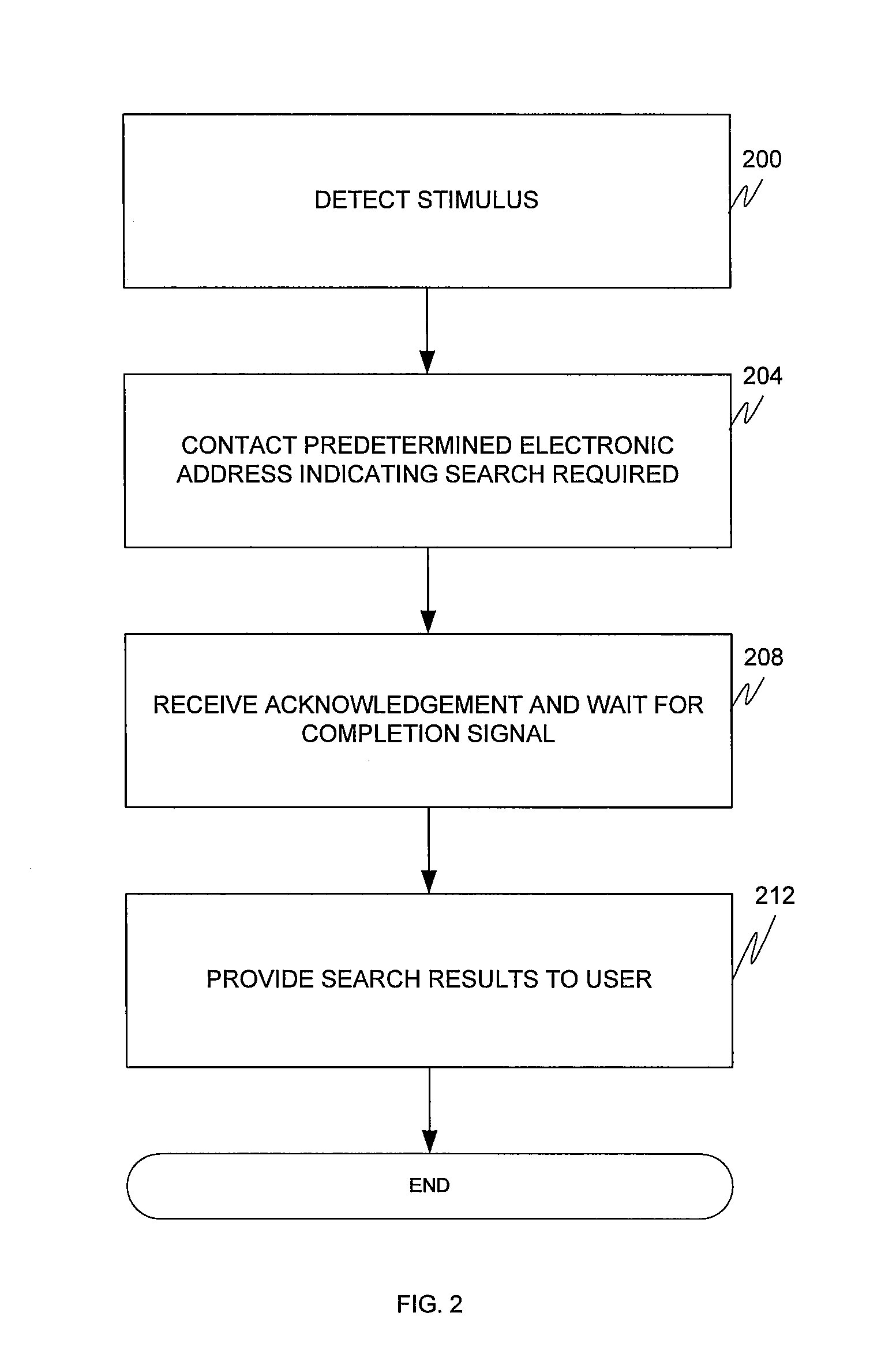
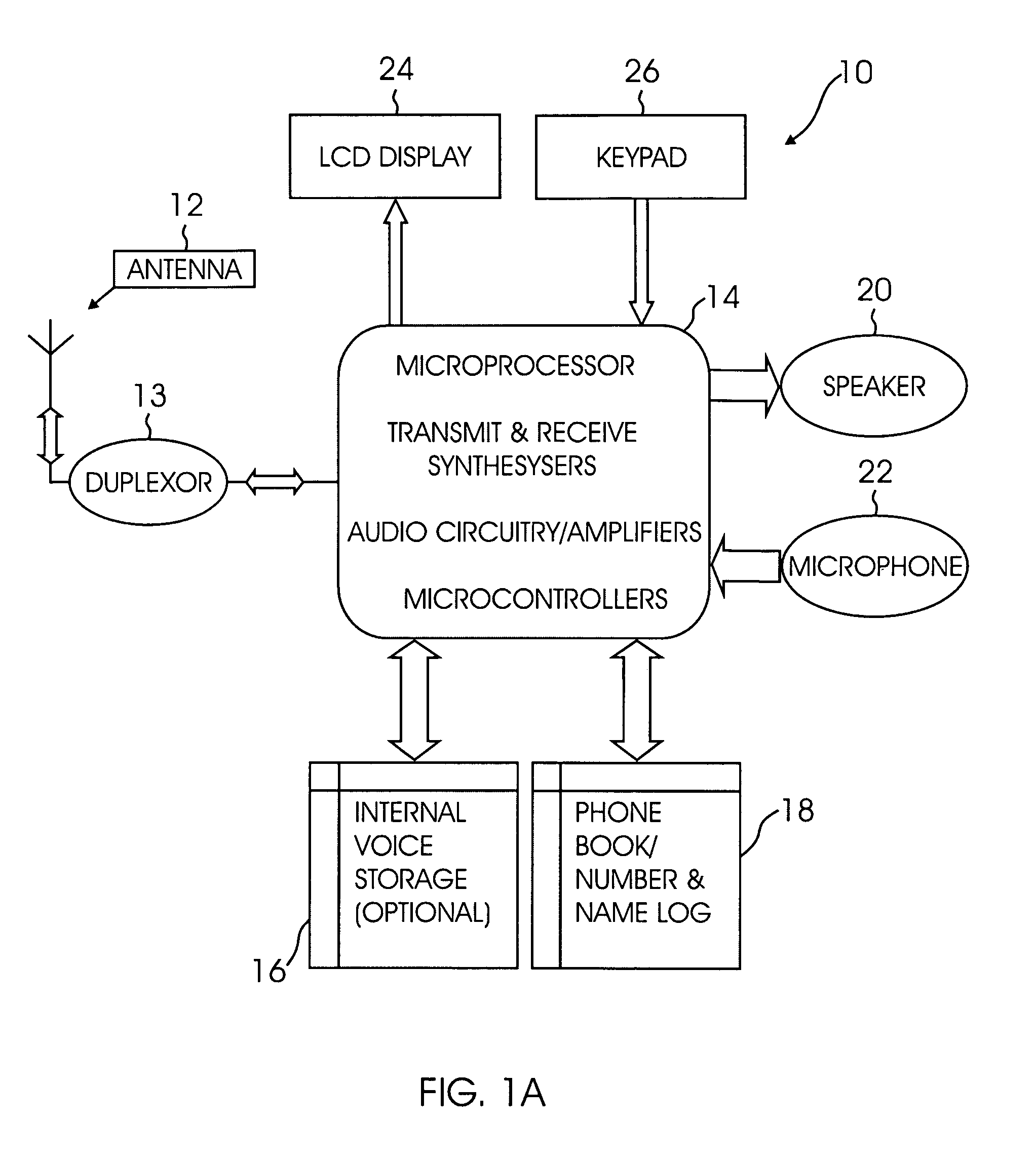
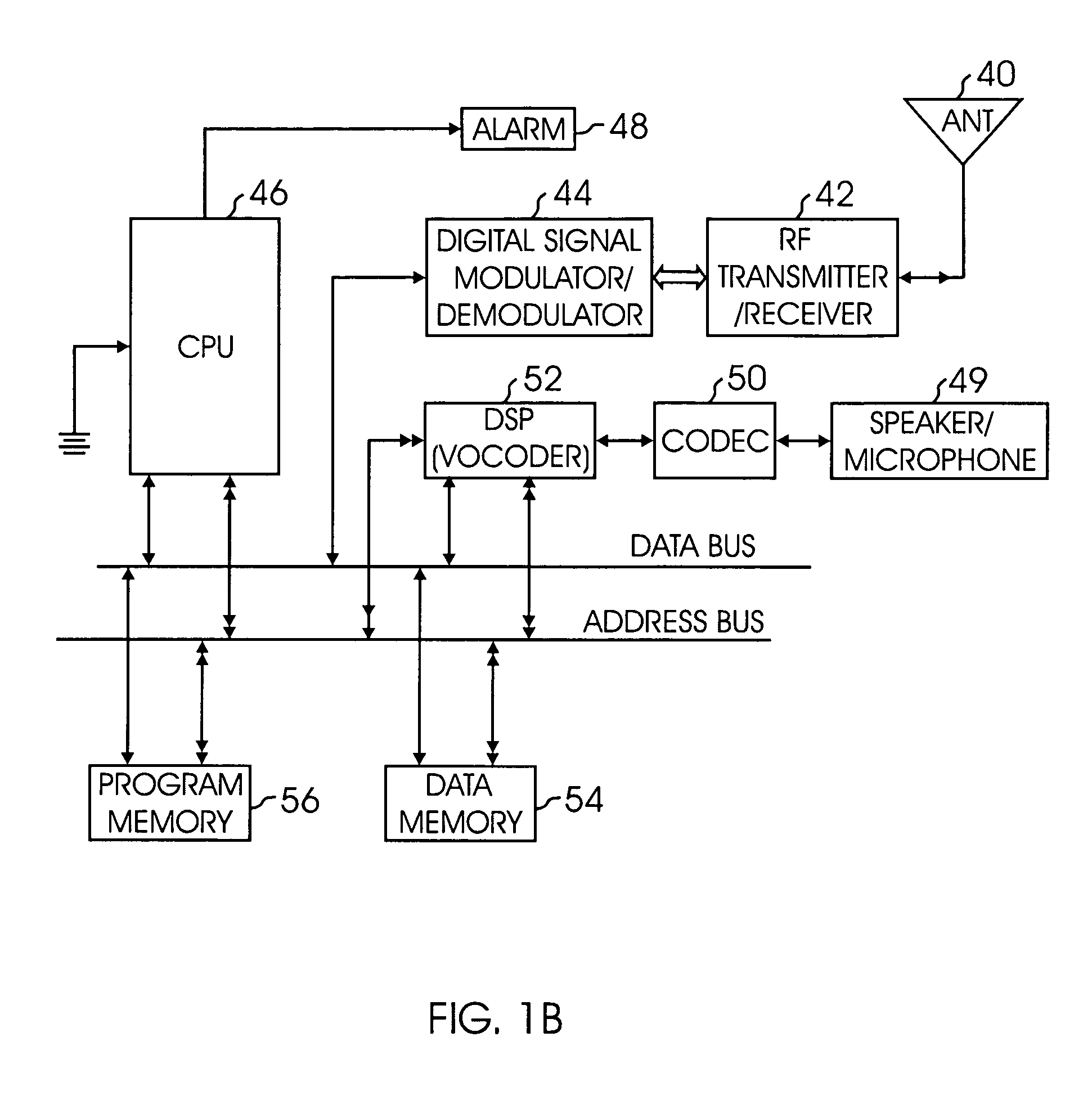
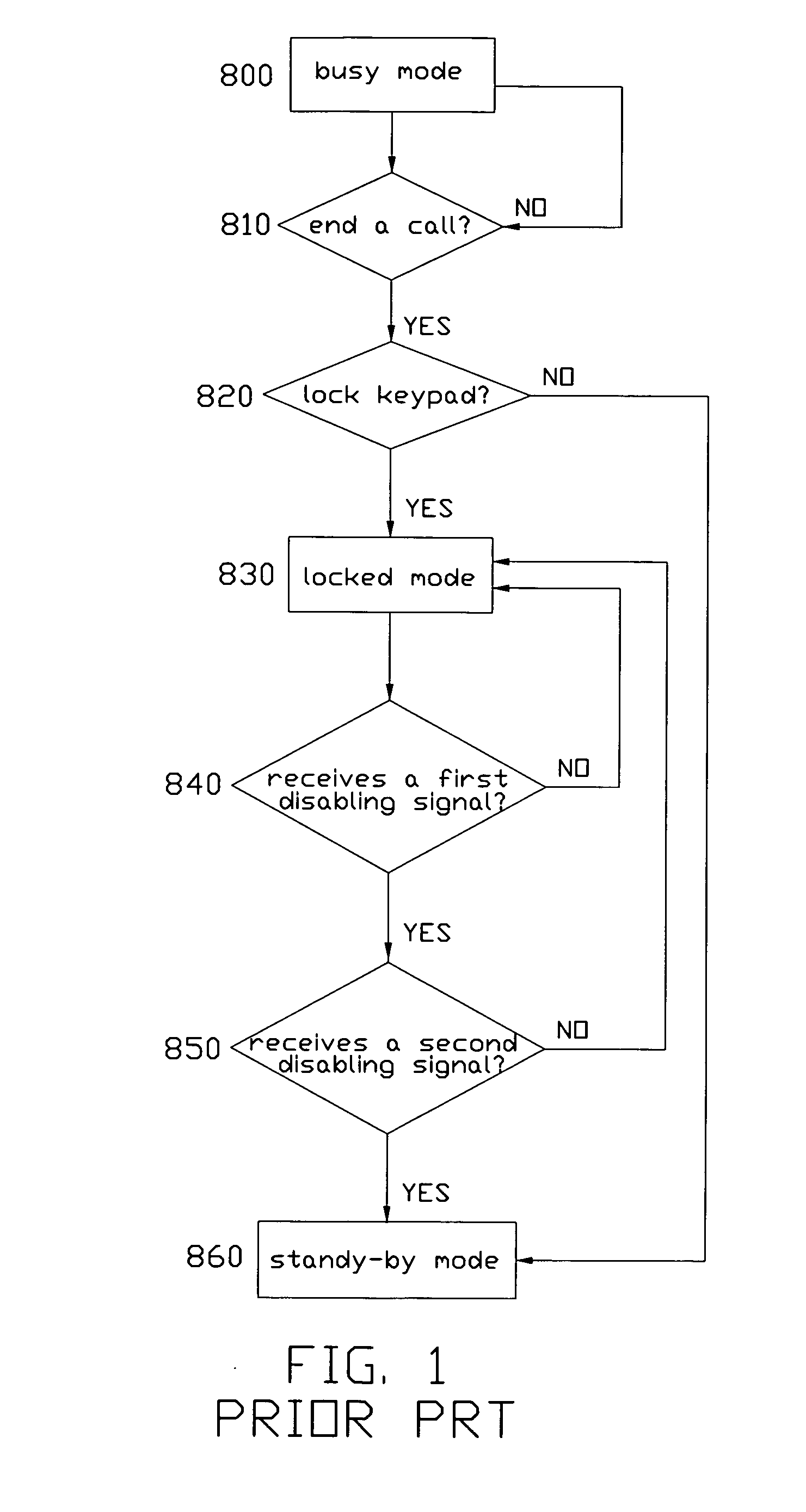
Patents
Literature
662 results about "Telephone number" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In mathematics, the telephone numbers or the involution numbers are a sequence of integers that count the ways n telephone lines can be connected to each other, where each line can be connected to at most one other line. These numbers also describe the number of matchings (the Hosoya index) of a complete graph on n vertices, the number of permutations on n elements that are involutions, the sum of absolute values of coefficients of the Hermite polynomials, the number of standard Young tableaux with n cells, and the sum of the degrees of the irreducible representations of the symmetric group. Involution numbers were first studied in 1800 by Heinrich August Rothe, who gave a recurrence equation by which they may be calculated, giving the values (starting from n = 0)
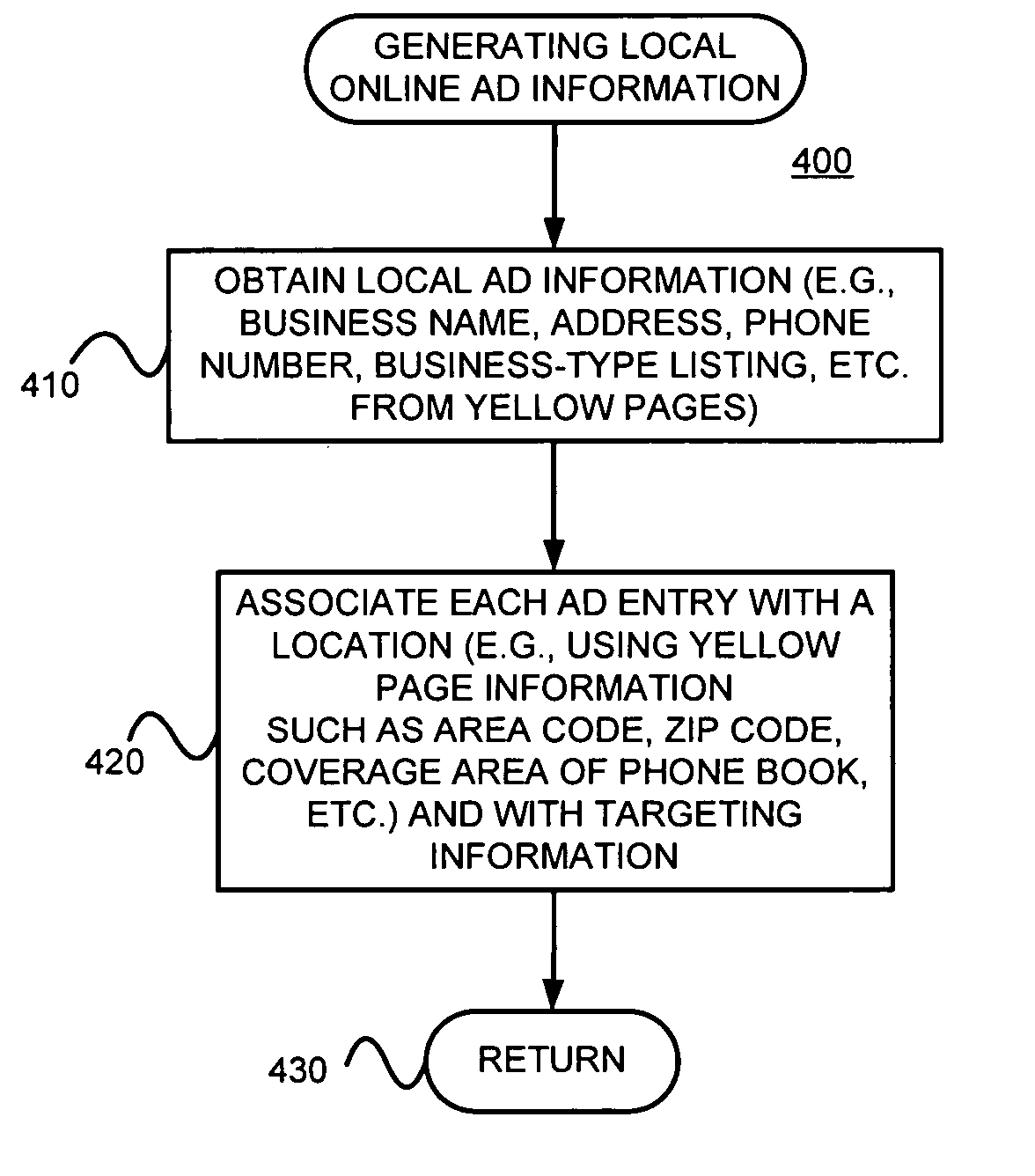
Generating and/or serving local area advertisements, such as advertisements for devices with call functionality
Sets of local, (e.g., online) ads may be generated by obtaining sets of information about (e.g., local) establishments, each set including a business address information and / or a telephone number, (b) determining, for each of the sets, a location using at least one of at least a portion of the business address information and at least a portion of the telephone number, and (c) generating, for each of the sets, an ad that includes targeting information that targets the serving of the ad to queries related to the determined location. A query, including information about a location of a client device, may be accepted and at least one of the generated ads that includes targeting information that targets the location of the client device may be determined.
Owner:GOOGLE LLC
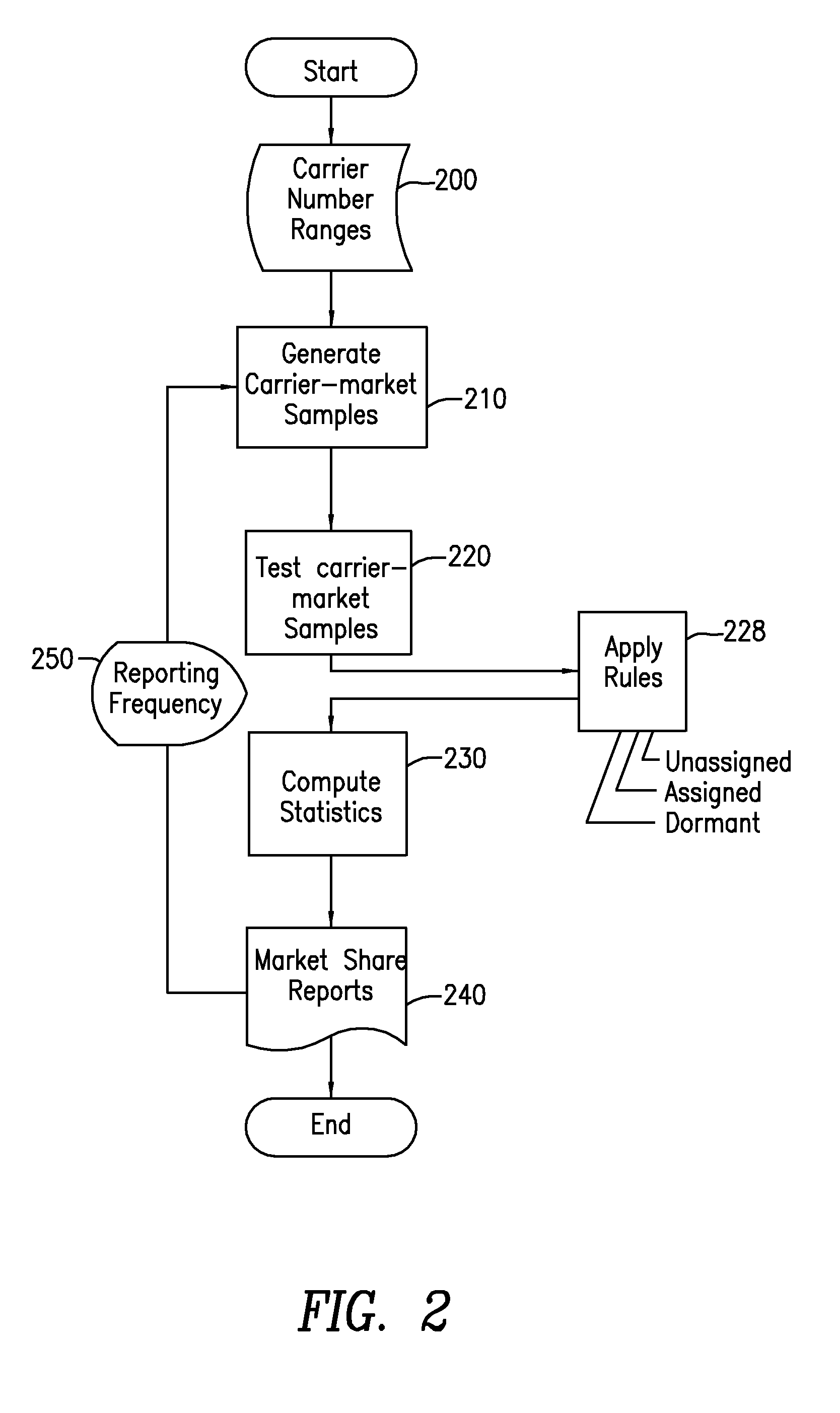
Method and apparatus for determining whether a cellular phone chip is dormant
InactiveUS20100167689A1Supervisory/monitoring/testing arrangementsWireless networksService provisionCellular telephone
Methods and systems are provided for determining whether a cellular telephone chip is dormant. Determinations are drawn from testing telephone numbers associated with chips and data collected is used to generate statistics. Methods are provided for determining the percentage of a wireless service provider's subscriber-base that consists of abandoned, or non-revenue-generating, customers.
Owner:MOBILE SCI
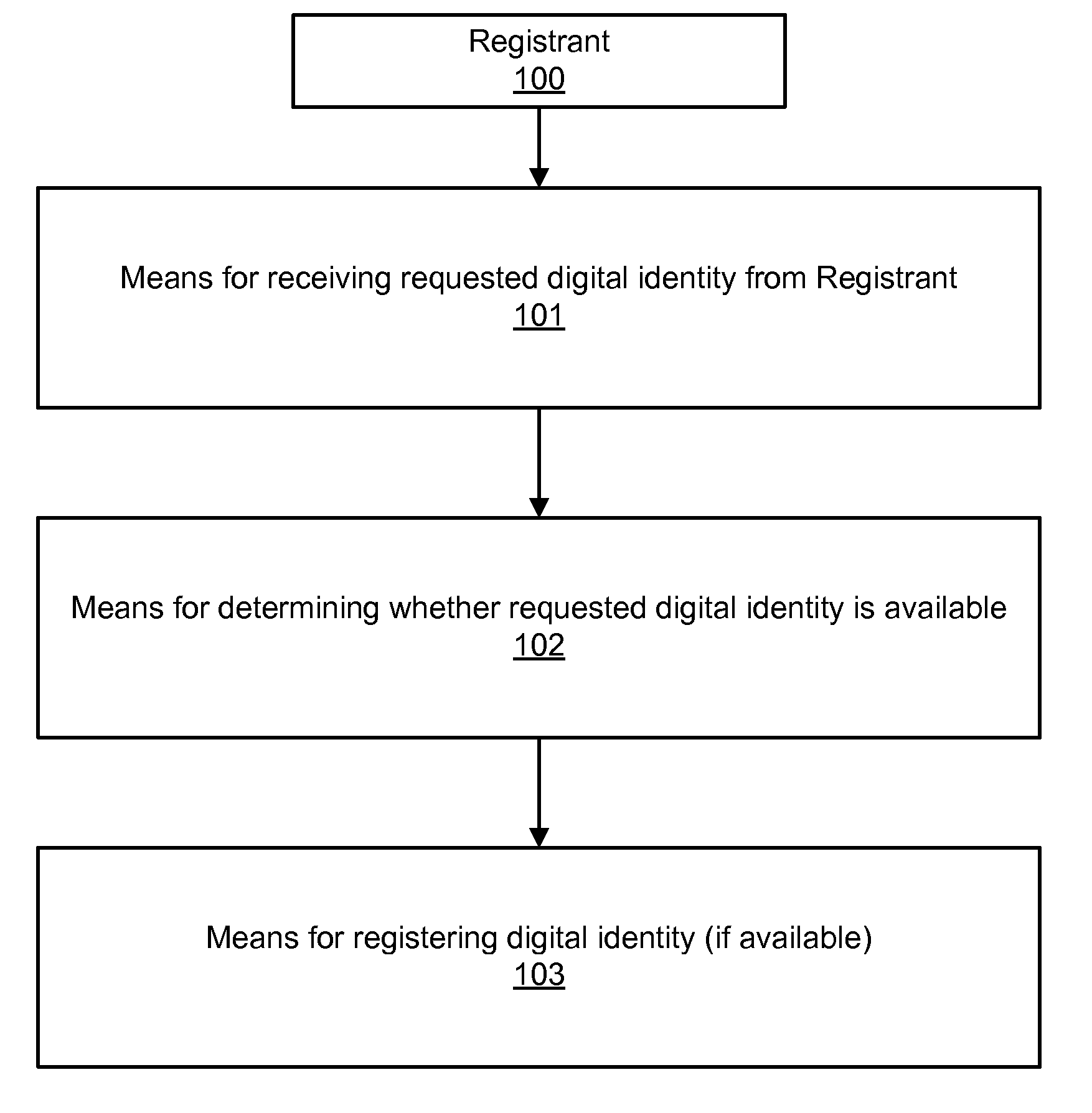
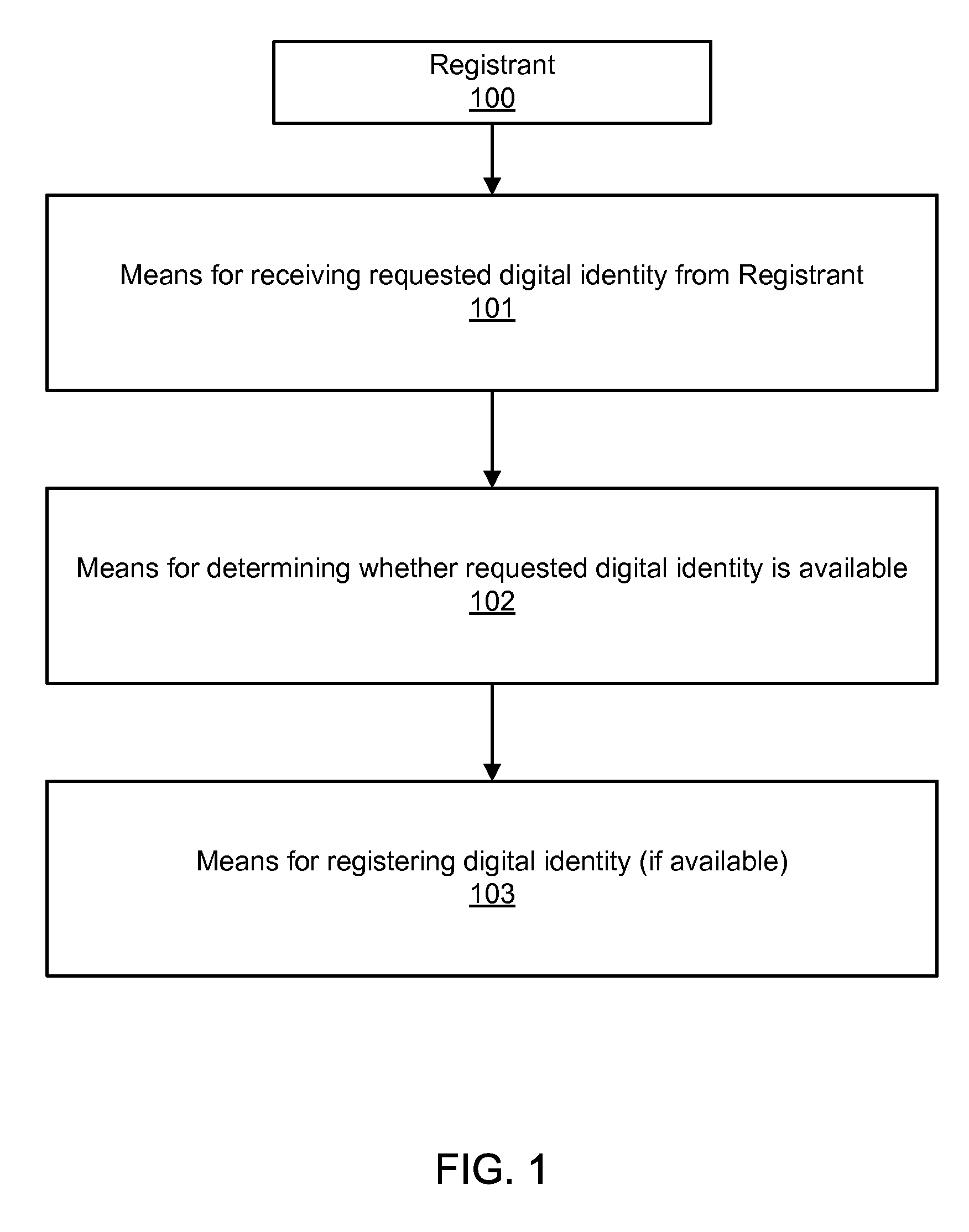
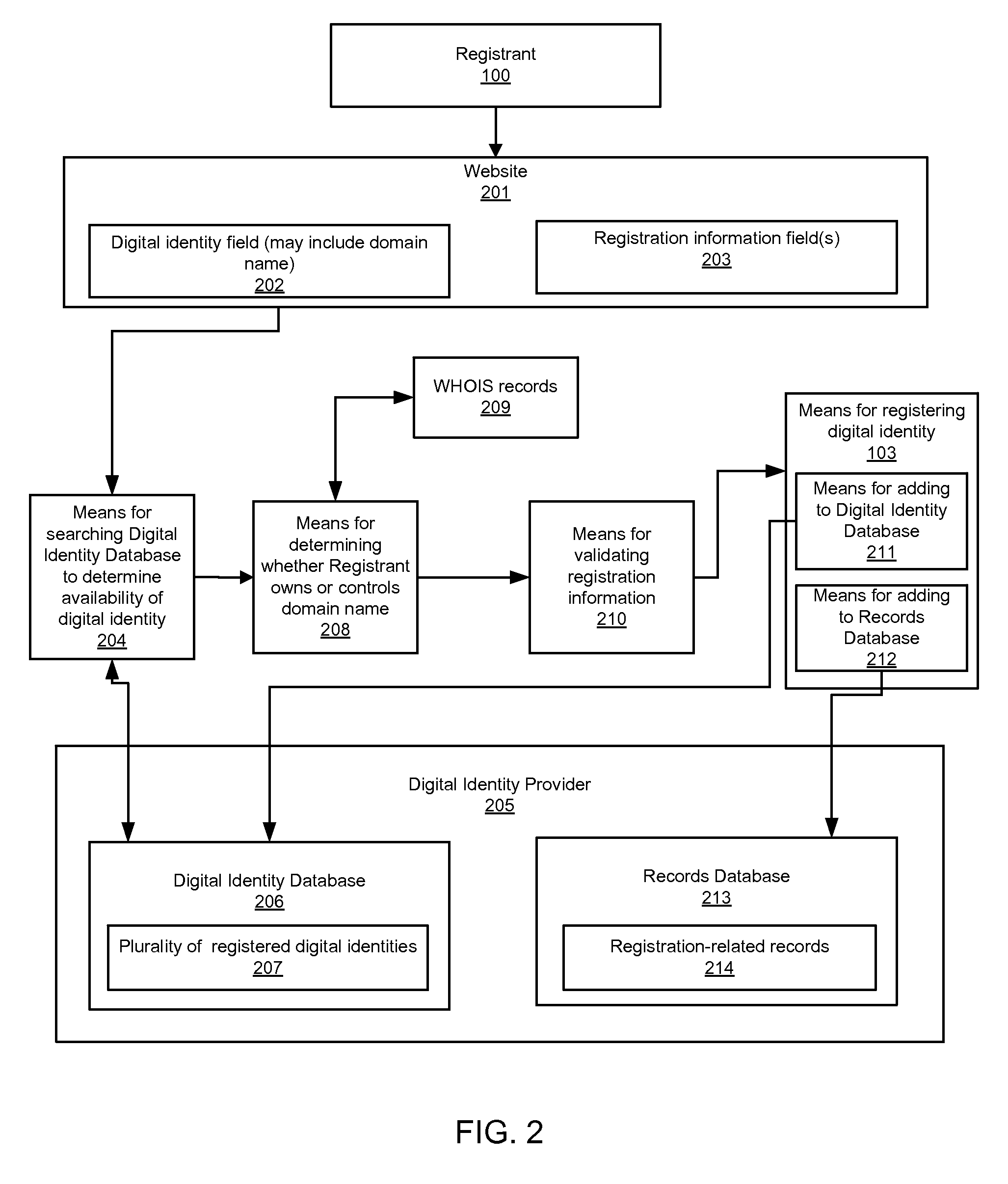
Digital identity validation
ActiveUS20070294431A1Effective registrationMultiple digital computer combinationsData switching networksDigital identityEmail address
Systems and processes of the present invention allow for digital identity validation. In an example embodiment, a digital identity is registered to a Registrant. During the registration process, one or more registration records are collected from the Registrant and stored in a Records Database. The registration records may include information regarding a digital identity, its Registrant, or another person or entity associated with the digital identity. They may also include name, address, phone number, email address, website, URL, or other information. The information is then verified, possibly by contacting a Registrant, administrative contact, technical contact, or another contact to confirm at least some information in the records. If the information is verified, the Digital Identity Provider may provide the Registrant with a Validation Marker indicating that the digital identity has been validated.
