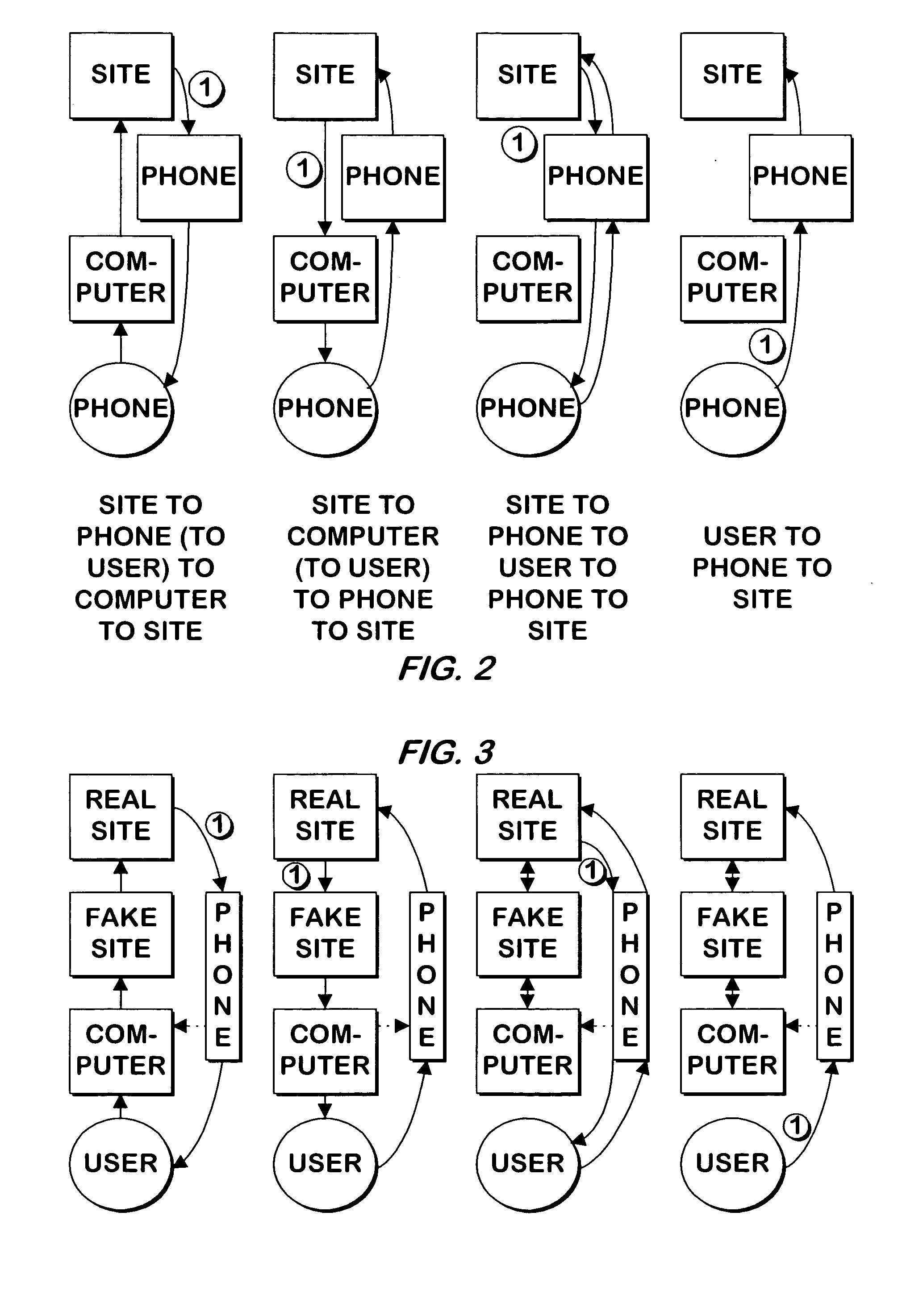
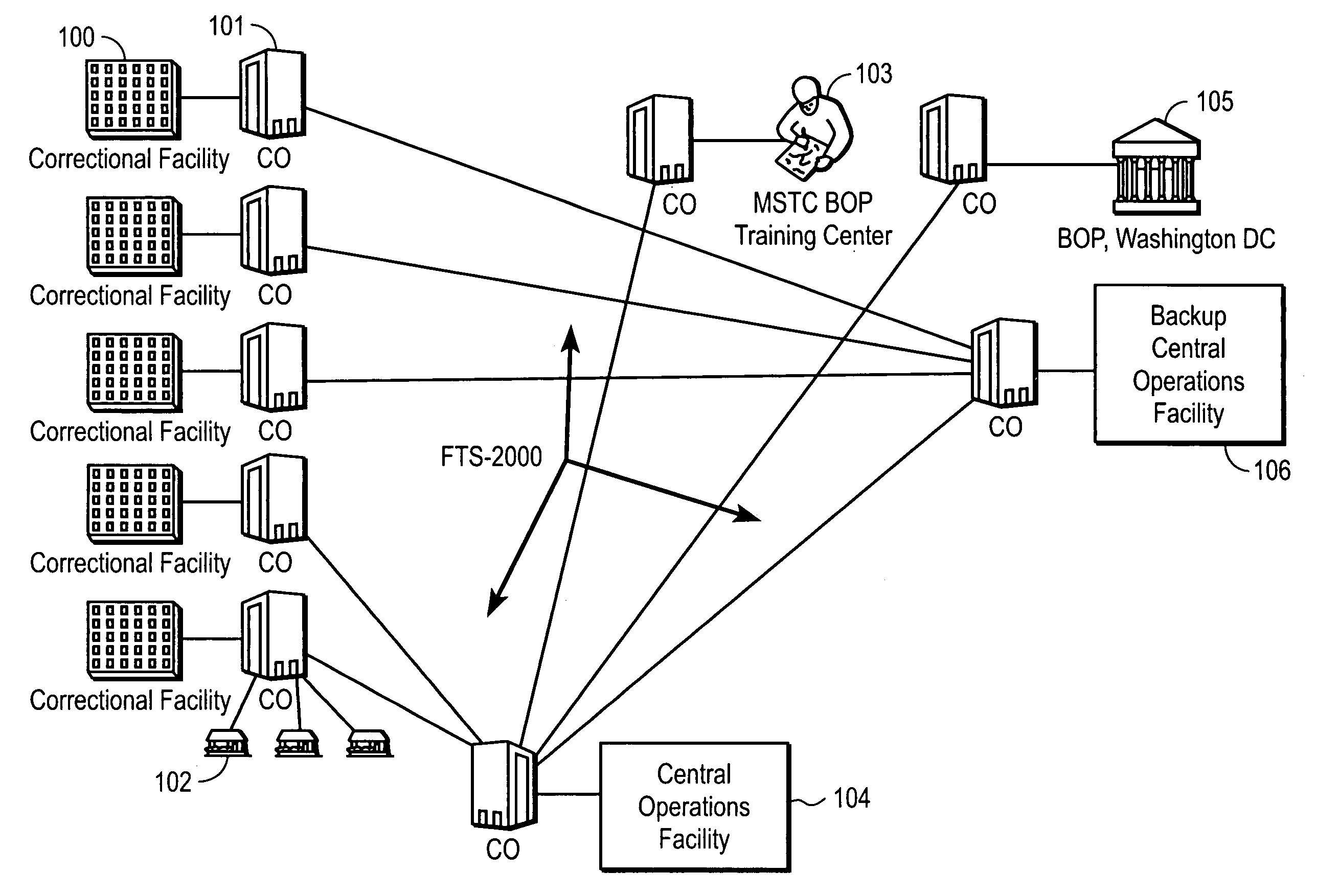
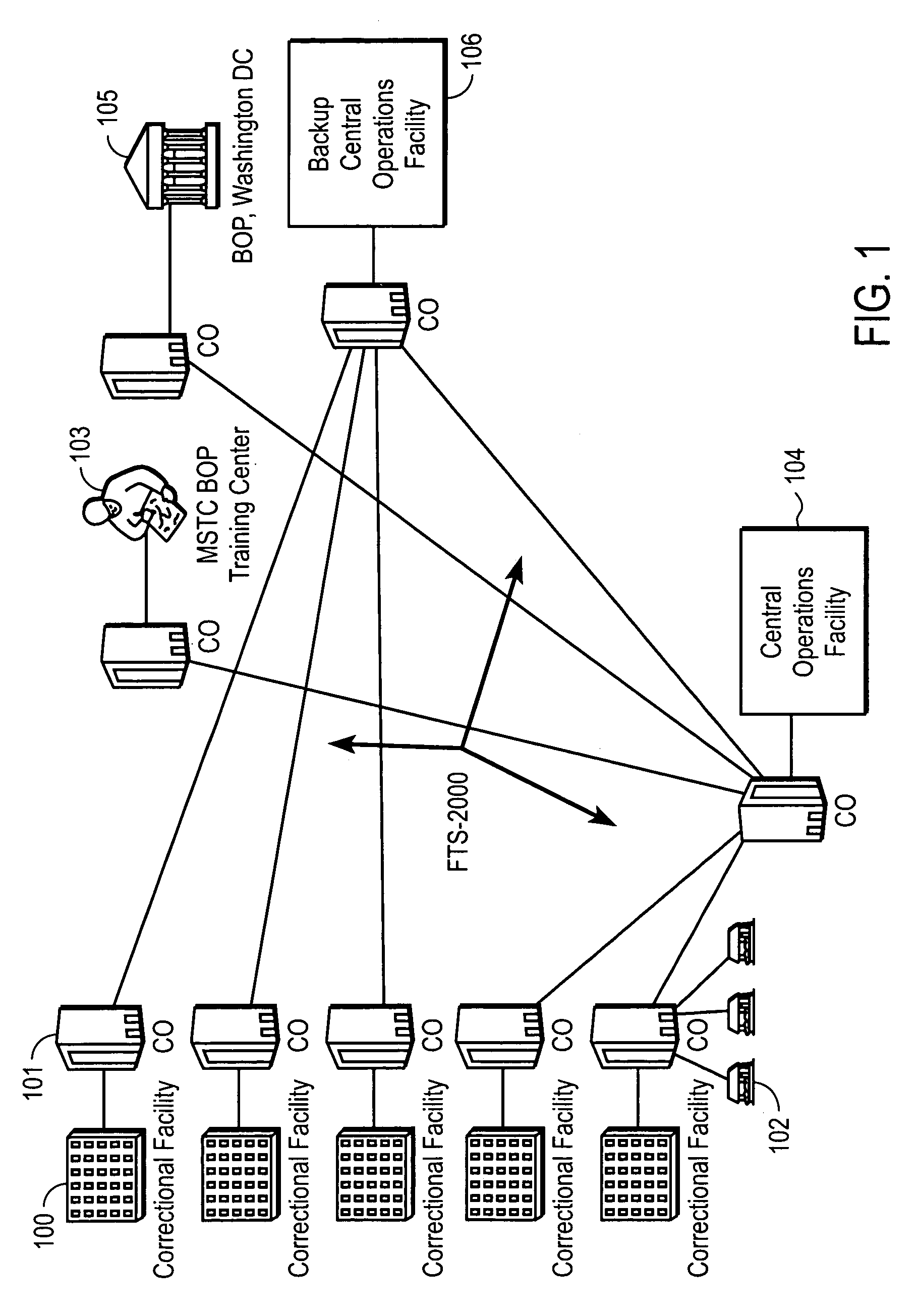
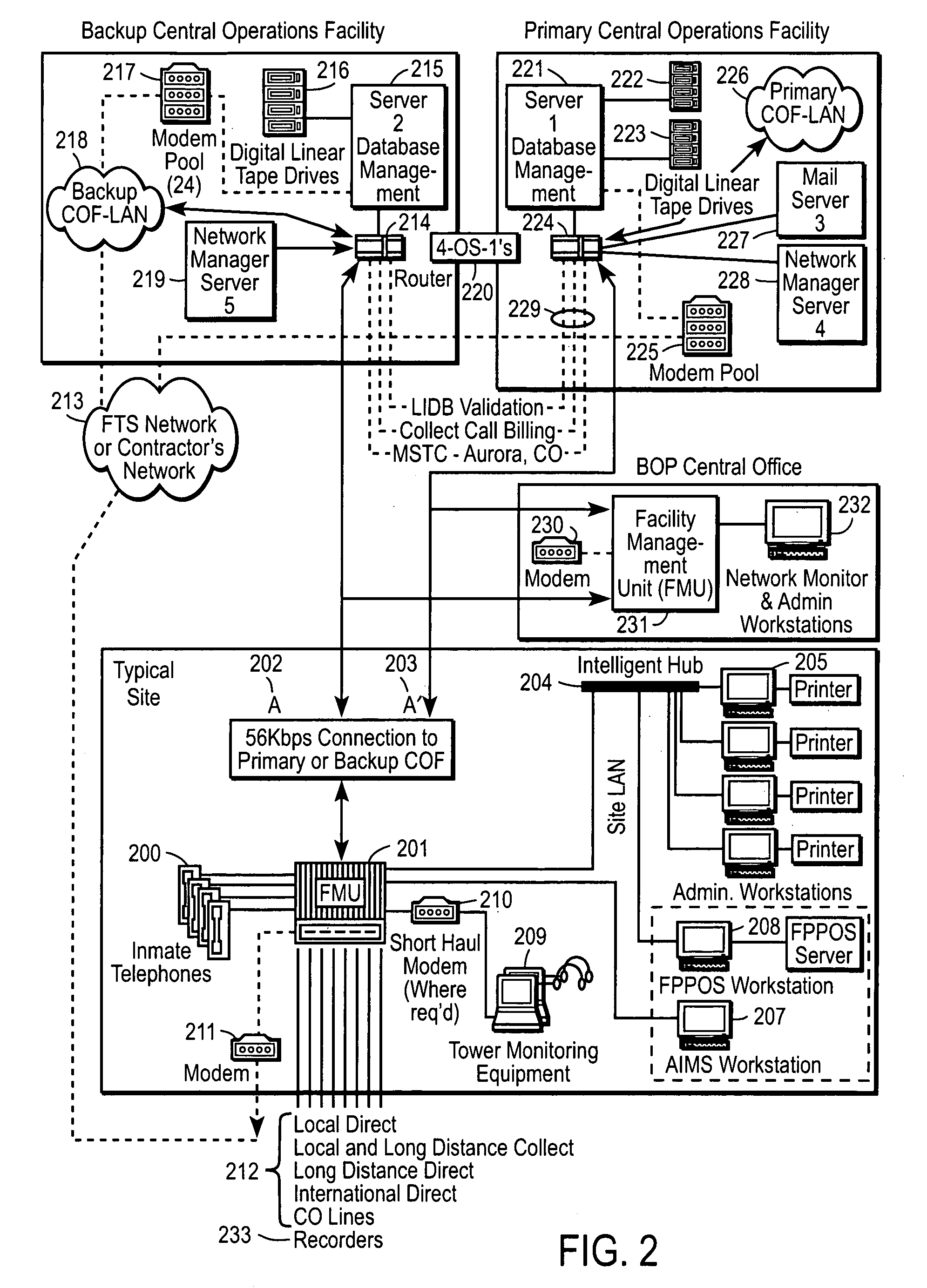
Patents
Literature
342598results about How to "Improve security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
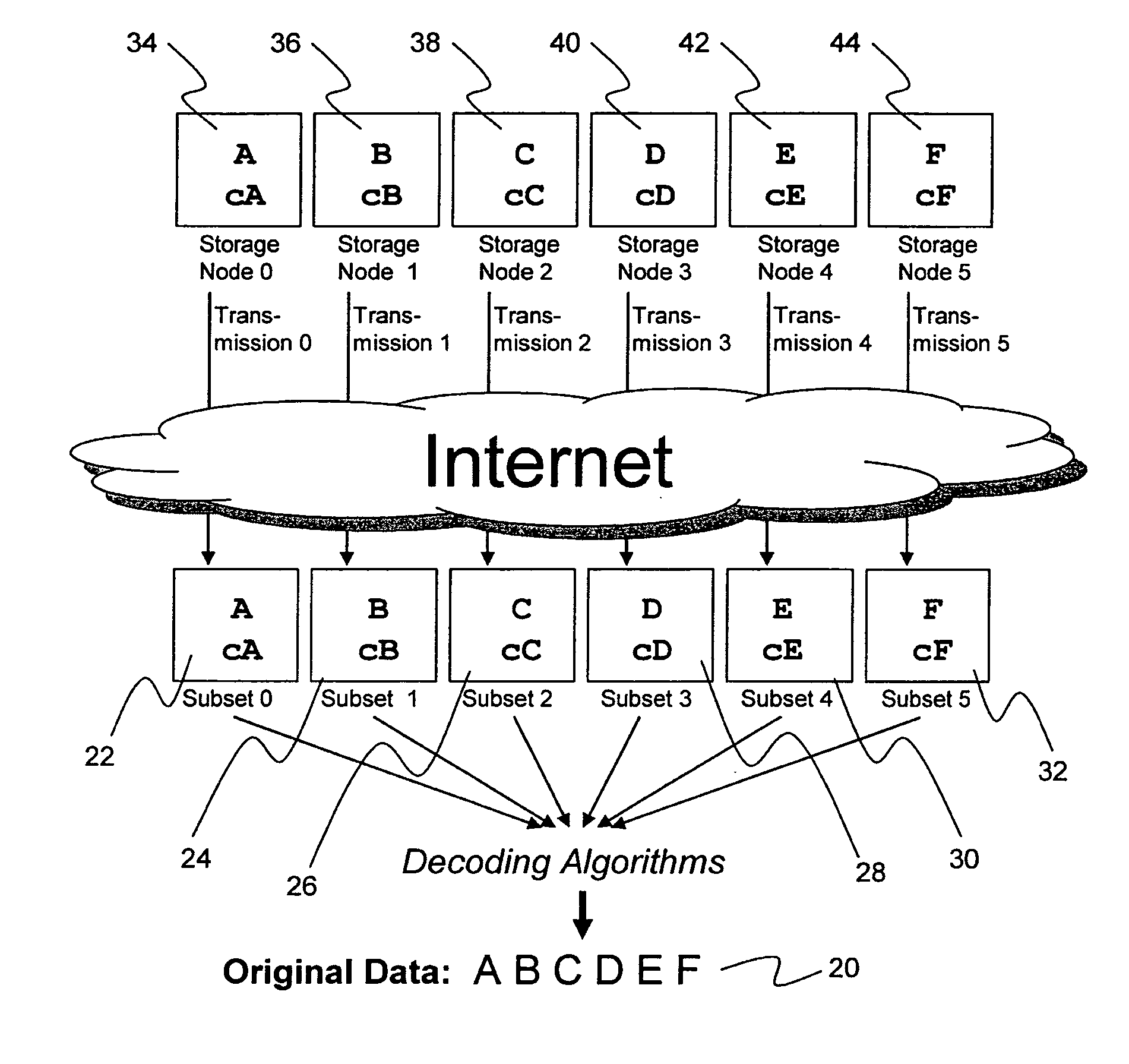
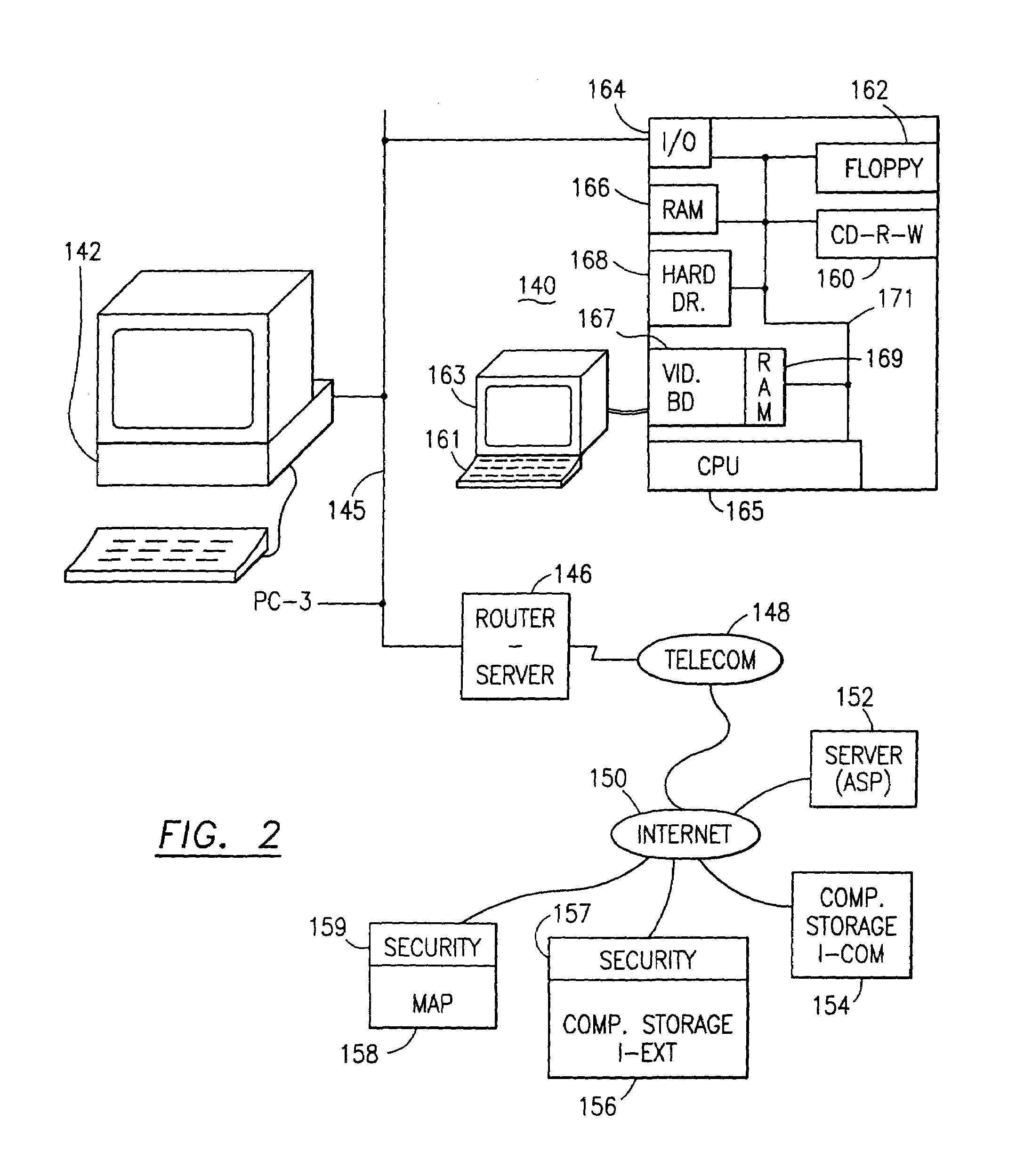
System for rebuilding dispersed data
ActiveUS20070079082A1Reliably and securely protectImprove privacyError detection/correctionDigital data protectionGrid resourcesInformation dispersal
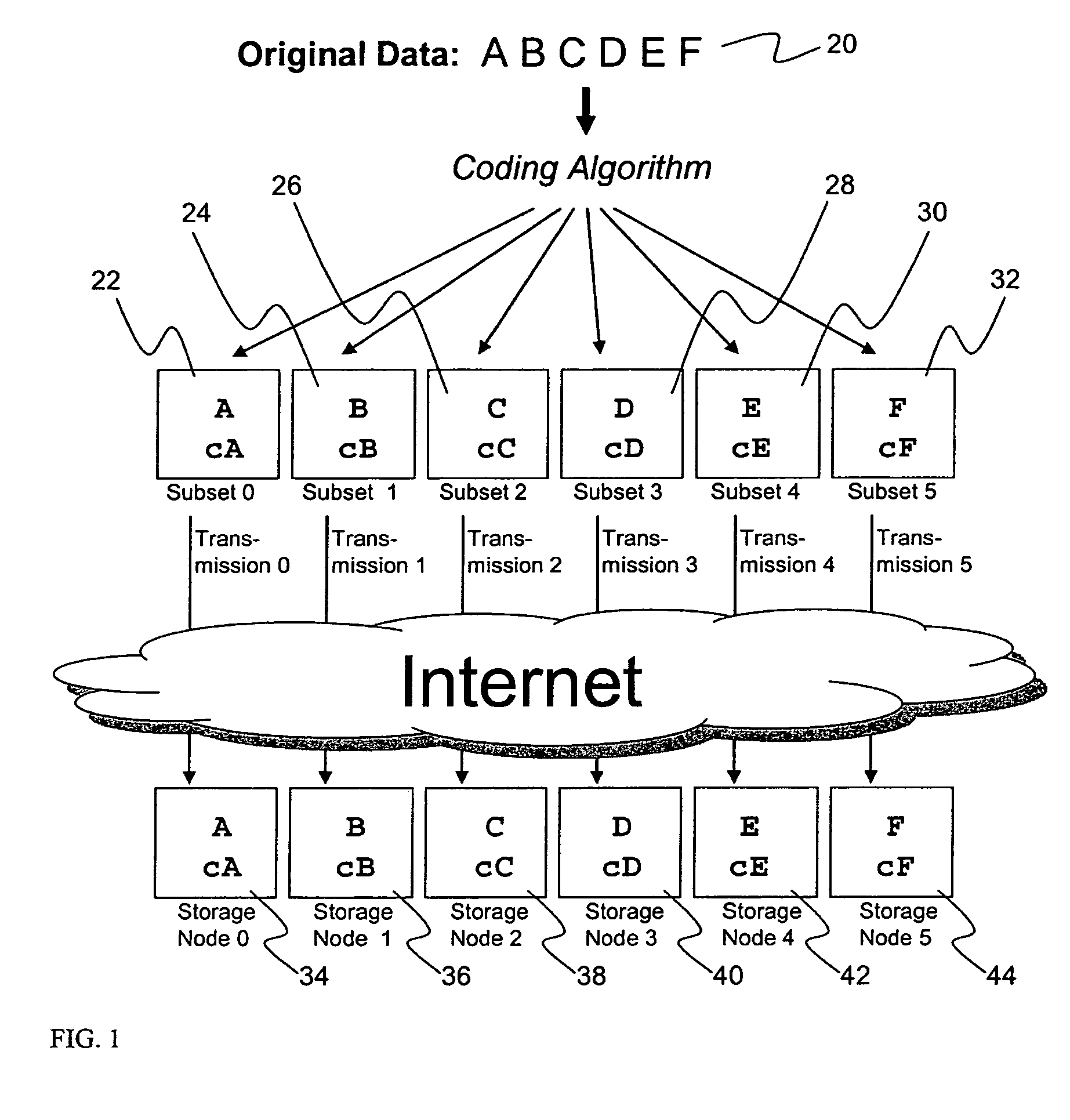
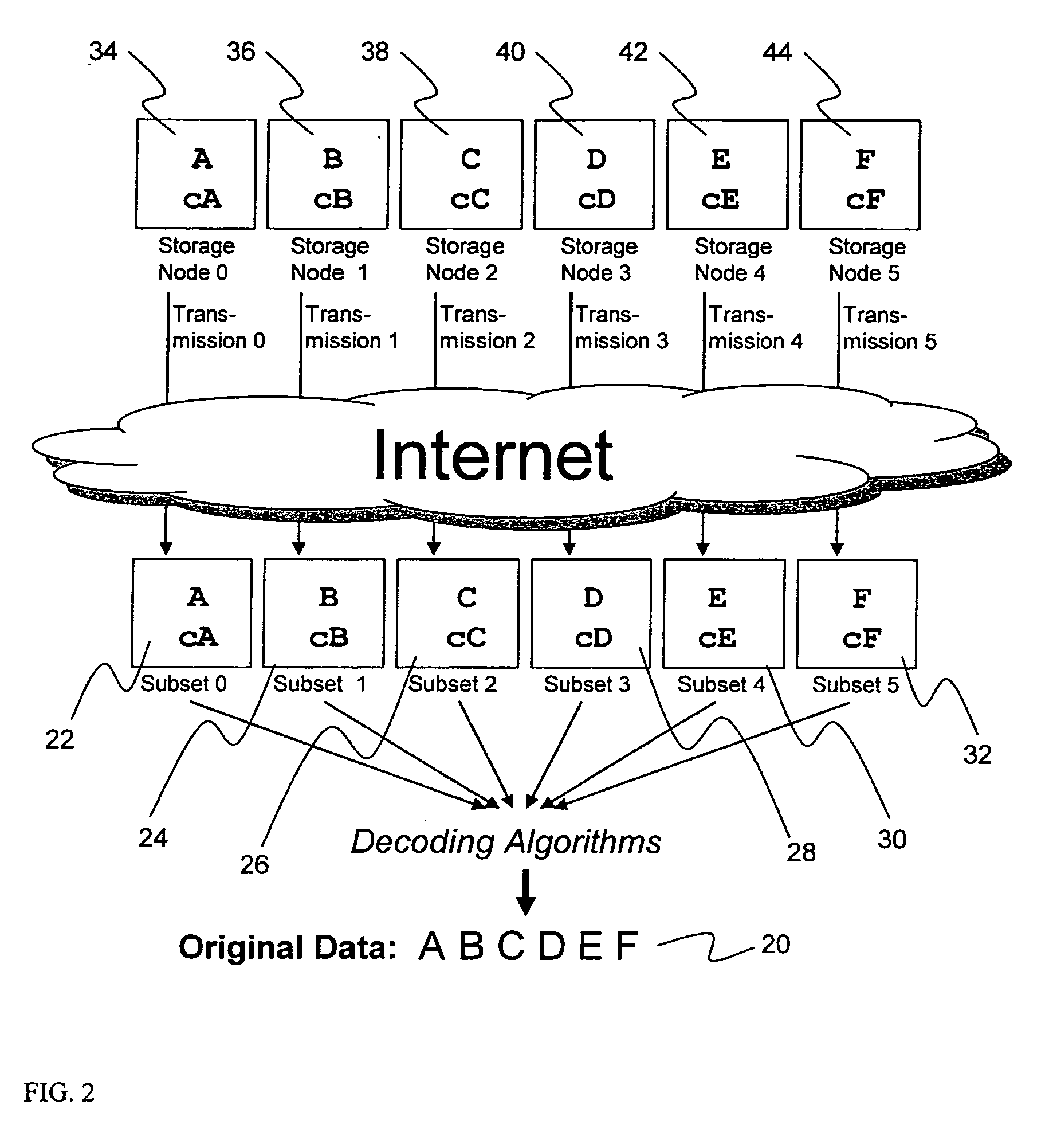
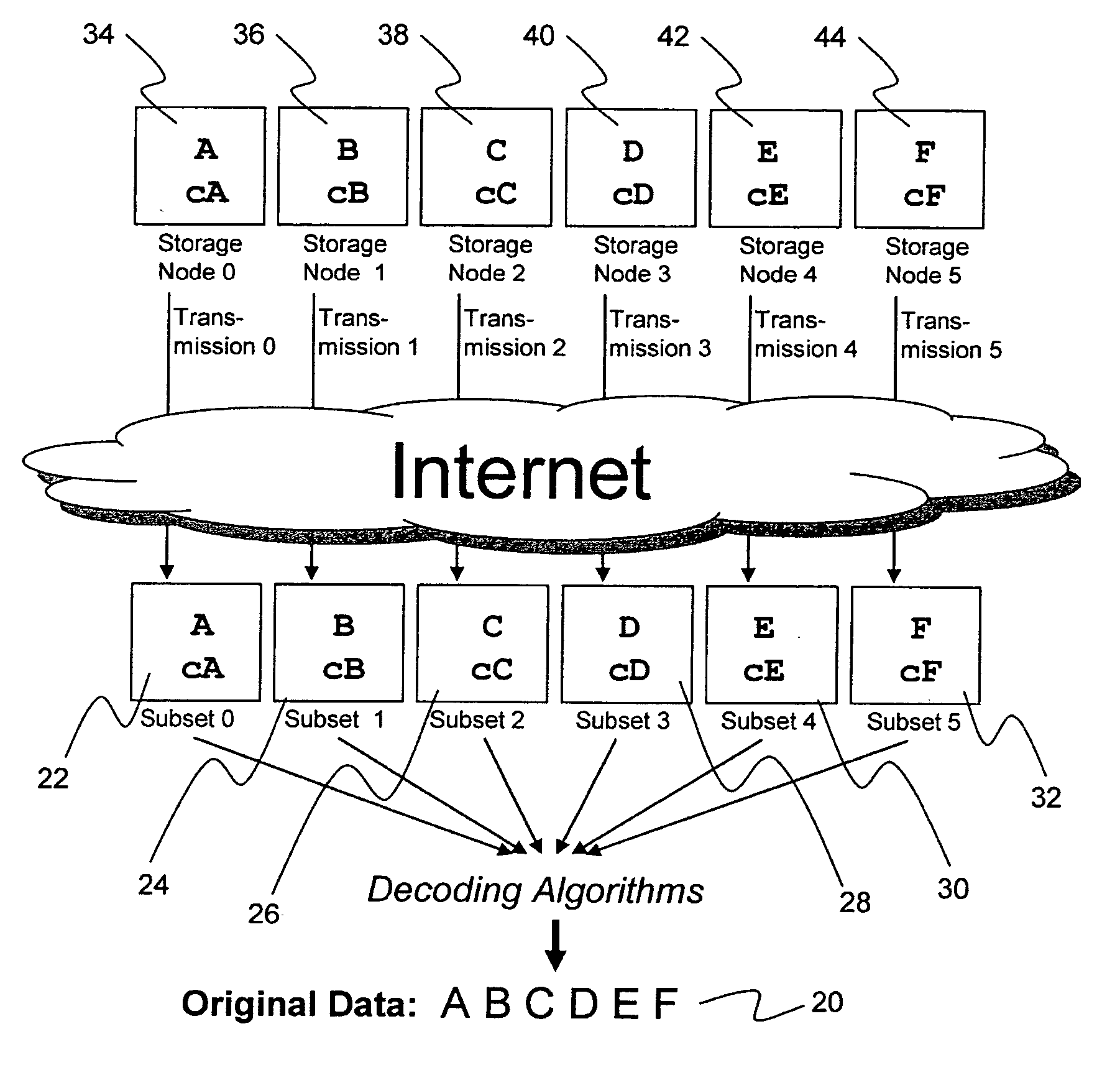
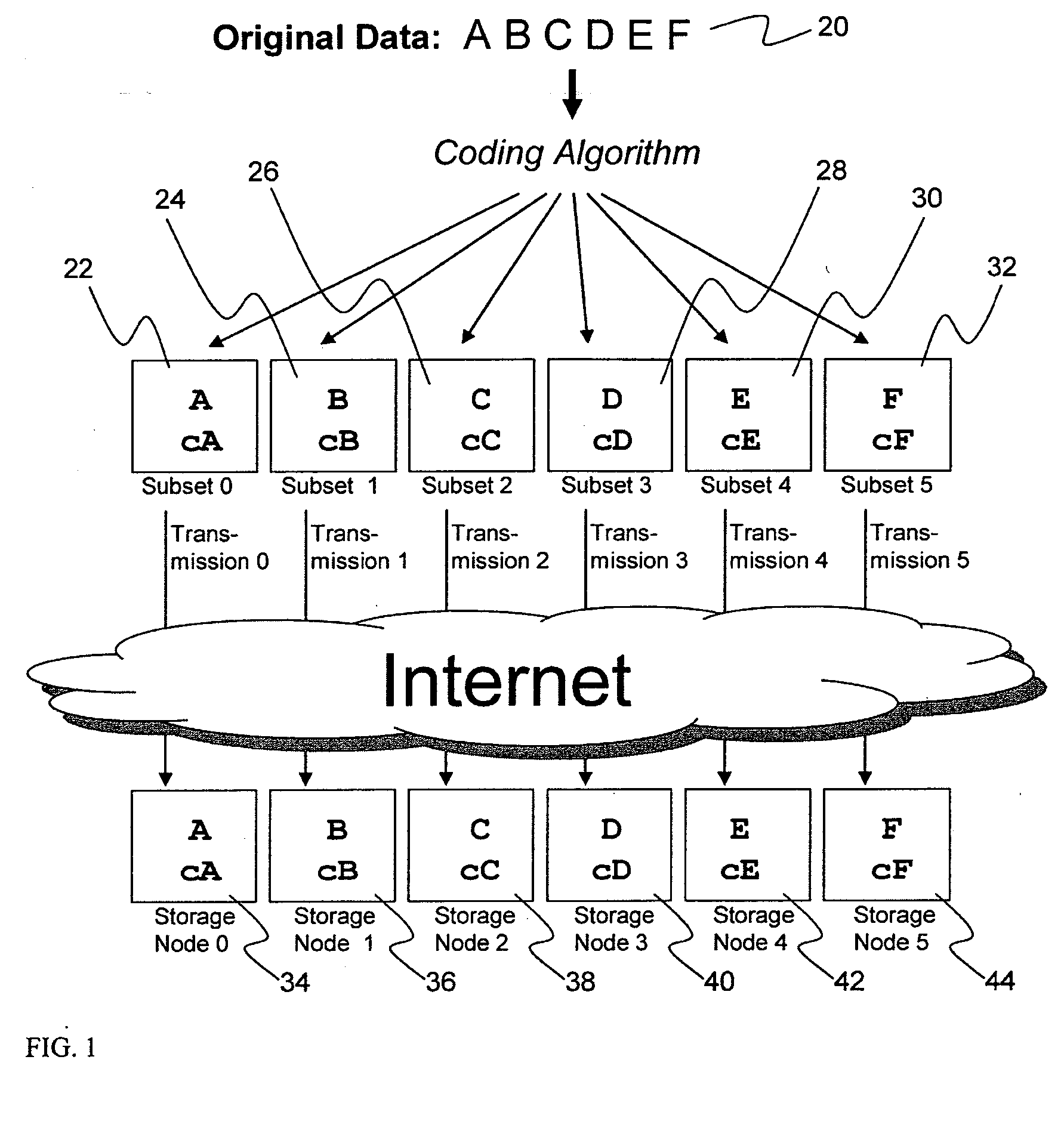
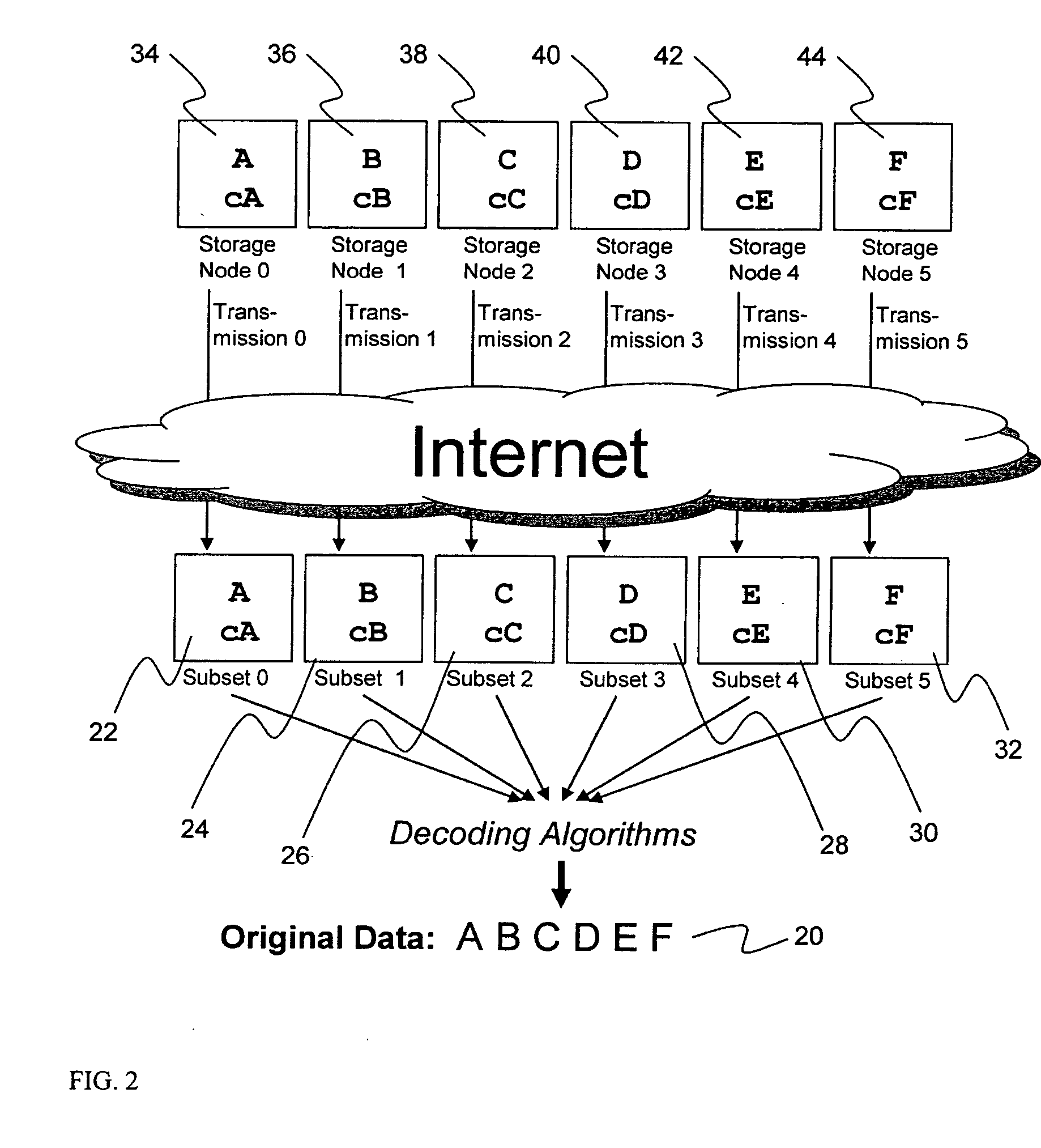
A digital data file storage system is disclosed in which original data files to be stored are dispersed using some form of information dispersal algorithm into a number of file “slices” or subsets in such a manner that the data in each file share is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other file shares. These file shares are stored on separate digital data storage devices as a way of increasing privacy and security. As dispersed file shares are being transferred to or stored on a grid of distributed storage locations, various grid resources may become non-operational or may operate below at a less than optimal level. When dispersed file shares are being written to a dispersed storage grid which not available, the grid clients designates the dispersed data shares that could not be written at that time on a Rebuild List. In addition when grid resources already storing dispersed data become non-available, a process within the dispersed storage grid designates the dispersed data shares that need to be recreated on the Rebuild List. At other points in time a separate process reads the set of Rebuild Lists used to create the corresponding dispersed data and stores that data on available grid resources.
Owner:PURE STORAGE
Metadata management system for an information dispersed storage system
ActiveUS20070079083A1Less usableImprove privacyComputer security arrangementsMemory systemsInformation dispersalMetadata management
Briefly, the present invention relates to an information dispersal sytem in which original data to be stored is separated into a number of data “slices” in such a manner that the data in each subset is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other data subsets. These data subsets are stored on separate storage devices as a way of increasing privacy and security. In accordance with an important aspect of the invention, a metadata management system stores and indexes user files across all of the storage nodes. A number of applications run on the servers supporting these storage nodes and are responsible for controlling the metadata. Metadata is the information about the data, the data slices or data subsets and the way in which these data subsets are dispersed among different storage nodes running over the network. As used herein, metadata includes data source names, their size, last modification date, authentication information etc. This information is required to keep track of dispersed data subsets among all the nodes in the system. Every time new data subsets are stored and old ones are removed from the storage nodes, the metadata