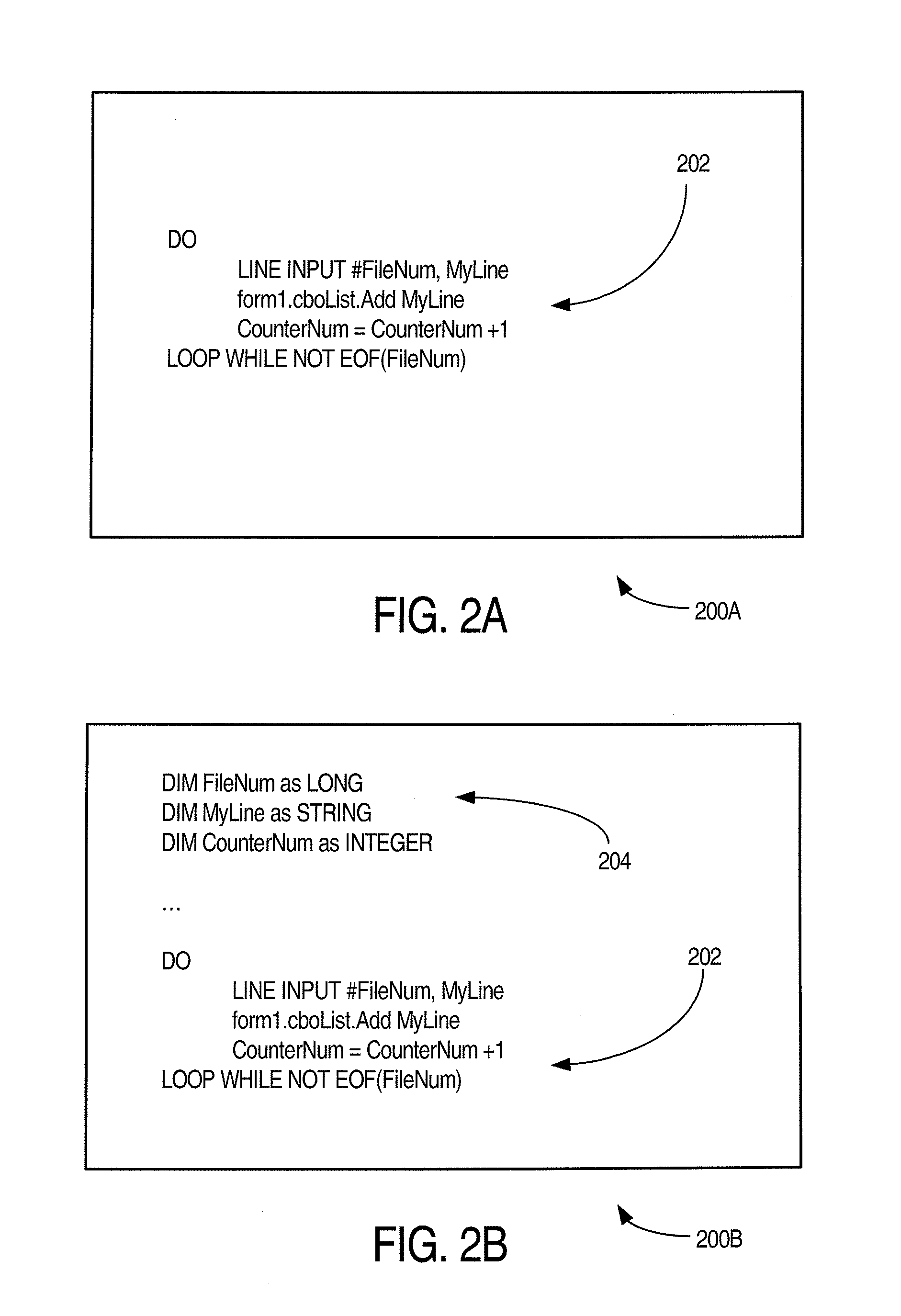
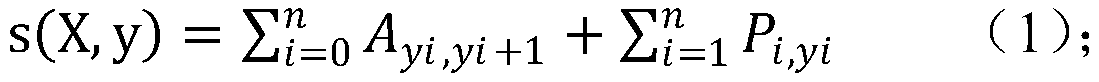Patents
Literature
67 results about "Declaration" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
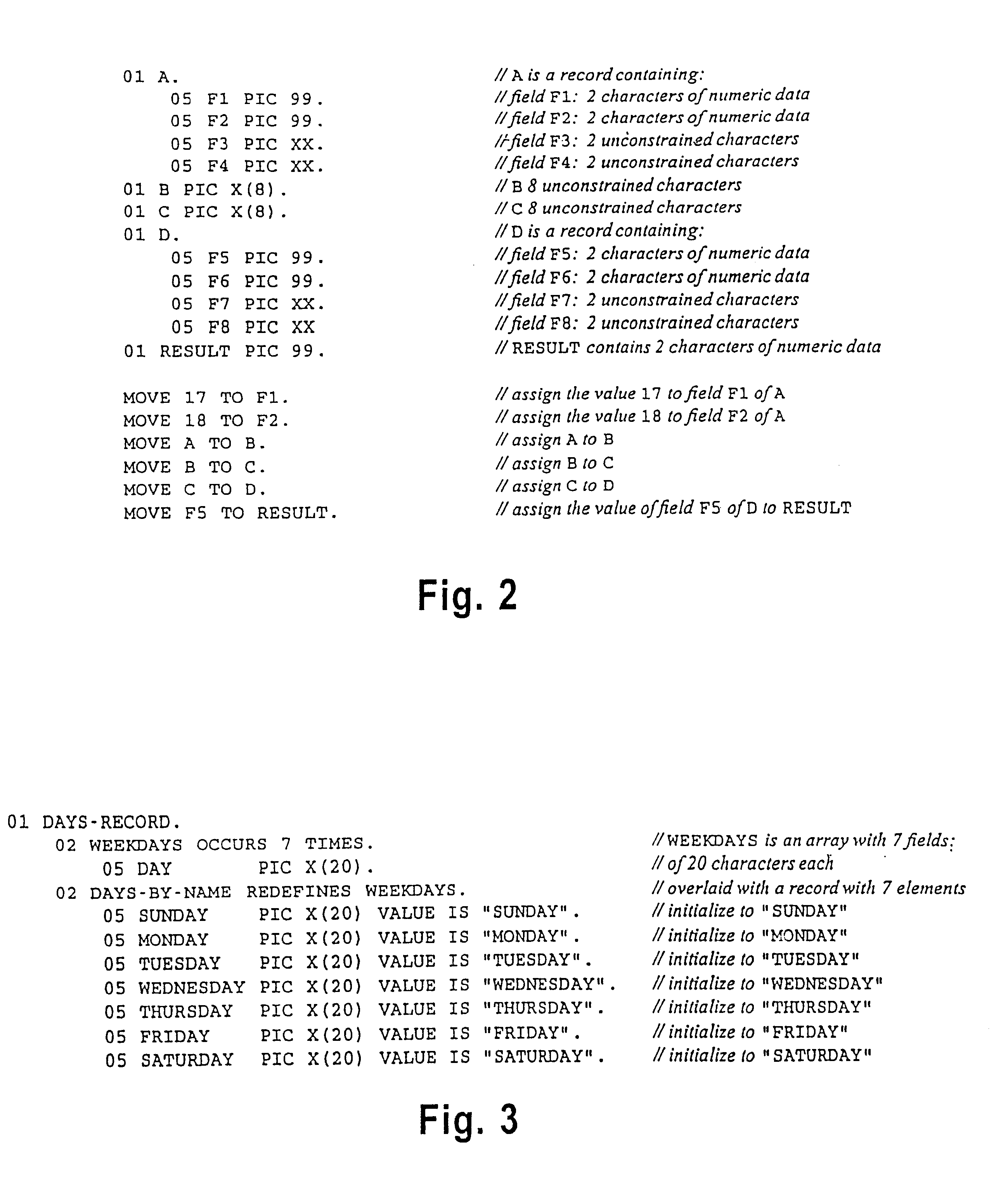
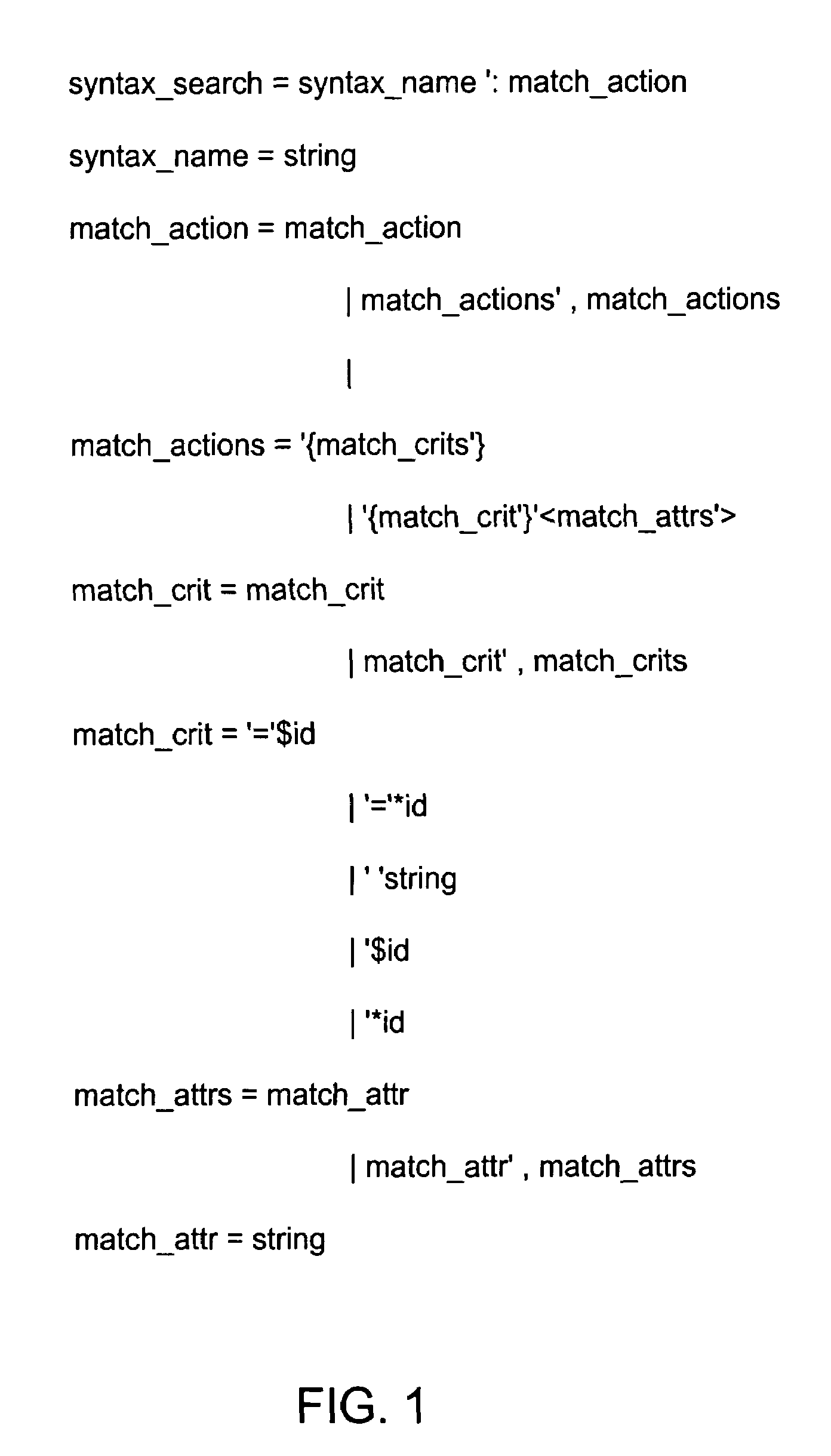
In computer programming, a declaration is a language construct that specifies properties of an identifier: it declares what a word (identifier) "means". Declarations are most commonly used for functions, variables, constants, and classes, but can also be used for other entities such as enumerations and type definitions. Beyond the name (the identifier itself) and the kind of entity (function, variable, etc.), declarations typically specify the data type (for variables and constants), or the type signature (for functions); types may also include dimensions, such as for arrays. A declaration is used to announce the existence of the entity to the compiler; this is important in those strongly typed languages that require functions, variables, and constants, and their types to be specified with a declaration before use, and is used in forward declaration. The term "declaration" is frequently contrasted with the term "definition", but meaning and usage varies significantly between languages; see below.
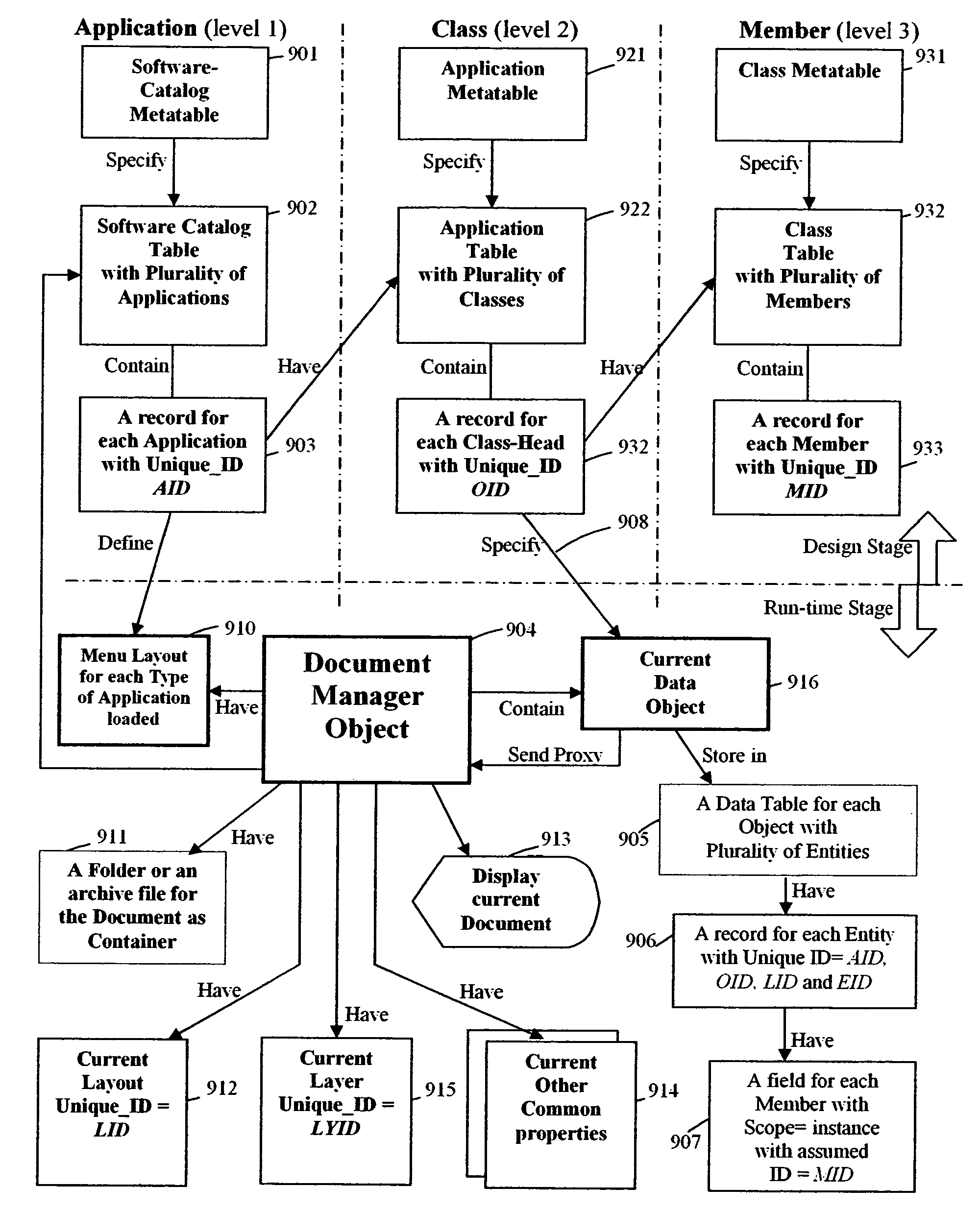
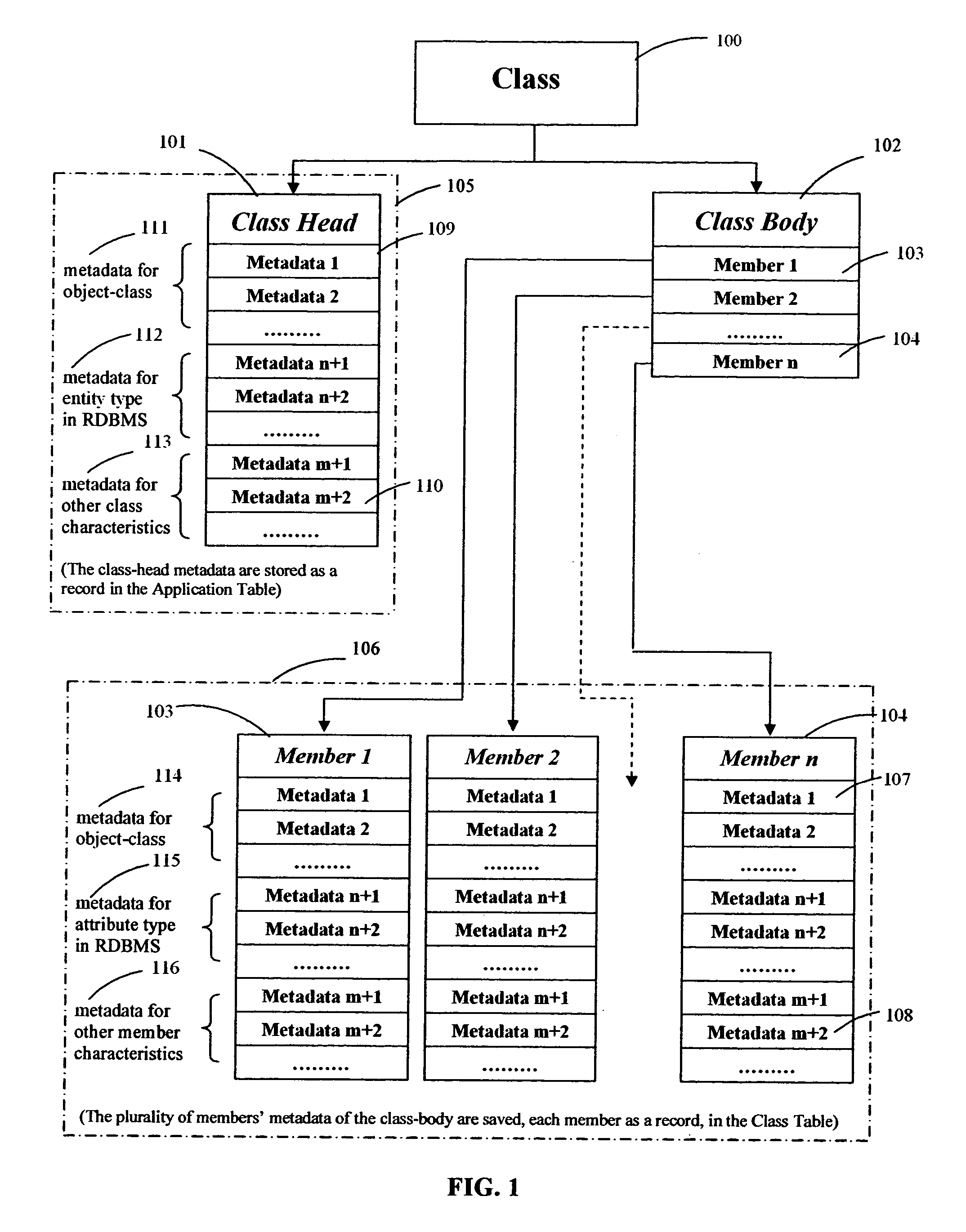
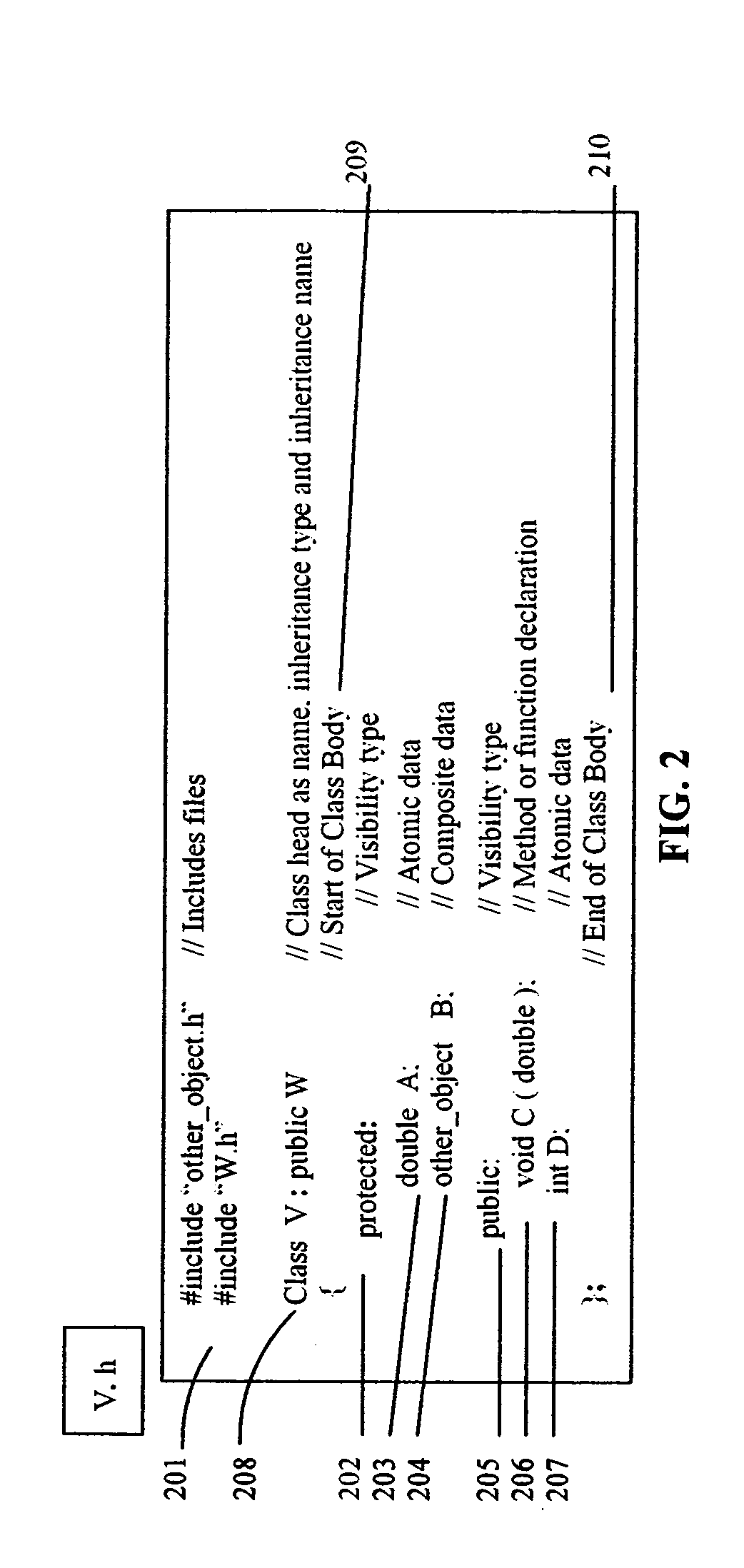
Method for enhancing object-oriented programming through extending metadata associated with class-body class-head by adding additional metadata to the database
ActiveUS7130863B2Achieve modularityEnhanced informationData processing applicationsDigital data processing detailsMetadataHuman language
The invention relates to a method for enhancing an object-oriented programming language. The method includes declaring one or more class structures in databases having metadata describing characteristics defining the class structures. The method also includes extending the metadata associated with the class structures by adding any number of additional metadata to the databases.
