Patents
Literature
611 results about "Digital identity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A digital identity is information on an entity used by computer systems to represent an external agent. That agent may be a person, organization, application, or device. ISO/IEC 24760-1 defines identity as "set of attributes related to an entity".
Blockchain identity management system based on public identities ledger
ActiveUS9635000B1Effectively prevents unauthorized sharingMultiple keys/algorithms usagePublic key for secure communicationSystems managementIdentity management system
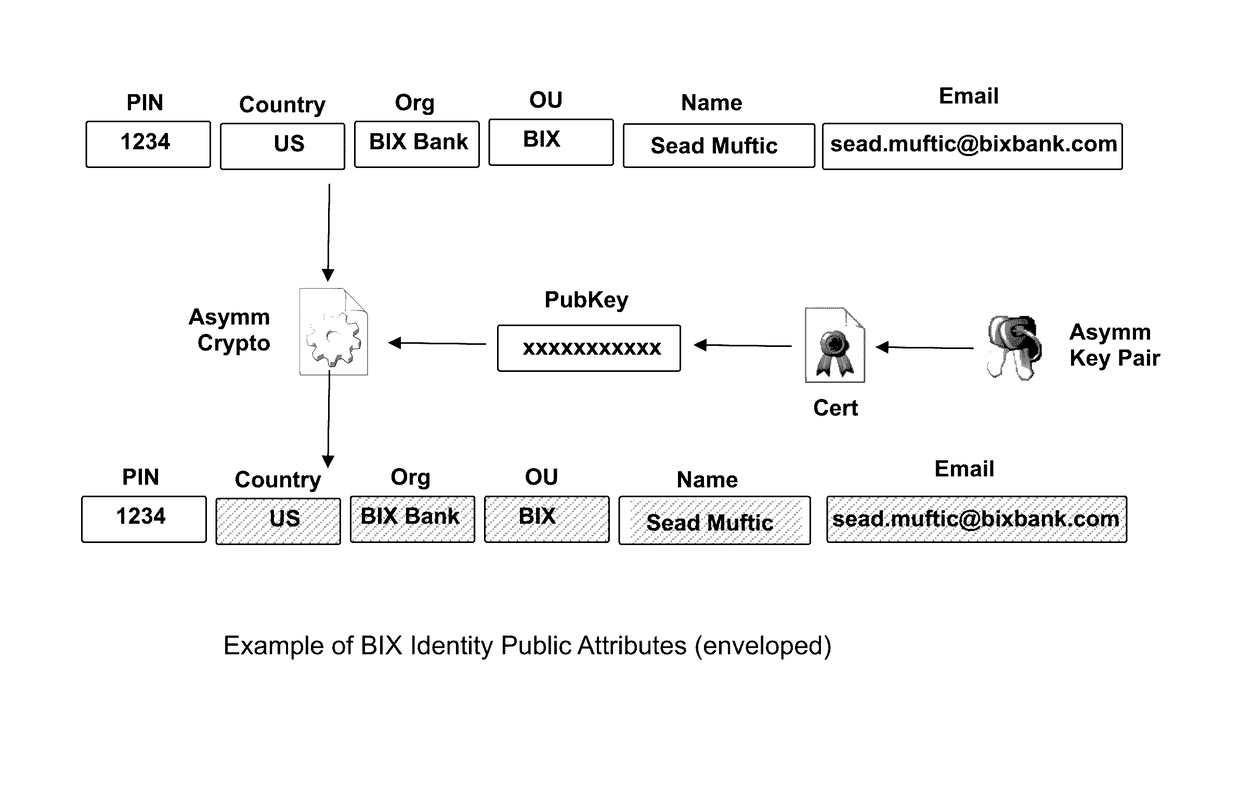
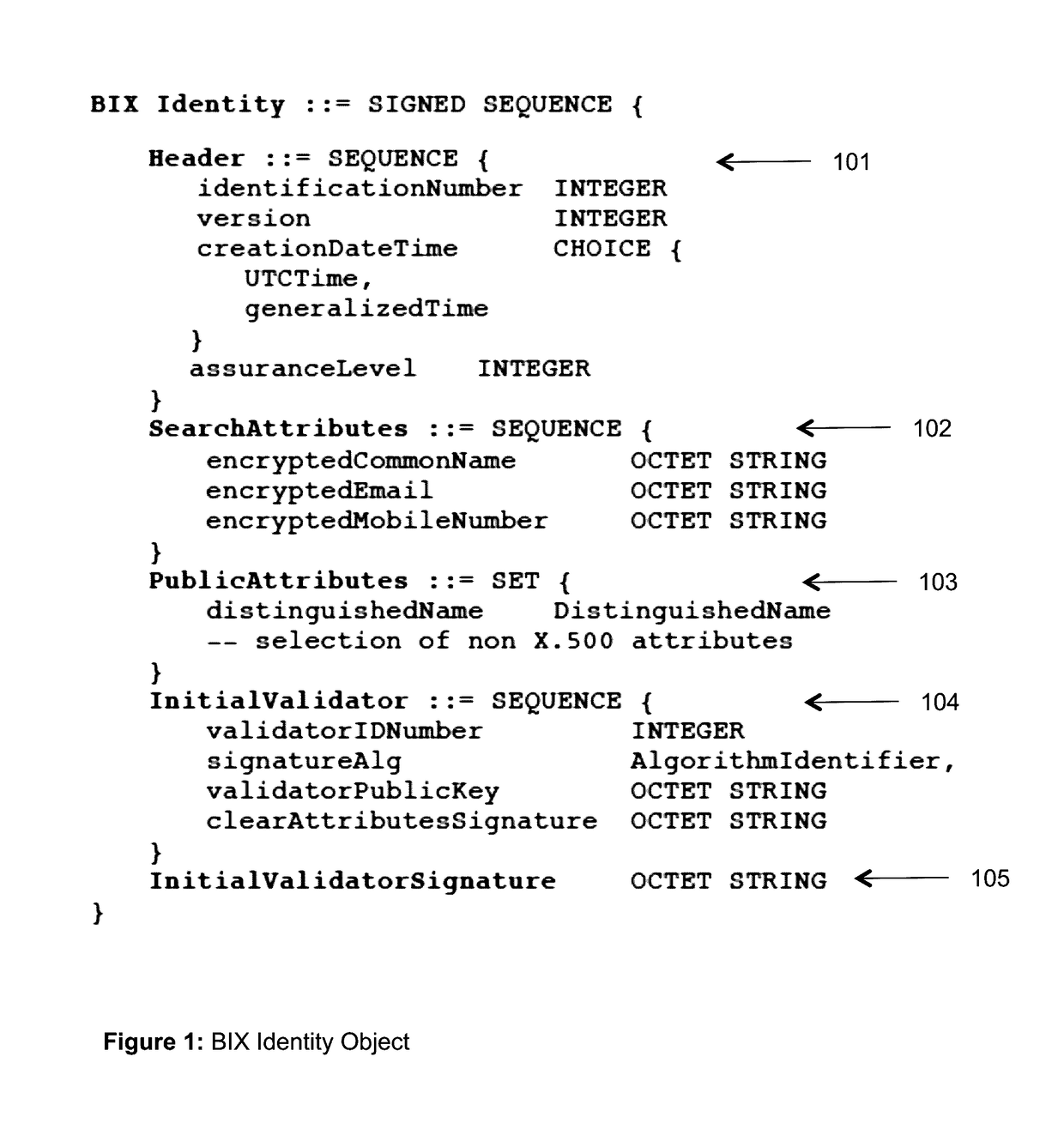
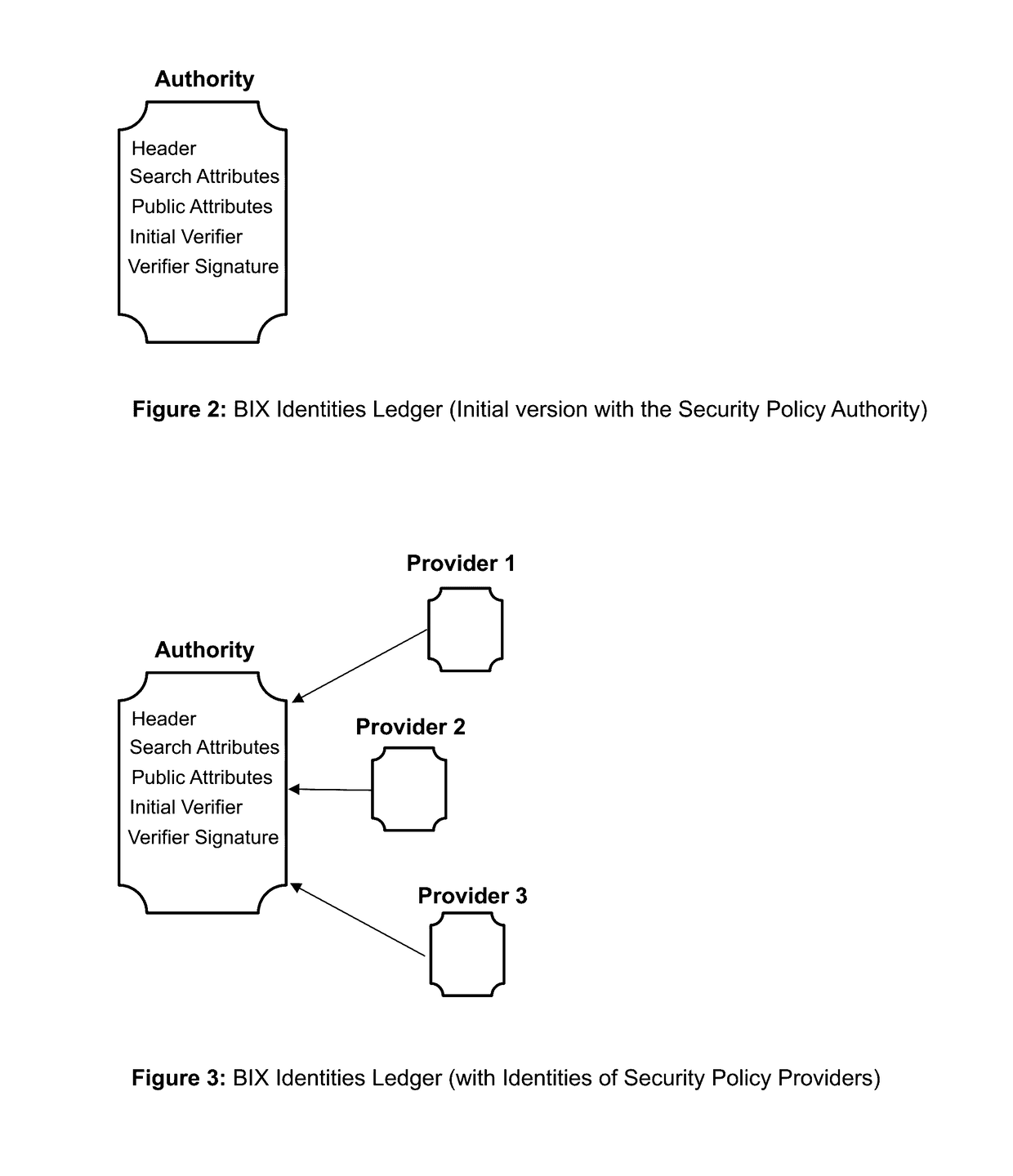
The invention describes an identity management system (IDMS) based on the concept of peer-to-peer protocols and the public identities ledger. The system manages digital identities, which are digital objects that contain attributes used for the identification of persons and other entities in an IT system and for making identity claims. The identity objects are encoded and cryptographically encapsulated. Identity management protocols include the creation of identities, the validation of their binding to real-world entities, and their secure and reliable storage, protection, distribution, verification, updates, and use. The identities are included in a specially constructed global, distributed, append-only public identities ledger. They are forward- and backward-linked using the mechanism of digital signatures. The linking of objects and their chaining in the ledger is based on and reflect their mutual validation relationships. The identities of individual members are organized in the form of linked structures called the personal identities chains. Identities of groups of users that validated identities of other users in a group are organized in community identities chains. The ledger and its chains support accurate and reliable validation of identities by other members of the system and by application services providers without the assistance of third parties. The ledger designed in this invention may be either permissioned or unpermissioned. Permissioned ledgers have special entities, called BIX Security Policy Providers, which validate the binding of digital identities to real-world entities based on the rules of a given security policy. In unpermissioned ledgers, community members mutually validate their identities. The identity management system provides security, privacy, and anonymity for digital identities and satisfies the requirements for decentralized, anonymous identities management systems.
Owner:MUFTIC SEAD
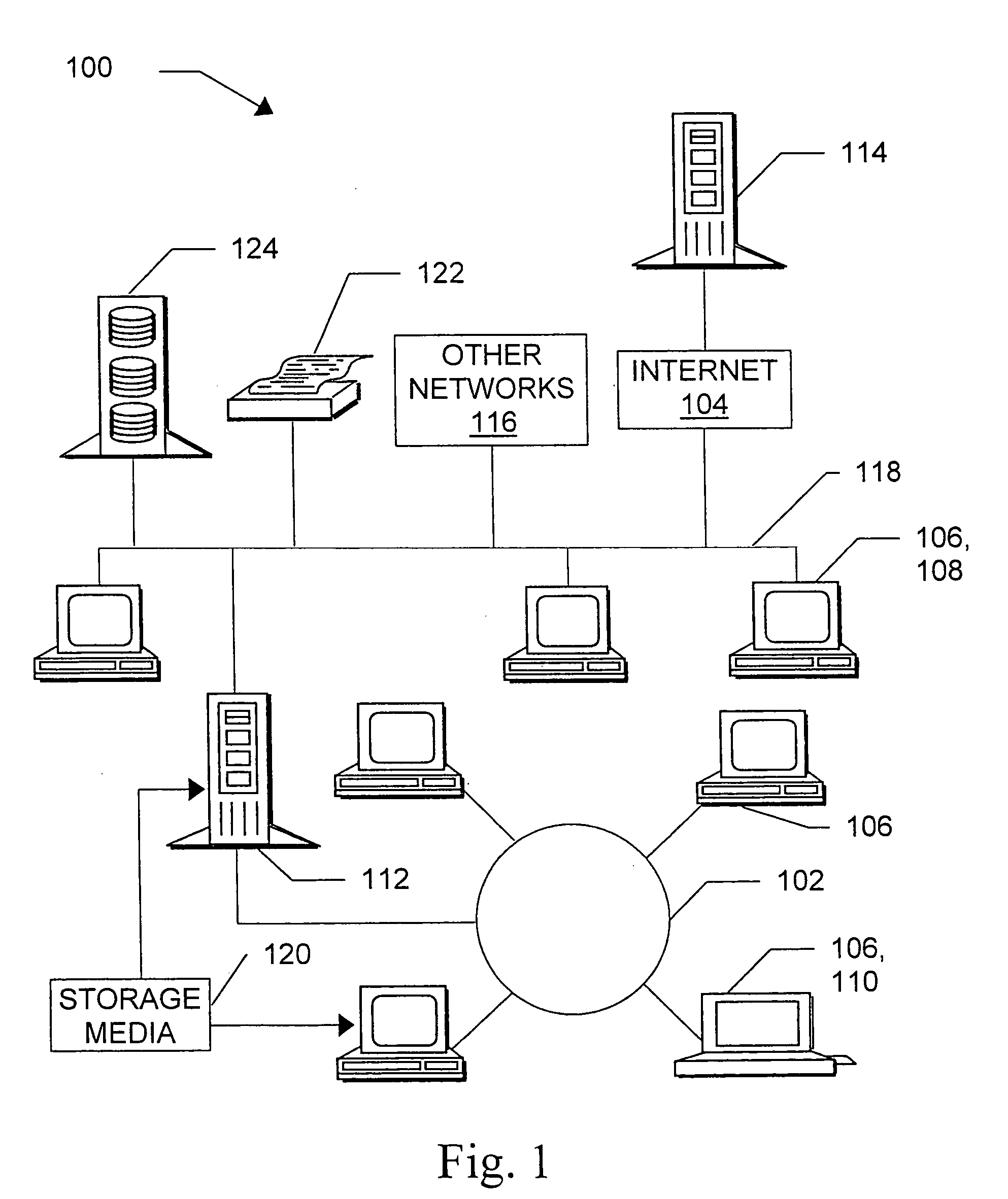
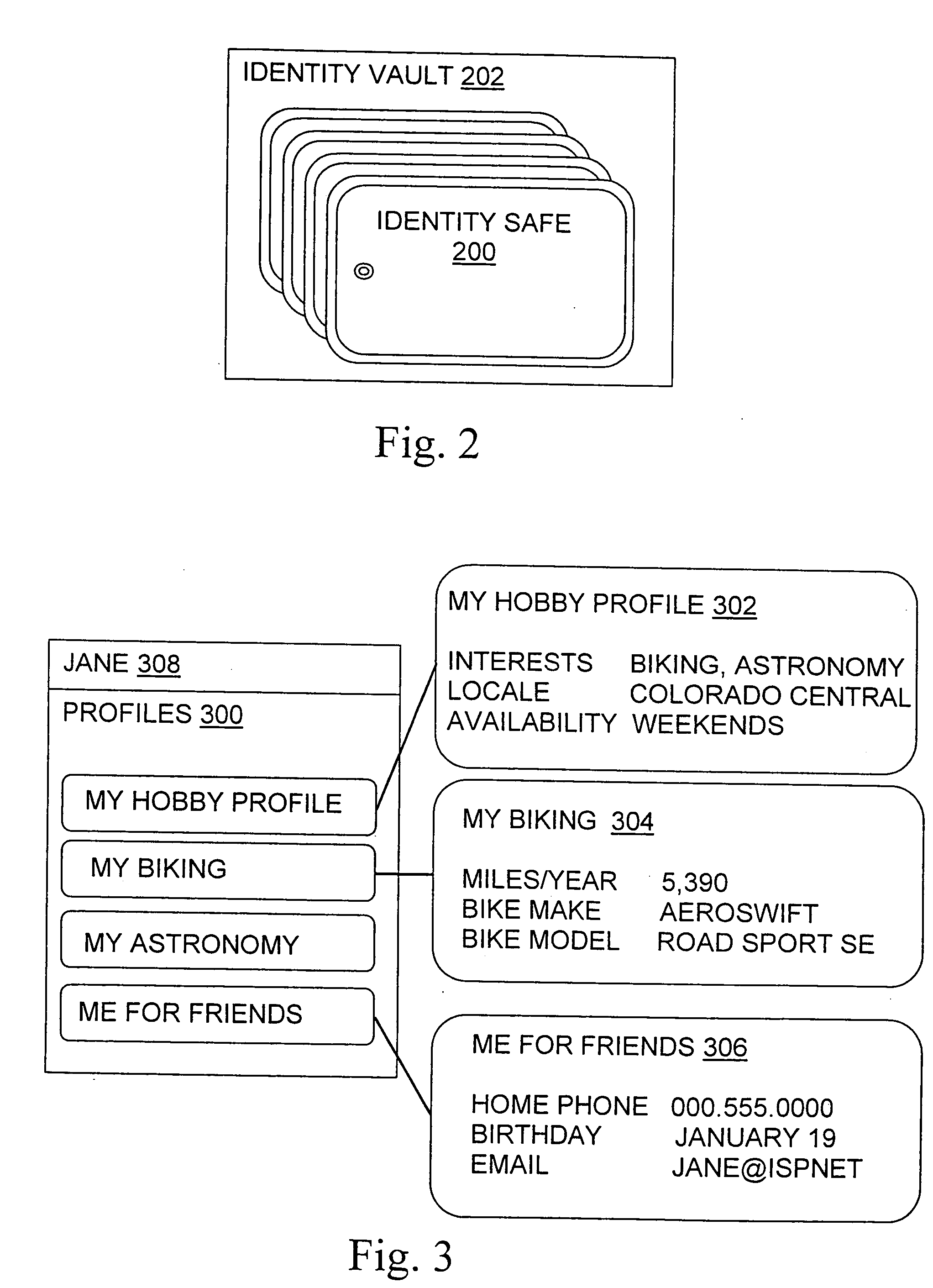
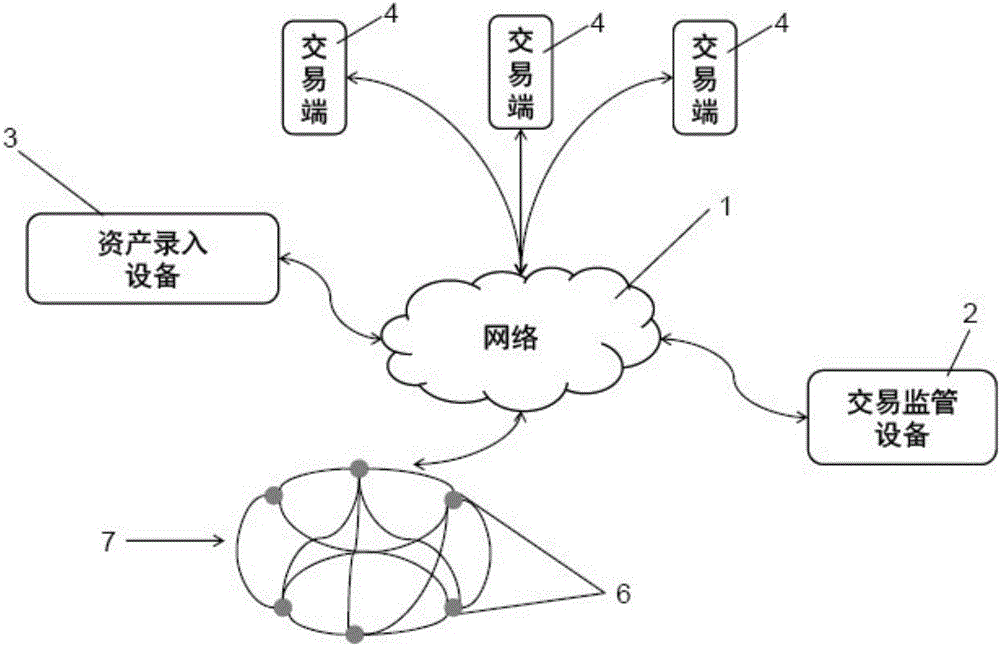
Managing digital identity information
ActiveUS20050044423A1Maintain the integrity of relationshipsAdvanced technologyDigital data processing detailsMultiple digital computer combinationsDigital identityPassword
A basic architecture for managing digital identity information in a network such as the World Wide Web is provided. A user of the architecture can organize his or her information into one or more profiles which reflect the nature of different relationships between the user and other entities, and grant or deny each entity access to a given profile. Various enhancements which may be provided through the architecture are also described, including tools for filtering email, controlling access to user web pages, locating other users and making one's own location known, browsing or mailing anonymously, filling in web forms automatically with information already provided once by hand, logging in automatically, securely logging in to multiple sites with a single password and doing so from any machine on the network, and other enhancements.
Owner:EMC IP HLDG CO LLC
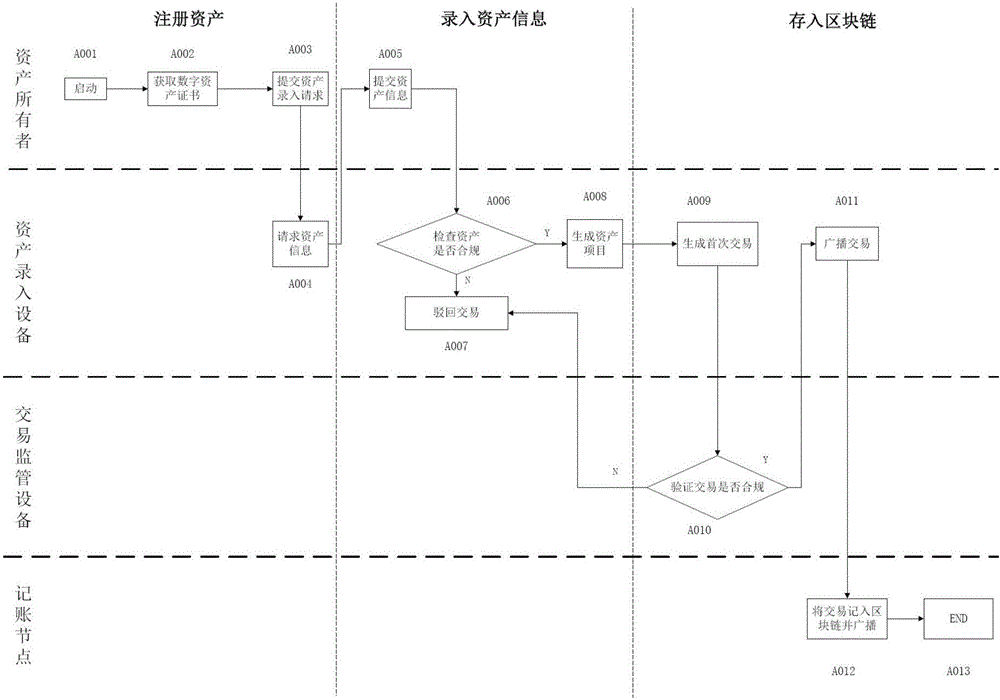
Asset transaction platform and digital certification and transaction method for assets
ActiveCN105956923AAchieve decentralizationGuarantee authenticityFinanceData synchronizationDigital identity
The present invention relates to a digital asset transaction platform, comprising an asset entry device and a distributed accounting network. An asset is validated by the asset entry device. When compliance is achieved, asset project information is generated and is input to the asset transaction platform, wherein the asset project information includes a hash value of a digital asset certificate of the asset. The distributed accounting network comprises a plurality of accounting nodes, which are connected in a point-to-point manner and each store a transaction data information general ledger which is synchronized with each other and is based on a block chain database. The asset transaction platform supports mutual transaction of at least two different types of assets. The asset transaction platform provided by the invention adopts the block chain technology and the digital identity identification technology of assets and realizes de-centralization and trusted quick transaction of various assets.
