Patents
Literature
8042 results about "Log data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Integrated routing/mapping information
InactiveUS6321158B1Enabling cooperationEnabling matingInstruments for road network navigationRoad vehicles traffic controlImage resolutionLevel of detail
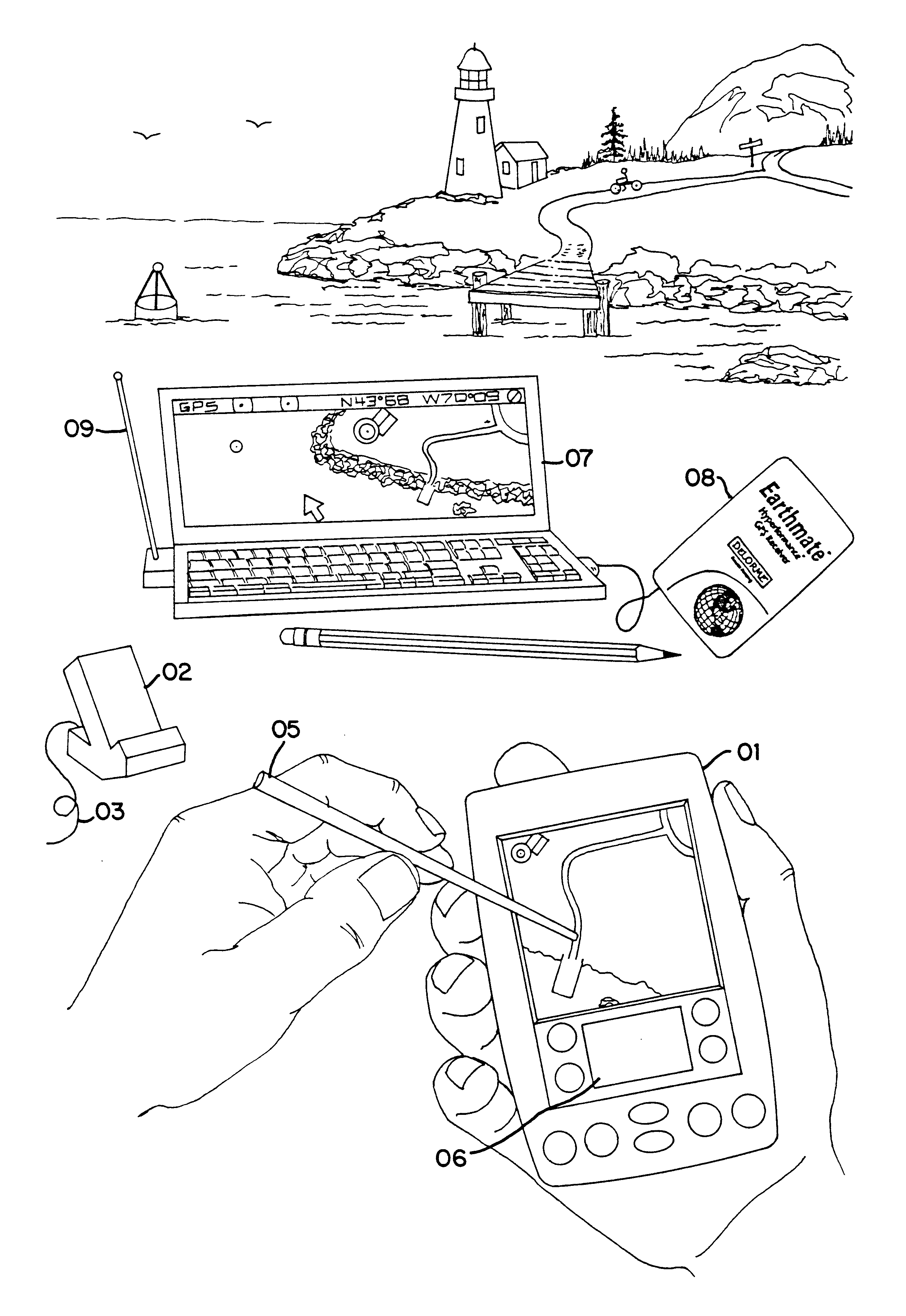
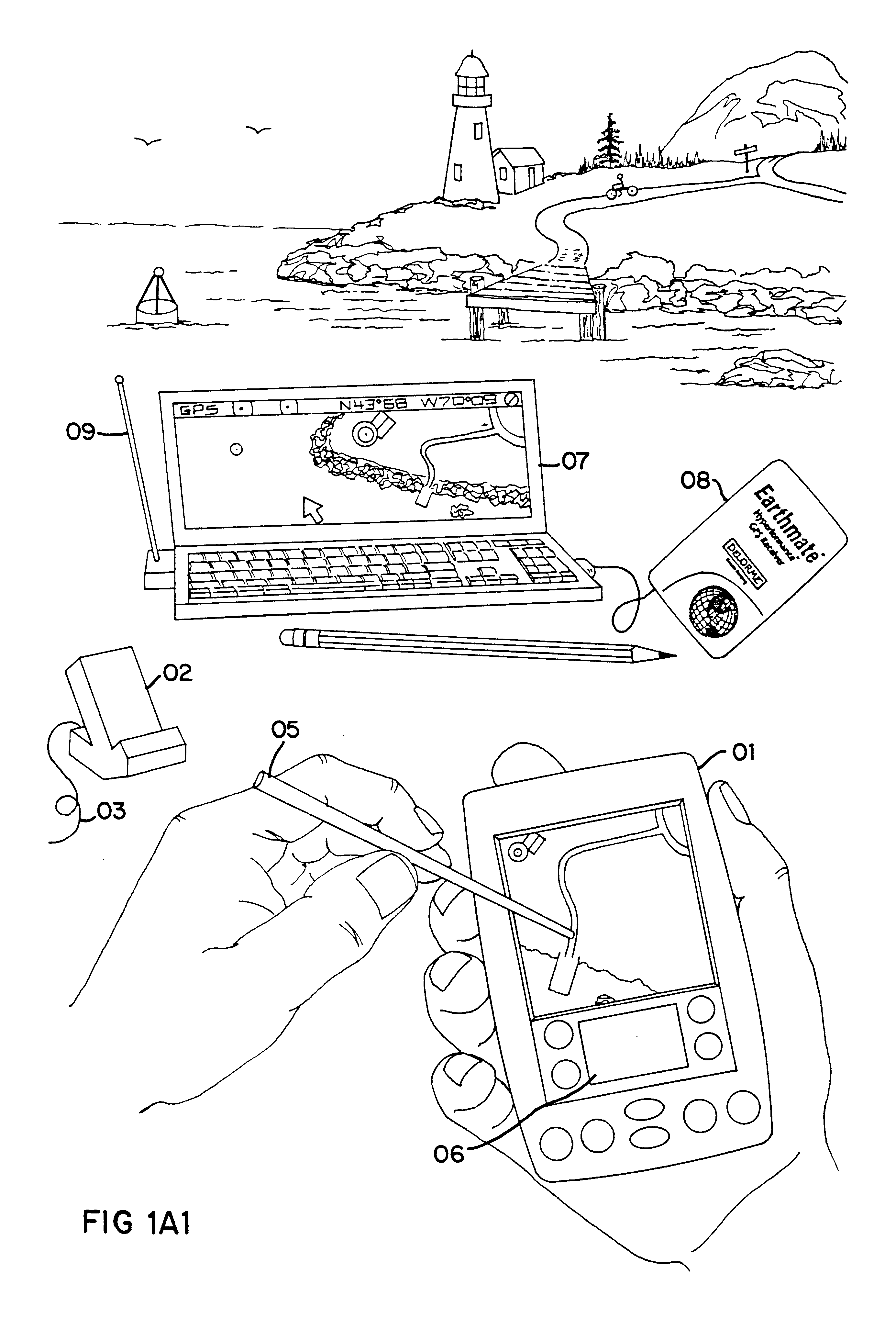
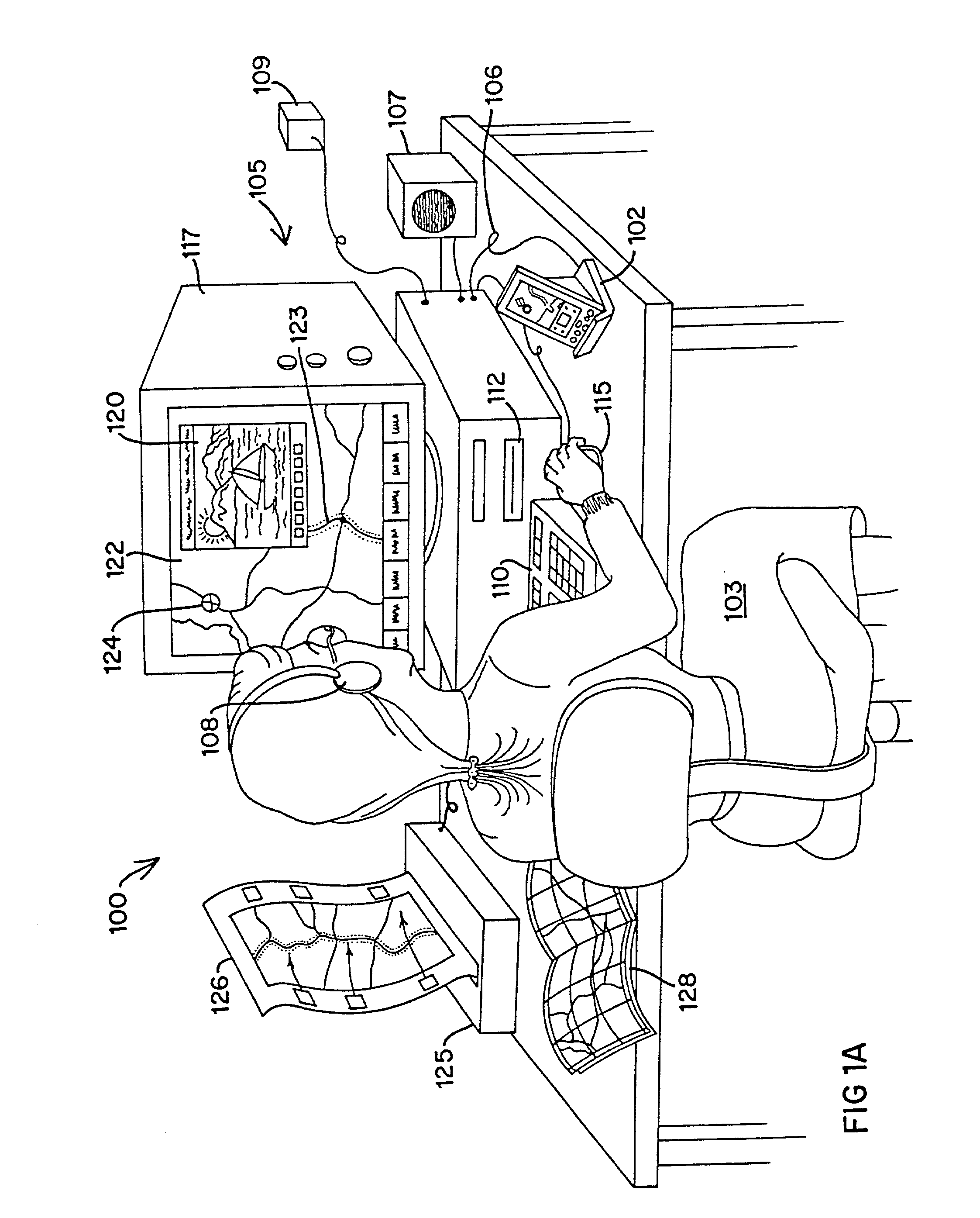
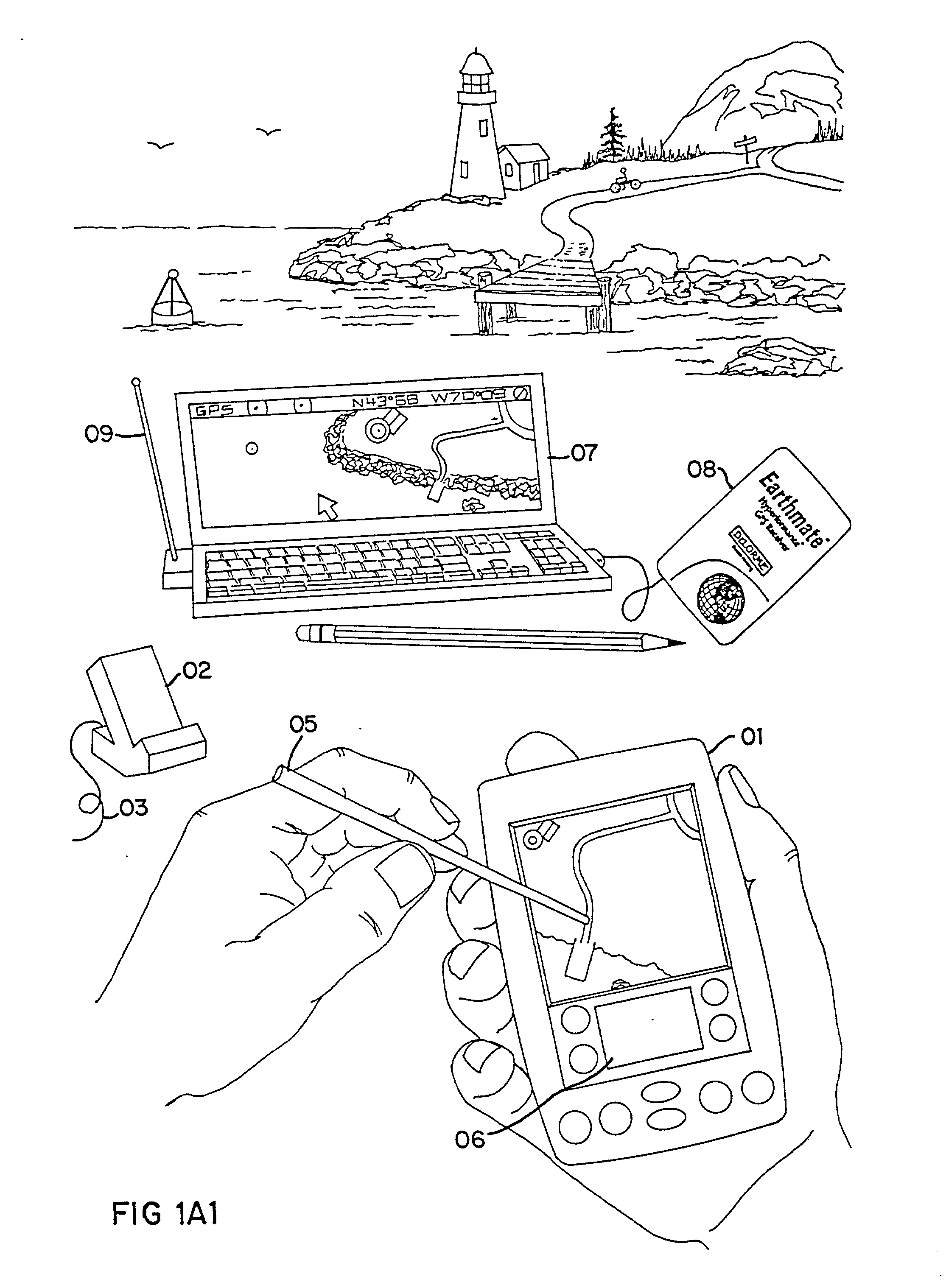
An Integrated Routing / Mapping Information System (IRMIS) links desktop personal computer cartographic applications to one or more handheld organizer, personal digital assistant (PDA) or "palmtop" devices. Such devices may be optionally equipped with, or connected to, portable Global Positioning System (GPS) or equivalent position sensing device. Desktop application facilitates user selection of areas, starts, stops, destinations, maps and / or point and / or route information. It optionally includes supplemental online information, preferably for transfer to the PDA or equivalent device. Users' options include route information, area, and route maps. Maps and related route information are configured with differential detail and levels of magnitude. Used in the field, in conjunction with GPS receiver, the PDA device is configured to display directions, text and map formats, the user's current position, heading, speed, elevation, and so forth. Audible signals identifying the next turn along the user's planned route are also provided. The user can pan across maps and zoom between two or more map scales, levels of detail, or magnitudes. The IRMIS also provides for "automatic zooming," e.g., to show greater detail or closer detail as the user approaches a destination, or to larger scale and lower resolution to show the user's overall planned route between points of interest. The IRMIS also enables the user to mark or record specific locations and / or log actual travel routes, using GPS position information. These annotated location marks and / or "breadcrumb" or GPS log data can be saved, uploaded, displayed, or otherwise processed on the user's desktop geographic information or cartographic system. The IRMIS application and data may be distributed online and / or in tangible media in limited and advanced manipulation formats.
Owner:GARMIN
Integrated routing/mapping information system
InactiveUS20030182052A1Enabling cooperationEnabling matingInstruments for road network navigationRoad vehicles traffic controlImage resolutionLevel of detail
An Integrated Routing / Mapping Information System (IRMIS) links desktop personal computer cartographic applications to one or more handheld organizer, personal digital assistant (PDA) or "palmtop" devices. Such devices may be optionally equipped with, or connected to, portable Global Positioning System (GPS) or equivalent position sensing device. Desktop application facilitates user selection of areas, starts, stops, destinations, maps and / or point and / or route information. It optionally includes supplemental online information, preferably for transfer to the PDA or equivalent device. Users' options include route information, area, and route maps. Maps and related route information are configured with differential detail and levels of magnitude. Used in the field, in conjunction with GPS receiver, the PDA device is configured to display directions, text and map formats, the user's current position, heading, speed, elevation, and so forth. Audible signals identifying the next turn along the user's planned route are also provided. The user can pan across maps and zoom between two or more map scales, levels of detail, or magnitudes. The IRMIS also provides for "automatic zooming," e.g., to show greater detail or closer detail as the user approaches a destination, or to larger scale and lower resolution to show the user's overall planned route between points of interest. The IRMIS also enables the user to mark or record specific locations and / or log actual travel routes, using GPS position information. These annotated location marks and / or "breadcrumb" or GPS log data can be saved, uploaded, displayed, or otherwise processed on the user's desktop geographic information or cartographic system. The IRMIS application and data may be distributed online and / or in tangible media in limited and advanced manipulation formats.
Owner:KHOURI ANTHONY
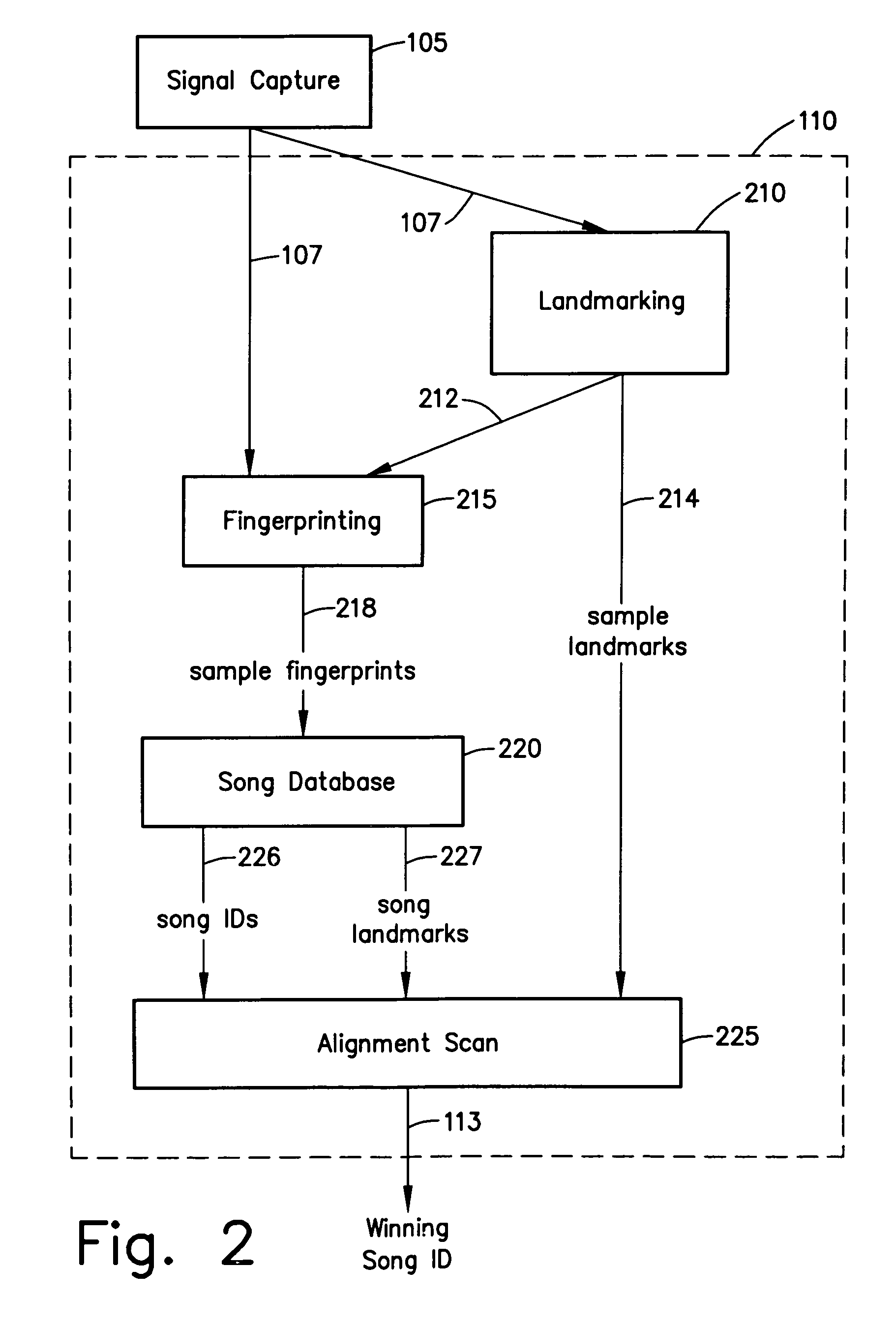
Method and system for purchasing pre-recorded music
ActiveUS7853664B1Automatic call-answering/message-recording/conversation-recordingRecord information storageAudio frequencyDistortion
A method and system is described which allows users to identify (pre-recorded) sounds such as music, radio broadcast, commercials, and other audio signals in almost any environment. The audio signal (or sound) must be a recording represented in a database of recordings. The service can quickly identify the signal from just a few seconds of excerption, while tolerating high noise and distortion. Once the signal is identified to the user, the user may perform transactions interactively in real-time or offline using the identification information.
Owner:APPLE INC
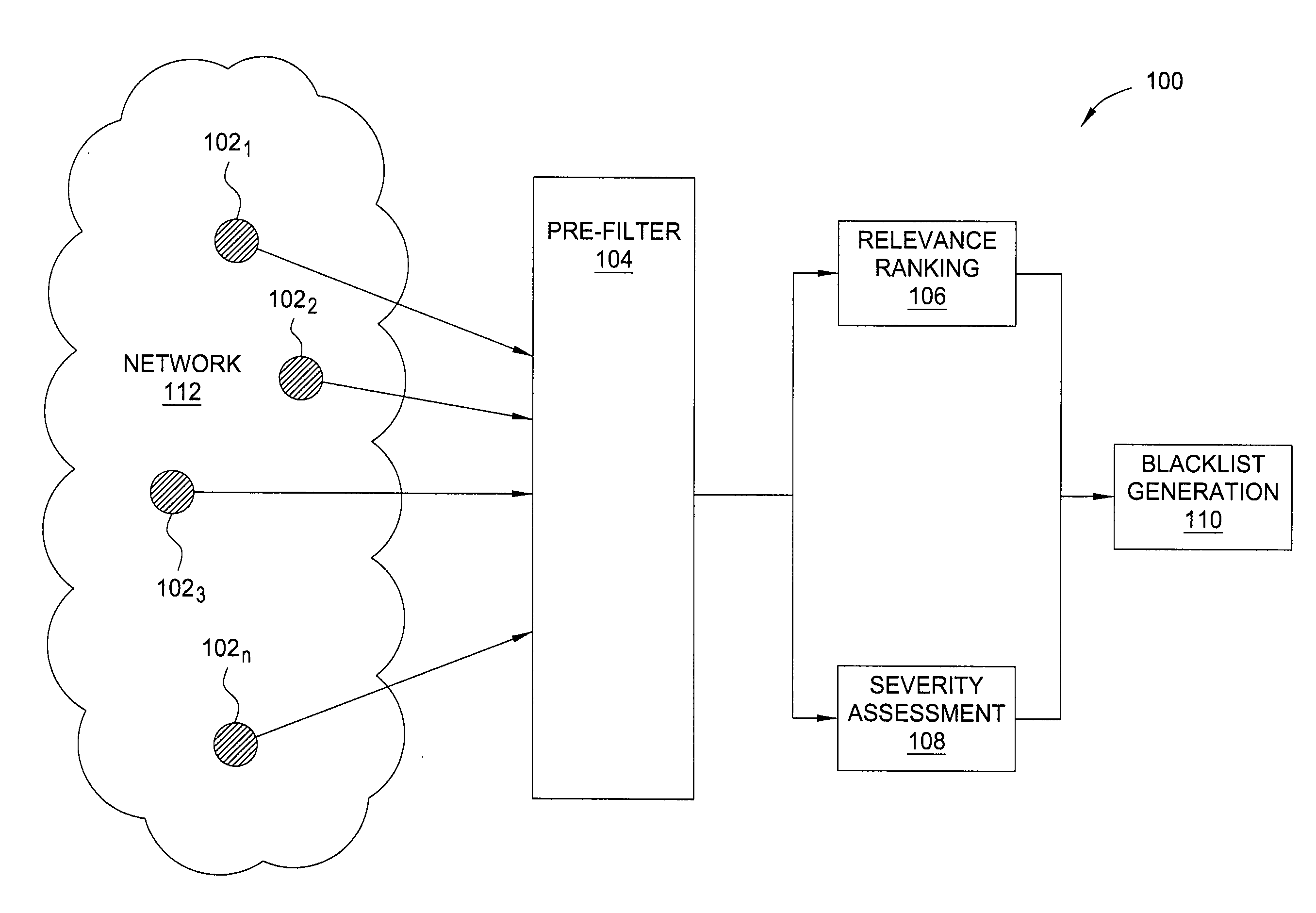
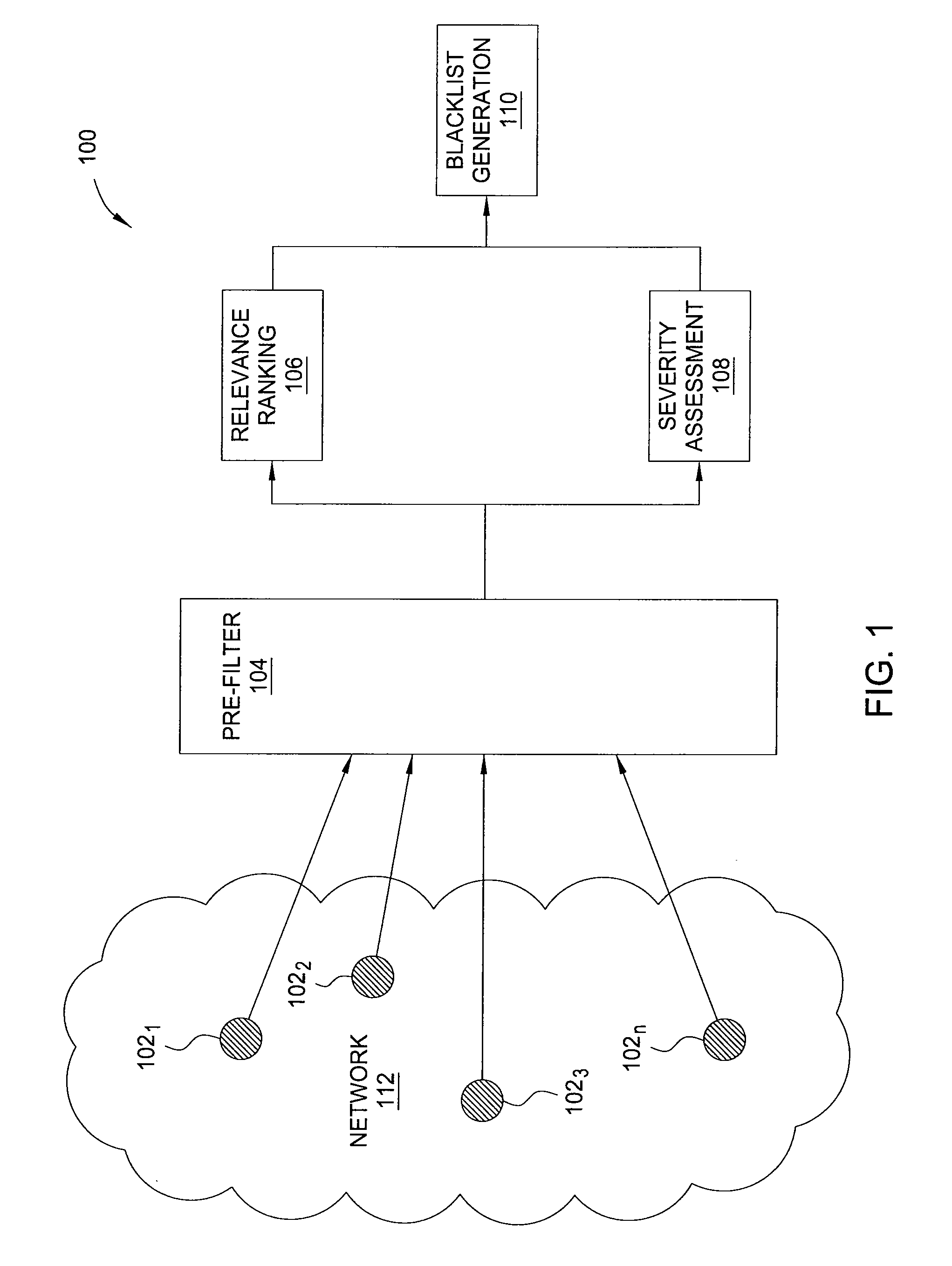
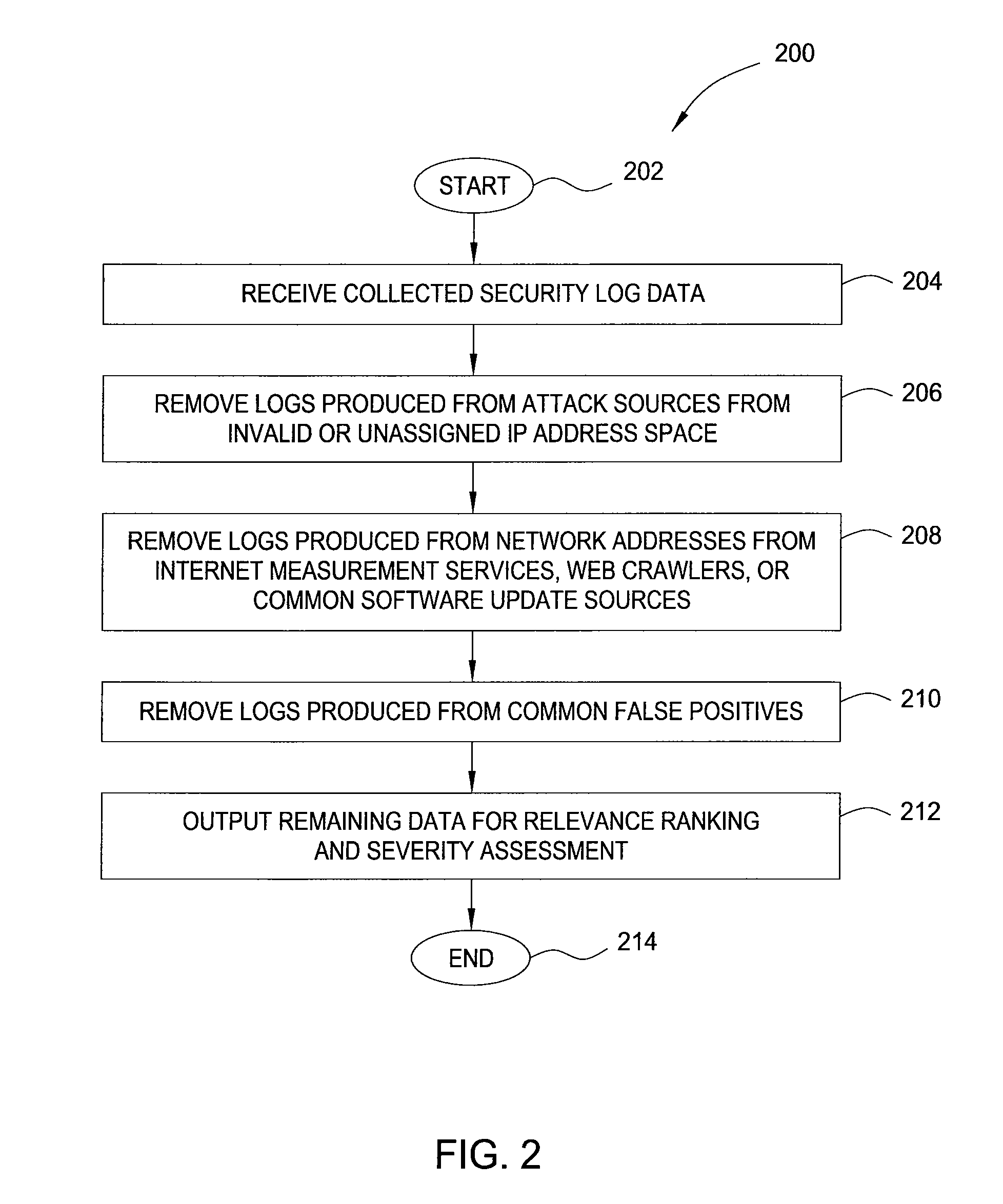
Method and apparatus for generating highly predictive blacklists
ActiveUS20090064332A1Memory loss protectionError detection/correctionNetwork addressingNetwork address
In one embodiment, the present invention is a method and apparatus for generating highly predictive blacklists. One embodiment of a method for generating a blacklist of network addresses for a user of a network includes collecting security log data from users of the network, the security log data identifying observed attacks by attack sources, assigning the attack sources to the blacklist based on a combination of the relevance each attack source to the user and the maliciousness of the attack source, and outputting the blacklist.