is updated. In accordance with an important aspect of the invention, the metadata management system stores metadata for dispersed data where: The dispersed data is in several pieces. The metadata is in a separate dataspace from the dispersed data. Accordingly, the metadata management system is able to manage the metadata in a manner that is computationally efficient relative to known systems in order to enable broad use of the invention using the types of computers generally used by businesses, consumers and other organizations currently.
Owner:PURE STORAGE
Data security system and method responsive to electronic attacks
ActiveUS7146644B2Ease overhead performanceHigh overhead performanceMemory loss protectionMultiple keys/algorithms usageInformation processingSelf adaptive
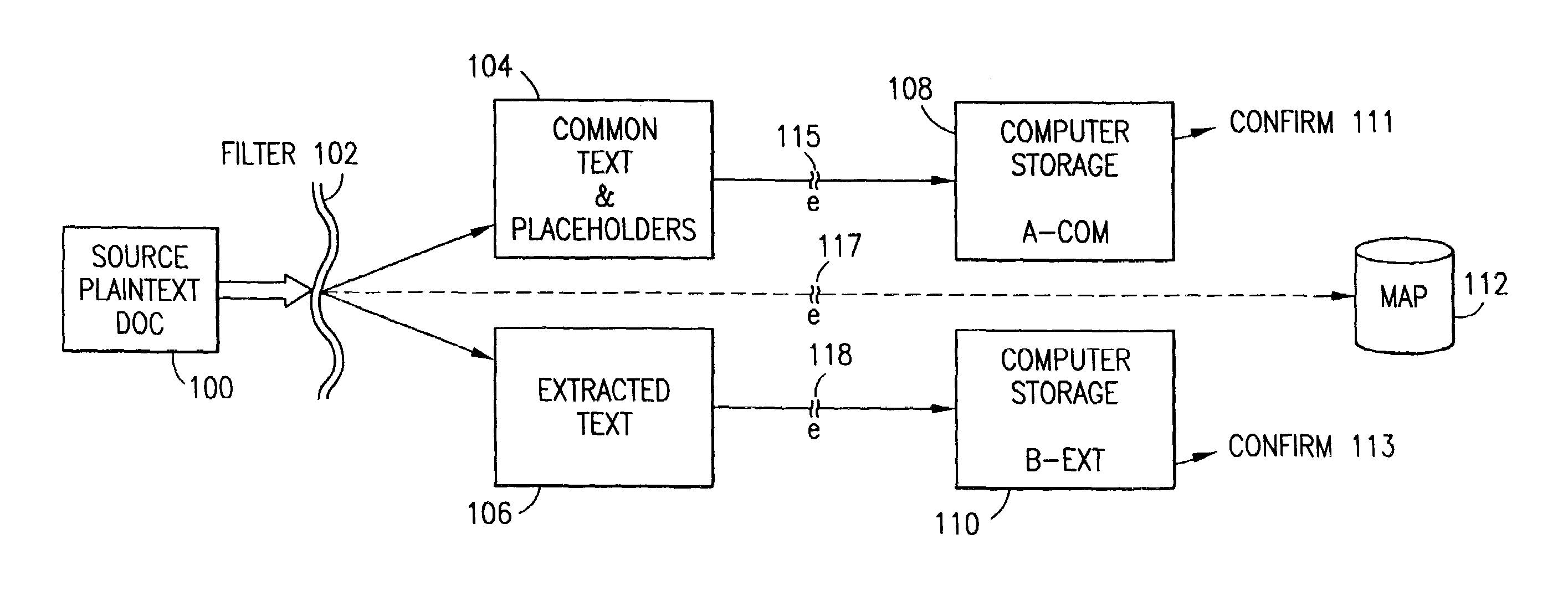
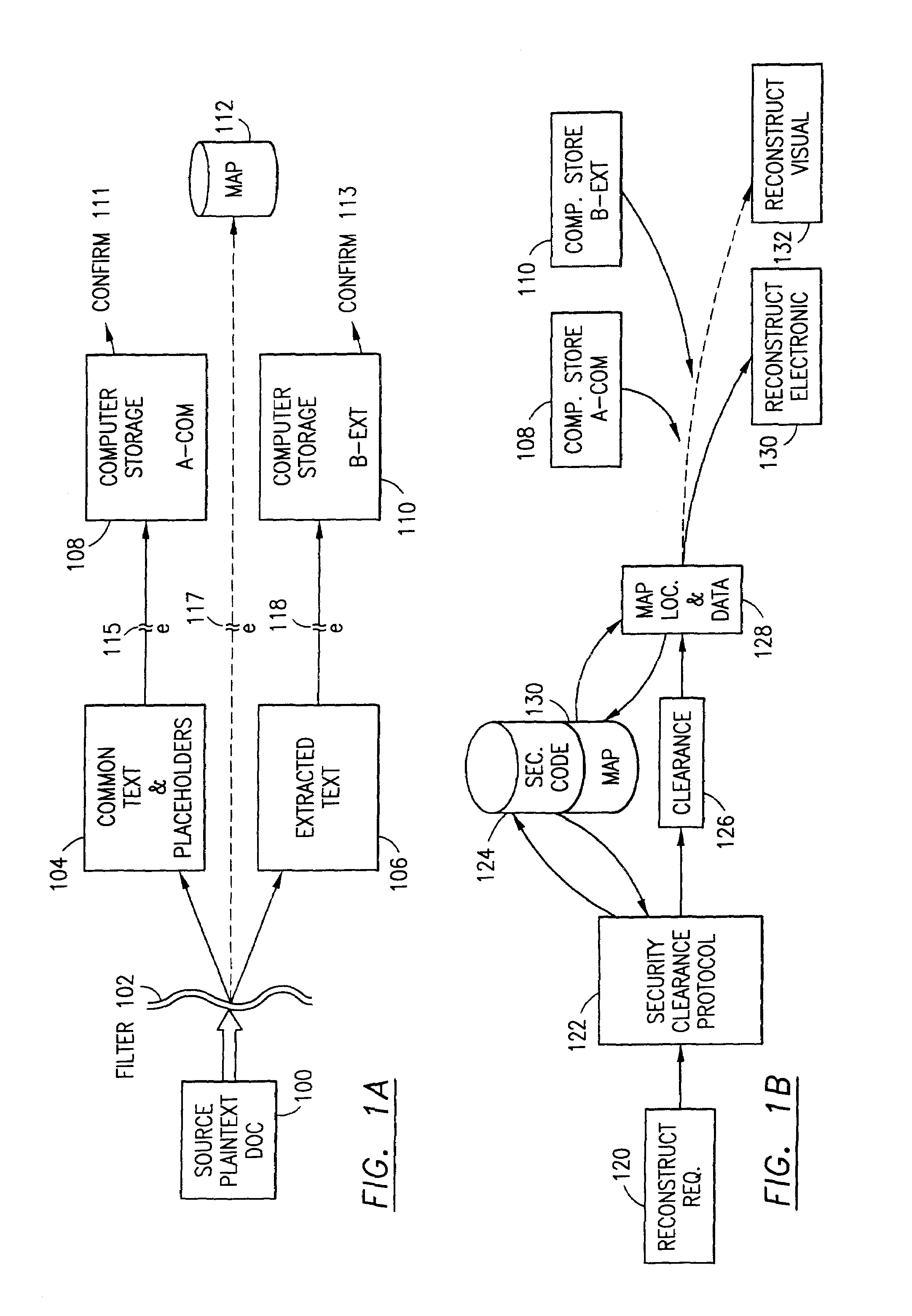
An adaptive method, system and program for securing data against a plurality of electronic and environmental events directed at computers utilizes a hacking monitor which generates attack warnings (such as a hacking warning) dependent upon the severity of the attack. Based upon these warnings, data is filtered to extract security sensitive words etc. and the extract and remainder data (if necessary) is stored in assigned memory. Full or partial reconstruction is permitted, manually or automatically, with a security clearance. Encryption is typically used dependent upon the warning. The information processing system includes a filter which is adjusted based upon the degree of attack warning to extract security sensitive words. A storage system stores extracted data and remainder data (if necessary) based upon the level of the warning and a compiler is used to reconstruct the data in the presence of the appropriate security clearance level.
Owner:DIGITAL DOORS
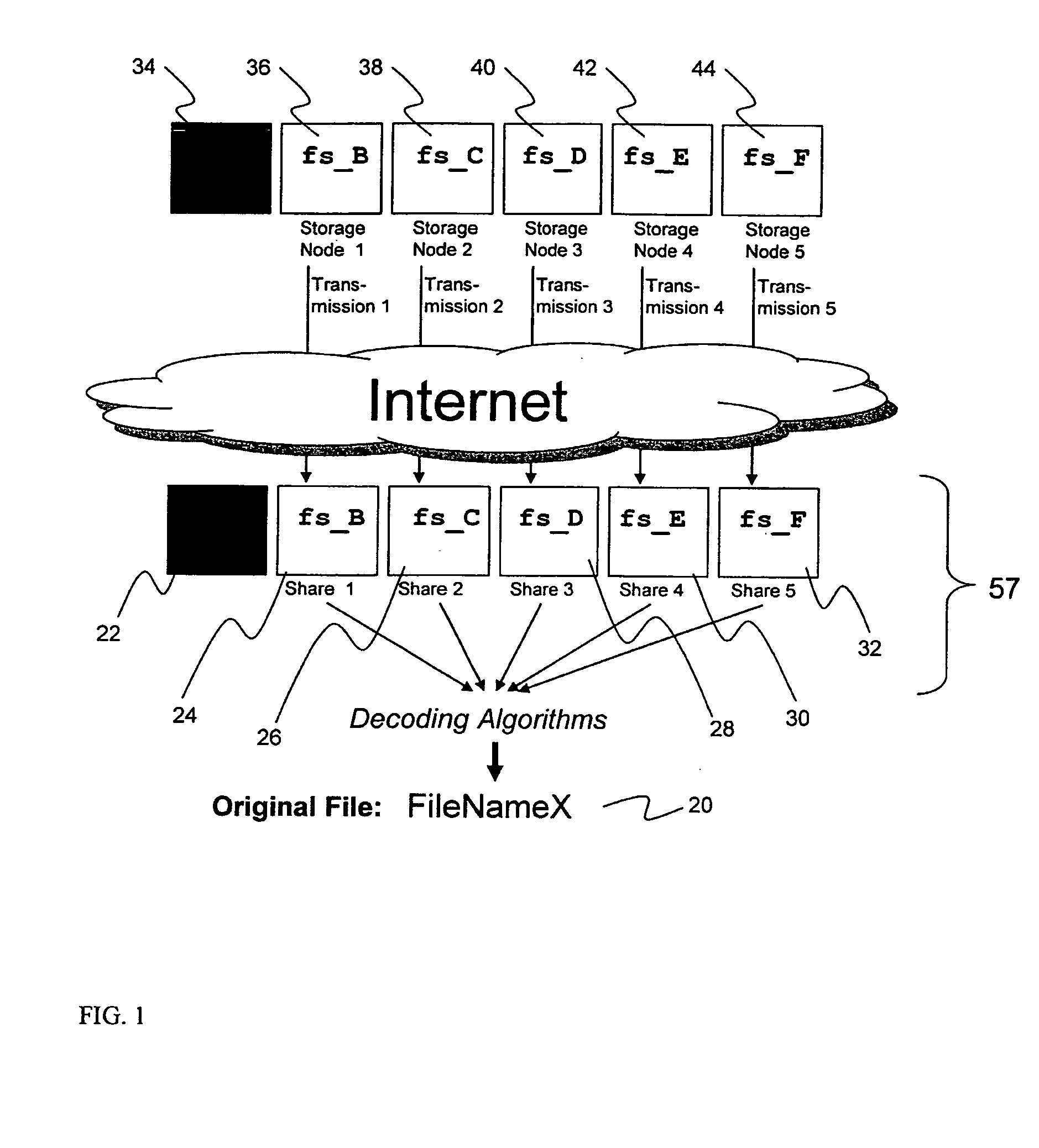
Billing system for information dispersal system
ActiveUS20070174192A1Less usableLess recognizableFinanceComputer security arrangementsInformation dispersalOriginal data
A billing process is disclosed for a information dispersal system or digital data storage system. In one embodiment of the invention, the original data to be stored is separated into a number of data “slices” or shares in such a manner that the data in each subset is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other data subsets. These data subsets are stored on separate digital data storage devices as a way of increasing privacy and security. As dispersed file shares are being stored or removed from a grid of distributed storage locations, a set of metadata tables are created, separate from the dispersed file share storage, to maintain information about the original data size of each block, file or set of file shares dispersed on the grid. The original data size information in these separate metadata tables is used to determine usage information based upon the original file size even though the file has been dispersed onto a storage grid that contains file slices who size may not relate to the original file size and the file slices may have been compressed by the system in order to reduce storage space or improve transmission time. As such, the billing process is able to enable a broad range of commercial billing options for billing for commercial data services on an information dispersal grid.