Owner:上海如鸽投资有限公司
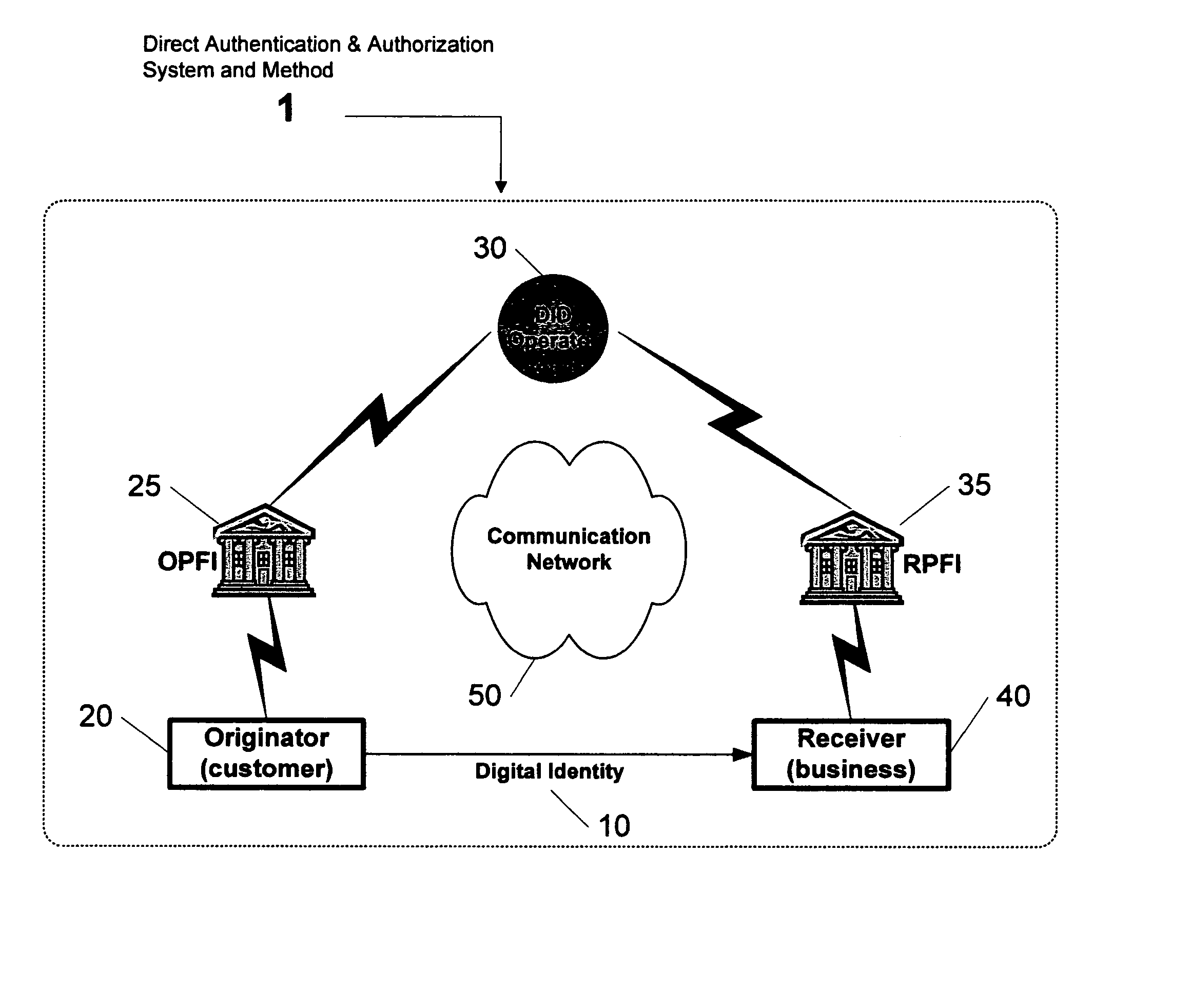
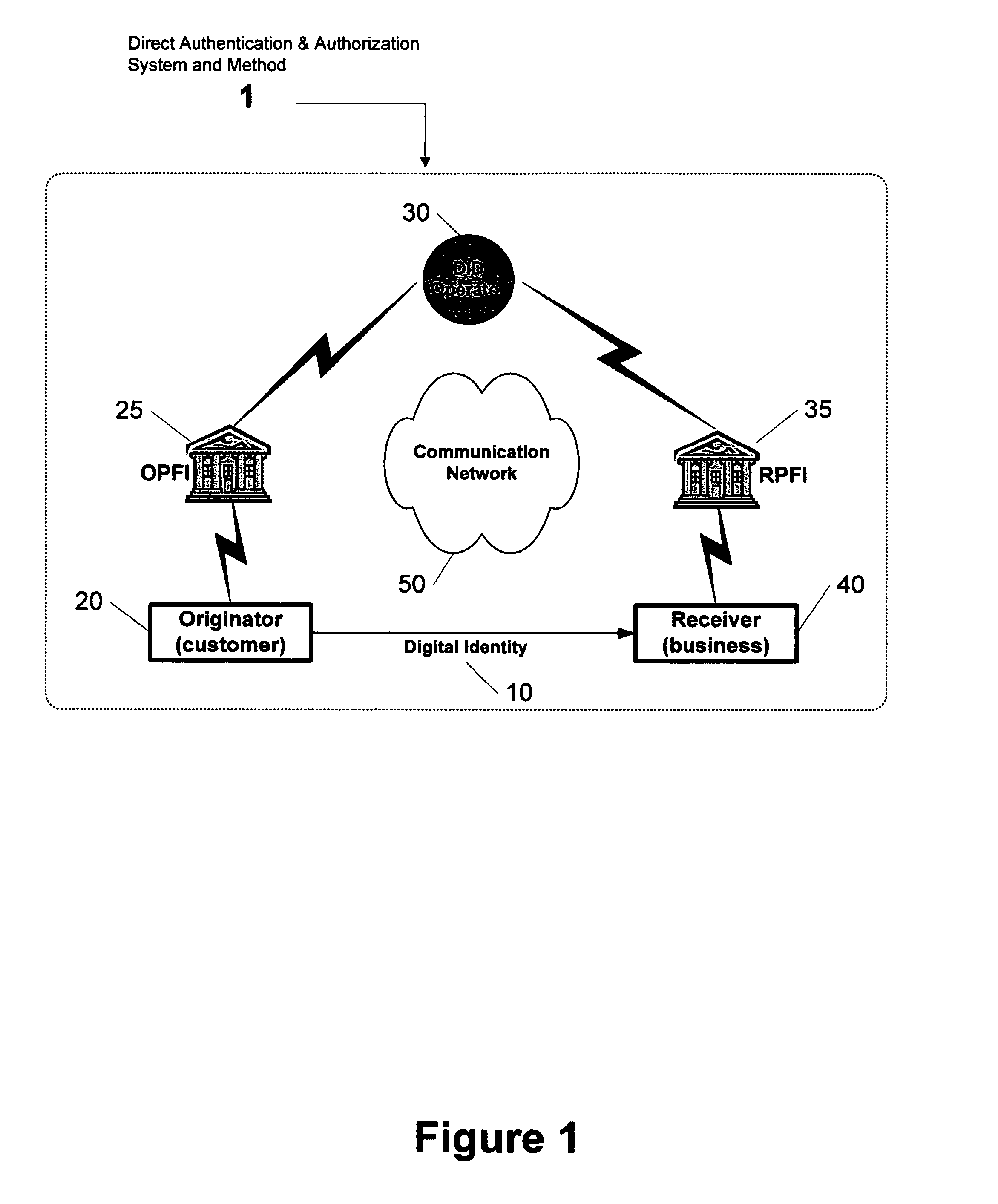
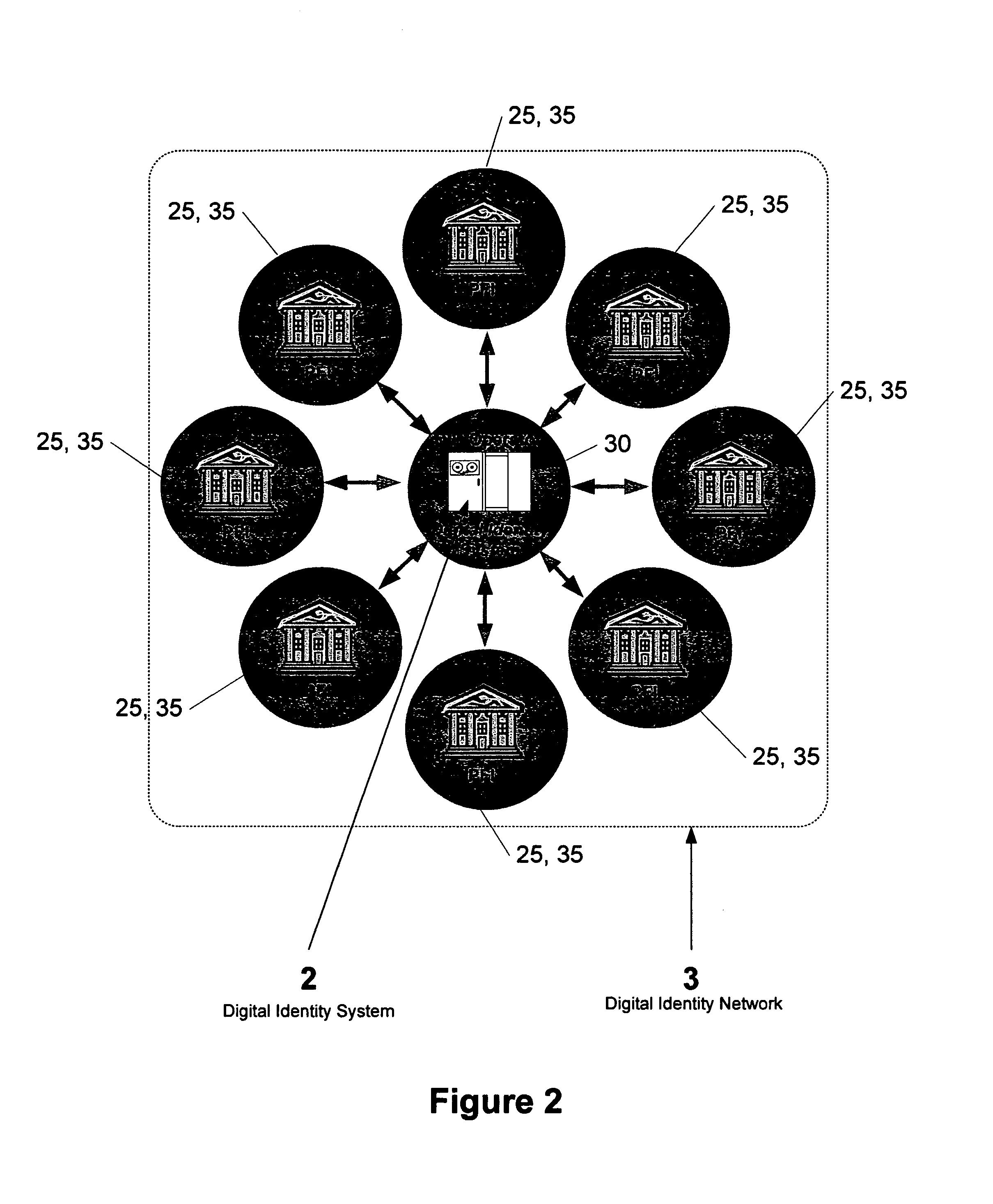
Direct authentication and authorization system and method for trusted network of financial institutions
A system and method for direct authentication and / or authorization of transactions. The system includes a trusted Digital Identity (DID) Network connecting an Originating Participating Financial Institution (OPFI) and a Receiving Participating Financial Institution (RPFI) through a DID Operator. The DID Operator may further be coupled to a DID System that calculates digital identities for Originators. According to the method, direct authentication of the Originator and / or authorization of the transaction is initiated upon the Originator communicating its digital identity to the Receiver. The Receiver subsequently provides the digital identity to the RPFI. The RPFI is then able to communicate with the OPFI for authentication of the Originator and / or authorization of the transaction through the DID Operator based on Originator's digital identity. The transaction between the Originator and Receiver can be financial or non-financial and may include, for example, account-to-account transfers, identity authentication or express agreements. In another embodiment, authentication and / or authorization may be performed in real time.
Owner:ASGHARI KAMRANI NADER +1
Managing digital identity information
ActiveUS7680819B1Maintain the integrity of relationshipsAdvanced technologyDigital data processing detailsMultiple digital computer combinationsDigital identityPassword
A basic architecture for managing digital identity information in a network such as the World Wide Web is provided. A user of the architecture can organize his or her information into one or more profiles which reflect the nature of different relationships between the user and other entities, and grant or deny each entity access to a given profile. Various enhancements which may be provided through the architecture are also described, including tools for filtering email, controlling access to user web pages, locating other users and making one's own location known, browsing or mailing anonymously, filling in web forms automatically with information already provided once by hand, logging in automatically, securely logging in to multiple sites with a single password and doing so from any machine on the network, and other enhancements.
Owner:EMC IP HLDG CO LLC
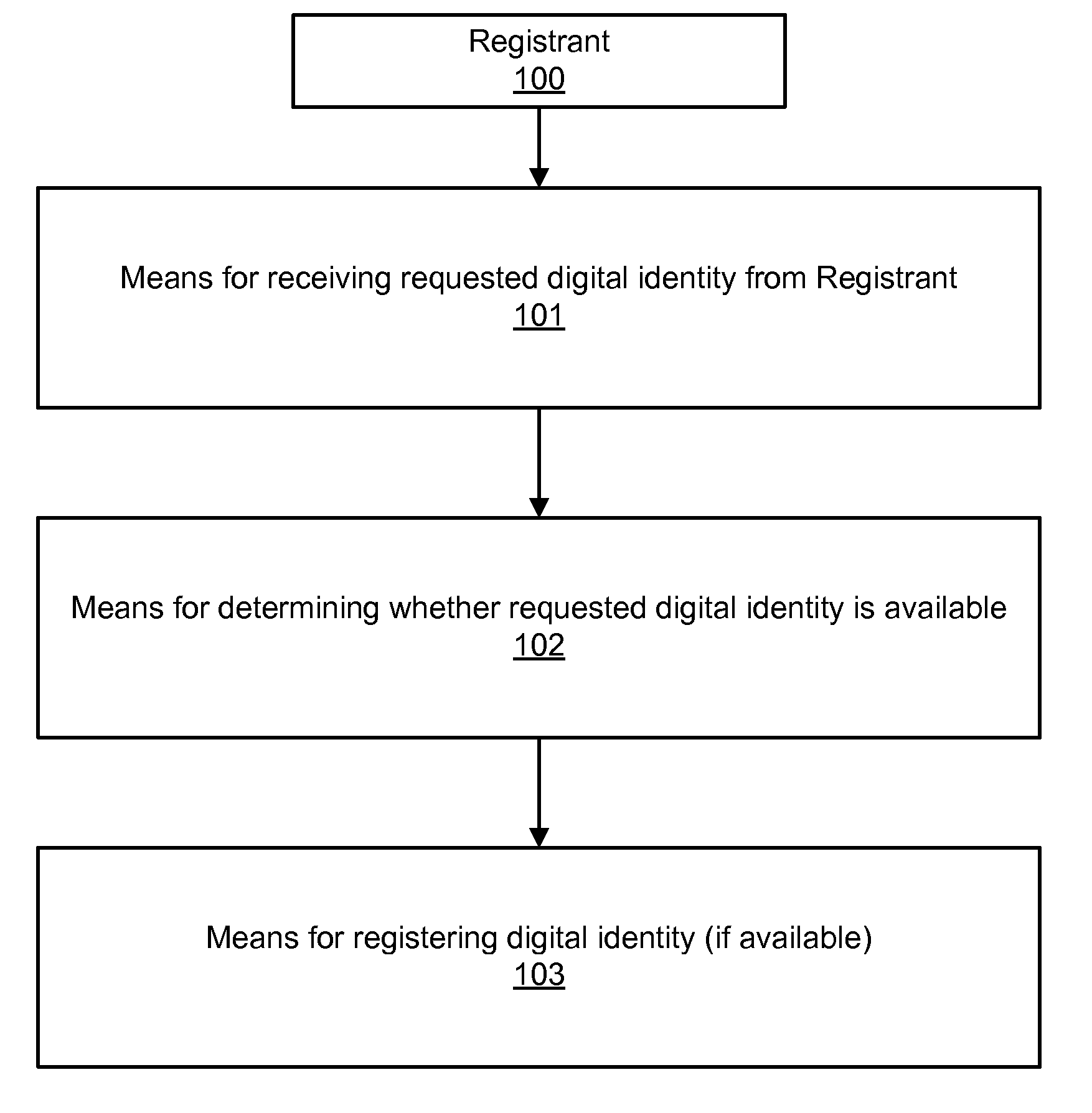
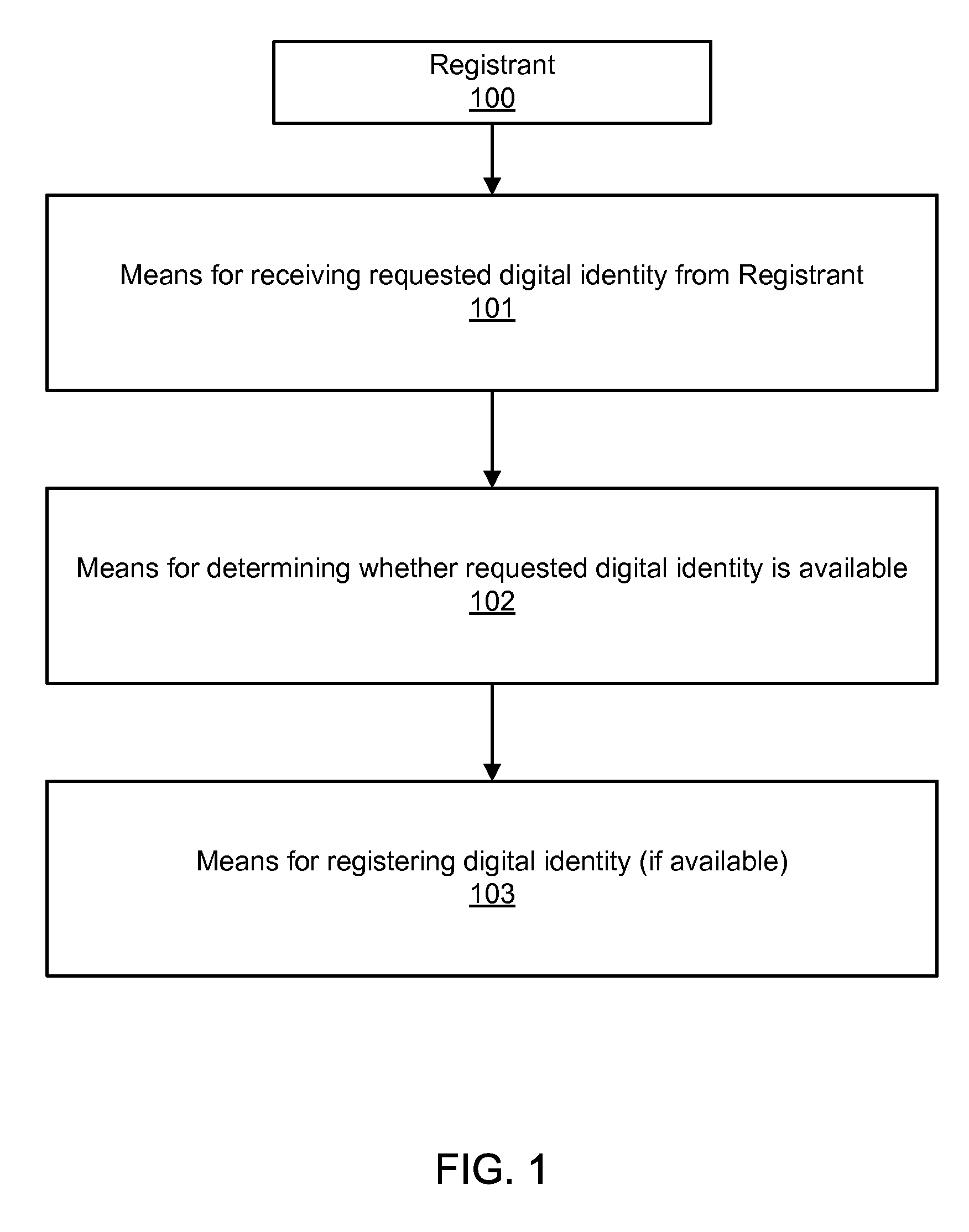
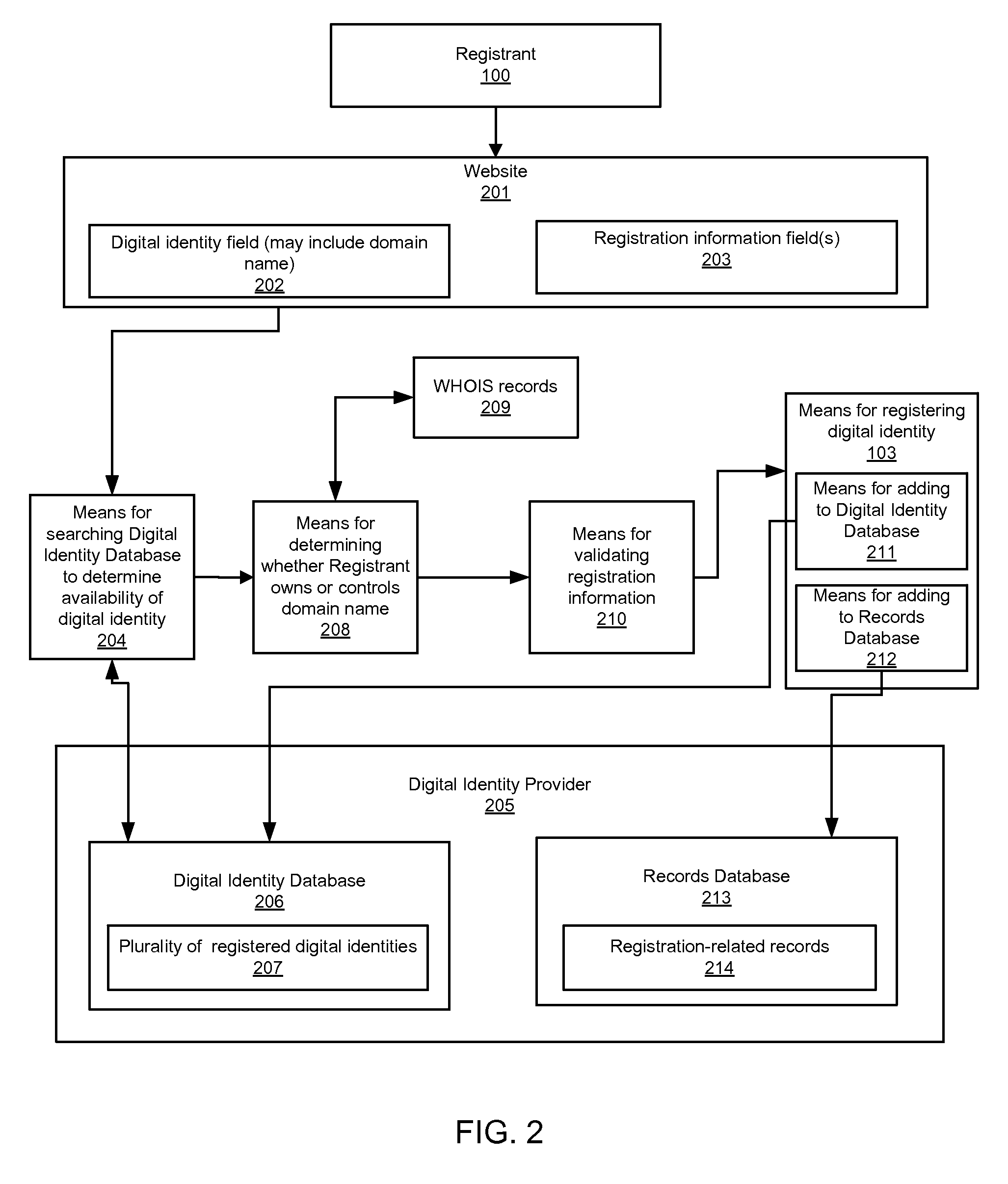
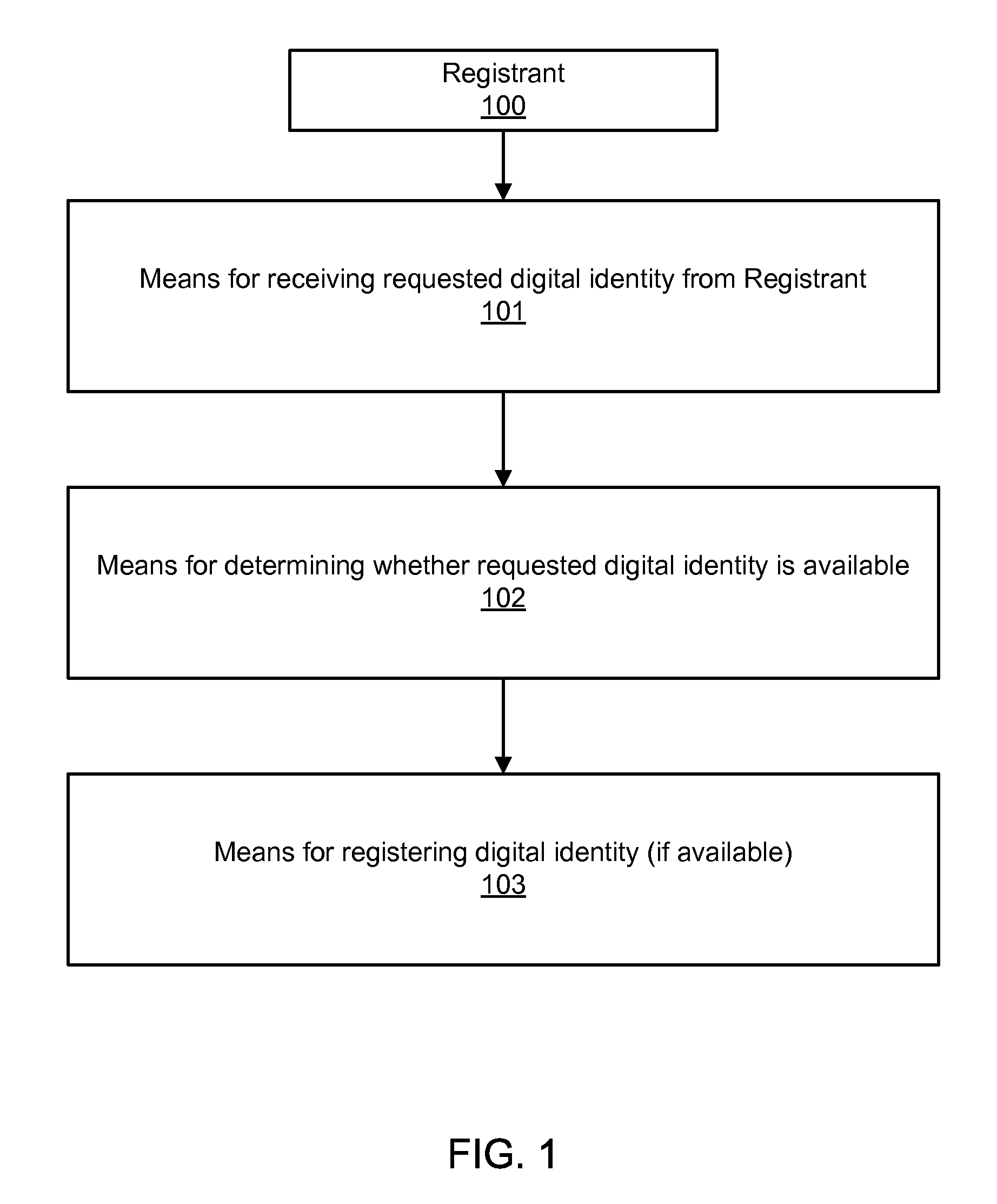
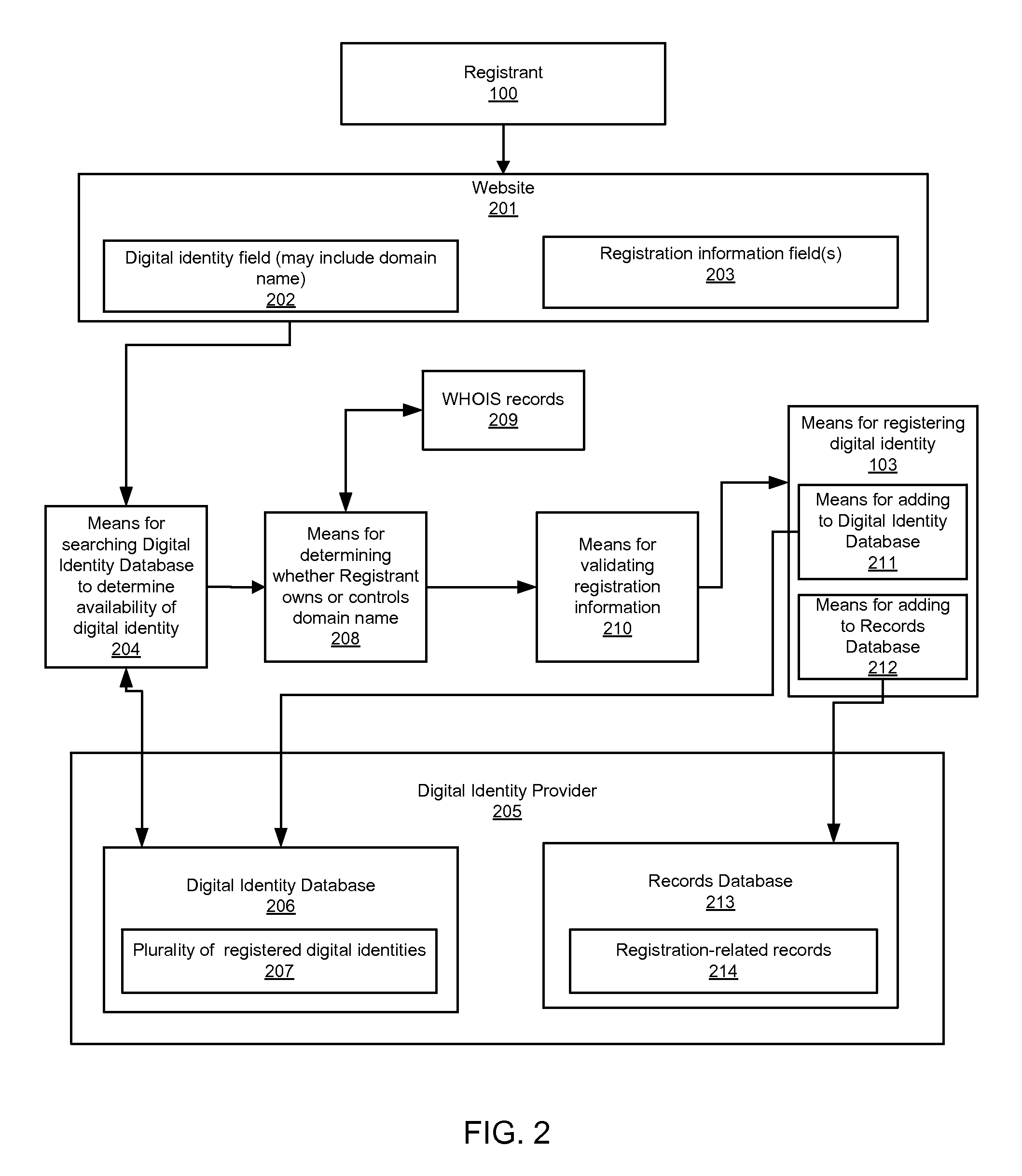
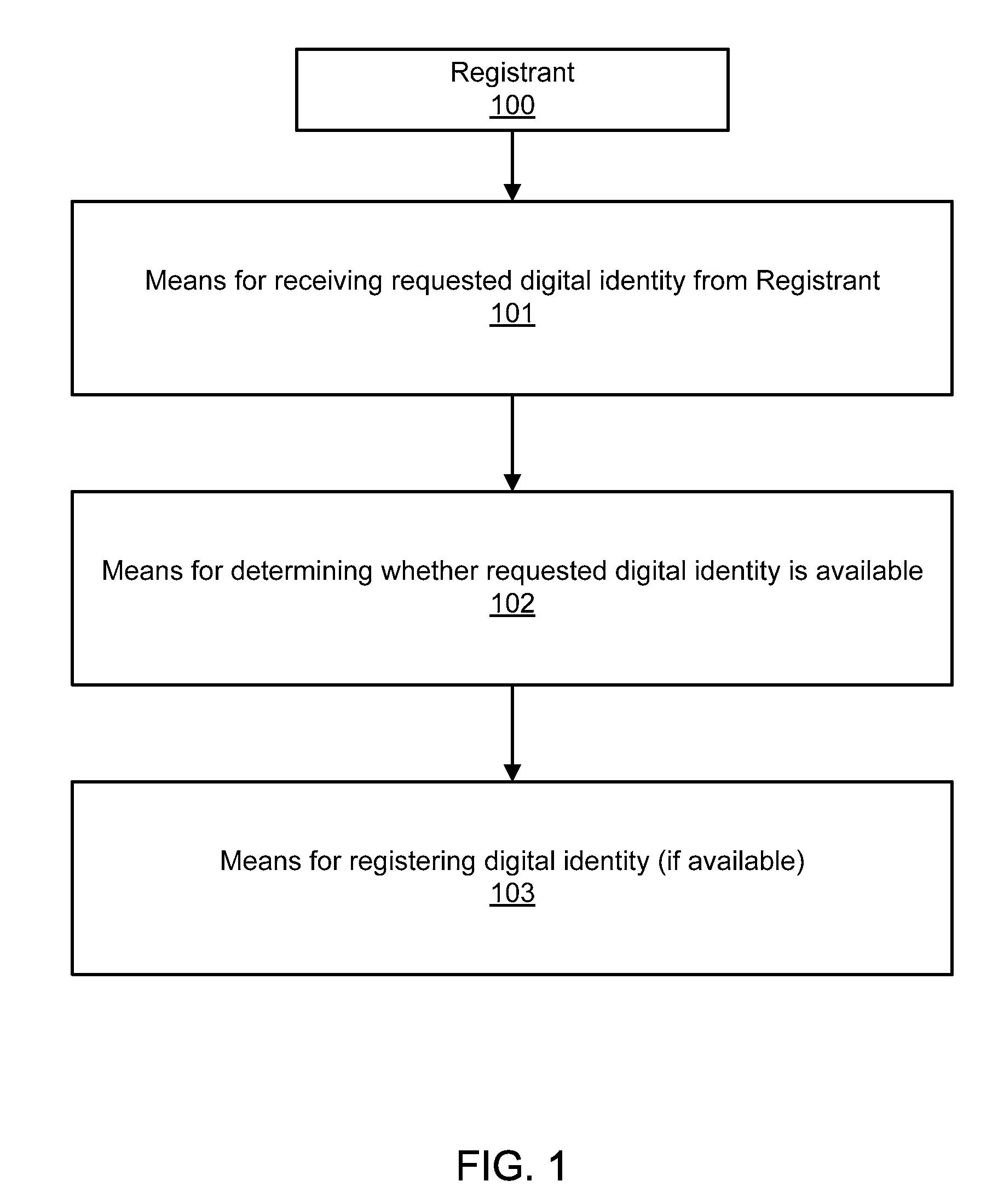
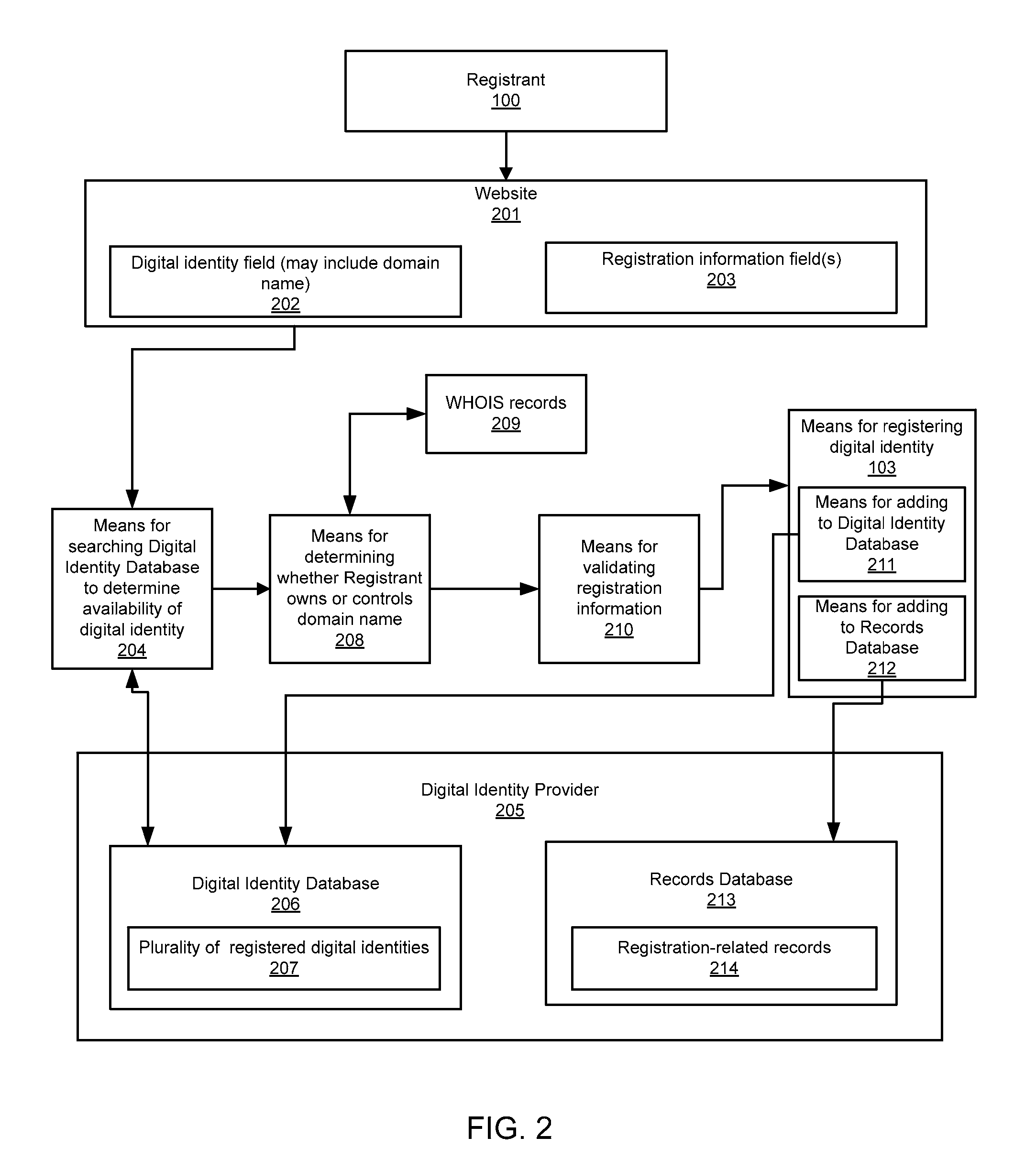
Digital identity validation
ActiveUS20070294431A1Effective registrationMultiple digital computer combinationsData switching networksDigital identityEmail address
Systems and processes of the present invention allow for digital identity validation. In an example embodiment, a digital identity is registered to a Registrant. During the registration process, one or more registration records are collected from the Registrant and stored in a Records Database. The registration records may include information regarding a digital identity, its Registrant, or another person or entity associated with the digital identity. They may also include name, address, phone number, email address, website, URL, or other information. The information is then verified, possibly by contacting a Registrant, administrative contact, technical contact, or another contact to confirm at least some information in the records. If the information is verified, the Digital Identity Provider may provide the Registrant with a Validation Marker indicating that the digital identity has been validated.
