Patents
Literature
1311 results about "Business function" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A Business Function is a concept used in the Organisation Architecture domain and represents what work is done by that organisation, organisation unit or business role. An organisation can be designed as a set of Business Functions and usually the structure of the organisation units within an organisation is closely based on the business functions.
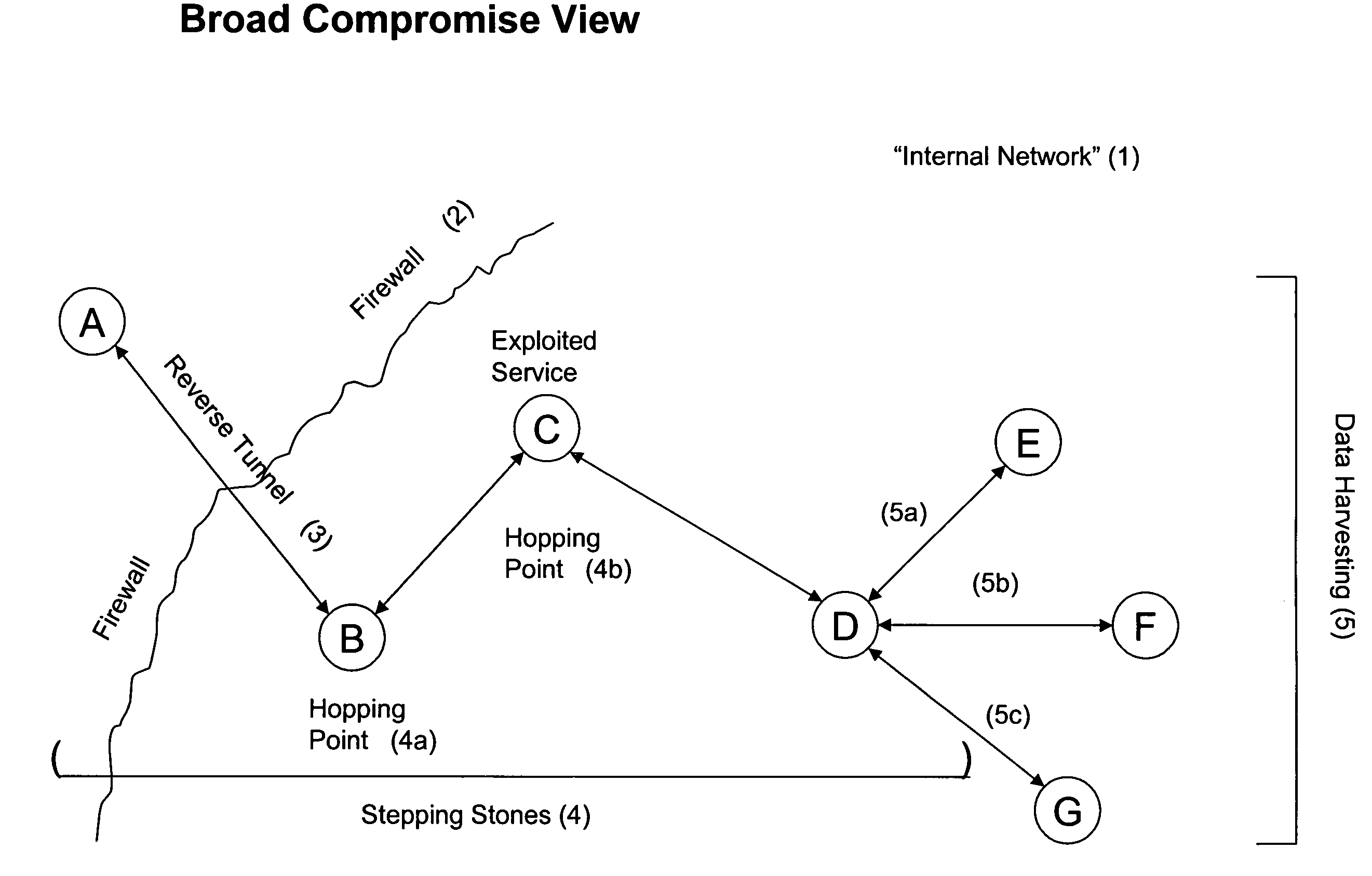
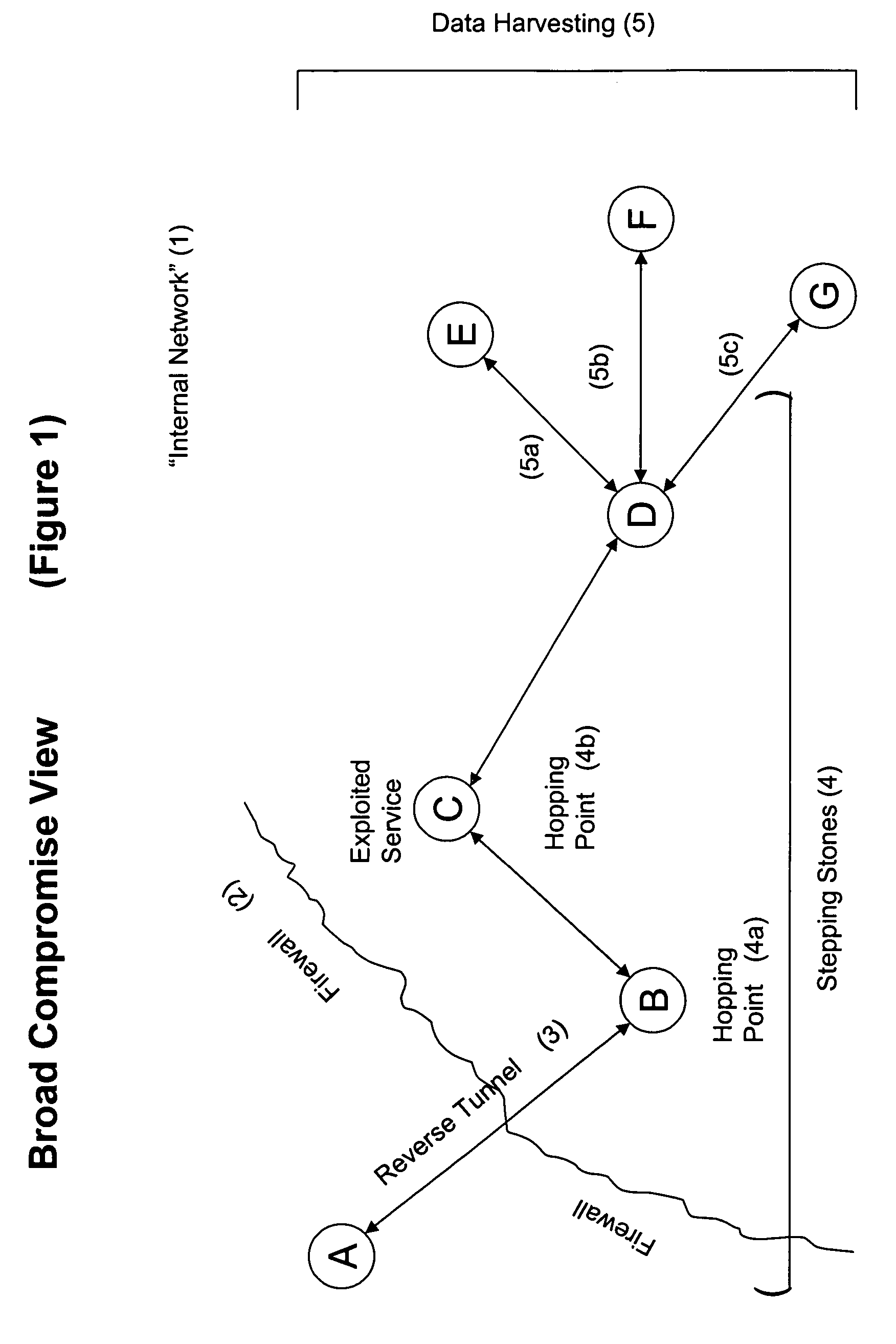
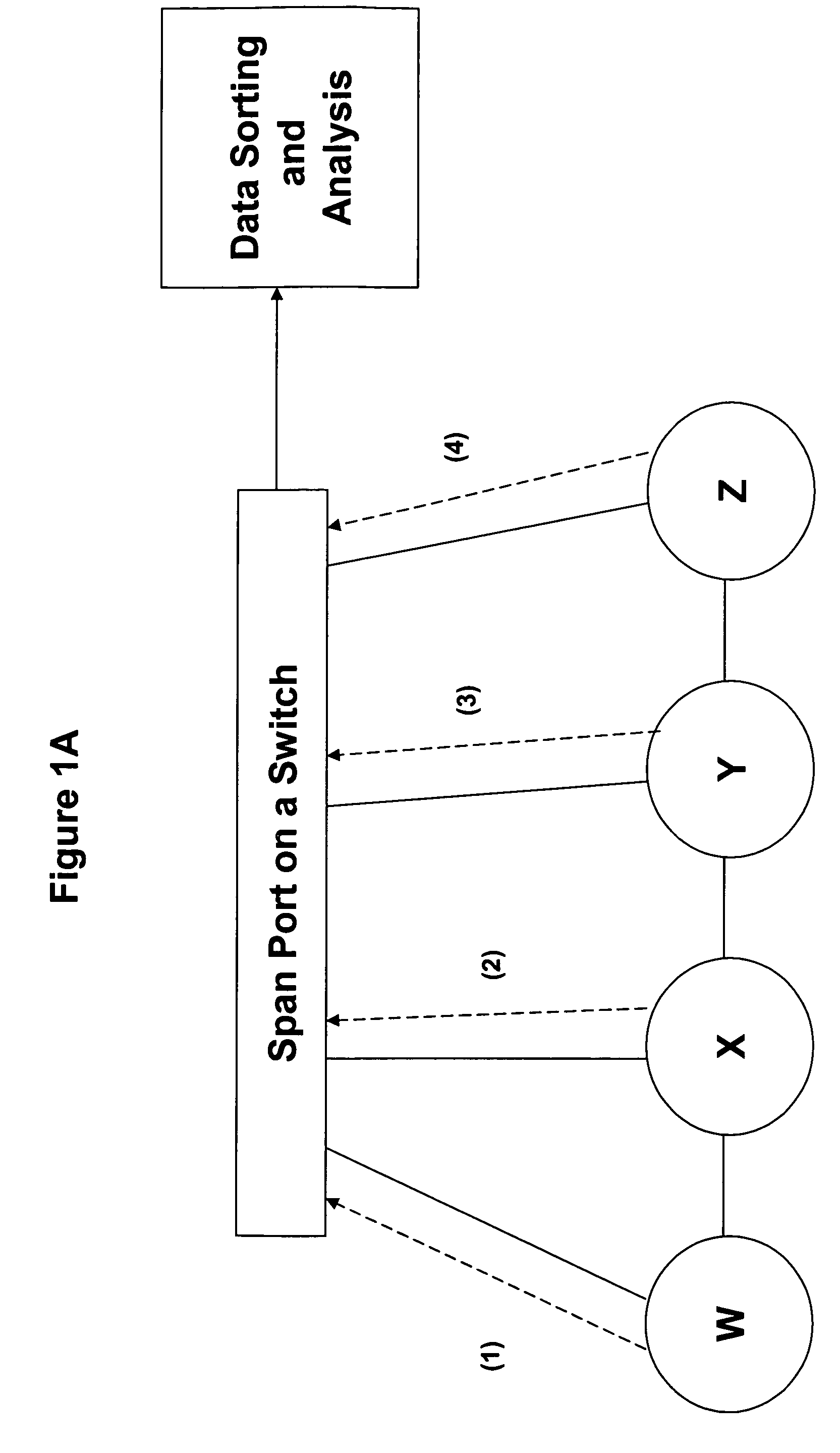
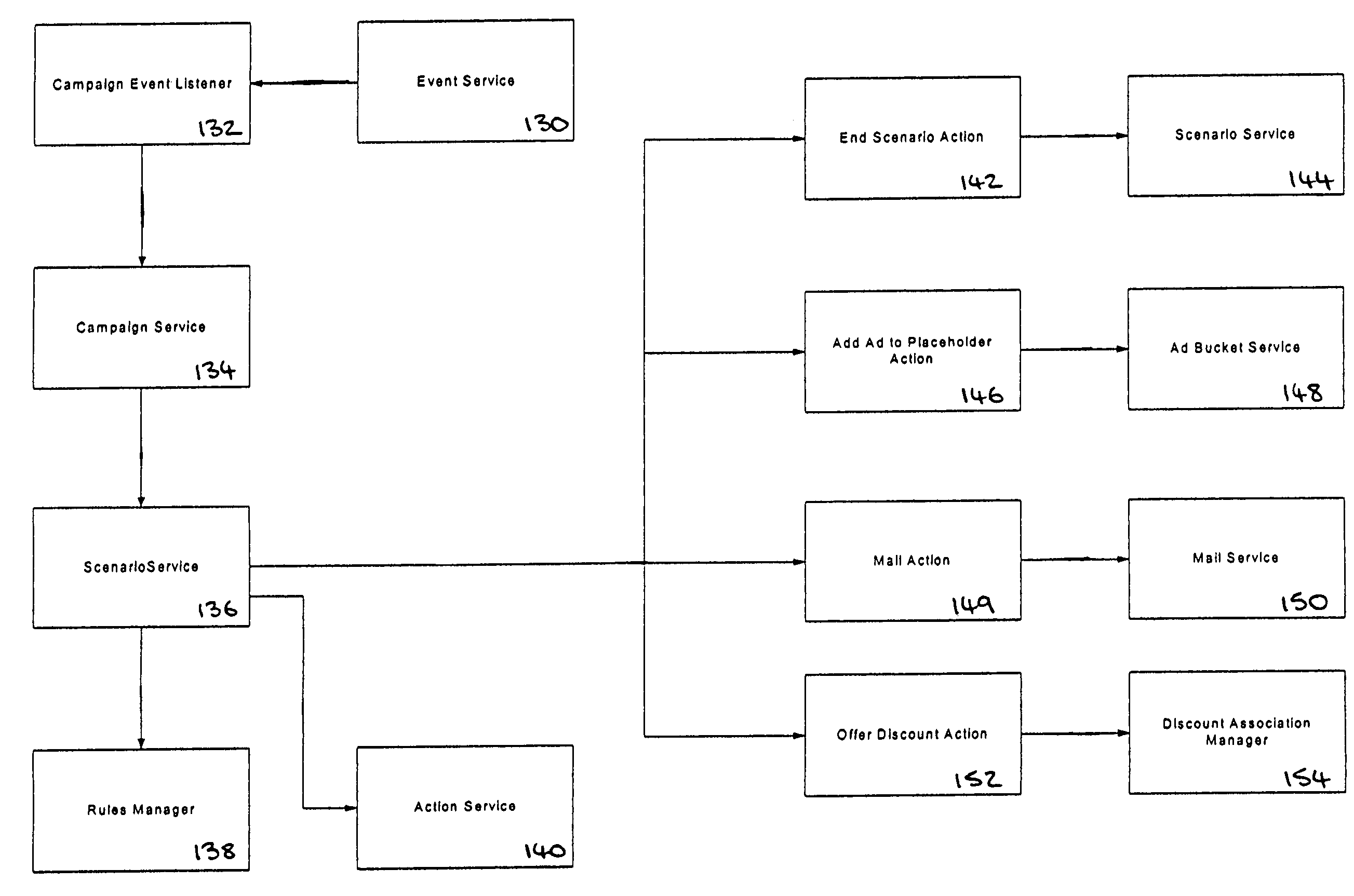
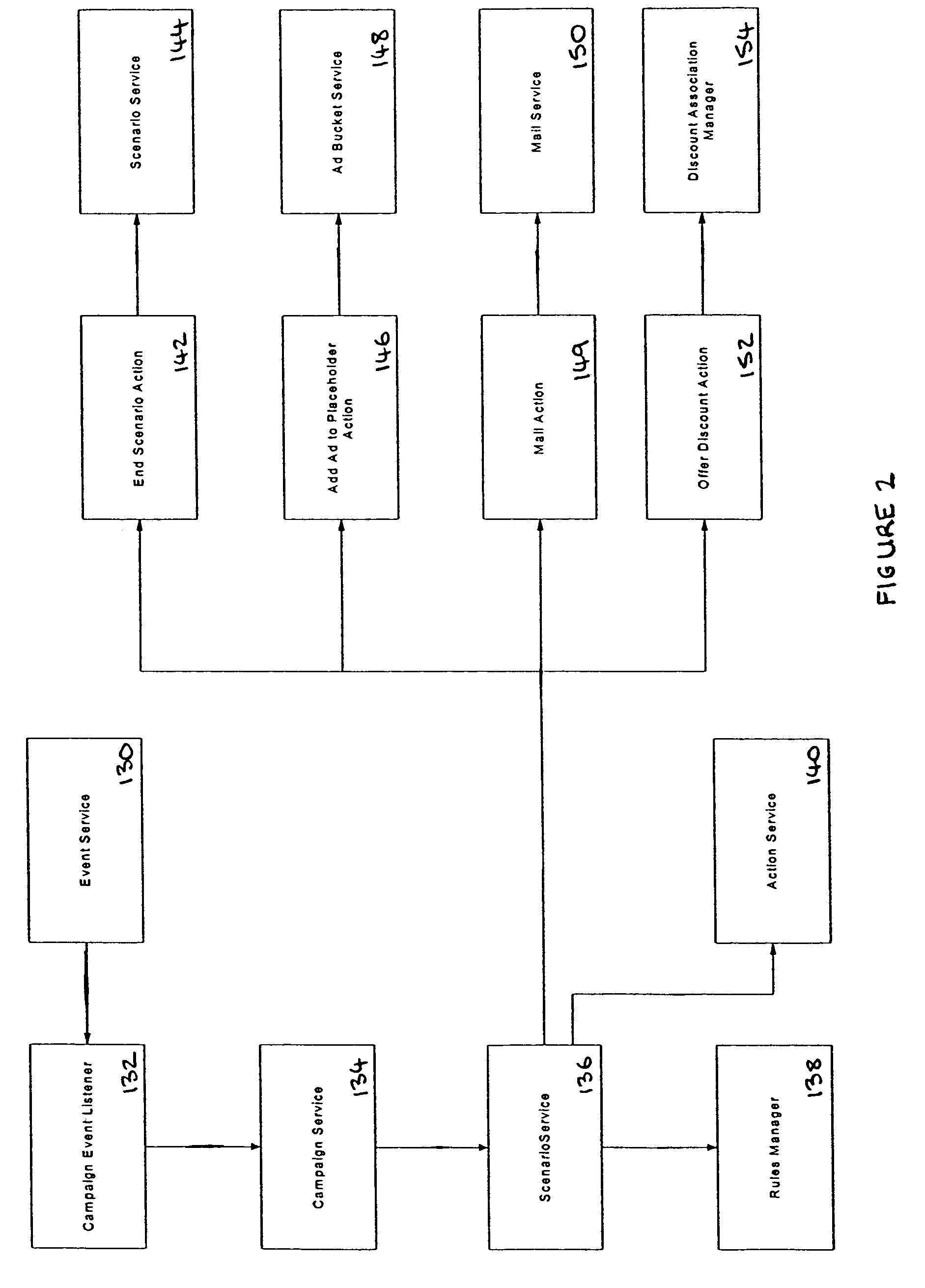
Systems and methods for detecting a compromised network
InactiveUS20050157662A1Reduce false positive resultsDigital data processing detailsComputer security arrangementsAnalysis dataData transmission
Systems and methods are disclosed for monitoring data transmissions on a network and detecting compromised networks. The systems and methods monitor communications involving network hosts and analyze the communications in view of the business function of the hosts. In certain embodiments the analysis is performed by associating a set of rules of operation for the sessions, hosts, and / or environment, and analyzing data packet transmissions to ascertain violations of the rules.
Owner:INTRUSIC
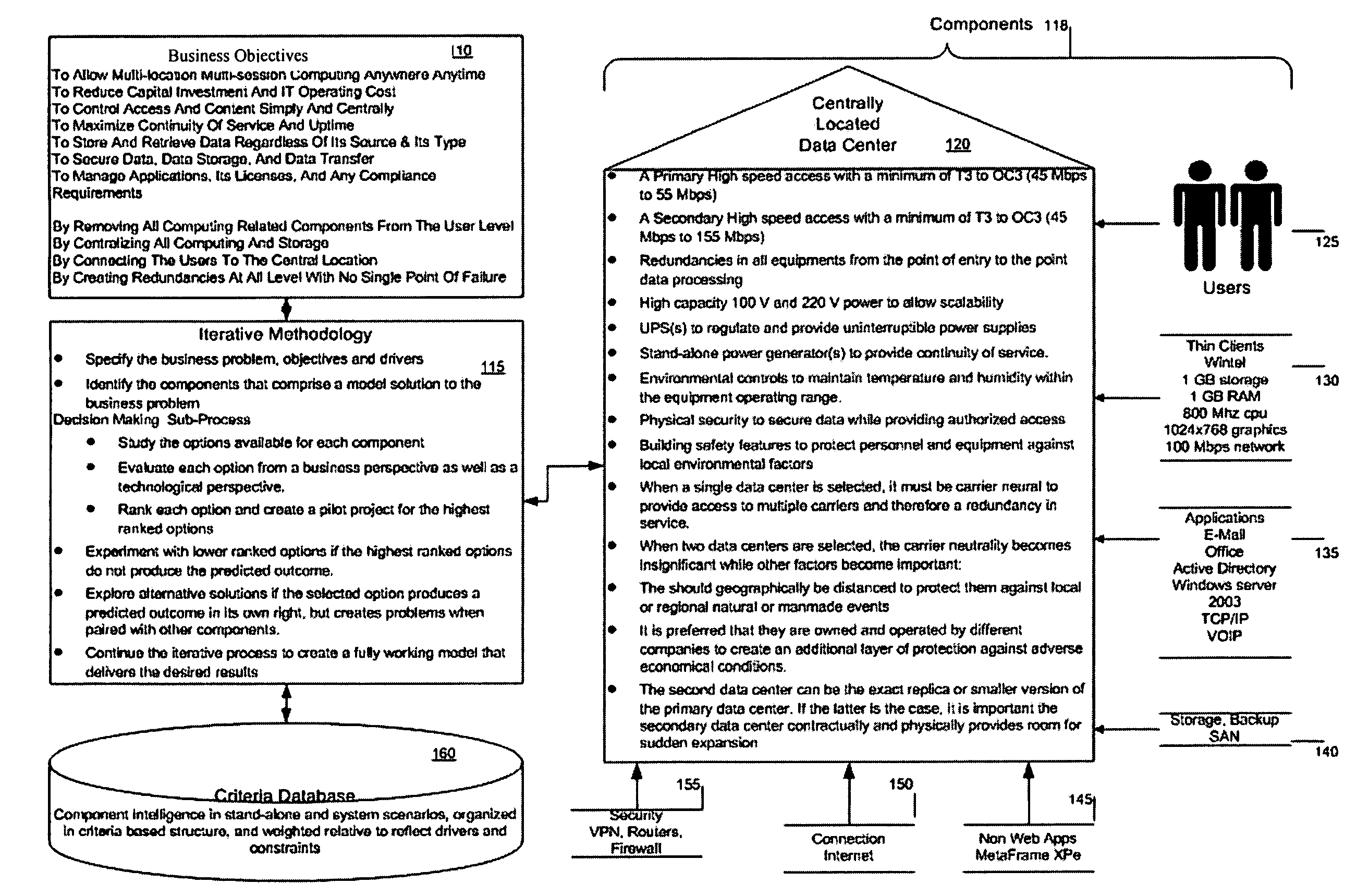
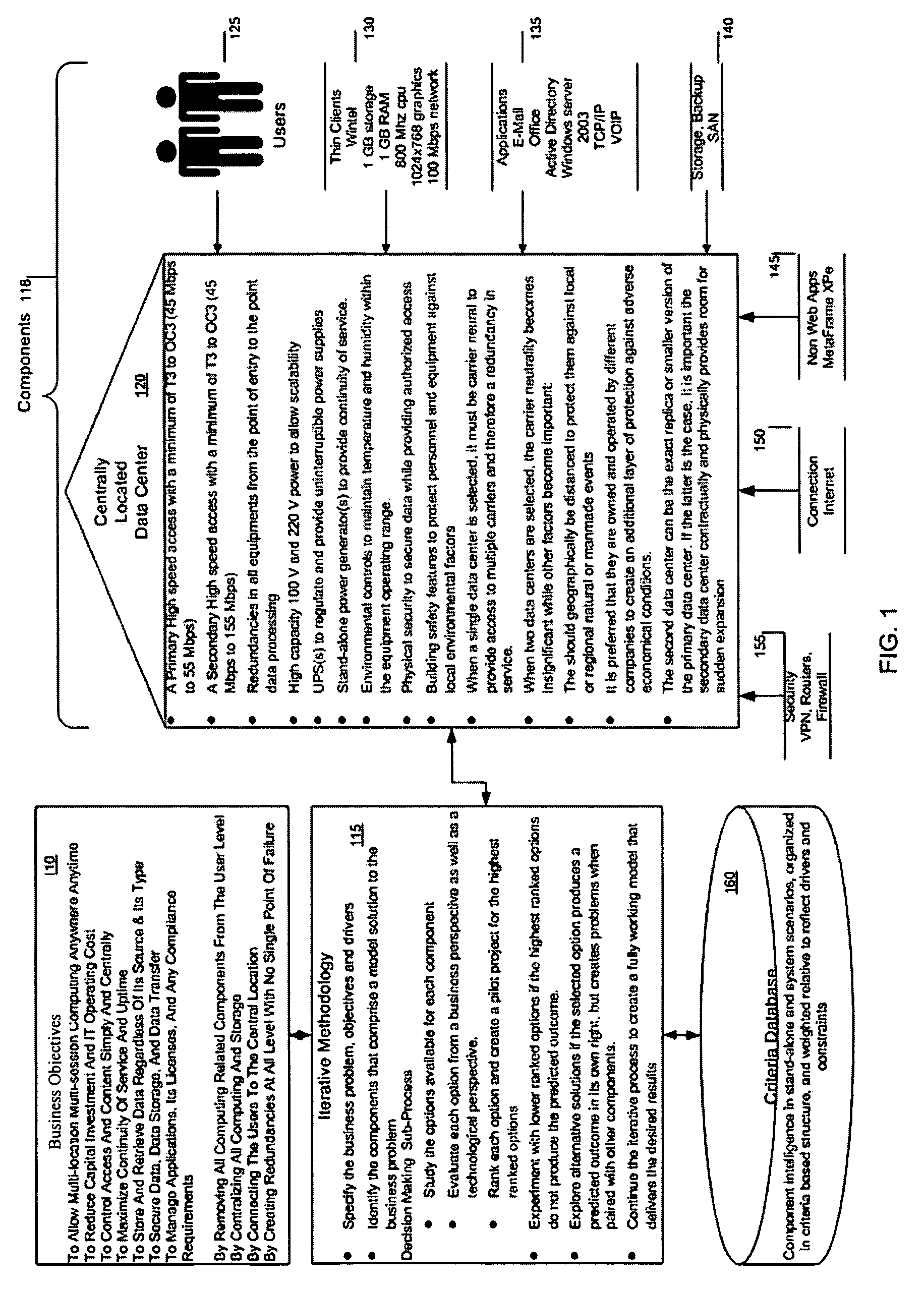
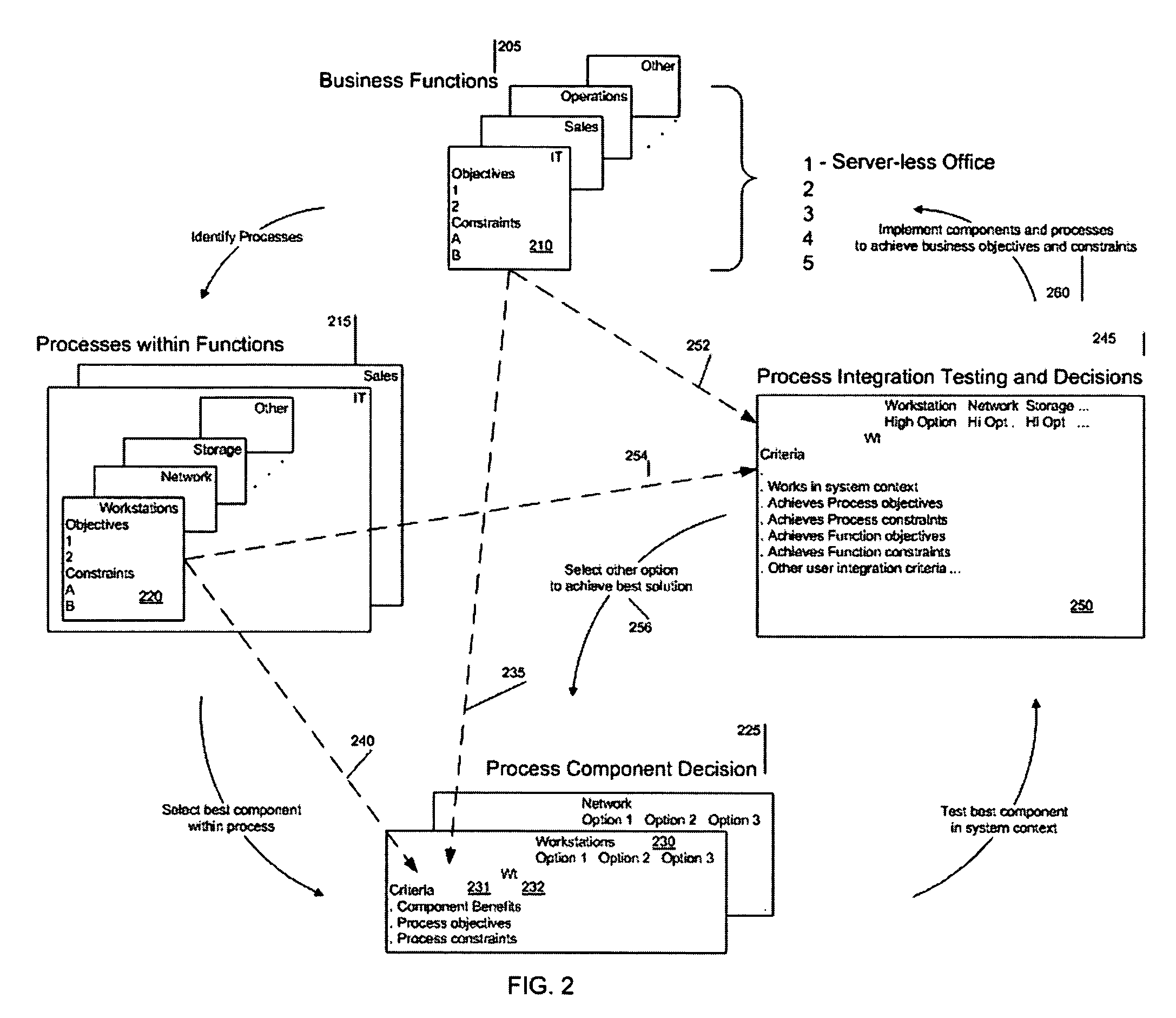
Method for a server-less office architecture
InactiveUS20050288961A1Easy to useImprove efficiencyDigital data authenticationOffice automationClient-sideFour component
A way is provided for architecting a server-less office that delivers anywhere anytime computing support to an organization. The server-less office comprises a plurality of information technology IT components selected based on business objectives and constraints associated with the business function of the organization to work together to deliver computing support functions to a plurality of end users who no longer have local computing support and may only have thin clients on their desks. A pre-determined server-less architecture is imposed by the present invention by including at least four architectural groupings of IT components that the organization must map the objectives and constraints of its business functions onto for IT component selection purposes. A local group is included in this minimum set of groups so that unique processing needs can be satisfied that are not met by the imposed pre-determined server-less office architectural groupings.