Owner:PURE STORAGE
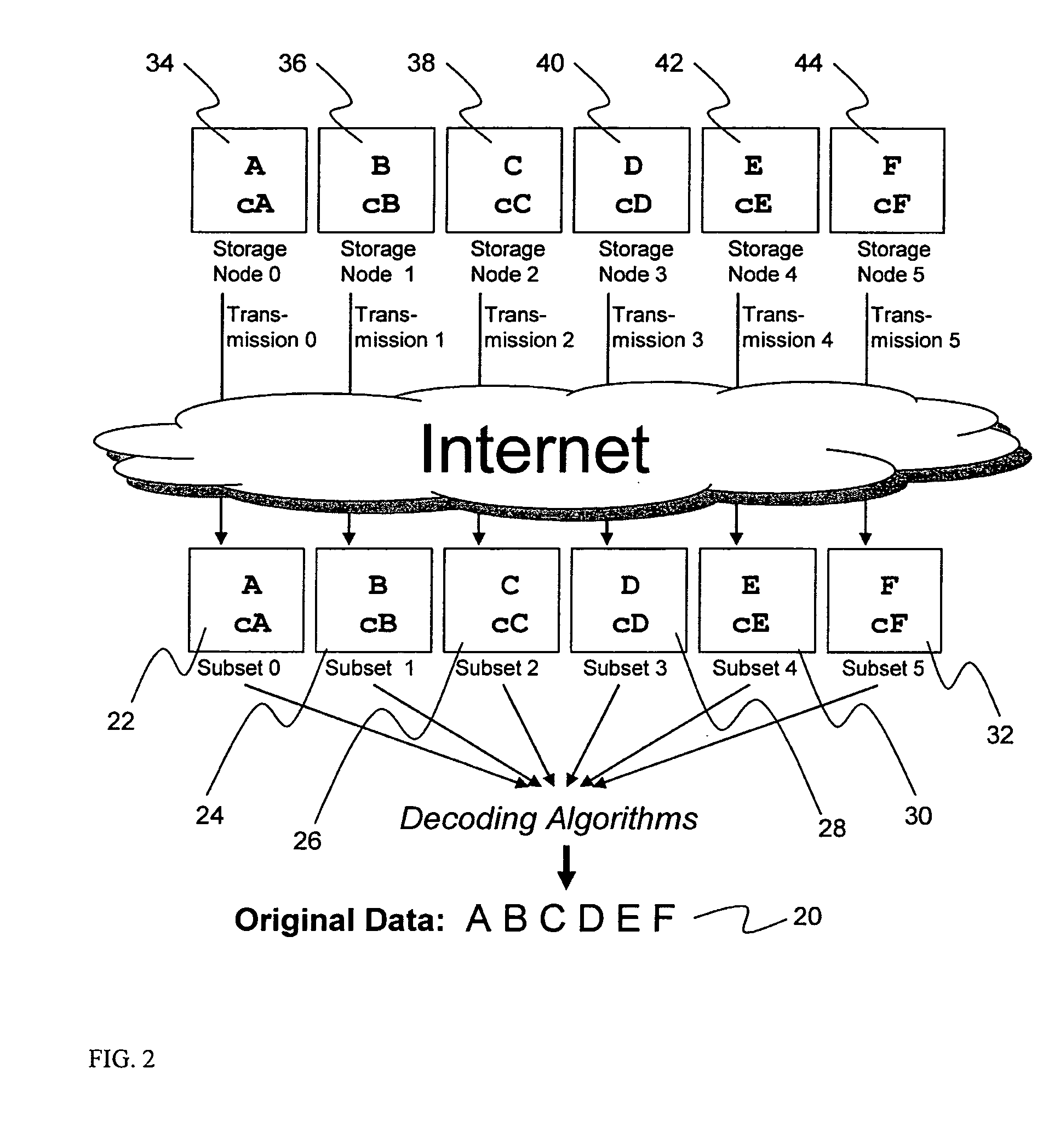
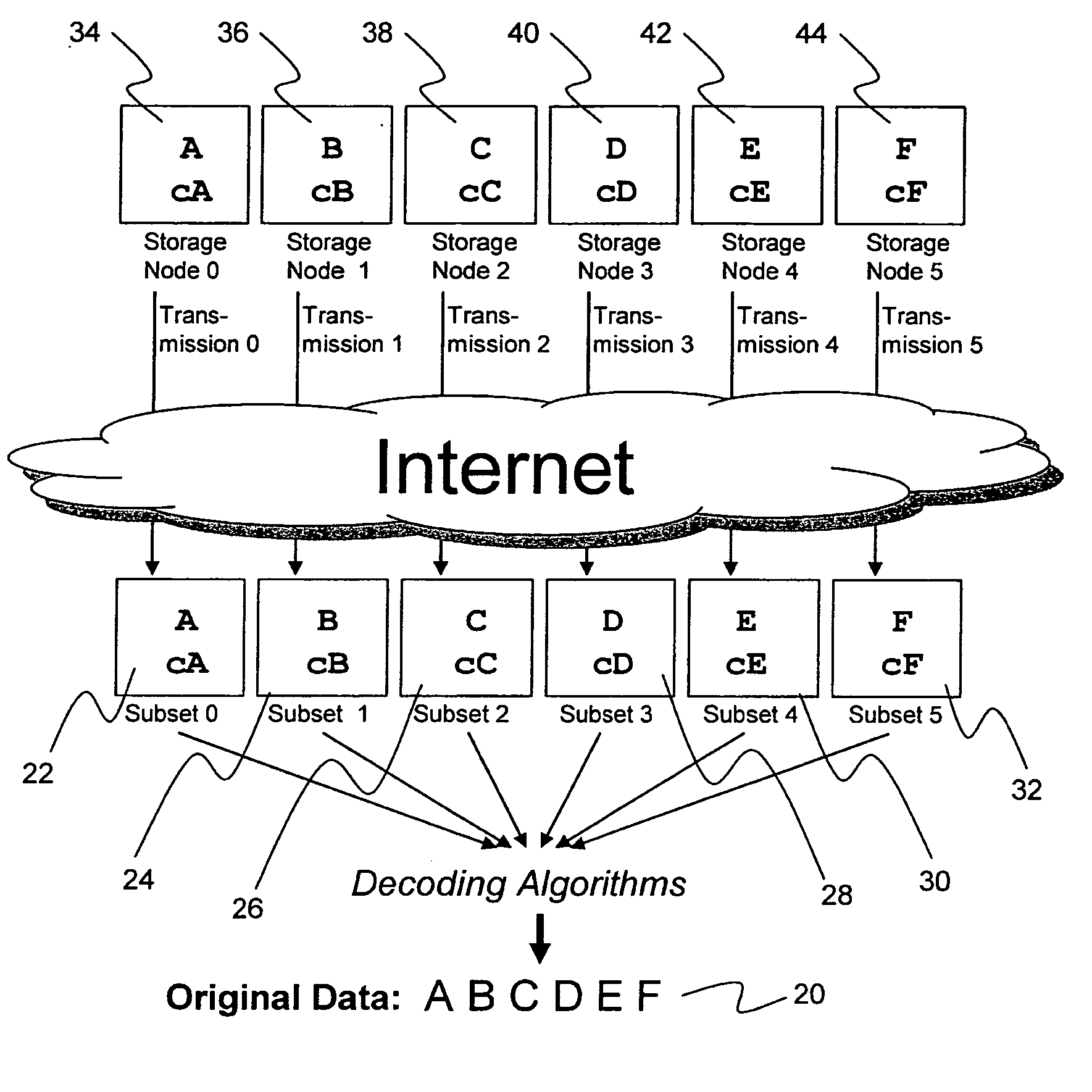
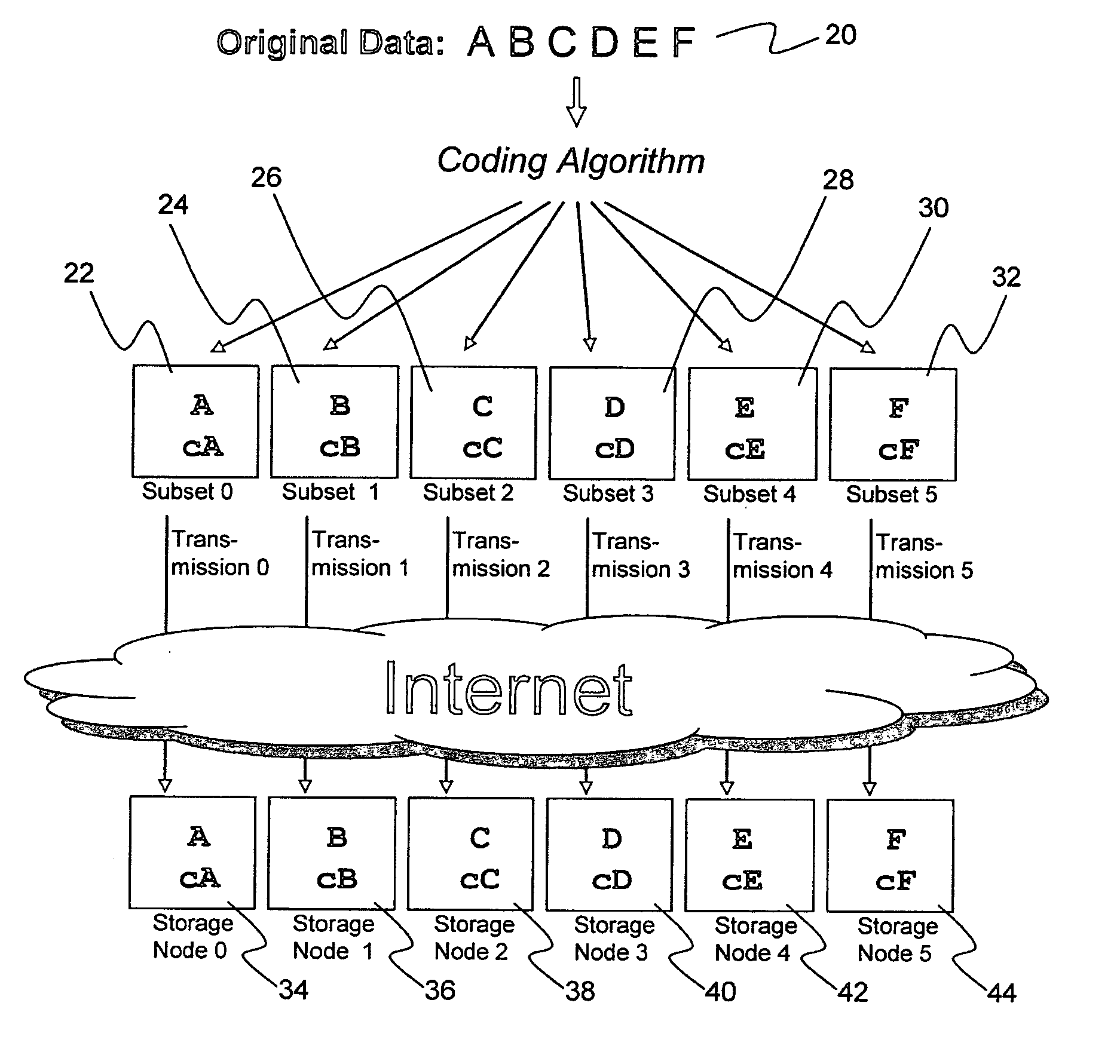
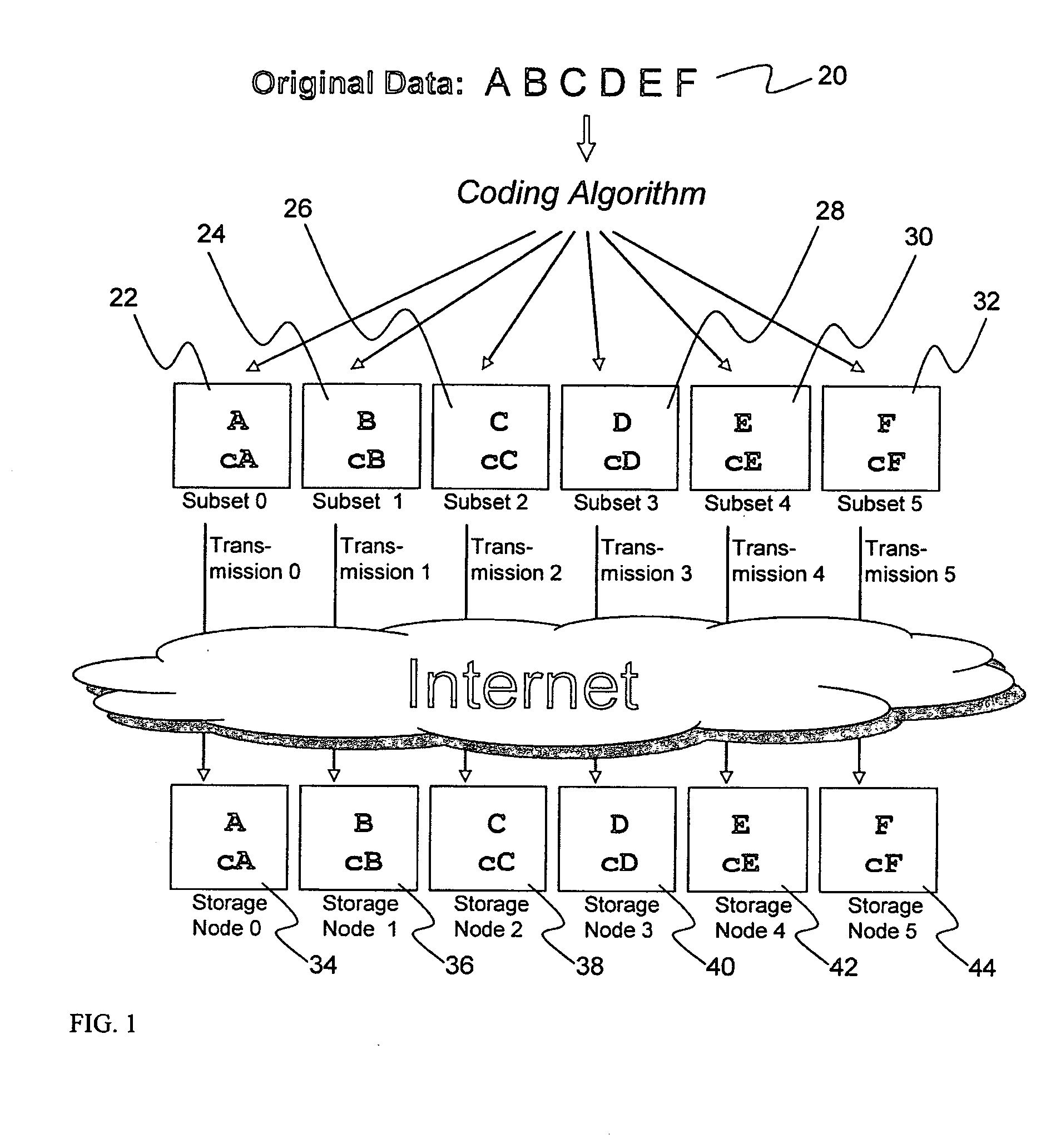
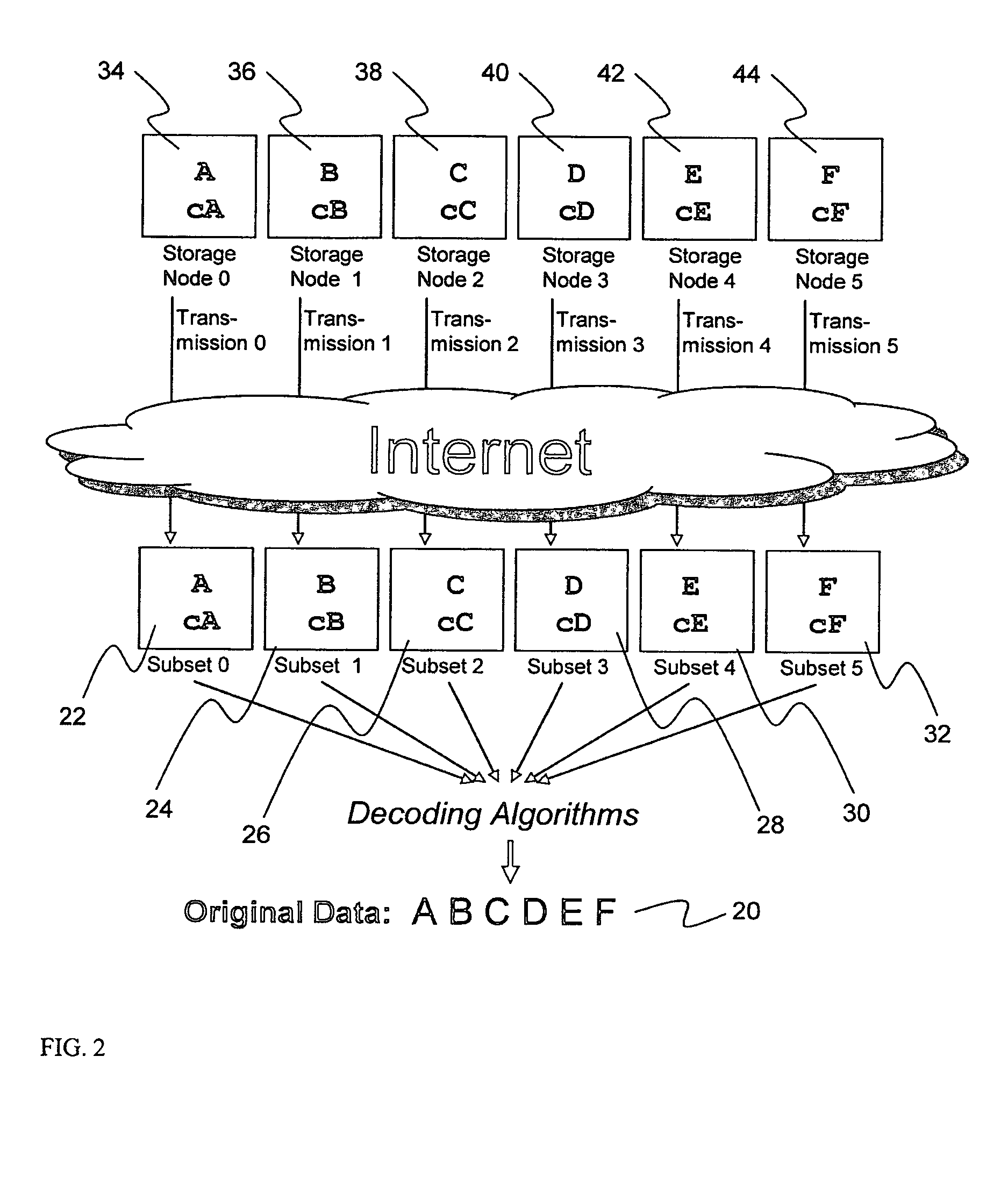
Digital data storage system
ActiveUS20070079081A1Less usableImprove privacyComputer security arrangementsMemory systemsOriginal dataSmall data
An efficient method for breaking source data into smaller data subsets and storing those subsets along with coded information about some of the other data subsets on different storage nodes such that the original data can be recreated from a portion of those data subsets in an efficient manner.
Owner:PURE STORAGE
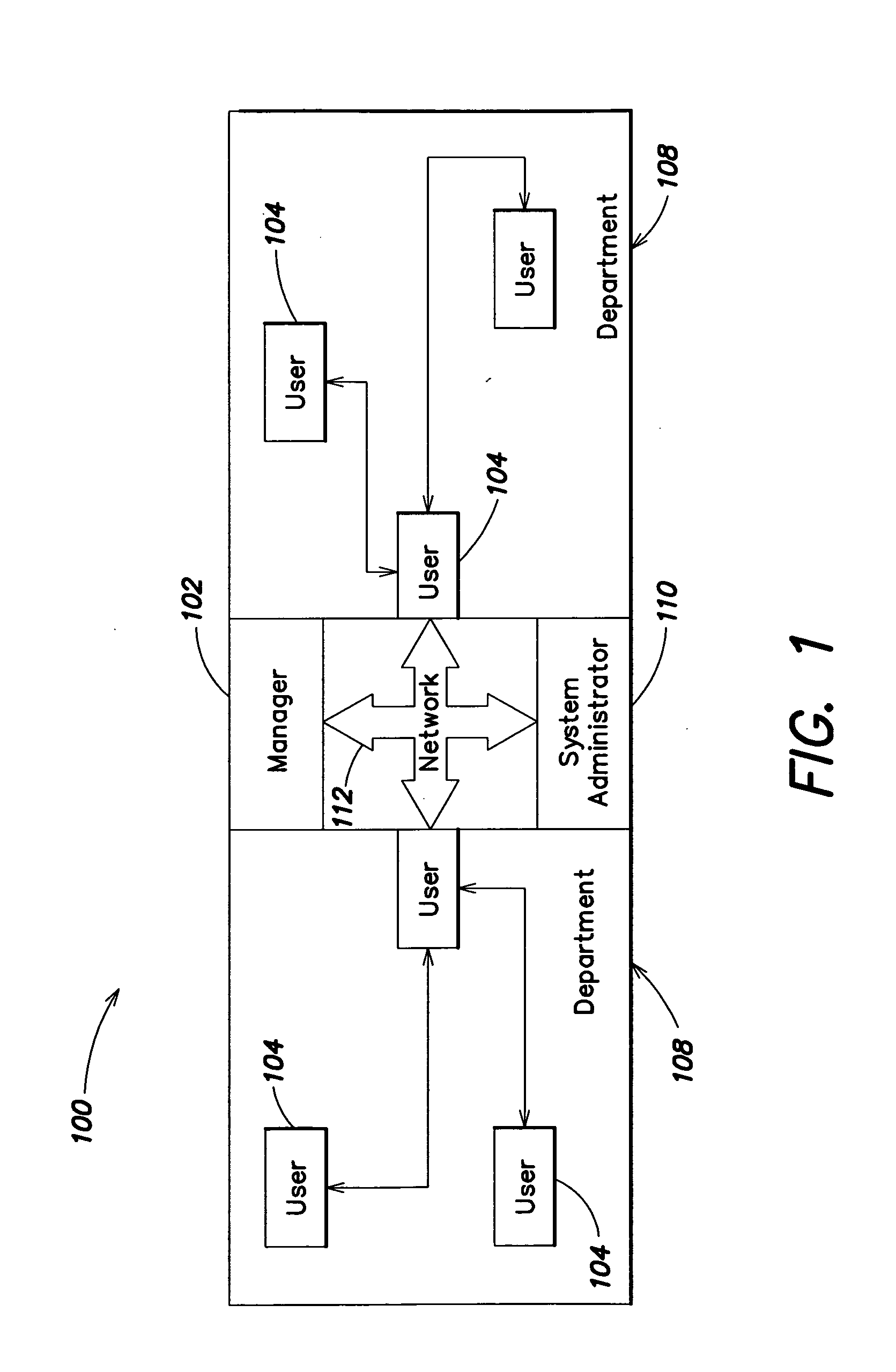
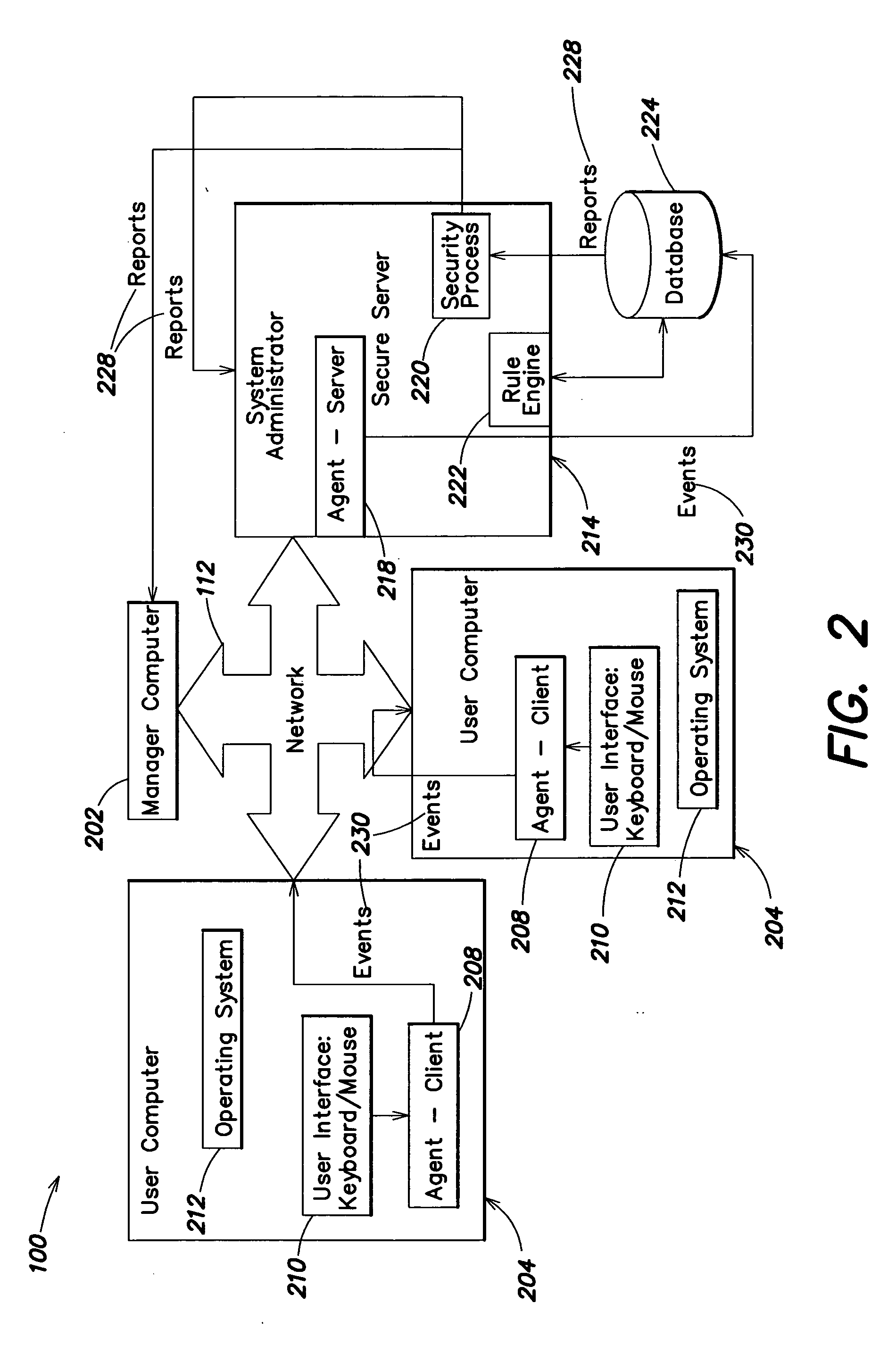
Methods and systems for monitoring user, application or device activity
InactiveUS20050183143A1Improve securityMemory loss protectionUnauthorized memory use protectionWorking environmentComputer usage
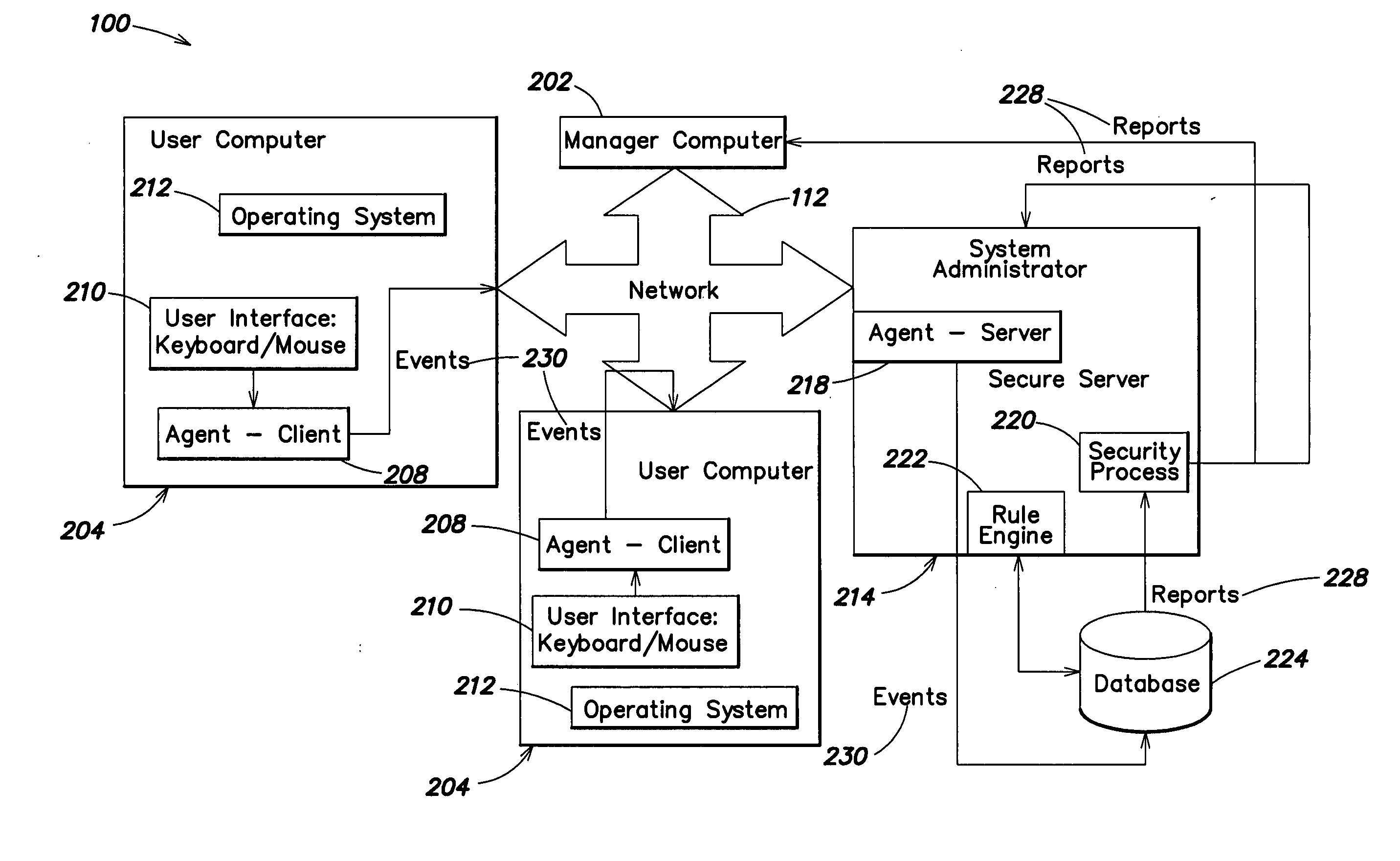
Methods and systems are provided for capturing usage data from a user computer, processing a subset of such data to form output, and offering access to selective views of such output, such as to assist a company's management in monitoring computer usage in a work environment. The output may be processed and viewed according to software application, device, or specified user. The output, or a report generated therefrom, may be accessible in differing degrees to individuals having appropriate levels of permission.