Owner:SRI INTERNATIONAL
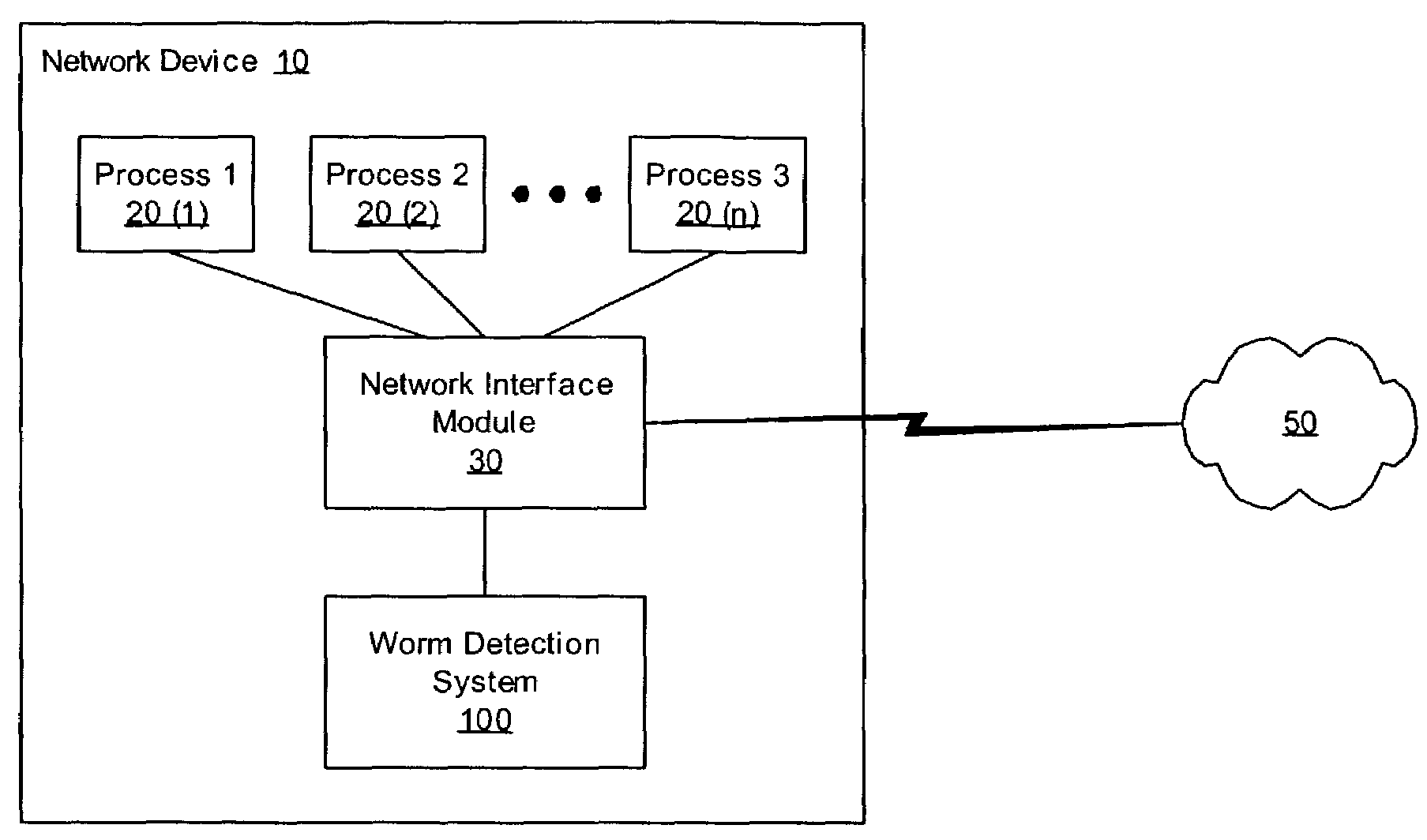
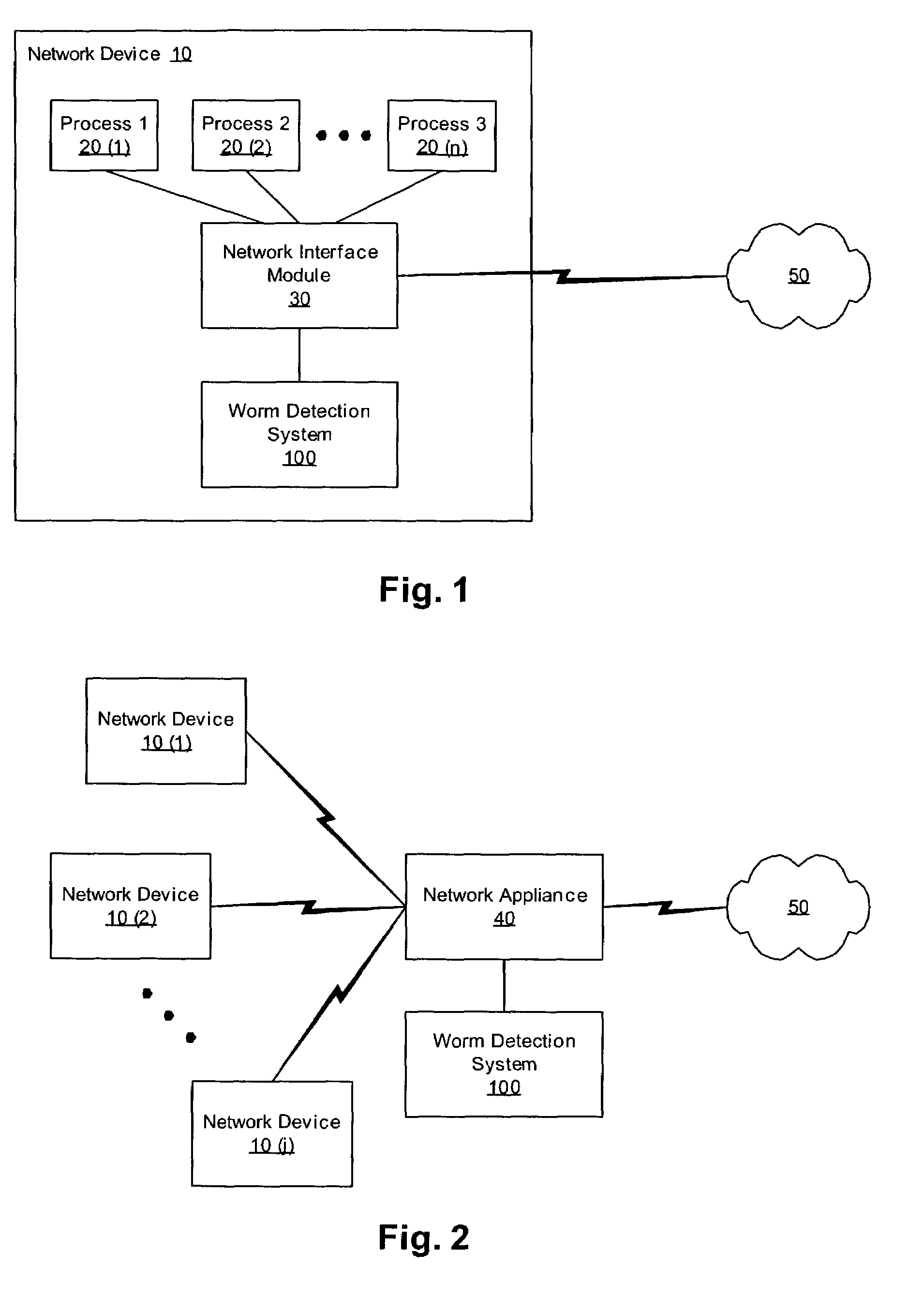
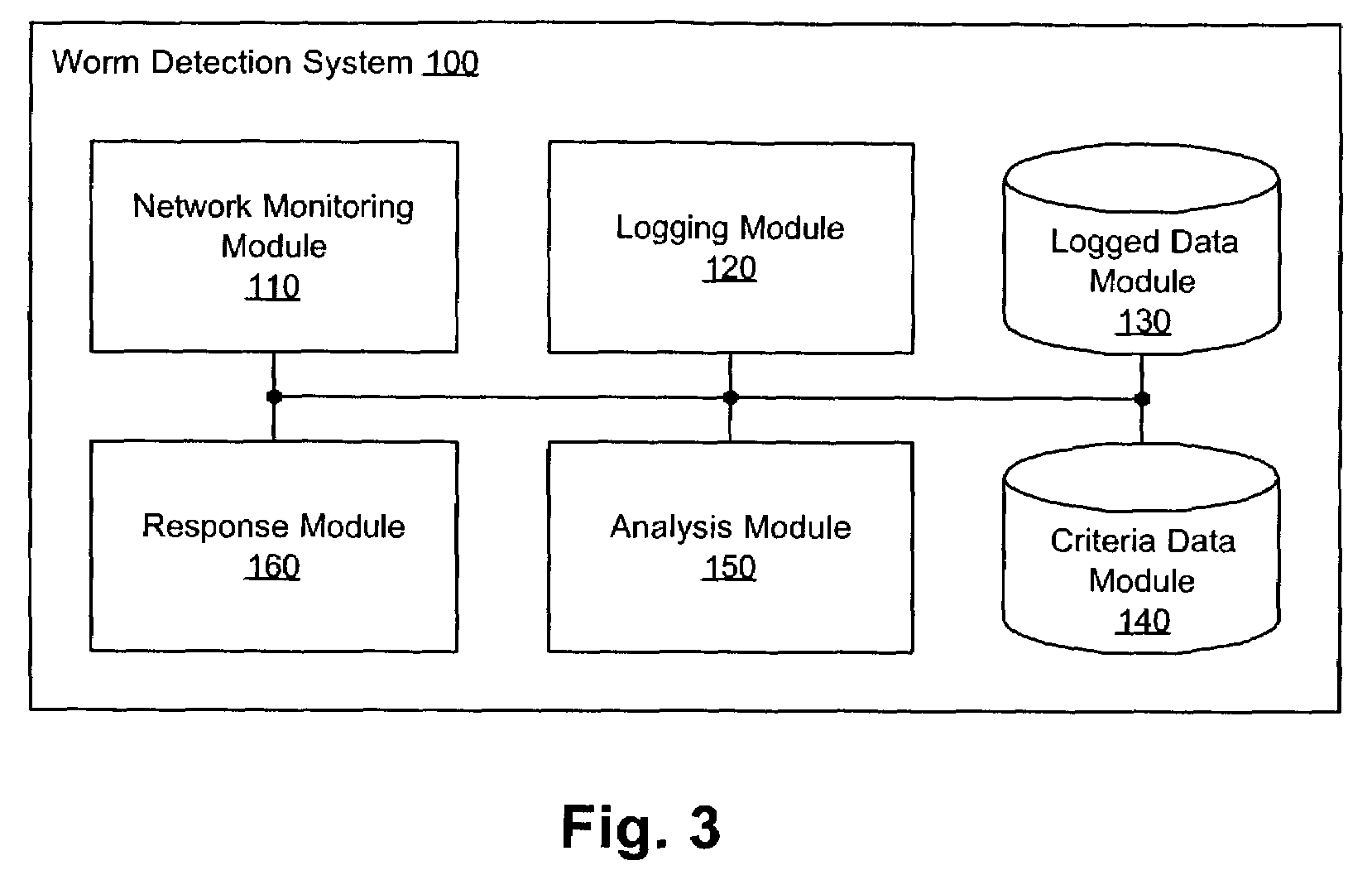
Heuristic detection and termination of fast spreading network worm attacks
Methods, apparati, and computer program products for detecting and responding to fast-spreading network worm attacks include a network monitoring module (110), which observes (205) failed network connection attempts from multiple sources. A logging module (120) logs (220) the failed connection attempts. An analysis module (150) uses the logged data on the failed connection attempts to determine (225) whether a sources is infected with a worm using a set of threshold criteria. The threshold criteria indicate whether a source's failed connection attempts are non-normal. In one embodiment, a response module (160) responds (240) to the computer worm by, e.g., alerting a user or system administrator, terminating an infected process (20), or terminating the infected source's network access.
Owner:CA TECH INC
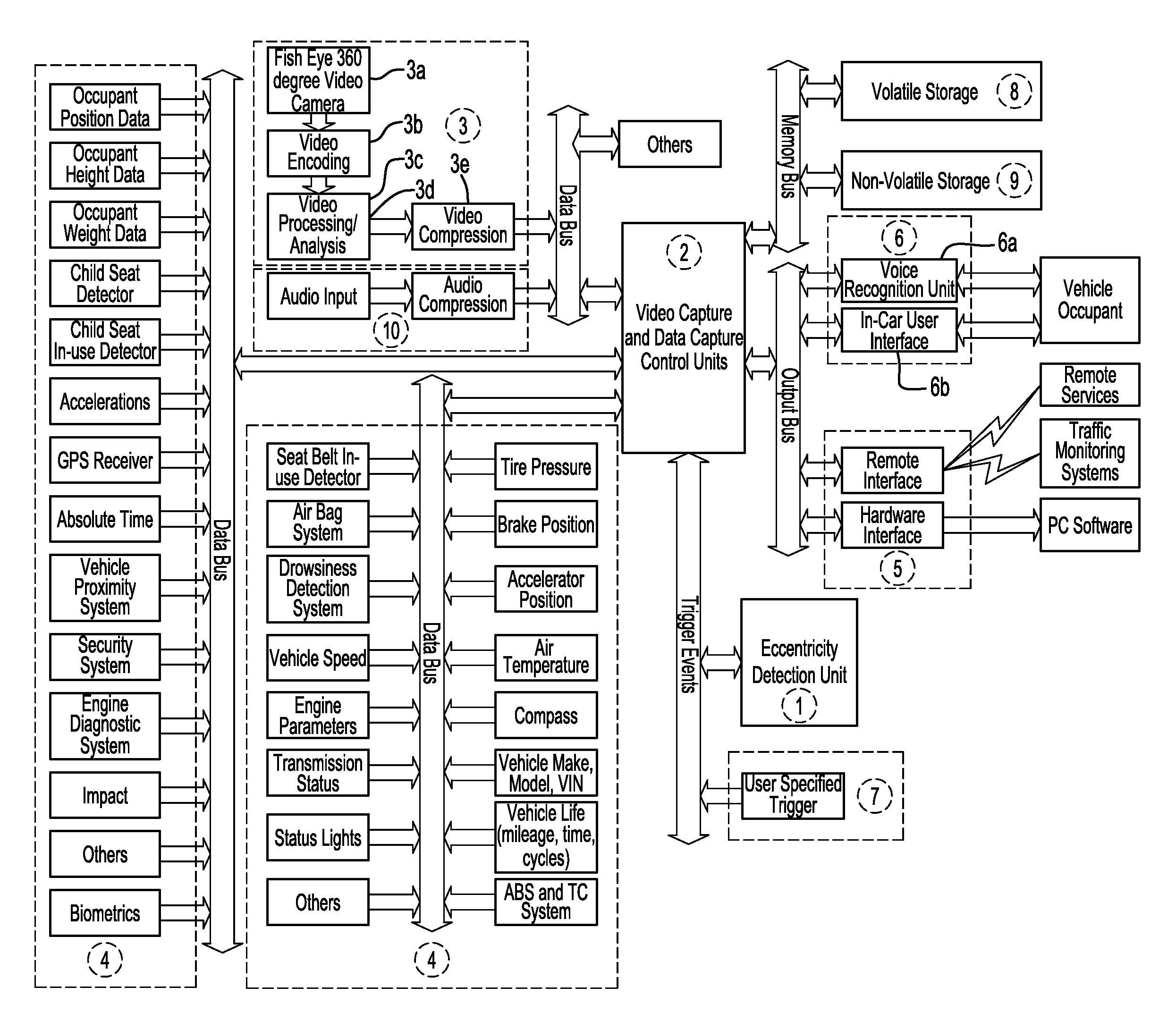
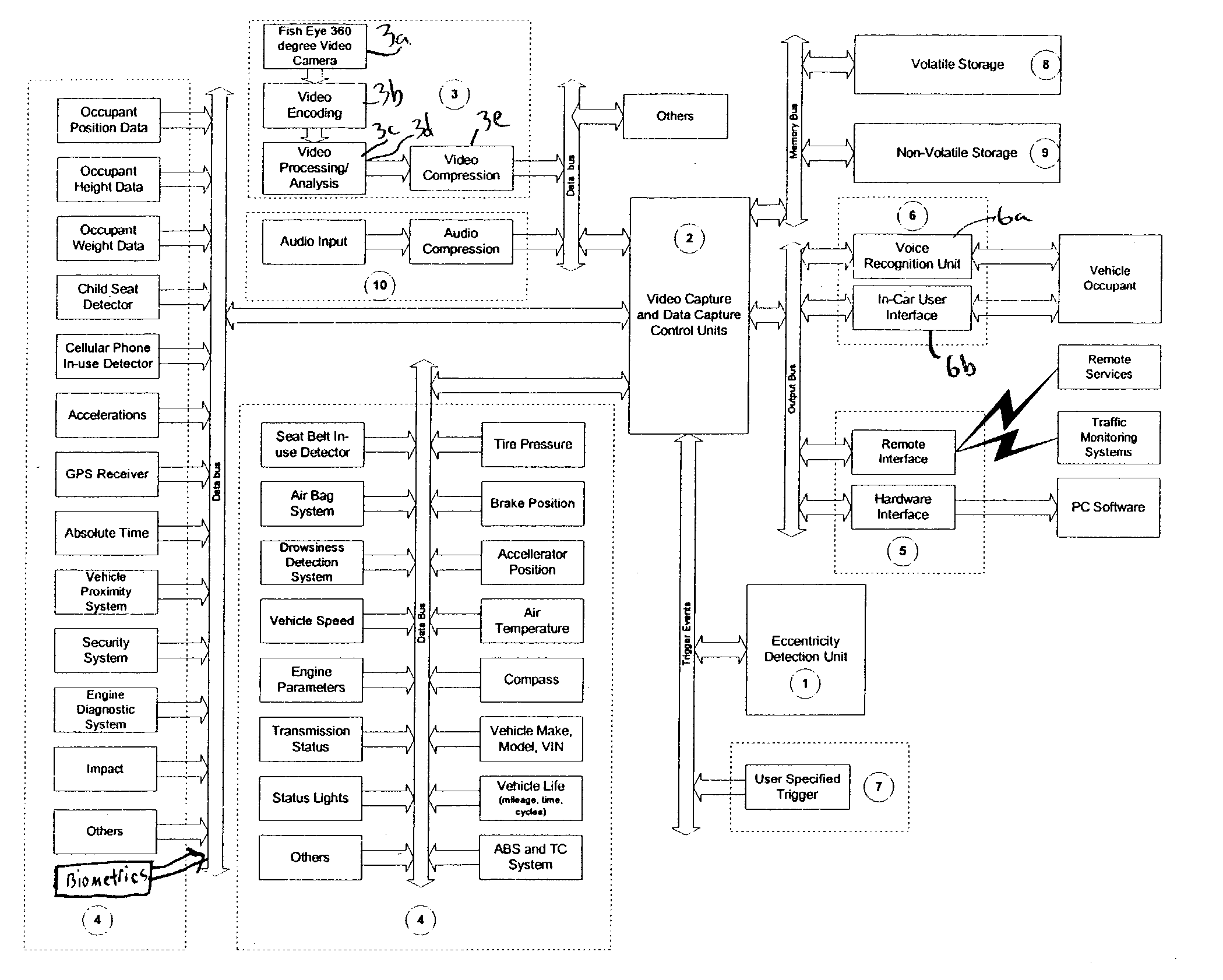
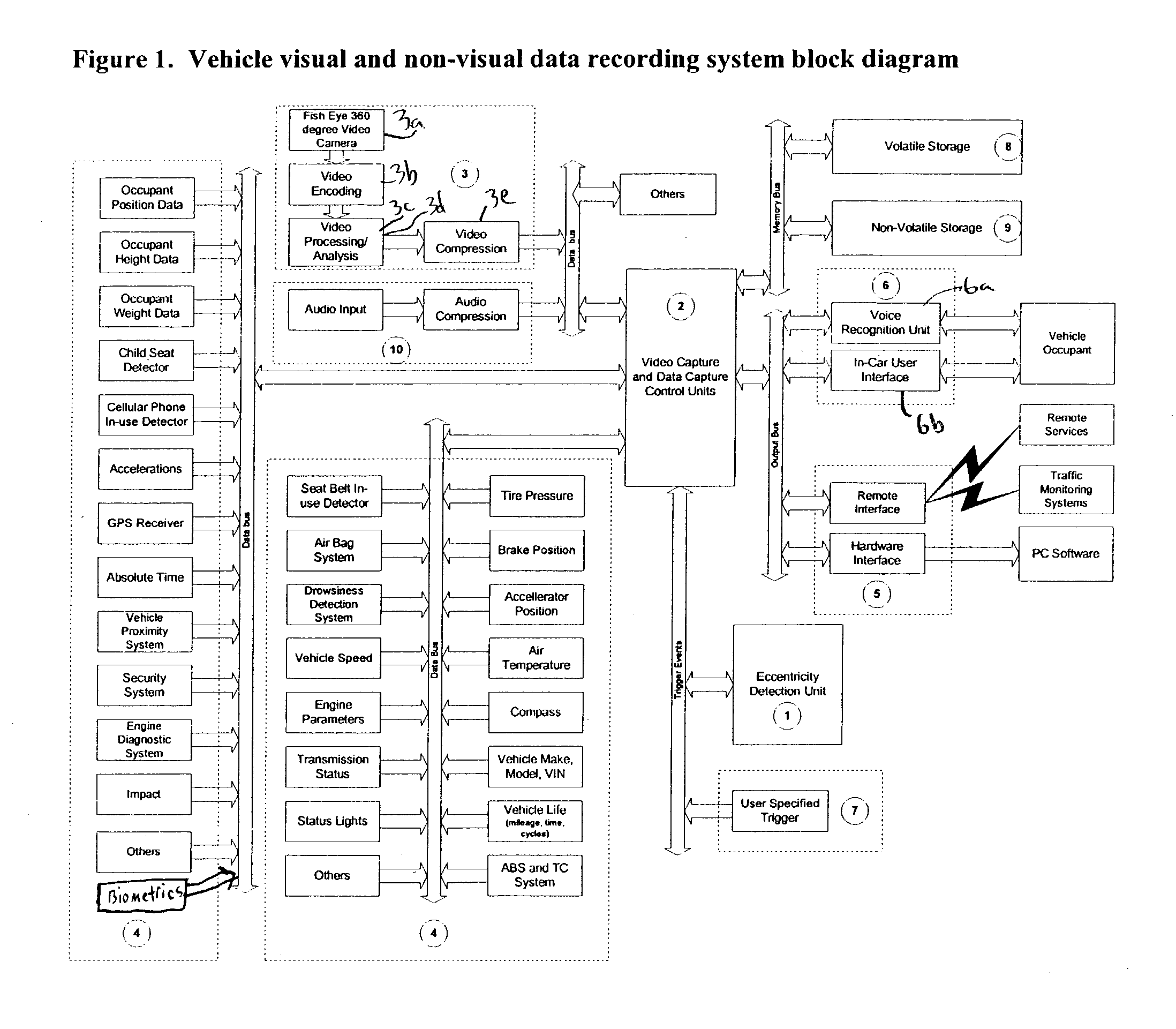
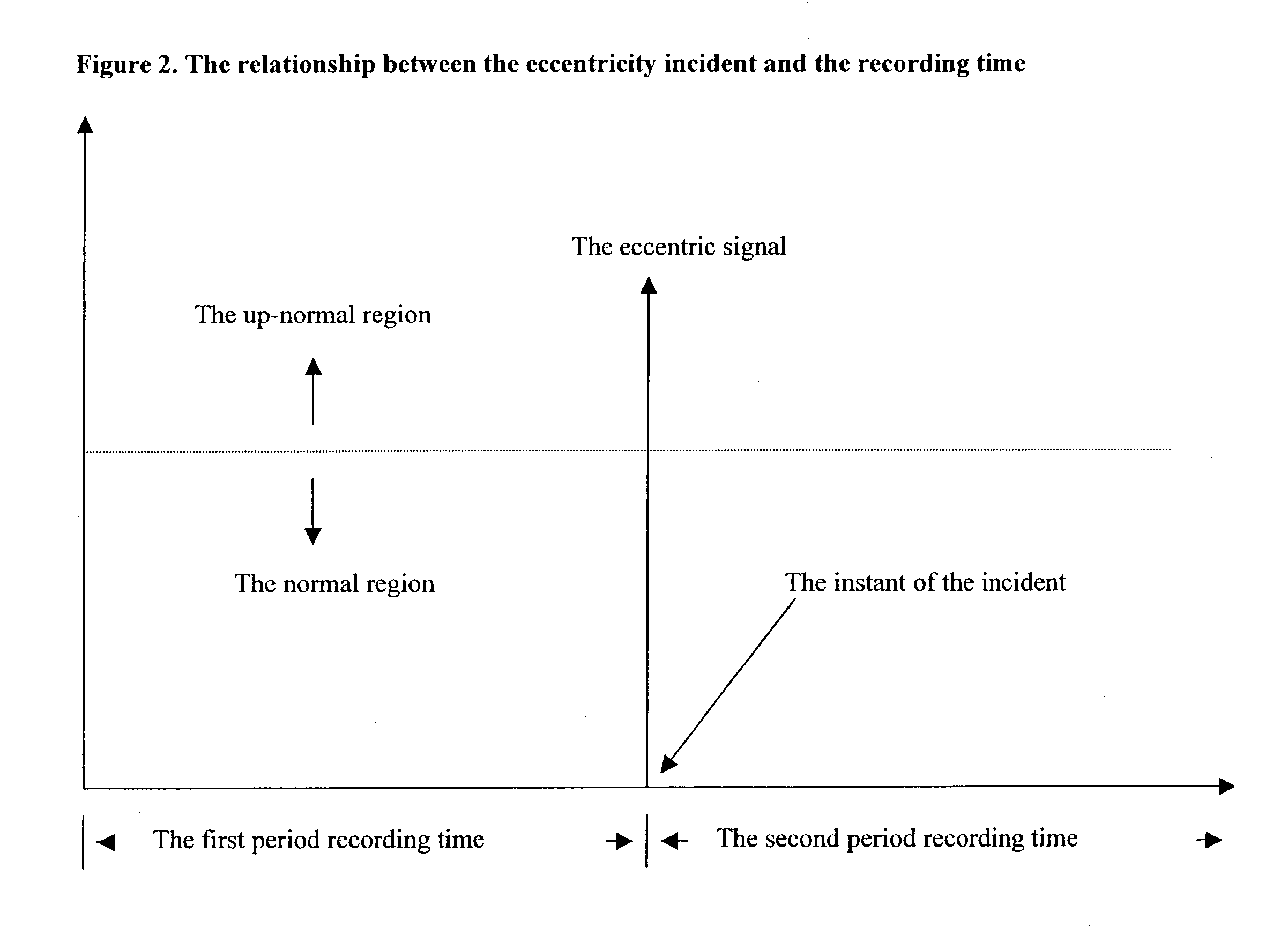
Vehicle visual and non-visual data recording system
ActiveUS7386376B2Vehicle testingRegistering/indicating working of vehiclesData synchronizationDriver/operator
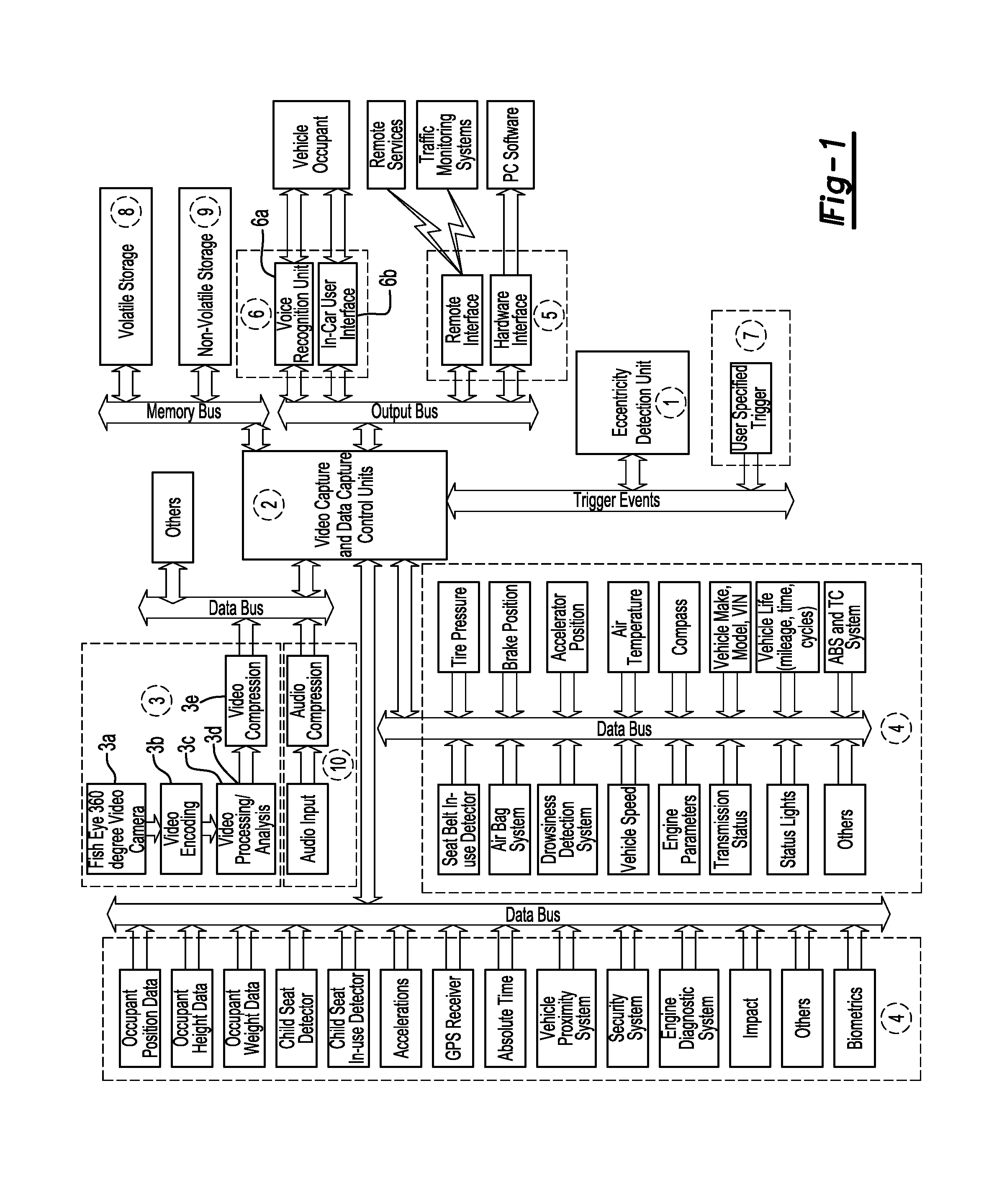
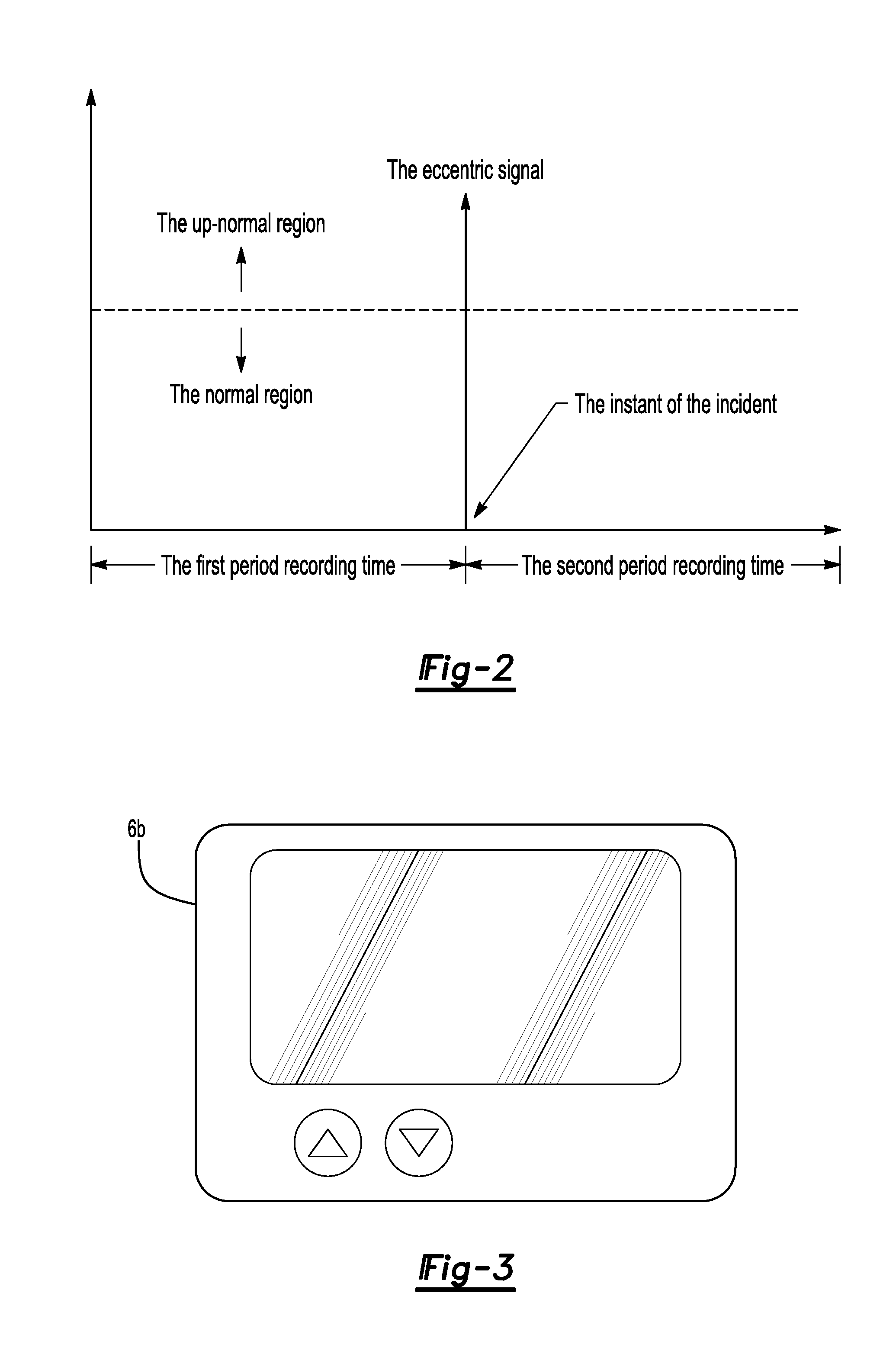
The system described in this invention can be used for monitoring and analyzing real time visual and non-visual information pertaining to the occupant, vehicle, and surroundings prior to, during and post eccentric operating conditions for a given period of time. The system stores vehicle and occupant data from sensors throughout the vehicle and also makes use of existing vehicle sensors that may already be present in the vehicle. The invention also includes a video recording module that makes use of a fish-eye camera to capture video from the inside and the outside of the vehicle. Real-time data analysis is performed to detect and to recognize vehicle occupants, and recognize impending eccentric events. Vehicle, occupant, and video data are stored in circular buffers. When an eccentric event, a collision for example, has been detected, the device continues to record data and video for a fixed period of time. Once this time has elapsed, the data is transferred from volatile to non-volatile memory for later retrieval. A computer may be used to retrieve and display the vehicle and occupant data in a synchronization with the video data for the purposes of accident recreation, driver or vehicle monitoring.
