Patents
Literature
4338 results about "Information sharing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The term "information sharing" gained popularity as a result of the 9/11 Commission Hearings and its report of the United States government's lack of response to information known about the planned terrorist attack on the New York City World Trade Center prior to the event. The resulting commission report led to the enactment of several executive orders by President Bush that mandated agencies implement policies to "share information" across organizational boundaries. In addition, an Information Sharing Environment Program Manager was appointed, tasked to implement the provisions of the Intelligence Reform and Prevention of Terrorism Act of 2004. In making recommendation toward the creation of an "Information Sharing Environment" the 9/11 Commission based itself on the findings and recommendations made by the Markle Task Force on National Security in the Information Age. The term "information sharing" in the information technology lexicon has a long history. Traditional information sharing referred to one-to-one exchanges of data between a sender and receiver. These information exchanges are implemented via dozens of open and proprietary protocols, message and file formats.
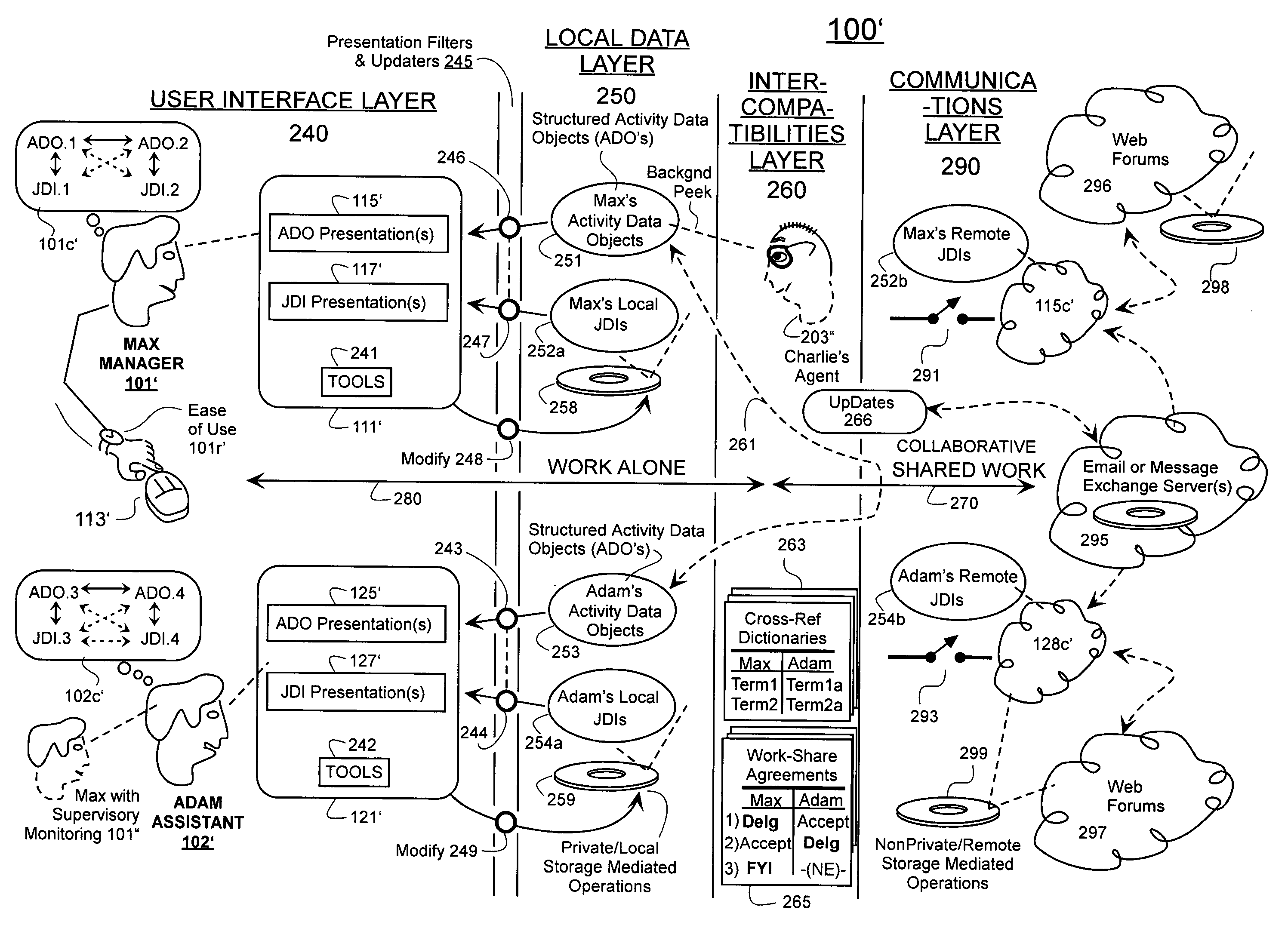
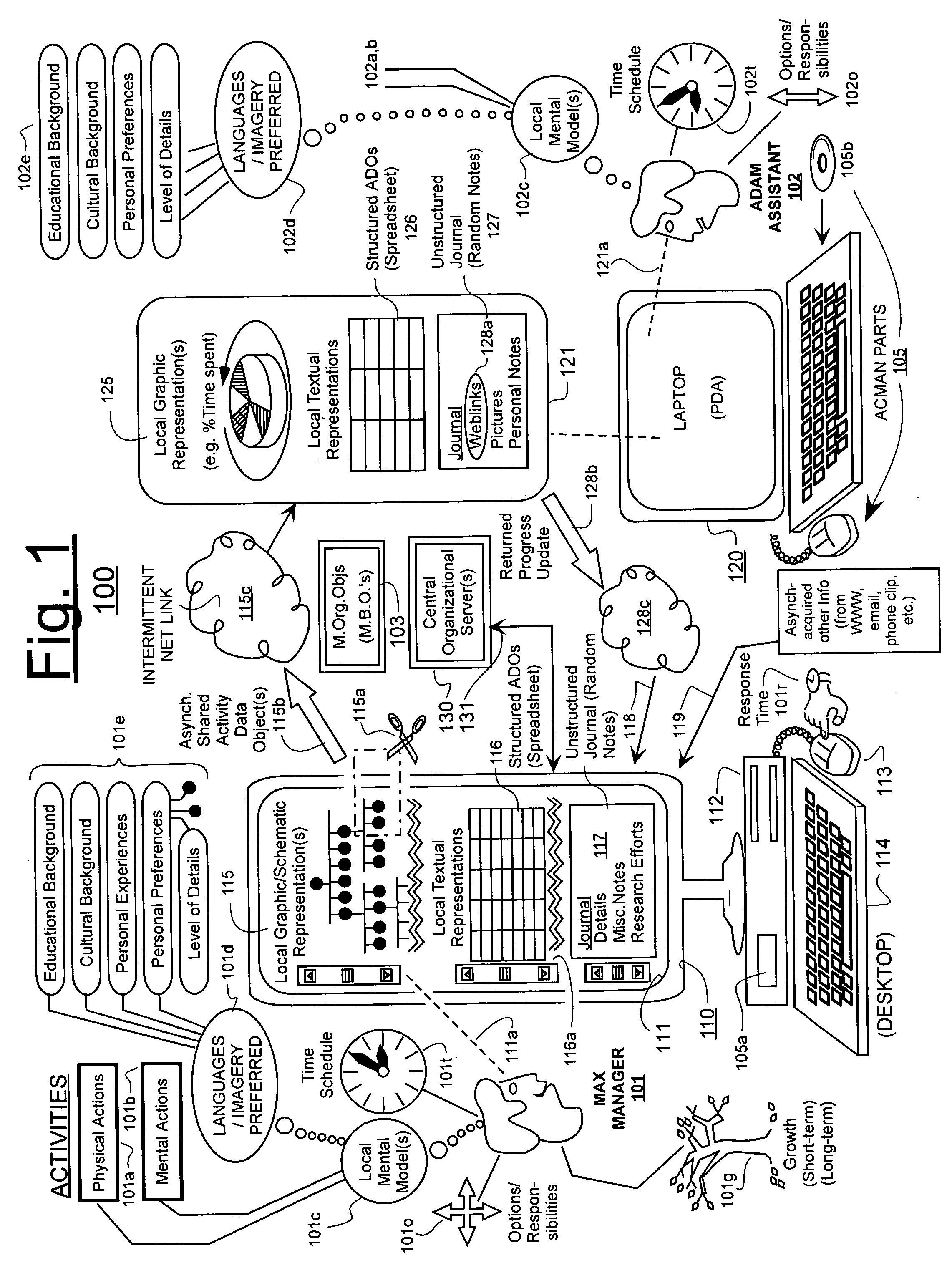
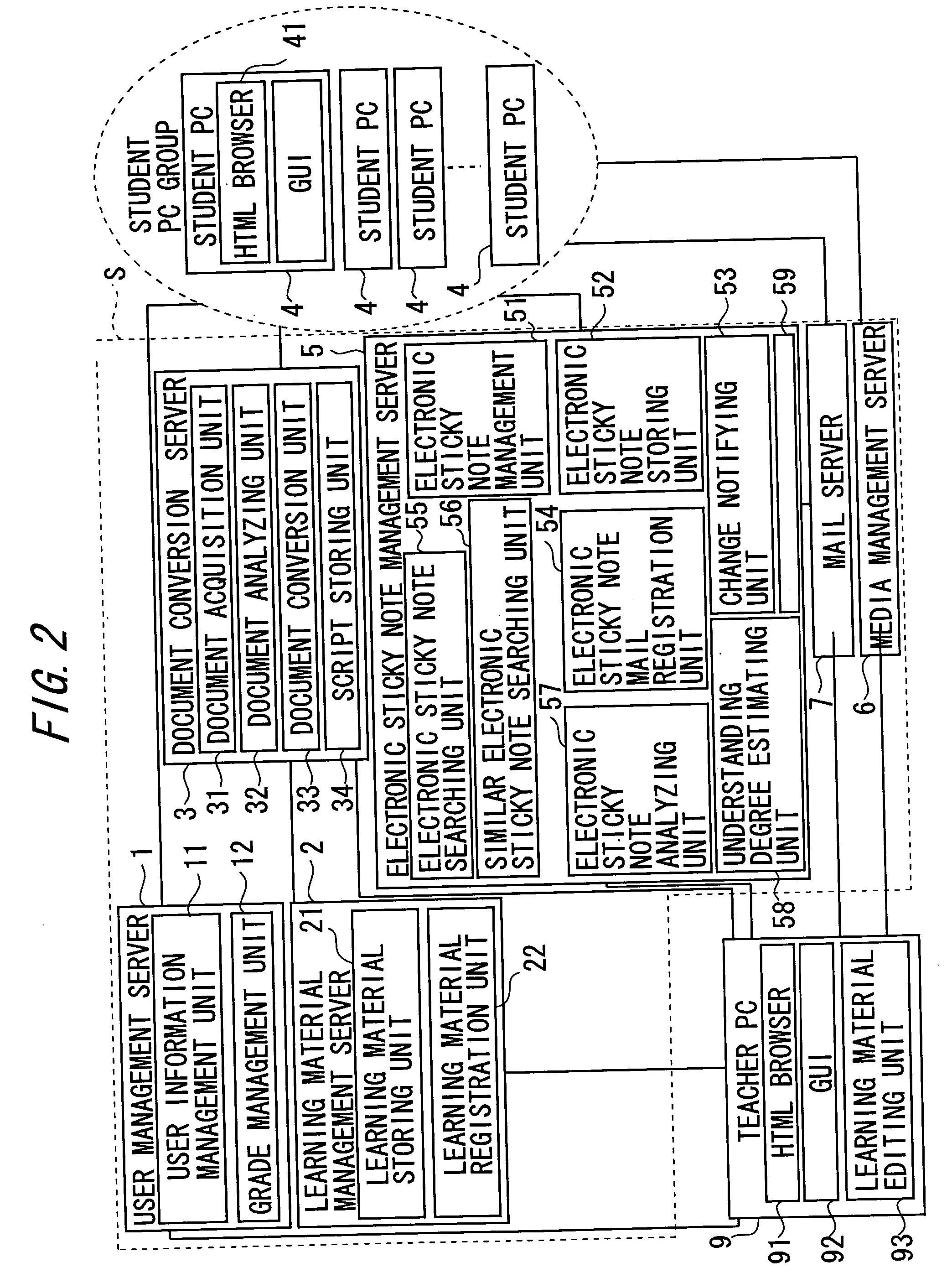
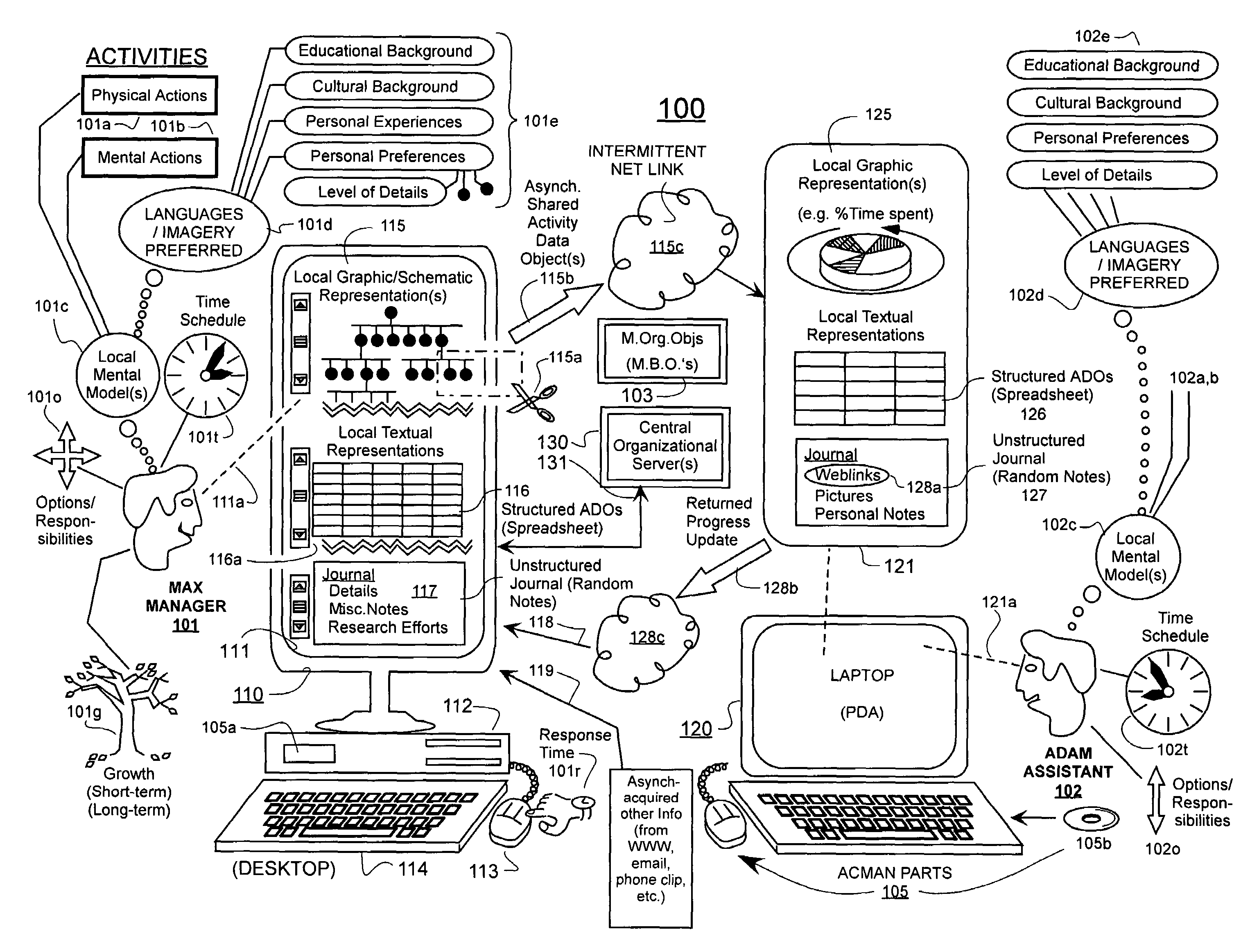
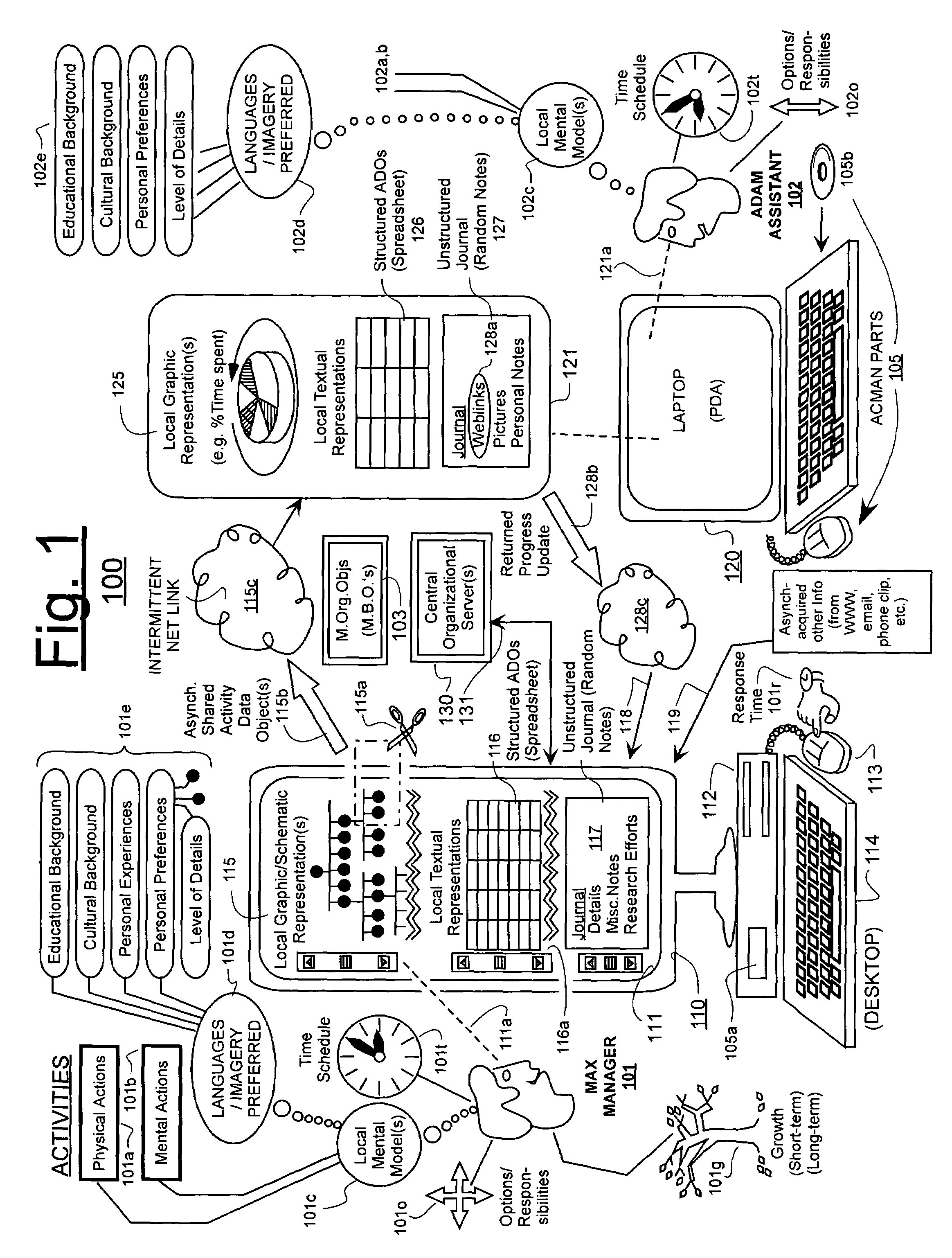
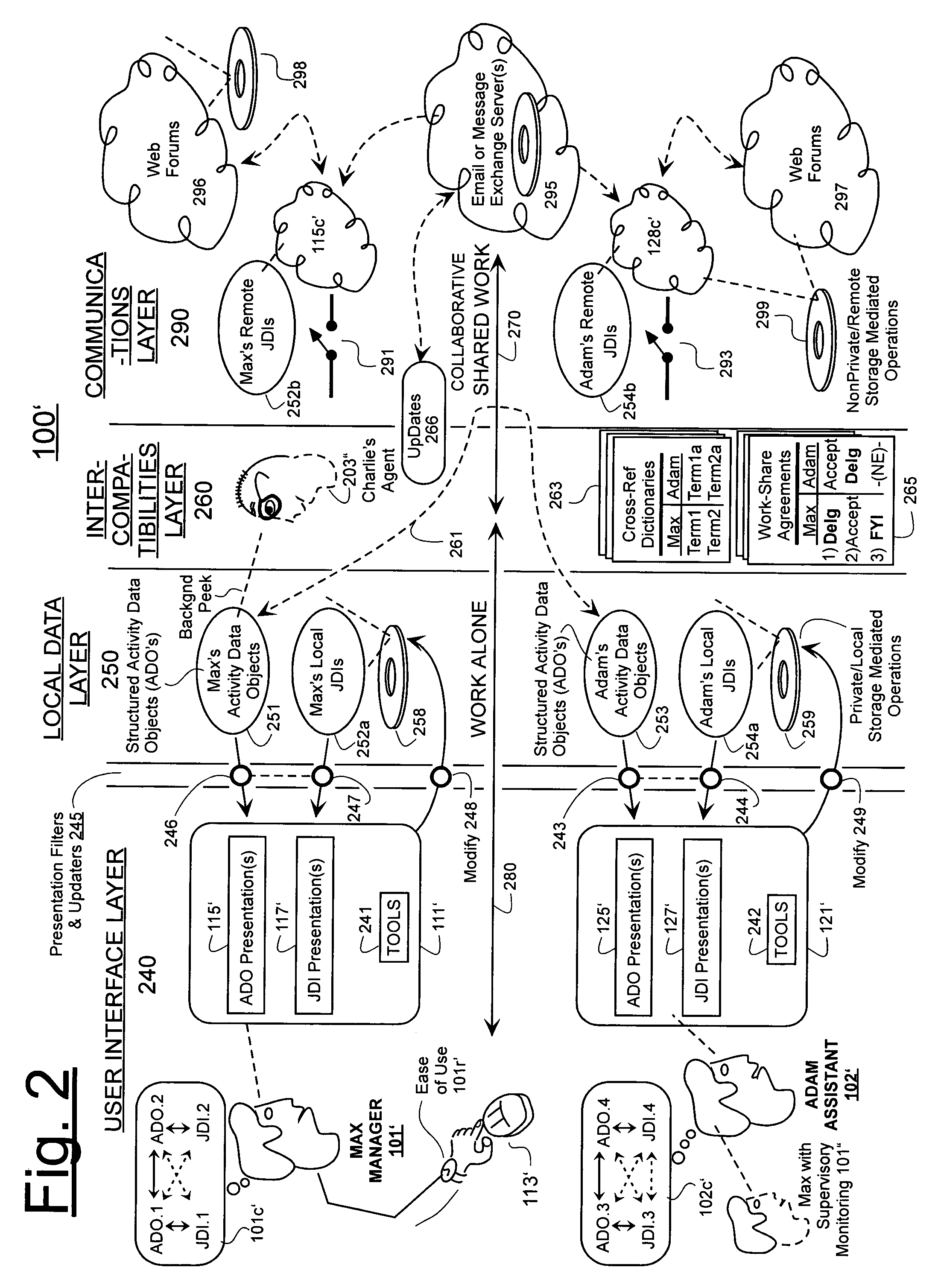
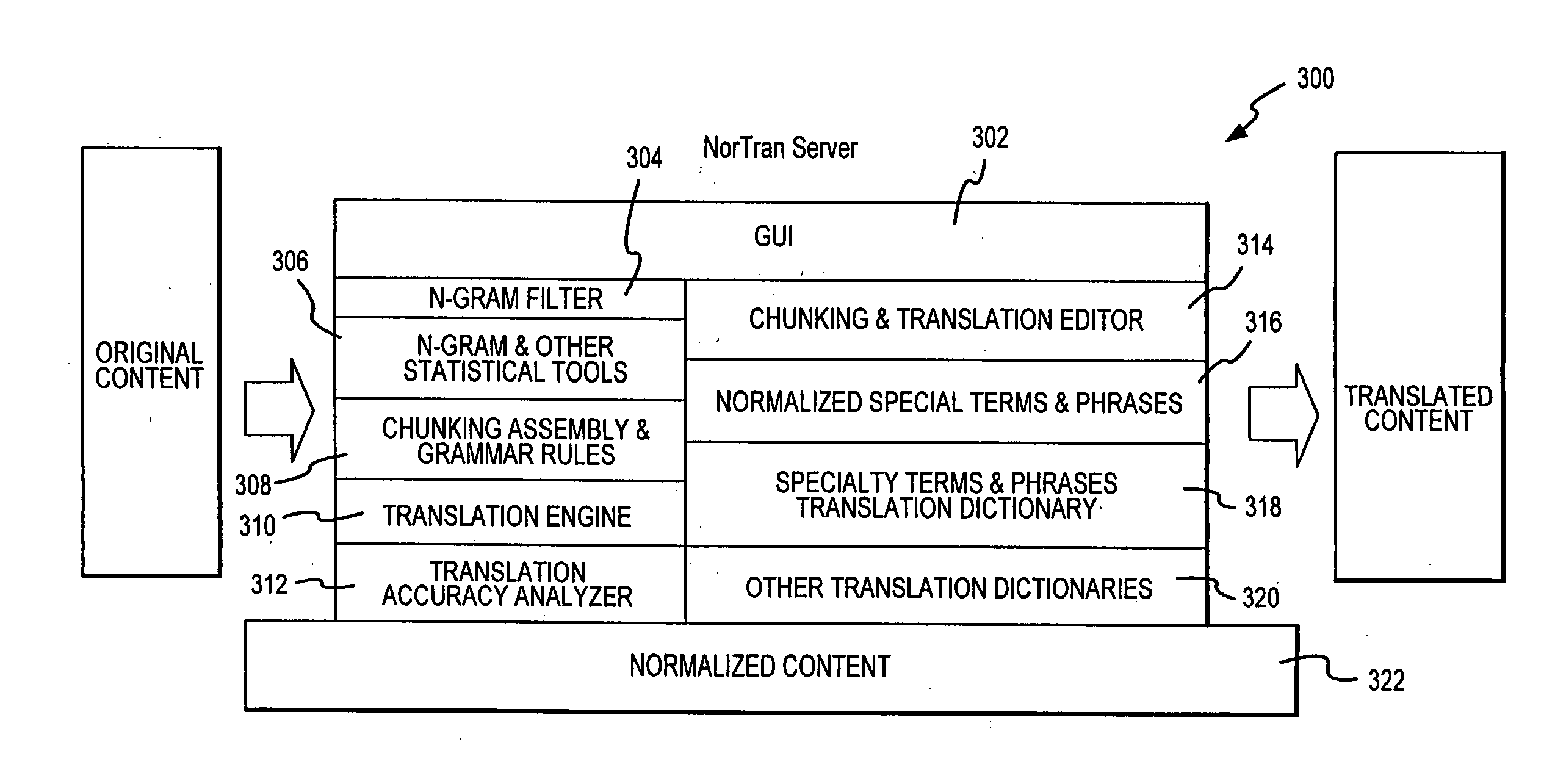
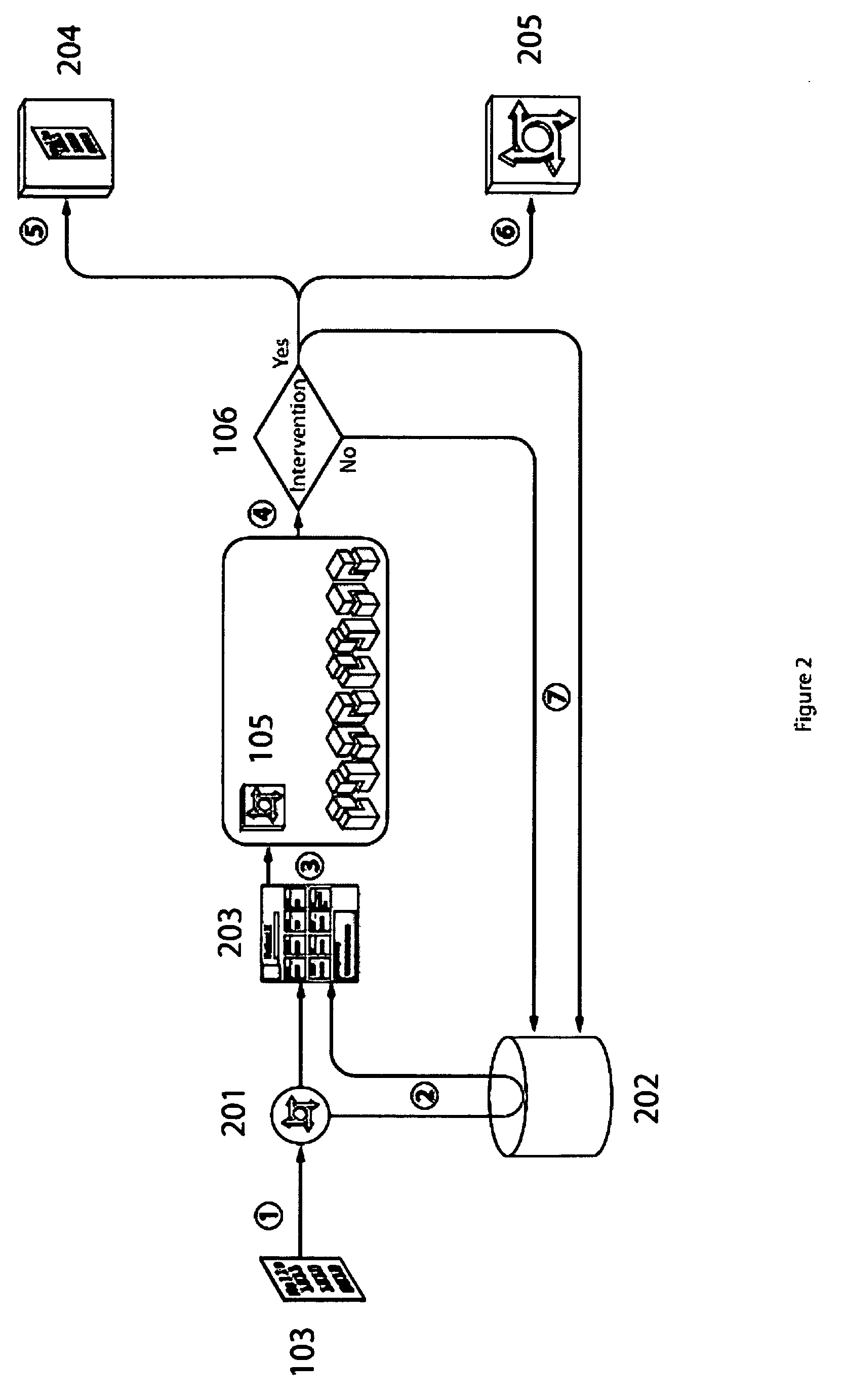
Machine-implemented activity management system using asynchronously shared activity data objects and journal data items
ActiveUS20050182773A1Improve developmentEasy to collectOffice automationBuying/selling/leasing transactionsJob sharingInformation sharing
Machine-assisted methods and apparatus are disclosed for allowing individual users to develop and organize respective activity descriptions and supporting journal items according to their respective preferences. Cross-referencing mappings may be created between activity descriptions and journal items in order to find, filter and organize disparate data. Cross-referencing mappings may also be created between the developed activity descriptions of different users so they can better understand each others perspectives and possibly overlapping goals. Different users' activity descriptions can be presented to a user even while the user may be disconnected from communication networks. Hierarchical relationships between activity descriptions may be provided. Machine-assisted means may be provided for creating work-sharing, work-delegating and / or informational sharing agreements between different users. Further machine-implemented means may be provided for automatically and asynchronously updating users on shared activities by other users even though all users are not necessarily connected to one or more respective communication networks at same time.