Owner:GO DADDY OPERATING
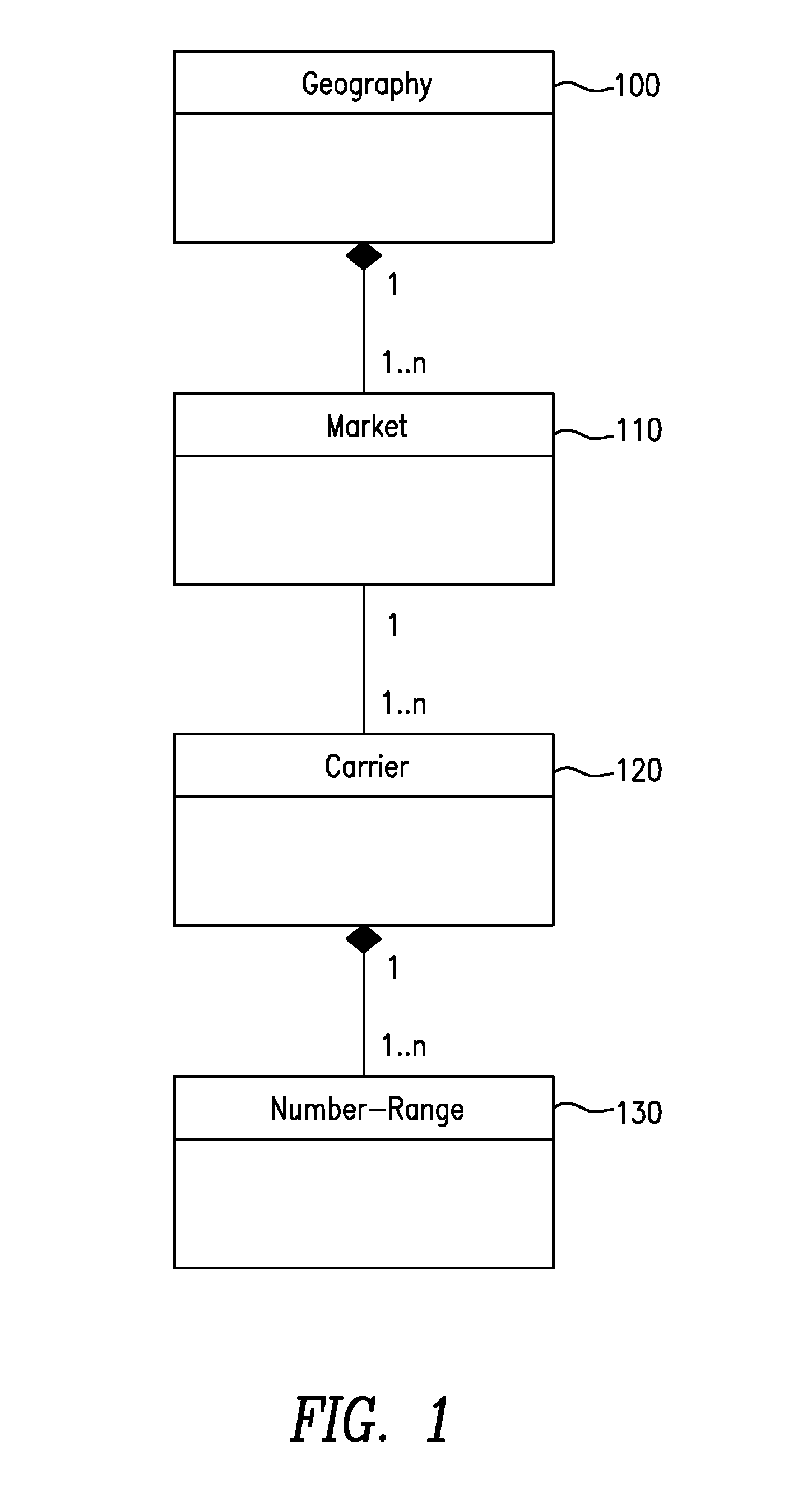
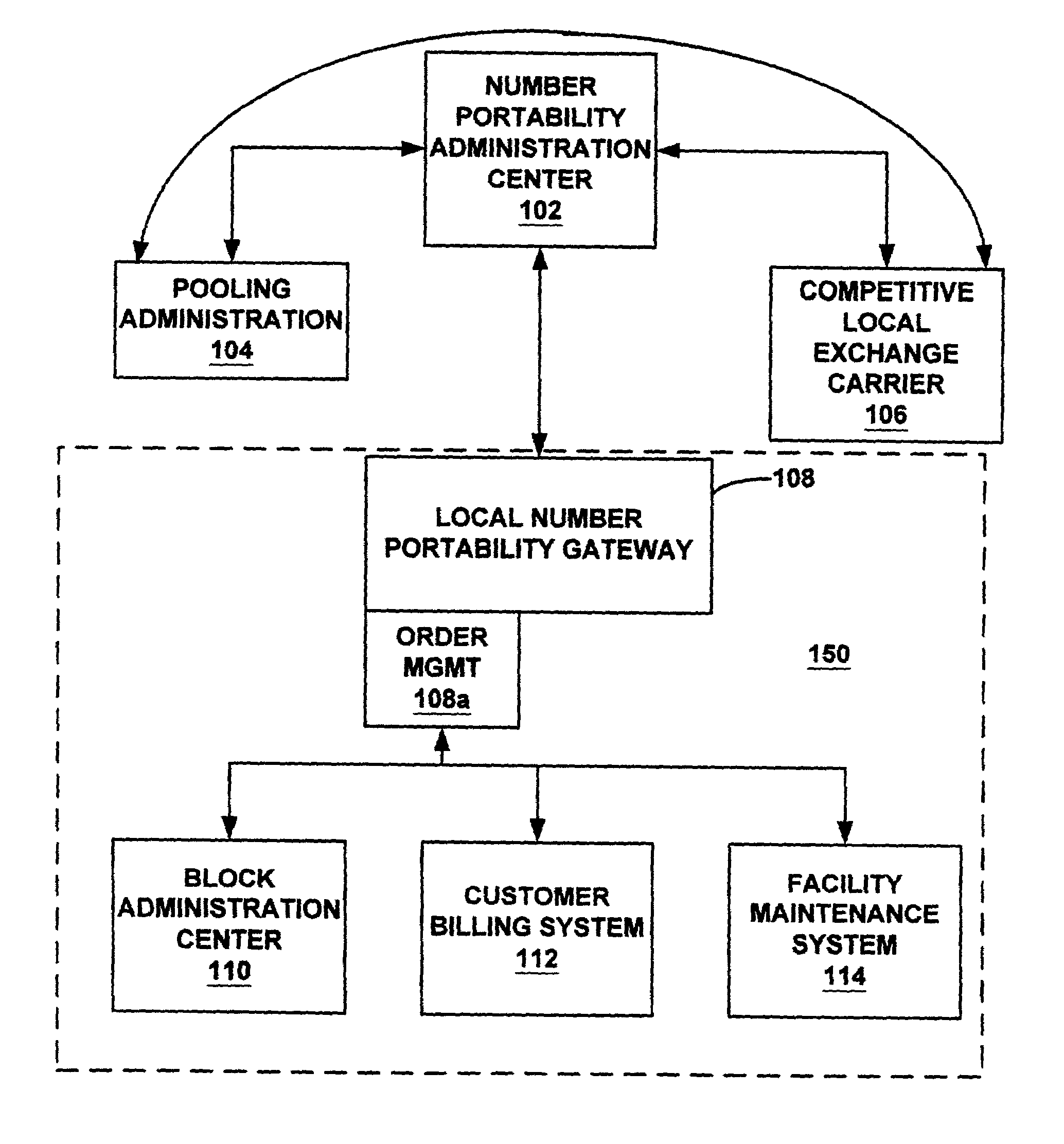
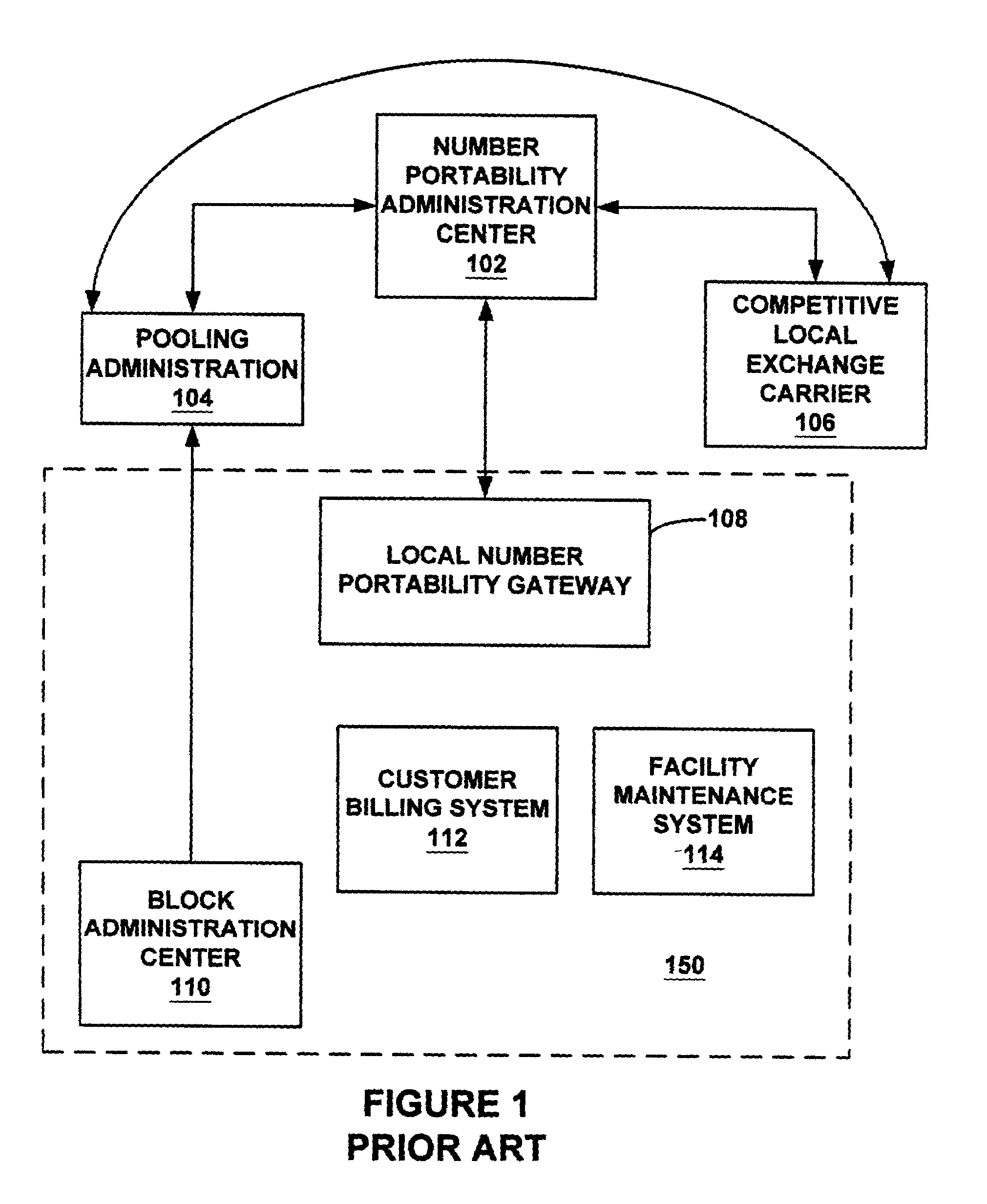
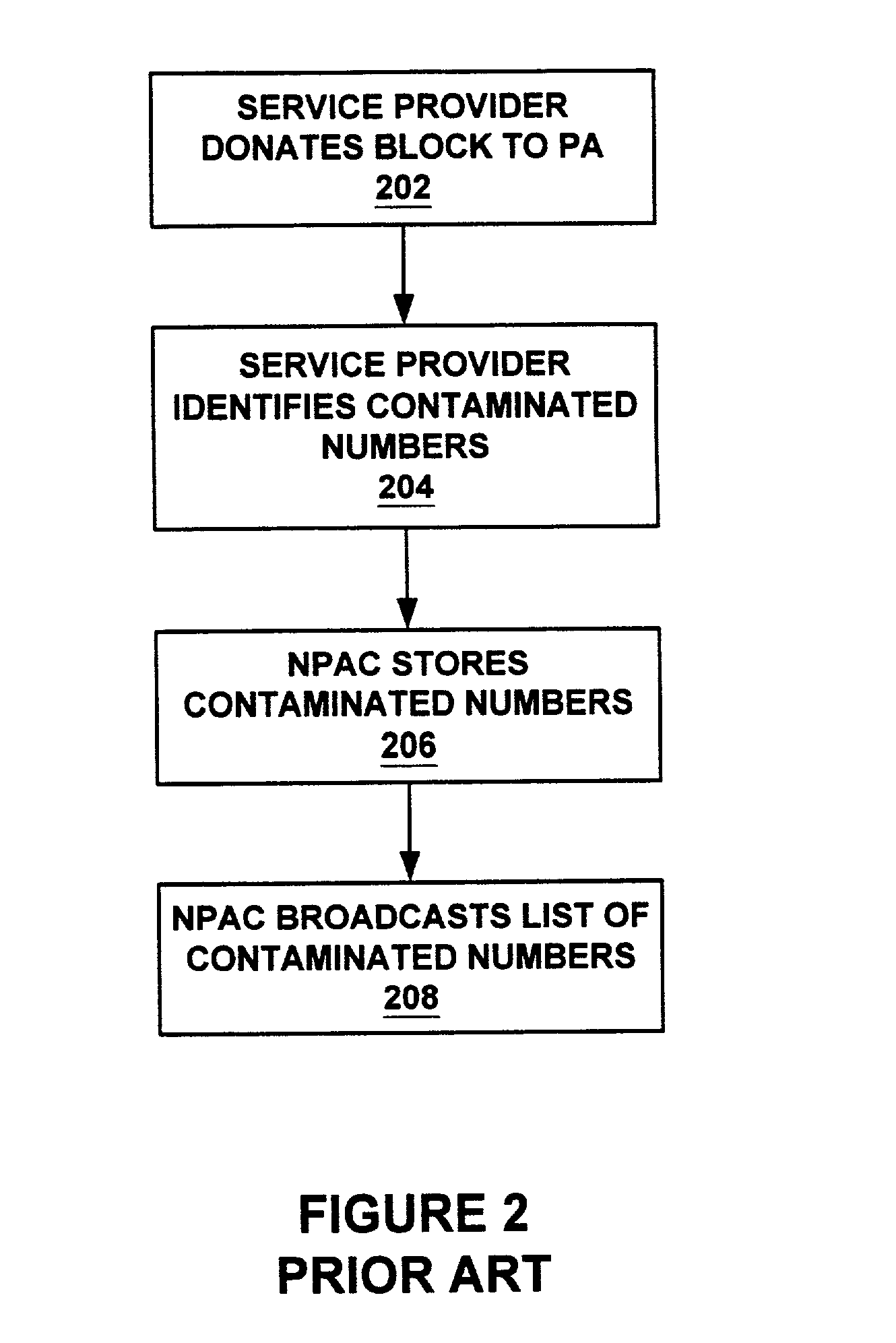
System and method for identifying contaminated telephone numbers and correct LRN under number pooling
InactiveUS7106844B1Interconnection arrangementsSpecial service for subscribersDistributed computingBilling system
A service provider's system components such as but not limited to a billing system and facilities maintenance system are sent a message that identifies contaminated telephone numbers contained within a block of numbers released to a service provider from a number pooling authority. The message also identifies the (location routing number) LRN associated with the switch of the uncontaminated numbers.
Owner:AT&T INTPROP I L P
System and method for advertising supported communications
InactiveUS6947531B1Discounts/incentivesTelephonic communicationTelecommunications networkTelephone number
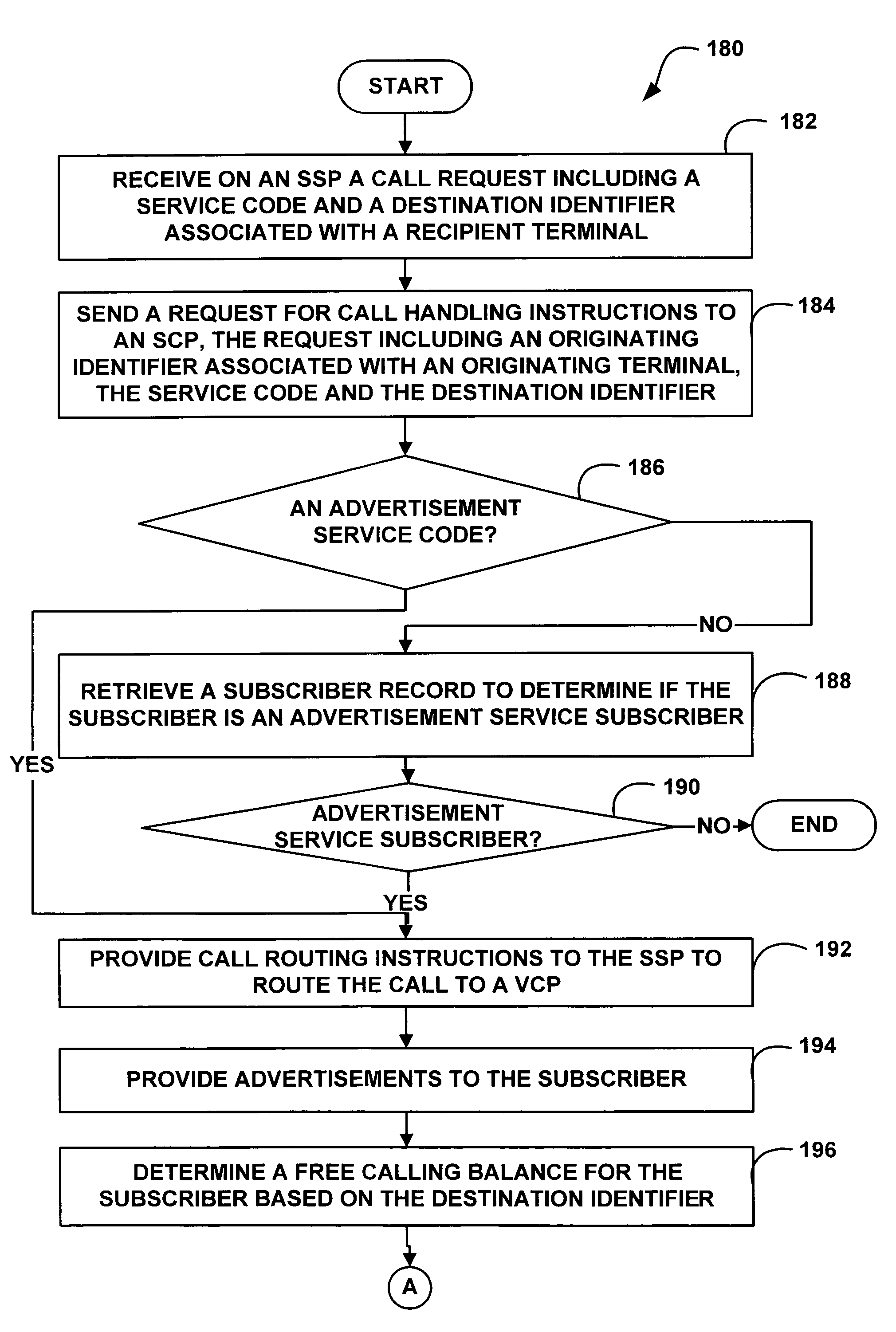
A system and method for advertising supported communications in a telecommunications network are described. One exemplary method includes receiving a call request to connect a call from an originating subscriber terminal to a destination subscriber terminal. The call request includes a destination identifier such as a MIN or a PSTN telephone number associated with the destination terminal. The method further includes providing at least one advertisement to a subscriber associated with the originating terminal, determining a free calling balance for the subscriber based on the advertisements being provided to the subscriber and the destination identifier, connecting the call from the originating terminal to the destination terminal, and monitoring as well as decrementing the free calling balance as the call progresses.
Owner:SPRINT SPECTRUM LLC
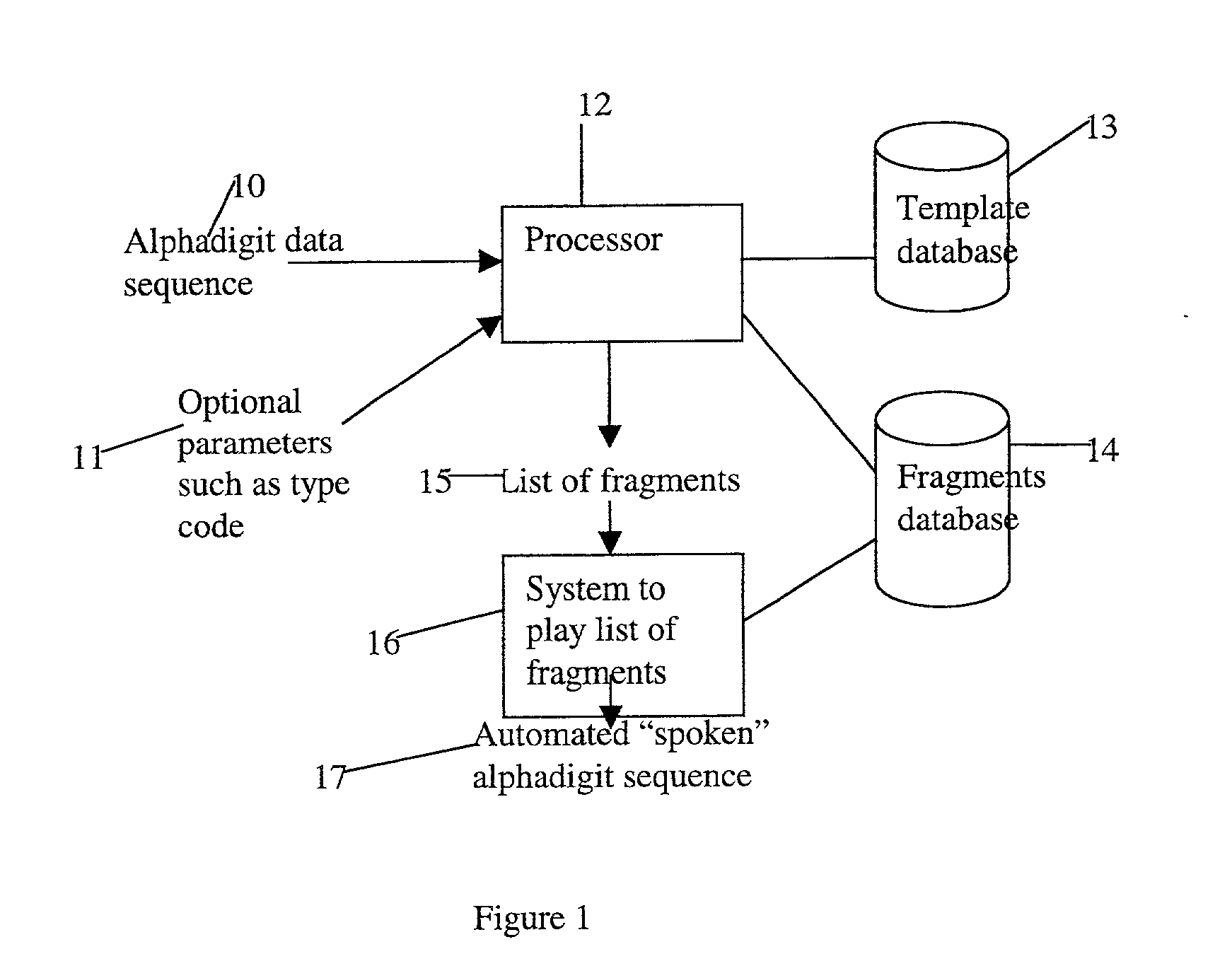
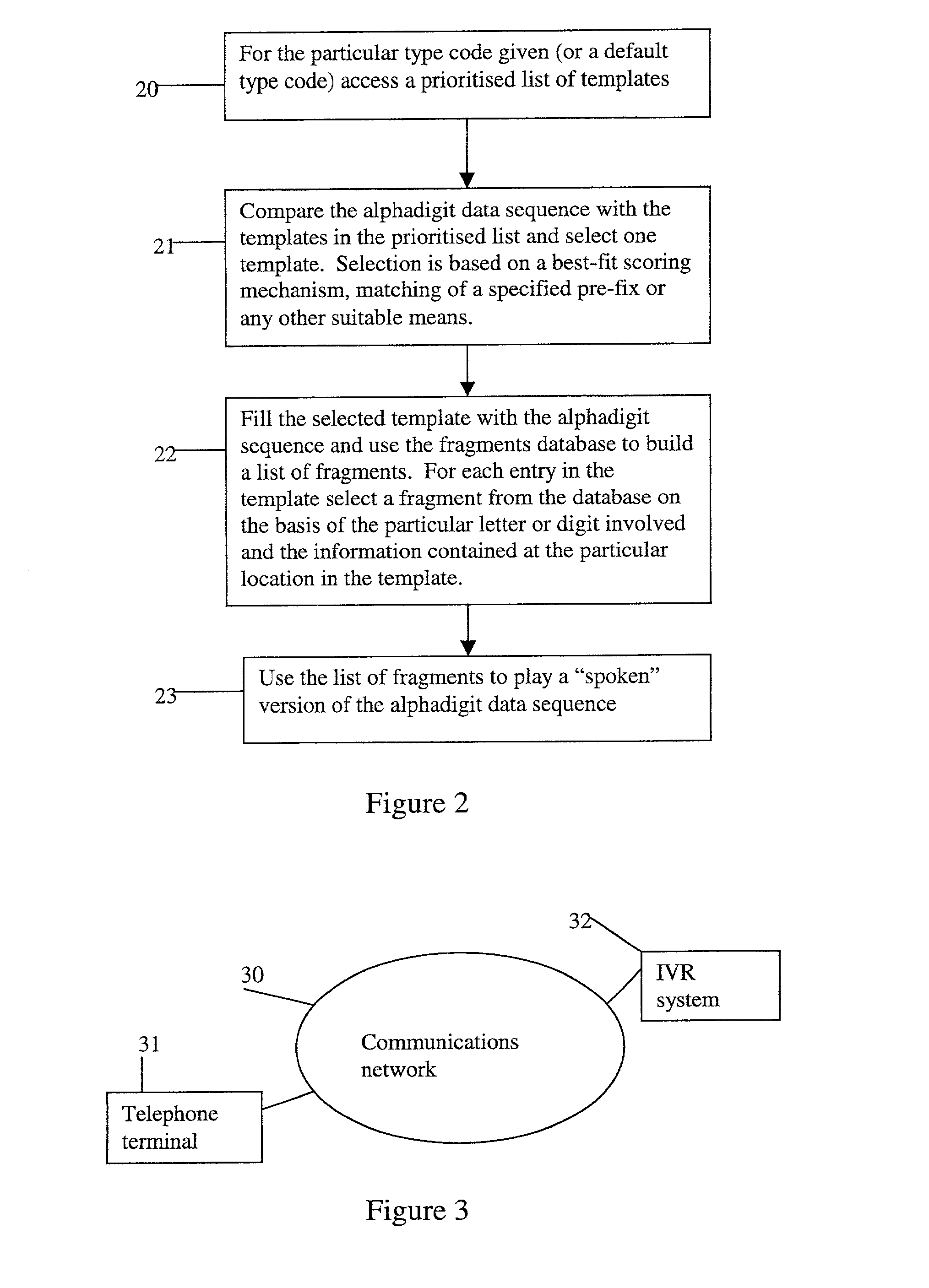
Method and apparatus for playing recordings of spoken alphanumeric characters
InactiveUS20030101045A1Simple configurationSpeech recognitionSpecial data processing applicationsSpoken languageLettering
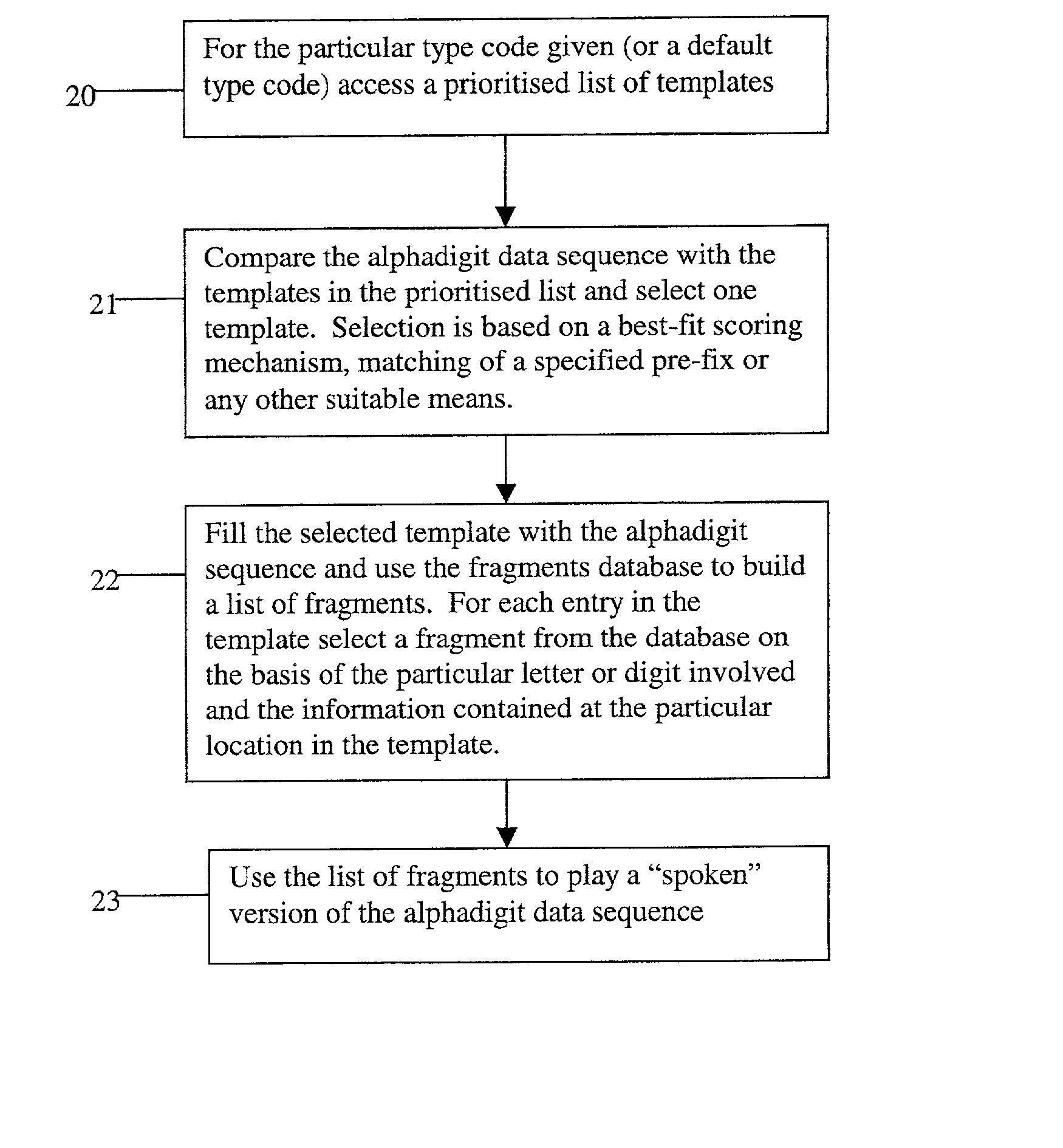
Automated systems for "speaking" telephone numbers, zip codes and the like typically produce unrealistic results that do not sound like an actual human speaking the telephone number or zip code. By using templates together with four or more types of fragment for each alphanumeric character this problem is addressed. A fragment is a recording of a spoken alphanumeric character as spoken at a particular location within an utterance. A template is a sequence of fields, each field representing part of a sequence of alphanumeric characters. Templates comprise information about the manner in which a sequence of alphanumeric characters is to be played, such as which fragments to use and when to use pauses. Using this method alphanumeric character sequences such as telephone numbers, zip codes and the like are played with human-like intonation in real time.
Owner:NORTEL NETWORKS LTD
Systems and methods for visual access to voicemail
InactiveUS20020154745A1Save effortShorten the timeAutomatic call-answering/message-recording/conversation-recordingCalling susbscriber number recording/indicationDisplay deviceTelephone number
Systems and methods for providing visual information to a telephone user regarding multiple voicemail services associated with the telephone user. The method includes providing a telephone comprising a display and organizing information relating to messages in the voicemail, wherein the information comprises an identifier indicating with which voicemail service each message is associated. Finally, the information is displayed on the display. Additional information may include the number of messages, a primary phone number from which each message was received, a name associated with each primary phone number, at least one alternative phone number associated with each primary phone number and a length of time for each message.