Owner:MINOTAUR SYST LLC
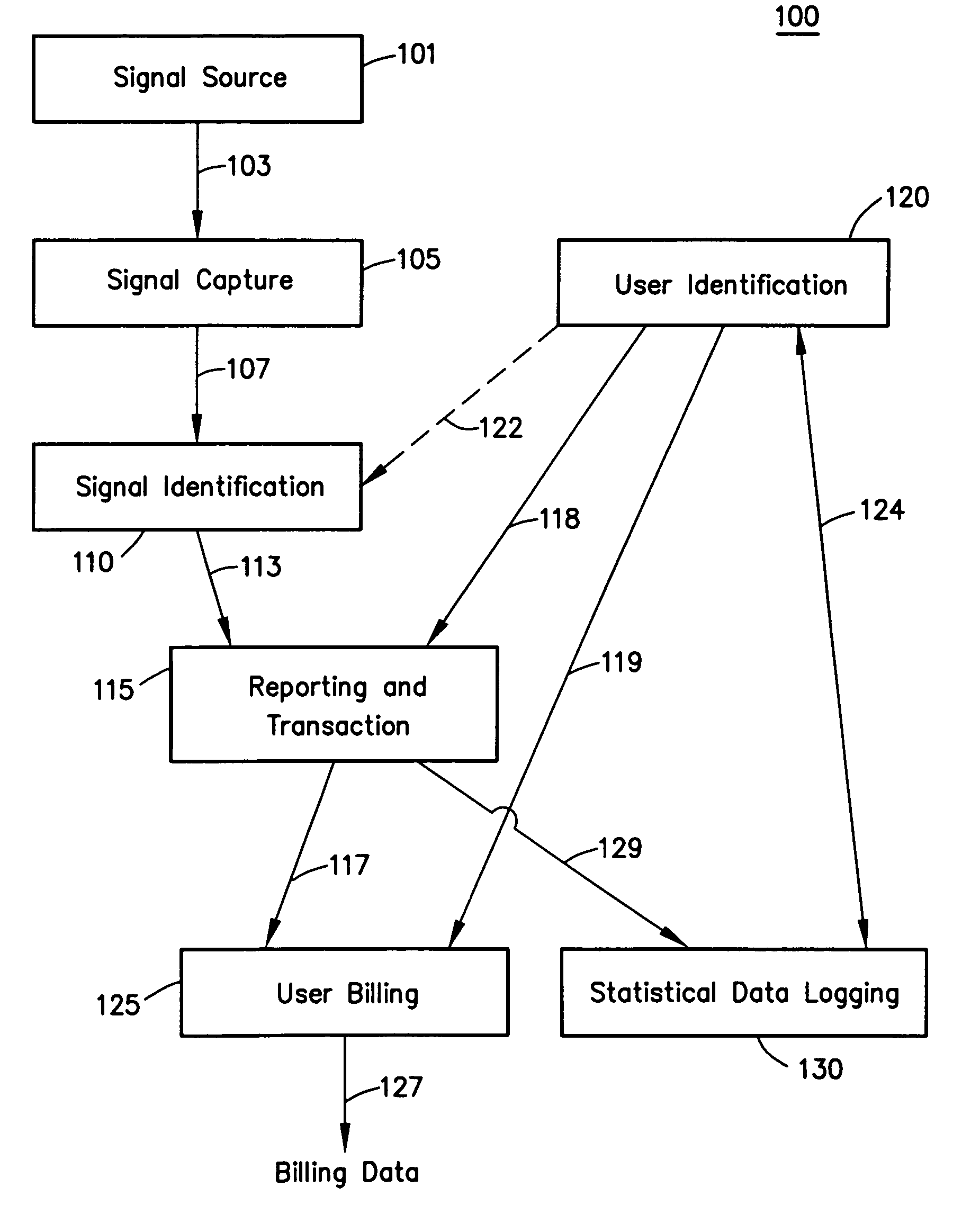
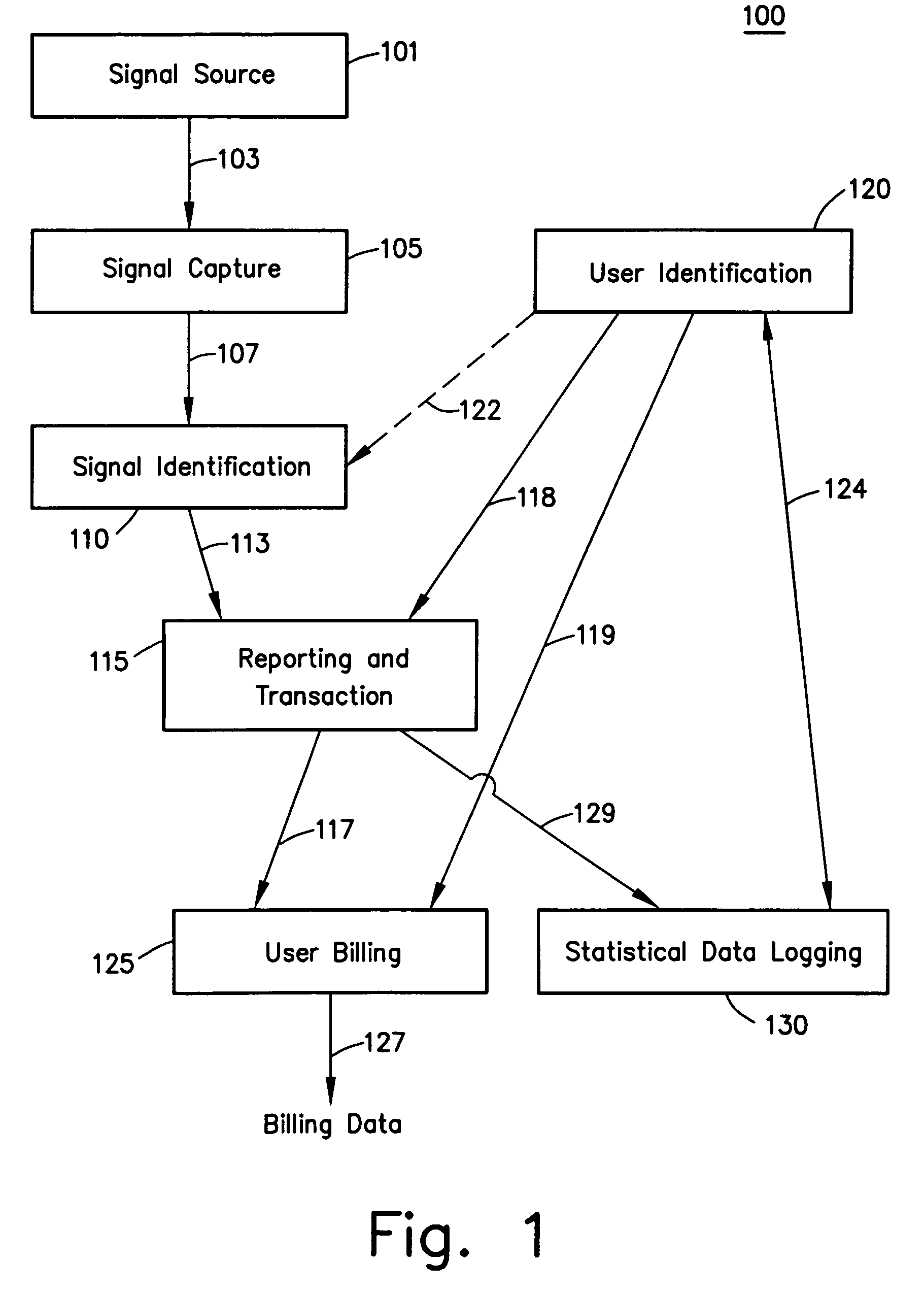
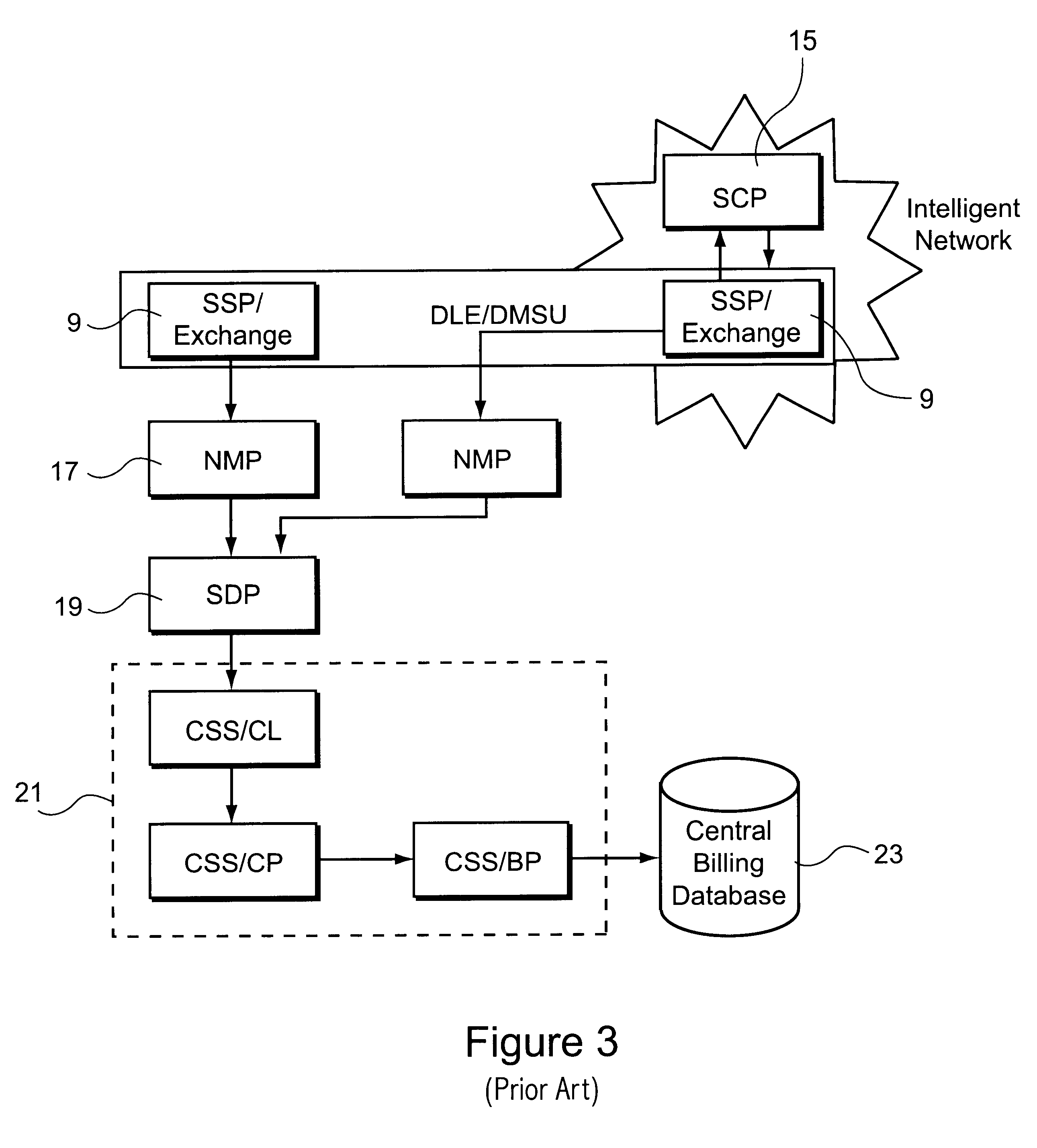
Billing system
A billing system for a telecommunications network uses a monitoring software agent to monitor messages, indicative of individual calls on the network, passing between a service switching point and a service control point. Call record information is extracted and is stored in a local call record database. Information from each call record database is then passed on to a central database, using updating mobile agents, the central database being accessible to such agents and report building agents which can extract billing information as requested by an operator. By monitoring the messages as they pass, the system can provide real time billing information without needing to poll the switch at the service switching point.
Owner:BRITISH TELECOMM PLC
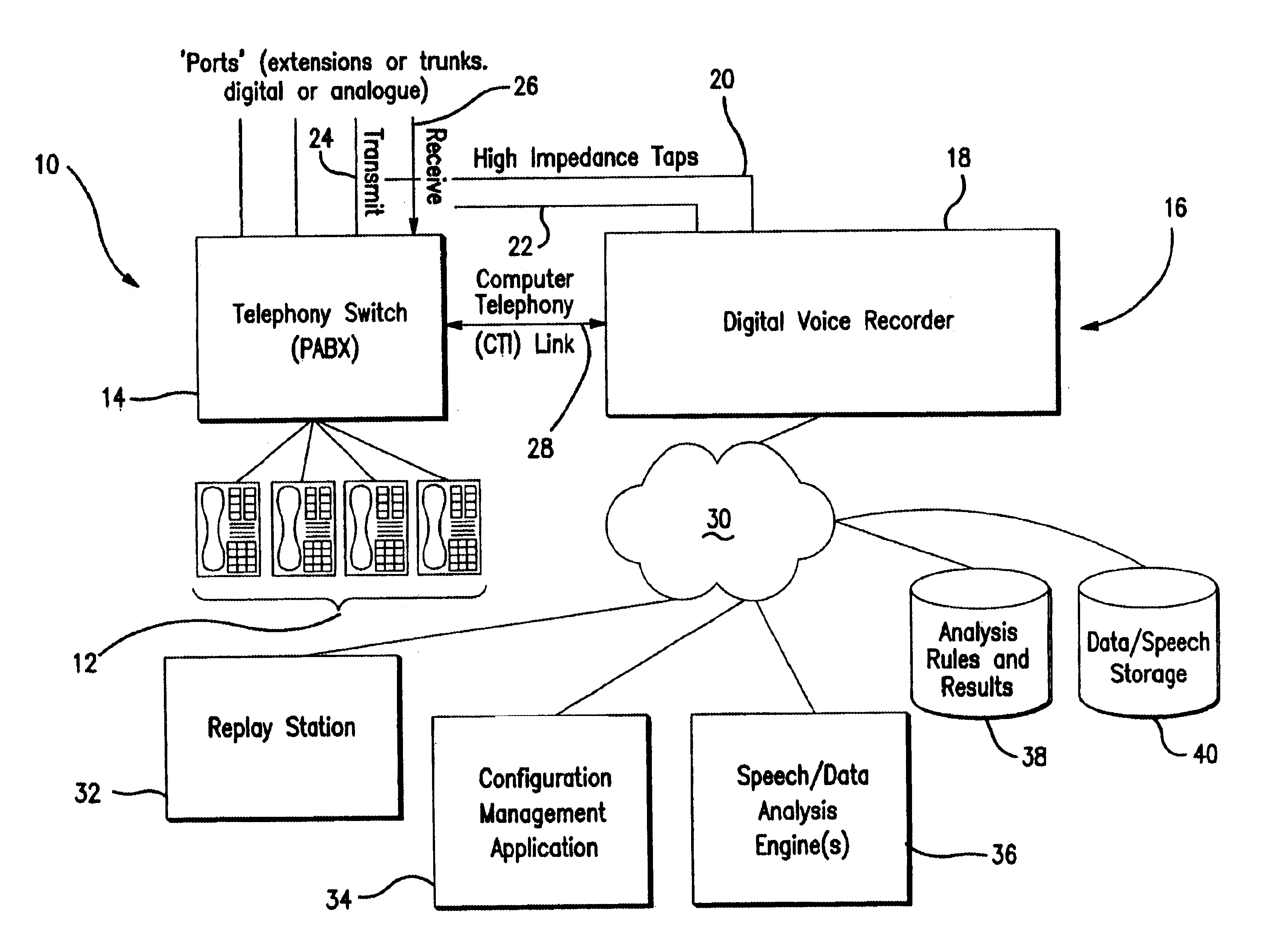
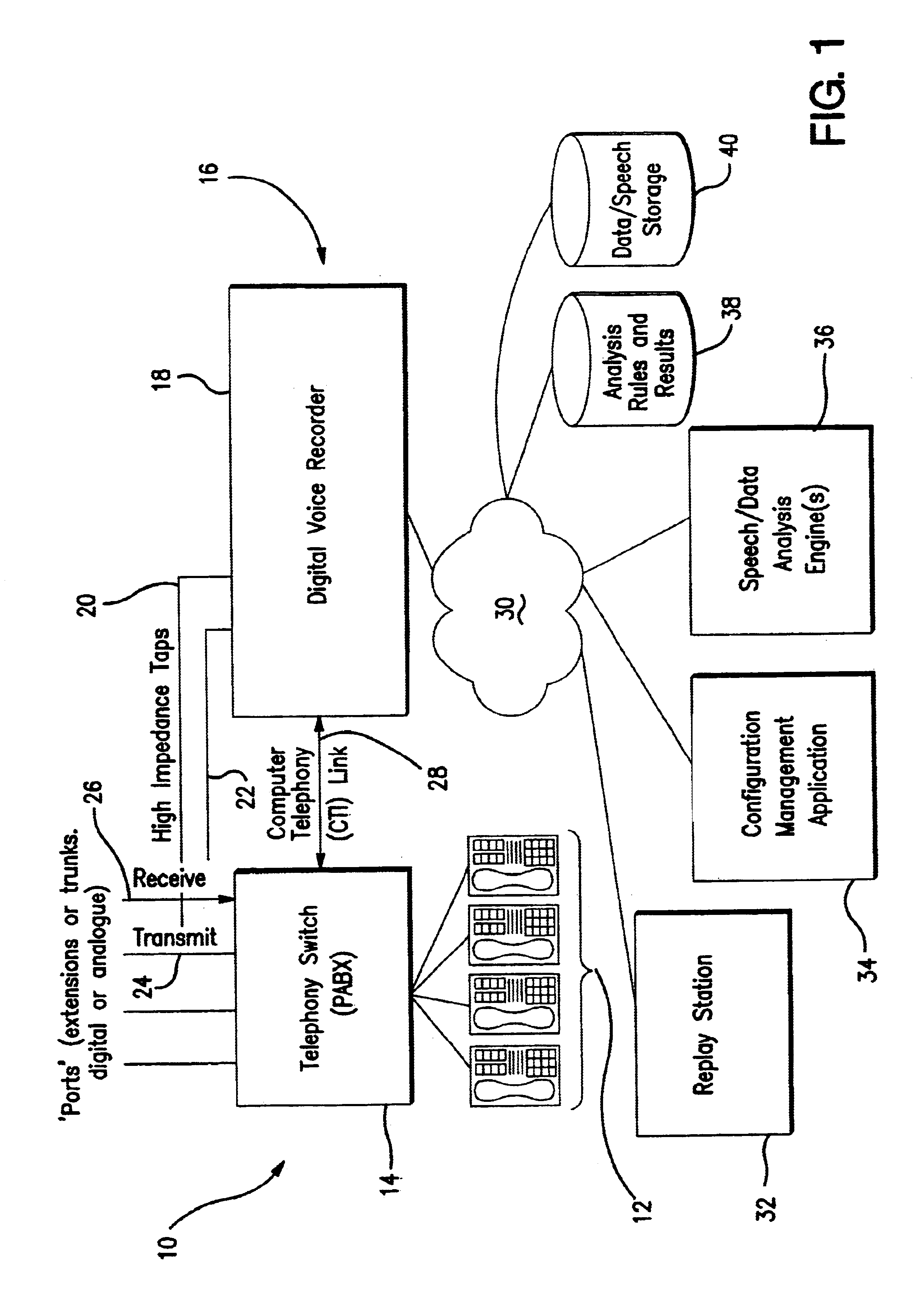
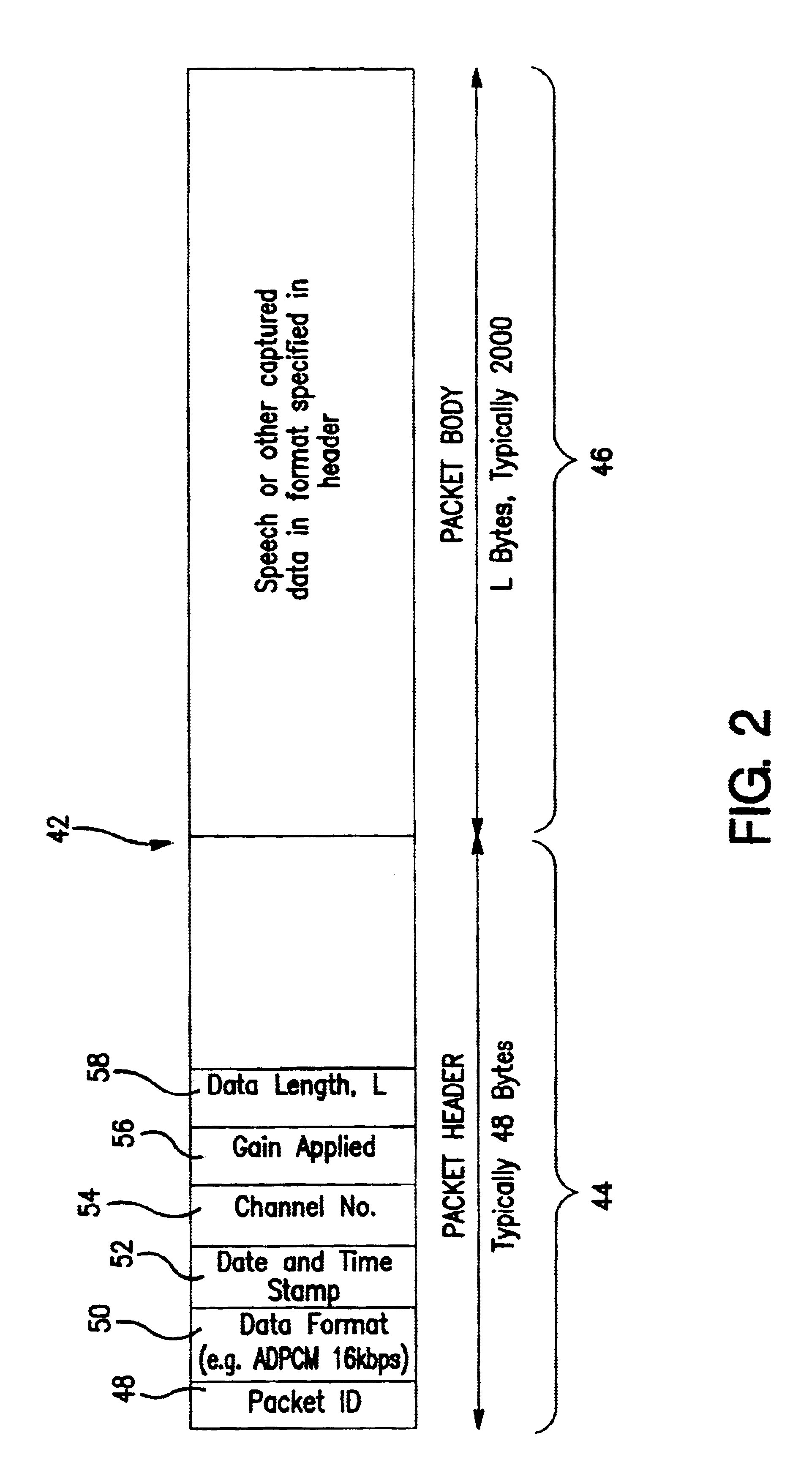
Signal monitoring apparatus analyzing voice communication content
InactiveUS6757361B2Easy to identifyInterconnection arrangementsSpecial service for subscribersVoice communicationSpeech sound
A signal monitoring apparatus and method involving devices for monitoring signals representing communications traffic, devices for identifying at least one predetermined parameter by analyzing the context of the at least one monitoring signal, a device for recording the occurrence of the identified parameter, a device for identifying the traffic stream associated with the identified parameter, a device for analyzing the recorded data relating to the occurrence, and a device, responsive to the analysis of the recorded data, for controlling the handling of communications traffic within the apparatus.
Owner:CREDIT SUISSE AS ADMINISTATIVE AGENT +1
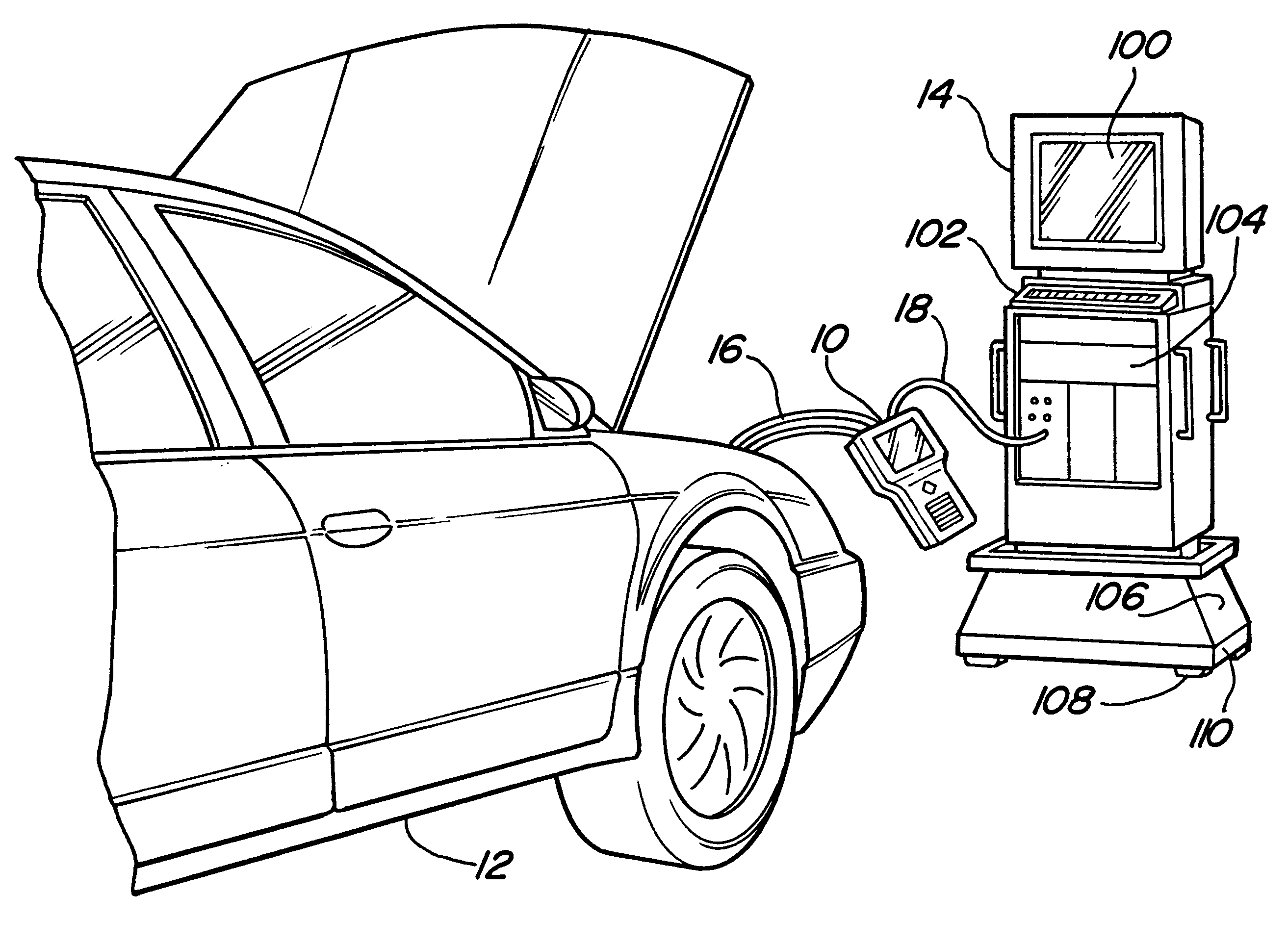
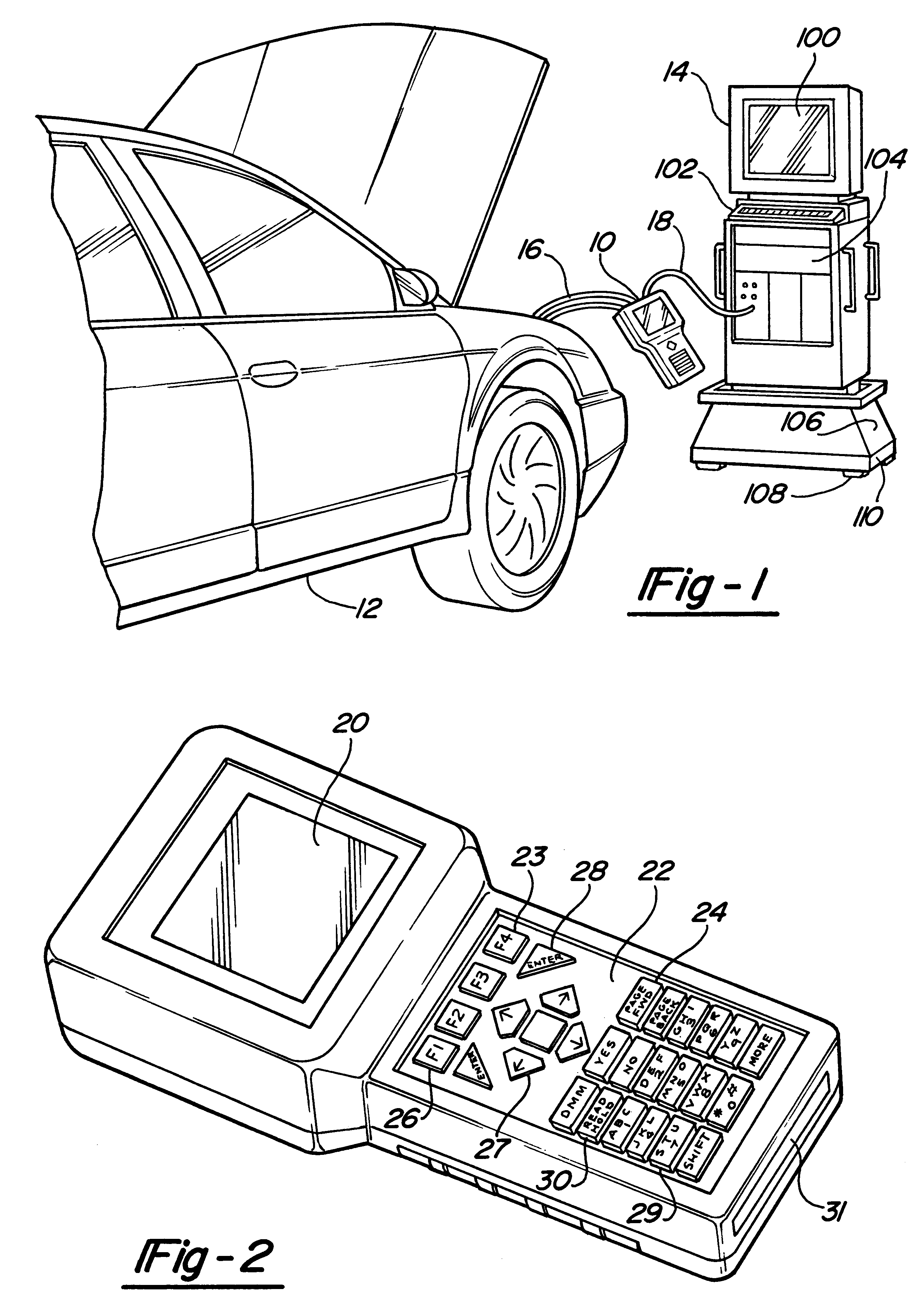
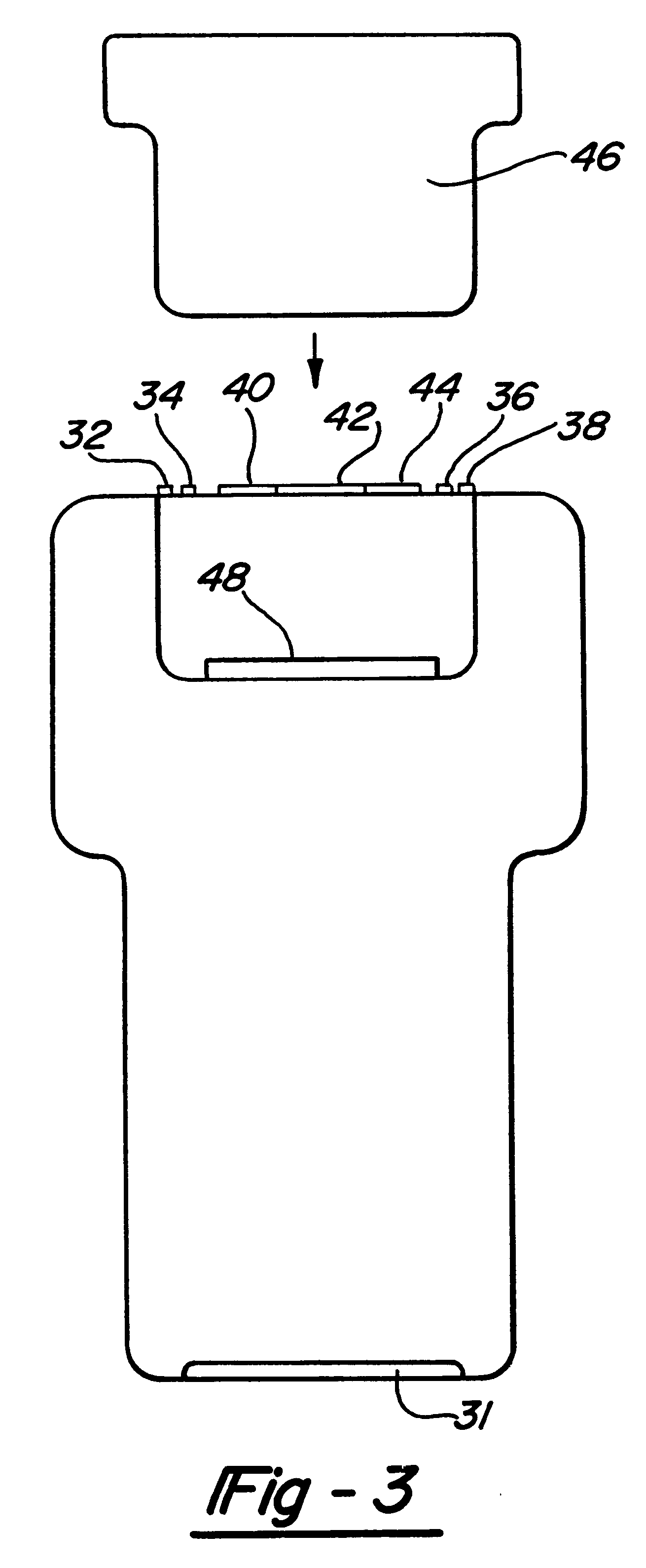
Automotive diagnostic service tool with hand held tool and master controller
InactiveUS6181992B1Reduce needQuick updateVehicle testingRegistering/indicating working of vehiclesOn boardMaster station
The present invention relates to a system and method for diagnosing and isolating problems and for monitoring operting conditions on an automobile. The system includes a hand held unit and a master station which can operate alone or in unison to accomplish functions such as logging and displaying data on a real-time basis, logging data remotely and displaying the data at a later time, diagnosing fault conditions, monitoring operating parameters, reprogramming on-board vehicle controllers, displaying service manual and service bulletin pages and ordering parts on-line.
