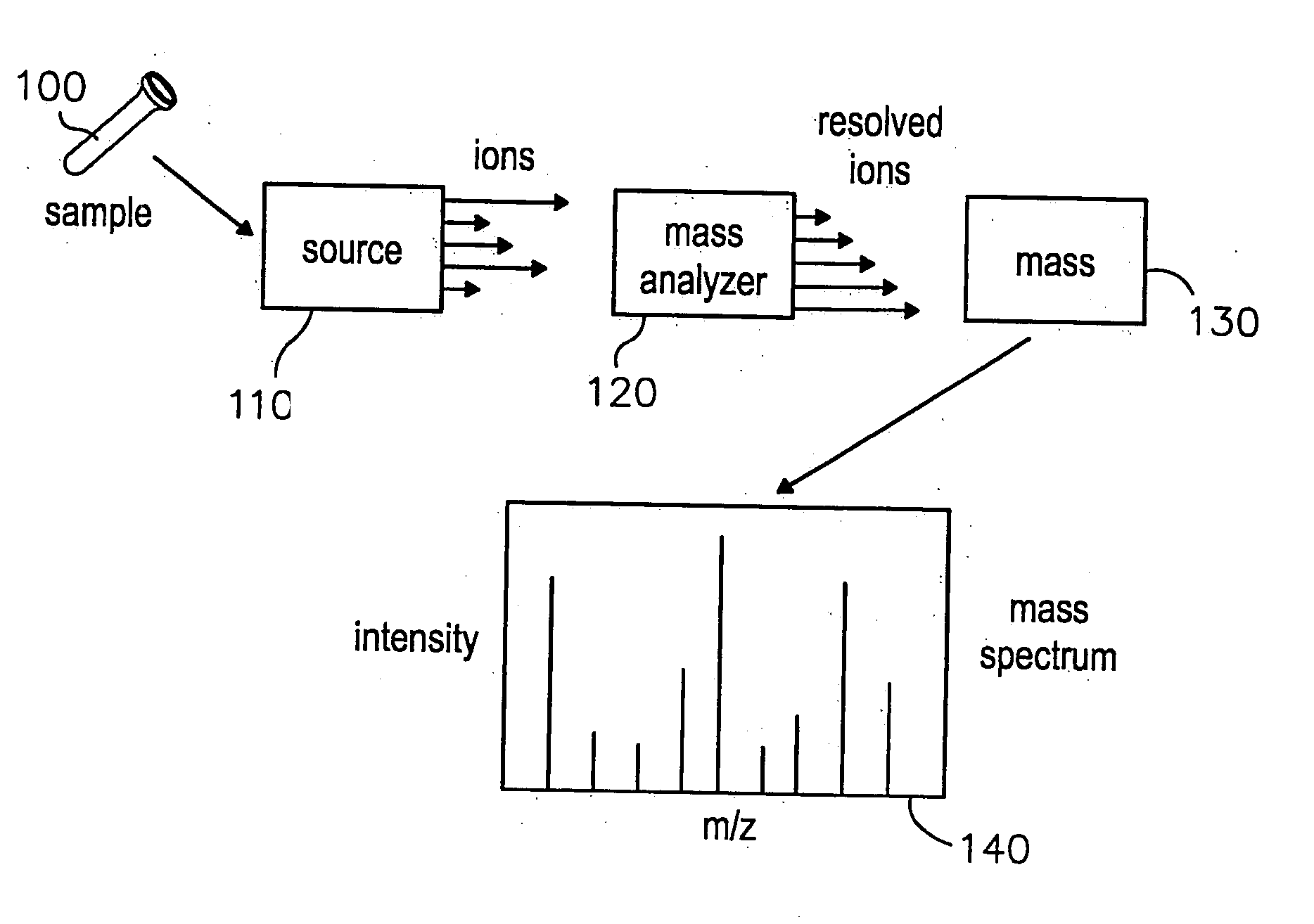
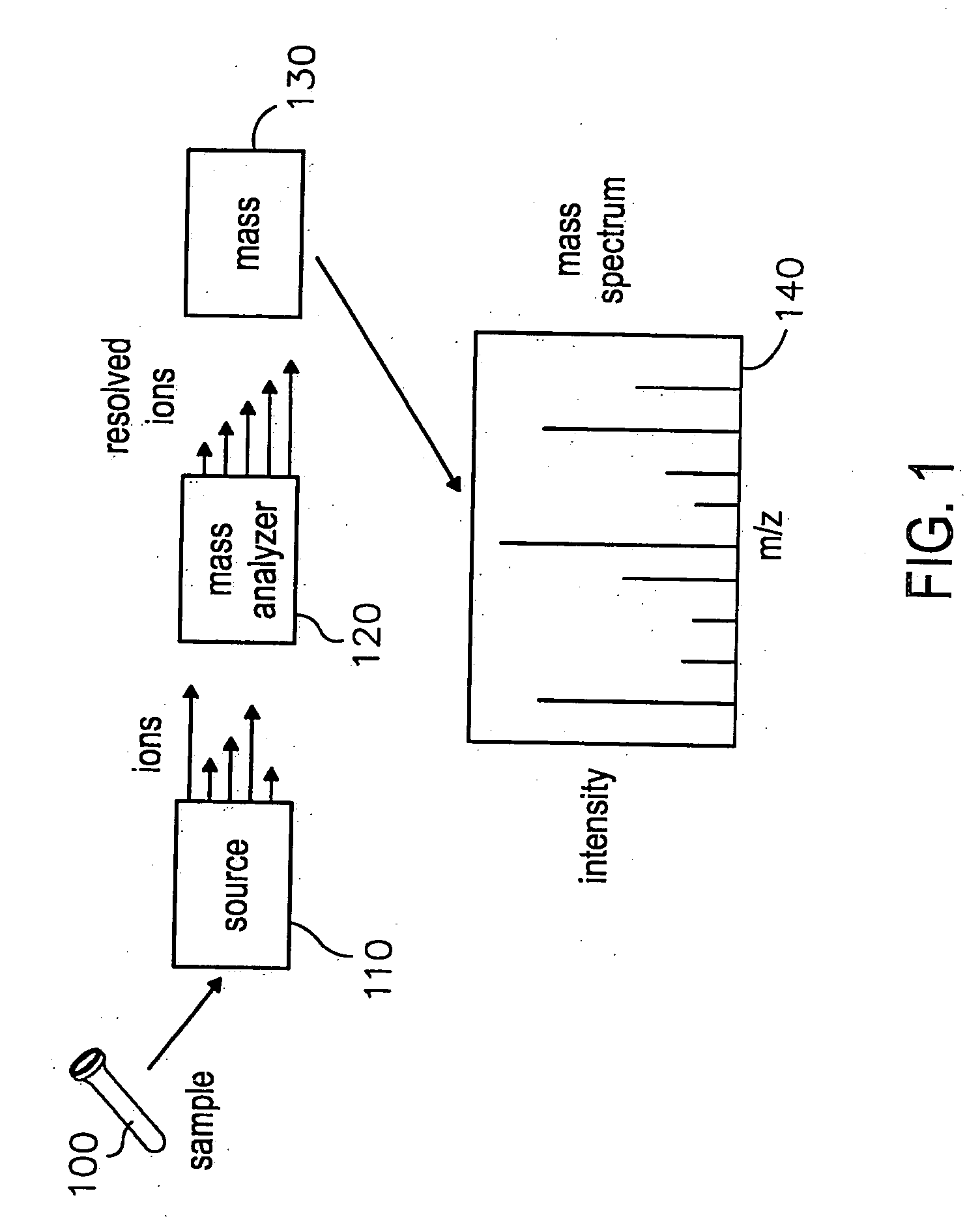
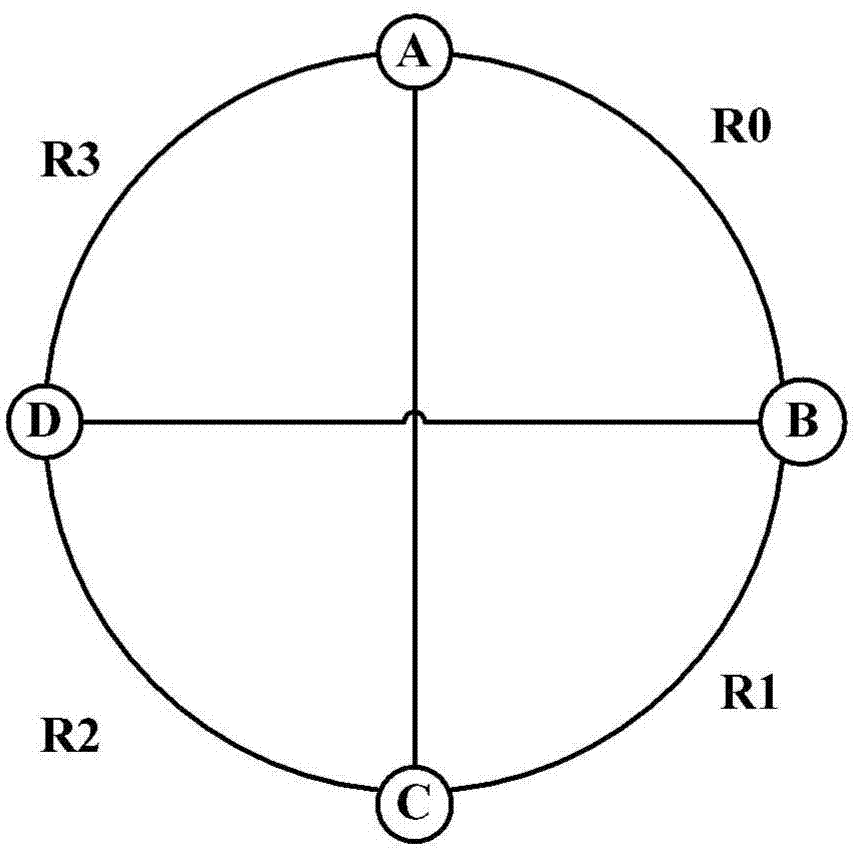
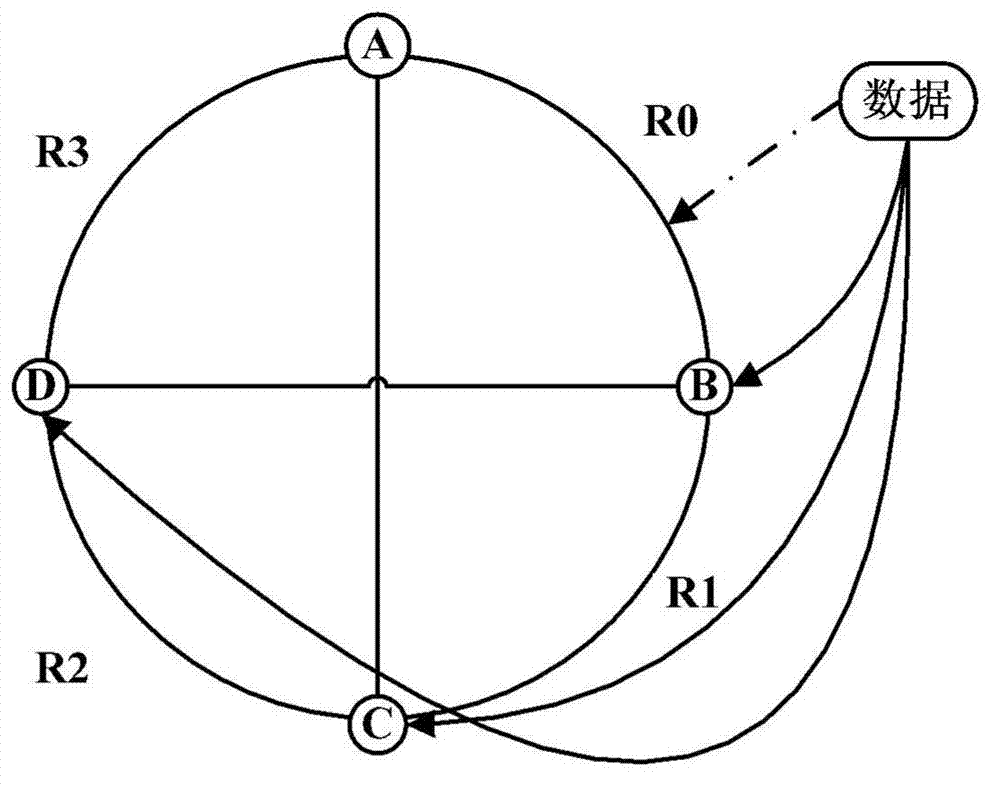
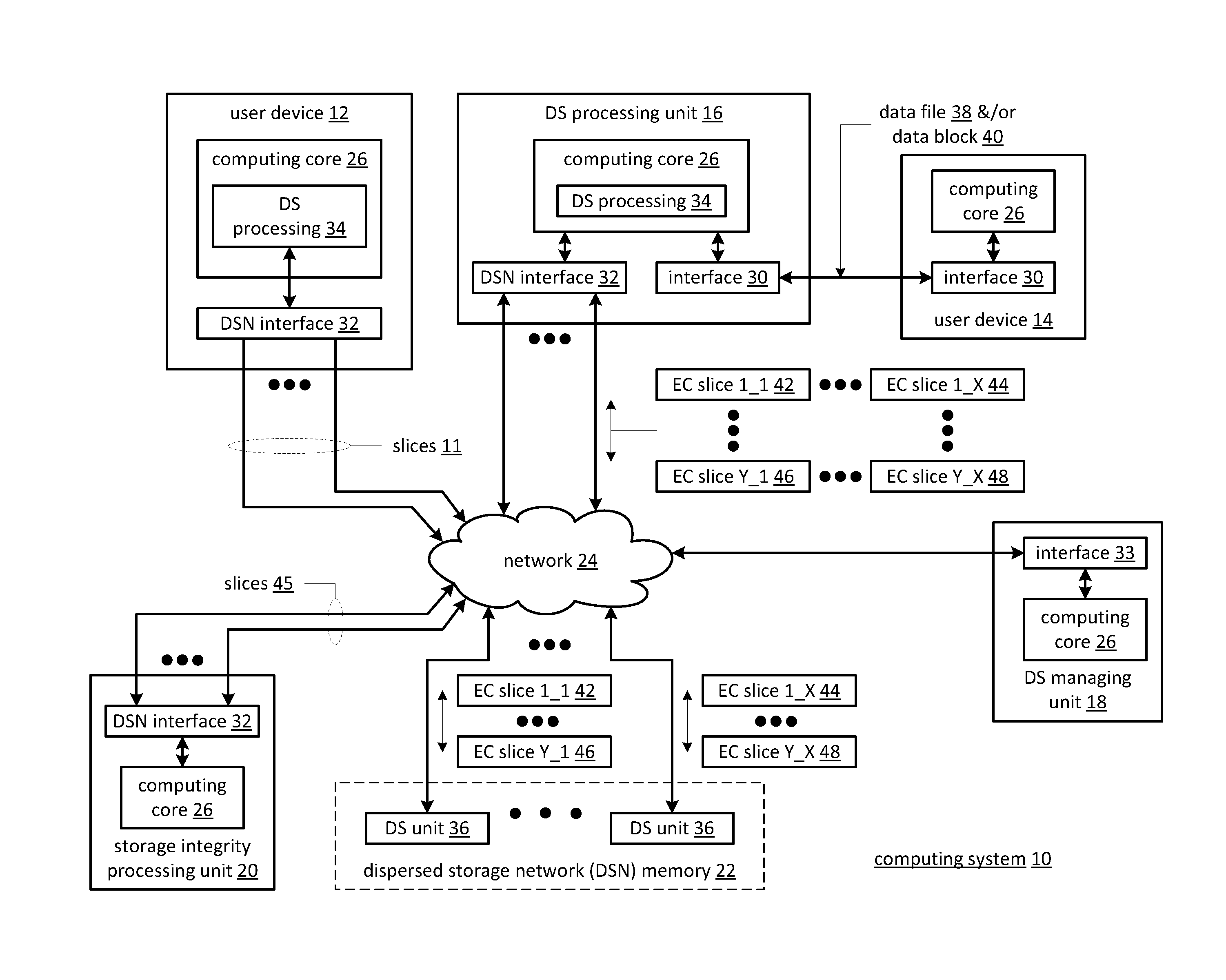
Patents
Literature
1234 results about "Data fragment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
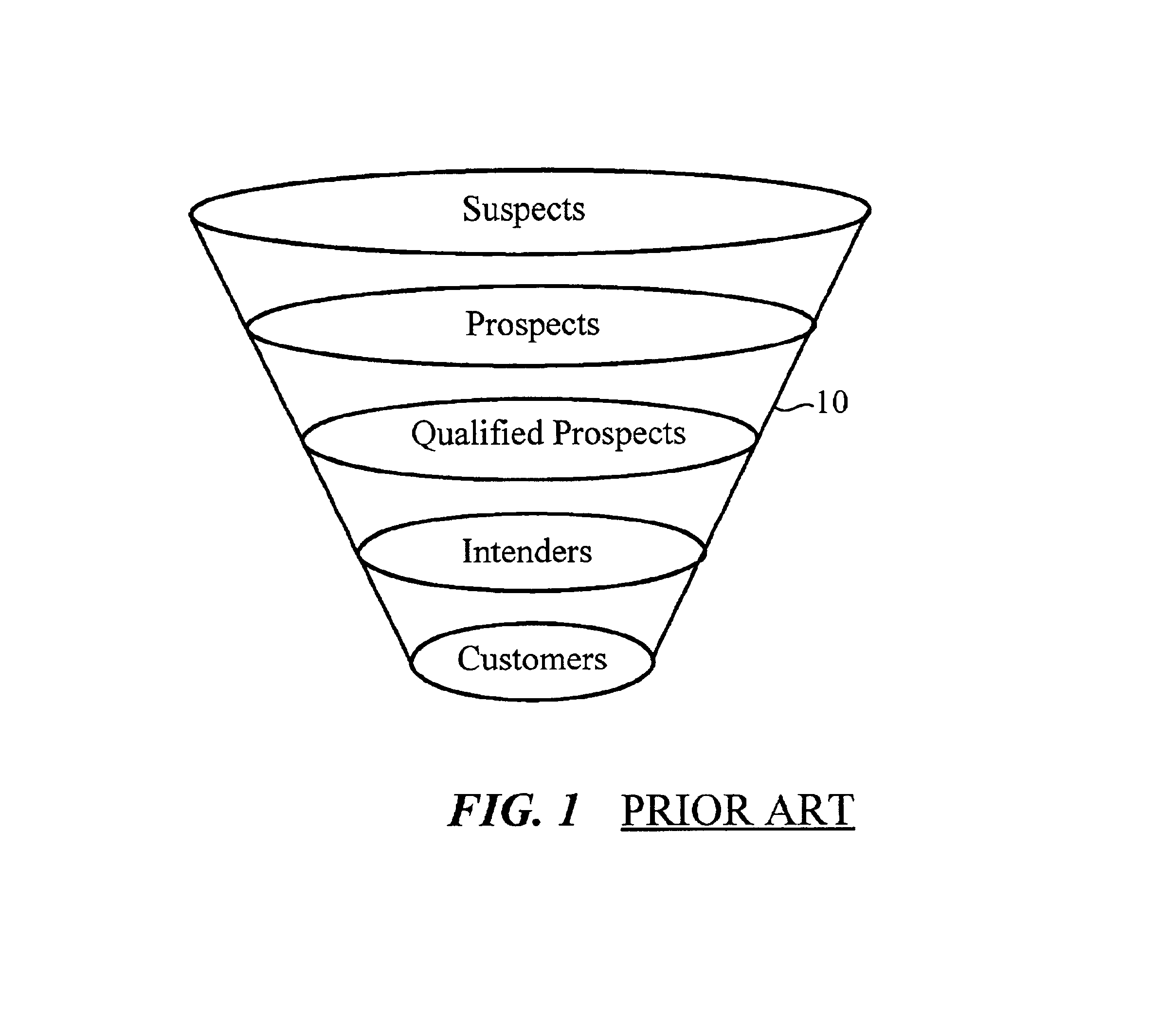
Data Fragments. There are small bits of time called data fragments. These data fragments became prevalent during the birth of the information age. When time is altered, the flow of time itself is diverted. Occasionally, small trickles of the previous flow stay in the current.
Query optimization in a multi-tenant database system
ActiveUS20050065925A1Great semantic knowledgeBroaden their knowledgeDigital data information retrievalData processing applicationsDatabase indexQuery optimization
More efficient querying of a multi-tenant database using dynamic tuning of database indices. A layer of meta-data associates data items with tenants, e.g., via tags, and the meta-data is used to optimize searches by channeling processing resources during a query to only those pieces of data bearing the relevant tenant's unique tag.
Owner:SALESFORCE COM INC
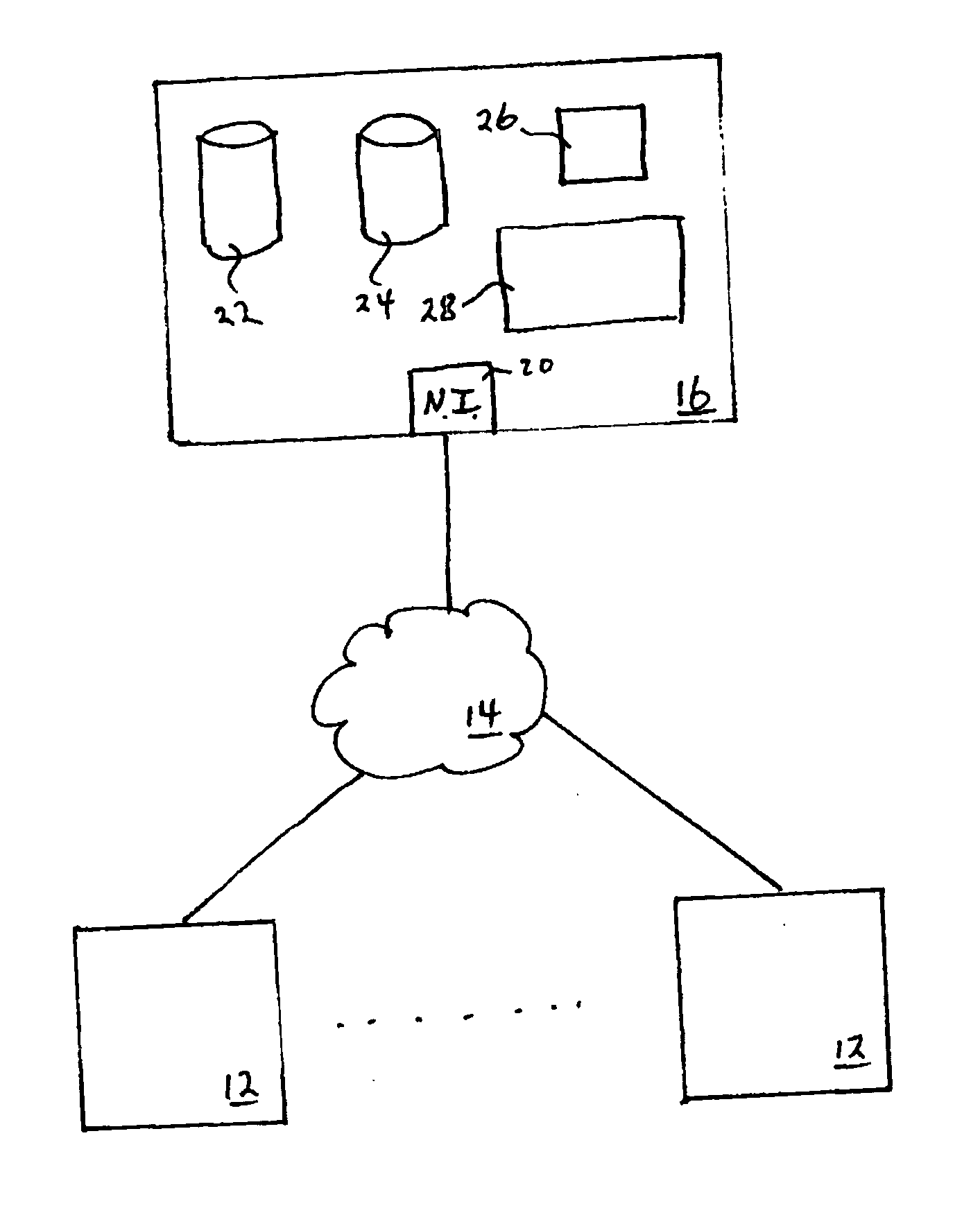
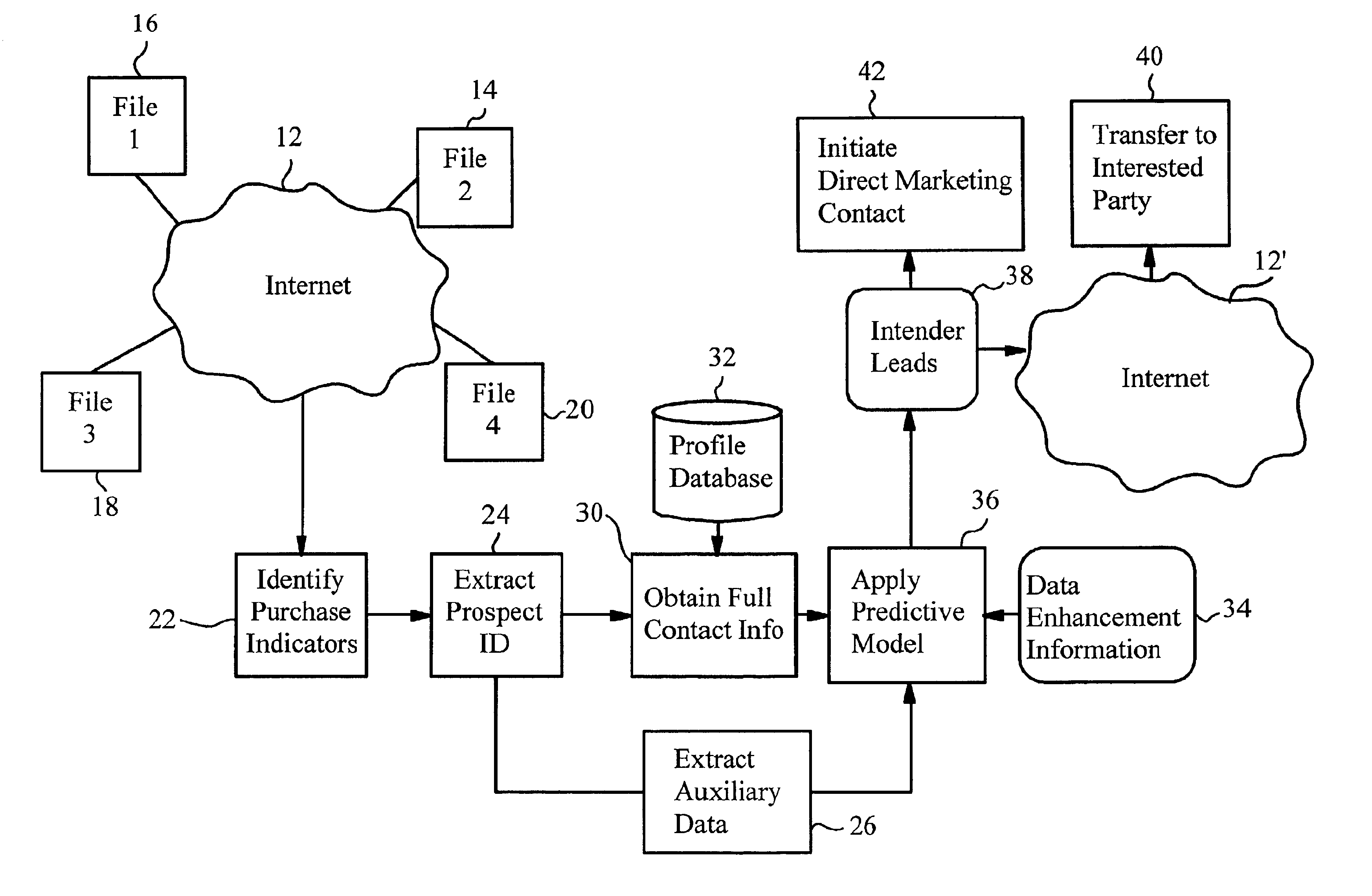
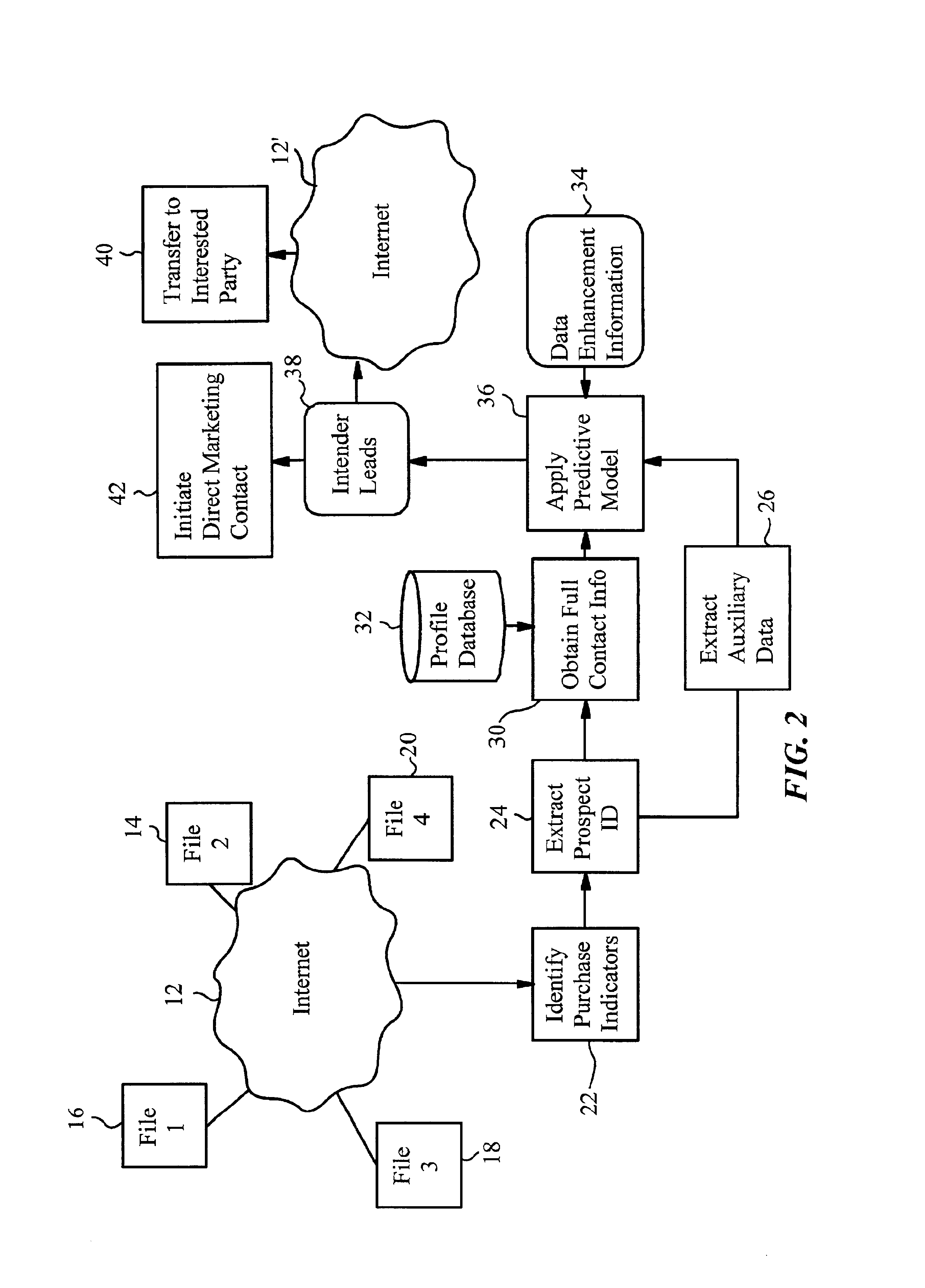
Internet-enabled lead generation
InactiveUS6868389B1Special data processing applicationsMarket data gatheringEmail addressThe Internet
A method of generating intender leads in a distributed computer system includes the steps of identifying purchase indicators and extracting prospect identifiers from the purchase indicators. Purchase indicators are pieces of data that represent a potential future purchase by a prospect. For example, an online classified advertisement selling an automobile is a purchase indicator for a potential future purchase of a new car by the old car seller. The prospect identifier, such as a telephone number or email address, uniquely identifies the prospect likely to make the future purchase. Preferably, the method also contains the steps of obtaining full contact information for the prospect from a profile database, applying a predictive model to the prospects to select intender leads, and transferring the intender leads to an interested party, such as a direct marketing service or sales force. An intender lead is a lead for a person intending to make a purchase of a particular product or service within a given time period. Only some of the prospects are actual intenders. Preferably, the method also includes the steps of extracting auxiliary data that is independent of the prospect from the purchase indicator, and obtaining data enhancement information about the prospect from data enhancement databases. The predictive model is preferably also applied to the data enhancement information and auxiliary data. The method is particularly well-suited for the Internet, which is a large source of publicly-available purchase indicators that is constantly updated. The intender leads are preferably transferred over the Internet, e.g. by email, so that they arrive at the sales force when they are still “hot.”