Owner:EPLUS CAPITAL
Object oriented based methodology for modeling business functionality for enabling implementation in a web based environment
A method of defining Business Classes for modeling business activities comprising the steps of representing business activities as the interaction between one or more Business Classes, and entering into a computer and storing in an electronic format the Business Classes and the relationships existing between the Business Classes.
Owner:GINEGAR LLC
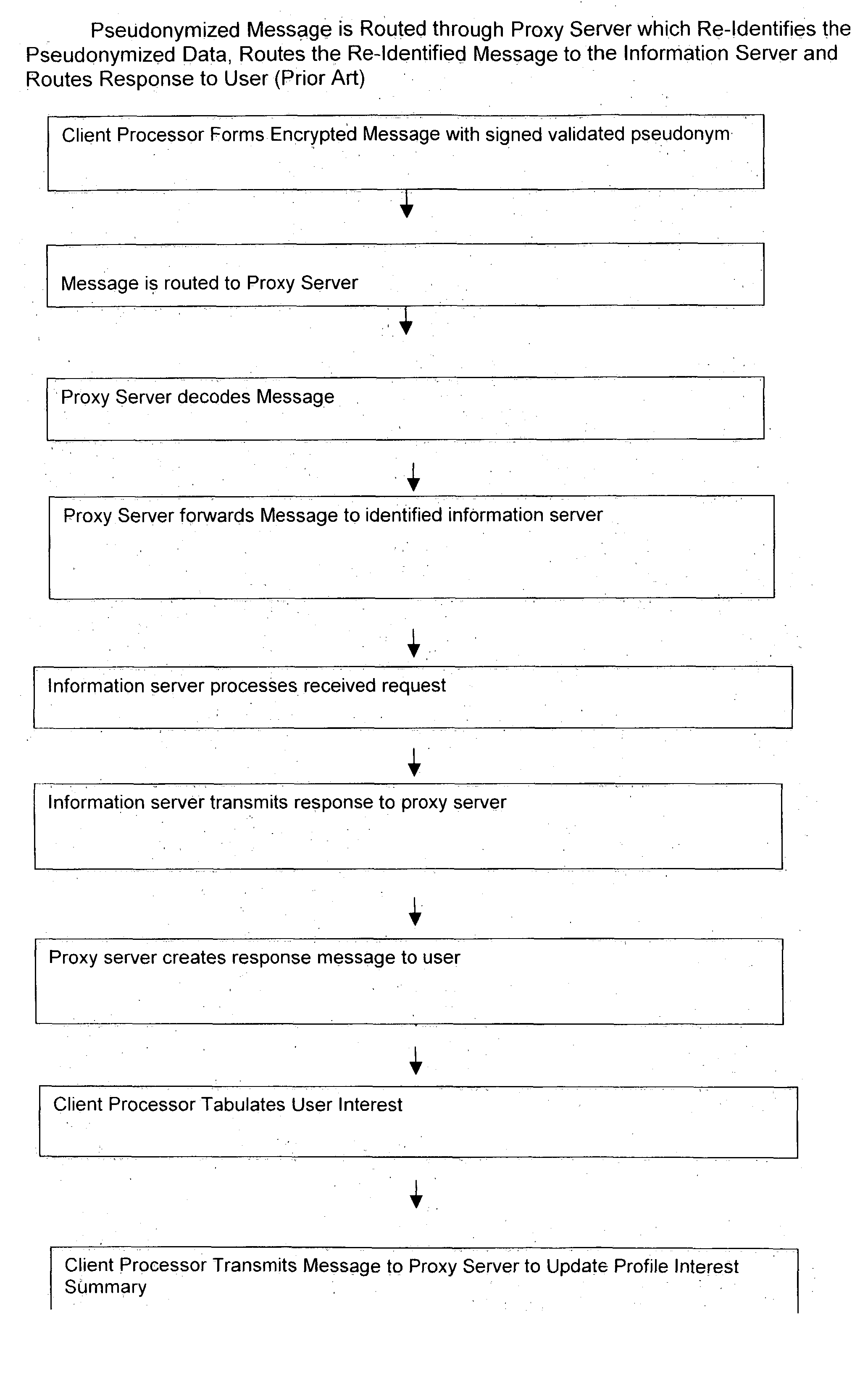
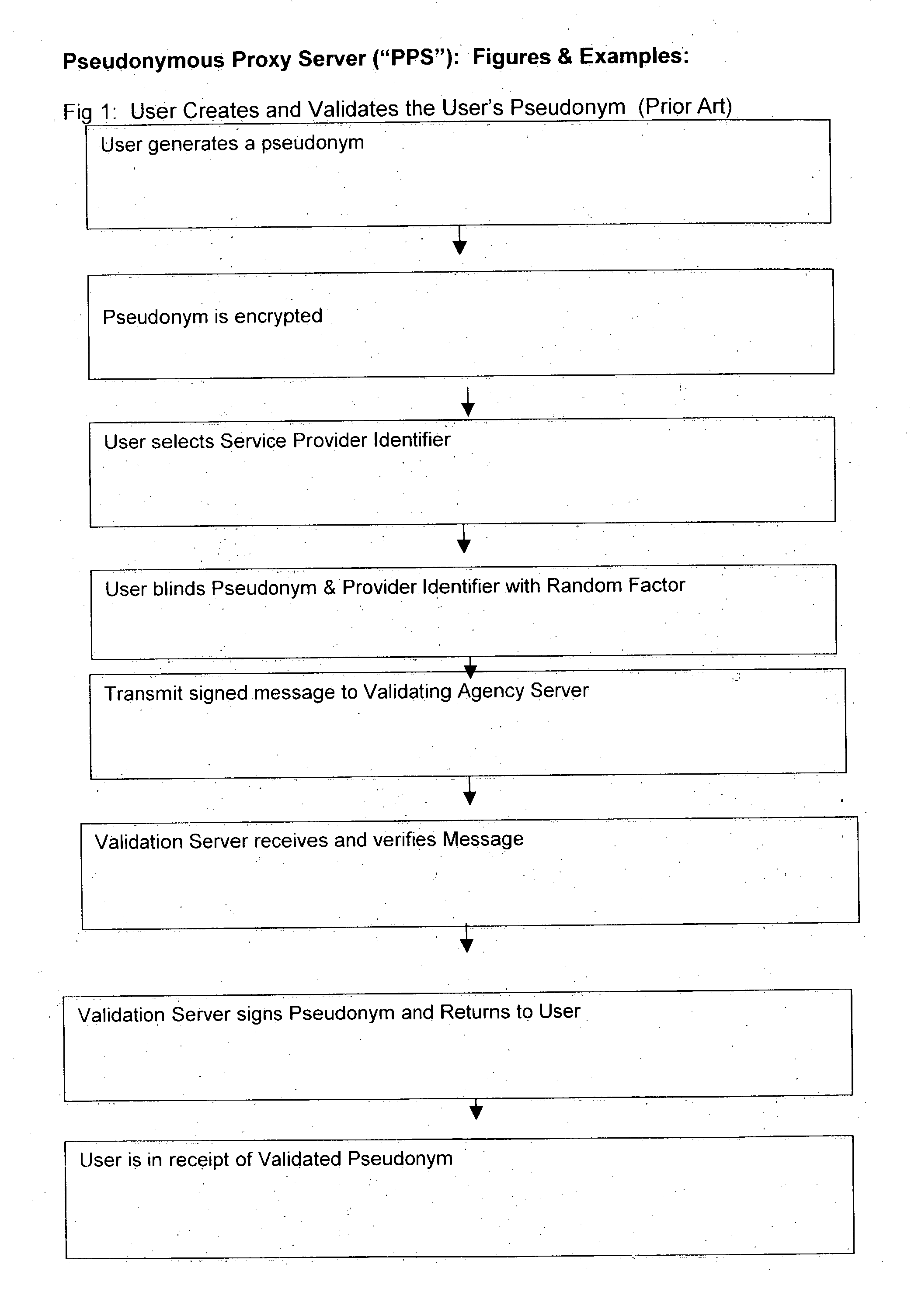
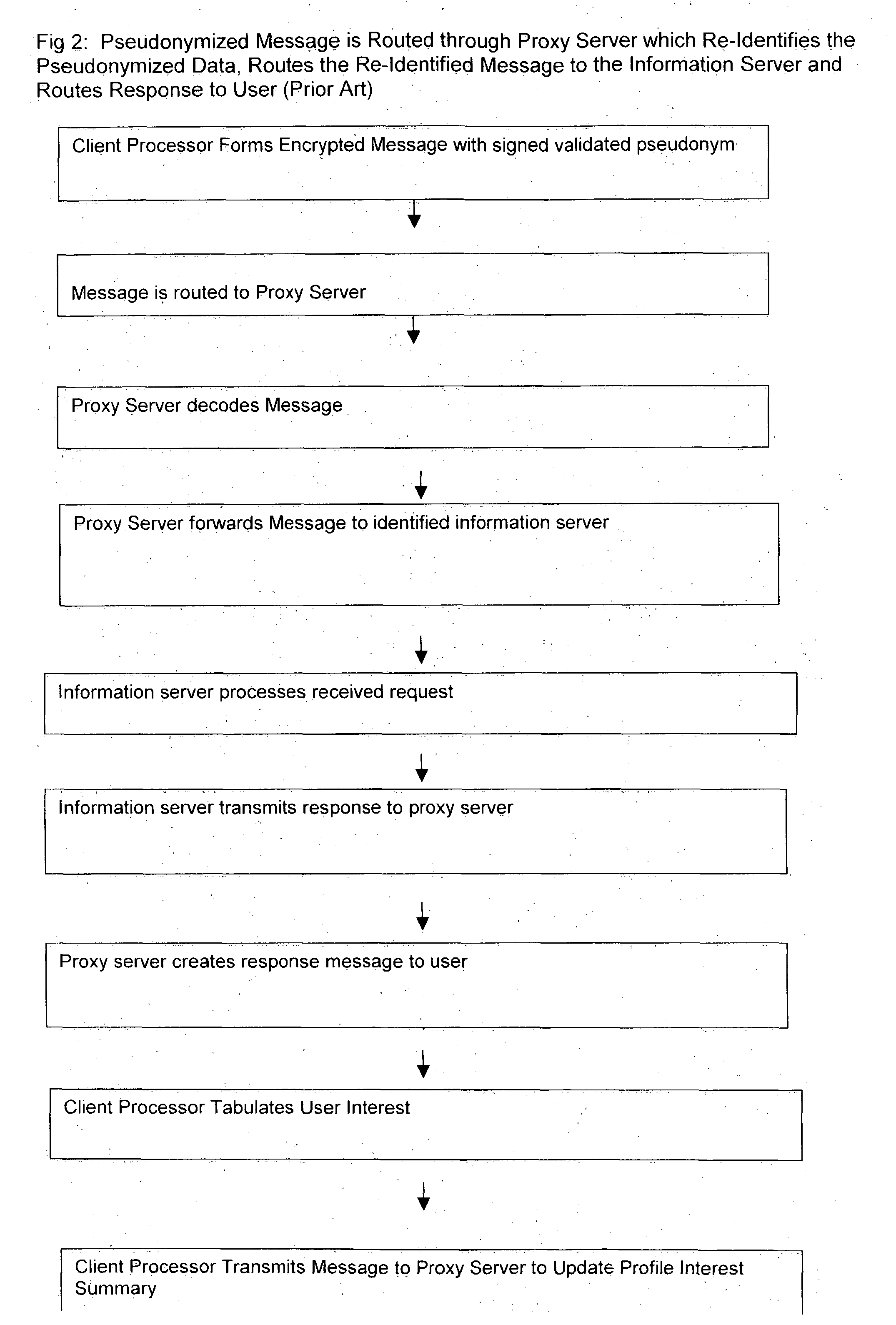
Use of proxy servers and pseudonymous transactions to maintain individual's privacy in the competitive business of maintaining personal history databases
InactiveUS20060031301A1Protect data privacyPrivacy can be assuredComputer security arrangementsMultiple digital computer combinationsInternet privacyData access
A system is provided that preserves data privacy for the Individual—I and Private Data Owner (PDO) while granting data access to the User-U and Accessor who need such data to perform their usual and customary business functions. The method and system completely control the User's access to the Private Data Owner's Private Data by replacing Identifying Information for the User—U, Individual—I, Accessor and PDO with pseudonyms. This assures the overall privacy of individuals, throughout the course of collecting, storing, accessing, analyzing and sharing detailed private records among different organizations engaged in providing and / or consuming services and / or products. Access Control Rule Sets (“ACRS”) consist of instructions which prescribe the terms and conditions for permitting Users to access the PDO's Pseudonymized and Actual Private data in accordance with the rules governing their authorization to access such data.
Owner:HERZ FREDERICK S M +2
System and method for web-based personalization and ecommerce management
InactiveUS7499948B2Strong incentiveQuickly attractDigital data processing detailsSpecial data processing applicationsPersonalizationE-commerce
A personalization system that uses rules to adjudicate and characterize a customer, or a customer's actions, and then to personalize a business function, such as a displayed page, based on the outcome of those rules. In one embodiment the invention provides a system for web-based personalization, that allows for personalizing the content or business functioning of a web-based application to reflect the characteristics of a particular user. The system comprises a user profiler, for determining a snapshot of a particular user of a web-based application, a rules editor for inputting a set of rules governing the business functioning of said web-based application, and a rules engine. The system then uses the set of rules to make decisions about the particular user and the business functioning of said web-based application, and to determine the content or business functioning of said web-based application as it applies to that user.
Owner:ORACLE INT CORP
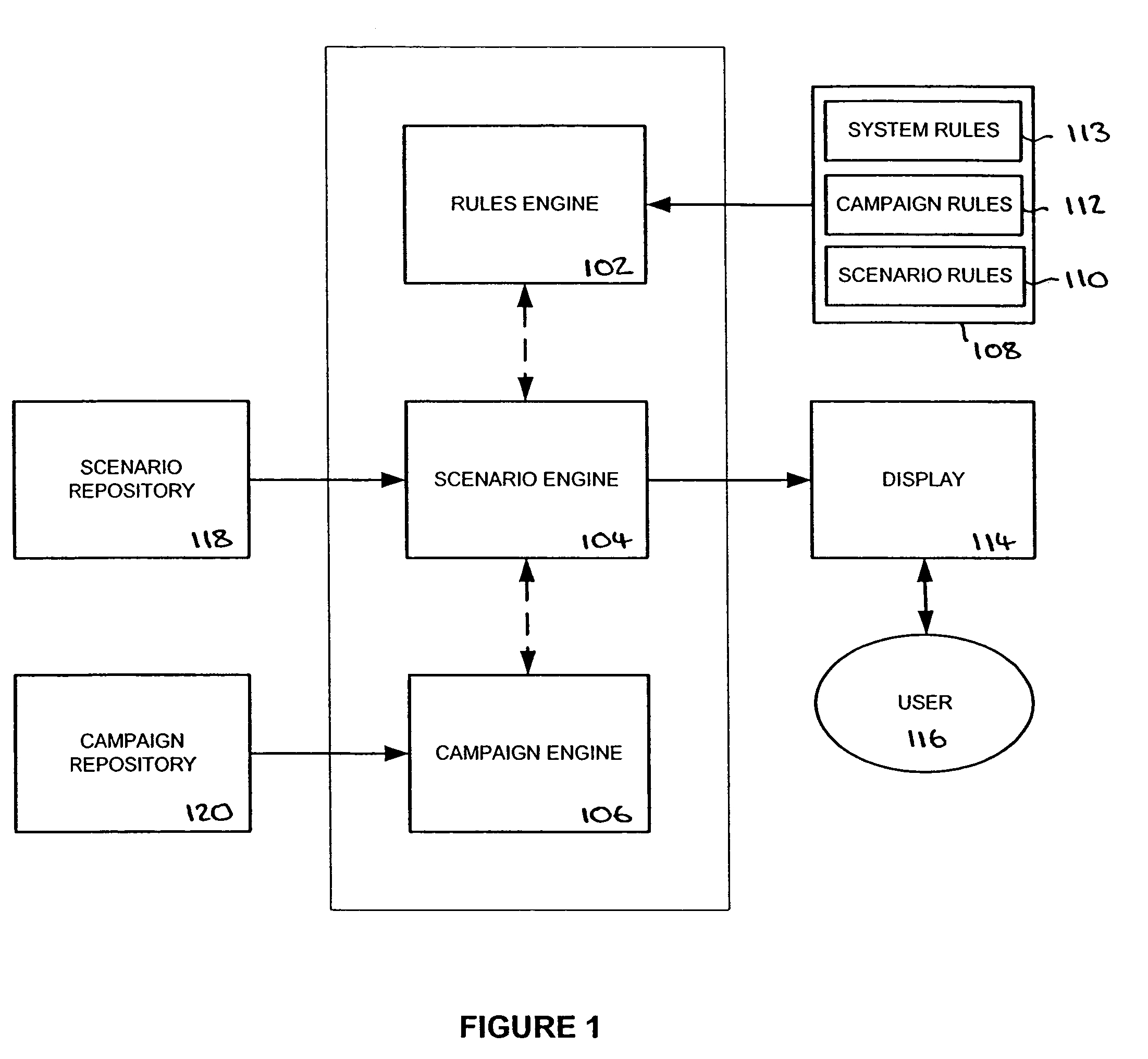
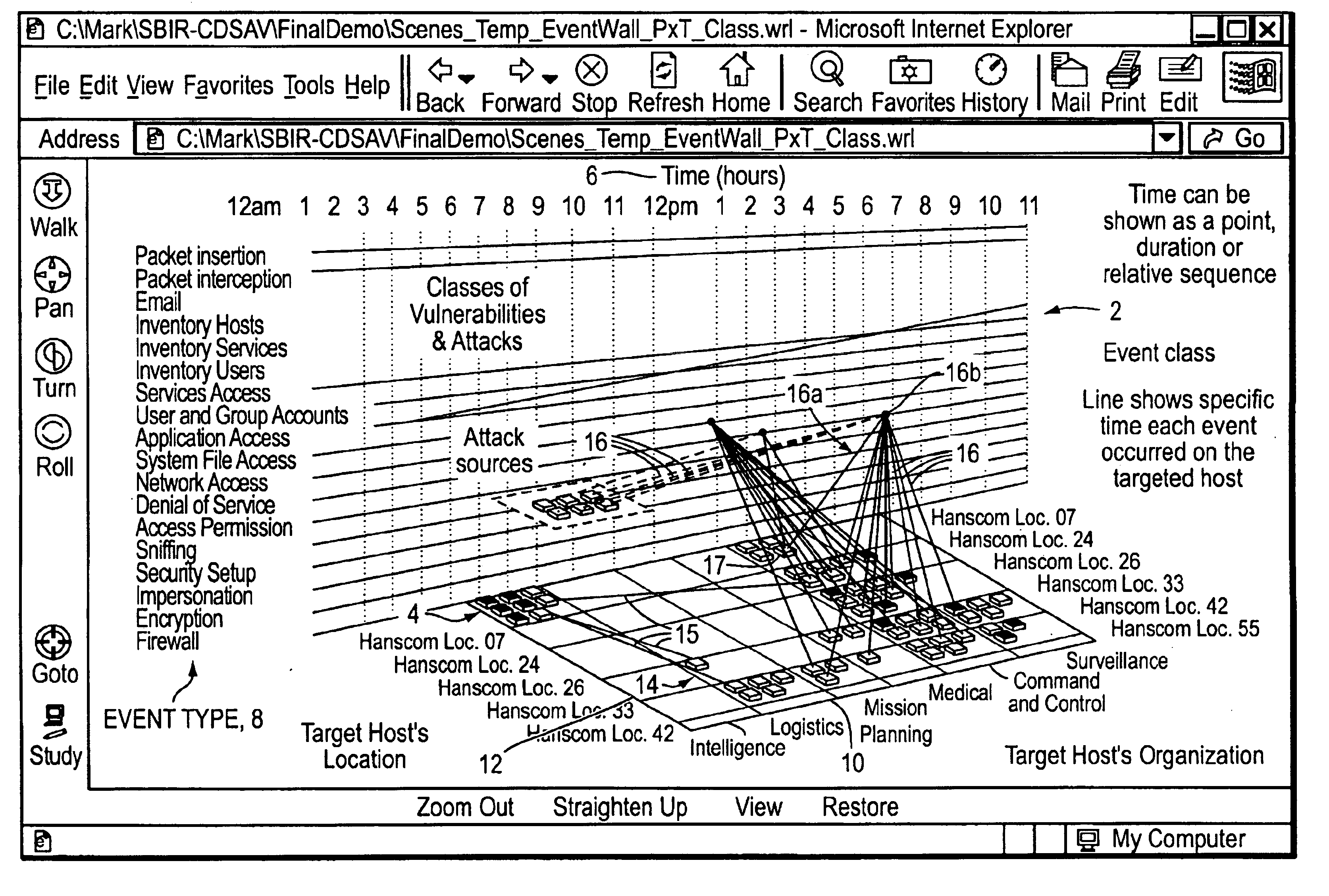
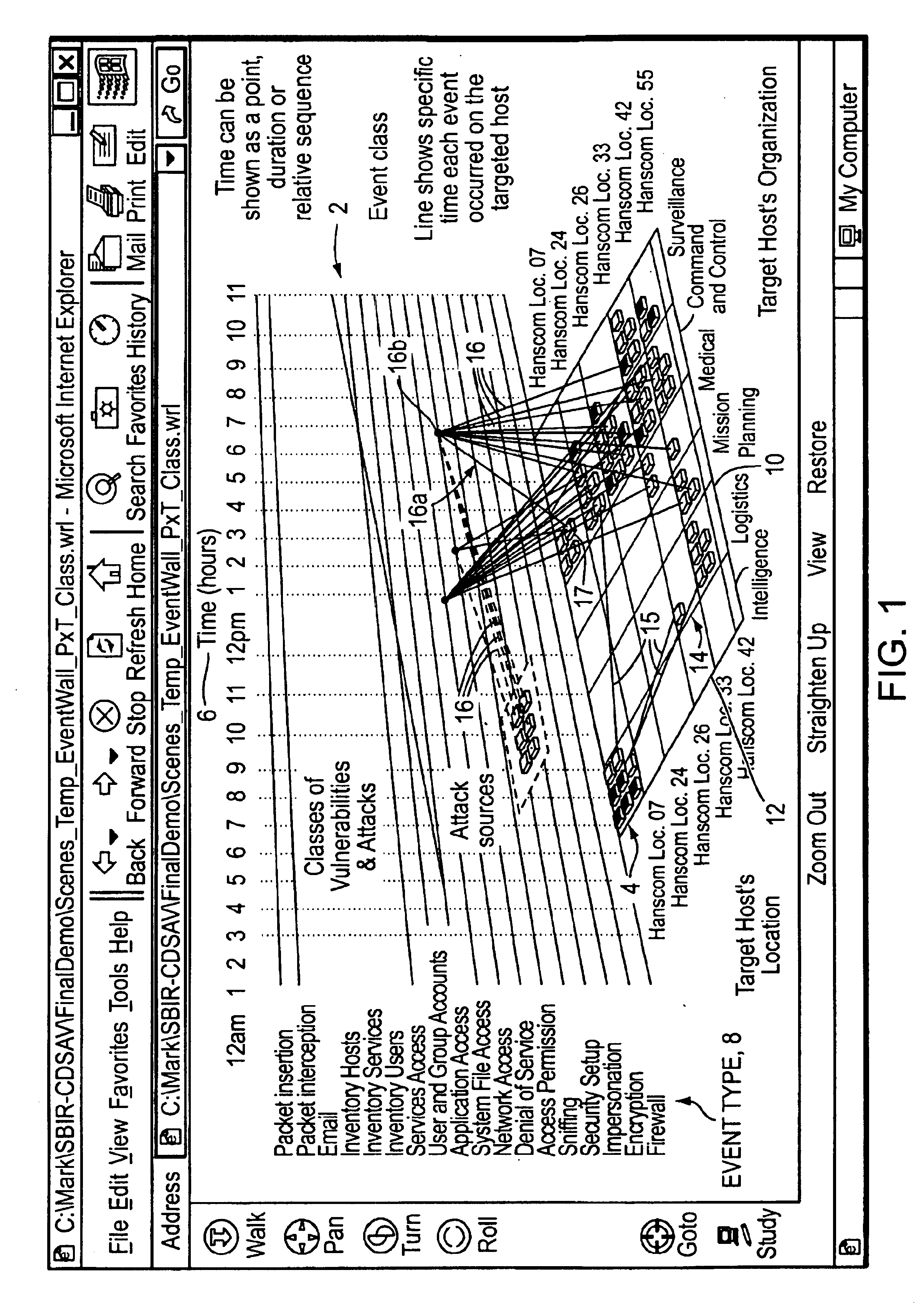
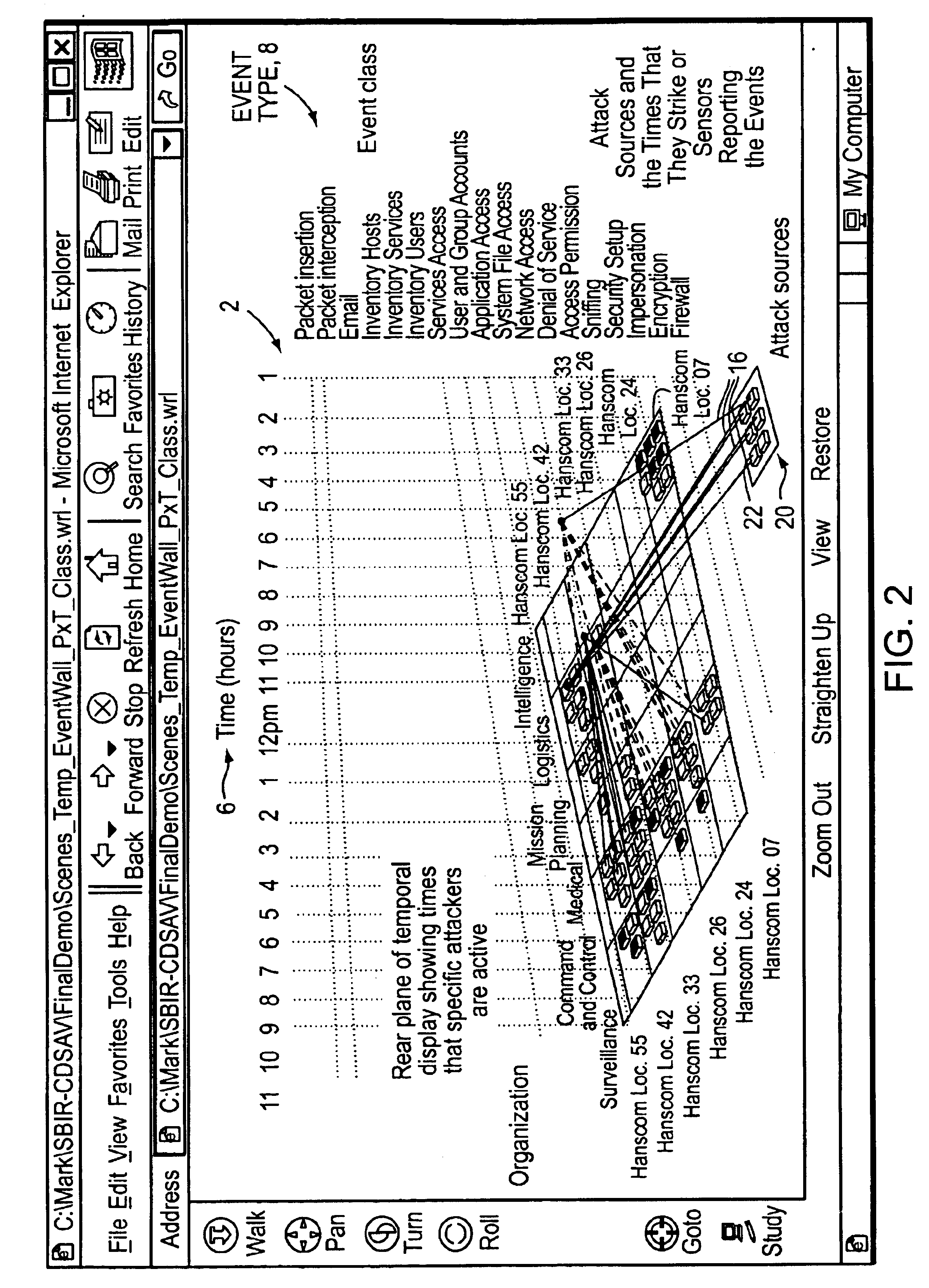
Visualizing security incidents in a computer network
InactiveUS6906709B1Enhanced Situational AwarenessFacilitate human perceptionTransmission3D-image renderingDatabase interfaceBusiness function
A method of visualizing the impact of security flaws or breaches in a network. A 3-D visualization tool that simulates 3-D space on a monitor interfaces with a security database which relationally associates security events with the network elements affected thereby. The security events are visually depicted in a first section of simulated 3-D space and the network elements are depicted in a second section of simulated 3-D space. Relationship lines are drawn between displayed categories of security events and the displayed network elements in order to aid an analyst to visualize the impact of security breaches on the organization. Various other properties of the network elements may also be displayed such as the role of the network device within the organization, and the business functions of the organization.
