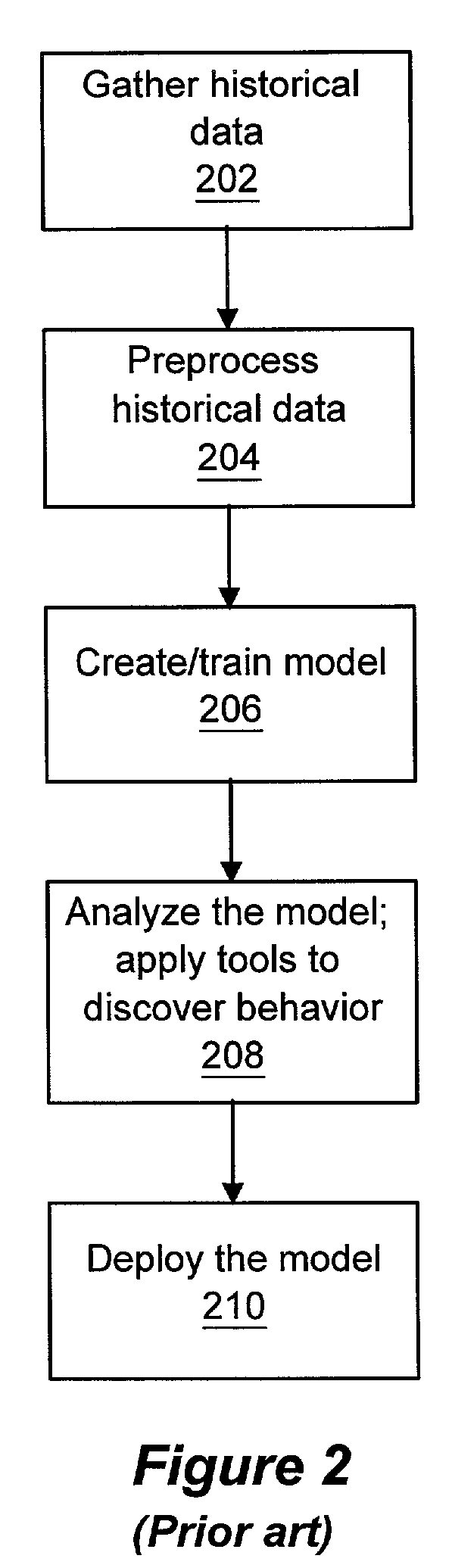
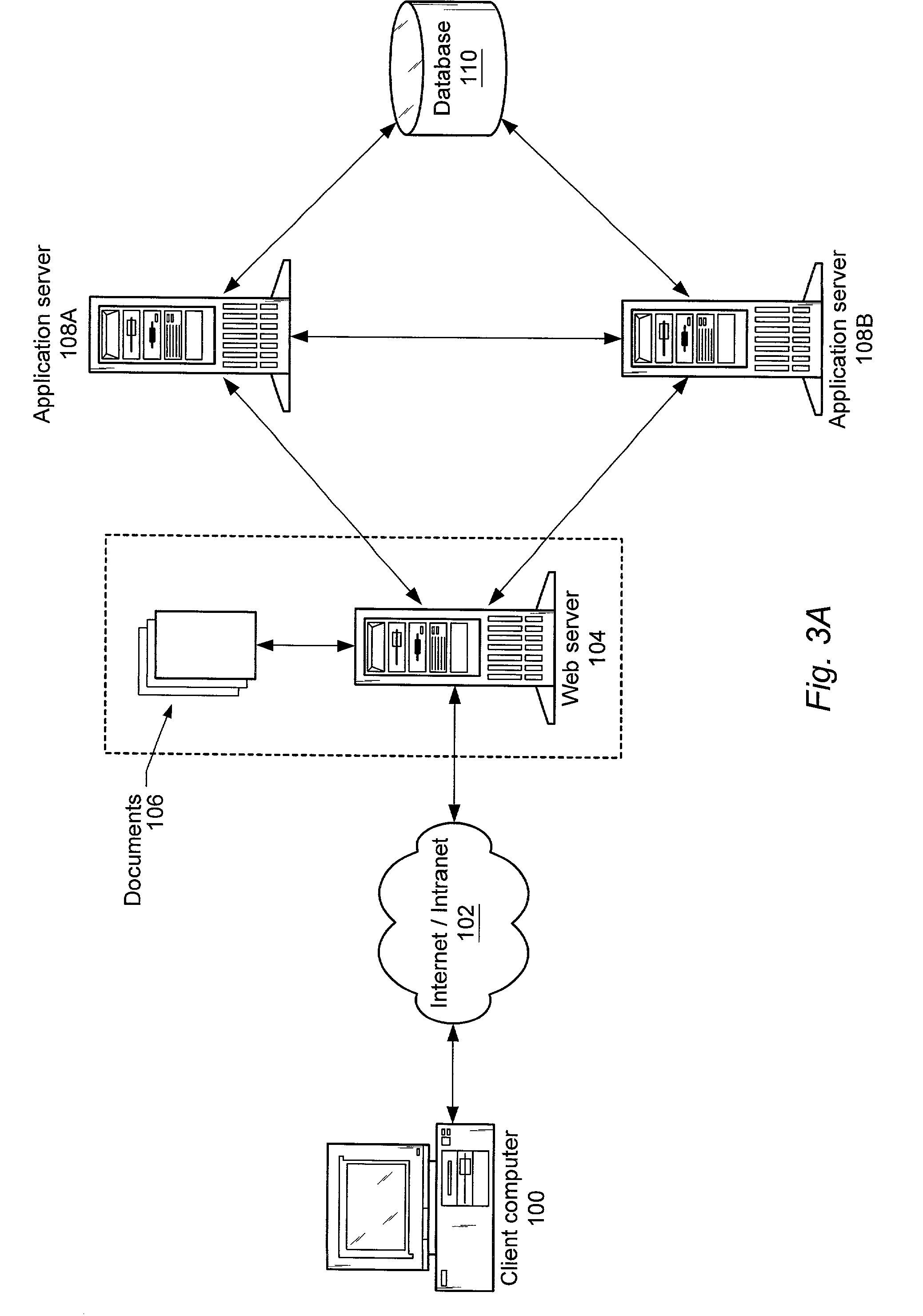
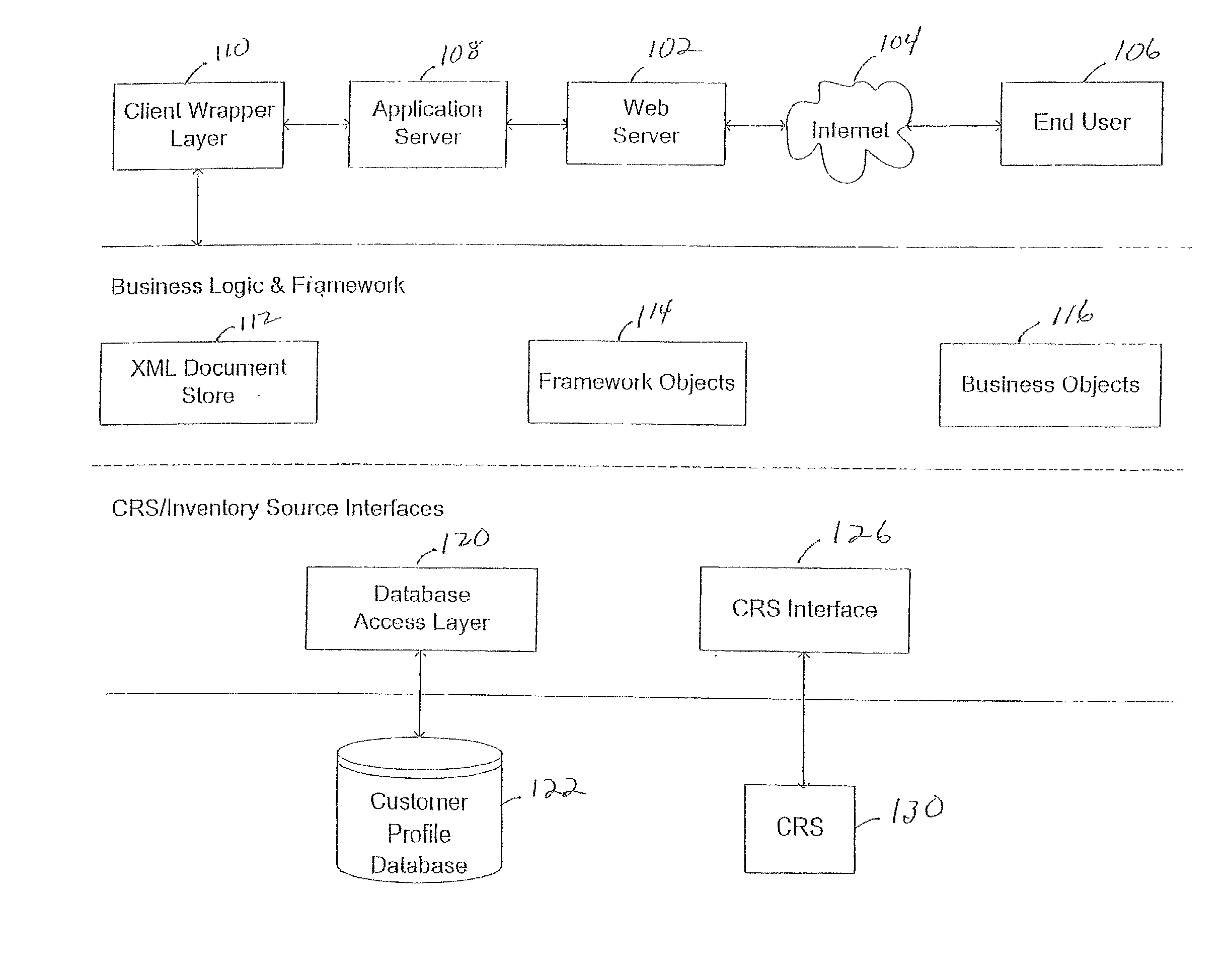
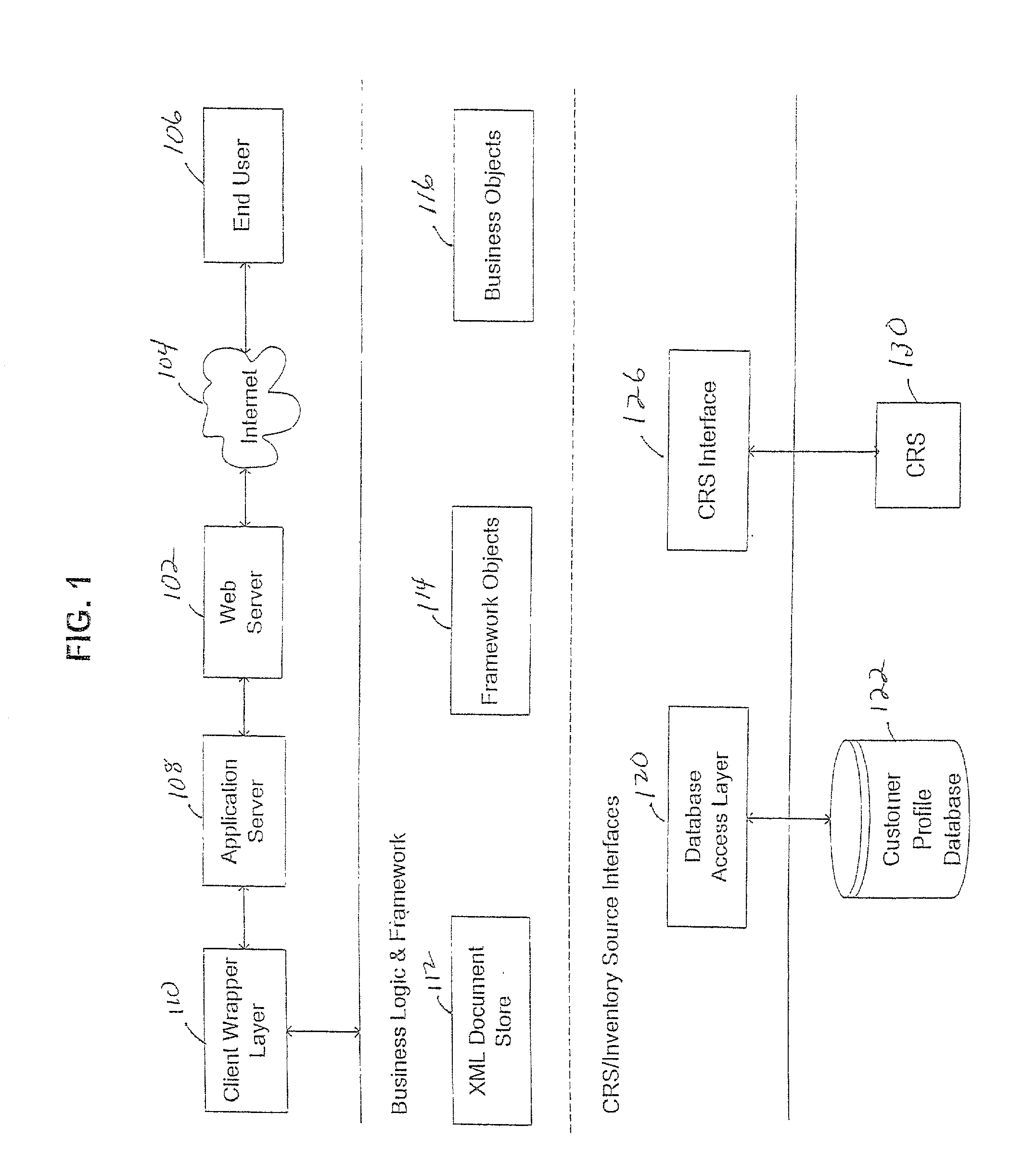
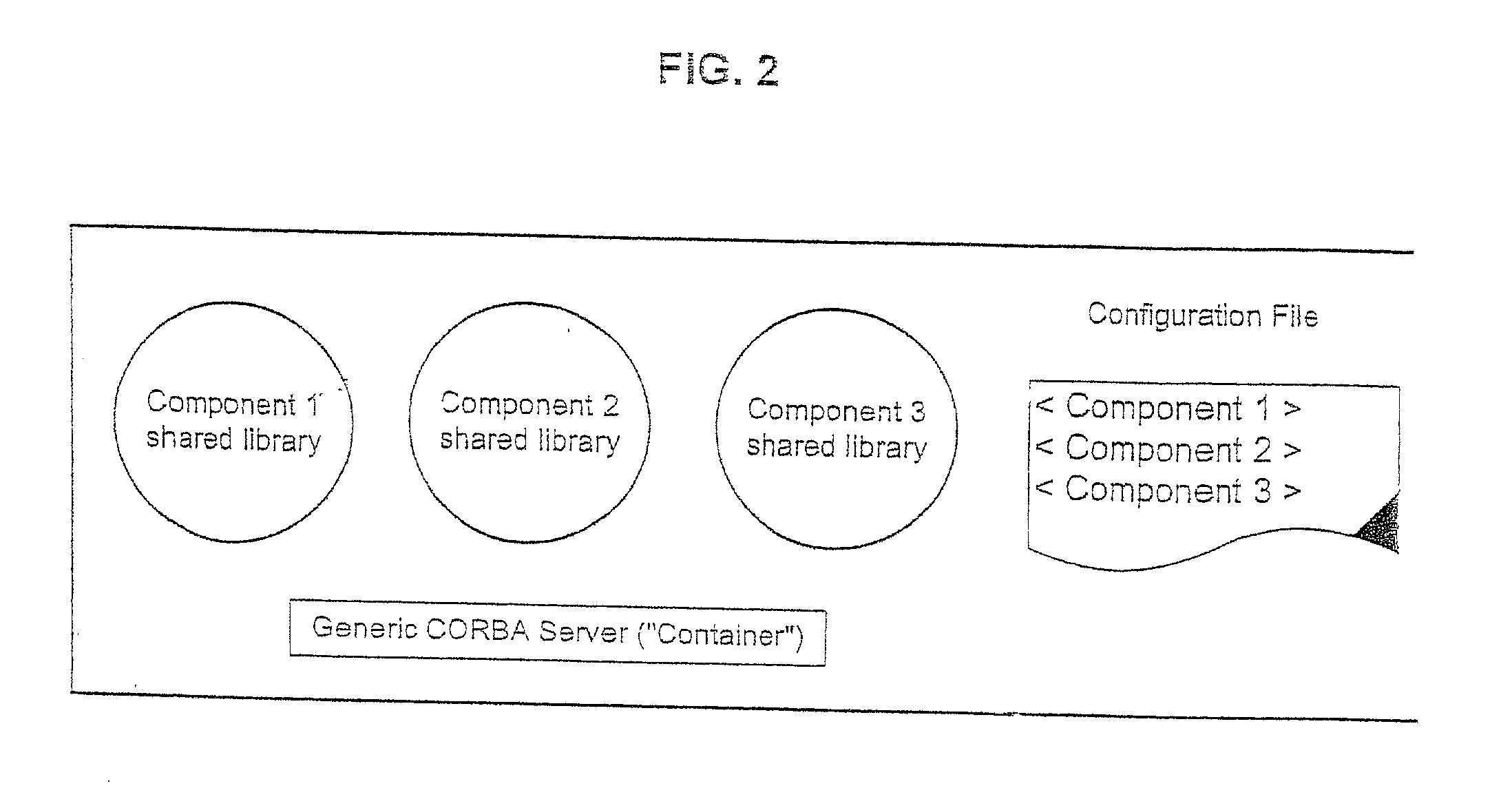
Patents
Literature
268 results about "Base class" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
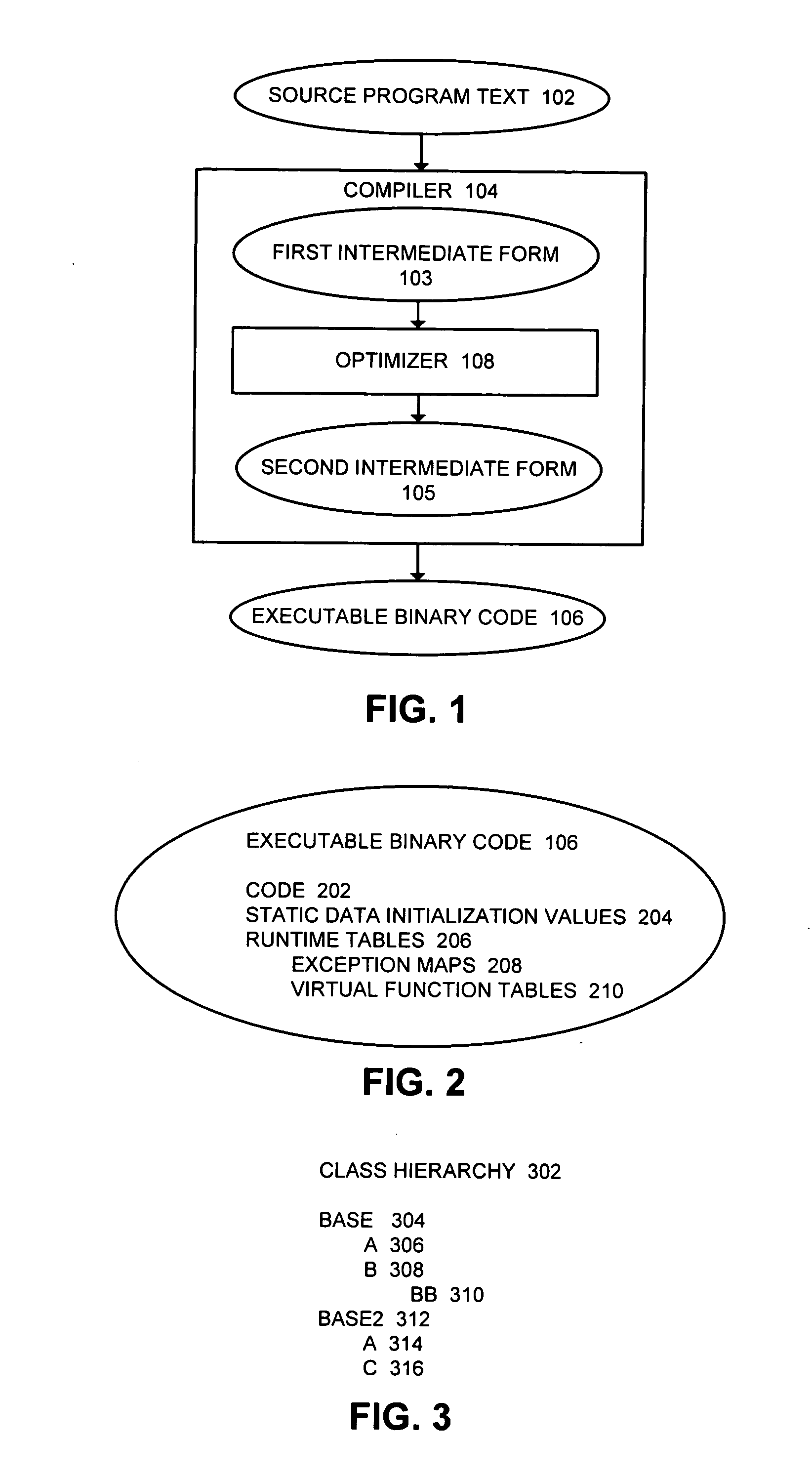
Base Class. Definition - What does Base Class mean? A base class is a class, in an object-oriented programming language, from which other classes are derived. It facilitates the creation of other classes that can reuse the code implicitly inherited from the base class (except constructors and destructors).
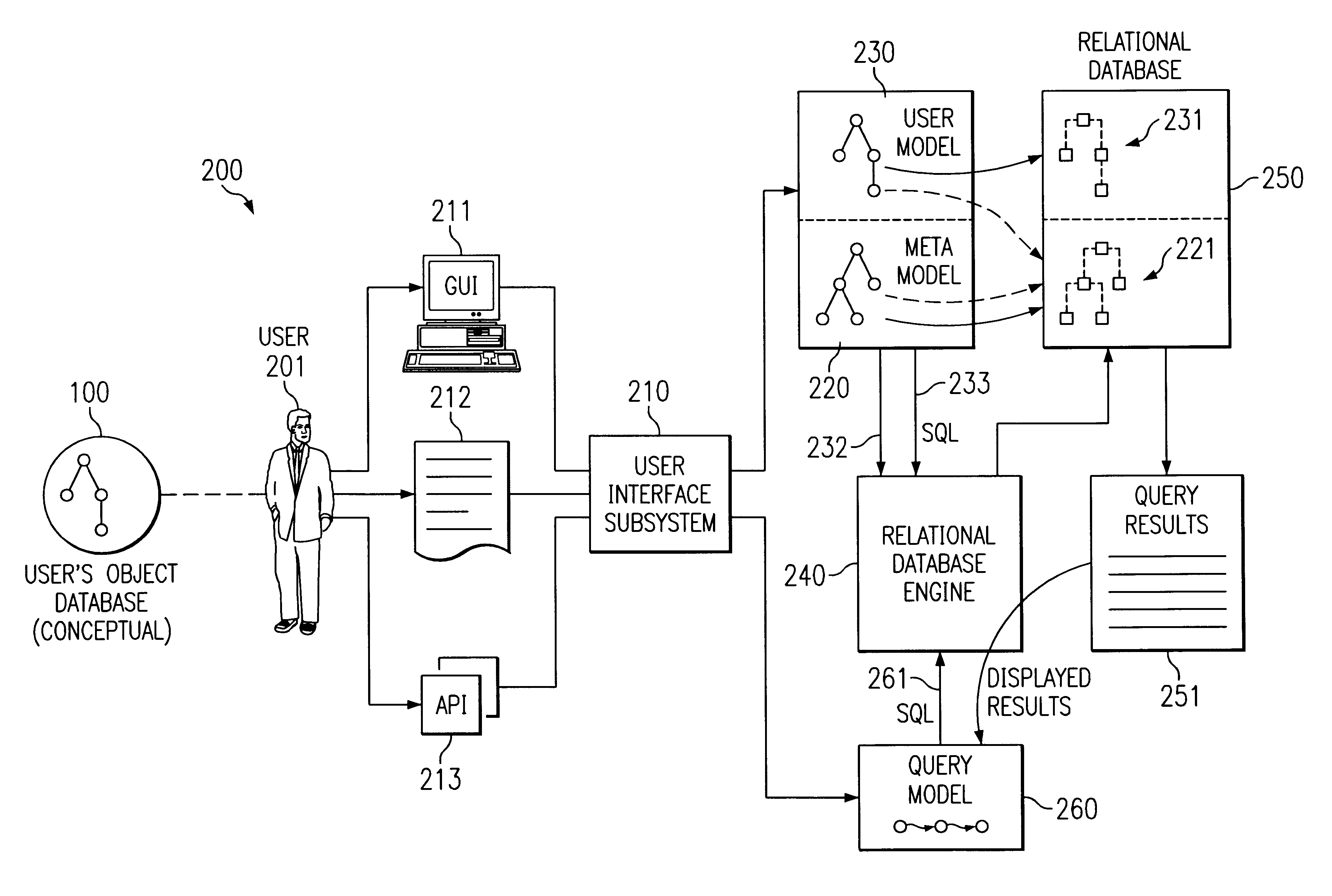
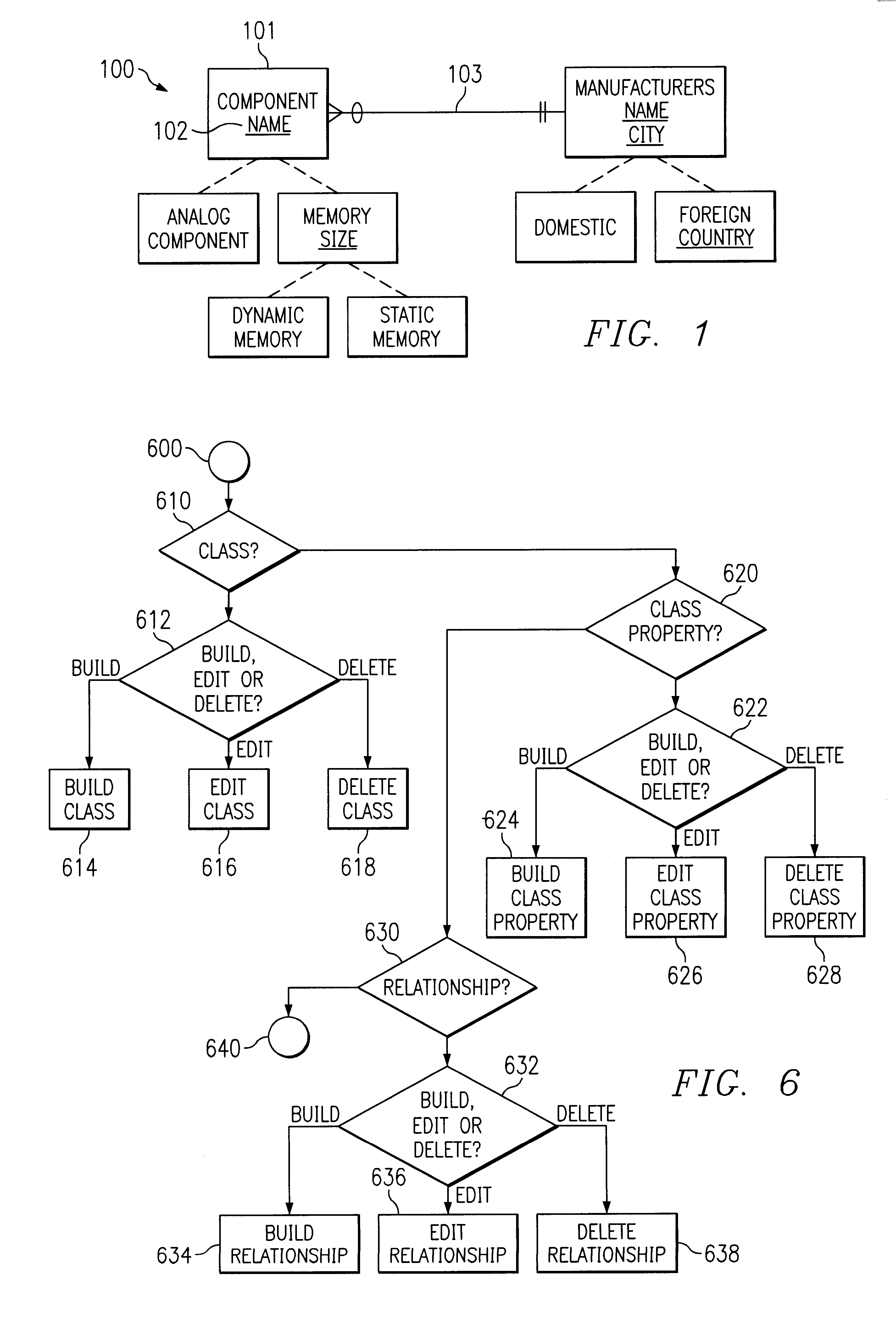
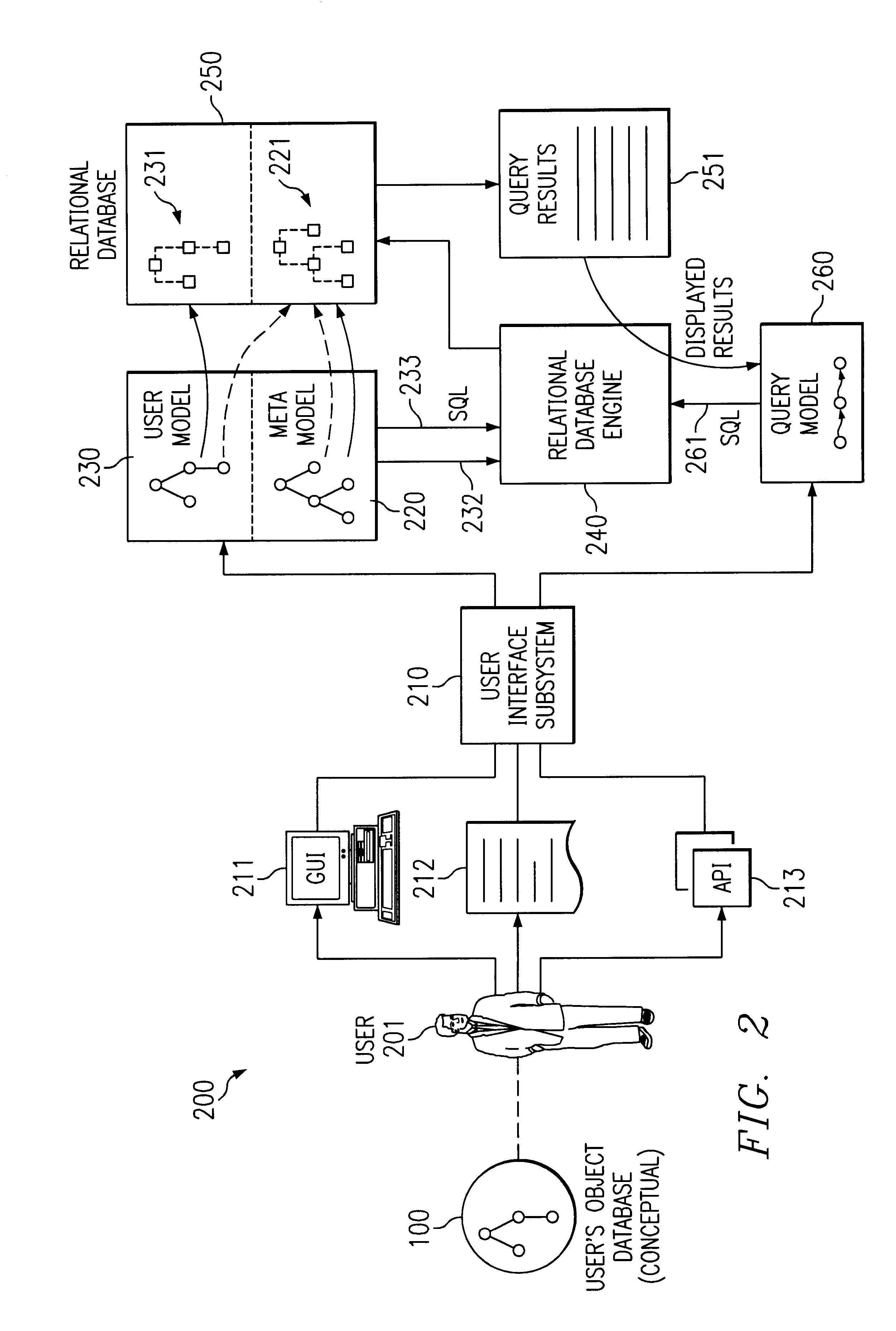
Modeling of object-oriented database structures, translation to relational database structures, and dynamic searches thereon
InactiveUS6374252B1Digital data information retrievalData processing applicationsBase classRelational database
A method and system for modeling of object-oriented database structures, translation to relational database structures, and dynamic searches thereon. The user may create, edit and manipulate a user's object database (dynamically translated into a set of relational database structures), to create, edit and manipulate objects for that object database (dynamically translated into data for those relational database structures), and to create, edit and manipulate queries to be applied to that object database (dynamically translated into queries to be applied to those relational database structures). A meta-model of the user's object database, which is itself an object database, and which has itself been translated into a set of relational database structures for manipulation by a relational database engine. The meta-model comprises a set of classes, objects, and relationships between classes which model the classes and relationships between classes of the system. Each of these classes may comprise a set of searchable properties, and each of these relationships may comprise an inheritance relationship (between a base class and a derived class) or a data-model relationship (such as a one-to-one, one-to-many, or many-to-many relationship). The data model of the user's object database is modeled by actual objects in the meta-model, and editing or manipulating the user's object database is modeled by creating, modifying, or deleting objects in the meta-model. The meta-model also models itself, in the same manner as it models the user's object database, and may be manipulated in the same manner as the user's object database.
Owner:JDA SOFTWARE GROUP
System and method for enterprise modeling, optimization and control
A system and method for performing modeling, prediction, optimization, and control, including an enterprise wide framework for constructing modeling, optimization, and control solutions. The framework includes a plurality of base classes that may be used to create primitive software objects. These objects may then be combined to create optimization and / or control solutions. The distributed event-driven component architecture allows much greater flexibility and power in creating, deploying, and modifying modeling, optimization and control solutions. The system also includes various techniques for performing improved modeling, optimization, and control, as well as improved scheduling and control. For example, the system may include a combination of batch and continuous processing frameworks, and a unified hybrid modeling framework which allows encapsulation and composition of different model types, such as first principles models and empirical models. The system further includes an integrated process scheduling solution referred to as process coordinator that seamlessly incorporates the capabilities of advanced control and execution into a real time event triggered optimal scheduling solution.