Owner:CALLAHAN CELLULAR L L C
Object model for Java TM
The mechanism includes three data structures: object data associated with each object O1, O2, O3 ... of a program, a class descriptor associated with the classes to which the objects O1, O2, O3 ... belong, and interface references. For each class Ci, the class descriptor corresponding to the class Ci includes: i) a class method table comprising one or more entries, wherein each entry identifies an implementation of a method inherited or defined by the class Ci; and ii) for each interface implemented by the class Ci, an interface method table comprising one or more entries, wherein each entry identifies an implementation of a method declared by the particular interface or an implementation of a method declared by an interface extended by the particular interface. An interface reference for an interface declaration ID associated with a given object OI, wherein the object OI implements methods that are declared by an interface declaration ID includes a pointer to the interface method table corresponding to the interface declaration ID within the class descriptor corresponding to the object OI. An efficient mechanism for method invocations is provided by generating an index that identifies the entry corresponding to the appropriate method in the interface method table pointed to by the pointer of the interface reference, reading the data stored by the entry identified by the index, and controlling the computer processing apparatus to jump to the address identified by the data.
Owner:IBM CORP
Aggregate structure identification and its application to program analysis
InactiveUS6279149B1Digital data processing detailsReverse engineeringArray data structureSimple component
An efficient program analysis method is provided for lazily decomposing aggregates (such as records and arrays) into simpler components based on the access patterns specific to a given program. This process allows us both to identify implicit aggregate structure not evident from declarative information in the program, and to simplify the representation of declared aggregates when references are made only to a subset of their components. The method can be exploited to yield: (i) a fast type analysis method applicable to program maintenance applications (such as date usage inference for the Year 2000 problem); and (ii) an efficient method for atomization of aggregates. More specifically, aggregate atomization decomposes all of the data that can be manipulated by the program into a set of disjoint atoms such that each data reference can be modeled as one or more references to atoms without loss of semantic information. Aggregate atomization can be used to adapt program analyses and representations designed for scalar data to aggregate data. In particular, atomization can be used to build more precise versions of program representations such as SSA form or PDGs. Such representations can in turn yield more accurate results for problems such as program slicing. Our techniques are especially useful in weakly-typed languages such as Cobol (where a variable need not be declared as an aggregate to store an aggregate value) and in languages where references to statically-defined sub-ranges of data such as arrays or strings are allowed.
Owner:IBM CORP
Parallelization security hole detecting method based on function call graph
InactiveCN102567200AEasy to analyzeEasy to detectSoftware testing/debuggingPlatform integrity maintainanceCall graphAccessibility
The invention relates to a parallelization security hole detecting method based on a function call graph, which is characterized in that a function set to be detected is determined by analyzing the function call relation in a C language module, instrumentation and assert analysis are performed for the function set by means of the preprocessing technology, and then security holes of a program are detected by the aid of model checking and the parallelization technology. The method mainly includes the steps: generating the function relation call graph, and determining C function information to be detected by analyzing the function relation call graph; extracting attribute information of a buffer area related to C program source codes by the aid of the constraint analysis technology, and inserting corresponding ASSERT statement information in a variable declaration, an assignment and a function call point by means of the attribute information of the buffer area; and performing accessibility judgment for the instrumented codes, and analyzing whether a dangerous point in the program includes an accessible path to discover the security holes in the source codes or not. The method detects the security holes such as buffer area overflow and the like by combining the constraint analysis static detecting technology, model checking and the parallelization technology, and the detecting precision of the method is higher than that of the general static detecting technology.
Owner:BEIHANG UNIV
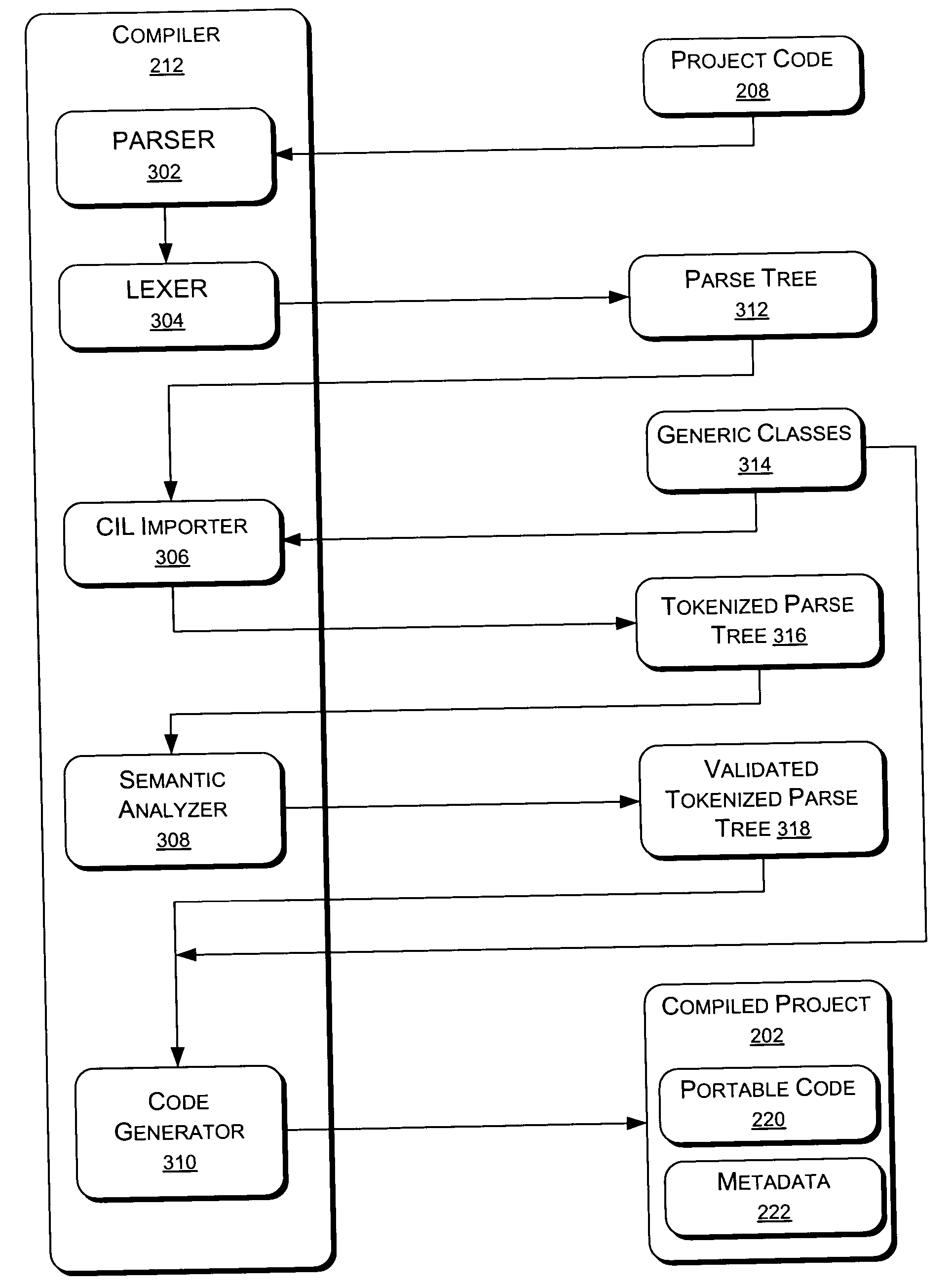
Compiling source code using generic classes
A method includes receiving a portion of JAVA™ language software having a declaration of an instance of a generic class, parsing the declaration into a token corresponding to the generic class, and generating an intermediate language code block corresponding to the parsed declaration. The intermediate language code block is executable by a runtime engine. A system for compiling includes a parser receiving JAVA™ language source code having an instruction referencing a generic class and specifying a type of the generic class, and a code generator generating intermediate language code representing the source code.
Owner:MICROSOFT TECH LICENSING LLC
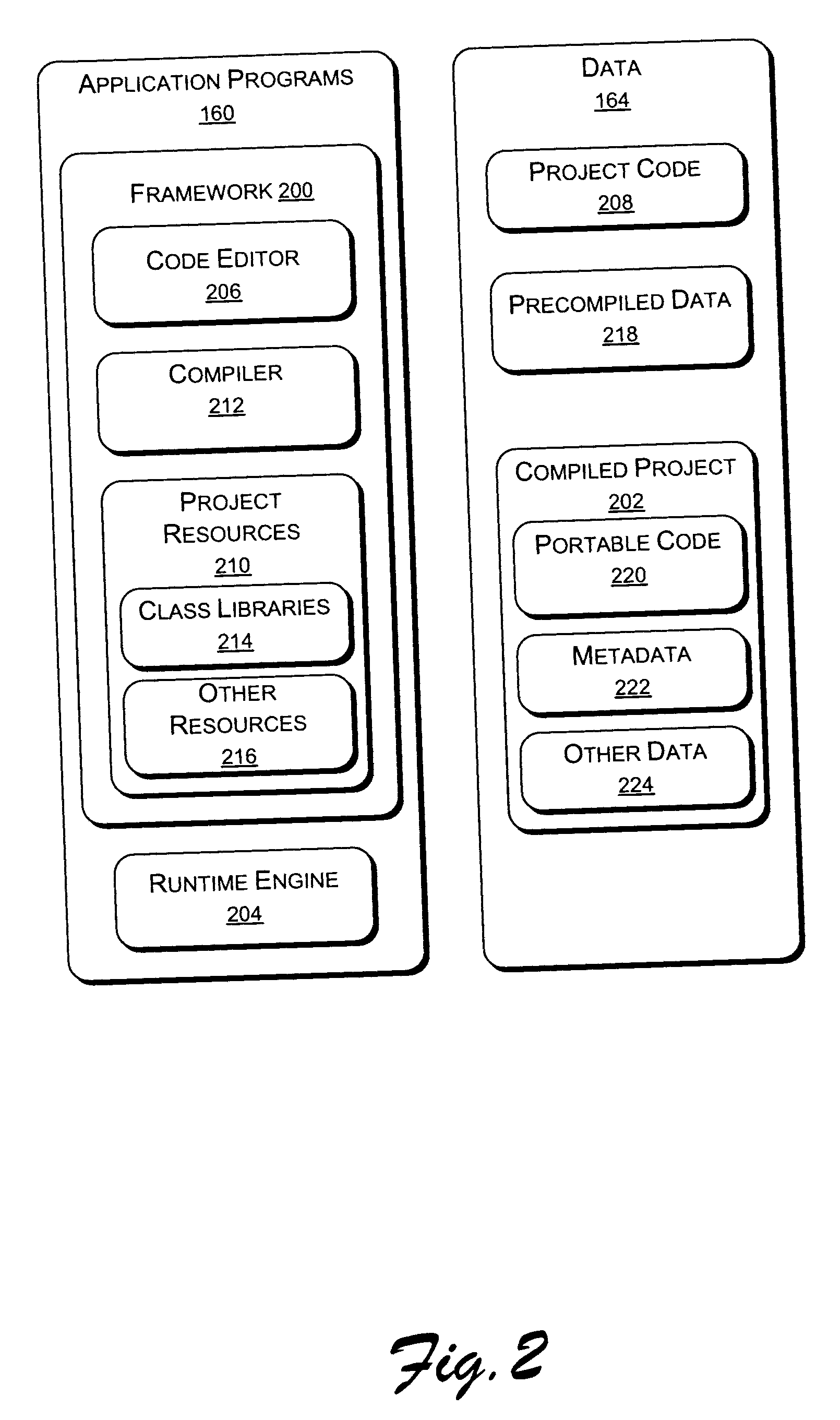
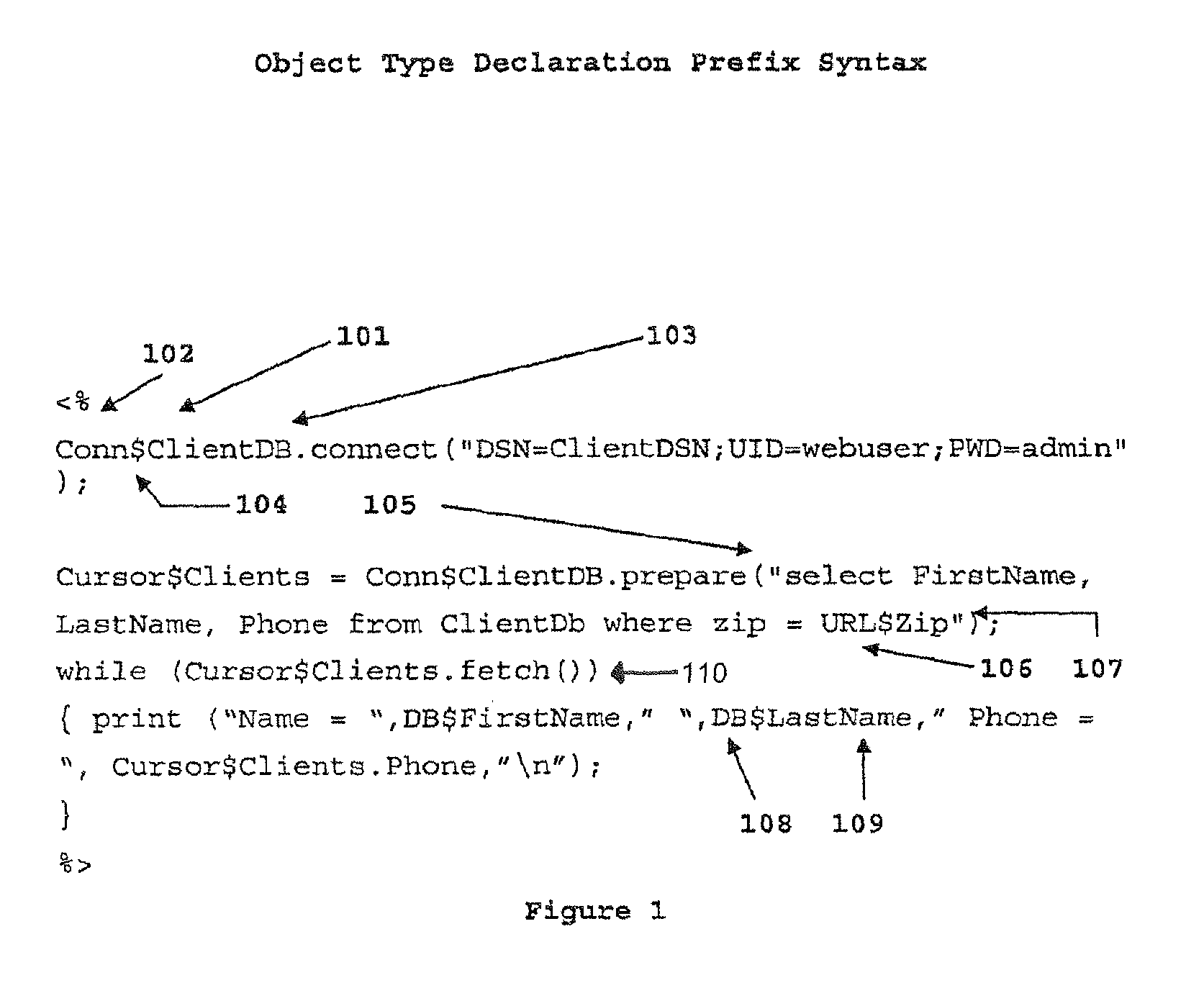
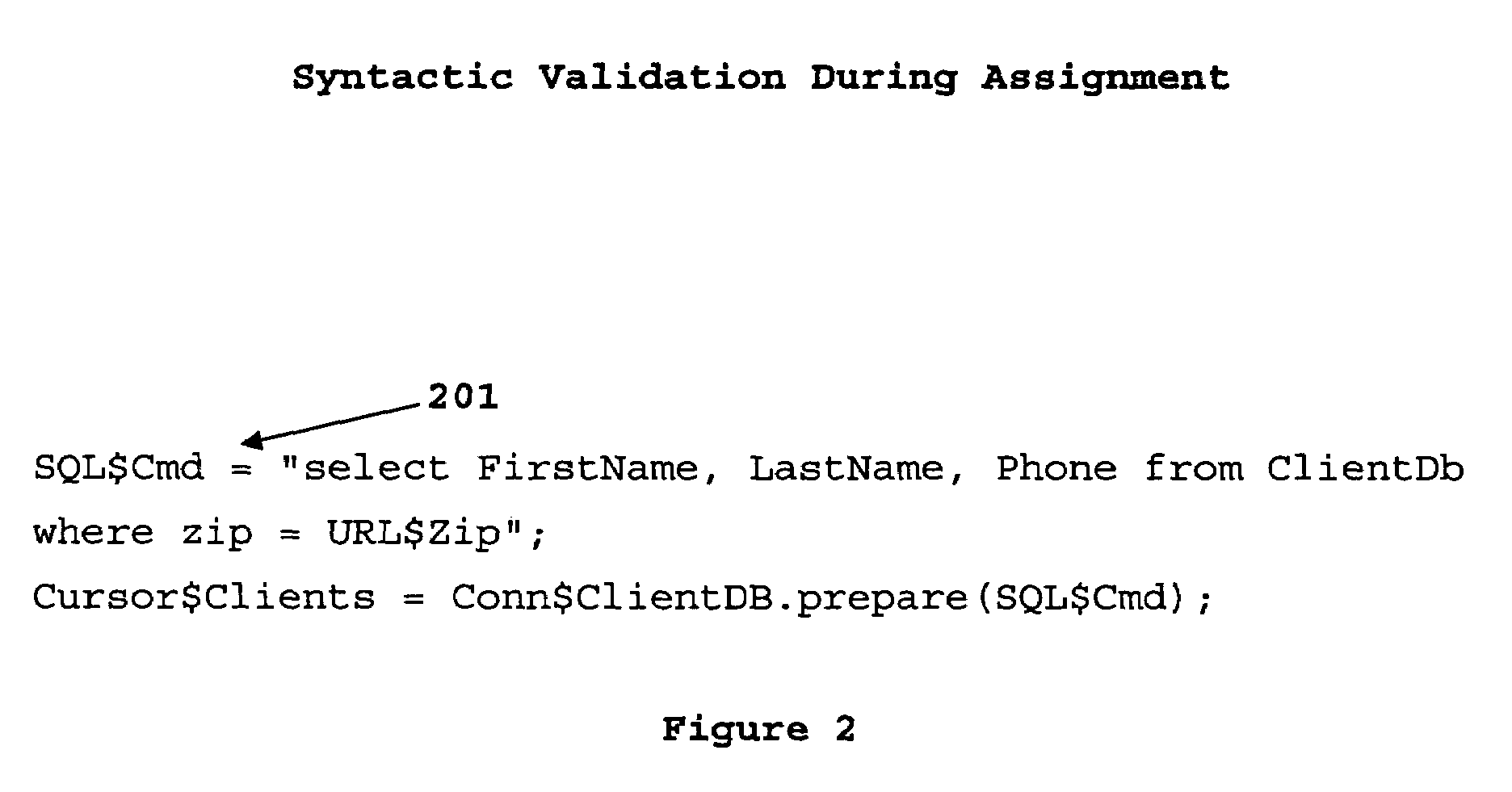
Object type-declaration prefix syntax
InactiveUS7539973B2Sure easyIncrease speedSoftware engineeringSpecific program execution arrangementsSelf-documentingUniform resource locator
A programming language syntax that embeds object type declaration in the object name. The objects are self-documenting because its object type is embedded in each object. In one embodiment, the object type-declaration prefix precedes the object name and explicitly declares the object type information. For example, a SQL object FirstName, may be implemented as SQL@FirstName, a URL object may be implemented as URL@FirstName, environment object from an environment table may be implemented as ENV@user.
Owner:HODGE BRUCE
Declarative computer programming language method and system
ActiveUS7836428B2Great degree of power and flexibilityHigh level of abstractionSoftware engineeringSpecific program execution arrangementsExtensibilityWeb site
Owner:III HLDG 3
Method for modifying the assembly output of a compiler
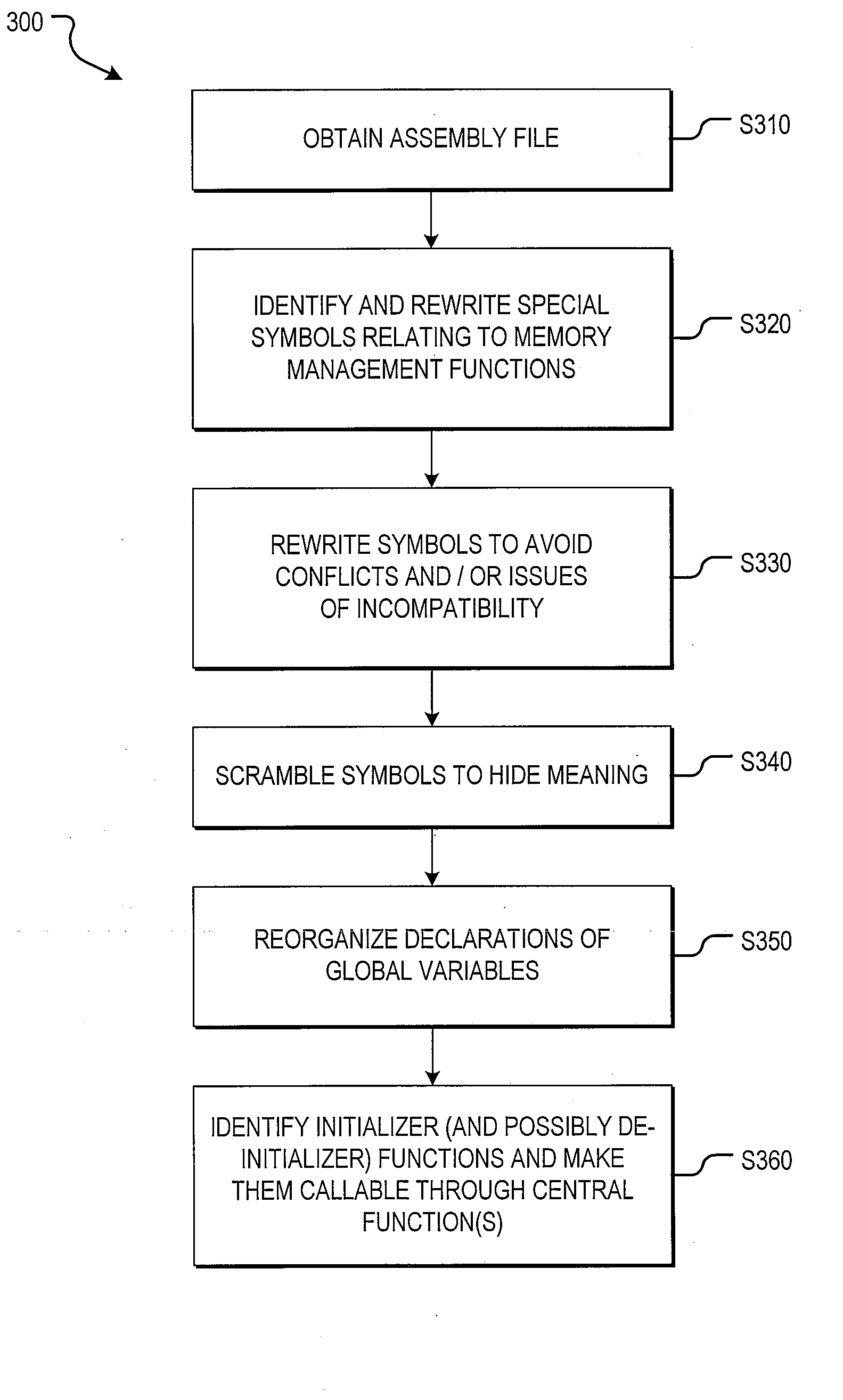
The present invention performs manipulations on the assembly file level. As a compiler outputs an assembly file, the assembly file may be inspected and modified before it is sent to the assembler. One or more of the following modifications may be made to the assembly file: rewrite certain symbols, scramble program symbols, reorganize declarations of global variables so that their layout and default values are known prior to linking, and identify initializer and de-initializer functions in order to make them callable through central initialization and de-initialization functions, respectively.
