Patents
Literature
28425 results about "Password" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A password, sometimes called a passcode, is a memorized secret used to confirm the identity of a user. Using the terminology of the NIST Digital Identity Guidelines, the secret is memorized by a party called the claimant while the party verifying the identity of the claimant is called the verifier. When the claimant successfully demonstrates knowledge of the password to the verifier through an established authentication protocol, the verifier is able to infer the claimant’s identity.
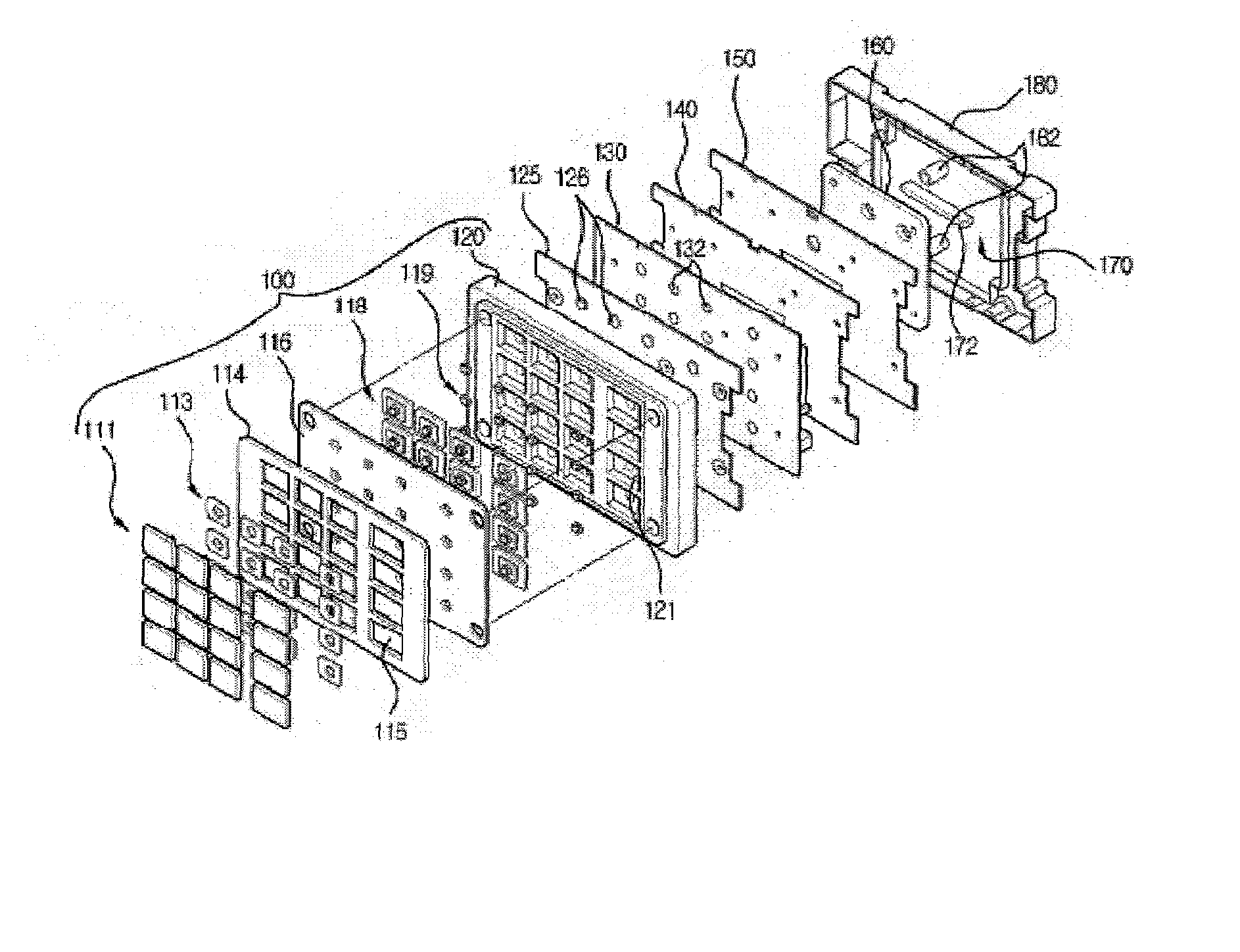
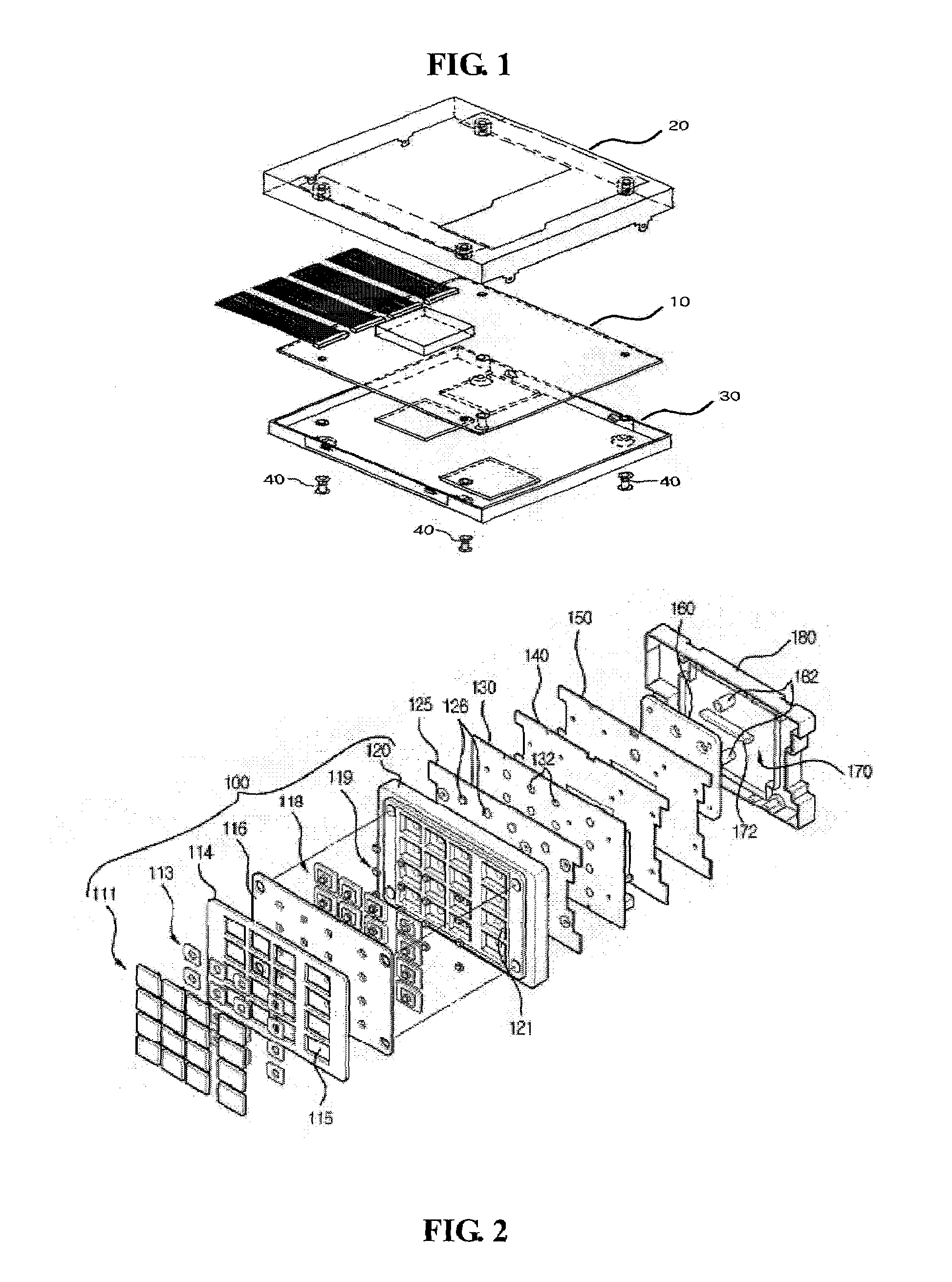
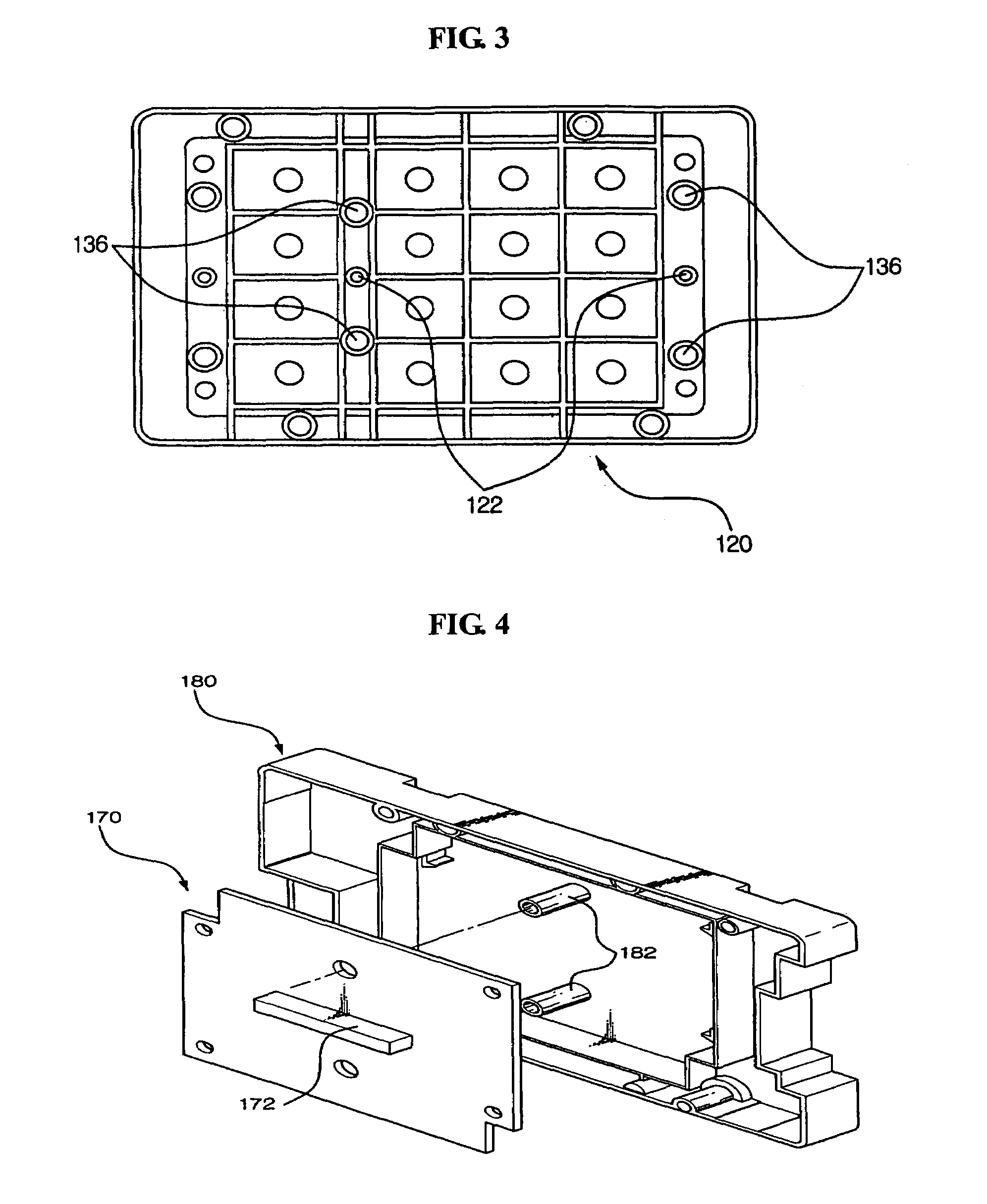
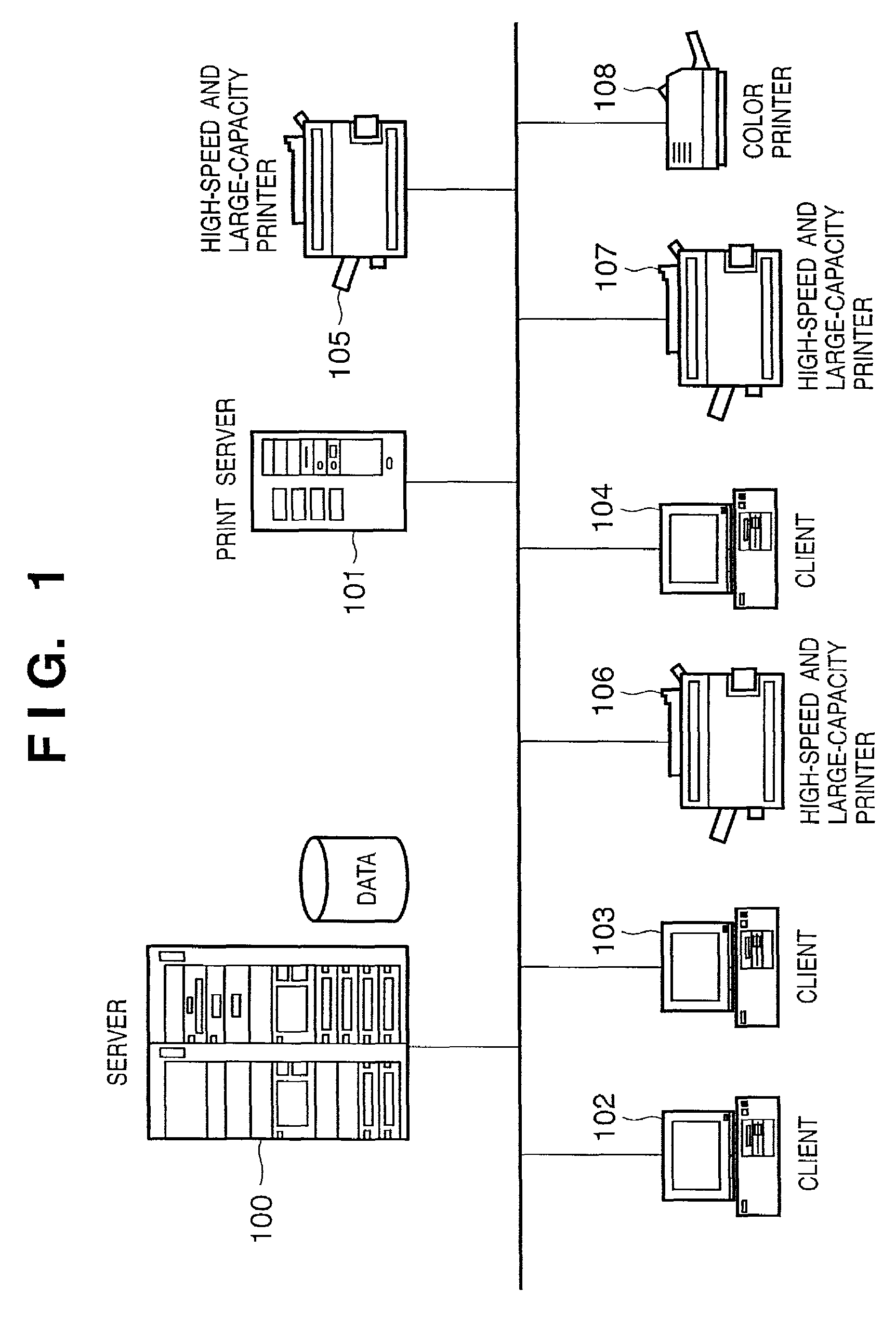
Tamper resistant pin entry apparatus
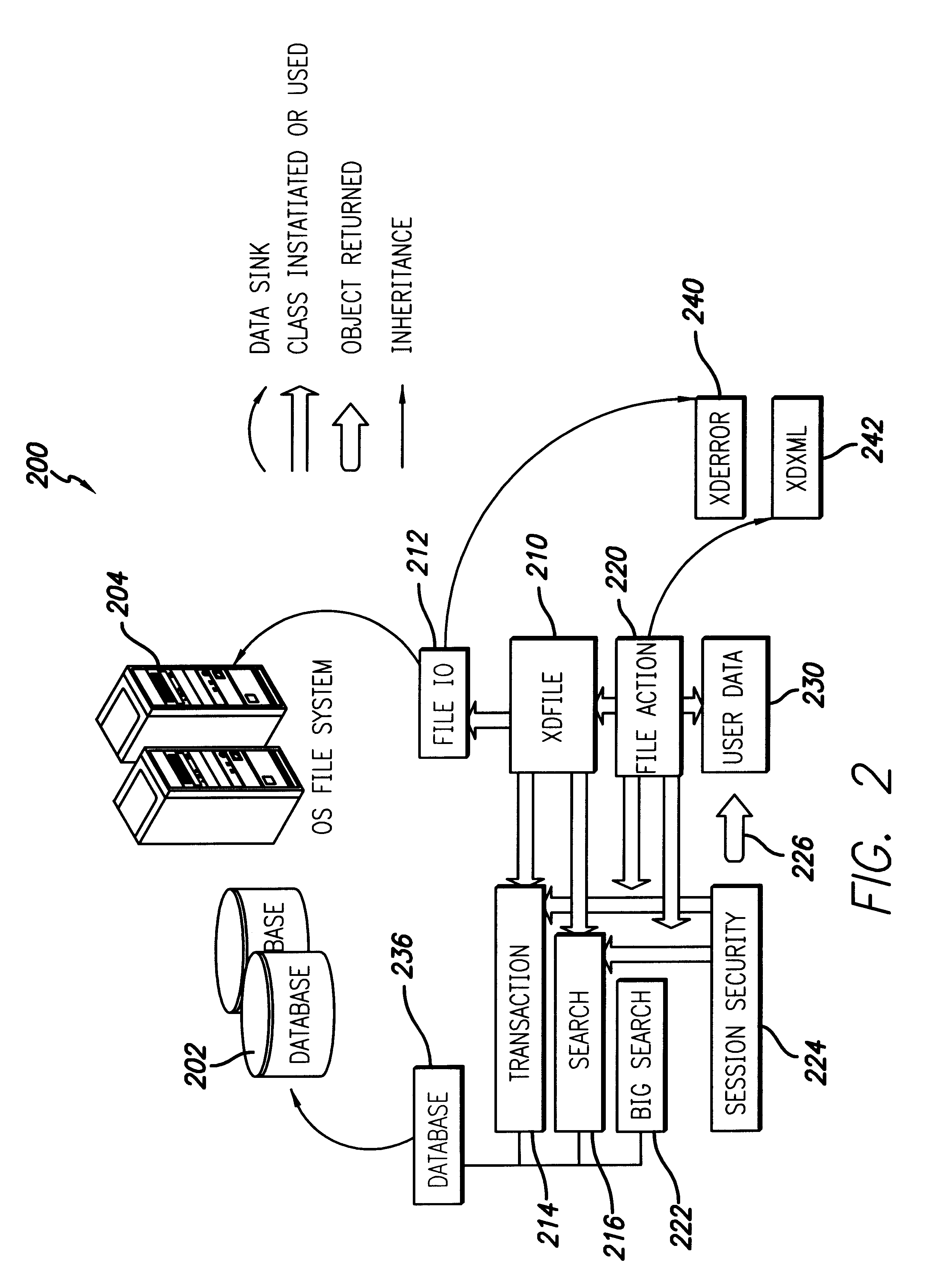
ActiveUS7238901B2Prevent leakagePrevent penetrationComplete banking machinesEmergency casingsPasswordElectric power system
Disclosed is a tamper resistant PIN entry apparatus for input of a key and for encryption of a password in a cash transaction machine. The PIN entry apparatus supplies the electric power to a memory of an electric circuit section, in such a manner that a first rod and a second rod of a rear case connect contacts of a key scan board, wherein the first rod is protruded on the rear of a key module including a button provided substantially on the front of the key module and the second rod of the rear case is coupled with the rear of the key module. At this time, in case that the rear case is removed from the key module or damaged, thereby changing the location of any one of the first and the second rods at the contact, the electric circuit section detects the event and destroys the memory itself physically. Otherwise, the electric circuit section makes information stored in the memory physically or softwarely unreadable, thereby preventing the leakage of the information.
Owner:NAUTILUS HYOSUNG
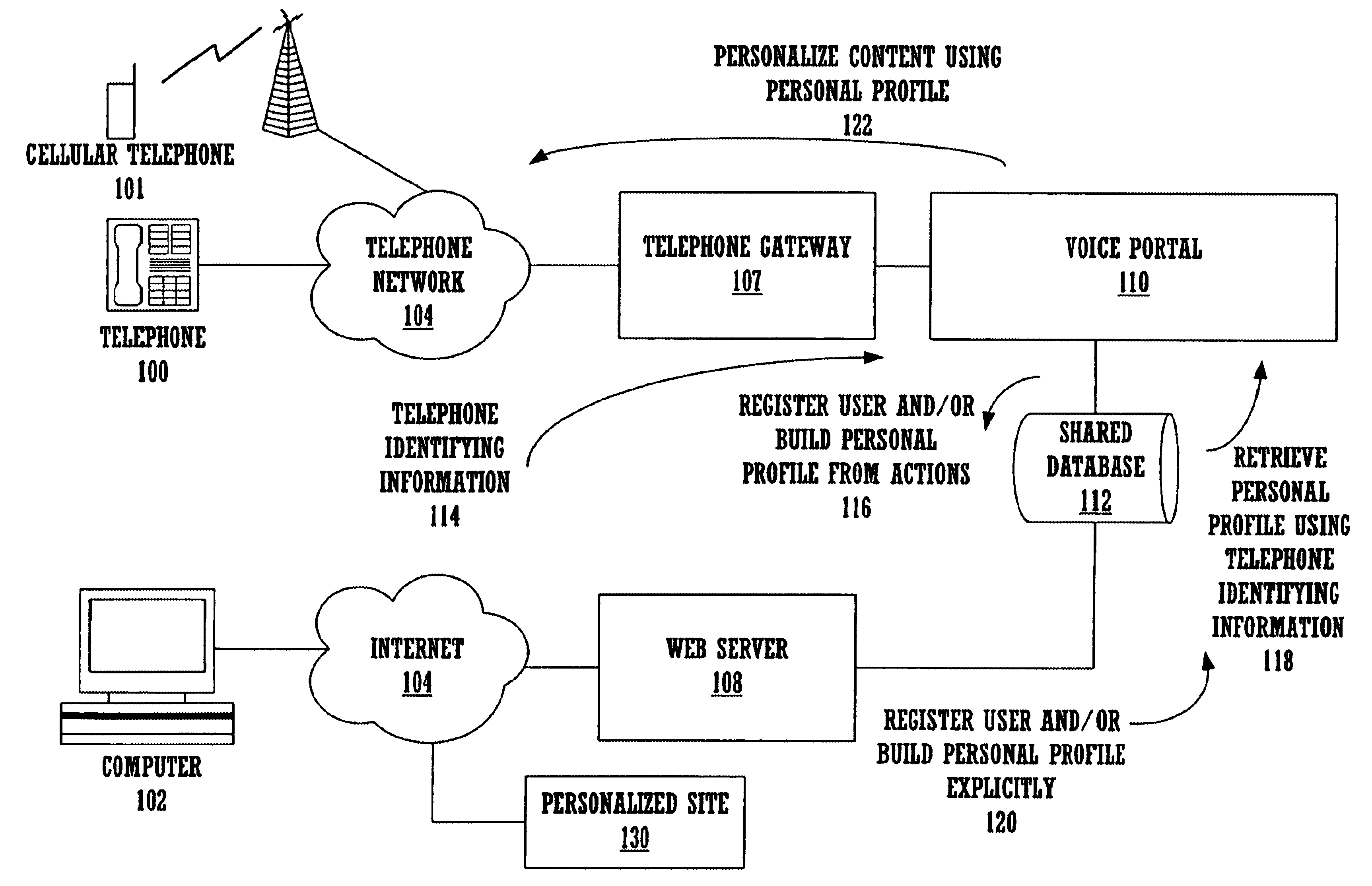
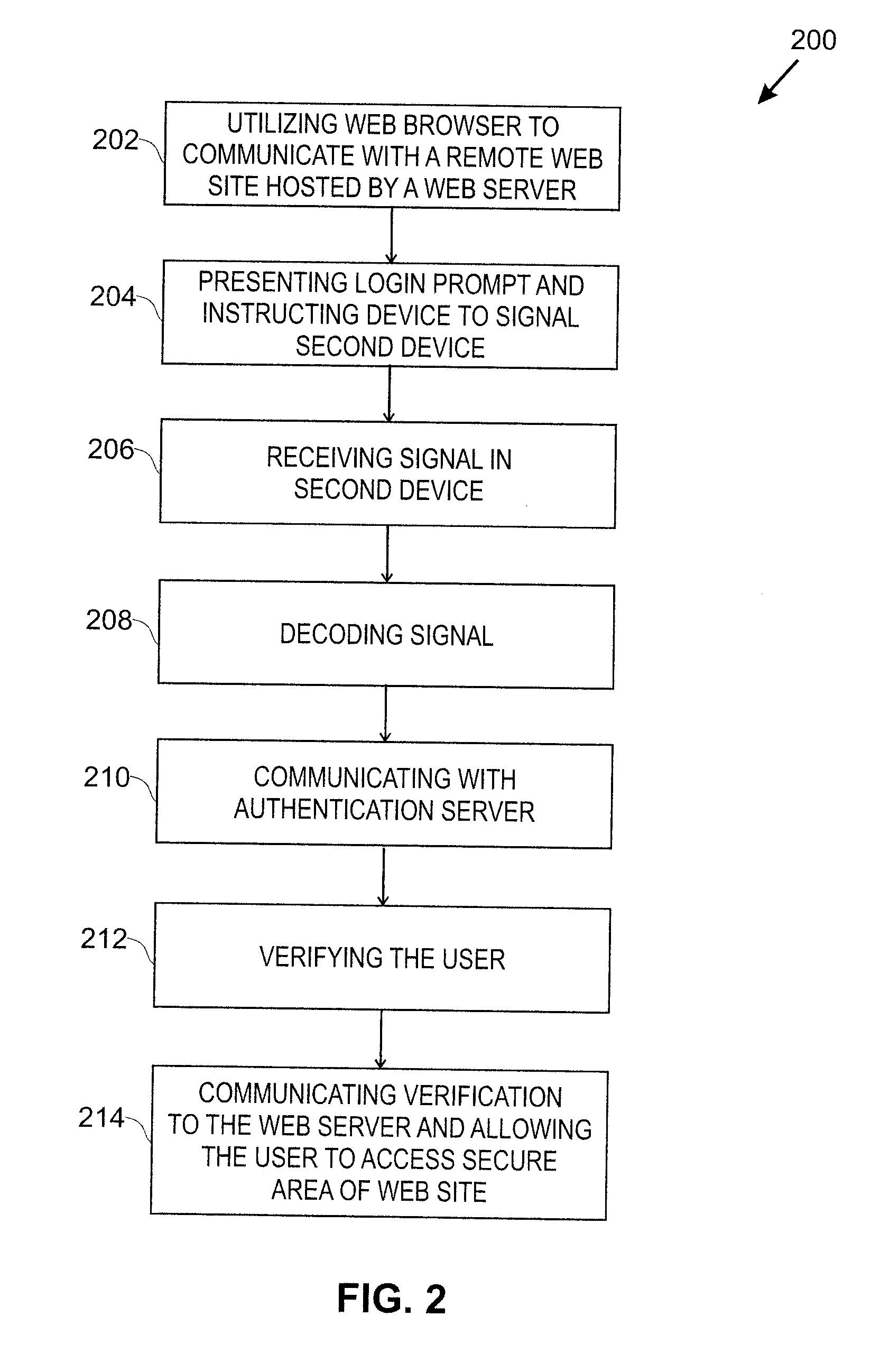
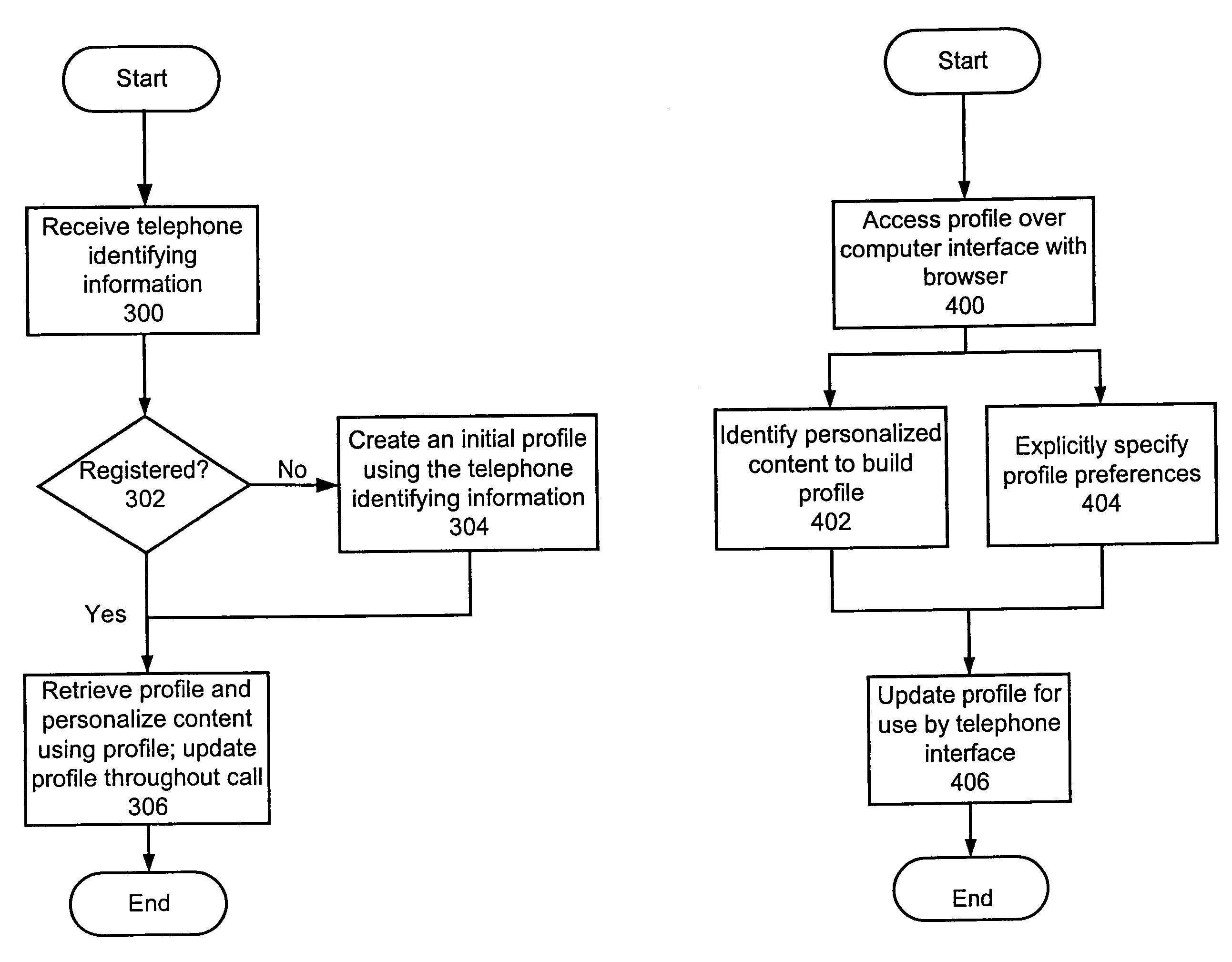
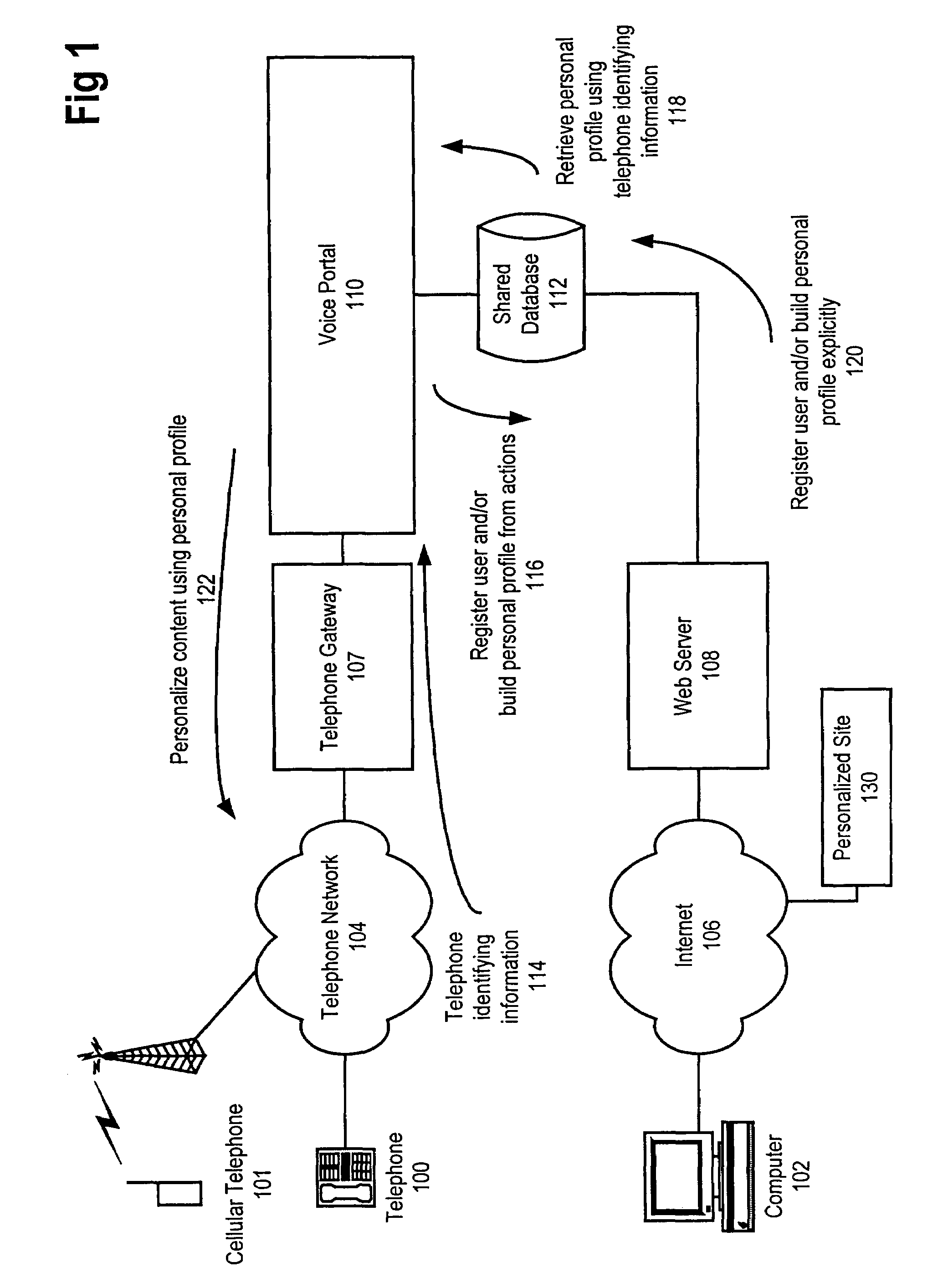
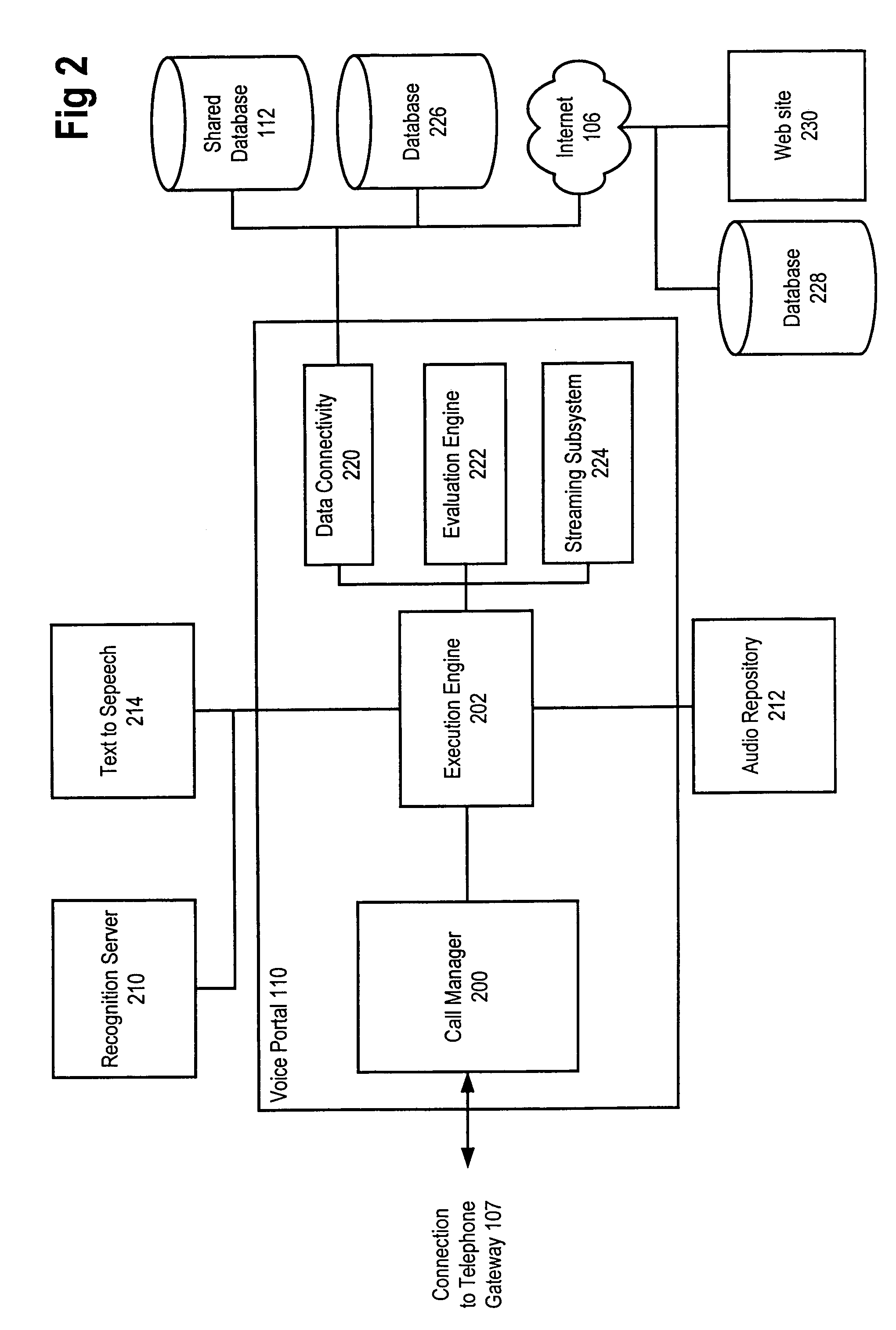
Method and apparatus for content personalization over a telephone interface with adaptive personalization
InactiveUS6842767B1Shorten speedIncrease volumeMultiple digital computer combinationsAutomatic exchangesPersonalizationHuman language
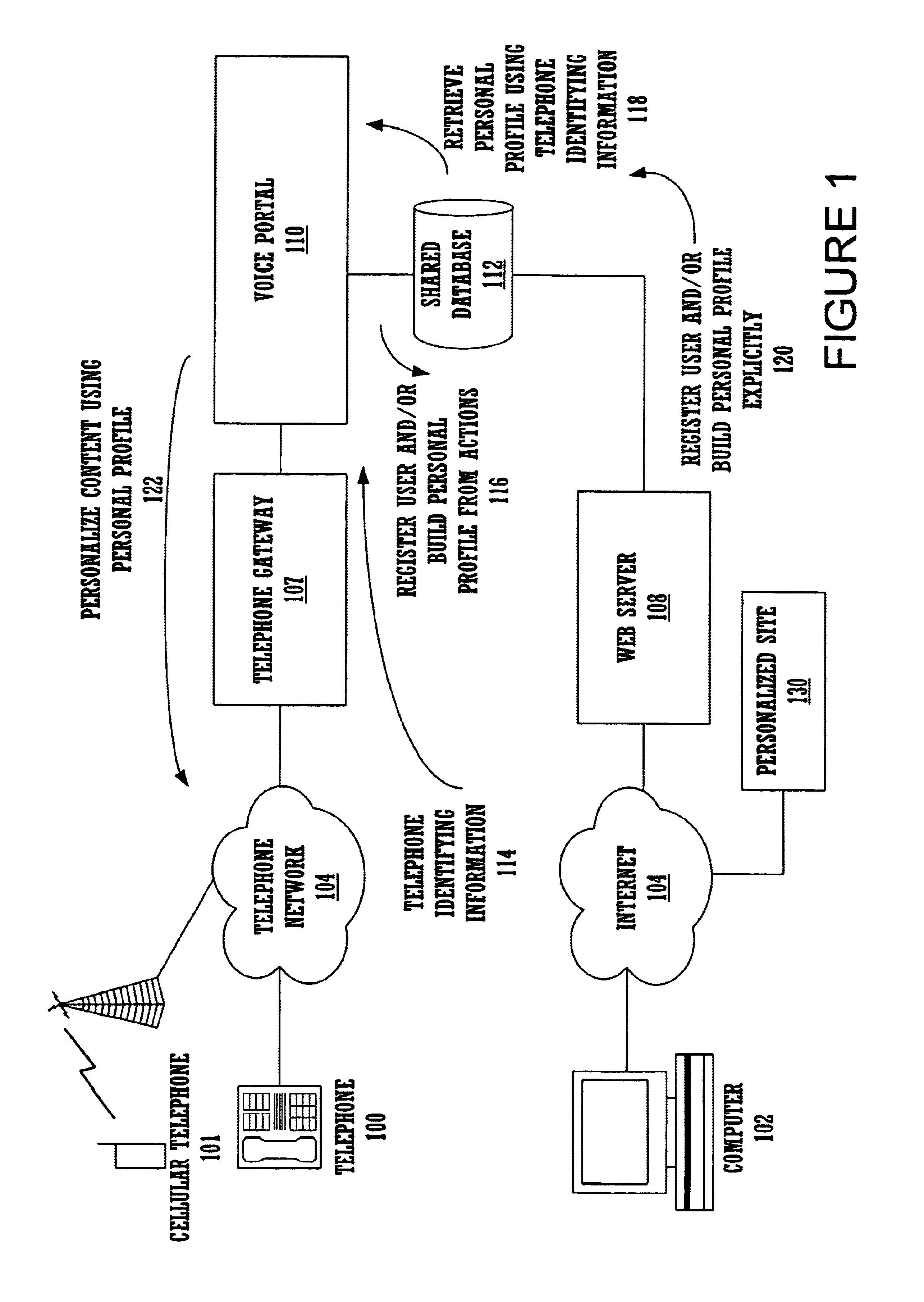
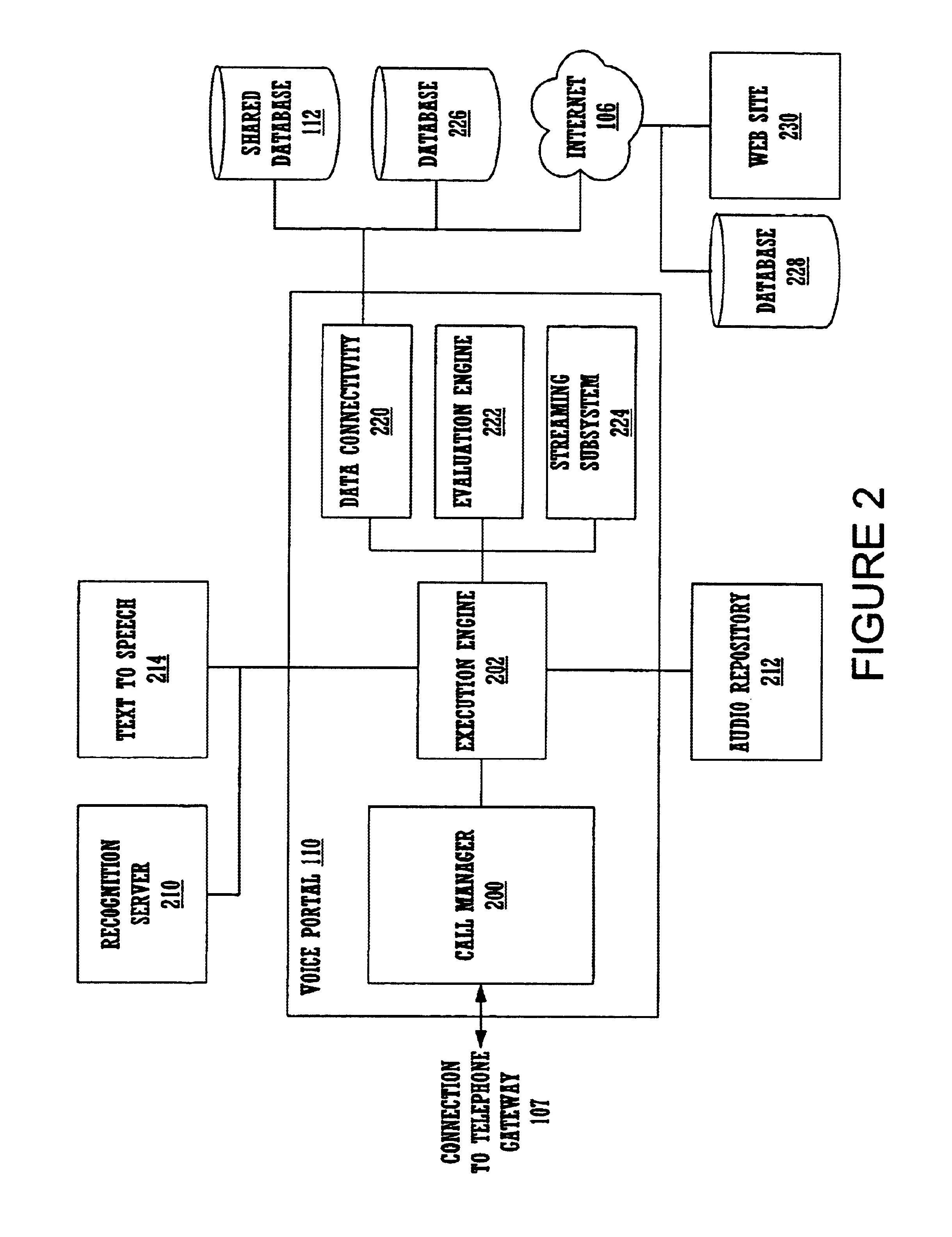
A method and apparatus for providing personalized information content over telephones is described. The creation of a voice portal is supported by the invention. Embodiments of the invention use telephone identifying information such as the calling party's number to identify, or create, user profiles for customization. The personalized content is specific to that user based on her / his telephone identifying information and may be further customized based on the current time, current date, the calling party's locales, and / or the calling party's dialect and speech patterns. Also, the telephone identifying information may support targeted advertising, content, and purchasing recommendations specific to that user. The system may use a voice password and / or touch-tone login system when appropriate to distinguish the caller or verify the caller's identity for specific activities. Typically, embodiments of the invention will immediately present a caller personalized content based on her / his profile using the appropriate dialect as well as the caller's preferred content. Profiles can be constructed as the caller uses embodiments of the invention as well as through explicit designation of preferences. For example, as the user selects topics, as well as particular content, a record of actions can be maintained. This record of actions can be used to provide suggestions and direct the personalization of the system for the user.
