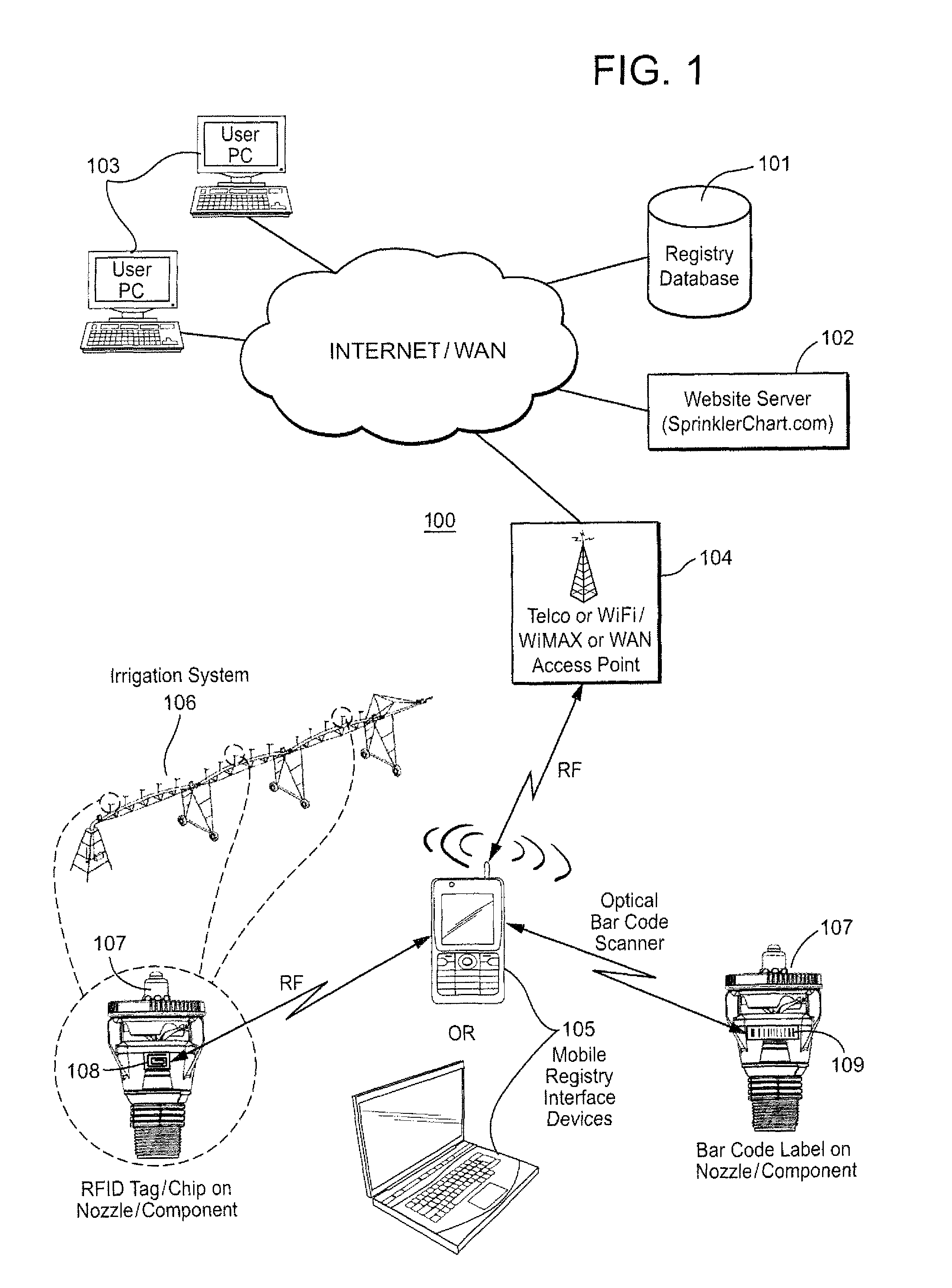
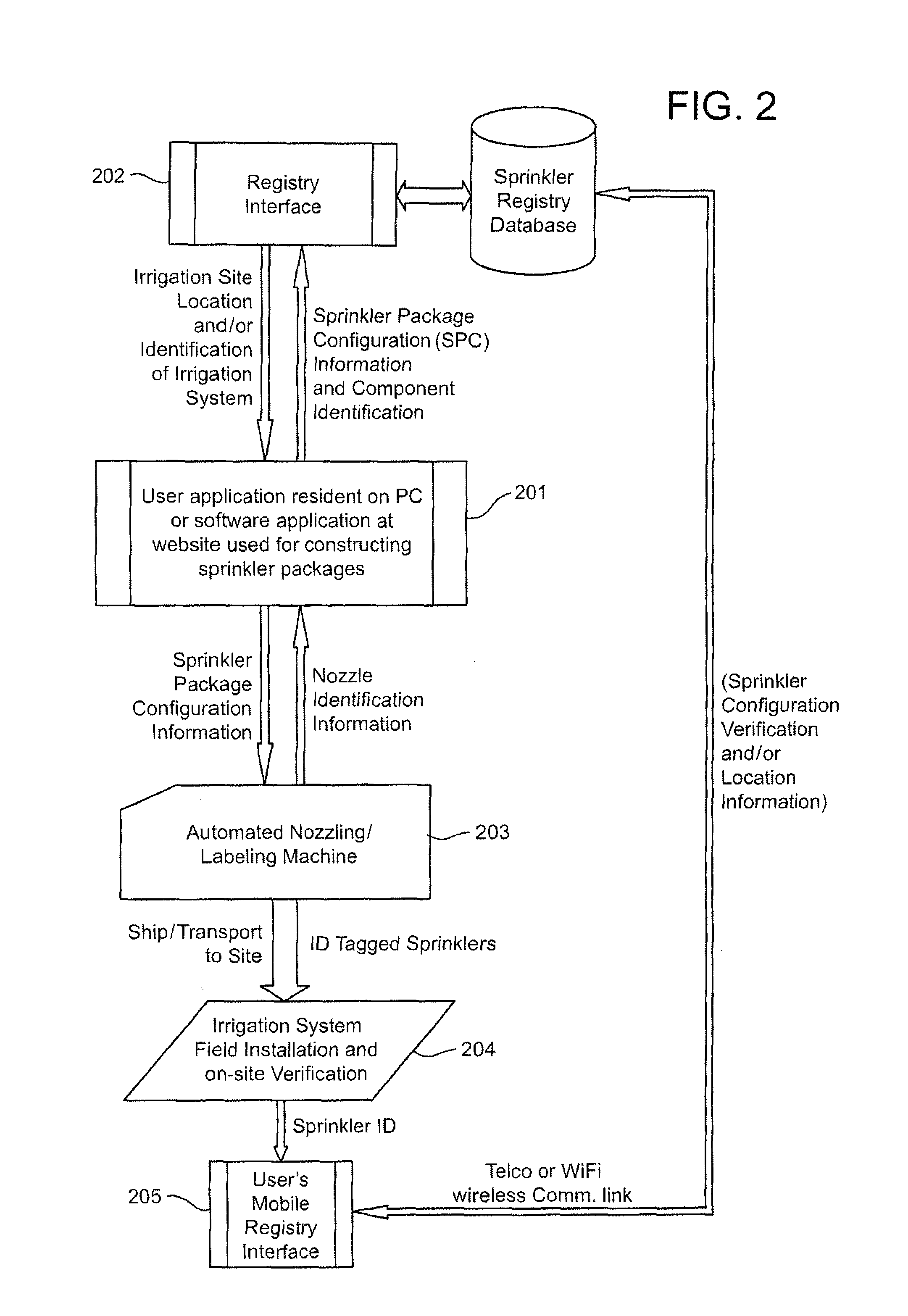
Method and apparatus for irrigation system design registration and on-site sprinkler package configuration verification
ActiveUS20120254784A1Convenient verificationMaximize efficiencyData processing applicationsInput/output processes for data processingSystems designLocation aware
Internet-accessible system and method for customized design and on-site verification of agriculture irrigation systems includes one or more of: 1) sprinkler package configuration software operable on a user's PC or accessible via an Internet website, 2) Internet-accessible proprietary irrigation system registry database and user interface, 3) computer-controlled automated component selection and labeling system for placing barcode or RFID information on components, and 4) portable wireless location-aware communication device operable at or near an irrigation site for accessing the registry database and obtaining sprinkler package configuration information specific to a particular irrigation system based on location and / or a particular irrigation system component detected in proximity to the portable communication device.
Owner:NELSON IRRIGATION
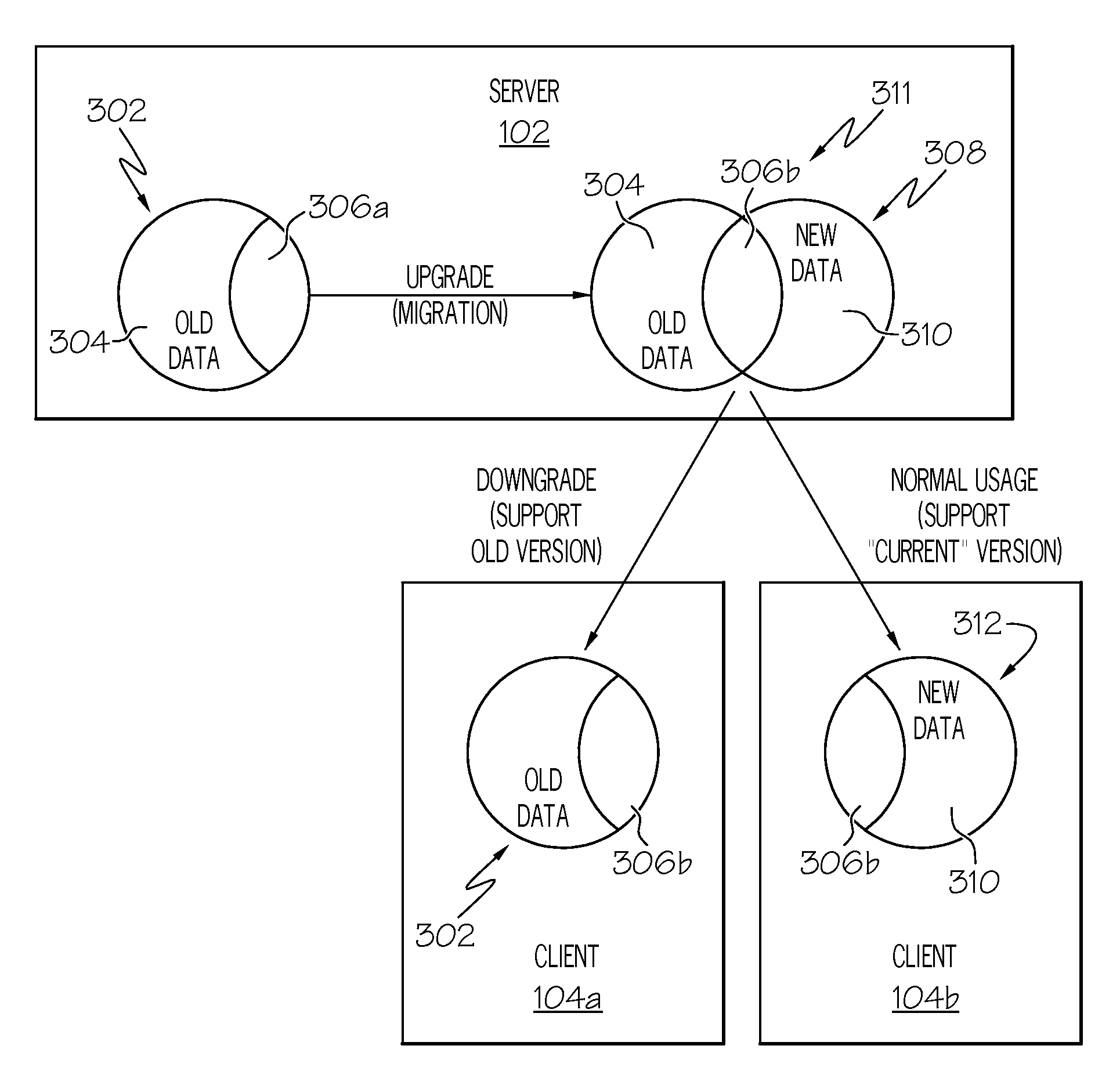
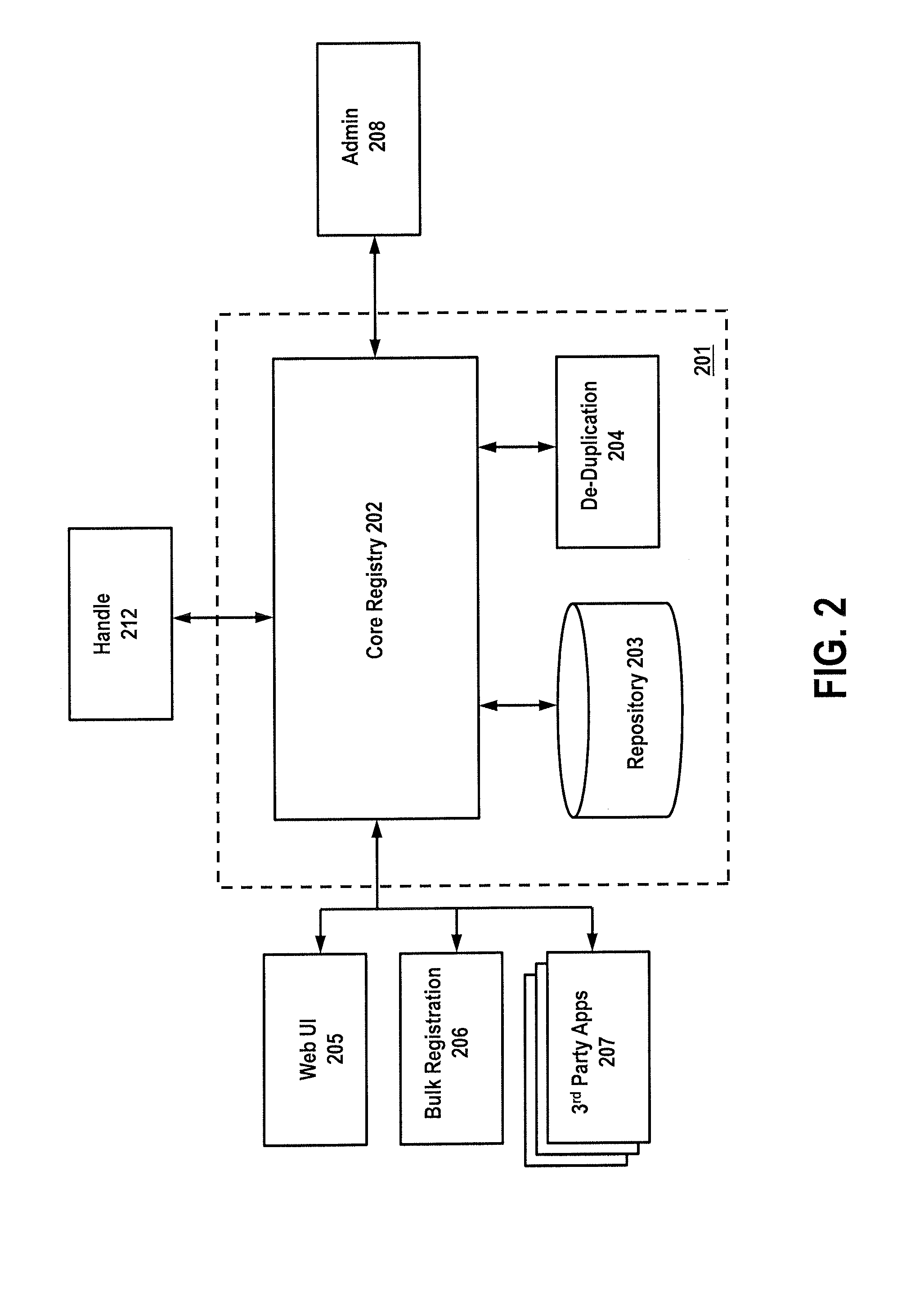
Configuration File Sharing
