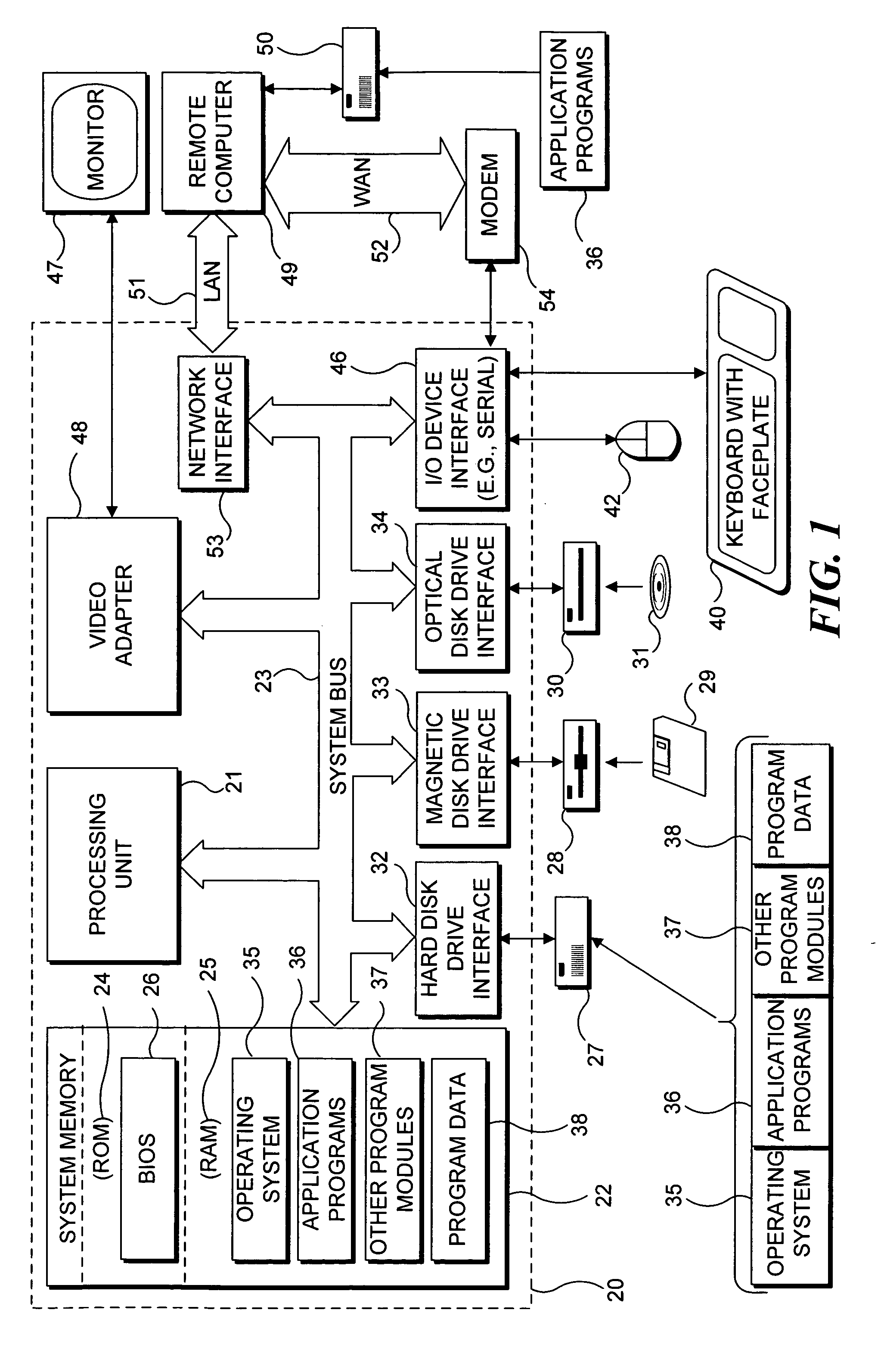
Patents
Literature
2945 results about "Verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
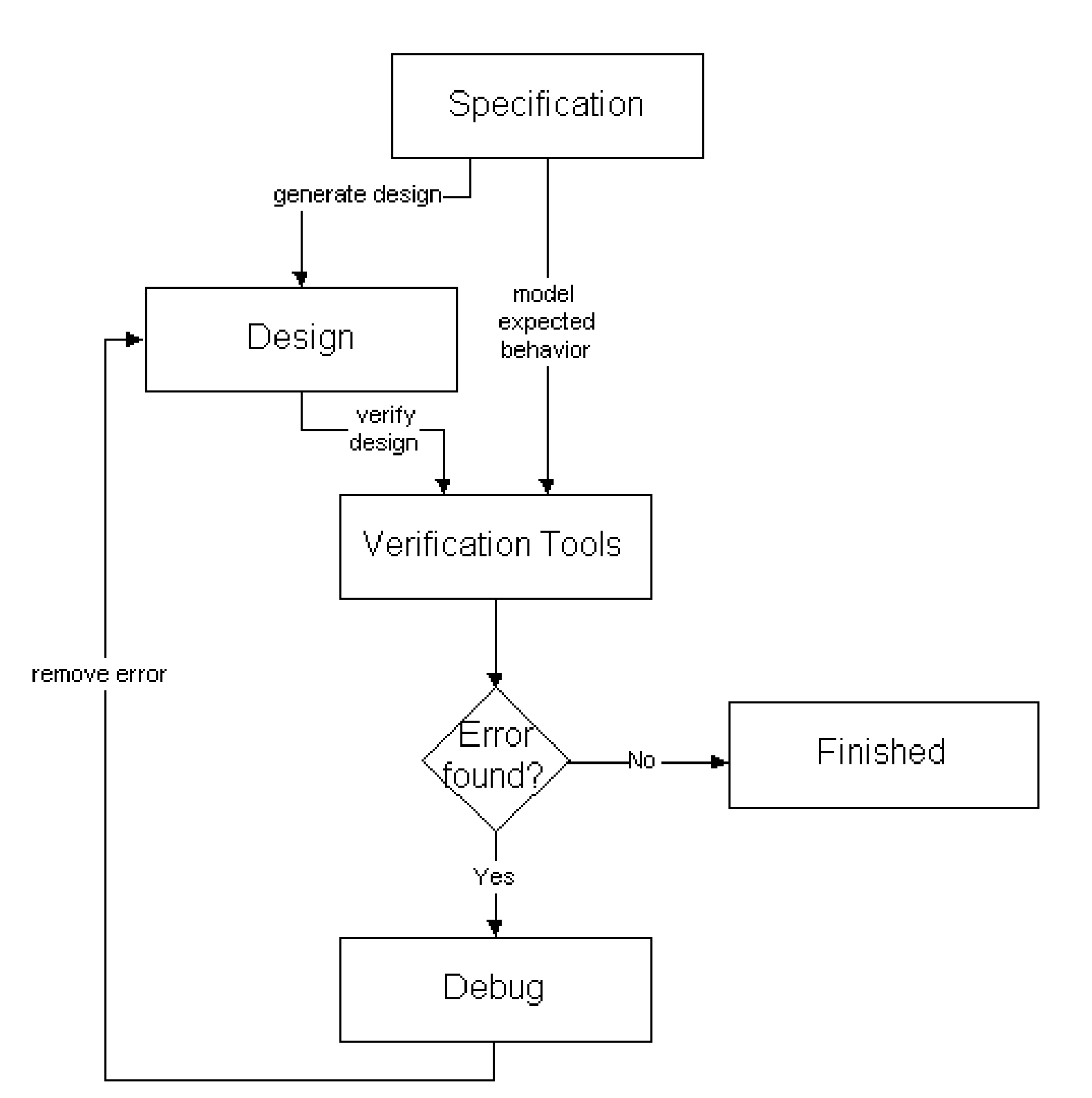
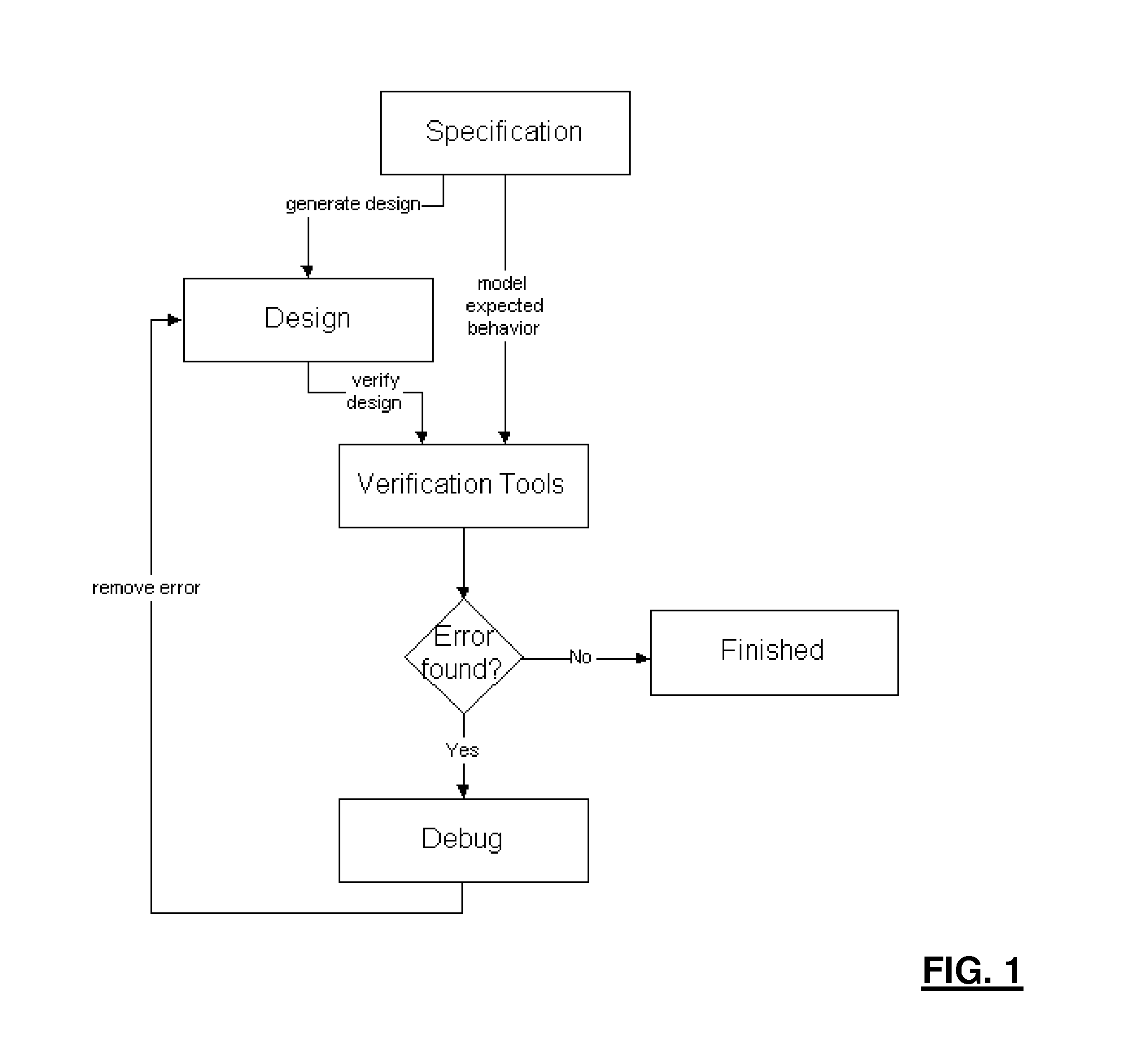
Verification in the field of space systems engineering covers two verification processes: Qualification and Acceptance
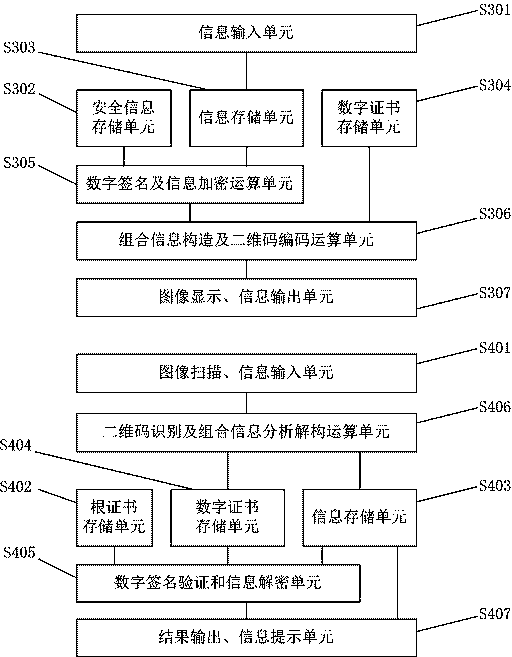
Construction verification method and device capable of verifying security two-dimensional code offline
ActiveCN106452756AEasy to useCannot be tampered withKey distribution for secure communicationUser identity/authority verificationInformation analysisEffective time
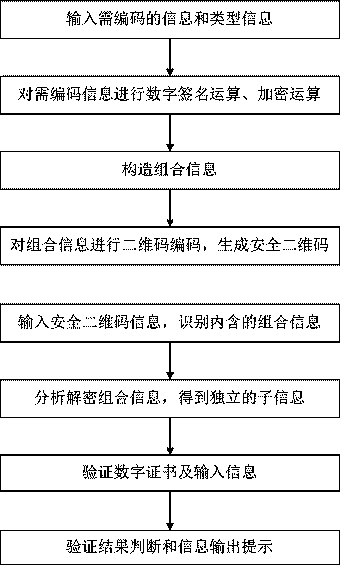
Embodiments of the invention provide a construction verification method and device capable of verifying a security two-dimensional code offline. The method comprises the following steps of inputting information that needs coding and type information, carrying out digital signature operation and encryption operation on the input information according to an information release type, constructing combination information, and encoding to generate a security two-dimensional code which can be verified off-line according to a two-dimensional code coding rule; inputting the information of the security two-dimensional code and identifying included combination information and type information, analyzing and decoding the combination information to obtain independent sub-information according to the type information of the two-dimensional code, and verifying digital certificate effectiveness information, a digital signature of the input information and an effective time limit of the input information; and if all verifications pass, showing that the offline verification of the security two-dimensional code is correct and the coding information source of the security two-dimensional code is credible, otherwise showing that the information release source of the security two-dimensional code is incredible. The method and the device have the beneficial effects that the security two-dimensional code cannot be tampered, counterfeited and denied, the public or private information can be released, and the integrity of the information of the security two-dimensional code and the authenticity of the source can be verified offline without a network connection.
Owner:王栋
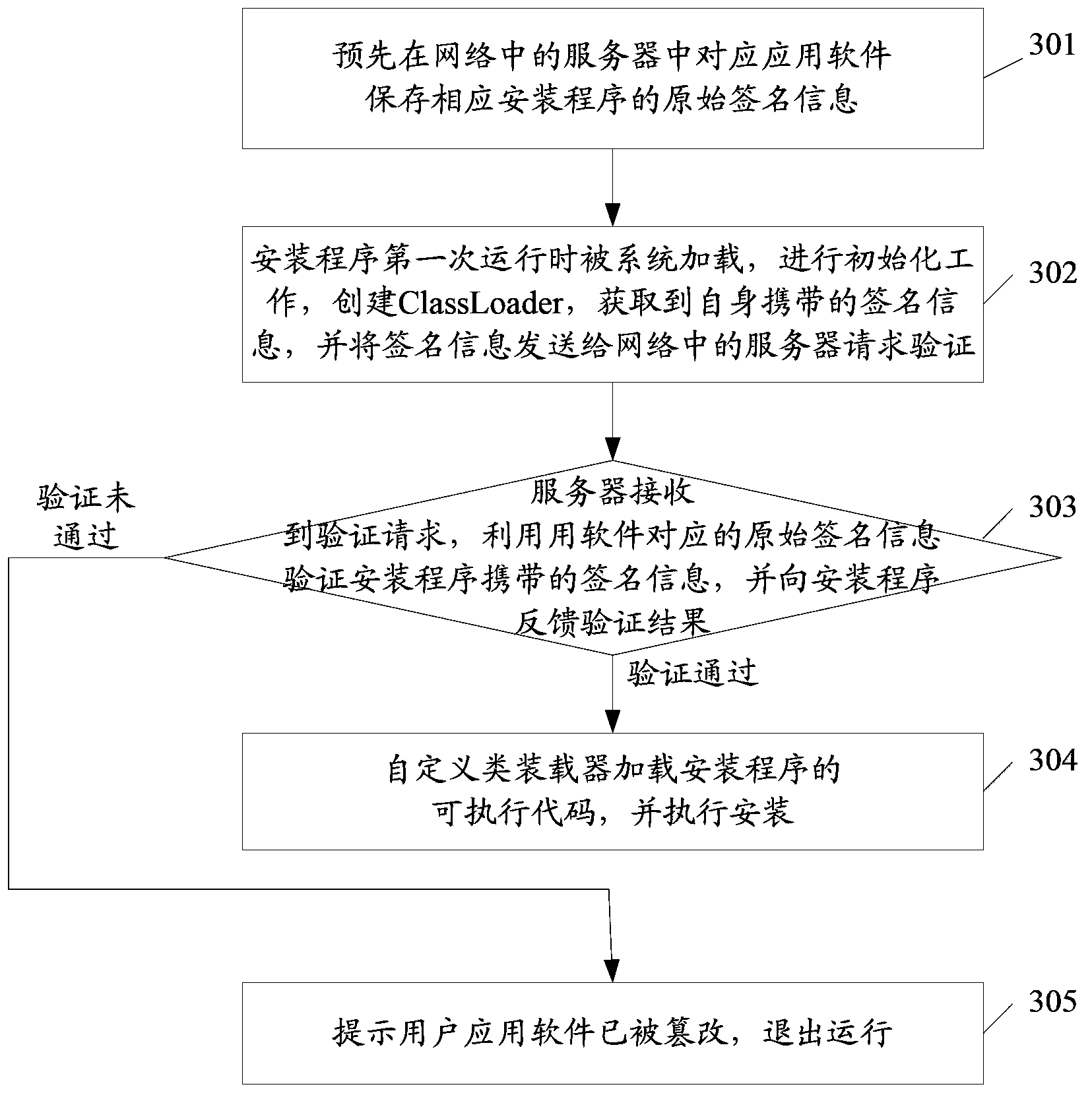
Method and device for installing application software
InactiveCN103577206AAvoid installationComputer security arrangementsProgram loading/initiatingOperational systemSoftware engineering
The invention discloses a method for installing application software. The method includes acquiring signature information carried by an installation program; utilizing prestored original signature information of an installation program of the application software to verify the signature information carried by the installation program, and if a verification result is unsuccessful, exiting installation of the application software; if the verification result is successful, executing an executable code of the installation program. The invention further discloses a device for installing the application software. By the method and the system, a tampered installation program can be effectively recognized, so that the application software which is maliciously modified is effectively avoided from being installed in an operation system.
Owner:BEIJING SAMSUNG TELECOM R&D CENT +1
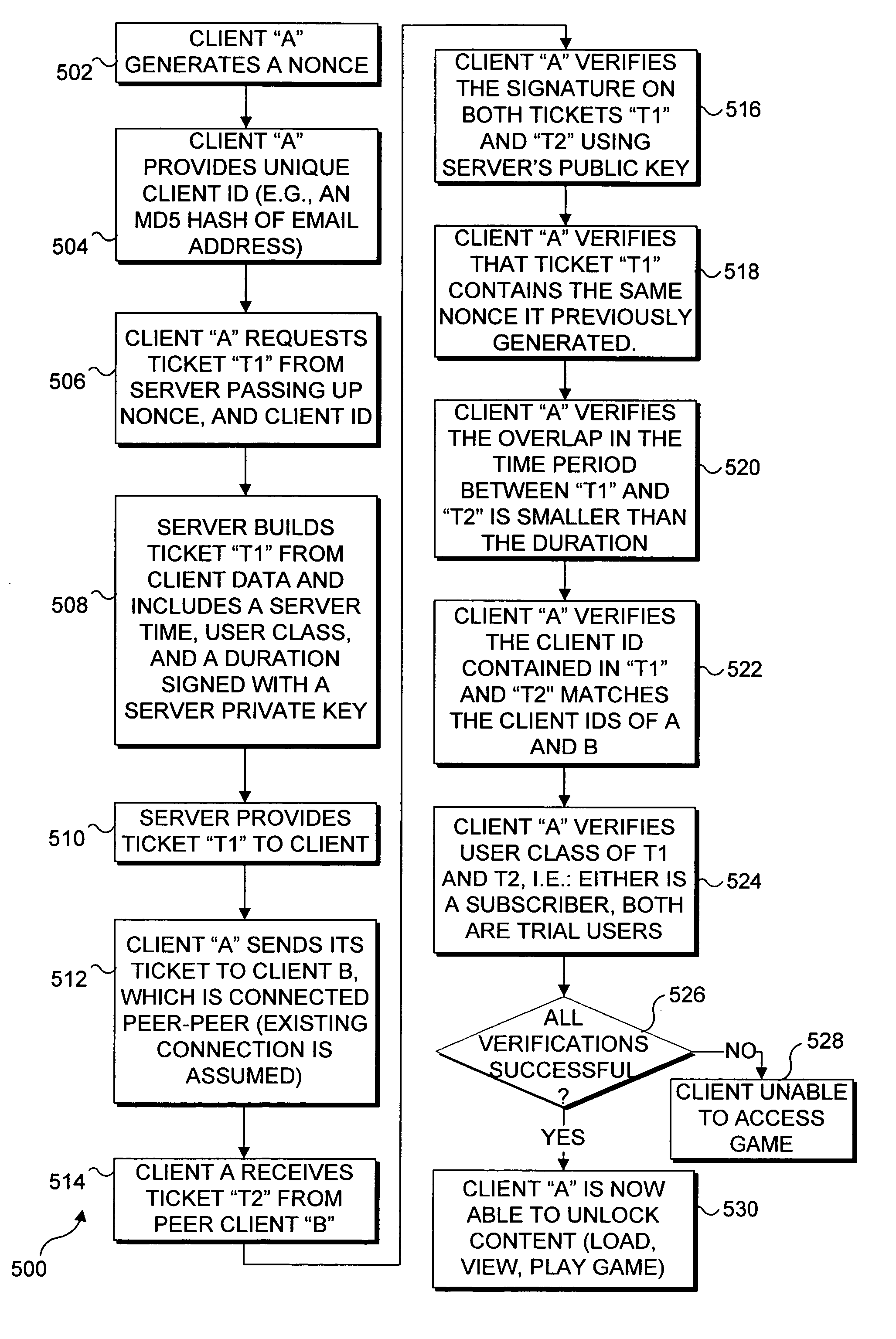
Trial-before-purchase subscription game infrastructure for peer-peer networks
InactiveUS20060123117A1Safety managementEnabling useDigital data processing detailsUnauthorized memory use protectionDigital signatureClient-side
A game or other software program is made accessible for execution by clients on a peer-peer network only after a plurality of verifications are made to ensure that control of the software is maintained. With a request sent to a server to access the software, a client includes a nonce and an ID of the user. The server digitally signs a portion of a ticket that is returned to the client, which includes the nonce, a time stamp, and the ID. The ticket is required to access the software. The clients are required to exchange the tickets, verify the digital signature on the portion of each ticket, and use the information therein to confirm that the tickets are current, issued by the correct server, issued to the proper users, and received from the users who are intended to execute the software.
Owner:MICROSOFT TECH LICENSING LLC
Familiar dynamic human challenge response test content
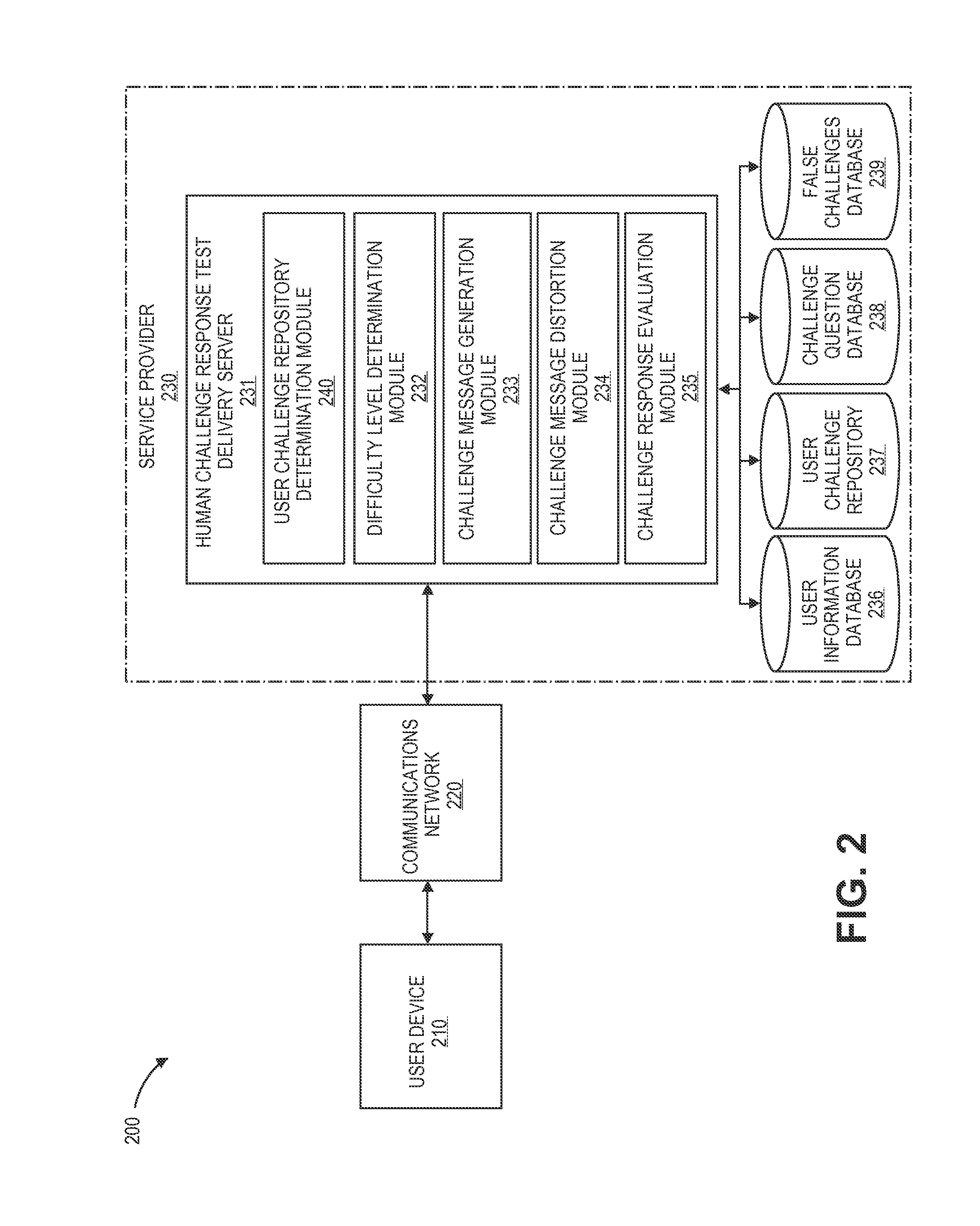
ActiveUS20130160098A1Easy to explainLimiting automated computer attackDigital data processing detailsMultiple digital computer combinationsUser deviceSoftware engineering
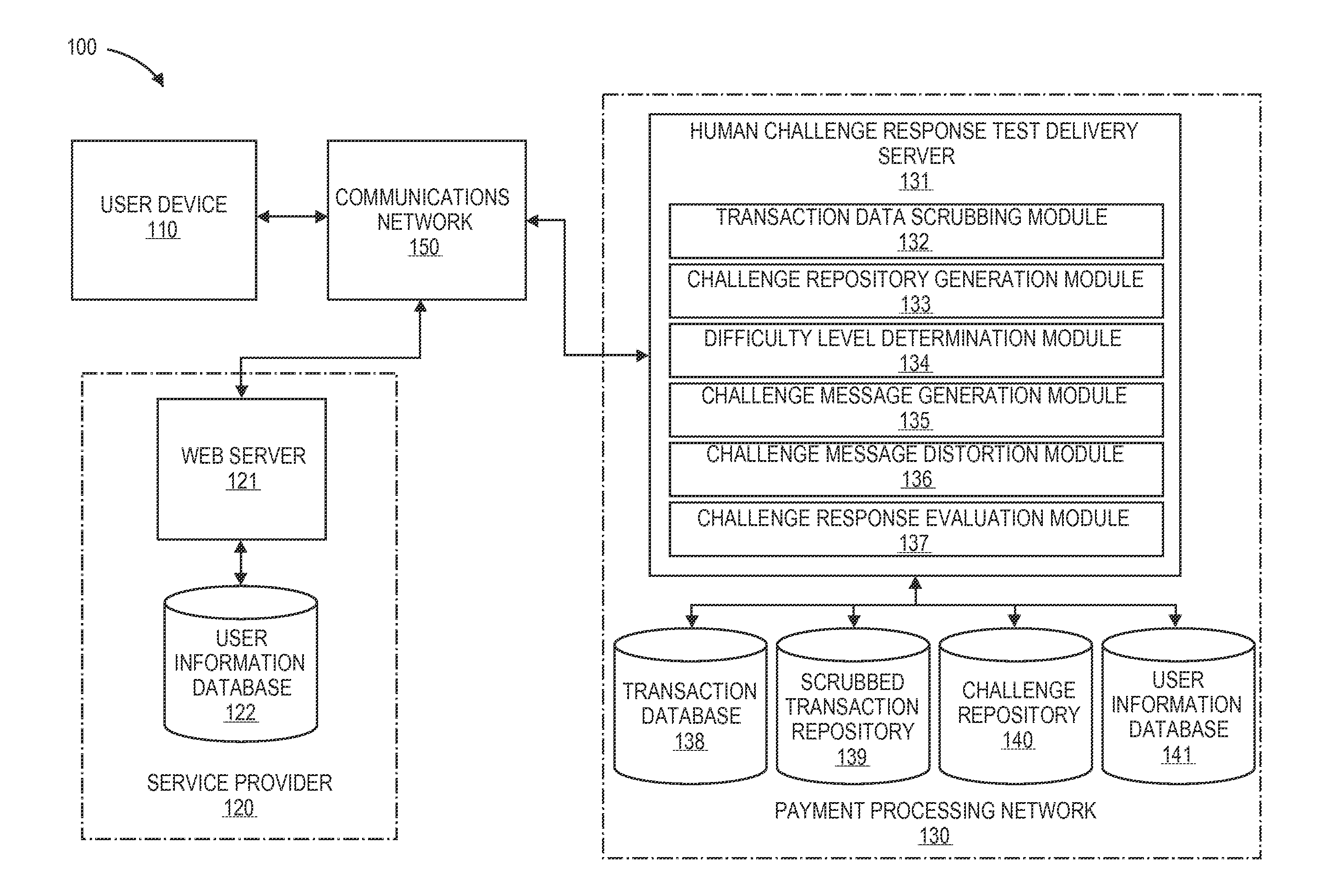
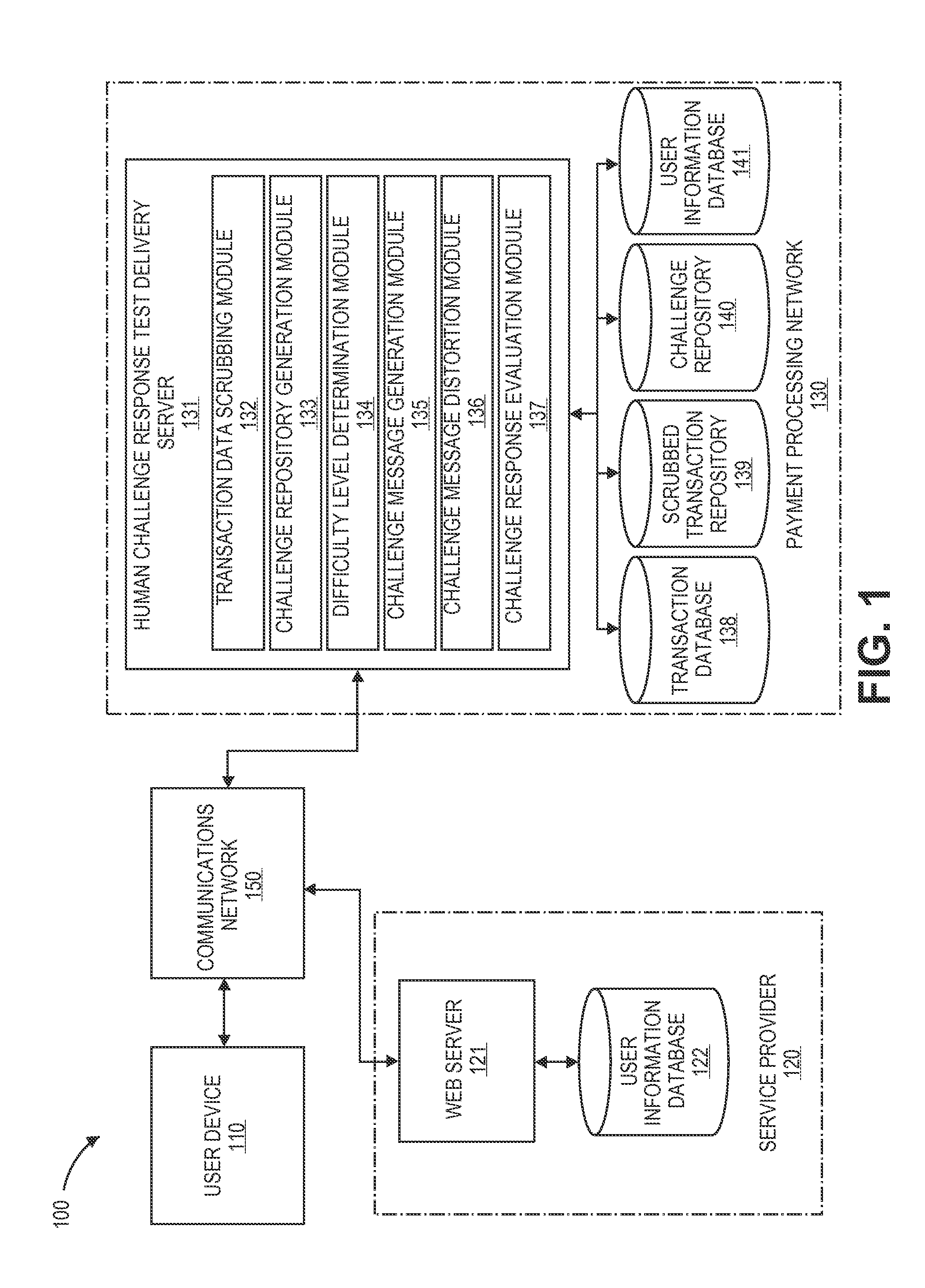
Embodiments of the invention are directed to human challenge response test delivery systems and methods. Specifically, embodiments of the present invention are directed to secure human challenge response test delivery services of configurable difficulty for user devices. One embodiment of the present invention is directed to methods and systems for implementing a familiar and dynamic human challenge response test challenge repository created from transaction data. The dynamic human challenge response test challenge repository may be created by a server computer receiving a plurality of transaction data. Challenge items may be extracted from the transaction data using an extraction algorithm. Furthermore, in some embodiments a challenge message may be sent to a requestor, a verification request may be received, and the verification request may be compared to the challenge message. Another embodiment may be directed at using user information in a human challenge response test to mutually authenticate a user and a service provider.