Owner:CALLAHAN CELLULAR L L C
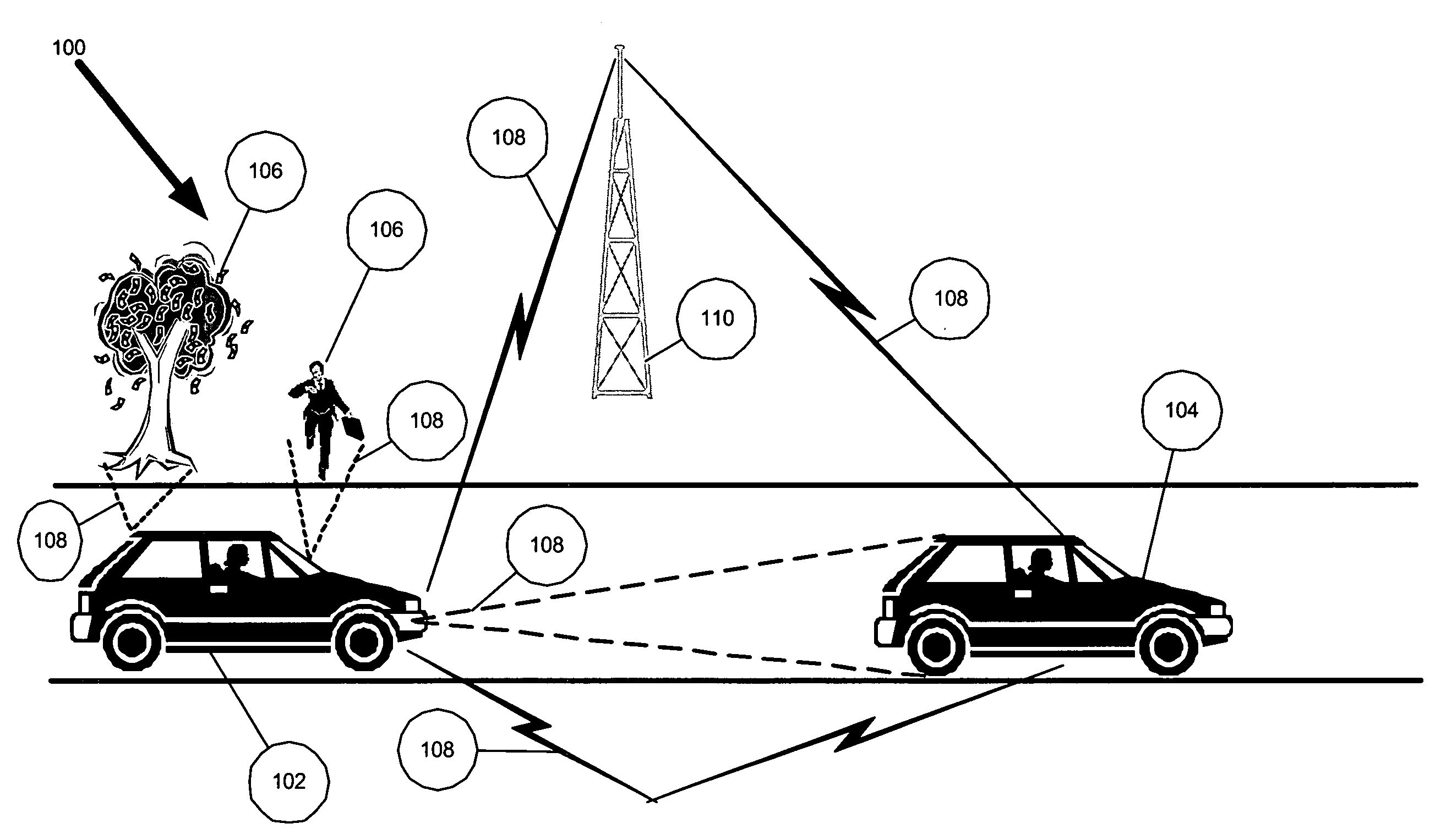
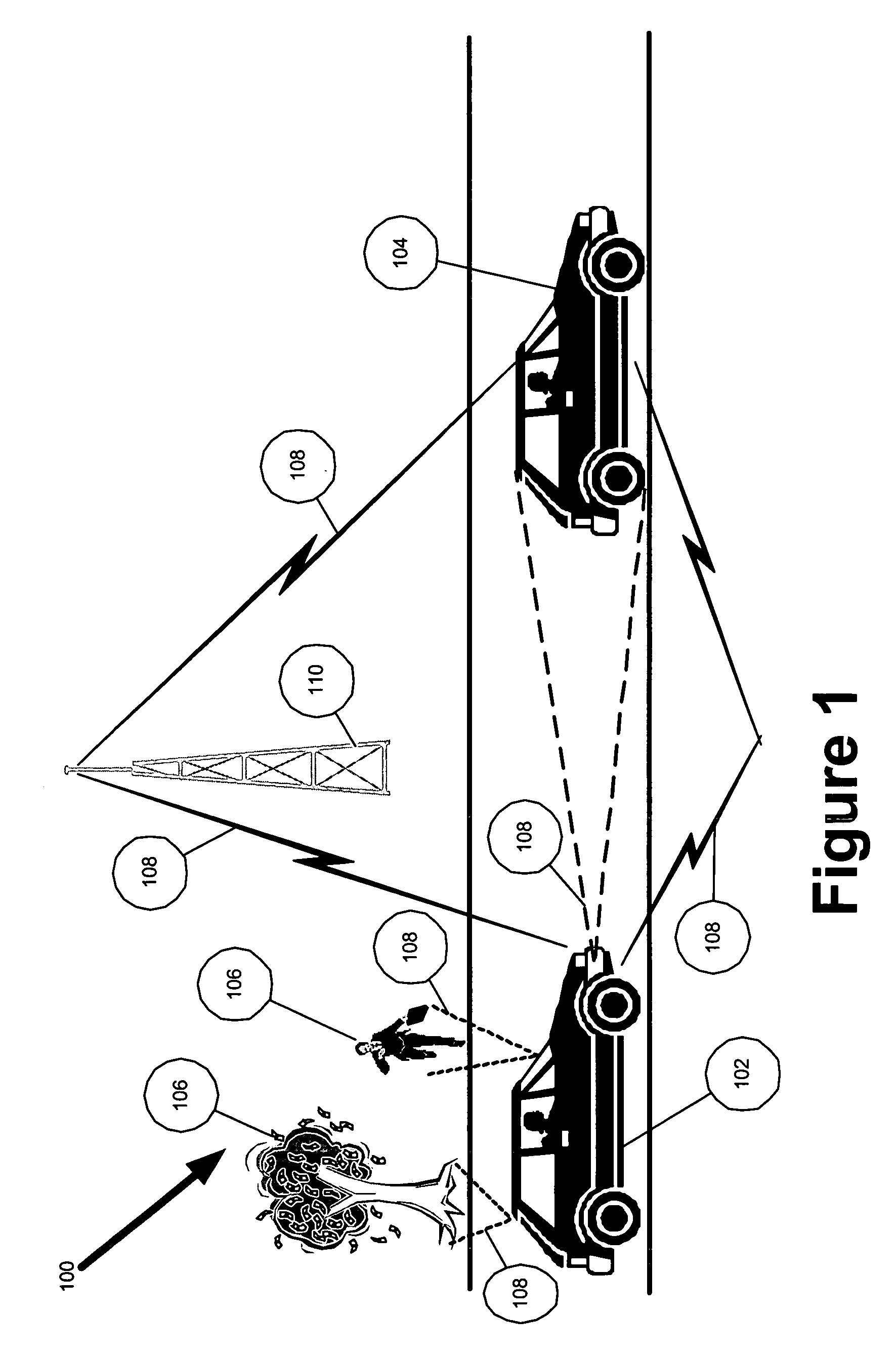
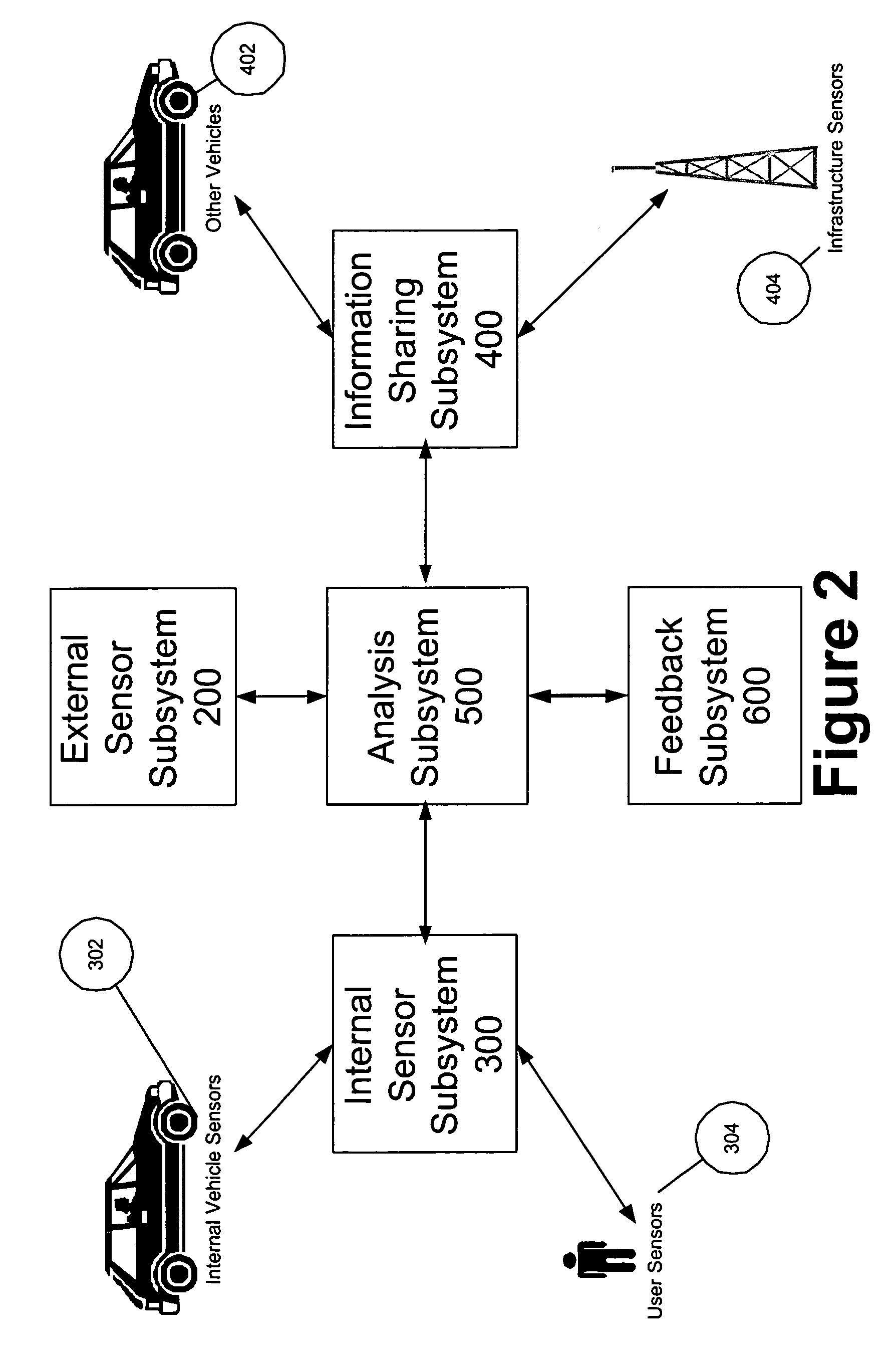
Multi-sensor integration for a vehicle
A sensor system for use in a vehicle that integrates sensor data from more than one sensor in an effort to facilitate collision avoidance and other types of sensor-related processing. The system include external sensors for capturing sensor data external to the vehicle. External sensors can include sensors of a wide variety of different sensor types, including radar, image processing, ultrasonic, infrared, and other sensor types. Each external sensor can be configured to focus on a particular sensor zone external to the vehicle. Each external sensor can also be configured to focus primarily on particular types of potential obstacles and obstructions based on the particular characteristics of the sensor zone and sensor type. All sensor data can be integrated in a comprehensive manner by a threat assessment subsystem within the sensor system. The system is not limited to sensor data from external sensors. Internal sensors can be used to capture internal sensor data, such a vehicle characteristics, user attributes, and other types of interior information. Moreover, the sensor system can also include an information sharing subsystem of exchanging information with other vehicle sensor systems or for exchanging information with non-vehicle systems such as a non-movable highway sensor system configured to transmit and receive information relating to traffic, weather, construction, and other conditions. The sensor system can potentially integrate data from all different sources in a comprehensive and integrated manner. The system can integrate information by assigning particular weights to particular determinations by particular sensors.
Owner:YAZAKI NORTH AMERICA
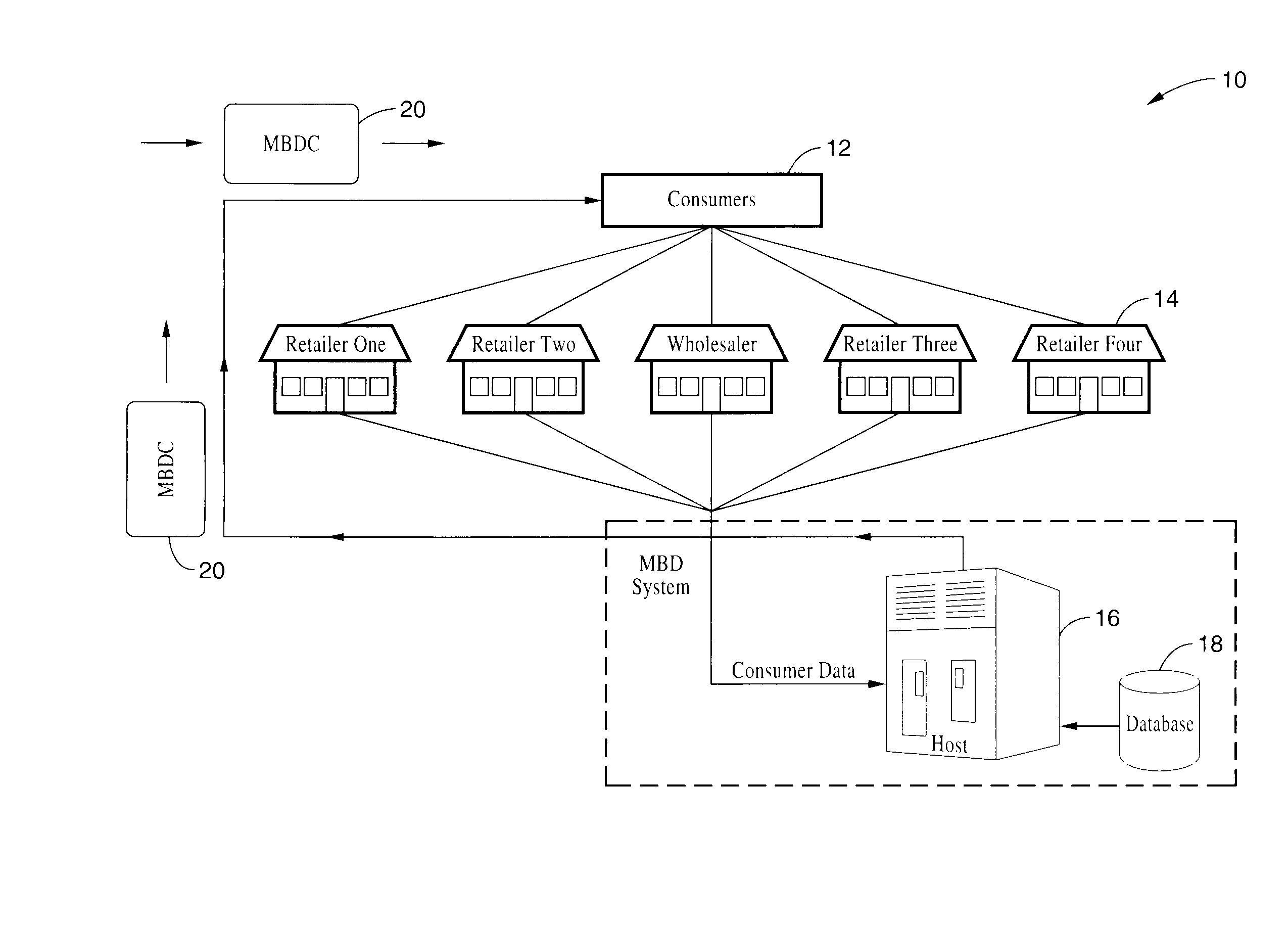
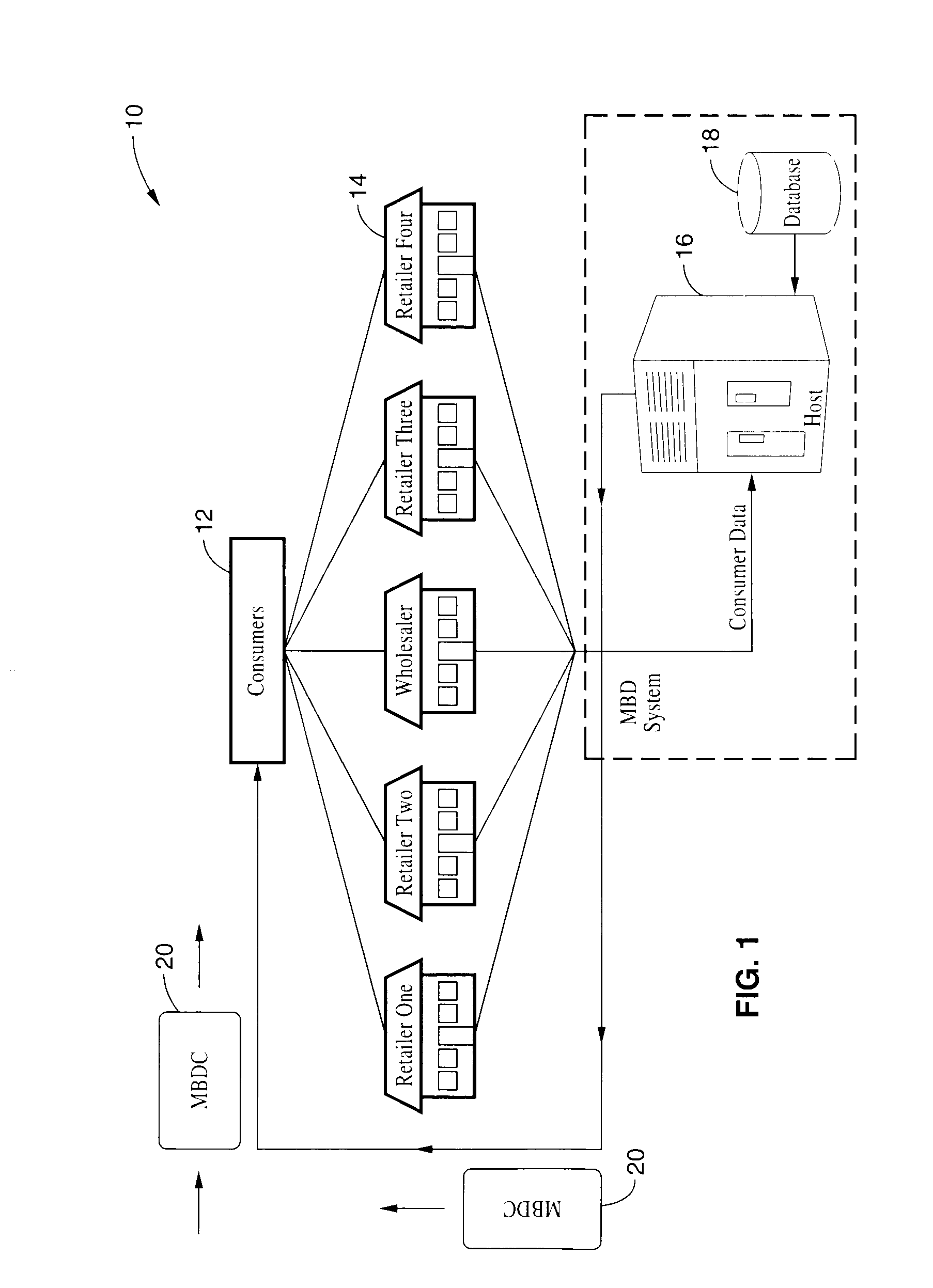
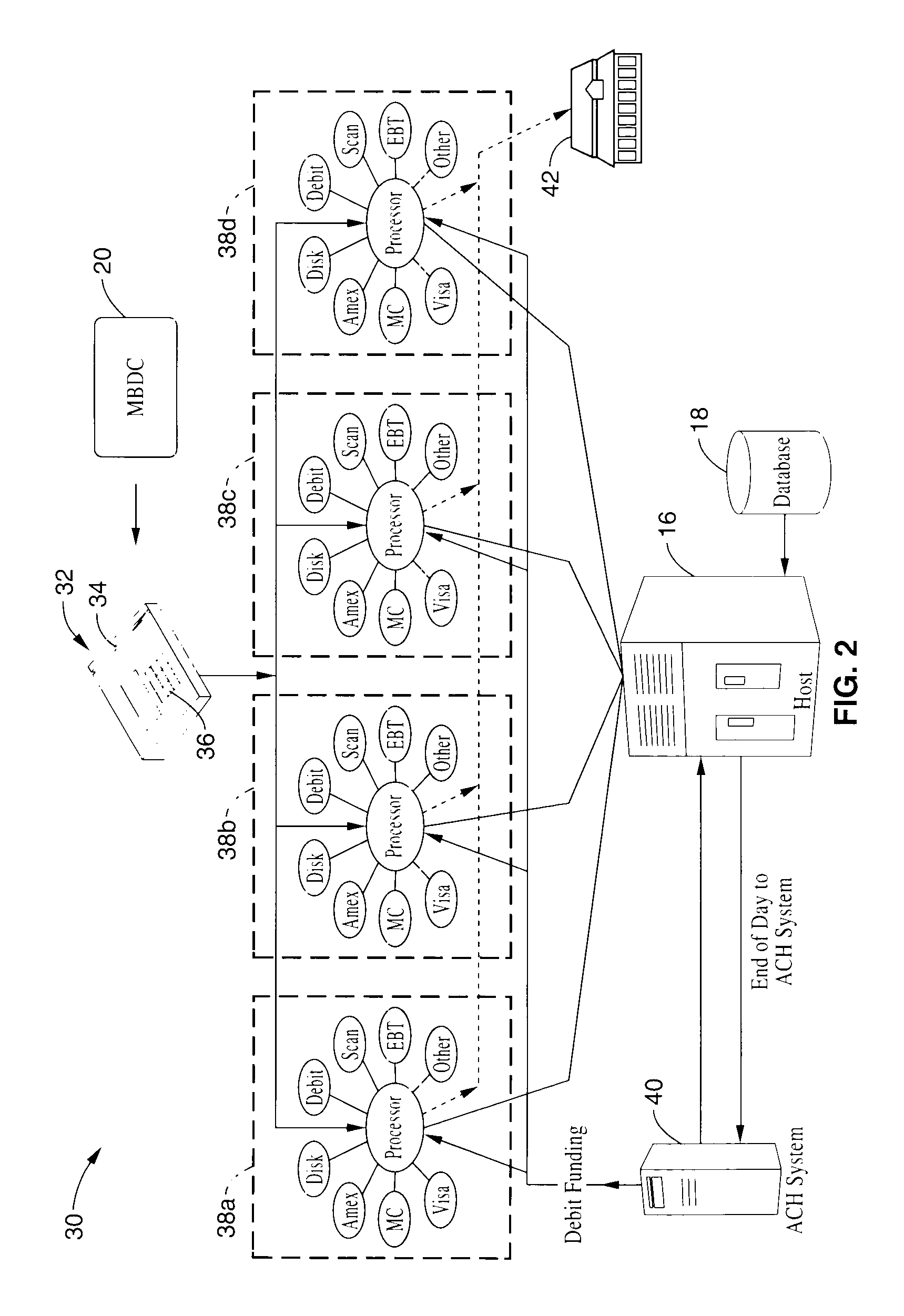
Method and system for facilitating electronic funds transactions
InactiveUS7104443B1Measurement is limitedReduce transaction costsComplete banking machinesFinanceInformation sharingMerchant account
A method and system for executing electronic funds transactions using a merchant based debit (MBD) card in a merchant-centric system that provides for reduced fees to acquiring merchants and remitting a portion of the collected fees to issuing merchants. The system also preferably provides information sharing on consumer transactions with merchants to facilitate consumer based incentive programs and the like. The system operates over conventional card processing infrastructure and utilizes the ACH network, or equivalent, to settle the transaction from a consumer checking account, or a merchant account in the case of a prepaid MBD card. Using the system, merchants may elect to qualify customers based on their own criterion. A portion of the interchange fee is distributed to the issuing merchant associated transaction executed using the merchant based debit card. Embodiments are described for prepaid, fixed value, programmable, and refillable, forms of merchant based debit cards.
Owner:KIOBA PROCESSING LLC
System and method for enhancing content using brain-state data
ActiveUS20140223462A1Easy to analyzeAnalogue secracy/subscription systemsBroadcast information monitoringInformation sharingUser input
A computer system or method may be provided for modulating content based on a person's brainwave data, including modifying presentation of digital content at at least one computing device. The content may also be modulated based on a set of rules maintained by or accessible to the computer system. The content may also be modulated based on user input, including through receipt of a presentation control command that may be processed by the computer system of the present invention to modify presentation of content. Content may also be shared with associated brain state information.
Owner:INTERAXON
Cryptographic method and system
InactiveUS20140164776A1Easy to useImprove abilitiesKey distribution for secure communicationMultiple keys/algorithms usageInformation sharingInternet privacy
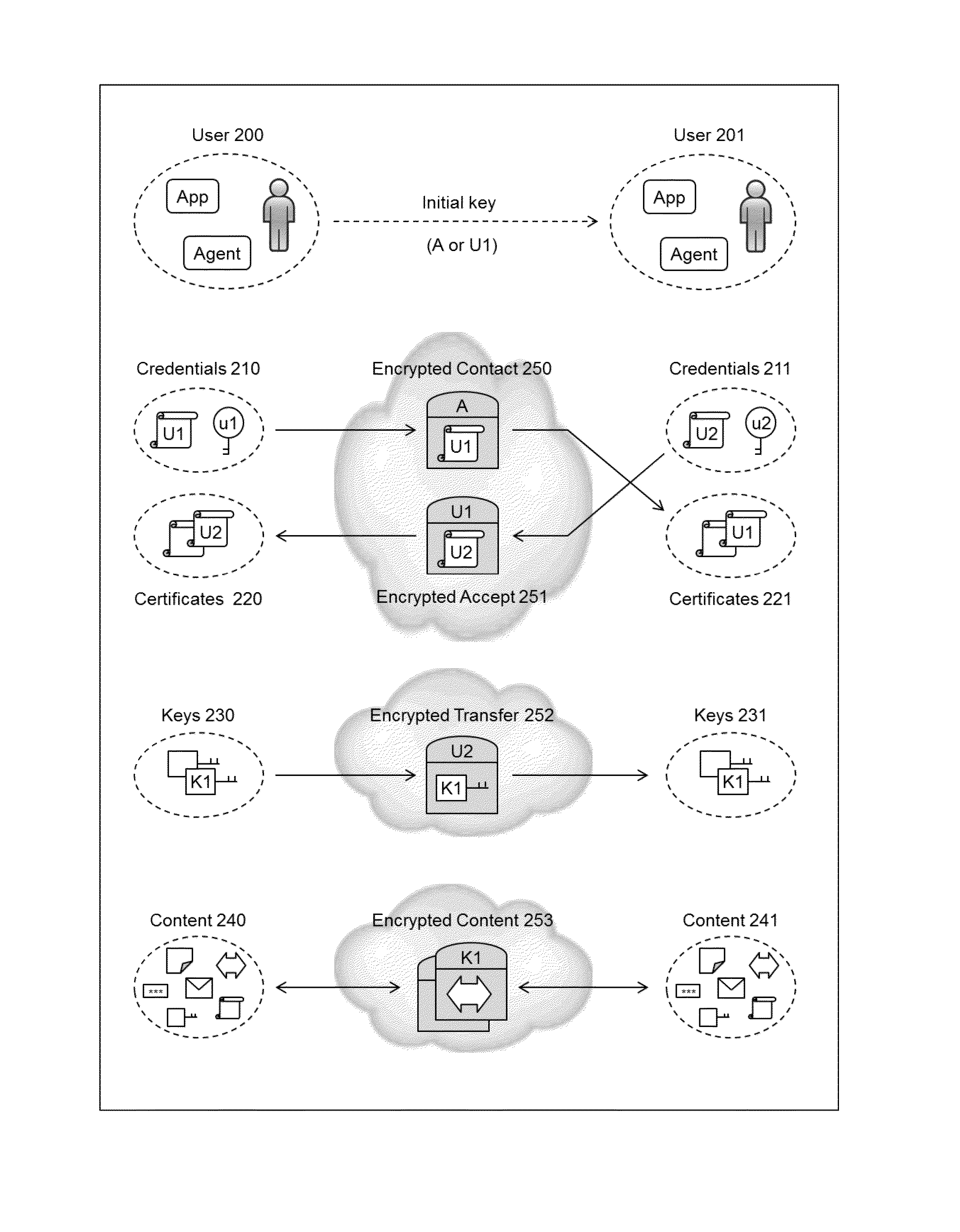
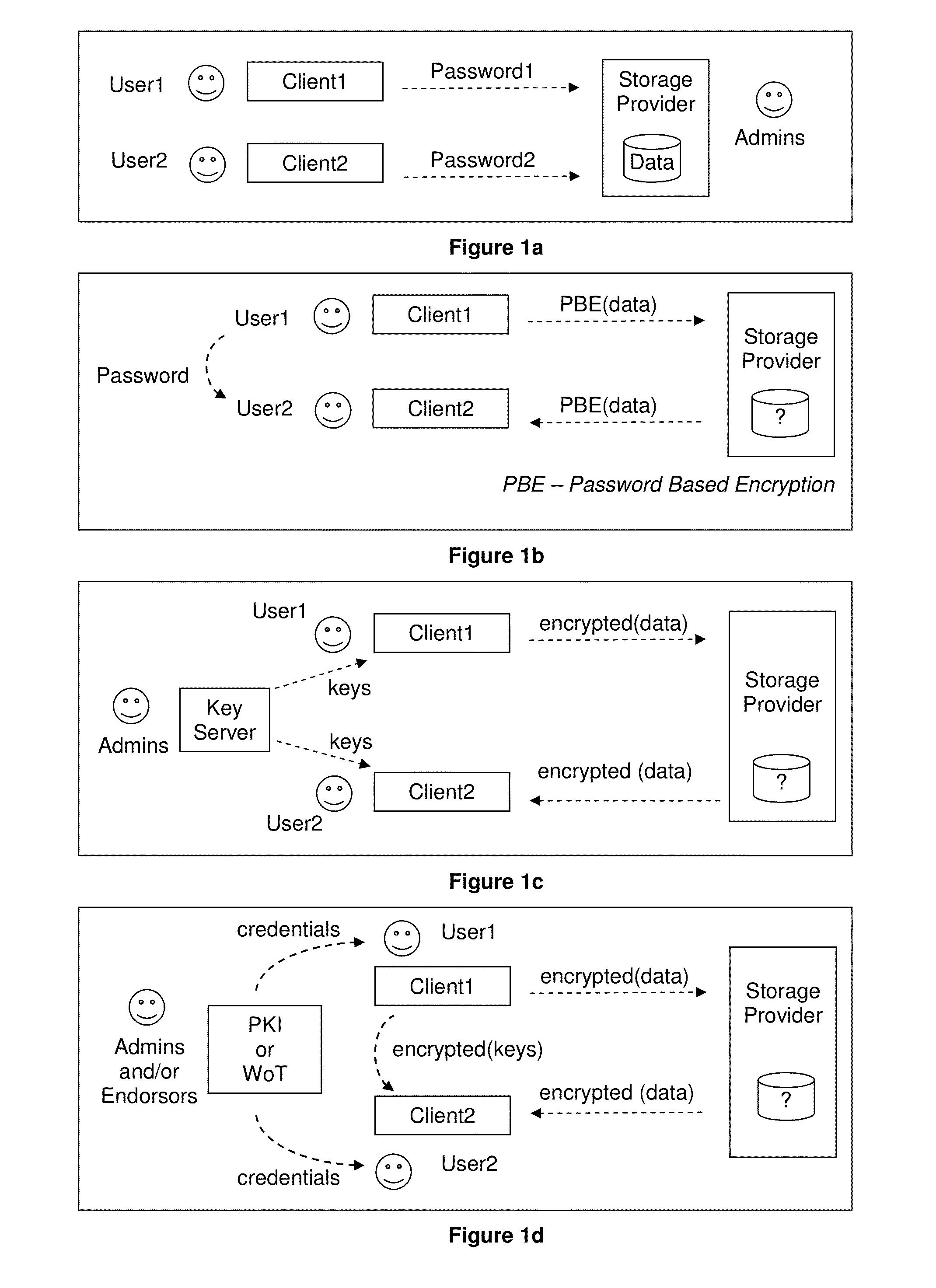
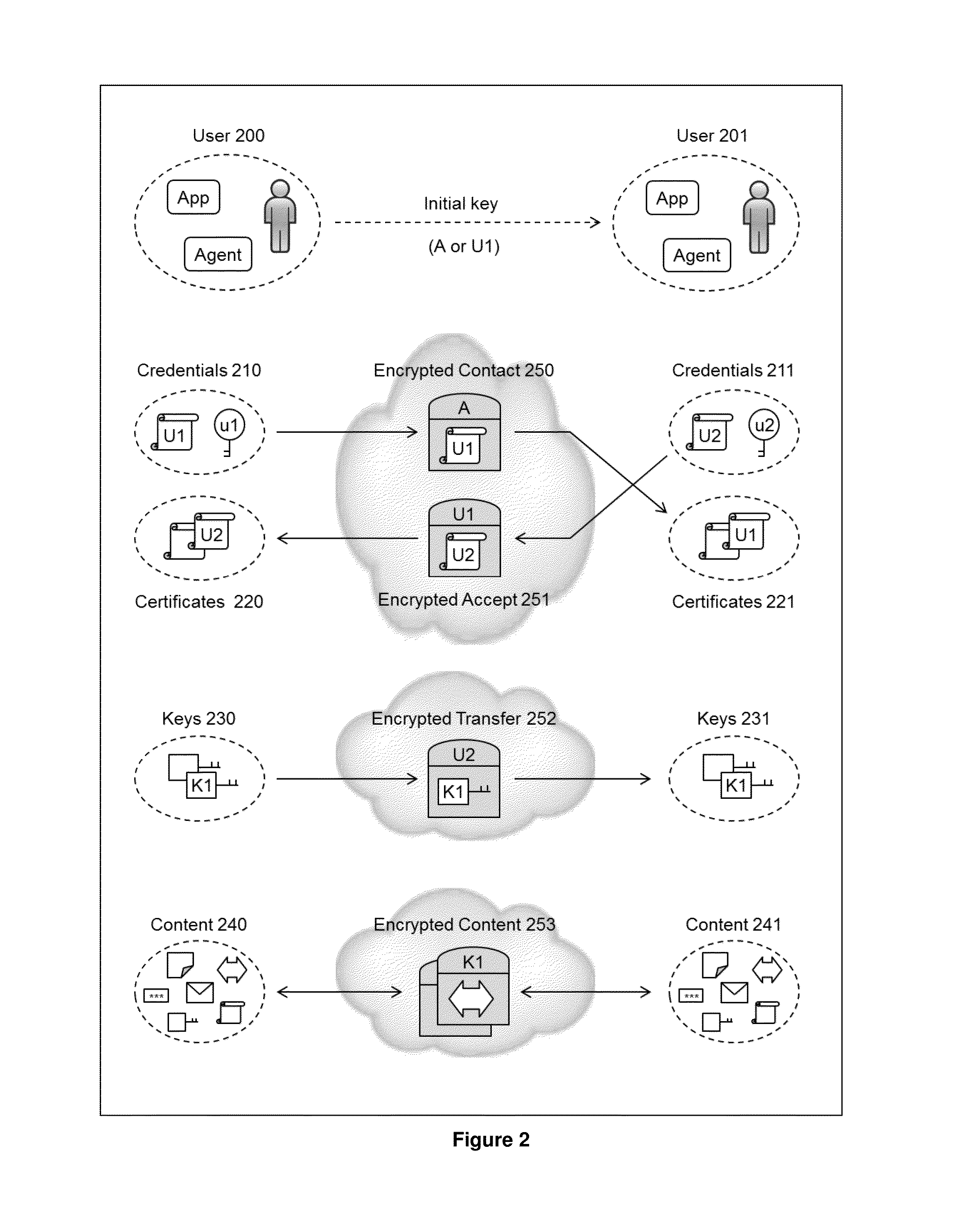
The present invention relates to the field of security of electronic data and / or communications. In one form, the invention relates to data security and / or privacy in a distributed and / or decentralised network environment. In another form, the invention relates to enabling private collaboration and / or information sharing between users, agents and / or applications. Embodiment(s) of the present invention enable the sharing of key(s) and / or content between a first user and / or agent and a second user and / or agent. Furthermore, embodiment(s) of the present invention have application in sharing encrypted information via information sharing services.A number of inventions, aspects and embodiments are disclosed herein.
Owner:LOCK BOX
Processes systems and networks for secure exchange of information and quality of service maintenance using computer hardware
InactiveUS20020040439A1Digital data processing detailsUser identity/authority verificationQuality of serviceData transformation
A system and method for providing external data-signal isolation, and signal-level information-preserving-data-transformations, to enable safe, operationally efficient, information sharing between protected information systems and networks and external, potentially hostile, information systems and networks which neutralizes any imbedded hostile executable codes such as viruses that may be in data-signals incoming from the external systems and networks. The system and method prevent untransformed external data-signals from entering protected systems and / or networks using an intermediate screen which is a computer hardware device. The intermediate screen (which may be implemented as a network of systems) is deployed between the protected systems and external systems and is used to process all incoming signals from the external system to obtain transformed data sets from which information is extracted before it is passed to the protected system. The incoming signals all remain confined in the intermediate screen.
Owner:KELLUM CHARLES W
Information sharing device and information sharing method
InactiveUS20050223315A1Easy to understandNatural language data processingElectrical appliancesElectronic documentInformation sharing
A technique is provided which enables users to add, with ease, annotation information to an electronic document on a network and to share the annotation information within a disclosure range set to the annotation information. An electronic information is provided in a state that allows the electronic information to have annotation in formation attached, annotation information to be attached to the electronic information is stored, attribute information indicating the disclosure range of the annotation information is stored and, when a user requests to provide annotation information, annotation information available to the user is provided to a terminal of the user by consulting the attribute information.
Owner:FUJITSU LTD
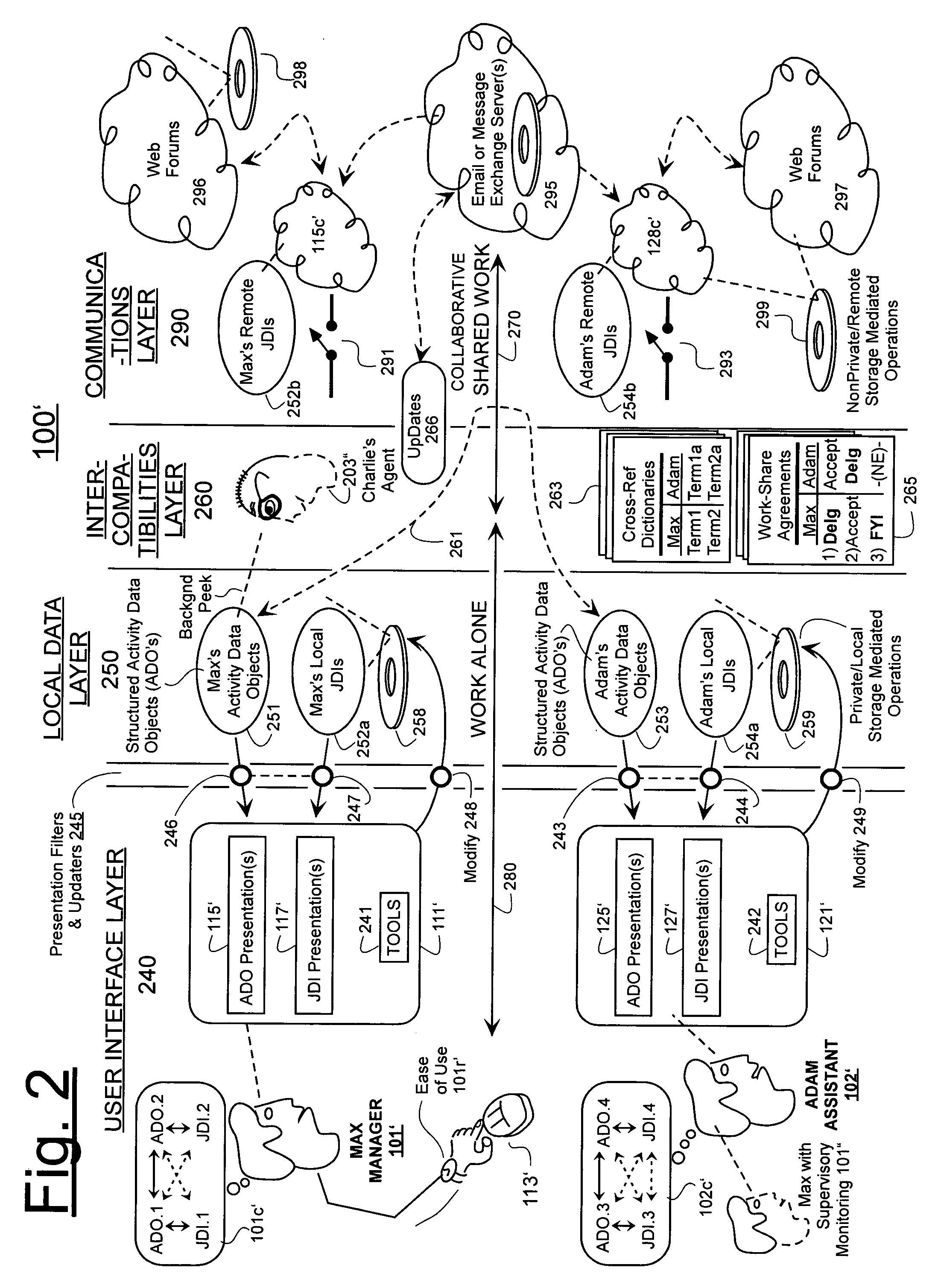
Machine-implemented activity management system using asynchronously shared activity data objects and journal data items
ActiveUS7197502B2ExchangeEasy to collectDigital data processing detailsOffice automationJob sharingInformation sharing
Machine-assisted methods and apparatus are disclosed for allowing individual users to develop and organize respective activity descriptions and supporting journal items according to their respective preferences. Cross-referencing mappings may be created between activity descriptions and journal items in order to find, filter and organize disparate data. Cross-referencing mappings may also be created between the developed activity descriptions of different users so they can better understand each others perspectives and possibly overlapping goals. Different users' activity descriptions can be presented to a user even while the user may be disconnected from communication networks. Hierarchical relationships between activity descriptions may be provided. Machine-assisted means may be provided for creating work-sharing, work-delegating and / or informational sharing agreements between different users. Further machine-implemented means may be provided for automatically and asynchronously updating users on shared activities by other users even though all users are not necessarily connected to one or more respective communication networks at same time.