Owner:APPLIED VISION
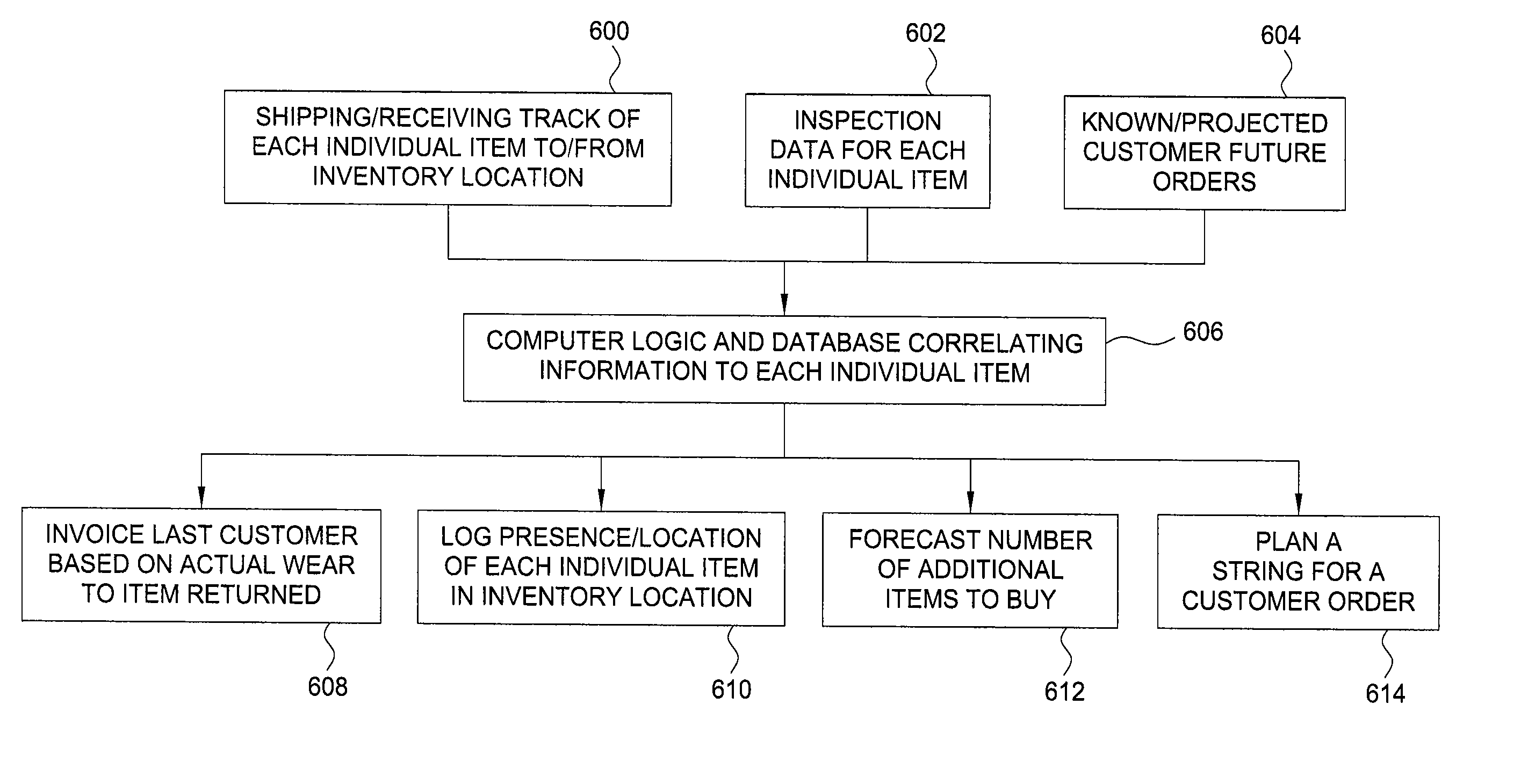
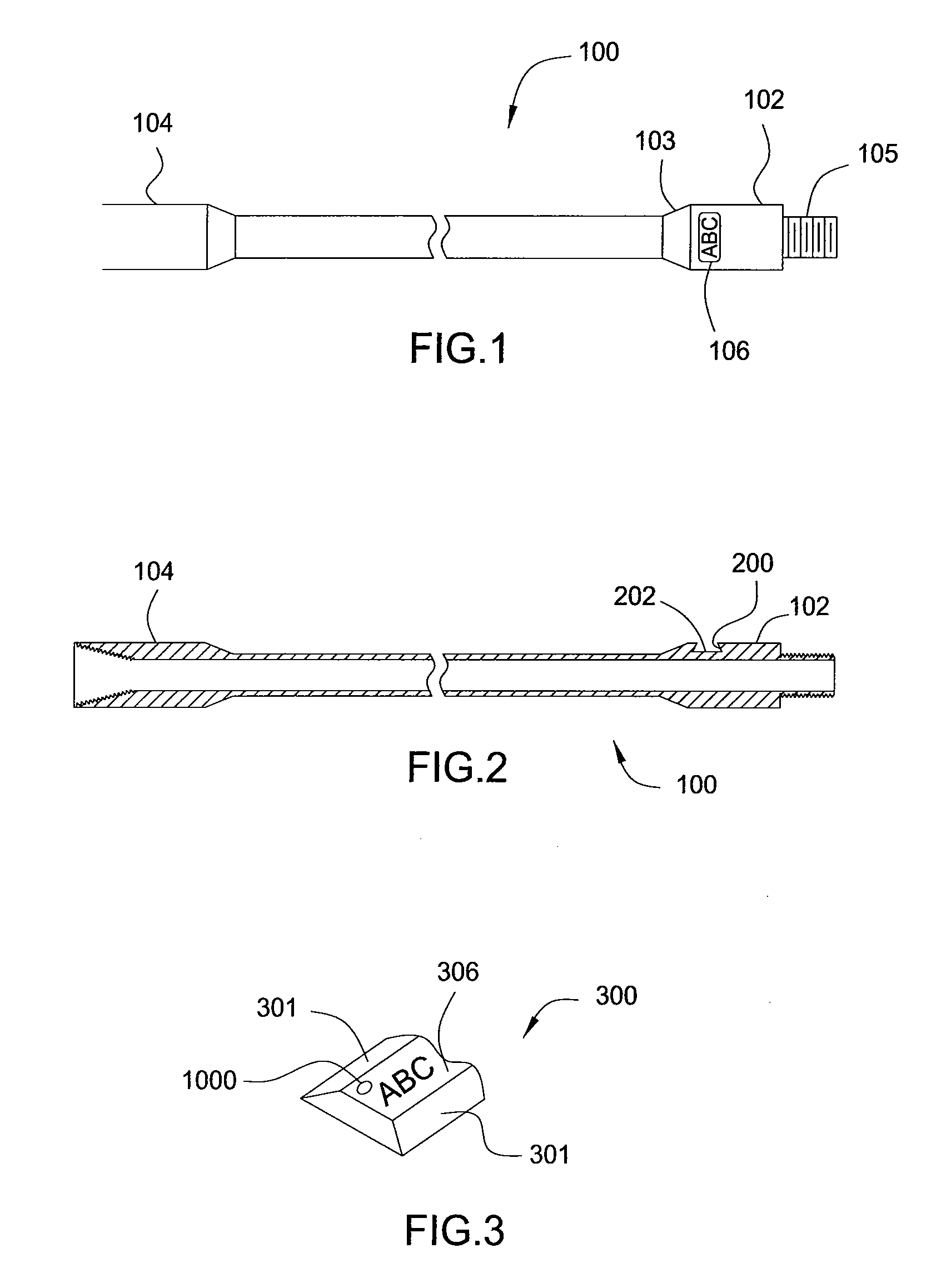
Serialization and database methods for tubulars and oilfield equipment
Methods and apparatus identify downhole equipment and correlate input data with the equipment to improve planning and / or inventory operations. For some embodiments, oilfield equipment or tubular goods such as drill pipe include a shaped recess along an outer circumference for receiving a tag cartridge by shrink fitting. Once tagged, detector system configurations at pipe yards may facilitate logging the presence and location of each drill pipe and correlating specific data, such as inspection data, to each drill pipe. Further, this correlation populates a database utilized to achieve other business functions such as forecasting number of additional drill pipe needed to purchase, invoicing customers according to actual tracked wear / use of the drill pipe being returned, and providing well or job specific drill string population using known history pipe joints.
Owner:WEATHERFORD TECH HLDG LLC
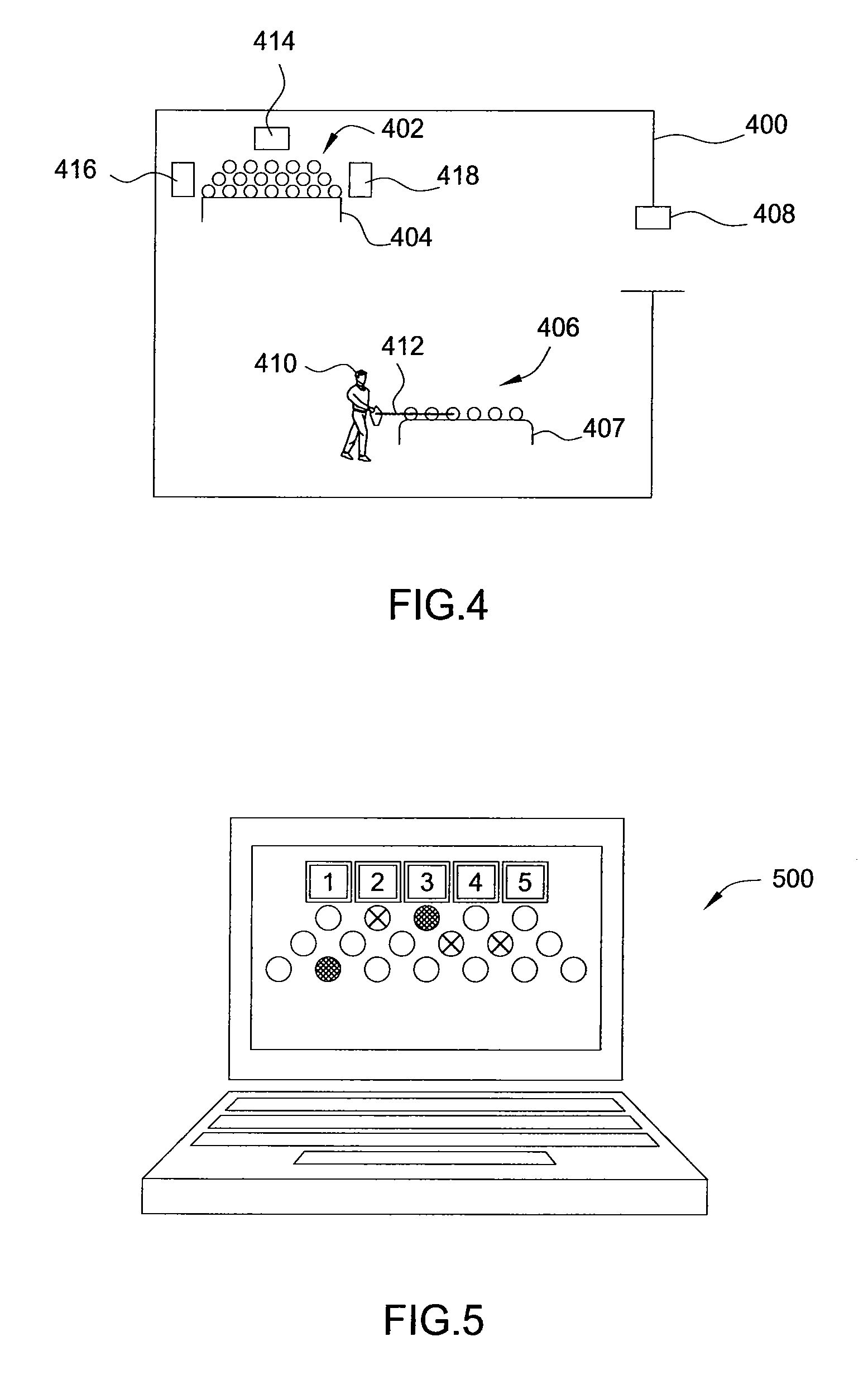
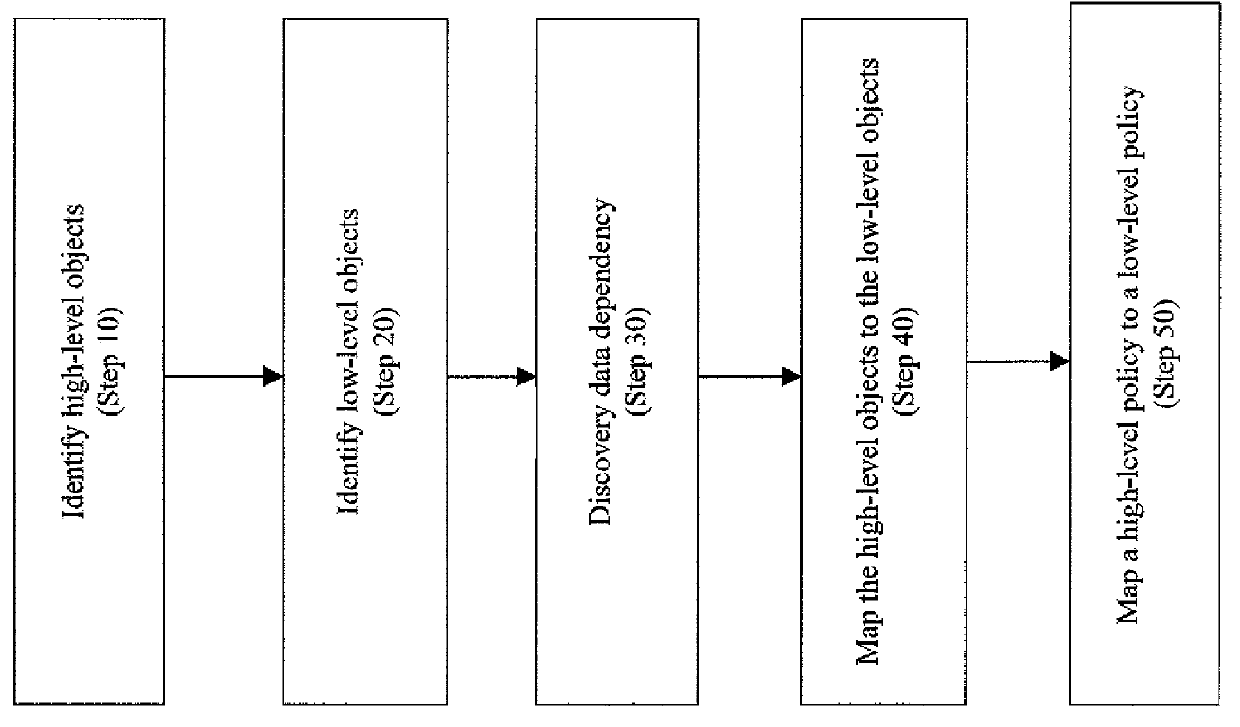
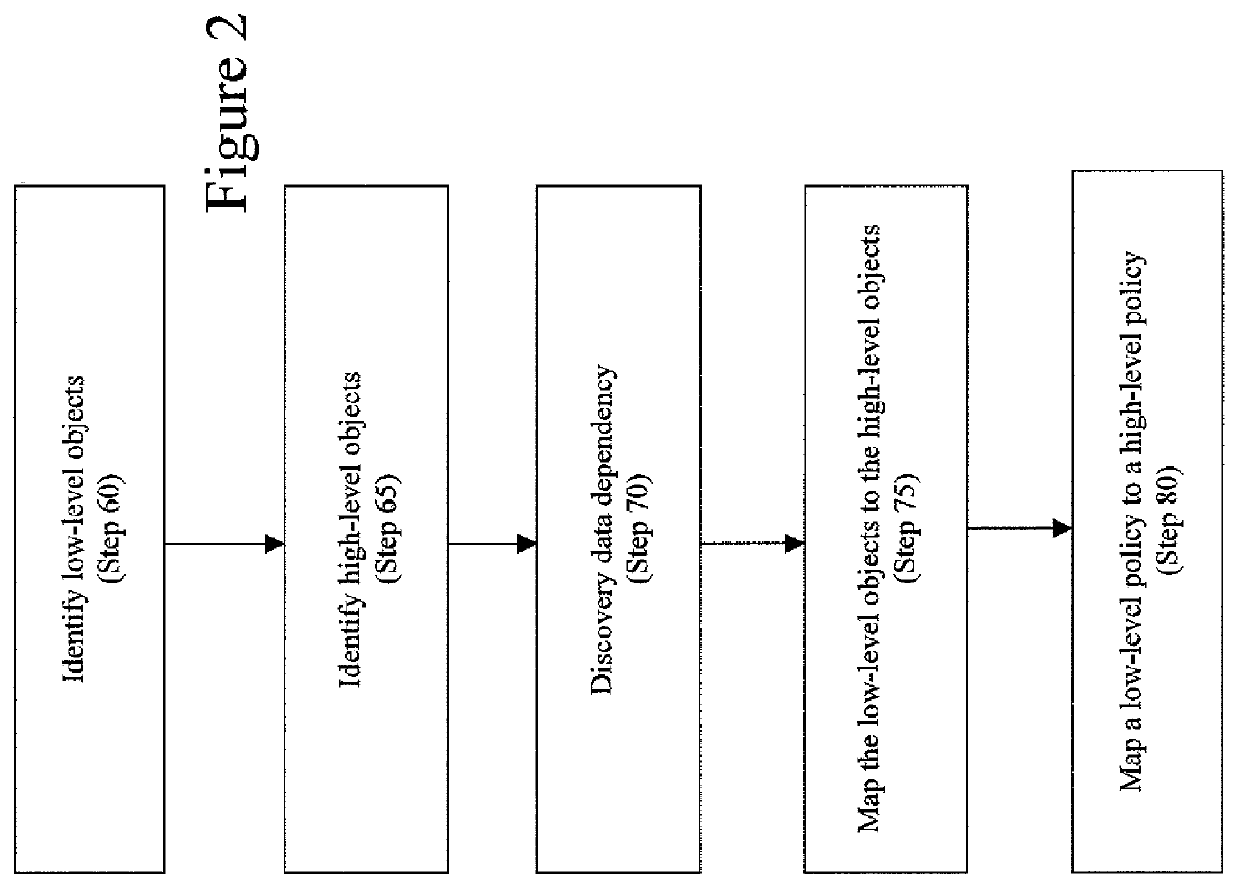
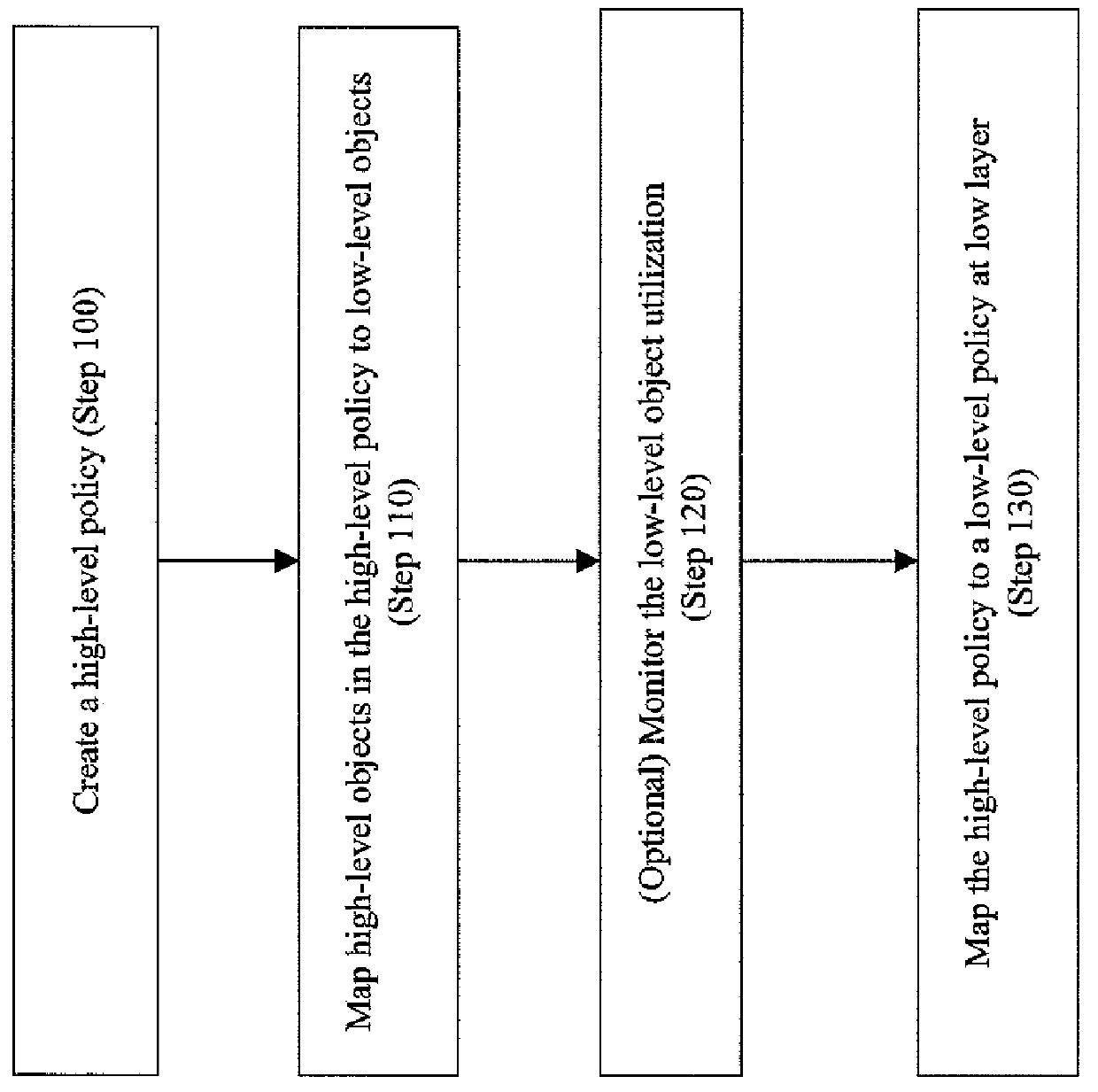
Method to automatically map business function level policies to it management policies
A method, system, computer program product, and computer program storage device for transforming a high-level policy associated with a high layer to a low-level policy associated with a low layer. Mapping between high-level objects in a high layer and low-level objects in a low layer is derived by an automated discovery tool. The high-level policy is mapped to the low-level policy according to the mapping (e.g., by substituting the high-level objects with the low-level objects and by performing a syntax transformation). In one embodiment, a low-level policy is transformed to a high-level policy according to the mapping. As exemplary embodiments, policy transformations in traffic shaping and data retention are disclosed.
Owner:INT BUSINESS MASCH CORP
Monitoring and performance management of component-based applications
ActiveUS7627671B1Error detection/correctionDigital computer detailsManagement toolApplication software
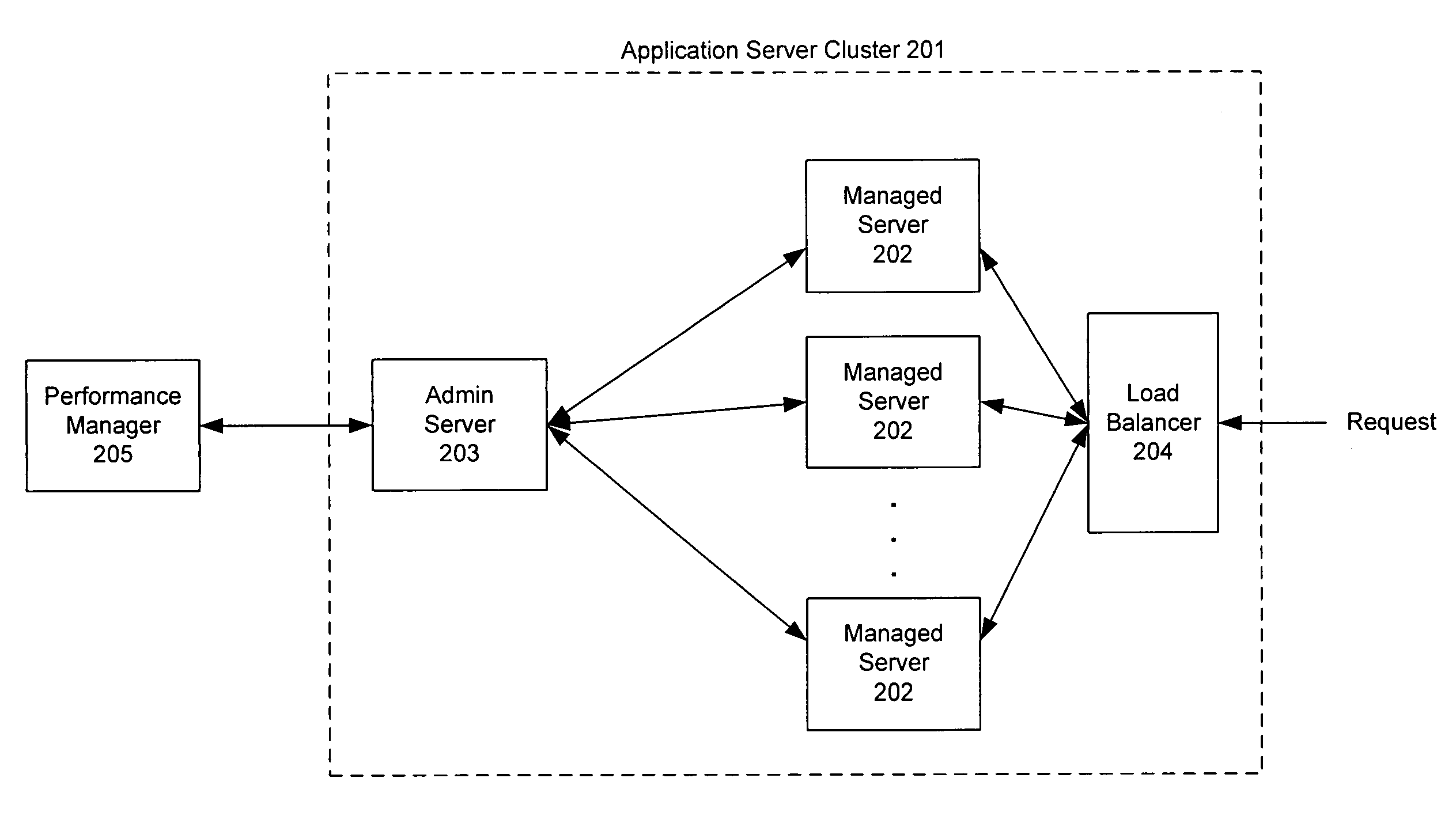
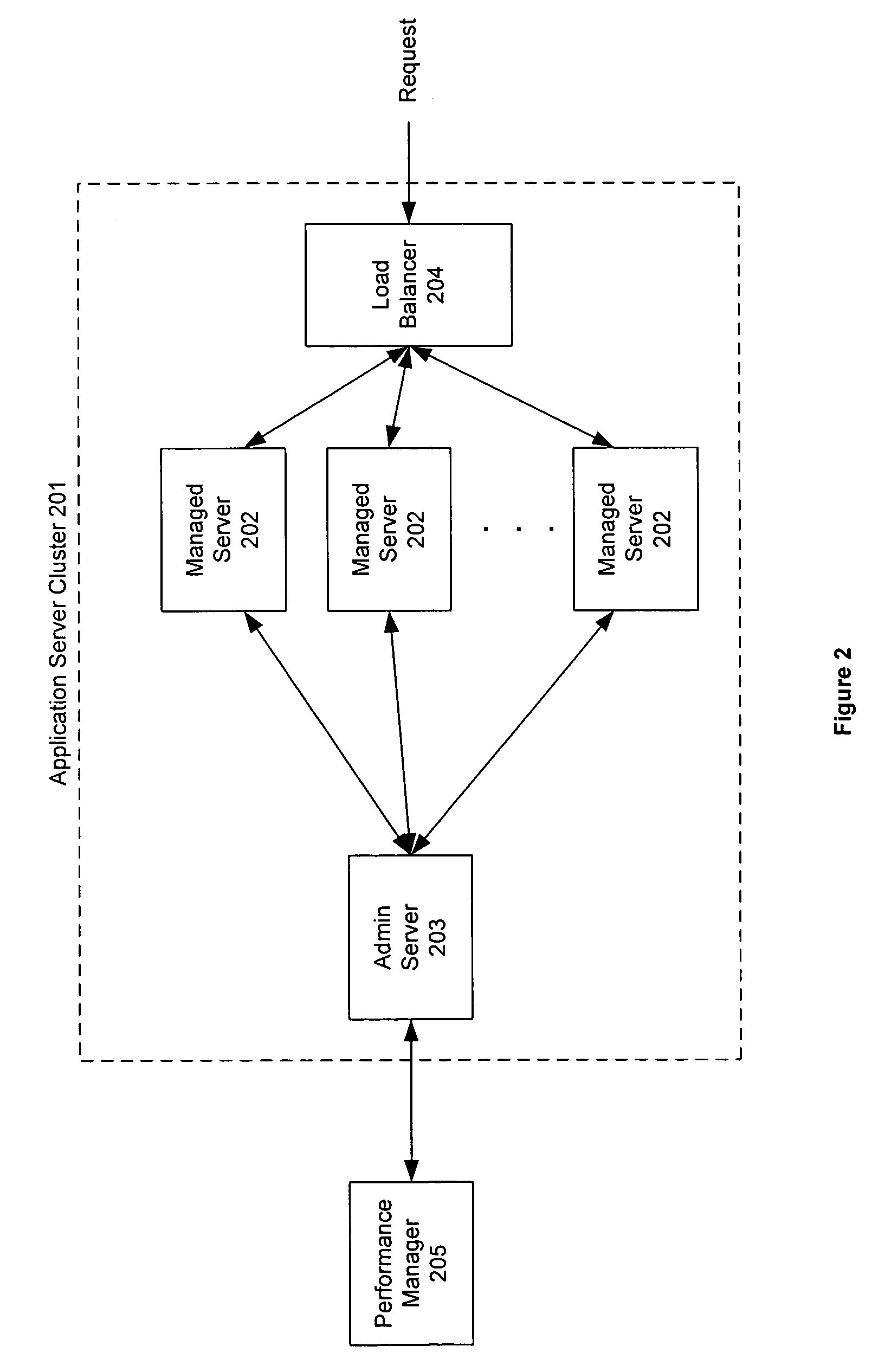
Invention manages underlying application objects that support implemented business functions. A performance manager accesses and interprets application metadata and execution environment metadata, using a hierarchical entity to model complex relationships between application abstractions, components and resources. The performance manager encodes common behavioral and architecture information in models resulting from analysis of component architecture standards, vendor application servers, development tools and administration tools. The performance manager conducts inter-component dependency and control flow analysis, for example by generating control flow graphs from application metadata and performing byte code analysis without access to application source code. The performance manager collects metrics from standardized and vendor-specific sources, instruments interpreters (such as the Java Virtual Machine), and collects and utilizes resource metrics, code performance metrics, configuration parameters, and transaction, failure and lifecycle events.