Owner:MEDIA DIRECT
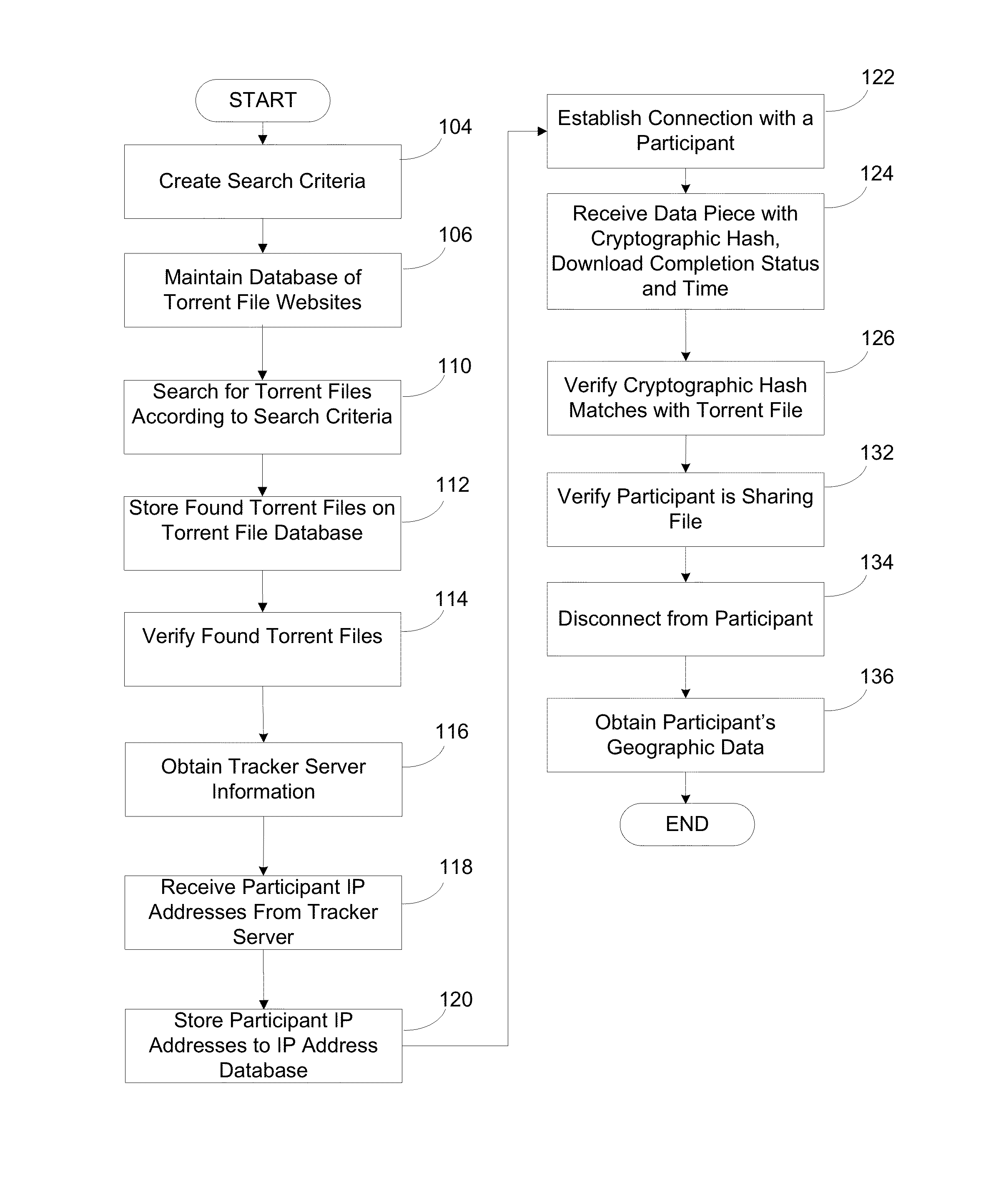
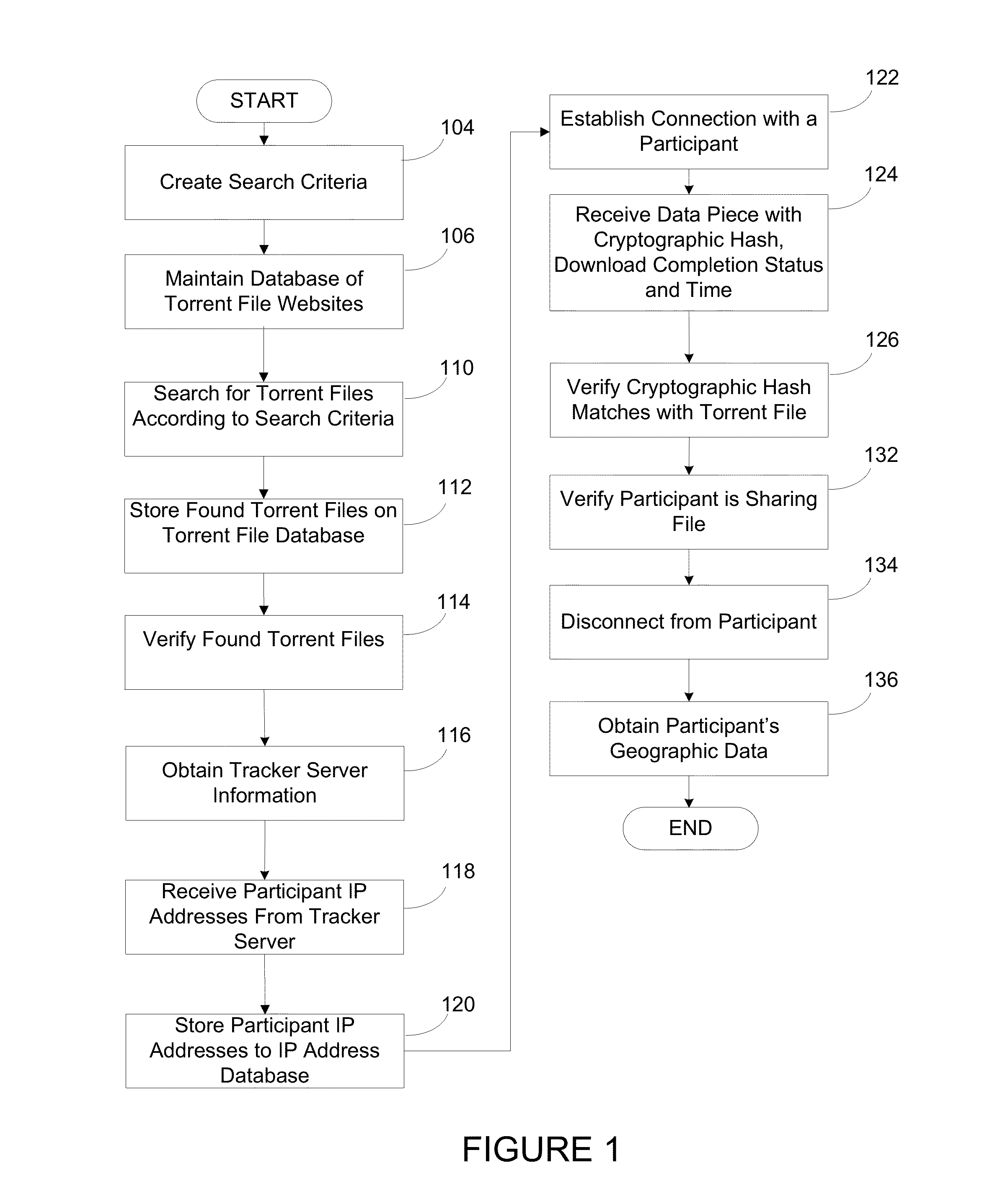
Systems and methods for managing data assets associated with peer-to-peer networks
ActiveUS20140289862A1Digital data processing detailsAnalogue secracy/subscription systemsIp addressComputer science
A system and method for targeting content to BitTorrent users is presented. The system searches torrent file websites for a torrent file according to specified search criteria and verifies that the torrent file corresponds to a media file containing the copyrighted work. The system obtains tracker server information from the torrent file and obtains the IP addresses of participants currently connected to the torrent file from the tracker server, attempts to establish a connection with a participant based on an IP address selected from the IP addresses and, if successful, receives a data piece with a cryptographic hash from the participant. The cryptographic hash is verified to correctly match with the torrent file. The system provides for correlation of information about participants in the peer-to-peer network and using the information to provide targeted campaign to each user based on the user's preferences.
Owner:IP SQUARED TECH HLDG
System and method for creating and inserting multiple data fragments into an electronic mail message
InactiveUS6510453B1Easy to identifyImprove performanceMultiple digital computer combinationsOffice automationComputer moduleWorld Wide Web
A method for creating and inserting an electronic mail signature fragment into an electronic mail message during the creation of the electronic mail message is disclosed. A computer-readable medium on which is stored a program module for creating and inserting an electronic mail signature fragment into an electronic mail message during the creation of the electronic mail message is also disclosed.
Owner:MICROSOFT TECH LICENSING LLC
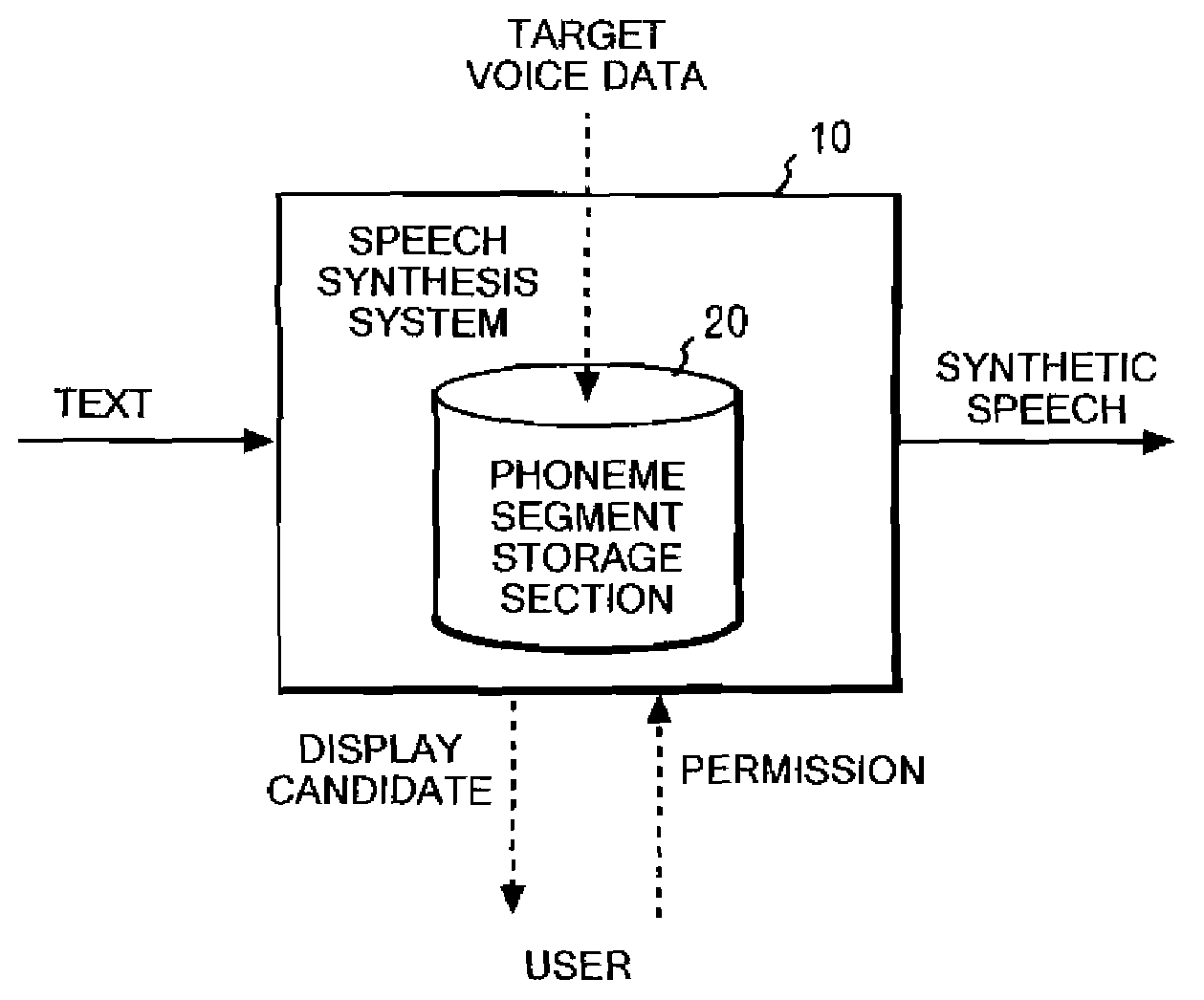
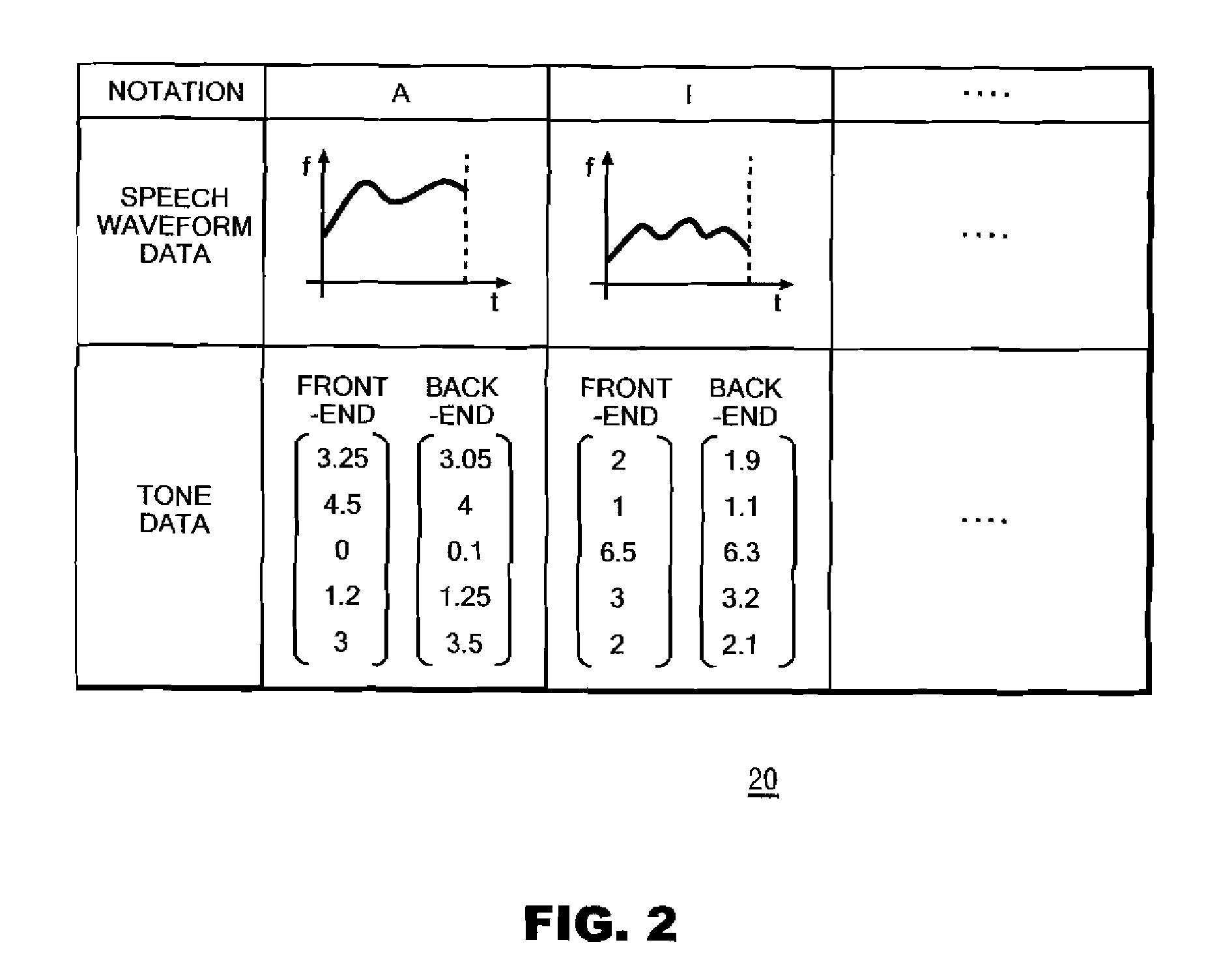
Technique of Generating High Quality Synthetic Speech