Owner:CALLAHAN CELLULAR L L C
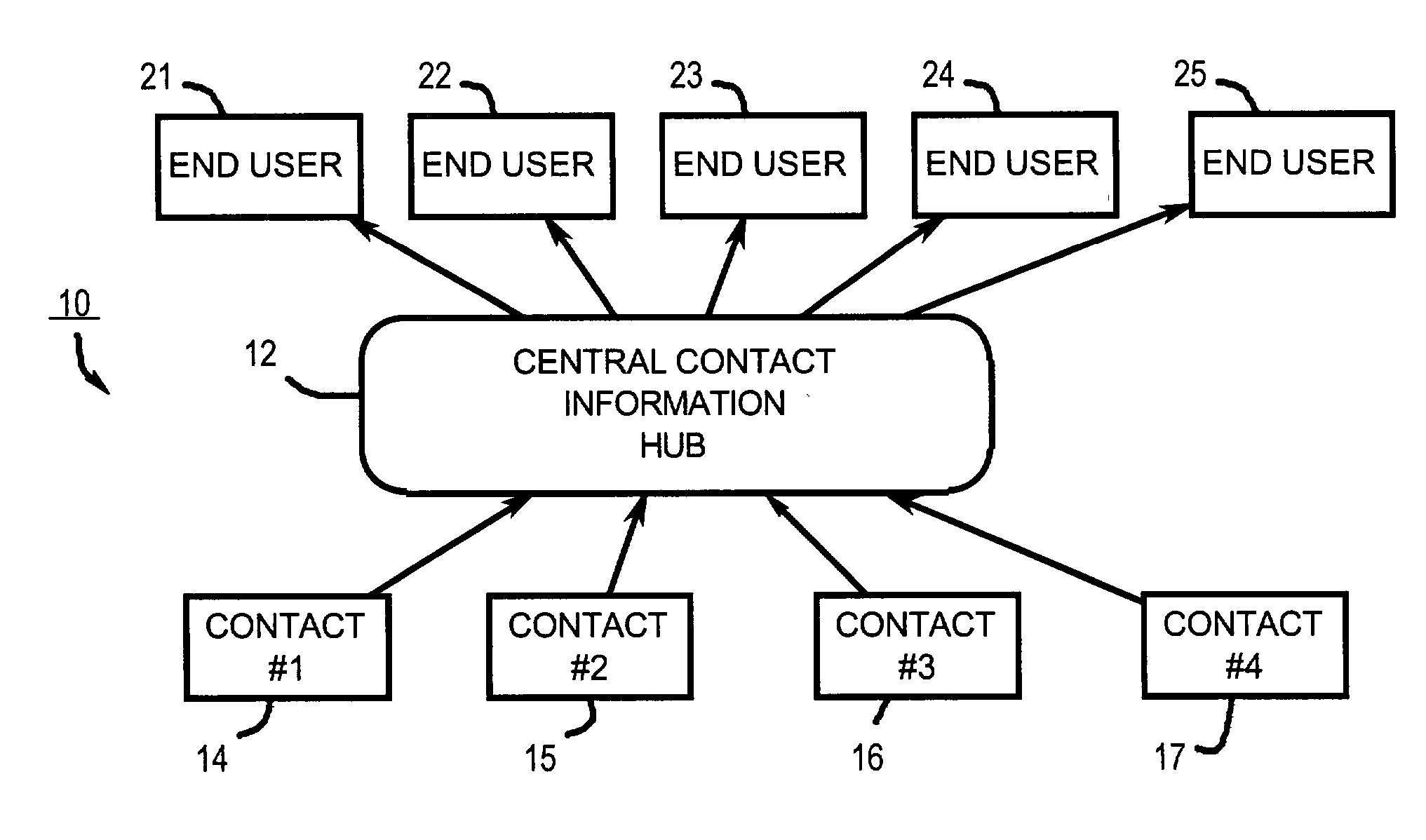
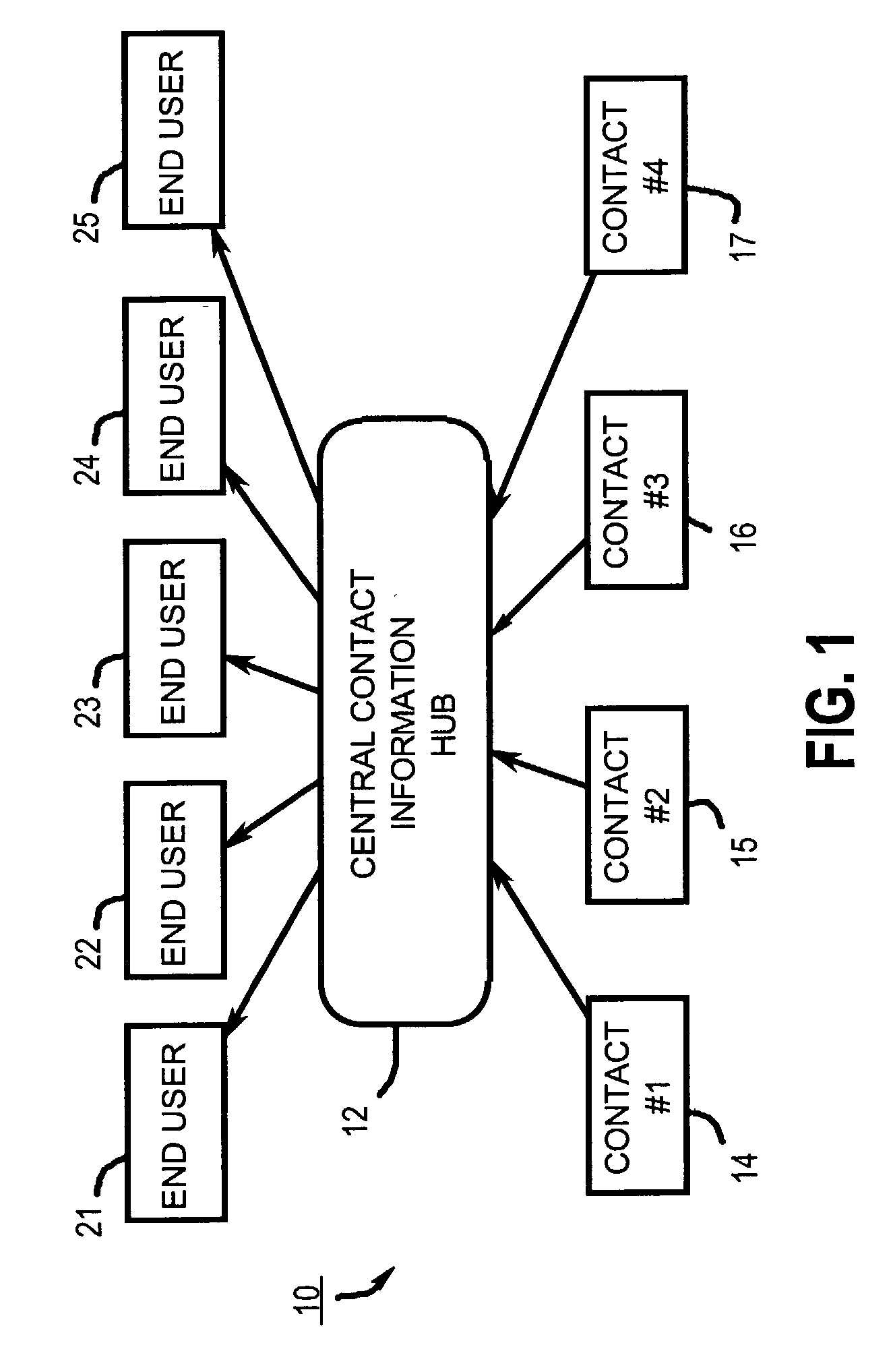
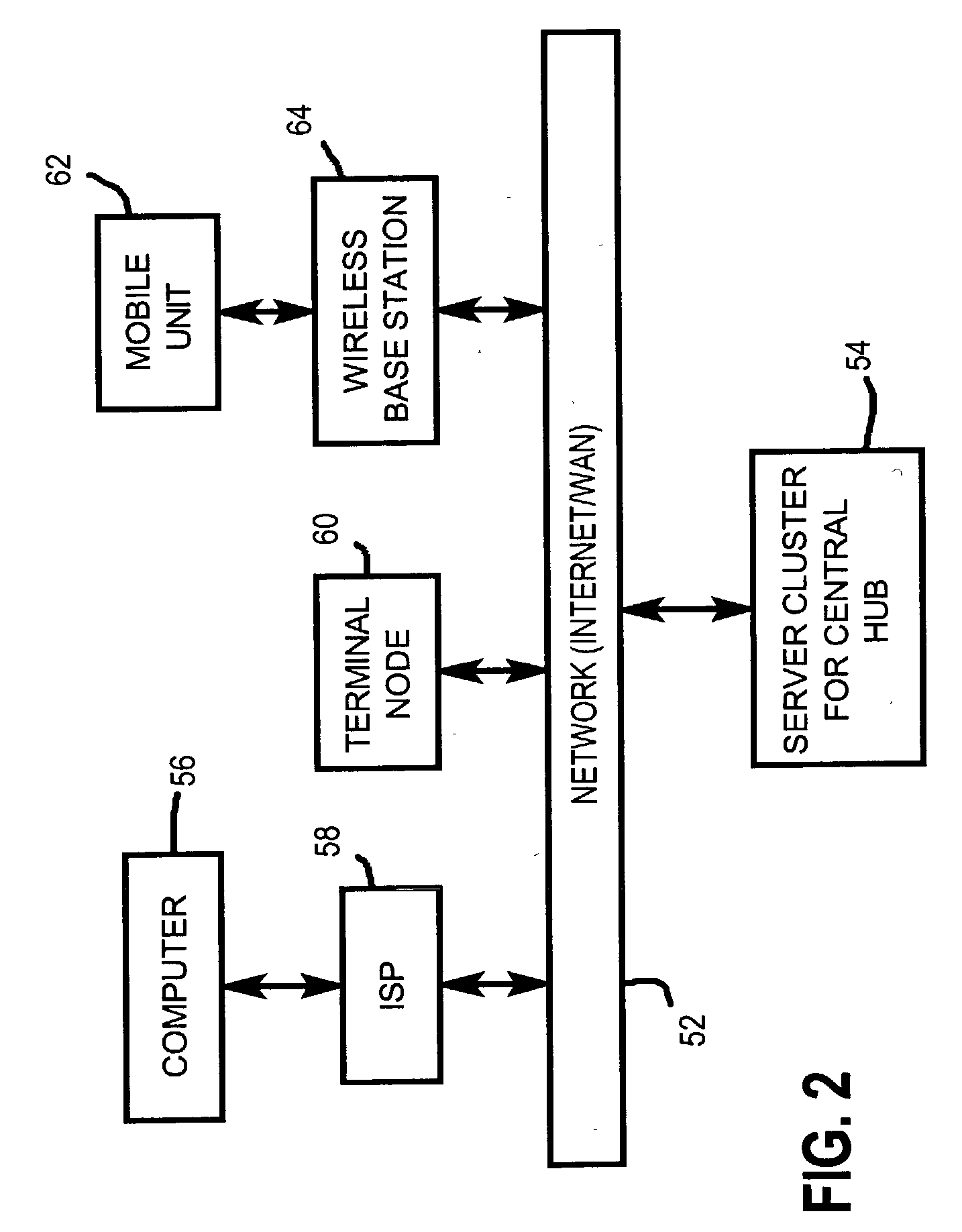
Automated contact information sharing
InactiveUS20040093317A1Digital data processing detailsSpecial service for subscribersInformation sharingInformation field
Provided is a system for controlling, distributing and receiving contact information. The system includes: central hub means for maintaining and distributing contact information, multiple terminal means electronically coupled to the central hub means for transmitting requests for contact information to the central hub means, and multiple contacts in communication with the central hub means. Each contact has an associated contact record maintained by the central hub means, each such contact record includes multiple different contact information fields, and each contact controls the content in the contact information fields for its associated contact record. Upon receipt of a request for a requested contact record from one of the terminal means, the central hub means automatically transmits the requested contact record to the requesting terminal means in a format that permits unambiguous identification of the different contact information fields upon application of pre-specified mechanical rules.
Owner:SWAN JOSEPH G
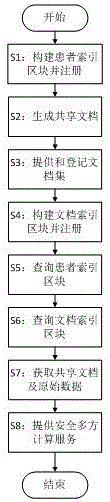
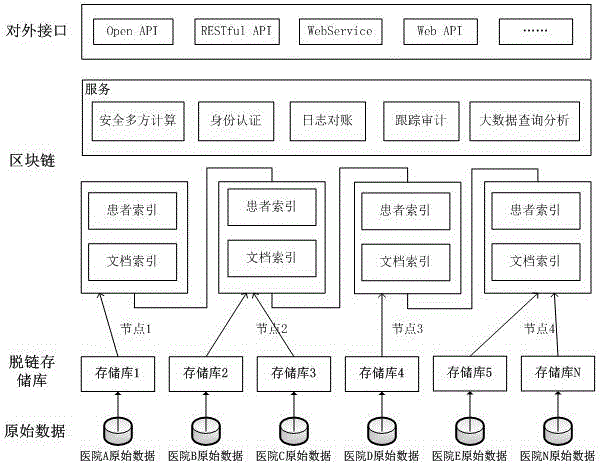
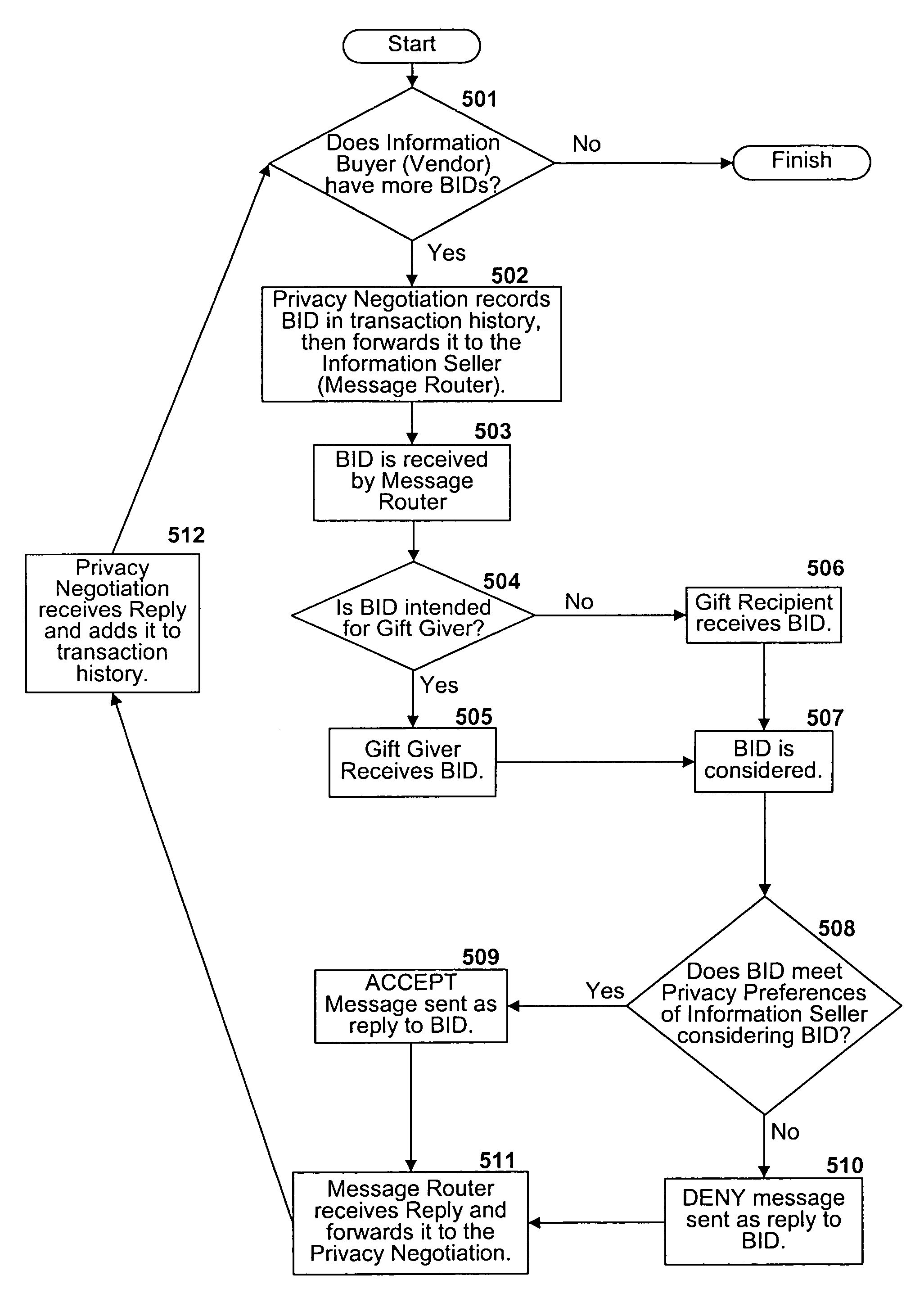
Method and device for medical information sharing privacy protection based on blockchain technology
InactiveCN106682530AAvoid privacyUse constraintsDigital data protectionInformation sharingPrivacy protection
The invention discloses a method and device for medical information sharing privacy protection based on a blockchain technology. According to the method, in aspects of privacy protection based on a blockchain technology, medical data on-chain and off-chain storage and forced privacy protection safety multiparty calculation, illegal medical data obtaining, use and tampering are avoided, and medical information sharing, big data analysis and utilization and patient privacy protection are implemented. The device comprises a data storage module, a service module provided based on the blockchain technology and a call service module provided externally, wherein a three-layer data storage frame is adopted for the data storage module; and the service module provided based on the blockchain technology mainly comprises forced privacy protection safety multiparty calculation. The method and device for medical information sharing privacy protection based on the blockchain technology are mainly applied to the fields of method and device for medical information sharing privacy protection based on a blockchain technology and medical big data analysis and the like, and technical guarantee is also provided for patient privacy protection while medical information sharing is achieved based on the blockchain technology.
Owner:HANGZHOU DIANZI UNIV
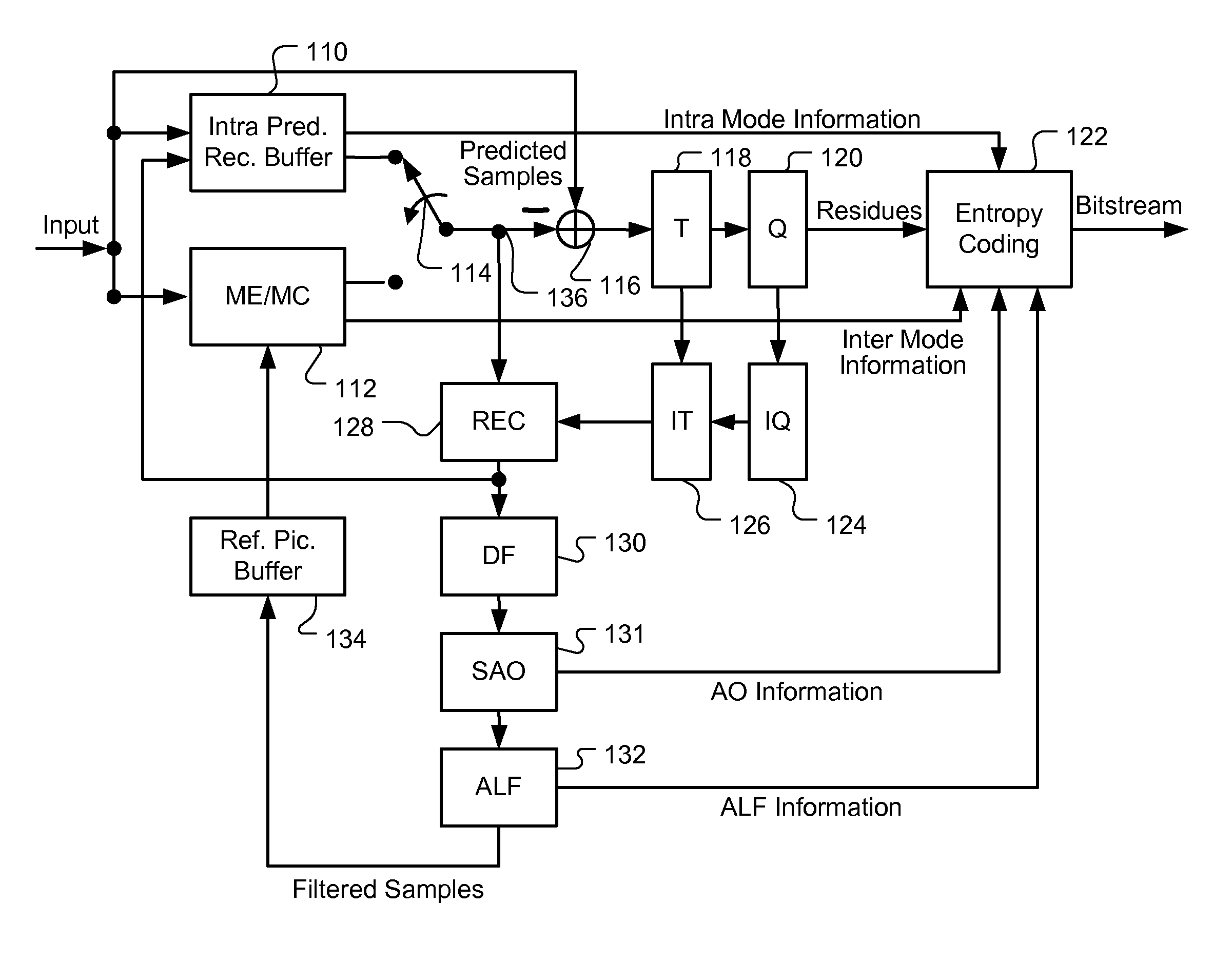
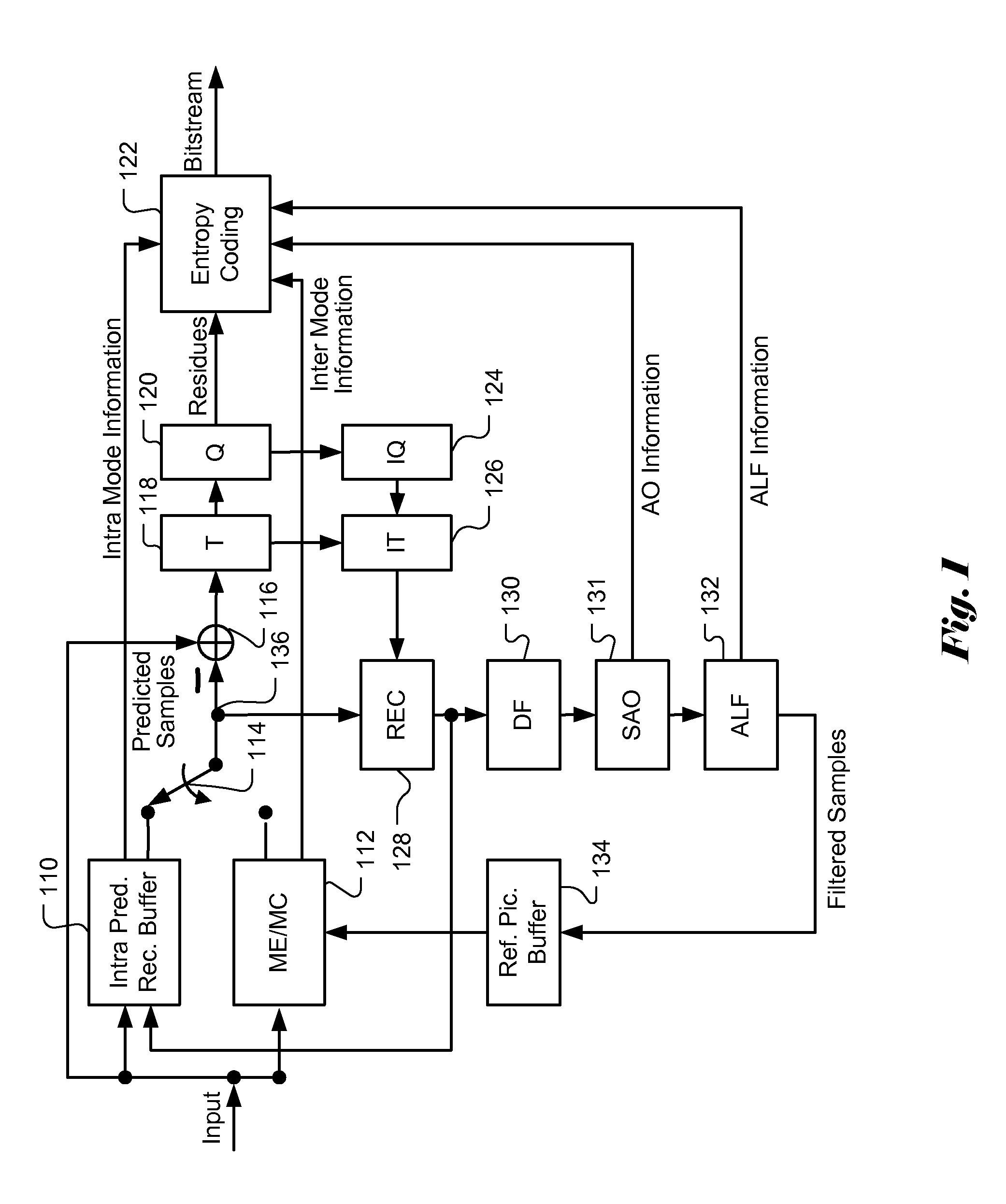
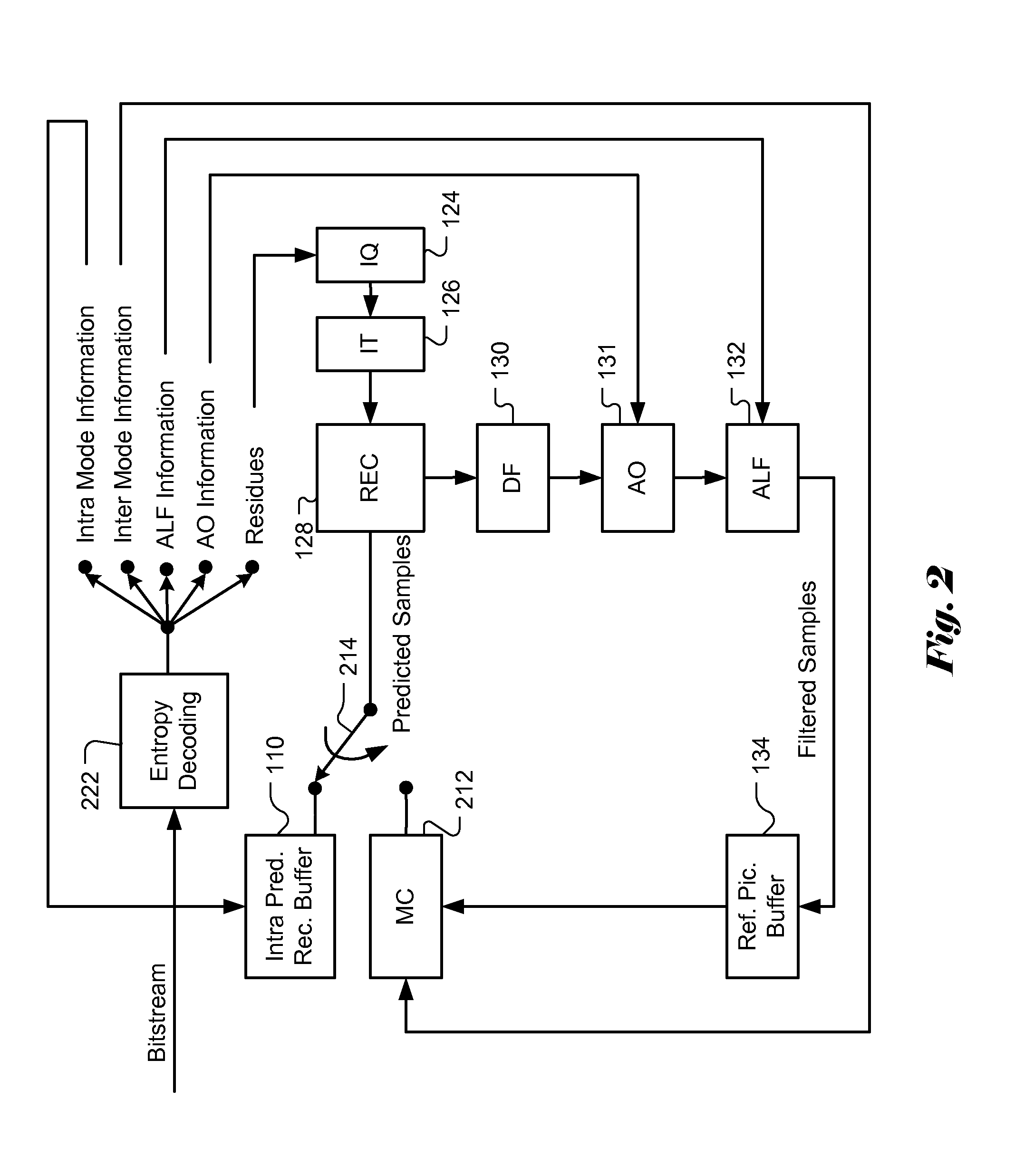
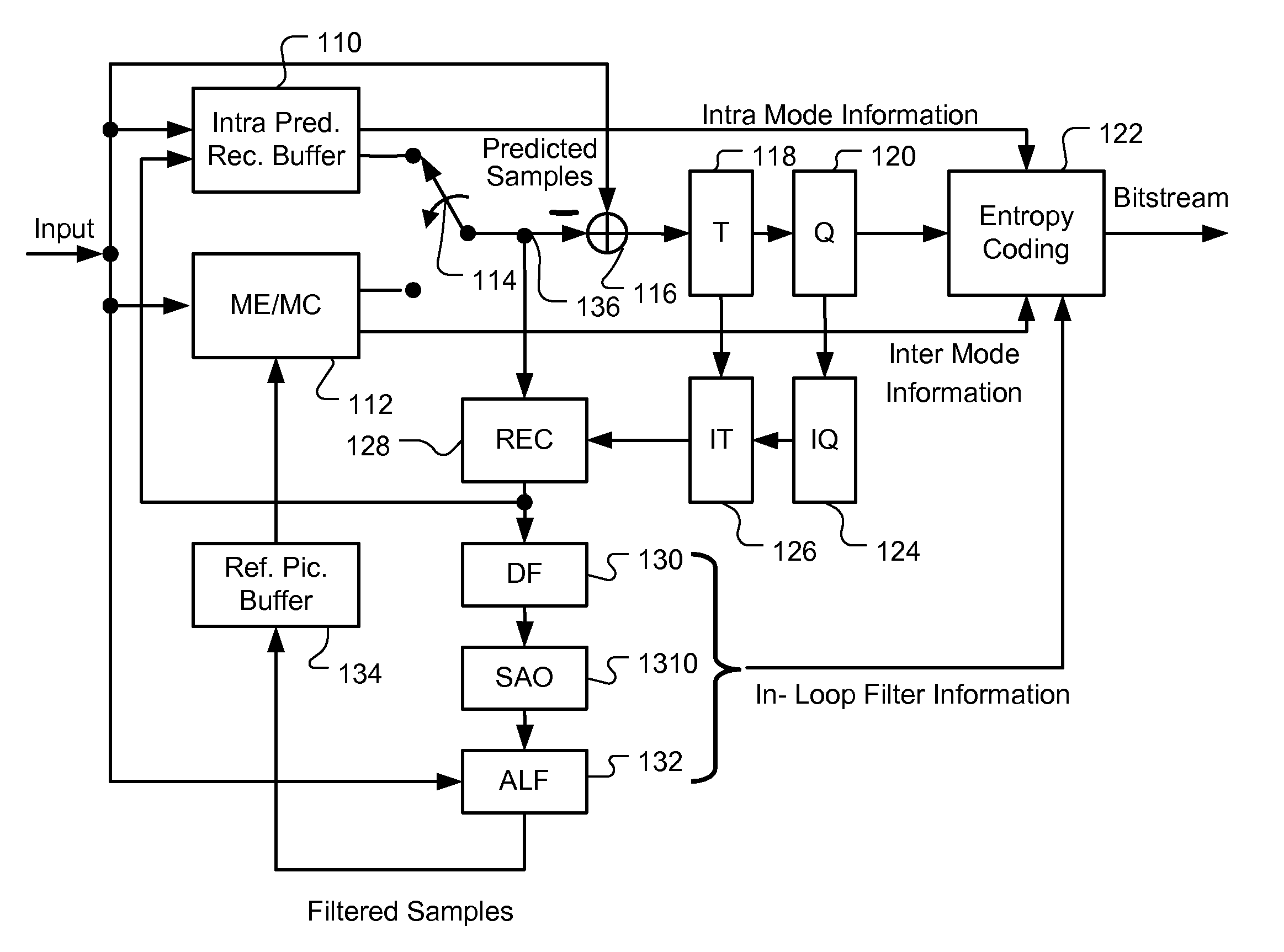
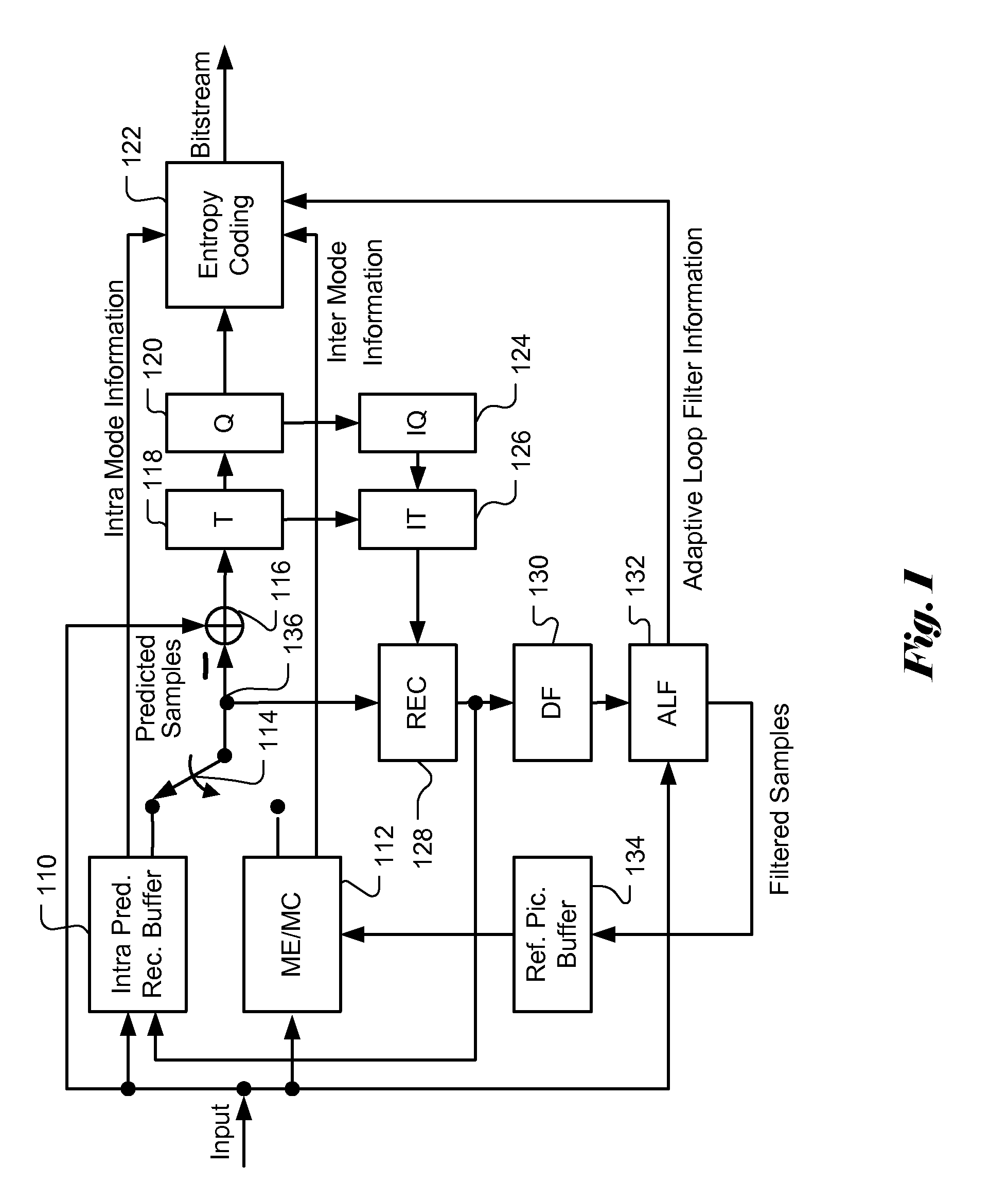
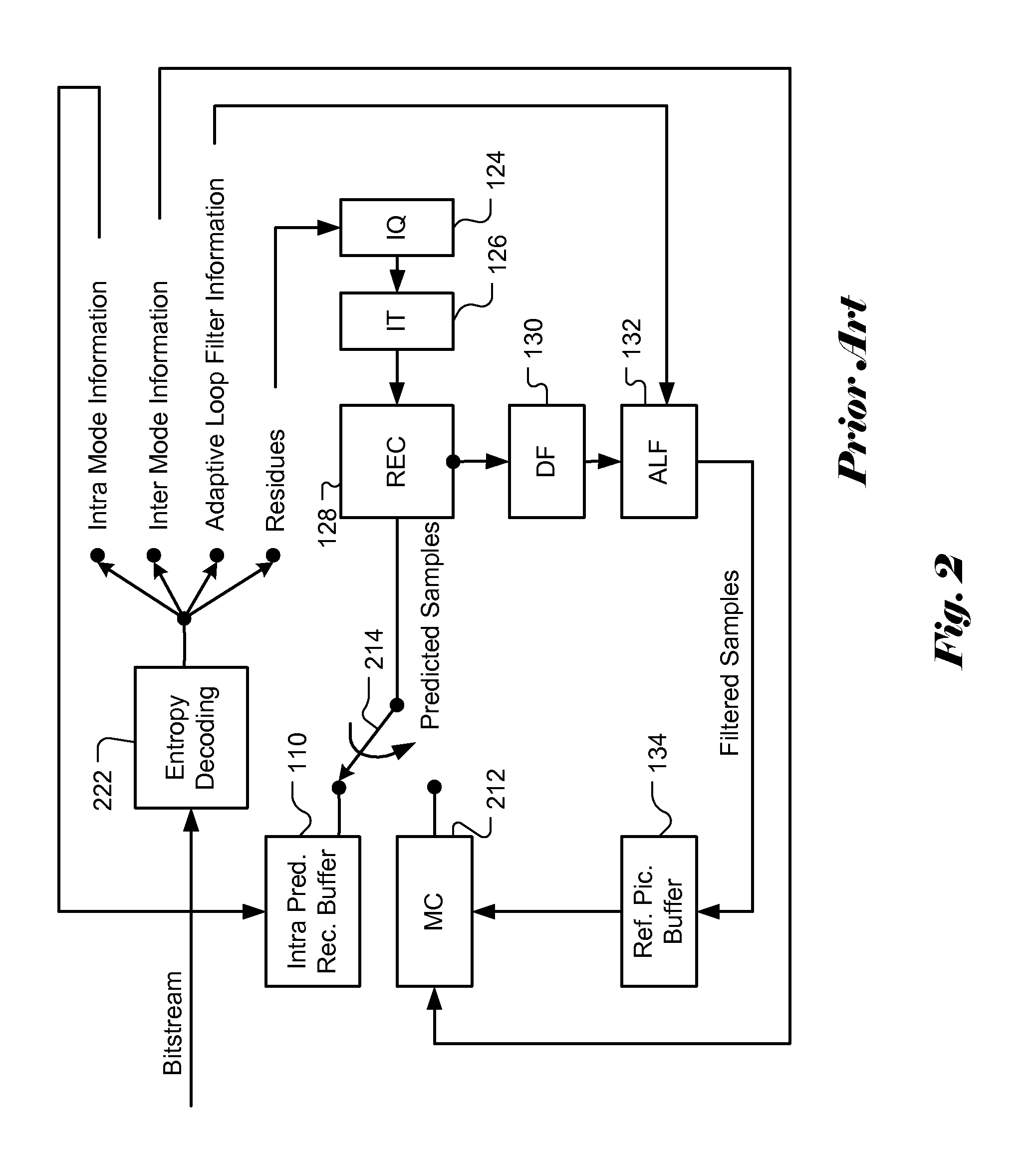
Apparatus and Method of Sample Adaptive Offset for Luma and Chroma Components
InactiveUS20120294353A1Improve coding efficiencyColor television with pulse code modulationColor television with bandwidth reductionComputational scienceLoop filter
A method and apparatus for processing reconstructed video using in-loop filter in a video coding system are disclosed. The method uses chroma in-loop filter indication to indicate whether chroma components are processed by in-loop filter when the luma in-loop filter indication indicates that in-loop filter processing is applied to the luma component. An additional flag may be used to indicate whether the in-loop filter processing is applied to an entire picture using same in-loop filter information or each block of the picture using individual in-loop filter information. Various embodiments according to the present invention to increase efficiency are disclosed, wherein various aspects of in-loop filter information are taken into consideration for efficient coding such as the property of quadtree-based partition, boundary conditions of a block, in-loop filter information sharing between luma and chroma components, indexing to a set of in-loop filter information, and prediction of in-loop filter information.