Owner:ORIX VENTURE FINANCE
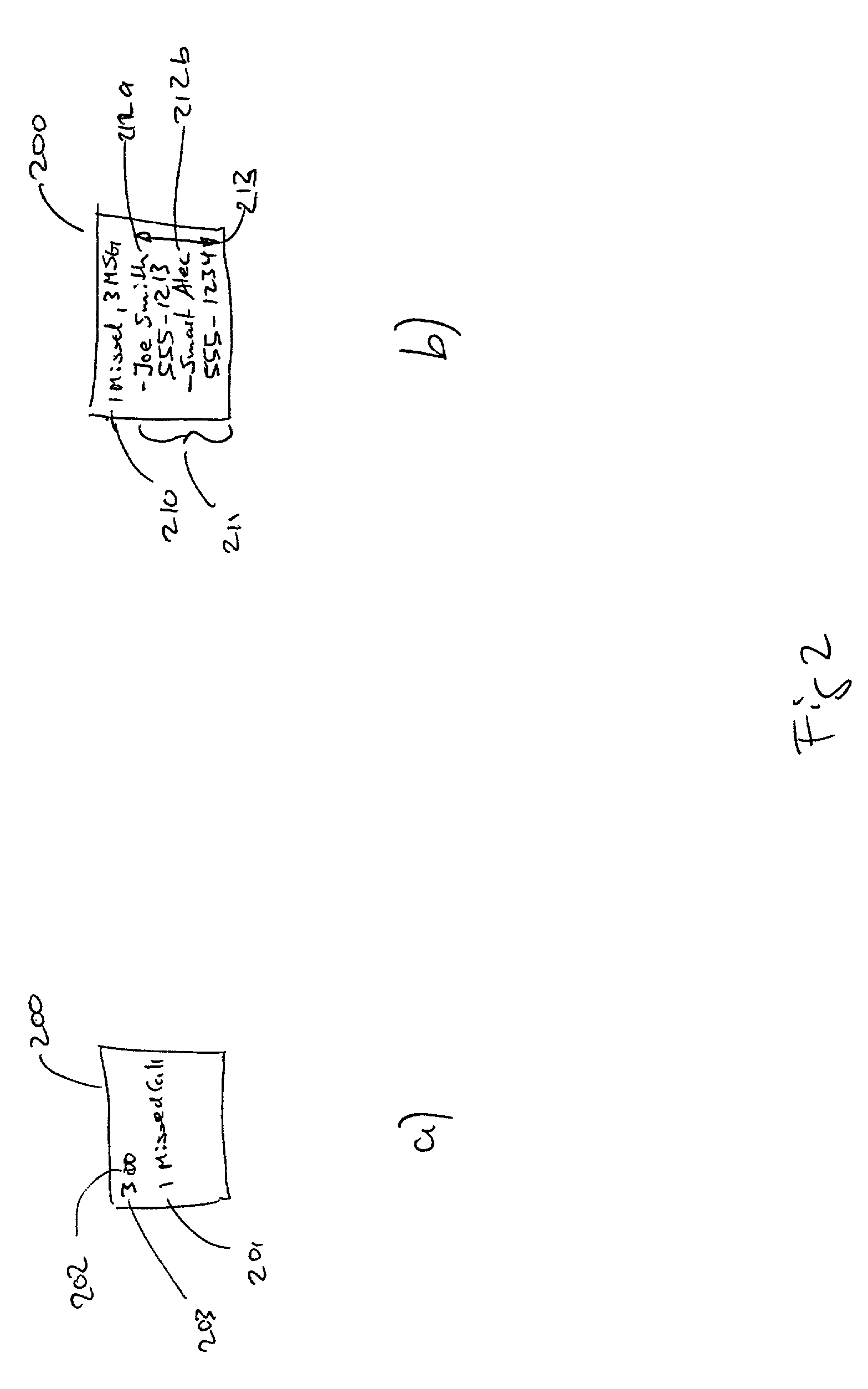
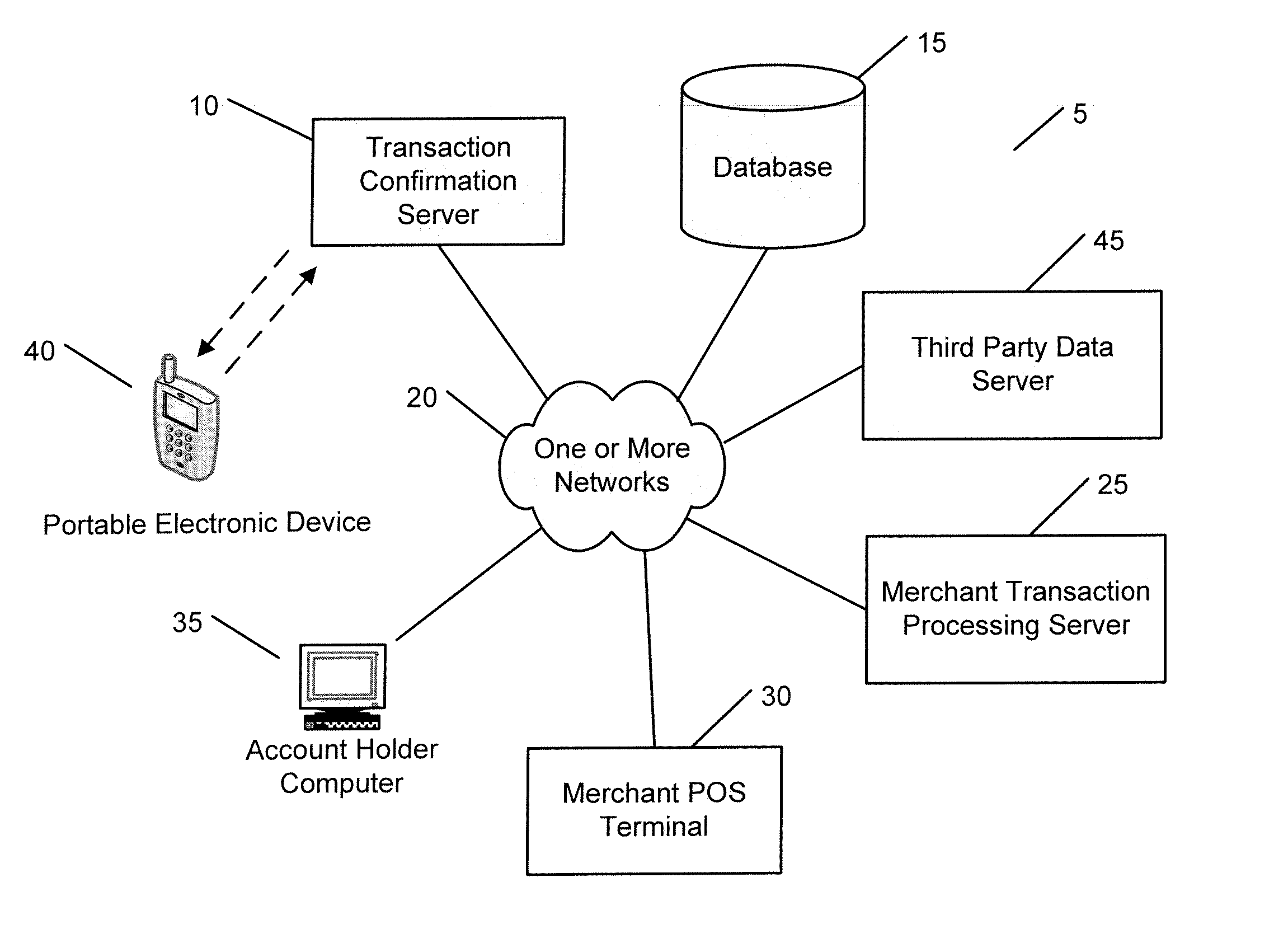
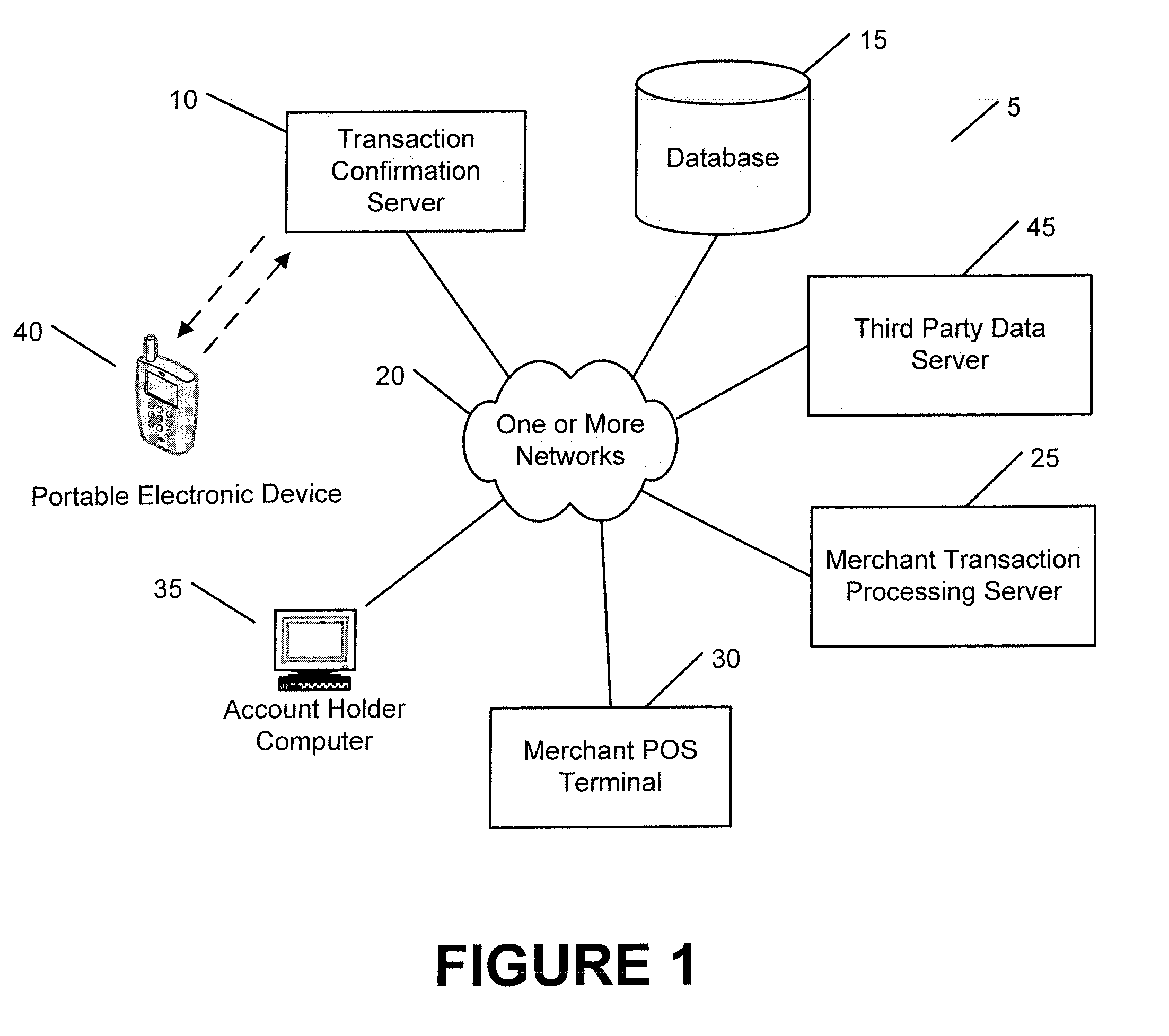
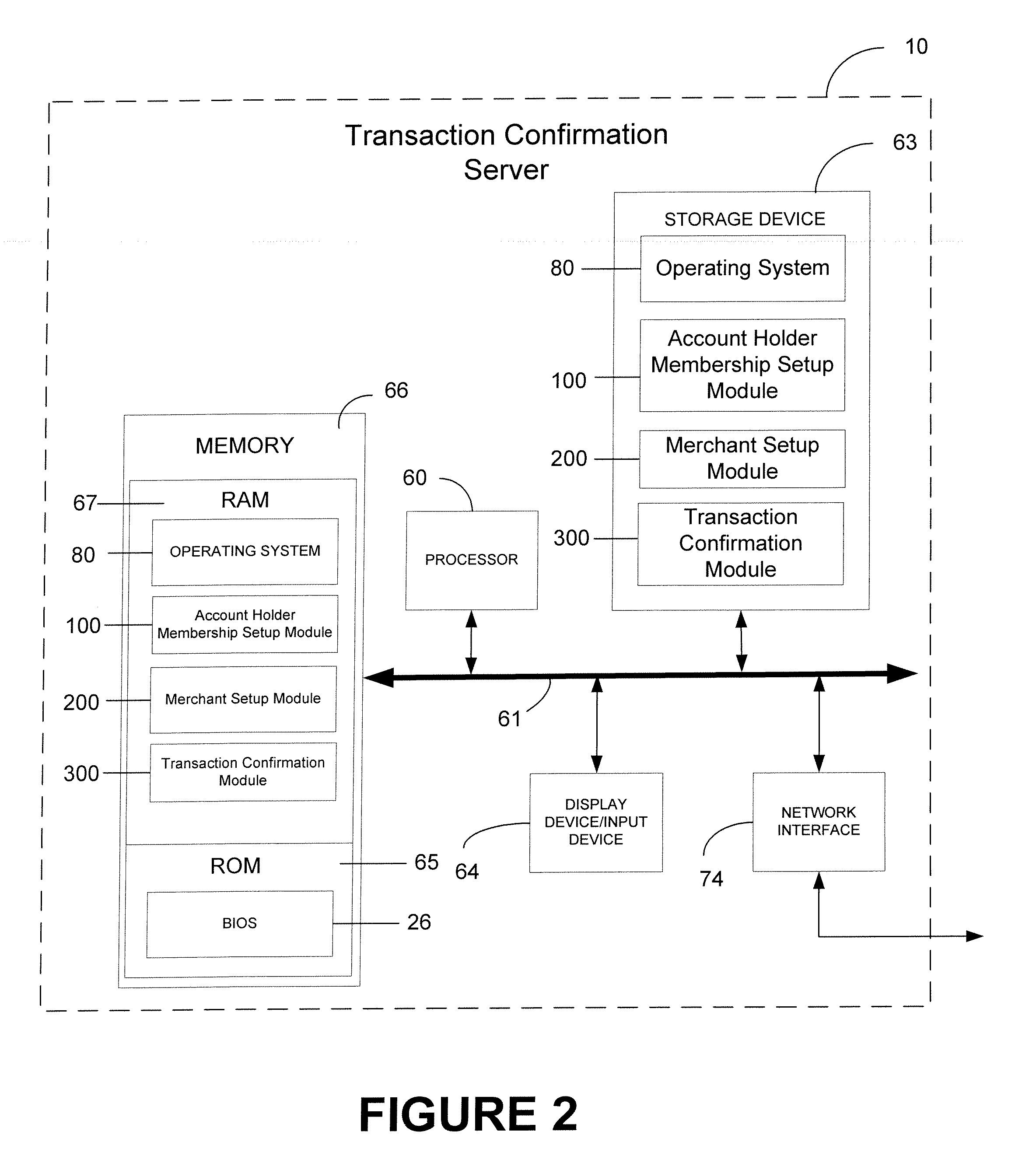
Transaction processing systems and methods
A transaction processing system according to various embodiments of the invention is adapted for: (1) associating a particular account (e.g., a credit card account) with a particular phone number; (2) at least partially in response to receiving a request to approve a transaction associated with the account, automatically transmitting a message (e.g., a text message) to the account holder via the phone number, requesting that the account holder confirm that the transaction is valid; and (3) using a response to the message to determine whether to approve or deny the transaction. In various embodiments, the request confirmation message requests that that the user answer a particular question (e.g., regarding out-of-wallet data), and the system is adapted to determine whether to approve or deny the transaction based on whether the response included a correct answer to the question.
Owner:GULA CONSULTING LLC
Method and system for making accessible wirelessly a network phonebook and journal database
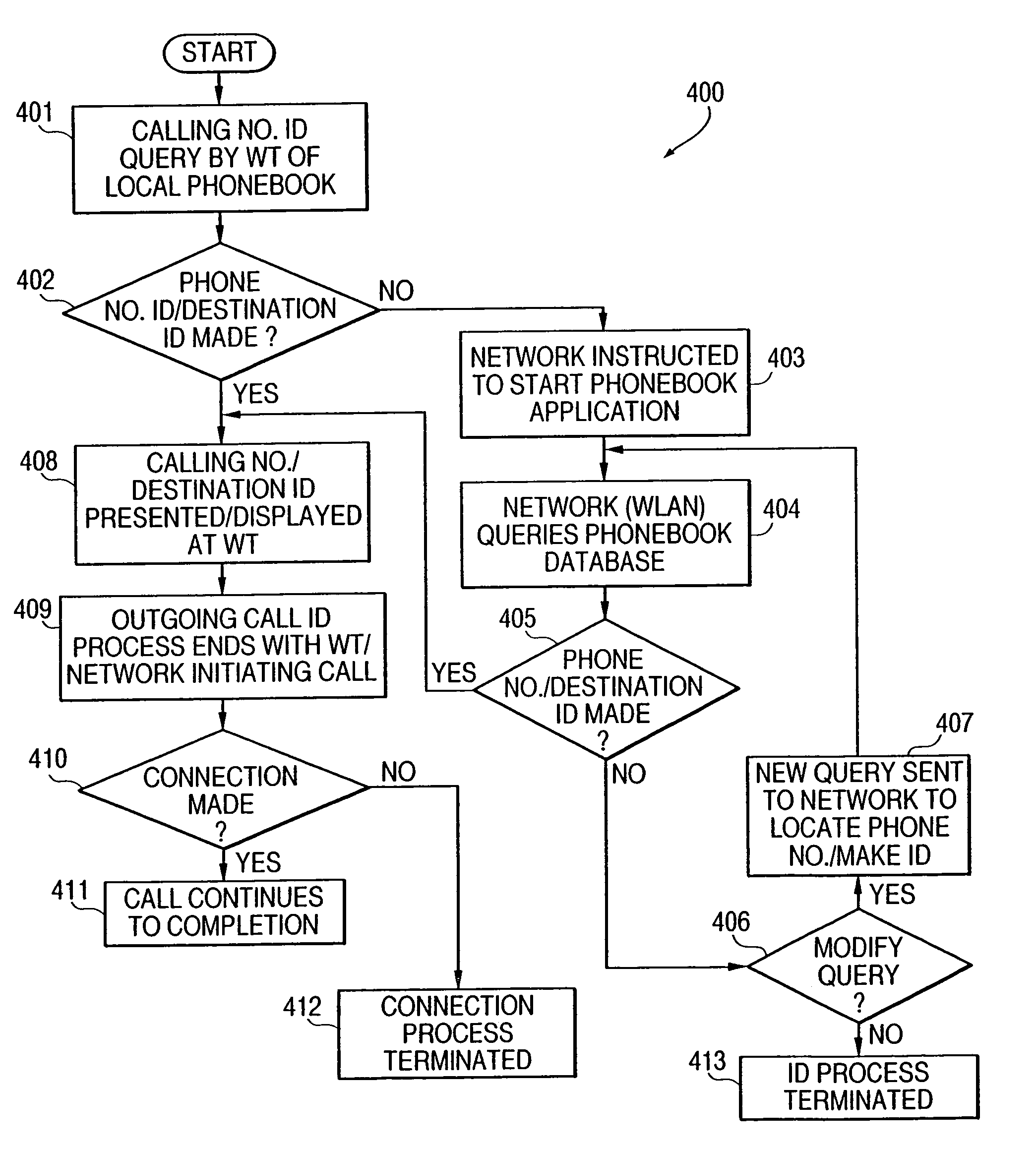
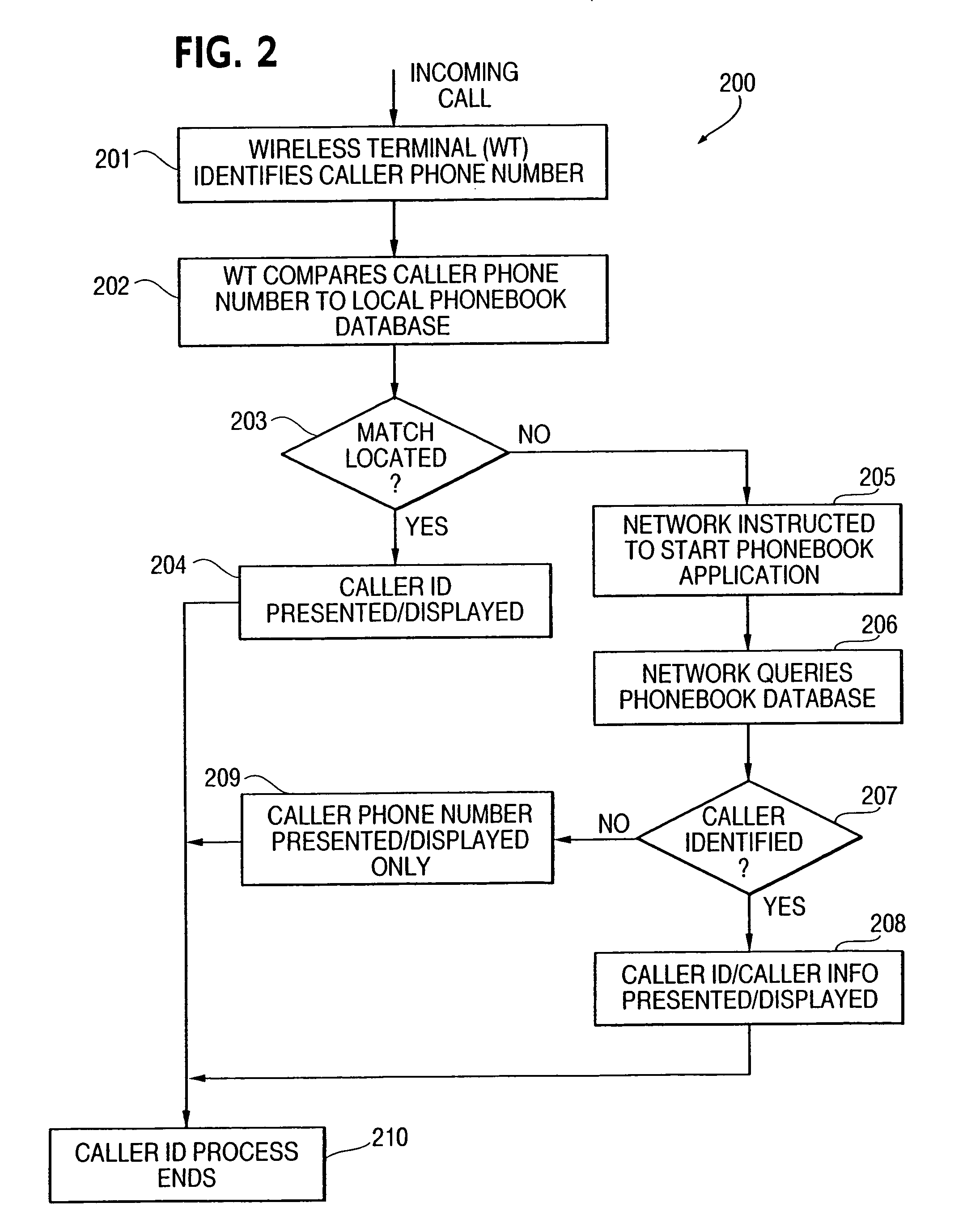
InactiveUS7085257B1Easy to callEasily keep trackNetwork topologiesSpecial service for subscribersEngineeringTelephone number
There is disclosed a method and system to provide a wireless terminal online access capability to a system phonebook, such as a WLAN, which calls for instructing the system to start a phonebook application such that for incoming calls the phonebook application commences in response to a phone number identification at the user terminal side and for outgoing calls the phonebook application commences through a User Interface (UI) of the user terminal; and performing a search query of the phonebook database to identify a caller corresponding to a phone number identification of an incoming call and / or at least one of a phone number and person or party of the call to be initiated.
Owner:VRINGO INFRASTRUCTURE +1
Callback services in a communication system
InactiveUS20060077965A1Interconnection arrangementsSpecial service for subscribersCommunications systemTelephone number
A method provides callback services in a communications system to a first party from a second party. The method includes supplying the second party with a telephone number of the first party in a first format. The method also includes selecting a numbering plan out of plurality of numbering plans based on at least one of the country and network where the second party is located. The method also includes converting the telephone number from the first format to a second format using the selected numbering plan.
Owner:NOKIA TECHNOLOGLES OY
Context sensitive, cloud-based telephony
ActiveUS20110202594A1OptimizationEasy accessSpecial service for subscribersMultiple digital computer combinationsThird partyCommunications system
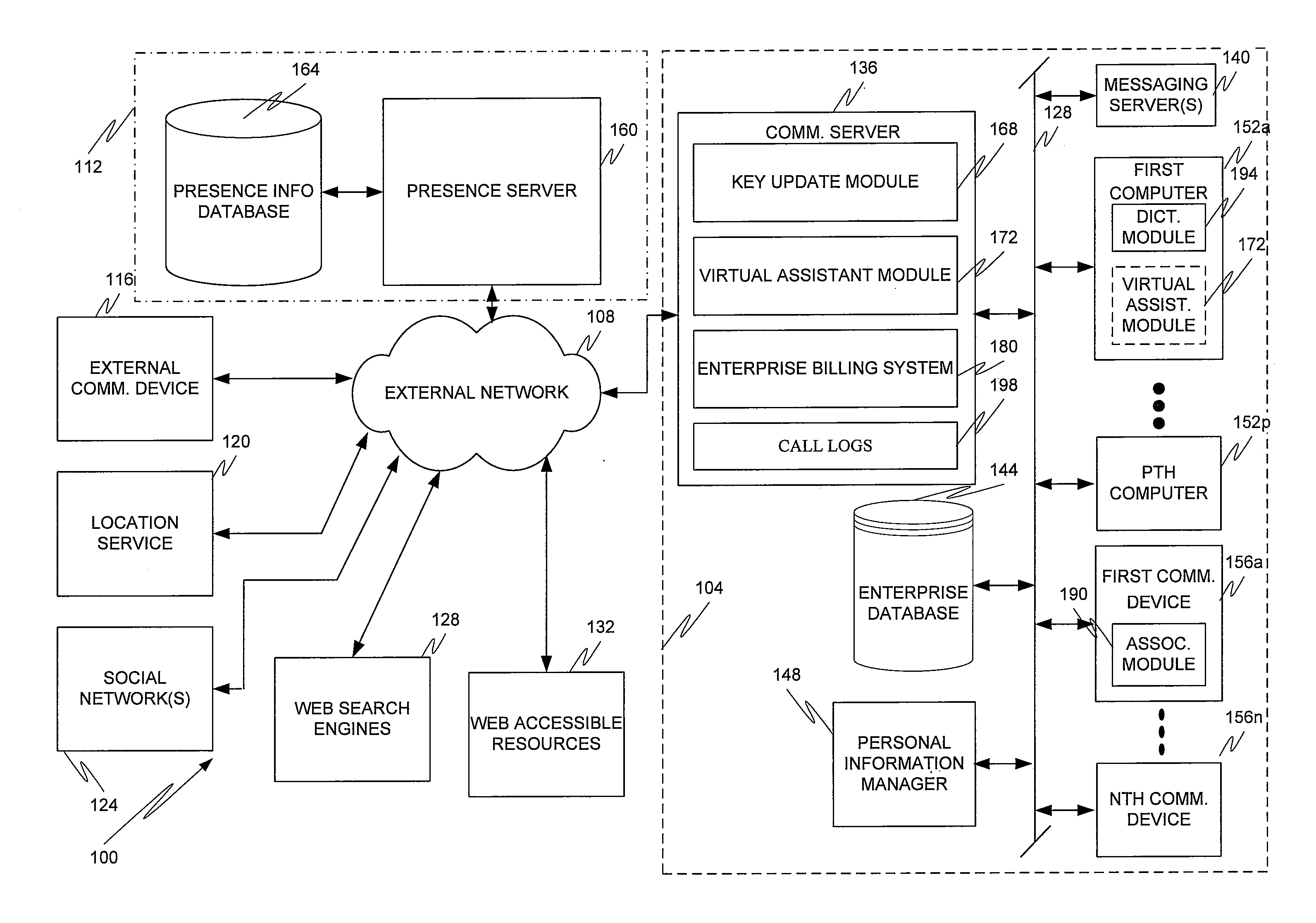
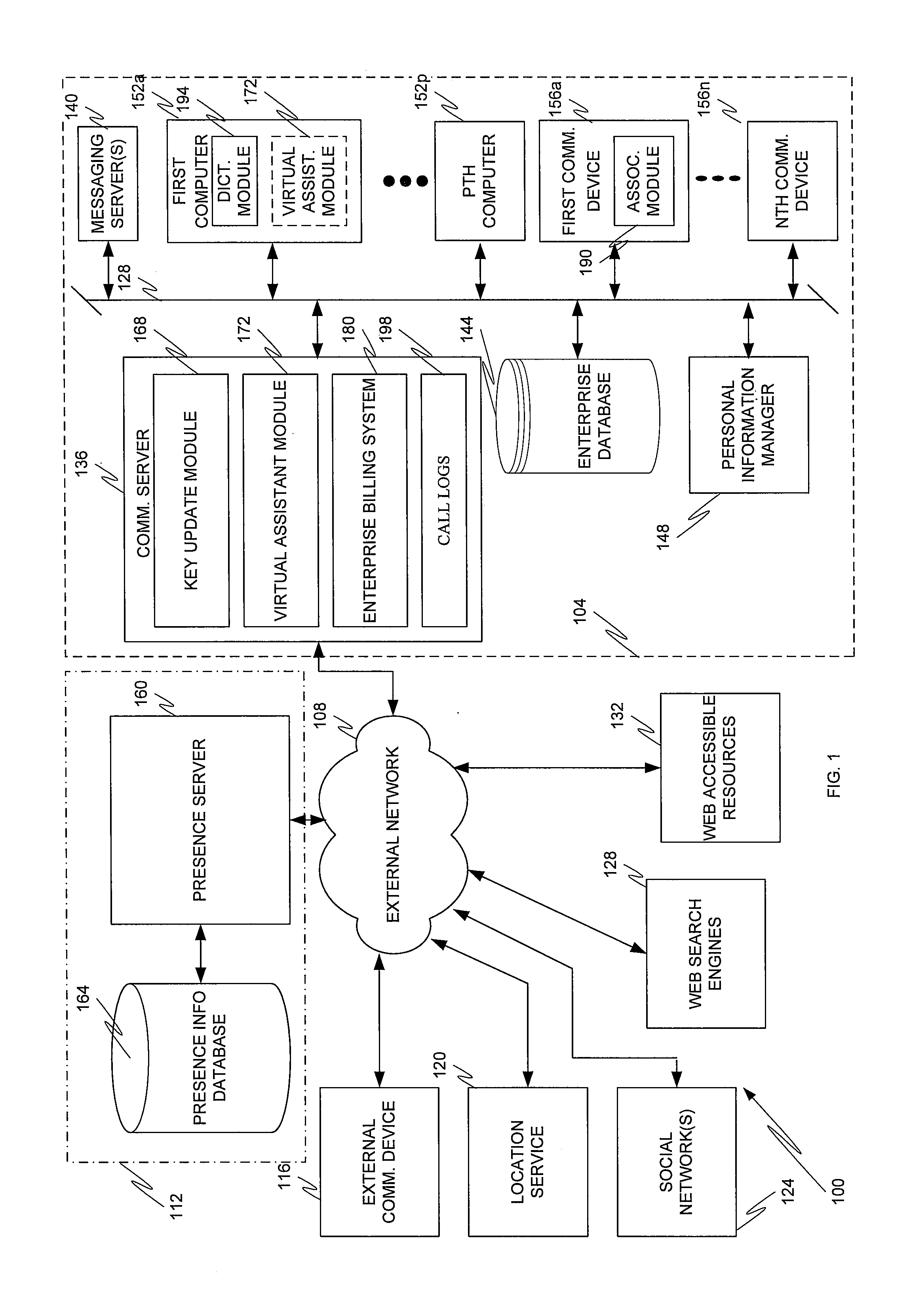
Embodiments of the present invention are directed to a communication system that provides various automated operations, including searches of public and private resources for third party information, performance of operations to assist a user in response to keyword identification in an audio, text or video stream, and speed dial updates based on calling frequencies to various telephone numbers.