Owner:ORACLE INT CORP
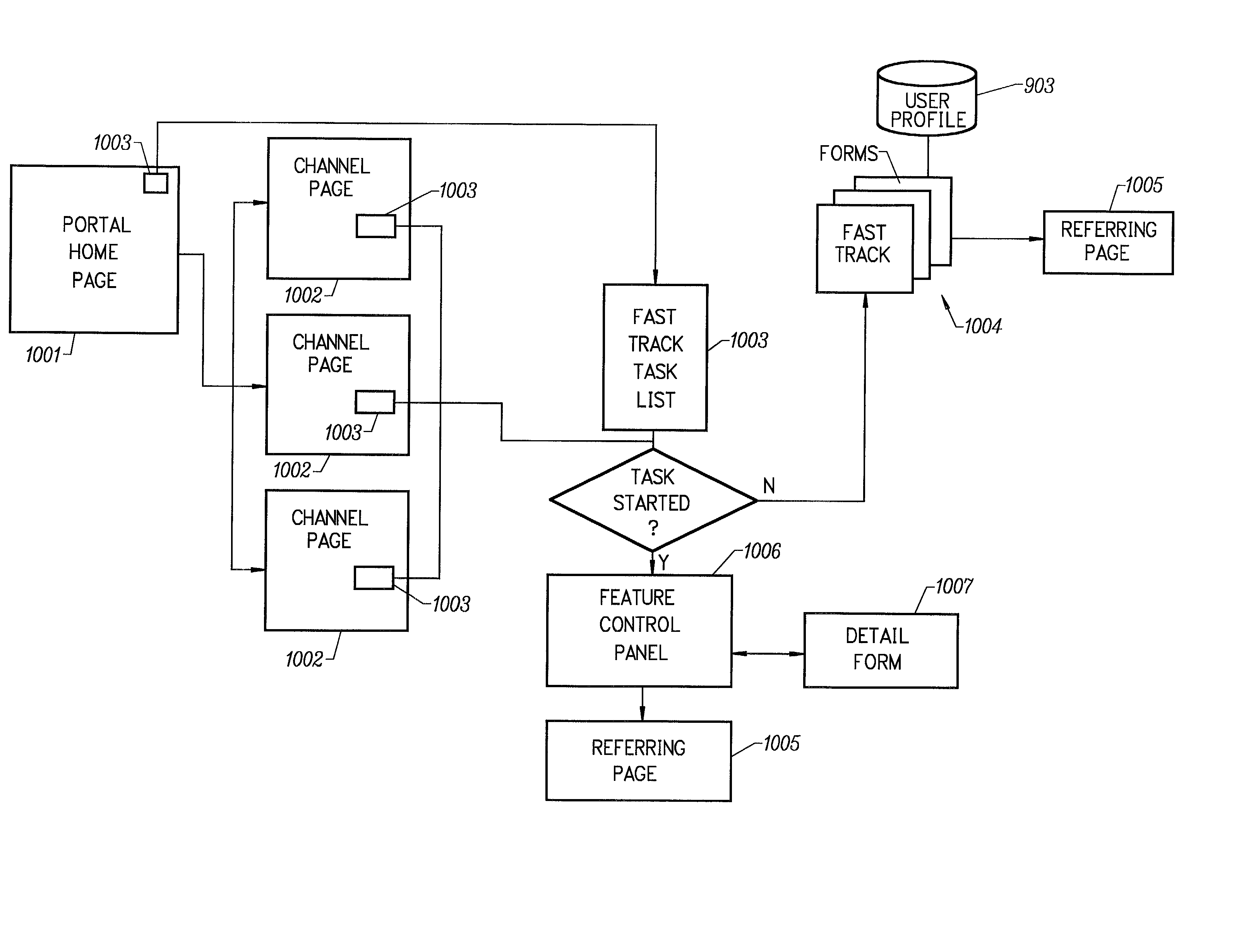
Method and apparatus for multi-vendor powered business portal with intelligent service promotion and user profile gathering
A personalized marketing and registration wizard for businesses is provided. Data is gleaned from a portal profile database to drive one-to-one marketing, registration, upselling, and cross-selling of partner services and centralized portal tools. Using the portal profile database, up-to-date user profile information is collected and shared across multiple vendors. The portal profile database preferably is not accessible by vendors, and each vendor is responsible for storing a desired subset of the user profile in the vendor's own database. In this way, a quasi-intelligent portal for multiple tasks is provided, where each task comprises a business function promoted to an end user in a logical fashion, and such that tasks from various vendors are promoted to the end user in a consistent fashion.
Owner:AOL LLC A DELAWARE LLC
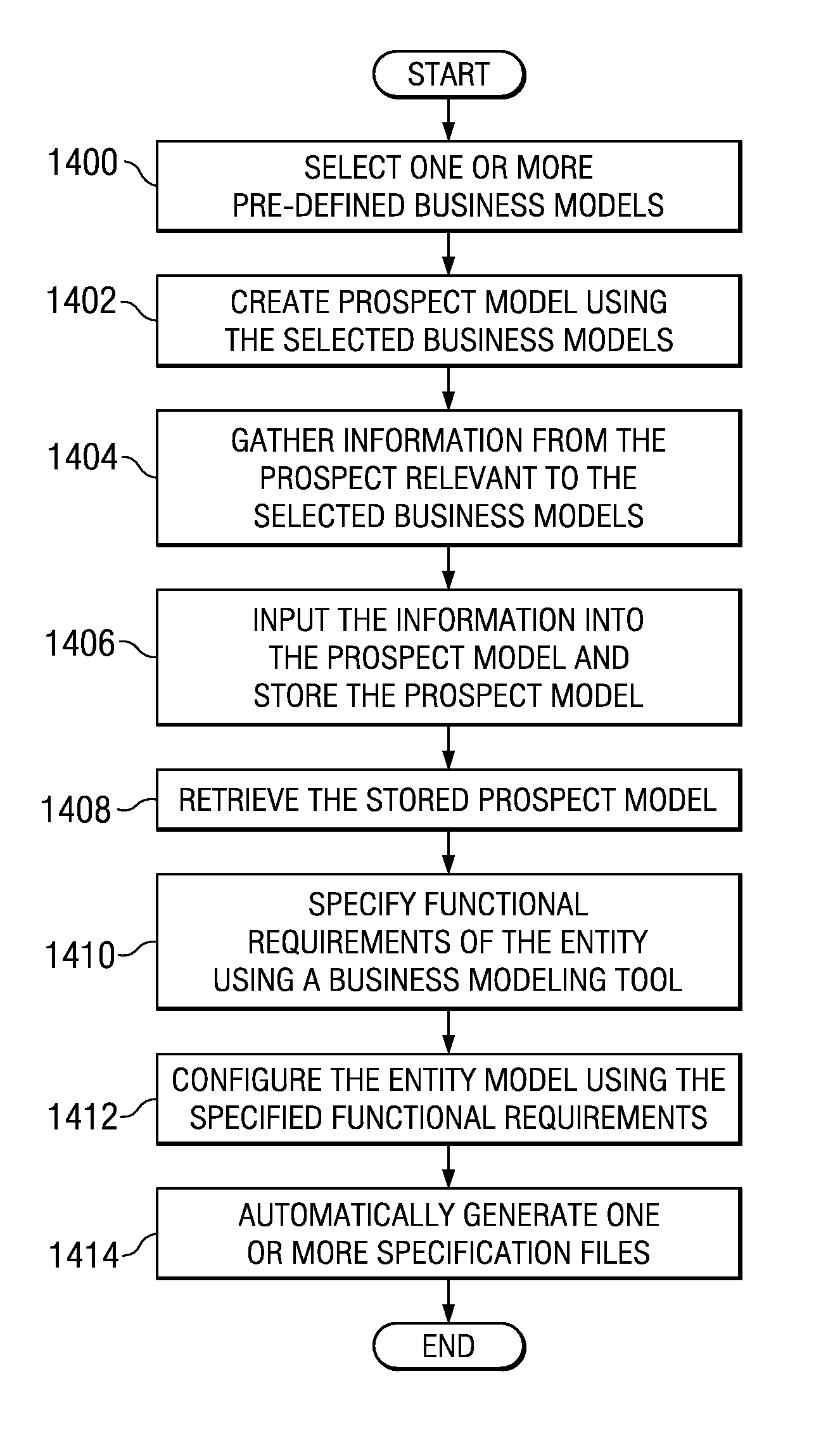
System and method for configuring software using a business modeling tool
InactiveUS7213232B1Disadvantages and reduced eliminatedShorten cycle timeProgram loading/initiatingMemory systemsKnowledge managementBusiness process
A method for configuring software includes communicating a business configuration interface to a user and receiving a selection of a business configuration from the user. In addition, the method includes communicating a business topology interface to the user that includes one or more functional elements associated with the selected business configuration. The method also includes receiving a selection of a functional element, which includes one or more business functions, from the user. In addition the method includes communicating a functional element interface to the user, the functional element interface including one or more business functions associated with the selected functional element, and receiving a selection of a business function from the user, the business function having one or more associated business processes. Furthermore, the method includes communicating one or more business process interfaces to the user and receiving software configuration information from the user via the one or more business process interfaces.
Owner:JDA SOFTWARE GROUP
Java server page (JSP) template-based intelligent table system capable of being defined freely and generating method
InactiveCN102135990AQuick buildTight and seamless integrationSpecial data processing applicationsExtensibilityData modeling
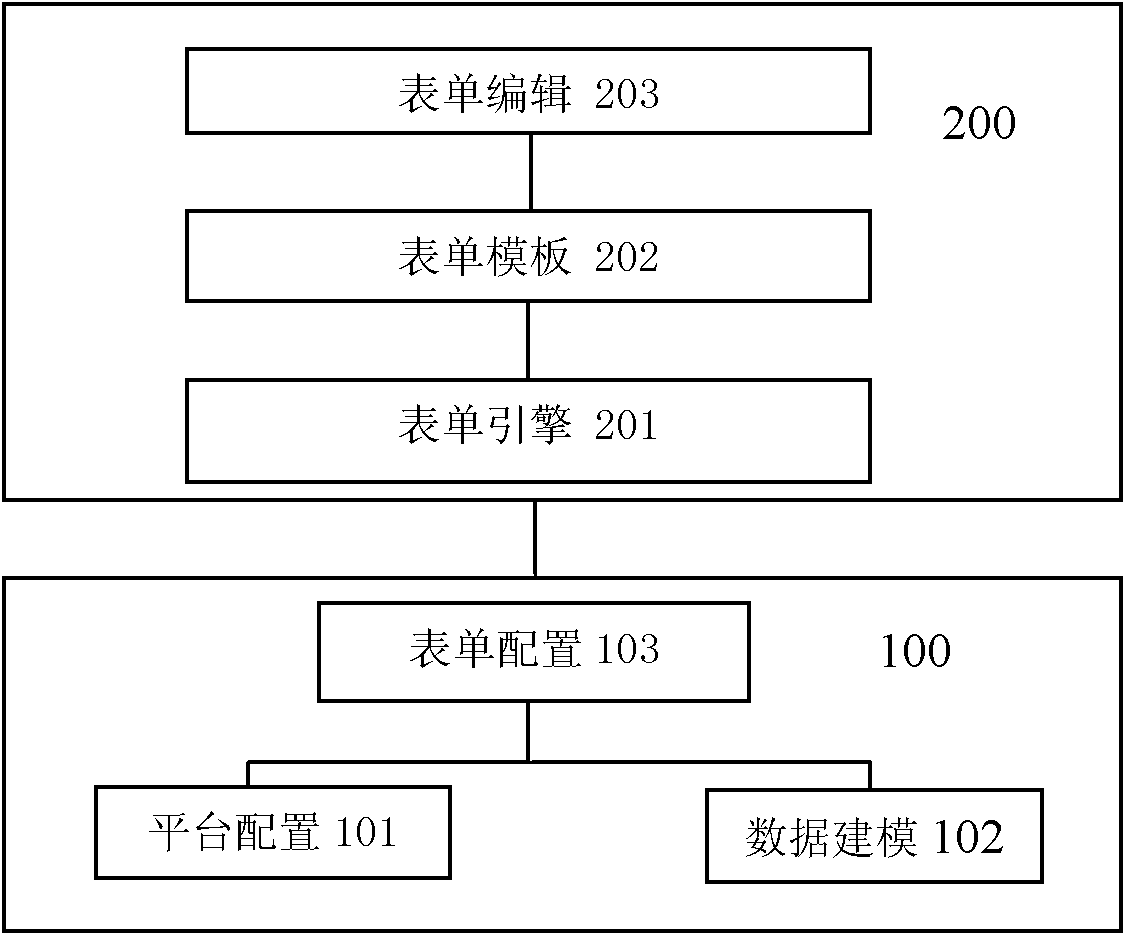
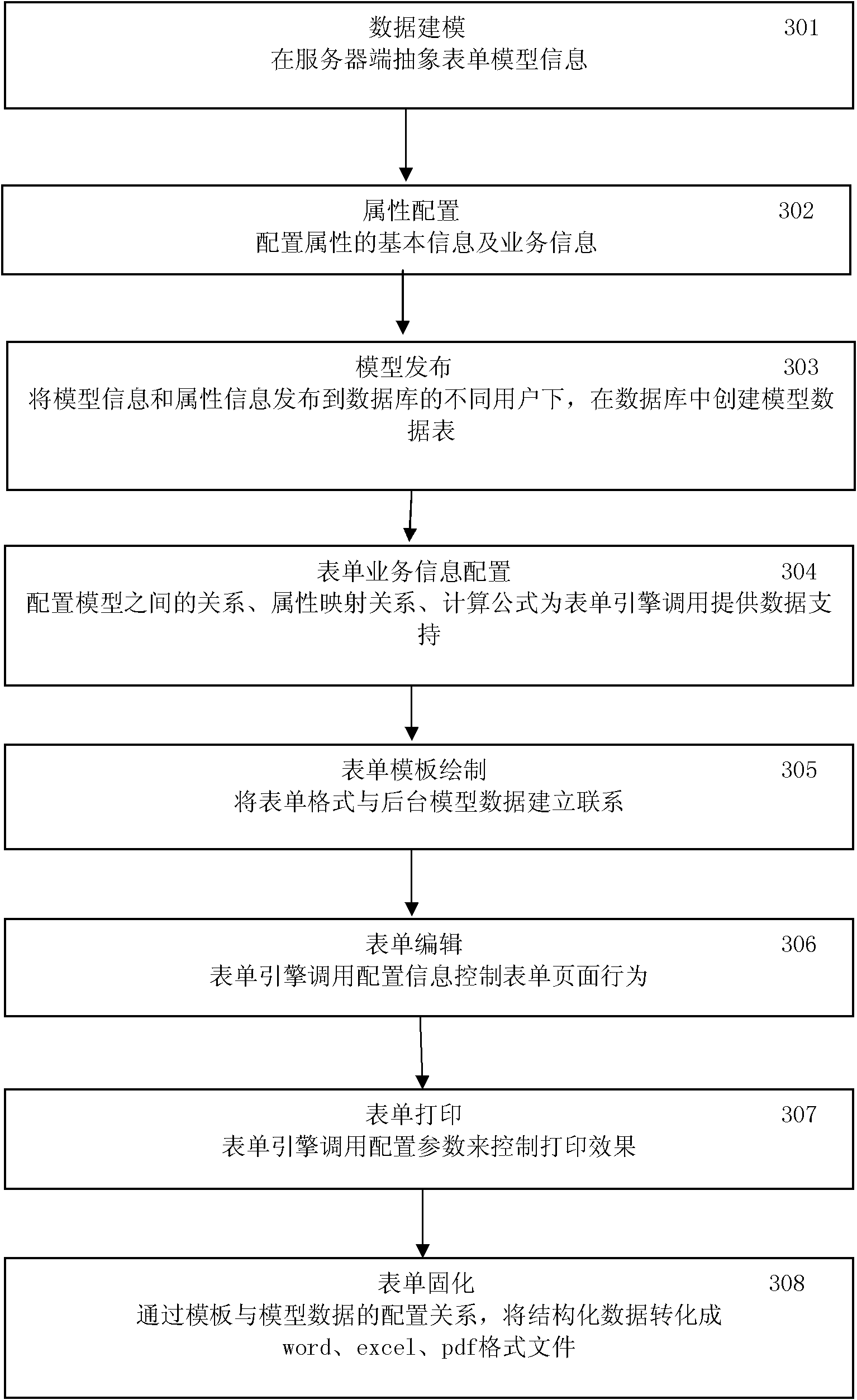
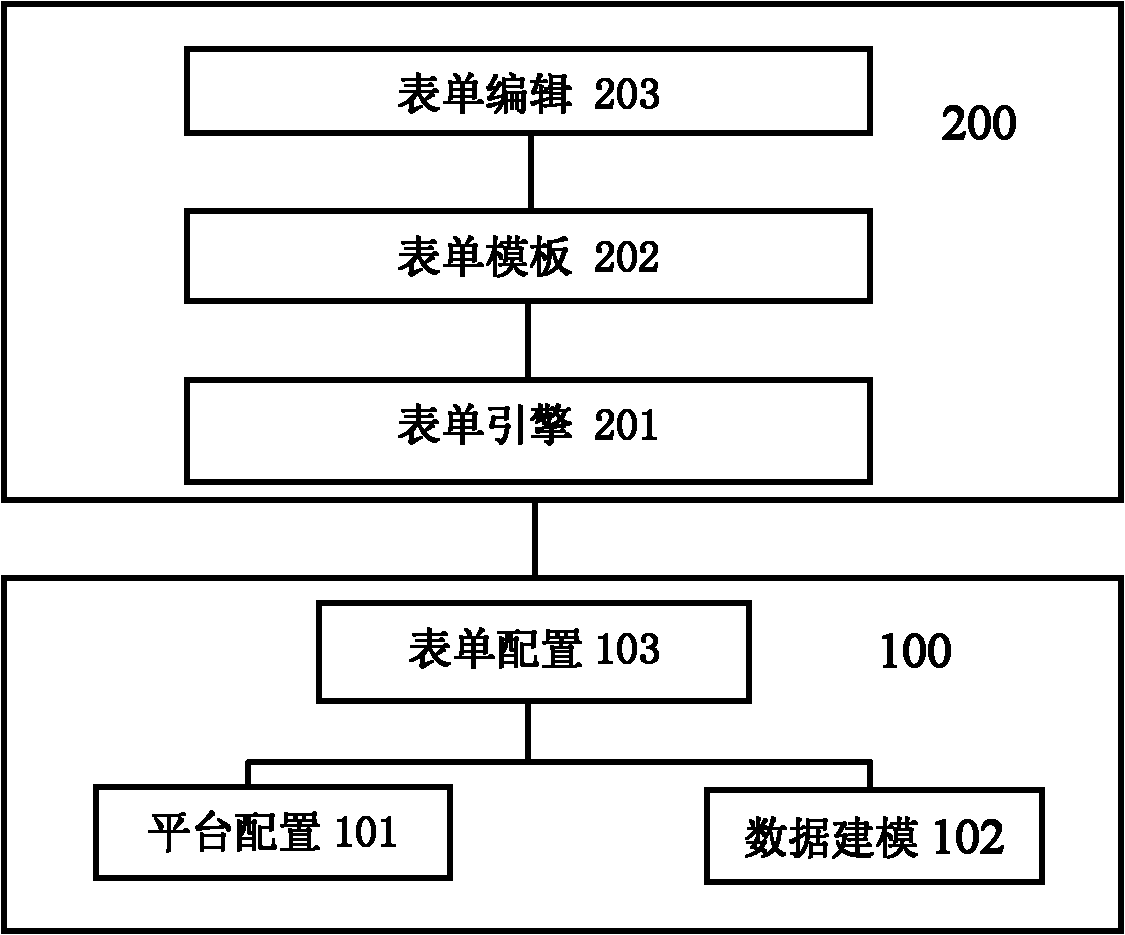
The invention relates to a java server page (JSP) template-based intelligent table system capable of being defined freely, which controls a table through system configuration under the driving of a table engine to complete various service functions on the basis of data modeling. The (JSP) template-based intelligent table system provides implementing mechanisms of data modeling, service configuration, table drawing, table editing and the like and can realize user-oriented free customization of the table, and a user can realize most service logics by configuring various parameters through pages, thereby greatly improving the flexibility and extensibility of the intelligent table system. In the system, the JSP file is used as a template of the table, and various configuration information controlling the table and the table template are connected through the table engine, thus that the effect that the table service comes into effect as long as configured can be realized. In the part of table editing, the system can realize automatic calculation of table attribute, addition and delete of sub-table rows, secondary authority control of the table, service implementation and control of the table and the like.
Owner:北京神舟航天软件技术股份有限公司
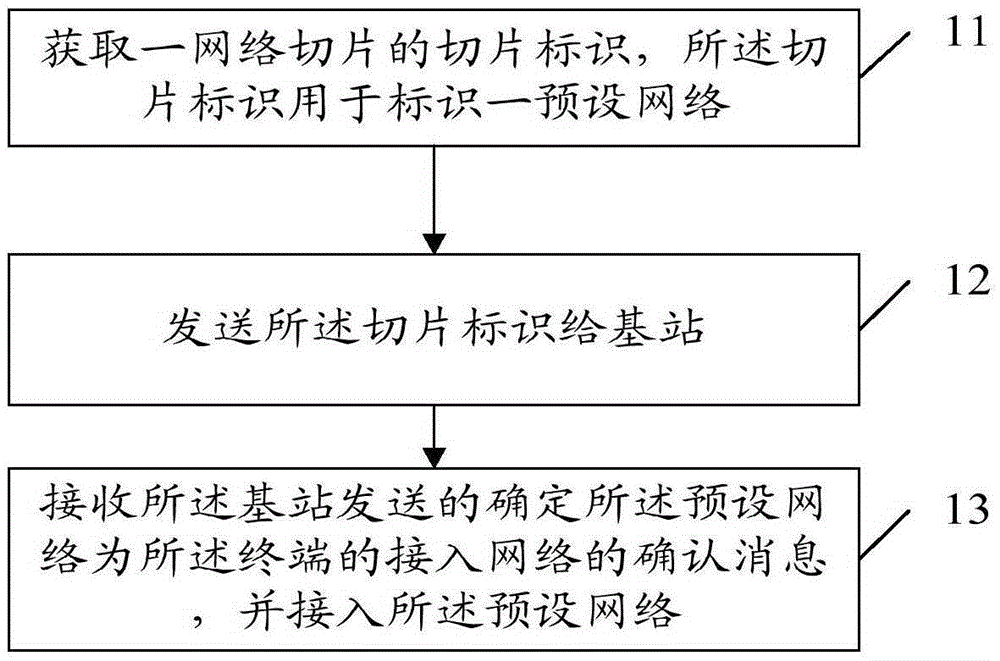
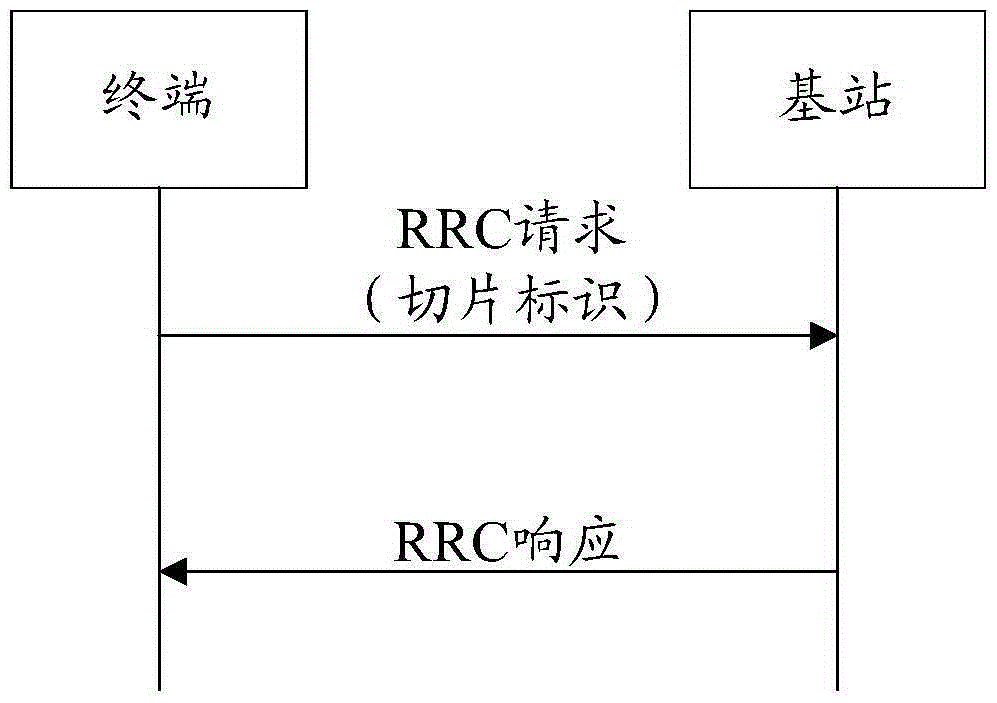
Network slice processing method, access network selecting method and apparatus
The invention provides a network slice processing method and an access network selecting method and apparatus. The network slice processing method applied to a terminal side includes the steps of obtaining a slicing identifier of a network slice, the slicing identifier marking a preset network, sending the slicing identifier to a base station, receiving a confirmation message sent by the base station for confirming that the preset network is the access network of the terminal, and accessing the preset network. Adding, deleting and changing can be flexibly conducted for the network slice in the embodiment, thereby satisfying the mobile network demand in diversity in the future. A terminal can flexibly select network business based on the network slicing identifier without specifically configuring the port of a network slice. Different network business functions correspond to different network slices, thereby preventing mutual influence of various businesses. The network stability is higher.
Owner:CHINA MOBILE COMM GRP CO LTD
Merchandising system method, and program product utilizing an intermittent network connection
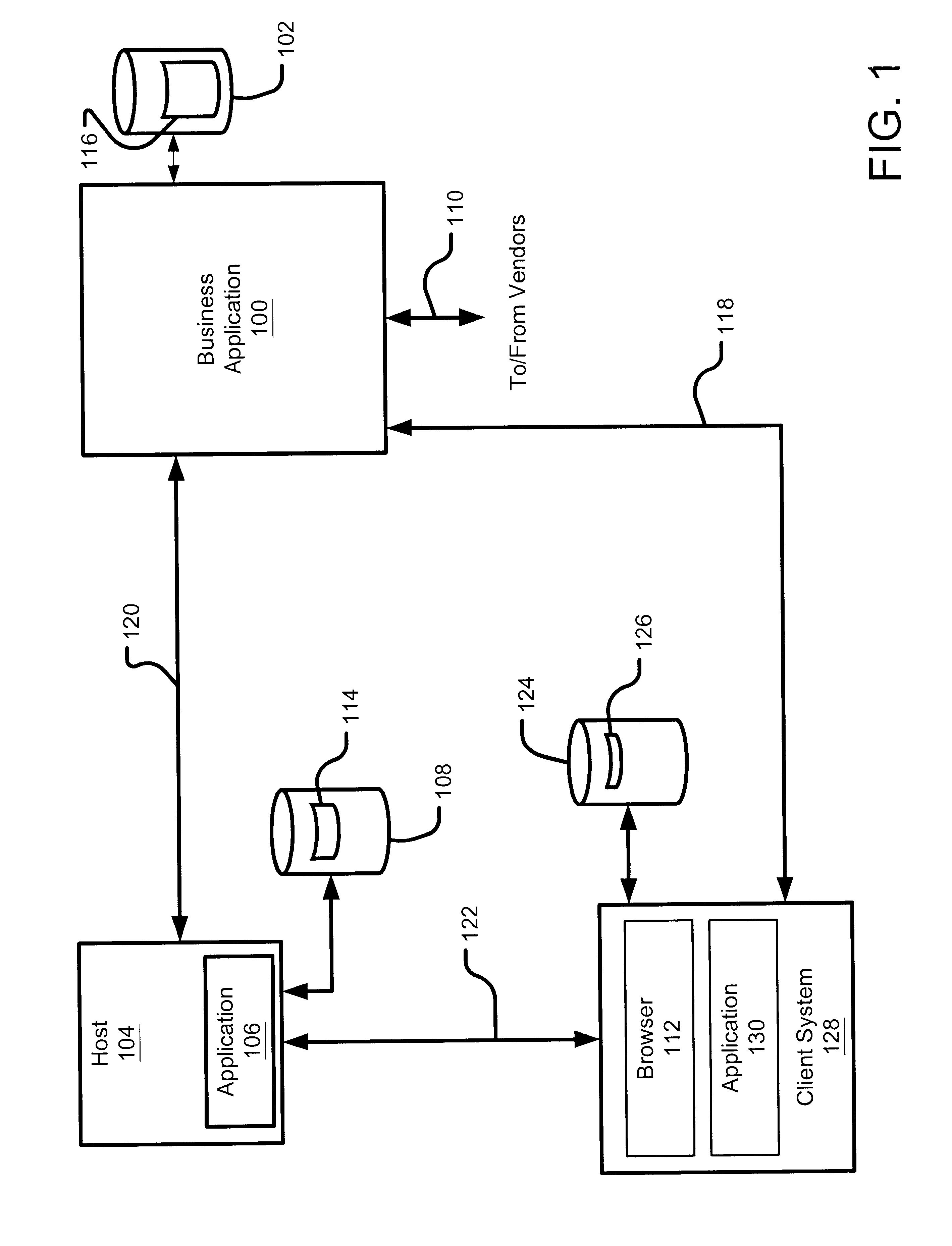
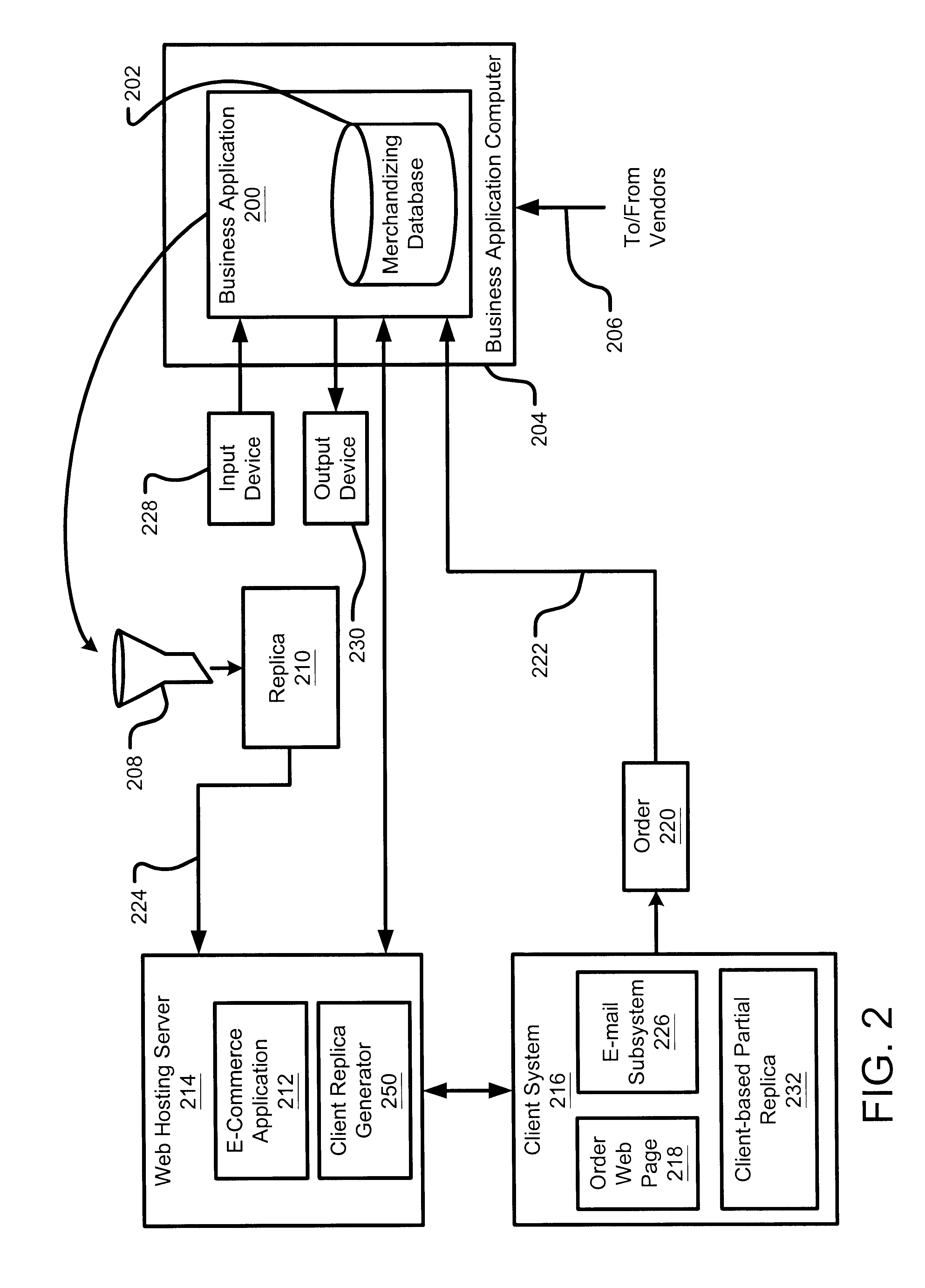
InactiveUS6901380B1Facilitate rapid synchronizationShorten the timeBuying/selling/leasing transactionsSpecial data processing applicationsNetwork connectionApplication software
A business application integrates a company's internal business systems with an e-commerce web site, so that company personnel can manage their business with a business application that seamlessly exports relevant, up-to-date data to a web site designed to interact with customers across the Web. The business application provides business functions for manipulating merchandising data stored in a merchandising database. In addition, to accommodate an intermittent connection to the Internet or otherwise to the web hosting server, the business application supports the generation of a replica, from the merchandising database, that can be exported to a web hosting server. A web application executing at the web hosting server generates web pages based on merchandising data stored in the partial replica. The customer can provide feedback, possibly representing purchase orders or customer information changes, for example, that can be automatically entered into the company's business system. Alternatively, the customer can download a client replica, generated from the partial replica at the web hosting server, for use during periods of disconnection from the web hosting server. Thereafter, the client replica and the partial replica can be synchronized to update each other with modified data. Furthermore, the partial replica and the merchandising database can also be synchronized.