Owner:HFI INNOVATION INC
Multi-user functionality for converting data from a first form to a second form
InactiveUS20050288920A1Efficient developmentEfficient processingNatural language translationSemantic analysisInformation sharingSyntax
In connection with a machine-based system for transforming data from a source form to a target form, a tool is provided for sharing information established in developing a transformation model. The shared information may relate to rules for mapping source collection terms to standardized terms, rules for ordering or syntax, rules for classifying terms or other transformation rules. Such information defines a knowledge base for the project. The knowledge base is divided into domains and subdomains that define a hierarchy that includes dependencies and references. These dependencies and references are used for domain management such that any conflicts and inconsistencies can be identified and arbitrated. In this manner, information sharing is accommodated, for example, for efficient knowledge base creation and multi-user functionality.
Owner:ORACLE INT CORP
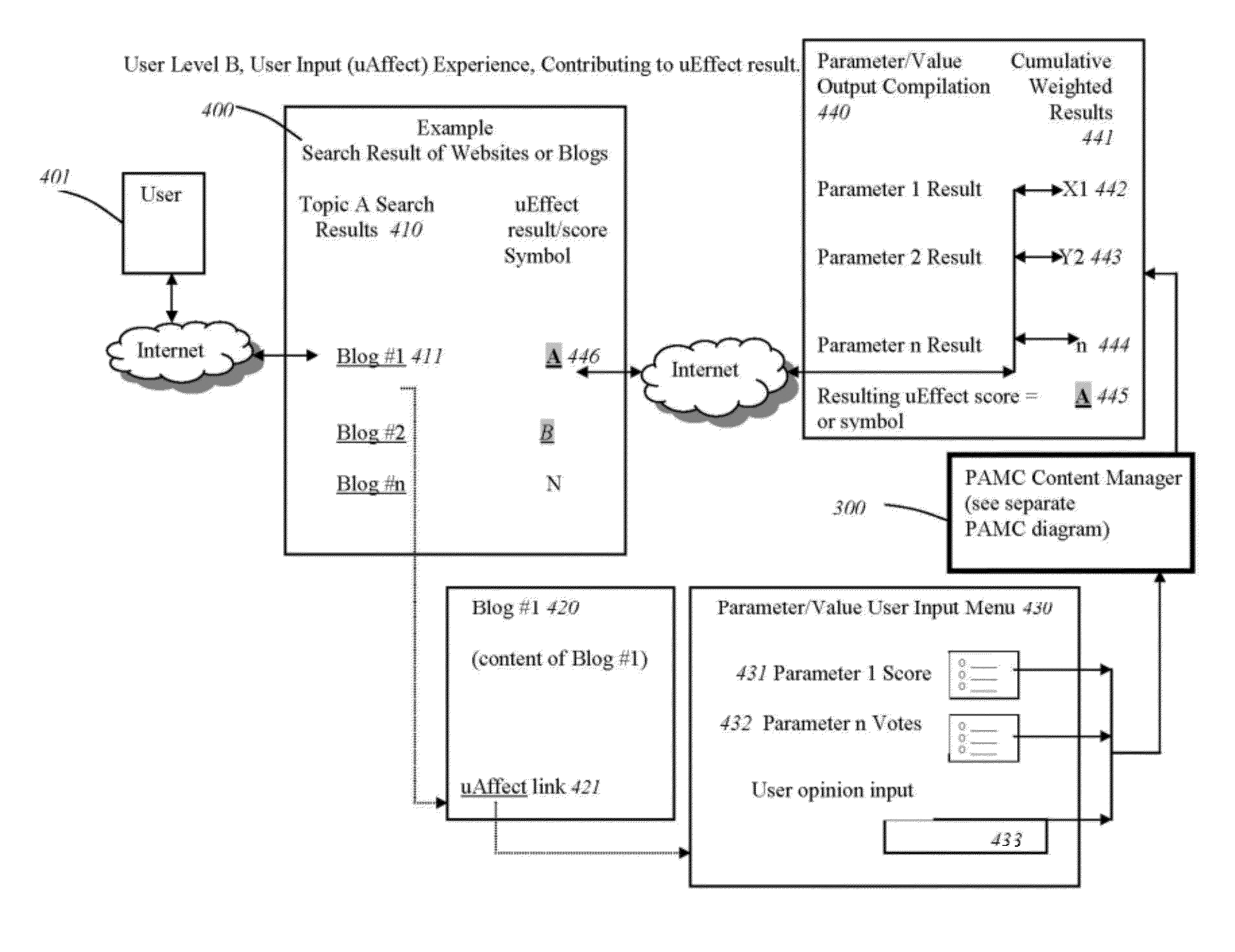
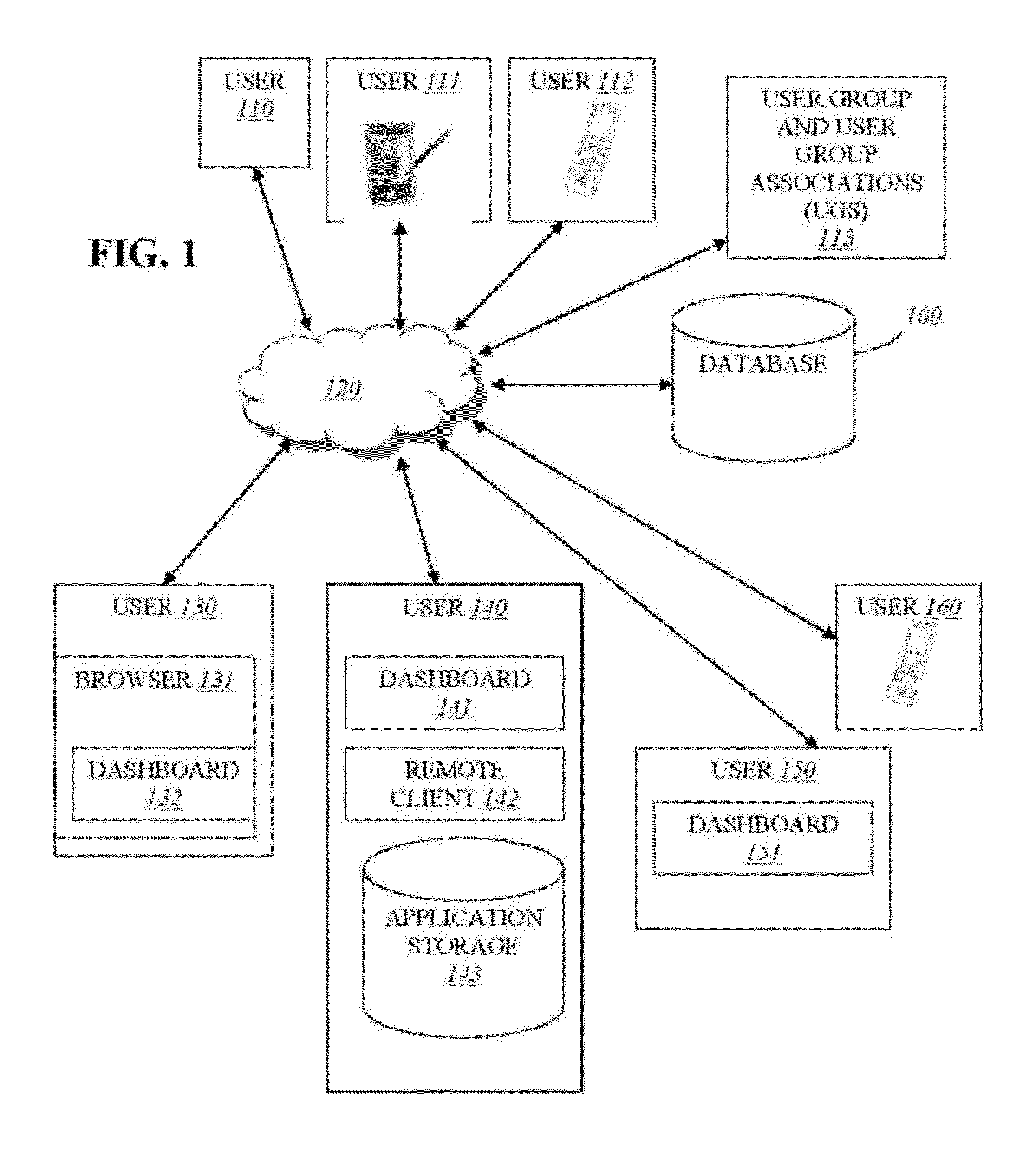
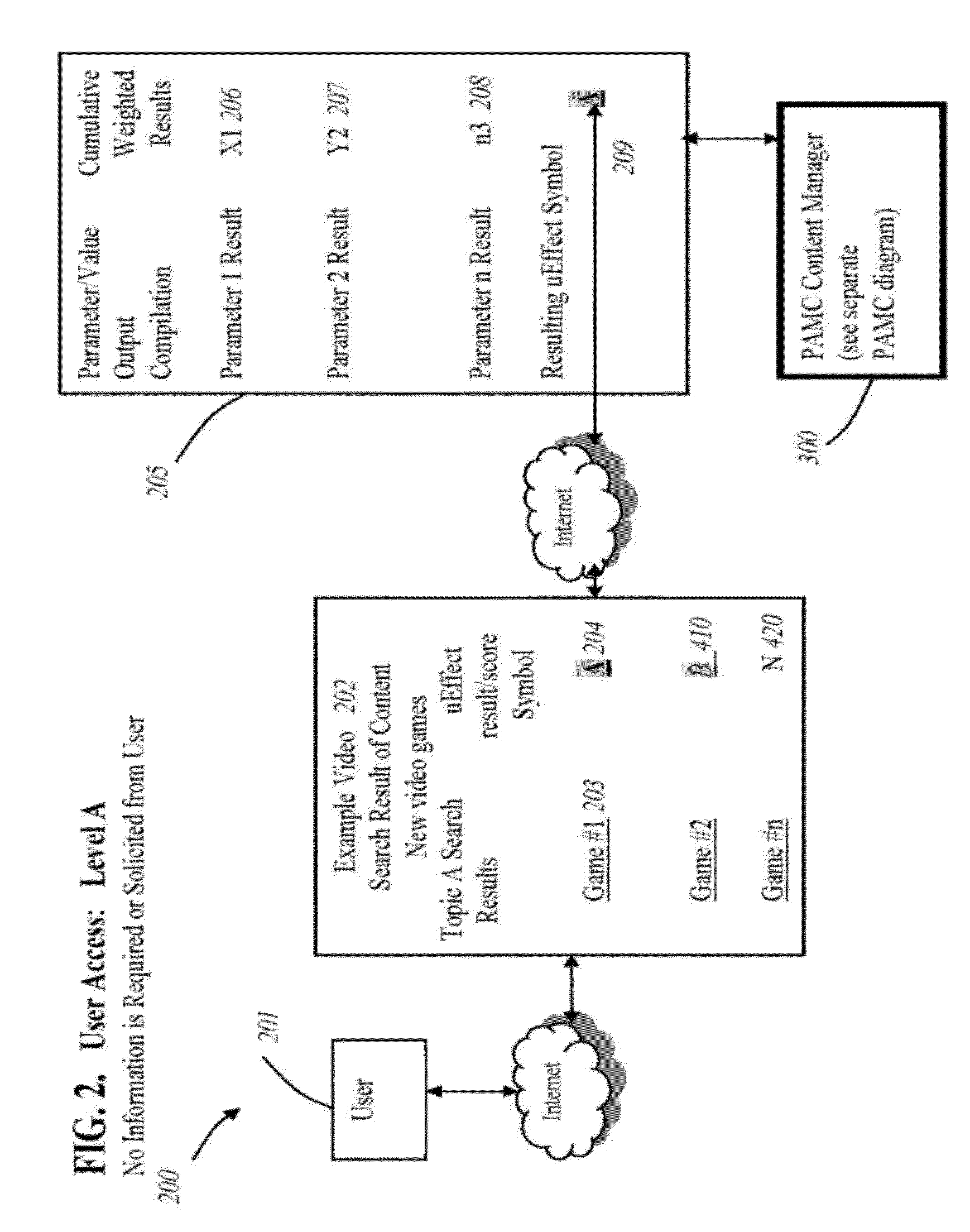
User-centric, user-weighted method and apparatus for improving relevance and analysis of information sharing and searching
InactiveUS8166026B1Facilitate data sharingEasy to switchWeb data indexingData sortingCommunity orRelevant information
A system and method that enables the user to search and identify meaningful and relevant information, based upon the weighted, custom parameters provided by the user and parameters or rules defined by the community of users as a group, with the option of utilizing user profile information to tune or detune searching, comparing or contrasting, and predicting. User profile information is collected and organized with data and feedback collected from other users. The results are then tailored to a weighted, cumulative summary result, for display that benefits the contributing user and subsequent future community or user group associations (UGA). The methods provide a summary, or result, that can be tailored specifically to the user based upon weighted rules (algorithms) and parameters defined by the user (or a user group as a whole), and the weighted rules and parameters defined as meaningful by the user (group).
Owner:UAFFECT ORG
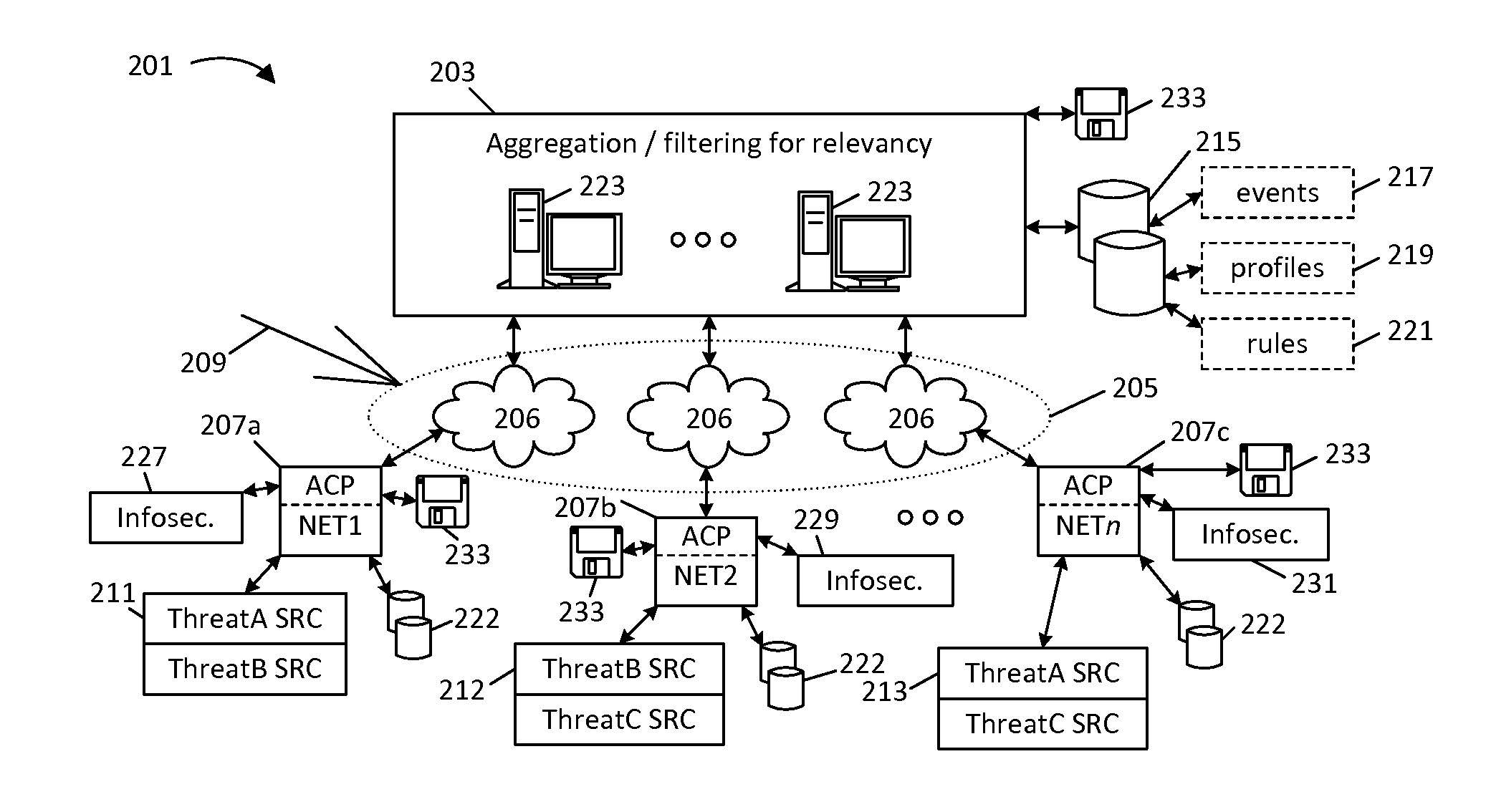
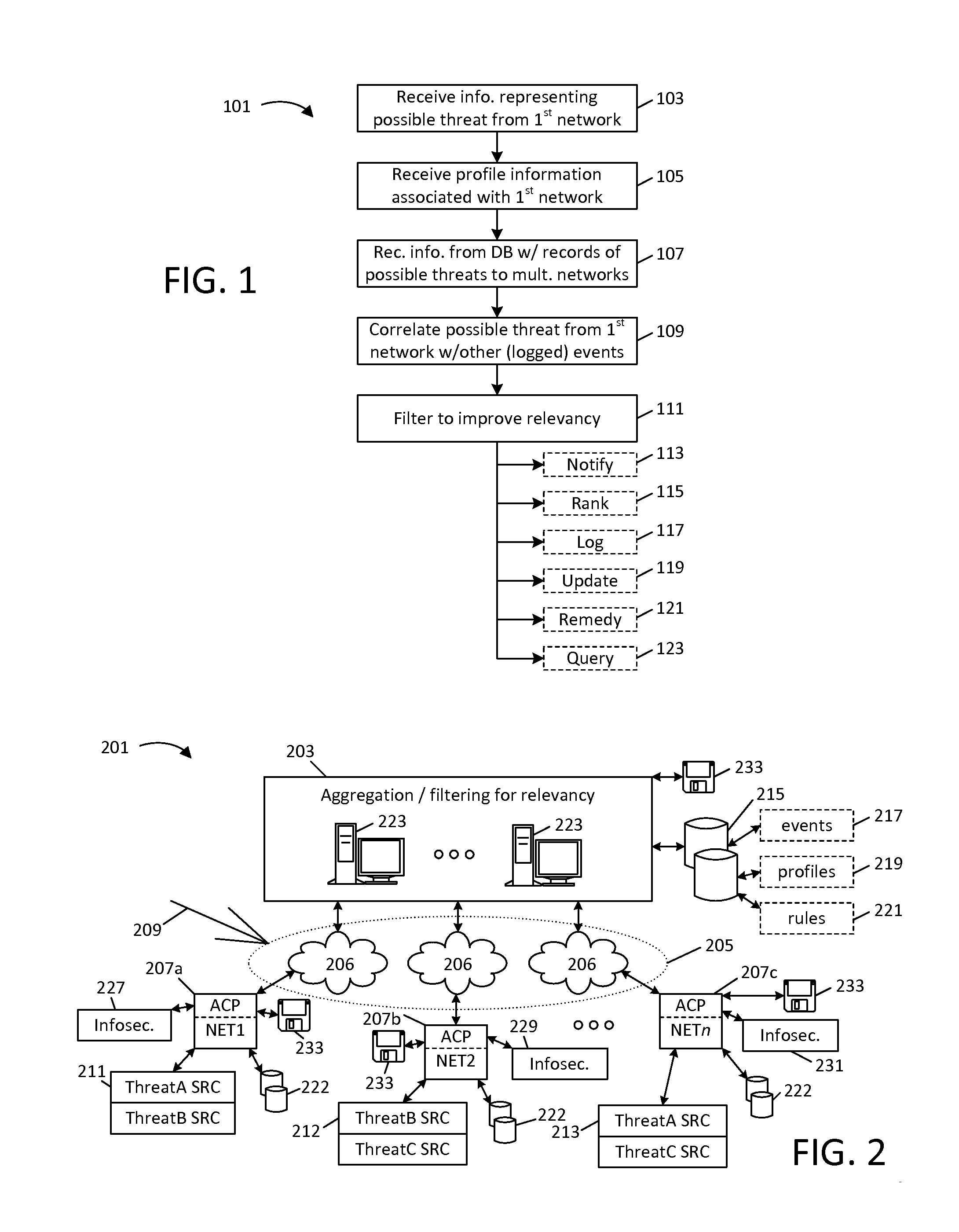
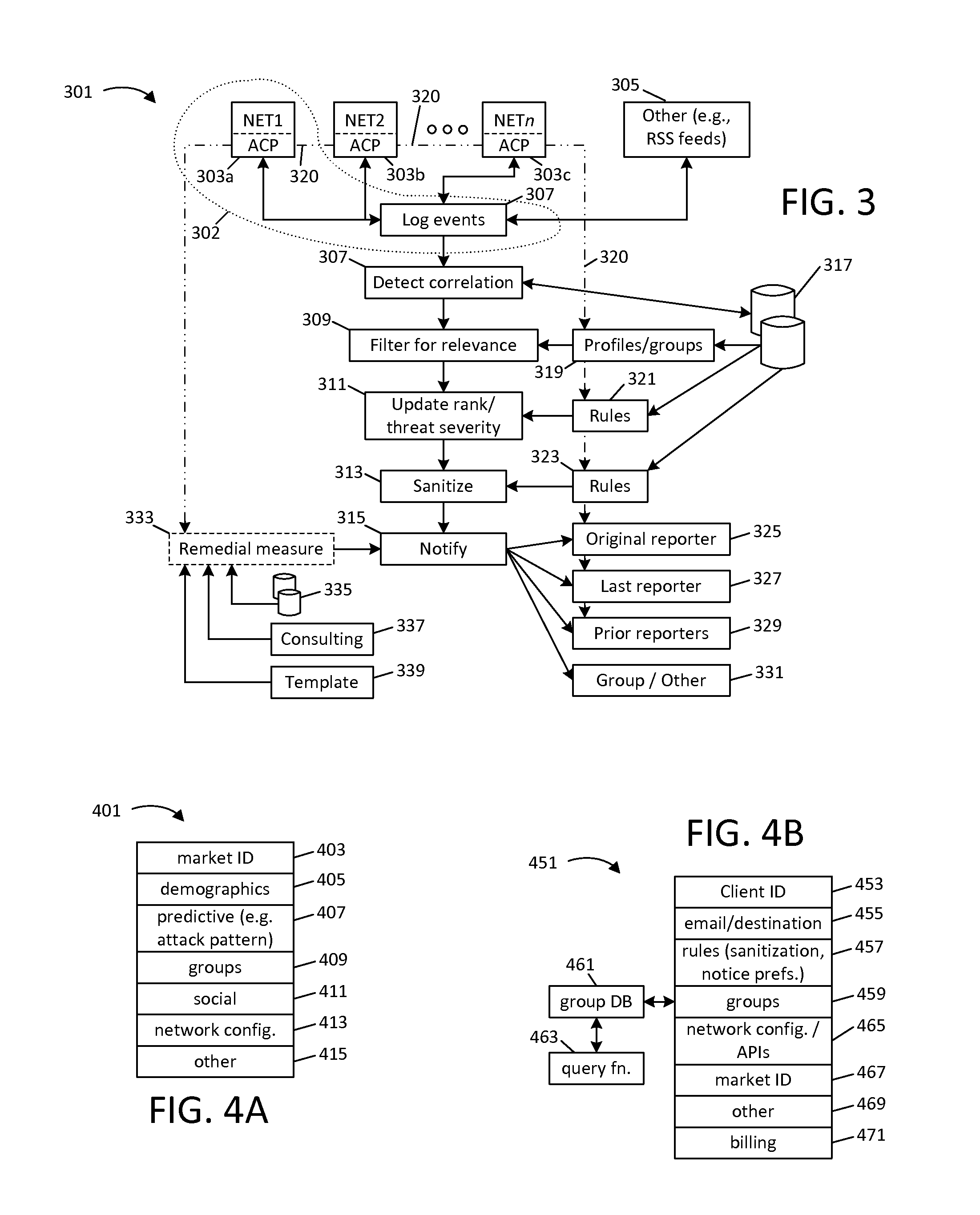
Techniques for sharing network security event information
ActiveUS20150207813A1Memory loss protectionError detection/correctionInformation sharingPrivate network
This disclosure provides techniques for pooling and searching network security events reported by multiple sources. As information representing a security event is received from one source, it is searched against a central or distributed database representing events reported from multiple, diverse sources (e.g., different client networks). Either the search or correlated results can be filtered and / or routed according at least one characteristic associated with the networks, for example, to limit correlation to events reported by what are presumed to be similarly situated networks. The disclosed techniques facilitate faster identification of high-relevancy security event information, and thereby help facilitate faster threat identification and mitigation. Various techniques can be implemented as standalone software (e.g., for use by a private network) or for a central pooling and / or query service. This disclosure also provides different examples of actions that can be taken in response to search results.
Owner:SERVICENOW INC
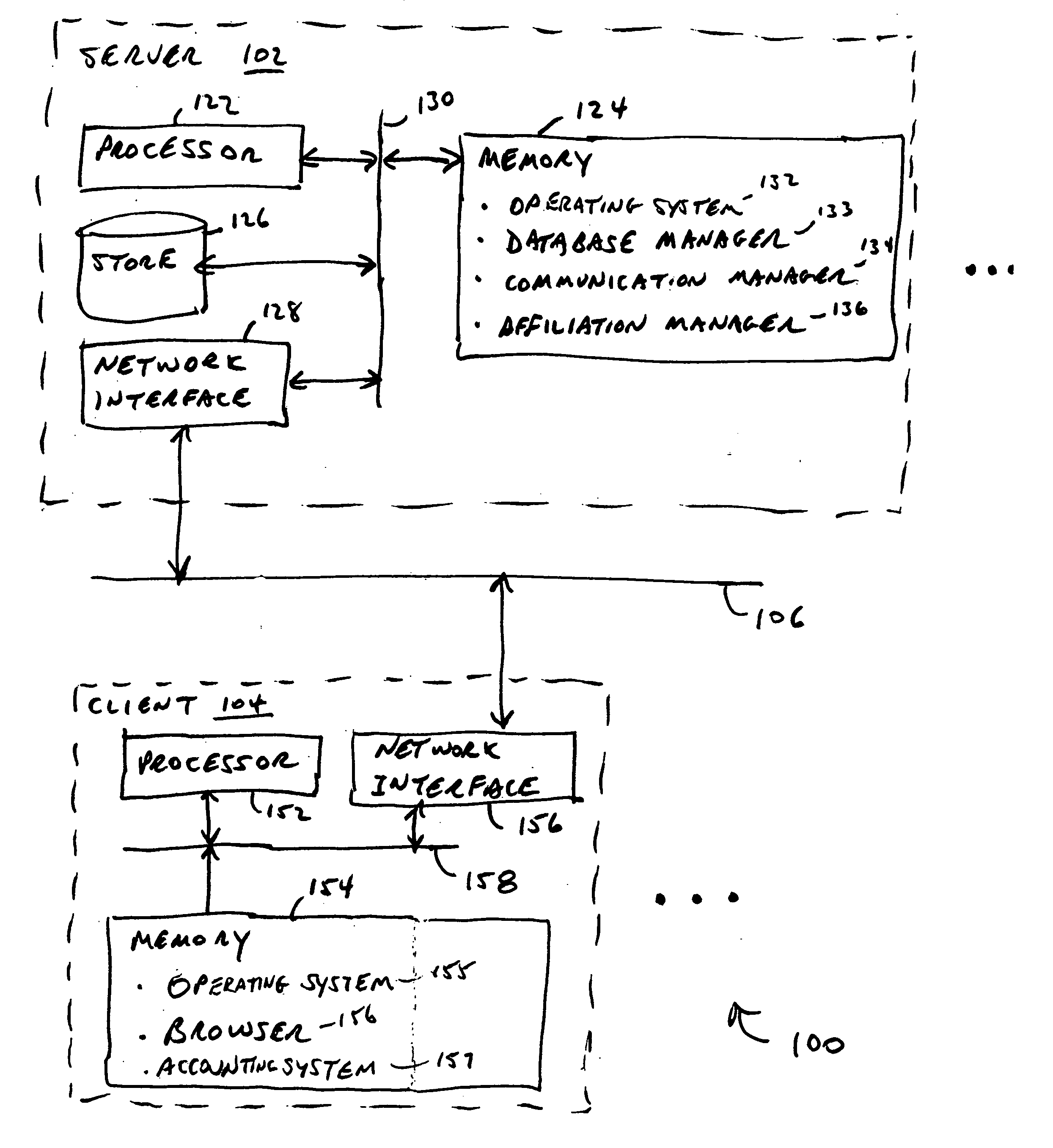
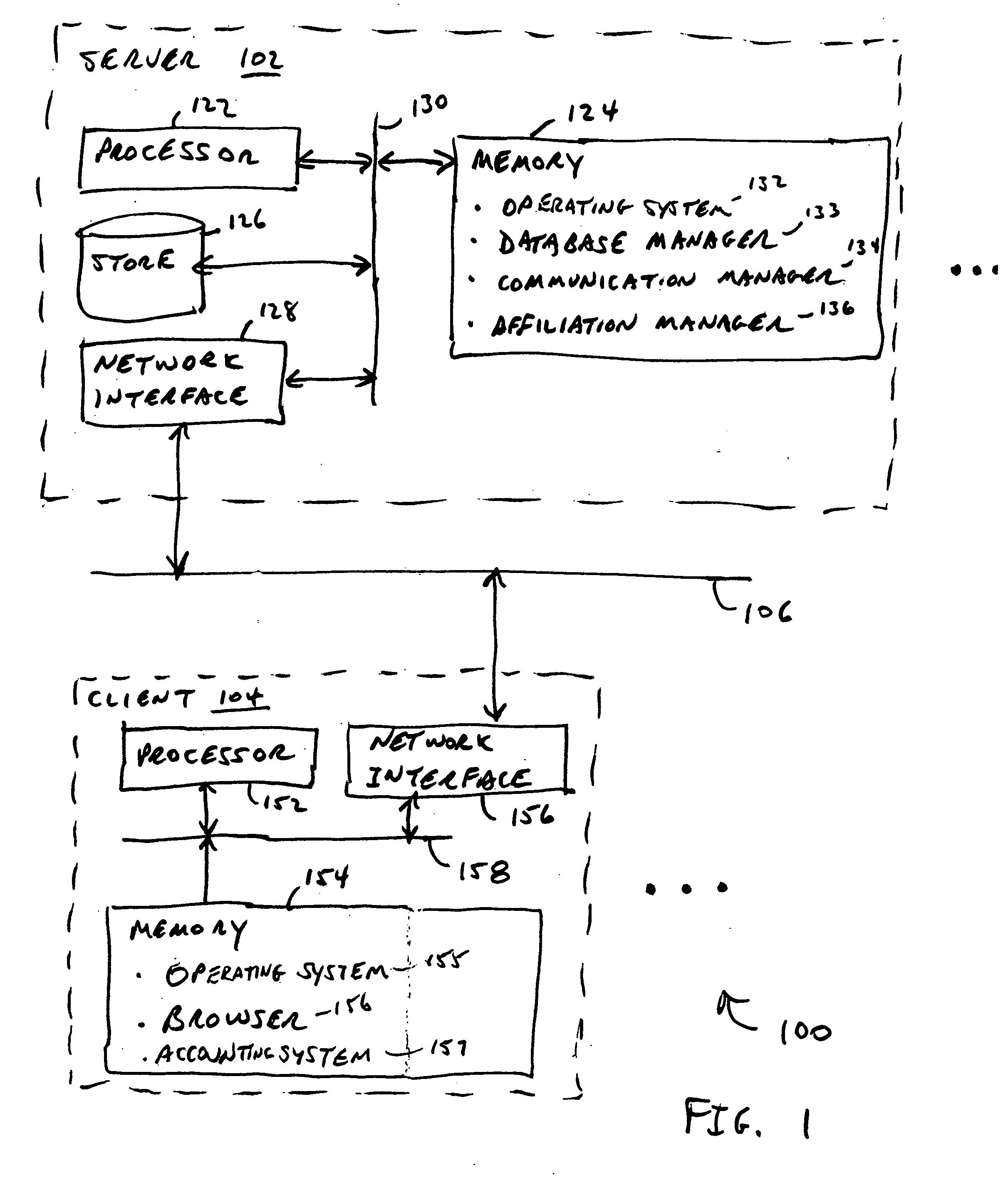
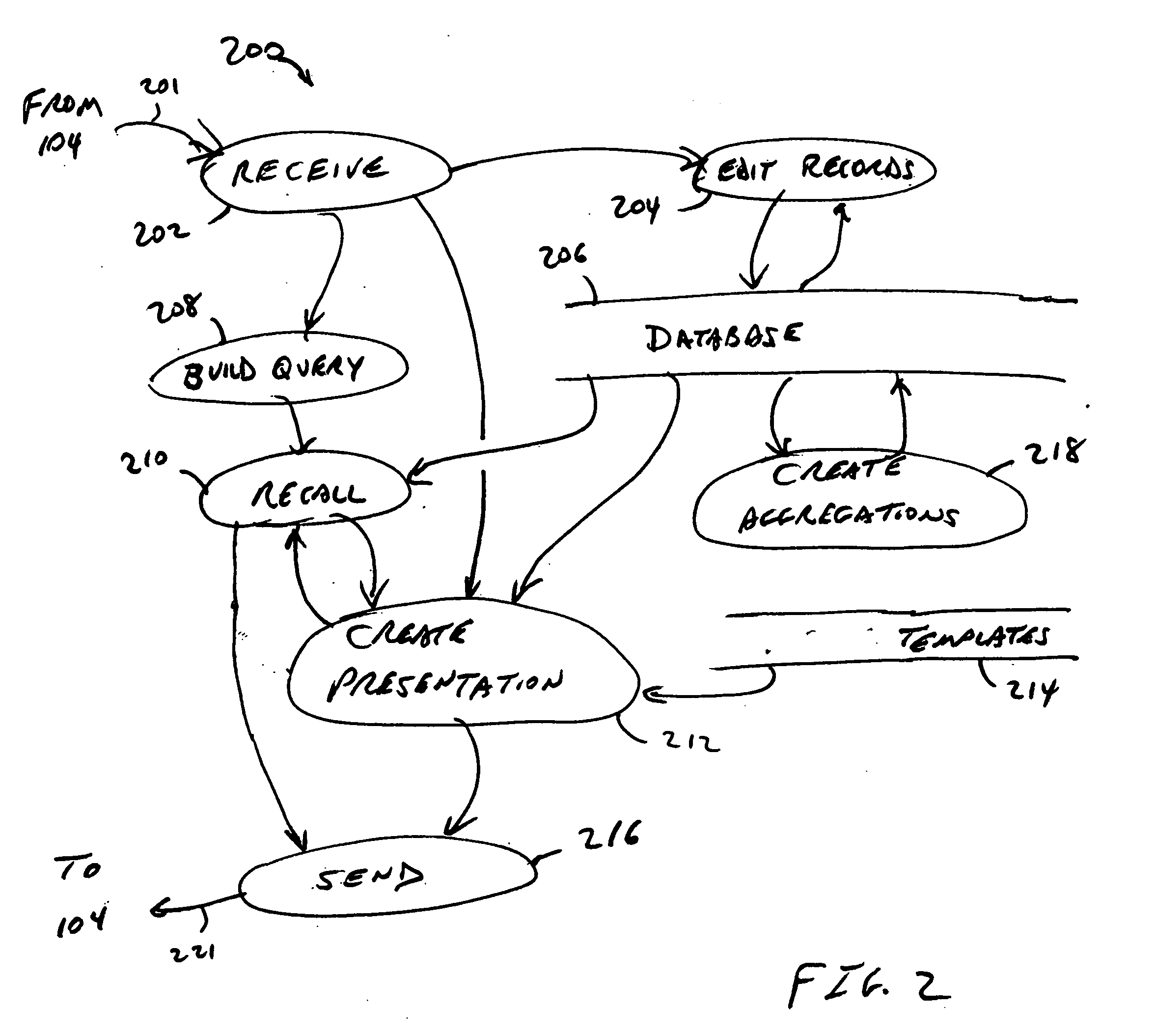
Systems and methods for managing affiliations
InactiveUS20050192822A1Facilitate communicationEasy to createData processing applicationsDigital data processing detailsInformation sharingCentral database
An affiliation manager provides each of typically hundreds of users with a calendar of appointments and a task list each including icons for capturing time and expenses accrued by the user when attending a particular appointment or performing a particular task. A subset of collected captured time and expenses may be transferred to each requesting client for use by independent accounting systems. Management of appointments and tasks from a central database promotes collaboration among users, simplifies sharing of schedule information among users, and provides context for data entry. Each user may create any number of affiliations, each affiliation describing affiliations of the user in numerous projects, organizations, employments, and activities. Each user may admit other users to share his or her affiliations, thereby promoting collaboration of many users for jointly attending meetings and jointly performing tasks. Context permits automatic intuitive association of email, chat messages, notes, and documents to records for persons, locations, resources, appointments, tasks, and projects for integrated affiliation management services. Requests for queries and forms are interpreted according to the context in which the user issued the request. Requests are made via a common set of icons and links on each item of a list provided by a prior query.