Owner:AVAYA INC
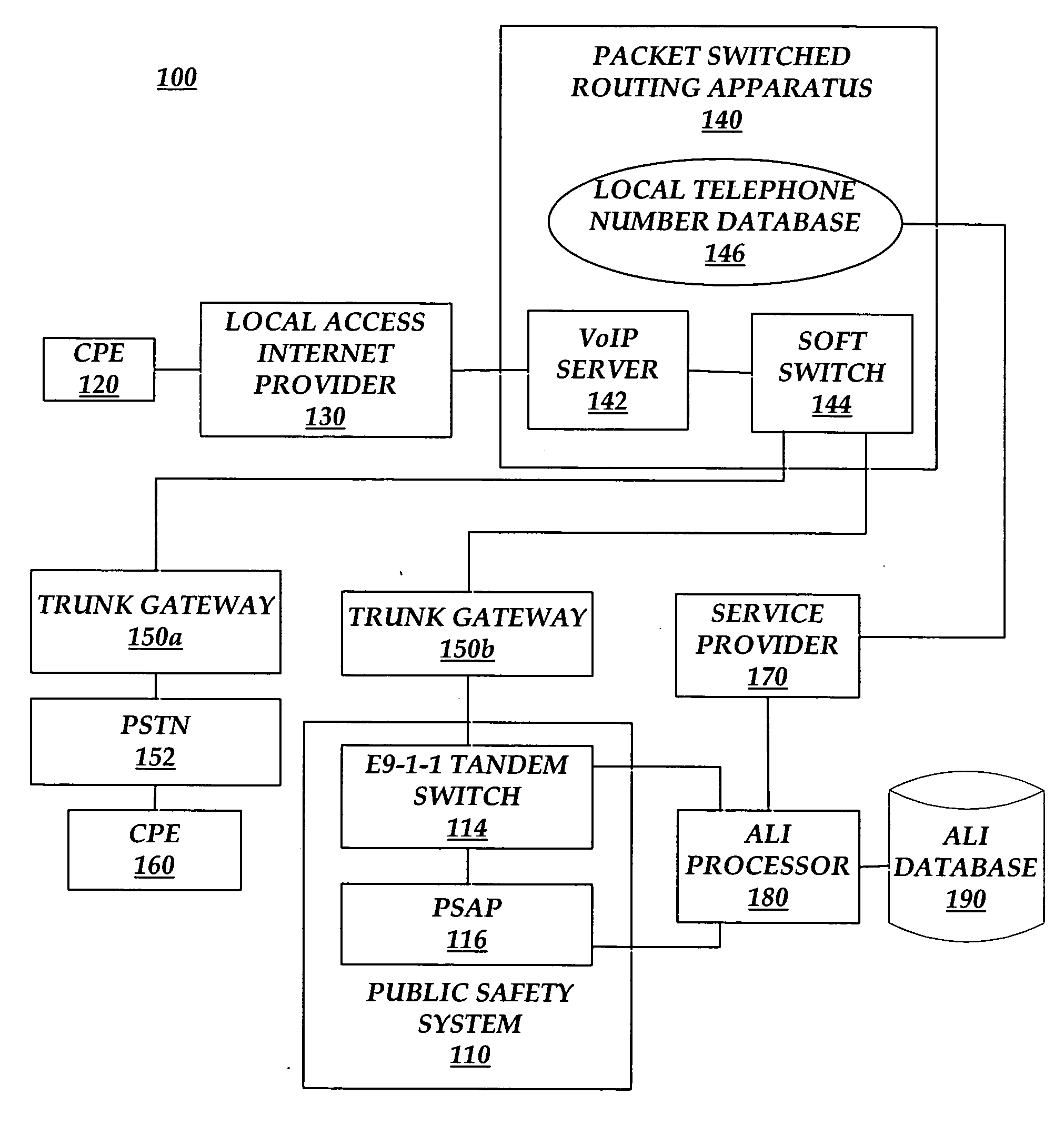
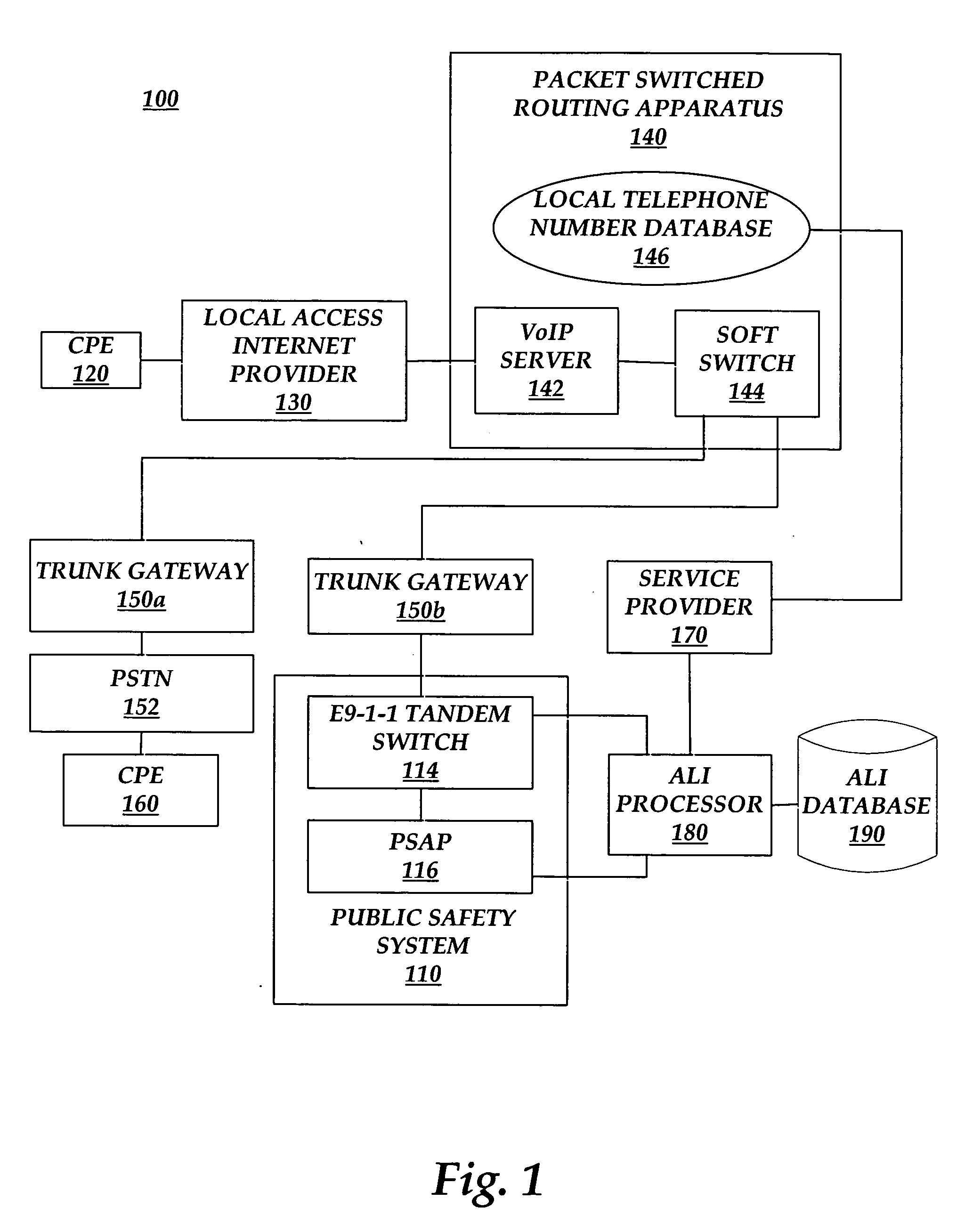
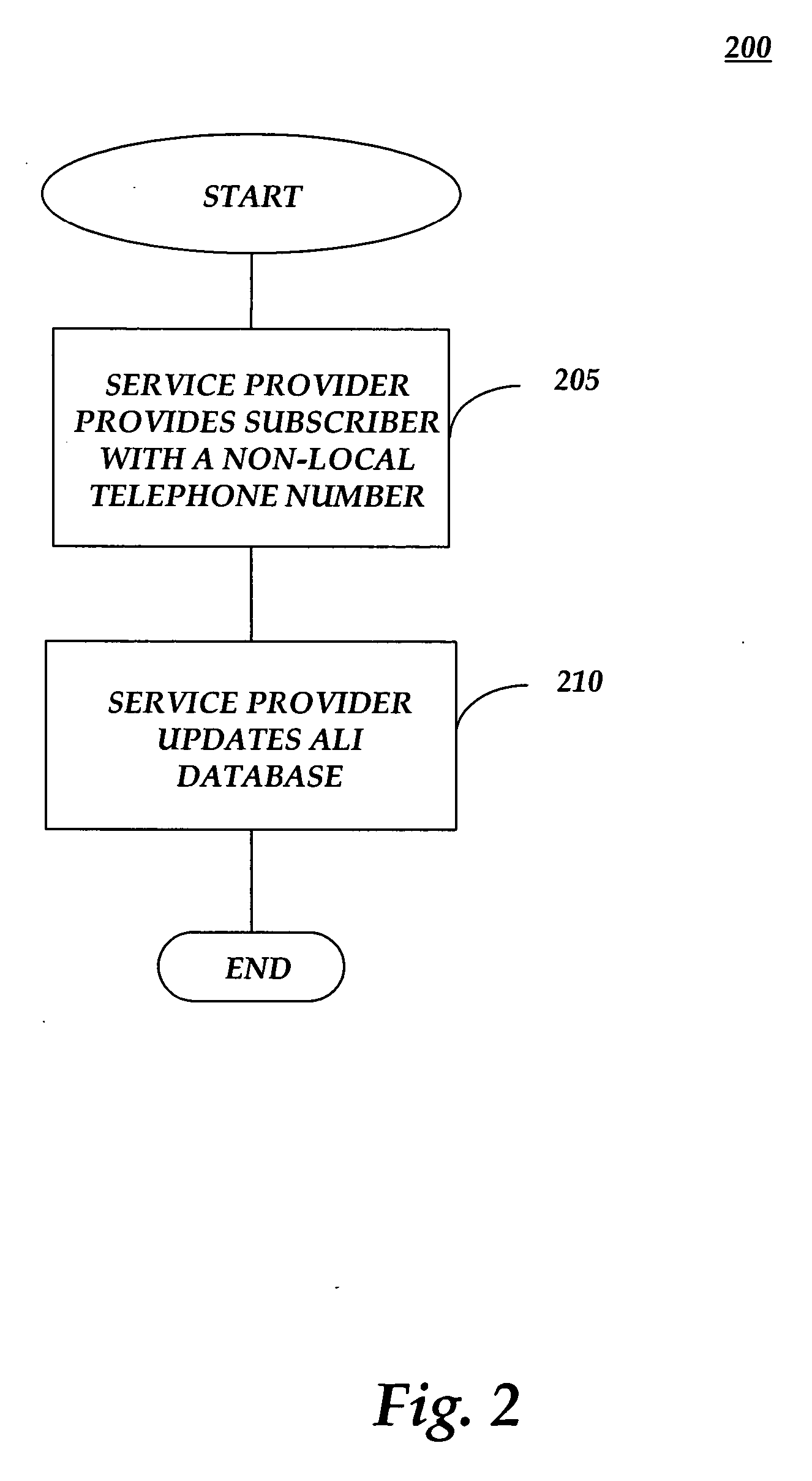
Methods and systems for providing foreign call back number compatibility for VoIP E9-1-1 calls
InactiveUS20060188083A1Provide compatibilityInterconnection arrangementsSpecial service for subscribersTelecommunicationsNon local
Systems and methods provide foreign call back number compatibility. The systems and methods receive a local telephone number assigned to a subscriber, the subscriber having a non-local telephone number as the normal calling number of the subscriber. Furthermore, the systems and methods query a database with the local telephone number to obtain the non-local telephone number and to provide the non-local telephone number. In addition, systems and methods provide a foreign call back number compatibility database. The systems and methods receive a local telephone number assigned to a subscriber and a non-local telephone number comprising the normal calling number of the subscriber and saving the local number and the non-local number to a database.
Owner:AT&T INTPROP I L P
Voice dialing using text names
InactiveUS6963633B1Easily integrateEnhance serviceInterconnection arrangementsAutomatic call-answering/message-recording/conversation-recordingLoudspeakerSpeech identification
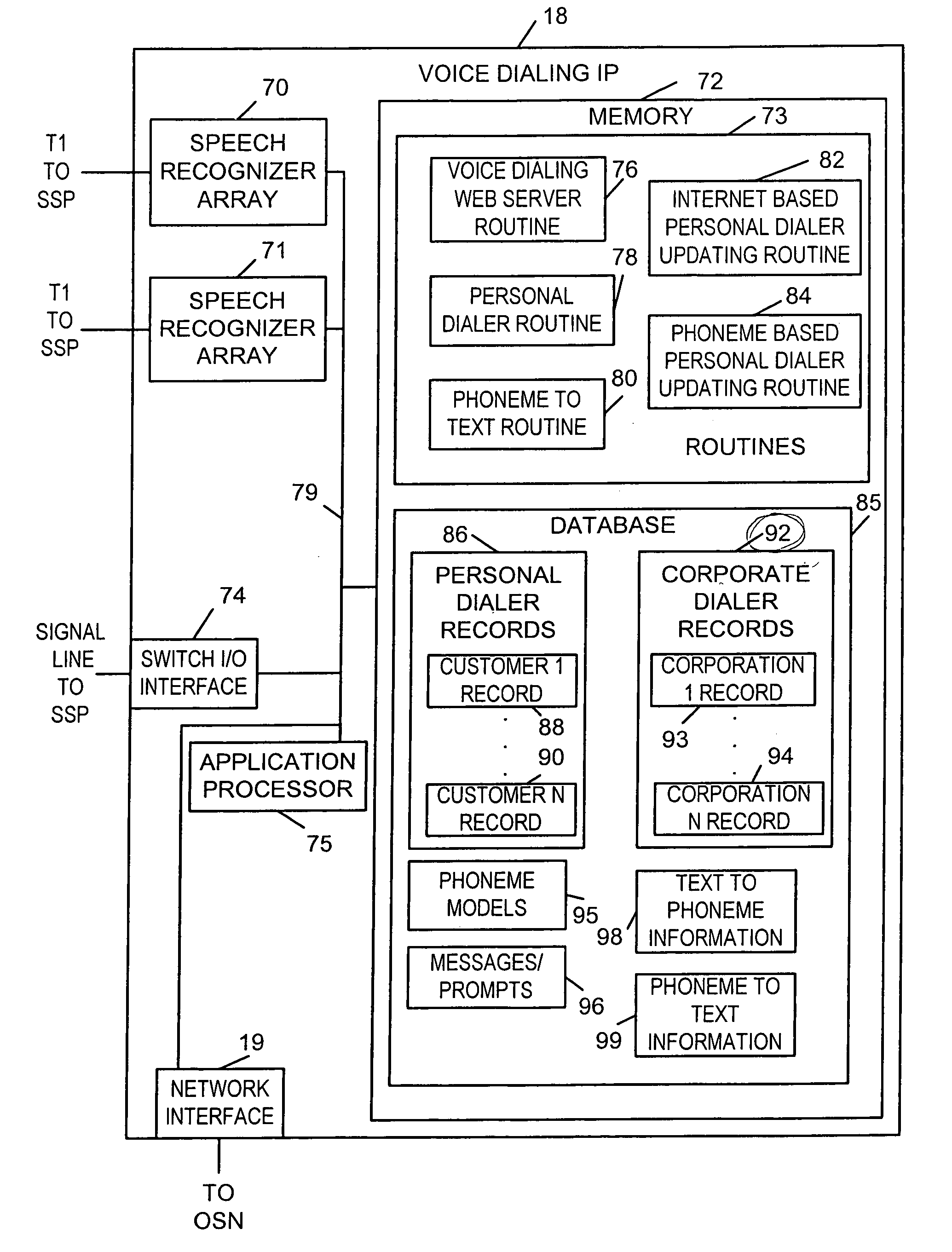
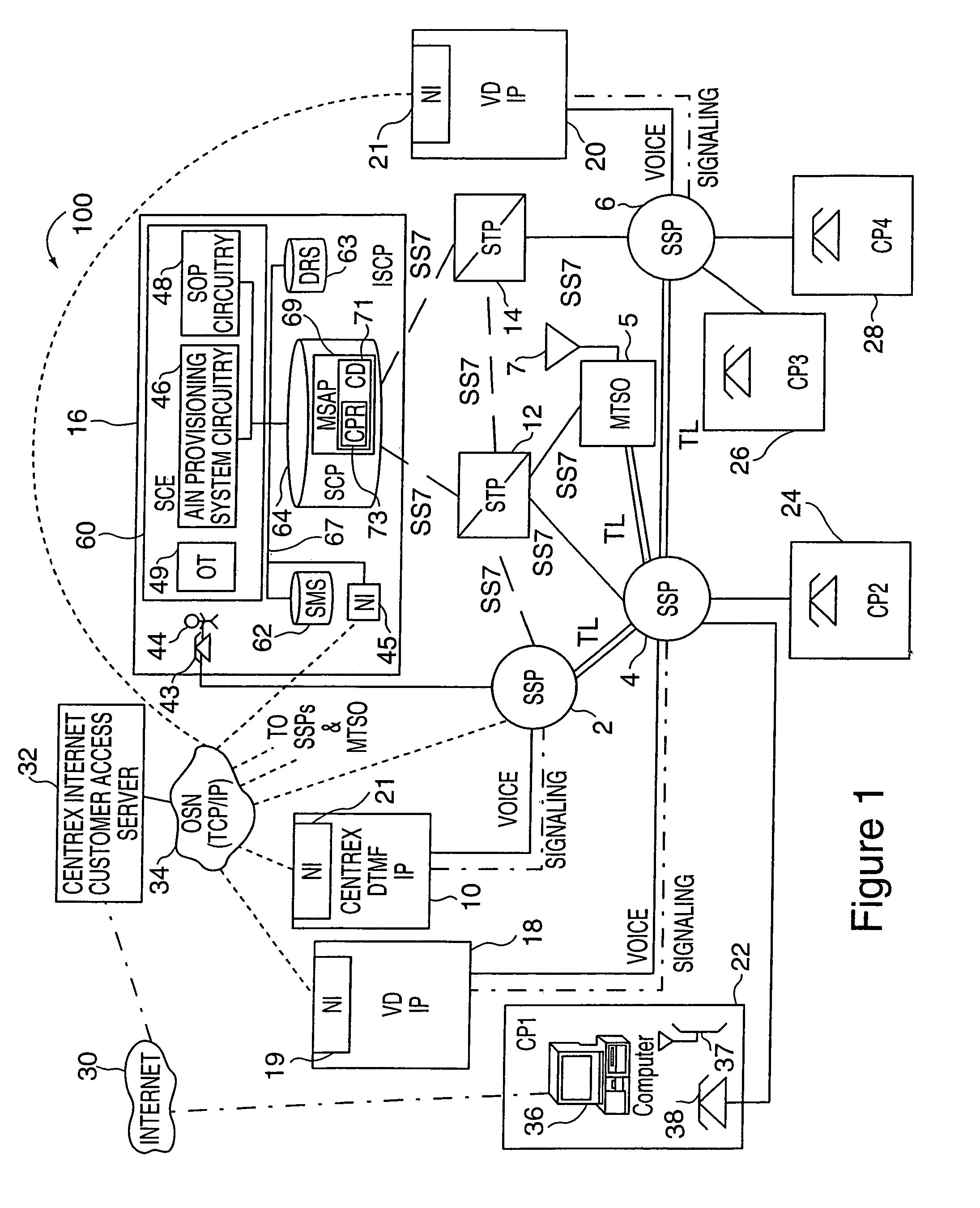
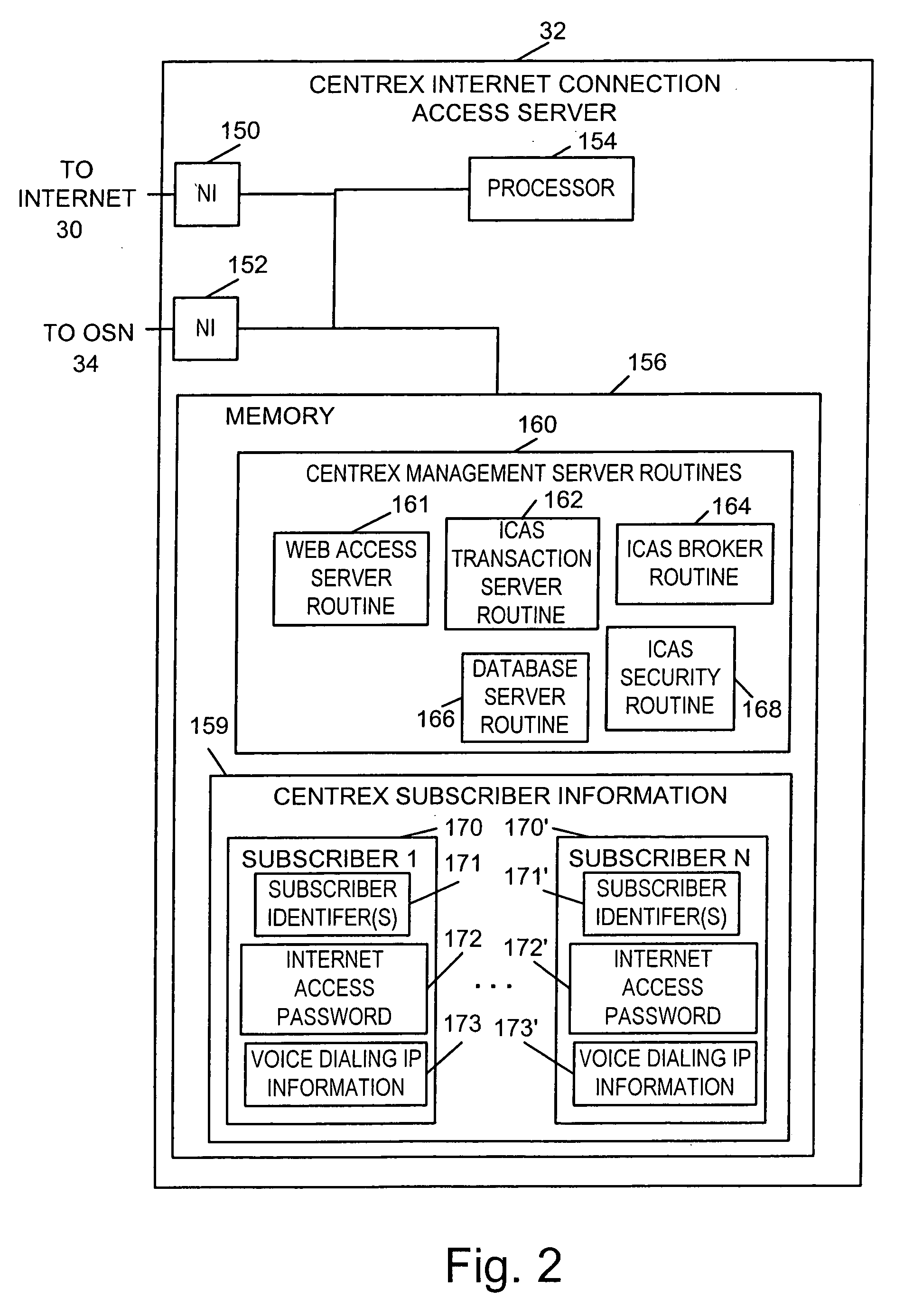
Methods and apparatus for implementing communication services such as voice dialing services are described. In one Centrex based voice dialing embodiment, voice dialing service subscribers are given access to personal voice dialing records including calling entries via the Internet as well as via telephone connections. Each calling entry normally includes the name and, optionally nickname, of a party to be called. It also includes one or more telephone numbers associated with each name. Different telephone number identifies, e.g. locations, can be associated with different names. A user can create or update entries in a voice dialing directory using text conveyed over the Internet or speech supplied via a telephone connection. In order to facilitate updating and maintenance of voice dialing directories over the Internet speaker independent (SI) speech recognition models are used. When a calling entry is created via the Internet the text of the name is processed to generate a corresponding speech recognition model there from. When an entry is created via speech obtained over the telephone, a speech recognition model is generated from the speech and a text name is generated is generated using speech to text technology. To avoid having to hang-up and initiate a new voice dialing call the outcome of a voice dialing call is monitored and the subscriber is provided the opportunity to initiate another call using voice dialing if the first call did not complete successfully e.g., goes unanswered.
Owner:GOOGLE LLC
One number, intelligent call processing system
InactiveUS7167553B2Expand coverageAutomatic call-answering/message-recording/conversation-recordingSpecial service for subscribersTelecommunications networkEngineering
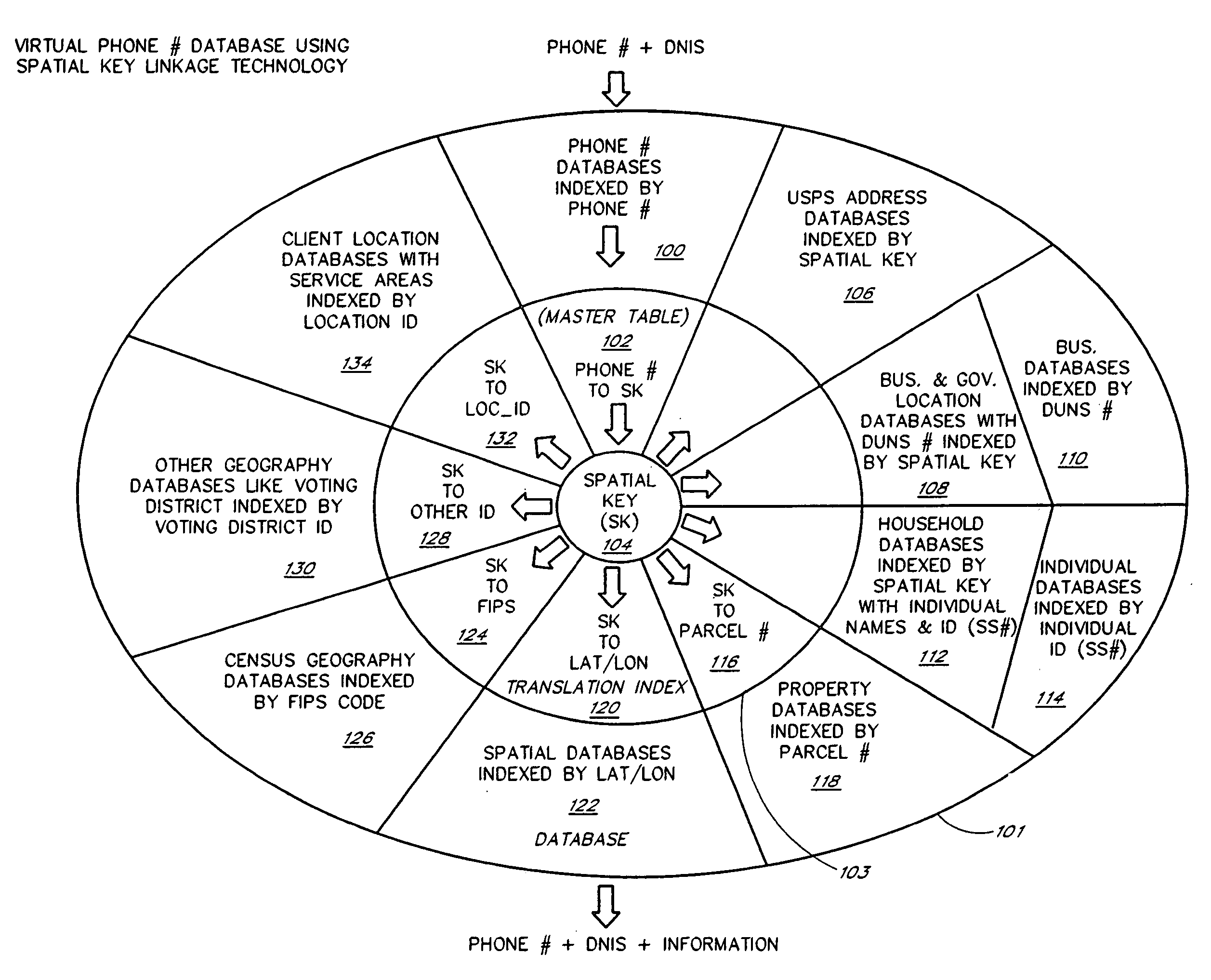
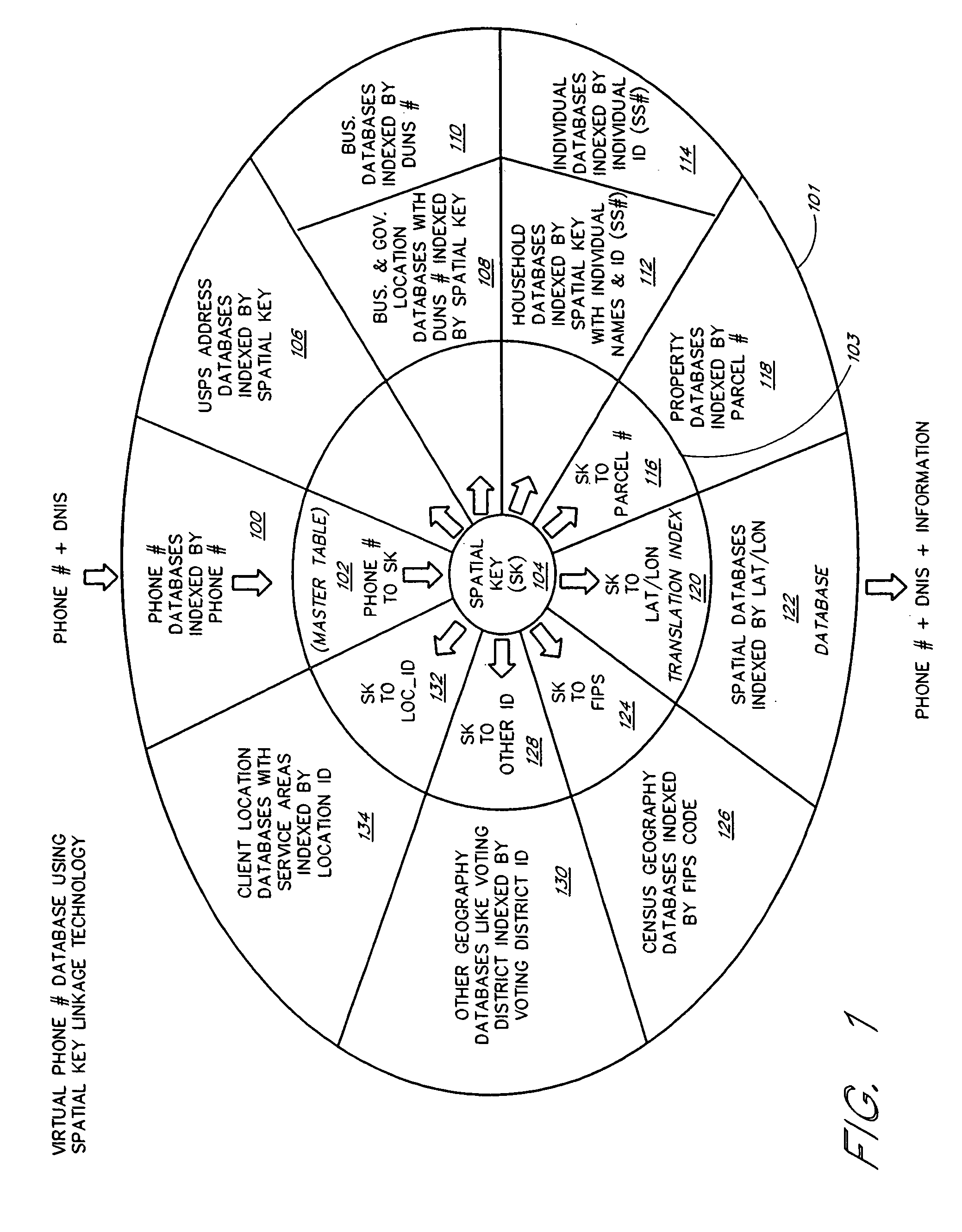
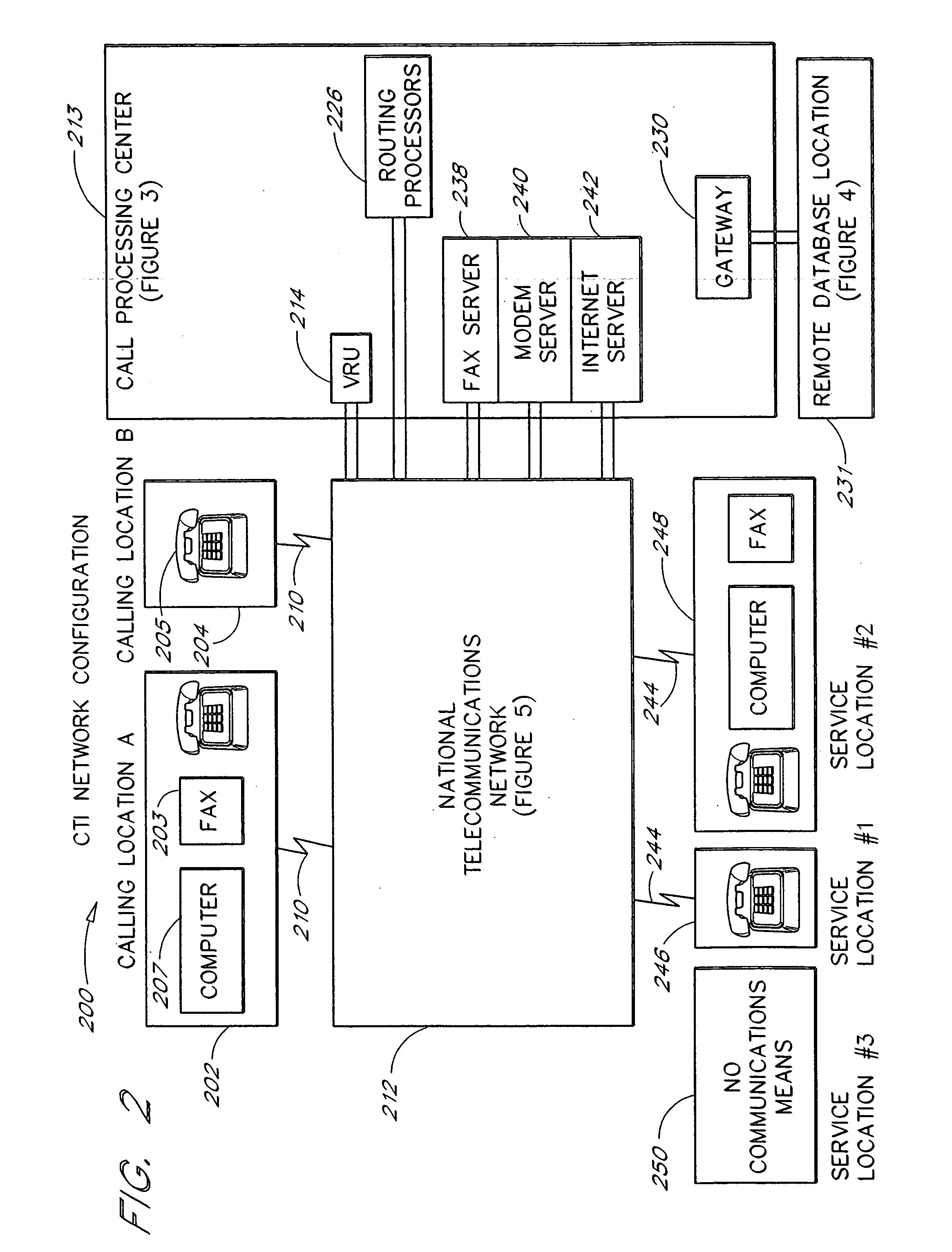
A one number, multi-application, intelligent call processing system provides service benefits to a caller, a servicing location and / or a vanity number advertiser during a call, parallel to the call and / or post call in an integrated common architecture. The system utilizes VRU technology in conjunction with the national telecommunications network connected via Computer Telephone Integration (CTI) to a virtual telephone number database containing a nationwide master list of telephone numbers with attribute data items associated by Spatial Key linkage to each telephone number. The process of the invention is initiated by a caller dialing a selected telephone number to request information and / or services. Based on the number dialed, a caller or network provided ten-digit telephone number and VRU prompted for and received caller input, the system retrieves the application requested data from the virtual telephone number database and provides it to the network.