Owner:ROCKWELL AUTOMATION TECH
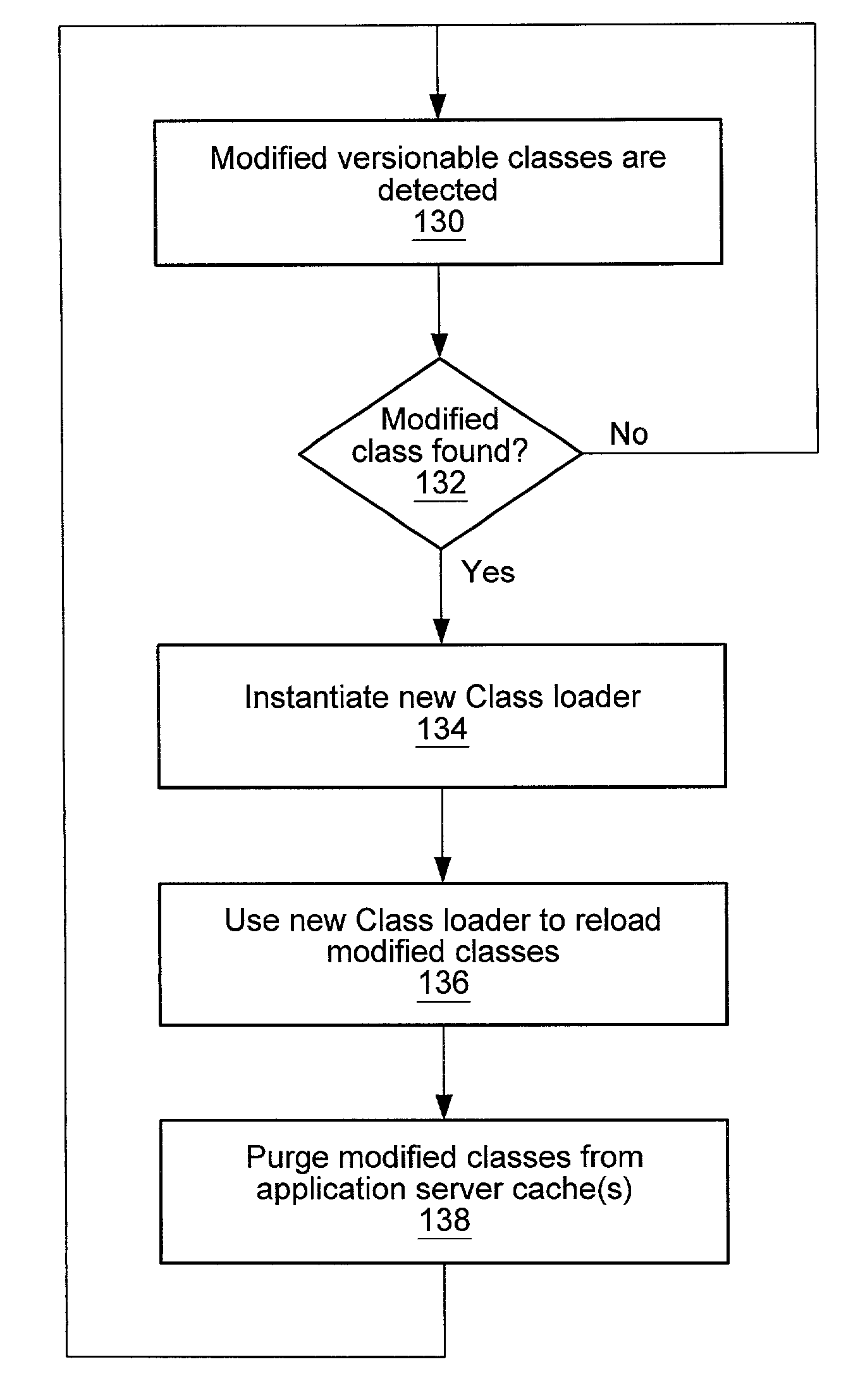
Class dependency graph-based class loading and reloading
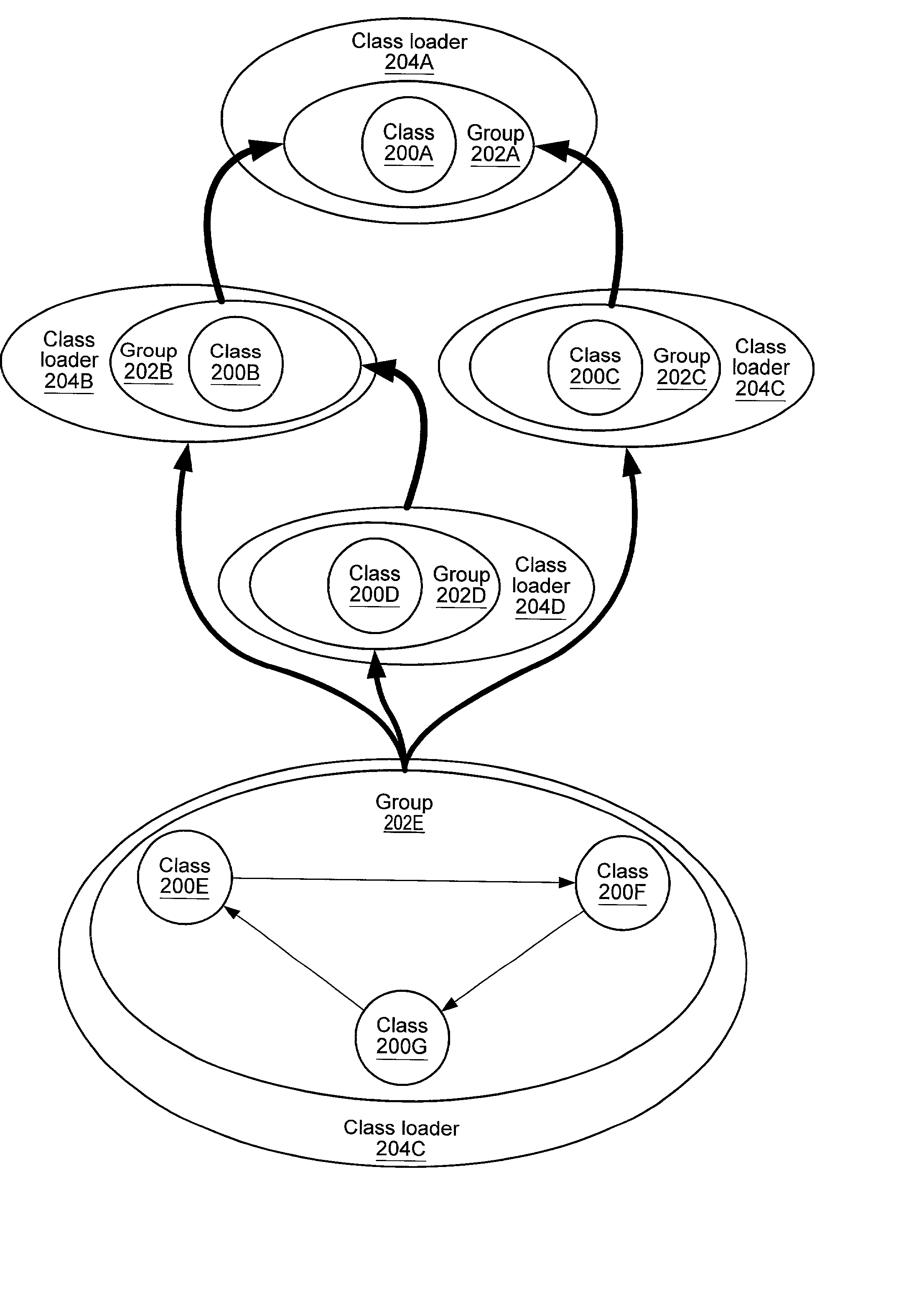
Embodiments of a system and method for providing class dependency graph-based class loading and reloading may be used to segregate namespaces in a graph-centric way, and may provide a set of normalized topologies that may be used to efficiently support hot-swapping of programmatic logic such as classes, applets, and beans, among other applications. Embodiments may provide a domain-independent, flexible and robust namespace segregation technique that is based on the dependency between the various classes and not on details like the roles the classes play. The problem of segregating namespaces is formulated as a graph theory problem, and a solution is sought through graph techniques. The graph may be normalized by identifying and grouping interdependent classes and non-interdependent classes in separate groups. A directed dependency relationship of the groups may be determined using the relationships between the member classes of the groups.
Owner:ORACLE INT CORP
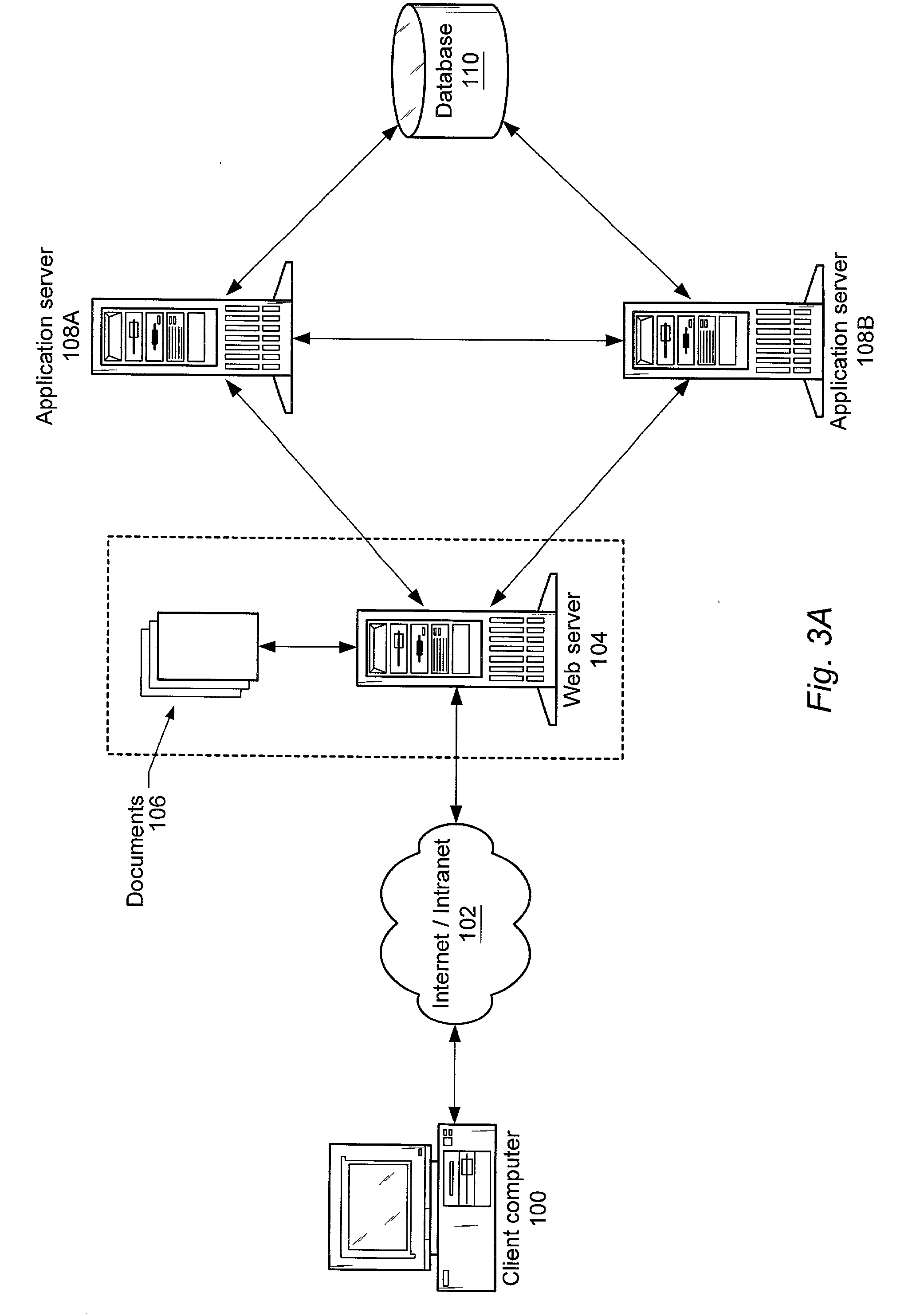
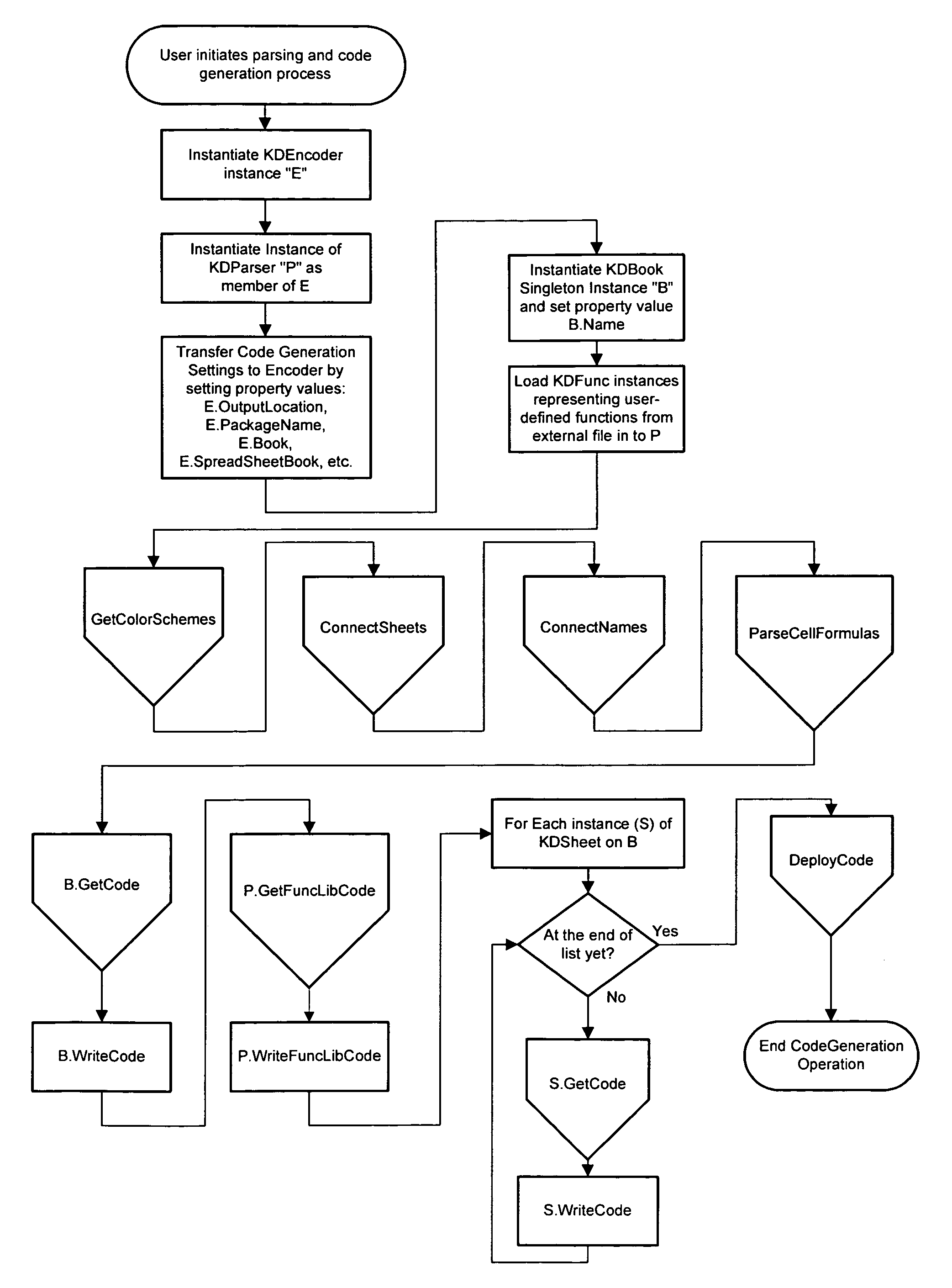
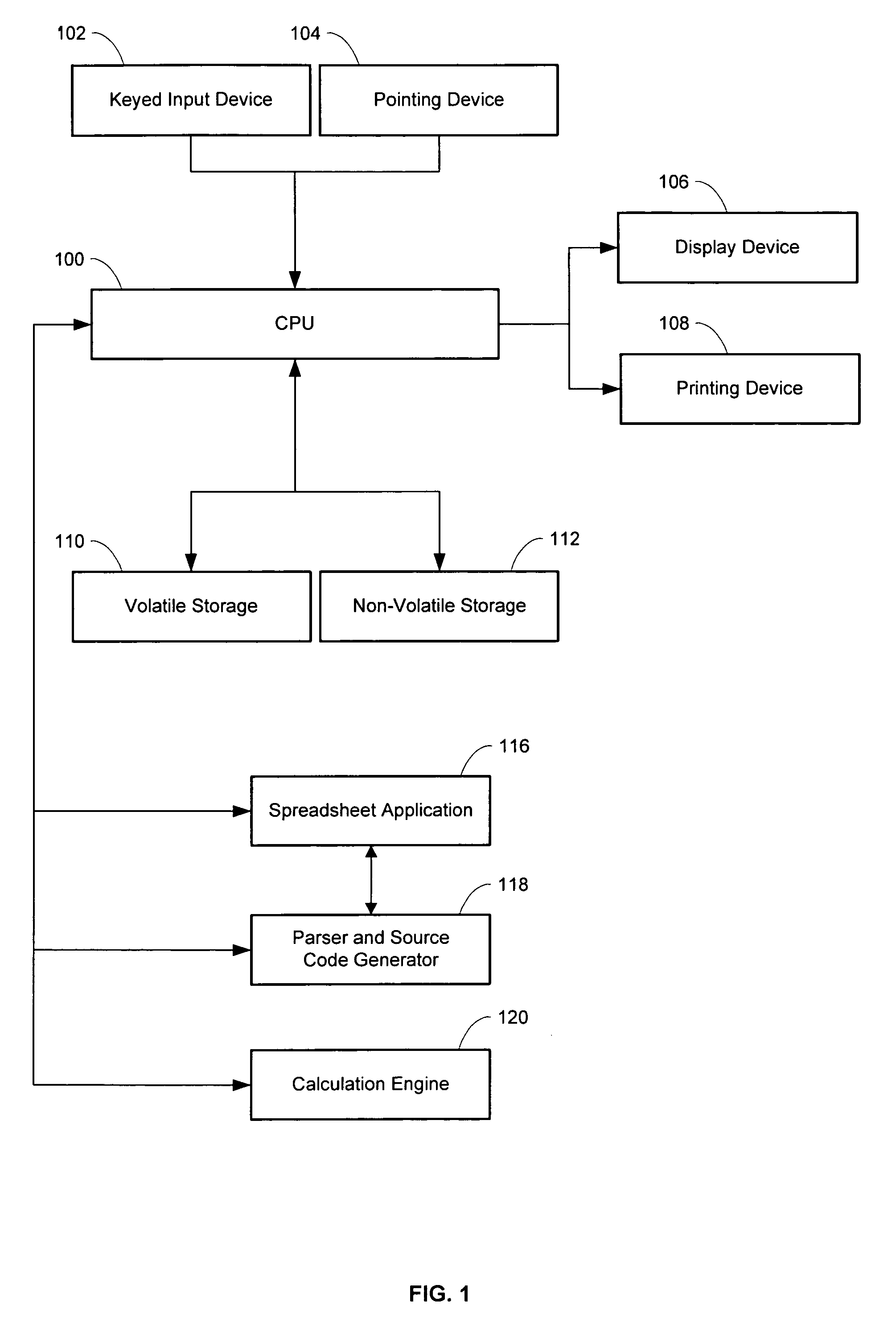
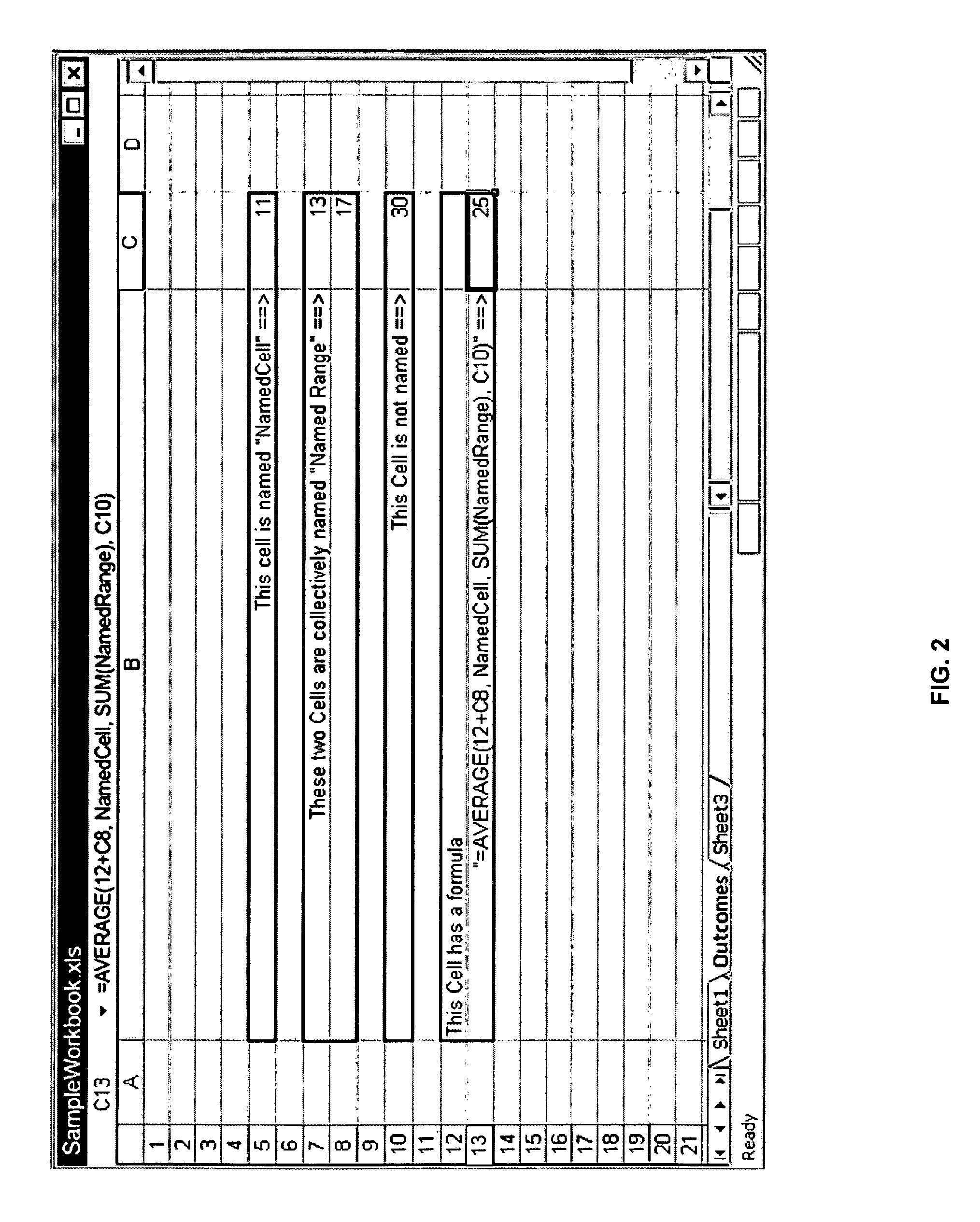
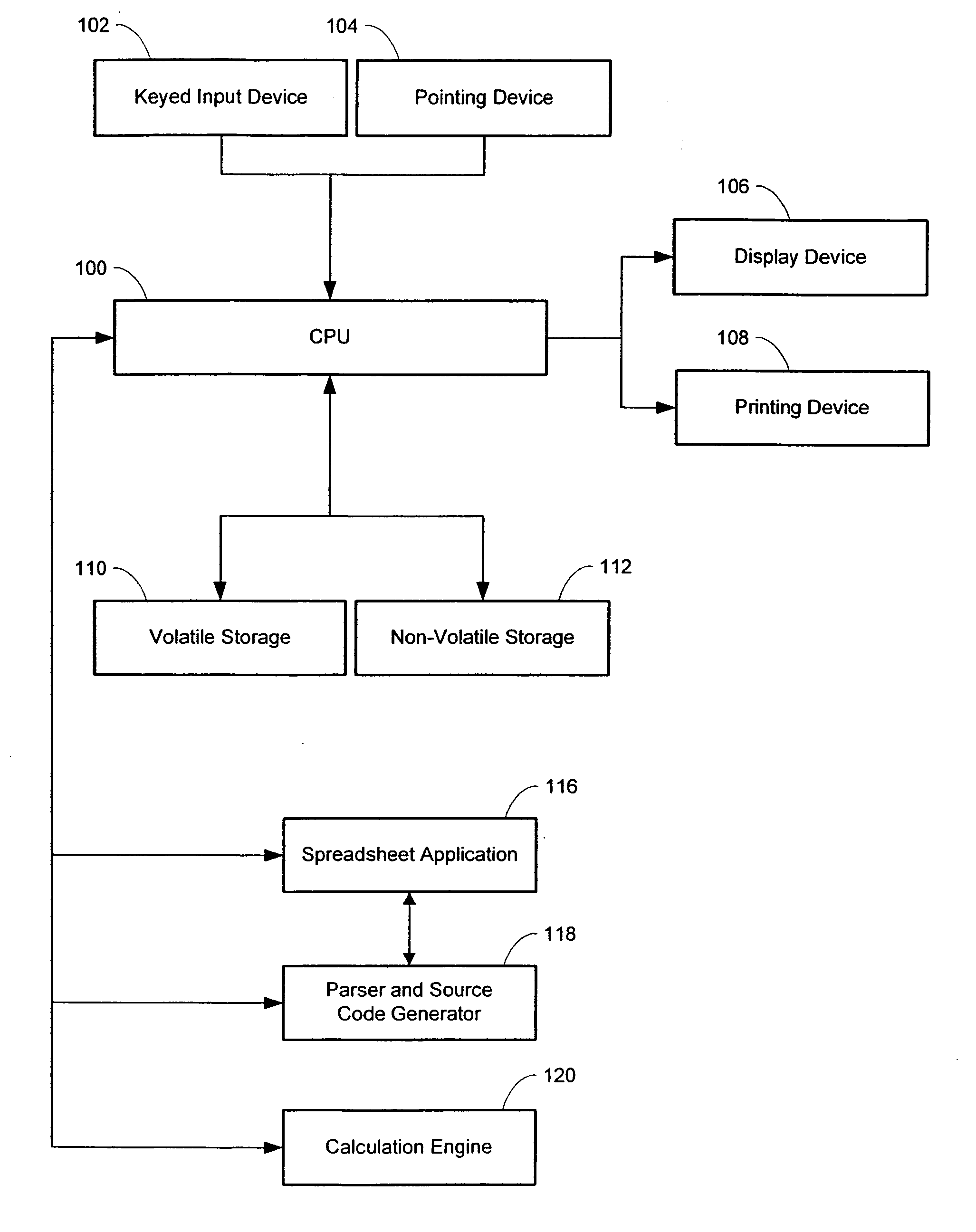
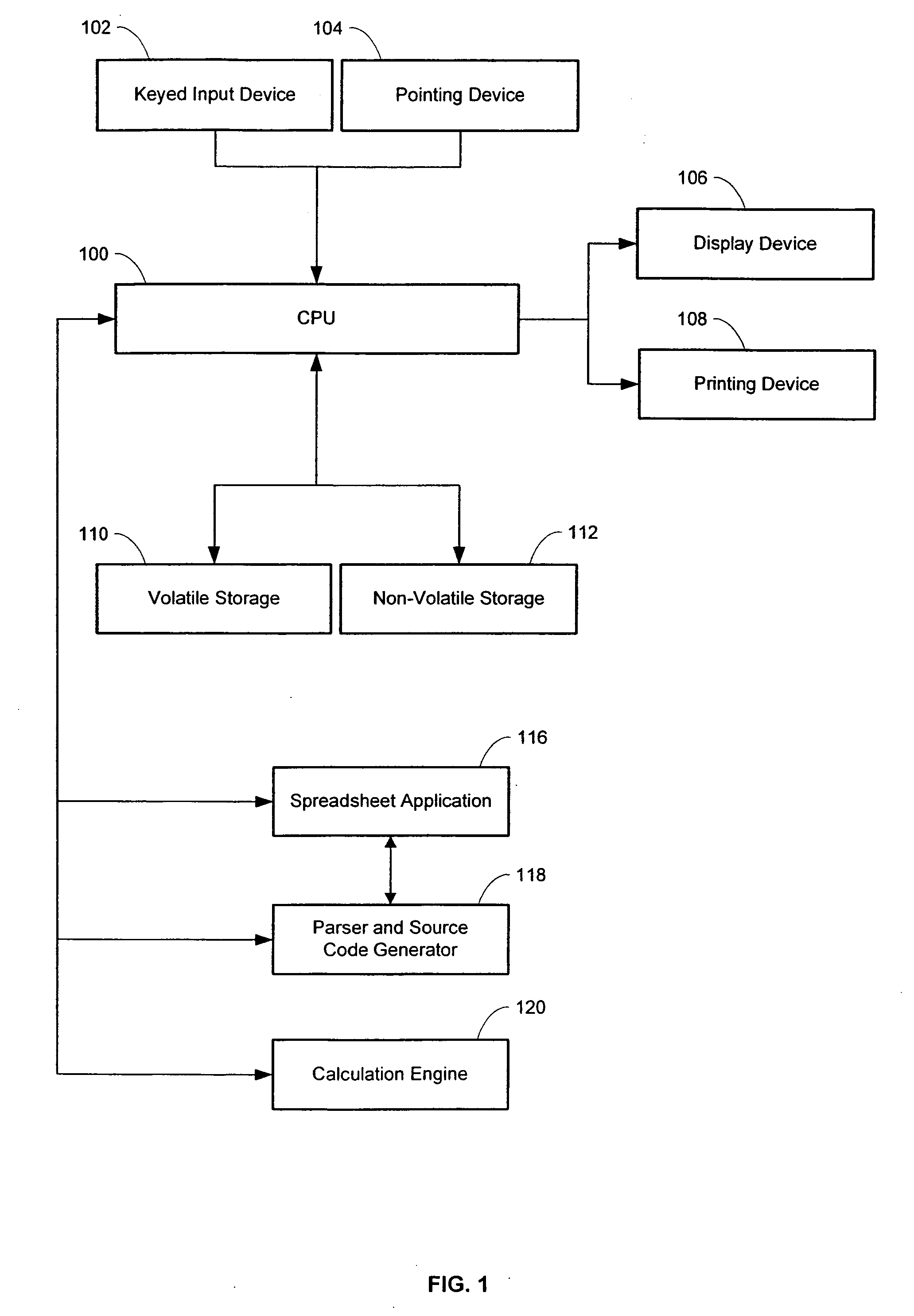
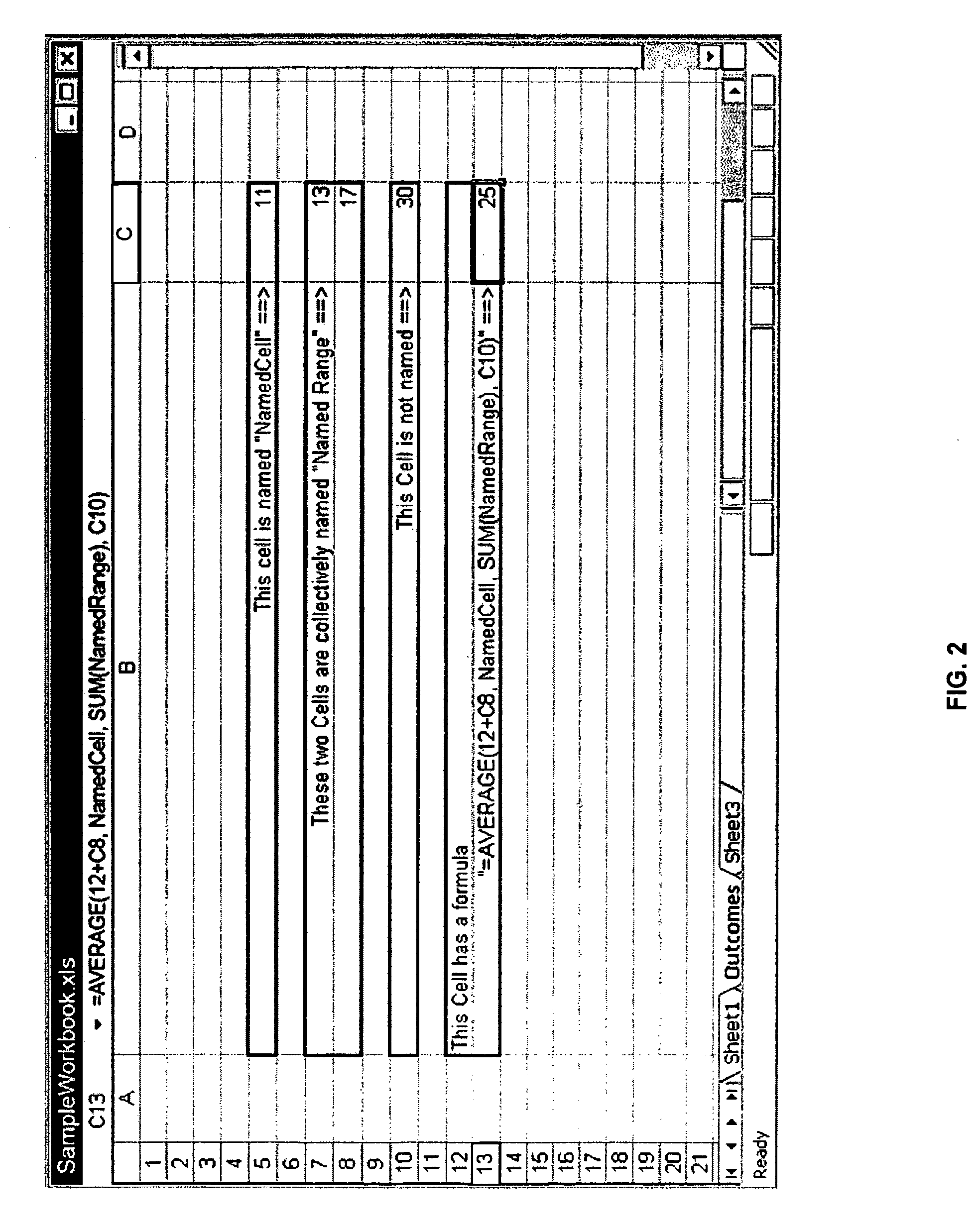
Parser, code generator, and data calculation and transformation engine for spreadsheet calculations
InactiveUS7010779B2EffectEfficient developmentDigital data information retrievalText processingData transformationBase class
A system including spreadsheet sheets, makes calculations and data transformations, which is available through a programming interface, and conforms to the grammar and syntax of a target software development language is presented. The system includes an Object Model with Data Structures representing entities involved in spreadsheets. The system includes a Parser and Code Generator that extracts data from a body of spreadsheet data, instantiates instances of Data Structures of the Object Model to represent the spreadsheet data, parses the data and formulas contained in the cells of the spreadsheets, iterates through the instantiated instances of the Data Structures, and generates source code that performs the calculations and data transformations embodied in the spreadsheet data. The system includes a Calculation Engine with software base classes that implement the common structural and data access features of spreadsheet data, and further implement the operations of common spreadsheet functions and operators.
