Patents
Literature
8272 results about "Temporary storage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Temporary storage is always allocated from the system disk pool—also known as the system auxiliary storage pool (ASP). This holds true for SQE temporary storage even if the permanent objects (tables and indexes) holding your data are located in user ASPs or in independent auxiliary storage pools (IASPs).
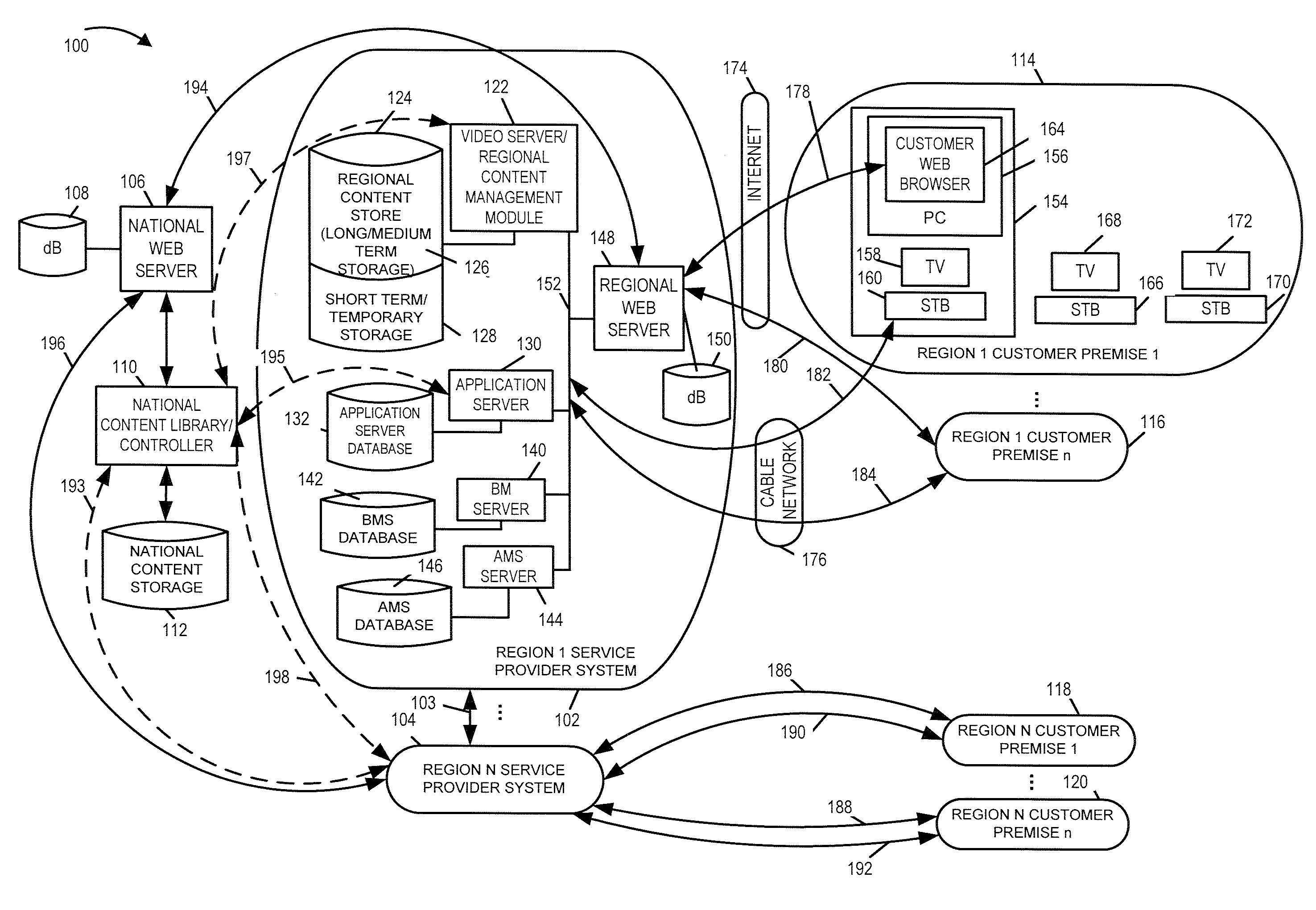
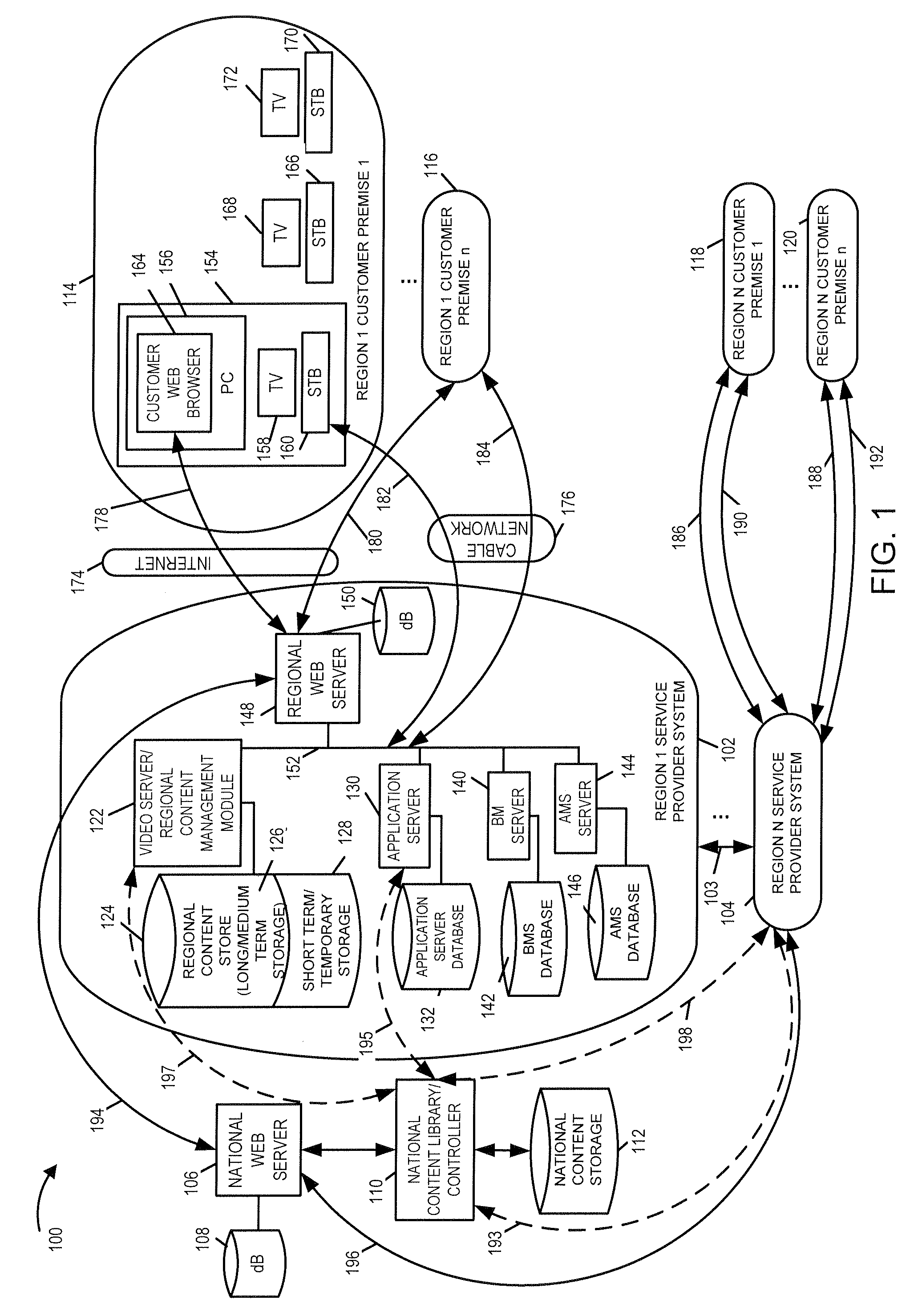
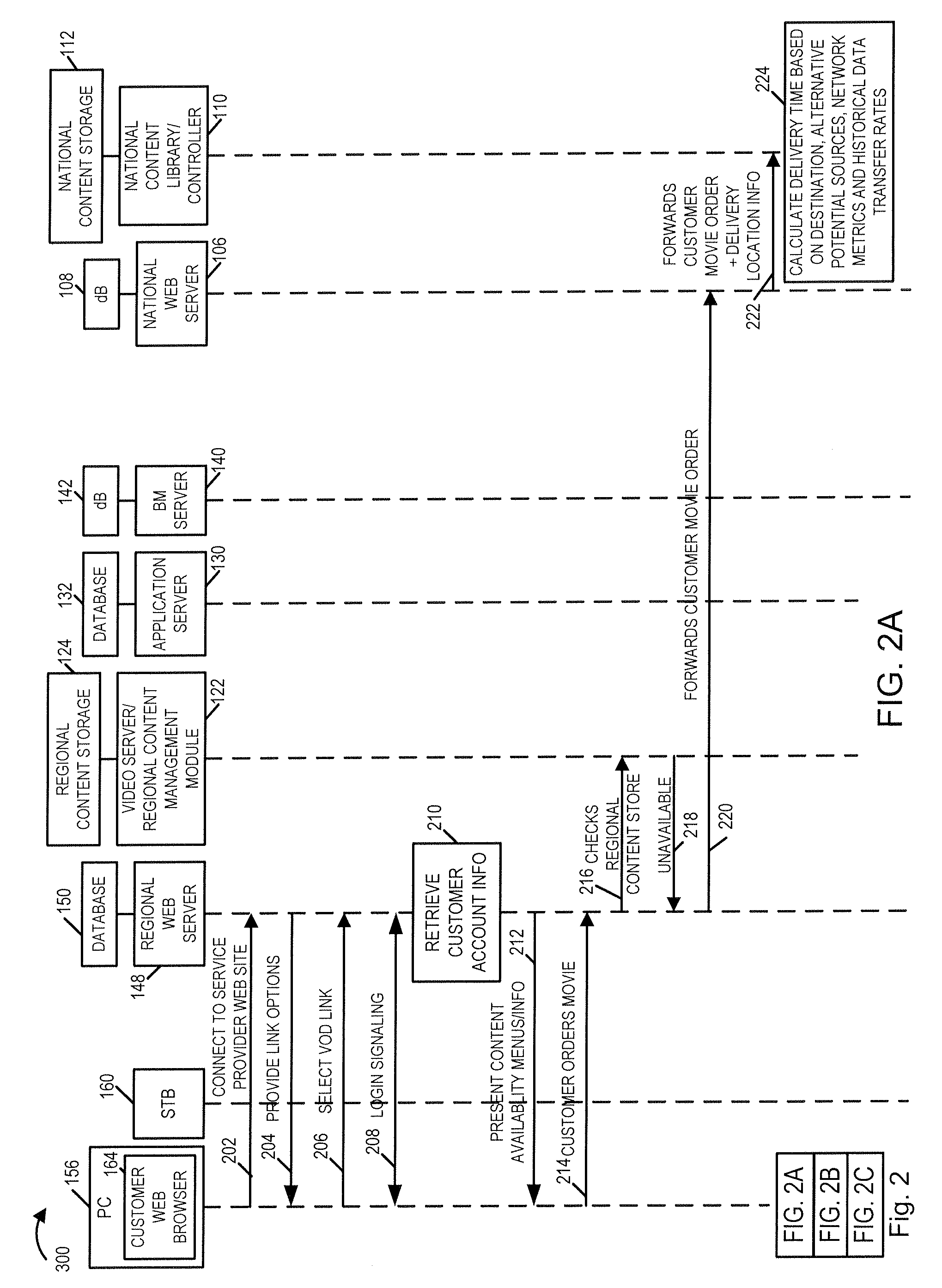
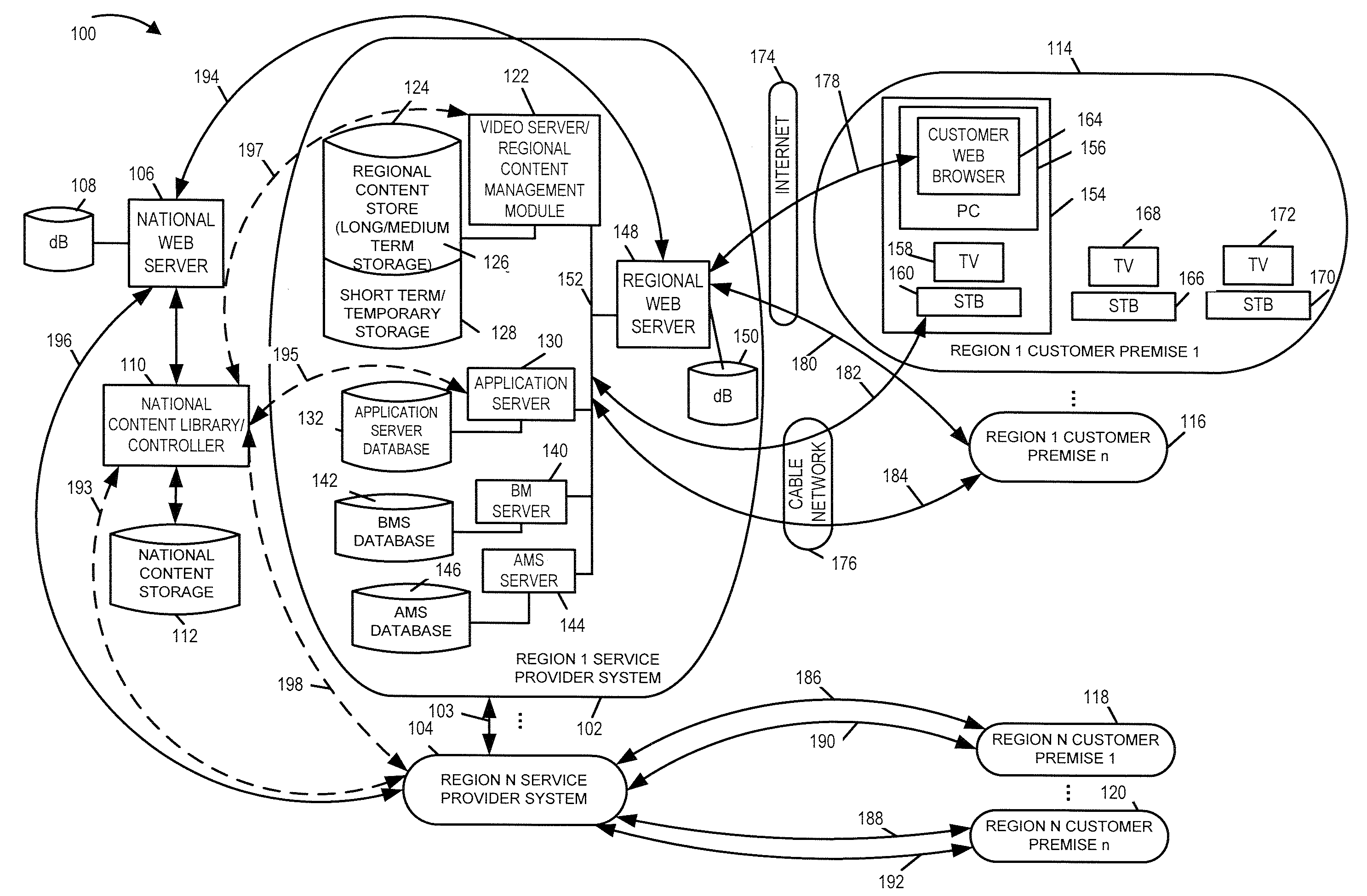
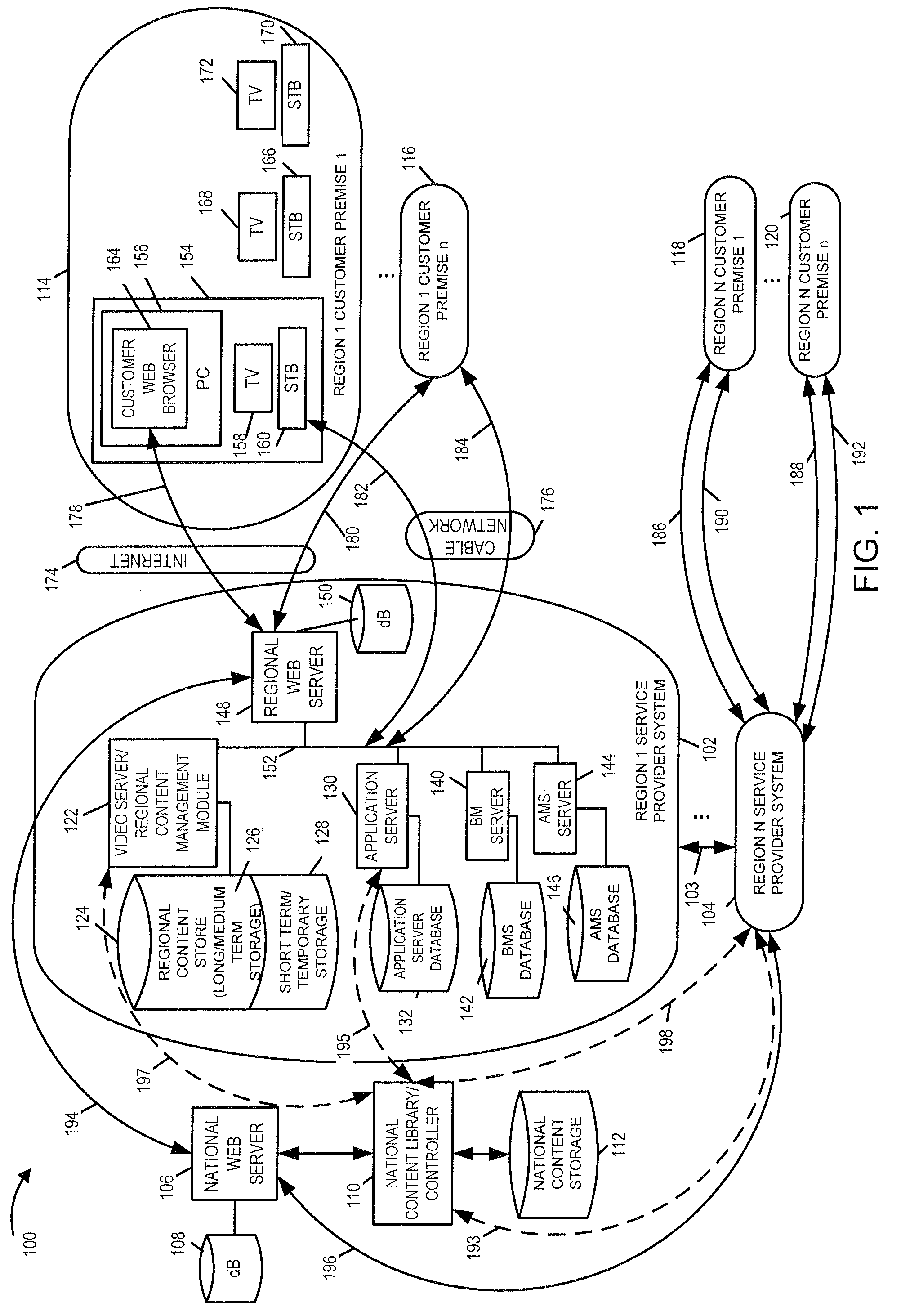
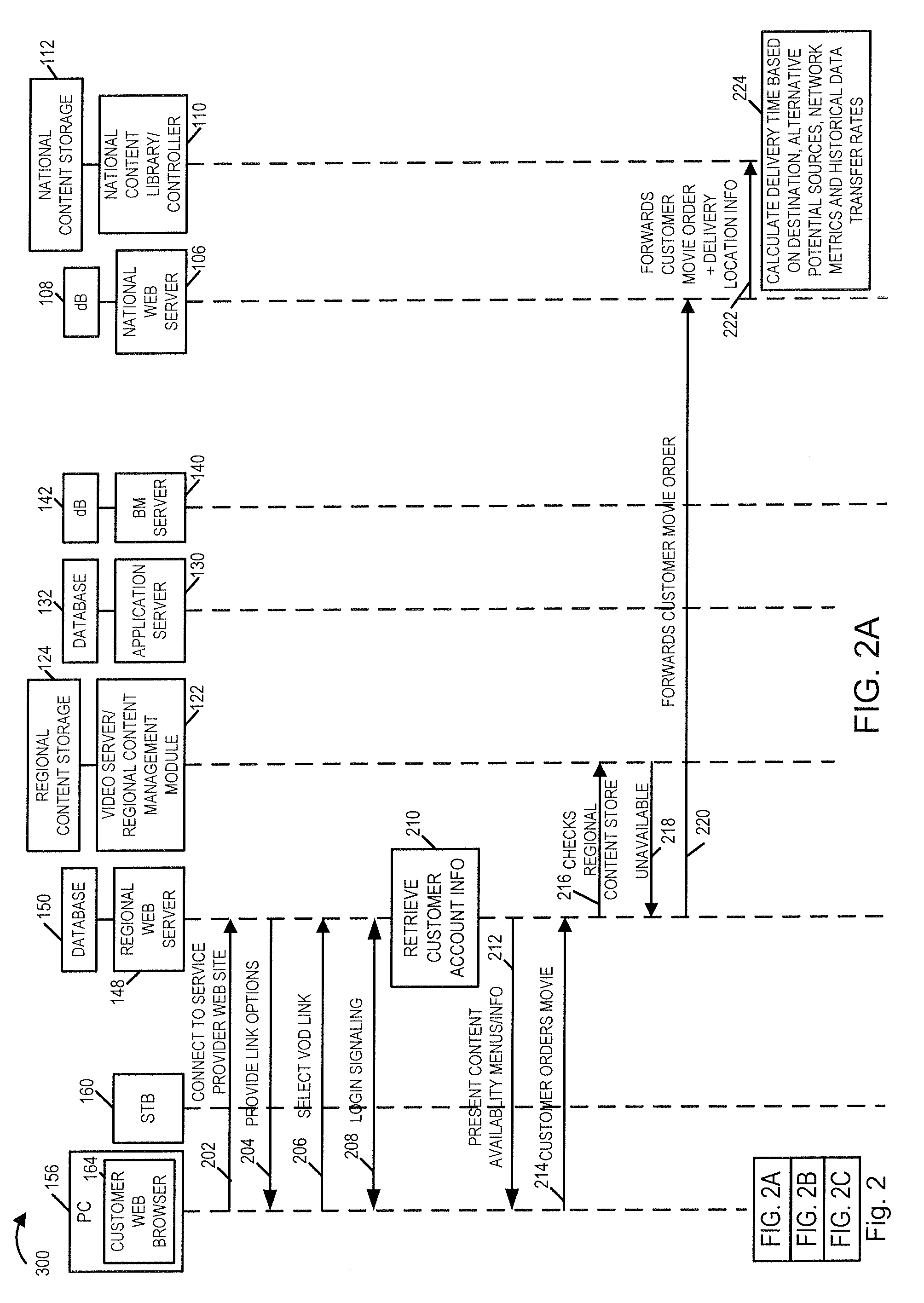
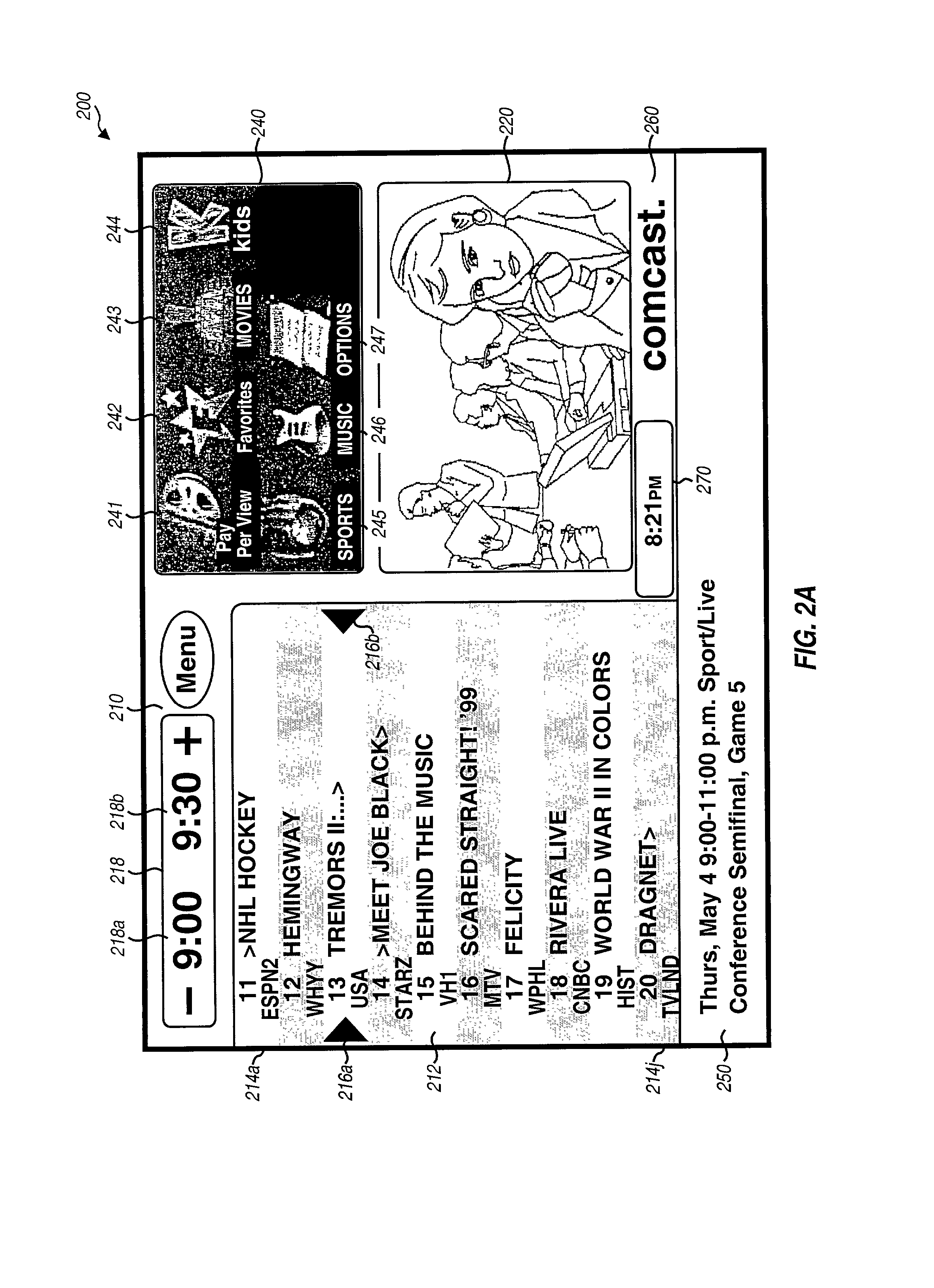
Methods, apparatus and user interface for providing content on demand
ActiveUS20080155613A1Increase storage capacityScalable approachTwo-way working systemsSelective content distributionWorld Wide WebUser interface
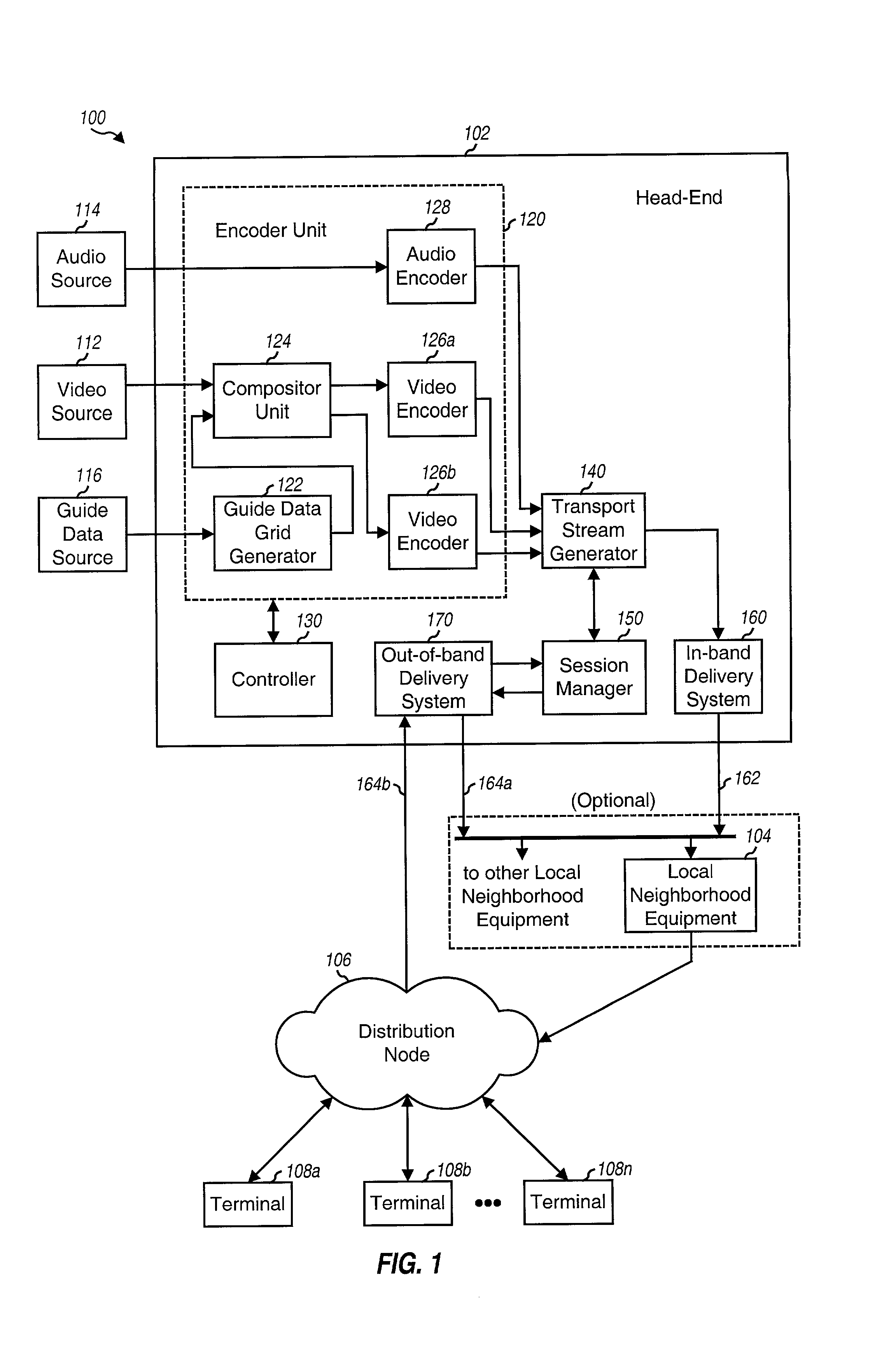
Methods and apparatus for supporting content delivery service are described. In accordance with the invention content can be supplied to temporary storage of a regional or local server used to supply the content to a customer's premises when the requested content is not already available in the regional or local server. A content server hierarchy may be implemented with servers higher up in the hierarchy including more content, e.g., titles, than the number of titles stored in the lower level servers. By storing less frequently accessed content in servers higher in the hierarchy and frequently requested titles lower in the hierarchy, a vast number of titles can be supported without overburdening the storage available at local and regional servers. In addition, a national or other server high in the hierarchy can be used to store, move, and distribute local or other content as part of an on demand service.