Owner:MICROSOFT TECH LICENSING LLC
System and method for displaying and selling goods and services
InactiveUS20010044751A1Easy to doDiscounts/incentivesBuying/selling/leasing transactionsPasswordLoyalty program
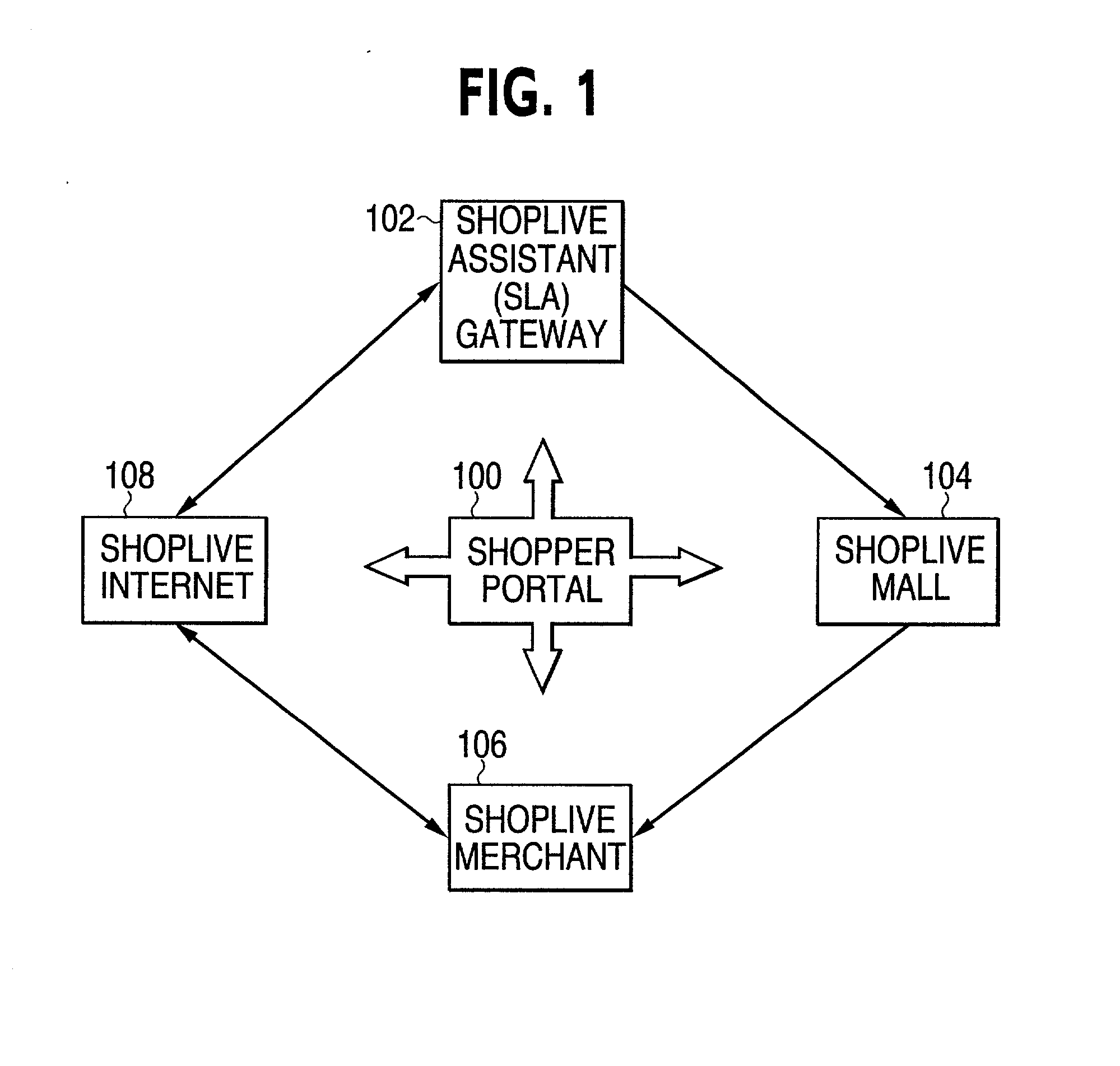
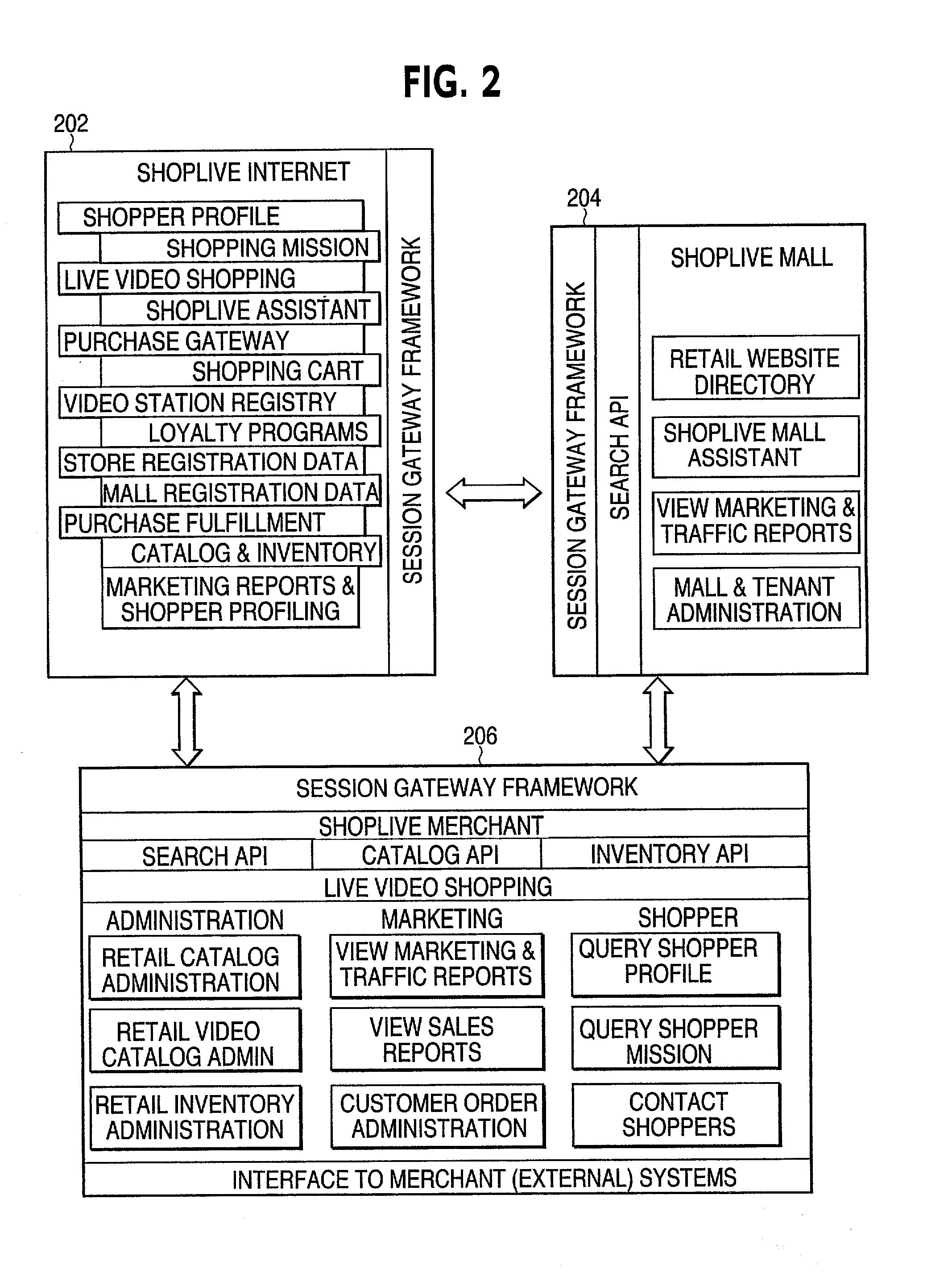
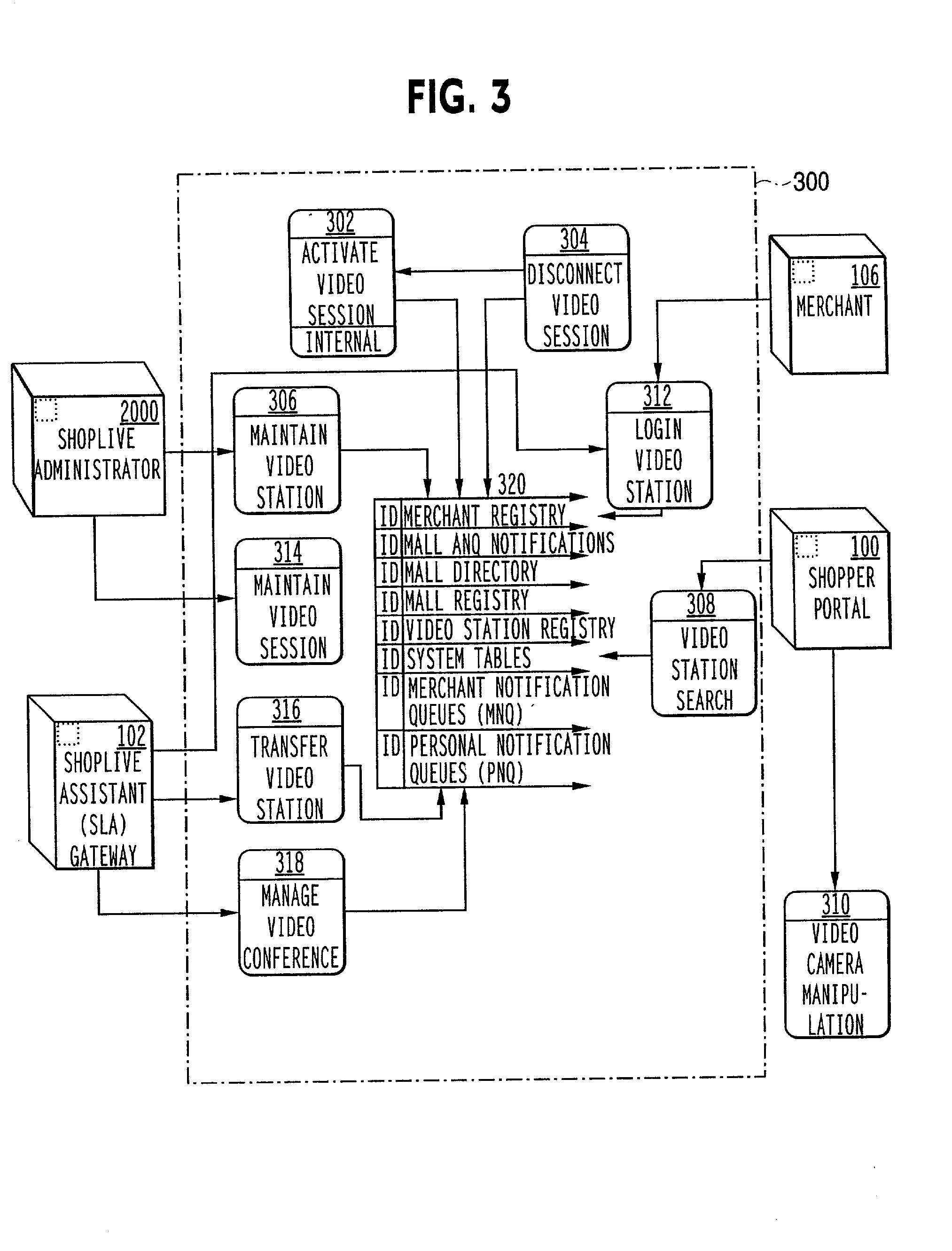
The ShopLive system supports existing merchants and malls to better serve customers by providing easy access to merchandise and sales assistance. The shopper accesses the ShopLive system through various portals. They can be a PC, Web TV, mall kiosk, store kiosk, mobile terminal, screen telephone or any other communication device capable of connecting to a communications network. When the shopper starts the shopping mission they can logon in or if already enrolled, they can use a password for a quick entry. They may chose to shop anonymously. A shopper can set up a shopping mission by defining class of goods, price, color and the like and set out to search for that either in their physical location or remotely. Once the items are located video cameras scan the merchandise to the shopper through the terminal. The cameras may be remotely operable to swing through different views to better display the goods. Or they can view items according to pre-determined scan patterns. Sound and other sensory stimulus such as tactile sensors may be used to enhance the shopping experience. The shopper may also ask for help from an assistant (SLA) that acts just like a sales person in a retail setting. This person can help select goods and can discuss the items selected. The SLA can also check product availability and help complete the purchase as in a normal sales transaction. Or, the shopper can use the ShopLive system to check out themselves. As the shopper moves through the shopping mission, they can add items to their electronic shopping cart and have a one-stop check out or they can check out with each merchant. The shopper is also entered into the available loyalty programs and presented with coupons and rebates. At the end of the shopping mission the shopper can either physically pick up the selections are arrange shipping. The ShopLive system supports multiple selling activities including auctions. It is also a rich data-base for merchants and allows targeted advertising. A live browser accesses the shopper to present sales and incentives to the customer. The ShopLive system connects the Shopper and the merchant to make the shopping experience more effective for both.
Owner:PUGLIESE ANTHONY V III +3
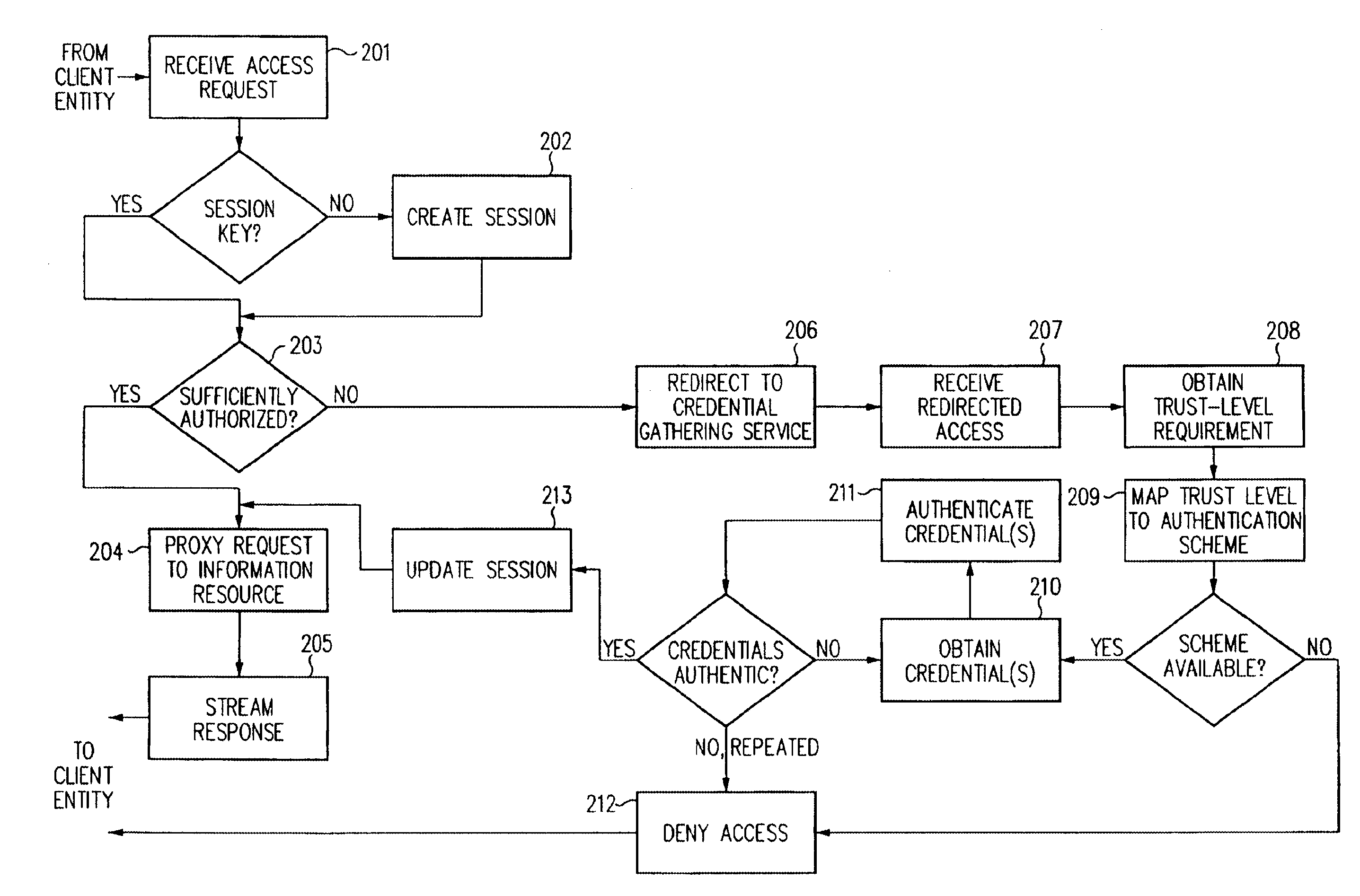
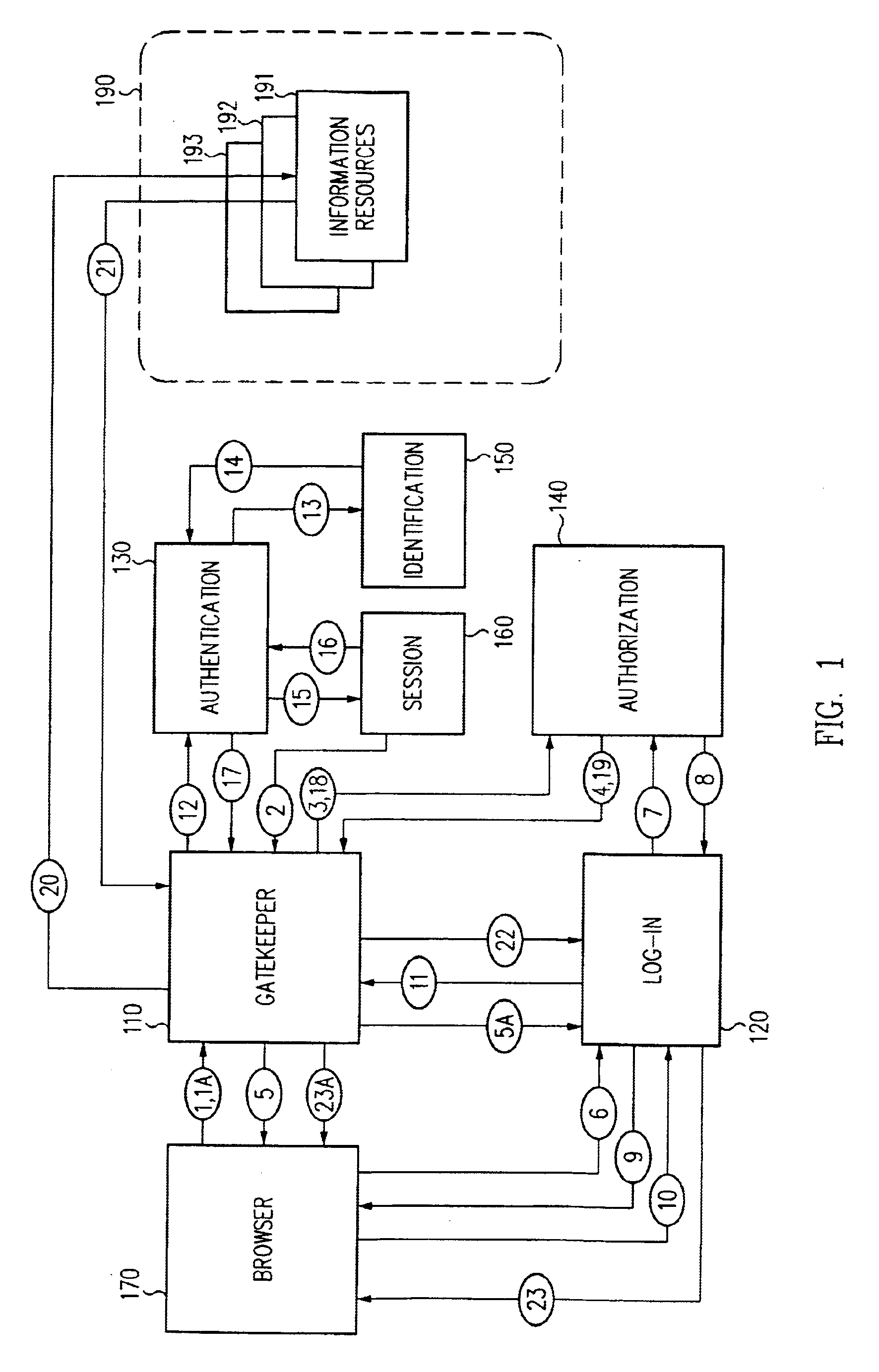
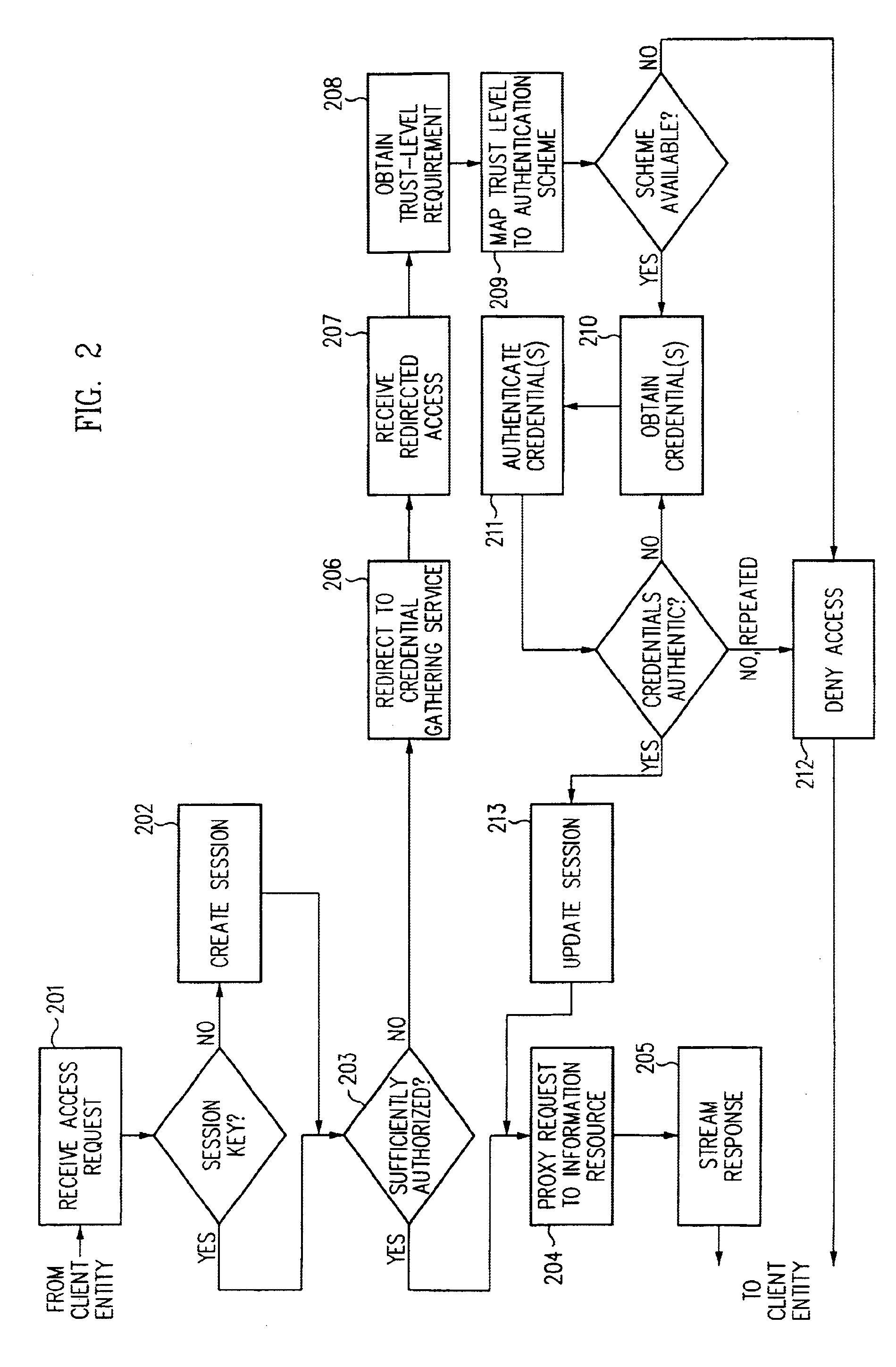
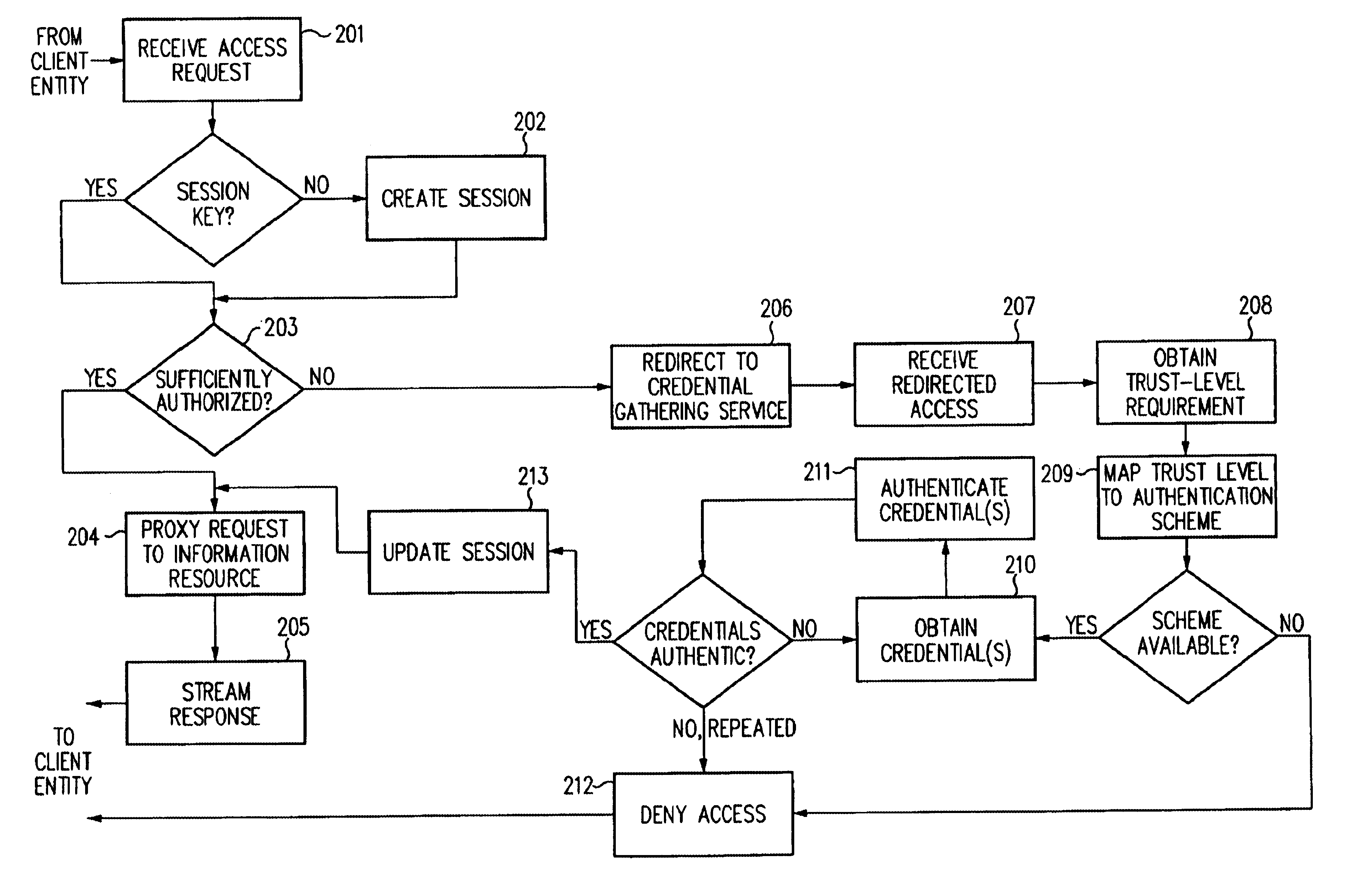
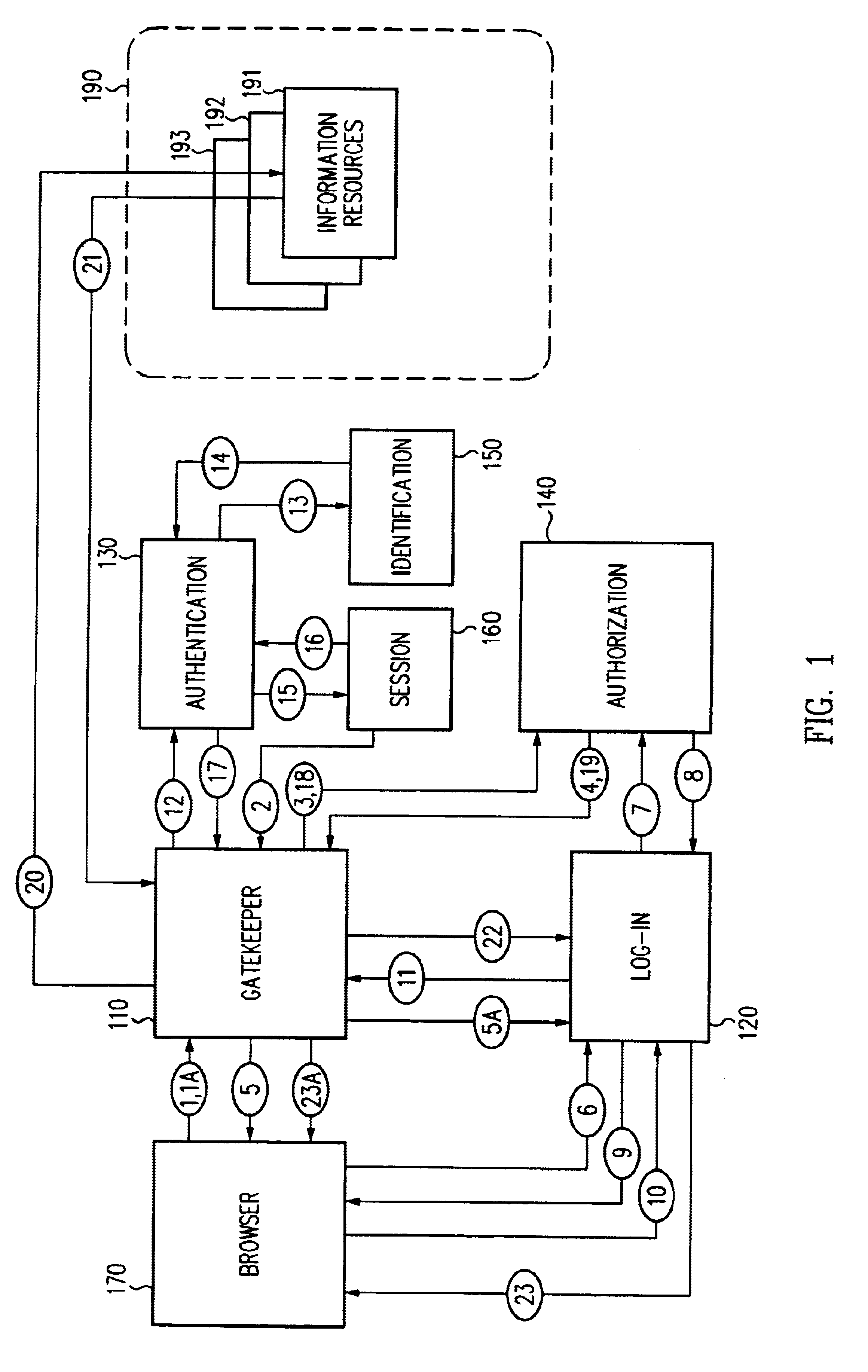
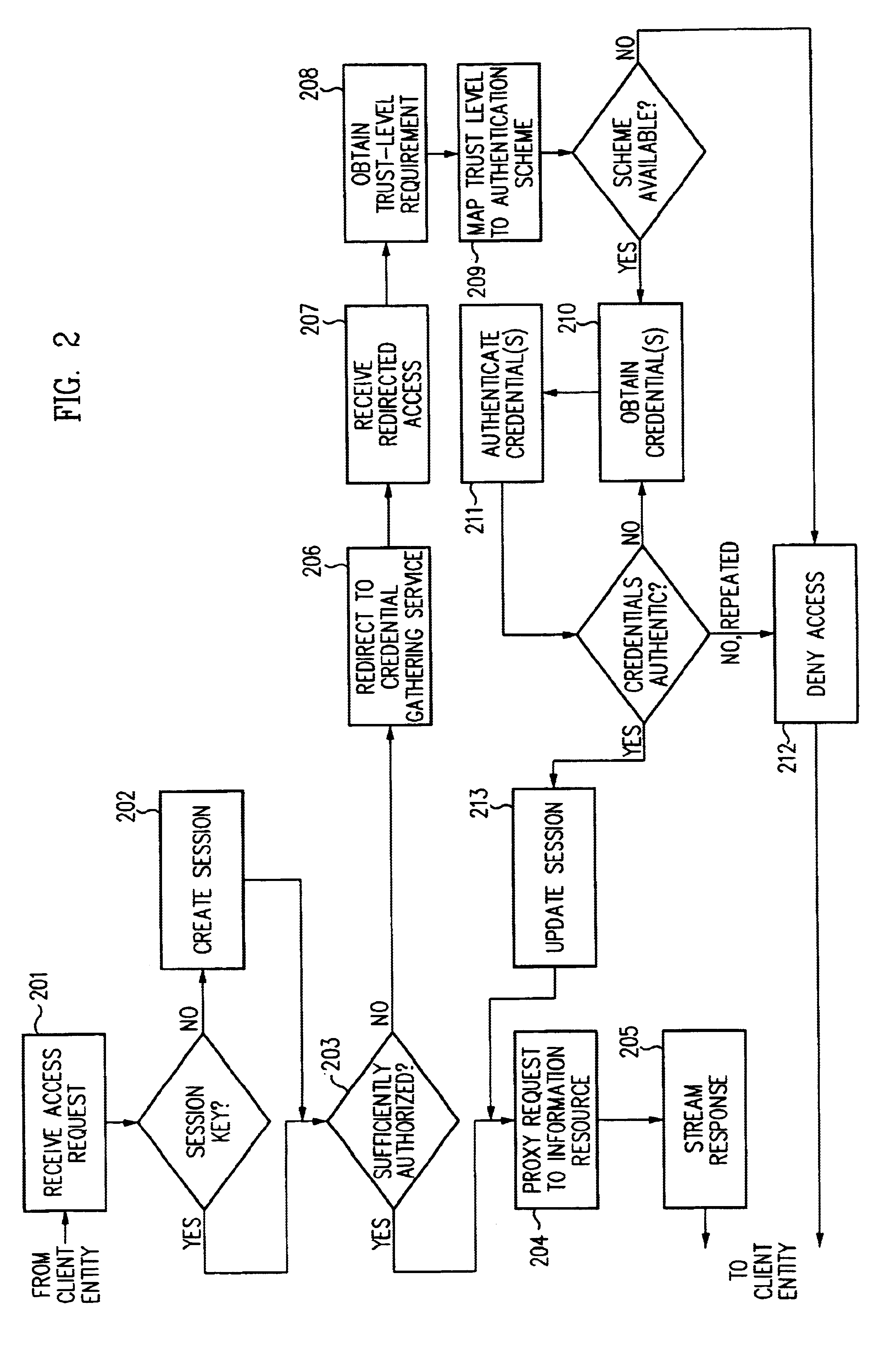
Log-on service providing credential level change without loss of session continuity
InactiveUS6609198B1Volume/mass flow measurementMultiple digital computer combinationsInformation resourceTrust level
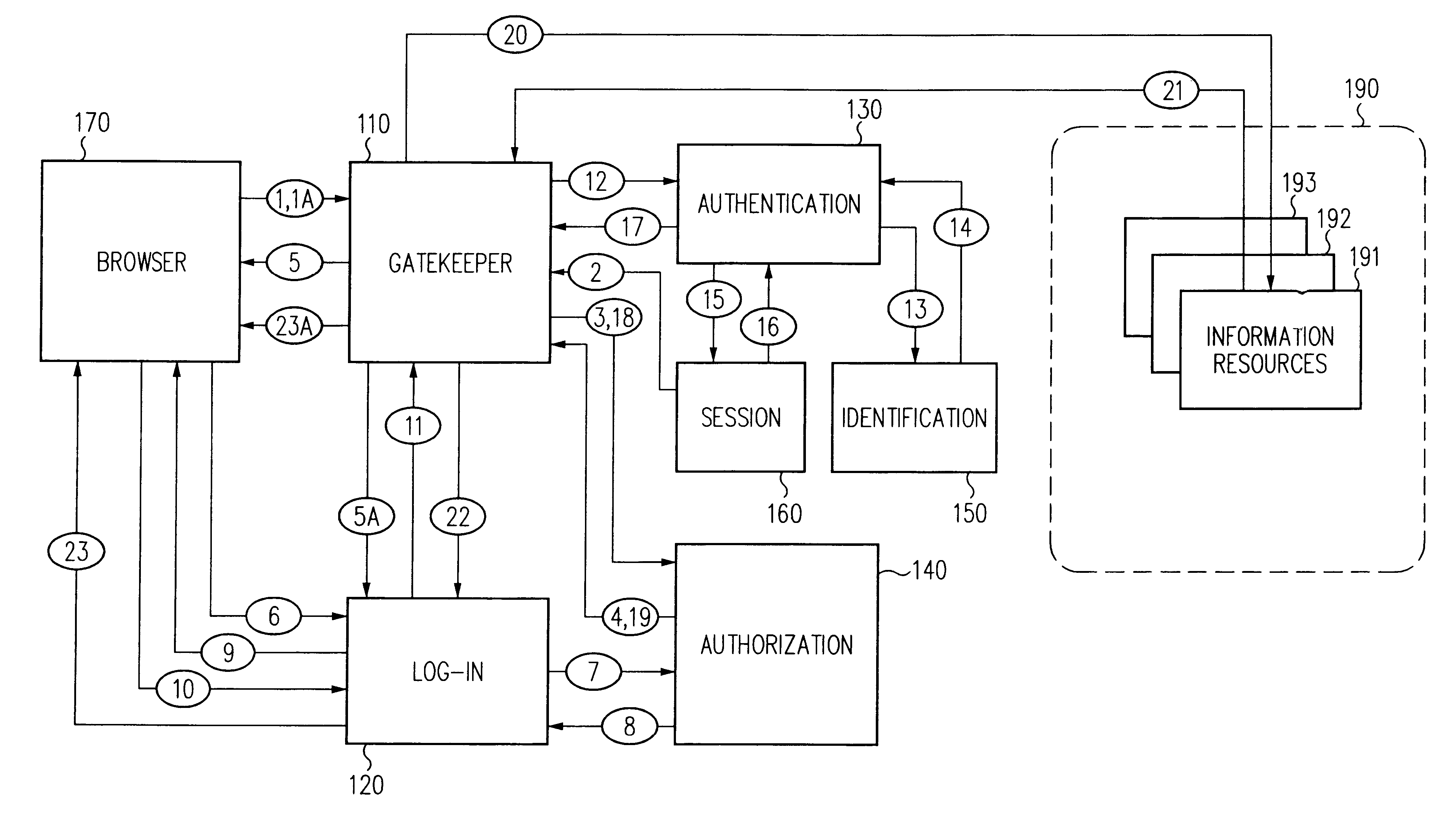
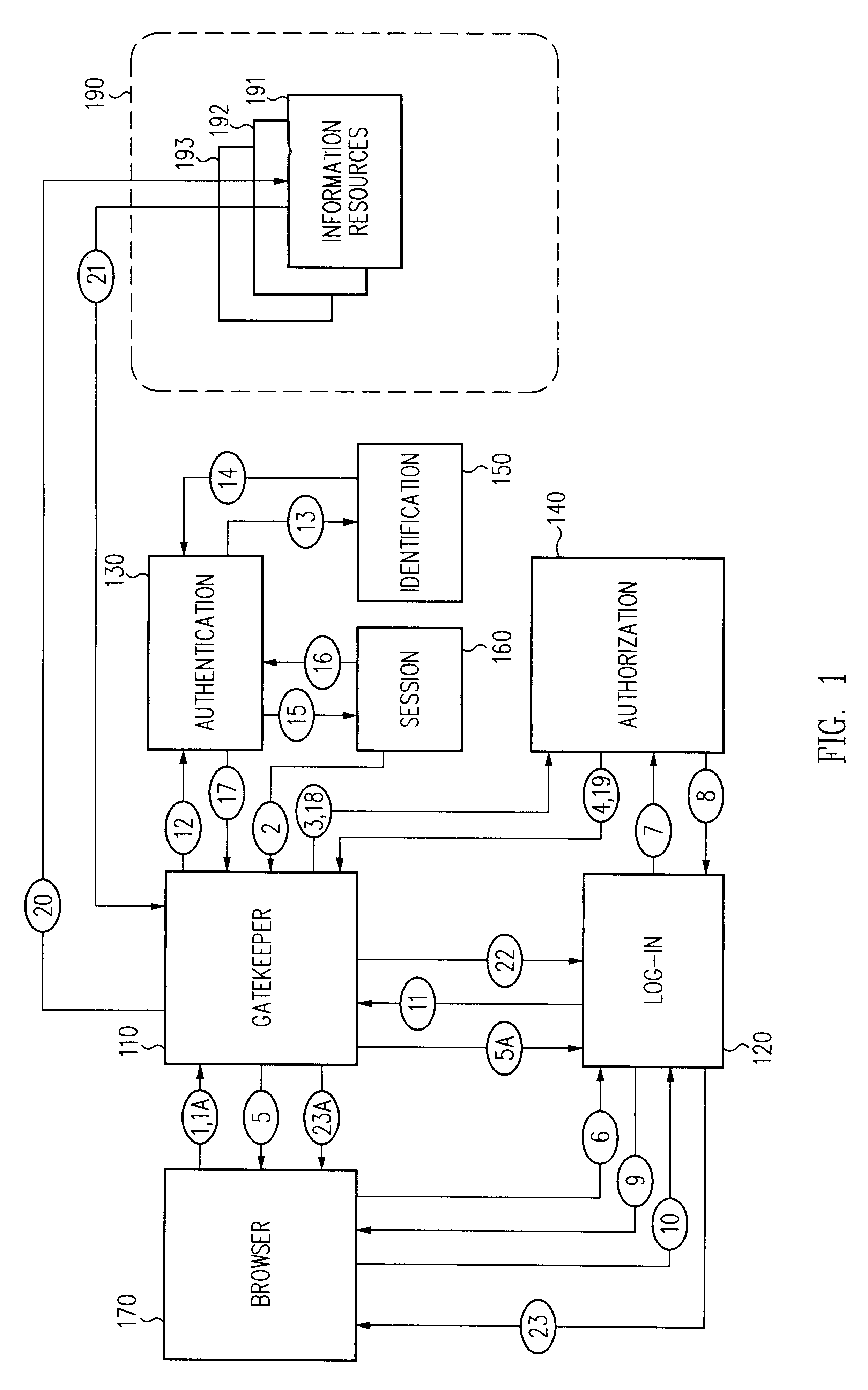
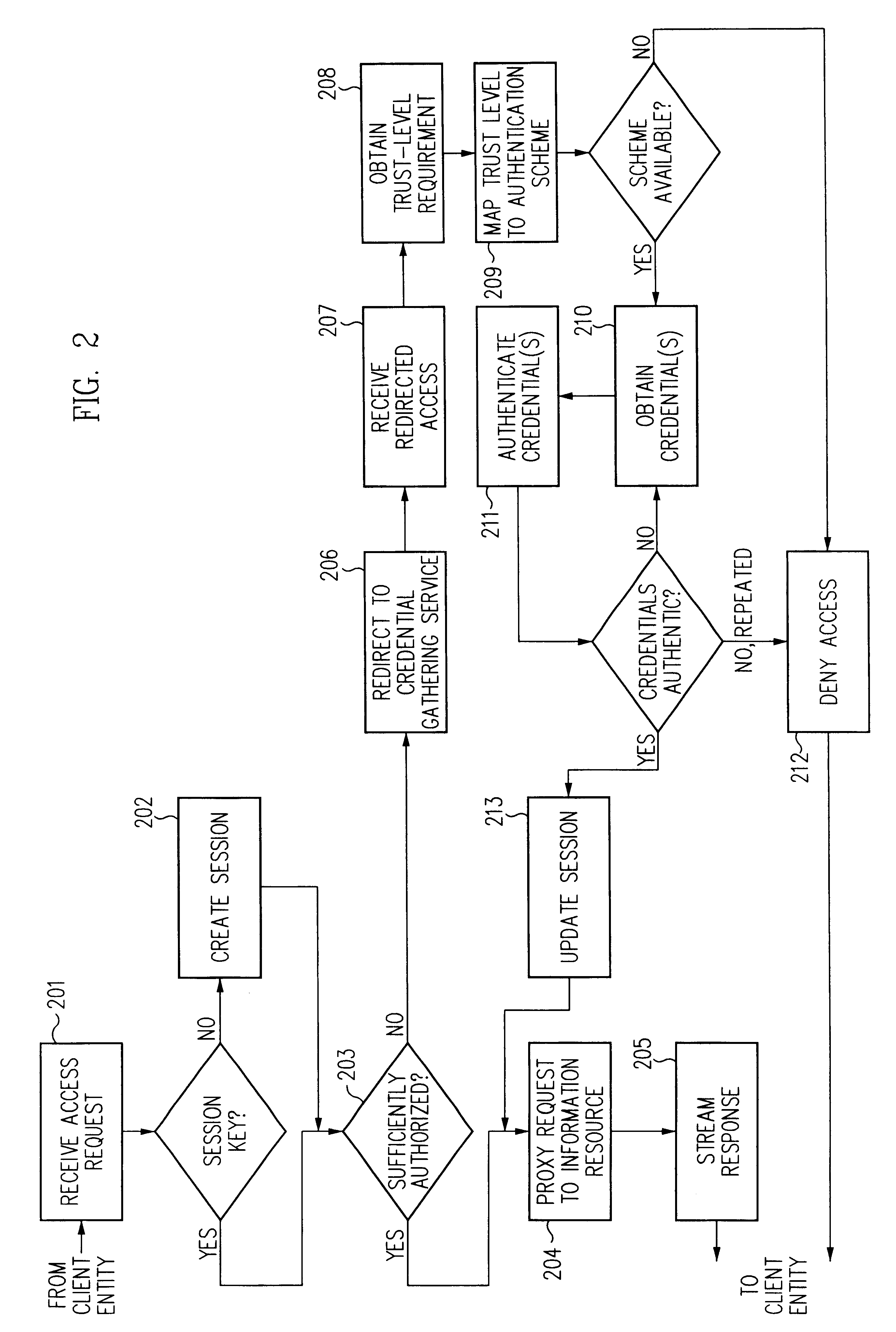
A security architecture has been developed in which a single sign-on is provided for multiple information resources. Rather than specifying a single authentication scheme for all information resources, the security architecture associates trust-level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are employed depending on the trust-level requirement(s) of an information resource (or information resources) to be accessed. Once credentials have been obtained for an entity and the entity has been authenticated to a given trust level, access is granted, without the need for further credentials and authentication, to information resources for which the authenticated trust level is sufficient. The security architecture allows upgrade of credentials for a given session. This capability is particularly advantageous in the context of a single, enterprise-wide log-on. An entity (e.g., a user or an application) may initially log-on with a credential suitable for one or more resources in an initial resource set, but then require access to resource requiring authentication at higher trust level. In such case, the log-on service allows additional credentials to be provided to authenticate at the higher trust level. The log-on service allows upgrading and / or downgrading without loss of session continuity (i.e., without loss of identity mappings, authorizations, permissions, and environmental variables, etc.).
Owner:ORACLE INT CORP
Single sign-on framework with trust-level mapping to authentication requirements
InactiveUS6892307B1Digital data processing detailsUser identity/authority verificationPasswordInformation resource