Owner:OPERA SOFTVEAR AS
System and method for automatically declaring variables
InactiveUS20080313604A1Intelligent editorsSpecific program execution arrangementsSoftwareCode module
A system and method for declaring variables during coding of a software program. The method includes, for each variable type, defining a unique string representing a variable declaration instruction and adapting a coding module wherein, when a string representing a variable declaration instruction is typed adjacent to a new variable name, the coding module automatically generates code for the corresponding variable declaration statement for a new variable having the new variable name and the specified variable type. The method further includes defining a reserved variable declaration area in the software program and placing any code generated by the coding module for the variable declaration statement into the reserved variable declaration area. Each unique string representing a variable declaration instruction may be a prefix or suffix that may be typed adjacent to the new variable name.
Owner:IBM CORP
Language extension for light weight threading in a JVM
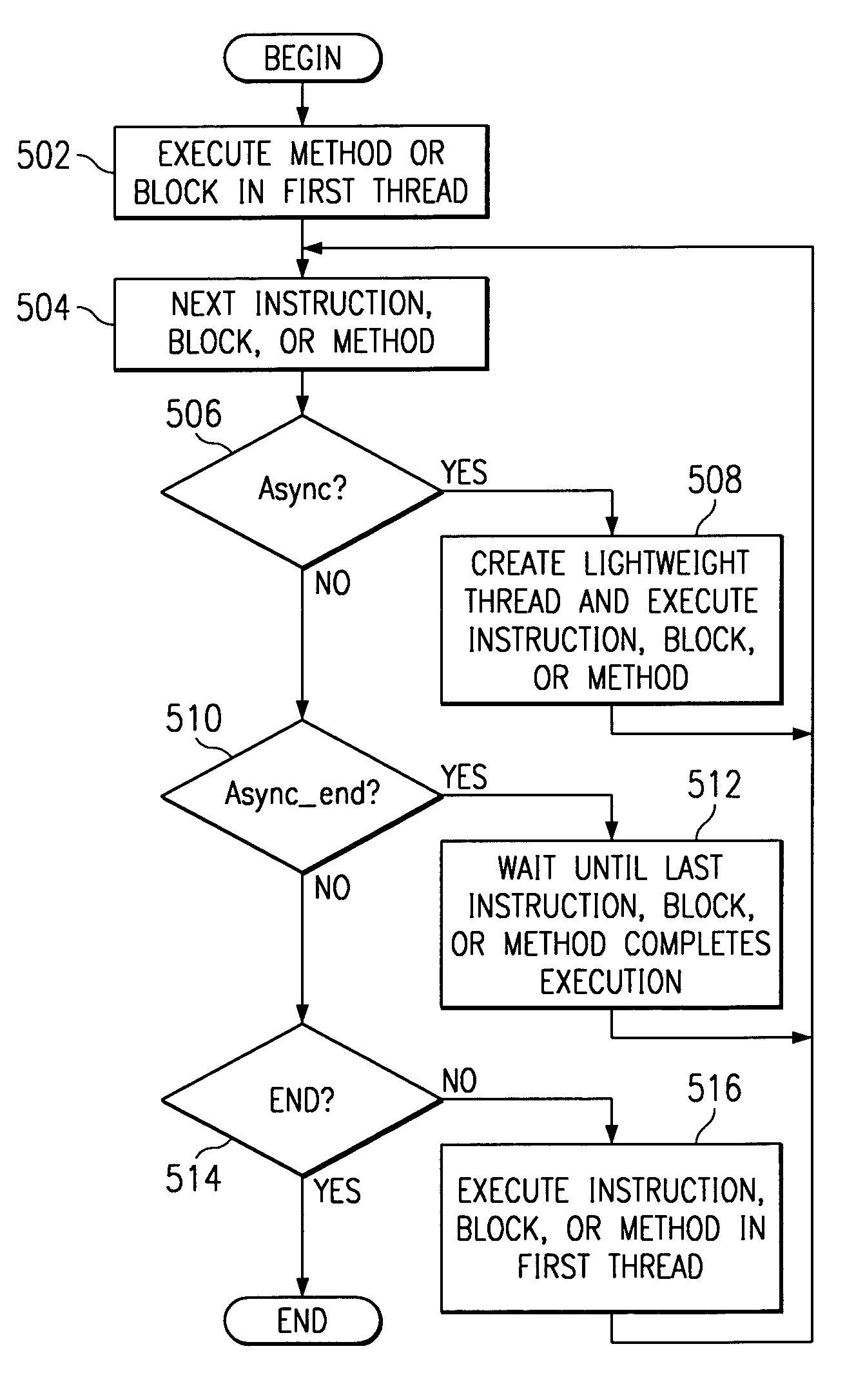
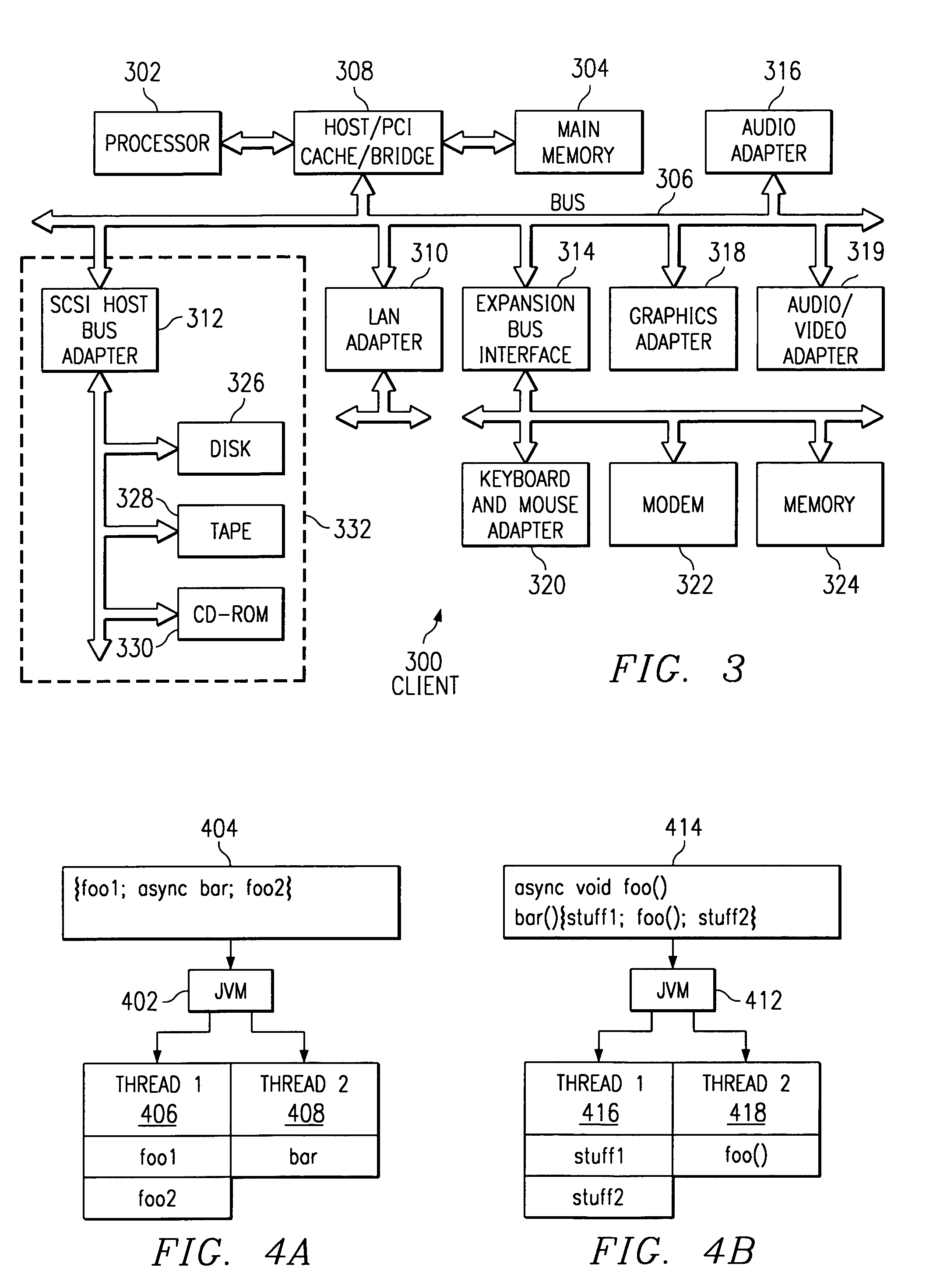
An asynchronous execution process to allow a compiler or interpreter to recognize code elements that may be executed out of order and to create a light weight thread for execution of the code element. This light weight thread may be executed on another processor in a multiprocessing environment. An “async” keyword is included in a language to indicate that a statement may be executed asynchronously with respect to the other statements at the same nesting level. The “async” keyword may also be used to modify the declaration of a function to indicate that it is safe to run the affected method out of order with other statements in a block. An “async_end” keyword is included in a language to indicate that asynchronous execution of a statement, block of code, or method must be complete before the next statement, block of code, or method may be executed.
Owner:LINKEDIN
System and method for validation of arguments provided to an application
InactiveUS20060130019A1Reduce riskReduce performance overheadPlatform integrity maintainanceSpecific program execution arrangementsBiological activationSource code
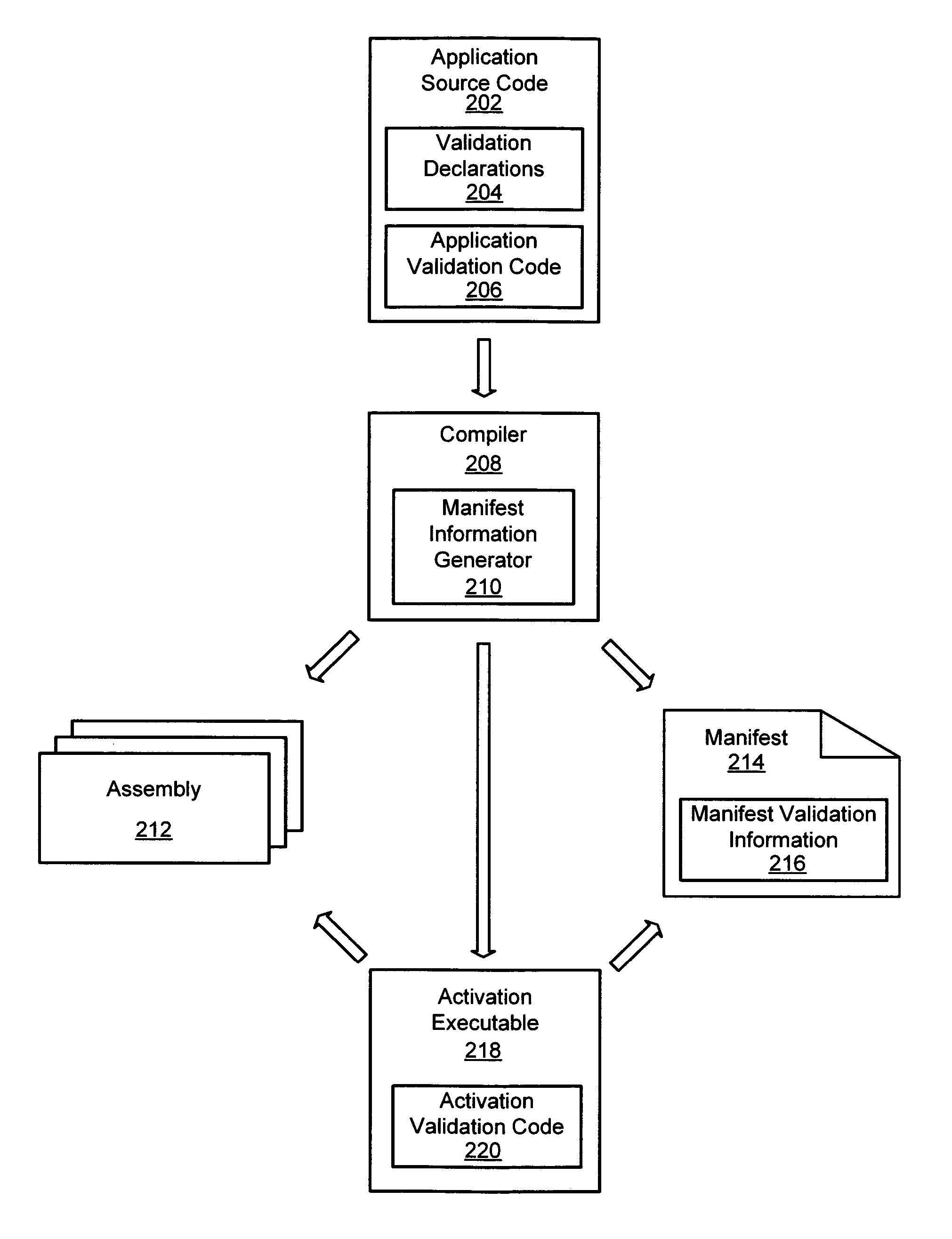
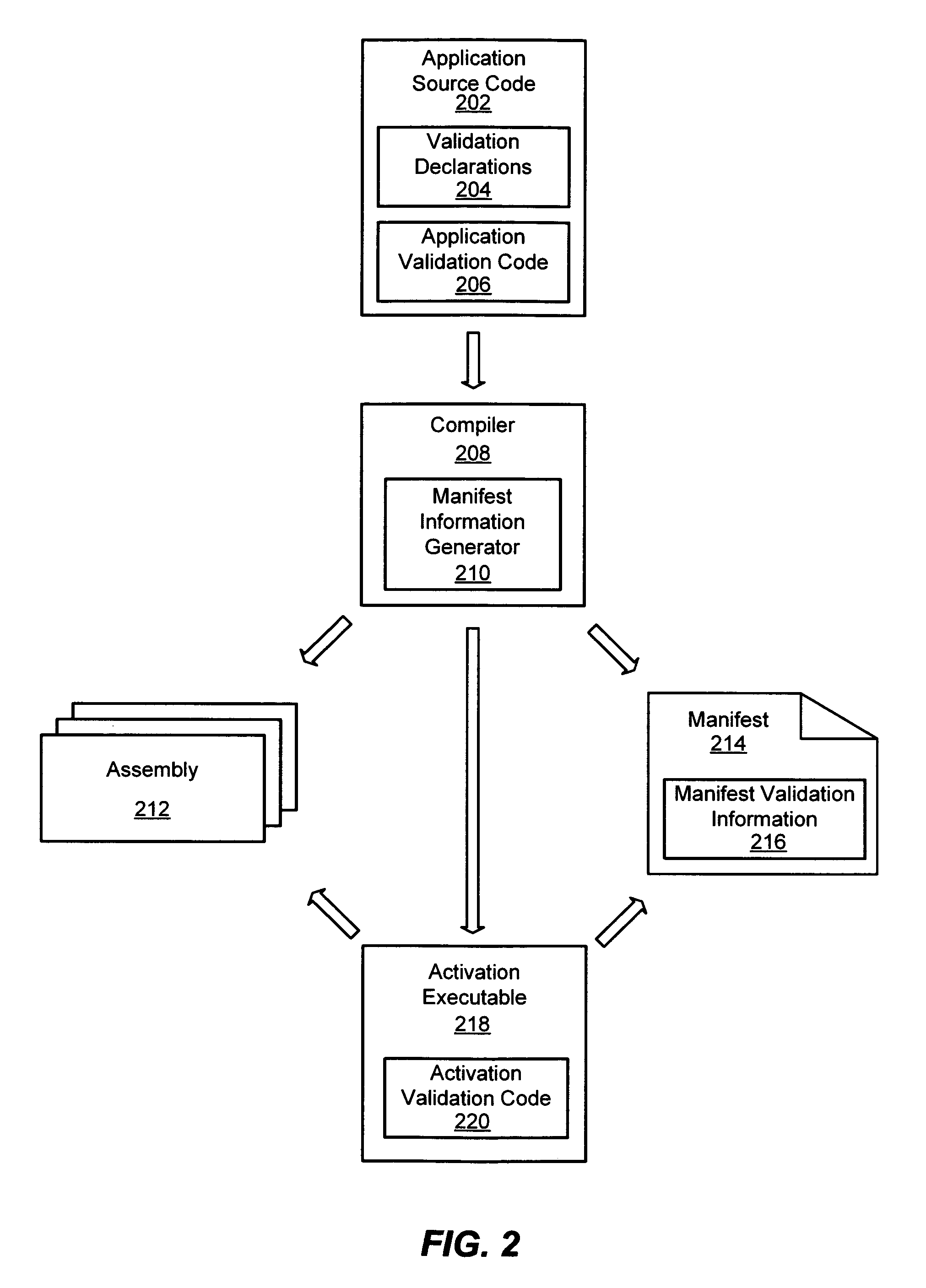
A system and method for validating arguments in a request to activate an application is provided. An application may include declarations with information for validating arguments provided with a request to activate the application. A compiler may then compile the source code of the application to generate an assembly with information for validating the arguments and may also generate an entry in a manifest with information identifying the assembly with the information for validating the arguments. The compiler may also generate an activation executable with executable code used for validating the arguments before the application may be executed. When a request may be received with arguments for activation of the application, activation code may validate the arguments and then execute the application code which may access the validated arguments.