Owner:GO DADDY OPERATING
User/product authentication and piracy management system
InactiveUS20050149759A1Reduce potentialPrevent illegal useDigital data processing detailsMultiple digital computer combinationsDigital identitySerialization
A system in the form of a software solution that provides new and unique solutions to the need to secure digital environments. The present invention uses innovative and new forms of multi-factor user authentication and digital identity management, providing levels of security unmatched in the industry. In addition, the system provides new and unique methods of software piracy management including CD media-based copy protection, remote CD media validation, embedded product serialization, protection of electronically distributed software, and remote product installation tracking.
Owner:MOVEMONEY
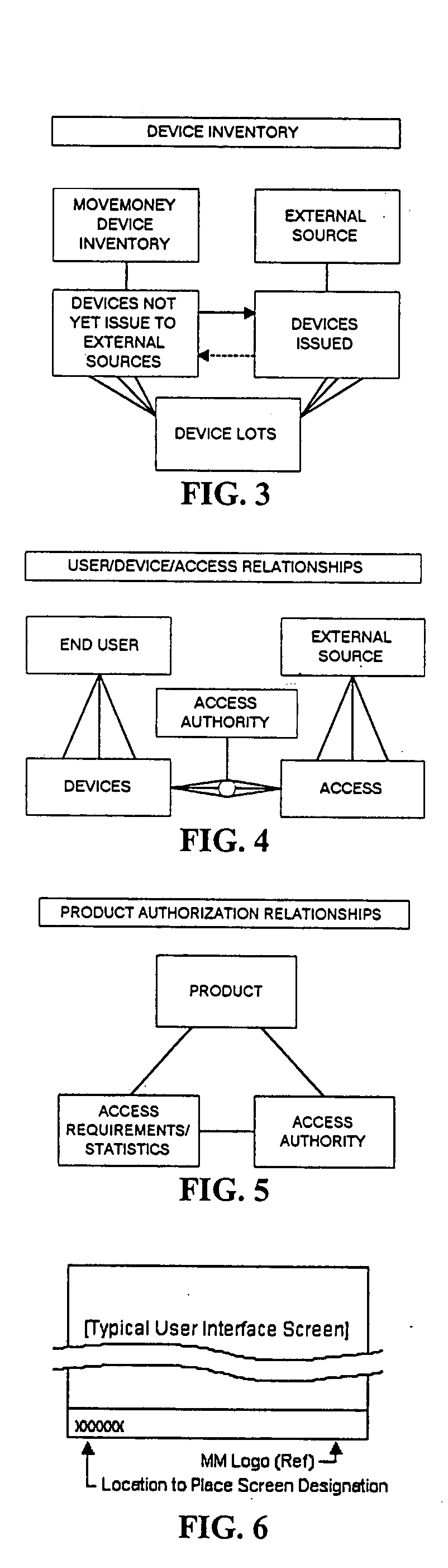
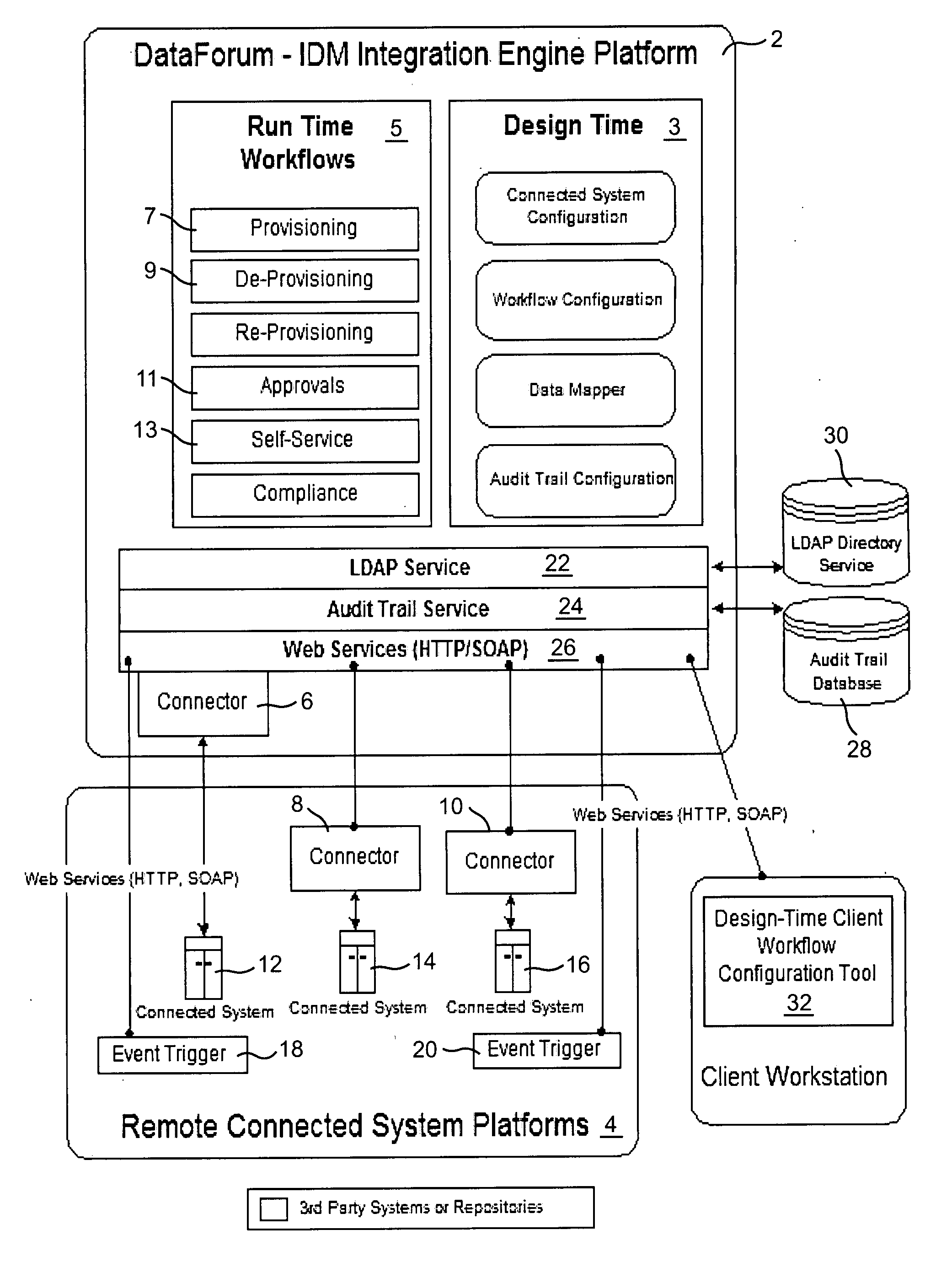
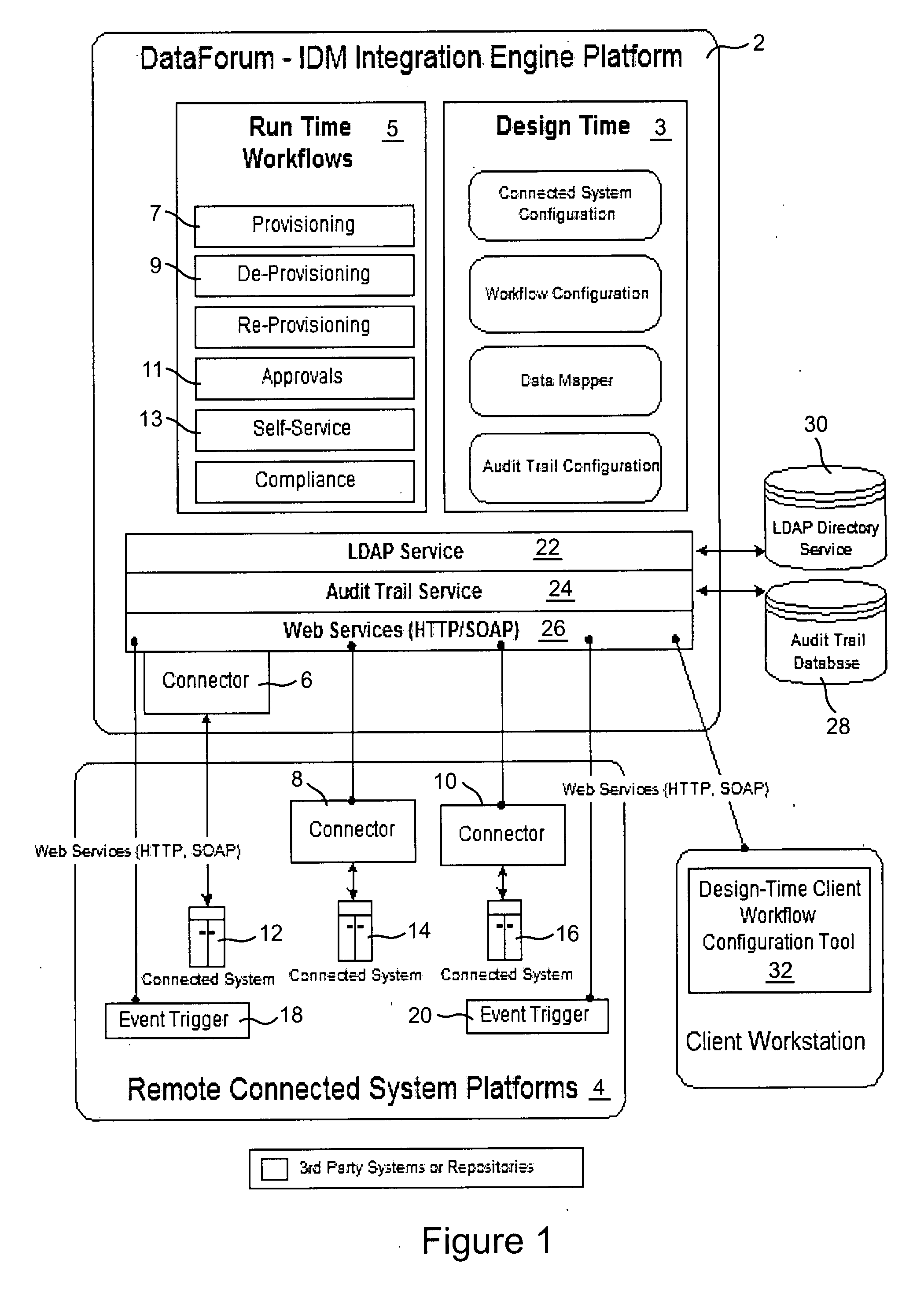
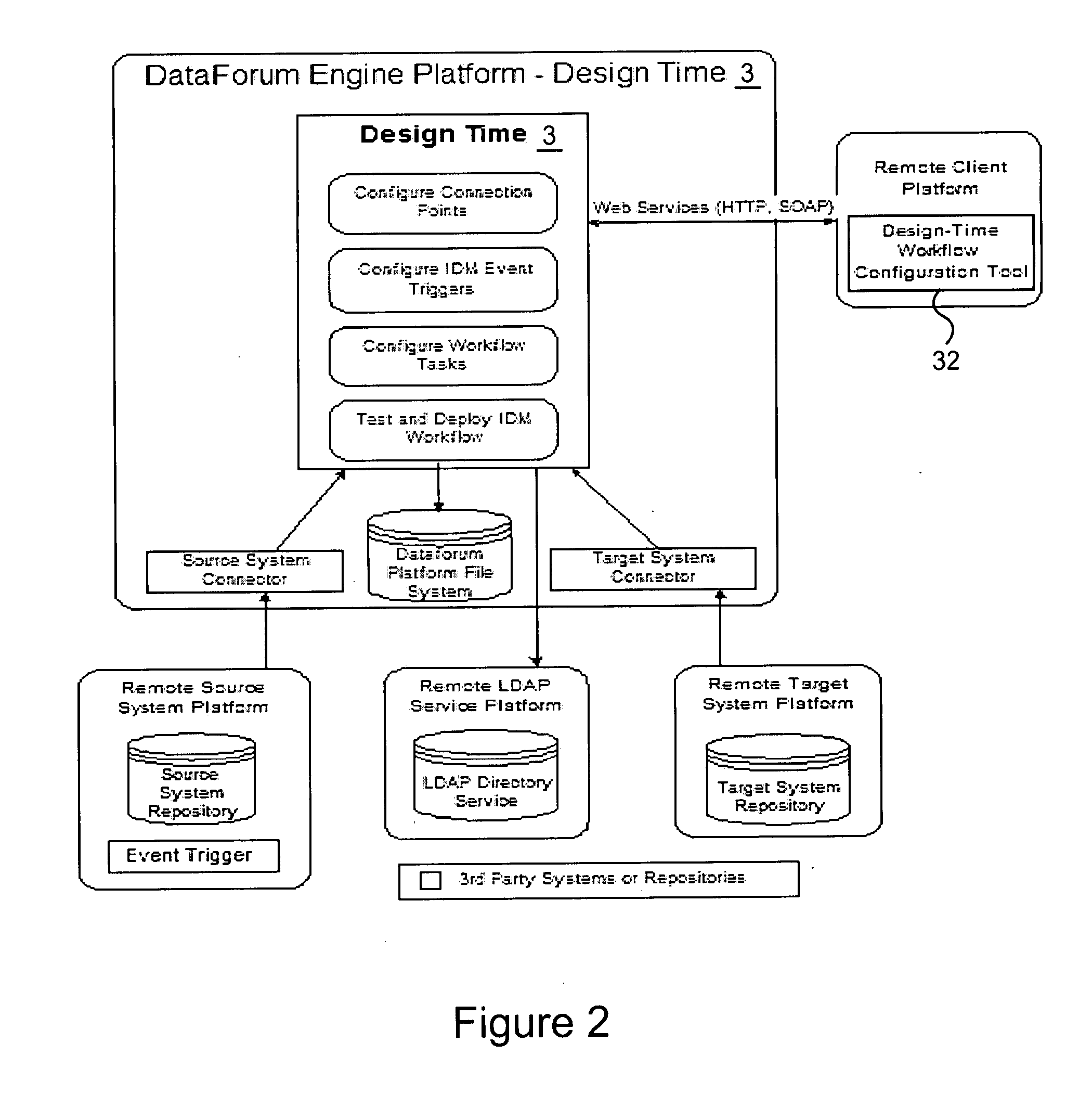
Cross domain provisioning methodology and apparatus
InactiveUS20070245013A1Increase valueKeep for a long timeDigital computer detailsComputer security arrangementsDigital identityCombined use
A cross domain provisioning method, system and architecture for securely managing digital identities across a wide variety of IT systems, providing unified administration, compliance and auditing, and simplified connectivity. The combined use of certain aspects of the illustrative IDM Provisioning Platform (DataForum™), Connectivity Component Architecture, Design-Time Client Workflow Tool, and the use of digital certificates to secure cross domain communication channels, collectively offer a unique approach to solving cross domain provisioning problems.
Owner:FISCHER INT IDENTITY
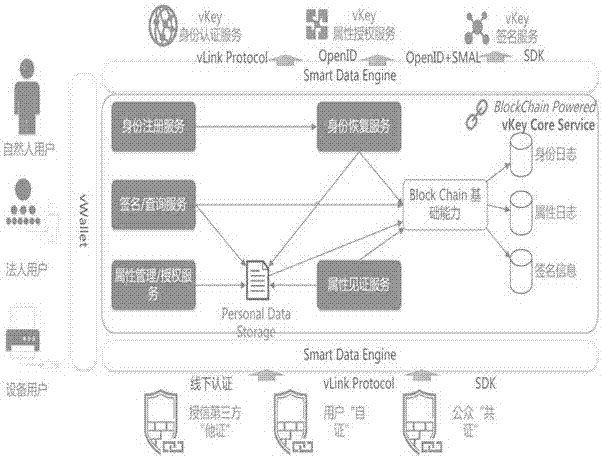
Block chain technology-based network digital identity authentication method
InactiveCN107181765AShorten confirmation timeAvoid the possibility of trending towards exclusive verificationUser identity/authority verificationDigital data protectionDigital identityInternet fraud
The present invention provides a block chain technology-based network digital identity authentication method. The method comprises the steps of 1) user registration: conducting the identity authentication service based on the vLink protocol, uploading a block chain if the identity of a user is legal, broadcasting the information of the user to the whole network by the block chain, and adding the information of the user into a corresponding block at each node, wherein blocks are mutually verified; 2) obtaining the information of the user, searching the information of the user through the vKey attribute authorization service, returning the user name, the gender and the age information of the user and returning a particular opened at the same time for distinguishing different users; 3) subjecting data to signature treatment during the digital identity authentication process based on the above block chain technology. According to the technical scheme of the invention, the personal data of a user are stored in a block chain, so that the occurrence of information leakage and internet fraud behaviors is radically avoided. The data security is ensured. During the data transmission process, the digital signature treatment is adopted. Therefore, the sensitive information is not tampered during the digital signature transmission process.
Owner:兰考同心互联数据管理有限公司
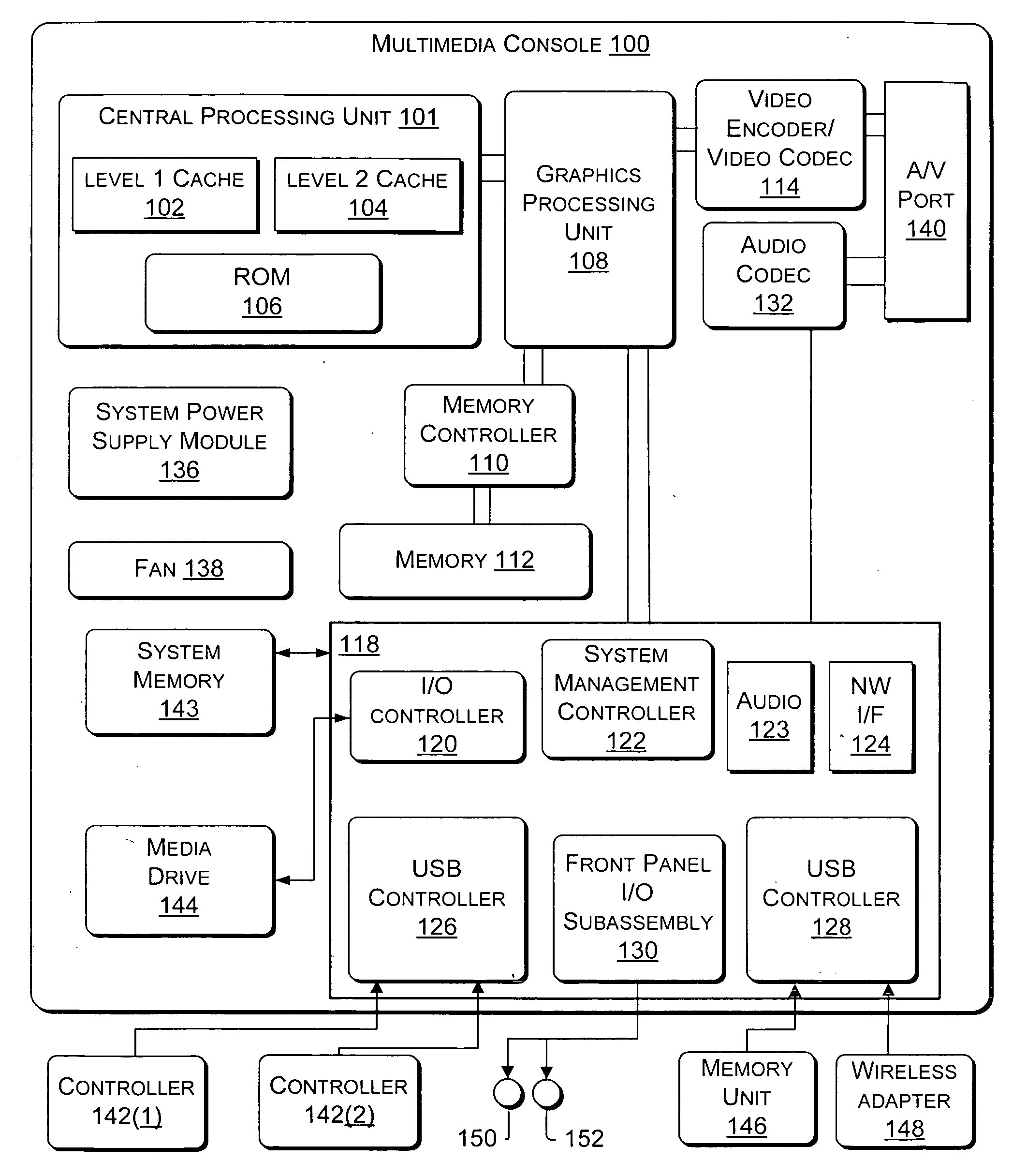
User-centric method of aggregating information sources to reinforce digital identity
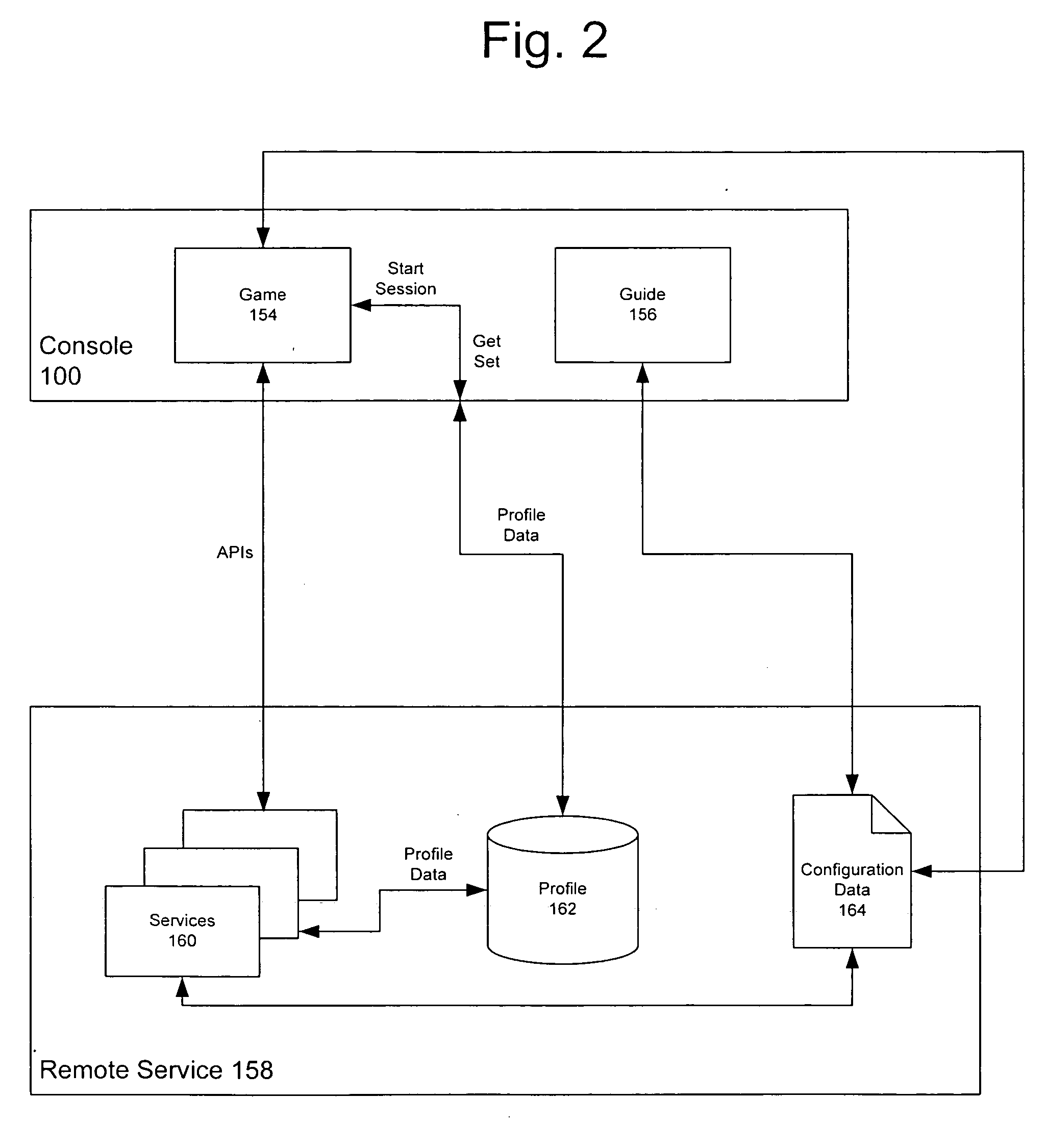
Systems and methods for providing a digital identity or profile in a gaming console that communicates to a remote service. A “Gamer Profile” is created that serves as a building block for services and applications that aim to create a social community of gamers and grow relationships among players. In accordance with the present invention, the Gamer Profile is the entirety of information (e.g., metadata) related to a specific user. The Gamer Profile is developed from a set of services that collect and expose this information in a meaningful way to the community. Feedback information may be included that is provided by other users to further enhance the profile. The Gamer Profile also provides for personalization such that users can customize their gaming experience.