Owner:SERGEANT LAB
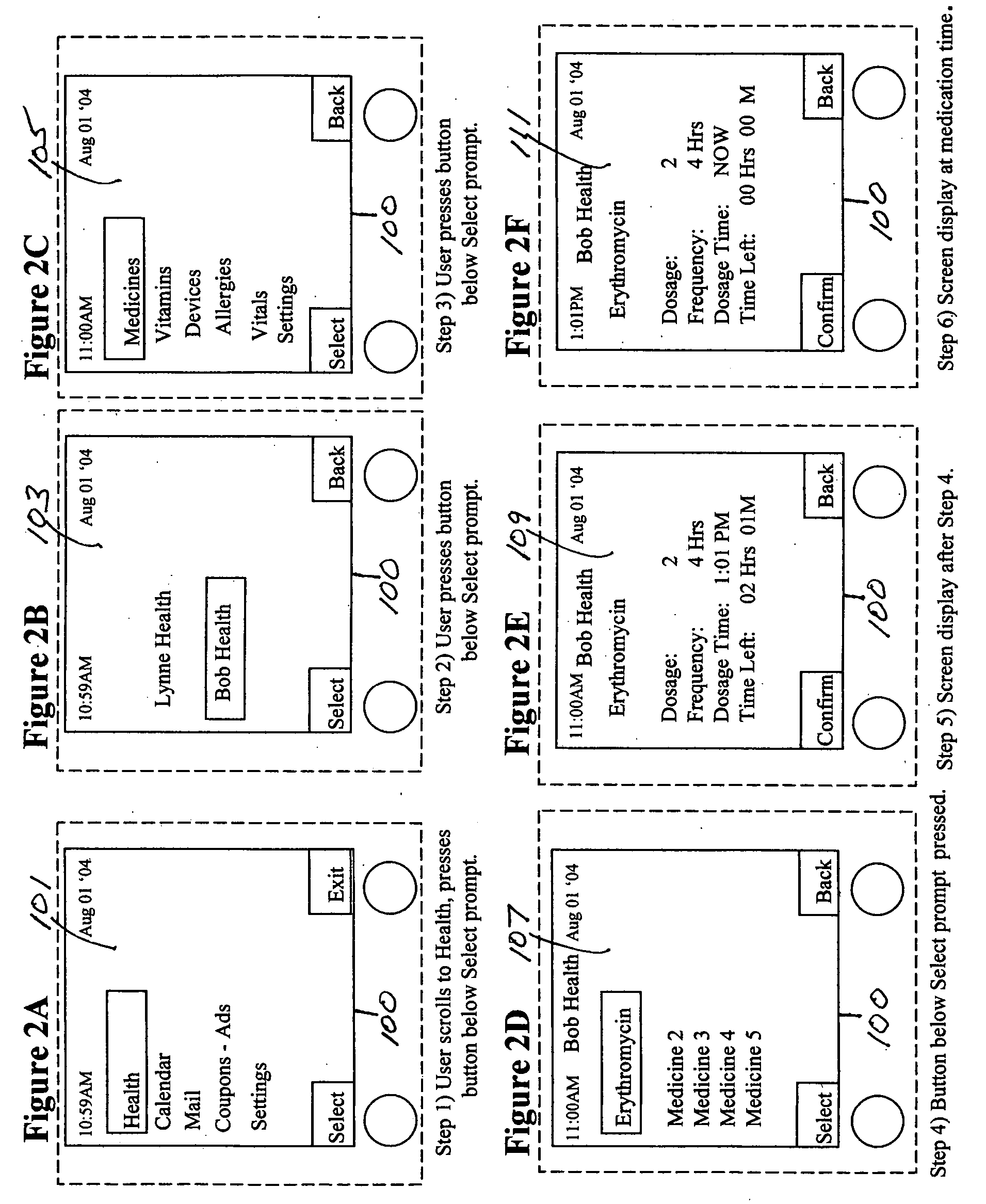
Medication & health, environmental, and security monitoring, alert, intervention, information and network system with associated and supporting apparatuses
InactiveUS20060154642A1Facilitate user and/or occupant well beingExtended stayDispersed particle filtrationDrug and medicationsNetworked systemHealth administration
Systems and apparatuses include devices, biosensors, environmental sensors, security related sensors, networked products, communications processors and components, alert and information components, processors, and software to support: 1) facilitating medication regimen and patient / user health administration, dosage control, tracking, compliance, information inquiry and presentation, reminder and notification; 2) providing monitoring, information, ordering, and intervention; 3) presenting the option of leveraging the preventative care, alert and notification components with other components to facilitate user or occupant well being, along with living, work area and dwelling environmental or security safety; and 4) enhancing the dwelling, living or work area with products that may be networked to support the widespread acceptance of these systems and apparatuses. The systems include a) processing, centralizing and communicating device commands and / or programs, e.g. a multifunctional device controller; b) device administration; c) patient / user information; d) dwelling environmental safety; e) security breach information; f) centralized and remote apparatus and system activations through primary component or at least one backup.
Owner:INSIGNIO TECH
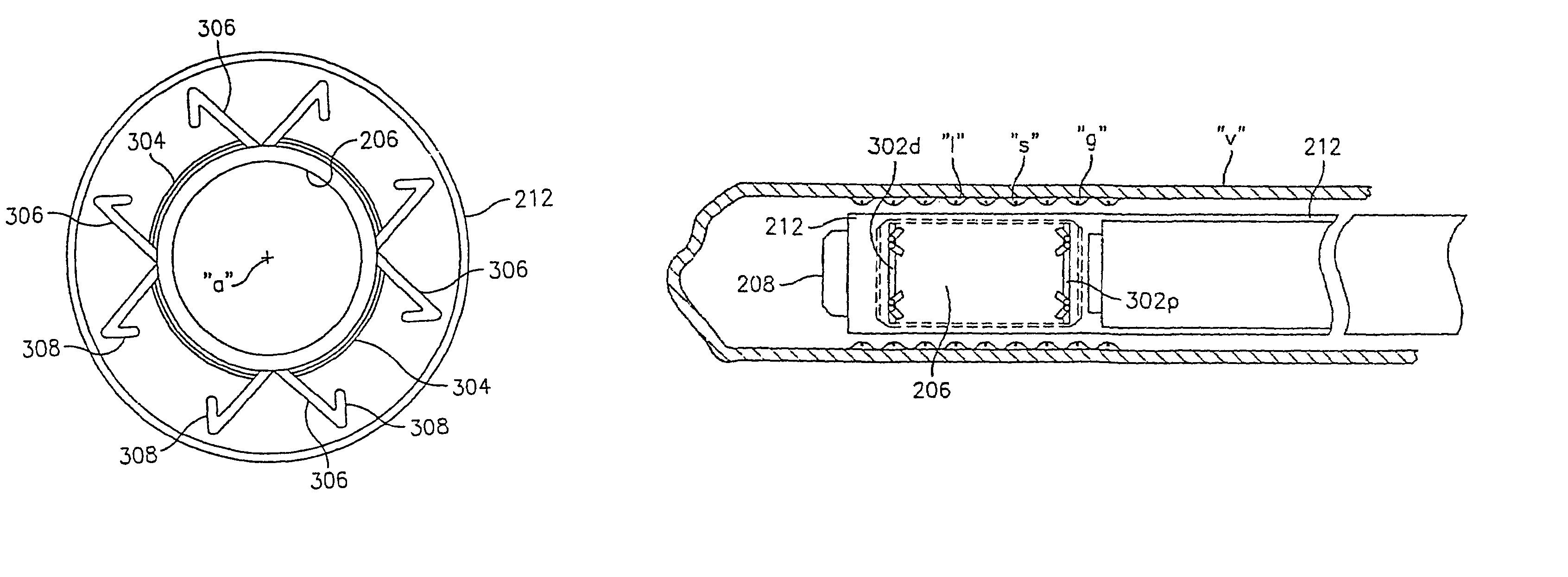
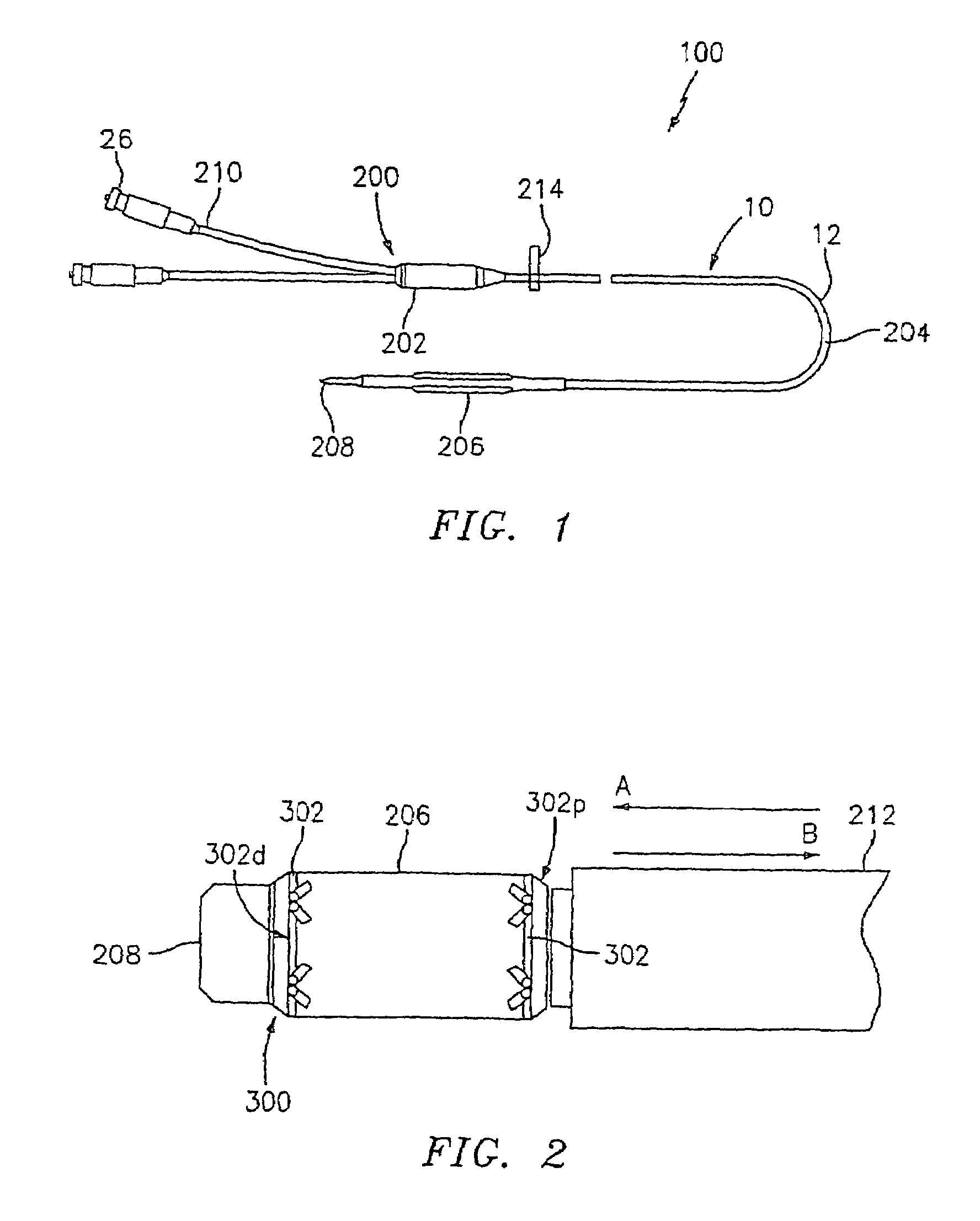
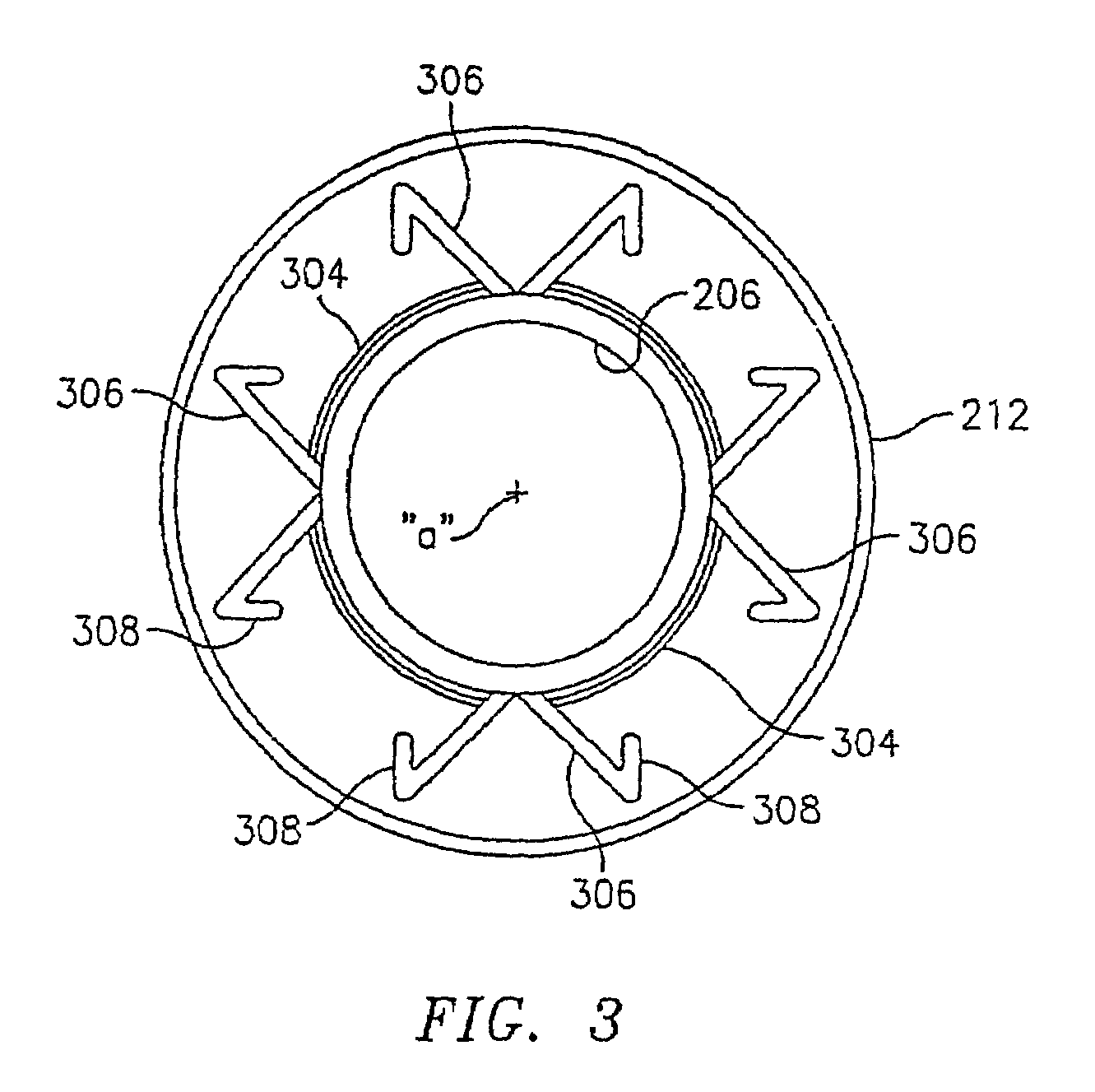
Apparatus and method for fixation of vascular grafts
InactiveUS7351258B2Reduce leakageOvercome disadvantagesStentsBlood vesselsThree vesselsVascular graft
An apparatus for facilitating securement of a vascular graft within a blood vessel, includes a shaft dimensioned for passage within a blood vessel and having an expansion member movable between a contracted condition and an expanded condition and a fastener array comprising at least one fastener disposed about a peripheral portion of the expansion member. The one fastener is deployable into a wall of the blood vessel upon movement of the expansion member to the expanded condition thereof, to thereby engage the vascular graft to secure the vascular graft to a wall of the blood vessel. The fastener array preferably includes a plurality of fasteners. The fasteners may be operatively connected to each other and releasably secured to the peripheral portion of the expansion member.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
Microprocessor controlled ambulatory medical apparatus with hand held communication device
InactiveUS6873268B2Enhance user interfaceReduce system sizeEnergy efficient ICTElectrotherapyDrugs infusionHand held
An implantable infusion pump possesses operational functionality that is, at least in part, controlled by software operating in two processor ICs which are configured to perform some different and some duplicate functions. The pump exchanges messages with an external device via telemetry. Each processor controls a different part of the drug infusion mechanism such that both processors must agree on the appropriateness of drug delivery for infusion to occur. Delivery accumulators are incremented and decremented with delivery requests and with deliveries made. When accumulated amounts reach or exceed, quantized deliverable amounts, infusion is made to occur. The accumulators are capable of being incremented by two or more independent types of delivery requests. Operational modes of the infusion device are changed automatically in view of various system errors that are trapped, various system alarm conditions that are detected, and when excess periods of time lapse between pump and external device interactions.
Owner:MEDTRONIC MIMIMED INC
Surgical apparatus including surgical buttress
ActiveUS9433420B2Facilitated releaseImprove securityDomestic articlesSurgical staplesButtressActuator
Owner:TYCO HEALTHCARE GRP LP
Method For Applying A Surgical Clip Having A Compliant Portion
Owner:CILAG GMBH INT +1
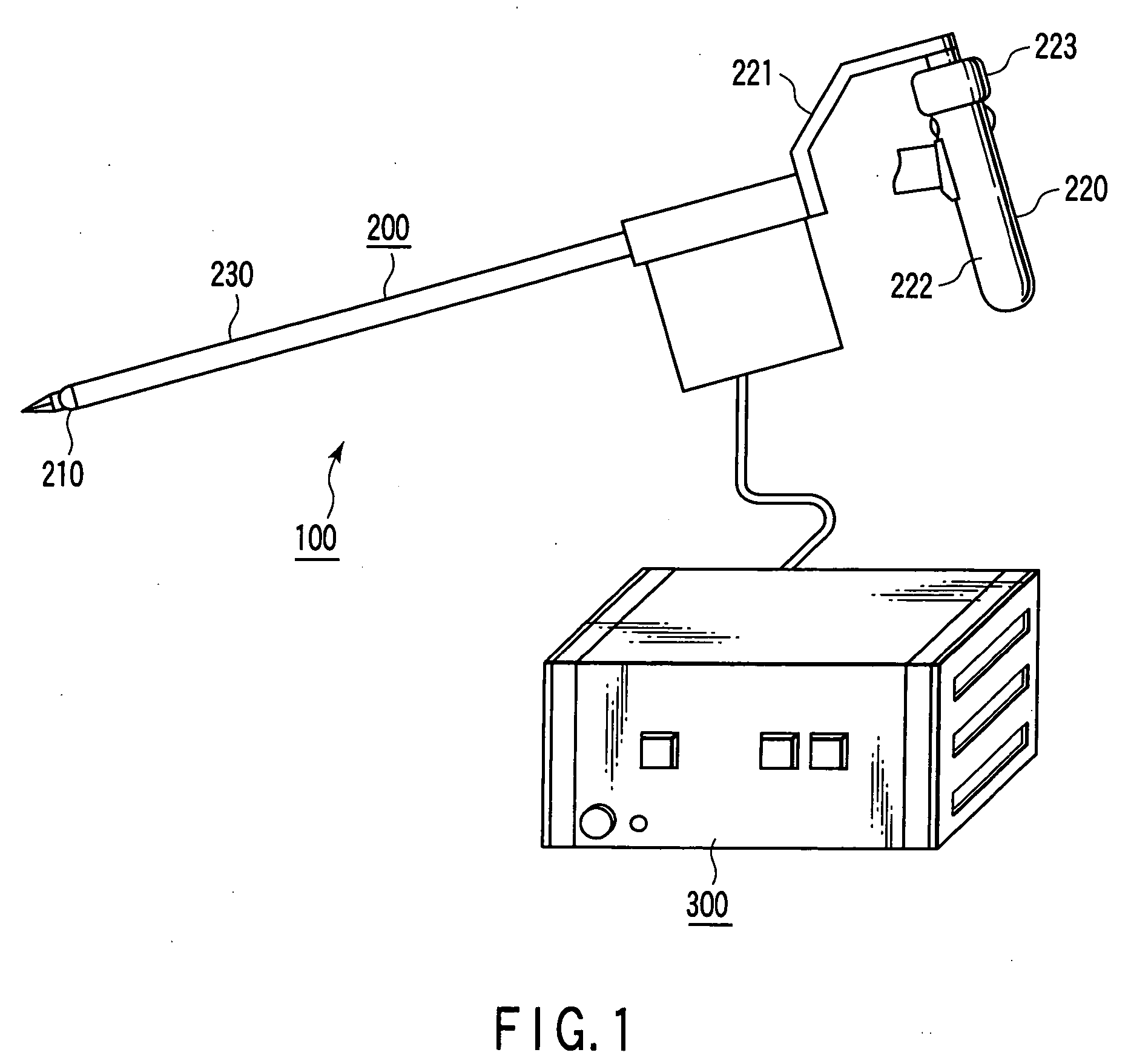
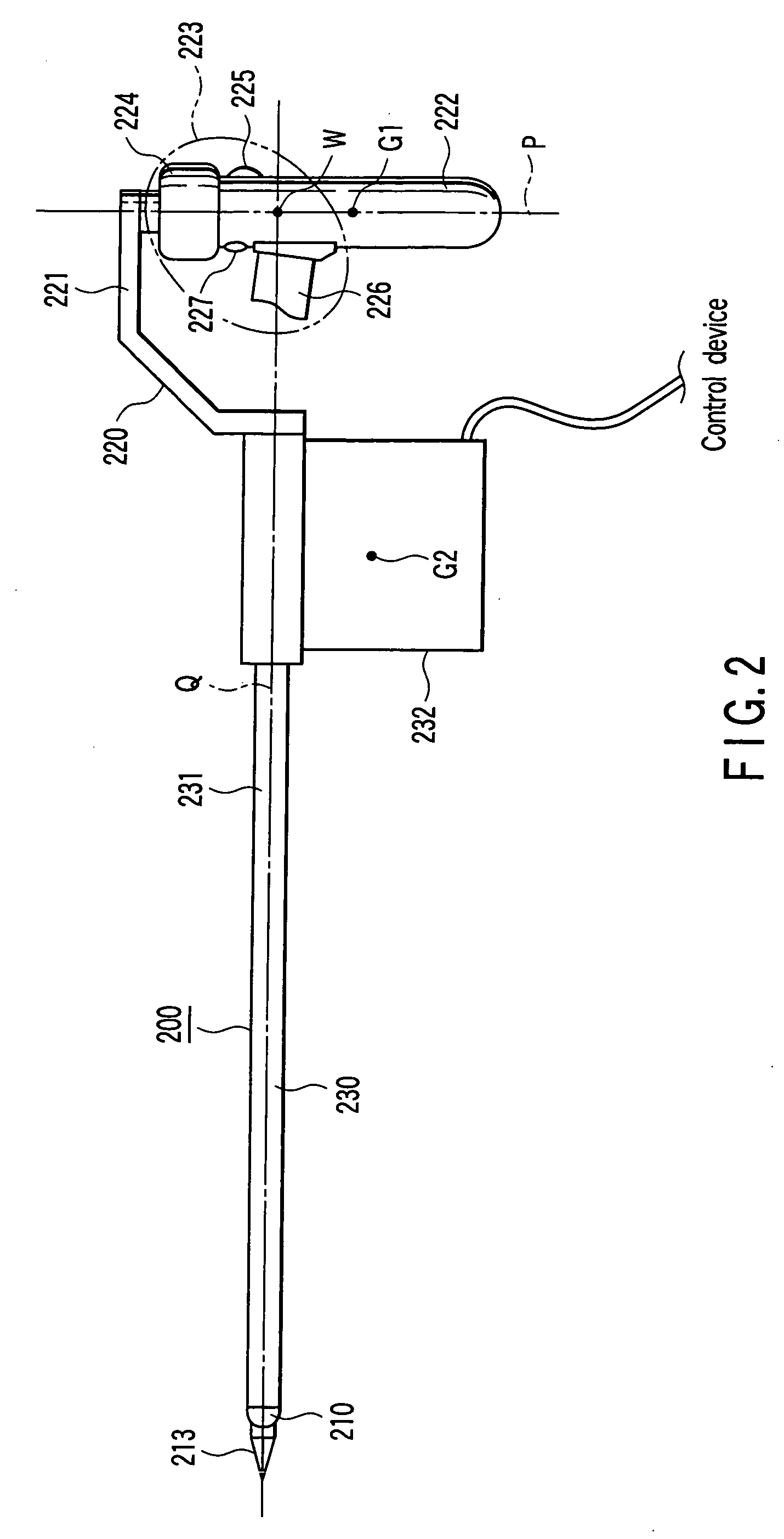
Manipulator and its control apparatus and method
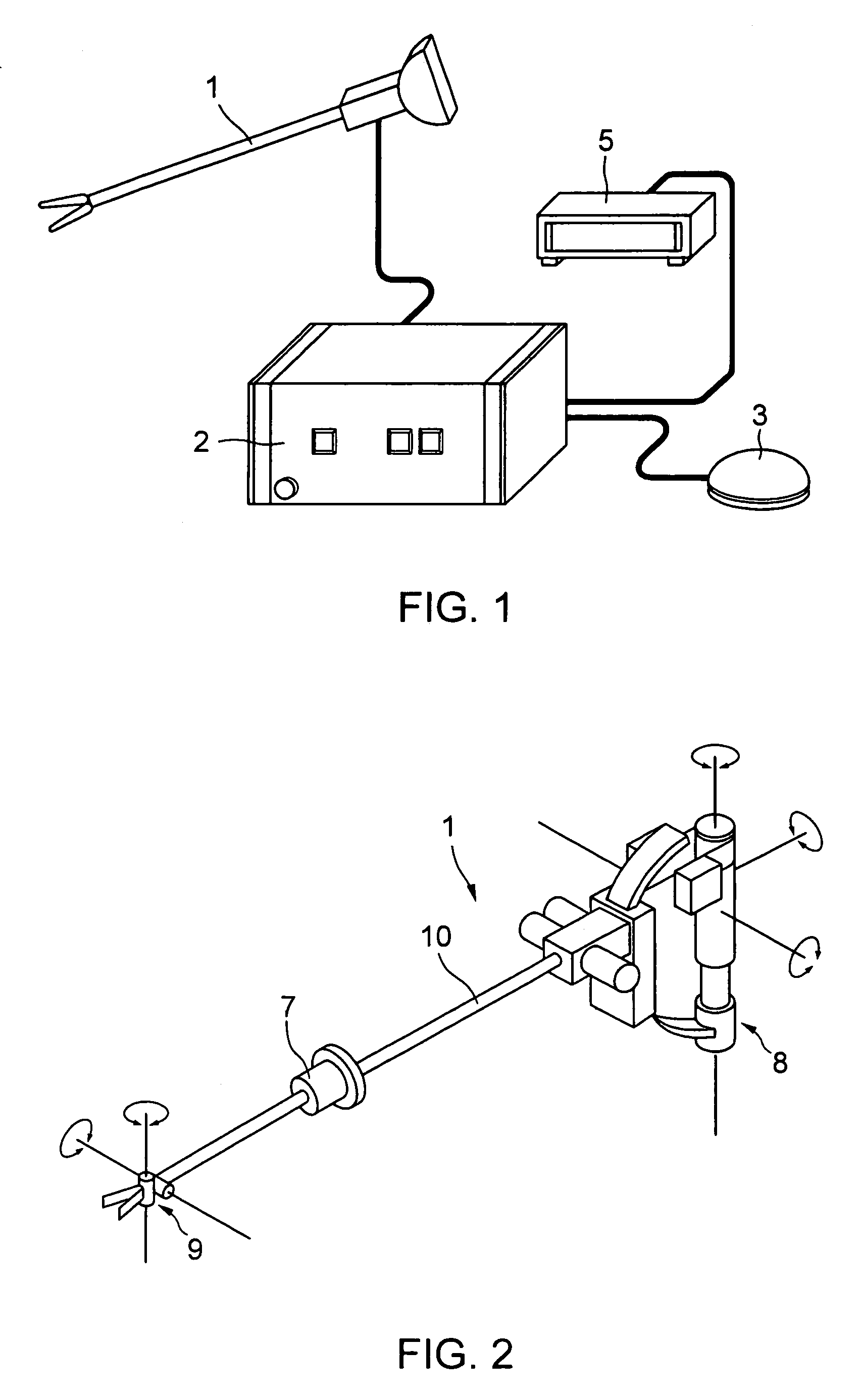
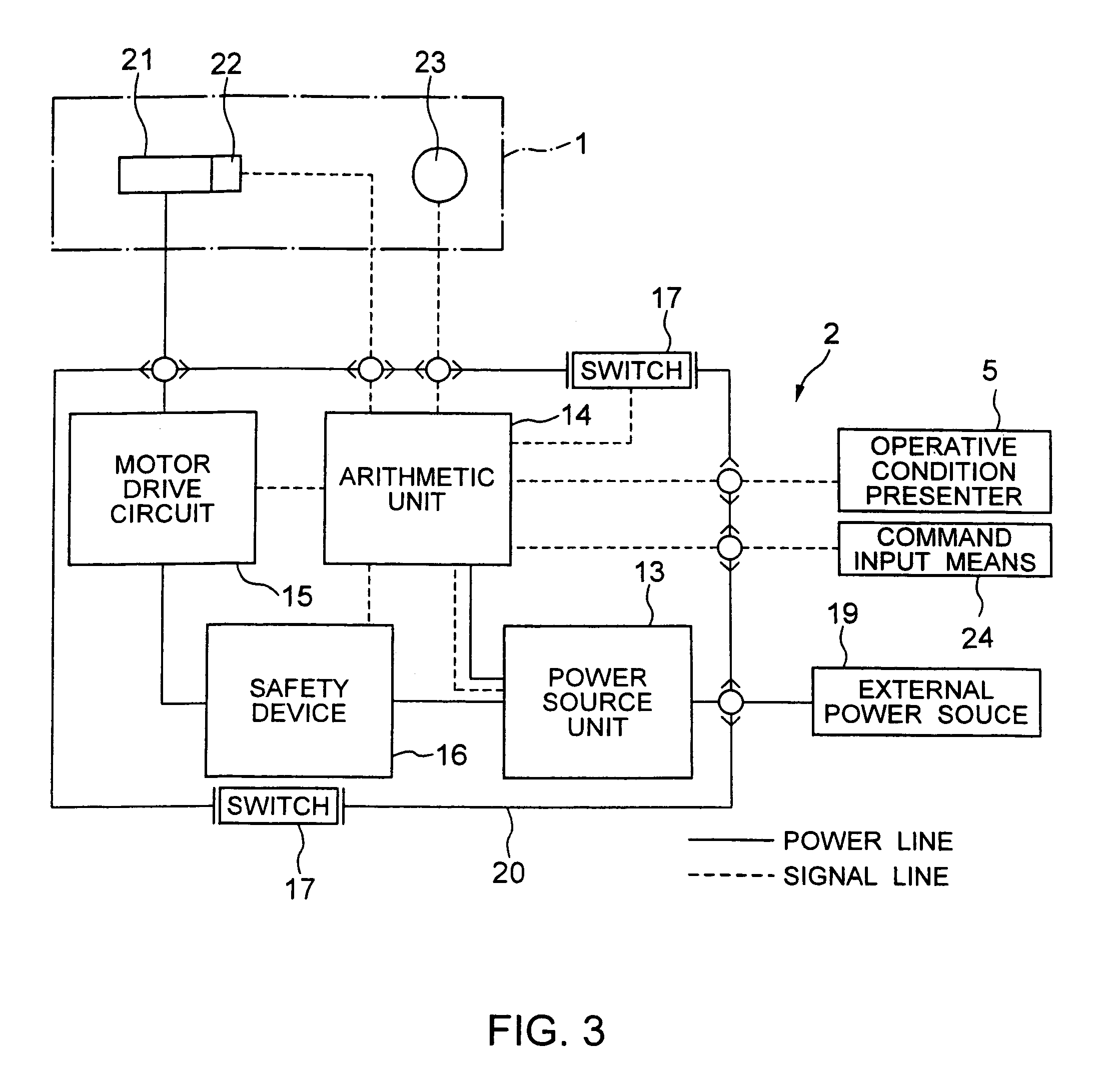
ActiveUS6993413B2Improve controllabilityImprove securityProgramme-controlled manipulatorGripping headsWork unitManipulator
A manipulator operative in a master / slave operative mode, comprising: a master unit commanding an operation; a slave unit having a work unit; a detector detecting the orientation of the master unit and the orientation of the slave unit; and a control device controlling the slave unit in response to the command from the master unit, wherein the control device includes: a function of determining a non-mater / slave operative mode or a master / slave operative mode; a function of calculating a difference between the orientation of the master unit and the orientationof the slave unit; and a function of comparing the absolute value of the difference with a preset reference value; and depending upon the result of the comparison, determining a normal master / slave operative mode or a transitional master / slave operative mode, in the master / slave operative mode, the transitional master / slave operative mode is a transitional mode from the non-master / slave operative mode to the master / slave operative mode.