Owner:TIME WARNER CABLE ENTERPRISES LLC
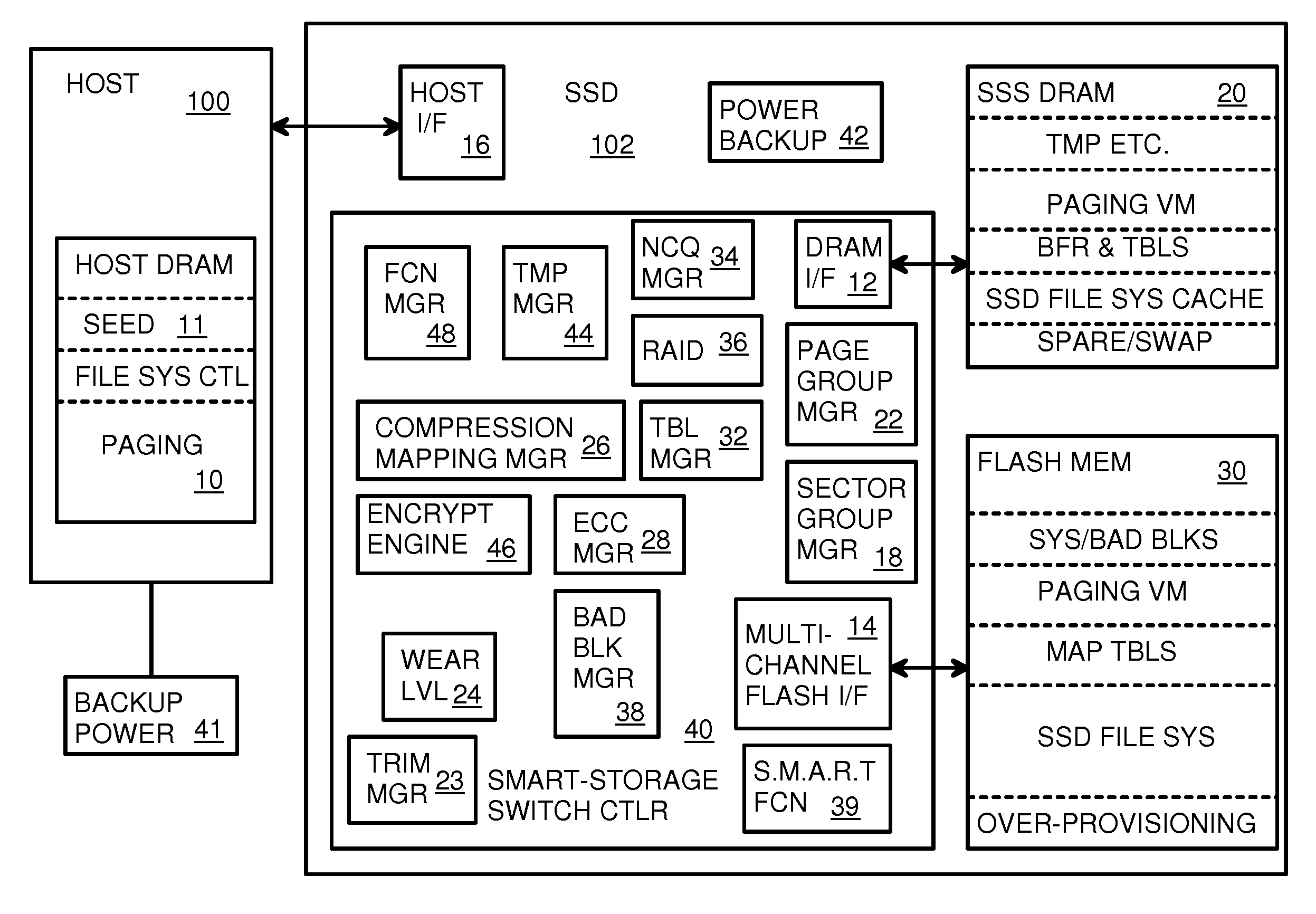
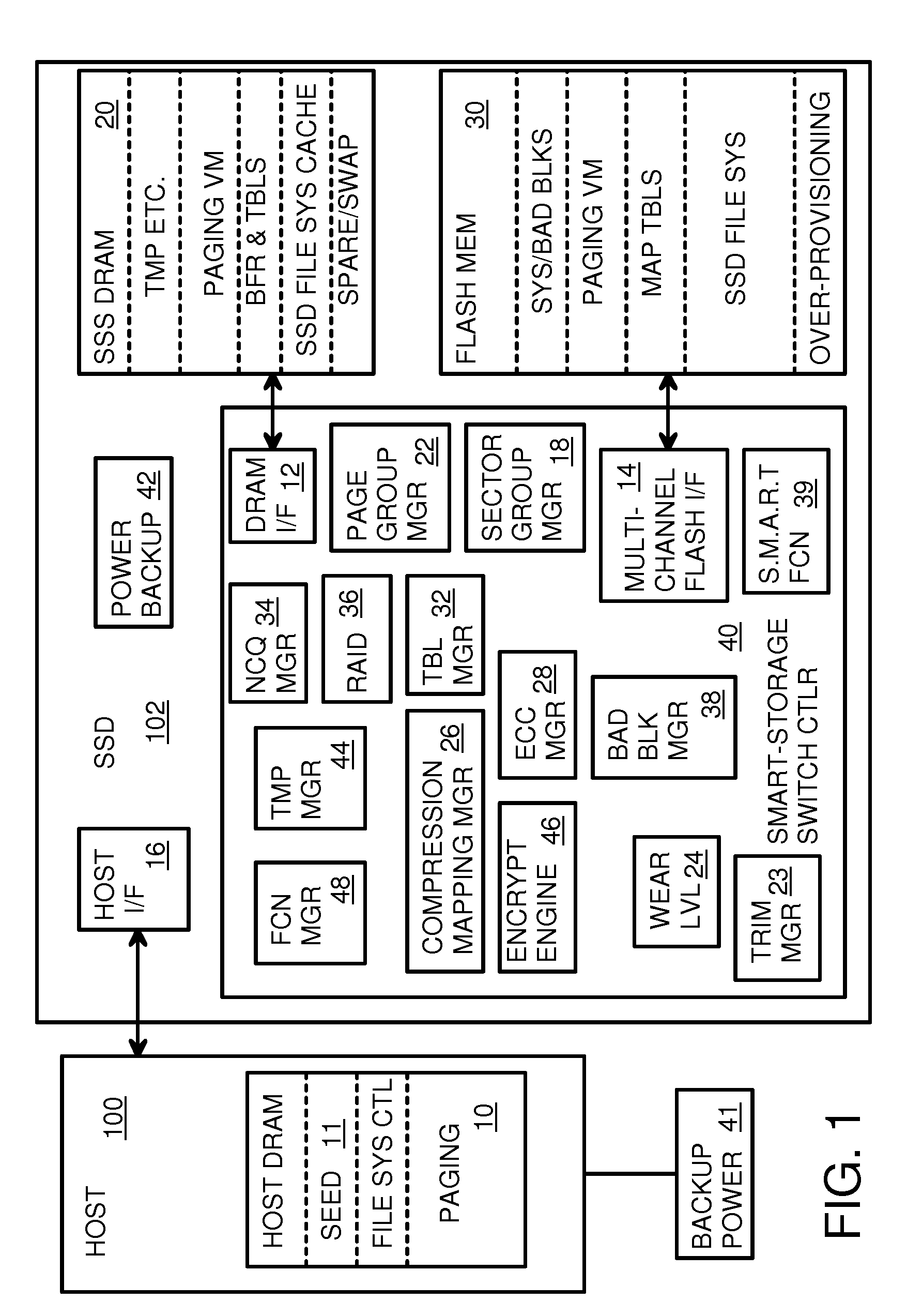
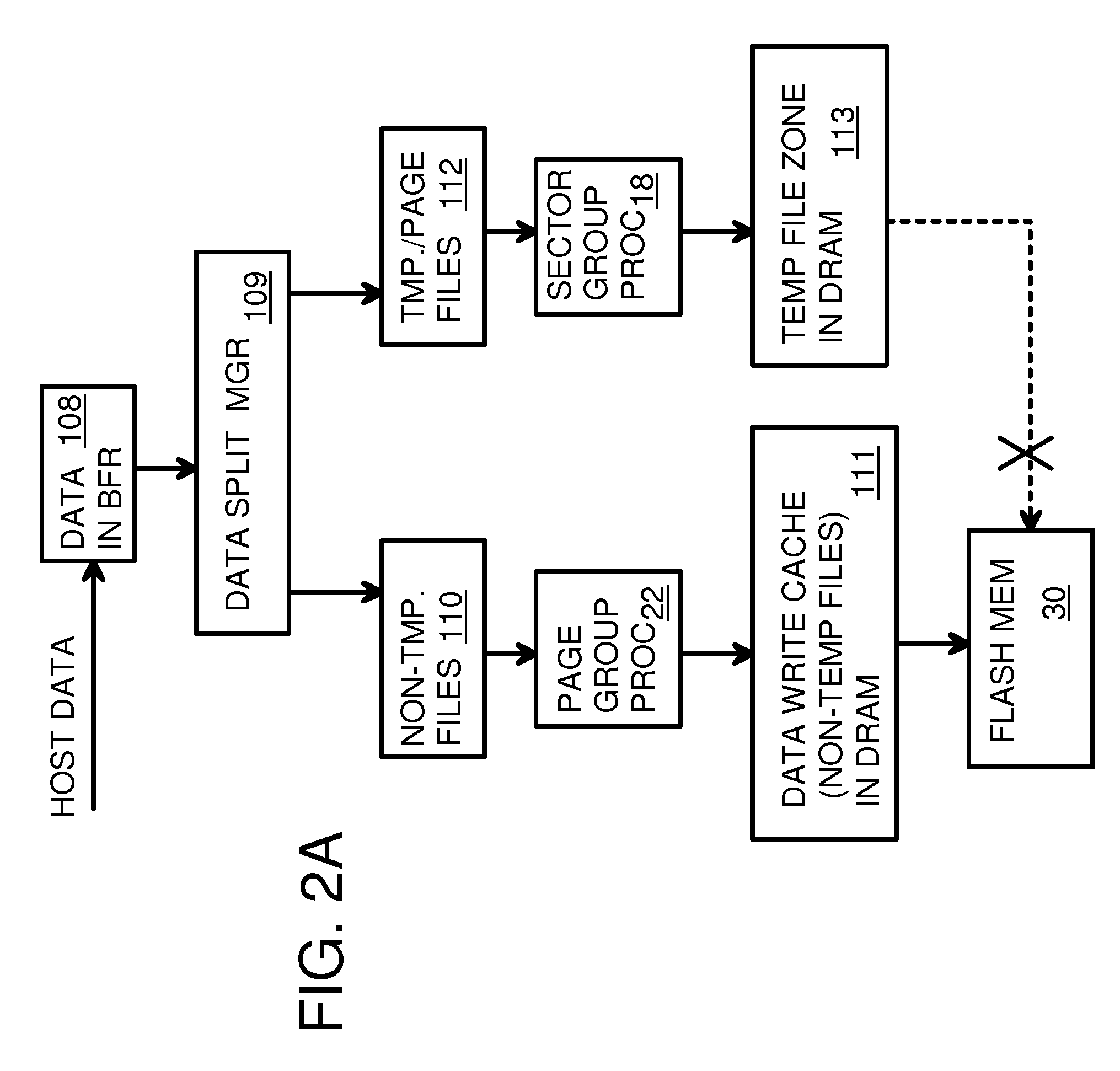
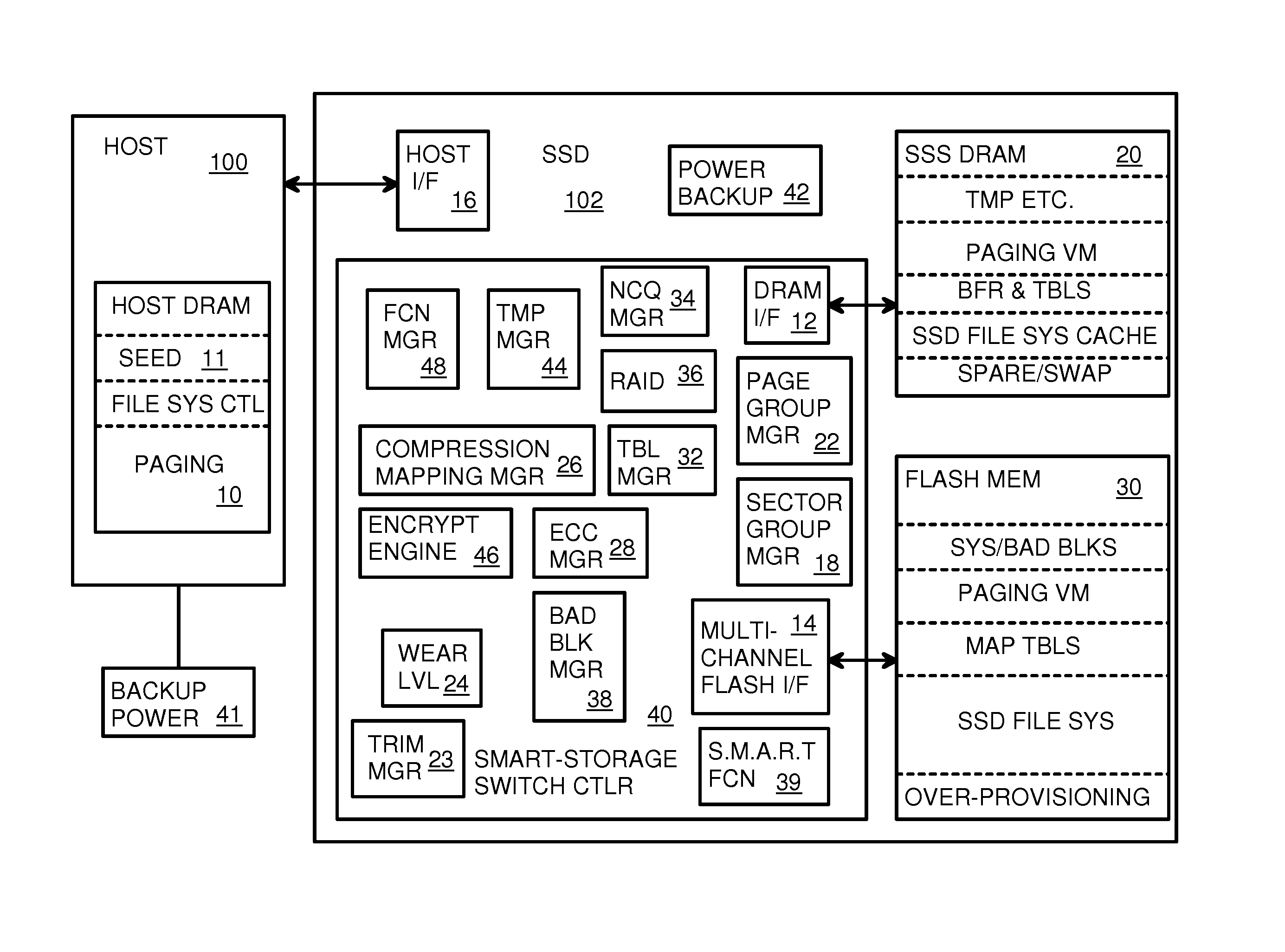
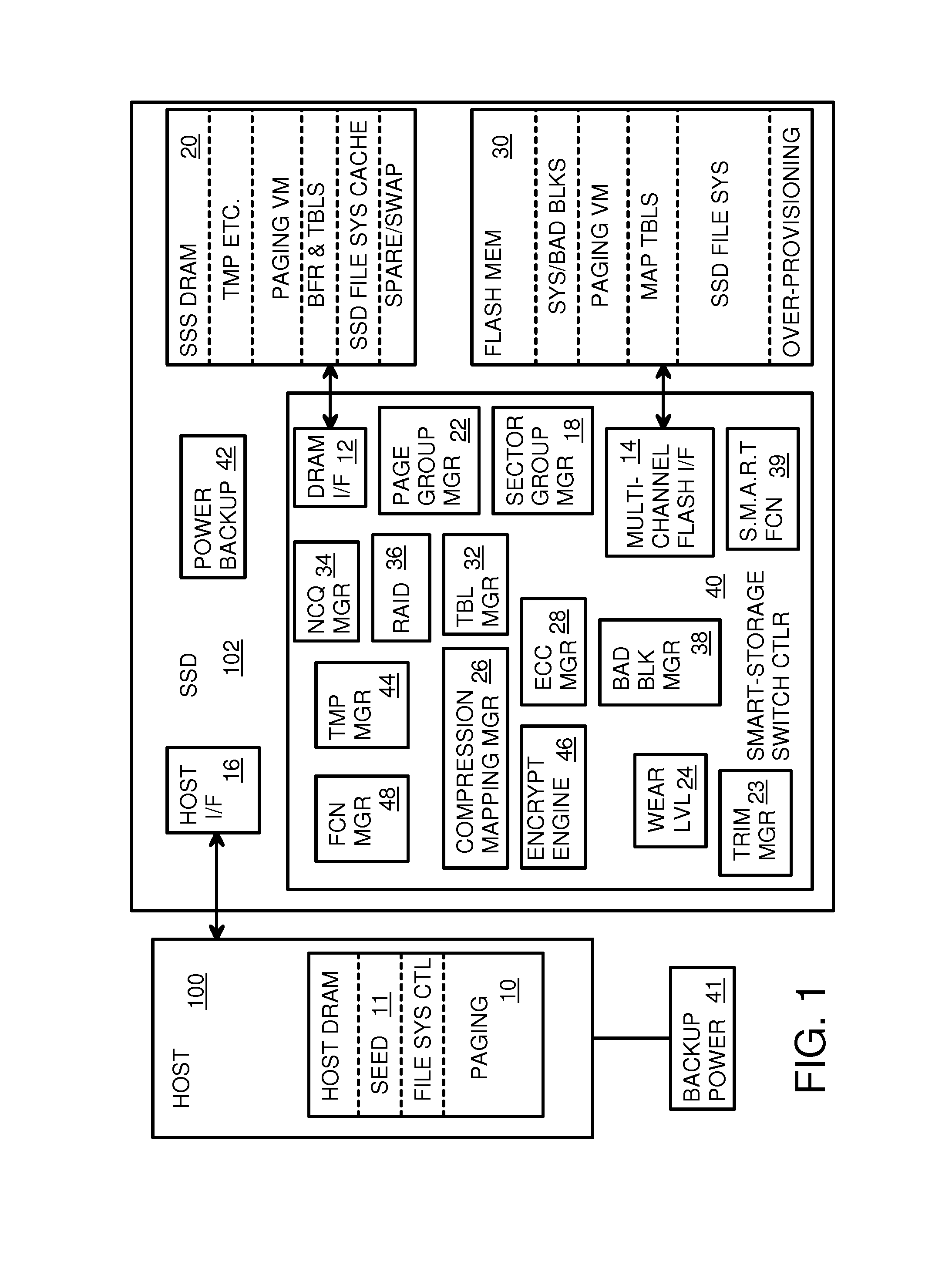
Super-Endurance Solid-State Drive with Endurance Translation Layer (ETL) and Diversion of Temp Files for Reduced Flash Wear
ActiveUS20120284587A1Memory architecture accessing/allocationDigital storageFilename extensionData file
A flash drive has increased endurance and longevity by reducing writes to flash. An Endurance Translation Layer (ETL) is created in a DRAM buffer and provides temporary storage to reduce flash wear. A Smart Storage Switch (SSS) controller assigns data-type bits when categorizing host accesses as paging files used by memory management, temporary files, File Allocation Table (FAT) and File Descriptor Block (FDB) entries, and user data files, using address ranges and file extensions read from FAT. Paging files and temporary files are never written to flash. Partial-page data is packed and sector mapped by sub-sector mapping tables that are pointed to by a unified mapping table that stores the data-type bits and pointers to data or tables in DRAM. Partial sectors are packed together to reduce DRAM usage and flash wear. A spare / swap area in DRAM reduces flash wear. Reference voltages are adjusted when error correction fails.
Owner:SUPER TALENT TECH CORP
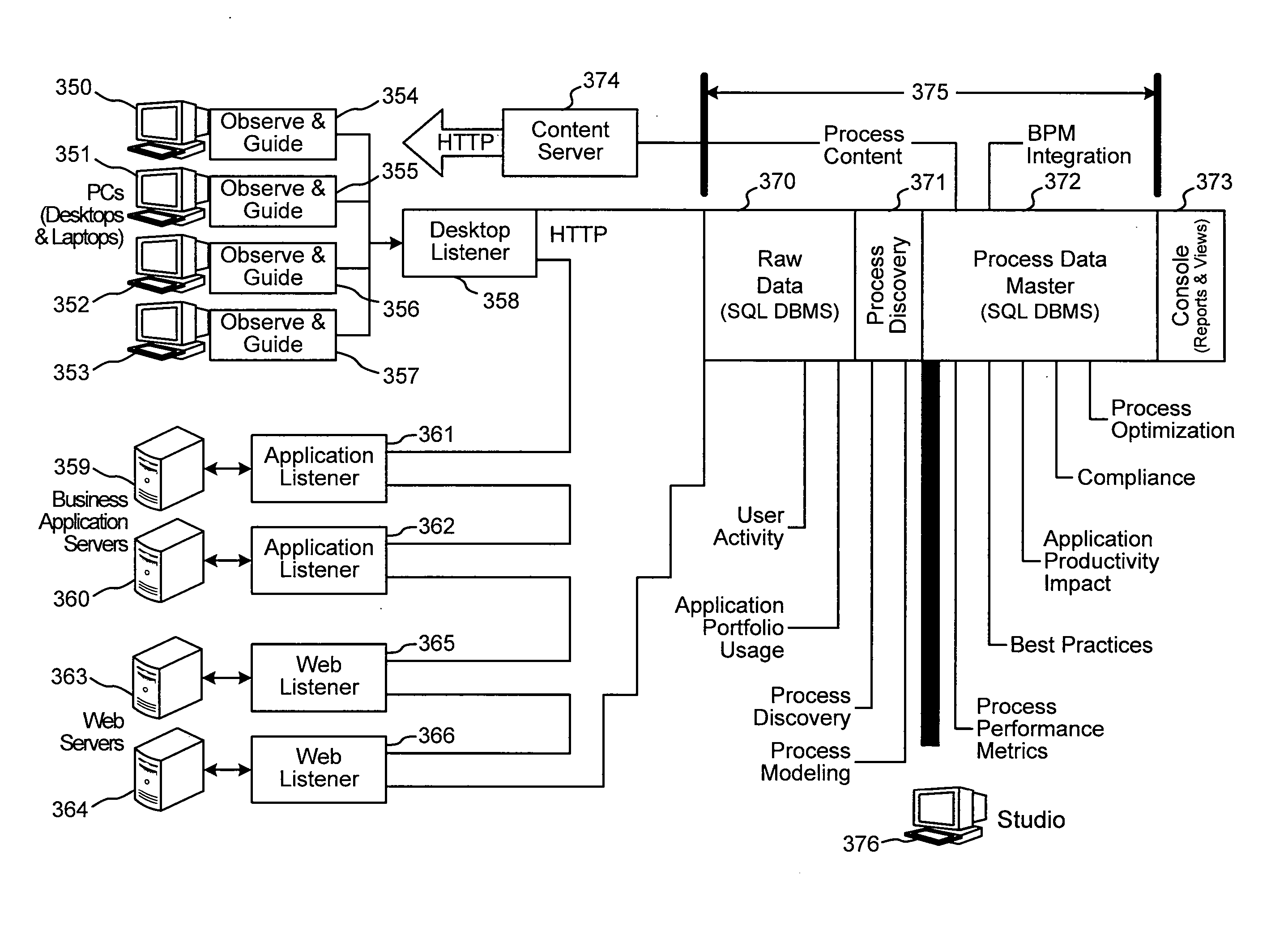
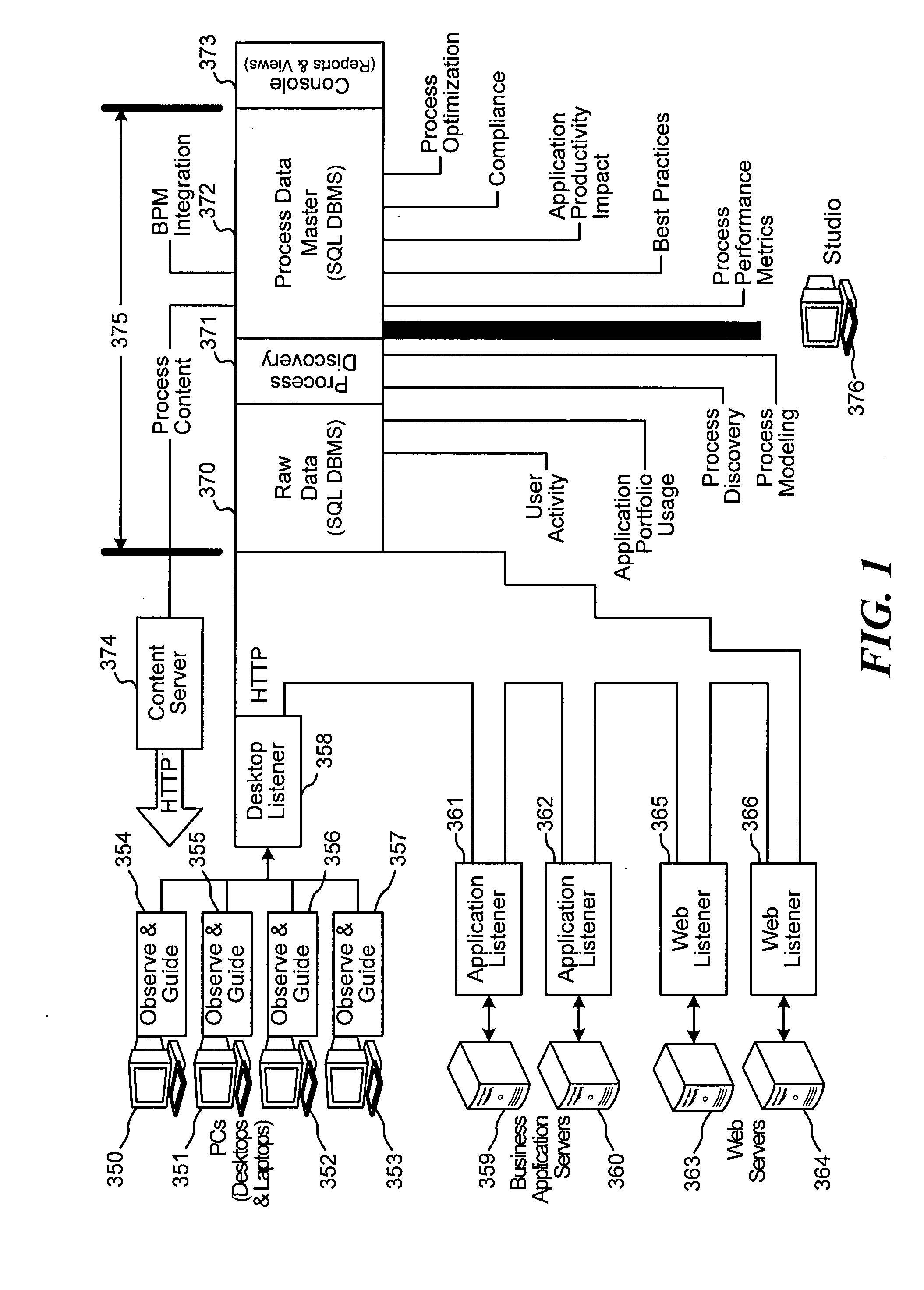
System and method for capture of user actions and use of capture data in business processes
InactiveUS20060184410A1Prevent wrong actionEnsure complianceDigital computer detailsOffice automationGood practiceData storing
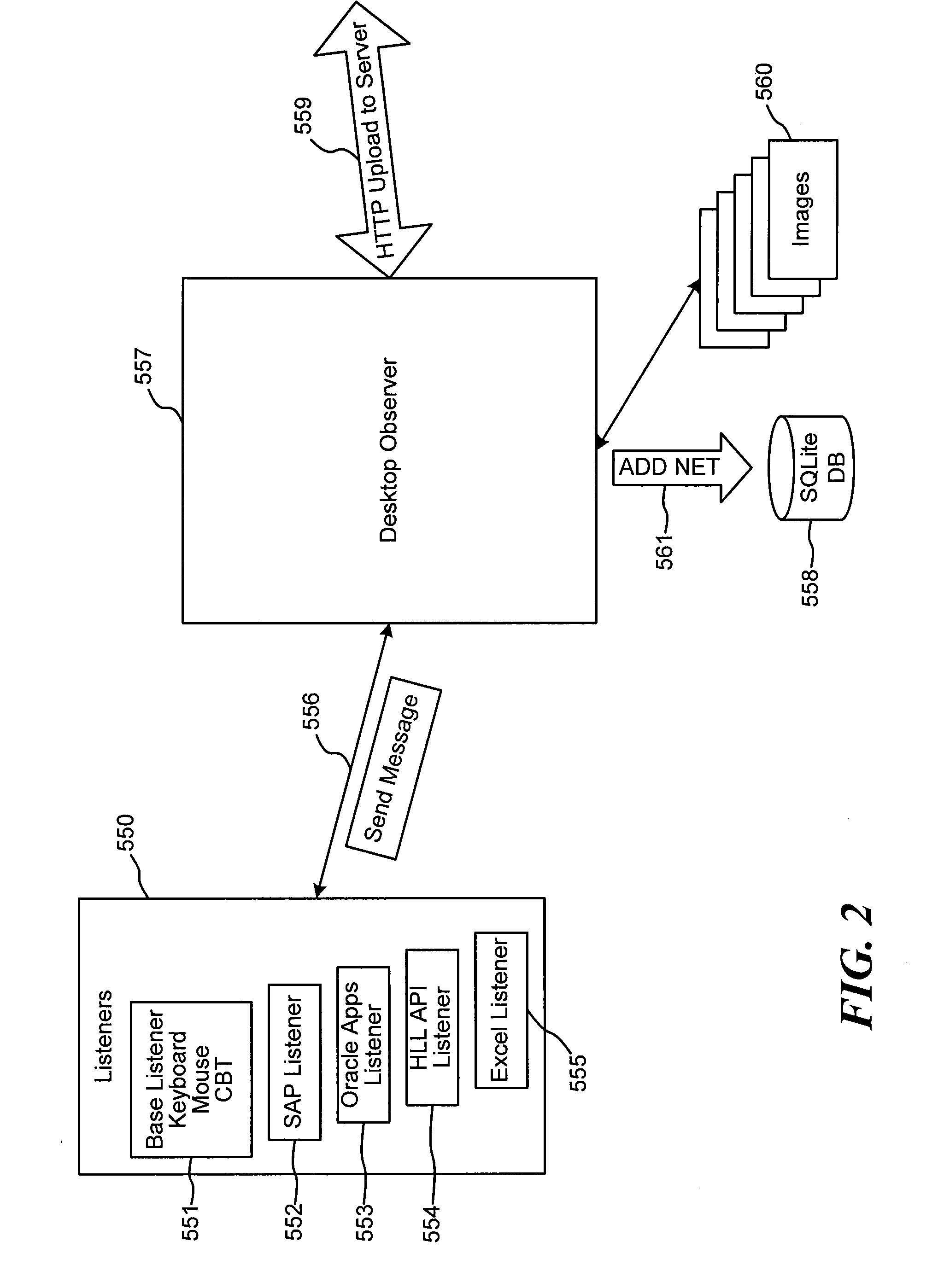
Systems and methods are disclosed for capturing data representative of user interactions with a desktop computer, and processing the capture data to identify and analyze business processes performed by the user. The disclosed system comprises listeners that capture key actuations, mouse-clicks, screen information, and other data representative of user interaction with a desktop computer. A desktop observer is provided to accept capture data from listeners, to temporarily store the capture data if necessary, and to pass the capture data to a process intelligence server. The process intelligence server includes a process discovery module the analyzes the capture data and identifies business processes corresponding to the capture data, or models business processes. A process data master storage is provided. A process analysis module is provided to determine performance metrics, best practices, application productivity impacts, compliance, and optimization analysis on the data stored in the process master storage. Methods are disclosed for capture, catalog, combination, correlation, change, compression, and certification.
Owner:QLIP MEDIA
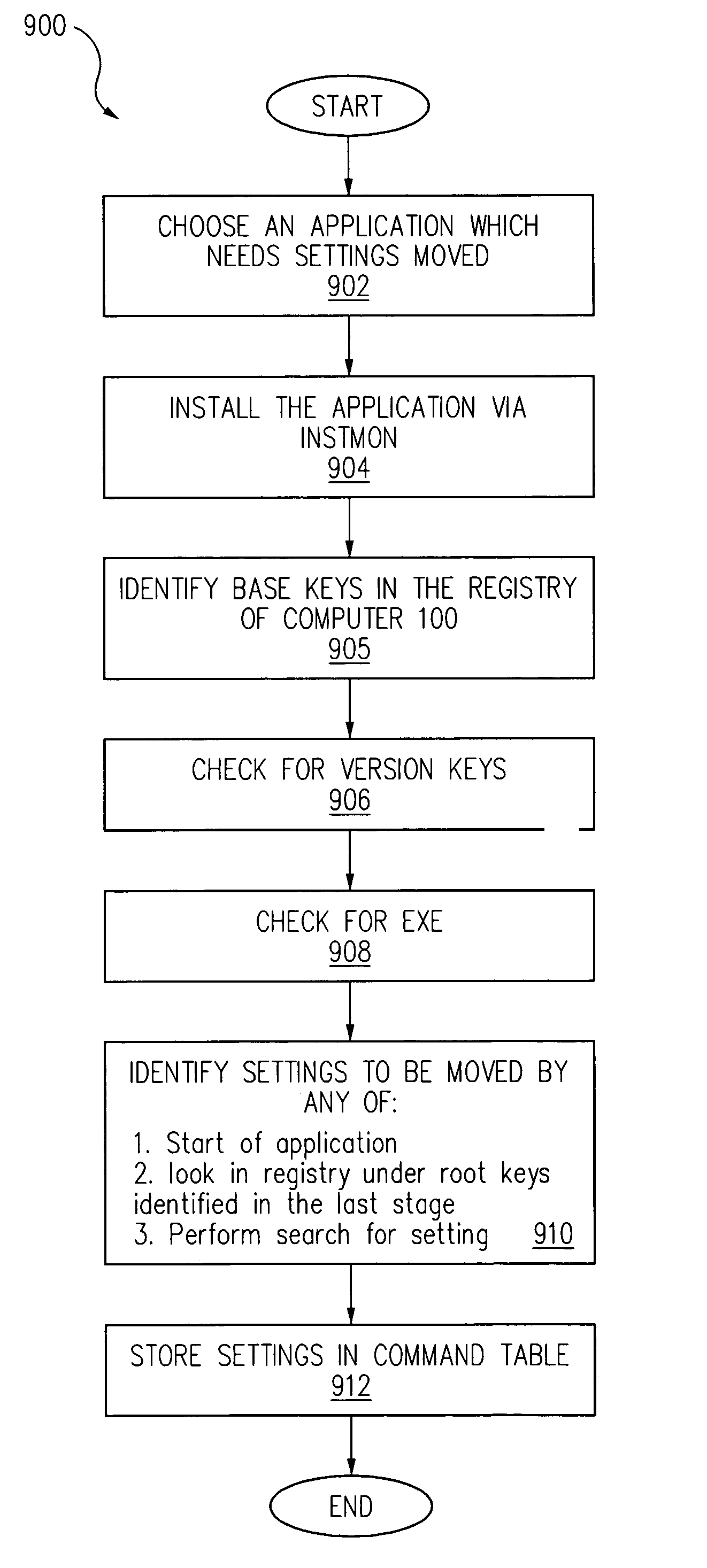
System for transferring customized hardware and software settings from one computer to another computer to provide personalized operating environments
InactiveUS6963908B1Simplify the shipping processOptimization mechanismDigital computer detailsProgram loading/initiatingPersonalizationWeb site
A method and system for transferring information from a first computer-based device to a web site, for temporary storage and later transfer of the stored information from the web site to a second computer-based device. First, a communication link is established between a first computer-based device and the web site. Next, the first computer-based device is scanned, via the web site, to determine the information contained on the first computer-based device. The user then selects which of the scanned information is to be uploaded from the first computer-based device onto the web site for temporary storage. Finally, the selected information is transferred from the first computer-based device onto the web site for temporary storage. Once retrieval of the temporarily stored information is desired, the user establishes a communication link between a second computer-based device and the web site. The second computer-based device is scanned, via the web site, to determine the information contained on the second computer-based device. The temporarily stored information, from the first computer-based device on the web site, is then displayed to the user and the user selects which of this temporary information, from the first computer-based device, is to be downloaded from the web site onto the second computer-based device. The selected information is finally downloaded from the website onto the second computer-based device.