Owner:KNOWLEDGE DYNAMICS
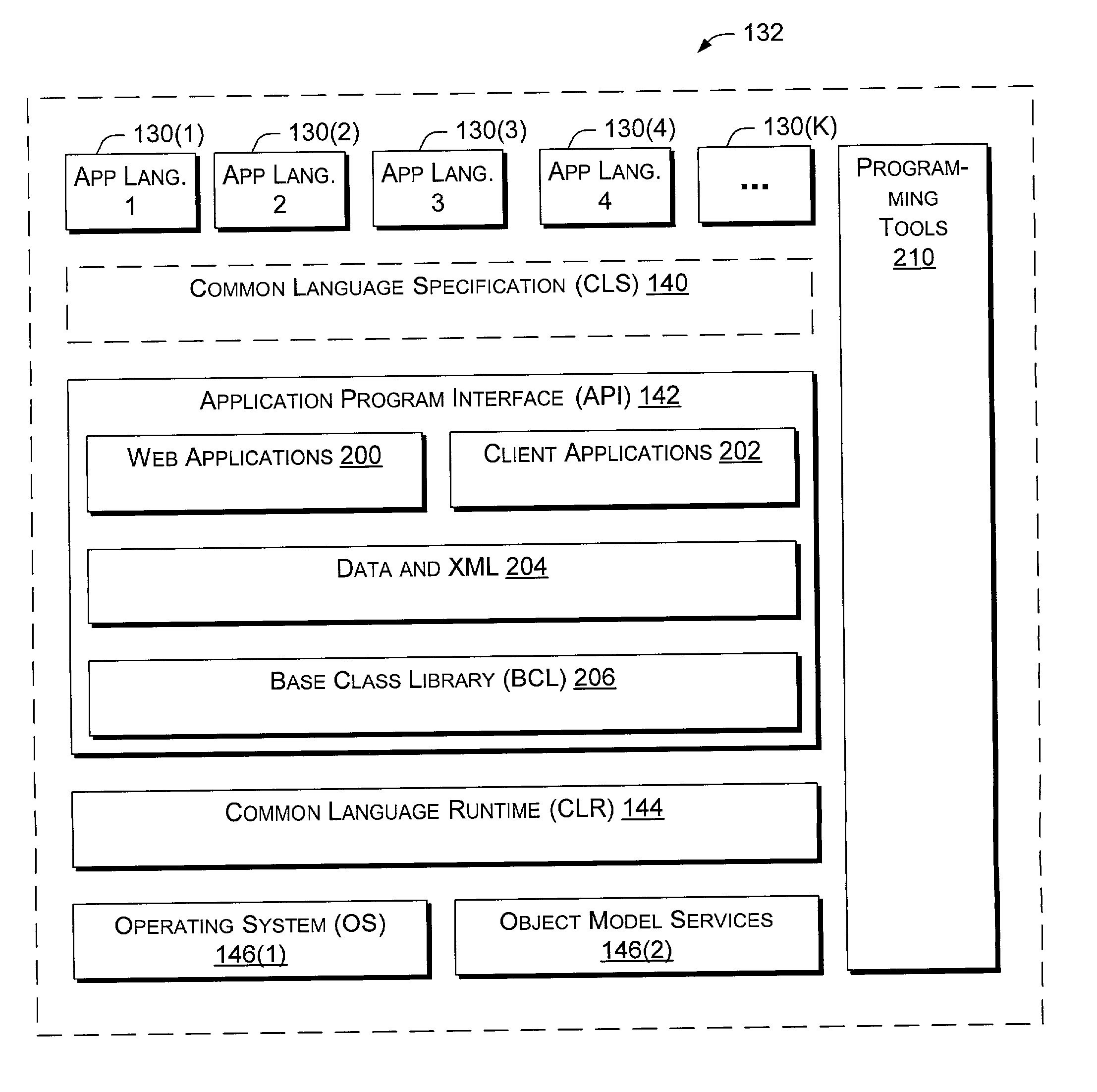
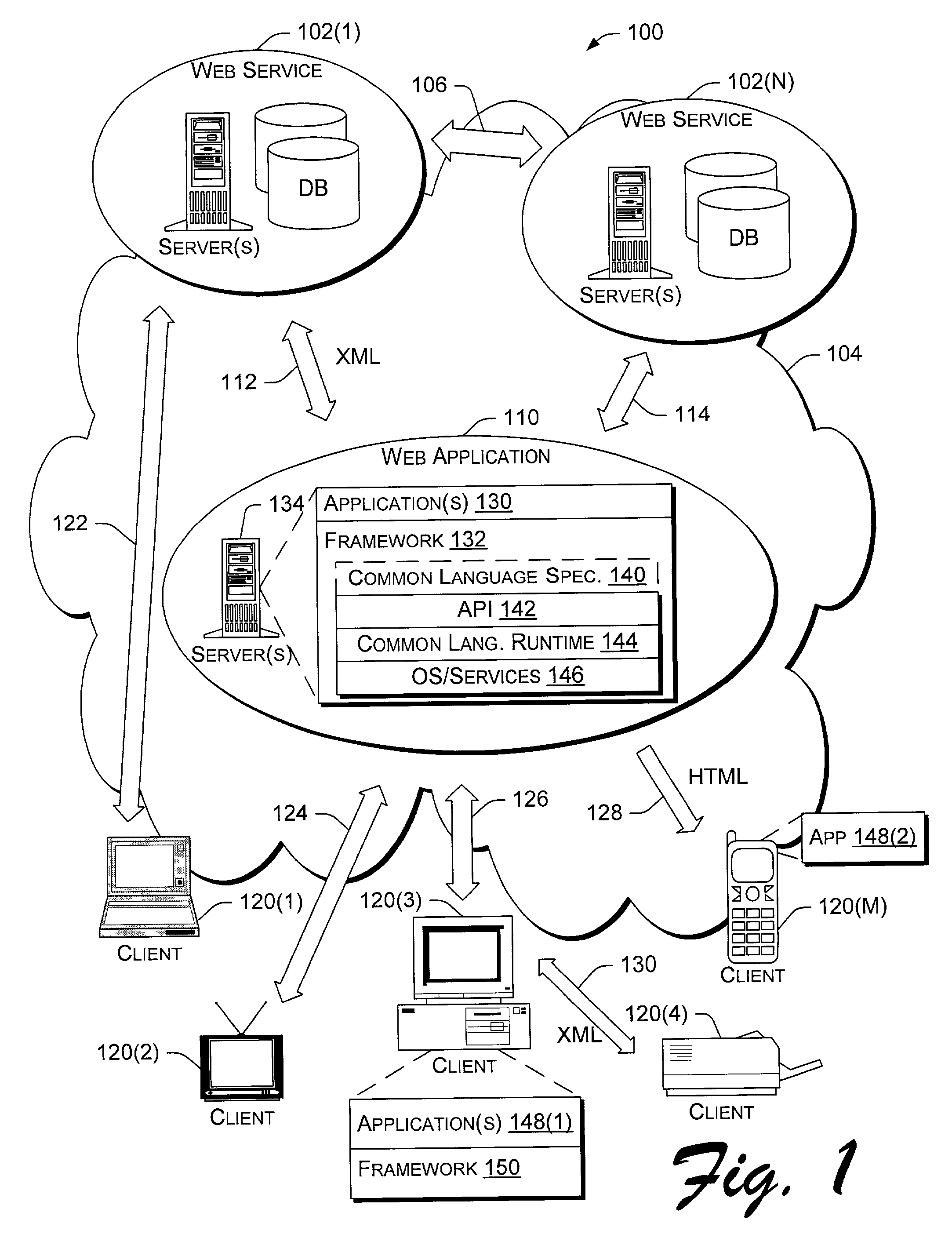
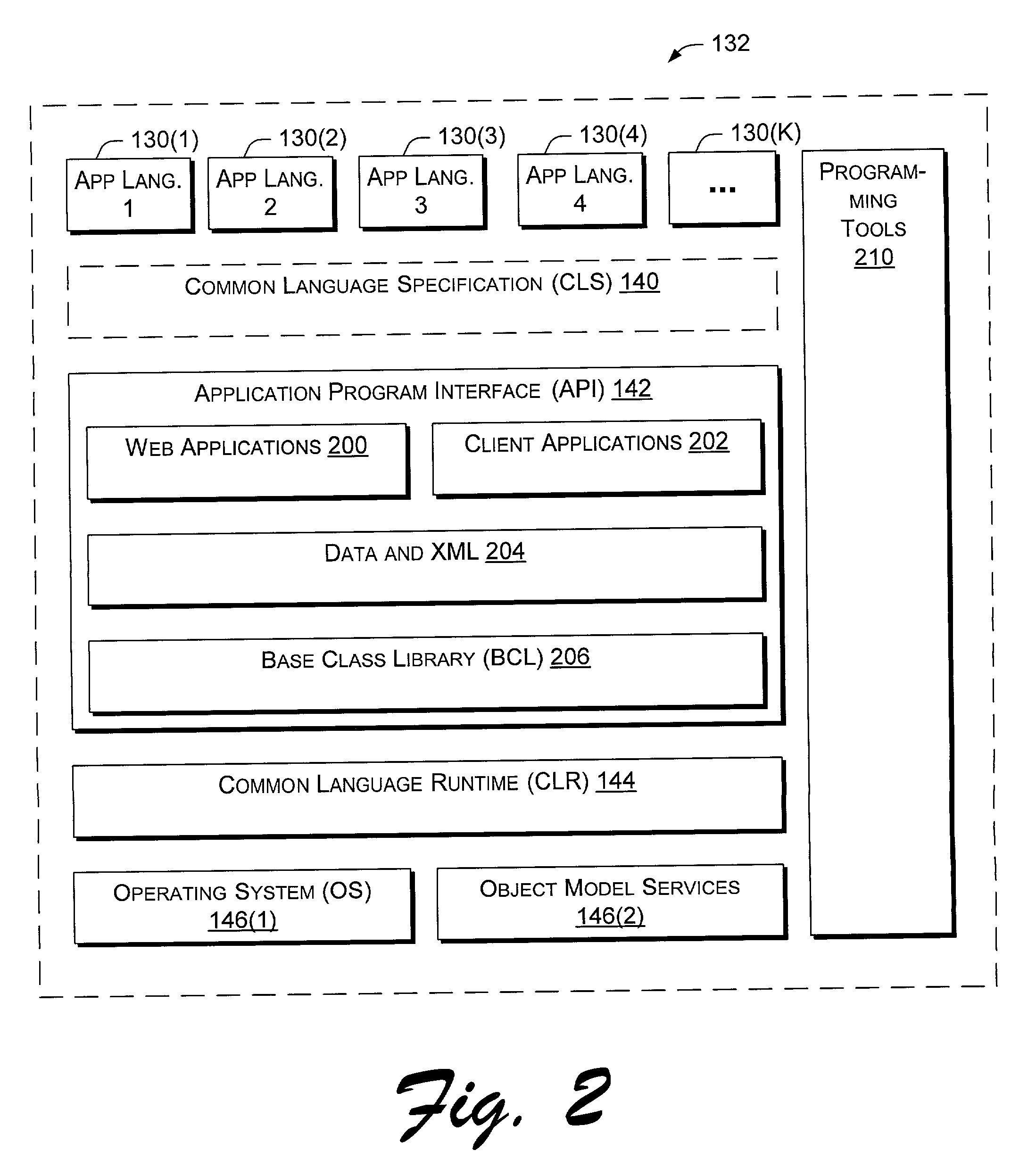
Application program interface for network software platform
InactiveUS20030167356A1Specific program execution arrangementsMemory systemsWeb applicationApplication programming interface
Owner:MICROSOFT TECH LICENSING LLC
Method of administering software components using asynchronous messaging in a multi-platform, multi-programming language environment
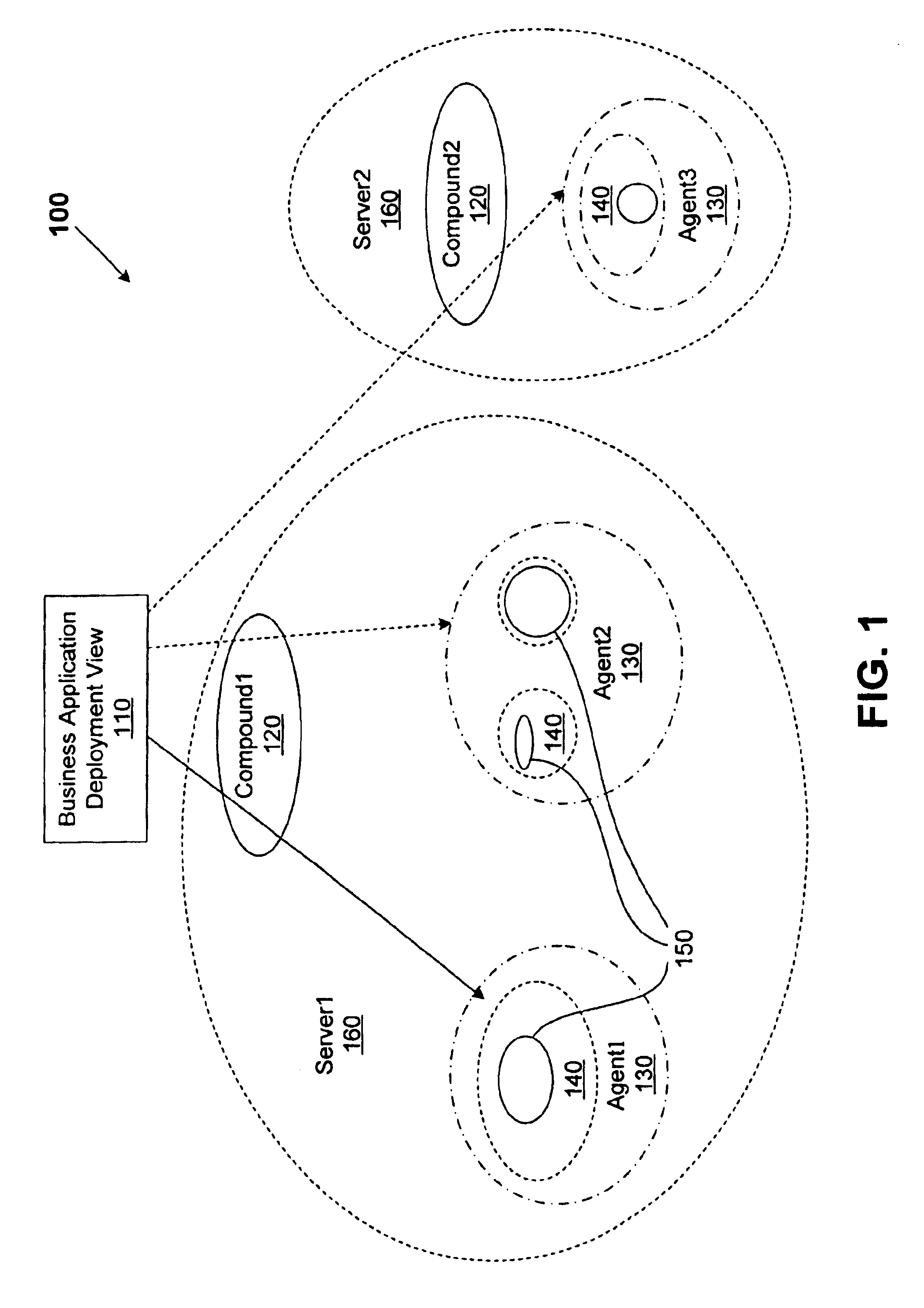
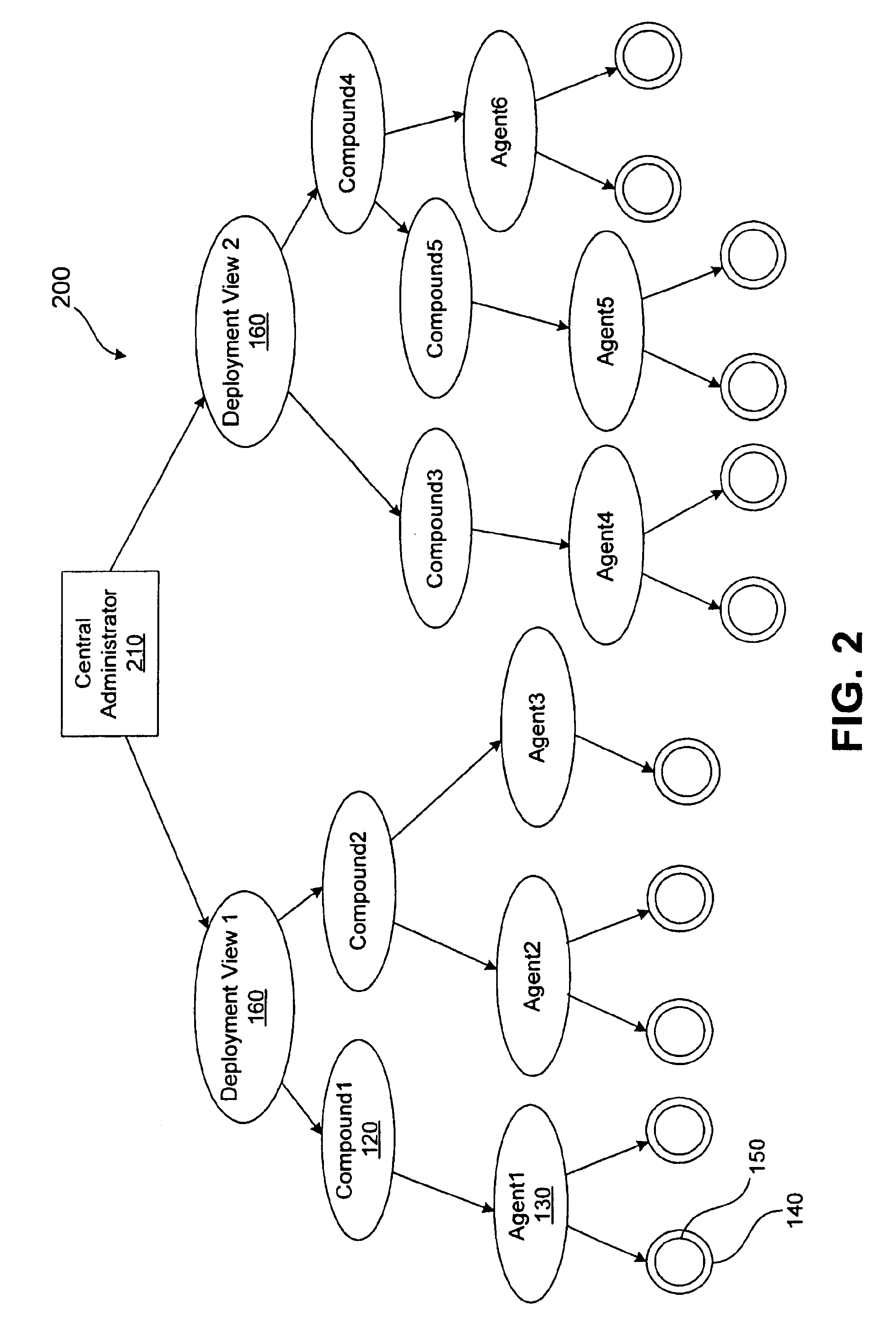
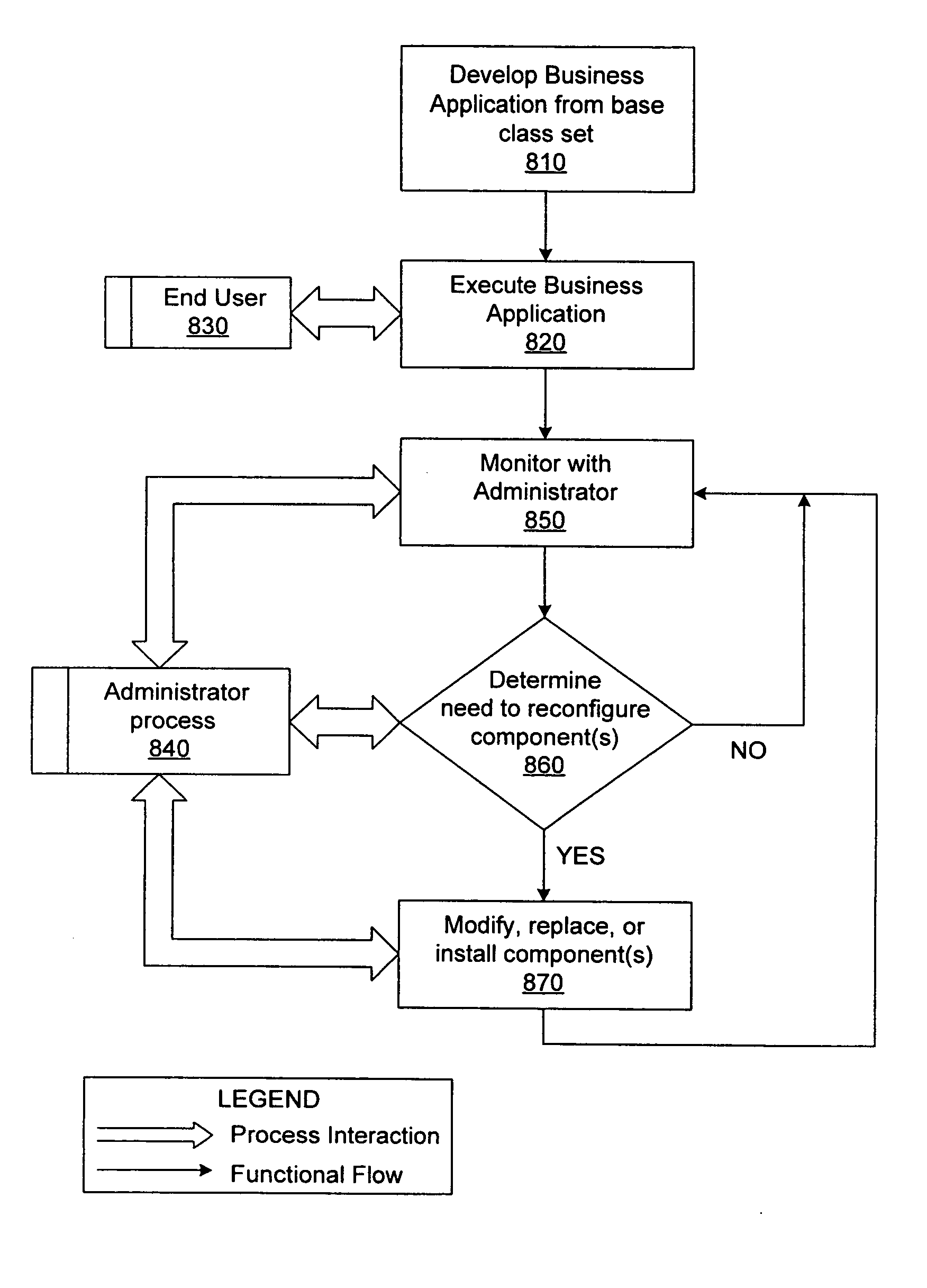
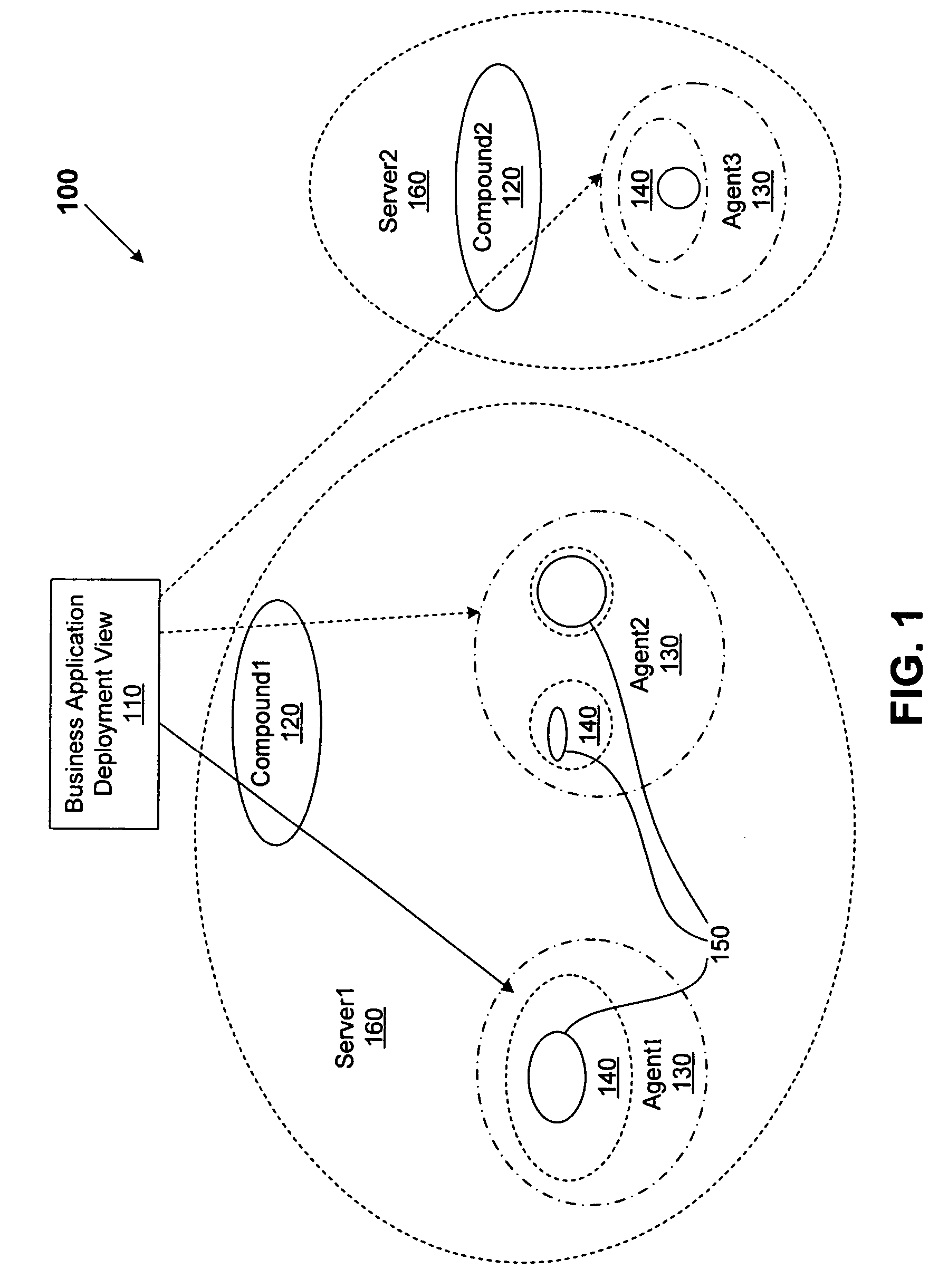
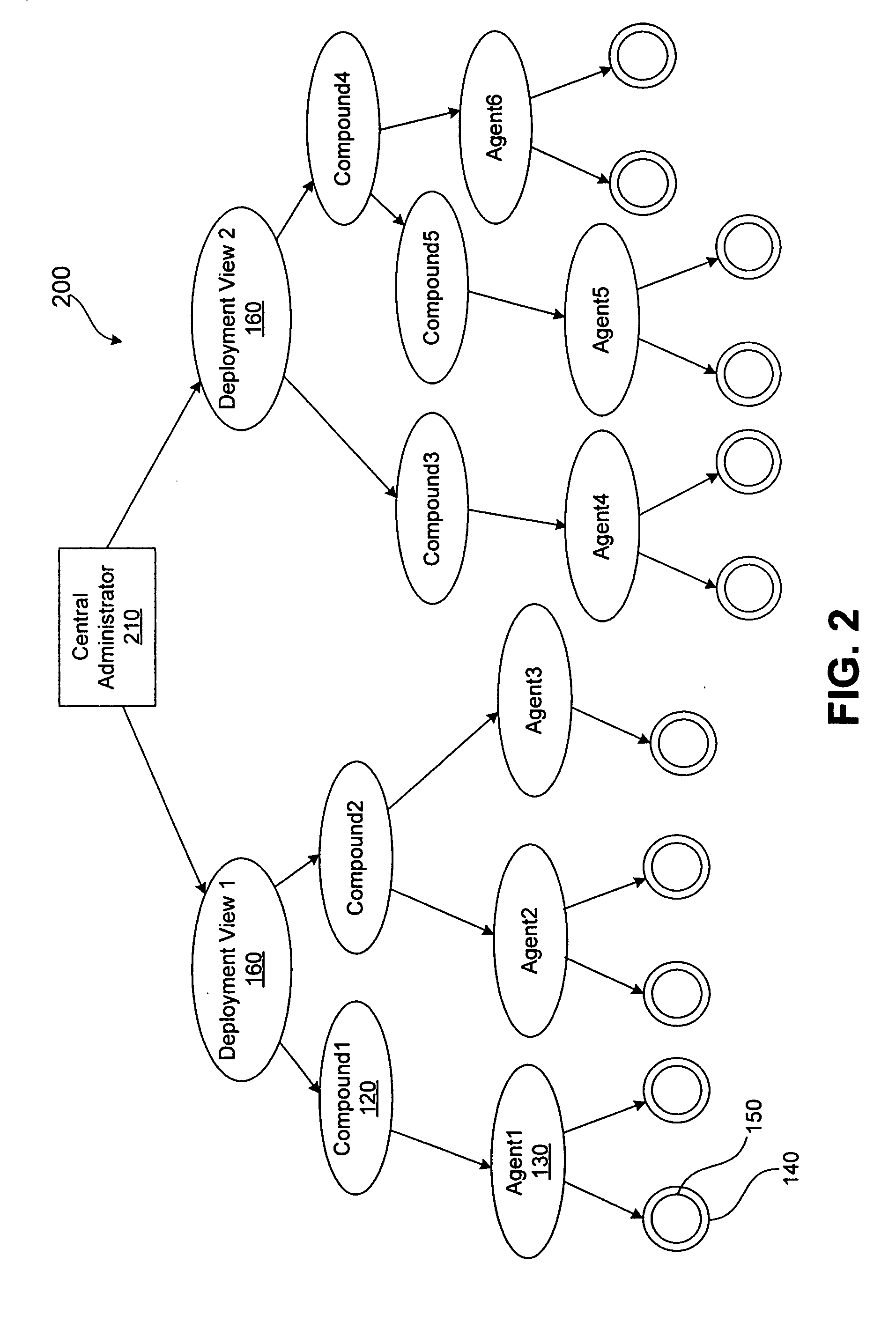
A method for performing life cycle management of business software applications and their components across a multiple-platform, multiple-language network. The method takes advantage of the inheritance properties of object-oriented programming (OOP) by developing all components of a business application from a set of base classes, thus deploying a common set of methods across all application components. The Central Administrator then determines when a need to reconfigure one or more components of the business application has arisen. The Central Administrator then modifies or replaces existing components of the business application or installs entirely new components over the network without end user interaction. In one embodiment of the present invention, the Central Administrator is aided by a set of Distributed Administrators located on each virtual node server / host computer of a business application operating over a network.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
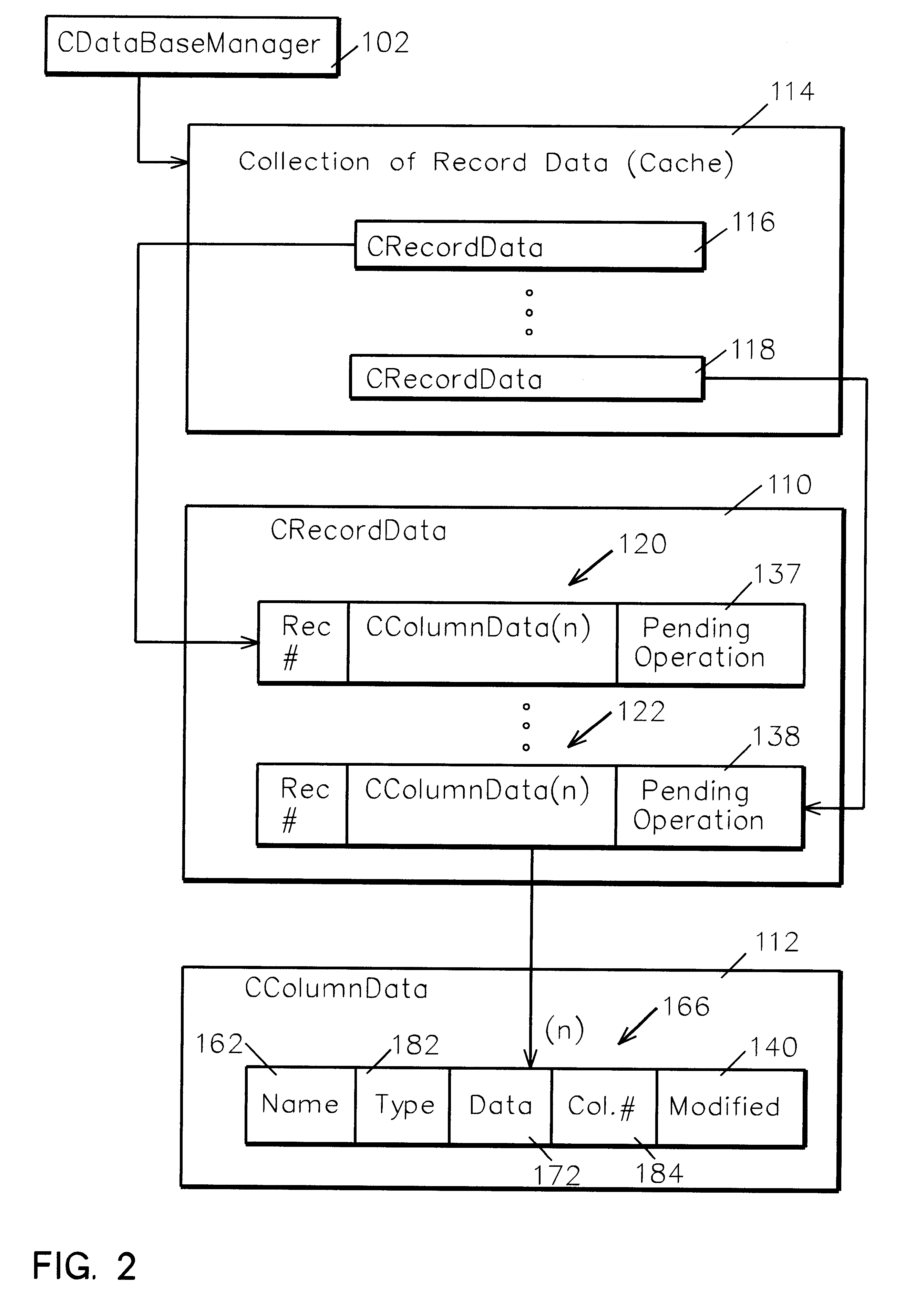
System and method for data manipulation in a dynamic object-based format
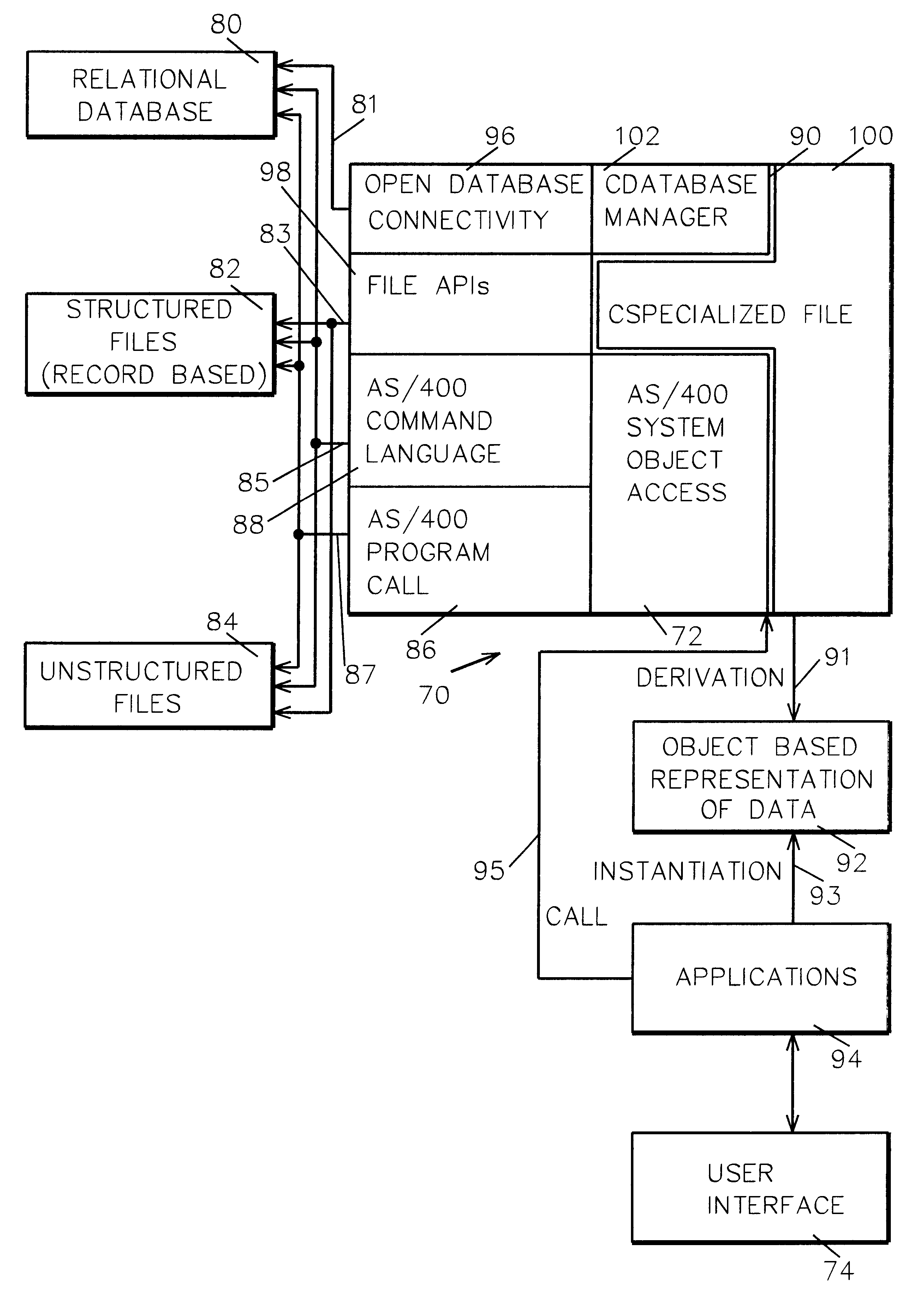
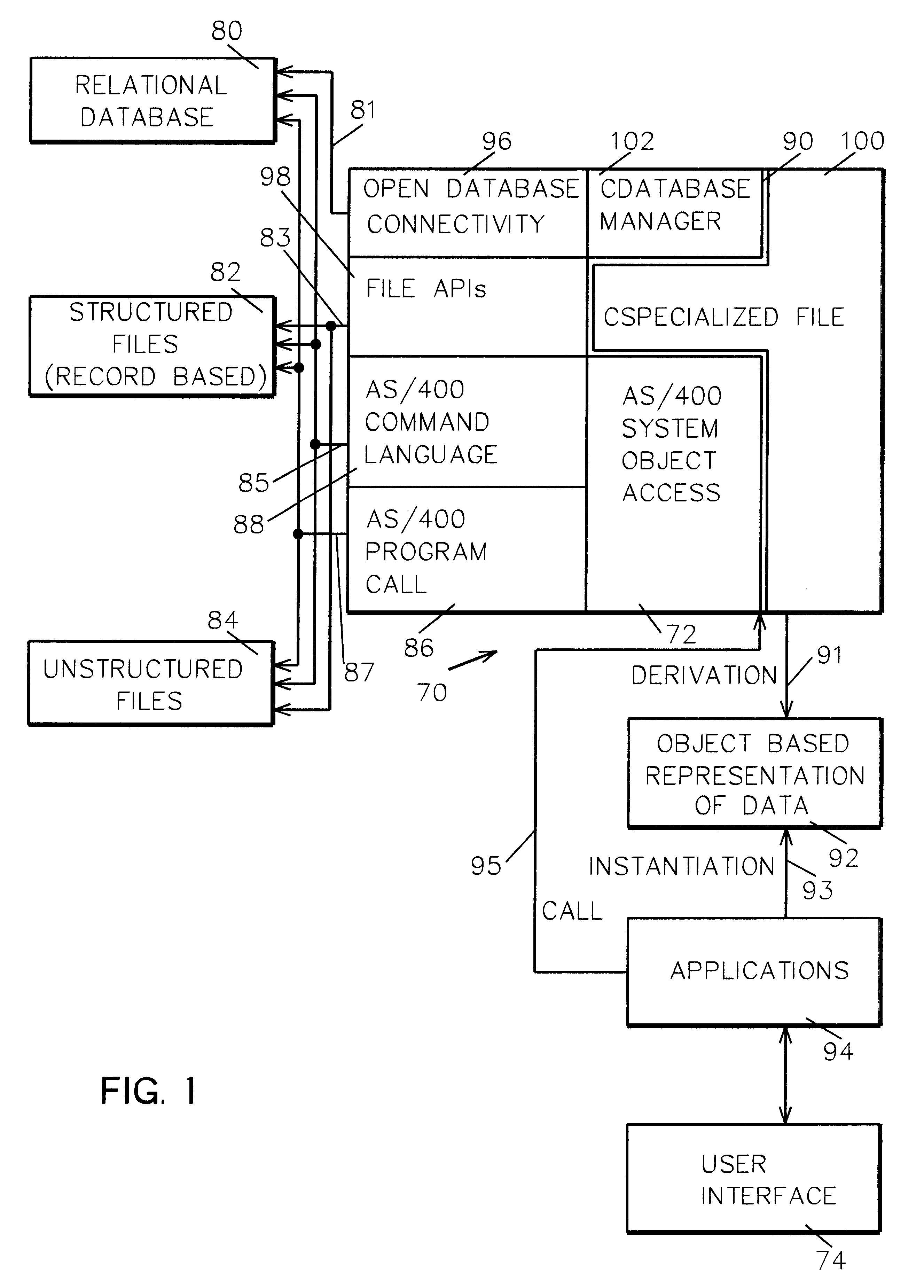
An extensible framework provides a unified interface for data manipulation in a dynamic object-based format. A data access layer of the Transmission Control Protocol / Internet Protocol (TCP / IP) Graphical User Interface (GUI) component uses ODBC to read and write files. Four abstractions implement the framework. These are (1) a CDatabaseManager class that provides access to data stored in a database; (2) a CSpecializedFile class which composes a CDatabaseManager that abstracts the management of reading and writing to database files and provides a unified interface for use by accessors. If the base class functionality of the CSpecializedFile class is not sufficient then derived specialized file classes are implemented to override the CSpecializedFile commit method and update the file in a different-fashion and / or implement specialized get / set methods by column data item and data type; (3) a CRecordArray class which manages vectored access to information stored as objects in a CColumnData class; and (4) a CColumnData object which manages changes made to the information and saves it when requested.