Owner:MUREX SECURITIES
Intelligent Call Mapping and Routing for Low Cost Global Calling on Mobile Devices Including SmartPhones
InactiveUS20100226362A1Metering/charging/biilling arrangementsAccounting/billing servicesApplication serverUser identifier
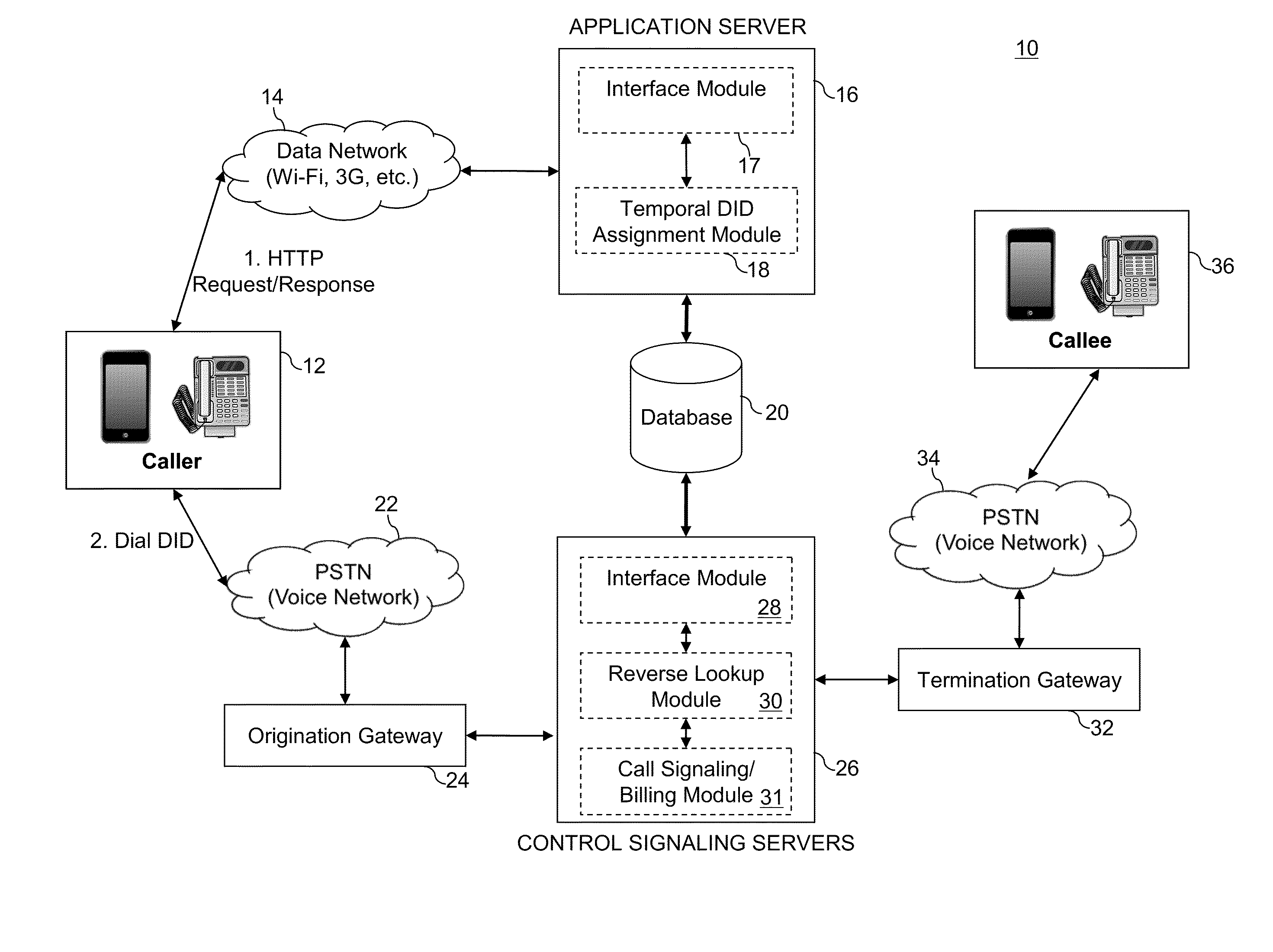
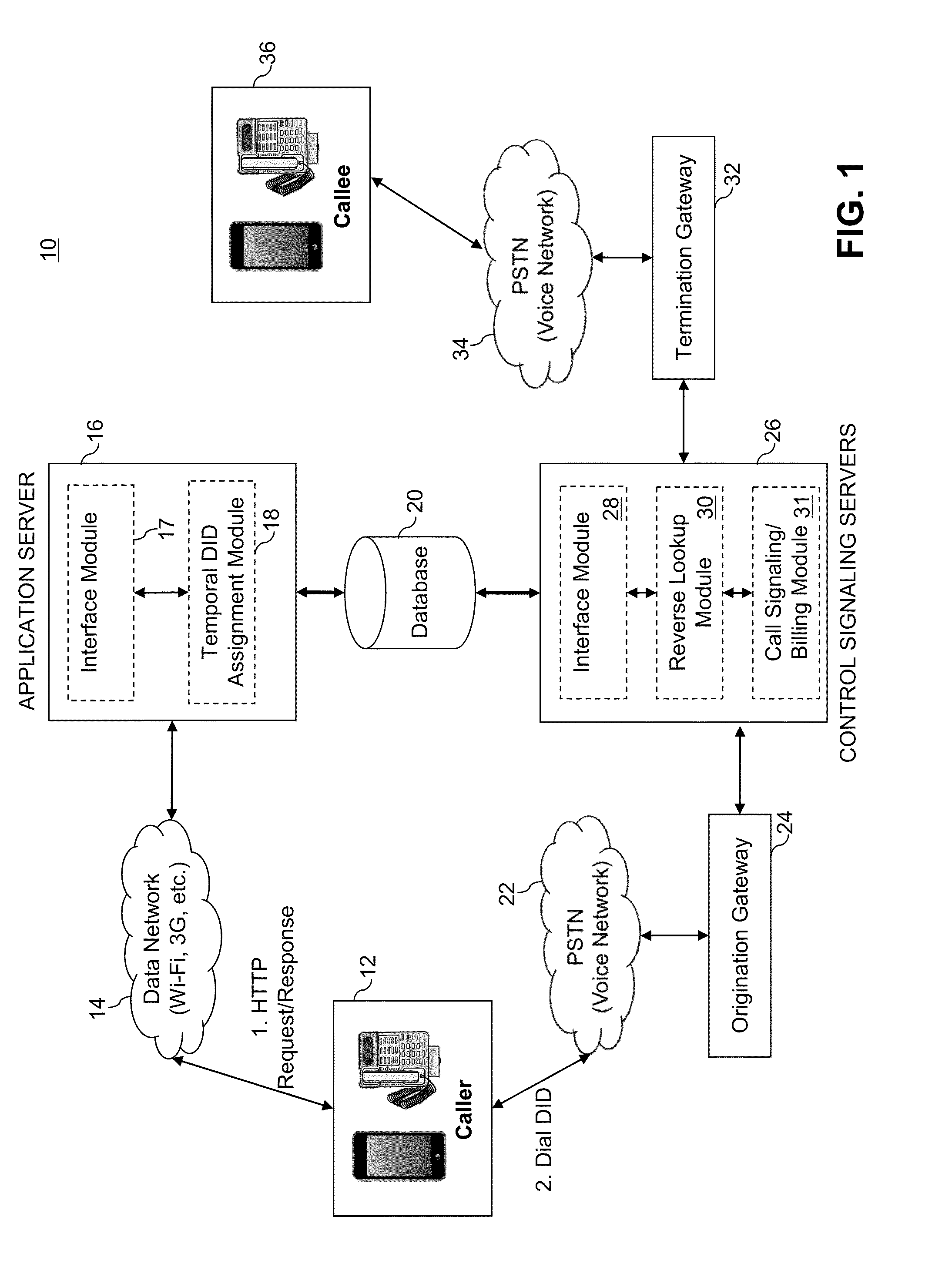
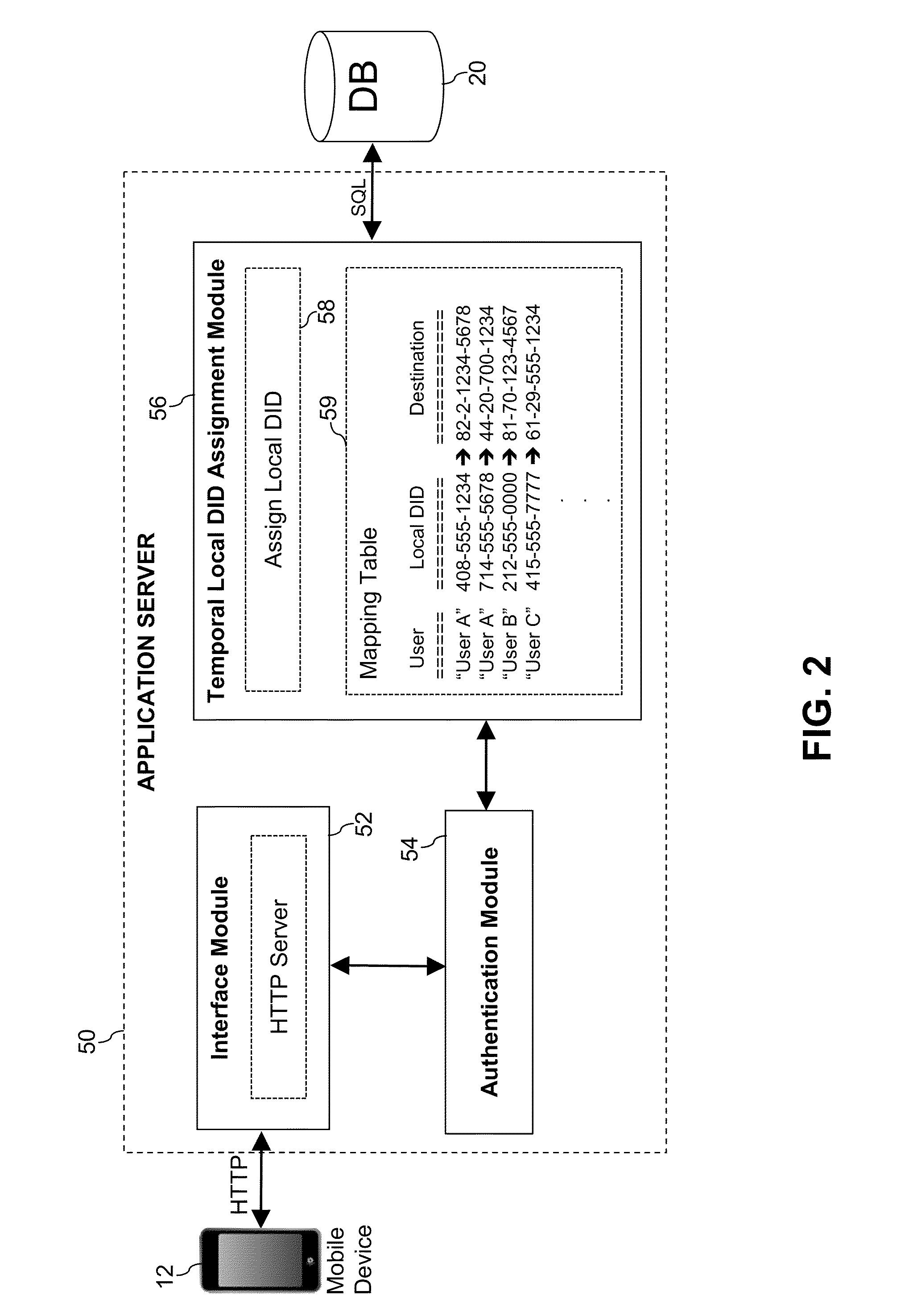
A method for providing international telephone call service to a calling party using a PSTN enabled communication device includes dialing the destination telephone number and establishing a connection between a software application installed on the communication device and an application server, authenticating the calling party using the user ID and the caller ID. When the calling party is authenticated, the method includes assigning a local DID number having the same or a nearby area code as the caller ID, notifying the communication device of the assigned local DID number, storing the destination telephone number and the assigned local DID number in a database, initiating a telephone connection over the PSTN to control signaling servers by dialing the assigned local DID number, retrieving the destination telephone number associated with the local DID number from the database, and establishing a voice-based connection between the caller and the callee.
Owner:INNODIAL COMM
Three-way call detection using steganography
ActiveUS7248685B2Improve reliabilityAccurate and reliable processSpecial service for subscribersSupervisory/monitoring/testing arrangementsSignal onCarrier signal
Owner:DSI ITI INC
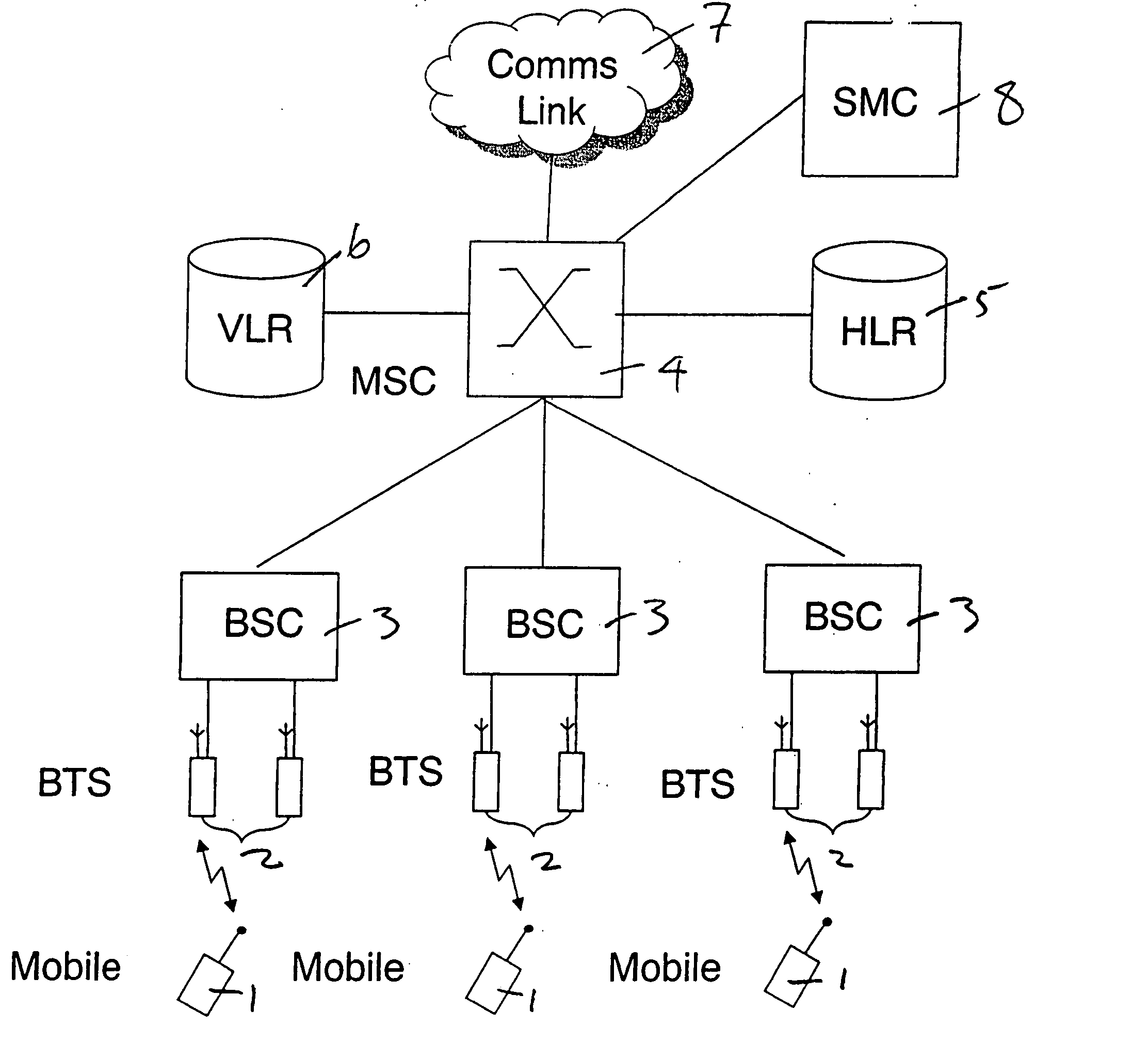
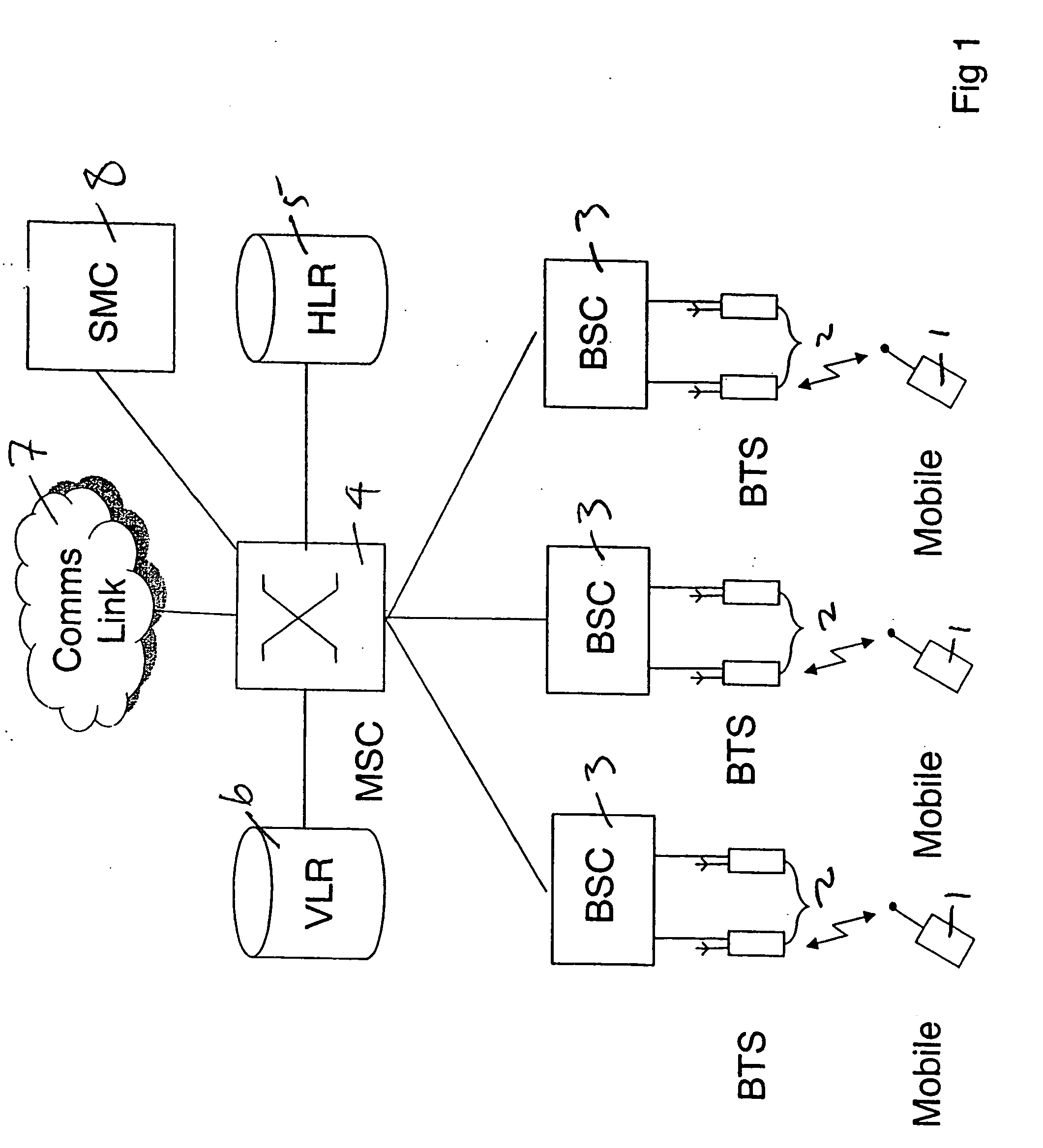
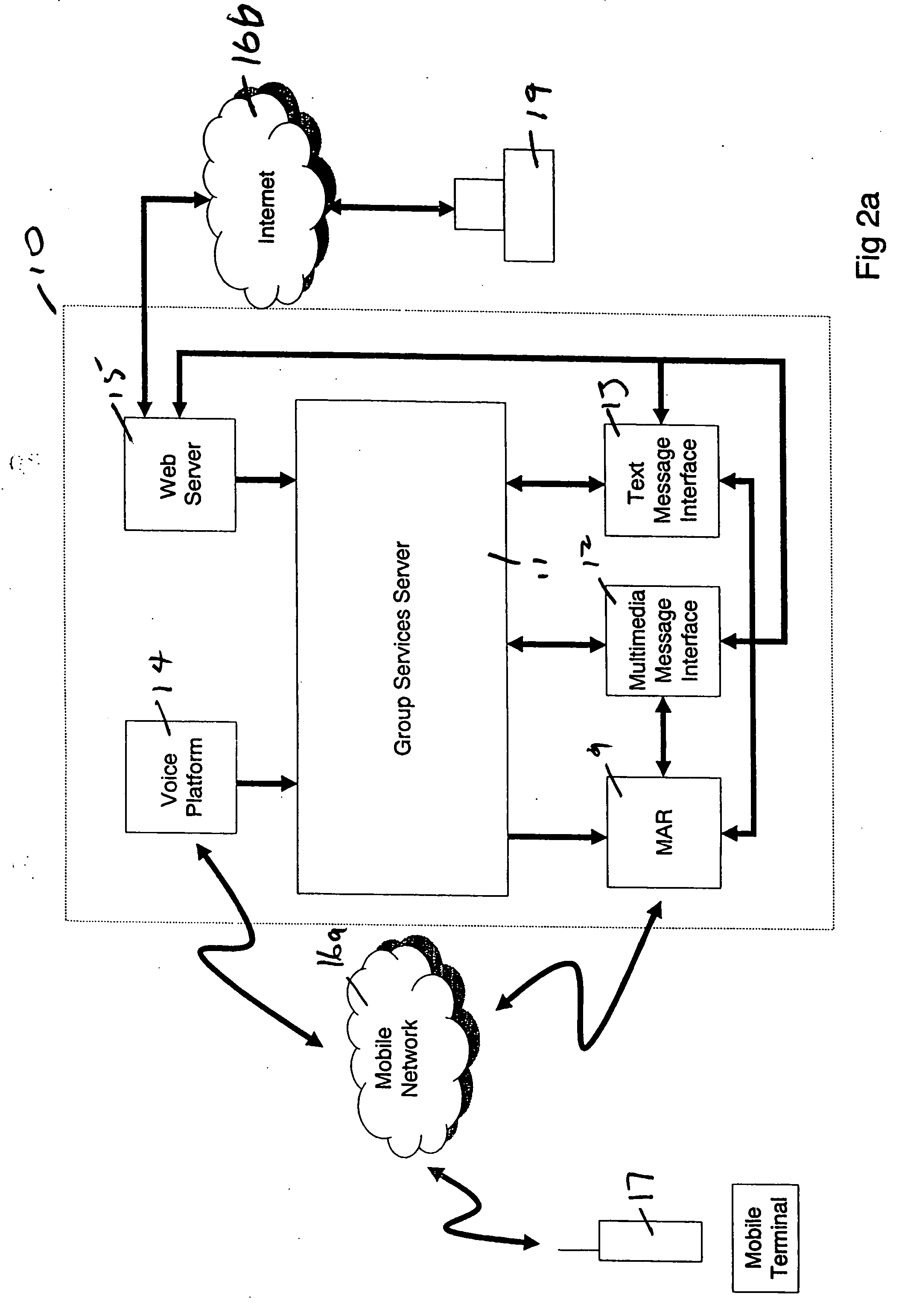
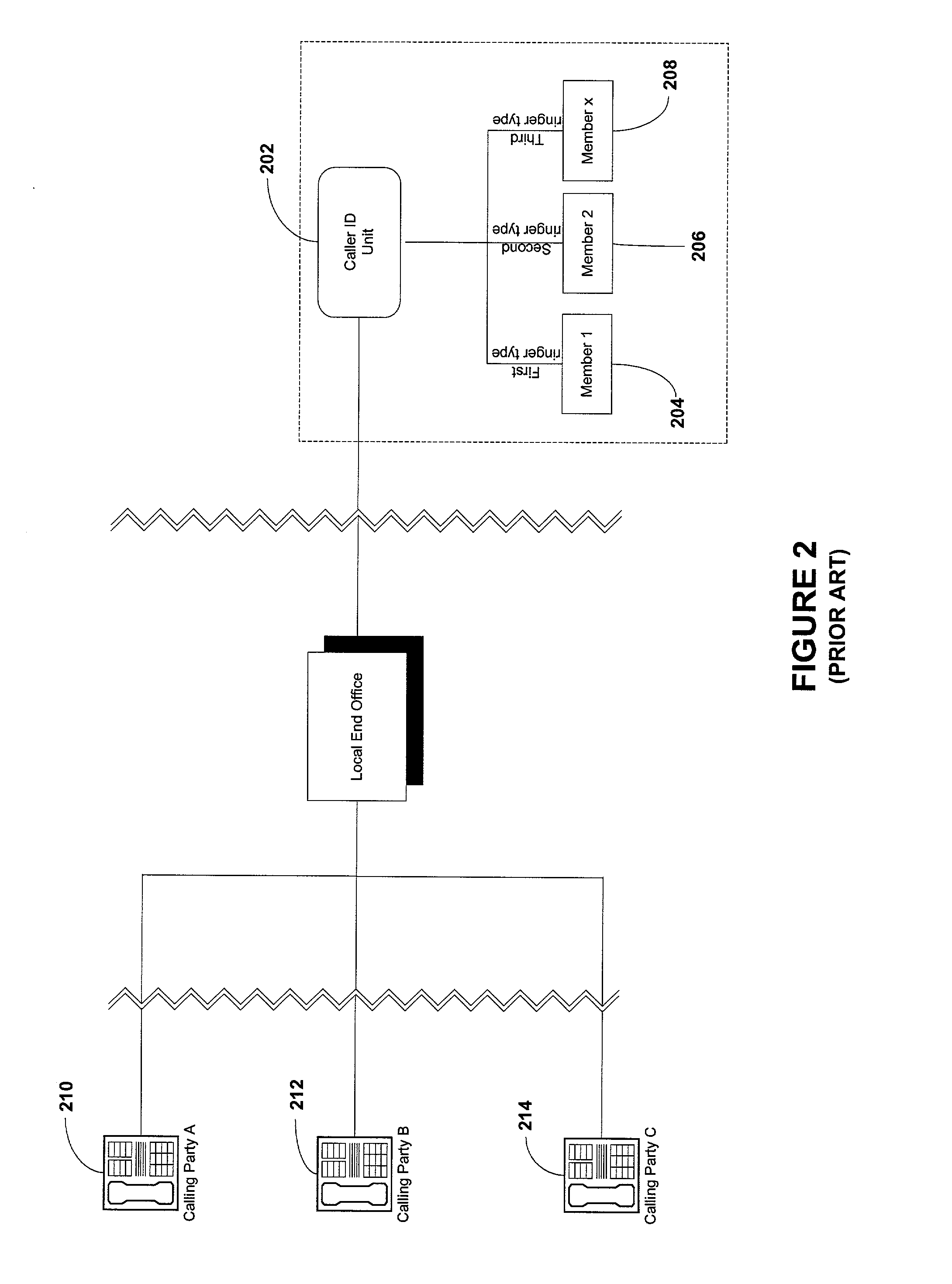
Provision of group services in a telecommunications network
InactiveUS20060067502A1Simple processSpecial service provision for substationNetwork topologiesTelecommunications networkTelephony
A method and system for providing group services in a telecommunications network. Groups of subscribers can be created and each group associated with its own telephone number. A member of a group can communicate with others in that group using a group service and the telephone number associated with the group. In one aspect, a number of different, and separately processed, group services are provided which can be accessed using a common group telephone dialing number.
Owner:FRANCE TELECOM SA
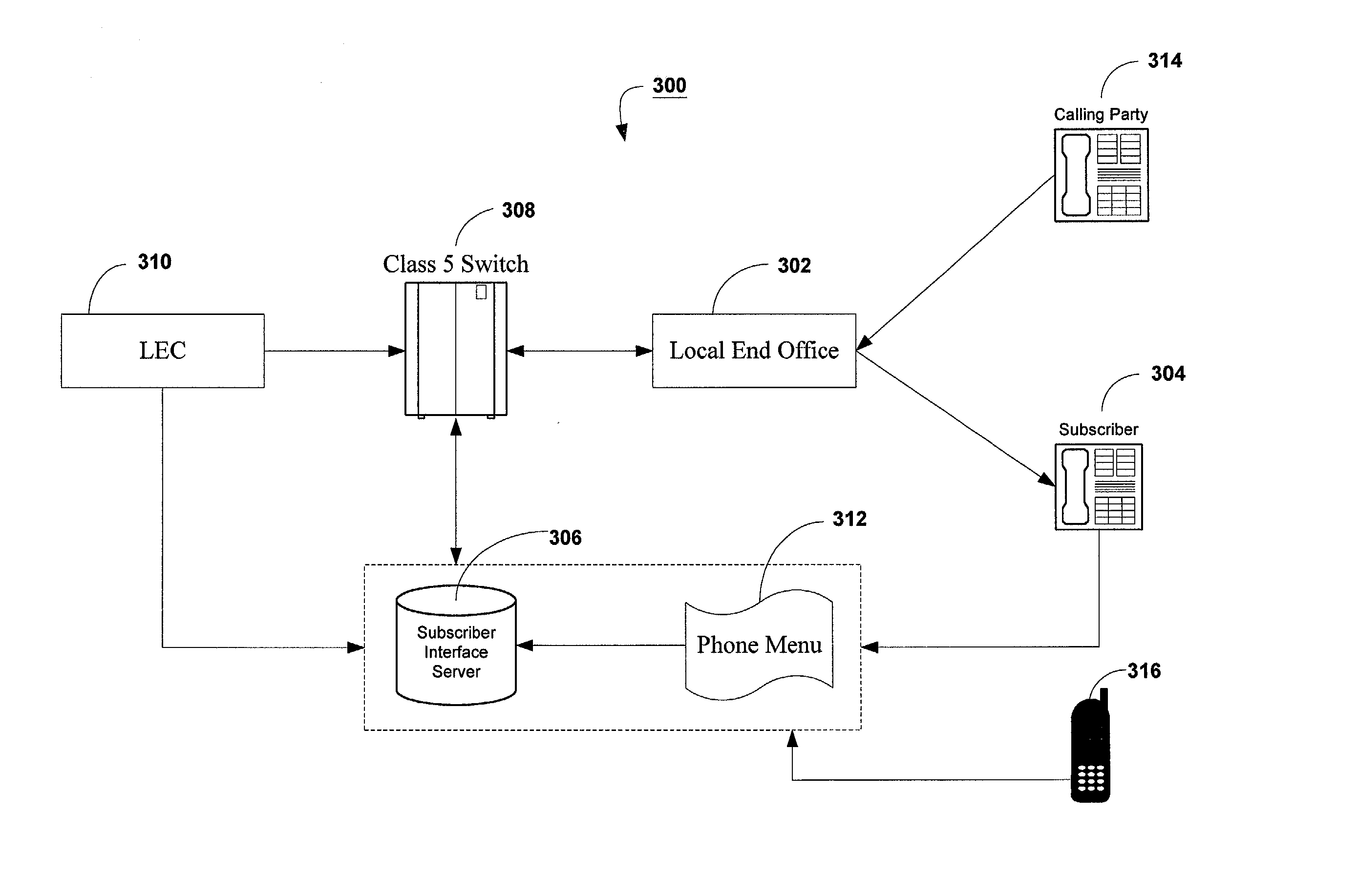
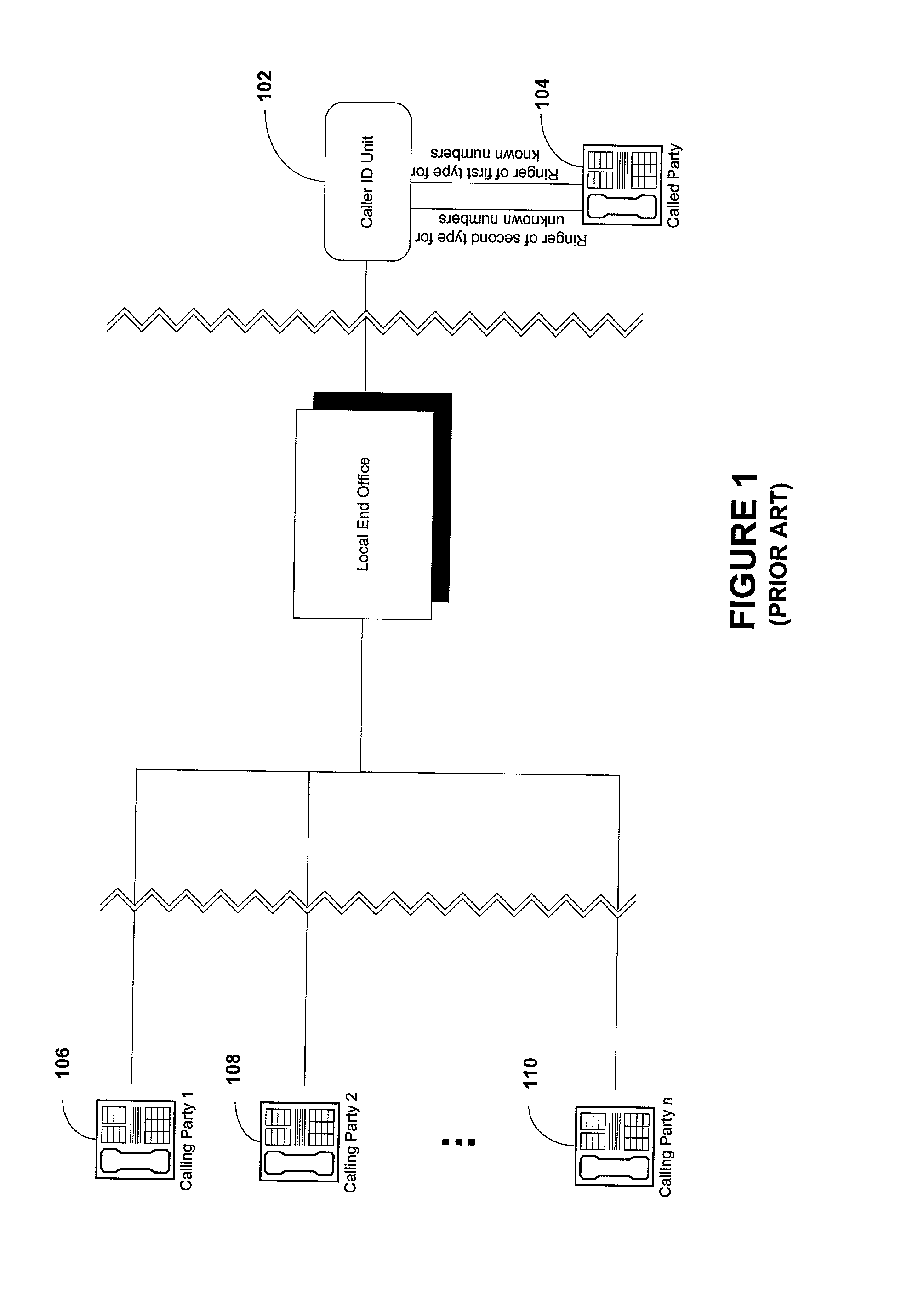
Ring that matters
InactiveUS20030198322A1Automatic call-answering/message-recording/conversation-recordingSpecial service for subscribersUser interfaceTelephony
An enhanced ringer service is described wherein subscribers are allowed to assign, via a menu, distinctive rings to telephone numbers of one or more callers. The enhanced ringer service is implemented via a subscriber interface server and a class 5 switch. Subscribers are able to interact, via a phone menu, with the customer user interface server and assign particular ringer types for incoming calls from one or more callers.