A synthetic speech system includes a phoneme segment storage section for storing multiple phoneme segment data pieces; a synthesis section for generating voice data from text by reading phoneme segment data pieces representing the pronunciation of an inputted text from the phoneme segment storage section and connecting the phoneme segment data pieces to each other; a computing section for computing a score indicating the unnaturalness of the voice data representing the synthetic speech of the text; a paraphrase storage section for storing multiple paraphrases of the multiple first phrases; a replacement section for searching the text and replacing with appropriate paraphrases; and a judgment section for outputting generated voice data on condition that the computed score is smaller than a reference value and for inputting the text after the replacement to the synthesis section to cause the synthesis section to further generate voice data for the text.
Owner:CERENCE OPERATING CO
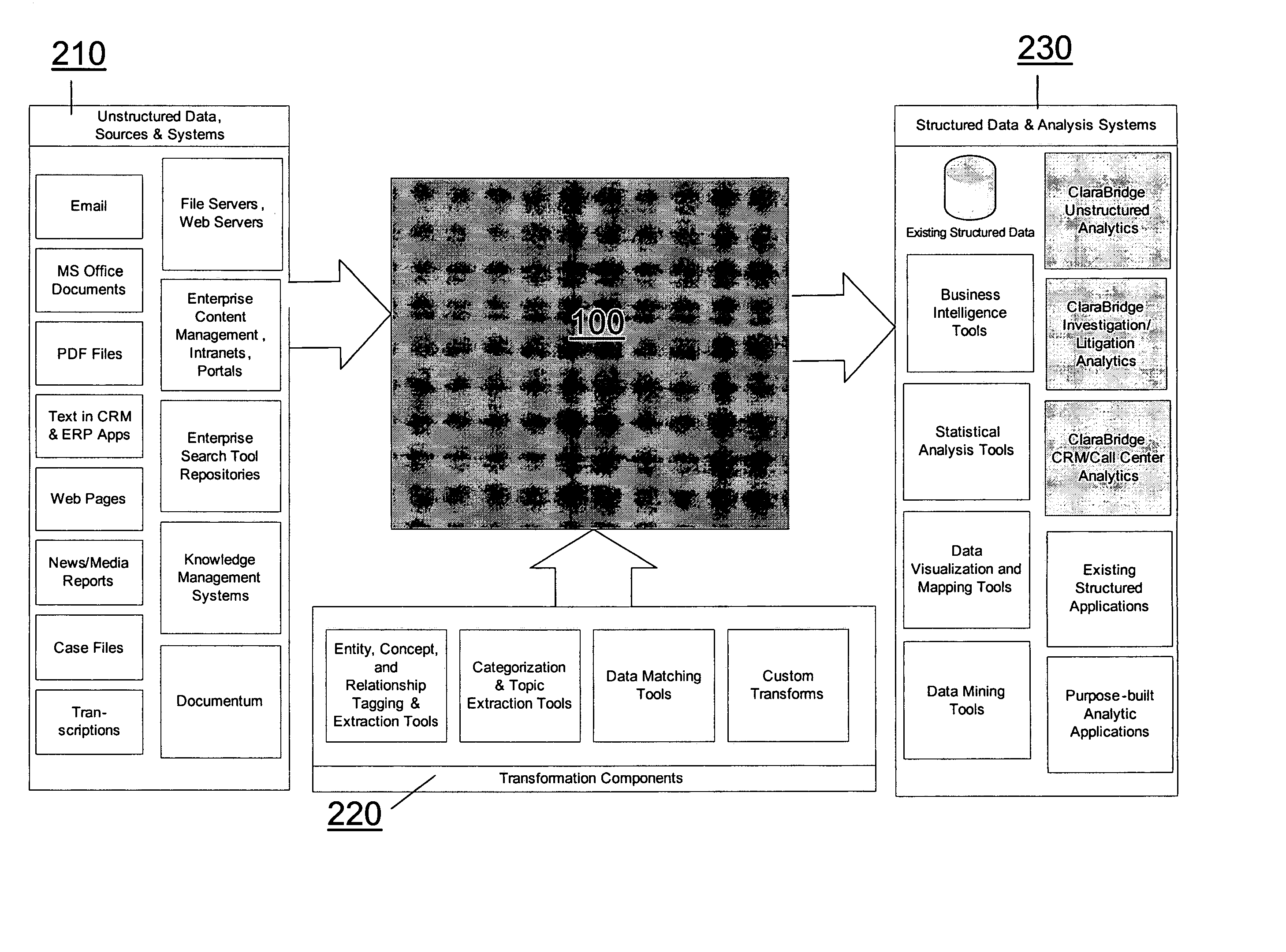
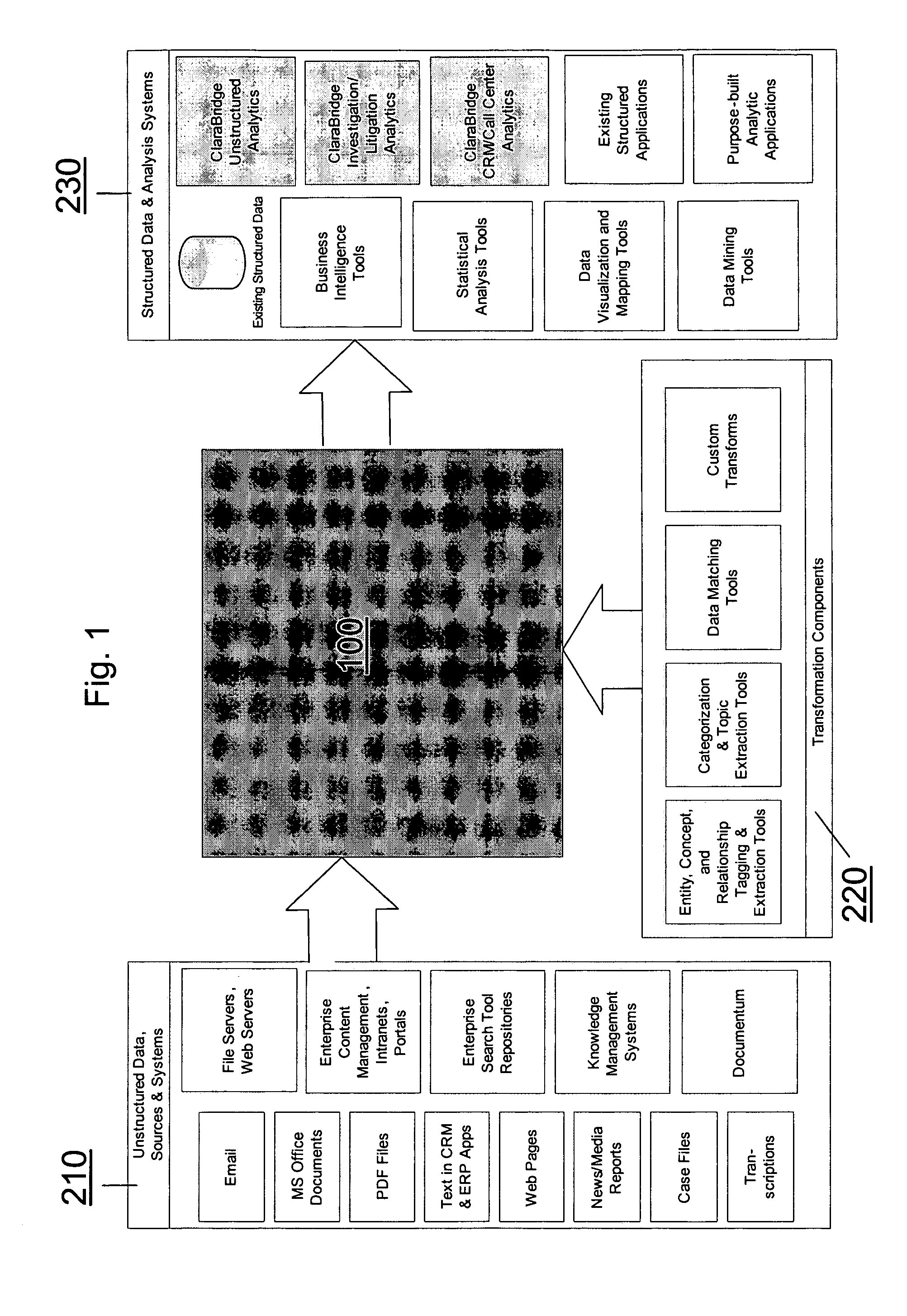
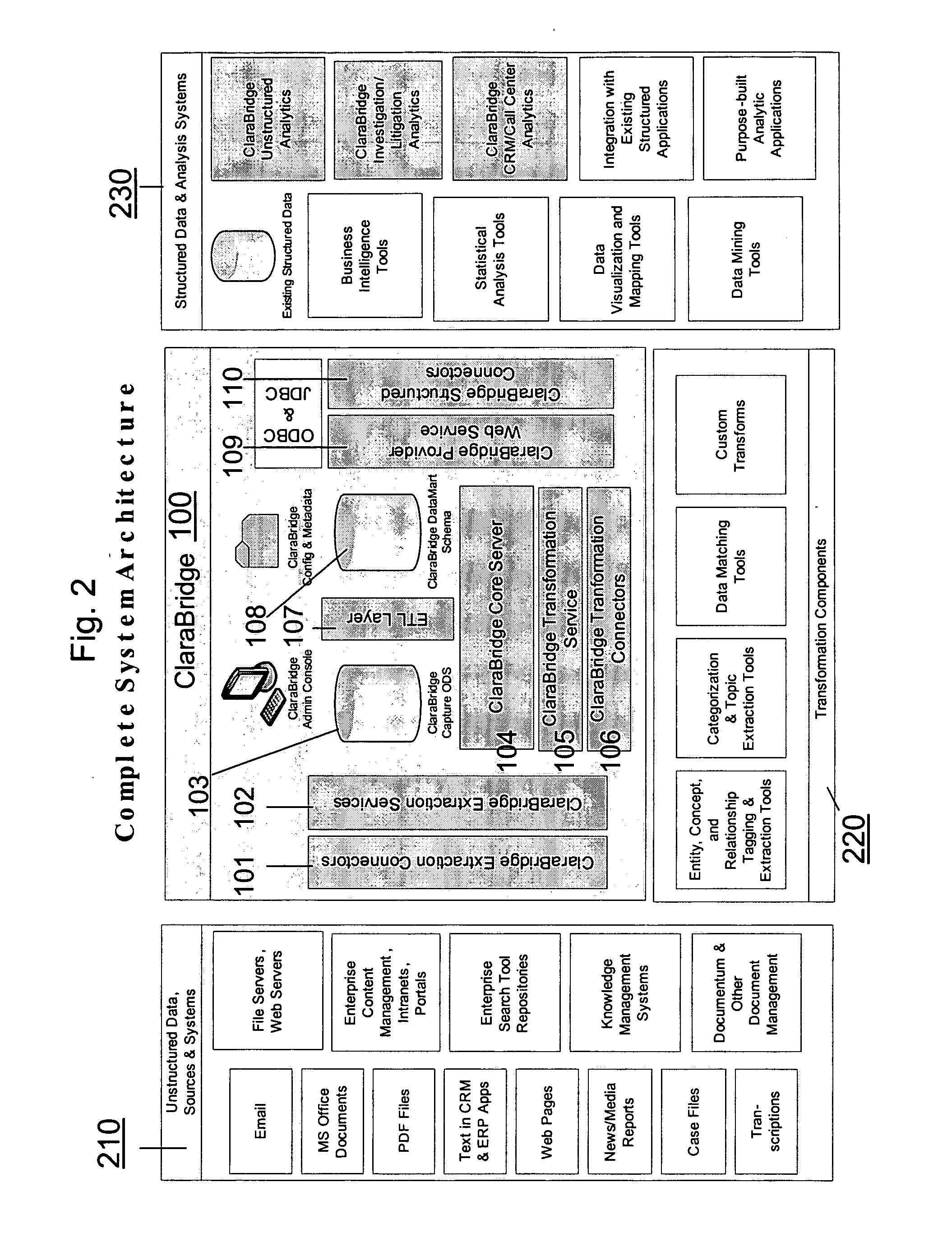
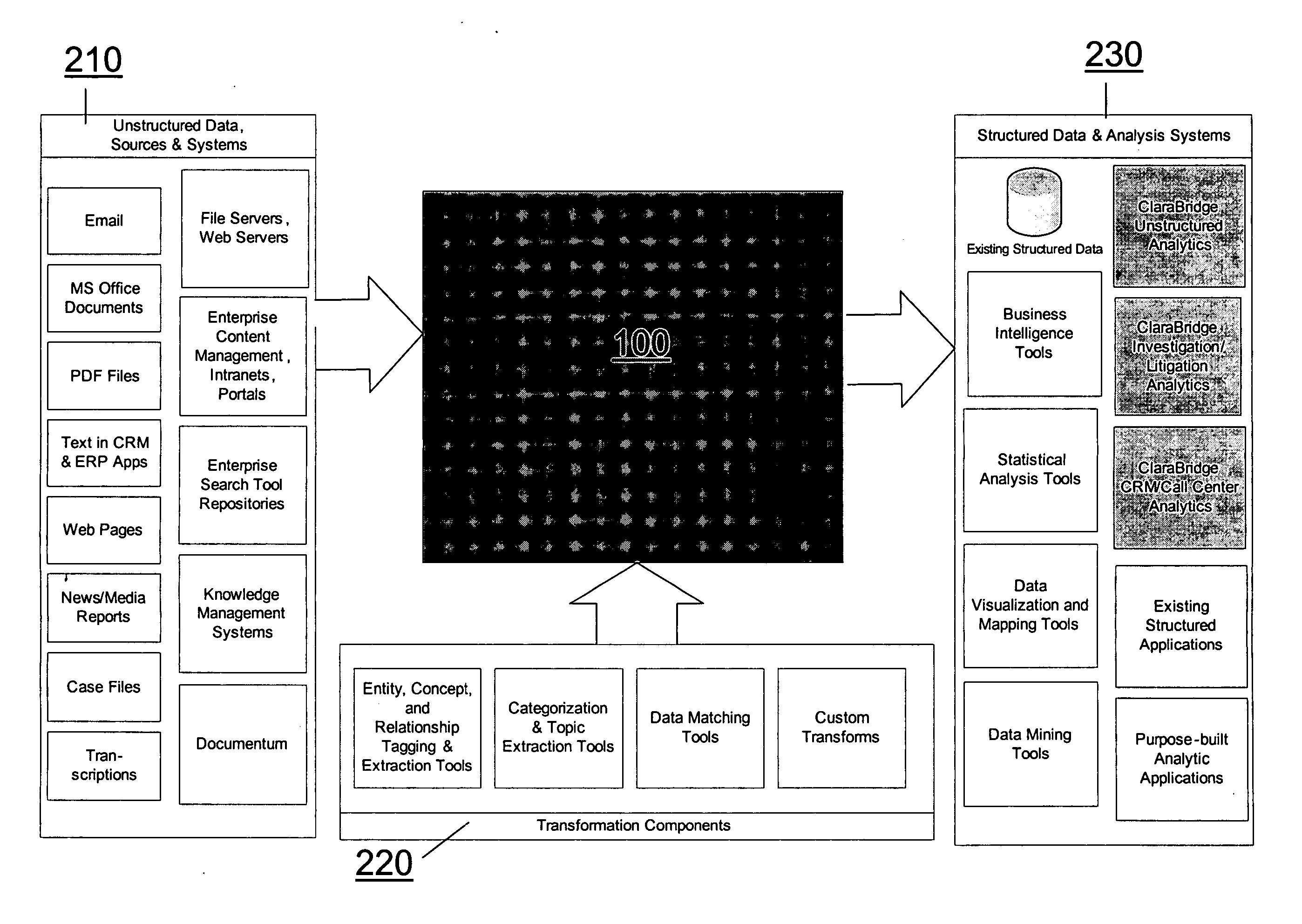
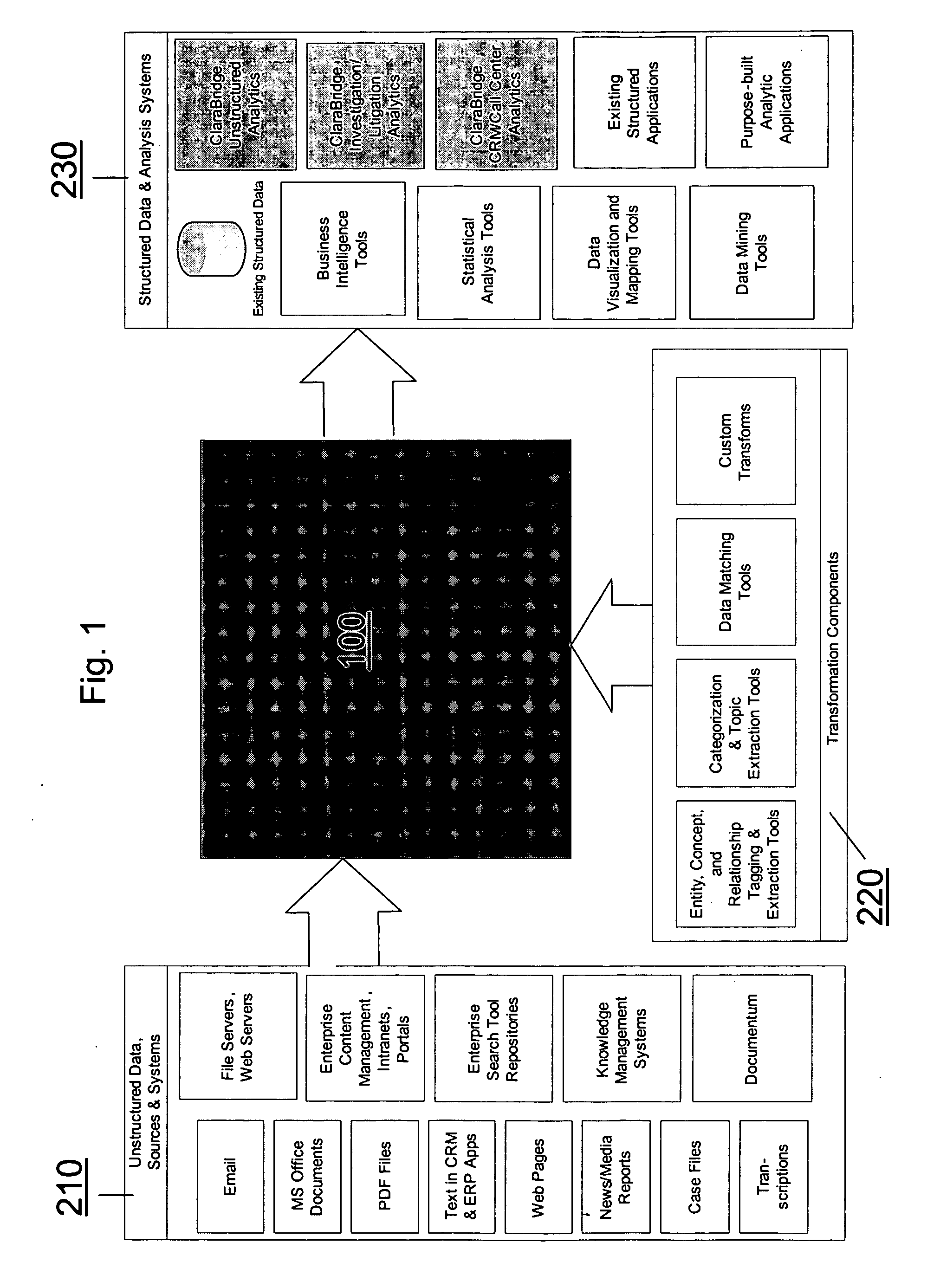
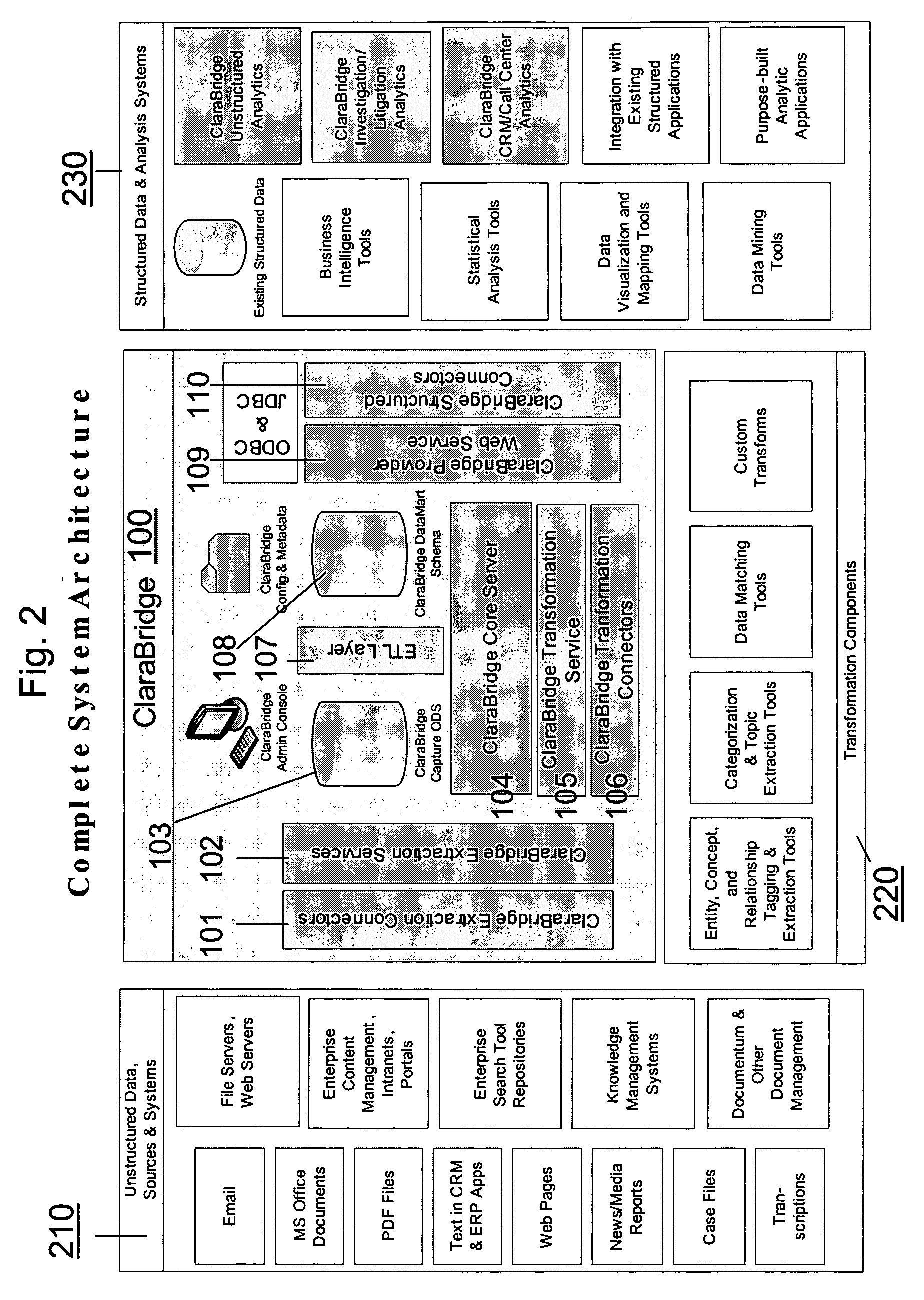
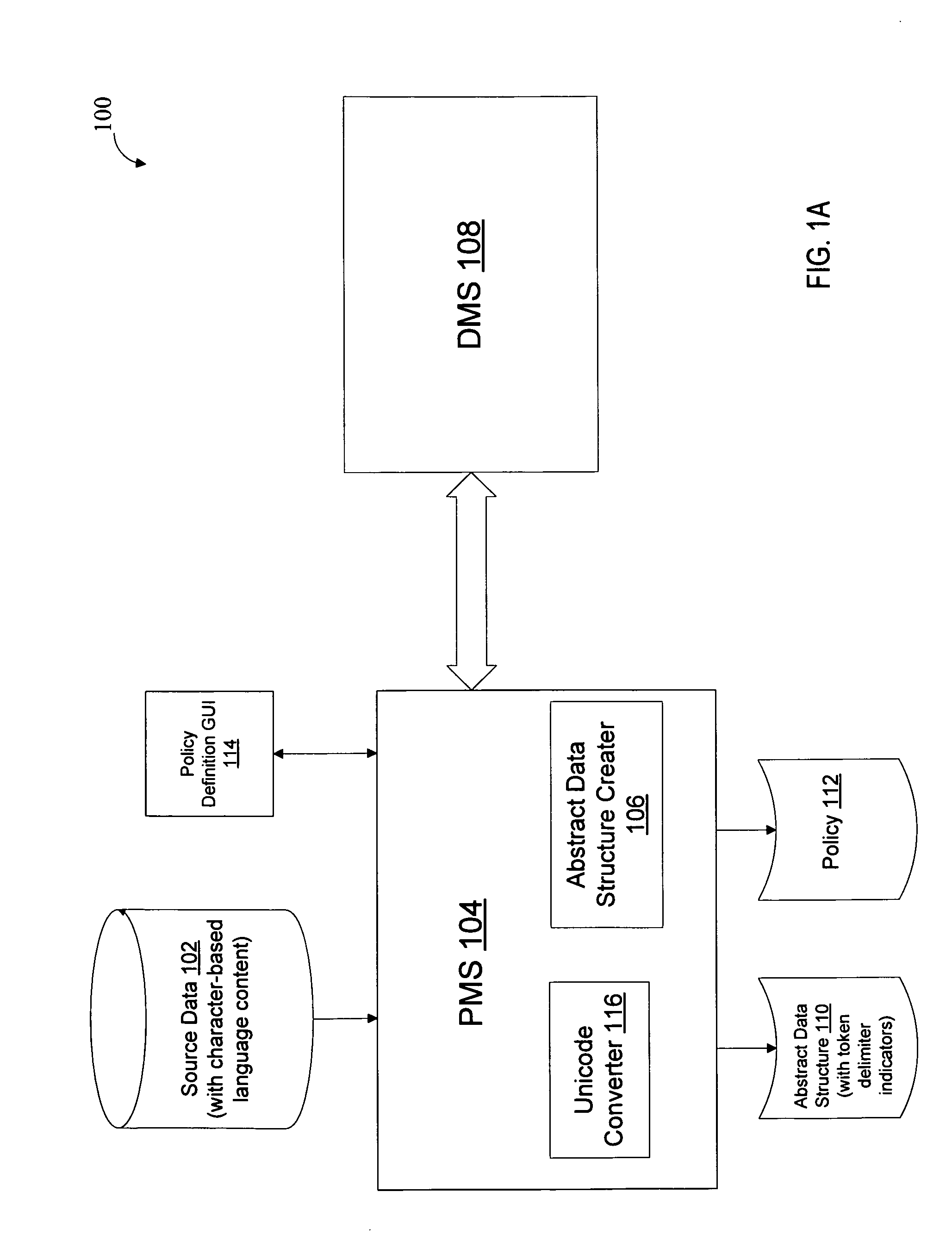
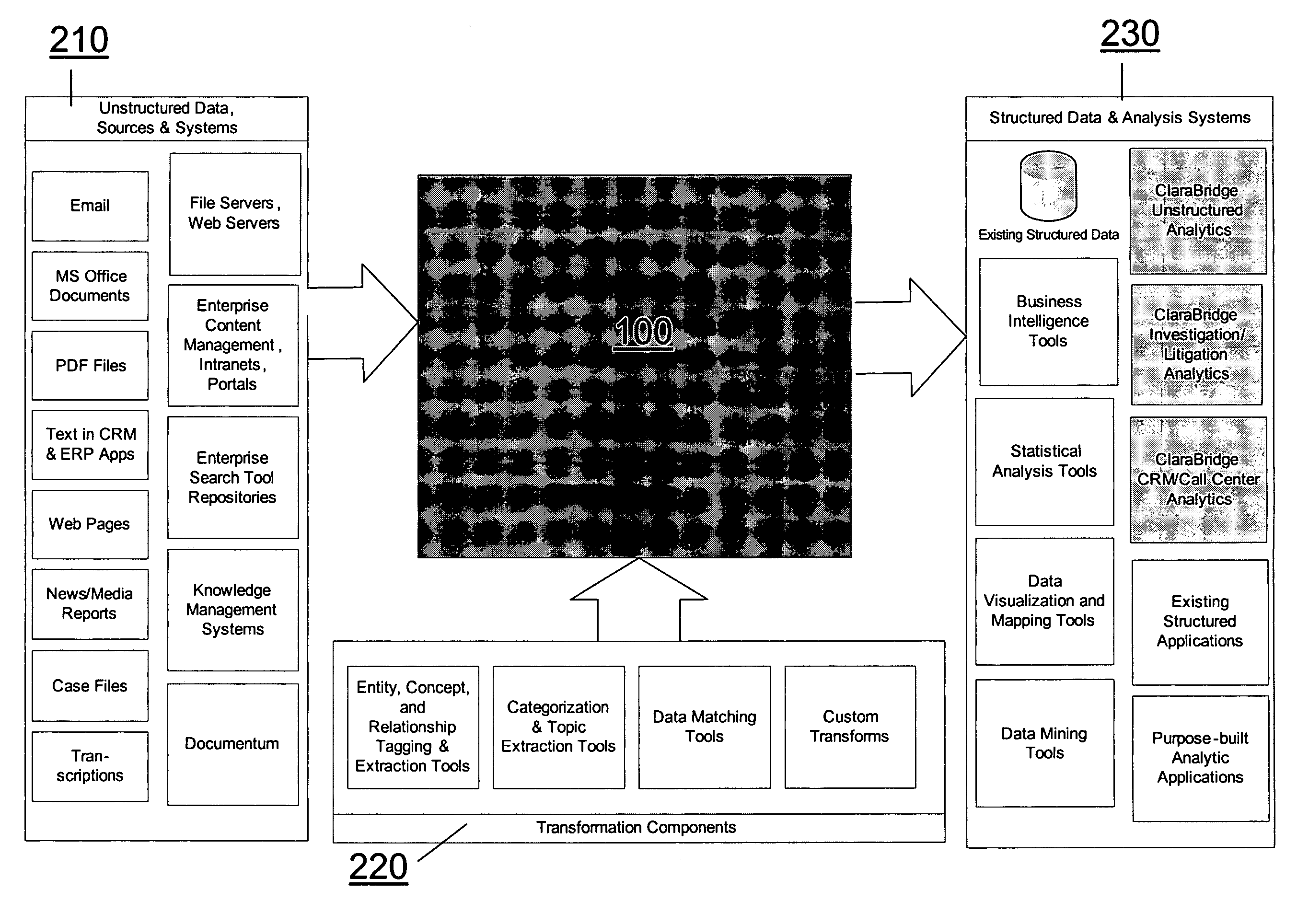
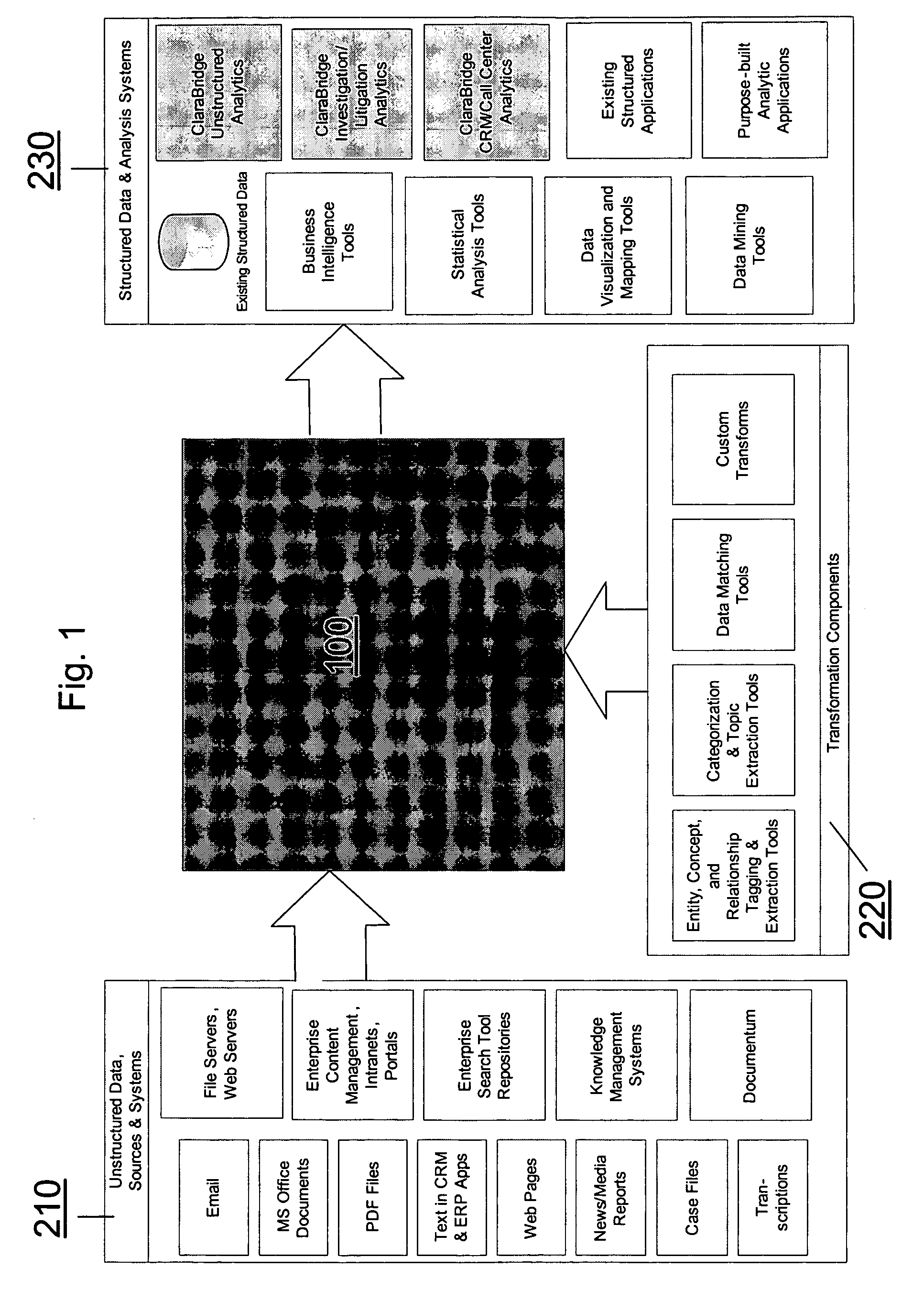
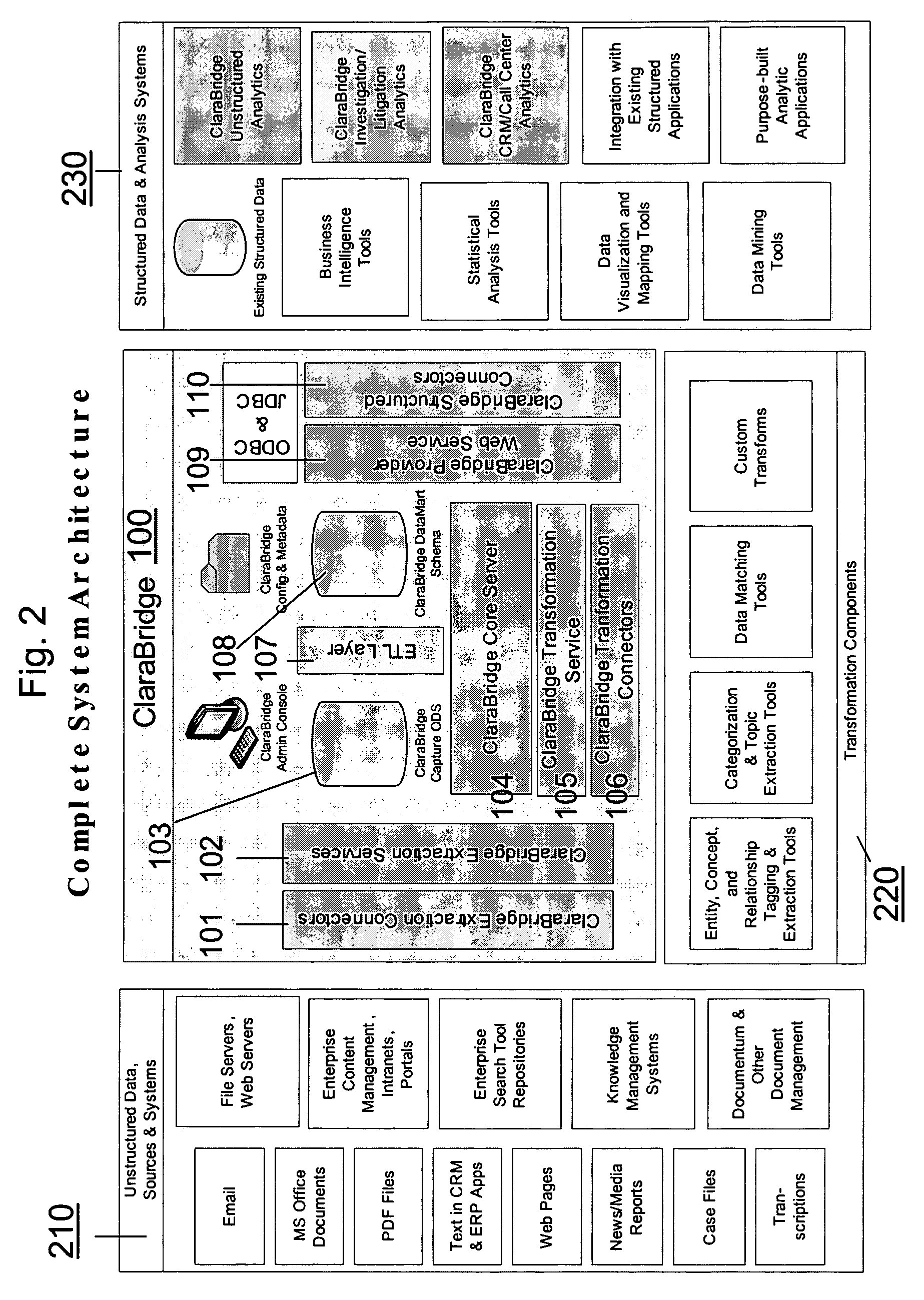
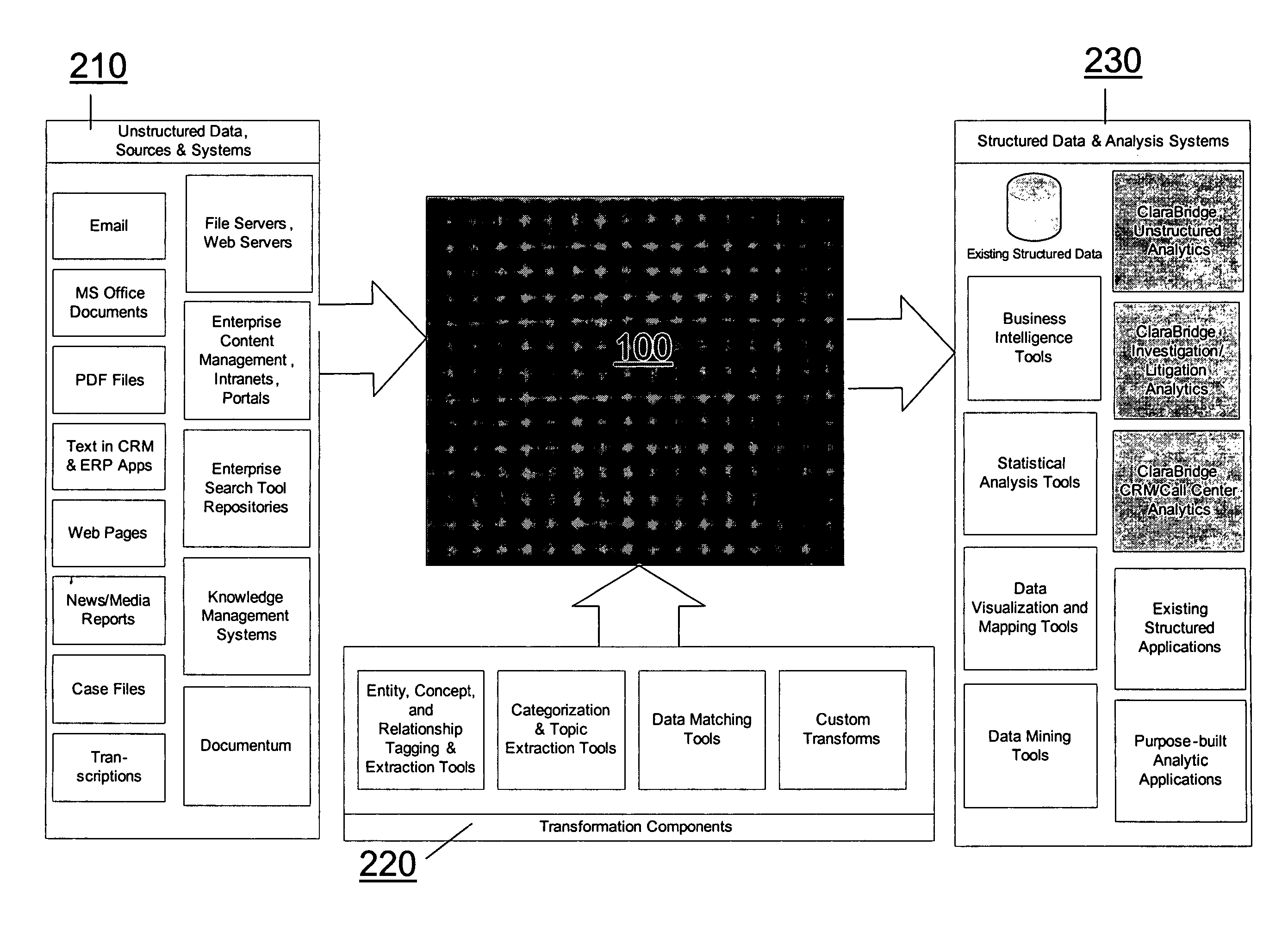
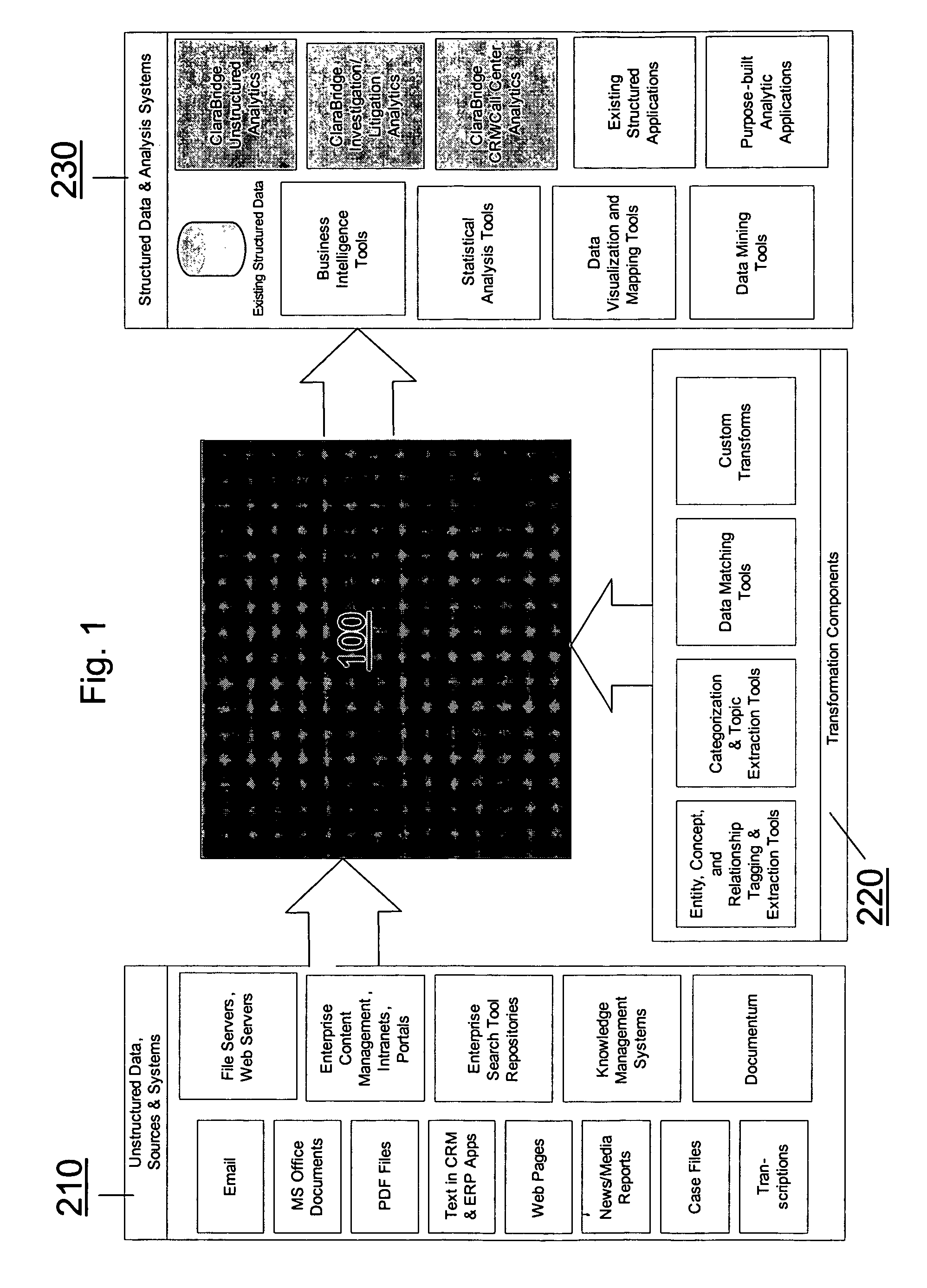
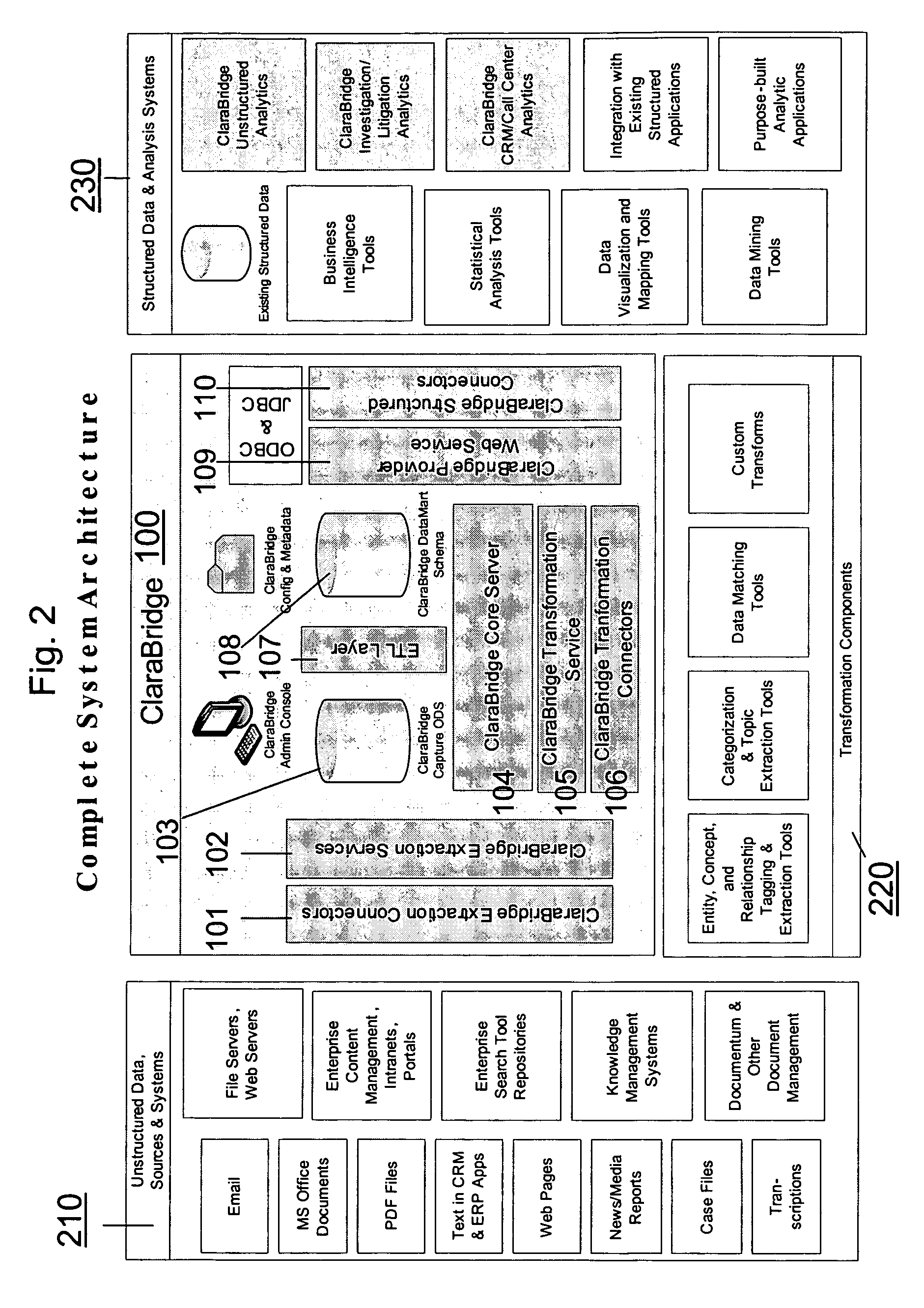
Analysis and transformation tools for structured and unstructured data
InactiveUS20070011183A1Digital data information retrievalDigital data processing detailsData transformationStructured data analysis
A system and method of making unstructured data available to structured data analysis tools. The system includes middleware software that can be used in combination with structured data tools to perform analysis on both structured and unstructured data. Data can be read from a wide variety of unstructured sources. The data may then be transformed with commercial data transformation products that may, for example, extract individual pieces of data and determine relationships between the extracted data. The transformed data and relationships may then be passed through an extraction / transform / load (ETL) layer and placed in a structured schema. The structured schema may then be made available to commercial or proprietary structured data analysis tools.