Owner:FCA US
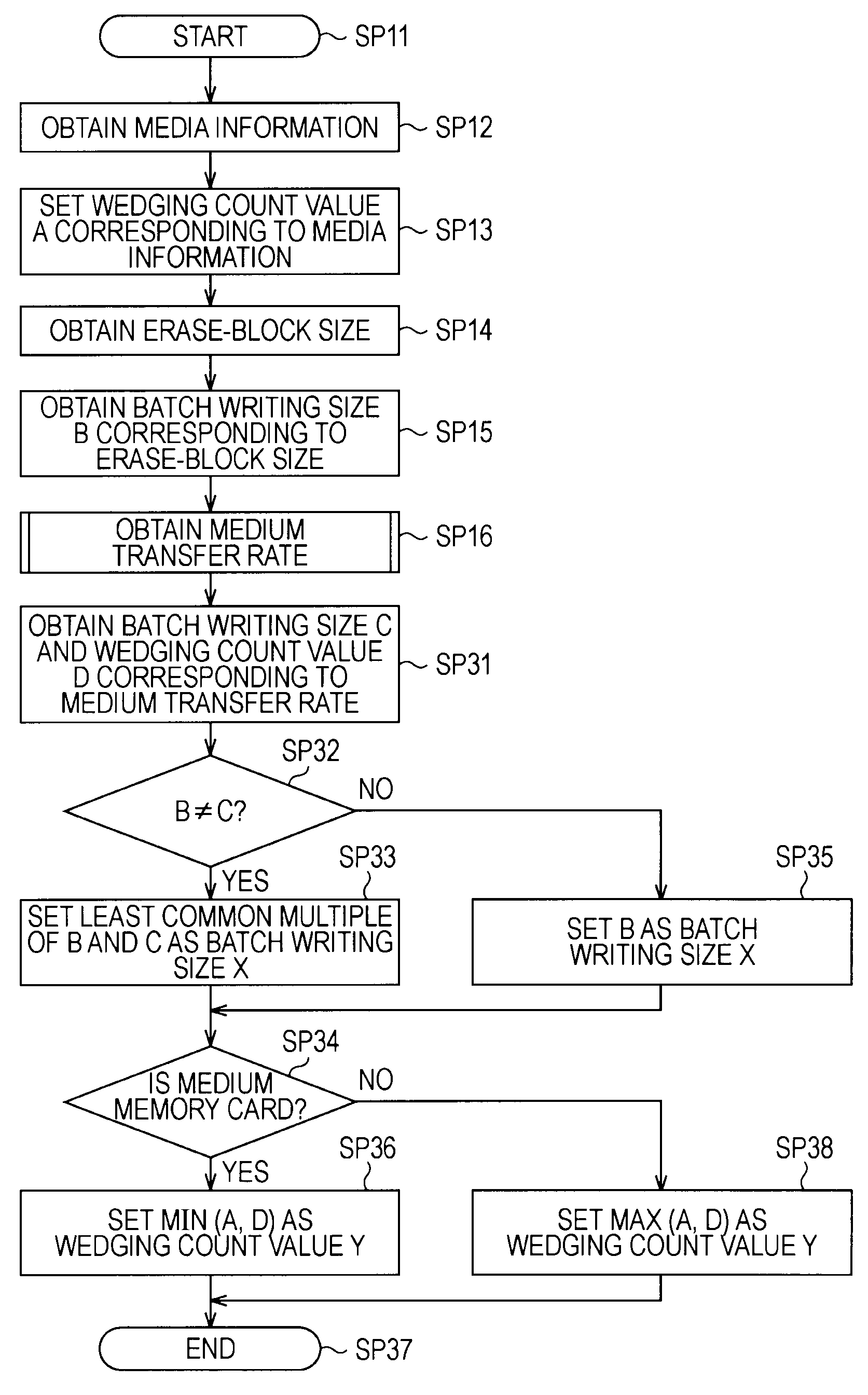
Recording apparatus, recording method, program for recording method, and storage medium that stores program for recording method
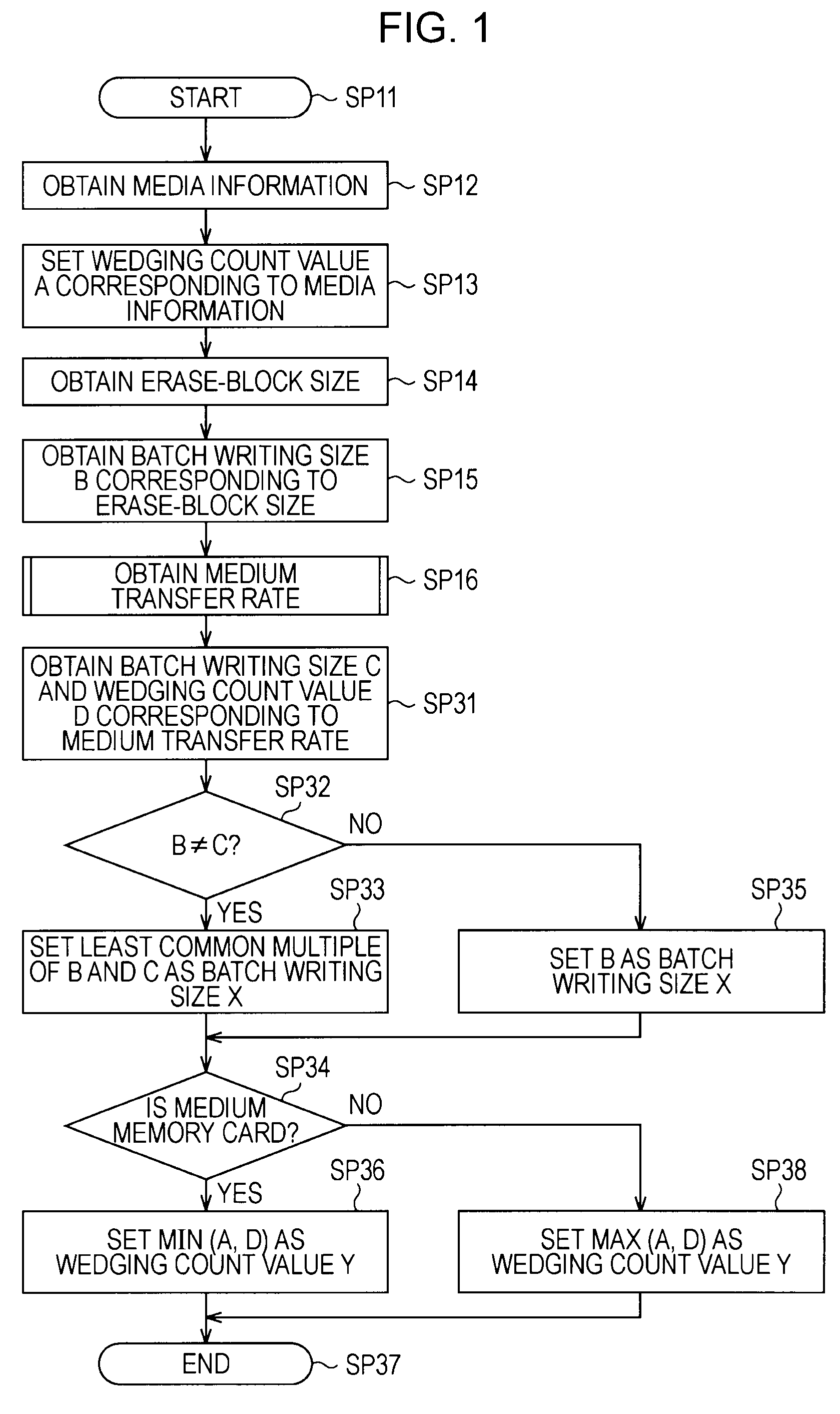
InactiveUS20090198889A1Suppress significant in serviceable lifeIncrease in sizeRecording carrier detailsInput/output to record carriersData recordingRecords management
A recording apparatus includes: a type detecting section that detects a type of storage medium; an erase-block size detecting section that detects an erase-block size of the storage medium; a recording section that records desired data to a data area in the storage medium and records management information of the data area to a management area in the storage medium; and a control section that controls the recording section by issuing a command to the recording section, on the basis of results of the detection. Each time a certain amount of data is recorded to the data area, the control section updates the management information in accordance with the recording, and when the storage medium is a storage medium in which recorded data is updated for each erase-block size, the control section increases the certain amount of data according to an increase in the erase-block size.
Owner:SONY CORP
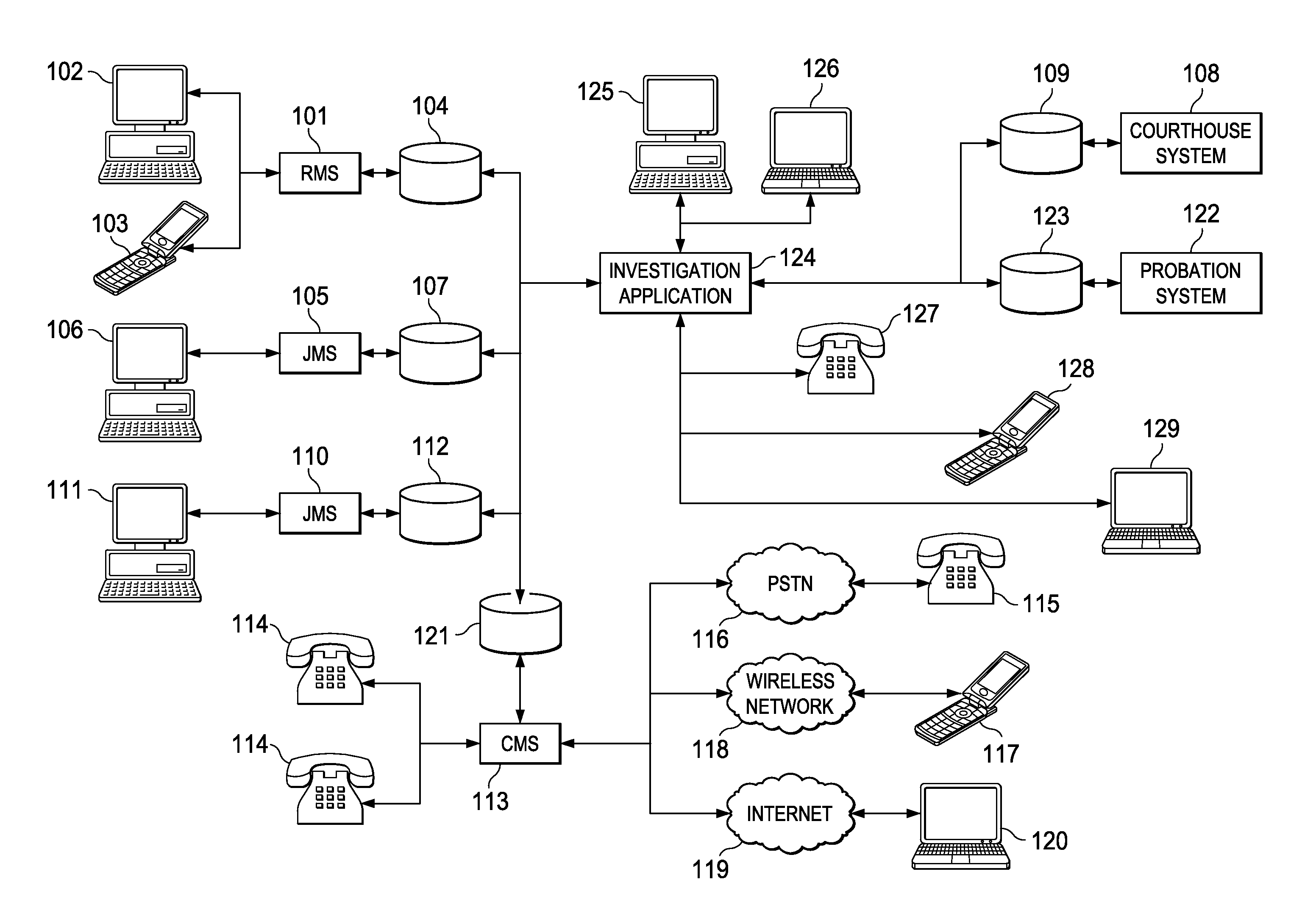
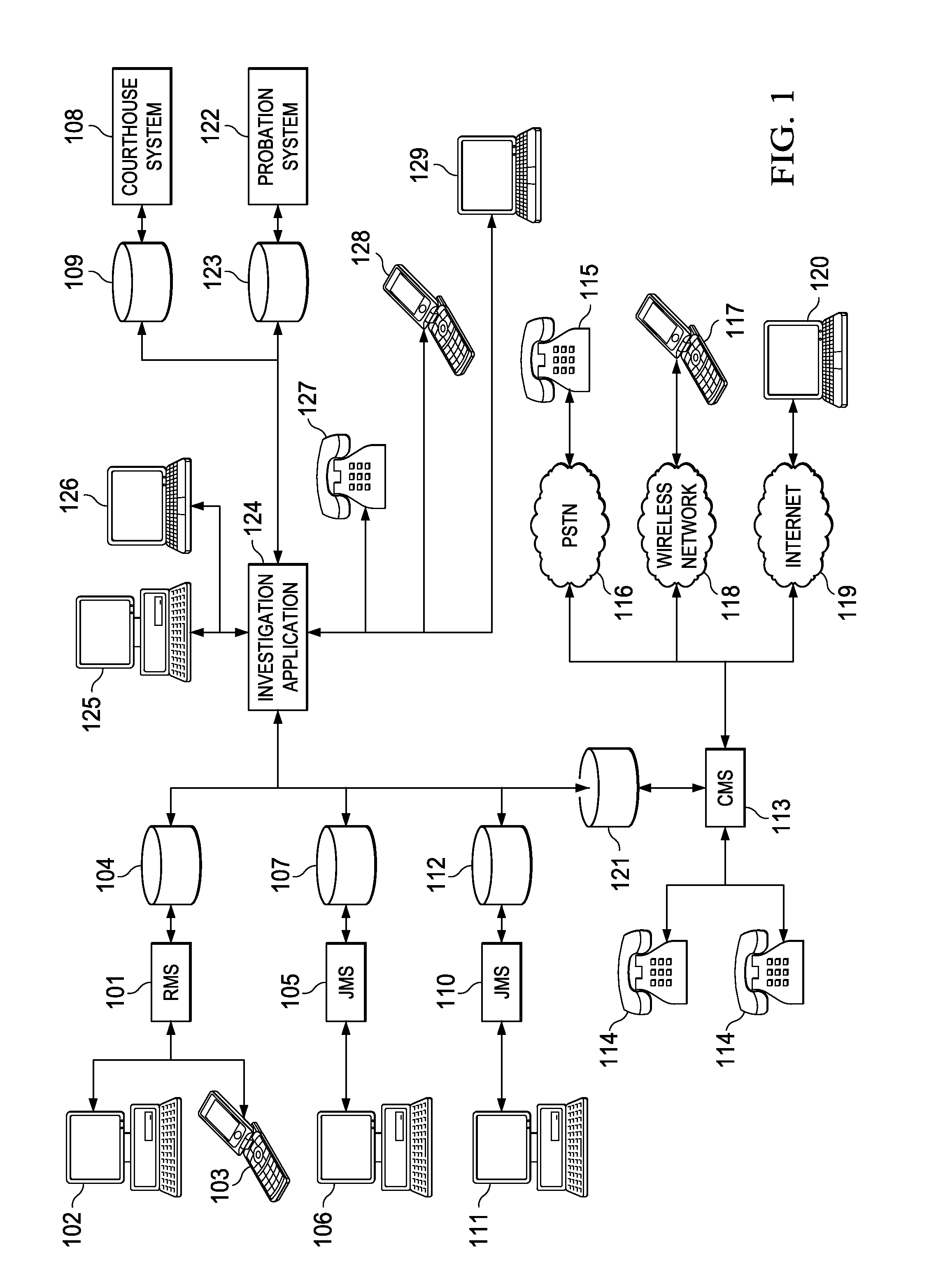
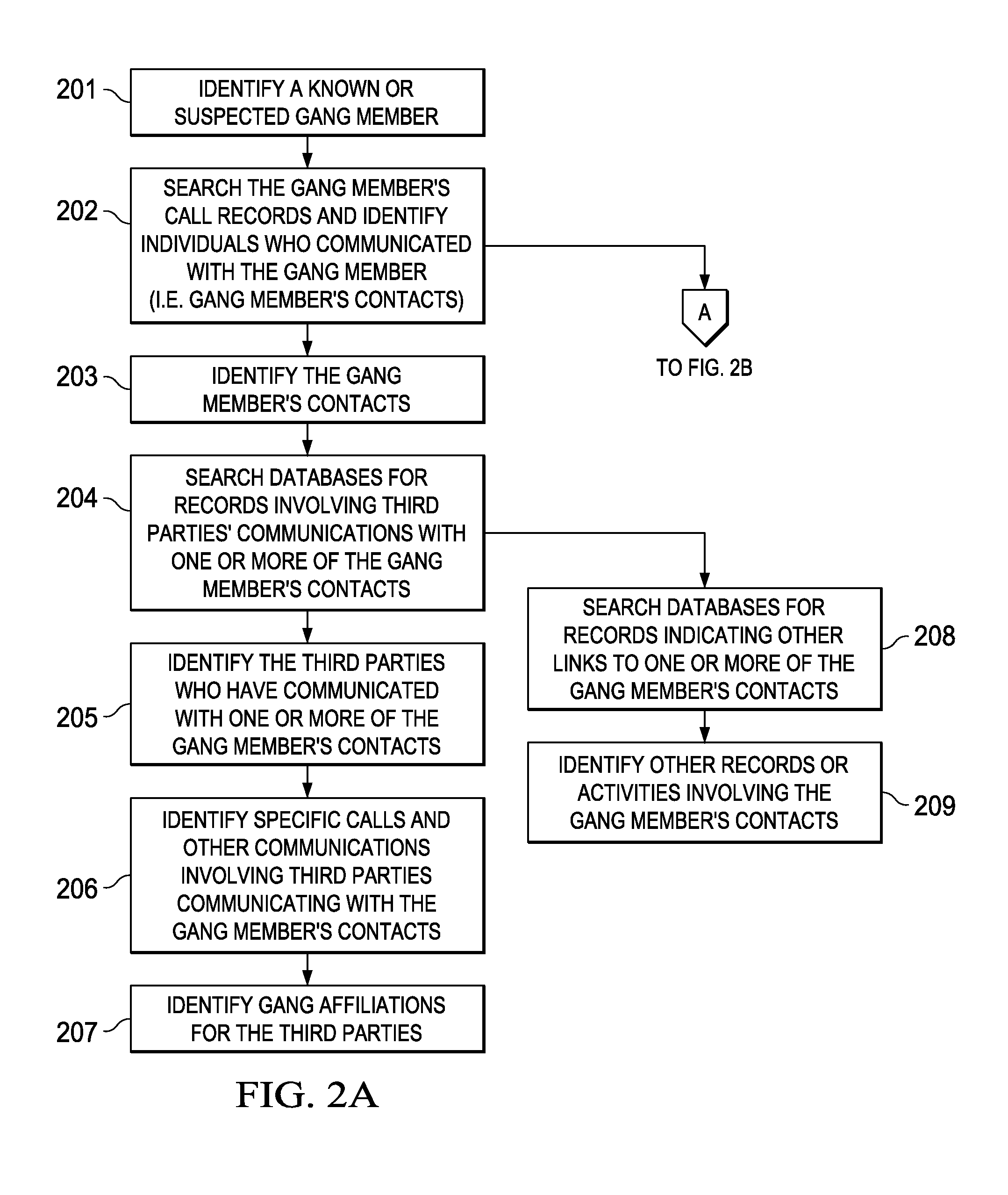
System and method for identifying members of a gang or security threat group
InactiveUS7805457B1Effectively “ connectingData processing applicationsDigital data processing detailsGroup systemData science
System and method for monitoring activity of detainees comprising identifying a detainee who is affiliated with a gang, searching one or more databases for information associated with the detainee, and correlating the information to identify individuals who may be affiliated with the gang. The databases may include call record databases, and the information associated with the detainee may include individuals called by the detainee, individuals who visit the detainee, telephone numbers called by the detainee, and sources of funding for the detainee's calls voice and / or facial biometric identifiers. An alert may be triggered when the detainee calls a specified individual or telephone number.
Owner:SECURUS TECH
Text mining system for web-based business intelligence applied to web site server logs
InactiveUS7330850B1Data processing applicationsMultiple digital computer combinationsClustered dataWeb site
A text mining system for collecting business intelligence about a client, as well as for identifying prospective customers of the client, for use in a lead generation system accessible by the client via the Internet. The text mining system has various components, including a data acquisition process that extracts textual data from Internet web sites, including their logs, content, processes, and transactions. The system compares log data to content and process data, and relates the results of the comparison to transaction data. This permits the system to provide aggregate cluster data representing statistics useful for customer lead generation.
Owner:CALLAHAN CELLULAR L L C +1
Vehicle visual and non-visual data recording system
ActiveUS20030154009A1Vehicle testingRegistering/indicating working of vehiclesData synchronizationDriver/operator
The system described in this invention can be used for monitoring and analyzing real time visual and non-visual information pertaining to the occupant, vehicle, and surroundings prior to, during and post eccentric operating conditions for a given period of time. The system stores vehicle and occupant data from sensors throughout the vehicle and also makes use of existing vehicle sensors that may already be present in the vehicle. The invention also includes a video recording module that makes use of a fish-eye camera to capture video from the inside and the outside of the vehicle. Real-time data analysis is performed to detect and to recognize vehicle occupants, and recognize impending eccentric events. Vehicle, occupant, and video data are stored in circular buffers. When an eccentric event, a collision for example, has been detected, the device continues to record data and video for a fixed period of time. Once this time has elapsed, the data is transferred from volatile to non-volatile memory for later retrieval. A computer may be used to retrieve and display the vehicle and occupant data in a synchronization with the video data for the purposes of accident recreation, driver or vehicle monitoring.