Owner:SOUTHWESTERN BELL COMM SERVICES
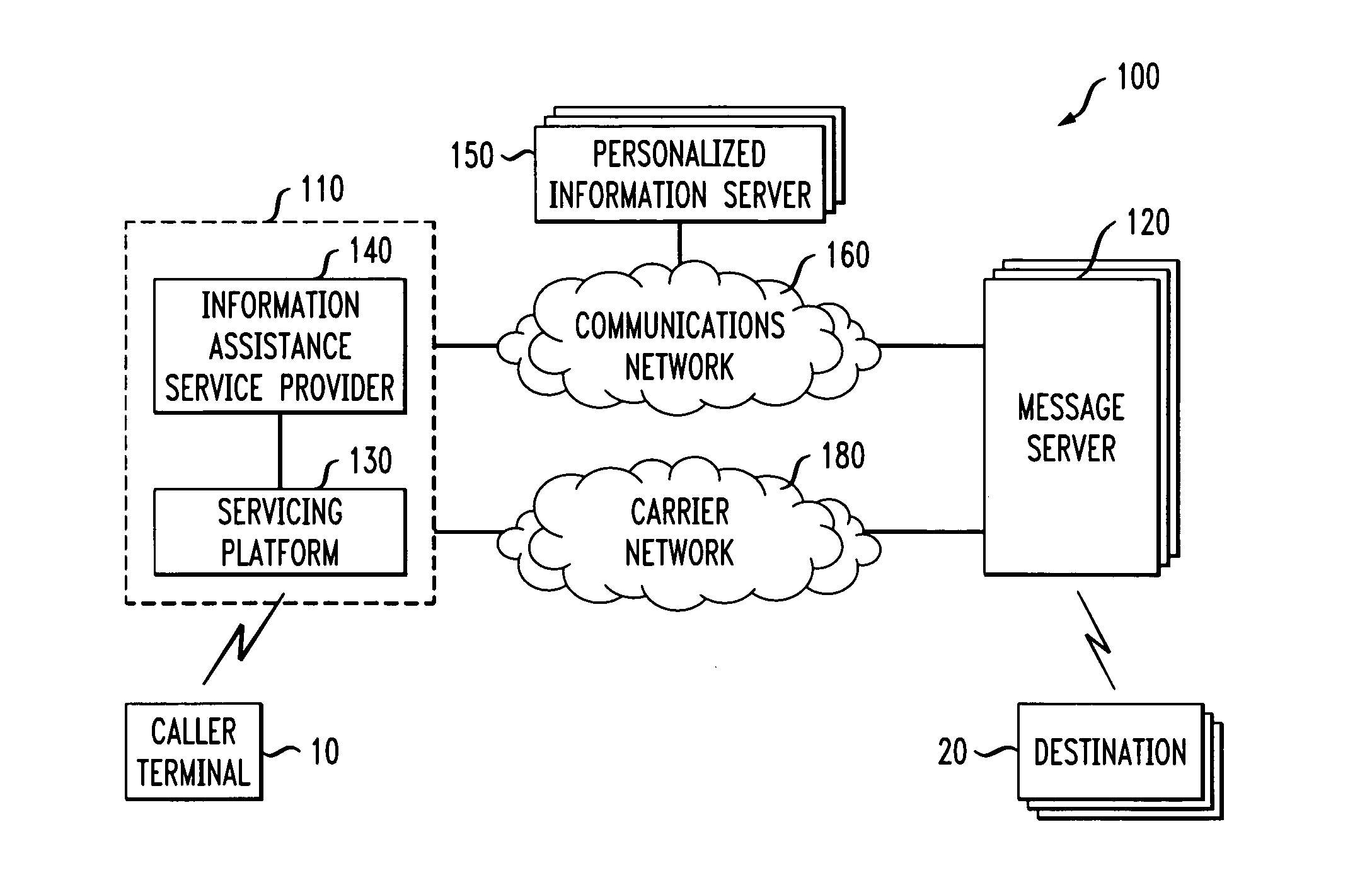
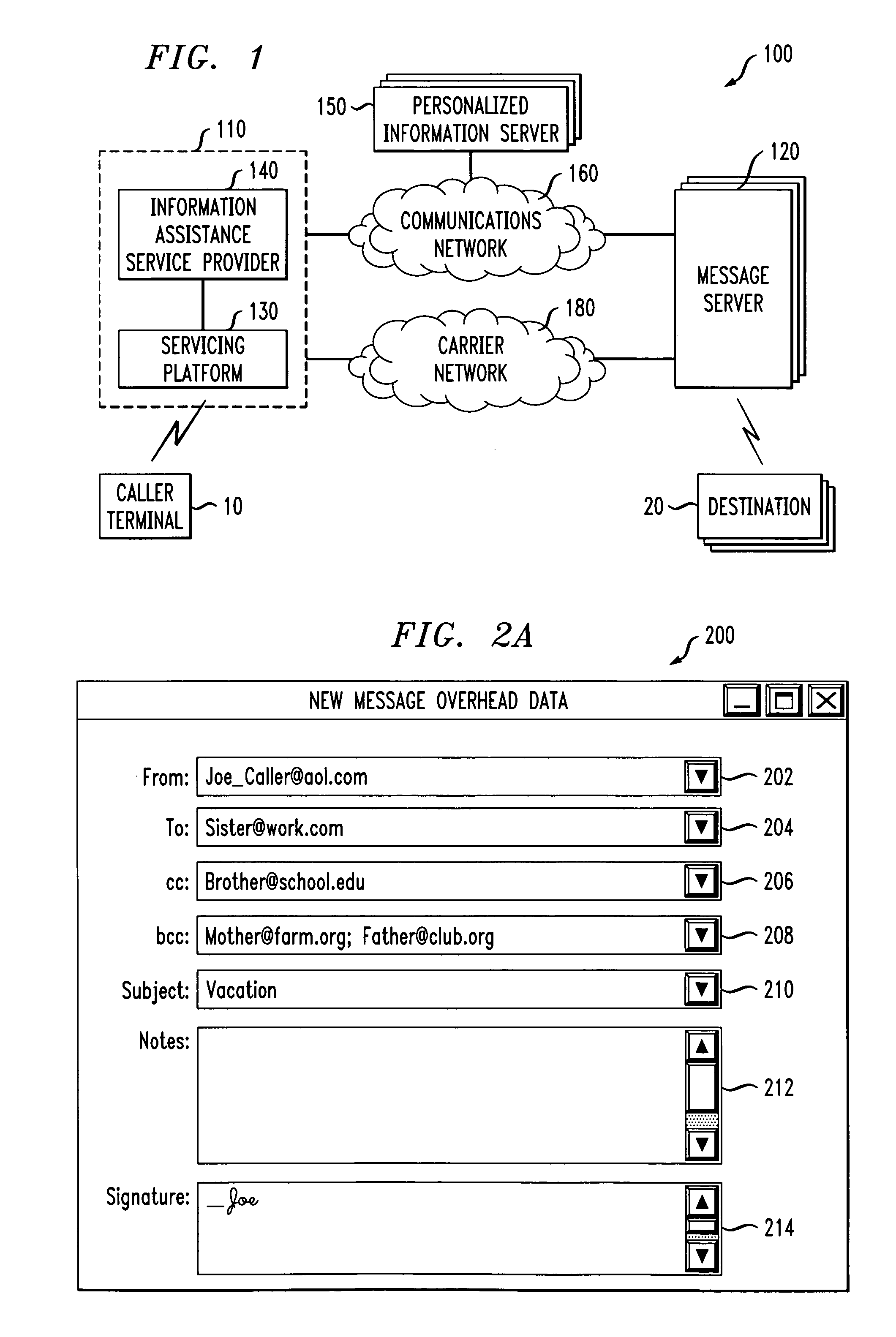
Technique for assisting a user with information services at an information/call center
InactiveUS20060018441A1Easy to replyInstruments for road network navigationArrangements for variable traffic instructionsEmail addressPersonal details
A service providing information assistance may maintain for a subscriber contacts folders comprising private directories of the subscriber, and a personal profile containing the subscriber's preferences. When a user calls the service to attempt to communicate with a desired party through the service, the service can ascertain whether the desired party has a personal profile and / or a contacts folder associated with him / her. If so, the caller is allowed to communicate with the desired party on the terms and conditions defined by the desired party in his / her personal profile and / or contacts folder. For instance, the desired party may have defined therein who should be allowed to contact him / her, when he / she should be contacted, by what communication means, and whether the caller can be told any of the desired party's communication addresses (e.g., telephone number, email address, etc.).
Owner:GRAPE TECH GROUP
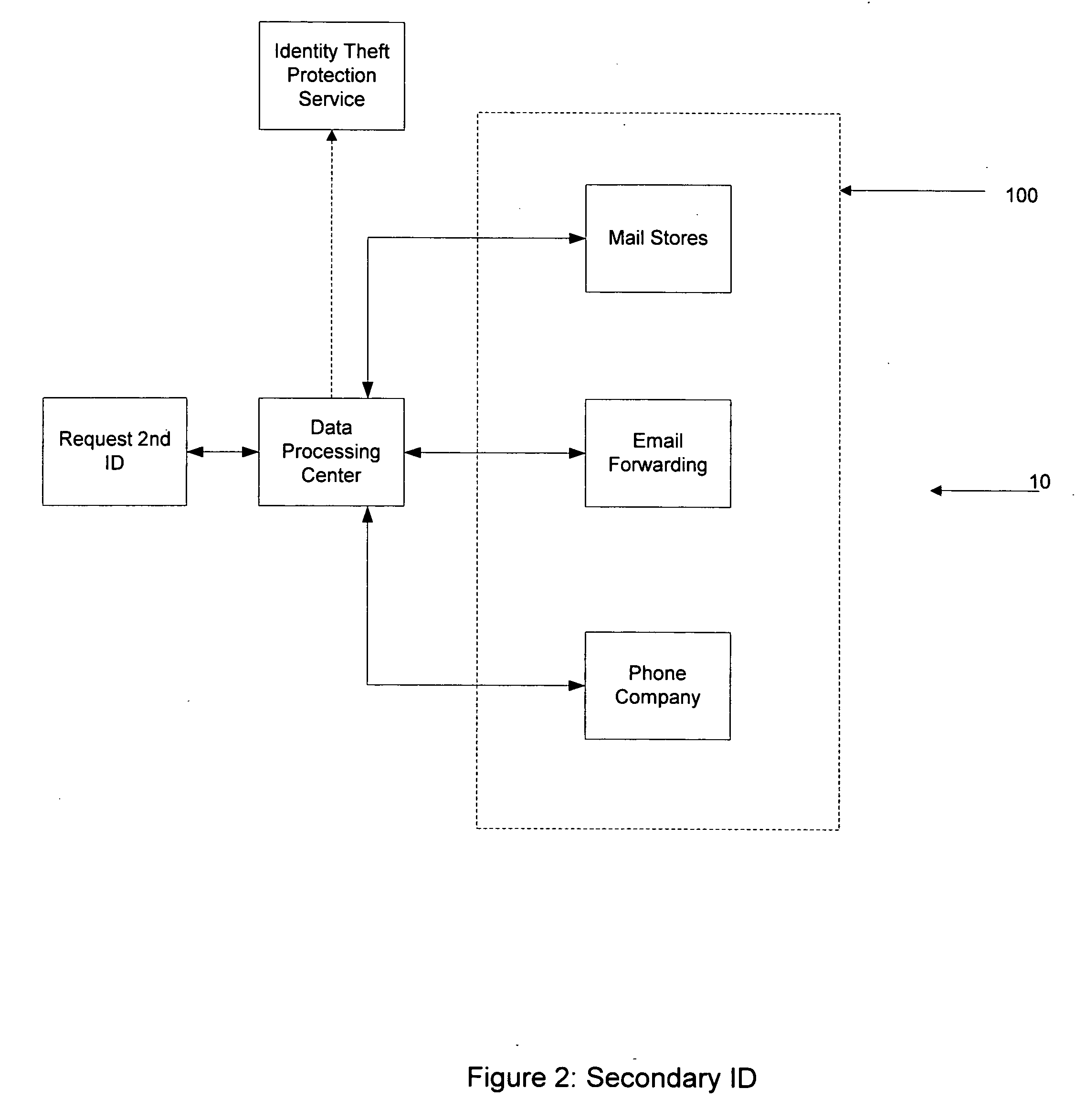
Methods and systems for protection of identity
InactiveUS20070078786A1Reduce harmImprove identityFinanceCharacter and pattern recognitionCredit cardEmail address
The present invention relates to a method to the creation and management of a secondary identification to avoid identify theft. Identity theft may occur over the internet, the purchase of goods and services by credit, and many other forms not yet known. The present invention creates a secondary identification for a person by creating one or more of the following secondary identifications which include a secondary email address, a secondary postal address, a secondary phone number, and any other identifying secondary information. The present invention describes methods and systems to create a secondary identification. Further, the present invention may be used to create a credit card containing the requestor's secondary identification.
Owner:SEAGATE TECH LLC
Method and apparatus for preconditioning mobile devices for network and other operations
ActiveUS20050130653A1Radio/inductive link selection arrangementsSubstation equipmentComputer hardwareQuality of service
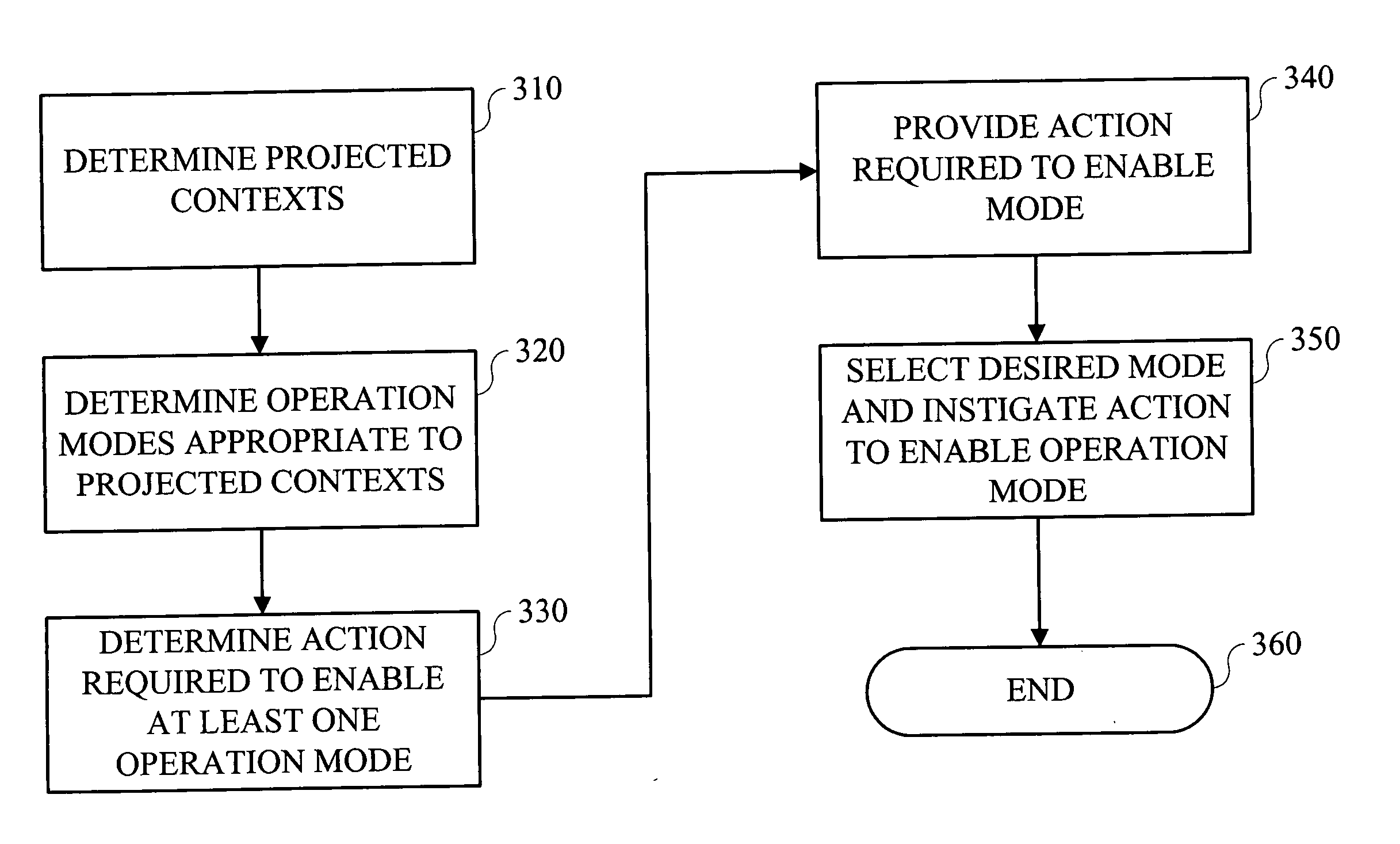
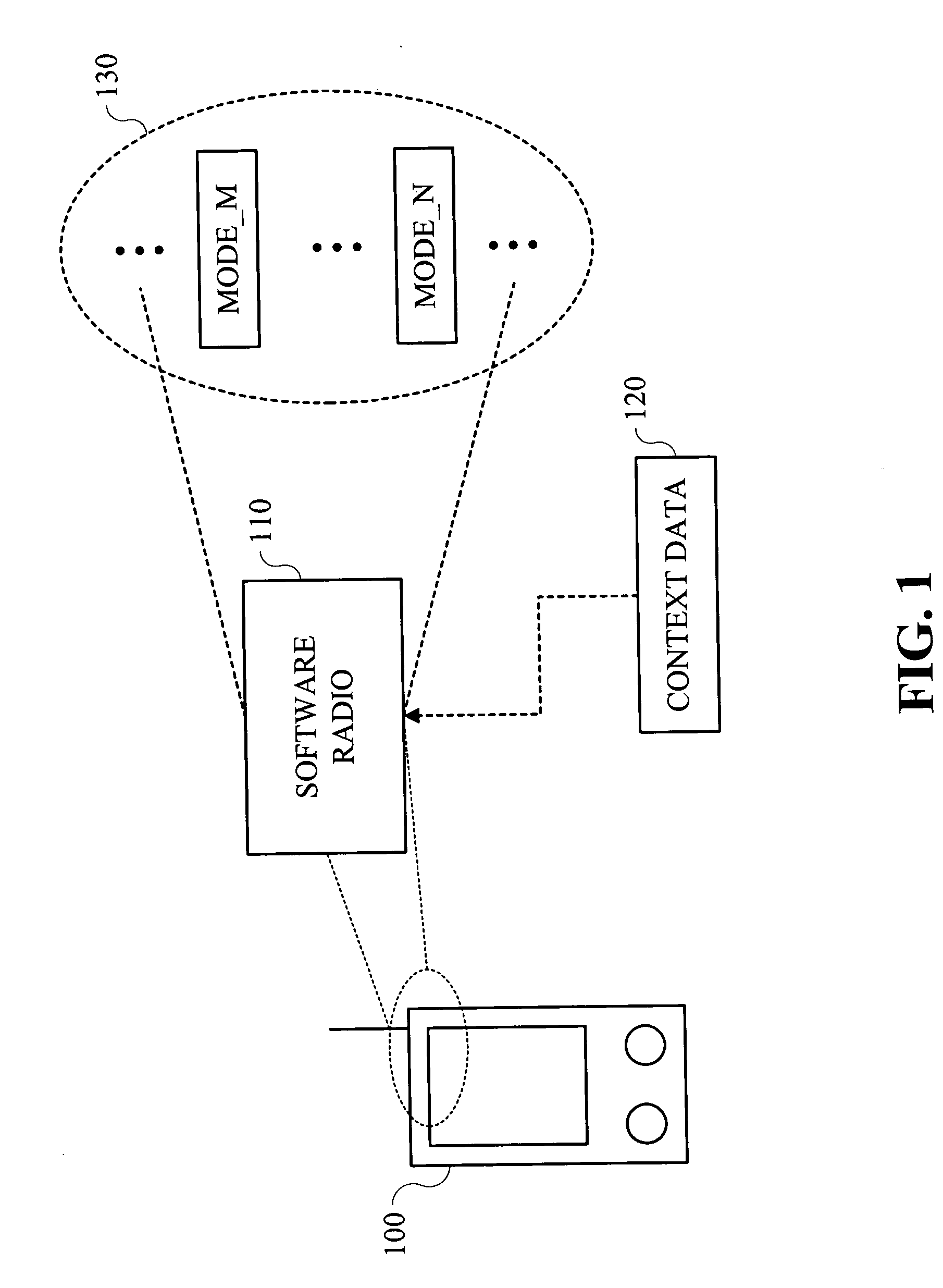
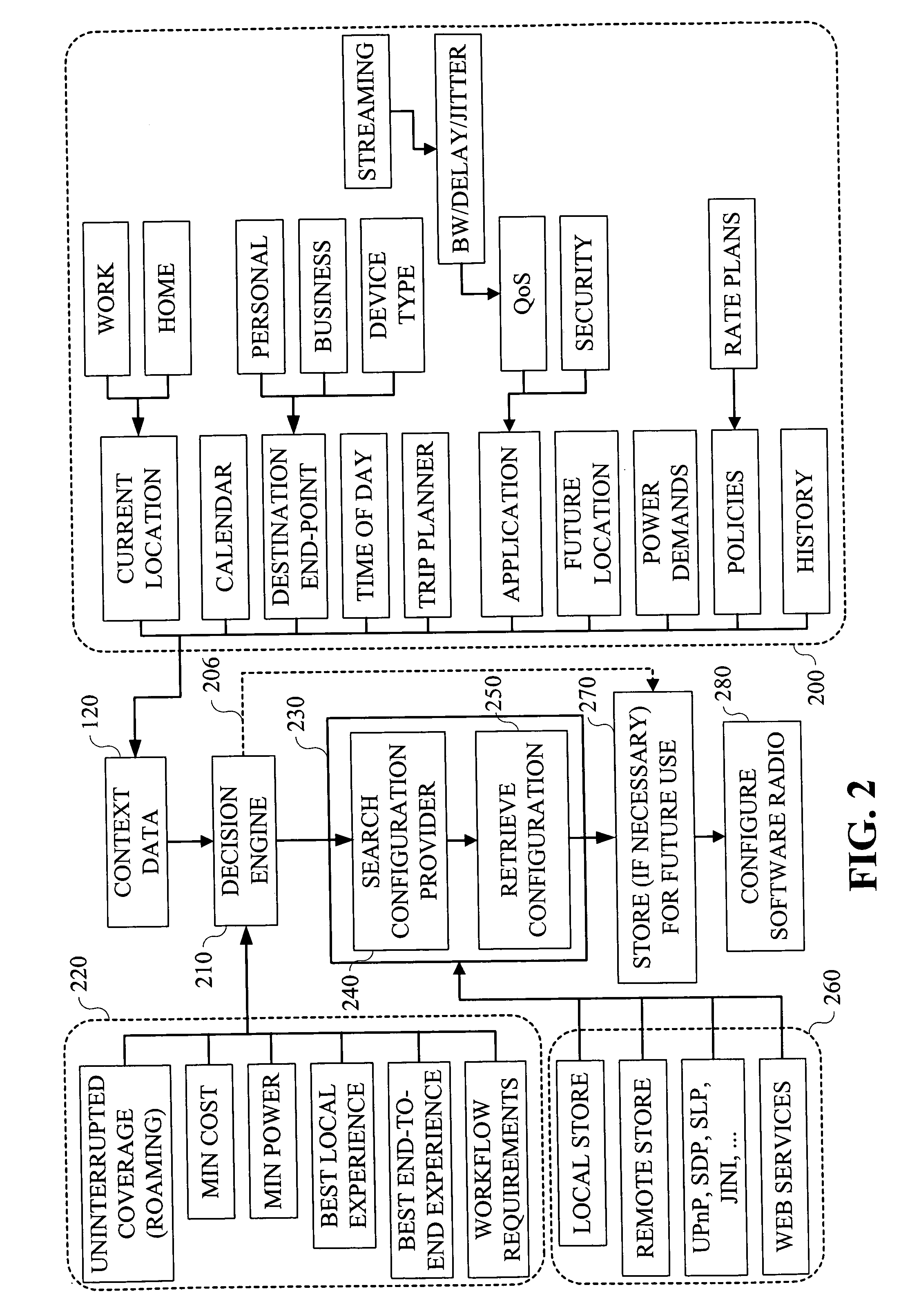
Techniques are provided for providing automated configuration of computing devices. More particularly, principles of the invention may use anticipated context to precondition a device whose operational mode is alterable via computer controllable operations. Anticipated context may be affected by any number of parameters including, but not limited to, current location, time of day, destination end-point, e.g., phone number to be called, past history, subscription rate plans, power requirements of device, application demands with respect to quality-of-service (QoS), security, calendar information, and so on. Further, principles of the invention may use locally derived knowledge about the intended use of a device and dynamically enable it in a desirable mode of operation using locally reachable configuration parameters stored in advance based on the anticipated context for the operation of the device. Still further, principles of the invention may dynamically locate necessary configuration parameters via a service discovery process.
Owner:DAEDALUS GRP LLC
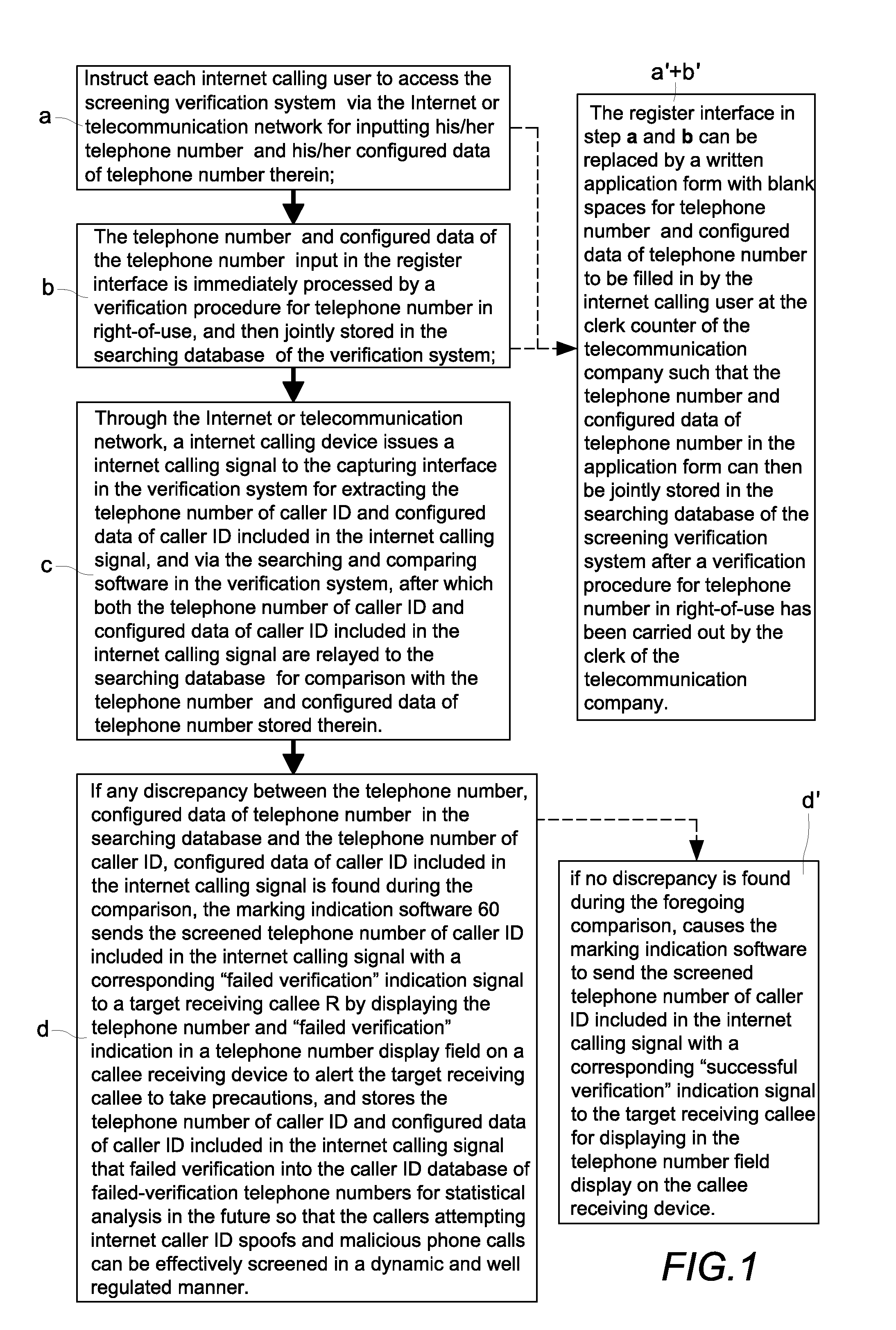
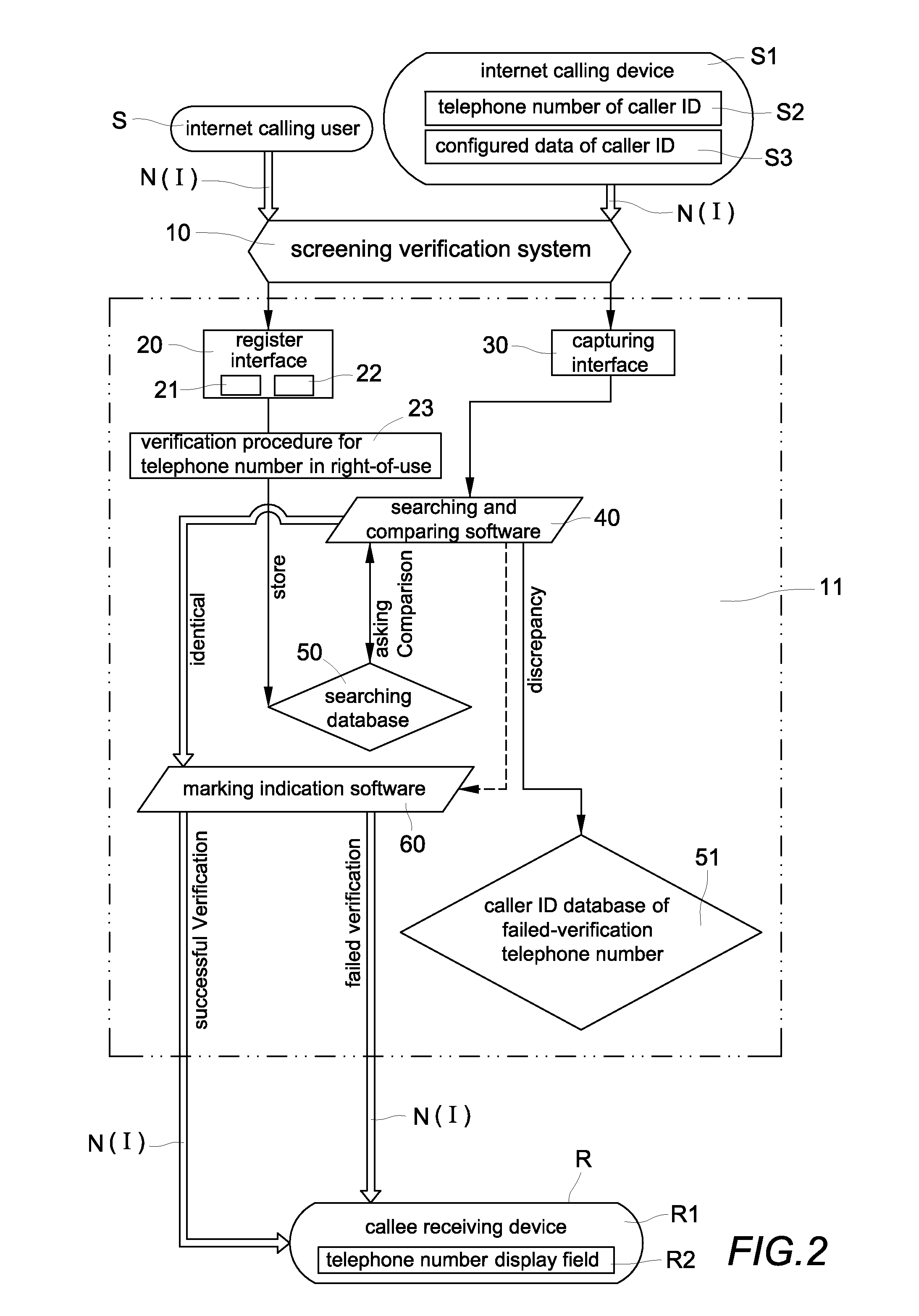
Verification method and system for screening internet caller id spoofs and malicious phone calls
InactiveUS20120287823A1Easy authenticationPrevent caller ID spoofing fraudSpecial service provision for substationMultiplex system selection arrangementsValidation methodsInternet users
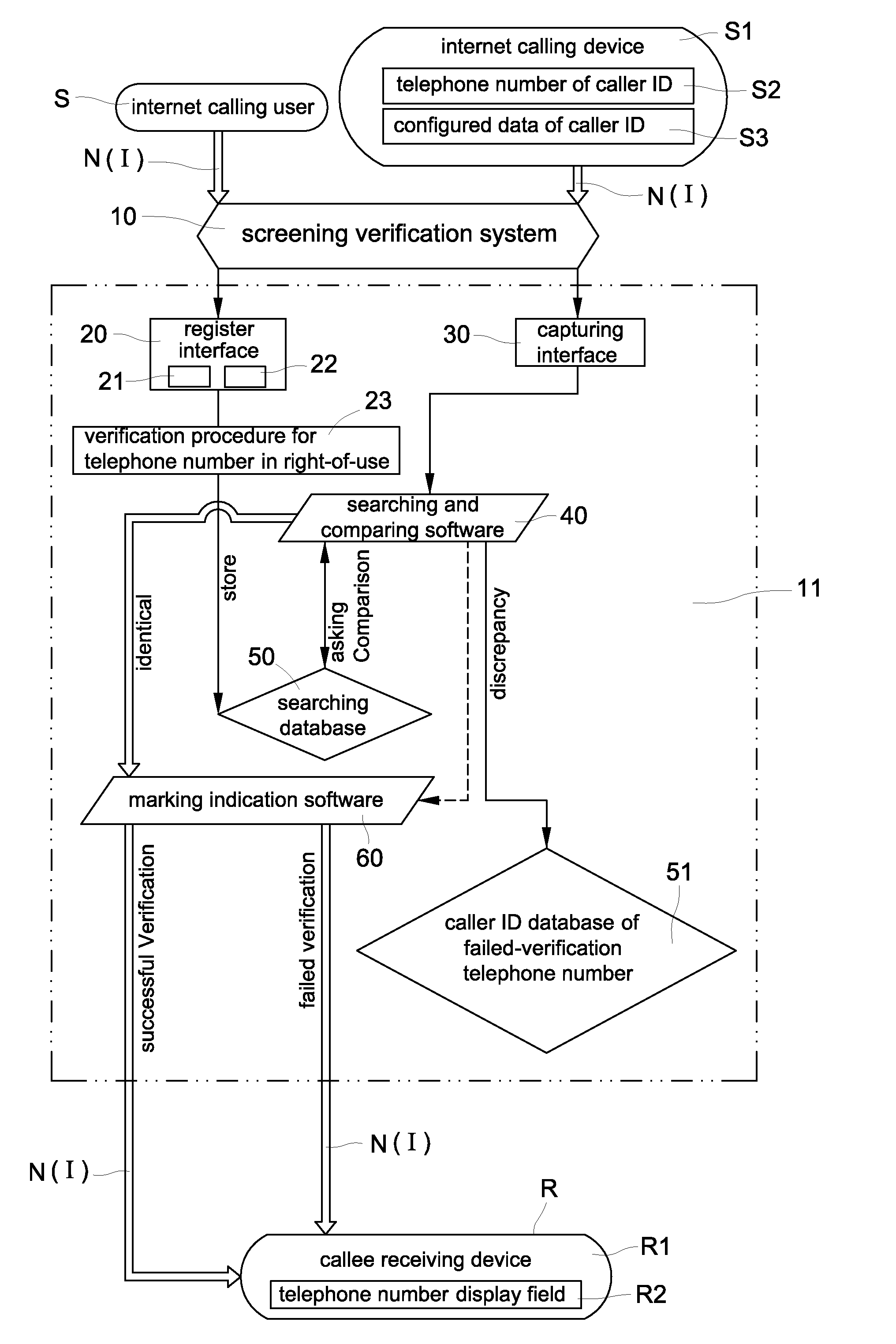
A verification system for screening internet caller ID spoofs and malicious phone calls includes a server, a register interface, a capturing interface, a searching and comparing software, a searching database, a caller ID database of failed-verification telephone numbers, and marking indication software. The searching database stores a telephone number of caller ID and configured data of telephone number of every internet user. The searching and comparing software compares the telephone number of caller ID and configured data of caller ID included in the internet calling signal with a corresponding telephone number and configured data of the telephone number stored in the searching database. The marking indication software sends a verified result of the comparison with a corresponding indication signal to a target receiving callee so that the callee can easily take suitable measures to prevent becoming the victim of telephone fraud.