Owner:CLARABRIDGE
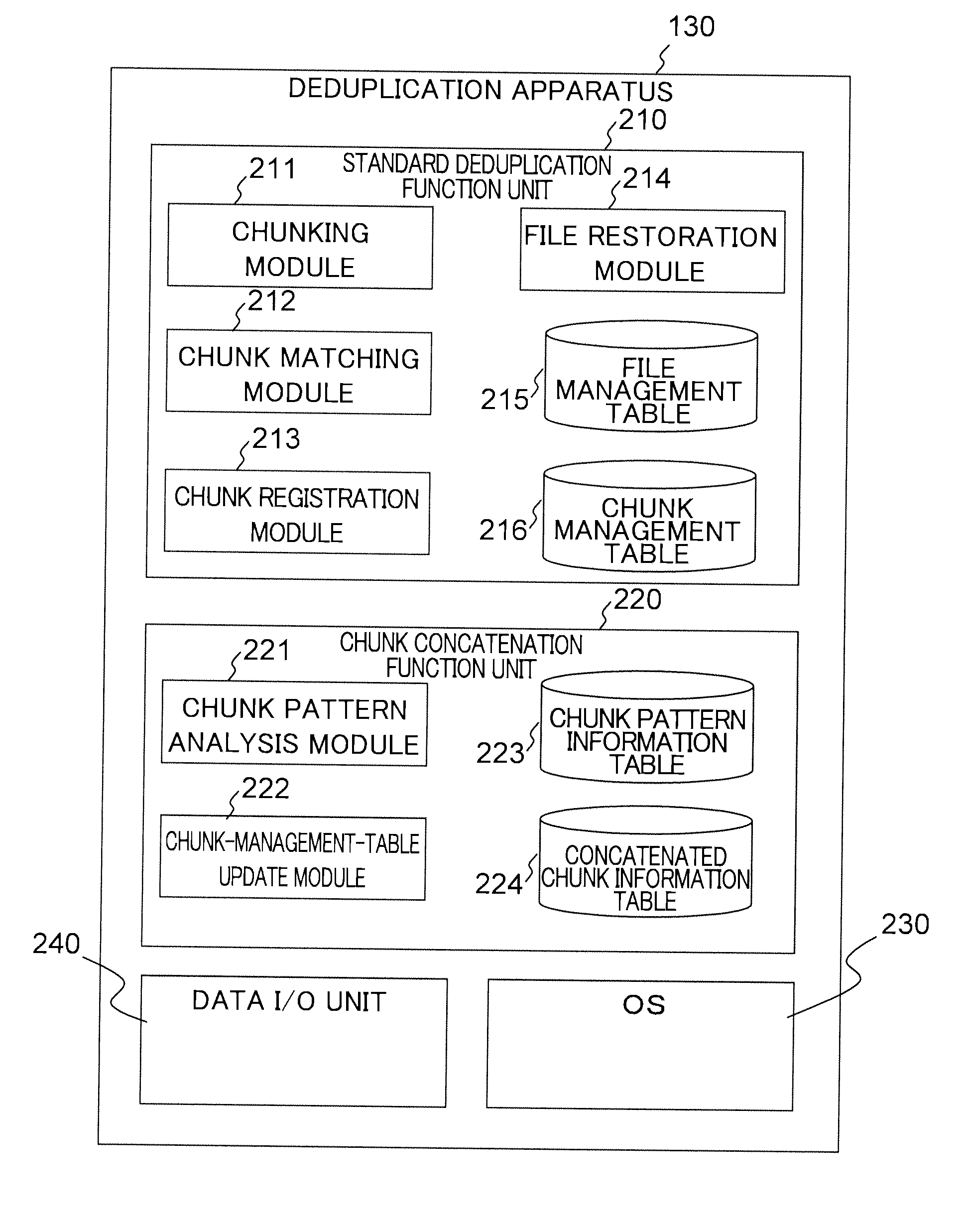
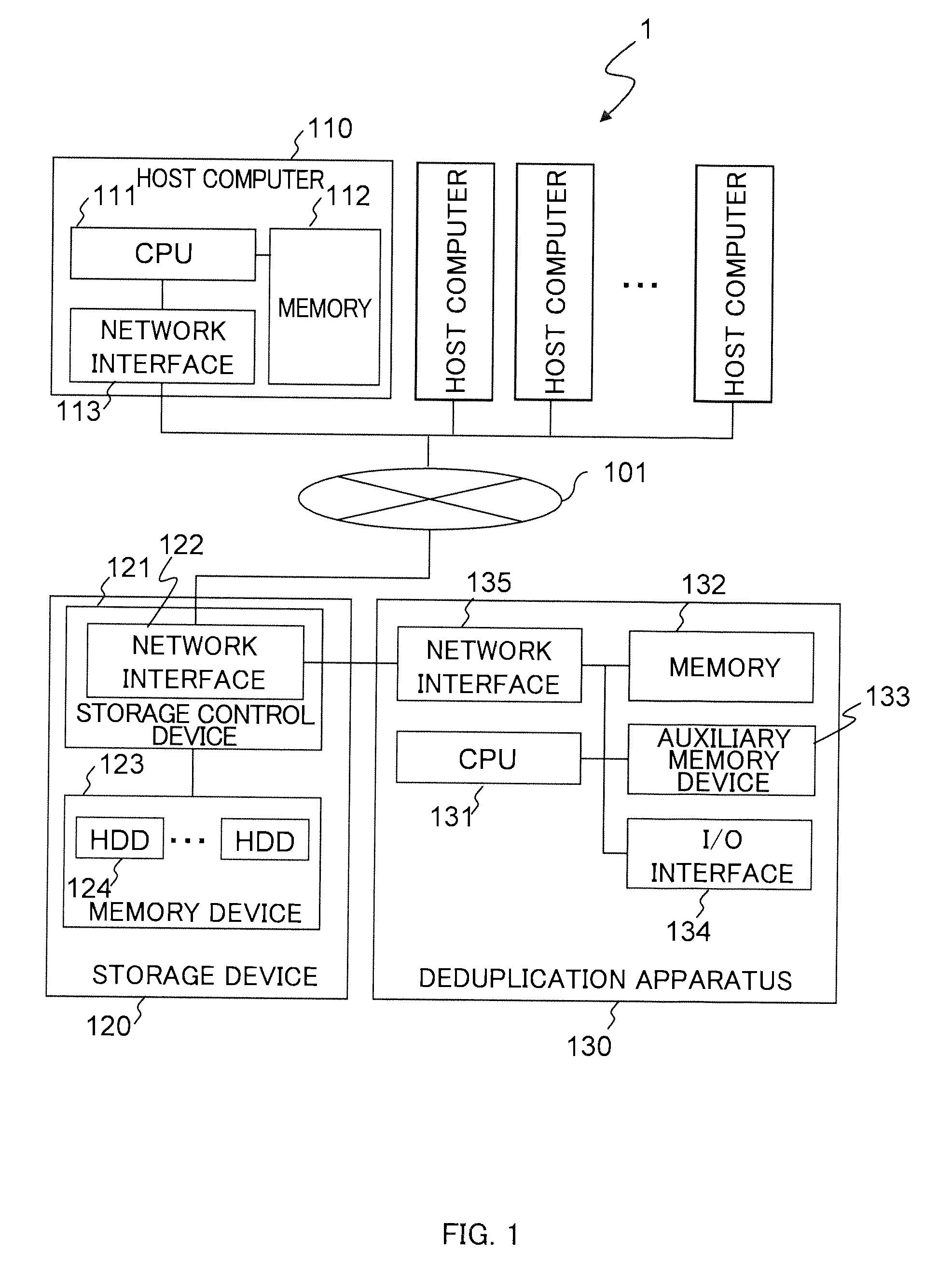
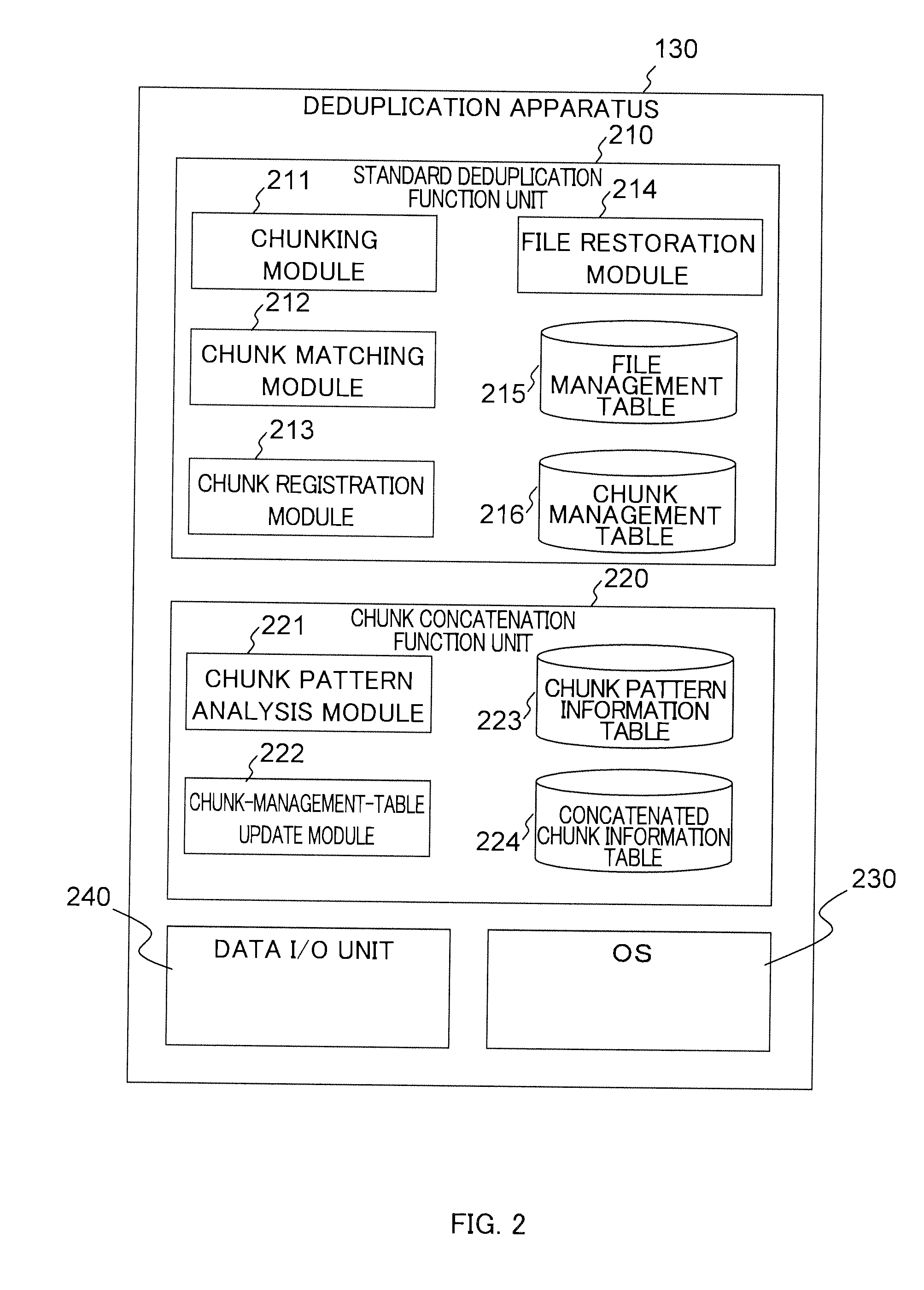
Stored data deduplication method, stored data deduplication apparatus, and deduplication program
InactiveUS20140229452A1Amount of timeDigital data information retrievalDigital data processing detailsData storingData store
Method of dividing data to be stored in storage device into data fragments; recording the data by using configurations of divided data fragments; judging whether identical data fragments exist in data fragments; when it is judged that identical data fragments exist, storing one of the identical data fragments in storage area of the storage device, and generating and recording data-fragment attribute information indicating an attribute unique to the data fragment stored; upon receipt of request to read data stored in the storage area of the storage device, acquiring the configurations of the data fragments forming the read-target data, reading the corresponding data fragments from the storage area of the storage device, and restoring the data; acquiring and coupling the recorded data fragments to generate concatenation target data targeted for judgment on whether chunk concatenation is possible or not, and detecting whether the concatenation target data has a repeated data pattern
Owner:HITACHI LTD
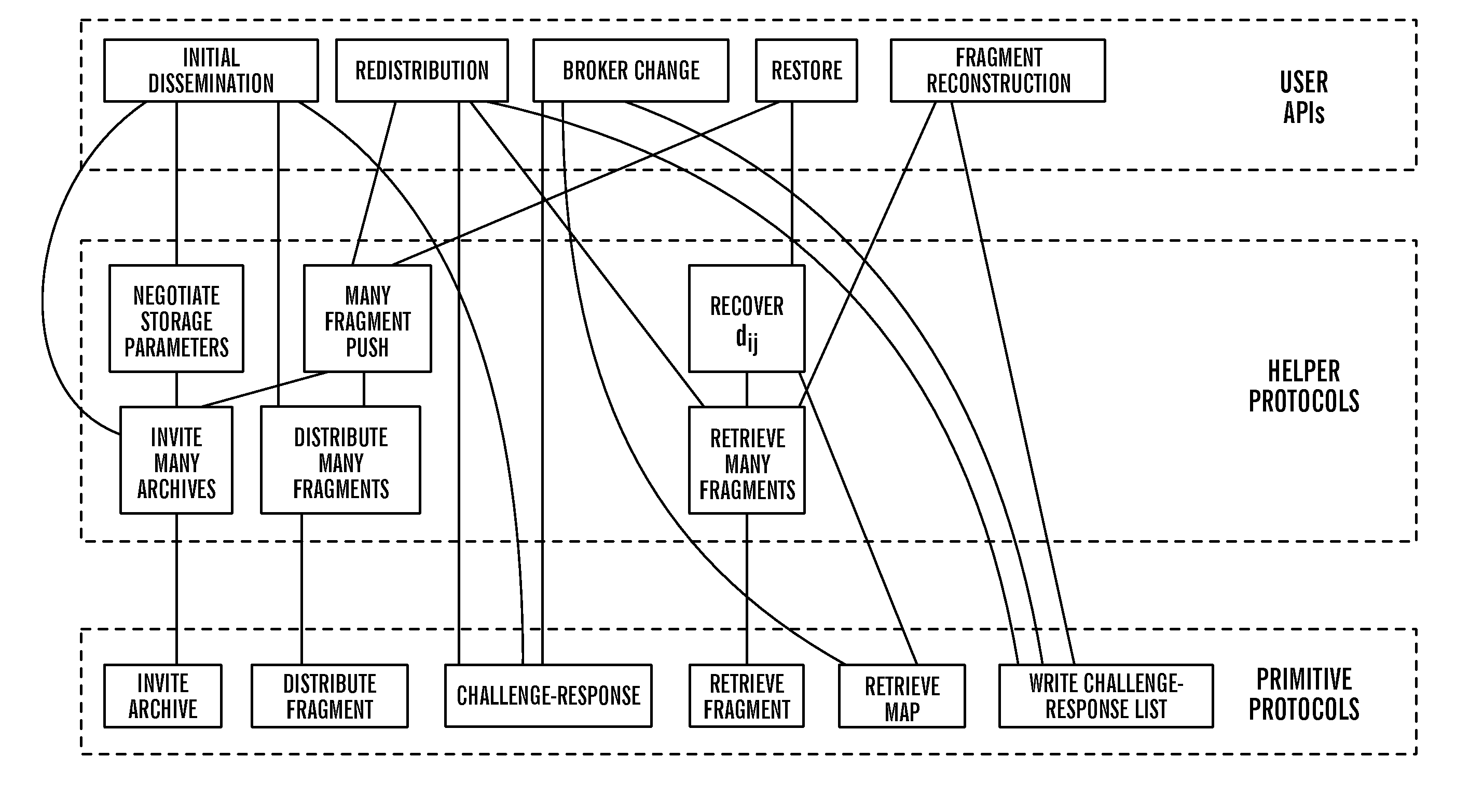
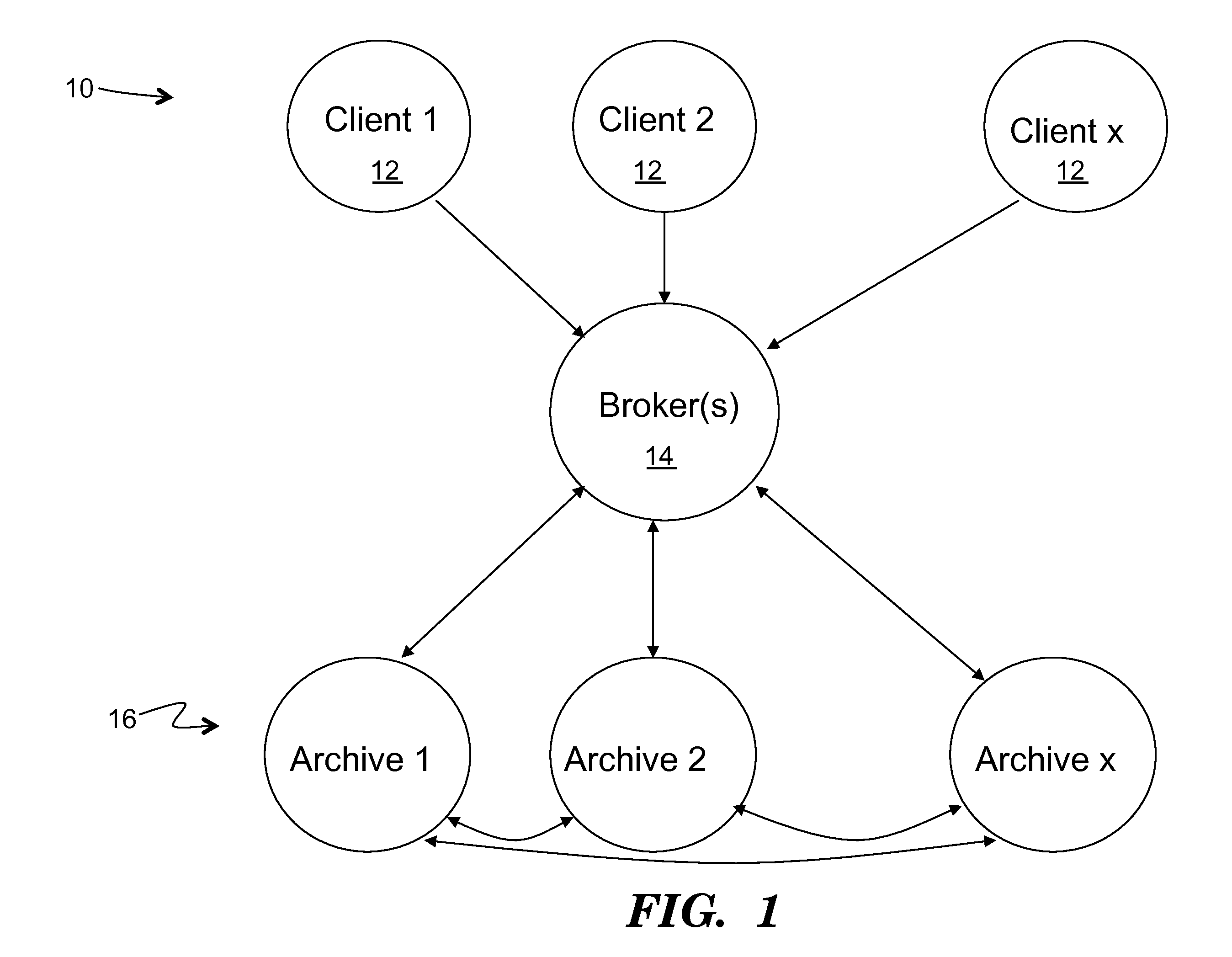
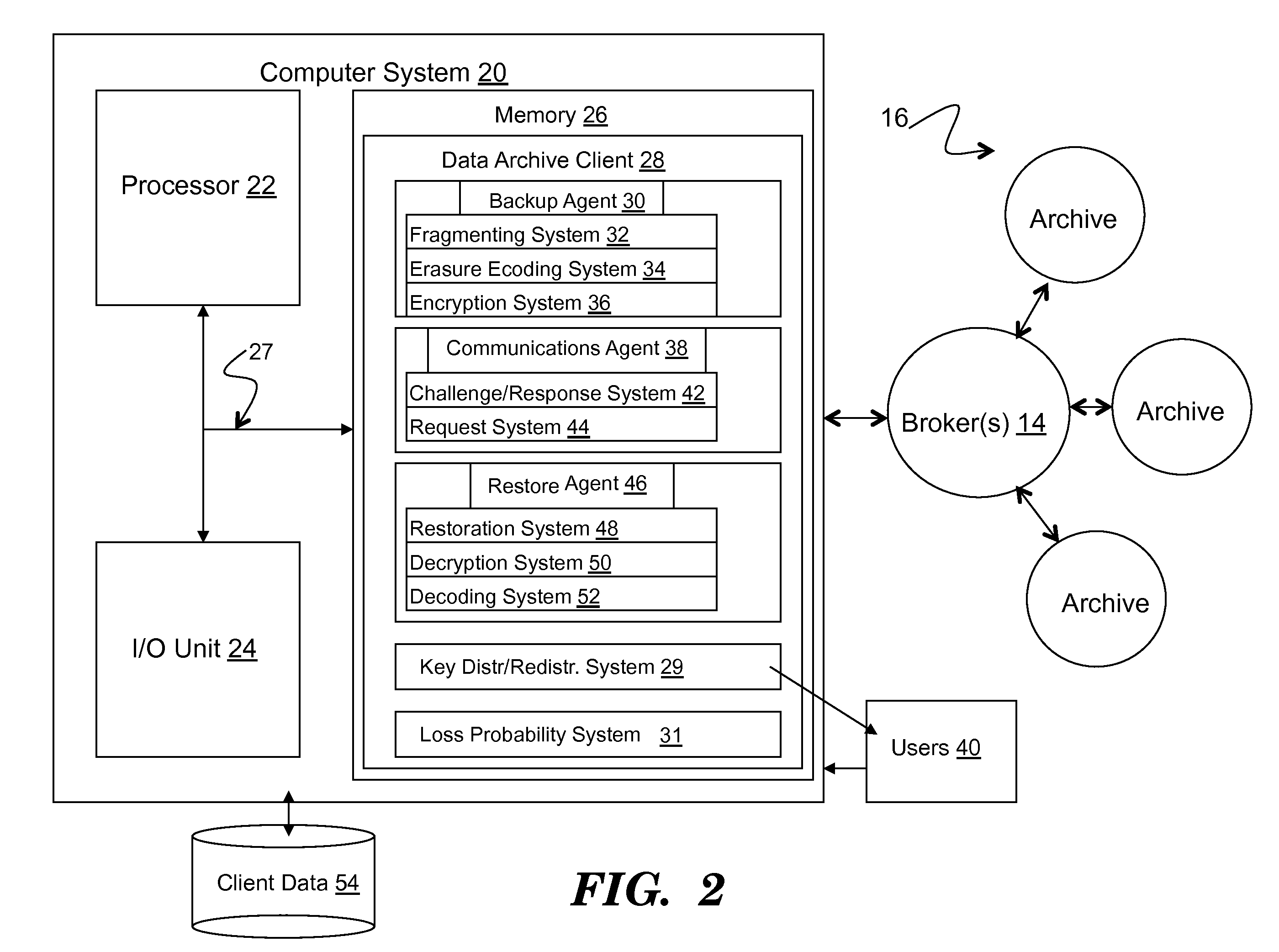
Method to support privacy preserving secure data management in archival systems
InactiveUS20100037056A1Digital data information retrievalUser identity/authority verificationInternet privacyPrivacy preserving
An infrastructure for archiving data among a client, a broker, and a plurality of archives, wherein the client comprises: a backup agent configured to fragment and erasure encode the data to create a set of erasure encoded data fragments; a communications agent configured to communicate the erasure encoded data fragments to the broker, issue a challenge for a challenge / response protocol to the broker, and to request data from the archives; and a restore agent configured to combine the data fragments obtained from the broker upon a data restore request.