Owner:DATAFORCE
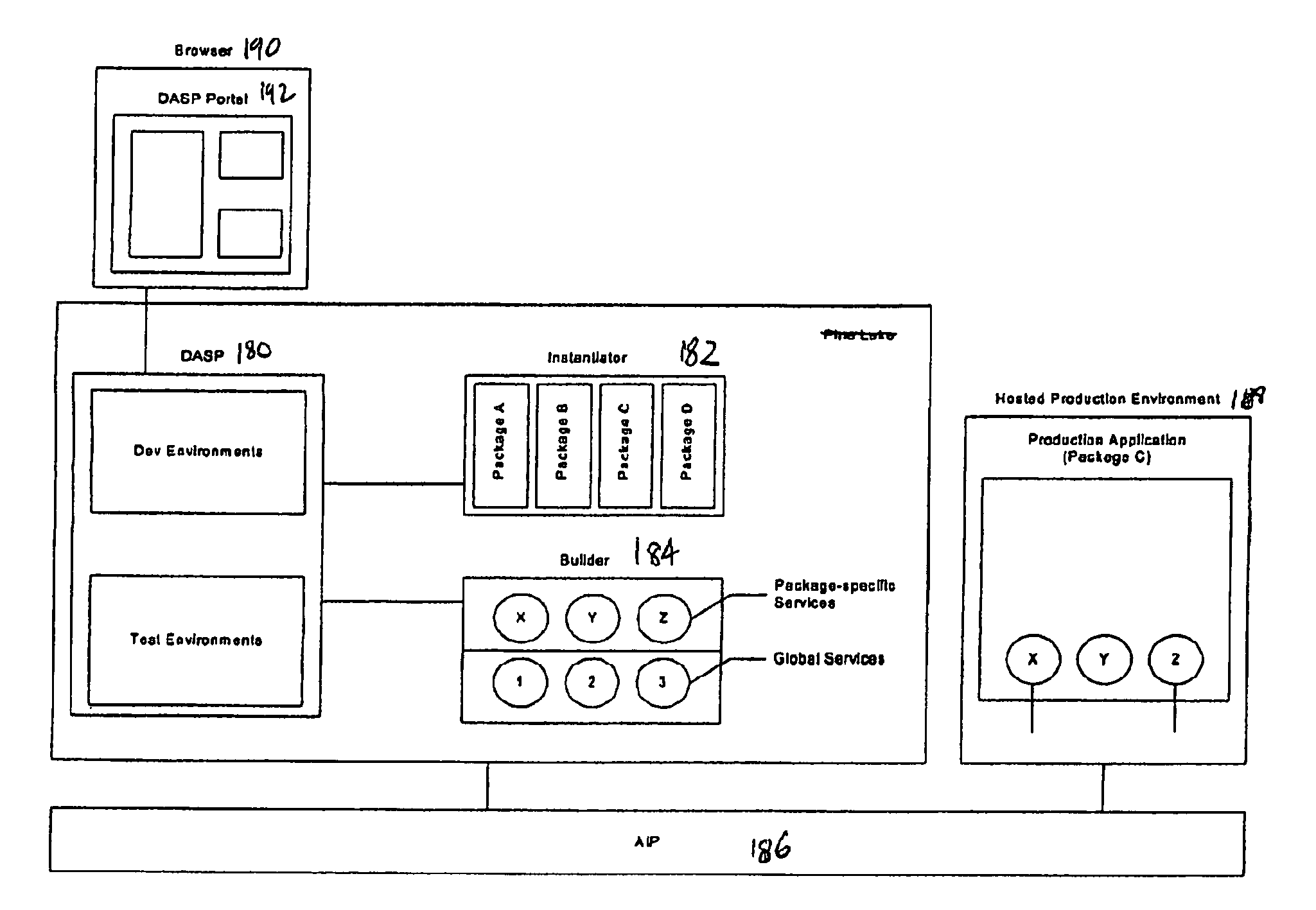
Distributed development environment for building internet applications by developers at remote locations
ActiveUS7870535B2Easy to createImprove skillsSoftware testing/debuggingSoftware designWeb serviceThe Internet
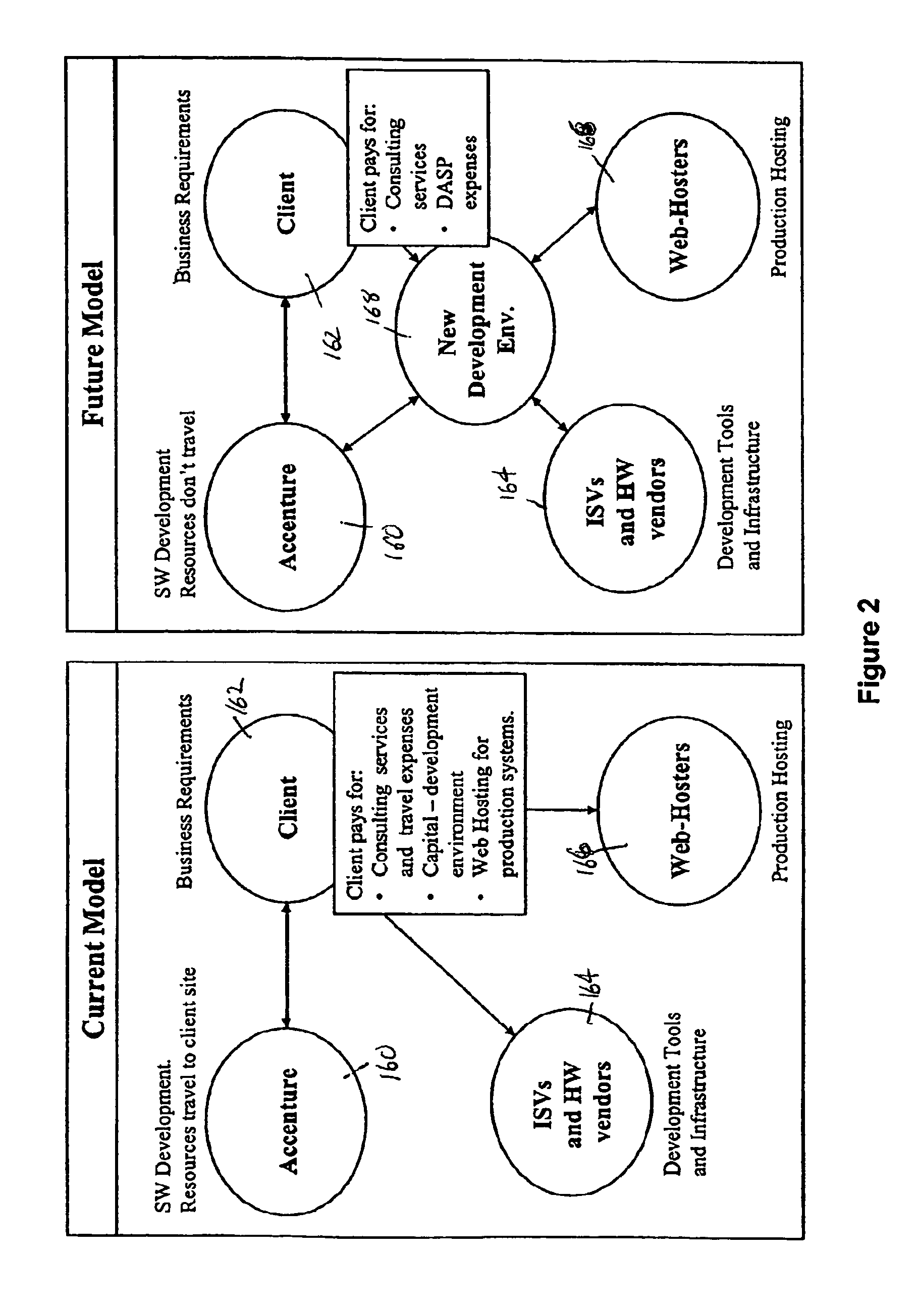
A system and a method for developing Internet-hosted business applications composed of web services and software for use in such environments where applications and application components interoperate to perform requested business functions. The system and method of the present invention utilize a software development application services provider module (DASP), an Instantiatior module, a Builder module, an Applications Service Provider (ASP) Infrastructure Platform (AIP) module, and a hosted production environment module. The system and method of the present invention seeks to maximize the use of prior work to eliminate repetition and reduce development cost and development time. With each new project the library and experience increases. The system and method of the present invention can use developers and testers situated in diverse locations so that a larger pool of skilled people can be employed, the work can be done around the clock by using people all over the globe, and the costs can be reduced by directing work to people in countries with lower labor rates. The system and method of the present invention increases efficiencies and reduces costs to all parties by partnering the developers with third parties who are brought in at the beginning of development.
Owner:ACCENTURE GLOBAL SERVICES LTD
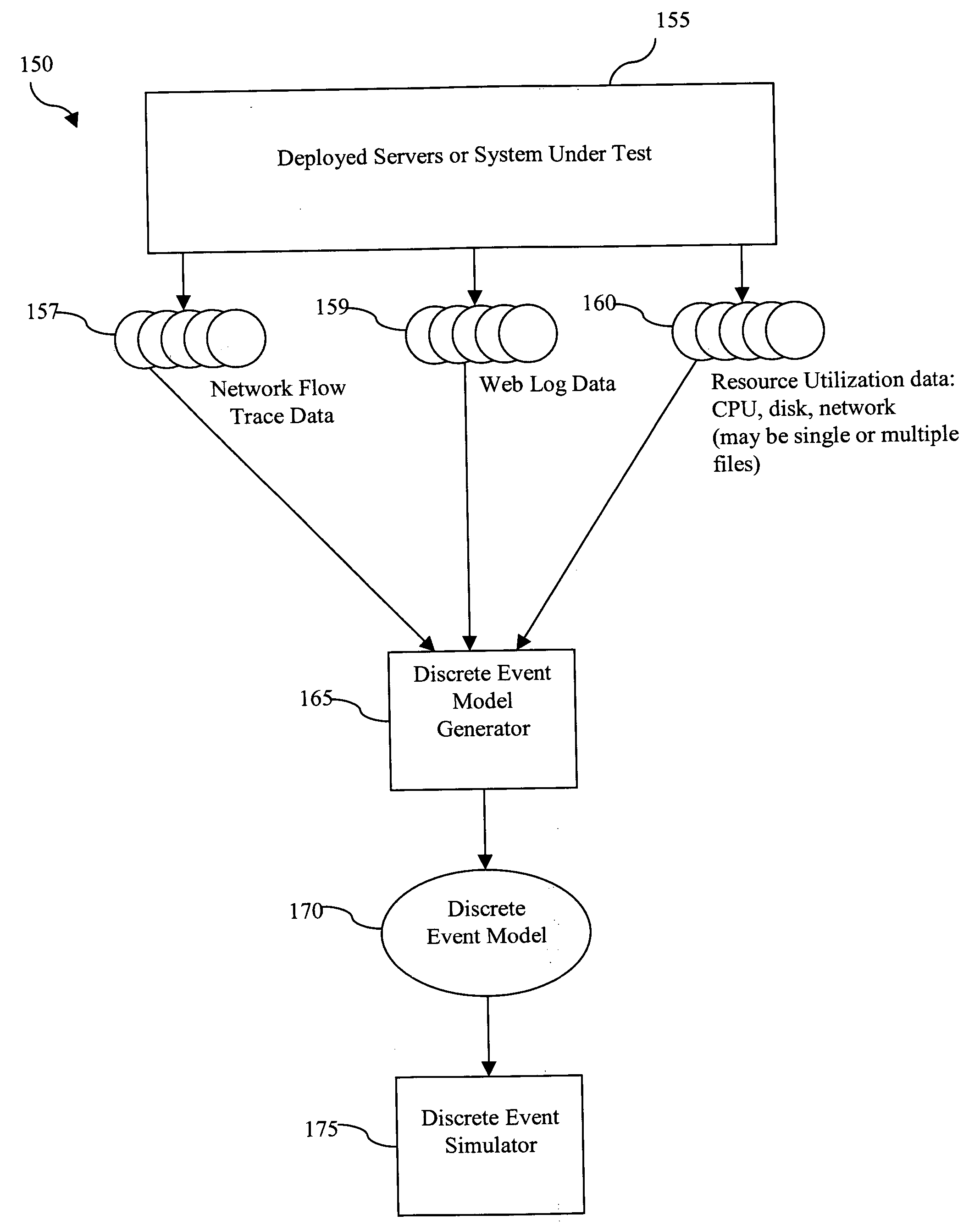
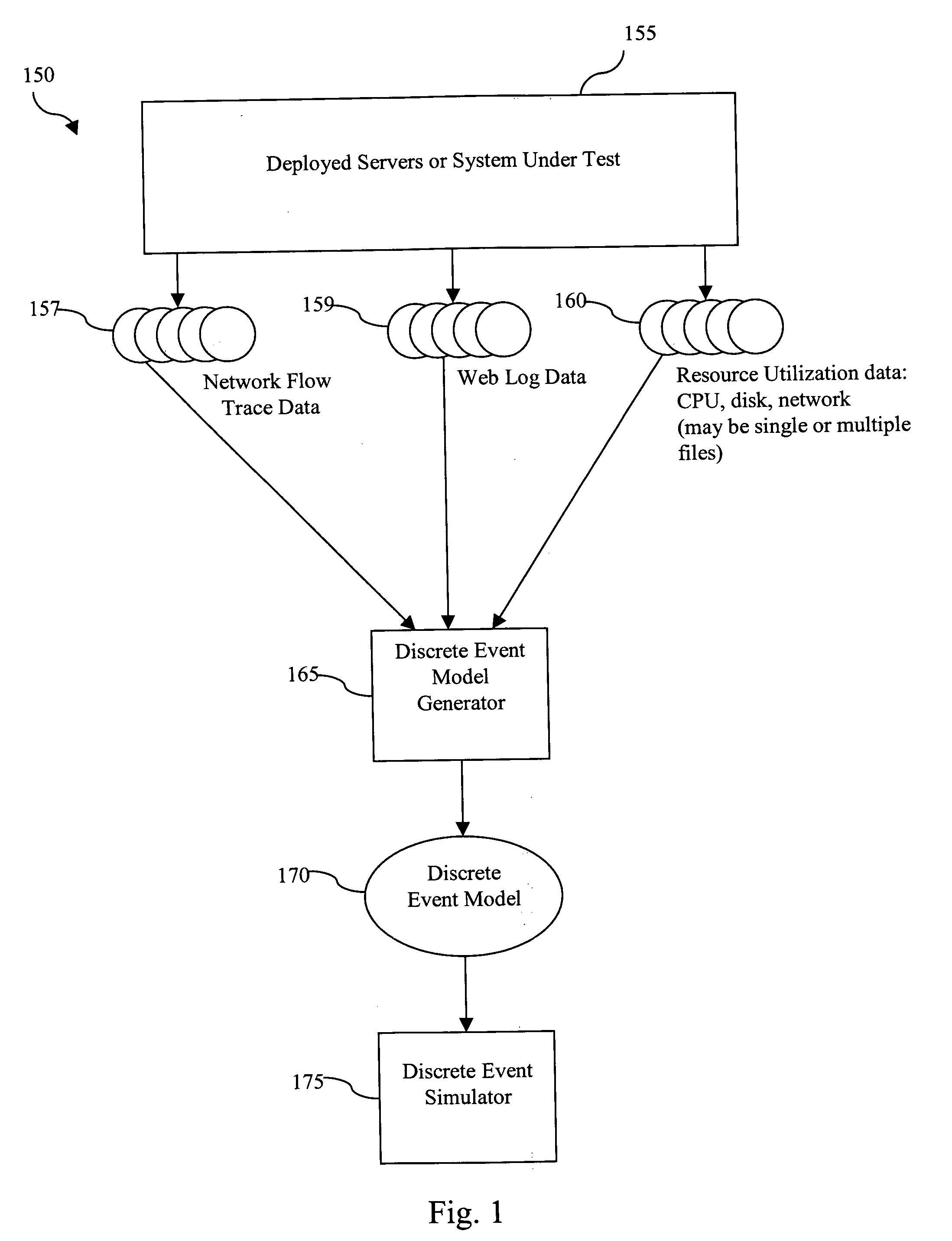
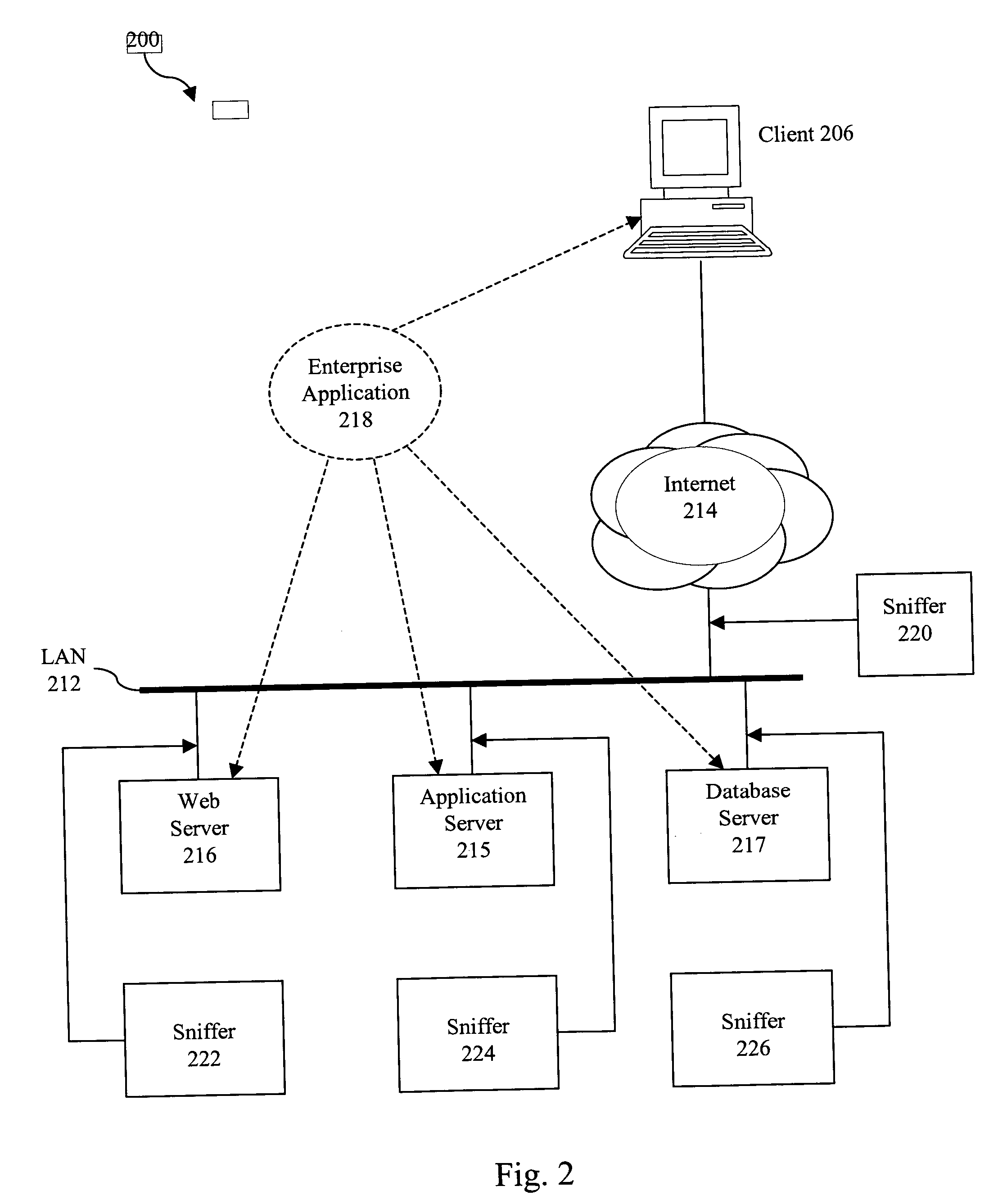
Method for building enterprise scalability models from load test and trace test data
A method is disclosed that preparing a discrete event simulation model of a production network is provided including a client and a plurality of servers connected by a network comprising the steps of initiating a single business function trace test on the production network; gathering network from trace data from the network; deriving a transaction summary from the network flow trace data; initiating a single business function load test on the production network; gathering resource data from the plurality of servers; normalizing the resource data; gathering web log data from at least one server from the plurality of servers; calculating a number of business functions running on the production network; calculating a consumption of resources used by the plurality of servers; calculating a business function cost associated with the consumption of resources; creating a business function profile from the transaction summary and the business function cost; and building a discrete event simulation model from the business function profile.
