Patents
Literature
299 results about "Public information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
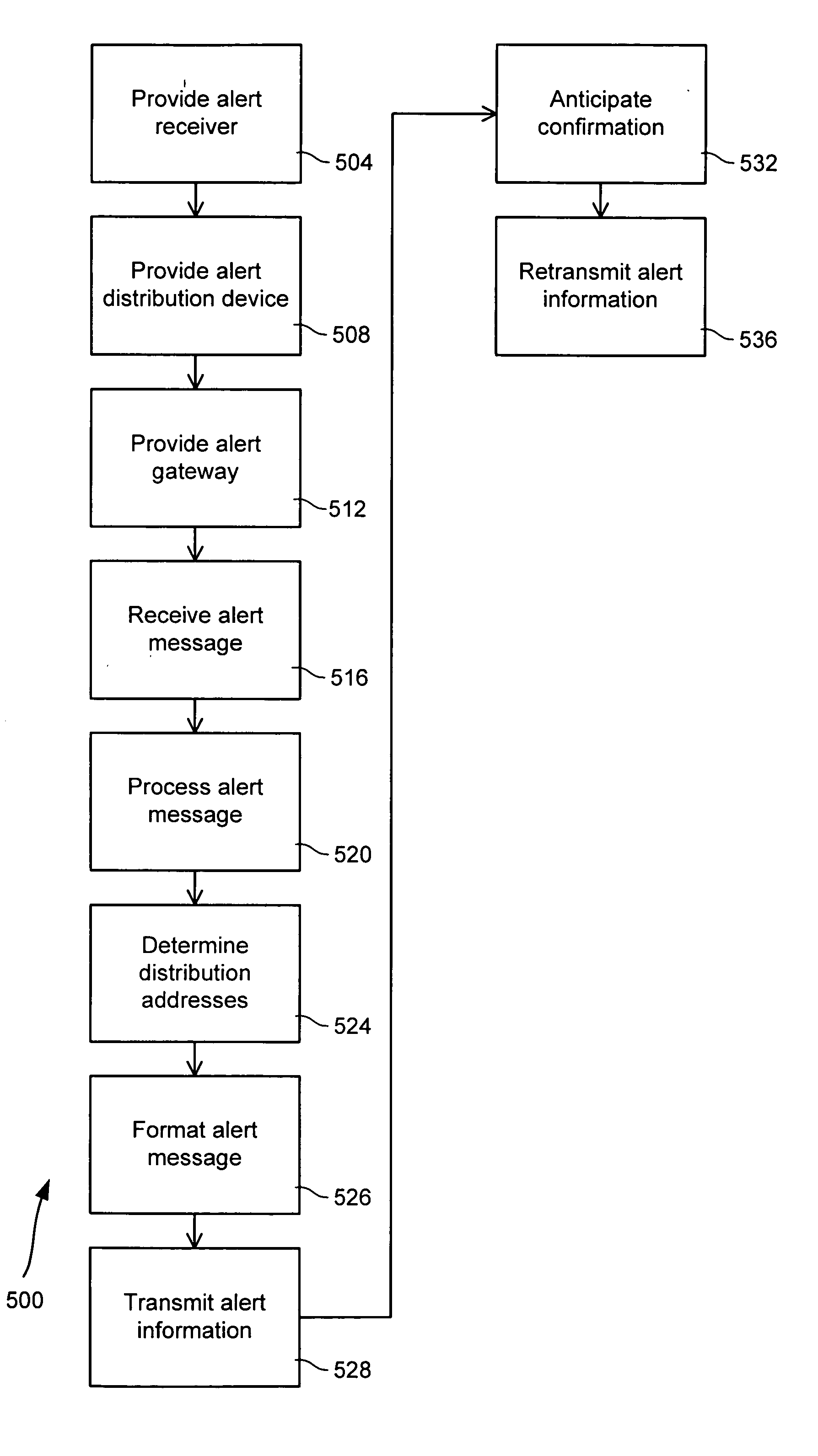
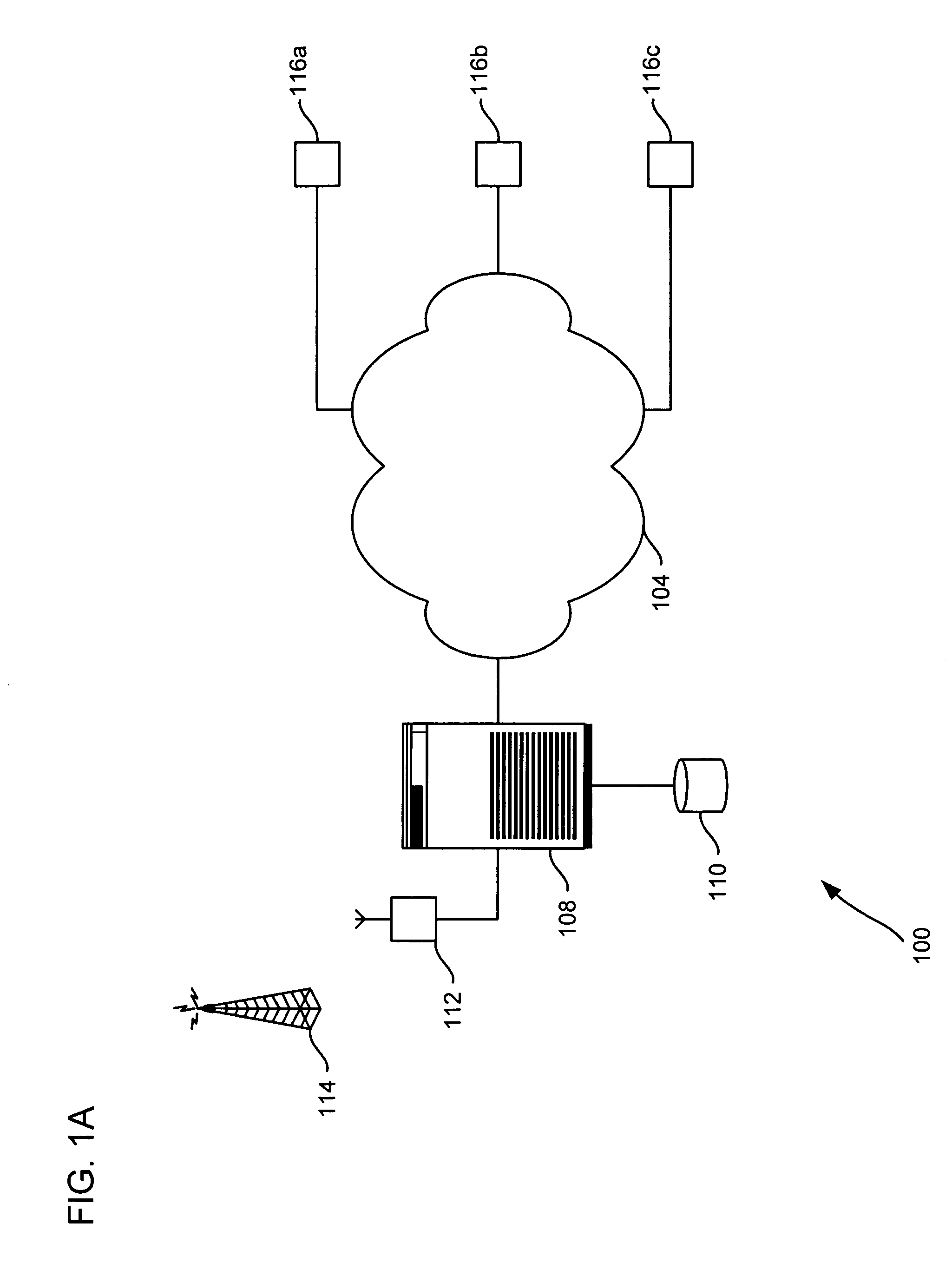
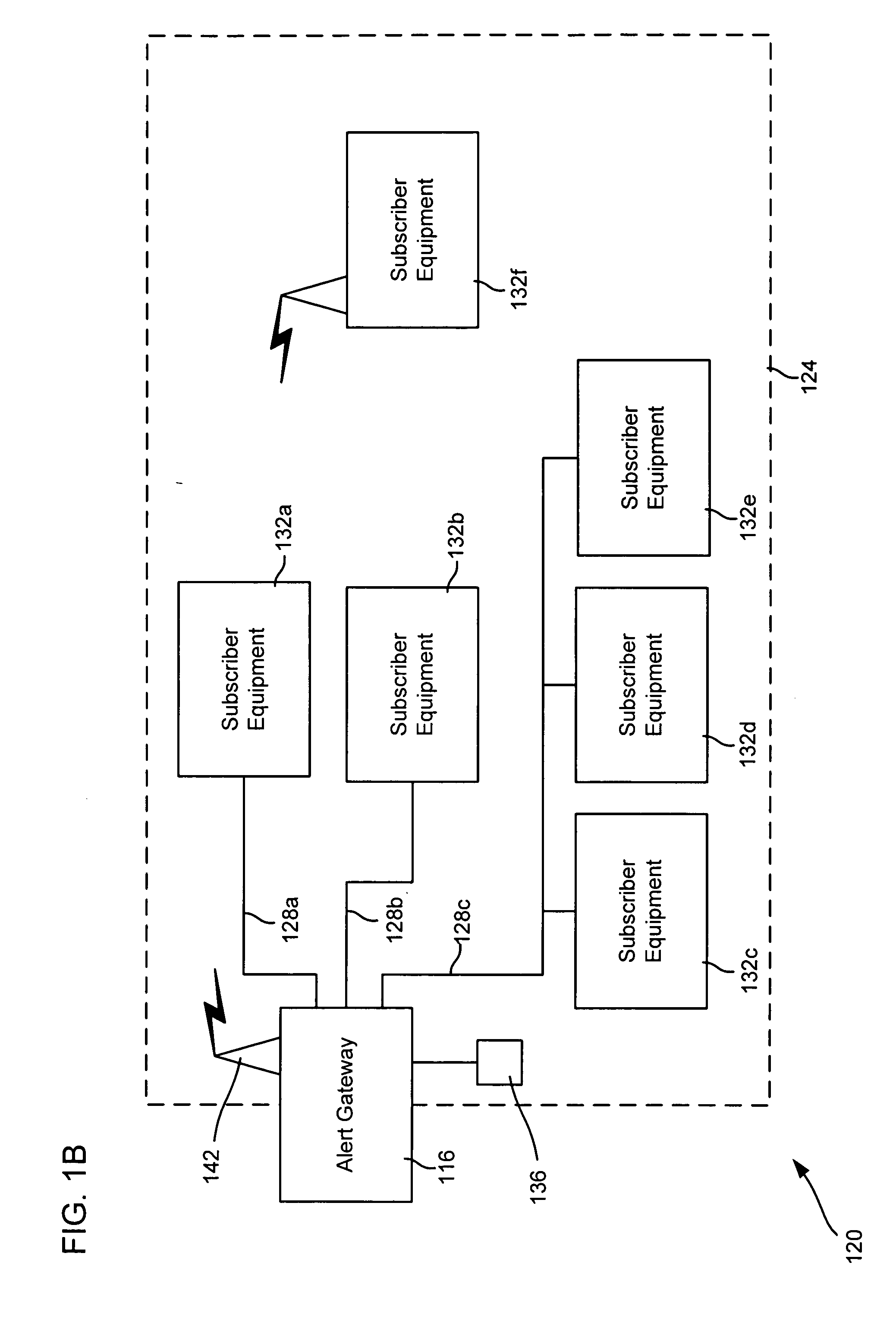
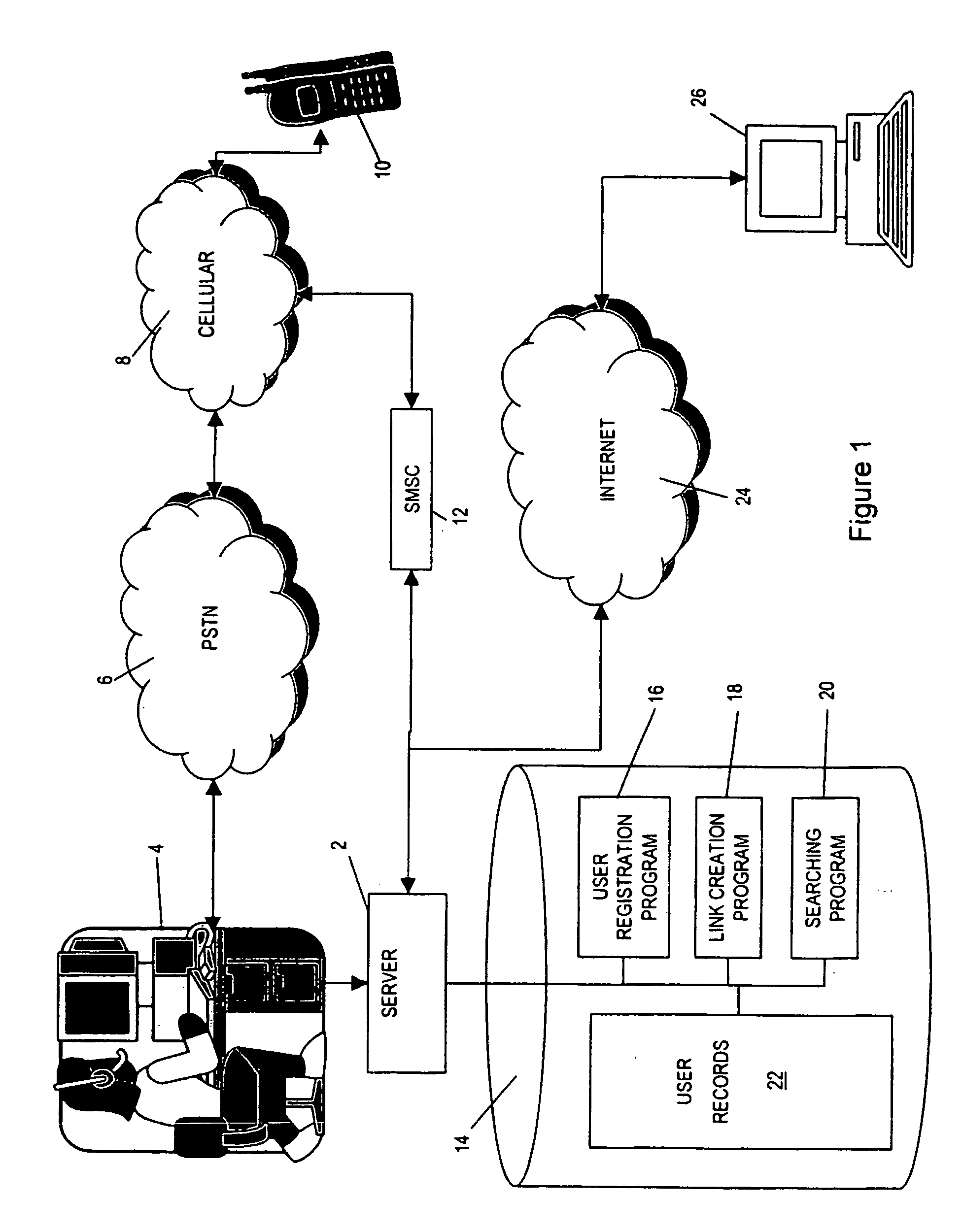
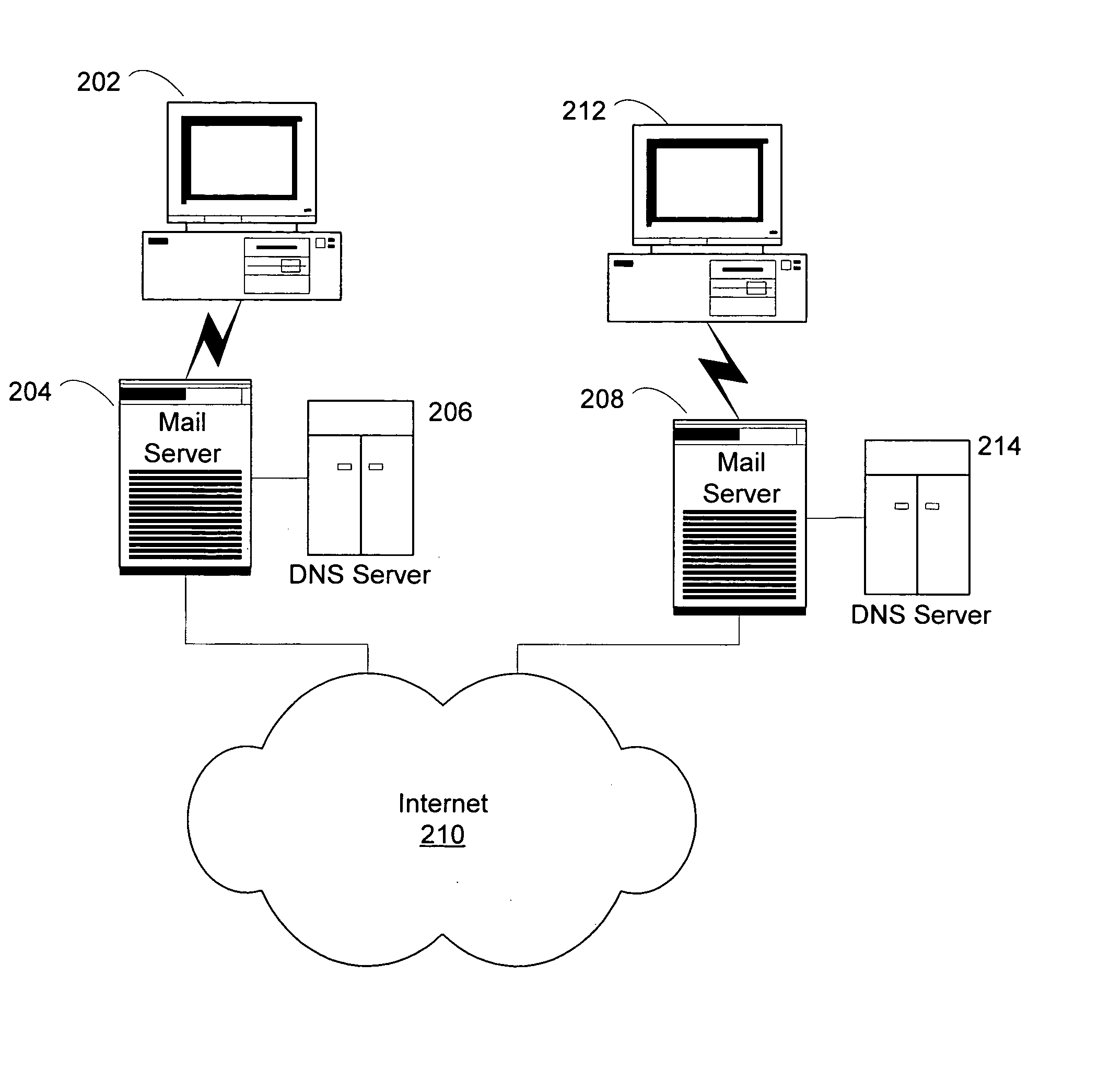
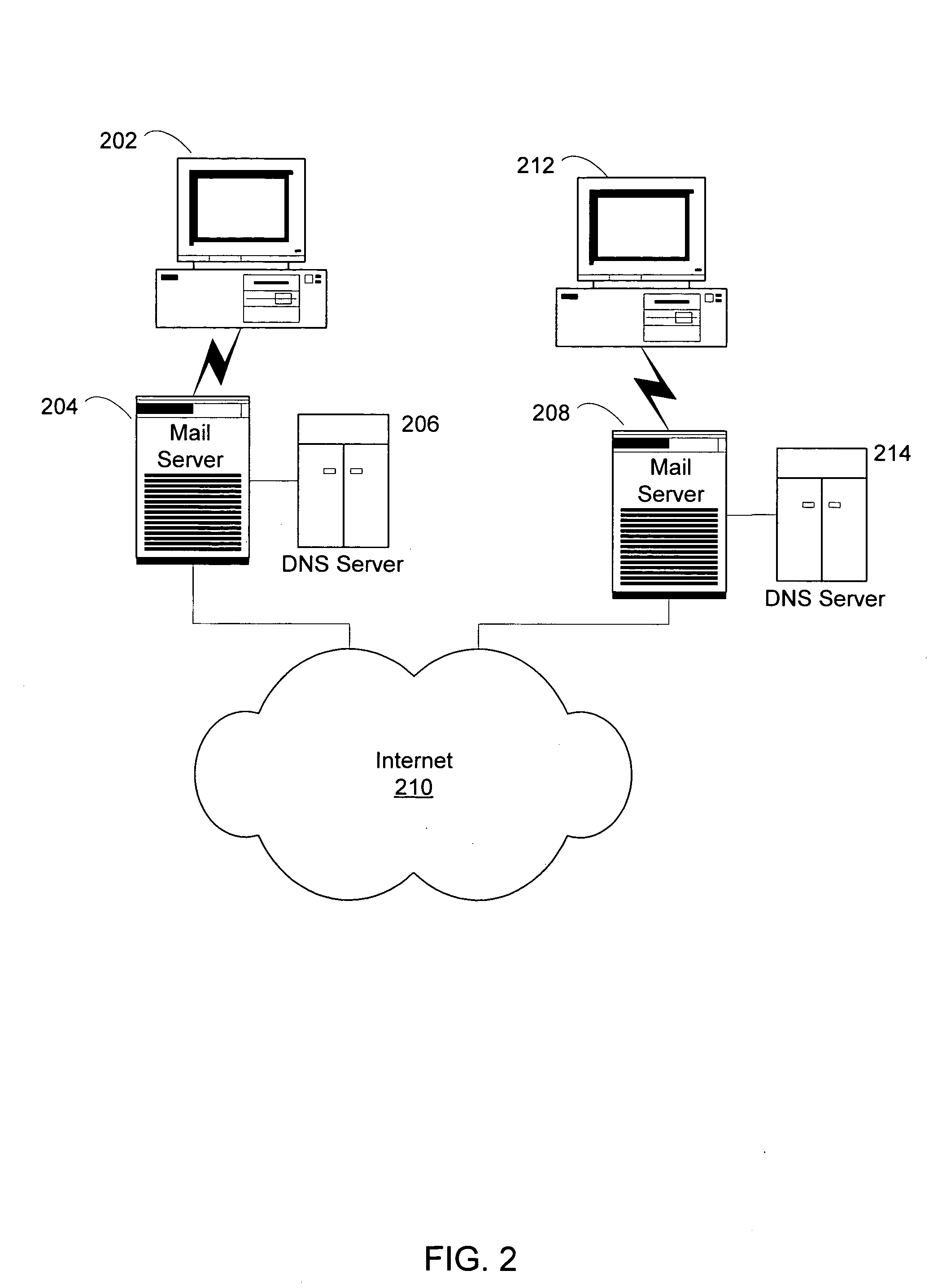
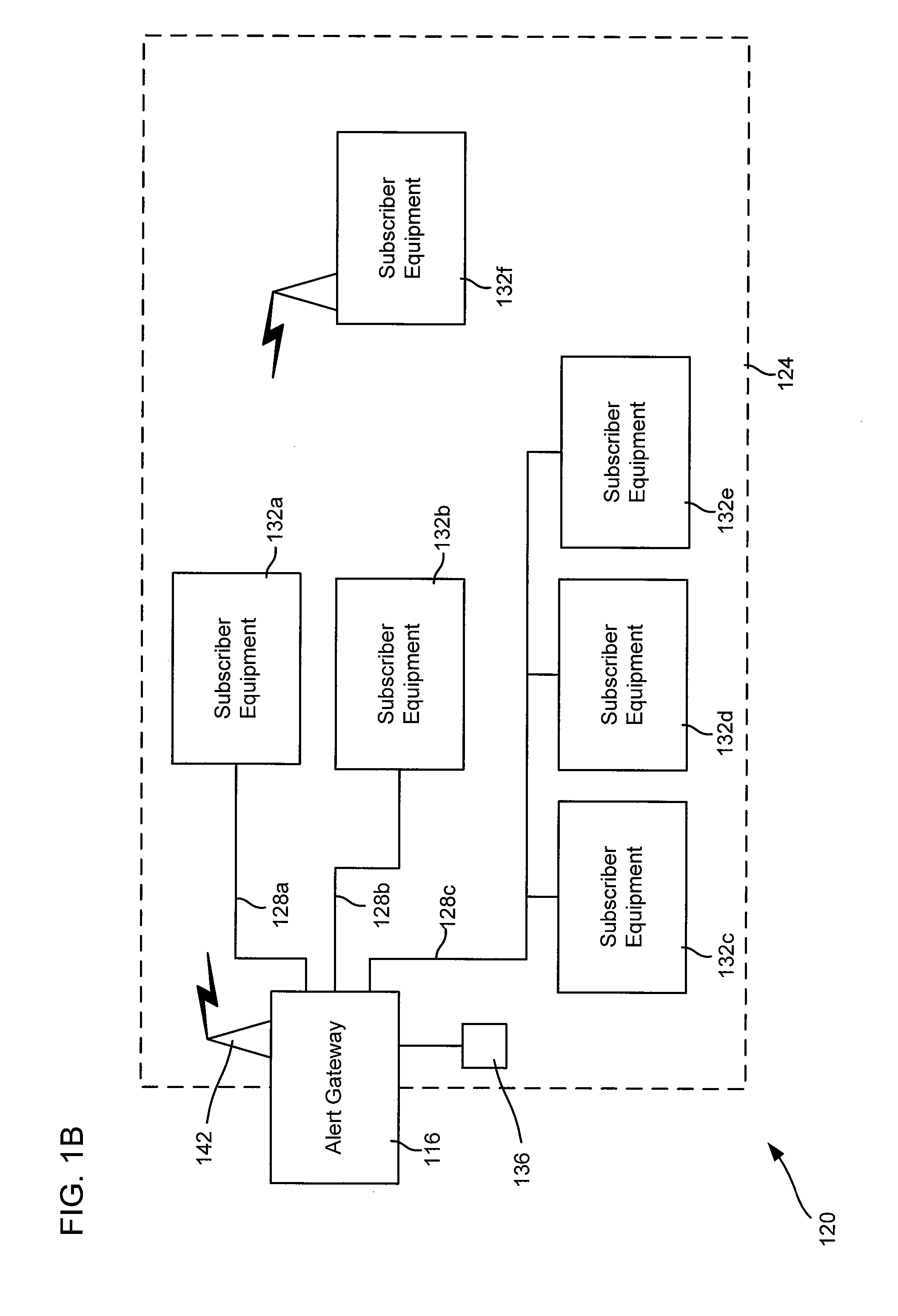
Alert gateway, systems and methods
ActiveUS20050030977A1Television system detailsPulse modulation television signal transmissionPublic informationReal-time computing
Embodiments of the invention provide systems and methods for distributing urgent public information. Merely by way of example, urgent public information, such as an alert message, may be received by, inter alia, an alert gateway device. The alert message may then be distributed to a subscriber in any of a variety of ways, including by telephone, by data message (e.g., to a computer), by video message (e.g., via a television), by display on an alert notification device. In some embodiments, the alert gateway device may process the alert message and / or may determine how to provide the alert message to the subscriber.