Owner:ALTAVAULT
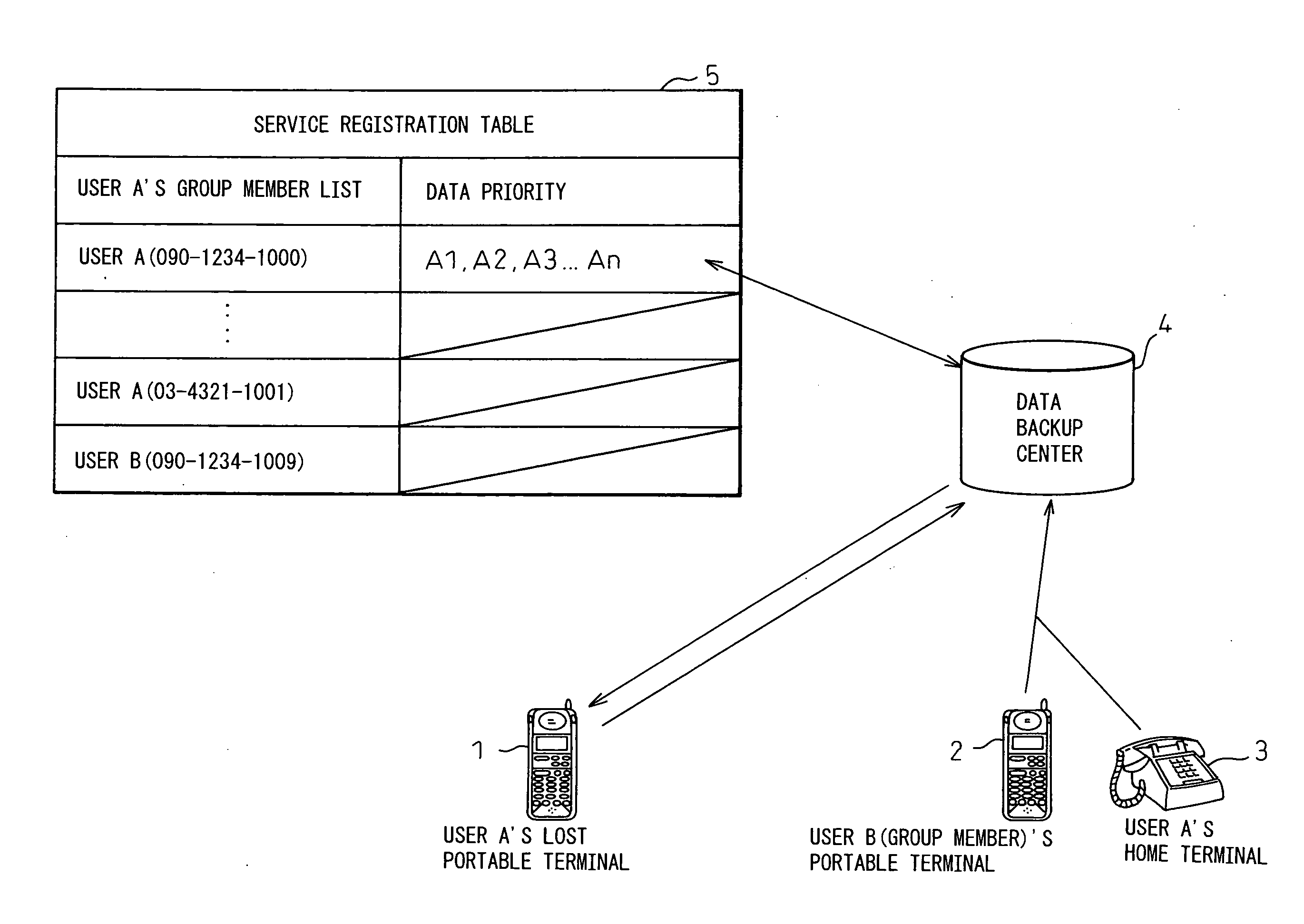
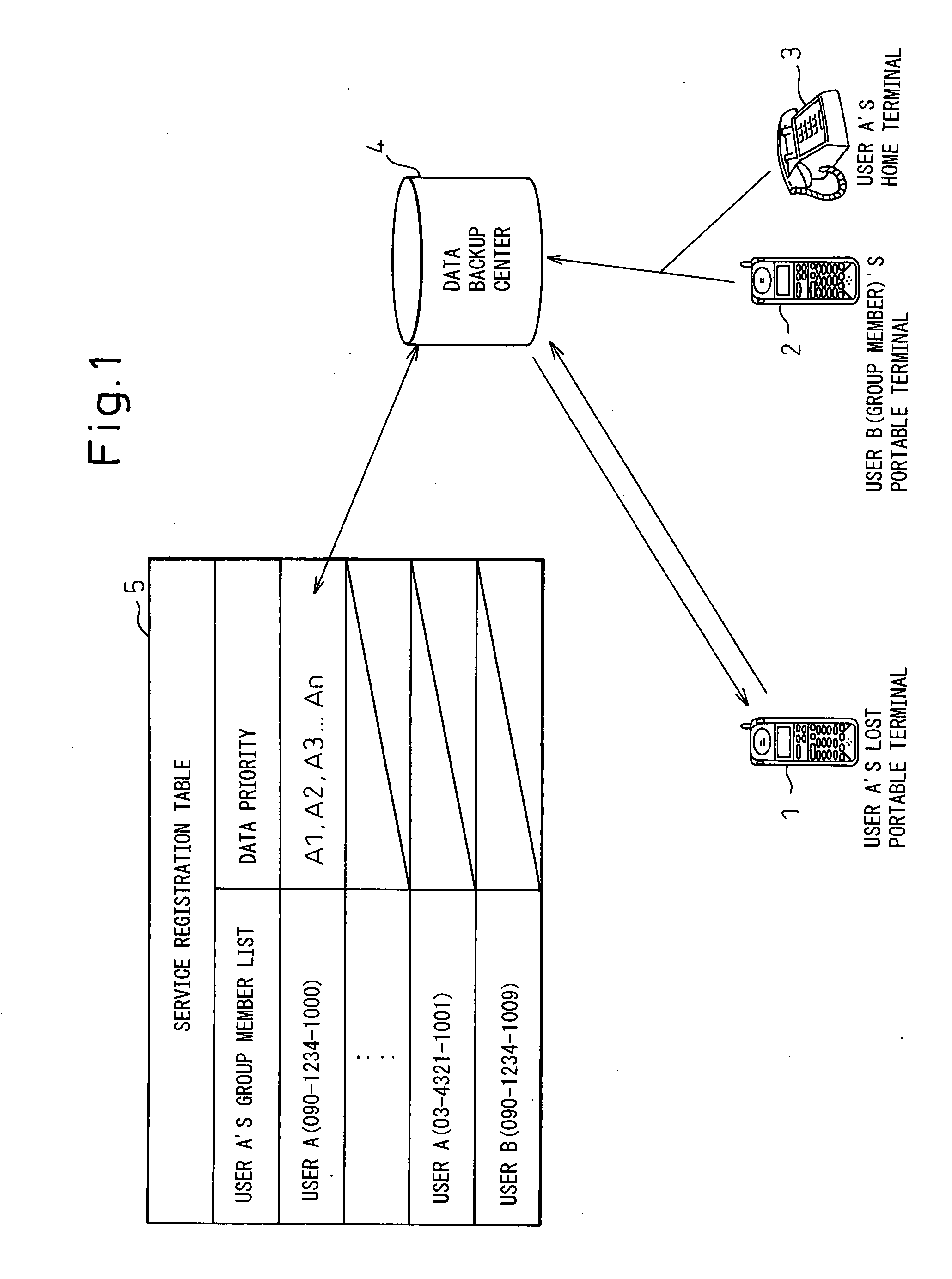
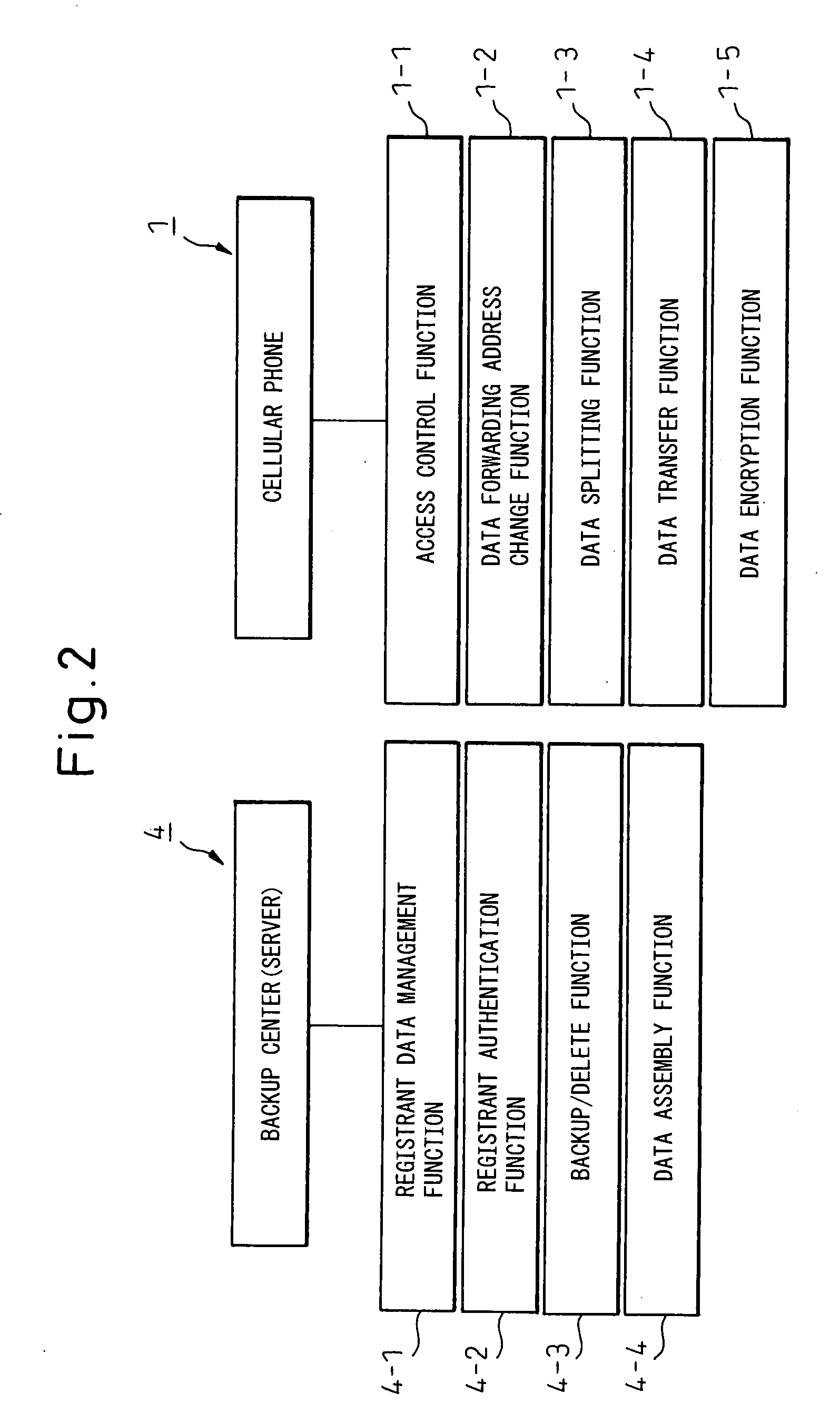
Portable wireless terminal and its security system
InactiveUS20070281664A1Avoid interceptionSafe removalUnauthorised/fraudulent call preventionEavesdropping prevention circuitsThird partyRemote control
The present invention relates to a portable wireless terminal, and in particular, a portable wireless terminal such as a cellular phone, etc., and its security system that can reliably prevent, by remote control, improper use of the portable wireless terminal by a third party when it is lost or stolen. The portable wireless terminal that uploads backup data to a center by remote control from the center via a wireless network includes: a data access control section 1-1 that, in response to an instructions from the center, prohibits access to the backup data retained by a portable wireless terminal or deletes the backup data; an encryption section 1-5 that encrypts the backup data by using a public key notified from the center or a public key owned by the portable wireless terminal itself in response to instructions from the center; and a data transmission section 1-2 to 1-4 that transmits the backup data split into a plurality of data fragments on a plurality of communication paths to the center according to transmission priority of the backup data that is notified from the center or owned by the portable wireless terminal itself.
Owner:FUJITSU LTD
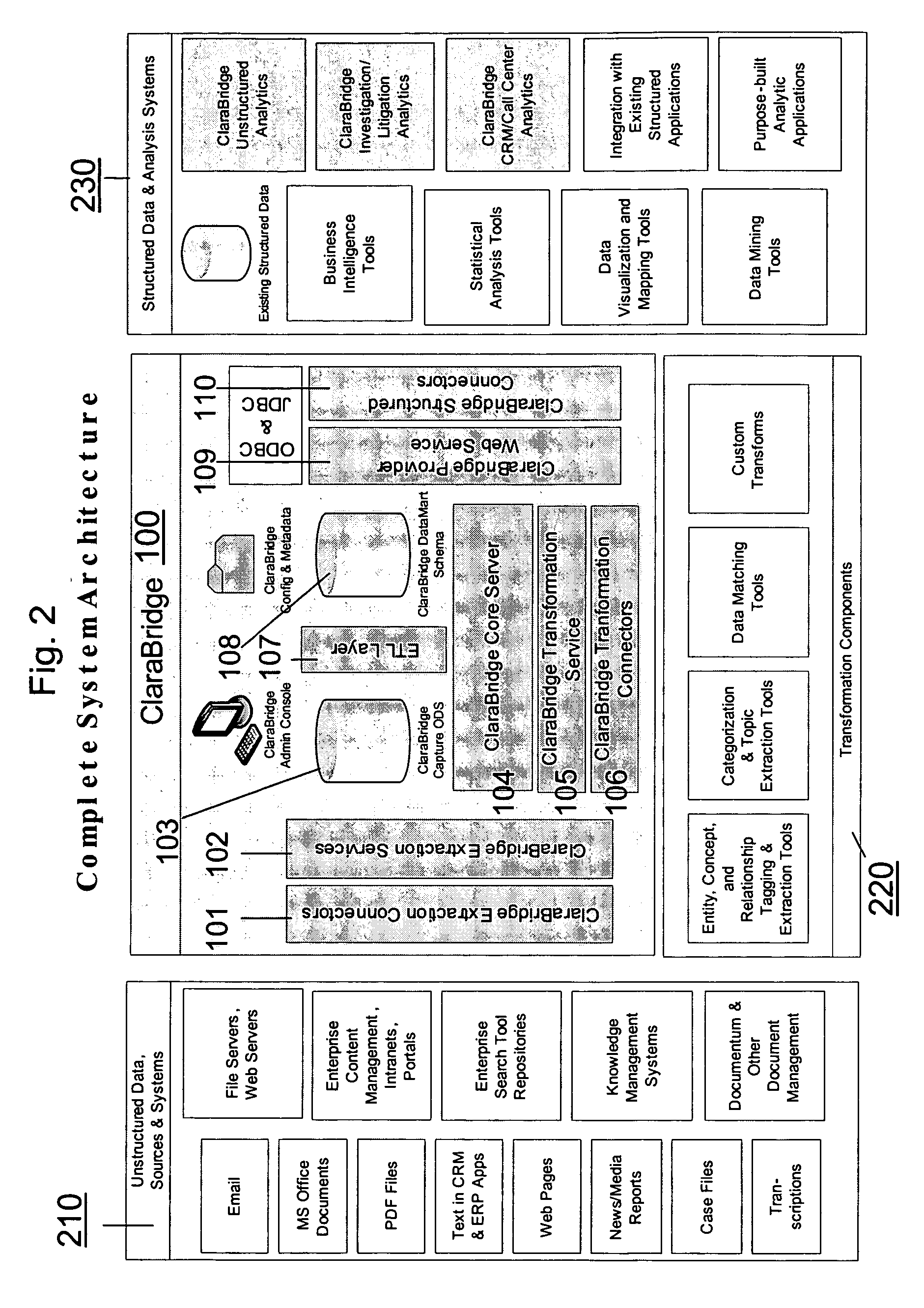
System and method of making unstructured data available to structured data analysis tools
ActiveUS20070011134A1Data processing applicationsDigital data information retrievalData transformationStructured data analysis
A system and method of making unstructured data available to structured data analysis tools. The system includes middleware software that can be used in combination with structured data tools to perform analysis on both structured and unstructured data. Data can be read from a wide variety of unstructured sources. The data may then be transformed with commercial data transformation products that may, for example, extract individual pieces of data and determine relationships between the extracted data. The transformed data and relationships may then be passed through an extraction / transform / load (ETL) layer and placed in a structured schema. The structured schema may then be made available to commercial or proprietary structured data analysis tools.
Owner:CLARABRIDGE
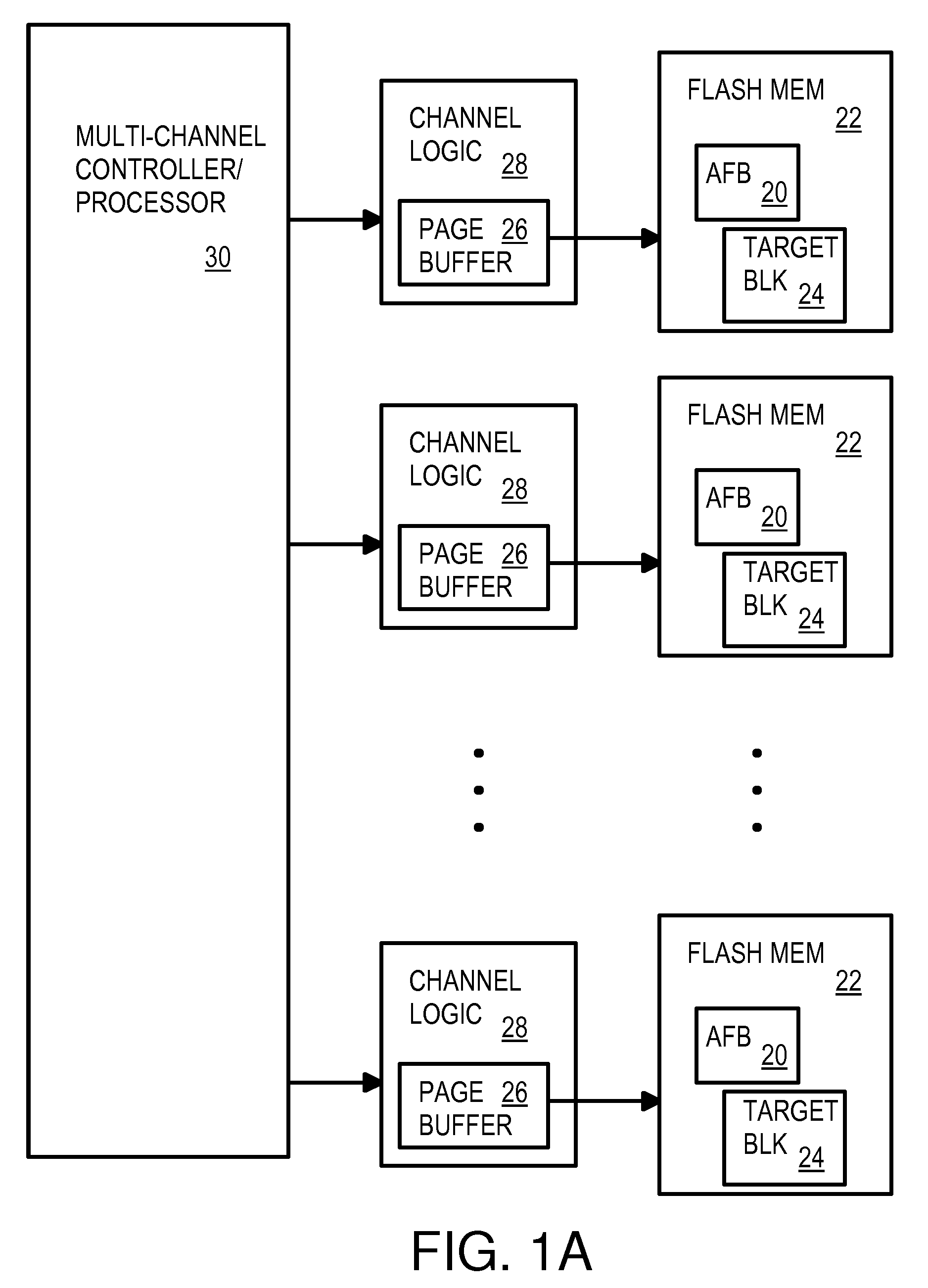
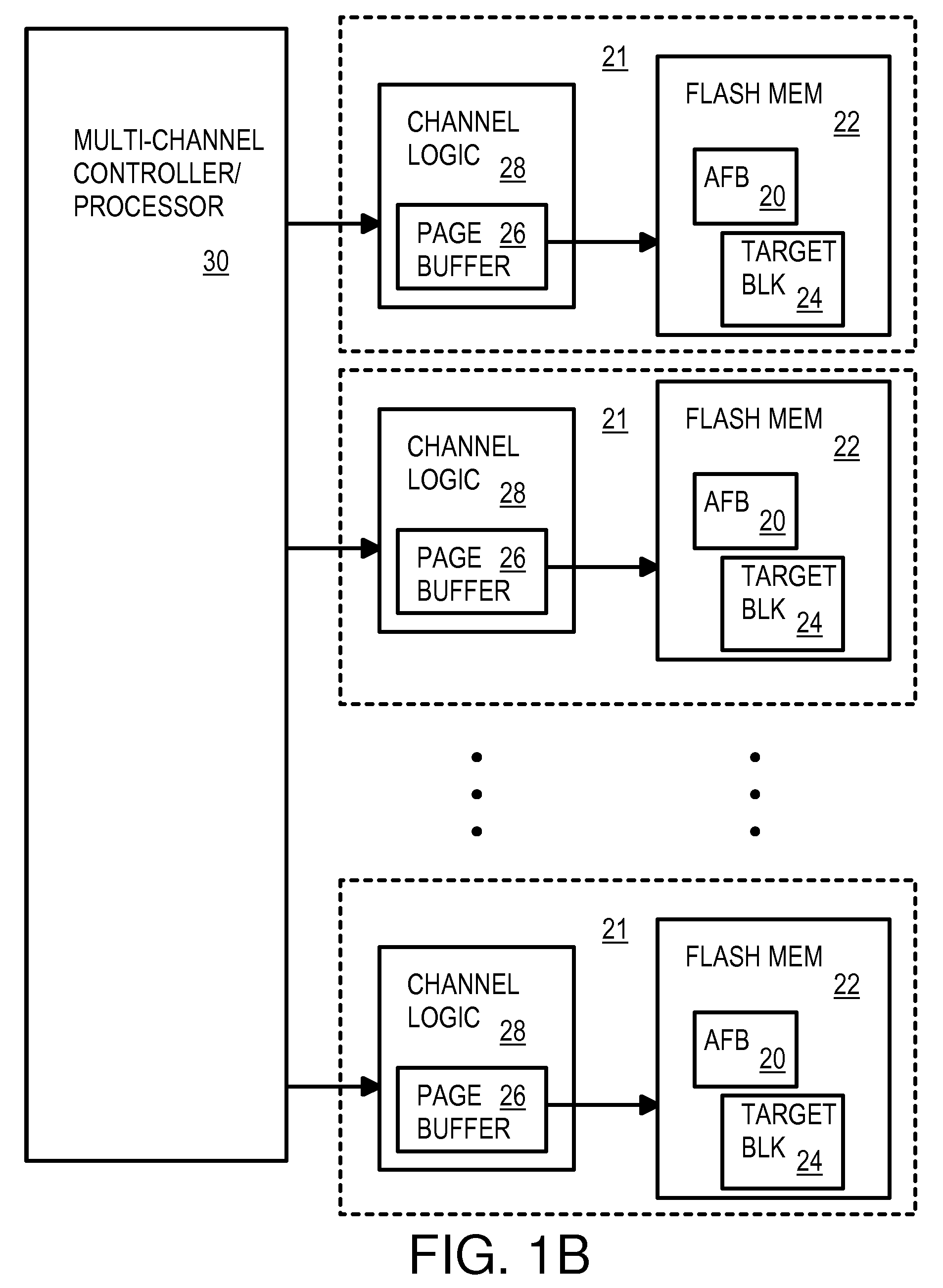
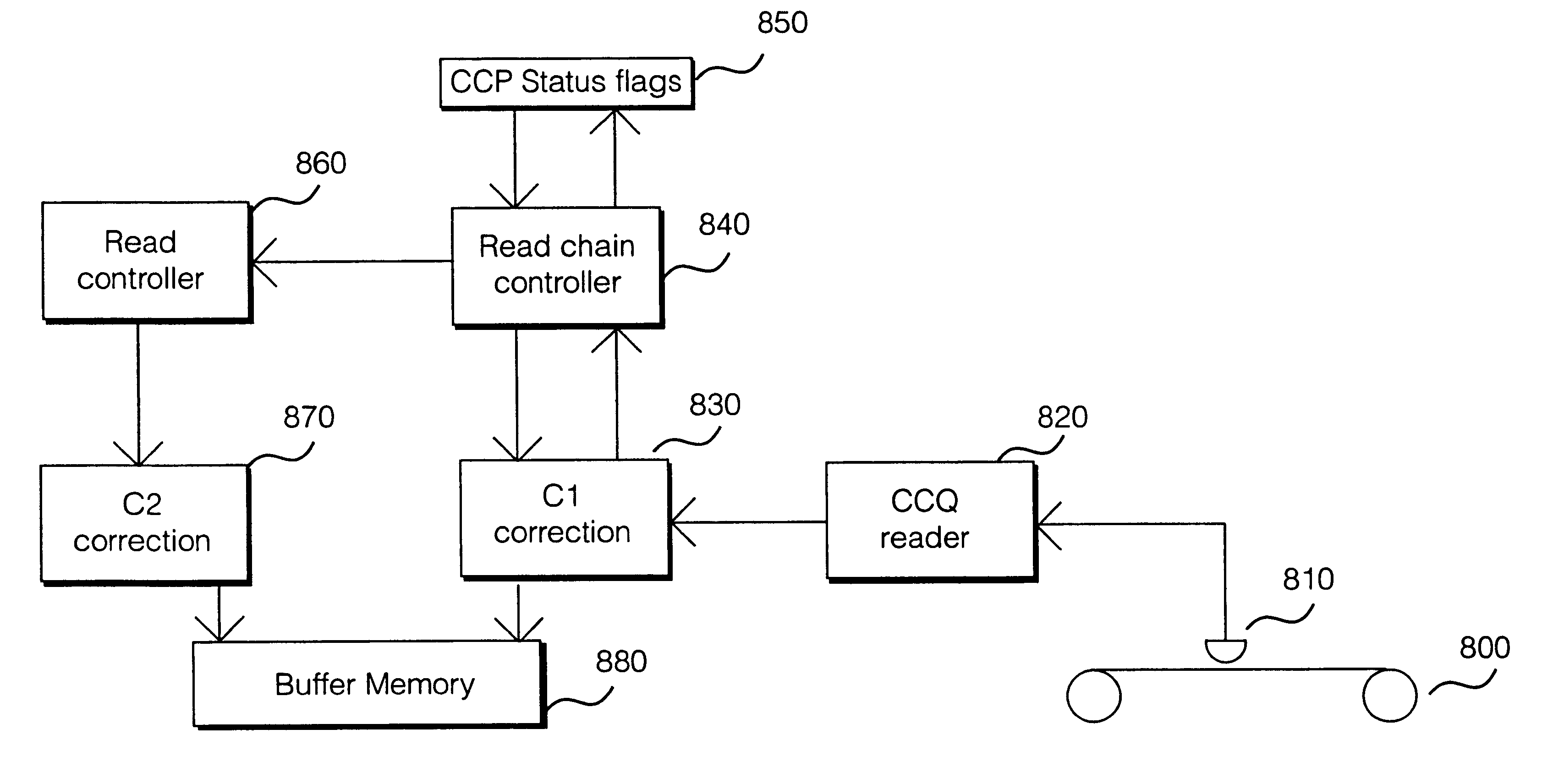
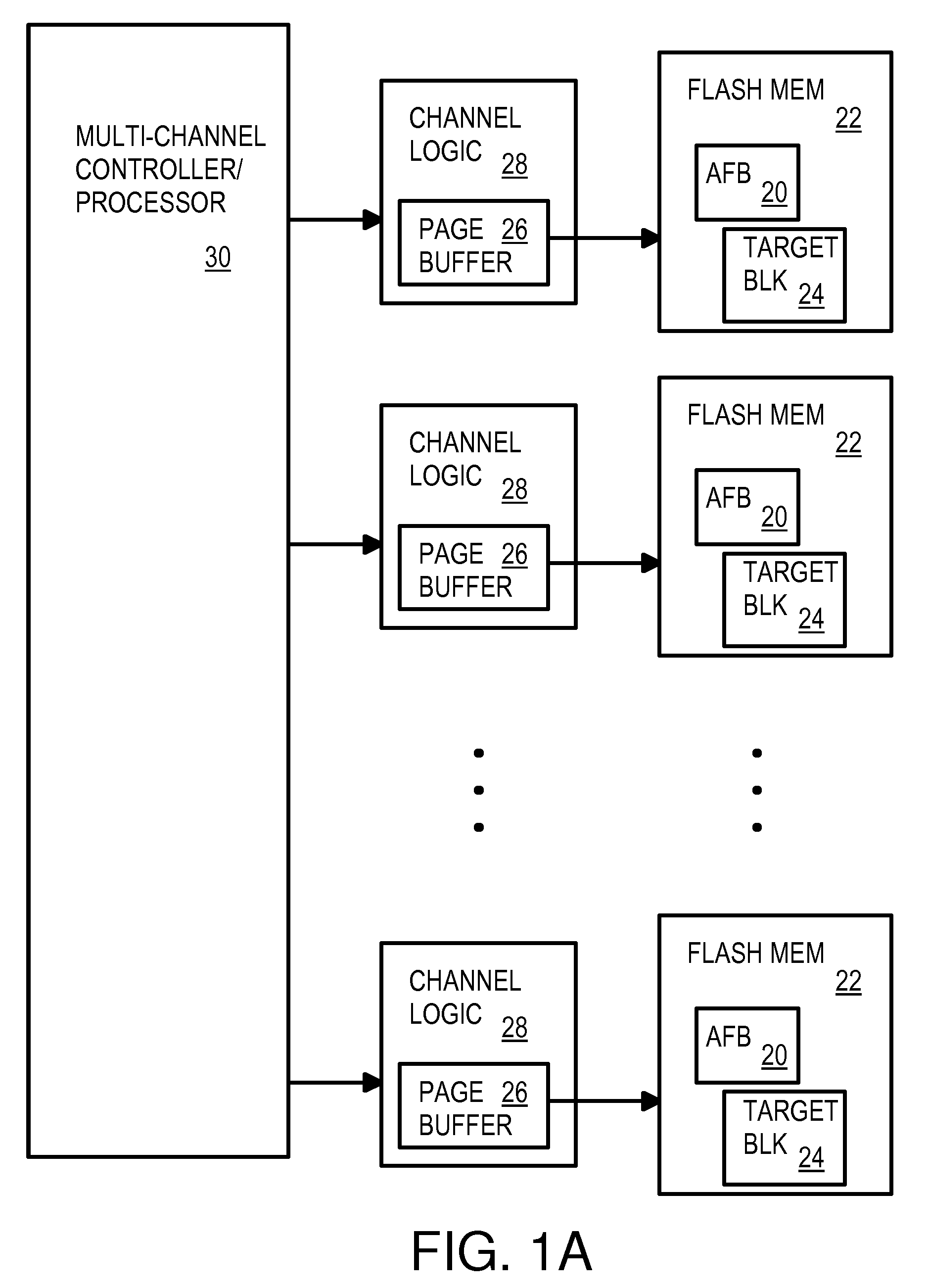
Multi-Operation Write Aggregator Using a Page Buffer and a Scratch Flash Block in Each of Multiple Channels of a Large Array of Flash Memory to Reduce Block Wear
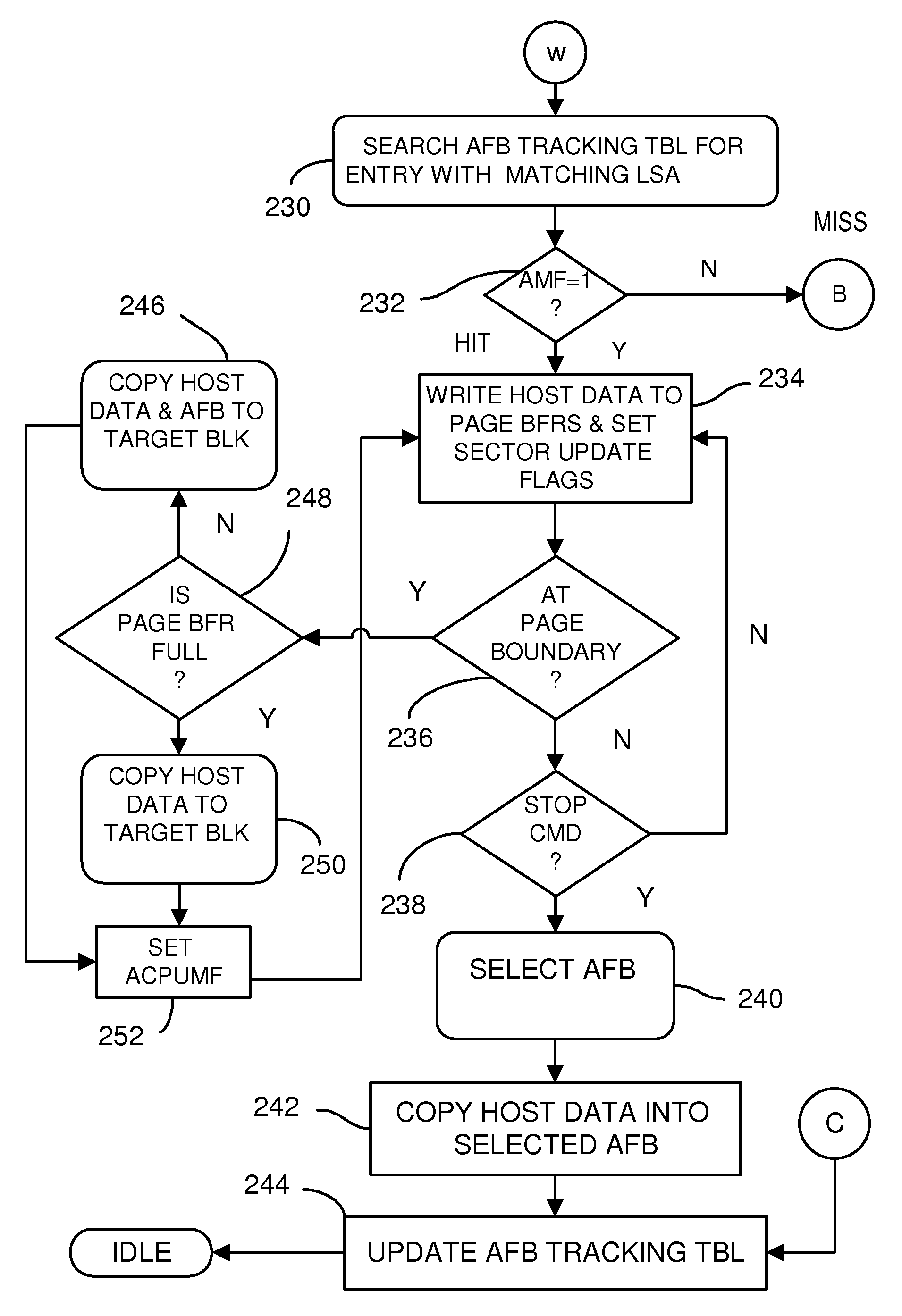
InactiveUS20080250195A1Memory architecture accessing/allocationMemory adressing/allocation/relocationSmall fragmentPage buffers
A flash system has multiple channels of flash memory chips that can be accessed in parallel. Host data is assigned to one of the channels by a multi-channel controller processor and accumulated in a multi-channel page buffer. When a page boundary in the page buffer is reached, the page buffer is written to a target physical block if full, or combined with old data fragments in an Aggregating Flash Block (AFB) when the logical-sector addresses (LSA's) match. Thus small fragments are aggregated using the AFB, reducing erases and wear of flash blocks. The page buffer is copied to the AFB when a STOP command occurs. Each channel has one or more AFB's, which are tracked by an AFB tracking table.
Owner:SUPER TALENT TECH CORP
Schema and ETL tools for structured and unstructured data
ActiveUS20070011175A1Data processing applicationsDigital data information retrievalData transformationStructured data analysis
A system and method of making unstructured data available to structured data analysis tools. The system includes middleware software that can be used in combination with structured data tools to perform analysis on both structured and unstructured data. Data can be read from a wide variety of unstructured sources. The data may then be transformed with commercial data transformation products that may, for example, extract individual pieces of data and determine relationships between the extracted data. The transformed data and relationships may then be passed through an extraction / transform / load (ETL) layer and placed in a structured schema. The structured schema may then be made available to commercial or proprietary structured data analysis tools.
