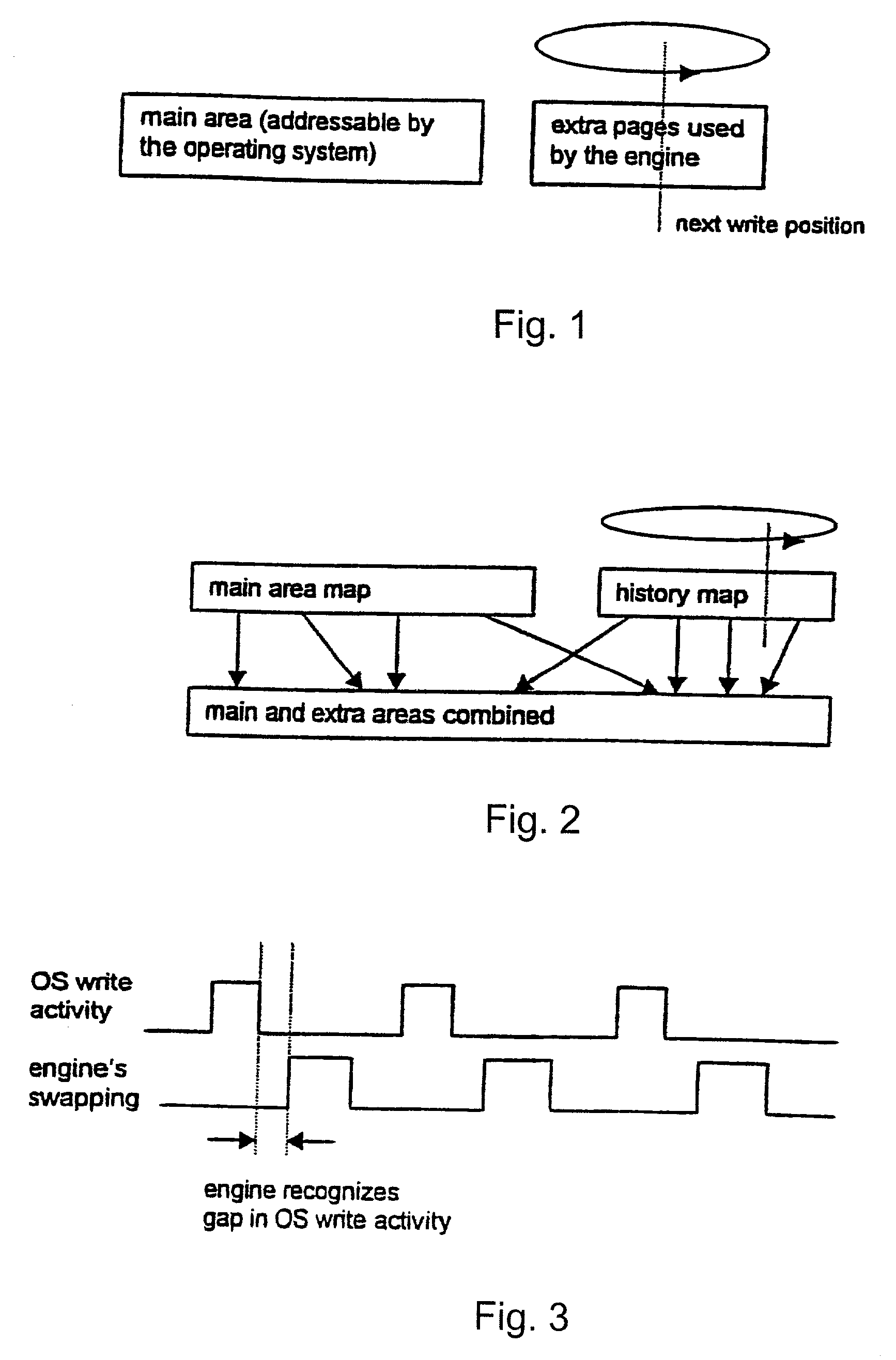
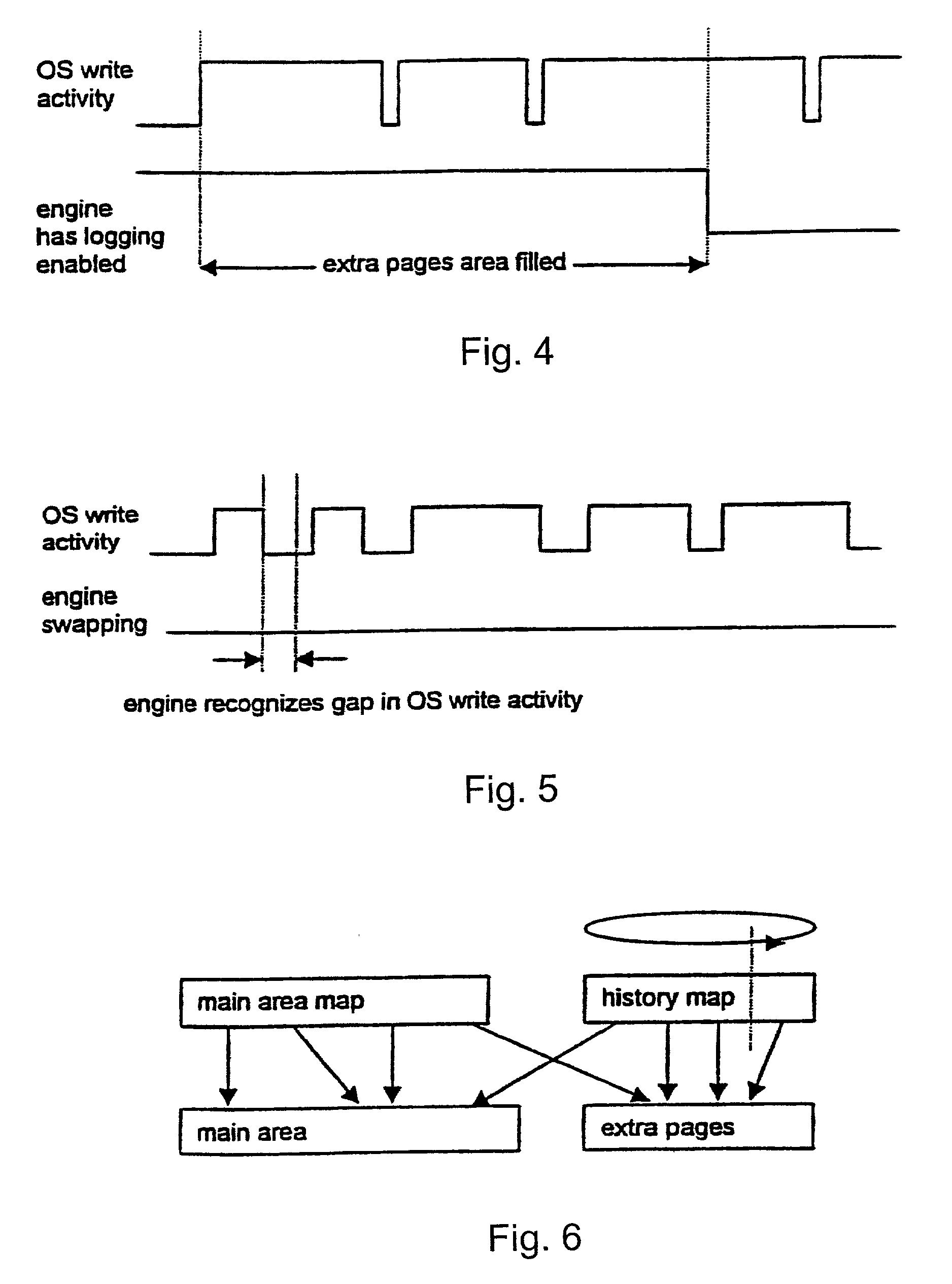
Patents
Literature
19948 results about "Original data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The Original Data Company is an independent full services data bureau and list broker founded on experience gained in the industry since 1984.
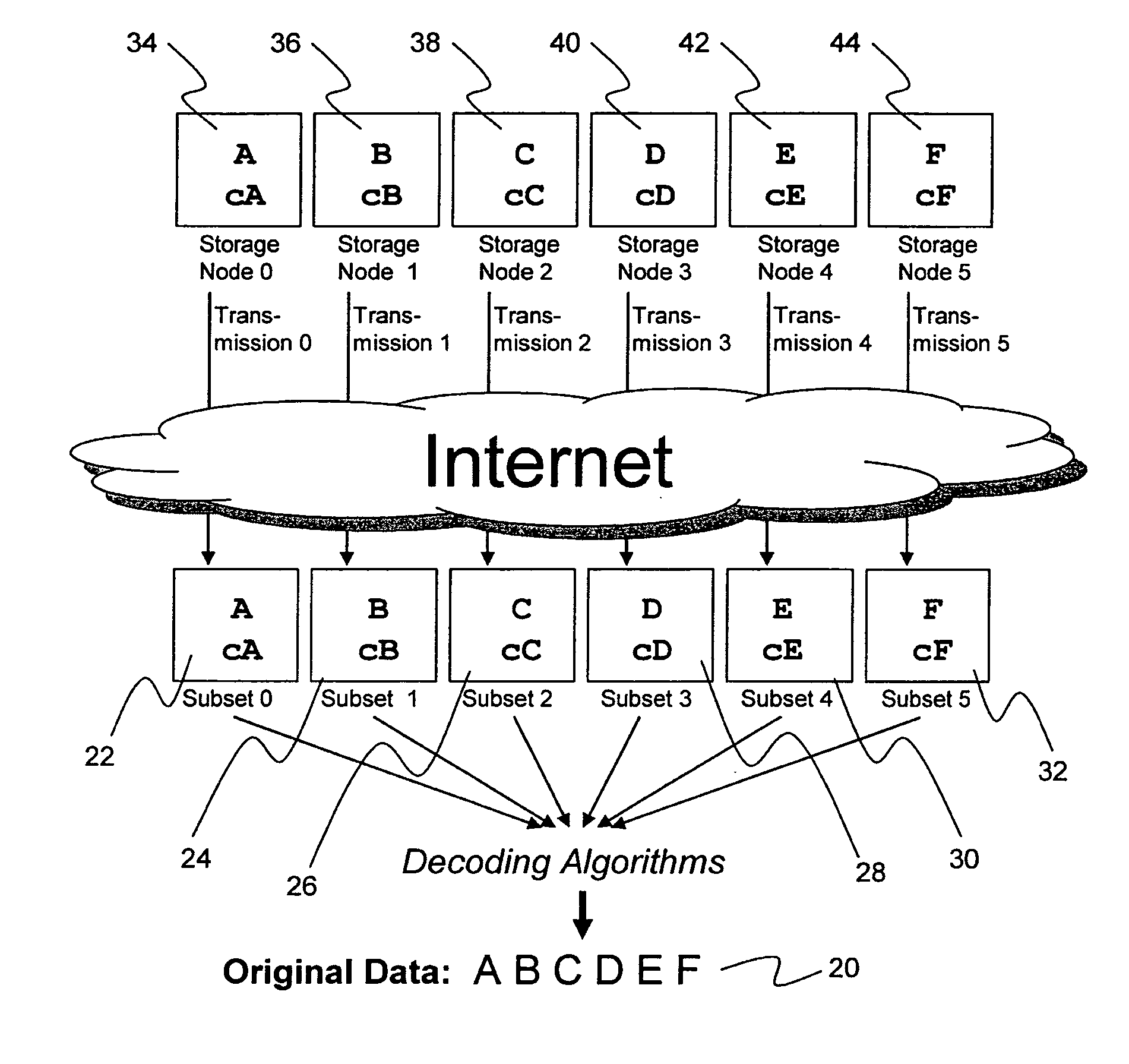
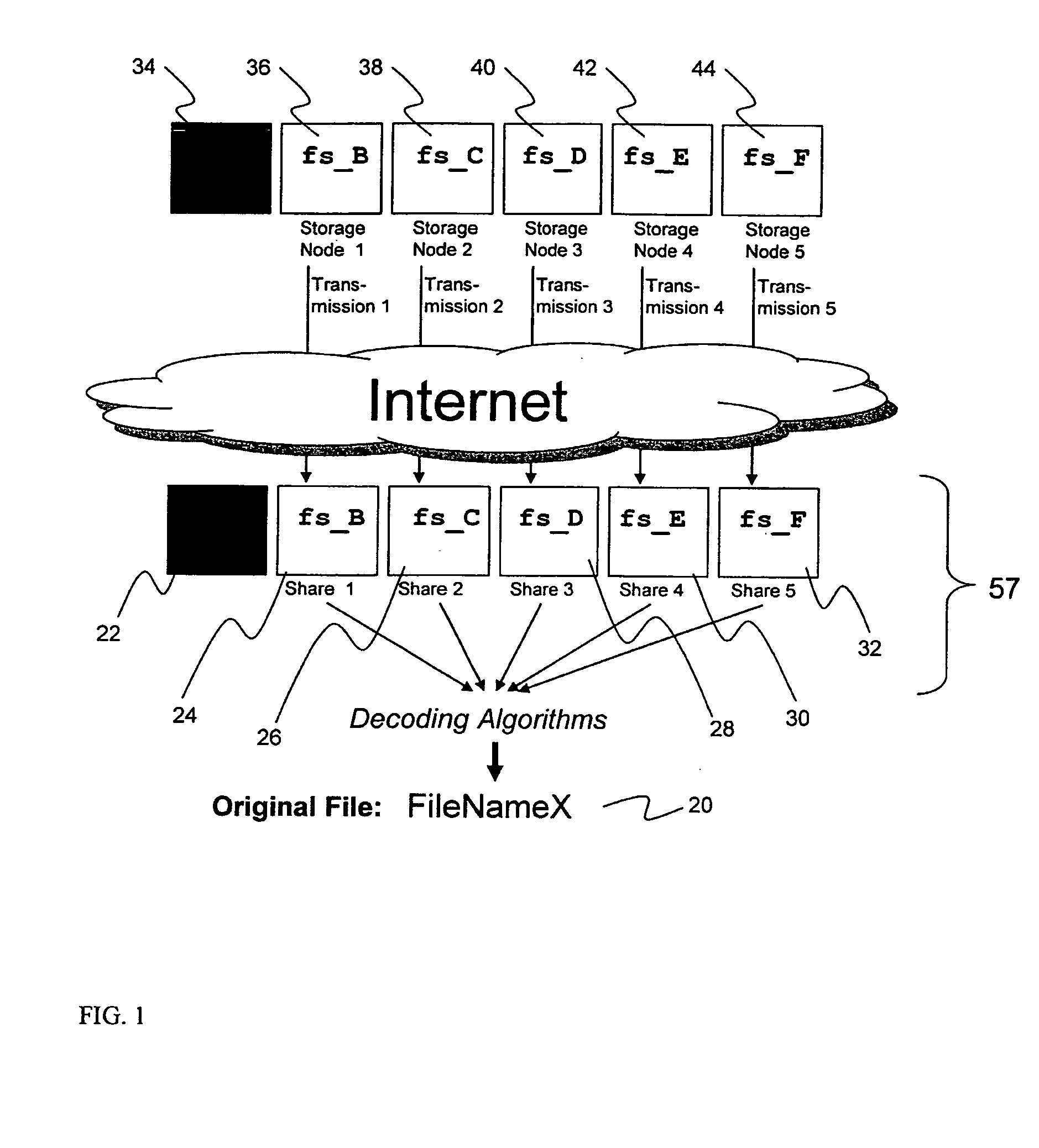
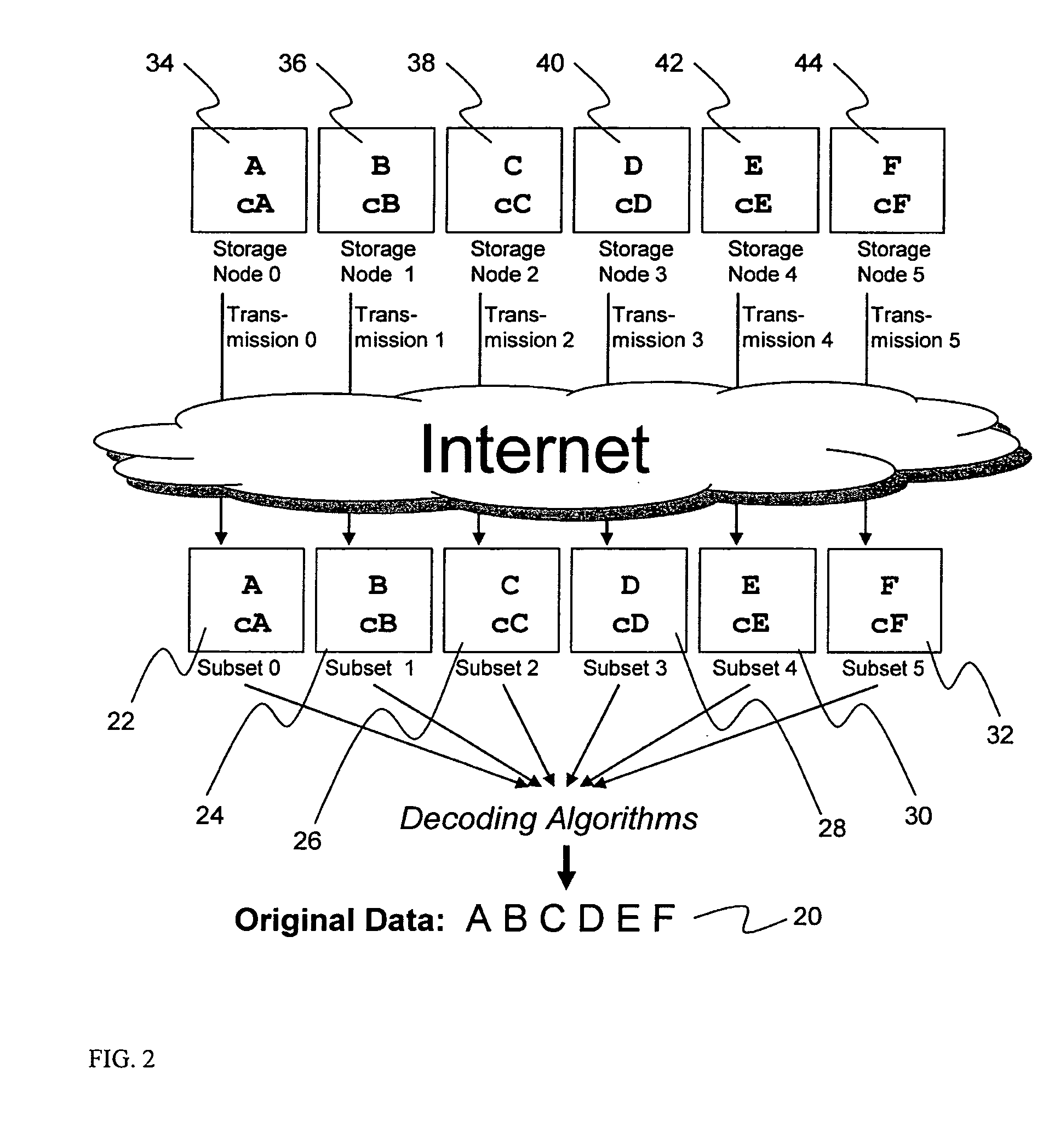
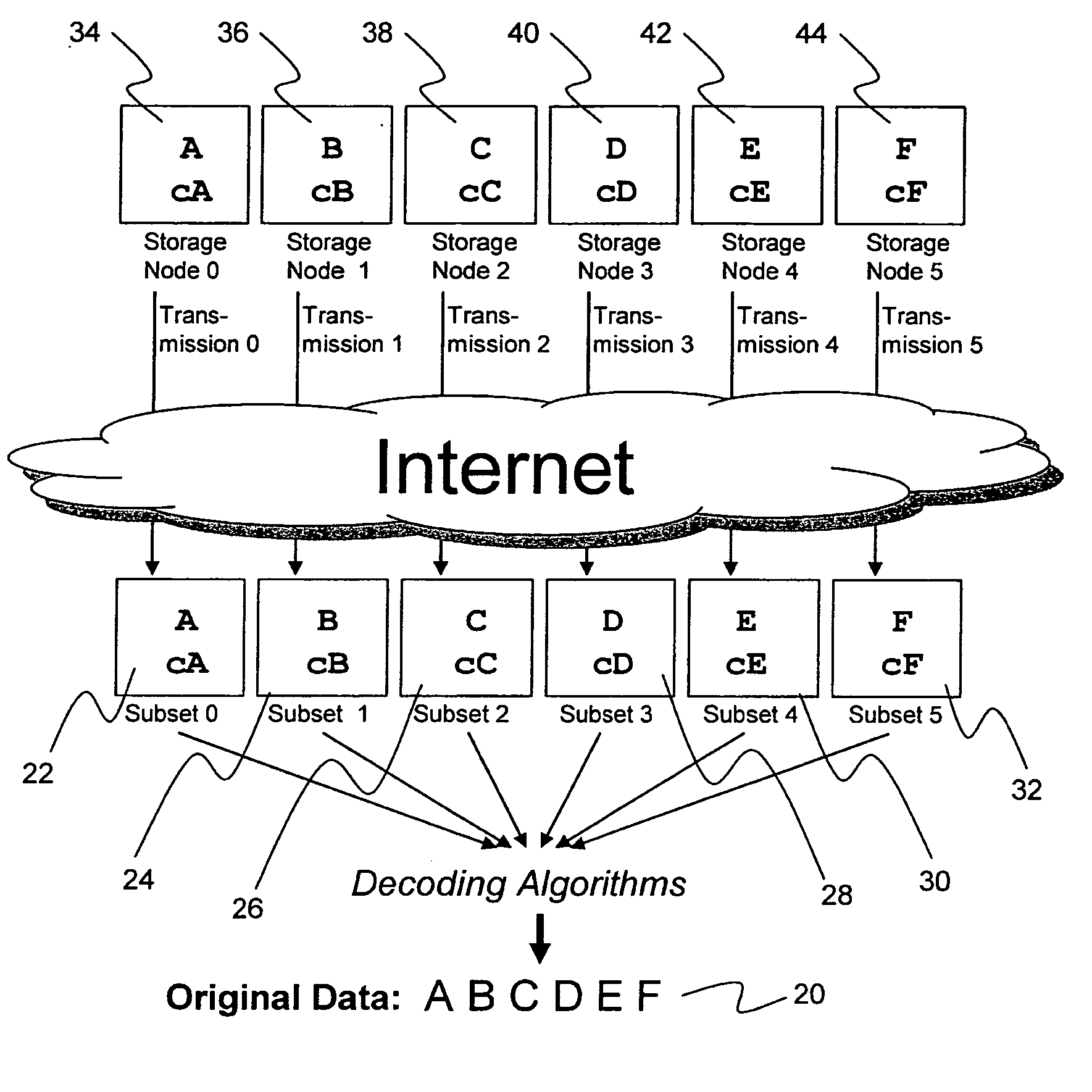
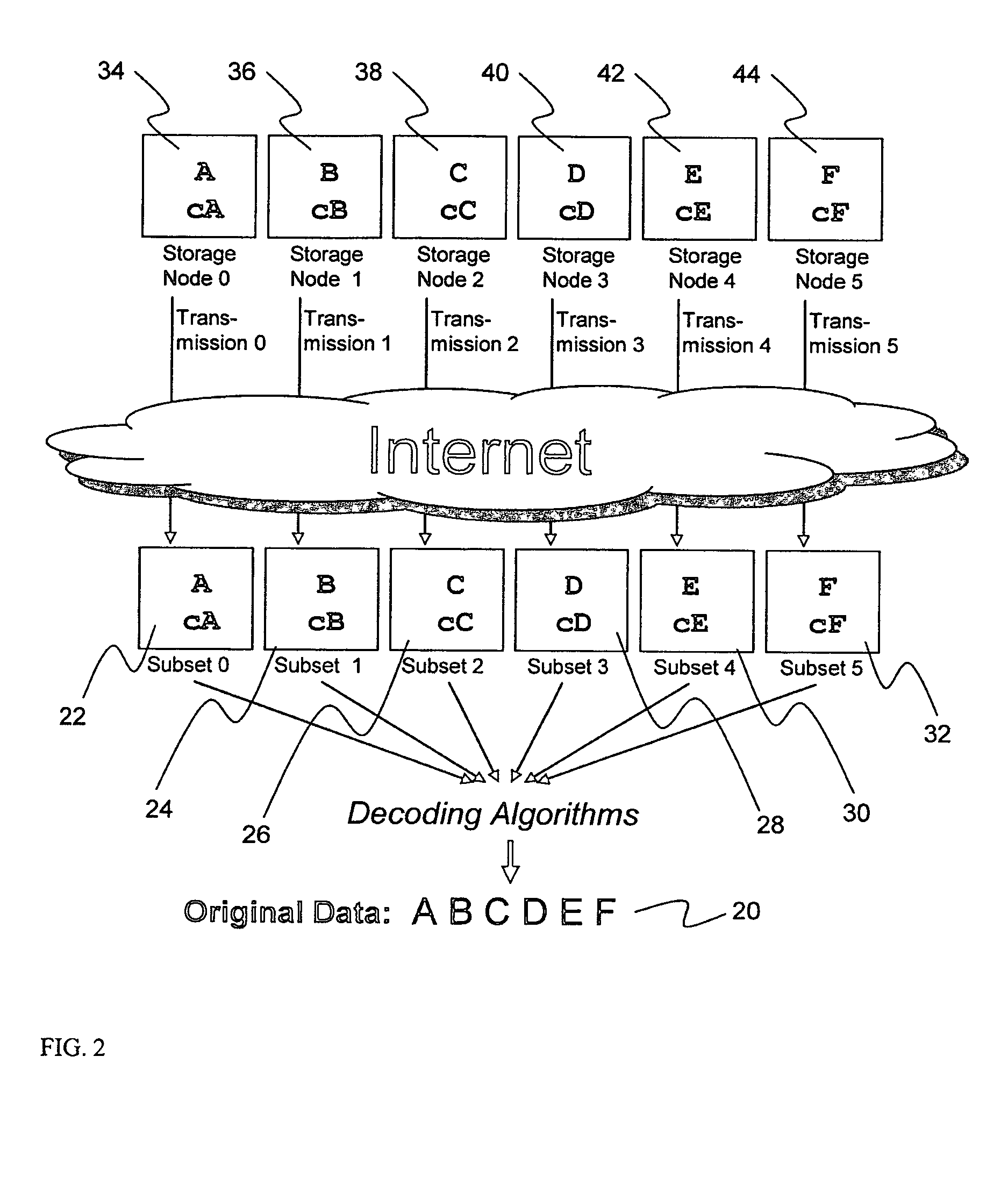
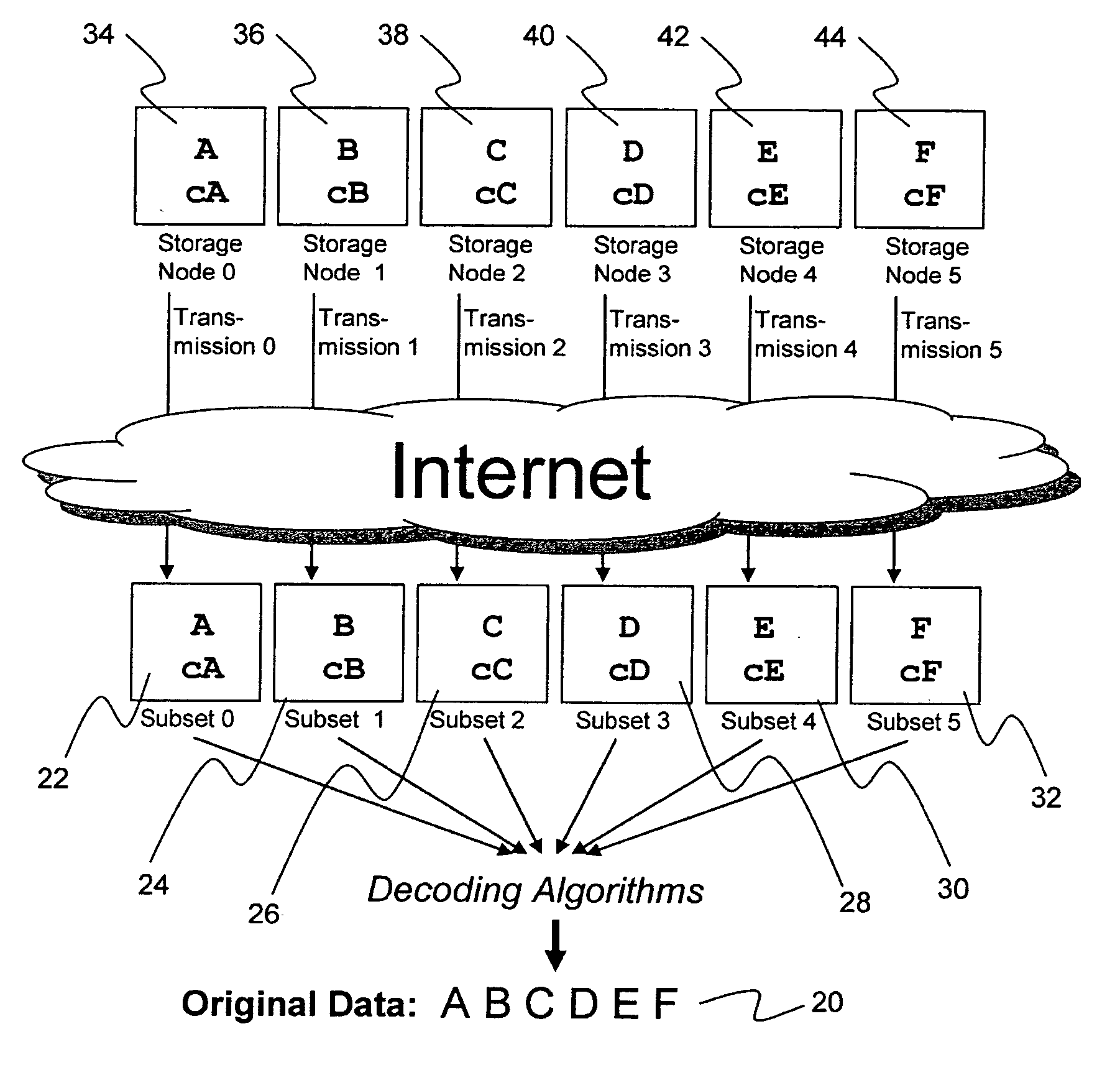
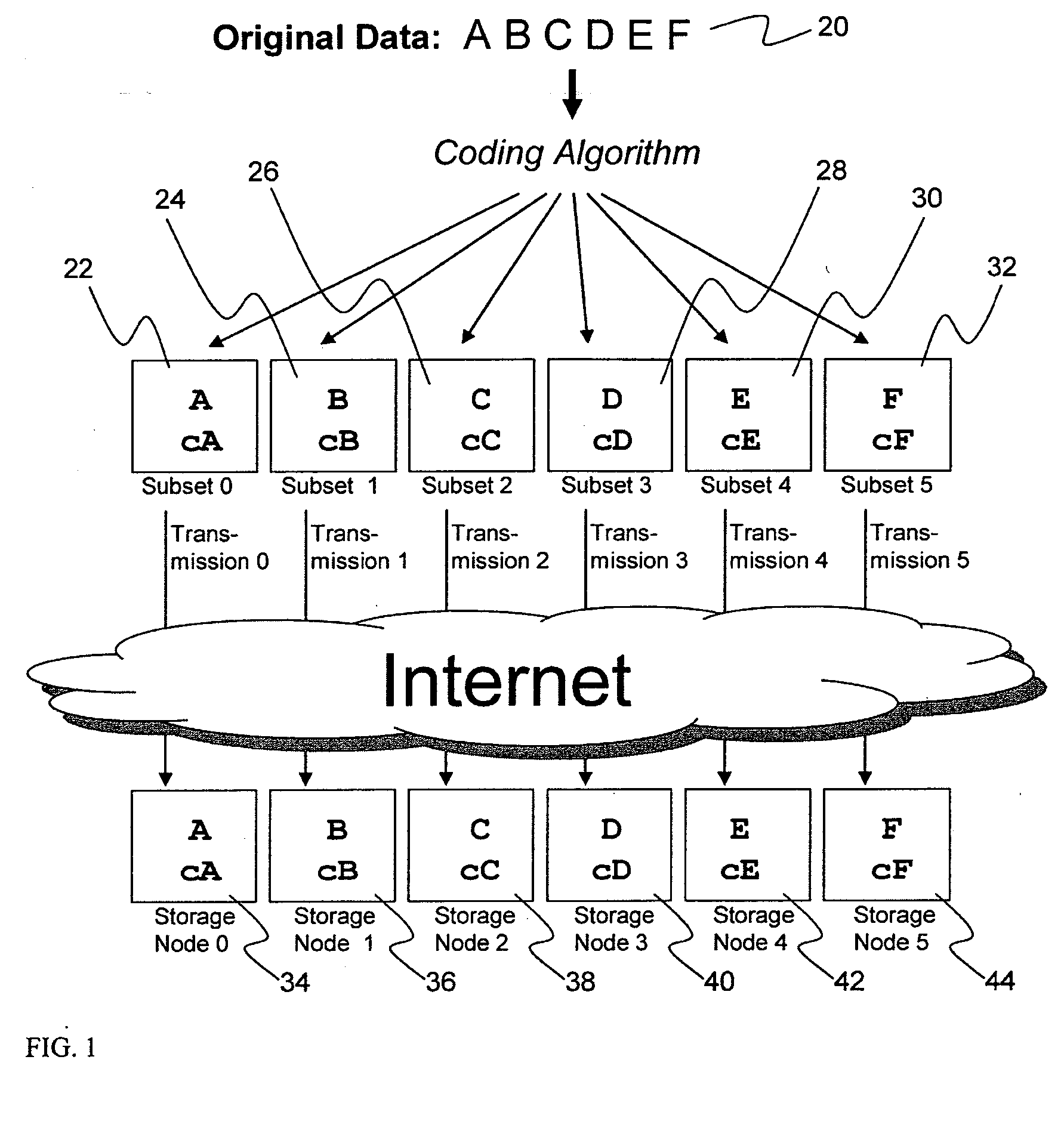
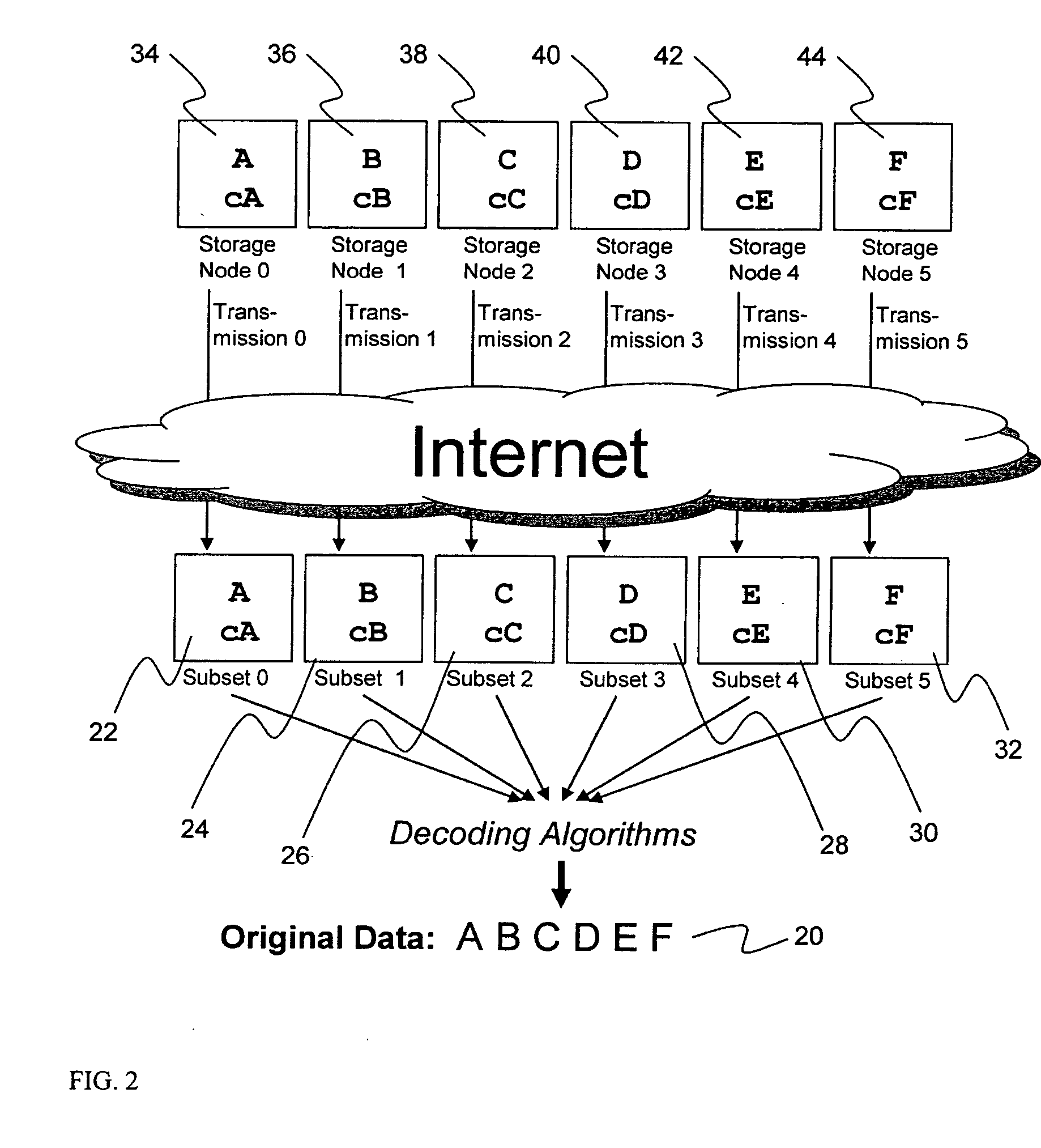
System for rebuilding dispersed data
ActiveUS20070079082A1Reliably and securely protectImprove privacyError detection/correctionDigital data protectionGrid resourcesInformation dispersal
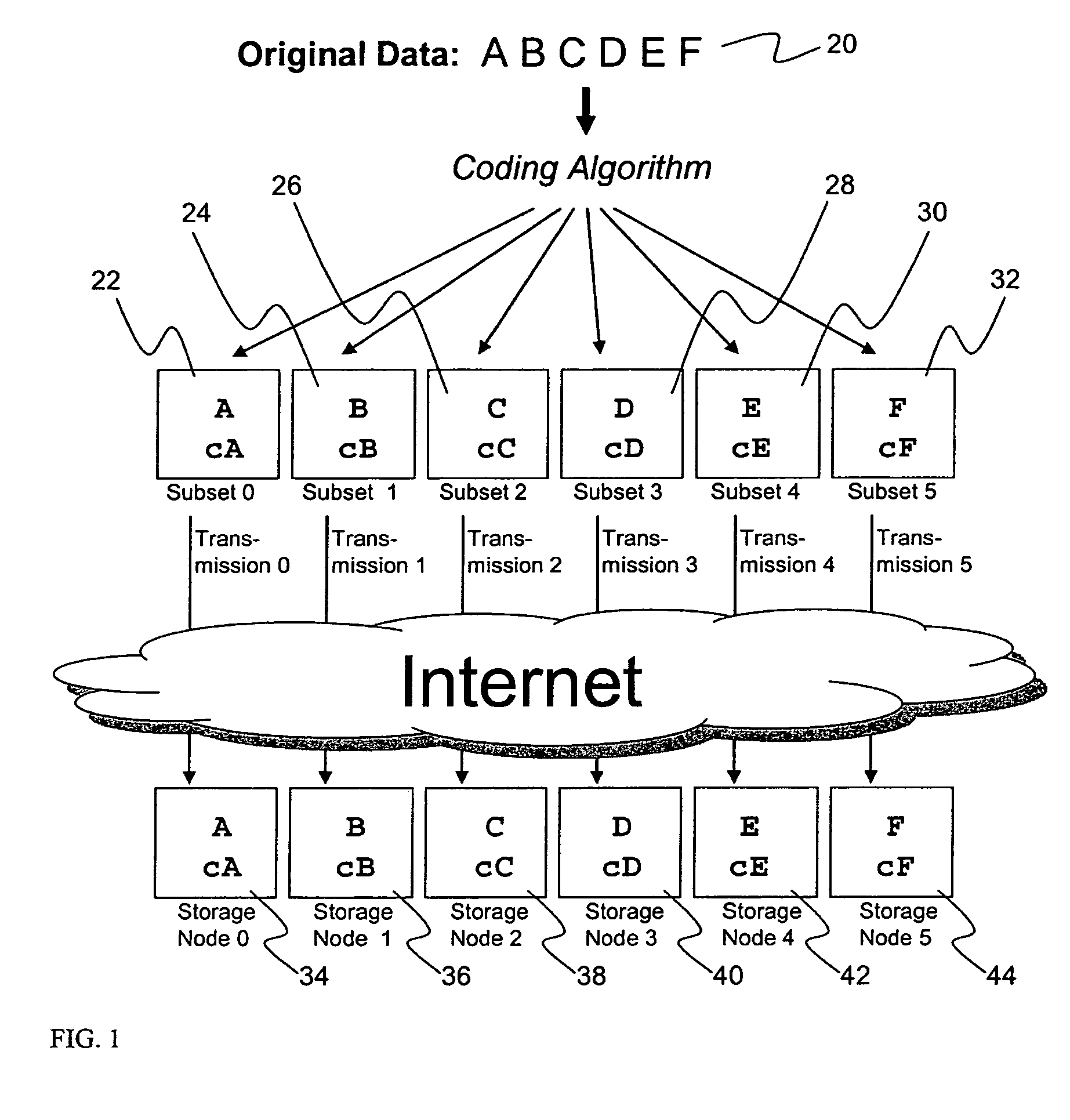
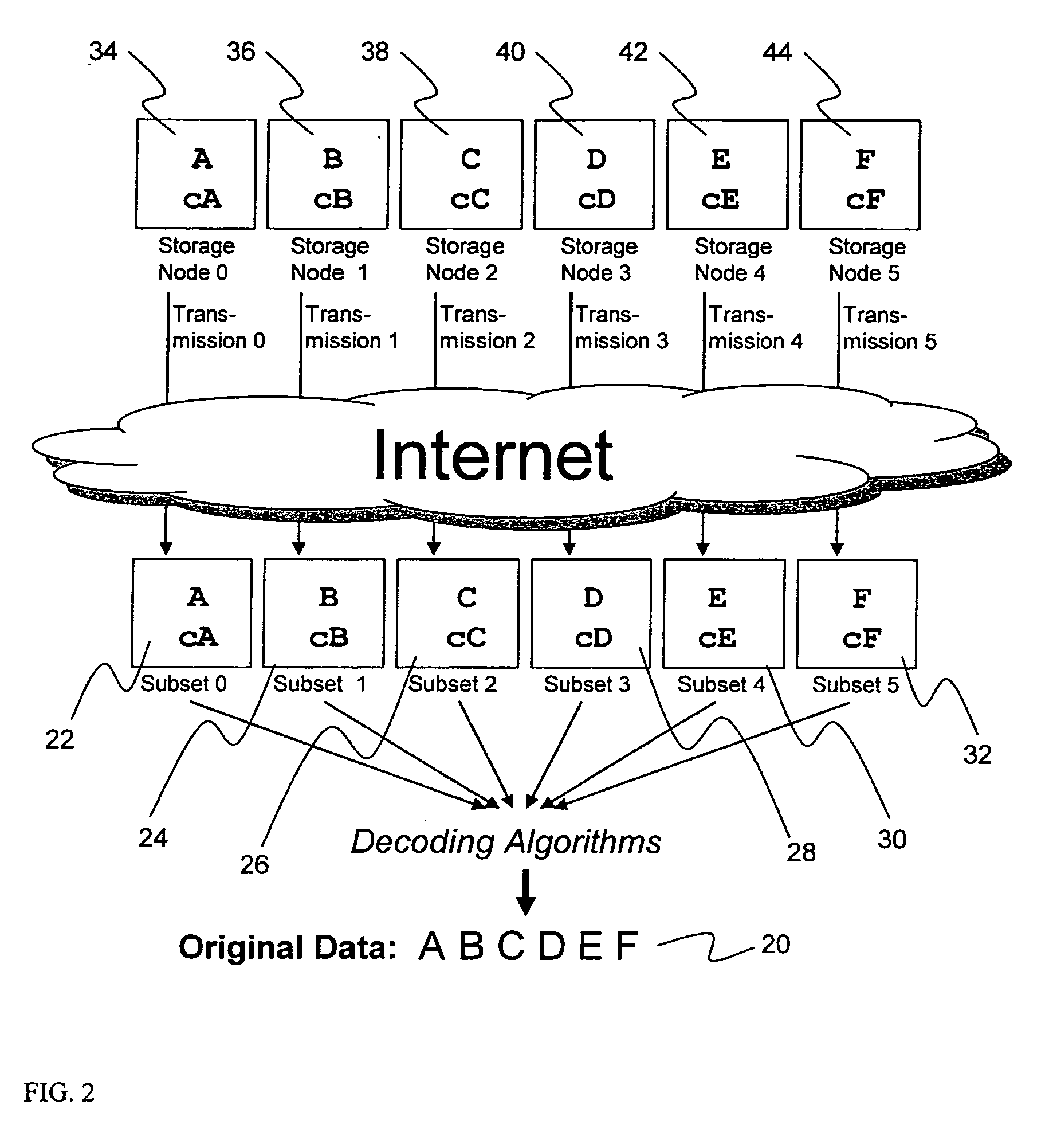
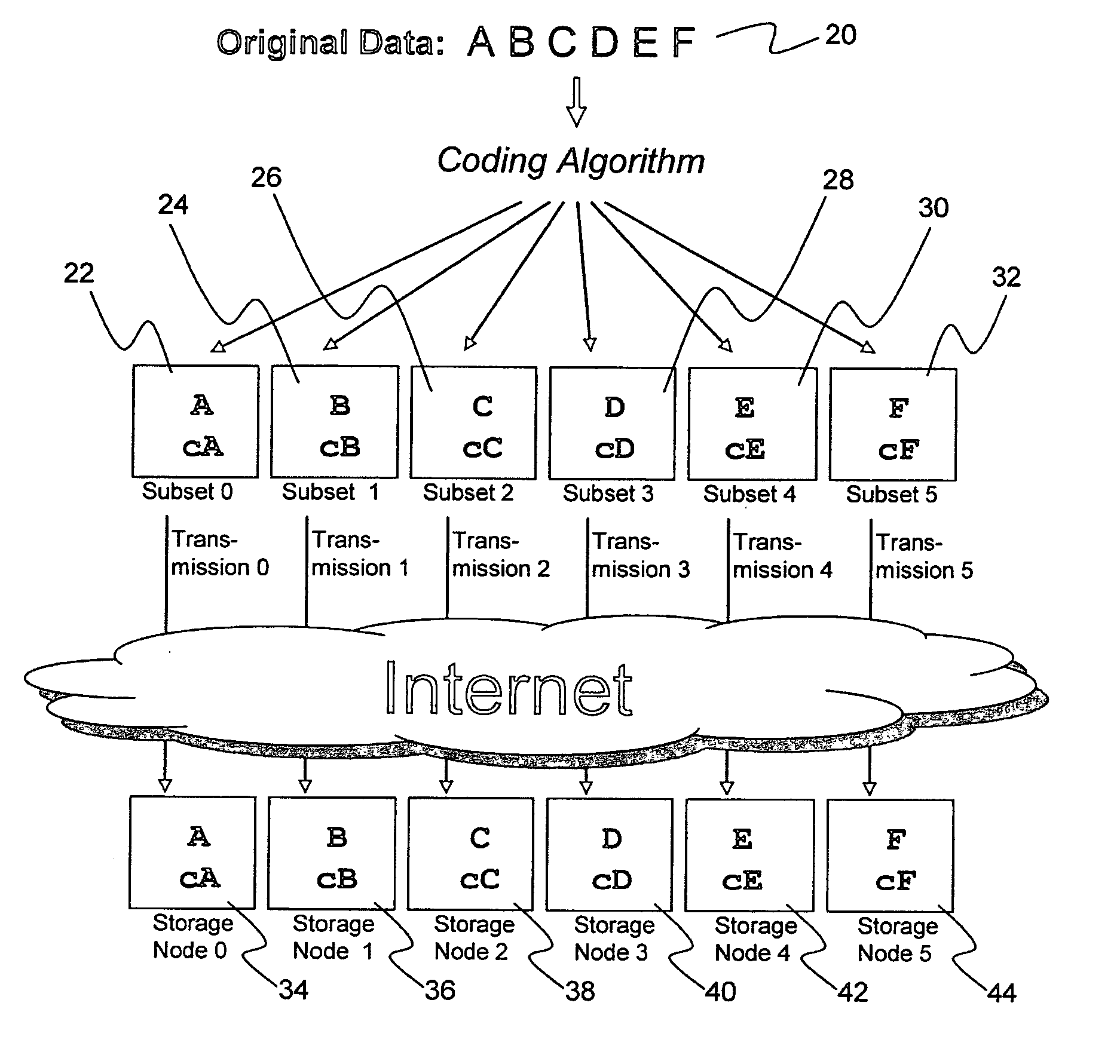
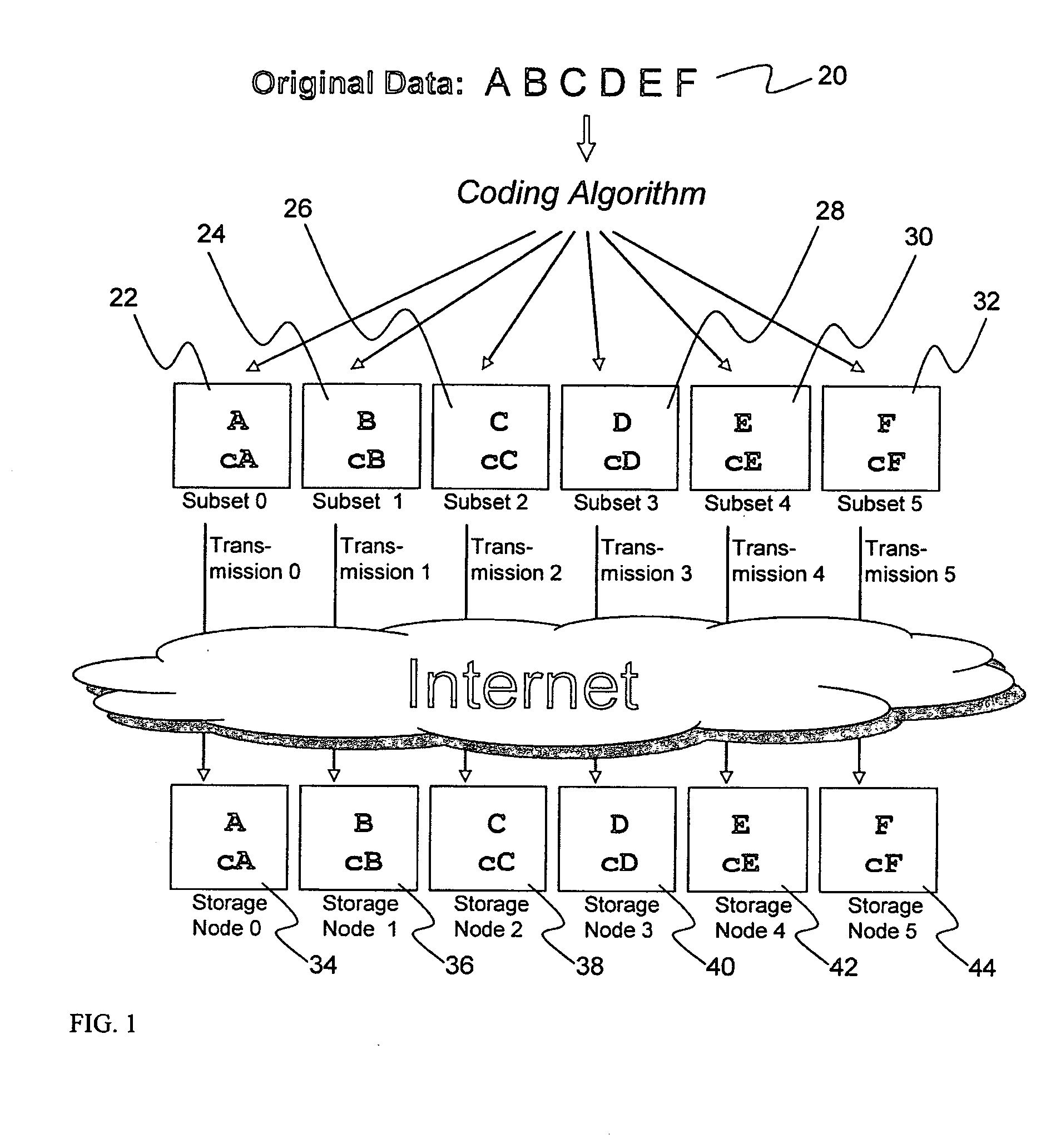
A digital data file storage system is disclosed in which original data files to be stored are dispersed using some form of information dispersal algorithm into a number of file “slices” or subsets in such a manner that the data in each file share is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other file shares. These file shares are stored on separate digital data storage devices as a way of increasing privacy and security. As dispersed file shares are being transferred to or stored on a grid of distributed storage locations, various grid resources may become non-operational or may operate below at a less than optimal level. When dispersed file shares are being written to a dispersed storage grid which not available, the grid clients designates the dispersed data shares that could not be written at that time on a Rebuild List. In addition when grid resources already storing dispersed data become non-available, a process within the dispersed storage grid designates the dispersed data shares that need to be recreated on the Rebuild List. At other points in time a separate process reads the set of Rebuild Lists used to create the corresponding dispersed data and stores that data on available grid resources.
Owner:PURE STORAGE
Metadata management system for an information dispersed storage system
ActiveUS20070079083A1Less usableImprove privacyComputer security arrangementsMemory systemsInformation dispersalMetadata management