Owner:MICROSOFT TECH LICENSING LLC
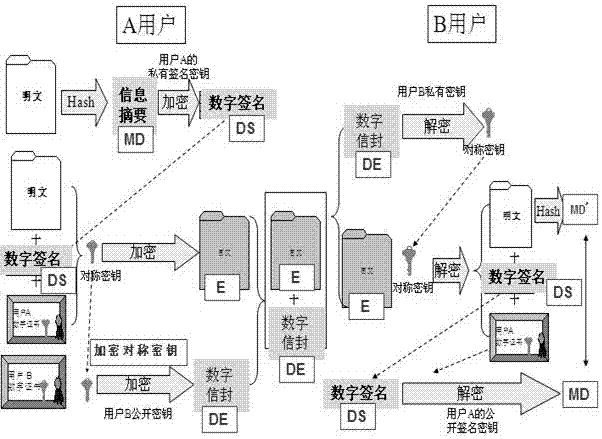
System and method for secure electronic communication in a partially keyless environment
InactiveUS7640427B2Reduce the burden onImprove securityPublic key for secure communicationMultiple digital computer combinationsDigital identityPlaintext
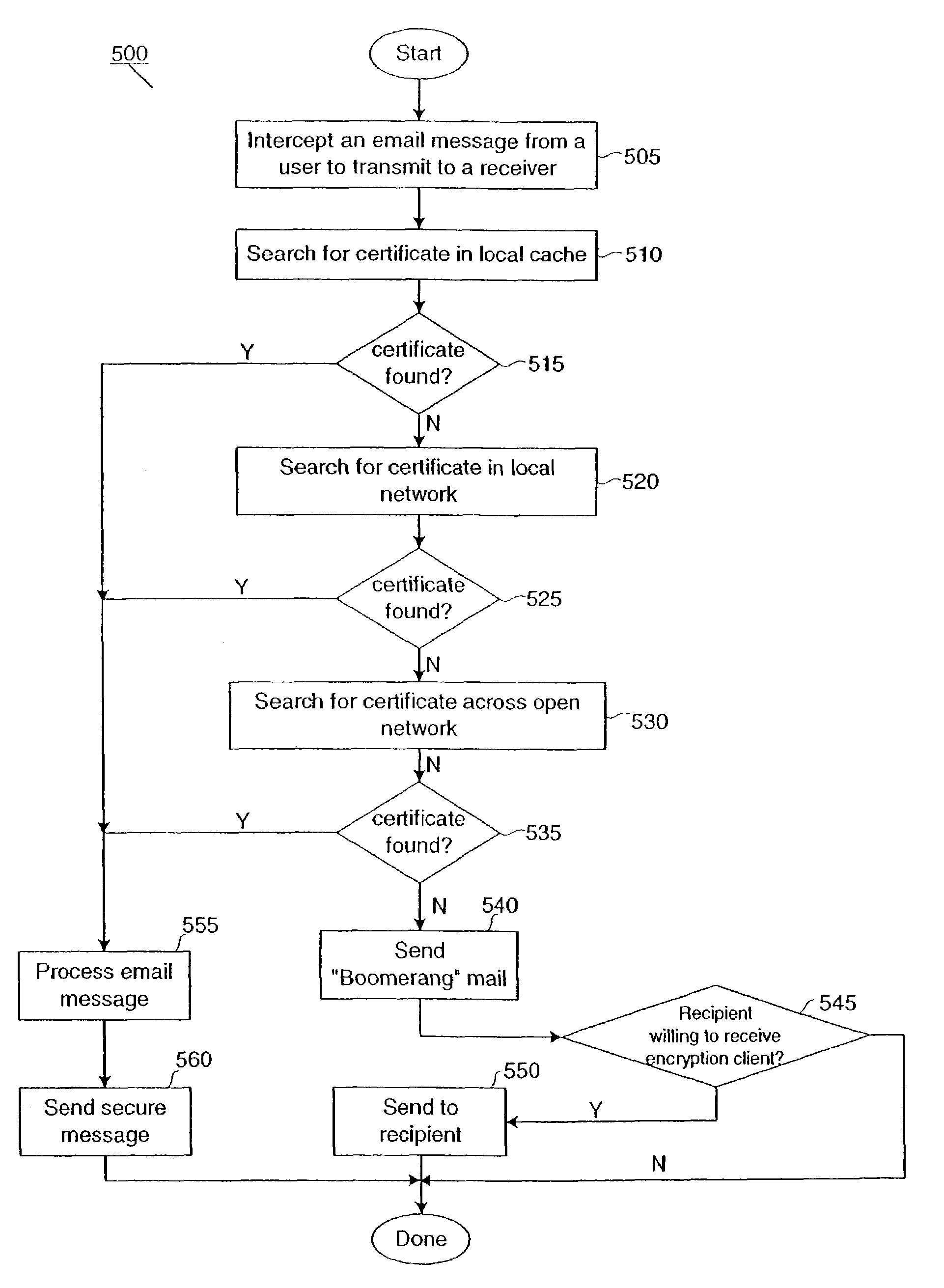
This present invention provides users with secure transparent electronic communication, allowing them to send and receive encrypted and / or signed messages with little or no user involvement. In various embodiments, the present invention provides a user with e-mail security via automated hierarchical techniques for transparently sending and receiving secure messages, and lowers the burden on administrators. Such a system can also manage cryptographic keys and certificates for the users, and creates such keys and certificates for the users when necessary. A server according to the present invention can intercept unsecured messages from a user, automatically transform those messages into secured messages, and transmit those secure messages to the intended recipients. The server can also automatically transform messages after the recipient sends a digital identity to the server and downloads the software necessary for transforming the secured messages back into readable messages (i.e., from ciphertext into plaintext). The server can further intercept an unsecured message from a user, search for a digital identity of the intended recipient, secure the unsecured message upon finding such a digital identity, and transparently send the secured message to the intended recipient.
Owner:CA TECH INC
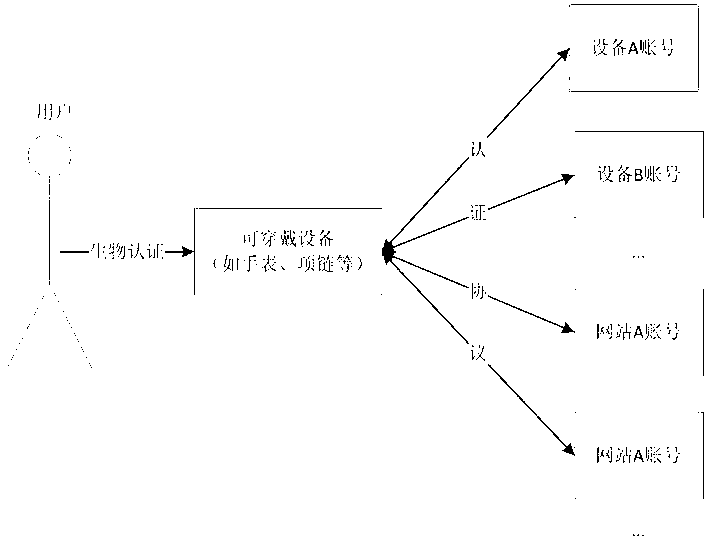
Man-machine fusion security authentication method based on wearable equipment
ActiveCN103310142AReduce dependenceEnsure safetyDigital data authenticationComputer hardwareDigital identity
The invention belongs to the field of personal identity authentication, and particularly relates to a man-machine fusion security authentication method based on wearable equipment. The wearable equipment in which user digital identity information is saved replaces a user to carry out identity authentication in a network space, and a command is not required to be inputted directly by the user. The method comprises the special steps as follows: a method user registers in the wearable equipment to become an authorized user; the method user stores the self digital identity into the wearable equipment; the method user passes the biometric-based identification authentication of the wearable equipment; and the wearable equipment automatically logs in other equipment or information systems in internet space through using the user digital identification stored in the wearable equipment. The method reduces the dependence of the user on a simple command, guarantees the information to be safer, and facilitates the monitoring and management better.
Owner:FUDAN UNIV
System for verification of pseudonymous credentials for digital identities with managed access to personal data on trust networks
InactiveUS20190333054A1Key distribution for secure communicationUser identity/authority verificationDigital identityThird party
The invention advantageously provides a system for the verification a user's identity and qualifications and authentication of credentials associated with a user's digital identity on a trust network (where service providers involved in a transaction may be independent parties operating with limited trust), in which a pseudonymized transaction record may be created for that digital identity and stored in a shared ledger; identifying information for a user may be retained in a custodial escrow account for that user; and transactions may be re-correlated with identifying information for authorized third parties under established “due process” rules that are appropriate for the applicable jurisdiction(s).
Owner:INFONETWORKS LLC
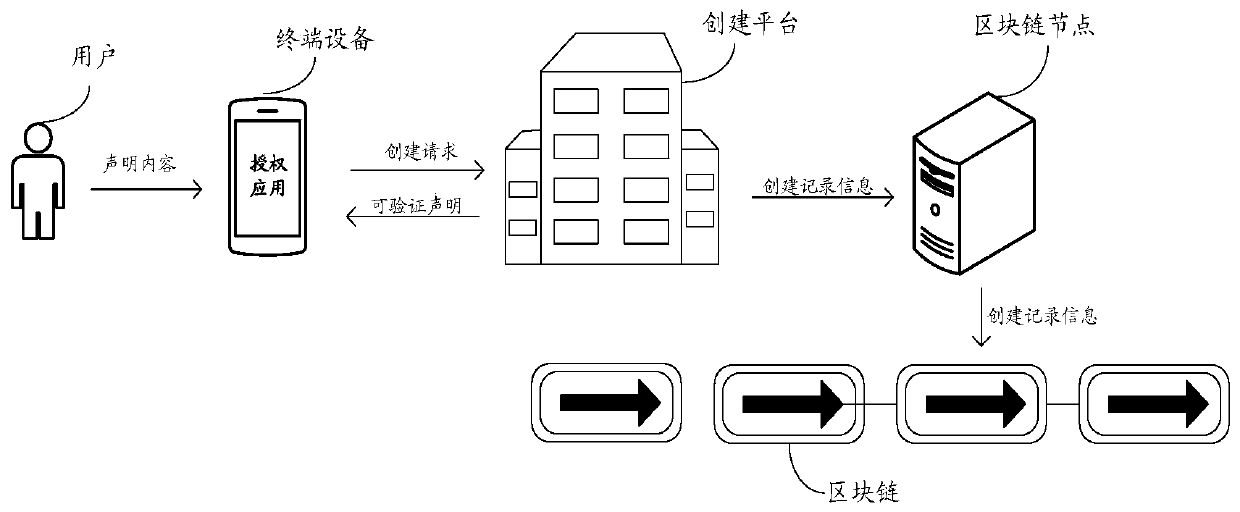
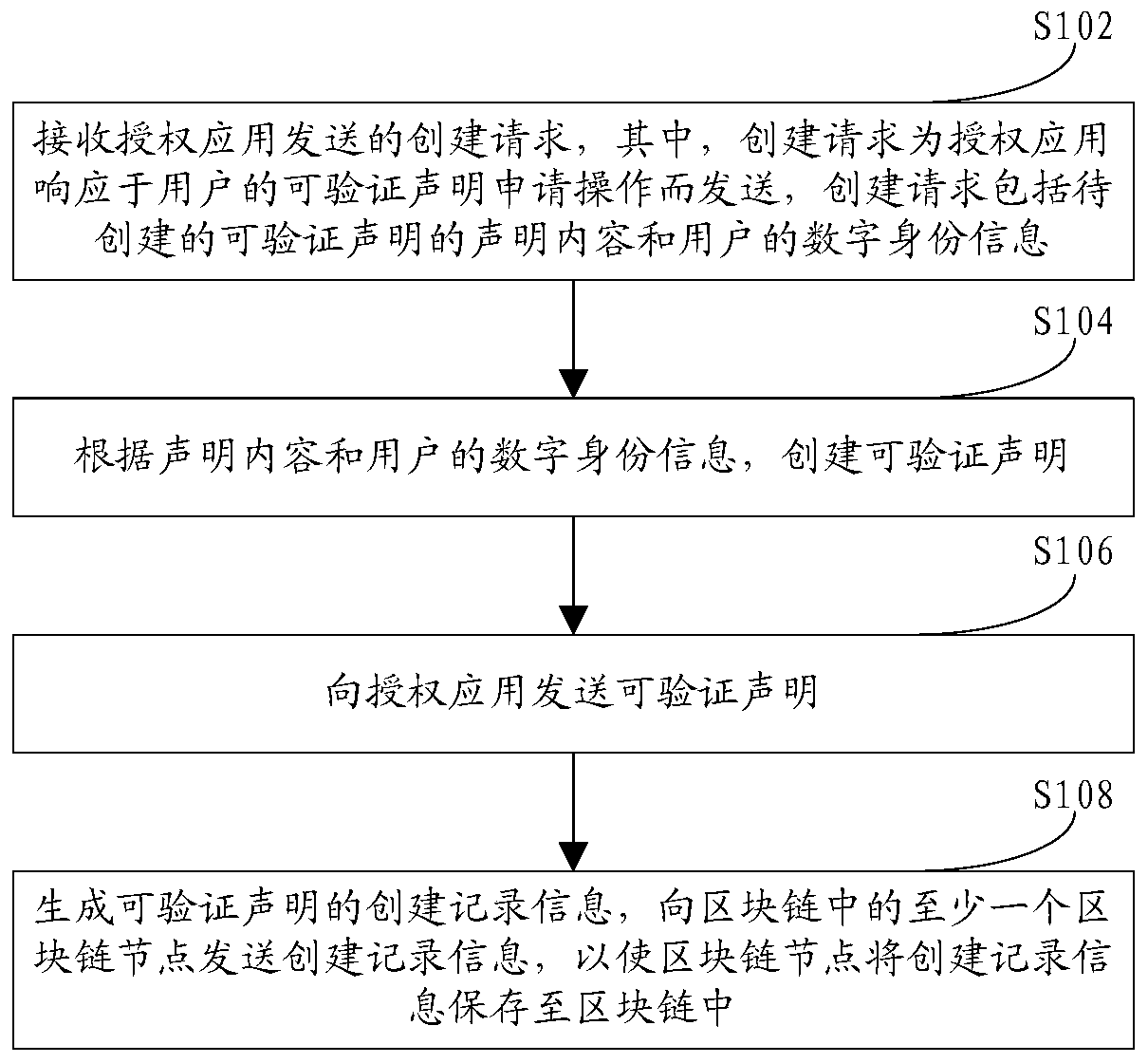
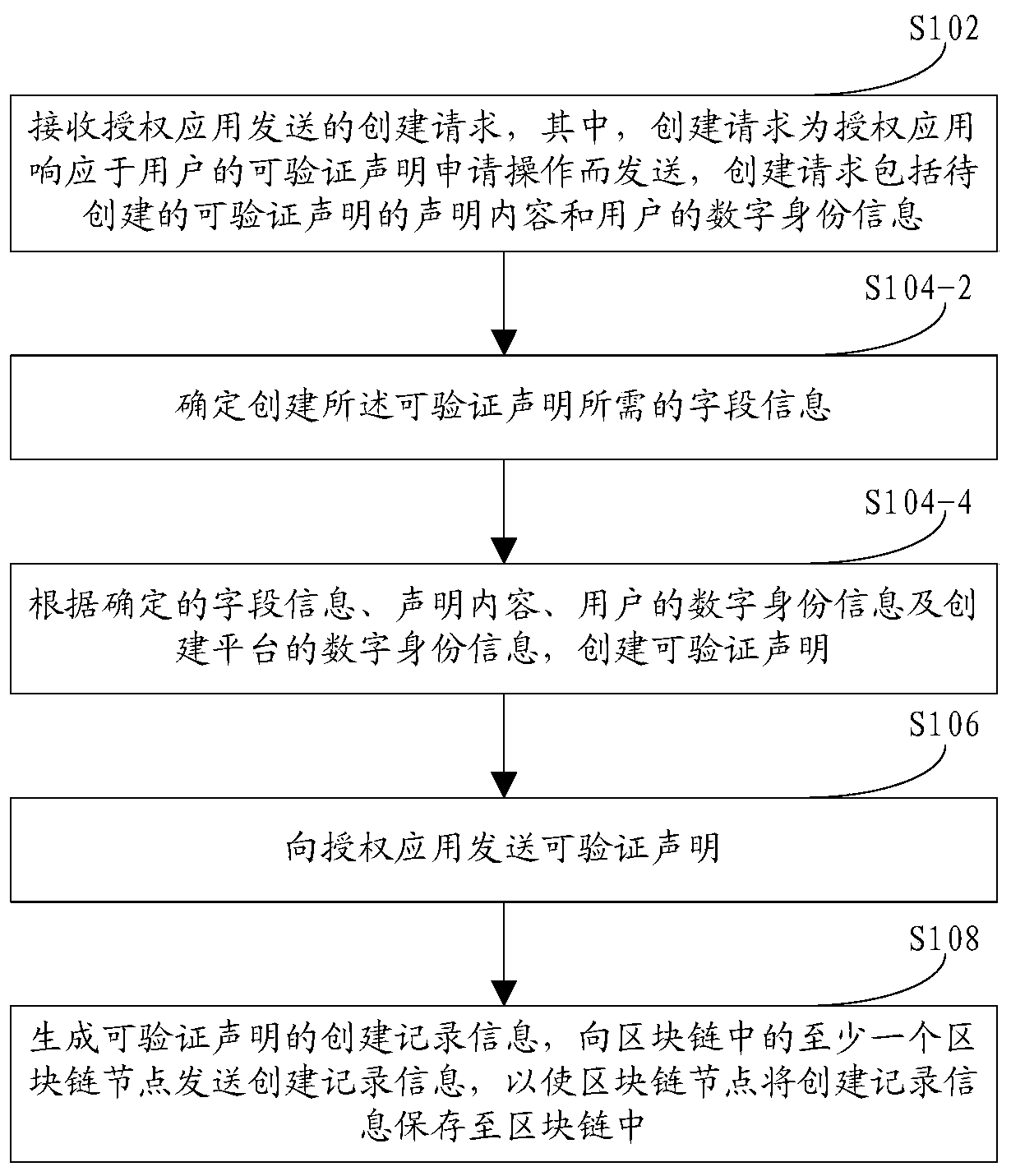
Verifiable declaration creation method, device, equipment and system based on block chain
Embodiments of the invention provide a blockchain-based verifiable declaration creation method, apparatus, device and system. The method comprises the steps of sending a creation request to a creationplatform by an authorization application in response to a verifiable declaration application operation of a user; the creation platform creates a verifiable declaration according to the declaration content included in the creation request and the digital identity information of the user, and sends the verifiable declaration to the authorization application; and generating creation record information capable of verifying the declaration, and sending the creation record information to at least one blockchain node in the blockchain, so that the blockchain node stores the creation record information into the blockchain.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Secure Electronic Payment
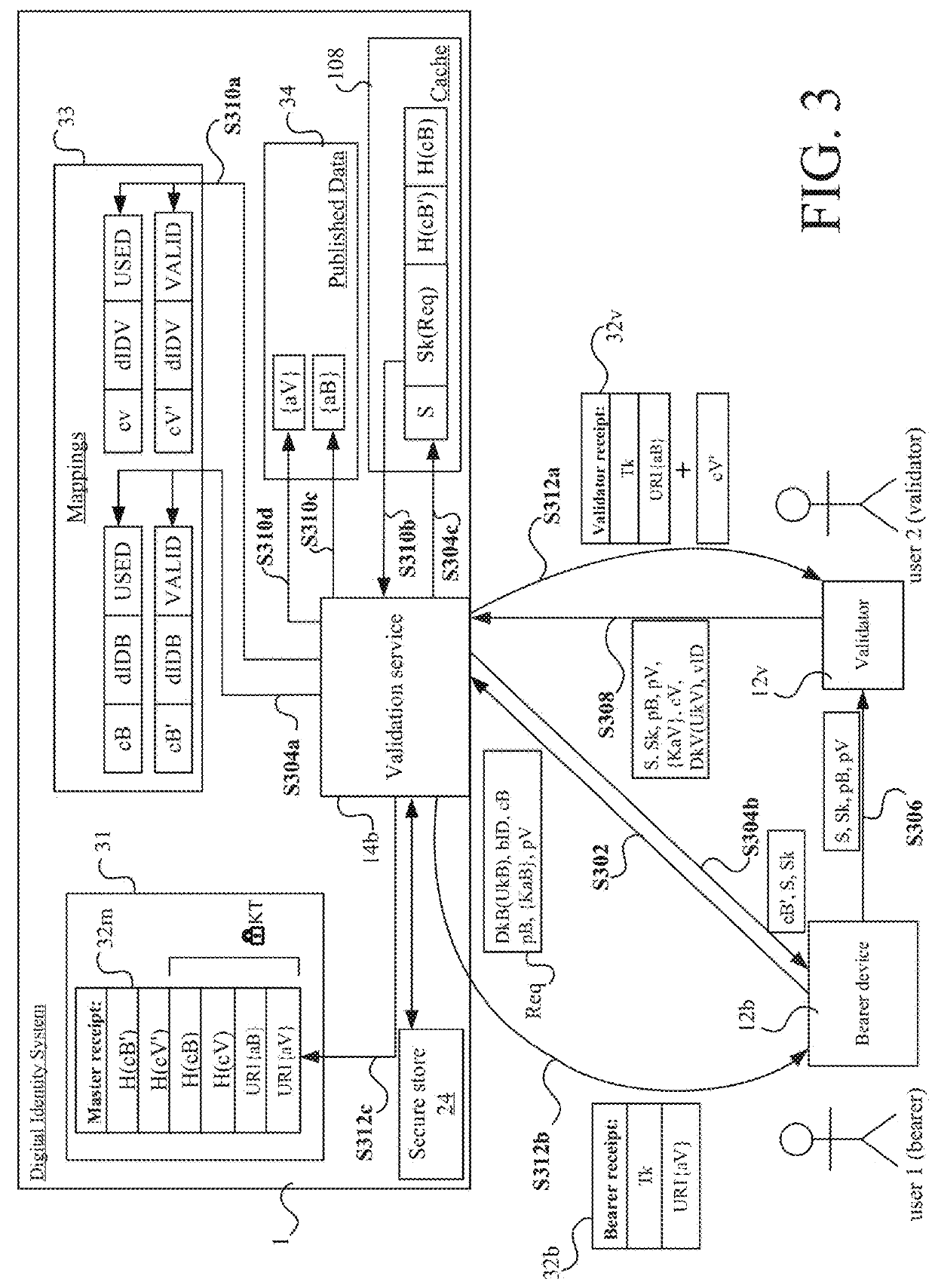
ActiveUS20180181964A1Secure and efficient mechanismElectronic credentialsProtocol authorisationDigital identityPayment
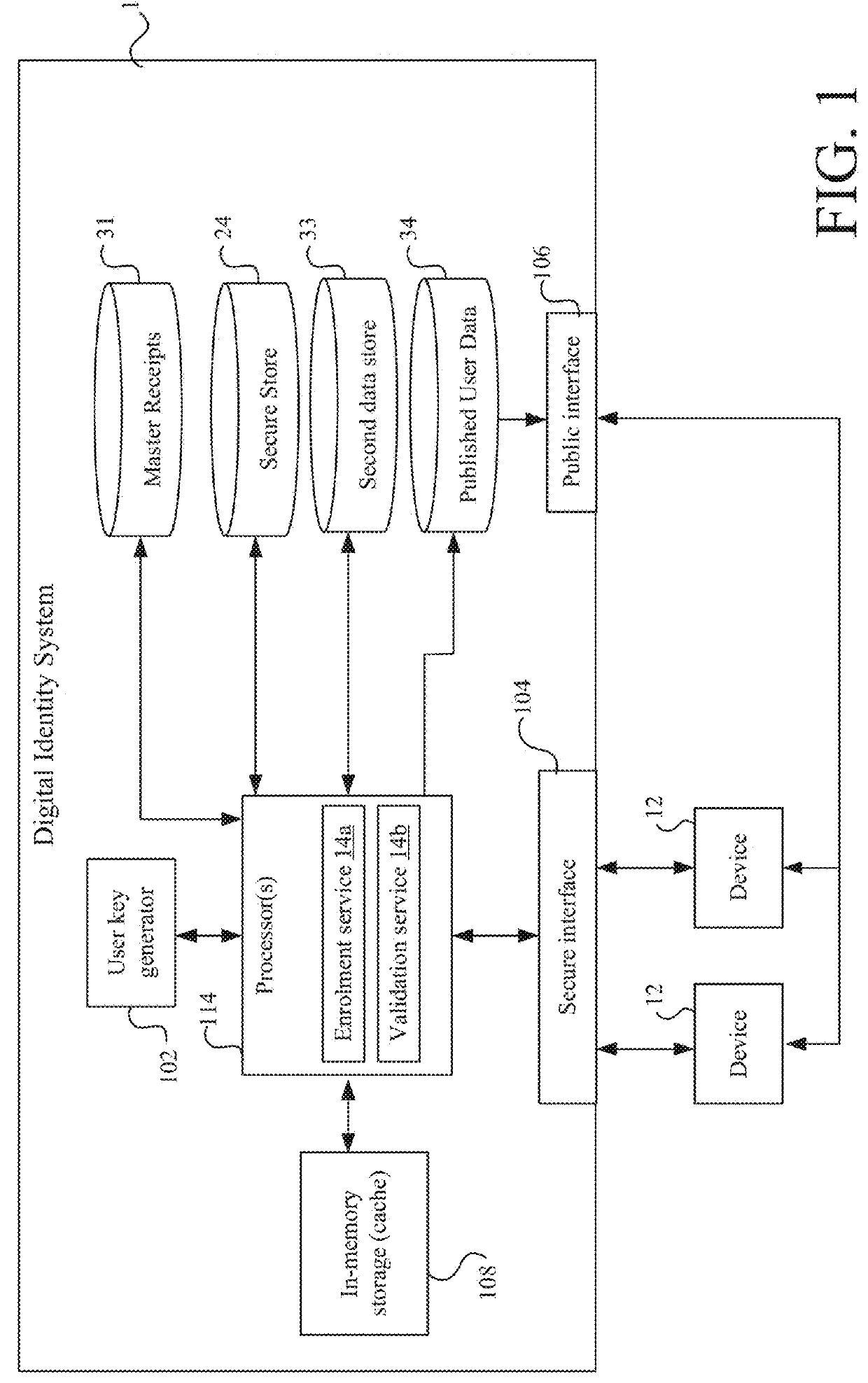
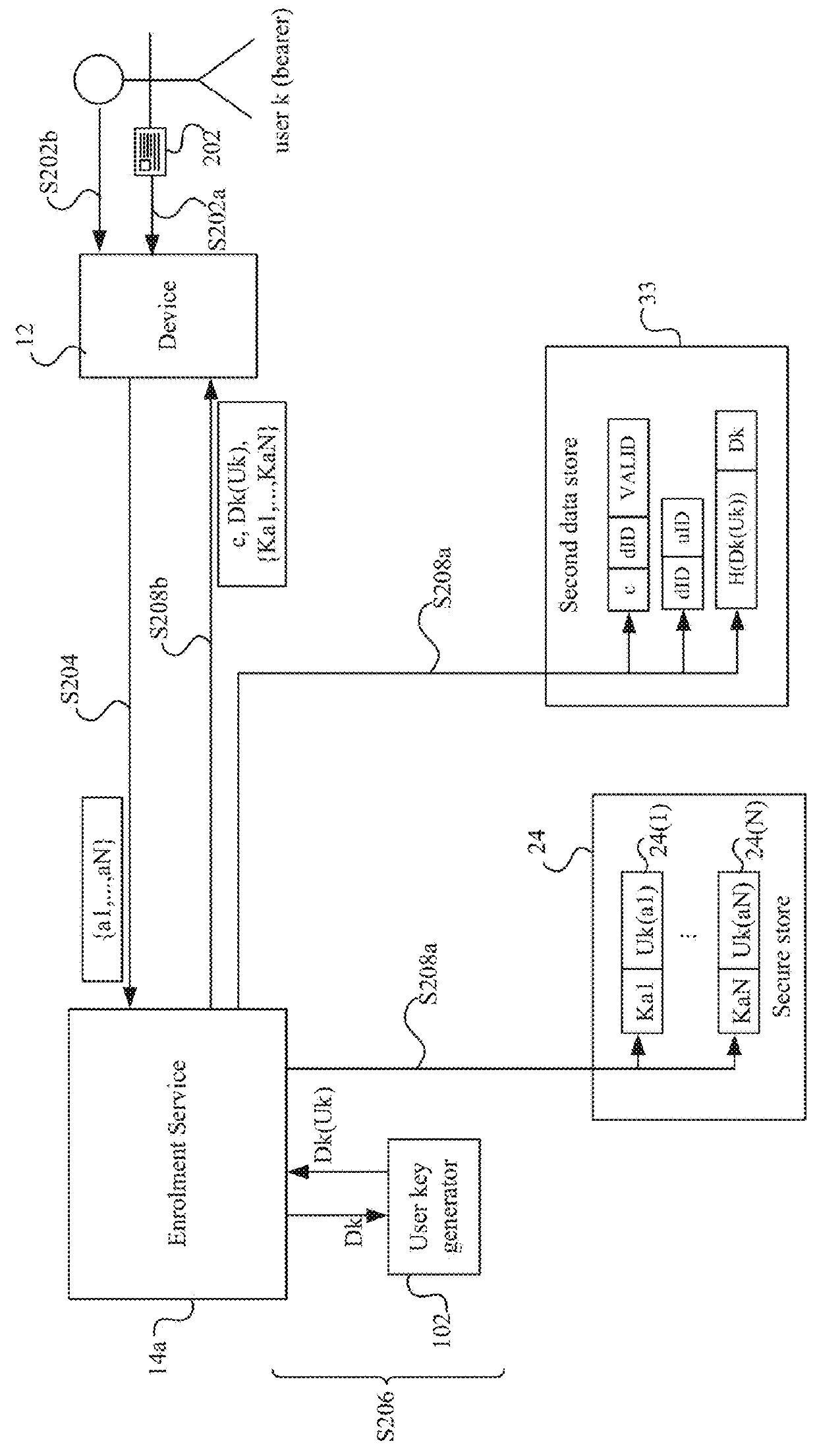
A method of authorizing a secure electronic payment from a payer to a payee. At a digital identity system, an electronic message is received, which comprises a payer credential and identifies a payee system. At the digital identity system, a digital identity associated with the payer credential is accessed, the digital identity comprising: 1) at least one identity attribute or data for deriving at least one identity attribute, and 2) a payment token or data for obtaining a payment token, the payment token for effecting an electronic payment from the payer to a recipient of the payment token. At least one electronic message is transmitted from the digital identity system to the payee system to render the identity attribute and the payment token available to the payee system, for determining, based on the identity attribute rendered available to the payee device, whether to use the available payment token to effect an electronic payment from the payer to the payee.