A method, system and computer-readable medium for configuration file sharing are presented. In a preferred embodiment, the method includes the steps of: creating, in a controller, a superset registry file that includes old registry data, new registry data, and kindred registry data, wherein the old registry data and the new registry data are incompatible, and wherein the kindred registry data is compatible with both the old registry data and the new registry data; and contemporaneously downloading the kindred registry data and software version-specific registry data, selected from the old registry data and the new registry data, to a requesting client.
Owner:IBM CORP
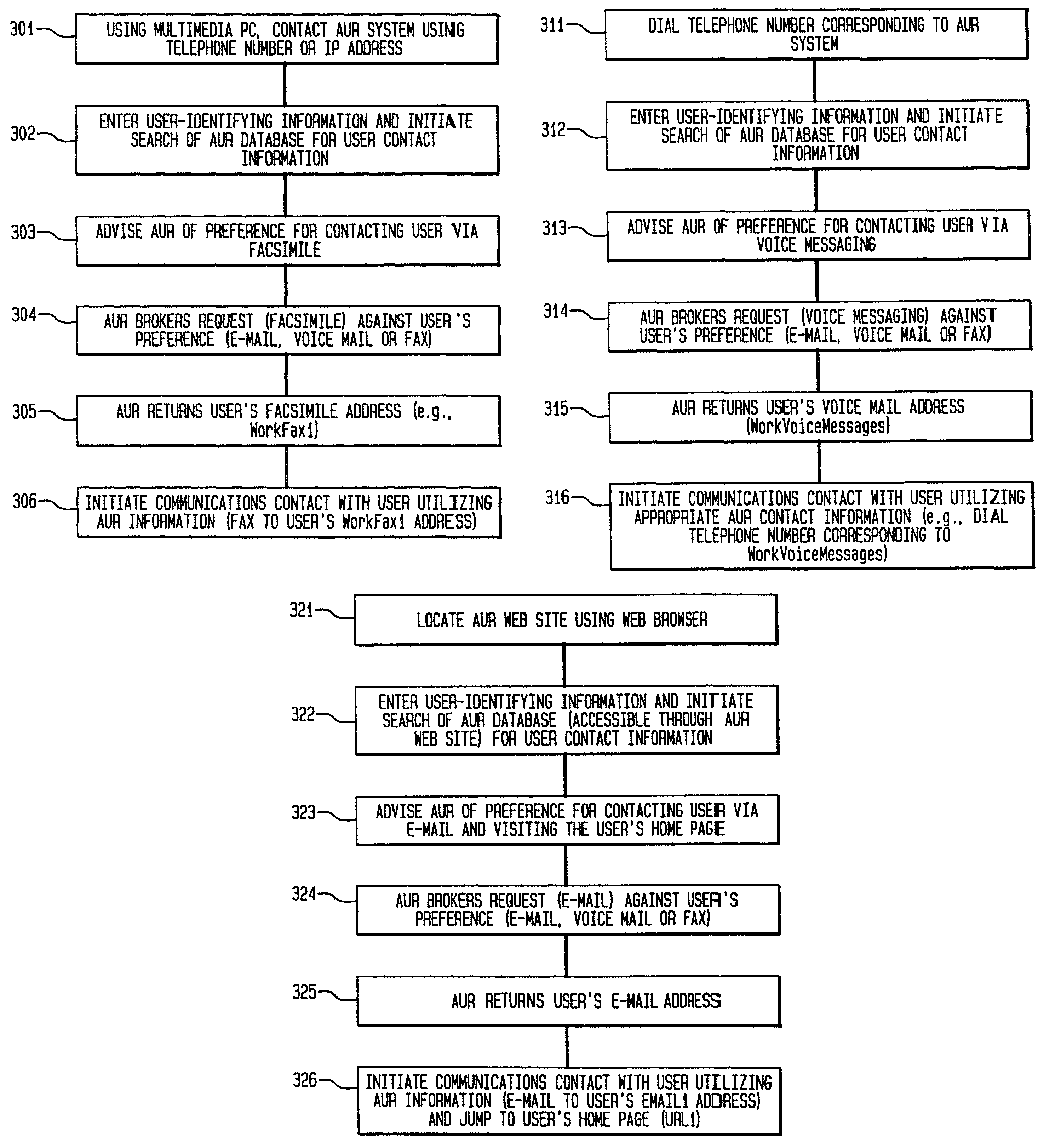
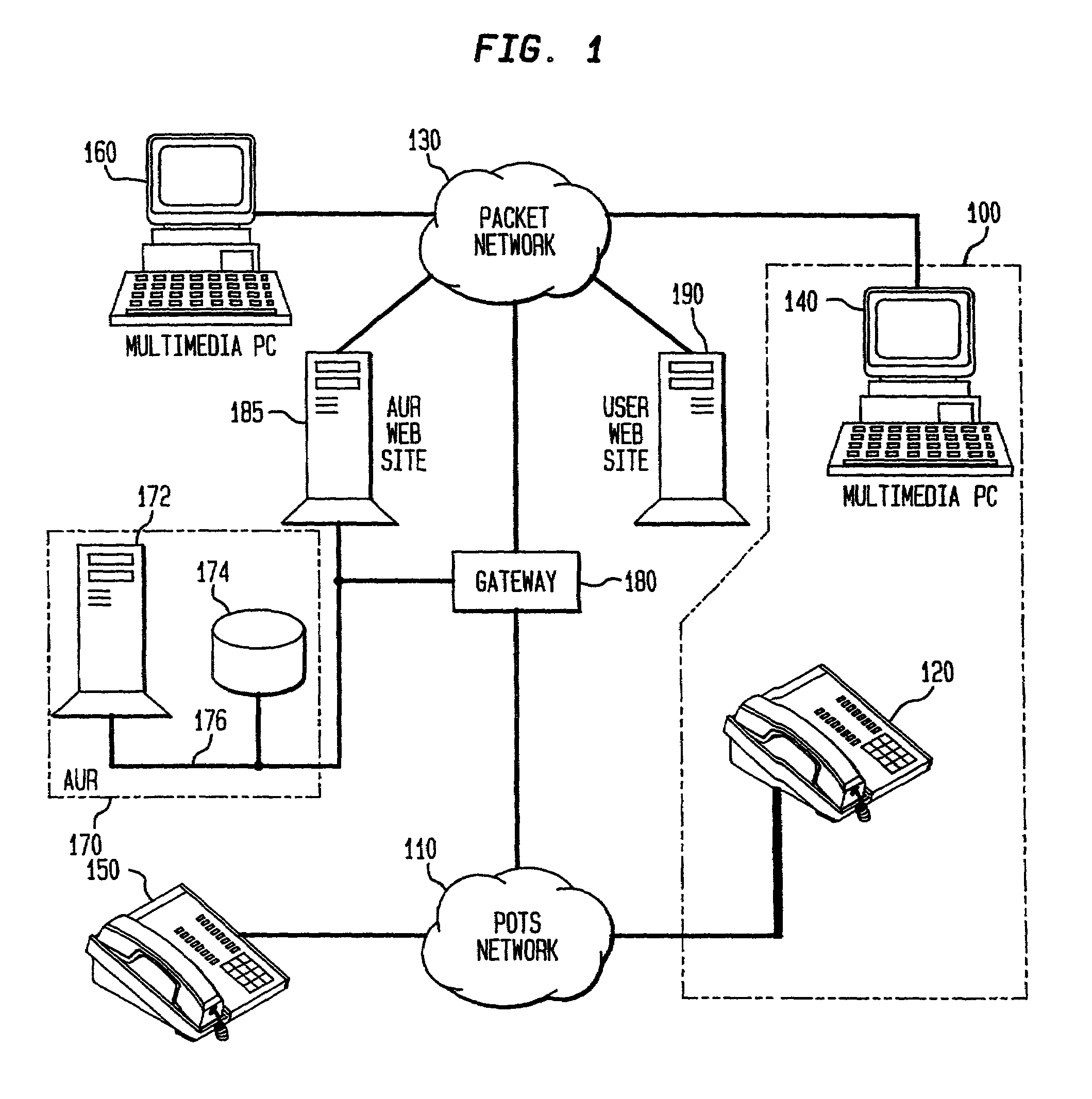
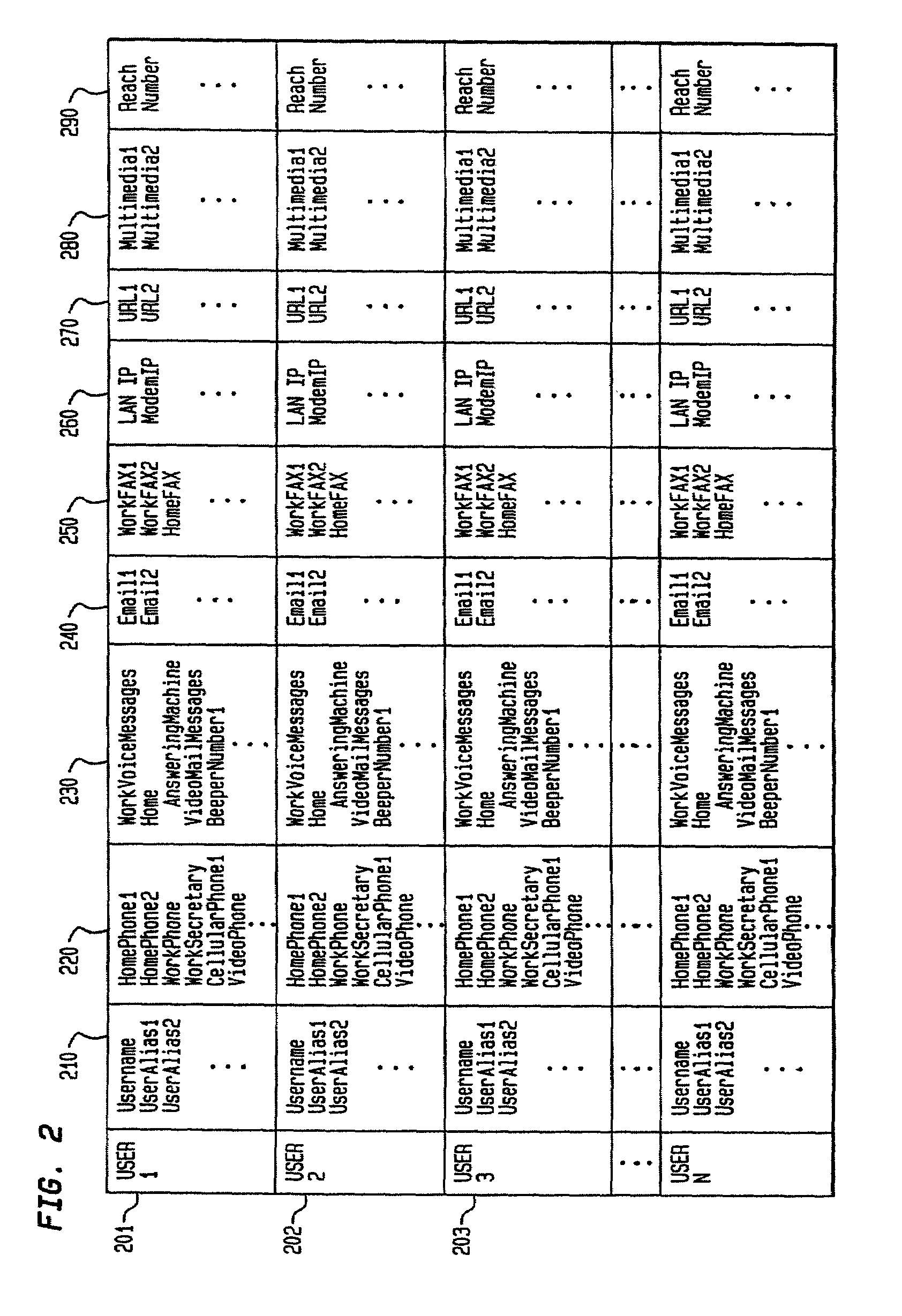
Active user registry
InactiveUS7408920B2Improve search capabilitiesInterconnection arrangementsData processing applicationsRegistry dataDynamic data structures
An Active User Registry system includes a database which is integrated with the POTS network and a packet network to exploit the outstanding strengths of both of its constituents. The Active User Registry database is a dynamic data structure of all the ways in which one or more users can be reached via some type of communication network. A key feature of the Active User Registry is the ability to broker between a subscriber's request for communications contact information corresponding to a user and the user's preferences of being reached by various communications alternatives.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