Briefly, the present invention relates to an information dispersal sytem in which original data to be stored is separated into a number of data “slices” in such a manner that the data in each subset is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other data subsets. These data subsets are stored on separate storage devices as a way of increasing privacy and security. In accordance with an important aspect of the invention, a metadata management system stores and indexes user files across all of the storage nodes. A number of applications run on the servers supporting these storage nodes and are responsible for controlling the metadata. Metadata is the information about the data, the data slices or data subsets and the way in which these data subsets are dispersed among different storage nodes running over the network. As used herein, metadata includes data source names, their size, last modification date, authentication information etc. This information is required to keep track of dispersed data subsets among all the nodes in the system. Every time new data subsets are stored and old ones are removed from the storage nodes, the metadata is updated. In accordance with an important aspect of the invention, the metadata management system stores metadata for dispersed data where: The dispersed data is in several pieces. The metadata is in a separate dataspace from the dispersed data. Accordingly, the metadata management system is able to manage the metadata in a manner that is computationally efficient relative to known systems in order to enable broad use of the invention using the types of computers generally used by businesses, consumers and other organizations currently.
Owner:PURE STORAGE
Billing system for information dispersal system
ActiveUS20070174192A1Less usableLess recognizableFinanceComputer security arrangementsInformation dispersalOriginal data
A billing process is disclosed for a information dispersal system or digital data storage system. In one embodiment of the invention, the original data to be stored is separated into a number of data “slices” or shares in such a manner that the data in each subset is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other data subsets. These data subsets are stored on separate digital data storage devices as a way of increasing privacy and security. As dispersed file shares are being stored or removed from a grid of distributed storage locations, a set of metadata tables are created, separate from the dispersed file share storage, to maintain information about the original data size of each block, file or set of file shares dispersed on the grid. The original data size information in these separate metadata tables is used