Owner:YOTI HLDG LTD
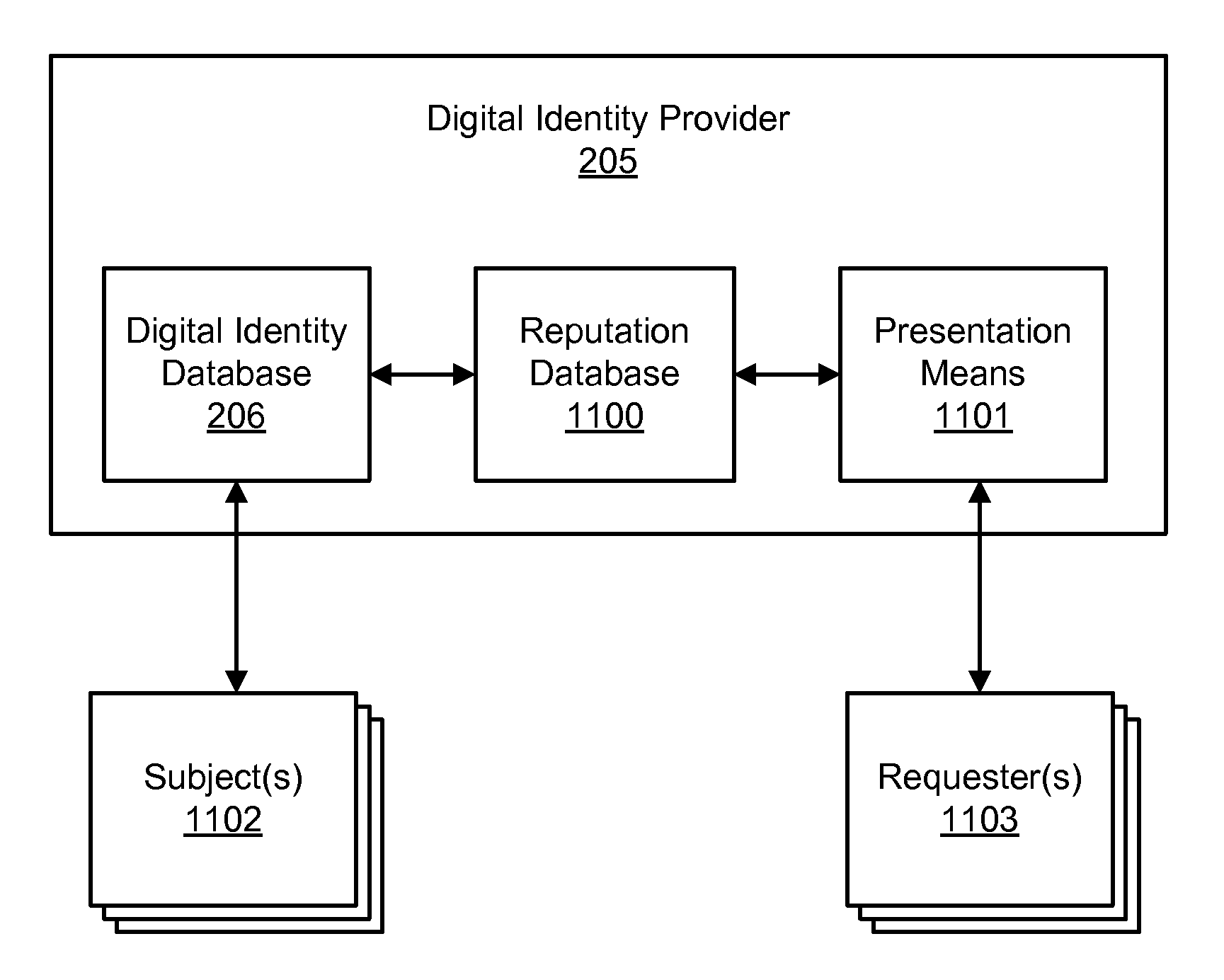
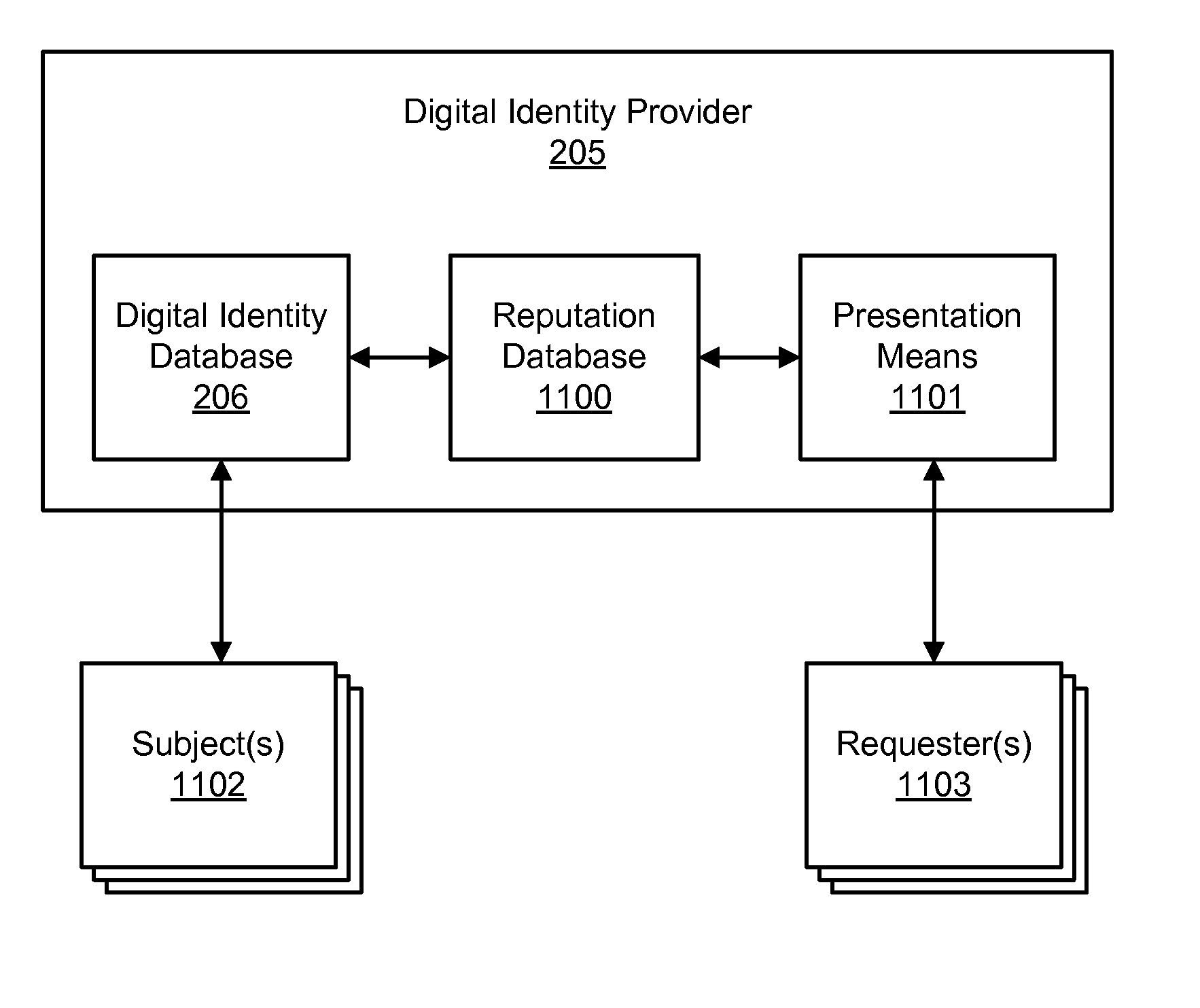
Accessing digital identity related reputation data
InactiveUS20090248623A1Effective registrationDigital data processing detailsData switching networksDigital identityDomain name
Systems and processes of the present invention allow for tracking and publishing digital identity related reputation. In an example embodiment, a Digital Identity Provider maintains a database with reputation data that can be accessed by Requesters. The Digital Identity Provider may update reputation data based on a variety of events related to a digital identity. The reputation data may be tracked regarding the digital identity itself, digital identity purchaser or registrant, or an email address, domain name, URL, or website associated with the digital identity. The reputation data may include various categories, such as email practices, website content, privacy policies and practices, fraudulent activities, domain name related complaints, overall reputation, etc. The reputation data may be published in a publicly-available database, a private database, or via other methods. The Registrant may opt for a reputation service while registering a digital identity. The Requester may decide whether to interact with a digital identity based on the digital identity related reputation.
Owner:GO DADDY OPERATING
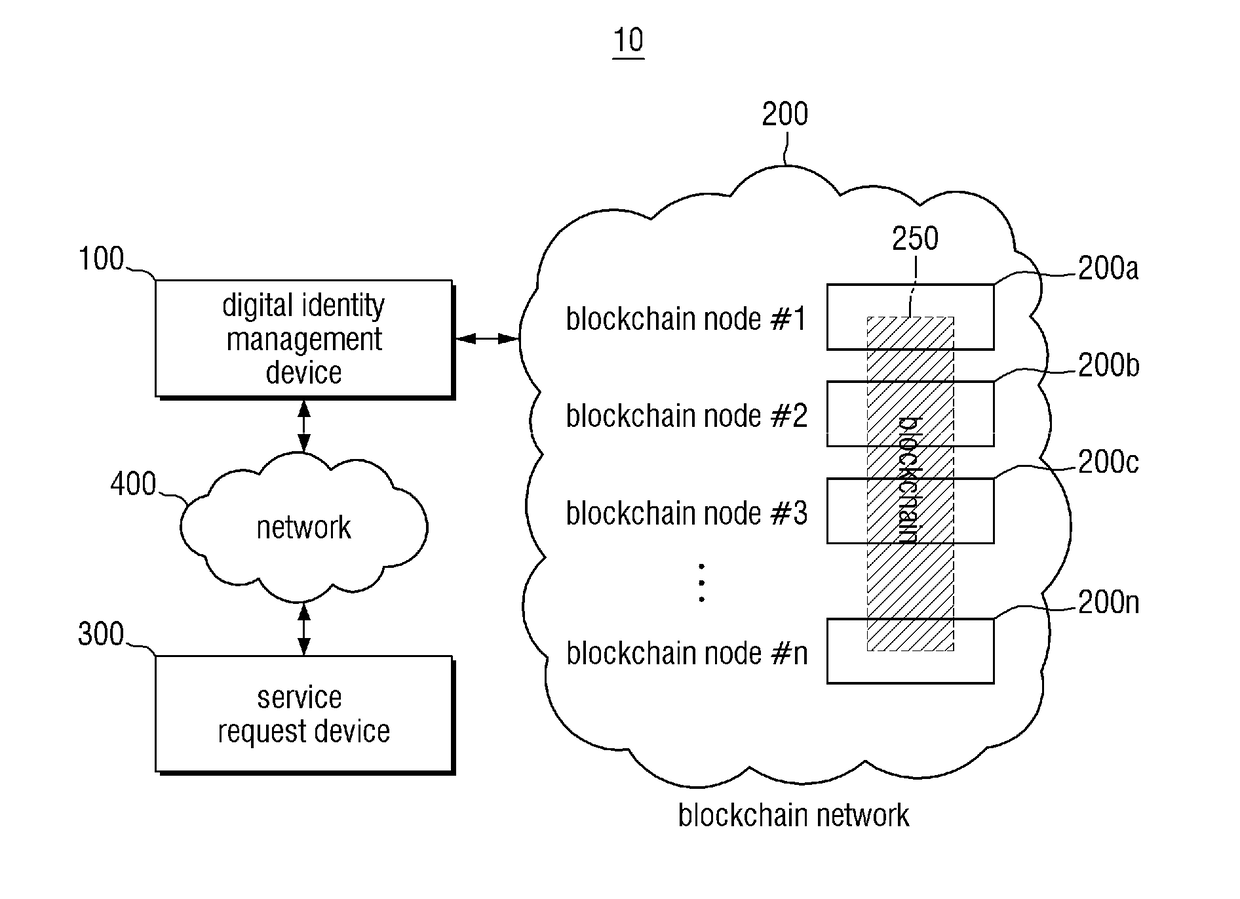
Blockchain-based digital identity management method
ActiveUS20180294966A1Improve securityUser identity/authority verificationDigital data authenticationComputer hardwareDigital identity
A digital identity management method based on a blockchain-based technology is provided. In some exemplary embodiments, the method comprises: performing a first process for storing identity identification information of a subscription request in a first block of a blockchain in response to the subscription request from a service request device and then obtaining a block hash value of the first block as a result of performing the first process, performing a second process for storing the block hash value of the first block and data of authentication information of the subscription request in a second block of the blockchain and then obtaining a block hash value of the second block as a result of performing the second process, and inserting the block hash value of the second block into a digital identity data structure as a result of processing the subscription request.
Owner:SAMSUNG SDS CO LTD
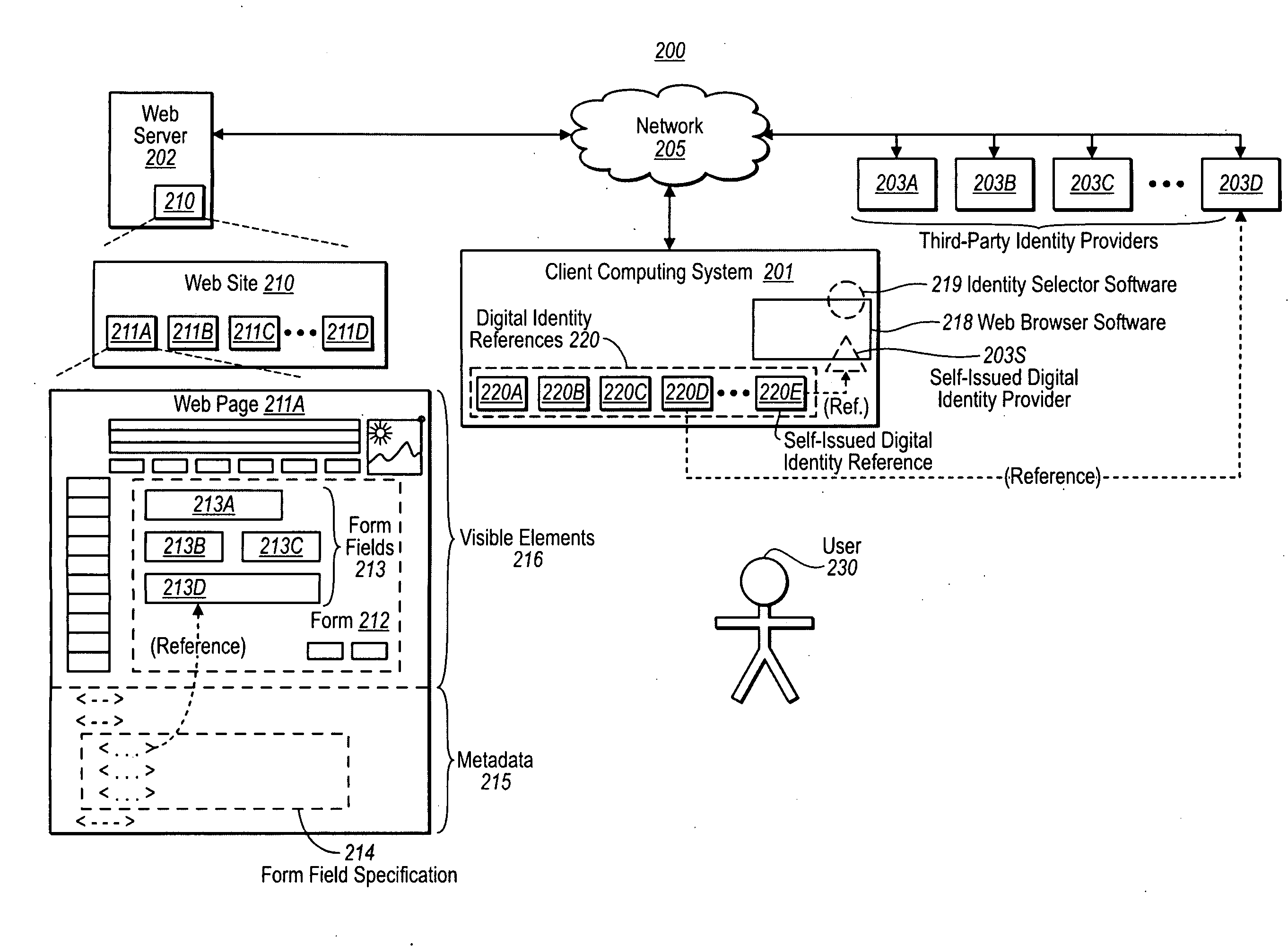
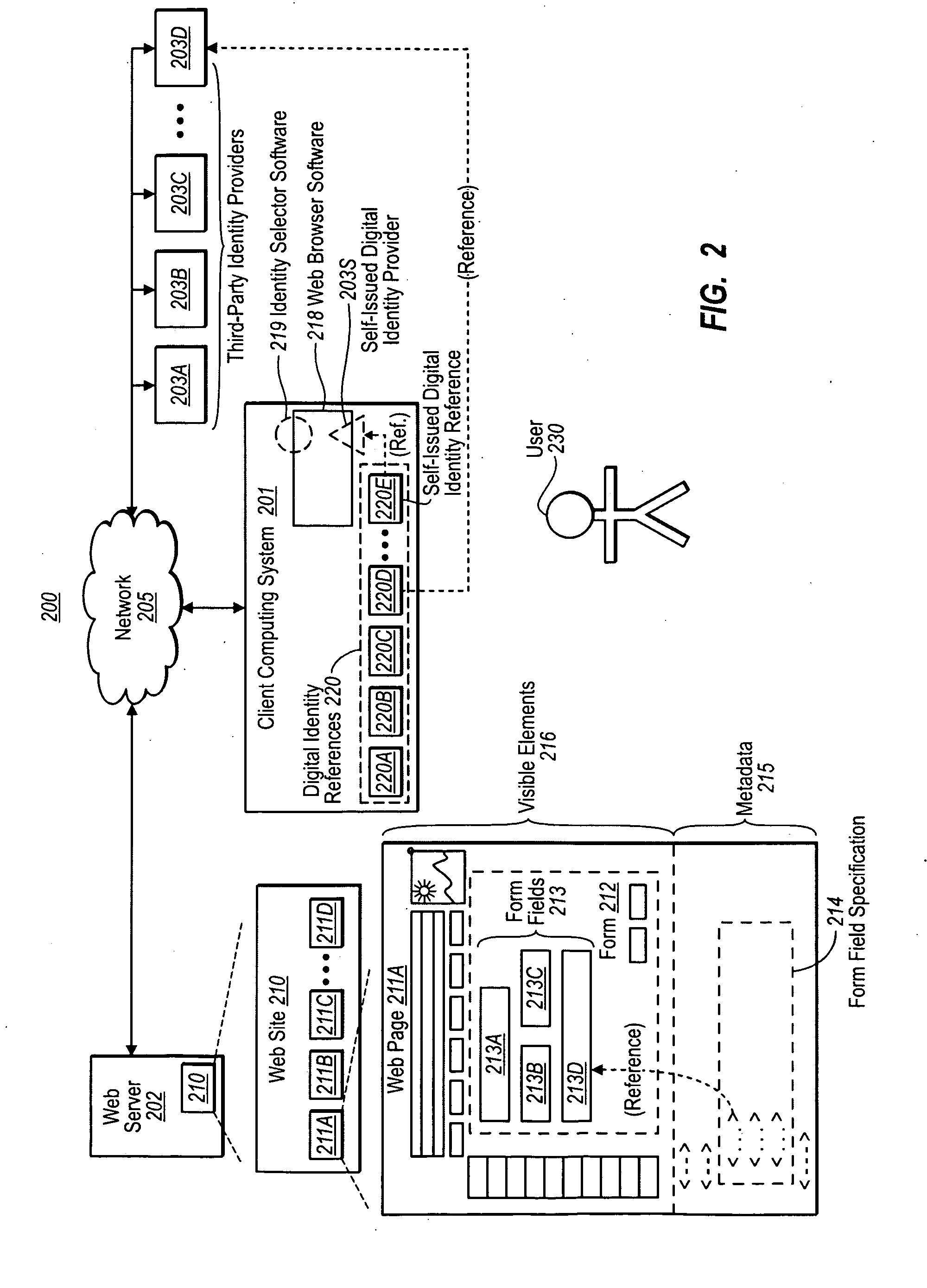
Form Filling with Digital Identities, and Automatic Password Generation
ActiveUS20100037303A1Less development effortLess effortDigital data processing detailsUser identity/authority verificationDigital identityField specification
In one implementation, form field(s) of a form of a website or application are populated with data obtained using a digital identity, and the populated form field(s) are submitted to the website or application. A form field specification specifying information about the form fields of the form is obtained. A user selects or creates a digital identity. Data is obtained using the digital identity, and the data is used to provide values to the form. The data is submitted to the website or application. In another implementation, a username and password are automatically generated. The username and password that are generated meet parameters that may be specified by the website or application. The username and password are submitted to the website or application for a purpose such as registration or authentication, and stored away for future authentication.
Owner:MICROSOFT TECH LICENSING LLC
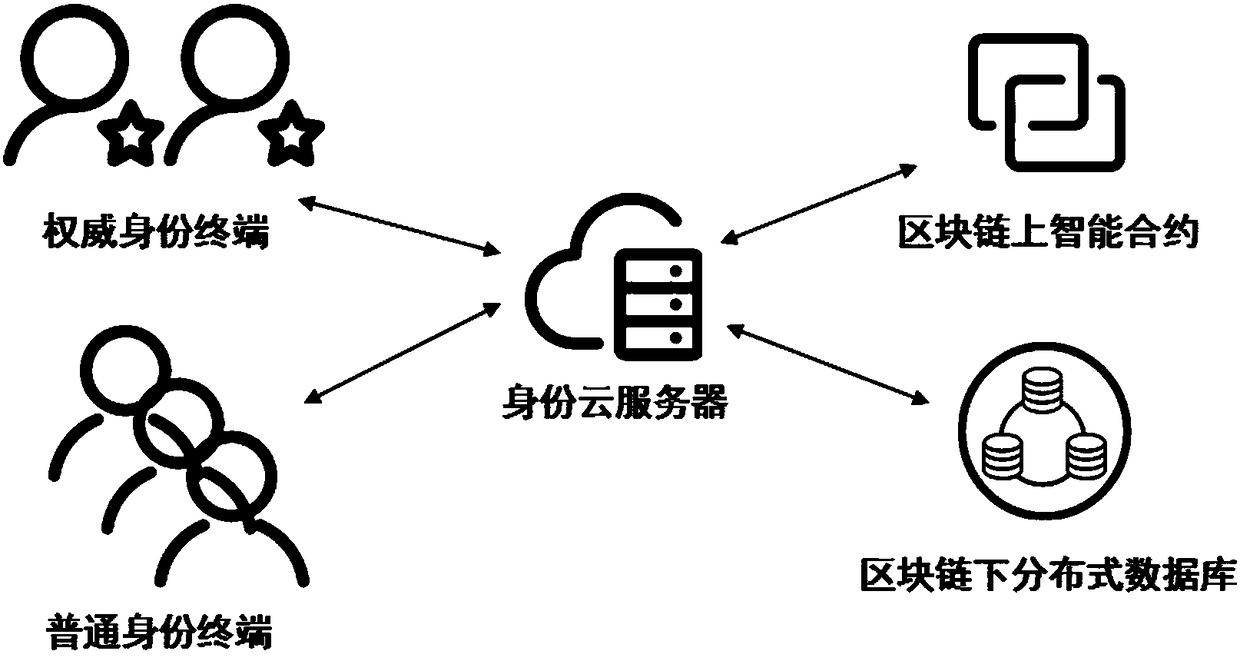
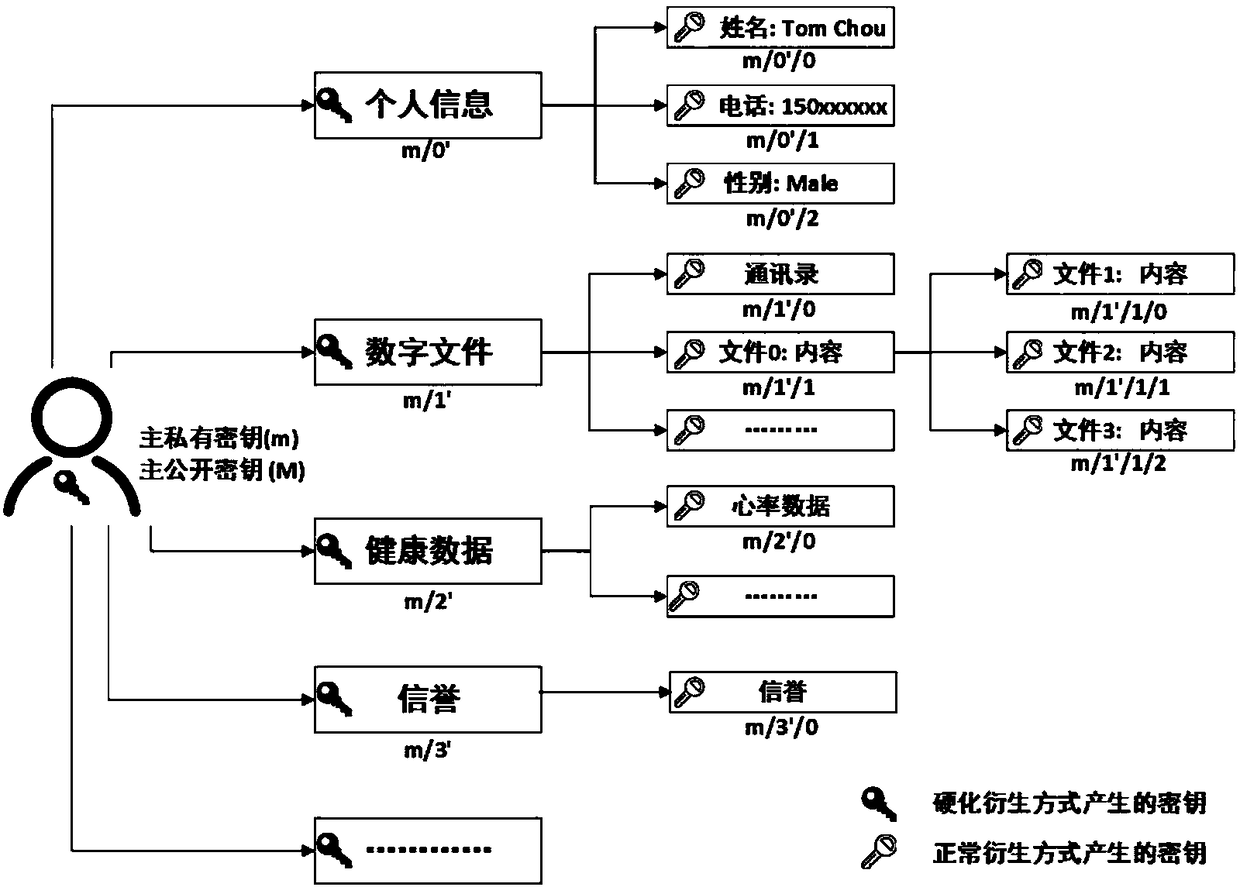
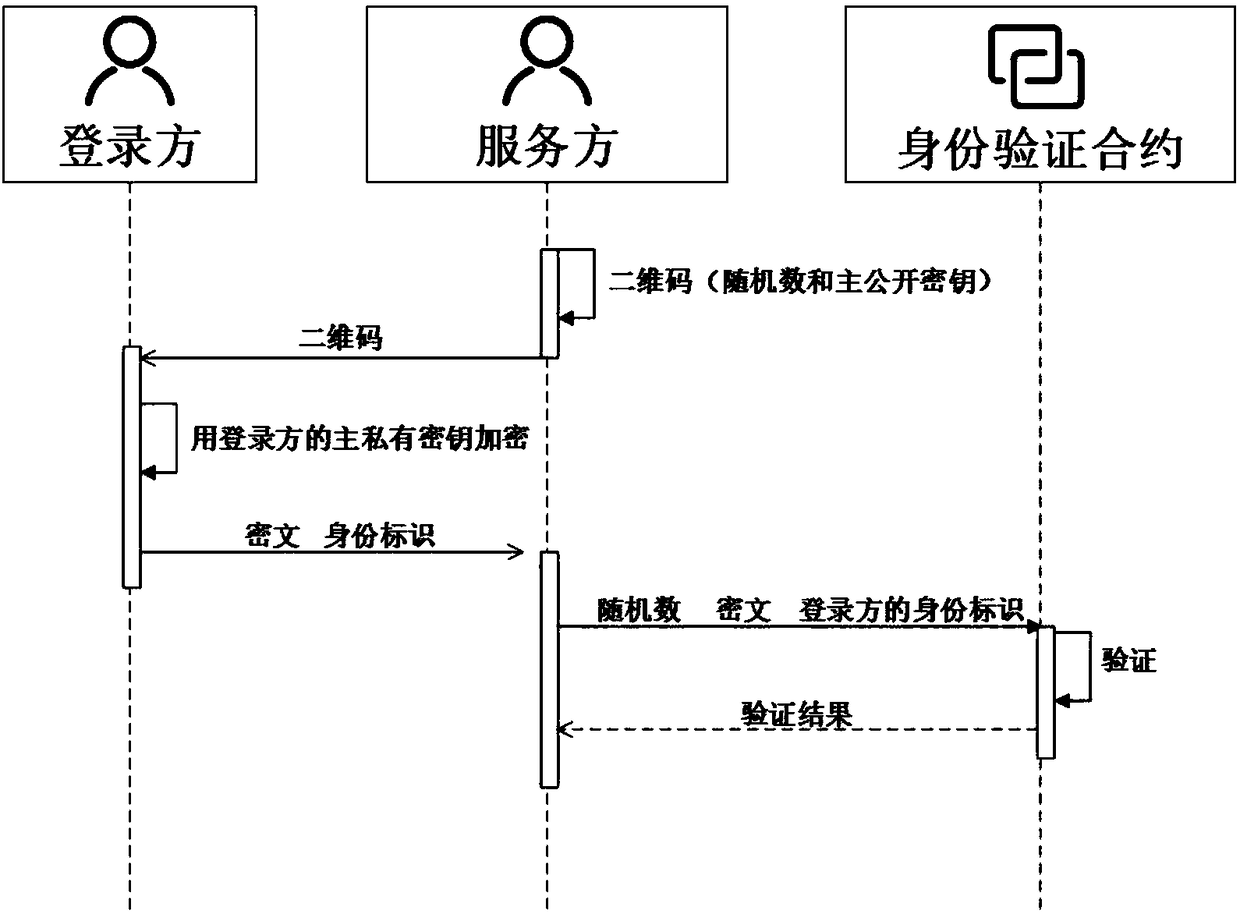
Self-certified digital identity management system and method based on smart contract
ActiveCN108234515AImplement passwordless loginMaster self-managementUser identity/authority verificationDigital identitySelf certified
The invention discloses a self-certified digital identity management system and method based on a smart contract. An identity terminal sends a public key and associated digital information to a cloudserver via the Internet, and accomplishes registration and login of digital identity, and the authorization, operation and verification of digital information depending on the smart contract on a block chain and a distributed database under the block chain. A unique identity of the whole network can be provided, passwordless login is achieved by scanning a two-dimensional code, the login mode of the traditional username and password is broken through, and a user entirety can securely and effectively manage the digital identity and the associated digital information, on-demand authorization, operation and verification of information are achieved, thus realizing a decentralized, self-certified digital identity management system.