Owner:TERUMO KK
Method for detecting transverse mode vibrations in an ultrasonic hand piece/blade
InactiveUS6588277B2Low costRecuperation increasedVibration measurement in solidsAnalysing solids using sonic/ultrasonic/infrasonic wavesResonanceEngineering
A method for detecting transverse mode vibrations in an ultrasonic hand piece / blade for determining the existence of unwanted vibration in the hand piece / blade. A tracking filter centered at the drive frequency of the generator, is used to monitor the drive frequency of the ultrasonic generator and attenuate the drive signal when it exceeds a predetermined level. The tracking filter has a wide pass band. Alternatively, a tracking filter having a pass band which is divided into several regions is used to avoid other longitudinal resonances, such as a resonance at a second harmonic, or other spectral features that would otherwise detract from the tracking accuracy of the filter.
Owner:ETHICON ENDO SURGERY INC
Manipulator apparatus
InactiveUS20050222587A1High operability , reliability and safetyMinimizing affectionDiagnosticsSurgical manipulatorsManipulatorEngineering
A manipulator apparatus comprises a surgical treatment section to be inserted into a subject body, a supporting section which turnably supports the surgical treatment section around a first axis and a second axis, an arm section having the supporting section connected to a distal end side thereof, a manipulating section provided at a proximal end side of the arm section, a manipulating lever provided at the manipulating section, the manipulating lever being turnably supported around a third axis provided at the proximal end side of the arm section, and a manipulating device provided at the manipulating lever, the manipulating device causing the surgical treatment section to turn around the first axis and the second axis.
Owner:TERUMO KK
Indwelling fecal diverting device
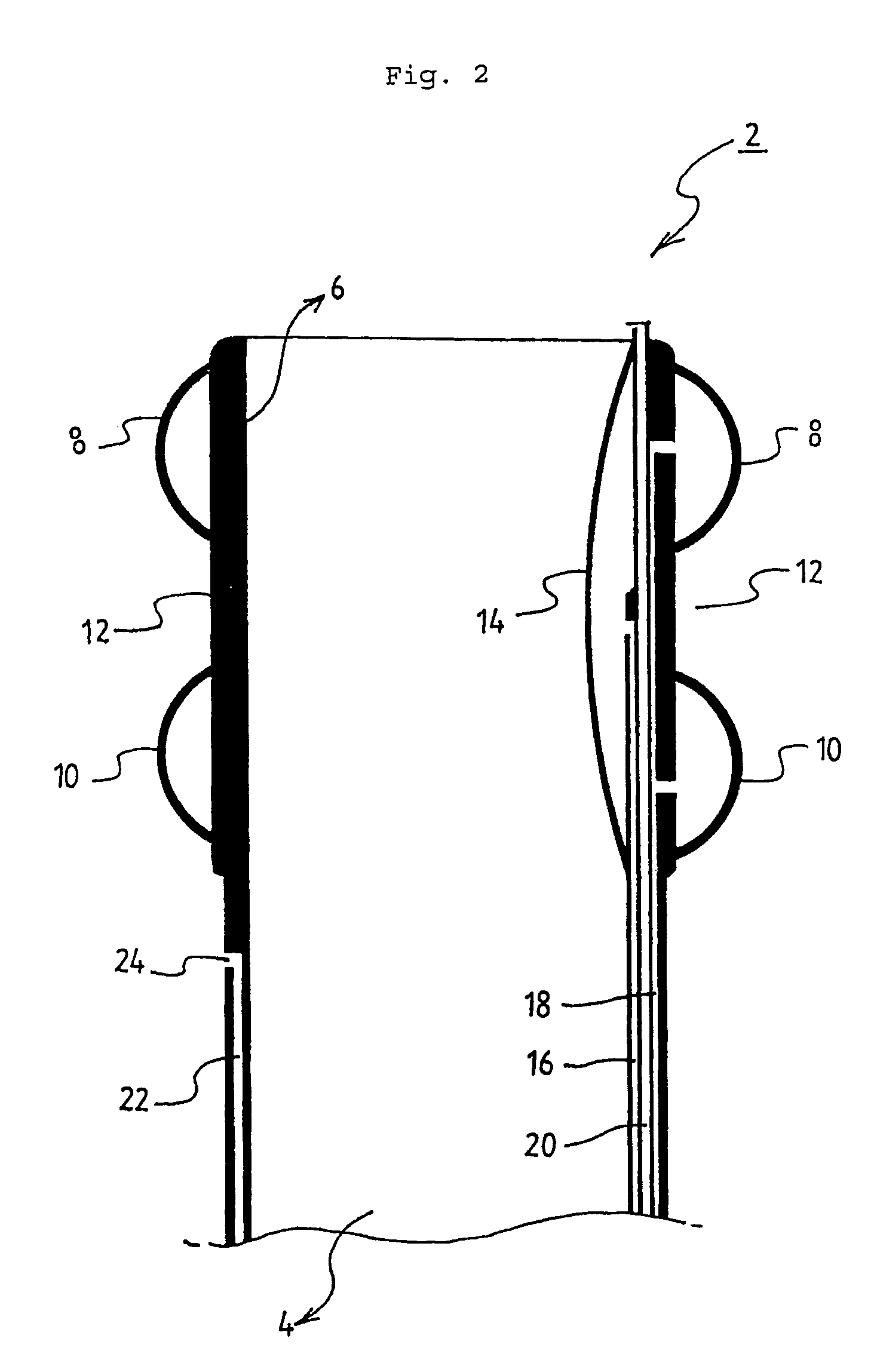
ActiveUS8398669B2Improve securityEasy to installBalloon catheterAnti-incontinence devicesFecesSurgery
Disclosed is an indwelling fecal diverting device. The device comprises an elongate tube formed, at an upper end thereof, with a tubular body part; a pair of fixing balloons attached up and down to an outer surface of the tubular body part such that a clamping portion is defined between the fixing balloons; and a tube opening and closing balloon attached to an inner surface of the tubular body part. An injection passage is defined in the tube so that a remedial liquid can be injected through the injection passage to the outside of the tube to medically treat an anastomosed portion of an intestinal tract of a patient. The indwelling fecal diverting device is fitted into the intestinal tract of the patient, air is supplied into the fixing balloons to inflate them, and the intestinal tract is clamped around the clamping portion using a clamping band.
Owner:YUSHIN MEDICAL +1
Atherectomy devices, systems, and methods
Owner:ATHEROMED
Arc-shaped cutting anastomat
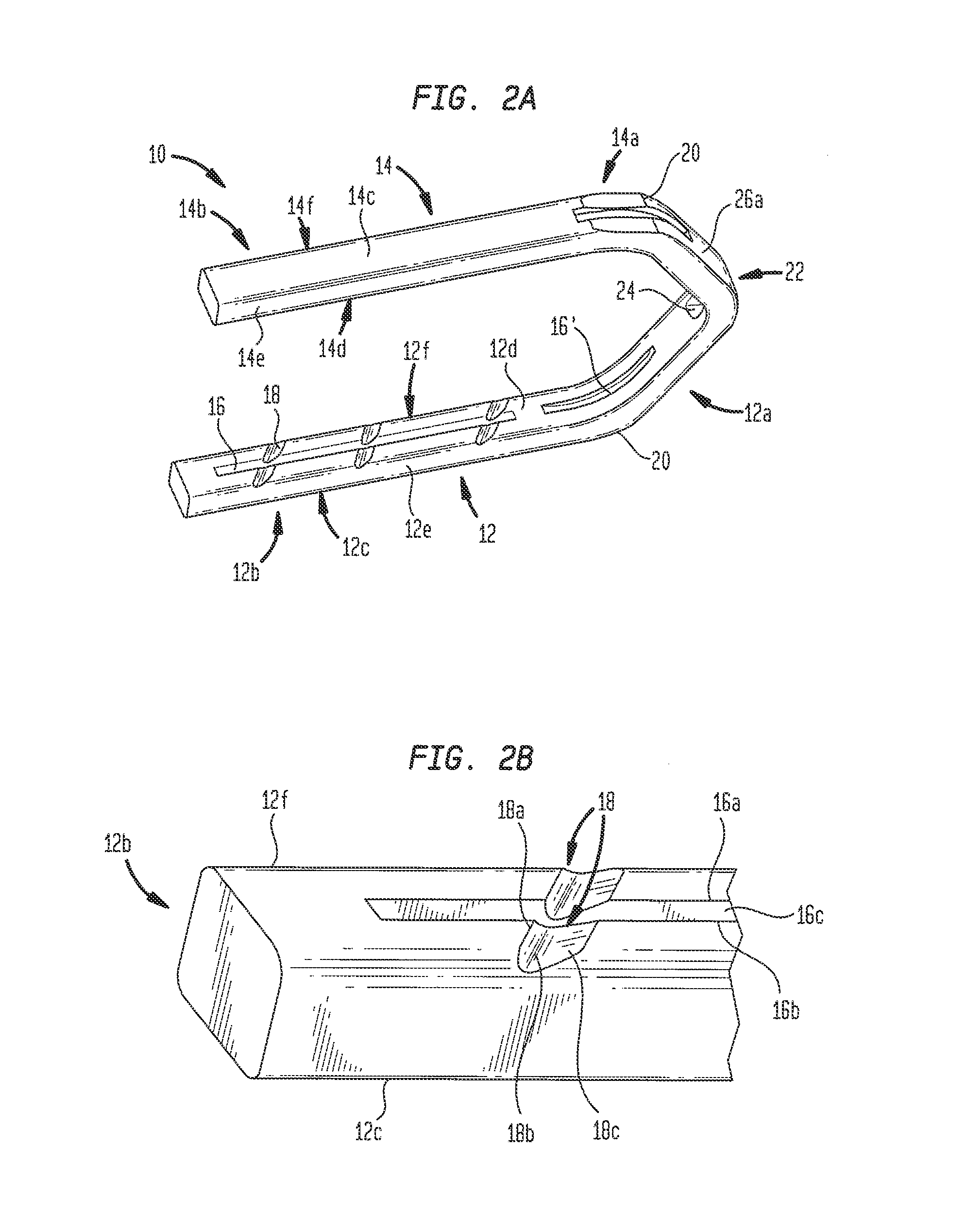
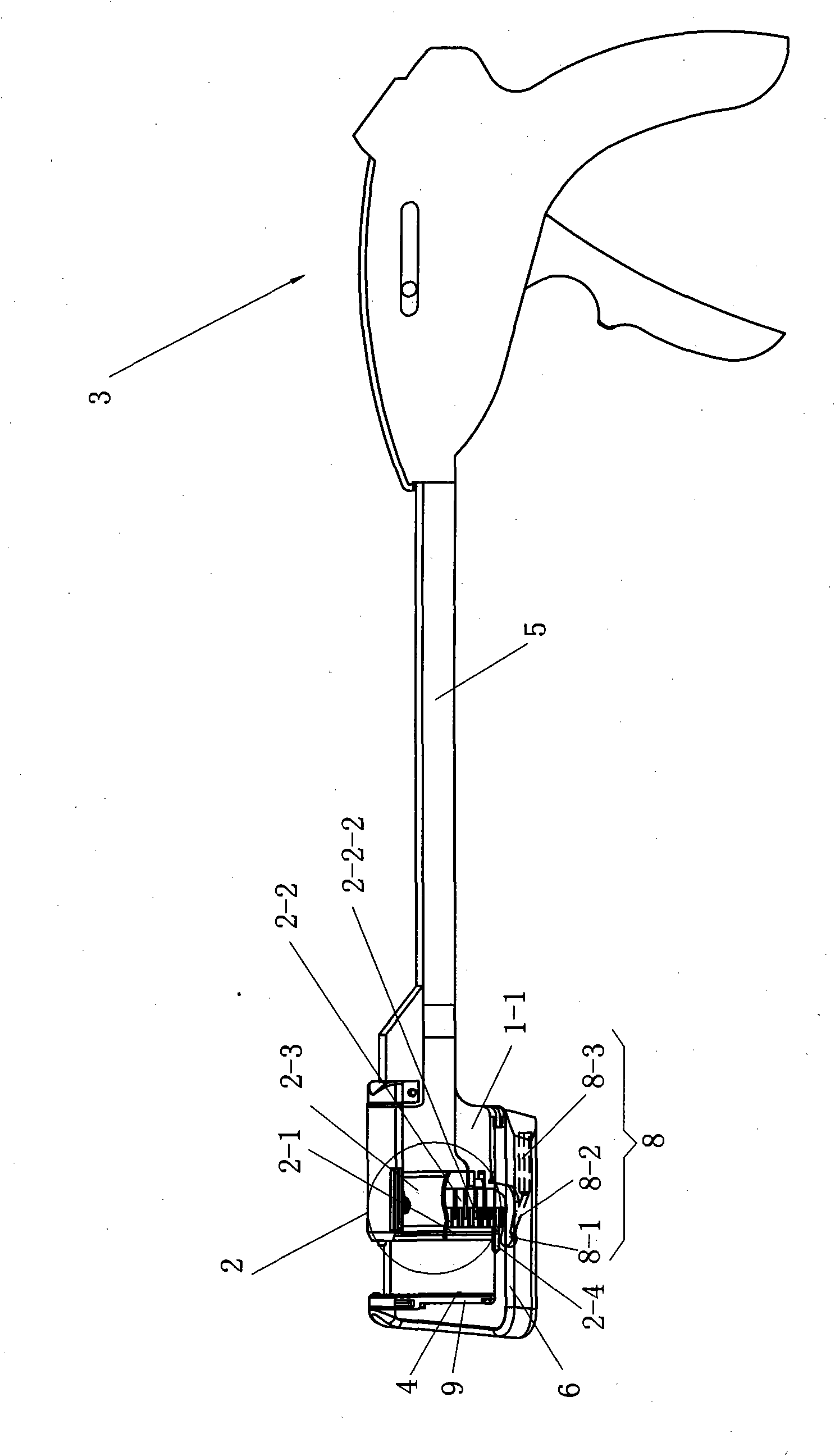
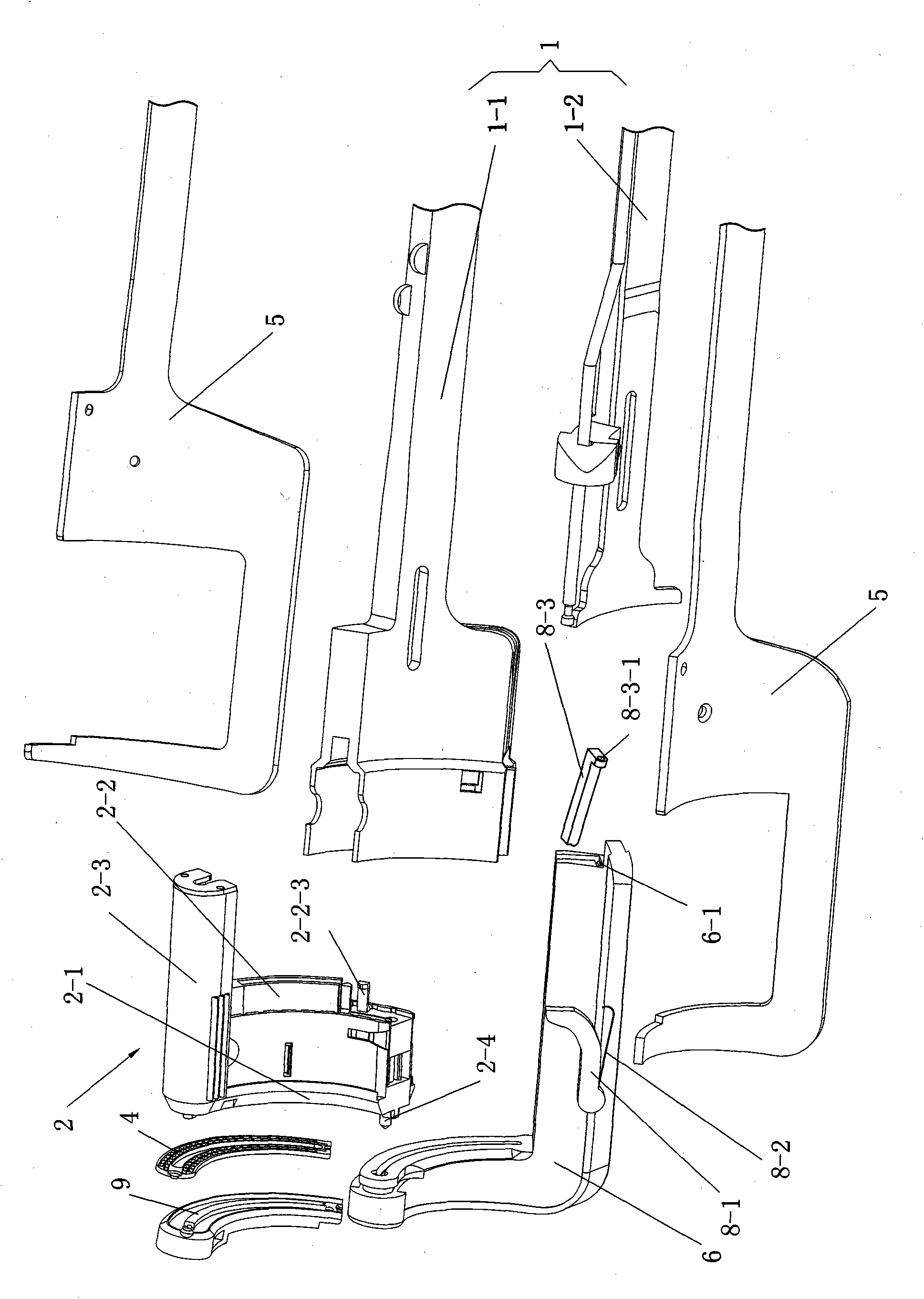
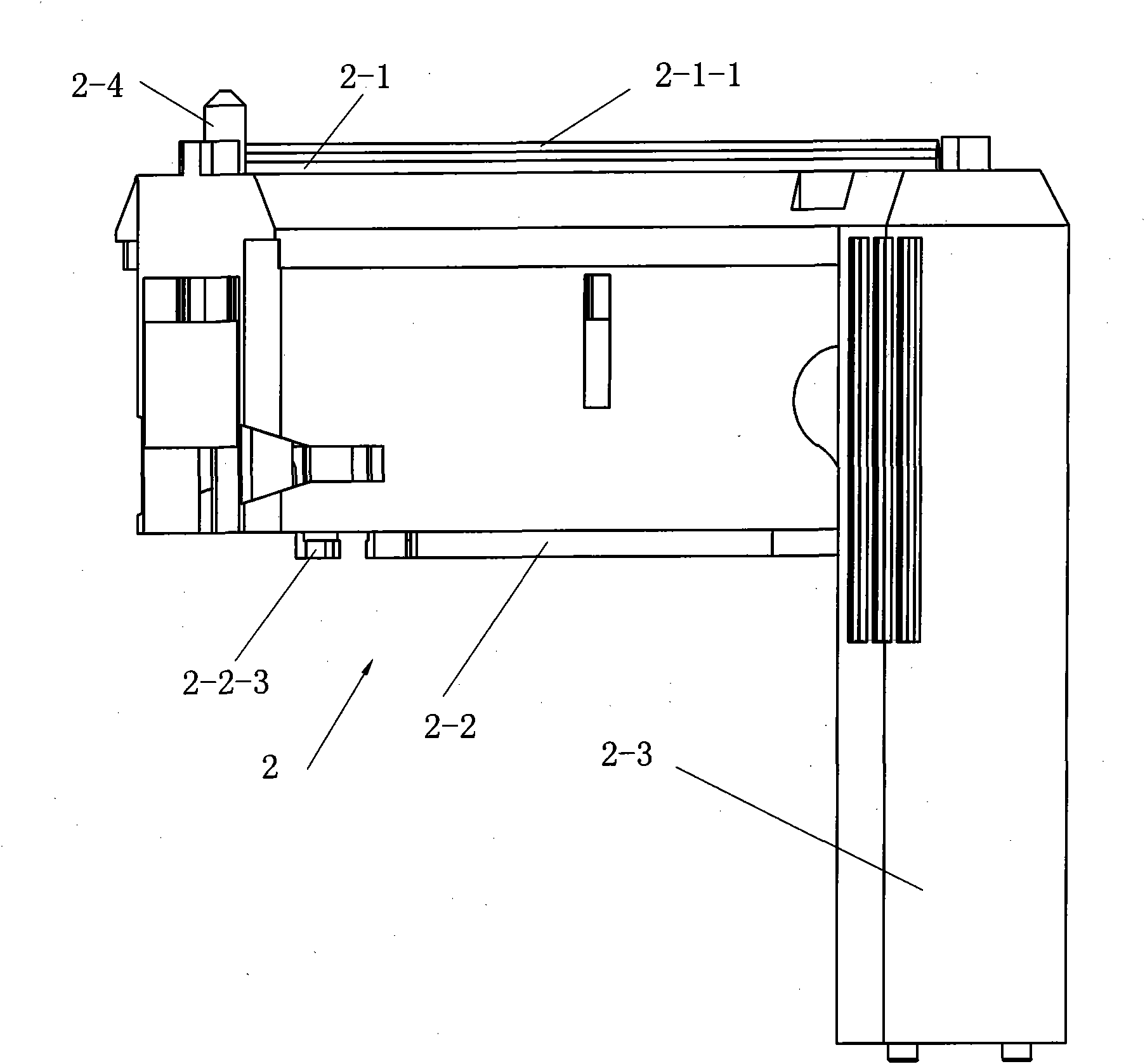
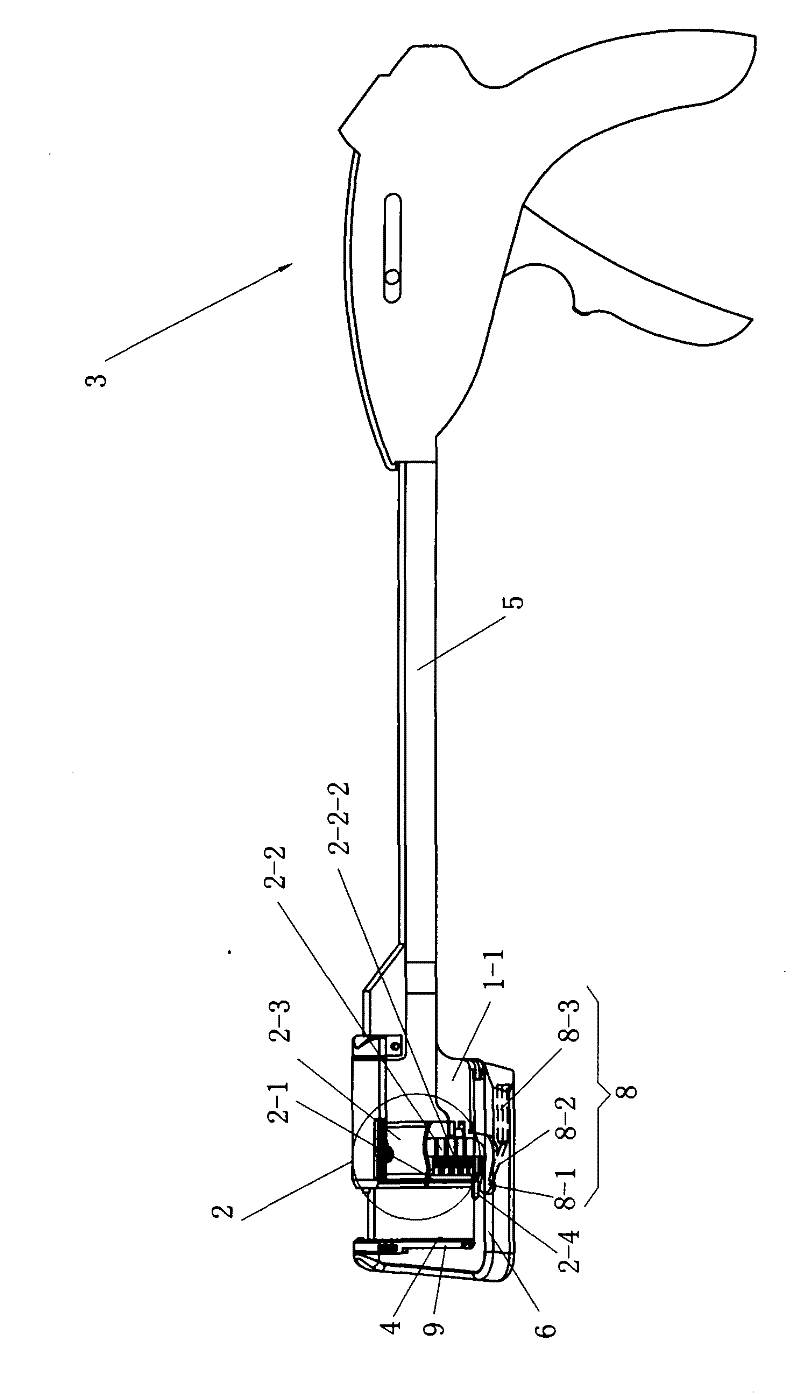
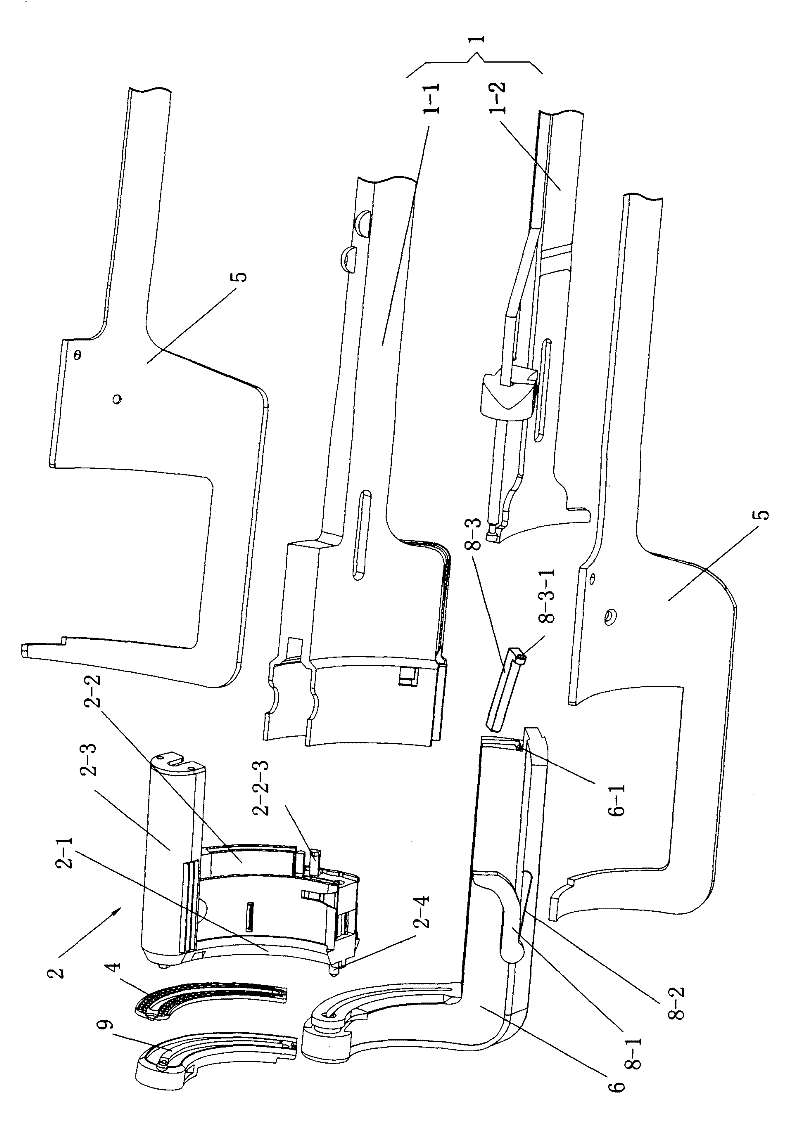
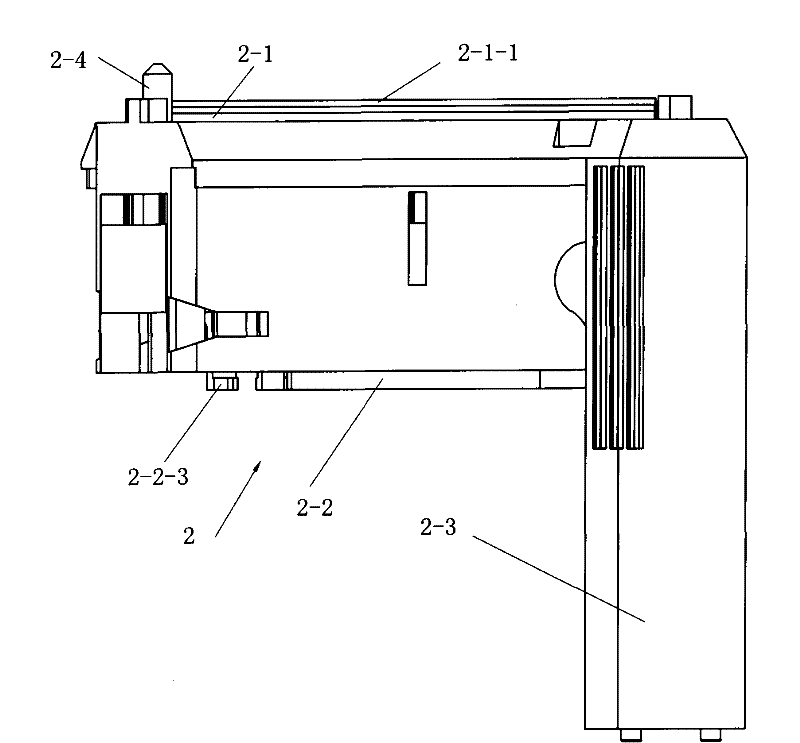
ActiveCN101912284AGood assembly firmnessImprove reliabilitySurgical staplesDistal anastomosisEngineering
The invention relates to an arc-shaped cutting anastomat comprising an anastomosis nail shaping mechanism, a nail pushing assembly, a trigger handle, a nail supporting seat, a base of the nail supporting seat, a knife cushioning ring and two splints, wherein the nail pushing assembly comprises a cutting knife, a nail pushing sheet, a nail bin and a guide post; the end of the nail pushing sheet and both sides of the cutting knife are respectively provided with a plurality of inner nail pushing dental sheets which are near the cutting knife and a plurality of outer nail pushing dental sheets which are far away from the cutting knife; the cutting knife and the nail pushing sheet are injected and molded at a time to be fixed together; the outer side of the each outer nail pushing dental sheet on the nail pushing sheet is provided with a reinforcing rib; the inner side of each nail pushing dental sheet on the nail pushing sheet is provided with a reinforcing rib; both ends of the first guide surfaces of the nail pushing dental sheets are respectively connected with the first contact surfaces and the second contact surfaces of the nail pushing dental sheets through concave arc-shaped connecting surfaces, and both ends of the second guide surfaces thereof are respectively connected with the first contact surfaces and the second contact surfaces through the concave arc-shaped connecting surfaces; and the first contact surfaces and the second contact surfaces are respectively in contact with the inner walls of the nail pushing dental sheet holes of the nail bin. The invention has the advantages of good trigger anastomosis shaping effect and high safety.