to determine usage information based upon the original file size even though the file has been dispersed onto a storage grid that contains file slices who size may not relate to the original file size and the file slices may have been compressed by the system in order to reduce storage space or improve transmission time. As such, the billing process is able to enable a broad range of commercial billing options for billing for commercial data services on an information dispersal grid.
Owner:PURE STORAGE
Digital data storage system
ActiveUS20070079081A1Less usableImprove privacyComputer security arrangementsMemory systemsOriginal dataSmall data
An efficient method for breaking source data into smaller data subsets and storing those subsets along with coded information about some of the other data subsets on different storage nodes such that the original data can be recreated from a portion of those data subsets in an efficient manner.
Owner:PURE STORAGE
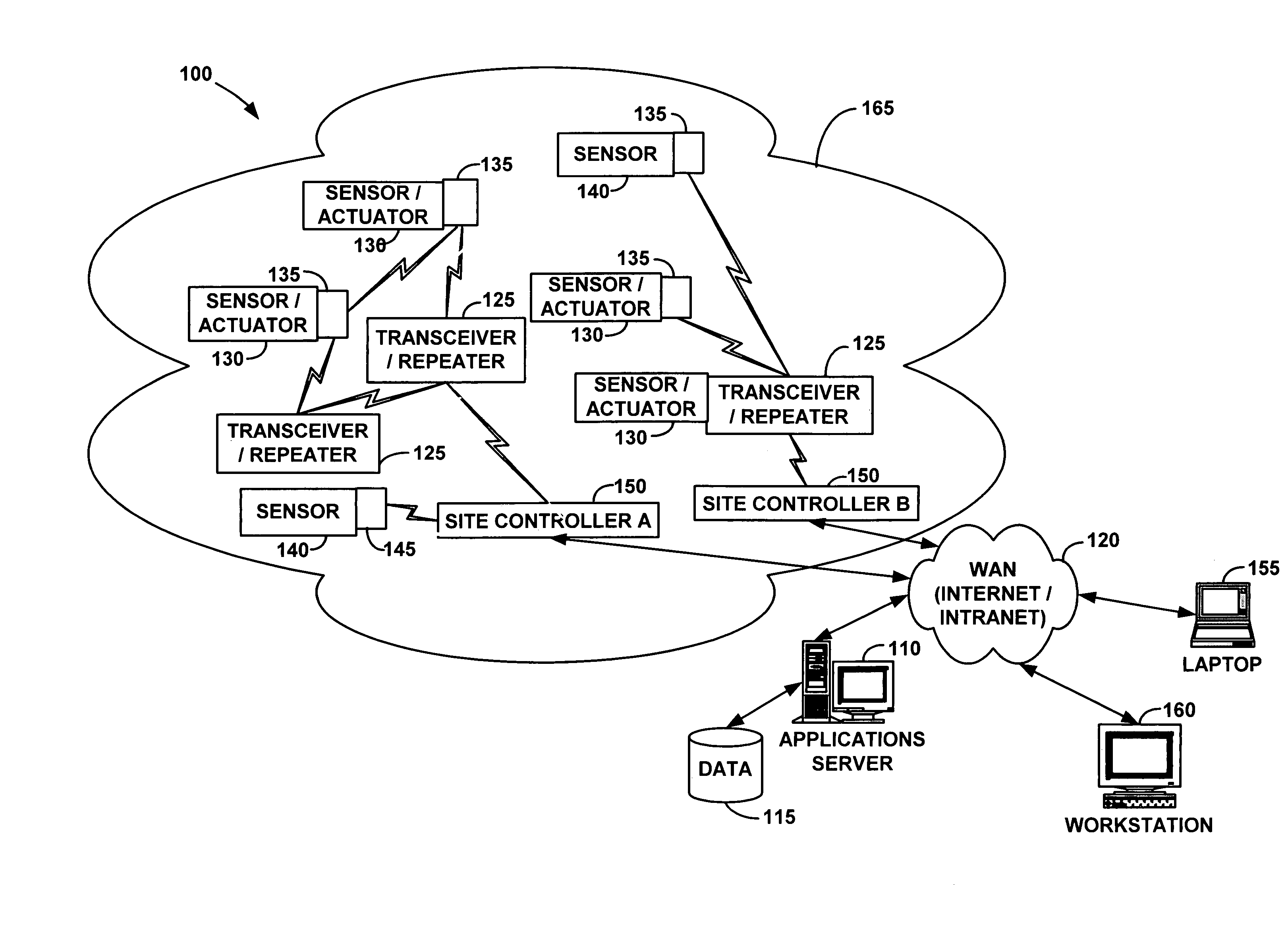
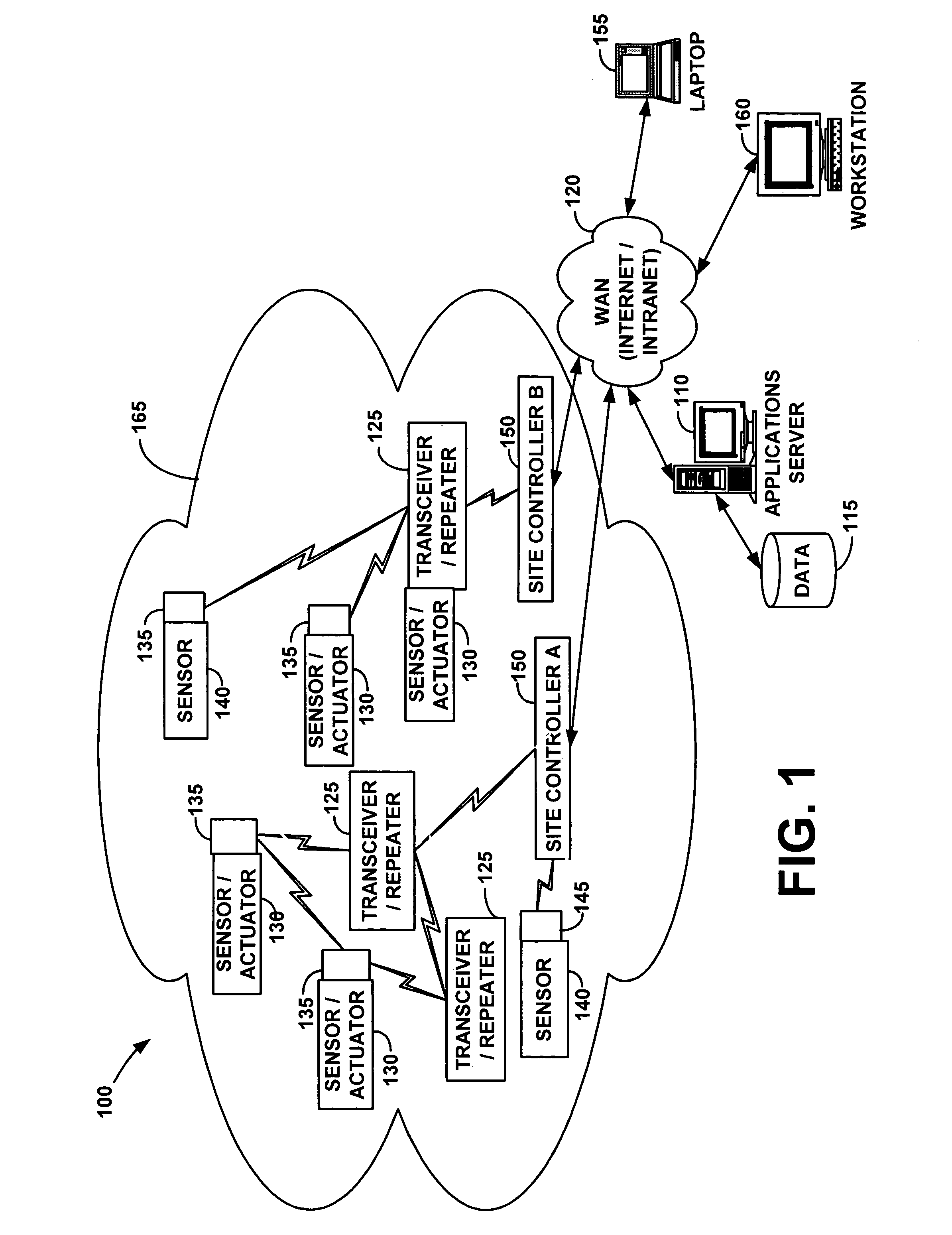
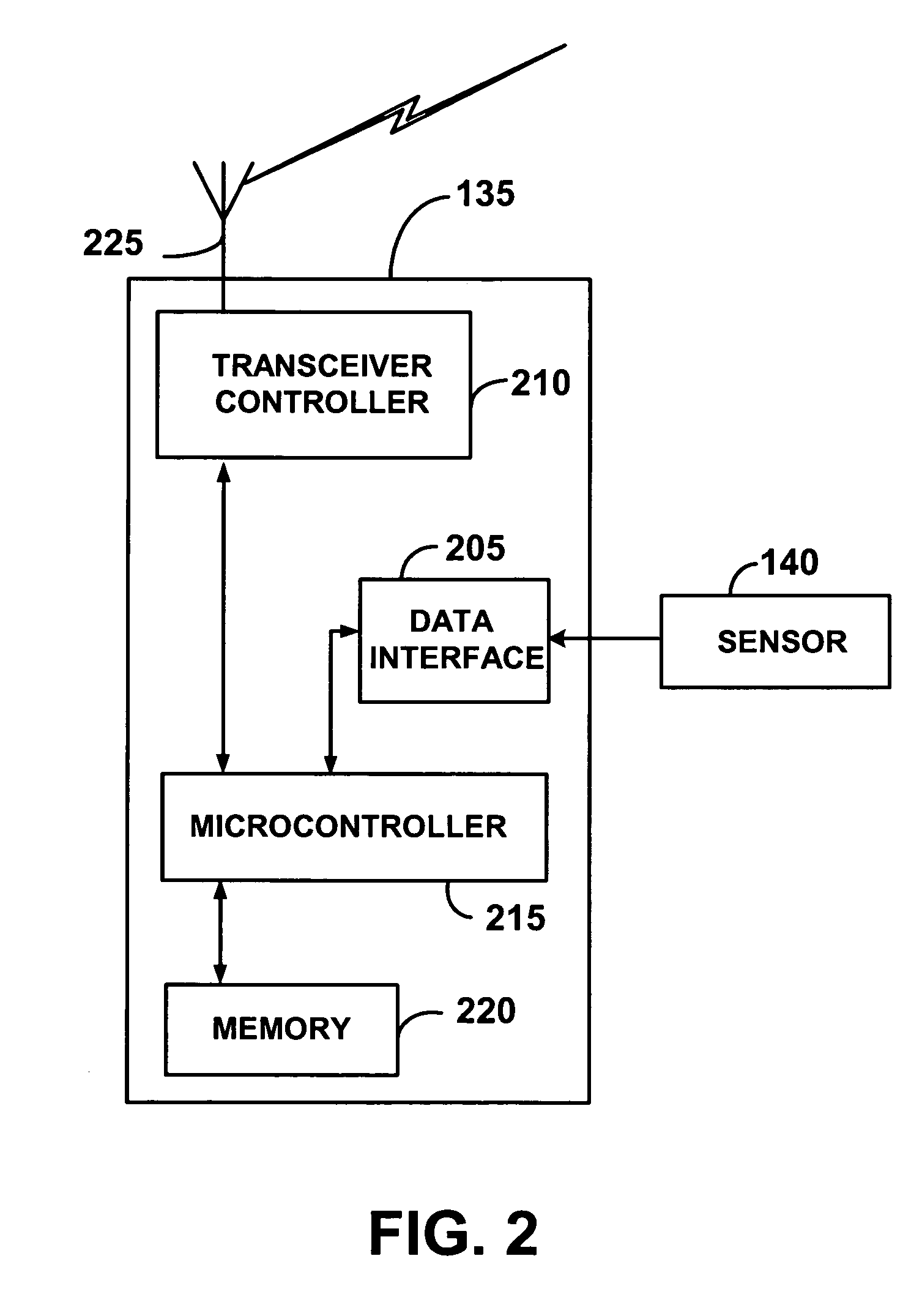
Wireless communication networks for providing remote monitoring of devices
InactiveUS7103511B2Cost-effectiveElectric signal transmission systemsError detection/correctionWireless communication protocolTransceiver
Wireless communication networks for monitoring and controlling a plurality of remote devices are provided. Briefly, one embodiment of a wireless communication network may comprise a plurality of wireless transceivers having unique identifiers. Each of the plurality of wireless transceivers may be configured to receive a sensor data signal from one of the plurality of remote devices and transmit an original data message using a predefined wireless communication protocol. The original data message may comprise the corresponding unique identifier and sensor data signal. Each of the plurality of wireless transceivers may be configured to receive the original data message transmitted by one of the other wireless transceivers and transmit a repeated data message using the predefined communication protocol. The repeated data message may include the sensor data signal and the corresponding unique identifier. Furthermore, at least one of the plurality of wireless transceivers may be further configured to provide the original data messages and the repeated data messages to a site controller connected to a wide area network. The site controller may be configured to manage communications between the wireless communication network and a host computer connected to the wide area network.