Owner:MICROSOFT TECH LICENSING LLC
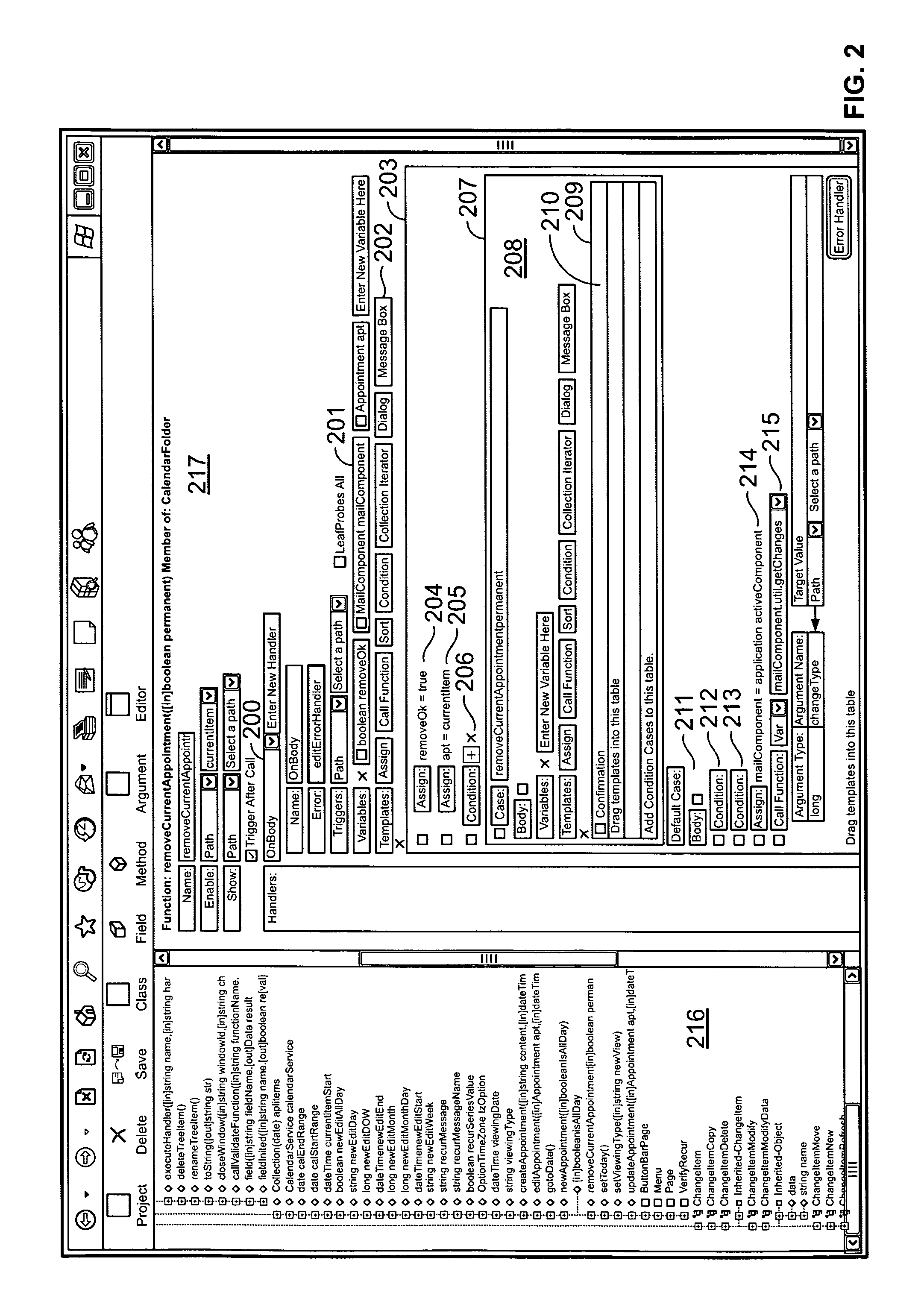
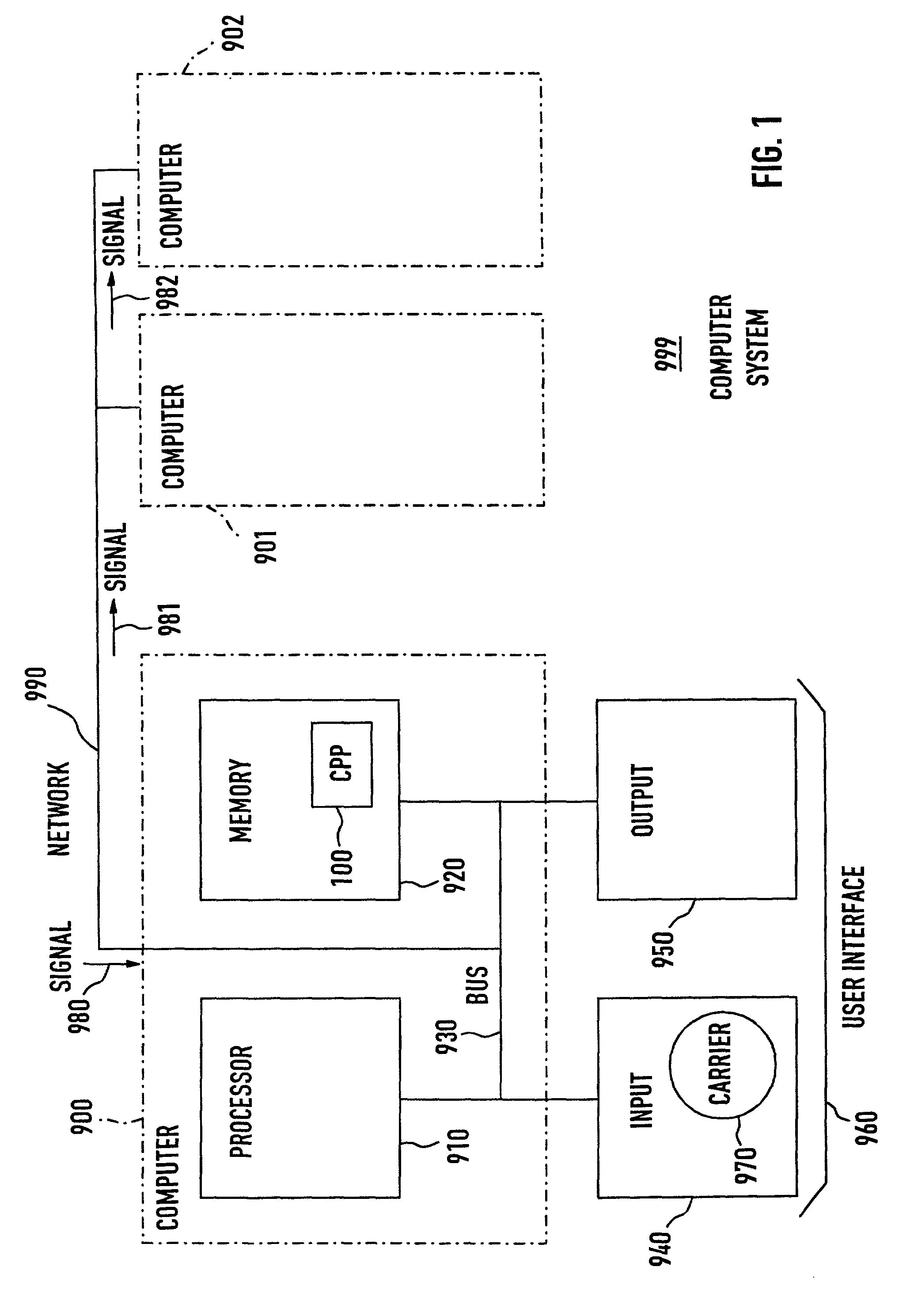
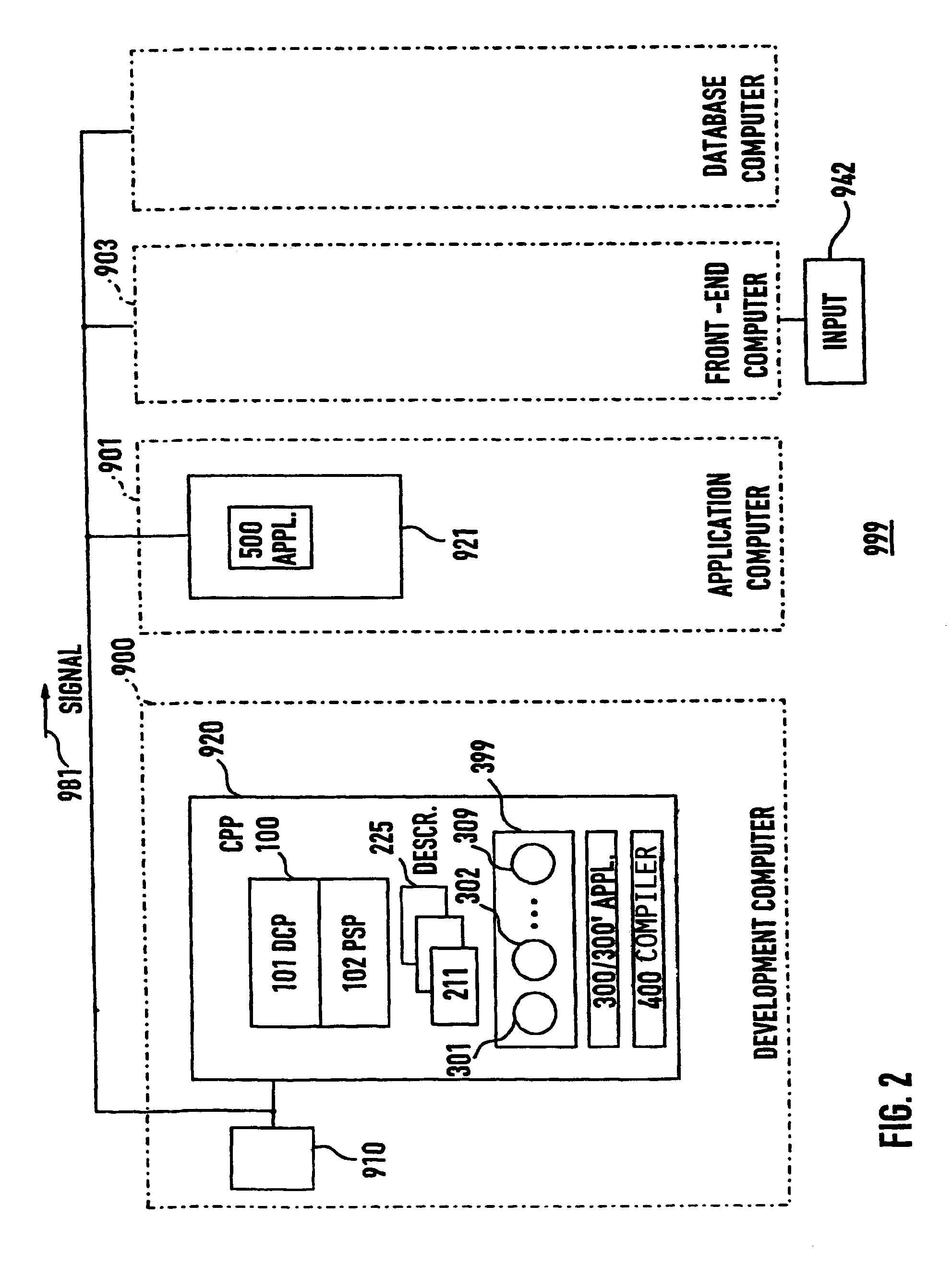
Development computer, development program for combining components to applications, using component descriptors related to the components, method, and computer program
ActiveUS7100148B2Specific access rightsDigital data processing detailsSoftware engineeringComponent (UML)
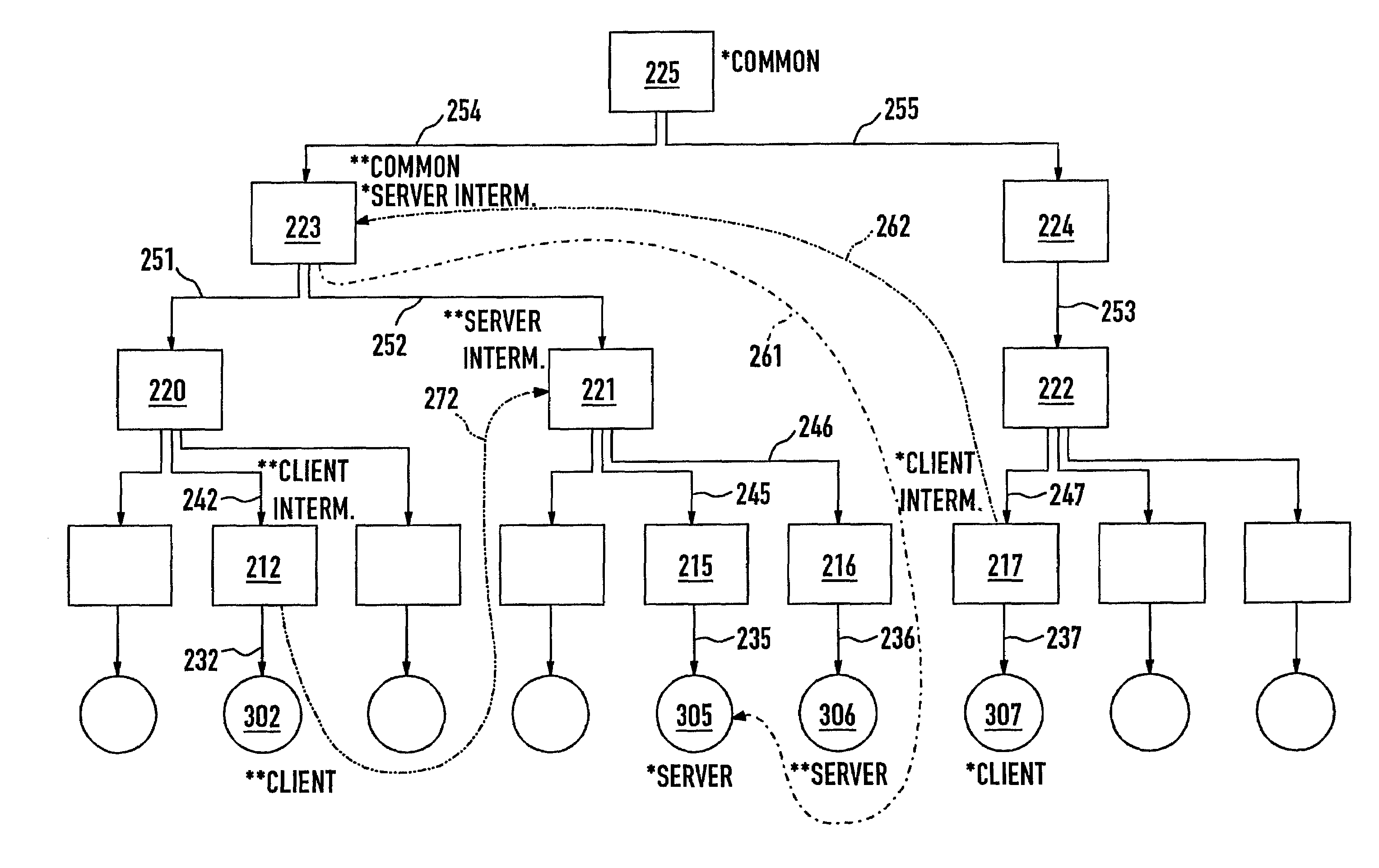
In a process of developing software applications from software components, the validity of component interactions is automatically validated by a program that determines a permission statement for any given utilization of a server component (305) by a client component (307). In a predefined structure (211–272), descriptors (211–219) are assigned (231–239) to components (301–309), descriptors (220–225) are assigned (241–255) to descriptors (211–224), some descriptors (223) have declarations to components (305), and some descriptors (217) have declarations to descriptors (223). The permission statement is true when 4 predefined conditions are all in compliance. The conditions are defined in relation to a common descriptor (225), to client (217) and server (223) intermediate descriptors, and to first (261) and second (262) declarations.
Owner:SAP AG
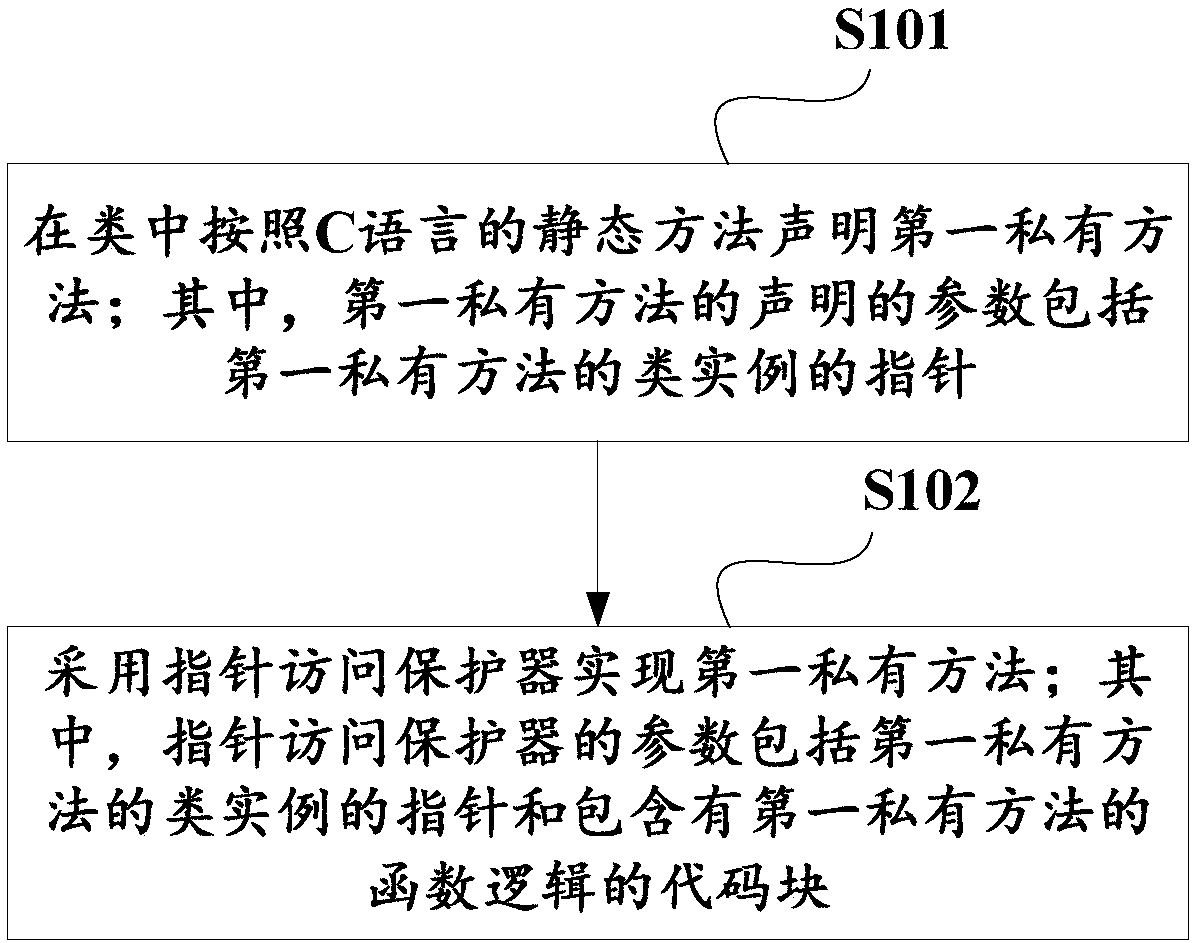
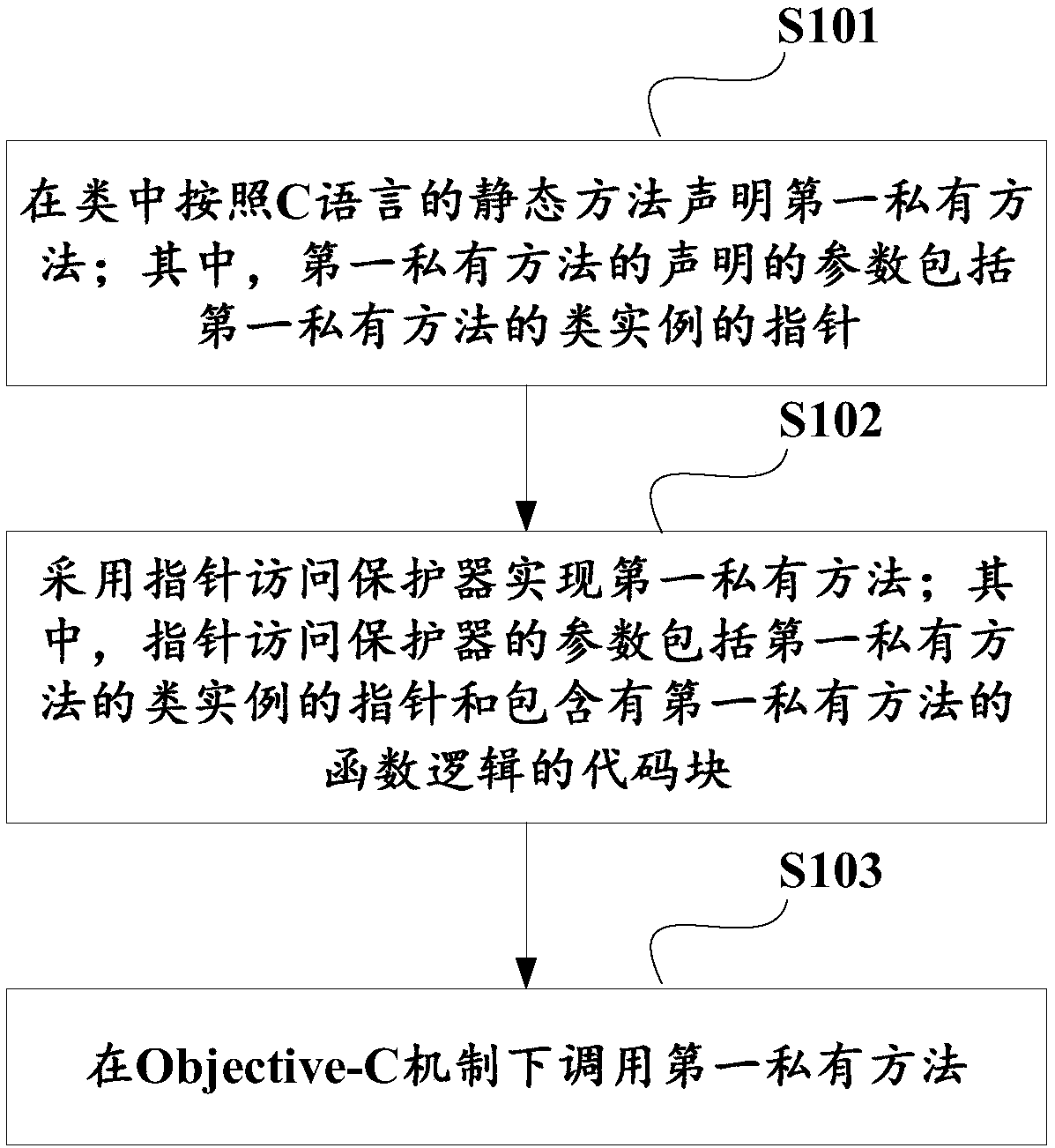
Implementing method and device and calling method and device for private method under programming environment
ActiveCN108733432AGuaranteed performanceAchieve operational performanceExecution paradigmsCreation/generation of source codePrivate variableFunction type
The invention discloses an implementation method, an implementation device, a calling method and a calling device for a private method under a programming environment. The implementation method comprises the steps of when the first private method carries a pointer of a class instance, stating the first private method in a class according to a static method of a programming language, wherein parameters of the statement of the first private method comprise a pointer of the class instance of the first private method; and implementing the private method according to a function implementation method of the programming language. When implementation of the first private method needs to access a private variable, the first private method also can be implemented by using a pointer access protector.The invention also discloses the calling method for the private method. The calling method comprises the step of using a function type converter to convert the first private method into a programmingenvironment method for calling, wherein the parameters of the function type converter comprise a function pointer of the first private method, a name identifier of the first private method, and a type identifier of the class to which the first private method belongs. According to the methods and devices provided by the invention, true sense of privatization of the private method under the programming environment is achieved under the premise of ensuring calling performance.