Owner:QWEST
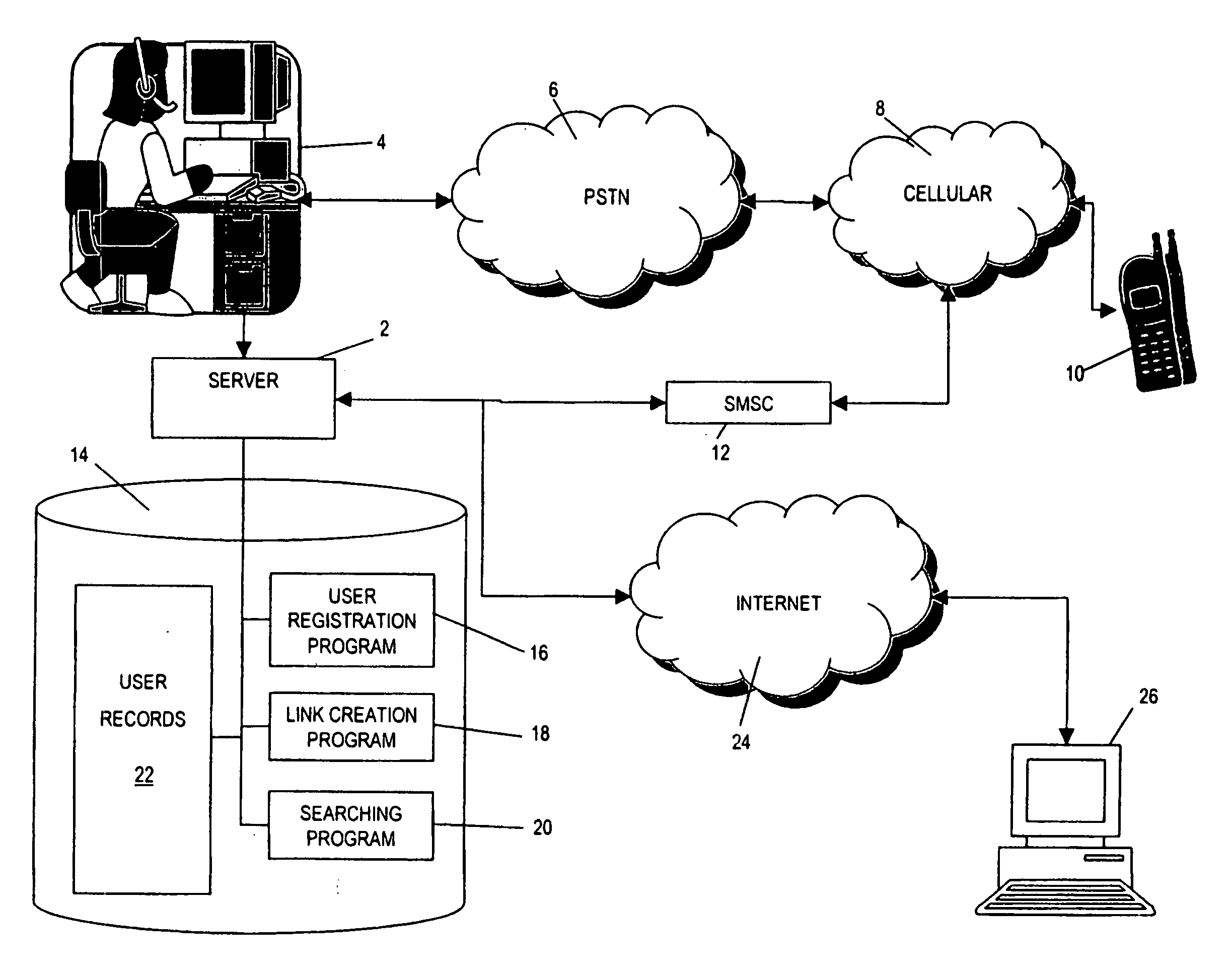
Method and system for processing or searching user records
ActiveUS20060080283A1Promote resultsImprove accuracyDigital data processing detailsAutomatic call-answering/message-recording/conversation-recordingAddress bookPublic information
Preferably for use in a directory enquires system, the invention provides a method and system for processing user records to determine common entries therebetween. When two user records are determined to store common information then link data is generated (18) and stored in each user record (22) indicating a link between the two records. This link information is then used in subsequent searching (20) of the user records to determine the most likely result from a list of possible results obtained from a search of the user records. In a directory enquiries system (14) the user records contain user ID and telephone number details as well as address book data of each user's friends, family, or other acquaintances. The address book data is used to determine whether a link between user records should be formed.
Owner:BRITISH TELECOMM PLC
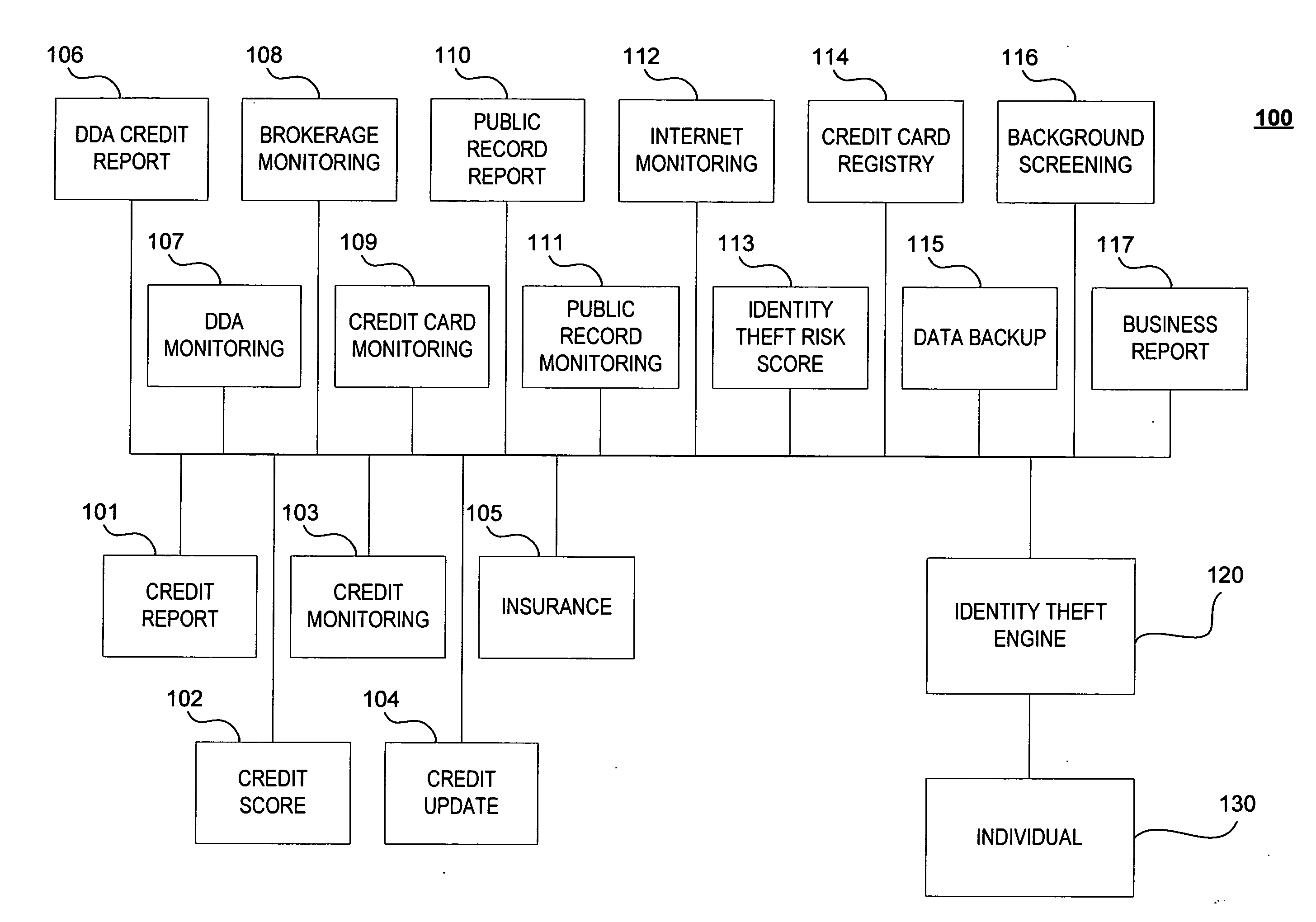
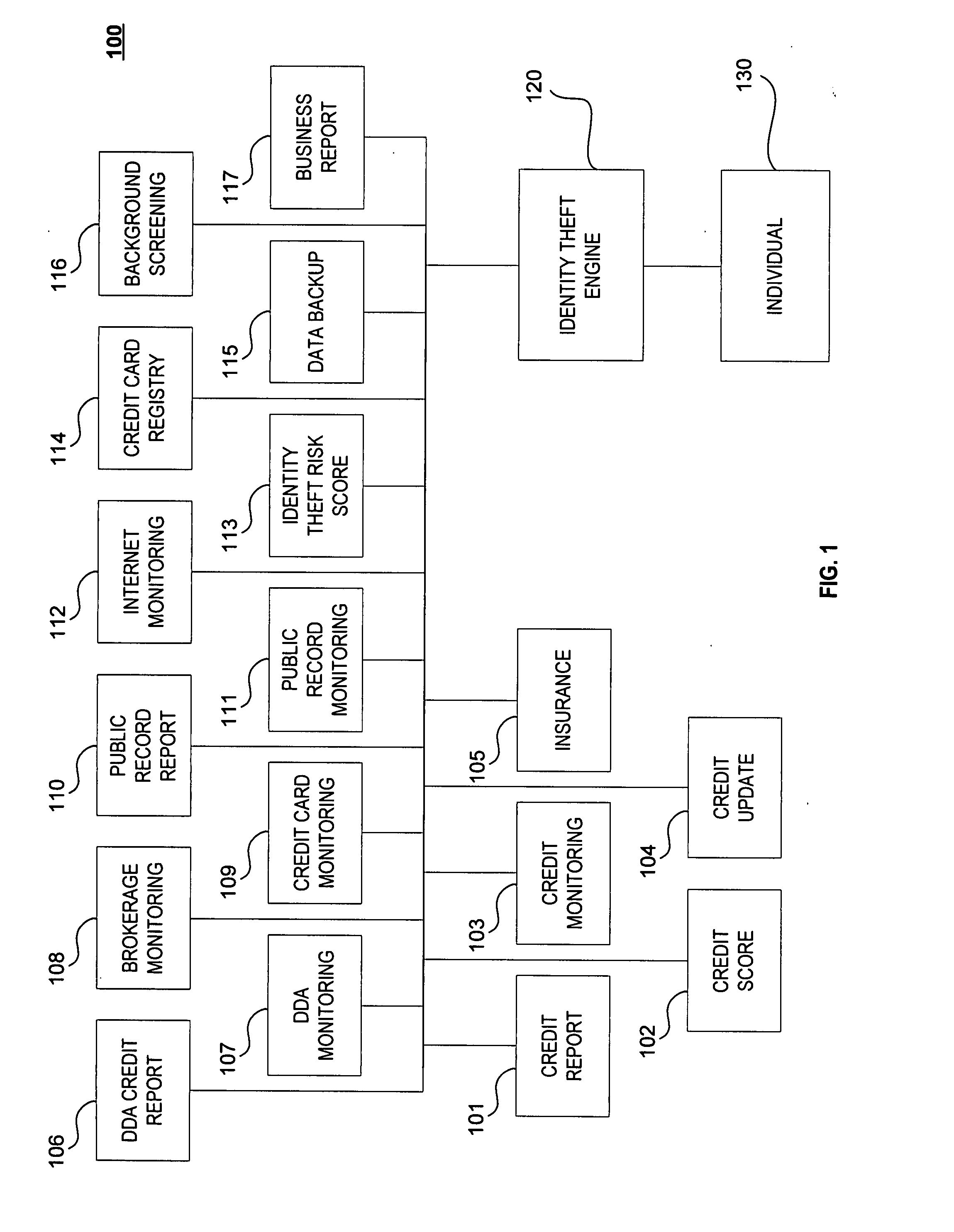
Method and system for preventing and detecting identity theft
ActiveUS20070244807A1Preventing and detecting identity theftStop in trackFinanceCredit cardData provider
A system, method and computer program product for receiving information relating to a financial account of an individual from at least one first data provider; receiving information relating to at least one of an identity theft expense reimbursement insurance policy of the individual, a public information relating to the individual, an identity theft risk score of the individual, a credit card registry of the individual, a backup data relating to the individual, a background information of the individual, and a business report relating to the individual, from at least one second data provider; and preparing a report relating to the individual's identity theft based on the information.
Owner:AURA SUB LLC +1
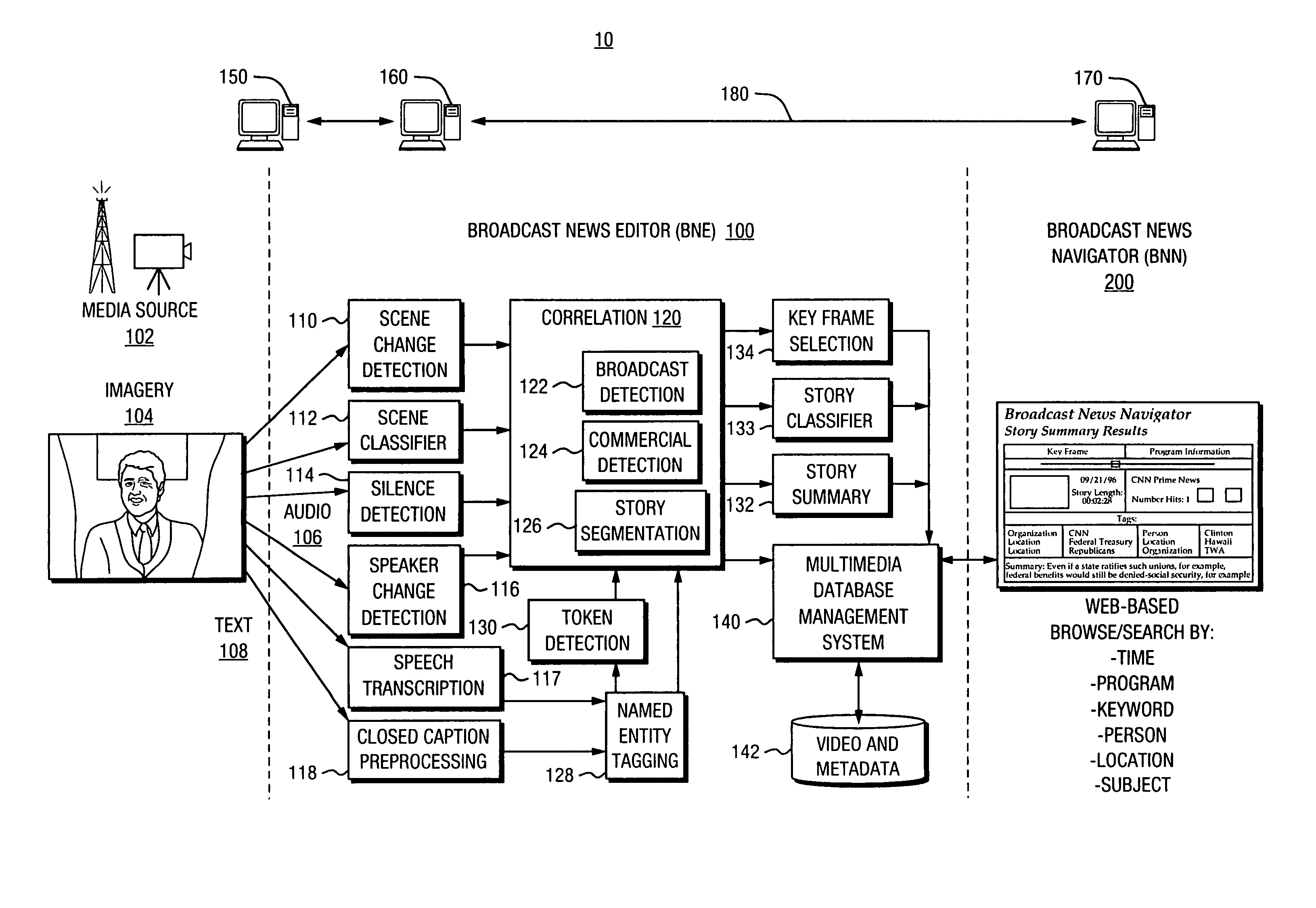
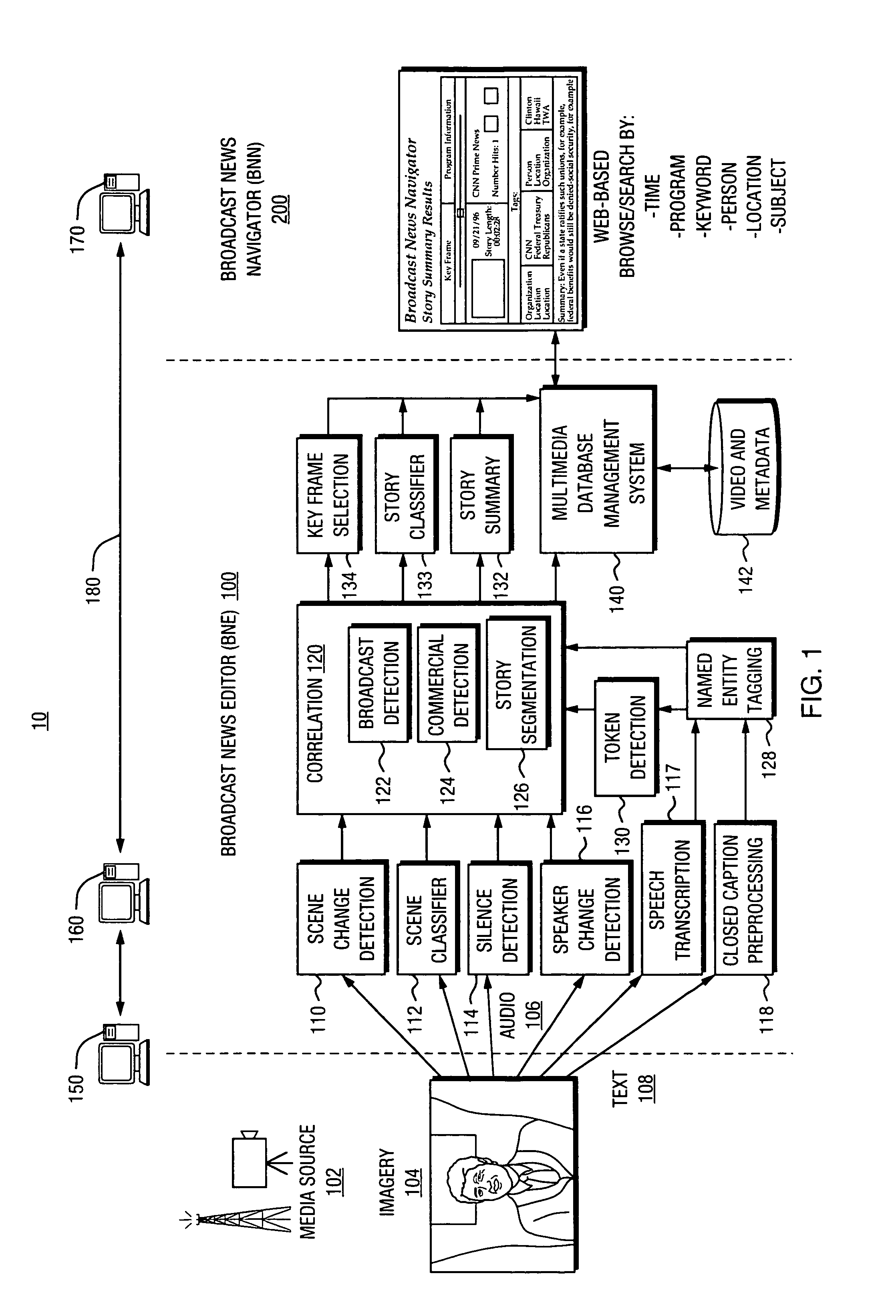
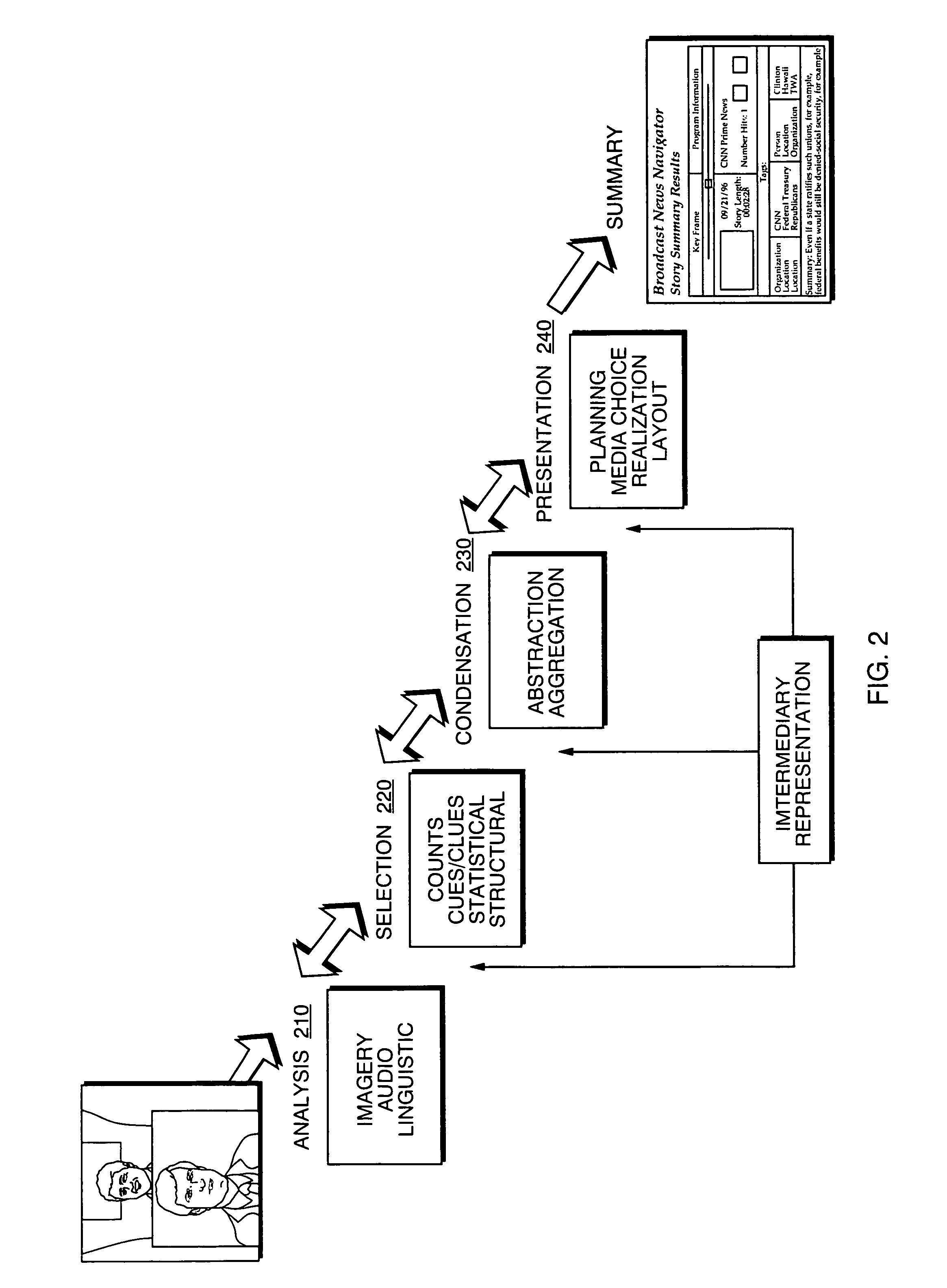
Automated segmentation and information extraction of broadcast news via finite state presentation model
InactiveUS7765574B1More efficientMore timelyTelevision system detailsDigital data information retrievalWeb browserPublic information
Owner:OAKHAM TECH
Conference support system with user operation rights and control within the conference
InactiveUS6266691B1Easily informationSimple treatmentOffice automationDigital output to display deviceSupporting systemInformation processing
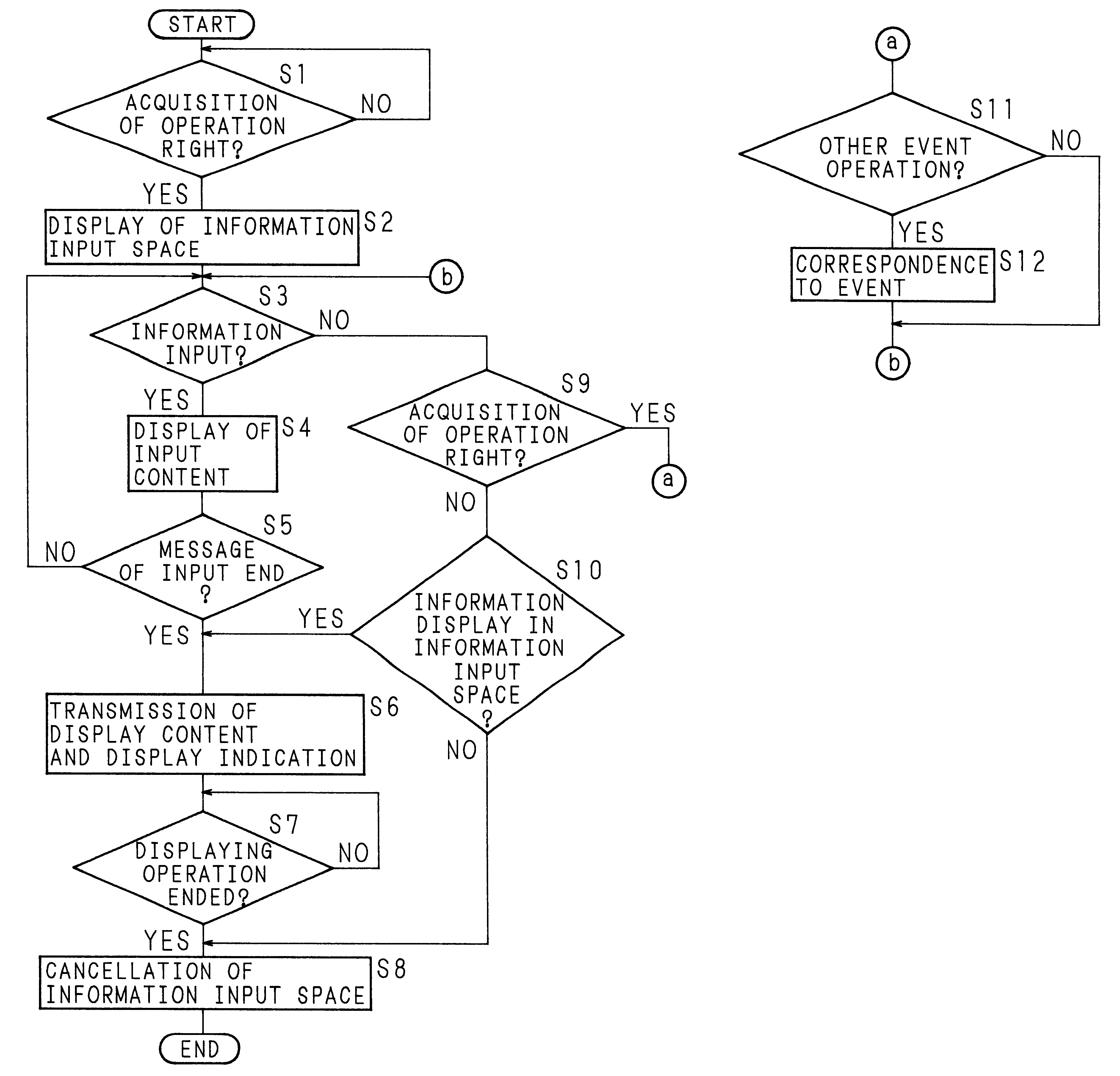
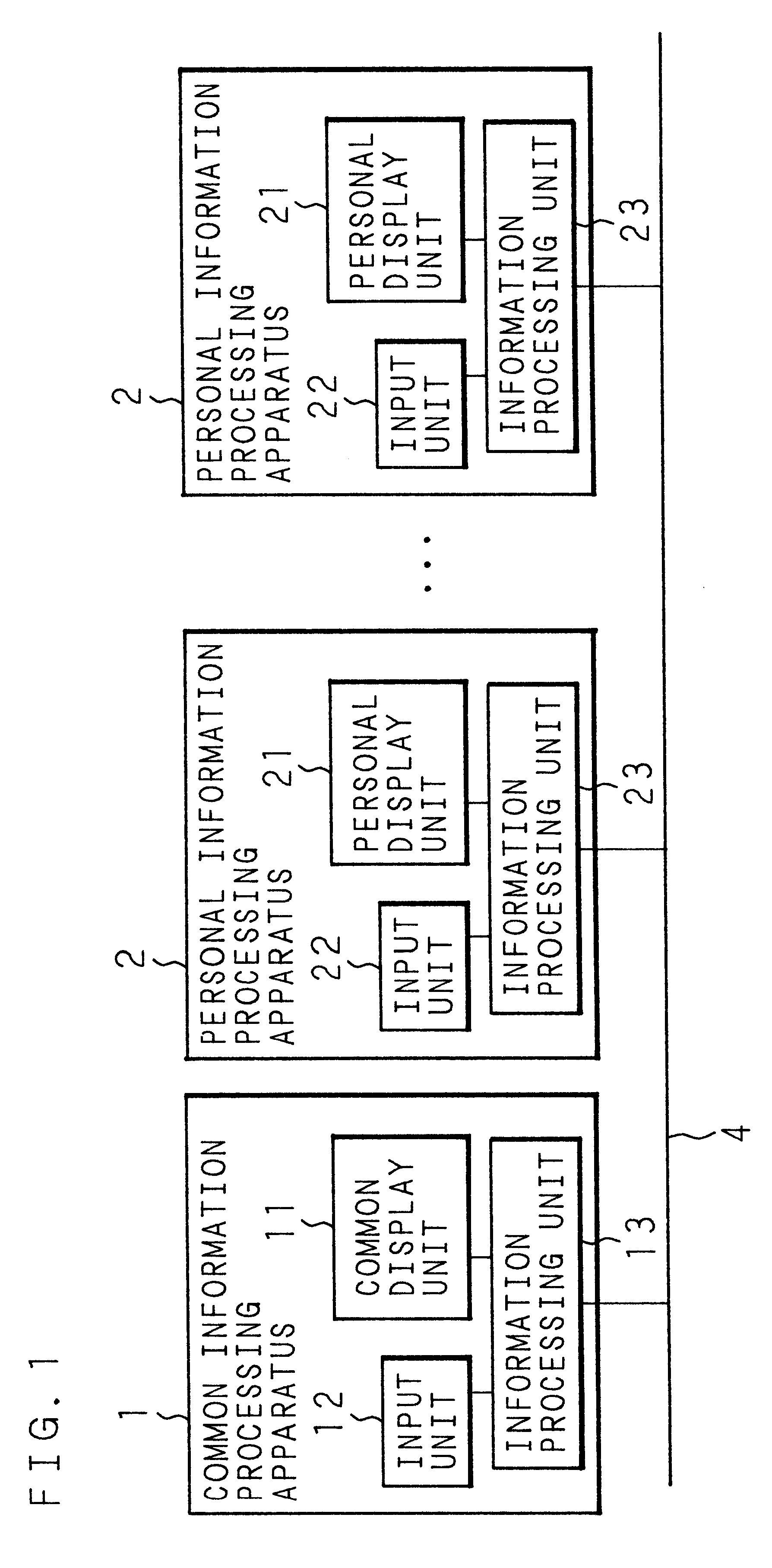
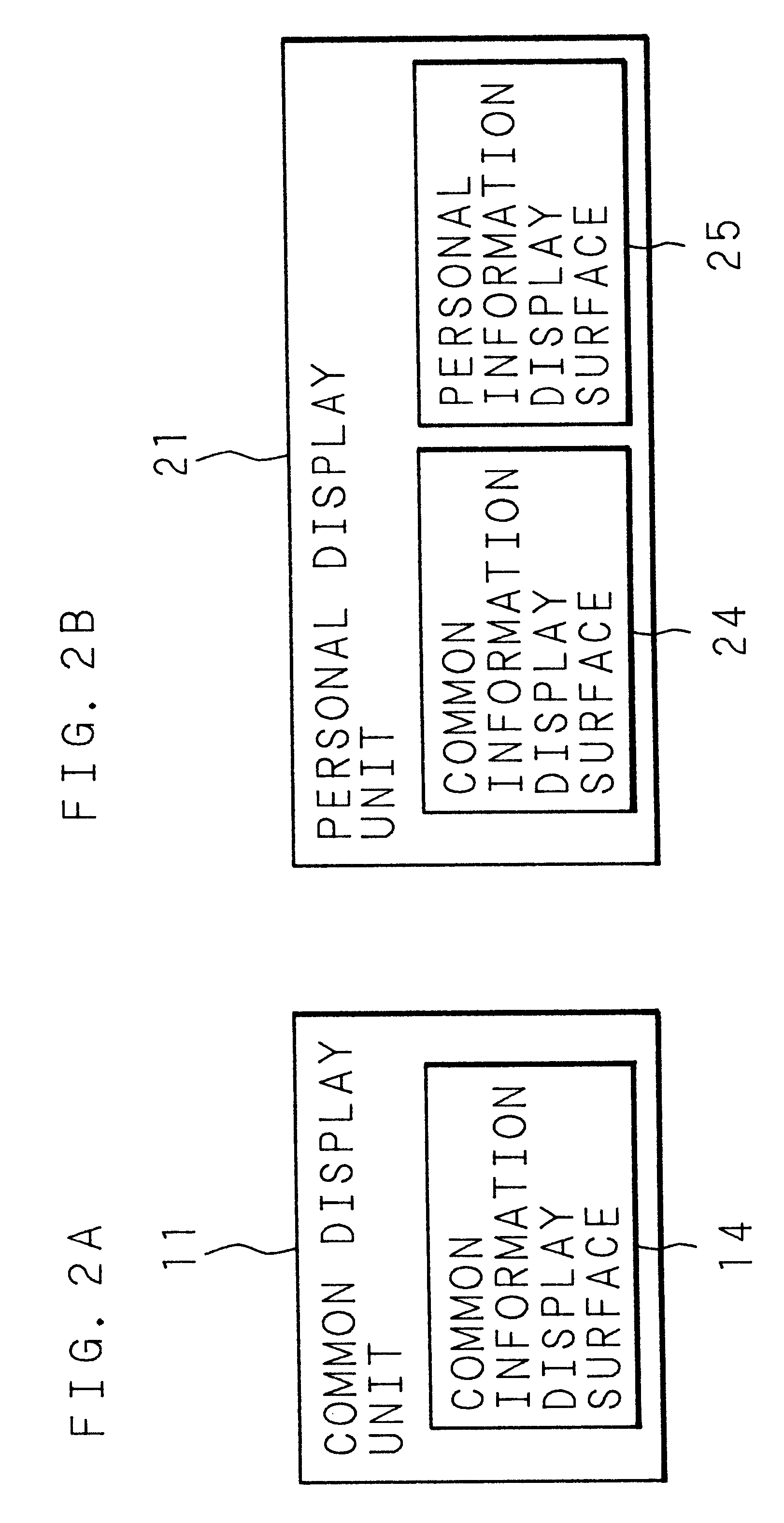
An electronic conference support system having a structure in which one main common information processing apparatus having a common display unit having a size sufficiently large for attendants to commonly look and some personal information processing apparatuses for permitting each attendant to exclusively create, display and edit information adjacent to each attendant are connected to one another to form a network communication structure through a data communication passage. When a certain attendant acquires an operation right, an information input space is displayed on the personal display unit of the attendant while permitting the attendant to input information. Information inputted to the information input space is, after completed and as an information object, displayed on the common display unit of the common information processing apparatus and the personal display units of all of the personal information processing apparatuses. The attendant of the conference is enabled to easily input information and other attendants who look the attendant's operation are enabled to be free from adverse stimulus.