Owner:SIPCO
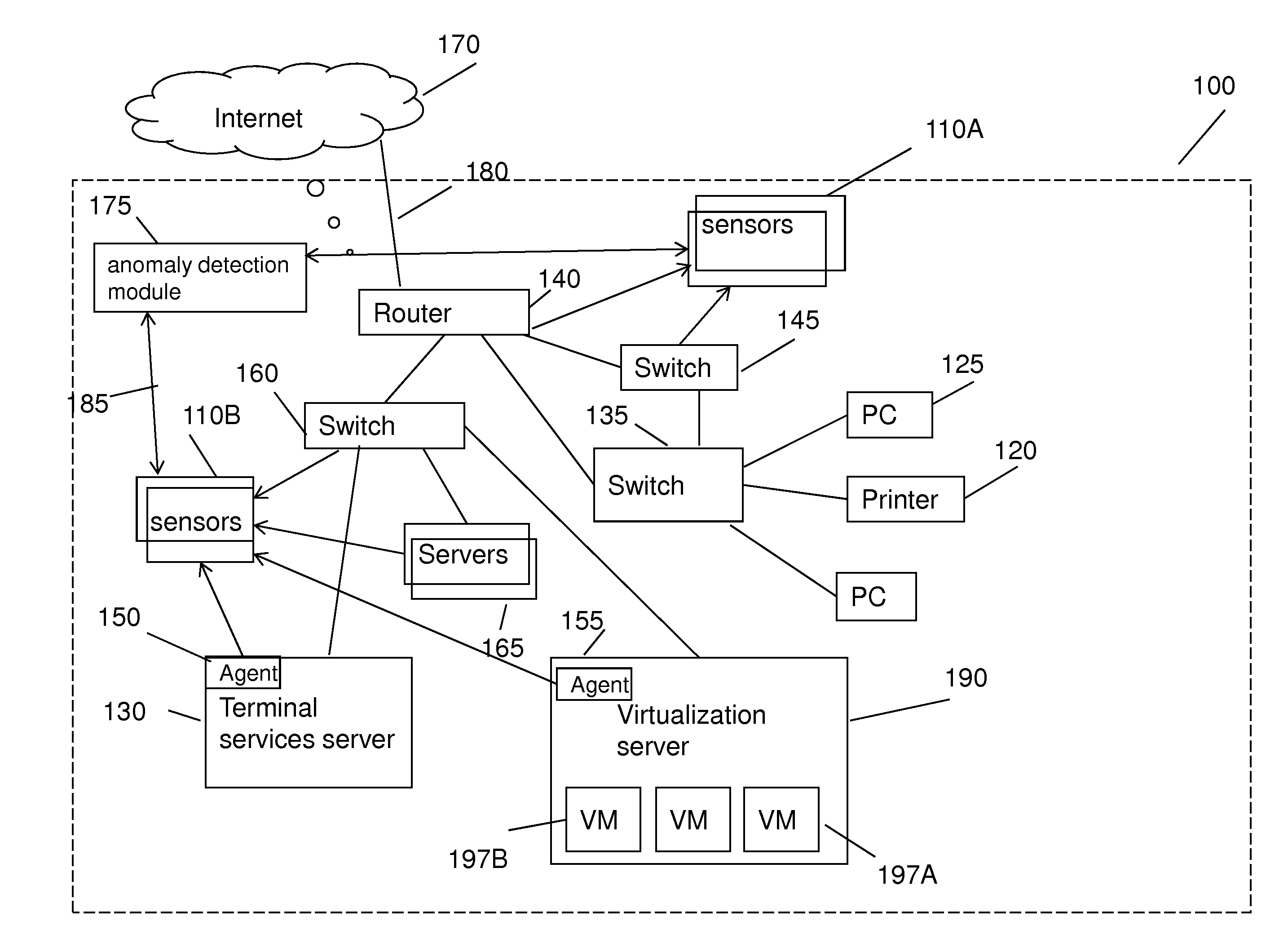
Method for detecting anomaly action within a computer network
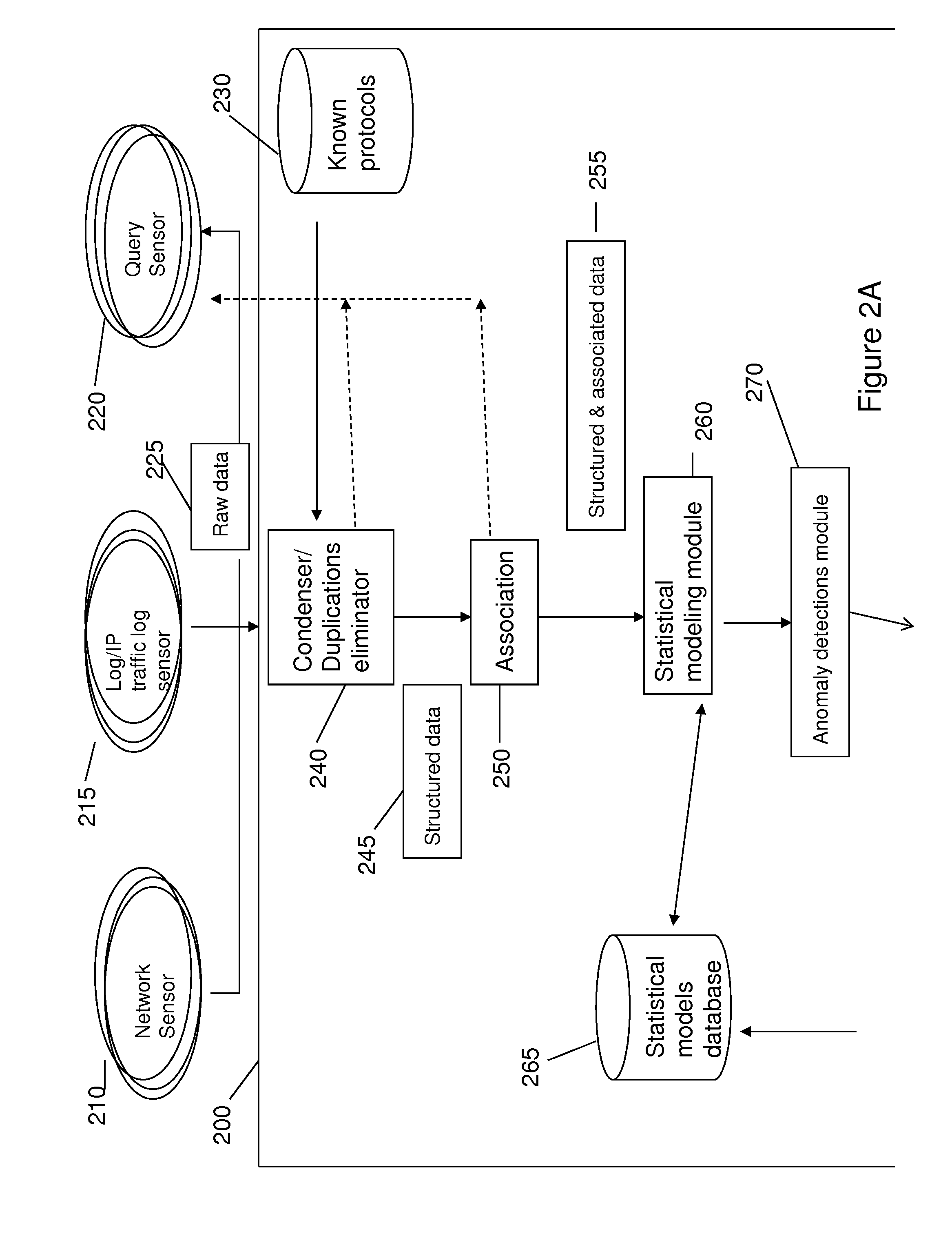
InactiveUS20140165207A1Eliminating duplication and processing dataMemory loss protectionError detection/correctionOriginal dataDistributed computing
A method and system for detecting anomalous action within a computer network is provided herein. The method starts with collecting raw data from at least one probe sensor that is associated with at least one router, switch or at least one server which are part of the computer network. Next, the raw data is being parsed and analyzed and meta-data is created from the raw data. Computer network actions are being identified based on existing knowledge about network protocols. The meta-data is associated with entities by analyzing the identified network actions and correlating between different computer network actions. Finally, creating at least one statistical model of the respective computer network said model including network actions' behavior pattern and online or batch detection of anomalous network actions associated with entities based on the statistical models.
Owner:LIGHT CYBER
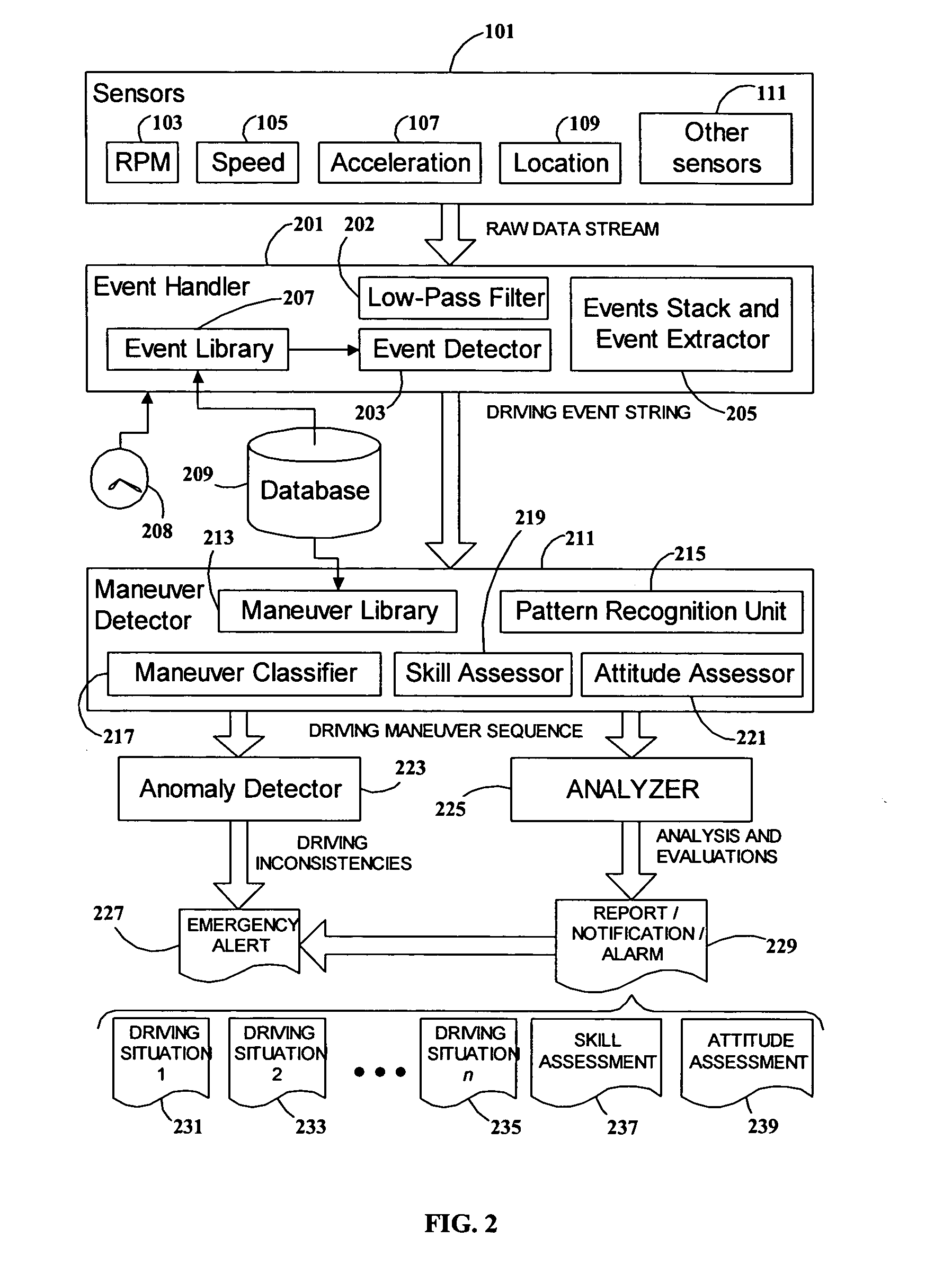
System and method for vehicle driver behavior analysis and evaluation
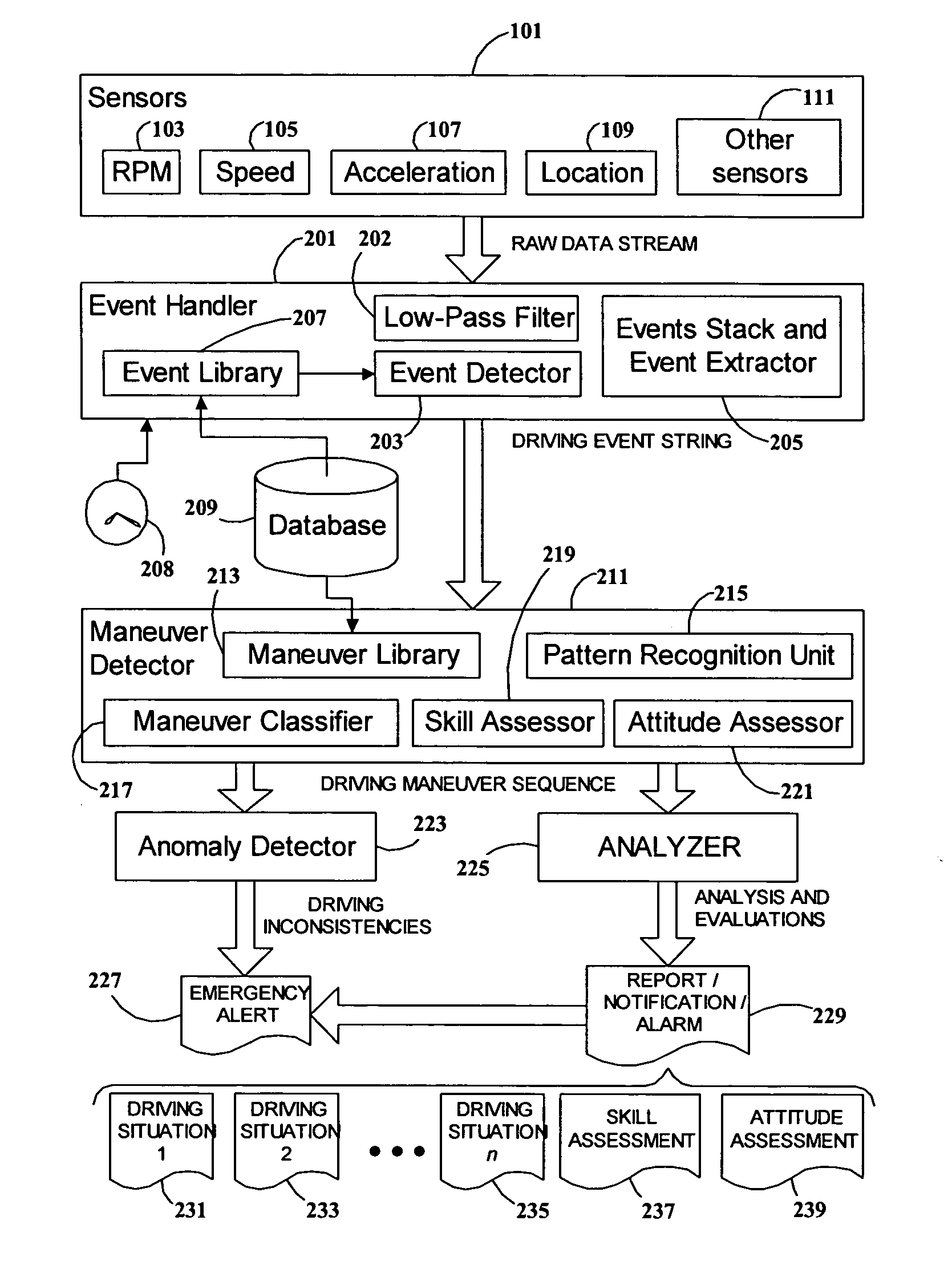
ActiveUS20050131597A1More informationEasy to useVehicle testingRegistering/indicating working of vehiclesData streamDriver/operator
A system and method for analyzing and evaluating the performance and attitude of a motor vehicle driver. A raw data stream from a set of vehicle sensors is filtered to eliminate extraneous noise, and then parsed to convert the stream into a string of driving event primitives. The string of driving events is then processed by a pattern-recognition system to derive a sequence of higher-level driving maneuvers. Driving maneuvers include such familiar procedures as lane changing, passing, and turn and brake. Driving events and maneuvers are quantified by parameters developed from the sensor data. The parameters and timing of the maneuvers can be analyzed to determine skill and attitude factors for evaluating the driver's abilities and safety ratings. The rendering of the data into common driving-related concepts allows more accurate and meaningful analysis and evaluation than is possible with ordinary statistical threshold-based analysis.
Owner:GREENROAD DRIVING TECH LTD
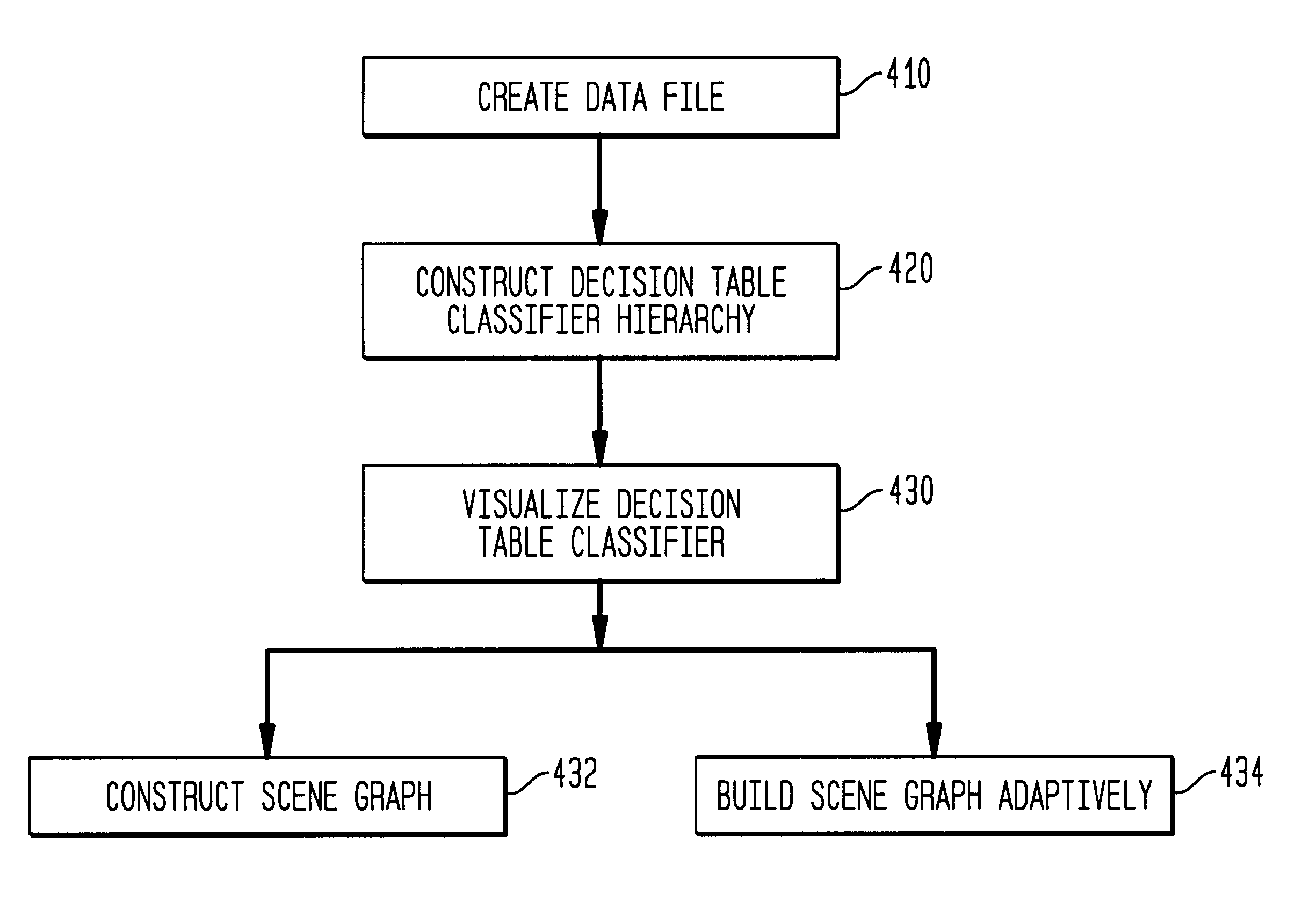
Method, system, and computer program product for visualizing a data structure
A data structure visualization tool visualizes a data structure such as a decision table classifier. A data file based on a data set of relational data is stored as a relational table, where each row represents an aggregate of all the records for each combination of values of the attributes used. Once loaded into memory, an inducer is used to construct a hierarchy of levels, called a decision table classifier, where each successive level in the hierarchy has two fewer attributes. Besides a column for each attribute, there is a column for the record count (or more generally, sum of record weights), and a column containing a vector of probabilities (each probability gives the proportion of records in each class). Finally, at the top-most level, a single row represents all the data. The decision table classifier is then passed to the visualization tool for display and the decision table classifier is visualized. By building a representative scene graph adaptively, the visualization application never loads the whole data set into memory. Interactive techniques, such as drill-down and drill-through are used view further levels of detail or to retrieve some subset of the original data. The decision table visualizer helps a user understand the importance of specific attribute values for classification.