Owner:TIME ECLIPSE
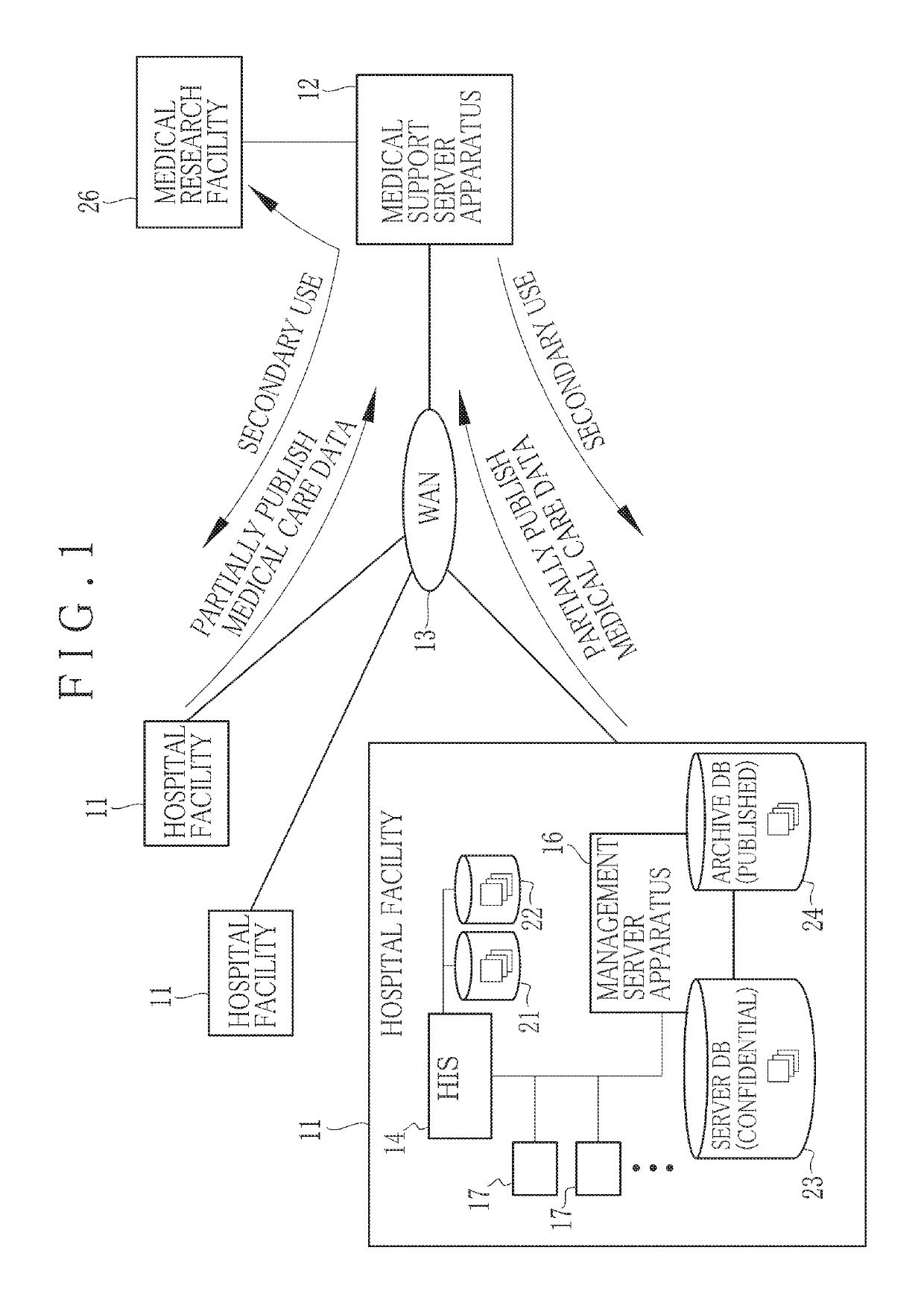
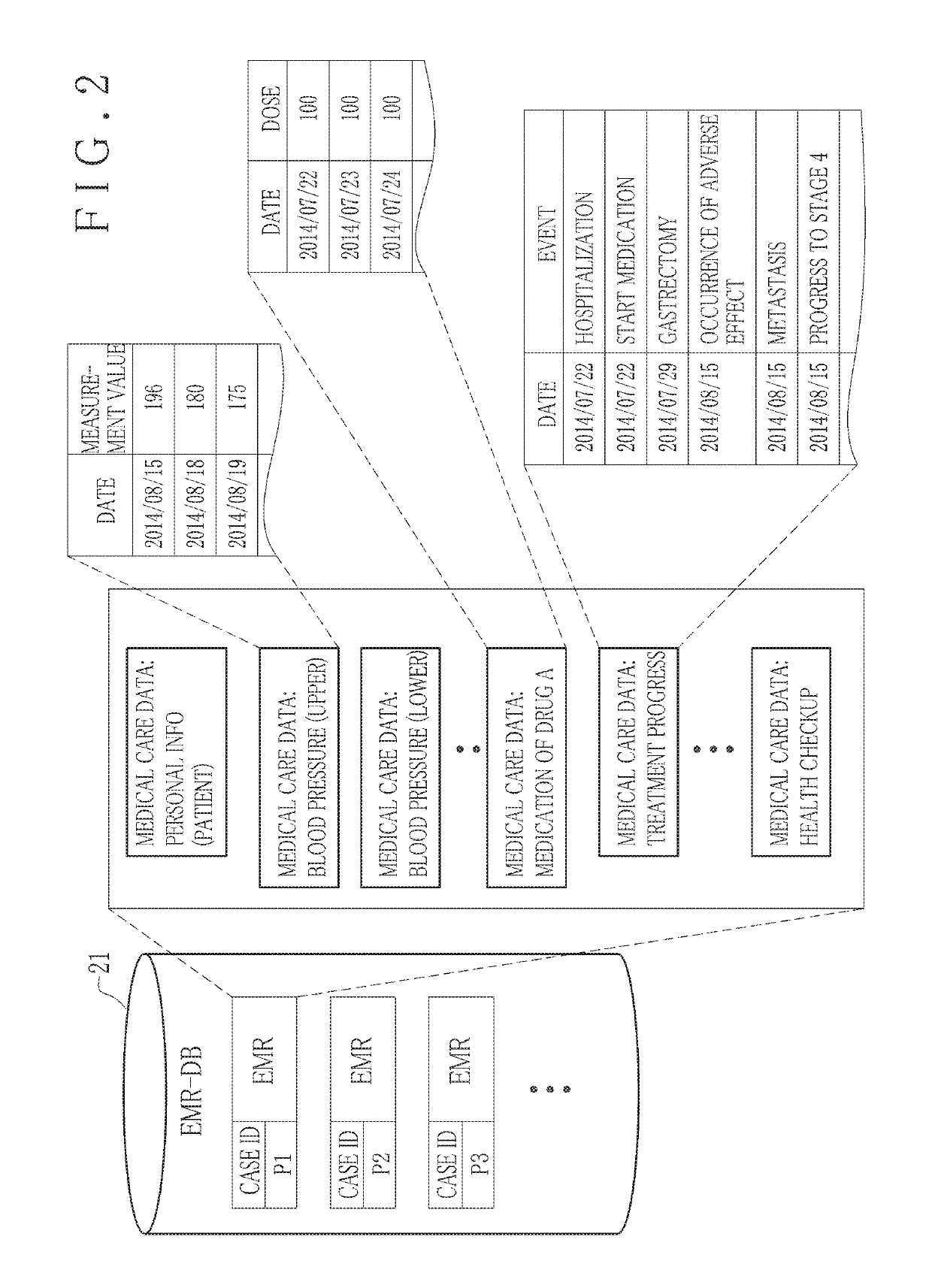
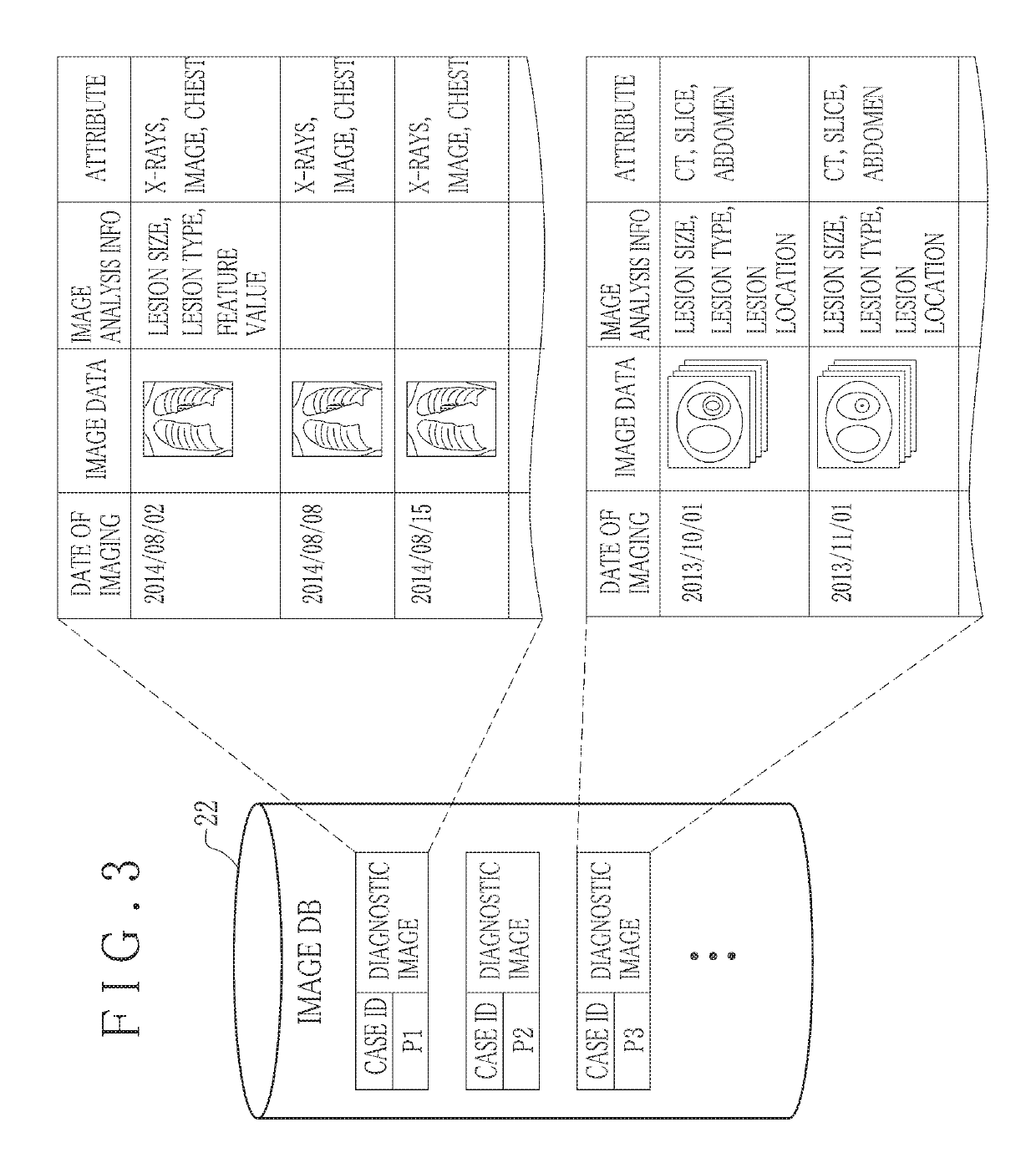
Information management apparatus and method for medical care data, and non-transitory computer readable medium
An information sharing apparatus (management apparatus) for medical care data of a patient body includes a data uploader for classifying the medical care data into confidential data for a primary use in medical care of the patient body, and published data published for a secondary use different from the primary use, to store the confidential data and the published data in a storage medium. A problem event detector monitors the confidential data being added or updated, to check occurrence of a problem event of clinical exacerbation of the patient body. An activation processor checks occurrence of a flag signal for activating relocation of the confidential data to the published data upon the occurrence of the problem event. A relocation unit filters the confidential data at least partially to produce published data upon occurrence of the flag signal after the occurrence of the problem event.
Owner:FUJIFILM CORP
Creating collaborative application sharing
InactiveUS7047279B1Multiple digital computer combinationsOffice automationInformation sharingNetwork connection
A system is disclosed that provides a goal based learning system utilizing a rule based expert training system to provide a cognitive educational experience. The system provides the user with a simulated environment that presents a training opportunity to understand and solve optimally. The technique establishes a collaborative training session, including the steps of establishing a network connection between a plurality of users, selecting a mode for the network connection between the plurality of users, establishing a network connection mode between the plurality of users, and synchronizing the mode between the plurality of users. Modes of operation include application sharing, whiteboarding, media sharing, newsgroup information sharing chatroom initiation and discussion group initiation.
Owner:ACCENTURE GLOBAL SERVICES LTD
Health information system and method
InactiveUS20060173715A1Reduce riskPrevent further degradationTelemedicineMedical automated diagnosisMedical recordDecision taking
The present invention relates to a distributed computer-based decision support technology for the healthcare industry. It also relates to a systematic knowledge diffusion technology for the healthcare industry. The tool and methodology packages and distributes computation and data processing software components in both centralized and federated fashions to process medical data in-situ and in real-time, applying the knowledge and best practices that can reflect the most recent advancement of medical sciences. This tool and methodology interacts with a healthcare organization's existing internal and external information sources, including those sources of its trading partners, such as practice management systems, health information systems, electronic medical records systems, lab systems, medical reference systems, and existing decision support systems. Due to this sharing of information and the ability to construct longitudinal medical records that was previously not possible, the quality of decision support can be rapidly improved, benchmarked, and standardized across the industry.
Owner:WANG HAO
Method for online information sharing for completing electronic forms
InactiveUS7334184B1Digital data information retrievalDigital computer detailsData setInformation sharing
Owner:CALLAHAN CELLULAR L L C +1
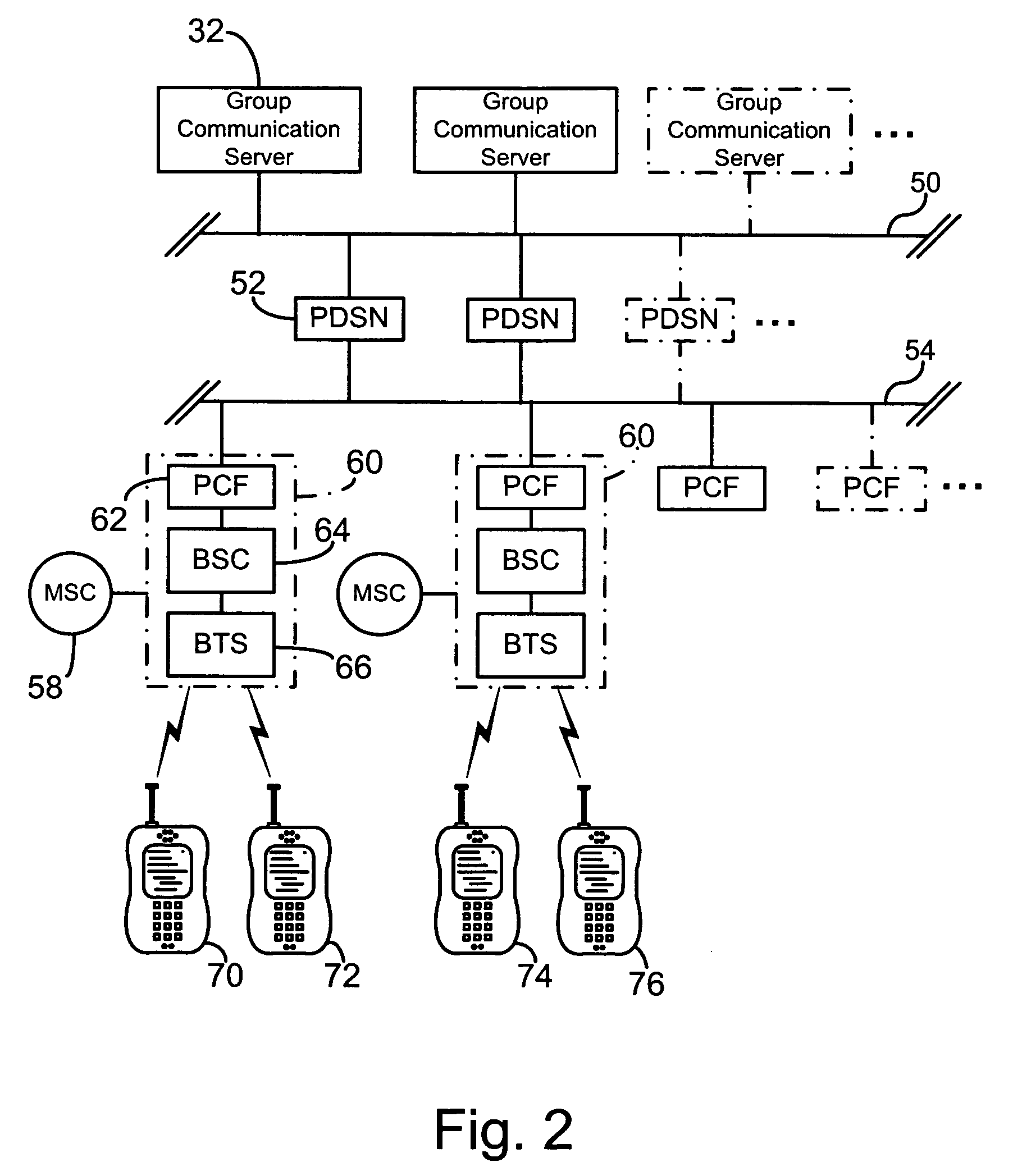
Peer to peer information exchange for mobile communications devices
The invention discloses various methods whereby mobile communications devices, connected to a communications network can share data by acting as both clients and servers. Specifically contemplated is the sharing of GPS assistance data. Also disclosed is the formation and use of hierarchical groups of mobile communications devices for the purpose of information sharing.
Owner:ERICSSON INC
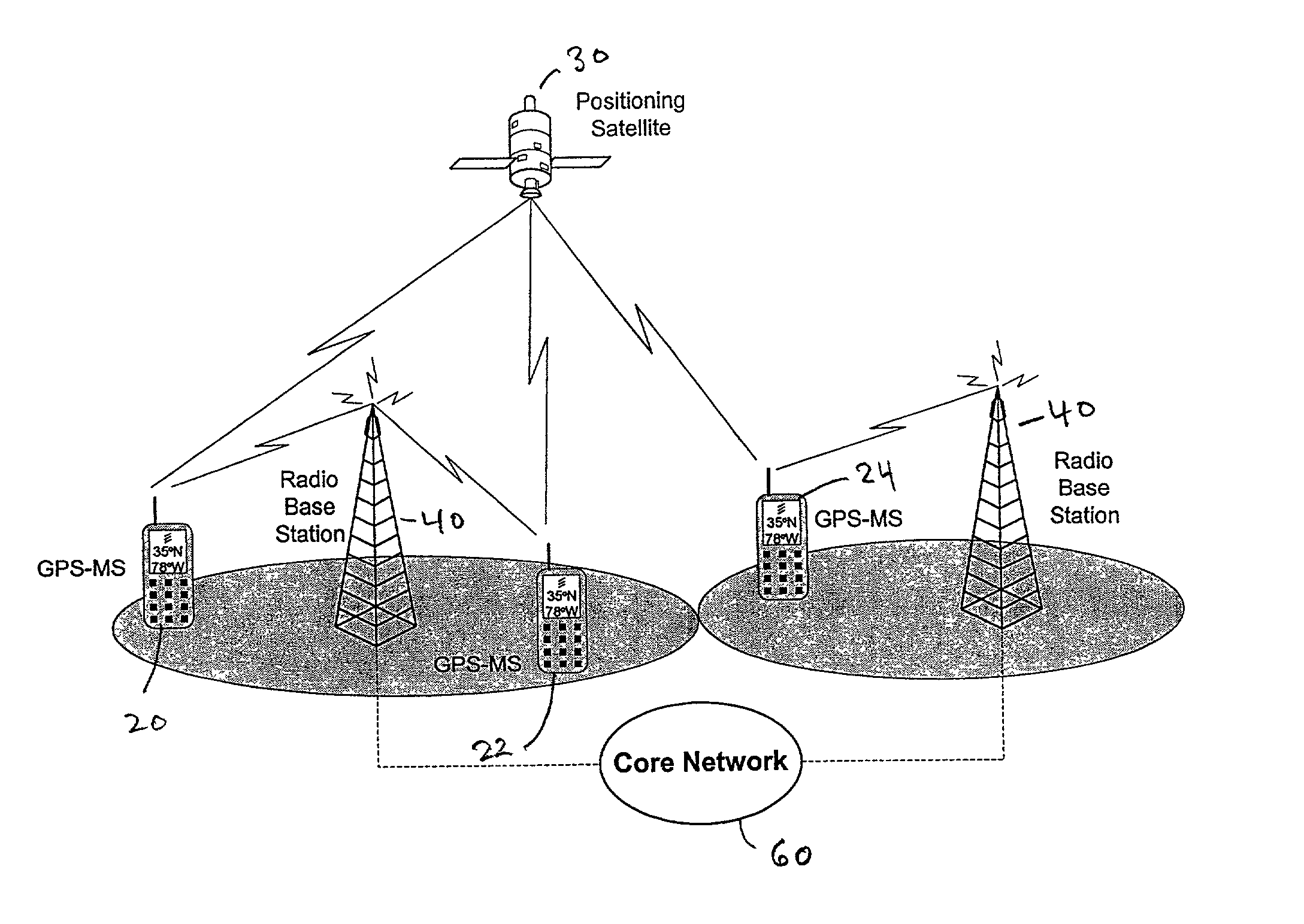
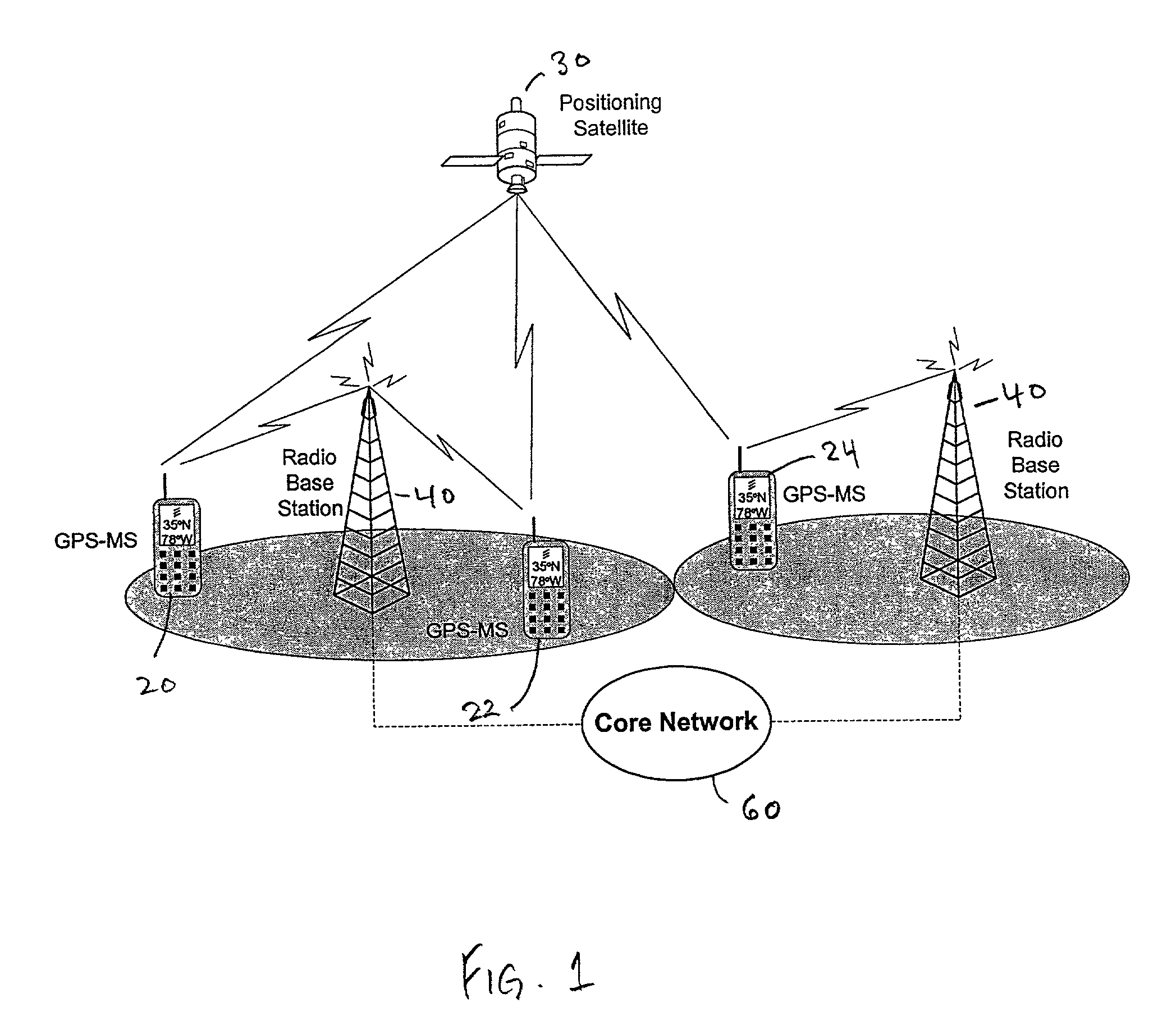
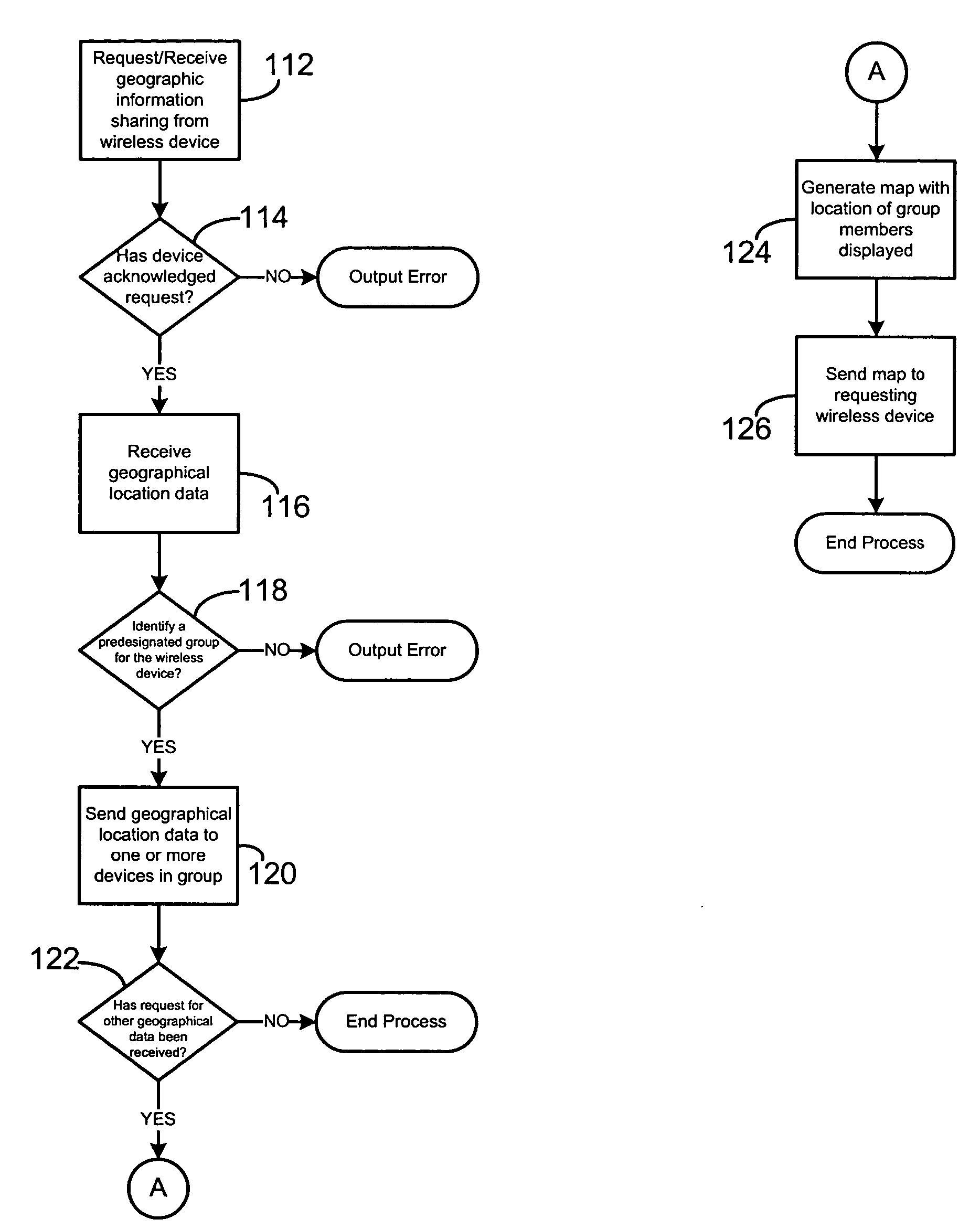
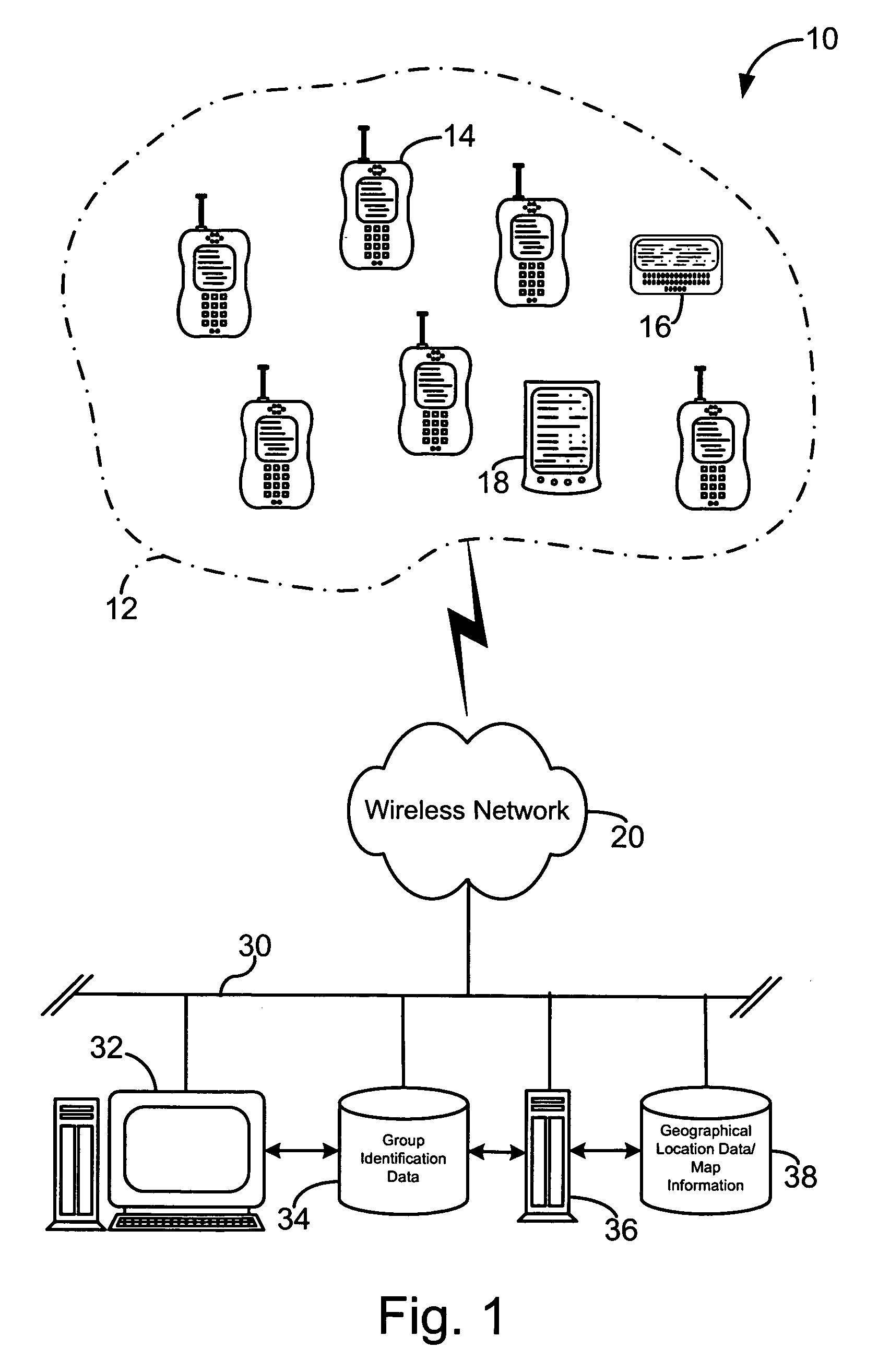
Geographical location information sharing among wireless devices
ActiveUS20050288036A1Radio/inductive link selection arrangementsRadio transmissionInformation sharingMobile telephony
A system and method for sharing geographical location information among a set of wireless telecommunication devices, such as mobile telephones. A first wireless telecommunication device generates geographical location information of that wireless telecommunication device, either through a resident device such as a GPS device, or has another computer device on the network provide the geographic location information, and then shares the geographical location information through sending the location information to one or more servers for relay to a predesignated target set of wireless telecommunication devices. The server stores the identity of member devices of the target set and controls communication between the first wireless telecommunications device and the member devices of the target set. A second server can be used to modify the geographical information, such as providing a map showing the location of the first wireless telecommunication device and other member devices of the target set.