Owner:FUJITSU LTD
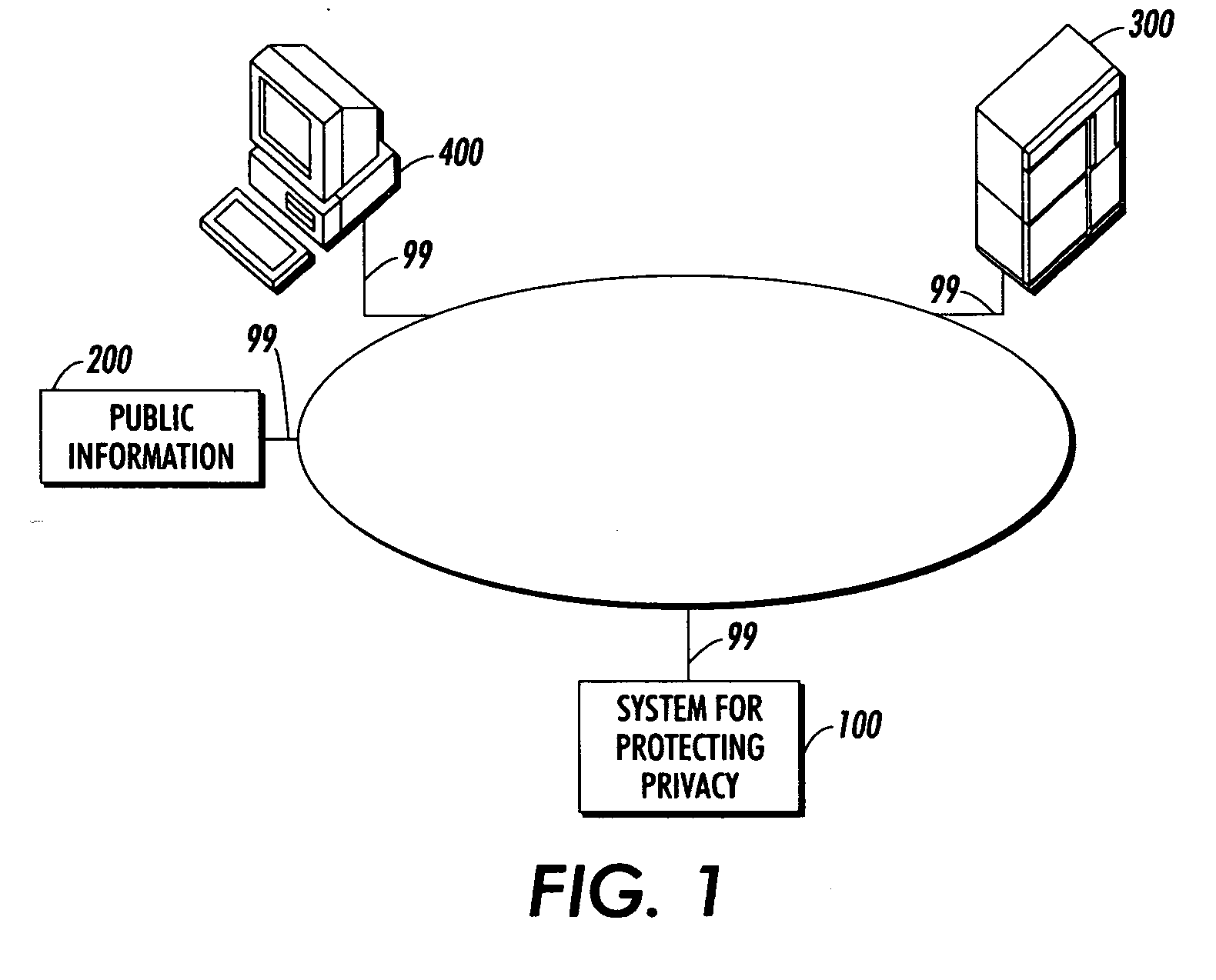
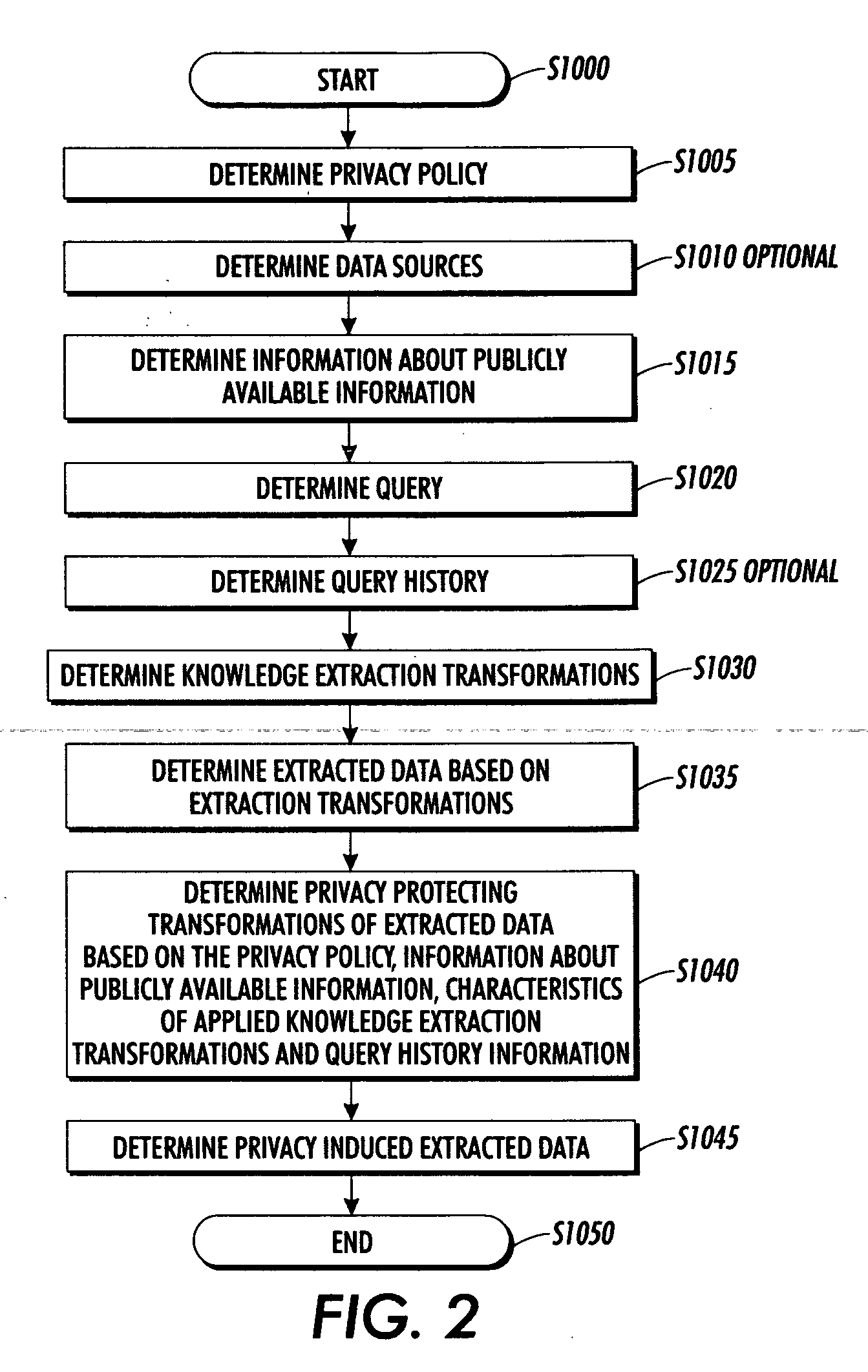
Systems and methods for protecting privacy
InactiveUS20060123461A1Digital data processing detailsComputer security arrangementsPrivacy protectionKnowledge extraction
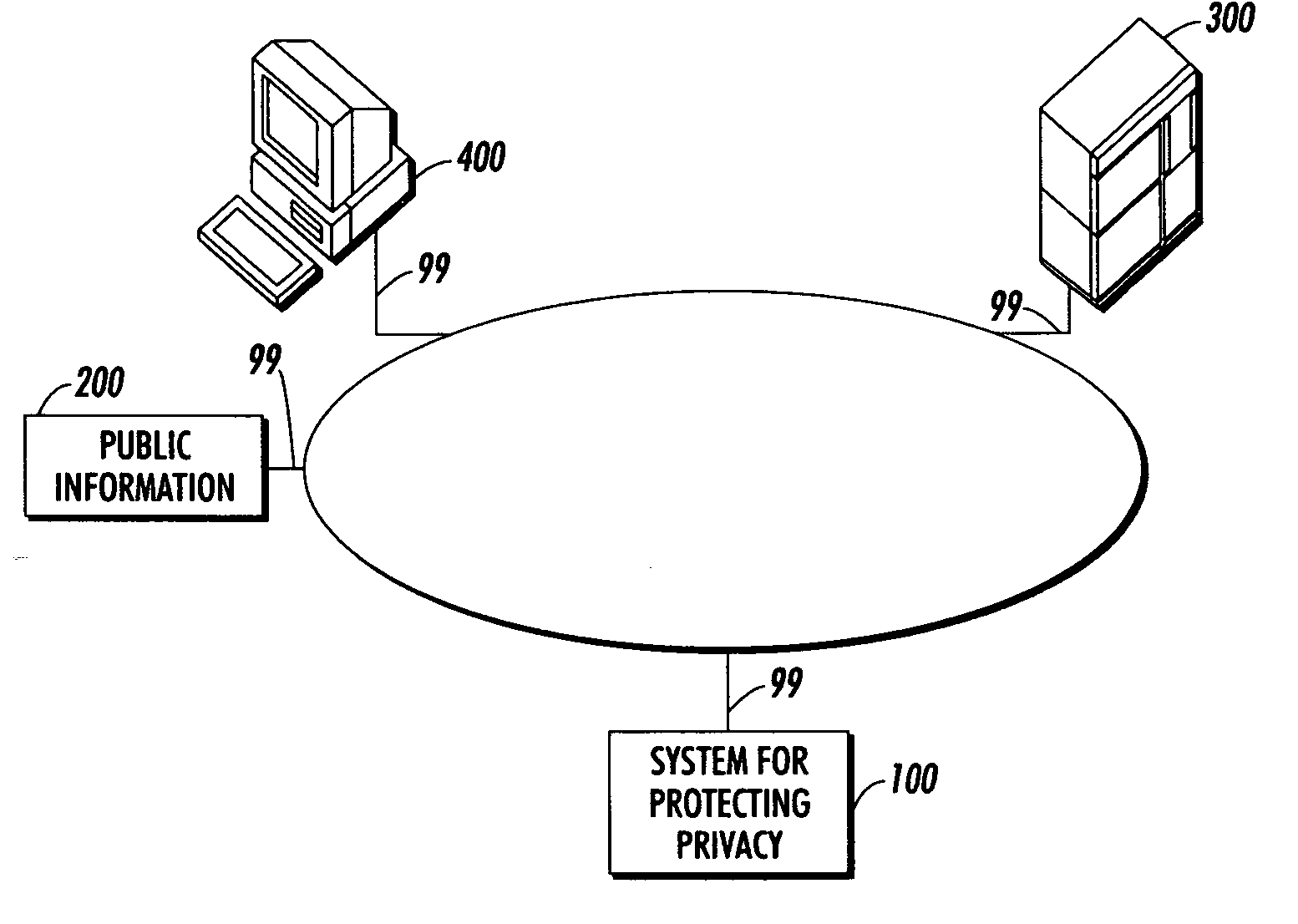
Techniques for providing privacy protection are provided. A query is received. Privacy policy information, extracted knowledge and optional information about available public information are determined. Information about the knowledge extraction transformations applied to create the extracted knowledge and the source data is determined. Privacy protecting transformations are determined and applied to transform the extracted knowledge based on the selected privacy policy, optional information about available public information, the characteristics of the applied knowledge extractions transformations, the source data and optional previous user queries.
Owner:PALO ALTO RES CENT INC
Method and apparatus for managing a digital inventory of multimedia files stored across a dynamic distributed network
InactiveUS20080228821A1Enhance reader comprehensionData processing applicationsSolid-state devicesPaymentHigh speed memory
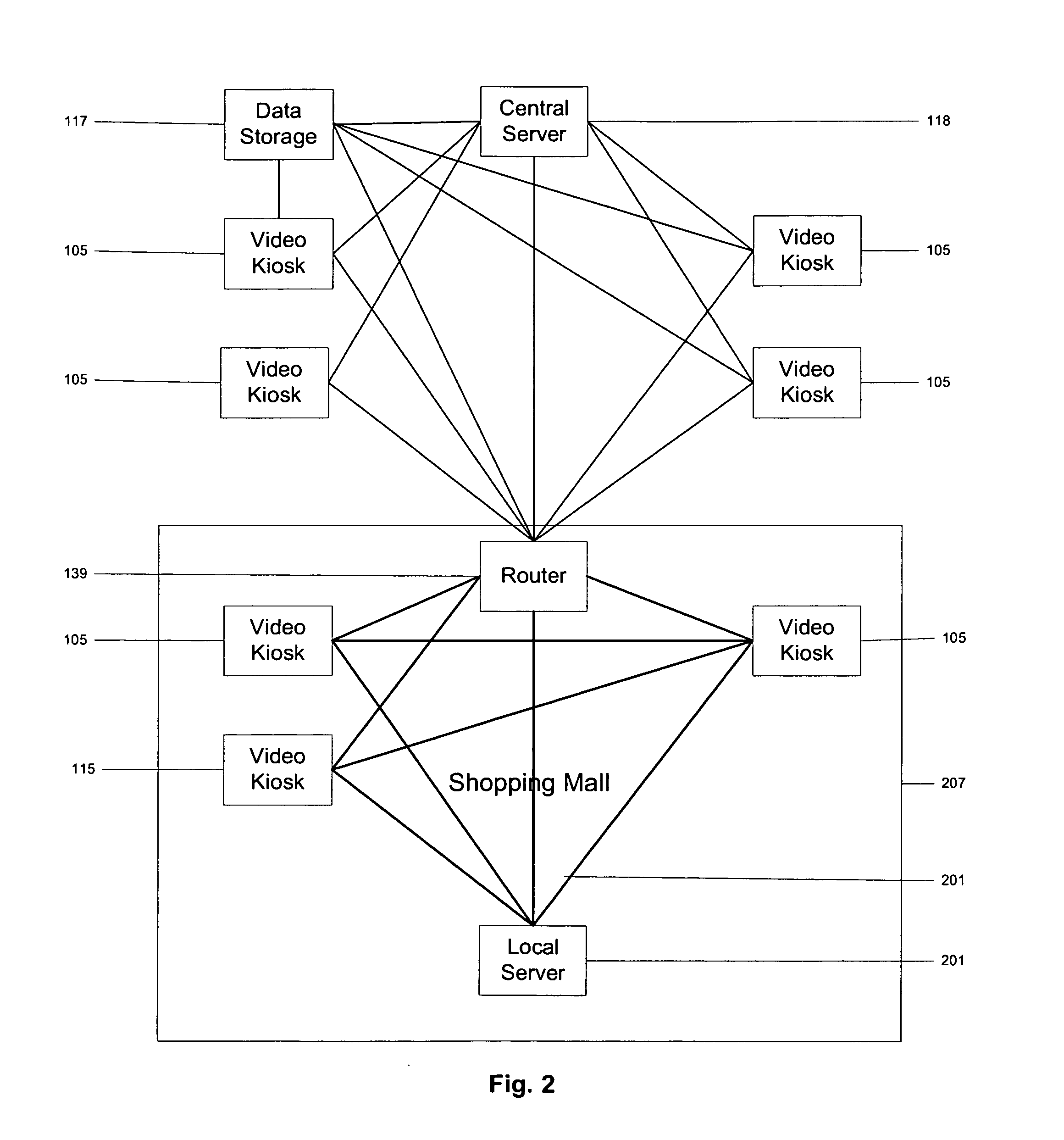
A video network includes public kiosks having digital storage capacity. Centralized inventory control manages the video files stored at individual kiosks or network LANs. A user requests a multimedia file for download, and selects various ancillary files and control features, such as languages, subtitles, control of nudity, etc. The requested file is encrypted according to an encryption key, watermarked, and downloaded from a high-speed port of a public kiosk to a hand-held proprietary high speed memory device of a user. Payment is received at the time of request or at the time of download, and royalties are distributed by the video network to copyright holders. Computer applications or playback devices allow users to store and / or play video files that have been downloaded to a hand-held device while managing and enforcing digital rights of content providers through the watermarking and / or encryption.