A security architecture has been developed in which a single sign-on is provided for multiple information resources. Rather than specifying a single authentication scheme for all information resources, the security architecture associates trust-level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are associated with trust levels and a log-on service obtains credentials for an entity commensurate with the trust-level requirement(s) of an information resource (or information resources) to be accessed. Once credentials have been obtained for an entity and the entity has been authenticated to a given trust level, access is granted, without the need for further credentials and authentication, to information resources for which the authenticated trust level is sufficient.
Owner:ORACLE INT CORP
Access management system and method employing secure credentials
InactiveUS6668322B1Digital data processing detailsUser identity/authority verificationInformation resourceTrust level
A security architecture has been developed in which a single sign-on is provided. Session credentials are used to maintain continuity of a persistent session across multiple accesses to one or more information resources, and in some embodiments, across credential level changes. Session credentials are secured, e.g., as a cryptographically secured session token, such that they may be inspected by a wide variety of entities or applications to verify an authenticated trust level, yet may not be prepared or altered except by a trusted authentication service. Some embodiments of the present invention associate trust level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are associated with trust levels, and in some embodiments, with environmental parameters. For example, in one configuration, a login service obtains login credentials for an entity commensurate with the trust level requirement(s) of an information resource (or information resources) to be accessed and with environment parameters that affect the sufficiency of a given credential type. Once login credentials have been obtained for an entity and have been authenticated to a given trust level, session credentials are issued and access is granted to information resources for which the trust level is sufficient. Advantageously, by using the session credentials access is granted without the need for further login credentials and authentication. In some configurations, session credentials evidencing an insufficient trust level may be remedied by a session continuity preserving upgrade of login credential.
Owner:ORACLE INT CORP
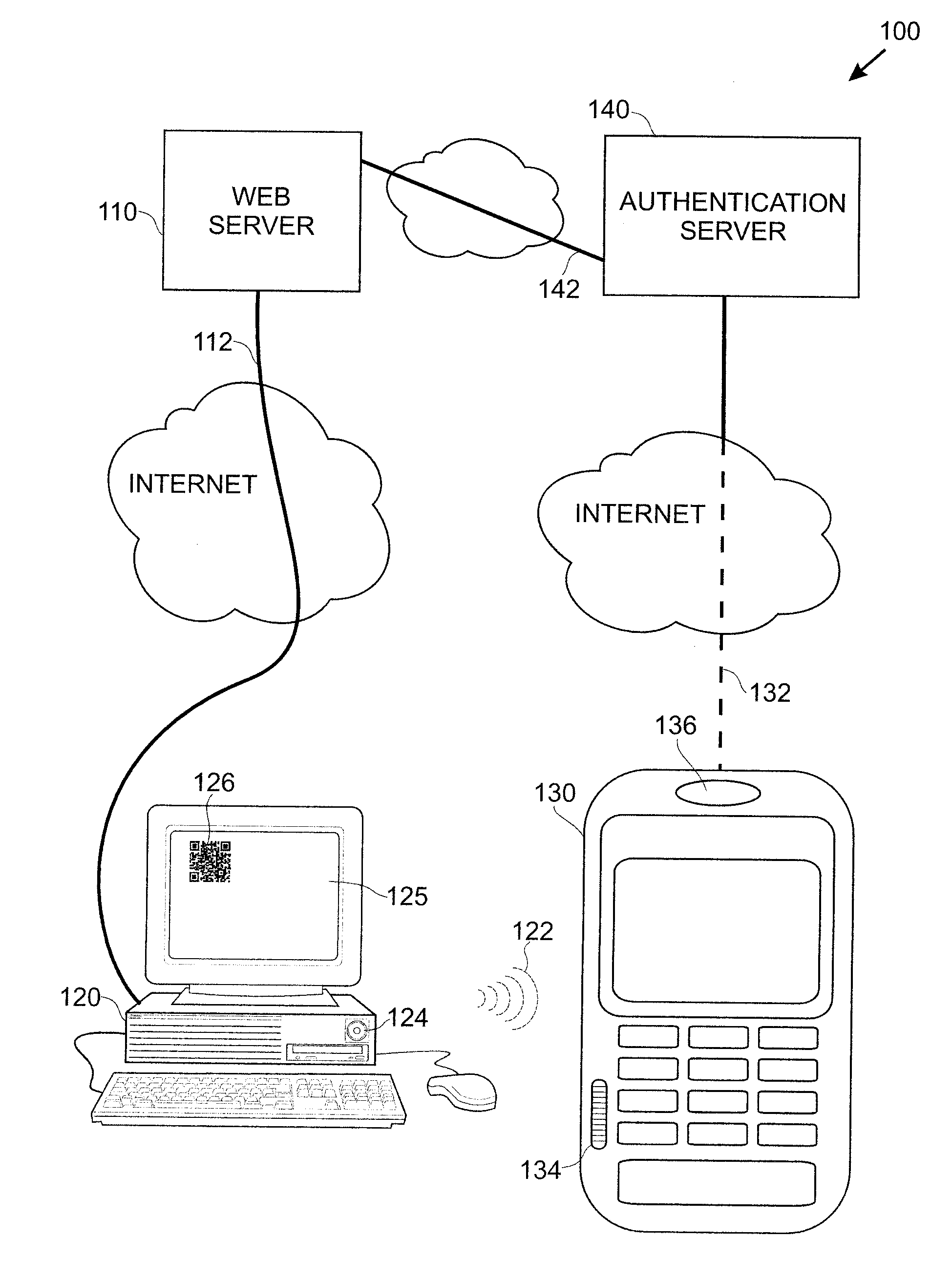
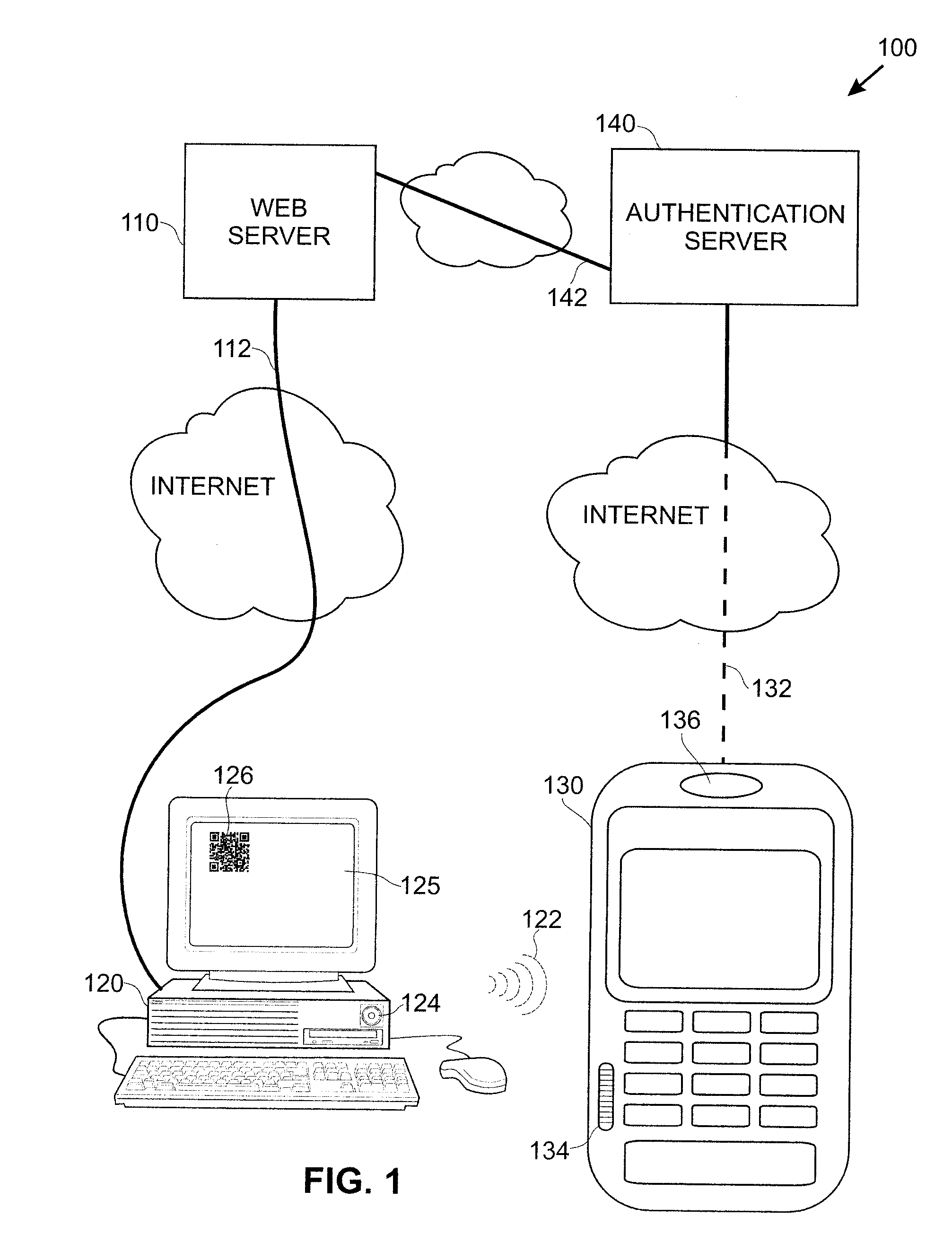
Smart Device User Authentication
InactiveUS20110219427A1Little and no burdenImprove securityDigital data processing detailsComputer security arrangementsUser deviceWeb service
Techniques for simplifying an authentication process from the viewpoint of a user while providing improved security to the many users currently employing no or weak security techniques. In logging into a web site hosted by a web server, a session begins by a user connecting and logging in with a device, such as a personal computer. Rather than a user name and password approach which is presently typical, the personal computer communicates with another user device, such as a smart phone. In one approach, an encoded acoustic signal is employed for this communication. The smart phone securely communicates with an authentication server which informs the web server whether the user has been authenticated or not.
Owner:RSSBUS
System for providing personalized content over a telephone interface to a user according to the corresponding personalization profile including the record of user actions or the record of user behavior
InactiveUS7330890B1Shorten speedIncrease volumeMultiple digital computer combinationsAutomatic exchangesPersonalizationPassword
Owner:MICROSOFT TECH LICENSING LLC
Method for blocking all unwanted e-mail (SPAM) using a header-based password
InactiveUS6266692B1Easy to sendEasy to solveOffice automationData switching networksEmail addressPassword
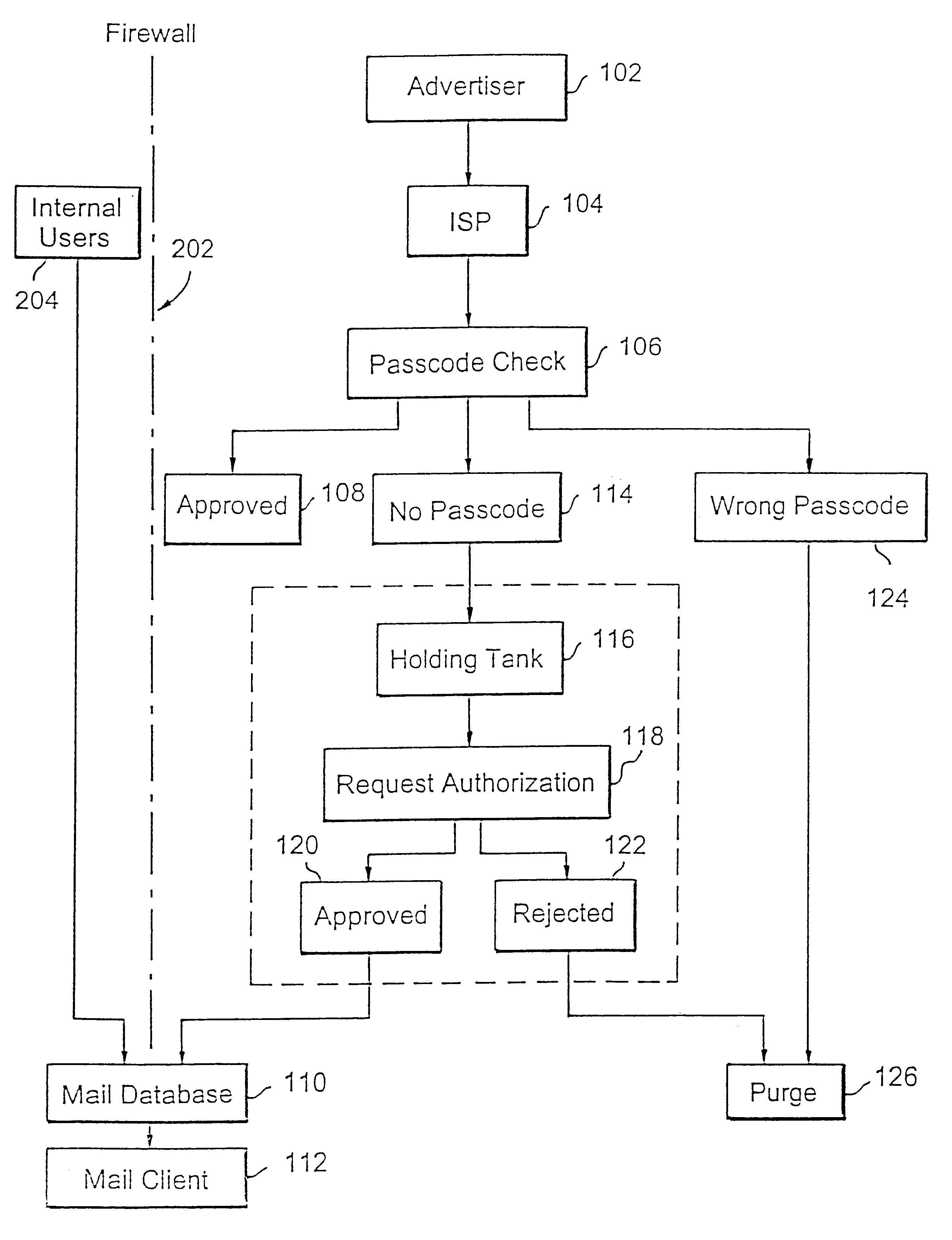
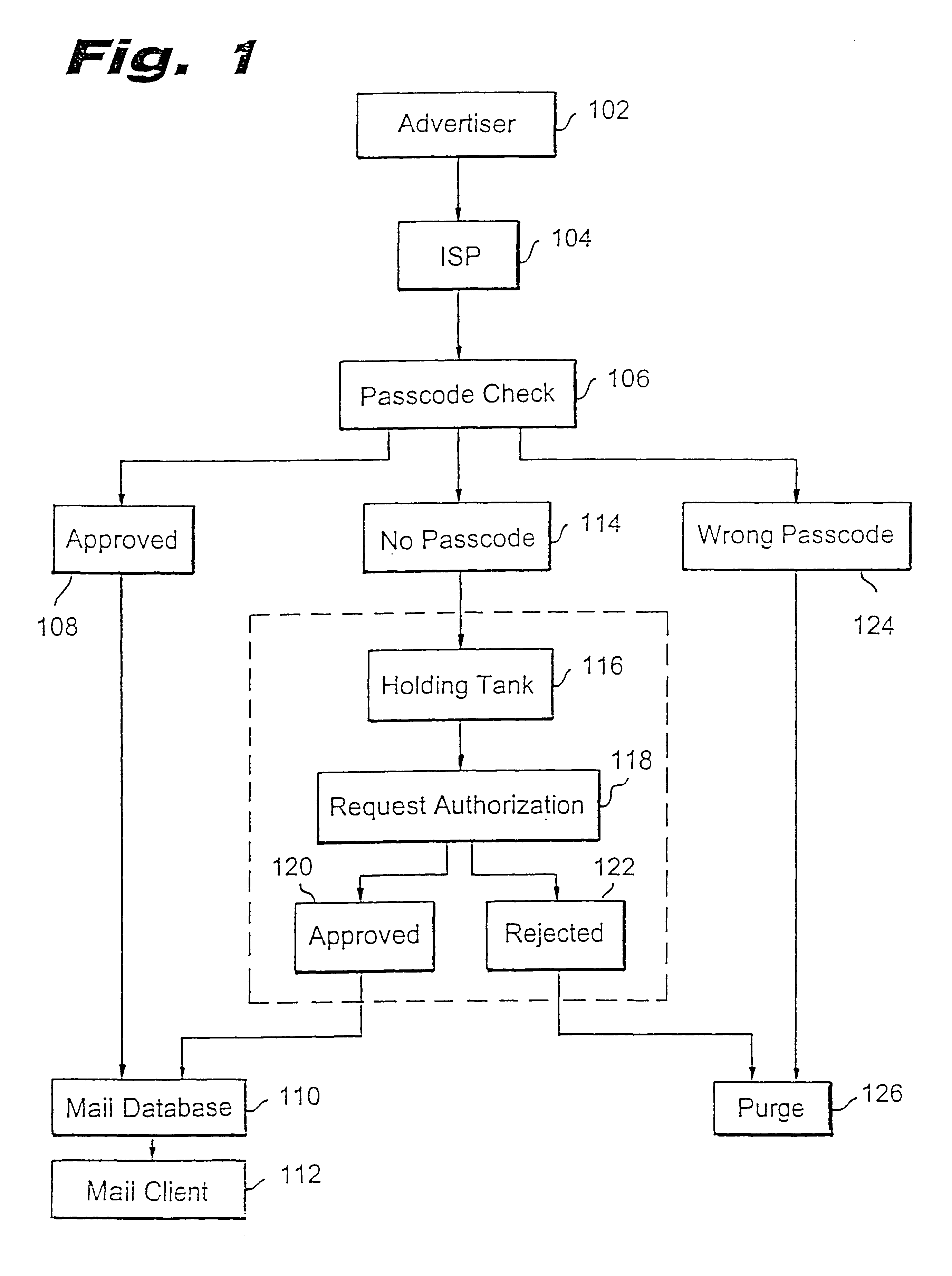
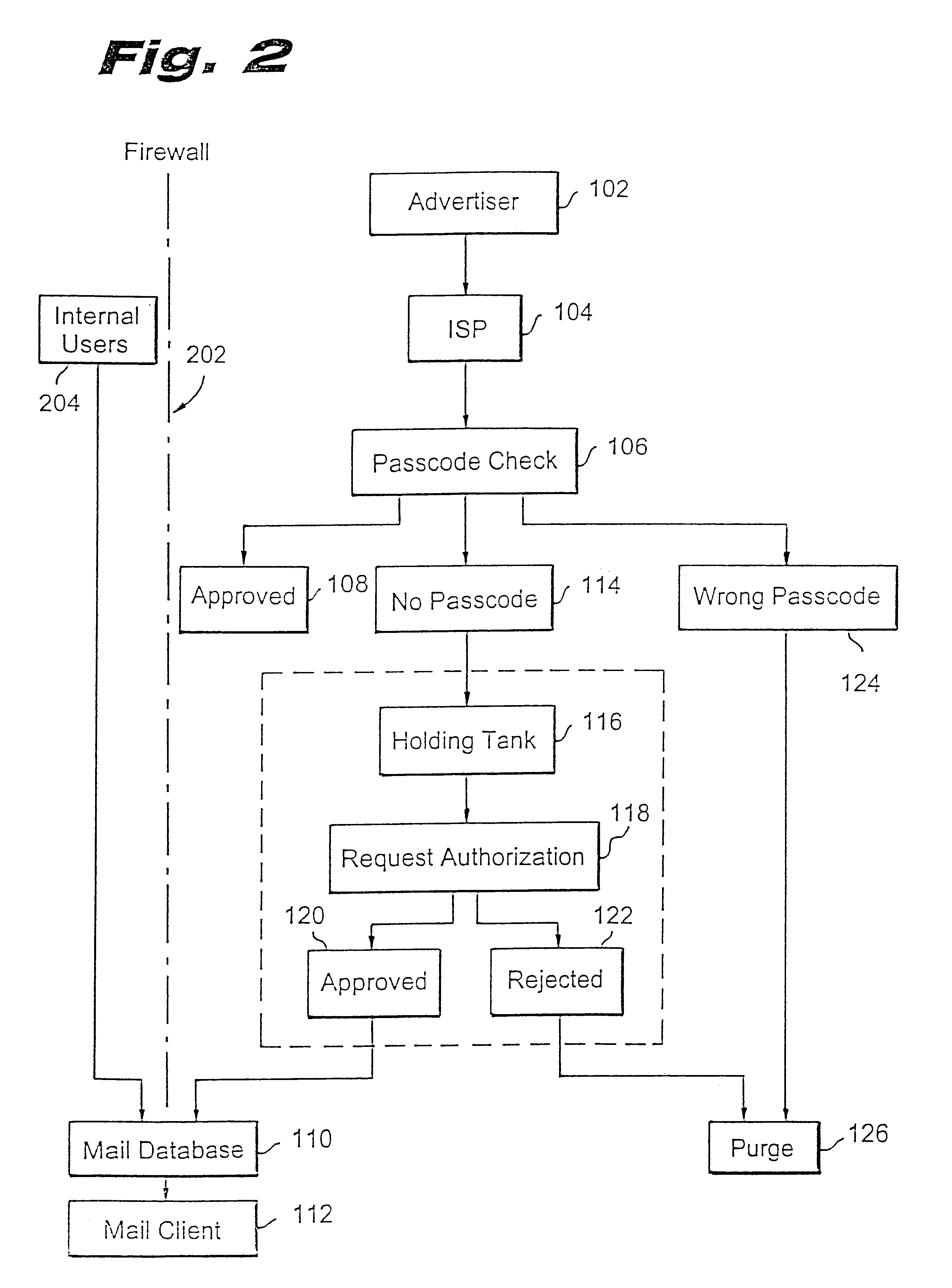
A method for blocking and / or filtering electronic mail. Selected senders are provided with a valid passcode associated with an e-mail address. When an e-mail is received at a mail server node, a field in a header of the e-mail is checked for a valid passcode associated with the destination e-mail address. If a valid passcode is detected, the e-mail is automatically sent to a receiver at the e-mail address. If an incorrect passcode is detected, the e-mail is automatically deleted at the server node and does not reach the receiver. If there is no passcode in the e-mail header, the e-mail is held temporarily, until the receiver approves to receive the e-mail. If the receiver rejects the e-mail, the e-mail is deleted. The present invention includes an additional capability for the senders of e-mails to request a passcode associated with a specific e-mail address in a lookup directory, before sending an e-mail to that address. Furthermore, the present invention enables firewall servers to block incoming e-mails only if they are received from the public Internet, thereby allowing all internal e-mails to reach the receiver without having to include valid passcodes.