Owner:RPX CORP +1
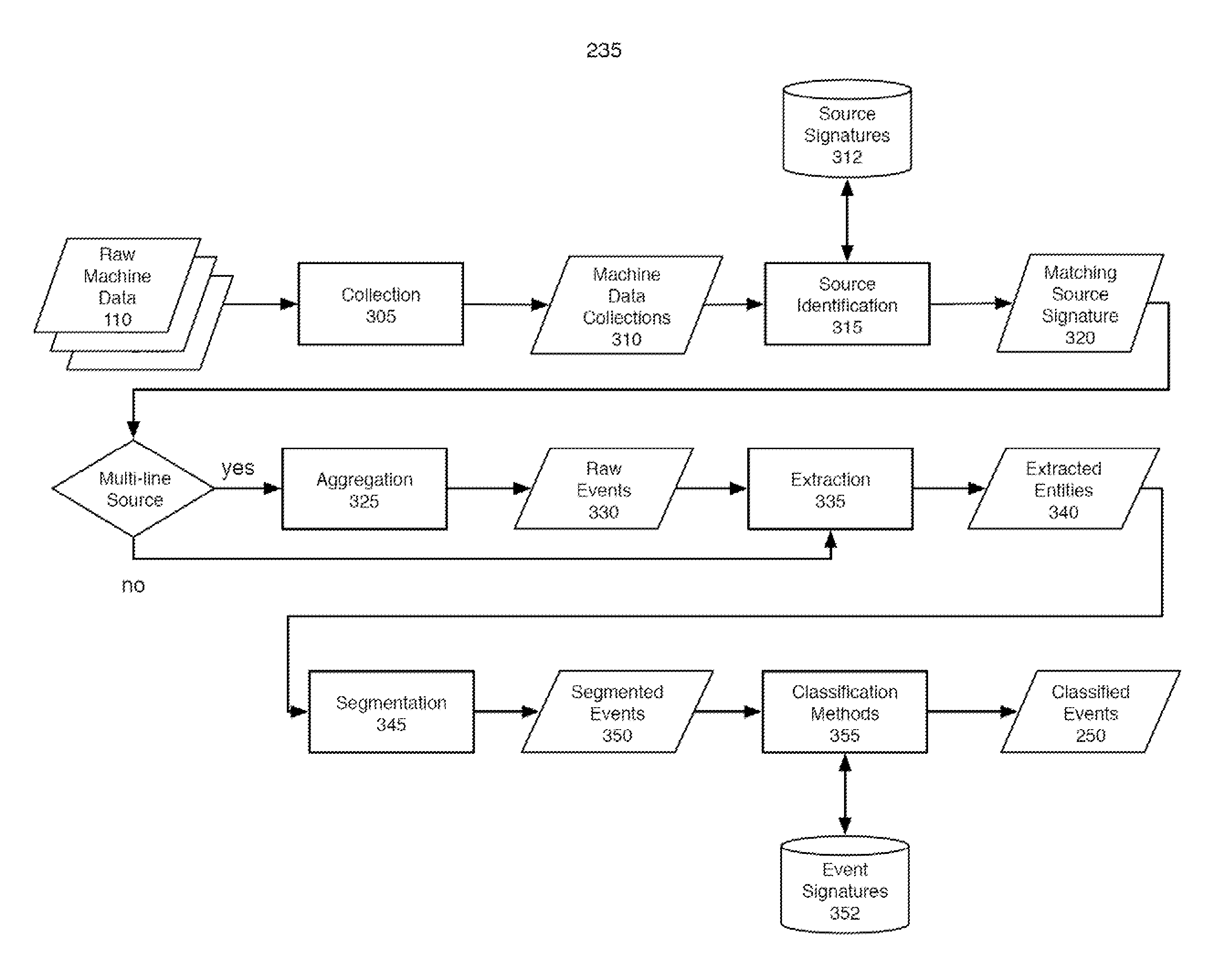
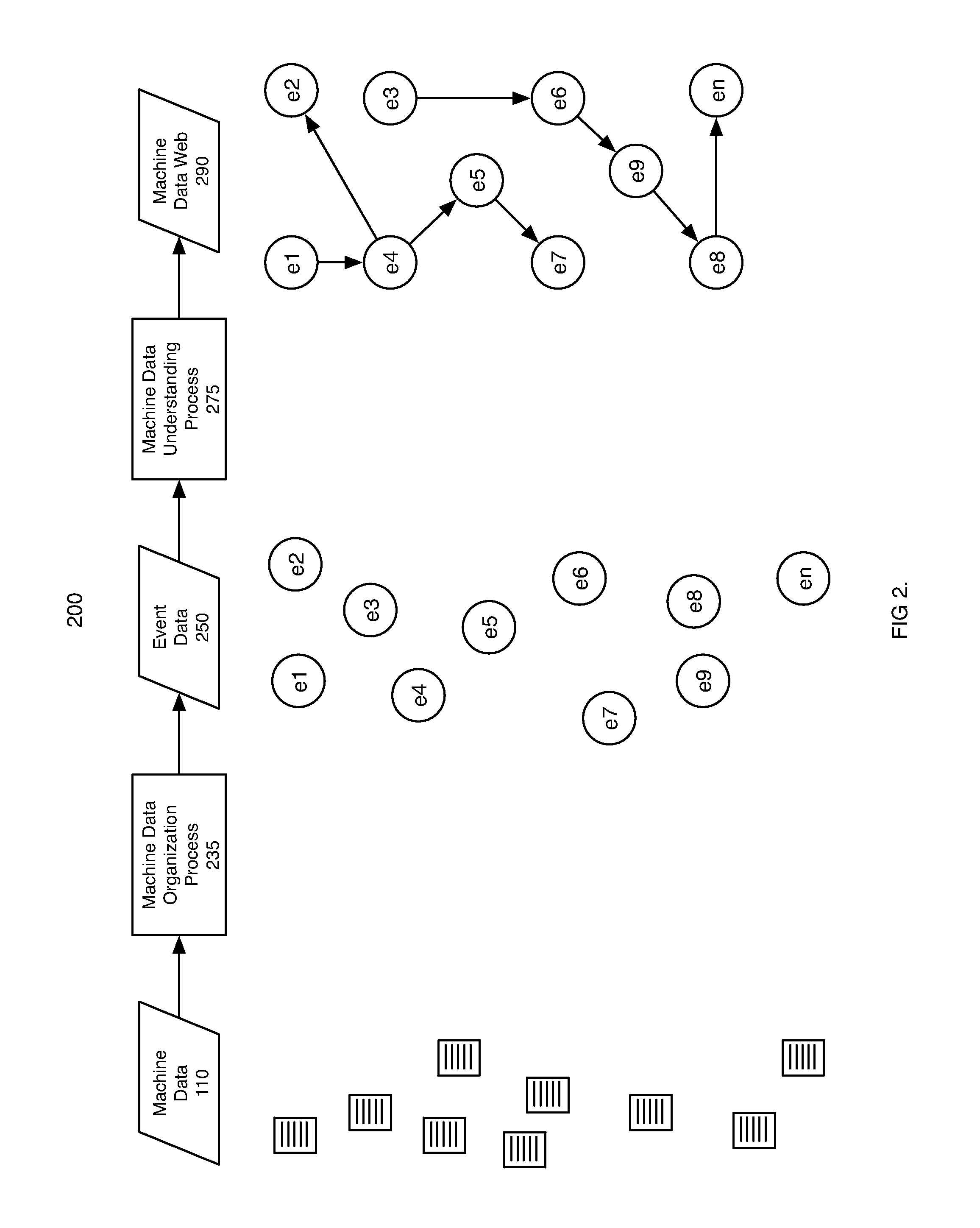
Machine data web
ActiveUS7937344B2Preserve integrityError detection/correctionInterprogram communicationInformation processingOriginal data
Methods and apparatus consistent with the invention provide the ability to organize and build understandings of machine data generated by a variety of information-processing environments. Machine data is a product of information-processing systems (e.g., activity logs, configuration files, messages, database records) and represents the evidence of particular events that have taken place and been recorded in raw data format. In one embodiment, machine data is turned into a machine data web by organizing machine data into events and then linking events together.
Owner:SPLUNK INC
Method, software and apparatus for saving, using and recovering data
InactiveUS6016553ADigital data information retrievalInput/output to record carriersOperational systemOriginal data
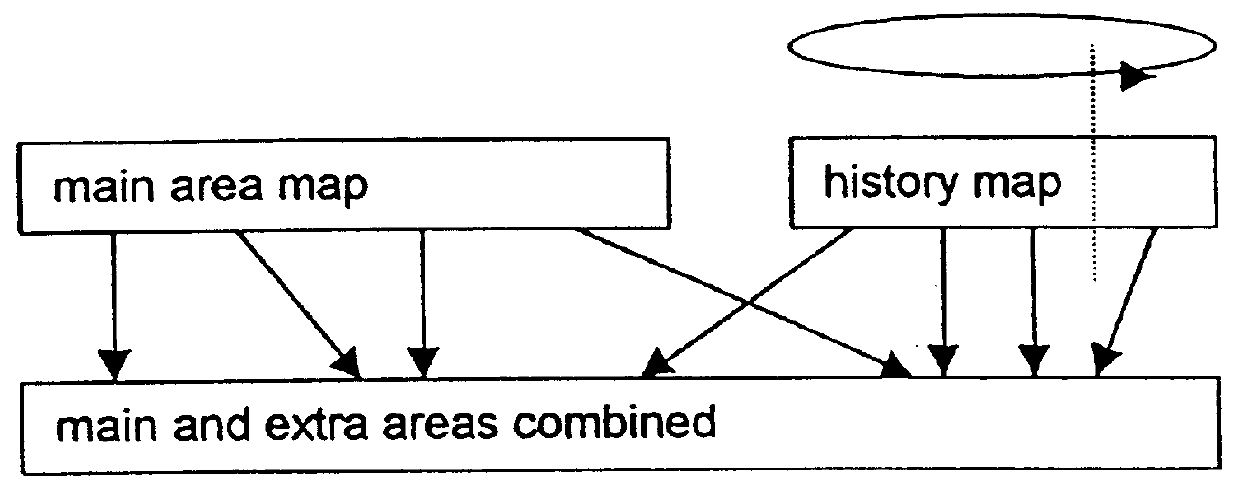
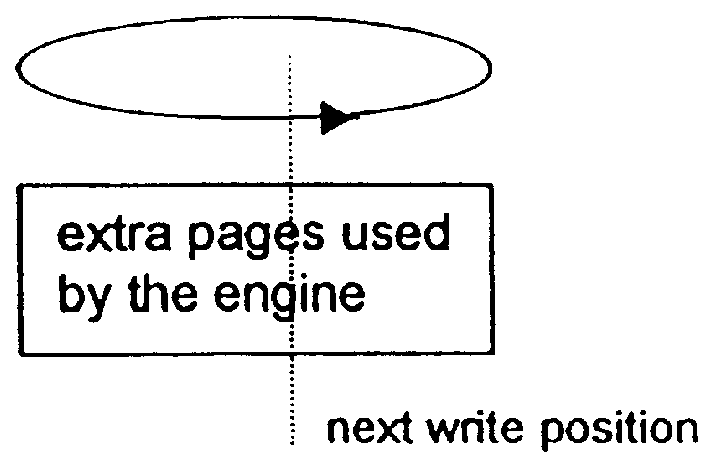
A method and apparatus for reverting a disk drive to an earlier point in time is disclosed. Changes made to the drive are saved in a circular history buffer which includes the old data, the time it was replaced by new data, and the original location of the data. The circular history buffer may also be implemented by saving new data elements into new locations and leaving the old data elements in their original locations. References to the new data elements are mapped to the new location. The disk drive is reverted to an earlier point in time by replacing the new data elements with the original data elements retrieved from the history buffer, or in the case of the other embodiment, reads to the disk are mapped to the old data elements stilled stored in their original locations. The method and apparatus may be implemented as part of an operating system, or as a separate program, or in the controller for the disk drive. The method and apparatus are applicable to other forms of data storage as well. Also disclosed are method and apparatus for providing firewall protection to data in a data storage medium of a computer system.
Owner:POWER MANAGEMENT ENTERPRISES
Secure data parser method and system
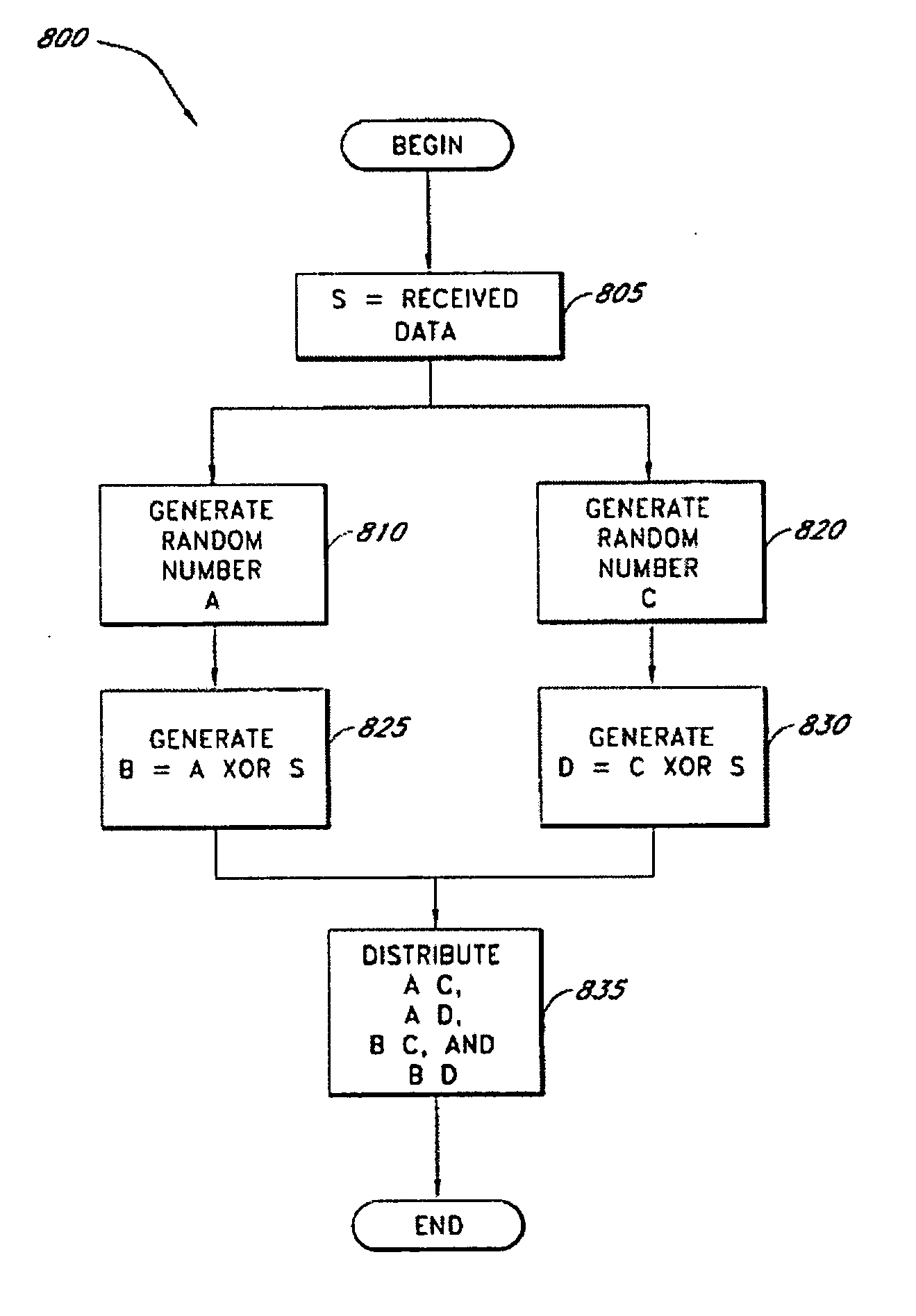
InactiveUS20060177061A1Minimal compute resourceAvoid the needKey distribution for secure communicationError detection/correctionOriginal dataEncryption
A secure data parser is provided that may be integrated into any suitable system for securely storing and communicating data. The secure data parser parses data and then splits the data into multiple portions that are stored or communicated distinctly. Encryption of the original data, the portions of data, or both may be employed for additional security. The secure data parser may be used to protect data in motion by splitting original data into portions of data, that may be communicated using multiple communications paths.
Owner:SECURITY FIRST INNOVATIONS LLC
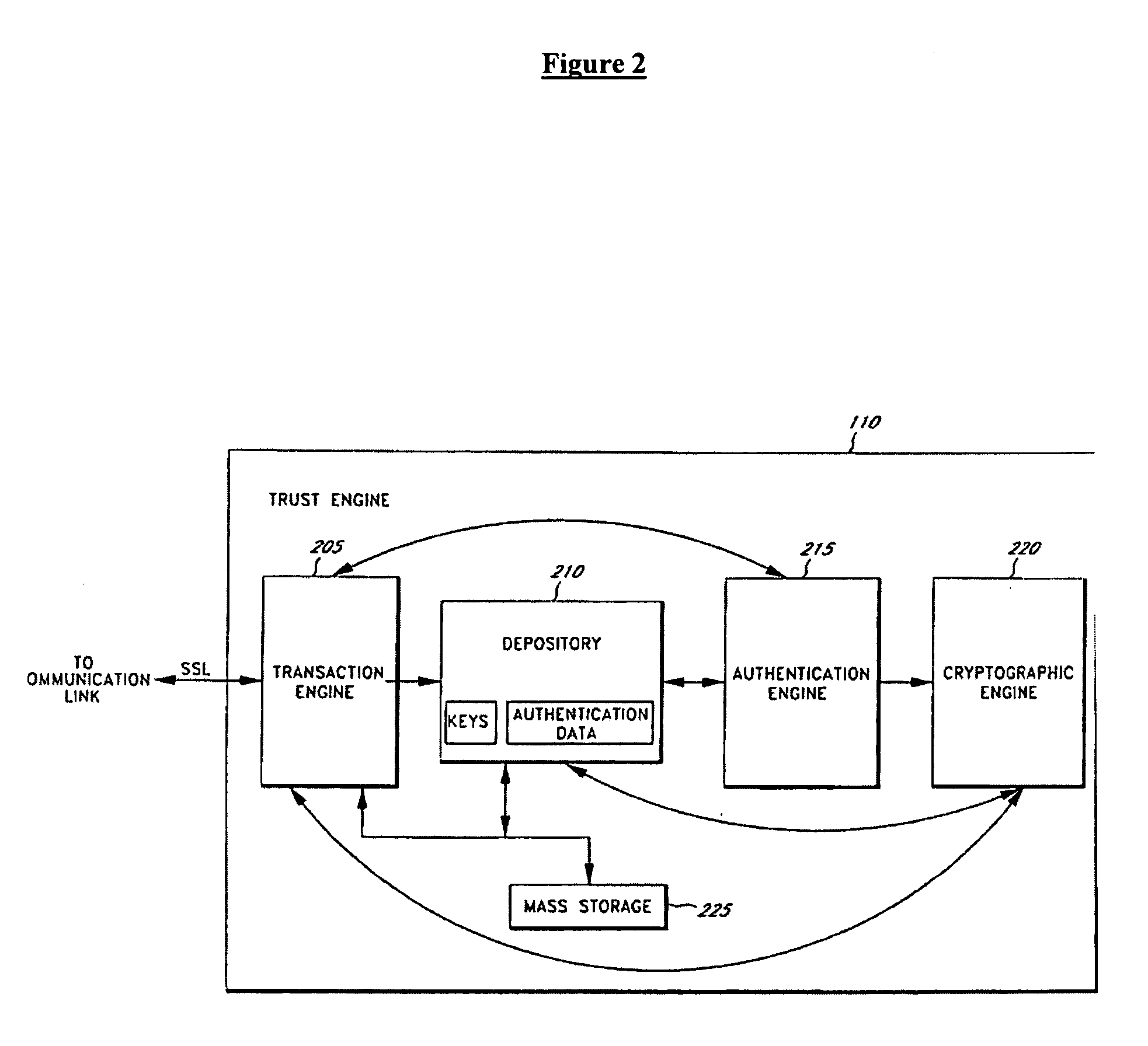
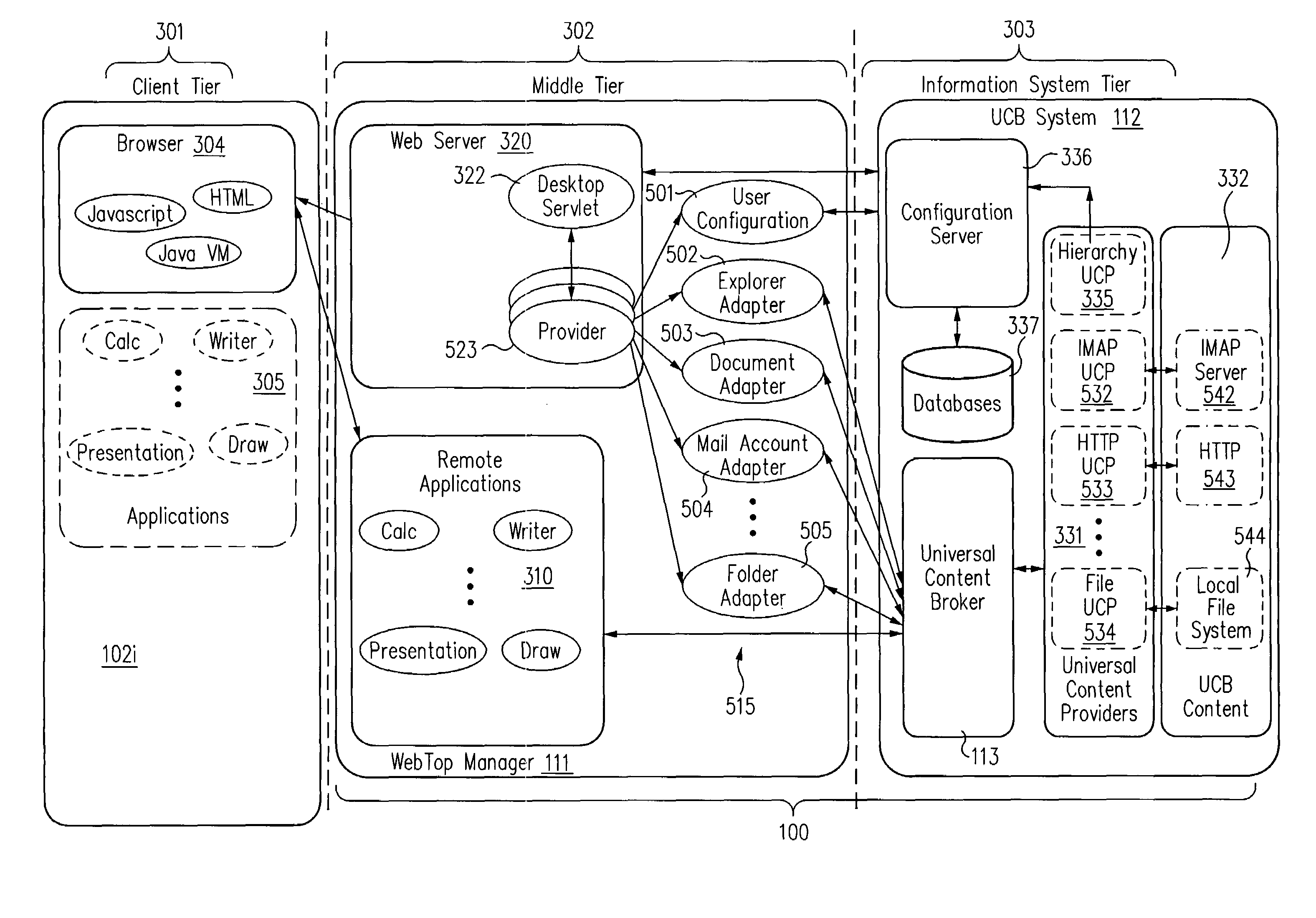
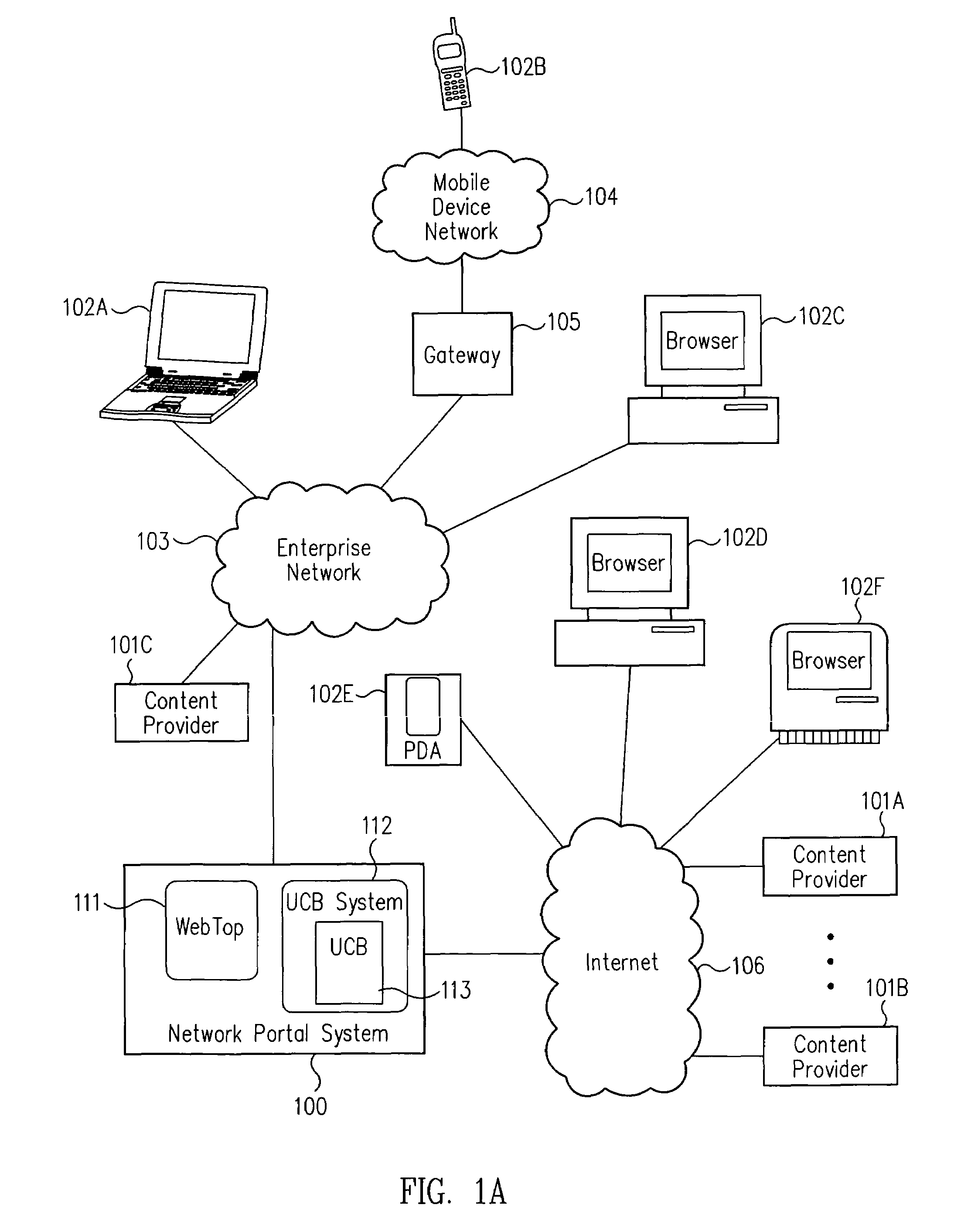
Network portal system and methods
InactiveUS7269664B2Improve scalabilityData processing applicationsText processingUser deviceOriginal data
A network portal system includes a web-top manager and a universal content broker system. The web-top manager is configured to receive a content request from a user device, where the content request includes a content provider identifier. The universal content broker system is coupled to the web-top manager. The universal content broker system includes a plurality of content providers. Each content provider in the plurality of content providers is associated with a different content provider identifier. Also, each content provider accesses content having a different raw data format. A universal content broker is coupled to the web-top manager and to the plurality of content providers. Upon the receipt of the content request from the web-top manager, the universal content broker passes the request to a content provider in the plurality of content providers that is associated with the content provider identifier.