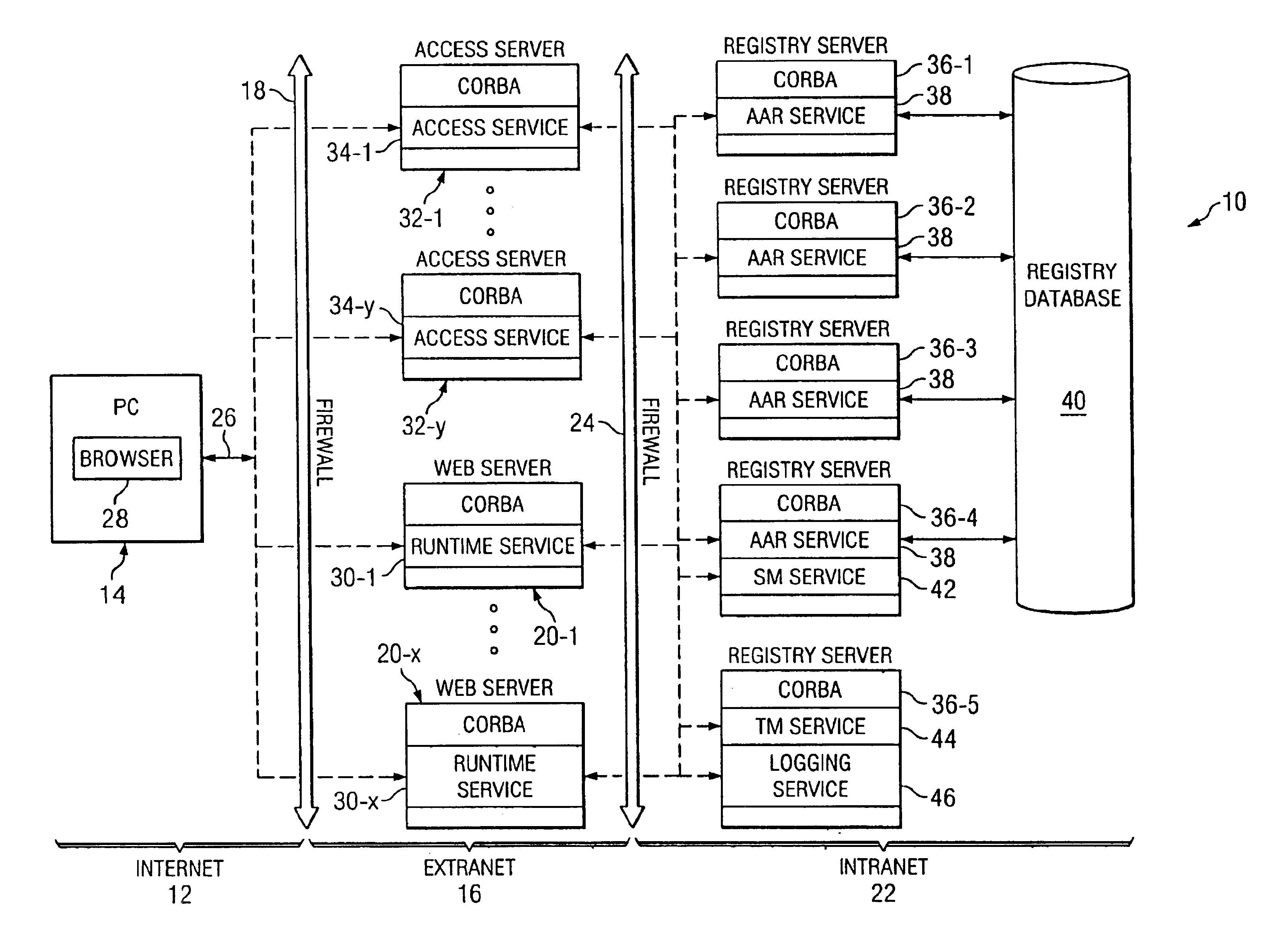
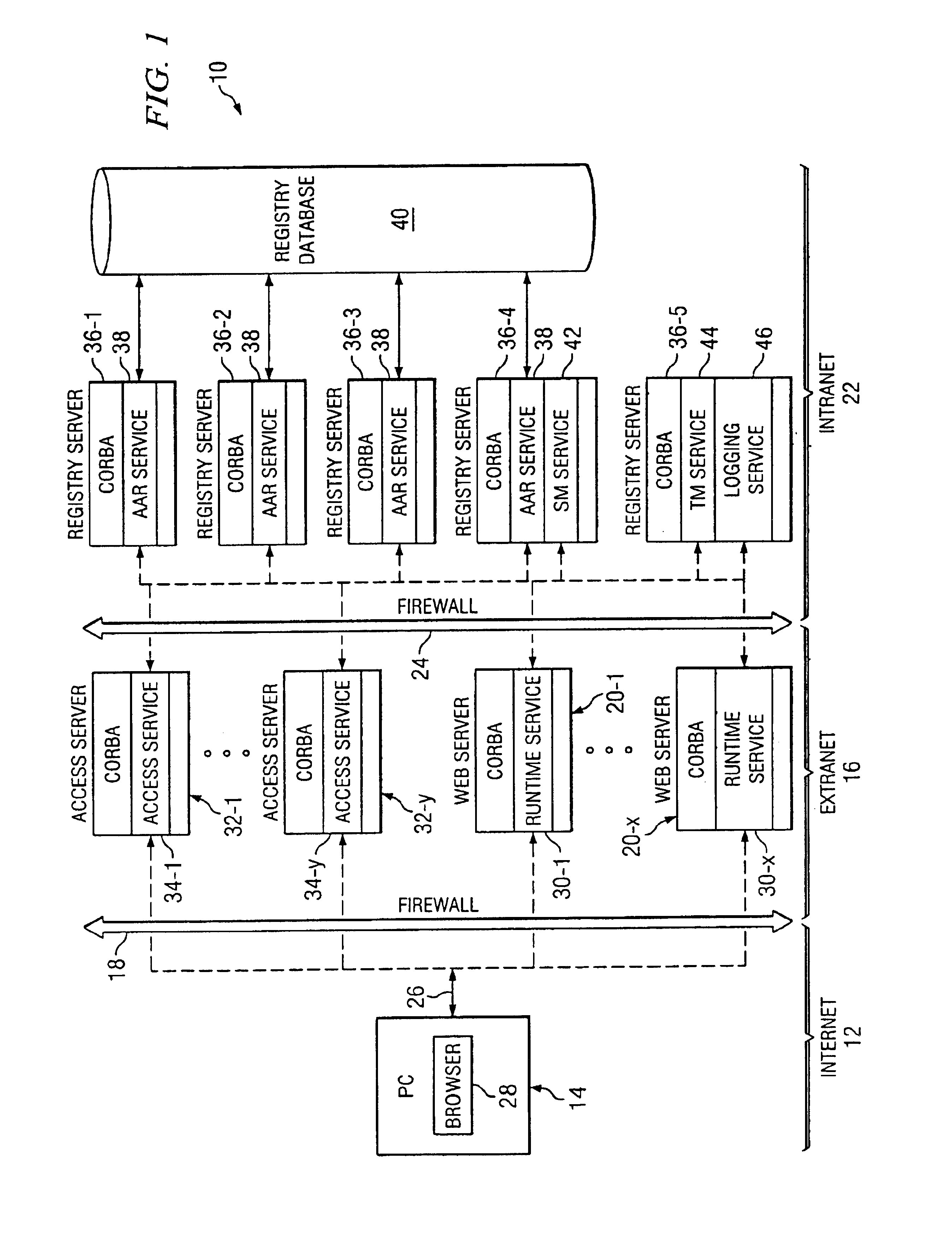
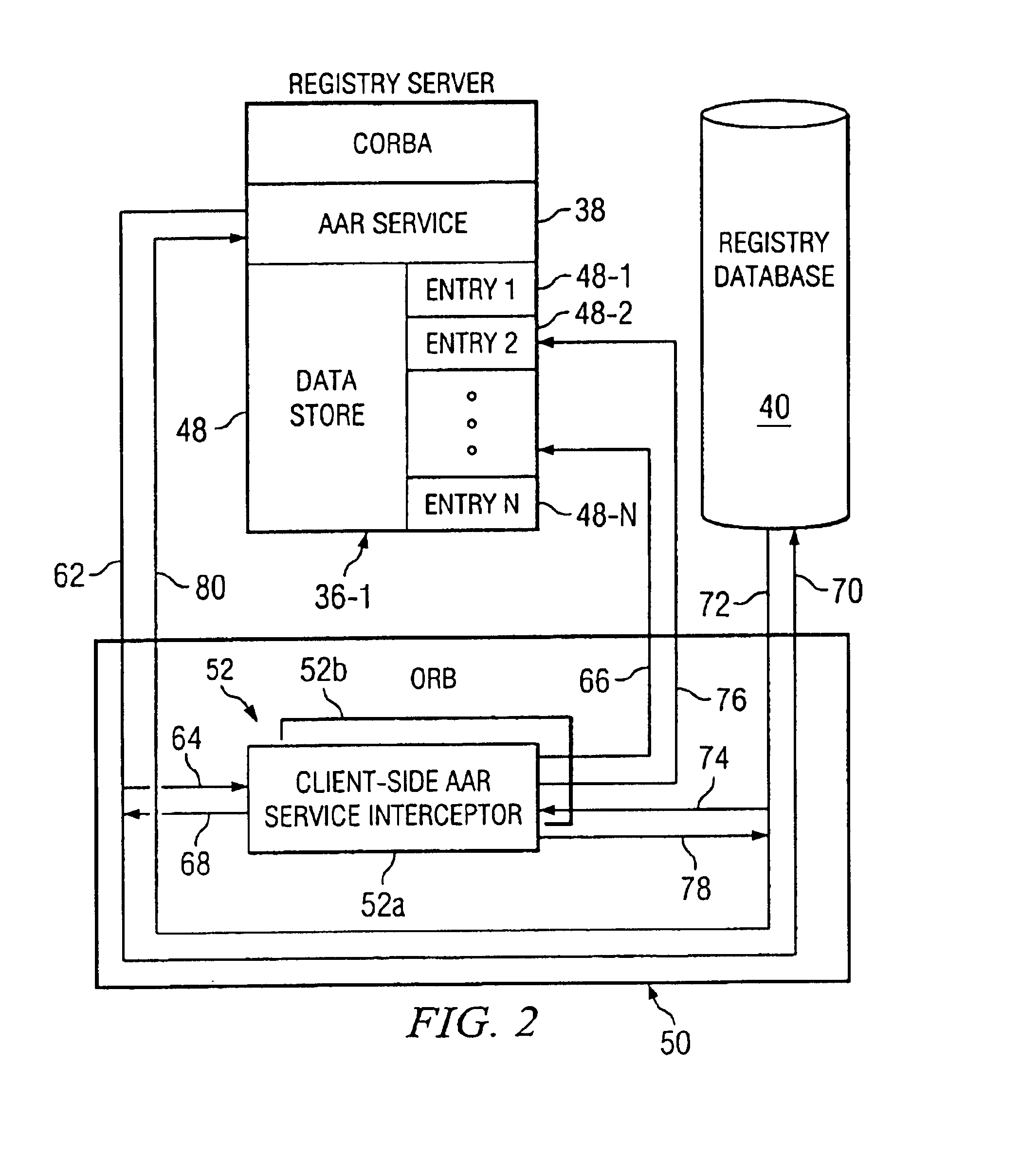
Computer system having an authentication and/or authorization routing service and a CORBA-compliant interceptor for monitoring the same
InactiveUS6839708B1Data switching networksSpecial data processing applicationsRegistry dataComputerized system
A CORBA-compliant computer network includes a registration server on which an AAR service resides, a registry database and an ORB which couples the registry server to the registry database. A CORBA-compliant interceptor residing on the ORB intercepts each message, generated by the AAR service, invoking the registry database and each message, generated by the registry database, responding to the invocation message generated by the service of the client server. The interceptor selects information useful in determining the cause of a failed usage of the service residing in the client server from each intercepted invocation and response messages, writes the selected information to a data store residing in the client server and then re-invokes the intercepted invocation and response messages. In the event of a network failure, the data written to the data store may be reviewed to obtain useful information regarding the network failure.