Owner:CLOUDING
Methods and apparatus for supporting content distribution
ActiveUS20080155059A1Reduce deliveryShort amount of timeMultiple digital computer combinationsTwo-way working systemsContent distributionWorld Wide Web
Methods and apparatus for supporting content delivery service are described. In accordance with the invention content can be supplied to temporary storage of a regional or local server used to supply the content to a customer's premises when the requested content is not already available in the regional or local server. A content server hierarchy may be implemented with servers higher up in the hierarchy including more content, e.g., titles, than the number of titles stored in the lower level servers. By storing less frequently accessed content in servers higher in the hierarchy and frequently requested titles lower in the hierarchy, a vast number of titles can be supported without overburdening the storage available at local and regional servers. In addition, a national or other server high in the hierarchy can be used to store, move, and distribute local or other content as part of an on demand service.
Owner:TIME WARNER CABLE ENTERPRISES LLC
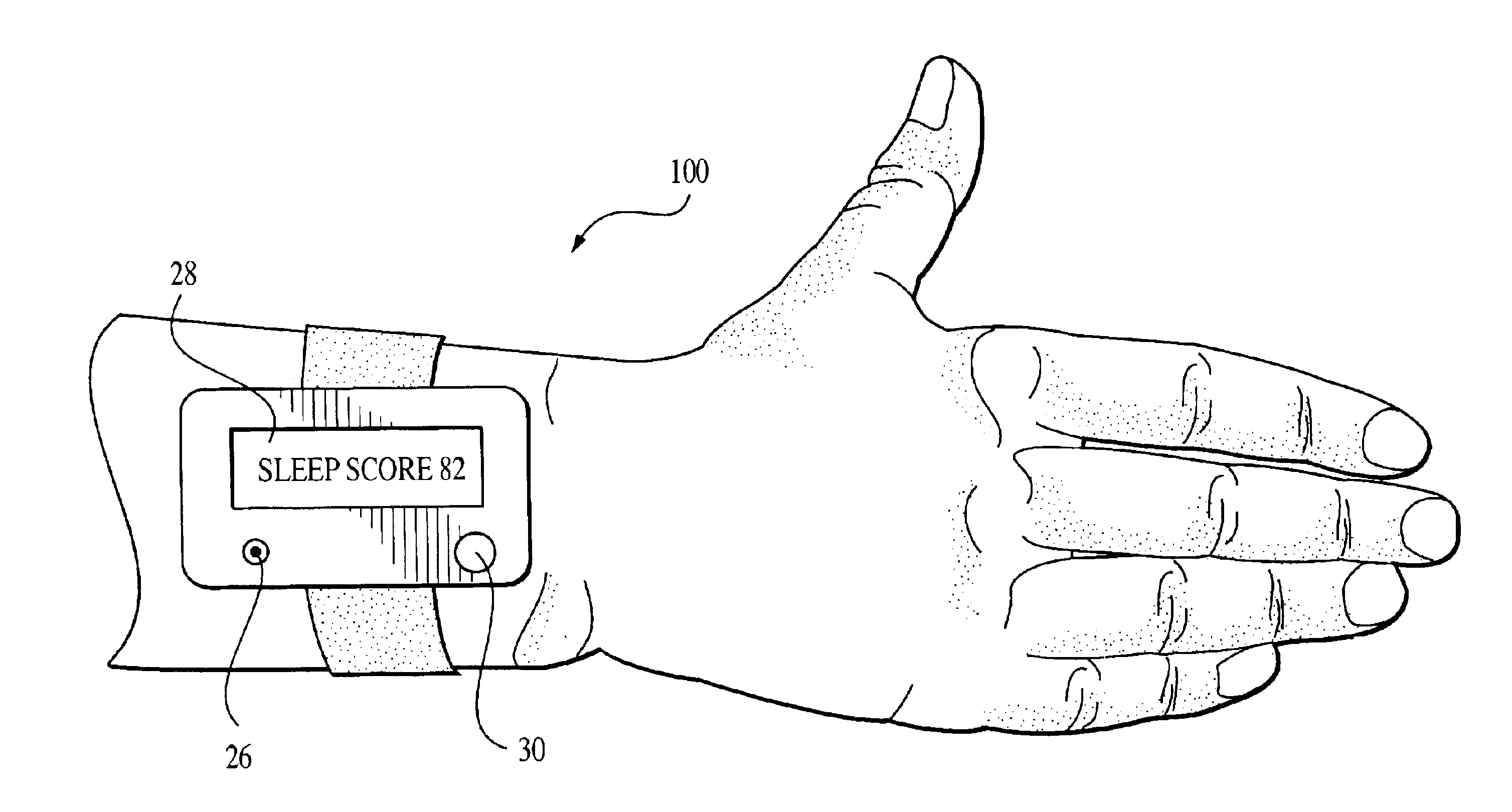
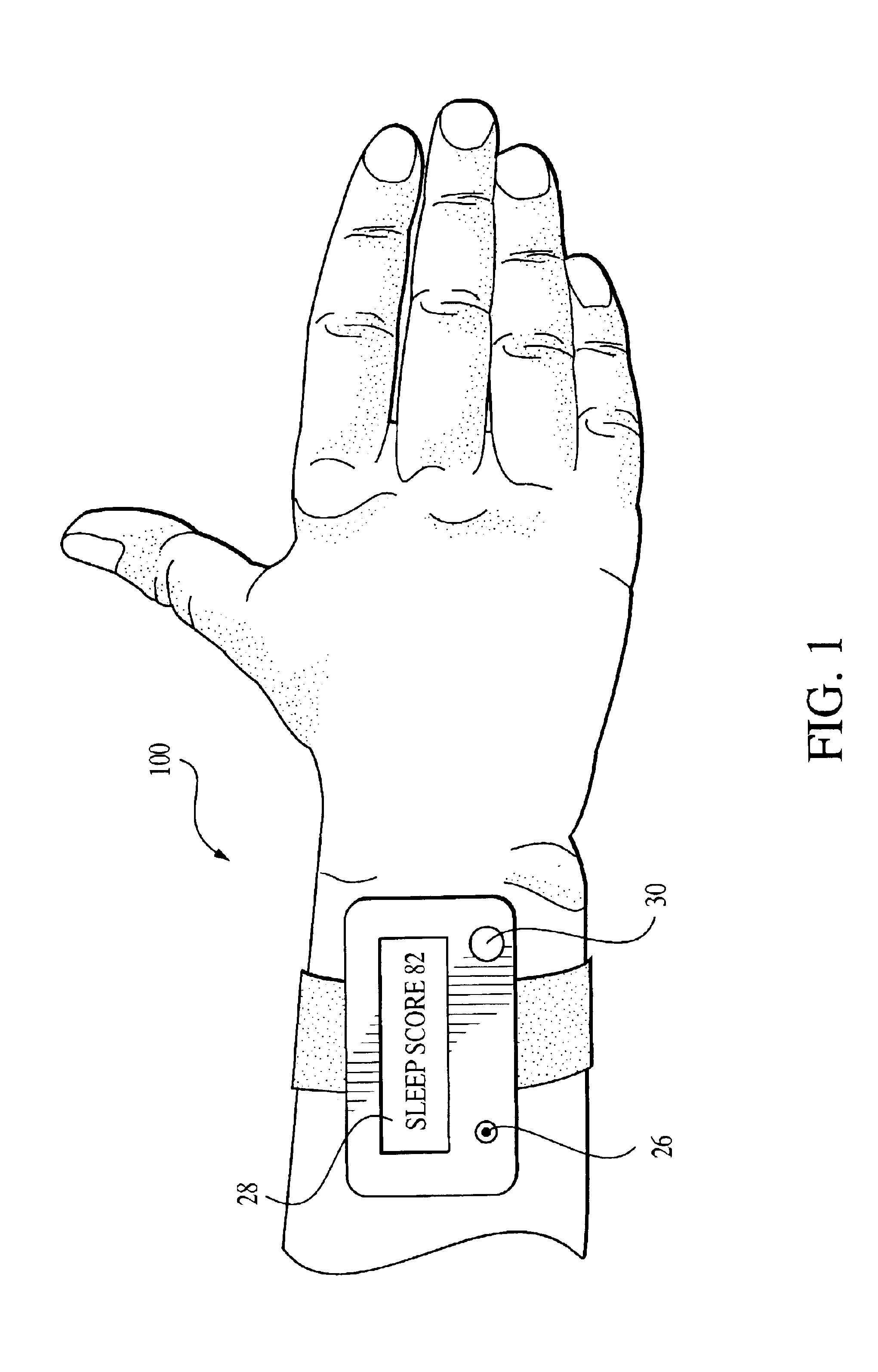
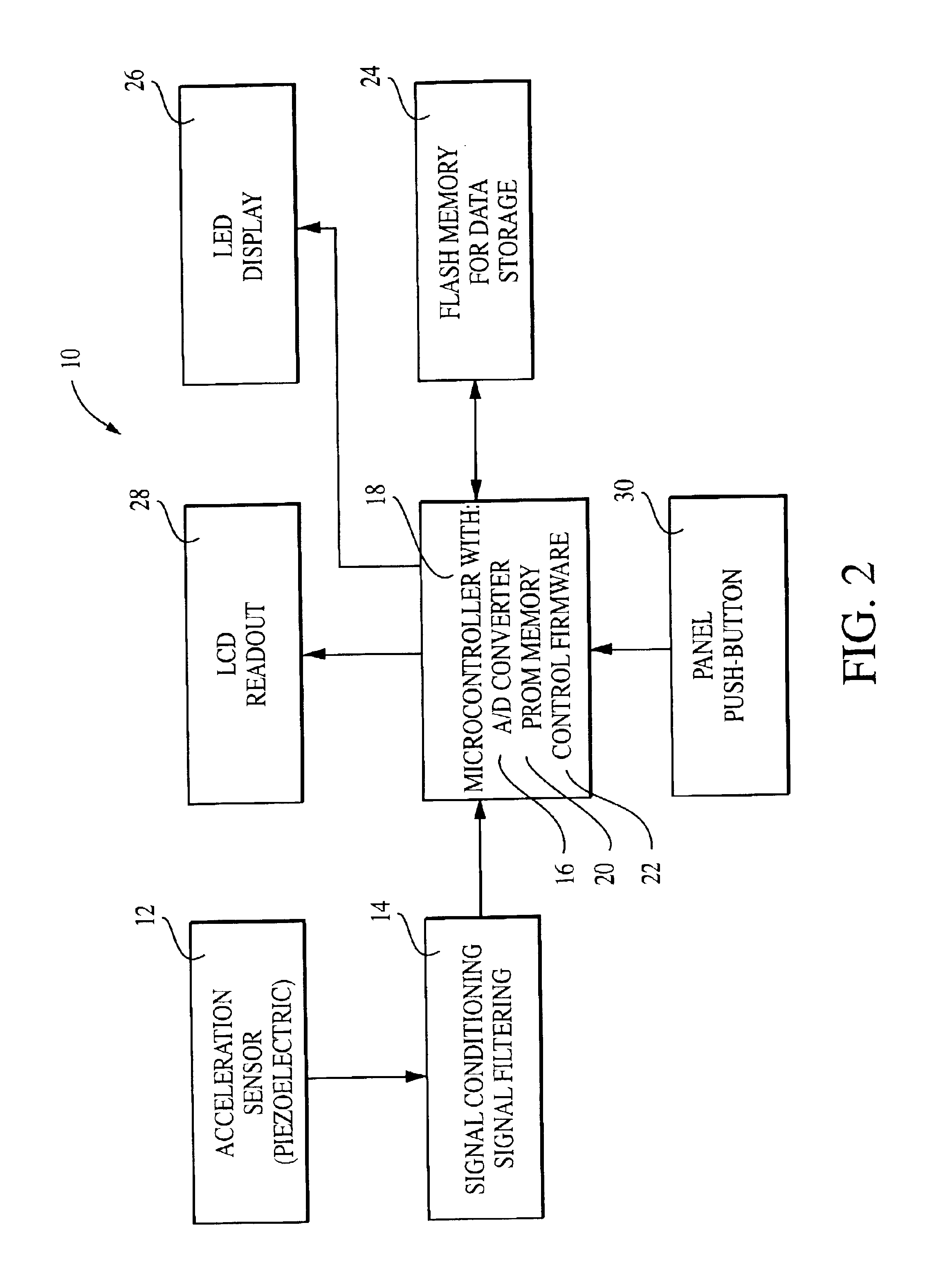
Sleep scoring apparatus and method
A method and an apparatus are disclosed for scoring the quality of sleep experienced by a subject wearing the apparatus for a specified period. This sleep monitoring apparatus includes a motion sensor that quantifies the temporal variation in the subject's motion, an analog to digital converter to sample the sensor data, a microprocessor with embedded programmable memory to store control and processing firmware, a memory device for data storage, a display means, and a switch for staring and resetting the device. The firmware for this apparatus: (i) directs the microprocessor to sample sensor output at a prescribed time interval and to temporarily store this data in the memory device, (ii) directs the microprocessor to analyze the temporarily stored data to compute a sleep score based on the magnitude of movements recorded during the monitoring period, and (iii) controls the operation of the display means. Upon termination of the sleep period, the apparatus' display means will display a sleep score based on a scale of 0 to 100. A high score indicates restful sleep (very low movements), while a low score indicates excessive restlessness during the monitored sleep period.
Owner:INDIVIDUAL MONITORING SYST
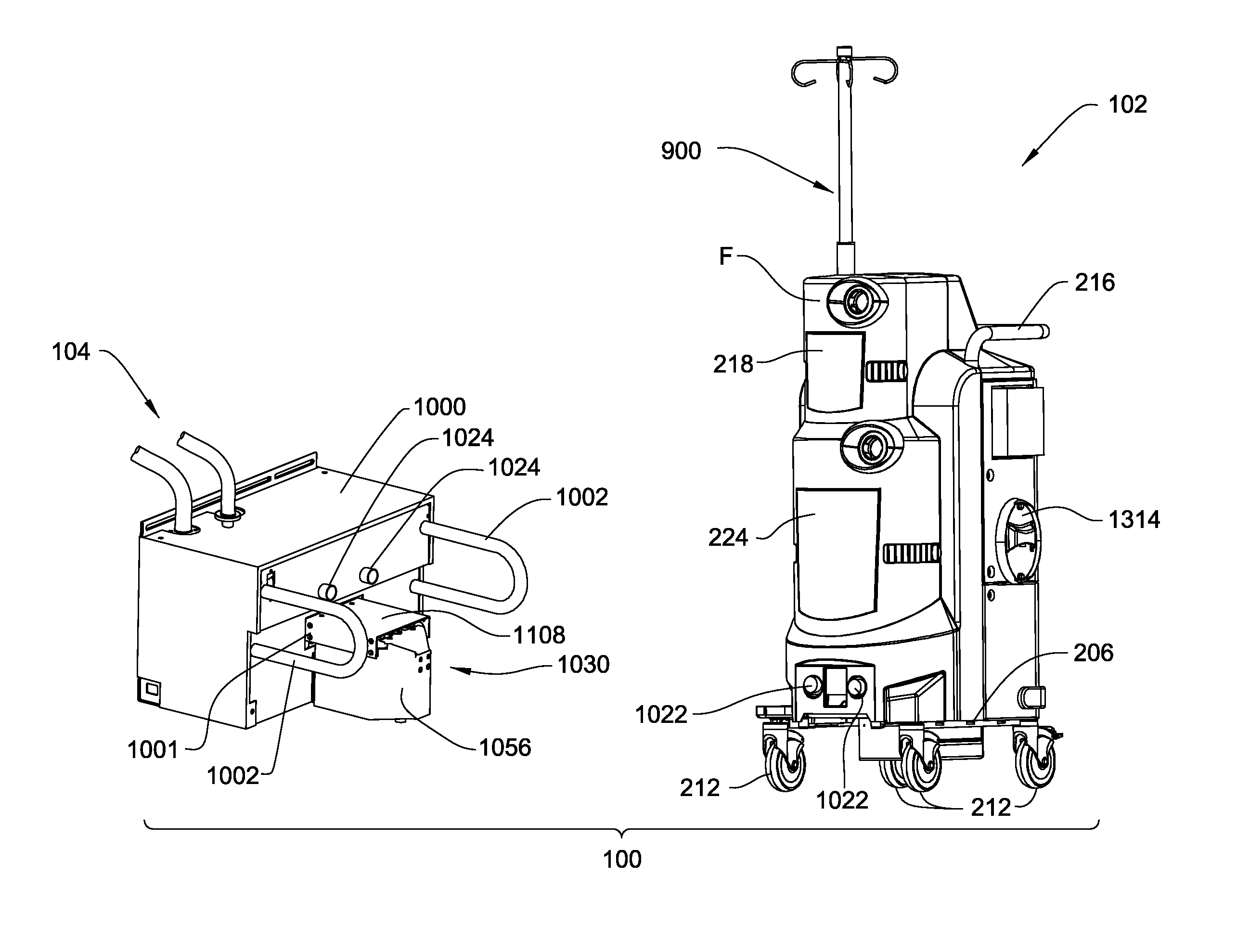
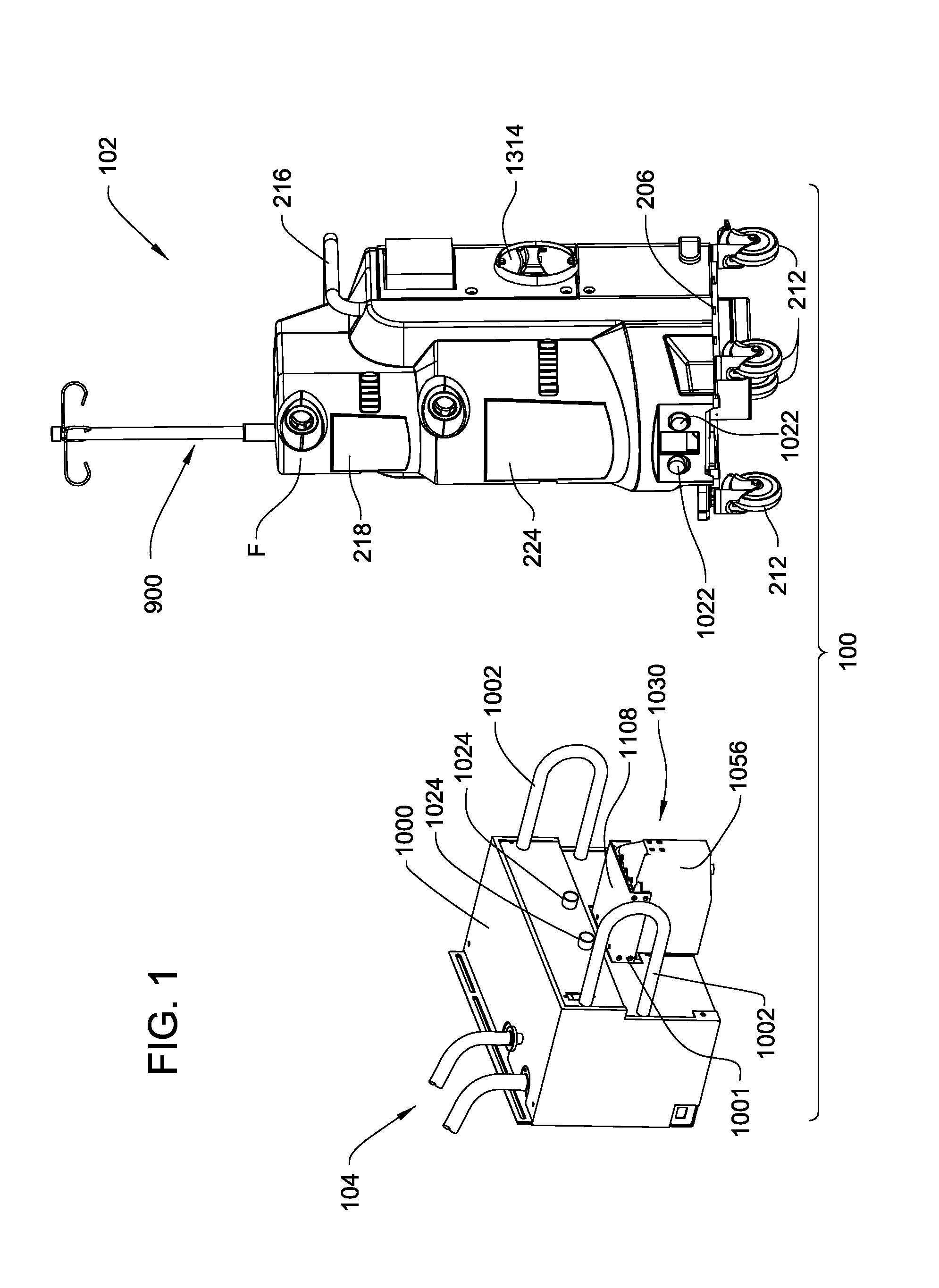
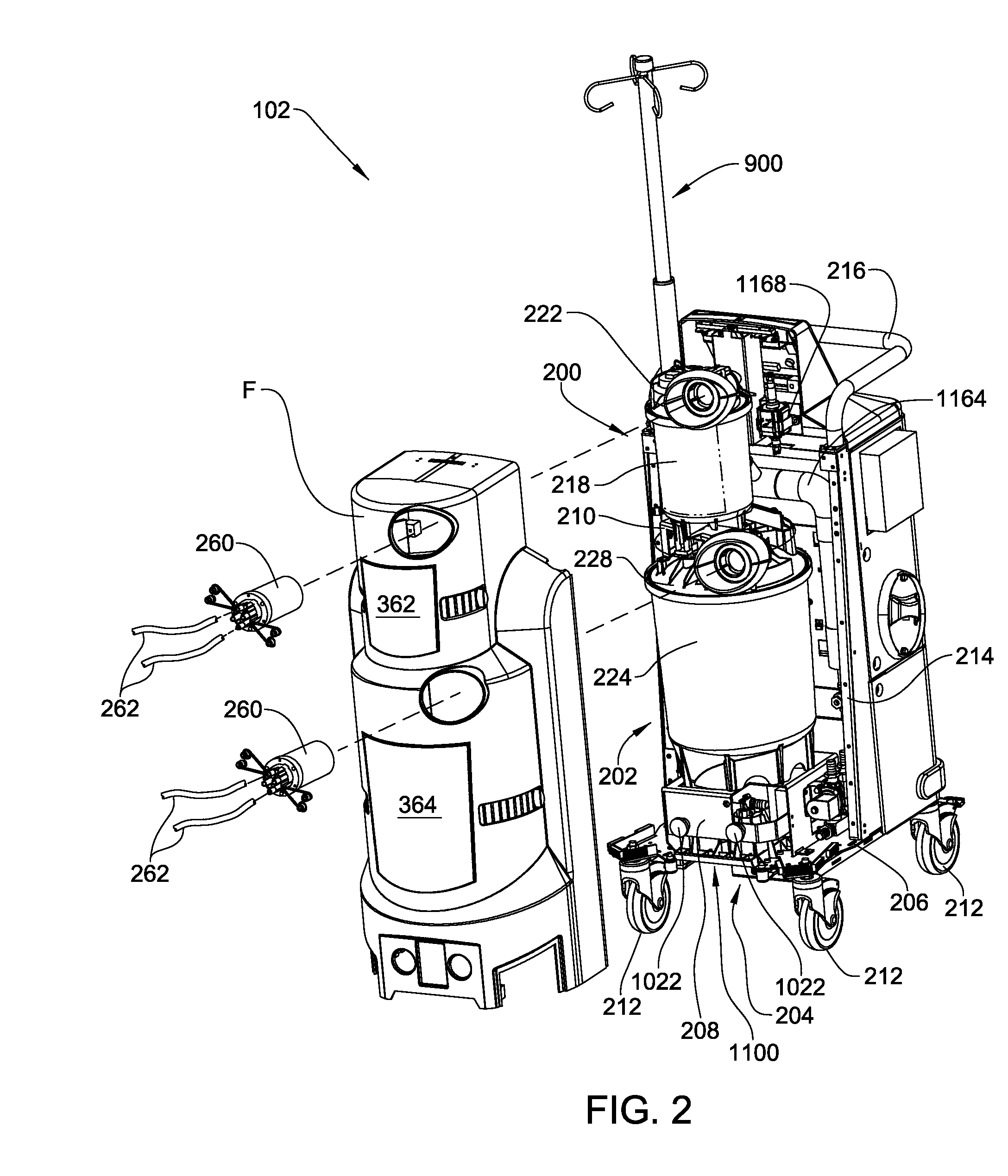
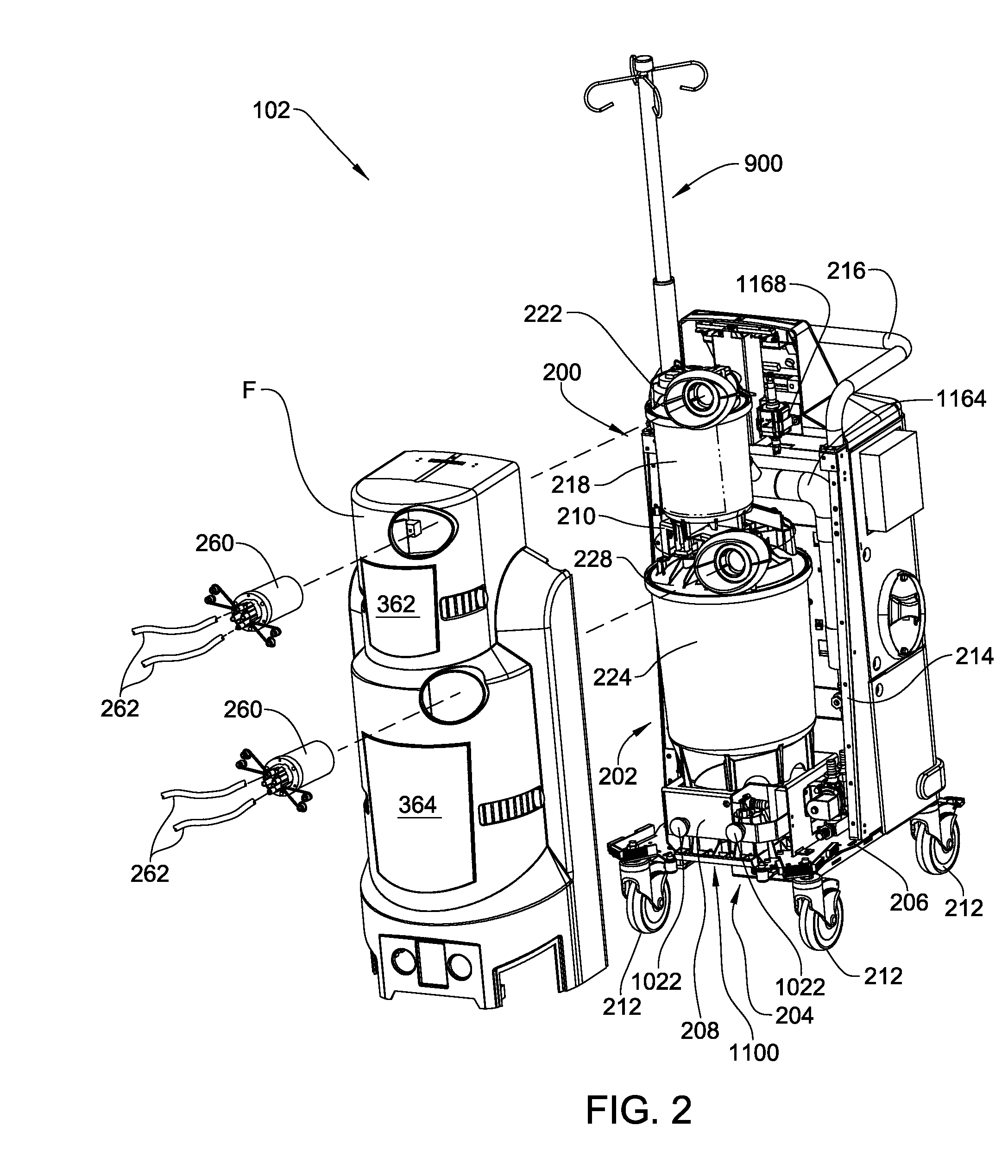
Medical/surgical waste collection unit including waste containers of different storage volumes with inter-container transfer valve and independently controlled vacuum levels
ActiveUS7621898B2Reduce in quantityLarge storage capacityMechanical apparatusDispersed particle filtrationDocking stationVacuum level
Owner:STRYKER CORP
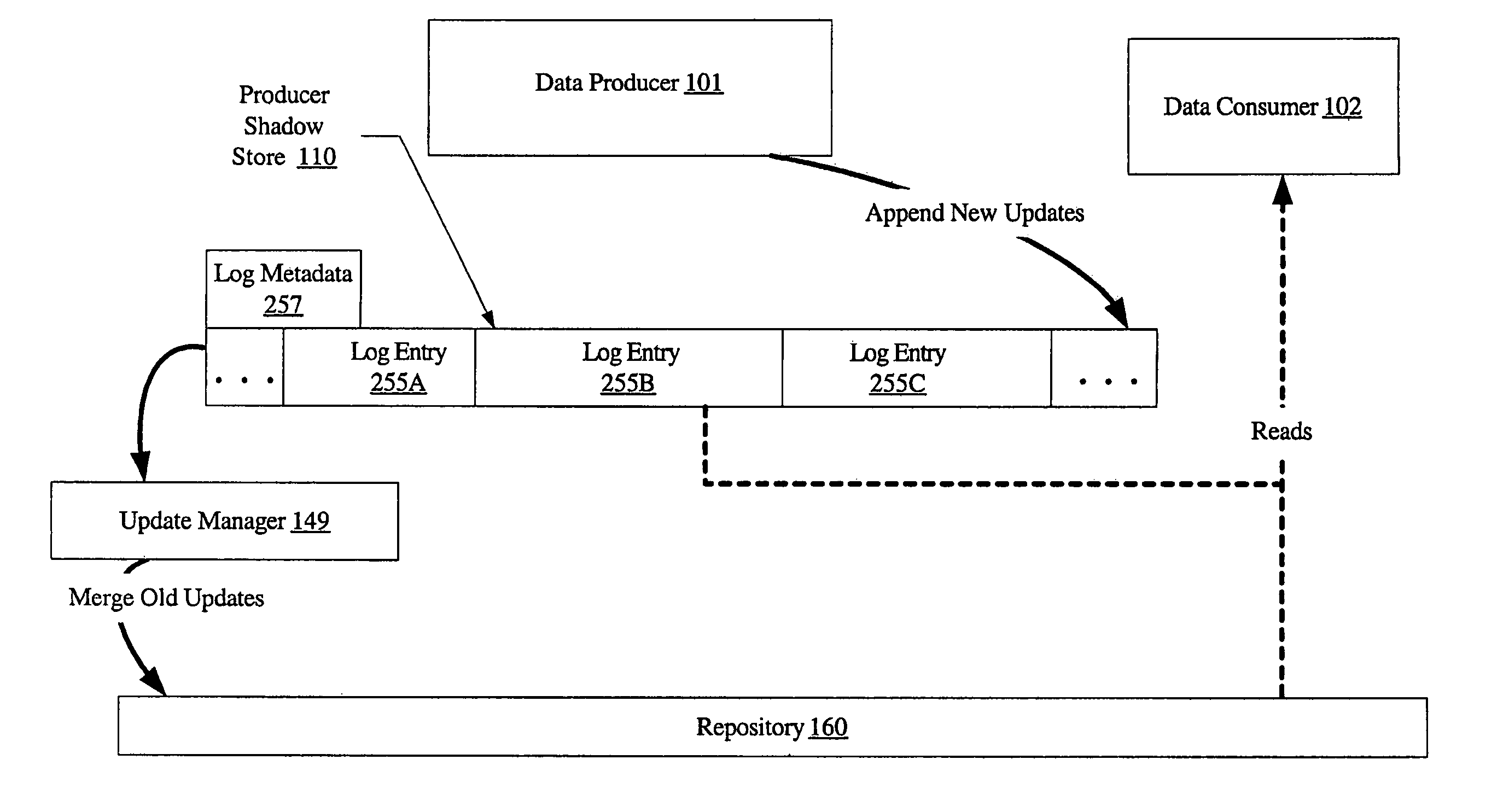
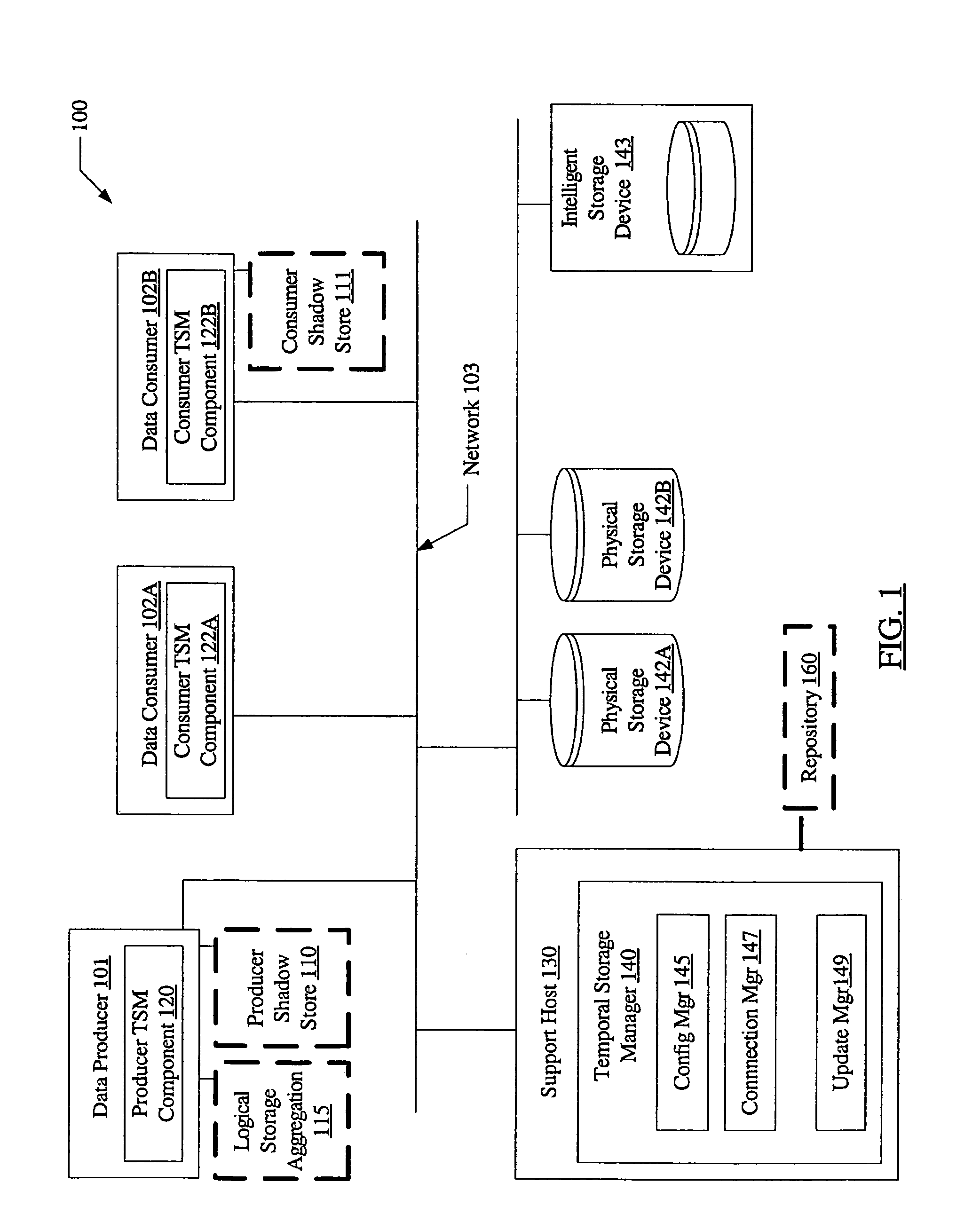
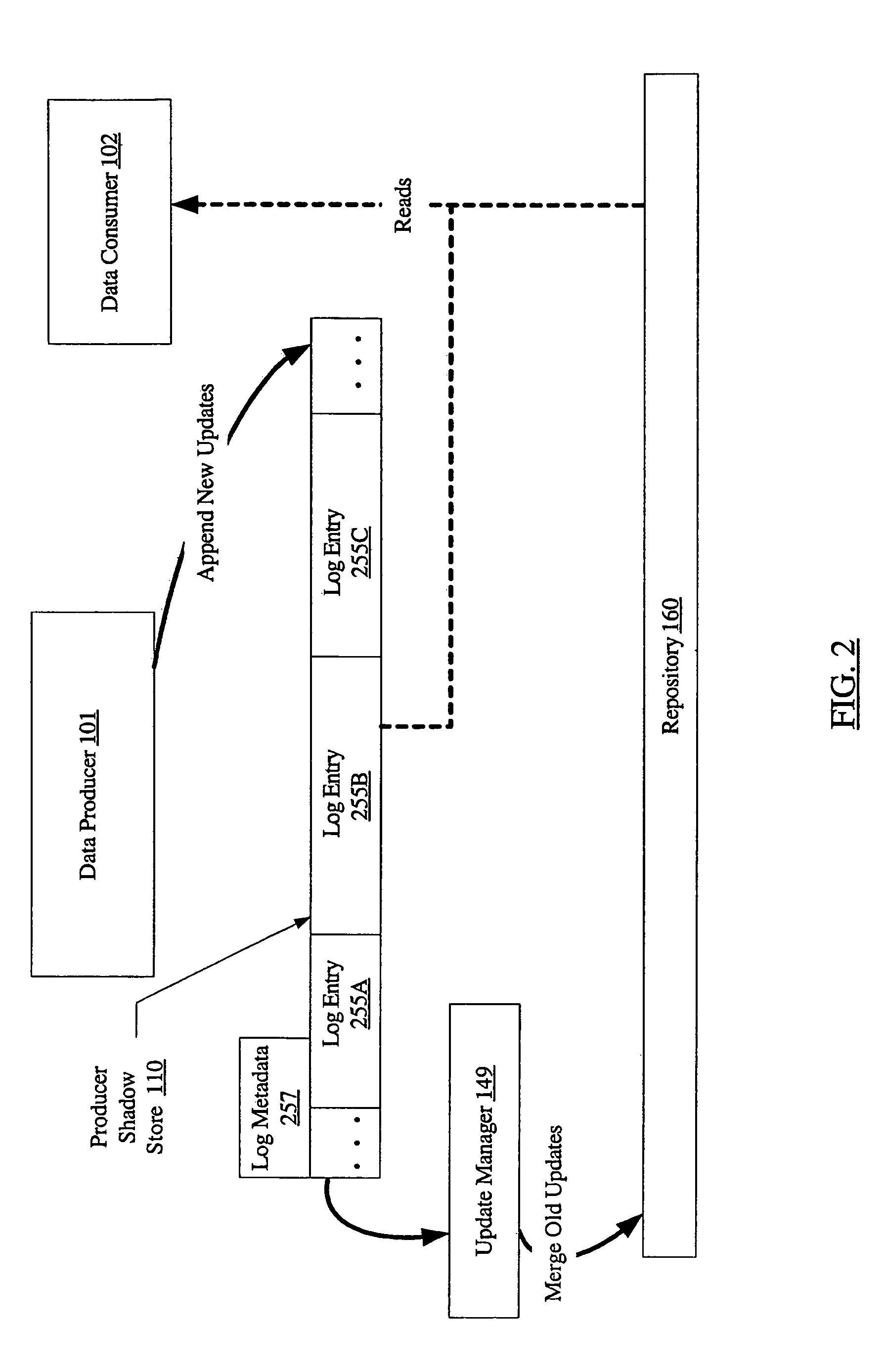
System and method for loosely coupled temporal storage management
ActiveUS7257689B1Prevent corruptionHigh degreeData processing applicationsDigital data information retrievalStorage managementDatabase
A system for loosely coupled temporal storage management includes a logical storage aggregation including a plurality of data blocks, a data producer, one or more data consumers, and a temporal storage manager. The temporal storage manager may be configured to maintain a producer shadow store including entries stored in a log-structured logical volume, where each entry is indicative of one or more data blocks of the logical storage aggregation that have been modified by the data producer. The temporal storage manager may also be configured to maintain a repository containing a baseline version of the logical storage aggregation, and to provide the data consumers with read-only access to the producer shadow store and the repository.