Owner:CLEAR GOSPEL CAMPAIGN
Single click synchronization of data from a public information store to a private information store
InactiveUS6944651B2Multiple digital computer combinationsWeb data navigationInformation spaceWeb site
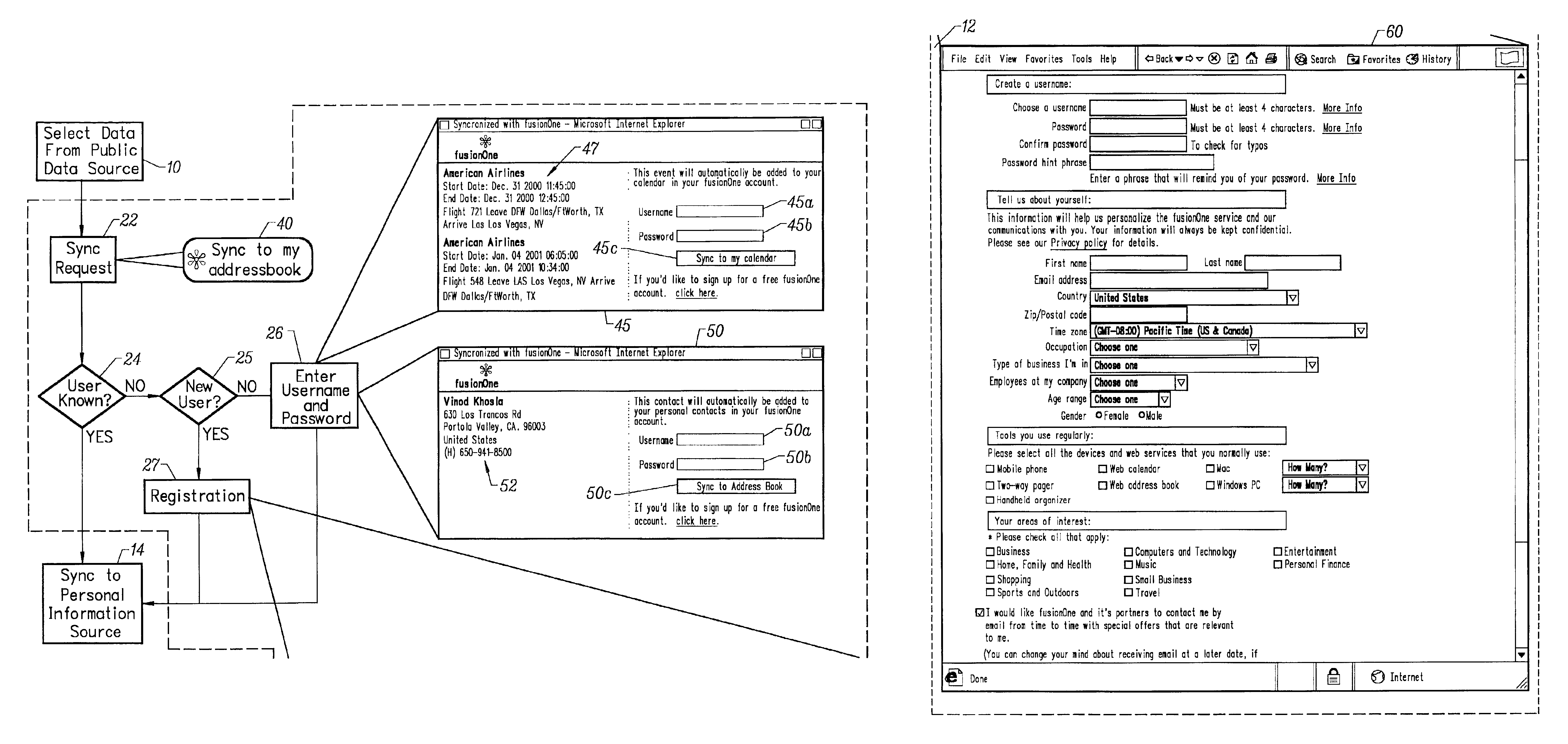
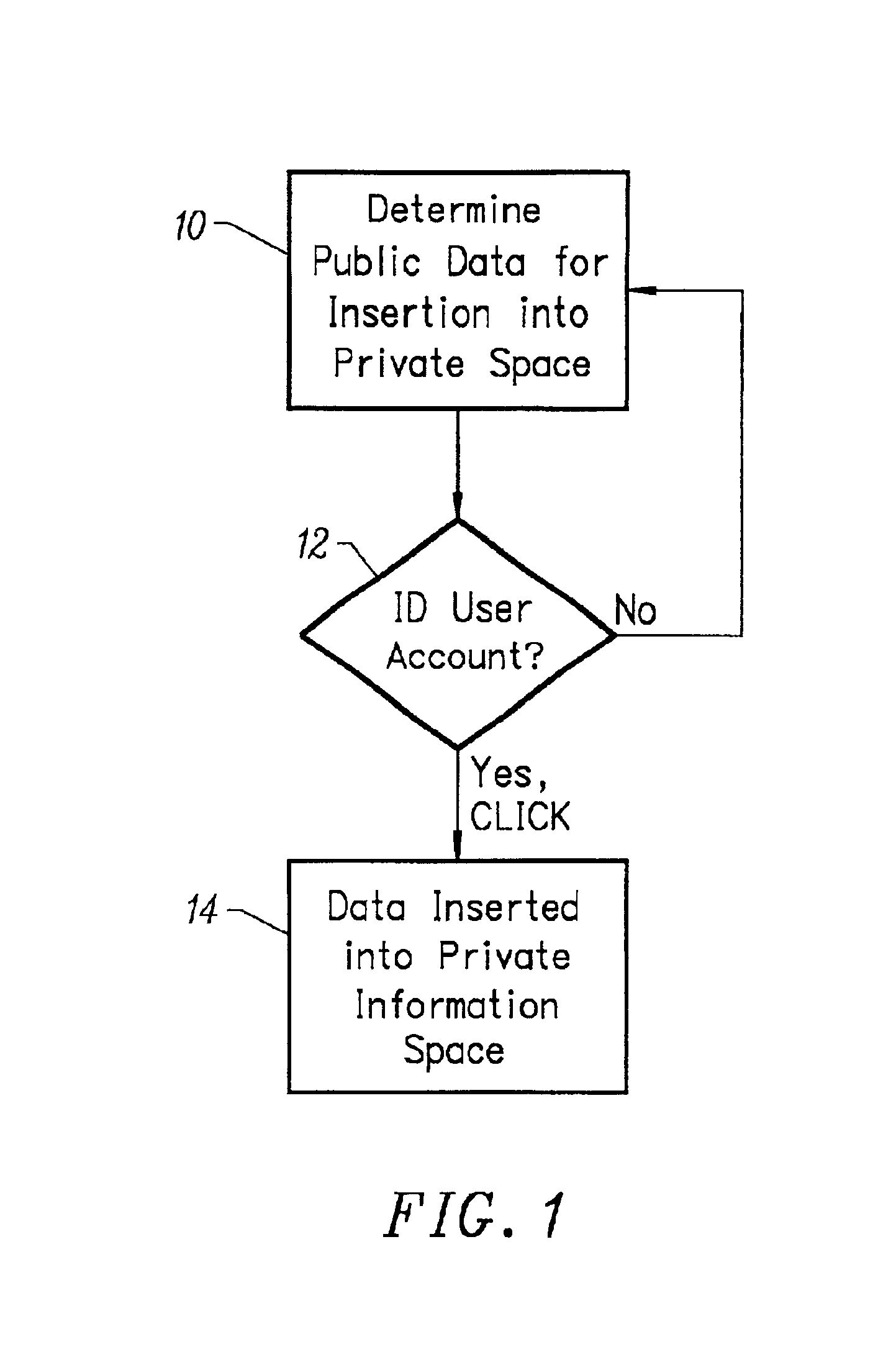
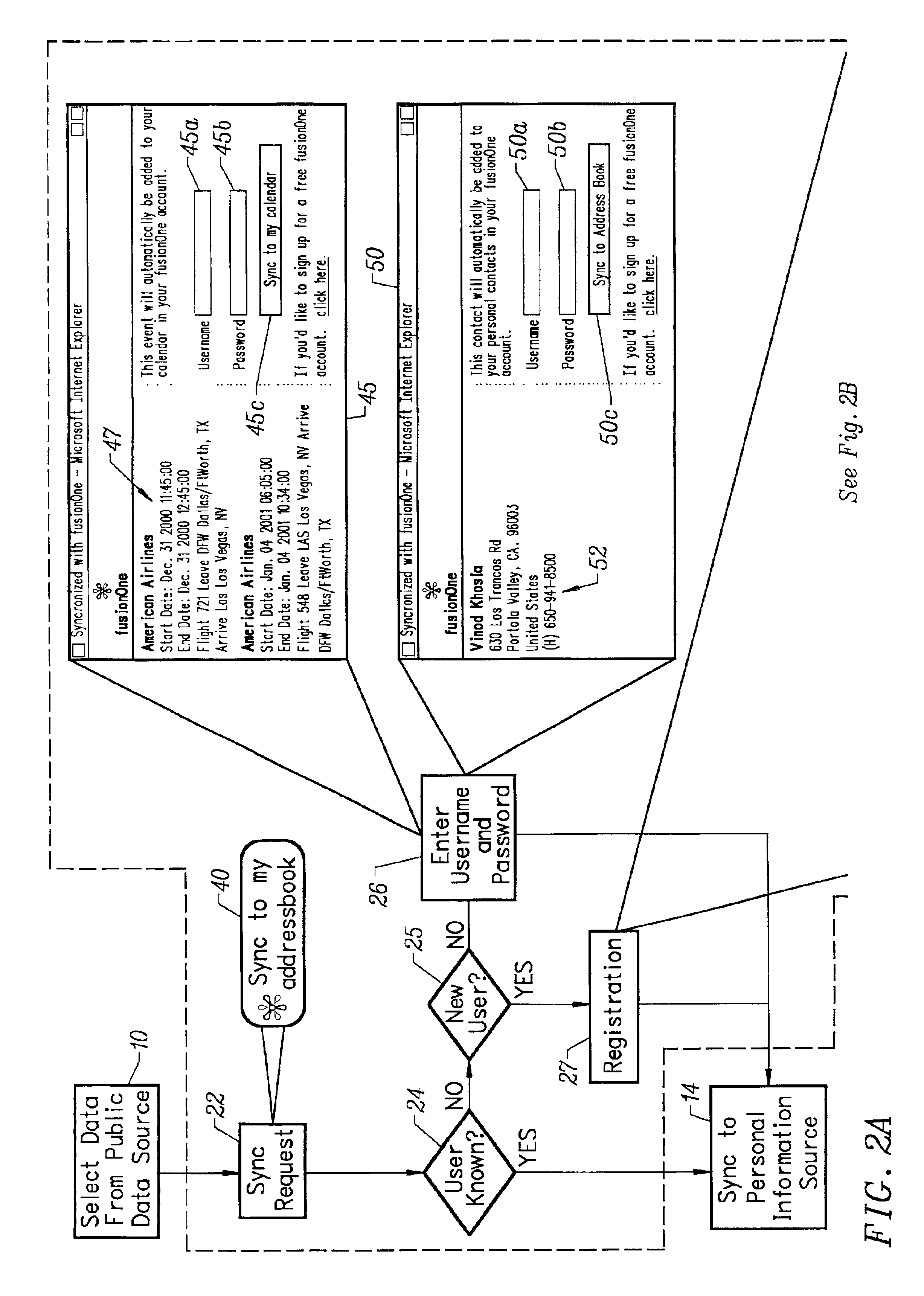
A method for transferring public information to a private information store maintained by a private information space manager. The method may include the steps of selecting public information from a public information source; initiating a sync request by selecting a sync request button on the public information web site; and identifying the private information space were the public information is to be stored. In a further aspect, the invention comprises a system for synchronizing public content from a public information web site to a private information store. The system may include a sync enable button on the public information web site; a pop-up window provided by a private information store provided responsive to the sync enable button on the public information web site; and a sync interface transfer button on the pop-up window initiating transfer of the public information to the private information store. In a further aspect, the public information web site is provided by an affiliate server and said affiliate server includes code enabling said sync button by directing a client web browser to the private information store provider. The system may further include at least one synchronization routine synchronizing the public information data with the private information space.
Owner:SYNCHRONOSS TECH
Non-symbolic data system for the automated completion of forms
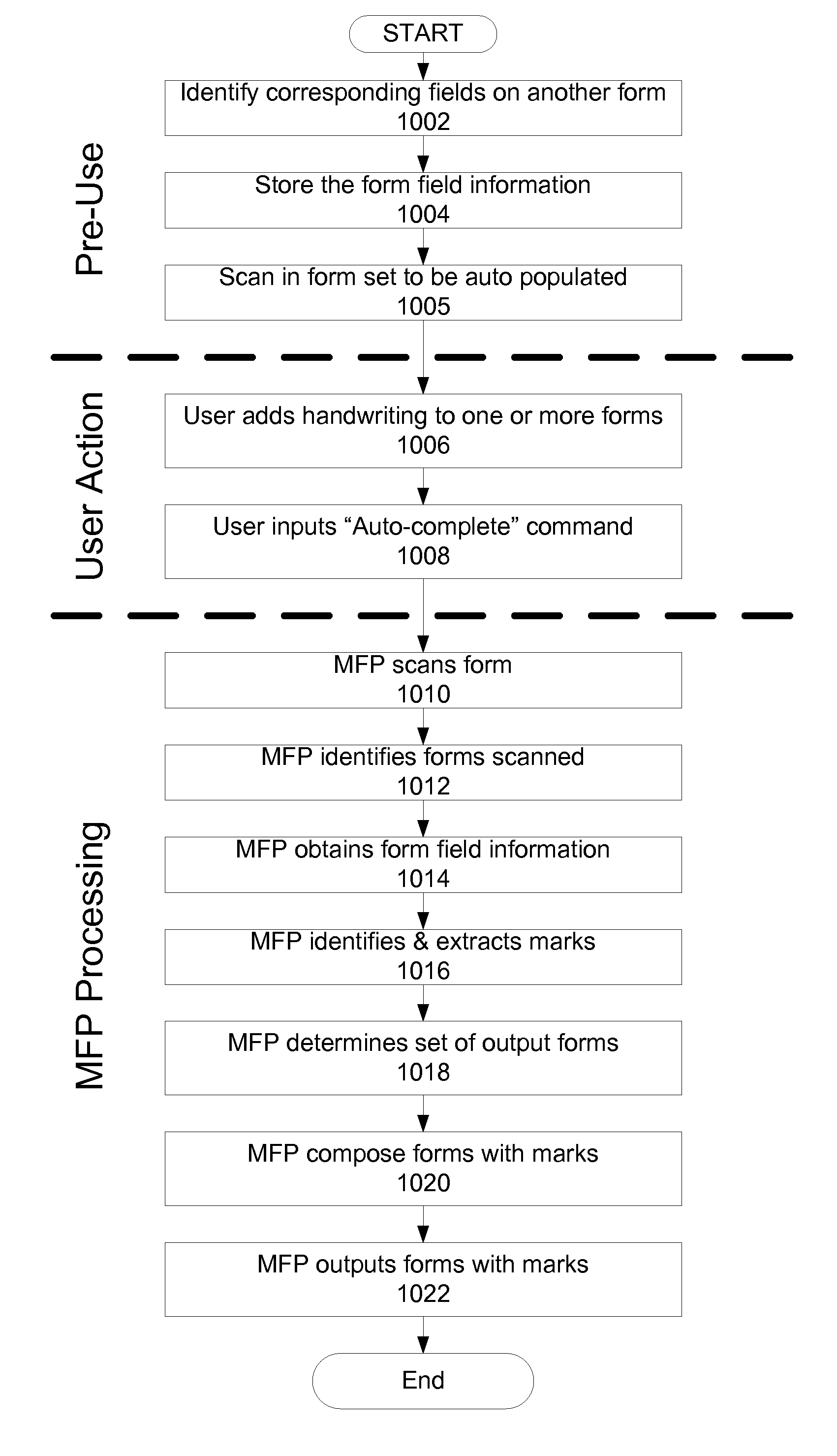
InactiveUS20070089049A1Computationally independentComputationally simpleNatural language data processingSpecial data processing applicationsMultiple formsPaper based
A system and method for paper-based, automated completion of forms allows a user charged with filling out multiple forms containing some common information to write each unique piece of information one time, and the system generates a set of completed forms with the required information on each form with no change to the use or structure of the current forms. The control module is operable on a processor to determine a mapping between common fields on multiple forms or multiple pages of the same form, copy information written in a field on one form to equivalent fields on other forms, and produce a set of completed forms. The system is computationally simple and independent of language because these operations can be performed without having to understand, translate or convert the writing. Furthermore, there is no loss of security or privacy beyond the use of paper forms because these operations can be performed without access to a centralized database and without connectivity to other systems. The system is advantageous because it does not change paper based workflows since the inputs and outputs of this system are paper.
Owner:RICOH KK
Method for transmitting protected information to a plurality of recipients
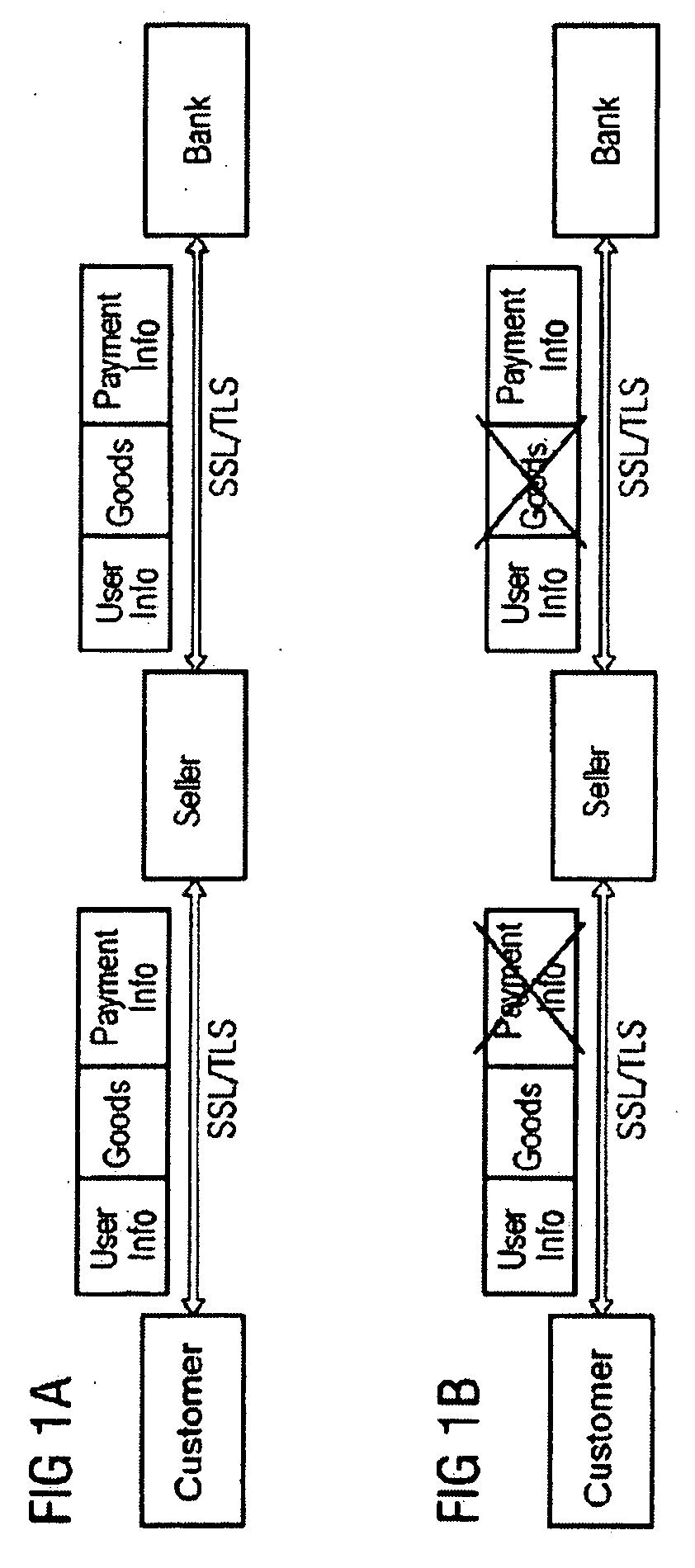
InactiveUS20070277013A1Complete banking machinesDigital computer detailsSide informationPublic information
The invention relates to first information which is determined for a first receiver. Said first information is transmitted together with secondary information, which is determined for a second receiver in a common information unit to the first receiver. The first information can be encrypted according to specifications of the first receiver. The secondary information, which can be made of several components, is encrypted according to the specifications of the second receiver, for example, with an open key, a so-called public key. Said public key encryption methods have various embodiments and security steps. Said methods ensure that the first receiver, upon receipt of the complete information, can not encrypt pieces of information therefor not intended therefor.
Owner:SIEMENS AG
Network intrusion detection and prevention system and method thereof
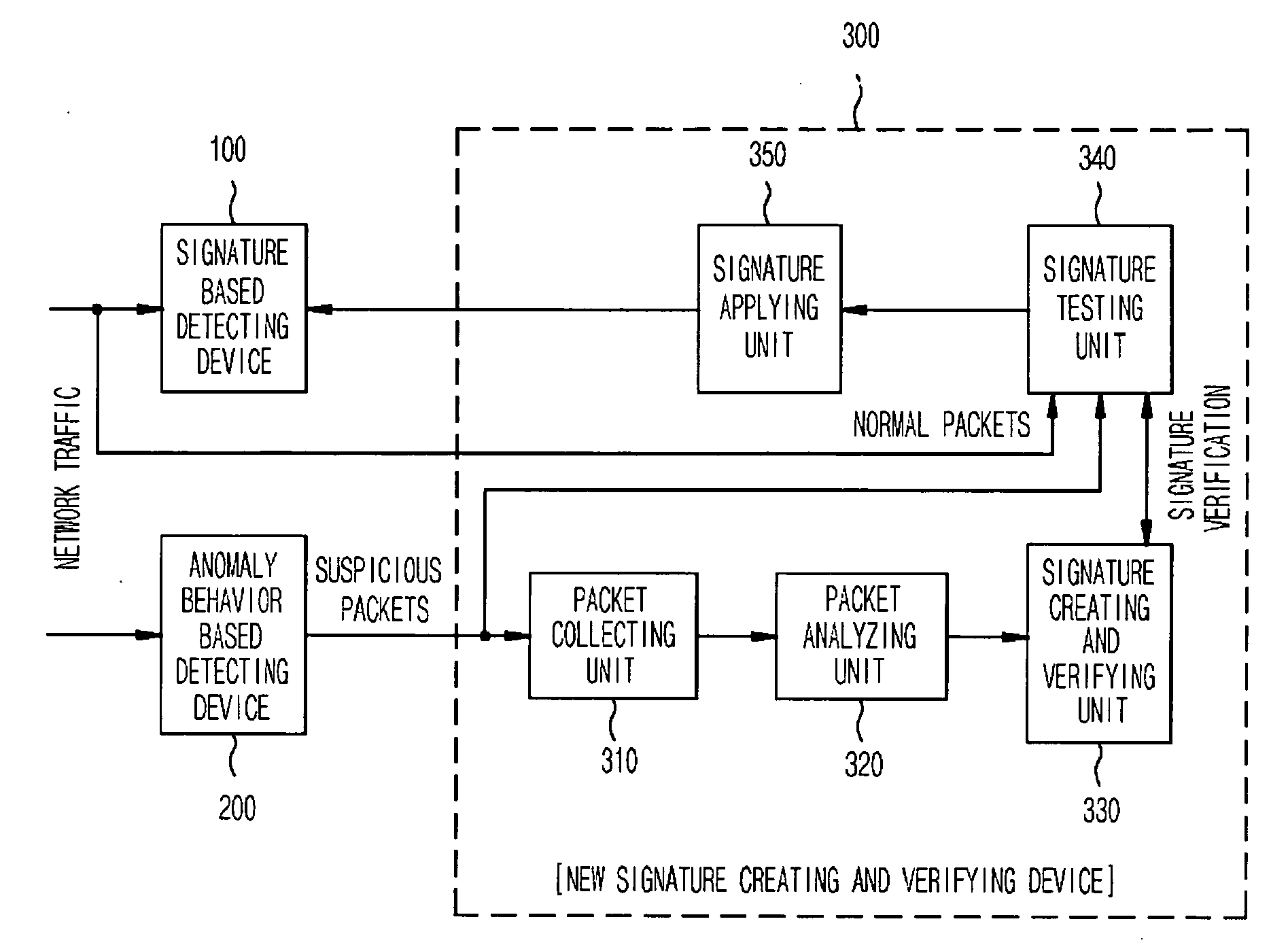
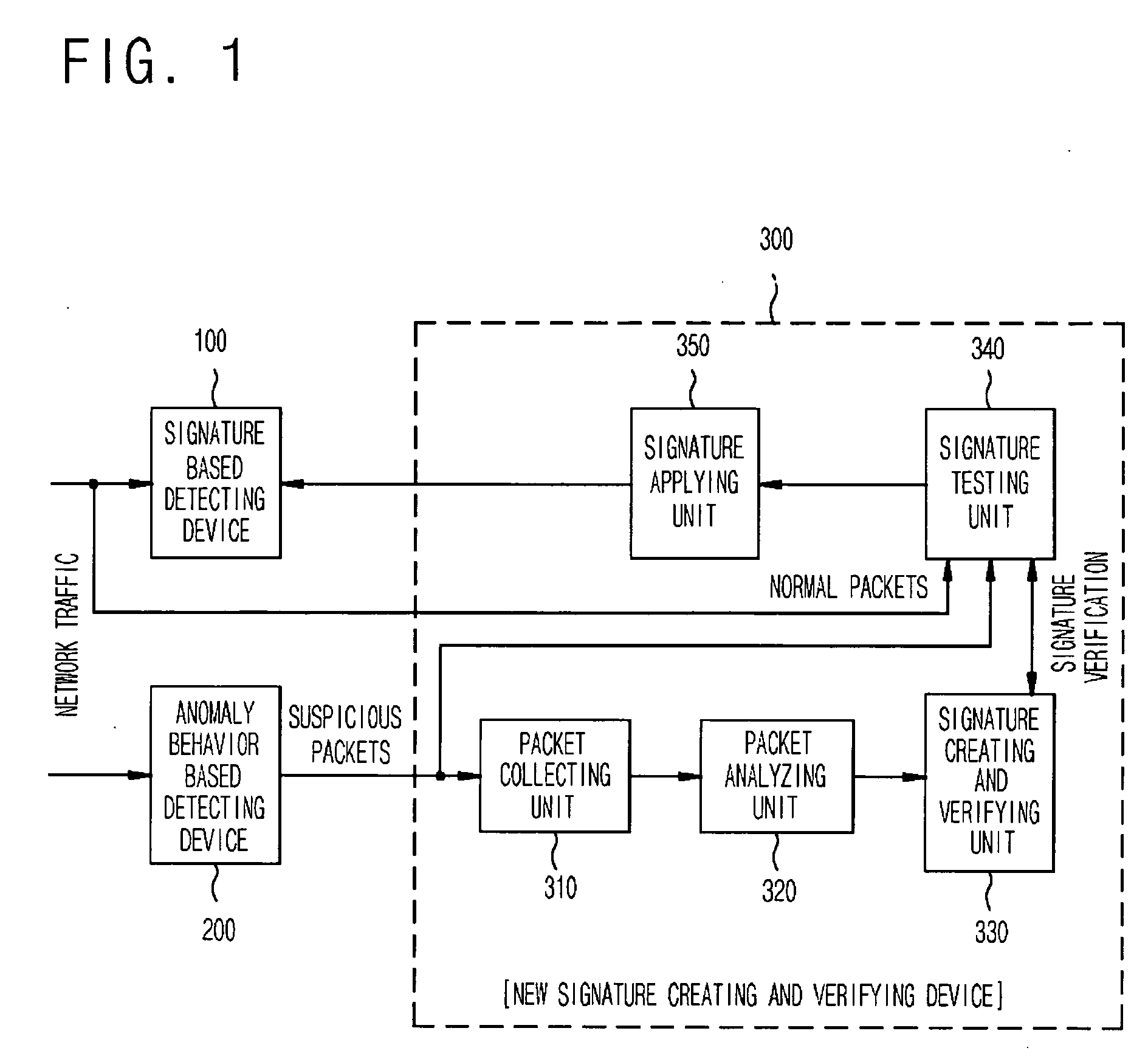
InactiveUS20060085855A1Maximize the effectCritical damageMemory loss protectionData taking preventionData packPublic information
The present invention relates to a network intrusion detection and prevention system. The system includes: a signature based detecting device; an anomaly behavior based detecting device; and a new signature creating and verifying device disposed between the signature based detecting device and the anomaly behavior based detecting device, wherein if the anomaly behavior based detecting device detects network-attack-suspicious packets, the new signature creating and verifying device collects and searches the detected suspicious packets for common information, and then creates a new signature on the basis of the searched common information and at the same time, verifies whether or not the created new signature is applicable to the signature based detecting device, and then registers the created new signature to the signature based detecting device if it is determined that the created new signature is applicable.