Owner:CHANGZHOU JIANRUIBAO MEDICAL DEVICES
Safety device for sampling tissue
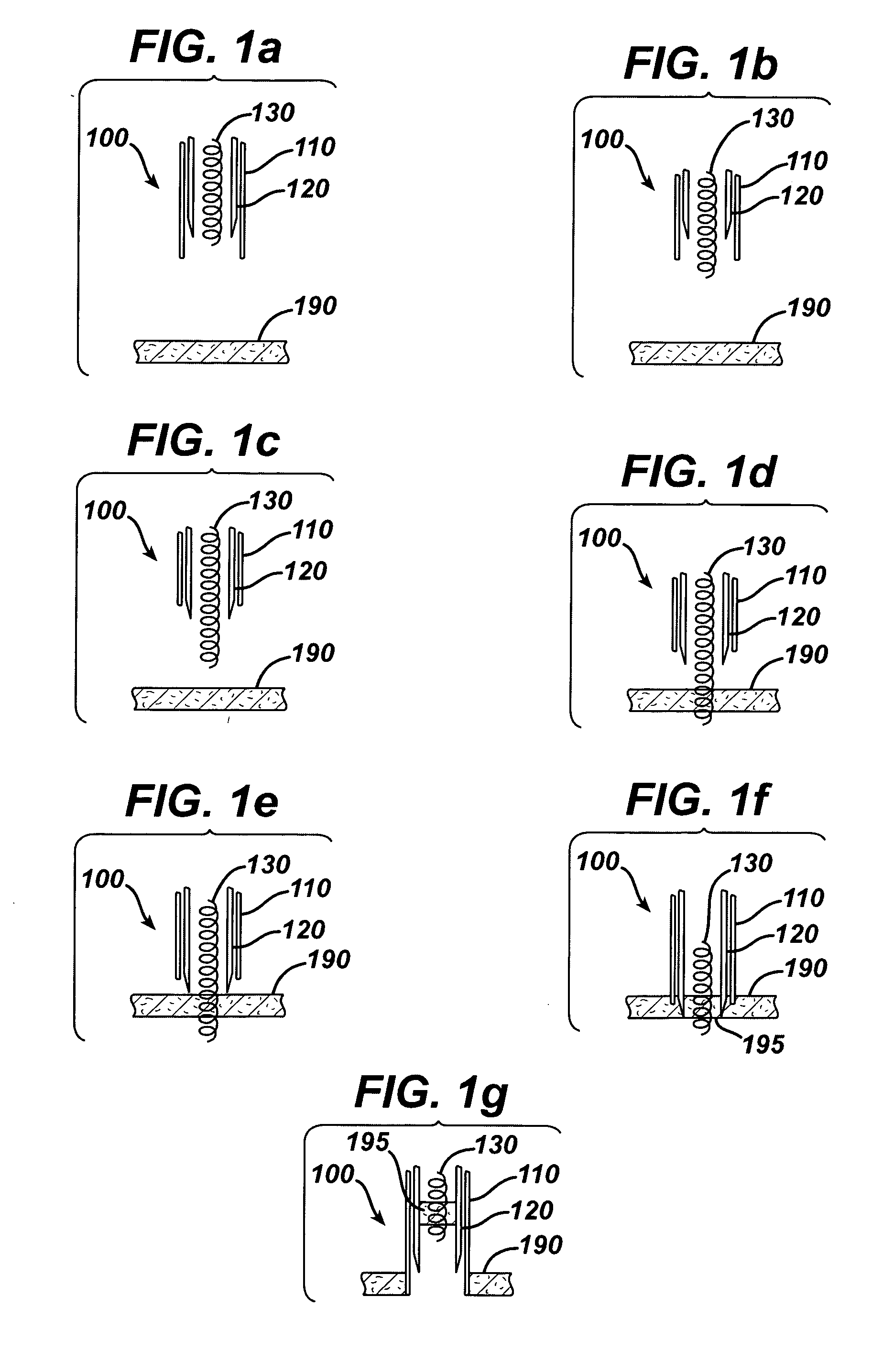
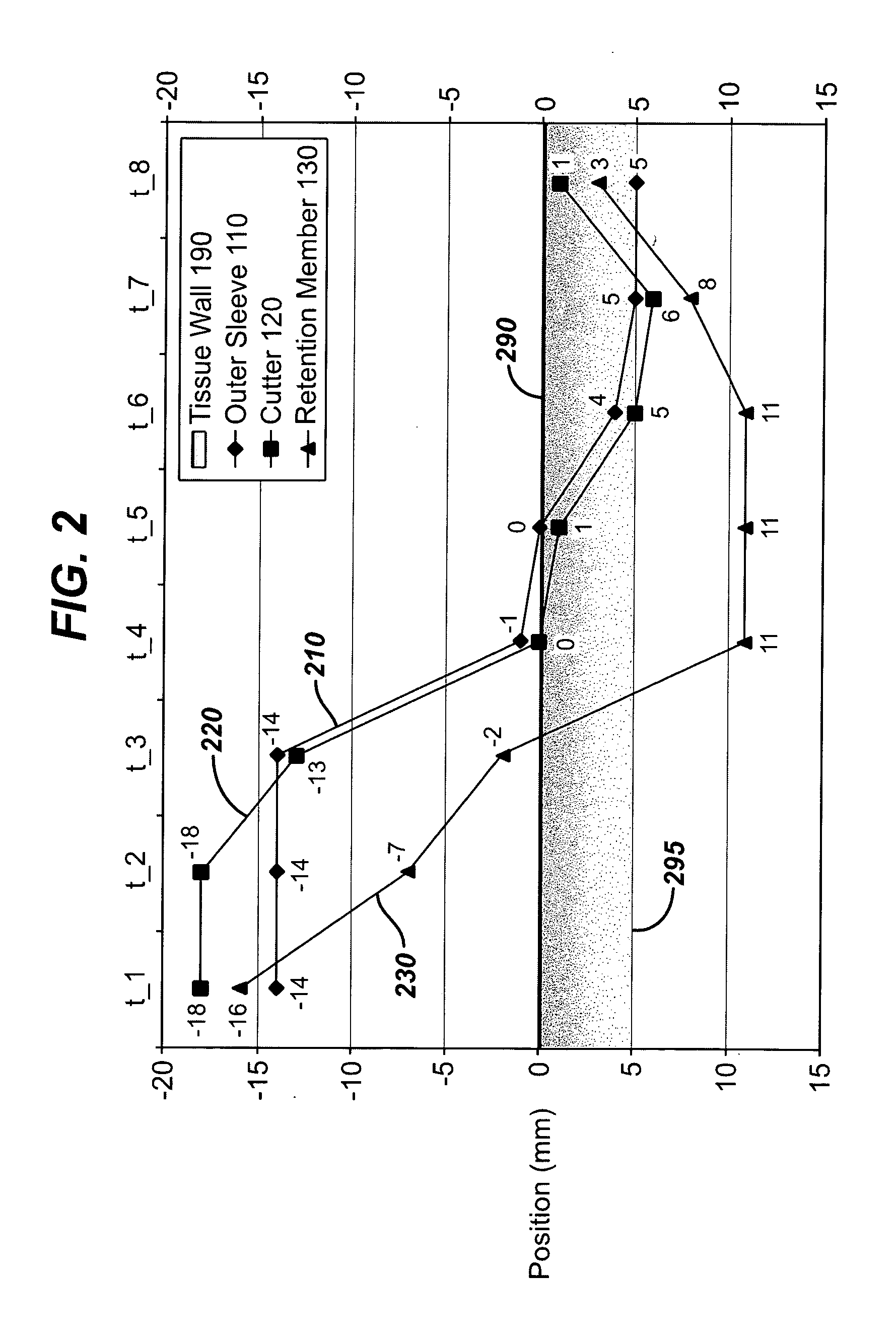
InactiveUS20050251063A1Eliminate needRobust designSurgical needlesVaccination/ovulation diagnosticsBiomedical engineering
An apparatus for sampling tissue includes a tissue engaging member for engaging and retaining a sample of a tissue structure, and a cutter surrounding the tissue engaging member. The tissue engaging member and cutter are both operative to translate longitudinally with respect to one another, and a mechanism prevents the cutter from moving distally, the mechanism being released and the cutter freed to move distally when the tissue engaging member is in a predetermined position, preferably distal of the cutter. Thereby, out of sequence operation, e.g., premature cutting of the tissue before the tissue engaging member is in position, is prevented.
Owner:ETHICON INC
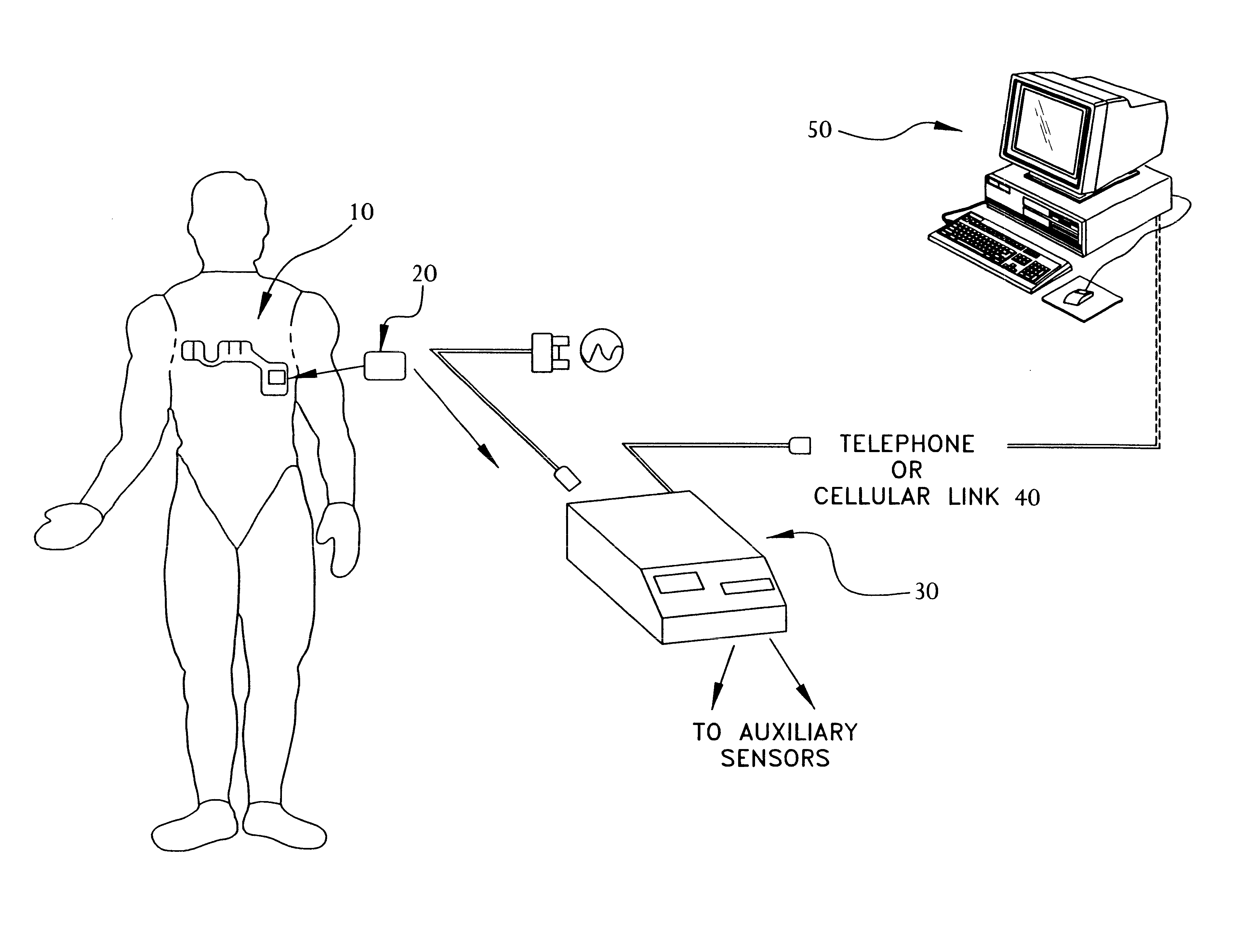
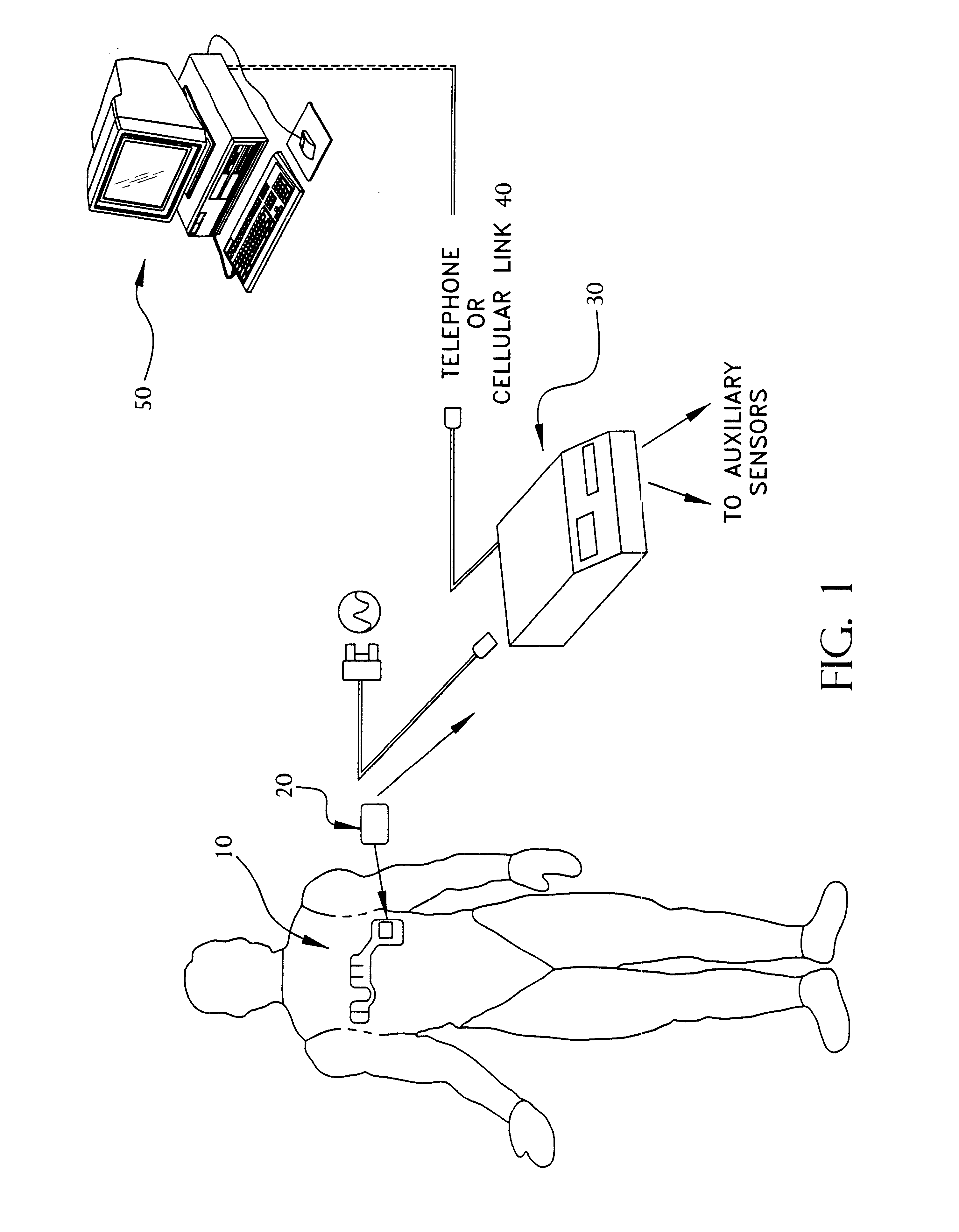
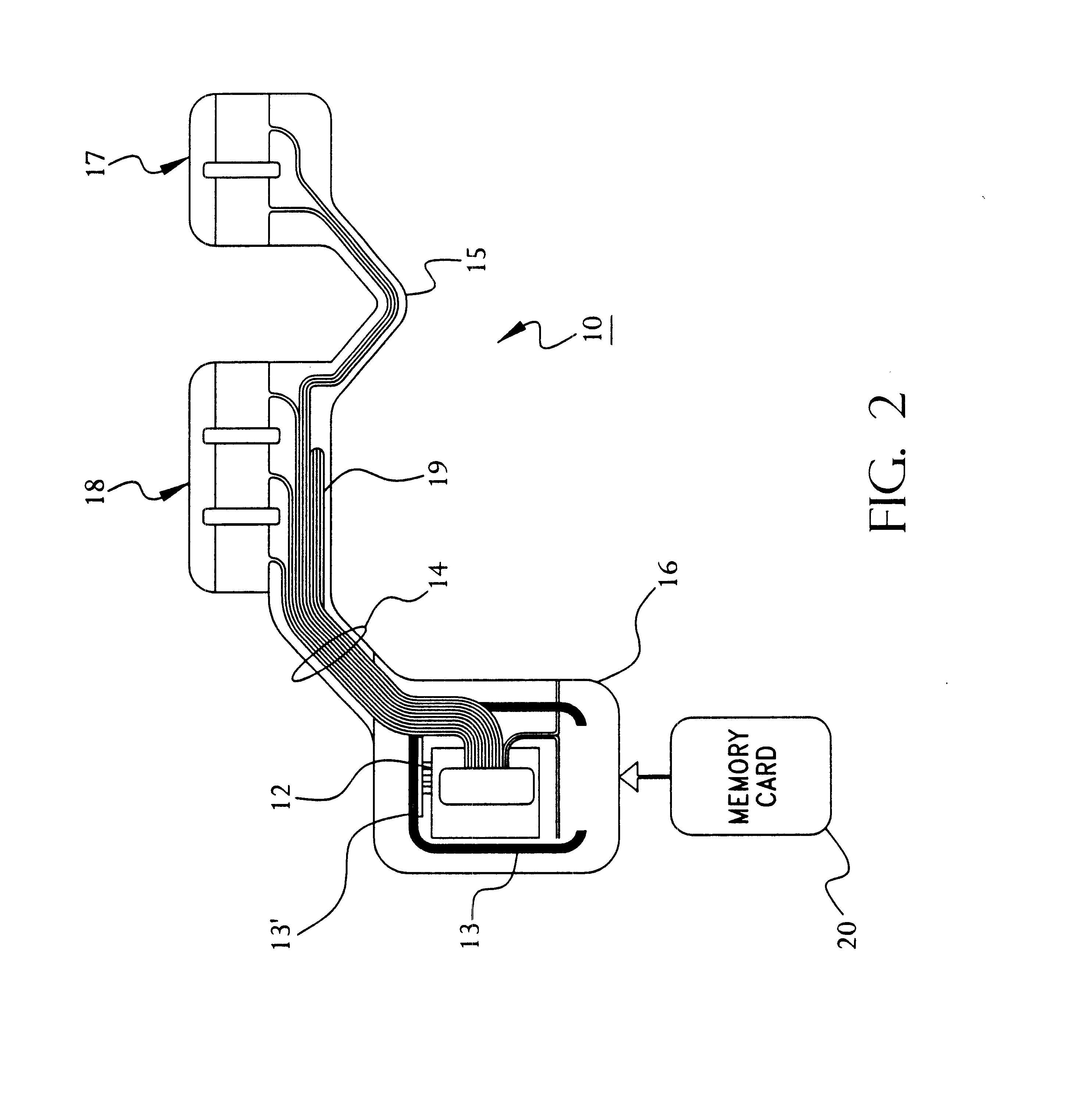
Portable remote patient telemonitoring system using a memory card or smart card
InactiveUS6454708B1Low costIncrease the number ofSurgeryRespiratory organ evaluationSmart cardFull waveform
A system and method for monitoring health parameters and capturing data from a subject. The system is characterized by a cordless, disposable sensor band with sensors for measuring full waveform ECG, full waveform respiration, skin temperature, and motion, and a connector which accepts a memory card or a smart card for storage of the measured data. After a predetermined period of time, such as when the sensor band is removed, the memory card or smart card is removed and inserted into a monitoring device which reads the stored health parameter data of the subject. The monitoring device includes a base station that includes a memory / smart card reader and is connected to conventional phone lines for transferring the collected data to a remote monitoring station. The base station may also capture additional clinical data, such as blood pressure data, and to perform data checks. Subject safety is enhanced by the ability of the base station to compare clinical data, e.g. ECG, against given profiles and to mark events when appropriate or when the base station is programmed to do so. The remote monitoring station allows the presentation and review of data (including events) forwarded by the sensor band. ECG analysis software and a user-friendly graphical user interface are provided to remotely analyze the transmitted data and to permit system maintenance and upkeep. In alternative embodiments, a smart card includes the sensor band's electronics and / or signal transmission circuitry in conjunction with a portable data logger so that the electronics may be reused from one disposable sensor band to the next without limiting the patient's range of movement. The system of the invention has useful application to the collection of subject clinical data during drug trials and medical testing for regulatory approvals as well as management of subjects with chronic diseases.