Owner:SYMANTEC OPERATING CORP
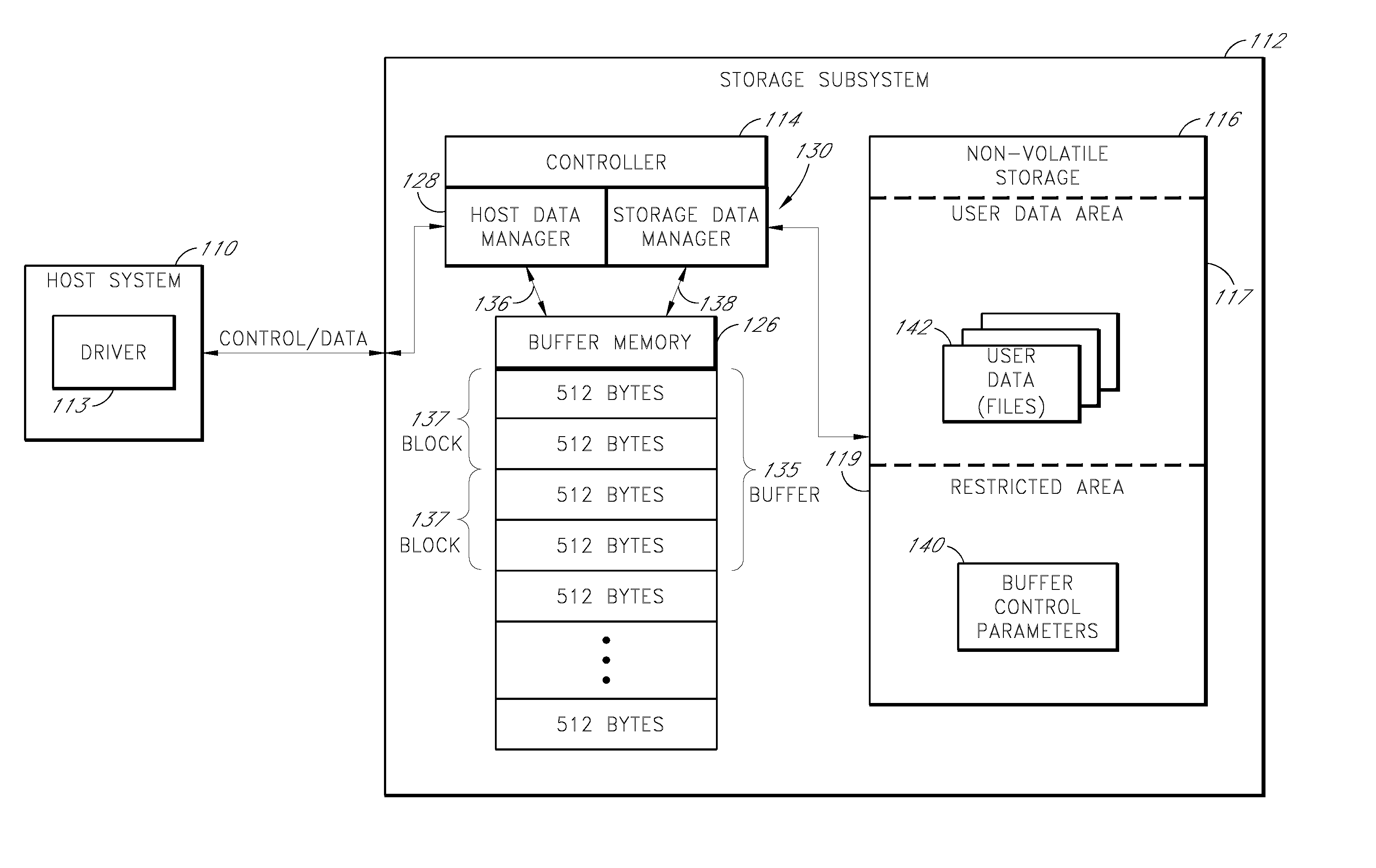
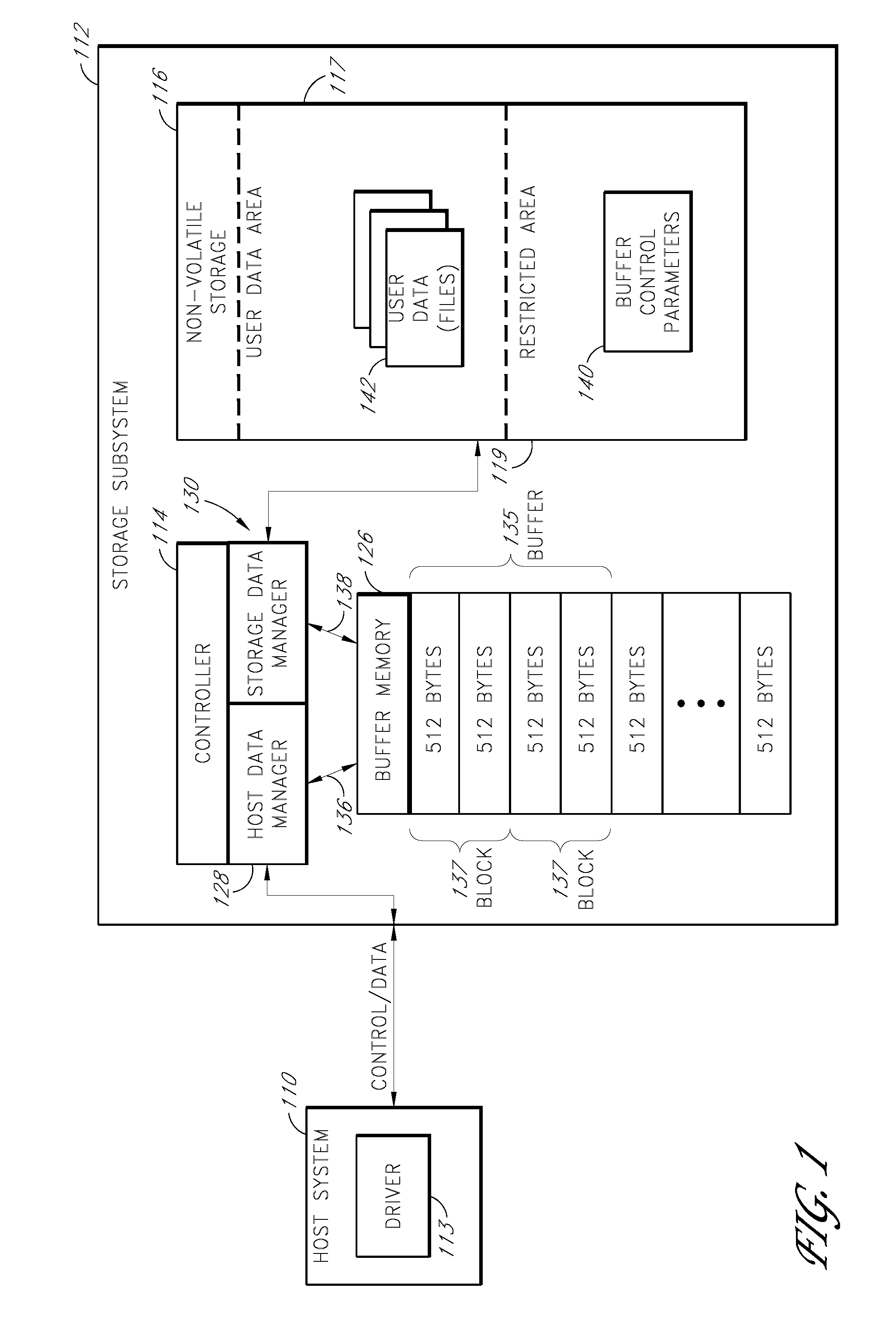
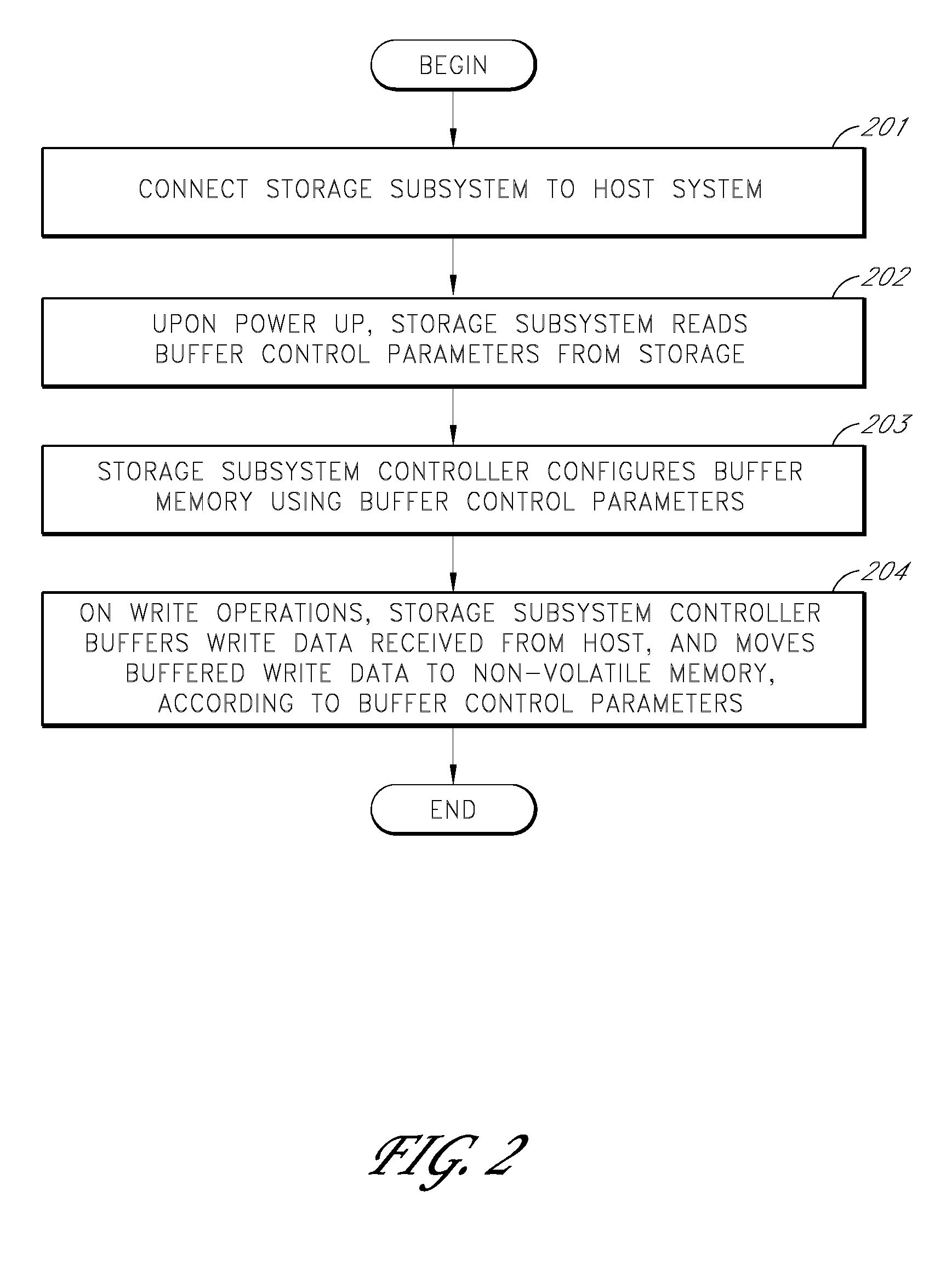
Storage subsystem with configurable buffer
ActiveUS7596643B2Reduce riskImprove performanceRecord information storageInput/output processes for data processingWrite bufferData loss
Owner:WESTERN DIGITAL TECH INC
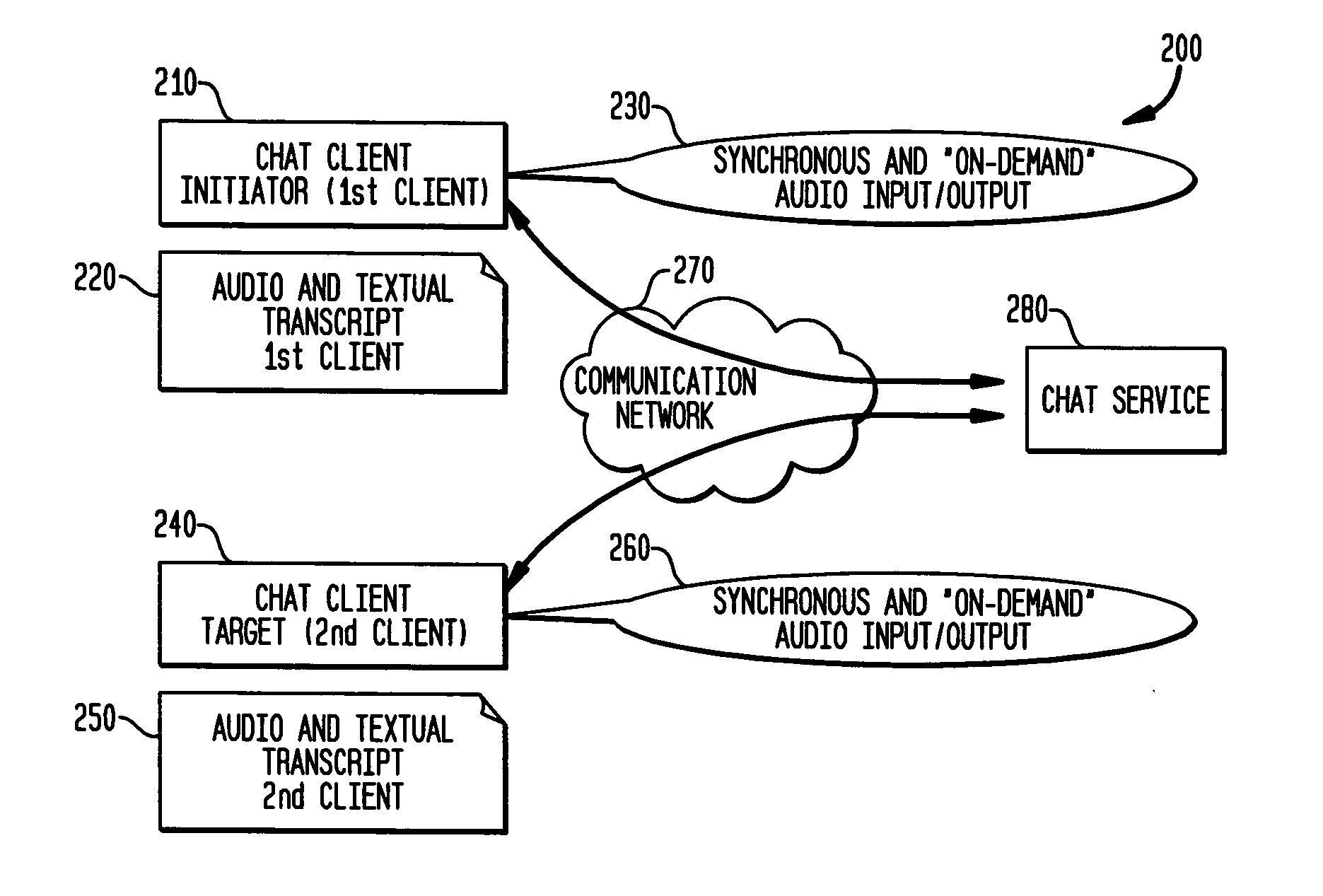
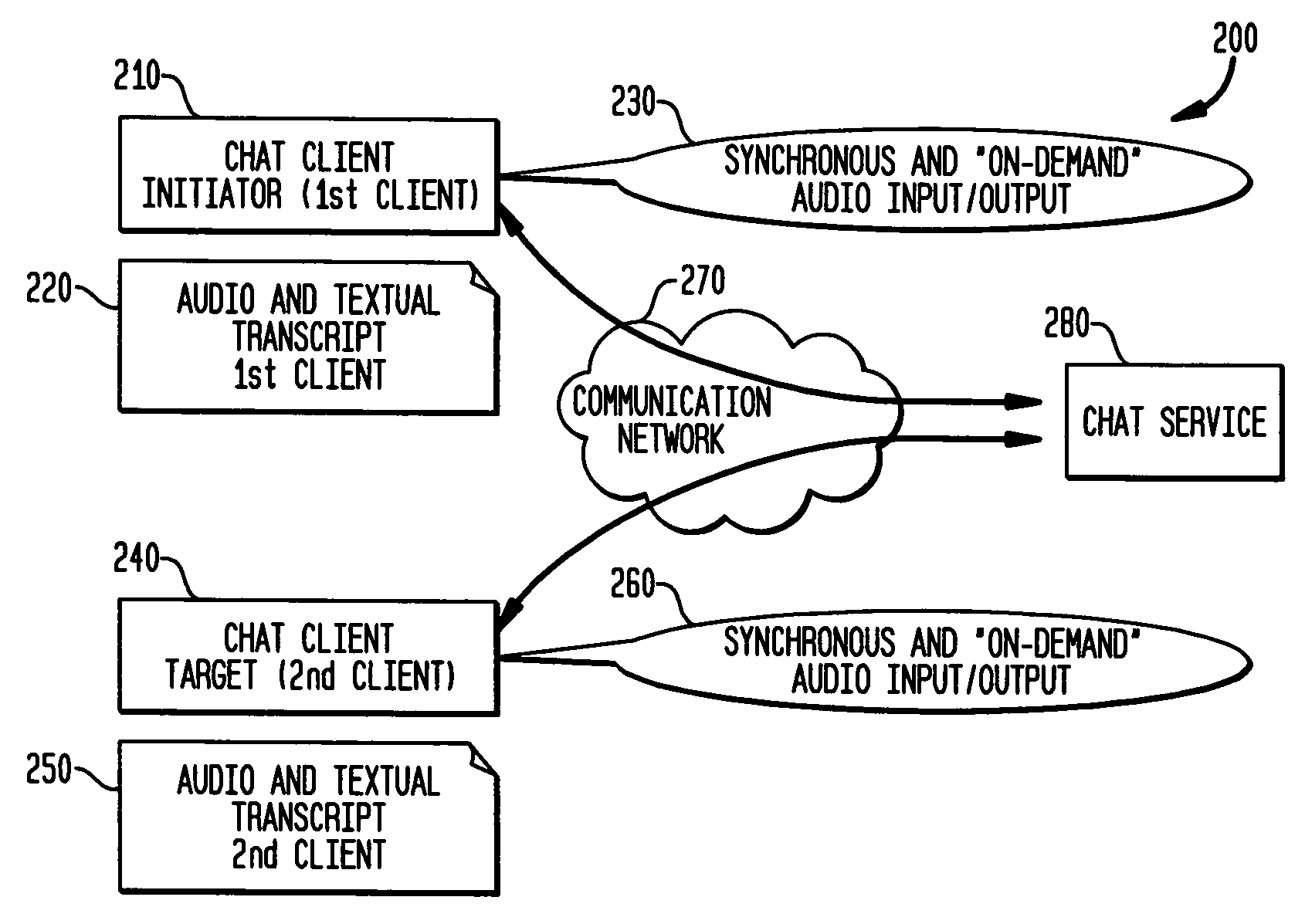
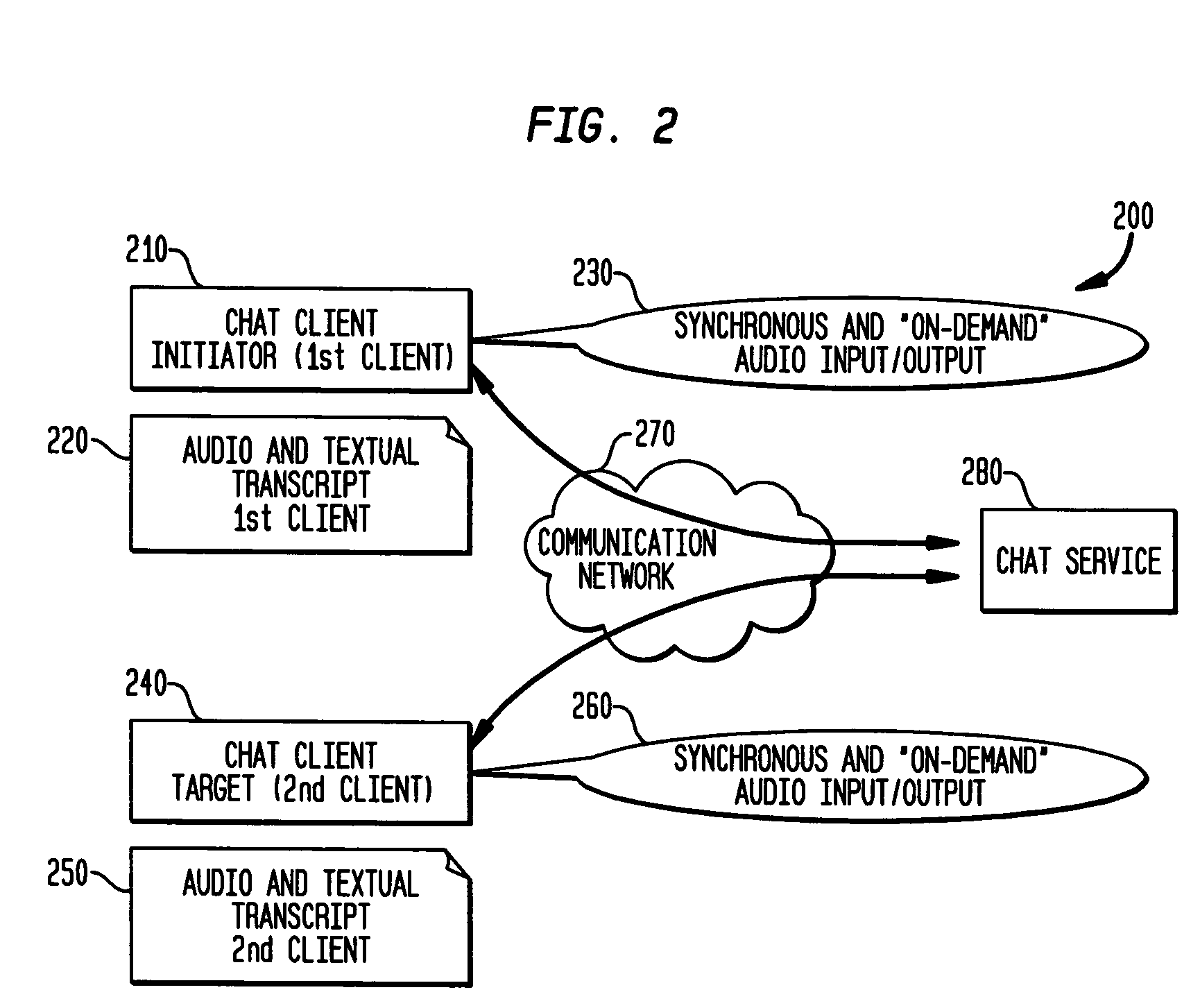
Method and system for voice on demand private message chat
ActiveUS20050144247A1Multiple digital computer combinationsData switching networksComputer hardwareText entry
A system and method for establishing a private message chat between electronic devices. The method includes steps of providing an indication as to the availability of a user for receiving a private message chat; receiving an audio input message from at least one first client; and transmitting the audio input message to at least one second client over a communications network, wherein the at least one second client can receive, temporarily store and play back the audio input message. The first client may receive a reply audio input message from the at least one second client or, receive a reply text input message from the at least one second client, and subsequently may further communicate back to the second client device via one of audio or text messaging, according to that user's discretion. The transmitting of any audio input message may be accomplished via VoIP or SIP.
Owner:ACTIVISION PUBLISHING
Medical/surgical waste collection and disposal system including waste containers of different storage volumes with inter-container transfer valve and independently controlled vacuum levels
ActiveUS20070135779A1Reduce the numberReduce tripsMechanical apparatusDispersed particle filtrationDocking stationWaste collection
A waste collection and disposal system for use in health care facilities is provided. The system includes a mobile waste collection unit for moving between use areas in the health care facility to collect waste material generated during medical procedures including body fluids, body tissues, saline, etc. The waste collection unit includes stacked upper and lower waste containers for receiving the waste material. During use, the upper waste container can be emptied into the lower waste container for temporary storage. In addition, different vacuum levels can be provided in the waste containers during complex procedures. Once a user desires to empty the waste collection unit, the waste collection unit is wheeled to a docking station. At the docking station, the waste material is off-loaded to a waste drain and the waste collection unit is cleaned and rinsed for further use.