Owner:SPRINT CORPORATION
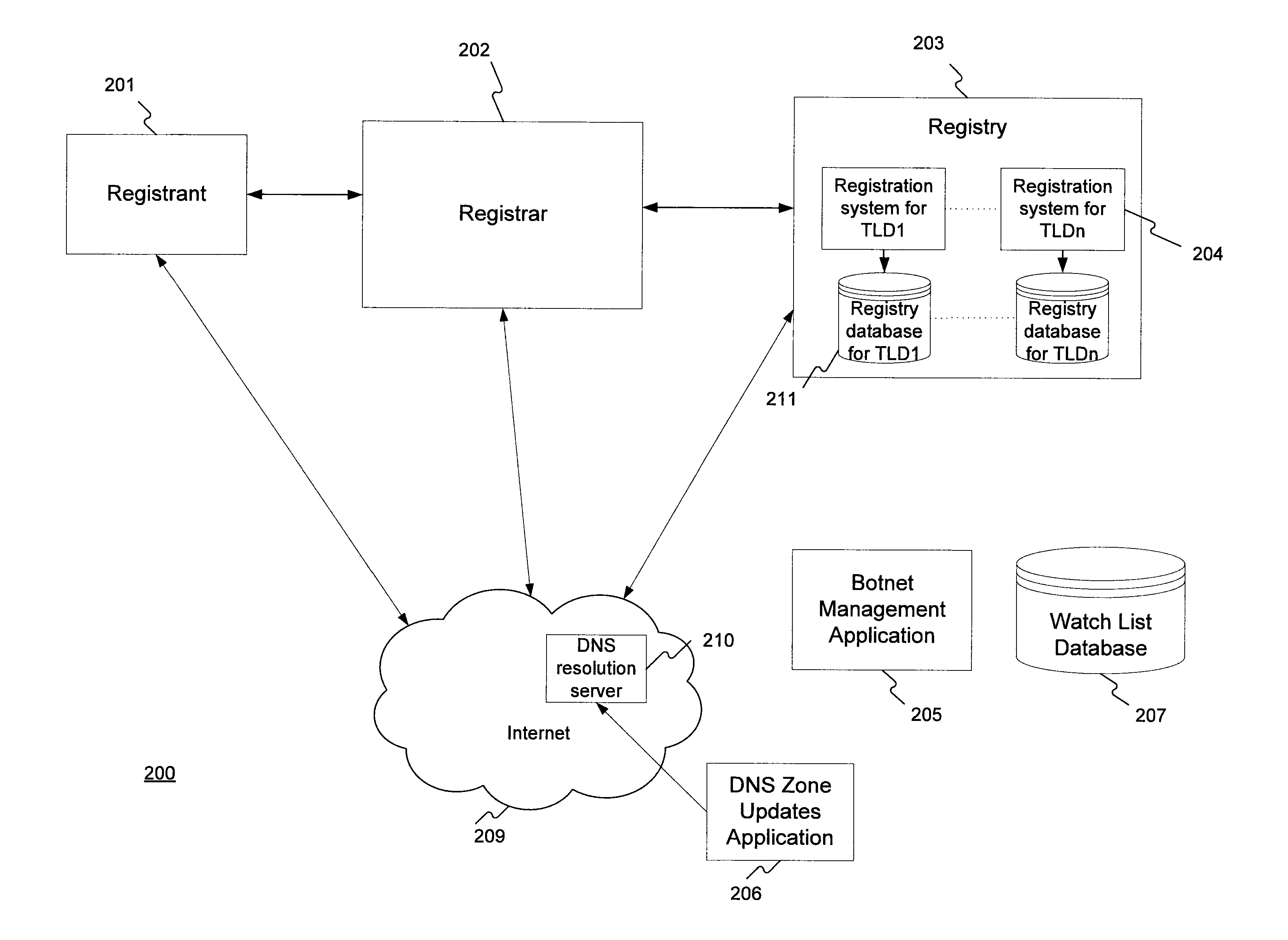
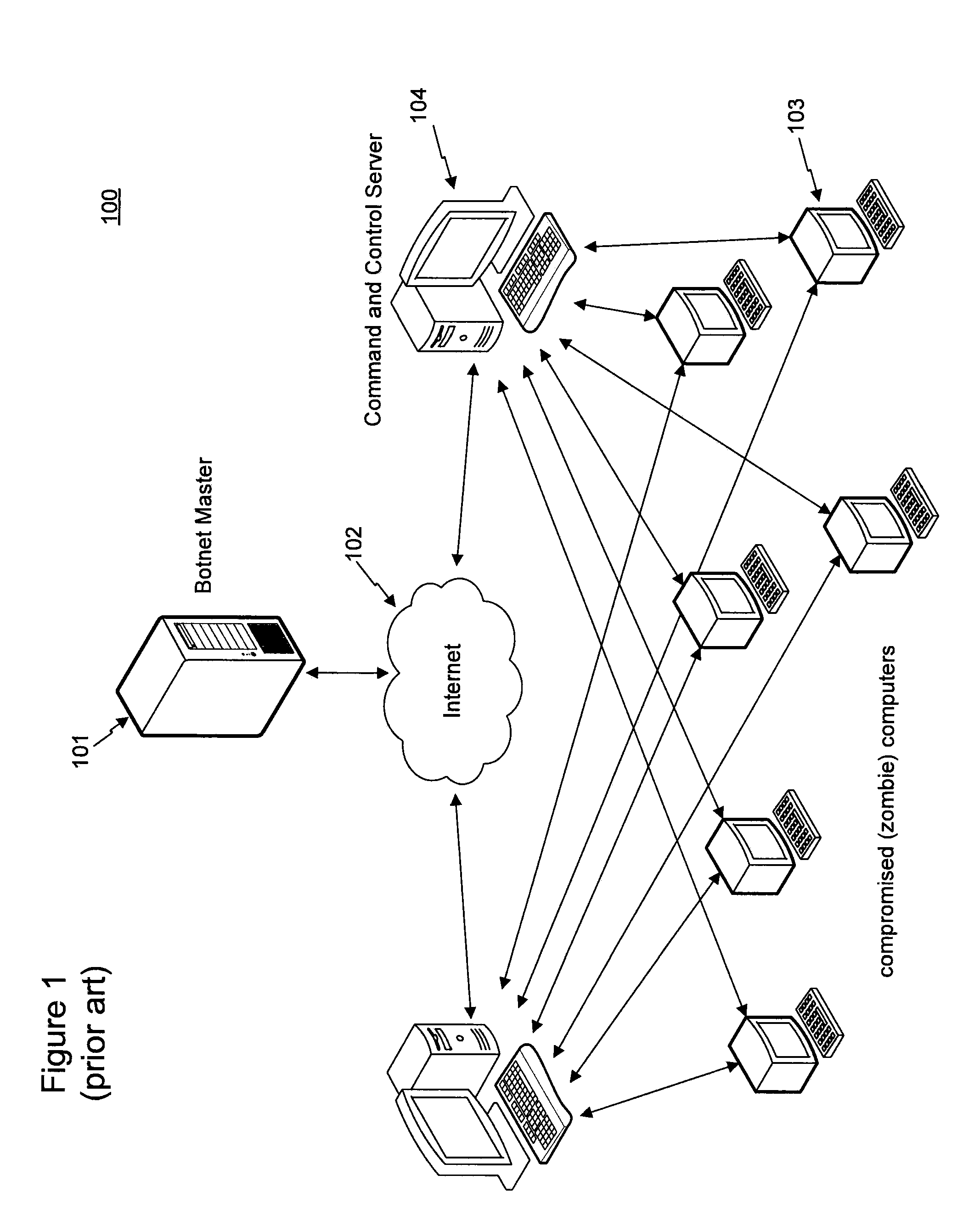
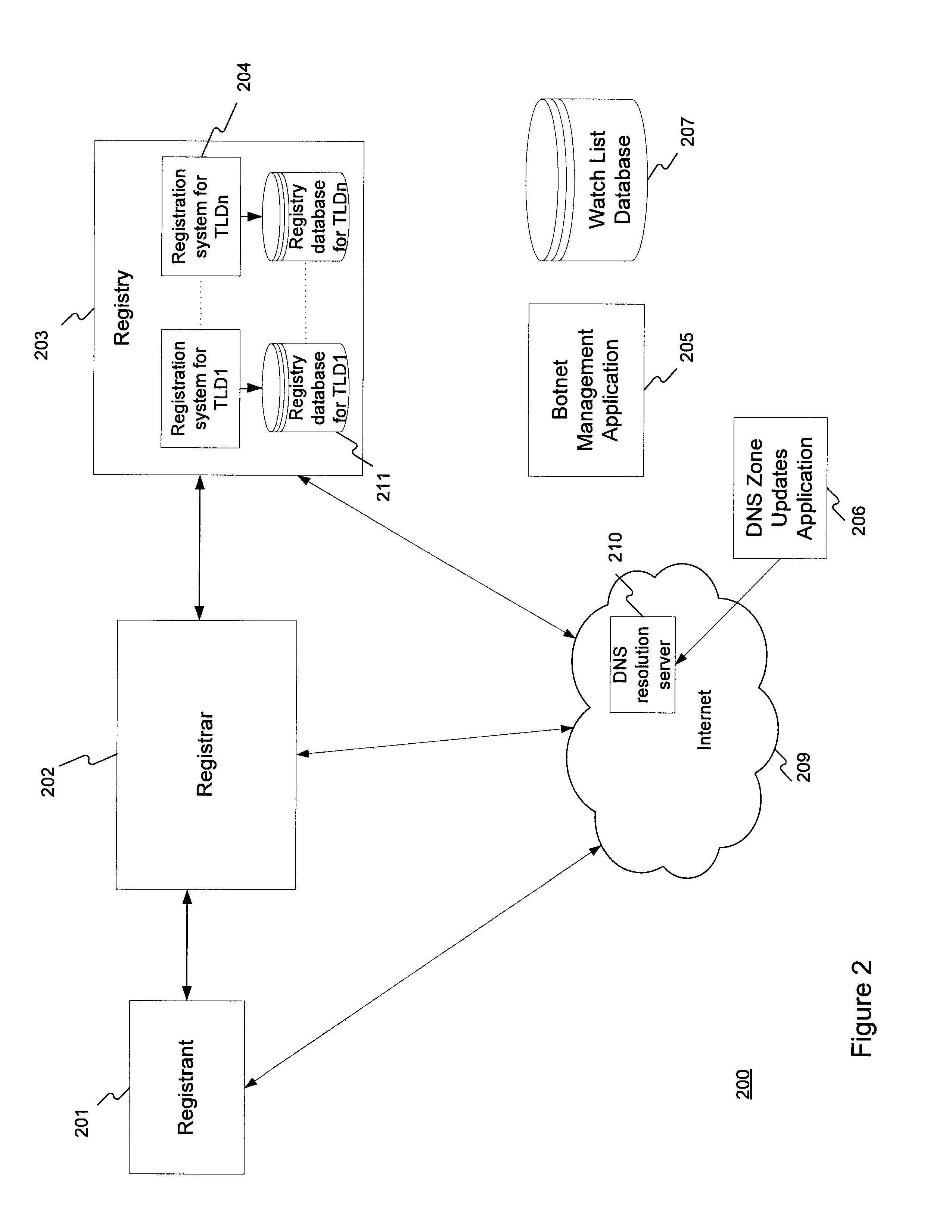
Method for administering a top-level domain
A method for administering a top-level domain by analyzing domain name registrations for requests for suspicious or malicious domain names. A request to register a domain name is received. The requested domain name's information may be stored in a registry database. The requested domain name may also be conditionally stored in the domain name system (DNS) zone. The requested domain name is compared to a list of botnet domain names stored in a watch list database. If the requested domain name corresponds to one of the botnet domain names, the requested domain name is prevented from being added to the DNS zone or is removed from the DNS zone, if it has already been stored there. The information regarding the requested domain name is stored in the registry database, even if the domain name does not ultimately stay in the DNS zone.