Owner:TREND MICRO INC
System and method for controlled access to shared-medium public and semi-public internet protocol (IP) networks
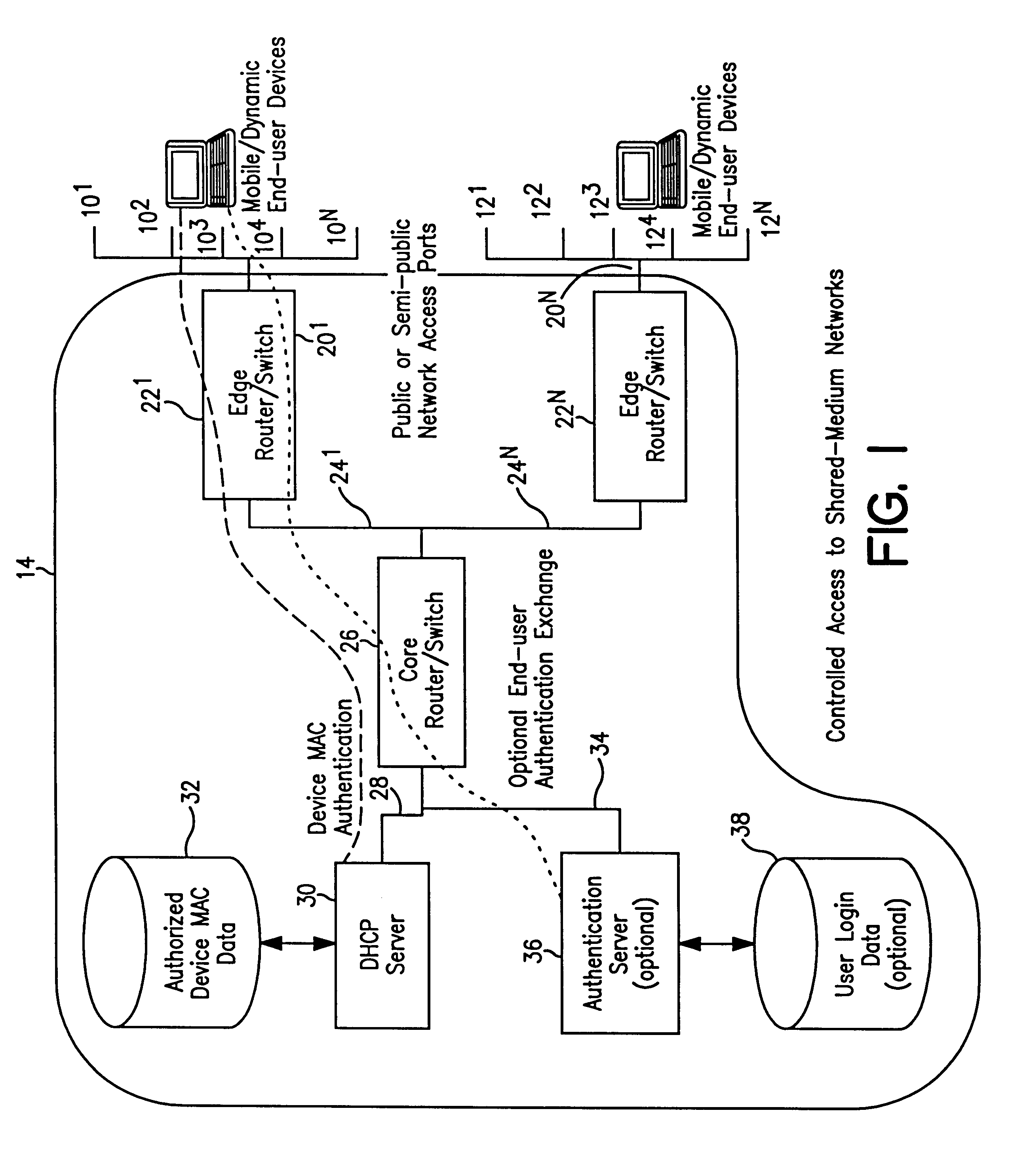
InactiveUS6393484B1Multiple digital computer combinationsTransmissionAddress Resolution ProtocolDevice register
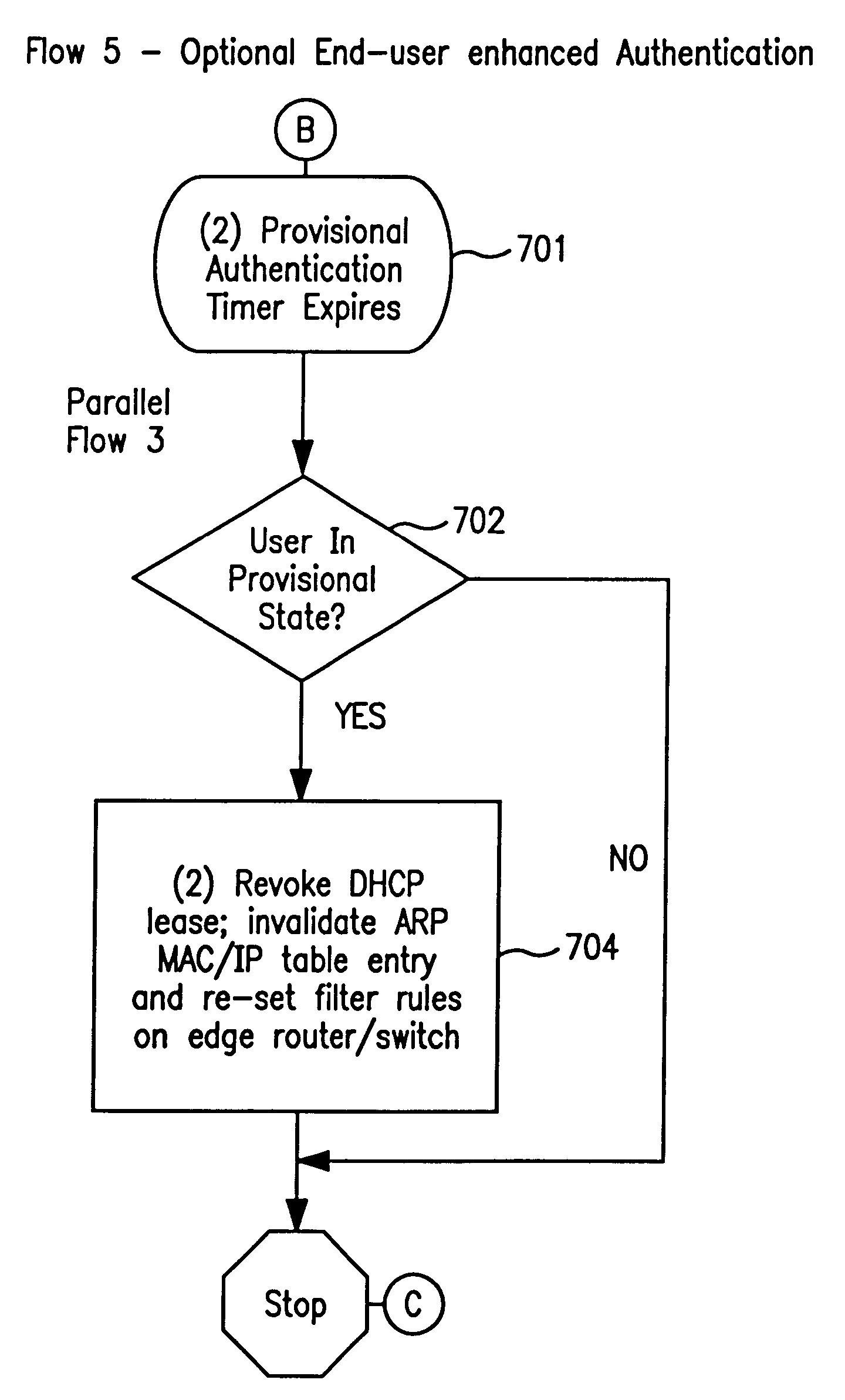
A system and method prevent unauthorized users and devices, in a dynamic user / device environment, from obtaining access to shared-medium public and semi-public IP networks. A network includes a layered communication system and routers / switches for coupling users and devices to a Dynamic Host Control Protocol (DHCP) server and an authentication server. Databases support the servers. The network incorporates Address Resolution Protocol (ARP). Authorized users and devices register for service by providing the DHCP with user identification for log-in, passwords, MAC addresses, etc. When users connect to the network access point, a DHCP exchange is initiated to obtain a valid IP address and other associated parameters. The DHCP client initiates a MAC broadcast for IP addresses which contain in the request the end user's device MAC address. The associated router switch will pick up and forward to a DHCP server the end user's device request. The DHCP server will process the end user's request and extract the end user's device MAC address. With the end user's MAC address, the DHCP server accesses its device and / or user information in the database. If the MAC address is not registered, the DHCP server refuses to handle the request and logs the attempt, potentially alerting network operators of a security breach. If the MAC address is registered, a DHCP server selects an appropriate IP address and associated parameters to be returned to the requesting end user and connects via programming or command interface to the router switch that is forwarding the DHCP request on behalf of the end user device. The server adds an ARP IP to the MAC address table entry with the selected IP address and end user's MAC address. End user device authentication and IP lease are marked as provisional. A timer is started for a suggested duration. Optionally, the DHCP dynamically sets up filter rules in the router switch limiting access to a subset of IP addresses such as the address of a log-in server. Initial DHCP processing is completed and an IP address is assigned to the requesting end user's device by DHCP. When the timer expires, if the DHCP server finds the authenticating user state is provisional, it will revoke the IP lease, invalidate the corresponding ARP to MAC table entry in the associated router switch, and reset any IP-permissive filtering for that device. If the user is in the full authenticated state, it will simply remove the restrictive filtering.
Owner:IBM CORP
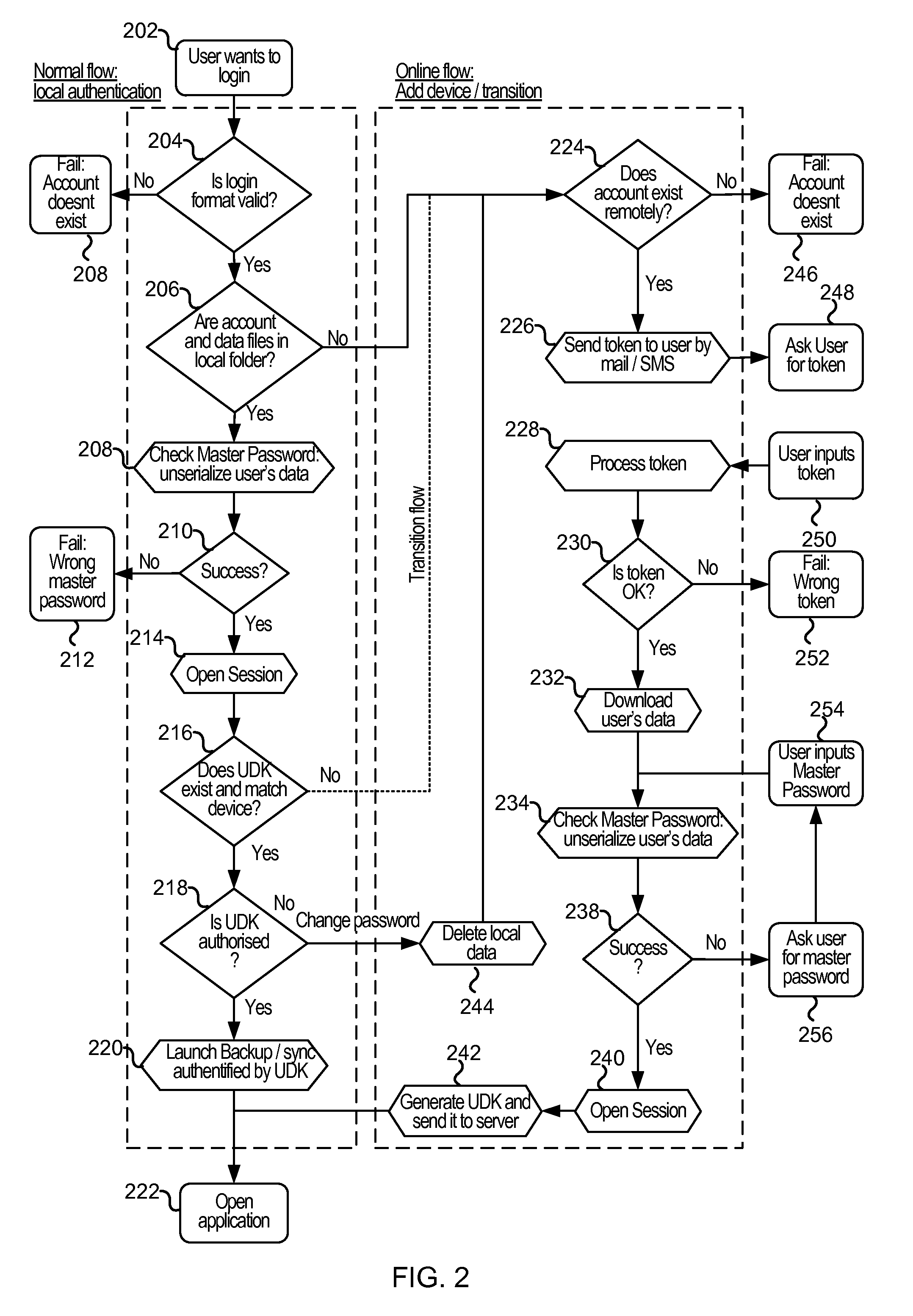
Cloud-based data backup and sync with secure local storage of access keys
ActiveUS20130145447A1Digital data processing detailsMultiple digital computer combinationsThree levelUser device
Methods and systems are provided for secure online data access. In one embodiment, three levels of security are provided where user master passwords are not required at a server. A user device may register with a storage service and receive a user device key that is stored on the device and at the service. The user device key may be used to authenticate the user device with the storage service. As data in the storage service is encrypted with a master password, the data may be protected from disclosure. As a user master key or derivative thereof is not used in authentication, the data may be protected from a disclosure or breach of the authentication credentials. Encryption and decryption may thus be performed on the user device with a user master key that may not be disclosed externally from the user device.
Owner:DASHLANE
Information server and mobile delivery system and method
InactiveUS20090249076A1Digital data processing detailsUser identity/authority verificationThird partyPassword
A user is provided with access to his or her account information using a client. The account information is stored on a server which receives the information from a feed source and transmits the information to the client. A method for downloading and installing specialized software for viewing the account information on the client is also provided. The information can be received from different feed sources in different formats and converted to a format that is compatible with the intended receiving client. Encryption can be used to protect the privacy of the users of the system and the account information therein. Additionally, a special access password and a privileged access routine can be used to provide access to an authorized third party user on a temporary basis.
Owner:ALLONE HEALTH GRP
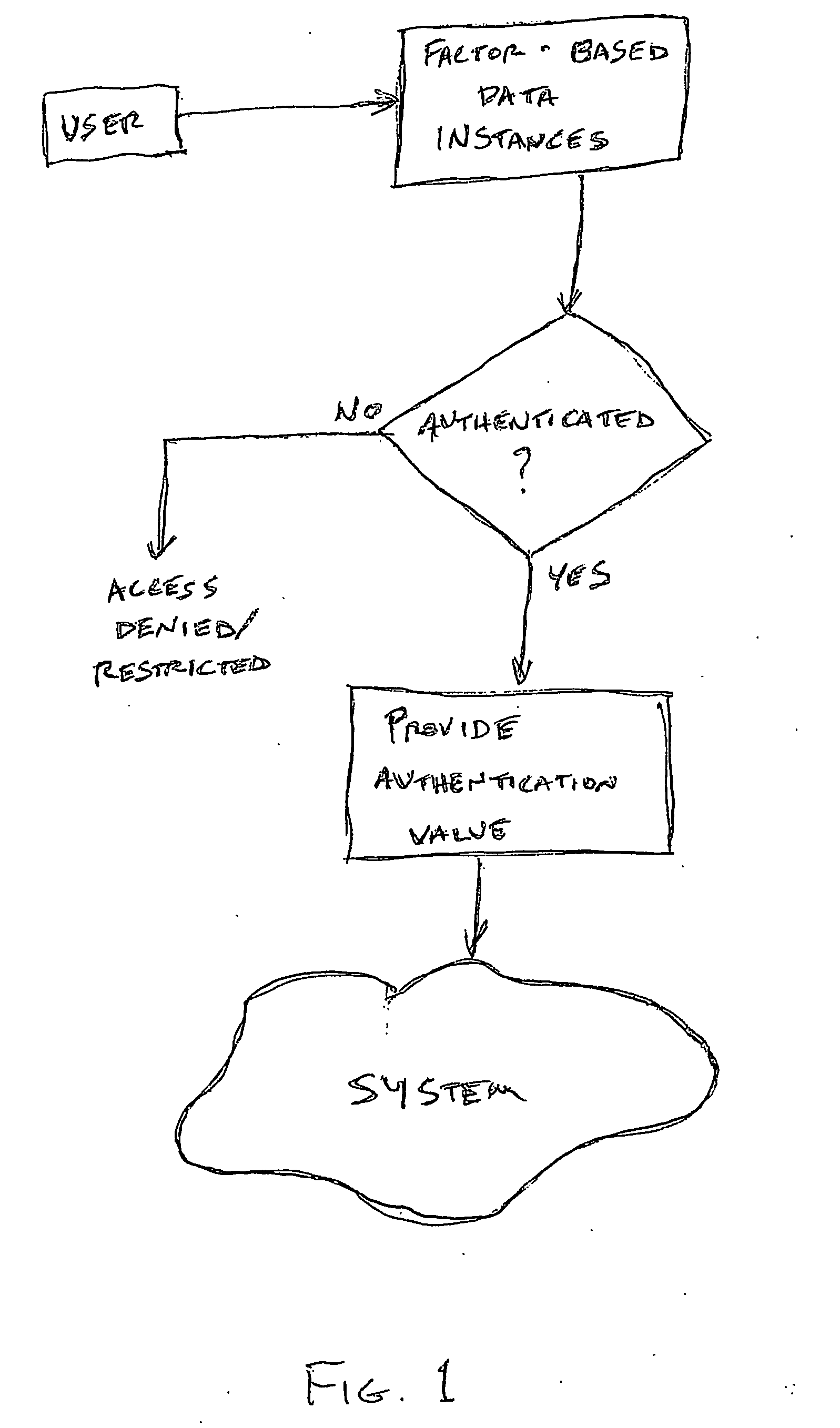
Multi-factor authentication system
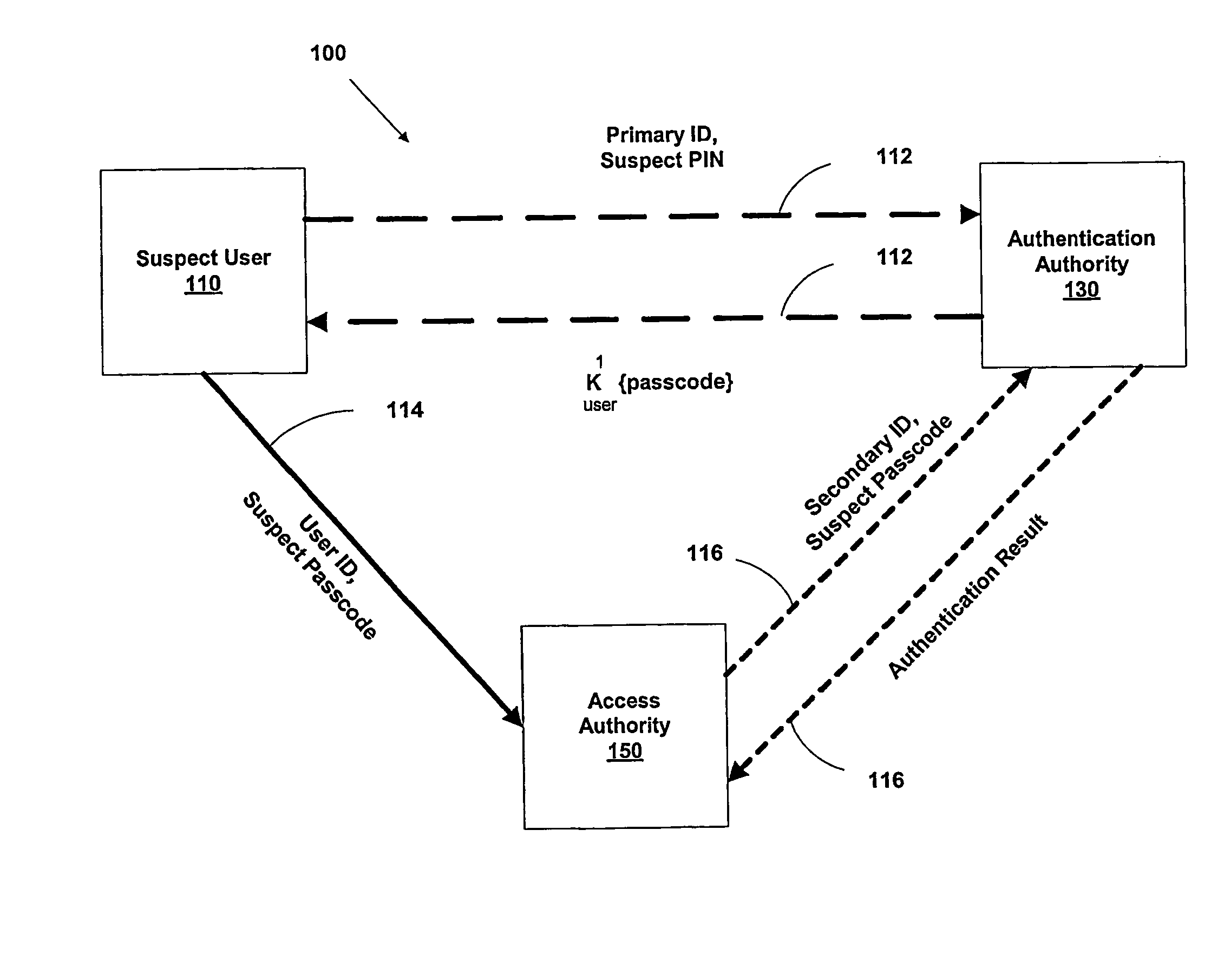
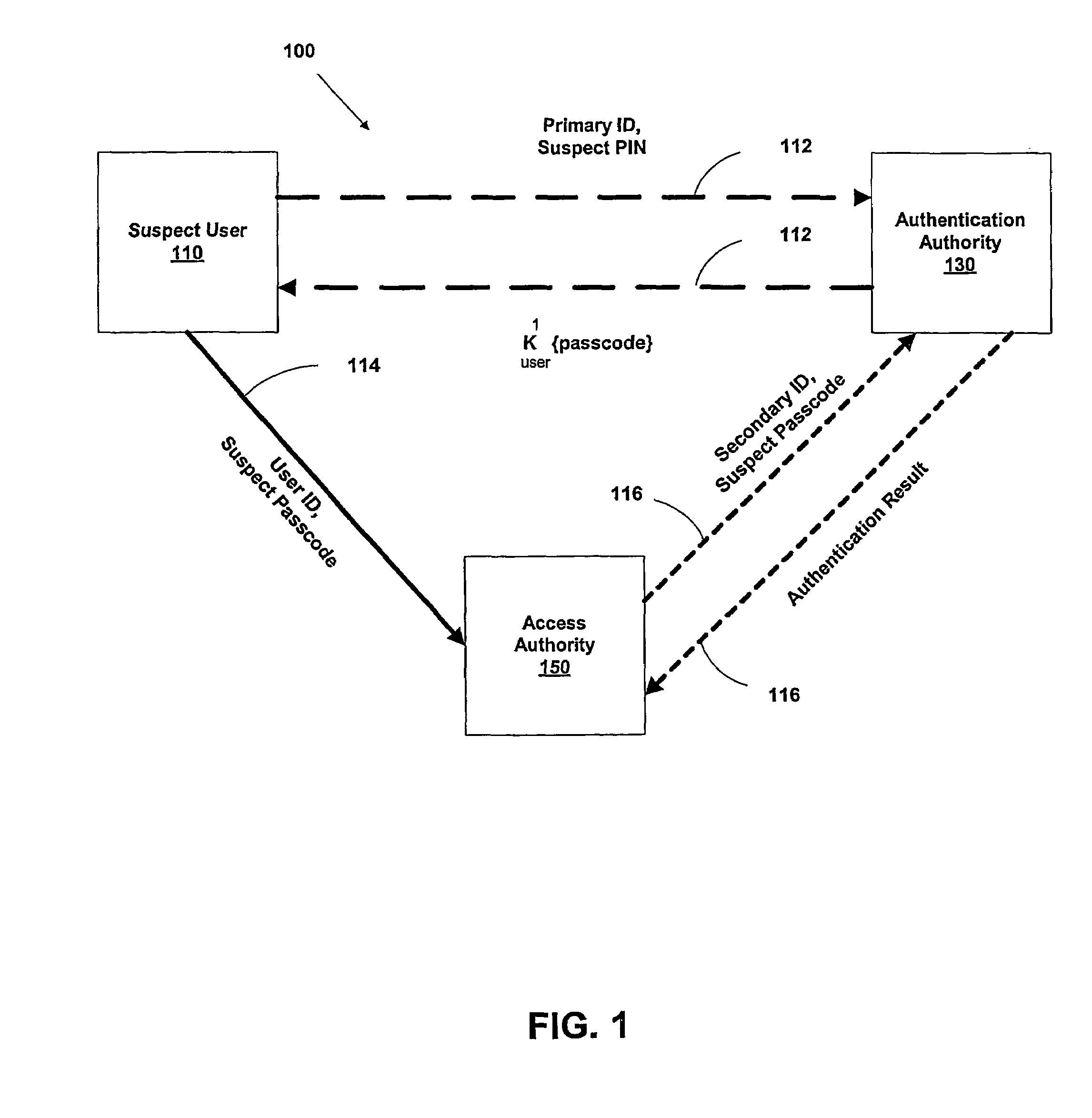
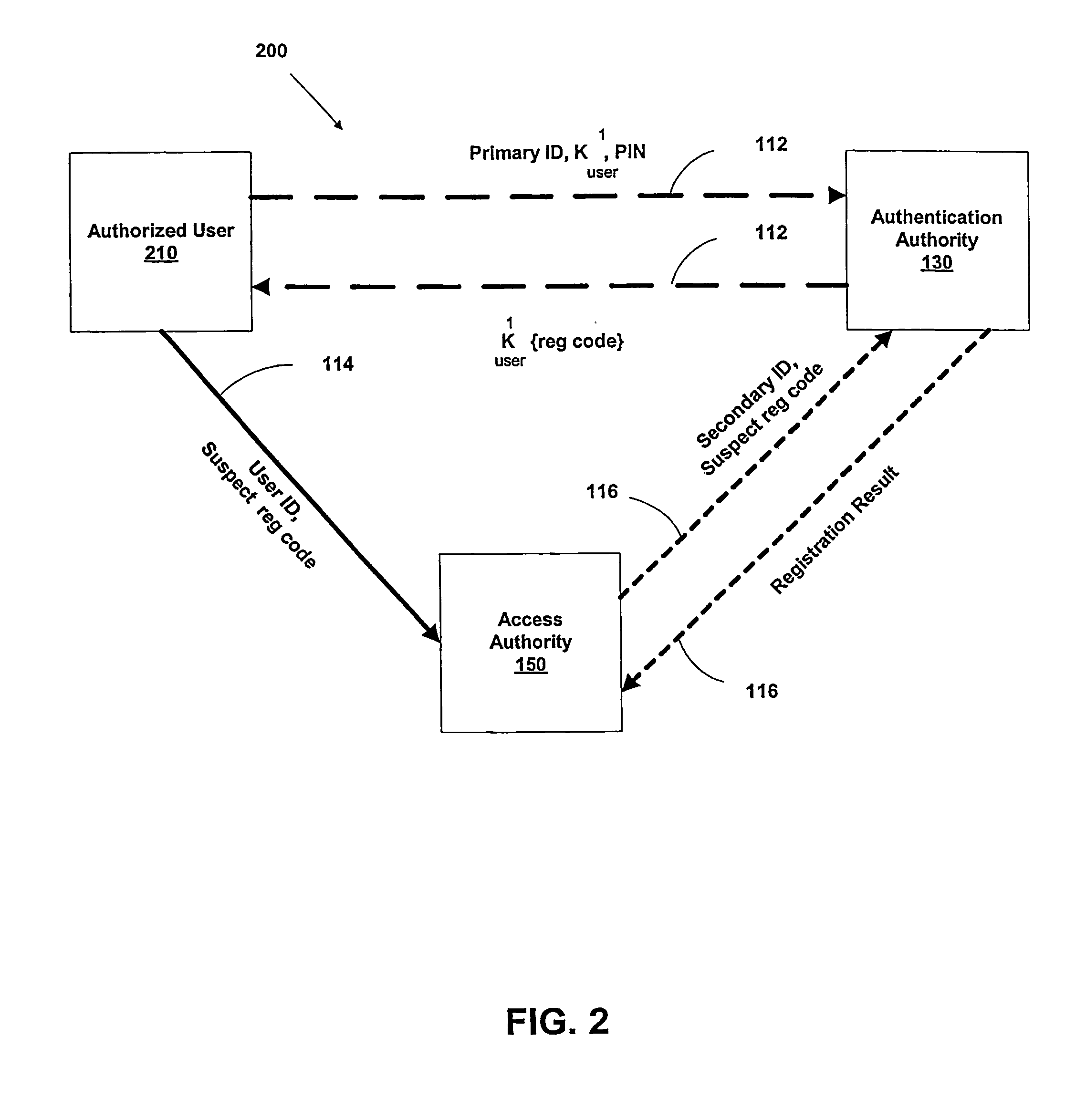
InactiveUS20040187018A1Easy to understandUser identity/authority verificationUnauthorized memory use protectionPasswordUser identifier
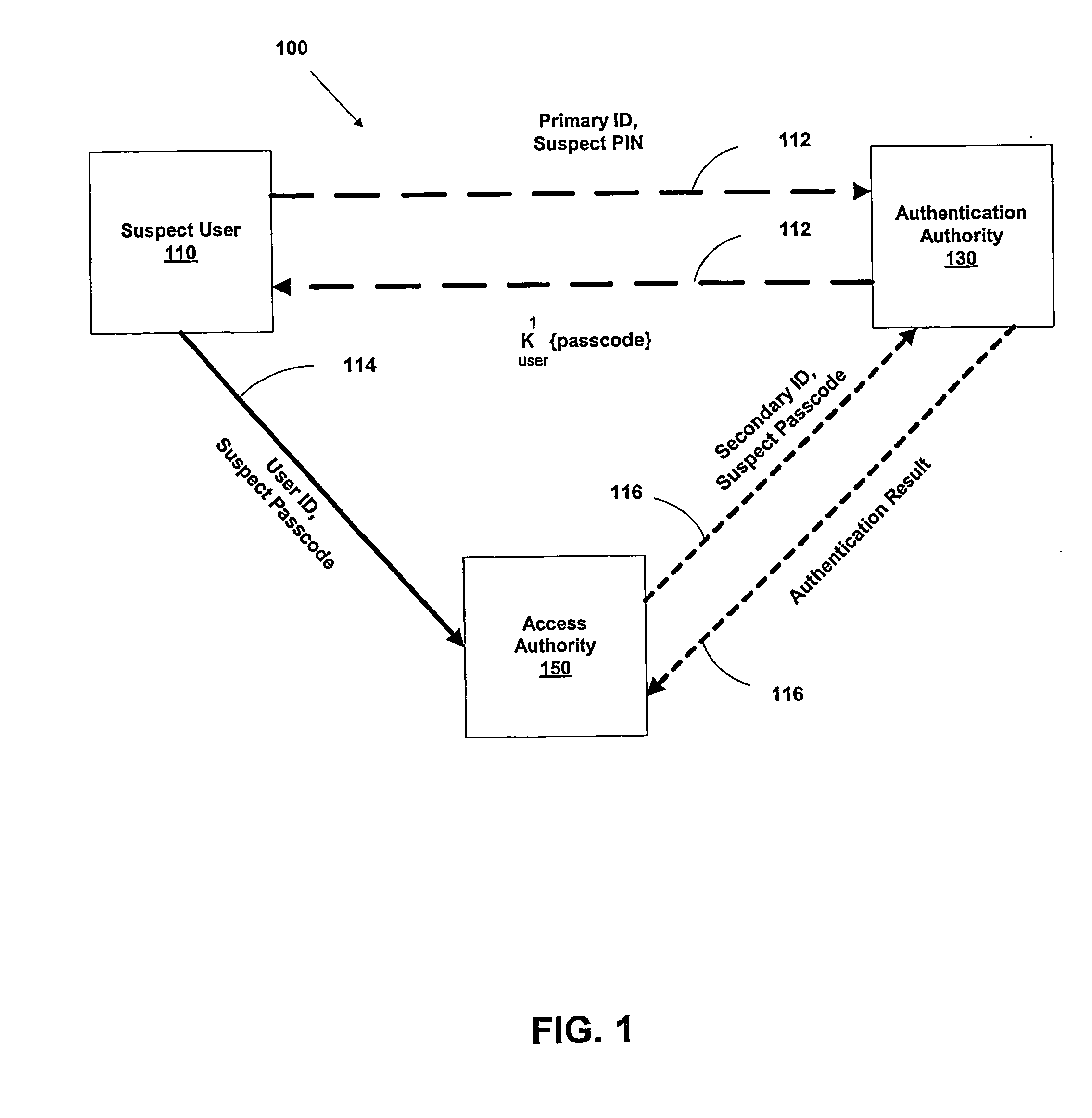
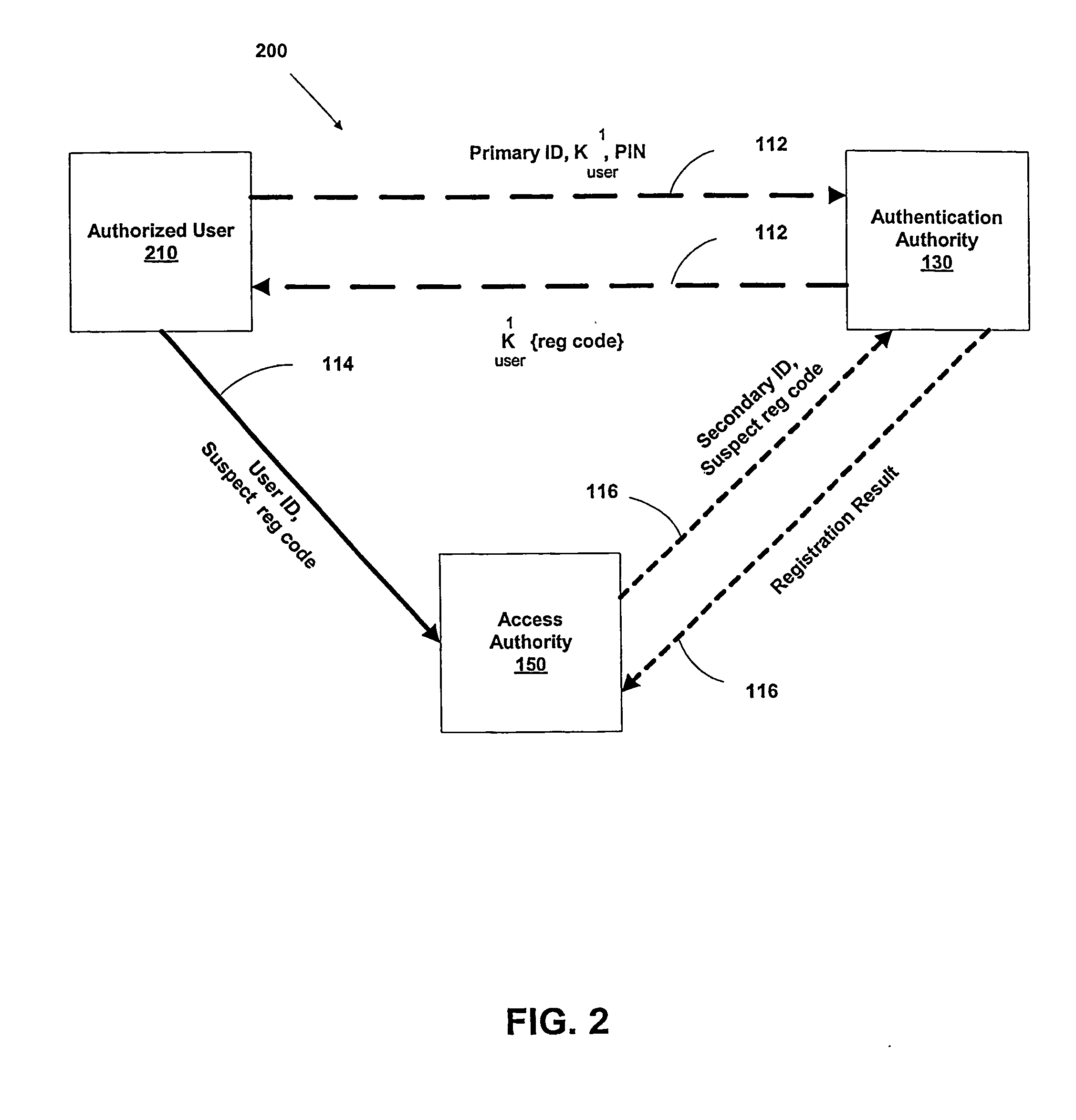
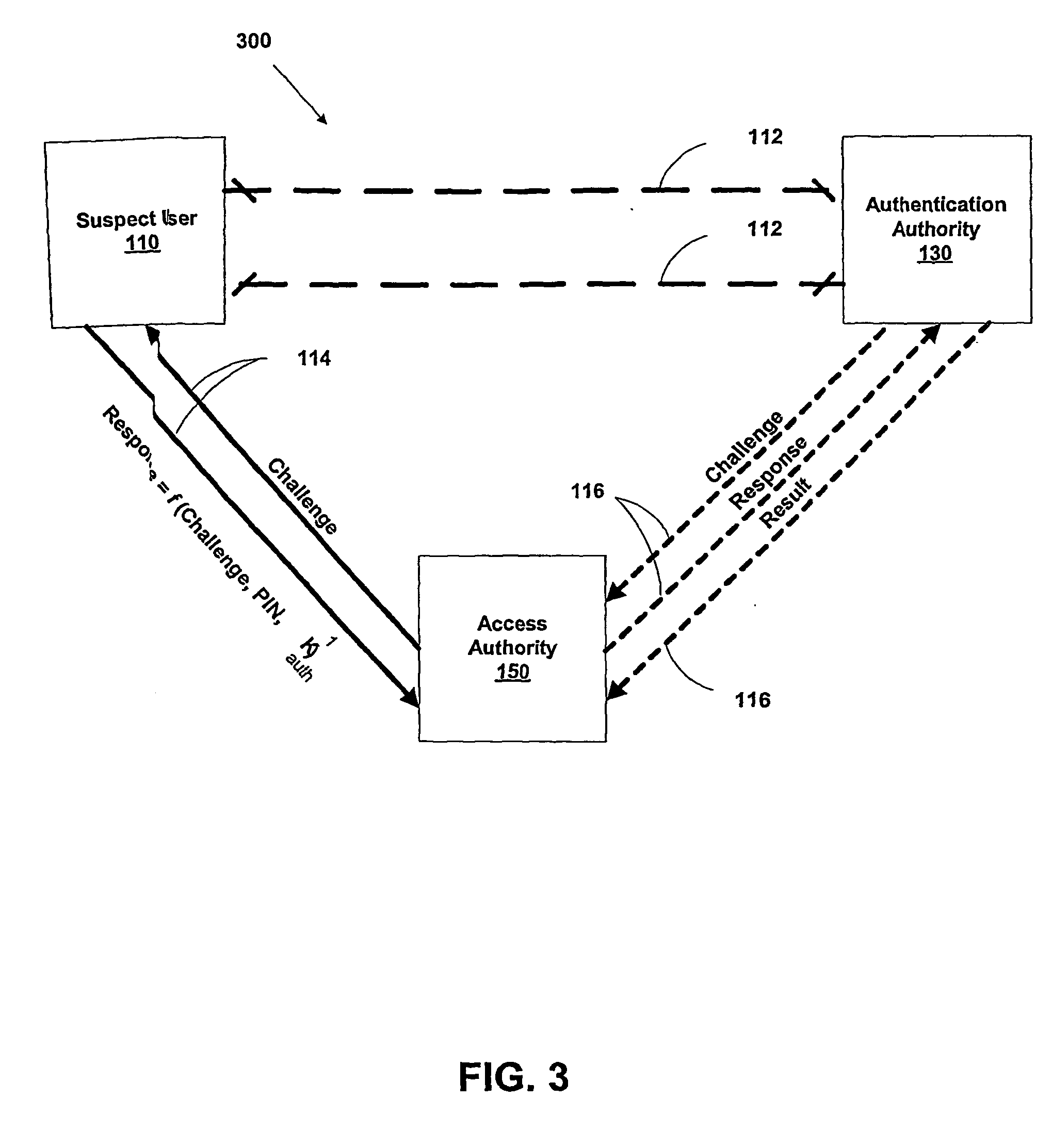
A suspect user (110) seeks access to a network resource from an access authority (150) utilizing a passcode received from an authentication authority (130). Initially, an ID of a device is bound with a PIN, the device ID is bound with a private key of the device, and the device ID is bound with a user ID that has been previously bound with a password of an authorized user. The device ID is bound with the user ID by authenticating the user ID using the password. Thereafter, the suspect user communicates the device ID and the PIN from the device over an ancillary communications network (112); the authentication authority responds back over the ancillary communications network with a passcode encrypted with the public key of the device; and the suspect user decrypts and communicates over a communications network (114) the passcode with the user ID to the access authority.