Owner:VISA INT SERVICE ASSOC
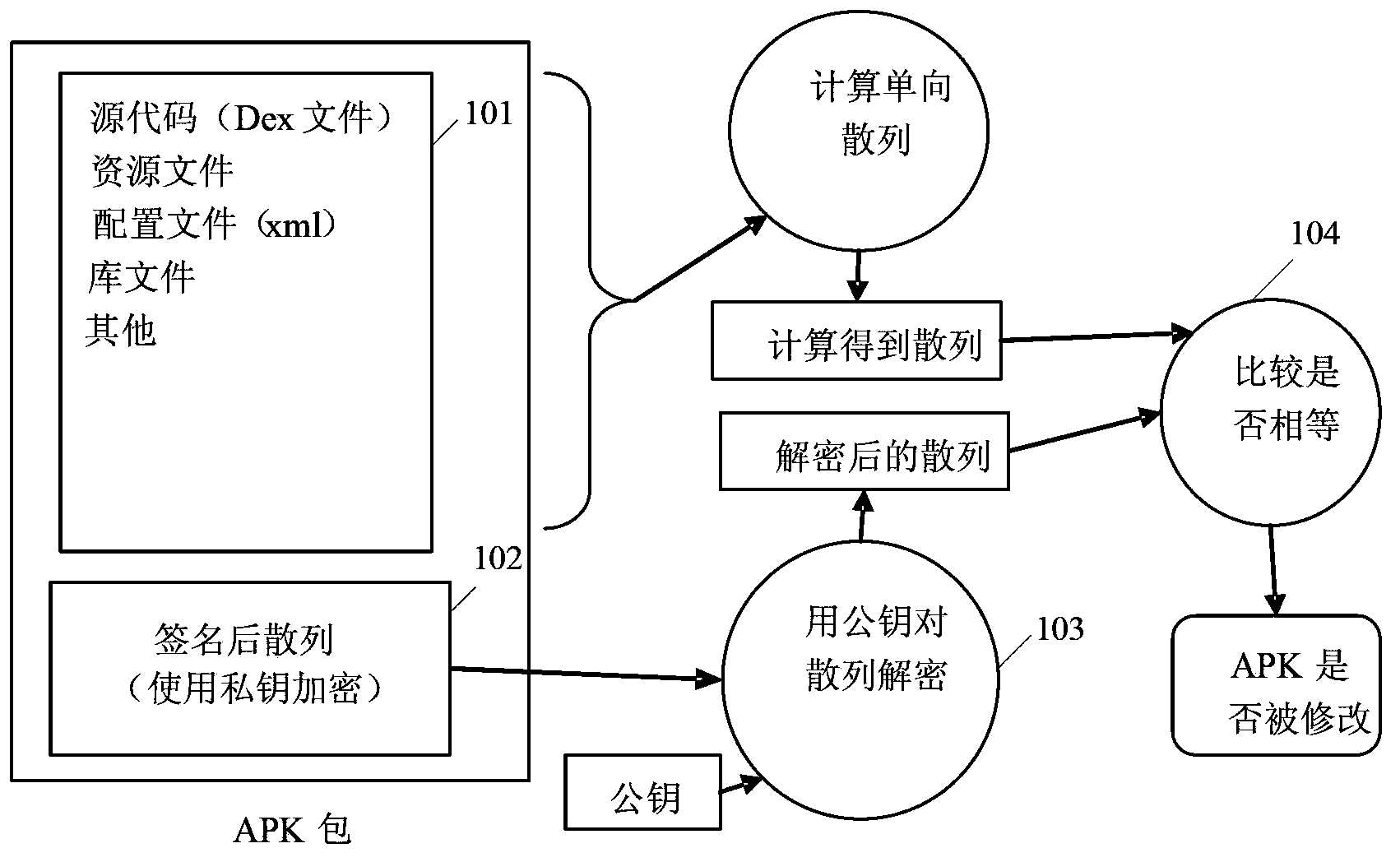
Verification of software application authenticity
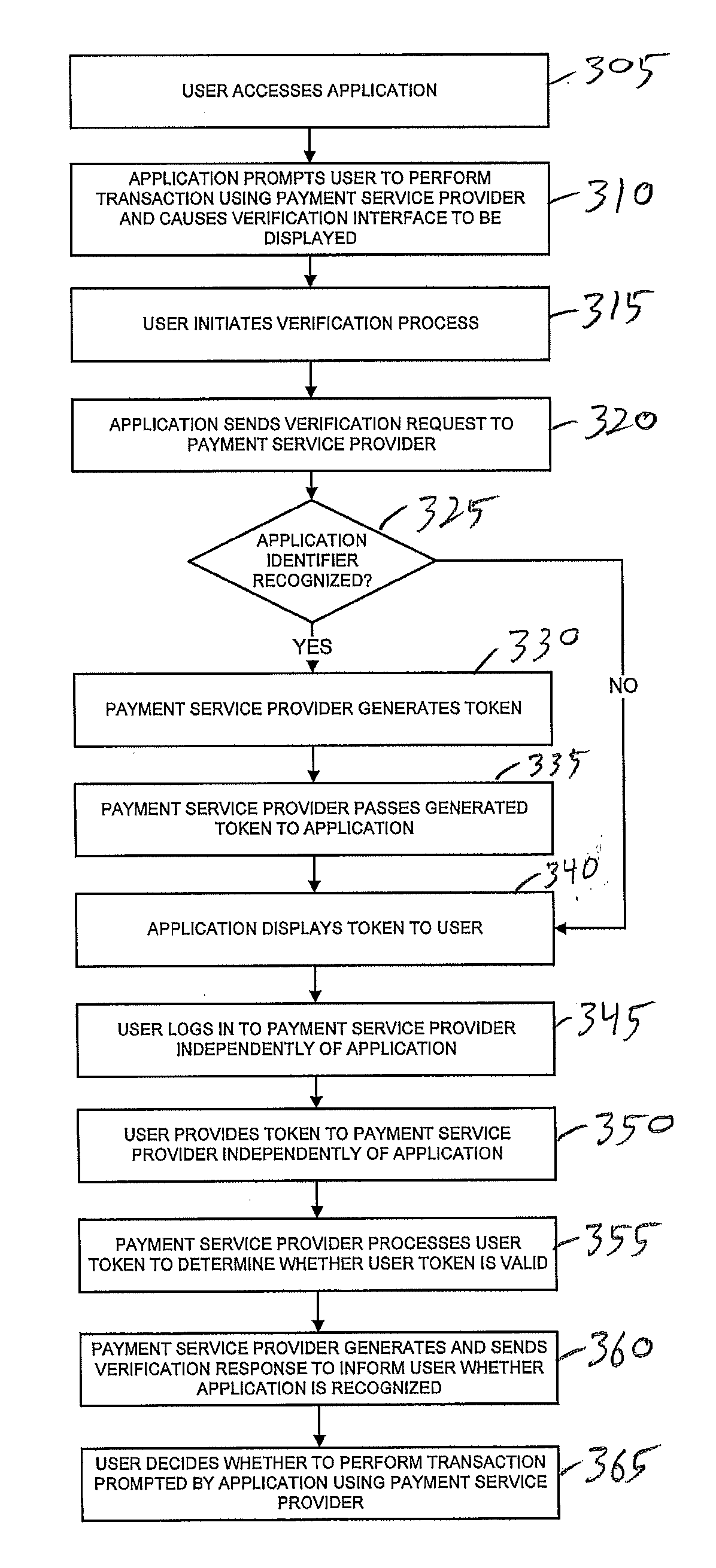
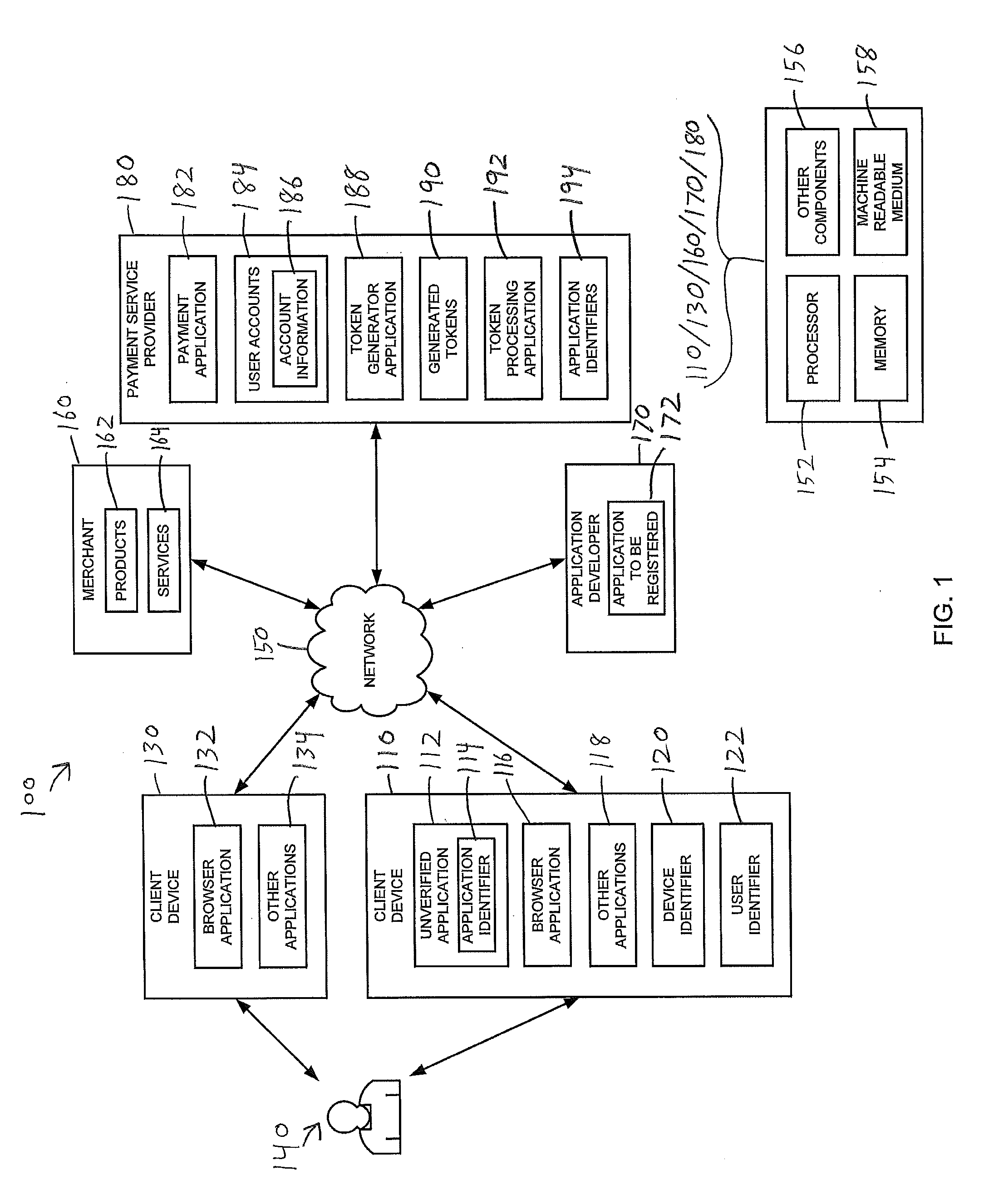
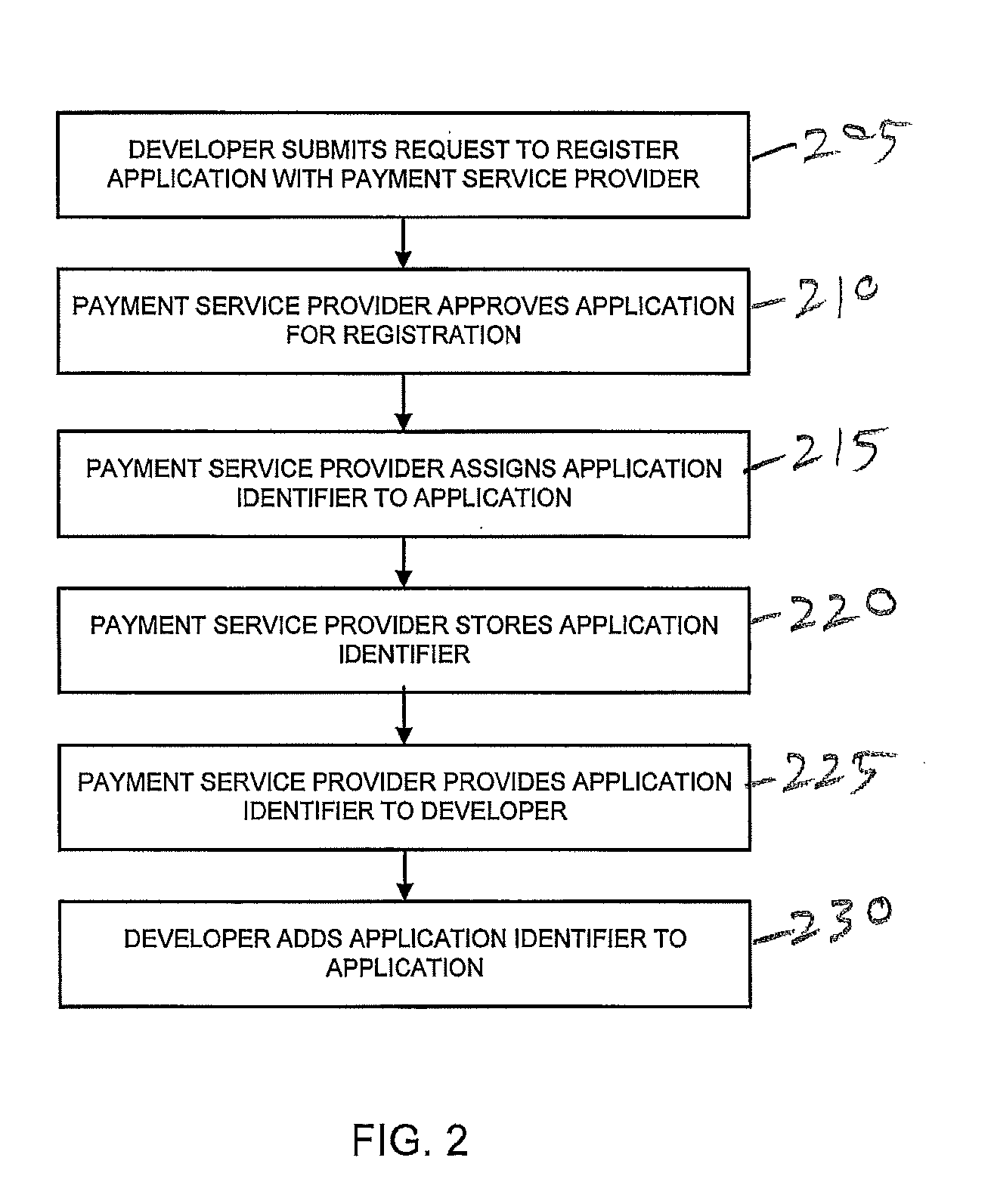
ActiveUS20090328207A1Memory loss protectionError detection/correctionApplication softwareApplication Identifier
Various techniques are provided for verifying the authenticity of software applications. Such techniques are particularly useful for verifying the authenticity of software applications used in online transactions involving users, payment service providers, and / or merchants. In one example, a set of application identifiers associated with a plurality of authenticated software applications are maintained and a verification request is received comprising an application identifier associated with an unverified software application. A token is generated in response to the verification request if the application identifier is in the set of application identifiers. The generated token is passed to the unverified software application. A user token is received and processed to determine whether the unverified software application is one of the authenticated software applications. A verification request is sent based on the processing. Additional methods and systems are also provided.
Owner:PAYPAL INC
Method for the static analysis of concurrent multi-threaded software
InactiveUS20070011671A1No loss in precisionReduce decreaseProgram synchronisationError detection/correctionTheoretical computer scienceSoftware
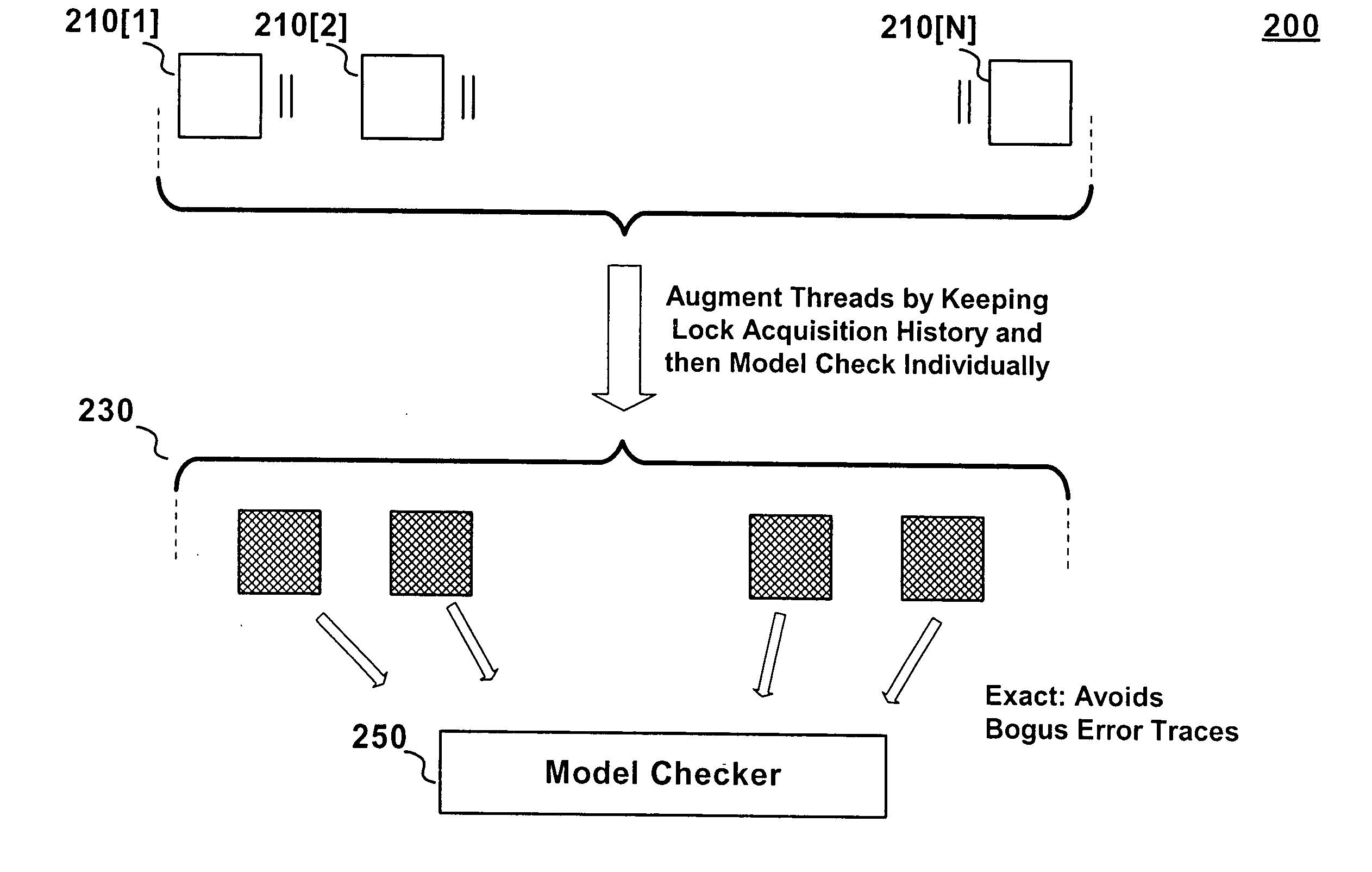
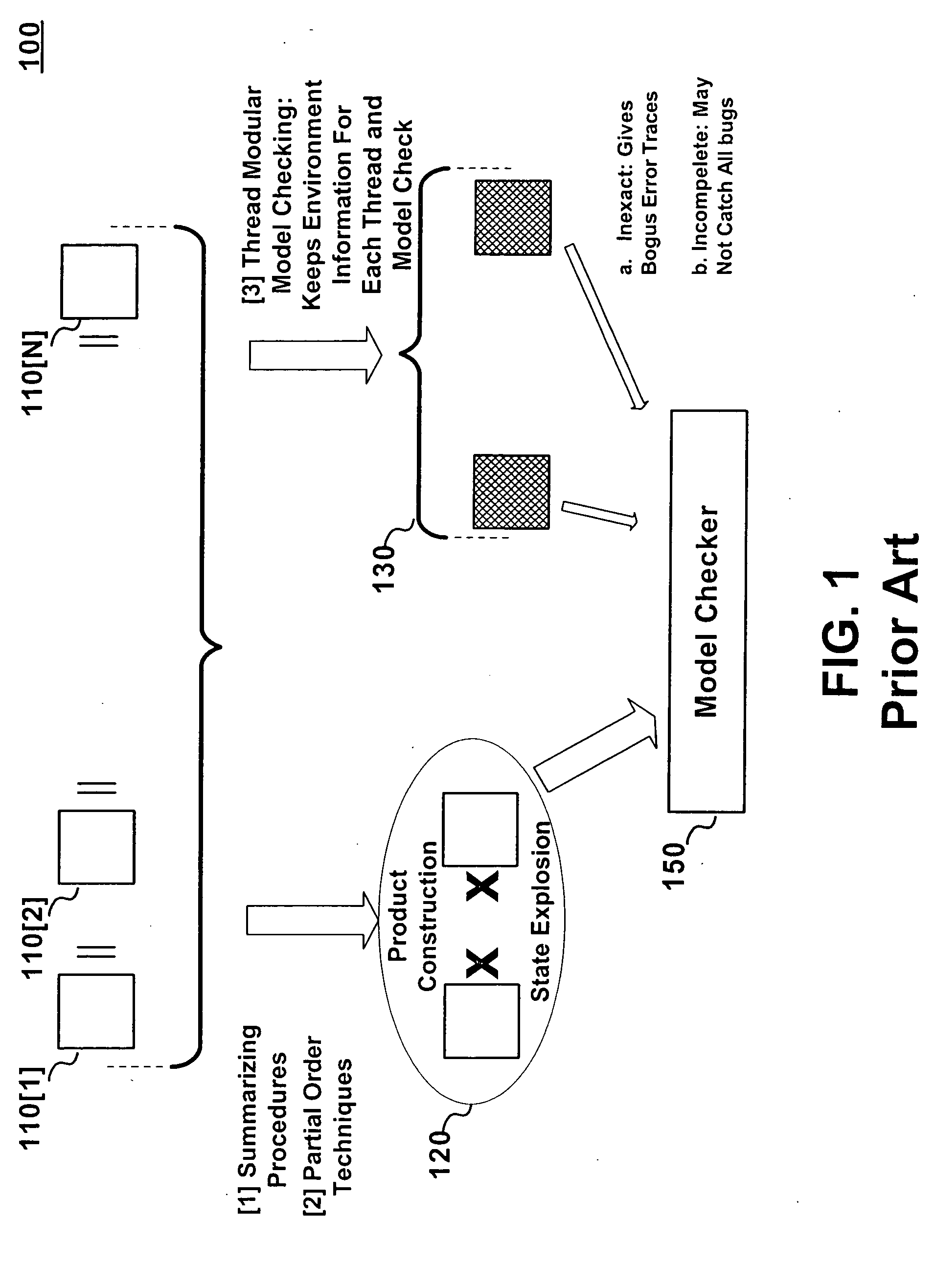
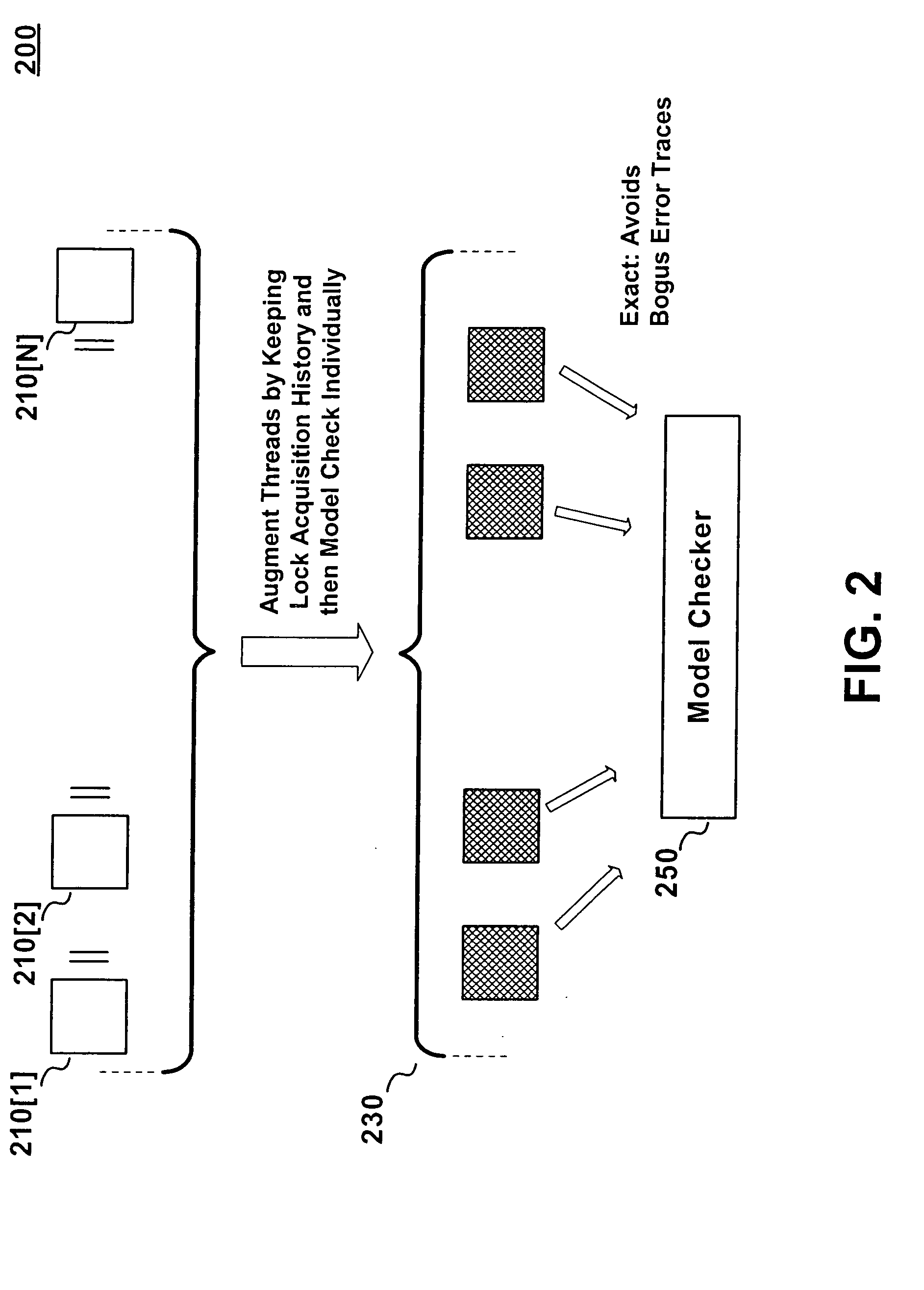
A method for the static analysis of concurrent multi-threaded software which bypasses the state explosion situation that plagues the prior art, thereby making our method scalable while—at the same time—producing no loss in precision. Our inventive method maintains patterns of lock acquisition and lock release by individual threads by constructing augmented versions of the threads. Once the augmented versions have been constructed, our inventive method verifies the concurrent program using existing tools for the verification of sequential programs—thereby greatly reducing implementation overhead. Finally, our inventive augmentation and method is carried out in an automatic manner—without requiring user intervention.