Owner:QUALCOMM INC
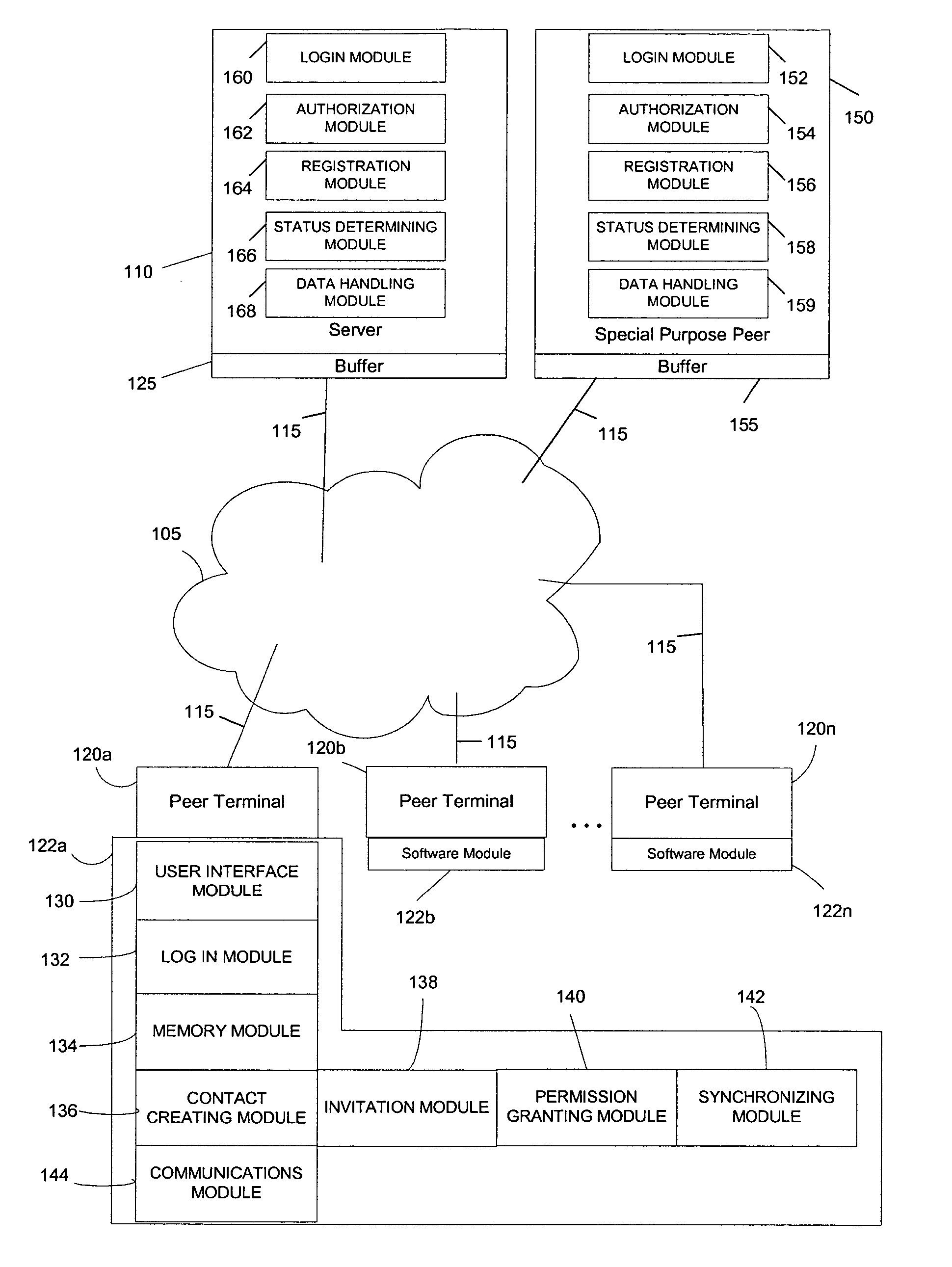
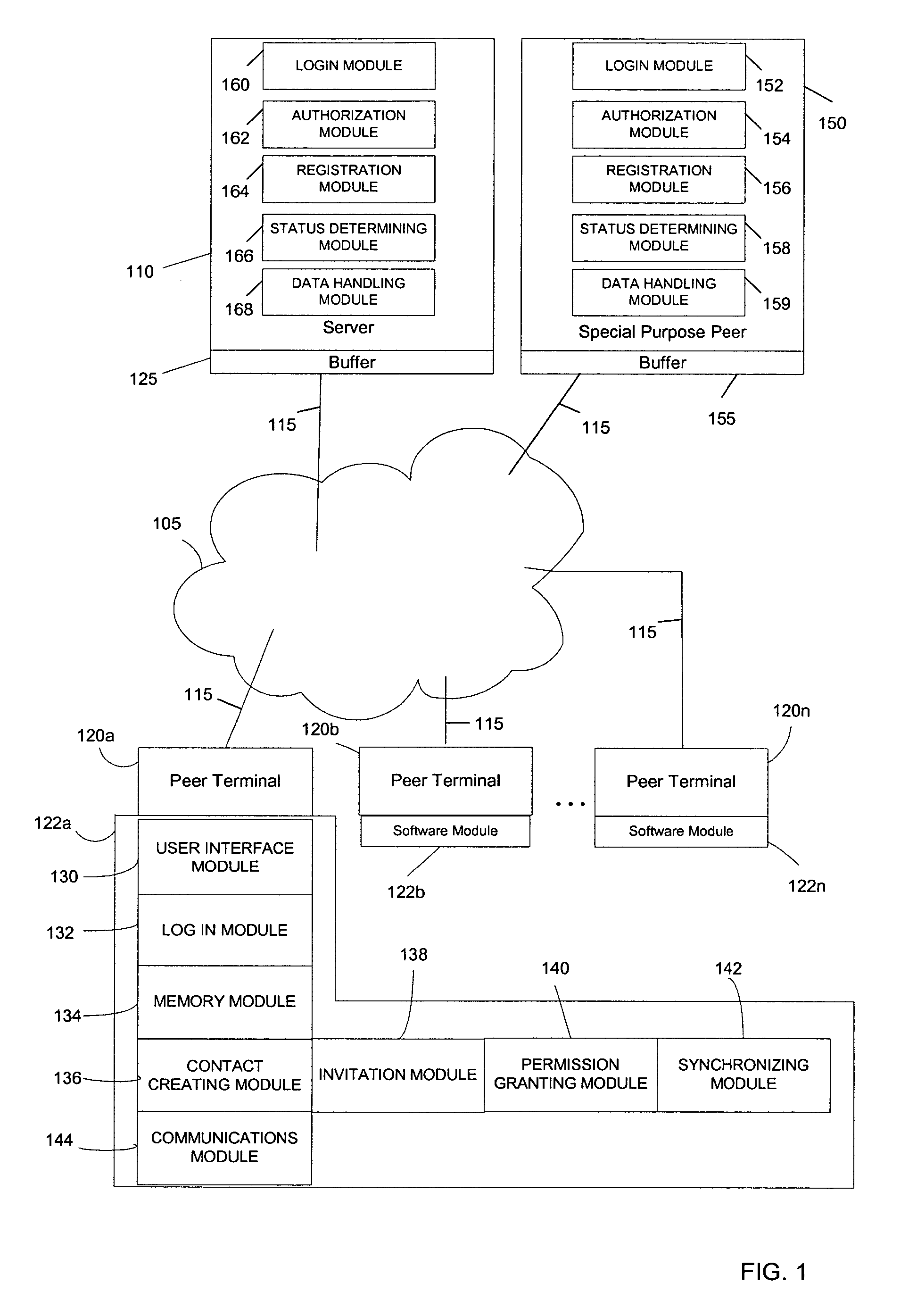
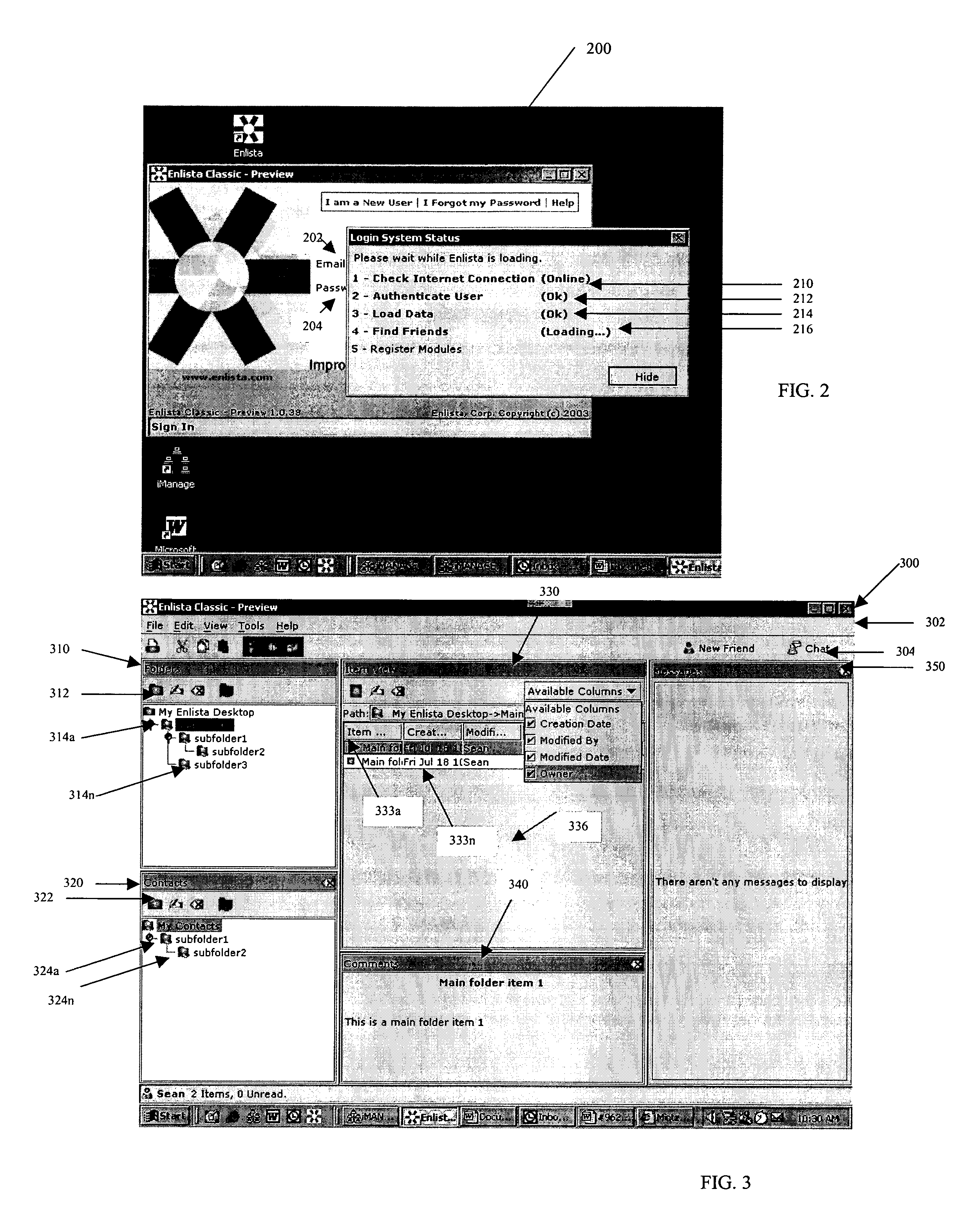
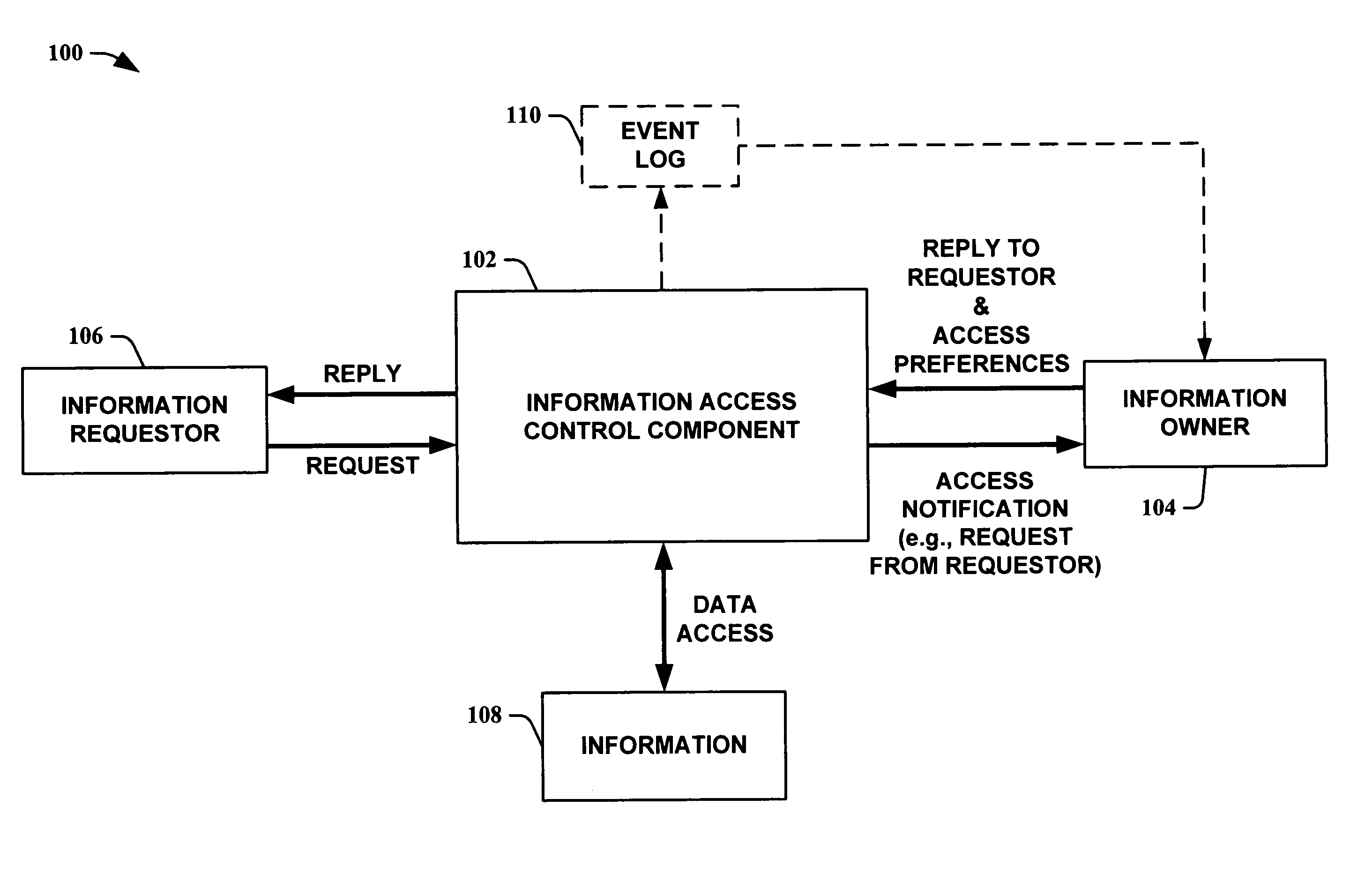
System and method for creating and selectively sharing data elements in a peer-to-peer network
InactiveUS20050091316A1Facilitate communicationFacilitate automatic synchronizationMultiple digital computer combinationsTransmissionInformation sharingData element
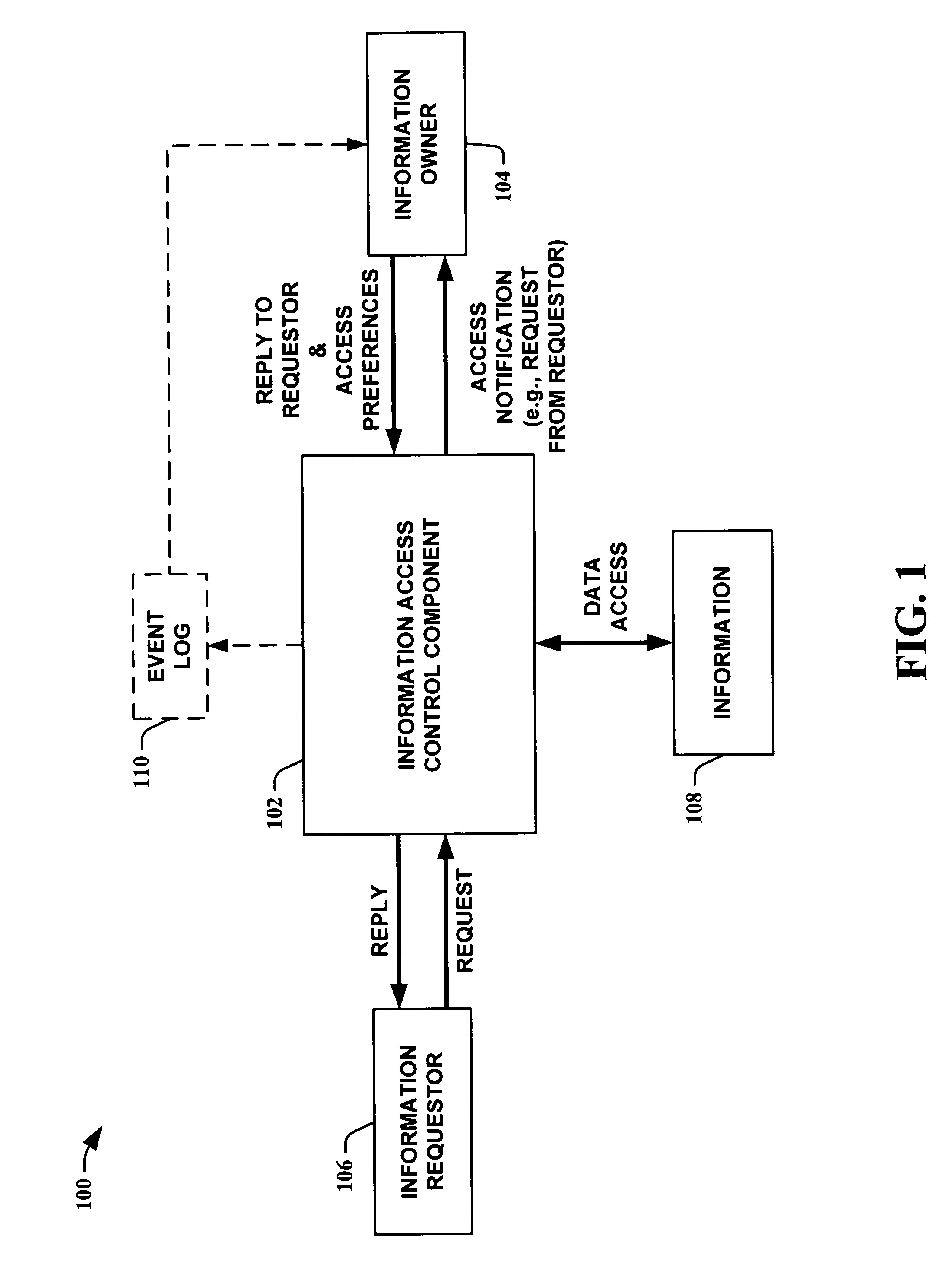
A system and method are provided for sharing information in a distributed peer-to-peer network wherein an information owner invites one or more trusted users to participate in information sharing and wherein the information owner designates permission levels for each of one or more trusted users. Upon accepting the invitation, the one or more trusted users may be granted with complete access, read only access, or blocked access to the shared information. The one or more trusted users may selectively decide to accept or decline to share information on a folder-to-folder basis. Any modifications made to the shared information may be disseminated to all the trusted users in real-time, upon log-in to a central server, or after a predetermined time delay.
Owner:ENLISTA
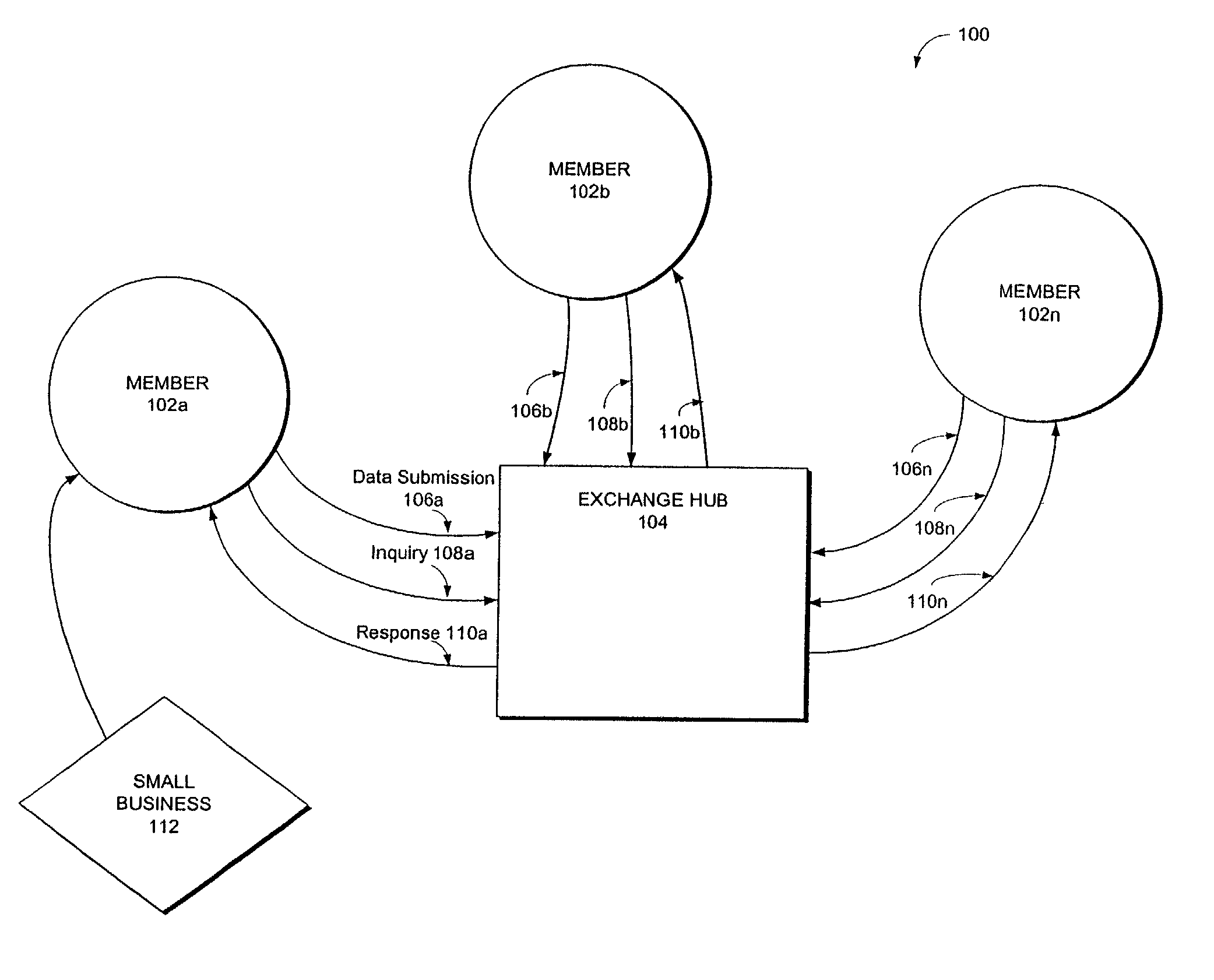
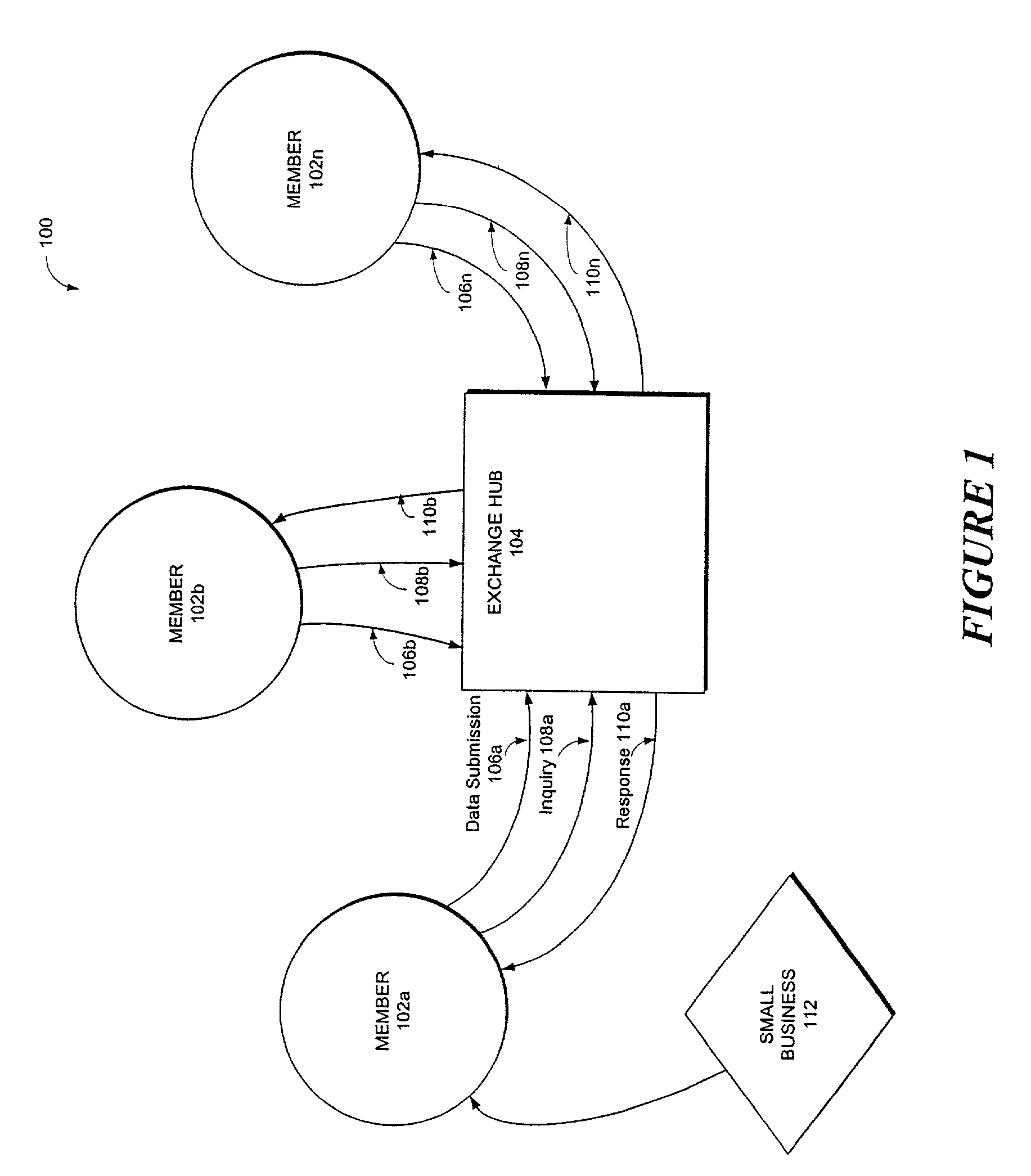
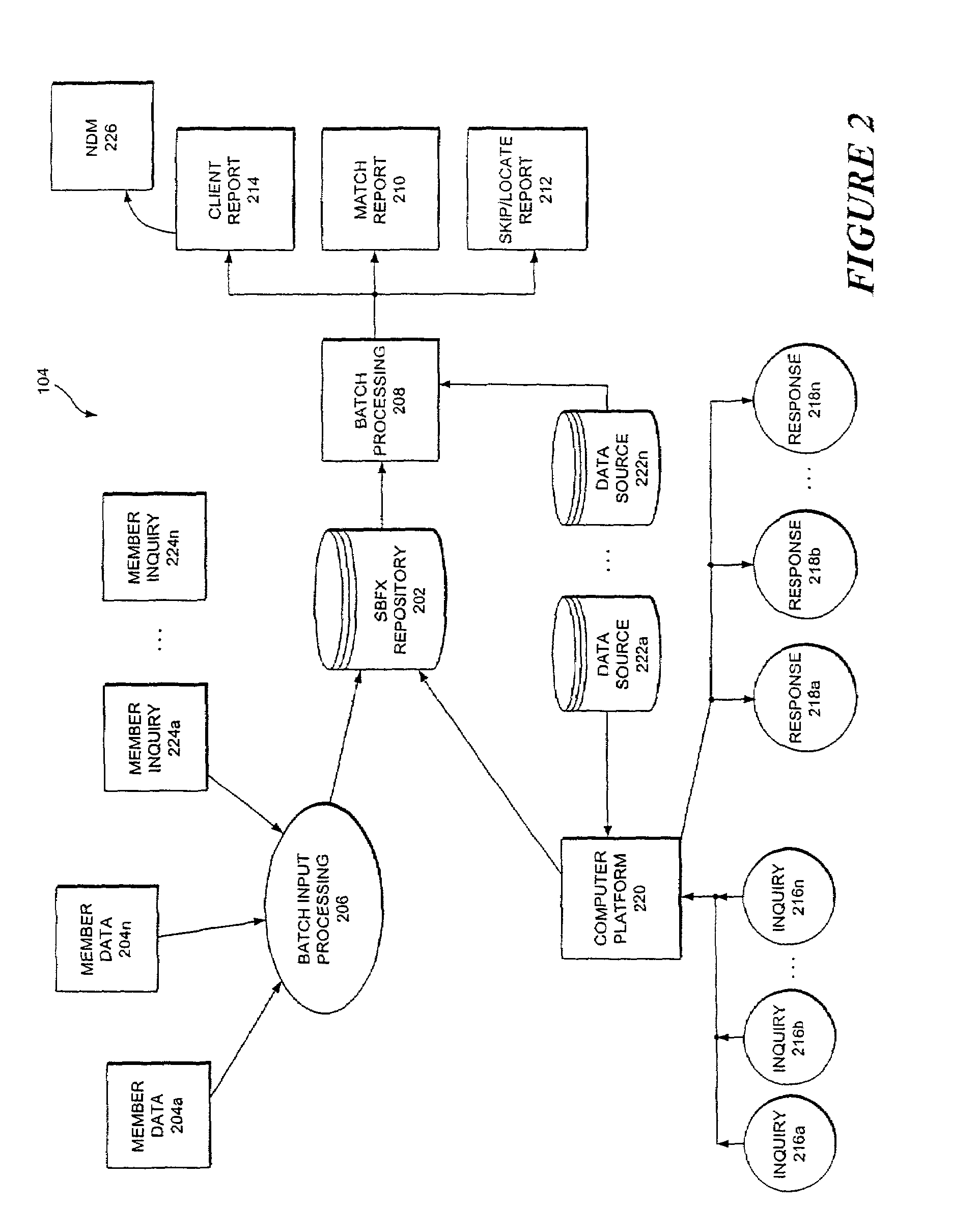
System and method for facilitating reciprocative small business financial information exchanges
ActiveUS7536346B2Improve protectionFacilitate information sharingFinanceMultiple digital computer combinationsEntity identifierInformation sharing
Systems and methods facilitate information sharing among a plurality of member institutions. Each member is associated with a member number and a corresponding member profile. A member contributes its data relating to small business entities to an exchange repository upon becoming a member, and thereafter on a periodic basis. Each member is eligible to query against the exchange repository. However, a response to a member's inquiry is determined by a reciprocity due to the inquiring member. If a member contributes comprehensive information regarding small business entities in its portfolio, then the member receives comprehensive information relating to a small business entity that becomes a subject of its inquiry. If a member contributes minimal information regarding the small business entities in its portfolio, the member receives minimal information relating to a small business entity that becomes a subject of its inquiry, regardless of the amount of information available in the exchange repository. Each business entity regarding which information is stored in the exchange repository is associated with a business entity identifier. A business entity identifier associates a record file for the corresponding small business entity. The record file includes trade data of the small business, data relating to one or more principals of the small business entity, as well as data relating to one or more guarantors of the small business entity, as appropriate.
Owner:EQUIFAX INC
Processes systems and networks for secured information exchange using computer hardware
InactiveUS20010039624A1Memory loss protectionUser identity/authority verificationData transformationData set
A system and method for providing external data-signal isolation, and signal-level information-preserving-data-transformations, to enable safe, operationally efficient, information sharing between protected information systems and networks and external, potentially hostile, information systems and networks which neutralizes any imbedded hostile executable codes such as viruses that may be in data-signals incoming from the external systems and networks. The system and method prevent un-transformed external data-signals from entering protected systems and / or networks using an intermediate screen which is a computer hardware device. The intermediate screen (which may be implemented as a network of systems) is deployed between the protected systems and external systems and is used to process all incoming signals from the external system to obtain transformed data sets from which information is extracted before it is passed to the protected system. The incoming signals all remain confined in the intermediate screen.