Owner:MINOTAUR SYST LLC
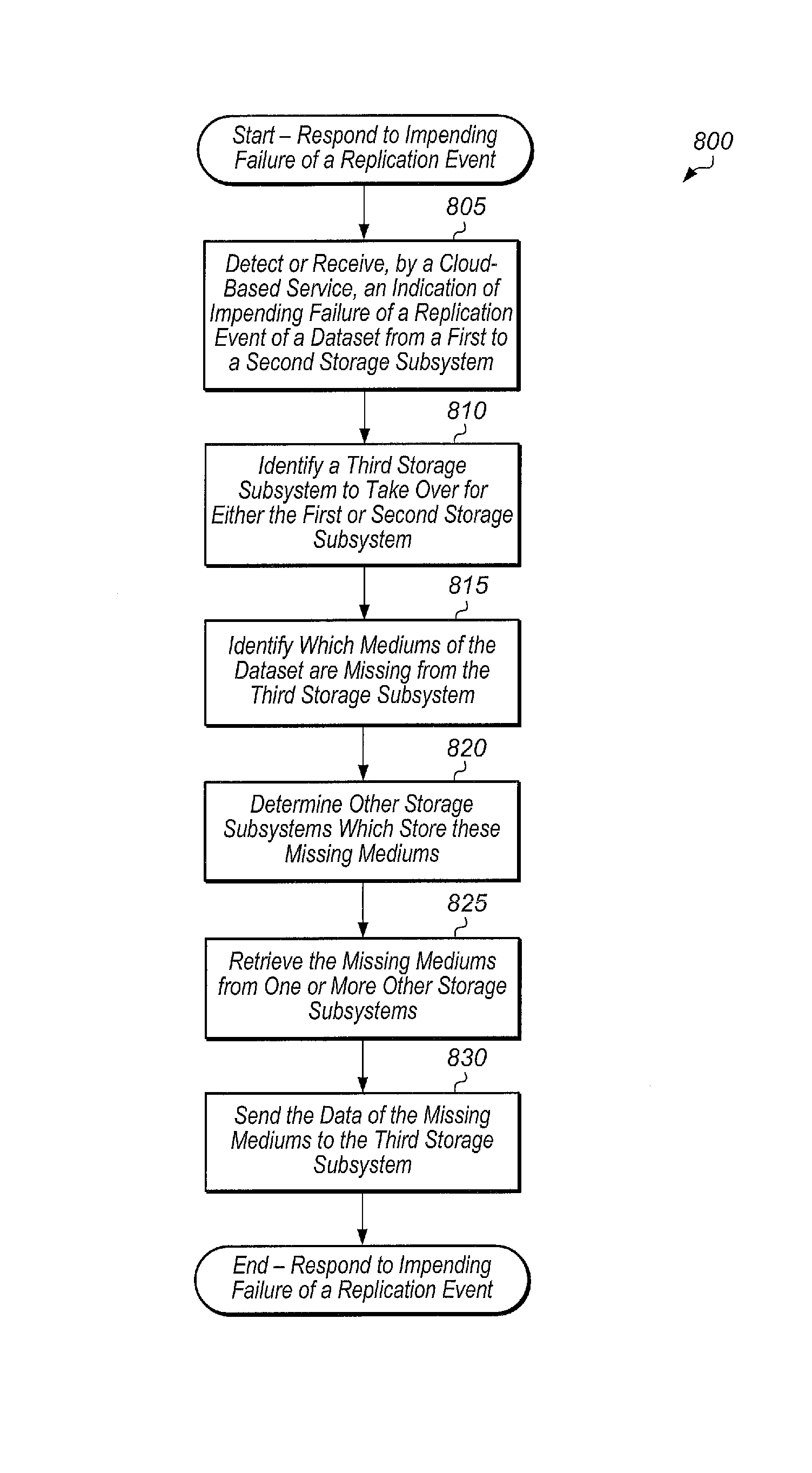
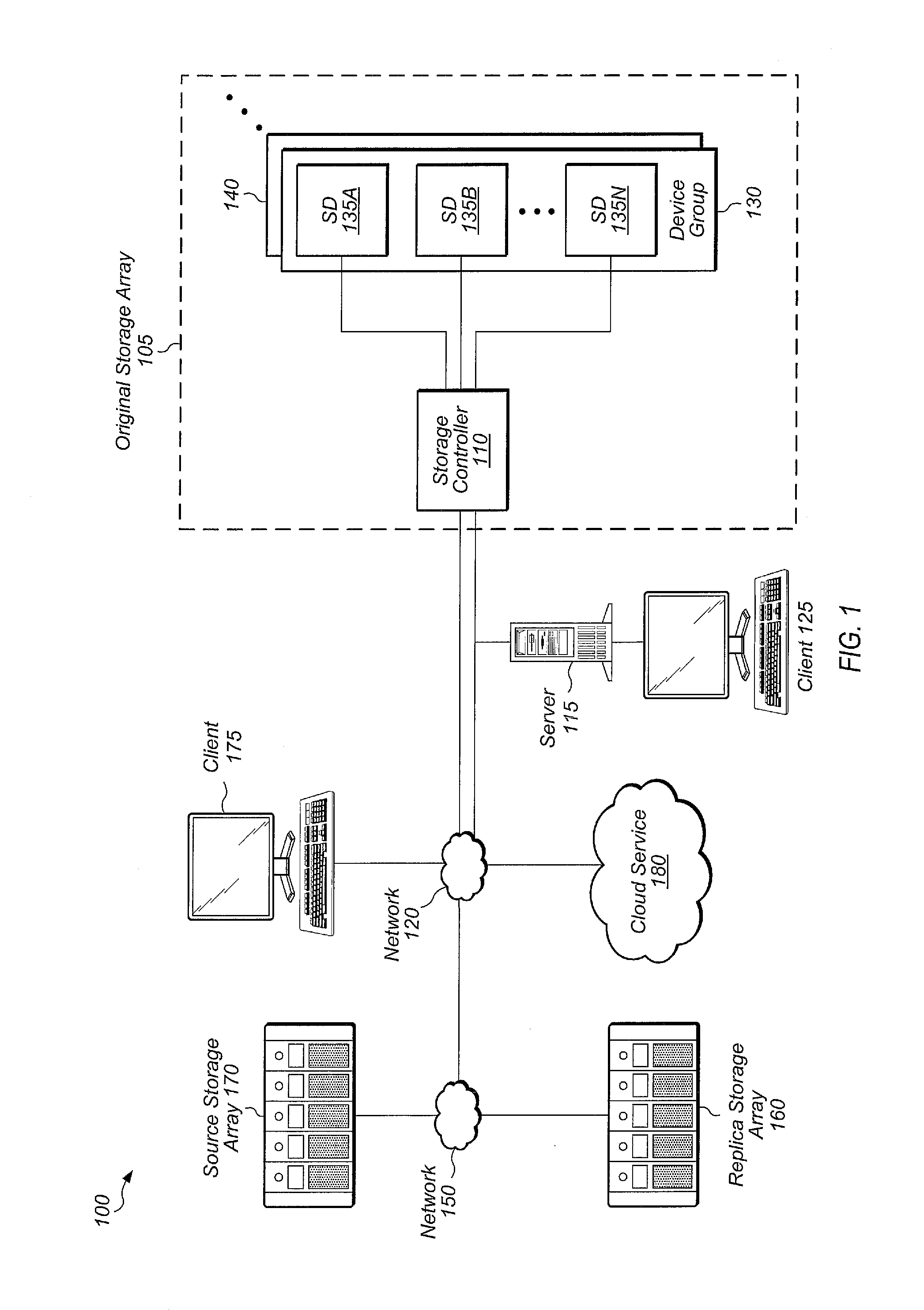
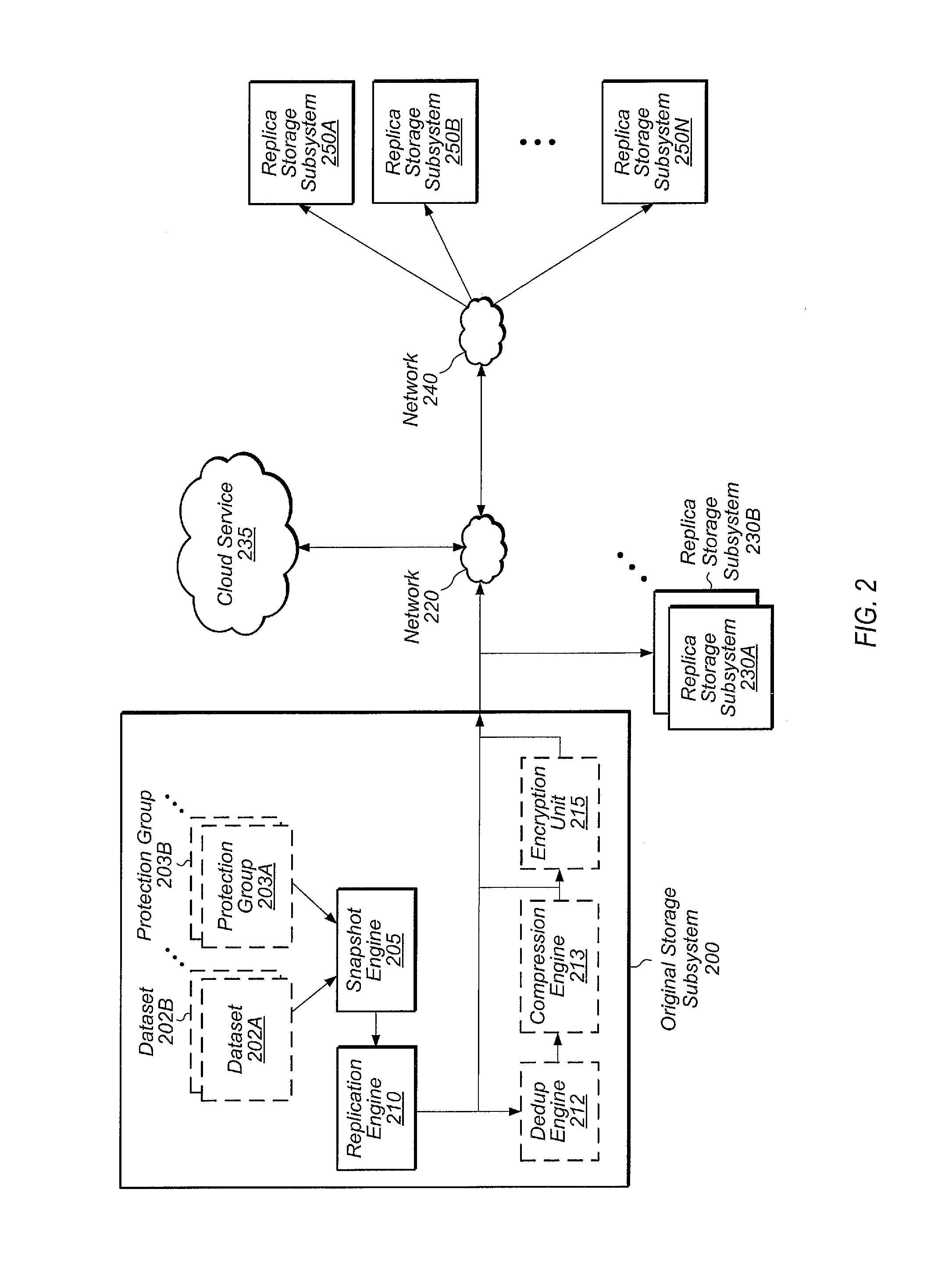
Cloud alert to replica
InactiveUS9552248B2Non-redundant fault processingRedundant operation error correctionComputer hardwareData set
Systems, methods, and computer readable storage mediums for generating an alert on a failure of a storage subsystem to phone home to the cloud in a replication environment. A dataset is replicated from a first storage subsystem to a second storage subsystem. The first and second storage subsystems also phone home log data to the cloud on a periodic basis. In response to detecting a failure of the first storage subsystem to phone home, the cloud generates and sends an alert to the second storage subsystem. In response to receiving this alert, the second storage subsystem starts disaster recovery operations for the dataset.
Owner:PURE STORAGE
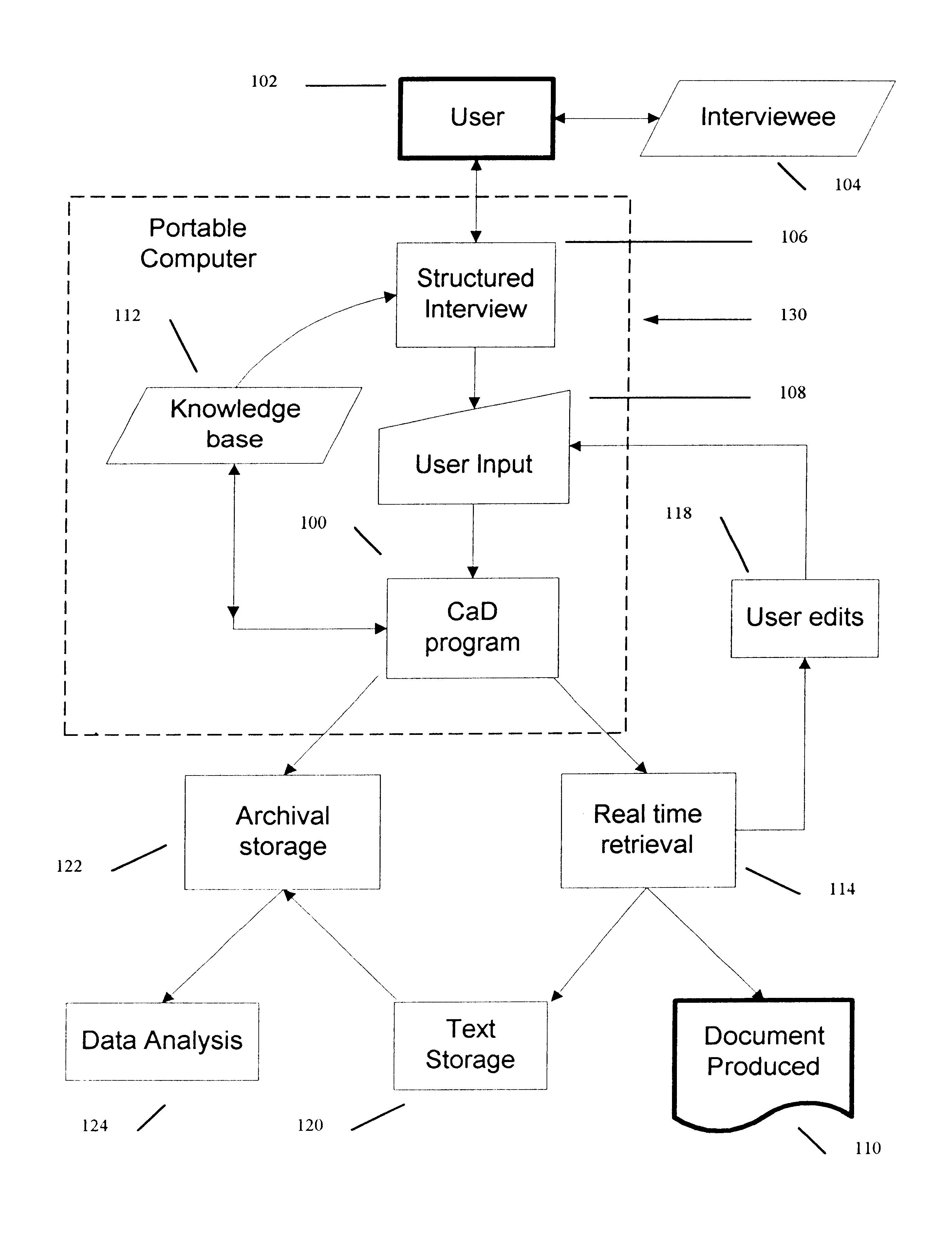
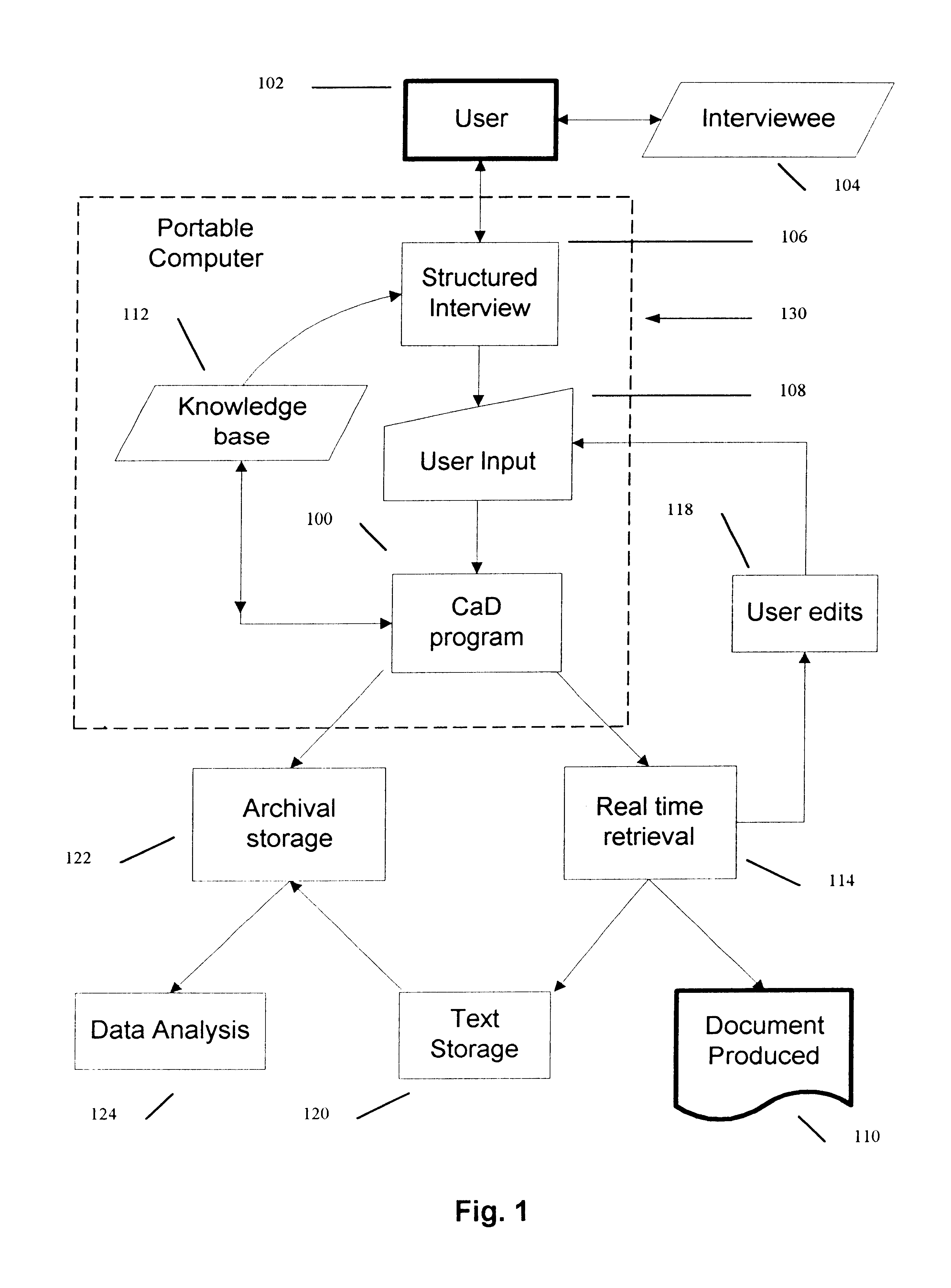
Method for production of medical records and other technical documents
InactiveUS6684188B1Improve overall utilizationEffective use timeData processing applicationsSurgeryMedical recordDocument preparation
A computer implemented system for the production of medical records, legal documents and other frequently produced semi-technical documents. This is accomplished by generating an intelligent computer-guided interview and the use of serialized scriptable objects. Major program elements include a knowledge base text file, a parse engine, and an execution module. The knowledge base uses a unique rule syntax. The parse engine converts the textual knowledge base file to a compiled binary representation which can then be interpreted by the execution module. The execution module leads the user through the interview by generating a series of questions and presents possible answers in the form of pick lists. The data is recorded with a computer pen and collated into a document file. This file is coded in binary format and can be written to and recalled from disk. If the file is recalled from disk the user can continue to answer questions or change answers previously given. The result is a mobile computing system whereby data is input in a structured format. When the program is executed the user is prompted for answers to questions and, based upon the user's response, the final document can change considerably. Depending upon each answer, the program may change the subsequent questions being asked, change the list associated with a question, change the text being generated, or change the entire structure of the document. The data collected may be also be stored in a database for analysis at a later date. Finally, the data collected is output in a narrative text format which can be tailored according to the traditions and expectations of the user's profession. The program will output the text via a printer or it can be transmitted via electronic means.
Owner:MITCHELL GEOFFREY C +1
Multi-tenant audit awareness in support of cloud environments
ActiveUS20120179646A1Facilitate compliance analysisEasy to analyzeDatabase management systemsDigital data processing detailsData miningComputer science
A cloud enablement aggregation proxy (CEAP) receives and processes audit data from audited resources before such data is stored in a database. The CEAP manages log data for resources hosted in a multi-tenant shared pool of configurable computing resources (e.g., a compute cloud). A method for managing log data begins by the proxy aggregating and normalizing log information received from a plurality of the resources. The aggregated and normalized log information is then parsed to identify a tenant associated with each of a set of transactions. For each of the set of transactions, the CEAP annotates log data associated with the tenant and the particular transaction to include a tenant-specific identifier. An optional tenant separation proxy (TSP) separates the annotated log data on a per tenant basis prior to storage, and the tenant-specific log data may be stored in per tenant data structures or dedicated tenant log event databases to facilitate subsequent compliance or other analysis.
Owner:IBM CORP
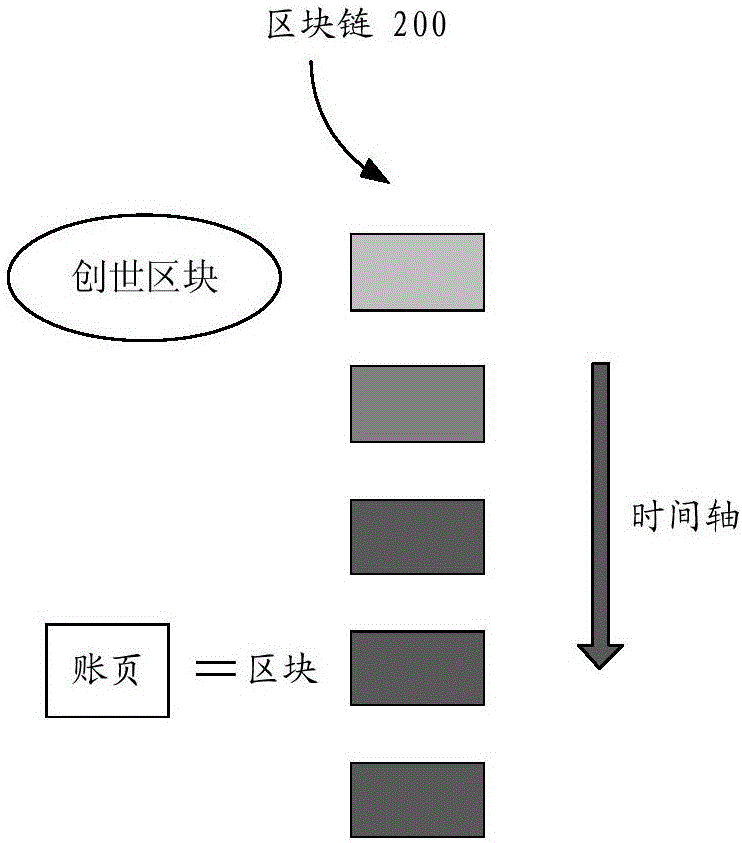
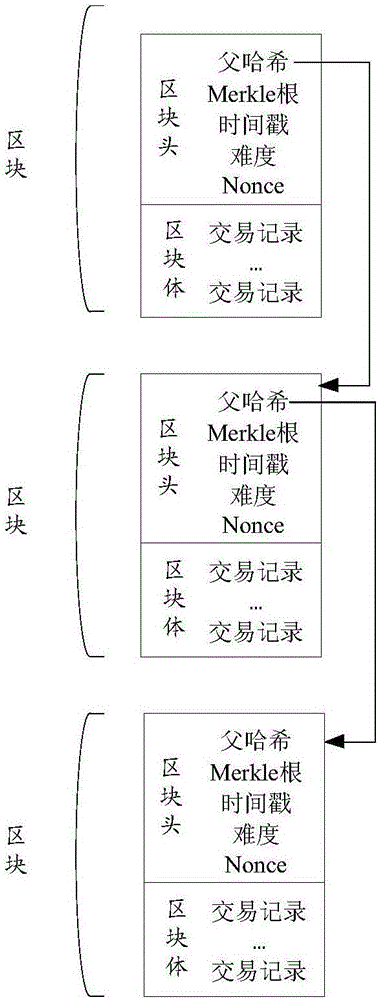
Block chain network, branch node and block chain network application method
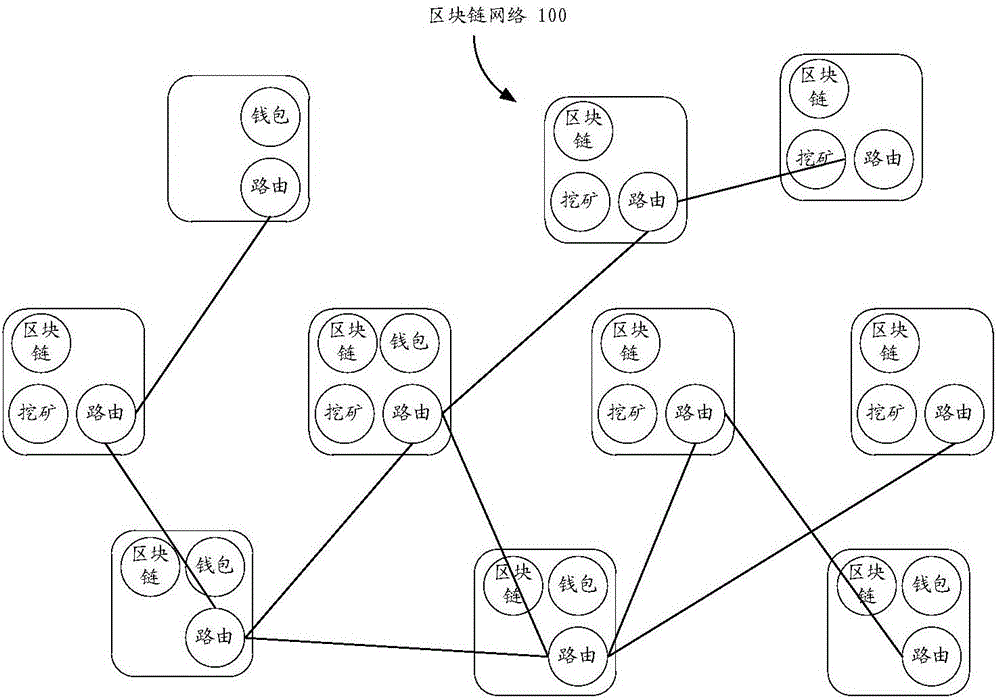
ActiveCN106452785ASave space resourcesSave computing resourcesUser identity/authority verificationPayment protocolsComputer terminalChain network
The invention discloses a block chain network, a branch node and a block chain network application method. The block chain network comprises a plurality of nodes used for separately storing blocks comprising recorded data and linking the blocks to form a block chain; the plurality of nodes comprise at least one branch node used for: when recorded data submitted by a specific user are received, sending the recorded data to other nodes in the block chain network, and returning a recorded data submission result to the specific user according to the number of effective confirmation results returned by other nodes for the recorded data; and the branch node is further used for: when a request of creating a new block of the specific user is received, sending the new block to the other nodes in the block chain network, and returning a result of creating the new block to the specific user according to verification results of the other nodes to the new block. By implementation of the block chain network disclosed by the invention, the implementation of the block chain technology on a mobile terminal of a user side is achieved, the application range of the block chain is expanded, and the resources of the mobile terminal of the user side can be saved.
Owner:TENPAY PAID TECH
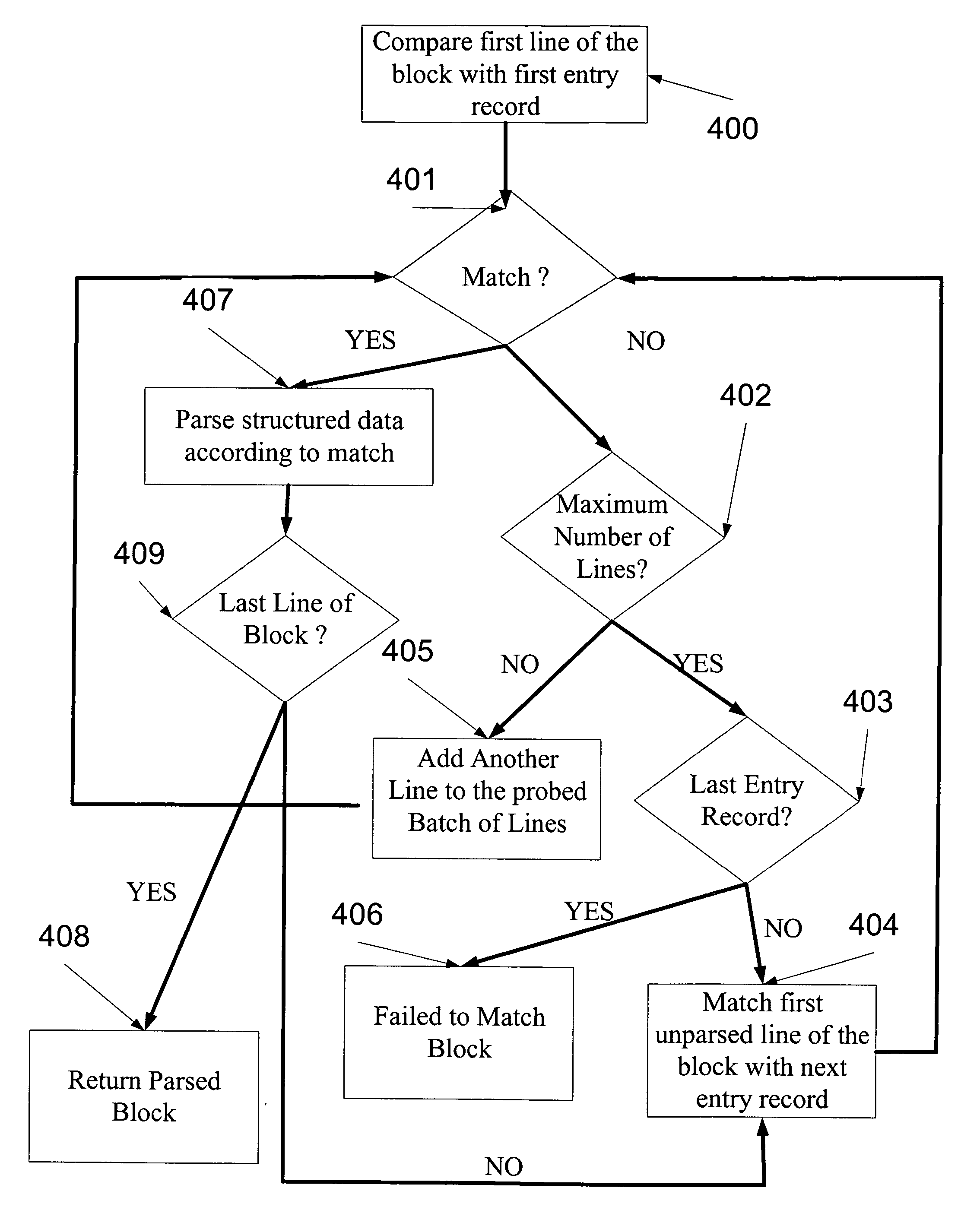
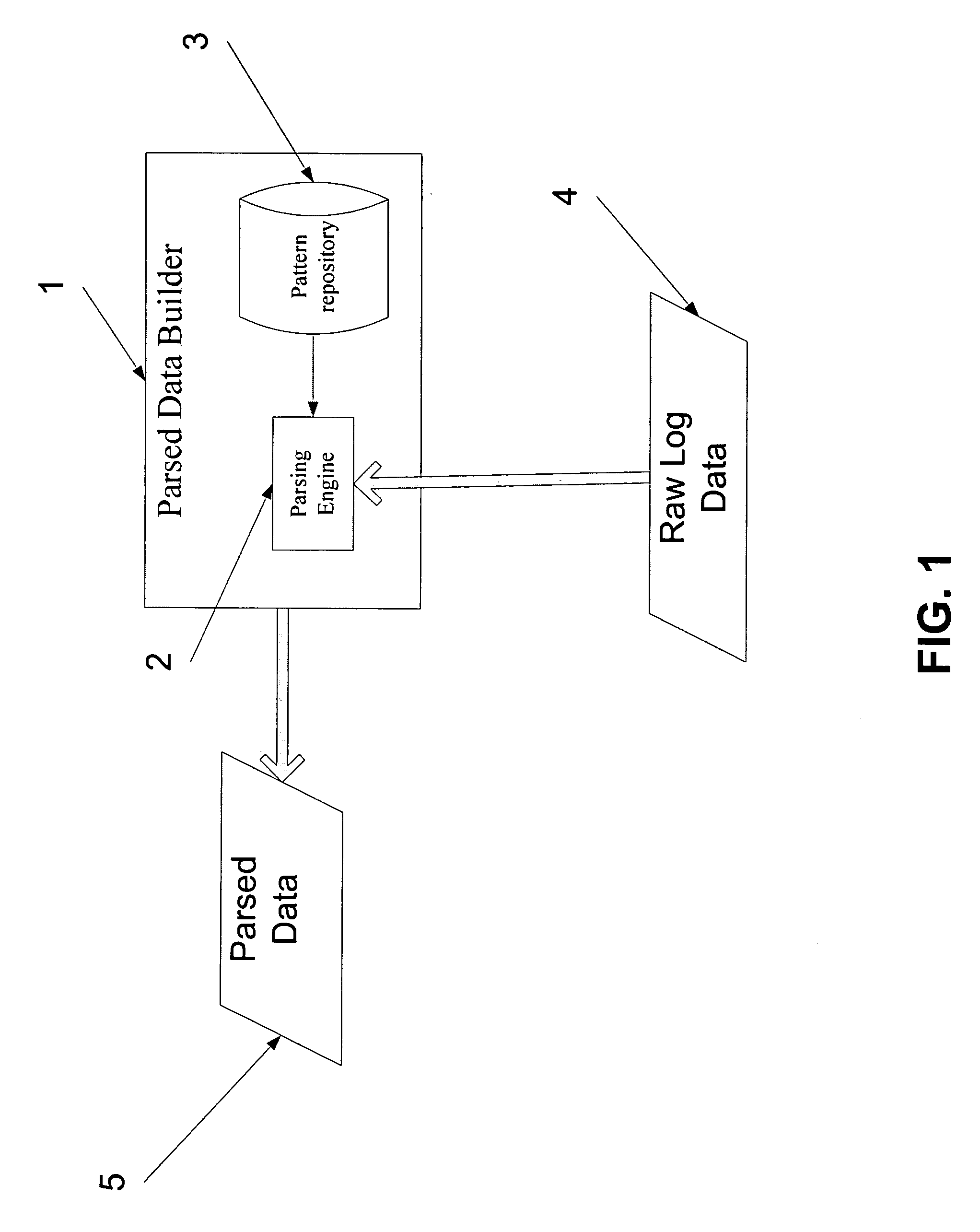
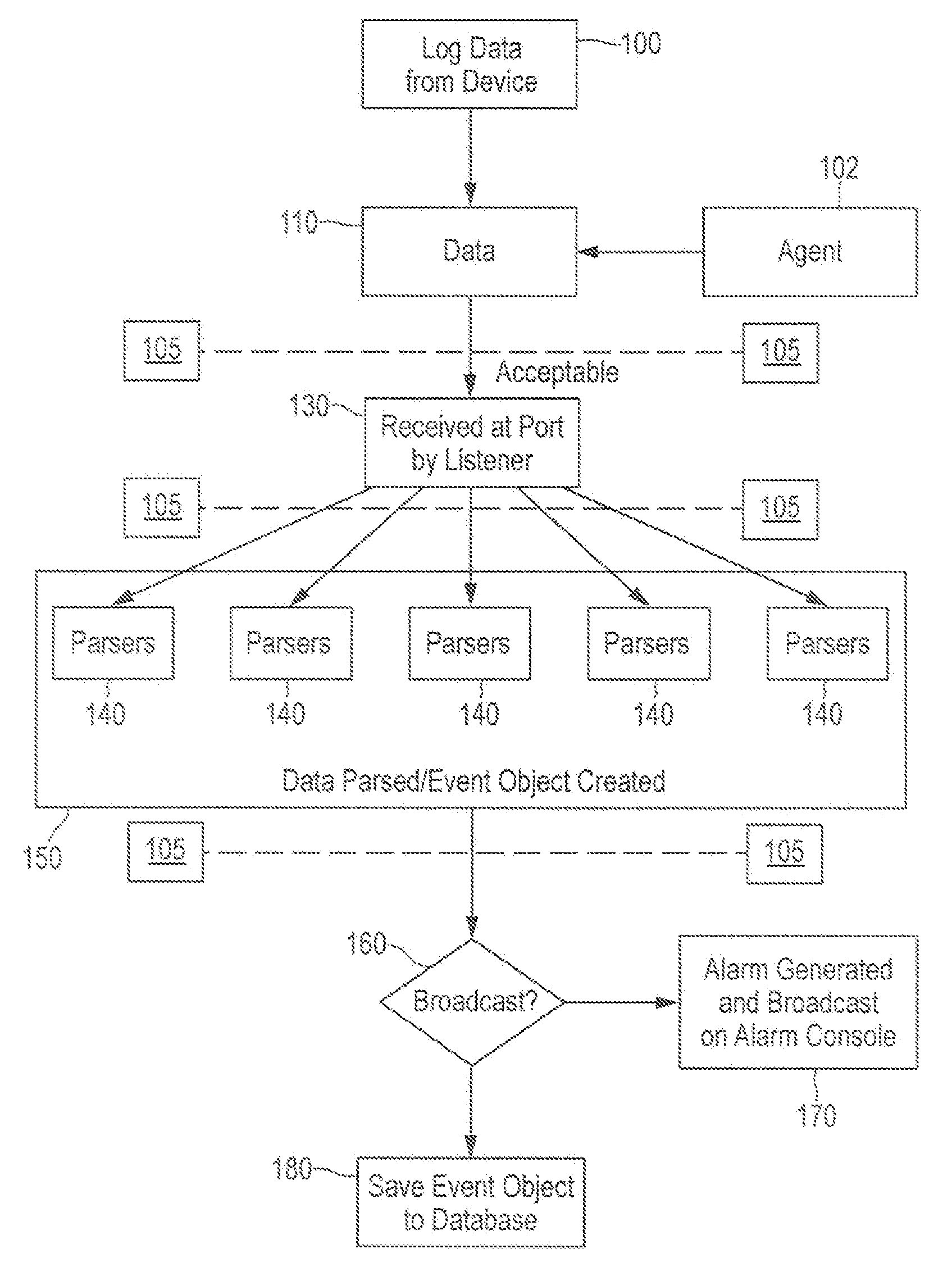
System and method for analysis and management of logs and events
ActiveUS20060184529A1Digital data processing detailsNon-redundant fault processingComputerized systemData mining
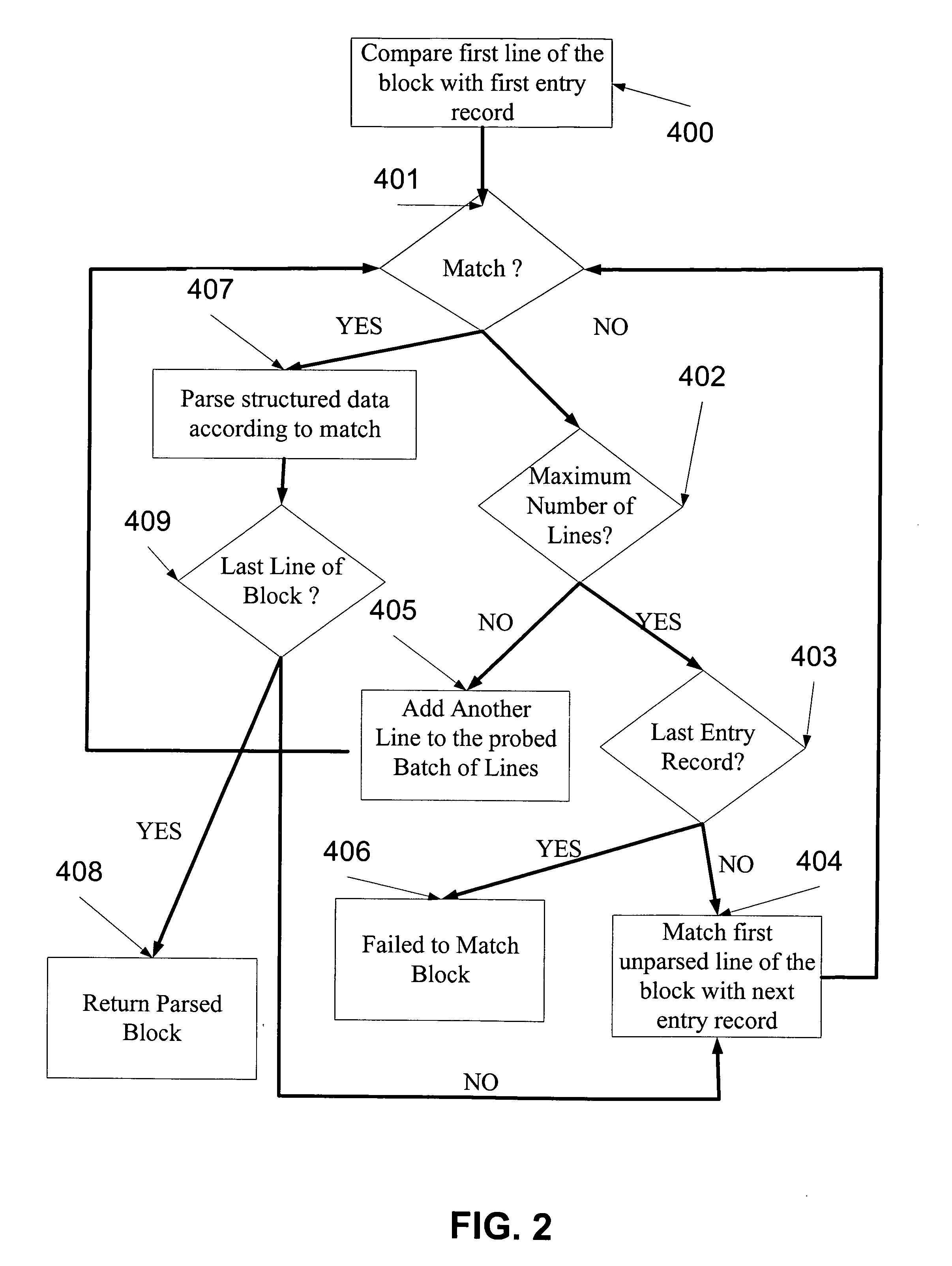
A log record analyzing system for monitoring log records from at least one computerized system. The log record analyzing system comprises a pattern repository that stores a plurality of pattern object records of different grammar types and a parsing engine which is adapted to receive a raw log data input. The parsing engine facilitates the matching between the raw log data input and at least one of the pattern object records. The parsing engine outputs parsed data according to the matching.