Owner:IBM CORP
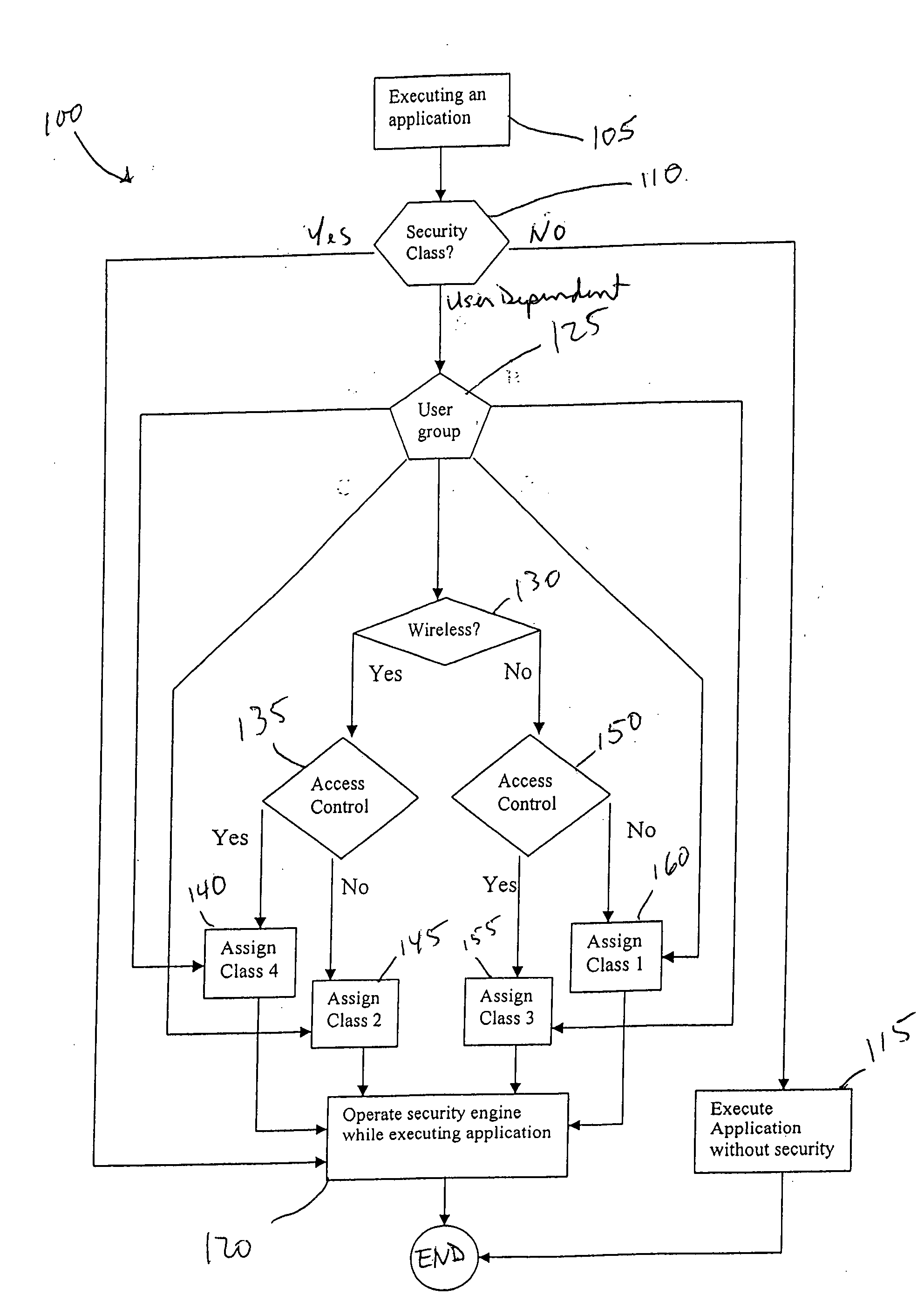
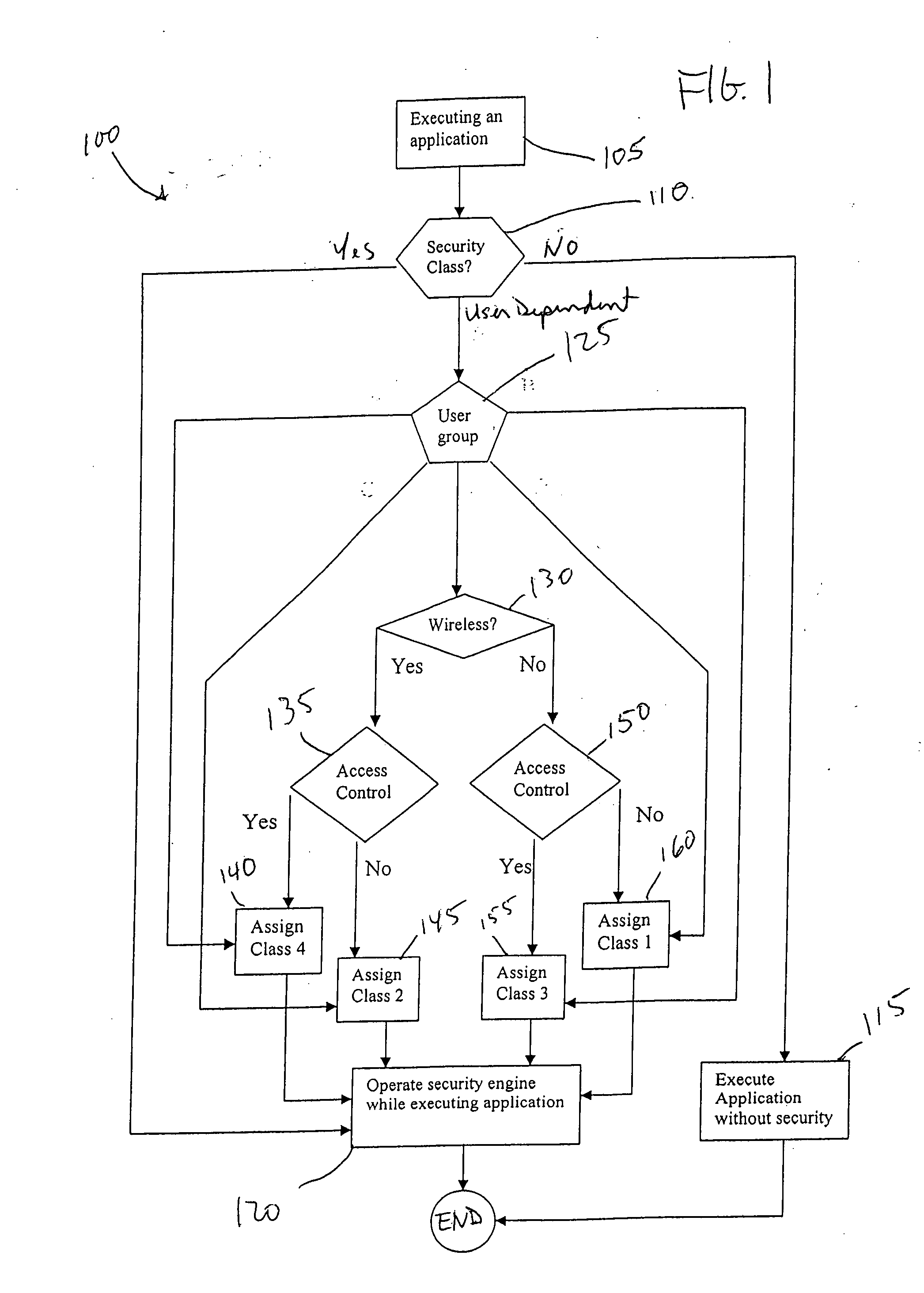
System and method for application and user-based class of security
InactiveUS20050015592A1Computer security arrangementsSecuring communicationInternet privacyBase class
A method for automatically adjusting the security level for a given application and specific user includes the steps of determining a security level assigned to the application, determining whether the security level is dependent upon a type of specific user, executing the application without security if no security level is assigned to the application and if the security level is not dependent upon the type of specific user, executing the application with security if the application has an assigned security level and if the security level is not dependent upon the type of specific user, assigning the security level if the security is dependent upon the type of specific user, and executing the application with the assigned security level dependent upon the type of specific user.
Owner:LIN JEOU KAI
Method and apparatus for executing multiple JAVA((TM)) applications on a single JAVA((TM)) virtual machine
InactiveUS6931544B1Big memorySignificant performance improvementProgram loading/initiatingSoftware simulation/interpretation/emulationOverlayUser Privilege
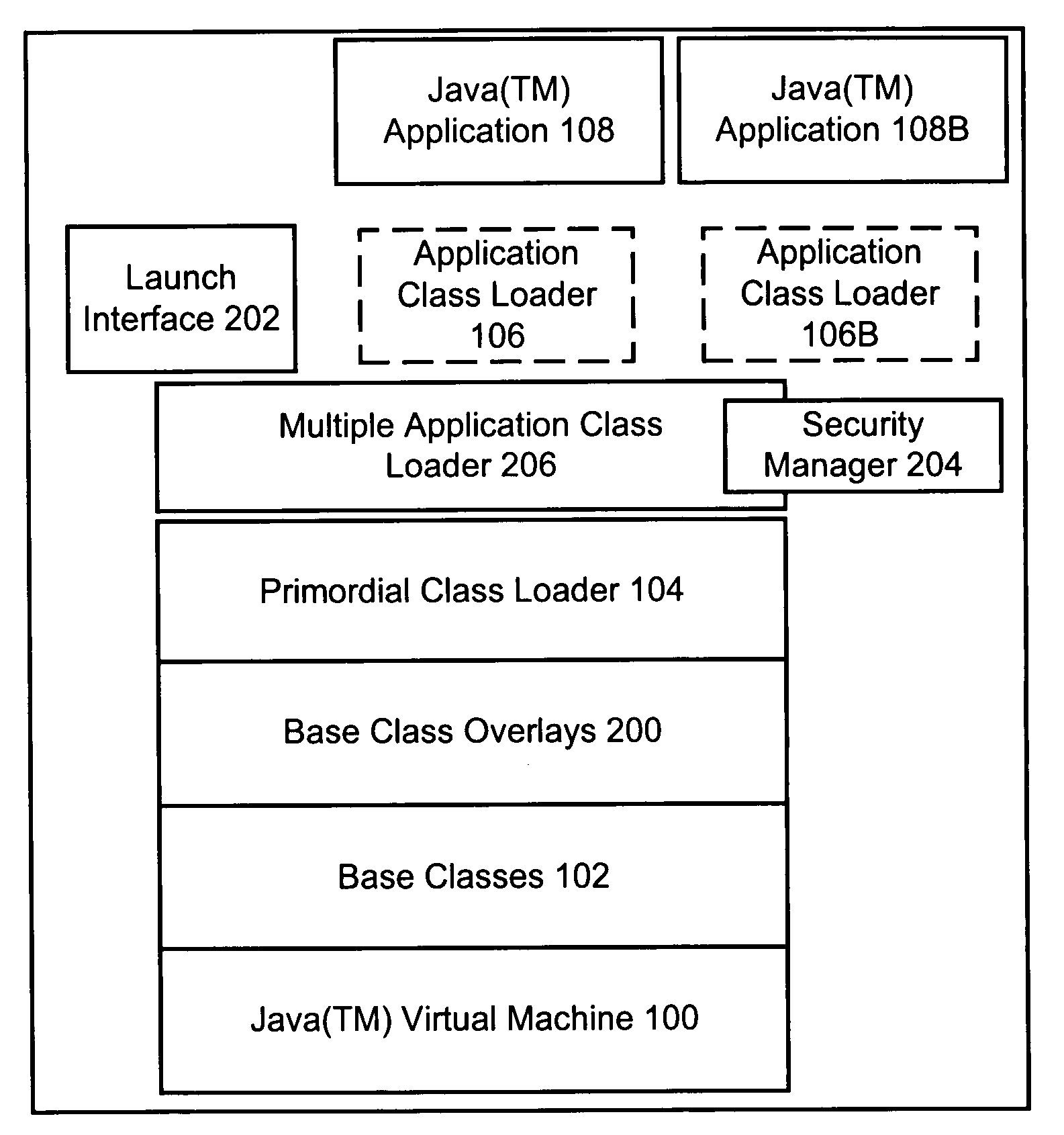
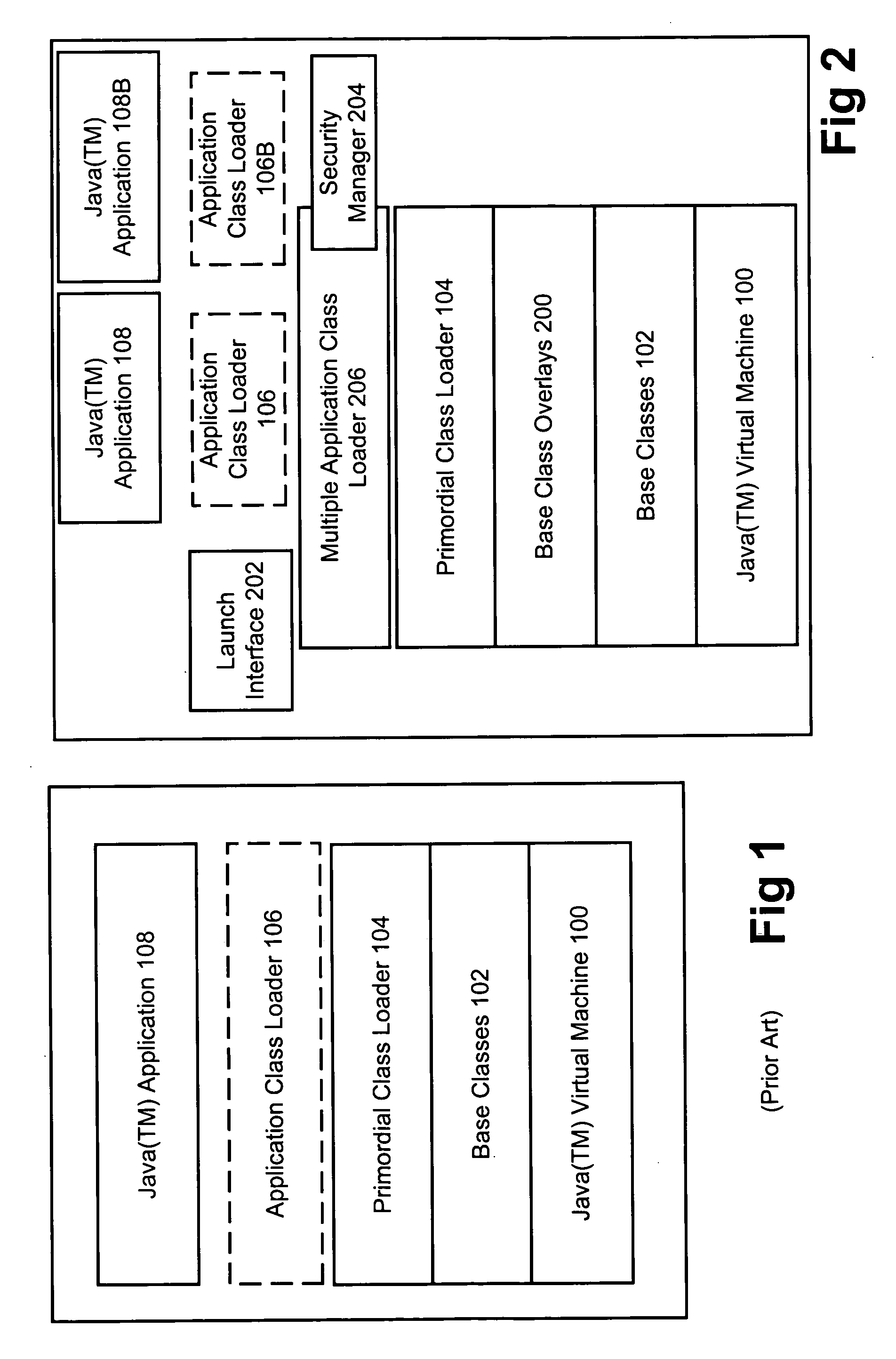
A modified JAVA(™) execution environment is described. The modified environment supports multiple JAVA(™) applications on a single JAVA(™) virtual machine (JVM). This modified environment provides significant memory and performance improvements when running multiple applications on a single computer system. Notably, no changes are needed to the source code of an application to take advantage of the modified environment. Further, embodiments of the invention may support shared access to base classes through the use of overlays. Additionally, system resource permissions can be enforced based upon the user permissions associated with a running application. Notably, embodiments of the invention allow multiple applications to share the abstract window toolkit (AWT) on a per display basis. Since only a single garbage collection routine is necessary, applications see improved performance relative to running in different JVMs. Further, the shared base classes eliminate significant memory overhead.
Owner:APPLE INC
Class dependency graph-based class loading and reloading
ActiveUS7039923B2Effective supportReduce in quantityVersion controlProgram loading/initiatingGraphicsAlgorithm
Embodiments of a system and method for providing class dependency graph-based class loading and reloading may be used to segregate namespaces in a graph-centric way, and may provide a set of normalized topologies that may be used to efficiently support hot-swapping of programmatic logic such as classes, applets, and beans, among other applications. Embodiments may provide a domain-independent, flexible and robust namespace segregation technique that is based on the dependency between the various classes and not on details like the roles the classes play. The problem of segregating namespaces is formulated as a graph theory problem, and a solution is sought through graph techniques. The graph may be normalized by identifying and grouping interdependent classes and non-interdependent classes in separate groups. A directed dependency relationship of the groups may be determined using the relationships between the member classes of the groups.
Owner:ORACLE INT CORP
Scripting business logic in a distributed object oriented environment
InactiveUS20020129345A1Program initiation/switchingProgram loading/initiatingScripting languageBase class
The software system of the present invention is a distributed object oriented software system that it is customizable and flexible enough to implement a wide variety of different "business logics" without the need to rewrite the basic components of the software system because it provides scripting capability in a distributed object-oriented software system. The present invention includes a rules-based scripting language that can be interpreted by a Rules Engine that is part of the base class of component for the software system. In accordance with the present invention each individual component of the software system may have one or more predetermined rule sets defined for it. Each predetermined rule set allows customization of the behavior of the associated component of the software system.
Owner:CONDUCTIVE TECH
Parser, code generator, and data calculation and transformation engine for spreadsheet calculations
InactiveUS20070006139A1EffectEfficient developmentDigital data information retrievalText processingData transformationBase class
Owner:KNOWLEDGE DYNAMICS
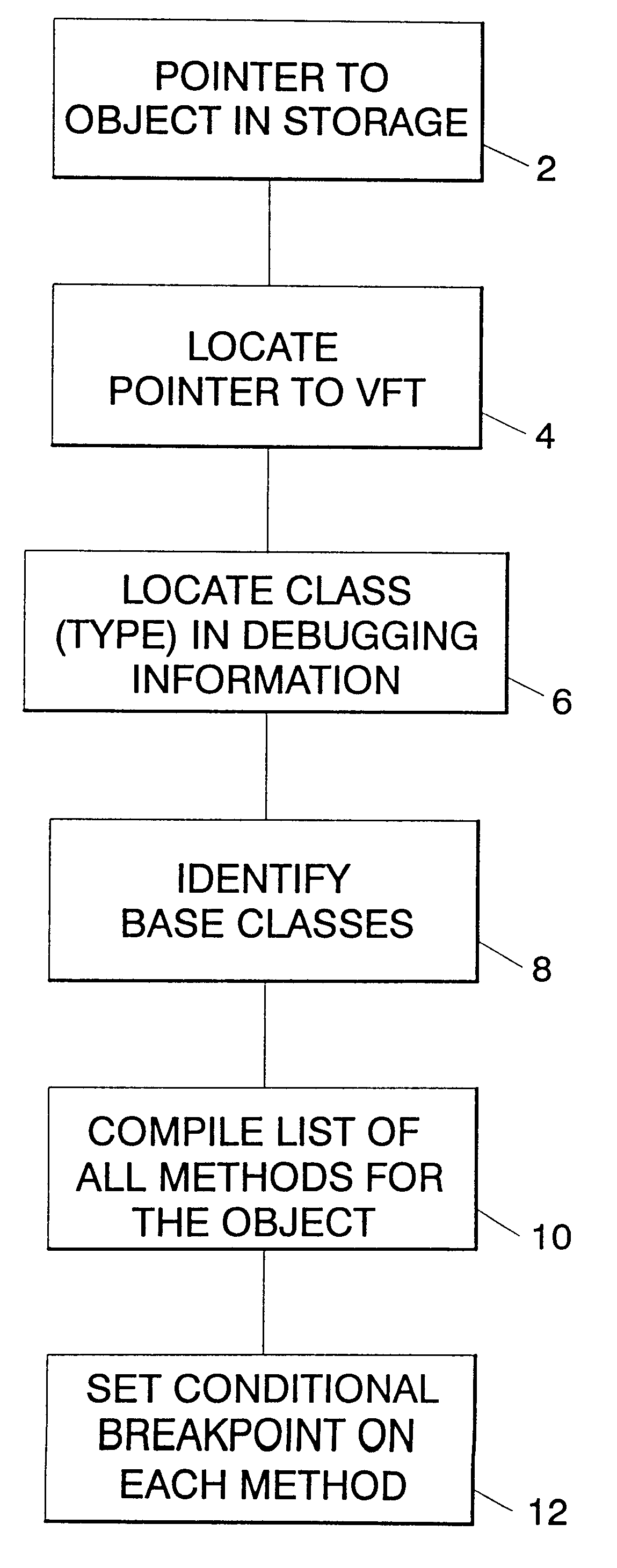
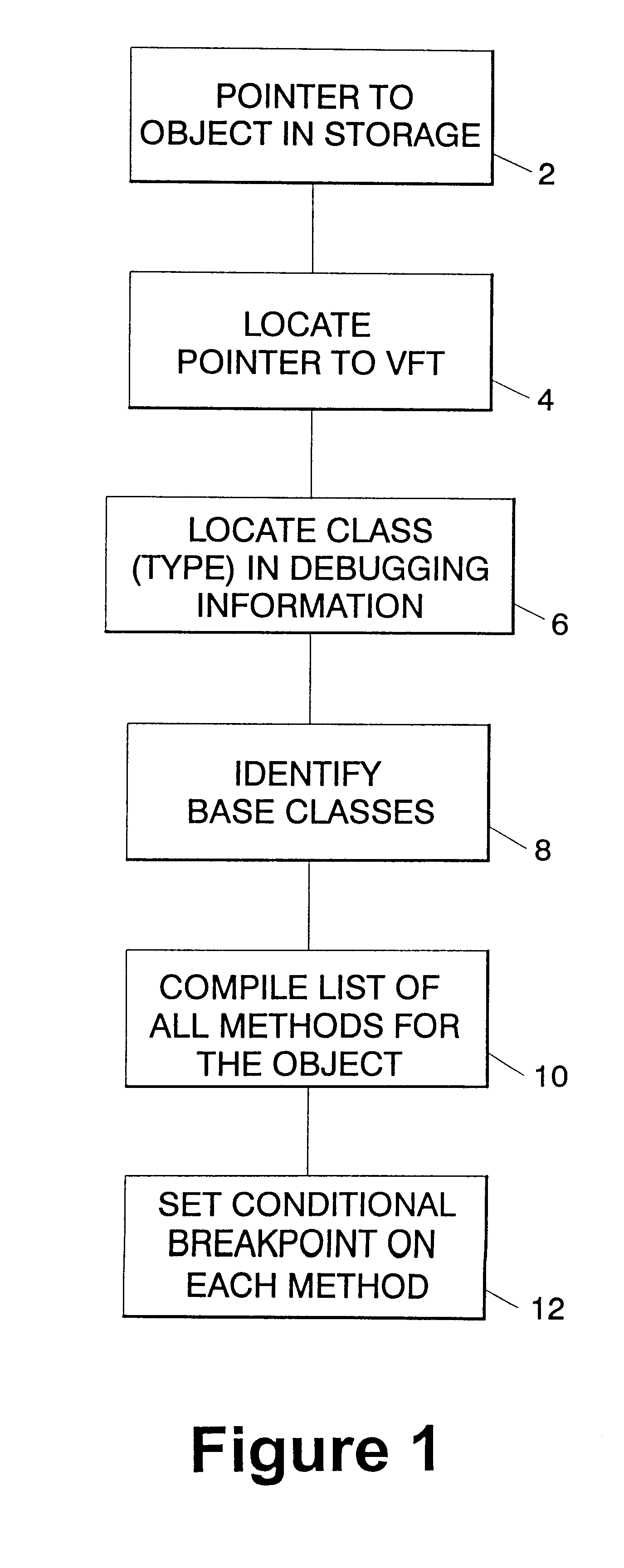
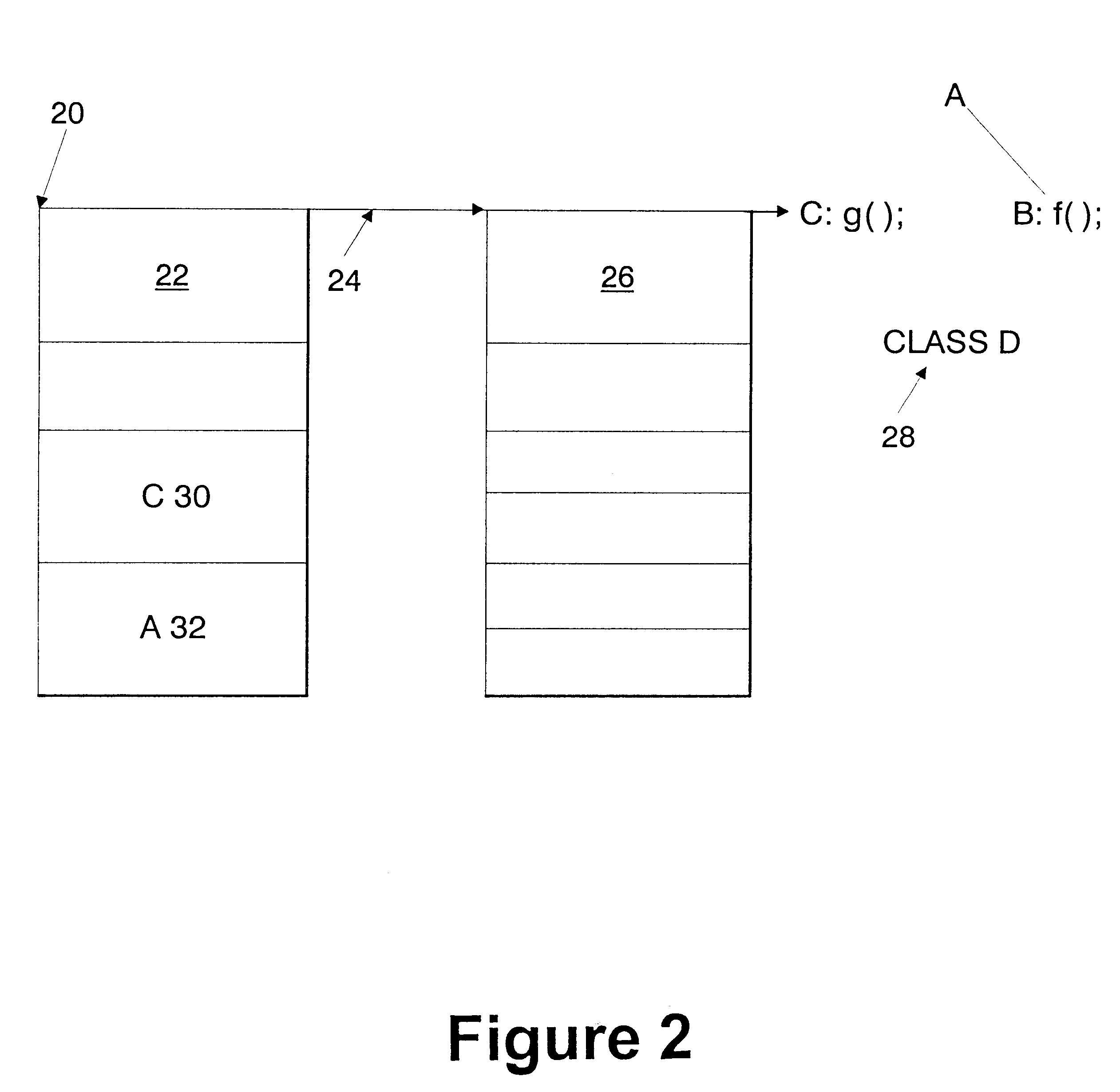
Setting instance breakpoints in object oriented computer programs
InactiveUS6240545B1Software testing/debuggingSpecific program execution arrangementsBase classClass hierarchy
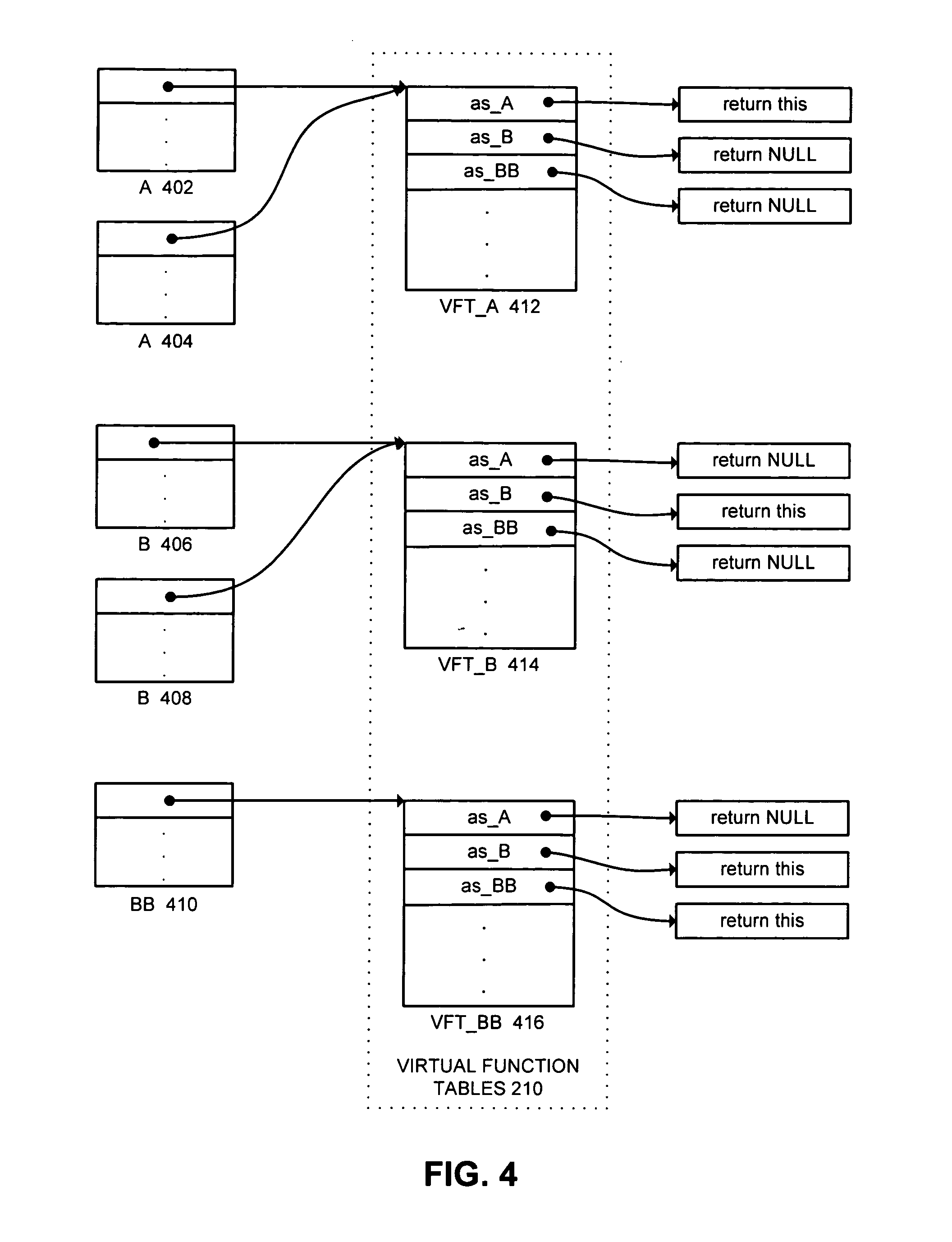
A mechanism for setting a conditional breakpoint on all methods called by a specific instance of a class. To set the instance breakpoint, the debugger determines all of the methods that can be applied to the object type or class. In an environment in which full debugging information includes the correspondence between virtual function tables and specific classes, and full class hierarchy information, the methods are located by locating the pointer to the type's virtual function table, and from the virtual function table, locating the specific class in the debugging information. Identifying the specific type permits all of the base classes of the type to be identified in the debugging information, and from the class hierarchy information, all methods for objects of the type can be compiled. The debugger then sets a conditional breakpoint on each method, the condition specifying that the breakpoint should cause program execution to automatically stop only if the method is being called for the particular object or instance for which the instance breakpoint was set.