Owner:CYBERDFNZ
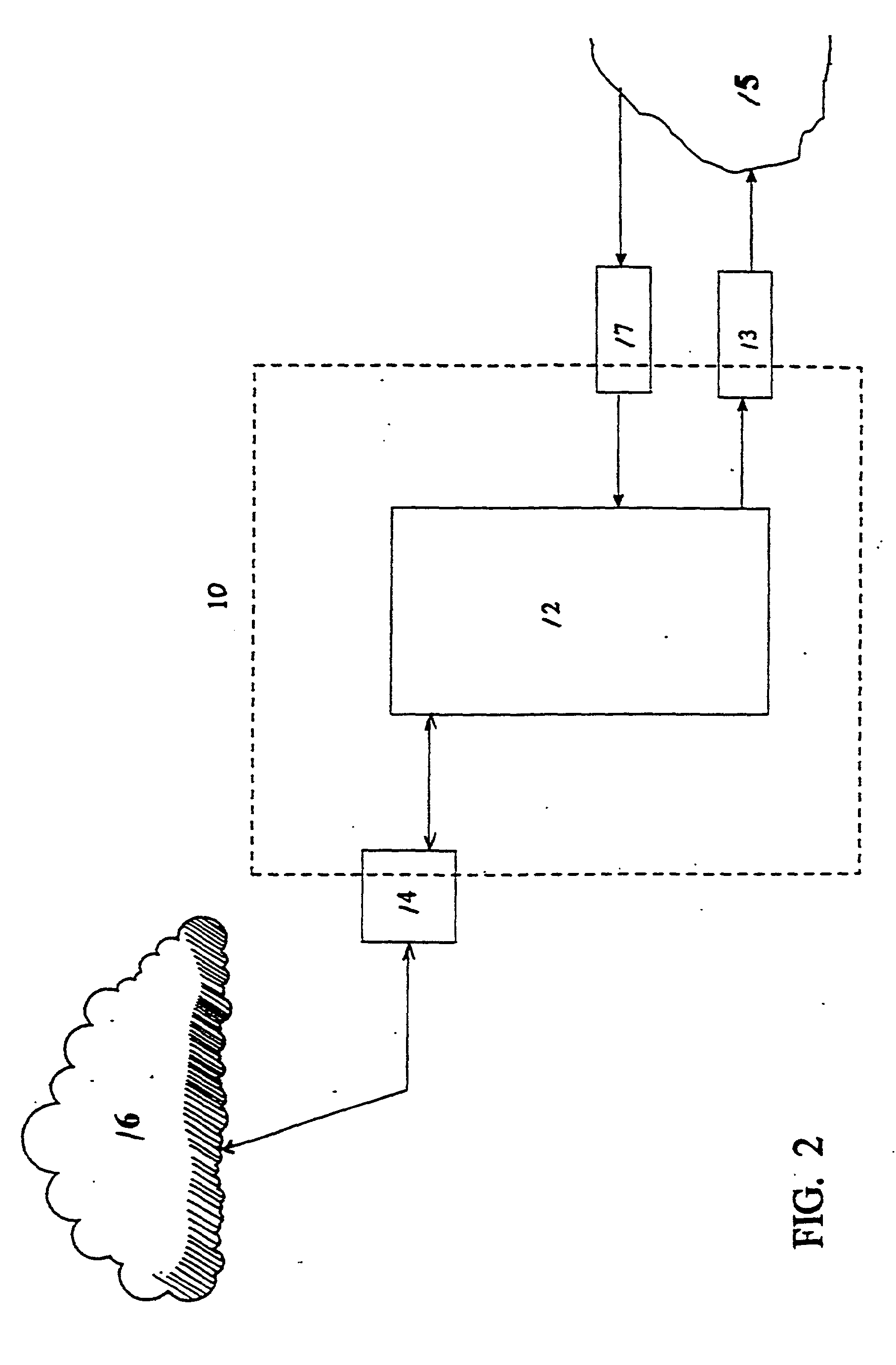
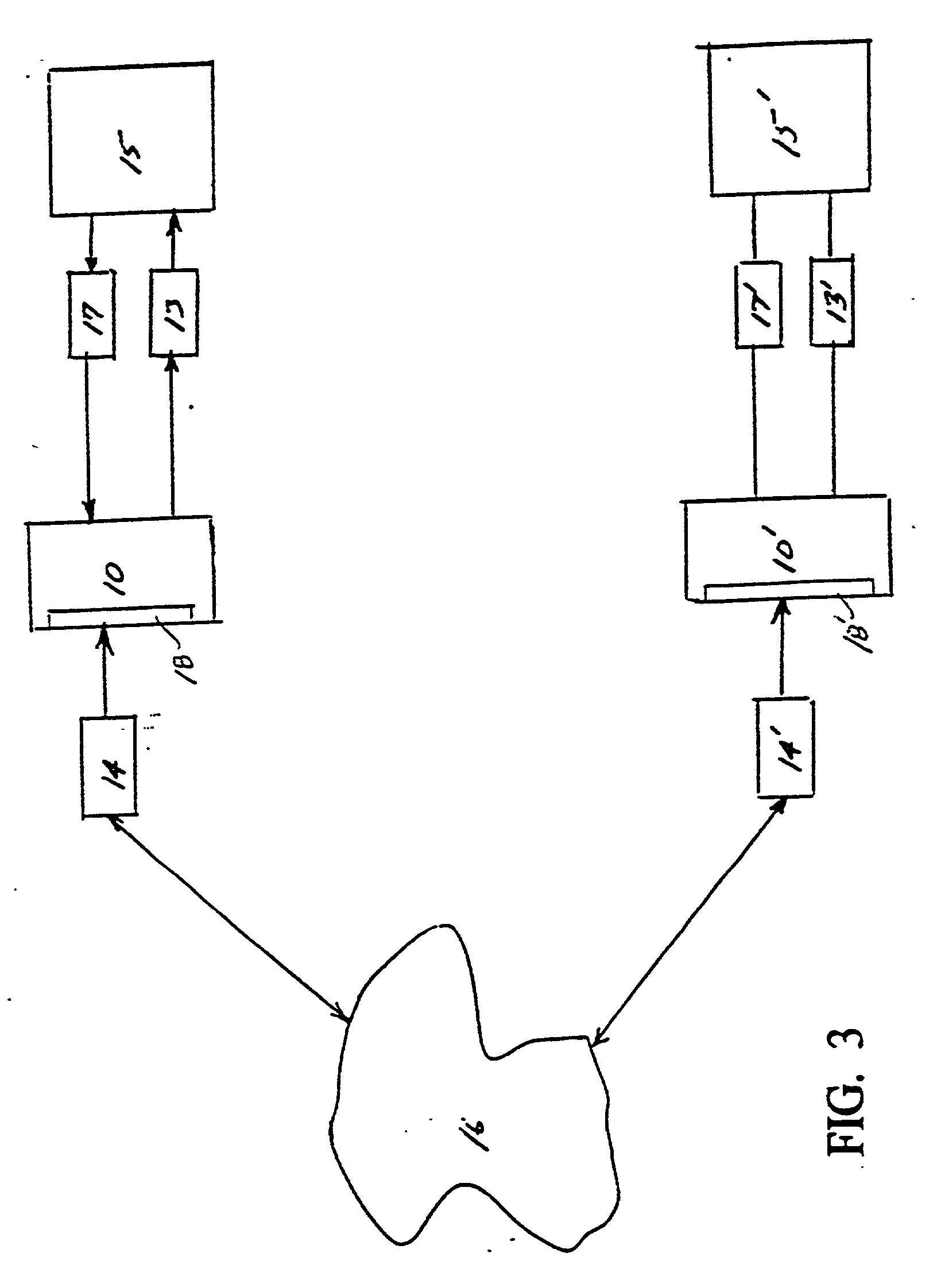
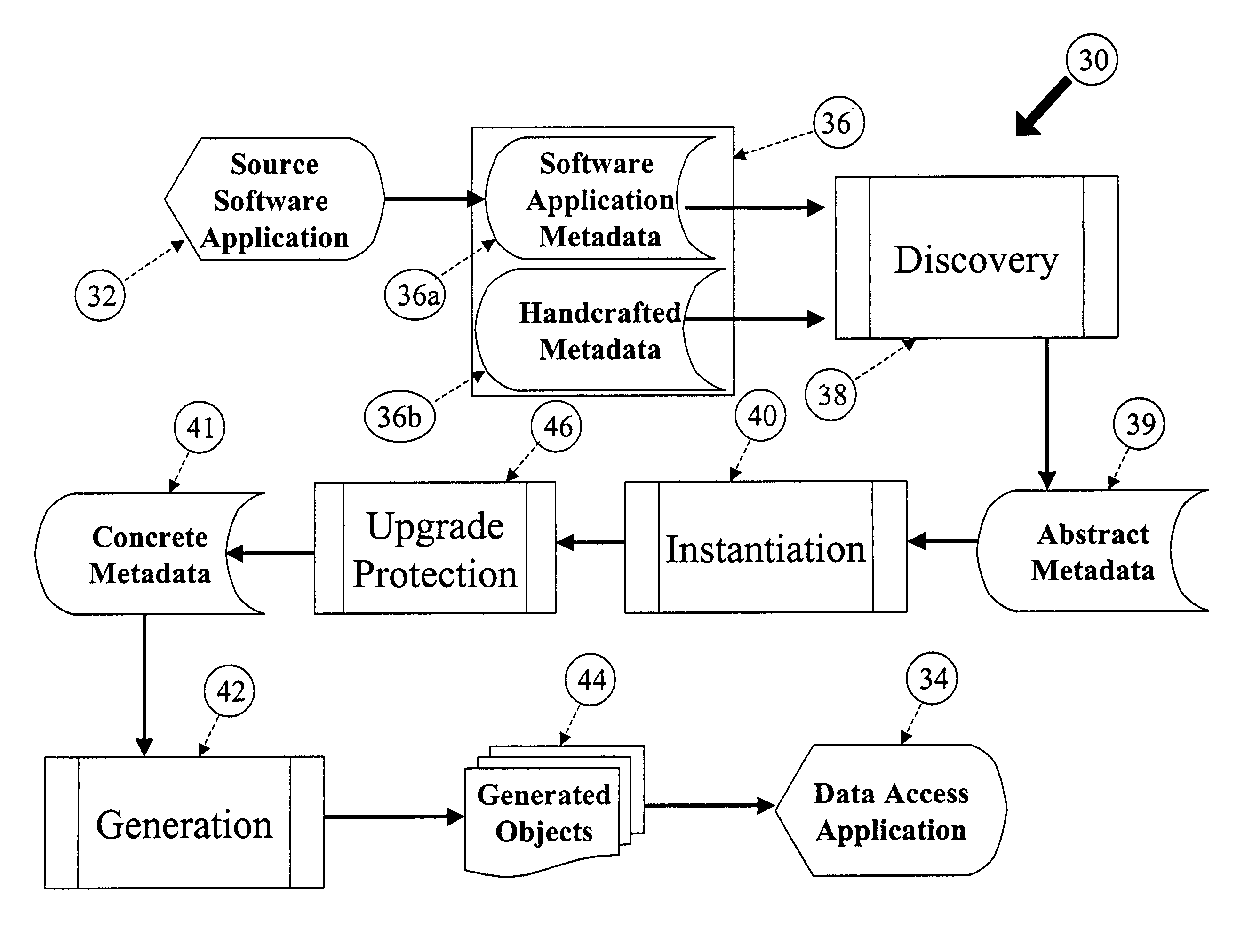
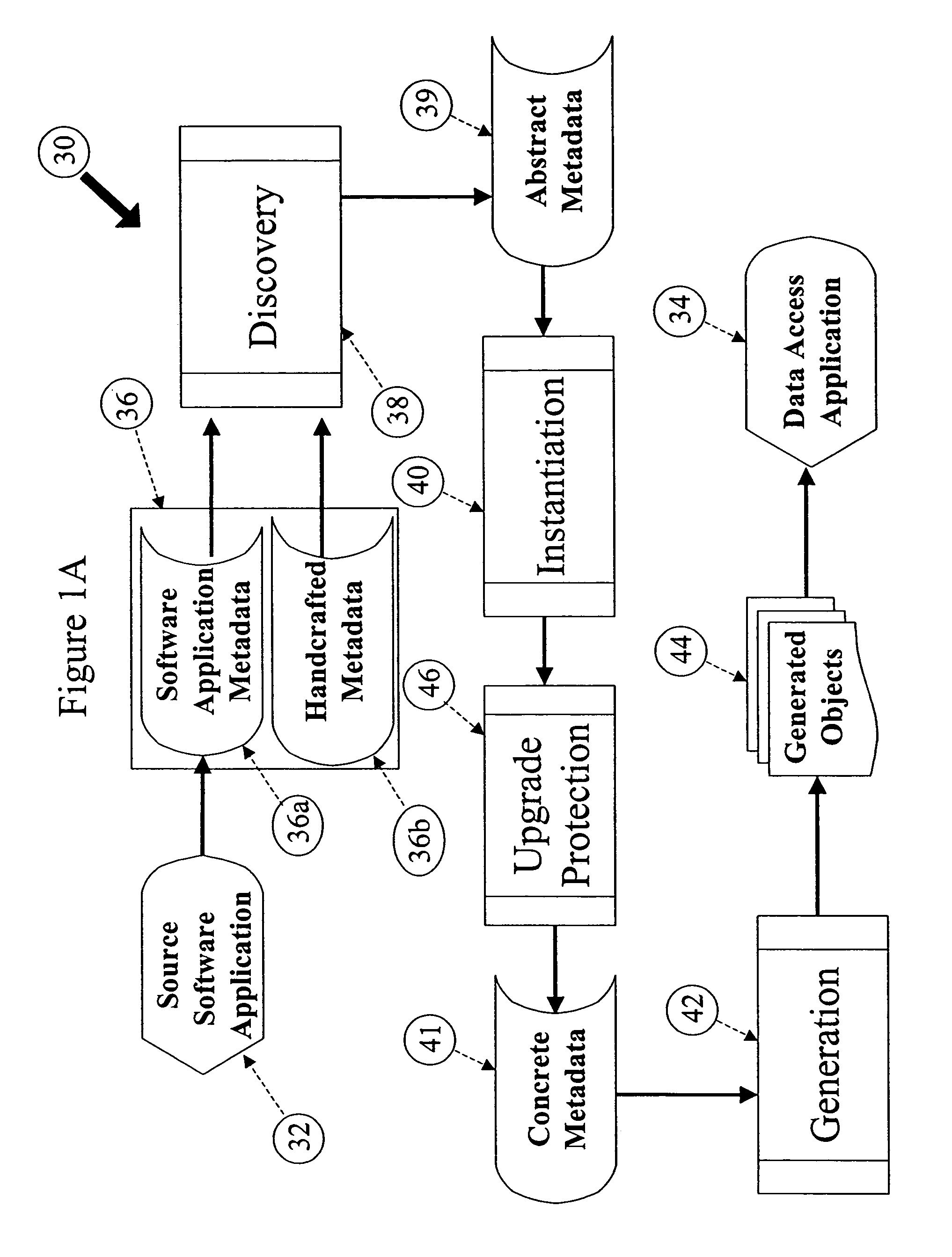
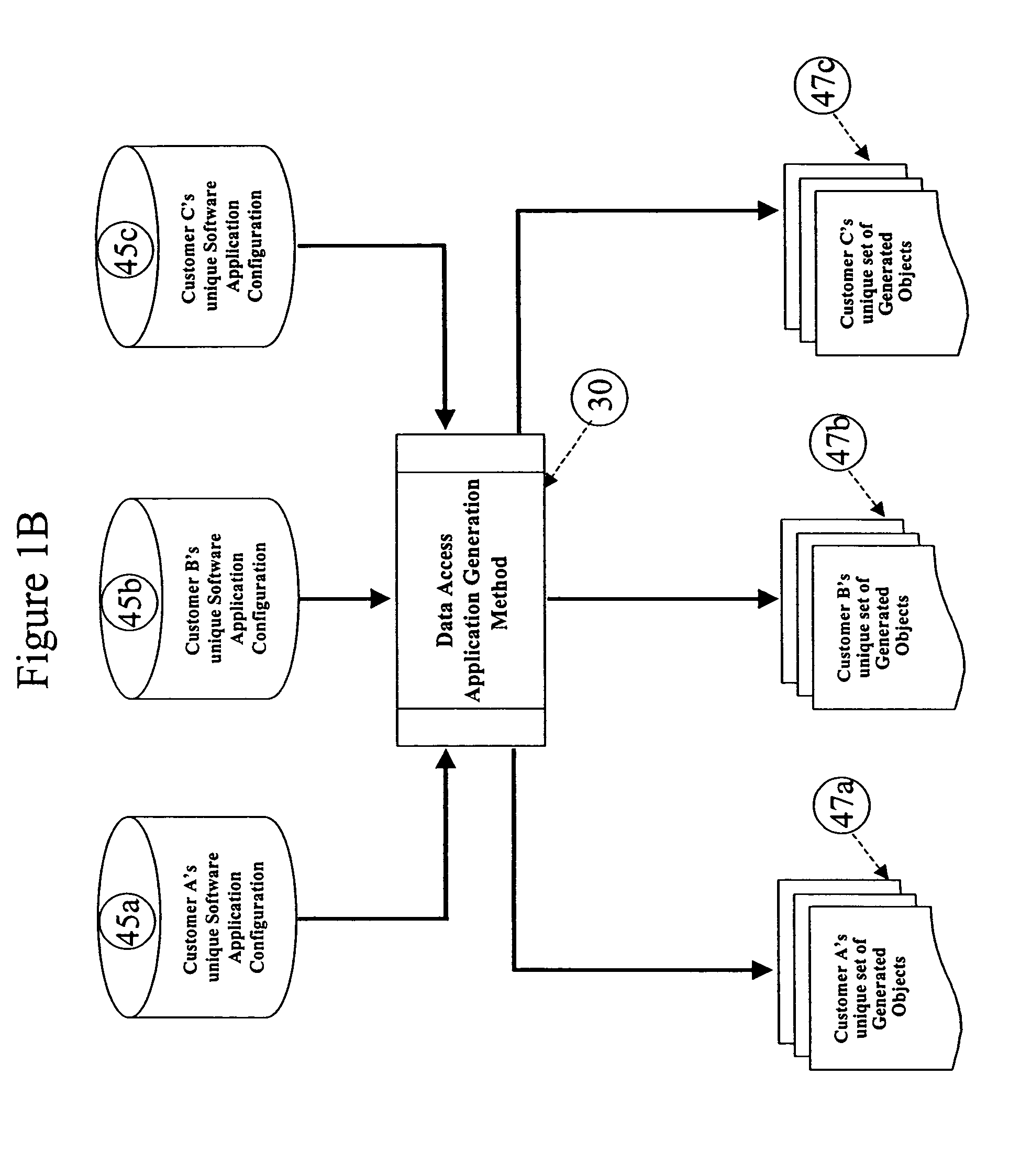
Computer implemented system and method for the generation of data access applications
InactiveUS7350191B1Increase valueImprove developmentDigital data processing detailsSpecific program execution arrangementsMultiple formsInformation sharing
A method and architecture is described that discovers software application metadata and generates data access applications based on the discovered software application metadata. The discovered metadata along with handcrafted metadata goes through a discovery process and is converted into common, generic abstract metadata objects. The abstract metadata objects then go through an instantiation process to be translated into concrete metadata objects that represent the unique configuration, context and terminology of the source software application. The concrete metadata objects can be generated into numerous forms for the purposes of data access and information sharing. The system also has upgrade protection.
Owner:NOETIX CORP
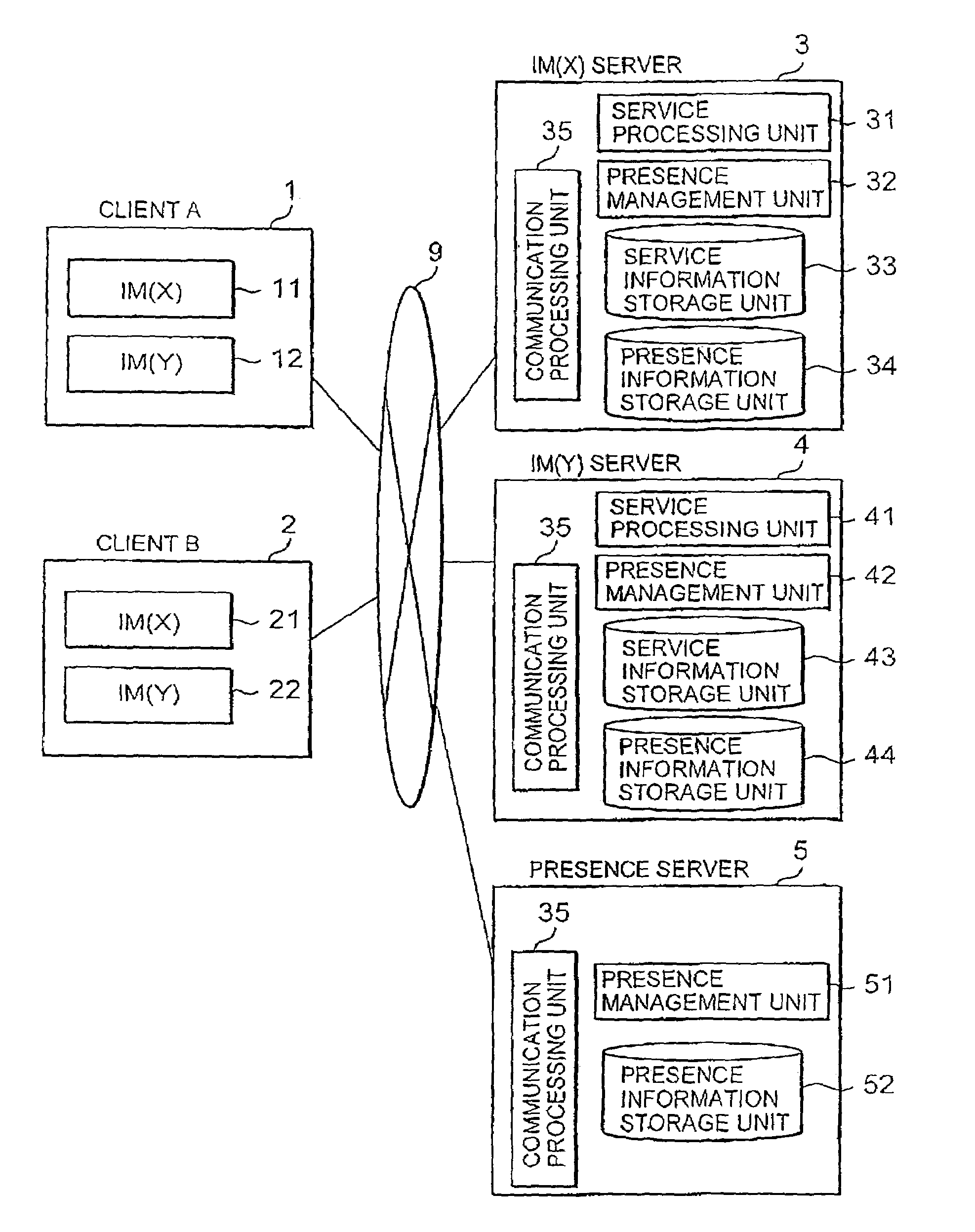
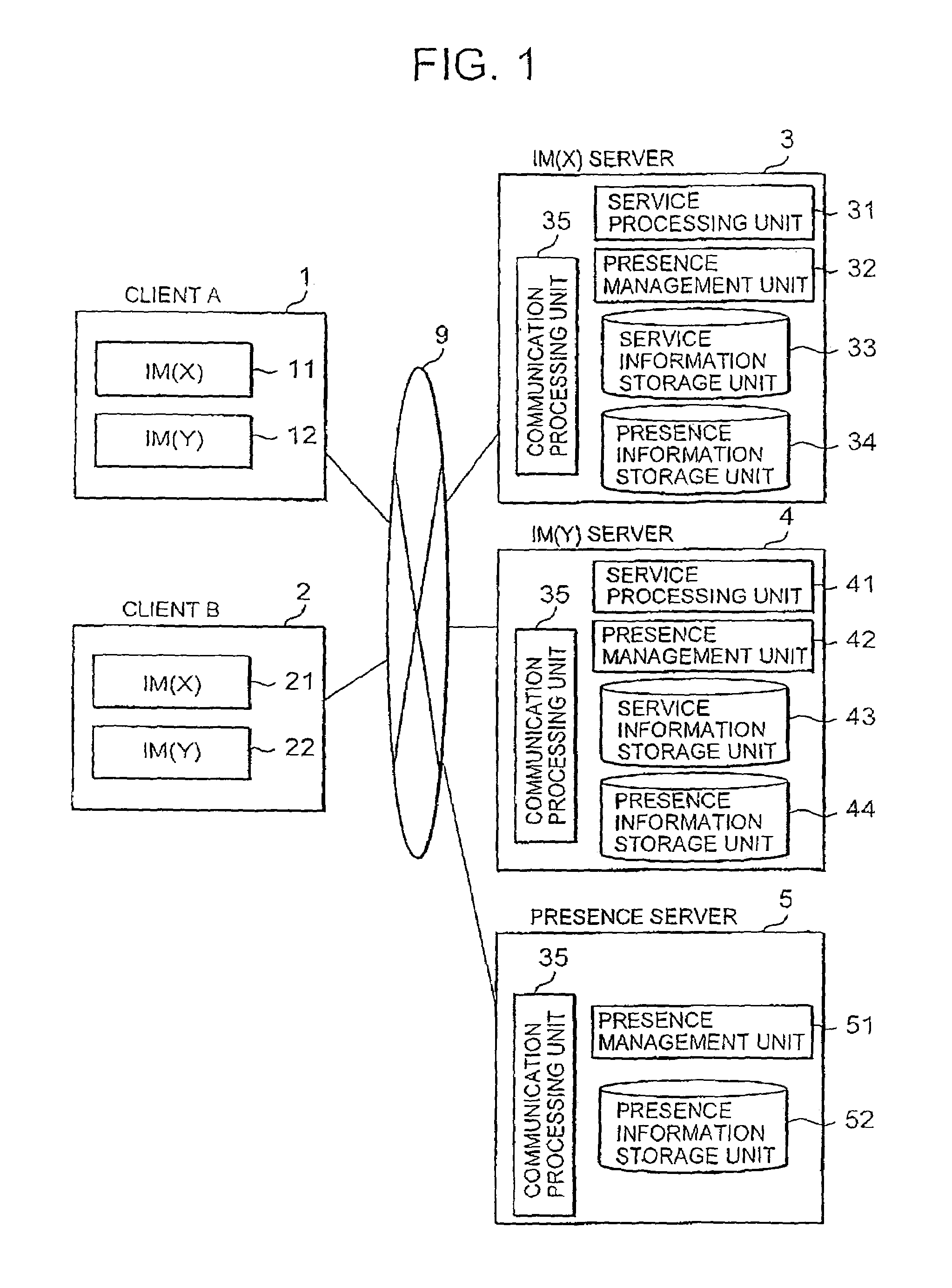
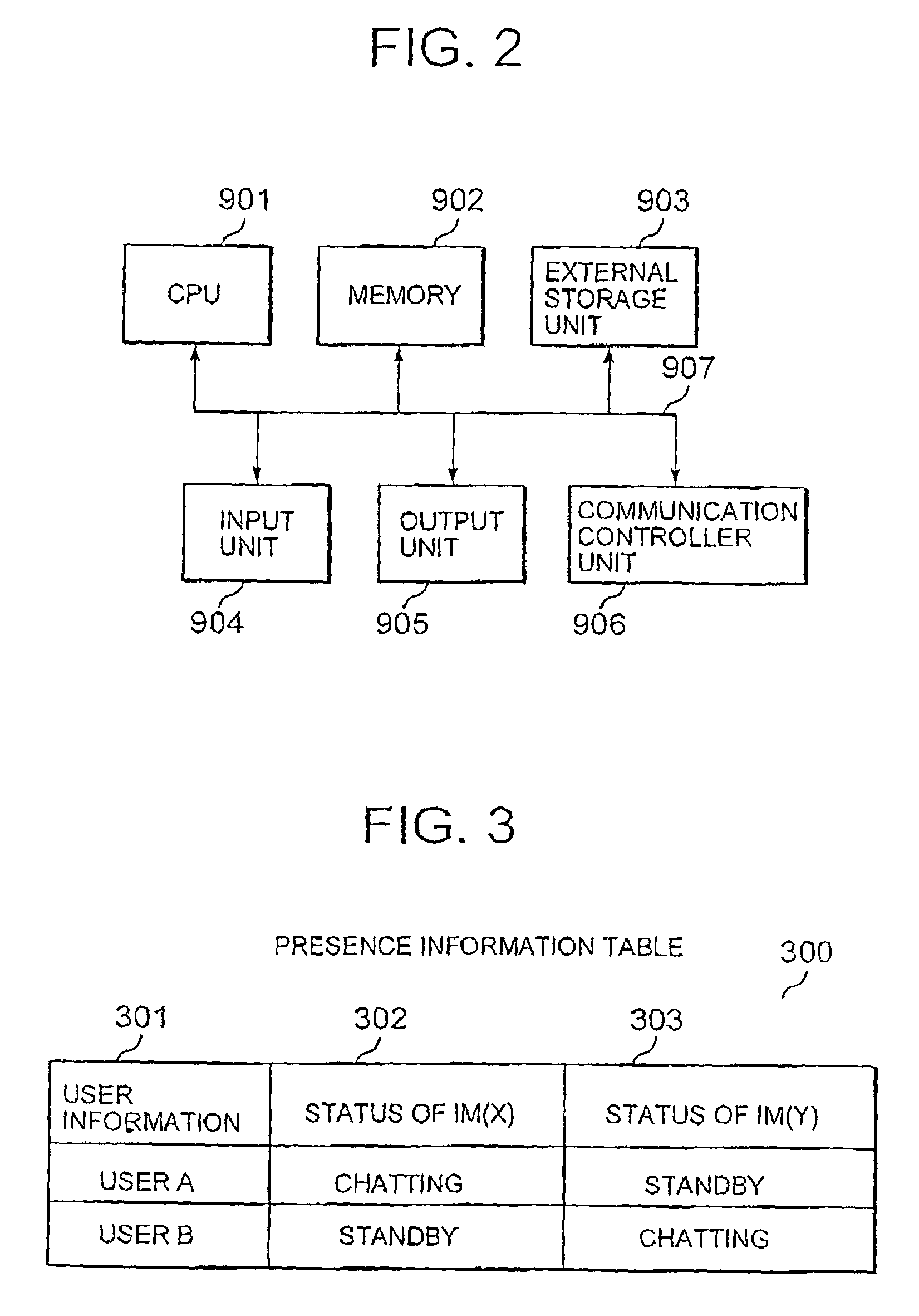
Presence information sharing method and system
ActiveUS7716293B2Special service provision for substationMultiple digital computer combinationsInformation sharingComputer network
Presence information is shared between a plurality of applications, to grasp a change of presence information of a different kind of application.An IM(X) server 3 receives a notification of a change of presence information from a client A1 (S902), and sends a change notification message for notifying the change of the presence information to a presence server 5 (S906). Then, the presence server 5 sends the change notification message received from the IM(X) server 3 to the IM(Y) server 4 (S908). The IM(Y) server 4 sends the change notification message received from the presence server 5 to a client B2 (S910).
Owner:HITACHI LTD
Method and Apparatus for Slice Common Information Sharing
ActiveUS20120207227A1Color television with pulse code modulationColor television with bandwidth reductionLoop filterInformation sharing
A method and apparatus for sharing information in a video coding system are disclosed. Embodiments according to the present invention use an information sharing flag to determine whether to share in-loop filter information in the picture level. The information sharing flag may be incorporated in the sequence level, the picture level or the slice level to indicate whether information sharing is enabled. Multiple information sharing flags may also be used to adaptively control information sharing. Furthermore, method and apparatus of using multiple Adaptation Parameter Sets (APSs) for information sharing of in-loop filters are disclosed. APS identifiers of in-loop filters may be incorporated in the slice header to allow each of the in-loop filters select respective filter information from the multiple APSs. A flag is incorporated in SPS to indicate whether multiple APS or single APS is used. Various exemplary syntax designs are disclosed to illustrate information sharing.