Owner:KARETEK HLDG LLC
Use of personal communication devices for user authentication
InactiveUS6993658B1Metering/charging/biilling arrangementsDigital data processing detailsPagerInternet privacy
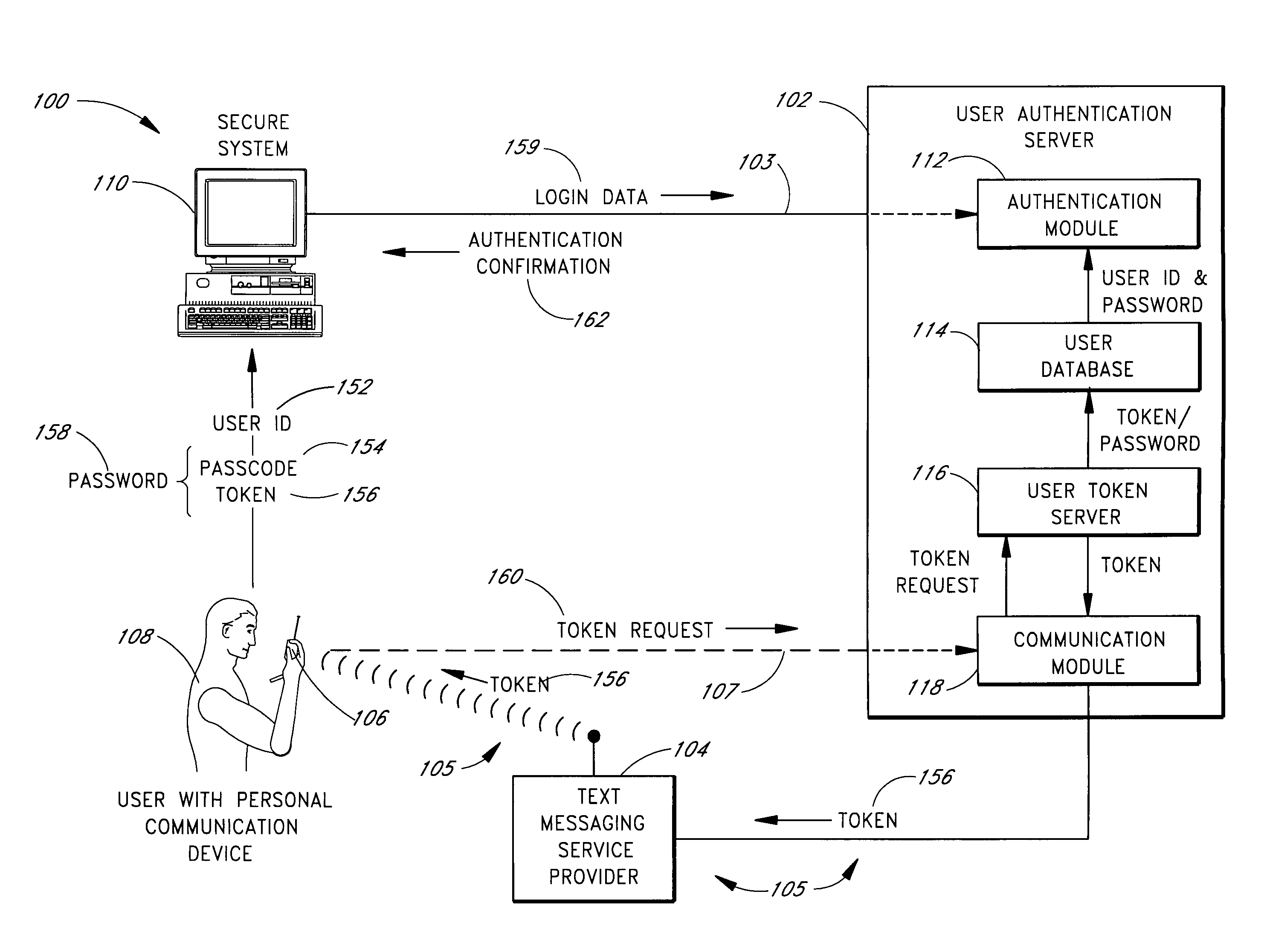
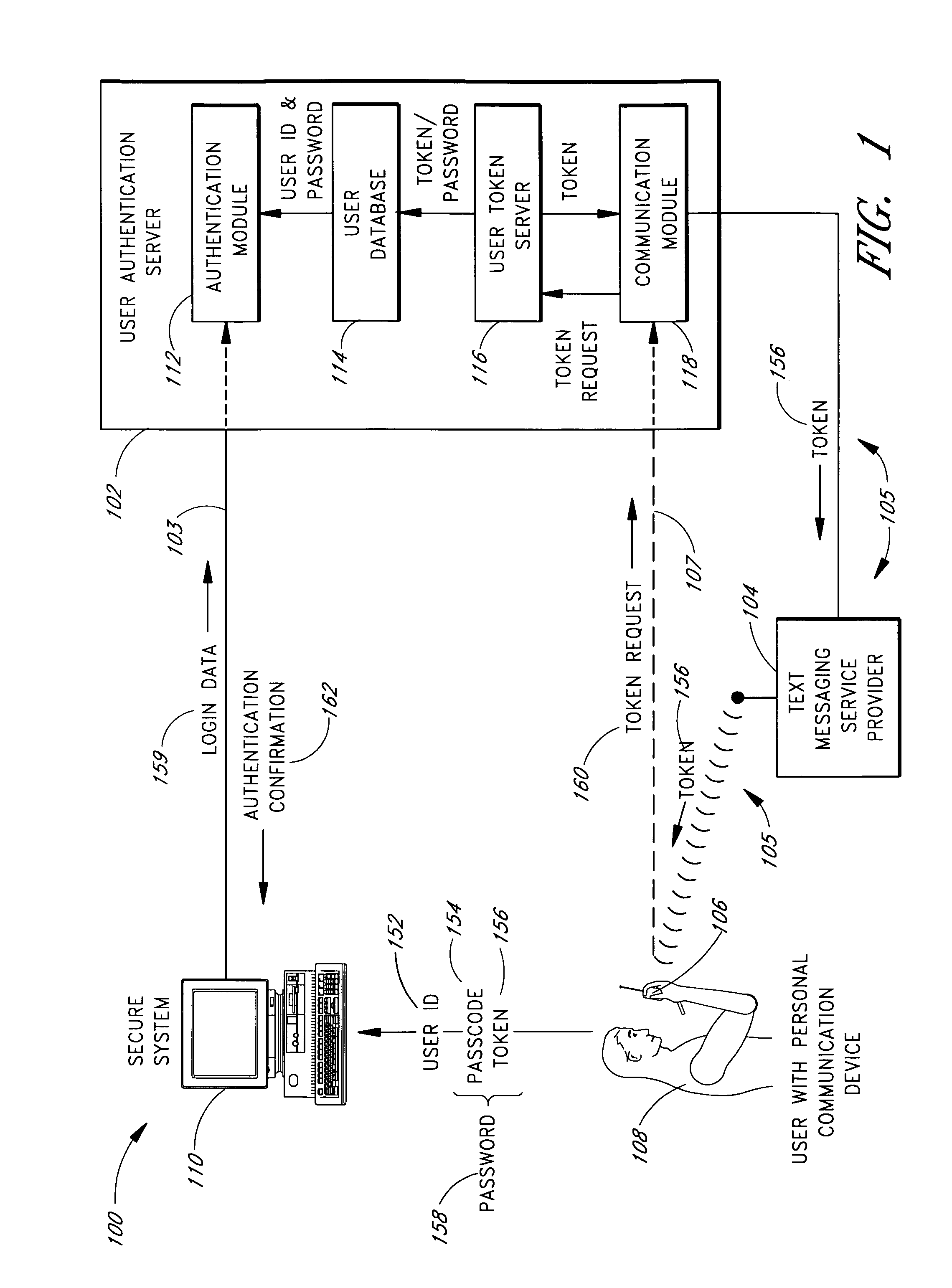
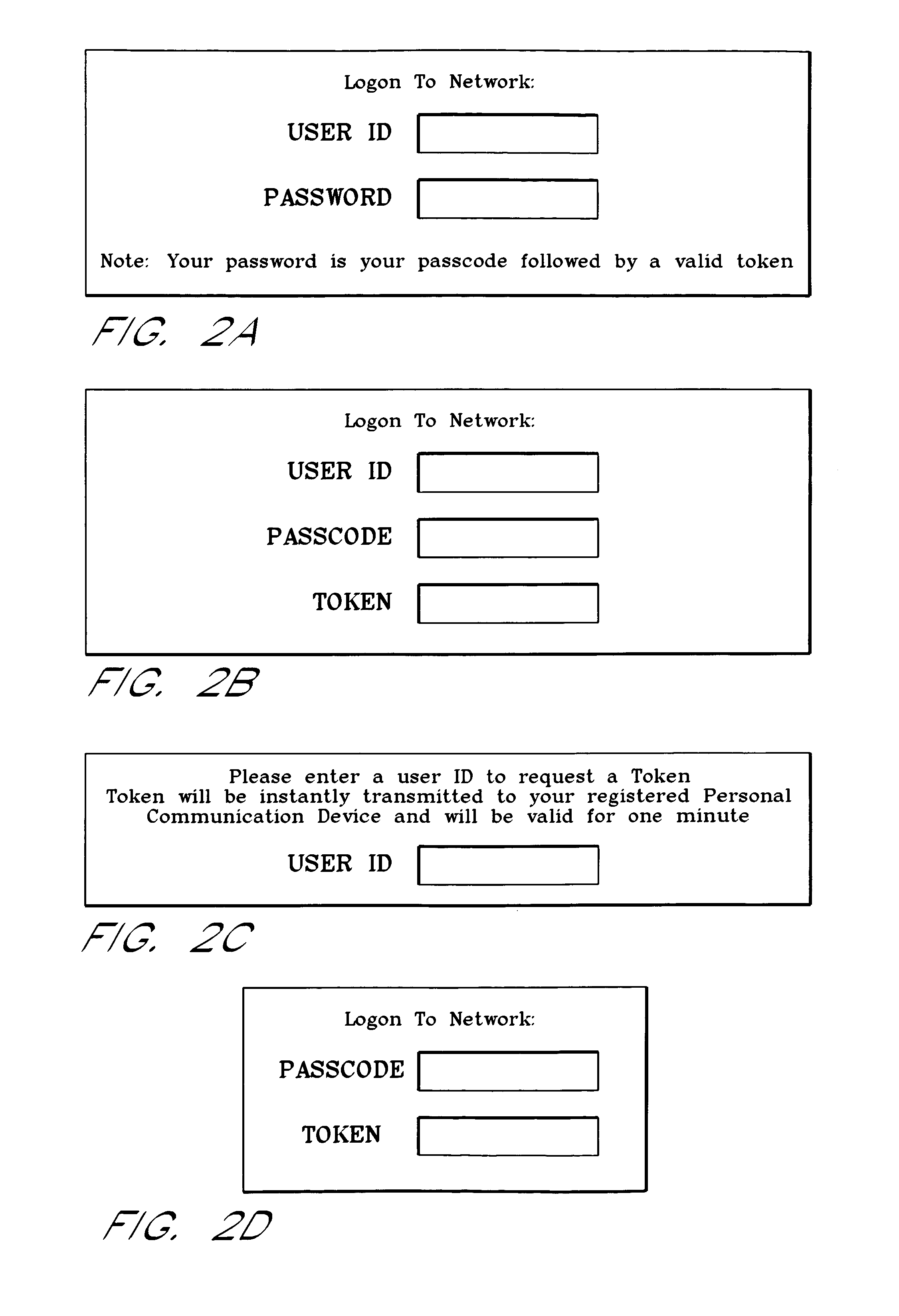
A password setting system for a secure system includes a user token server and a communication module. The user token server generates a random token in response to a request for a new password from a user. The server creates a new password by concatenating a secret passcode that is known to the user with the token. The server sets the password associated with the user's user ID to be the new password. The communication module transmits the token to a personal communication device, such as a mobile phone or a pager carried by the user. The user concatenates the secret passcode with the received token in order to form a valid password, which the user submits to gain access to the secure system. Accordingly, access to the system is based upon: nonsecret information known to the user, such as the user ID; secret information known to the user, such as the passcode; and information provided to the user through an object possessed by the user, such as the token.
Owner:DYNAPASS IP HLDG LLC
Secure data storage and retrieval with key management and user authentication
InactiveUS6947556B1Key distribution for secure communicationUser identity/authority verificationDigital dataPassphrase
Methods, systems and computer program products are provided which provide for controlling access to digital data in a file by encrypting the data with a first key, encrypting the first key with a second personal key generated from a password / passphrase associated with the file and further encrypting the encrypted first key with a control key which is managed by the system. In certain embodiments, user authentication may also be provided by issuing a ticket which is utilized to create, access and administer the files in the system.
Owner:IBM CORP
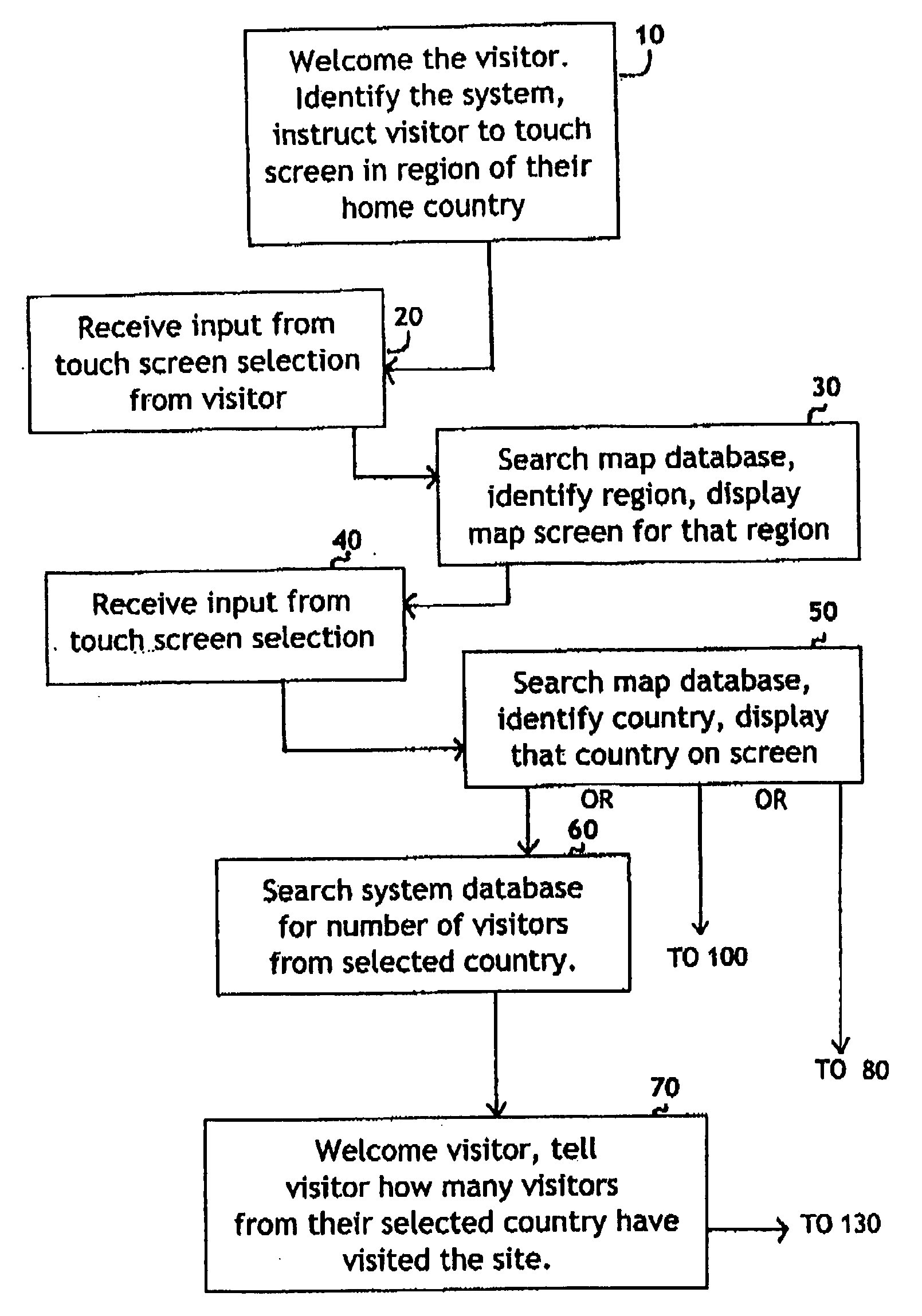
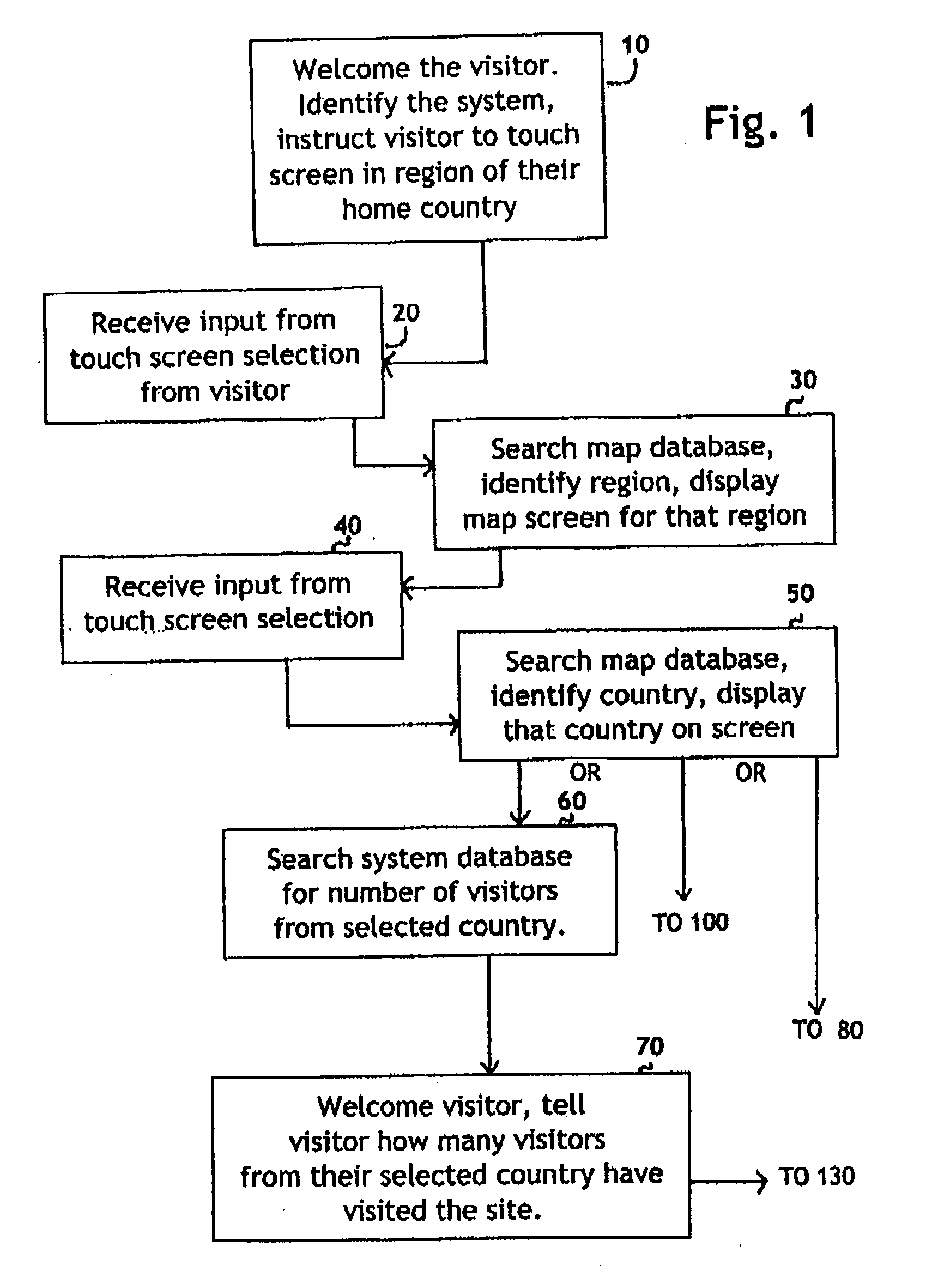
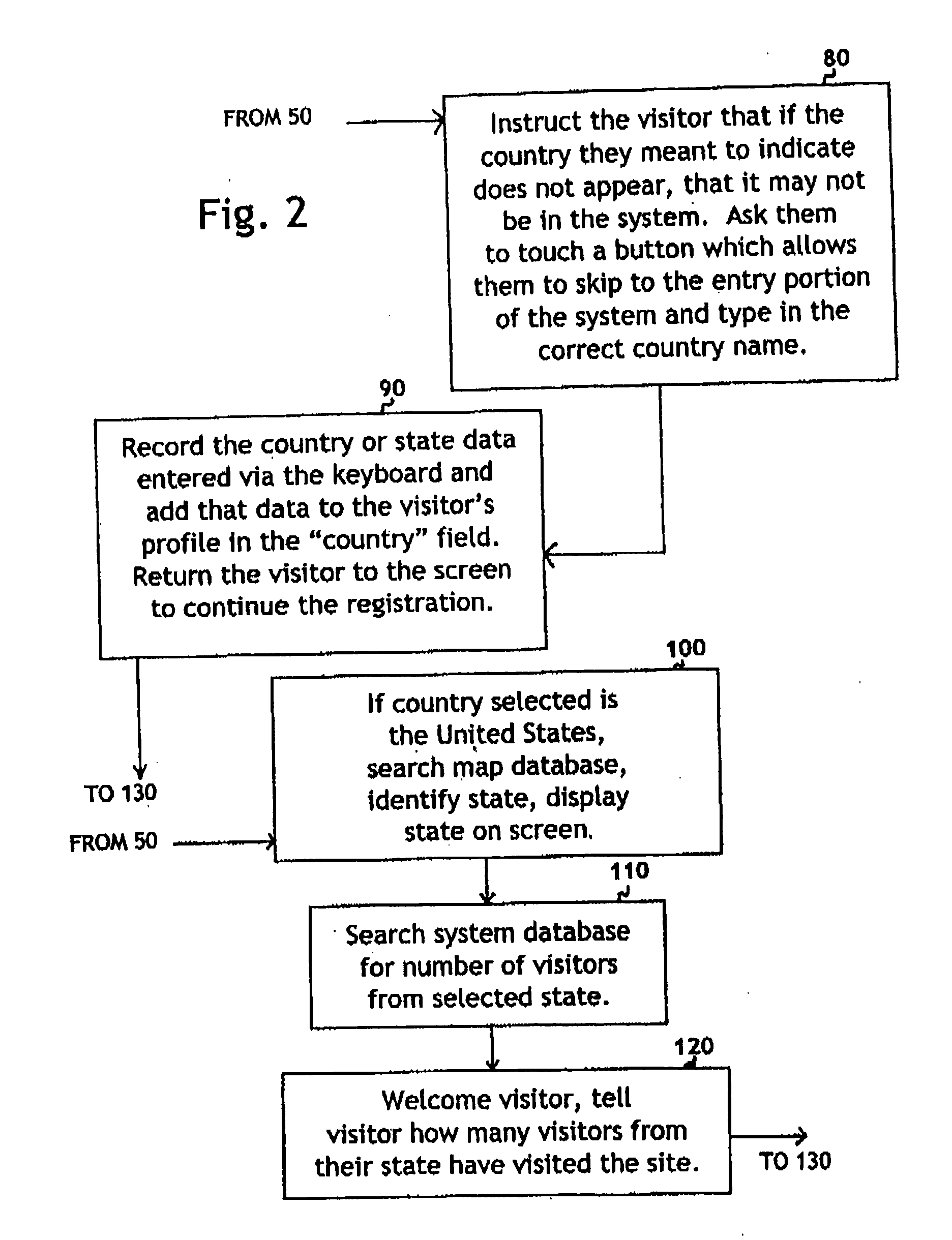
System for self-registering visitor information with geographic specificity and searchable fields
InactiveUS20080270938A1Easy retrievalBetter servedOffice automationGeographical information databasesEmail addressGeographic feature
An interactive visitor self-registration system for visitors to museums or other public sites using a digital computer or internet appliance device and a touchscreen monitor, which accesses a dedicated website, through a global computer network such as the Internet. It focuses on gathering information regarding residence of visitors as well as the information gathered by a traditional paper guest book. The system is searchable by visitors and by site staff. The information gathered by the system is stored on a dedicated website. A second, administration website, also password protected with an unpublished web address can be used by Site Administrators to customize the looks and options of their specific visitor self-registration system. Additionally, there is a public website which is accessible via the Internet which stores travel information for every signer to the system who logs on with his or her email address. These visitors can track their own travel via a map displayed on the website and be linked to the website for the sites they visit.
Owner:CARLSON ELIZABETH MARIE
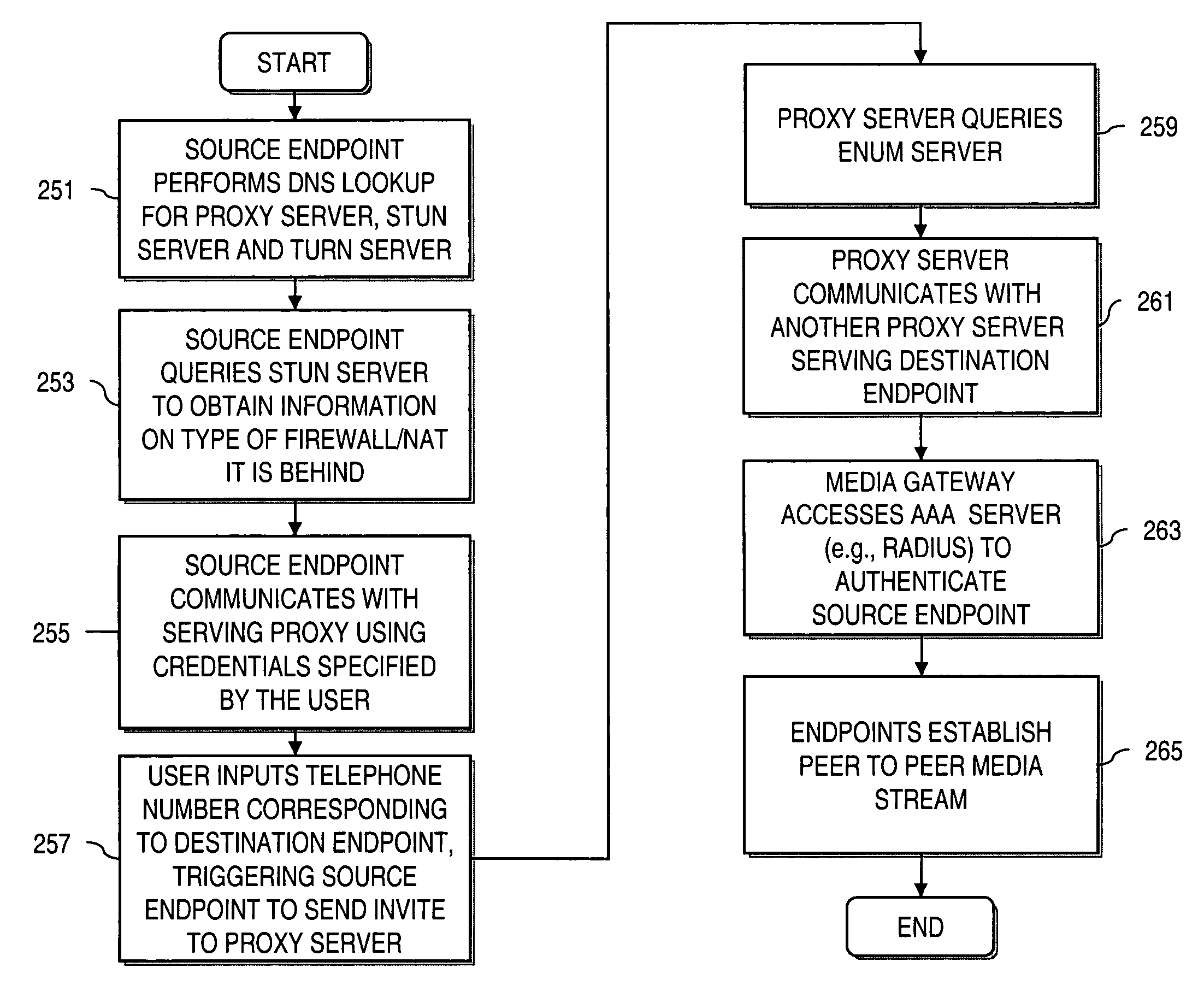
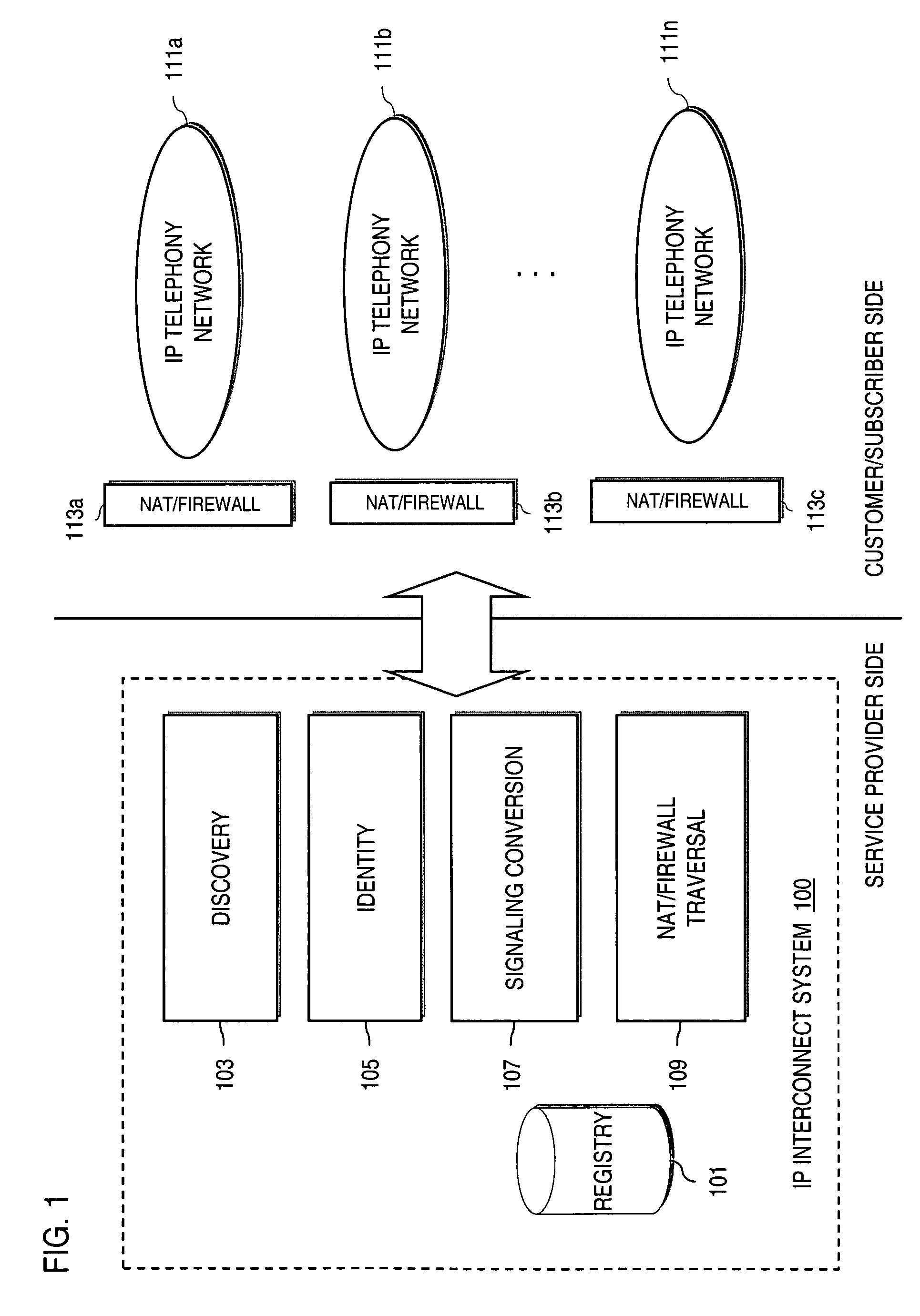
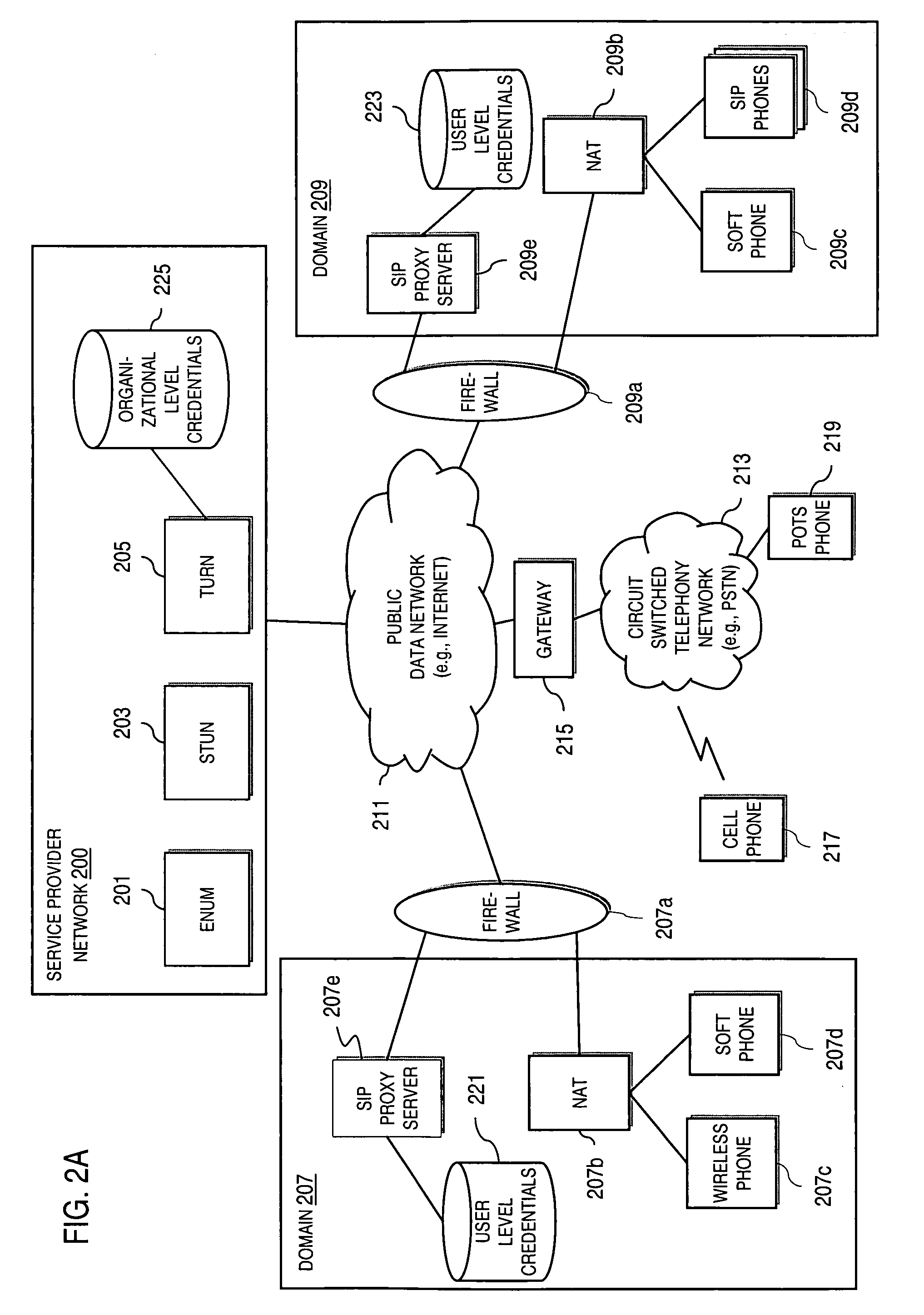
Method and system for providing secure credential storage to support interdomain traversal
An approach provides interdomain traversal to support packetized voice transmissions. A request is received from a first endpoint of a first domain for establishing a communication session with a second endpoint of a second domain. Encrypted user credential information is retrieved from a credentials database resident within the first domain, wherein the encrypted user credential includes a password associated with a user associated with the first endpoint. Further, the encrypted user credential information is transmitted to a tunneling server in response to the request, wherein the tunneling server is configured to selectively setup a tunnel to support the communication session based on the encrypted user credential information. The tunnel traverses a first firewall and a first network address translator of the first domain and a second firewall and a second network address translator of the second domain to reach the second endpoint.