Owner:IBM CORP
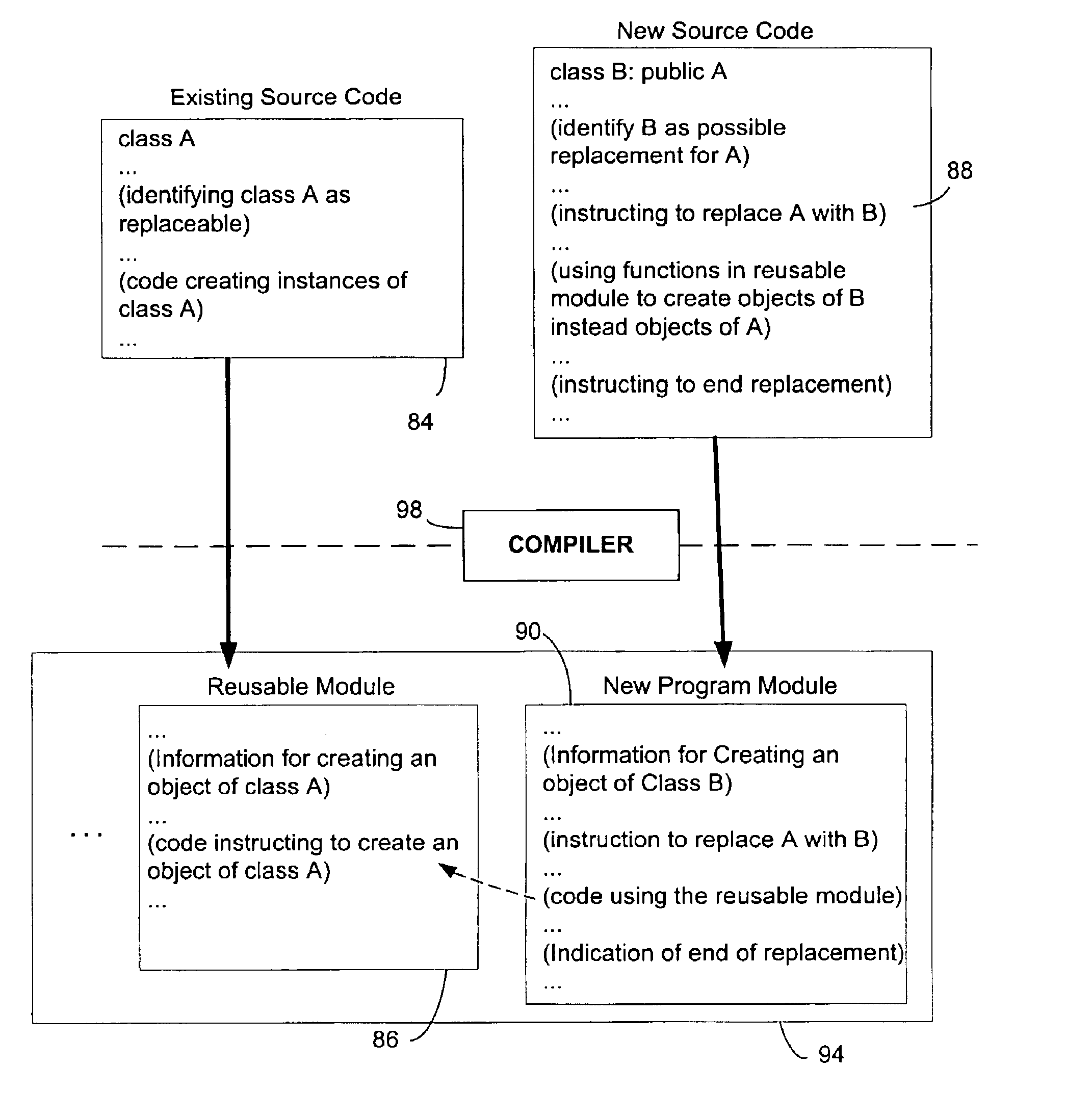
Replaceable classes and virtual constructors for object-oriented programming languages
InactiveUS6895581B1Facilitate software developmentFunction increaseSpecific program execution arrangementsMemory systemsCompiled languageBase class
An extension of object-oriented programming languages enables the use of replaceable classes and virtual constructors, thereby allowing existing code that creates objects of a base class to be reusable for creating instances of a new class derived from the base class. A base class intended to be replaceable later is declared to be replaceable. In the case of a compiled language, the programming code defining and using the base class is compiled into a reusable module. Later, a new class derived from the base class is identified as a replacement for the base class and is used in new programming code that uses the existing reusable module. The replacement relationship between the old base class and the new class is registered. During execution of the program, when the old code of the reusable module indicates the creation of an object of the base class, the registered replacement information is referenced. If the old class is to be replaced with the new class, the creation information for the new class is passed instead so that an object of the new class is created. The class replacement may be implemented with compiled and interpreted programming languages. When a compiled language is used, the class replacement may be implemented with new compiler-supported features that emit data for class replacement into the .obj files, but may also be implemented without requiring changes to existing compilers.
Owner:MICROSOFT TECH LICENSING LLC
System and method for delivering versatile security, digital rights management, and privacy services from storage controllers
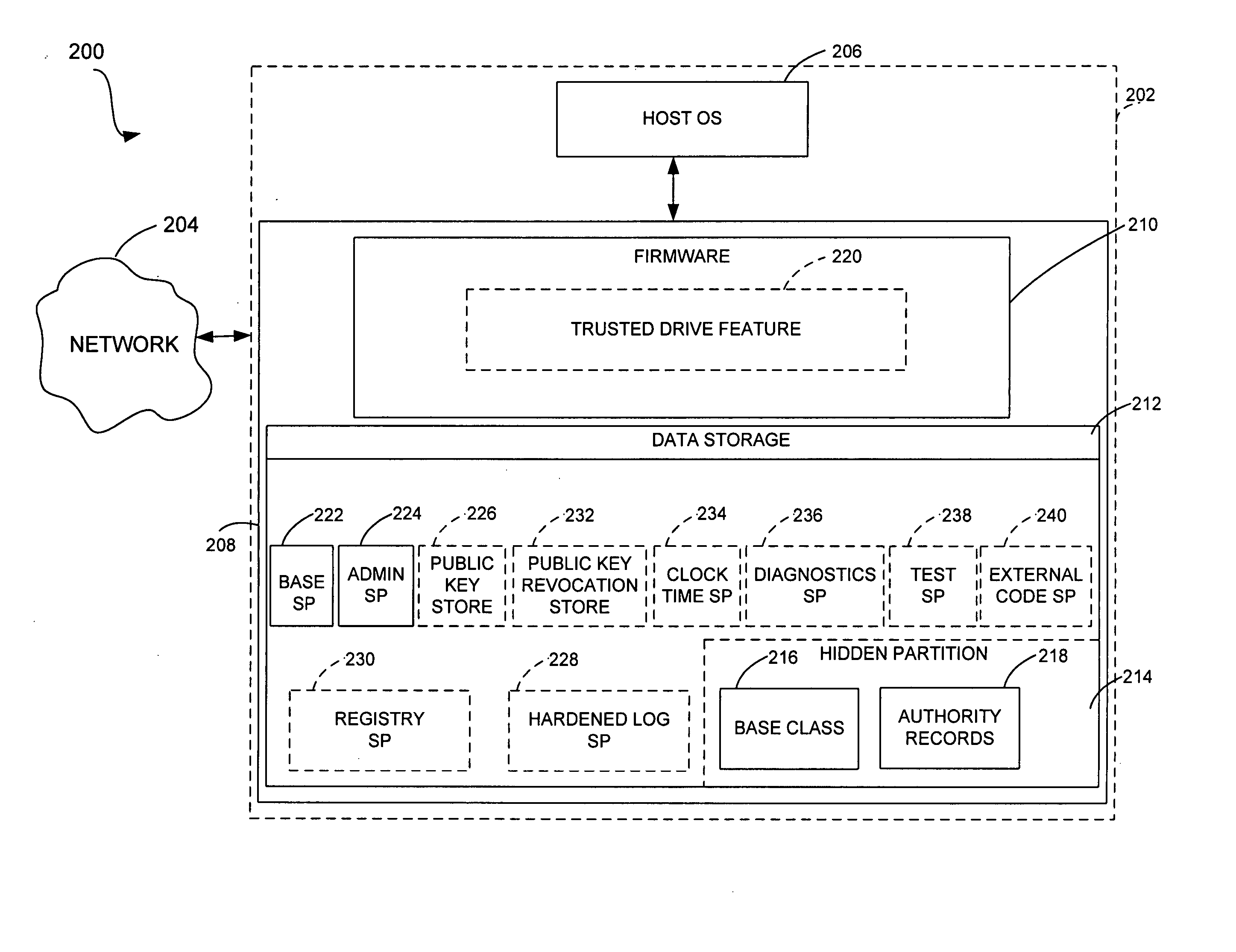
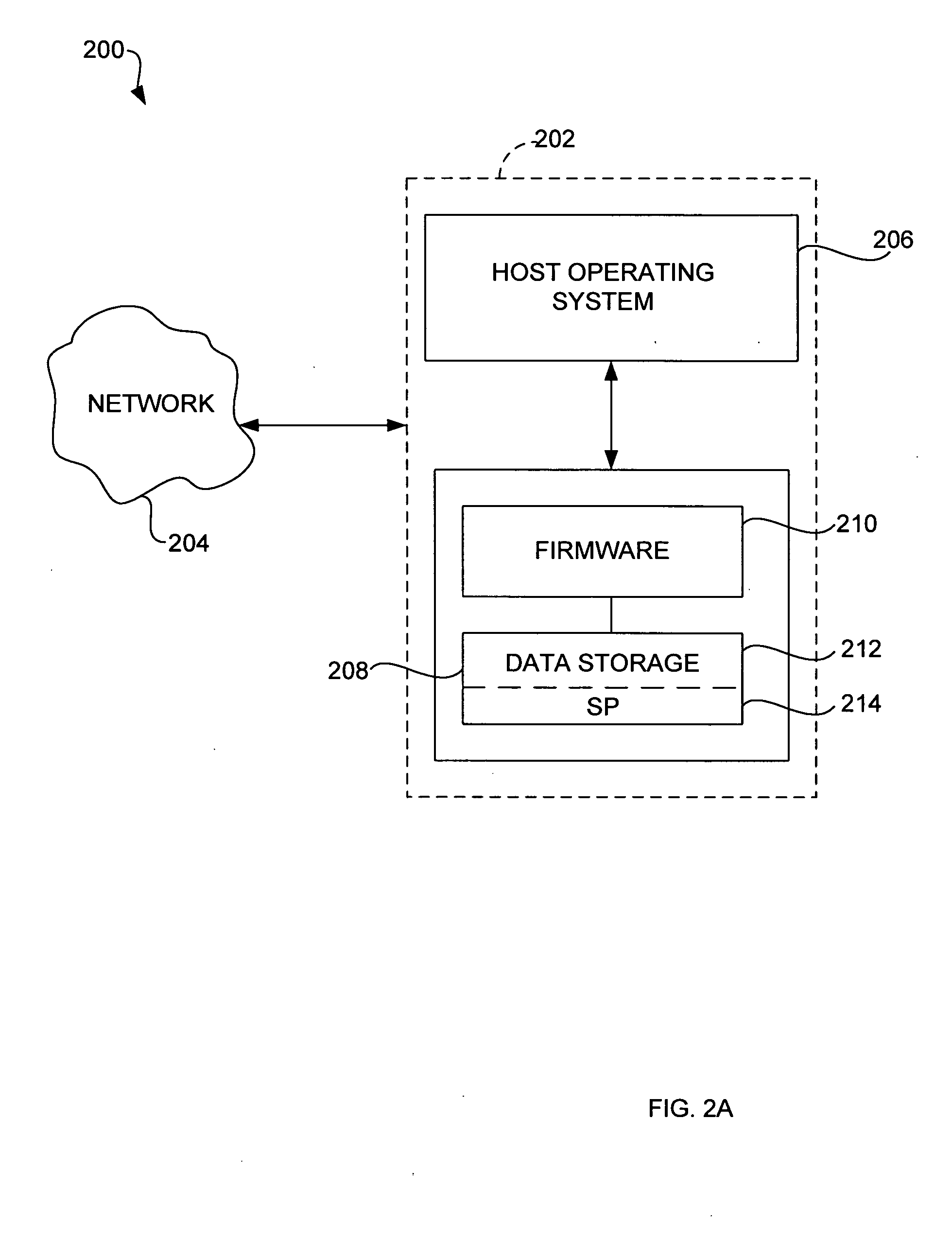
InactiveUS20050066191A1Input/output to record carriersDigital data processing detailsControl storeBase class
A method for providing enhanced security features in a storage device involves partitioning a storage media in the storage device into a hidden partition and a storage partition in the storage media. A base class is written to the hidden partition. A security provider base class is instantiated from the base class. The security provider base class is adapted to control access to the storage media.
Owner:SEAGATE TECH LLC
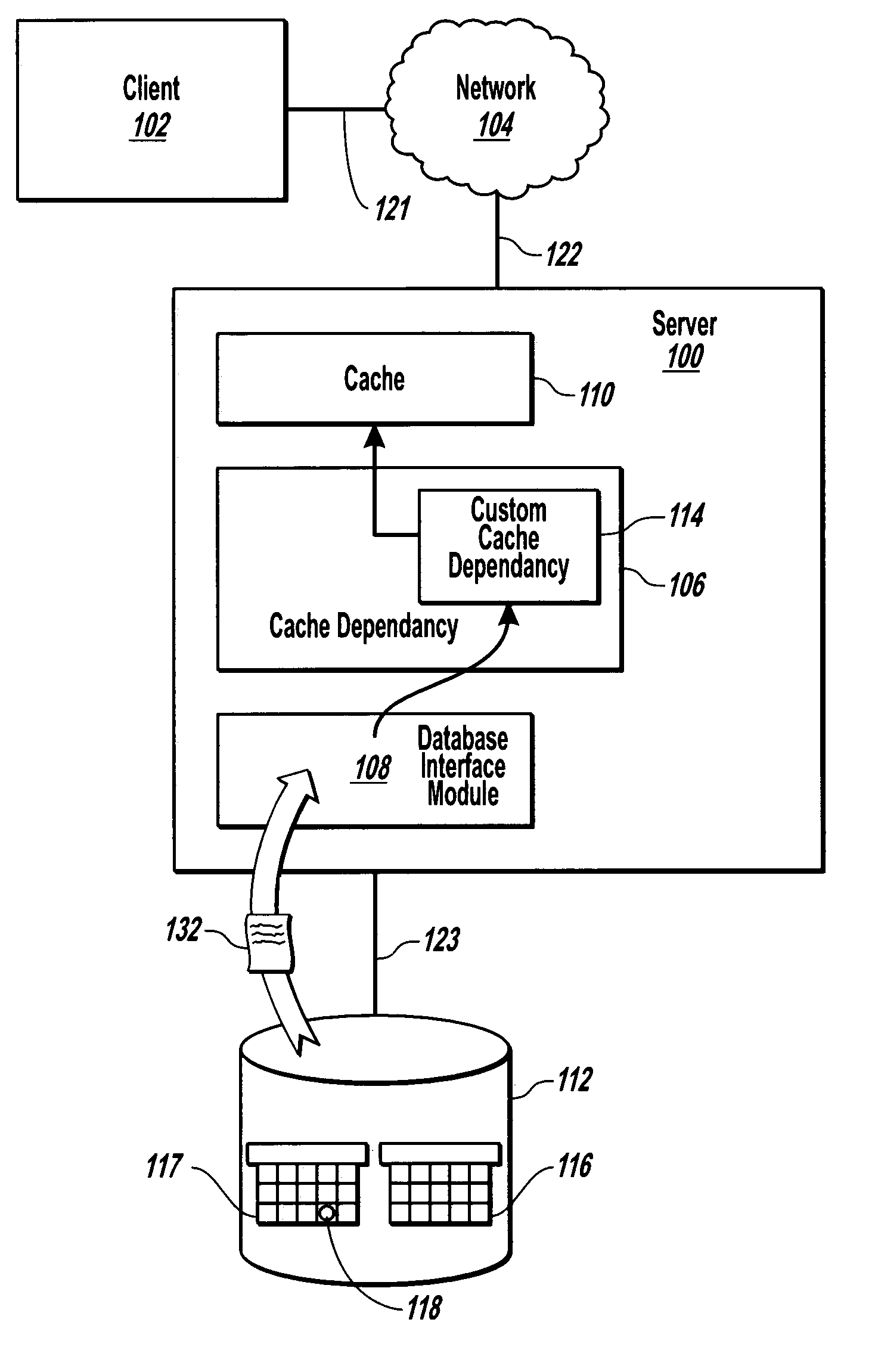
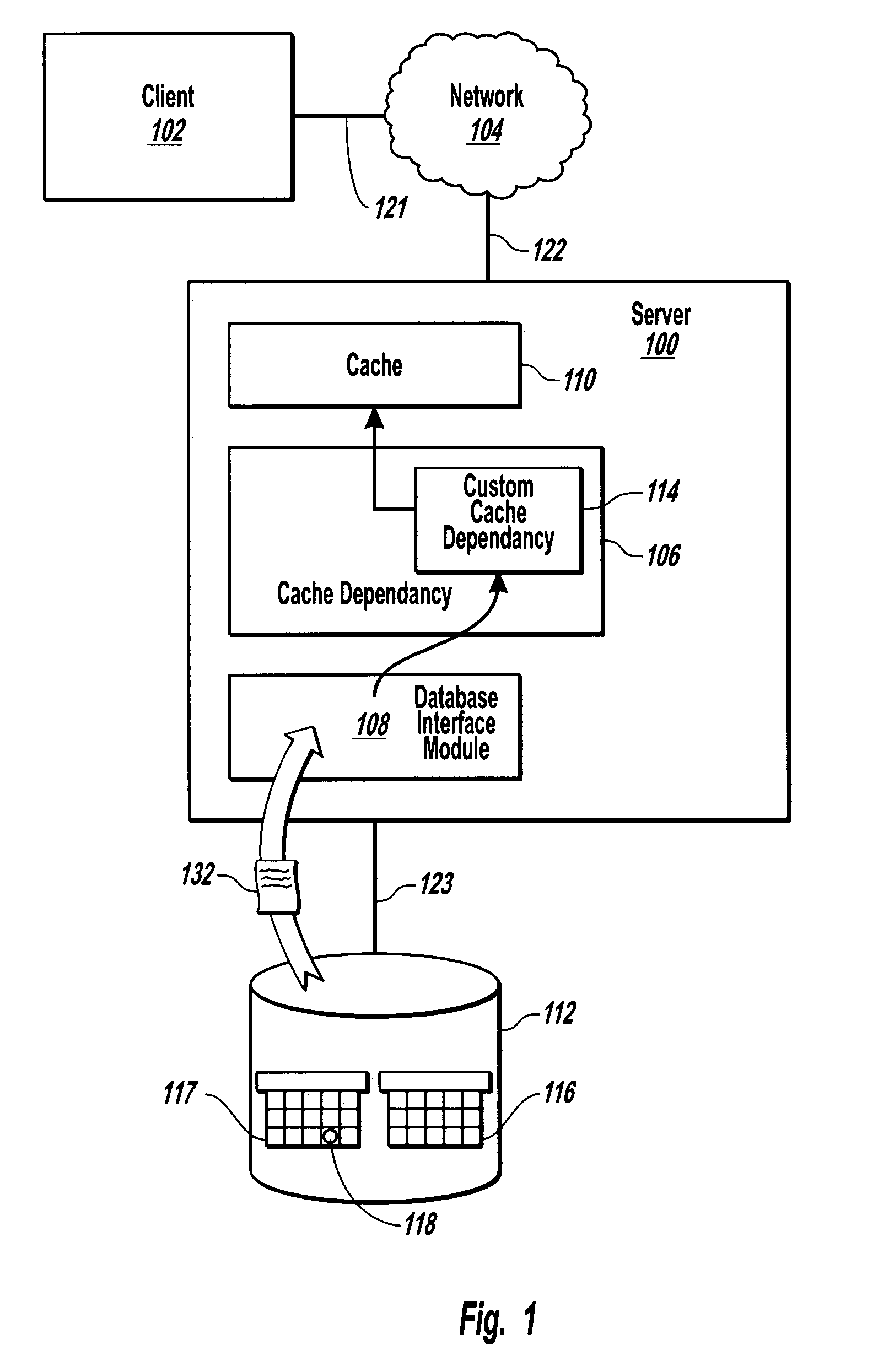
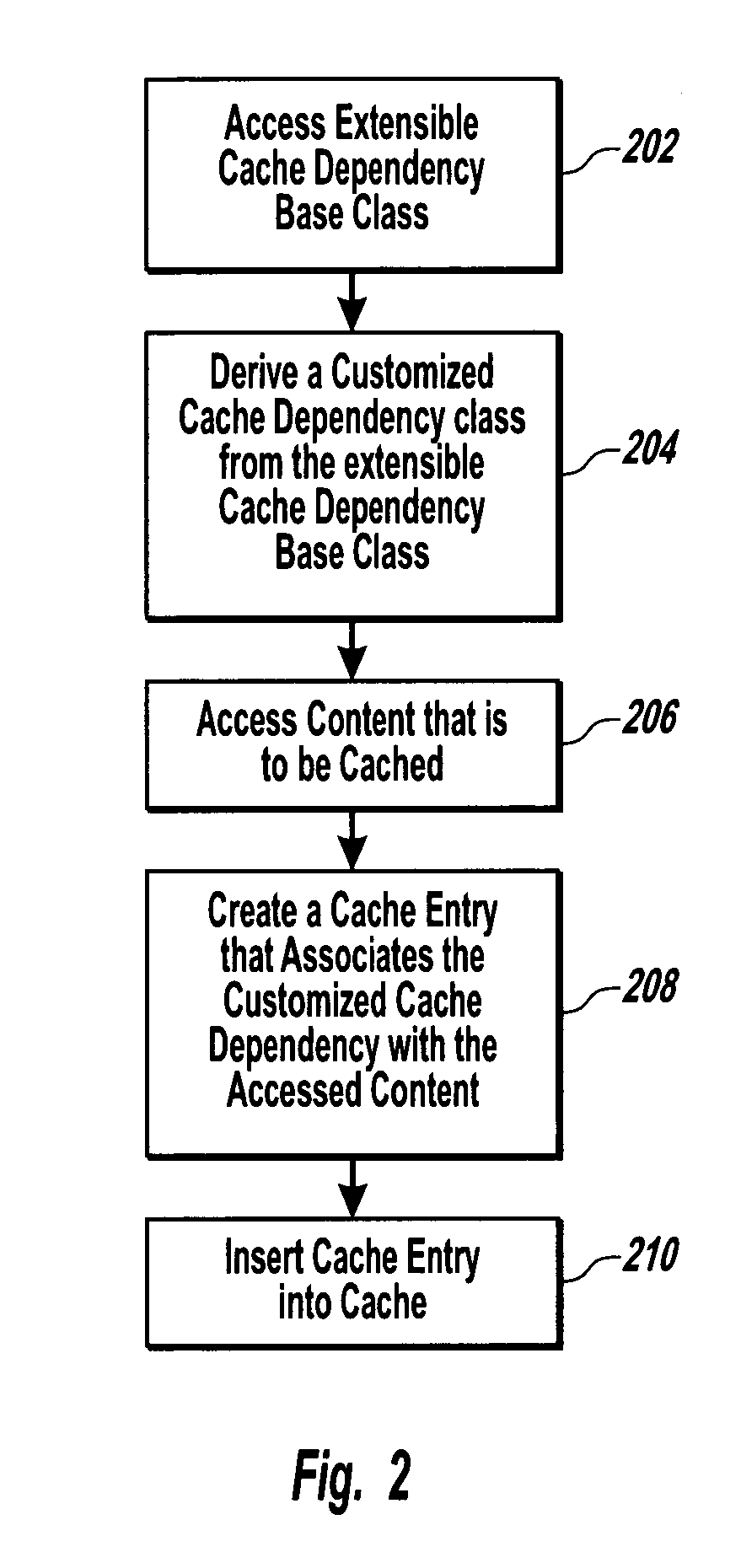
General dependency model for invalidating cache entries
InactiveUS7398304B2Digital data information retrievalMemory adressing/allocation/relocationBase classWeb service
Owner:MICROSOFT TECH LICENSING LLC
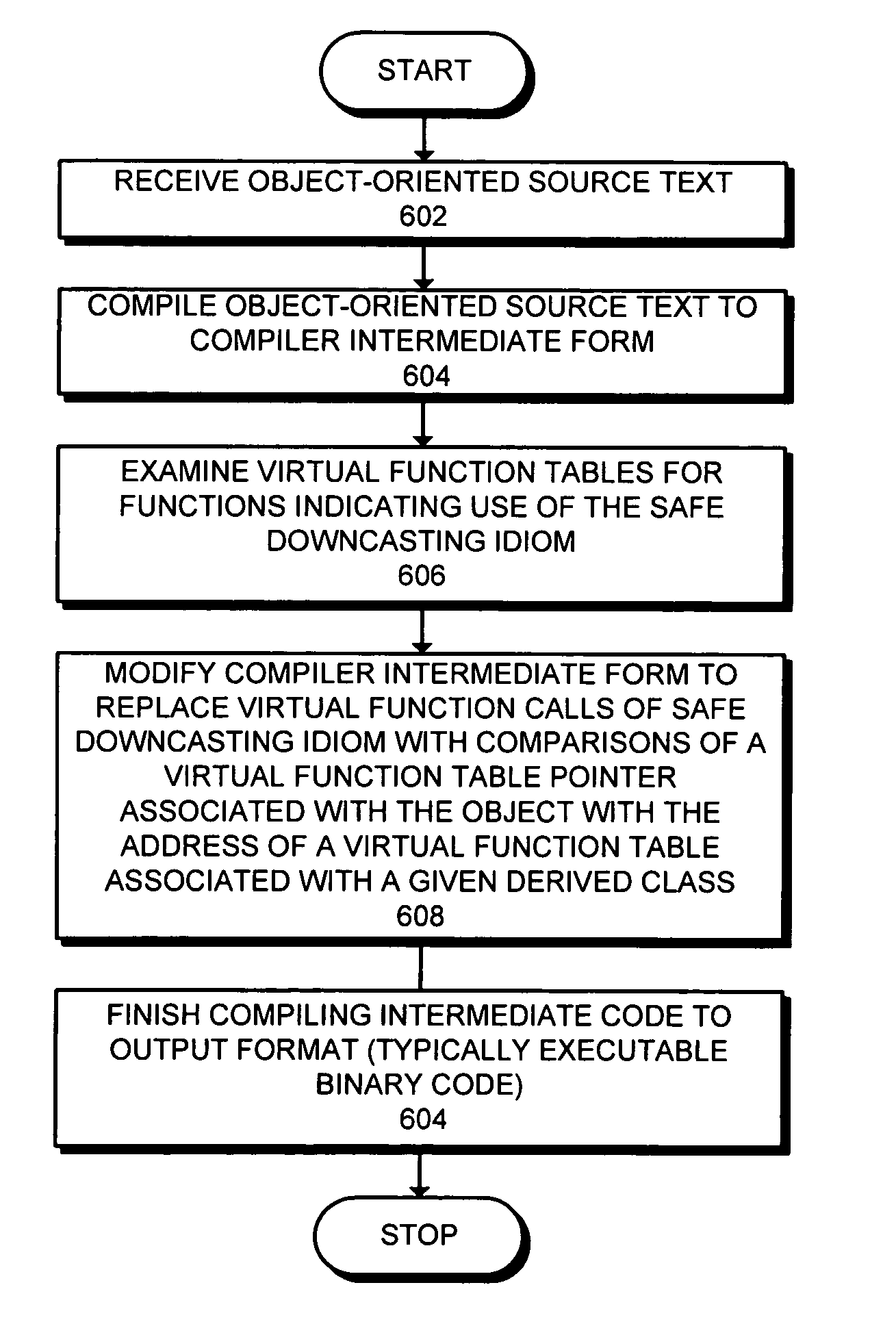
Optimizing safe downcasting in an object-oriented programming language
ActiveUS7171649B1Facilitates safe downcastingOptimizing safe downcasting and similar programming idiomsSpecific program execution arrangementsMemory systemsBase classProgramming idiom
A system is presented for optimizing safe downcasting and similar programming idioms in an object-oriented programming language. The system operates by receiving a source program written in the object-oriented programming language. The system compiles this source program into an intermediate representation. Next, the system examines the intermediate representation to identify the use of a virtual function call to determine if an object of a given base class is a member of a given derived class. Such usage facilitates safe downcasting of the object from the given base class to the given derived class. If the intermediate representation uses the virtual function call in this manner, the system replaces the virtual function call with a comparison of a virtual function table pointer associated with the object to an address of a virtual function table associated with the given derived class. The compiler finishes compiling the intermediate representation into executable binary code.