Owner:STRYKER CORP
Method and system for voice on demand private message chat
ActiveUS7305438B2Multiple digital computer combinationsData switching networksComputer hardwareText entry
A system and method for establishing a private message chat between electronic devices. The method includes steps of providing an indication as to the availability of a user for receiving a private message chat; receiving an audio input message from at least one first client; and transmitting the audio input message to at least one second client over a communications network, wherein the at least one second client can receive, temporarily store and play back the audio input message. The first client may receive a reply audio input message from the at least one second client or, receive a reply text input message from the at least one second client, and subsequently may further communicate back to the second client device via one of audio or text messaging, according to that user's discretion. The transmitting of any audio input message may be accomplished via VoIP or SIP.
Owner:ACTIVISION PUBLISHING
Massive role-playing games or other multiplayer games system and method using cellular phone or device
A massive multiplayer role-playing game platform utilizing mobile devices such as cellular phones is disclosed. The invention links massive amounts of players, each holding at least one mobile device, via a cellular or wireless network. The system provides the user with the game data in a client-server method or in a streaming / buffering mode of operation. Most of the game data is stored on the game servers, and only the minimal amount of data is temporarily stored on the device's memory. The user may play in a single mode or group mode and several groups can join together to make a larger group. A game may be downloaded onto the mobile devices which may be linked to a base station. The base station in turn is connected to the network, which links it to the game server.
Owner:INNOVATION SYST
System and method for multi-tiered rule filtering
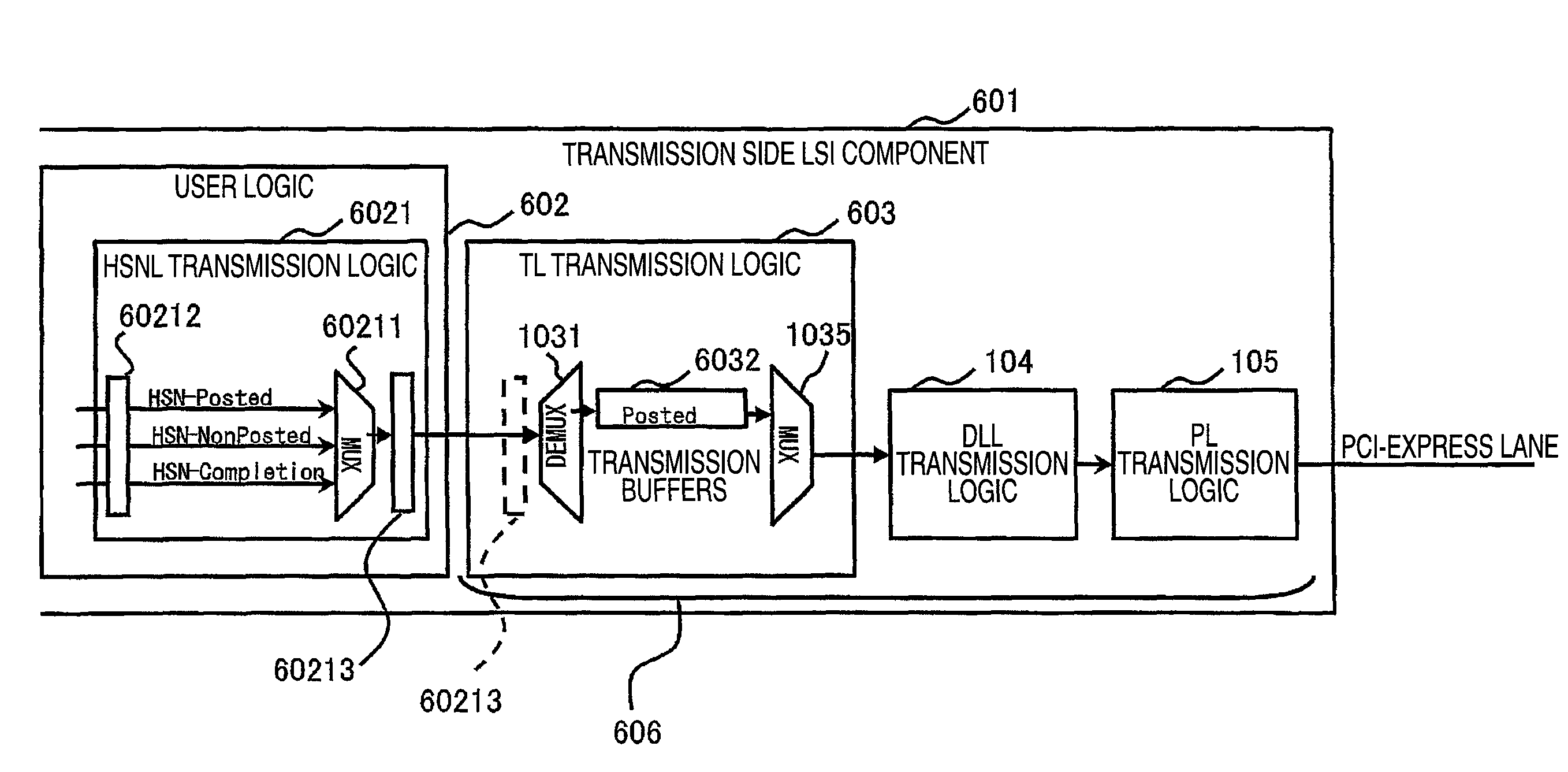
ActiveUS7027463B2Interconnection arrangementsData switching by path configurationRule setsTemporary storage
A system is described for processing messages and calls comprising: a plurality of filtering modules to apply a corresponding plurality of rule sets in succession to filter incoming and / or outgoing electronic messages and to apply the highest priority rule from among a plurality of rule sets to calls; and a pre-inbox for temporarily storing the calls and / or electronic messages as each of the plurality of rule sets are applied, the calls and / or electronic messages being removed from the pre-inbox and disposed of only after each of the plurality of rule sets have been applied to the calls and / or electronic messages.
Owner:CATALYSTWEB
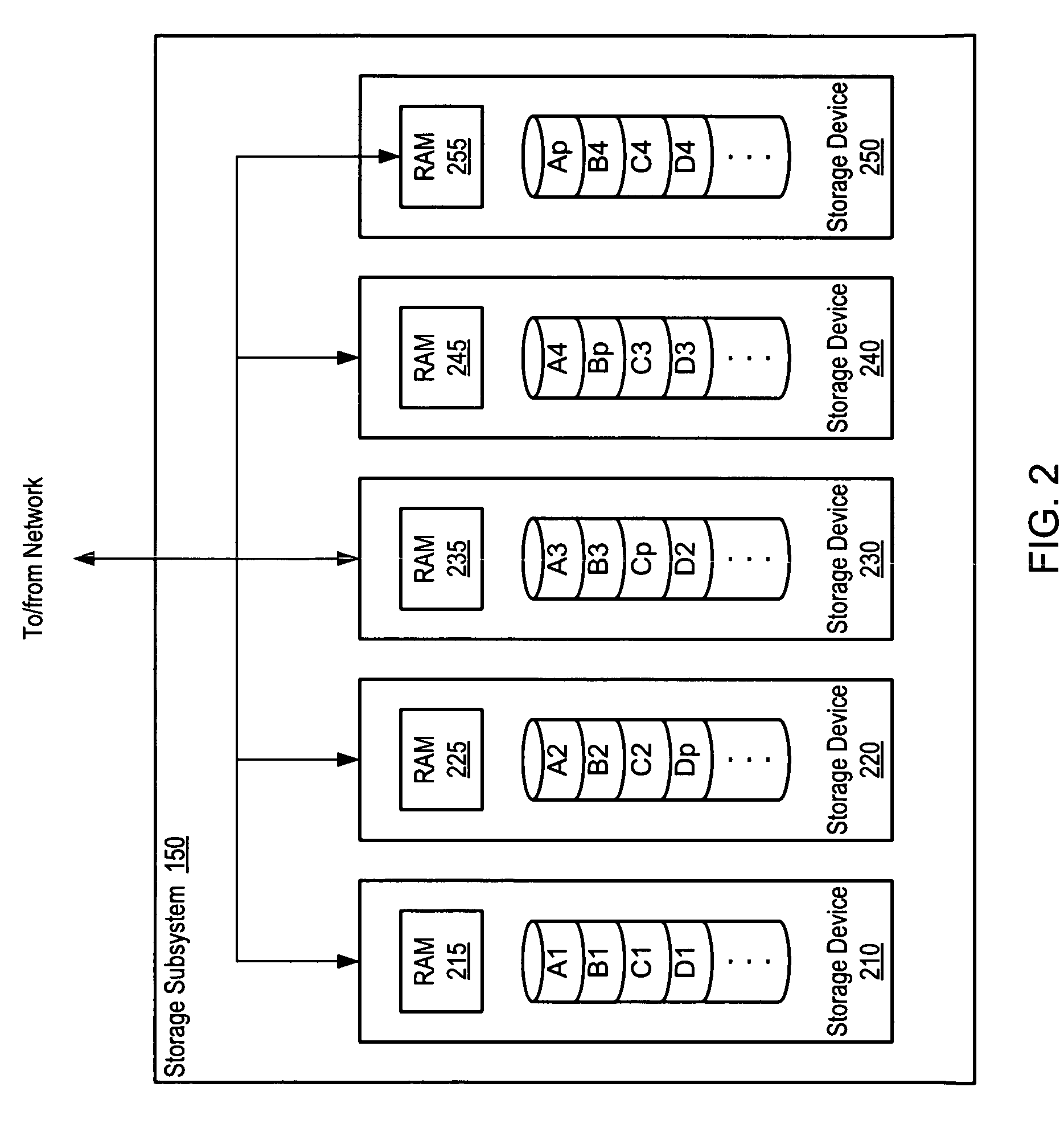
System and method of redundantly storing and retrieving data with cooperating storage devices
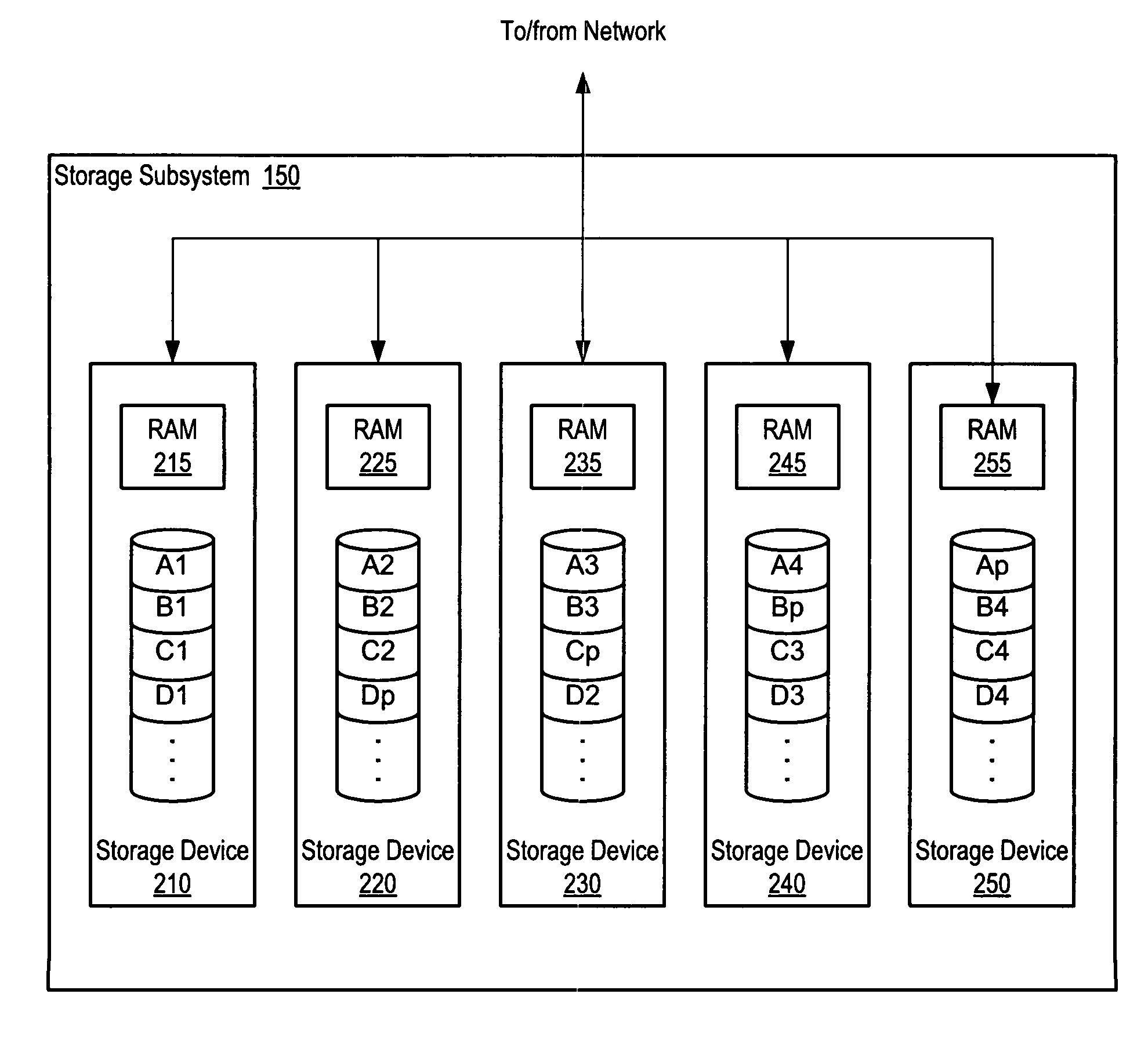
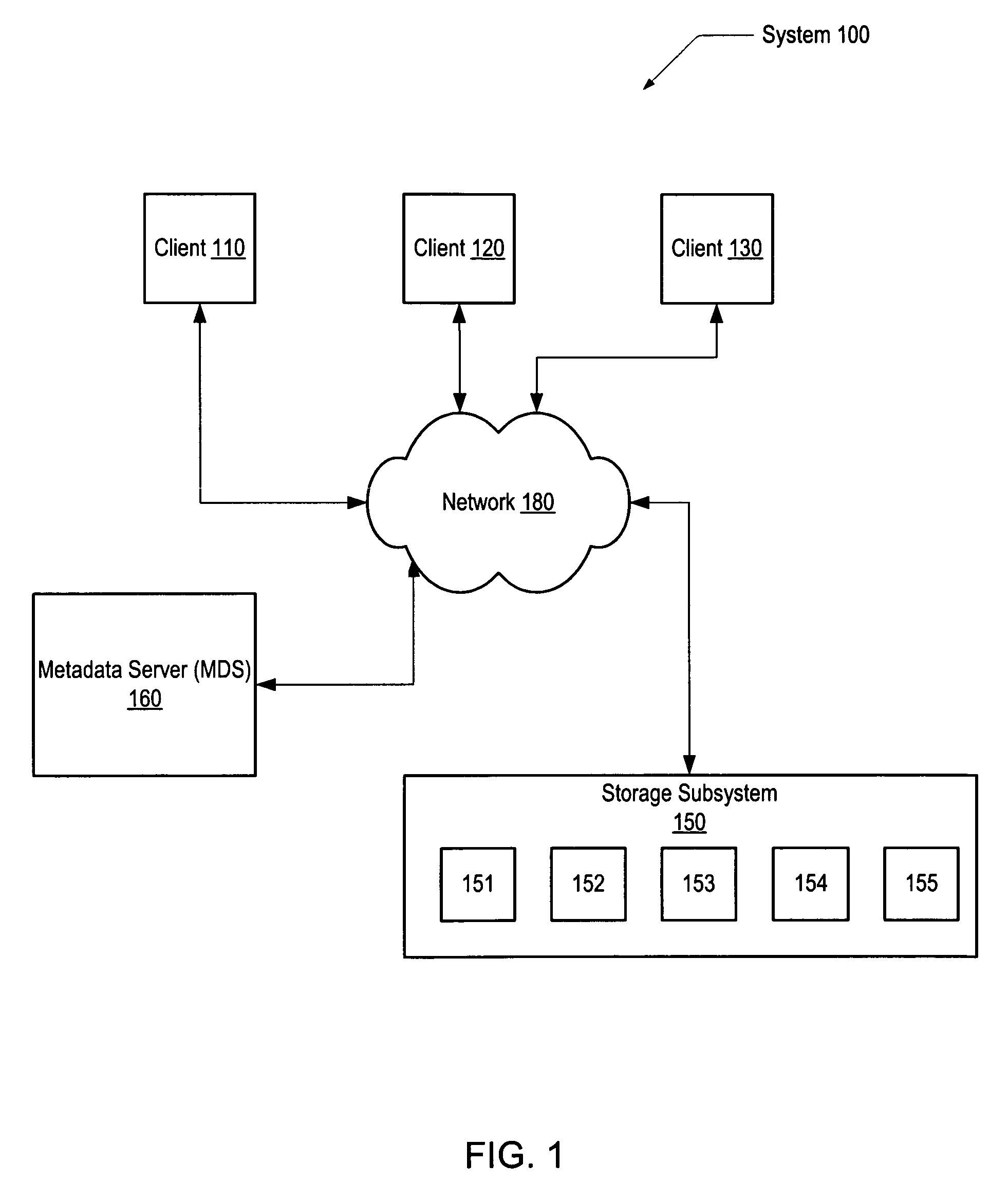
A system and method for data storage in an array. A system includes a client coupled to a storage subsystem. The storage subsystem comprises data storage locations addressable as rows and columns in an array. Each column comprises a separate storage device. Each row includes redundant data. For a given row, a coordinating storage device receives data from the client, coordinates computation and storage of redundant data, and forwards data to other storage devices. In response to receiving data targeted for storage in a given storage location, a non-volatile, temporary storage device that is associated with the separate storage device that includes the given storage location buffers the received data. The coordinating storage device conveys a write completion message to the client in response to detecting that the data has been buffered in the non-volatile, temporary storage devices. At least two storage devices are coordinating storage devices in separate rows.
Owner:VERITAS TECH
Method and apparatus for interacting with broadcast programming
ActiveUS20060062363A1Television system detailsReceiver side switchingBroadcast channelsRelevant information
A method of and apparatus for allowing a user using a communications device to interact with first media material that is broadcast on a first broadcast channel y a first broadcast media source and second media material that is broadcast on a second broadcast channel by a second broadcast media source, the first media material and the second media material include a first media item and a second media item, respectively, the first media item and the second media item are associated with a first representation of the first media item and a representation of the second media item, respectively, that are received and presented by a broadcast reception device while the broadcast reception device is tuned to a third broadcast channel. The method includes maintaining in a temporary storage an item identifier, the item identifier identifies one of a first media item-related information and a second media item-related information. Additionally, when the broadcast reception device is tuned to the third broadcast channel and presents the first representation of the first media item, the method includes providing the item identifier as a basis for identifying the first media item-related information, the first media item-related information is a basis for a response to an interactivity activation made in reaction to presentation of the first representation of the first media item by the broadcast reception device. When the broadcast reception device is tuned to the third broadcast channel and presents the first representation of the second media item, the method includes providing the item identifier as a basis for identifying the second media item-related information, the second media item-related information is a basis for a response to an interactivity activation made in reaction to presentation of the representation of the second media item by the broadcast reception device.
Owner:ADAM ALBRETT +1
Endurance Translation Layer (ETL) and Diversion of Temp Files for Reduced Flash Wear of a Super-Endurance Solid-State Drive
ActiveUS20150106556A1Memory architecture accessing/allocationMemory adressing/allocation/relocationFilename extensionData file
A flash drive has increased endurance and longevity by reducing writes to flash. An Endurance Translation Layer (ETL) is created in a DRAM buffer and provides temporary storage to reduce flash wear. A Smart Storage Switch (SSS) controller assigns data-type bits when categorizing host accesses as paging files used by memory management, temporary files, File Allocation Table (FAT) and File Descriptor Block (FDB) entries, and user data files, using address ranges and file extensions read from FAT. Paging files and temporary files are never written to flash. Partial-page data is packed and sector mapped by sub-sector mapping tables that are pointed to by a unified mapping table that stores the data-type bits and pointers to data or tables in DRAM. Partial sectors are packed together to reduce DRAM usage and flash wear. A spare / swap area in DRAM reduces flash wear. Reference voltages are adjusted when error correction fails.
Owner:SUPER TALENT TECH CORP
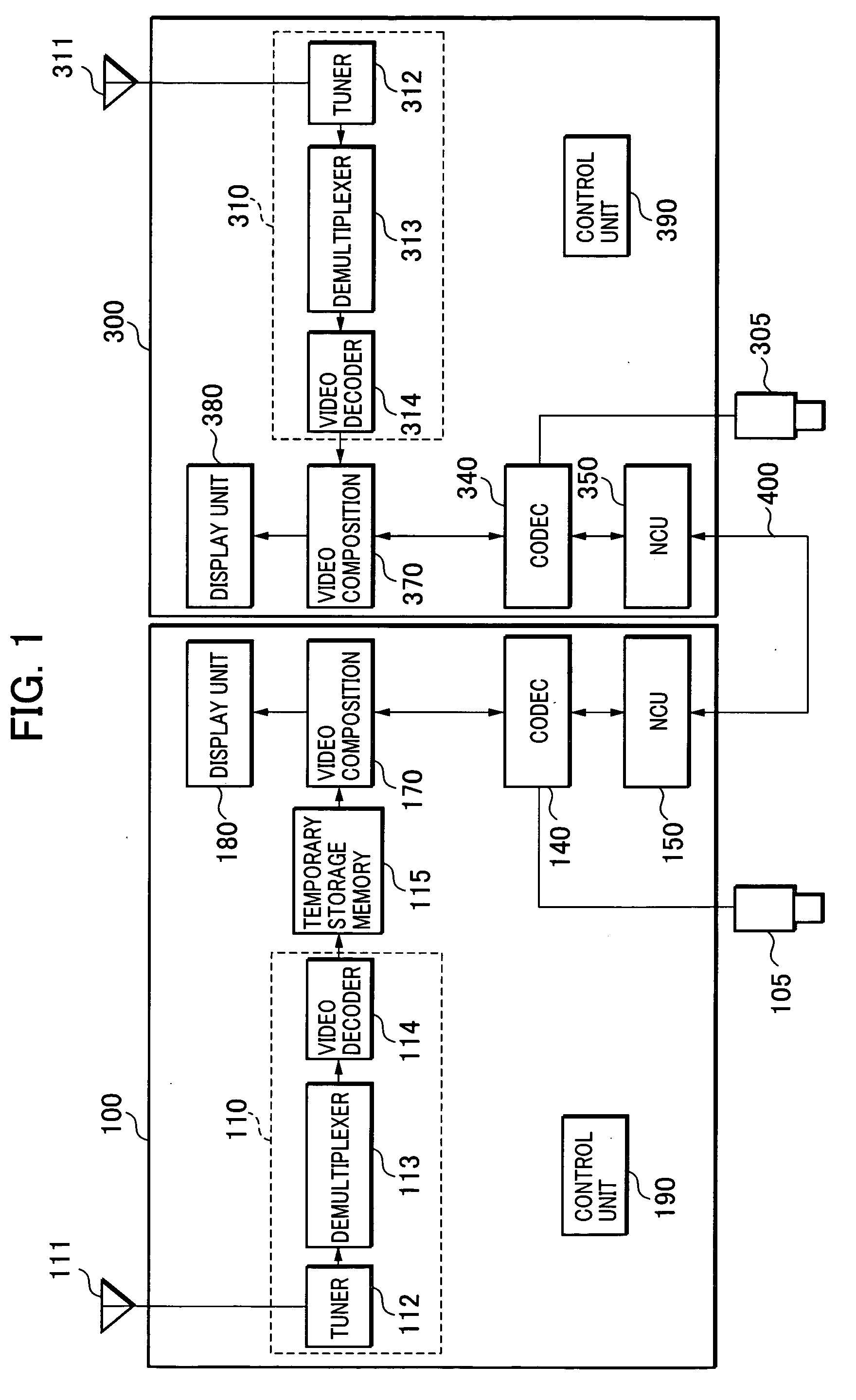
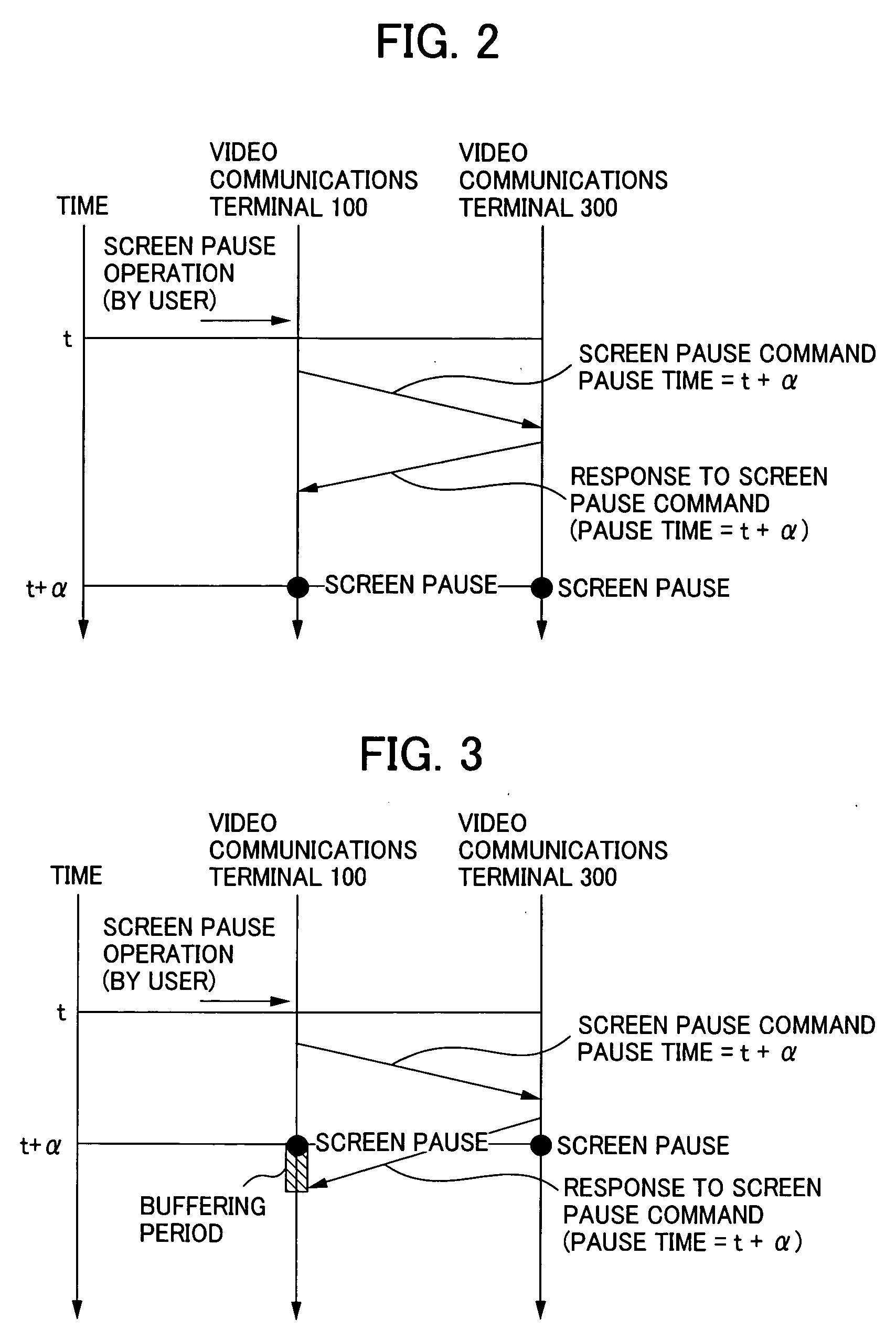
Visual communications system and method of controlling the same
InactiveUS20050166242A1Television system detailsAnalogue secracy/subscription systemsCommunications systemComputer science
A visual communications system and a method of controlling the same for pausing the screens of two terminals at quite the same image. Video communications terminals receive the same channel in their respective broadcast program receiving units. A first video communications terminal temporarily stores the video of the received channel in the temporary storage memory. When a user pauses operation of the first terminal, it temporarily stores a screen pause time obtained by adding a predetermined time to the current time, and transmits a screen pause command and the screen pause time to a second video communications terminal. The second terminal pauses the video at the screen pause time if possible in time. Otherwise, it pauses the video immediately, and transmits a response with its own image pause time to the first terminal. The first terminal displays an image corresponding to the image pause time of the second terminal memory.