Owner:VERIZON PATENT & LICENSING INC
Managing digital identity information
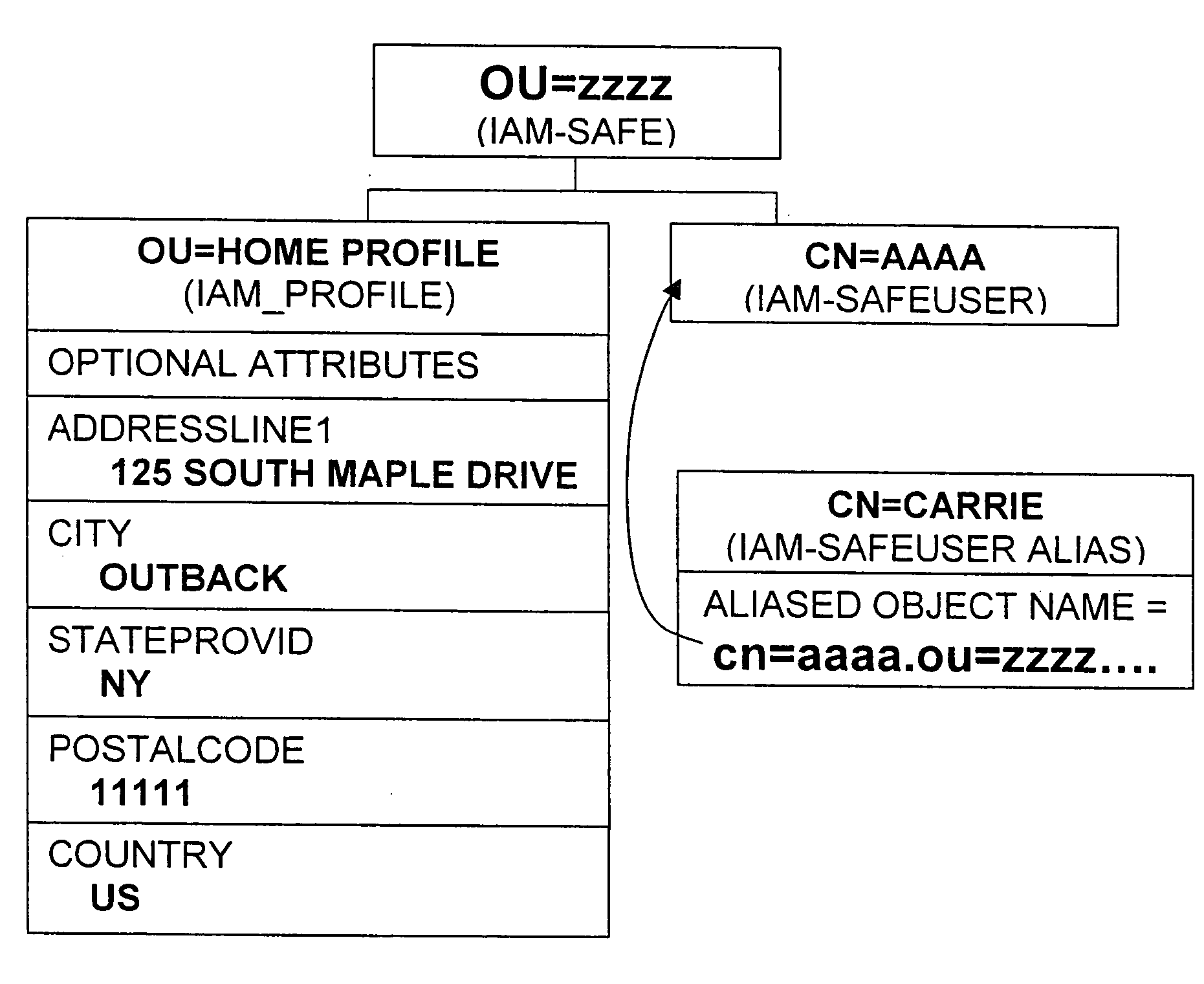
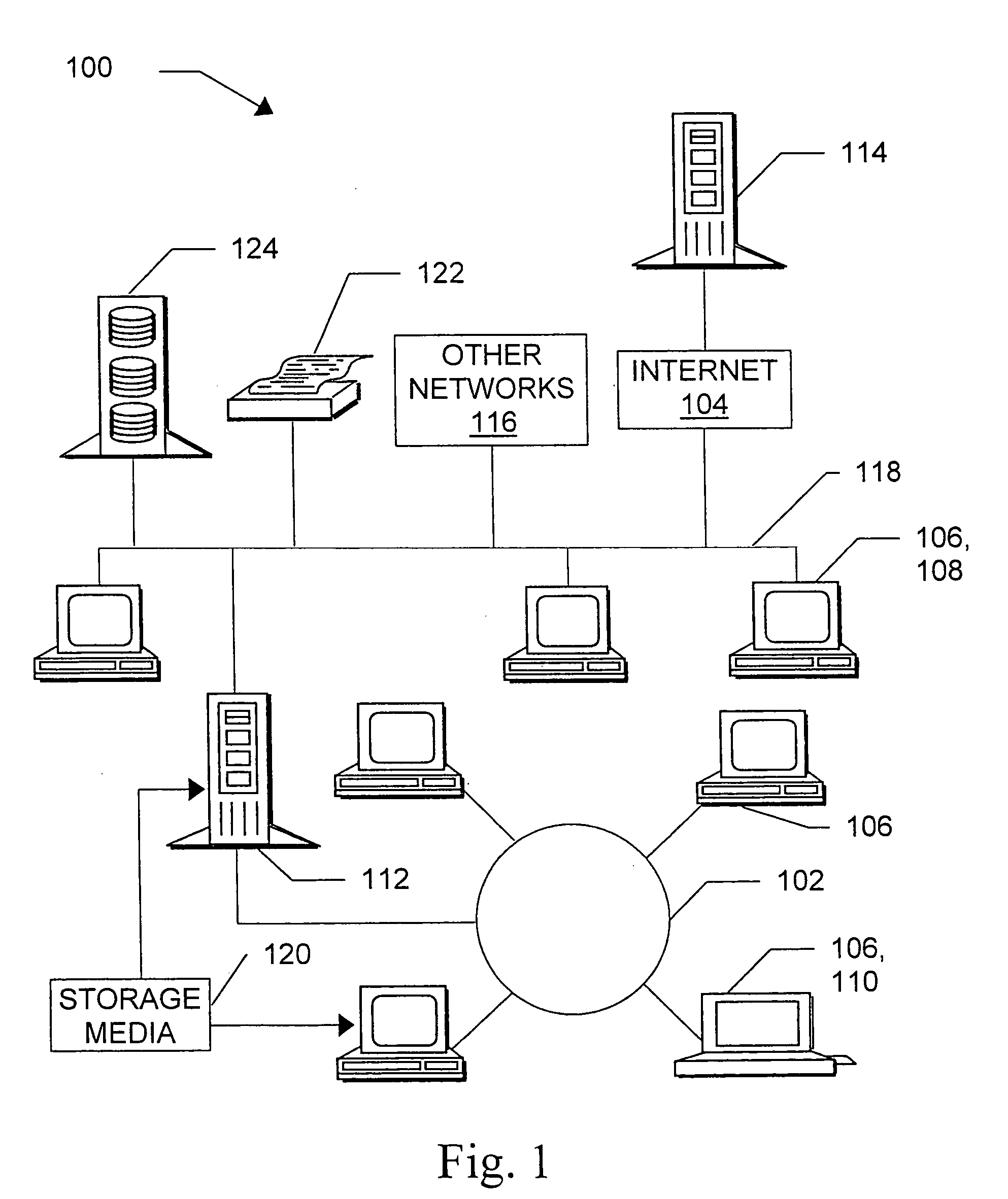
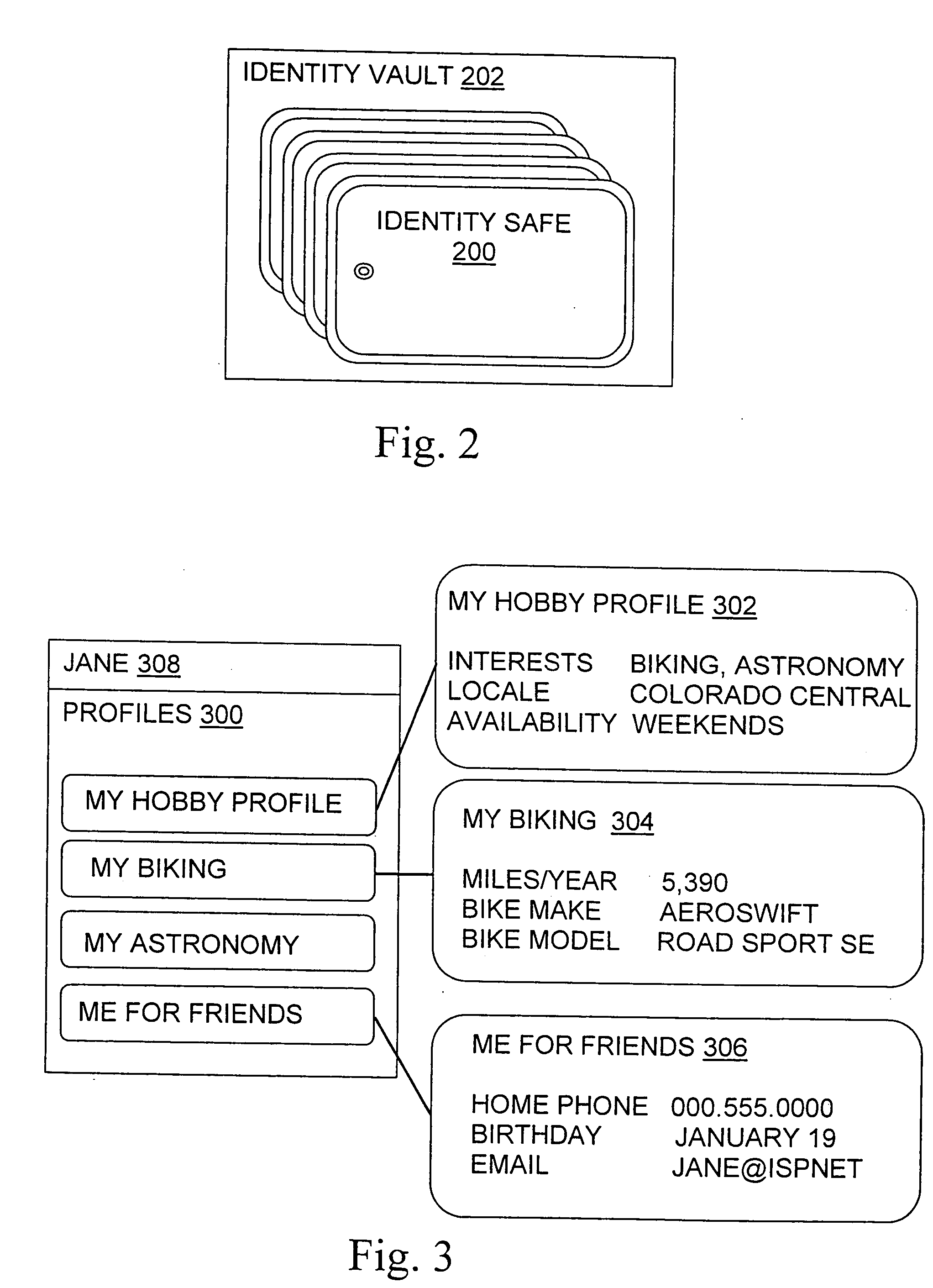
ActiveUS20050044423A1Maintain the integrity of relationshipsAdvanced technologyDigital data processing detailsMultiple digital computer combinationsDigital identityPassword
A basic architecture for managing digital identity information in a network such as the World Wide Web is provided. A user of the architecture can organize his or her information into one or more profiles which reflect the nature of different relationships between the user and other entities, and grant or deny each entity access to a given profile. Various enhancements which may be provided through the architecture are also described, including tools for filtering email, controlling access to user web pages, locating other users and making one's own location known, browsing or mailing anonymously, filling in web forms automatically with information already provided once by hand, logging in automatically, securely logging in to multiple sites with a single password and doing so from any machine on the network, and other enhancements.
Owner:EMC IP HLDG CO LLC
Multi-factor authentication system
InactiveUS7373515B2User identity/authority verificationUnauthorized memory use protectionPasswordUser identifier
Owner:KARETEK HLDG LLC
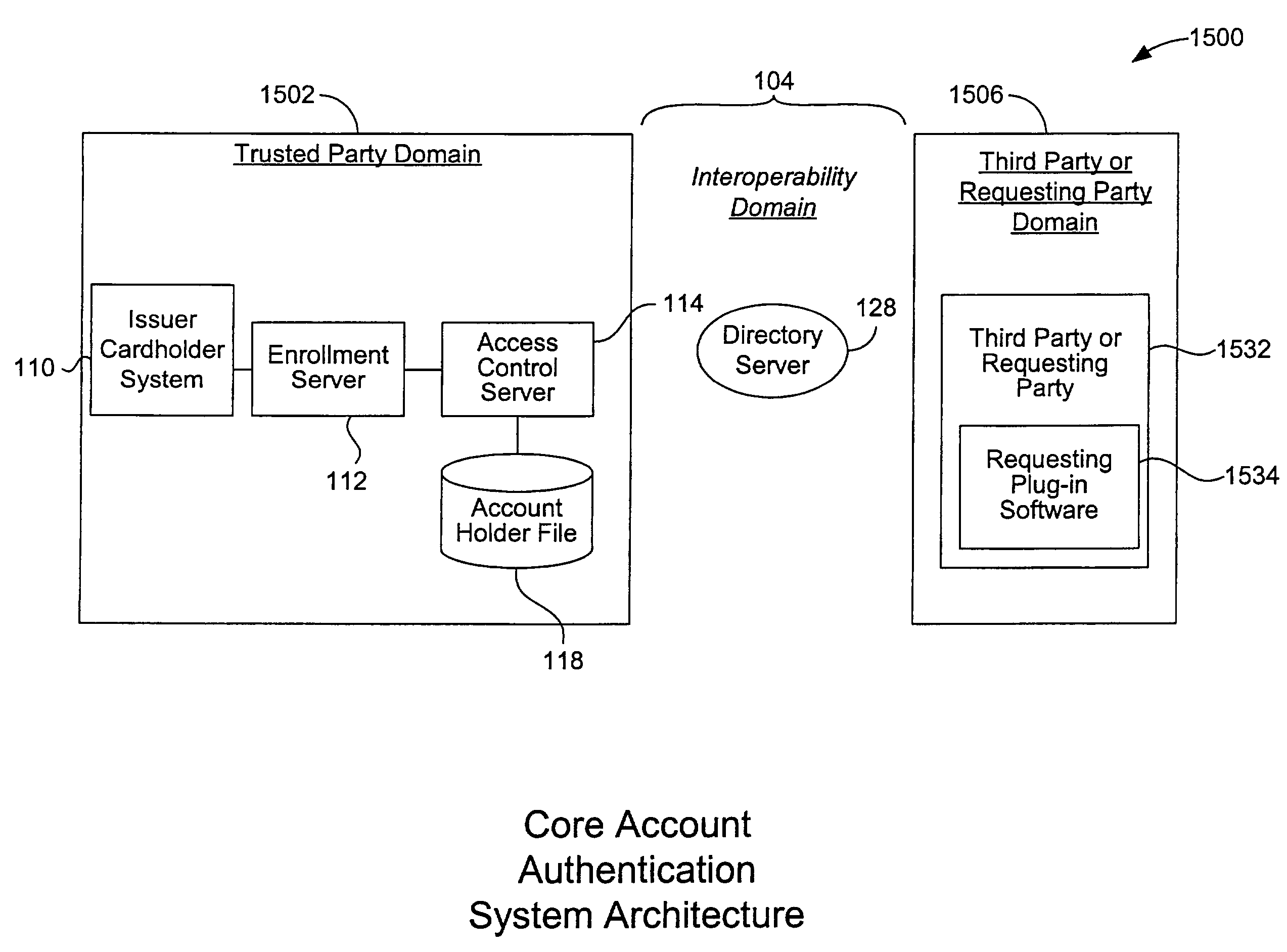
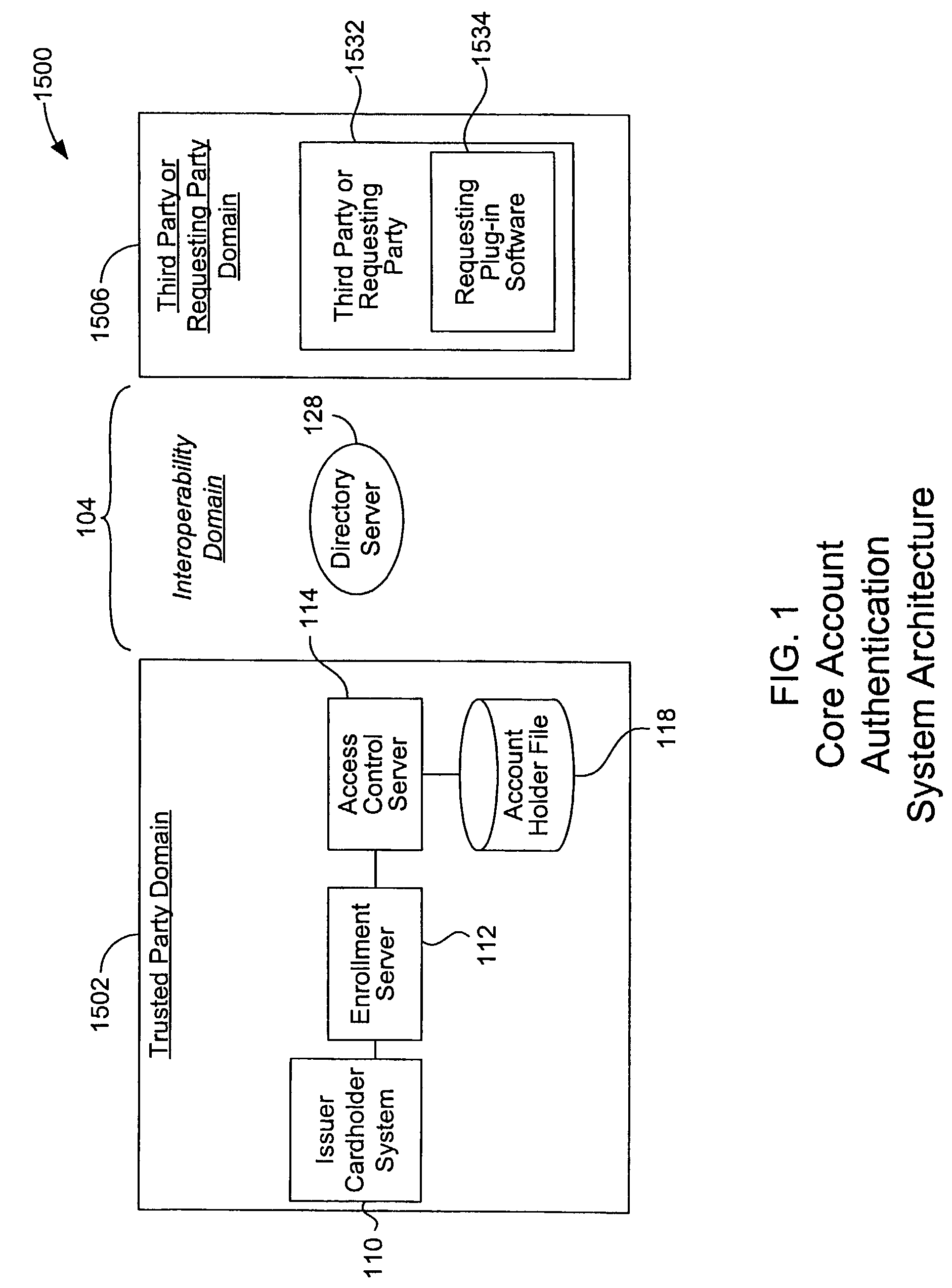
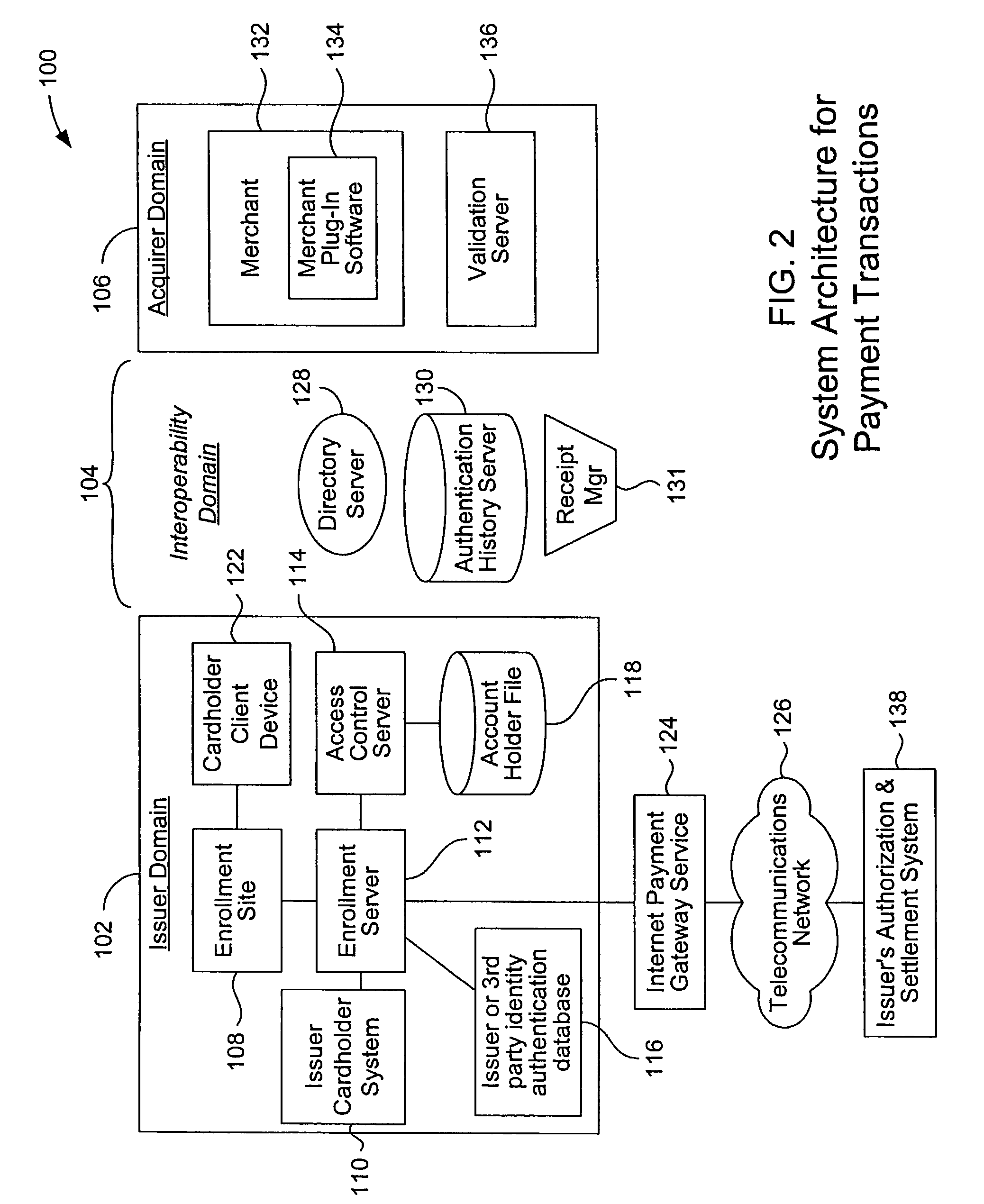
Mobile account authentication service
ActiveUS7707120B2Minimal investmentHigh level of interoperabilityComplete banking machinesFinanceInternet Authentication ServicePayment
A payment authentication service authenticates the identity of a payer during online transactions. The authentication service allows a card issuer to verify a cardholder's identity using a variety of authentication methods, such as with the use of tokens. Authenticating the identity of a cardholder during an online transaction involves querying an access control server to determine if a cardholder is enrolled in the payment authentication service, requesting a password from the cardholder, verifying the password, and notifying a merchant whether the cardholder's authenticity has been verified. Systems for implementing the authentication service in which a cardholder uses a mobile device capable of transmitting messages via the Internet are described. Systems for implementing the authentication service in which a cardholder uses a mobile device capable of transmitting messages through voice and messaging channels is also described.
Owner:VISA INT SERVICE ASSOC
Robust visual passwords
InactiveUS7219368B2Easy to rememberKey distribution for secure communicationPublic key for secure communicationGraphicsUser input
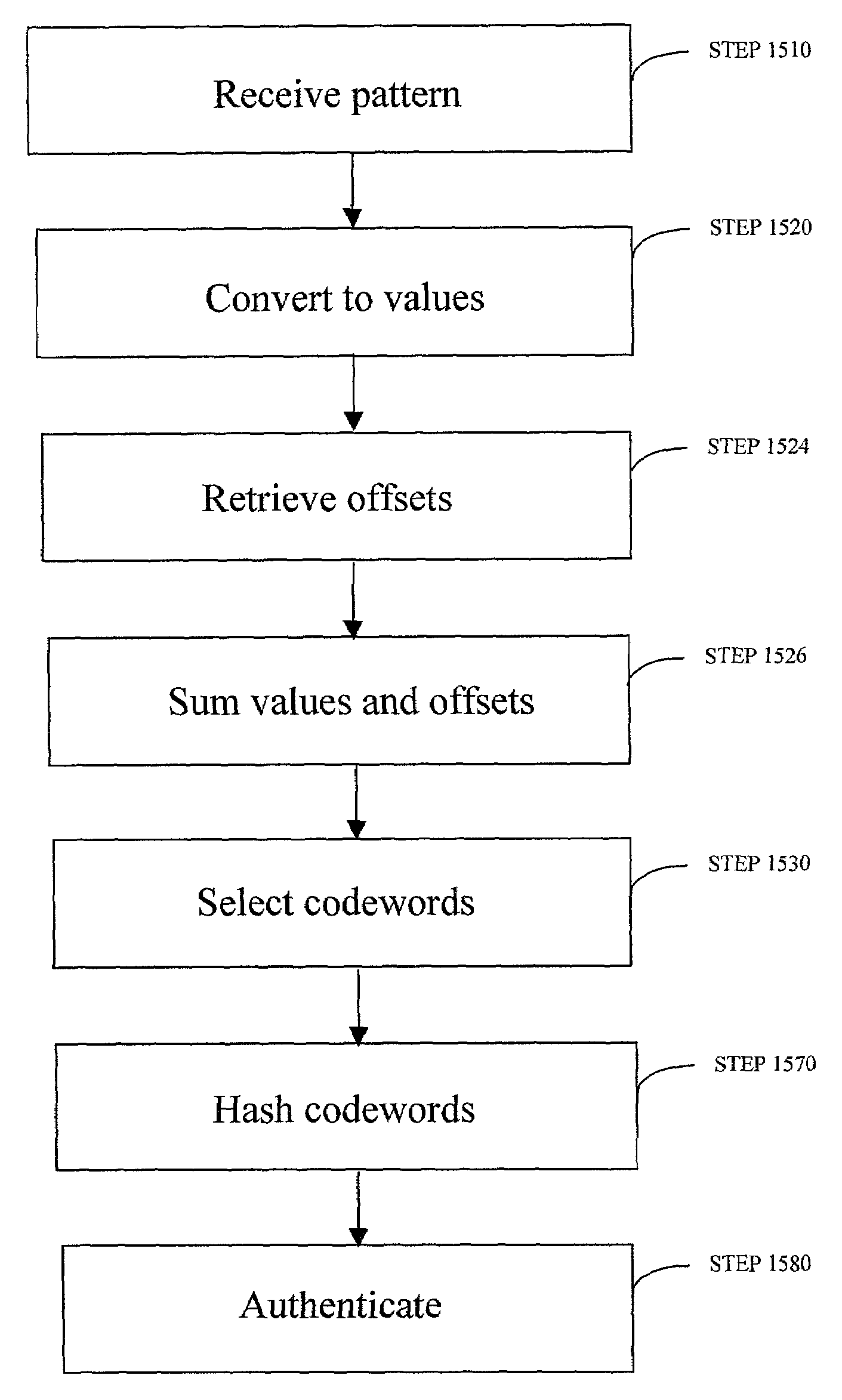
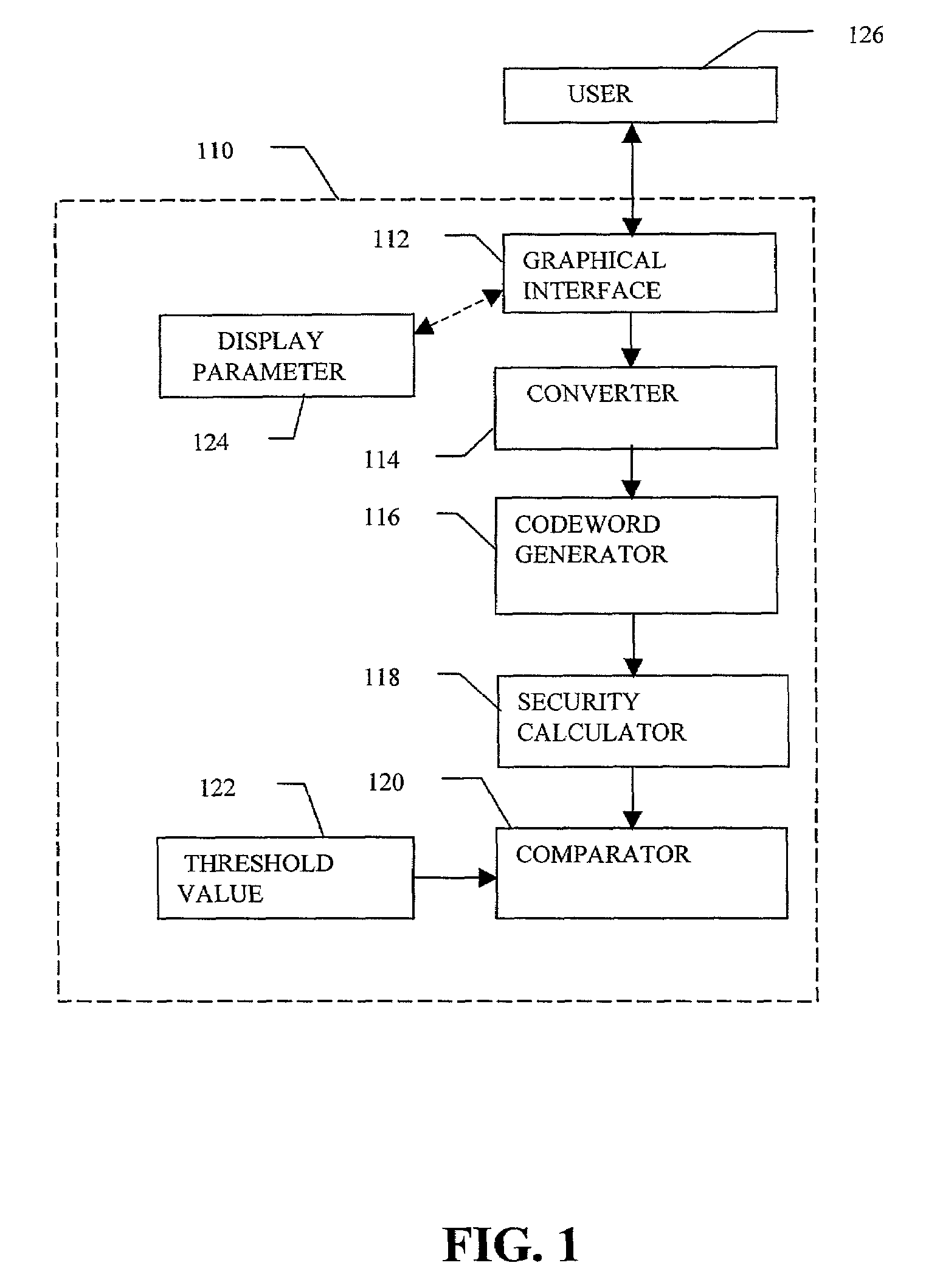
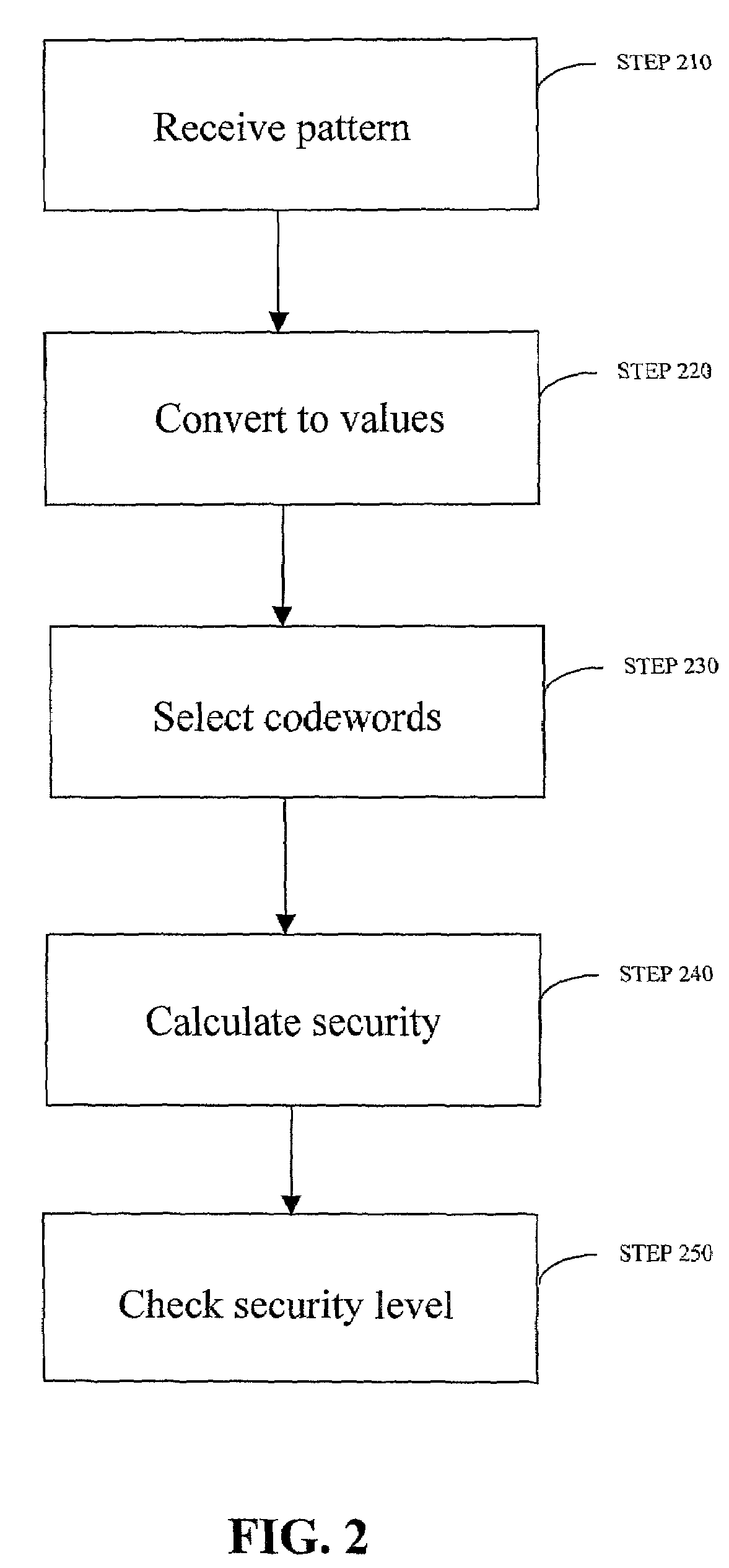
Enrollment and authentication of a user based on a sequence of discrete graphical choices is described. A graphical interface presents various images and memory cues that a user may associate with their original graphical choices. Enrollment may require the input to have a security parameter value that meets or exceeds a threshold. An acceptable sequence of graphical choices is converted to a sequence of values and mapped to a sequence of codewords. Both a hash of the sequence of codewords and a sequence of offsets are stored for use in authenticating the user. An offset is the difference between a value and its corresponding codeword. Authentication requires the user to enter another sequence of discrete graphical choices that is approximately the same as original. The offsets are summed with the corresponding values before mapping to codewords. Authentication requires the sequence of codewords, or a hash thereof, to match.