Owner:ADVANCED NEW TECH CO LTD
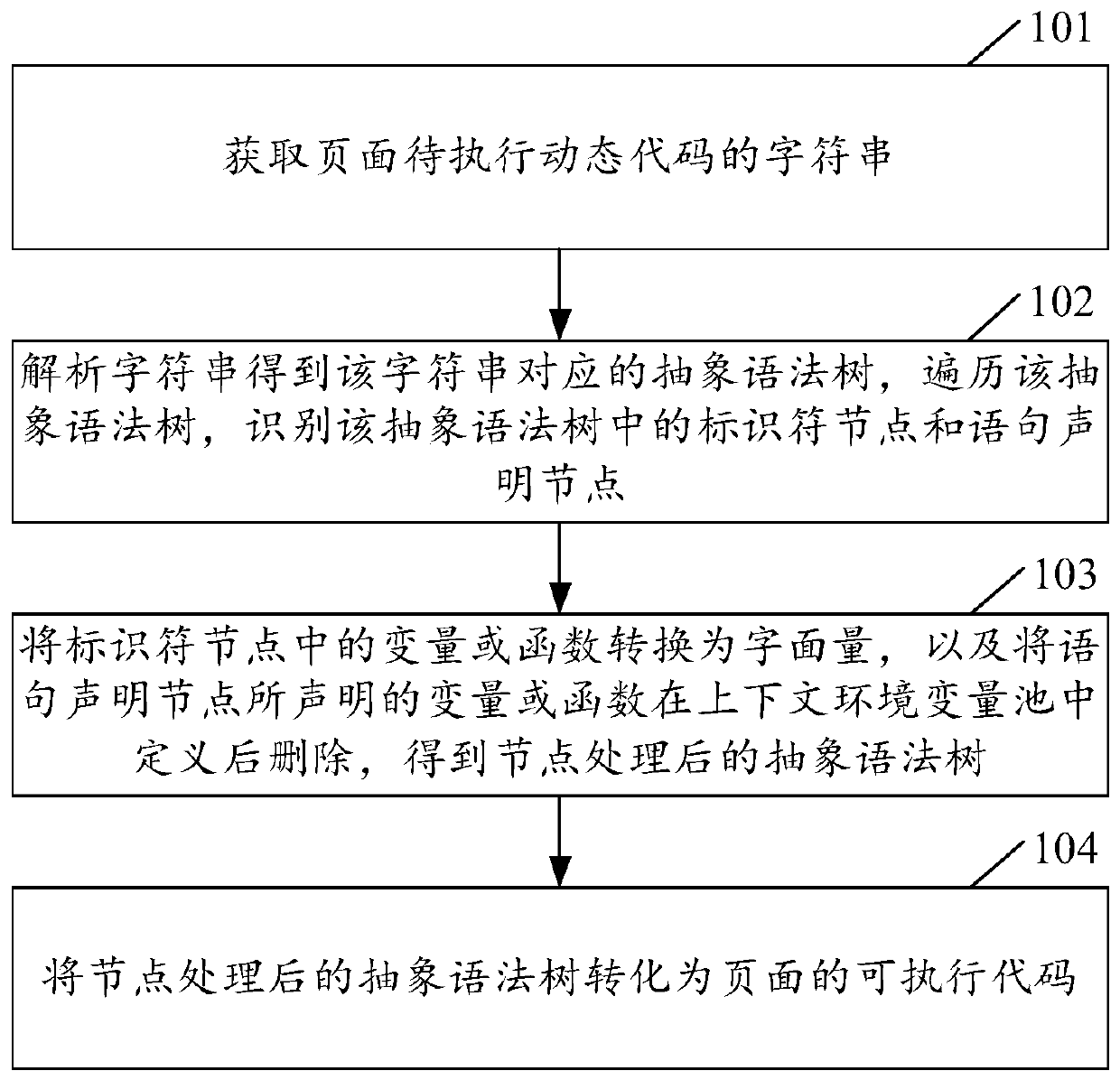
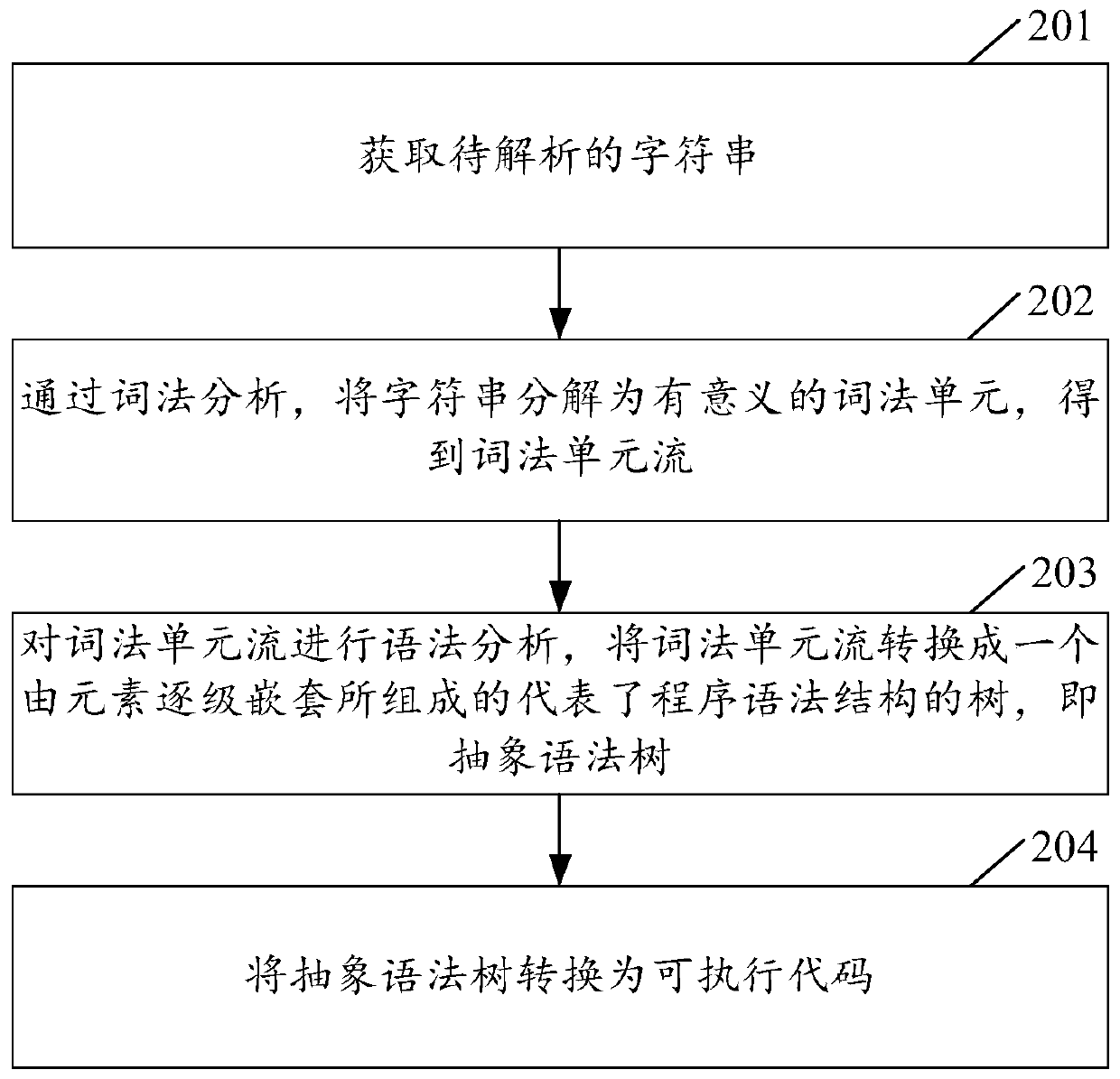
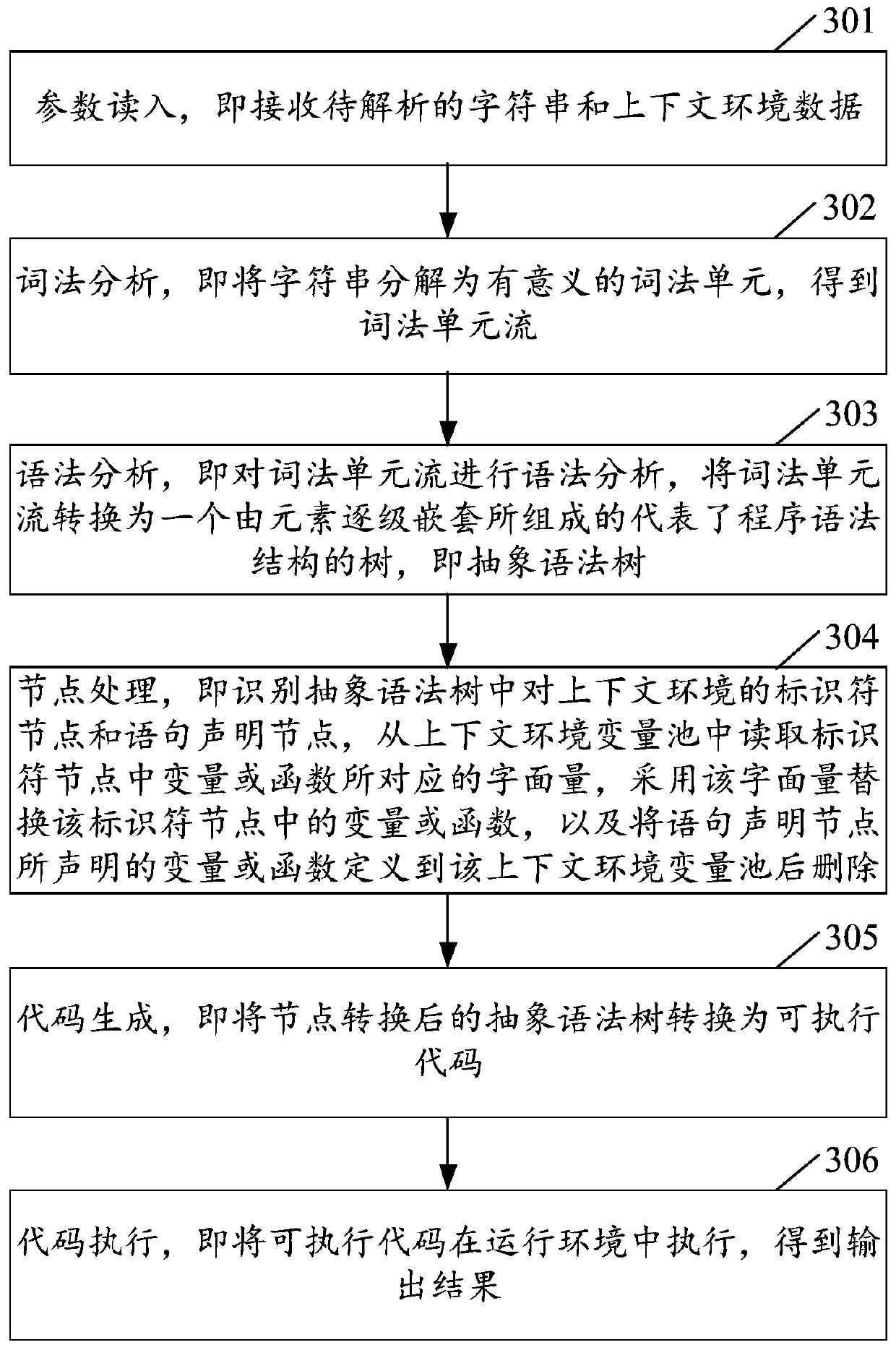
Method, device and equipment for executing dynamic codes on page and storage medium
PendingCN111045678AEliminate dependenciesAvoid missing reference exceptionsTransformation of program codeTheoretical computer sciencePool
The invention relates to a page execution dynamic code method and device, page execution dynamic code equipment and a storage medium. The method comprises: obtaining a character string of a to-be-executed dynamic code of a page; parsing the character string to obtain an abstract syntax tree corresponding to the character string, traversing the abstract syntax tree, and identifying an identifier node and a statement declaration node in the abstract syntax tree; converting variables or functions in the identifier nodes into literal quantities, defining the variables or functions declared by thestatement declaration nodes in a context environment variable pool, and deleting the variables or functions to obtain an abstract syntax tree processed by the nodes; and converting the abstract syntaxtree processed by the node into an executable code of the page. The invention is used for solving the problem that after the dynamic code depending on the context is converted into the executable code through the abstract syntax tree, when the executable code is operated by a component of a page, wrong interaction is generated, and loss is caused to a user.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
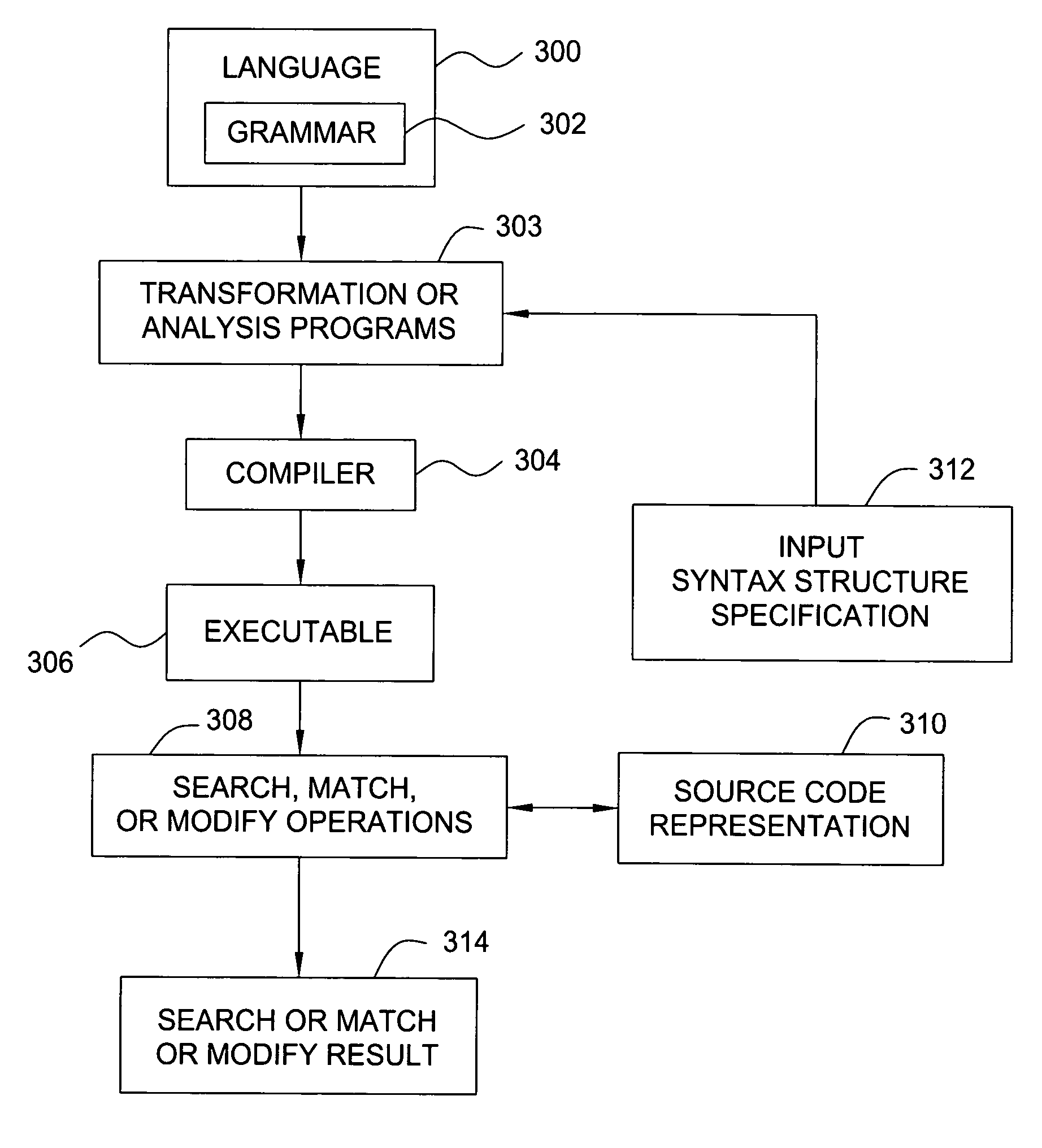
Technique for constructing syntax-directed search and modifications in program transformation systems
A front end component and a technique are provided. The front end component allows a transformation rule writer to specify syntax structure of interest, as well as what action to take when a syntax structure of interest is found. Example syntax structures include function call, variable declaration, math expression, etc. Typical actions include matching, replacement, or copying. The technique allows transformation tool writers to translate the specification into actual query and manipulation commands on the program representation. It is structured to be target language agnostic and, therefore, can be easily re-targeted to different programming languages.
Owner:WSOU INVESTMENTS LLC
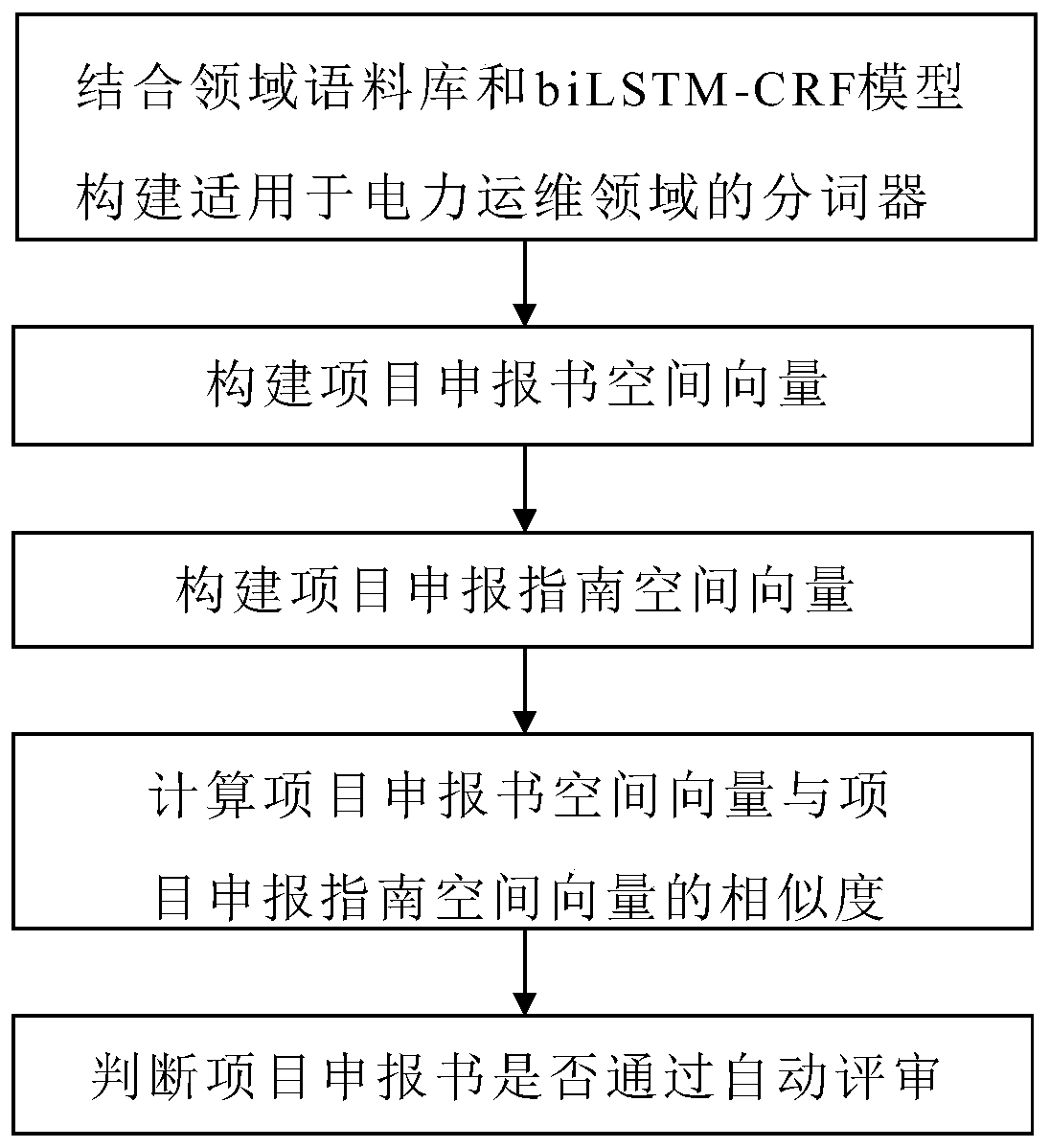
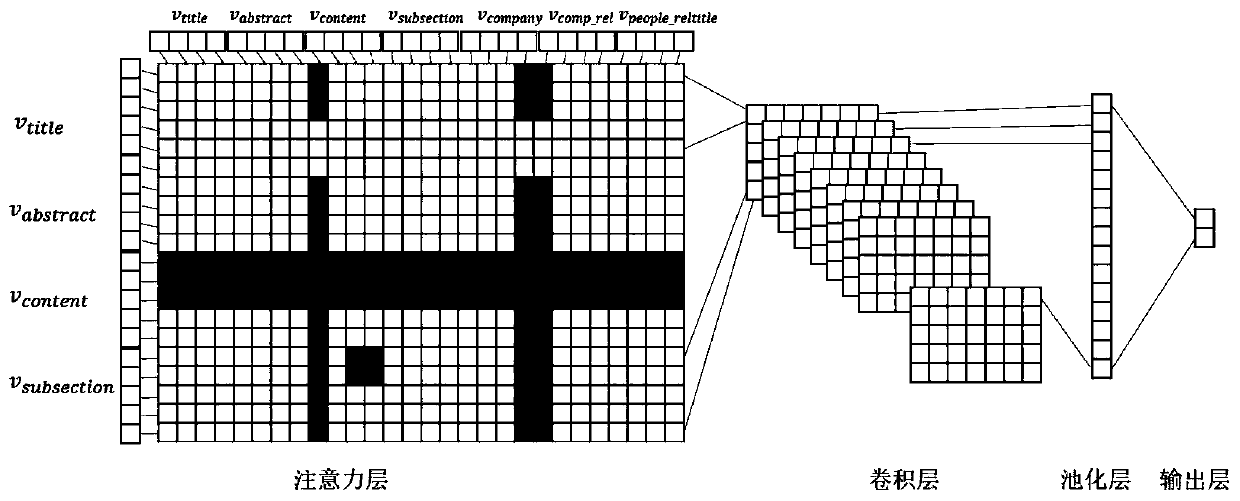
Operation and maintenance project management method based on intelligent word segmentation and deep learning
ActiveCN110852089AShorten the reporting periodOptimize the declaration processNatural language data processingNeural architecturesEngineeringProject management
The invention discloses an operation and maintenance project management method based on intelligent word segmentation and deep learning. The method comprises the steps of performing intelligent word segmentation on a declaration text and a declaration guide text in a project declaration according to a domain corpus biLSTM-CRF model; constructing a project declaration form space vector and a project declaration guide space vector; calculating a similarity value between a project declaration form space vector and a project declaration guide space vector through a convolutional neural network enhanced by an attention mechanism; finally, judging whether the project declaration passes automatic review or not through the similarity value. The project declaration process can be optimized, the project declaration period can be shortened, meanwhile, the declaration labor cost can be reduced, and the production efficiency can be improved.