Owner:VERISIGN
E-mail server registry and method
InactiveUS20050055404A1Multiple digital computer combinationsData switching networksRegistry dataInternet privacy
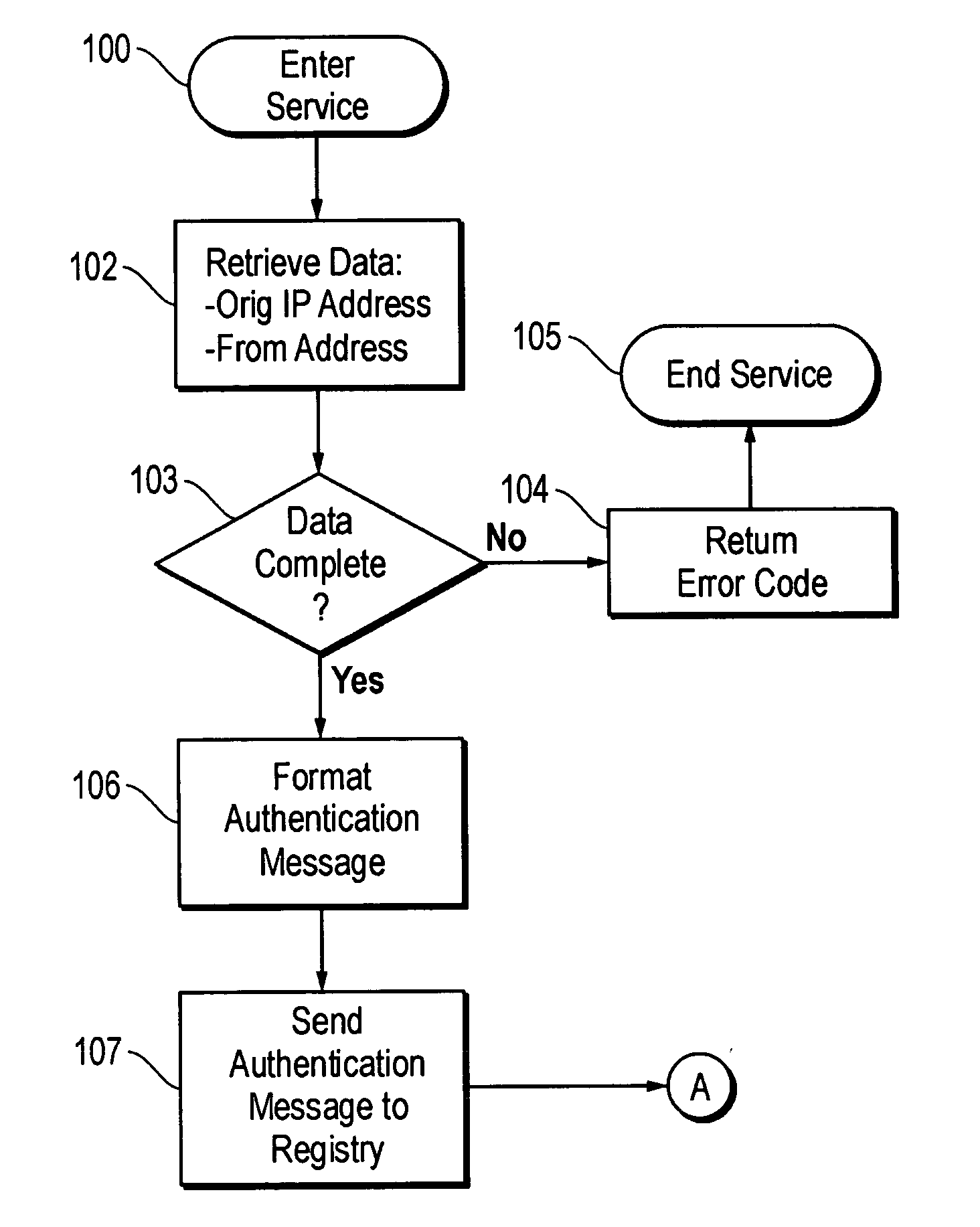
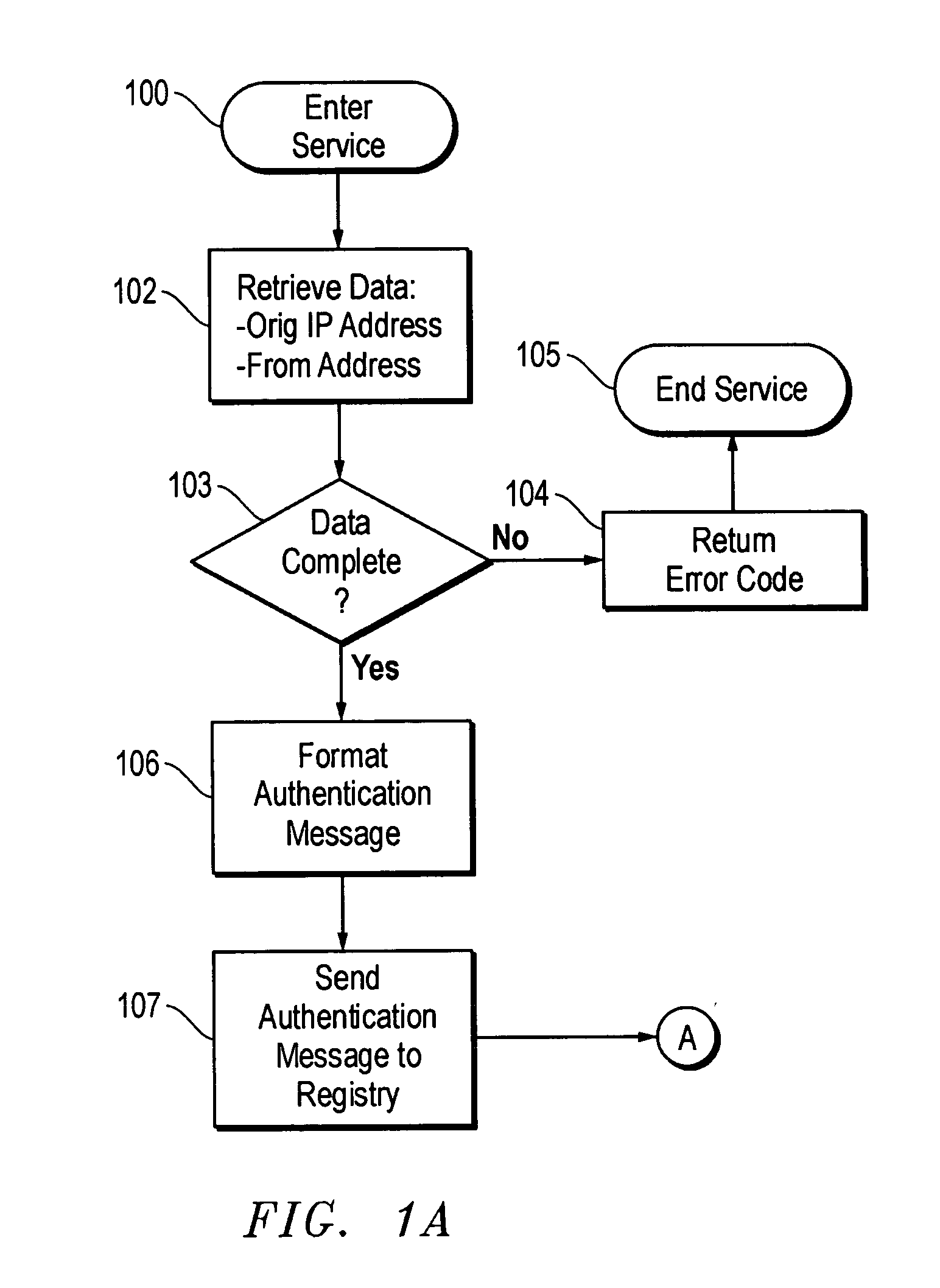
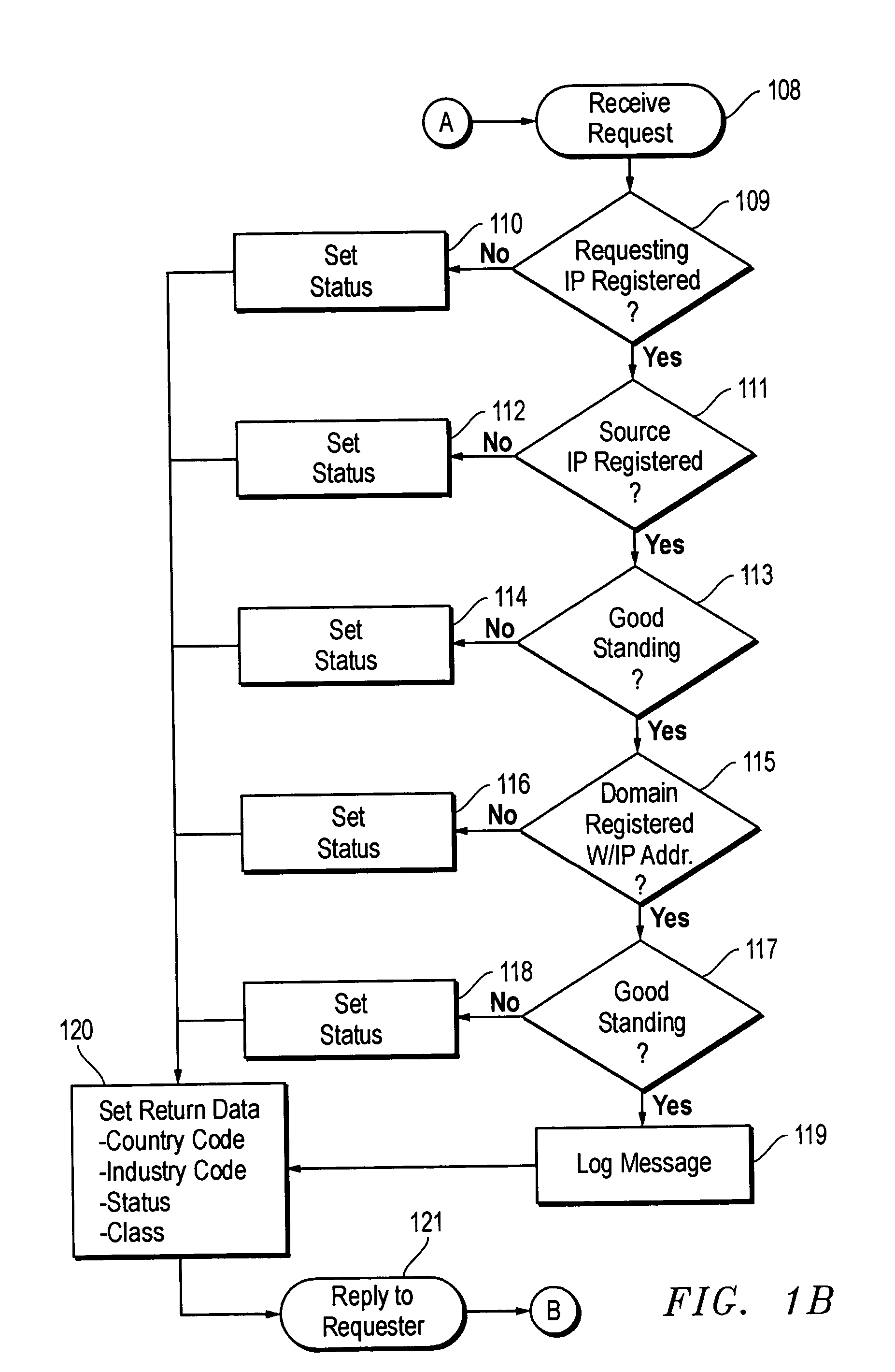
A system for denying or allowing delivery of an incoming electronic mail (e-mail) message that indicates a source e-mail server, source domain, and an addressee for the message. A central e-mail server registry database stores information for all e-mail servers authorized to send e-mail messages over the Internet. Each e-mail recipient can specify characteristics of domains that are authorized to send e-mail messages to the recipient. When an incoming e-mail message arrives at the recipient's e-mail server, the server accesses the registry database to determine whether the source e-mail server and / or domain are registered, and if so, whether the registration in good standing, and whether the source domain possesses the specified characteristics. If these conditions are not met, delivery of the e-mail is denied. Registered e-mail servers can download specified server information from the central registry and store it in a local registry. When incoming messages arrive at the server, the local registry is checked first, if unsuccessful, the central registry is checked.