Owner:RSA
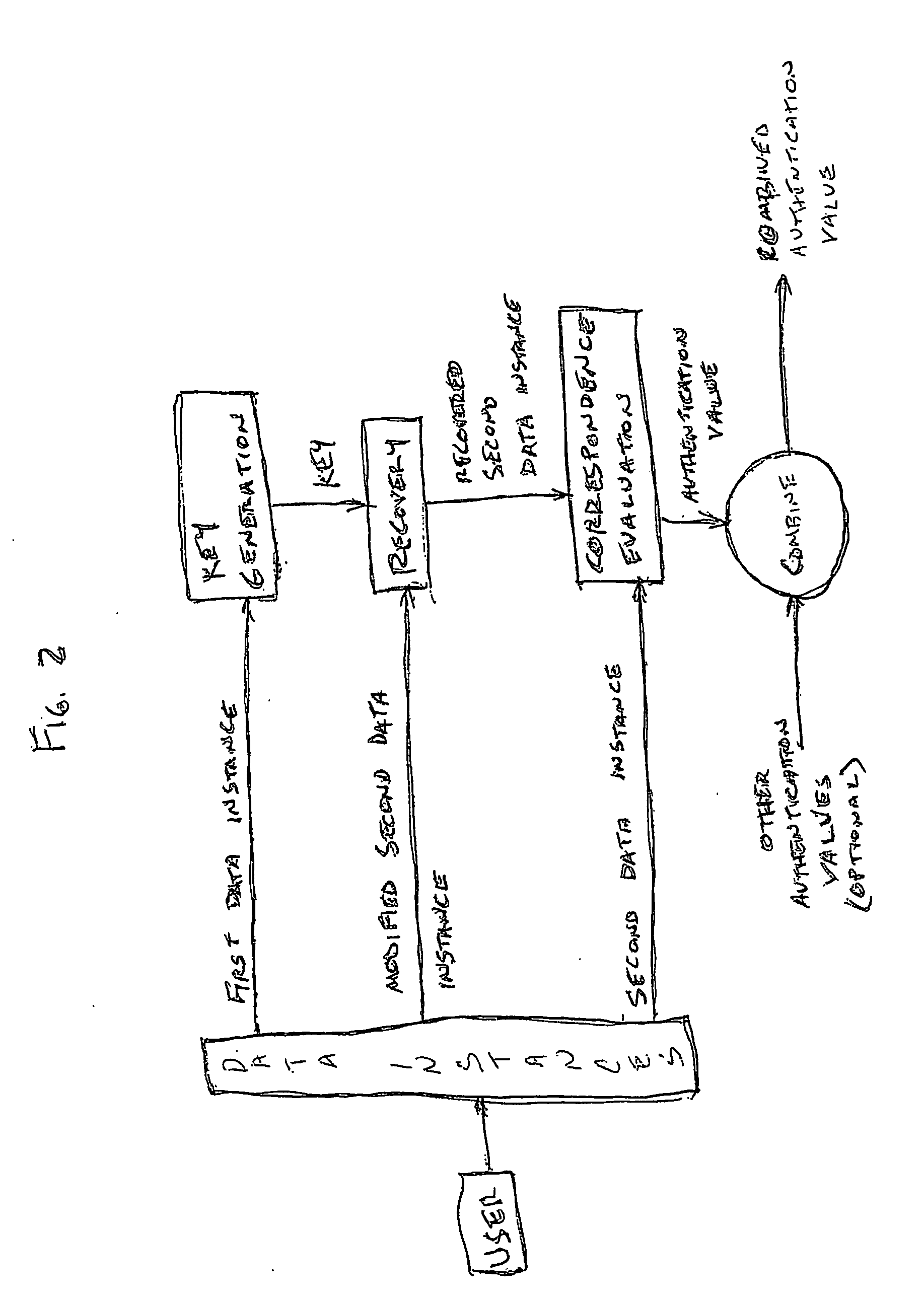
Access system utilizing multiple factor identification and authentication
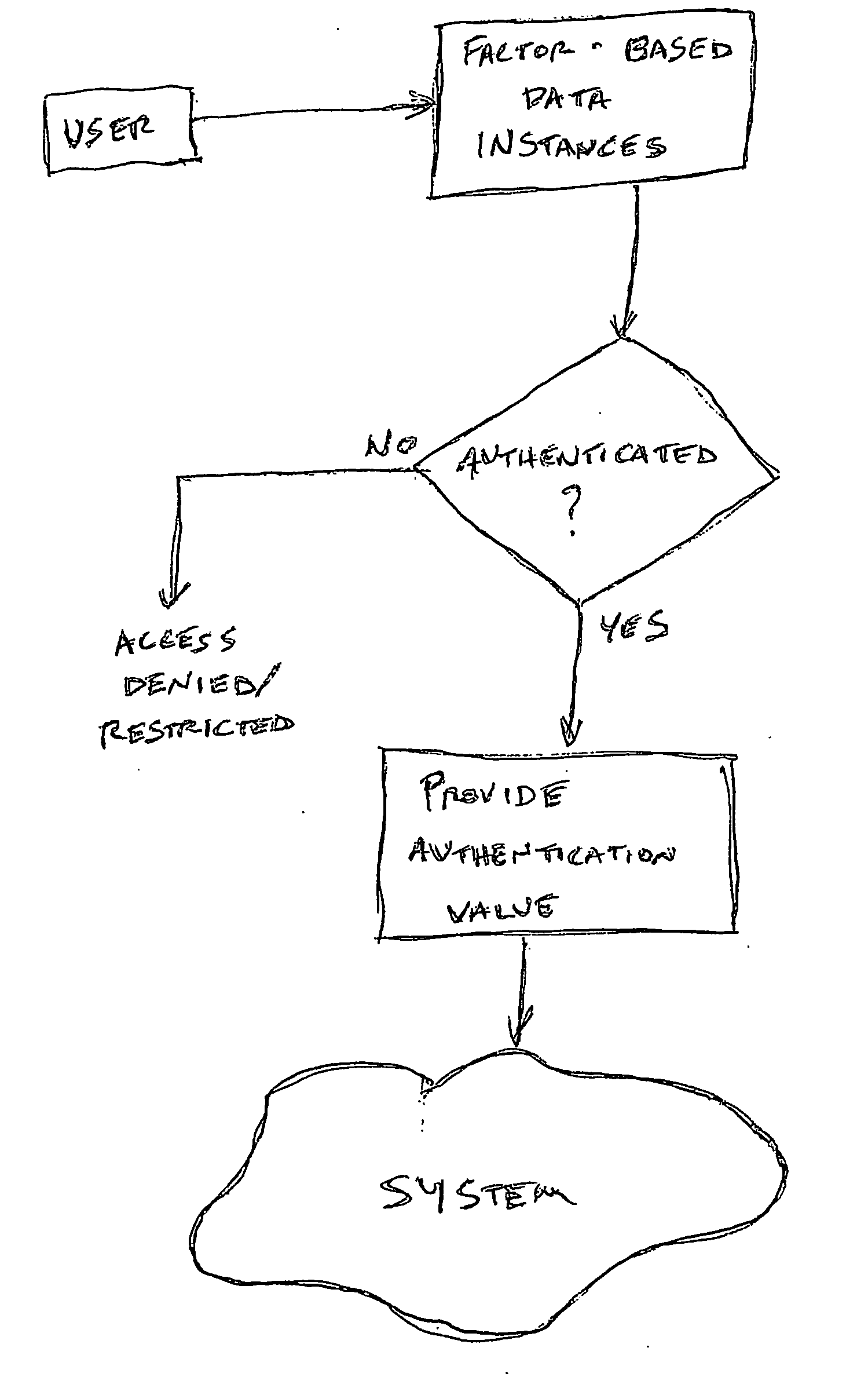
InactiveUS20050235148A1Flexible approachEasy to useKey distribution for secure communicationPublic key for secure communicationTransfer systemPassword
A method of authenticating a user to use a system includes using a provider token to generate a random value. The token generates a derived key based at least in part on a token-provided salt value and a user-provided password. The provider generates a token unlock key based at least in part on the derived key and sends it to the token. First and second challenge data instances are generated by the provider and the token, respectively, and the process is terminated if the challenge data instances are determined not to match. If the challenge data instances are determined to match, then an encrypted data transfer system is established between the token and the provider, and the token unlocks locked private data stored on the token. The user is authenticated for secured use of the system based at least in part on the unlocked private data.
Owner:TECSEC
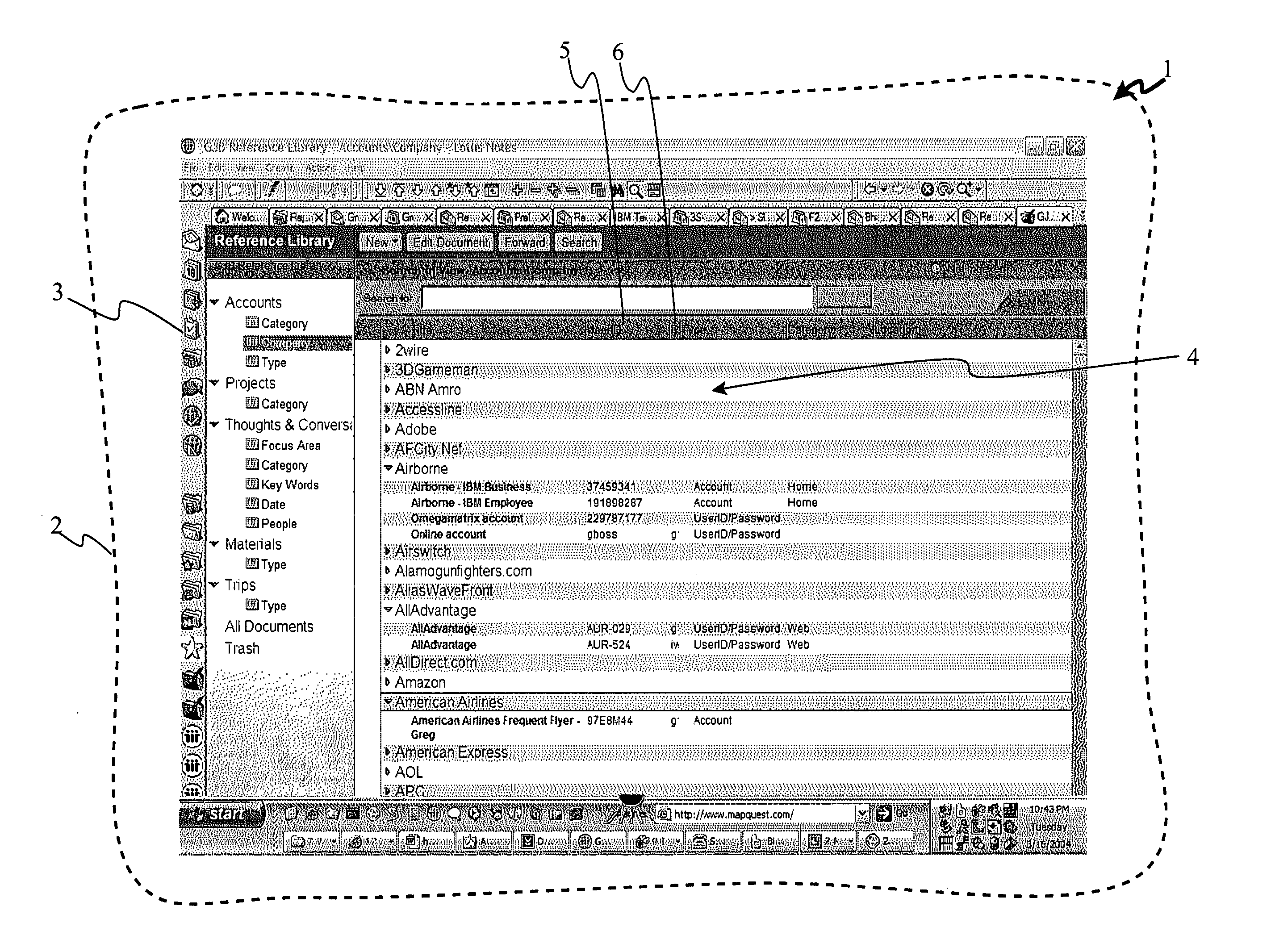
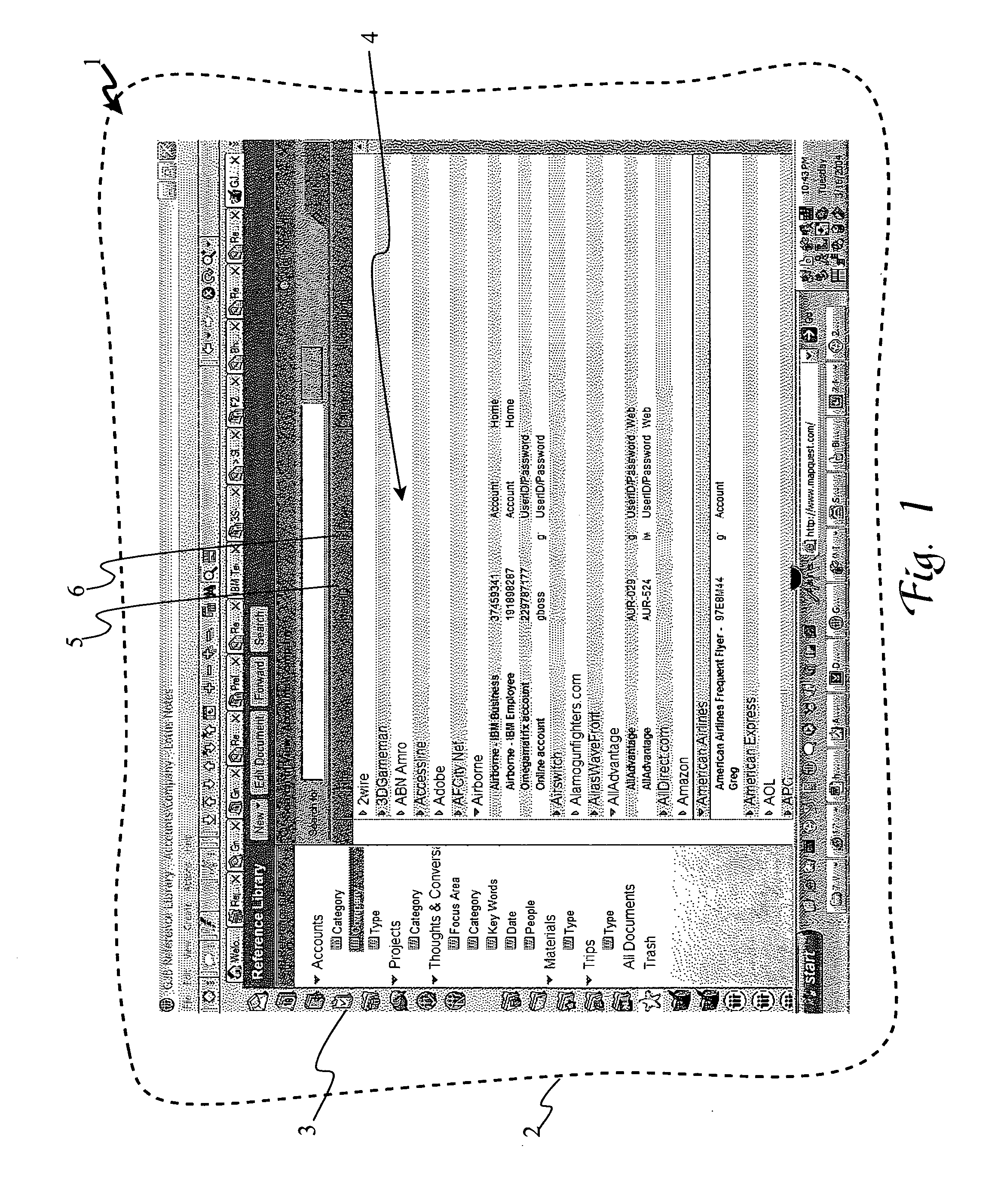
System and method to capture and manage input values for automatic form fill
ActiveUS20060059434A1Quickly select desired valueEasy to fillNatural language data processingDigital data authenticationWeb siteRecordset
A system for automatically completing fields in online forms, such as login forms and new user registration forms, which employs a Master Cookie File containing sets of records associated with the user, his or her accounts or web sites, and registered values associated with form tags (e.g. username, password, address, email, telephone, etc.). When the user encounters another form, the MCF is automatically searched for matching values and form tags, primarily from the same account or web site, or alternatively from other accounts or sites. A flowing pop-up menu is displayed nearby the form fields from which the user can select values to automatically complete the form. Automatic account information updating, value expiration management, mapping of favorite values, and sharing of values are optional, enhanced functions of the invention.
Owner:KYNDRYL INC
Automatic protection of partial document content
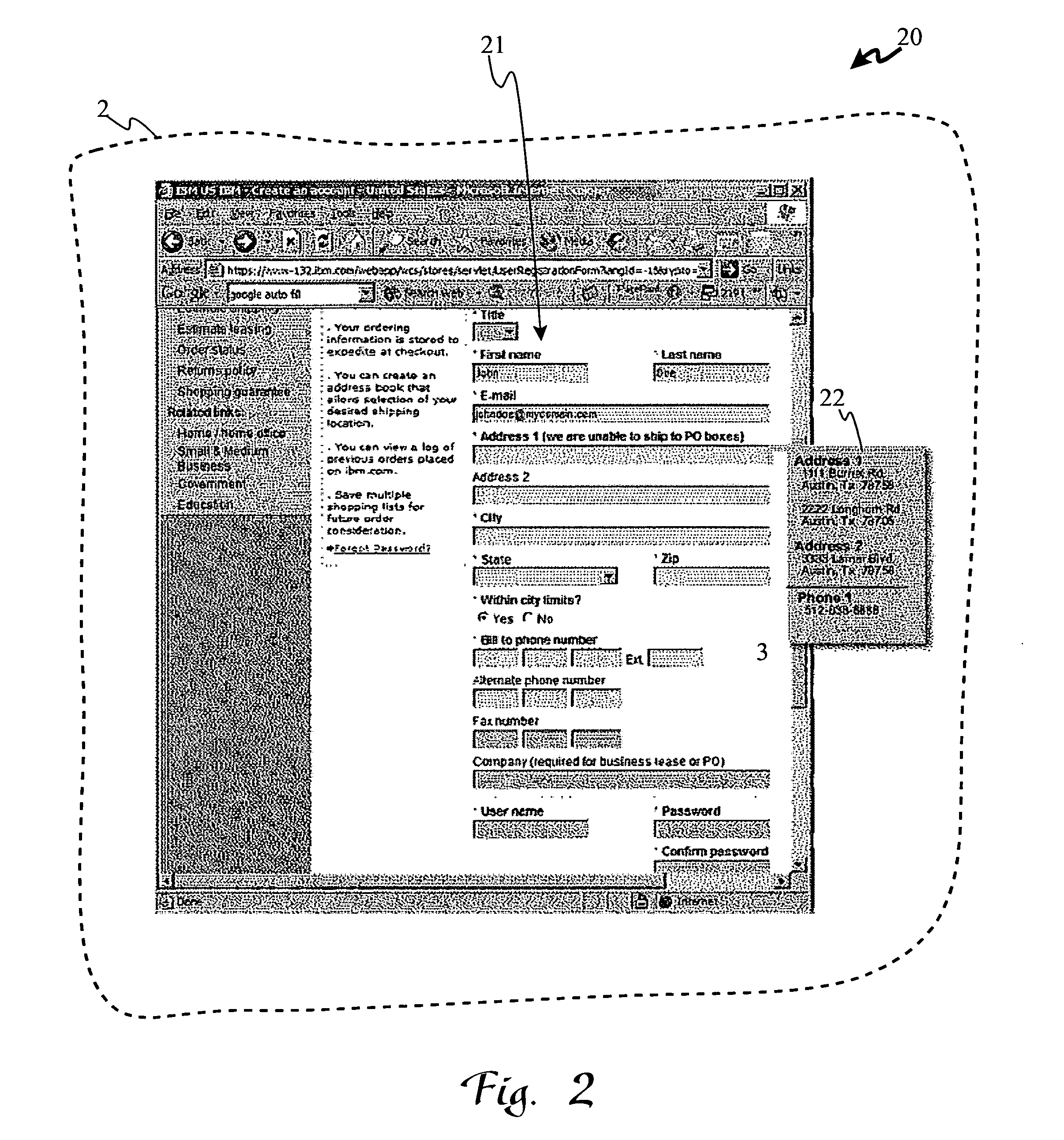
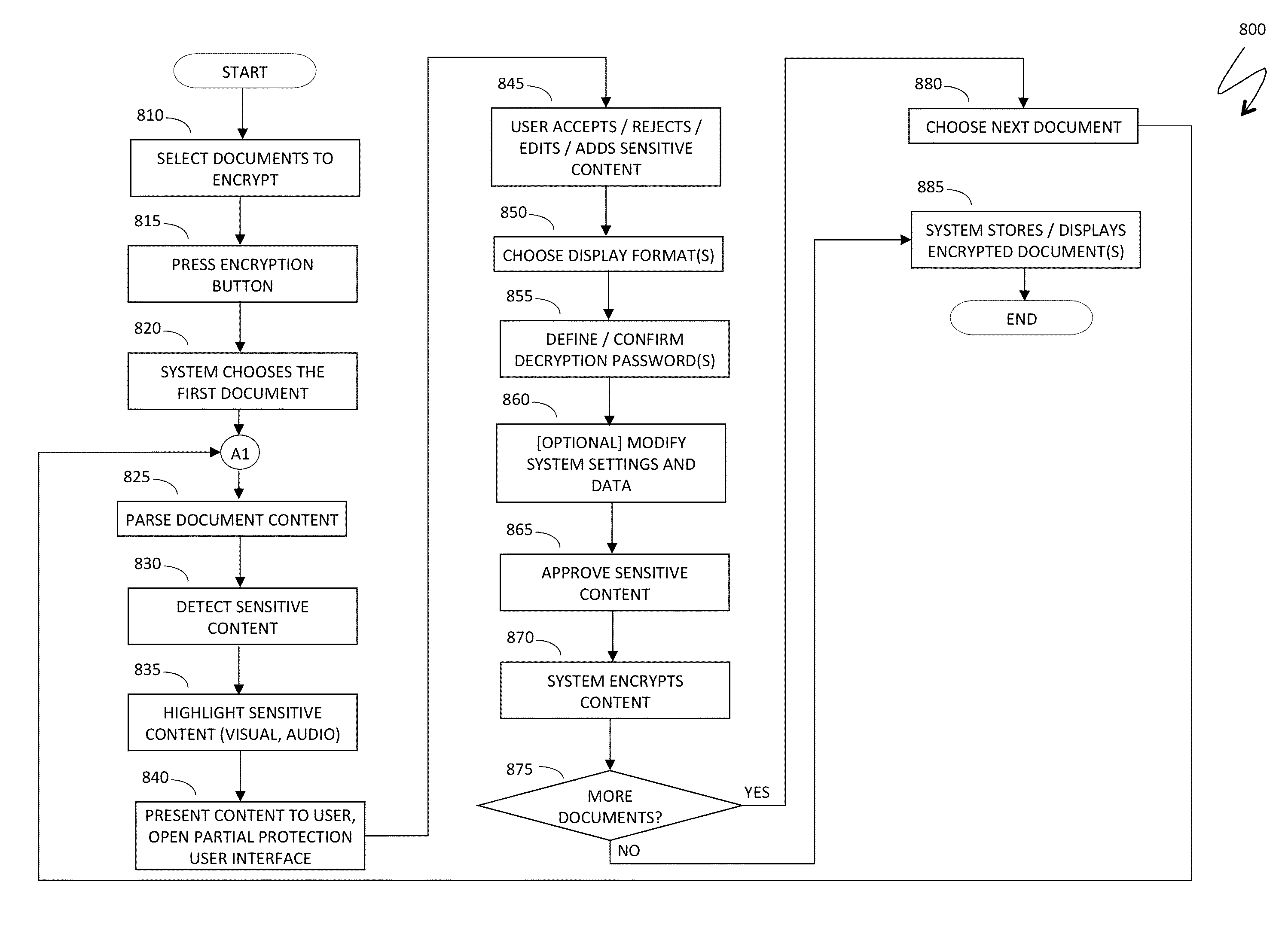
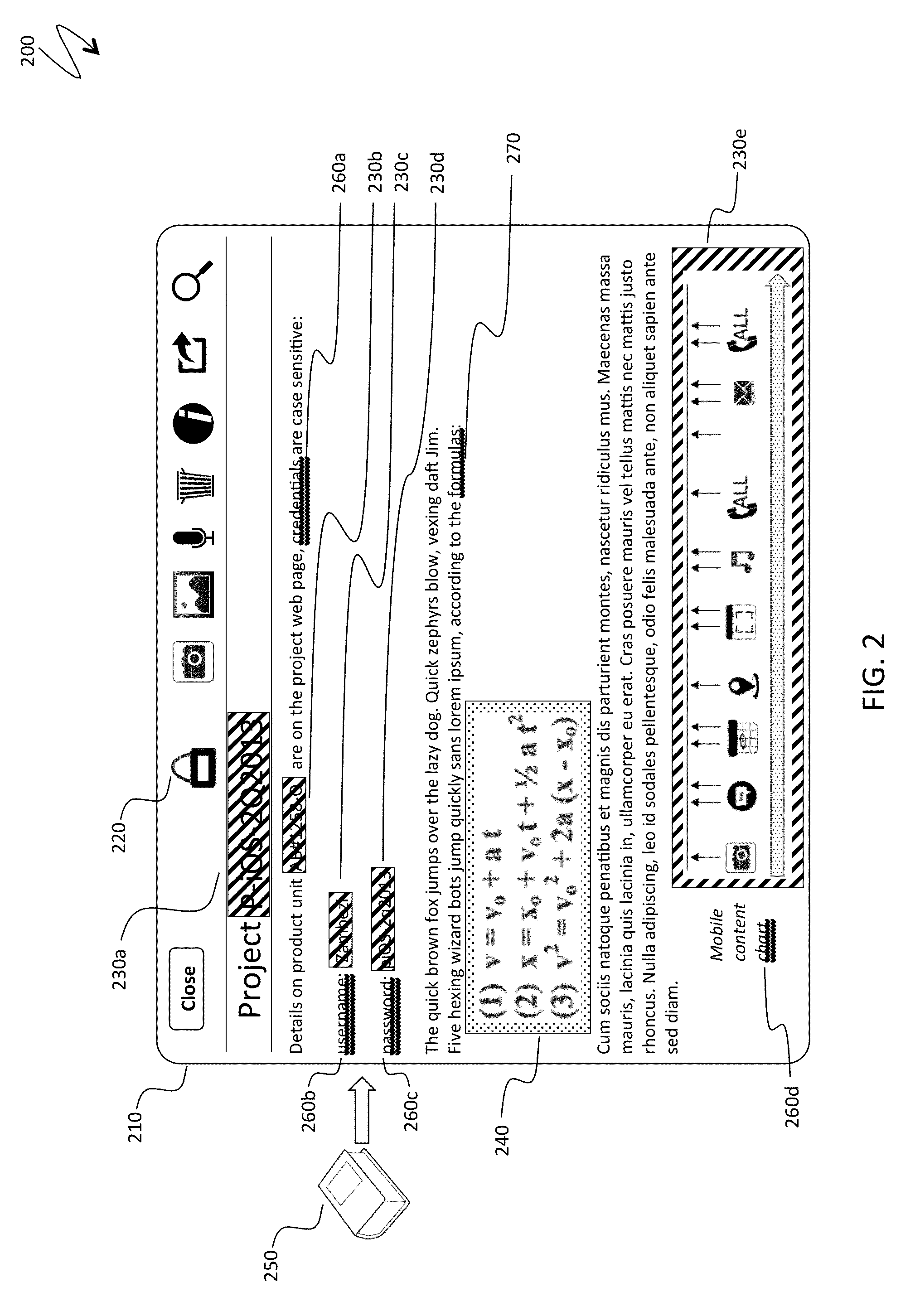
ActiveUS20140208418A1Reduce the amount requiredDigital data processing detailsUnauthorized memory use protectionPasswordDocumentation
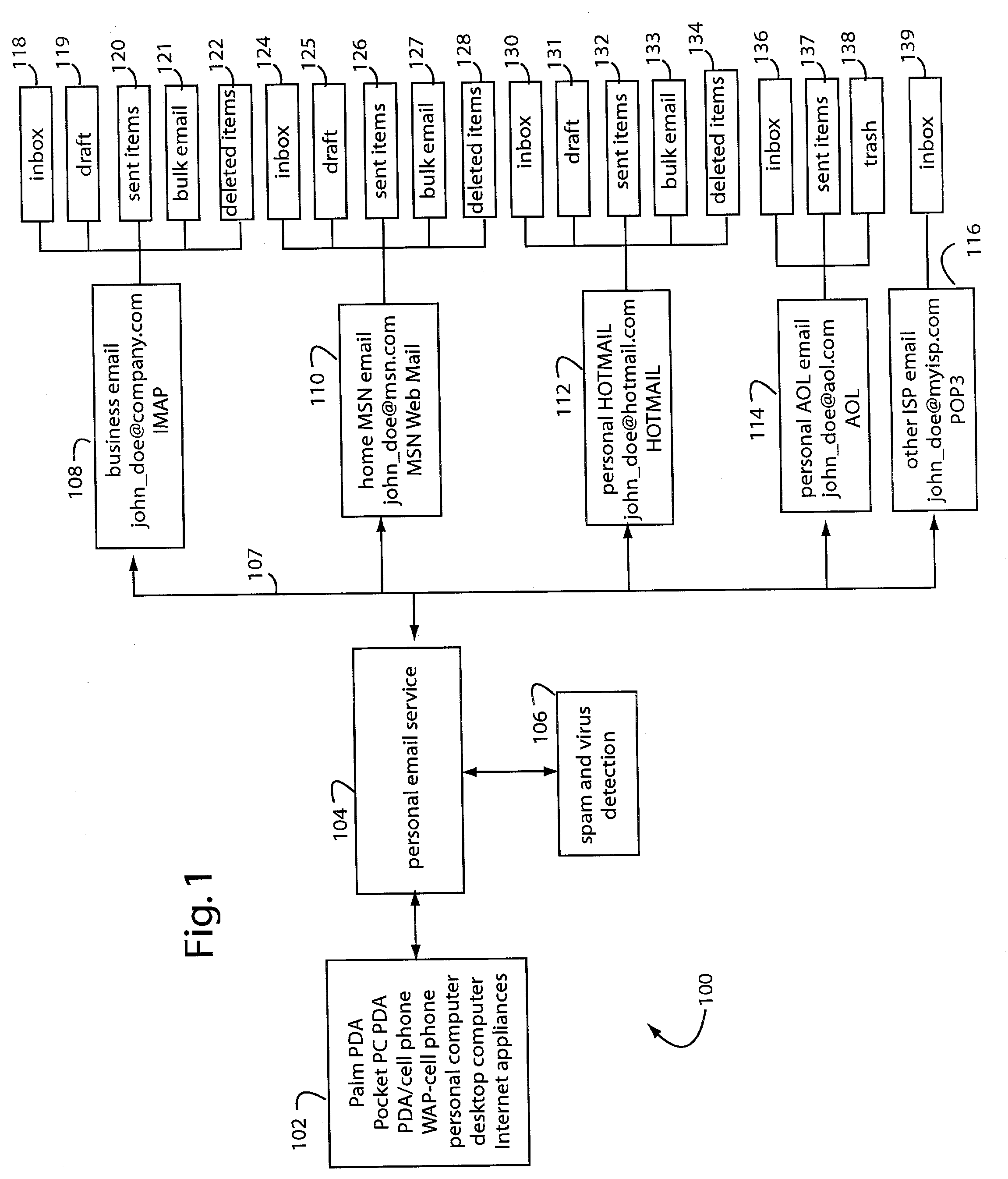
Protecting a fragment of a document includes automatically detecting the fragment without user intervention based on the content of the fragment and / or the context of the fragment within a set of documents, selectively encrypting the fragment to prevent unauthorized access, and providing an alternative view of the fragment that prevents viewing and access of content corresponding to the fragment unless a decryption password is provided. Automatically detecting the fragment may include detecting numbers and alphanumeric sequences of sufficient length that do not represent commonly known abbreviations, detecting generic terms, detecting proper names, detecting terms signifying a type of content, detecting mutual location of terms and sensitive content, and / or detecting user defined terms. The generic terms may correspond to password, passcode, credentials, user name, account, ID, login, confidential, and / or sensitive. The proper names may be names of financial organizations and security organizations.
Owner:EVERNOTE
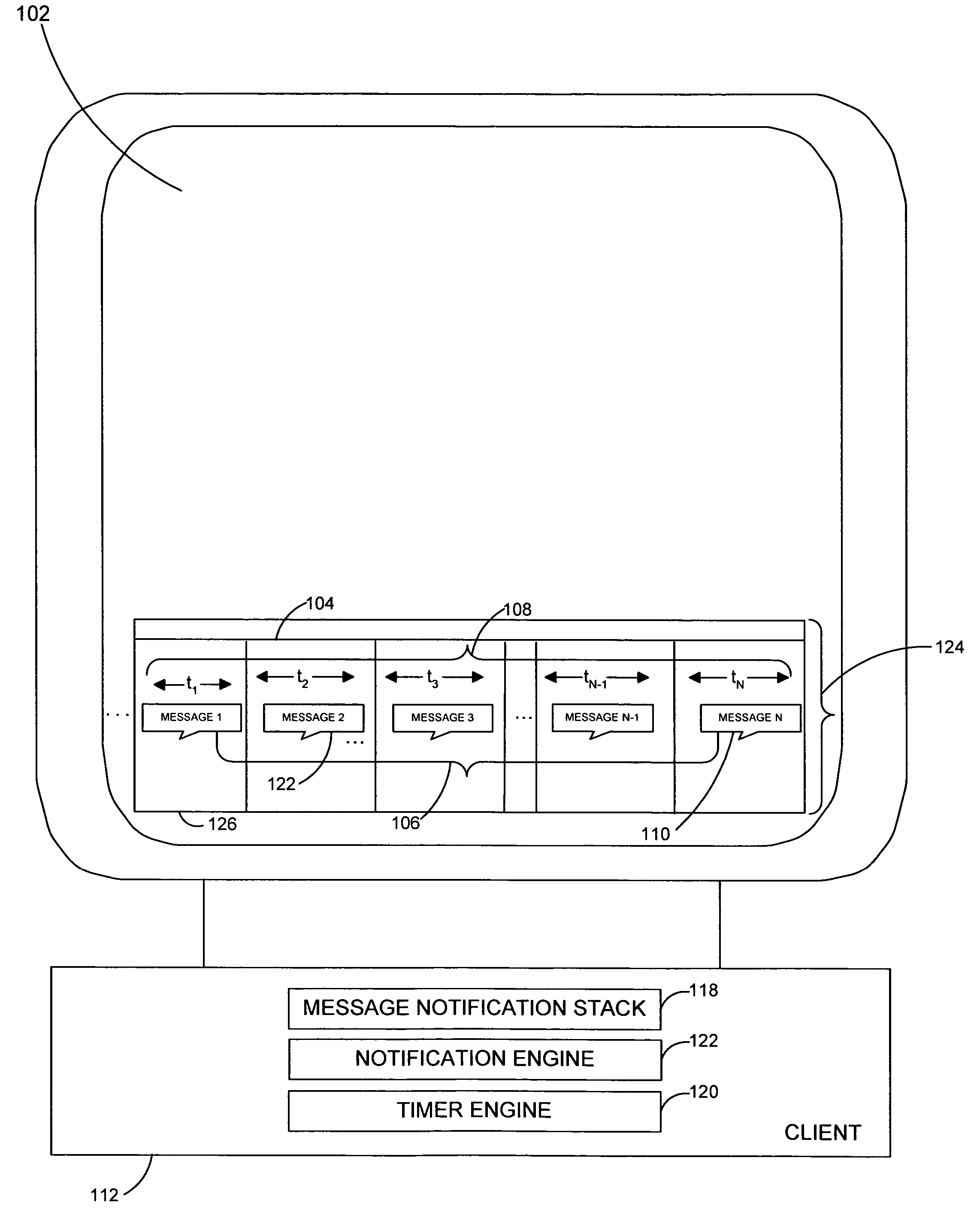
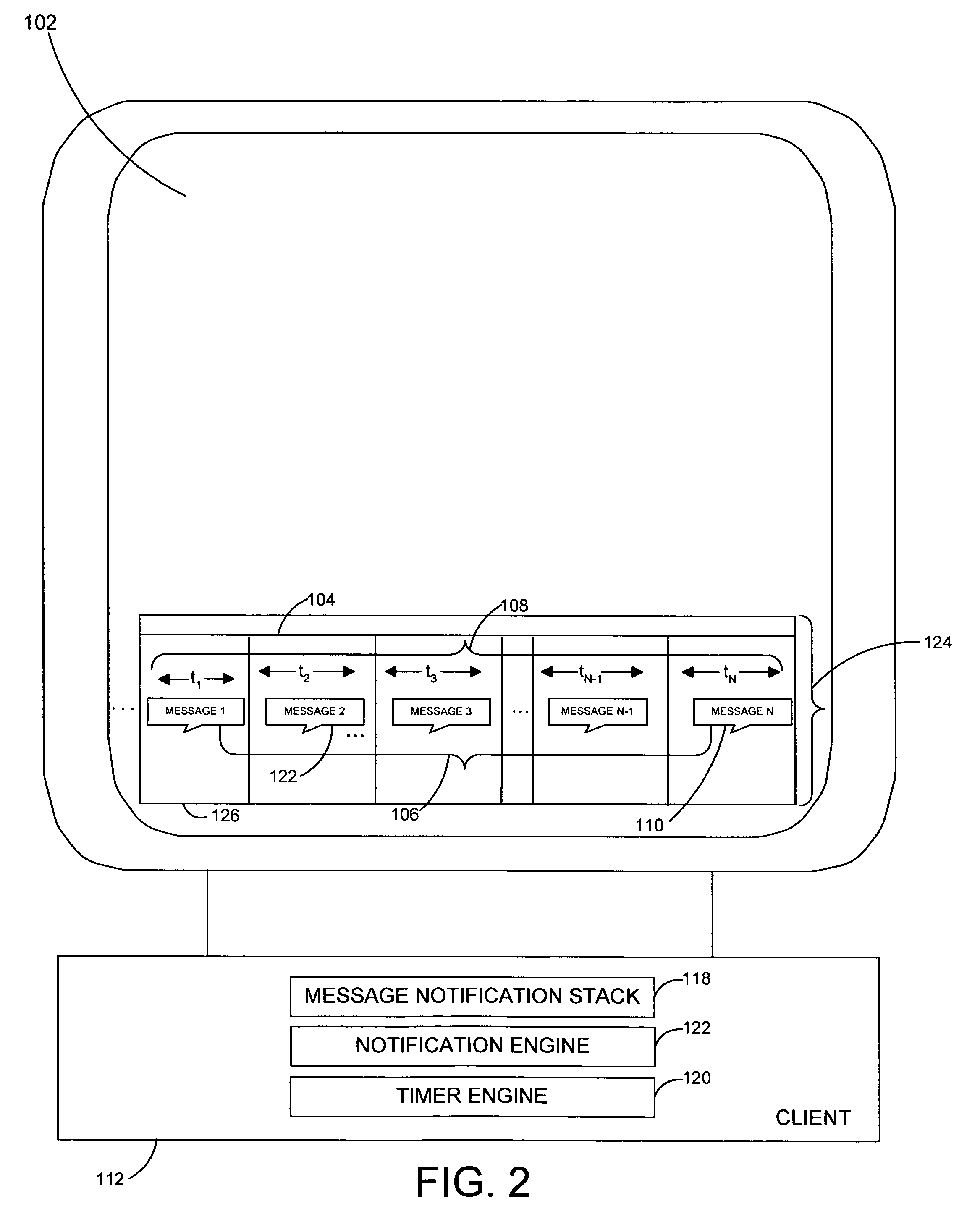
System and method for generating message notification objects on dynamically scaled timeline
InactiveUS20050268237A1Preserving spaceData processing applicationsMultiple digital computer combinationsEmail addressPassword
A system and related techniques to collect and manage a set of incoming message notification objects, such as instant message notifications, email notifications, download notifications, transaction notifications and others and present those objects to the user an icon, tile or other representation on a dynamically scaled timeline. According to embodiments, the dynamically scaled timeline may present the most recently received object farthest to the right on a notifications bar or facility, and slide objects to the left to represent that passage of time as those objects age. Instead of presenting those objects on a linear scale, according to the invention the time intervals in which the objects may be presented may be scaled to cause the oldest message objects to be presented on a relatively compressed dimension. The most recently received messages in contrast may be presented on wider intervals, to permit the user to perceive the differences in arrival of those items more clearly. According to embodiments, when more than one message object slides to an overlapping point with another, those objects may be stacked into a cascading message stack. When two or more stacks touch, they may be merged into a single stack. According to embodiments of the invention in another regard, when the user hovers over a given message object a popup box may appear which displays attributes of that object, such as message or other notification type, the date and time which the object was received, the source of the underlying message or other data. In further embodiments, one or more of the message notification objects may be clickable or otherwise reactivatable to reveal actions, dialogs, inputs or other interactions which were presented at the time the message was originally received, such as a query box to input a password or a selection for an email address.