Owner:CANON KK
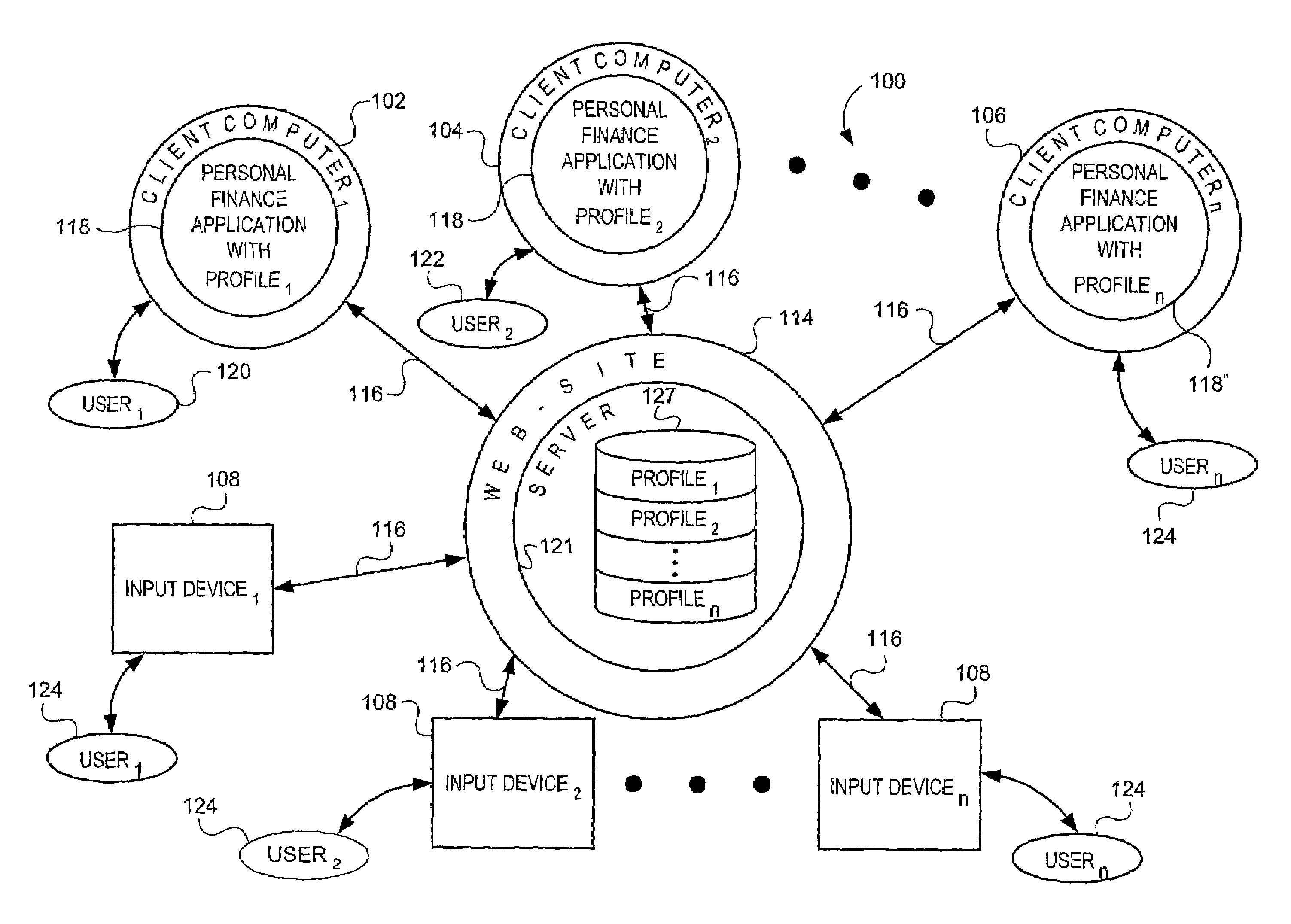
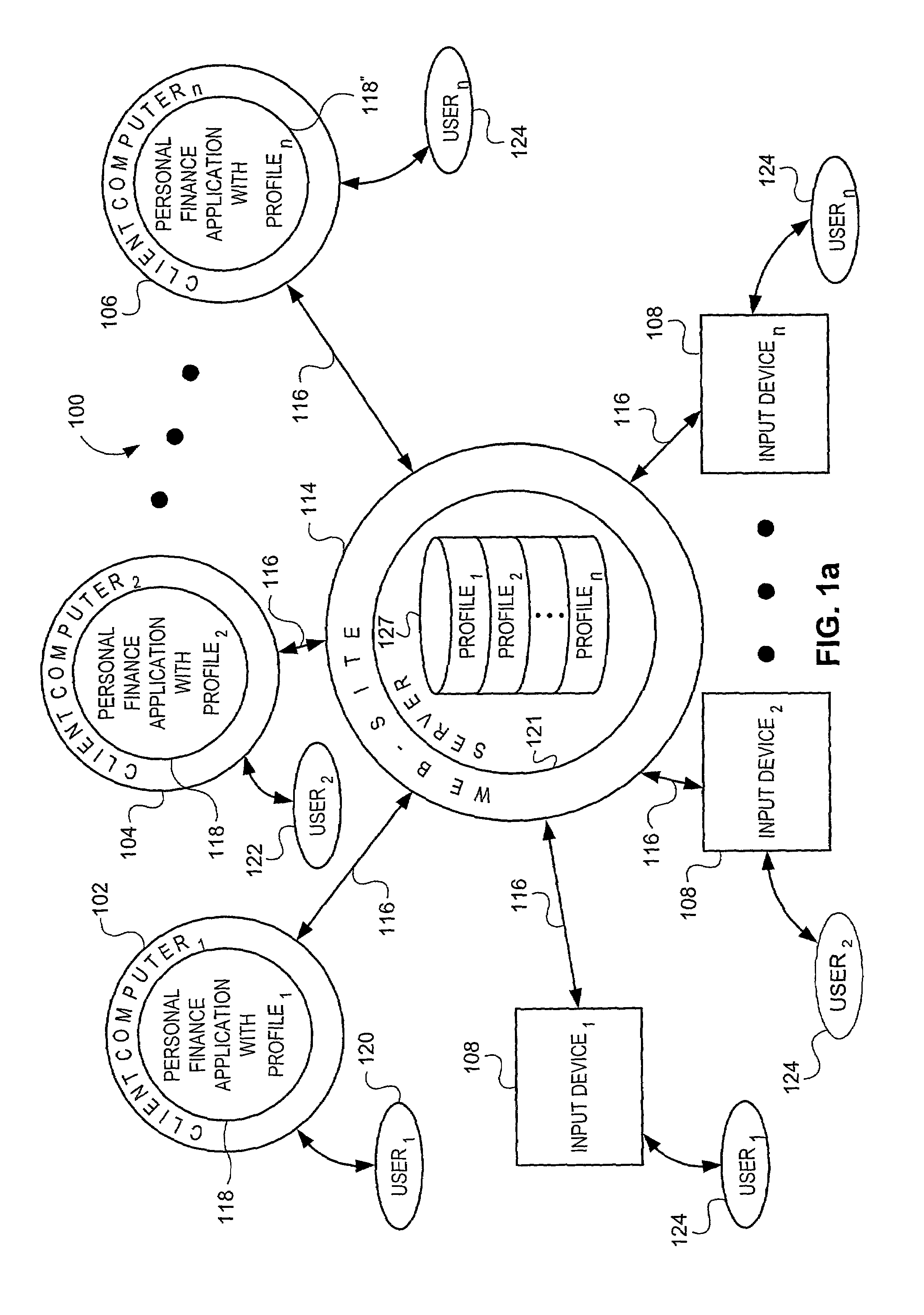
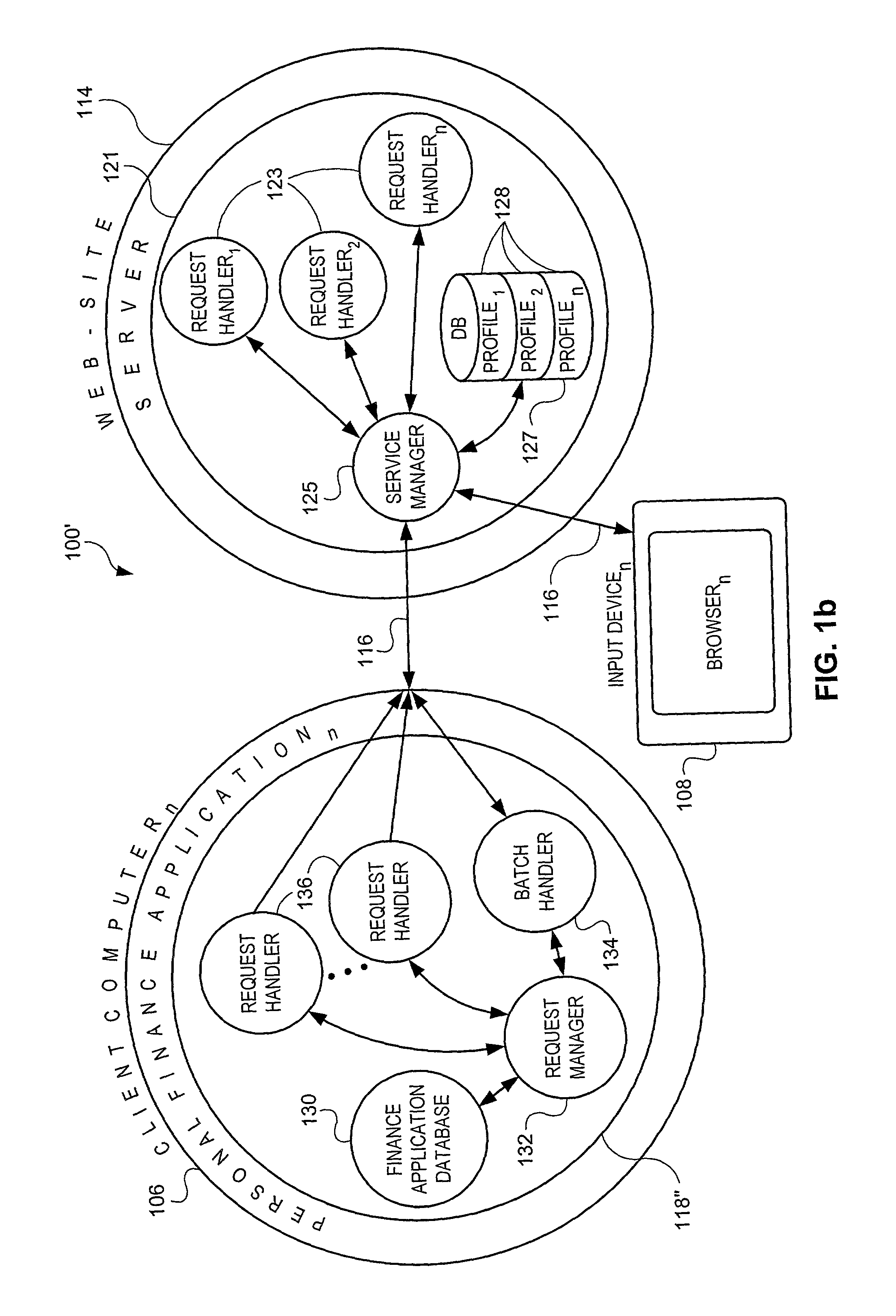
Web-based entry of financial transaction information and subsequent download of such information
InactiveUS7729959B1Reduce probabilityImprove timelinessComplete banking machinesFinanceWeb siteFinancial transaction
The systems, methods and related software products which enable users to temporarily store and subsequently retrieve information are disclosed. The system includes a plurality of input devices, client computers (each having a user-specific personal finance application) and a web-site server with a database. The input devices, client computers and server are communicatively linked via a communication network so that a plurality of users can temporarily store and / or manipulate financial transaction information on the server from any of the input devices. Each user can also transmit financial profile information to the server. This information enables the server to replicate the unique profile characteristics for each of the finance applications. This, in turn, simplifies remote entry of information, subsequent download of that information and integration of such information into each user's personal finance application.
Owner:INTUIT INC
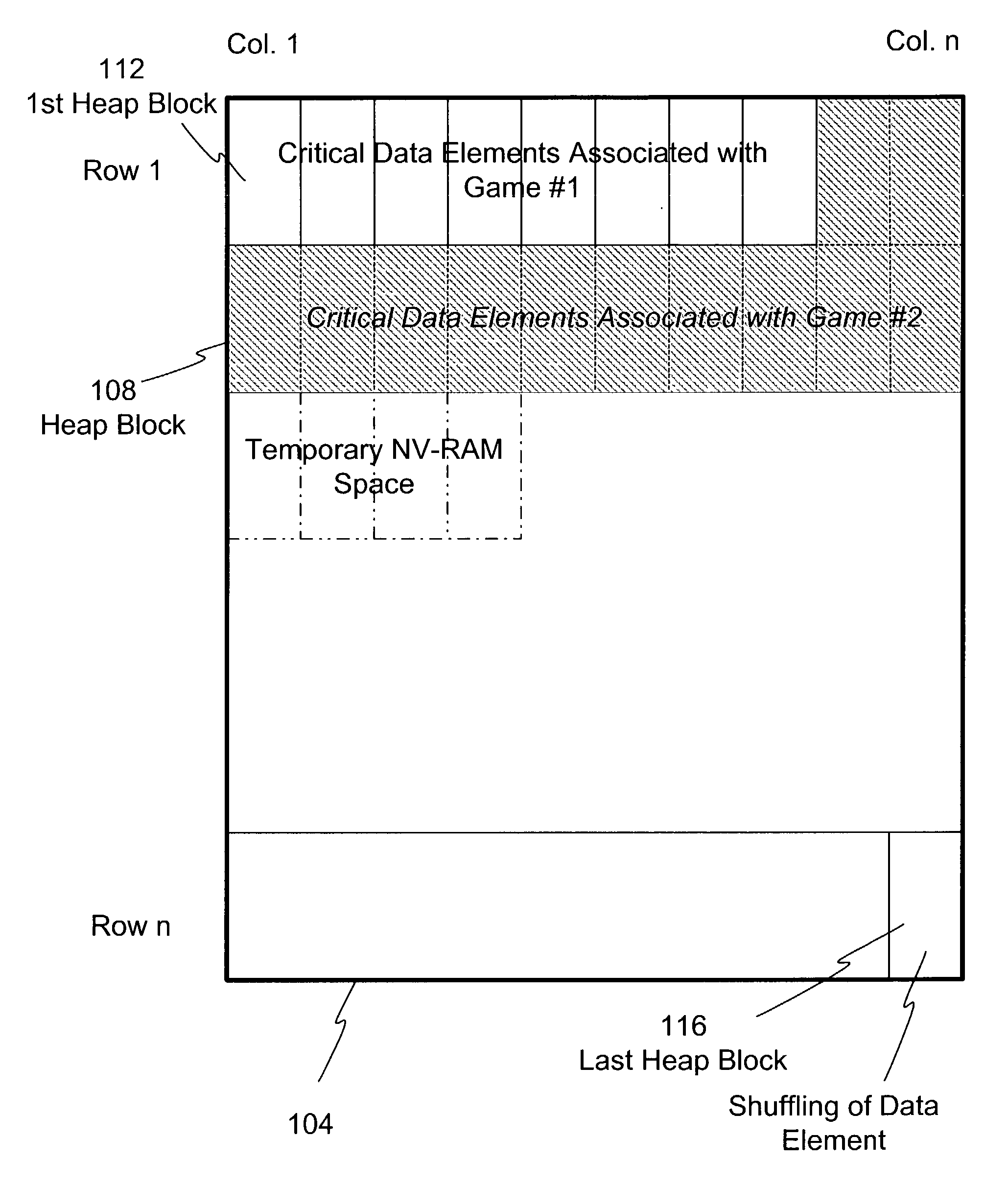
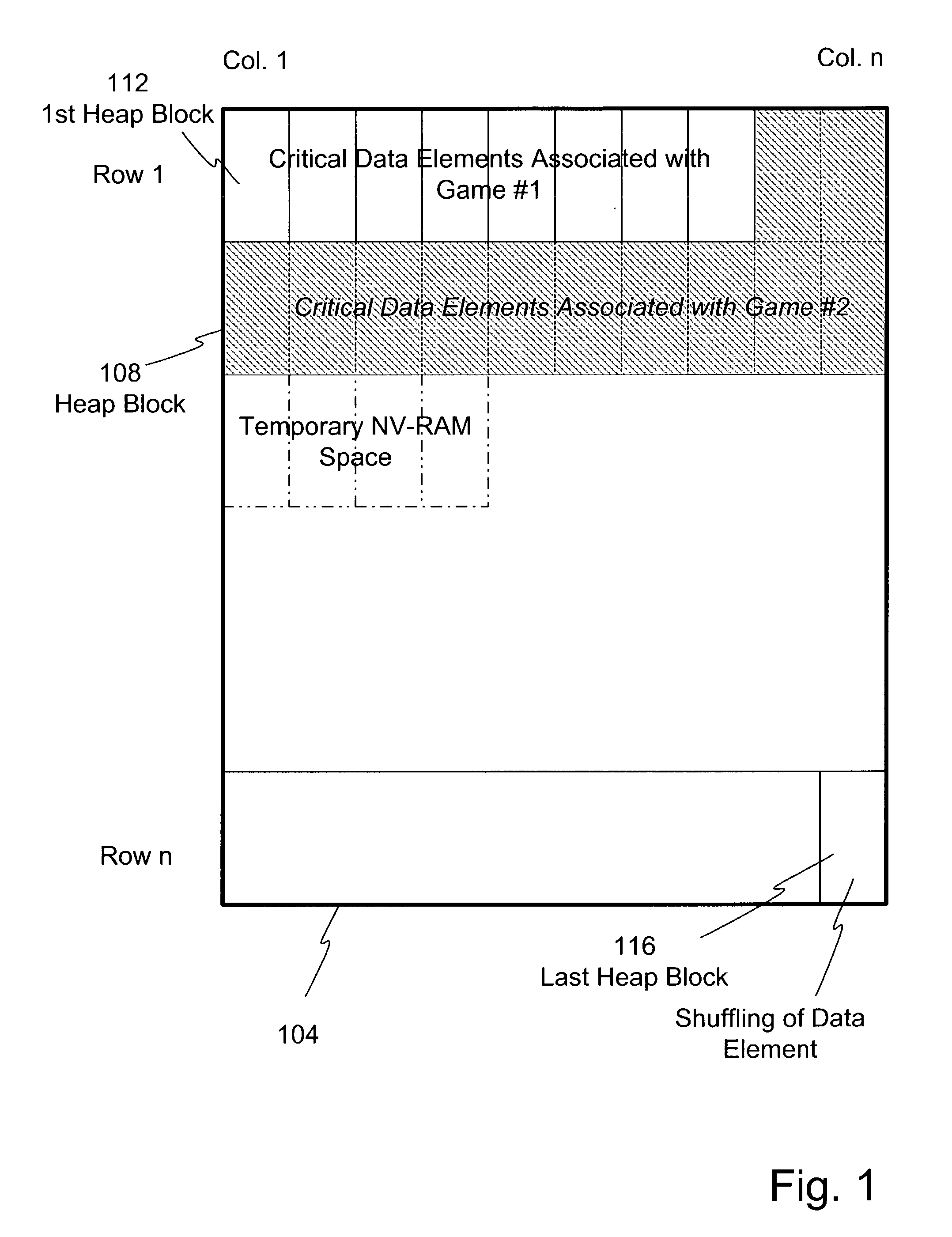
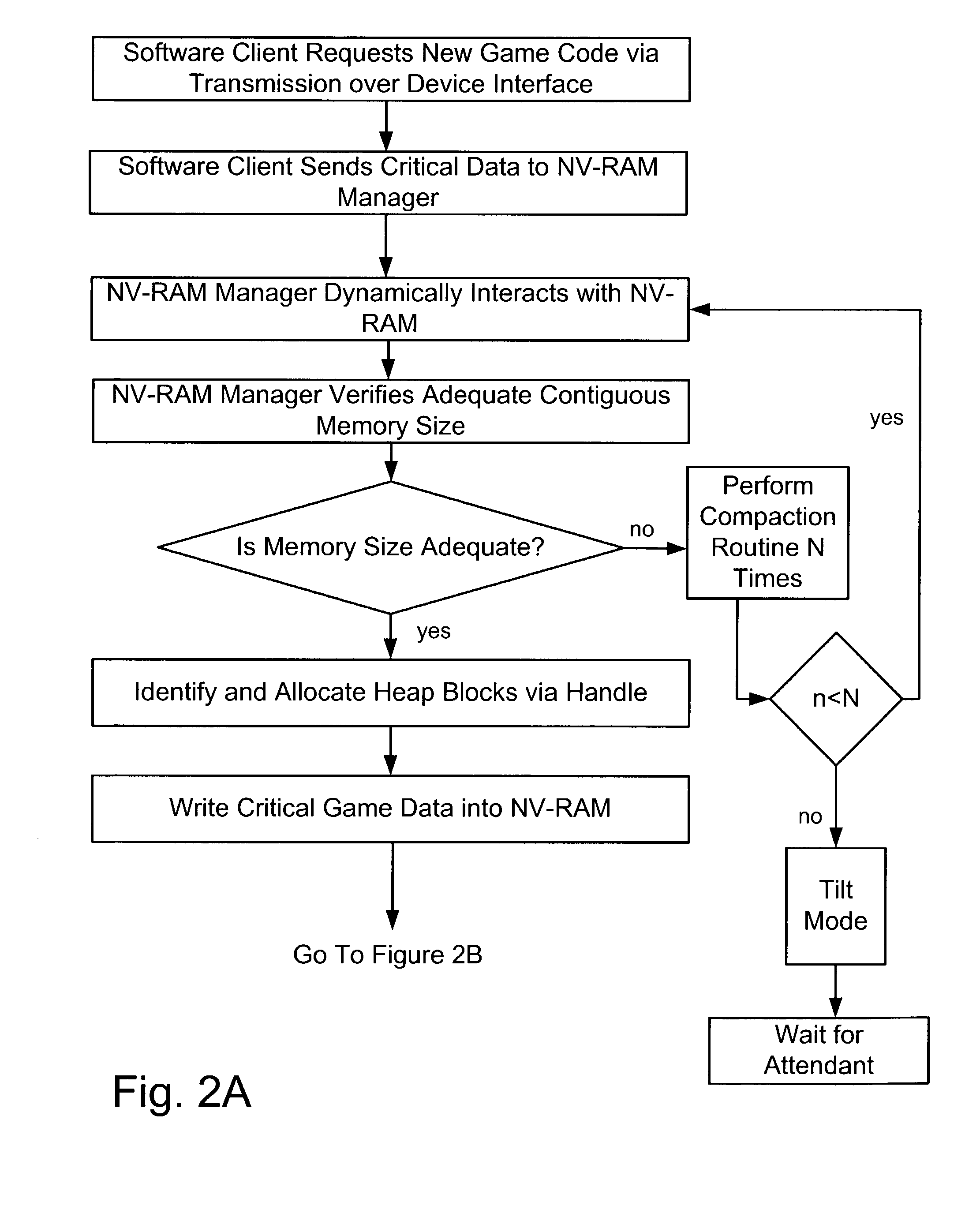
Dynamic NV-RAM
InactiveUS7111141B2Maximize useMemory architecture accessing/allocationMemory adressing/allocation/relocationParallel computingDynamic storage
A method and apparatus of dynamically storing critical data of a gaming machine by allocating and deallocating memory space in a gaming machine is disclosed. One or more embodiments describe downloading or removing a new game to a gaming machine such that all existing critical data in NV-RAM memory is left intact. In one embodiment, the invention discloses a method and apparatus for dynamically allocating and deallocating memory space to accommodate either permanent or temporary storage in an NV-RAM. A method and apparatus is provided to monitor available memory space and dynamically resize the memory in NV-RAM. In one embodiment, a method is disclosed for performing an integrity check of the NV-RAM and determining whether a critical data error has occurred. In one or more embodiments, methods of compacting and shifting contents of an NV-RAM are described to consolidate available memory space or to prevent unauthorized access of NV-RAM memory.
Owner:IGT
Storage system disposed with plural integrated circuits
InactiveUS8010720B2Increase profitImprove utilization efficiencyTransmissionInput/output processes for data processingSystem configurationEngineering
Owner:HITACHI LTD
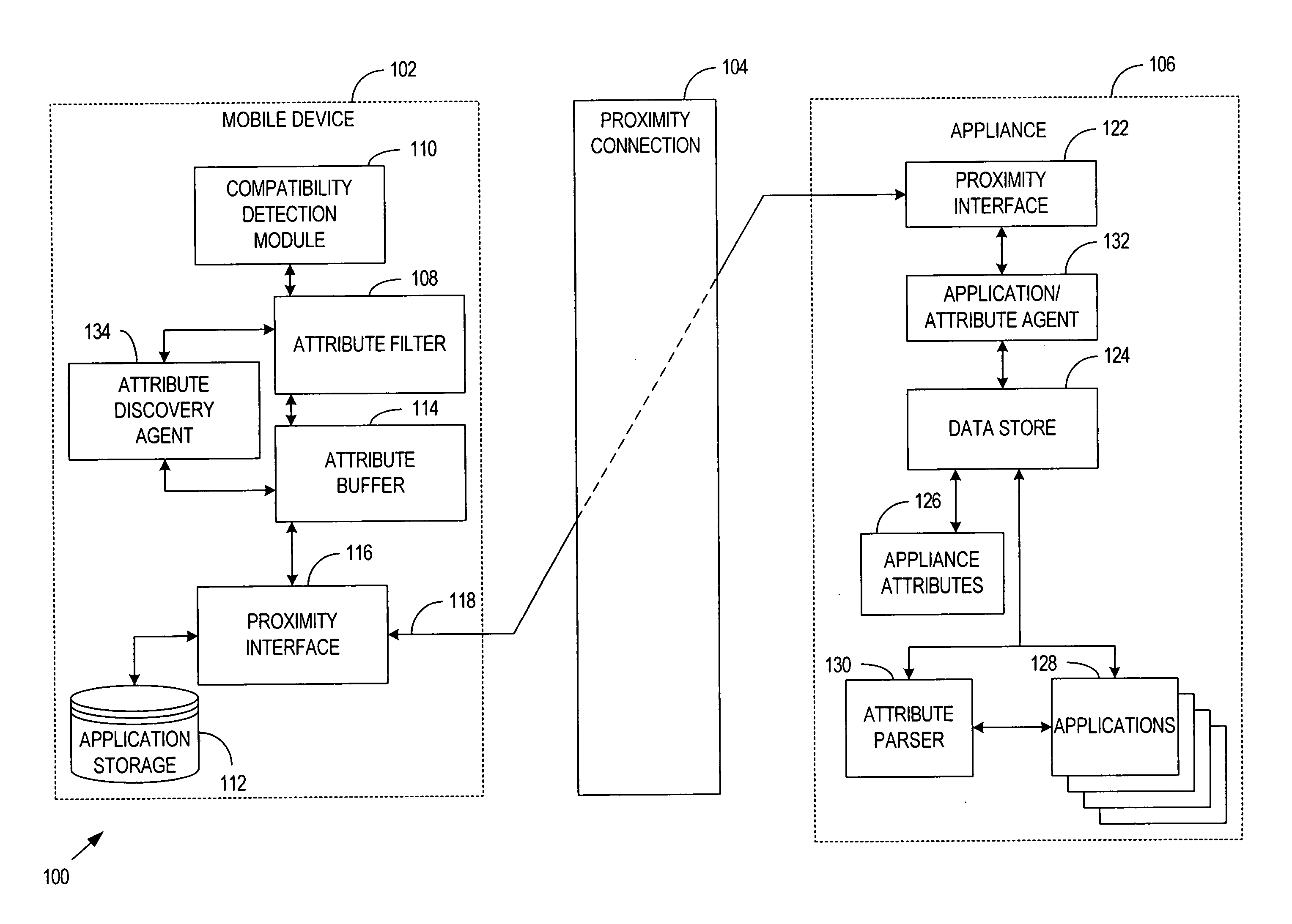
System, method and apparatus for data transfer between computing hosts
A system, method and apparatus to facilitate application and data transfer between a computation host acting as an application source and a computation host acting as an application target. Sufficient execution logic and static data exists between the two computation hosts and a third party interrogation device to allow a determination of the compatibility of applications resident within the source computation host and the application target, as well as the determination of the compatibility between the applications and the interrogation device itself. If compatibility exists, transfer of the applications between the computation hosts via the third party interrogation device is facilitated, whereby the interrogation device supplies temporary storage for the applications.
Owner:NOKIA SOLUTIONS & NETWORKS OY
Processing apparatus and recording medium
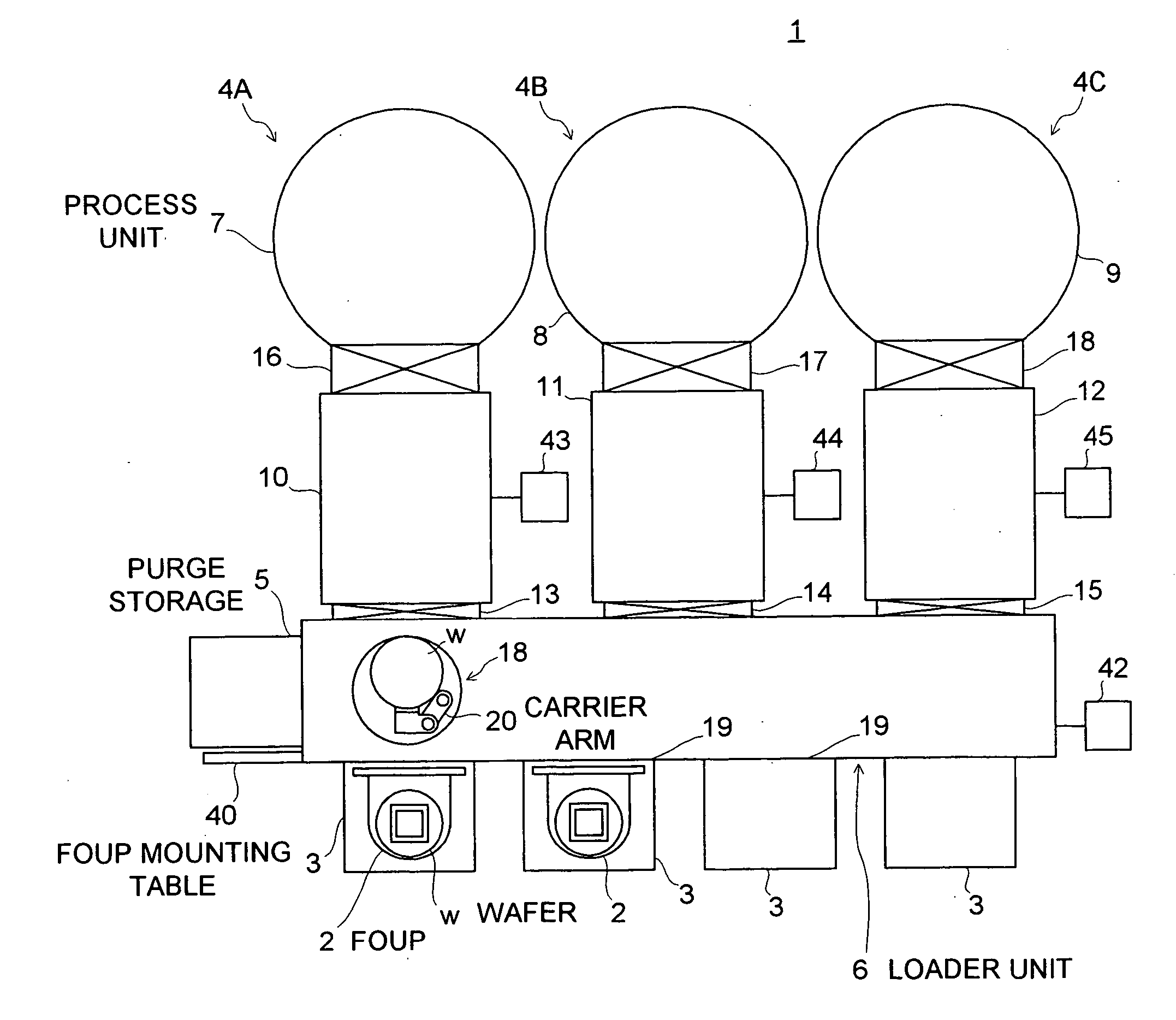
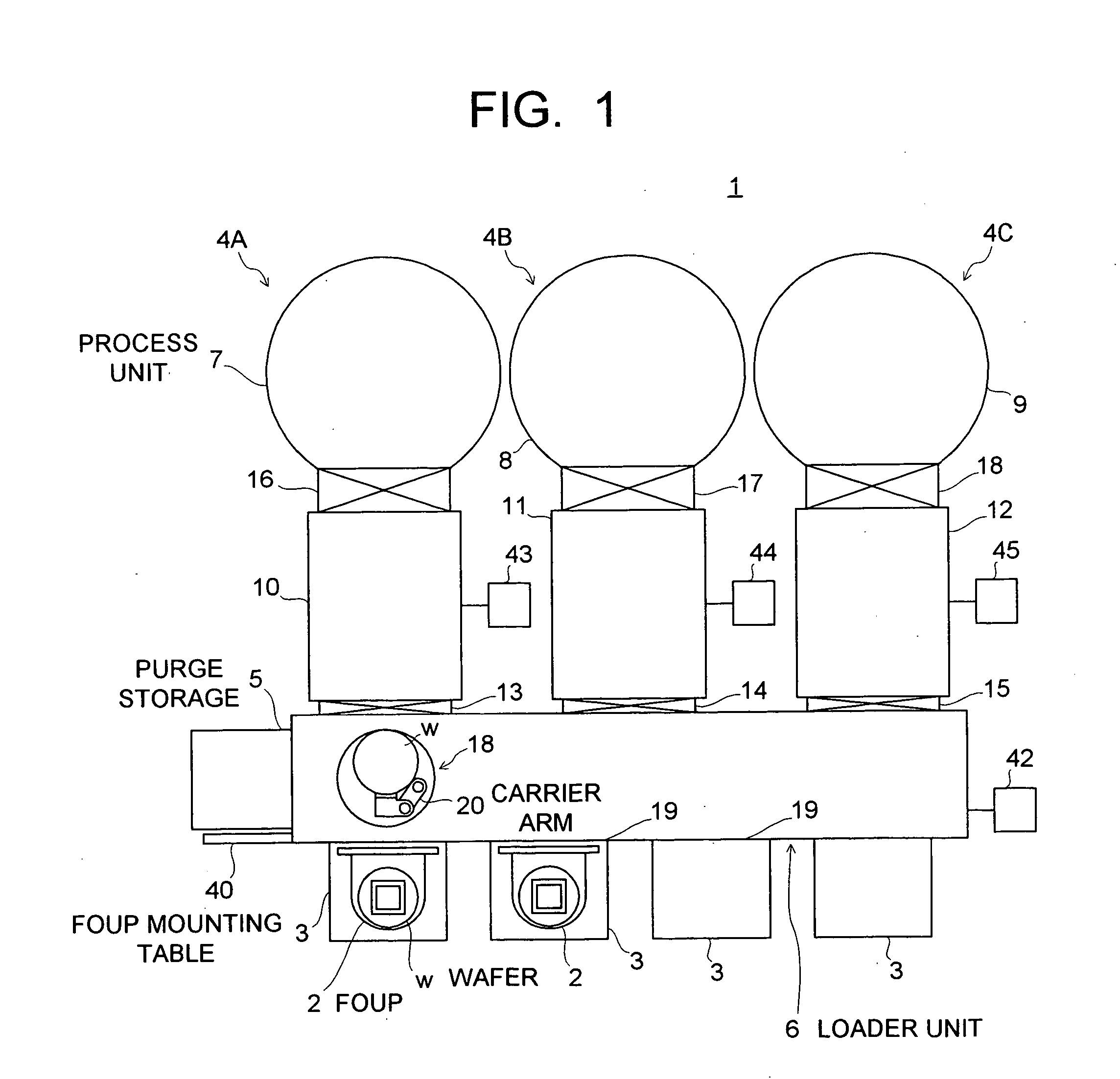
InactiveUS20060215347A1Easy to detectAvoid breakingSemiconductor/solid-state device manufacturingEngineeringMechanical engineering
A processing apparatus includes: a mounting table on which a carriage container containing a plurality of substrates is placed; a process chamber in which predetermined processing is applied to the substrate; a temporary storage unit having a substrate loading part on which the plural processed substrates are loaded in multi-tiers; a transfer unit having a carrier arm carrying the substrate to / from the carriage container on the mounting table, the process chamber, and the temporary storage unit; a vibration sensor detecting vibration of the substrate loading part; and a control unit which compares a current detection value of the vibration sensor with a predetermined set value to judge whether or not the vibration is abnormal vibration and to stop the carrier arm when judging that the vibration is the abnormal vibration.