Owner:ORACLE INT CORP
Secure data parser method and system
ActiveUS20070160198A1Minimal compute resourceAvoid the needDigital data protectionSecret communicationOriginal dataComputer science
A secure data parser is provided that may be integrated into any suitable system for securely storing and communicating data. The secure data parser parses data and then splits the data into multiple portions that are stored or communicated distinctly. Encryption of the original data, the portions of data, or both may be employed for additional security. The secure data parser may be used to protect data in motion by splitting original data into portions of data, that may be communicated using multiple communications paths.
Owner:SECURITY FIRST INNOVATIONS LLC
System and method for restoring a computer system after a failure
InactiveUS20020049883A1Memory adressing/allocation/relocationInternal/peripheral component protectionOperational systemOriginal data
A method and apparatus for reverting a disk drive to an earlier point in time is disclosed. Changes made to the drive are saved in a circular history buffer which includes the old data, the time it was replaced by new data, and the original location of the data. The circular history buffer may also be implemented by saving new data elements into new locations and leaving the old data elements in their original locations. References to the new data elements are mapped to the new location. The disk drive is reverted to an earlier point in time by replacing the new data elements with the original data elements retrieved from the history buffer, or in the case of the other embodiment, reads to the disk are mapped to the old data elements stilled stored in their original locations. The method and apparatus may be implemented as part of an operating system, or as a separate program, or in the controller for the disk drive. The method and apparatus are applicable to other forms of data storage as well. Also disclosed are method and apparatus for providing firewall protection to data in a data storage medium of a computer system.
Owner:NORTONLIFELOCK INC
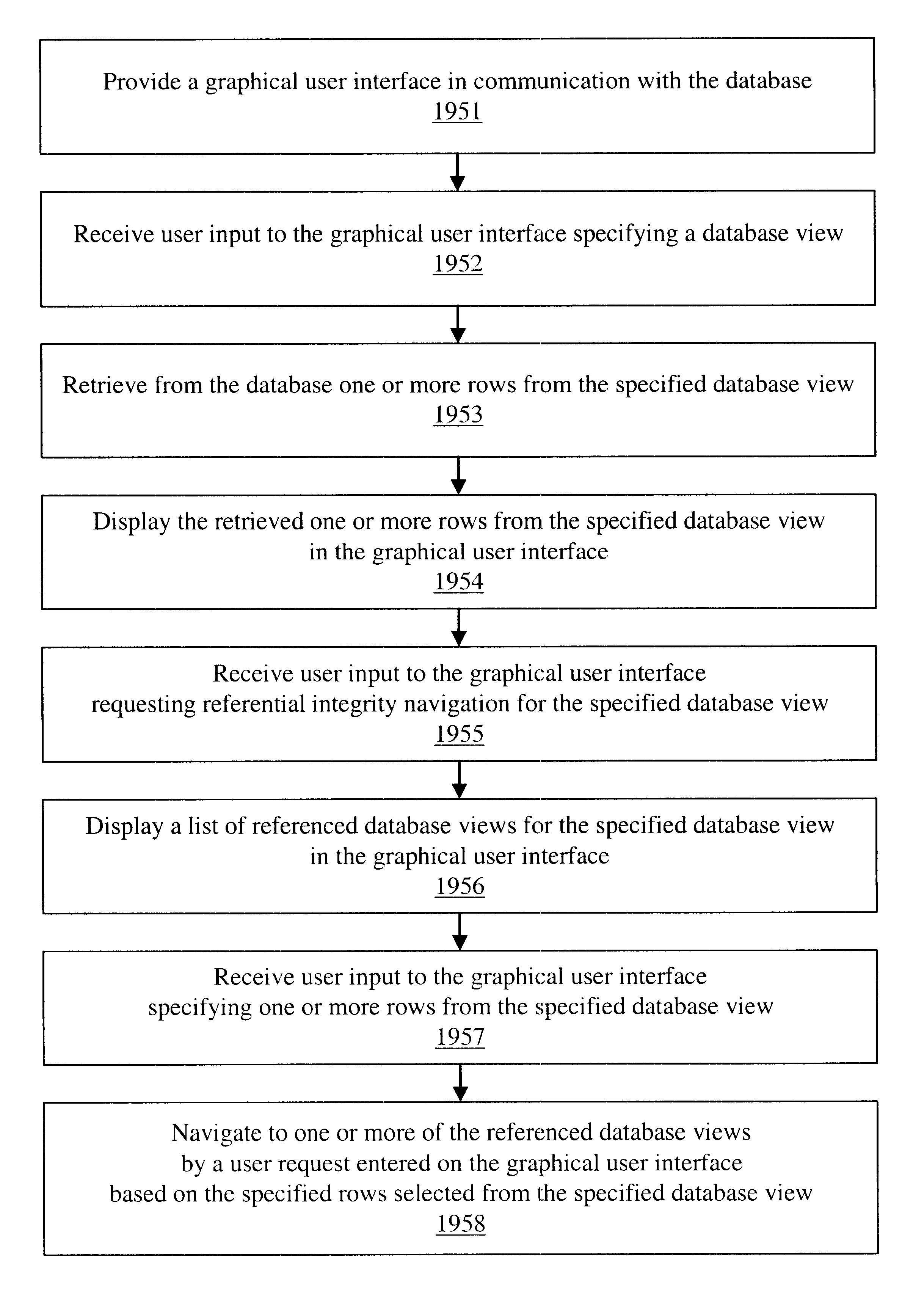
Navigation of view relationships in database system
InactiveUS6609122B1Maintaining correctness and consistency of dataData inconsistencyData processing applicationsDigital data processing detailsOriginal dataApplication software
The invention is an improved system and method for browsing and editing data residing in database tables. The method of the present invention includes the steps of providing a graphical user interface in communication with a database, receiving user input to the graphical user interface, retrieving data from the database, displaying the retrieved data in the graphical user interface, and navigating to one or more referenced database tables or views by user request entered on the graphical user interface. The purpose of referential integrity is to prevent database users or applications from entering inconsistent data into a database. The goal of referential integrity navigation is to allow the user, having retrieved one or more rows of data, to navigate easily to the data in other tables that either refers to or is referred to by that data. These relationships are defined by referential integrity constraints, and the data thus retrieved by navigation is then available for all the operations possible on the original data, including data editing and further relational navigation. By storing a catalog of the relationships known to exist between Oracle's V$ views, the same form of navigation can be provided between these data sources.
Owner:BMC SOFTWARE
Management of non-volatile memory systems having large erase blocks
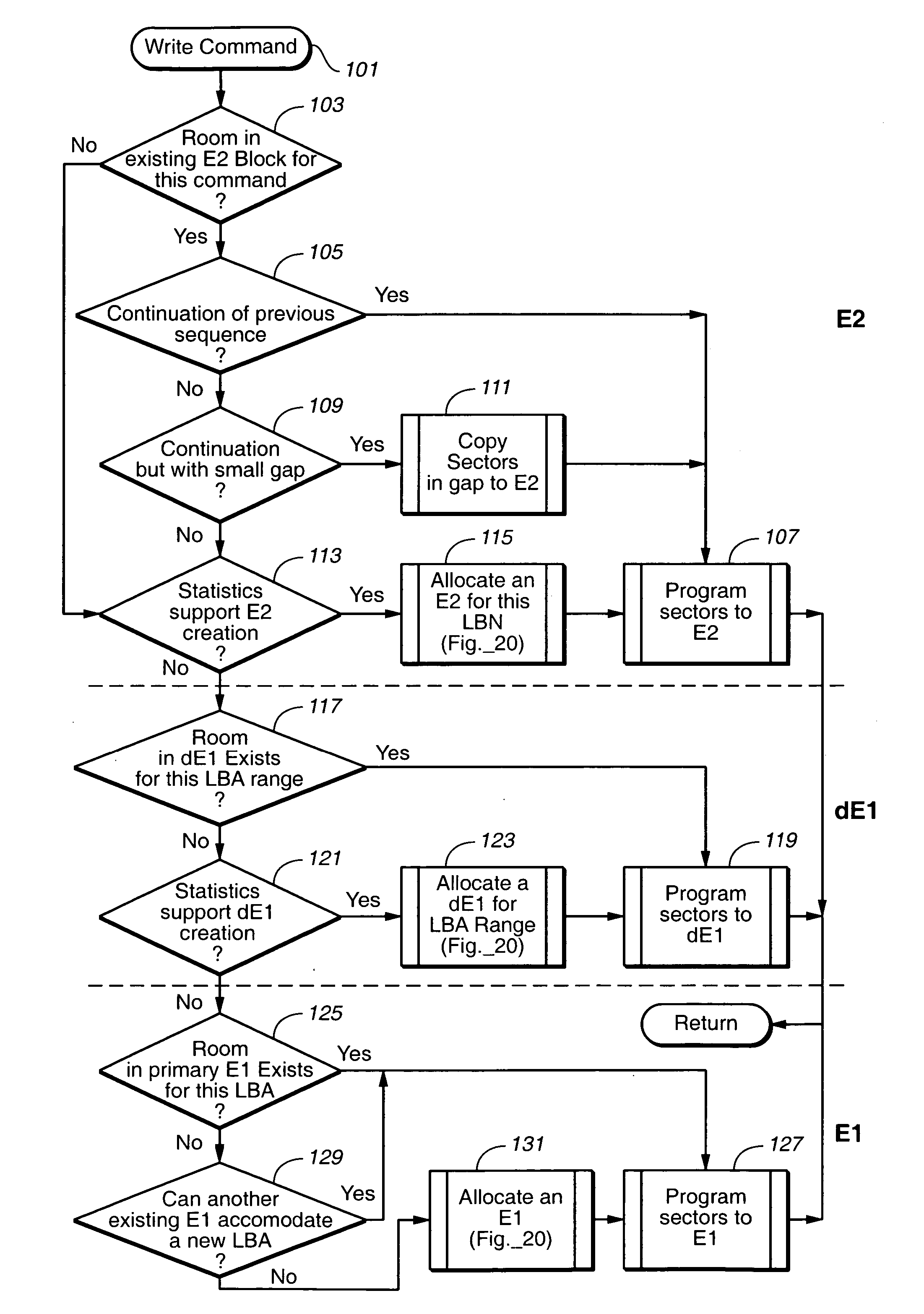
ActiveUS20050144358A1Reduce amountImprove system performanceMemory architecture accessing/allocationMemory adressing/allocation/relocationOriginal dataTerm memory
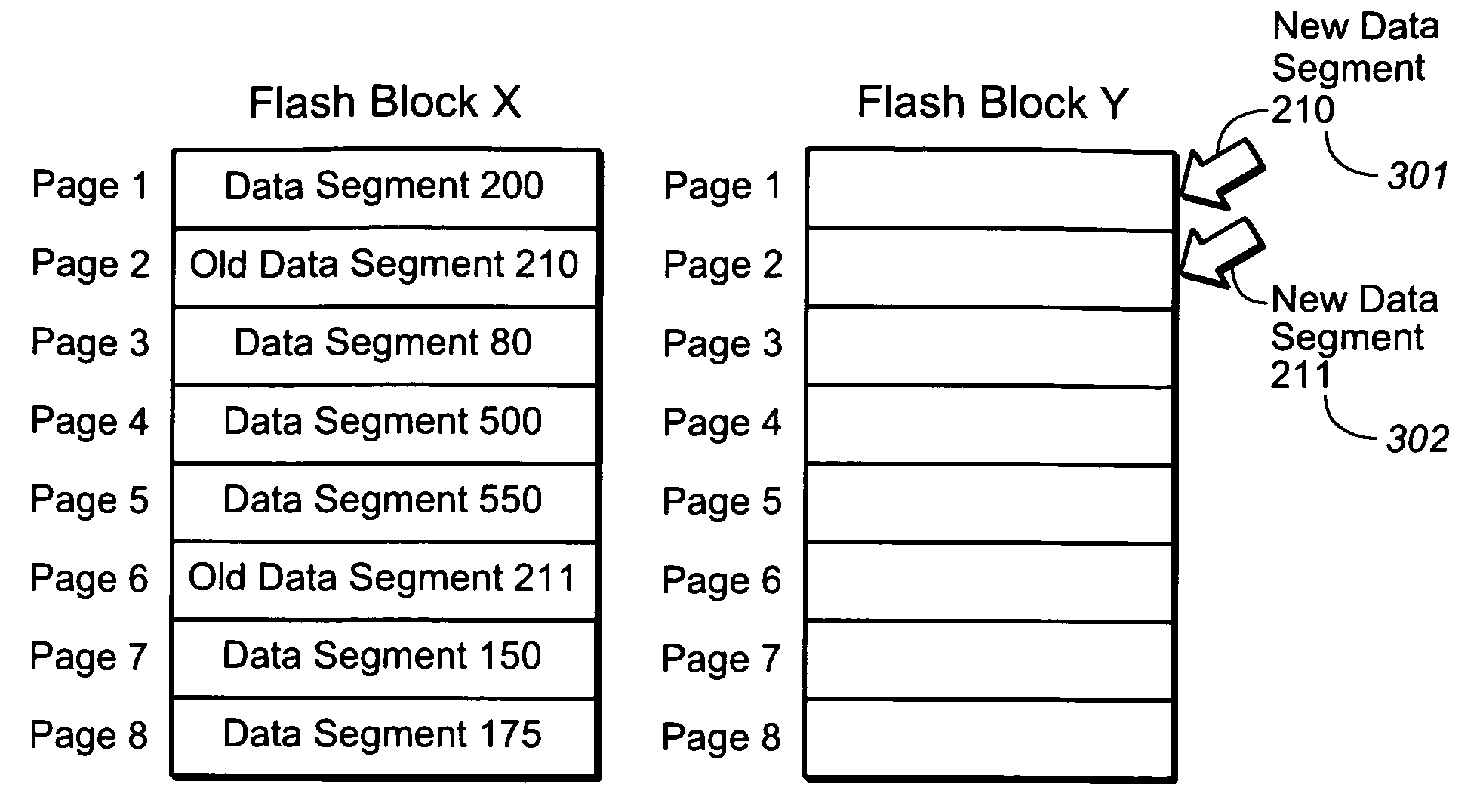
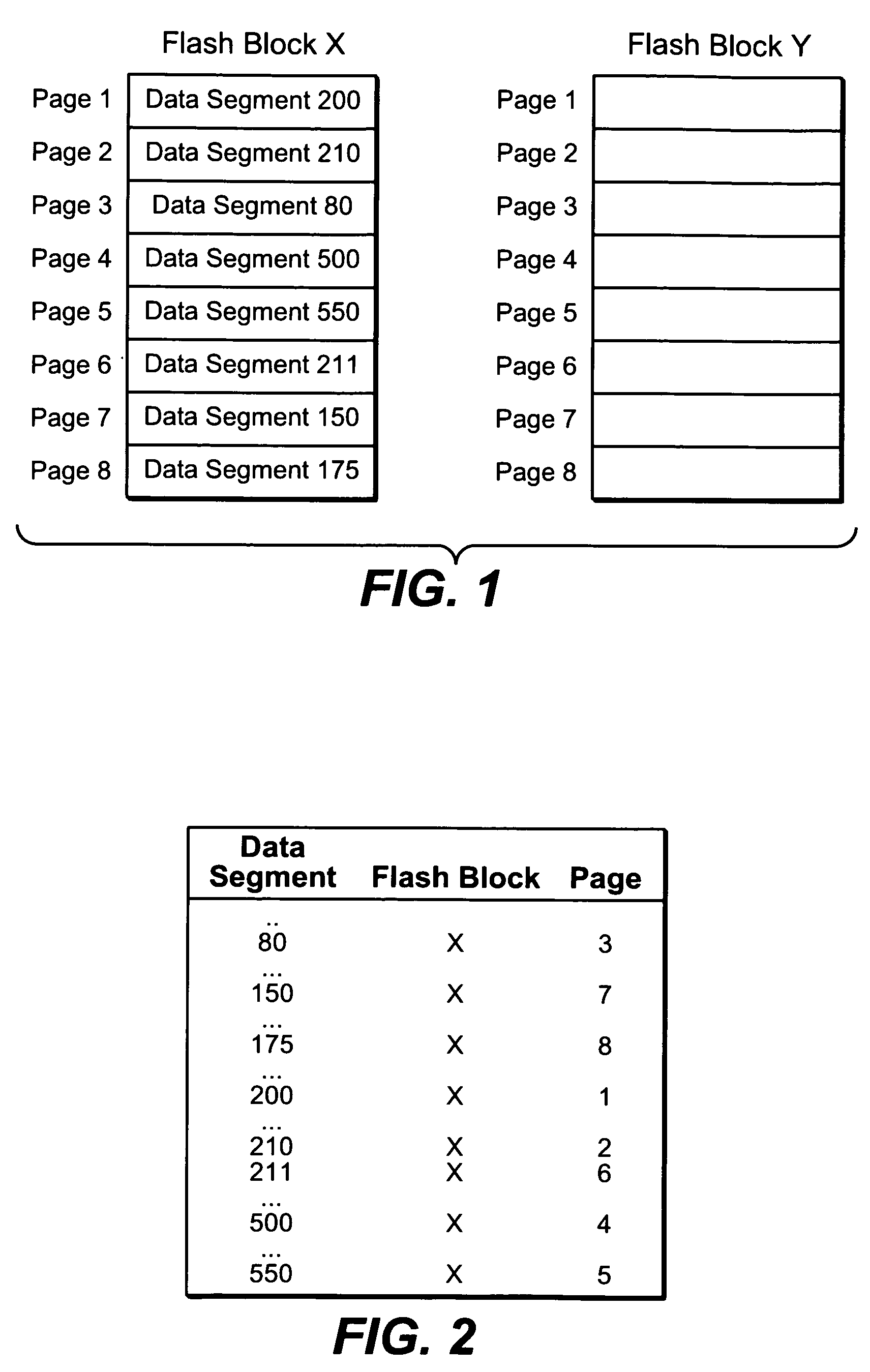
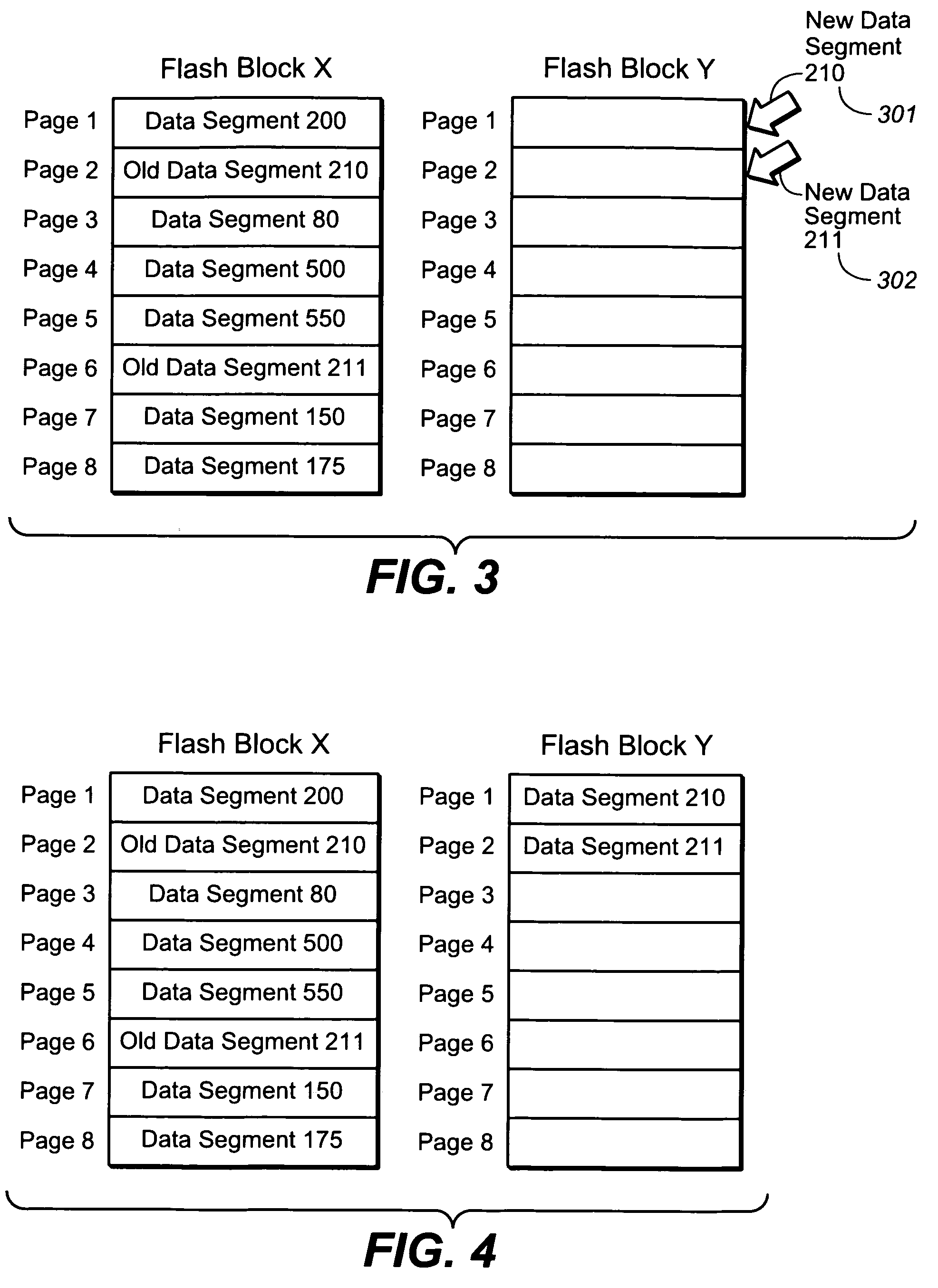
A non-volatile memory system of a type having blocks of memory cells erased together and which are programmable from an erased state in units of a large number of pages per block. If the data of only a few pages of a block are to be updated, the updated pages are written into another block provided for this purpose. Updated pages from multiple blocks are programmed into this other block in an order that does not necessarily correspond with their original address offsets. The valid original and updated data are then combined at a later time, when doing so does not impact on the performance of the memory. If the data of a large number of pages of a block are to be updated, however, the updated pages are written into an unused erased block and the unchanged pages are also written to the same unused block. By handling the updating of a few pages differently, memory performance is improved when small updates are being made. The memory controller can dynamically create and operate these other blocks in response to usage by the host of the memory system.