Owner:INFORMATION PROCESSING CORP
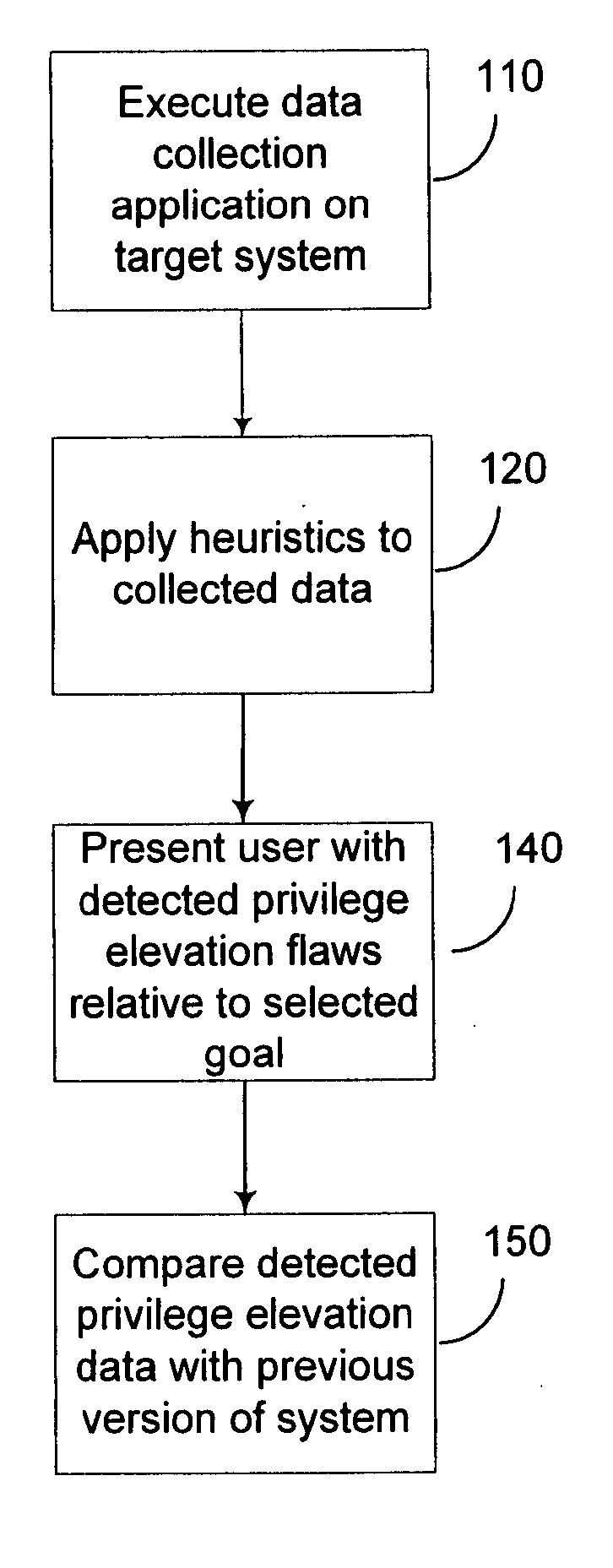
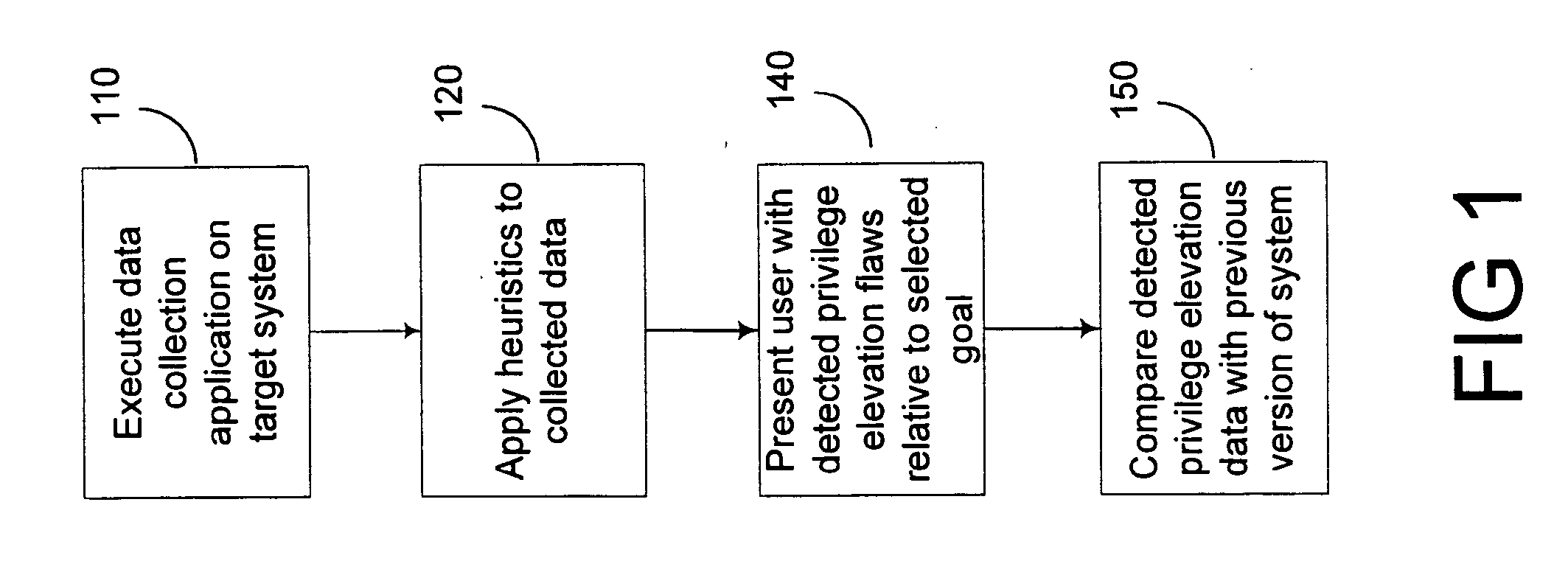
Expert system analysis and graphical display of privilege elevation pathways in a computing environment
A data collection application is executed on a target system. Various data indicative of privilege elevation pathways is collected, including user account data, file permission data, and system registry data. The collected data is analyzed according to heuristics. System accounts are displayed on a graph as nodes. Detected privilege elevations between the accounts are displayed as edges between their corresponding accounts. A user may customize the displayed graph to focus on particular goal accounts, and categories of privilege elevations.