Owner:NEC CORP
Production line design and optimization method based on digital twinning
PendingCN111061232AEasy to controlHave assessmentForecastingTotal factory controlProduction lineStatistical analysis
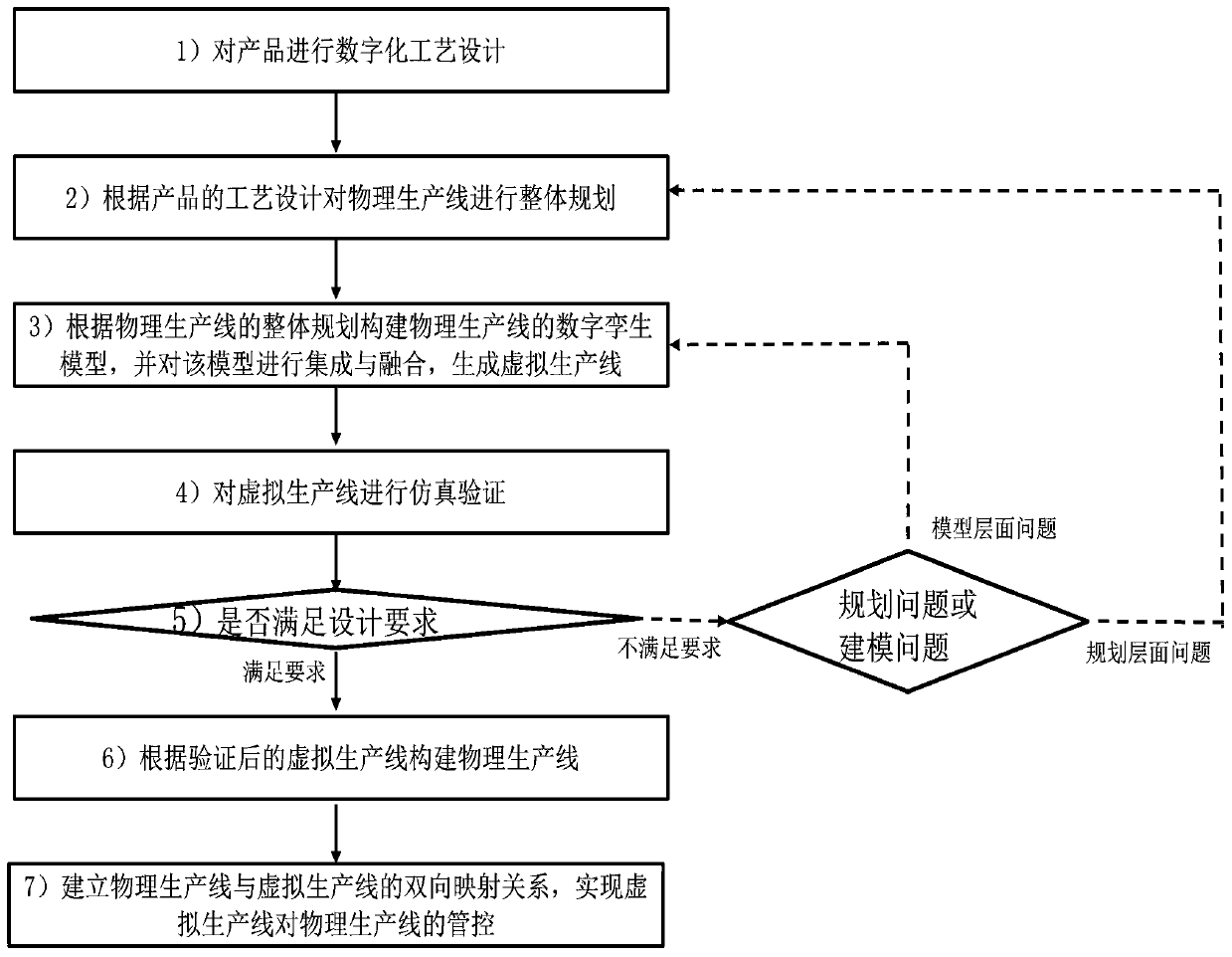
The invention relates to a production line design and optimization method based on digital twinning. The production line design and optimization method comprises the following steps: performing digital process design on a product, integrally planning a production line, constructing and integrating a digital twinning model of the production line, performing simulation verification on a virtual production line, constructing and implementing a physical production line, and performing virtual-real mapping and optimization on the production lines. According to the invention, the digital twinning model is constructed according to three levels of elements, behaviors and rules, and has production line evaluation, evolution and reasoning capabilities; a virtual production line model is established,virtual debugging and simulation operation of the virtual production line are achieved, the production line does not need to be constructed firstly, design risks are avoided, and debugging time is saved; and a virtual-real mapping relationship and an interaction mechanism between the virtual production line and the physical production line are established, statistical analysis is performed on theoperation data of the virtual production line, and optimization and management and control on the physical production line are realized.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
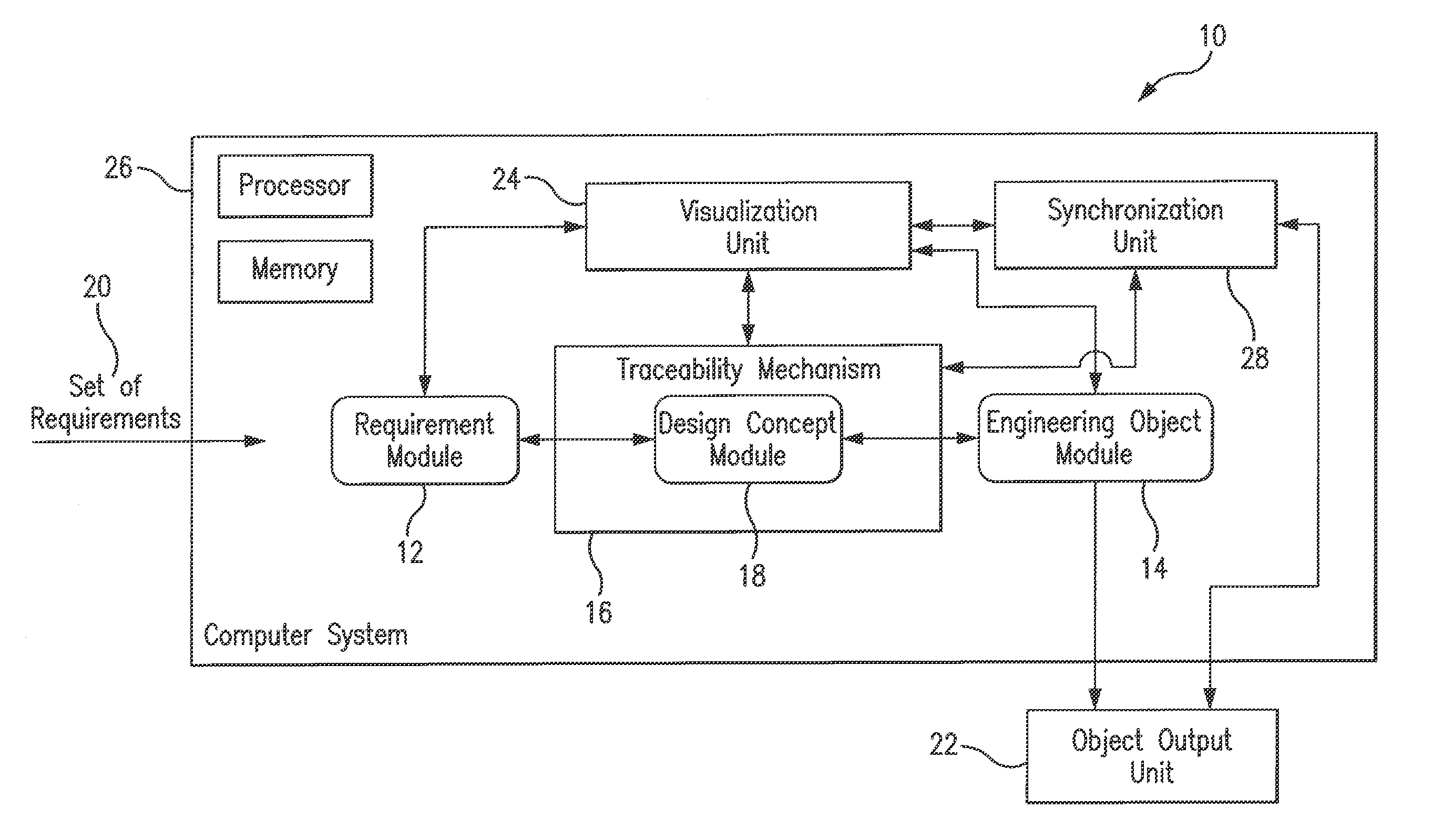
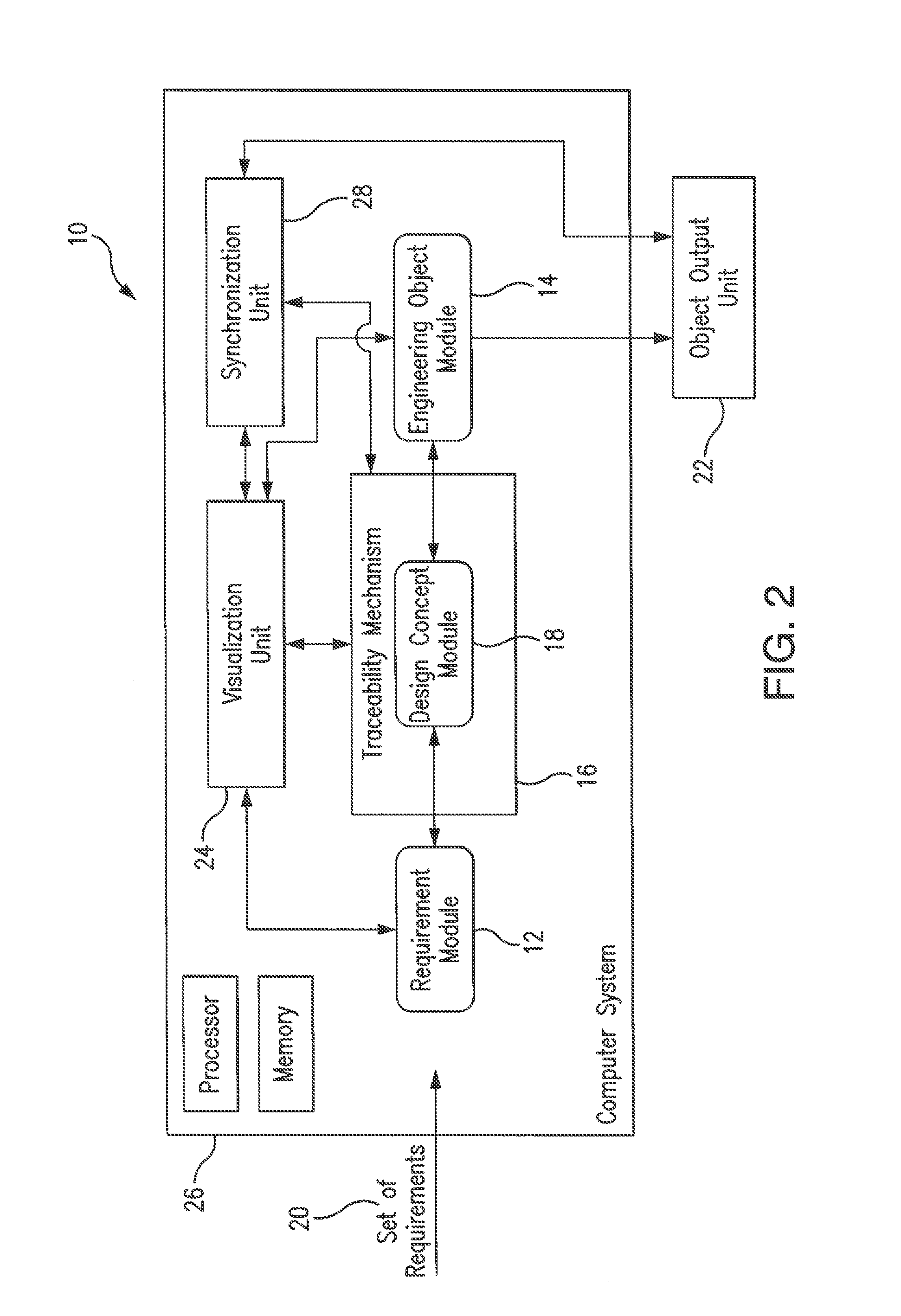
Method and system for ontology-enabled traceability in design and management applications
InactiveUS20120143570A1Enhanced Semantic RepresentationSpecial data processing applicationsNetwork management applicationDesign rule checking
A system and method for ontology-enhanced traceability in design and management applications employ ontology nodes embedded in a processor executable traceability link (network) coupling processor executable requirement modules to processor executable engineering object modules to facilitate in all stages of engineering object development. The engineering object development occurs through multiple models of computation, control, and visualization platform networked together via ontology-enhanced traceability mechanism. Processor executable design rule checking module embedded in the design concept nodes creates a pathway for the development process validation and verification at early stages of the object lifecycle. Linking of ontologies / meta-models is performed for the purposes of supporting ontology-enabled traceability across multiple domains.
Owner:UNIV OF MARYLAND
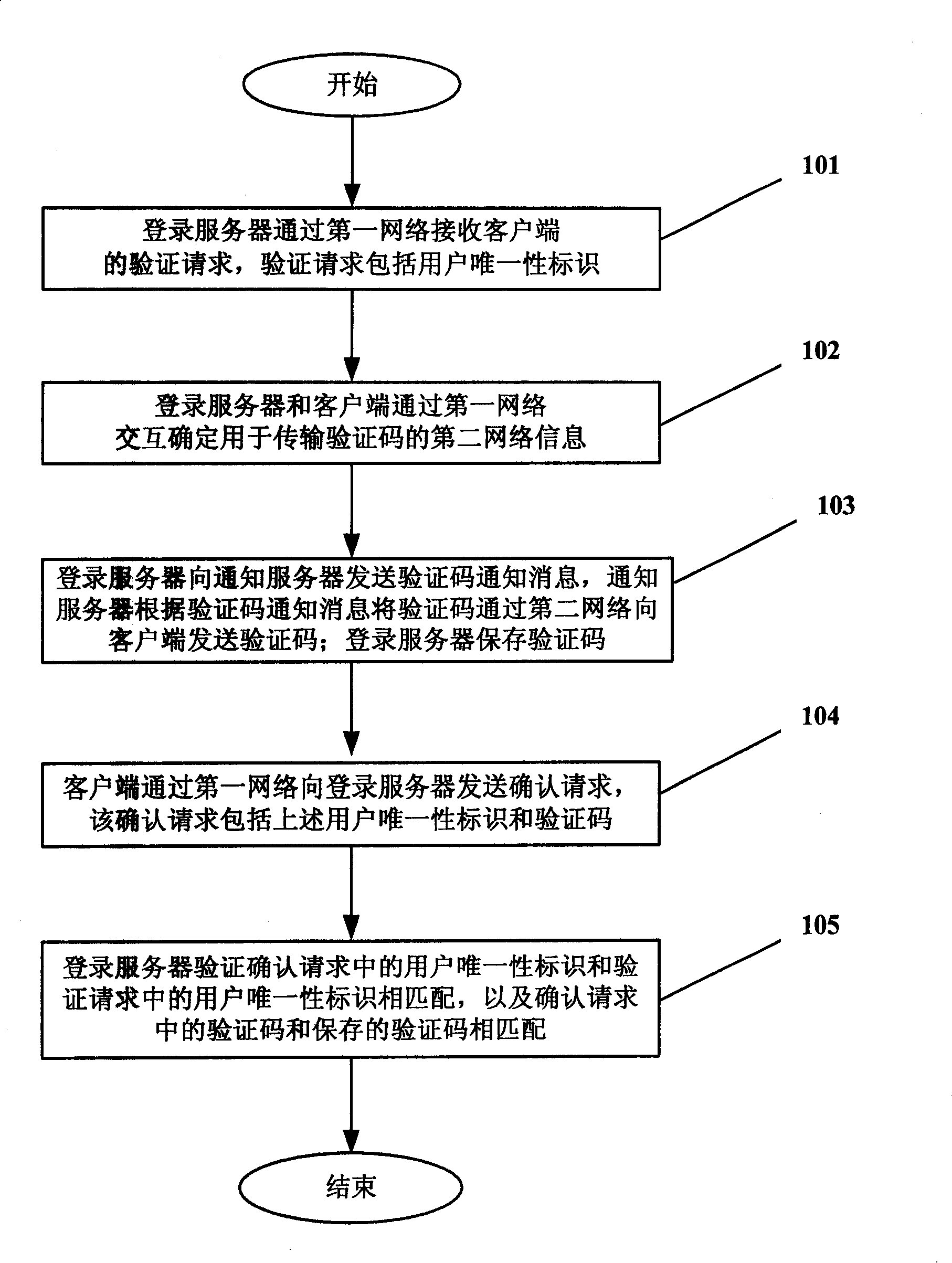
A validation method and system based on heterogeneous network
ActiveCN101242404AHigh selectivityReduce interventionSecuring communicationValidation methodsHeterogeneous network
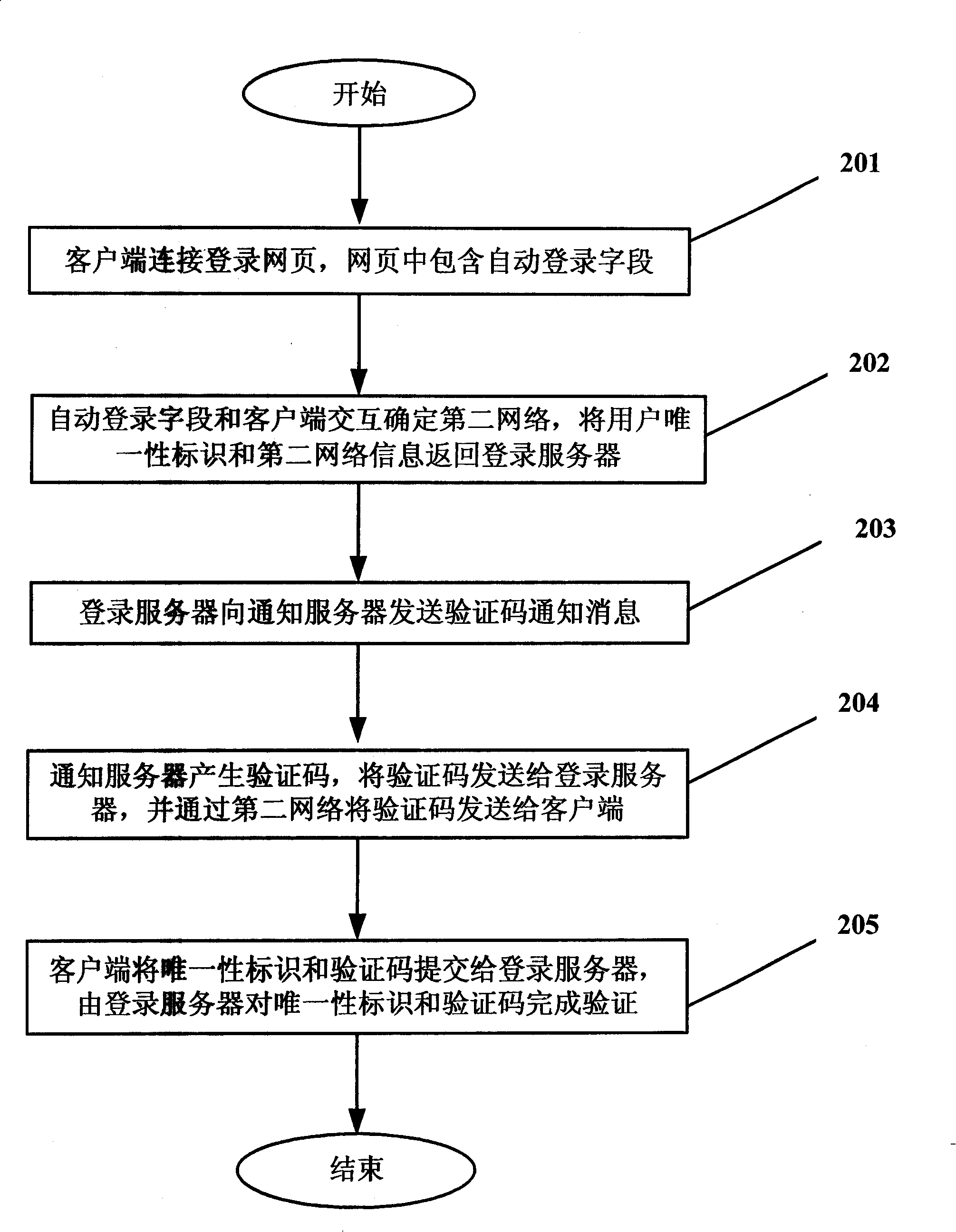
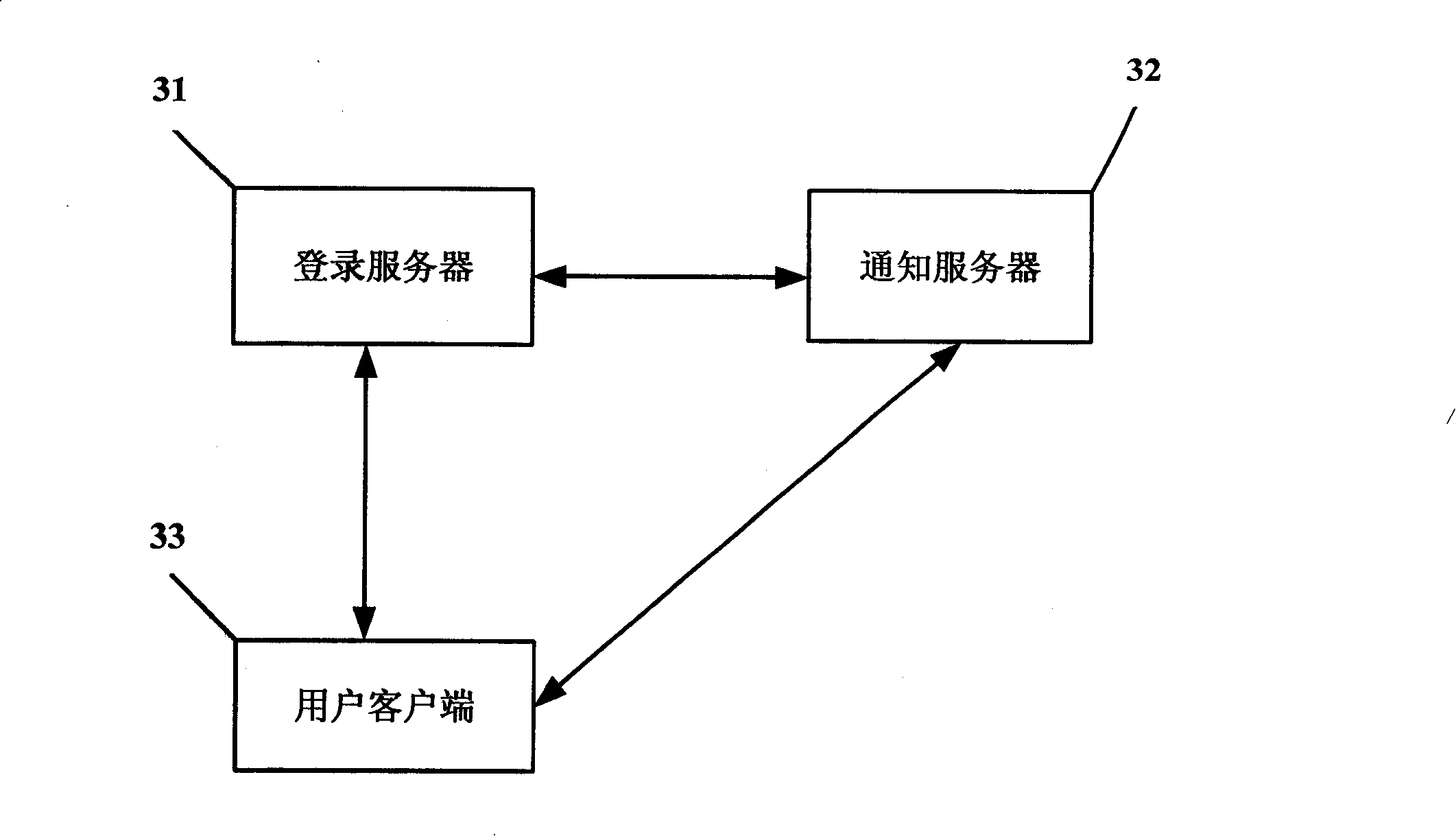
The invention discloses a validation method and a system based on a heterogeneous network, comprising the steps that: a log server receives a unique label of a client; the log server and the client interactively determine second network information for transmitting a verification code by a first network; the log server sends a verification code notification massage to a notice server, the notification server sends the verification code to the client by a second network according to the verification code notification massage; the log server saves the verification code; the client sends a confirmation request including a unique label and a verification code to the log server by the first network; the log server verifies the unique label in the confirmation request, matches the unique label in the confirmation request with the unique label in the verification request, as well as matches the verification code in the confirmation request with the saved verification code. The validation method and the system based on the heterogeneous network improve the convenience and flexibility of a validation process based on the heterogeneous network.