Owner:HFI INNOVATION INC
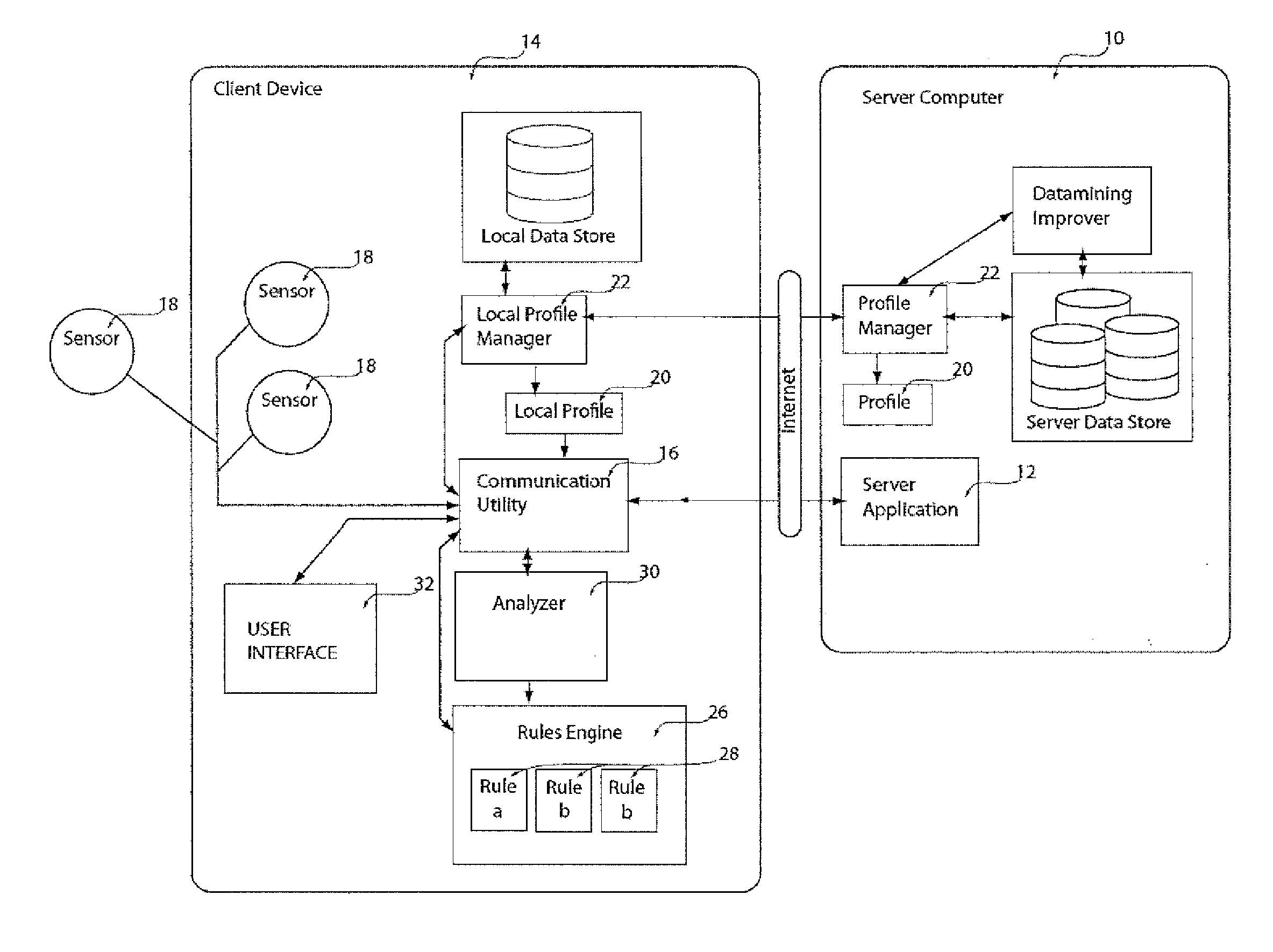
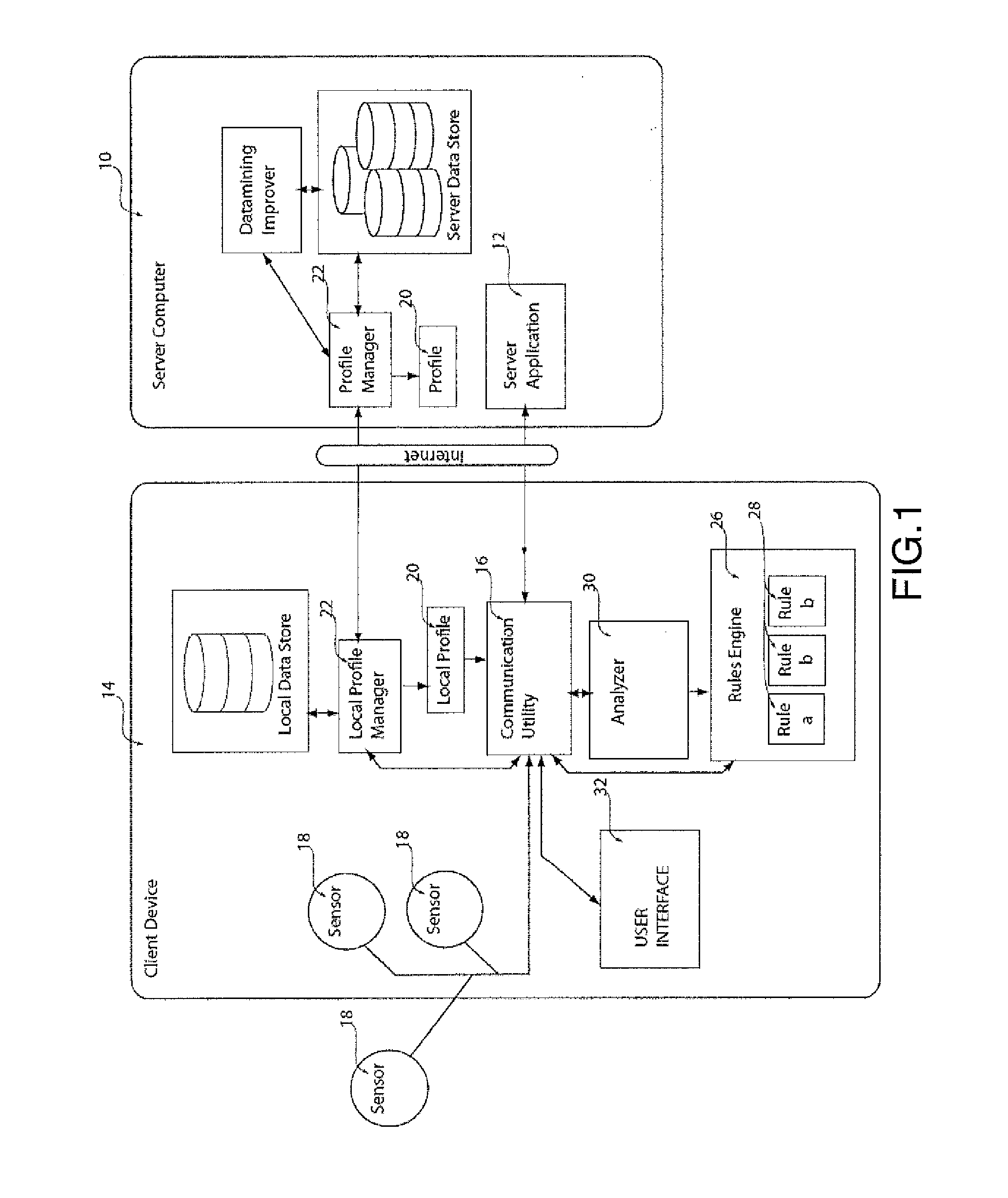
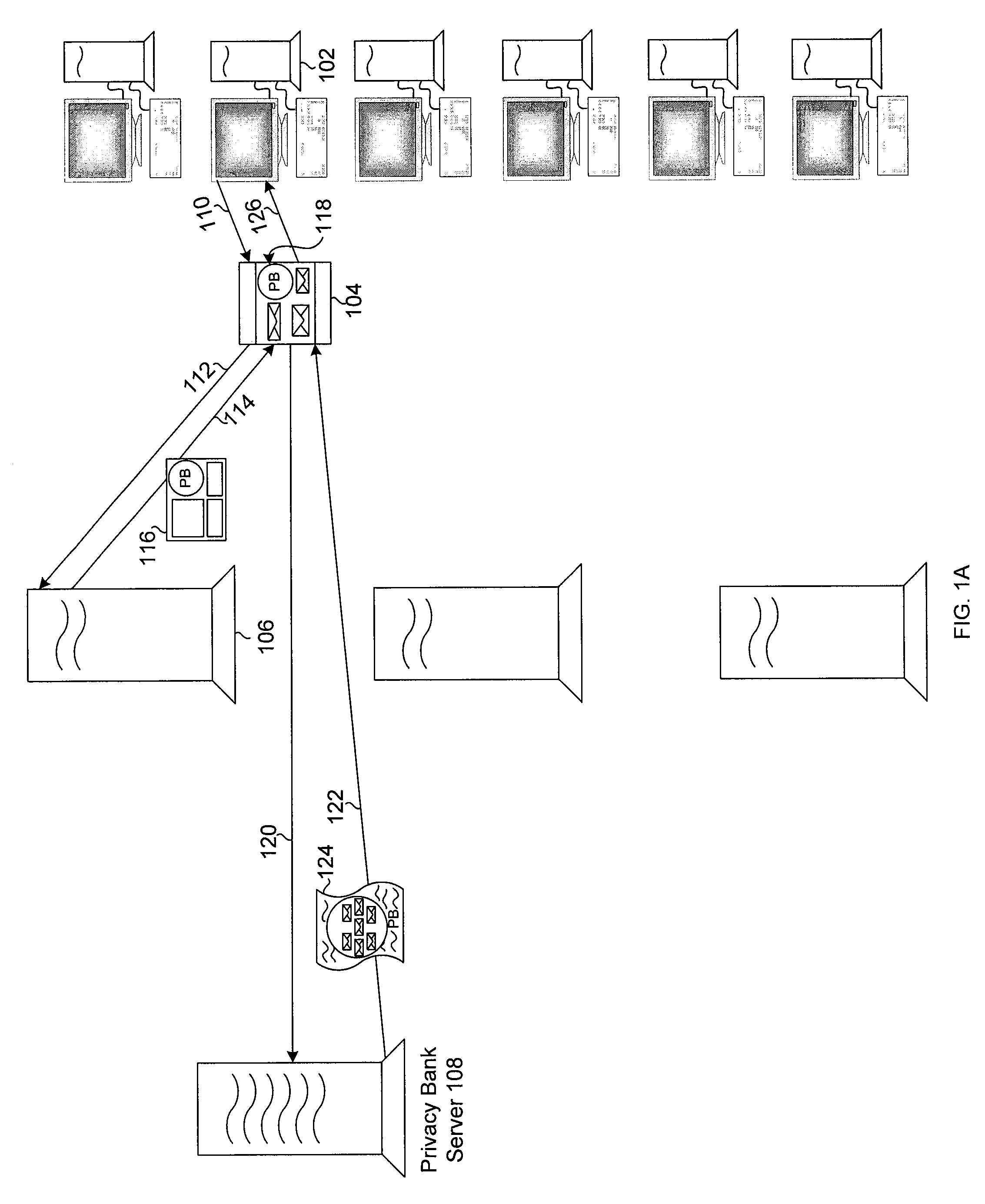
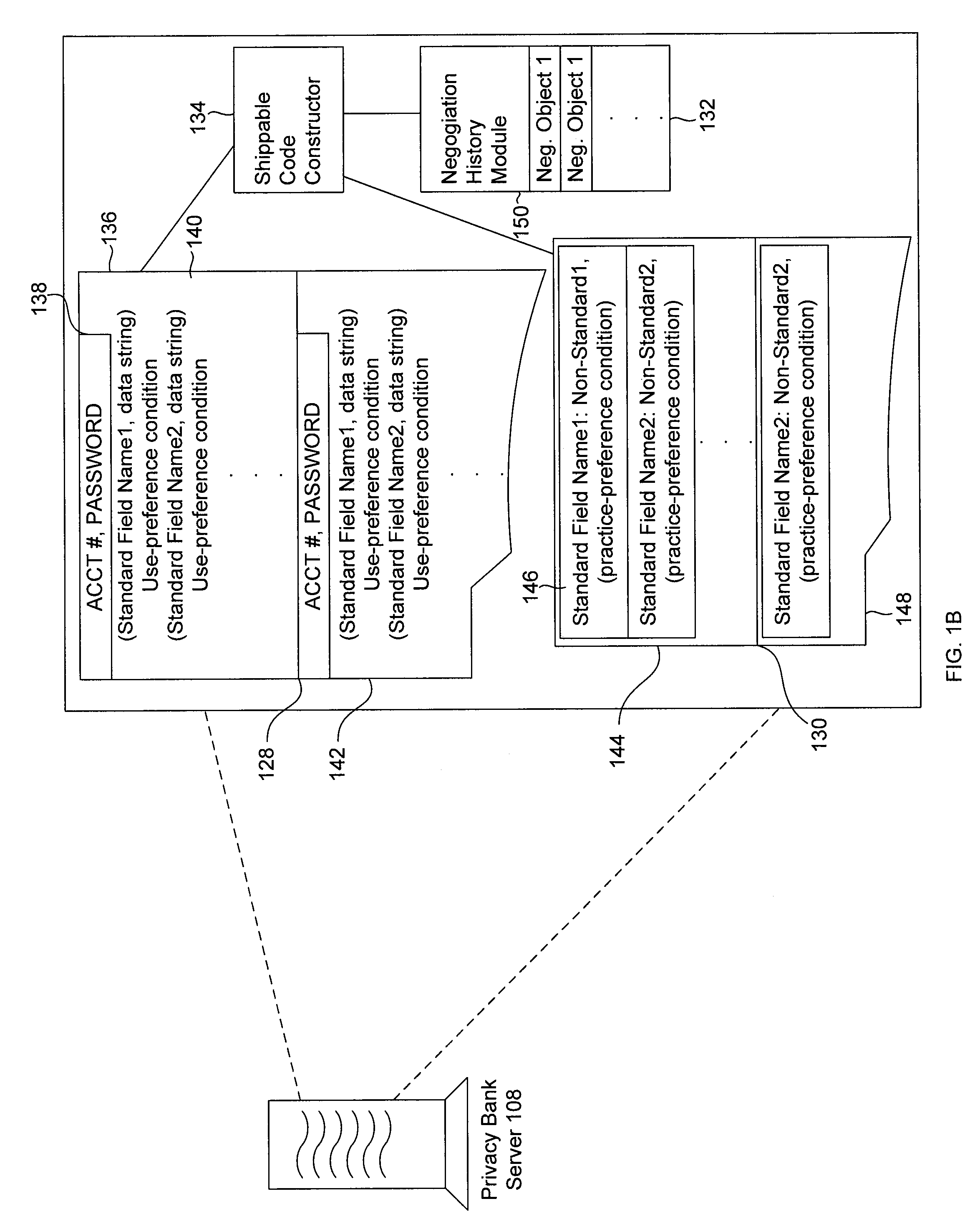
Abstractions and automation for enhanced sharing and collaboration
InactiveUS20050232423A1Optimal information privacyReduce the burden onDigital data processing detailsUser identity/authority verificationInformation sharingCrowds
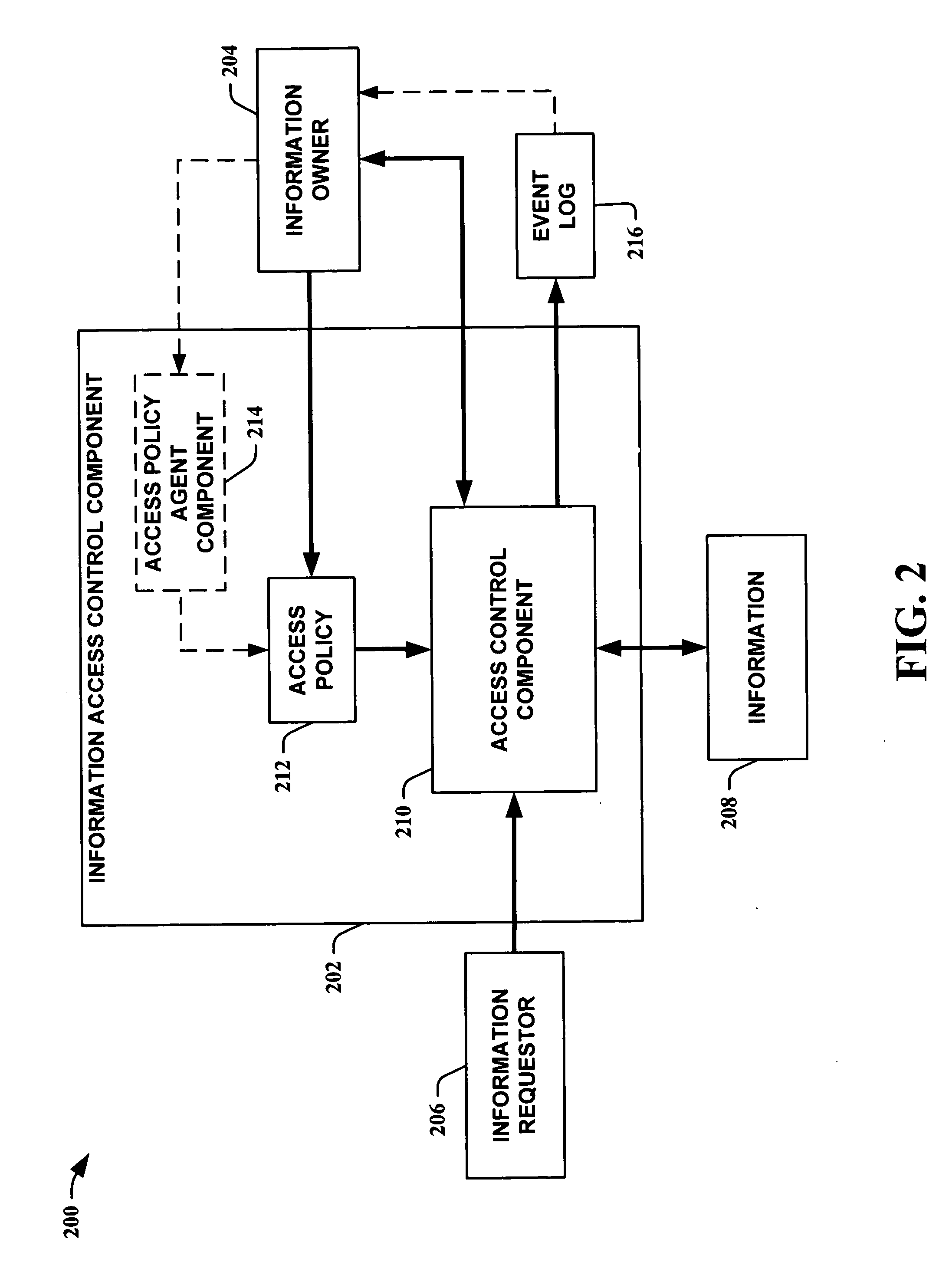
The present invention provides methods for using abstractions of people, including dynamic and static groups of people, to enhance the efficiency of the specification and automation of policies for sharing information between users with a “need-to-know.” An instance of the present invention can also provide these users information based on a “time-to-know.” By providing access to information based on group affiliation and properties of the content of the information, the present invention maintains optimal information privacy while minimizing encumbrances to sharing data with appropriate users and even at appropriate times. The present invention can be integrated with other communication technologies to facilitate access to information in a time appropriate manner. Other instances of the present invention employ automated and semi-automated, mixed-initiative techniques, to make information-sharing decisions. Additional instances of the present invention include the employment of machine-learning techniques to facilitate construction of access policies from the actions or profile of a single user or a community of users, including the construction of automated sharing agents that work in an automated or mixed-initiative manner to respond to real-time requests for information.
Owner:MICROSOFT TECH LICENSING LLC
Dynamic creation of information sharing social networks
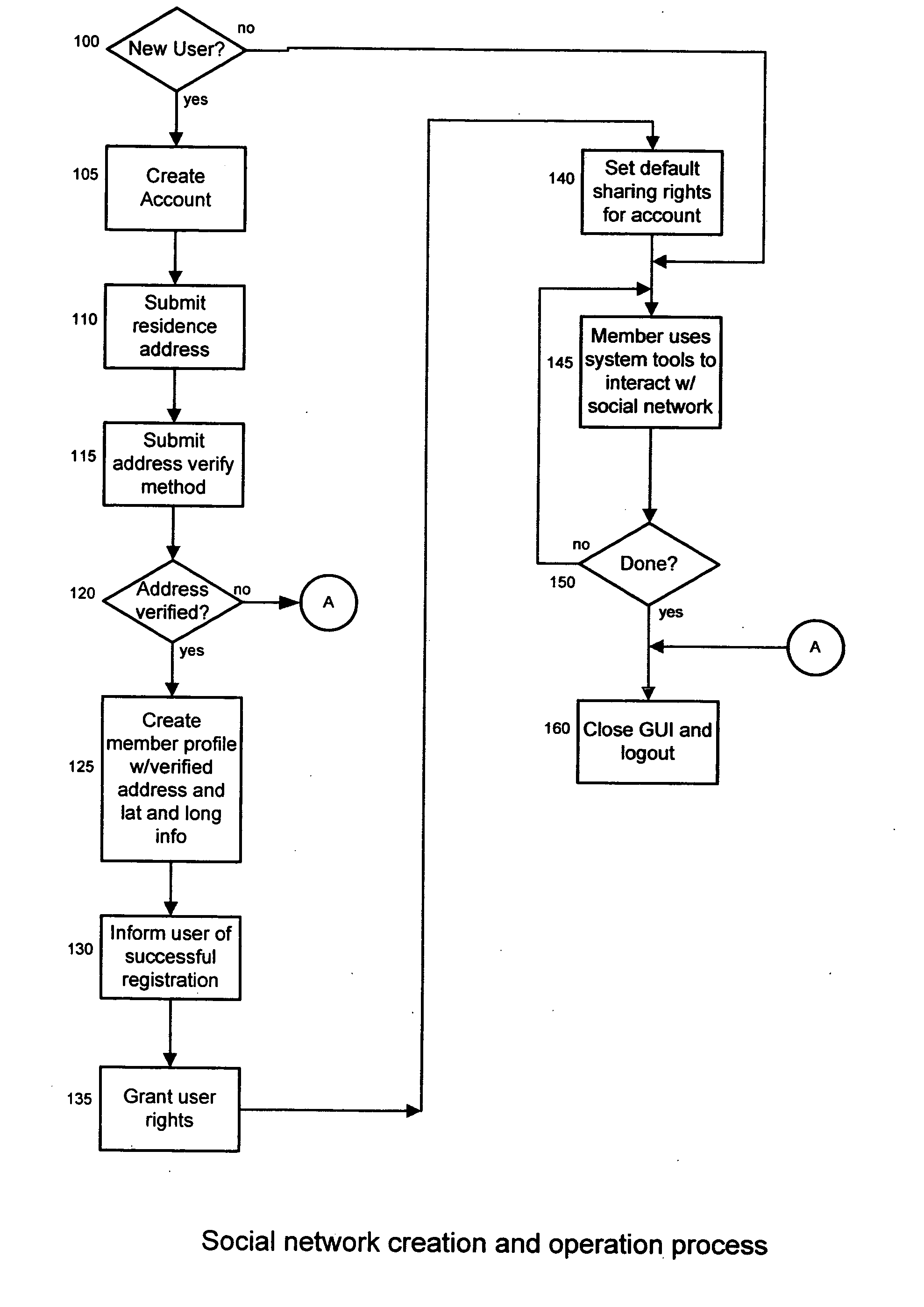
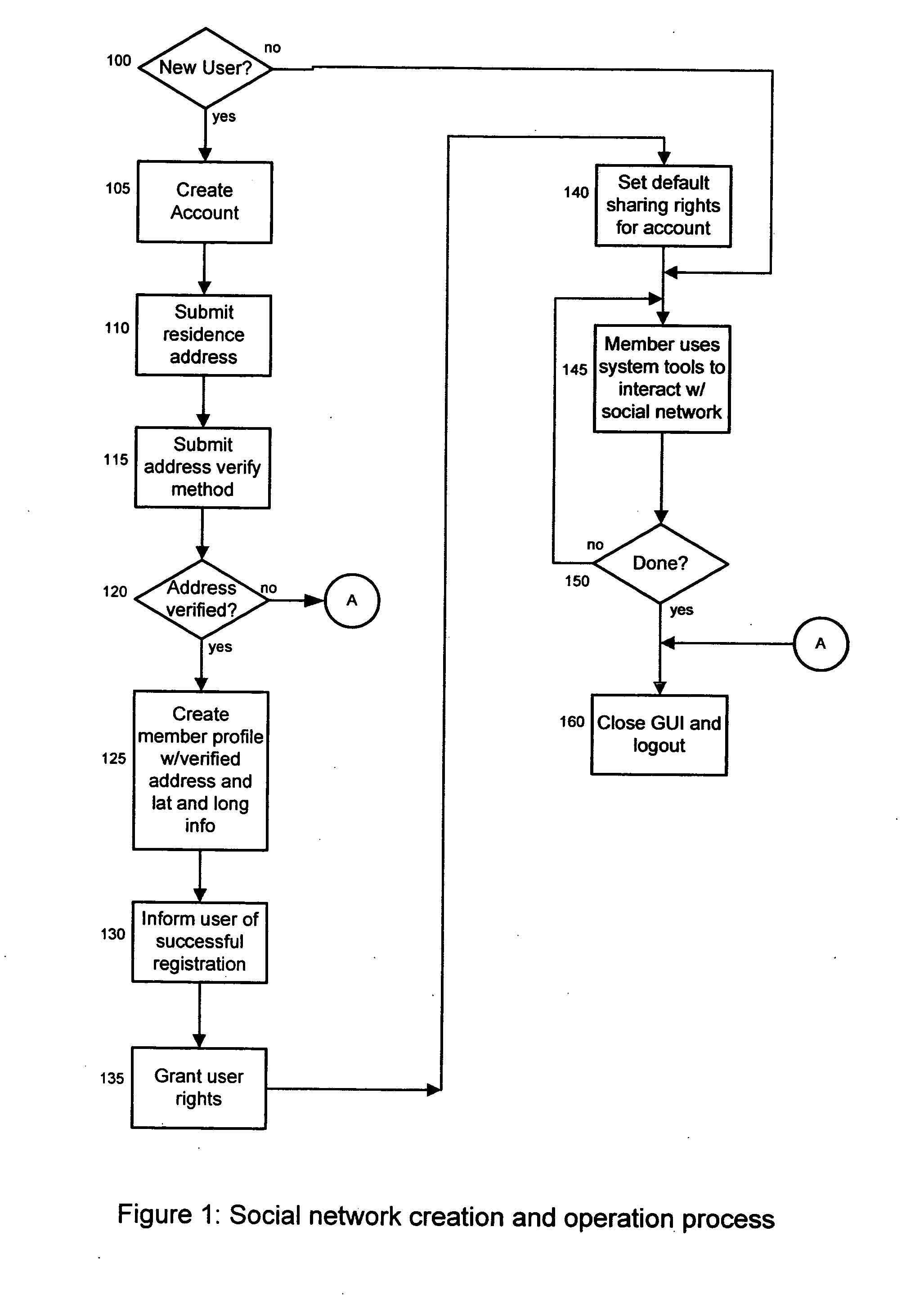
InactiveUS20080097999A1Reduce usageSimple and systematicOffice automationLocation information based serviceInformation sharingNetwork connection
A system and method for creating and using a searchable and browsable directory of verified, network connected and geo-coded users, listing members according to their proximity to each other and according to the longitude and latitude coordinates of each user. By making the member directory accessible to users dynamically the system eases the connection and interaction of neighbors and members of the same physical community.
Owner:HORAN TIM
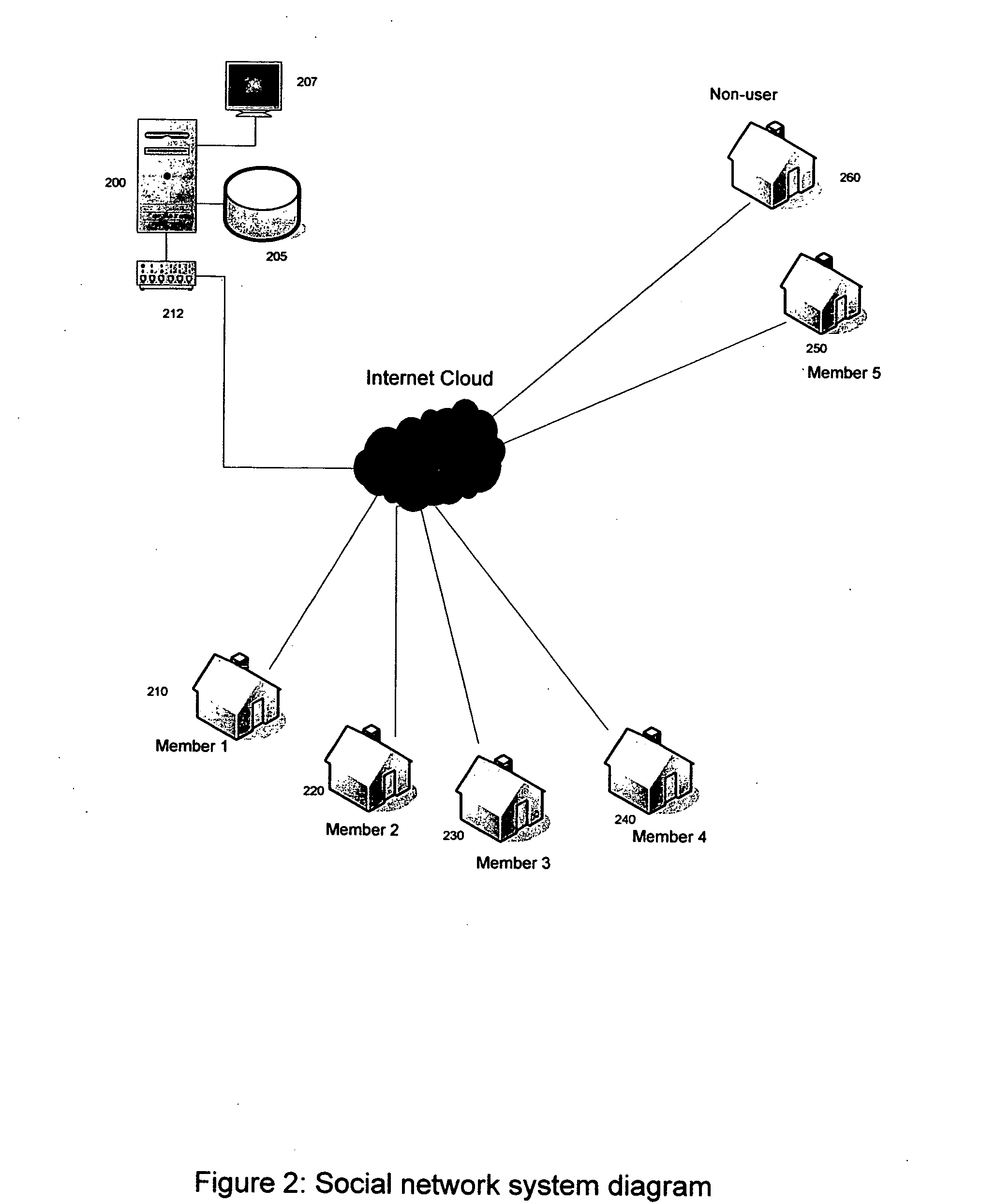
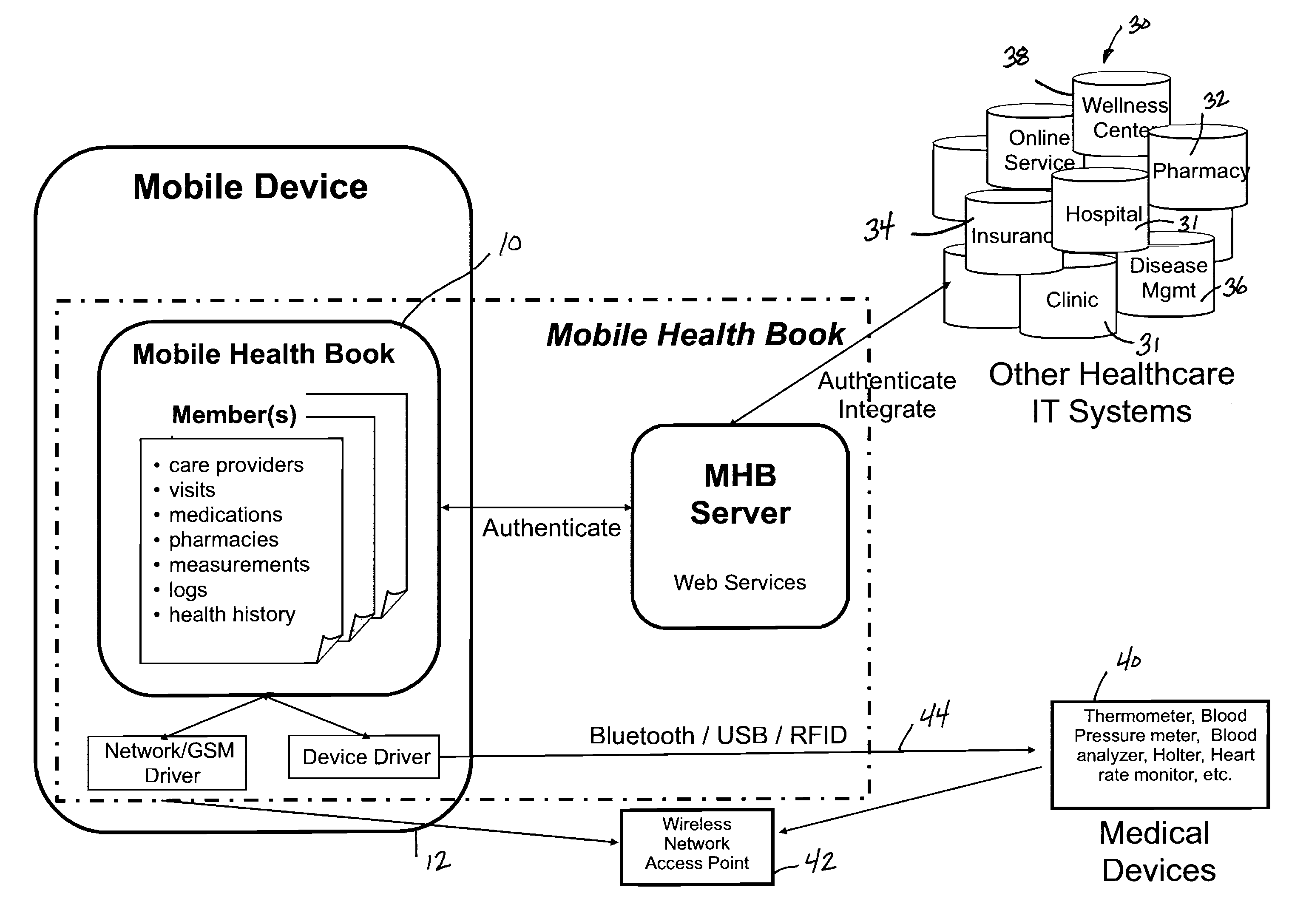
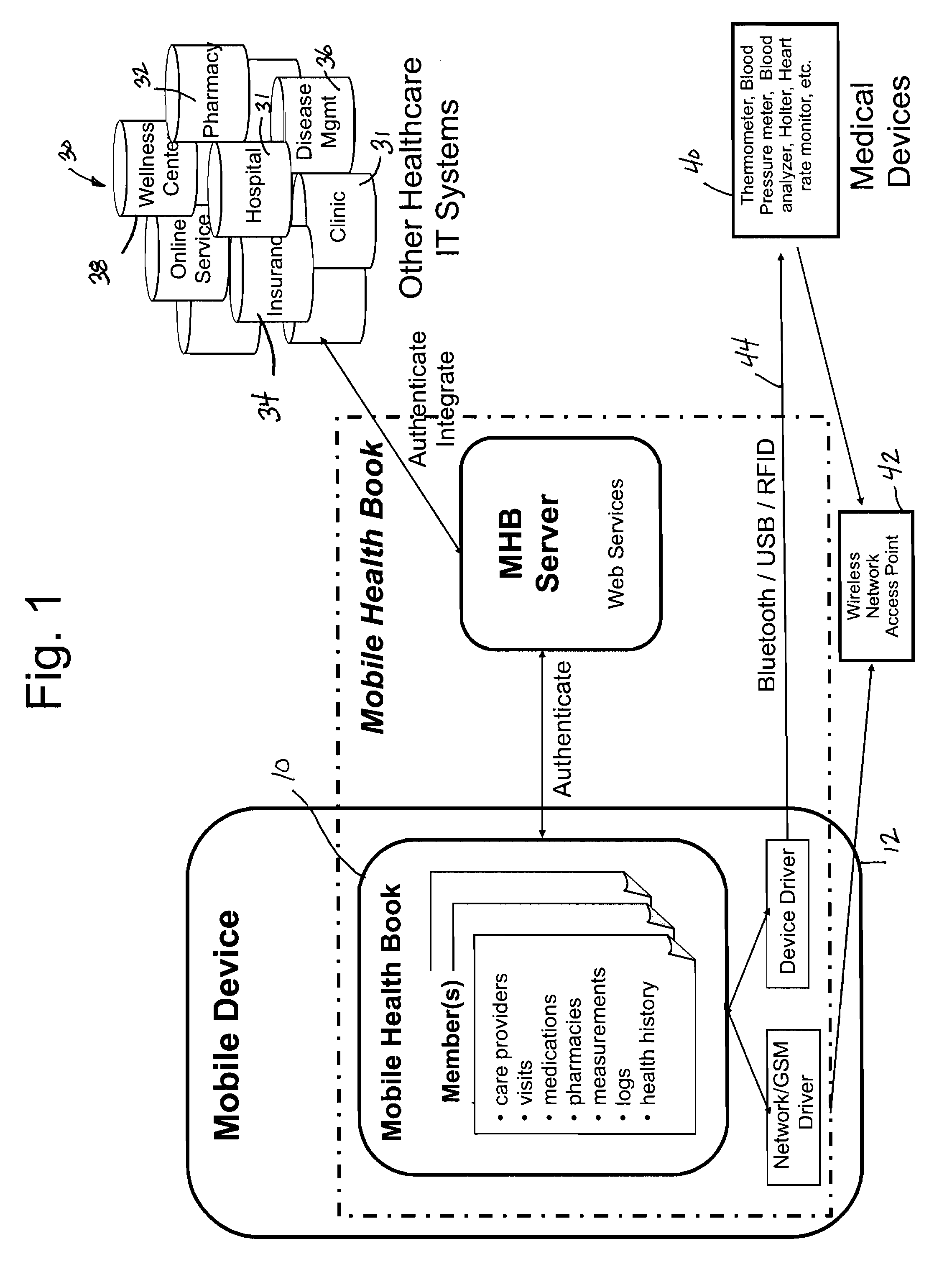
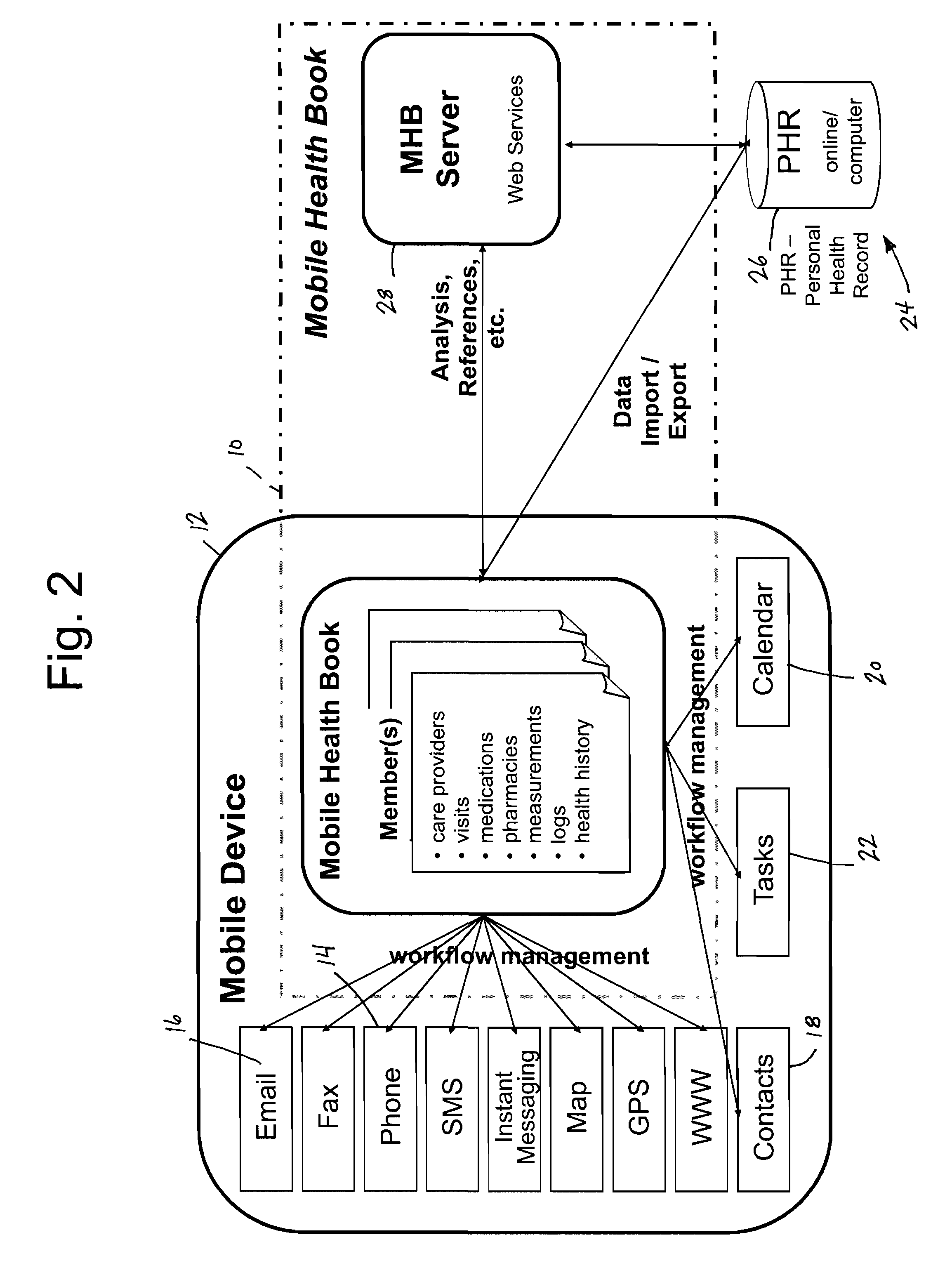
Mobile health book
InactiveUS20090259493A1Local control/monitoringDrug and medicationsHealth related informationInformation sharing
A mobile health book (MHB) is incorporated into a mobile device such that users can manage and track health care related information for the user. The mobile health book includes a health tracking software program stored on the memory of the mobile device. The health tracking software receives and stores various health related information for the user. The health tracking software program communicates with at least the contact management program and calendar program on the mobile device to integrate the function of these programs with the health tracking software. The mobile device is able to communicate with other mobile devices such that health related information from the mobile device can be shared and synchronized with similar information on a second mobile device. The synchronization and sharing of health related information between multiple mobile devices allows the user of one mobile device to track and monitor health related information for a second user through the wireless sharing of information.
Owner:VENON MEDHI O +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com