Owner:MICROSOFT TECH LICENSING LLC
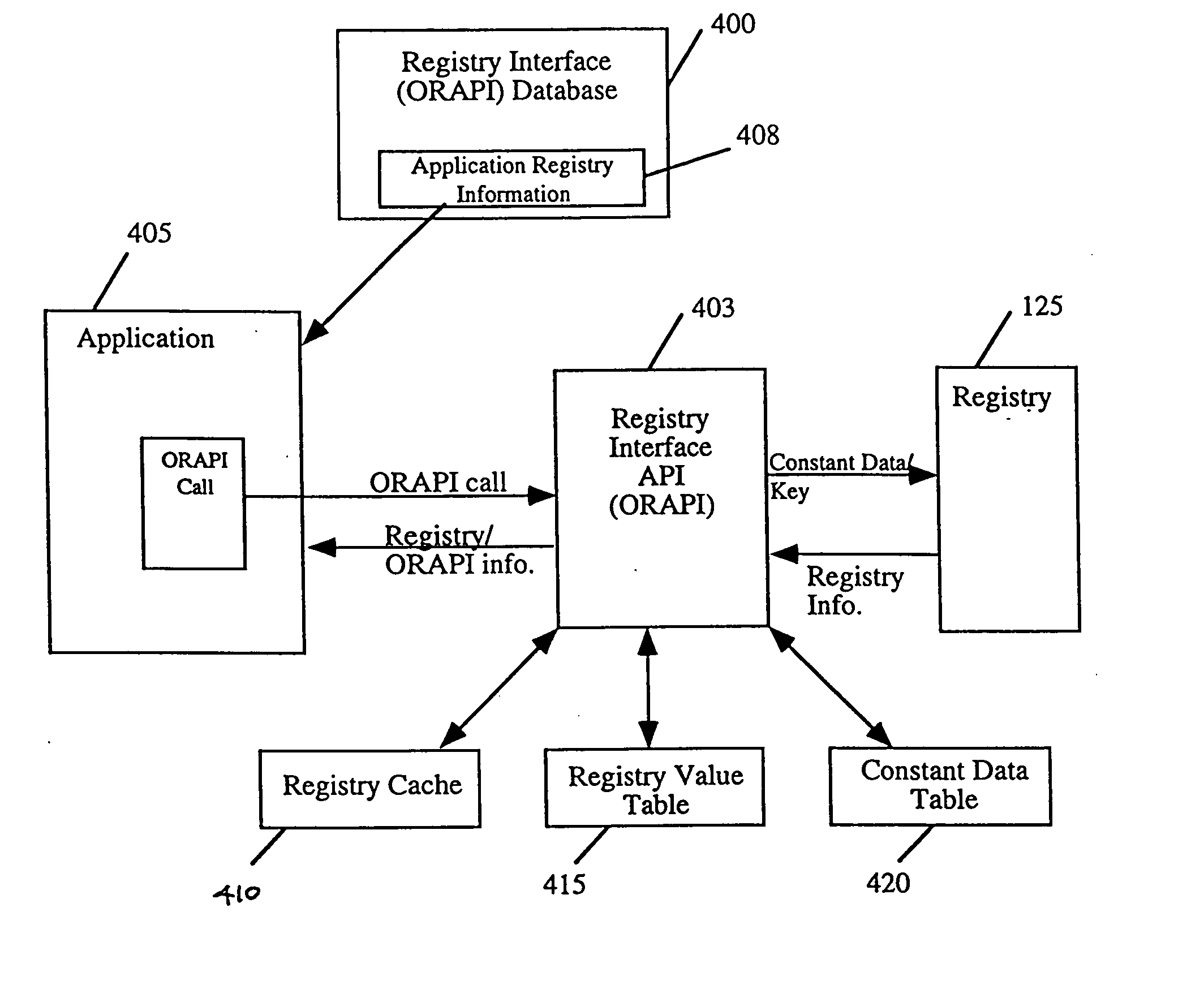
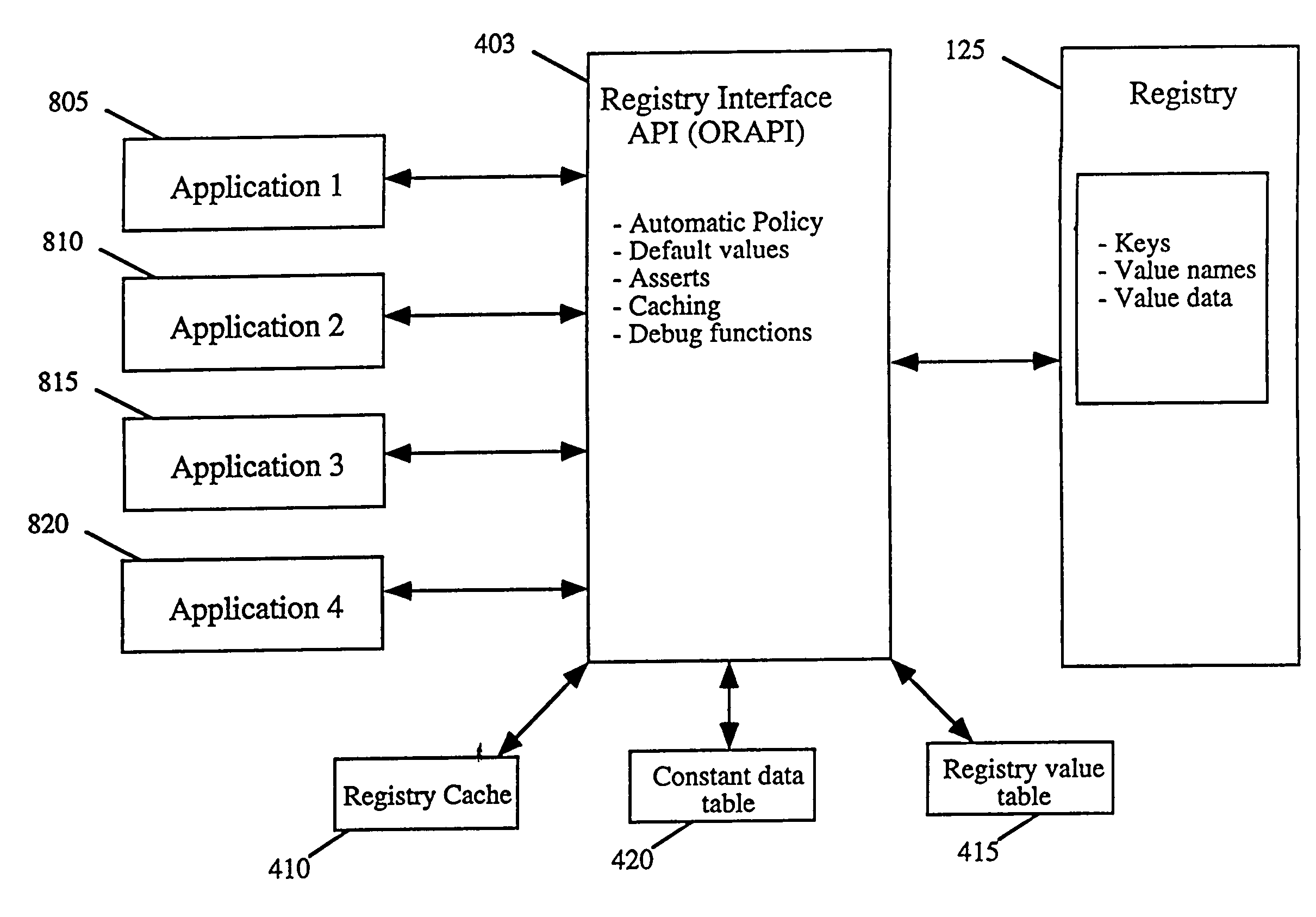
System and method for retrieving registry data
InactiveUS20050038773A1Reduce registry bloatStreamline application codeData processing applicationsDigital data information retrievalRegistry dataData information
Information is retrieved from the registry by creating a registry interface database containing information regarding registry data and uniquely identifying every registry entry for a registry interface. Source header files are generated using information about a program module, such as an application, contained in the registry interface database. The source header files are compiled with the application to generate the application's executable file. During run-time of the application, the registry interface is called by the application to retrieve registry data. If available, the registry interface retrieves the registry data and forwards this information to the application. In the event that the registry data is not available, the registry interface retrieves a default value in place of the registry data and forwards that default data to the application. A policy may be implemented by checking a policy area of the registry for the registry data and invoking the policy.
Owner:MICROSOFT TECH LICENSING LLC
Internet domain name registration system
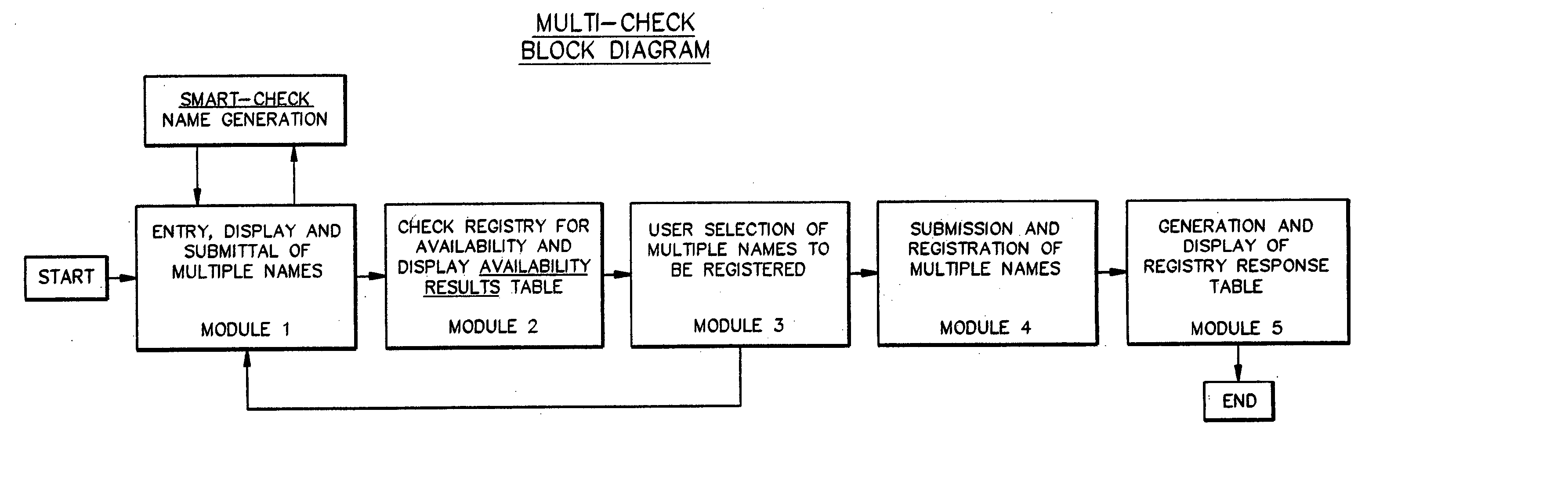
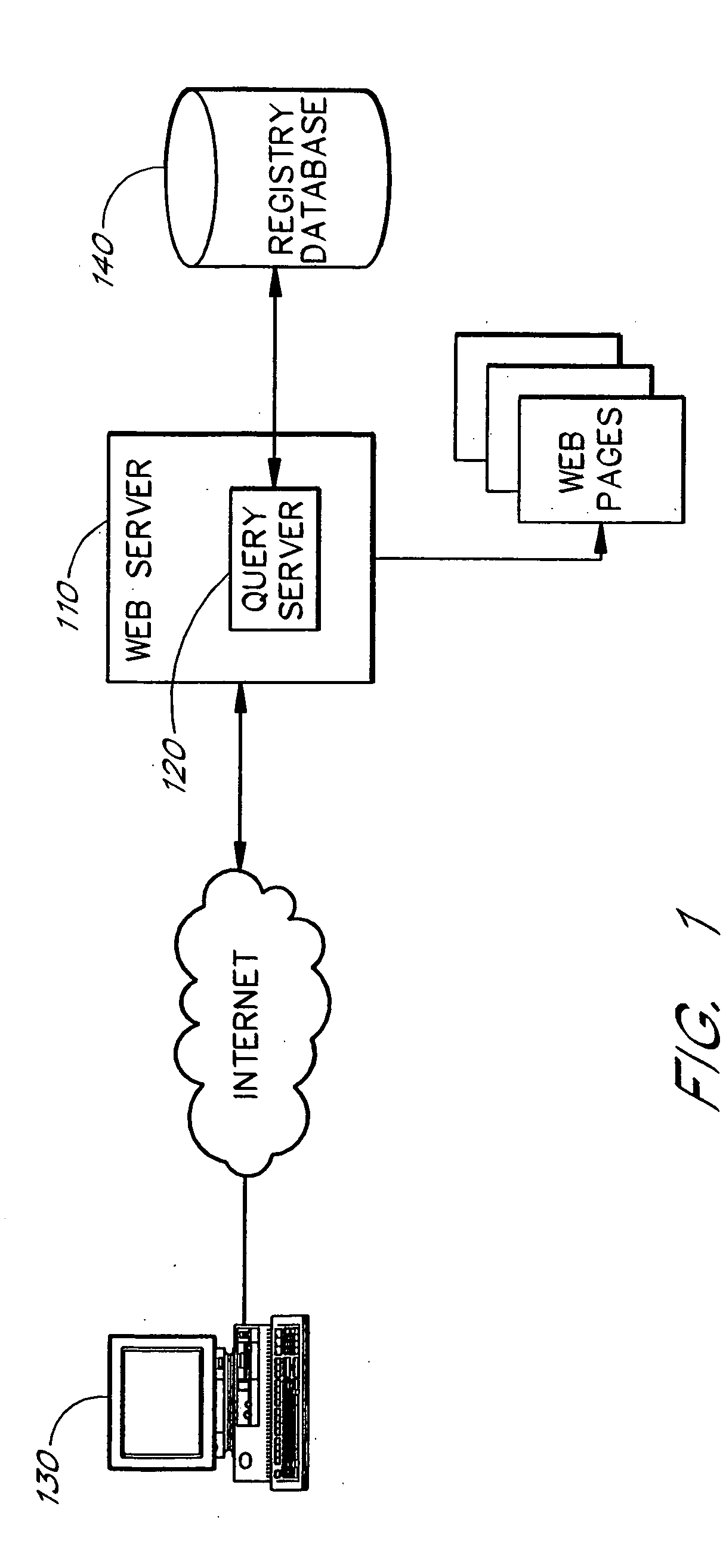
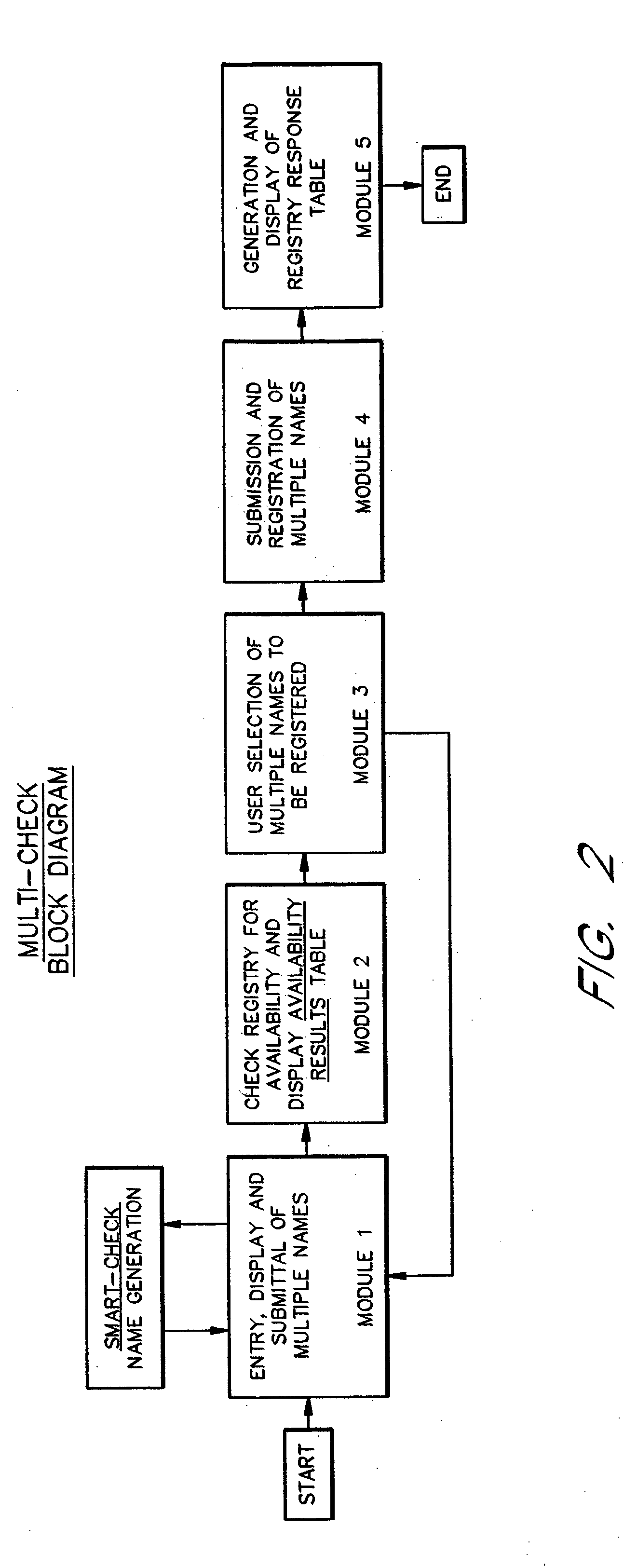
InactiveUS20050256853A1Convenient queryReduce amountData processing applicationsDigital data processing detailsRegistry dataResponse table
A domain name registration system includes a user interface through which a user can submit multiple names to a query server to determine the availability of the names for domain name registration. After the query results are returned for each of the multiple names submitted, the user is presented with a table listing the availability of each name in combination with multiple Top-Level Domain (TLD) extensions. The user is able to select one or more names from the table for registration in the registry database. After the query server has attempted to register each of the selected names, the user is presented with a Registry Response Table indicating which of the selected names were successfully registered as domain names. Thus, the system and method increases the speed and productivity of querying and updating a domain name registry or other database.