Owner:LENOVO (BEIJING) CO LTD
Multi-version test method and device
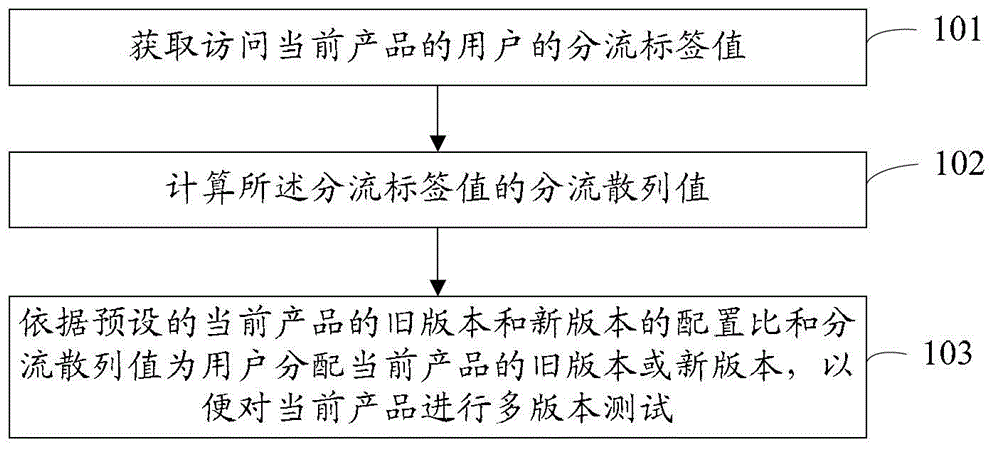
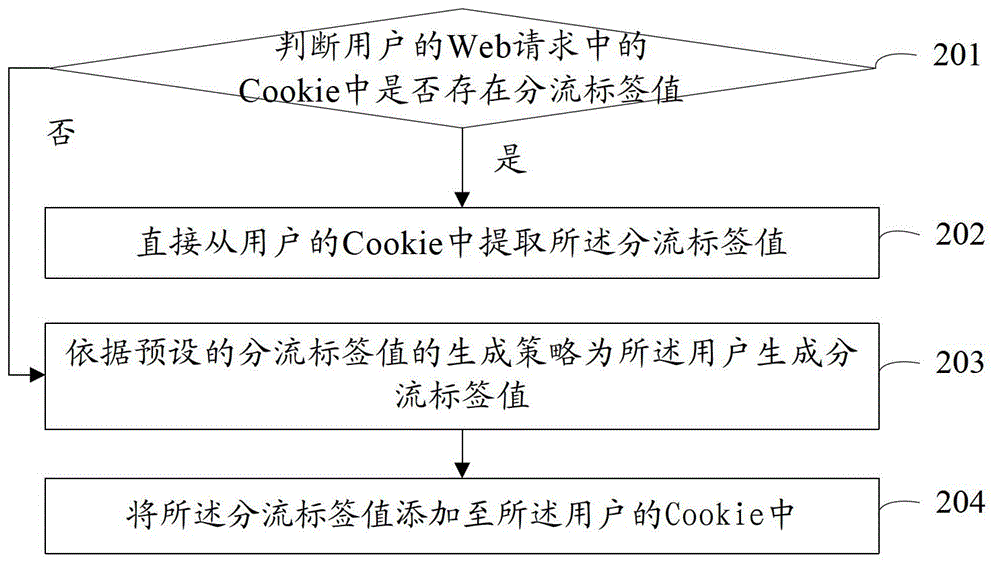
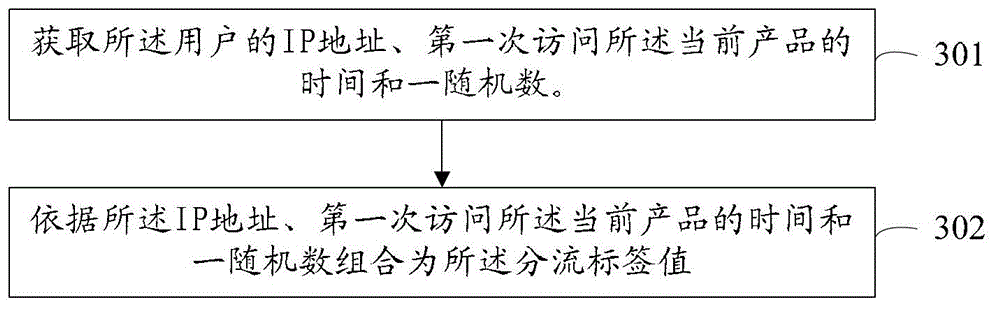
InactiveCN104102576AConvenient multi-version testing methodImprove effectivenessSoftware testing/debuggingCommerceAlgorithmValidation methods
The invention provides a multi-version test method and a multi-version test device. The method comprises the following steps that a shunting label value of a user visiting a current product is obtained, and the shunting label value is used for uniquely identifying the user; a shunting hash value of the shunting label value is calculated; the old version or the new version of the current product is allocated to the user according to the preset configuration ratio of the old version and the new version of the current product and the shunting hash value, so that the current product can be subjected to multi-version test. When the method or the device provided by the embodiment of the invention is adopted, a universal convenient multi-version test method realized on the basis of the shunting hash value can be provided, further, the problems of effectiveness and accuracy of the multi-version test results caused by user differences can be solved, an effective verification method is provided, and the problem of mutual interference of shunting during the parallel proceeding of the multiple multi-version tests on the same product can also be solved.
Owner:ALIBABA GRP HLDG LTD
Reliable firmware upgrading realizing method for distributed control system
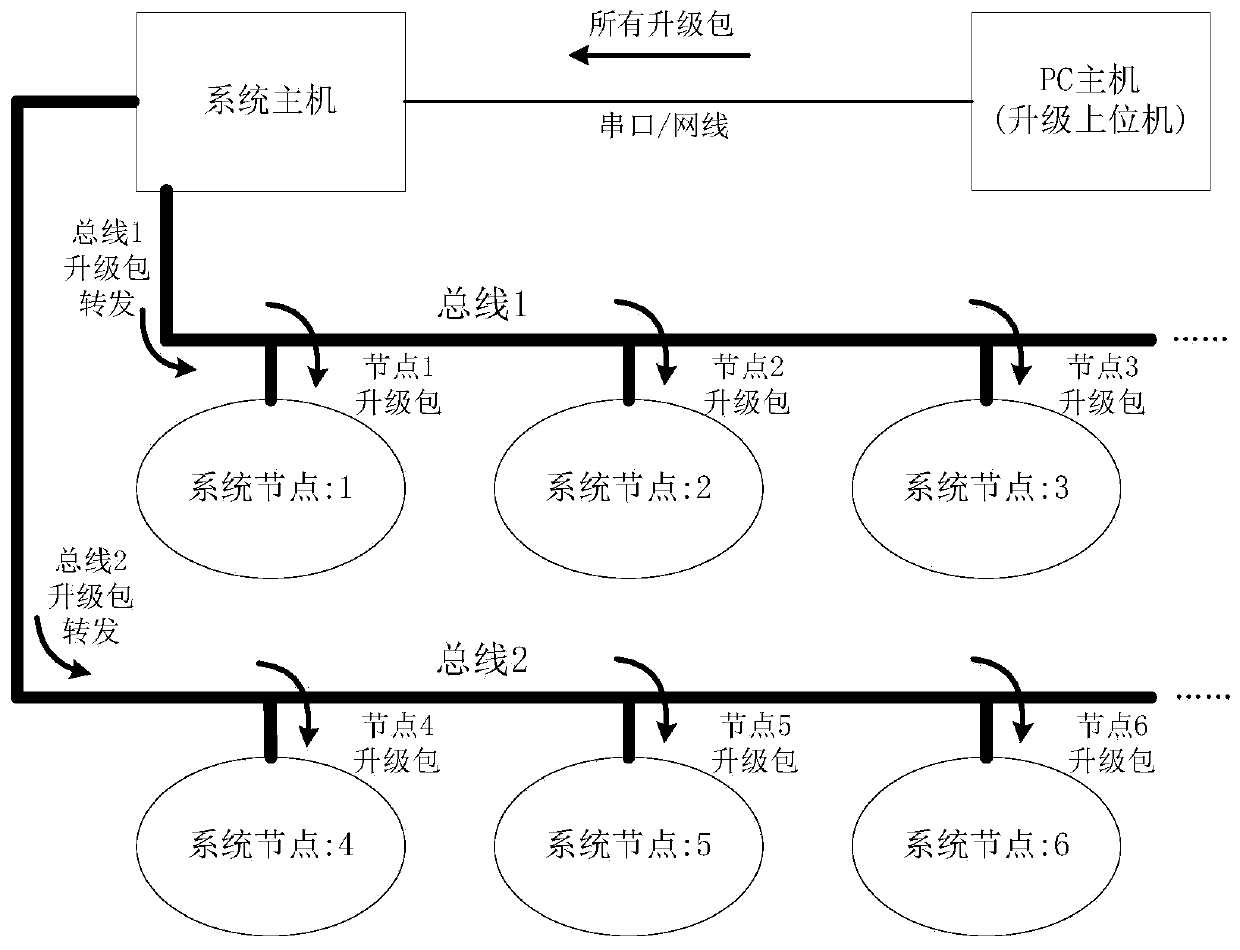
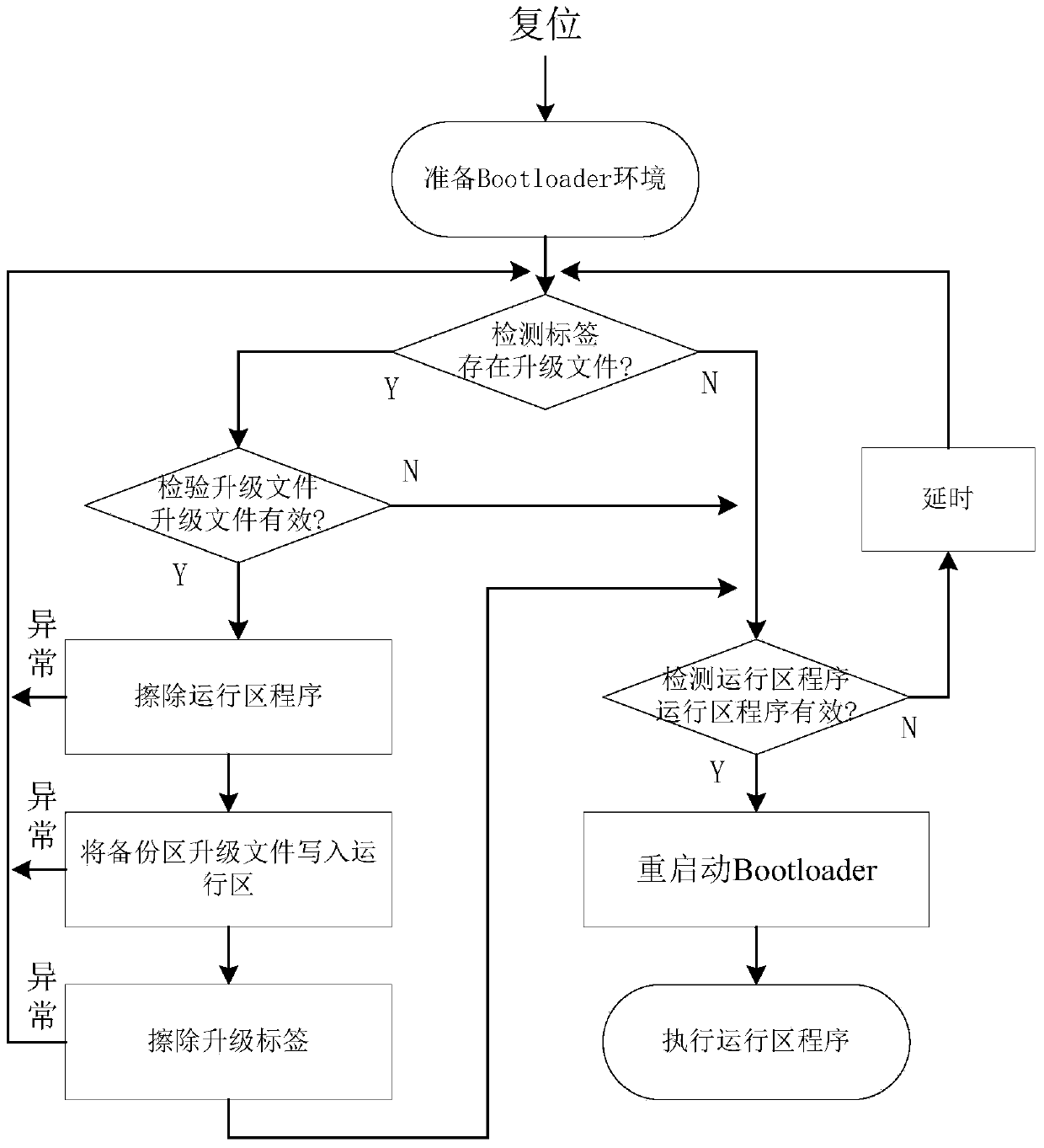
ActiveCN104007996AAvoid accidentsIncomplete replacement will not occurProgram loading/initiatingTransmissionNetwork packetDistributed control system
The invention provides a reliable firmware upgrading realizing method applied to a distributed control system. The reliable firmware upgrading realizing method enables any controller nodes or a host in the system to have program upgrading capacity, greatly improves the expansion capacity of hardware equipment and the customizing performance of the system and reduces later maintenance and upgrading cost. The reliable firmware upgrading realizing method is different from a traditional method in that receiving of a target program package is realized in an application program, the received data package is stored into a backup program area at first, after the target program package is completely received and CRC verification is passed, parameter information marks are generated in an IAP mark area, and a Boot loader is called for to realize program upgrading. Even if an unpredictable failure occurs in any link, existing programs cannot be replaced, and therefore the stability of the system is greatly improved.
Owner:南京润教科技有限公司
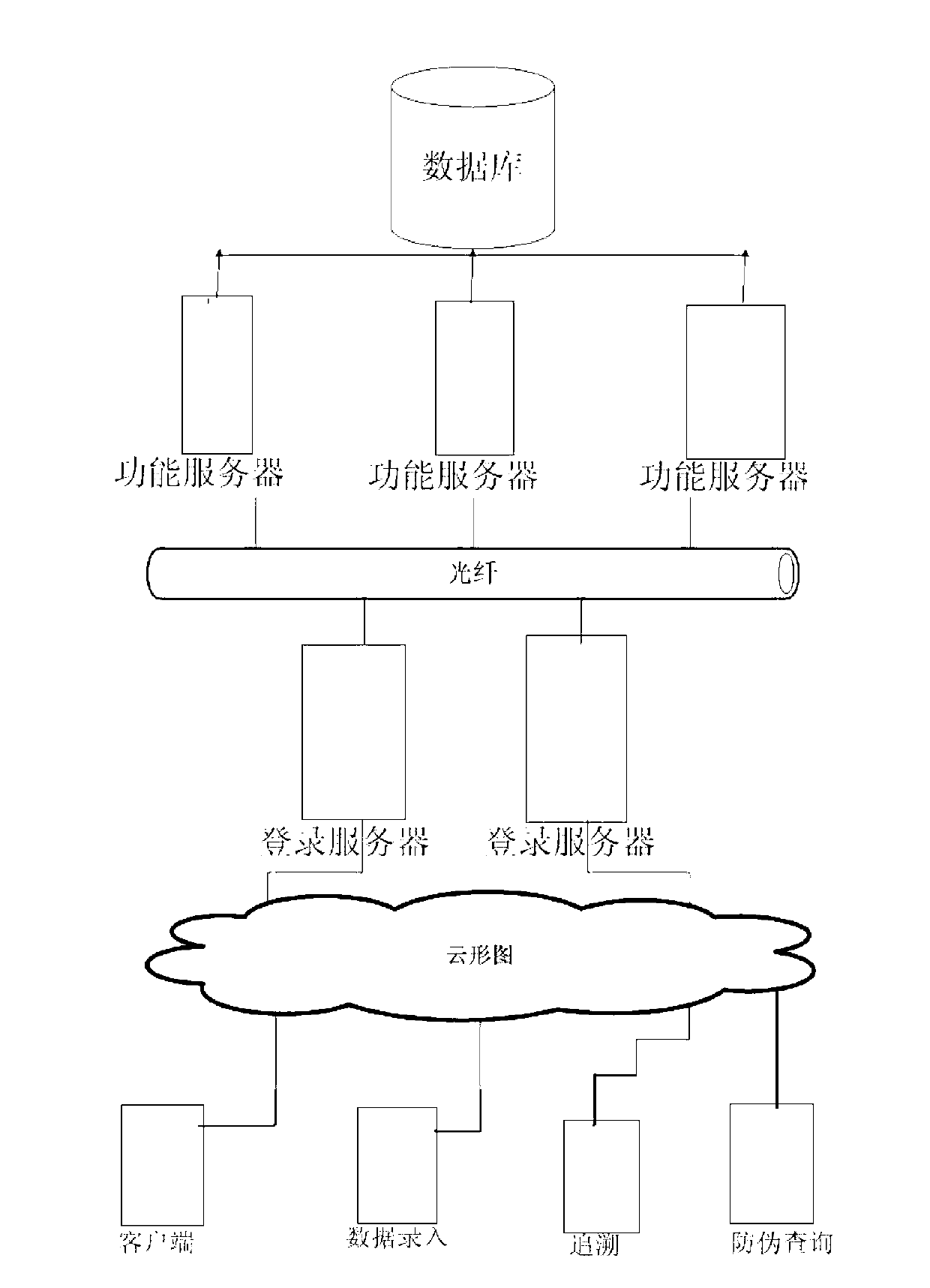
Bar-code-based information verification system
InactiveCN103123709AImprove securityImprove response speedCommerceSensing by electromagnetic radiationProgramming languageEngineering
The invention discloses a bar-code-based information verification system. The information verification system comprises a bar code, a database subsystem, a management subsystem, a server cluster, a fixed terminal and a mobile terminal, wherein the bar code is used for identifying and encoding a product and comprises encrypted product information; the database subsystem is used for storing bar code information and the position information of the terminals; the management subsystem is used for information management and operation maintenance; the server cluster is used for providing support for verification service; the fixed terminal is used for reading the bar code information and sending the bar code information to the server cluster for processing; and the mobile terminal is used for real-time anti-counterfeiting verification. The bar-code-based information verification system has the advantages that (1) system safety is improved by using a dynamic encryption algorithm; (2) the response speed and throughput of the system are increased by using the server cluster; (3) data safety is improved by data backup; and (4) the improved bar code design is suitable for the anti-counterfeiting traceability of commodity.
Owner:广州众码汇信息科技有限公司
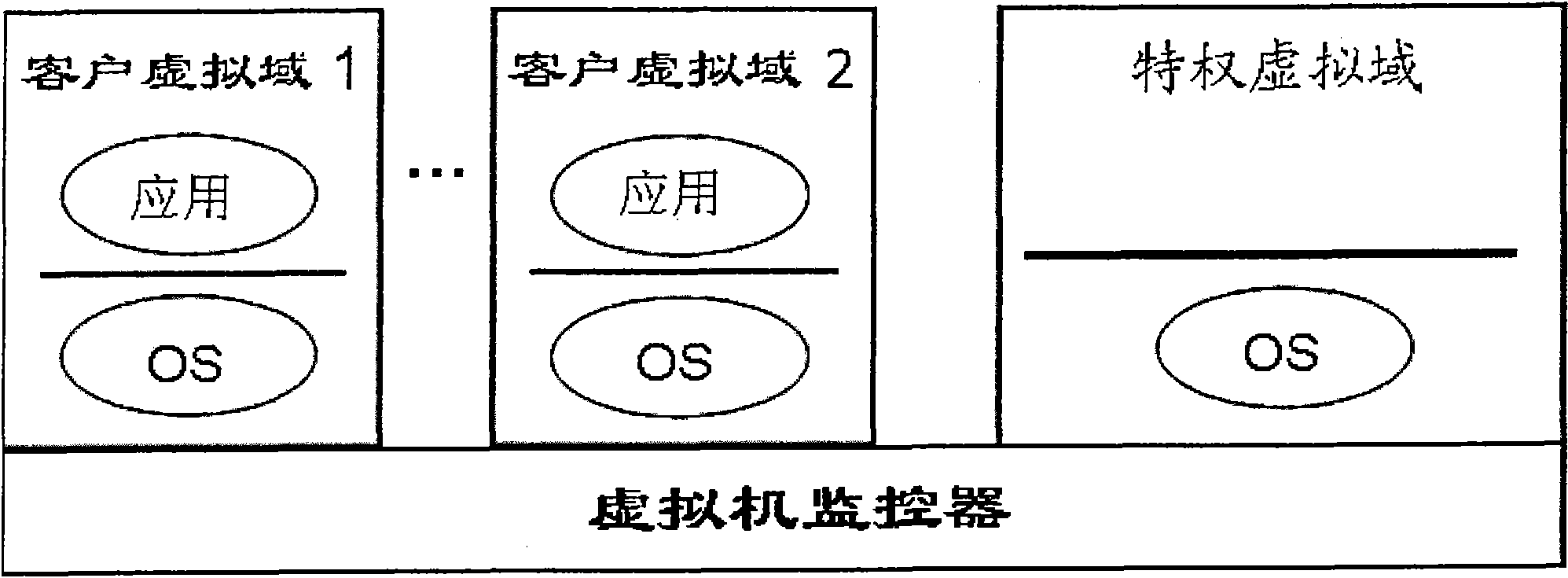
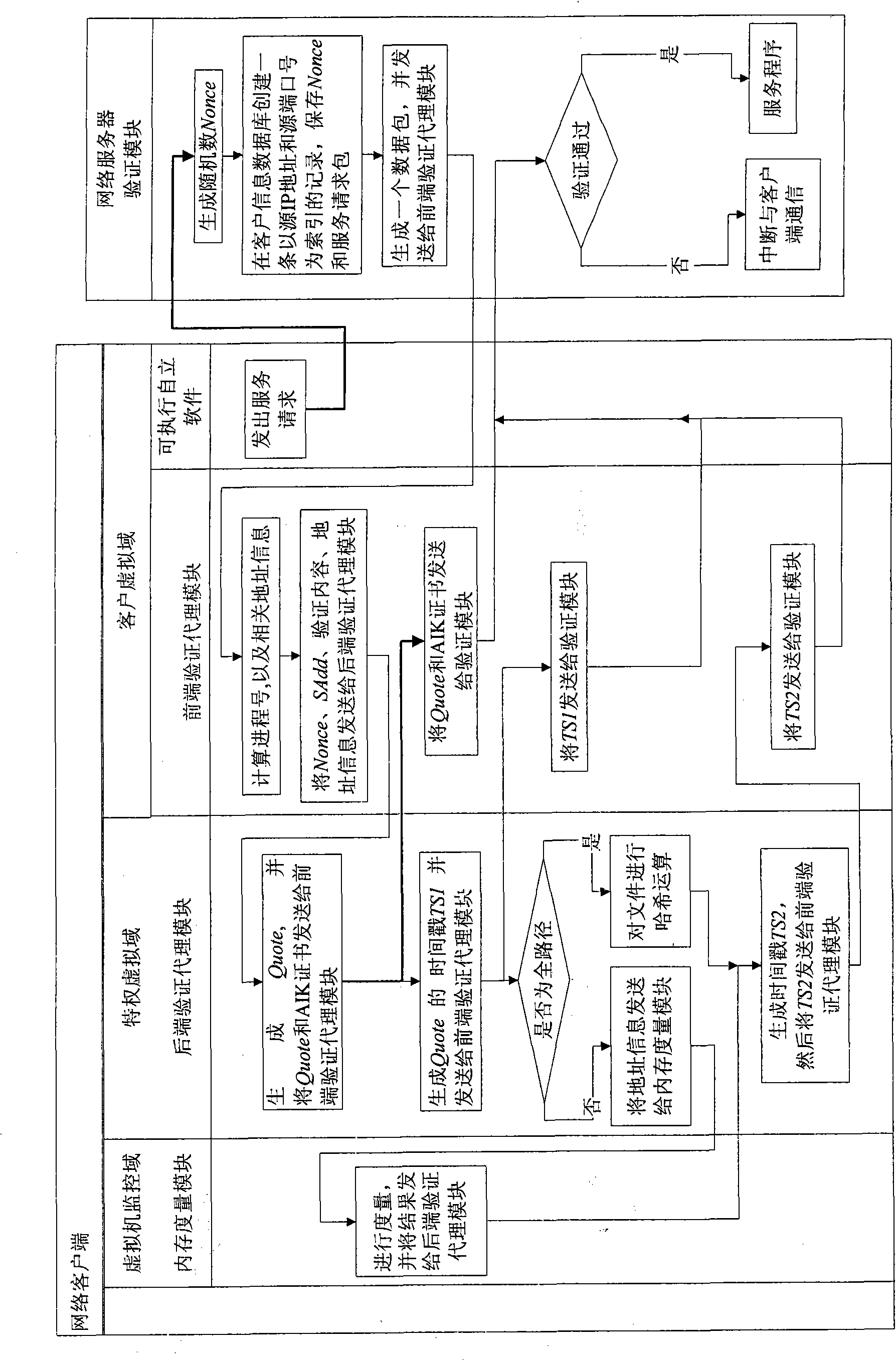
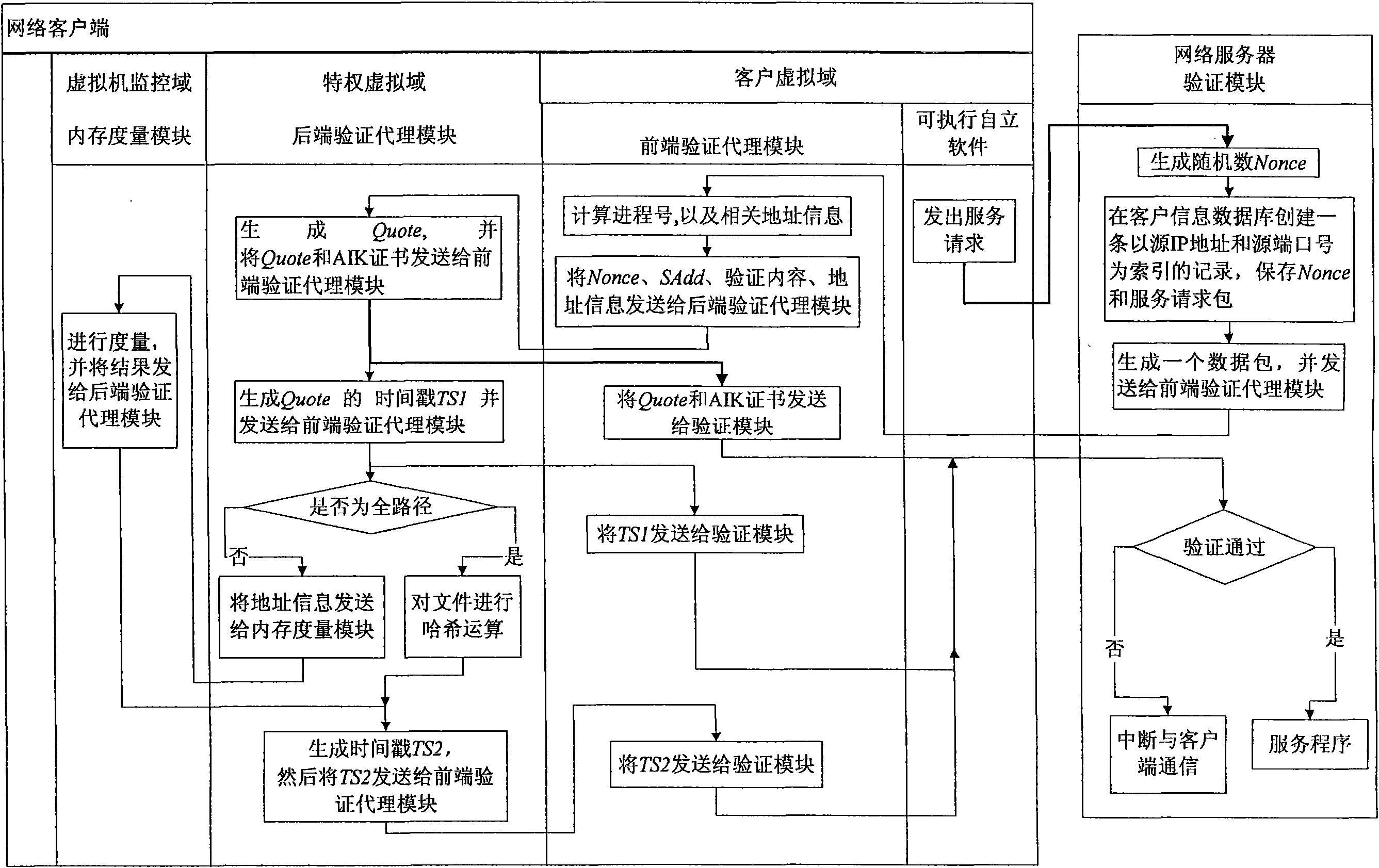
Method for remote dynamic verification on integrality of client software
The invention provides a method for remote dynamic verification on integrality of client software. In the method, a TCG (Trusted Computing Group) remote verification method, an Xen virtual machine security isolation property and a Trusted Platform Module (TPM) timestamp function are adopted to realize remote dynamic verification of a network server on self-contained executables of a network client untrusted client virtual domain. The network client is configured with a security chip TPM (Trusted Platform Module) and an Xen virtual machine system is also installed. A remote dynamic verification framework adopted by the method comprises three parts of an integrality measuring mechanism, a reporting mechanism and a verification mechanism, wherein the integrality measuring mechanism is completed by a back-end verification agent module installed in a network client privileged virtual domain and a memory measuring module installed in a network client virtual machine monitor; the reporting mechanism is completed by a front-end verification agent module installed in the network client virtual domain; and the verification mechanism is completed by a verification module installed d in the network server.