Owner:XPOLOG
Apparatus and method for downloading desired data signal to user-selectable storage unit
InactiveUS6931198B1Facilitates user operationImprove reliabilityTelevision system detailsPulse modulation television signal transmissionData signalLog data
Owner:SONY CORP
Flexible marking of recording data by a recording unit
InactiveUS7194186B1Improve abilitiesLow attentionTelevision system detailsRecording carrier detailsComputer scienceLog data
Owner:VULCAN PATENTS
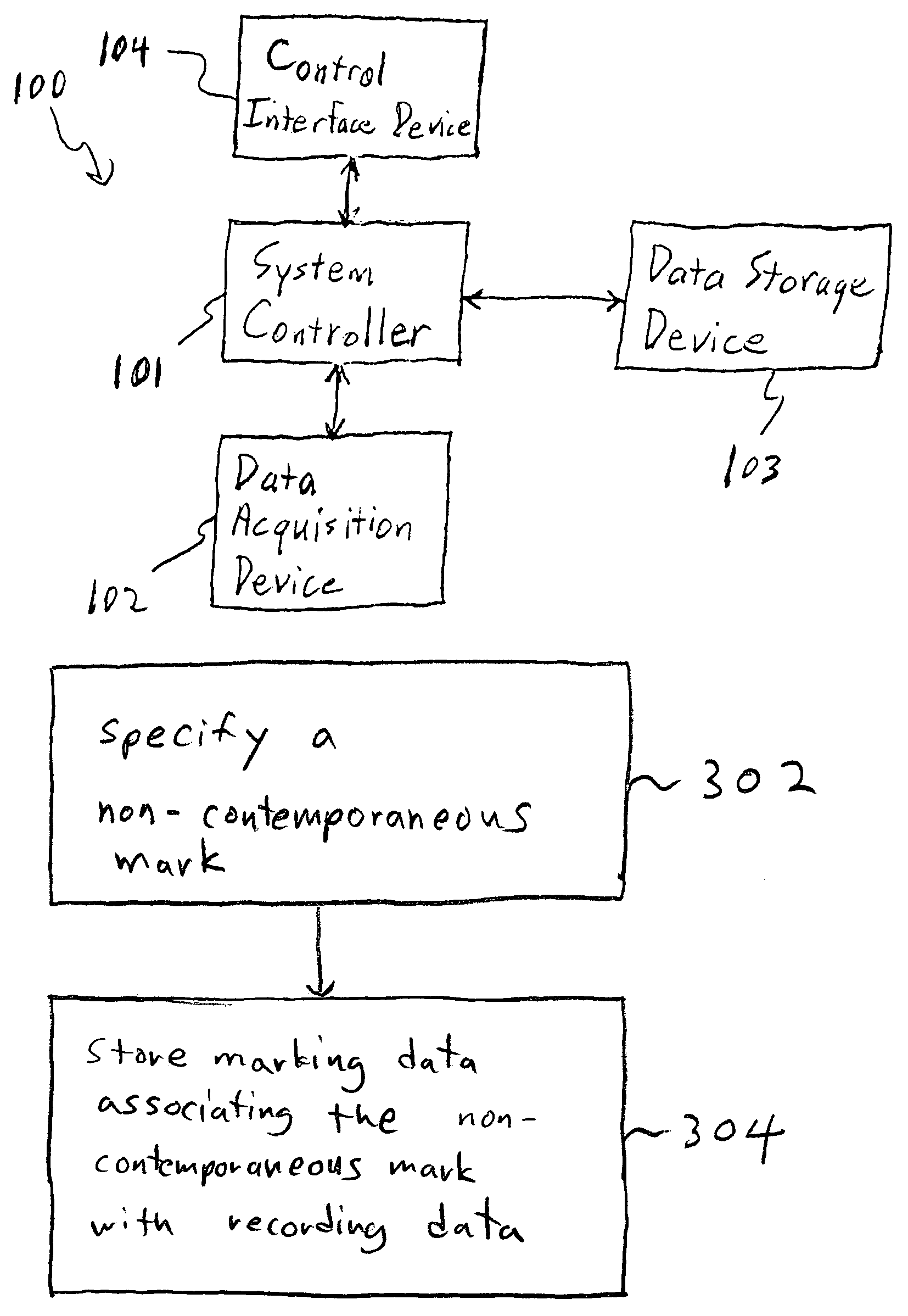
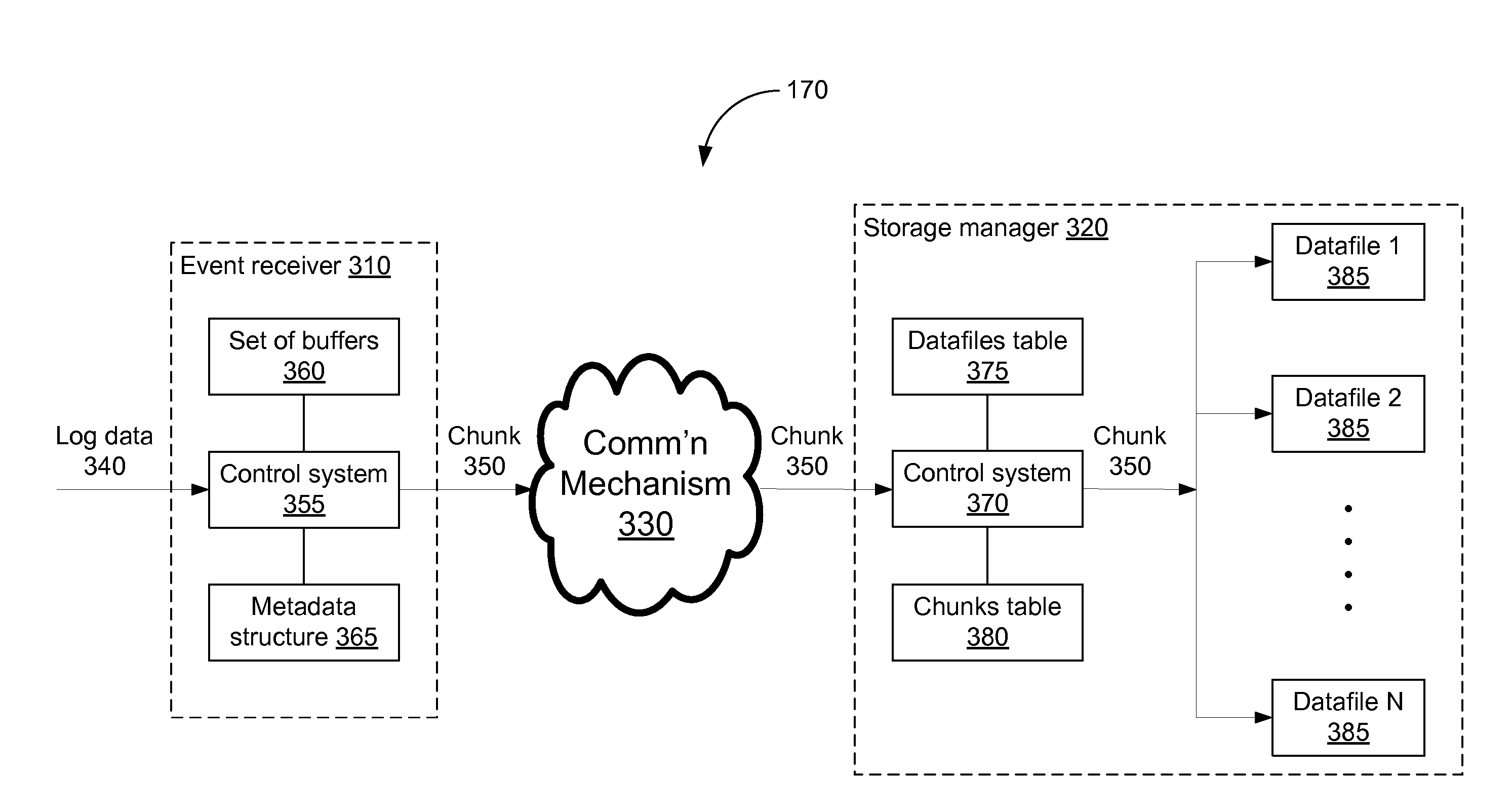
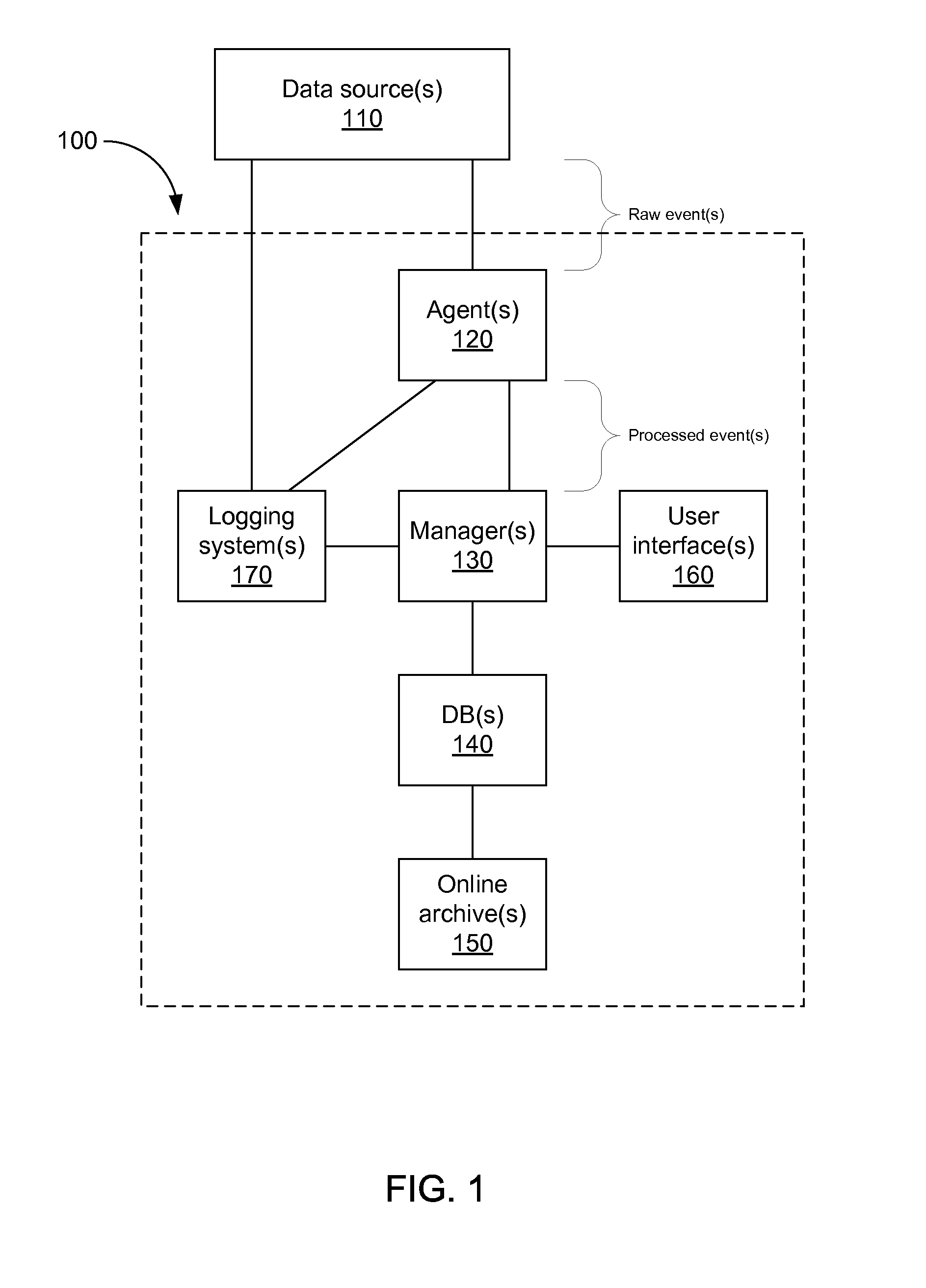
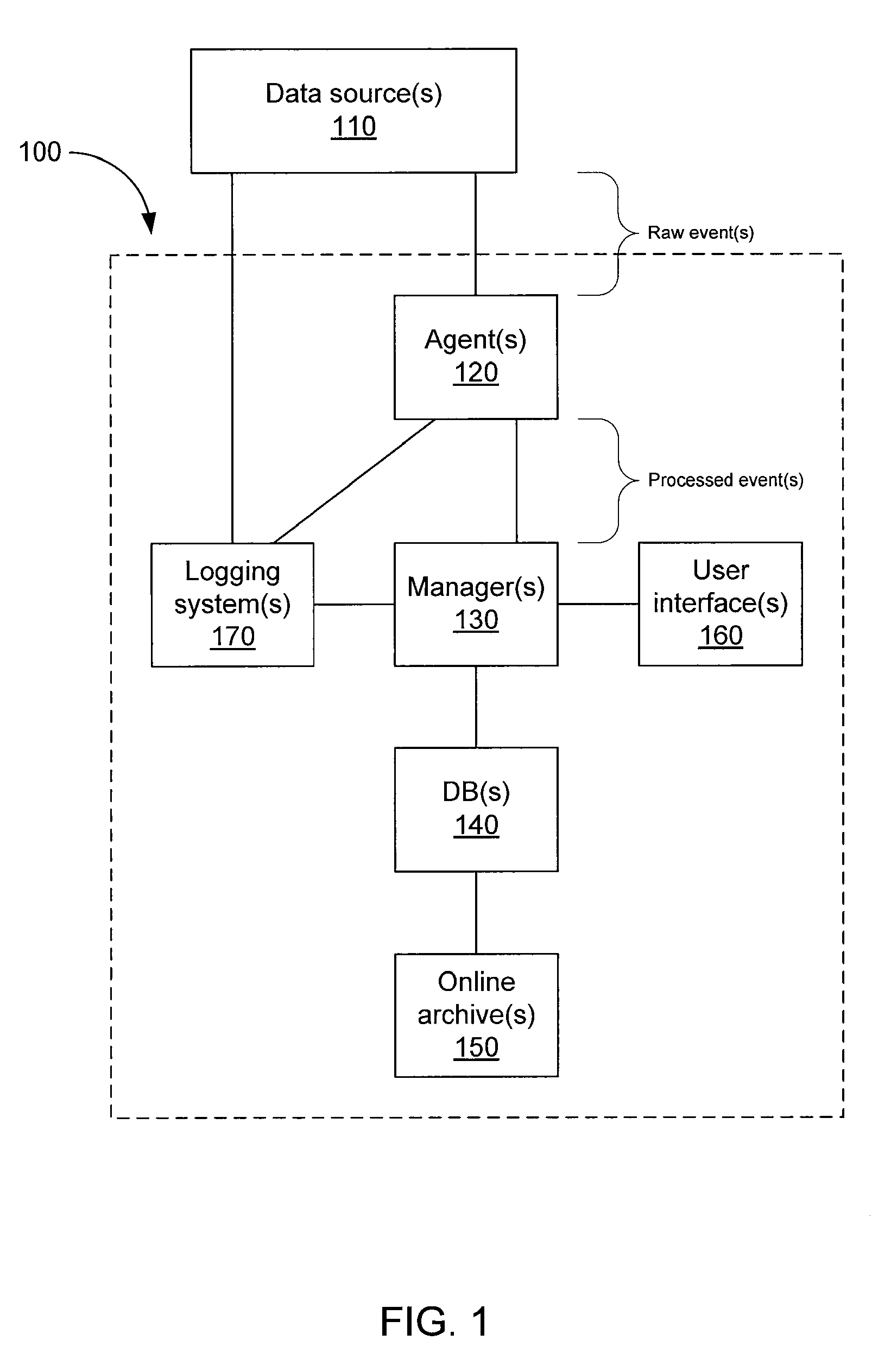
Storing log data efficiently while supporting querying
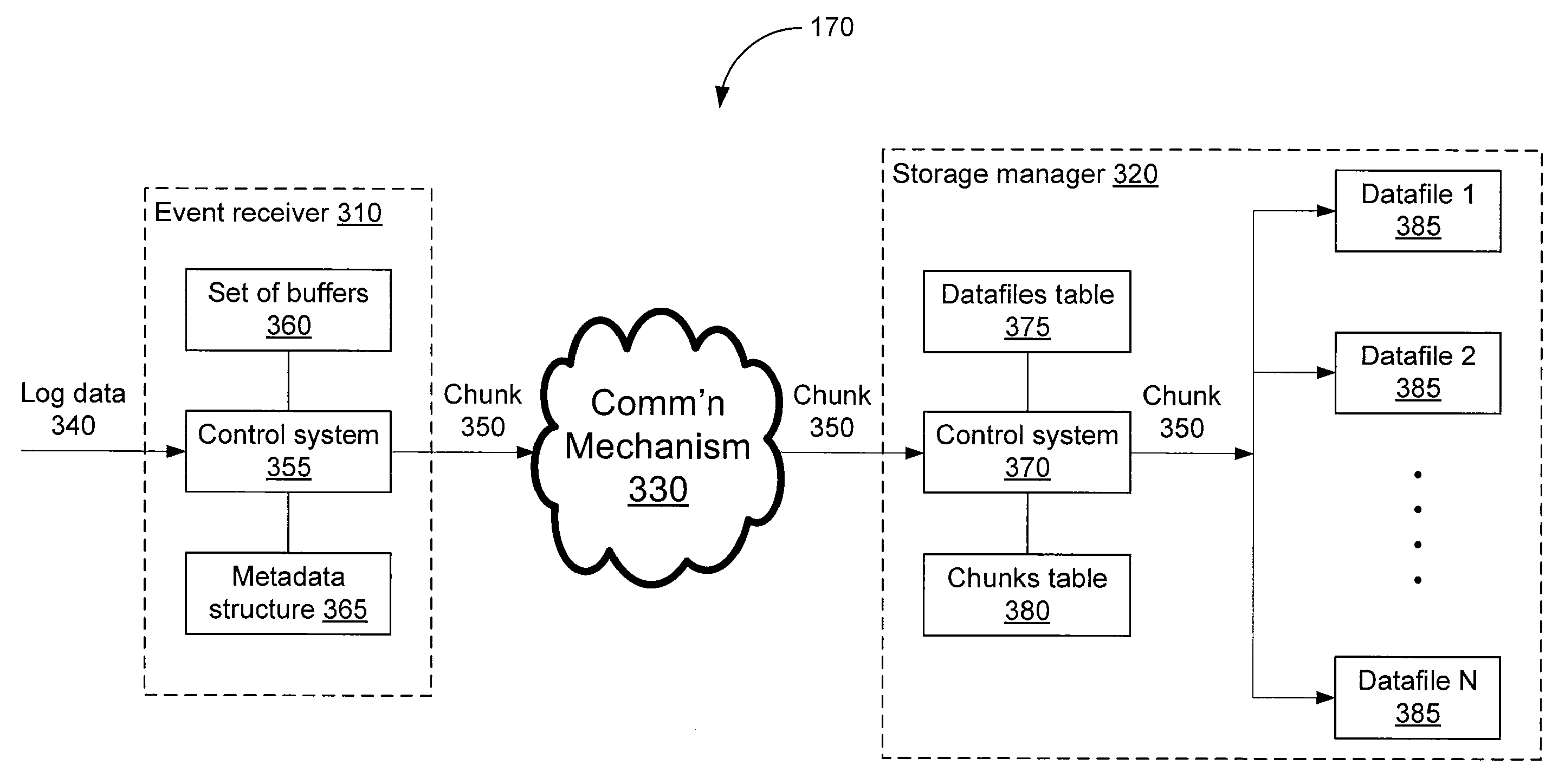
A logging system includes an event receiver and a storage manager. The receiver receives log data, processes it, and outputs a column-based data “chunk.” The manager receives and stores chunks. The receiver includes buffers that store events and a metadata structure that stores metadata about the contents of the buffers. Each buffer is associated with a particular event field and includes values from that field from one or more events. The metadata includes, for each “field of interest,” a minimum value and a maximum value that reflect the range of values of that field over all of the events in the buffers. A chunk is generated for each buffer and includes the metadata structure and a compressed version of the buffer contents. The metadata structure acts as a search index when querying event data. The logging system can be used in conjunction with a security information / event management (SIEM) system.
Owner:MICRO FOCUS LLC
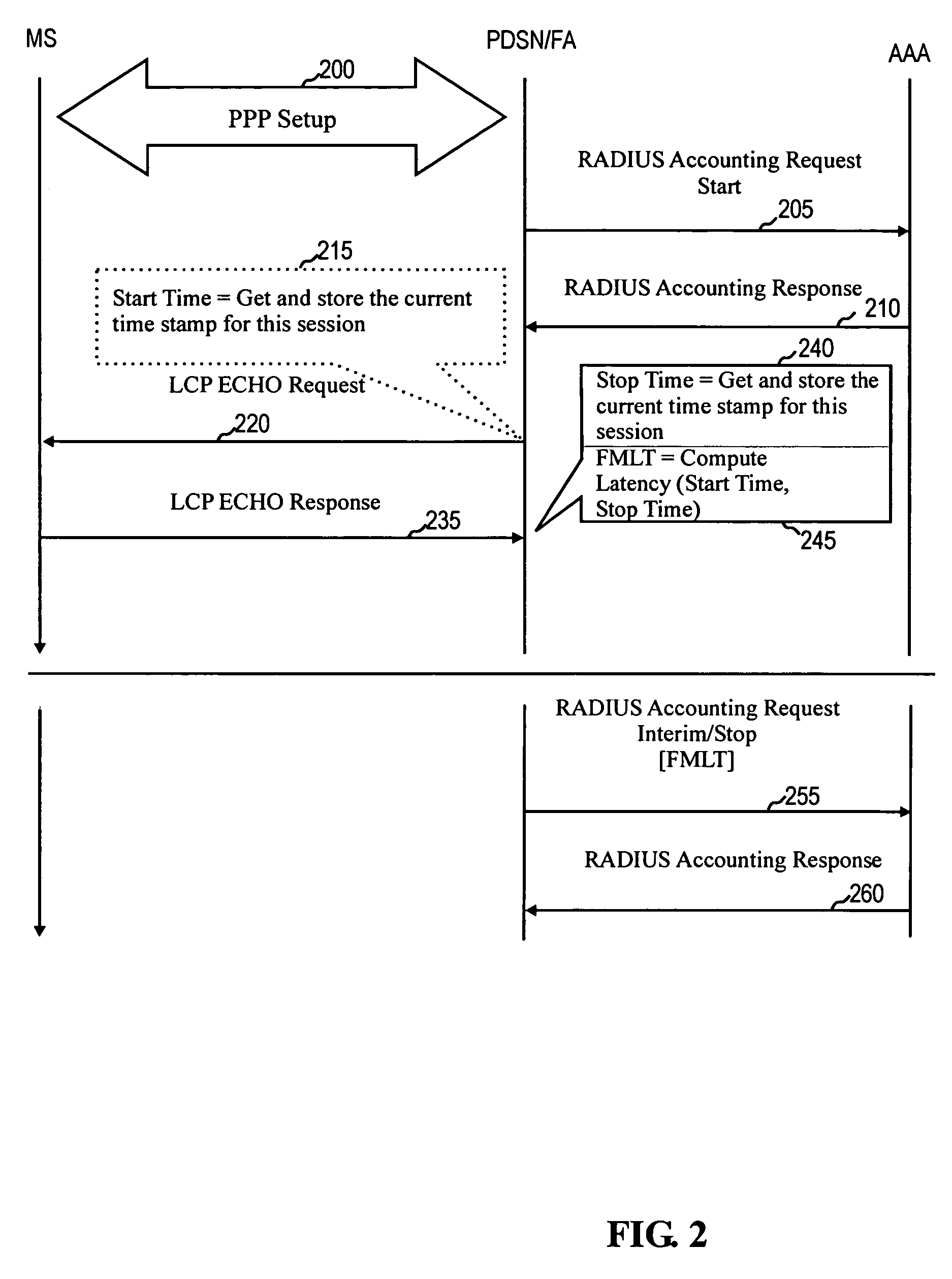
System and method for measuring and recording latency in internet protocol networks
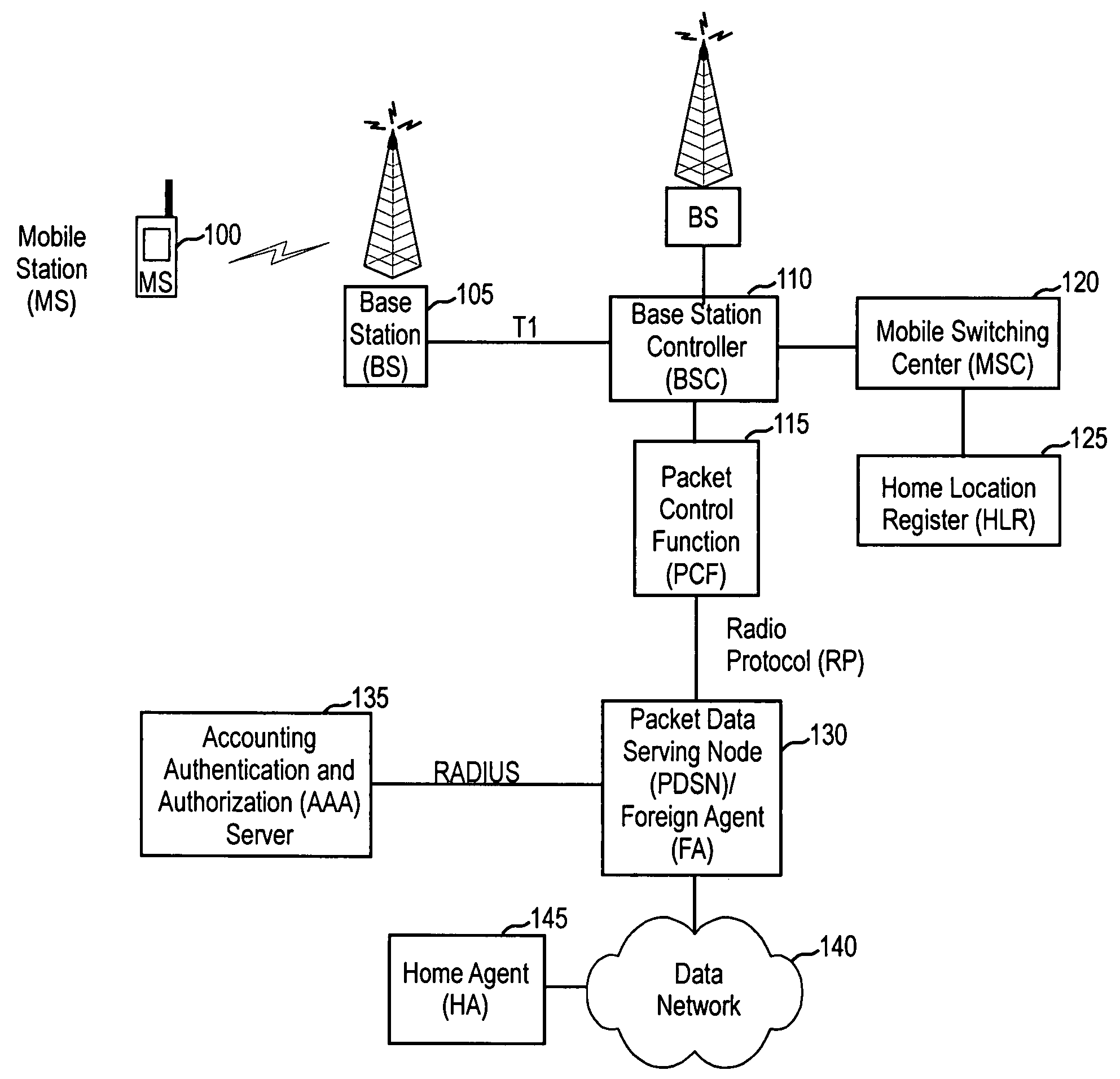
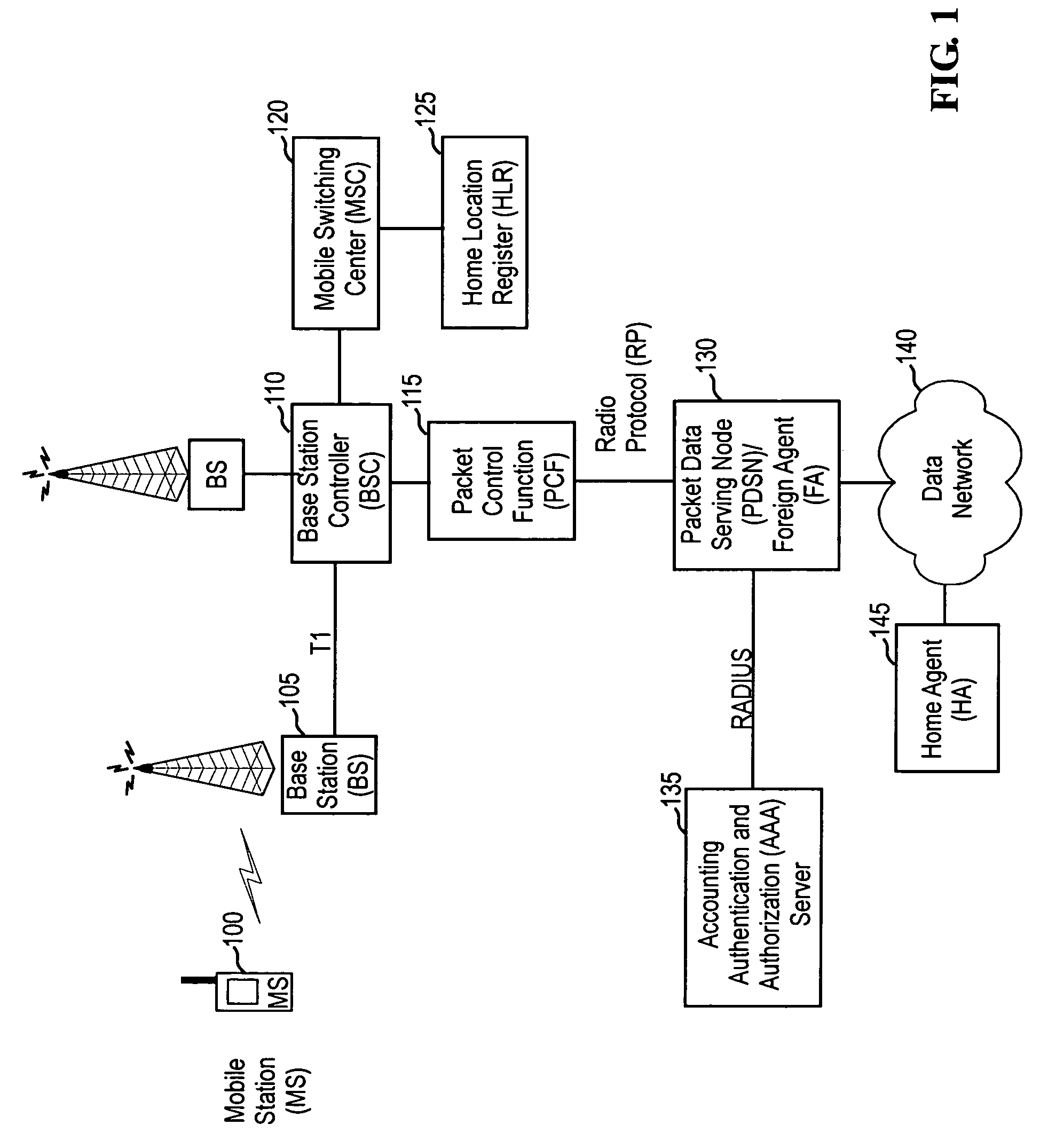
ActiveUS7610396B2Metering/charging/biilling arrangementsTelephonic communicationComputer scienceMobile IP
A system and method for measuring and recording latency in data networks. The system and method can be used to measure and record latency in a Simple IP network or a Mobile IP network. One embodiment of the present invention is a system and method for measuring latency between a first device and a second device, the first and second devices communicating in accordance with a communications specification. The system and method comprises the second device transmitting, during a communication session, a message to the first device; receiving a response message from the first device; computing an elapsed time from transmission of the message to receipt of the response message to determine the latency; and recording the latency in a latency parameter. The message and the response message are provided by the communications specification.