Owner:LIN CHUNG YU
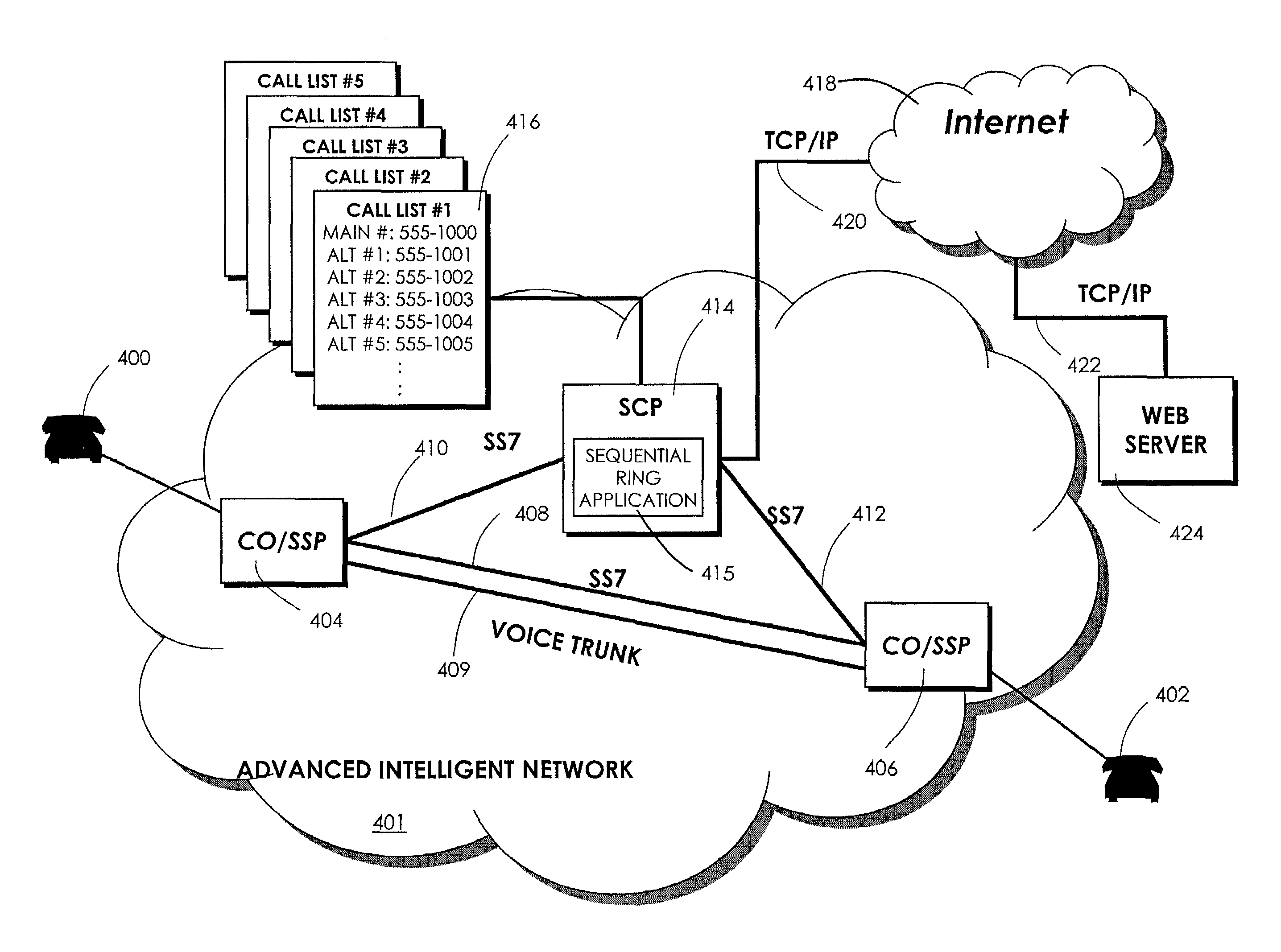
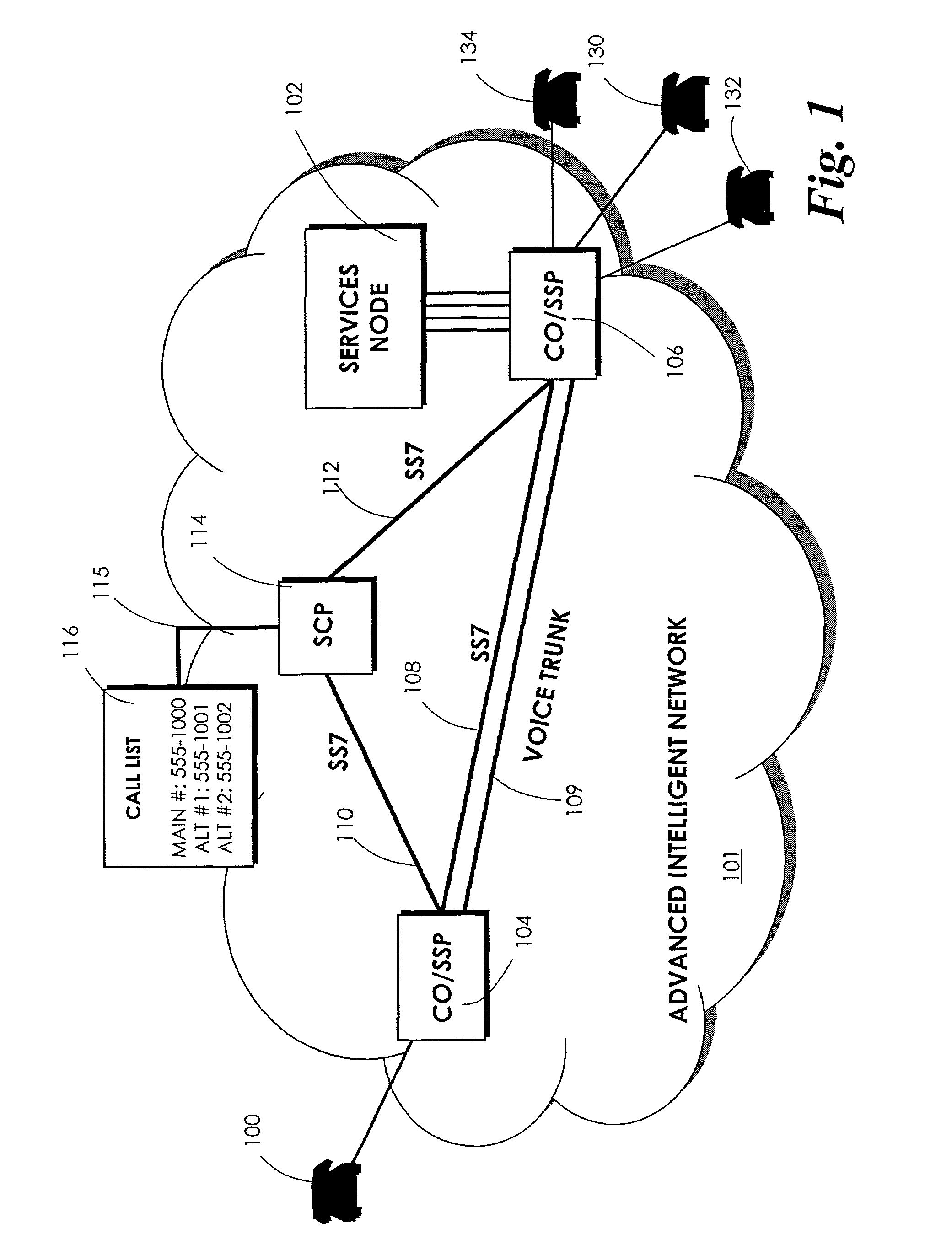
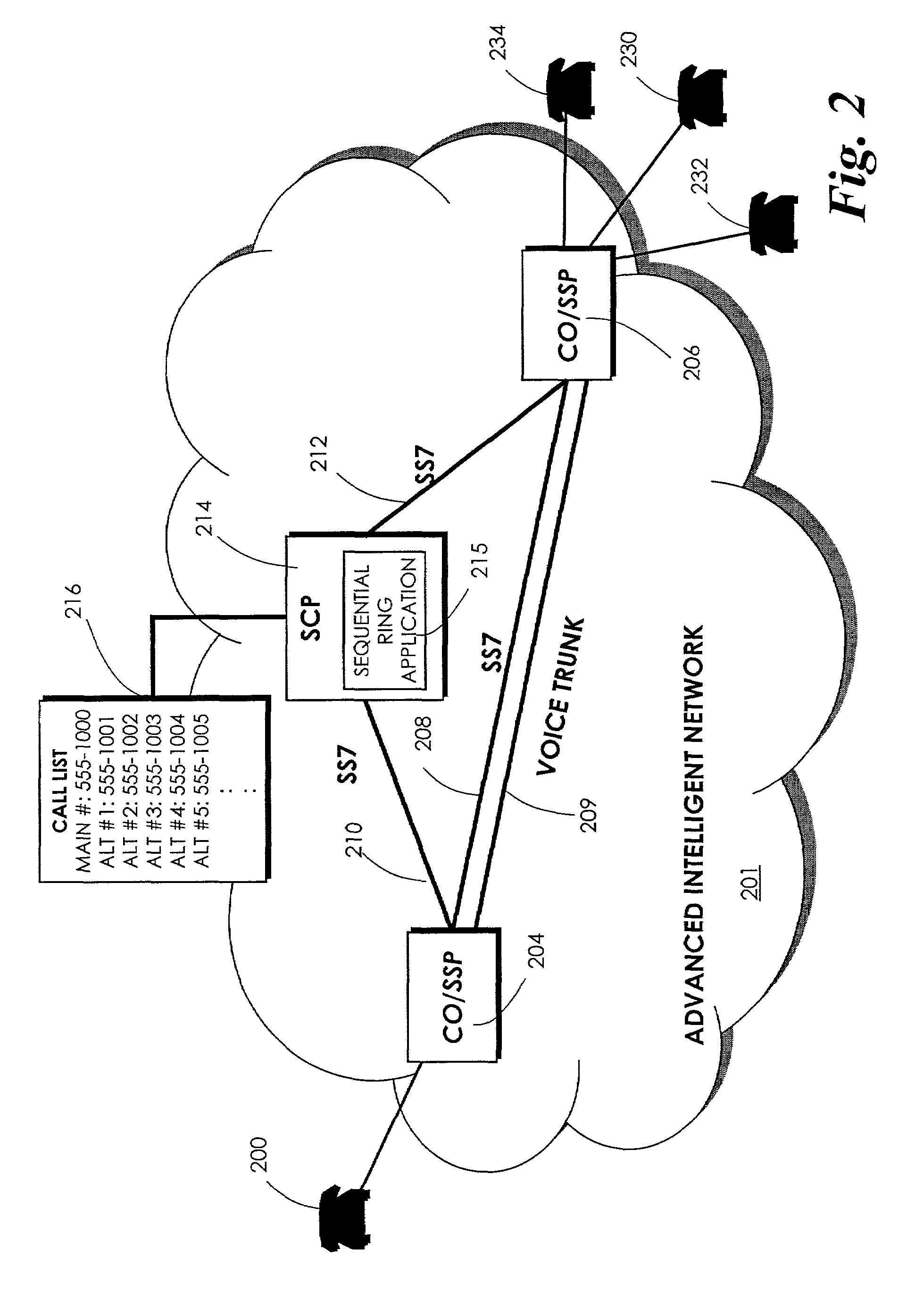
Automatically sequentially ringing alternative telephone numbers
InactiveUS7194080B2Efficient implementationEliminate useIntelligent networksInterconnection arrangementsTelecommunicationsSpeech sound
A Service Control Point (SCP) has a call list associated with the main telephone number of a called party. When a calling party attempts to contact the called party by calling the main number, but cannot reach the main number, a Service Switching Point (SSP) fires a trigger. One trigger is a T_No_Answer trigger, which is fired in response to a call to the main number that is not answered within a predefined number of rings. Another trigger is a T_Busy trigger that is fired in response to a call to the main number that is made when the main number is busy. Each trigger causes the SCP to access the call list and to cause the SSP to ring an alternative telephone number associated with the main telephone number. If this attempt to reach the called party also fails, then the SSP again fires the trigger and an attempt is made to connect the calling party to the next number on the call list. If the call list is exhausted before the calling party is connected to a number on the called party's call list, then a message can be played to the calling party. Alternatively, the calling party may be connected to a voice mailbox associated with the called party or may receive a busy tone.
Owner:BELLSOUTH INTPROP COR
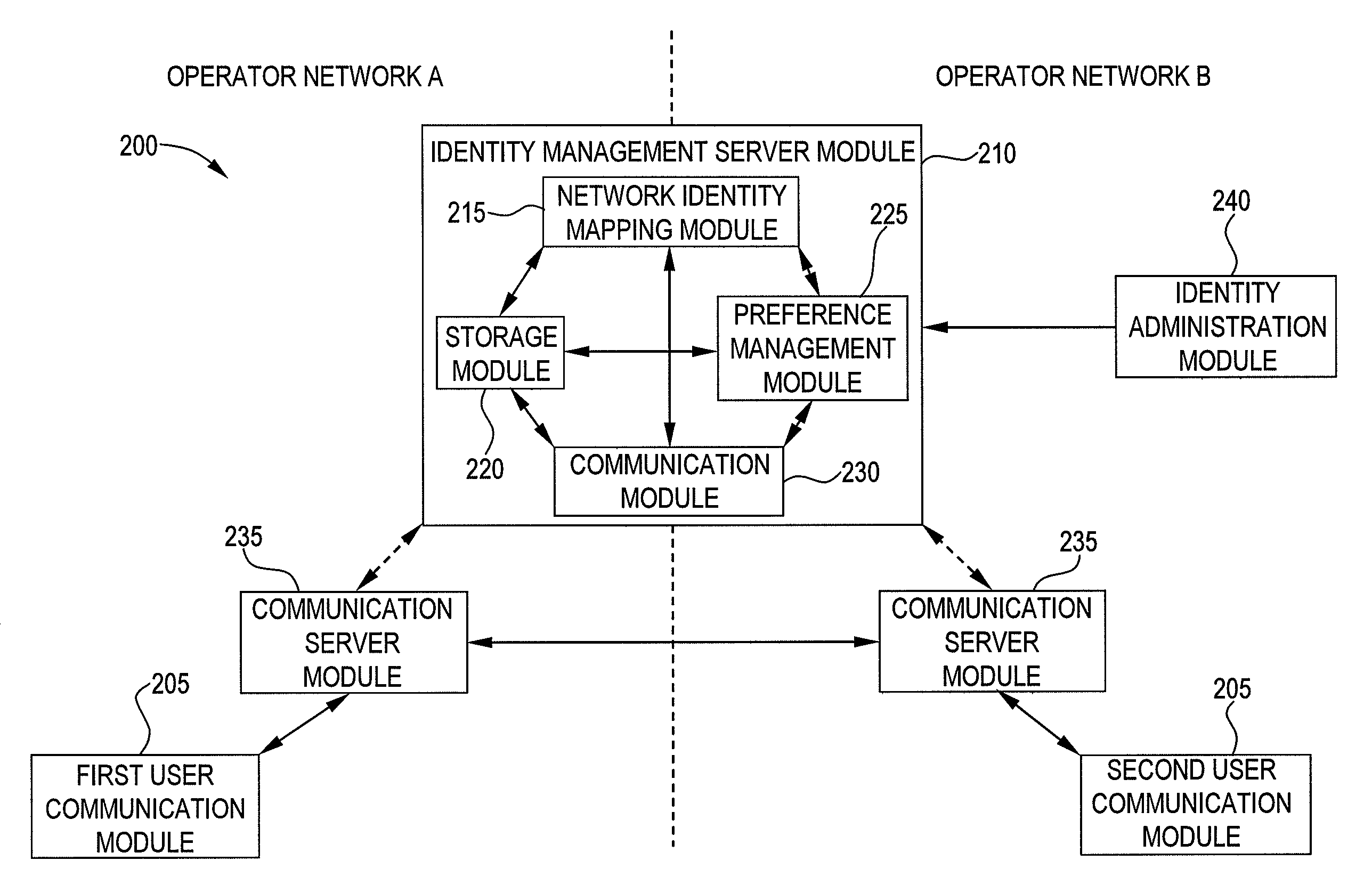
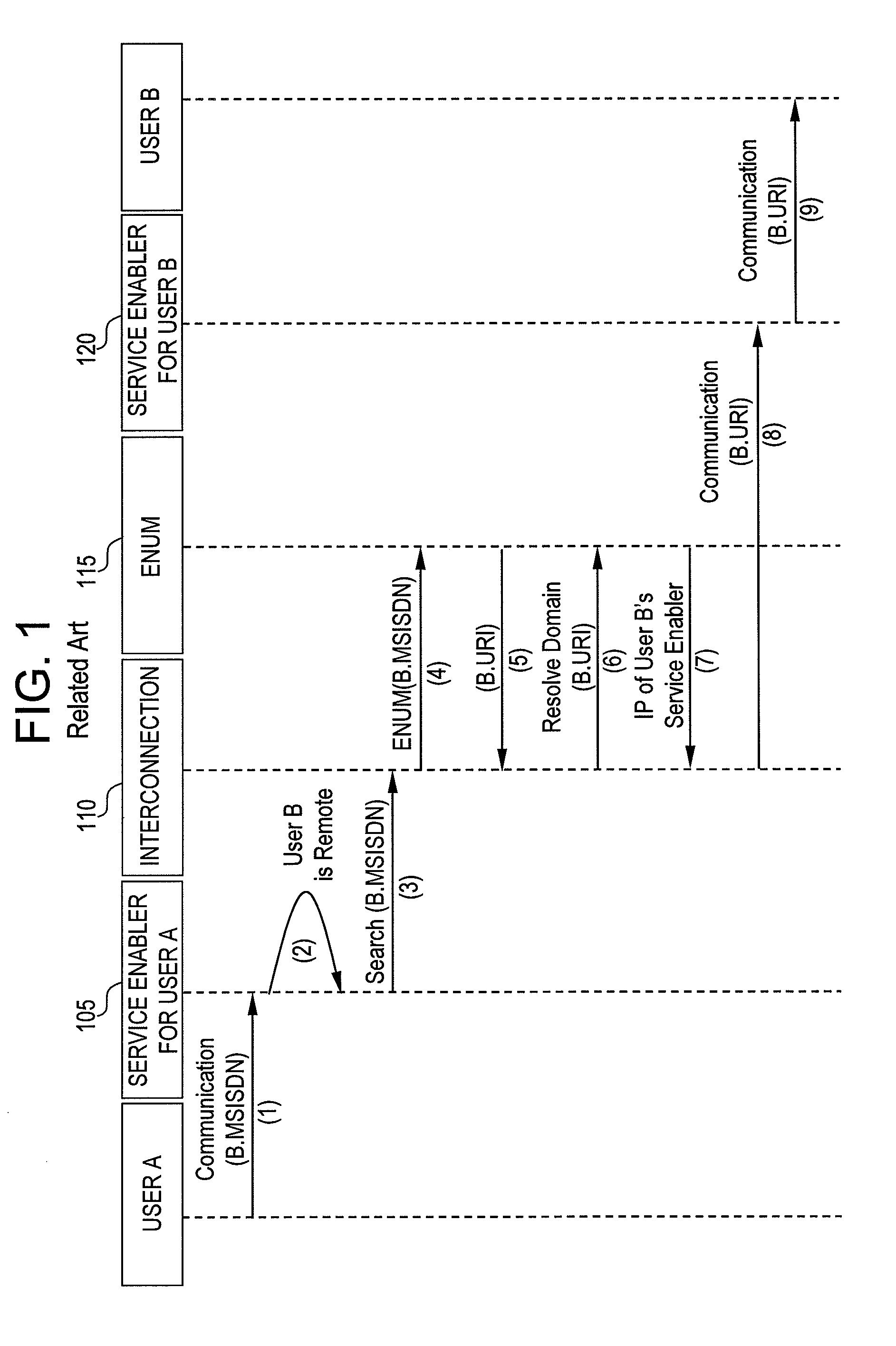
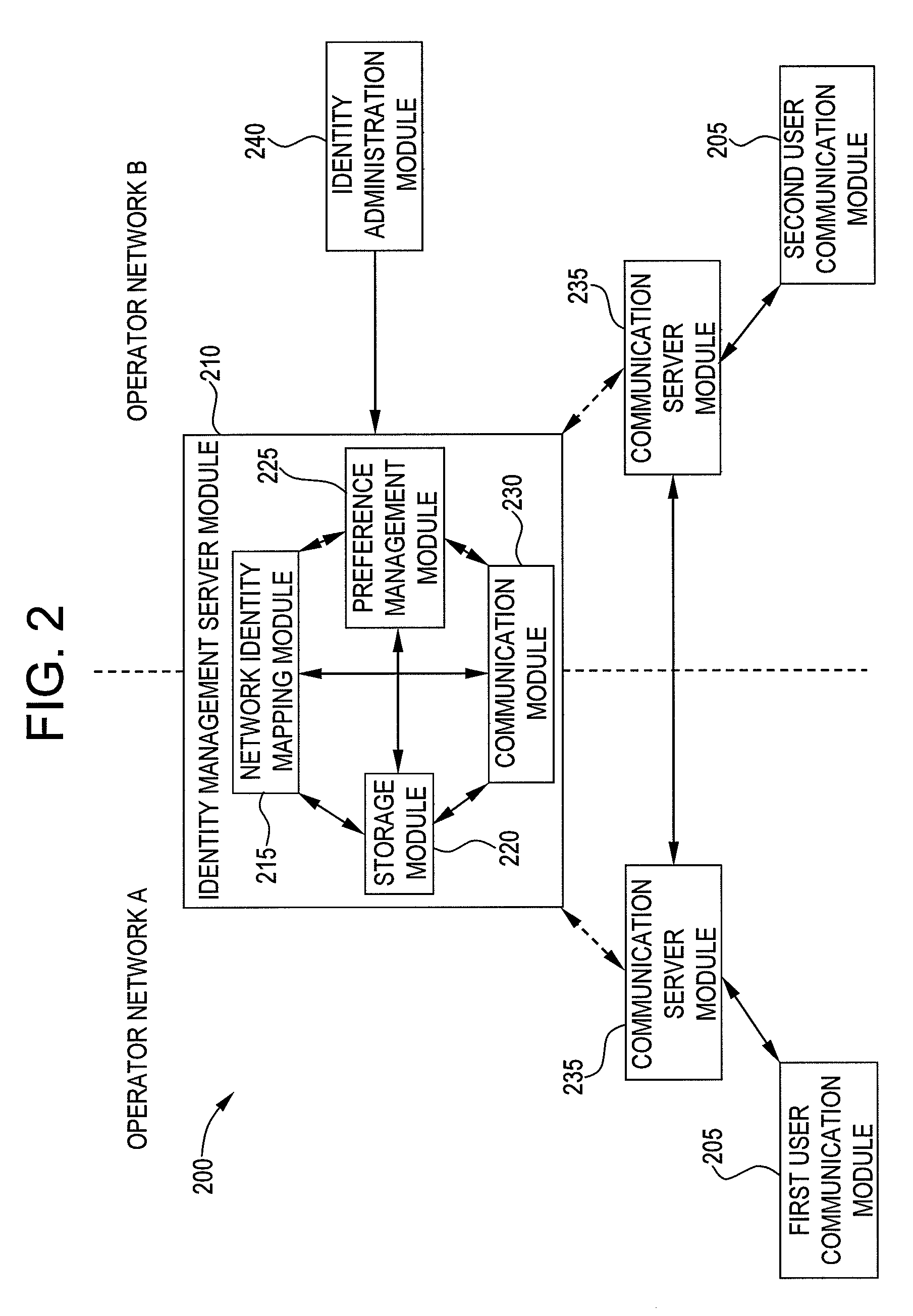
System and method for user identity portability in communication systems
InactiveUS20080130523A1Maintain privacySpecial service provision for substationMultiplex system selection arrangementsCommunications systemInternet privacy
Exemplary embodiments of the present invention are directed to a system and method for user identity portability in communication systems. The present invention can provide user identity portability across communication networks that do not necessarily impose a phone number as the identity, addressing, or routing identifier. According to exemplary embodiments, a user identified by any suitable user identifier can switch network operators (e.g., from operator A to operator B) and retain their user identifier. For example, an identity server can support reverse lookup ENUM usage for URI and other identity correlation. Thus, all communication contacts that the user had while with operator A can seamlessly continue communications with the user even after the user switches to operator B.
Owner:NEUSTAR
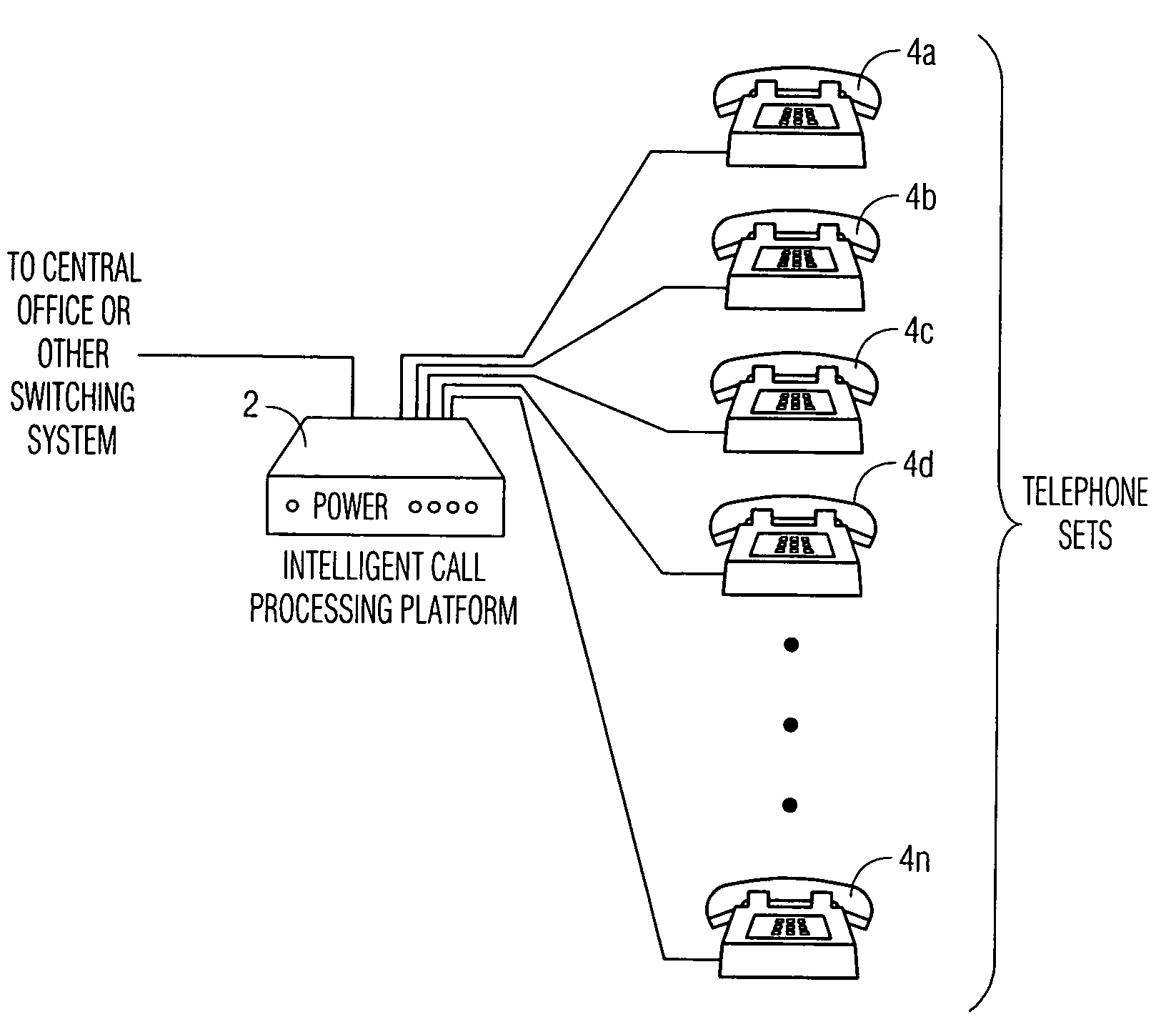
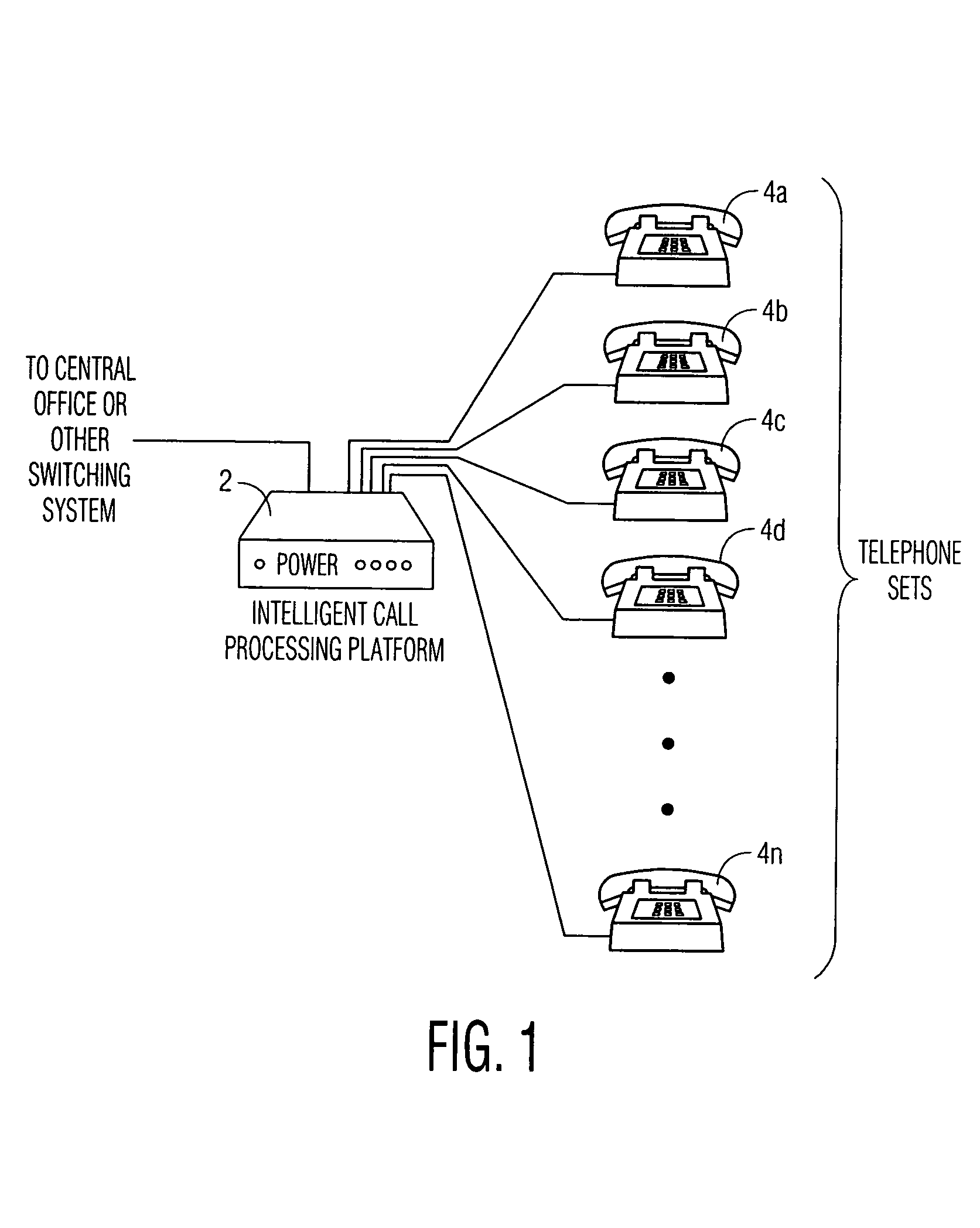
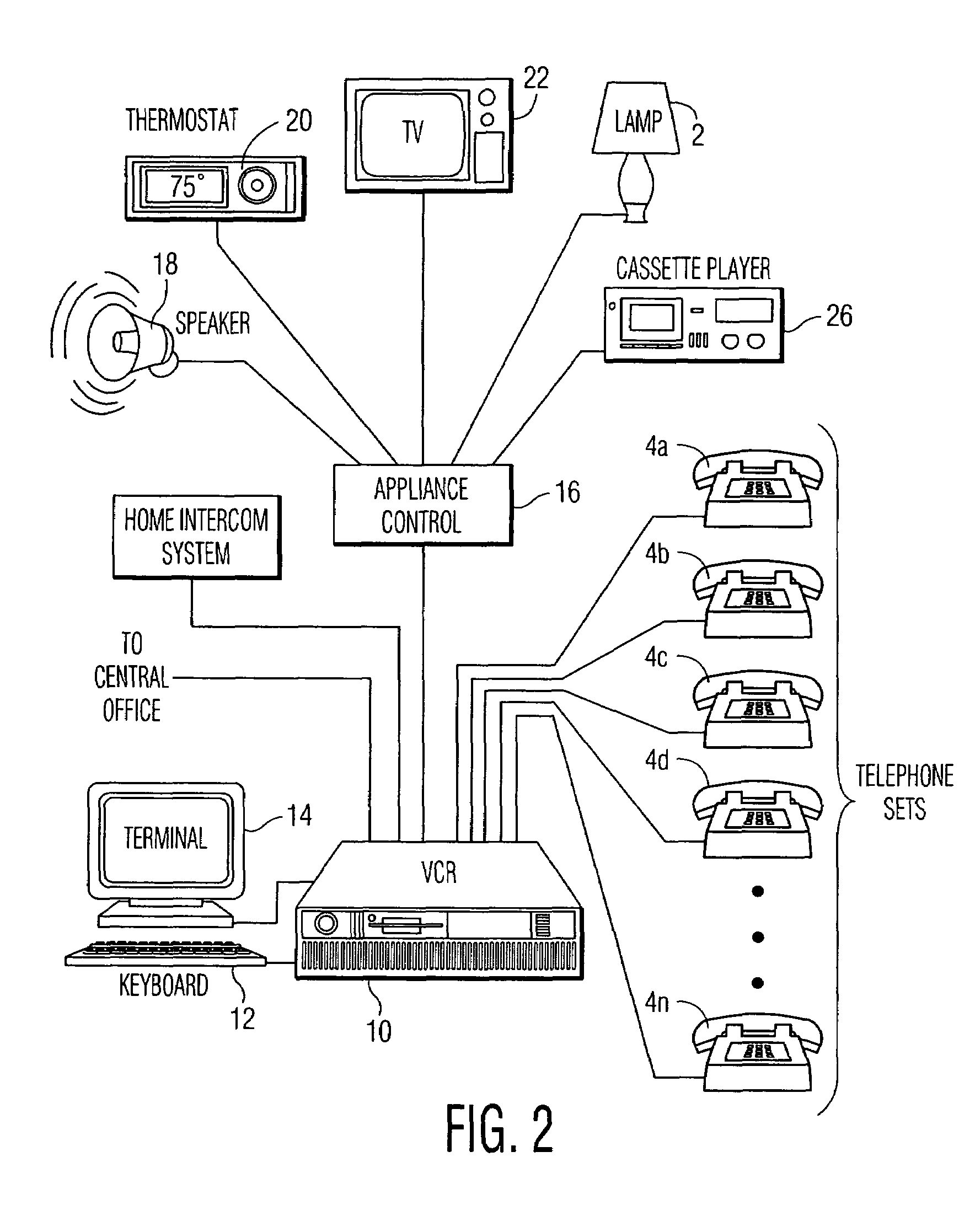
Intelligent call processing platform for home telephone system
InactiveUS6931104B1Facilitate implementationEasy to implementCordless telephonesSpecial service for subscribersHandsetSpeech sound
The present invention comprises an intelligent call processing platform for use with a home telephone system. The system consists of a processing unit interfaced with a variety of memory storage areas, a switching central office providing local telephone service and a plurality of telephone handsets. Using a variety of voice and / or pushbutton commands, a user is able to access a variety of telephone services from any telephone interfaced with the platform. Services provided include identification of incoming callers, automatic speed dialing of user-stored telephone numbers, storage of new numbers to the user-stored list of telephone numbers, and control of peripheral systems interconnected with the intelligent call processing platform.