Owner:BEIJING JIAOTONG UNIV
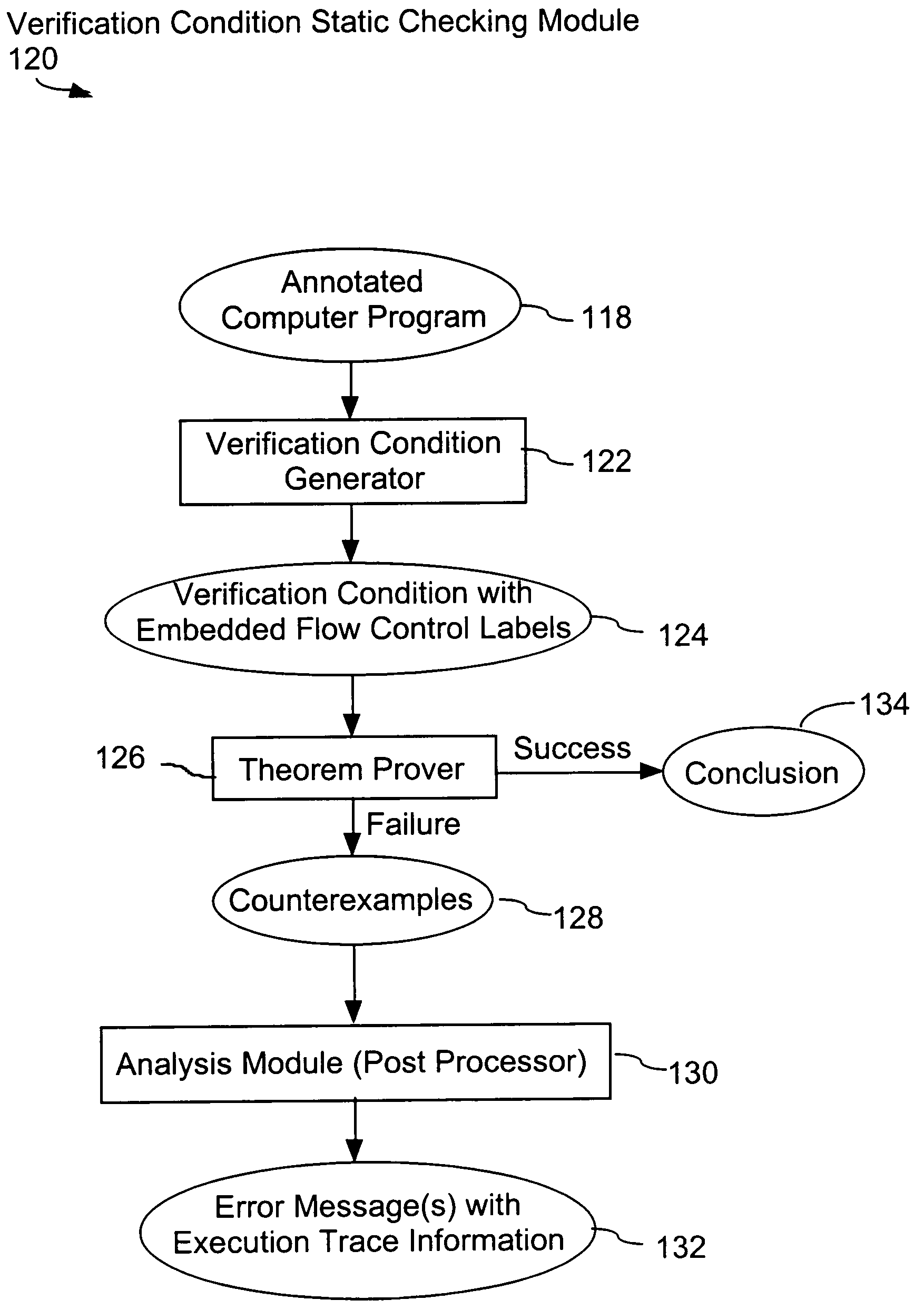
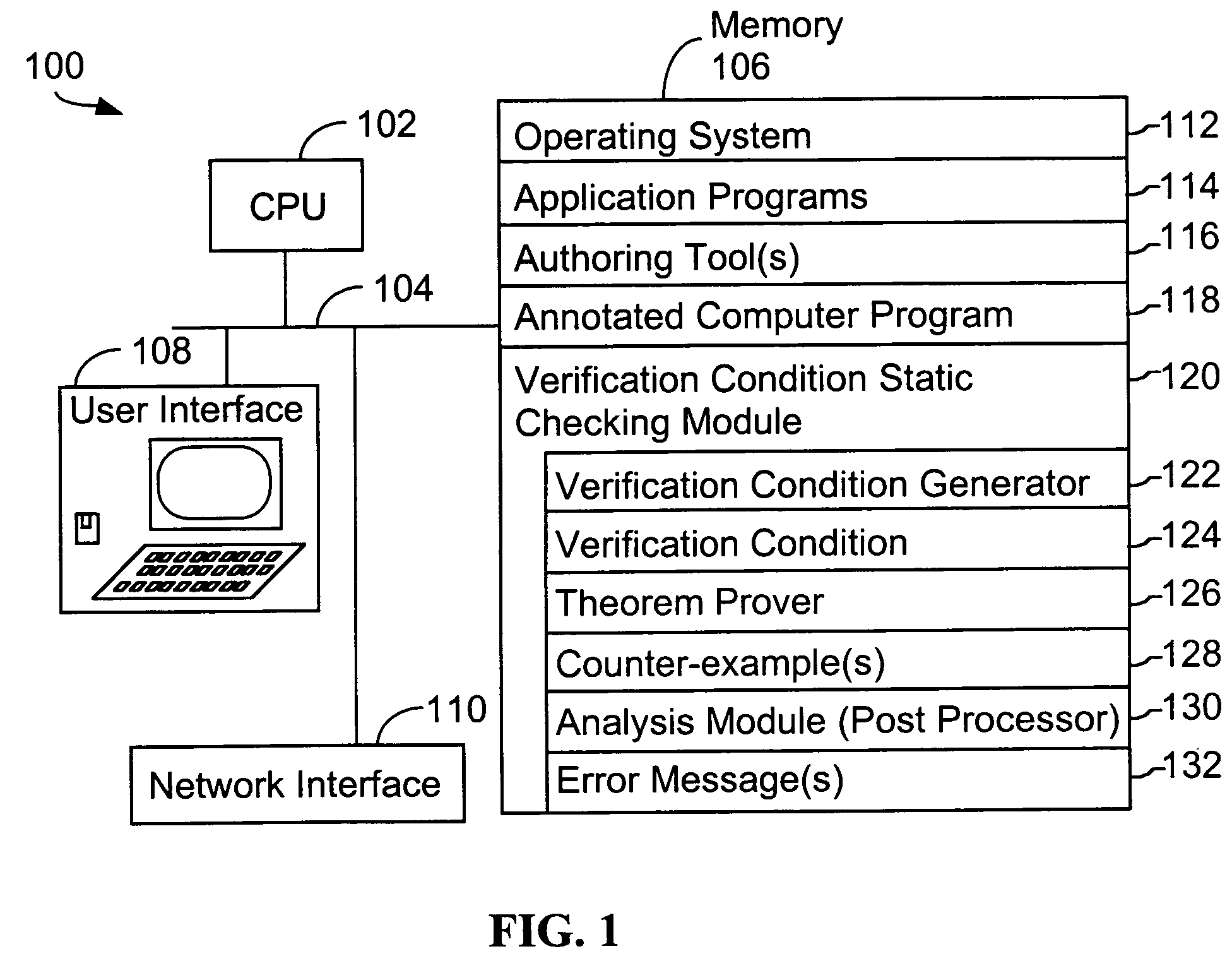
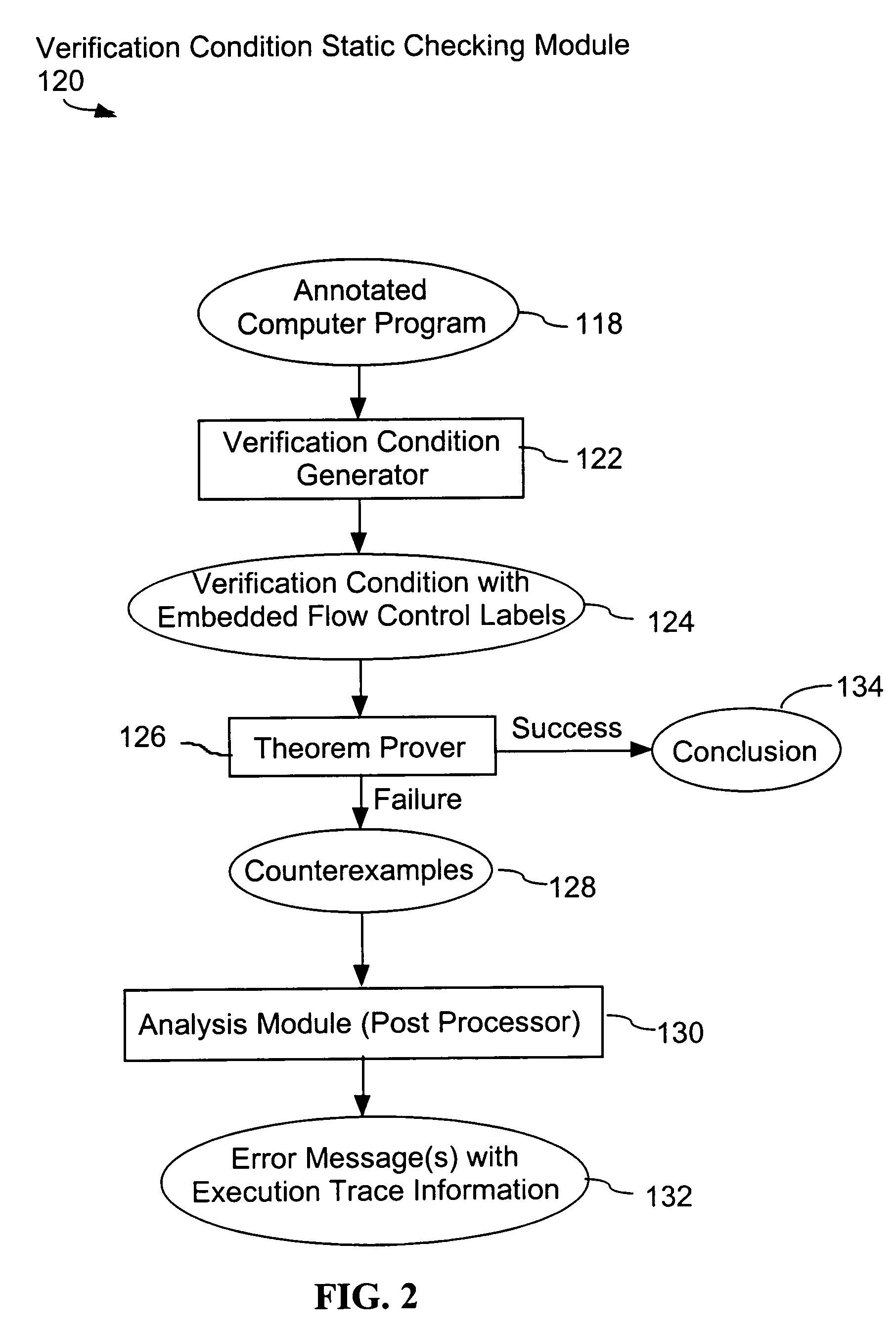
System and method for verifying computer program correctness and providing recoverable execution trace information
In a system for statically analyzing a specified computer, a verification condition generator converts the program into a logical equation, called a verification condition, and inserts program flow control labels into the sub-equations of the verification condition. The flow control labels identify conditional branch points in the specified computer program. A theorem prover is applied to the logical equation to determine truth of the logical equation, and when the truth of the logical equation cannot be proved, the theorem prover generates at least one counter-example identifying one of the conditions, one or more variable values inconsistent with that condition, and any of the flow control labels for conditional branch points of the program associated with the identified variable values. A post processing module converts each counter-example into an error message that includes a program trace when the counter-example identifies one or more of the flow control labels.
Owner:HEWLETT PACKARD DEV CO LP
Software upgrading bag packaging method and software upgrading method
InactiveCN101425114AGuaranteed Safe UpgradesDigital data authenticationProgram loading/initiatingPlaintextDigital signature
The invention relates to a technique for safely updating a software and provides a software update packet packaging method for ensuring the legality and completeness of an updated software, as well as a software updating method. Digital certificates of trustworthy authentication institutes are prearranged in a terminal apparatus, or a server is used for determining the trustworthy authentication institutes; the authentication institutes respectively perform digital signing to the software and transmit an original cleartext software together with all digital signatures and digital certificates to the terminal apparatus; the terminal apparatus verifies whether all digital certificates are legal and judges the authentication institutes working together for updating the software; if all conditions are satisfied, the terminal apparatus verifies all digital signatures and then updates the software after the verification. As the legality of a software update packet is verified according to the digital certificates of the authentication institutes, the completeness of the software update packet is verified according to the digital signatures of the authentication institutes and a plurality of parties participate the concerted signing to the software, the safe update of the software is ensured.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Partial grant set evaluation from partial evidence in an evidence-based security policy manager
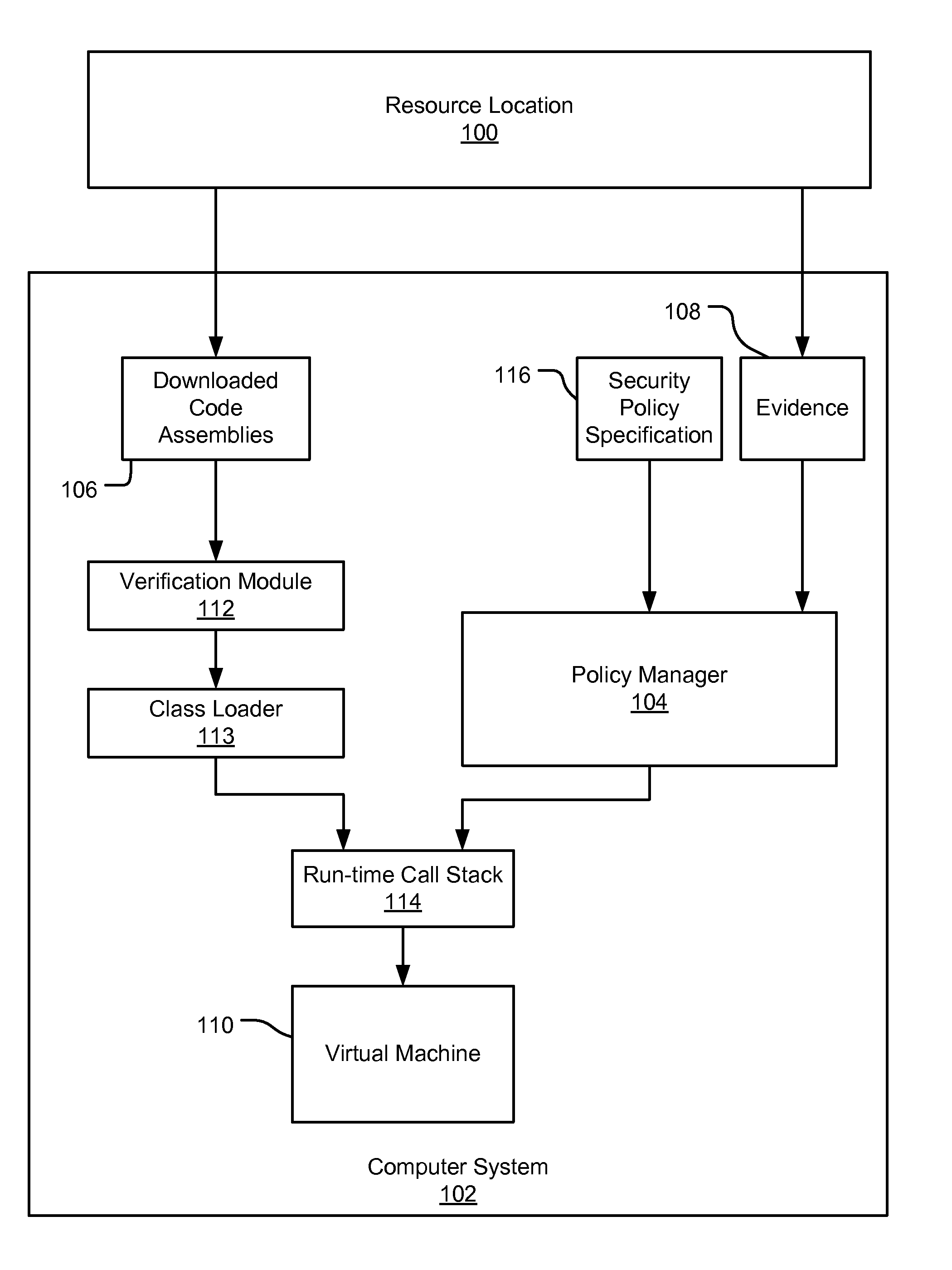
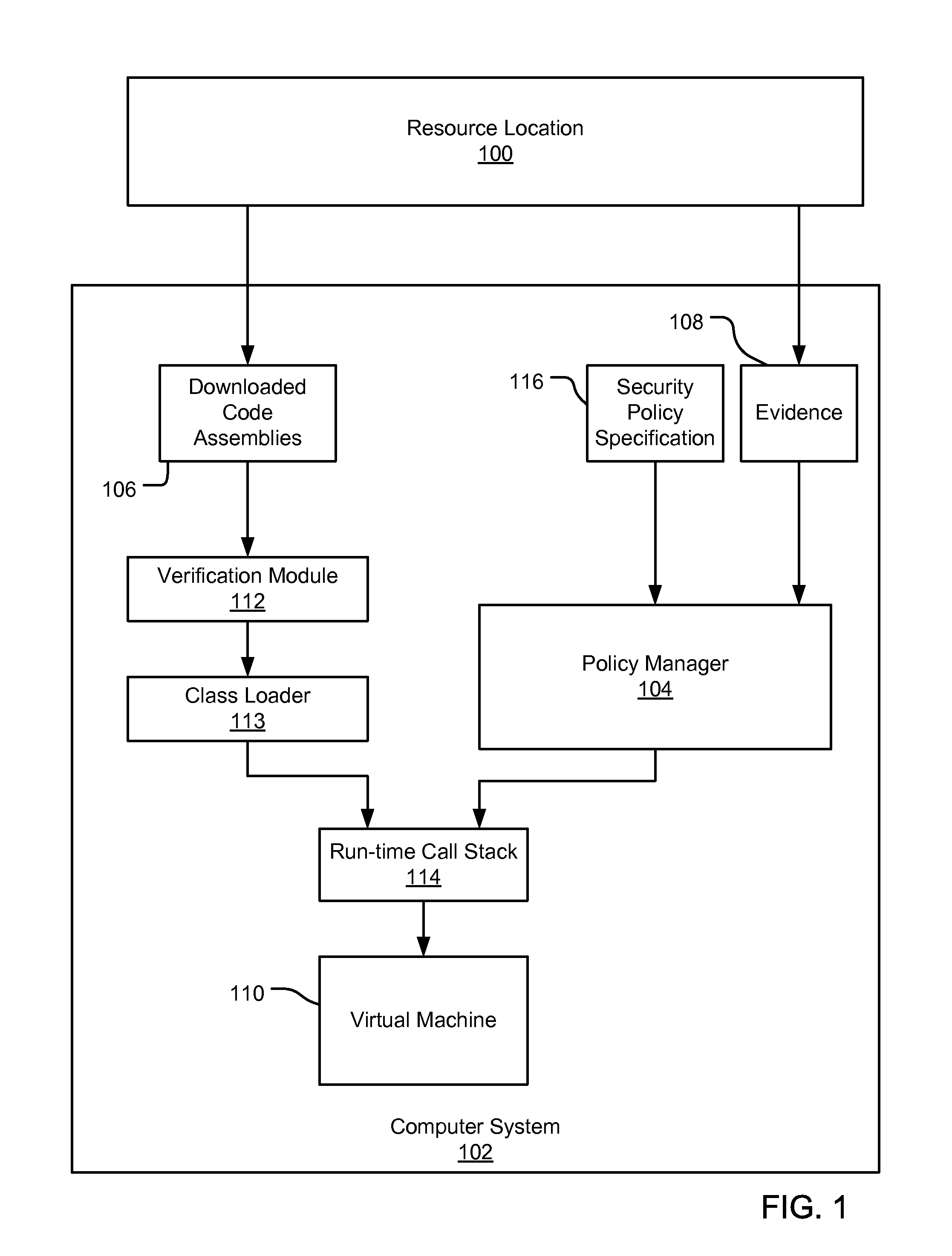
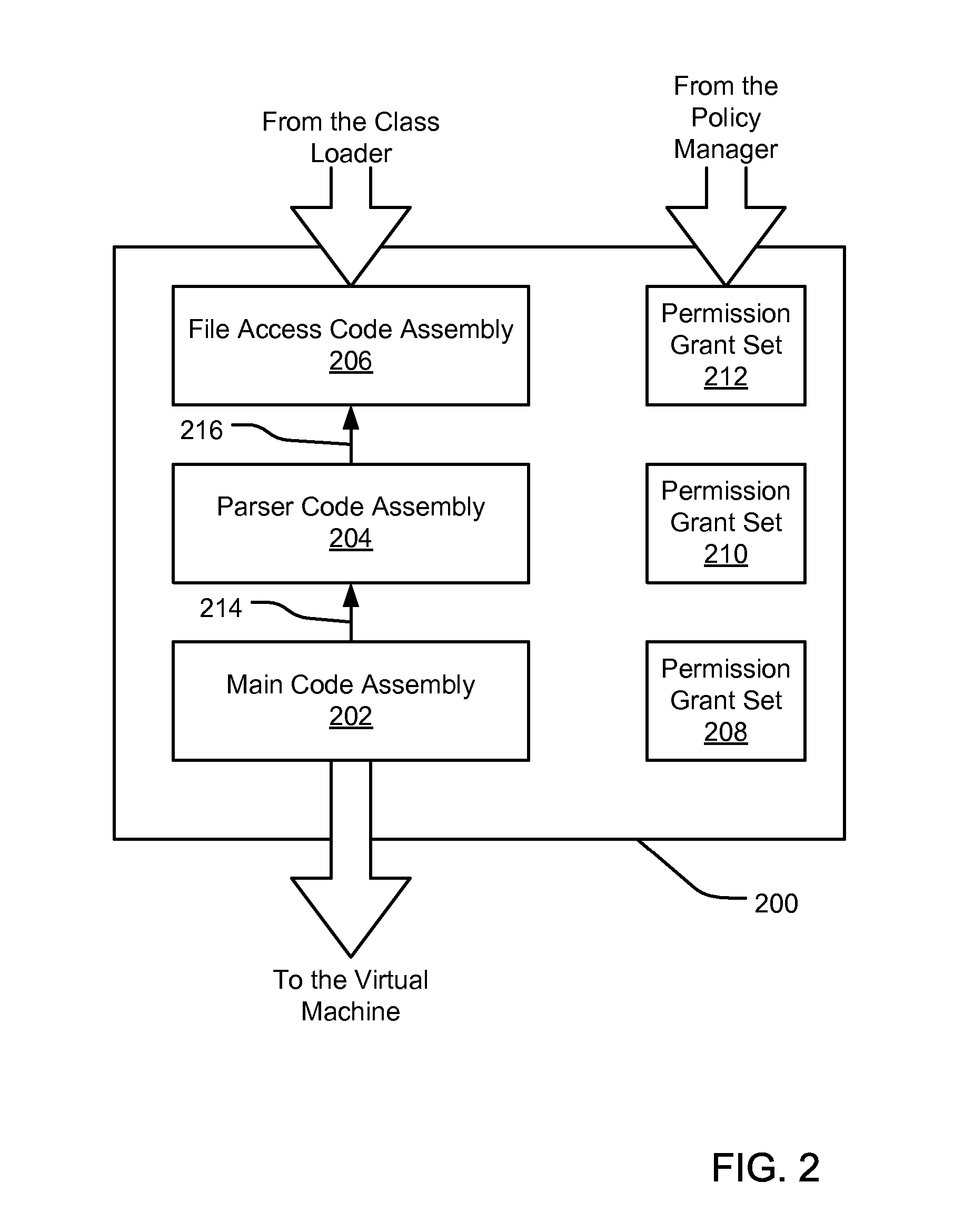
InactiveUS20070192839A1Digital data processing detailsUser identity/authority verificationCall stackEngineering
An evidence-based policy manager generates a permission grant set for a code assembly received from a resource location. The policy manager executes in a computer system (e.g., a Web client or server) in combination with the verification module and class loader of the run-time environment. The permission grant set generated for a code assembly is applied in the run-time call stack to help the system determine whether a given system operation by the code assembly is authorized. The policy manager may determine a subset of the permission grant set based on a subset of the received code assembly's evidence, in order to expedite processing of the code assembly. When the evidence subset does not yield the desired permission subset, the policy manager may then perform an evaluation of all evidence received.
Owner:MICROSOFT TECH LICENSING LLC
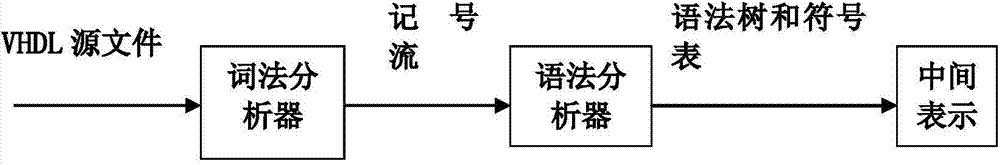
System for automatically converting hardware language VHDL (Vhsic Hardware Description Language) into MSVL (Modeling, Simulation and Verification Language)
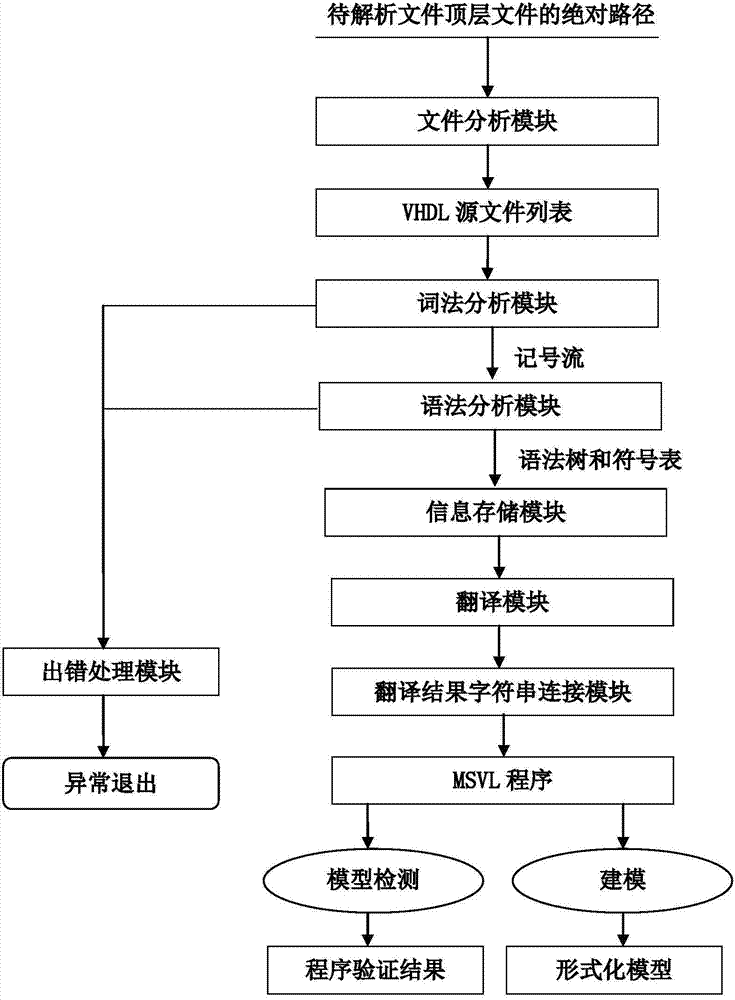
ActiveCN104503816AGuaranteed correctnessProgram controlMemory systemsVhsic hardware description languageLexical analysis
The invention relates to a system for automatically converting a hardware language VHDL (Vhsic Hardware Description Language) into an MSVL (Modeling, Simulation and Verification Language). The system can convert a VHDL language program file into an MSVL language program file; the conversion system comprises a file analysis module, a lexical analysis module, a syntactic analysis, an information storage module, a translation module and a translation result character string connection module. After a VHDL program is converted into an MSVL program, model construction and property description use the same language, so that verification is carried out in the same logic framework and indirect model detection on the VHDL language program is conveniently realized. In the converting process, the VHDL program is converted into the semantic equivalent MSVL program by making conversion rules of different grammatical structure through a plurality of additional auxiliary means, so that correctness of a source VHDL program can be ensured by carrying out simulation, model construction and verification on the equivalent MSVL program.