Owner:CLEARPATH PARTNERS
Microprocessor controlled ambulatory medical apparatus with hand held communication device
ActiveUS20050010269A1Enhance capacityReduce in sizeEnergy efficient ICTElectrotherapyTelemetry EquipmentBiomedical engineering
An implantable infusion pump possesses operational functionality that is, at least in part, controlled by software operating in two processor ICs which are configured to perform some different and some duplicate functions. The pump exchanges messages with an external device via telemetry. Each processor controls a different part of the drug infusion mechanism such that both processors must agree on the appropriateness of drug delivery for infusion to occur. Delivery accumulators are incremented and decremented with delivery requests and with deliveries made. When accumulated amounts reach or exceed, quantized deliverable amounts, infusion is made to occur. The accumulators are capable of being incremented by two or more independent types of delivery requests. Operational modes of the infusion device are changed automatically in view of various system errors that are trapped, various system alarm conditions that are detected, and when excess periods of time lapse between pump and external device interactions.
Owner:MEDTRONIC MIMIMED INC
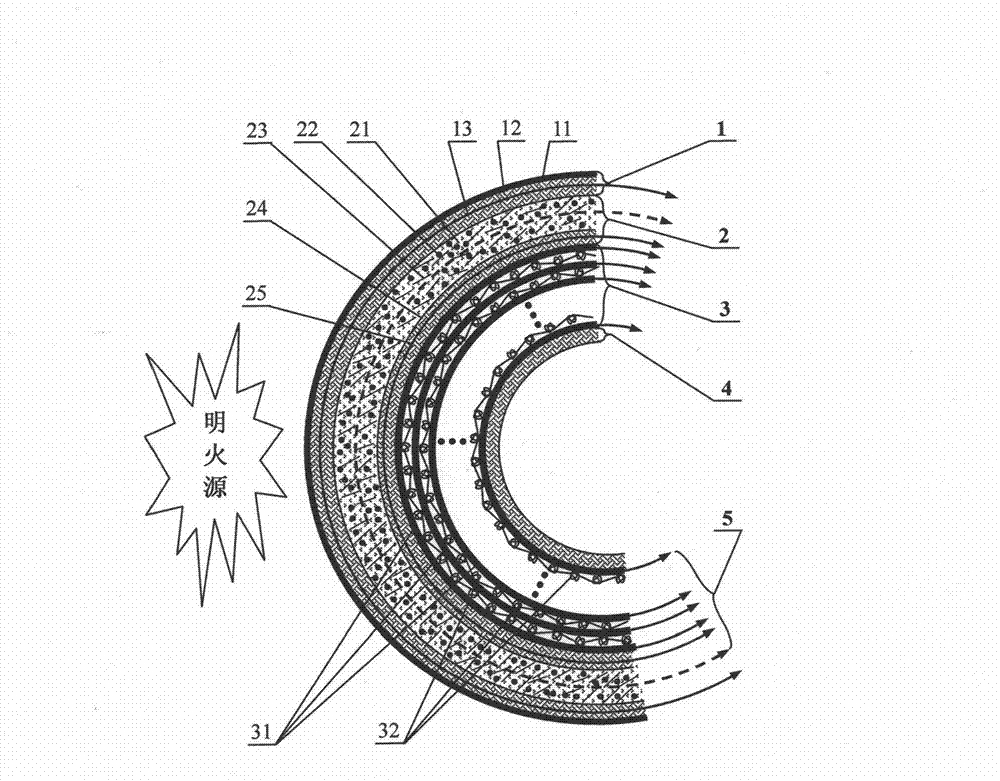
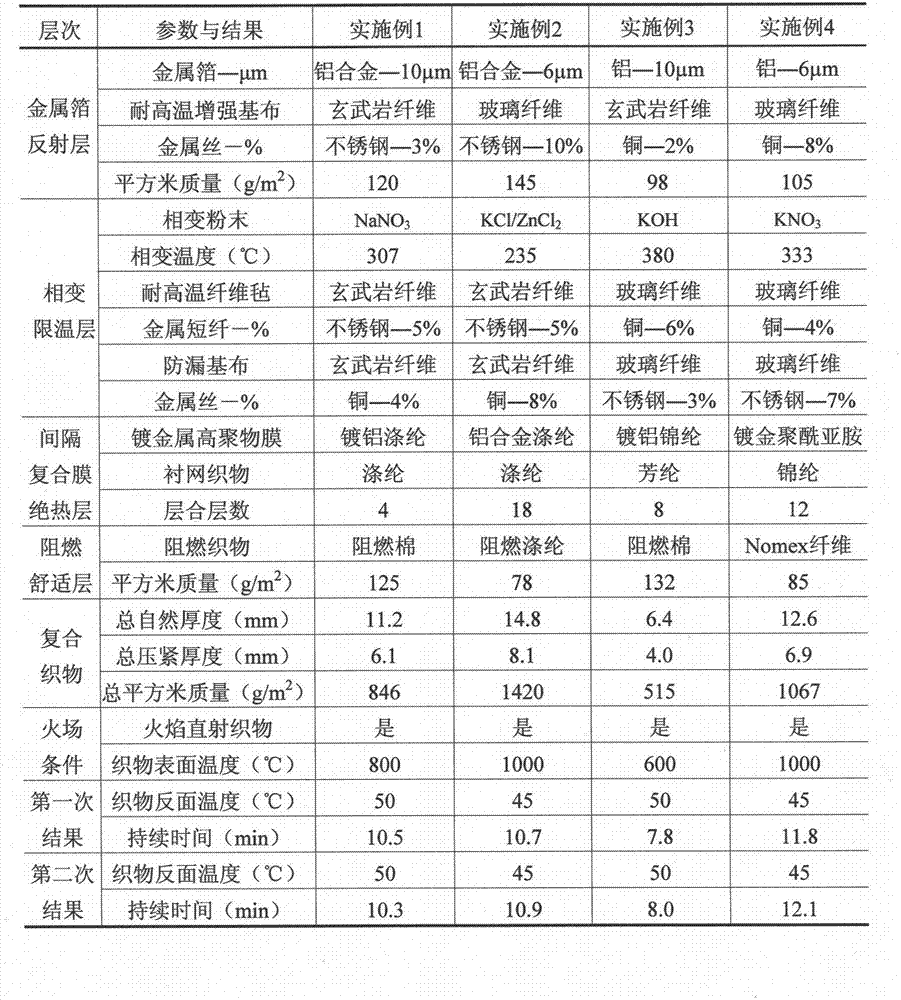
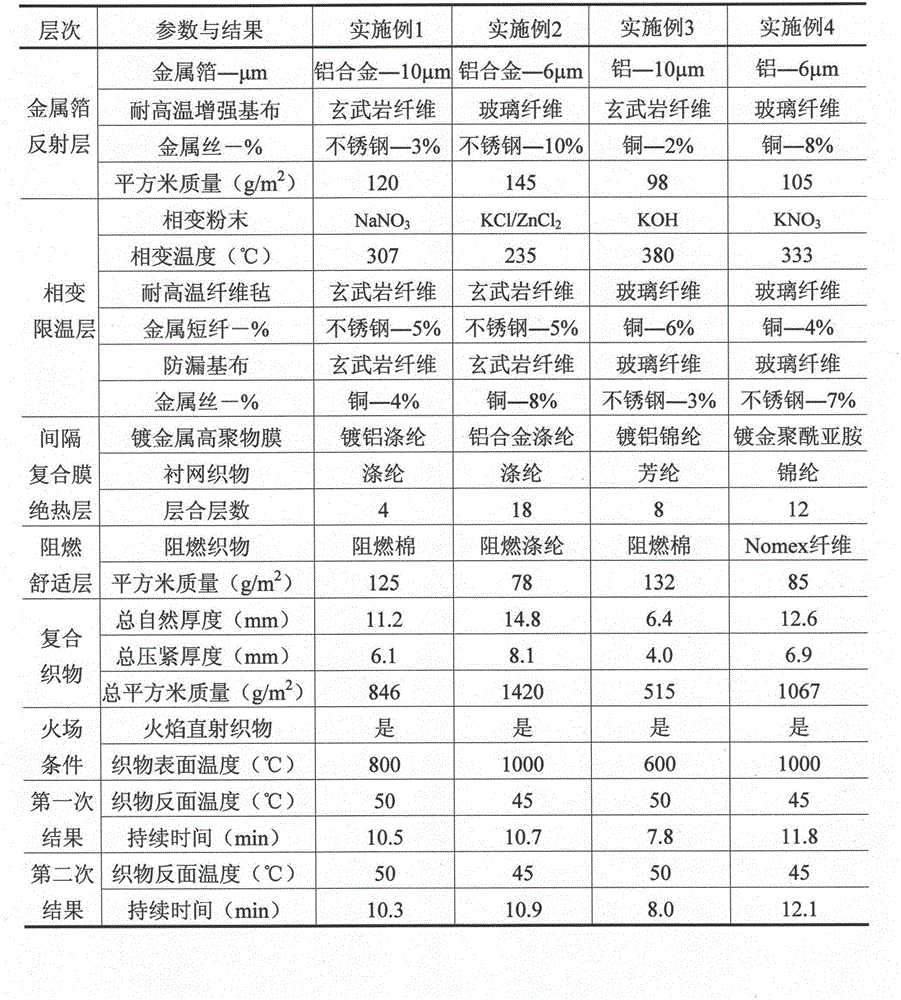
Multistage-spreading heat-dissipation fire-proof heat-insulation composite fabric, preparation method and application
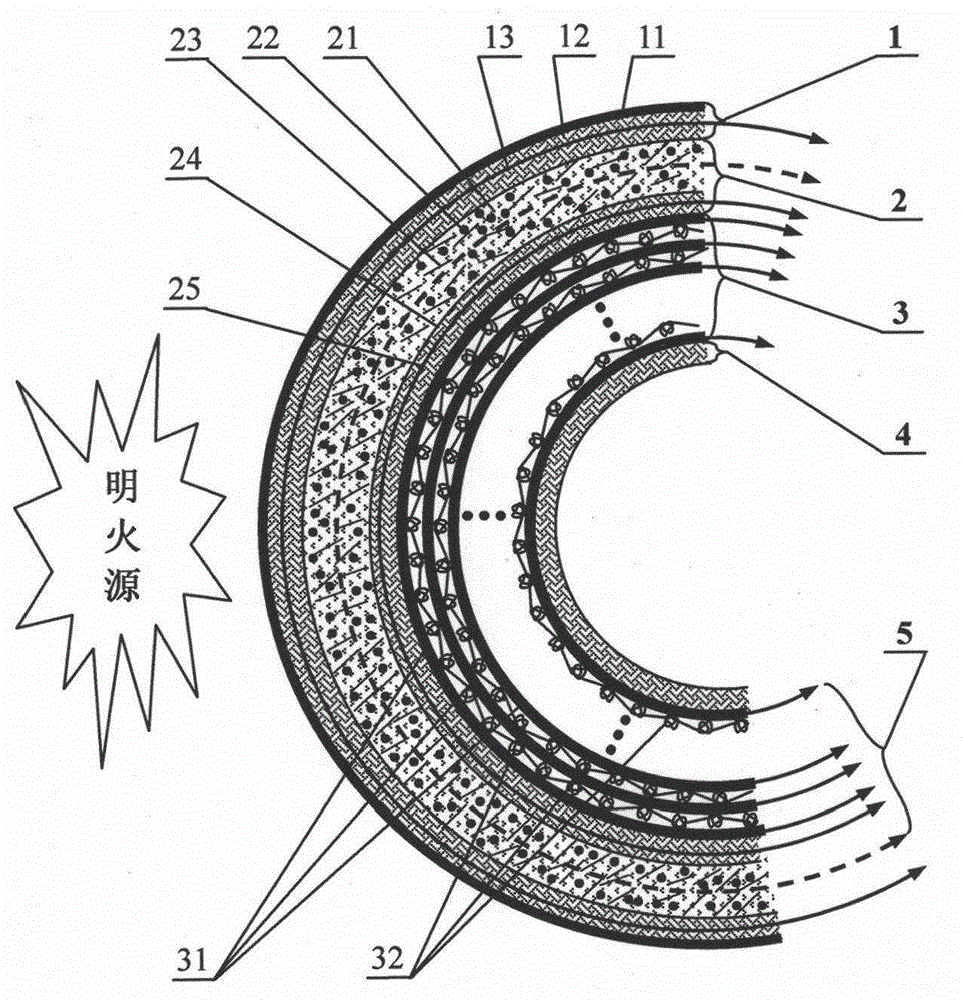
ActiveCN102783741AImprove permeabilityPromote absorptionLaminationLamination apparatusInsulation layerMetal foil
The invention relates to a preparation method and an application of multistage-spreading heat-dissipation fire-proof heat-insulation composite fabric. The multistage-spreading heat-dissipation fire-proof heat-insulation composite fabric is formed by successively arranging and laminating a metal foil reflection layer, a phase change temperature limitation layer, an interval composite membrane heat-insulation layer and a flame-retardant comfortable layer, wherein the metal foil reflection layer has high reflectivity and an enhanced heat-dissipation function; the phase change temperature limitation layer has functions of high energy consumption absorption and evenly-distributed heat conduction; the interval composite membrane heat-insulation layer has the functions of reflection insulation and even distribution of heat; and the flame-retardant comfortable layer has the functions of low-contact heat conduction, heat insulation and comfort. When the front side of the multistage-spreading heat-dissipation fire-proof heat-insulation composite fabric is under the action of open fire and strong heat flow environment, the back side of the multistage-spreading heat-dissipation fire-proof heat-insulation composite fabric can be kept below 50DEG C which is near the safe temperature state of the human skin, and the integral structural form and the mechanical property are stable. The natural thickness of the composite fabric is 5-15mm, the compression thickness of the composite fabric is 3-8mm, and the square meter quality of the composite fabric is 400-1500g / m<2>. The composite fabric is fire-proof heat-insulation material which is totally sealed, stuck and sewn and can be used for individual protection and environment heat insulation in special high-temperature occasions, such as fire control, military, exploration, safe escape and industry and the like.
Owner:DONGHUA UNIV
Method and apparatus for the free licensing of digital media content
ActiveUS20040003398A1Improve securityReduce partAnalogue secracy/subscription systemsTwo-way working systemsDigital contentControl signal
A system and method for displaying digital media files with compulsory advertisement files is disclosed. In one embodiment, the system includes a user interface, a media file decryptor, an ad manager, an intersplicer, and a media player. The user interface receives input from a user indicating the selection of media files to be presented. The media file decryptor receives and decrypts the selected media files. The ad manager receives and manages ad files from an ad file source. The intersplicer combines the media files with the ad files by providing control signals to the media player, causing the media player to present the ad files with the selected media files. Various embodiments of the invention facilitate the wide distribution of media content in a way that allows the free use of media properties, on demand, with direct consumer exchange capabilities, while at the same time enabling compensation to copyright holders.
Owner:PIRANHA MEDIA DISTRIBUTION LLC
Video-Based Privacy Supporting System
ActiveUS20100205667A1Improve securityPrivacy protectionDigital data processing detailsUnauthorized memory use protectionDisplay deviceOutput device
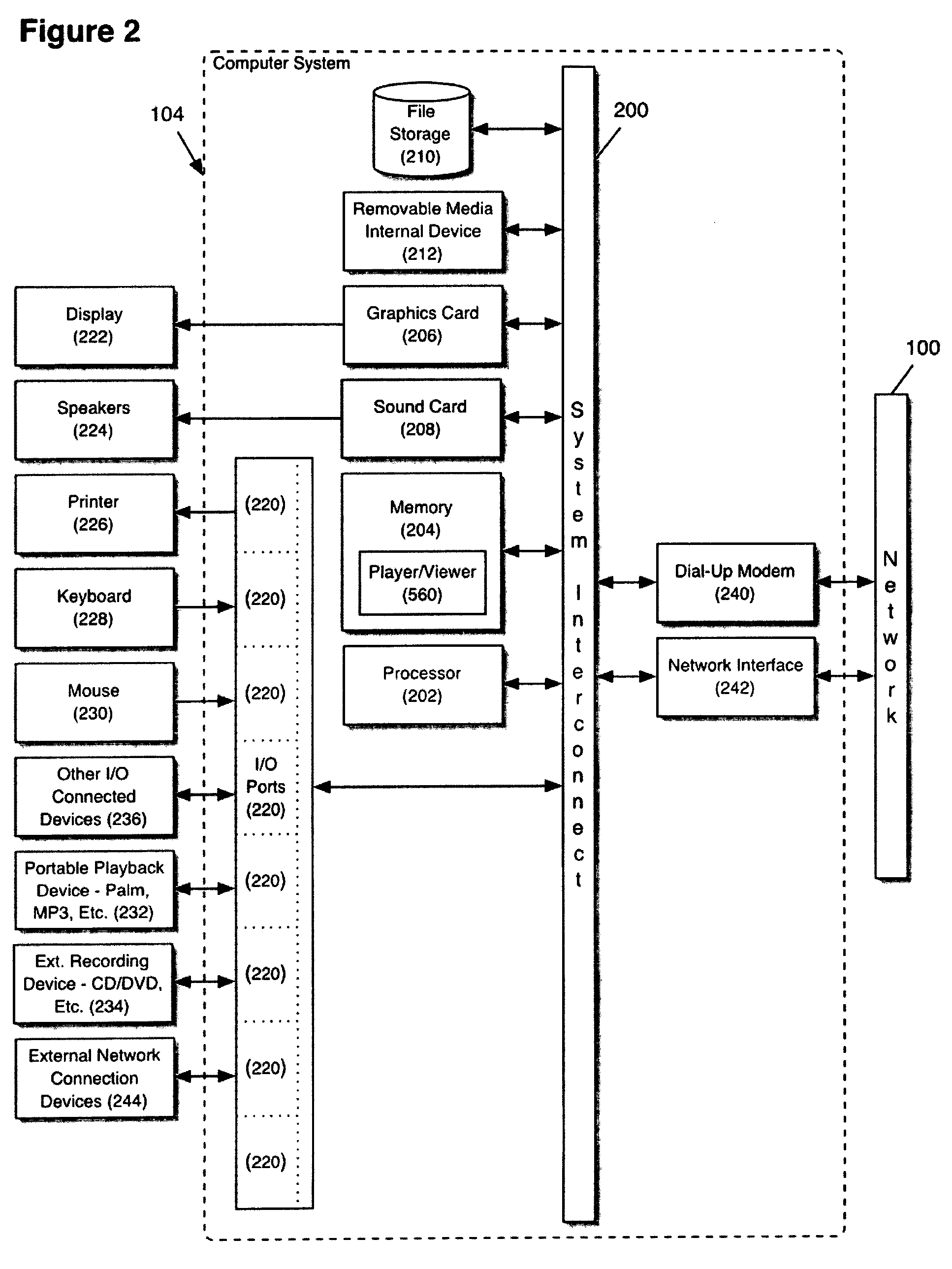
Computer display privacy and security for computer systems. In one aspect, the invention provides a computer-controlled system for regulating the interaction between a computer and a user of the computer based on the environment of the computer and the user. For example, the computer-controlled system provided by the invention comprises an input-output device including an image sensor configured to collect facial recognition data proximate to the computer. The system also includes a user security parameter database encoding security parameters associated with the user; the database is also configured to communicate with the security processor. The security processor is configured to receive the facial recognition data and the security parameters associated with the user, and is further configured to at least partially control the operation of the data input device and the data output device in response to the facial recognition data and the security parameters associated with the user.
Owner:TOBII TECH AB
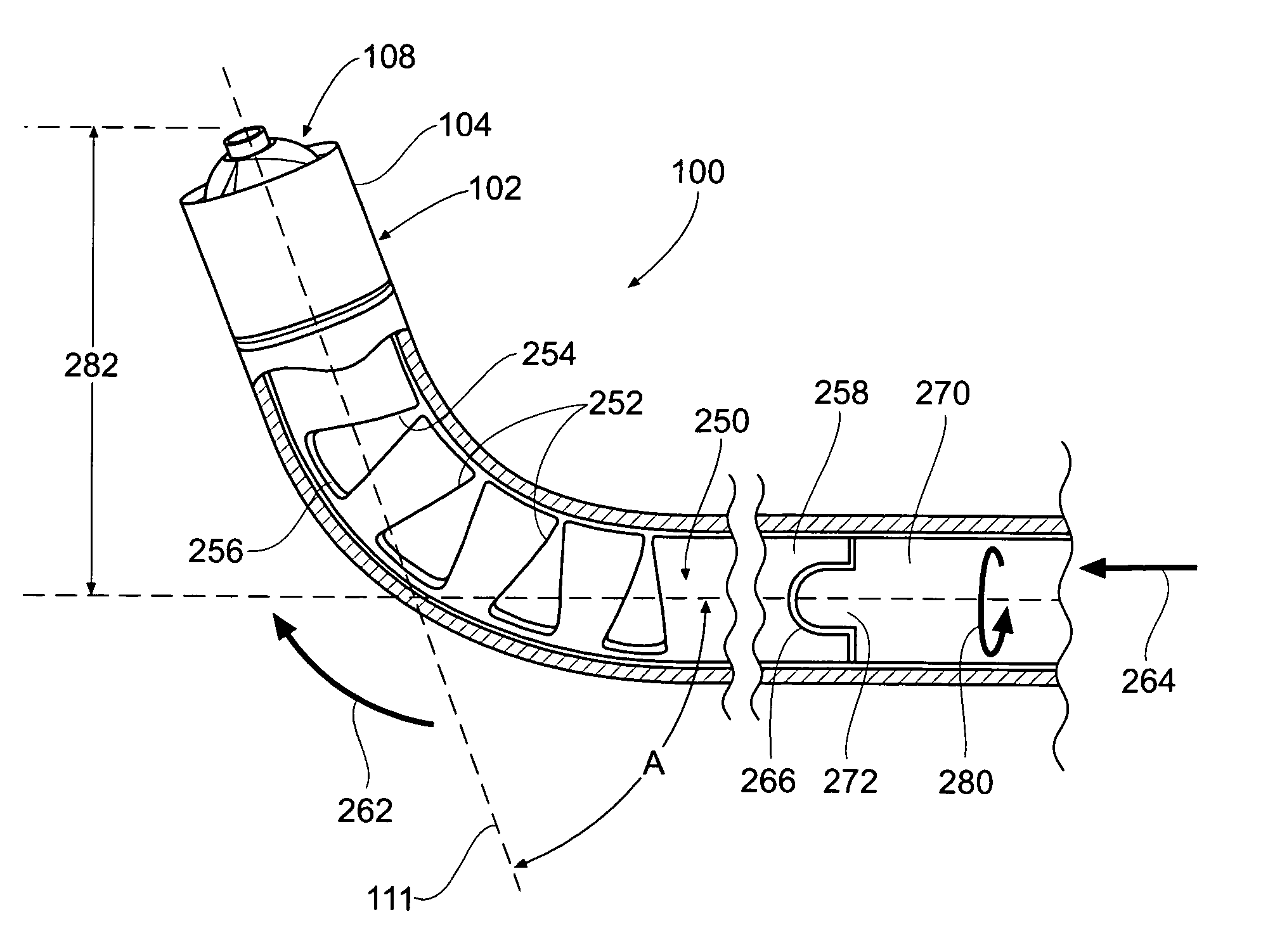
Portable drilling device
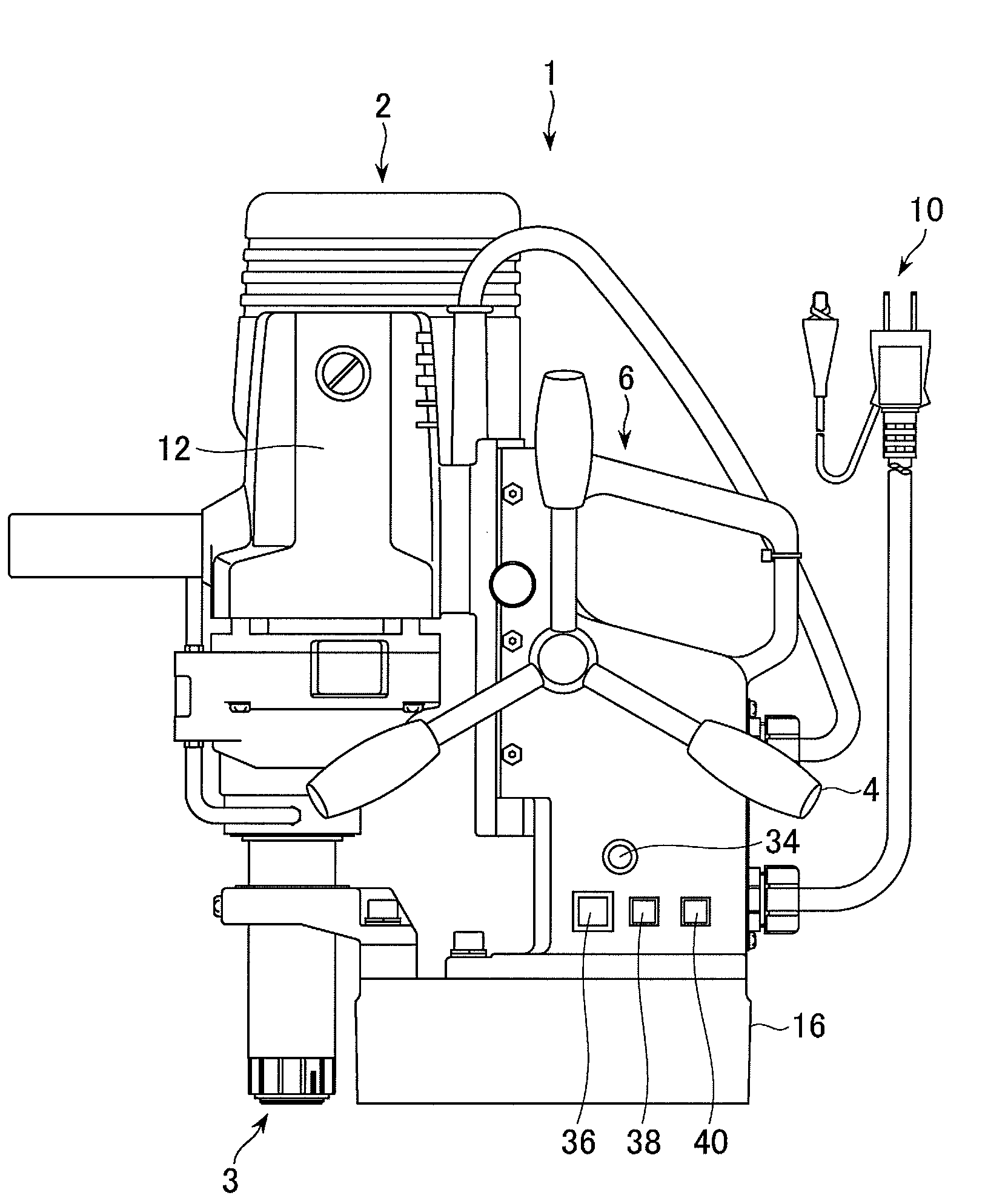
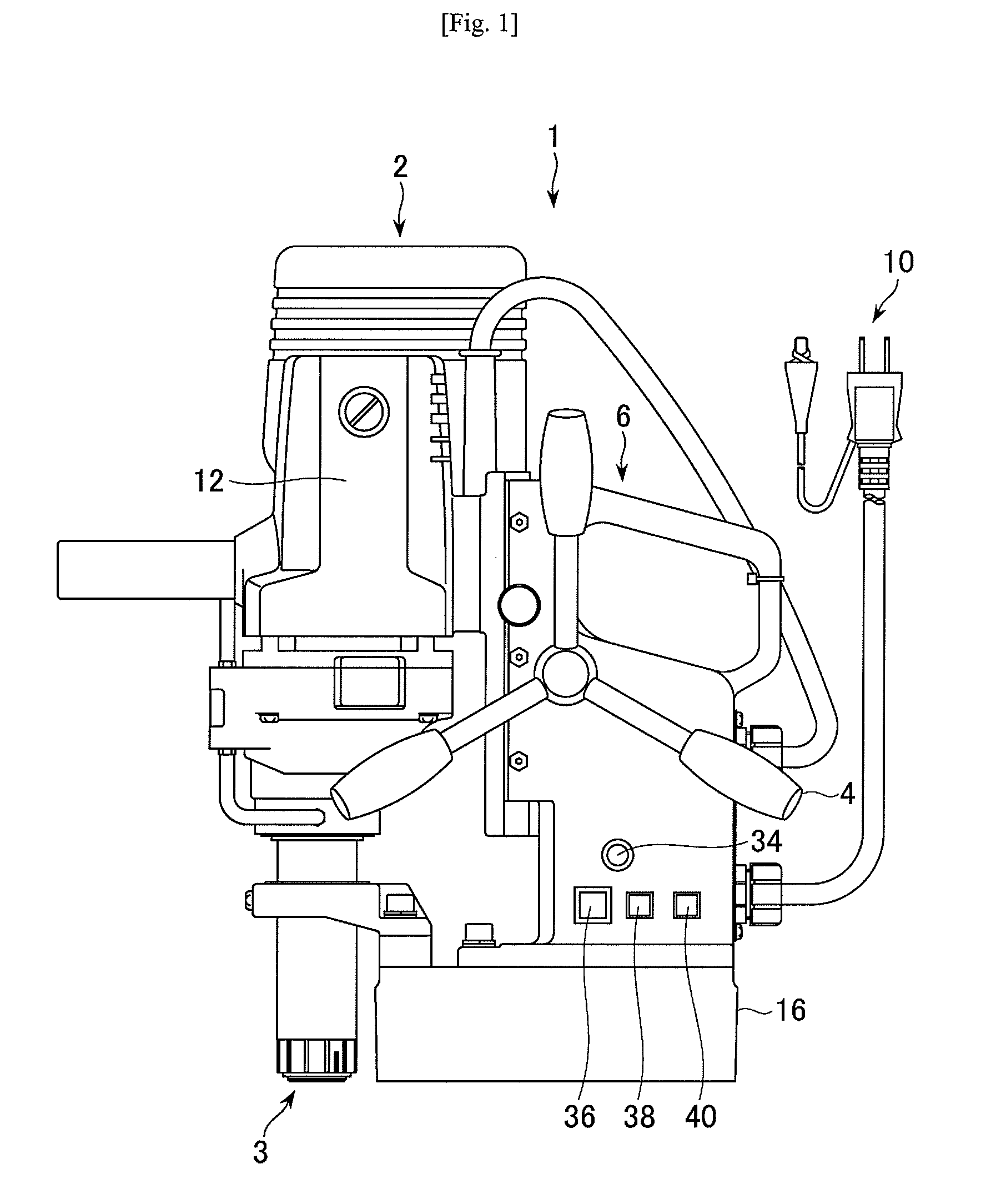
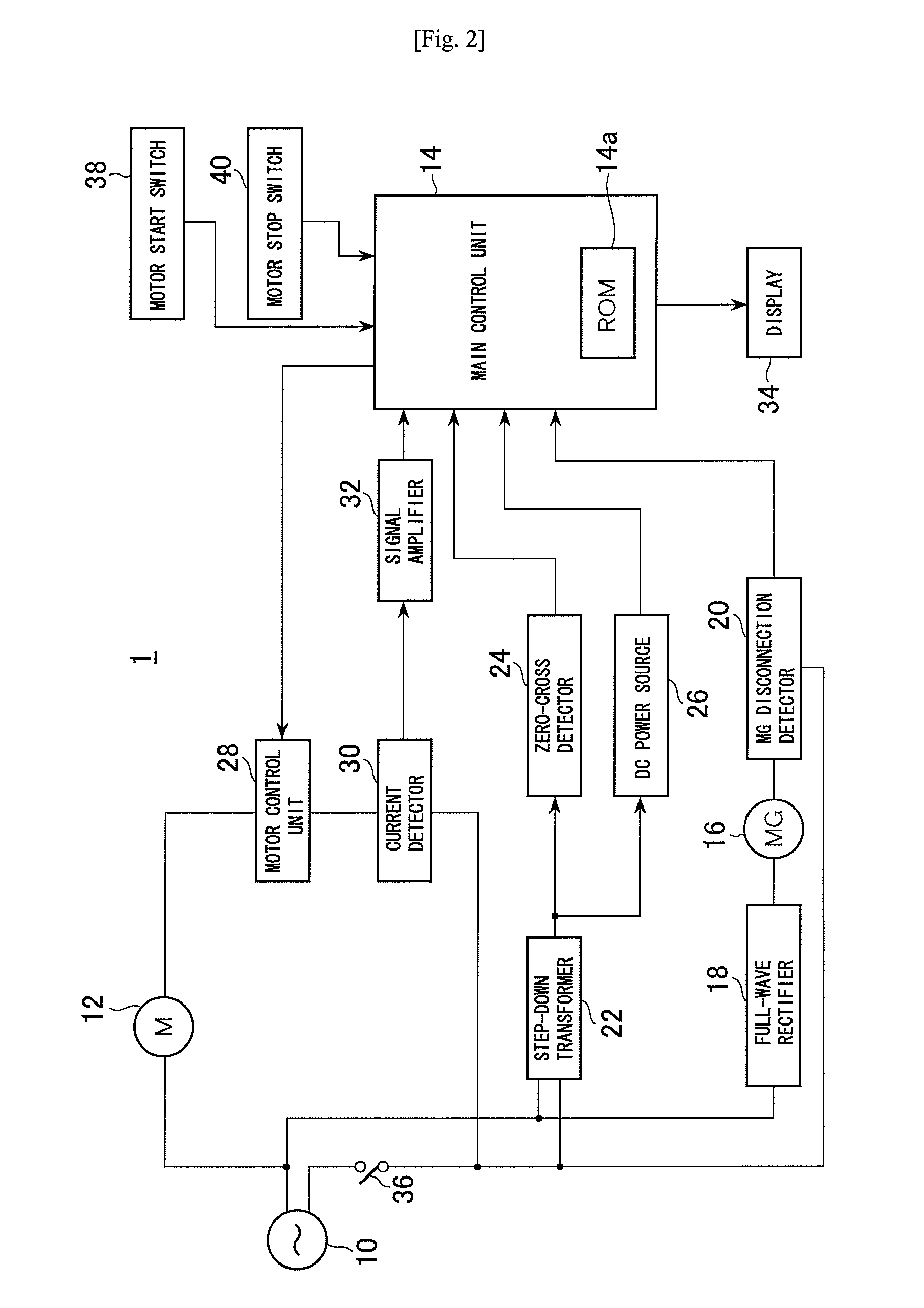
ActiveUS7936142B2Easy to operateImprove securityAC motor controlDC motor speed/torque controlFull waveEngineering
A drilling device prevents recurrence of an overload condition after occurrence of the overload condition, thereby improving operability and safety in the drilling device. A motor for rotating a drill is connected to an AC power source through a motor control unit, a current detector, and a power switch. A magnet is also connected to the AC power source through the power switch and a full-wave rectifier. The motor control unit rotationally drives the motor on the basis of a signal sent from a main control unit according to a state in which a motor start switch is on. The main control unit controls the motor control unit to gradually reduce a supply voltage to the motor when the motor becomes overloaded, to gradually increase the voltage to the normal power supply condition when the overload condition is vanished, and to stop power supply to the motor if the overload condition continues for a predetermined period.