Owner:HYPERFORMIX
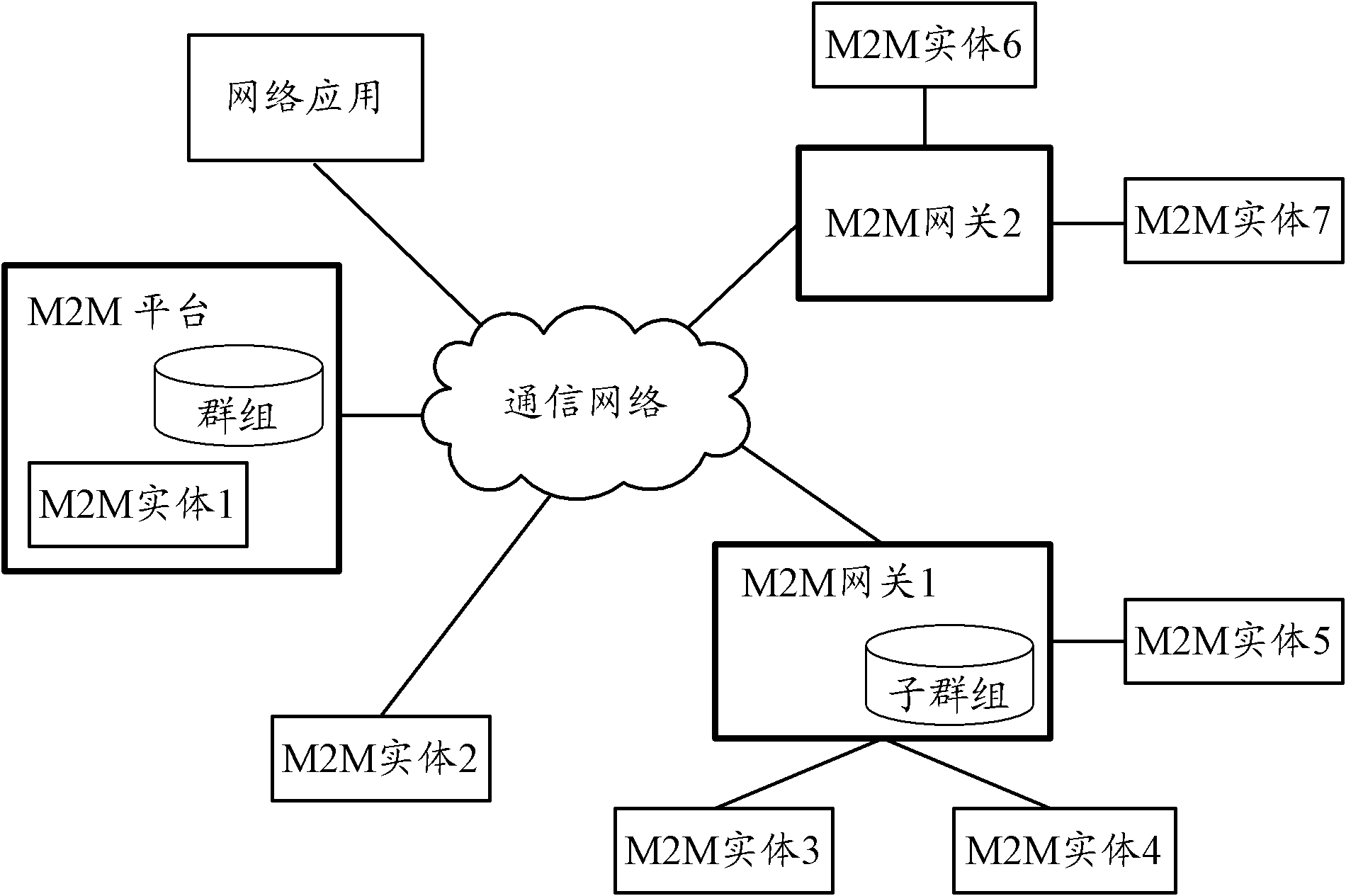
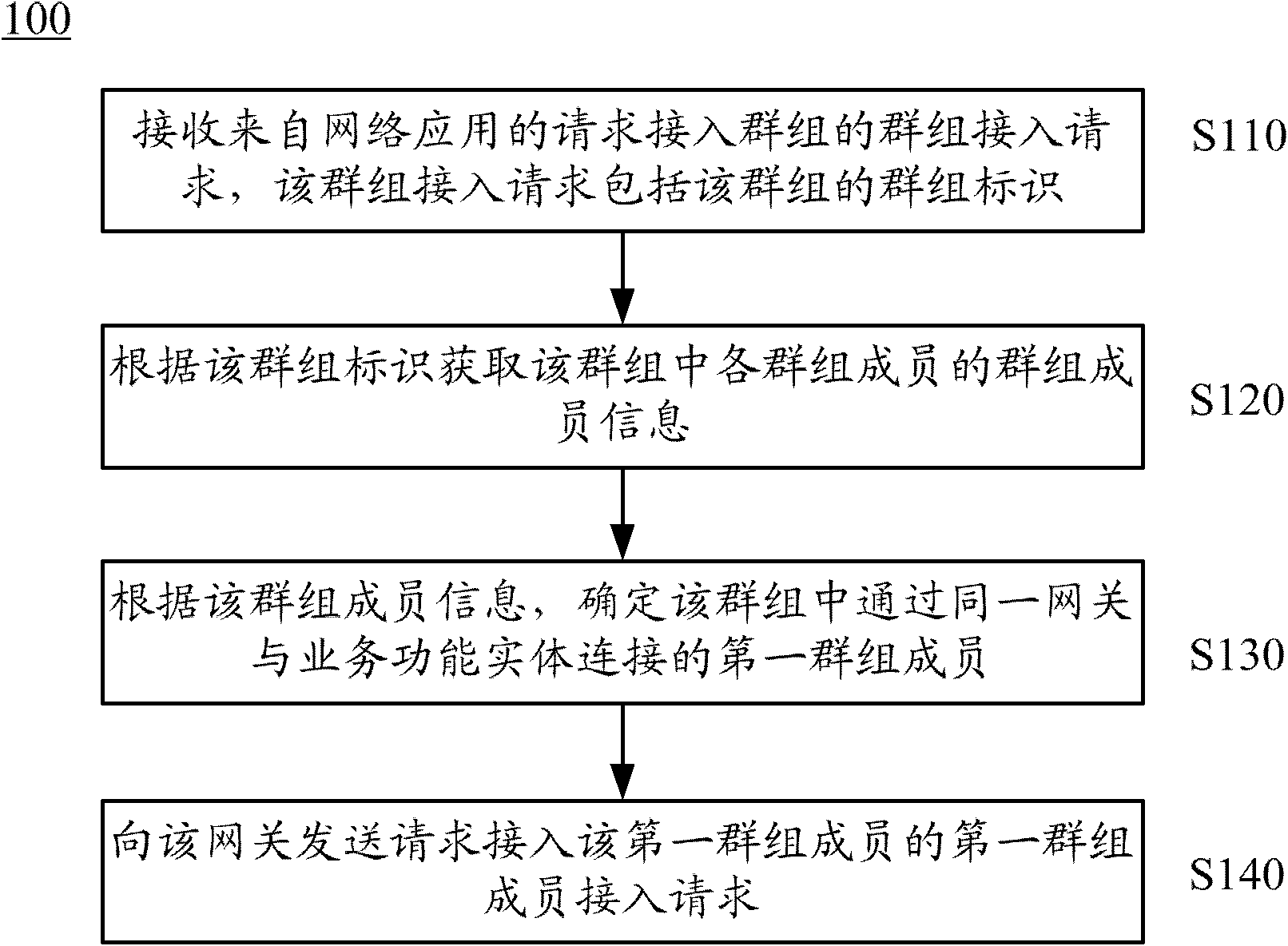
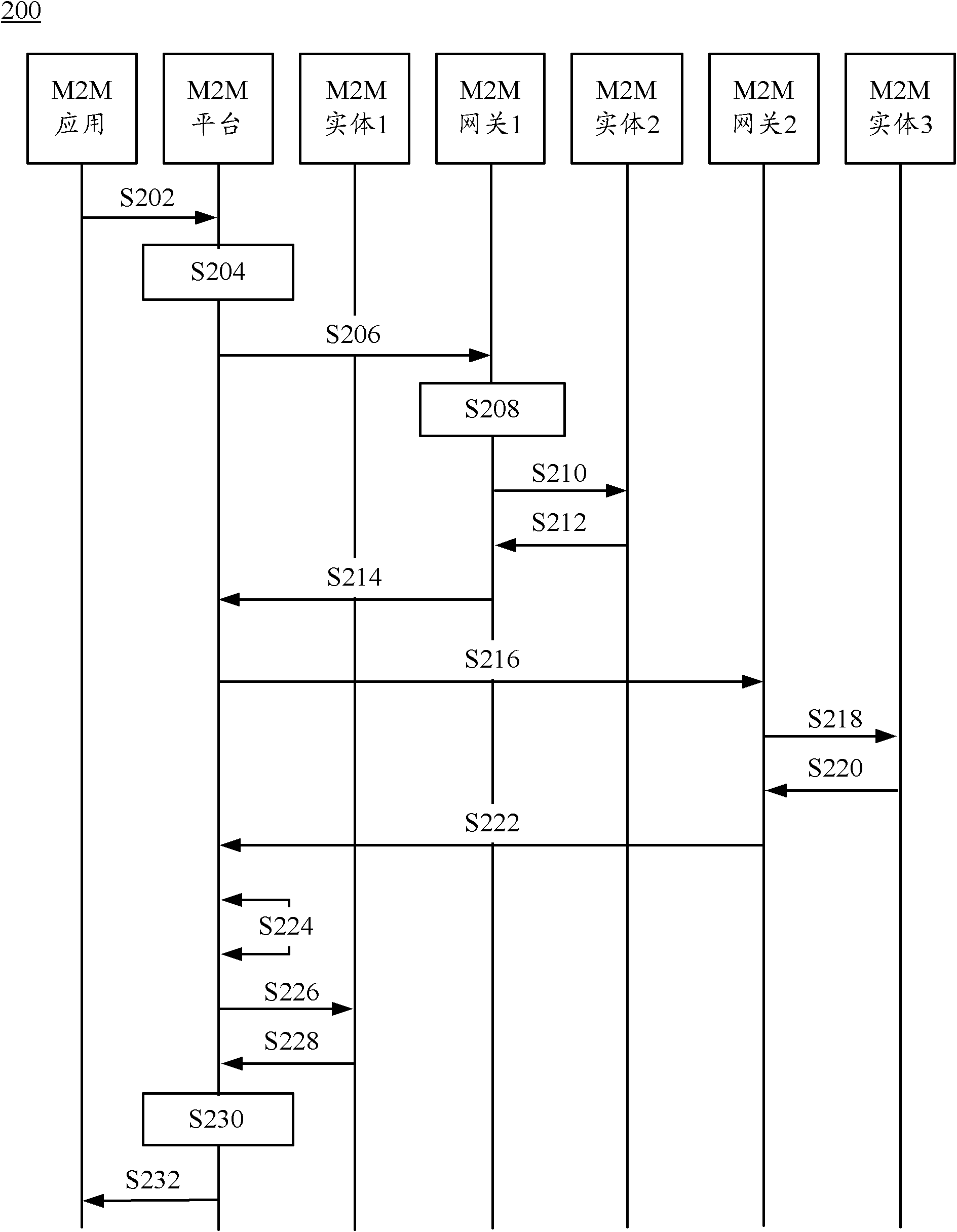
Group communication method and device
ActiveCN102130773AImprove efficiencyReduce overheadSpecial service provision for substationBroadcast service distributionTelecommunicationsNetwork application
The invention discloses a group communication method and device. The method comprises the following steps of: receiving a group access request for accessing a group from a network application, wherein the group access request comprises a group identifier of the group; acquiring the group member information of each group member in the group according to the group identifier; determining first group members connected with a service functional entity through the same gateway according to the group member information; and transmitting a first group member access request for accessing the first group members to the gateway. The device comprises the service functional entity and the gateway, wherein the service functional entity comprises a first receiving module, an acquiring module, a first determining module and a first transmitting module. Due to the adoption of the method and the service functional entity, signaling overhead during group communication can be reduced and the efficiency of group communication is increased.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
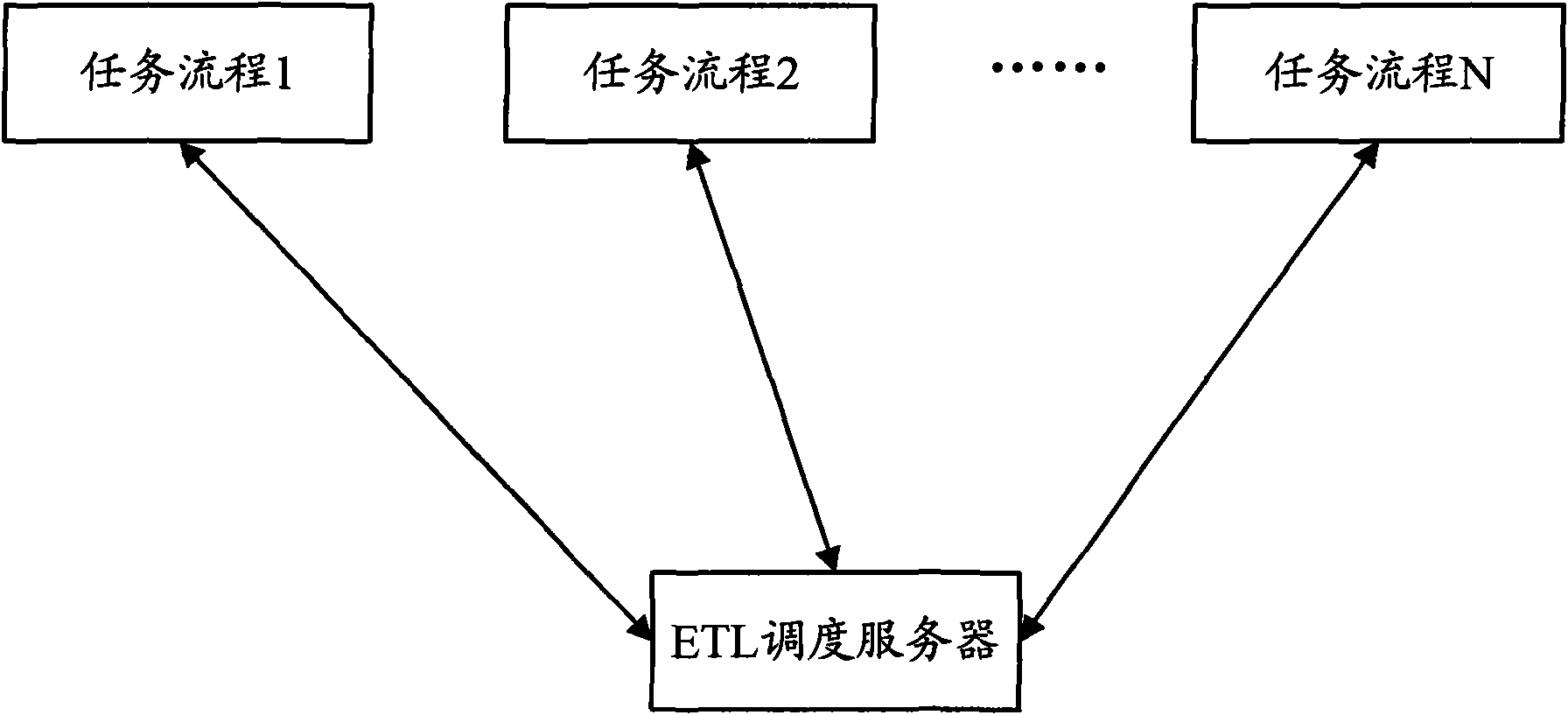
Method and apparatus for implementing ETL scheduling
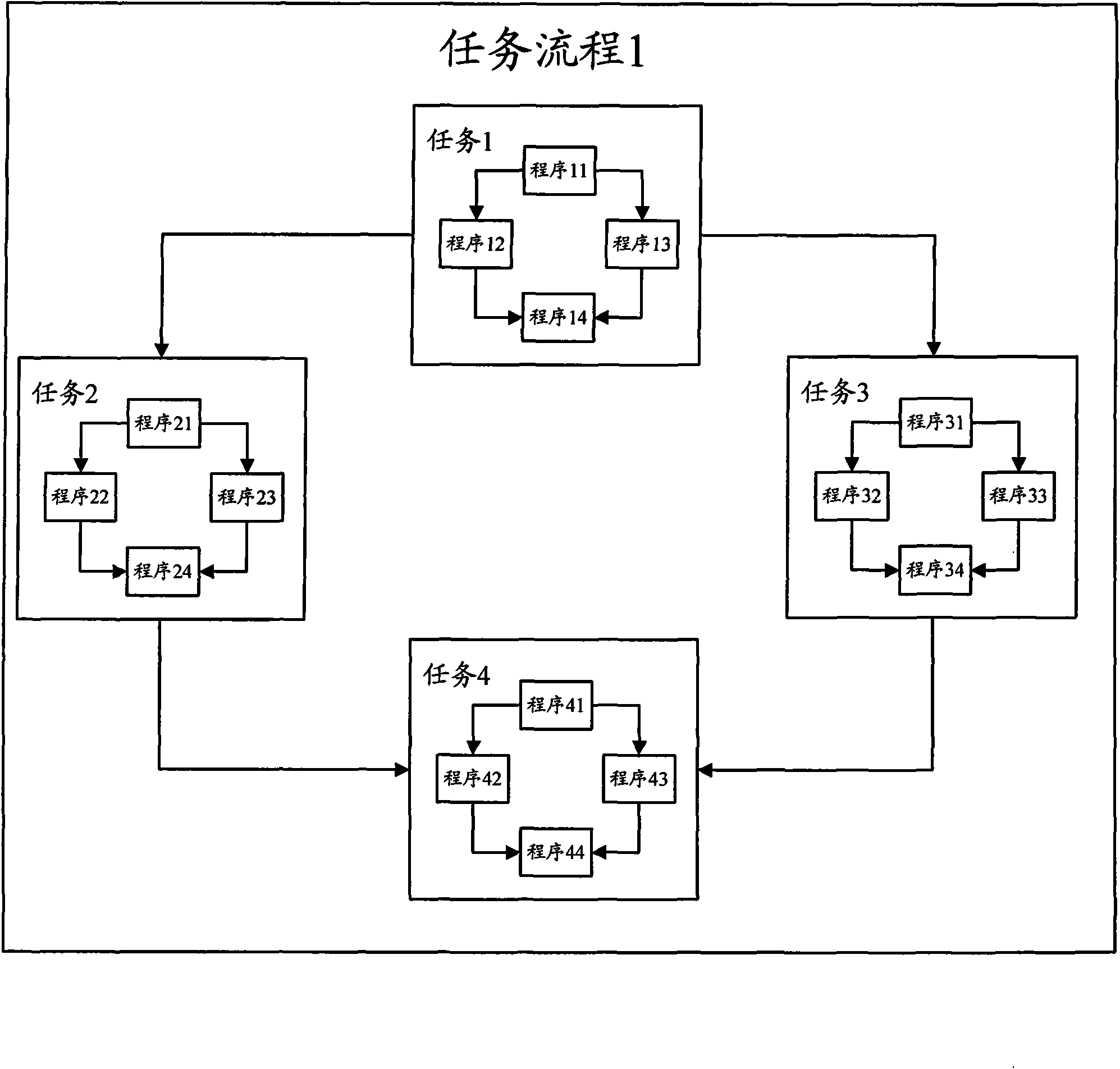
ActiveCN101567013AImprove execution efficiencyClear business logicSpecial data processing applicationsMutual dependencyDistributed computing
The invention discloses a method for scheduling ETL, comprising: determining the triggering mode, operation sequence and mutual dependency relationship of each subtask flow included in the task flow based on preset configuration file aiming at an optional task flow when implementing plural task flows included in the ETL scheduling; triggering corresponding subtask flows in turn according to the set triggering mode and implementing the triggered subtask flow according to set sequence, wherein after determining that at least a subtask flow is implemented, starting to implement other subtask flows depending on at least a subtask flow and other triggered subtasks based on the dependency relationship between subtask flows. Thus, subtask flow in each task flow has clear service logic and service function so as to effectively enhance the implementing efficiency of the ETL scheduling flow. The invention also discloses an apparatus for implementing ETL scheduling.
Owner:ADVANCED NEW TECH CO LTD
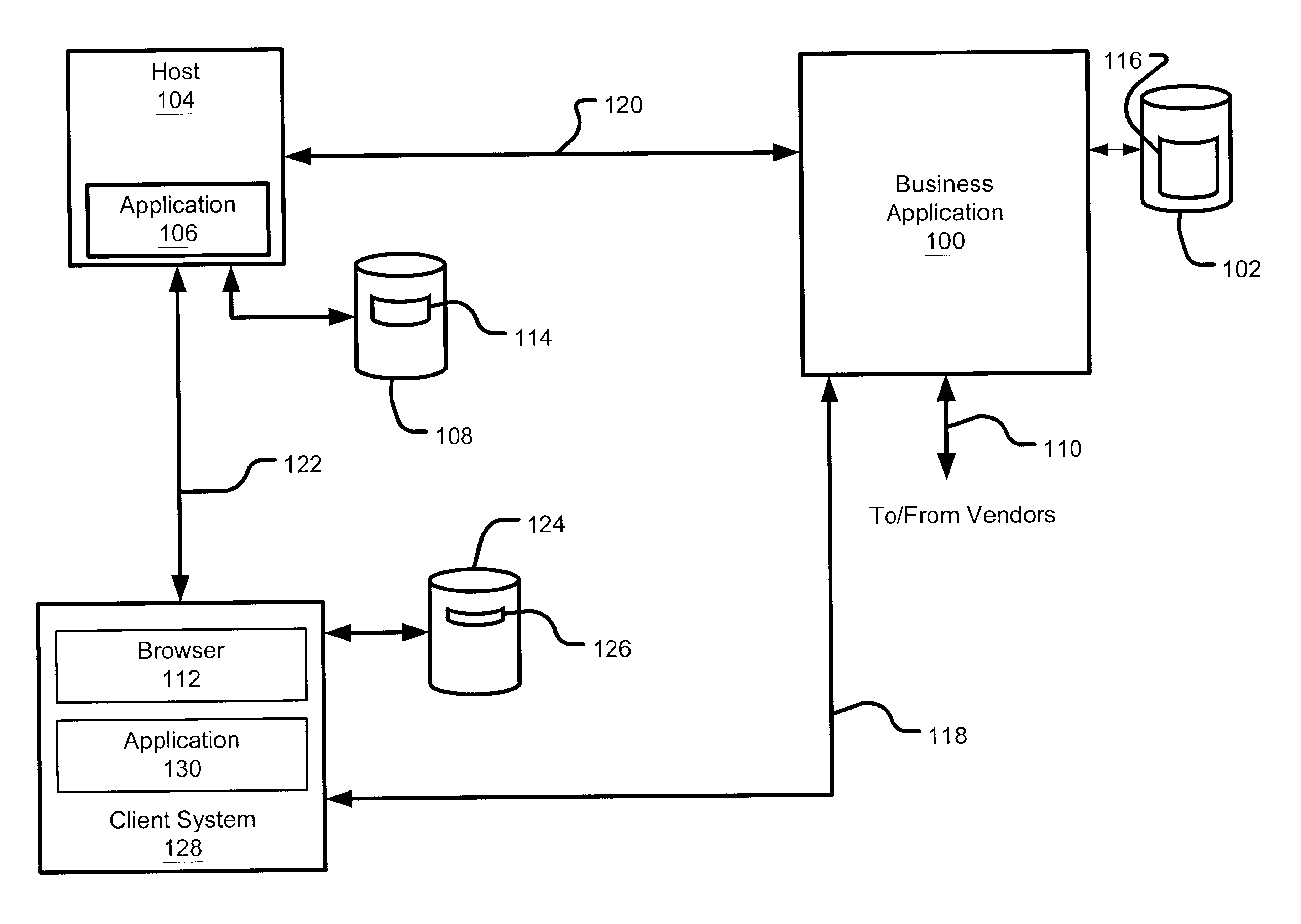
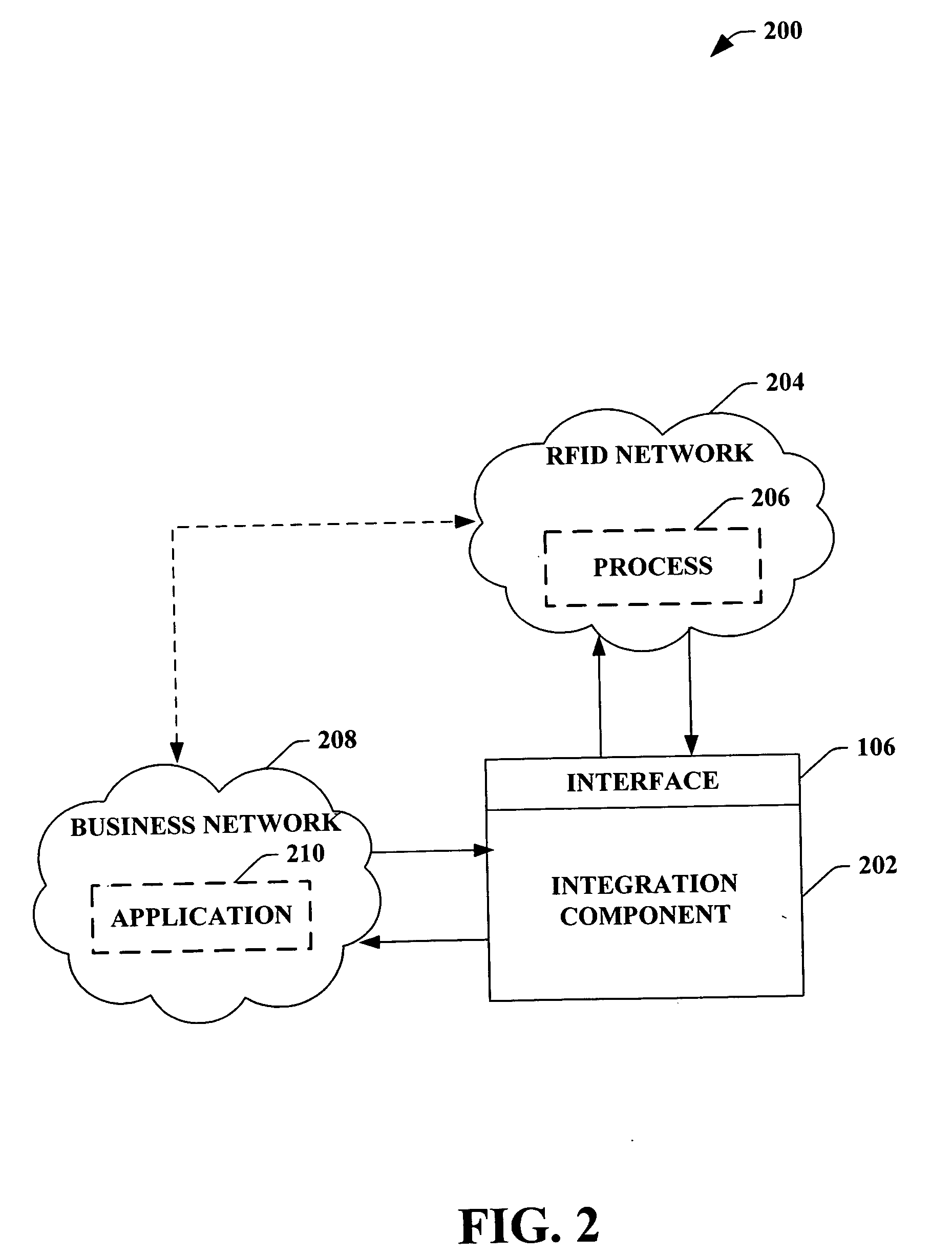
RFID enabled information systems utiling a business application
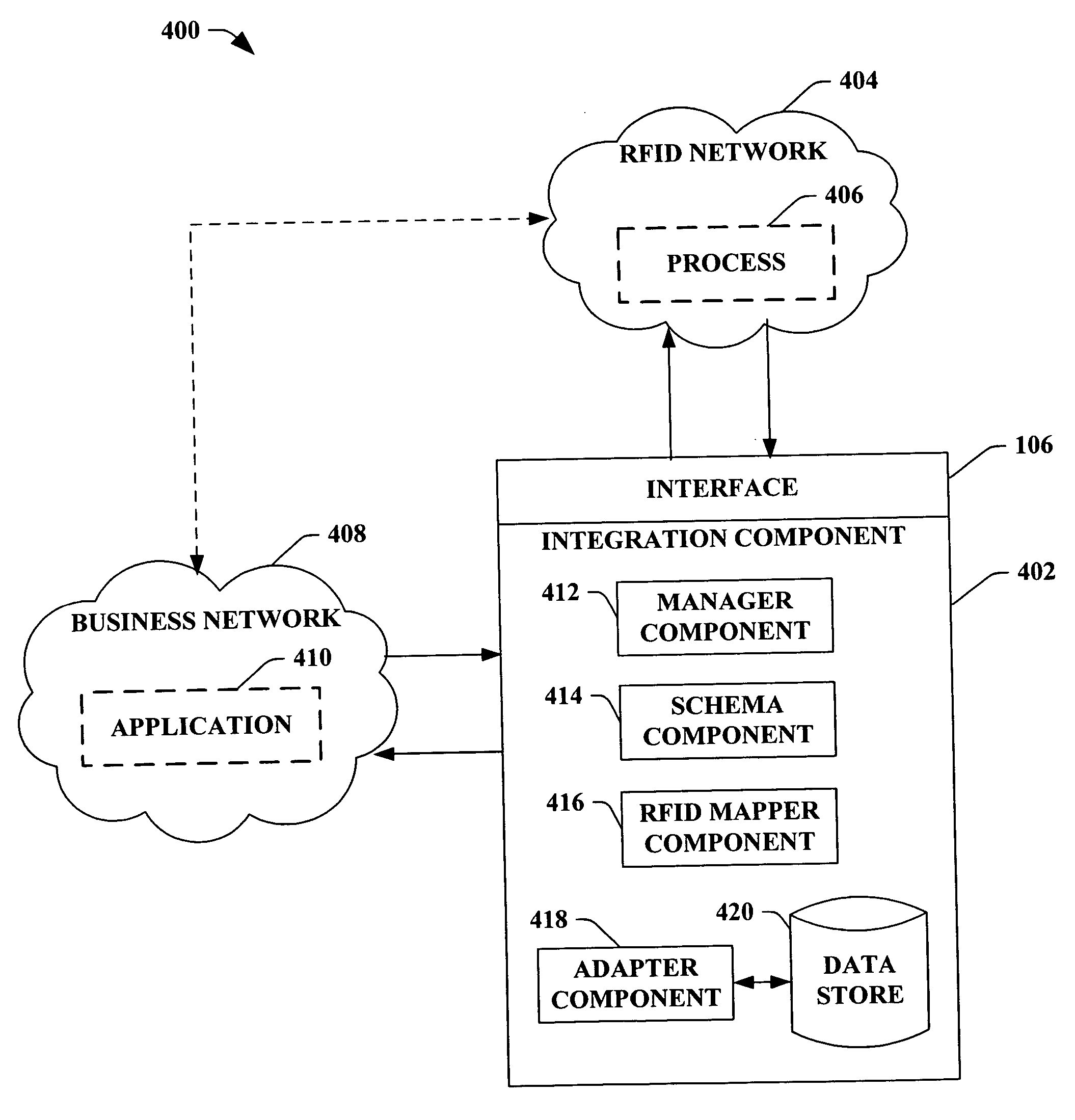
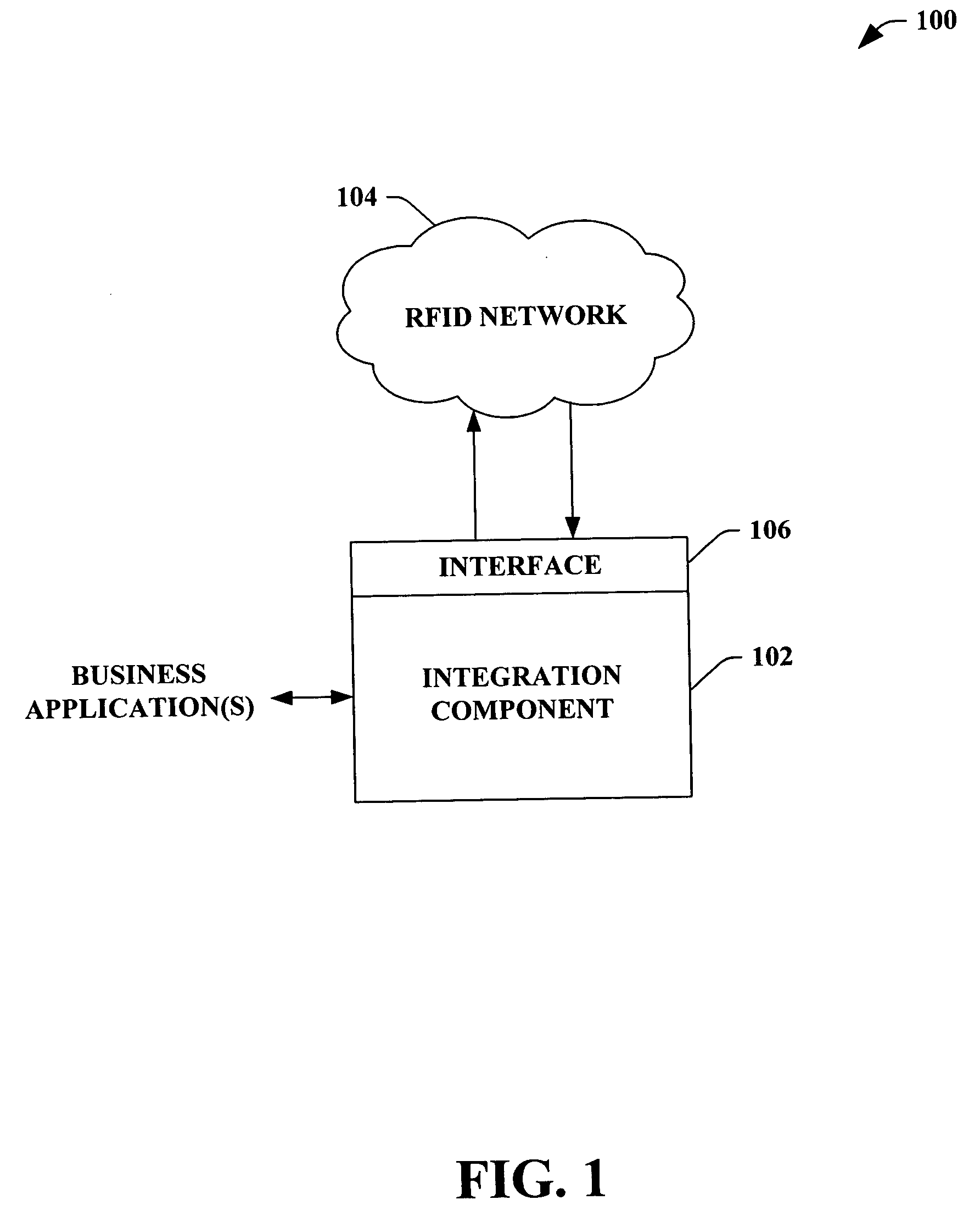
ActiveUS20060047545A1Easy to integrateDigital data processing detailsCo-operative working arrangementsReal-time dataComputer science
The subject invention provides a system and / or a method that facilitates extending data within an RFID network to a business application. An interface can receive real-time RFID data from a process with at least one device collection within the RFID network. An integration component can seamlessly expose such real-time RFID data to a business application to achieve a critical business function in real-time. The business application can be associated to a business network that connects applications within a single organization and / or connects applications in different organizations. Moreover, the integration component can allow the business application to manipulate the RFID network based at least in part upon the real-time output.