Owner:安徽中科晶格技术有限公司
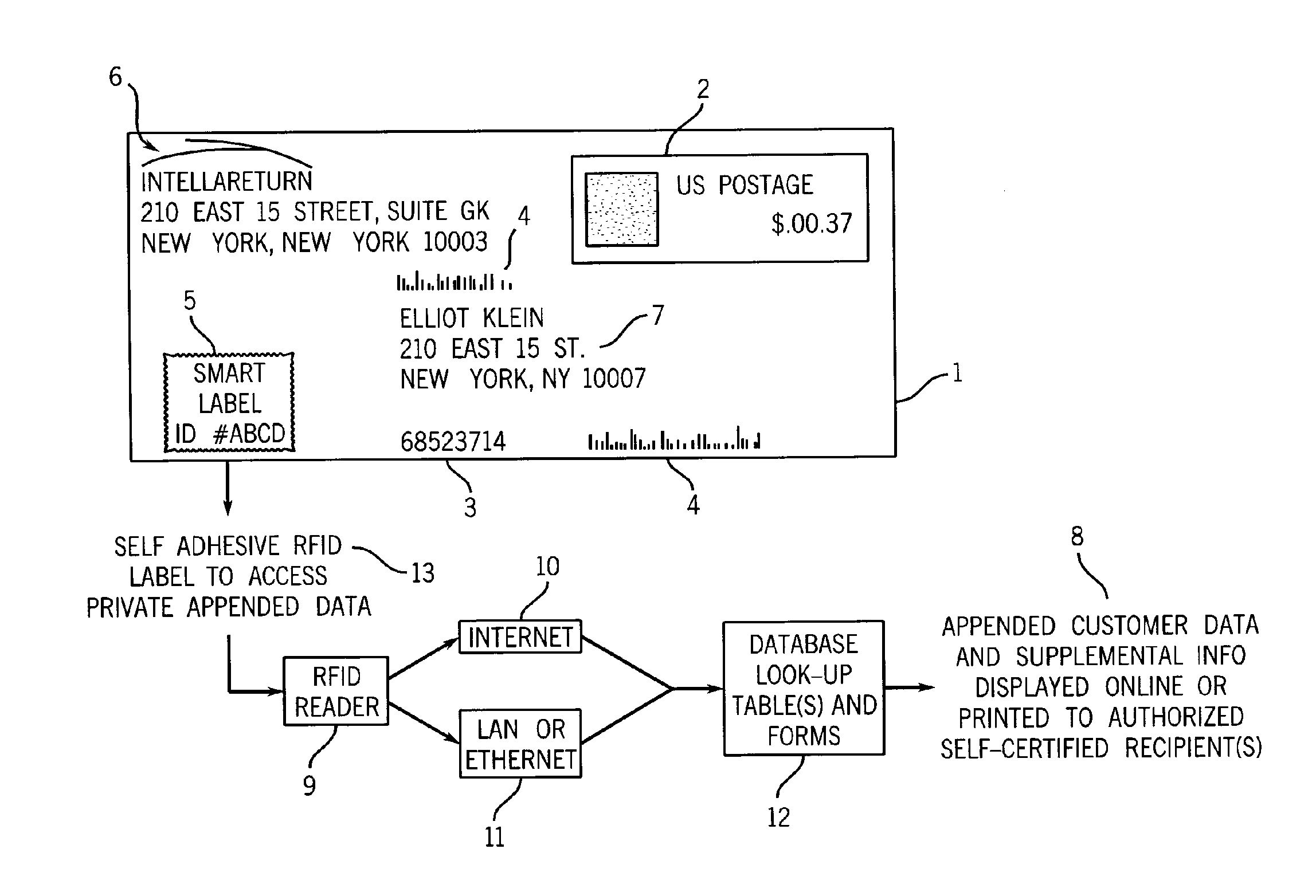
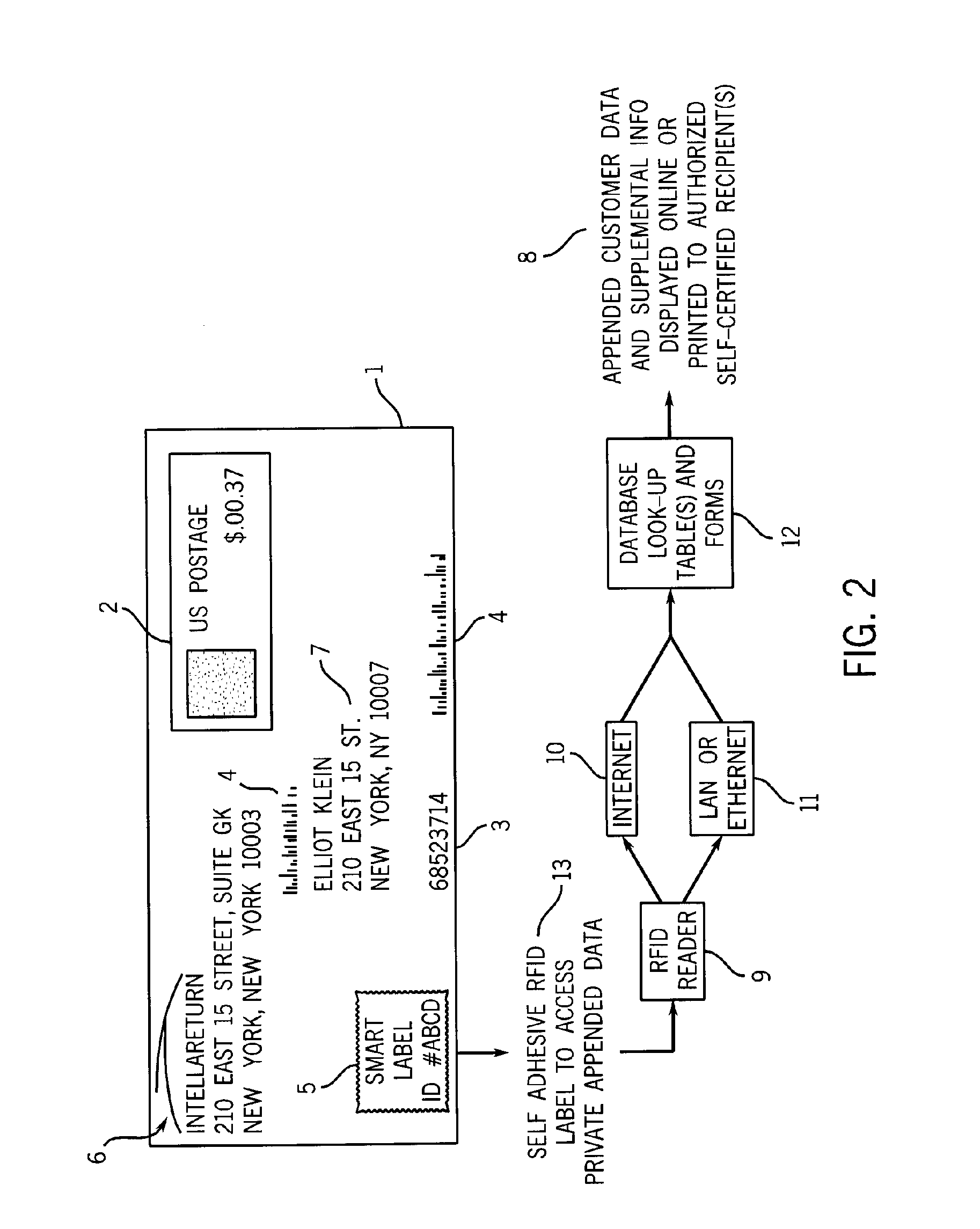
Data append method for sent postal mail
InactiveUS20060010086A1Expand the role of U.SFranking apparatusProgram controlDigital identitySelf certified
Method to manage an electronic interface by radio-frequency identification (“RIFD”) transponder to retrieve supplemental data for U.S. Postal Service sent mailings under non-negotiable privacy and digital identity registration policy standards, pursuant to data registration templates and self-certification standards.
Owner:KLEIN ELLIOT S
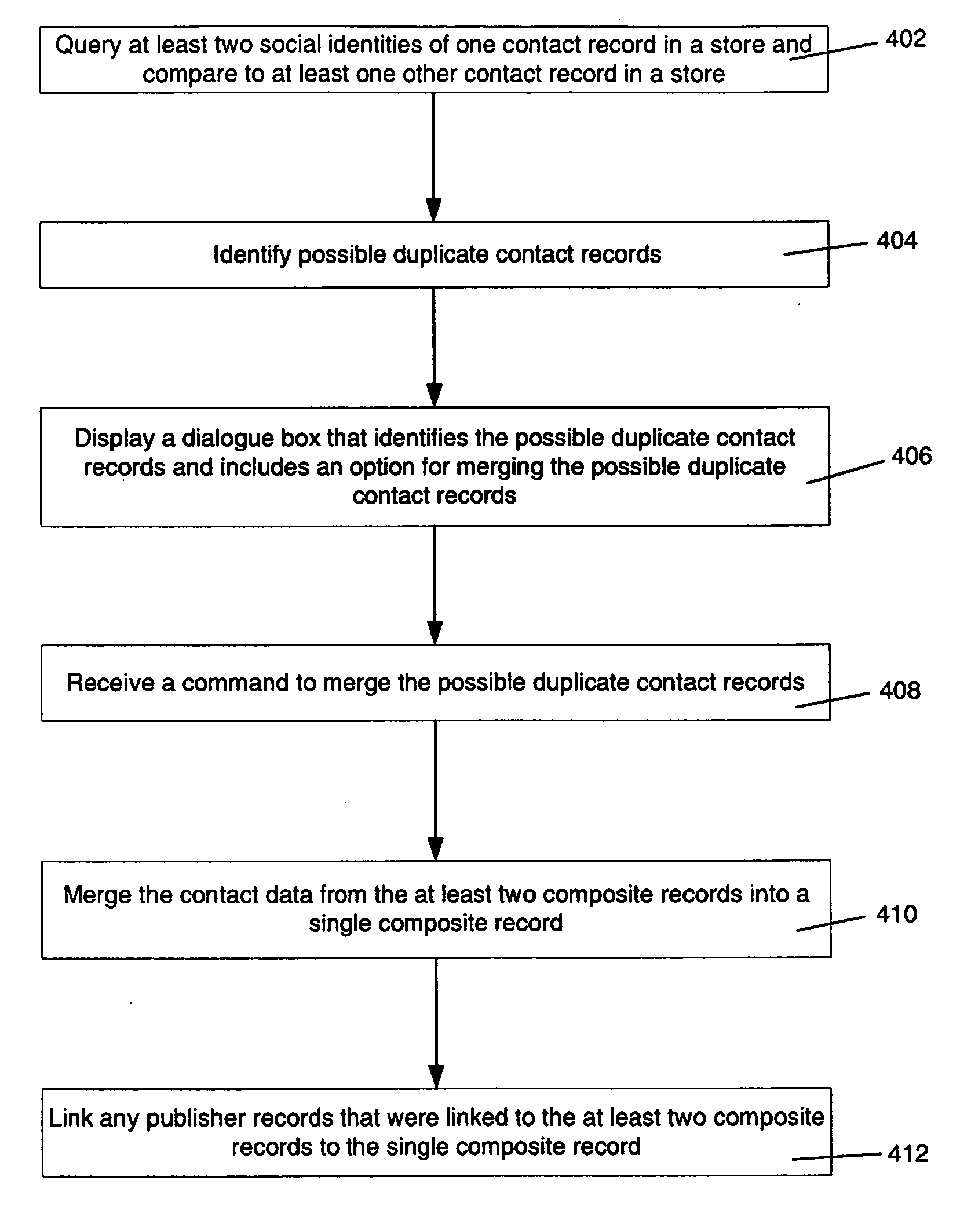
Contact merge auto-suggest
InactiveUS20060184584A1Structured data retrievalSpecial data processing applicationsDigital identityData science
Aspects of the present invention identify duplicate entries across multiple sources of information, such as databases. Further aspects of the invention relate to auto-suggesting entries as duplicates. Embodiments of the invention relate to an algorithm constructed to match or discard duplicates based upon information relating to at least two social identities in one store. Further embodiments of the invention relate to an algorithm constructed to match or discard duplicate entries based upon a legal and / or digital identity. This can be in conjunction with information relating to social identity.
Owner:MICROSOFT TECH LICENSING LLC
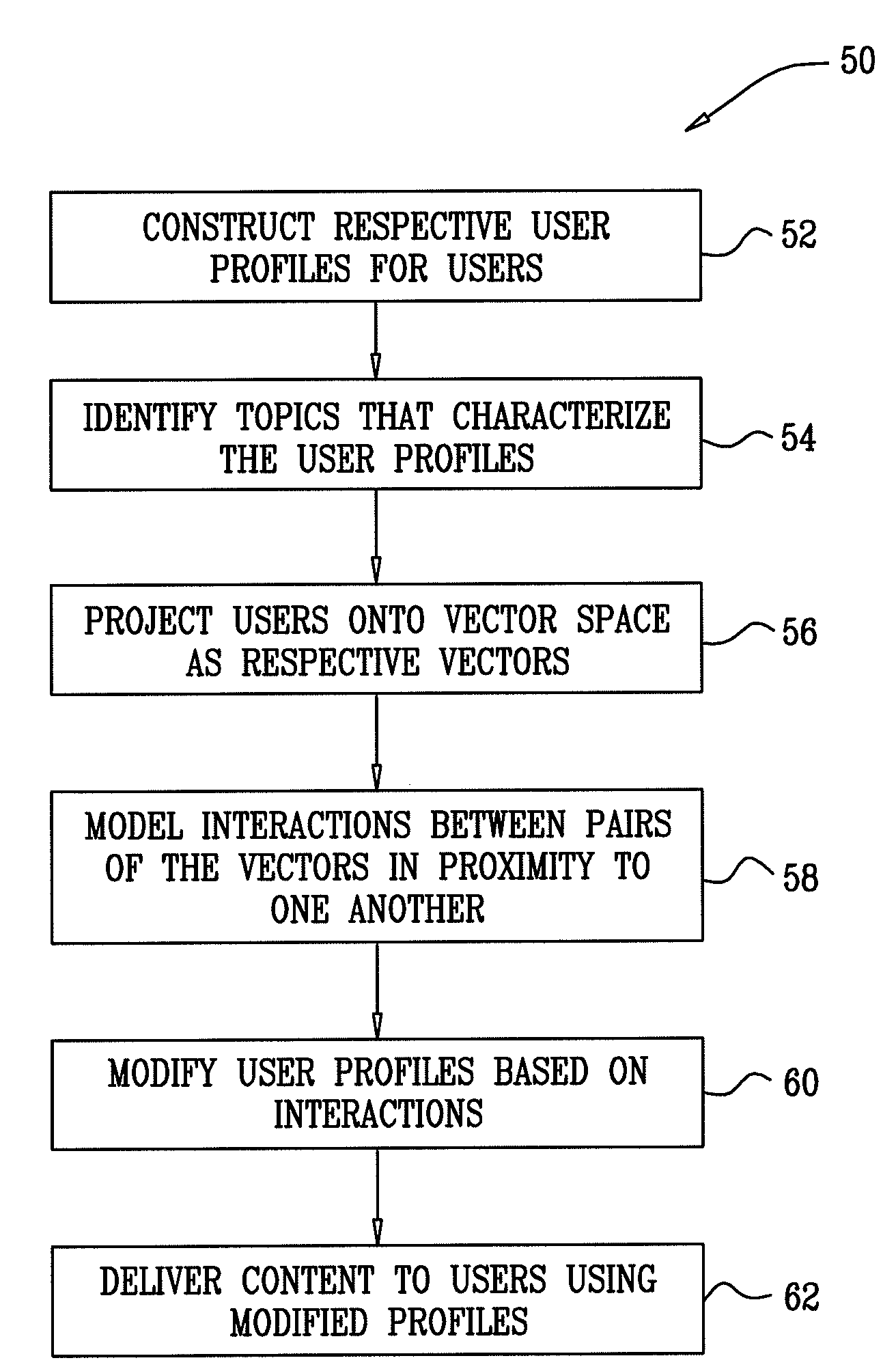
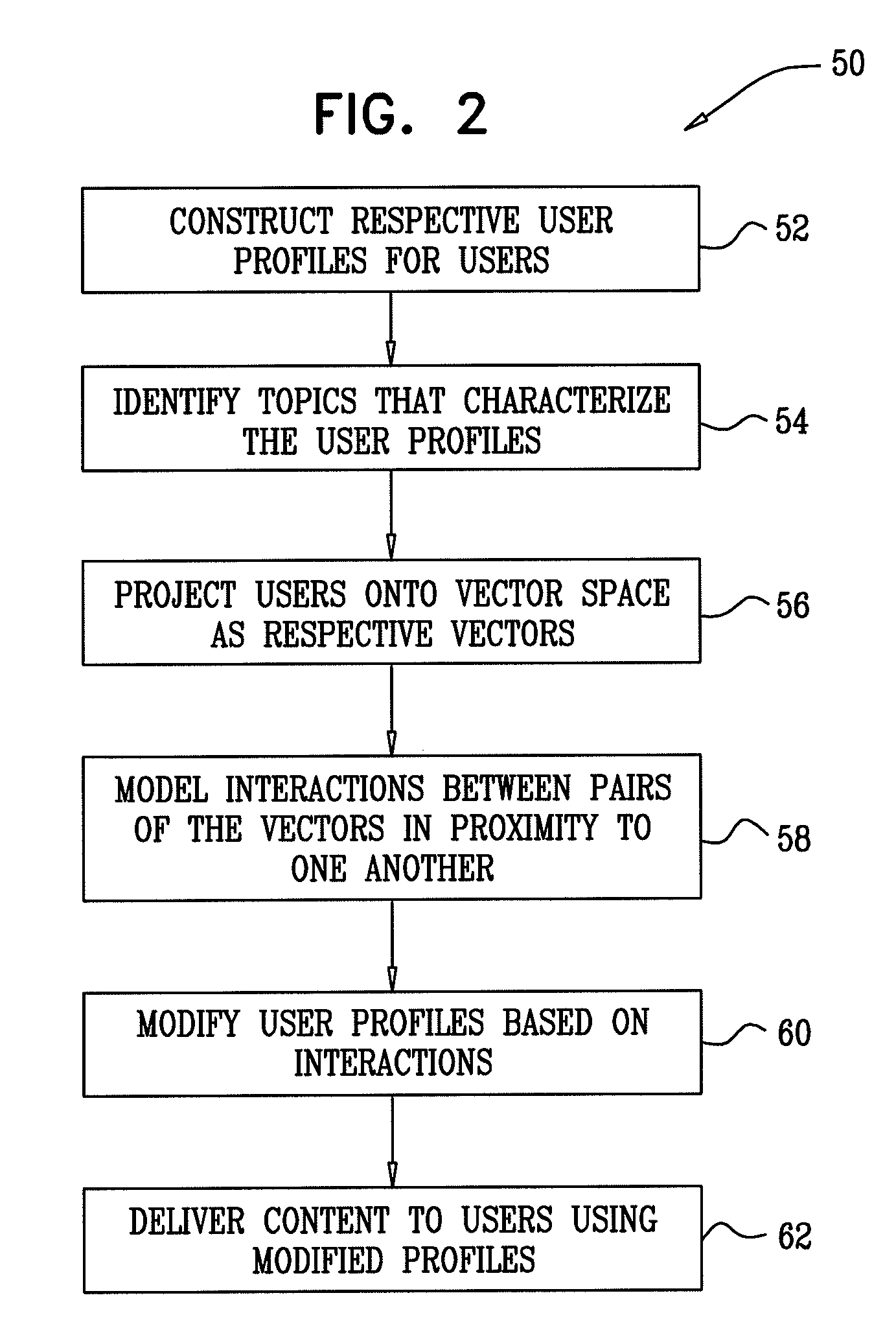
Interactions among online digital identities
InactiveUS20100049770A1Increased its relevancyDigital data processing detailsMultiple digital computer combinationsDigital identityHuman–computer interaction
A computer-implemented method is provided, which includes constructing first and second user profiles for respective first and second users, by observing respective online behaviors of the first and second users. The first and second user profiles are projected onto an N-dimensional vector space as respective first and second vectors. An interaction between the first and second vectors in the vector space is modeled. Responsively to the modeled interaction, at least one entity is modified, the entity selected from the group consisting of: the first user profile, and the first vector. Content is presented to the first user responsively to the modified entity. Other embodiments are also described.
Owner:COLLARITY
Digital identity related reputation tracking and publishing
InactiveUS20070208940A1Effective registrationUser identity/authority verificationData switching networksDomain nameDigital identity
Systems and processes of the present invention allow for tracking and publishing digital identity related reputation. In an example embodiment, a Digital Identity Provider maintains a database with reputation data that can be accessed by Requesters. The Digital Identity Provider may update reputation data based on a variety of events related to a digital identity. The reputation data may be tracked regarding the digital identity itself, digital identity purchaser or registrant, or an email address, domain name, URL, or website associated with the digital identity. The reputation data may include various categories, such as email practices, website content, privacy policies and practices, fraudulent activities, domain name related complaints, overall reputation, etc. The reputation data may be published in a publicly-available database, a private database, or via other methods. The Registrant may opt for a reputation service while registering a digital identity. The Requester may decide whether to interact with a digital identity based on the digital identity related reputation.
Owner:GO DADDY OPERATING
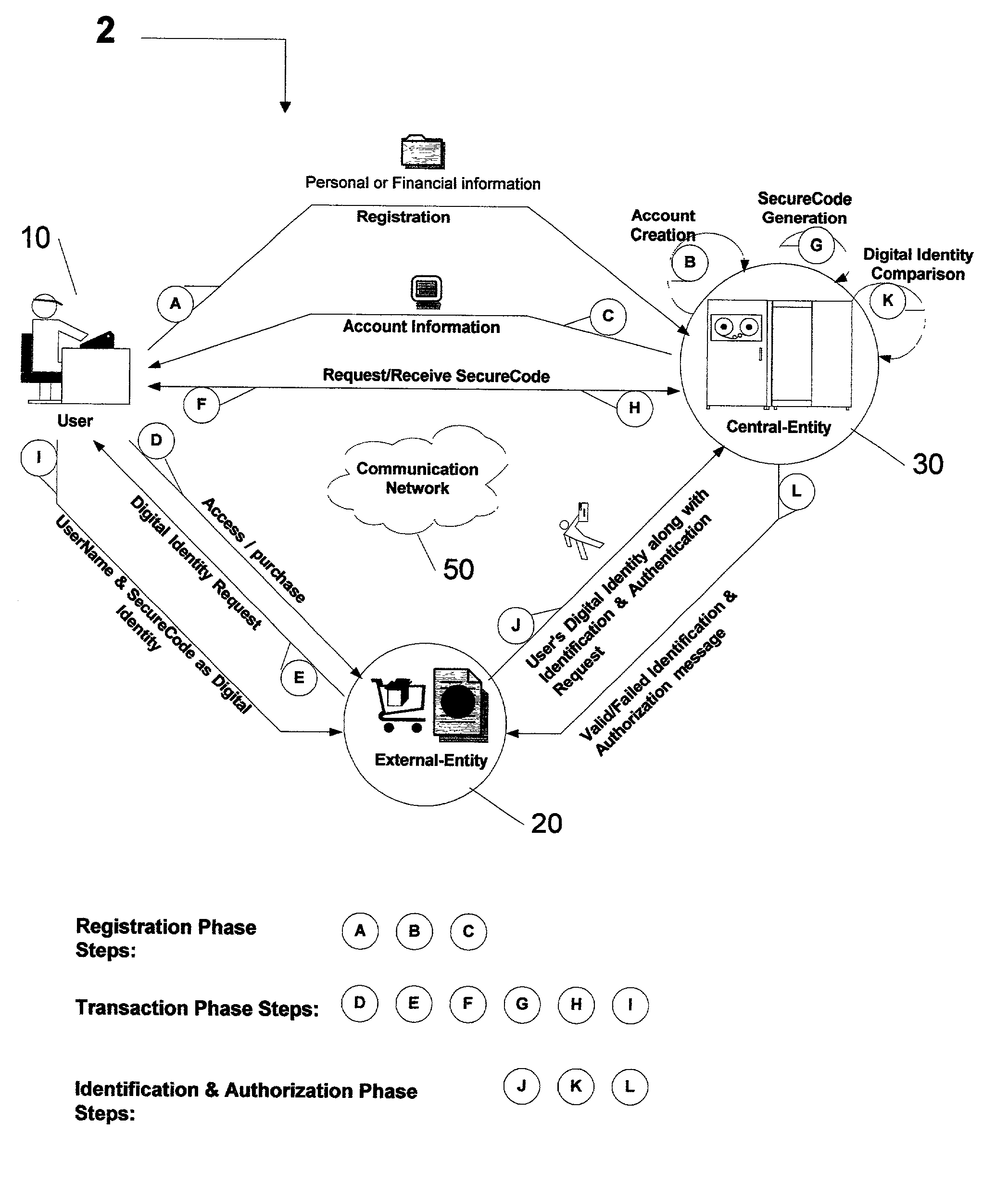
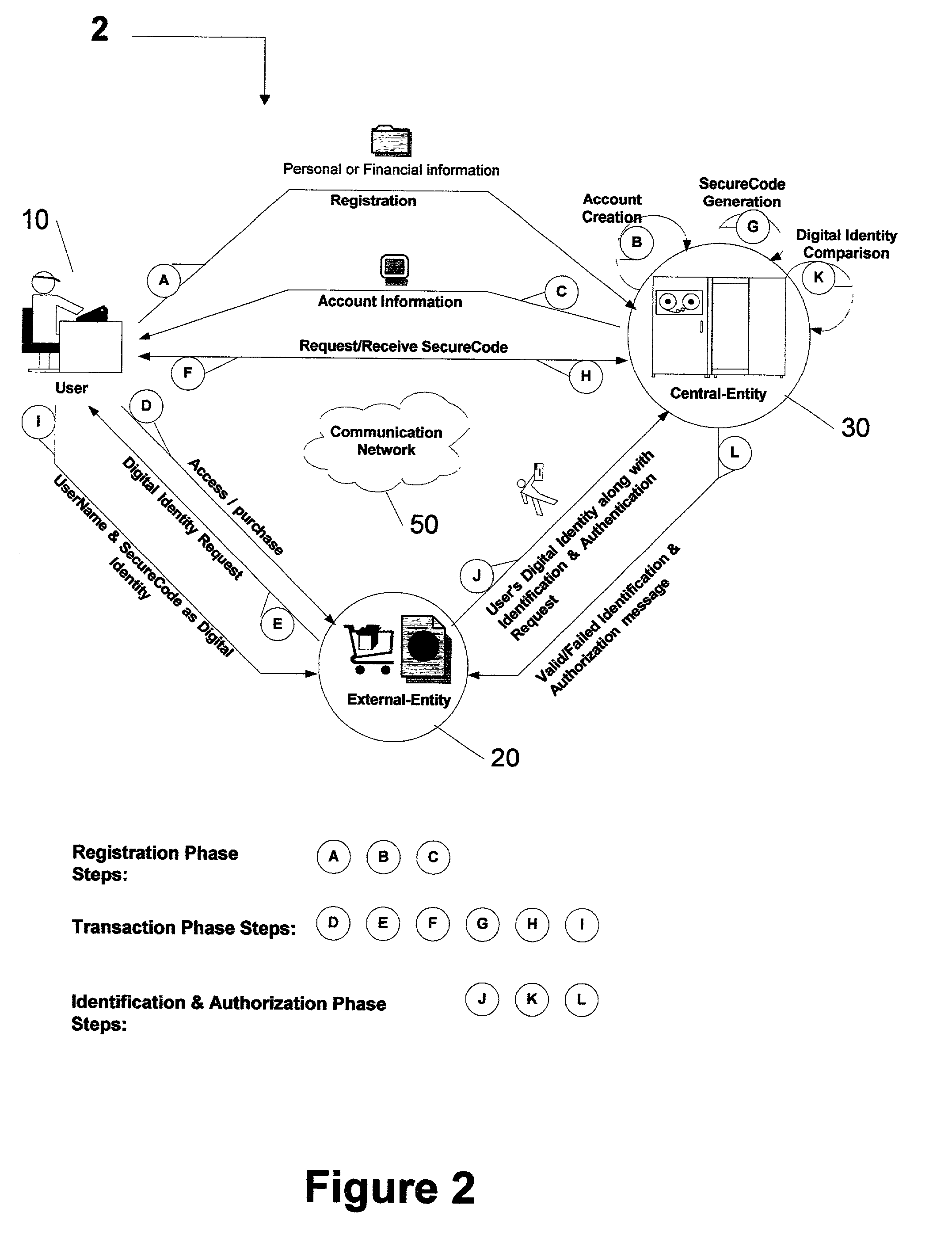
Centralized identification and authentication system and method
ActiveUS7356837B2Reduce fraudImprove securityFinanceDigital data processing detailsDigital identityService provision
A method and system is provided by a Central-Entity, for identification and authorization of users over a communication network such as Internet. Central-Entity centralizes users personal and financial information in a secure environment in order to prevent the distribution of user's information in e-commerce. This information is then used to create digital identity for the users. The digital identity of each user is dynamic, non predictable and time dependable, because it is a combination of user name and a dynamic, non predictable and time dependable secure code that will be provided to the user for his identification.The user will provide his digital identity to an External-Entity such as merchant or service provider. The External-Entity is dependent on Central-Entity to identify the user based on the digital identity given by the user. The External-Entity forwards user's digital identity to the Central-Entity for identification and authentication of the user and the transaction.The identification and authentication system provided by the Central-Entity, determines whether the user is an authorized user by checking whether the digital identity provided by the user to the External-Entity, corresponds to the digital identity being held for the user by the authentication system. If they correspond, then the authentication system identifies the user as an authorized user, and sends an approval identification and authorization message to the External-Entity, otherwise the authentication system will not identify the user as an authorized user and sends a denial identification and authorization message to the External-Entity.