Owner:ELECTRONICS & TELECOMM RES INST
Secure file format
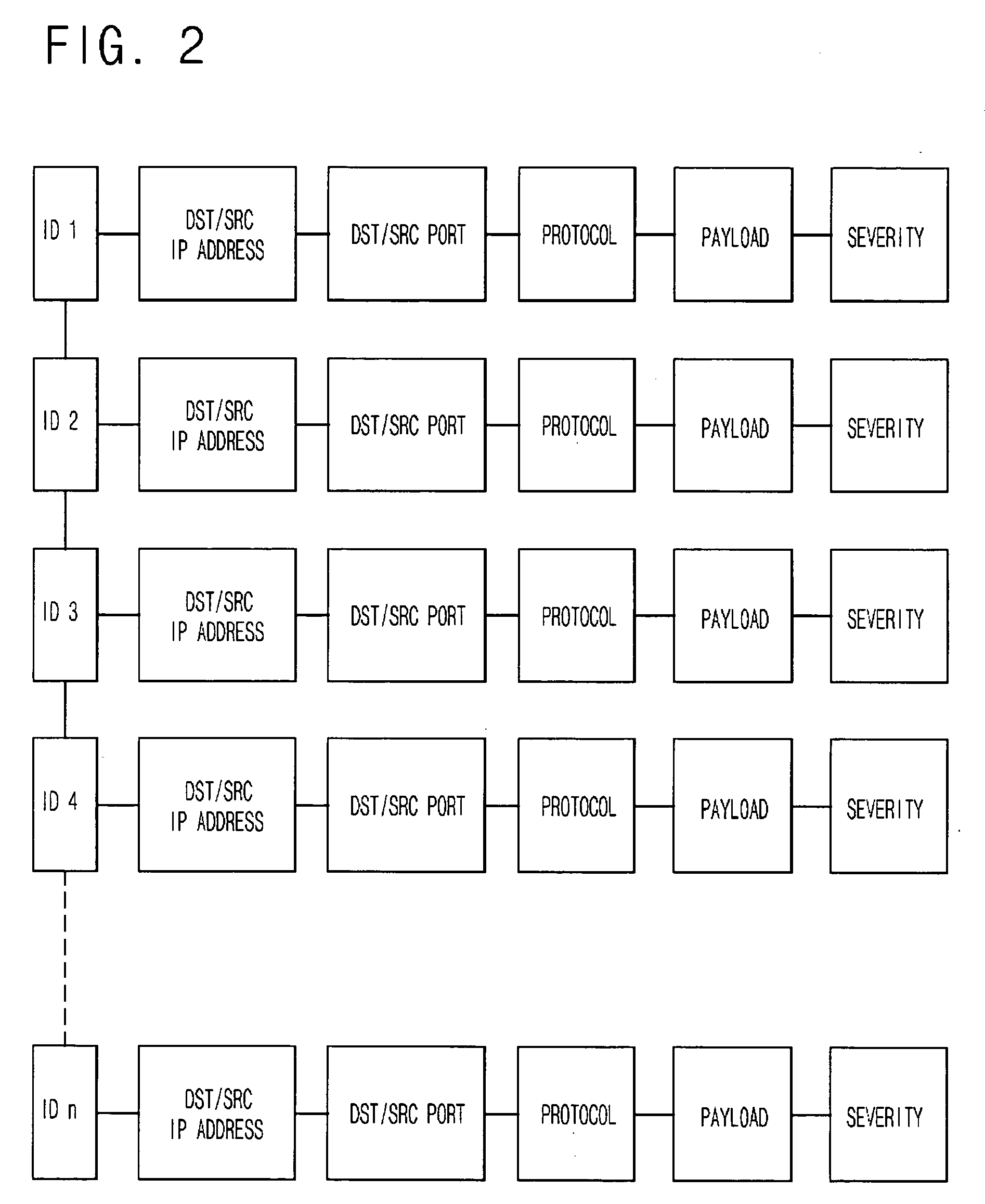
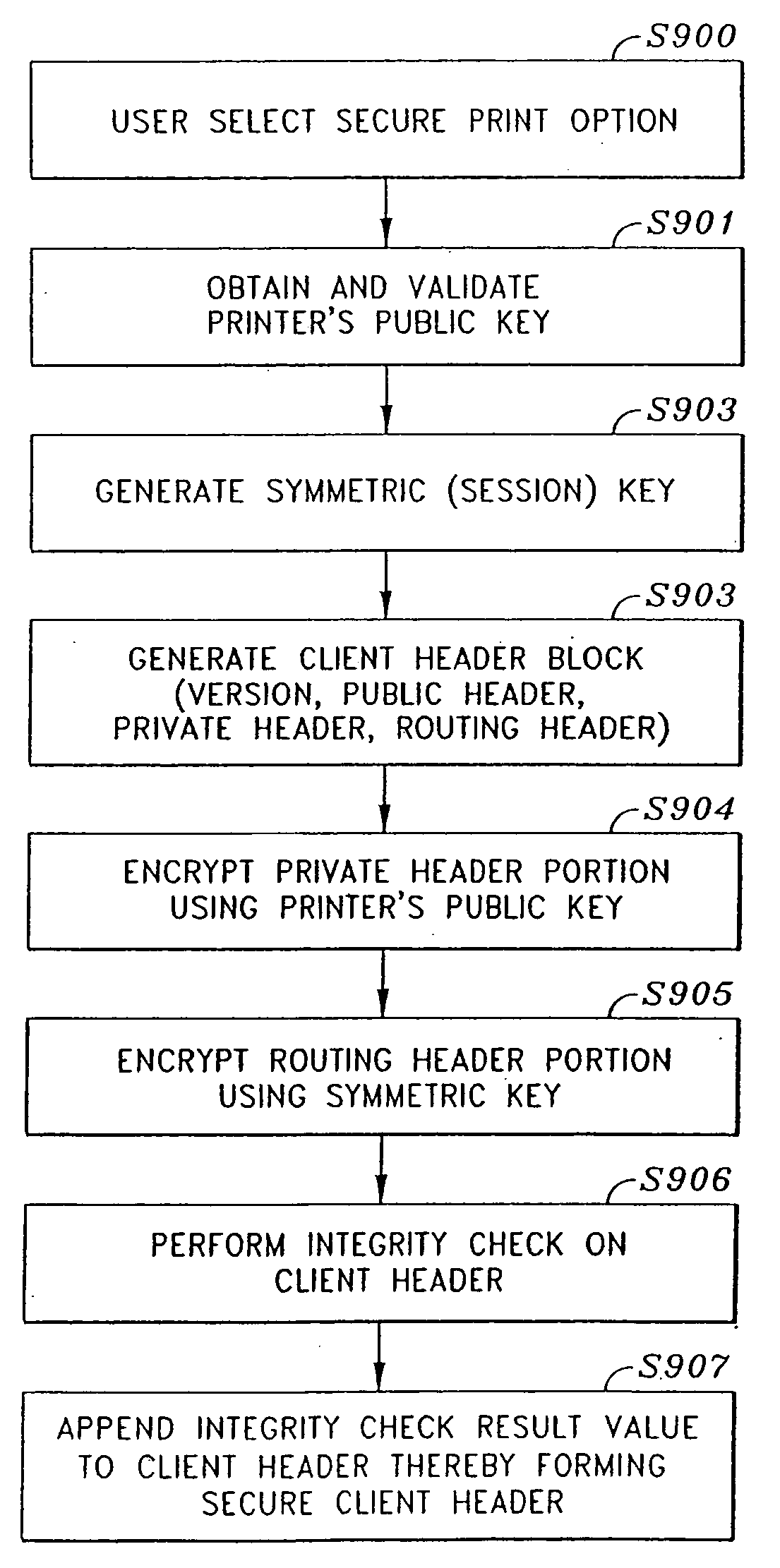
A file format for a secure file for use with a block cipher or a stream cipher, the secure file having a secure client header and a data block appended to the secure client header. The client header has a client information block comprised of a public information block, a private information block and an initialization vector. At least a portion of the private information block is encrypted, and a client information block integrity check value is appended to the client information block, the client information block integrity check value being obtained by performing an integrity check on the client information block. The data block is preferably encrypted and is comprised of a plurality of encrypted data blocks each appended with its own respective integrity check result value. Each of the plurality of data blocks and their respective integrity check result values are obtained by dividing the encrypted data block into n encrypted data blocks, performing an integrity check on a first one of the n encrypted data blocks and the client information integrity check result value appended to the client information block, so as to obtain a first encrypted data block integrity check result value, appending the first encrypted data block integrity check result value to the first encrypted data block, and repeatedly performing, for each of the subsequent n encrypted data blocks, an integrity check on the subsequent encrypted data block and an integrity check result value appended to a previous one of the n encrypted data blocks, so as to obtain an integrity check result value for the subsequent encrypted data block, and appending the subsequent integrity check result value to the subsequent encrypted data block.
Owner:CANON KK
Moving picture coding method and moving picture decoding method
InactiveUS20050147375A1Easy to copyEasy to specifyTelevision system detailsPulse modulation television signal transmissionVariable-length codePublic information
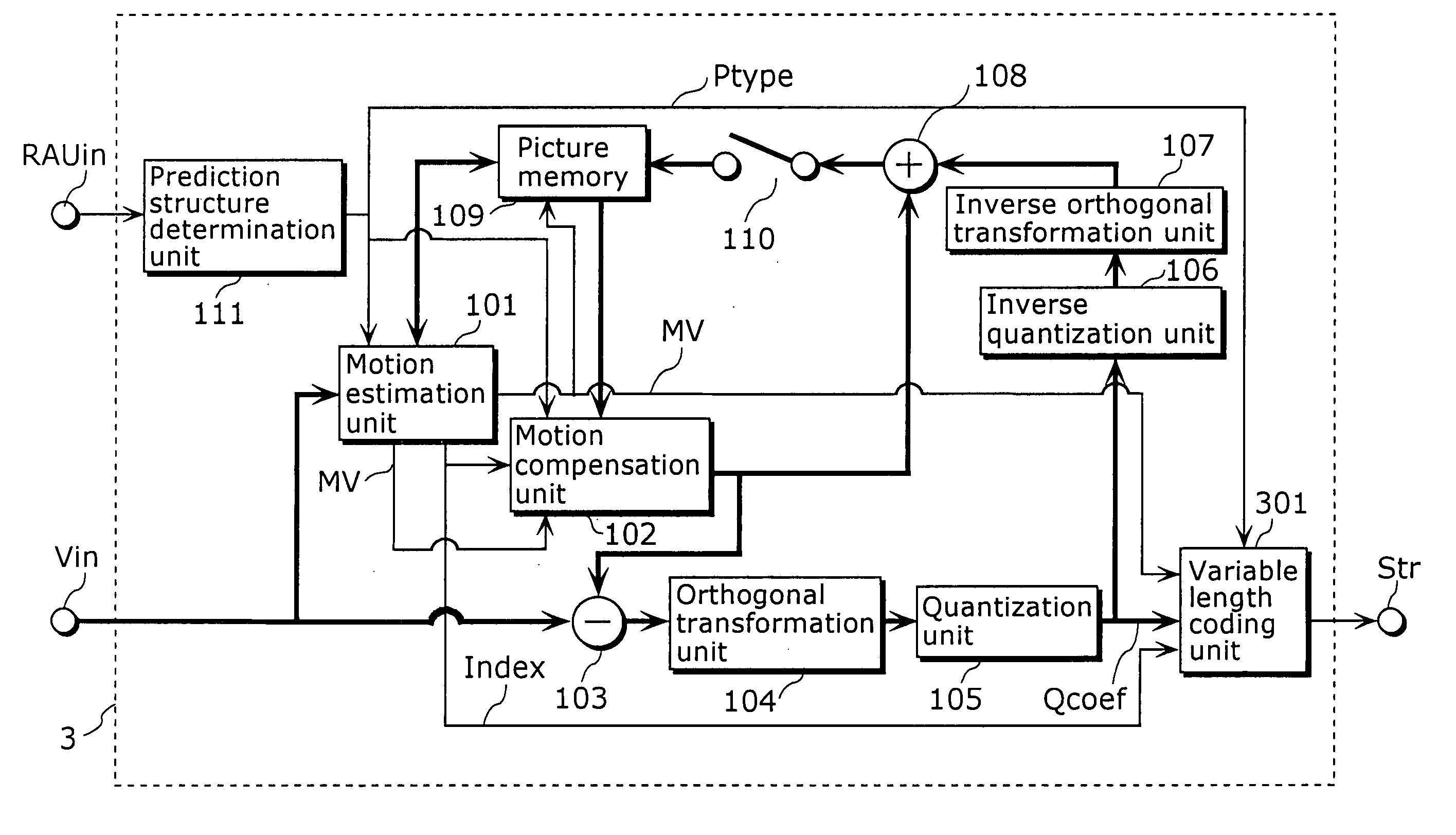
A moving picture coding apparatus (1) includes: a map creation unit (113) for creating variable speed reproduction information Map that is information necessary for variable speed reproduction according to a picture type Ptype; a variable length coding unit (112) for coding the variable speed reproduction information Map and placing it in a bit stream Str; a detection unit (114) for detecting the need of coding a picture parameter set PPS referred to by a current picture to be coded; and a common information addition unit (115) for adding the picture parameter set PPS to the current picture to be coded when the detection unit (114) detects the need of coding the picture parameter set PPS.
Owner:PANASONIC CORP
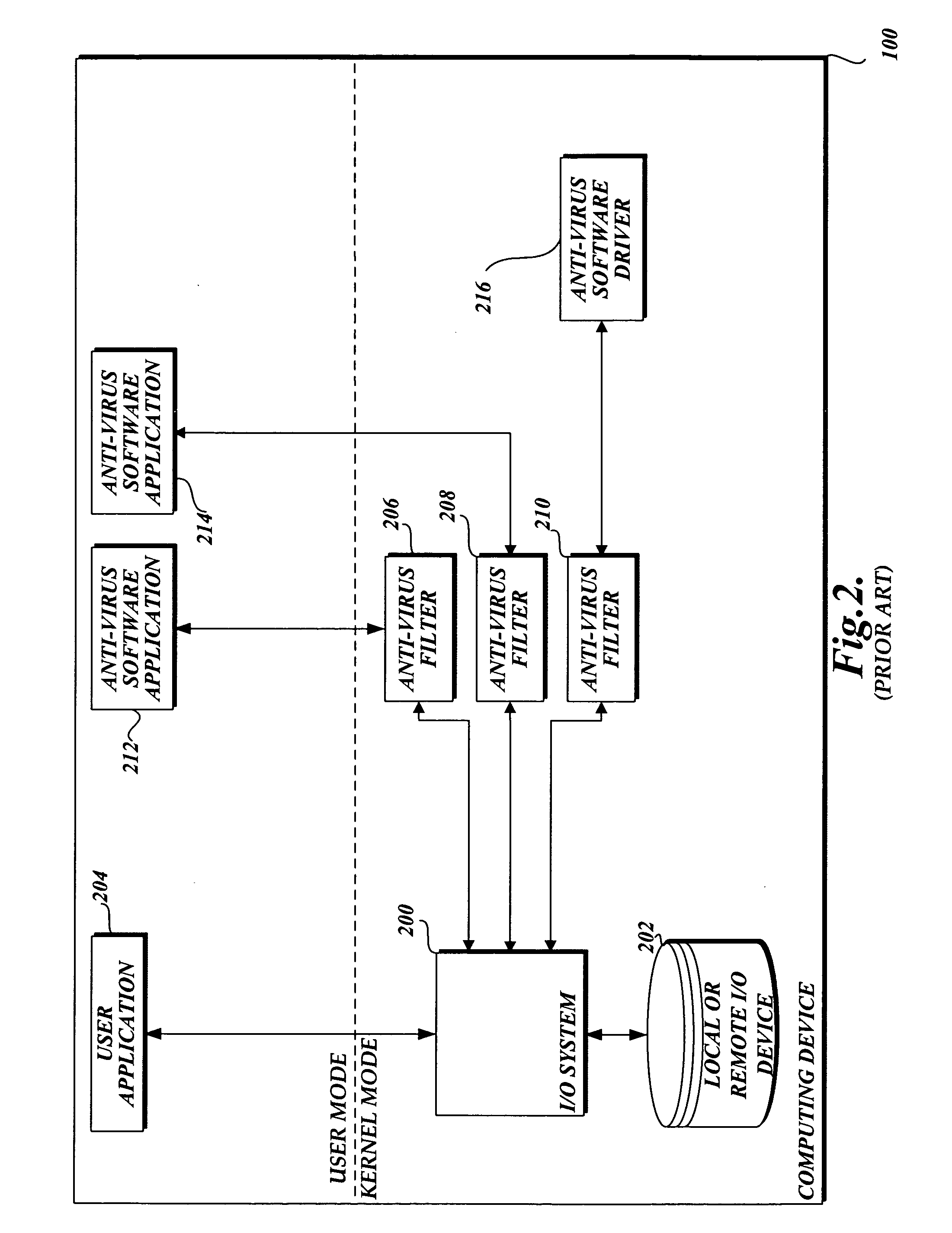
System and method of aggregating the knowledge base of antivirus software applications
InactiveUS20060101282A1Attempt have been hamperedIncrease speedMemory loss protectionDigital data processing detailsFile systemPublic information
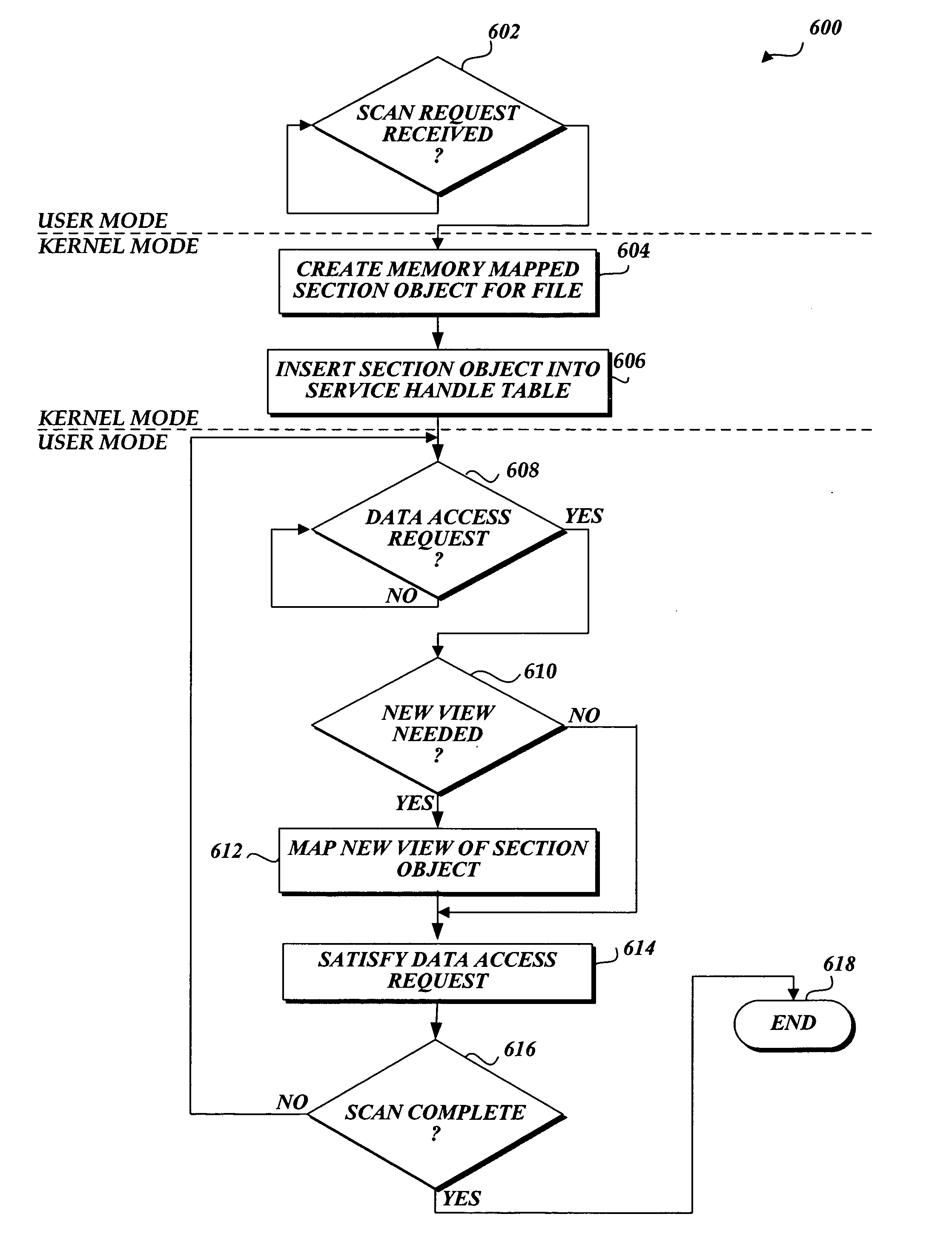
In accordance with this invention, a system, method, and computer-readable medium that aggregates the knowledge base of a plurality of antivirus software applications are provided. User mode applications, such as antivirus software applications, gain access to file system operations through a common information model, which obviates the need for antivirus software vendors to create kernel mode filters. When file system operations are available to antivirus software applications, the present invention may cause each antivirus software application installed on a computing device to perform a scan to determine if the data is malware.
Owner:MICROSOFT TECH LICENSING LLC
Method and device for realizing information sharing between SCADA and GIS
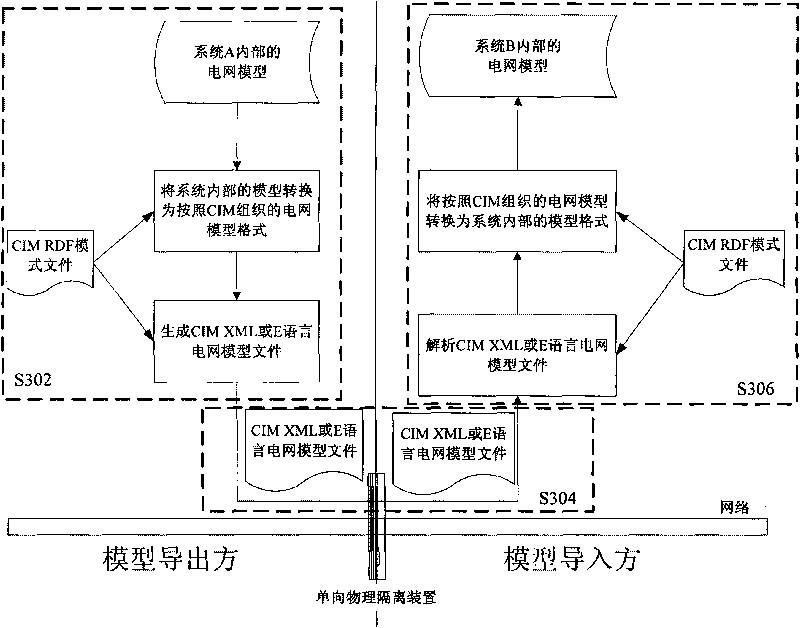
InactiveCN101751426AAchieve sharingReduce maintenance workloadSpecial data processing applicationsData transformationEngineering
The invention discloses a method for realizing information sharing between data collection and monitoring system and geographic information system. The method includes the following steps: taking one of the data collection and monitoring system and the geographic information system as a model export party, converting an electric system model inside thereof into an electric system model document meeting public information model regulations; transmitting the converted electric system model system into another system from the data collection and monitoring system and the geographic information system as the model export party; the model export party resolves the electric system model document according to the public information model regulations and converts the data obtained through resolving into an electric system model inside the model export party. The invention can meet the regulation of physical isolation required in General Framework for Secondary System Safety Protection of National Electric Systems, and can realize excellent interface generality simultaneously.
Owner:STATE GRID CORP OF CHINA +1
Information delivery system, delivery request program, transfer program, delivery program, and the like
InactiveUS20070283043A1Digital data processing detailsMultiple digital computer combinationsRelevant informationPublic information
A first node device transmits to a second node device unique identification information corresponding to specific common information, receives from the information saving node device the relevant information regarding the information saving node device, and requests to a selected information saving node device delivery of the specific common information, the second node device searches the node information and, in a case where there is node information, transfers the identification information to the information saving node device, which is indicated by node information, and the information saving node device, in a case where the transmission of the specific common information indicated by the identification information is available, transmits to the first node device the relevant information regarding the information saving node device, and, in a case where delivery request for the specific common information is received from the first node device, delivers specific common information.