Owner:MICROSOFT TECH LICENSING LLC
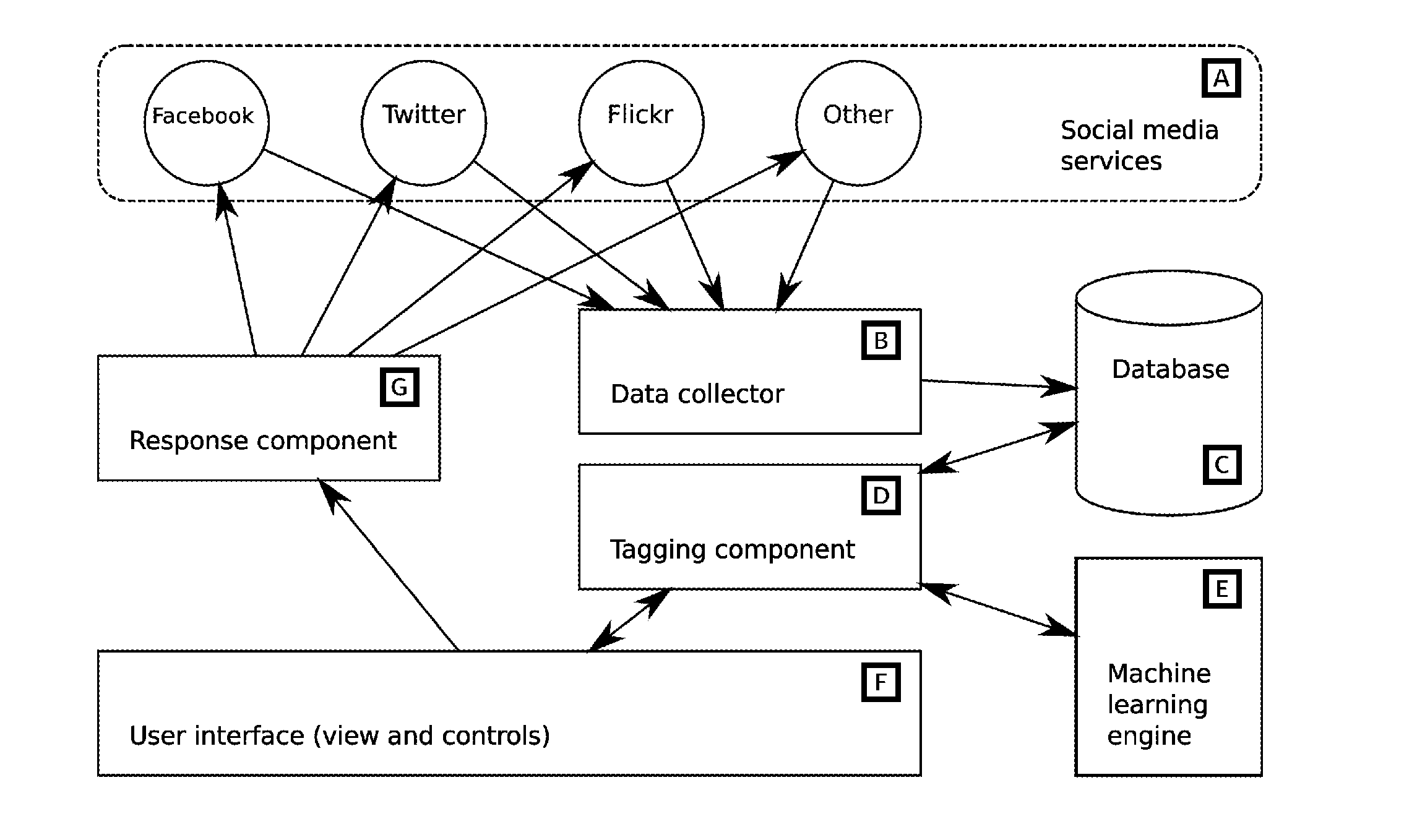
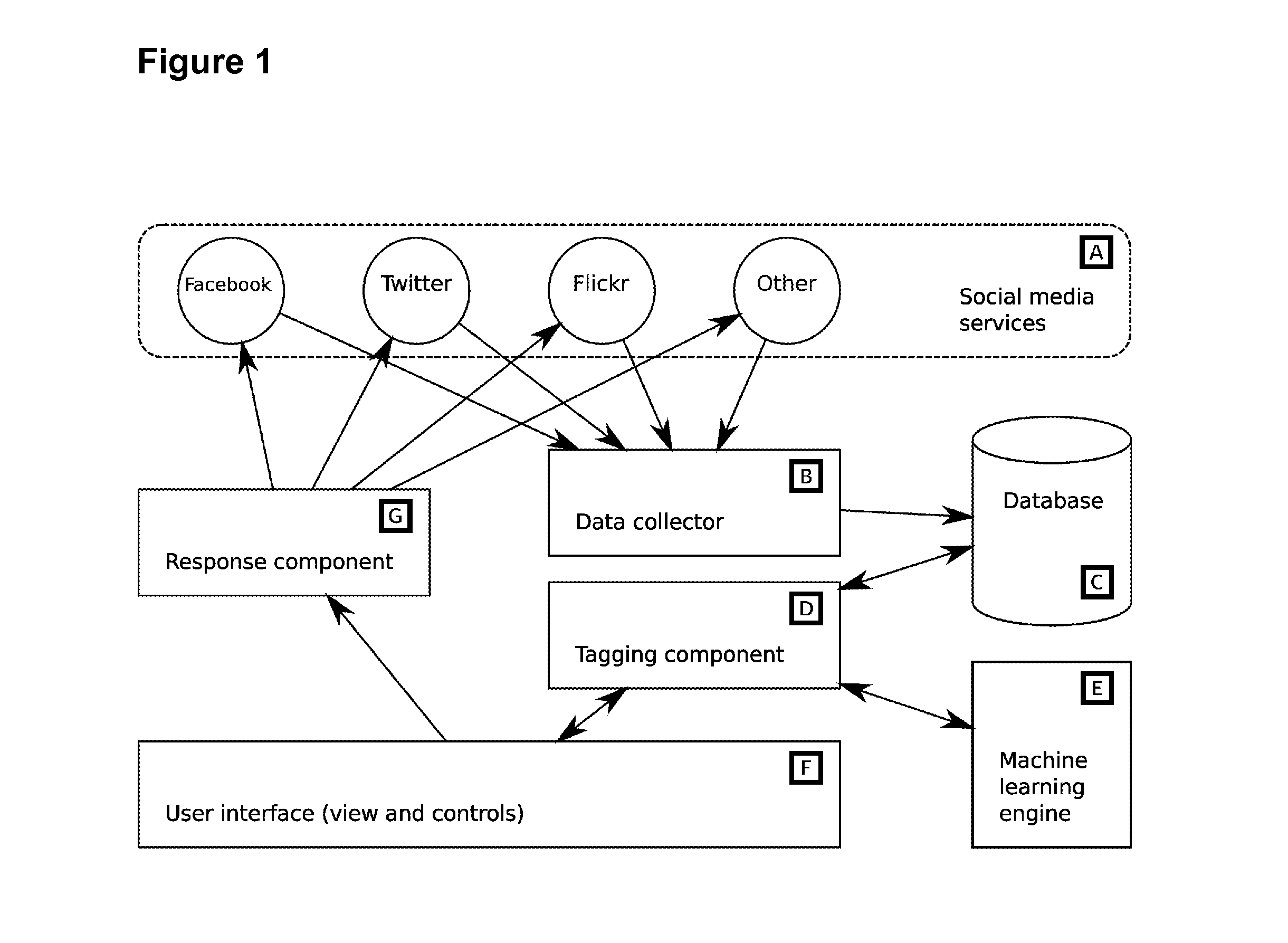
System for organising social media content to support analysis, workflow and automation
InactiveUS20110078584A1Optimize volumeEasy to handleInput/output for user-computer interactionDigital computer detailsSocial mediaApplication software
A social media workflow application includes a social media search component executable by a computing system, a tagging system for annotating search results with textual tags, and a user interface enabling the display of filtered results based on tag, and potentially other, criteria. The new invention is a system to automate tagging and other actions, and the use of such automation to provide a flexible semi-automated workflow tool for the improved use of social media, with particular relevance for marketing and public communications business functions.
Owner:WINTERWELL ASSOCS
Structured products based enterprise management system
InactiveUS20050144033A1Suppress detailSuppress complexityFinanceResourcesElectricitySystems management
The field of invention is in Information Technology based management systems for the natural gas, data communications, electricity, medical, government supply chain and vehicle markets. The disclosed system manages core commercial activities and business for companies in these industries. These systems are specifically designed to not only handle complex transactions but to also allow the same system to be used across all core business functions, including: marketing, sales, contracting, production, delivery, business optimization and financial settlement.
Owner:RATIONAL SYST
Secure Credit Transactions
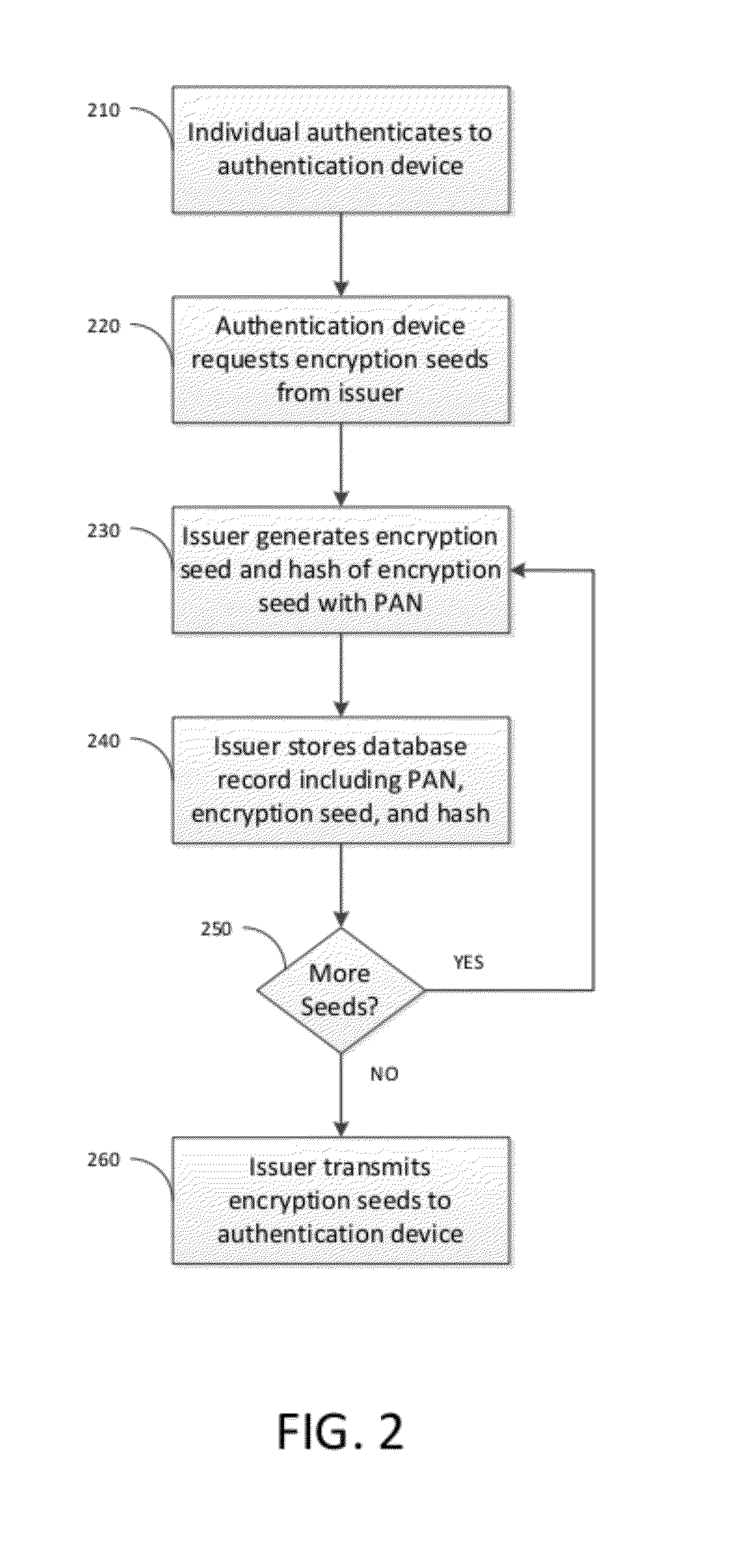
InactiveUS20120191615A1Public key for secure communicationElectronic credentialsCredit cardTransaction data
A system and method for engaging in a credit or debit transaction do not transmit an individual's account number to a vendor or merchant. The individual provides the account number to a transaction acquiring device (TAD). The TAD requires the individual to provide one or more pseudo-random numbers that identify the individual. These numbers are only obtainable from an authentication device that can be unlocked only by passing an authentication challenge. The TAD then provides transaction data to a credit or debit issuer and the vendor, but does not provide or store the account number. The issuer provides the merchant with an identifier other than the account number that is nevertheless unique to the individual. This identifier may be used to track the individual's purchase history or perform other business functions.
Owner:SURIDX
Business level metric for information technology
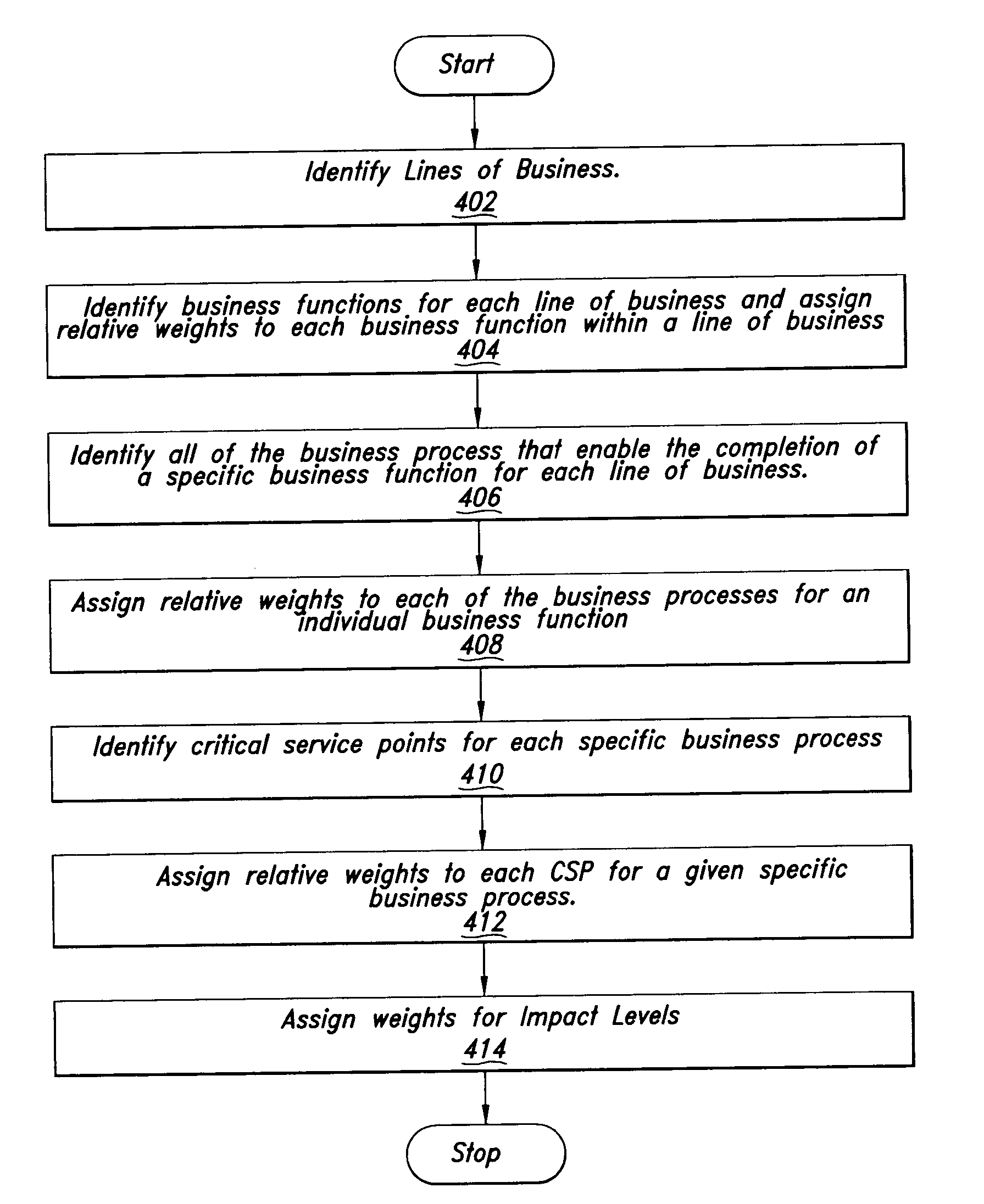
ActiveUS20050086091A1Data processing applicationsSpecial data processing applicationsKnowledge managementBusiness process
A method, system, and computer program product for determining a business level metric for assessing the impact of performance degradation of IT components upon the revenue stream of an entity is provided. In one embodiment, the business level metric is determined by determining business functions that comprises a revenue stream for a line of business. Weights are then assigned to each business function, wherein the weights indicate the relative importance of each business function in relation to the other business functions. For each business function, the business processes that enable the completion of a specific business function are determined and weights. For each business process, critical service points for measuring the performance of supporting information technology components for the business process are determined and weights are assigned. The critical service points are then monitored and a partial business level metric raw score is determined.
Owner:ENT SERVICES DEV CORP LP
Automatic interface test system
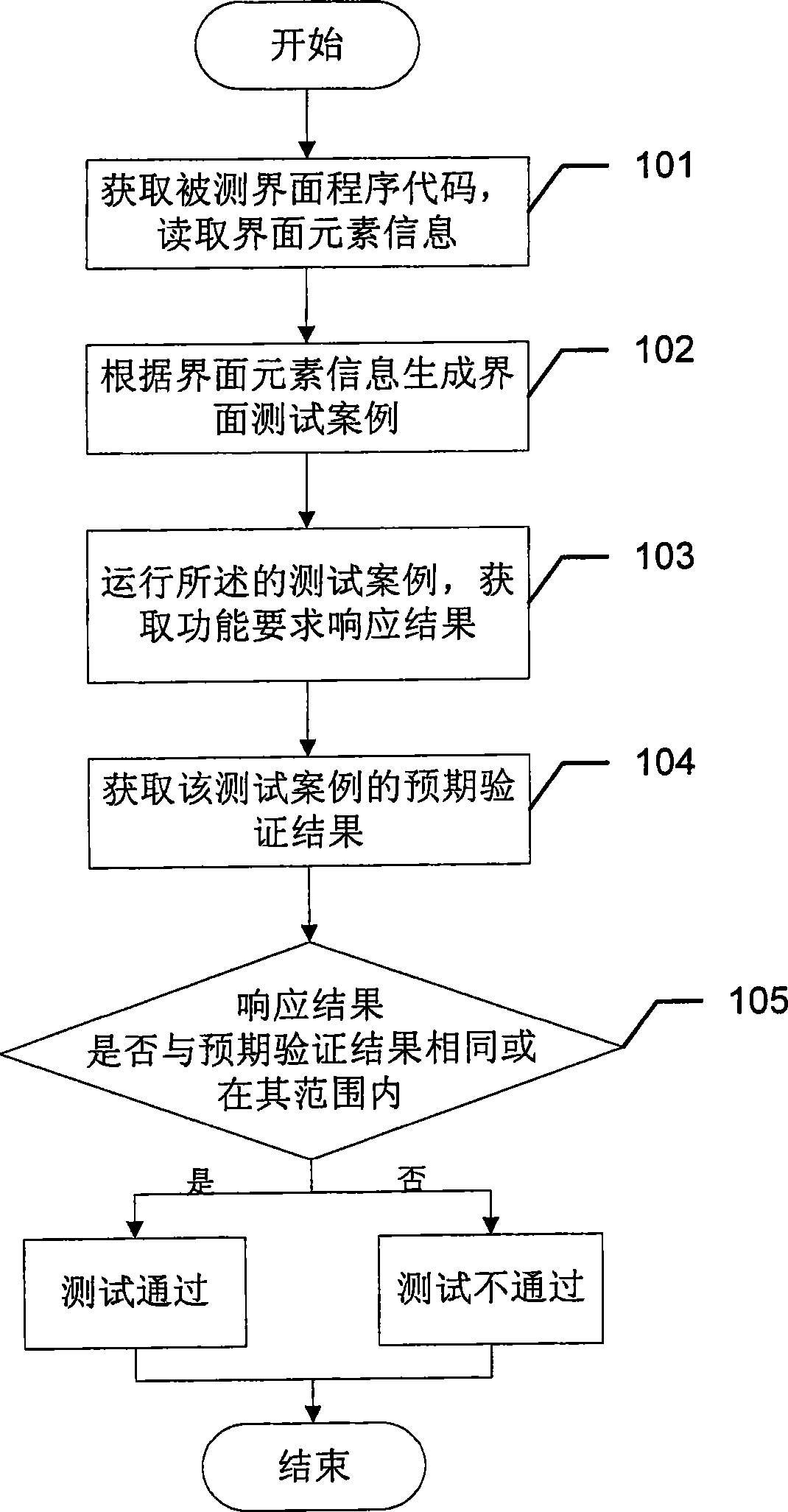
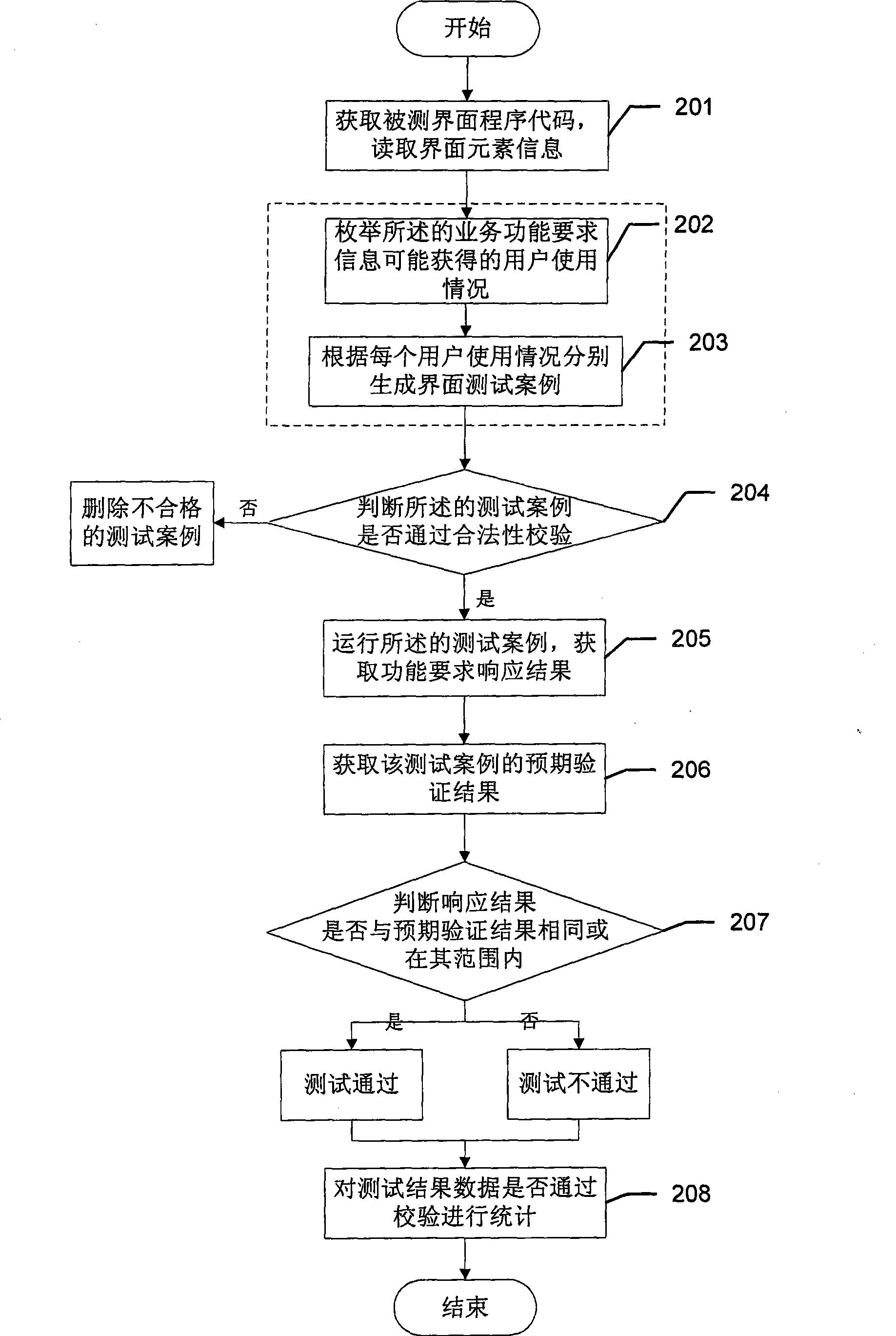
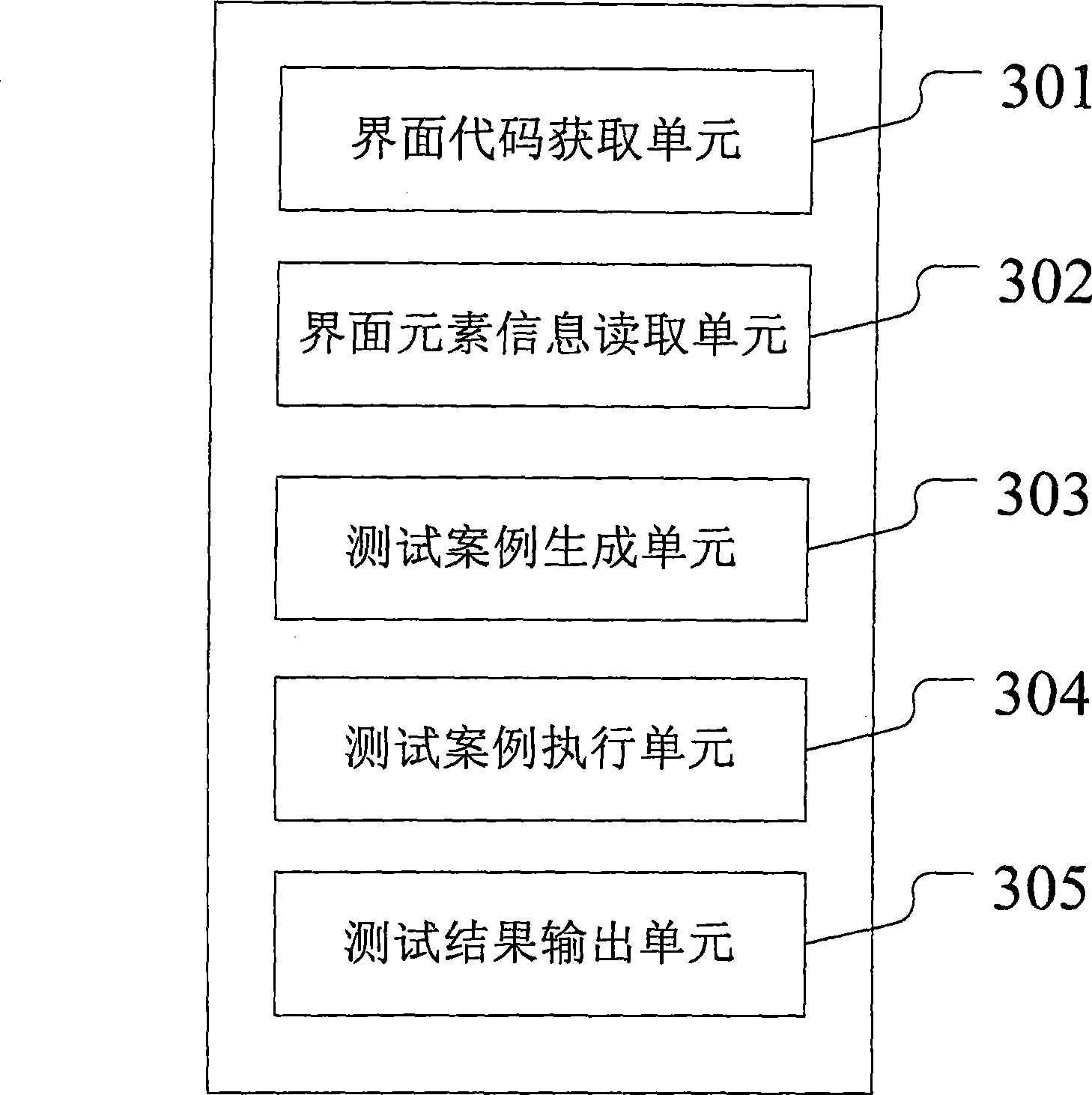
ActiveCN101377759AThe solution cannot be reusedSolve difficult batch case executionSoftware testing/debuggingComputer hardwareTest efficiency
The invention provides an automatic interface test system, which comprises an interface code acquisition unit used for acquiring the codes of tested interface programs; an interface element information read unit used for reading interface element information including interface element names, interface element types and service function requirement information from the codes of the tested interface programs; a test case generation unit used for generating interface test cases according to the business function requirement information; a test case execution unit used for running the test cases and responding to the functional requirements in the running of the test cases as well as acquiring the responding results of the functional requirements; a test result output unit used for acquiring expected verification results of the test cases from the running test cases, comparing the responding results of the functional requirements with the expected verification results for uniformity, and outputting uniform or nonuniform test results. The test efficiency of the automatic interface test system is significantly improved by comparing the test with the automatic interface test system with manual test.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
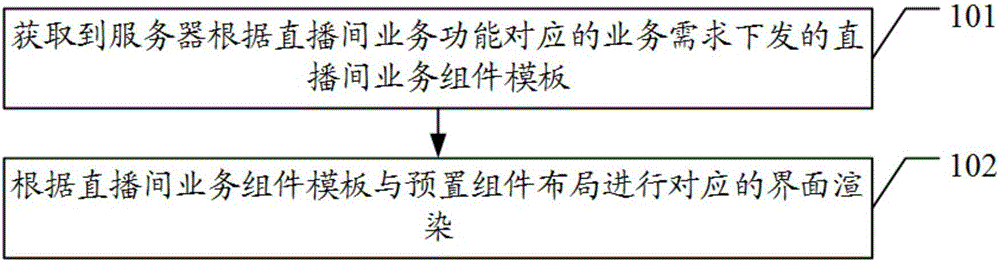
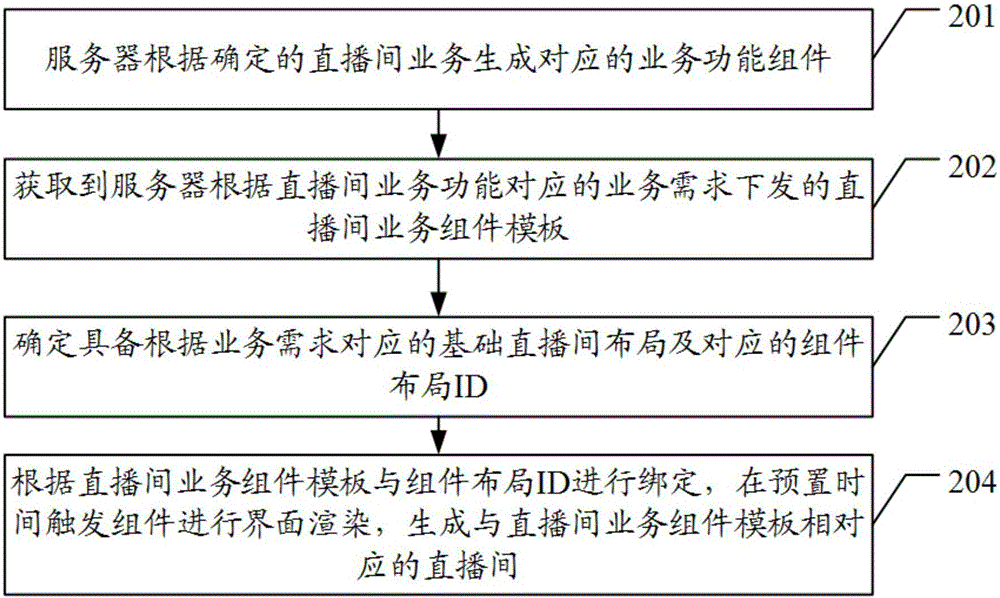
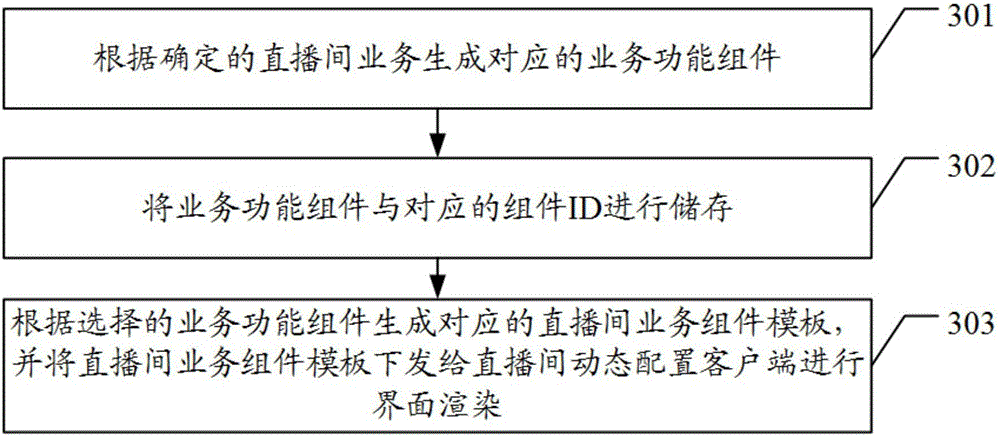
Live broadcasting room dynamic configuration method, device, system and server
The embodiment of the present invention discloses a live broadcasting room dynamic configuration method, device, system and a server which solve the technical problems at present that when different types of live broadcasting rooms need to change the UI templates, the on-line configuration and dynamic switching can not realized, so that the dynamic repair can not be realized when problems occur, but the continuous iterative development is needed; moreover, users are required to upgrade the versions and install the applications again, and the personnel of multiple service lines develop in a same engineering, so that the coordinated development and positioning problems are difficult, and accordingly, the efficiency of updating the configuration is low. The live broadcasting room dynamic configuration method of the embodiment of the present invention comprises the steps of obtaining the live broadcasting room service assembly templates issued according to the service demands corresponding to the live broadcasting room service functions; and carrying out the corresponding interface rendering according to the live broadcasting room service assembly templates and the preset assembly layout.