Owner:AMERITECH SOLUTIONS INC
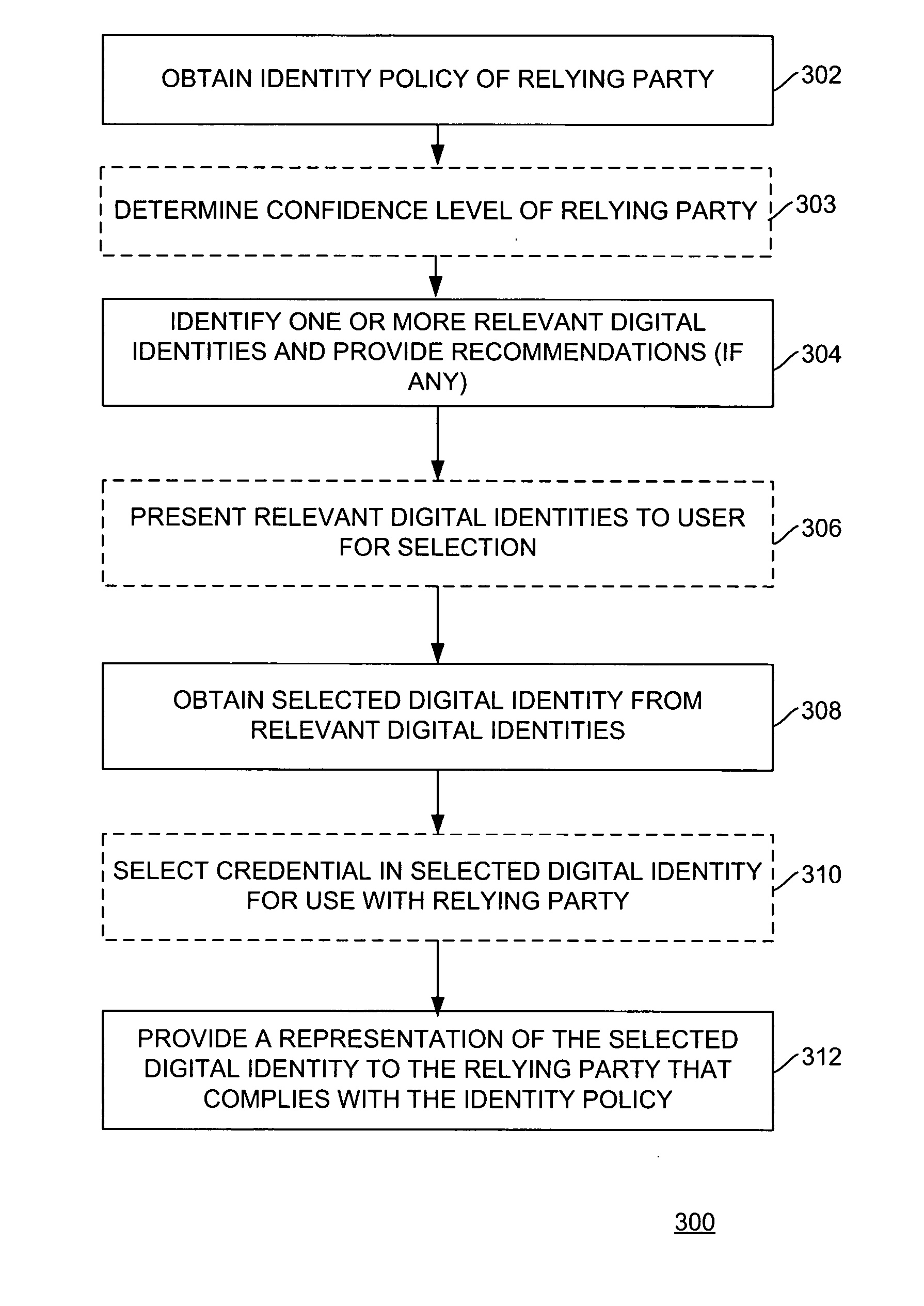
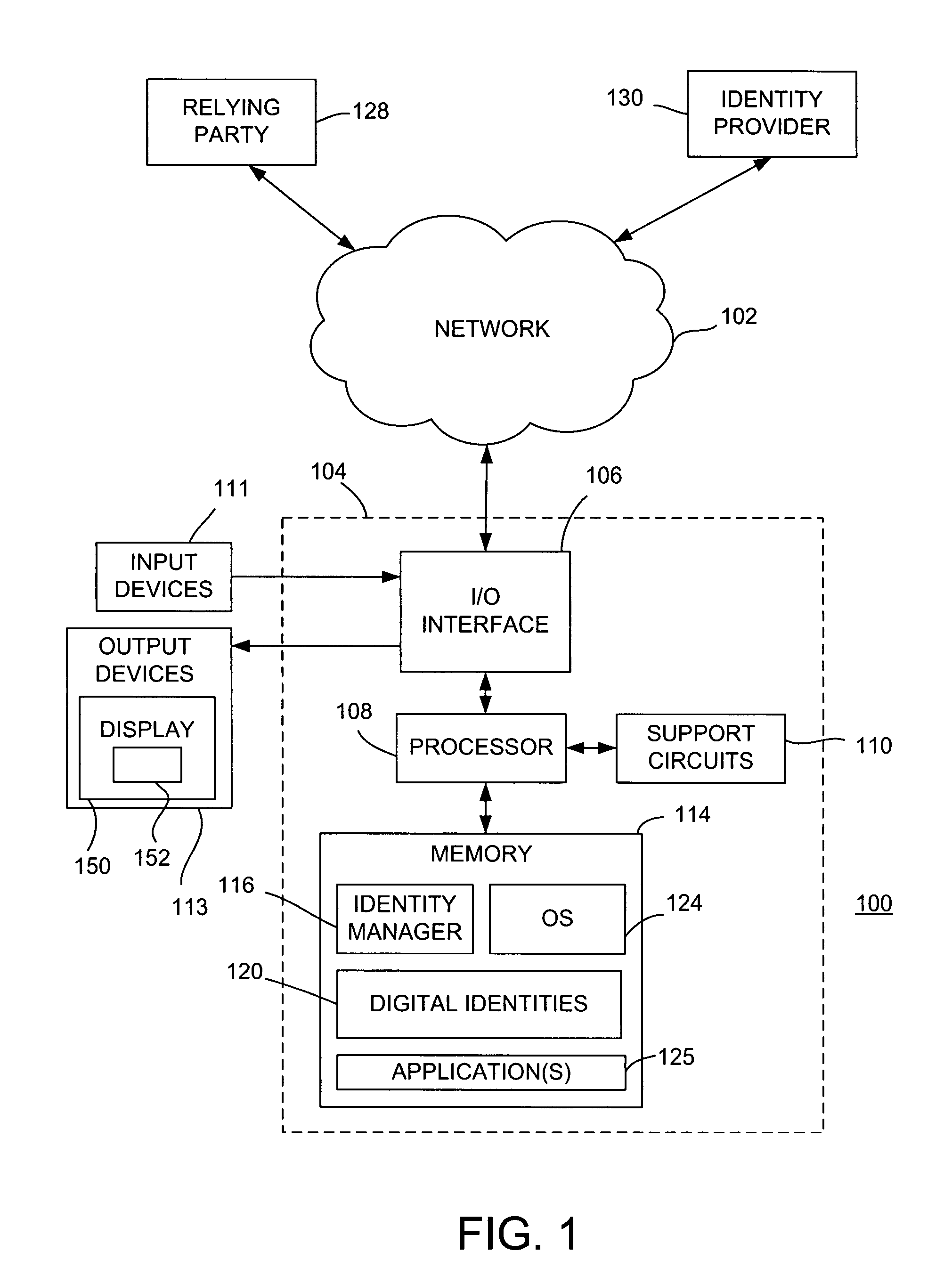
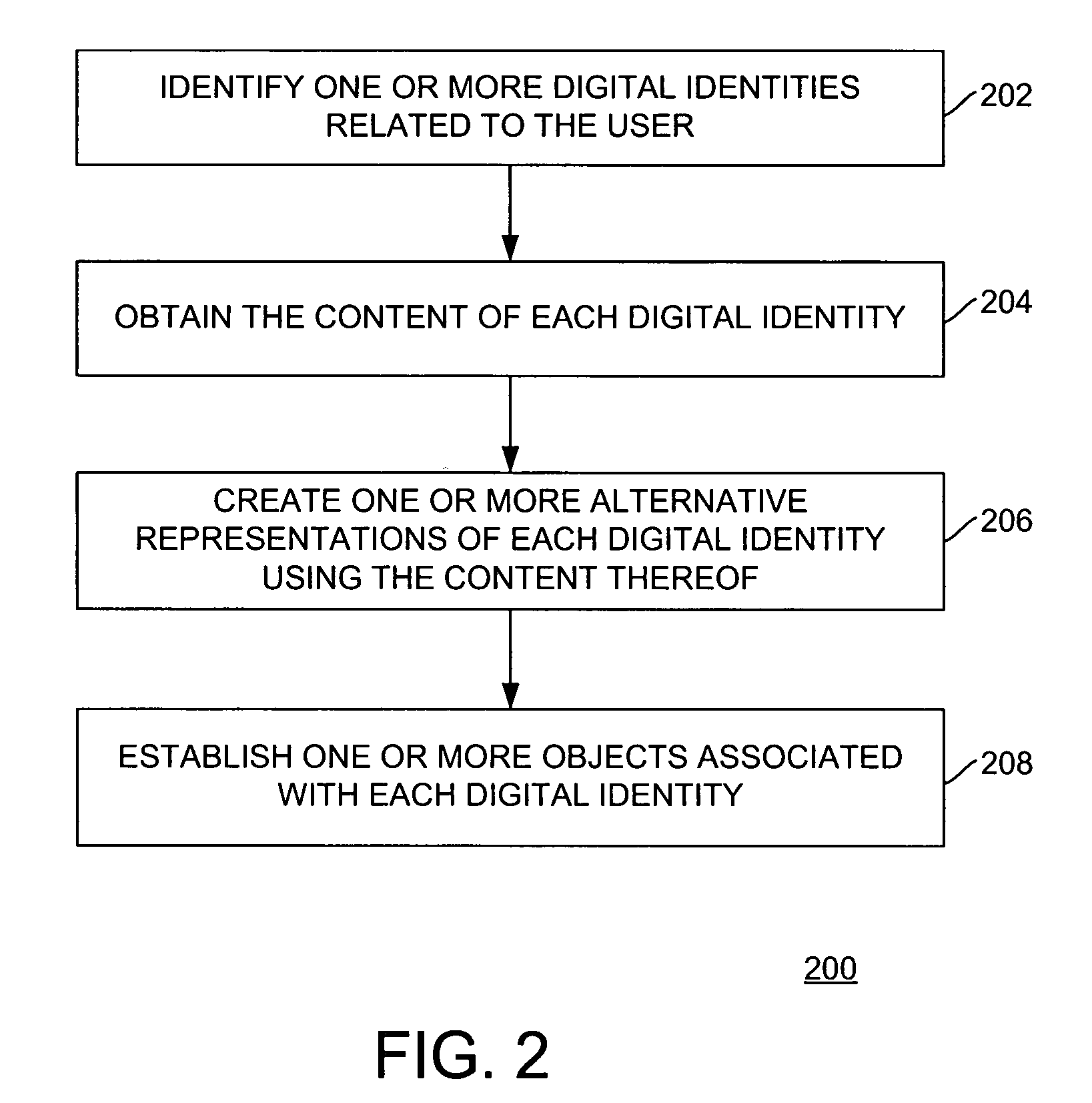
Method and apparatus for managing digital identities through a single interface
ActiveUS20080256594A1Digital data authenticationSpecial data processing applicationsDigital identity
Method and apparatus for managing digital identities through a single interface is described. One aspect of the invention relates to managing digital identities related to a user. An identity policy of an entity is obtained. At least one relevant digital identity is selected from the digital identities. Each relevant digital identity includes information required by the identity policy. A selected digital identity is obtained from the relevant digital identity or identities. A representation of the selected digital identity is provided to the entity that complies with the identity policy.
Owner:GEN DIGITAL INC
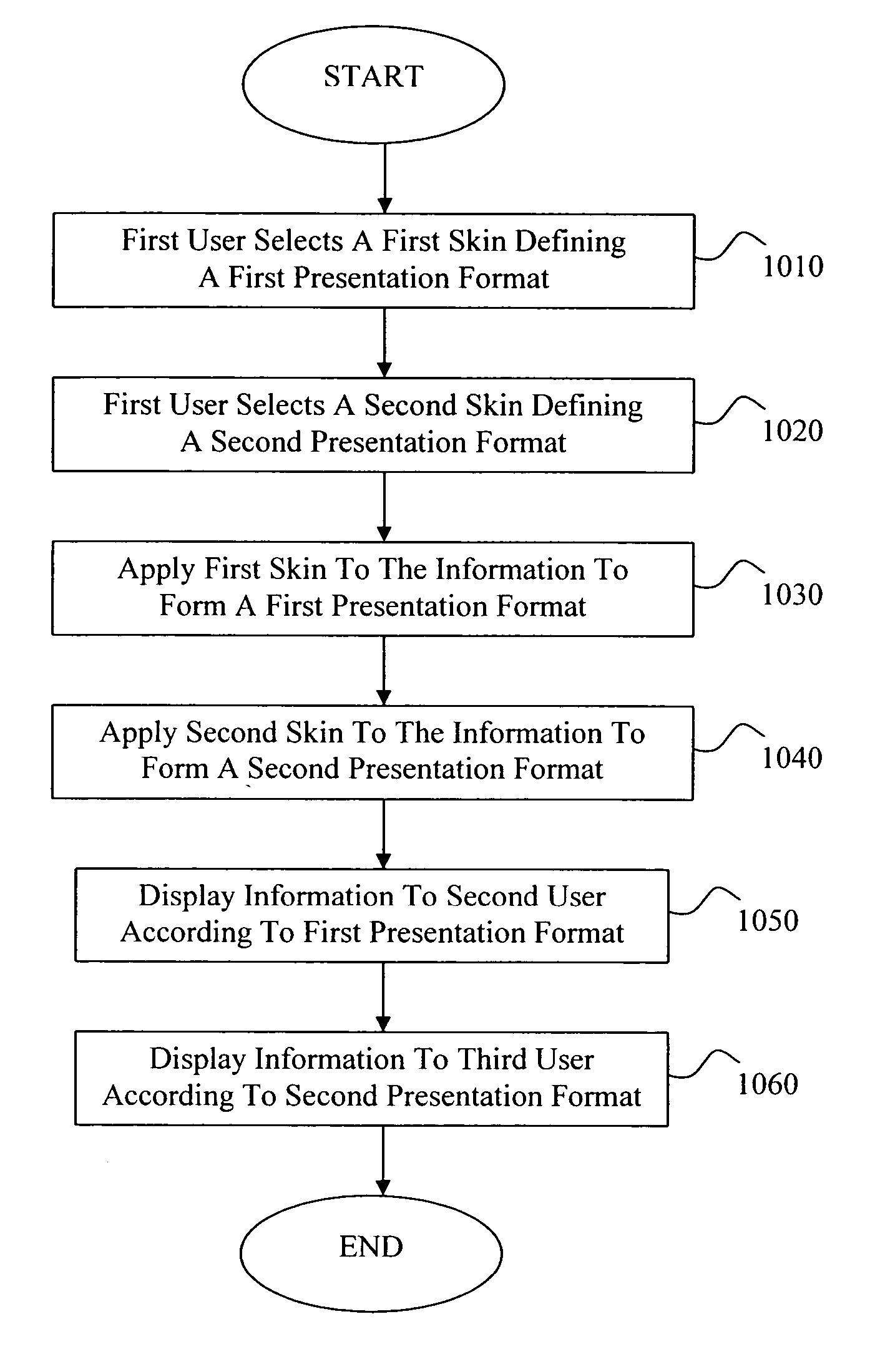
Presentation of information based on digital identities
InactiveUS20050289474A1Special data processing applicationsInput/output processes for data processingDigital identityHuman–computer interaction
Methods for controlling the display of information shared between users are disclosed. For example, an individual may agree to share his or her contact information with other users, for example, by exchanging one or more vCards of which the individual is considered the owner. The owner has a first relationship with a first user and a second relationship with a second user. Using dynamic electronic presentation skins, which are selected based on the relationships between the parties, the owner's contact information is presented to the first user in a first fashion and presented to the second user in a second fashion. If the relationship between the owner and the first and / or second user changes, a different dynamic presentation skin can be applied to the owner's contact information in the form of a vCard to alter the presentation of the information contained therein.
Owner:AYMAN
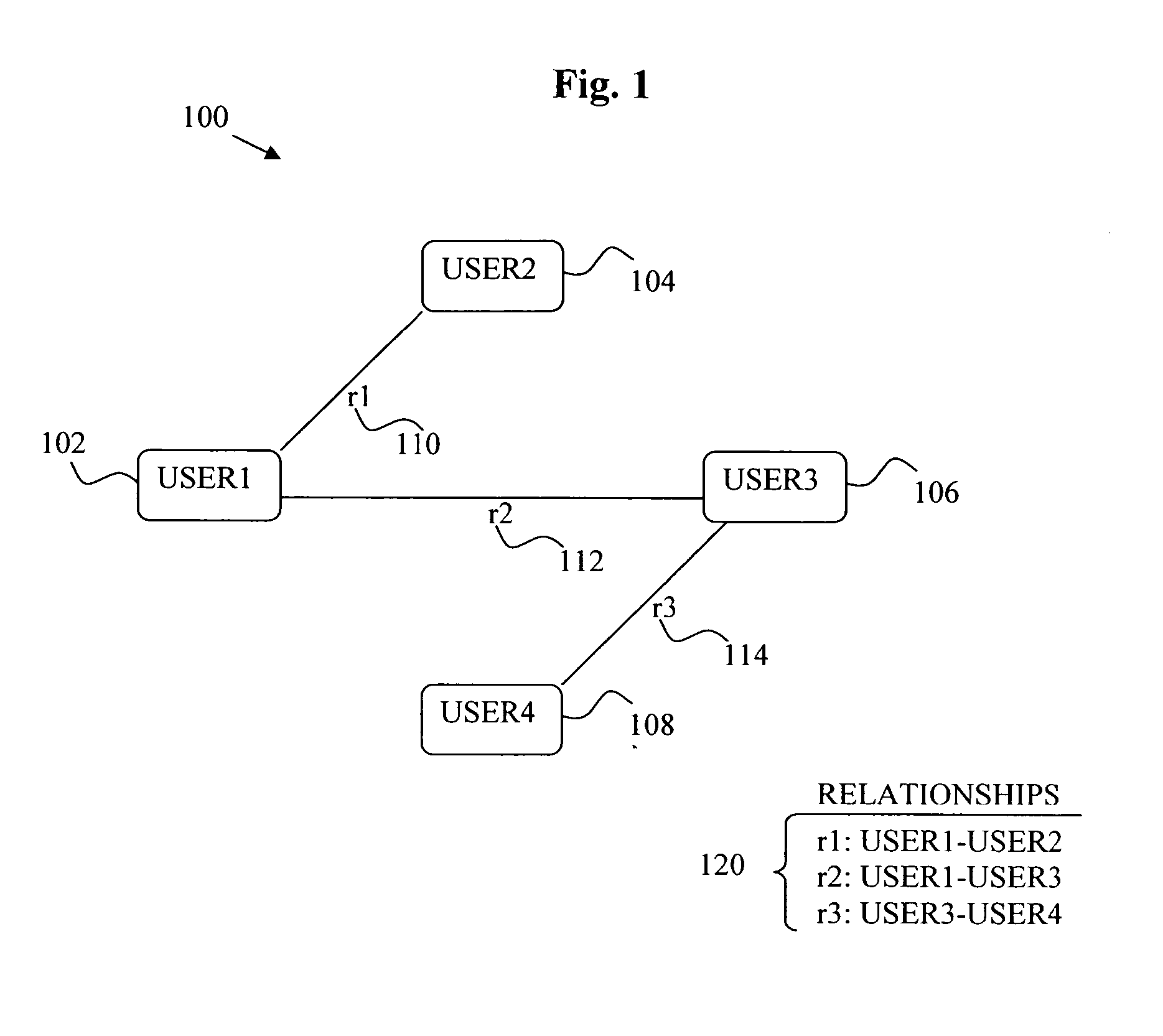
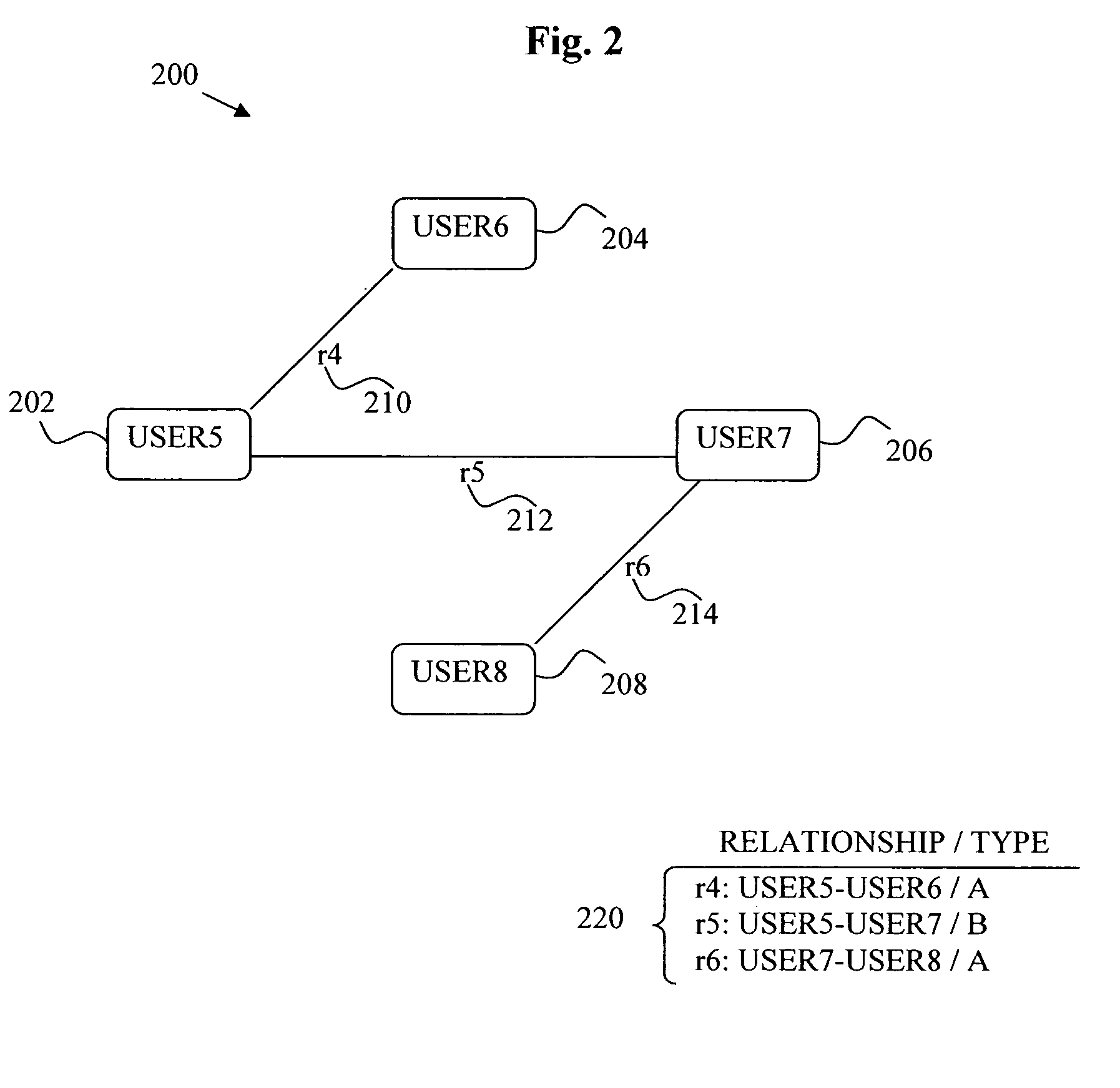
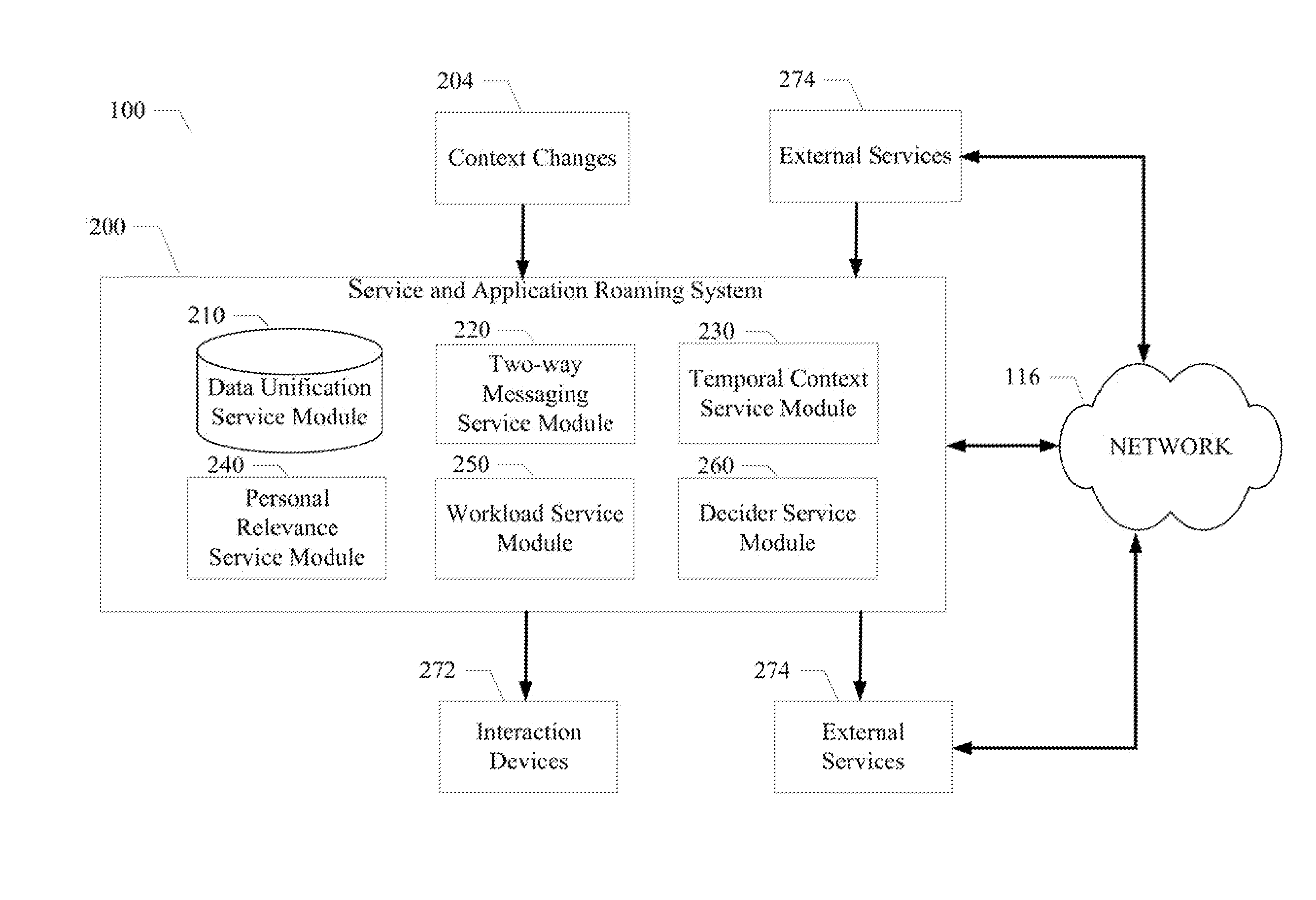
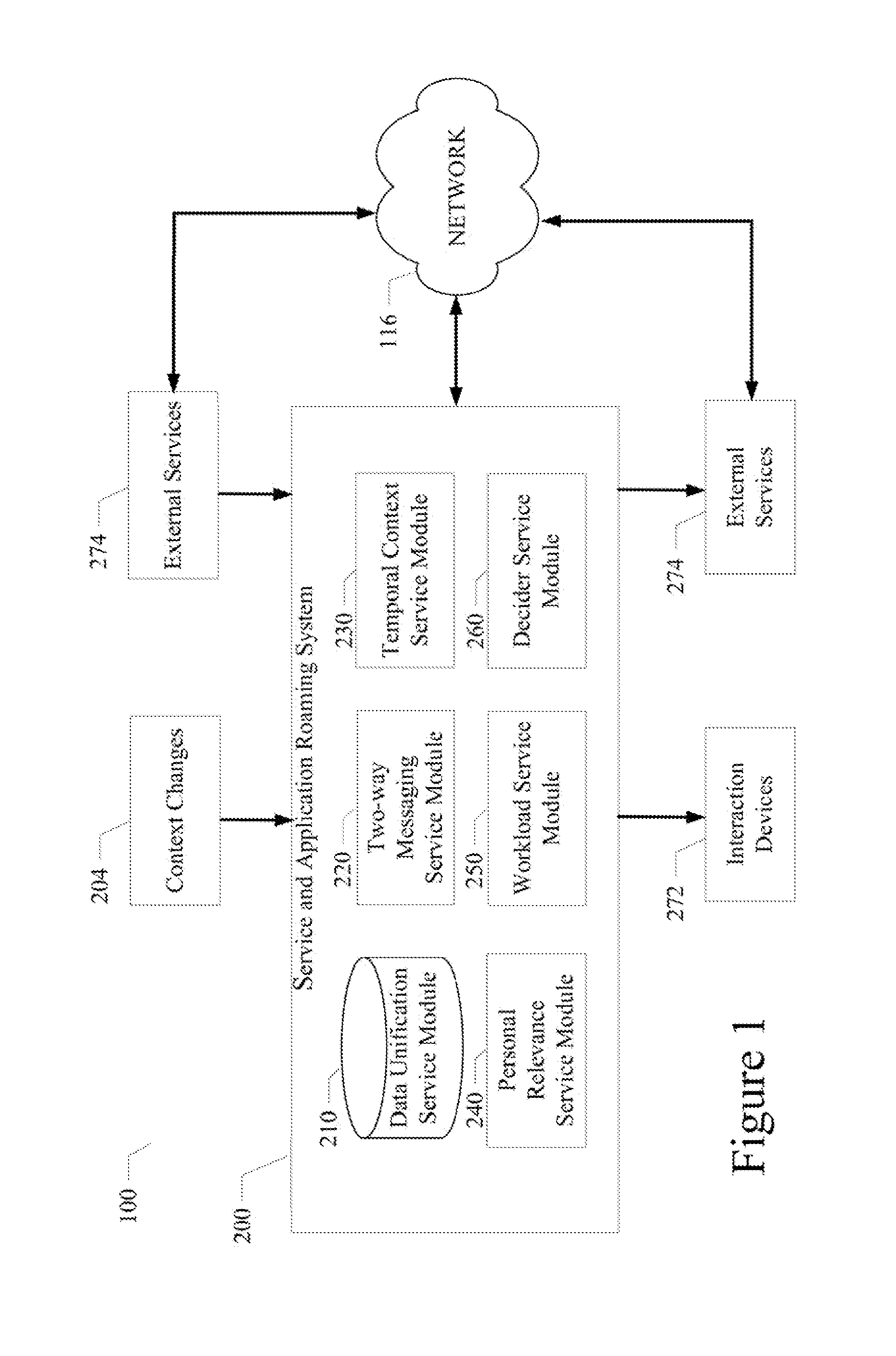
System and method enabling service and application roaming
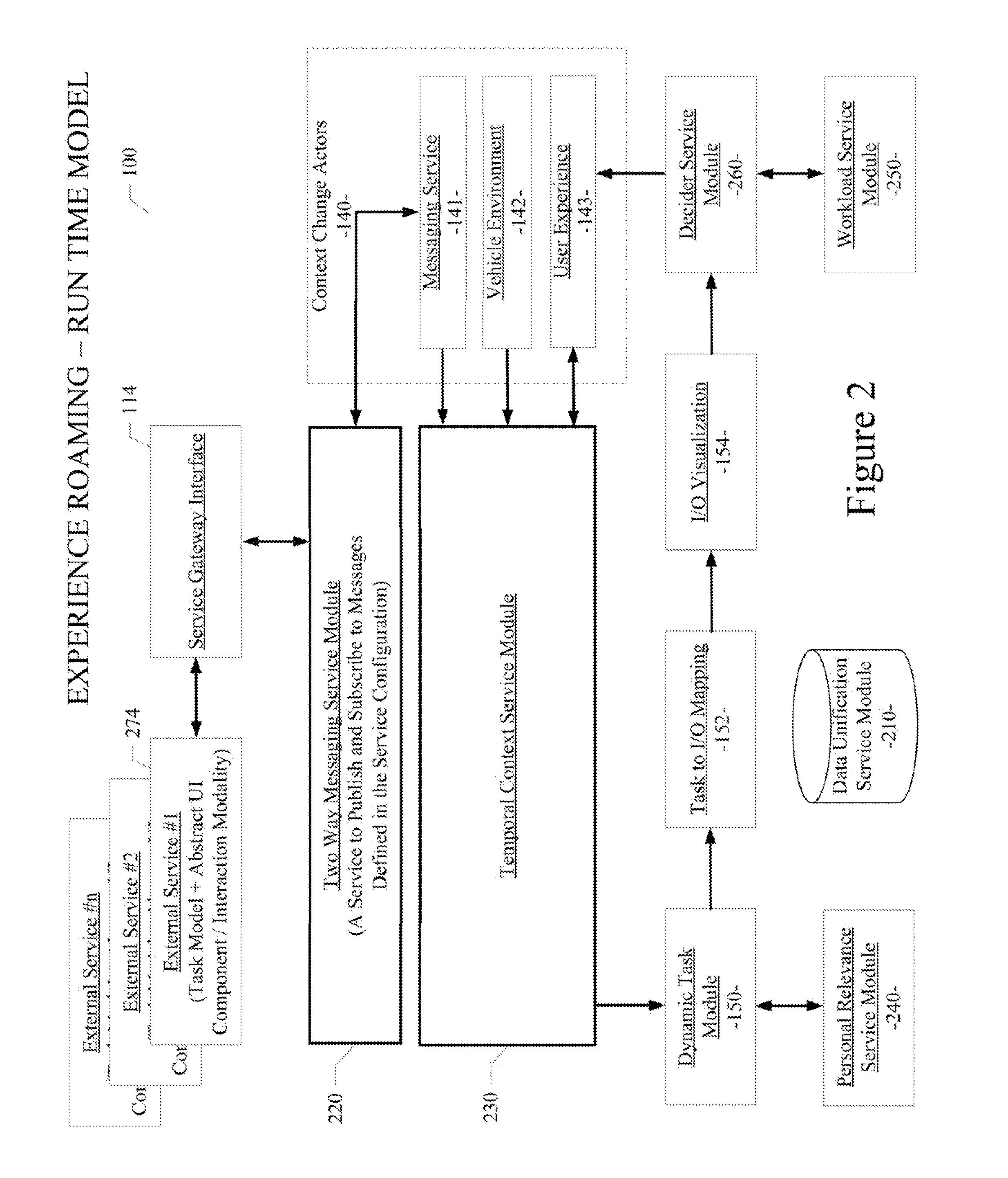
A system and method enabling service and application roaming are disclosed. A particular embodiment includes: unifying a plurality of user services and applications from a plurality of sources in an environment into a shared ecosystem of services and applications; assigning, by use of a data processor, a digital identity to the shared ecosystem of services and applications; detecting a context change in the environment causing a transition to a current context; causing a task set to be performed in response to the context change; and dispatching a set of interaction resources, corresponding to the task set, to present a state of the current context to a user by use of a plurality of interaction devices corresponding to the set of interaction resources, the set of interaction resources being accessed using the plurality of user services and applications in the shared ecosystem of services and applications.