Owner:BROTHER KOGYO KK +1
Method to secure credit card information stored electronically
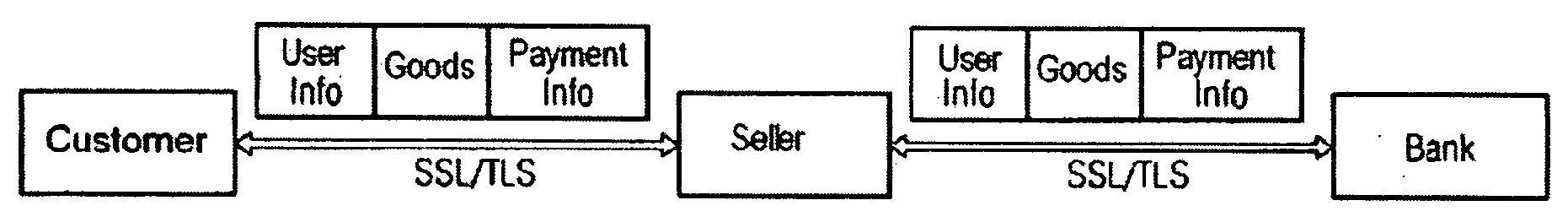
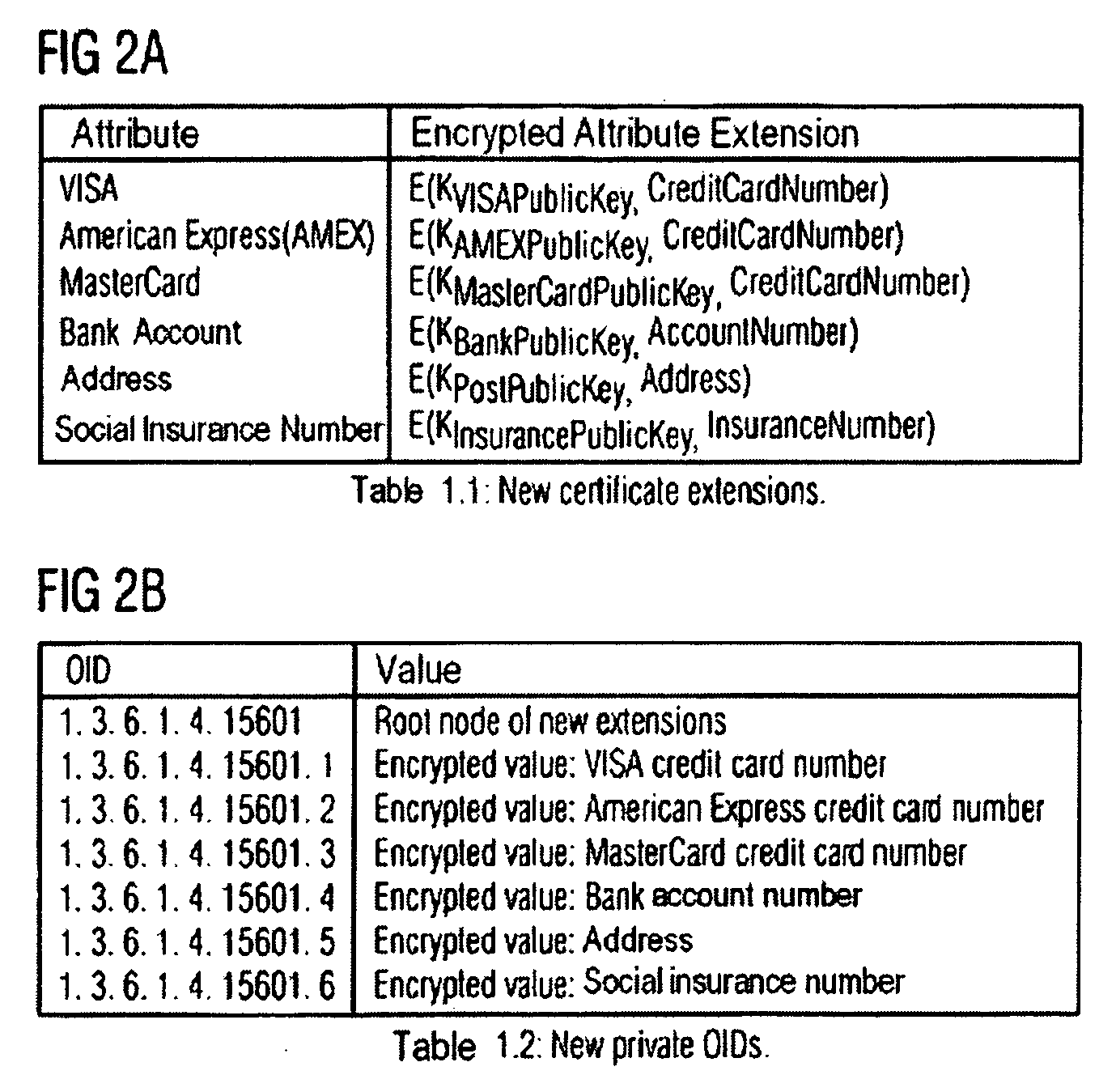
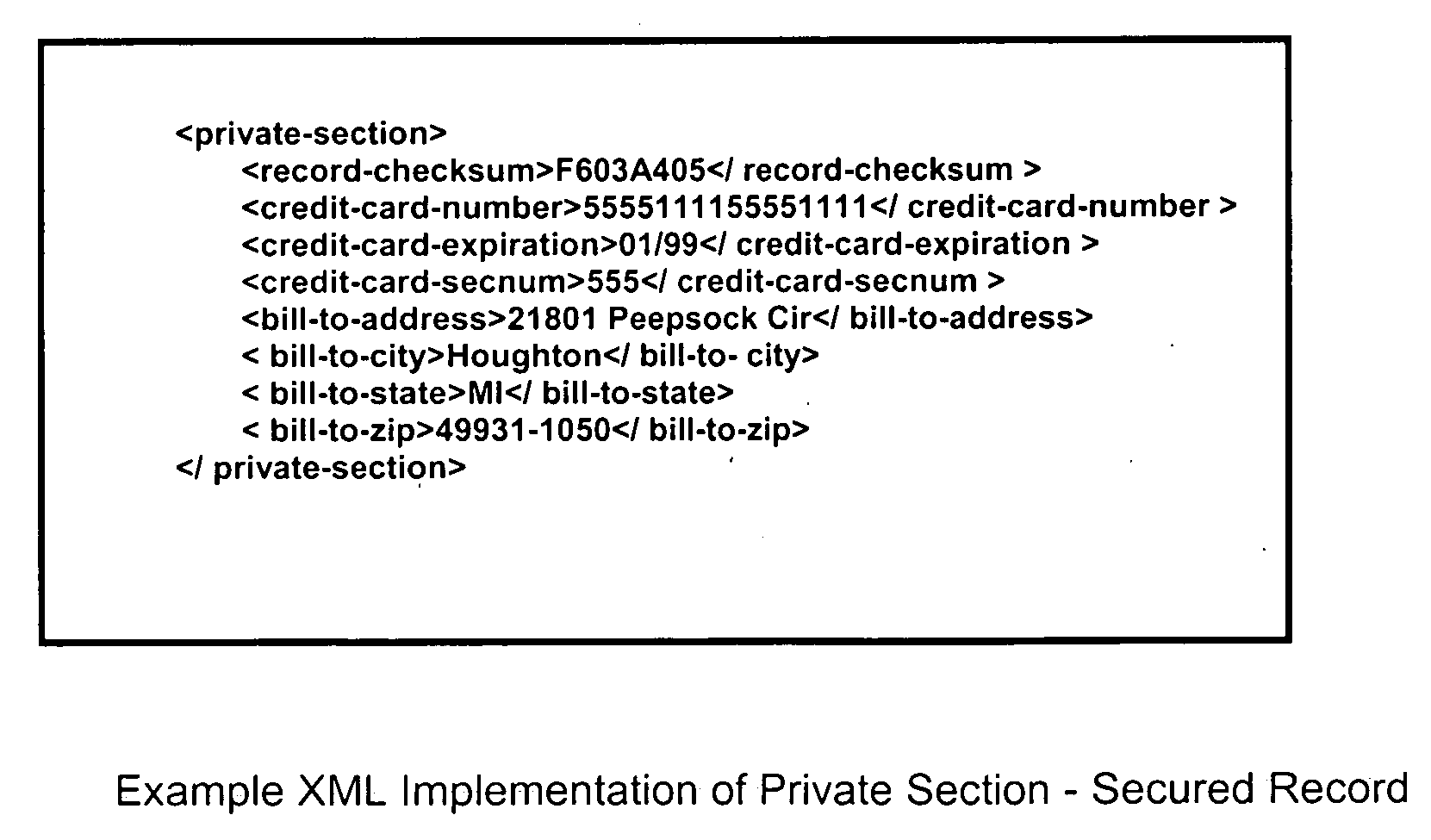
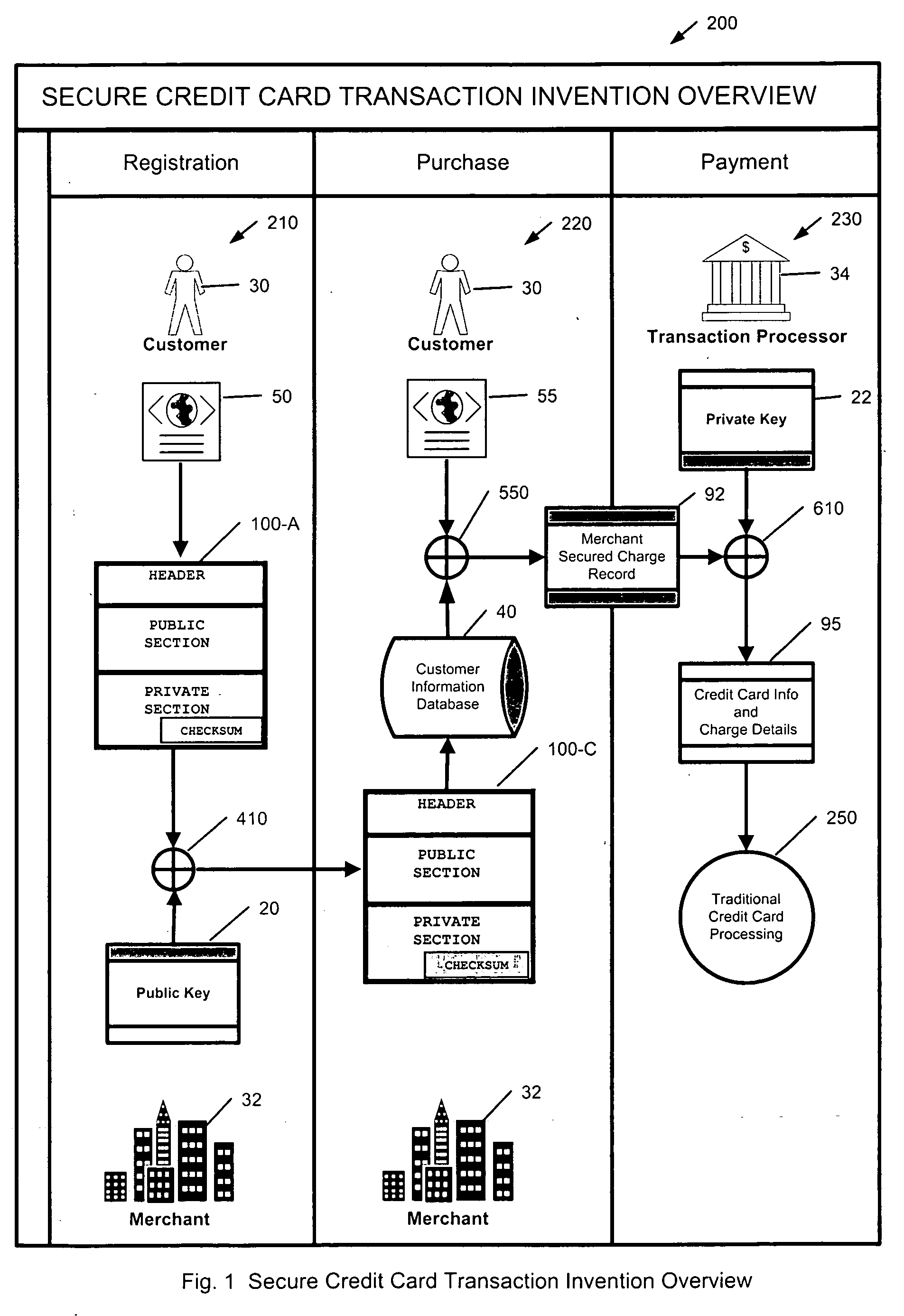
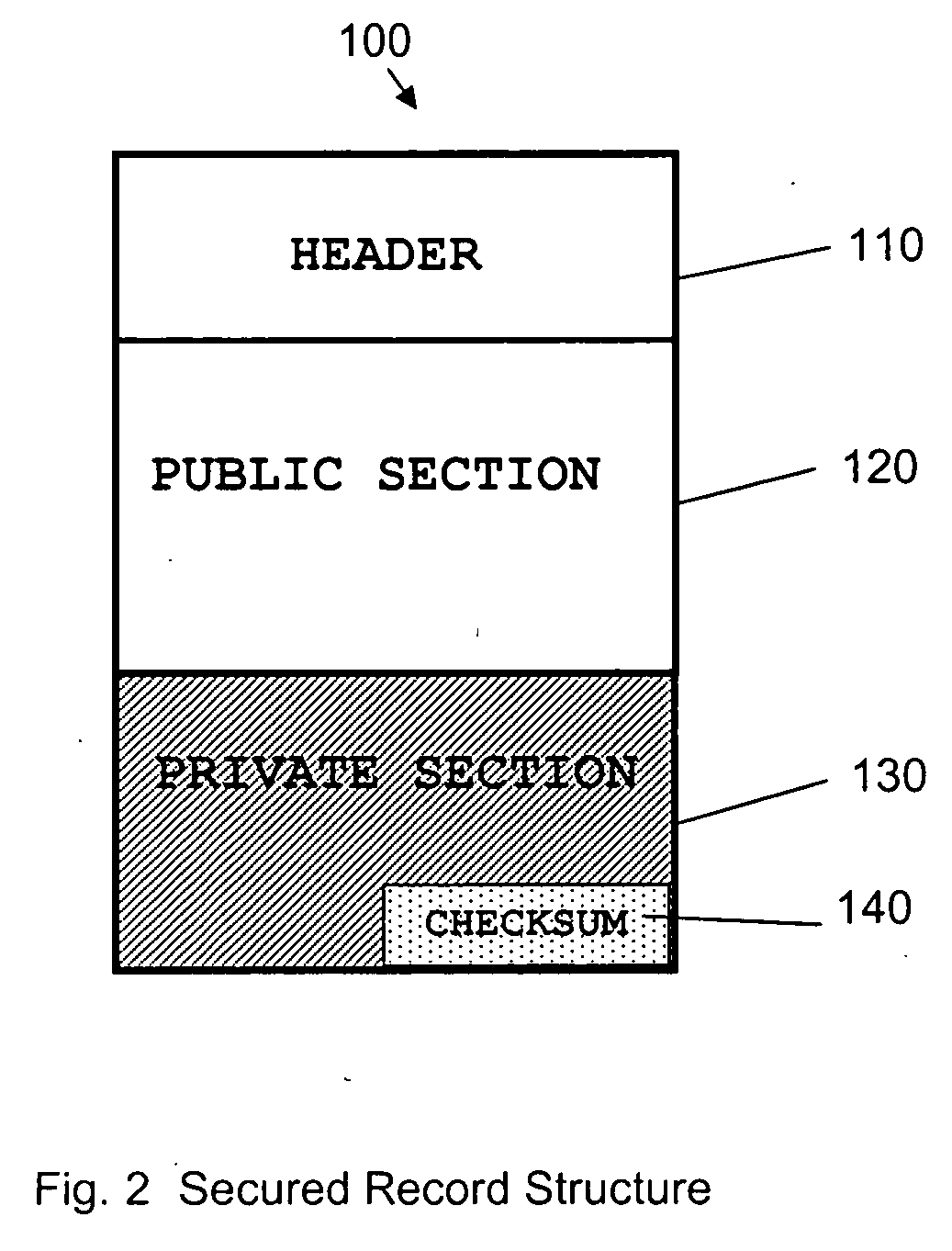
InactiveUS20060282372A1Ensure integrityMinimize expirationAcutation objectsFinanceCredit cardChecksum
A method by which merchants who store sensitive credit card information can secure the information from theft, while minimizing the impact on the customer, as well as minimizing the cost of implementation. The merchant uses a special secured record for the storage of the credit card information for a specific customer. The record consists of two parts. The first part of the record contains public information which is visible to anyone with access to the record. The public information includes the merchant identity, along with information that constrains the use of the record, such as limits on the type of purchase, amount of purchase, or frequency of purchase, as well as the expiration date of the record, approved shipping addresses, and other constraints that make the record effectively useless to anyone except the merchant who created and stored the record, as well as limiting possible abuse by said merchant. The second part of the record contains private information which is encrypted so as to be visible only to parties authorized to view the information. The private part of the record will contain the sensitive credit card information, along with a checksum of the contents of the record. When the record is submitted to the clearing entity, the private part of the record is decrypted using the appropriate key. The checksum is used to verify that the record has not been modified, and that the public and private sections correspond to each other. Once the record is validated, constraints are applied, and if met, the credit card information is used to process the transaction.
Owner:ENDRES TIMOTHY GERARD +1
Method and apparatus for end-to-end content publishing system using XML with an object dependency graph
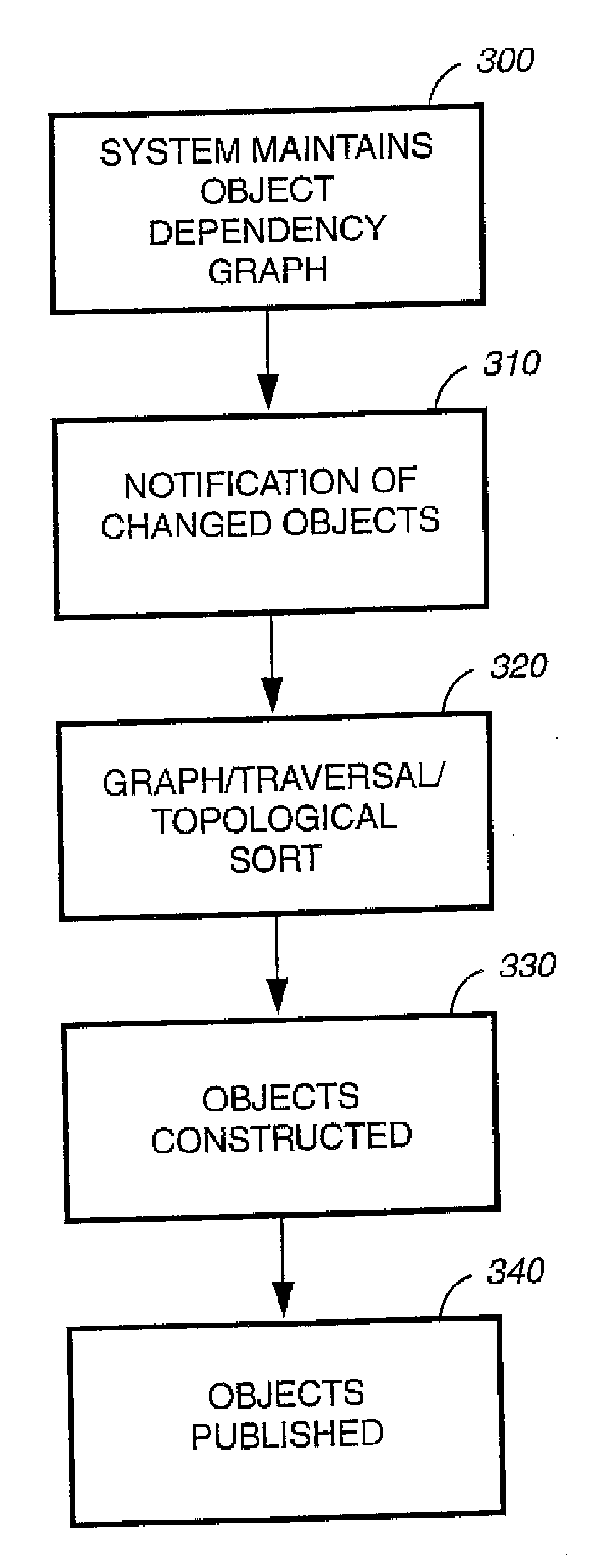
InactiveUS20060294459A1Avoid scattering and duplicationReusabilityDigital computer detailsNatural language data processingData integrityReusability
The system for end-to-end content publishing using XML with an object dependency graph is based on the following two design principles: First, separation of content and style: Information stored in the content management system is independent on how it is going to be presented. The presentation style is encapsulated elsewhere and can be used to customize the look and feel based on the end-user preferences as well as the delivery methods and devices. Second, reusability of information content: By encapsulating common information in fragments and subfragments and making these fragments insertable in other fragments, thereby avoid scattering and duplication of information. This enables a user to restrict the edit operations to a limited number of relevant fragments, to affect global changes. In addition, the present invention provides data consistency and data integrity in the content management.
Owner:INT BUSINESS MASCH CORP
Information delivery system, delivery request program, transfer program, delivery program, and the like
ActiveUS20070297422A1Effective preservationDigital data information retrievalDigital computer detailsComputer networkPublic information
In an information delivery system including a plurality of node devices connected each other to thereby configure a network, a first node device includes a device for transmitting request information based on unique identification information corresponding to specific common information and request number information indicative of request number of node information to a second node device to thereby request transmission of the node information concerning a plurality of information saving node devices, included in the plurality of node devices and saving specific common information, which is specified out of common information to be shared among the plurality of node devices, and the second node device includes : a device for searching node information corresponding to the identification information and indicated by request number information included in the request information as many as request number upon receipt of request for the specific common information and a device for transmitting the node information as many as at least the requested amount to the first node device when the node information as many as the request number or more is found and to transmit only node information thus found to the first node device in case where the requested amount of node information cannot be found.
Owner:BROTHER KOGYO KK +1
Platform for management of Internet based public communications and public comment
InactiveUS20050240623A1Efficient use ofLow costData processing applicationsDigital data processing detailsWeb siteGraphics
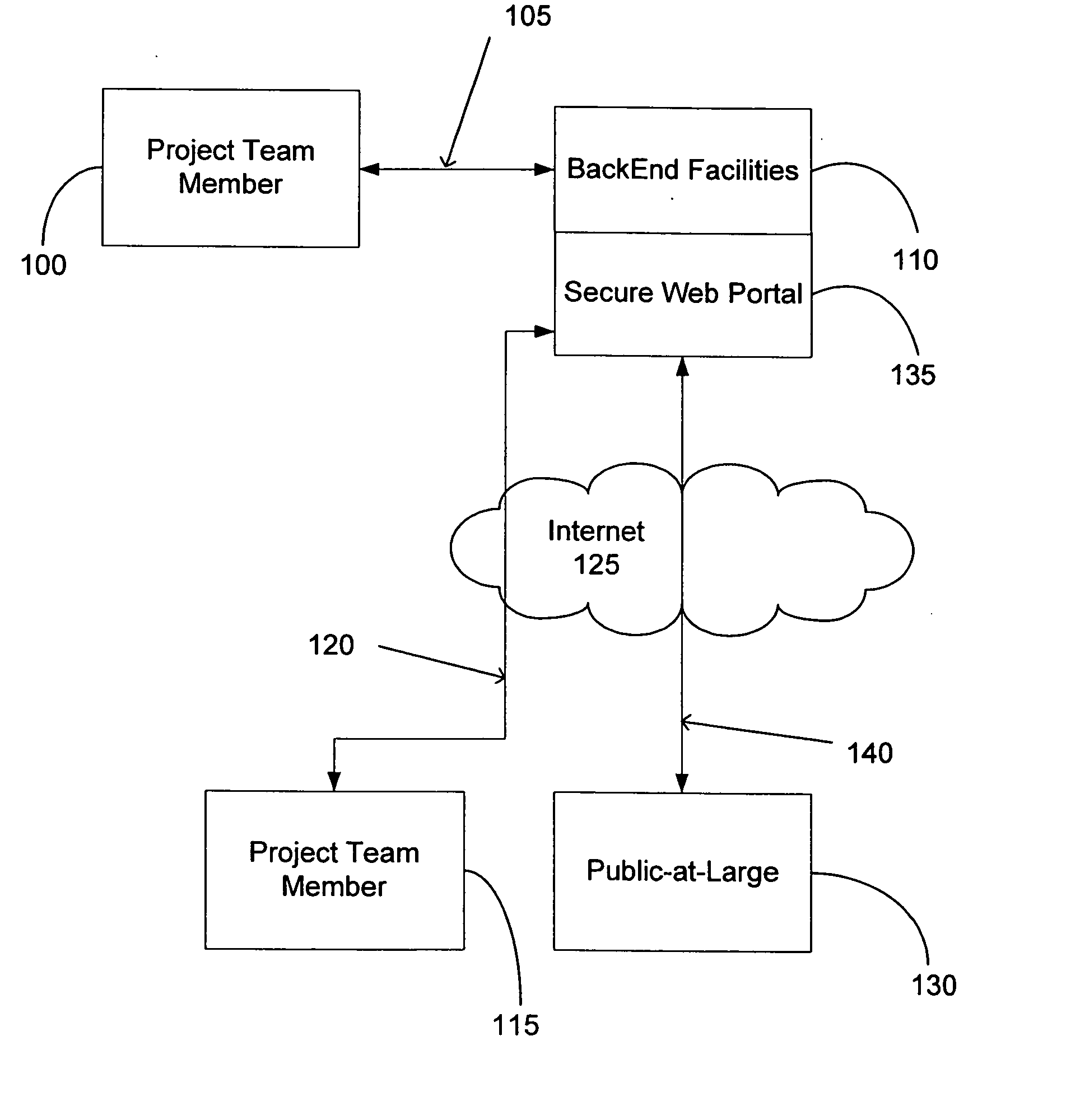
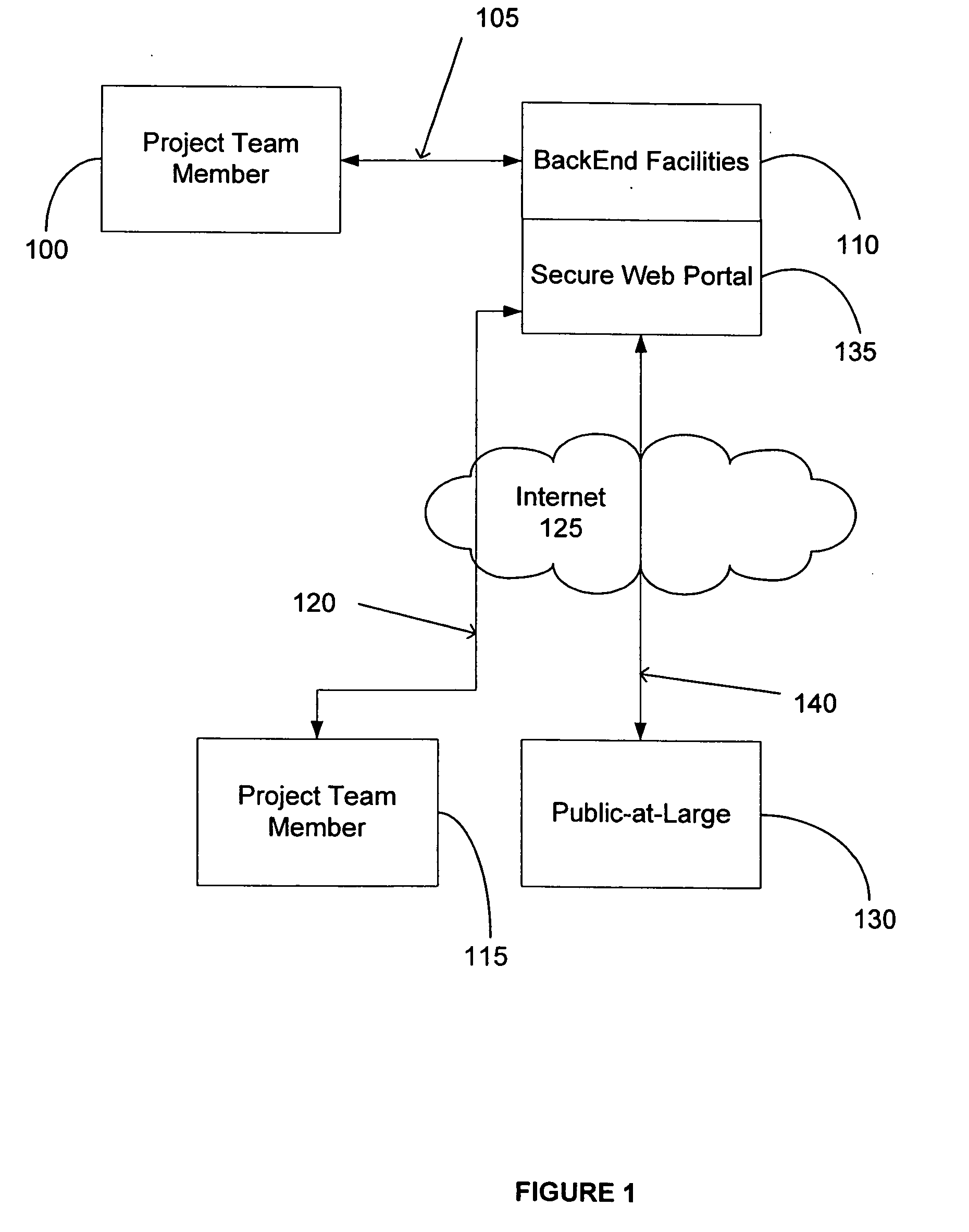
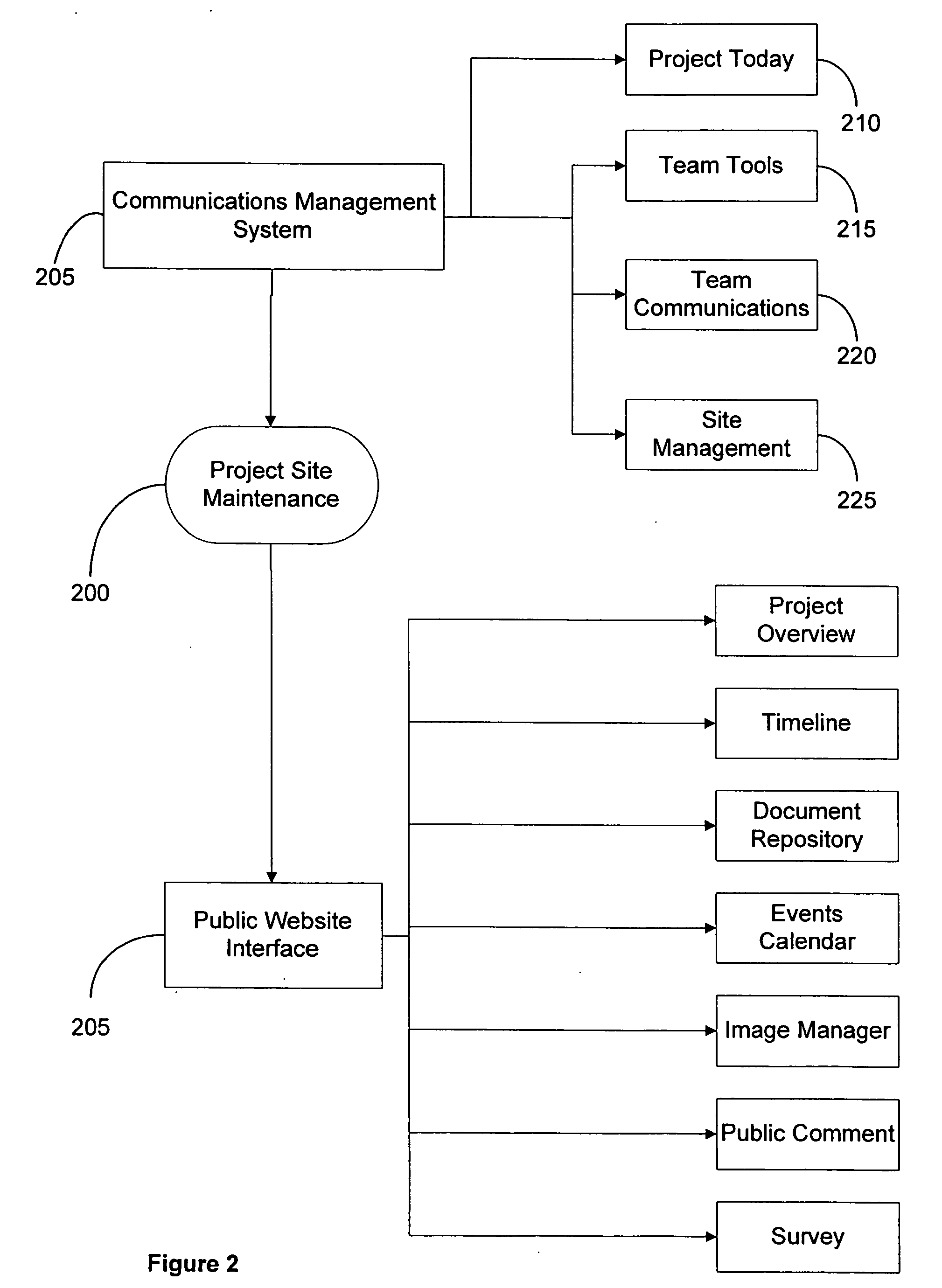
An Internet-based integrated technology platform that simultaneously supports the management of Public Information Sites—Web sites used to both (1) inform the public; and (2) capture and manage public comment (including submission of images)—while at the same time providing support for electronic communication for project teams that manage public involvement projects. The support includes sharing of graphic, text and collaborative tasks. The system and method allow revisions to comments and dynamic feedback in agency decision making based on comments with greater responsiveness. The system is also suited for implementing charettes with a large number of participants.