Owner:CLARABRIDGE
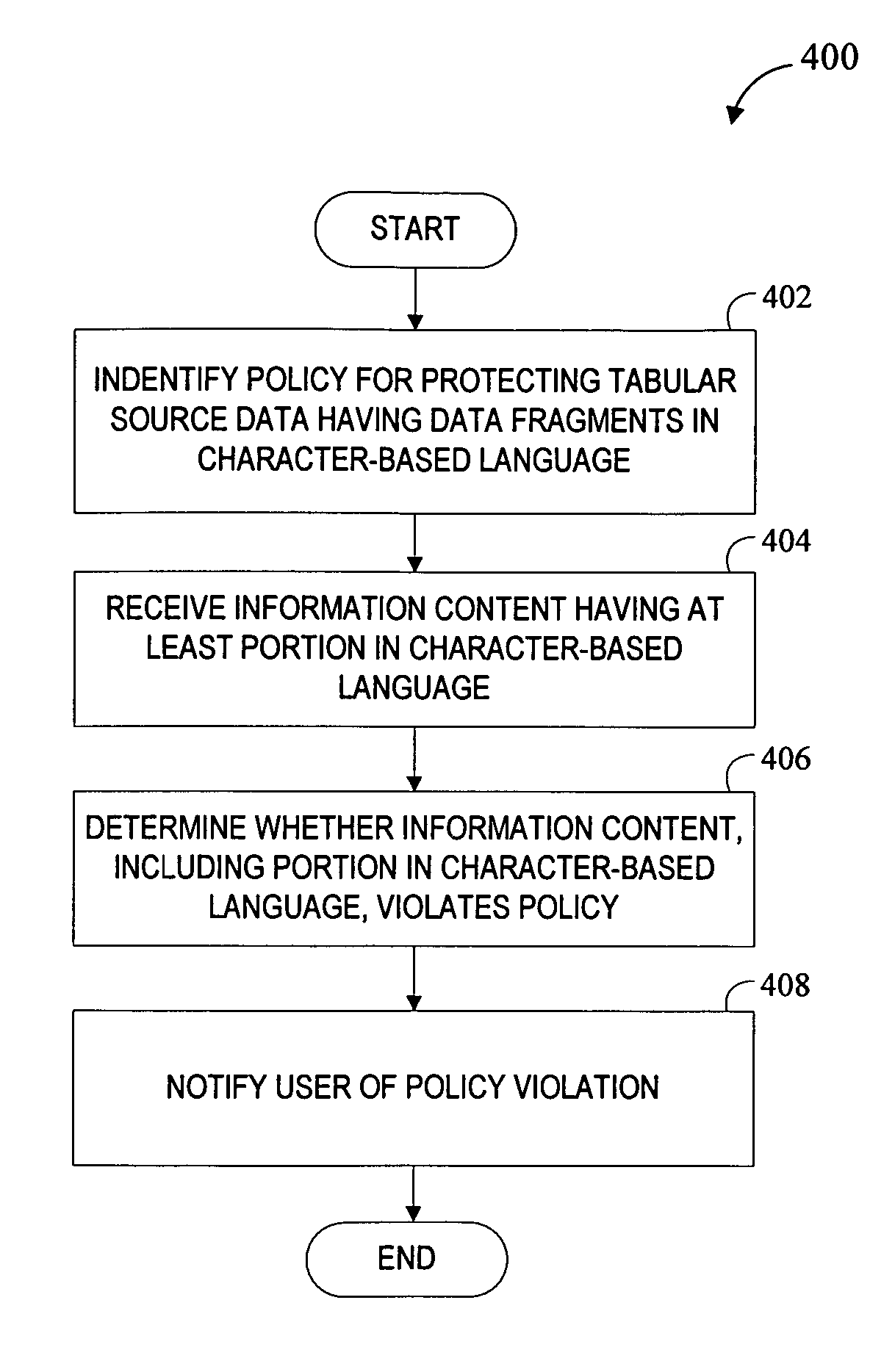
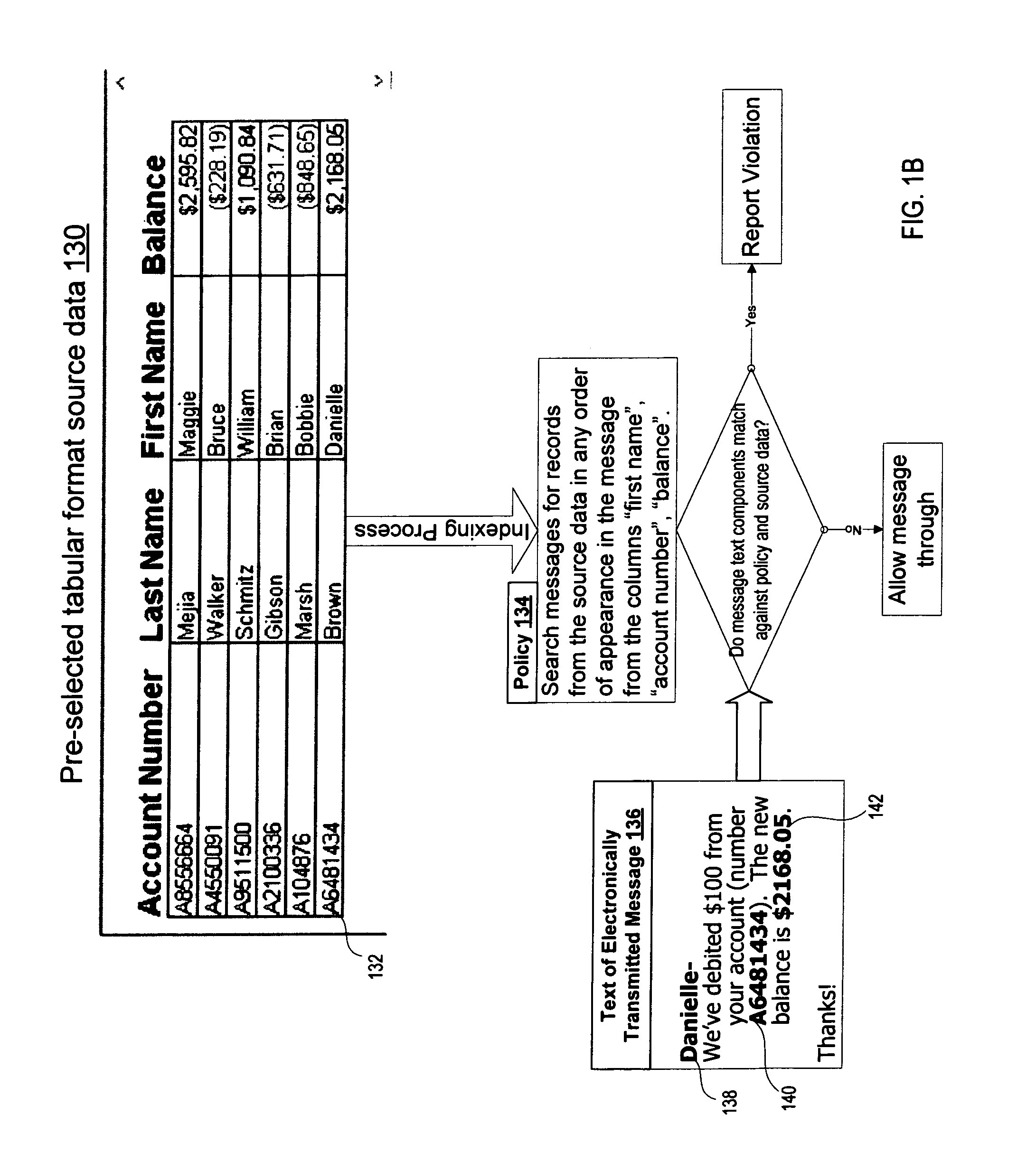
Detecting policy violations in information content containing data in a character-based language
ActiveUS8065739B1Digital data processing detailsAnalogue secracy/subscription systemsInternet privacyHuman language
A method and apparatus for detecting policy violations in information content containing data in a character-based language is described. In one embodiment, the method includes identifying a policy for protecting source data having a tabular format. The source data contains one or more data fragments in the character-based language. The method further includes receiving information content having at least a portion in the character-based language, and determining whether any part of the information content, including the portion in the character-based language, violates the policy.
Owner:CA TECH INC
Schema and ETL tools for structured and unstructured data
ActiveUS7849049B2Digital data information retrievalData processing applicationsData transformationStructured data analysis
Owner:CLARABRIDGE
System and method of making unstructured data available to structured data analysis tools
ActiveUS7849048B2Data processing applicationsDigital data information retrievalData transformationStructured data analysis
A system and method of making unstructured data available to structured data analysis tools. The system includes middleware software that can be used in combination with structured data tools to perform analysis on both structured and unstructured data. Data can be read from a wide variety of unstructured sources. The data may then be transformed with commercial data transformation products that may, for example, extract individual pieces of data and determine relationships between the extracted data. The transformed data and relationships may then be passed through an extraction / transform / load (ETL) layer and placed in a structured schema. The structured schema may then be made available to commercial or proprietary structured data analysis tools.
Owner:CLARABRIDGE
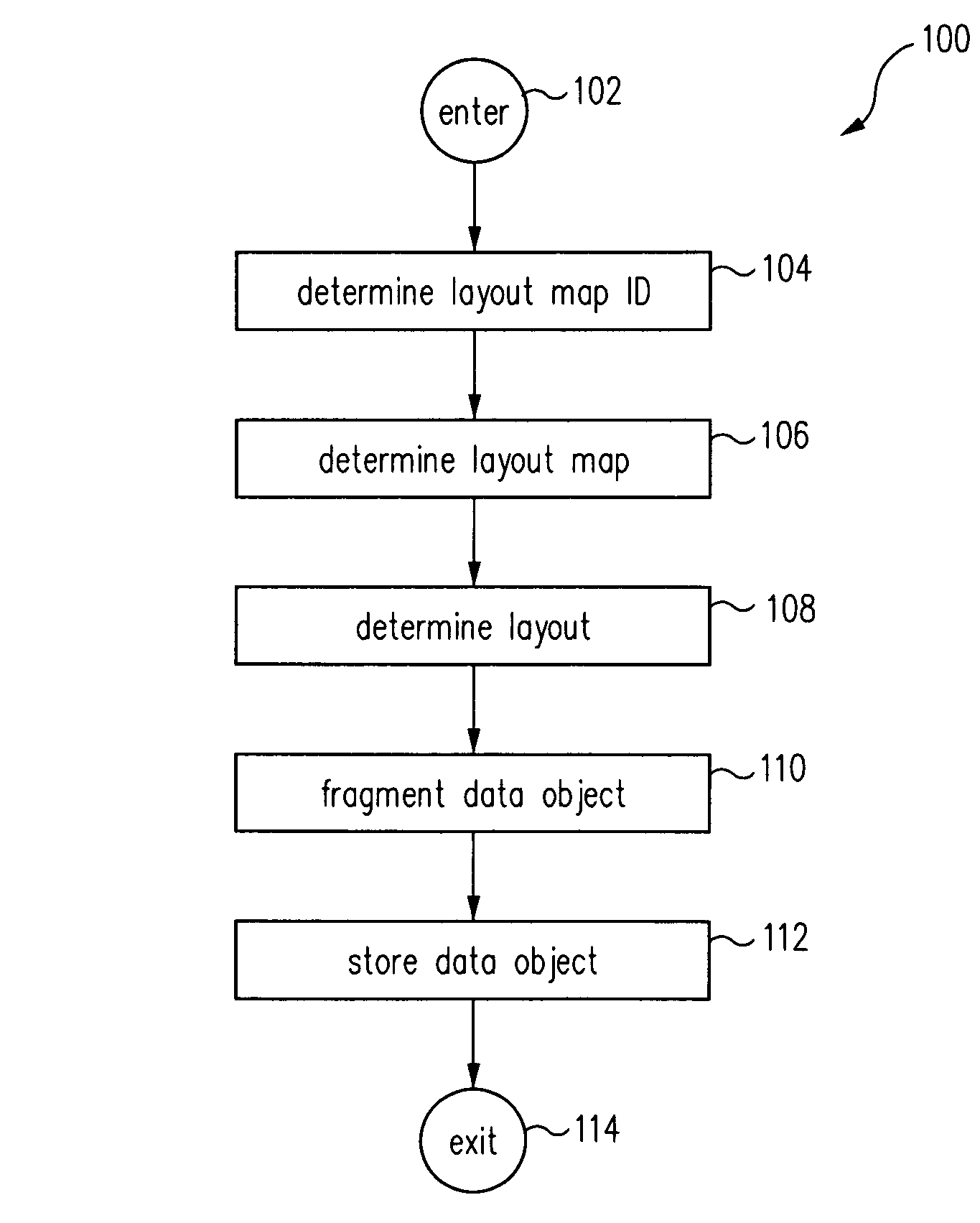
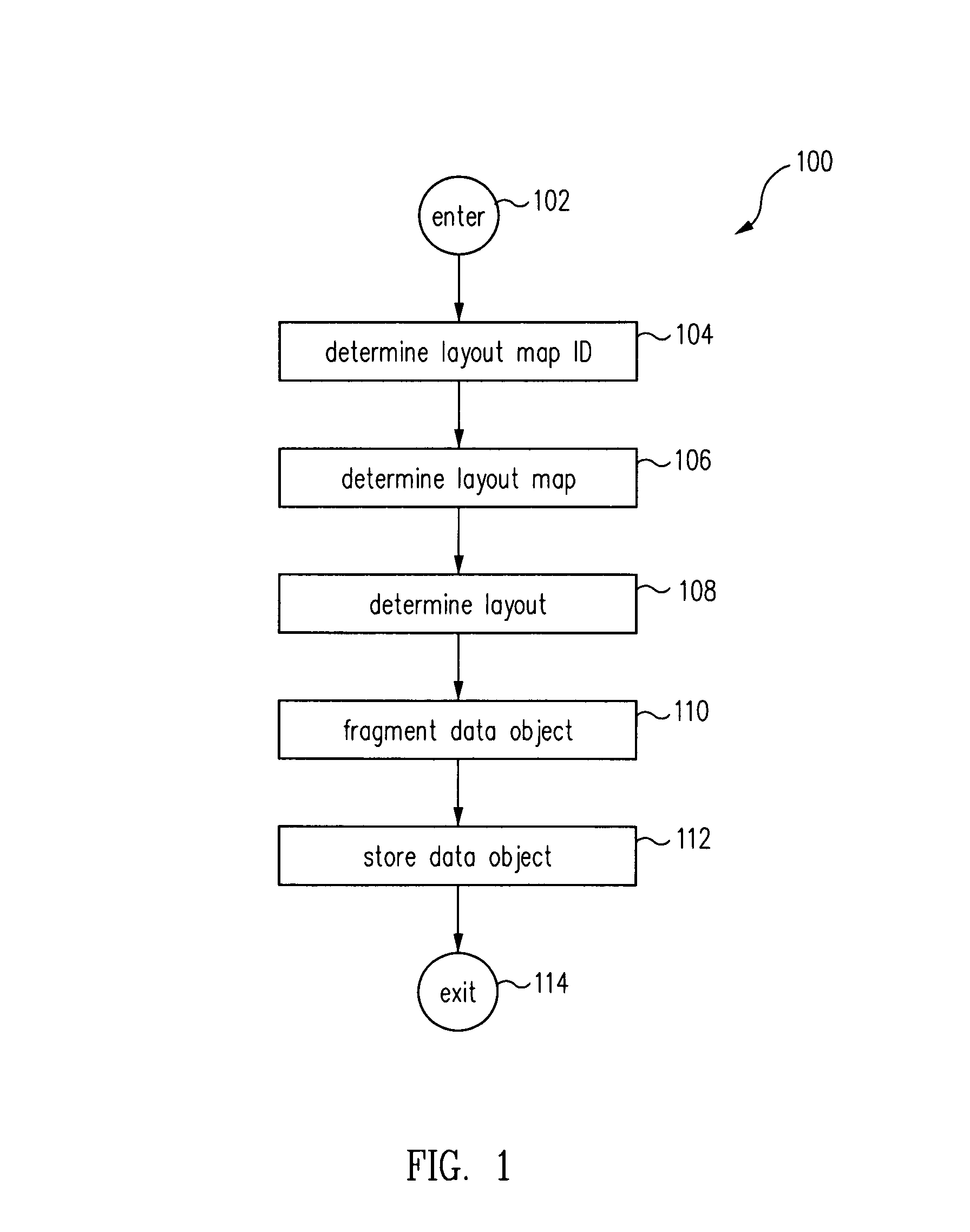
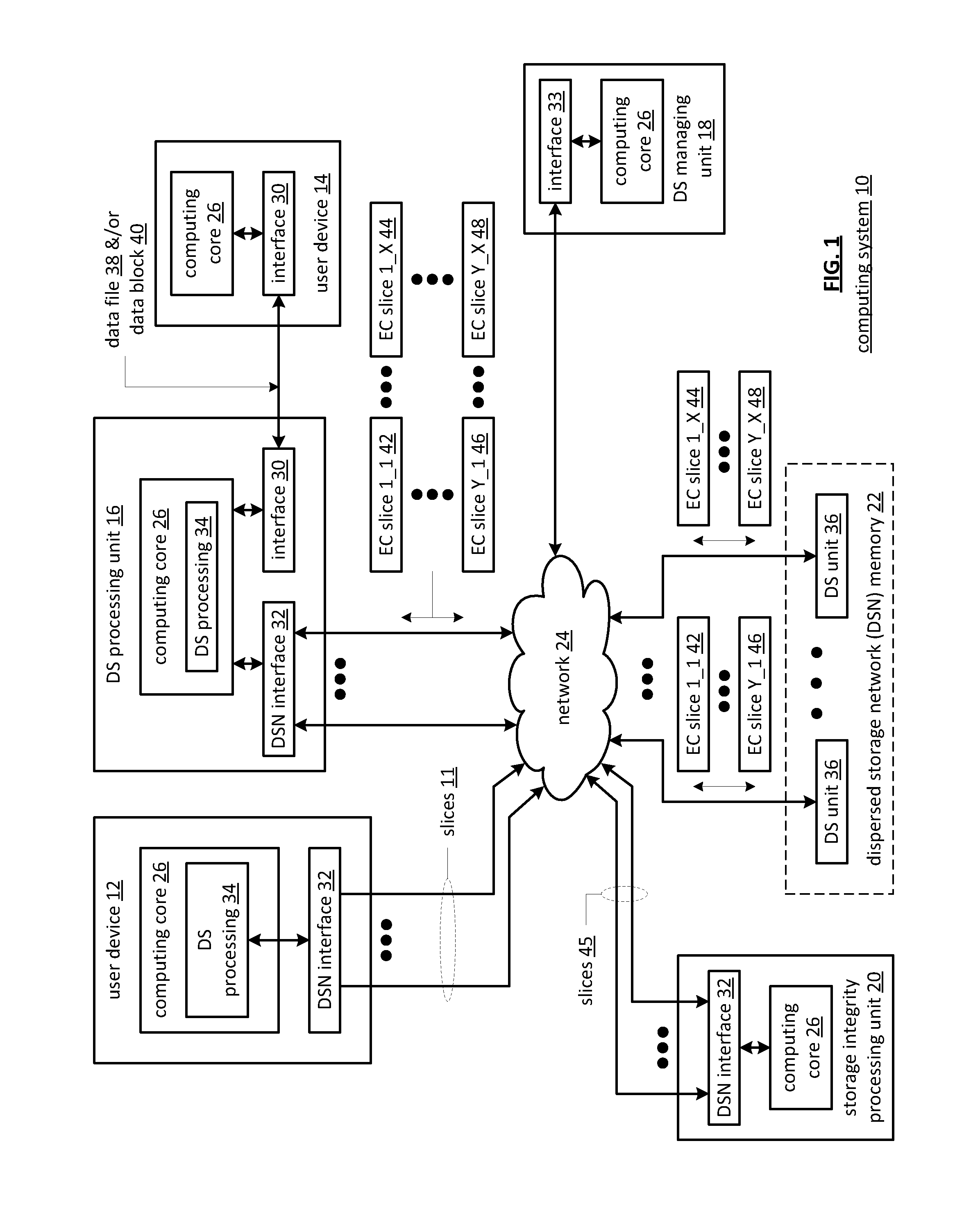
Method for distributed storage of data
ActiveUS7734643B1Digital data processing detailsSpecial data processing applicationsParallel computingData store
A method for distributively storing a data object on a data storage system includes determining a layout map ID and associating the layout map ID with the data object. The layout map ID is used in determining a layout map, and the layout map is used in determining a layout given a current configuration of the data storage system. The data object is fragmented into data fragments and parity fragments, and the data fragments and parity fragments are distributively stored on data storage system in accordance with the layout.
Owner:ORACLE INT CORP
System and methods for navigating and visualizing multi-dimensional biological data
InactiveUS20060036425A1Easy to identifyFacilitate correlation2D-image generationData visualisationData setEeg data
Methods systems and computer readable media for manipulating and displaying sparse data contained within very large datasets. Particular applications includes those to proteomics and metabolomics. Navigation of the large data sets from a global perspective may be practically implemented, so that a user is not confined to a narrow slice of data at a time, thus providing context of the whole dataset while viewing data within the dataset.
Owner:AGILENT TECH INC
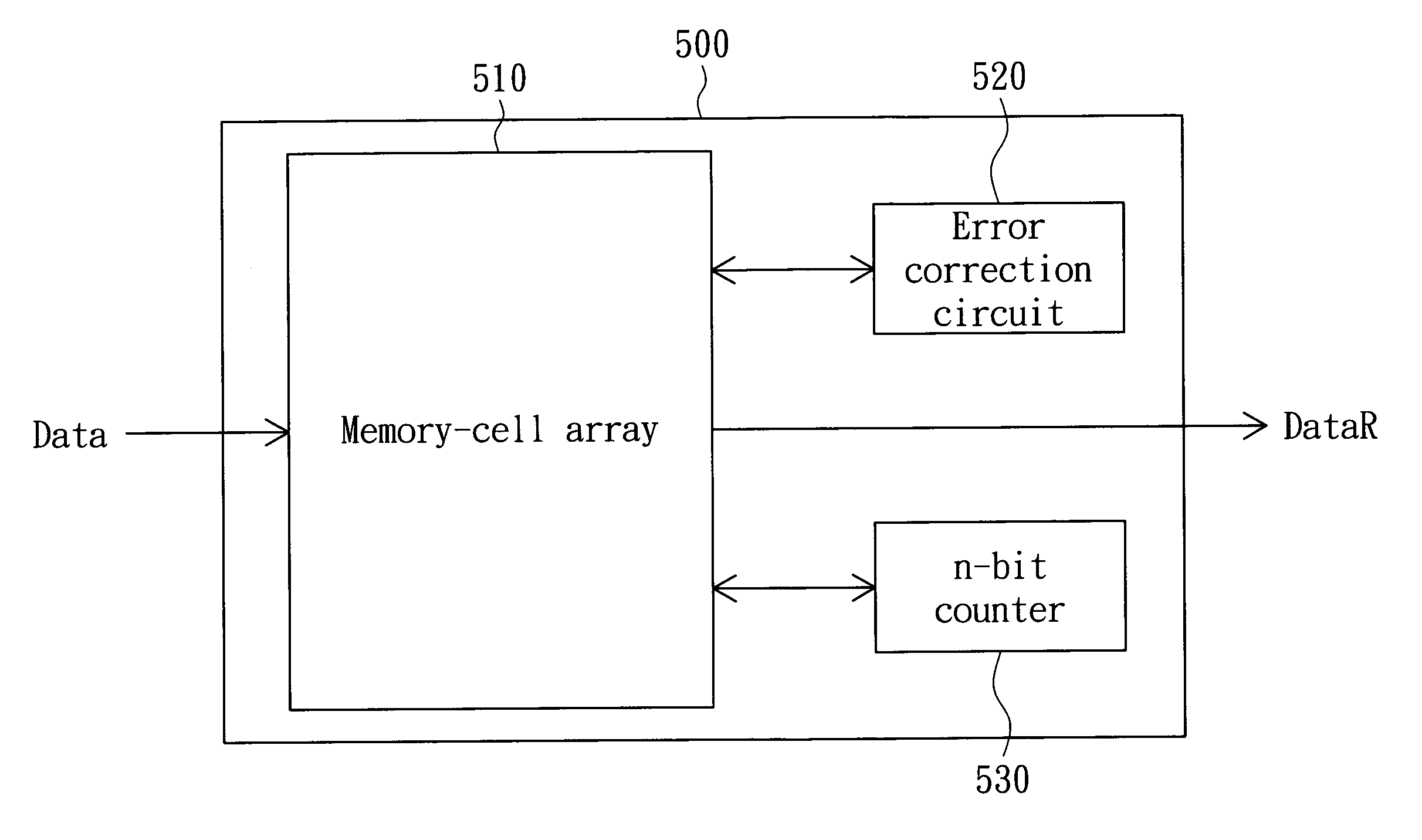
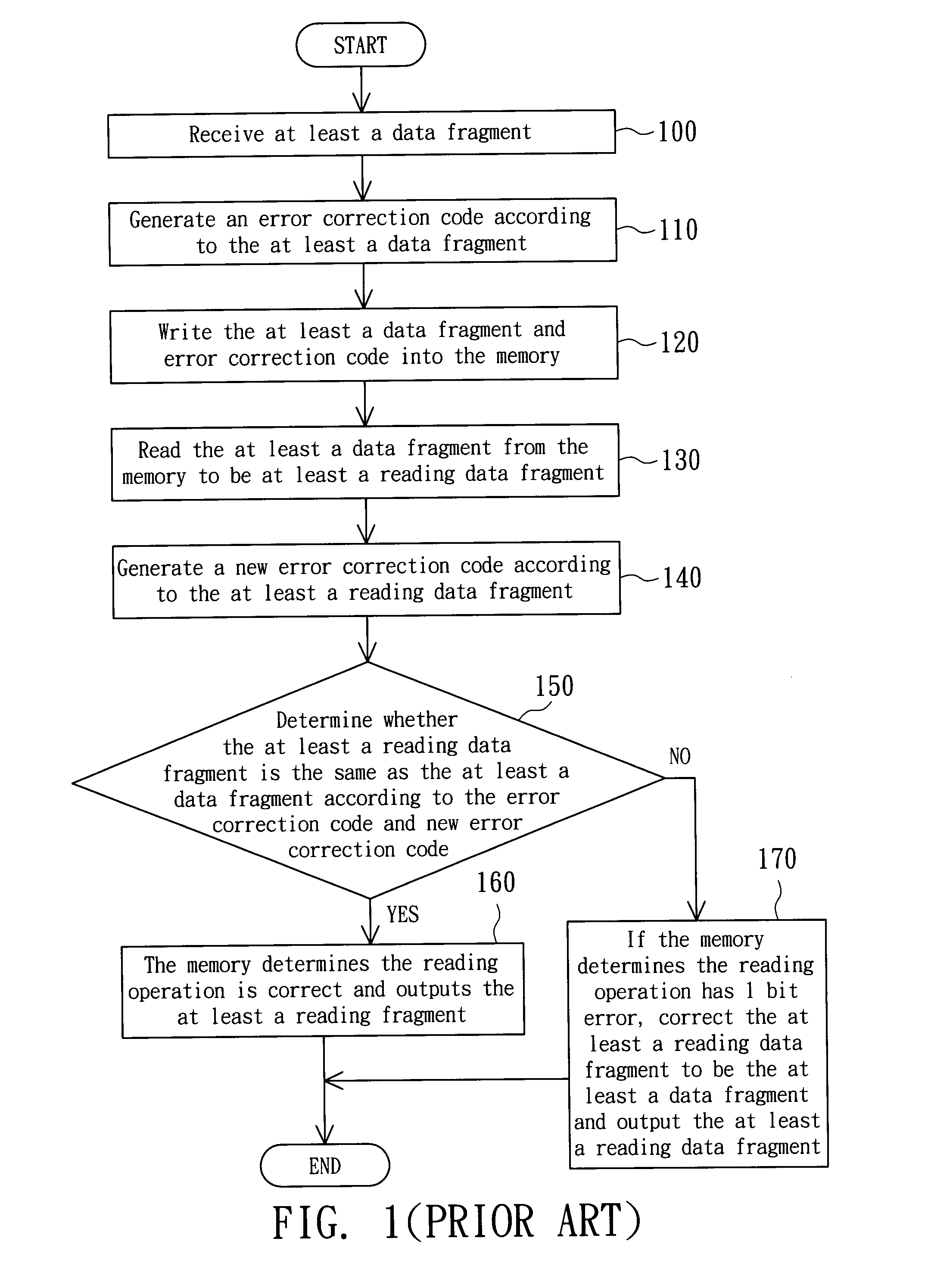
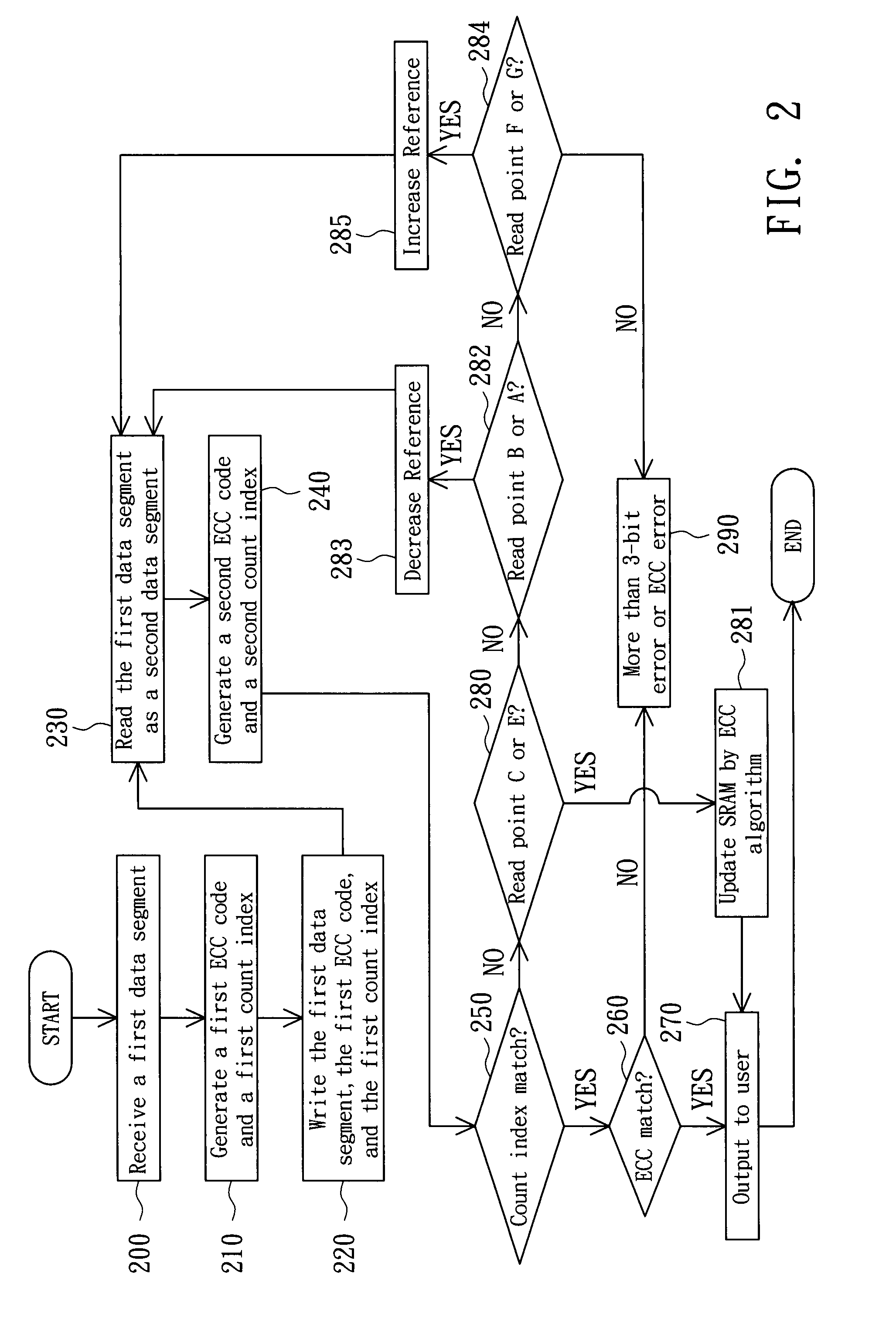
Memory and method for checking reading errors thereof
ActiveUS7925960B2Improve accuracySave memory spaceError detection/correctionCode conversionComputer scienceData fragment
Owner:MACRONIX INT CO LTD
Method for structuring and searching information
InactiveUS6691123B1Low costEasy to add and deleteDigital data information retrievalData processing applicationsThe InternetDigital storage
A system for structuring digitally stored information and methods for searching the resulting structure are described. The structuring system comprises a database comprising a number of cells arranged in rows and columns for holding pieces of data representing the information. Only one piece of data may be stored in each cell and the pieces of data contained in cells in one row of the database constitutes a certain information. This information may be files on a computer hard disk, pages on the www etc. An index for each unique piece of data occurring in the database, where each index table providing information concerning all locations of that unique piece of data in the database, a main index listing once all the unique pieces of data in the database together with a corresponding index table identifier, the index table identifier providing a link to the corresponding index table for that particular piece of data, are also necessary elements in the structuring system, The structure of the database / index system in itself provides fast and simple access to the information contained therein. The information structuring system and the methods for structuring and searching digitally stored information may e.g. be used in a search engine for the Internet, in a mobile phone, WAP or as a search system for retrieving files and controlling the information stored in a LAN or computer hard disk.