Owner:SANDISK TECH LLC
Private information storage system
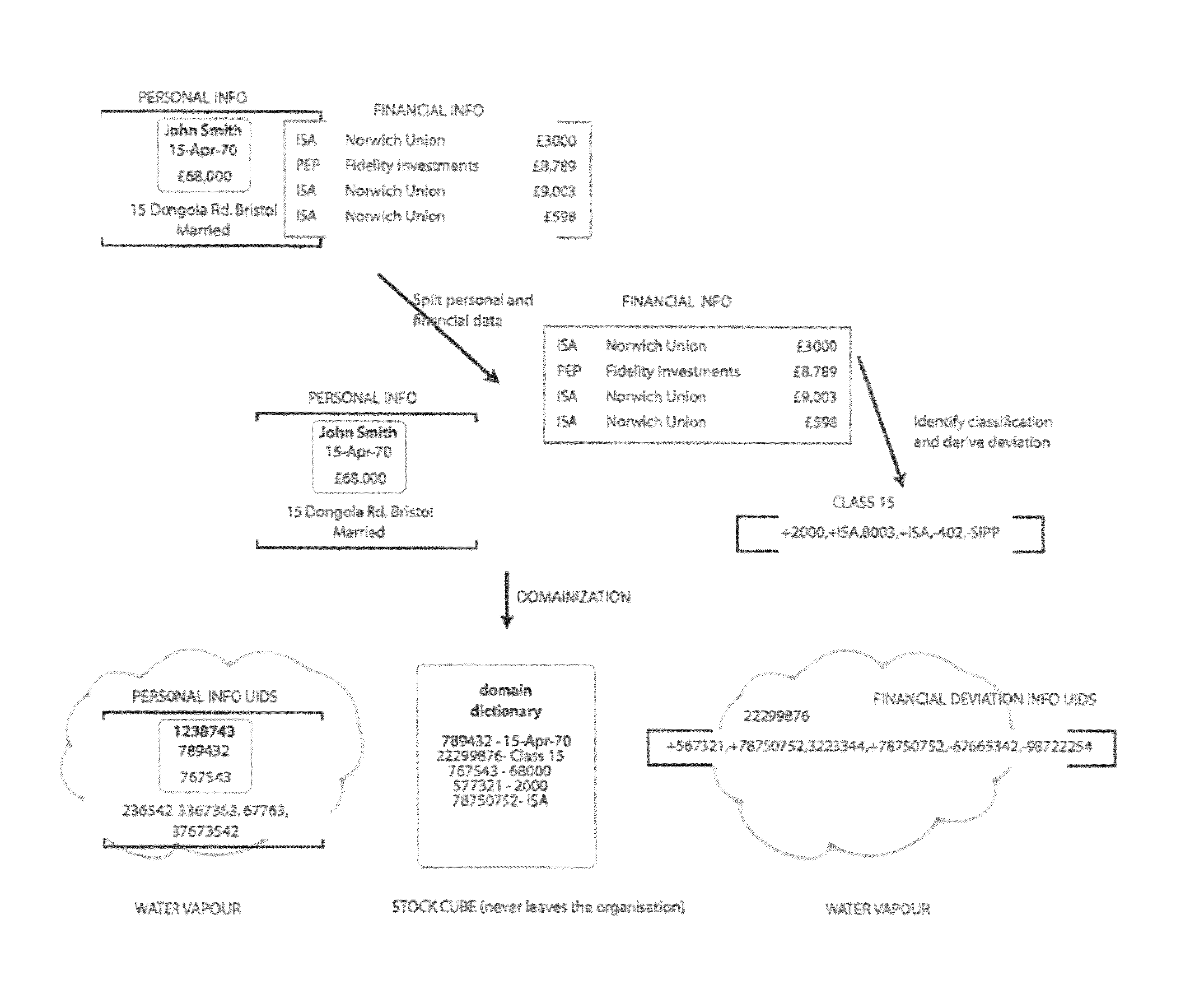
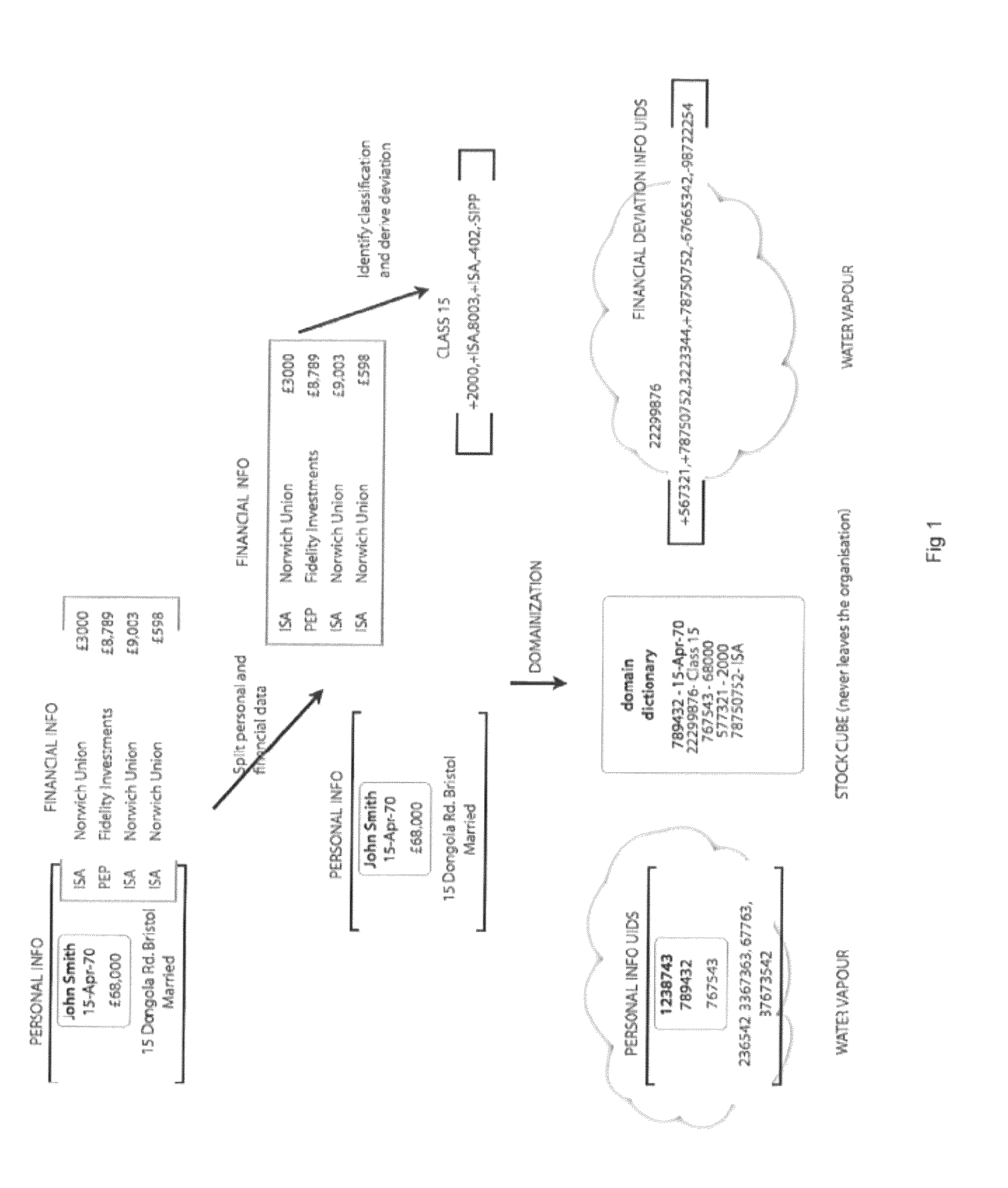
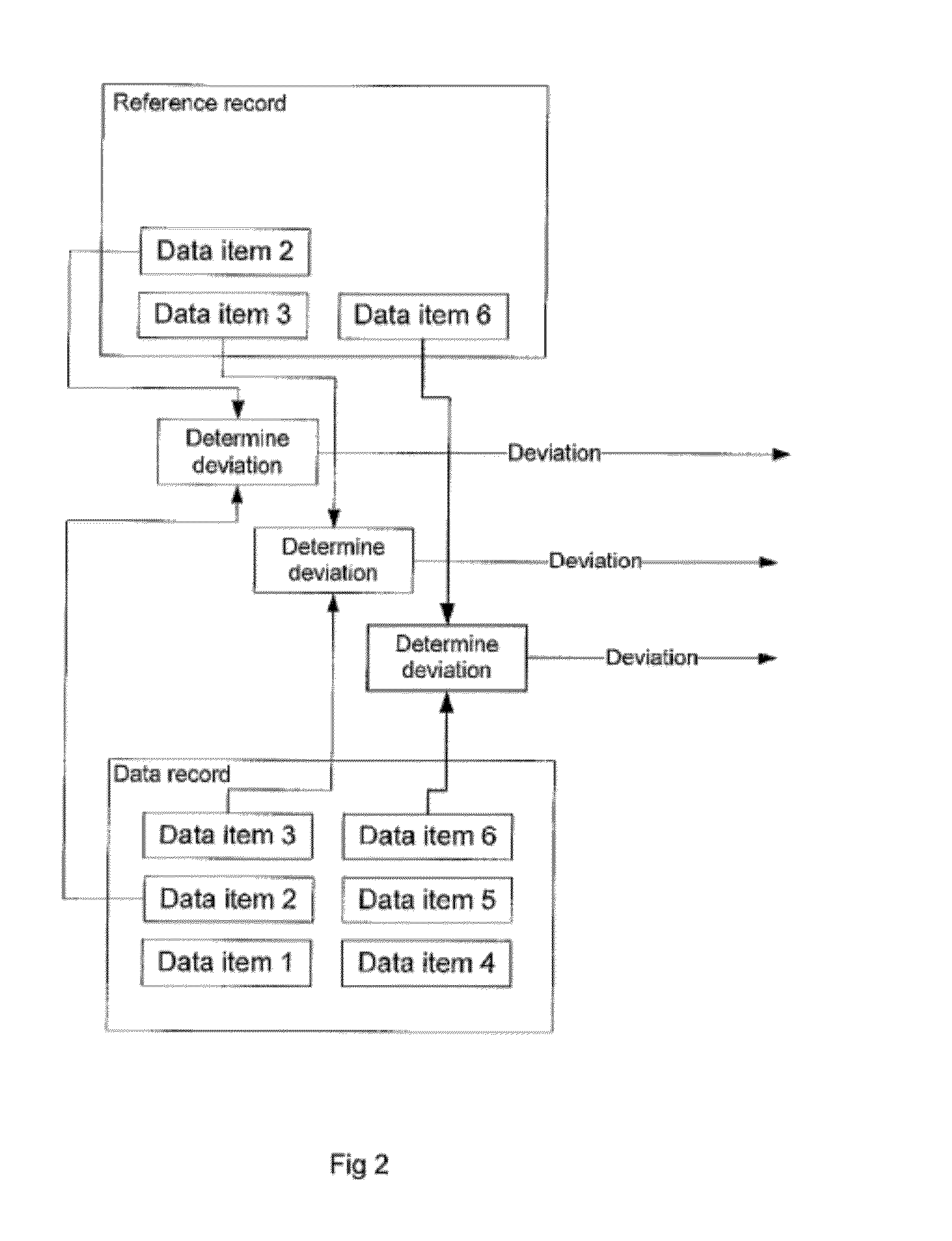
This invention relates to a scheme for storage of private information on a cloud computing platform without contravention of territorial privacy laws. A method of anonymising a database of personal data is described whereby data identifiers are assigned to data items and deviation identifiers are assigned to deviations for selected data items derived from reference records. Such information can then be uploaded to a cloud based storage platform. A translation table maps the data items, data identifiers and deviation identifiers to the original data entries. This translation table is stored locally and separate to the anonymised information uploaded to the cloud. The invention further describes a method of decoding the database anonymised according to the above method.