Owner:STATE GRID CORP OF CHINA +1
Custom logic method and system using domain-specific language, and readable medium
ActiveCN112231068AImprove efficiencyImplement customizationSoftware simulation/interpretation/emulationCode compilationUser inputSoftware engineering
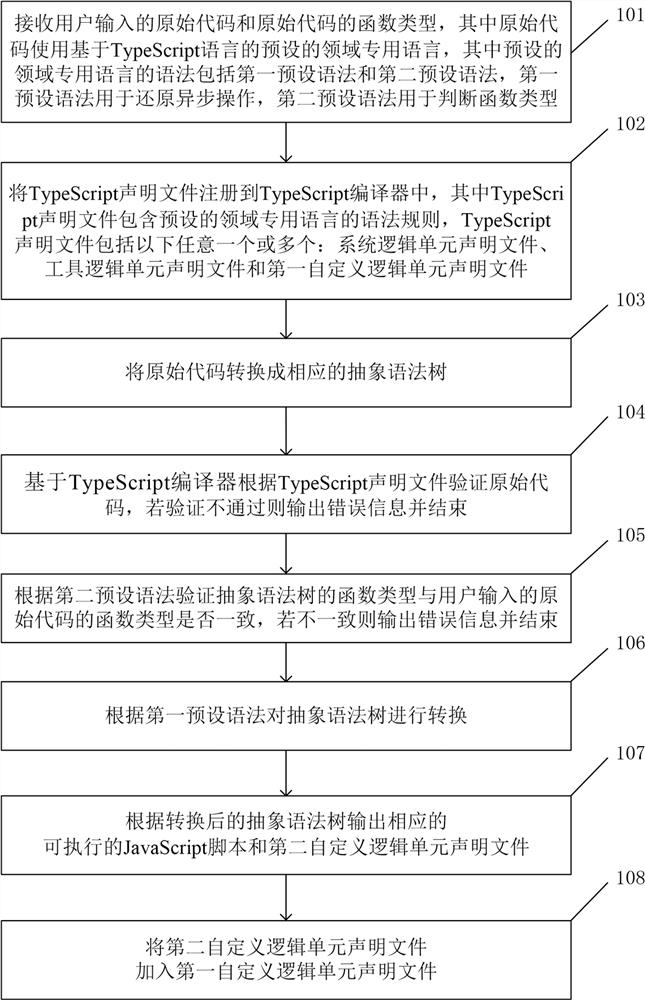
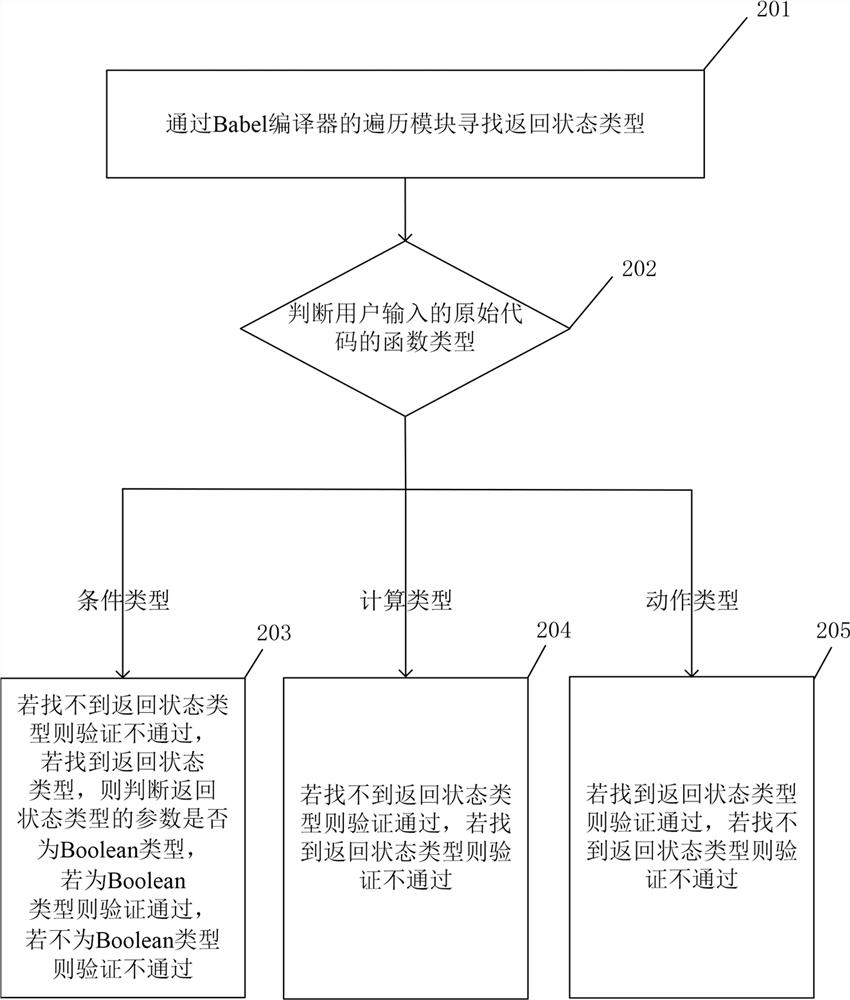
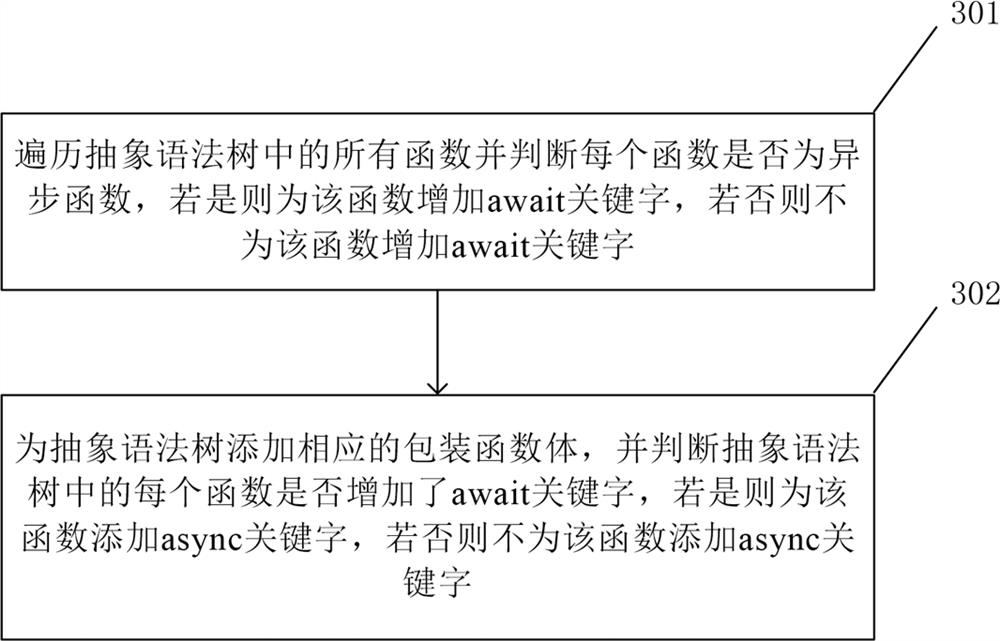
The invention provides a custom logic method and system using domain-specific language, and a computer readable medium. The method comprises the steps: receiving an original code input by a user and afunction type of the original code, wherein the original code uses a preset domain-specific language based on a Type Script language, and grammars of the preset domain-specific language comprise a first preset grammar and a second preset grammar; registering the TypeScript statement file into a compiler; converting the original code into an abstract syntax tree; verifying the original code according to the Type Script declaration file; verifying whether the function type of the abstract syntax tree is consistent with the function type of the original code input by the user or not according toa second preset syntax; converting the abstract syntax tree according to a first preset syntax; and outputting the executable script according to the abstract syntax tree. The method can achieve custom complex logic with low user learning cost and is suitable for a large-scale system.
Owner:浙江太美医疗科技股份有限公司
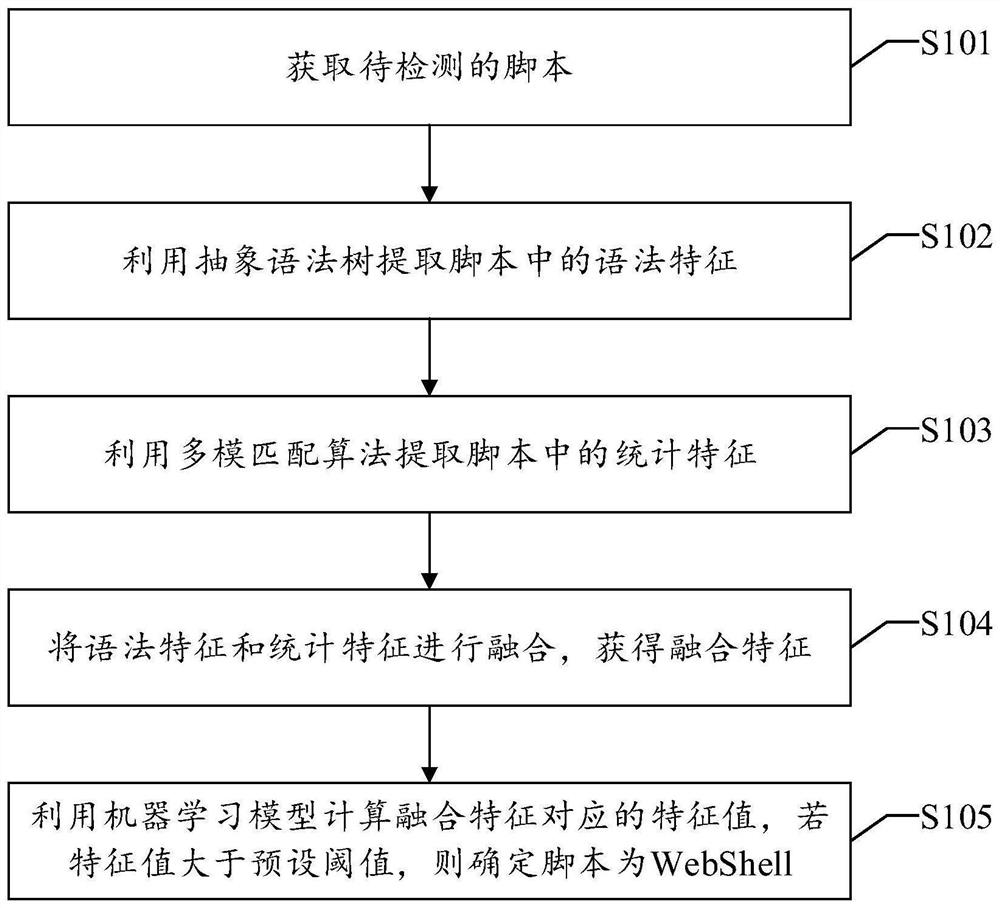
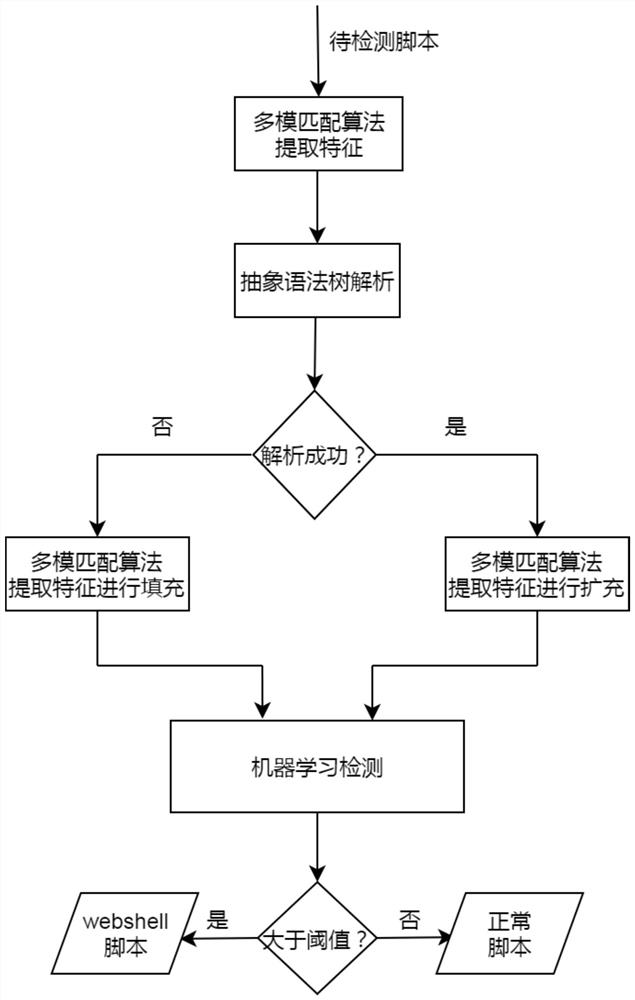
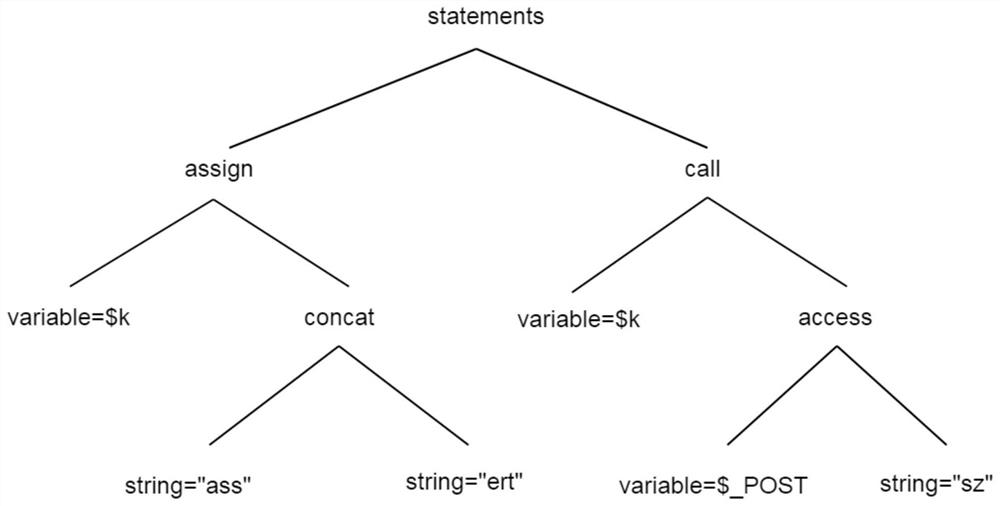
WebShell detection method, device and equipment and readable storage medium
PendingCN113094706AImprove accuracyImprove efficiencyPlatform integrity maintainanceMachine learningAlgorithmMatch algorithms
The invention discloses a WebShell detection method, device and equipment and a readable storage medium. The method disclosed by the invention comprises the following steps: acquiring a script to be detected; extracting grammatical features in the script by using the abstract syntax tree, wherein the grammatical features comprise a function dependency relationship, a class declaration and a function keyword; utilizing a multimode matching algorithm to extract statistical characteristics in the script; fusing the grammar features and the statistical features; and utilizing a machine learning model to calculate a feature value corresponding to the fused feature after fusion, and if the feature value is greater than a preset threshold, determining that the script is WebShell. According to the invention, the abstract syntax tree and the multimode matching algorithm are used for extracting the multi-dimensional features from the script, and then the features are fused, so that the features of all the dimensions complement one another, the defect of a single detection mode is overcome, missing report or false report can be avoided, and the accuracy and efficiency of WebShell detection are improved. Correspondingly, the invention discloses a WebShell detection device and equipment and a readable storage medium, which also have the above technical effects.
Owner:SANGFOR TECH INC
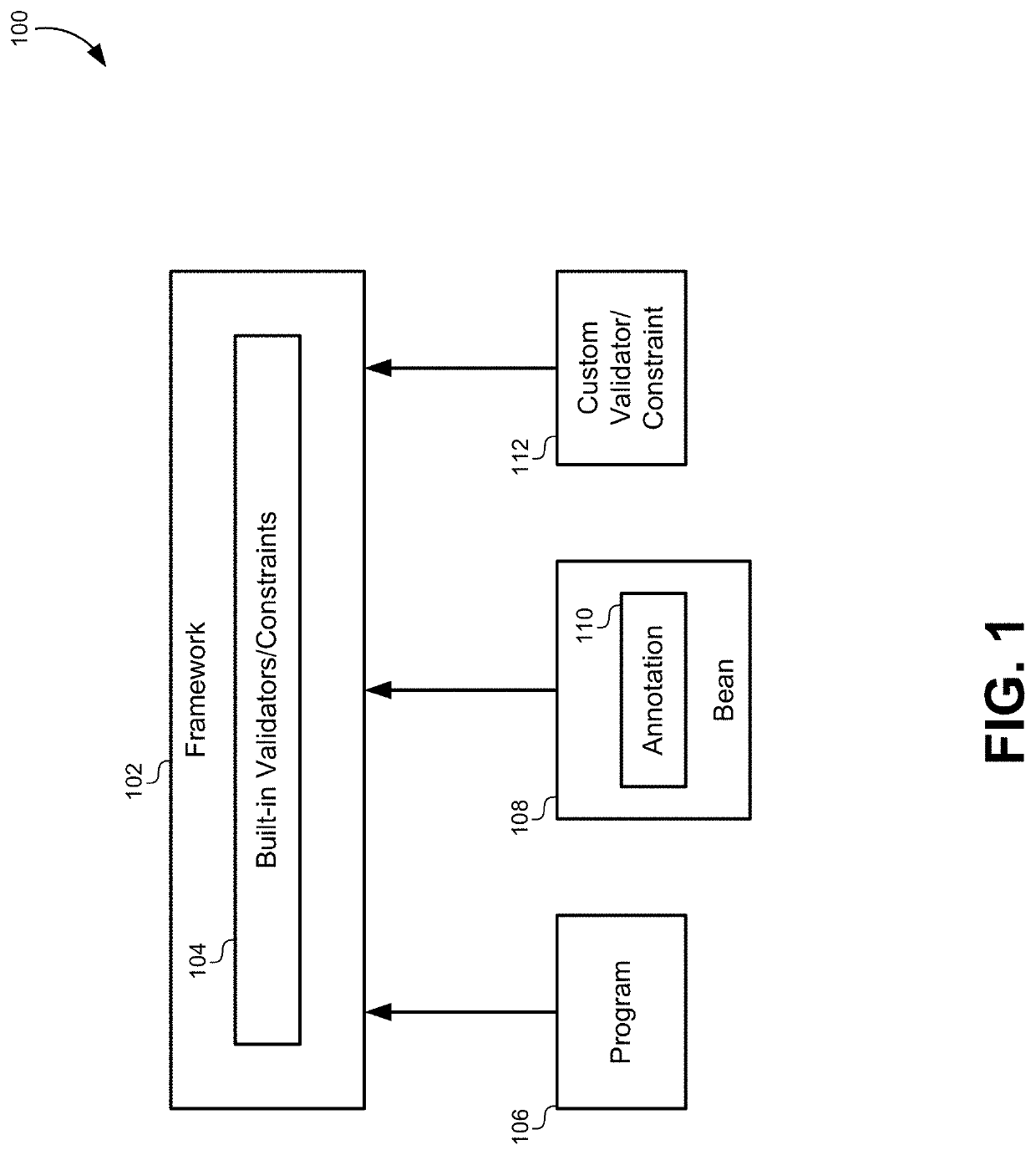
Dynamic validation framework extension
ActiveUS11113033B1Easy to addError detection/correctionSoftware designTheoretical computer scienceProgrammer
A programming language framework may be enhanced to provide for dynamic validation. Dynamic validation allows the validator function for any variable to be selected at runtime rather than statically declared at programming-time. Instead of annotating a variable with an annotation that refers to a specific validator function or constraint type, programmers can annotate a variable with an annotation that indicates that the validator function will be selected dynamically at runtime. When a runtime instance of the variable is created, the programming language framework may identify the dynamic validation annotation on the variable, and then use the runtime values in the variable to determine which validator function(s) should be used.
Owner:ORACLE INT CORP
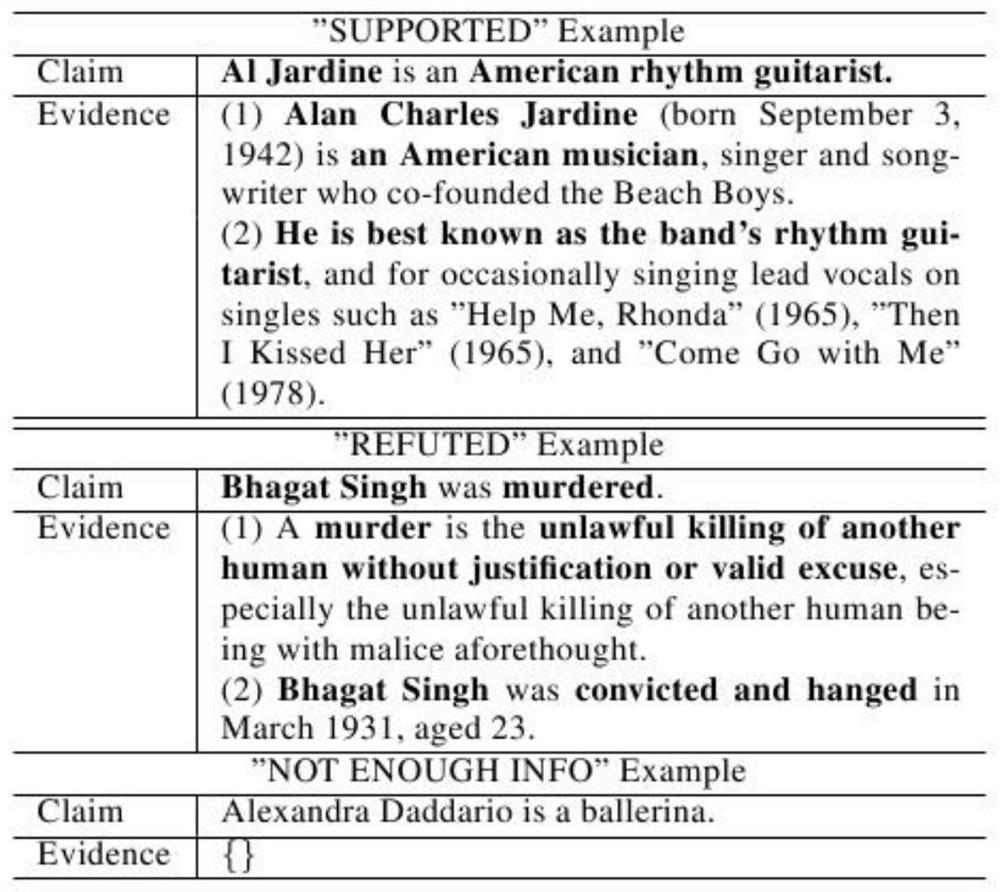
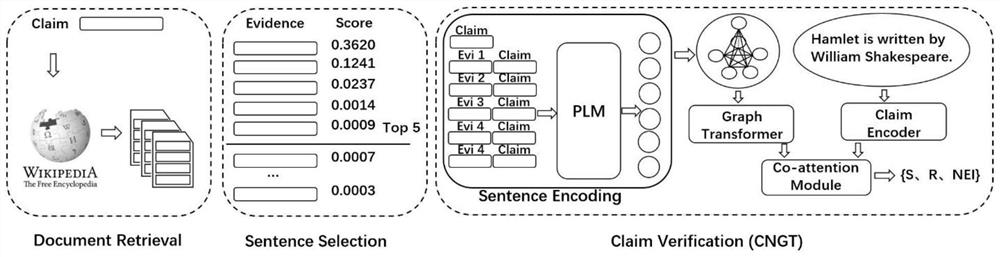
Automatic fact verification method fusing graph converter and common attention network
PendingCN114048286AImprove performanceNode said goodData processing applicationsCharacter and pattern recognitionEntity linkingEngineering
The invention discloses an automatic fact verification method fusing a graph converter and a common attention network, and belongs to the technical field of artificial intelligence. An automatic fact verification method based on deep learning is constructed by using the declaration and the retrieved evidence as input data. The method includes: firstly, recognizing entities in declarations through an entity linking method, and retrieving related documents in Wikipedia according to the extracted entities; secondly, selecting five sentences most relevant to the declaration from the retrieved document by using a sorting model as evidences; thirdly, constructing (evidence and declaration) pairs, and inputting the (evidence and declaration) pairs into the fine-tuned pre-training language model for coding; and finally, by constructing a fact verification model based on the graph converter and the common attention network, learning declarations and evidences and potential relationships between the evidences, and completing fact verification. Experimental results show that the method is superior to the existing automatic fact verification method, and meanwhile, the method has interpretability.
Owner:NANKAI UNIV
Method and system for enlarge and configuing corresponding extensible sofrware
InactiveCN100478874CTransformation of program codeSoftware maintainance/managementExtensibilityTheoretical computer science
Methods and systems are described herein for extending configuration dependent extensible software programs. Classes of a core extensible software program may be extended by adding a configuration dependent extension. The extensions may be added statically prior to compiling the core version of a software program or dynamically at runtime. The declaration of extensible core classes may include an extensibility attribute with an indication of whether the class is statically extensible or dynamically extensible. An object description language is also described herein for appropriately declaring configuration dependent extensible classes. Also, a preprocessor is described herein for processing the object description language to generate a source code representation of the extensible class declarations and their extensions. The source code representation may then be used to generate the extended version of the core software program.