Owner:PHILIPS ELECTRONICS NORTH AMERICA
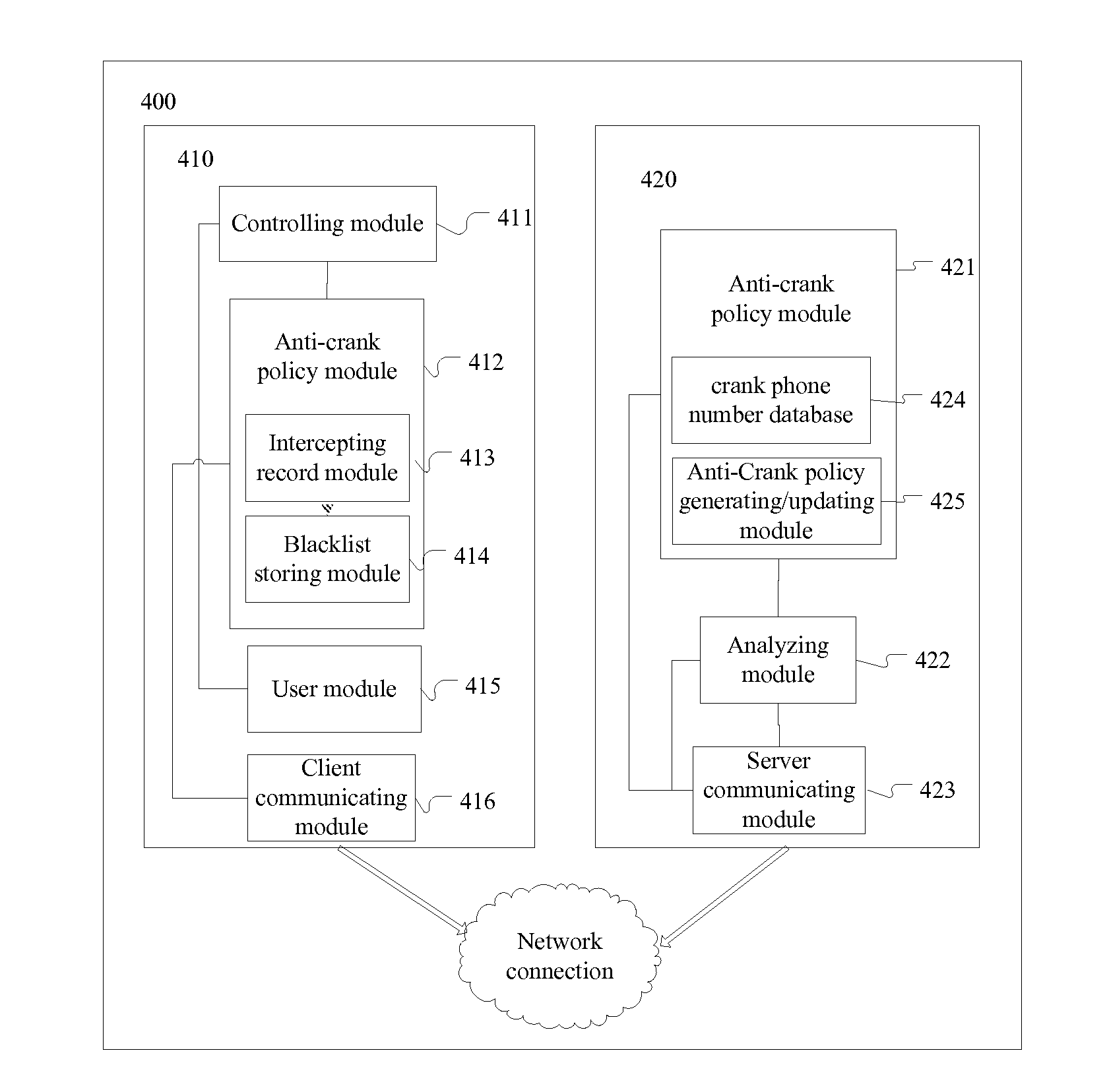
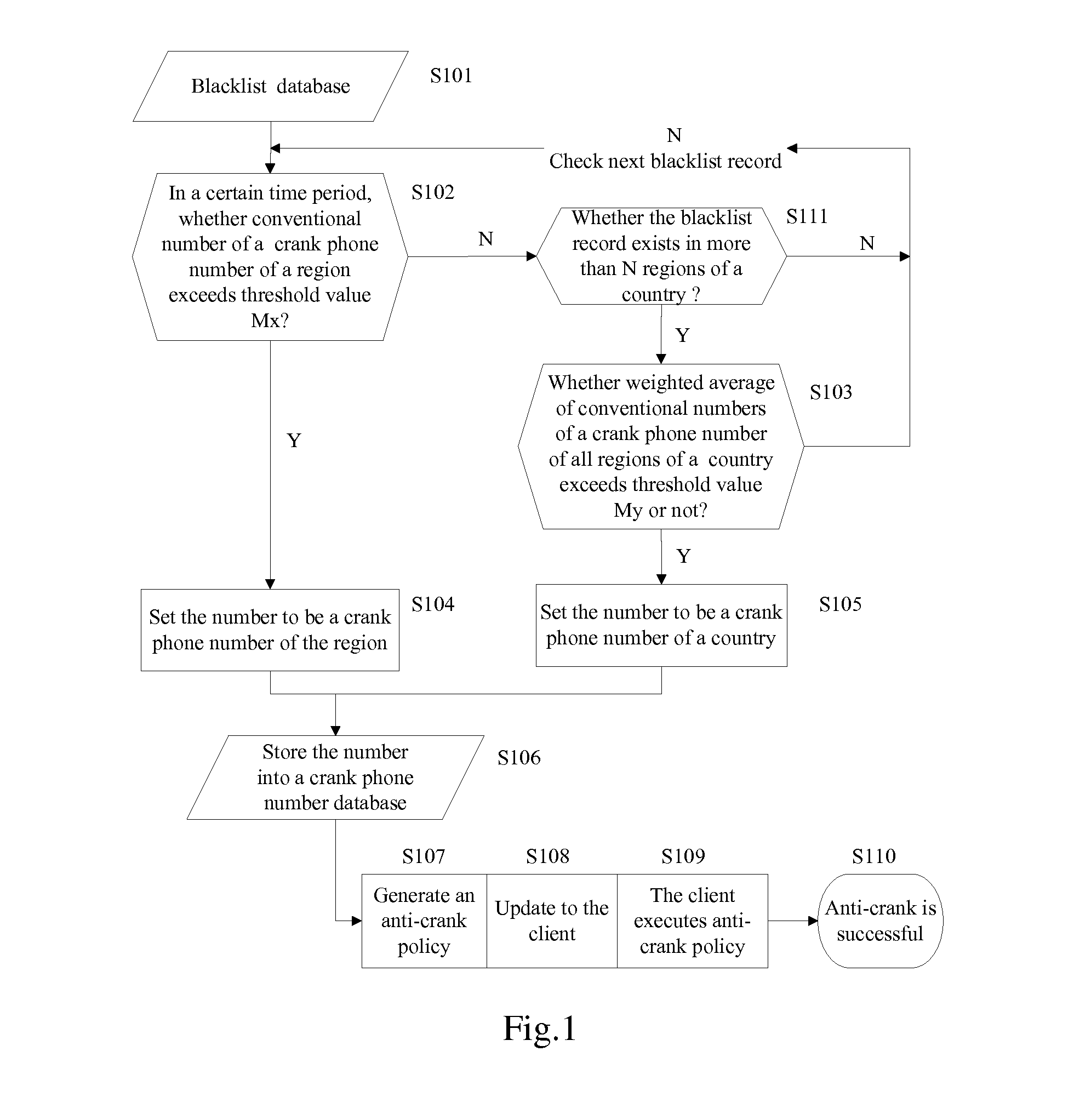
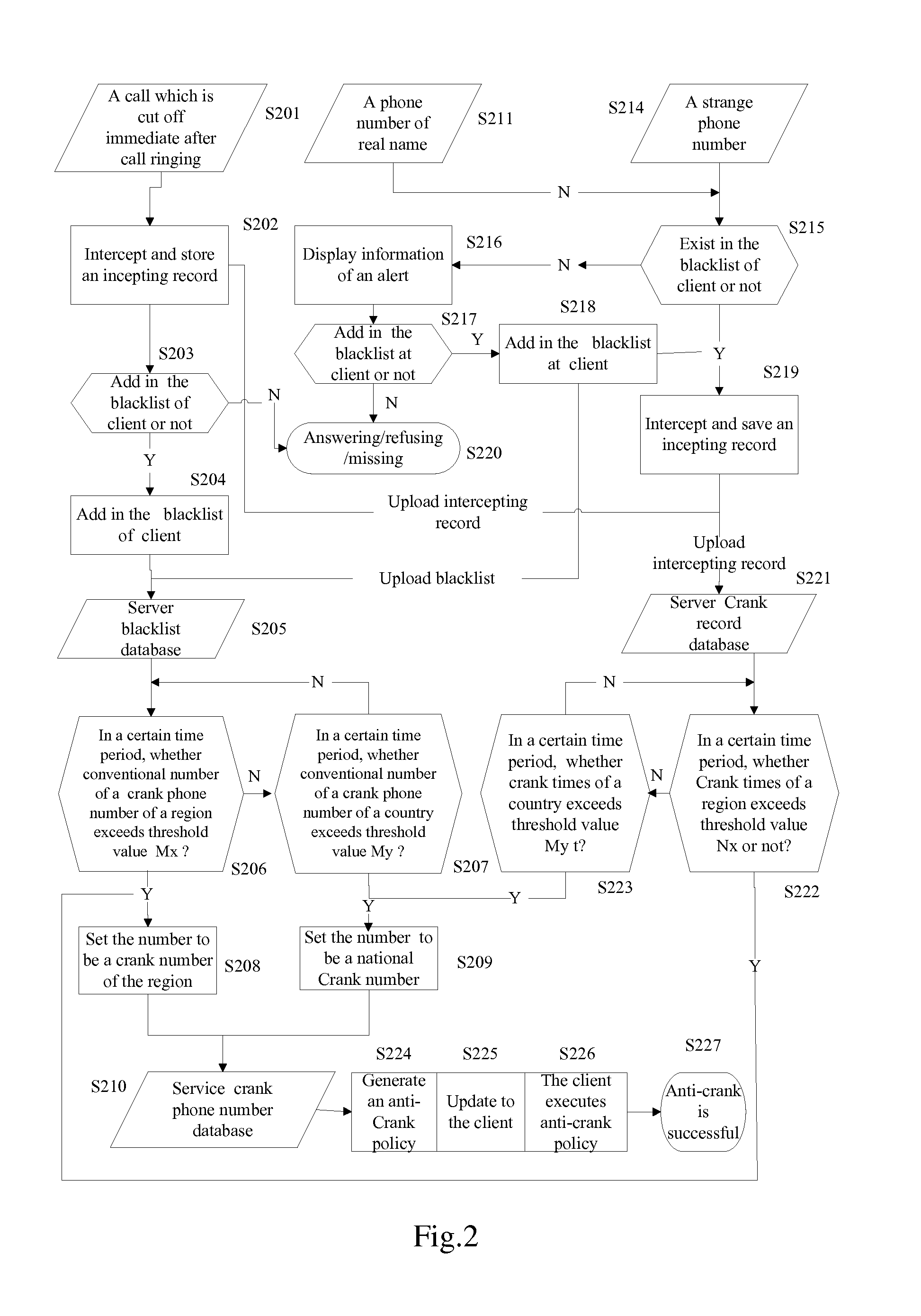
Method for blocking crank calls by using cloud computing and a system thereof
InactiveUS20120309365A1Increase quantityNot be correctSpecial service for subscribersCalling susbscriber number recording/indicationCloud computingEngineering
The present disclosure provides a method for blocking crank calls by using cloud computing and a system thereof. In the method, a client(s) uploads a blacklist to a server; the server makes statistic according to blacklist data uploaded by the client(s) and determines a particular phone number be a crank phone number, generates an anti-crank policy and updates the generated anti-crank policy to the client(s); when receiving a call or a message from the crank phone number, the client executes the anti-crank policy.
Owner:NETQIN MOBILE BEIJING
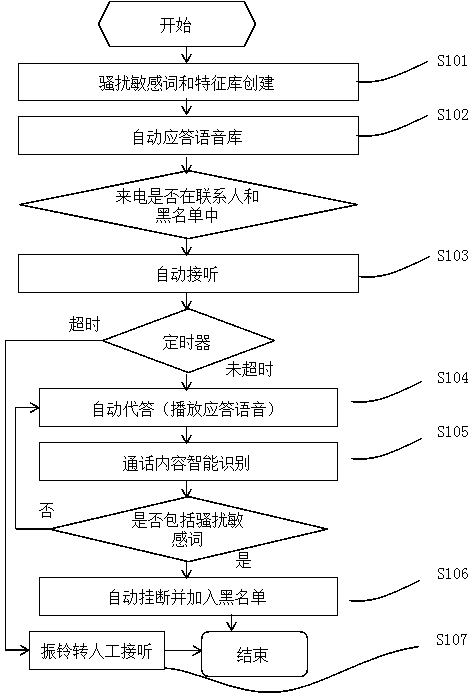
Crank call preventing mobile phone achieving method based on conversation content
InactiveCN104184872AEasy to detectImplement interceptionSubstation equipmentTelecommunicationsMobile phone
The invention discloses a crank call preventing mobile phone achieving method based on conversation content. The technology of auto-answering at the forepart of calling, the intelligent crank call sensitive word recognizing technology, the intelligent sensitive word feature matching technology, the automatic crank call hanging up and recording technology, the non-crank-call manual switching over reminding technology and other key technologies are adopted, the crank call detection and interception at the conversation stage are achieved, the accurate crank call defense based on the true conversation content is achieved, the single mode that traditionally, whether the phone call is the crank call or not is judged only based on the phone number before conversation is avoided, and an accurate and efficient crank call preventing effect is achieved.
Owner:陈桂芳
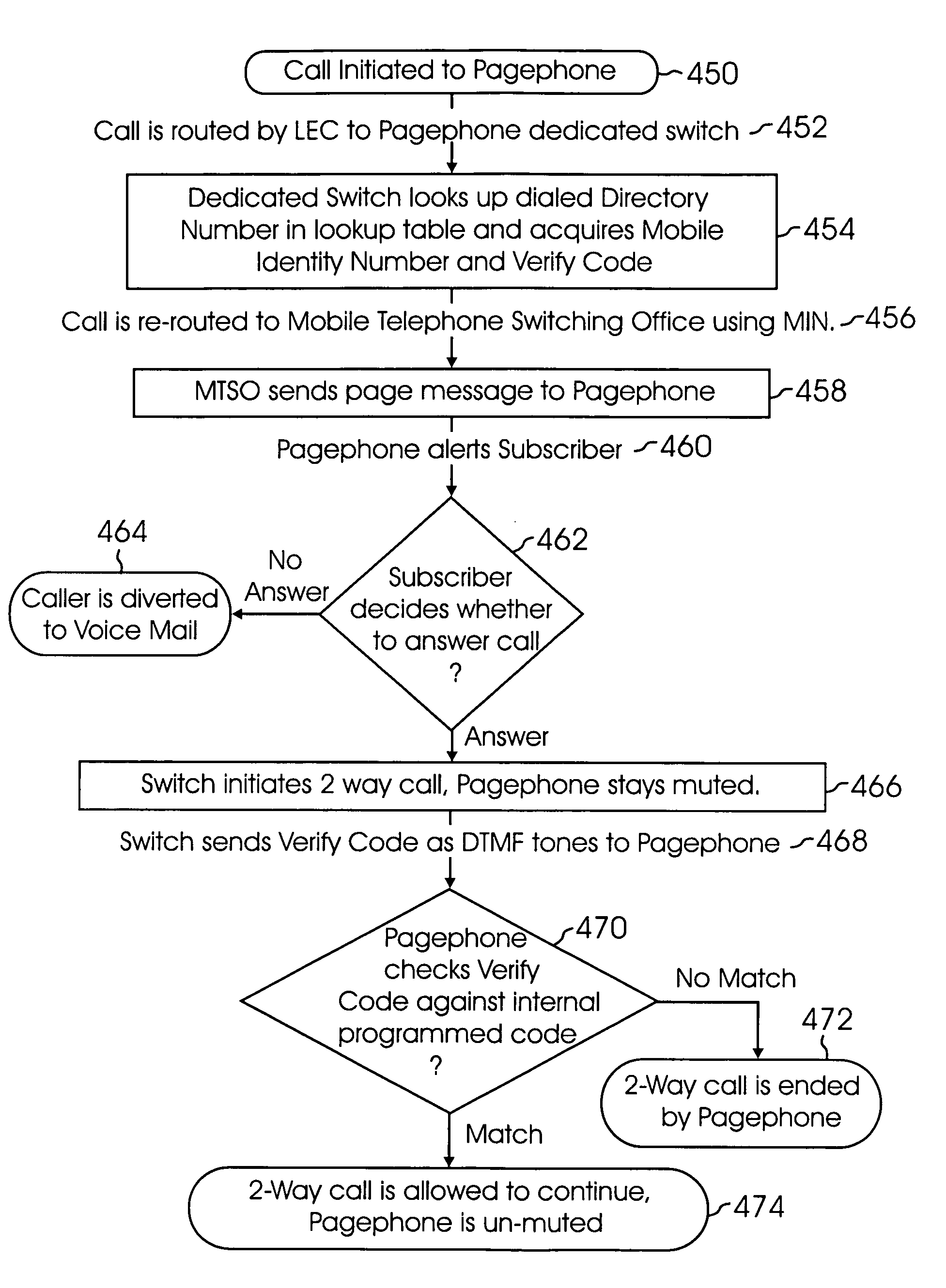
Call receiving method and apparatus having two-way text messaging and automatic retrieval of call numbers making calls to apparatus
InactiveUS7005963B1Reduce fraudInterconnection arrangementsAccounting/billing servicesPagerMessage passing
A system and method for a call receiving pager apparatus, system and method utilizing a dedicated switch for providing proprietary access, billing functions and other enhanced features is described. The system utilizes a subscriber apparatus having pager or radiotelephone functions whereby a caller may call the apparatus and gain direct two-way communication with the subscriber. The caller is billed for the communication. A call receiving pager apparatus, system and method which enables two-way text messaging as well as the storage, retrieval, and recall of telephone numbers making calls to the pager apparatus where the recalls are made by way of sending a data package to the stored caller number is described. The subscriber is unable to initiate any real time two-way communication with the outgoing connection.
Owner:LBT IP LLC
Method and apparatus for automatically deactivating a keypad lock
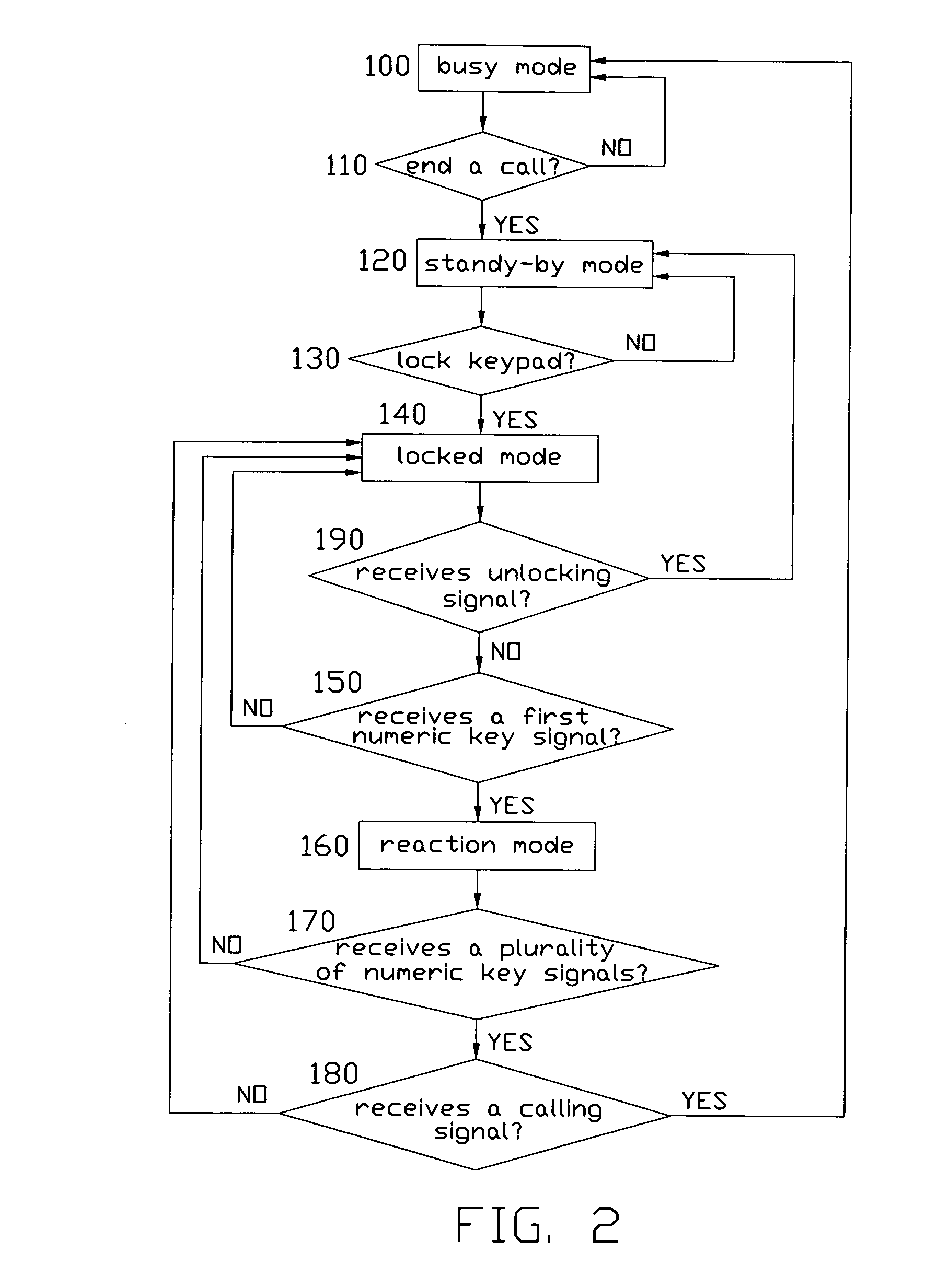
InactiveUS20060046694A1Automatically deactivate the keypad lockUnauthorised/fraudulent call preventionEavesdropping prevention circuitsReal-time computingCommunication device
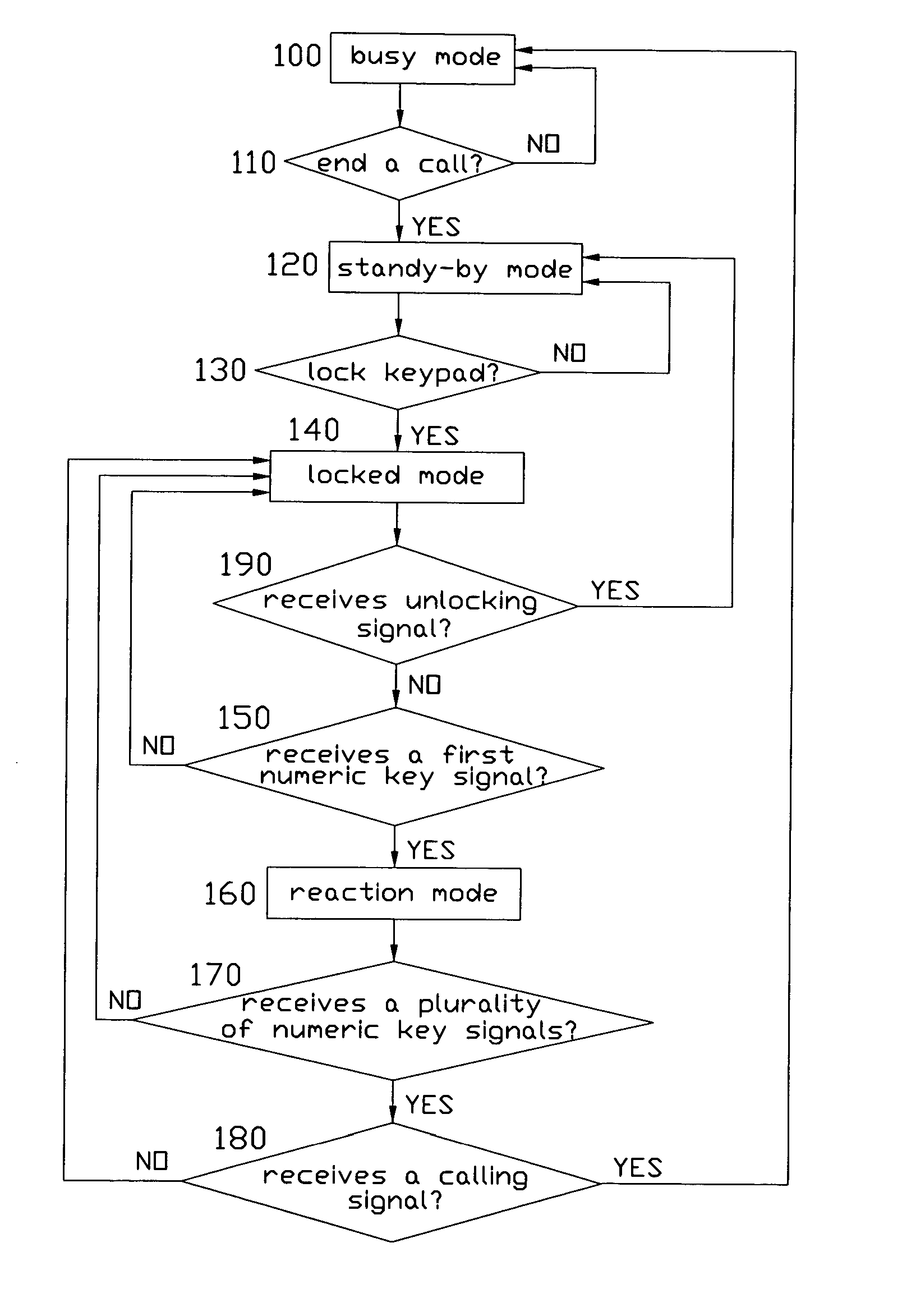
The present invention relates to a method for automatically deactivating a keypad lock and a communication apparatus for performing the method, wherein when in locked mode, the communication apparatus does not react to any other keypad command but a predetermined unlocking signals and signals from numeric keys. It is not necessary that the user should have to input unlocking signals before dialing a phone number. The method comprises the steps of: 1) determining whether or not it receives a first numeric key signal from the keypad, 2) then waiting for a first waiting delay to determine whether it receives a plurality of numeric key signals, 3) and at last determining whether it receives a dialing signal in a second waiting delay, 4) if all answer of above is yes, the keypad lock being deactivated and a communication connection being setup.
Owner:ASIA OPTICAL CO INC
Activation of electronic lock using telecommunications network
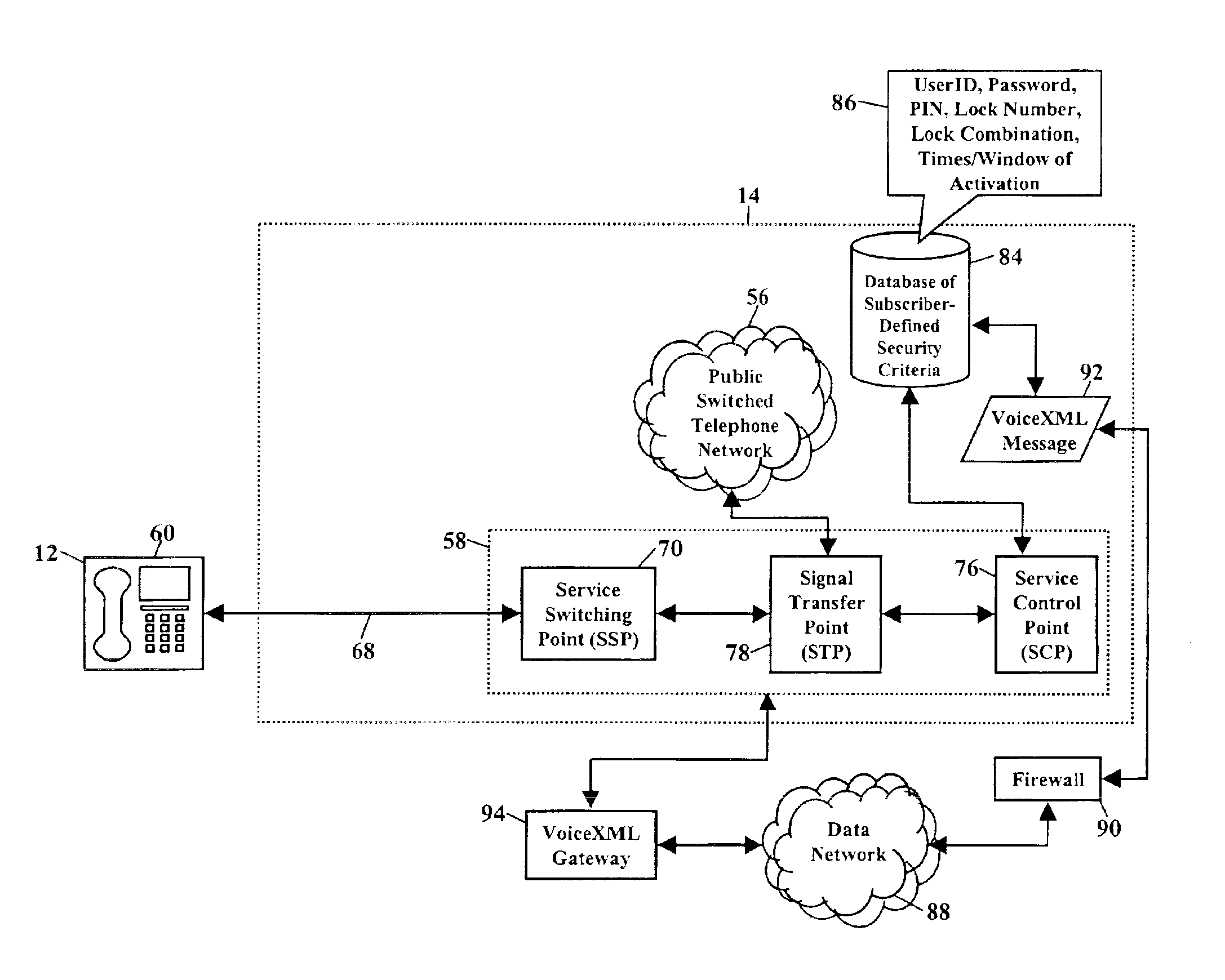
InactiveUS6885738B2Reduce the burden onCalled number recording/indicationNetwork connectionsIntelligent NetworkTelecommunications network
Methods and systems are disclosed for activating an electronic lock in an intelligent switched telecommunications network having a plurality of Advanced Intelligent Network (AIN) components. A call is received from a device communicating with the telecommunications network. The call is from a calling party to a called party. Processing of the call within the telecommunications network is suspended. A database is queried for a telephone number of the called party. The database stores telephone numbers of called parties subscribing to a lock service provided by a telecommunications service provider. The lock service allows a user to remotely activate an electronic lock using the telecommunications network. If the query is successful, processing of the call within the telecommunications network is resumed. The call is used to activate the electronic lock.
Owner:OPEN INVENTION NEWTORK LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com