Owner:U S CELLULAR
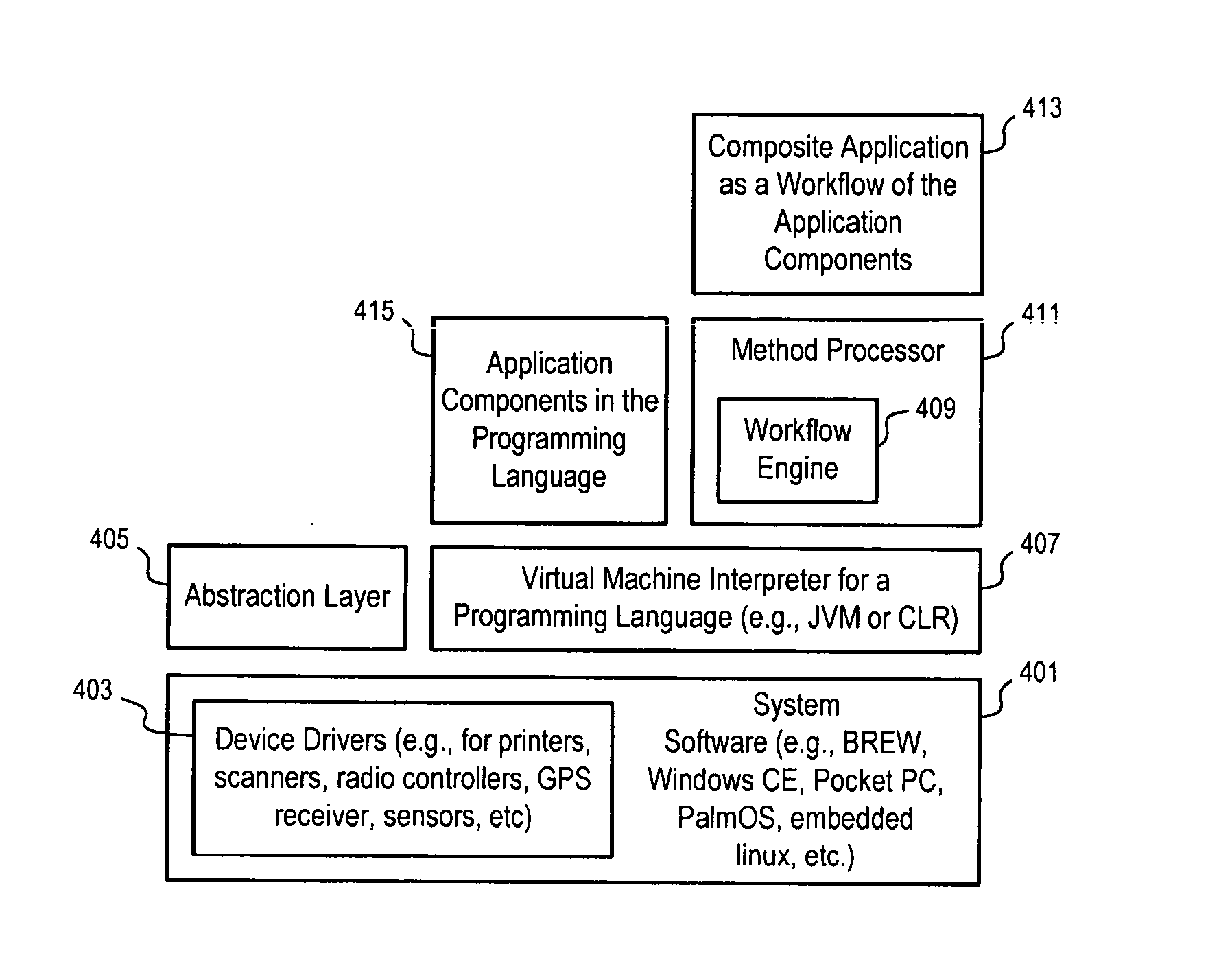
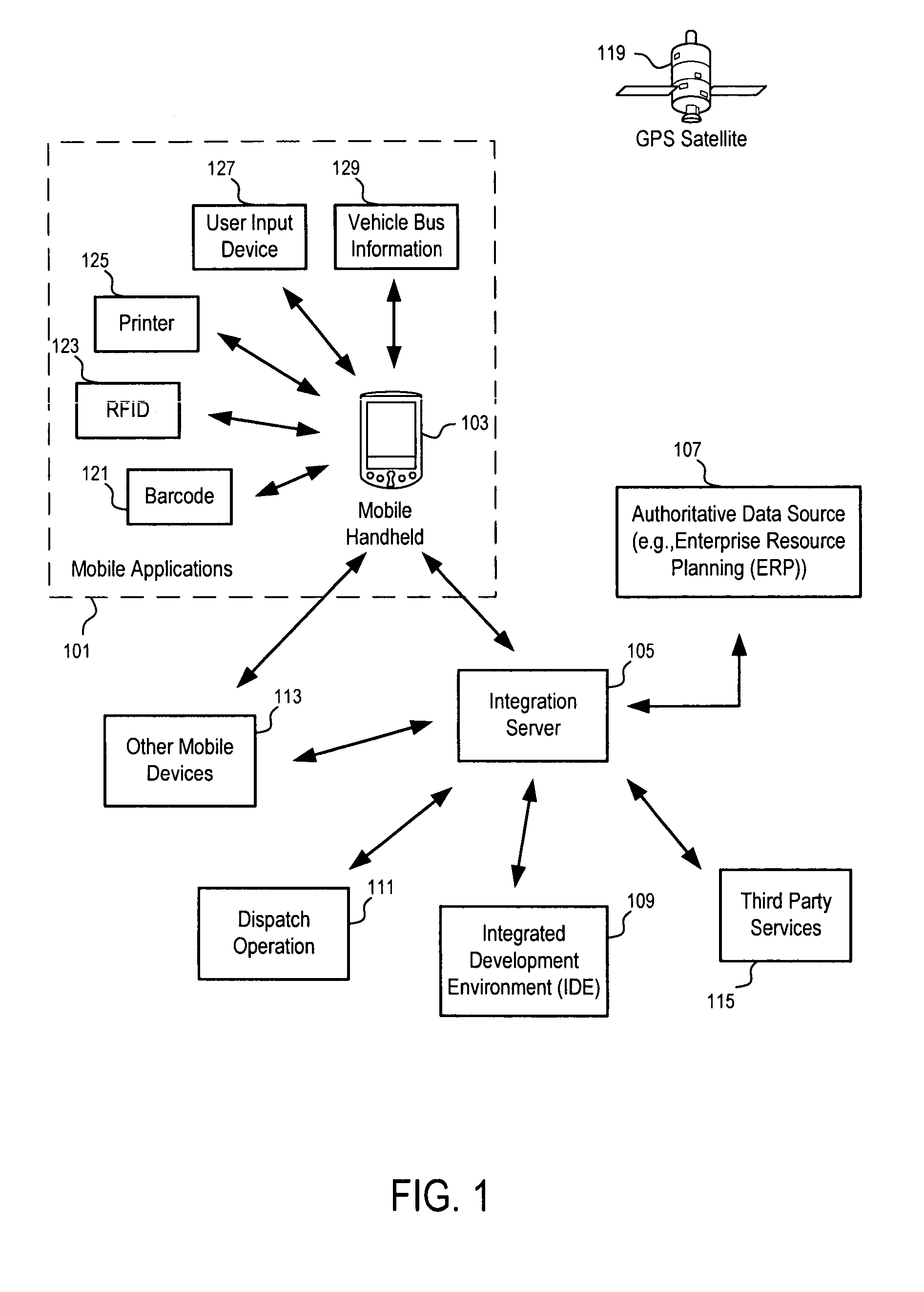
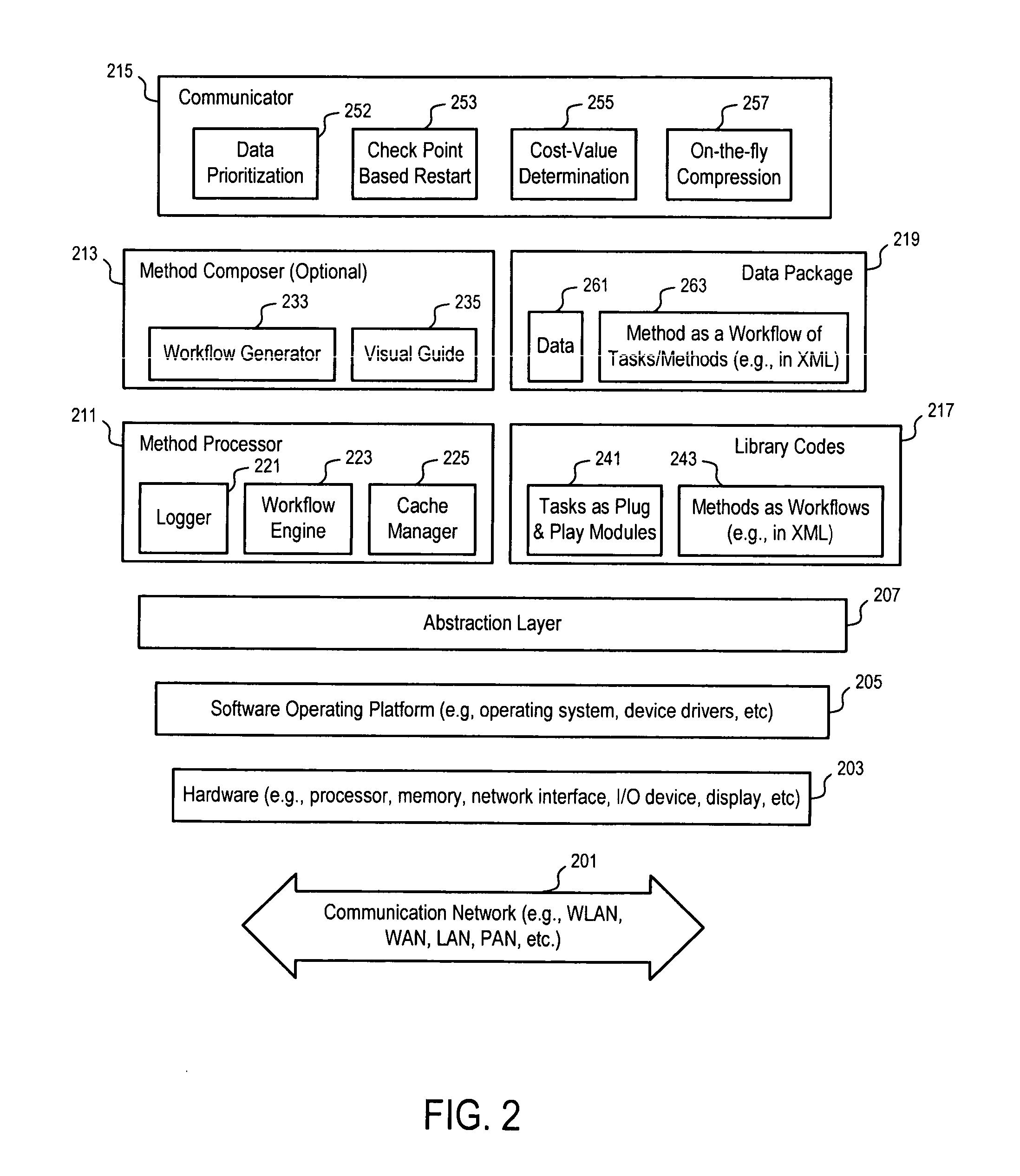
Methods and apparatuses to provide composite applications
InactiveUS20070011334A1Eliminate flickeringError detection/correctionMultiple digital computer combinationsData streamComposite application
Methods and apparatuses to enable the development, deployment and update of composite applications on mobile devices. In one embodiment, a method processor in a mobile device may include a workflow engine and a cache manager which looks ahead of the current execution of a workflow to preload modules. The method processor may present modal user interfaces in a non-modal way to eliminate flicker, and use a logger to stamp the workflow related data with real time measurements, such as time, location, and vehicle bus information. The logger may capture screen images and global data of the workflow during the execution. The log data stream may be collected and sent from the mobile device in real time, or in a batch mode, for monitoring, debugging, diagnosing or tuning the execution of a workflow, for providing hot update, help and guidance against deviation during the execution, and for other features.
Owner:APACHETA CORP
System for reducing server loading during content delivery
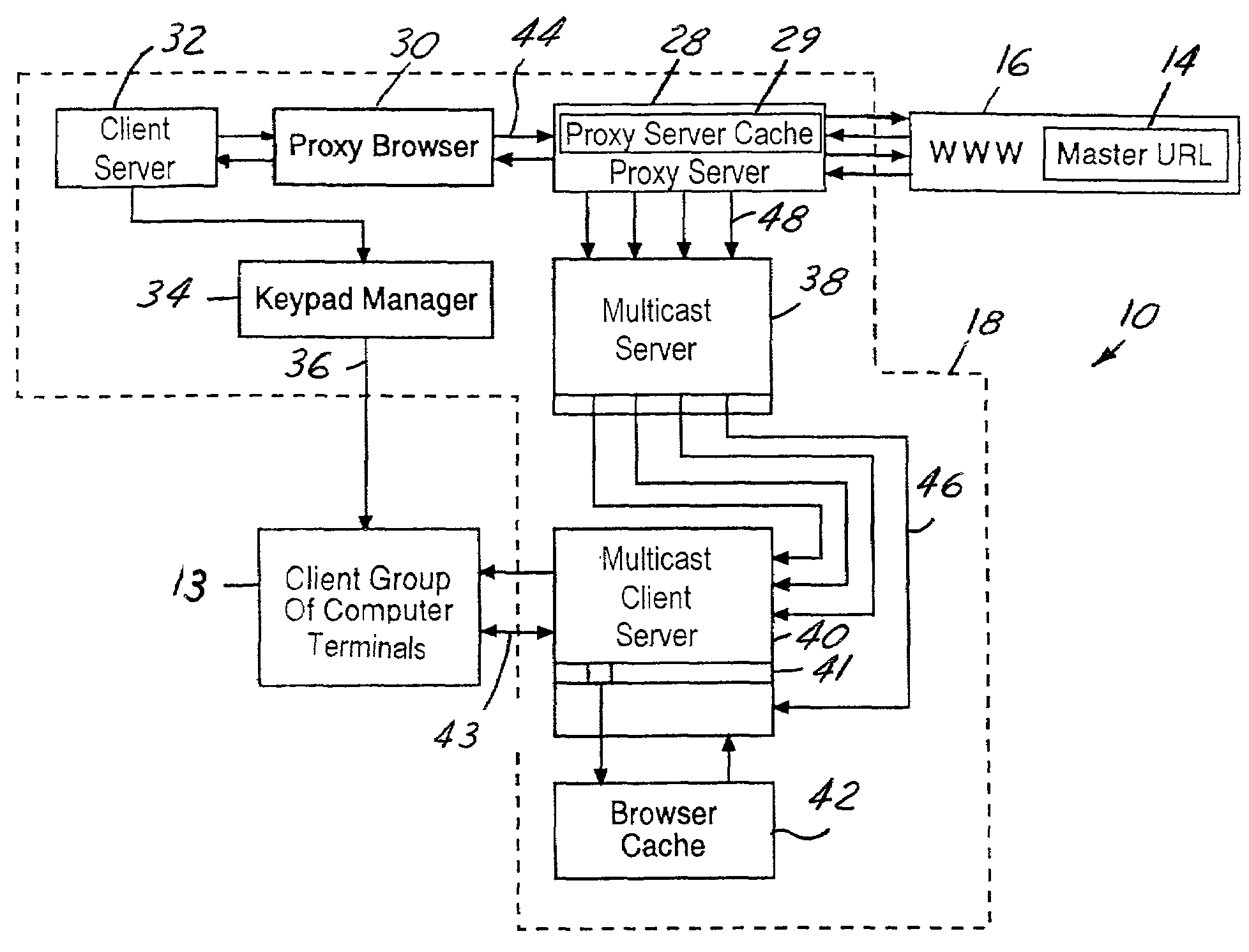
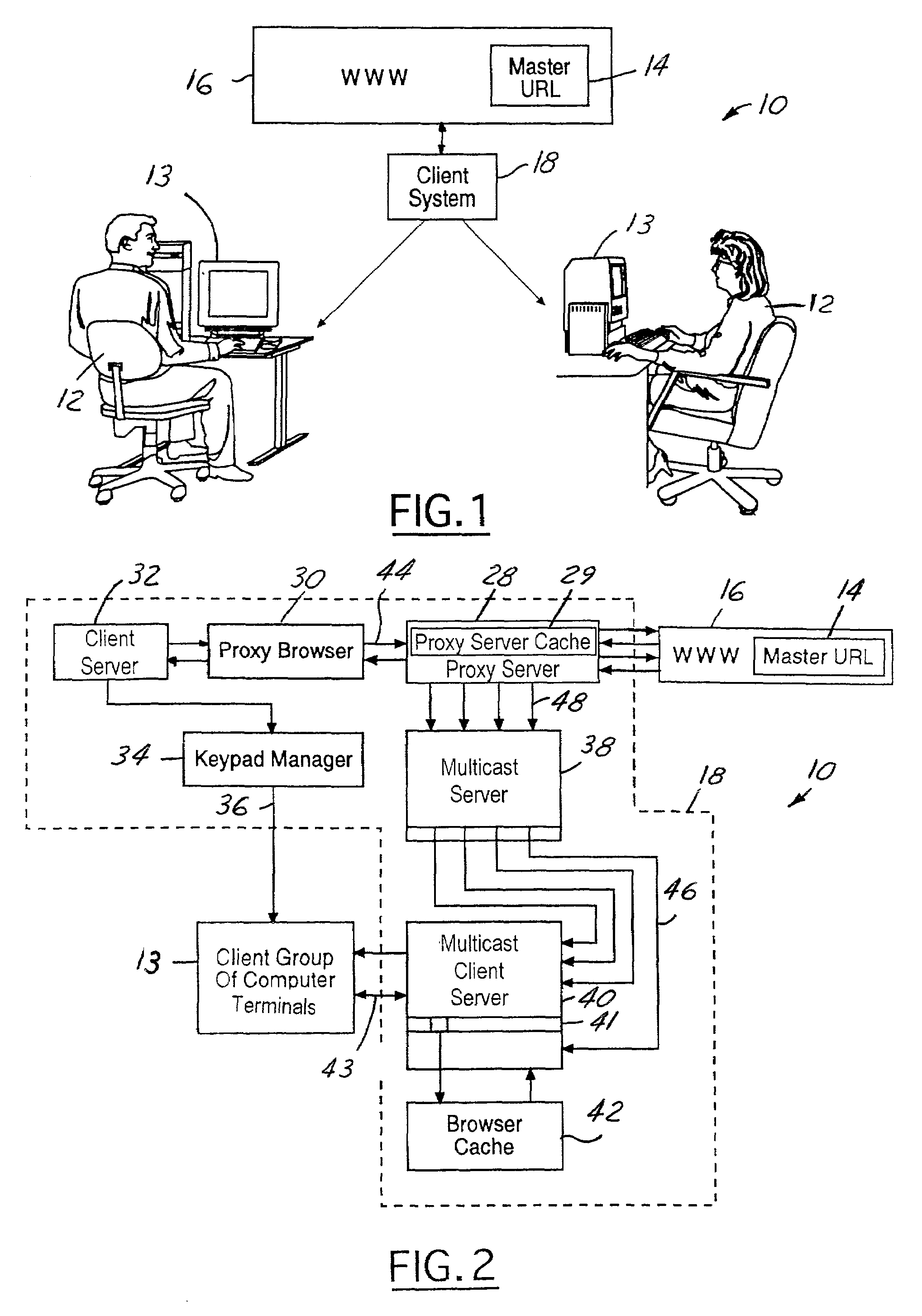
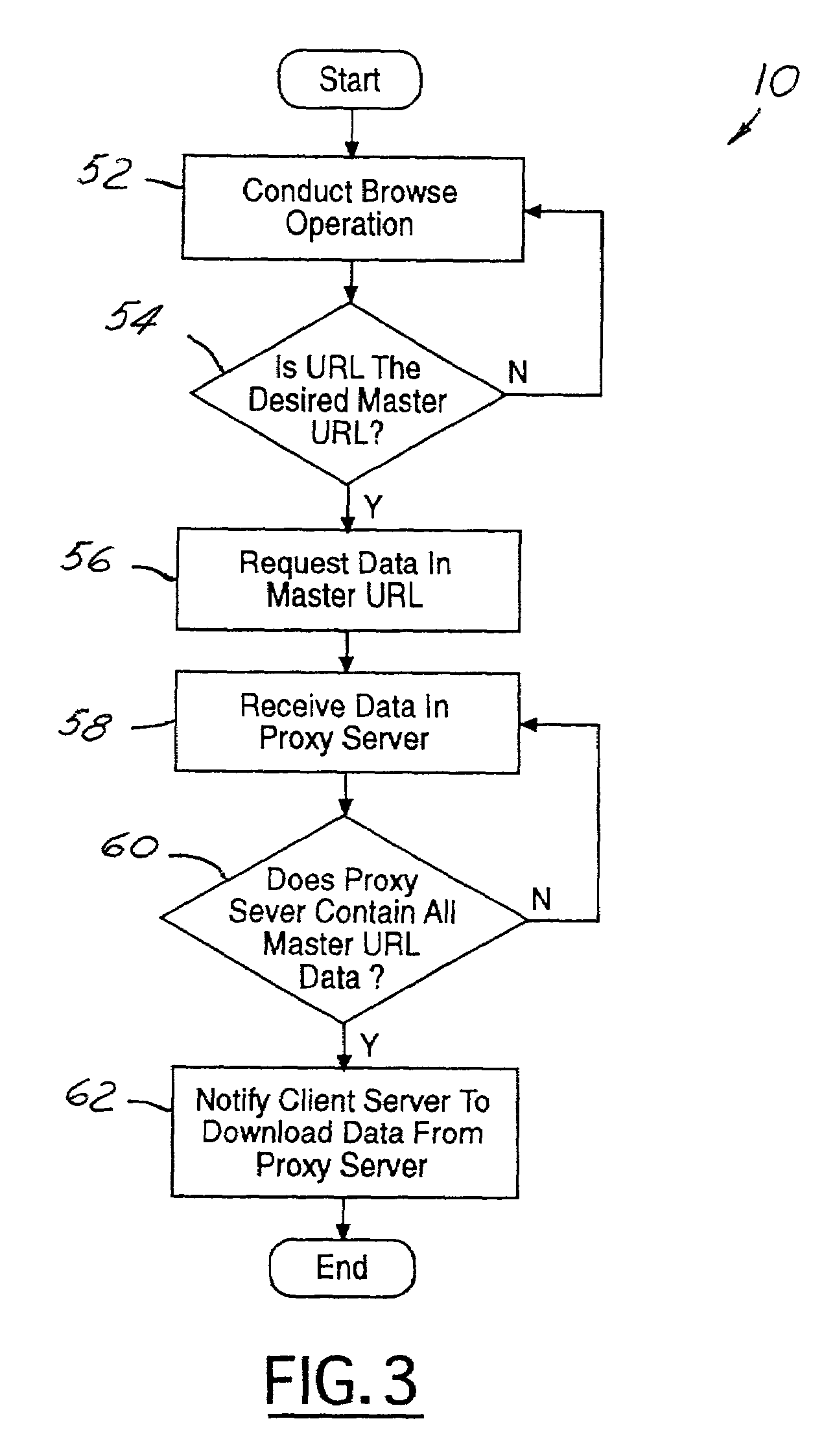
InactiveUS7149809B2Rapidly and efficiently downloadMinimize outdated information transferMultiple digital computer combinationsProgram controlUniform resource locatorClient-side
A server load reduction system includes a master URL containing data. The system further includes a proxy browser, which conducts a browse operation to request the data contained in the master URL. This browse operation is conducted through a proxy server. The proxy server is capable of receiving the data from the master URL. The proxy server includes logic operative to record and distribute the data to a client server. Logic contained in the proxy browser is operative to notify a client server to load the data when the proxy server contains all of the data.
Owner:ONE TOUCH SYST
Storing log data efficiently while supporting querying to assist in computer network security
ActiveUS20080162592A1Data processing applicationsError detection/correctionSystem of recordEvent management
A logging system includes an event receiver and a storage manager. The receiver receives log data, processes it, and outputs a data “chunk.” The manager receives data chunks and stores them so that they can be queried. The receiver includes buffers that store events and a metadata structure that stores metadata about the contents of the buffers. The metadata includes a unique identifier associated with the receiver, the number of events in the buffers, and, for each “field of interest,” a minimum value and a maximum value that reflect the range of values of that field over all of the events in the buffers. A chunk includes the metadata structure and a compressed version of the contents of the buffers. The metadata structure acts as a search index when querying event data. The logging system can be used in conjunction with a security information / event management (SIEM) system.