Owner:IMP TECH
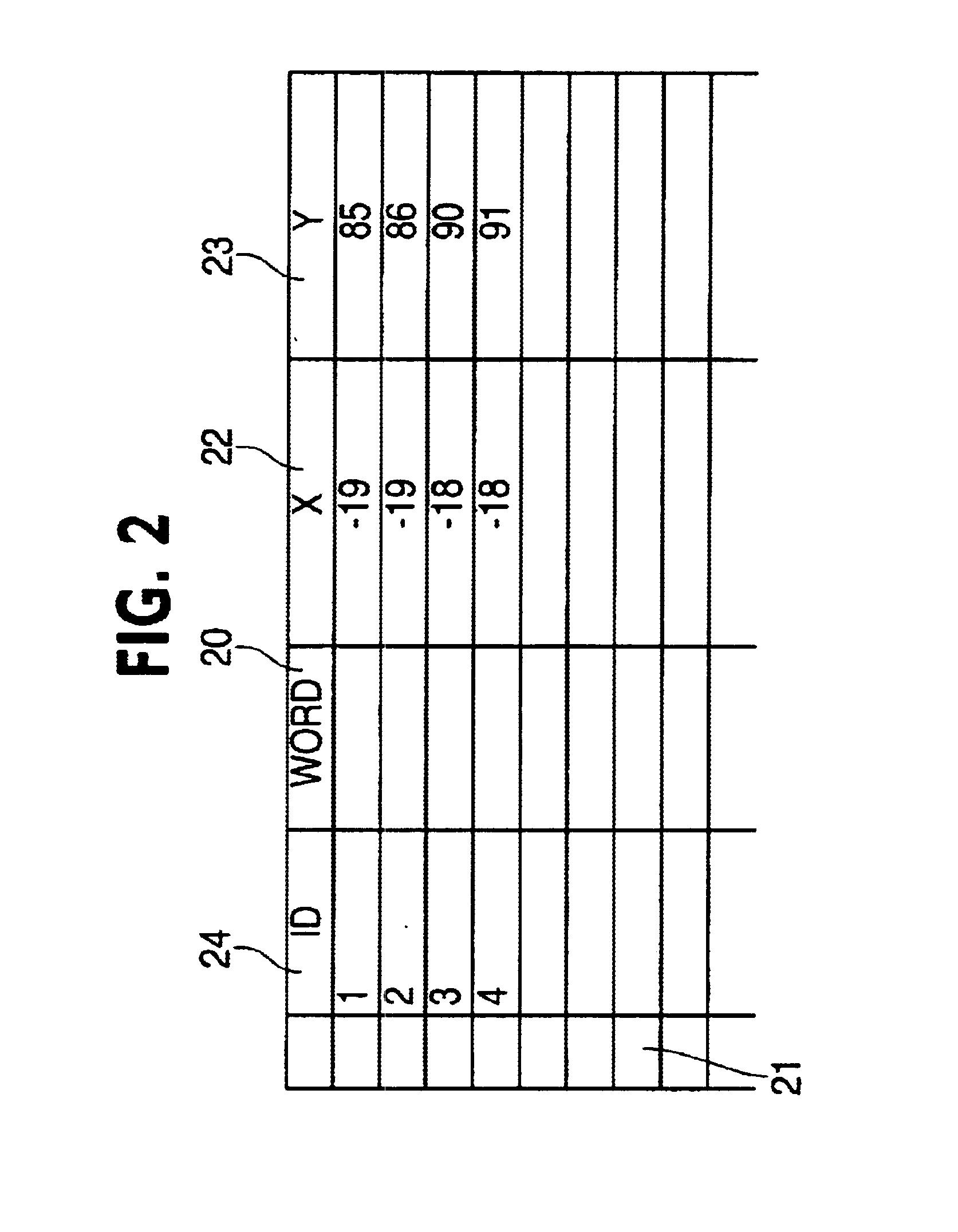
Data set recovery by codeword overlay
A method for recovering user data from a host device stored on a data storage medium where a said data may become corrupted during a read operation comprises: performing a read operation to read at least one encoded data fragment of said plurality of encoded data fragments from said data storage medium; storing status data indicating whether said at least one data fragment was correctly read; writing said read at least one data fragment to a buffer memory; attempting to decode said at least one encoded data fragment in said buffer memory wherein if said attempted decoding is unsuccessful then said method further comprises the steps of: re-reading incorrectly read encoded data fragments from said data storage medium; and attempting to decode said encoded data fragments located in said buffer memory.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
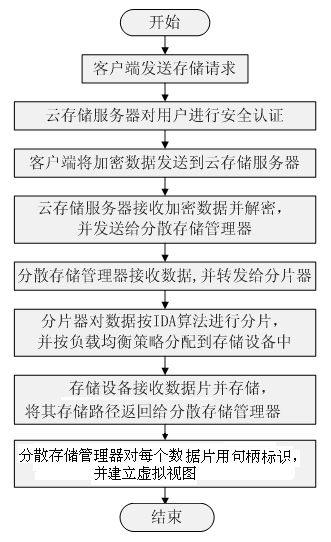
Data storage method of cloud storage system
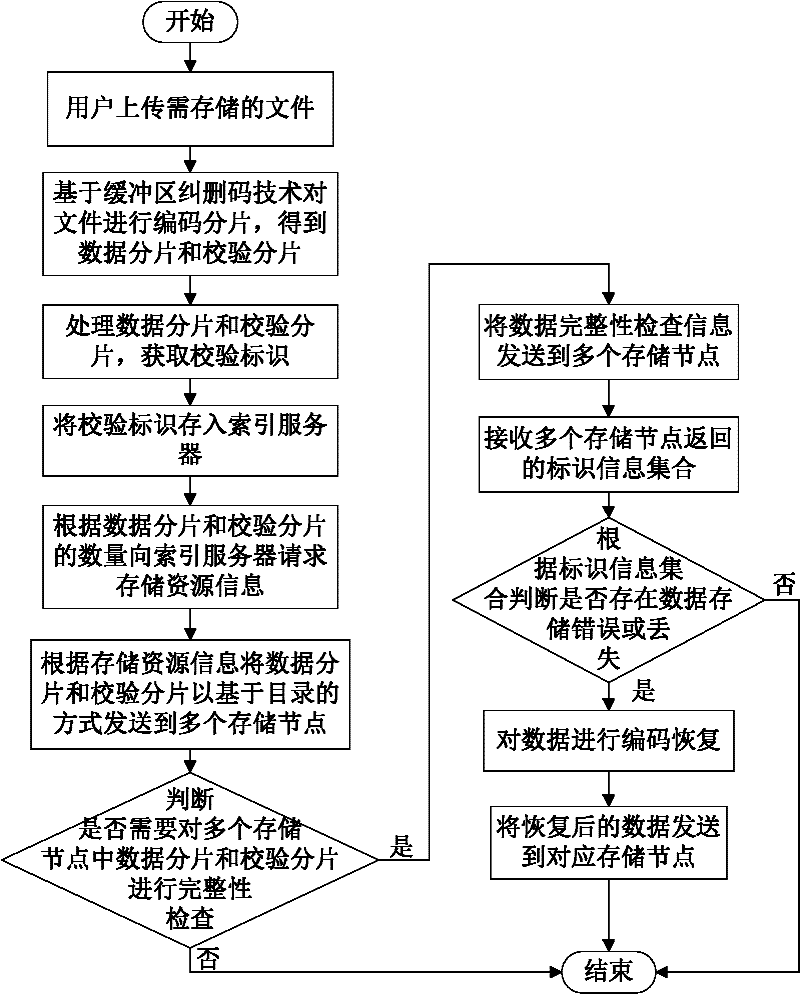
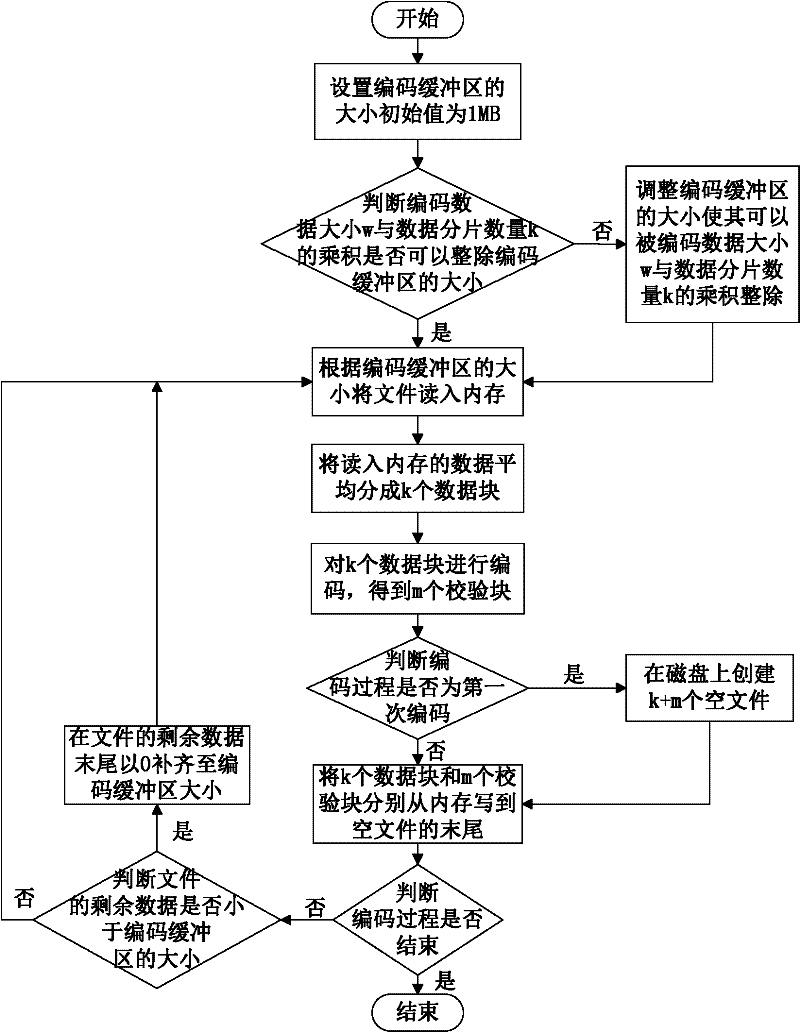
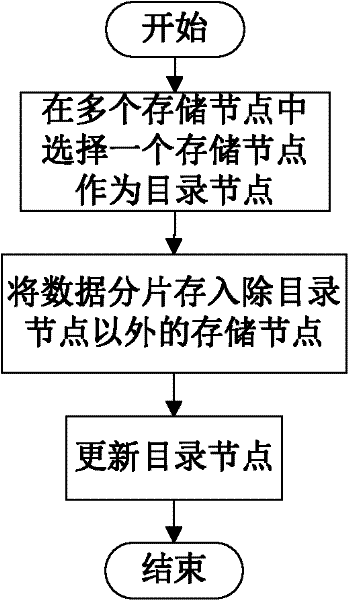
InactiveCN102546755ADoes not affect recoveryImprove data availabilityTransmissionSpecial data processing applicationsComputer hardwareData integrity
The invention discloses a data storage method of a cloud storage system, which comprises the steps of: carrying out coding fragmentation on a file on the basis of a buffer zone erasure code technology to obtain data fragments and check fragments; processing the data fragments and the check fragments to obtain a check identification; storing the check identification in an index server; requesting storage resource information to the index server according to the quantity of the data fragments and the check fragments; sending the data fragments and the check fragments to a plurality of storage nodes according to the storage resource information; judging whether needing to carry out integrity check on the data fragments and the check fragments in the storage nodes; if needing to carry out integrity check on the data fragments and the check fragments in the storage nodes, sending the data integrity check information to the storage nodes, receiving an identification information set returned by the storage nodes, and judging whether data storage errors or data losses exist according to the identification information set, if yes, coding for recovering the data, and sending the recovered data to the corresponding storage nodes.
Owner:HUAZHONG UNIV OF SCI & TECH
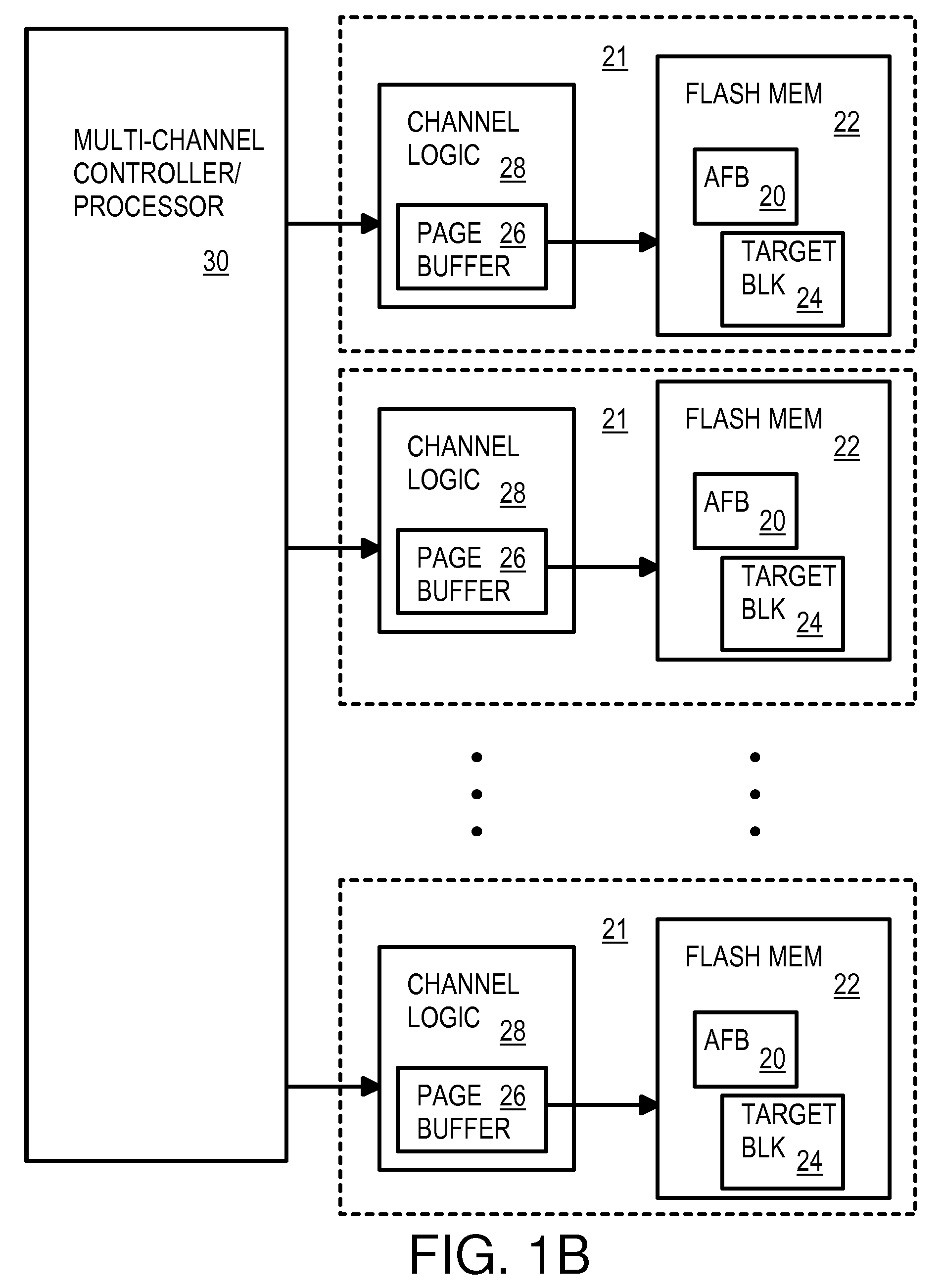
Multi-operation write aggregator using a page buffer and a scratch flash block in each of multiple channels of a large array of flash memory to reduce block wear
InactiveUS8108590B2Memory architecture accessing/allocationMemory adressing/allocation/relocationSmall fragmentPage buffers
A flash system has multiple channels of flash memory chips that can be accessed in parallel. Host data is assigned to one of the channels by a multi-channel controller processor and accumulated in a multi-channel page buffer. When a page boundary in the page buffer is reached, the page buffer is written to a target physical block if full, or combined with old data fragments in an Aggregating Flash Block (AFB) when the logical-sector addresses (LSA's) match. Thus small fragments are aggregated using the AFB, reducing erases and wear of flash blocks. The page buffer is copied to the AFB when a STOP command occurs. Each channel has one or more AFB's, which are tracked by an AFB tracking table.
Owner:SUPER TALENT TECH CORP
Distributed storage oriented cloud storage security architecture and data access method thereof
InactiveCN102088491AImprove usabilityImprove reliabilityTransmissionStorage area networkConfidentiality
The invention discloses a distributed storage oriented cloud storage security architecture and a data access method thereof. The distributed cloud storage oriented security architecture comprises a cloud storage server, a distributed storage manager, a wafer breaker and storage devices, wherein the distributed storage manager and the cloud storage server are respectively connected with a client-side; the distributed storage manager and the cloud storage server are connected by a fiber channel (FC) or a routing switch; the wafer breaker is imbedded in the distributed storage manager; the distributed storage manager is connected with the storage devices by the FC or Iscsi; and the storage devices are connected by a network attached storage (NAS) or a storage area network (SAN). The storage devices are located at different places and are redundant mutually, thus improving the fault-tolerant ability of the devices and the optimal storage use ratio; the wafer breaker is used for carrying out fragment on stored data, so that the data are fragmented into data fragments which can not be identified by other authentication systems, and the fragmented data have relative confidentiality and security in the process of network transmission and data storage; and the storage devices and the server are the devices with higher cost performance, thus reducing the cost.
Owner:XI'AN UNIVERSITY OF ARCHITECTURE AND TECHNOLOGY
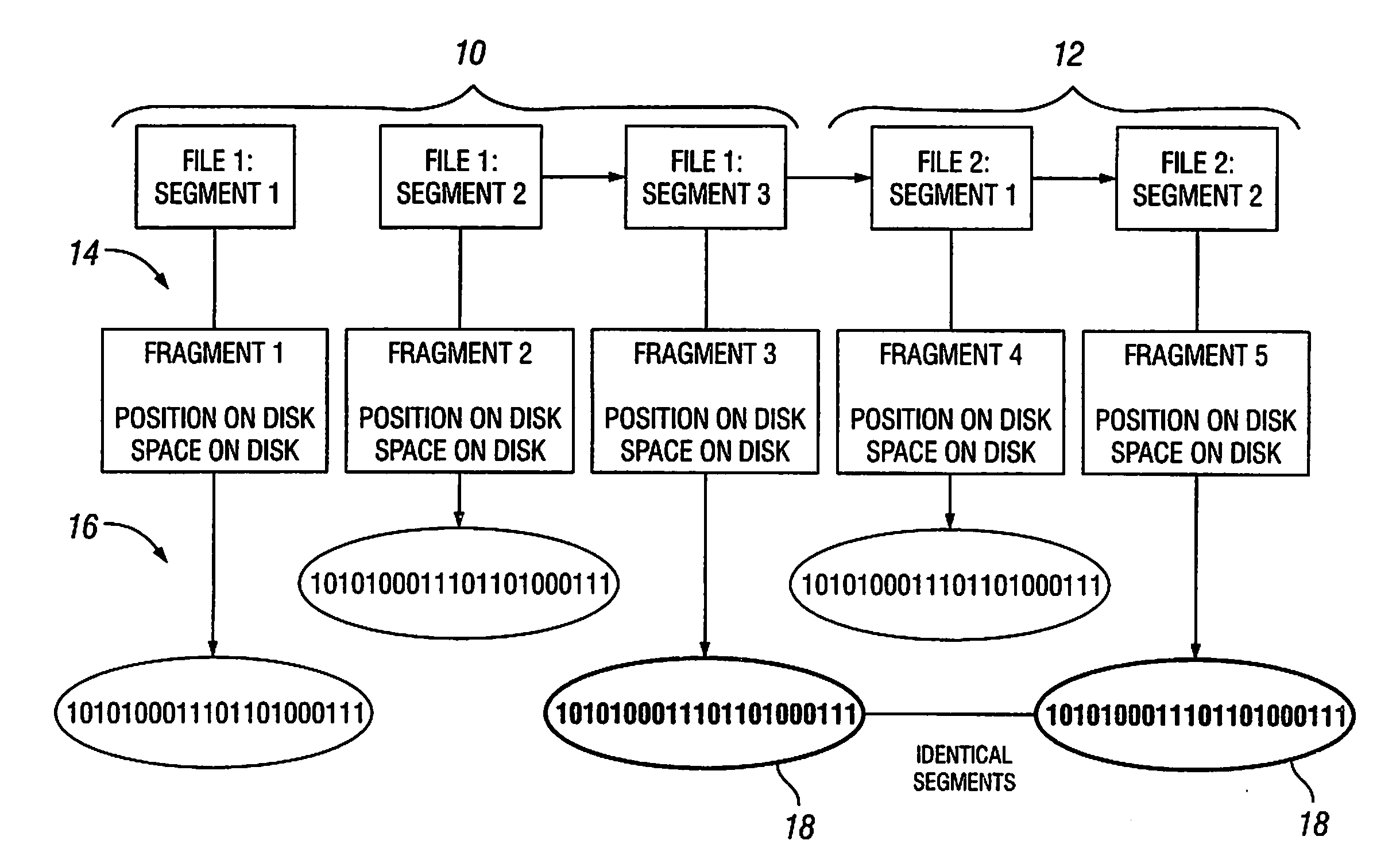
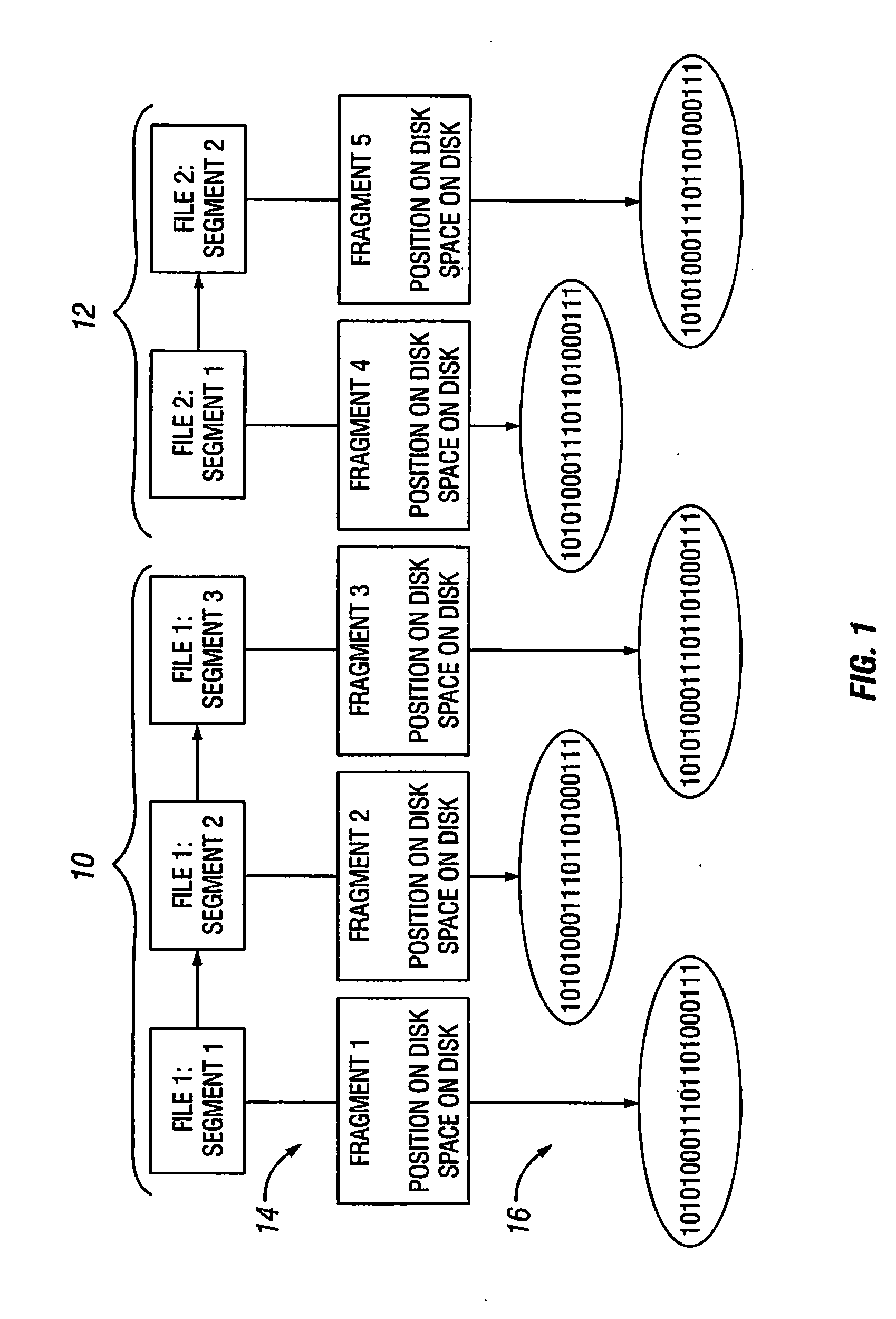
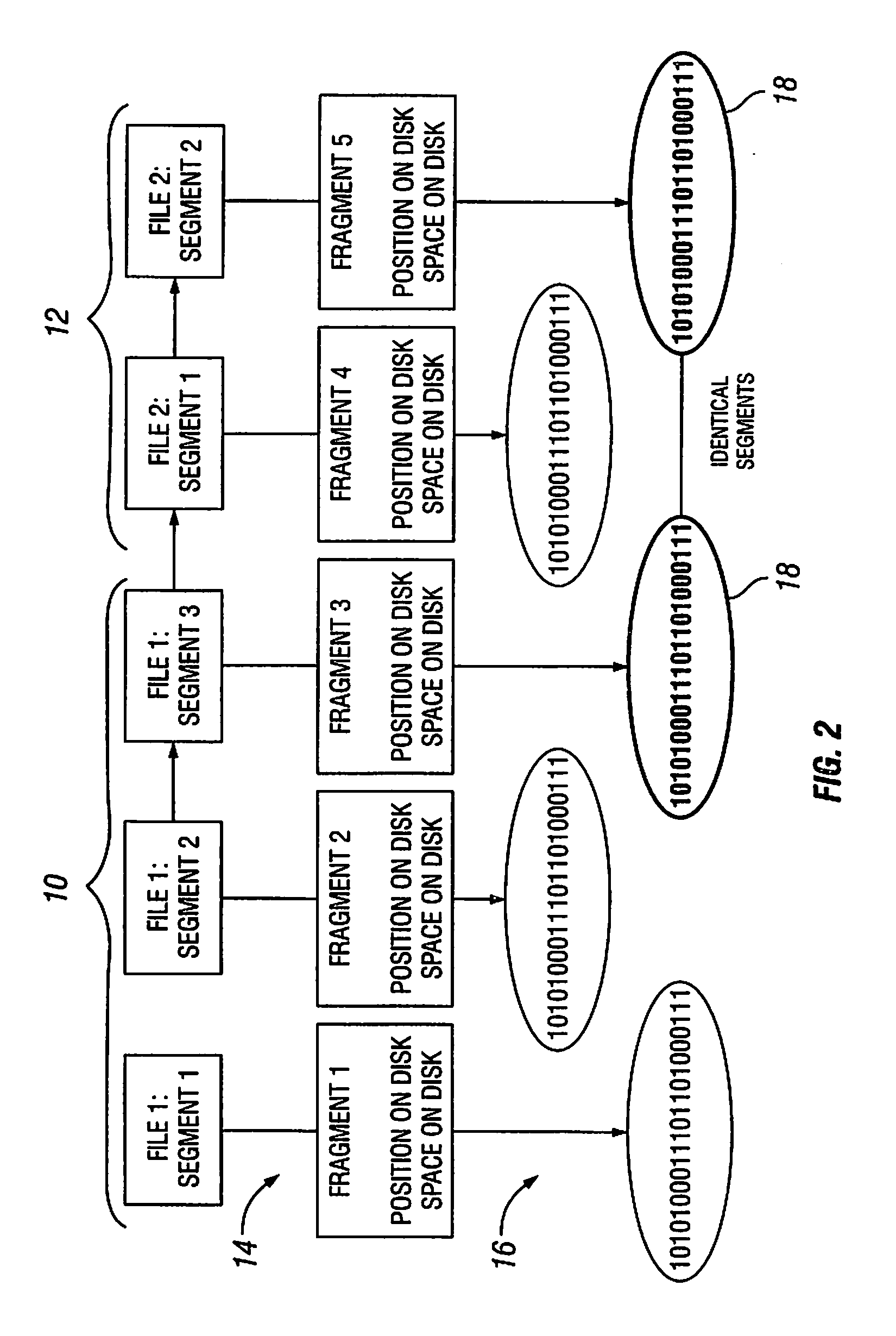
Fragmentation Compression Management
InactiveUS20080172430A1Digital data information retrievalSpecial data processing applicationsData segmentData file
A method of managing data fragments on computer readable storage media includes identifying an identical data segment within both of first and second data files, establishing a single instance of the identical data segment as a shared data fragment, modifying file headers associated with the first and second data files so that each file header associates with the shared data fragment, and reclaiming storage space that contains a redundant instance of the identical data segment. A data file or data fragment may be divided or further divided into data fragments if the file or fragment is identified as having a data segment that is identical to a data segment in a different data file or fragment. The method should require that amount of identical data reclaimed is greater than the amount of new header information stored with each fragment.
Owner:IBM CORP
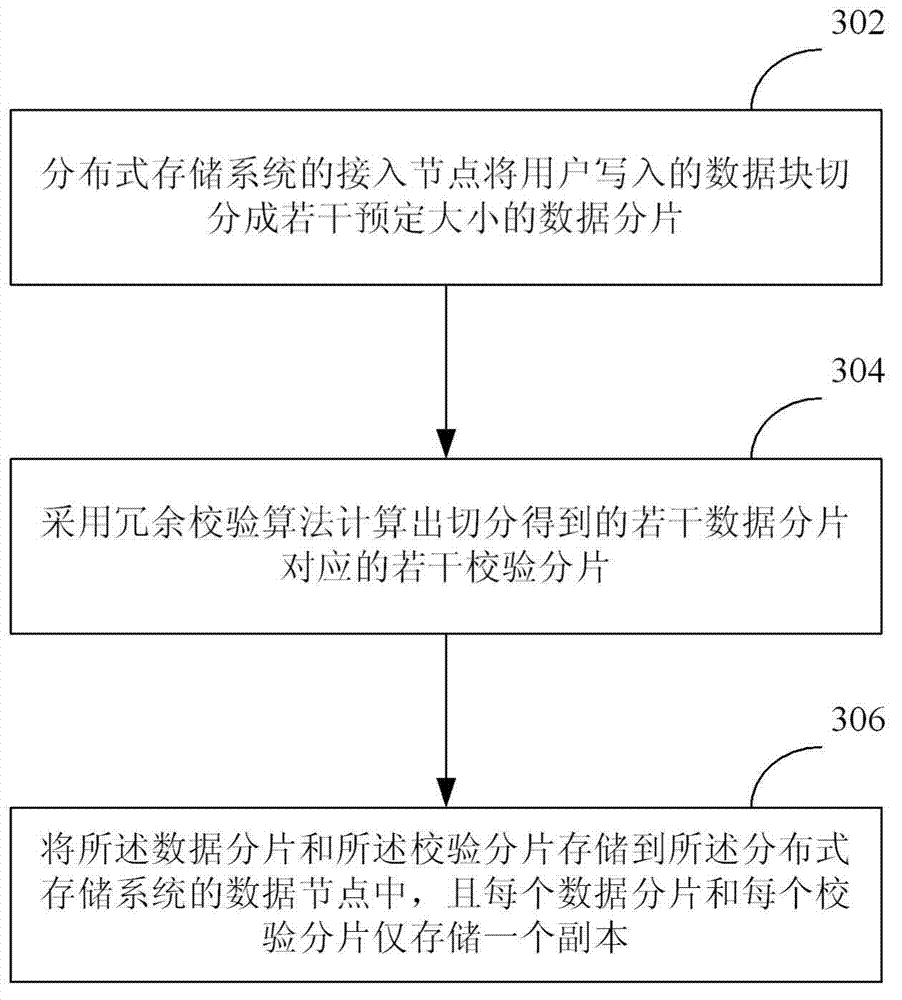
Data storage method, data storage equipment and distributed storage system
InactiveCN103699494AGuaranteed reliabilityReduce the proportionMemory adressing/allocation/relocationRedundant data error correctionData nodeData reliability
The invention discloses a data storage method, data storage equipment and a distributed storage system. The method, the equipment and the system belong to the technical field of computers. The data storage method comprises the steps that access nodes of the distributed storage system cut a data block which is written in by a user into a plurality of data fragments with preset sizes; a plurality of check fragments corresponding to the data fragments which are obtained by cutting are calculated through a redundancy check algorithm; the data fragments and the check fragments are stored into the data nodes of the distributed storage system, and each data fragment and each check fragment only store one copy. According to the data storage method, the data storage equipment and the distributed storage system, the proportion of redundant data can be reduced on the premise of ensuring data reliability, so as to save the storage space.