Owner:MICROSOFT TECH LICENSING LLC
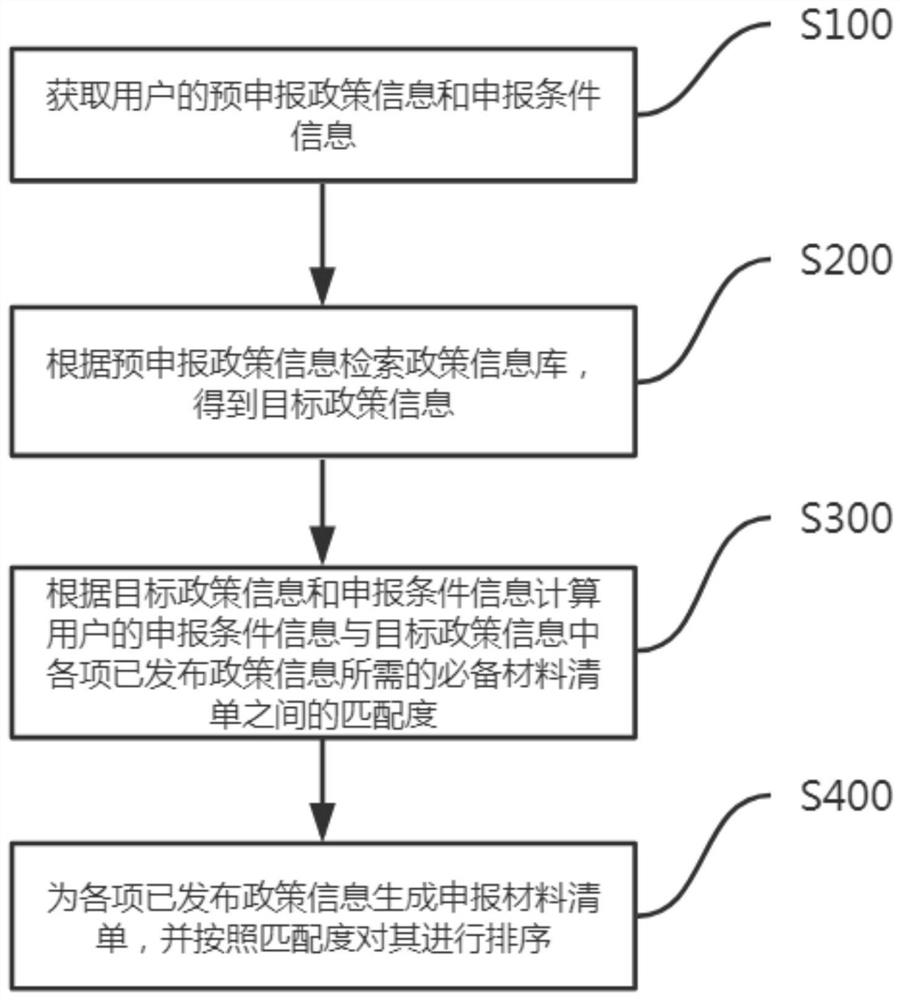
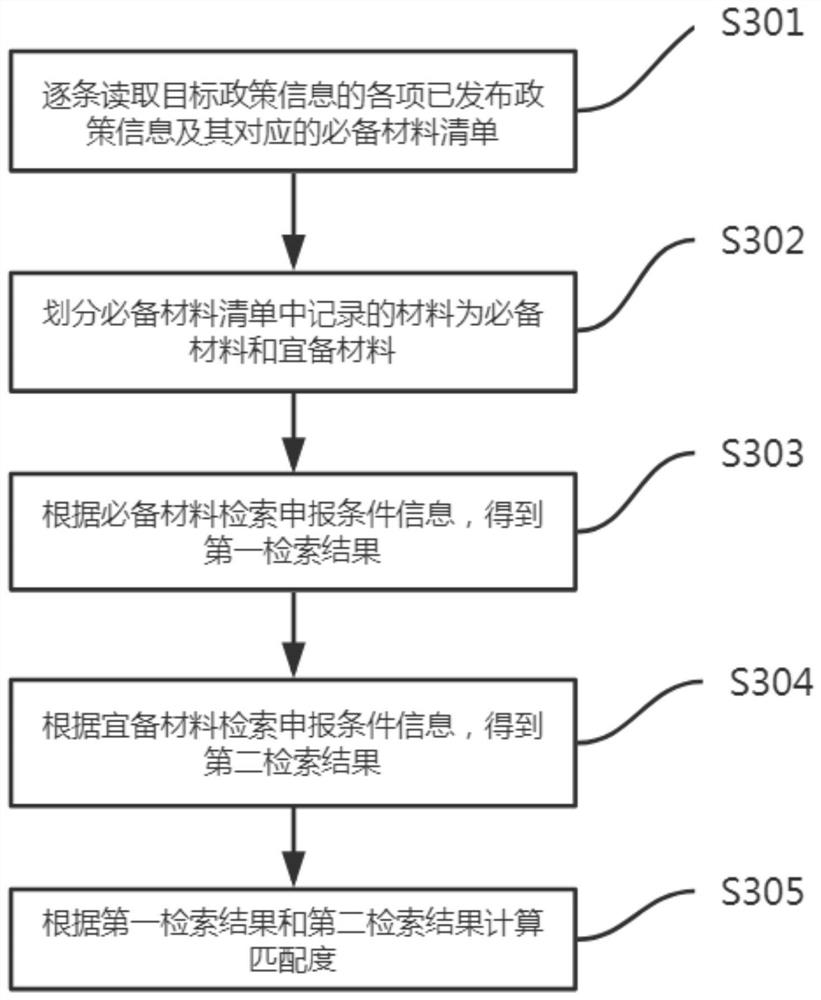
Policy matching degree calculation method and system, computer equipment and storage medium
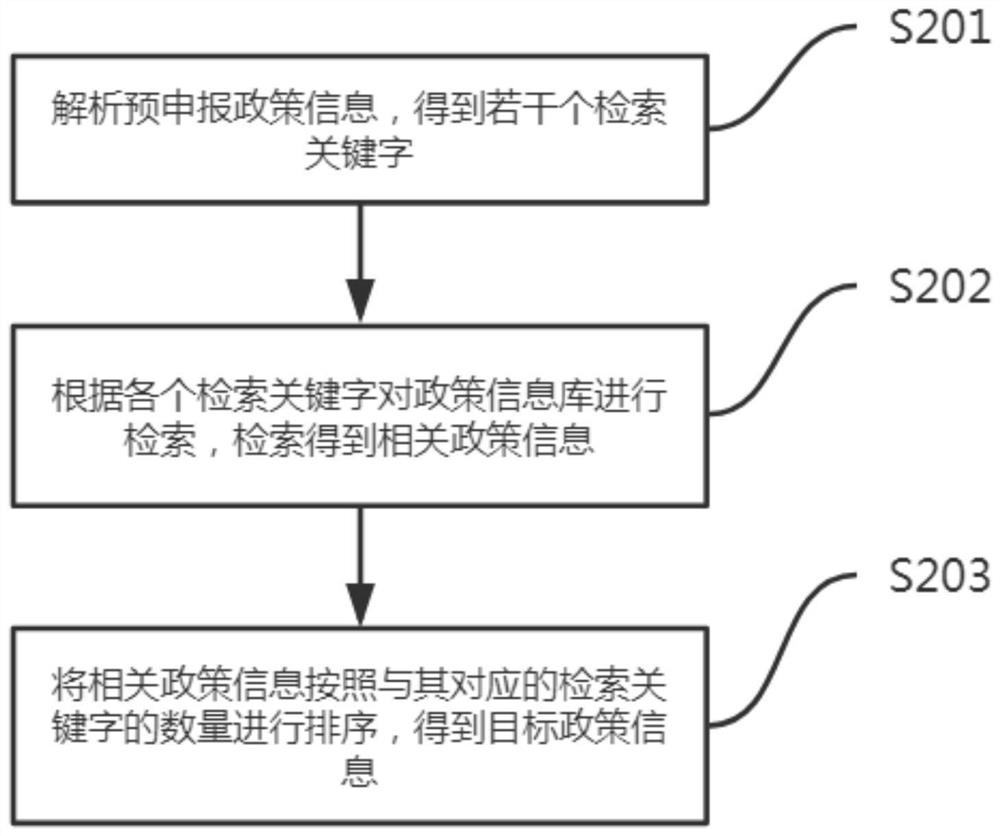
InactiveCN113255742ATroubleshoot Self-Lookup PoliciesKnow quicklyCharacter and pattern recognitionText database queryingInformation repositoryCollation
The invention belongs to the technical field of software management, and particularly relates to a policy matching degree calculation method and system, computer equipment and a storage medium, and the method comprises the steps: obtaining pre-declaration policy information and declaration condition information of a user; retrieving a policy information base according to the pre-declaration policy information to obtain target policy information; calculating a matching degree according to the target policy information and the declaration condition information; and generating a declaration material list for each published policy information, and sorting the declaration material list according to the matching degree. According to the method and system, the type of the policy to be declared by the current user is judged according to the policy information to be declared of the user, so that the related policy is determined, the matching degree is calculated according to the declared condition information of the user, and the basis for judging the policy declared possibility is provided for the user, so that on one hand, the problem that the user needs to autonomously search the policy is solved; and on the other hand, the user can be helped to quickly know the declarable policy, and a required material list is generated.
Owner:广西东创大数据有限公司
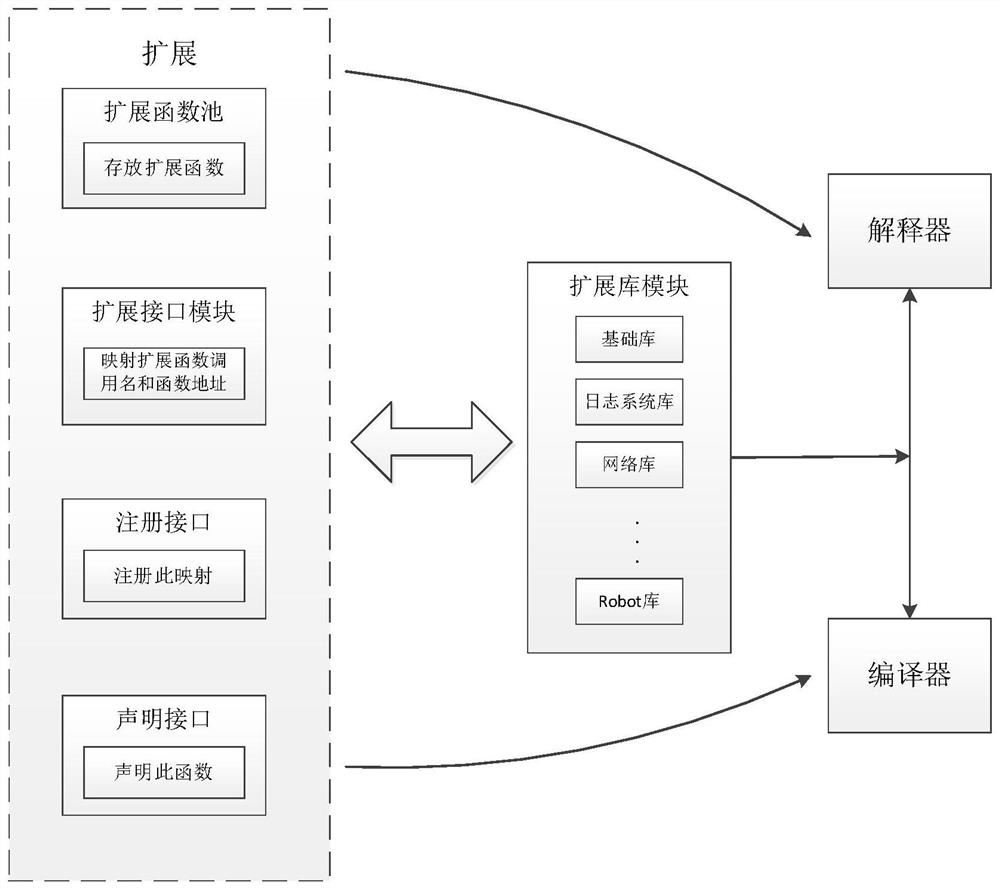
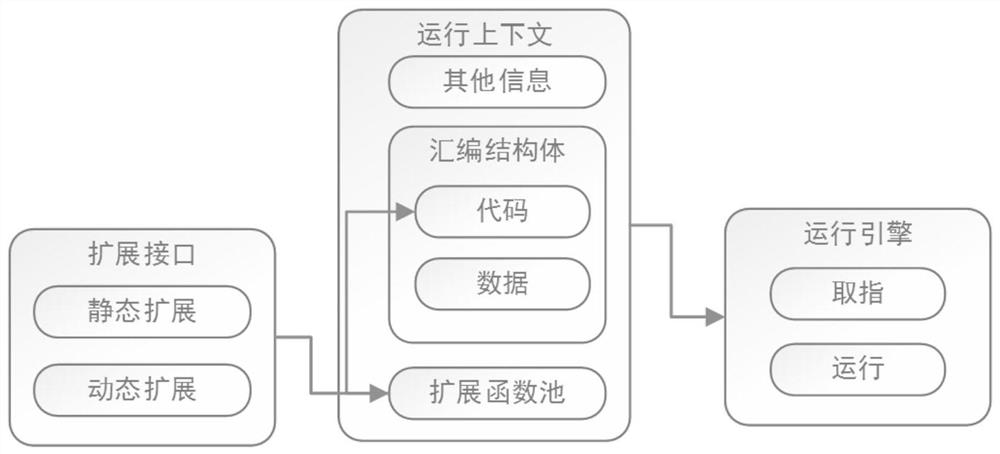
Programming system for mechanical arm program development and function extension method
PendingCN111767033AAdd supportWith secondary development functionProgramme-controlled manipulatorLink editingFunctional expansionSoftware engineering
The invention provides a programming system for mechanical arm program development and a function extension method, and the programming system comprises an extension function pool which is used for storing extension functions; an expansion interface module which is used for generating a mapping relationship between the function call name and the address based on a received mapping instruction containing the call name and the function address of the expansion function, and storing the mapping relationship; a registration interface which is used for registering the mapping relationship based ona received registration instruction containing a mapped expansion function, and adding the registered expansion function into an operation function pool; a declaration interface which is used for declaring the extension function on the basis of a received declaration instruction containing the call name of the registered extension function and storing the declaration; and an extension library module which is used for classifying the extension functions into corresponding sub-libraries in an extension library based on the attribute information of the extension functions and storing the classification information of the extension functions, wherein the extension library comprises a plurality of sub-libraries. The programming system is more convenient to integrate and has very strong expansibility.
Owner:江苏中科重德智能科技有限公司
Universal description language data system for directed acyclic graph type automatic task flow
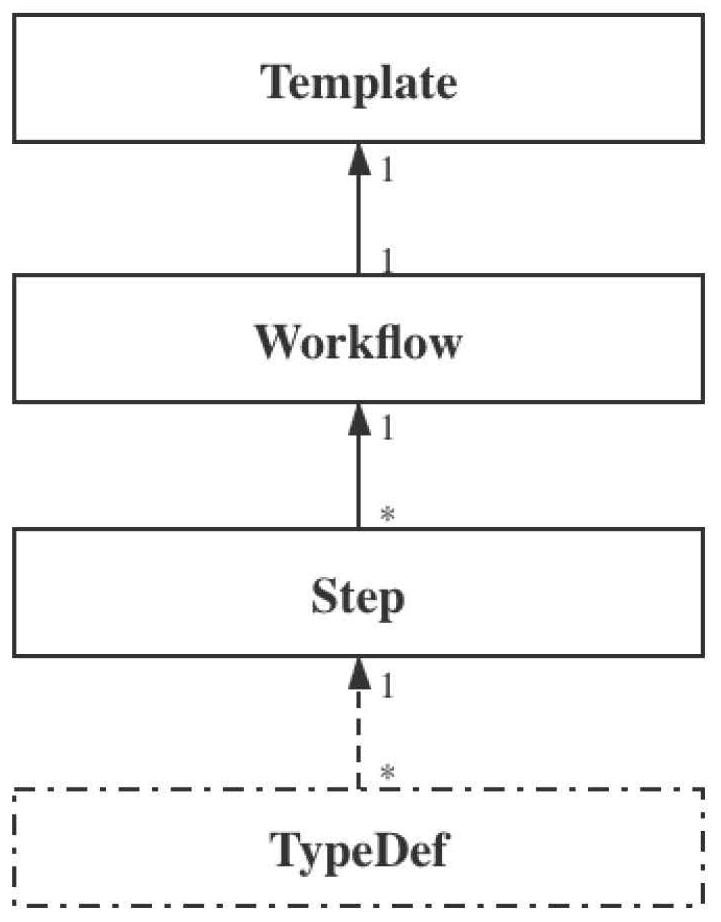
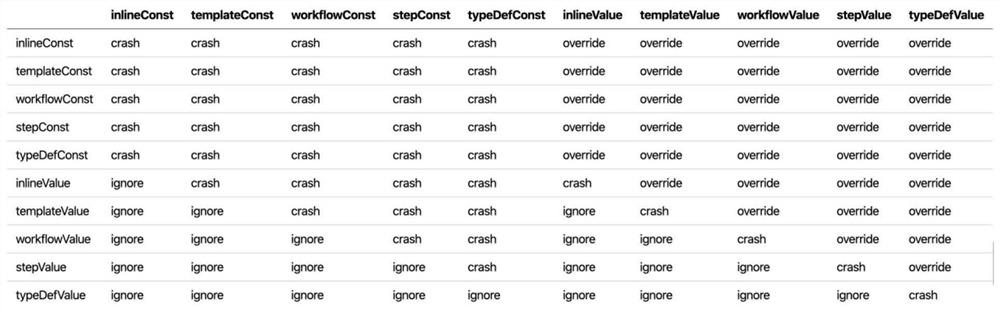
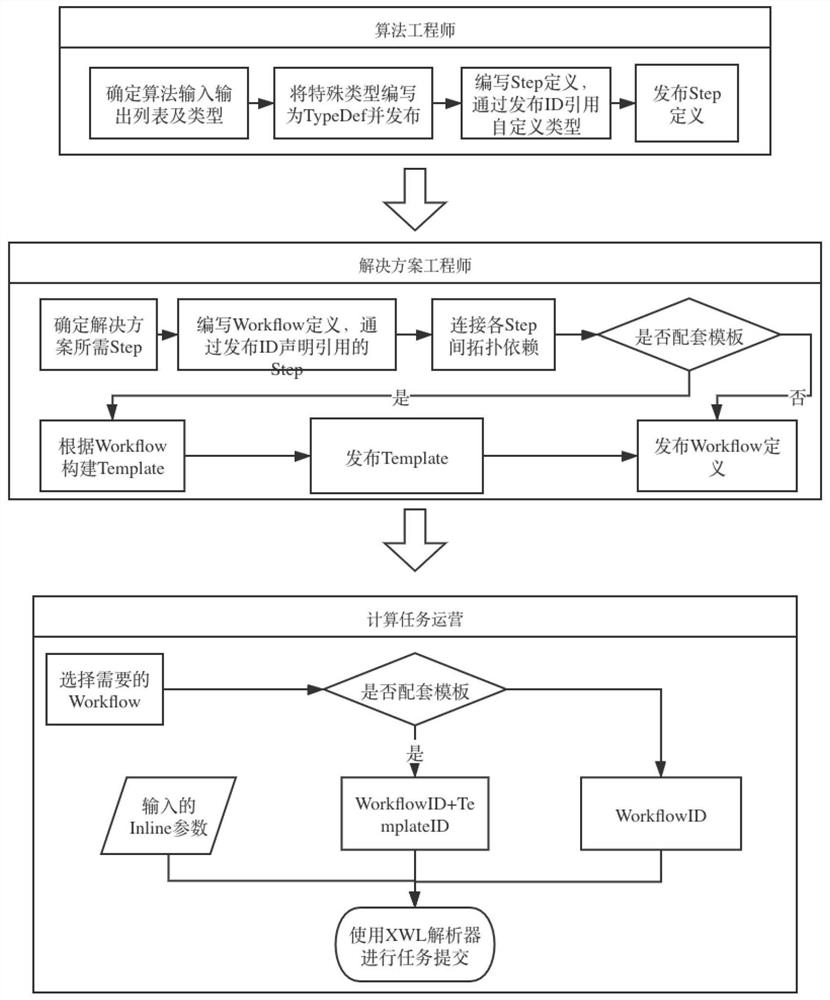
PendingCN112162737AImprove description granularityComplete task descriptionCreation/generation of source codeInformation layerData center
The invention provides a universal description language data system for directed acyclic graph type automatic task flow. The universal description language data system comprises a Step definition layer, a Workflow definition layer and a Template definition layer, The Step layer is description of a single task, and information such as names, types, documents and parameters of input and output itemsneeds to be declared specifically for input and output declarations of a docker mirror image or other actuators; the Workflow layer is a workflow composed of one or more Steps, the dependency topology of the Steps needs to be defined, and shared parameters can also be defined; the Template layer is based on a Workflow definition, and the template is used for presetting parameters, explaining supplementary parameters, and defining an inspector or a data source. The data center and a task execution tool are used, and a programming language needs to be used for achieving a corresponding tool. Adata center needs to store each definition document and indexes the definition documents to the corresponding documents through reference links, and an interpreter needs to read all definition contents and assign corresponding data to a definition structure according to the reference links.
Owner:SHENZHEN JINGTAI TECH CO LTD
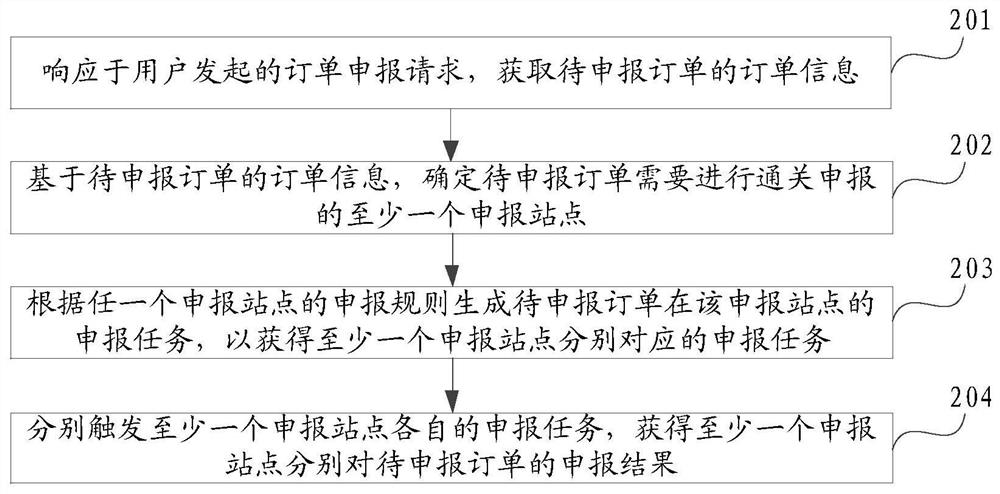
Order cross-border declaration method, system and device and computing equipment
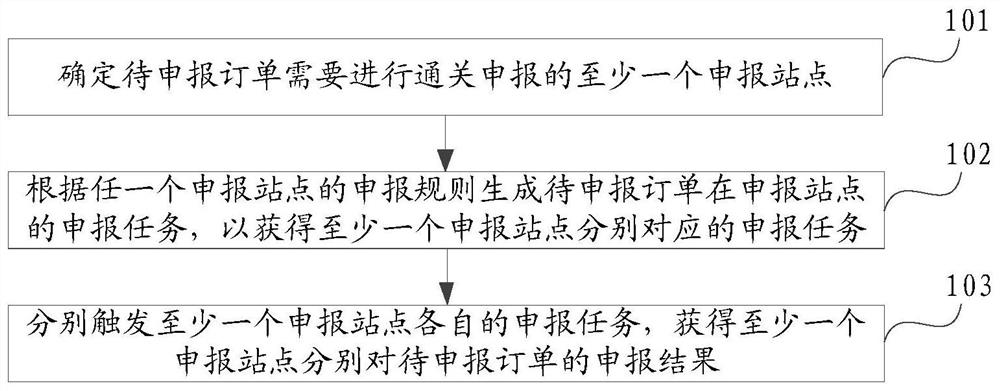
PendingCN113298459ARealize automatic executionReduce reporting workloadBuying/selling/leasing transactionsResourcesDeclarationReliability engineering
The embodiment of the invention provides an order cross-border declaration method, system and device and computing equipment. The method comprises the steps of determining at least one declaration site where a to-be-declarated order needs to be subjected to customs clearance declaration; generating a declaration task of the to-be-declarated order at the declaration site according to the declaration rule of any declaration site so as to obtain a declaration task corresponding to the at least one declaration site; and respectively triggering a declaration task of the at least one declaration site, and obtaining a declaration result of the at least one declaration site for the order to be declarated. According to the embodiment of the invention, the customs clearance declaration efficiency of the cross-border order is improved.