Owner:广州方硅信息技术有限公司
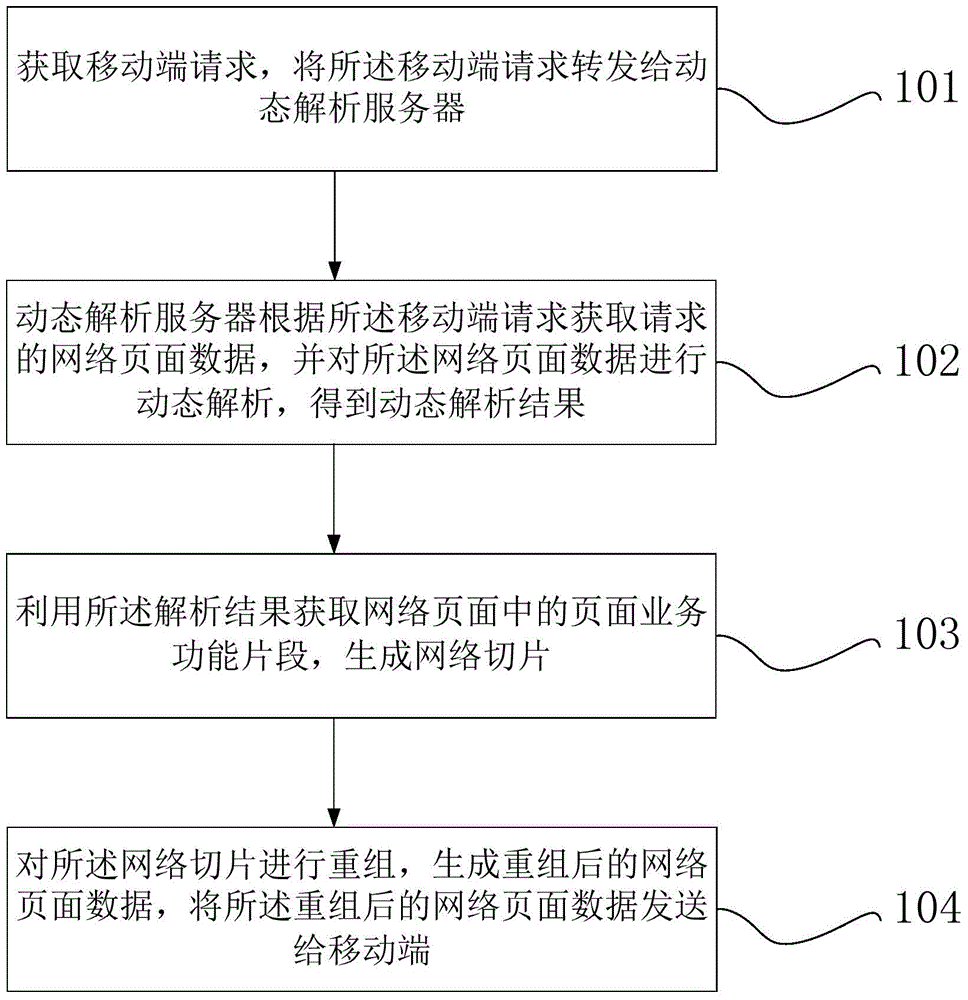
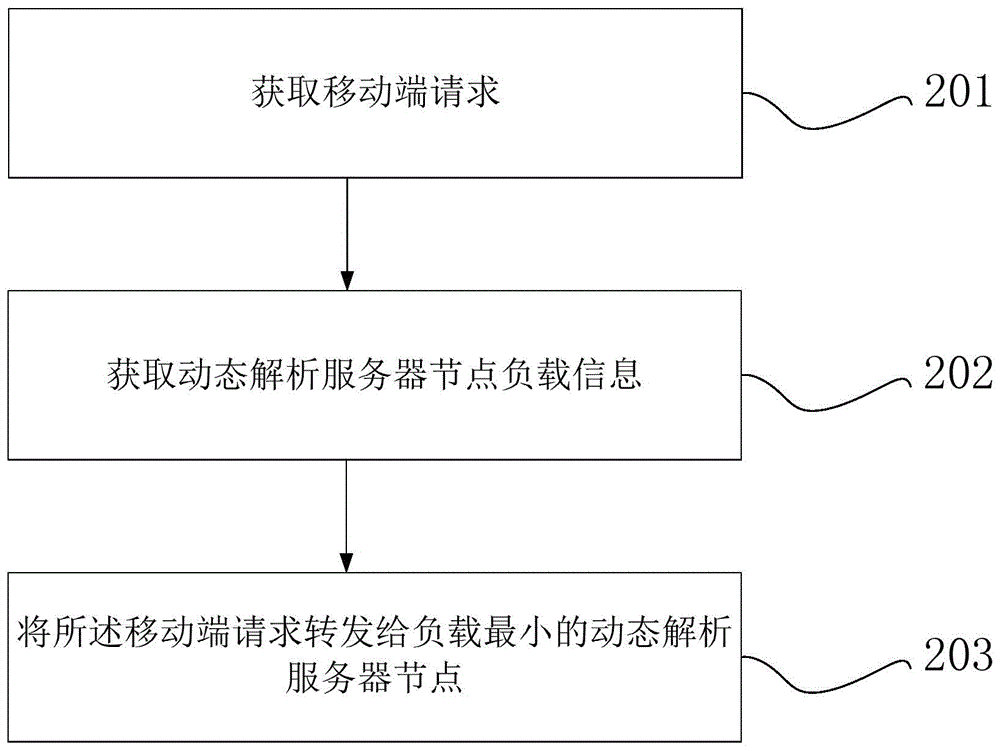
Self-adaptive method and system based on cloud architecture
The invention provides a self-adaptive method and a system based on a cloud architecture. The method comprises the following steps of obtaining a mobile terminal request, and forwarding the mobile terminal request to a dynamic analysis server; enabling the dynamic analysis server to obtain the requested network webpage data according to the mobile terminal request, and dynamically analyzing the network webpage data, so as to obtain a dynamic analysis result; utilizing the analysis result to obtain a webpage service function fragment in a network webpage, and generating network slices; regrouping the network slices, generating the regrouped network webpage data, and sending the regrouped network webpage data to a mobile terminal.
Owner:BEIJING HANDSCAPE TECH
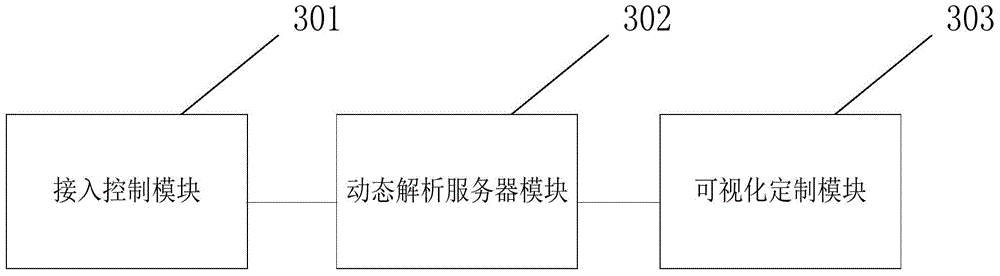
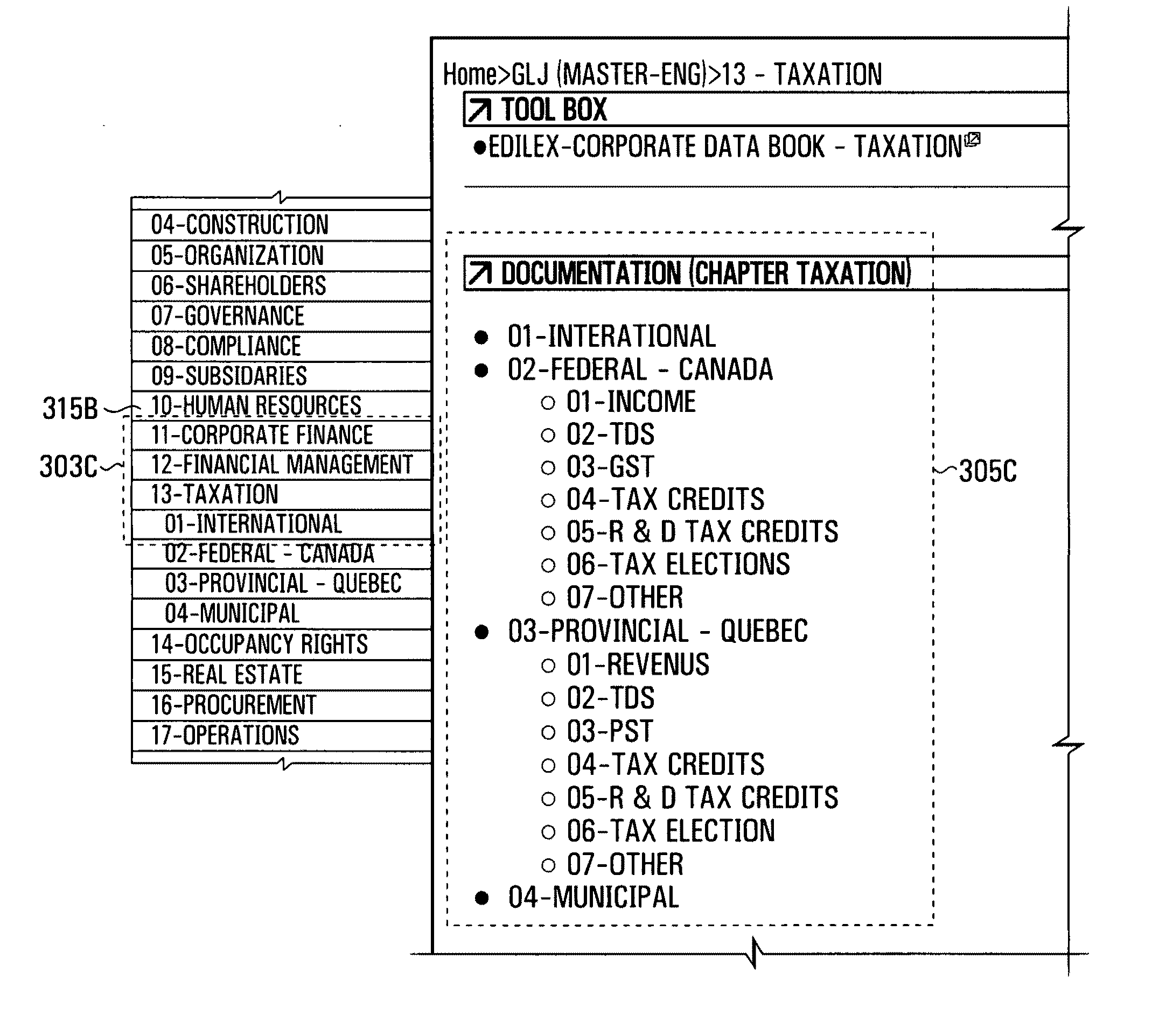
Business document system
A hierarchical organization of business documents, system and graphical user interface related thereto, allowing the efficient organization of business documents such as contracts and other legal documents. In a non-limiting example, three-tier organization is made possible, the first tier relating to major business function, the second to business tasks or processes and the last to individual business documents. The business documents may themselves be made up of hierarchical sections. Reference to particular portions of the hierarchy may take the form of a coordinate or address. A graphical user interface includes means of navigating through the hierarchy towards a particular business document.
Owner:THIBAULT GILLES
Method and device for extending software function based on micro service architecture
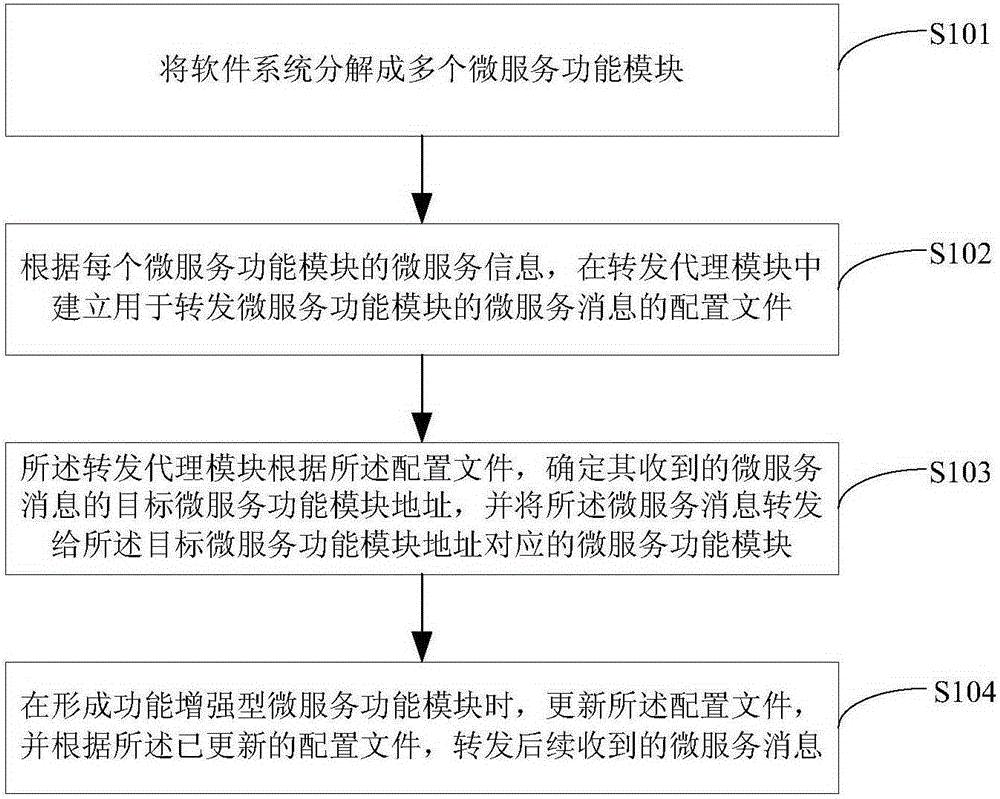
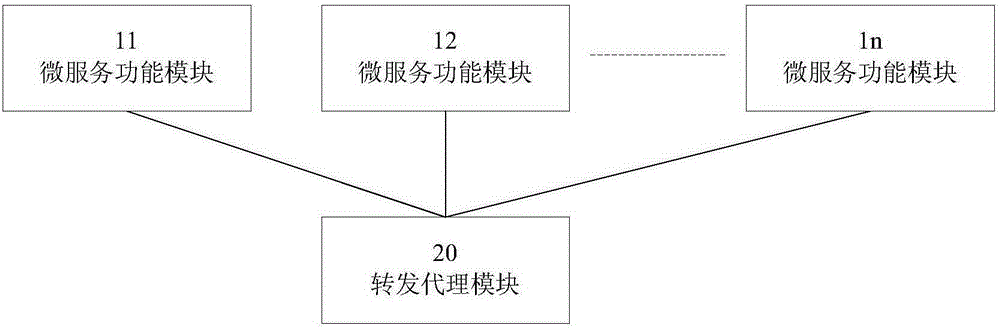
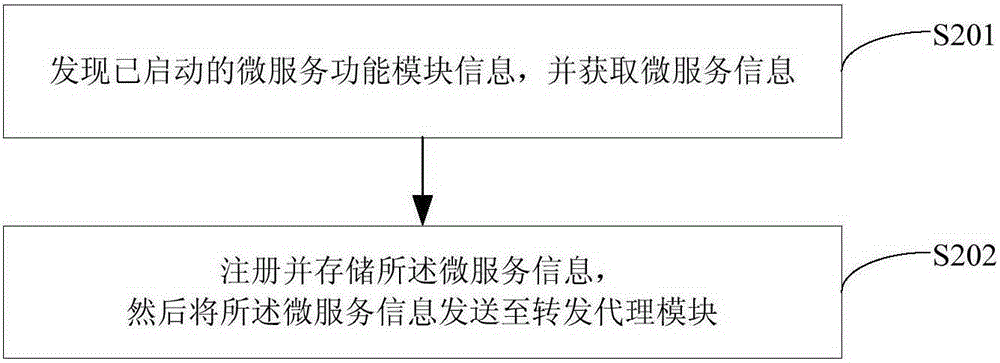
InactiveCN106612188AImprove acceleration performanceImprove usabilityProgram loading/initiatingData switching networksSoftware systemBusiness function
The invention discloses a method and a device for extending a software function based on a micro service architecture. The method comprises steps: a software system is decomposed into multiple micro service function modules; according to the micro service information of each micro service function module, a configuration file for forwarding the micro service information of the micro service function module is built in a forwarding agent module; according to the configuration file, the forwarding agent module determines a target micro service function module address of the received micro service information, and the micro service information is forwarded to the micro service function module corresponding to the target micro service function module address; and when a function enhancement-type micro service function model is formed in the software system according to service function requirements, the forwarding agent module updates the configuration file according to the micro service information of the function enhancement-type micro service function model, and according to the already-updated configuration file, subsequently-received micro service information is forwarded. Thus, the software function can be dynamically extended.
Owner:ZTE CORP
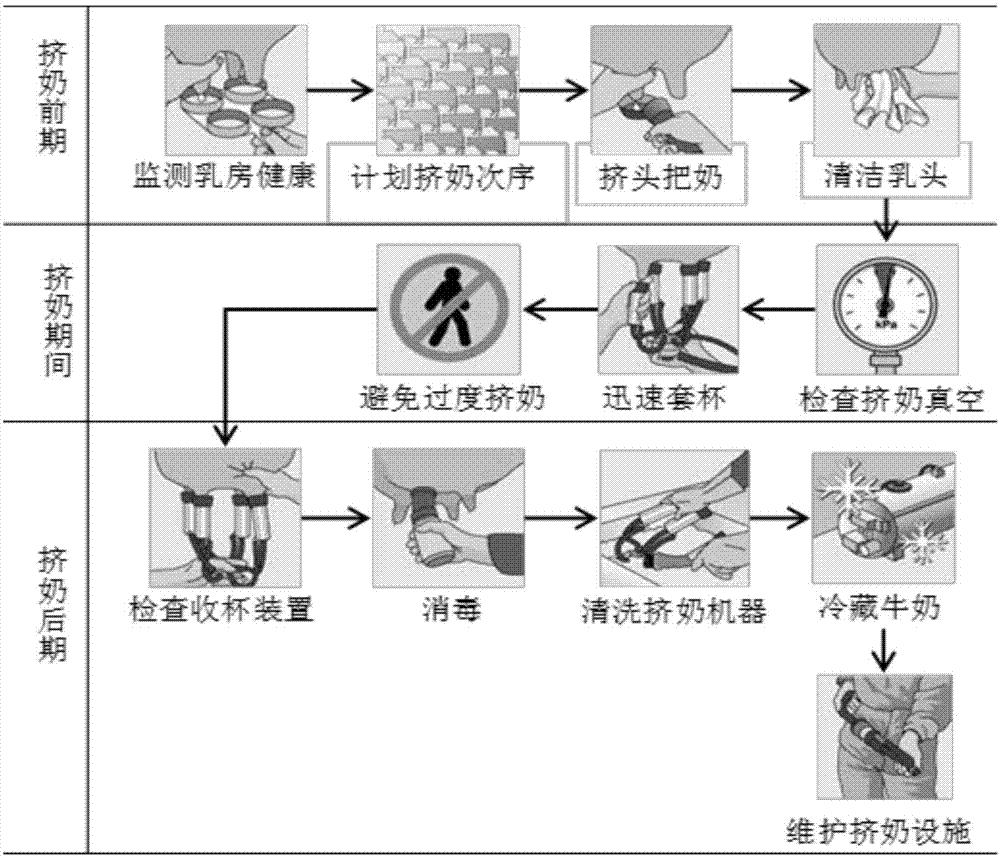
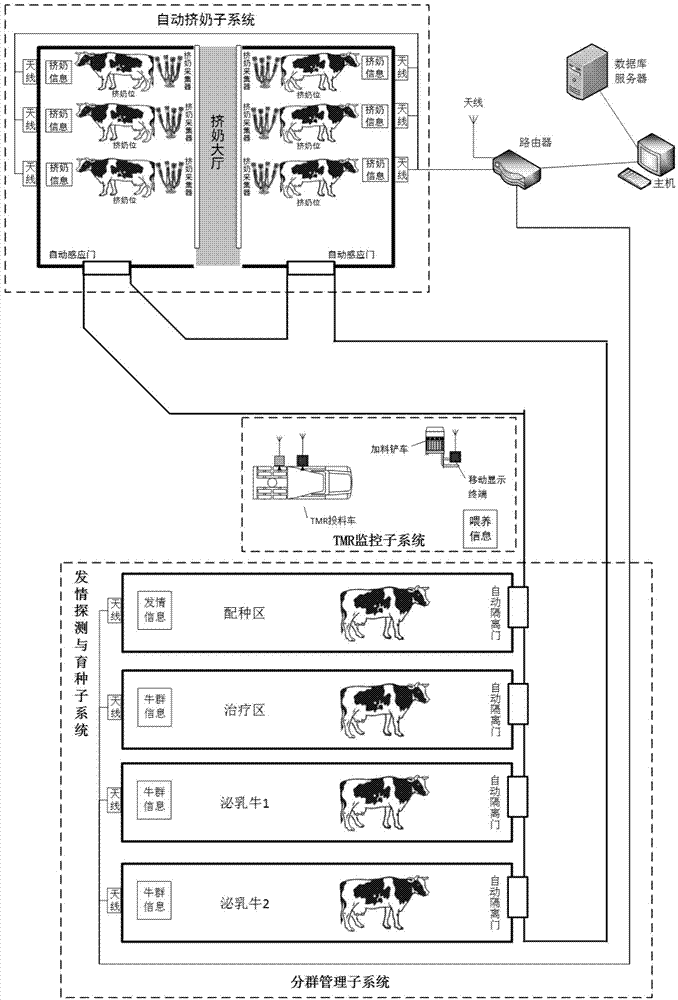
Cow fine breeding method based on RFID technology
ActiveCN103782954AImplement dynamic configurationImprove efficiencyClimate change adaptationCo-operative working arrangementsAgricultural scienceBusiness function
The invention discloses a cow fine breeding method based on the RFID technology. The method includes the following steps that 1, the milk production of cows is recorded through an automatic milk production recording subsystem where the RFID technology and milking are combined; 2, automatic clustering management is performed on the cows through an automatic cow isolation door based on the RFID technology; 3, appropriate nutritious daily ration is prepared for cow groups through a TMR monitoring subsystem based on the RFID technology; 4, cow movement and oestrus sensors are installed on cow neckbands so as to monitor movement conditions of the cows in real time. In the cow fine breeding method, the cow breeding management business relates to various fields of milking management and fodder management, and the cow fine breeding method is applied and deployed from the aspects of automatic milk production counting, clustering management, fodder management and oestrus hybridization management according to different business functions of cow farms.
Owner:GUANGDONG YANTANG DAIRY
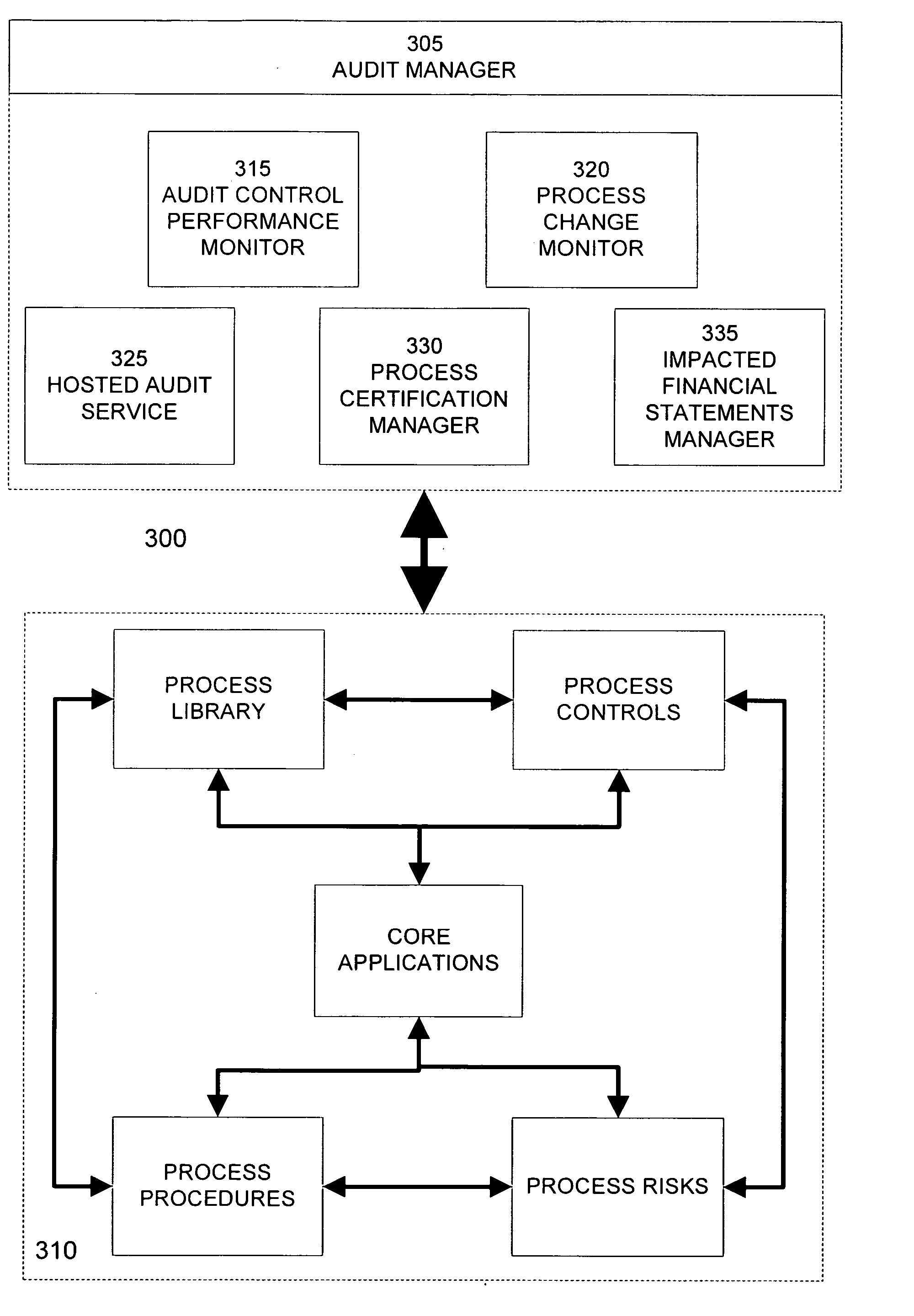
Segregation of duties reporting
InactiveUS20050209899A1Efficiently determinedPrevent employee accessFinanceSpecial data processing applicationsBusiness processComputer science
An embodiment of the invention is an audit system including a set of business processes that describe the operations of an enterprise. The audit system has a registry of incompatible business functions. The registry of incompatible business functions is created from a library of business processes. Additional business functions can be added to the registry by auditors to suit the specific needs of an enterprise. A report generator determines the business functions available to each employee and compares these functions with the registry to ensure that proper segregation of duties is observed. Additionally, if a new business function is assigned to an employee, an alert is sent by the audit system if this business function is incompatible with other business functions assigned to the employee.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com