Owner:TOKYO ELECTRON LTD
Method for preventing malicious software installation on an internet-connected computer
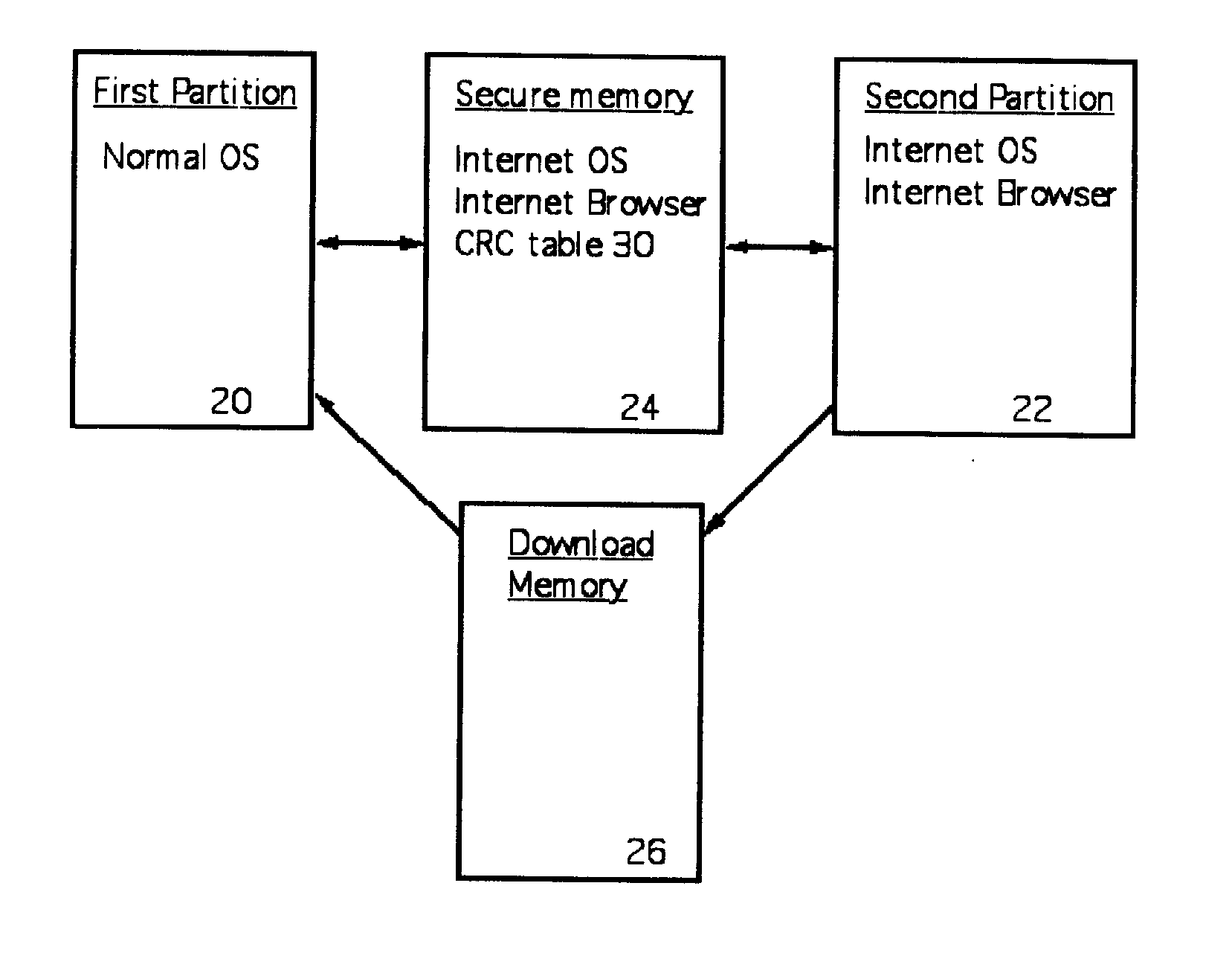
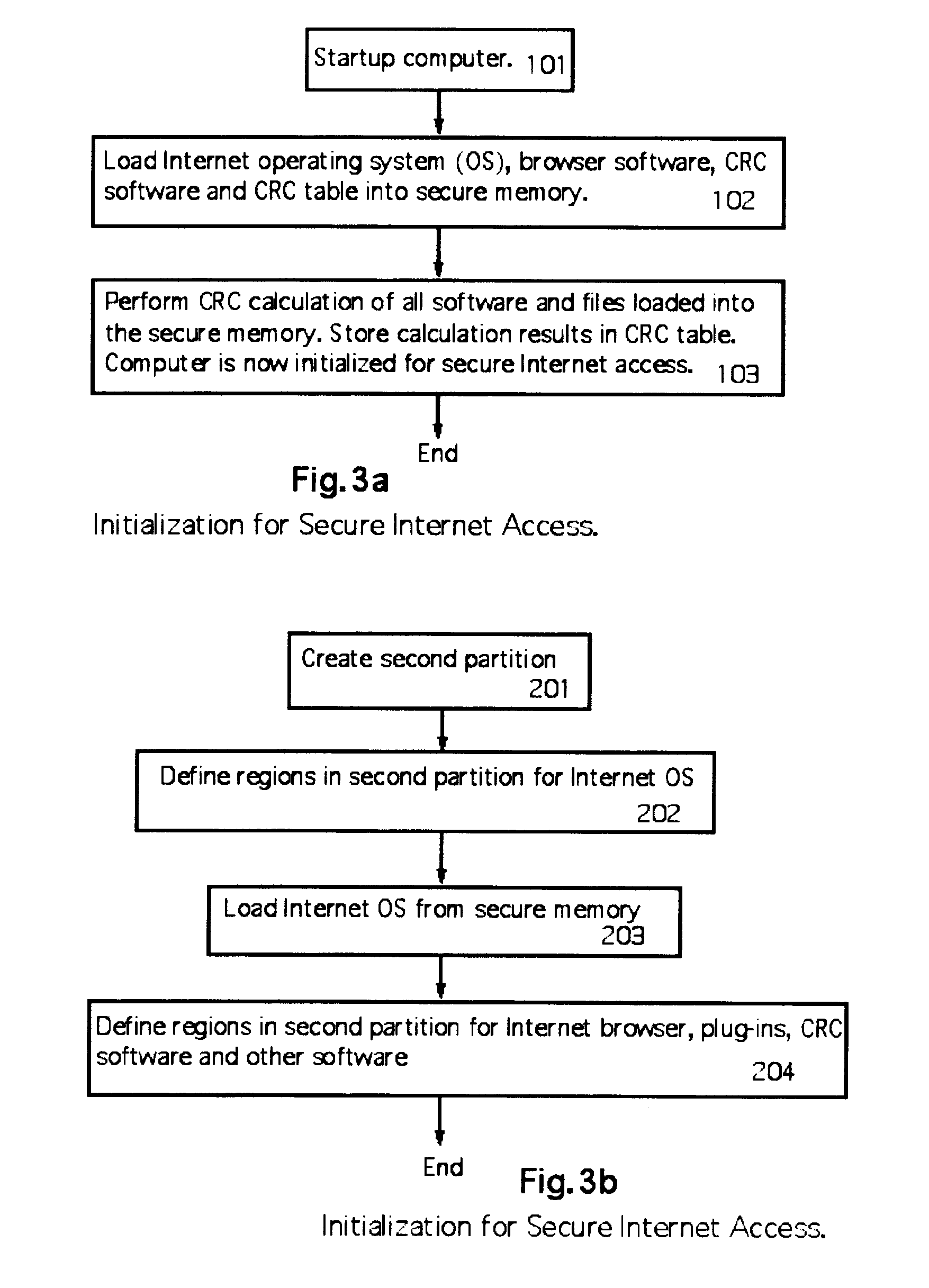
ActiveUS20070192854A1Prevents gaining accessAvoid accessMemory loss protectionDigital data processing detailsOperational systemTerm memory
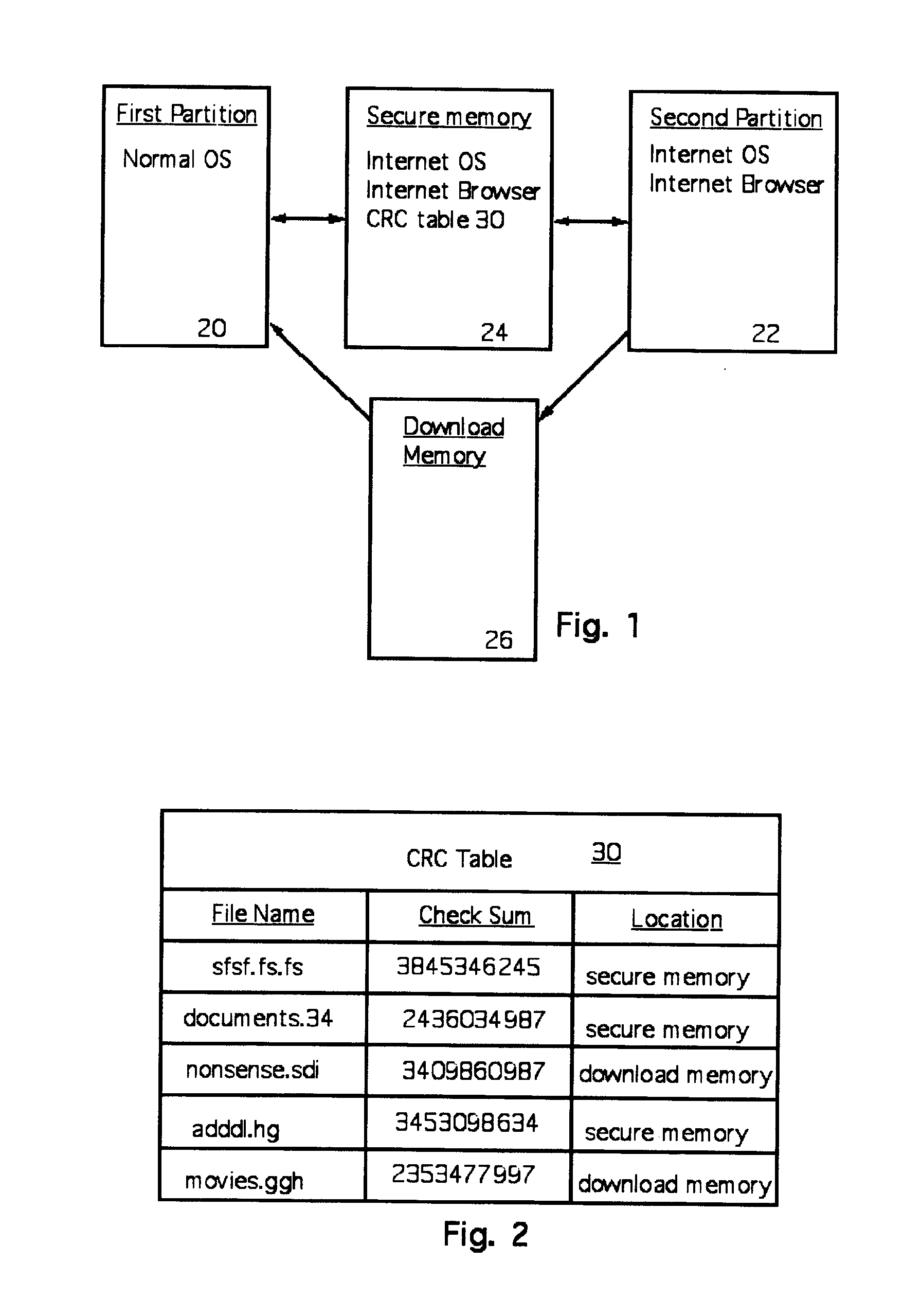
A computer random access memory is divided into first and second partitions. Each partition has its own operating system (OS). The first partition has a conventional OS and is designated for non-Internet use. The second partition is designated for secure Internet access, and has an OS specific for Internet usage. Software in the second partition cannot write or copy files in the second partition. The size of the second partition is fixed and unchangeable while said second partition is open. Each software application in the second partition is allocated a memory region that cannot be changed, thereby preventing memory overflow attacks. A secure memory is designated for temporary storage of software used in the second partition. Cyclic redundancy check (CRC) values are calculated for all files in the secure memory. To detect unauthorized file changes, CRC values are calculated for all files used in the second partition, and checked against values stored in the secure memory. The second partition can write only to a secure memory using a security arrangement such as password protection or a download memory separate from the first partition to allow files stored in the download memory to be examined by scanning and testing from the first partition prior to being stored elsewhere in the computer.
Owner:KYNDRYL INC
System and method for improving the effectiveness of web advertising
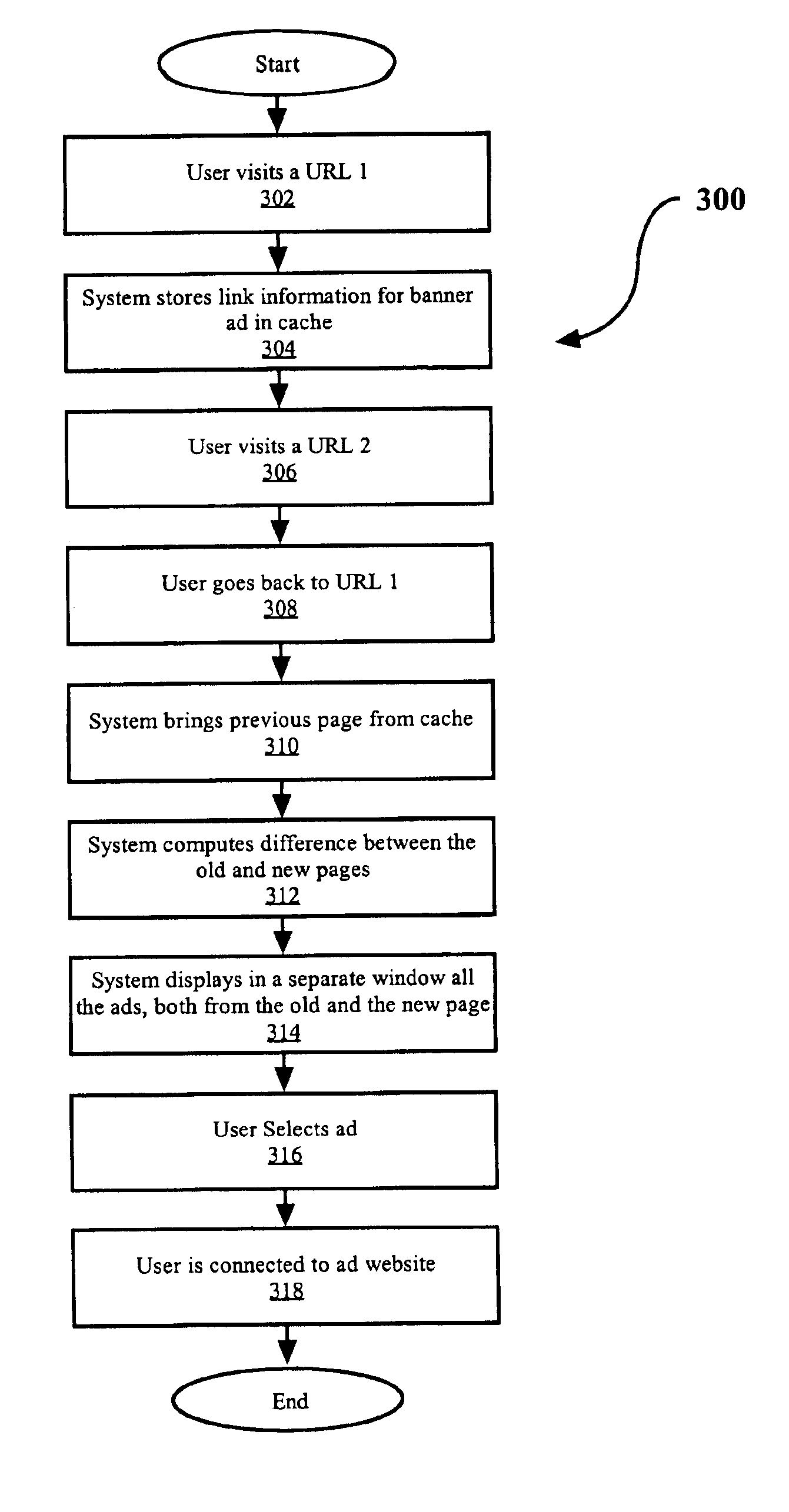
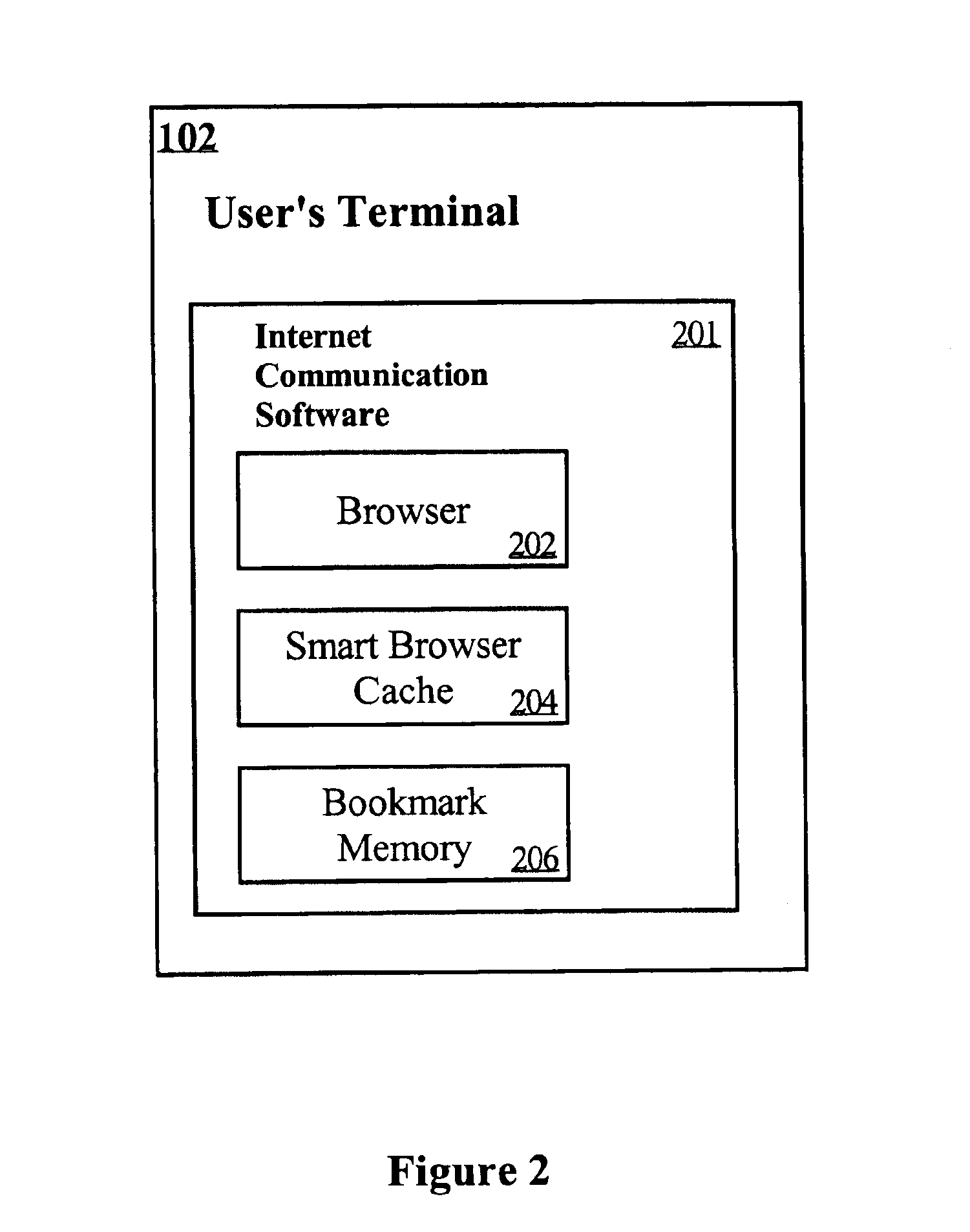
InactiveUS6892181B1Improve efficiencyAdvertisementsSpecial data processing applicationsHyperlinkOnline advertising
A system and method for improving the effectiveness of web advertising by allowing a user to return and request a previously displayed ad that appeals to the user. Generally, the system employs an intelligent browser cache maintained within a user's terminal to keep web pages in cache and maintain information about hyperlinks contained therein. Furthermore, the system allows for the storing of ads in a bookmark memory without clicking on the ads. The bookmark memory is either permanently maintained or temporarily stored for a predetermined time period at the user's terminal to allow the user view all the stored ads at a later time. The system further includes an algorithm for computing the differences between previously visited pages stored in the intelligent browser cache and a new page in terms of their hyperlinks. Presented to the user in separate windows are all the ads from both the old and new pages to aid the user in deciding whether to click and visit a different page or to save the displayed page for later use. Finally, the system permits the user to request for ads previously displayed at a particular position by pointing his mouse to the current ad at such a location.
Owner:IBM CORP
System and method for processing transaction data
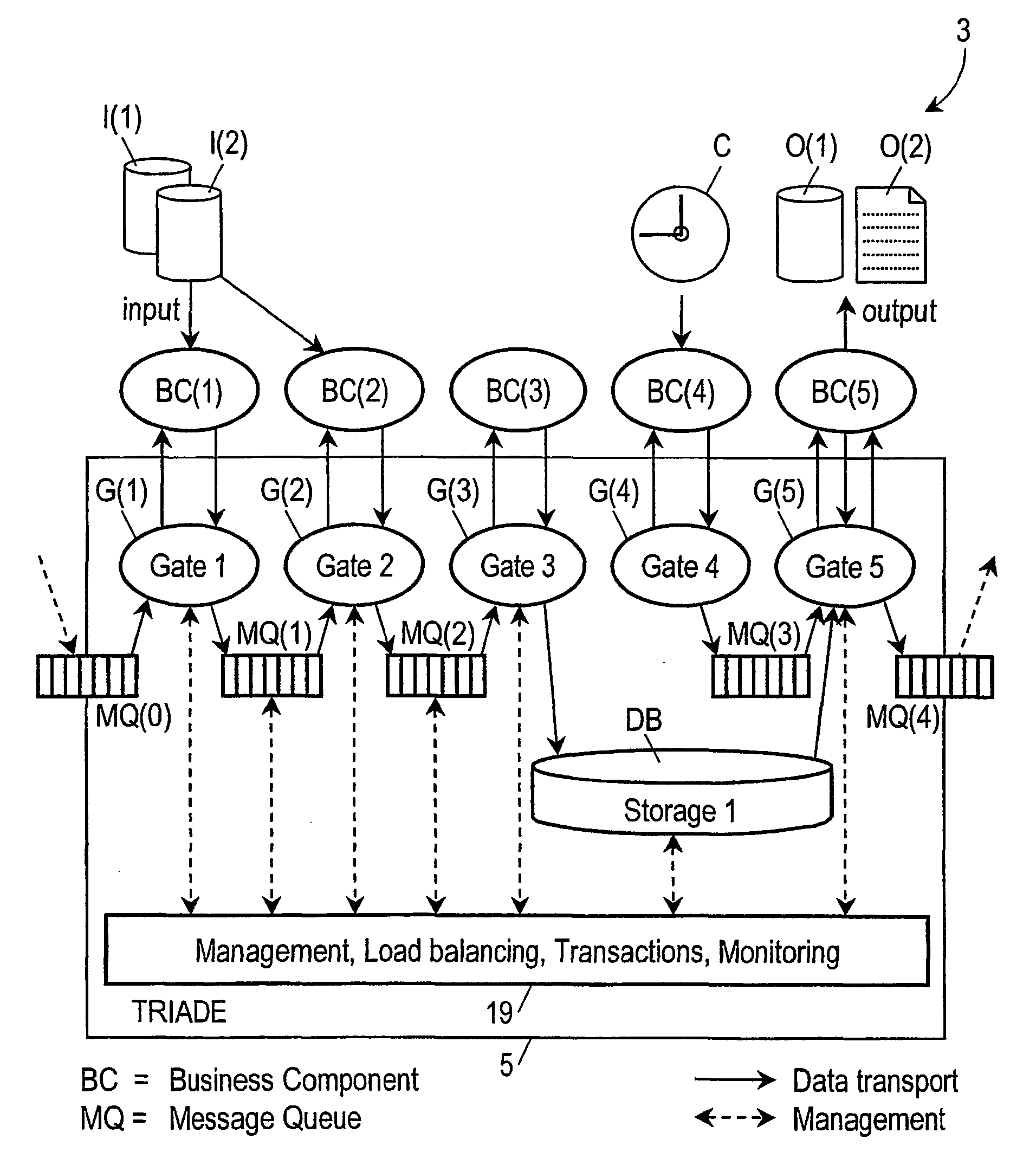
InactiveUS20040024626A1FinanceMultiple digital computer combinationsMessage queueSoftware architecture
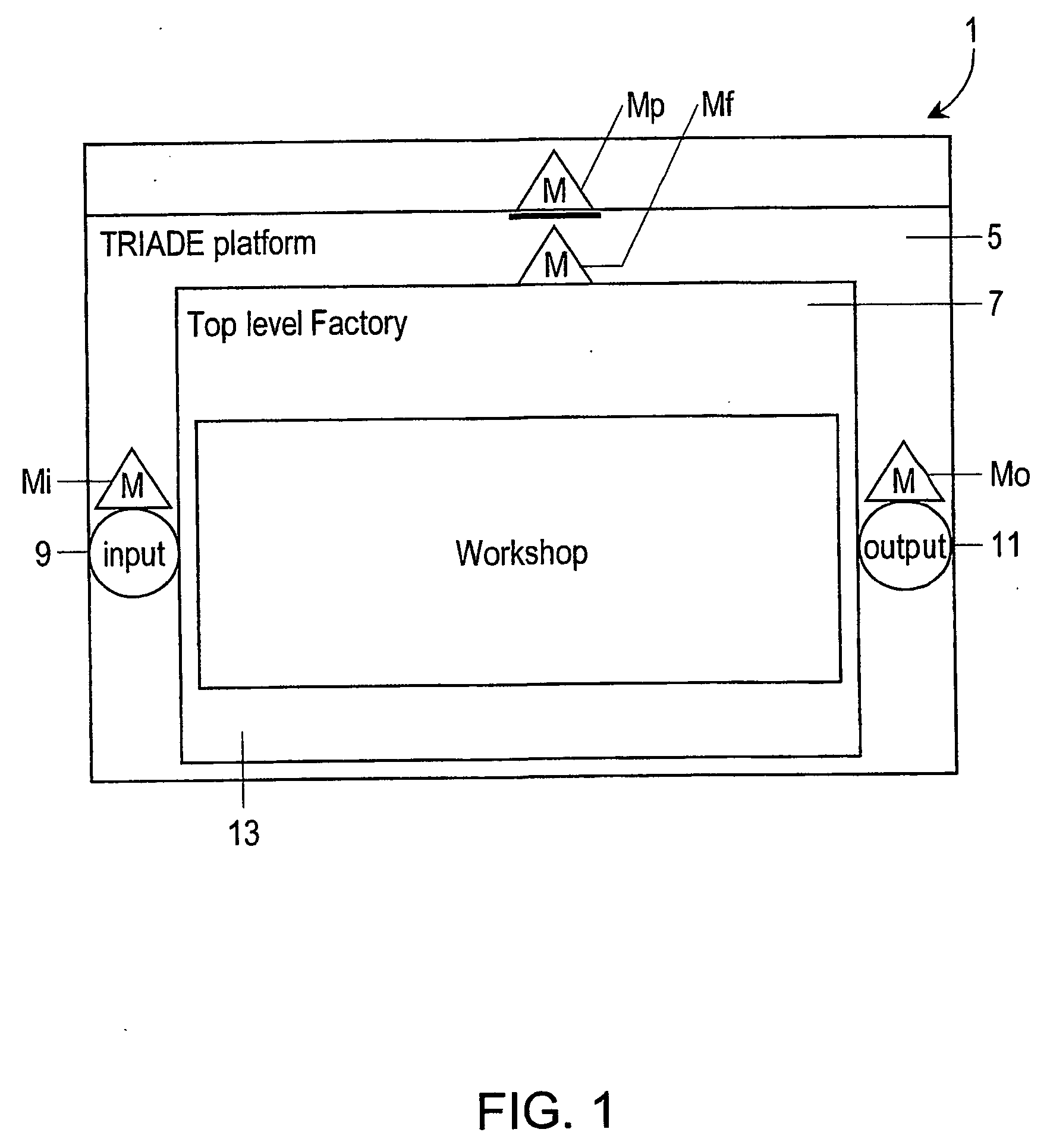
Computer system provided with a software architecture for processing transaction data which comprises a platform (5) with at least one logical processing unit (21) comprising the following components: a plurality of gates (G(k)); one or more message queues (MQ(k)), these being memories for temporary storage of data; one or more databases (DB); a hierarchical structure of managers in the form of software modules for the control of the gates (G(j)), the messages queues (MQ(k)), the one or more databases, the at least one logical processing unit (21) and the platform (5), wherein the gates are defined as software modules with the task of communicating with corresponding business components (BC(j)) located outside the platform (5), which are defined as software modules for carrying out a predetermined transformation on a received set of data.
Owner:NEDERLANDSE ORG VOOR TOEGEPAST-NATUURWETENSCHAPPELIJK ONDERZOEK (TNO)
Method and apparatus for collecting and reporting consumer trend data in an information distribution system
InactiveUS20020077880A1Better serveTelevision system detailsMarket predictionsData selectionDistribution system
Techniques to collect data indicative of viewer habits and preferences relating to television viewing and / or use of a user interface (e.g., an interactive program guide) provided at the terminal. Various types of information may be collected to identify and track the habits and preferences of the viewers. For example, the viewers' interaction with the terminals, selections made by the viewers, requests for particular programming, demographic information, and others, may be collected for the viewers. These various types of information (i.e., "trend" data) may be continually collected by an application executing at the terminal, temporarily stored in a storage unit, and thereafter reported (e.g., periodically, or upon request) to a head-end of an information distribution system. The head-end may analyze the trend data, and may select and provide programming, advertisements, and other contents targeted to the terminals based on the analyzed data.