Owner:ORACLE INT CORP
System and method for delivering versatile security, digital rights management, and privacy services
InactiveUS20050160281A1Input/output to record carriersUnauthorized memory use protectionBase classDigital rights management
A method for providing enhanced security features in a storage device involves partitioning a storage media in the storage device into a hidden partition and a storage partition in the storage media. A base class is written to the hidden partition. A security provider base class is instantiated from the base class. The security provider base class is adapted to control access to the storage media.
Owner:SEAGATE TECH LLC
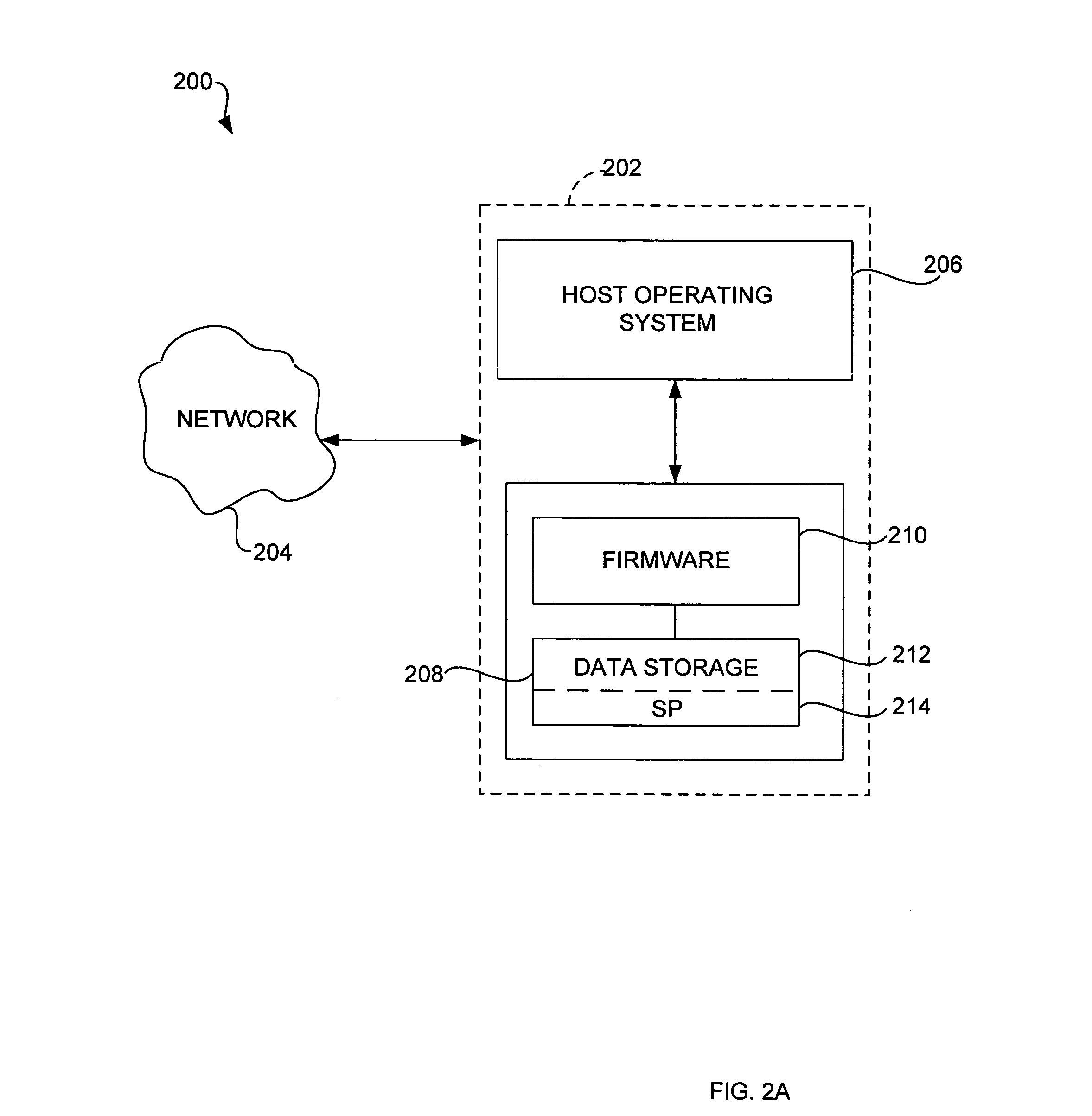
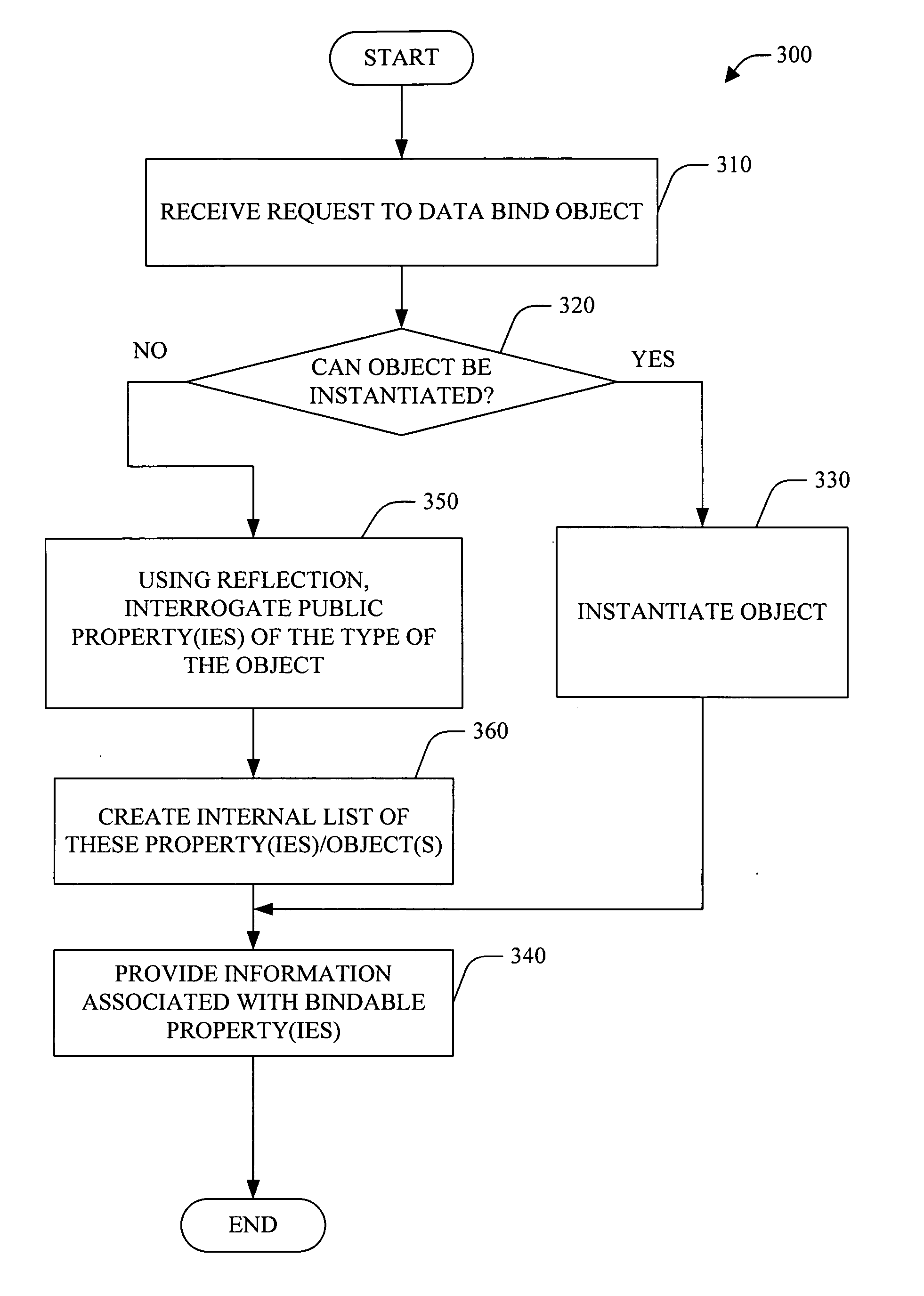
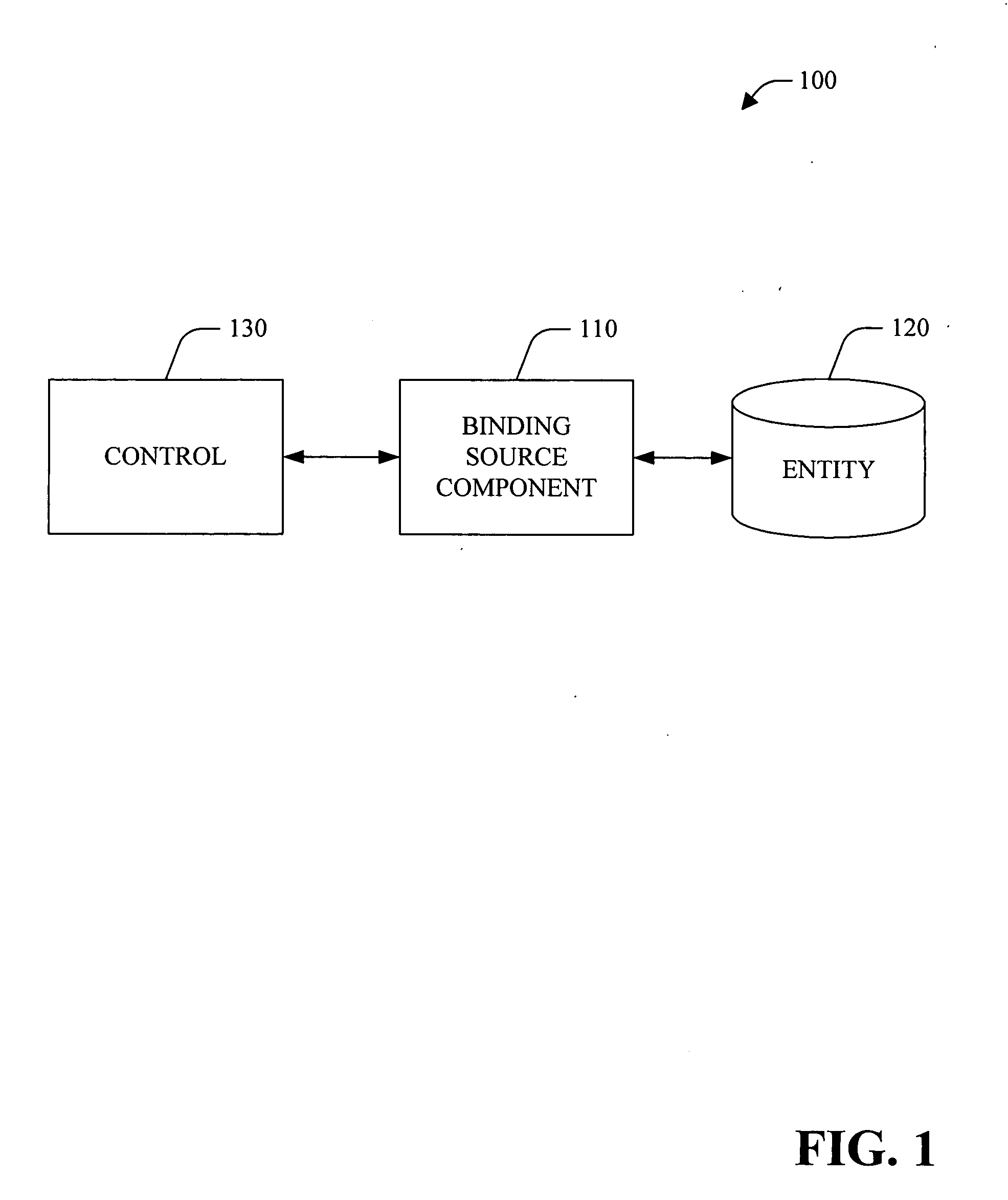
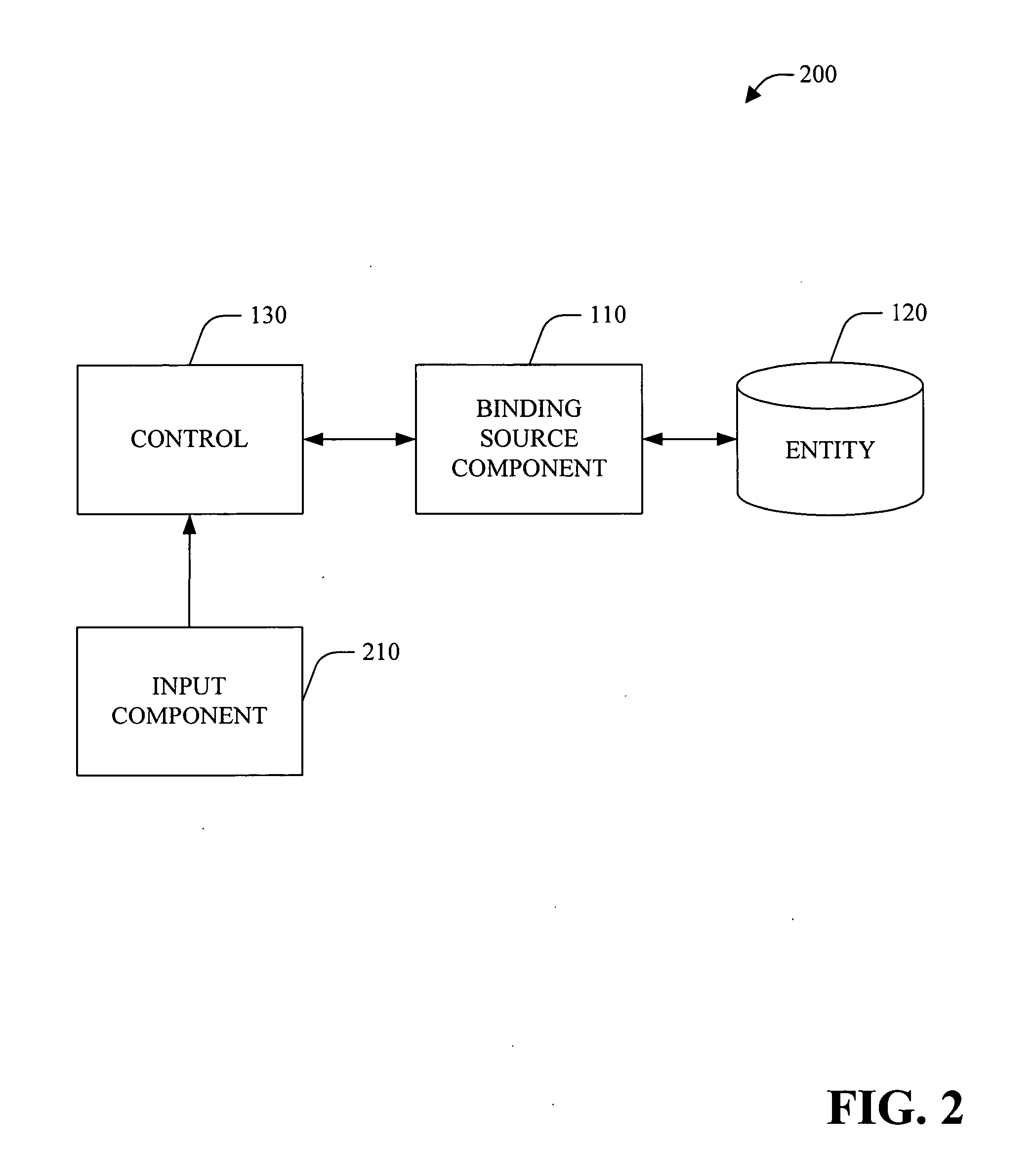
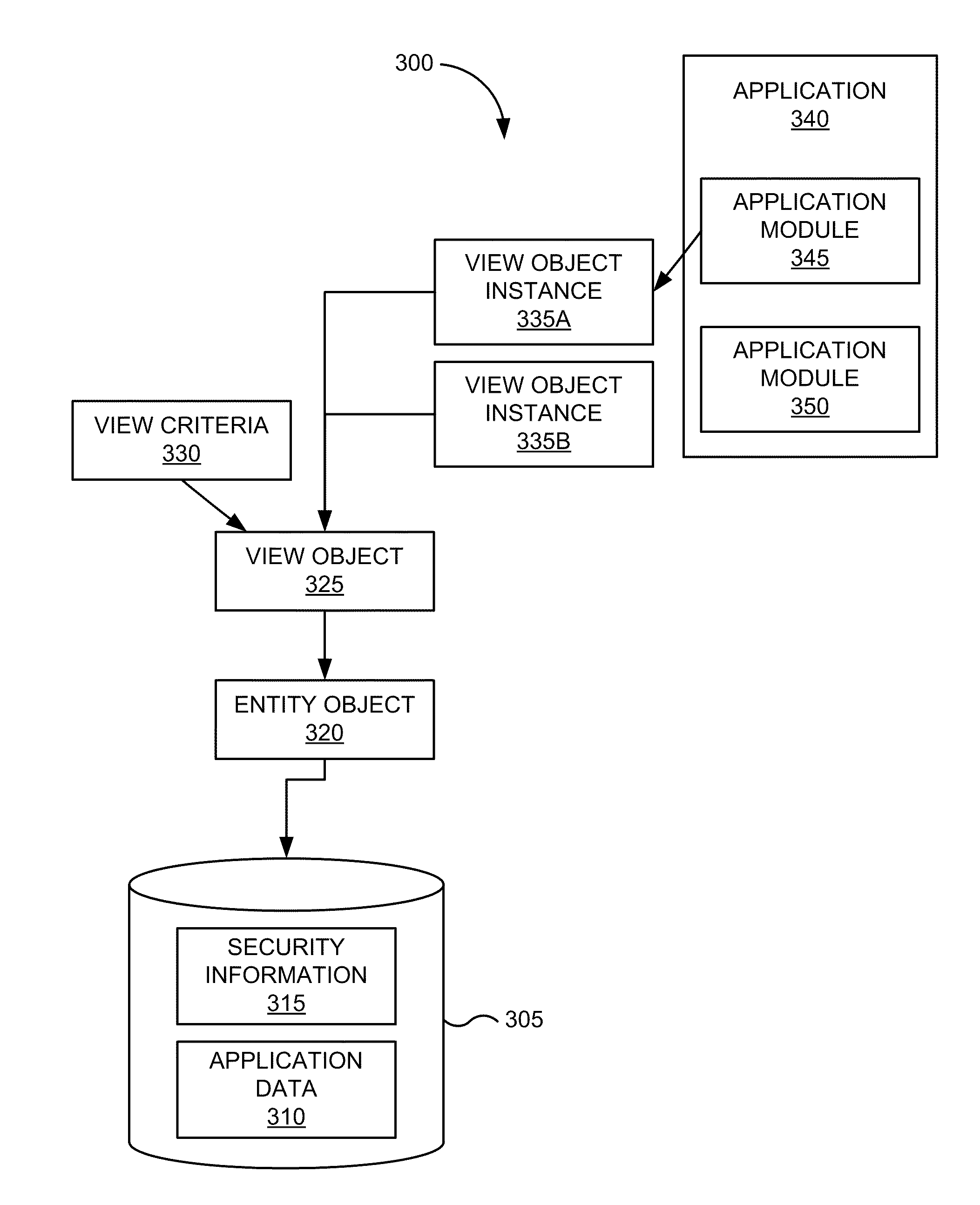
Binding to types
InactiveUS20060150172A1Well formedSoftware designSpecific program execution arrangementsEntity typeWeb service
A system and method for system and method data binding to type(s) of object(s) is provided. The system can be employed in a software application development environment to facilitate data binding to types of entity(ies) (e.g., object(s), web service(s) and / or a hierarchy of objects) rather than instance(s) of the entity(ies). With the ability to bind to types, the system provides the ability to abstract schema by which the control(s) are bound from the source of data. The system allows developer(s) and / or architect(s) to specify their own base classes for their own object(s). The system includes a binding source component that supports the ability to set its data source to a type, rather then a specific instance. For example, when the data source is changed, the binding source component can evaluate whether the data source (e.g., object) can be instanced and whether the data source (e.g., object) supports necessary designer interface(s). If the type isn't supported by the designer, using reflection, the binding source component can interrogate the public properties of the type. Additionally, the binding source component can analyze complex object(s).
Owner:MICROSOFT TECH LICENSING LLC
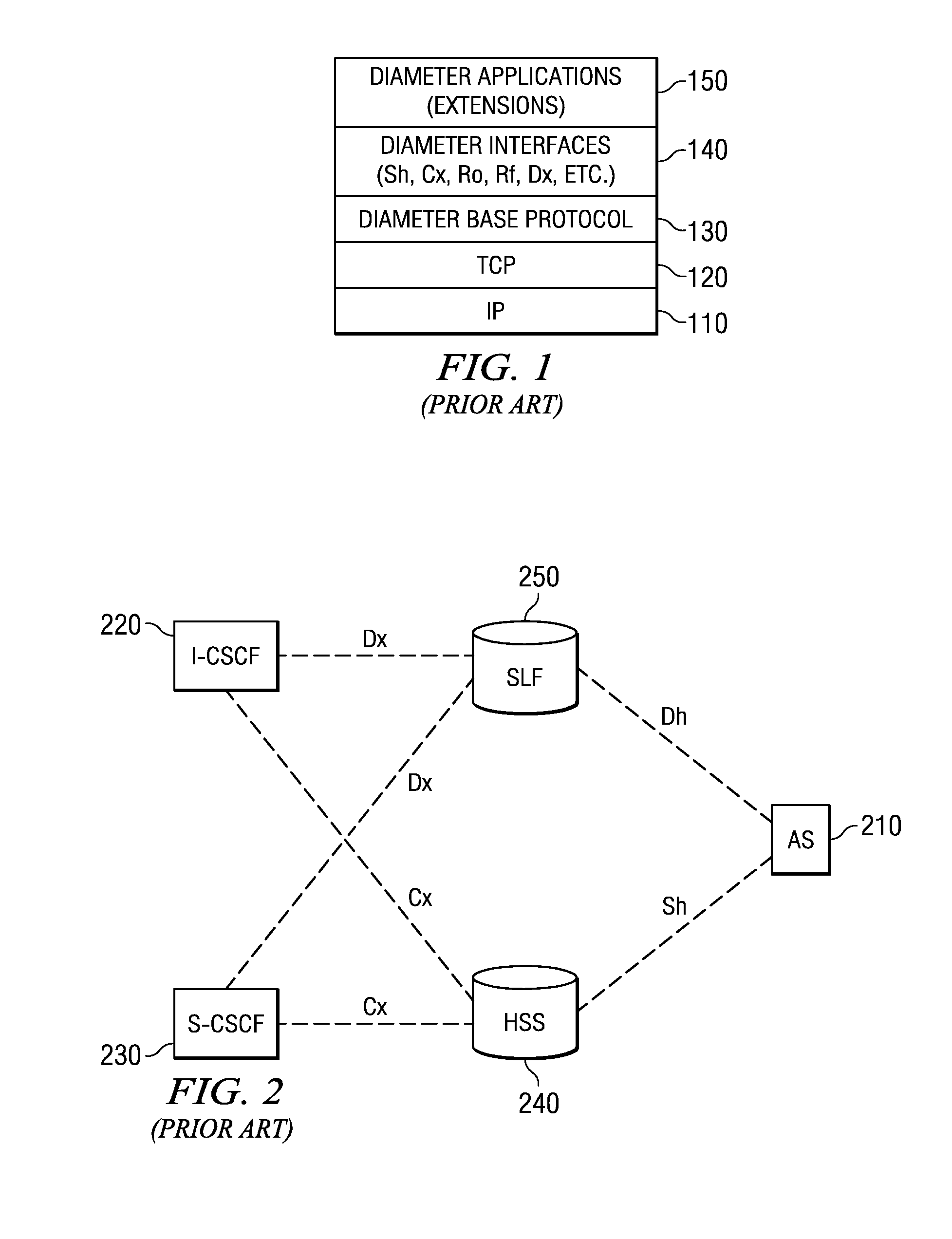
System and Method for Developing Diameter Applications
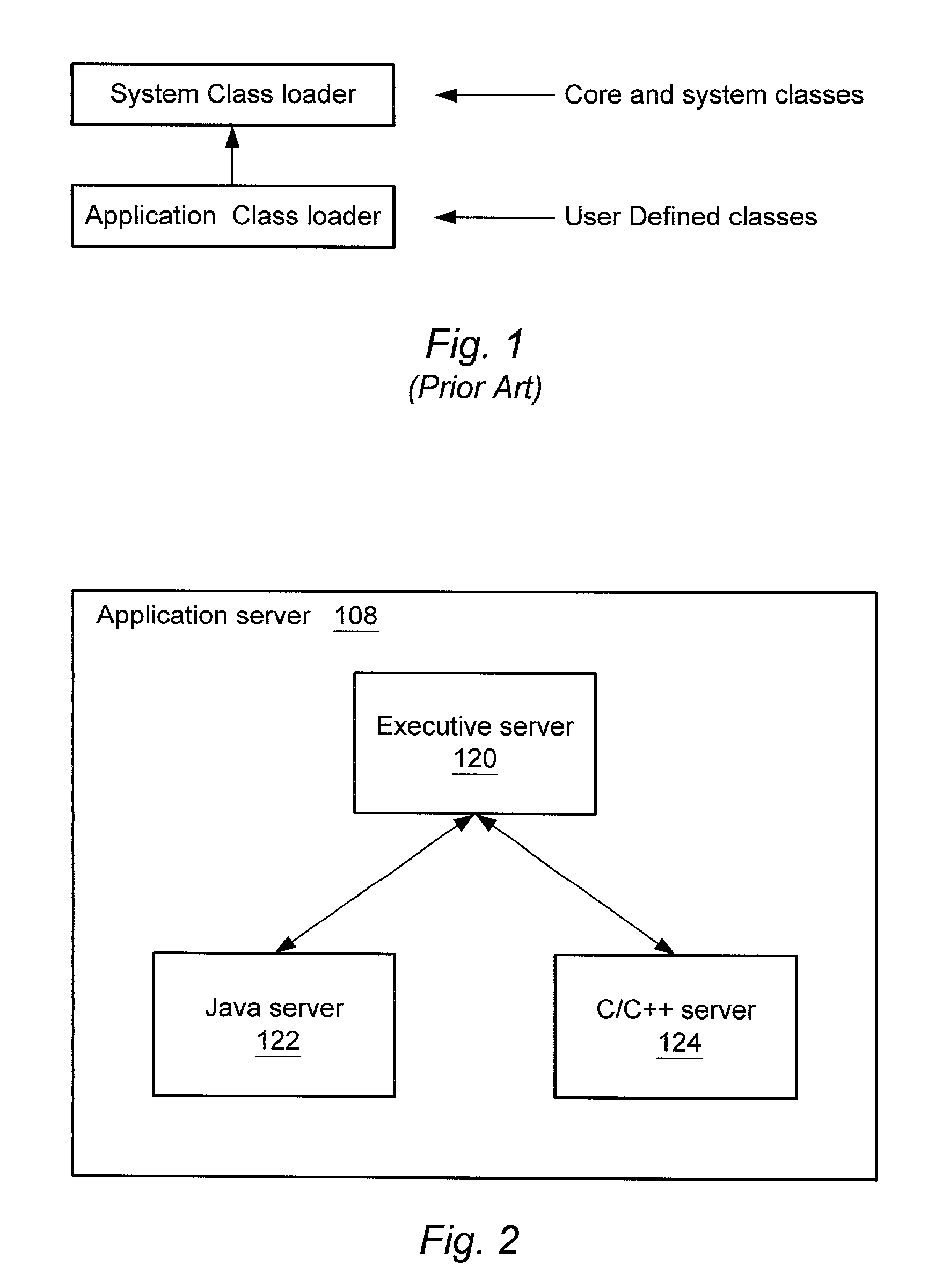
ActiveUS20080195742A1Improve usabilityFacilitate communicationMultiple digital computer combinationsTransmissionApplication serverBase class
A system and method for developing Diameter applications are provided. The system and method extend the application server servlet model to support Diameter applications. A “base protocol” servlet is provided that handles the basic Diameter protocol functionality. Base application servlets are provided for each Diameter interface (for example, an “Sh” base servlet for the IMS “Sh” interface). These servlets are base classes for application code. The base application servlets implement additional semantics on top of the base protocol servlet to support additional attribute-value pair semantics. With the system and method, Diameter servlets share the same ServletContext as HTTP and SIP servlets. This mechanism facilitates communication between the various application entities and facilitates generation of converged applications.
Owner:SNAPCHAT
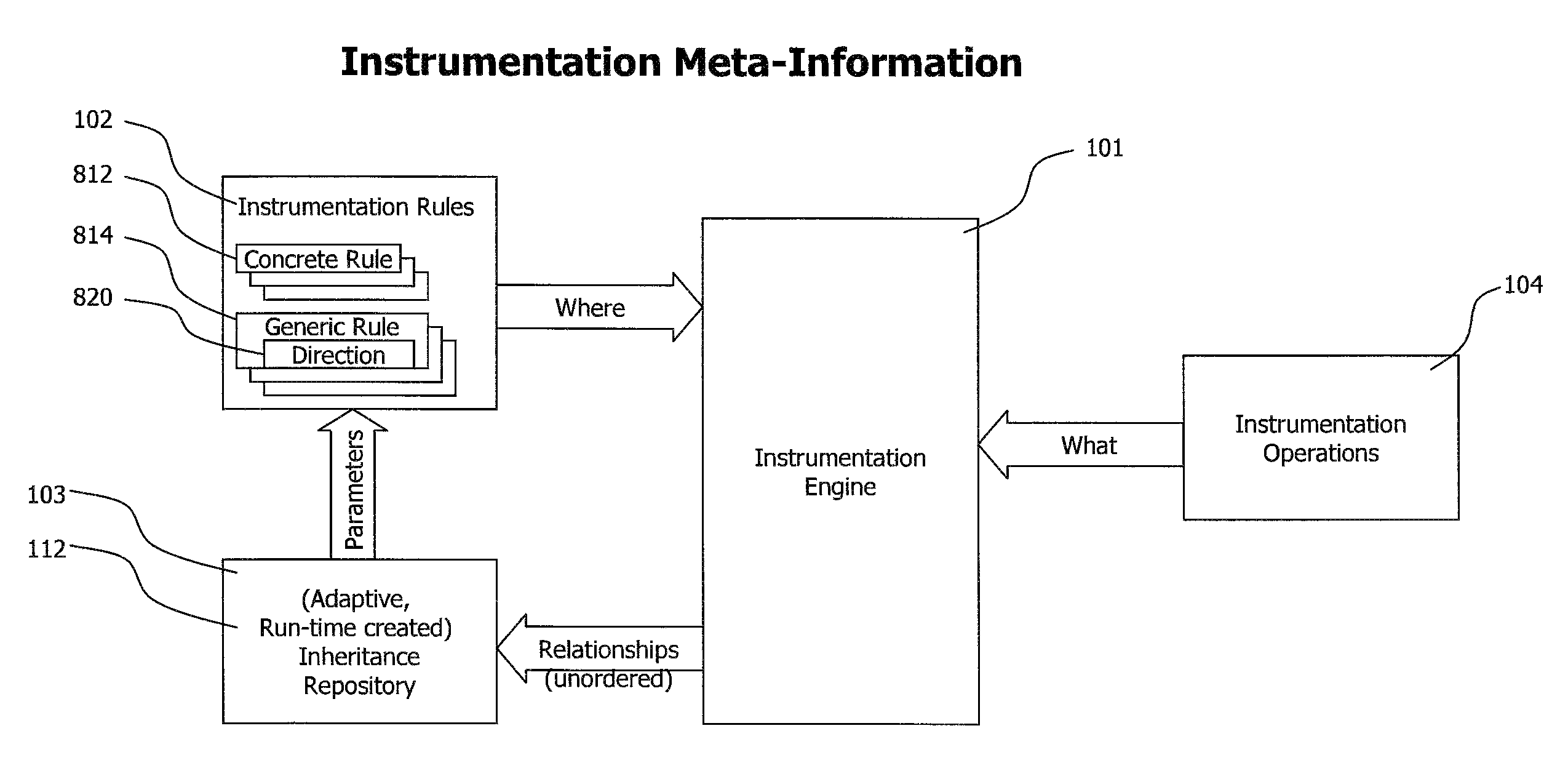
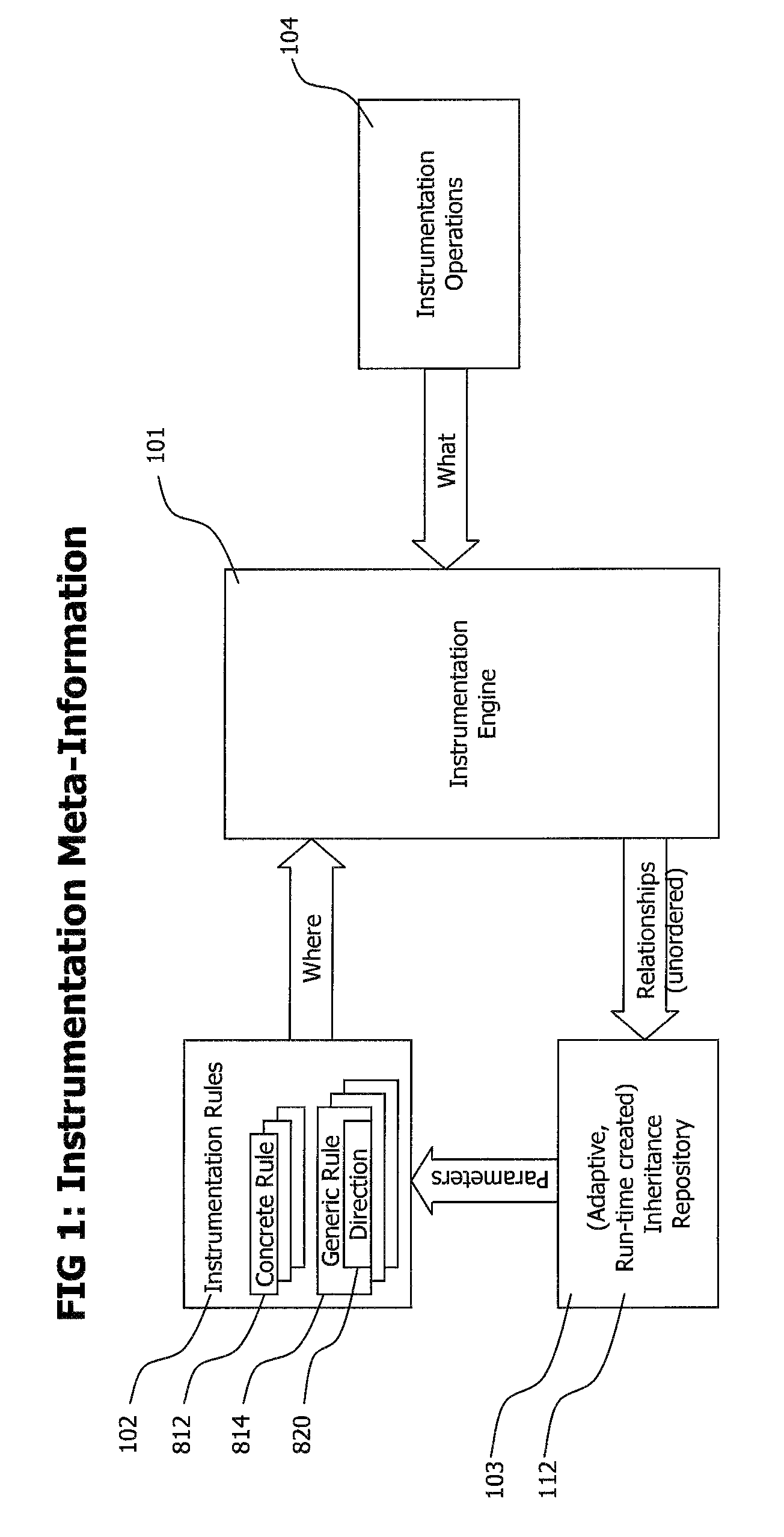
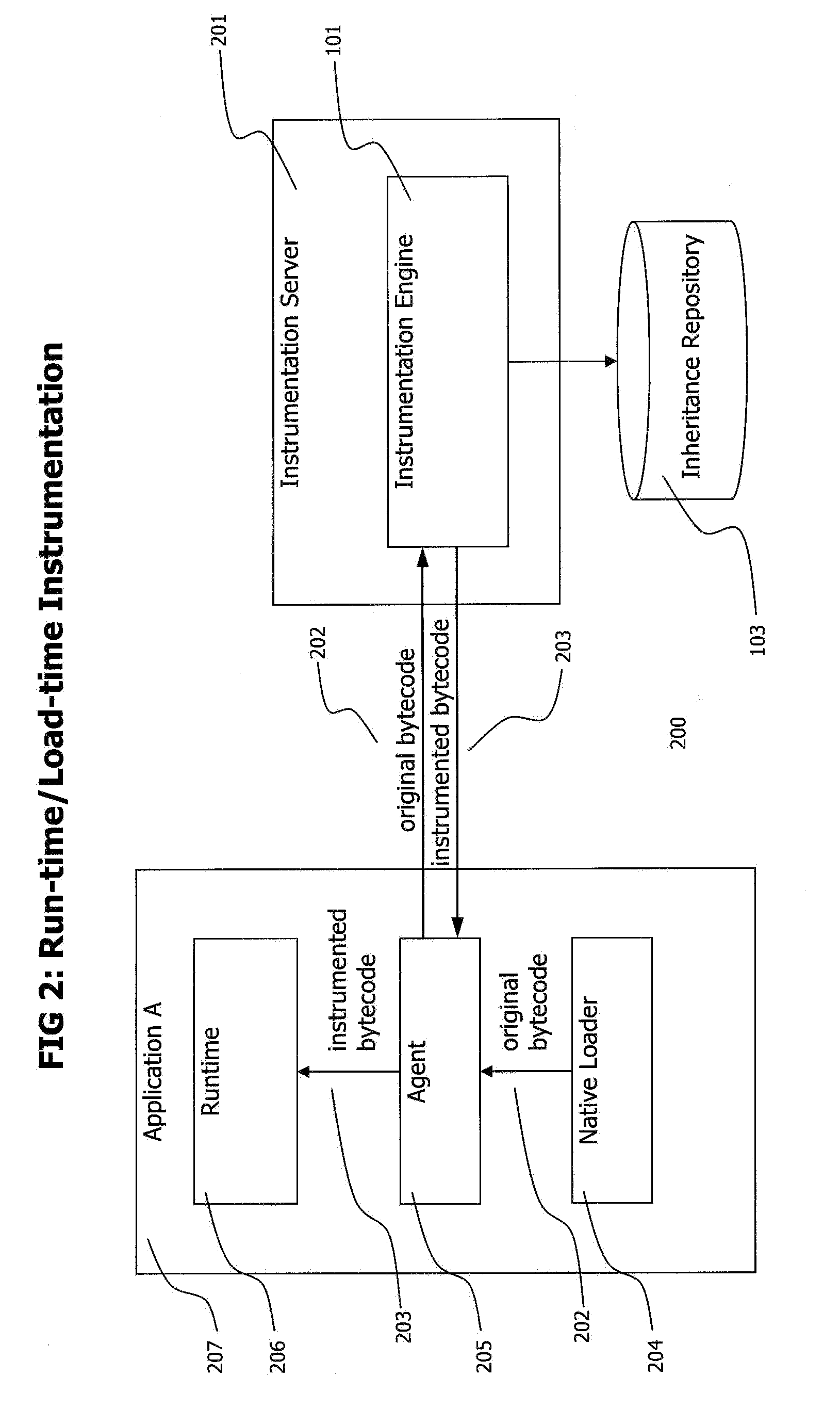
Method and system for adaptive, generic code instrumentation using run-time or load-time generated inheritance information for diagnosis and monitoring application performance and failure
ActiveUS8464225B2Error detection/correctionSpecific program execution arrangementsBase classApplication procedure
A system for generic, run-time adaptive placement of byte code instrumentation takes into account object oriented inheritance relationships that are stored in an inheritance repository. The inheritance repository, which mirrors the structure of the monitored application, is created at run-time and is updated if the code base of the monitored application changes either dynamically at run-time or by manually changing the configuration and restarting the application. The inheritance repository contains meta-data of application classes and their relationships, like direct and indirect inheritance. The inheritance repository information is used to evaluate generic instrumentation placement rules, like rules that match to methods of classes that inherit from a specific base class. The inheritance repository is generated concurrently with instrumentation placement at application load-time or run-time and persists between application runs to enable dedicated adaptation runs to create the repository.