Owner:INGAGE NETWORKS
Trusted user interface for a secure mobile wireless device
InactiveUS20050166064A1No costly hardware duplicationAvoid dataDigital data processing detailsUser identity/authority verificationComputer hardwareMemory address
A mobile wireless device programmed with software which provides a trusted user interface for the device by allowing the content of a secure screen memory to be modifiable only by authorised applications. Normally, the entire screen memory address is public information, making the entire screen memory fully available to any application; hence, even sensitive dialogs would use screen memory which can in theory be looked at by malicious software, enabling that malicious code to grab PIN data etc. or corrupt a trusted user interface. But with the present invention, unauthorised applications are prevented from accessing the data displayed by the secure frame buffer because they are able to access only the non-secure screen memory. Hence, malicious applications cannot retrieve data from a trusted dialog or compromise that data. Further, as the present invention is a software only solution, it requires no new hardware per se—the only requirement is that components (e.g. a software window server; a video chip etc.) can select content from different parts of screen memory—i.e. secure and non-secure frame buffers.
Owner:NOKIA CORP
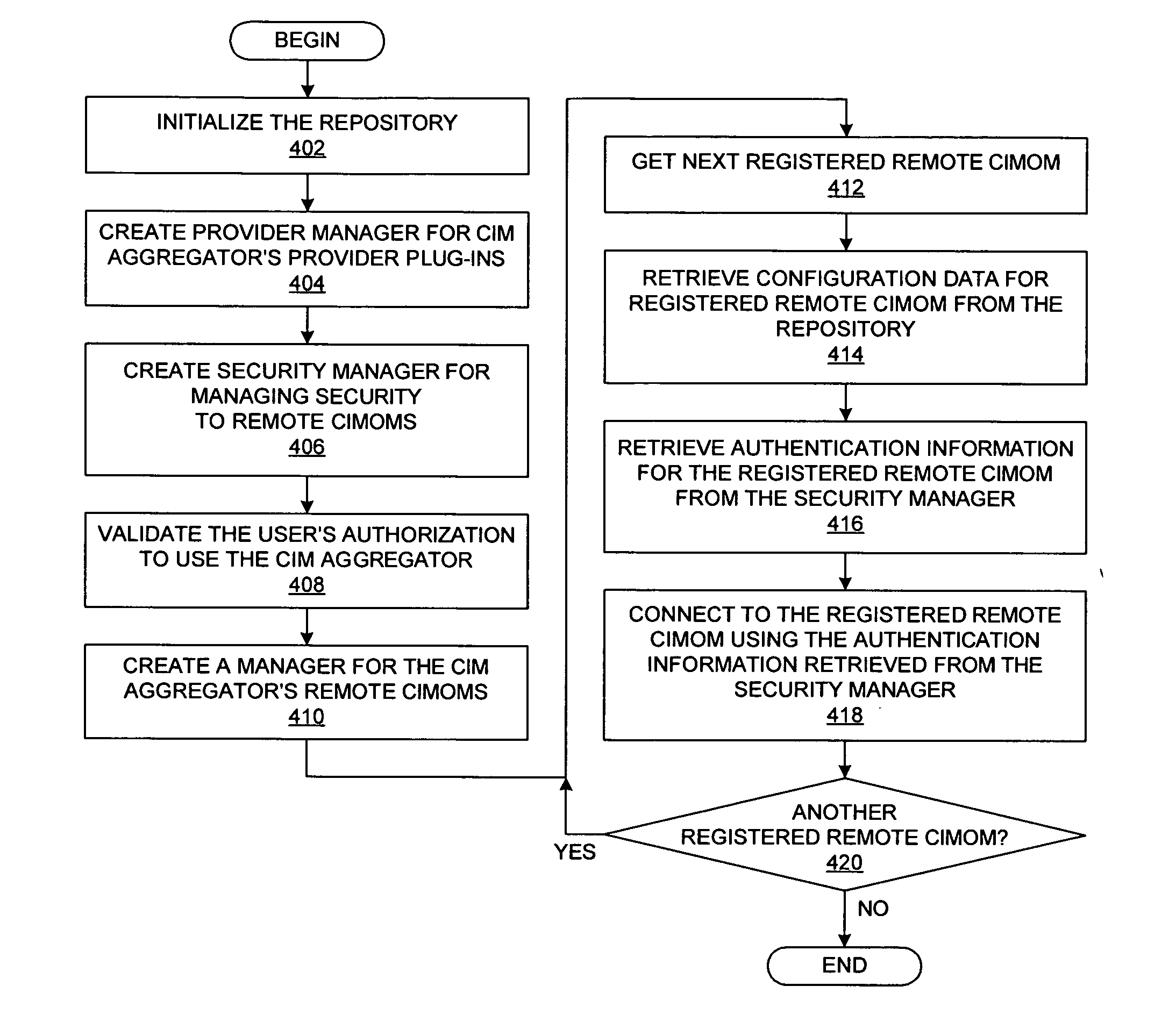
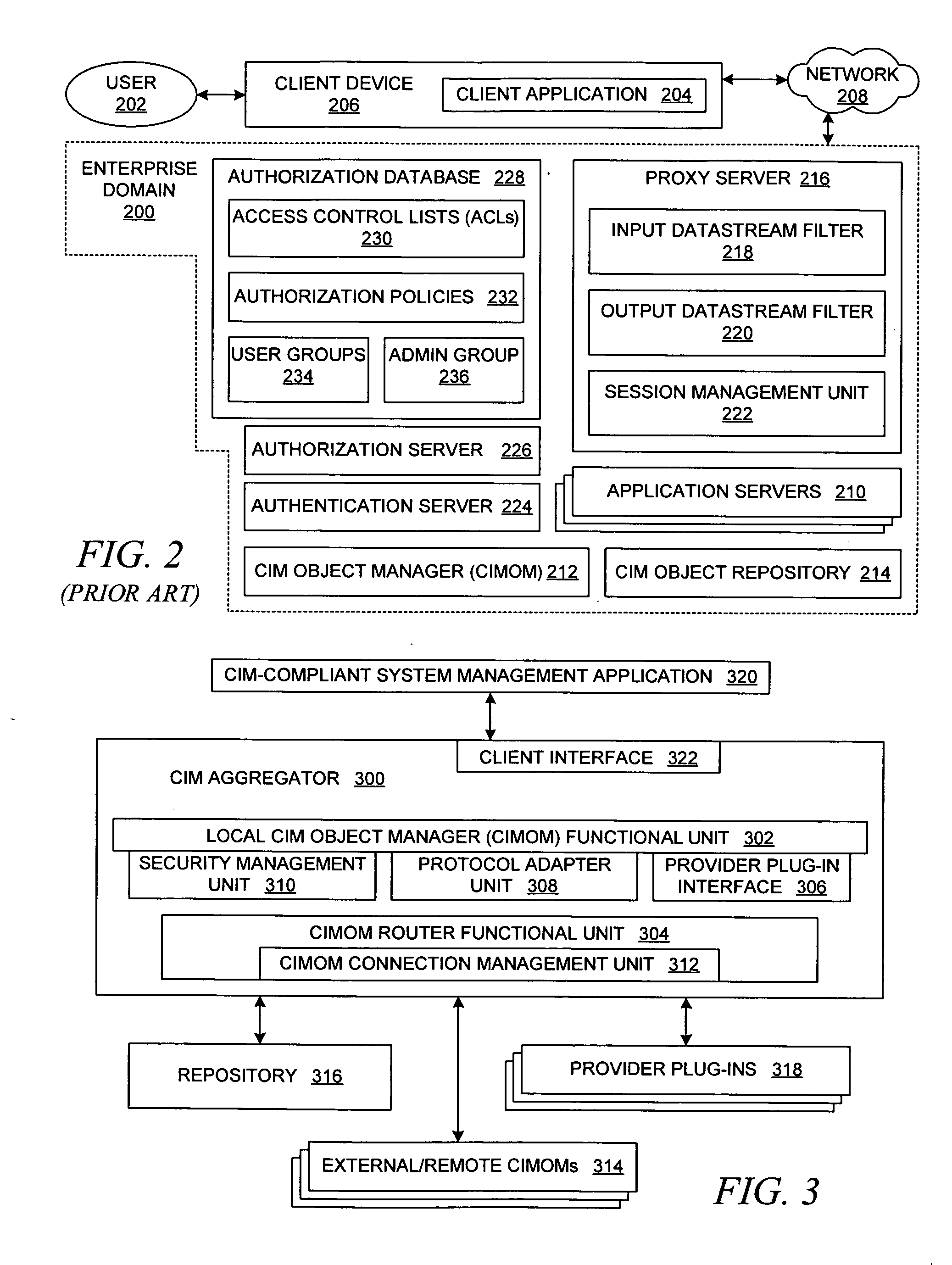
Method and system for unified support of multiple system management information models in a multiple host environment
InactiveUS20070073877A1Energy efficient ICTData processing applicationsData processing systemSystems management
Owner:IBM CORP +1
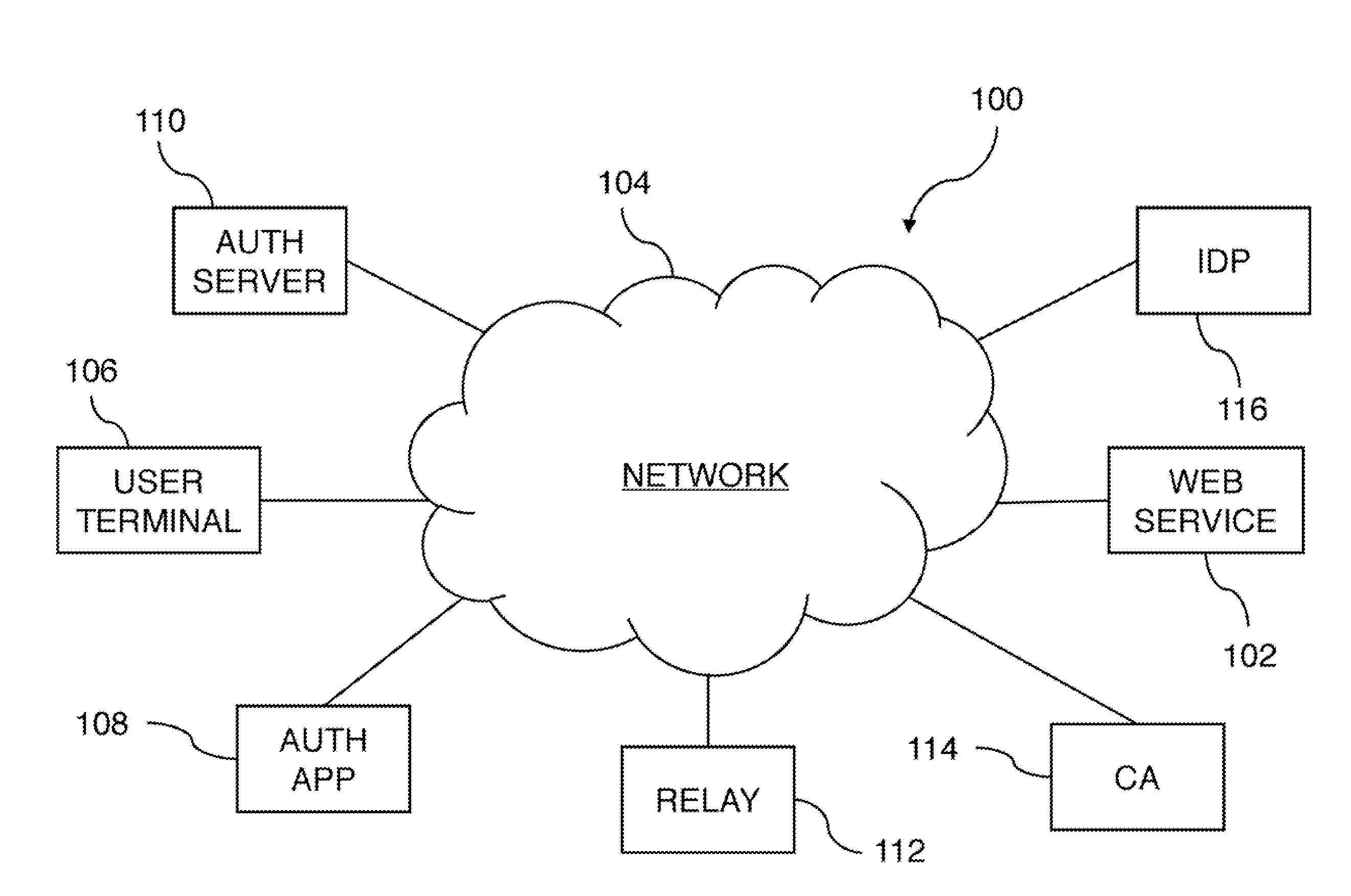
Password-less Authentication System, Method and Device
ActiveUS20150304847A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsPasswordWeb service
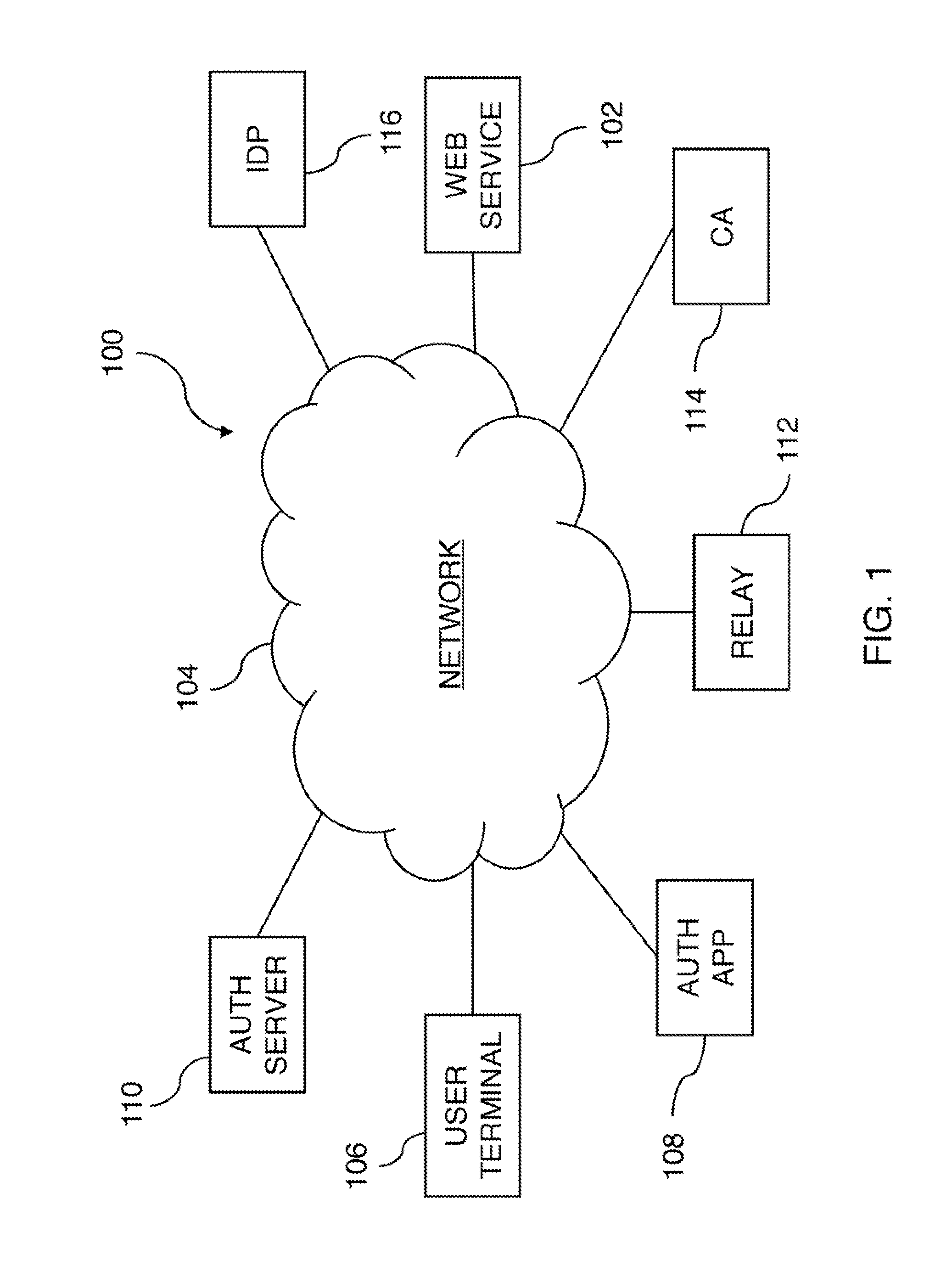
A password-less authentication system is described herein. Also described are the devices used for such a system and the method and process implemented. The system employs asymmetric cryptography to enable users to log in to various systems or services on different platforms or computers by the aid of a mobile device. Users' credentials are kept privately in the mobile device, and not leaked to the network or any web service. In addition, the web service can verify users' authentication request by solely public information of users' credentials.
Owner:GONG GUANG +2
Bandwidth allocation signalling
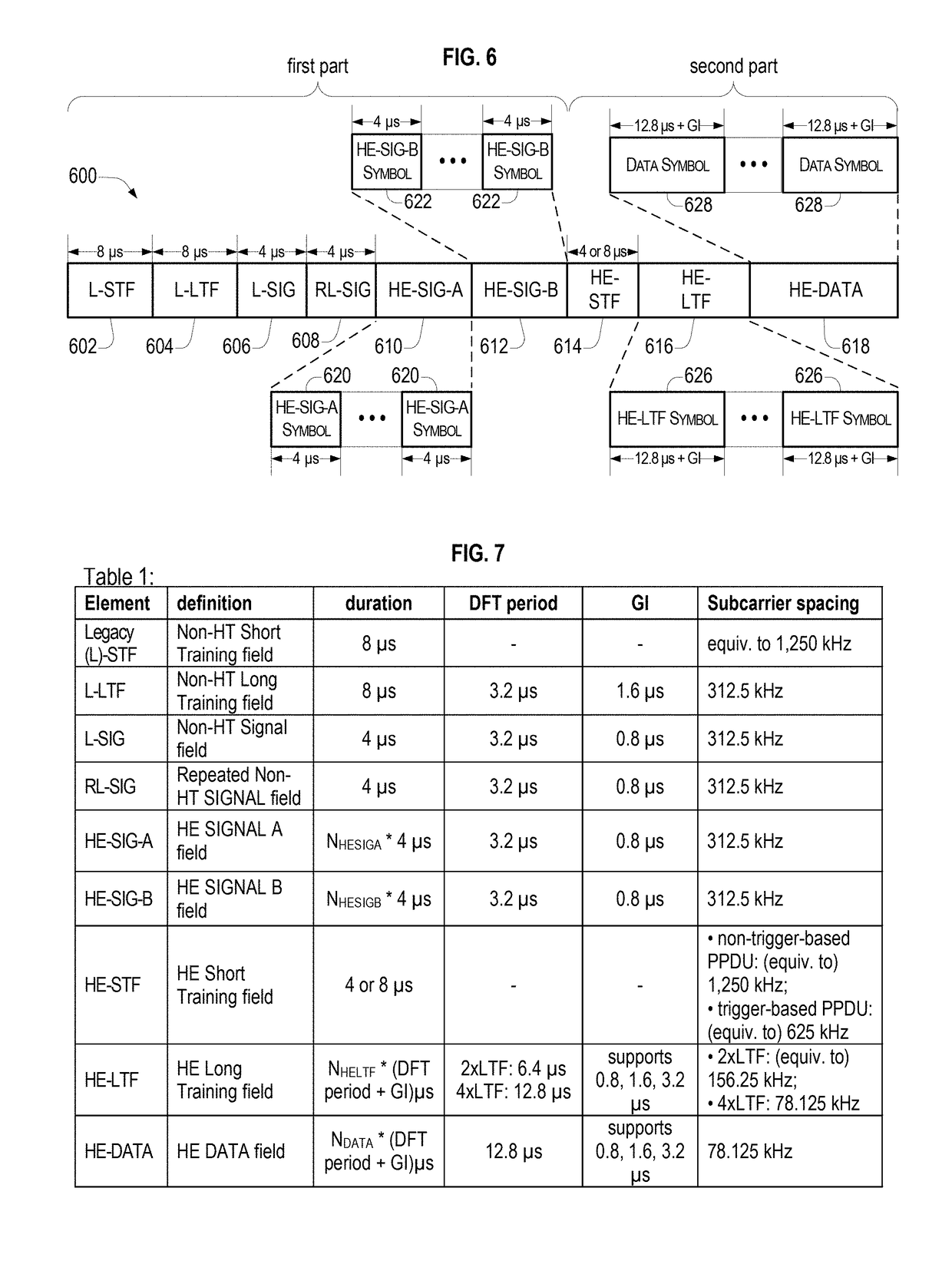
ActiveUS10219271B1Improve efficiencySignal allocationWireless communicationTelecommunicationsPublic information
An Access Point (AP) may allocate Resource Units (RUs) of a bandwidth of a Multi-User (MU) frame, including determining that an RU is not allocated to a station; determine a value of an RU Allocation Subfield according to the allocation of the RUs, the value of the RU Allocation Subfield indicating that the RU is not allocated; and generate a High Efficiency Signal B (HE-SIG-B) field including the RU Allocation Subfield in a common info field thereof. An AP may perform an MU transmission by transmitting a length to a station; determining identifiers each having the length; and transmitting an HE-SIG-B field including one of the identifiers to the station after transmitting the length. An AP may perform an MU transmission by allocating RUs and responding to receiving a frame from a station by transmitting a Multi-User Acknowledgement (MU-ACK) frame that includes information on the allocation of the RUs.
Owner:SAMSUNG ELECTRONICS CO LTD
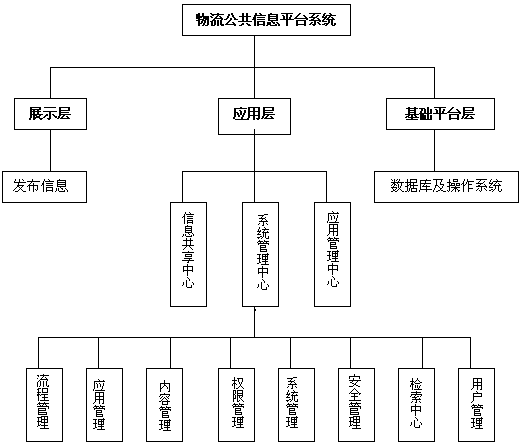
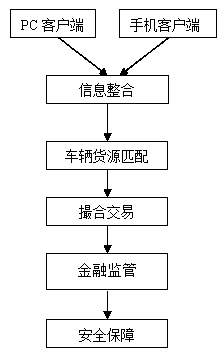
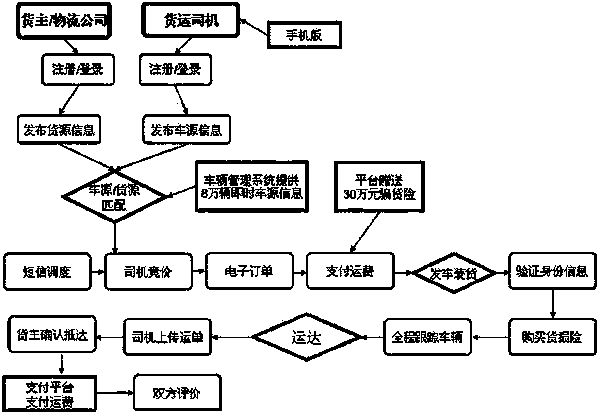
Logistic public information platform system
InactiveCN103699979AEasy to operateRealize human-computer interactionResourcesTransaction managementInformation resource
The invention provides a logistic public information platform system, which is oriented towards production and manufacturing enterprises, drivers and logistics companies, has the functions of logistic information management, information retrieval, identity authentication, vehicle positioning, online insurance effecting and online traction, combines with a logistic information system and an electronic business system for realizing logistic information resource sharing and provides online parking lot one-stop service vehicle and cargo marching for a user. The system is an electronic information platform which is based on Internet and is developed by adopting a B2C (Business to Customer) mode, i.e. an enterprise and consumer transaction mode, wherein the electronic information platform comprises a foreground website and a background management system, the user can log in the foreground website for performing user registration, find required vehicle source information or cargo source information through an information searching function of the website, and submitting an electronic order for concluding a transaction, and an administrator can maintain the content of the foreground website through the background management system. The logistic public information platform system is suitable for logistic information transaction.
Owner:JIAN WANJI LOGISTICS TRANSPORTATION
Authenticated exchange of public information using electronic mail
InactiveUS20050223226A1Improve trustKey distribution for secure communicationUser identity/authority verificationPublic informationProtocol for Carrying Authentication for Network Access
Methods and systems are provided for using an existing email transfer protocol, such as SMTP, to exchange digital objects in an authenticated manner. The provided methods and systems solve the bootstrapping problem of computer identities for P2P communication by authenticating the exchange of public information. If the electronic mail protocols are strong, in that sending an email message to a given address results in the message reaching that address with a high degree of confidence, then the exchange of public information performed in accordance with embodiments of the invention is confidently authenticated.