Owner:BEIJING QIHOO TECH CO LTD +1
Selecting storage units to rebuild an encoded data slice
ActiveUS20140331100A1Error detection/correctionError correction/detection using multiple parity bitsData segmentAlgorithm
A method begins with a processing module of a dispersed storage network (DSN) identifying an encoded data slice of a set of encoded data slices that requires rebuilding and identifying storage units of the DSN that store the set of encoded data slices. The method continues with the processing module determining a rebuilding metric regarding the identified encoded data slice and selecting a sub-set of the storage units for retrieving a decode threshold number of encoded data slices of the set of encoded data slices based on the rebuilding metric. When the decode threshold number of encoded data slices have been retrieved, the method continues with the processing module decoding the decode threshold number of encoded data slices to produce a reconstructed data segment and generating a rebuilt encoded data slice from the reconstructed data segment.
Owner:PURE STORAGE
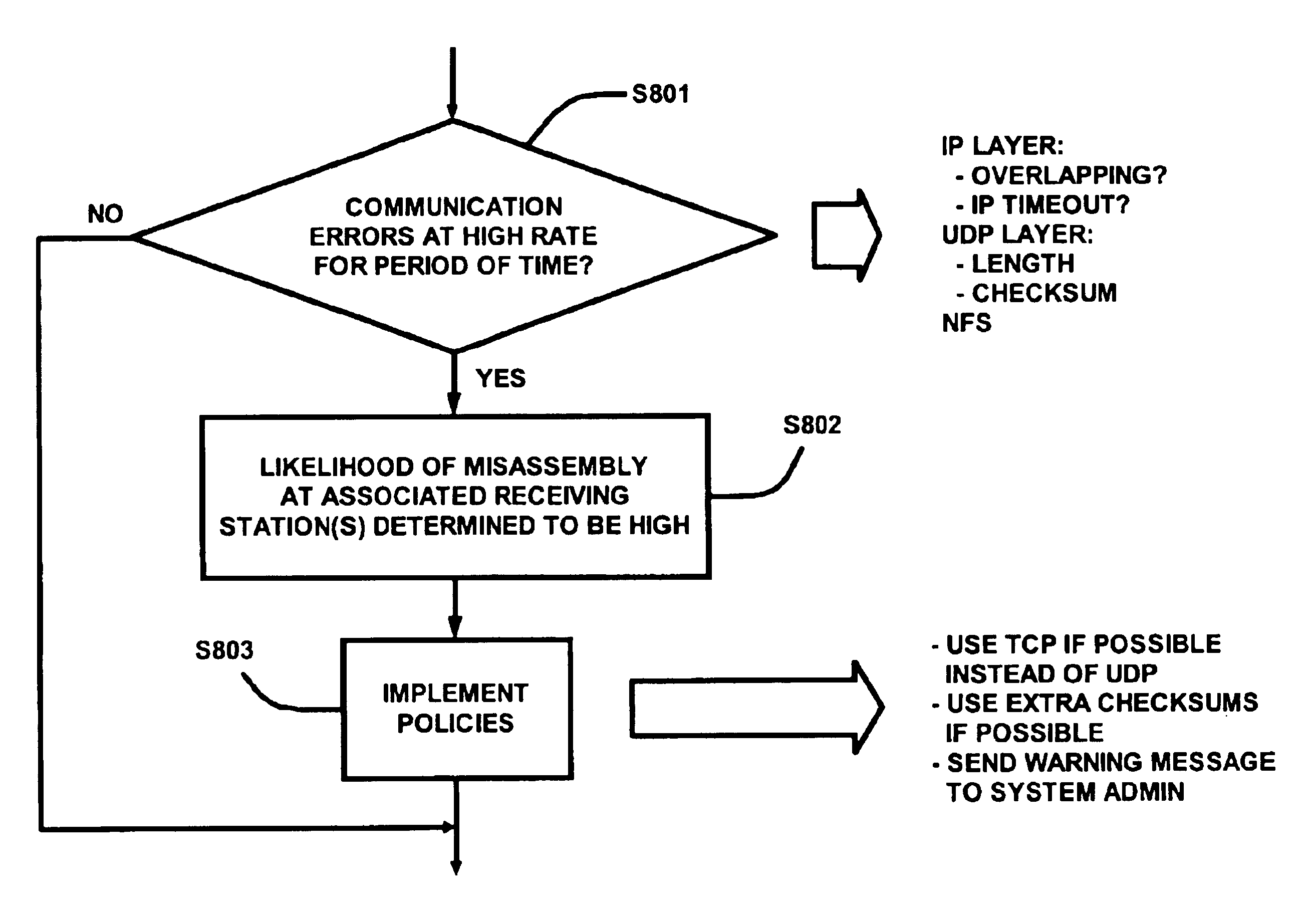
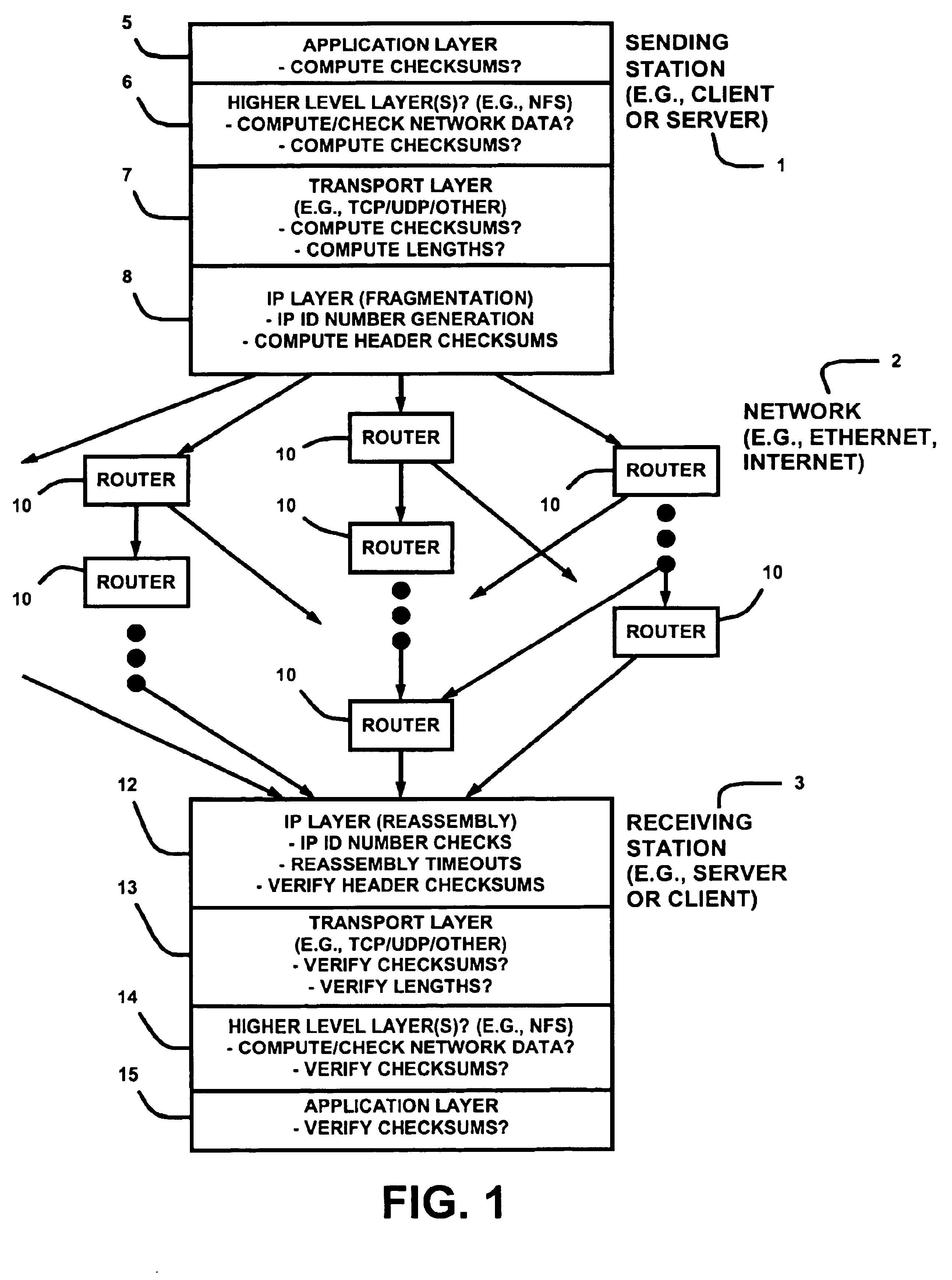
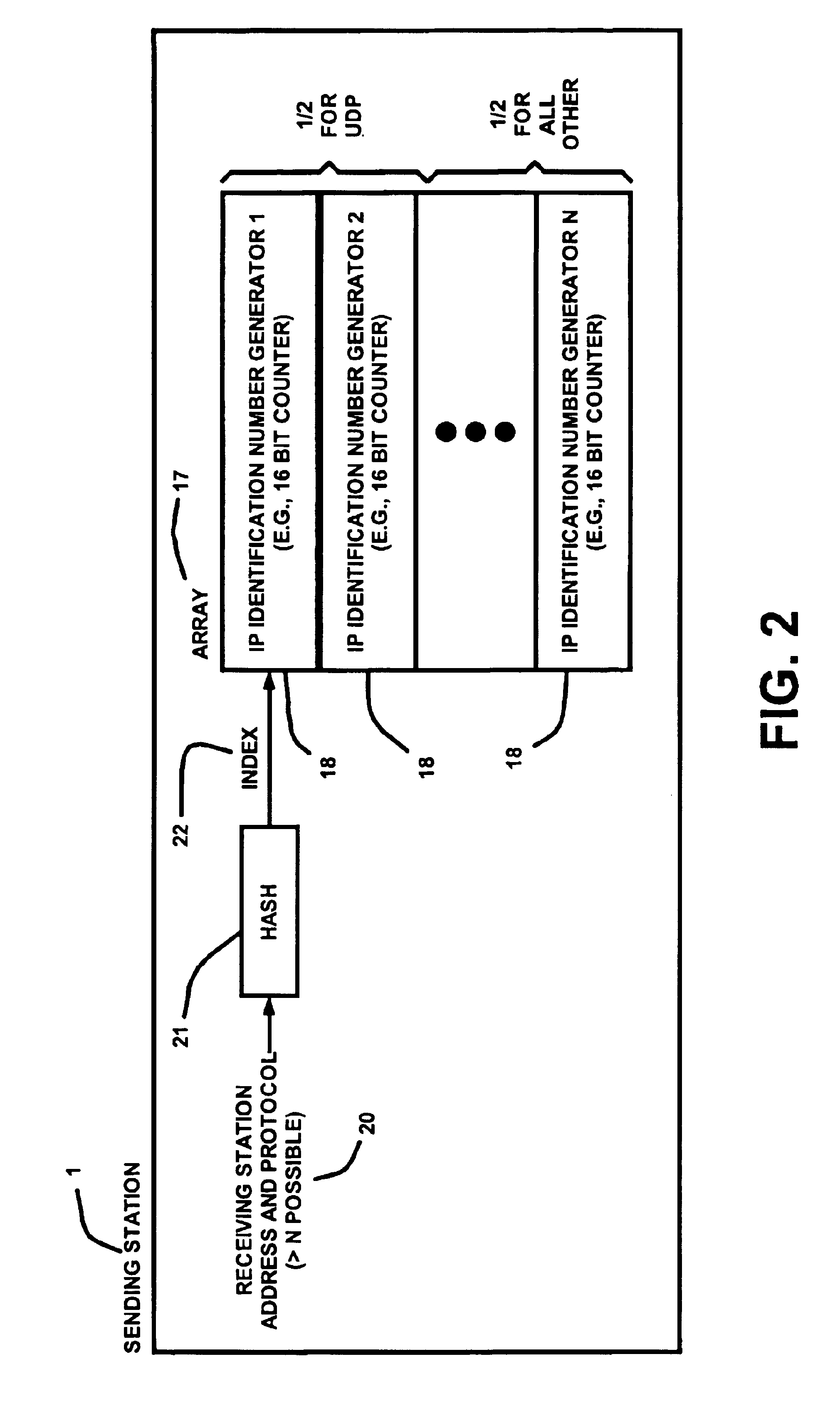
Prevention and detection of IP identification wraparound errors
InactiveUS6894976B1Reduce likelihood of misassemblyRaise the possibilityError preventionTransmission systemsTelecommunicationsNumber generator
A method of generating IP identification numbers for IP datagrams. A plurality of IP identification number generators are maintained. A plurality of receiving stations are associated with the plurality of IP identification number generators such that each receiving station has an IP identification number generator associated therewith. An IP identification number is generated for a datagram sent to a receiving station based on an output of the associated IP identification number generator. Also, a method of reducing a likelihood of misassembly of received data fragments from fragmented IP datagrams. The data fragments have an IP identification number. All received data fragments of the datagram are discarded upon detection of receipt of an overlapping data fragment having the IP identification number. Timeouts for reassembling datagrams are reduced. First, timeouts for reassembling the datagrams are reduced to less than a standard timeout. Second, timeouts are reduced upon detection of a gap in the received data fragments. Third, timeouts are reduced upon detection of a datagram having the same protocol identification number and source address, but having a different IP identification number. Furthermore, a method of detecting a likelihood of misassembly of data fragments from fragmented IP datagrams. Communication errors between a sending station and a receiving station are detected. A rate is determined at which an IP identification number generator associated with the receiving station wraps around. NFS re-transmissions are determined. Based on one or more of these, a likelihood of misassembly at the receiving station is determined to be high.
Owner:NETWORK APPLIANCE INC
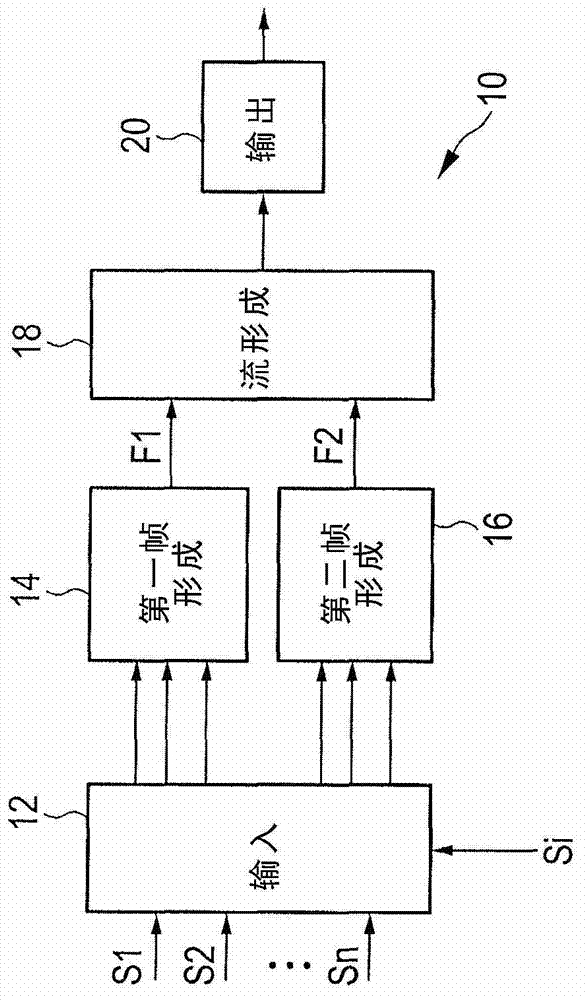
Mapping apparatus and method for transmission of data in a multi-carrier broadcast system
The present invention relates to an apparatus and a corresponding method for mapping payload data of mapping input data streams (S1, S2,..., Sp) onto a mapping output data stream (Q) having a channel bandwidth for transmission in a multi- carrier broadcast system. To enable the selection of the robustness for the transmission of data, said apparatus comprises a frame forming means (16, 64) for mapping the data blocks of said at least two mapping input data streams (S1, S2,..., Sp) onto frames (F) of said mapping output data stream (Q) covering said channel bandwidth, each frame (F) comprising a payload portion (50), said payload portion (50) comprising a plurality of data symbols (52)and being segmented into data segments (51) each covering a bandwidth portion of said channel bandwidth, wherein the frame forming means (64); is adapted for mapping the data blocks of said at least two mapping input data streams (S1, S2,..., Sp) onto the data symbols (52) of said pay-load portion (50) and comprises a MIMO mode selection means (1614, 1682) for selecting the MIMO mode of the data blocks per data segment (51) and / or per map- ping input data stream (S1, S2,..., Sp).
Owner:SONY CORP
Data storage method, data recovery method, and relevant device and system
ActiveCN105095013AImprove storage consistencyRedundant data error correctionInput/output processes for data processingRecovery methodData segment
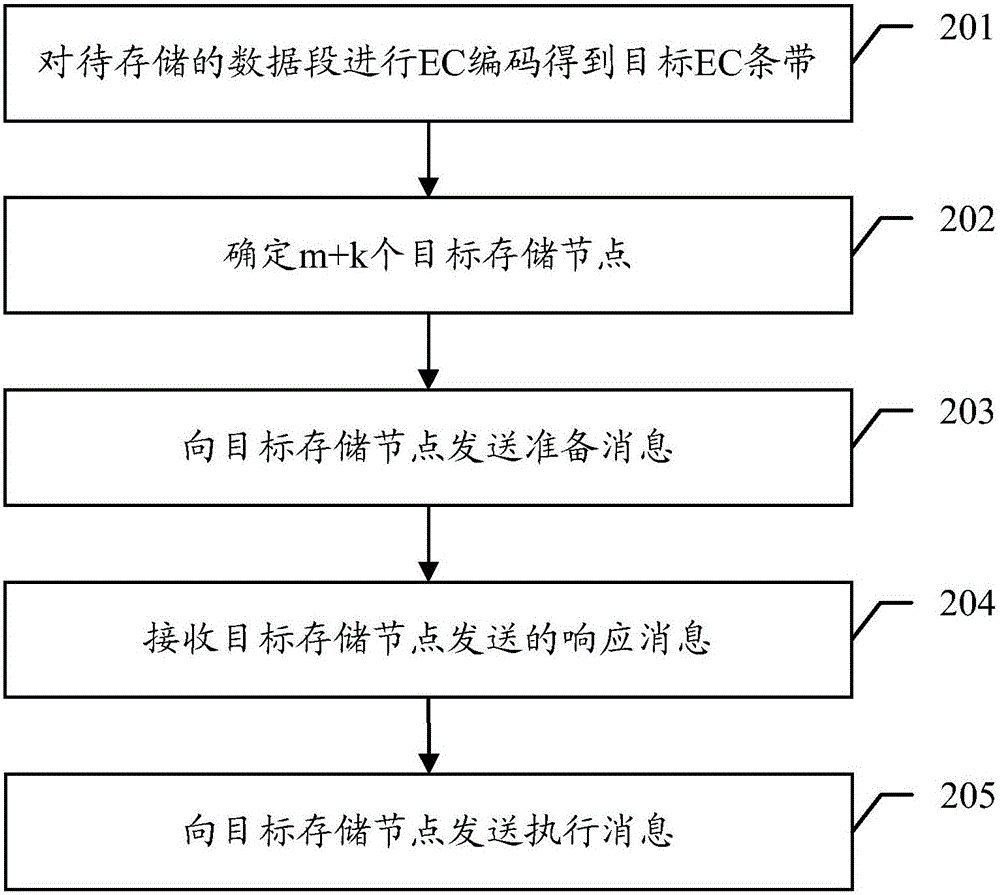
The invention discloses a data storage method for improving the storage consistency of a distributed memory system in an embodiment. The method comprises: a major storage node performs EC coding on a data fragment to be stored to obtain a target EC stripe; (m+k) target storage nodes for storing (m+k) target EC blocks of the target EC stripe are determined in a storage node group; a preparation message is sent to the target storage nodes; a response sent by each target storage node is received; and after the response messages of all the target storage nodes are received, an execution message is sent to the target storage nodes to instruct the target storage nodes to write in the target EC blocs in a preparation log. The embodiment of the invention further provides a data recovery method and a relevant device.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
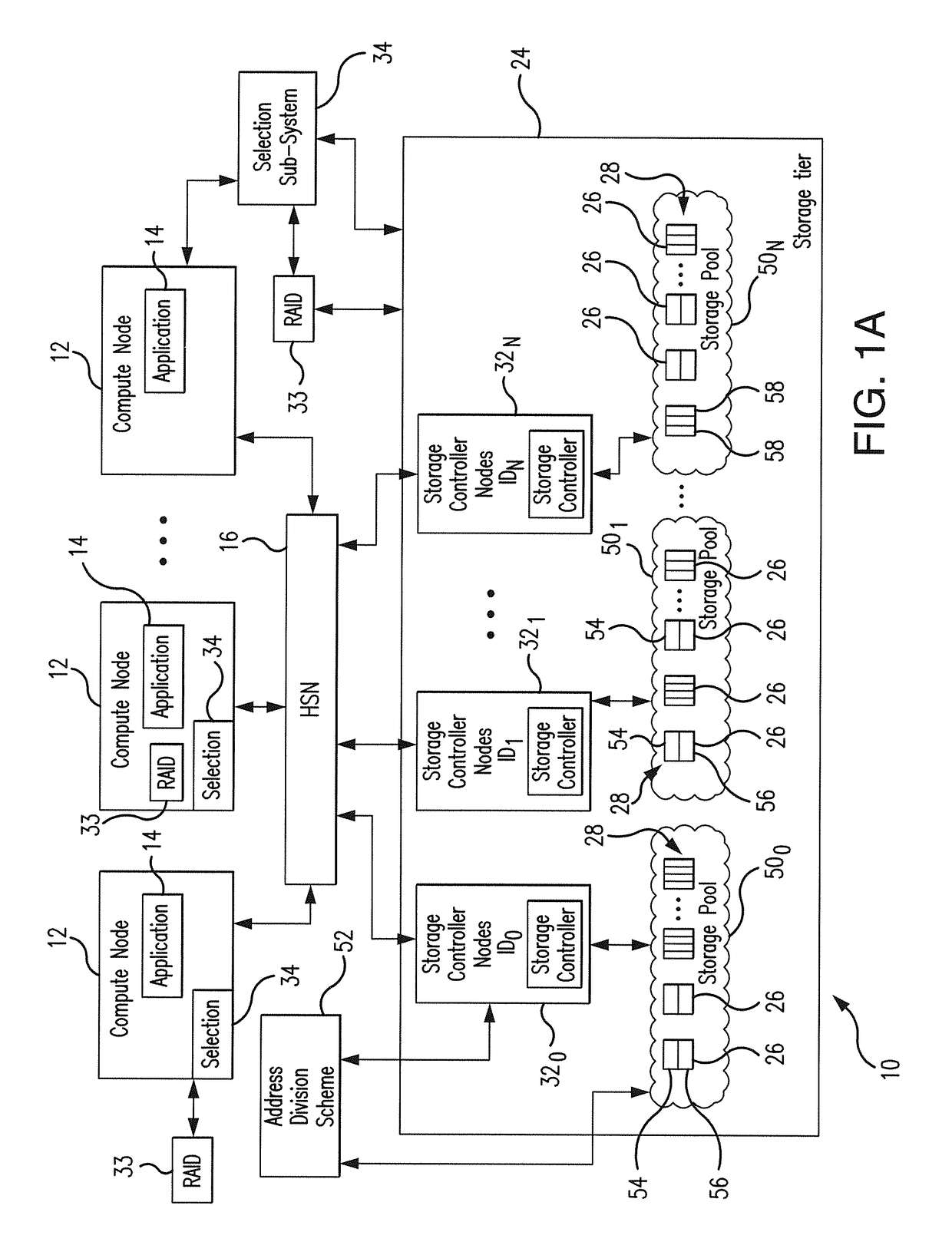
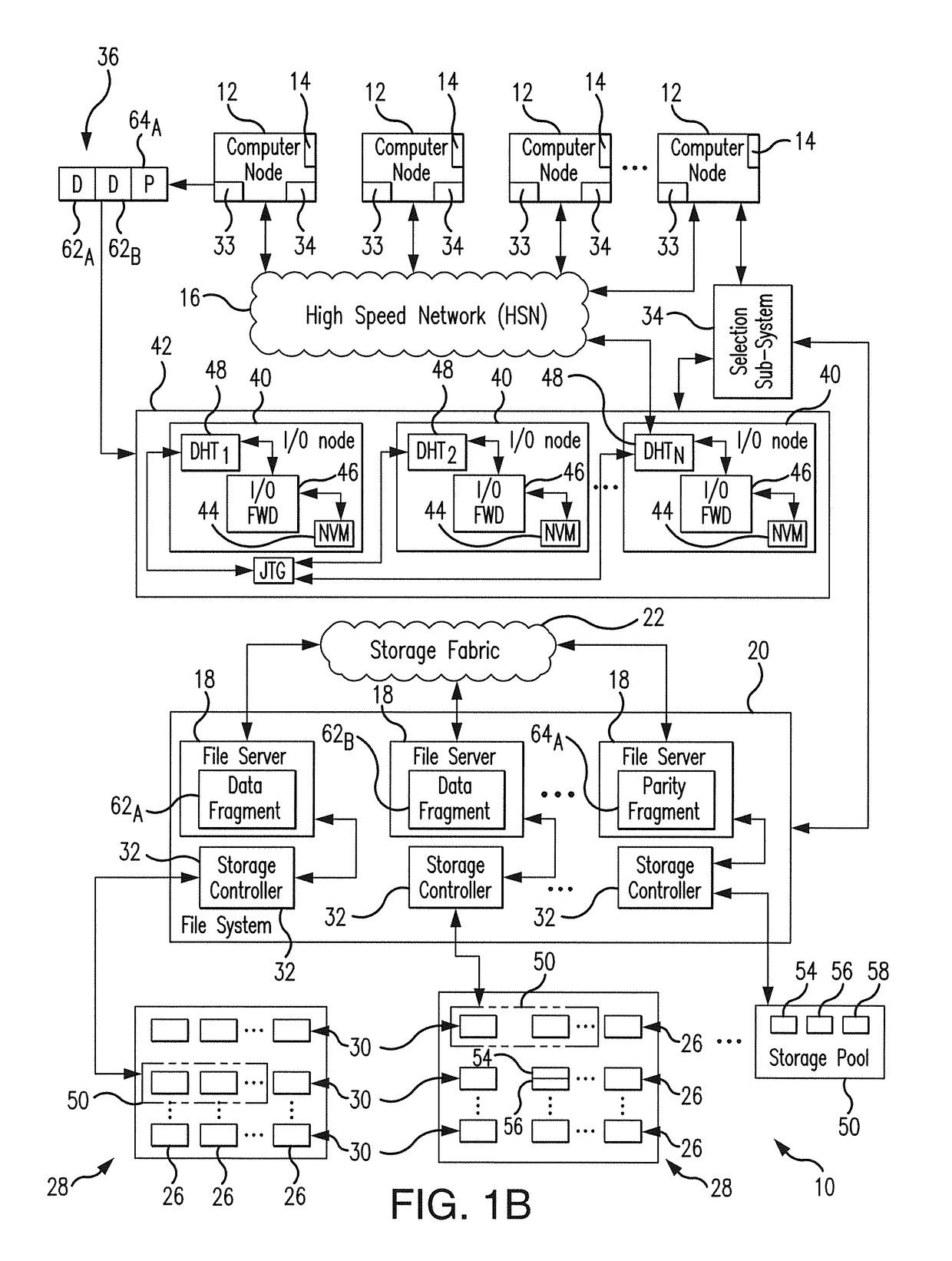
Low latency and reduced overhead data storage system and method for sharing multiple storage devices by high performance computing architectures
ActiveUS9959062B1Improve the level ofReliable rebuildInput/output to record carriersRedundant hardware error correctionData setPerformance computing
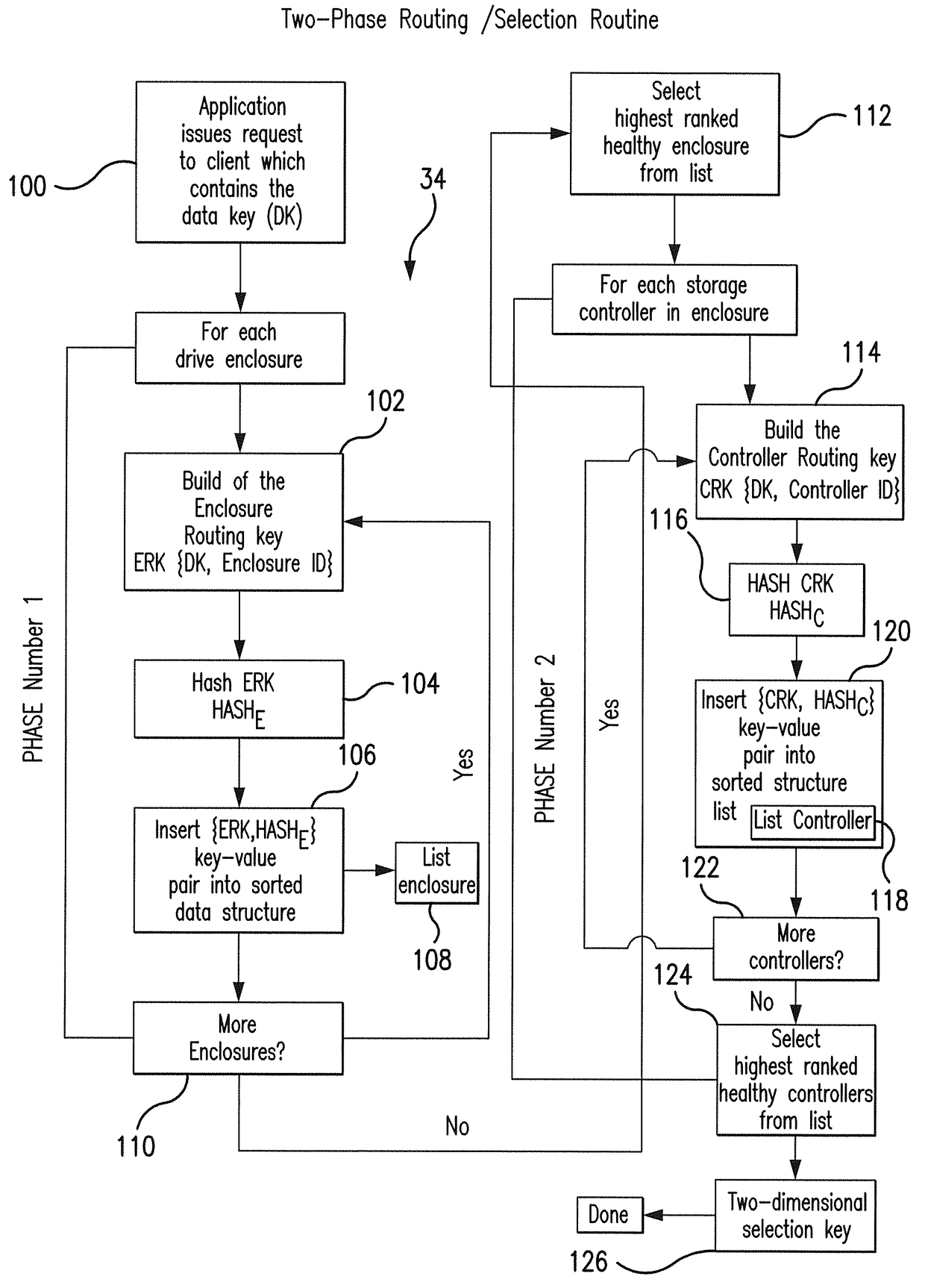
A data migration system supports a low-latency and reduced overhead data storage protocol for data storage sharing in a non-collision fashion which does not require inter-communication and permanent arbitration between data storage controllers to decide on the data placement / routing. The multiple data fragments of data sets are prevented from routing to the same storage devices by a multi-step selection protocol which selects (in a first phase of the selection routine) a healthy highest ranked drive enclosure, and further selects (in a second phase of the selection routine) a healthy highest-ranked data storage controller residing in the selected drive enclosure, for routing data fragments to different storage pools assigned to the selected data storage devices for exclusive “writing” and data modification. The selection protocol also contemplates various failure scenarios in a data placement collision free manner.
Owner:DATADIRECT NETWORKS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com