Owner:MICRO FOCUS LLC
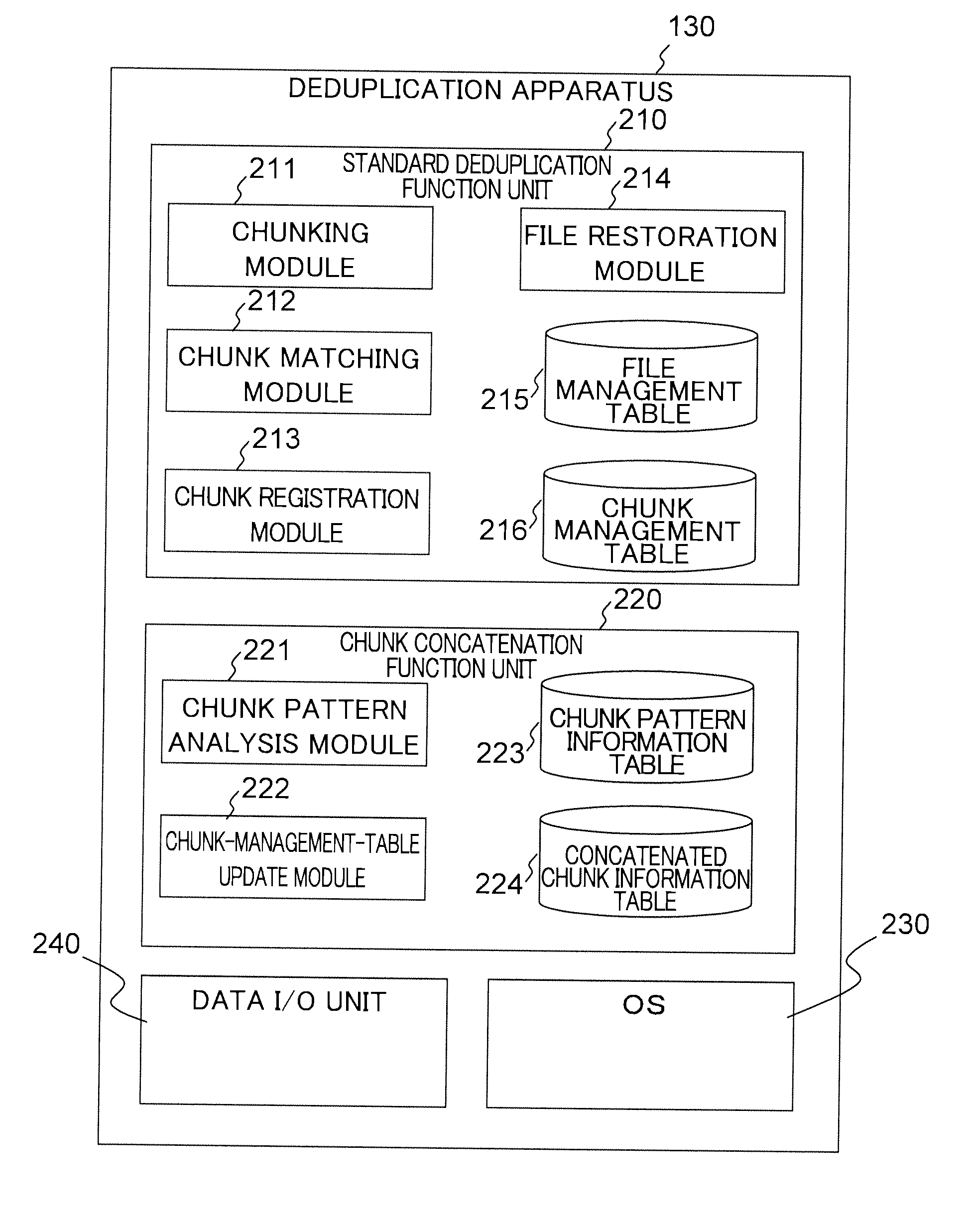
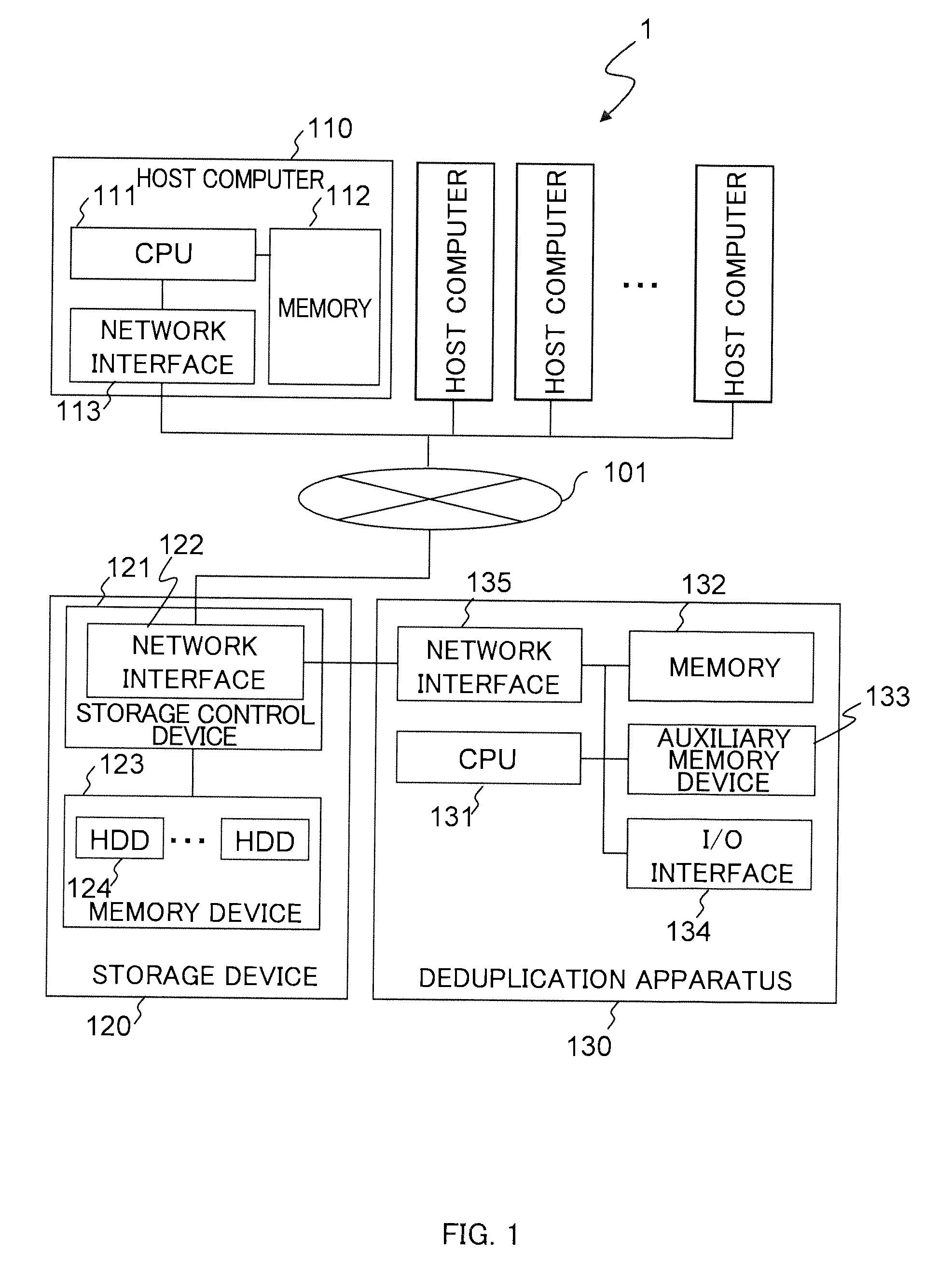
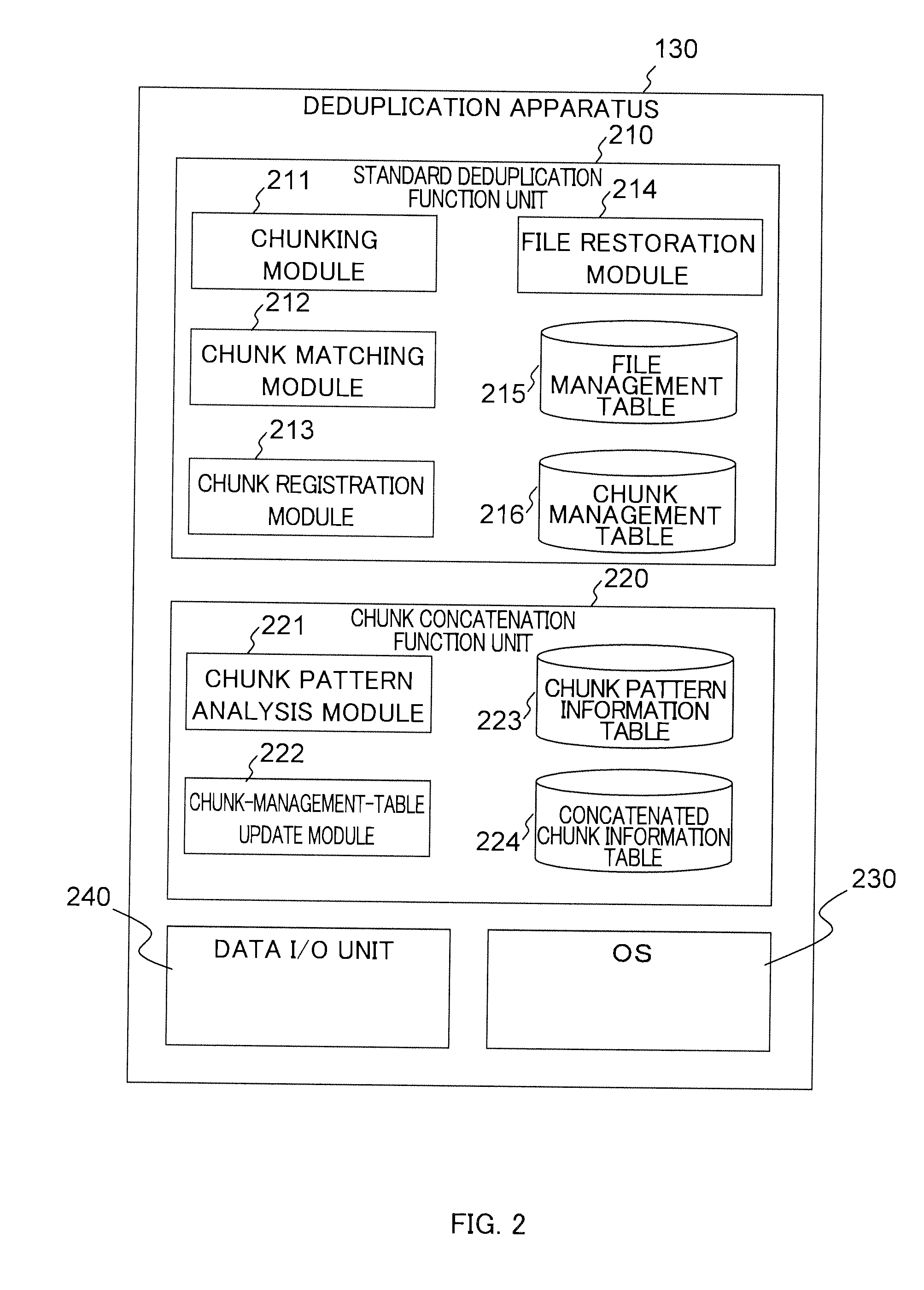
Stored data deduplication method, stored data deduplication apparatus, and deduplication program
InactiveUS20140229452A1Amount of timeDigital data information retrievalDigital data processing detailsData storingData store
Method of dividing data to be stored in storage device into data fragments; recording the data by using configurations of divided data fragments; judging whether identical data fragments exist in data fragments; when it is judged that identical data fragments exist, storing one of the identical data fragments in storage area of the storage device, and generating and recording data-fragment attribute information indicating an attribute unique to the data fragment stored; upon receipt of request to read data stored in the storage area of the storage device, acquiring the configurations of the data fragments forming the read-target data, reading the corresponding data fragments from the storage area of the storage device, and restoring the data; acquiring and coupling the recorded data fragments to generate concatenation target data targeted for judgment on whether chunk concatenation is possible or not, and detecting whether the concatenation target data has a repeated data pattern
Owner:HITACHI LTD
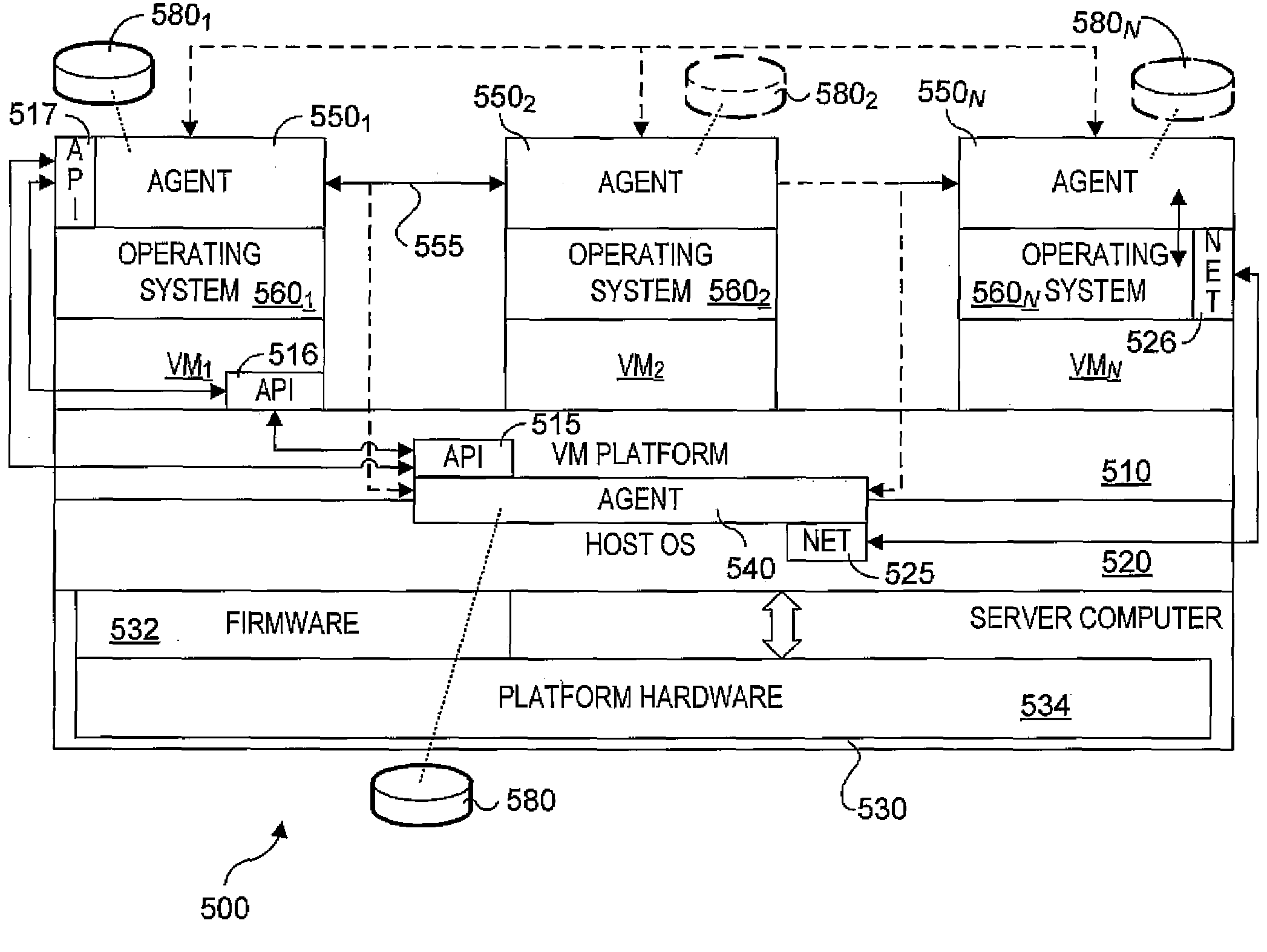
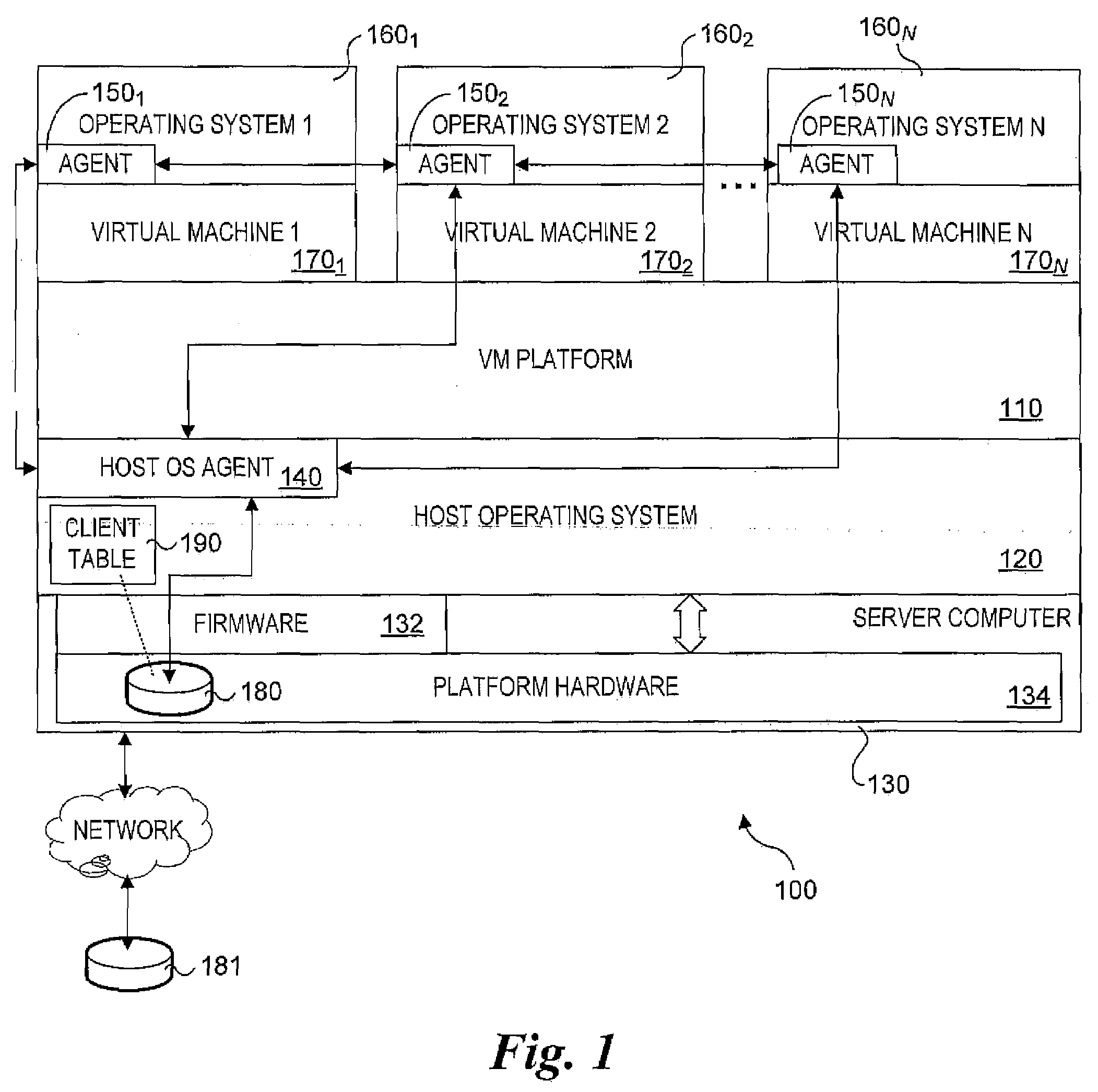
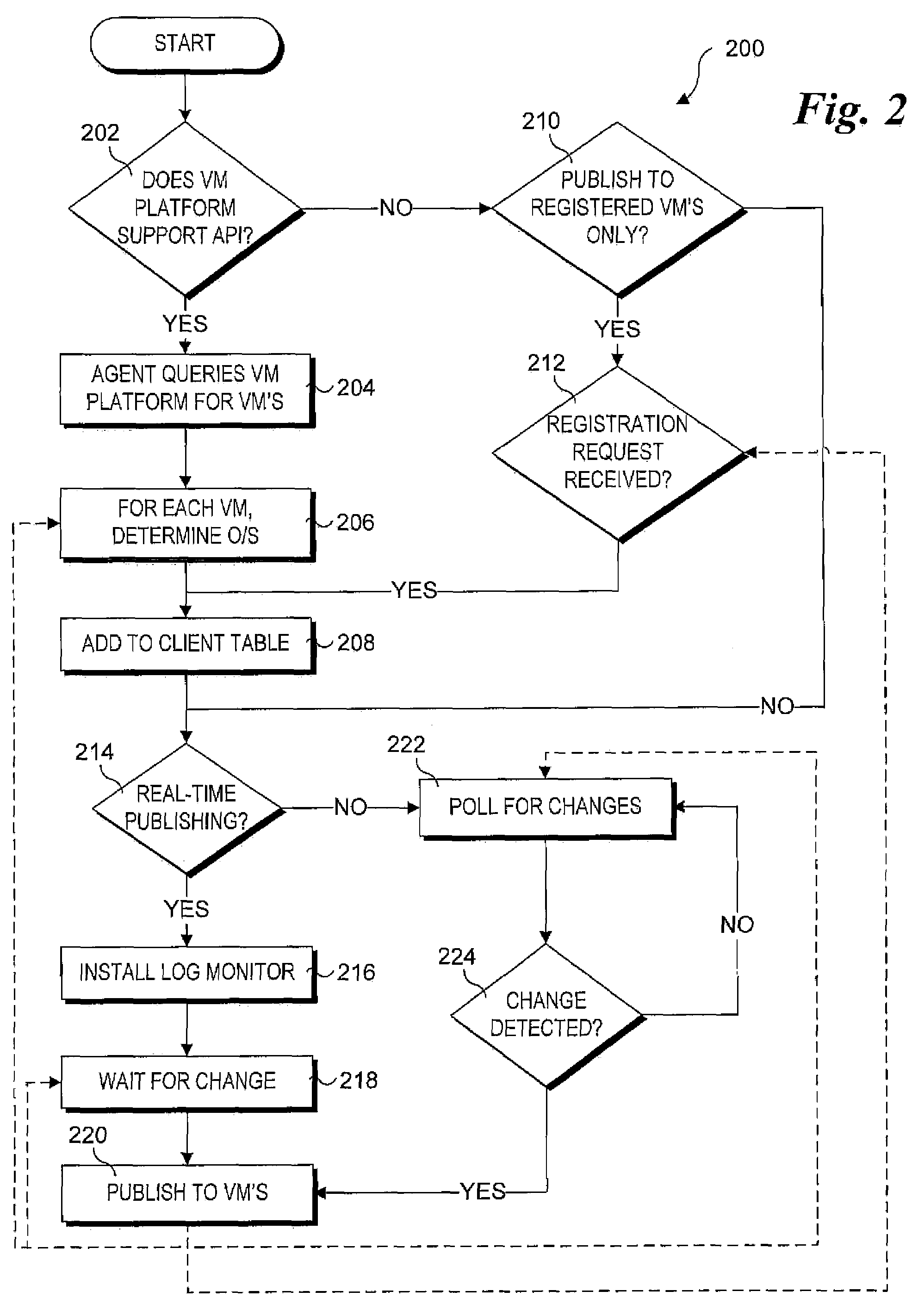
System and method for host and virtual machine administration
InactiveUS20080196043A1Reduce dependenceResource allocationError detection/correctionOperational systemEvent data
Methods, architectures, software / firmware and systems for enabling concurrent administration of host operating systems and virtual machine-hosted operating systems. Techniques are disclosed for monitoring and reporting various administrative data (e.g., performance data, event data, log data, etc.), as well as enabling allocation and reallocation of system resources, such as physical memory and disk space. The techniques support implementation of user-interfaces hosted by a virtual machine operating system or a host operating system that enable administrators and the like to manage operations of virtual machines and hosts via a unified interface. Moreover, the techniques support concurrent management of different operating system types.
Owner:FEINLEIB DAVID +2
On-line service/application monitoring and reporting system
ActiveUS7379999B1Improve service qualityImprove stabilityError detection/correctionMultiple digital computer combinationsRelevant informationData file
An event monitoring and logging system, including apparatuses and methods, for instrumenting an on-line application program, or service, for generating and communicating events upon the occurrence of certain conditions during the execution thereof, for monitoring generated events in real and near-real time in accordance with configurable rules, for generating and communicating selected alerts to appropriate personnel upon the exceeding of configurable thresholds, for logging generated events and related information in data files and databases for subsequent analysis, and for producing reports related to such instrumentation and generated events.
Owner:MICROSOFT TECH LICENSING LLC
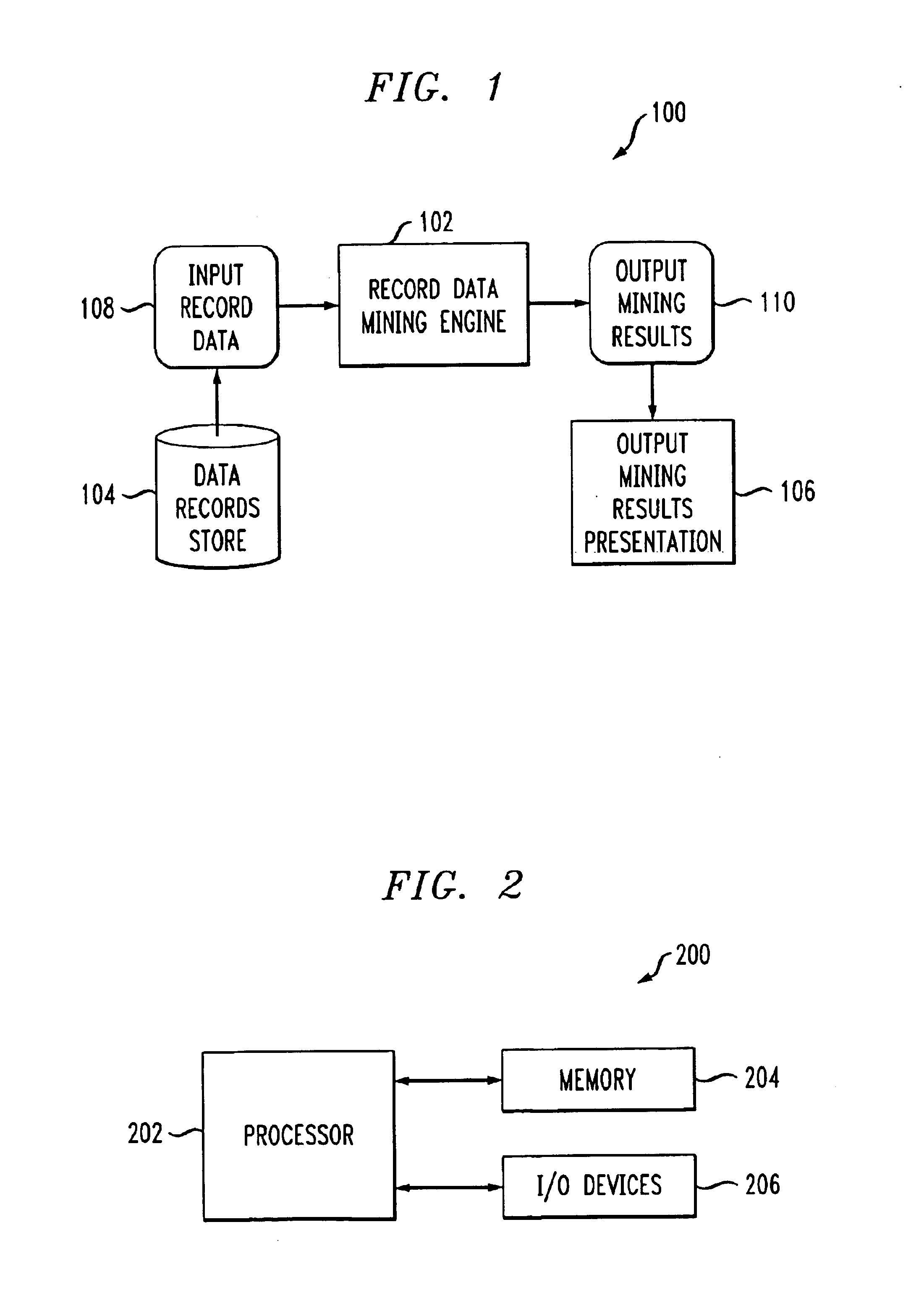
Method and apparatus for data mining to discover associations and covariances associated with data
ActiveUS7043476B2Efficient and effectiveData processing applicationsDigital data processing detailsData dredgingHigh dimensionality
Data mining techniques are provided which are effective and efficient for discovering useful information from an amorphous collection or data set of records. For example, the present invention provides for the mining of data, e.g., of several or many records, to discover interesting associations between entries of qualitative text, and covariances between data of quantitative numerical types, in records. Although not limited thereto, the invention has particular application and advantage when the data is of a type such as clinical, pharmacogenomic, forensic, police and financial records, which are characterized by many varied entries, since the problem is then said to be one of “high dimensionality” which has posed mathematical and technical difficulties for researchers. This is especially true when considering strong negative associations and negative covariance, i.e., between items of data which may so rarely come together that their concurrence is never seen in any record, yet the fact that this is not expected is of potential great interest.
Owner:IBM CORP
Comprehensive security structure platform for network managers
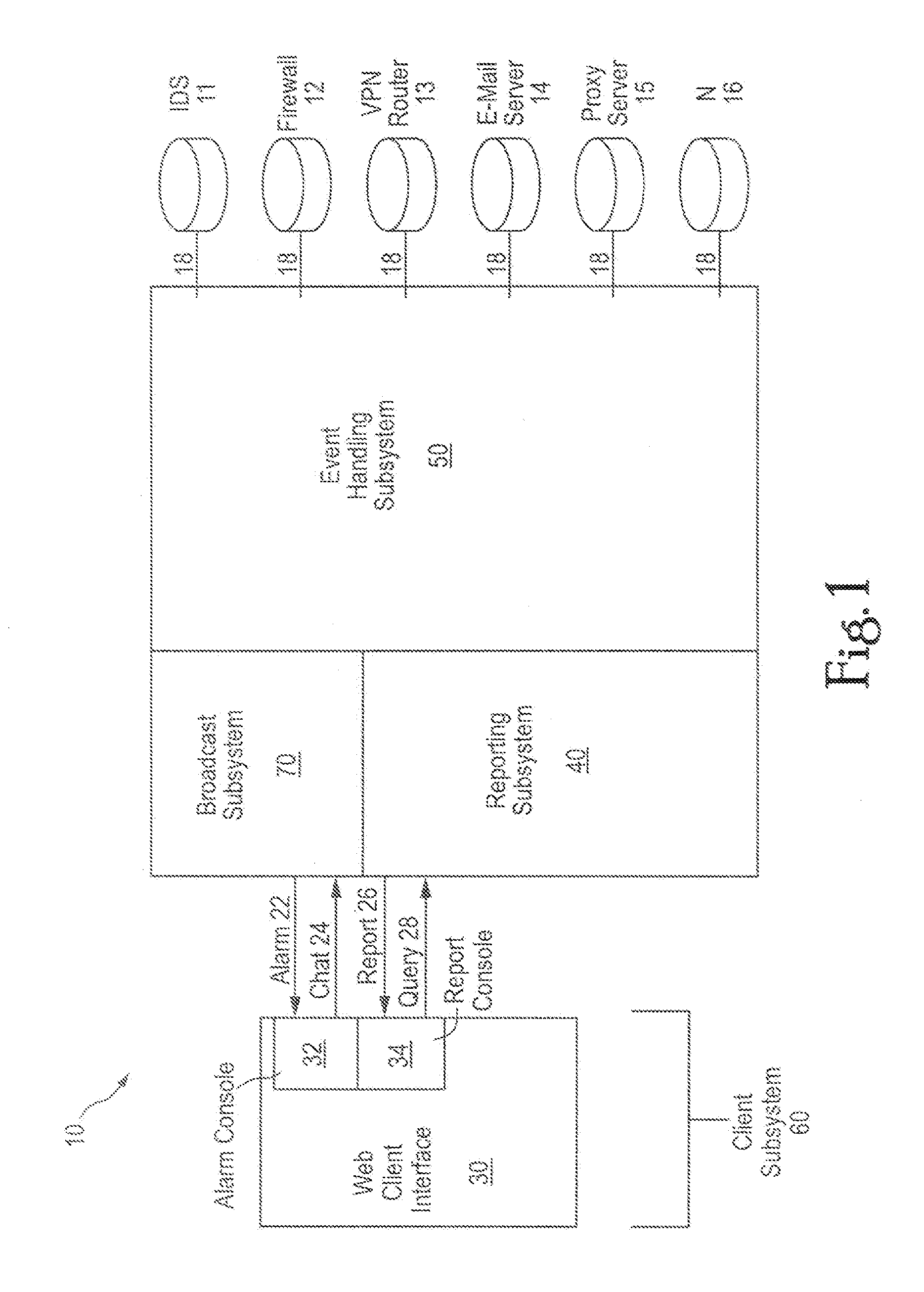
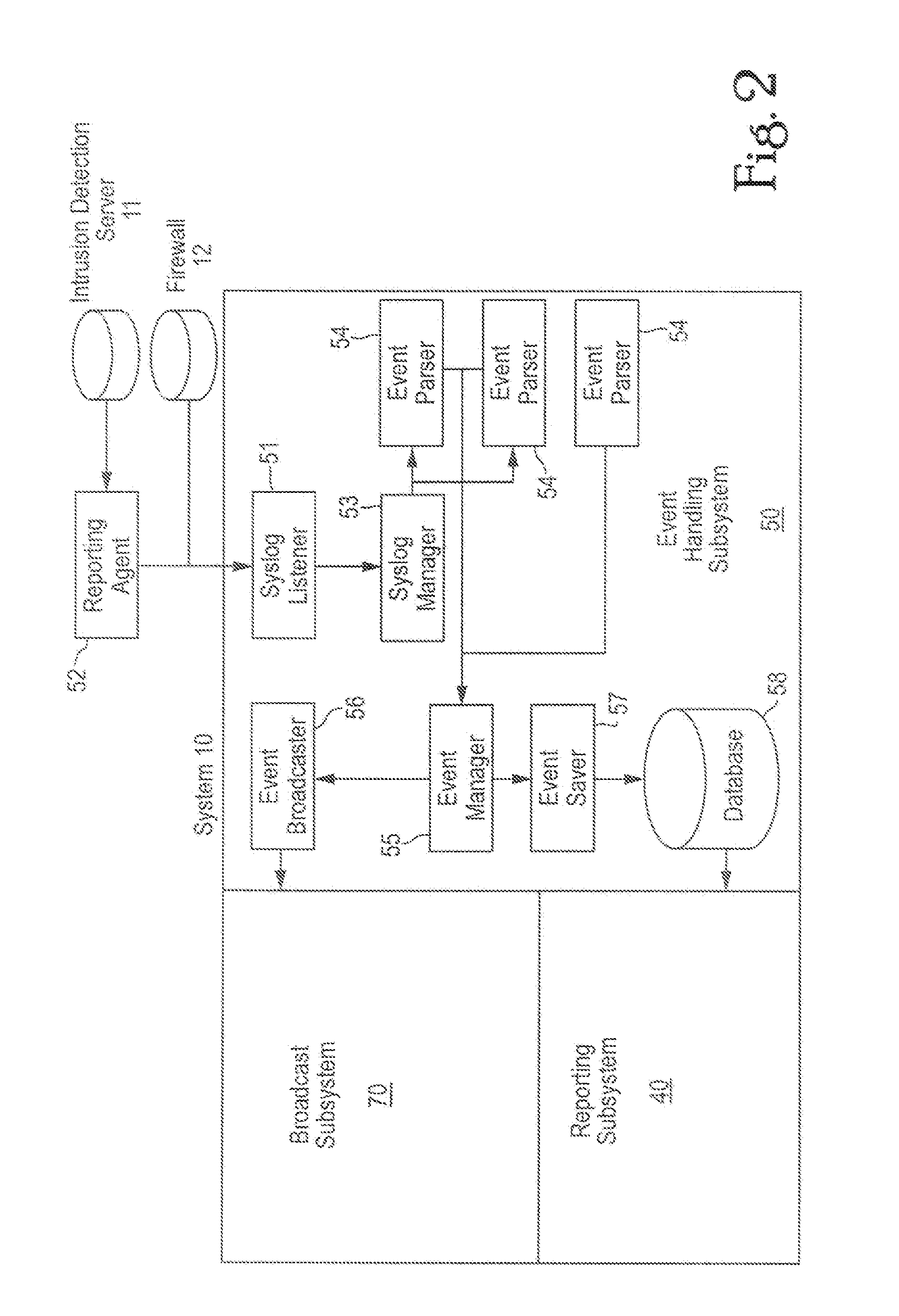
InactiveUS7127743B1Convenient reviewMemory loss protectionError detection/correctionComputerized systemNetwork service
An embodiment includes a computer system for detecting and monitoring network intrusion events from log data received from network service devices in a computer network. An embodiment may include an event parser in communication with multiple network service devices. The event parser may parse information to create corresponding event objects concerning intrusion events. The system may include an event manager in communication with the event parser. The event manager may be configured to evaluate the event objects according to at least one predetermined threshold condition. The system may include an event broadcaster in communication with the event manager for receiving event objects designated by the event manager for broadcast. The event broadcaster may be able to transmit the event objects in real time. The system may also include means for alerting the user that a network intrusion event has occurred.
Owner:BLACKSTRATUS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com