Owner:MICROSOFT TECH LICENSING LLC
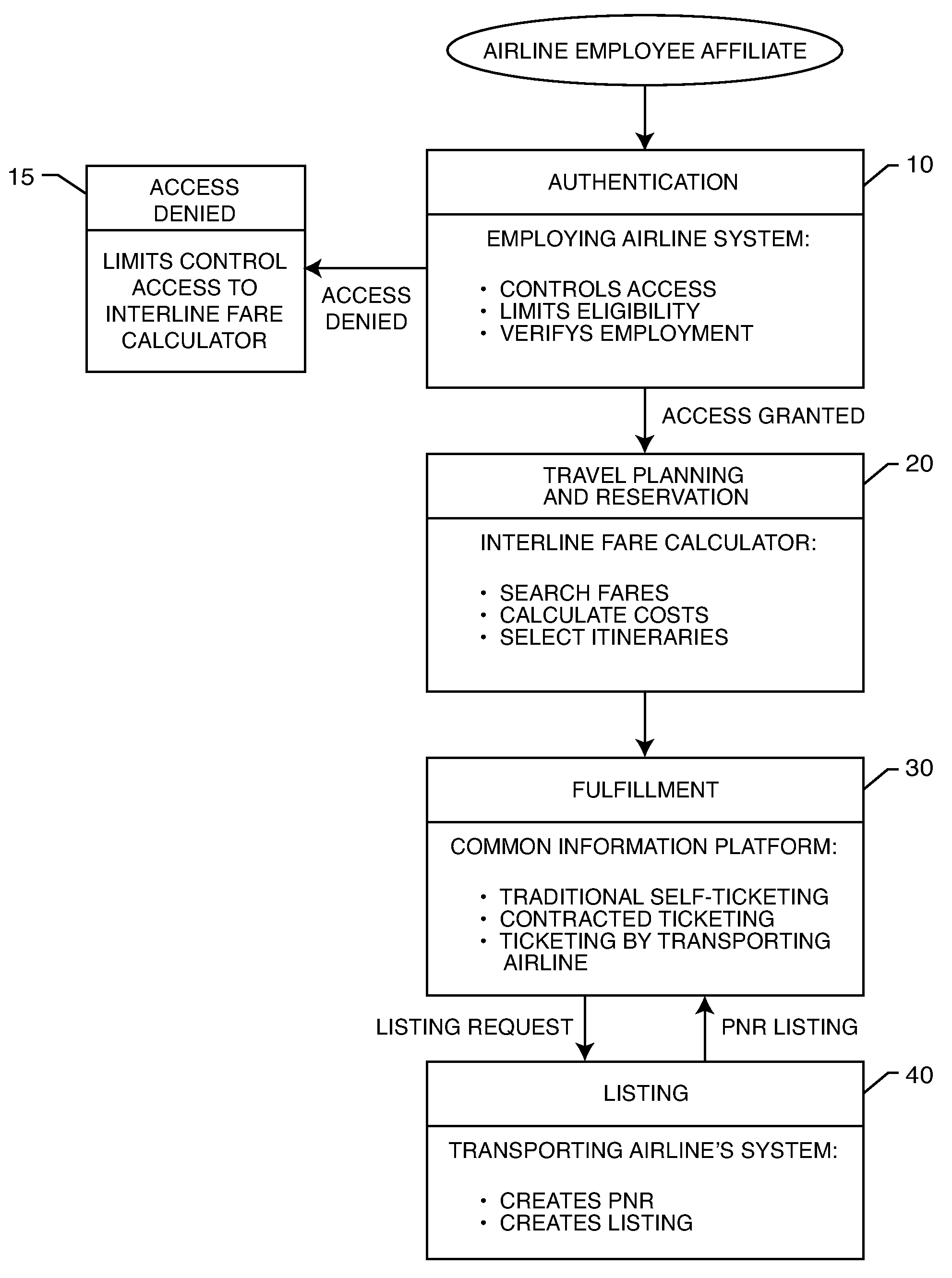
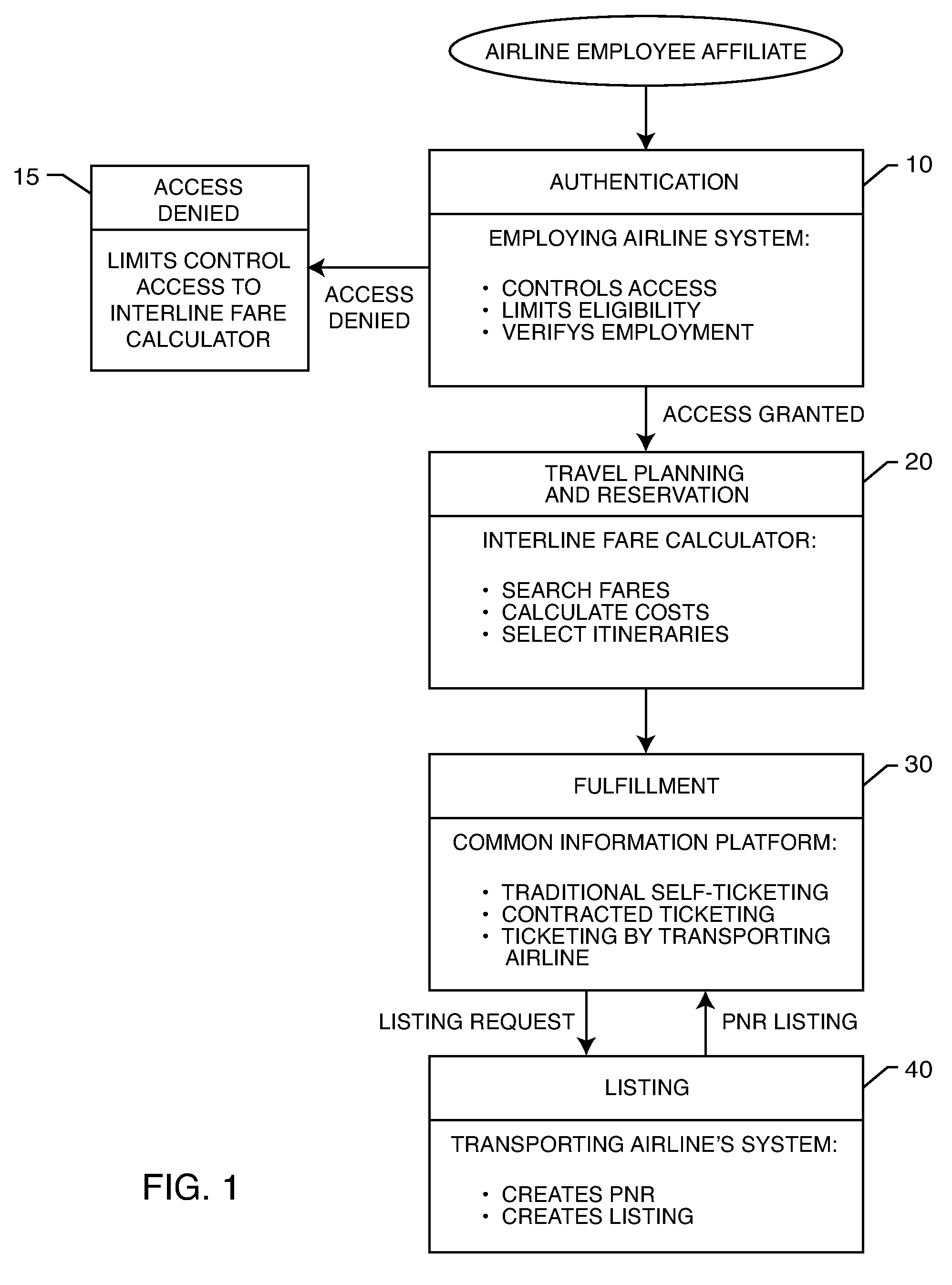
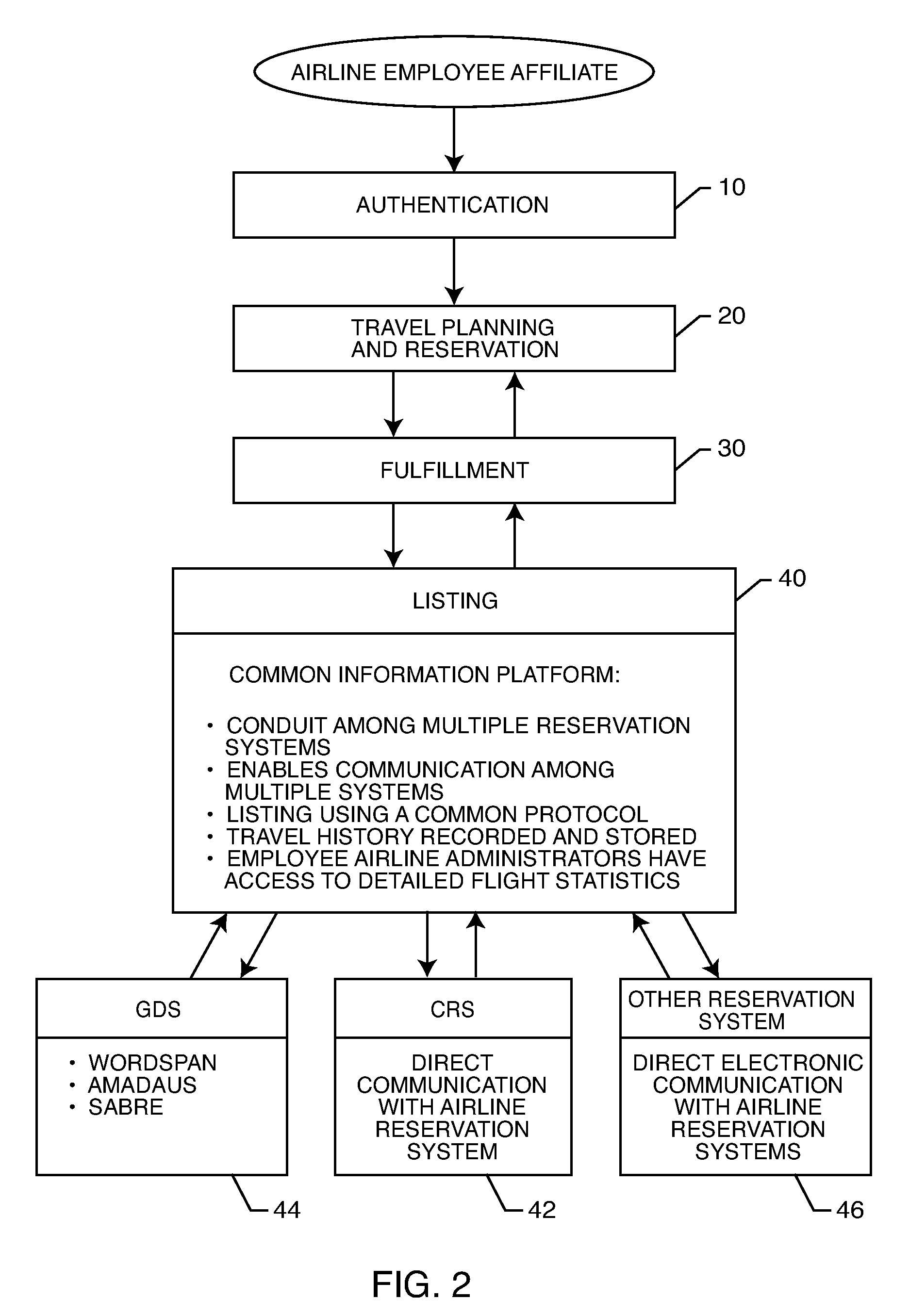
Reservation and ticketing process for space-available seats to airline employees
A process for reserving and ticketing interline travel for an airline employee affiliate. The airline employee affiliate develops a travel itinerary for interline travel. The travel itinerary is processed in electronic form in a common information platform administered by a third party purchase facilitator. An electronic ticket data is associated with the travel itinerary in the common information platform, wherein the electronic ticket data is in an electronic format compatible with a transporting airline reservation system. Finally, the electronic ticket data and travel itinerary are transmitted to a carrier reservation system for listing the airline employee affiliate for travel on the transporting airline.
Owner:NON REVENUE HLDG
City management intelligent streetlamp
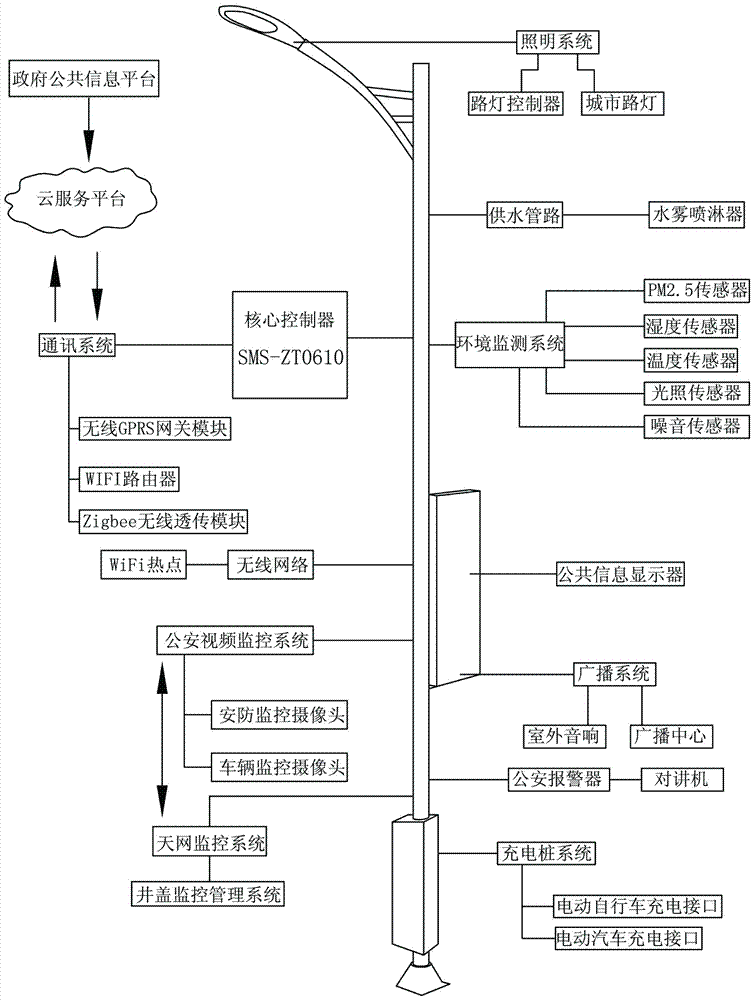
PendingCN107062108AEnsure safetyReduce the temperatureProgramme controlMechanical apparatusVideo monitoringDisplay device
The invention discloses a city management intelligent streetlamp which comprises a streetlamp body arranged on a municipal road. A core controller is arranged in a lamp post of the streetlamp body. The core controller is connected with an illumination system, a water supply pipeline, an environment monitoring system and a communication system. The illumination system comprises a city streetlamp and a streetlamp controller. The streetlamp controller is in controlled connection through the core controller. The communication system comprises a wireless GPRS gateway module, a WiFi router and a ZigBee wireless unvarnished transmission module. The communication system is connected to a cloud service platform. The cloud service platform is connected with a government public information platform. A public information display is installed on the streetlamp body. The core controller is connected to a public security video monitoring system, a sky net monitoring system and a well lid monitoring managing system. By means of the city management intelligent streetlamp, the air humidity and temperature can be adjusted to a certain degree, the PM2.5 value in the air is reduced, the public information display is further arranged and can play government public information in real time, and due to the arranged public security video monitoring system and the interconnected sky net monitoring system and well lid monitoring managing system, good security work can be done.
Owner:江西中天景建设有限公司
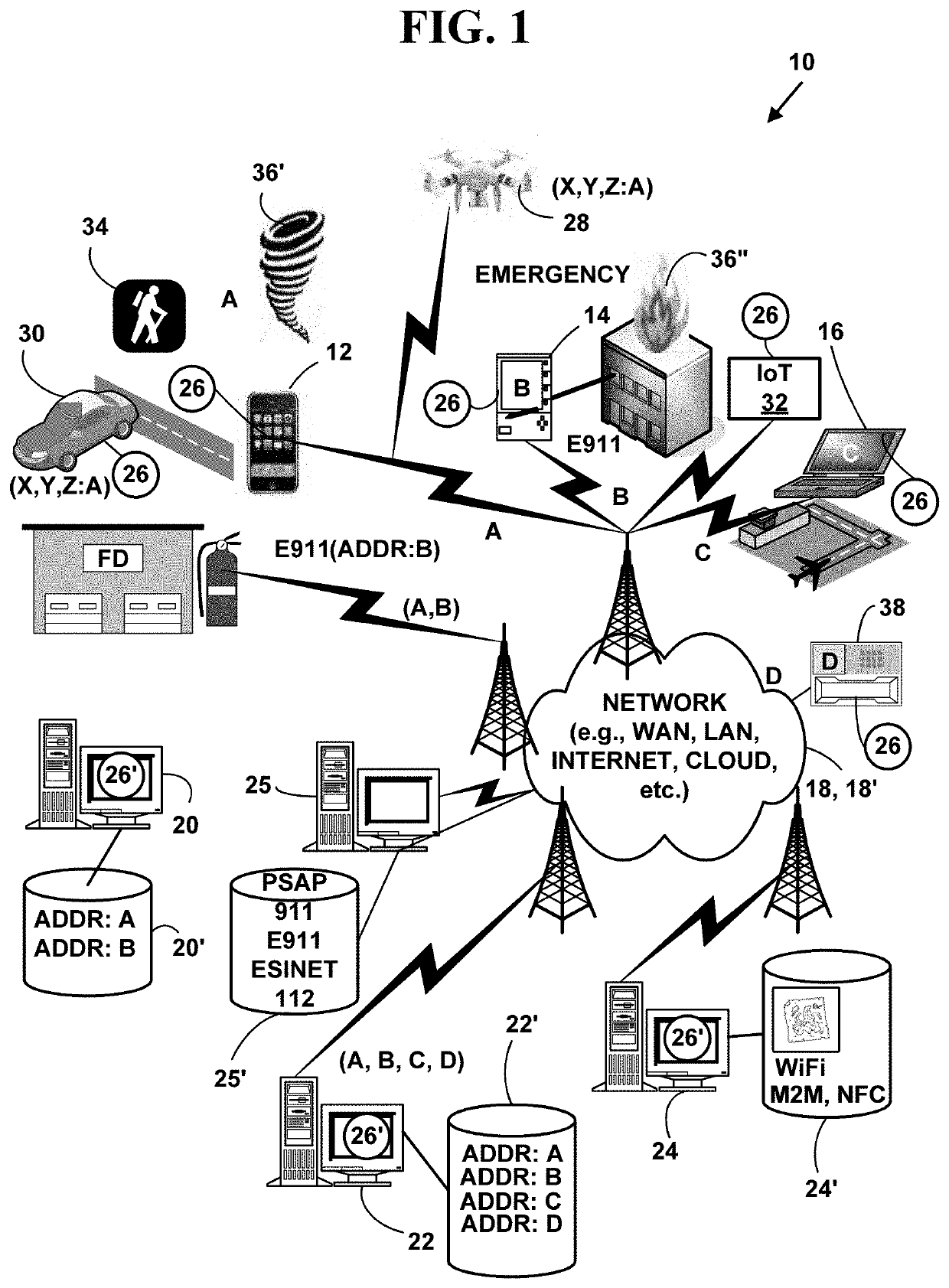
Method and system for locating a network device in an emergency situation including public location information
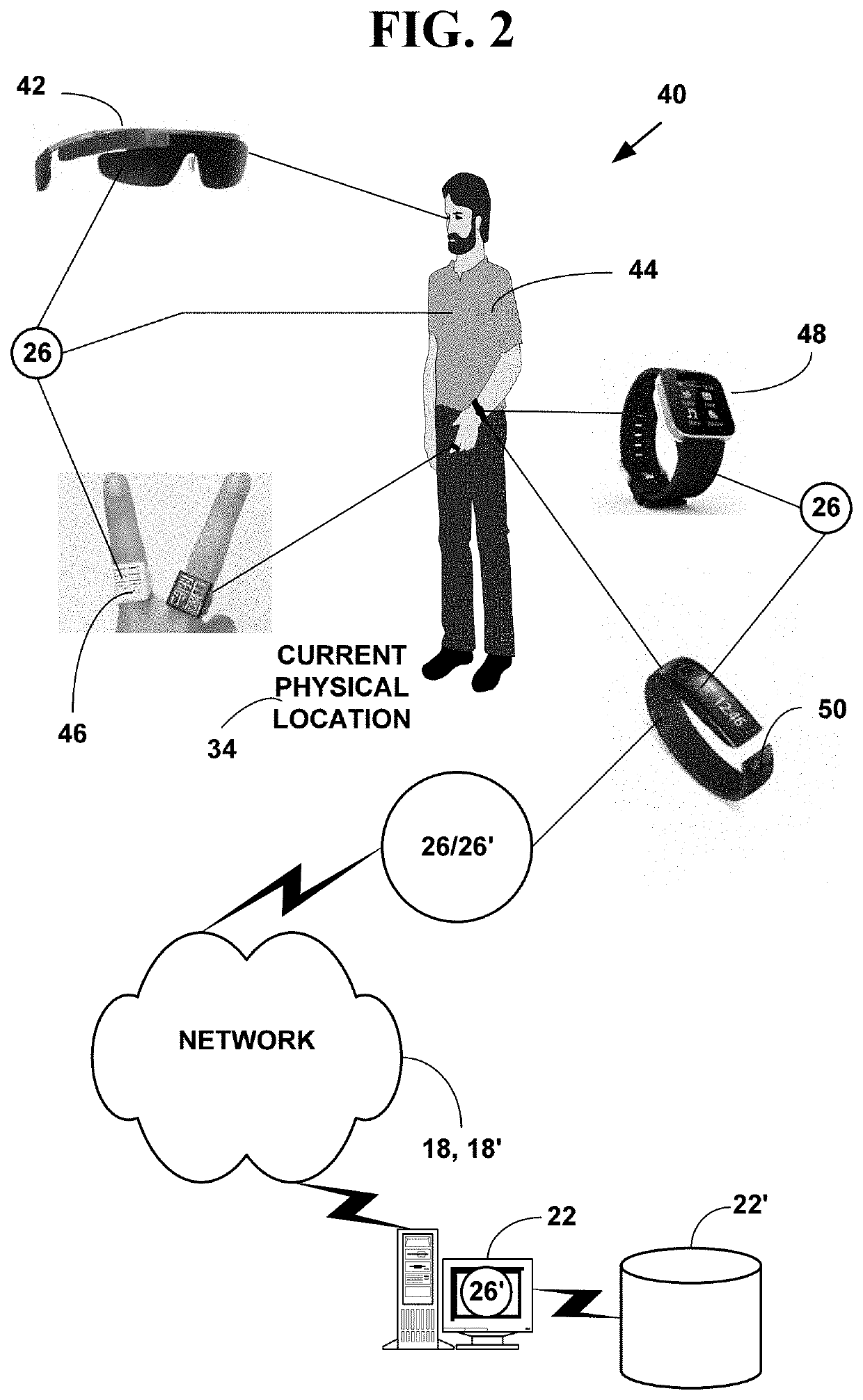
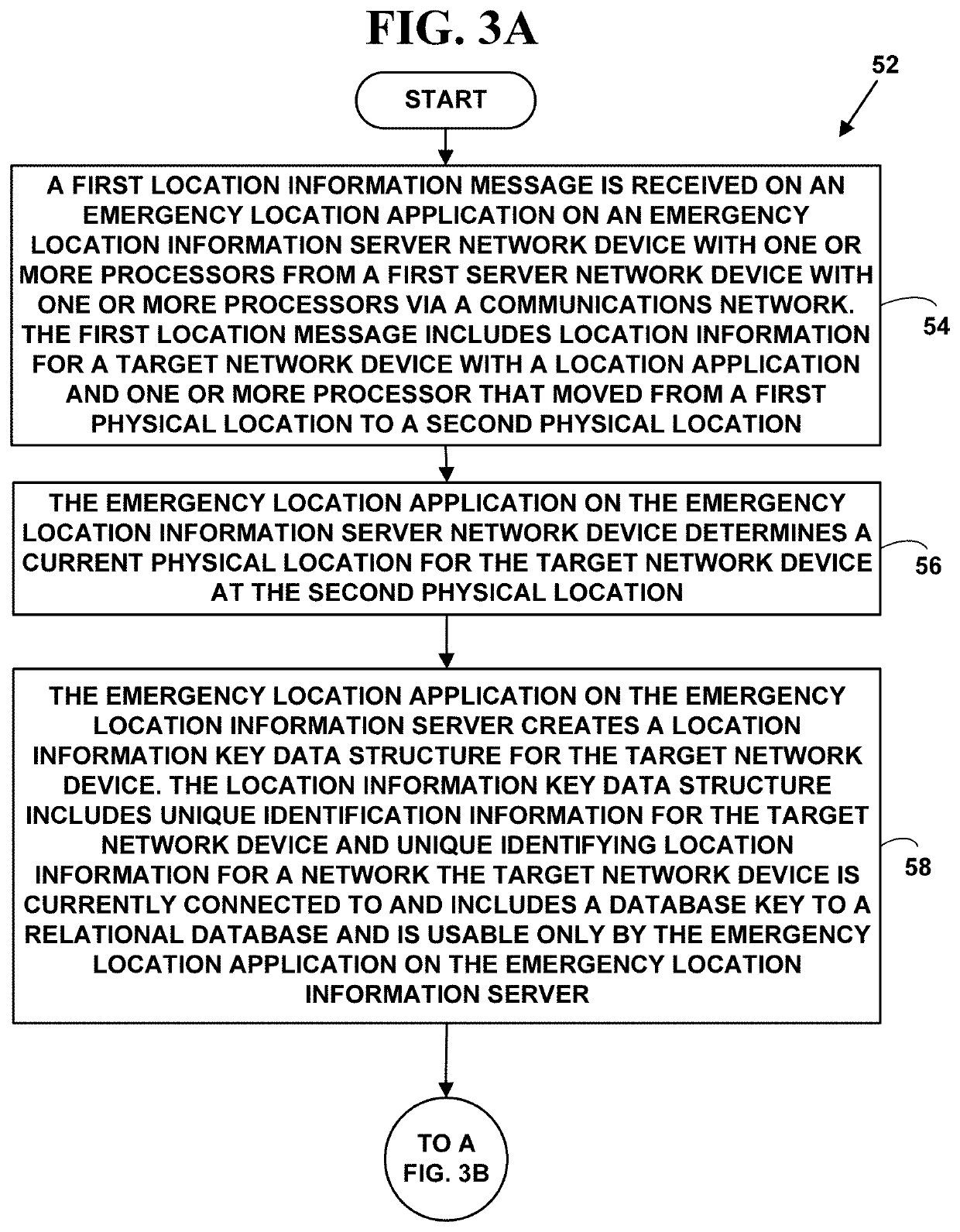
A method and system for locating a network device in an emergency situation including public information. Current physical location information is obtained for a network device every time it registers on a network or moves to a new physical location. The current physical location is sent and received in an encrypted format to and from the network device. When the network device initiates an emergency message (e.g. 911, E911, NG911, text-to-911, 112, etc.) based on an emergency event (e.g., weather, crime, fire, natural disaster, medical, terrorist, military, etc.), the emergency message includes the encrypted current physical location information for the network device. The current physical location information is decrypted. Additional information is collected from one or more public location information sources for the current physical location of the network device. The emergency message with the additional information is routed in real-time to an appropriate Public Safety Answering Point (PSAP). The appropriate PSAP is immediately notified in real-time so emergency responders (e.g., police, fire, medical, etc.) can be dispatched to the current physical location of the network device.
Owner:EVERBRIDGE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com