Owner:XIDIAN UNIV
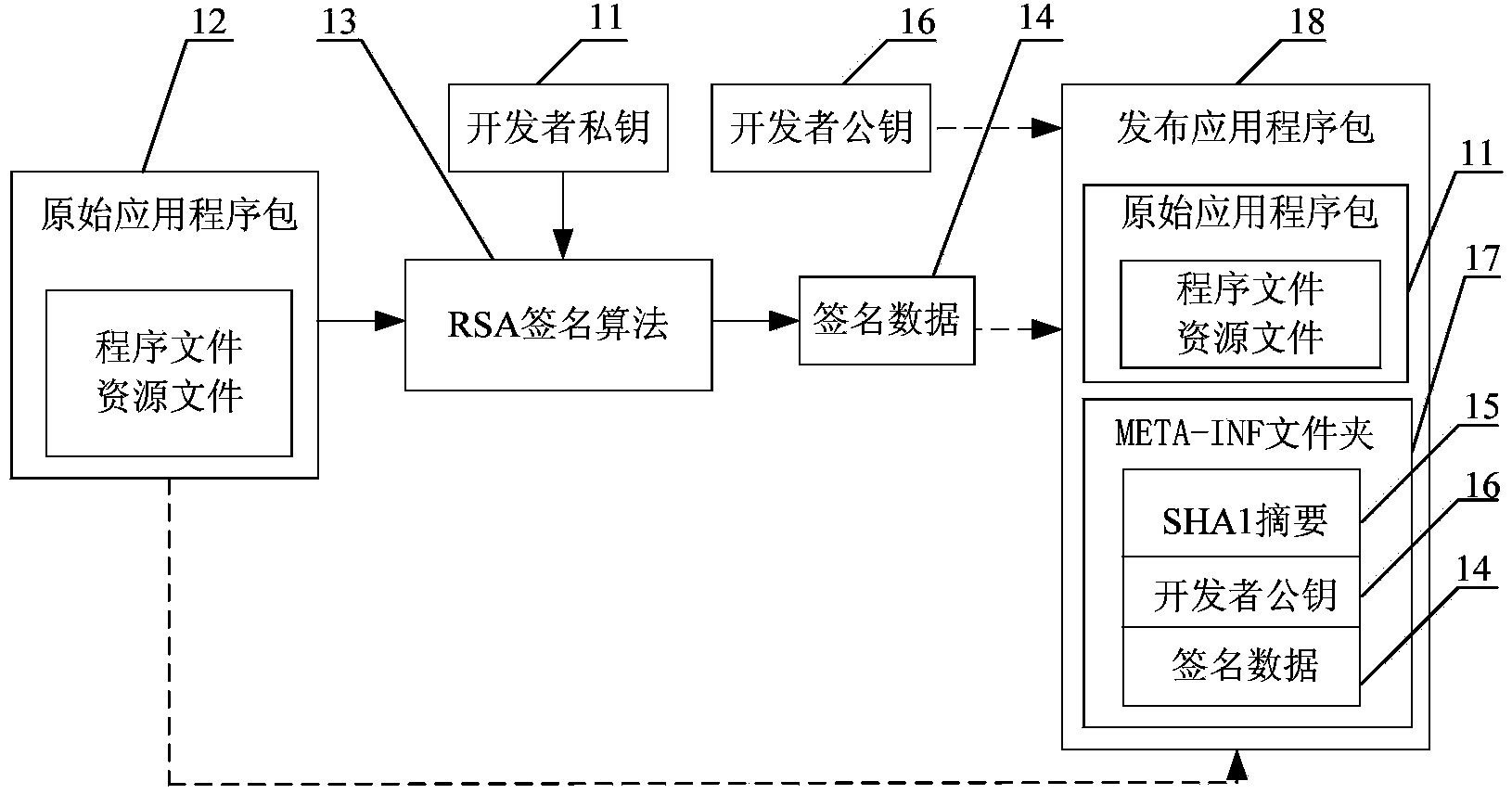
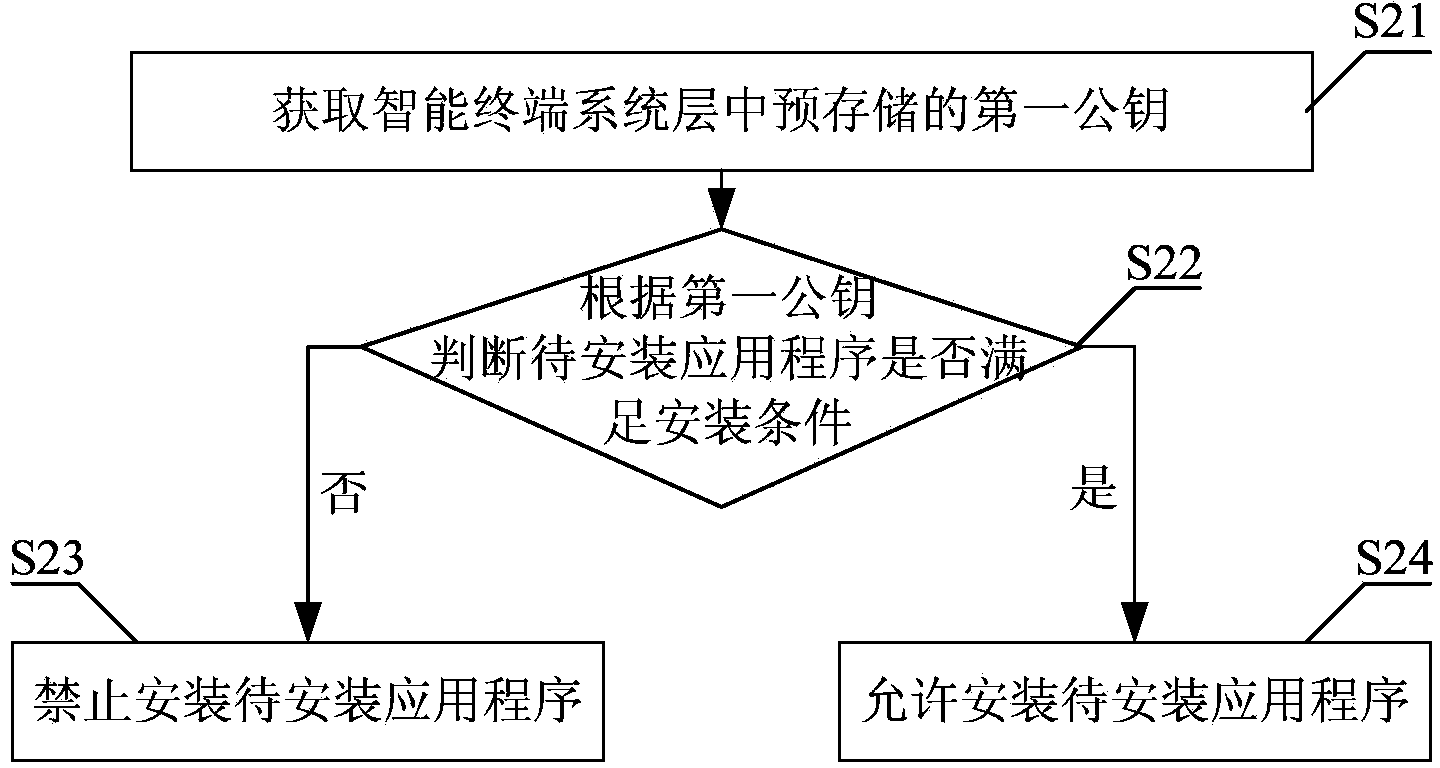
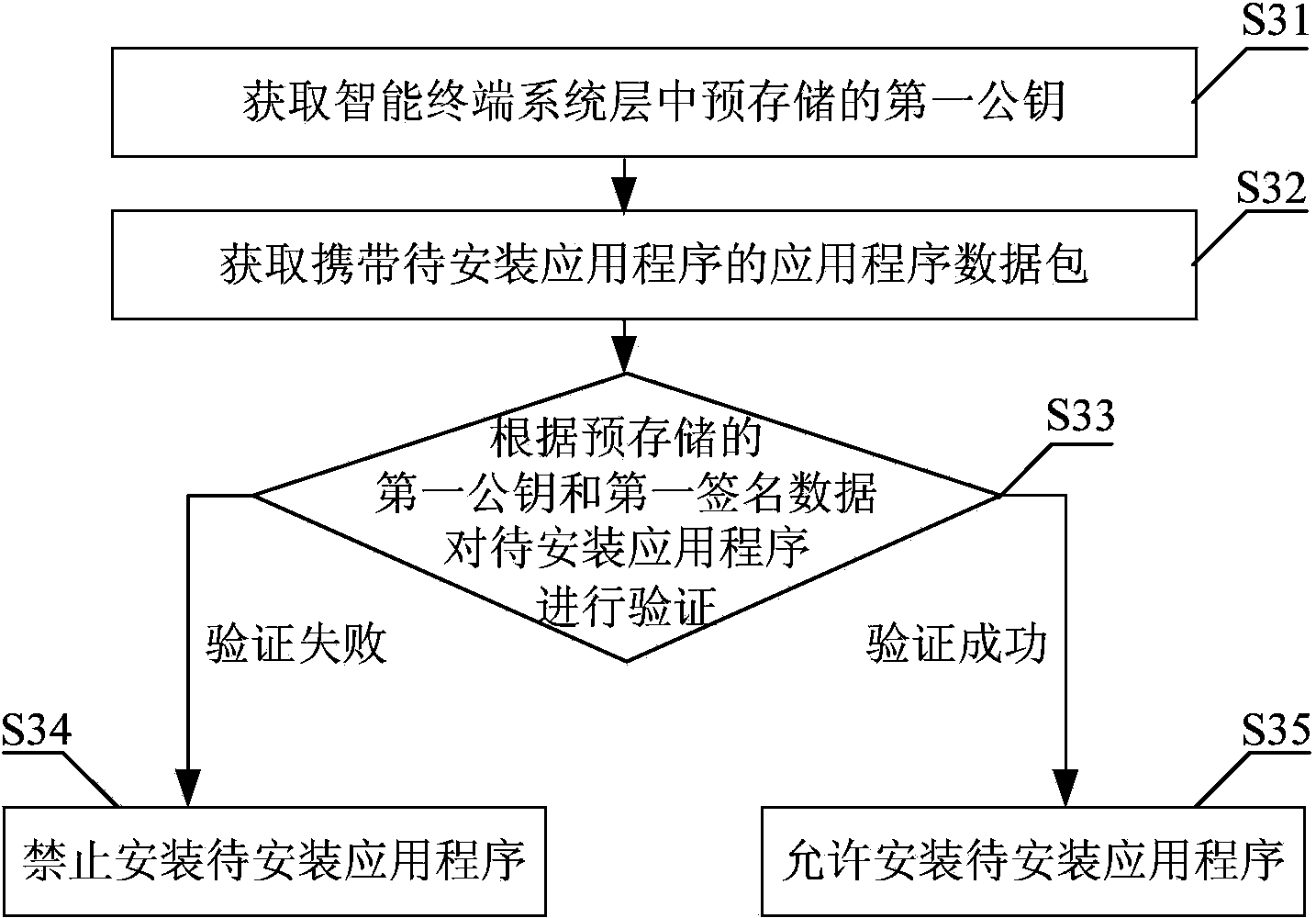
Installing verification method for intelligent terminal application program and system
InactiveCN104331658APrevent trespassAvoid spreadingComputer security arrangementsValidation methodsTerminal equipment
The invention discloses an installing verification method for an intelligent terminal application program. The method comprises the following steps: acquiring a first public key pre-stored in an intelligent terminal system layer; judging if a to-be-installed application program meets an installing condition according to the pre-stored first public key; if yes, allowing to install the to-be-installed application program; if not, forbidding the installing for the to-be-installed application program. The invention also provides a system for realizing the method. According to the installing verification method for the intelligent terminal application program provided by the invention, before the application program is installed, the pre-stored first public key of the system layer is utilized to judge if the application program meets the installing condition, and the application program can be installed when the installing condition is met, so that the application program on the terminal equipment being an authenticated legal program can be ensured; the installing for an illegal application program can be effectively prevented; the manageable and controllable terminal application can be ensured; the illegal entry and spreading of harmful information can be prevented; the benefits of operators and users can be protected.
Owner:北京视博数字电视科技有限公司
Method, system and computer program for automated hardware design debugging
InactiveUS20080127009A1Bulky designEasy to handleError detection/correctionComputer aided designComputer hardwareComputer architecture
The present invention provides a method, system and computer program for automated debugging for pre-fabricated digital synchronous hardware designs implemented in Hardware Description Language (HDL). Required information is captured by interacting with the verification environment after verification fails. This capture information is used to build a diagnosis problem where the solution is a set of logic level error sources. Using the HDL information, the error at the logic level is translated to gates, modules, statements, and signals in the HDL description. The diagnosis problem can be solved efficiently formulating a Quantified Boolean Formula (QBF) problem and also by using the hierarchical and modular nature of the HDL design during diagnosis.
Owner:VENERIS ANDREAS +3
Software simulation verification method based on Cache coherence protocol
InactiveCN102880537AEasy diagnosisSpeed up the debugging processFunctional testingTheoretical computer scienceLogisim
The invention provides a software simulation verification method based on a Cache coherence protocol. According to the method, pseudo random test which is capable of compiling constraint models and also carrying out band constraint in a manual mode is subject to software simulation and verification; specific objects are verified, and the accuracy and defect of the protocols are fed back. The method based on software simulation comprises the following steps of: firstly determining a multi-stage coherence description mode based on an expanded Cache Coherence protocol; and subsequently realizing the software simulation verification method, counting the coverage rate and carrying out error report. With the adoption of the method, the Cache Coherence protocol in multi-stage domains in a multi-state space can be verified effectively so as to enable a protocol table to realize the establishment of corresponding logic relationship, judge whether the state transition of a system in accordance with the protocol table accords with the coherence definition through an overall checker, and primarily judge whether a mode established in accordance with the protocol table has expected properties. The model system has the remarkable advantages that counter-examples can be generated automatically so as to assist in debugging errors of the system and accelerating system diagnosis and debugging.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Partitionless Multi User Support For Hardware Assisted Verification
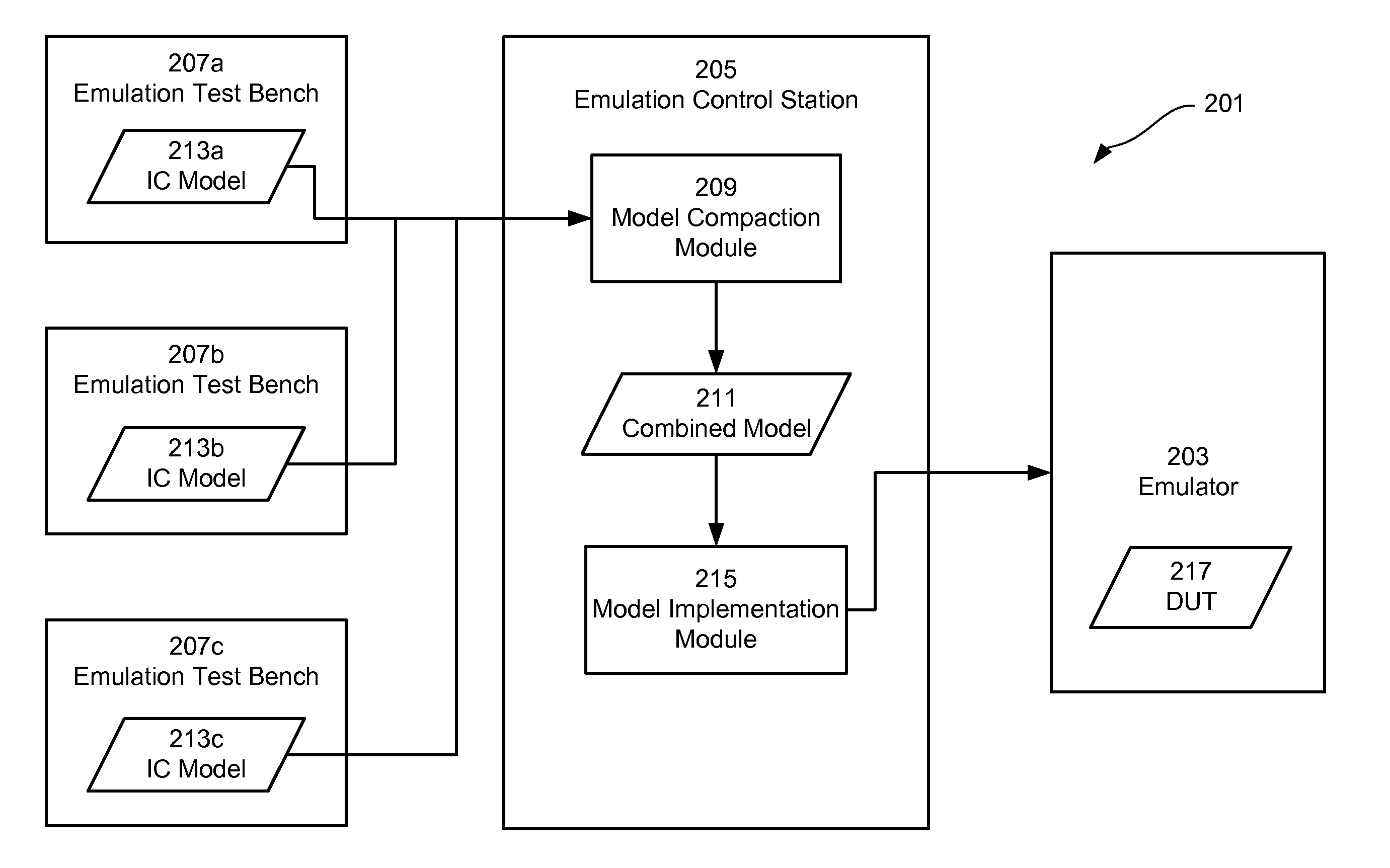
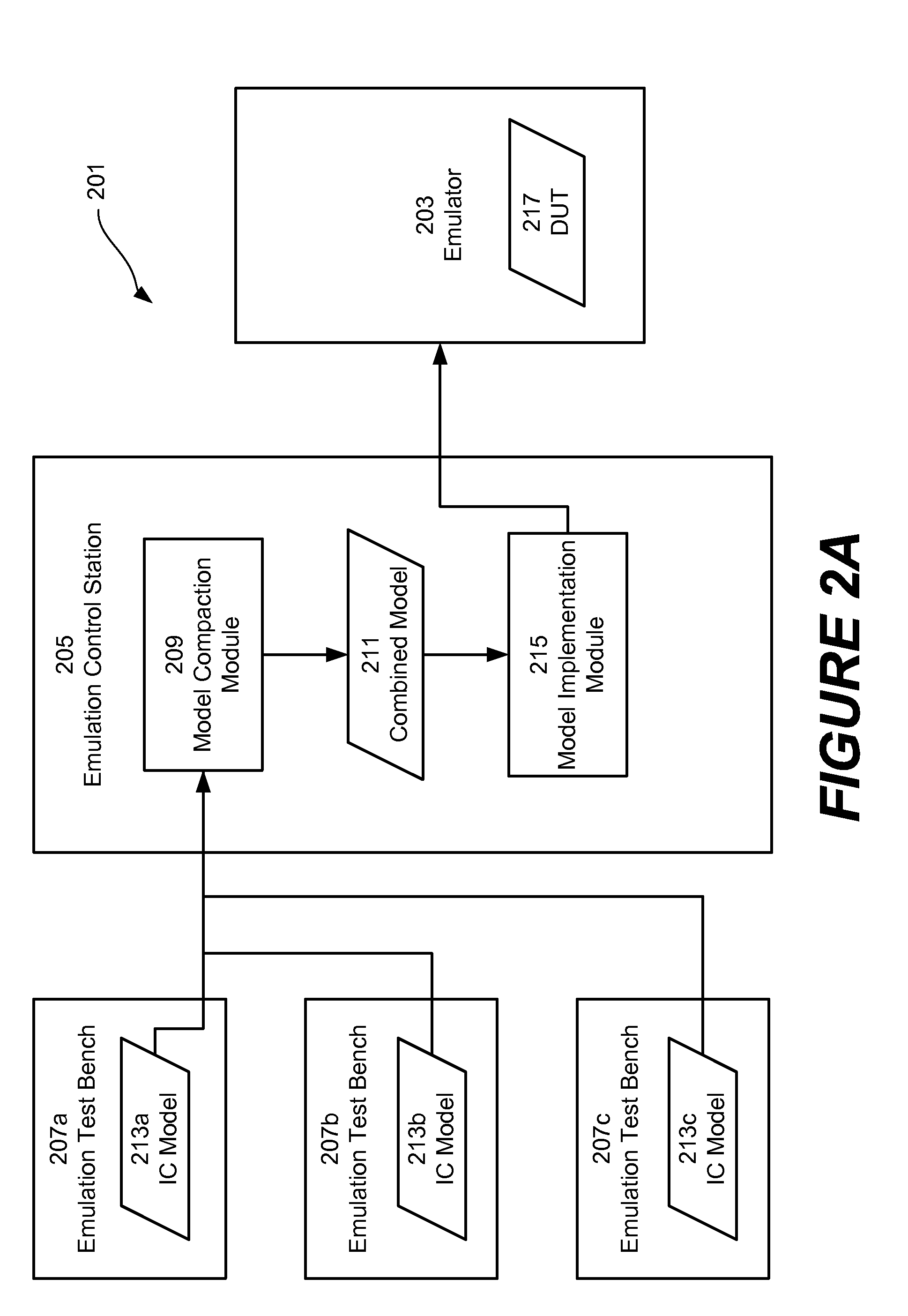
InactiveUS20140052430A1High simulationCAD circuit designSpecial data processing applicationsParallel computingComputer module
Embodiments of the disclosed technology are directed toward facilitating the concurrent emulation of multiple electronic designs in a single emulator without partition restrictions. In certain exemplary embodiments, an emulation environment comprising an emulator and an emulation control station is provided. The emulation control station includes a model compaction module that is configured to combine multiple design models into a combined model. In some implementations, the design models are merged to form the combined model, where each design model is represented as a virtual design with the combined model. Subsequently, the emulator can be configured to implement the combined model. Furthermore, an emulation clock control component is provided that allows for portions of the emulated combined model to be “stalled” during emulation without affecting other portions.
Owner:MENTOR GRAPHICS CORP
Software updating apparatus, software updating system, alteration verification method and alteration verification program
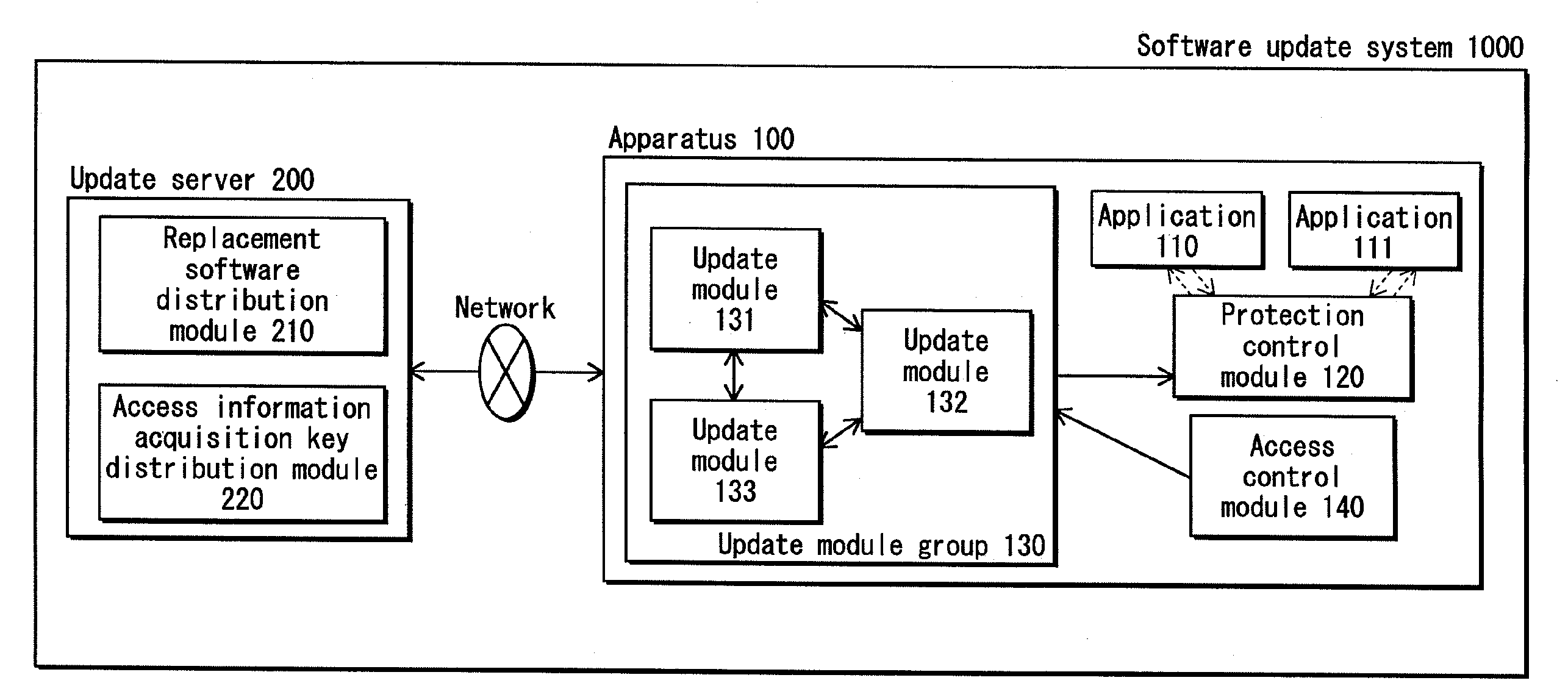
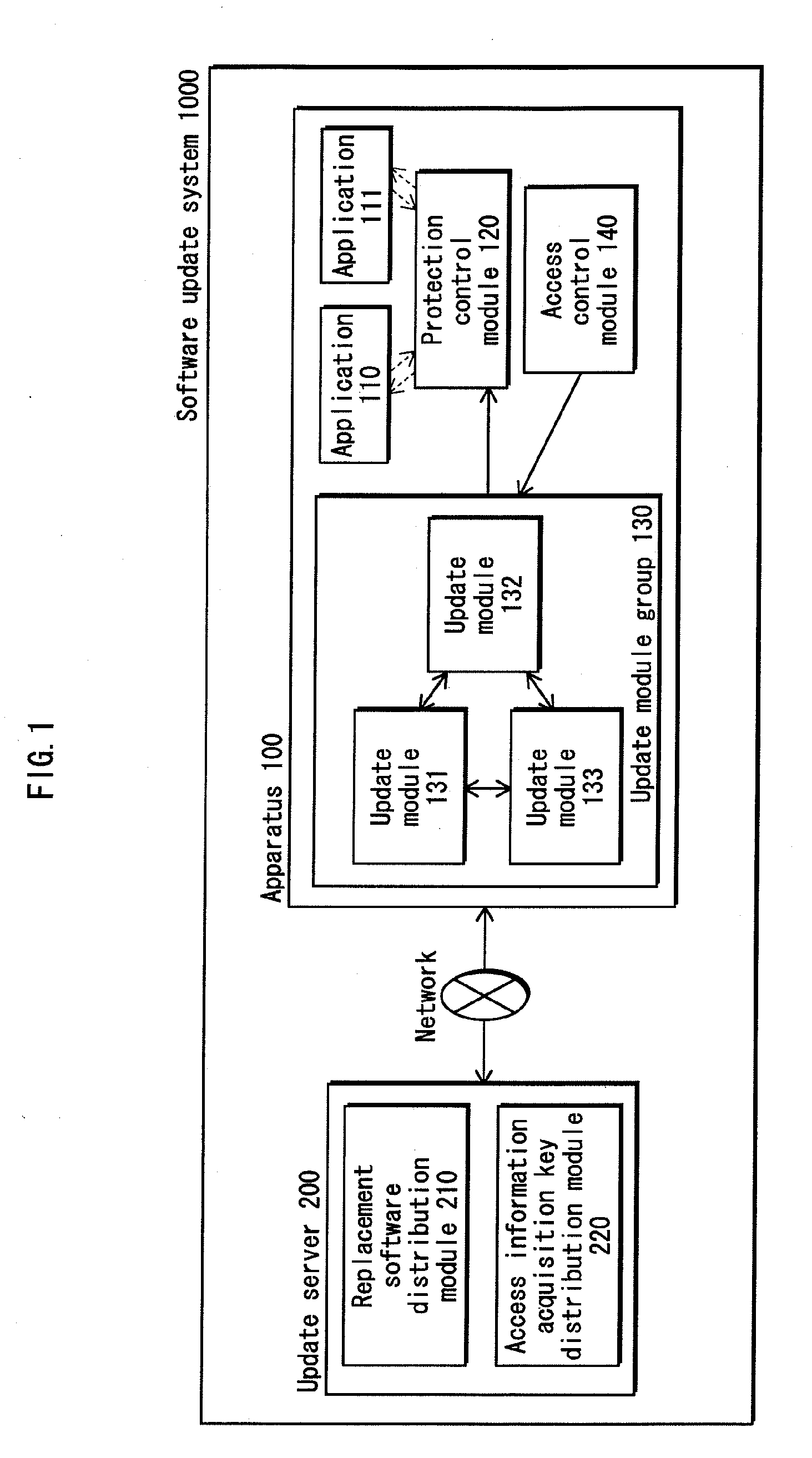
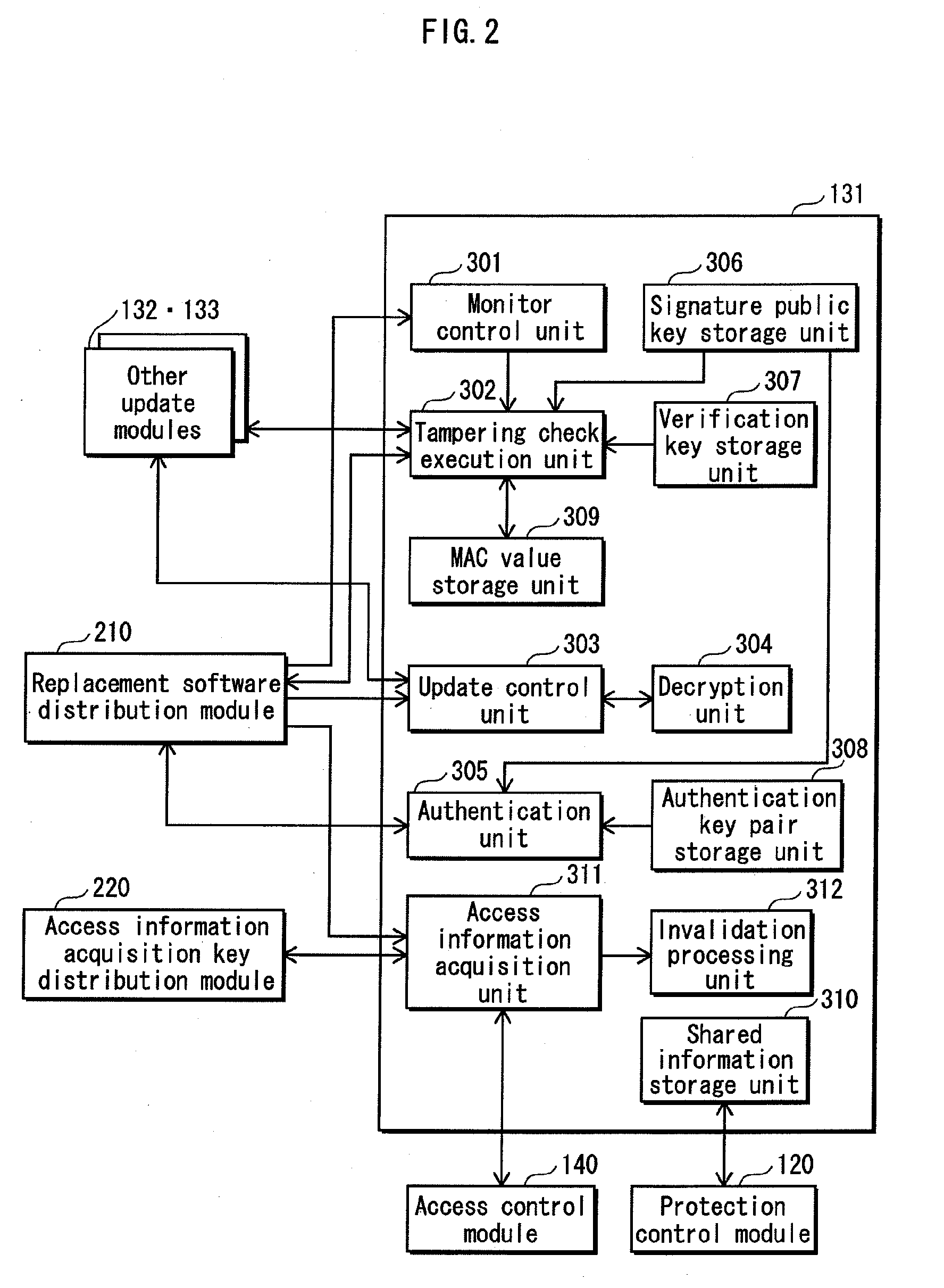
ActiveUS20100180343A1Increase probabilityPrevent protection controlKey distribution for secure communicationMemory loss protectionValidation methodsSoftware update
To aim provide a software update apparatus including an install module group (130) composed of a plurality of install modules. Each of the install modules has a function of receiving, from an external server (200), a replacement protection control module (121) to be used for updating a protection control module (120) having a function of verifying whether a predetermined application has been tampered with. Each of the install modules simultaneously running is verified by at least another one of the install modules simultaneously running, as to whether the install module has a possibility of performing malicious operations.