Owner:NITTO KOHKI CO LTD
Forced discharge mechanism and safety switch device for storage battery
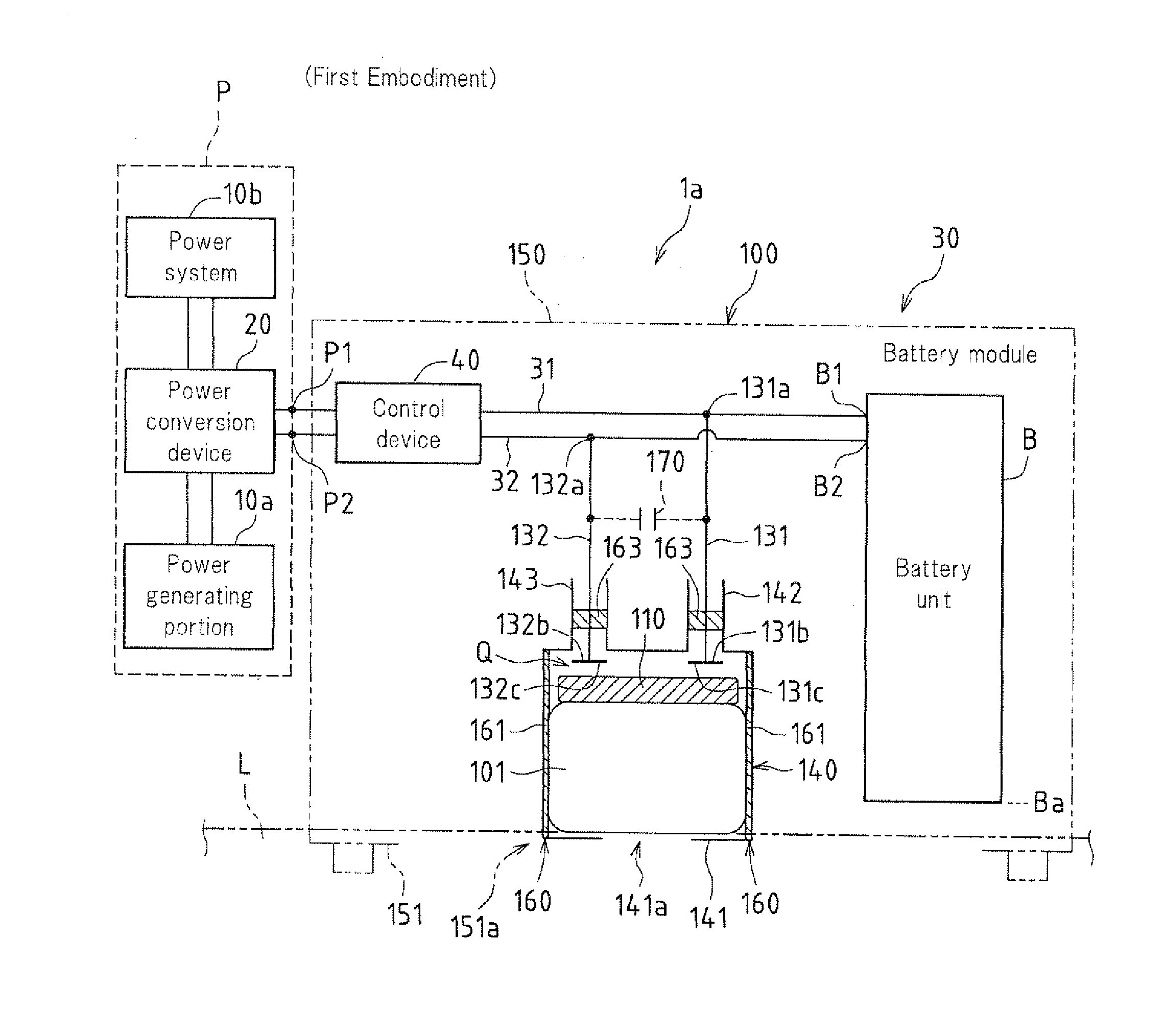
InactiveUS20110127945A1Improve securityReduce the amount requiredHybrid vehiclesCell temperature controlEngineeringElectrical and Electronics engineering
A forced discharge mechanism for a storage battery for forcibly establishing conduction between a pair of power transport paths that are respectively connected to a positive electrode terminal and a negative electrode terminal of the storage battery includes an electric resistor for establishing conduction between the power transport paths, and the electric resistor is movable due to a buoyant force of liquid that has entered.
Owner:SHARP KK
System and method for authenticating users using two or more factors
ActiveUS20050268107A1Easy to useLess increased securityPayment architectureDigital data authenticationComputer science
A system and method authenticates users via any two or three of 1) Something the user knows; 2) Something the user has; and 3) A physical characteristic of the user.
Owner:EMC IP HLDG CO LLC
Computer-based method and apparatus for controlling, monitoring, recording and reporting telephone access
InactiveUS7106843B1Improve securityLow costUnauthorised/fraudulent call preventionEavesdropping prevention circuitsManagement unitCentralized management
A method and apparatus for managing institutional telephone activity utilizing a computer-based telephony management unit to connect institutional telephones with outside telephone lines. The unit provides institutional users with fully automated, direct dial and collect calling privileges for local, long distance, and international calls. The unit contains a database for storing the calling privileges and restrictions of institutional users, for recording calling transactions made by the users, and for managing user monetary accounts. The unit can record up to 400 hours of conversation in a digital format. The unit provides various administrative capabilities, including user account management, audit trails, transaction reports, centralized management and report capabilities, and detection of fraudulent calling.
Owner:AMERICAN CAPITAL FINANCIAL SERVICES +1
Arc-shaped cutting anastomat
The invention relates to an arc-shaped cutting anastomat comprising an anastomosis nail shaping mechanism, a nail pushing assembly, a trigger handle, a nail supporting seat, a base of the nail supporting seat, a knife cushioning ring and two splints, wherein the nail pushing assembly comprises a cutting knife, a nail pushing sheet, a nail bin and a guide post; the end of the nail pushing sheet and both sides of the cutting knife are respectively provided with a plurality of inner nail pushing dental sheets which are near the cutting knife and a plurality of outer nail pushing dental sheets which are far away from the cutting knife; the cutting knife and the nail pushing sheet are injected and molded at a time to be fixed together; the outer side of the each outer nail pushing dental sheeton the nail pushing sheet is provided with a reinforcing rib; the inner side of each nail pushing dental sheet on the nail pushing sheet is provided with a reinforcing rib; both ends of the first guide surfaces of the nail pushing dental sheets are respectively connected with the first contact surfaces and the second contact surfaces of the nail pushing dental sheets through concave arc-shaped connecting surfaces, and both ends of the second guide surfaces thereof are respectively connected with the first contact surfaces and the second contact surfaces through the concave arc-shaped connecting surfaces; and the first contact surfaces and the second contact surfaces are respectively in contact with the inner walls of the nail pushing dental sheet holes of the nail bin. The invention has the advantages of good trigger anastomosis shaping effect and high safety.
Owner:CHANGZHOU JIANRUIBAO MEDICAL DEVICES
Fire-proof and heat-insulating composite fabric with multi-stage expansion and heat dissipation, preparation method and application
ActiveCN102783741BImprove permeabilityPromote absorptionLaminationLamination apparatusInsulation layerMetal foil
The invention relates to a preparation method and an application of multistage-spreading heat-dissipation fire-proof heat-insulation composite fabric. The multistage-spreading heat-dissipation fire-proof heat-insulation composite fabric is formed by successively arranging and laminating a metal foil reflection layer, a phase change temperature limitation layer, an interval composite membrane heat-insulation layer and a flame-retardant comfortable layer, wherein the metal foil reflection layer has high reflectivity and an enhanced heat-dissipation function; the phase change temperature limitation layer has functions of high energy consumption absorption and evenly-distributed heat conduction; the interval composite membrane heat-insulation layer has the functions of reflection insulation and even distribution of heat; and the flame-retardant comfortable layer has the functions of low-contact heat conduction, heat insulation and comfort. When the front side of the multistage-spreading heat-dissipation fire-proof heat-insulation composite fabric is under the action of open fire and strong heat flow environment, the back side of the multistage-spreading heat-dissipation fire-proof heat-insulation composite fabric can be kept below 50DEG C which is near the safe temperature state of the human skin, and the integral structural form and the mechanical property are stable. The natural thickness of the composite fabric is 5-15mm, the compression thickness of the composite fabric is 3-8mm, and the square meter quality of the composite fabric is 400-1500g / m<2>. The composite fabric is fire-proof heat-insulation material which is totally sealed, stuck and sewn and can be used for individual protection and environment heat insulation in special high-temperature occasions, such as fire control, military, exploration, safe escape and industry and the like.
Owner:DONGHUA UNIV
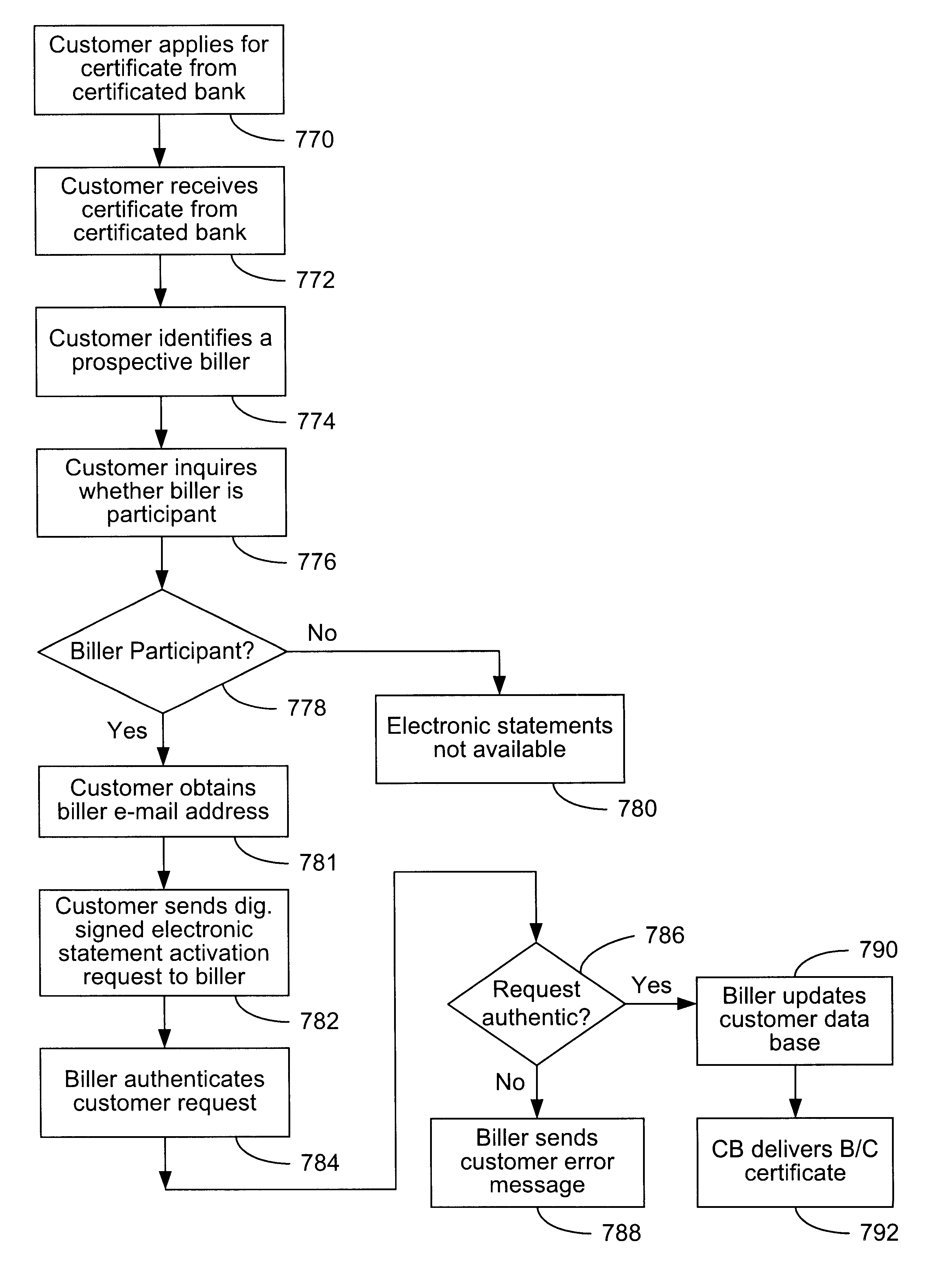
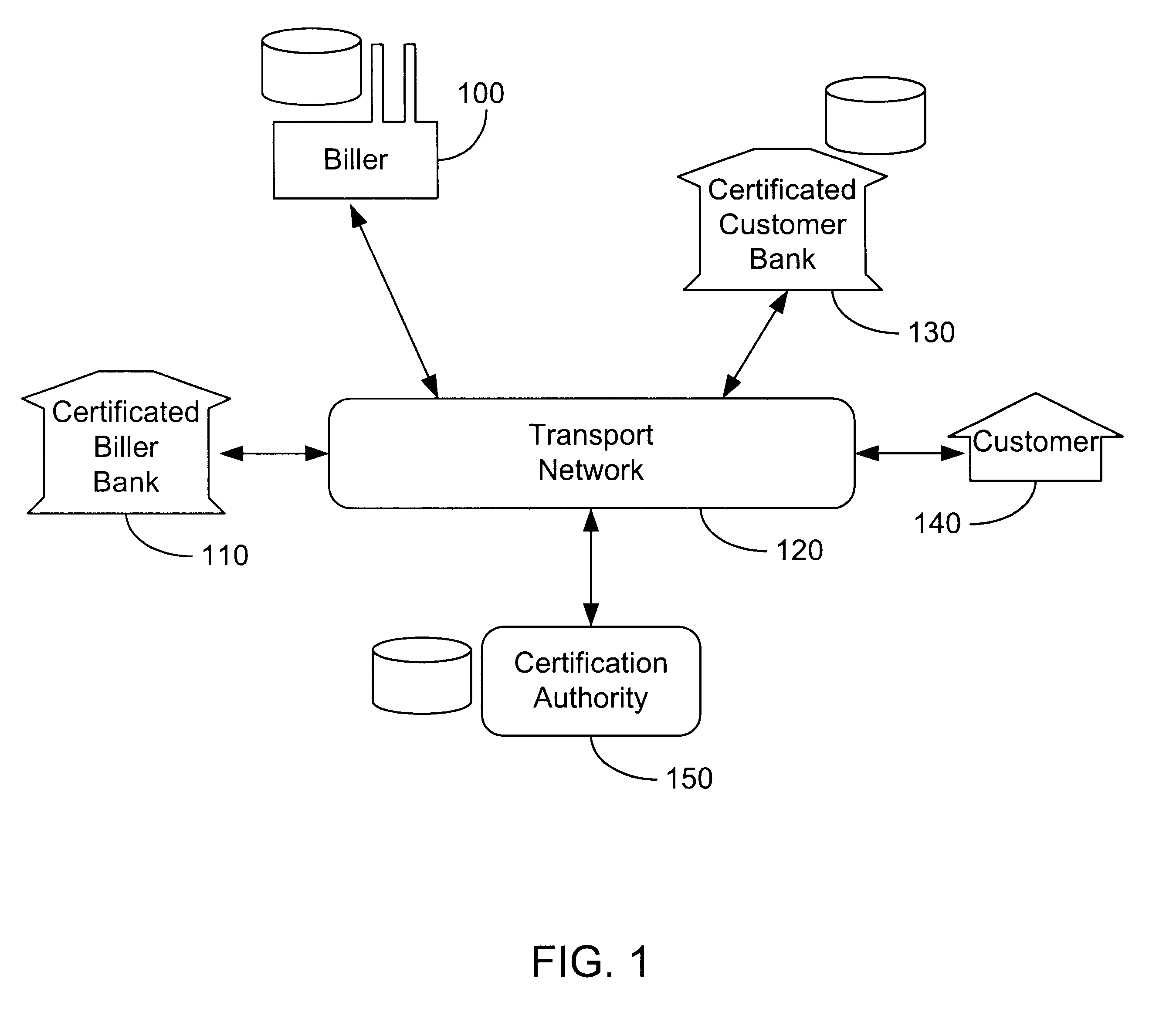
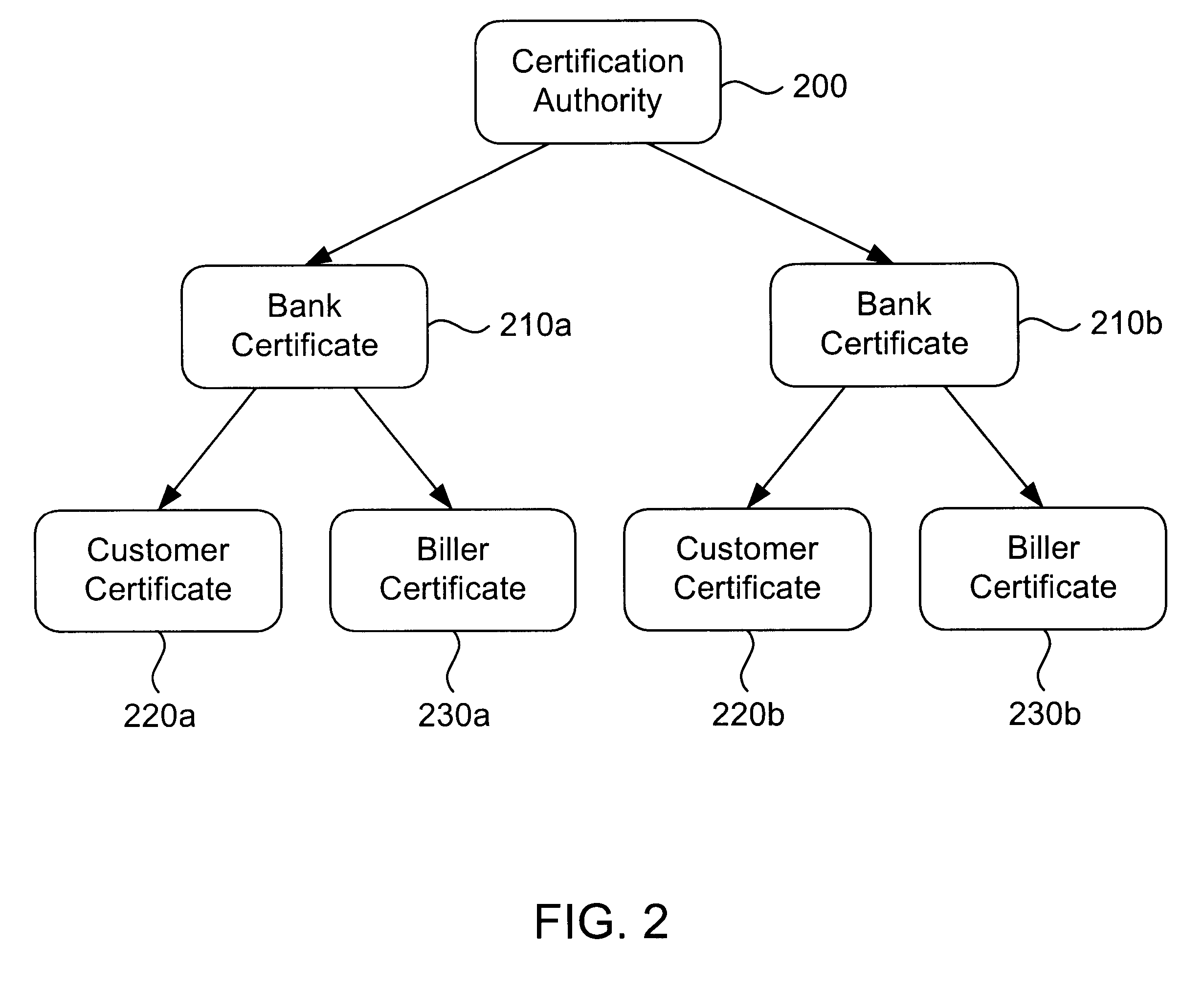
Secure interactive electronic account statement delivery system
InactiveUS6285991B1Good flexibilityBilling is thereby complicatedFinanceUser identity/authority verificationDigital dataNetwork communication
The present invention consists of a secure interactive electronic account statement delivery system suitable for use over open networks such as the Internet. The invention utilizes a certification hierarchy to insure that electronic bills, invoices, and other account statements can be securely sent over open networks. The participants in the system are a certification authority, certificated banks, billers, and customers. The certification authority grants digital certificates to the certificated banks, which in turn grant digital certificates to billers and customers. Digital certificates form the basis for encryption and authentication of network communications, using public and private keys. The certificates associate a customer and biller with a certificated bank and with the electronic billing system, much like payment cards associate a customer with a payment card issuer and a particular payment card system. Digital signatures are used for authentication and non-repudiation. The certificates may be stored as digital data on storage media of a customer's or biller's computer system, or may be contained in integrated circuit or chip cards physically issued to billers and customers. The electronic bill itself may be a simple text message containing the equivalent of summary information for the bill, or may be more elaborate. In one embodiment of the invention, the electronic bill contains a number of embedded links, for example an embedded URL of a biller's world wide web server that allows the customer to interactively bring up detailed billing information by activating the link. The e-mail message may also include links to third party websites.
Owner:VISA INT SERVICE ASSOC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com