Owner:DYNATRACE
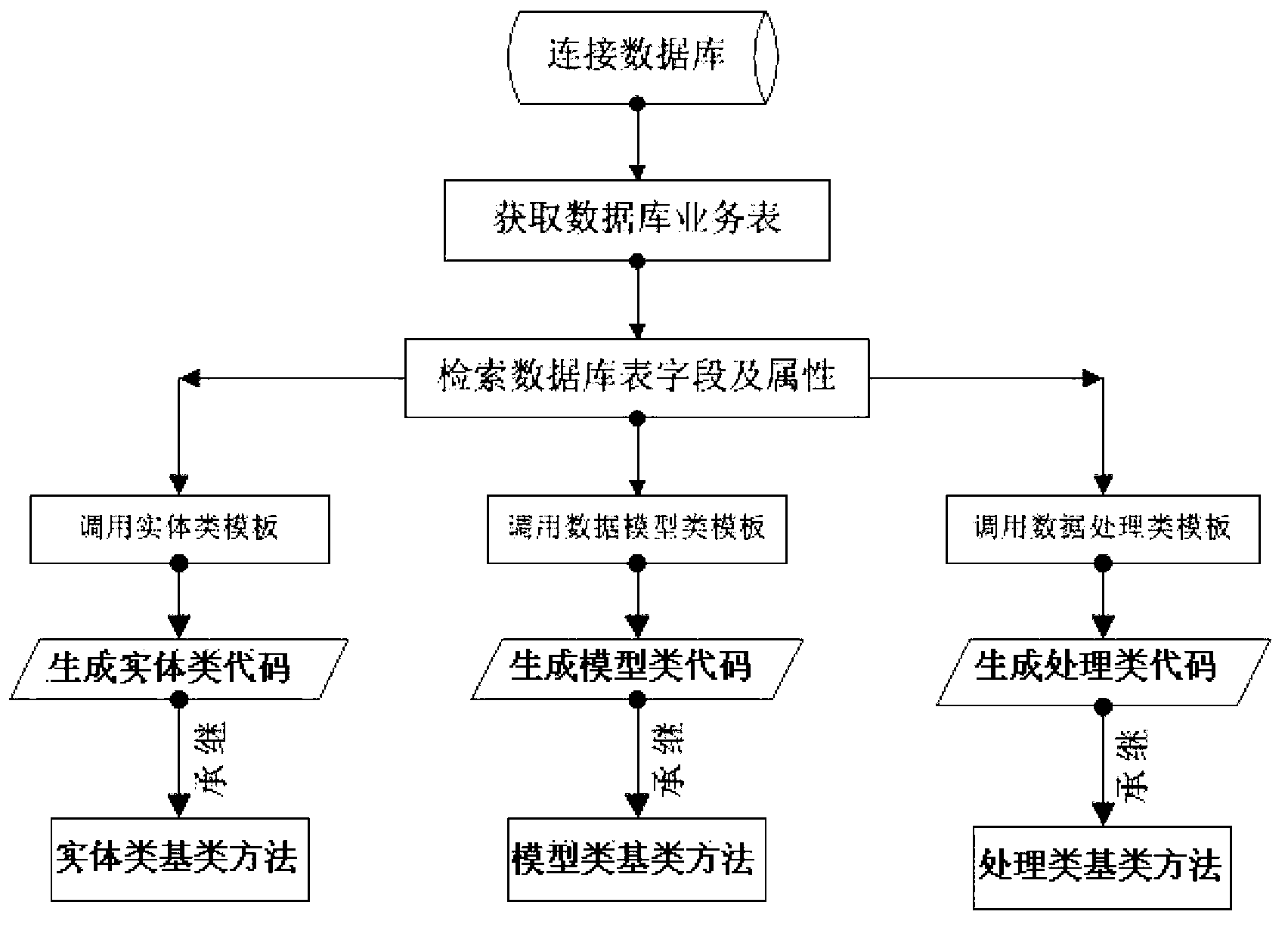
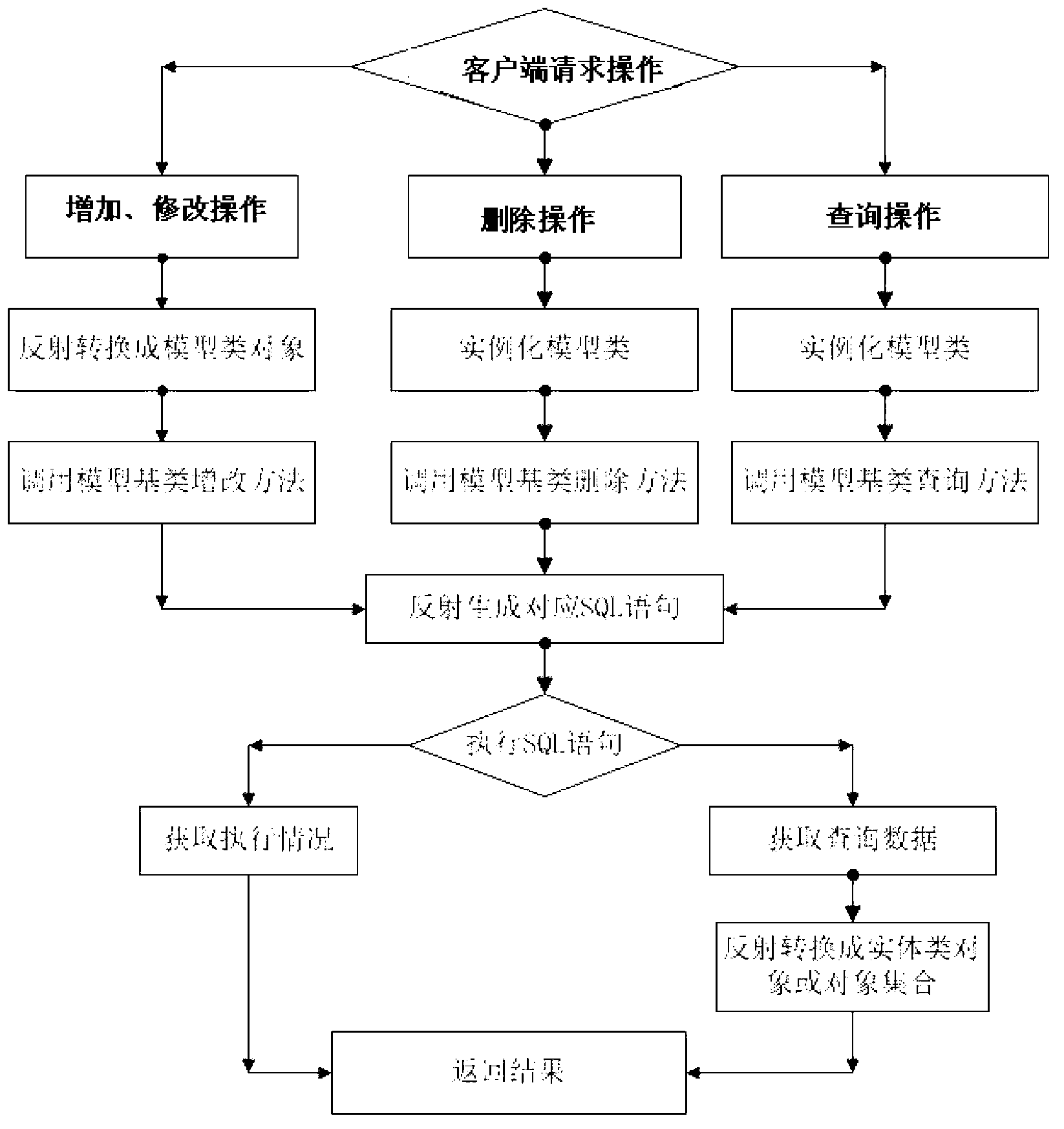
Method for automatically generating and using code
ActiveCN103226478AReduce frequent changesImprove simplicitySpecific program execution arrangementsSpecial data processing applicationsBase classMaintainability
The invention discloses a method for automatically generating and using a code. The method is characterized by comprising the following steps that: 1, a data acquiring module acquires system attributes of a database and a database service table; 2, a code generating module splices the acquired corresponding system attributes into an entity class code, a mode class code and a data processing class code and stores the entity class code, the mode class code and the data processing class code; 3, a base class inherited by the class codes generated in the step 2 is a corresponding base class method; and 4, when a user sends an operating request to the service table data at a client end, a data processing class module instantiates a data type requested by the user to the corresponding model class code and carries out SQL (Structured Query Language) statement splicing through a reflection mechanism, and a database processing assembly receives and executes an SQL statement and returns a generated operating result. According to the method, by using a reflection technology and the SQL statement capable of being executed by a dynamics splicing database, the error rate is reduced and the program simplicity, maintainability and readability are improved.
Owner:BEIJING JINHER SOFTWARE
Method of administering software components using asynchronous messaging in a multi-platform, multi-programming language environment
InactiveUS20050177827A1Specific program execution arrangementsMemory systemsBase classSoftware engineering
A method for performing life cycle management of business software applications and their components across a multiple-platform, multiple-language network. The method takes advantage of the inheritance properties of object-oriented programming (OOP) by developing all components of a business application from a set of base classes, thus deploying a common set of methods across all application components. These methods enable monitoring by a Central Administrator element without interdependence between any of the business application components and the Central Administrator. The Central Administrator then determines when a need to reconfigure one or more components of the business application has arisen. The Central Administrator then modifies or replaces existing components of the business application or installs entirely new components over the network without end user interaction. In one embodiment of the present invention, the Central Administrator is aided by a set of Distributed Administrators located on each virtual node server / host computer of a business application operating over a network. The business application can thus reconfigured without terminating the application's business function in a scaleable, extensible manner without regard to platform or language.
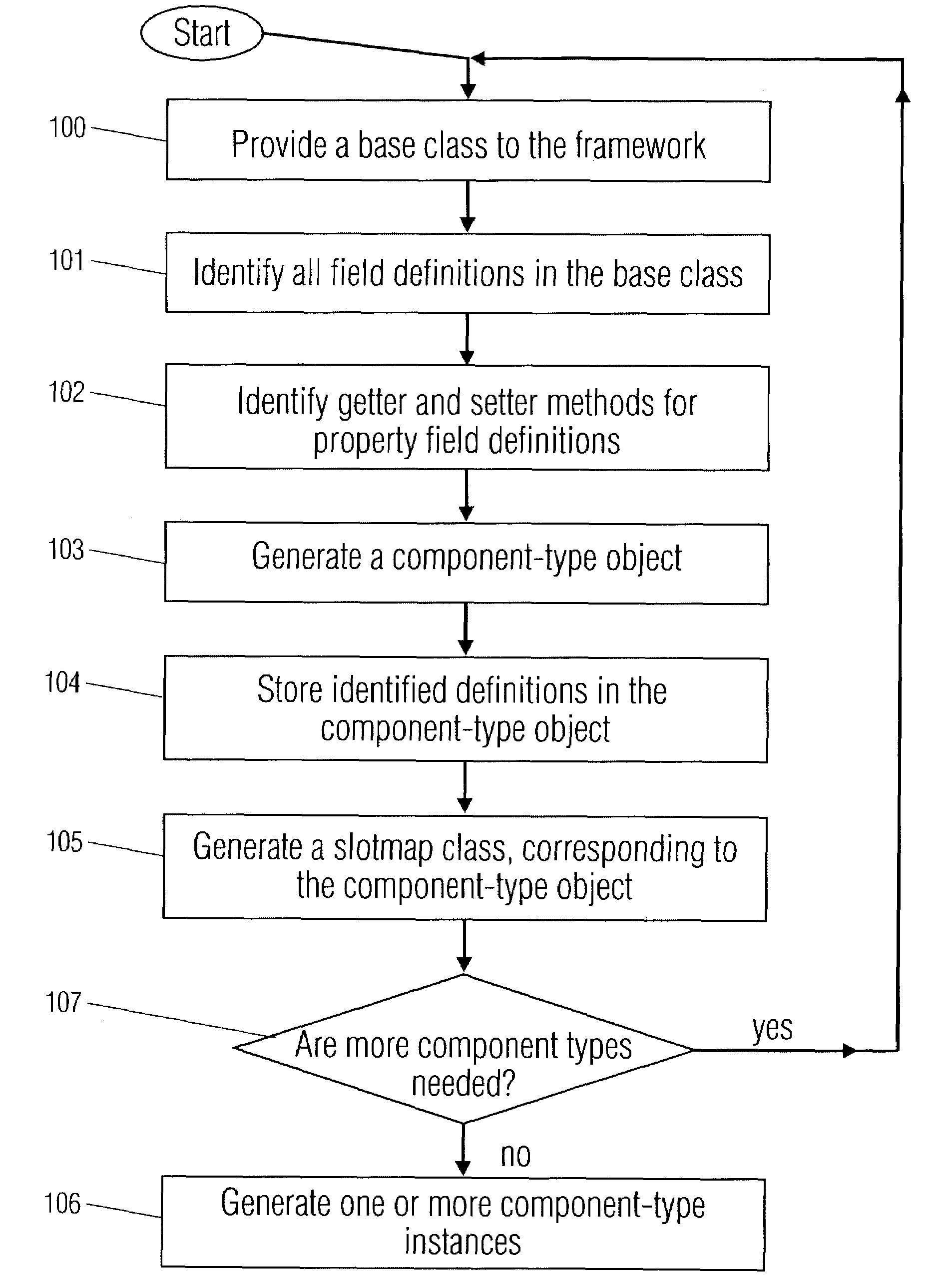
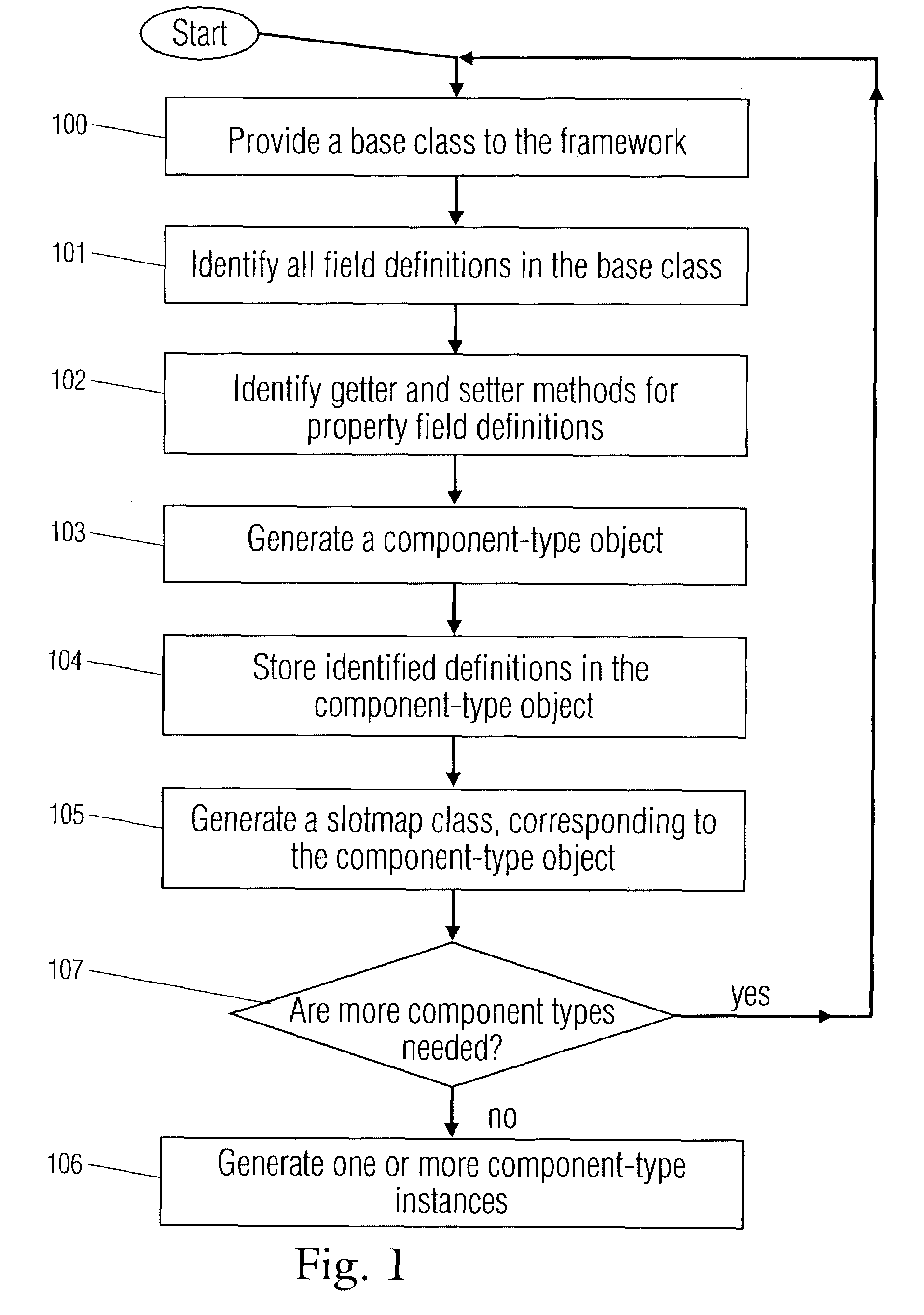
Owner:VERIFONE INTERMEDIATE HLDG INC & VERIFONE
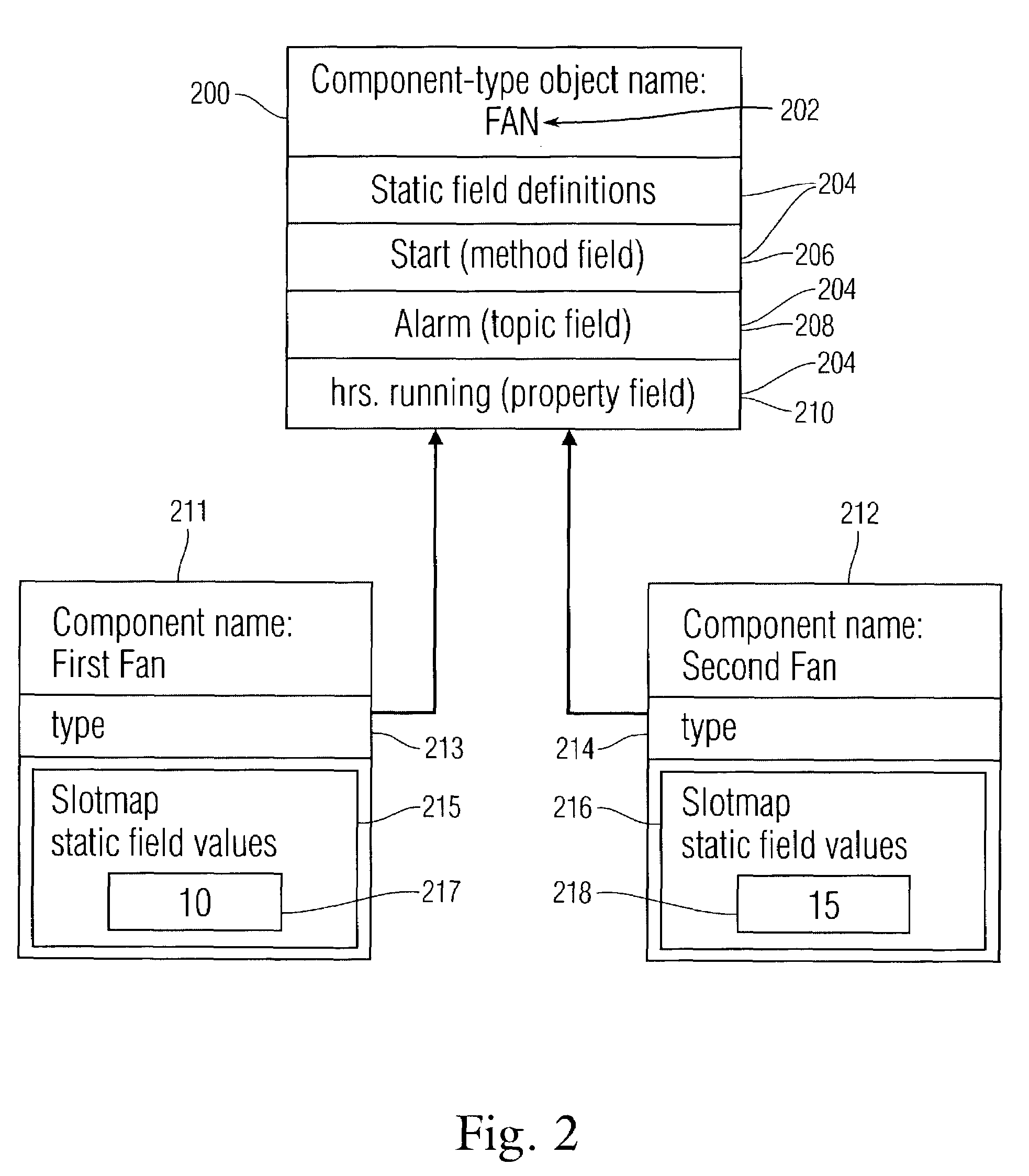
Dynamic objects with property slot definition and runtime mechanisms
ActiveUS7225426B2Multiple digital computer combinationsVisual/graphical programmingBase classTheoretical computer science
A component based software program, where each component is based on a component-type. Component-types are created from base classes comprising slot definitions. The slot definitions are identified and stored in a component-type object. One or more components of the component-type are created, each comprising a reference, to a component-type object and a slotmap having storage locations for values associated with property slots definitions, in the component-type object. Values for property slots are entered into components by being placed in the storage locations. Also disclosed is a method for automatically designating unique names to components. One root component is created. Further non-root components are placed within the root component or within other components, so that all components form a tree structure. A component is assigned a unique identification string, comprising a sequential list of all of the component's ancestors and the component's name.
Owner:TRIDIUM
On-line business processing system middleware package method
InactiveCN101122852AOvercome the disadvantage of having to understand middleware technologyOvercome the disadvantage of not being able to support arbitrary data typesSpecific program execution arrangementsSpecial data processing applicationsBase classBusiness class
The present invention discloses an encapsulation method for middleware of an online transaction processing system (OLTP). The method includes the following steps: a business processing class basic class is established and data members and parameters of member functions are used to represent the data type processed by the middleware. The member function of the business processing class basic class calls the application program interface of middleware, achieving the data processing function of middleware. A business entity class basic class is established, different member functions of which serialize and anti-serialize the objects. A root basic class is established which derives business processing class basic classes and business entity class basic classes. The business processing basic classes derive at least a business processing class, the member functions of which encapsulate the function of middleware of OLTP. The business entity class basic classes derive at least a business entity class, the member functions of which serialize and anti-serialize the objects.