Owner:PANASONIC CORP
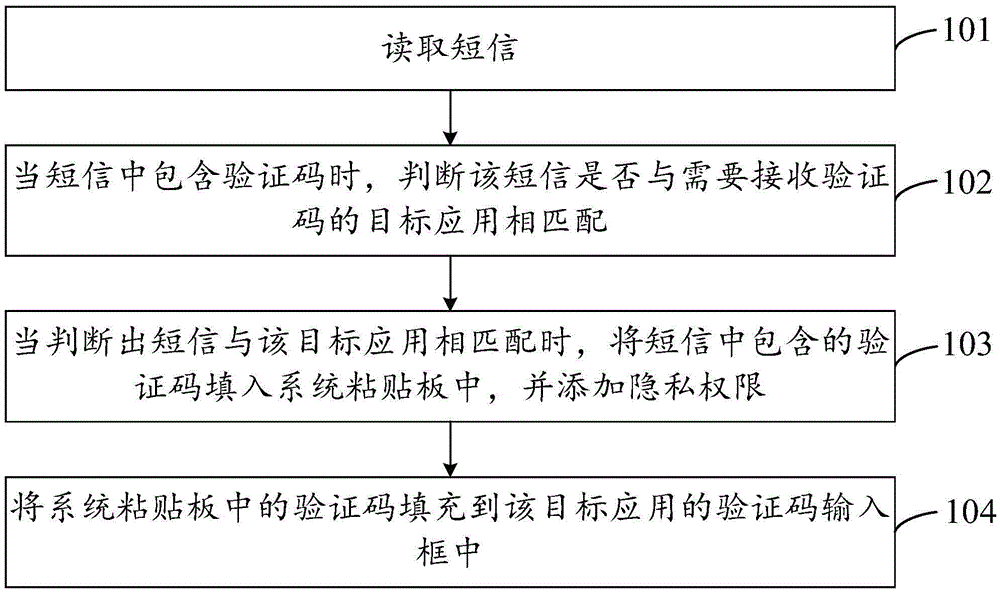
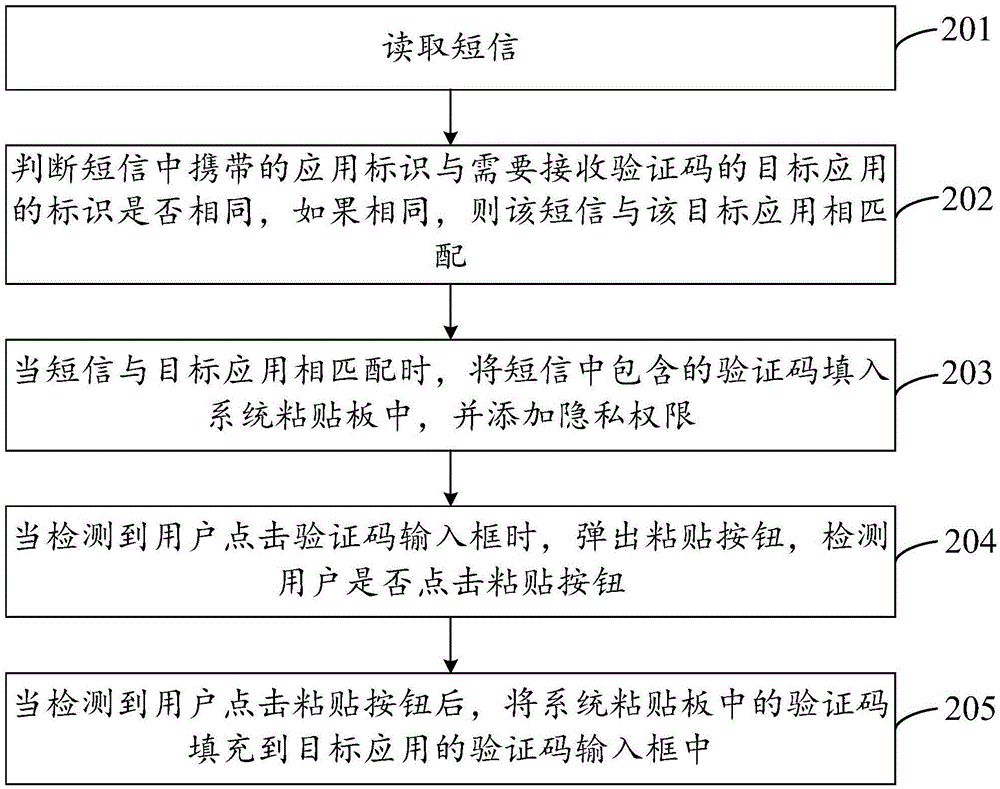
Verification code input method and device
InactiveCN105553663AIncrease privacy permissionsEasy to operateUser identity/authority verificationMessaging/mailboxes/announcementsComputer hardwareFilling-in
The invention provides a verification code input method and device, and the method comprises the steps: reading a short message; judging whether the short message is matched with a target application which needs to receive a verification code or not when the short message contains the verification code; enabling the verification code in the short message to be filled in a system paste board when the short message is matched with the target application, and adding privacy authority, wherein the privacy authority is used for shielding other applications different from the target application; and enabling the verification code in the system paste board to be filled in a verification input frame of the target application. In conclusion, the method can automatically analyzes the verification code, matched with the target application which needs to receive the verification code, from the content of the short message, and fills the verification code into the corresponding verification input frame. A user does not need to specially search the verification code from the short message, so the method and device are relatively simple in operation. In addition, the method adds privacy authority to the content of the system paste board, thereby preventing the leakage of the privacy of the user.
Owner:XIAOMI INC
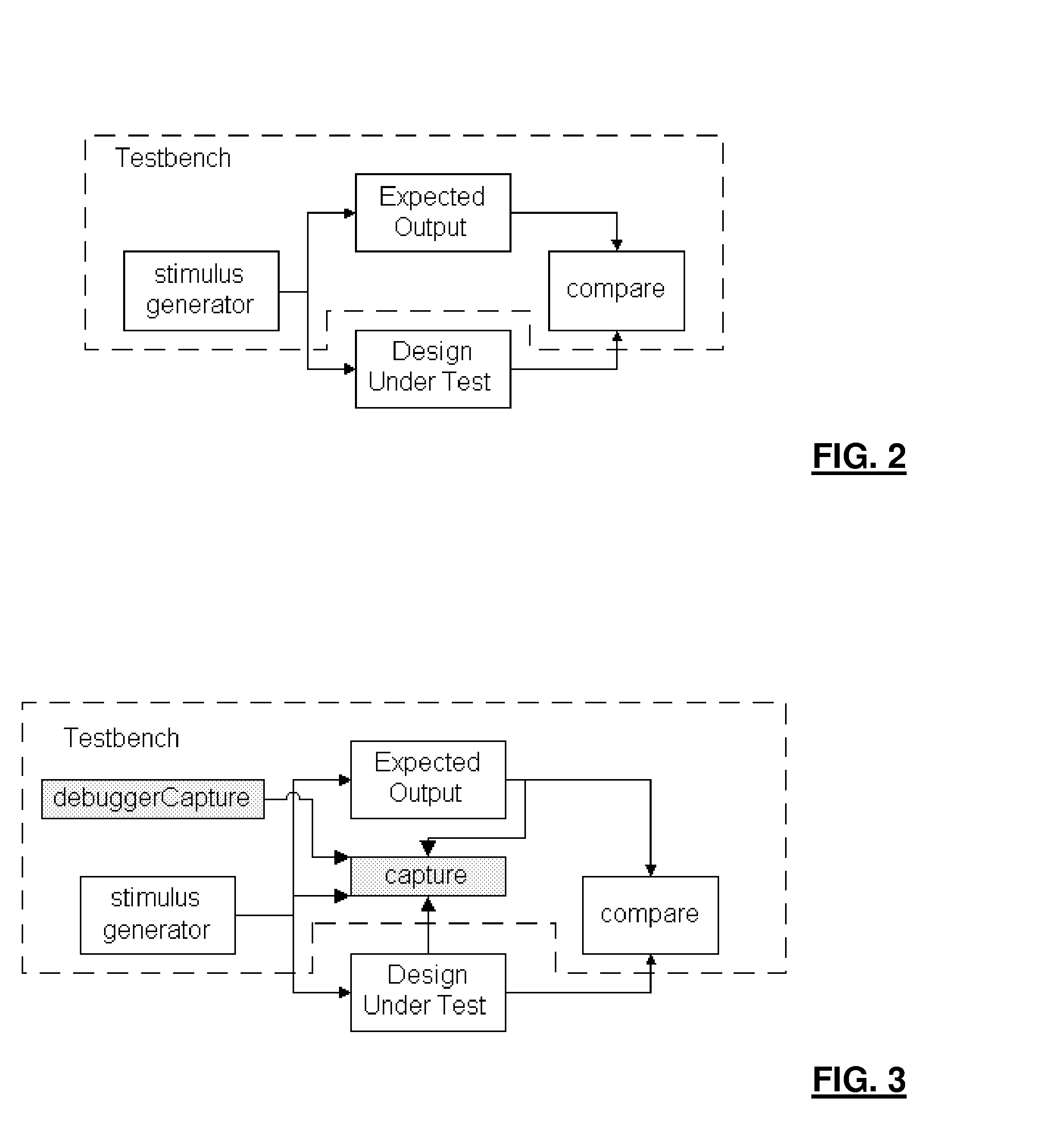
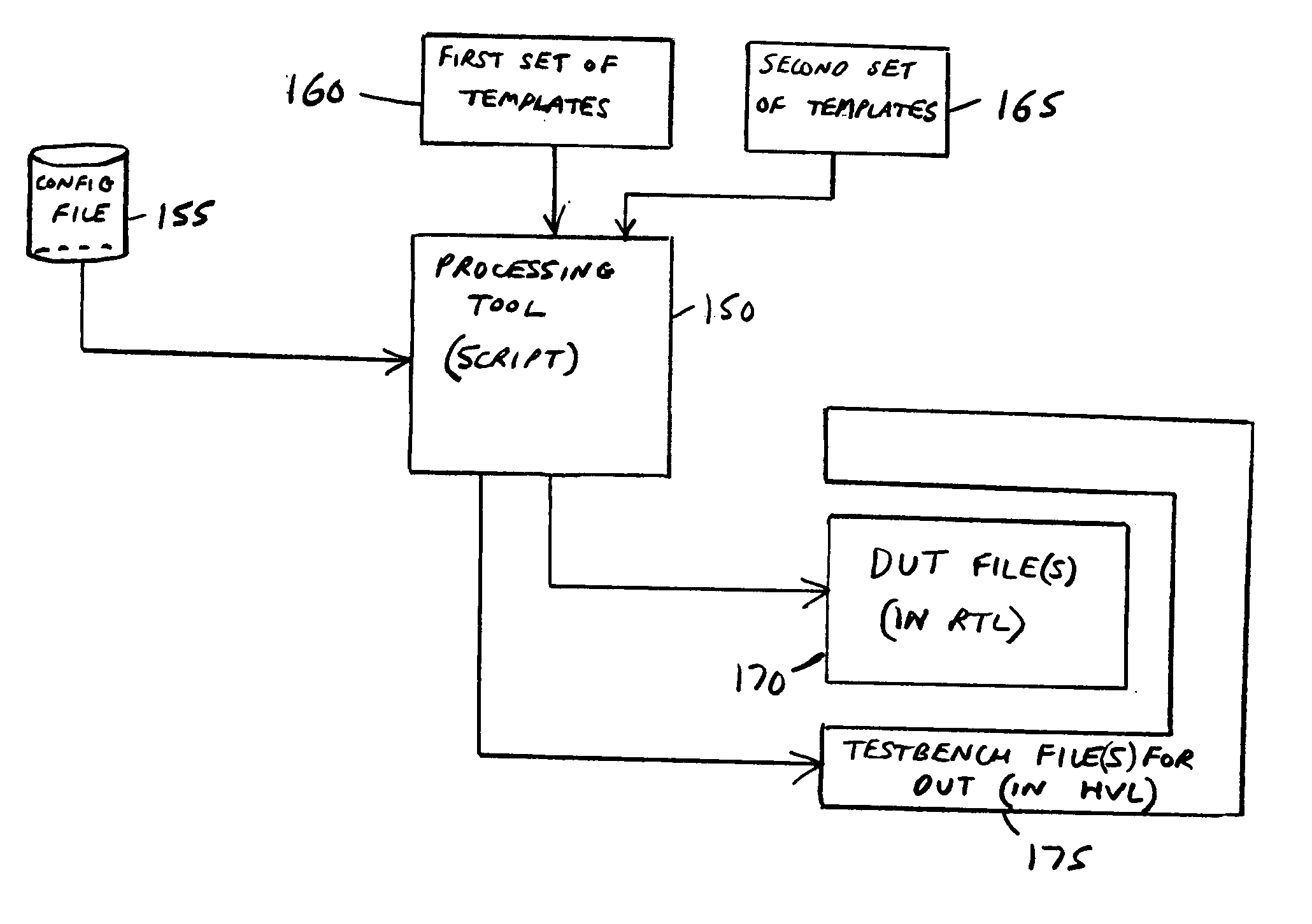
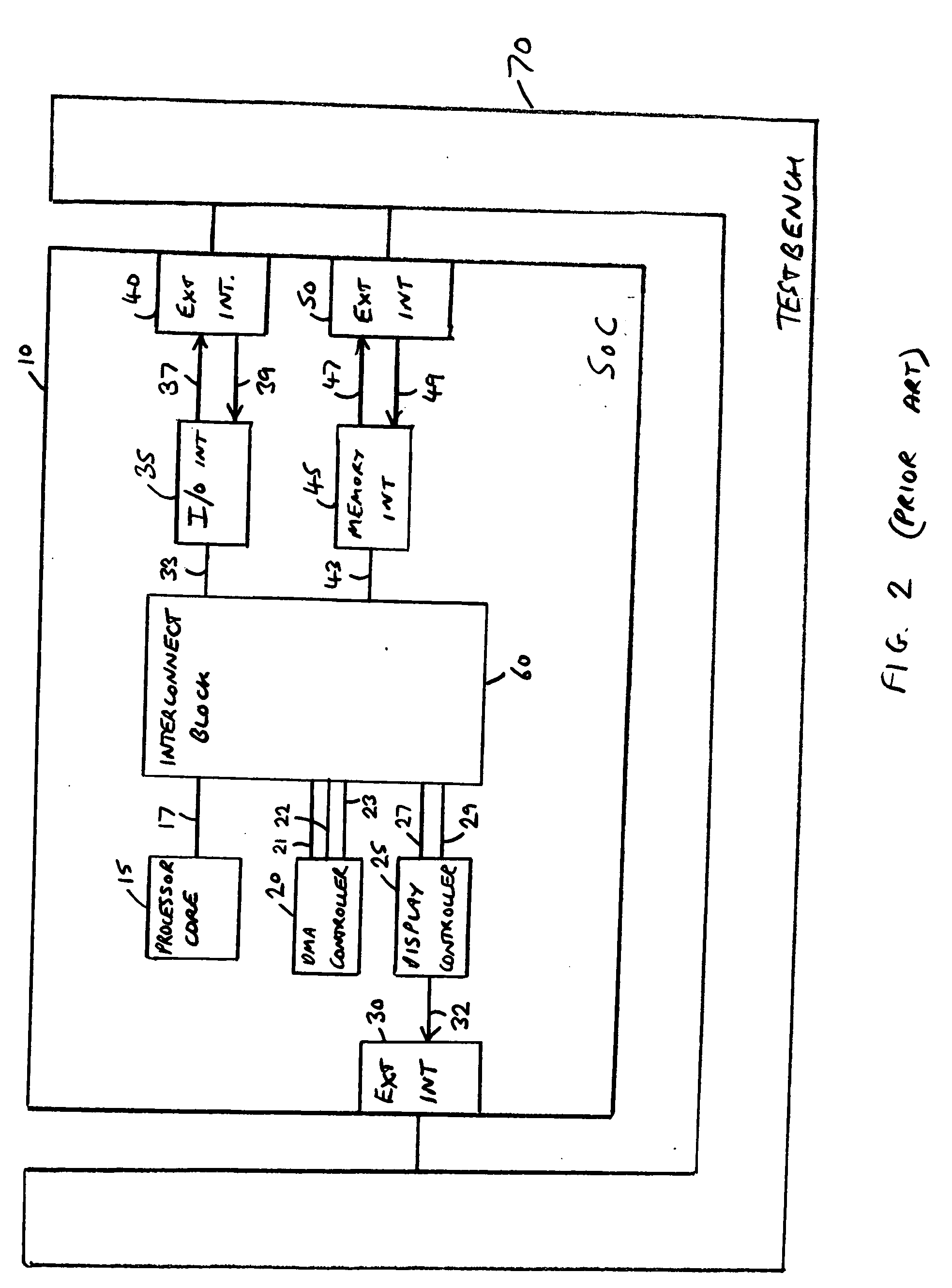
Generation of a testbench for a representation of a device
A system and method for generating a testbench for a representation of a device to be incorporated in a data processing apparatus is provided. The representation of the device is configurable based on configuration data specifying predetermined attributes of one or more components of the data processing apparatus with which that device is to be coupled, and the testbench provides a test environment that represents those one or more components. The method comprises the steps of receiving the configuration data used to configure the representation of the device, and generating the testbench with reference to the configuration data and a first set of templates defining the test environment. By this approach, a matching testbench can automatically be generated for any particular instantiation of the configurable representation of the device to enable thorough verification testing of that instantiation of the device to be performed.
Owner:ARM LTD
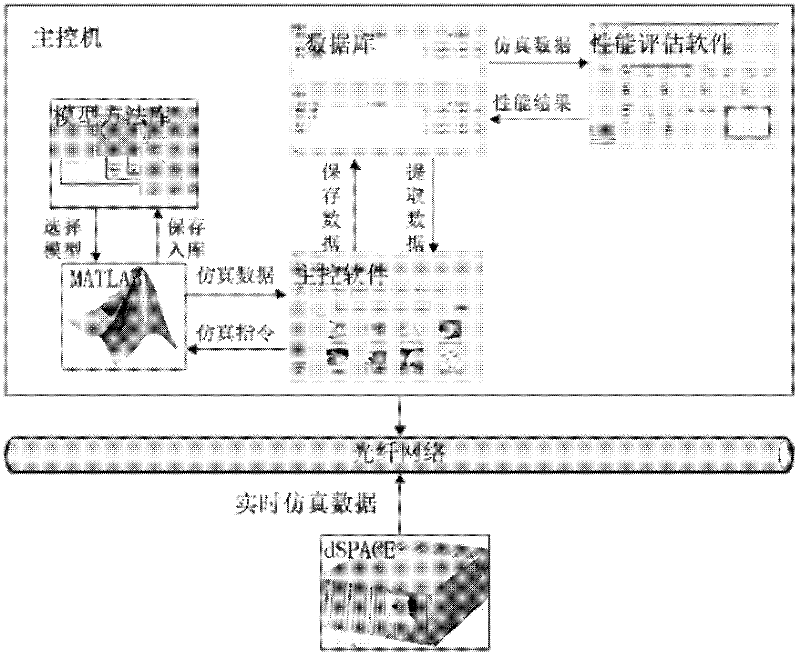
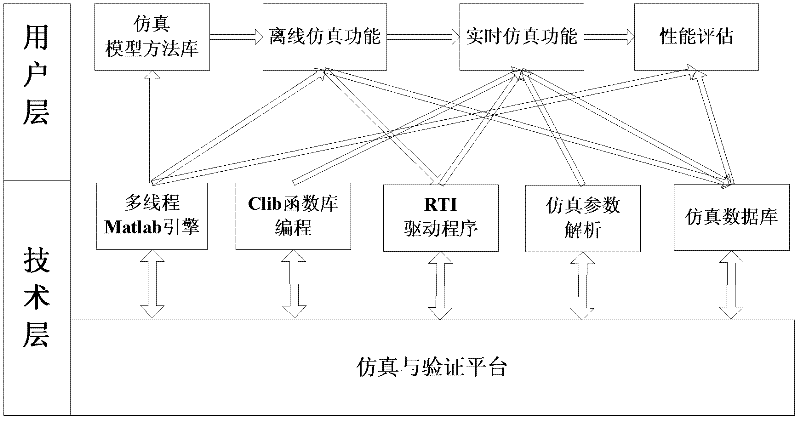
Simulation and verification method of control method of near space aircraft
ActiveCN102508692AStrong computing powerSpeed up developmentSoftware simulation/interpretation/emulationCommunication interfaceReal-time simulation
The invention relates to the simulation and the verification of a control method in the field of aerospace. In order to provide a simulation and verification platform capable of supporting a near space aircraft to real-time simulation tests and performance evaluation from the design of a flight control system, the technical scheme adopted by the invention is as follows: a simulation and verification method of the control method of the near space aircraft is realized by virtue of the following devices: a simulation master control machine and a dSPACE real-time simulation machine, wherein the simulation master control machine is provided with a DS817 high-speed serial communication interface plate; and the simulation master control machine is communicated with the DS814 high-speed serial communication interface plate of the dSPACE real-time simulation machine through an optical fiber. The method comprises the following steps of: operating master control software; dividing a whole evaluation process into two parts, namely a control system efficiency evaluation process and an evaluation confirmation process, by performance evaluation software; and obtaining data, which is needed by control system efficiency evaluation, by the control system efficiency evaluation process through three steps. The simulation and verification method of the control method of the near space aircraft is mainly applied to simulation and verification in the field of aerospace.
Owner:TIANJIN UNIV
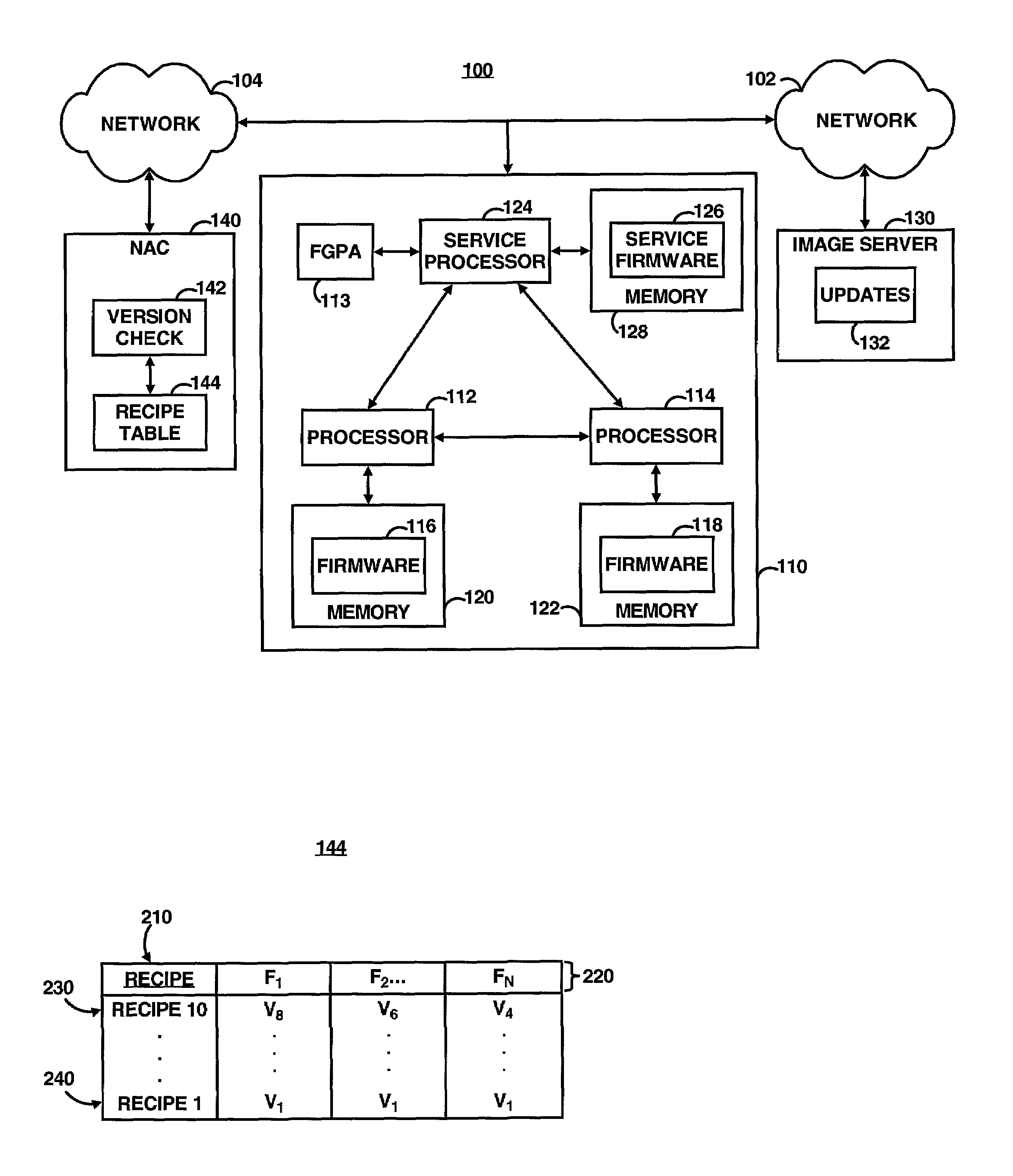
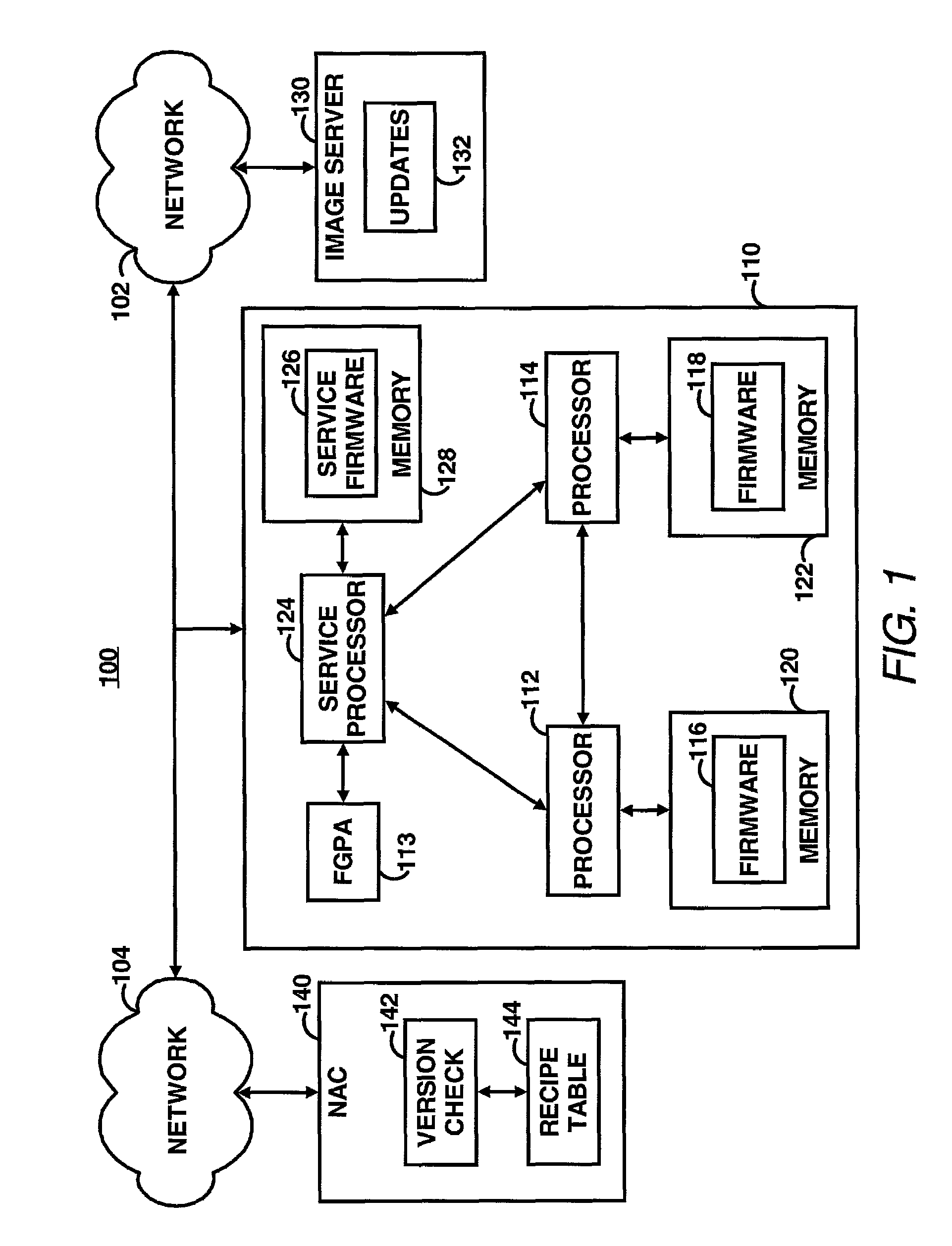
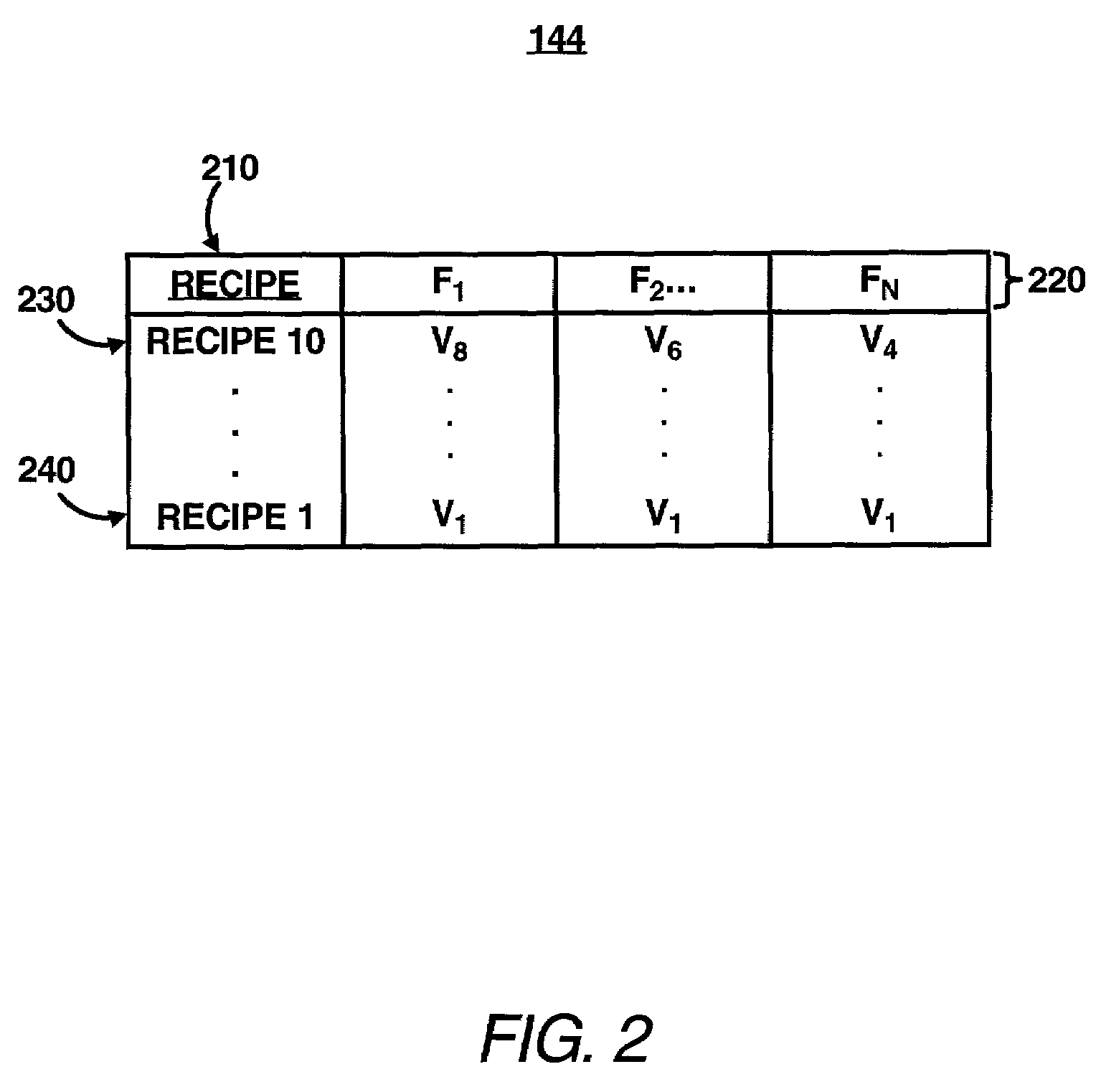
Verification of computer program versions based on a selected recipe from a recipe table
InactiveUS7065560B2Version controlMultiple digital computer combinationsParallel computingComputer program
A computer program version checking system checks at least one version of software running on a computing device including a plurality of programmable devices. A version of software running on the computing device is identified and compared to a version of the software in a recipe that is previously determined to be a correct version of the software. A determination is made as to whether the versions match.