Owner:SEDNA PATENT SERVICES
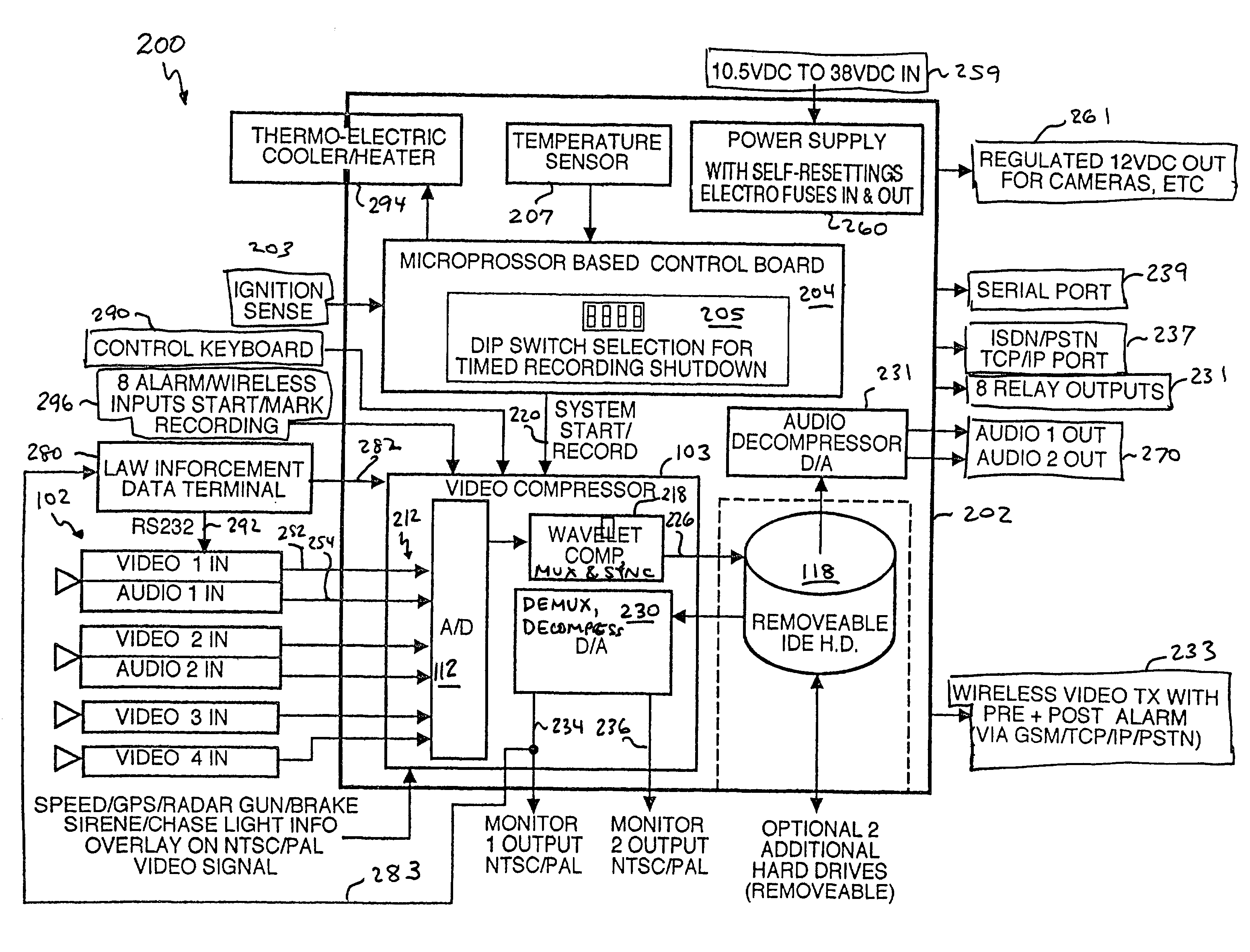
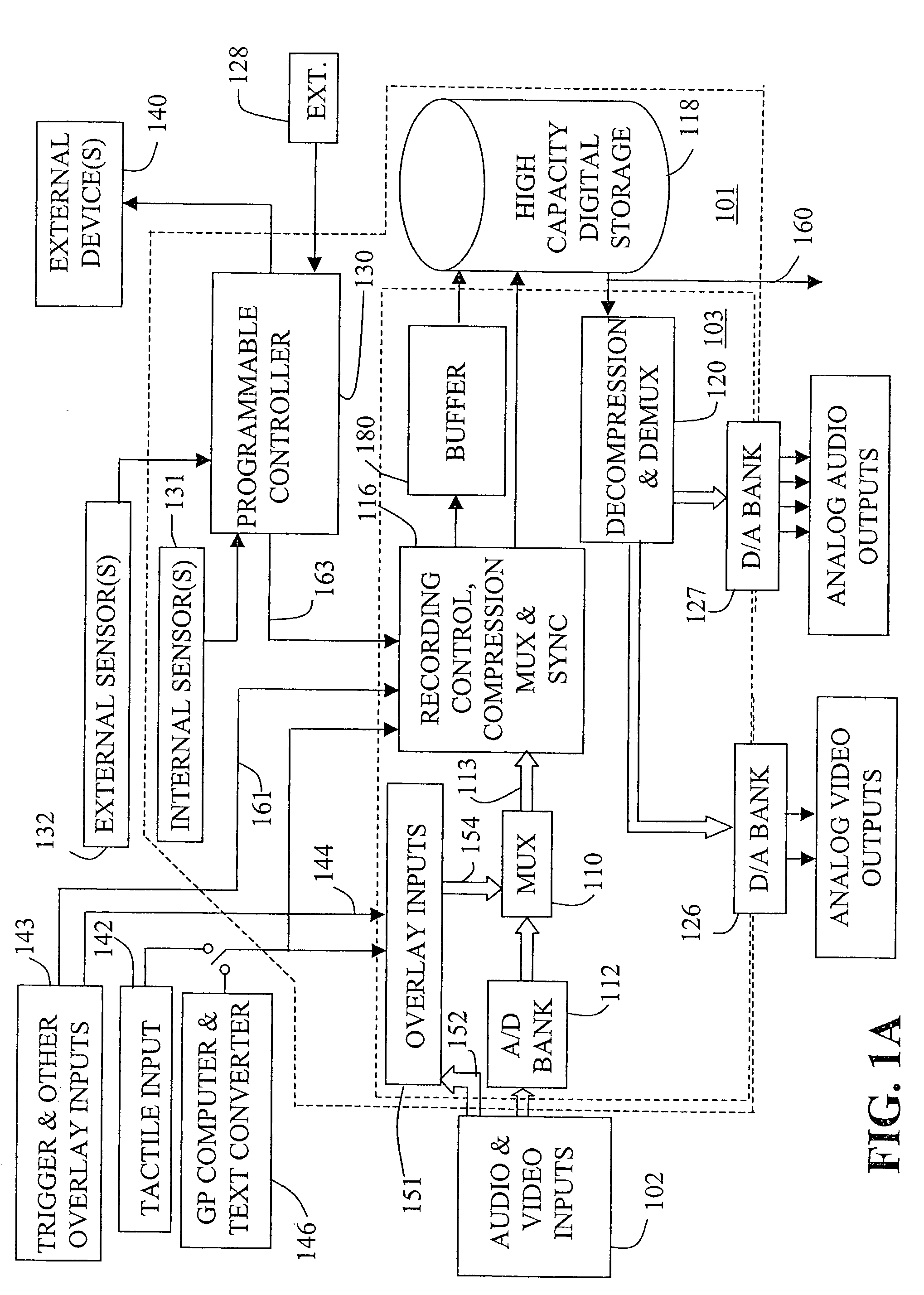
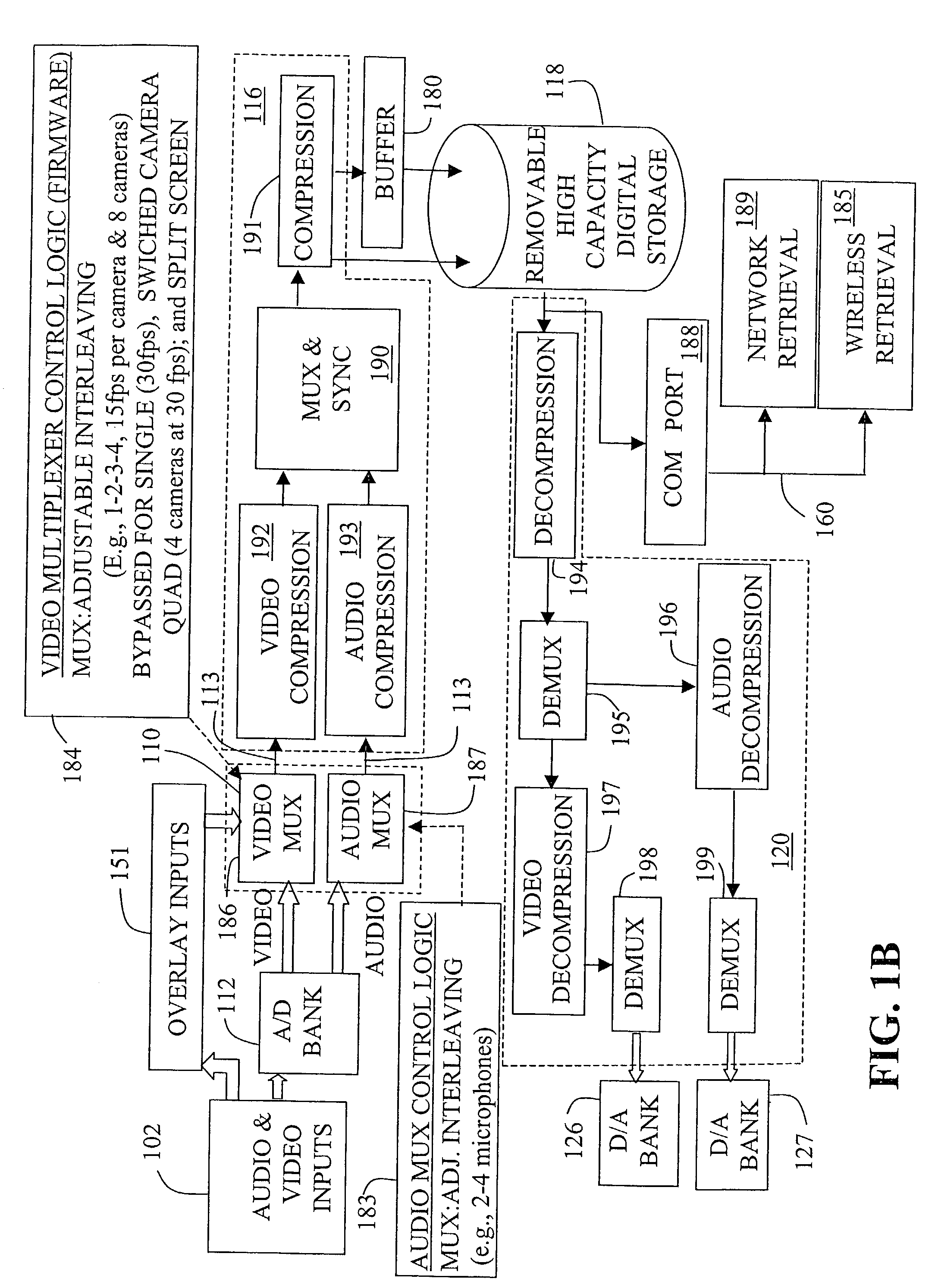
Heating and cooling of a mobile video recorder
InactiveUS20030081128A1Quick analysisSimple processReducing temperature influence on carrierTelevision system detailsDigital videoMultiplexing
Provided is a mobile event-recording device contained within an airtight chassis with its internal temperature regulated according to pre-programmable operational thresholds via a controller using a temperature sensor and a solid-state heat pump attached to or proximate with the chassis. The mobile event-recording device further includes multiplexors, compressors and a buffer for the temporary storage of video signals during a sliding time window for the recording of compressed digital video and audio onto a hard disk or other high-capacity long-term storage medium. With regard to the buffer, the device responds to receipt of a trigger signal by initiating live recording of the video signal by the video recorder and transferring the temporarily stored video signal to the storage means (or otherwise preserving the temporarily stored video signal for permanent storage).
Owner:HUBB SYST
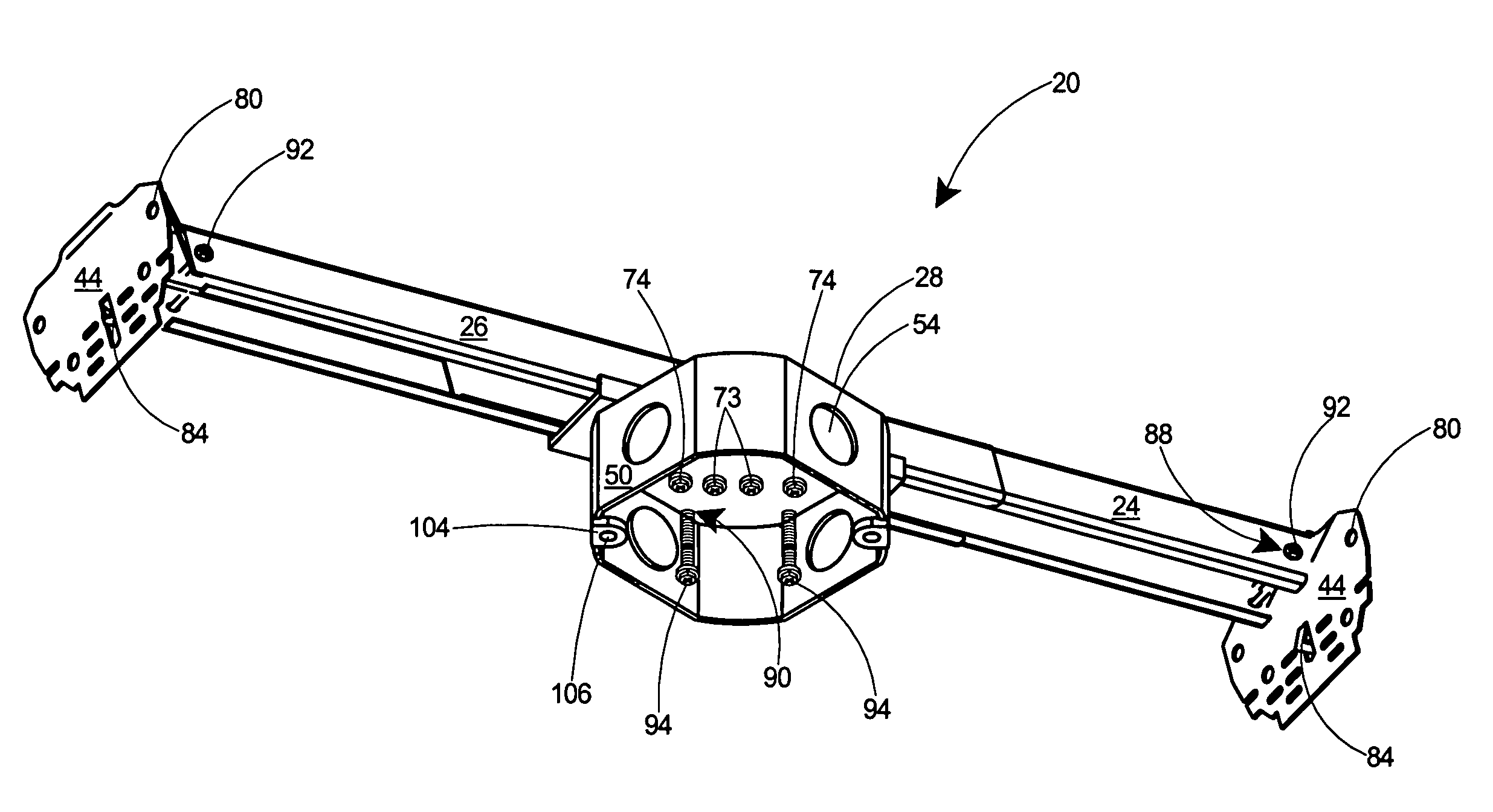
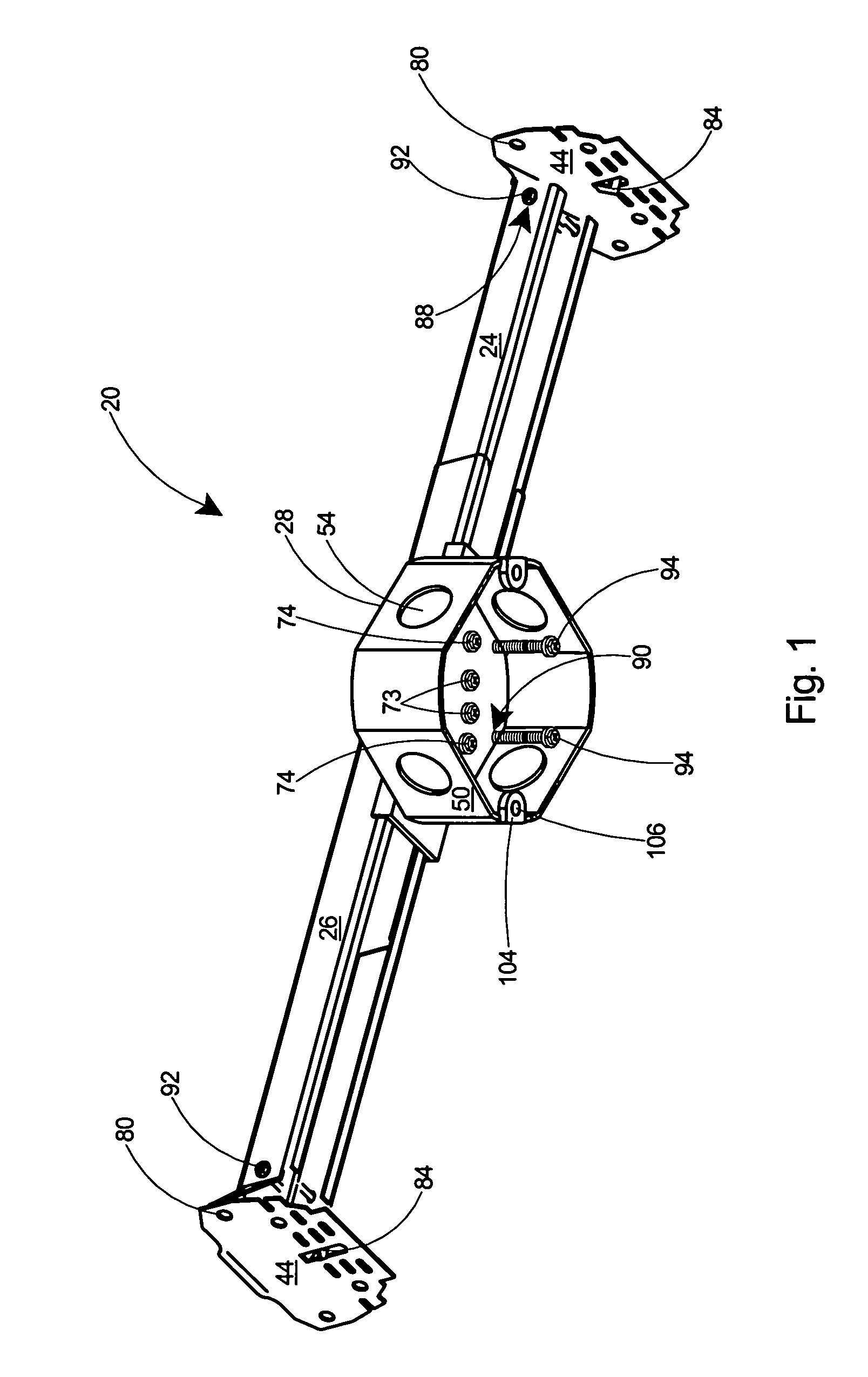
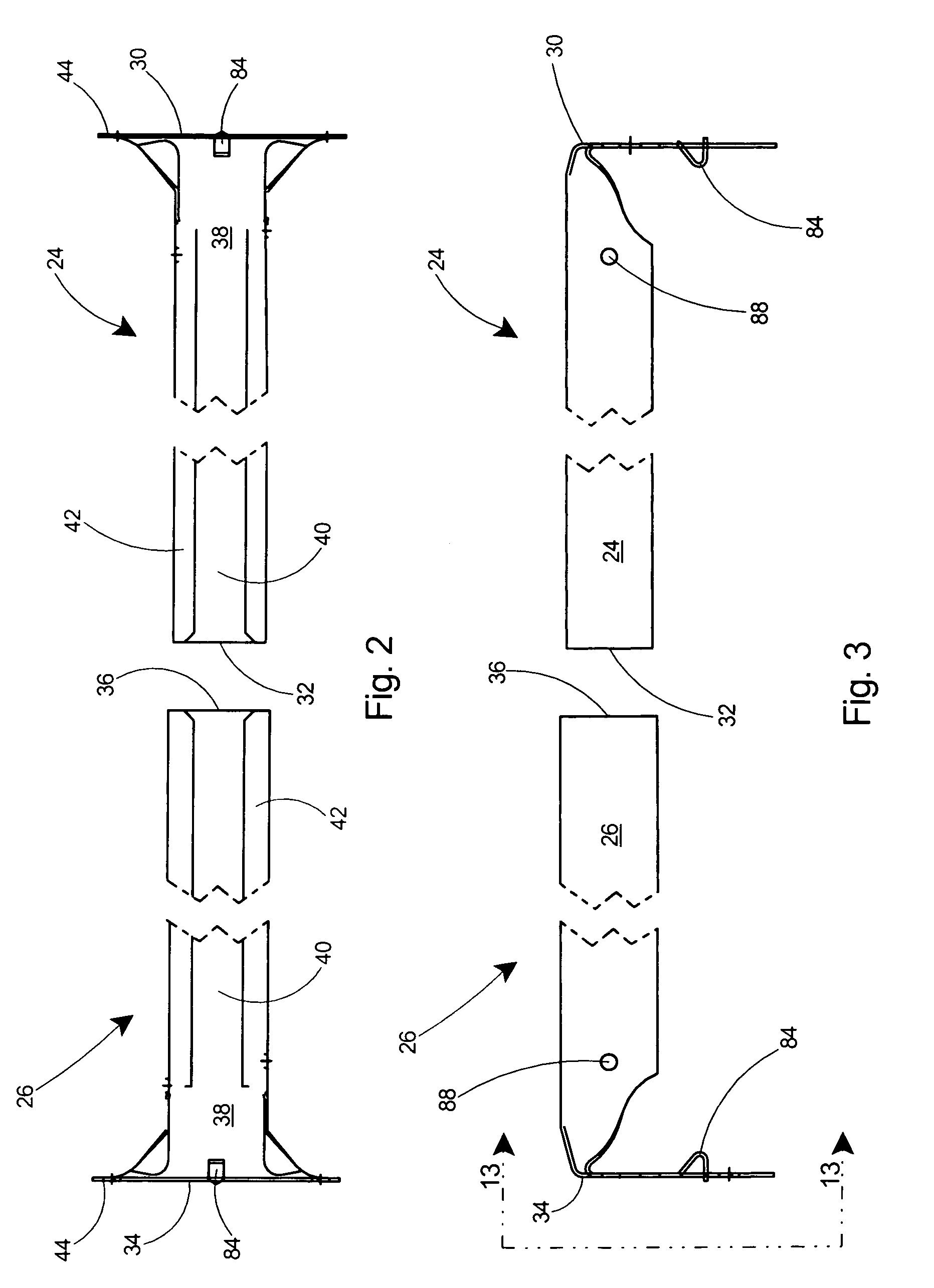
Electrical box mounting assembly
An adjustable mounting bar and electrical box assembly for hanging a light fixture, fan, or other electrical device from a ceiling. All hardware required for mounting the electrical device is included with the assembly. The adjustable mounting bar includes sliding tubular members with end flanges for spanning between adjacent overhead joists. An electrical box is connected to the tubular members by a clamp and outer clamping fasteners, which can be loosened to adjust the length of the adjustable mounting bar. The end flanges include penetrable tabs that can be driven into the overhead joists to temporarily secure the adjustable mounting bar to the joists and thereby free the installer's hands. The outer face of the end flanges include a series of rows of slots arranged horizontally thereon and forming a plurality of bend lines. To accommodate ceiling coverings of various thickness, the end flanges can be bent outwards at the proper bend line to position the lower end of the electrical box flush with the ceiling surface. Load bearing bar fasteners threadably engaged in temporary storage receptacles in the sliding tubular members are removed therefrom and fastened through the end flanges to securely fasten the mounting bar to the joists. Load bearing device fasteners threadably engaged in temporary storage receptacles in the electrical box are removed therefrom and driven into receptacles in the clamp to secure the electrical device to the mounting bar. Oversize openings are provided in the top wall of the electrical box to ensure that the entire suspended load is borne by the clamp and mounting bar and not the electrical box.
Owner:ARLINGTON INDS
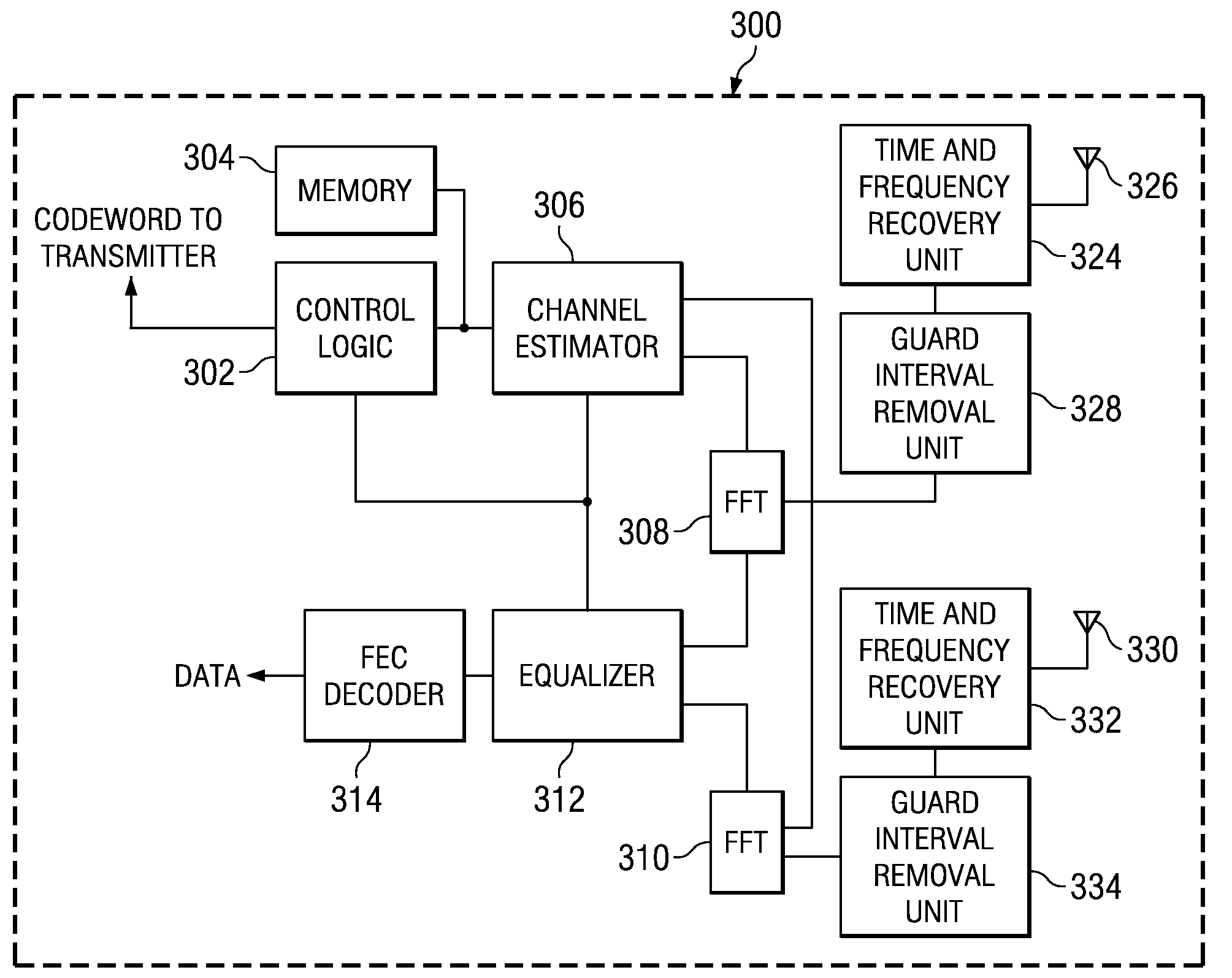
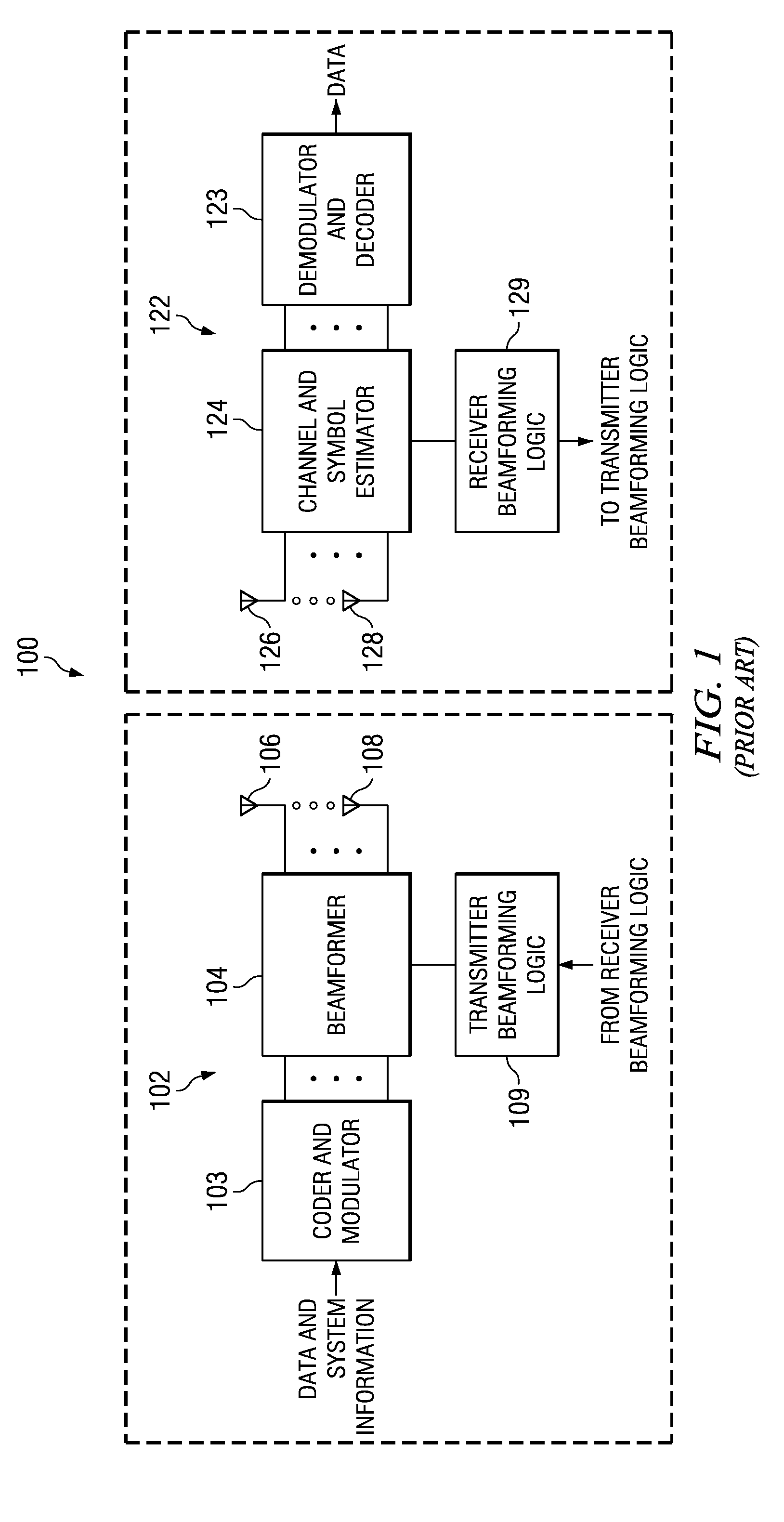
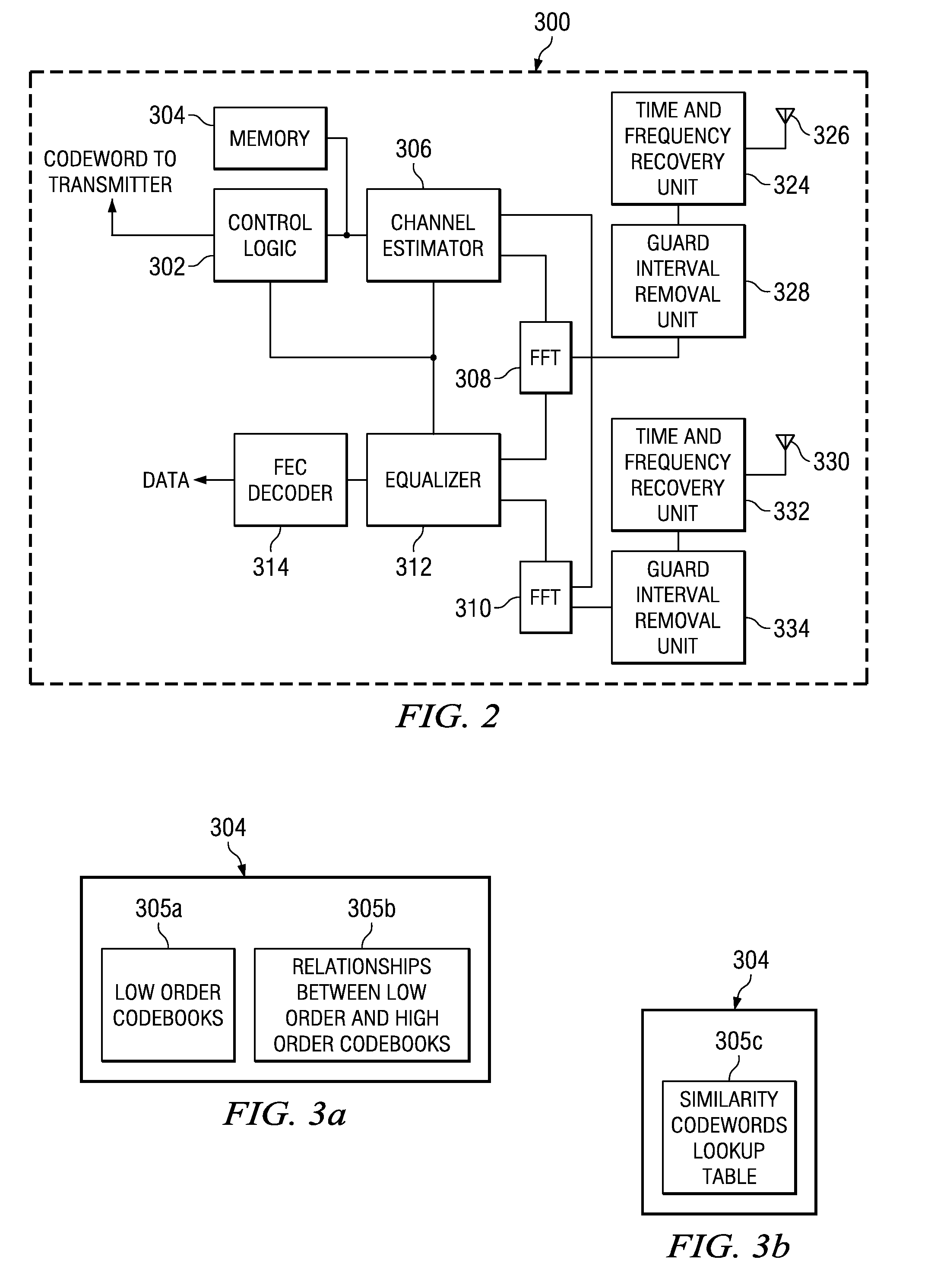
Low complexity precoding matrix selection
ActiveUS20080304464A1Transmission path divisionDiversity/multi-antenna systemsLow complexityTransmitter
A method of determining indices for matrix codewords in a matrix codeword codebook. The matrix codewords are adapted for communicating information between a transmitter and a receiver. The method includes retrieving from temporary storage, an eigenmode representation for a communications channel, where the eigenmode representation is based upon on a received signal precoded by a first matrix codeword. The method also includes performing a test on multiple vector codewords to identify a first vector codeword among the multiple vector codewords, where the test includes determining a relationship between the first vector codeword and the representation of an eigenmode. The first vector codeword is associated with a first vector codeword index that identifies the first vector codeword. The method also includes generating a matrix codeword index associated with a second matrix codeword in the matrix codeword codebook. The matrix codeword index is based upon the first vector codeword index, and the order of the first vector codeword is different from the order of the second matrix codeword.
Owner:TEXAS INSTR INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com