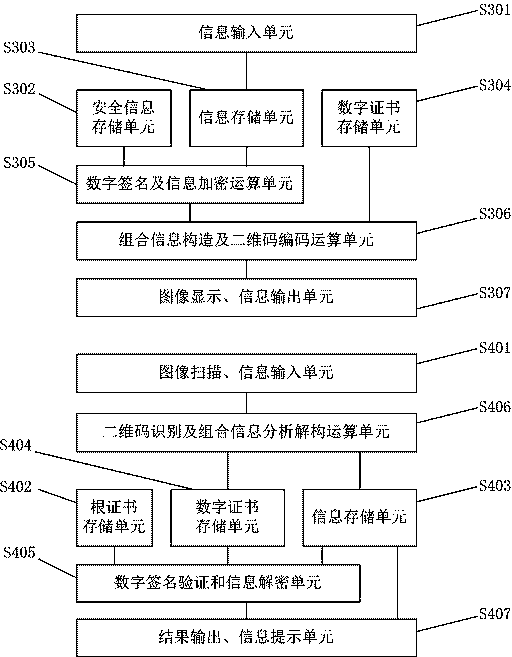
Construction verification method and device capable of verifying security two-dimensional code offline
A verification method and two-dimensional code technology, applied in the field of offline verification of secure two-dimensional code construction verification, can solve problems such as difficulty in verification of publishing sources, inability to read and verify sources, and verification of two-dimensional code security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0127] The specific implementation steps are as follows:
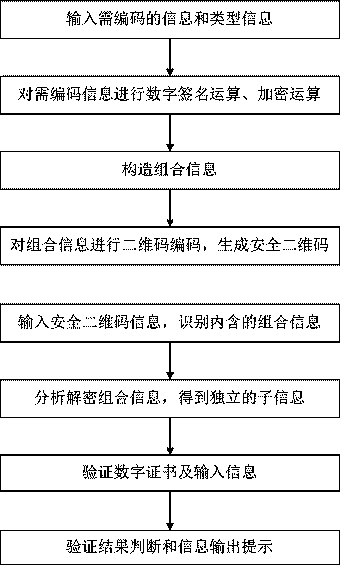
[0128] 1. Enter the information and type information to be encoded
[0129] The information to be coded includes basic information, target information, and dynamic information. Basic information: Base:{Name:ABC Bank}, target information: OBJ:{URI:https: / / www.abc.com}, dynamic information: DYN:{Created:2016-1-1 12:00 :00|Expired:2026-1-1 12:00:00}. The type information is a public information security QR code.
[0130] Connect the input information with vertical bars and brackets, as shown in Table 1.
[0131] Table 1 Information to be encoded in Example 1
[0132] [OBJ:{URI:https: / / www.abc.com}Base:{Name:ABC Bank}DYN:{Created:2016-1-112:00:00|Expired:2026-1-1 12:00: 00}]
[0133] 2. Perform digital signature operations and encryption operations on the information to be encoded
[0134] Using the SHA256 hash algorithm, the hash value of the information to be encoded in Table 1 is calculated as:
[0135] sha256: 9f2a8e9ace06537b...
Embodiment 2
[0191] The specific implementation steps are as follows:
[0192] 1. Enter the information to be encoded and type information
[0193] The information to be coded includes basic information, target information, and dynamic information. The basic information is: Base:{TaxiID:沪A12345|LicenseID:123456|UserID:12345678|Domain:abcpay.com}, the target information is: OBJ:{URI:https: / / sqr.abcpay.com / zrk1rjziurlr2w3ira}, dynamic The information is: DYN:{Created:2016-1-112:00:00|Expired:2017-1-1 12:00:00}. The type information is a QR code for public information security.
[0194] Connect the input information with vertical bars and brackets, as shown in Table 8.
[0195] Table 8 Information to be encoded in Example 2
[0196] [OBJ:{URI:https: / / sqr.abcpay.com / zrk1rjziurlr2w3ira}Base:{TaxiID:沪A12345|LicenseID:123456|UserID:12345678|Domain:abcpay.com}DYN:{Created:2016-1-1 12:00:00|Expired:2017-1-1 12:00:00}]
[0197] In this embodiment, the encoding information needs to include multi-byte chara...
Embodiment 3
[0226] The specific implementation steps are as follows:
[0227] 1. Enter the information to be encoded and type information
[0228] The information to be coded includes basic information, target information, and dynamic information. The basic information is: Base:{Name:ABC Mall|Addr:No.1288,ABC Rd.,Shanghai|Domain:abcpay.com}, and the target information is: OBJ:{URI:https: / / pay.abcpay.com / dkri67zin9oo8tzxy9ojquz8mcaedhzcljix1jeu}, the dynamic information is: DYN:{Created:2016-5-1 12:00:00|Expired:2016-5-1 12:10:00|PaymentID:e7db7c48642c78a669fd|Total:580.00RMB}. The type information is a QR code for public information security.
[0229] Connect the input information with vertical bars and brackets, as shown in Table 12.
[0230] Table 12 Information to be encoded in Embodiment 3
[0231] [OBJ:{URI:https: / / pay.abcpay.com / dkri67zin9oo8tzxy9ojquz8mcaedhzcljix1jeu}Base:{Name:ABC Mall|Addr:No.1288,ABC Rd.,Shanghai|Domain:abcpay.com}DYN:{Created:2016 -5-1 12:00:00|Expired:2016-5-1 12...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com