Owner:HEWLETT PACKARD DEV CO LP
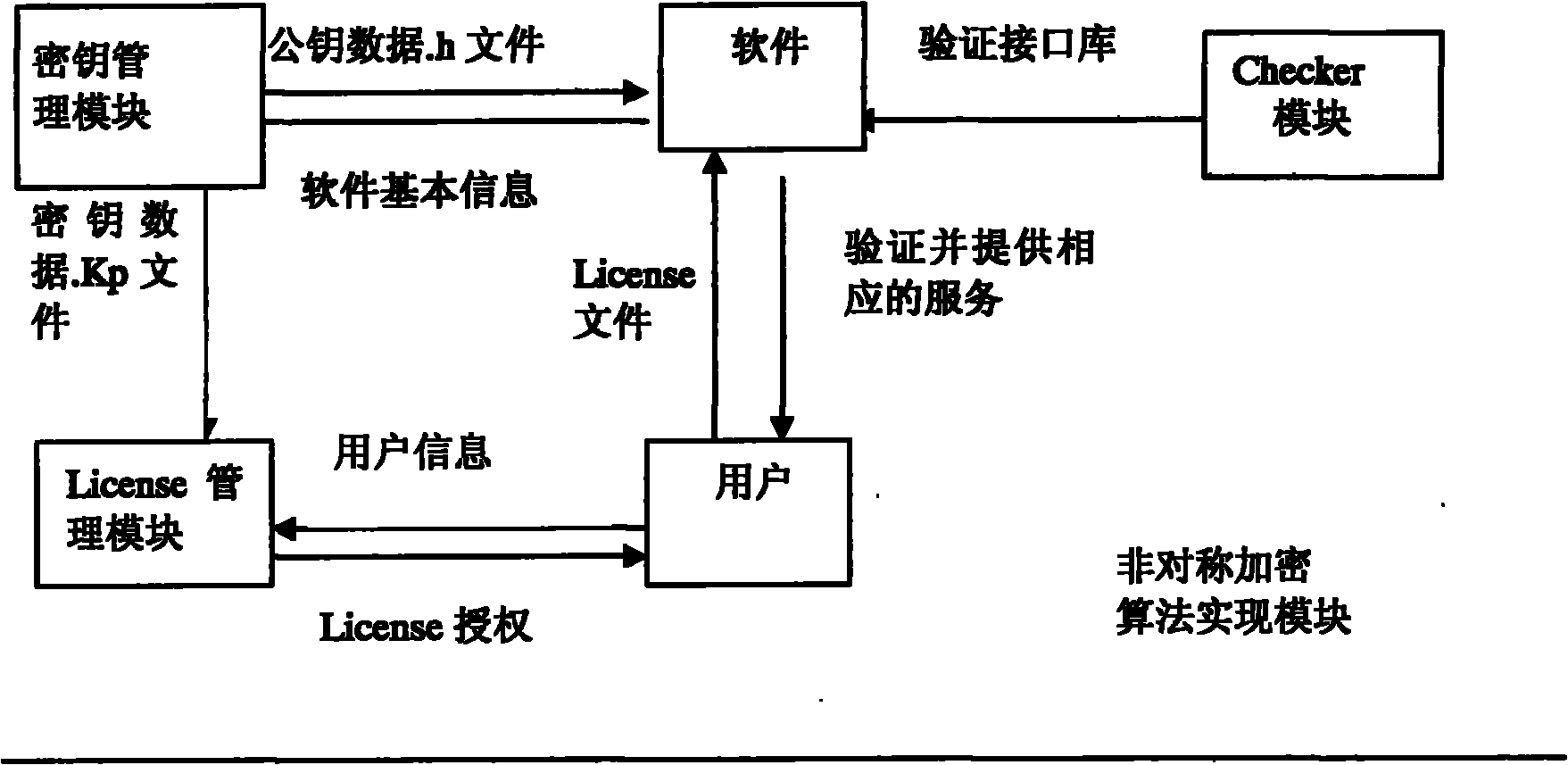
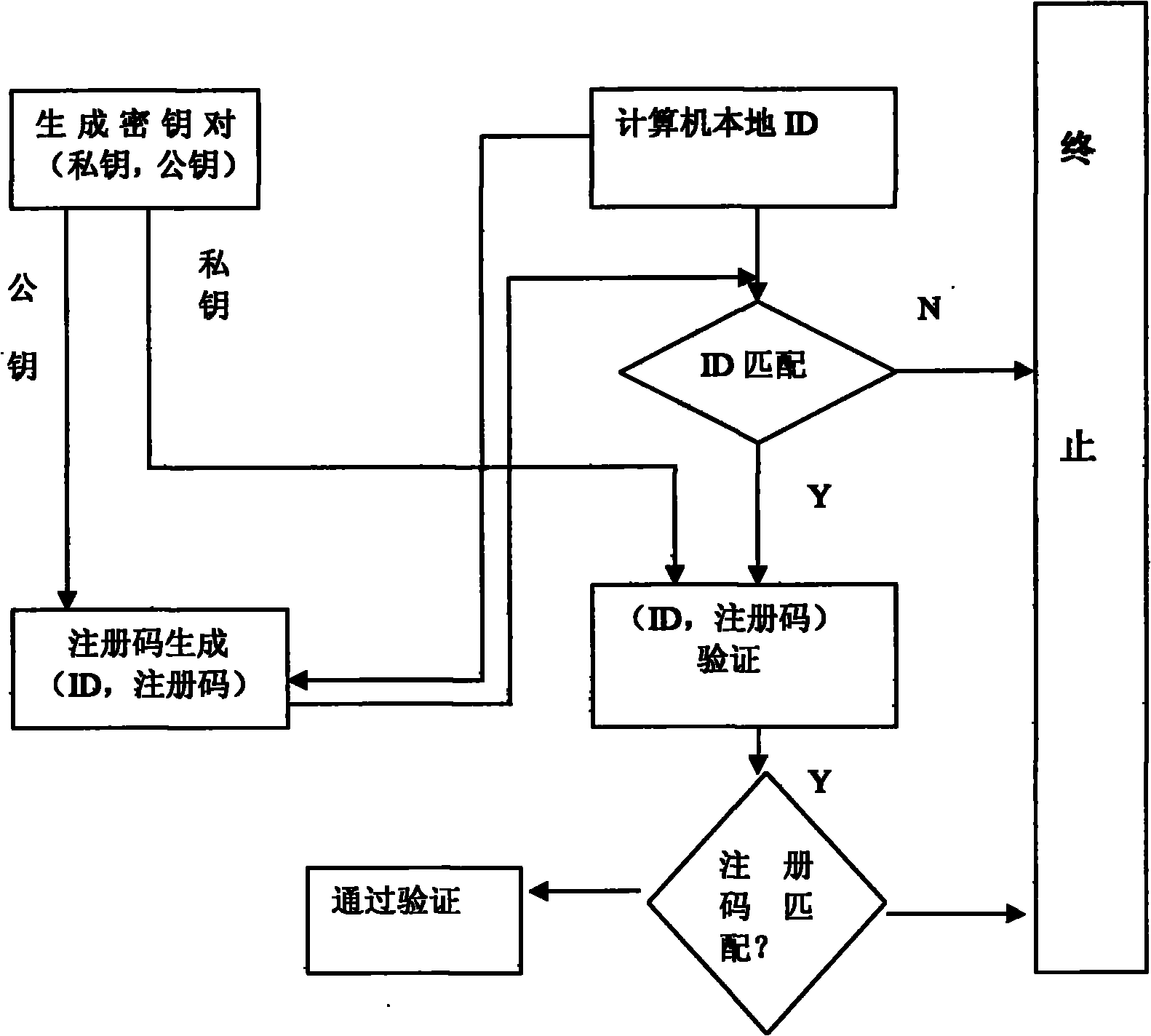
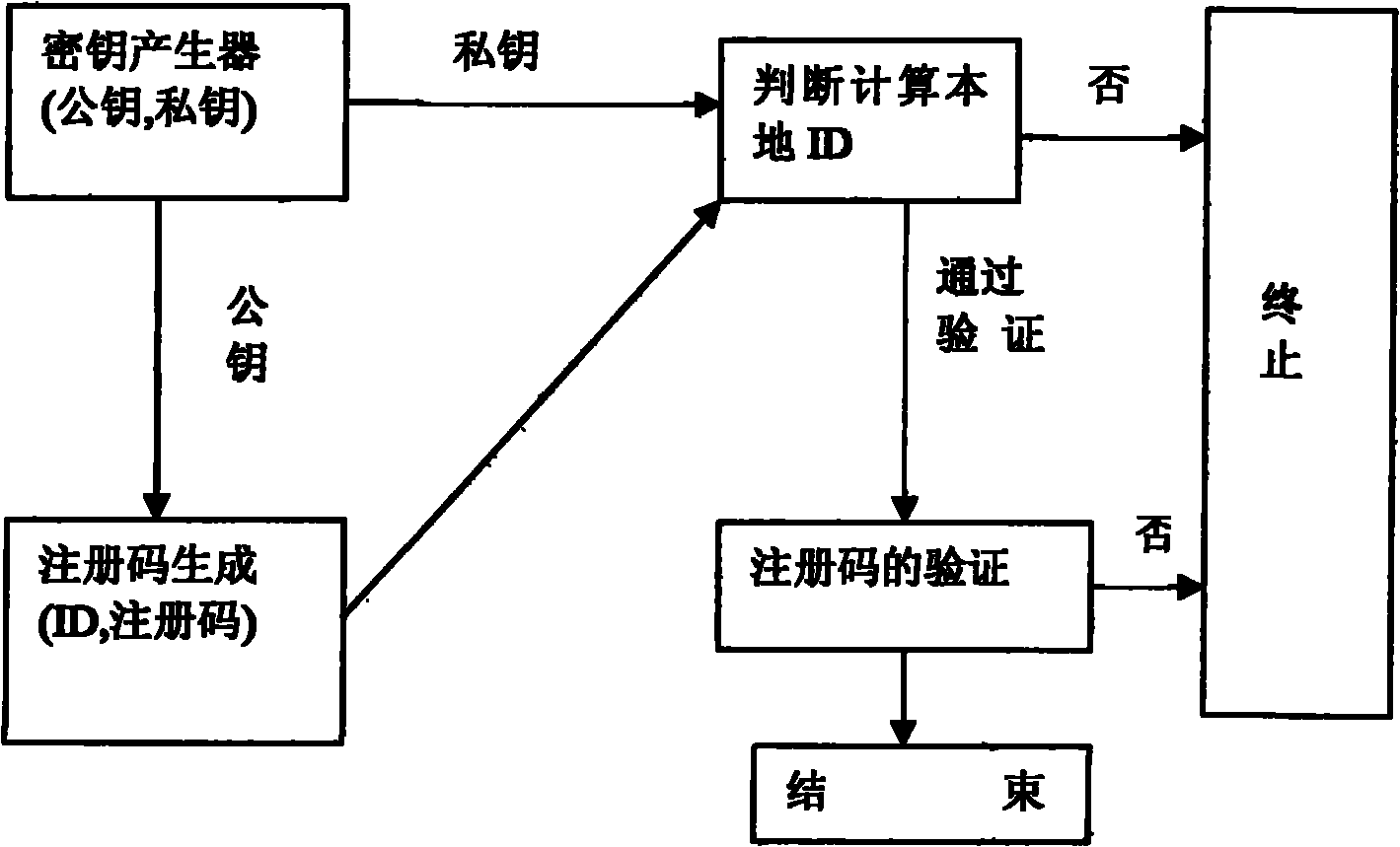
Method for utilizing Elagamal public key algorithm to generate software license code
InactiveCN102110199APublic key for secure communicationProgram/content distribution protectionComputer hardwareSoftware license
The invention discloses a method for utilizing Elagamal public key algorithm to generate a software license code to solve the problem of the software license code. The method comprises steps as follows: a cipher key generating module generates a public key / private key pair with a certain length through a random cipher key generator; secondly, a host computer ID generating module computes an ID with a fixed length according to the hardware information of the host computer and by combining with a random number Rand, and a software user submits the host computer ID to a software developer; a license code computing module computes a corresponding license code according to the host computer ID and the random number Rand, the private key provided by the cipher key generating module is used for signing, and the software developer submits an ordered pair, namely, the ID and the license code, to the user; and the legality of the ID must be determined at first by a license code verification module before operating the software program, and if the ID is illegal, the program terminates.
Owner:BEIJING SAFE CODE TECH
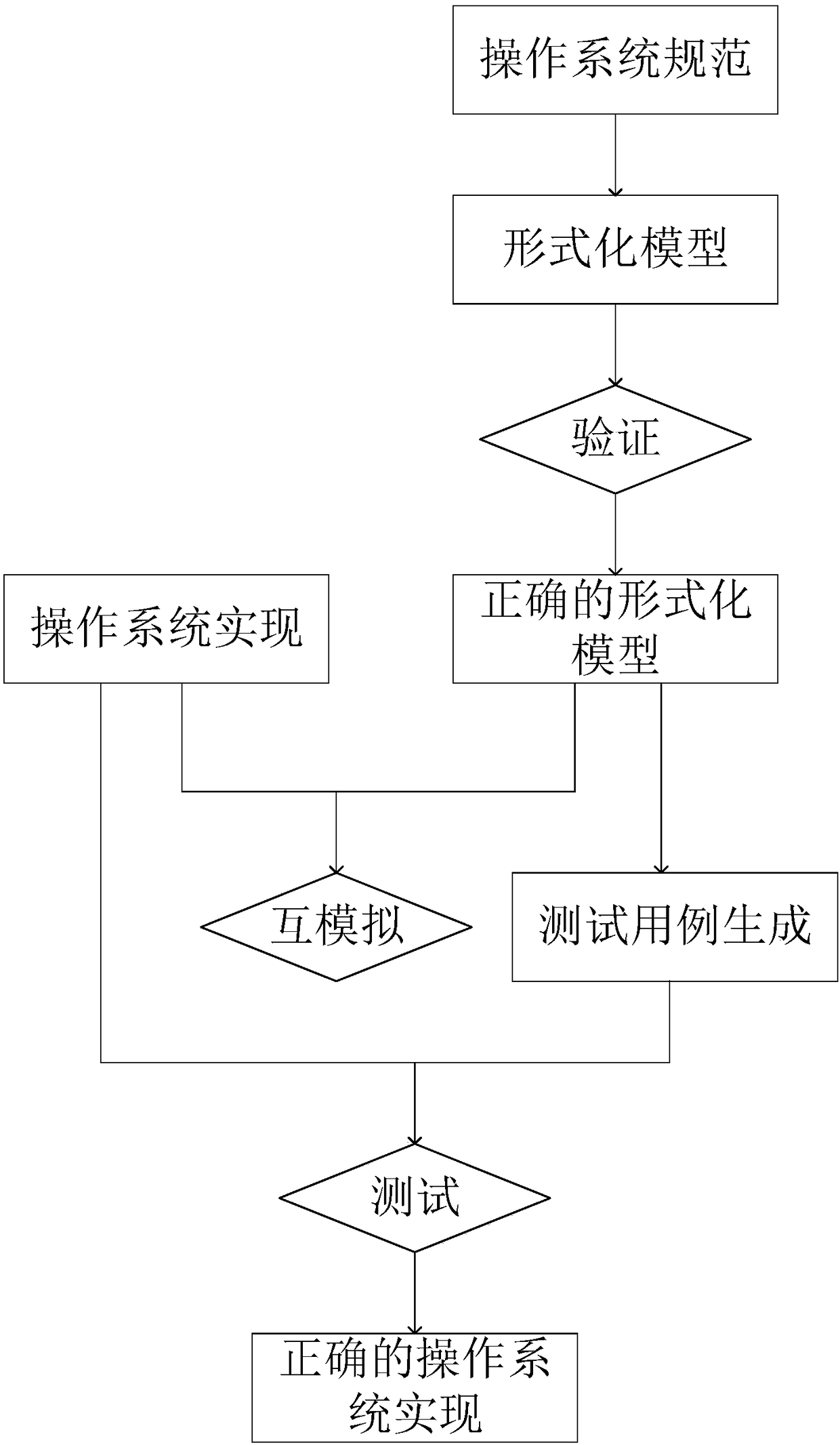
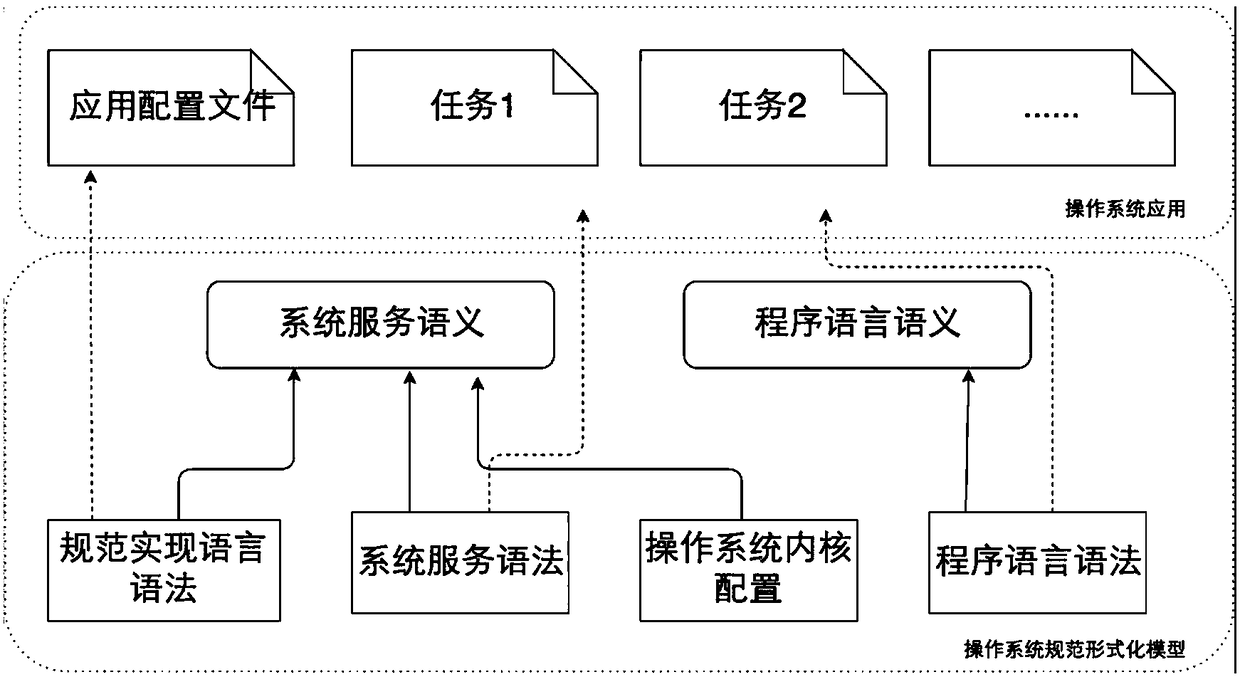
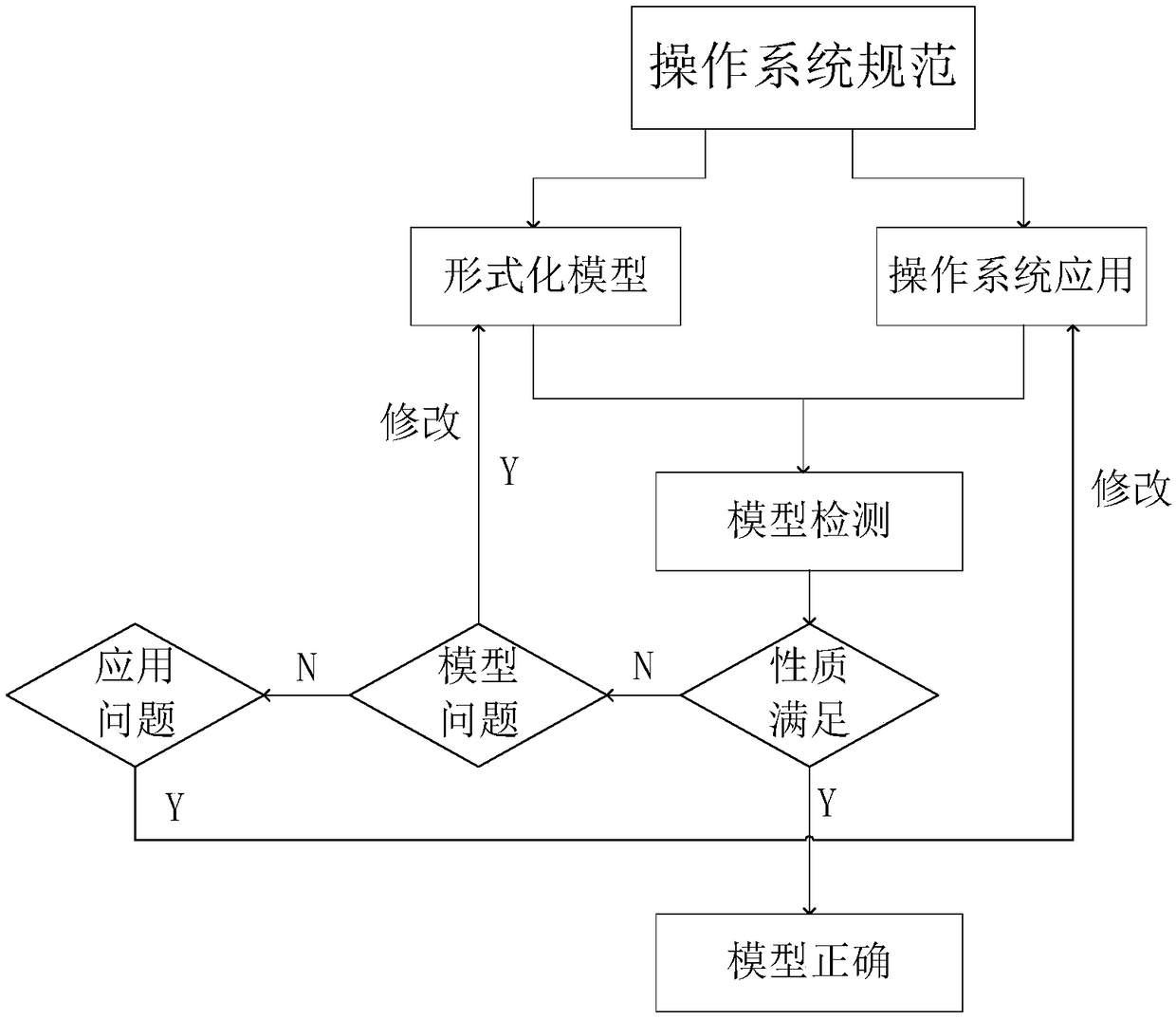
Operation system specification formal verification and test method
ActiveCN108509336AAchieve correctnessSoftware testing/debuggingCode compilationConstraint specificationPre conditioning
The invention discloses an operation system specification formal verification and test method. The method comprises the steps of firstly extracting constraints of pre-conditions and post-conditions about system service execution in operation system specifications; according to the extracted constraint specifications, building a formal semantic model; verifying the formal semantic model and an operation system application, and if the verification is not passed, correcting the formal semantic model or the operation system application, until the formal semantic model and the operation system application meet the specifications; automatically generating a test case realized by an operation system kernel from the correct formal semantic model by using a model check method; testing the correctness of operation system kernel implementation; and executing the verified application in the formal semantic model and the operation system kernel implementation, extracting two executive tracks, comparing the consistency of the two executive tracks by applying a mutual simulation method, and if the two executive tracks are inconsistent, correcting the operation system kernel implementation until the operation system kernel implementation is correct. The method is applied to formal verification of the operation system specifications and test of the operation system kernel implementation, thereby improving the security and reliability of an operation system.
Owner:EAST CHINA NORMAL UNIVERSITY
Signature verification method and device for application
InactiveCN106022098APrevent secondary packagingComputer security arrangementsApplication softwareData mining
An embodiment of the present application provides a method for verifying the signature of an application program, including: calling a target function in a preset dynamic link library; obtaining the dynamic signature information of the application program through the target function; and verifying the dynamic signature information Whether it is consistent with the first signature information pre-embedded in the dynamic link library; if not, close the application program; if consistent, run the application program. In the embodiment of the present application, the dynamic signature information of the application program is acquired by calling a function in the dynamic link library, and the dynamic signature information is compared with the pre-embedded first signature information. If they are inconsistent, the application program is closed. Since it is difficult to crack the dynamic link library, the method of obtaining the signature information by calling the function of the JAVA layer in the dynamic link library is also difficult to crack. This makes it difficult for counterfeiters to obtain the signature information of the application, thereby preventing the program from being repackaged.
Owner:JUHAOKAN TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com