Owner:ALIBABA (CHINA) CO LTD
Natural language semantic representation method and device based on function declaration and electronic equipment
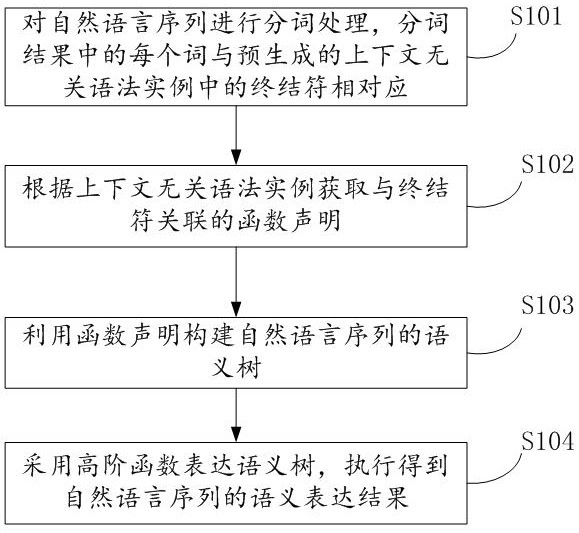
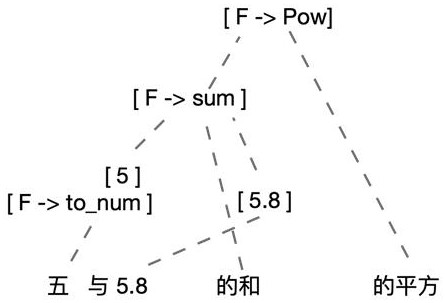
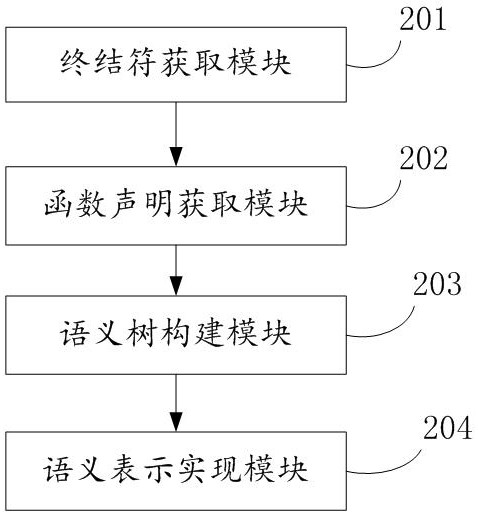
InactiveCN111967247AIncrease flexibilityNo strong couplingSemantic analysisCode compilationSemantic treeSemantic representation
The invention discloses a natural language semantic representation method and device based on function declaration and electronic equipment. The method comprises the steps: performing word segmentation processing on a natural language sequence, wherein each word in a word segmentation result corresponds to a terminator in a pre-generated context-independent grammar instance; obtaining a function statement associated with the terminator according to the context-independent grammar instance; utilizing the function statement to construct a semantic tree of the natural language sequence; expressing the semantic tree by adopting a high-order function, and executing to obtain a semantic expression result of the natural language sequence. Free combination and nesting of different grammars can beachieved, and then semantic structure representation of complex natural languages is achieved; the specific implementation mode of the function is separated from the semantic representation process declared by the function, the reusability is good, and the flexibility is high; in addition, a semantic representation result can be represented and realized by a function nested executed by a computer,and can be directly executed to complete a specific task.
Owner:北京智源人工智能研究院
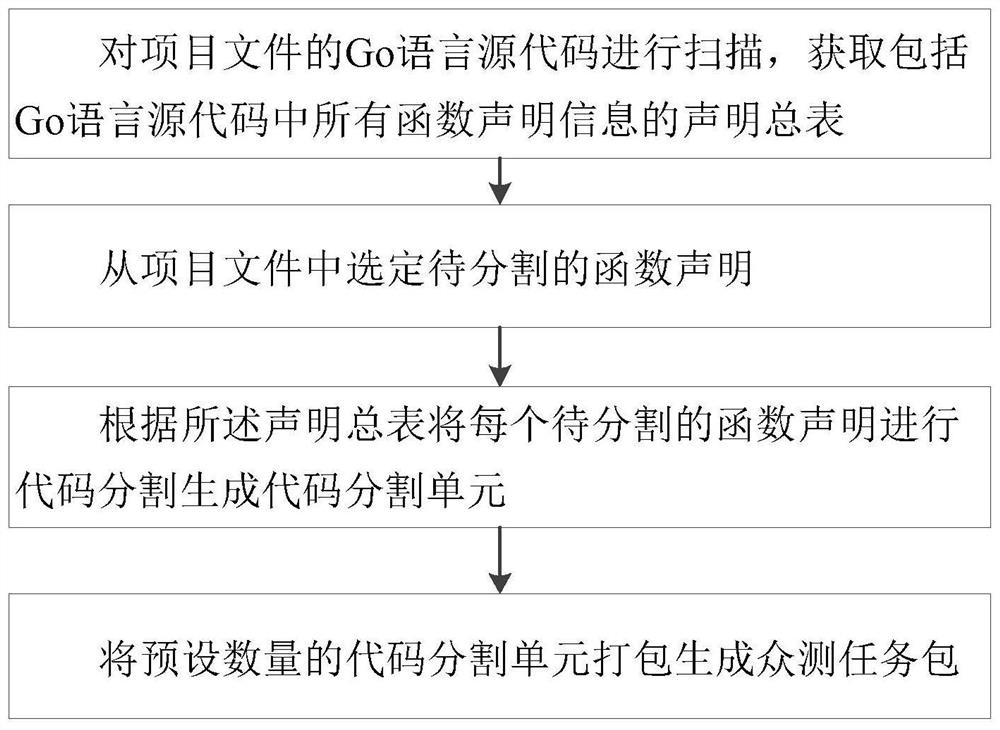
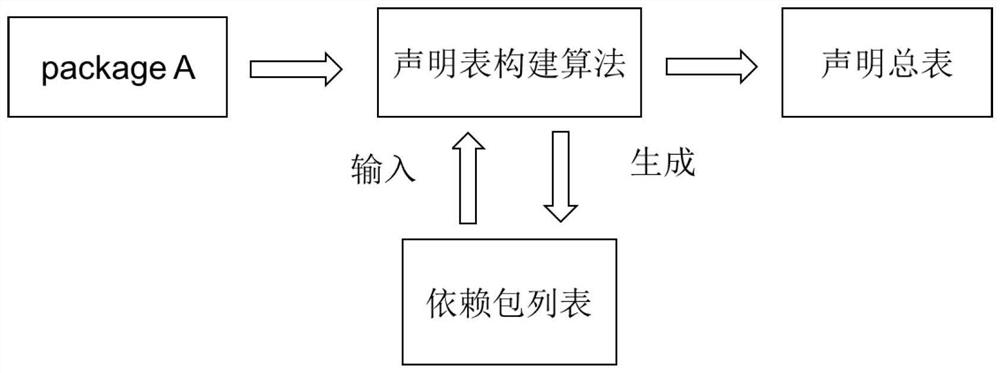
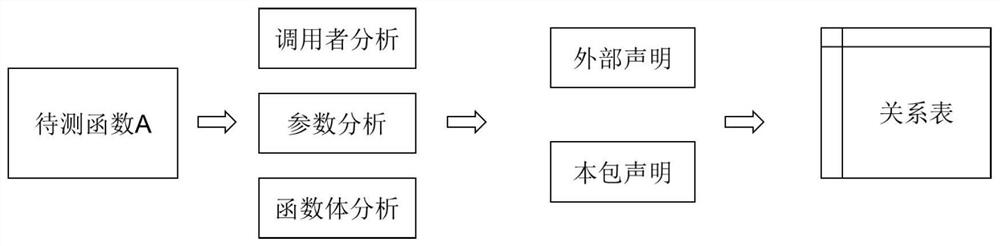
Public test task package generation method and protection method based on Go language code segmentation
PendingCN113946800AReduce complexityEasy to completeSoftware testing/debuggingProgram/content distribution protectionSoftware engineeringSource code
The invention discloses a crowd test task package generation method and protection method based on Go language code segmentation, and the production method comprises the steps of scanning a Go language source code of a project file, and obtaining a declaration general table comprising all function declaration information in the Go language source code; selecting a function statement to be segmented from the project file; performing code segmentation on each to-be-segmented function statement according to the statement general table to generate code segmentation units; packaging the preset number of code segmentation units to generate a crowd test task package; according to the invention, the problem of source code leakage in the unit crowdsourcing software testing process can be effectively solved.
Owner:ARMY ENG UNIV OF PLA
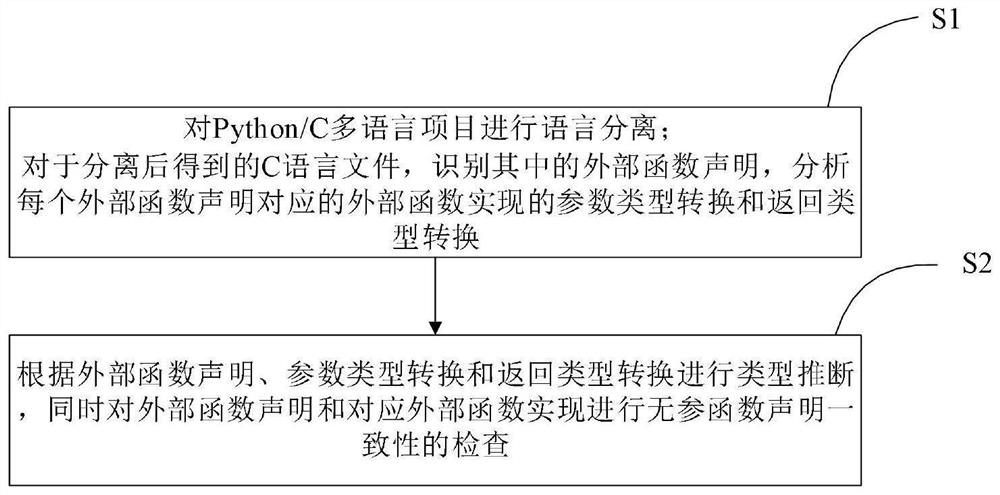
Static type inference method and system for Python external function
PendingCN113885854AReliable inferenceAvoid mistakesPlatform integrity maintainanceVisual/graphical programmingSoftware engineeringType inference
The invention relates to a static type inference method and system for a Python external function. The method comprises the following steps: S1, performing language separation on a Python / C multi-language project; for a C language file obtained after separation, identifying external function declarations in the C language file, and analyzing parameter type conversion and return type conversion realized by an external function corresponding to each external function declaration; S2, carrying out type inference according to each external function declaration, the parameter type conversion, and the return type conversion, and carrying out parameter-free function declaration consistency check on each external function declaration and the corresponding external function. According to the method provided by the invention, the type signature of an external function can be inferred, and a Python static type inference tool in the prior art is enhanced, so that the Python static type inference tool can analyze external function calling in a program and check vulnerabilities that external function declarations are inconsistent with the implementation thereof.
Owner:UNIV OF SCI & TECH OF CHINA
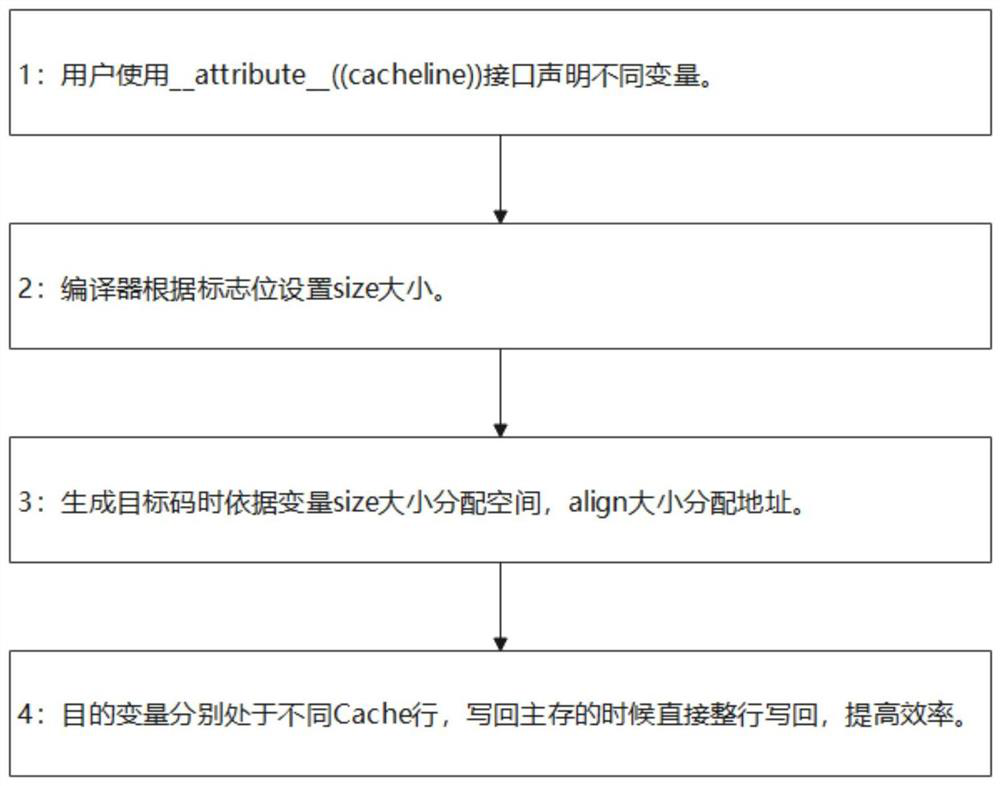
Compiler support method for alleviating false sharing problem
PendingCN114217937AImprove write-back efficiencyIncrease intervalResource allocationCode compilationBase classParallel computing
The invention discloses a compiler support method for relieving a false sharing problem, which comprises the following steps of: S1, respectively using an attrite (cache) interface for variable declarations which possibly have false sharing among multi-thread Caches in a program by a user; and S2, the compiler sets a flag bit cache in a base class treeclcommon structural body of the declaration tree node as 1, sets an align as the size of a Cache Line, and sets a user align in a base class treebase structural body of the treeclcommon as 1. According to the method, the problem of false sharing caused by the fact that certain Cache structures do not guarantee transverse consistency is solved.
Owner:JIANGNAN INST OF COMPUTING TECH
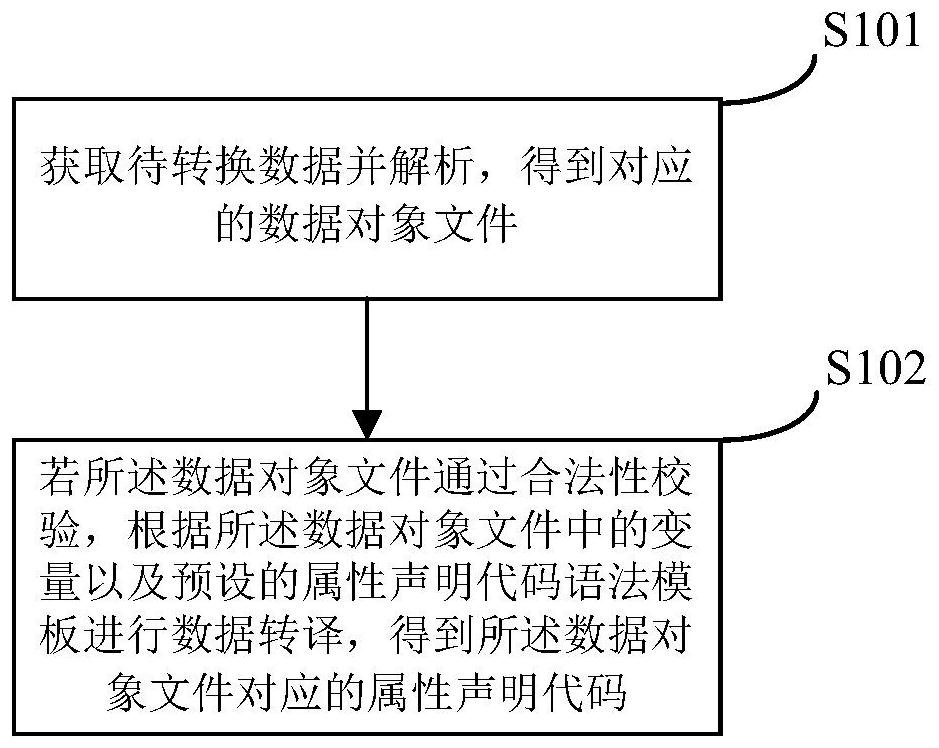
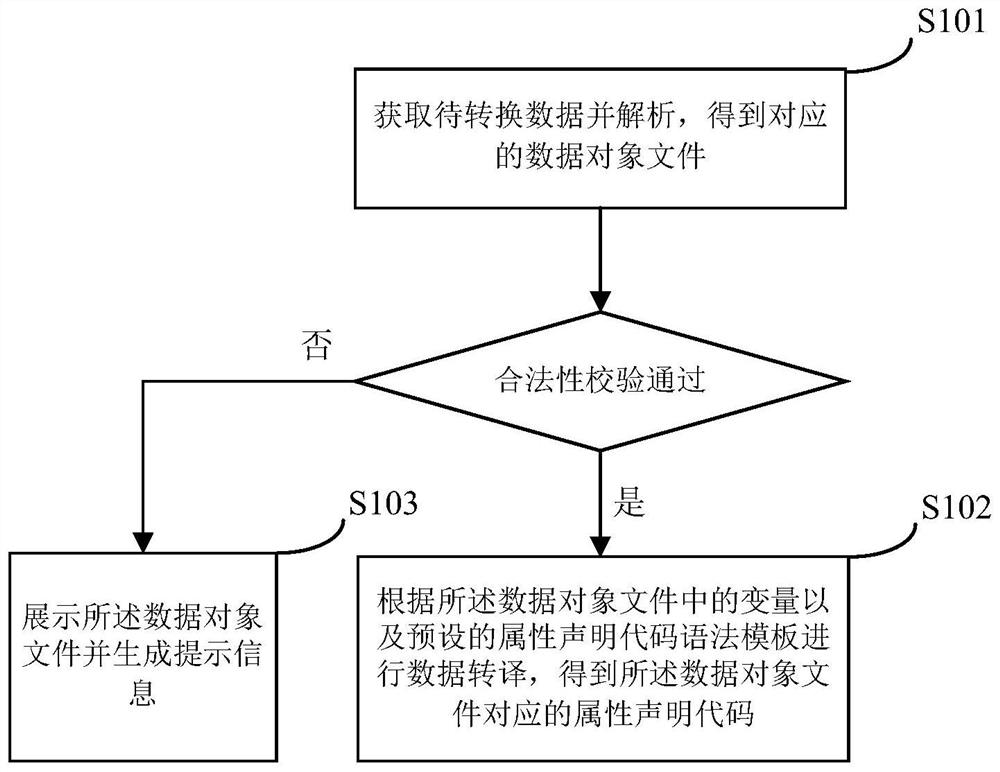
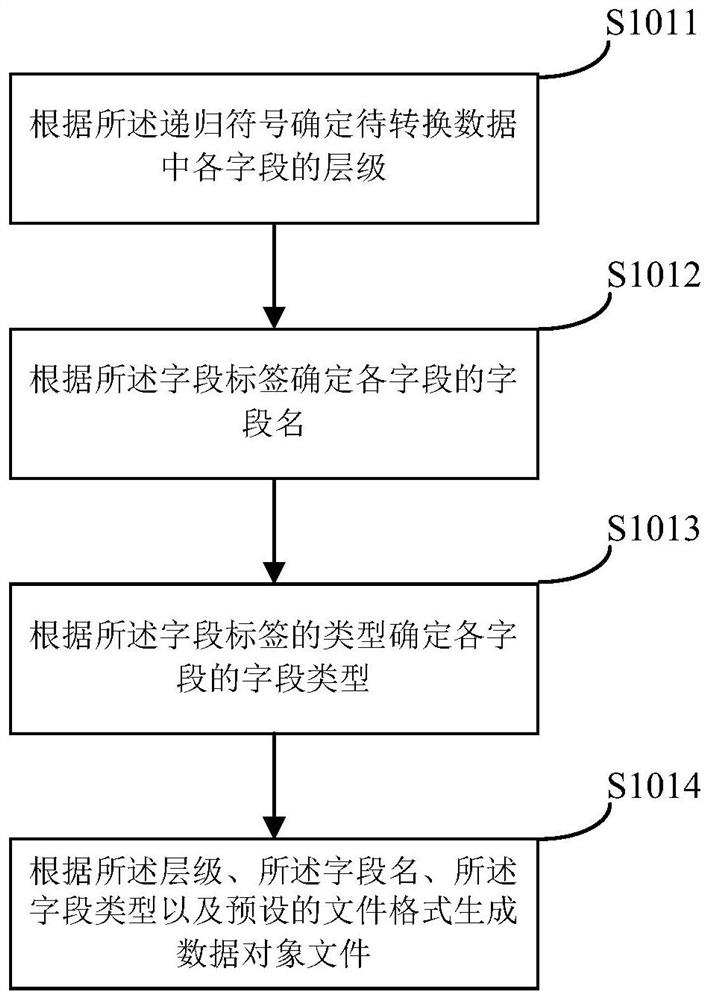
Automatic generation method and device of attribute declaration code based on iOS
PendingCN114675833AImprove accuracyAvoid wastingCode compilationData translationSoftware engineering
The invention provides an automatic generation method and device of an attribute declaration code based on iOS, and relates to the field of program research and development, the technical field of mobile internet and the field of finance. The automatic generation method comprises the following steps: acquiring and analyzing to-be-converted data to obtain a corresponding data object file; and if the data object passes the legality verification, performing data translation according to variables in the data object file and a preset attribute declaration code grammar template to obtain an attribute declaration code corresponding to the data object file. According to the method and the device, the process of automatically generating the attribute declaration code file from the data objects in various formats is realized, repeated work of developers is not needed, and waste of human resources caused by extra workload is avoided; meanwhile, the application of the method is beneficial to reducing the error rate of the attribute declaration code.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com