Owner:LENNY INSURANCE LTD
System for digital identity authentication and methods of use
ActiveUS20190149334A1Improve securityMore securityKey distribution for secure communicationMultiple keys/algorithms usageDigital identityComputerized system
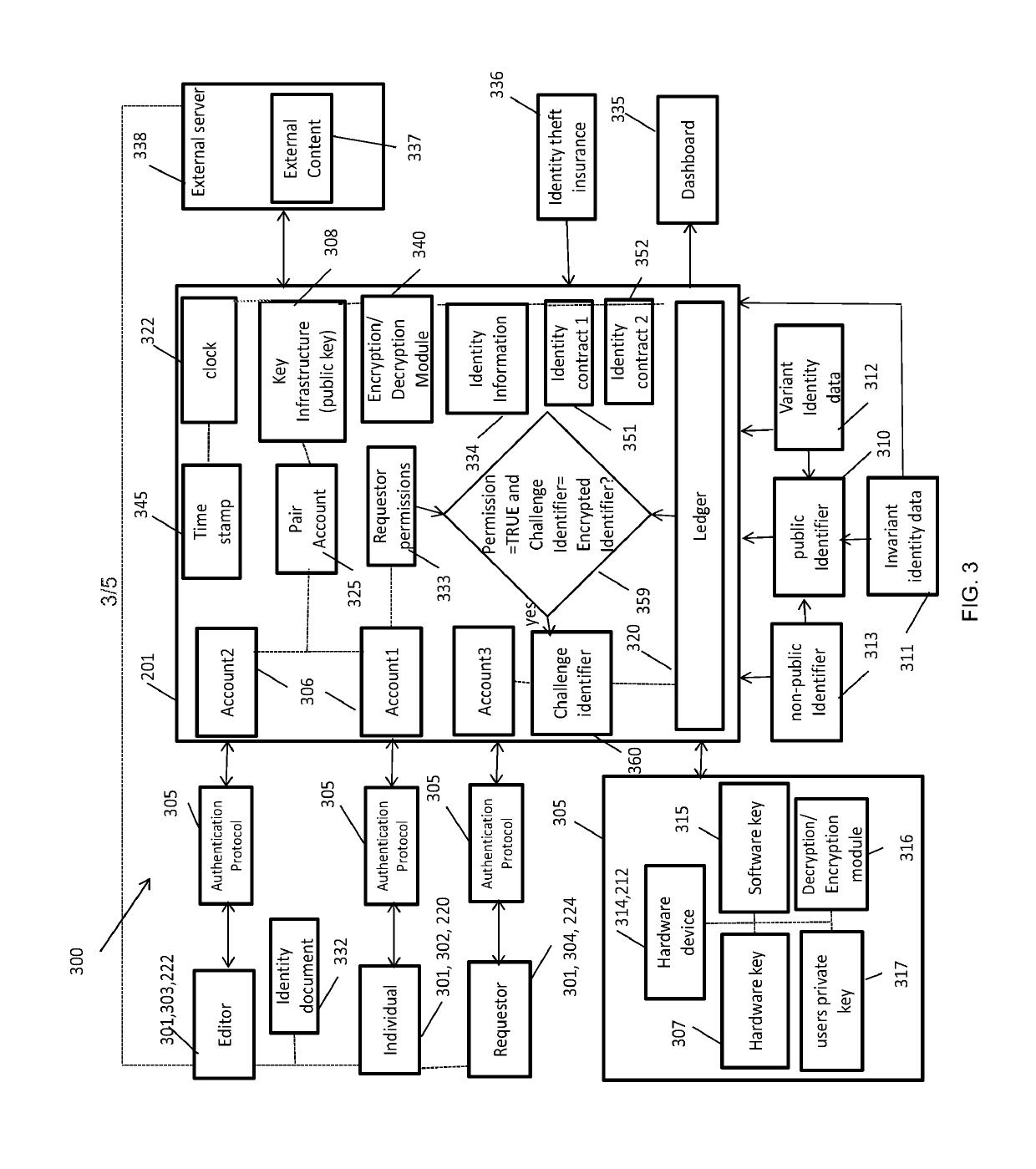
A system for digital identity authentication including a computer system or platform to enable users (individual, identity editor, requestor) using invariant and variant data on an identity server which uses multi-factor authentication to: 1) The paired identity editor creates a public identifier of the individuals constructed from invariant data and signs / encrypts the individual's user data (including public identifier) with identity editor's private key (hardware) and links the public identifier to the encrypted data record; 2) a requestor obtains public identifier from the individual who wants to disclose his identity and executes an identity verification request (challenge) to an identity server, identity server sends identity verification request (challenge) to individual; 3) individual utilizes individual's private key (hardware) to sign / authenticate identity verification request (challenge); 4) identity server then uses the public key of the paired identity editor to decrypt the individuals data and to compare the public identifier to the decrypted public identifier of the individual. If the decrypted public identifier matches the one provided by the requestor the identity is confirmed as well as the fact that the decrypted data belongs to this individual.
Owner:VAN DER VELDEN ALEXANDER J M
Method and system for human face comparison identity identification
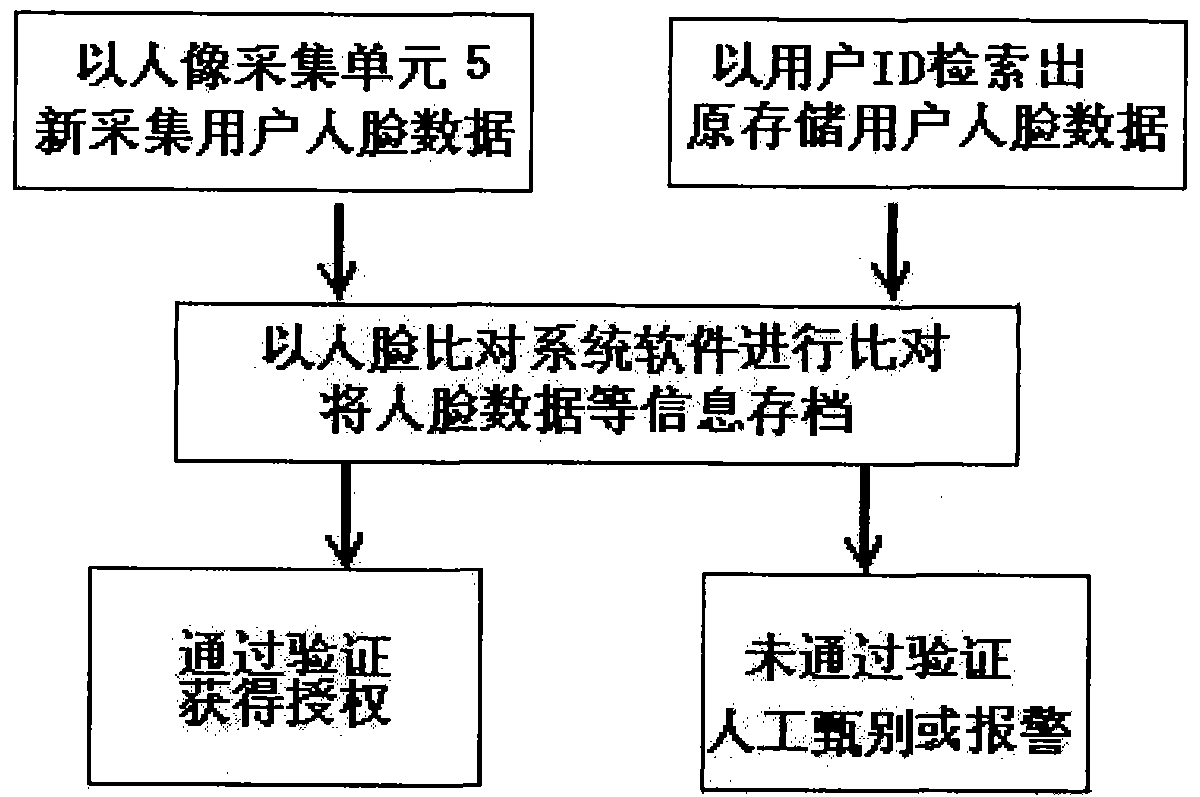
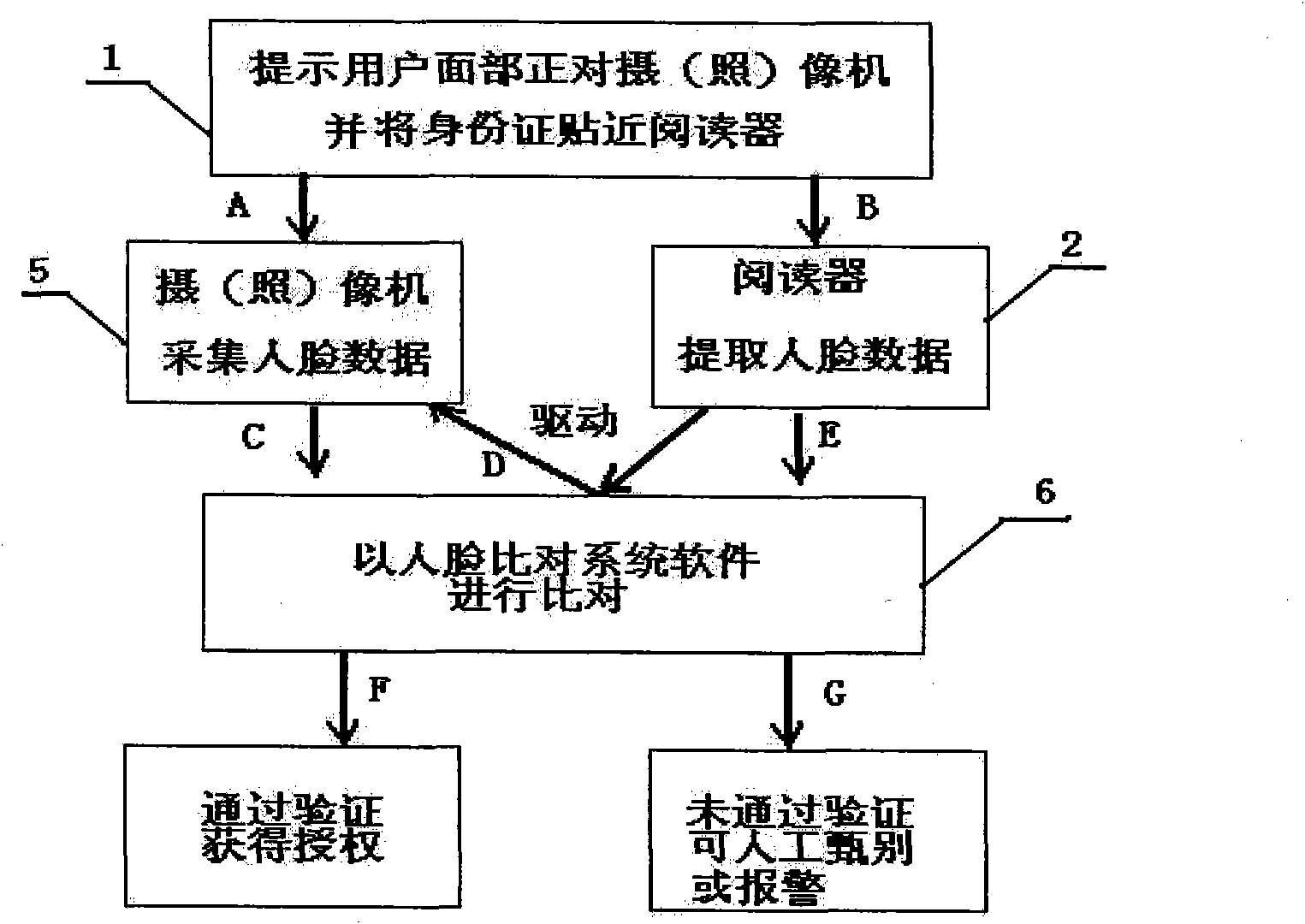
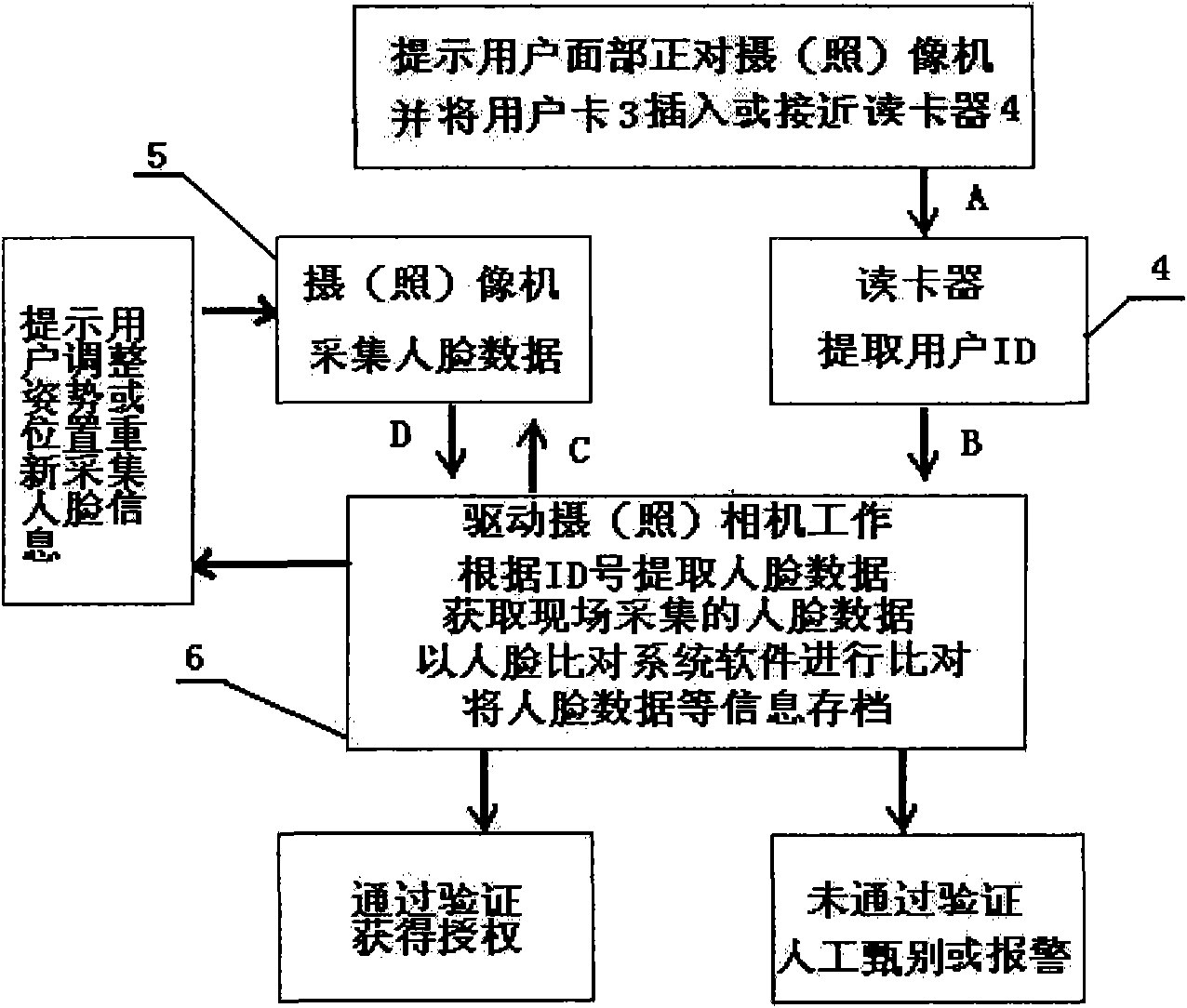
InactiveCN101826151AAvoid human errorImprove management levelCharacter and pattern recognitionDigital identityFace verification
The invention relates to a method and a system for human face comparison identity identification, which comprises the following steps: searching human face data stored in a database and an IC card by identified personnel through identity marks of the identified personnel; obtaining identification human face data of the identified personnel through image picking, photo taking and scanning; using a computer human face identification system; and carrying out coidentity comparison on the originally stored human face data and the later obtained identification human face data for realizing the identity identification. The system comprises identity mark, identity mark carrier and corresponding identifying and reading units, units for obtaining the identification human face data of identified personnel and units for storing, processing and recording the human face data. The invention can be used for industries such as banks, public security, telecommunications, medical insurance, civil aviation, education, military and the like, can effectively avoid the manual careless omission, and can automatically, conveniently efficiently and accurately realize the digital identity identification and passageway control and the like.
Owner:赵毅
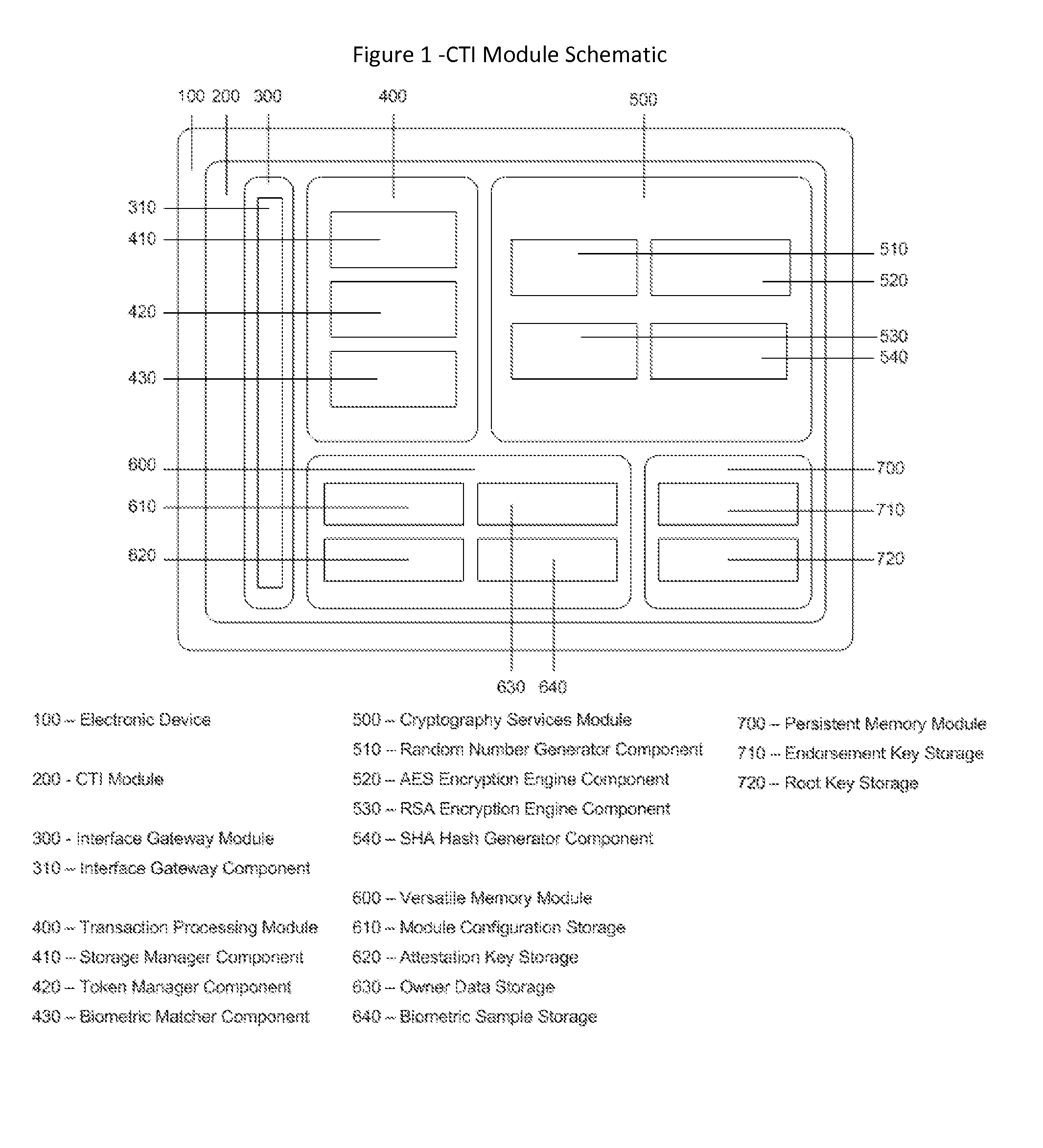
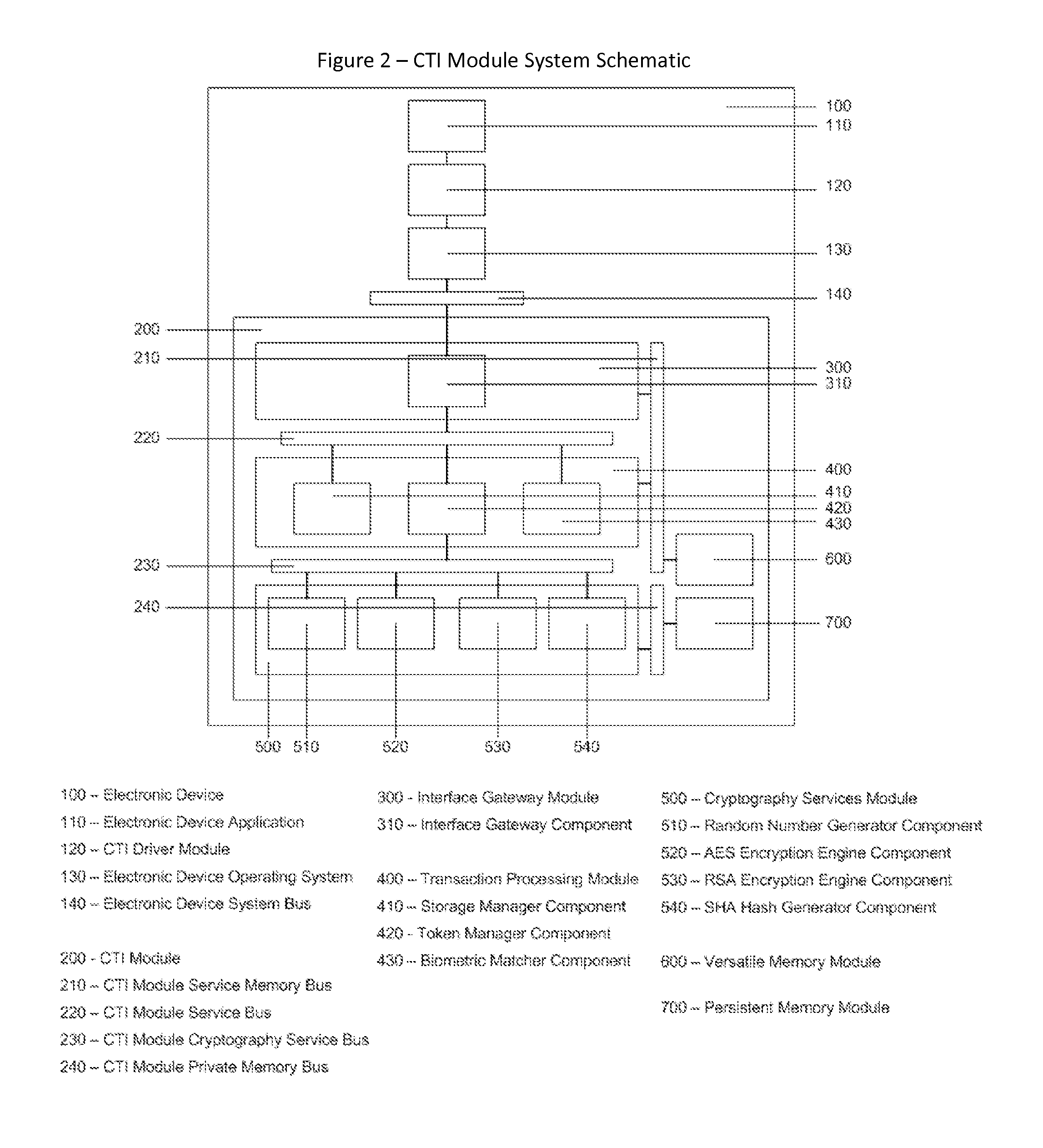
Cyberspace Trusted Identity (CTI) Module
InactiveUS20130219481A1Eliminate needIncrease storage capacityDigital data processing detailsMultiple digital computer combinationsTrusted authorityDigital identity
The Cyberspace Trusted Identity (CTI) module provides secure storage of a cyberspace user's personal identity information and a security infrastructure to guarantee the integrity and privacy of a cyberspace transaction. When the owner of an electronic device registers their biometric samples on the CTI module the module becomes locked and the information stored on the module can only be accessed when the device owner provides a live biometric sample, which matches the registered biometric sample. When the CTI Module is registered under a trusted third party system; a Cyberspace Identification Trust Authority (CITA) system, the module provides a secure mechanism for storing a cyberspace user's digital identity tokens and for conducting safe and reliable cyberspace transactions between two cyberspace users. The CTI Module eliminates the need to carry man-made identity tokens, or the need to remember and / or openly exchange personal identity information, when conducting a cyberspace transaction.
Owner:VOLTZ ROBERT MATTHEW
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com