Owner:MICROSOFT TECH LICENSING LLC
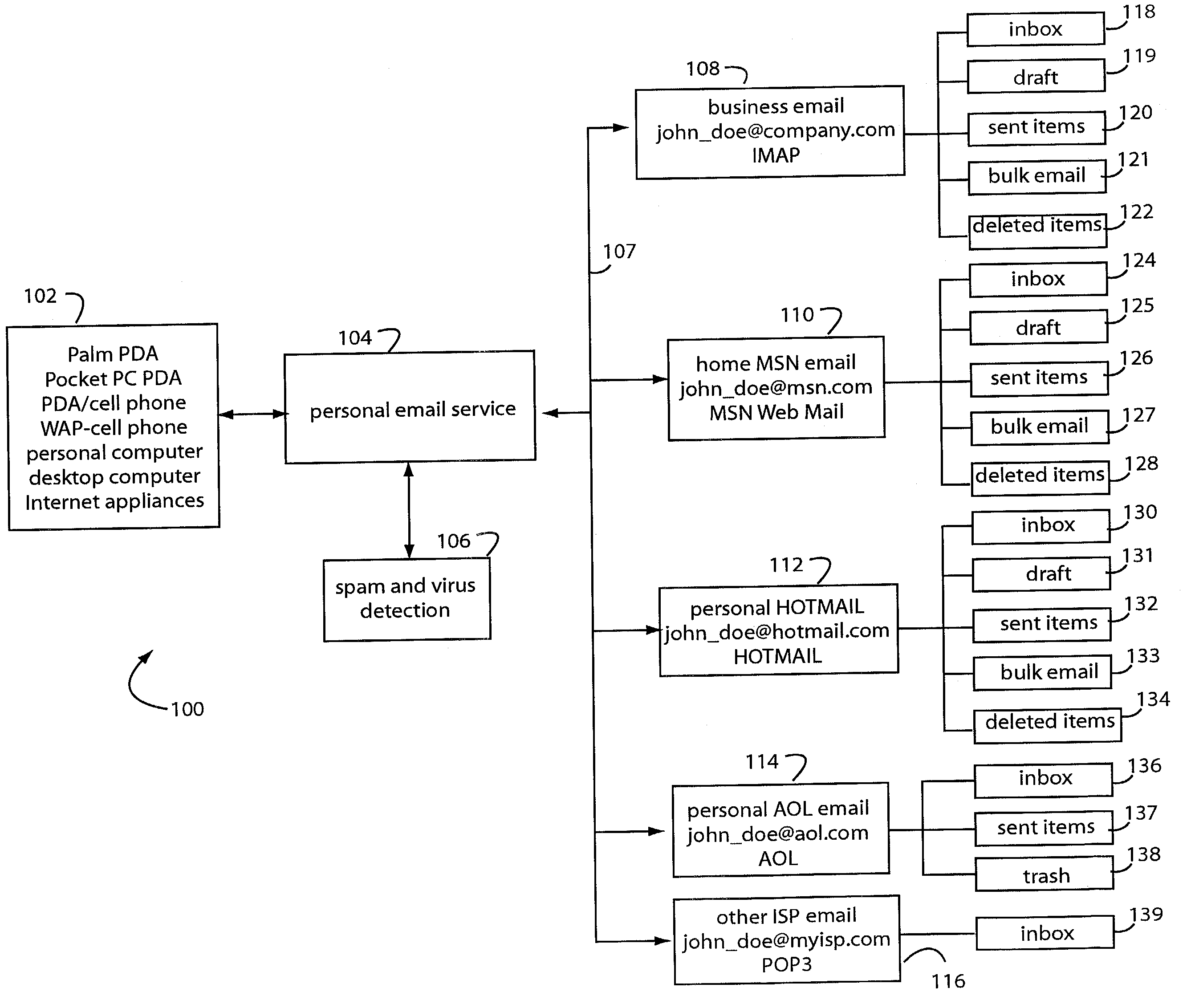
Personal e-mail system and method
InactiveUS20030231207A1Expand accessSimplify choreCathode-ray tube indicatorsData switching networksPasswordInternet privacy
A personal e-mail system comprises an ad-hoc computer host platform loaded with a personal e-mail application program. The host has Internet access and a user has previously established e-mail accounts at a variety of provider sites. The user is periodically delivered e-mail messages that are collected from such provider sites, and such are displayed according to any display limitations that exist with the particular host platform. The personal e-mail application program automatically and dynamically adjusts the protocols it uses to suit the particular provider site it is accessing, and uses user-provided user names and passwords to access the provider site to appear as if the user themselves has properly logged in. The personal e-mail application program then can send responses or issue new messages that are accepted by the provider site and issued by it as if originated from there.
Owner:GOPHER KING
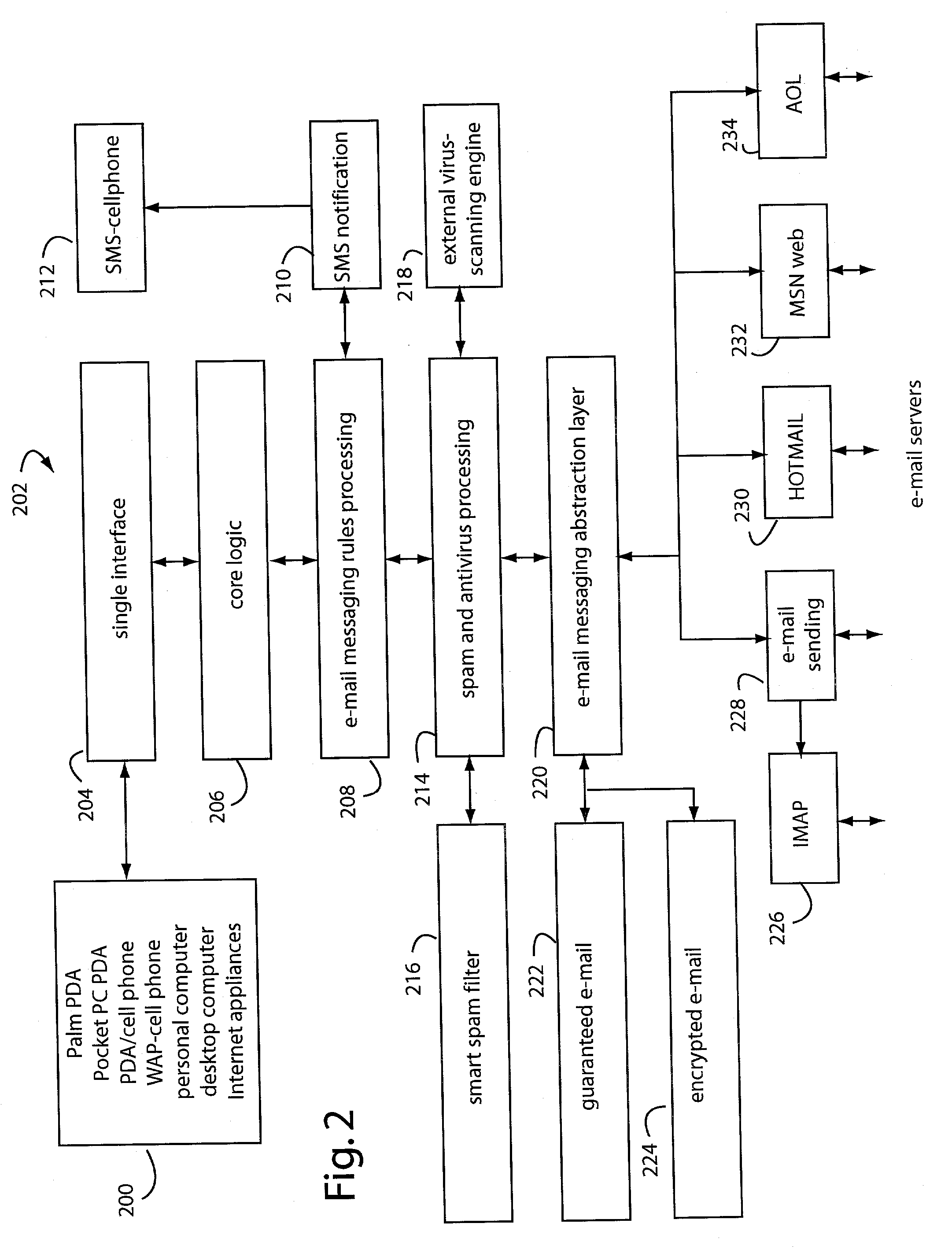
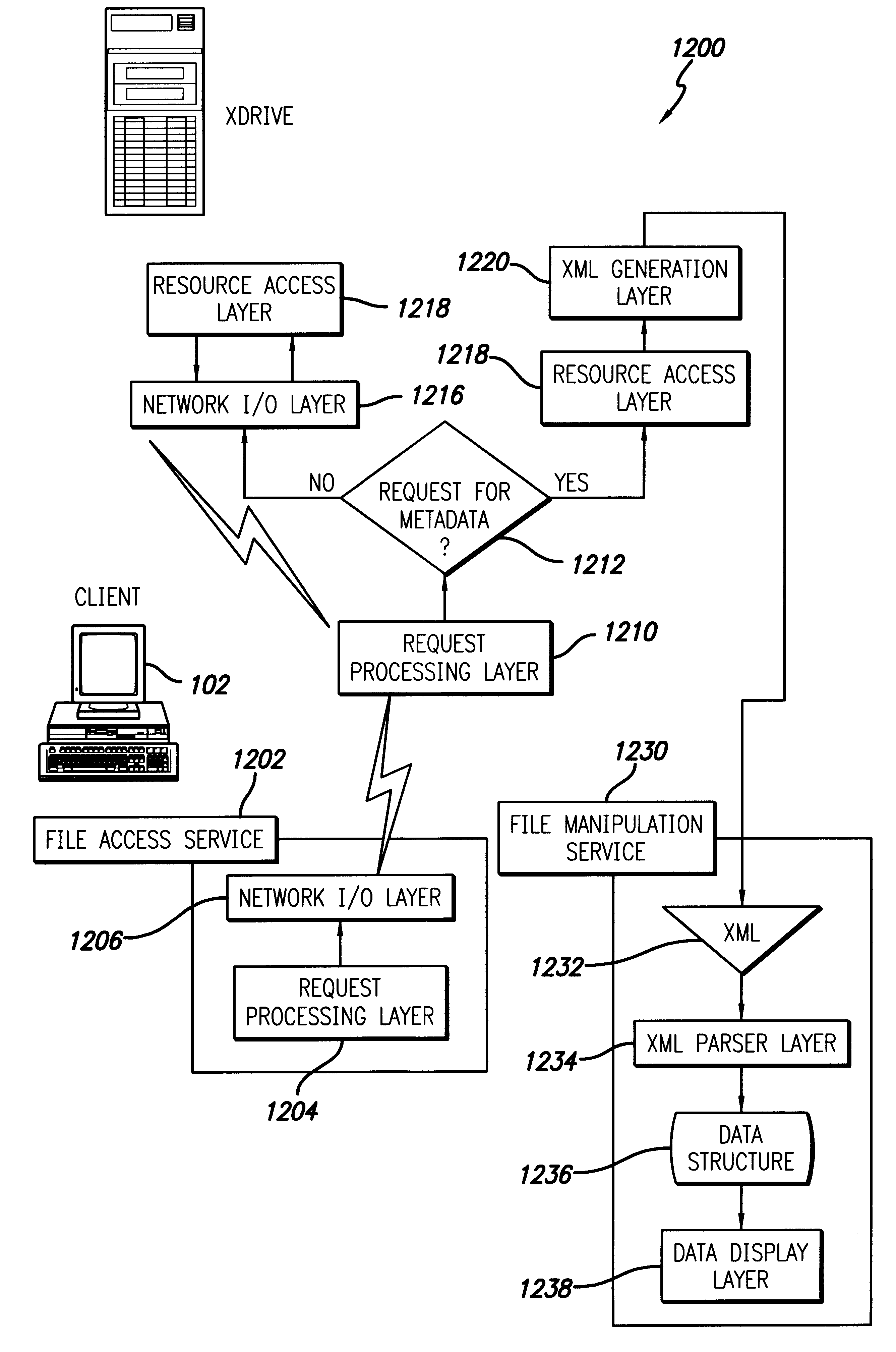
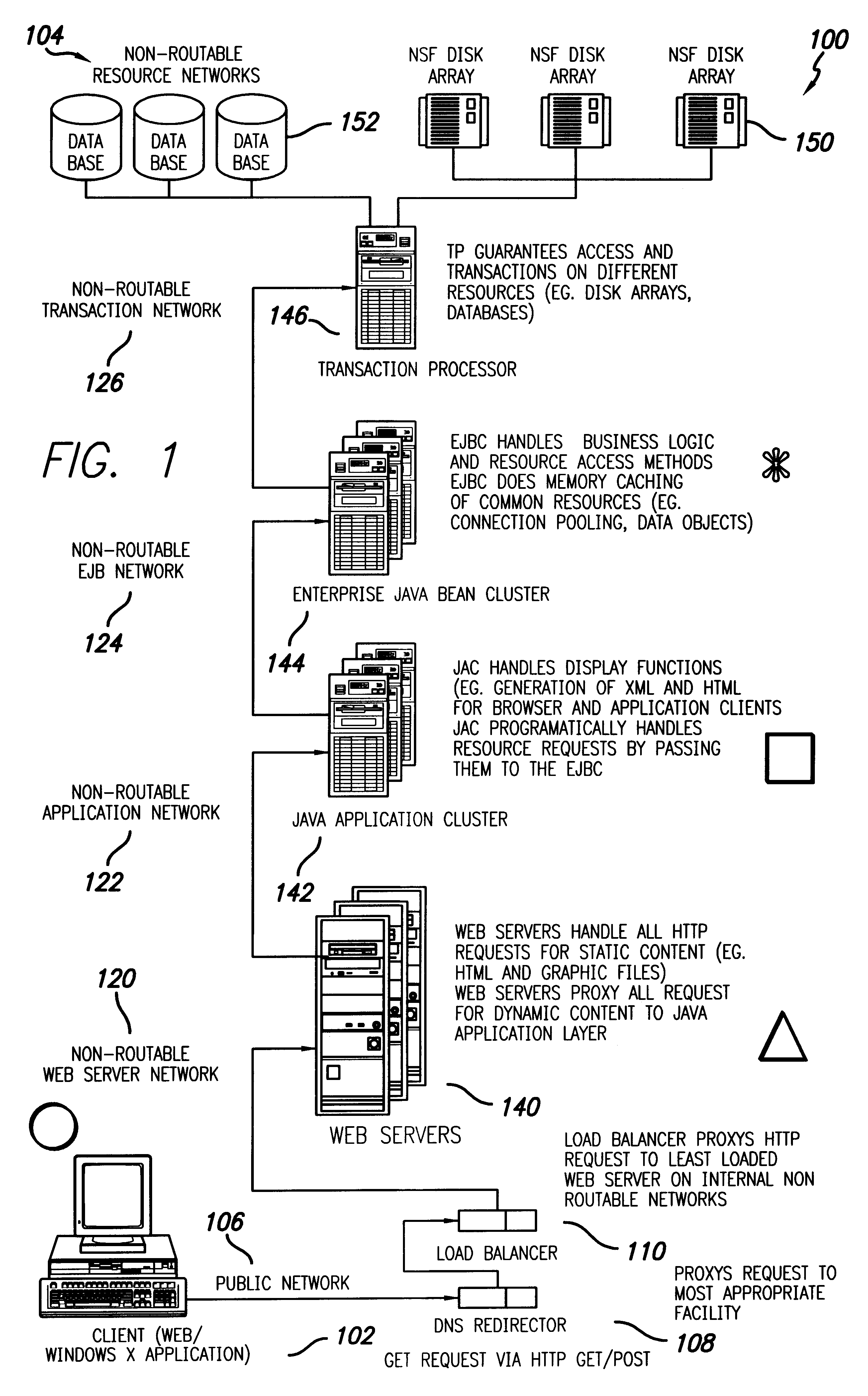
Shared internet storage resource, user interface system, and method
InactiveUS6351776B1Easy to understandData processing applicationsWeb data indexingData streamWeb service
The Shared Internet Storage Resource provides Internet-based file storage, retrieval, access, control, and manipulation for a user. Additionally, an easy-to-use user interface is provided both for a browser or stand-alone application. The entire method provides means by which users can establish, use, and maintain files on the Internet in a manner remote from their local computers yet in a manner that is similar to the file manipulation used on their local computers. A high capacity or other storage system is attached to the Internet via an optional internal network that also serves to generate and direct metadata regarding the stored files. A web server using a CGI, Java(R)-based, or other interface transmits and retrieves TCP / IP packets or other Internet information through a load balancer / firewall by using XML to wrap the data packets. File instructions may be transmitted over the Internet to the Shared Resource System. The user's account may be password protected so that only the user may access his or her files. On the user's side, a stand-alone client application or JavaScript object interpreted through a browser provide two means by which the XML or other markup language data stream may be received and put to use by the user. Internet-to-Internet file transfers may be effected by directly downloading to the user's account space.
Owner:TIME WARNER
Tamper resistant software encoding
InactiveUS6842862B2Improvement in tamper-resistanceIncreased complexityMemory loss protectionUnauthorized memory use protectionTamper resistancePassword
The present invention relates generally to computer software, and more specifically, to a method and system of making computer software resistant to tampering and reverse-engineering. “Tampering” occurs when an attacker makes unauthorized changes to a computer software program such as overcoming password access, copy protection or timeout algorithms. Broadly speaking, the method of the invention is to increase the tamper-resistance and obscurity of computer software code by transforming the data flow of the computer software so that the observable operation is dissociated from the intent of the original software code. This way, the attacker can not understand and decode the data flow by observing the execution of the code. A number of techniques for performing the invention are given, including encoding software arguments using polynomials, prime number residues, converting variables to new sets of boolean variables, and defining variables on a new n-dimensional vector space.
Owner:IRDETO ACCESS
System to control content and prohibit certain interactive attempts by a person using a personal computer
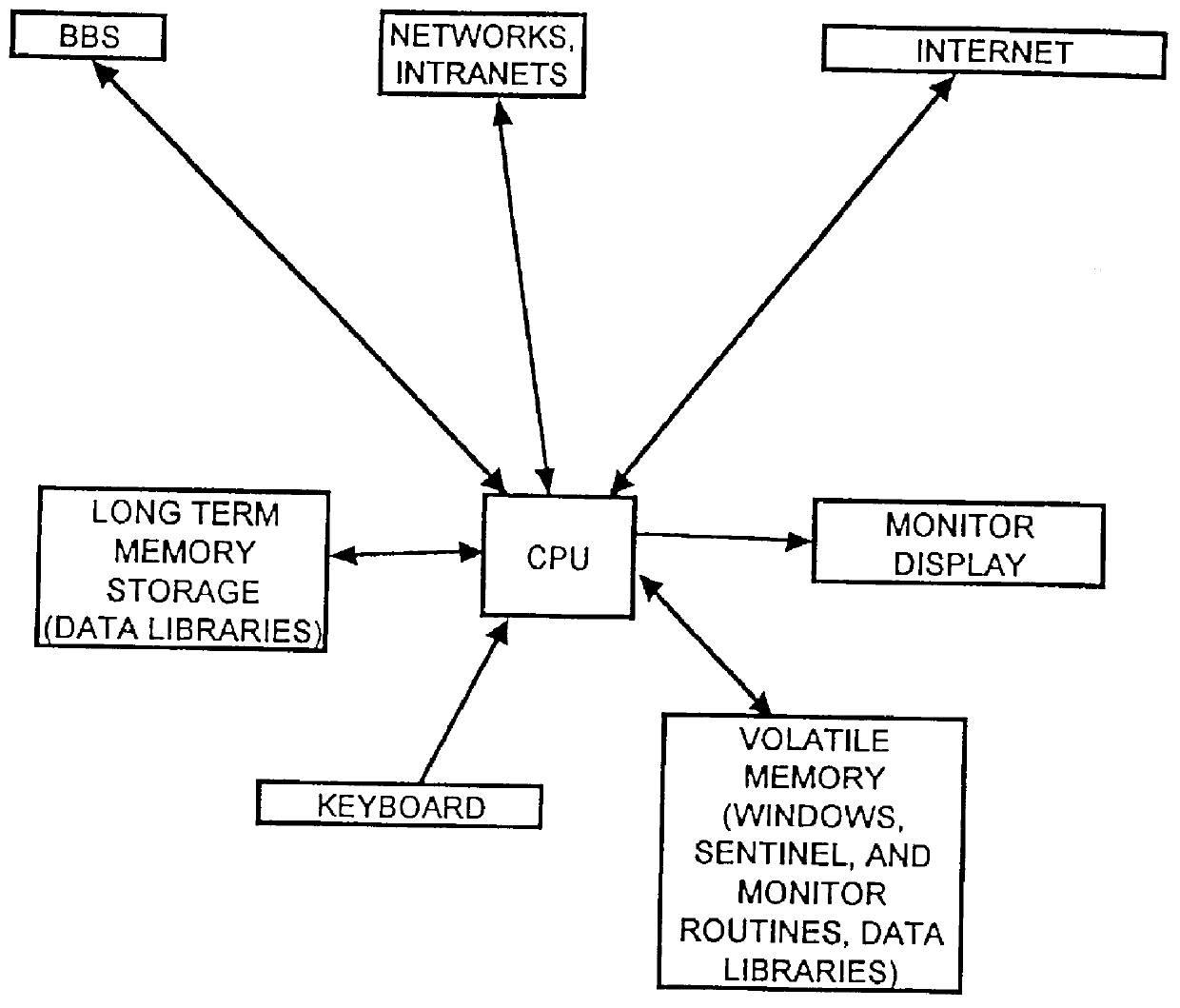
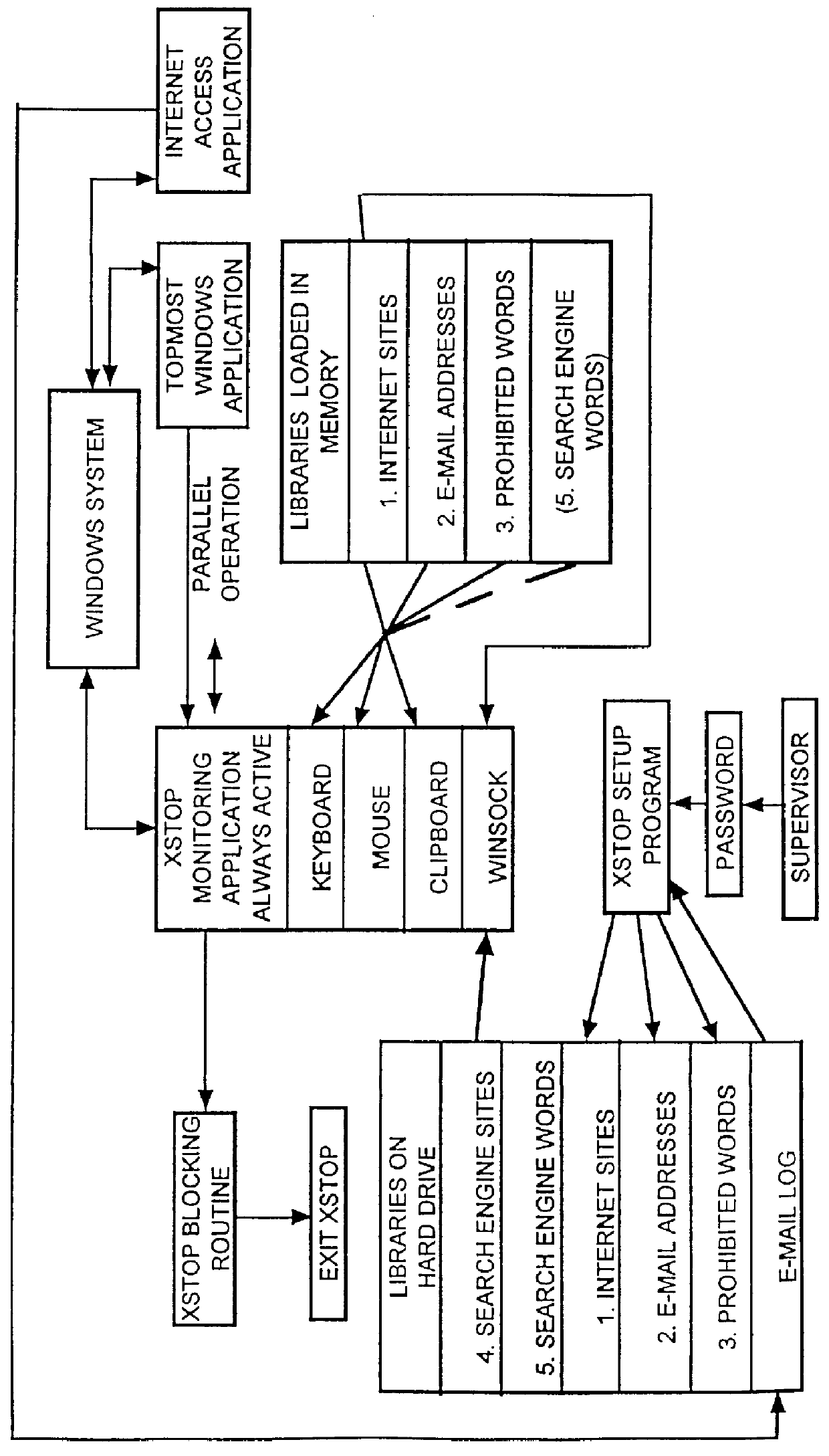
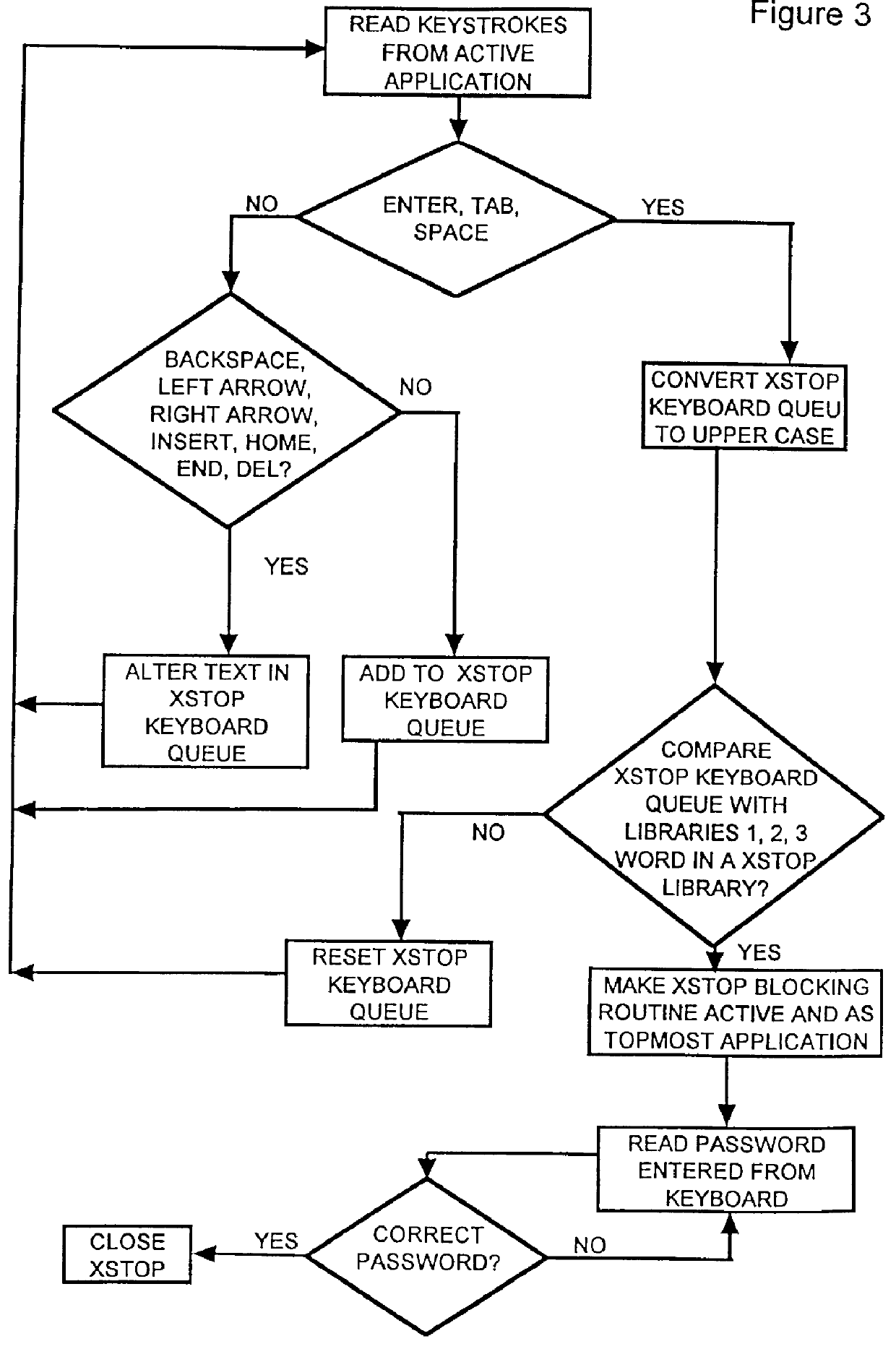
InactiveUS6065056AReduce usageAvoid spreadingDigital data information retrievalMultiple digital computer combinationsPasswordWord search
A computer, terminal and a method for blocking the use and creating of vulgar and pornographic material in a responsive and interactive matter that comprehensively monitors computer operations for creation or transmission of vulgar and pornographic material. Data created by the keyboard, data passing through the clipboard, data selected by the mouse pointer, and data passing through the Internet interface are monitored for content and further operation of the computer terminal is blocked. The computer terminal may only be unblocked by a supervisory intervention, such as by entering of a password, or by restarting or resetting the terminal. Key word searches, such as those in Internet search engines, are also monitored, but the terminal adapts to monitor not only for words of a profane and vulgar nature, but also for words that are behaviorally tested to produce lists containing vulgar and profane items, e.g., Internet sites. The computer terminal and method can be modified to block other forms of communication or computer operation, such as blocking transmission of secret business data, blocking execution or opening of certain programs or files, and the like.
Owner:TW SECURITY CORP
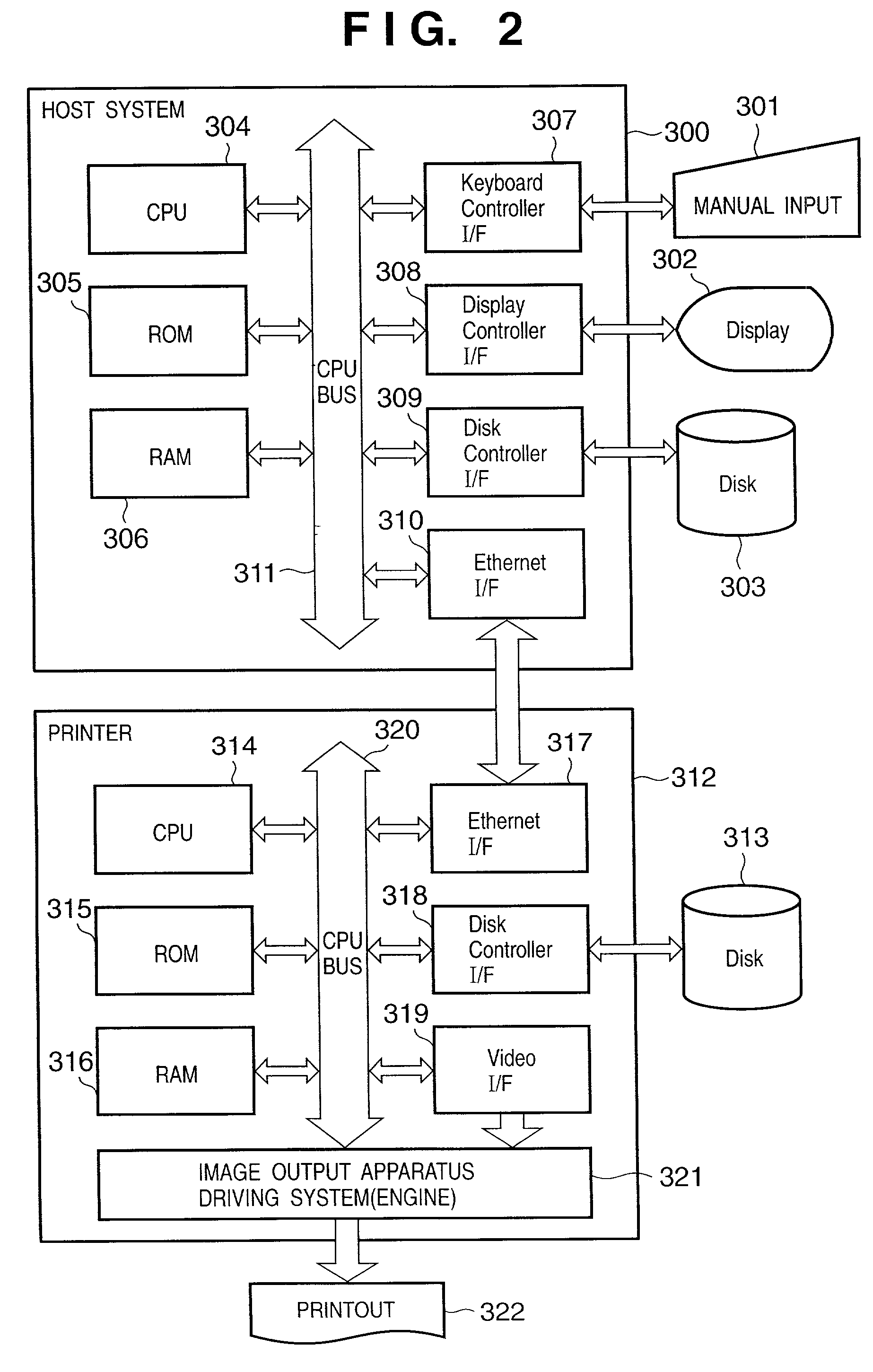
Automatic authentication method and system in print process
ActiveUS7313699B2Improve securityEliminate needDigital data processing detailsUser identity/authority verificationUser authenticationUser identifier
This invention provides an automatic authentication method and system in a print process, which can obviate the need for user's input operations of the user ID and password and can improve security since authentication is automatically done based on print information embedded in a file or information from an application program without any user's input.In a print process that requires user authentication, a printer driver extracts information related to an application and / or a document for the print process as attribute information, and user authentication is made by comparing the attribute information with information stored in a user registration information database of a server. If user authentication has succeeded, the printer driver controls a printer to print, and the server manages and stores accounting information and the like for respective departments in a department management information database.
Owner:CANON KK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com