Owner:HUAWEI TECH CO LTD
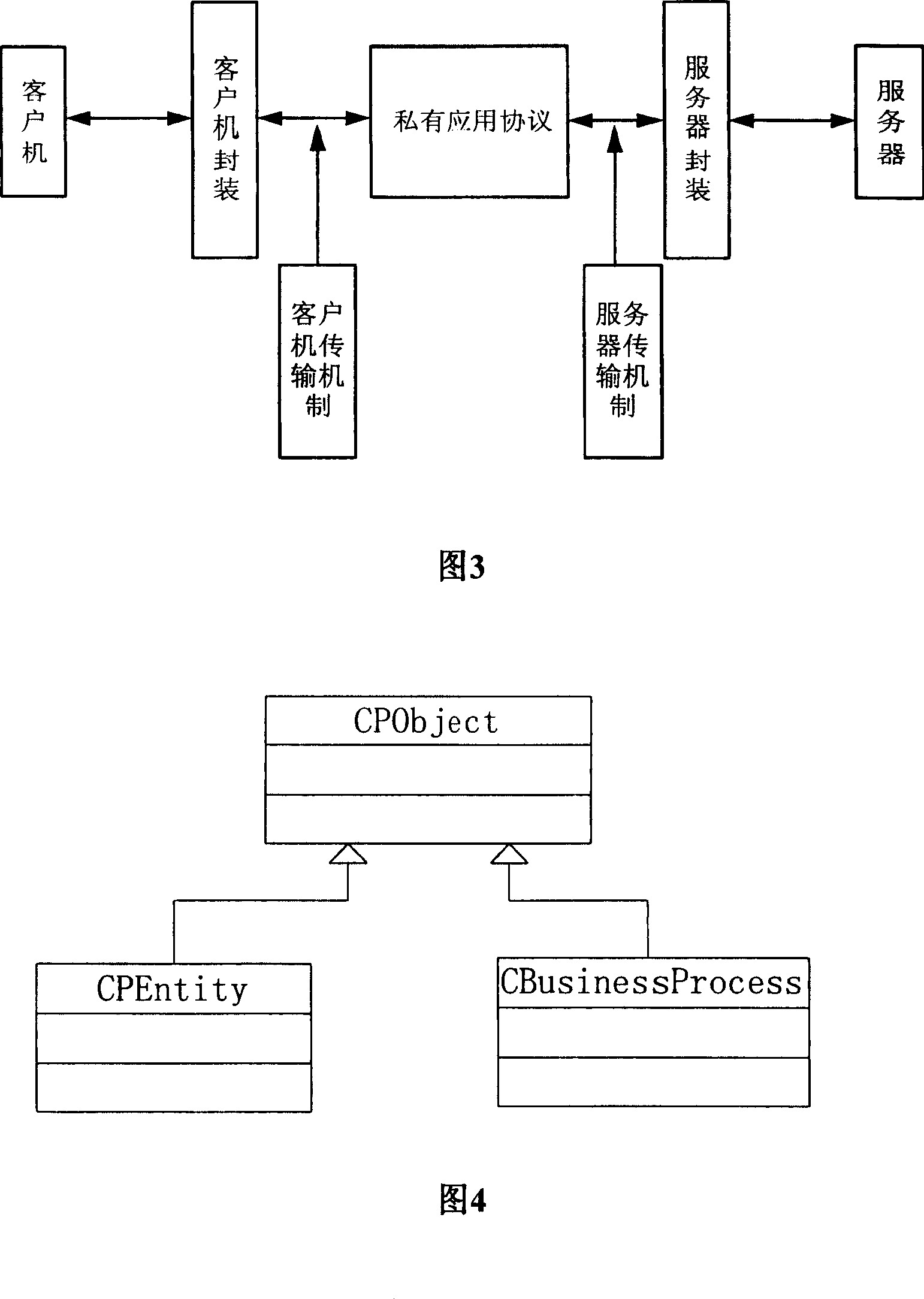
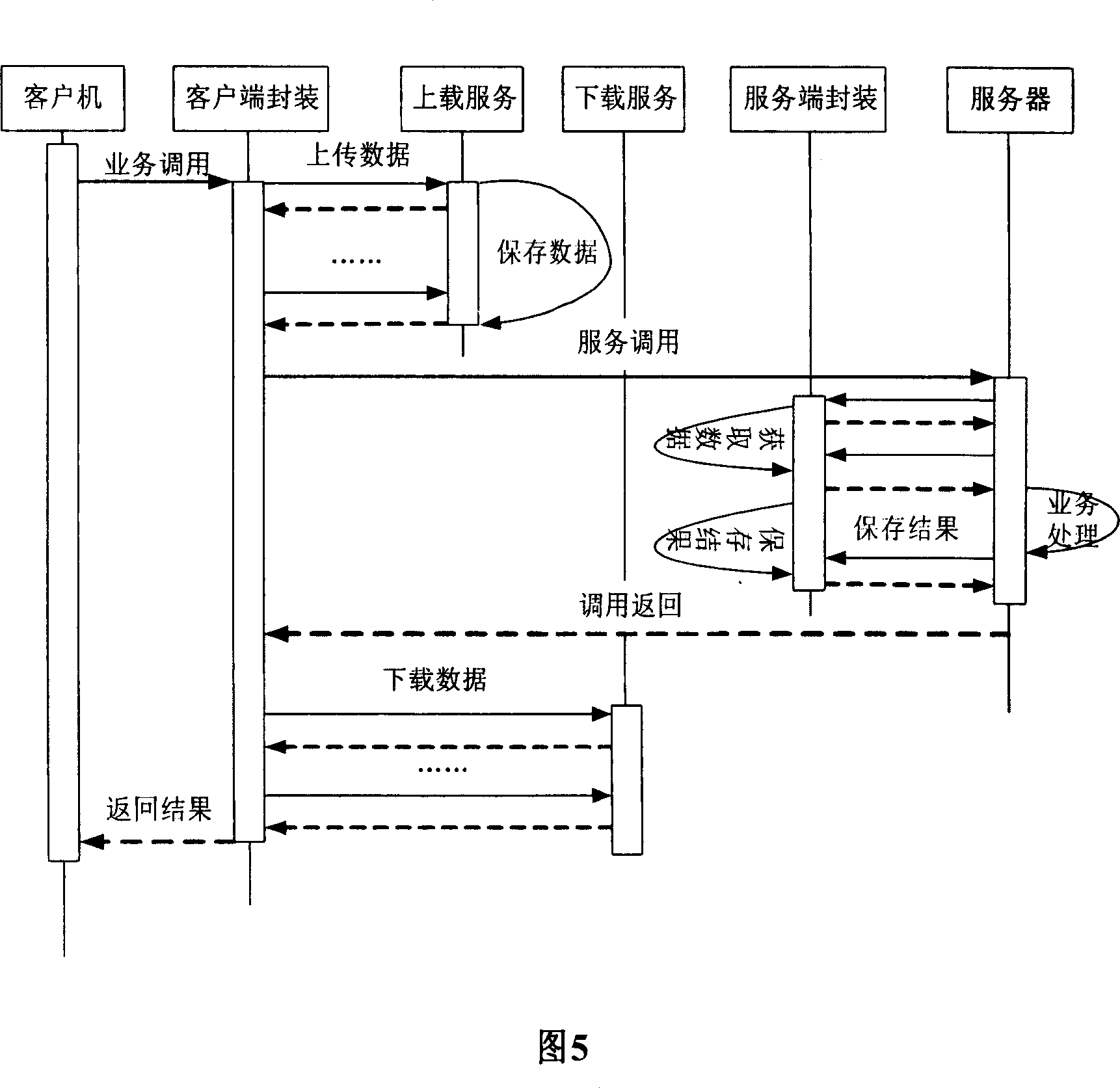
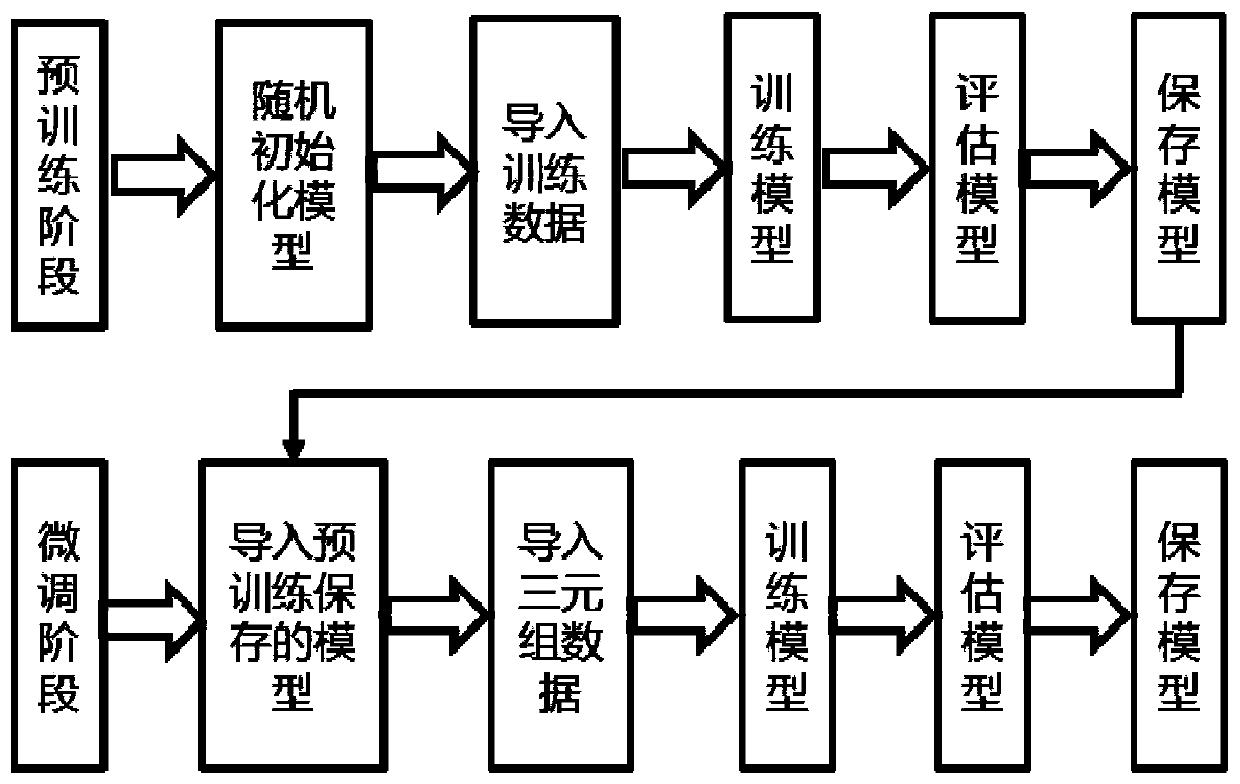
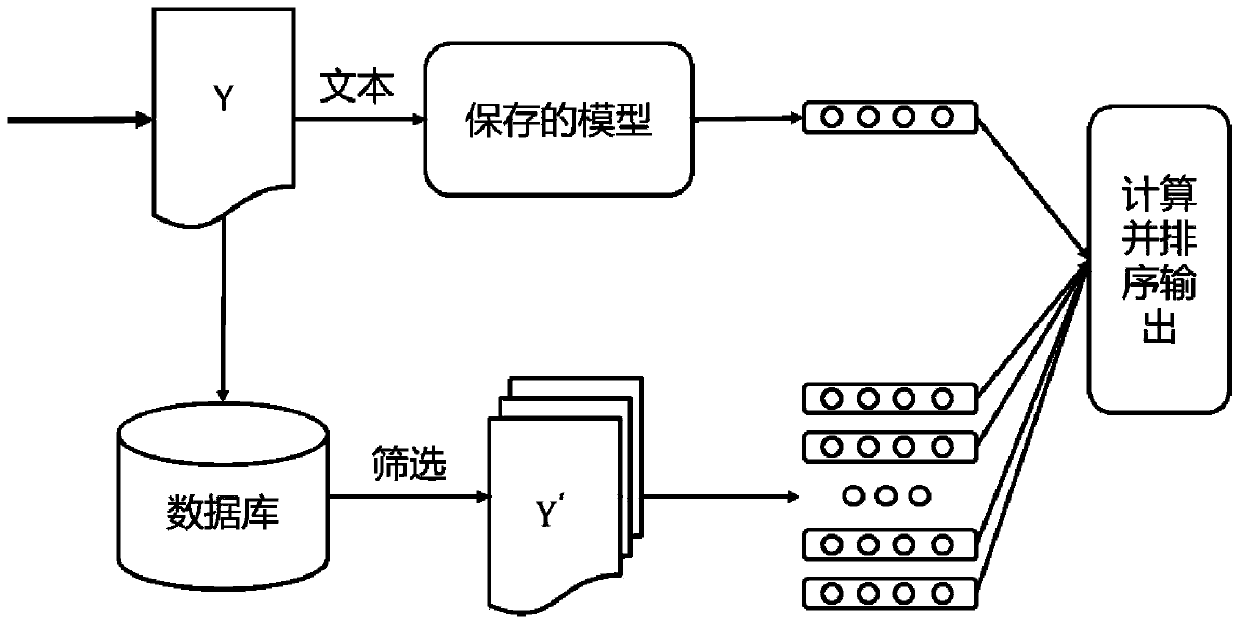
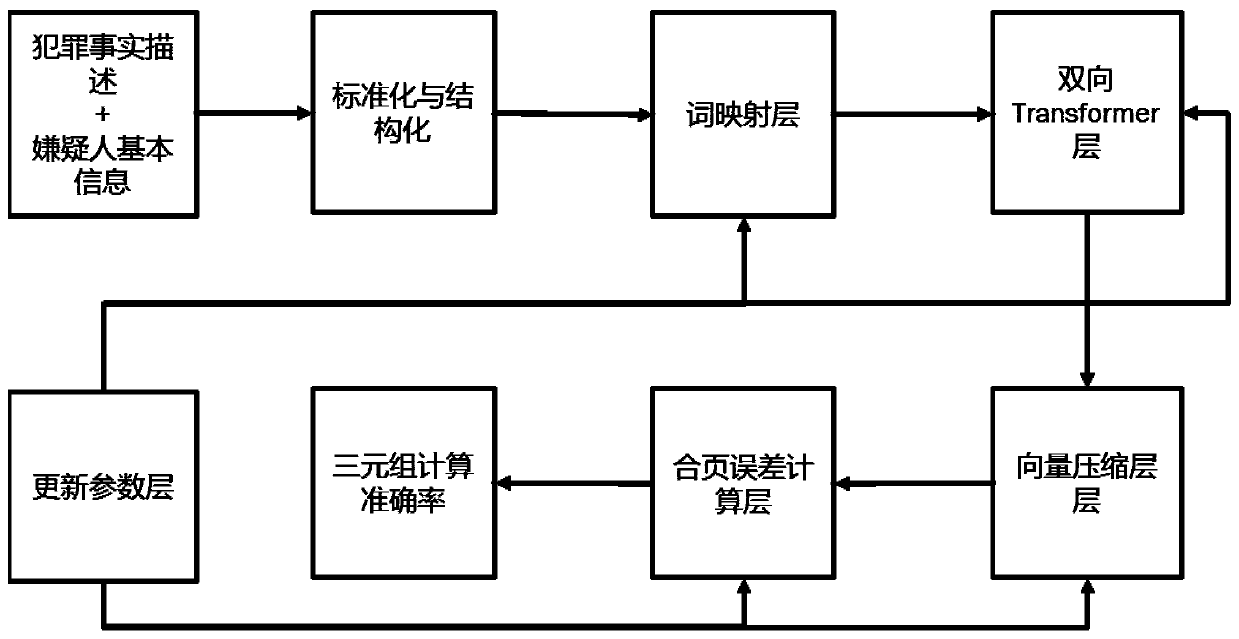
Class case recommendation method based on text content
ActiveCN110442684AImprove recommendation effectFully expressive semanticsCharacter and pattern recognitionNeural architecturesBase classDocument preparation
The invention relates to a class case recommendation method based on text content. The method is divided into a pre-training part and a fine adjustment part. The pre-training part adopts a transformerencoder as a main structure, a Chinese language model is trained, Chinese language knowledge is learned from other corpora, and a high-quality language model is obtained. A triad model is used as a framework of the fine adjustment part, a preprocessed judicial document is used as training data, more knowledge about judgment is learned from the judicial field, and a better text vector representation is obtained. Compared with a traditional keyword-based class case recommendation method and a single-task neural network-based class case recommendation method, the content-based class case recommendation method provided by the invention is better in effect, and has better robustness based on a semantic training model, which indicates that the method provided by the invention is effective and practical.
Owner:SHANDONG UNIV +1
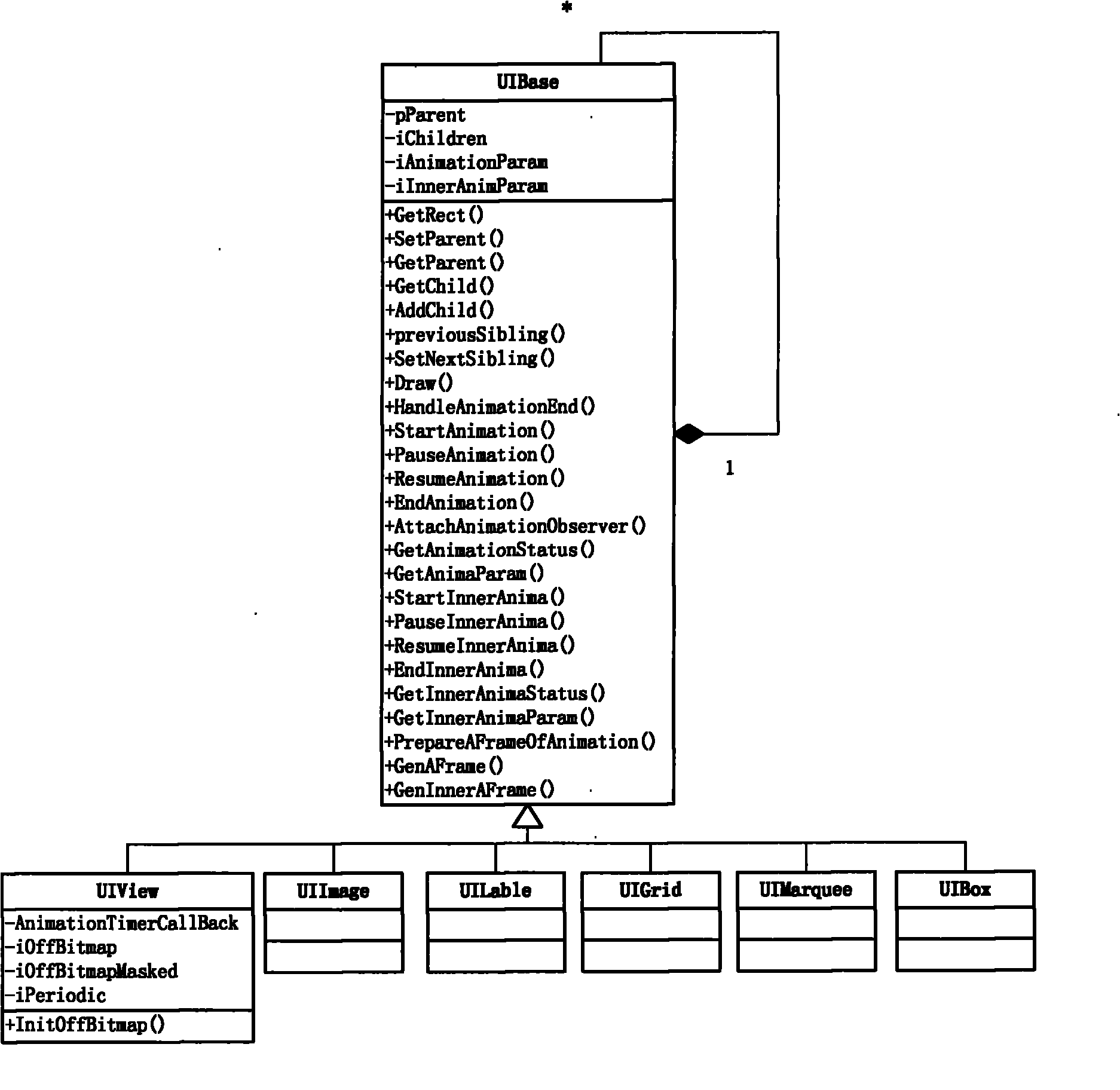
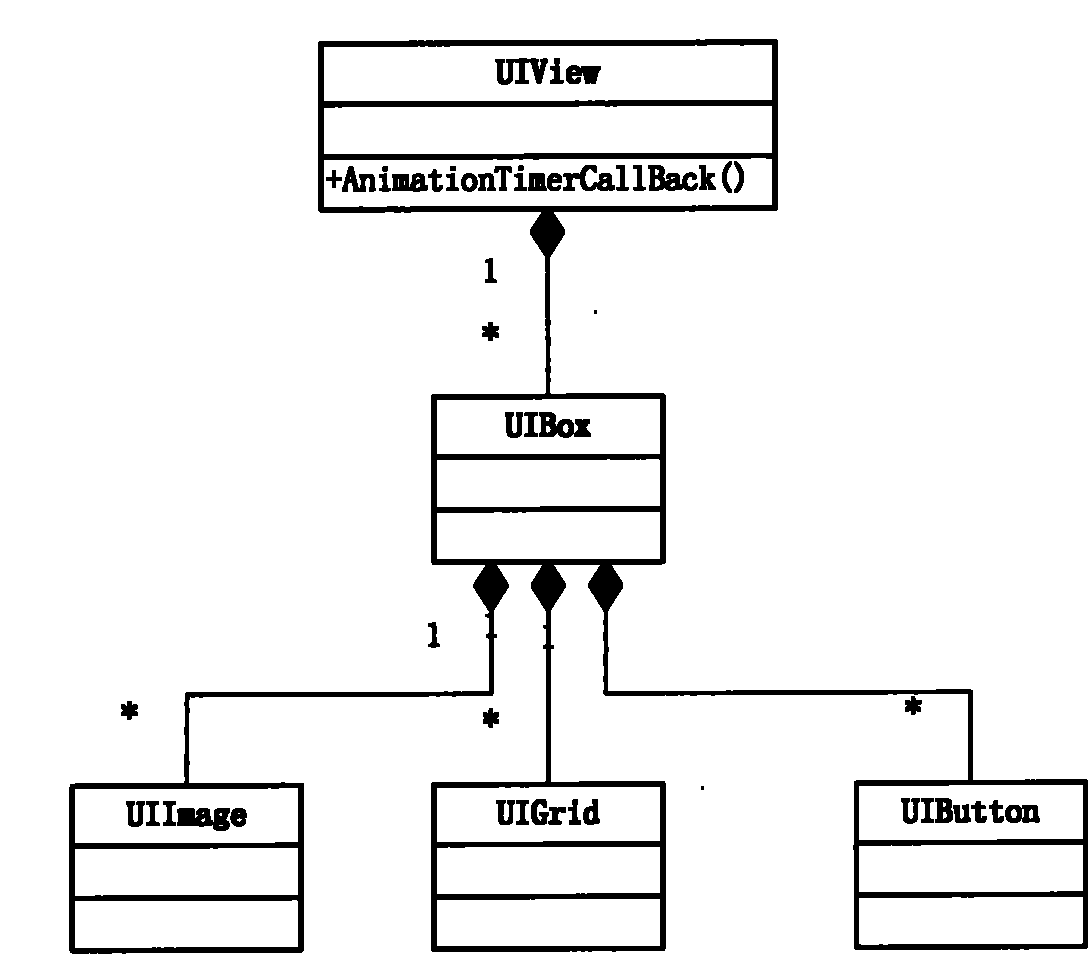
Method and system for creating and drawing interface control tree and mobile terminal
InactiveCN101980154ARealize the animation effectSoftware engineeringSpecific program execution arrangementsRelationship - FatherControl system
The invention discloses a method and a system for creating and drawing an interface control tree and a mobile terminal. A specific control class derived from an interface control base class is created to generate animating nodes, interface container controls and interface control nodes, timer callback functions of the animating nodes are created, and the interface control tree and class objects are created and generated by combing father-son-brother relations of all control nodes by creating the interface control base class and operational functions of the interface control base class, animation control functions and tag status, the current frame animation content preparation functions and animating content functions. Only drawing preparation functions of root node animating nodes are interacted with the system to achieve the aim of animation effect of the drawn interface control tree. The drawing effects of the control tree are uniformed through the time cycle of an animation timer; the technical problems that interface controls are difficult to mutually contain so as to form complicated control systems are solved; and a complicated control layout is organized in a screen page to efficiently achieve the animation effects of the whole system.
Owner:融创天下(上海)科技发展有限公司
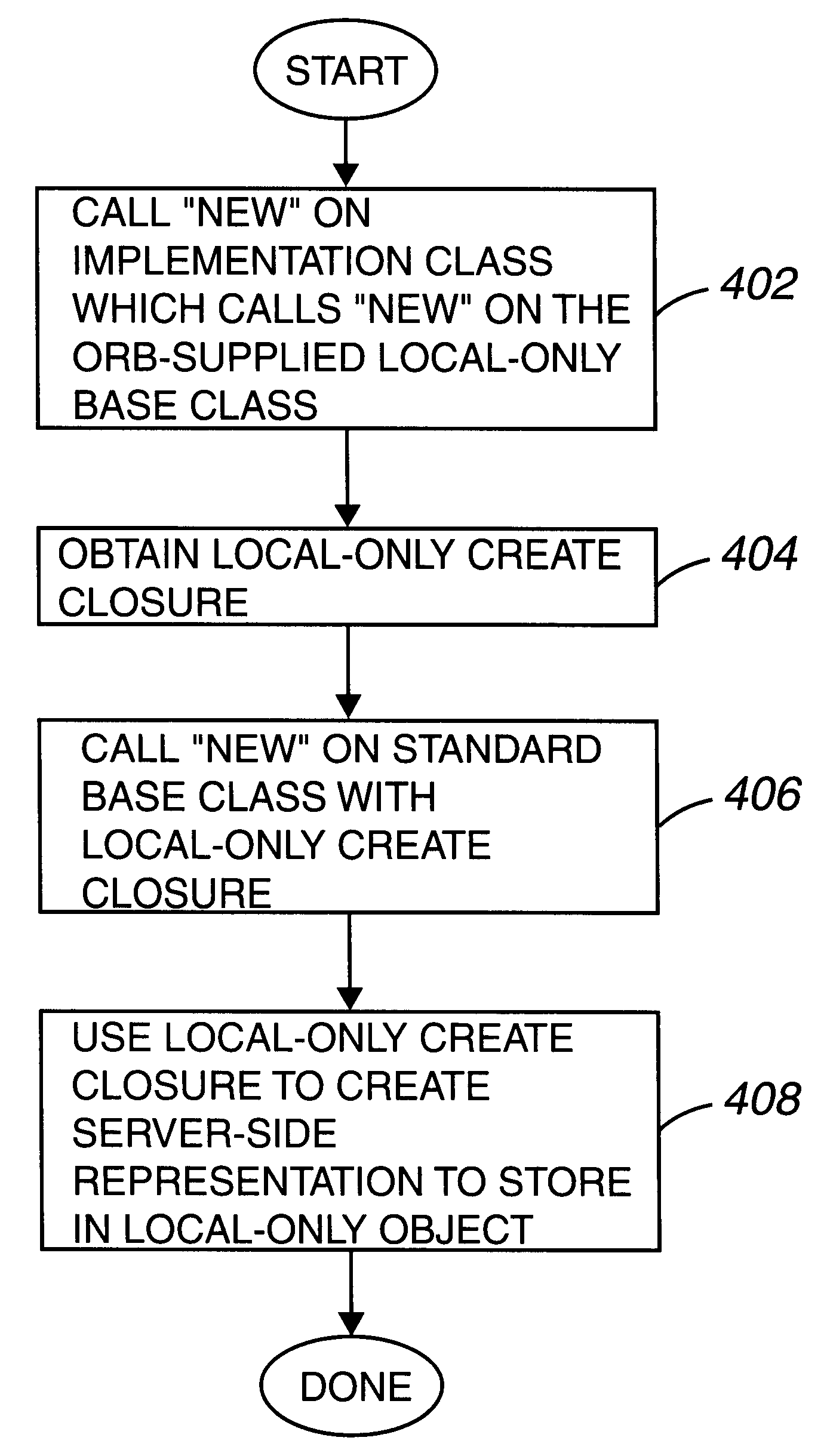
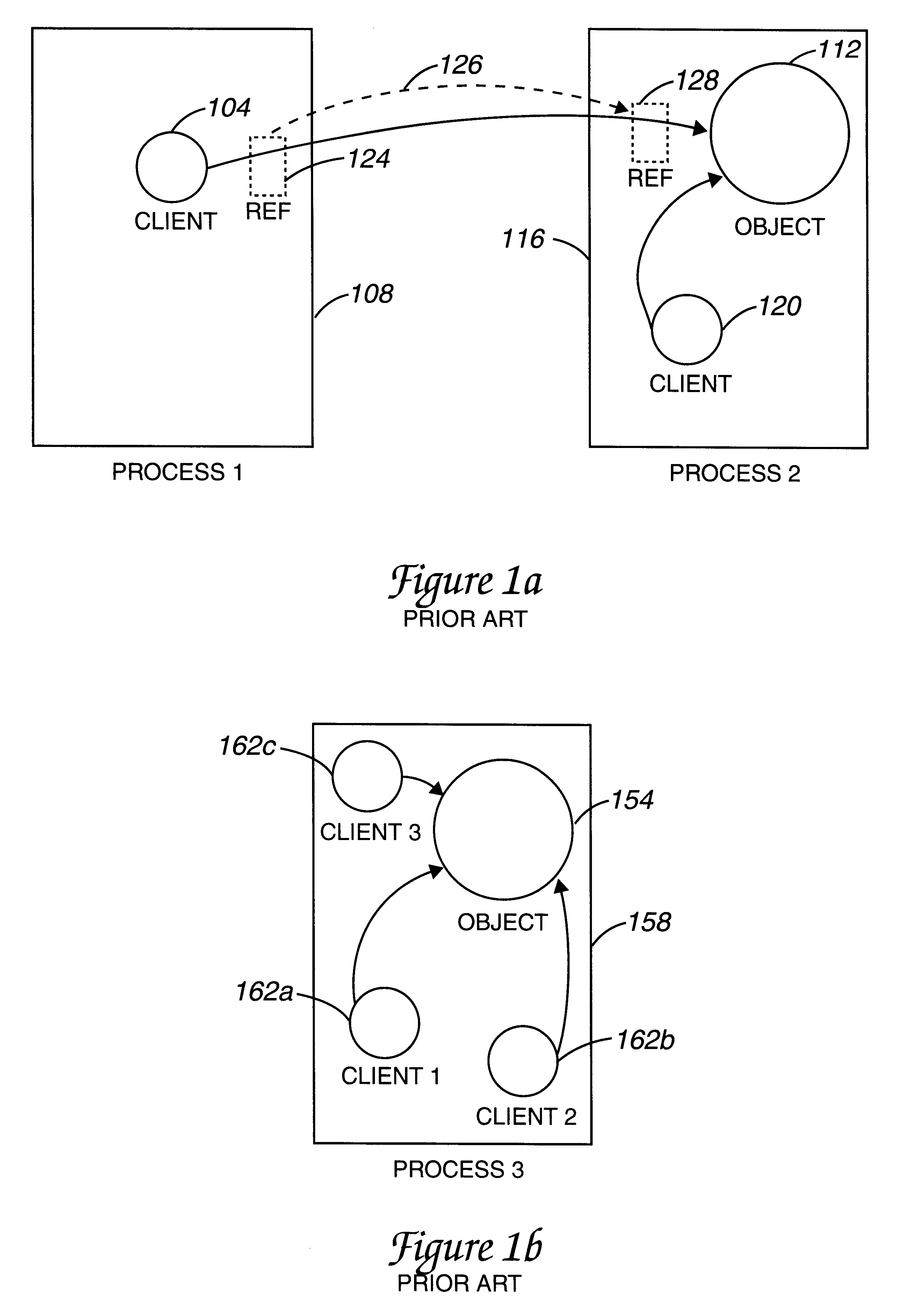
Method and apparatus for fast, local corba object references
InactiveUS6438616B1Multiprogramming arrangementsMultiple digital computer combinationsObject basedBase class
Methods and apparatus for reducing computing overhead by creating fast, local-only objects in a distributed client / server based computing system are disclosed. In one aspect of the invention, within an object-based computing system, a method for creating an object reference that is associated with a local-only servant object includes implementing a first base class to create a first object that represents the object reference, and obtaining a local-only create closure. An operation is called on a second base class using the local-only create closure. The operation creates a server-side representation associated with the local-only servant object, and is stored in the first object that represents the object reference. In one embodiment, creating the local-only create closure includes creating a skeleton object and calling a local m-table builder for the skeleton object.
Owner:ORACLE INT CORP
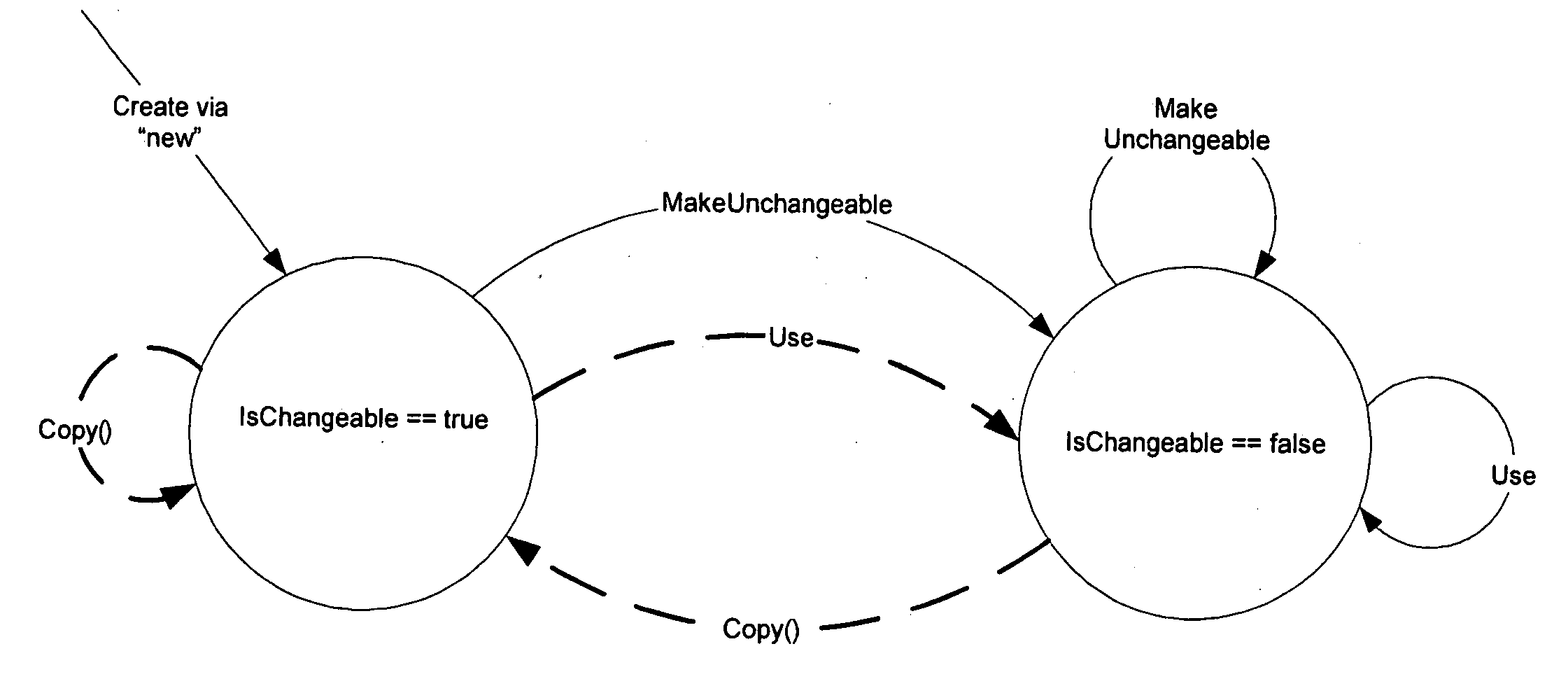
Changeable class and pattern to provide selective mutability in computer programming environments
InactiveUS20050091637A1Increase flexibilityReduce the amount requiredProgramming languages/paradigmsSpecific program execution arrangementsBase classComputer programming
A changeable pattern and implementation is presented in which types (used in programming environments and virtual machines) may be mutable as controlled by a programmer, and share many of the benefits of value types, without the drawbacks of value types. The changeable pattern provides flexibility for restricting the modifiability of the resultant uses of the values, as well as providing a means for providing notifications upon changes. In one implementation, a single set of changeable types is provided that derive from a common Changeable base class, and any type for which mutability is desired may derive from the Changeable class. Properties associated with the changeable define state that determines cloning and / or changeability characteristics on subsequent uses of the type. True mutability is provided via a status property of next use being set to a changeable reference state such that subsequent uses of the type do not cause a state change.
Owner:MICROSOFT TECH LICENSING LLC
Declarative attribute security using custom properties
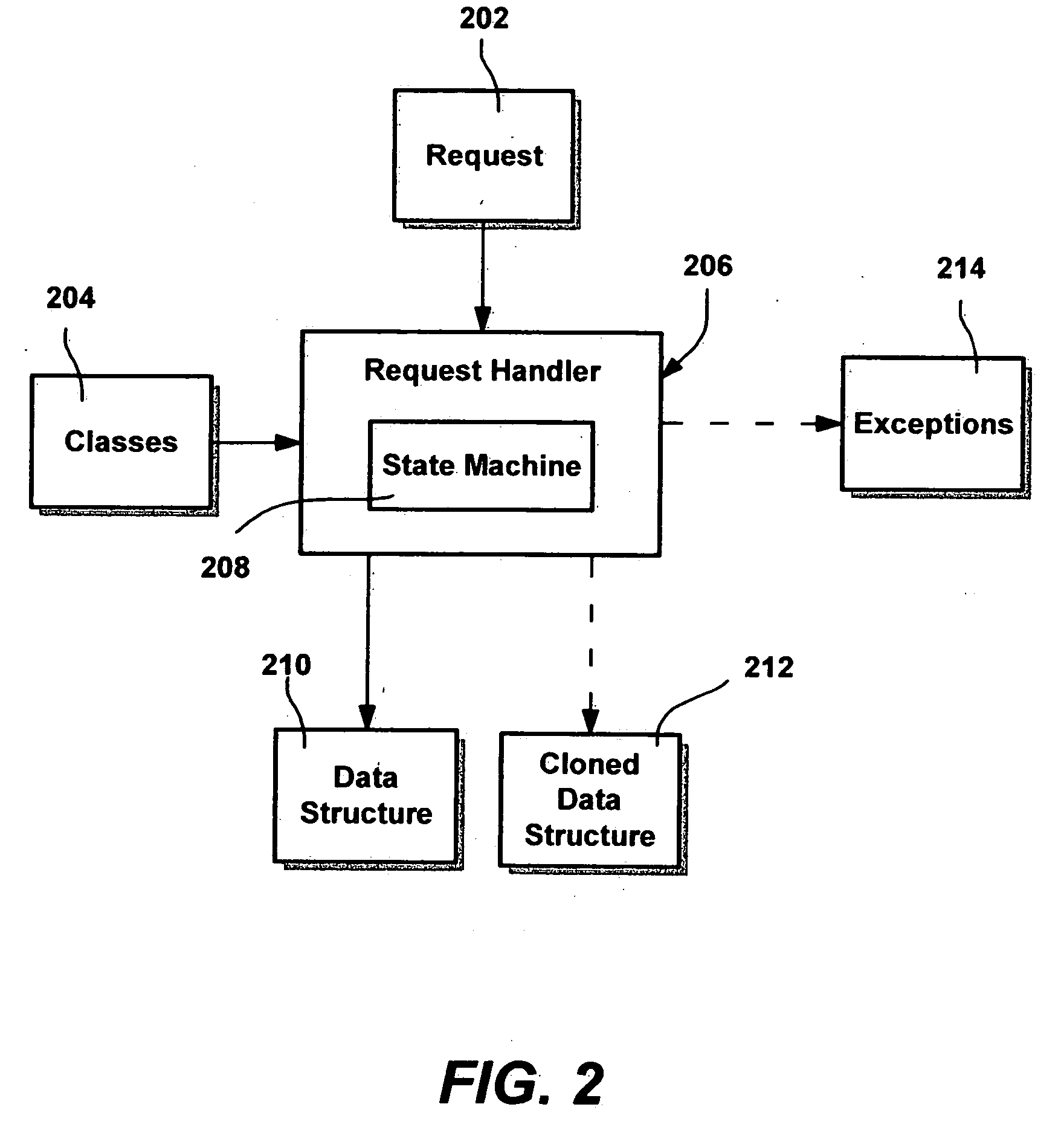
ActiveUS20110191751A1Provide securityComputer security arrangementsSpecific program execution arrangementsBase classApplication software
In various embodiments, application development tools can allow developers to control whether or not an attribute of a view object is displayed by declaratively associating a data security privilege with the attribute. Associating a data security privilege with the attribute can be done by adding a specially named custom property on the view object attribute. Modifications to a base class can provide any necessary support to retrieve the privilege and determine whether a current user is allowed to view the attribute for the current record / row. If the user is authorized to view the attribute for the current record / row, then the attribute value is returned and displayed. Otherwise, redacting information, such as “*****” can be returned and displayed.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com