Owner:MULTICHECK SYST
System and method for retrieving registry data
InactiveUS7379948B2Efficient administrationReduce registry bloatDigital data information retrievalData processing applicationsRegistry dataData information
Information is retrieved from the registry by creating a registry interface database containing information regarding registry data and uniquely identifying every registry entry for a registry interface. Source header files are generated using information about a program module, such as an application, contained in the registry interface database. The source header files are compiled with the application to generate the application's executable file. During run-time of the application, the registry interface is called by the application to retrieve registry data. If available, the registry interface retrieves the registry data and forwards this information to the application. In the event that the registry data is not available, the registry interface retrieves a default value in place of the registry data and forwards that default data to the application. A policy may be implemented by checking a policy area of the registry for the registry data and invoking the policy.
Owner:MICROSOFT TECH LICENSING LLC
Real-time trading and purchasing of value documents
This disclosure describes a system for real-time trading and purchasing of value documents. Described is providing access over the internet with a device to a registry server with a registry database. Next, described is setting up a registry for a plurality of value documents. Further described is the registration of owners and their value documents in a log file. And further described is keeping entries of the registered value documents. Next described is the opening an e-wallet account by a buyer that defines an exit account and then verifying it. Further described is interconnecting the e-wallet, the registry and the exit account. Additionally described is the pre-order validation of all orders. And, then described is the trading and settlement of funds and the value documents between the owner and the buyer. And then described is updating and recording information when a trade of the documents is executed.
Owner:XTRADESOFT
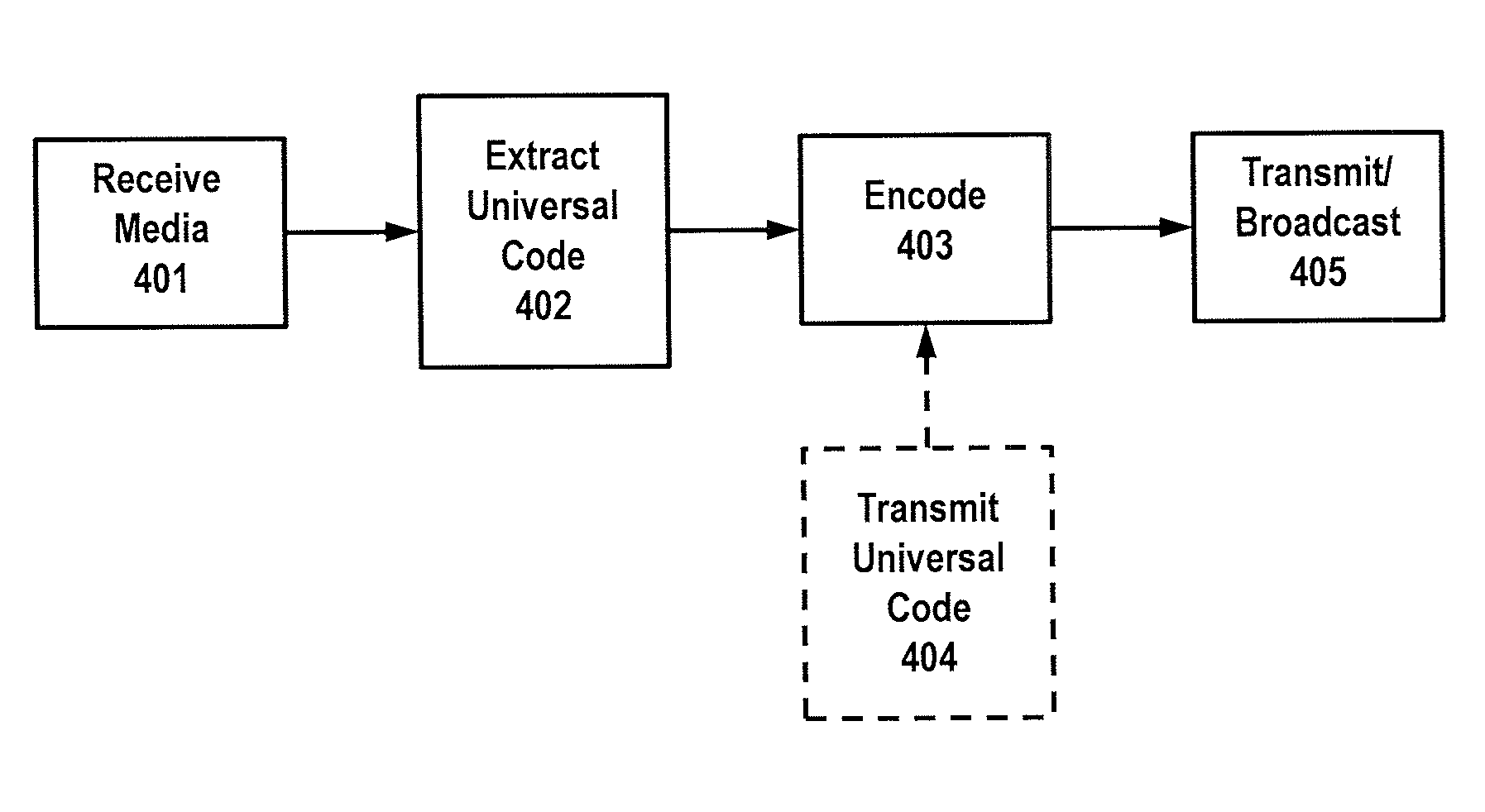
Systems Apparatus and Methods for Encoding/Decoding Persistent Universal Media Codes to Encoded Audio
ActiveUS20150039320A1Speech analysisSpecial data processing applicationsRegistry dataComputer hardware
Apparatus, system and method for encoding and / or decoding persistent universal media identification (ID) codes embedded in audio. For encoding, a persistent identifier code is generated or received from a registry database, where the code includes data for uniquely identifying a media object. Audio code components including frequency characteristics are generated to represent symbols of the persistent identifier code and the audio code components are psychoacoustically embedded into an audio portion of the media object to include the persistent identifier code within one or more of a plurality of encoding layers. Such embedded audio may be subsequently decoded by transforming the audio data into a frequency domain and processing the transformed audio data to detect the persistent identifier code.
Owner:THE NIELSEN CO (US) LLC
Method and apparatus for irrigation system design registration and on-site sprinkler package configuration verification
Internet-accessible system and method for customized design and on-site verification of agriculture irrigation systems includes one or more of: 1) sprinkler package configuration software operable on a user's PC or accessible via an Internet website, 2) Internet-accessible proprietary irrigation system registry database and user interface, 3) computer-controlled automated component selection and labeling system for placing barcode or RFID information on components, and 4) portable wireless location-aware communication device operable at or near an irrigation site for accessing the registry database and obtaining sprinkler package configuration information specific to a particular irrigation system based on location and / or a particular irrigation system component detected in proximity to the portable communication device.
Owner:NELSON IRRIGATION
Telephone Call Screening System and Method and Caller Registration System and Method For Use Therewith
InactiveUS20060193453A1Automatic call-answering/message-recording/conversation-recordingSpecial service for subscribersRegistry dataRegistration system
A telephone call screening system screens telephone calls placed to a subscriber based upon a preferred caller database established by the subscriber from a networked caller registry database. A caller registration system allows callers to select a private identifier unique to the caller and registers the callers in a caller registry database. The subscriber establishes the preferred caller database by connecting to the caller registration system and selecting the preferred callers. The private identifiers associated with the selected preferred callers are then stored in the preferred caller database. When a caller calls the subscriber, the caller is asked to enter the caller's private identifier. A caller disposition process is initiated based on whether the private identifier is in the preferred caller database.
Owner:PROLOGUE COMM
RFID enabled media system and method that provides dynamic downloadable media content
ActiveUS8341752B2Easy to identifyShort timeDigital data processing detailsAnalogue secracy/subscription systemsRegistry dataComputer network
An audio and / or video media content providing device includes a controller, such as a server, that is responsive to RFID tag based information obtained from a remote RFID enabled media object. The controller is operative to facilitate access to media content associated with a stored periodically changing media content list. For example, a content registry database may be periodically updated through a suitable user interface to change a link between content identification information read from a remote RFID enabled media object, with media application information so that the same RFID tag may allow the downloading of different media. The link between the content ID and the media ID may be dynamically changed through the controller. This may be advantageous, to provide for example, a Top 10 song card or other RFID enabled object that stays the same but can be used to securely download different media over time.
Owner:ACCENTURE GLOBAL SERVICES LTD
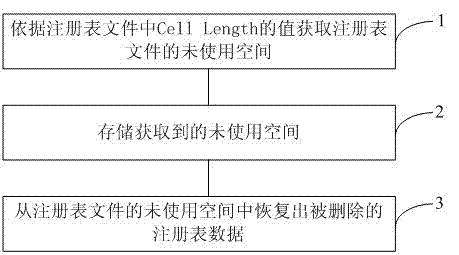
Recovery method and recovery device of registry deleted data
ActiveCN103092726AIntegrity guaranteedGuaranteed accuracySpecial data processing applicationsRedundant operation error correctionRegistry dataEngineering
The invention provides a recovery method and a recovery device of registry deleted data. The recovery method of registry deleted data comprises the following steps: acquiring unused space of registry files according to values of CellLength in the registry files, marking the unused space using Cell in the deleted data, storing the achieved unused space, and recovering deleted registry data from the unused space of the registry files. According to the recovery method of registry deleted data, on the condition that data are not written into a registry when a registry key is deleted, the deleted registry key can be recovered 100%, integrity of a directory structure can be guaranteed, and integrity and accuracy of recovered data are guaranteed to a large extent. The recovery method of registry deleted data provides solutions for the loss of the registry data caused by misoperations or vicious operations.
Owner:XIAMEN MEIYA PICO INFORMATION
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com