Owner:ANZEN TECH SYST LTD
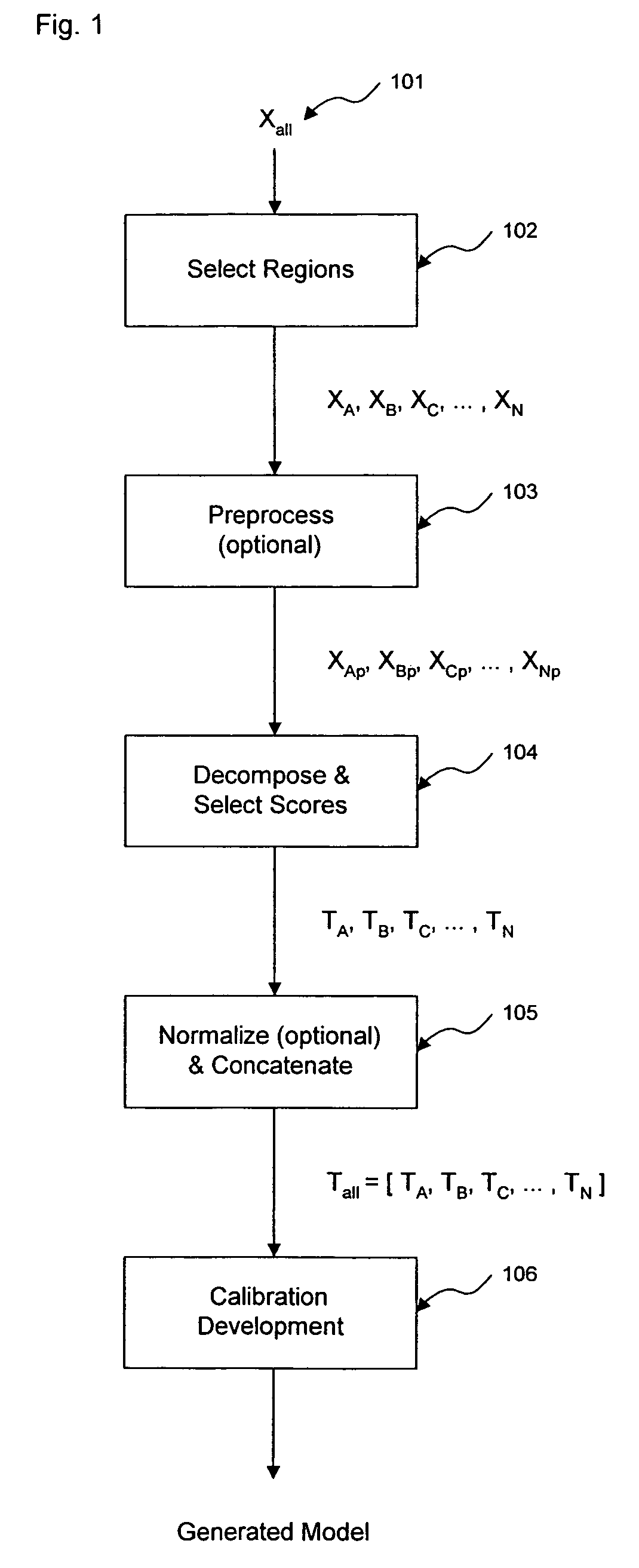
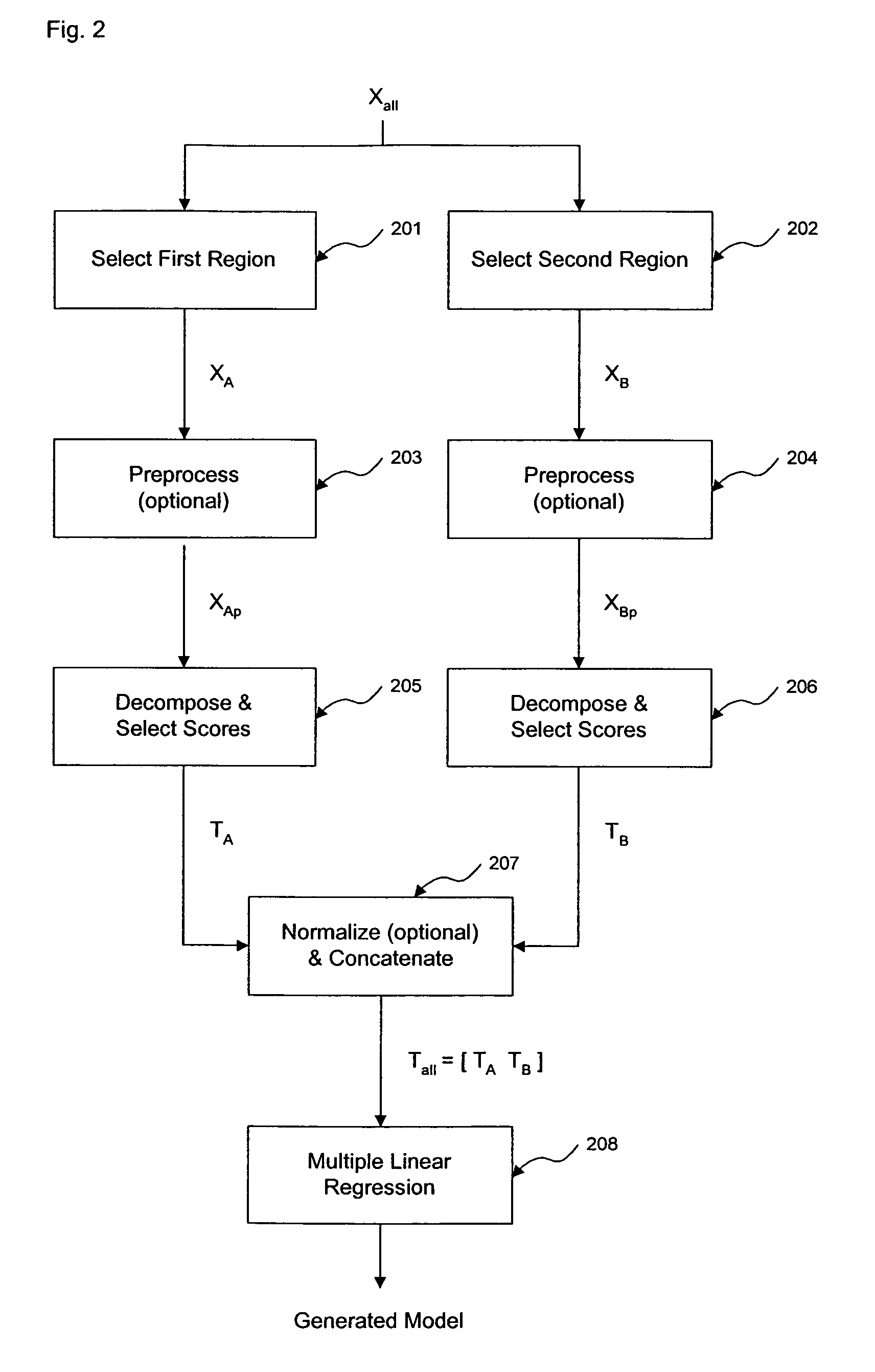
Method and apparatus for enhanced estimation of an analyte property through multiple region transformation
ActiveUS7620674B2Computation using non-denominational number representationDiagnostic recording/measuringAnalyteDecomposition
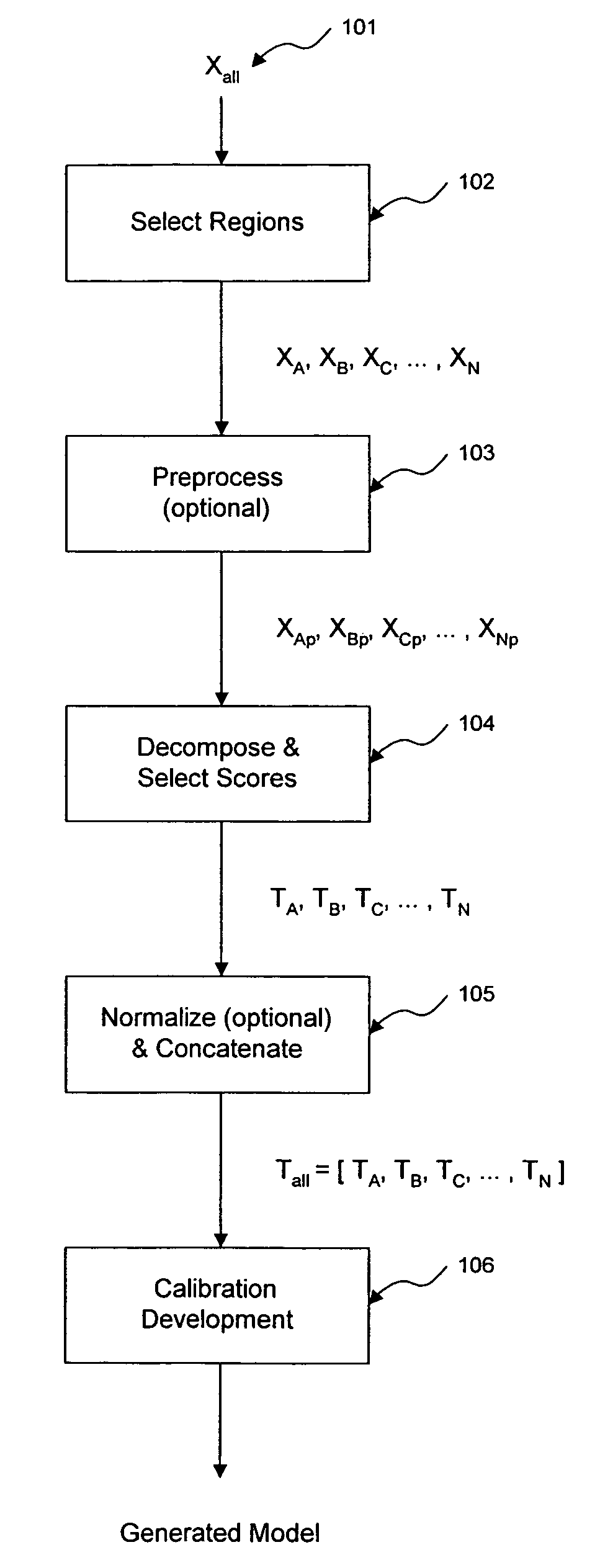
The invention comprises transformation of a section of a data block independently of the transformation of separate or overlapping data blocks to determine a property related to the original matrix, where each of the separate or overlapping data blocks are derived from an original data matrix. The transformation enhances parameters of a first data block over a given region of an axis of the data matrix, such as signal-to-noise, without affecting analysis of a second data block derived from the data matrix. This allows for enhancement of analysis of an analyte property, such as concentration, represented within the original data matrix. A separate decomposition and factor selection for each selected data matrix is performed with subsequent score matrix concatenization. The combined score matrix is used to generate a model that is subsequently used to estimate a property, such as concentration represented in the original data matrix.
Owner:GLT ACQUISITION
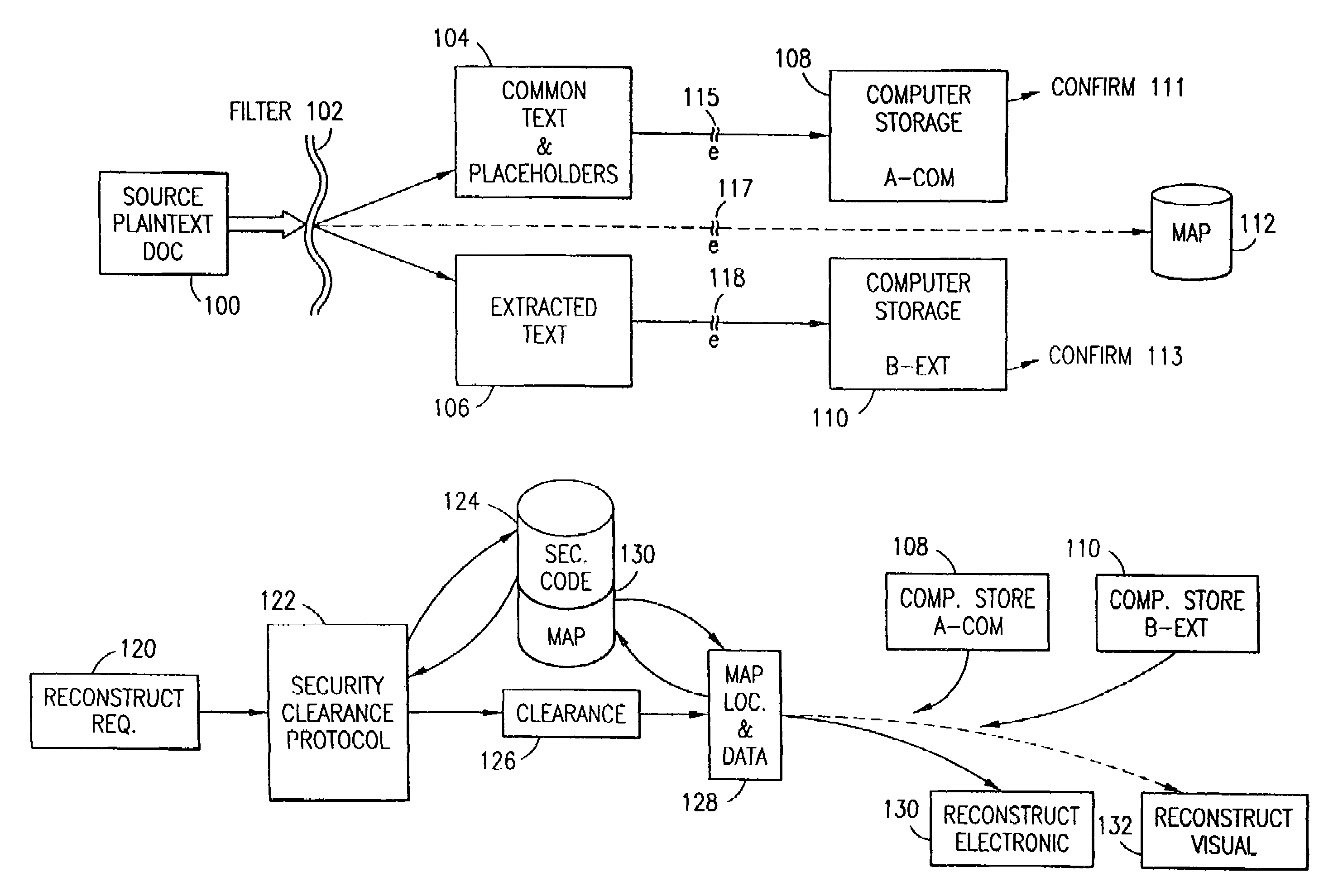
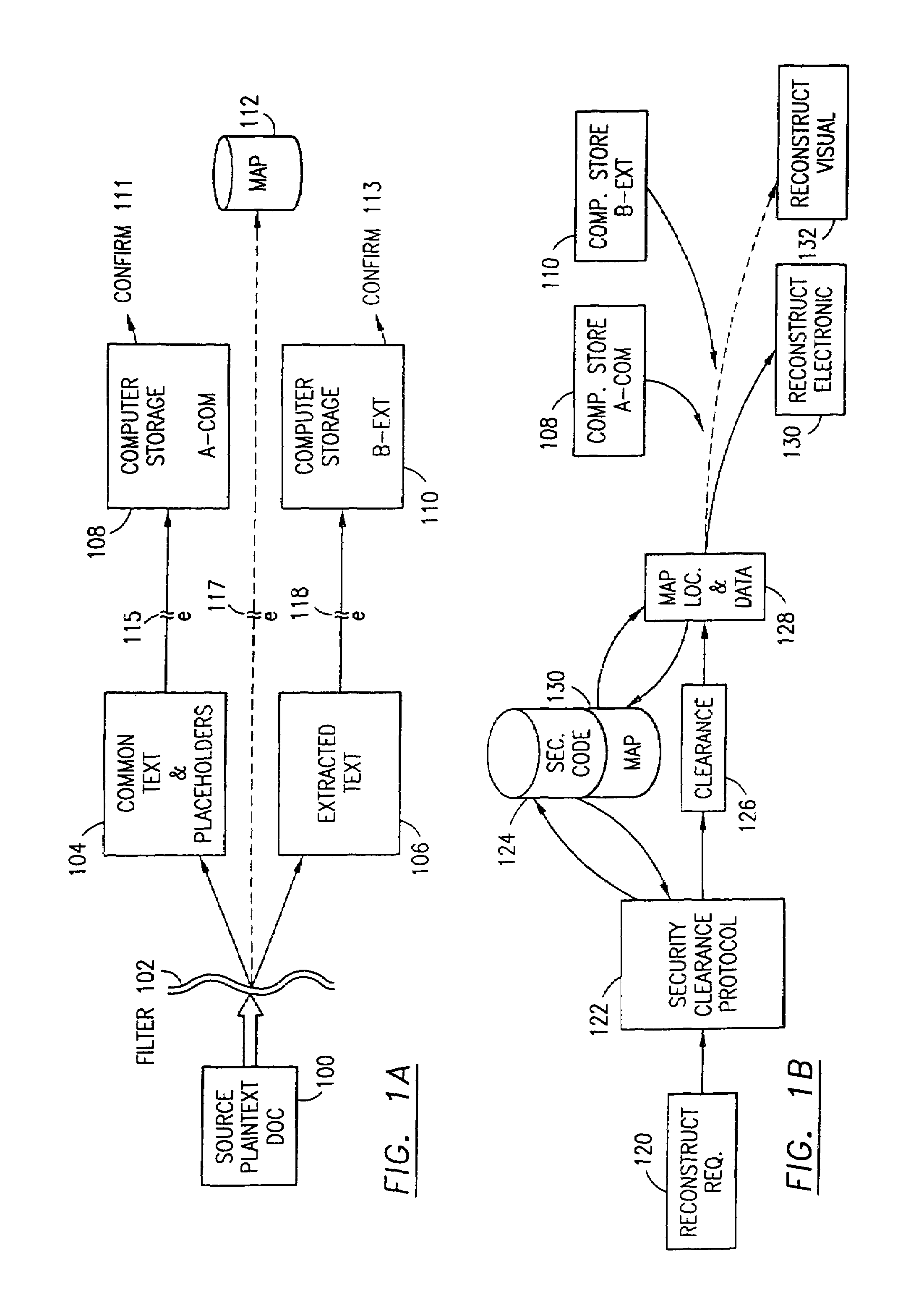
Data security system and method associated with data mining
ActiveUS7322047B2Ease overhead performanceHigh overhead performancePeptide/protein ingredientsMultiple keys/algorithms usagePlaintextInternet privacy
The data security method, system and associated data mining enables multiple users, each having a respective security clearance level to access security sensitive words, data objects, characters or icons. The method extracts security sensitive words, data objects, characters or icons from plaintext or other source documents to obtain (a) subsets of extracted data and (b) remainder data. The extracted data is, in one embodiment, stored in a multilevel security system (MLS) which separates extract data of different security levels with MLS guards. Some or all of the original data is reconstructed via one or more of the subsets of extracted data and remainder data only in the presence of a predetermined security level. In this manner, an inquiring party, with the proper security clearance, can data mine the data in the MLS secured storage.
Owner:DIGITAL DOORS
Systems and methods for securing data using multi-factor or keyed dispersal
ActiveUS20090177894A1Minimal compute resourceAvoid the needUnauthorized memory use protectionHardware monitoringInformation dispersalOriginal data
A secure data parser is provided that may be integrated into any suitable system for securely storing and communicating data. The secure data parser parses data and then splits the data into multiple portions that are stored or communicated distinctly. Encryption of the original data, the portions of data, or both may be employed for additional security. The secure data parser may be used to protect data in motion by splitting original data into portions of data, that may be communicated using multiple communications paths. A keyed information dispersal algorithm (keyed IDA) may also be used. The key for the keyed IDA may additionally be protected by an external workgroup key, resulting in a multi-factor secret sharing scheme.
Owner:SECURITY FIRST INNOVATIONS LLC
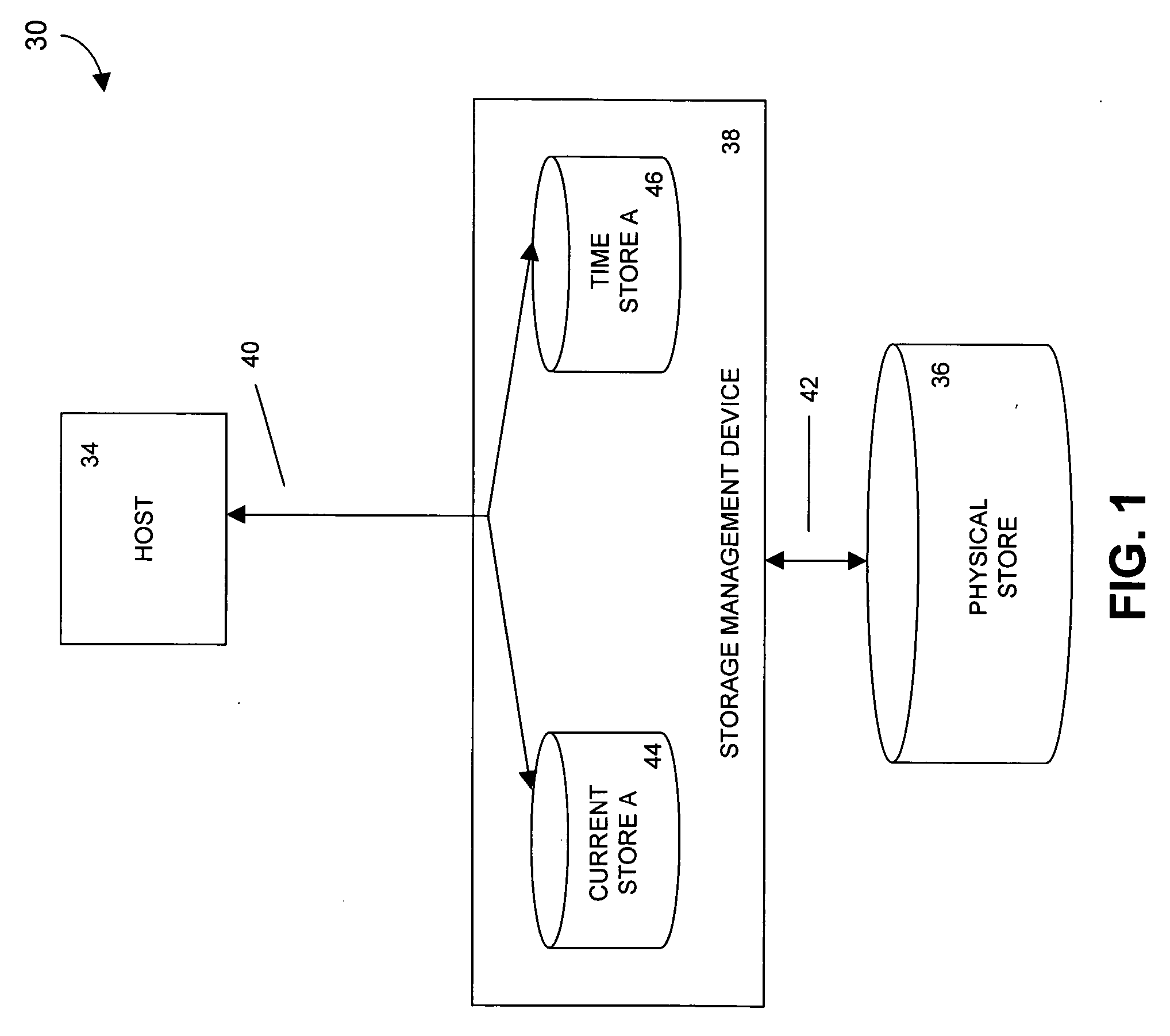
Storage system snapshot assisted by SSD technology
ActiveUS20100153620A1Memory architecture accessing/allocationMemory loss protectionOriginal dataData needs
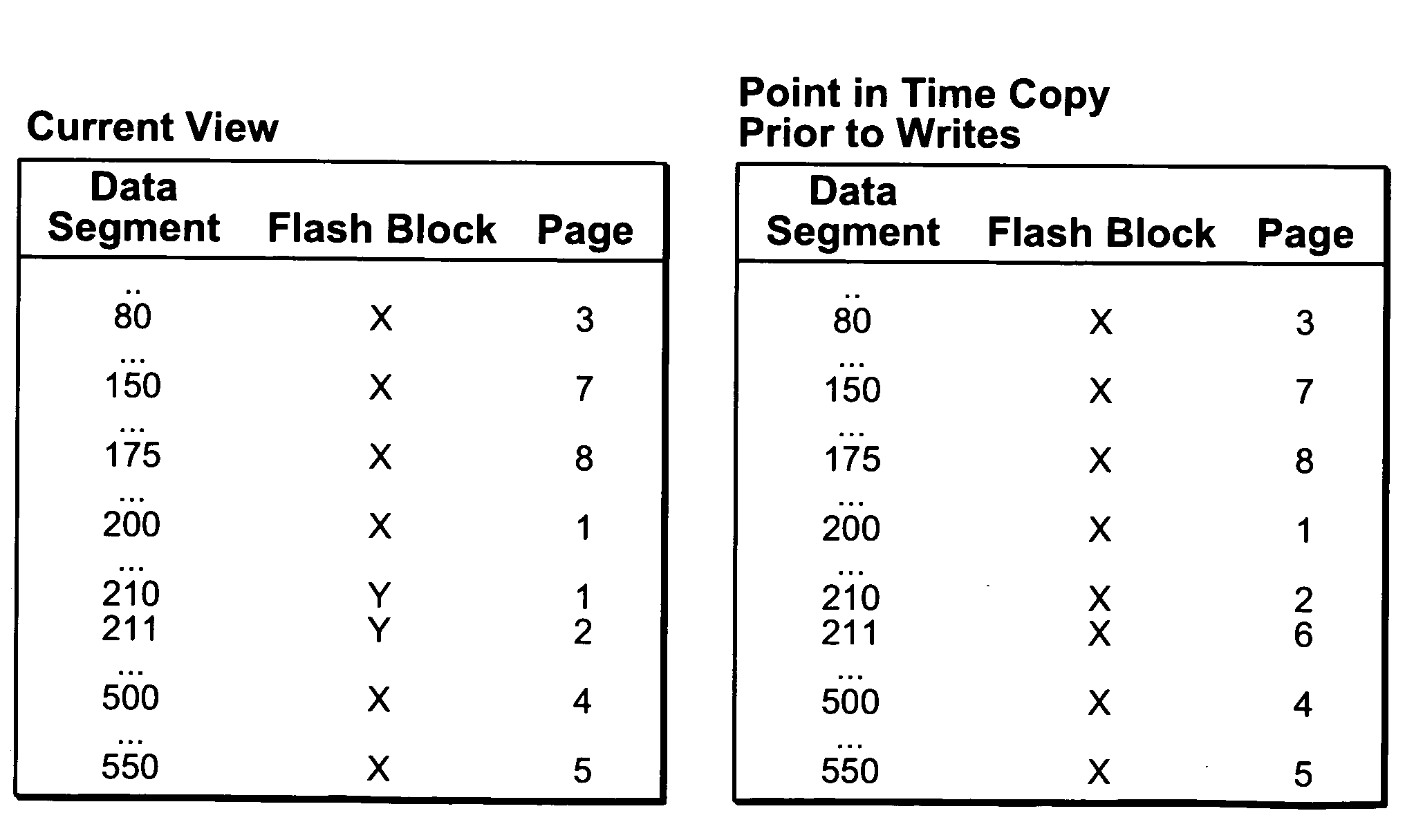
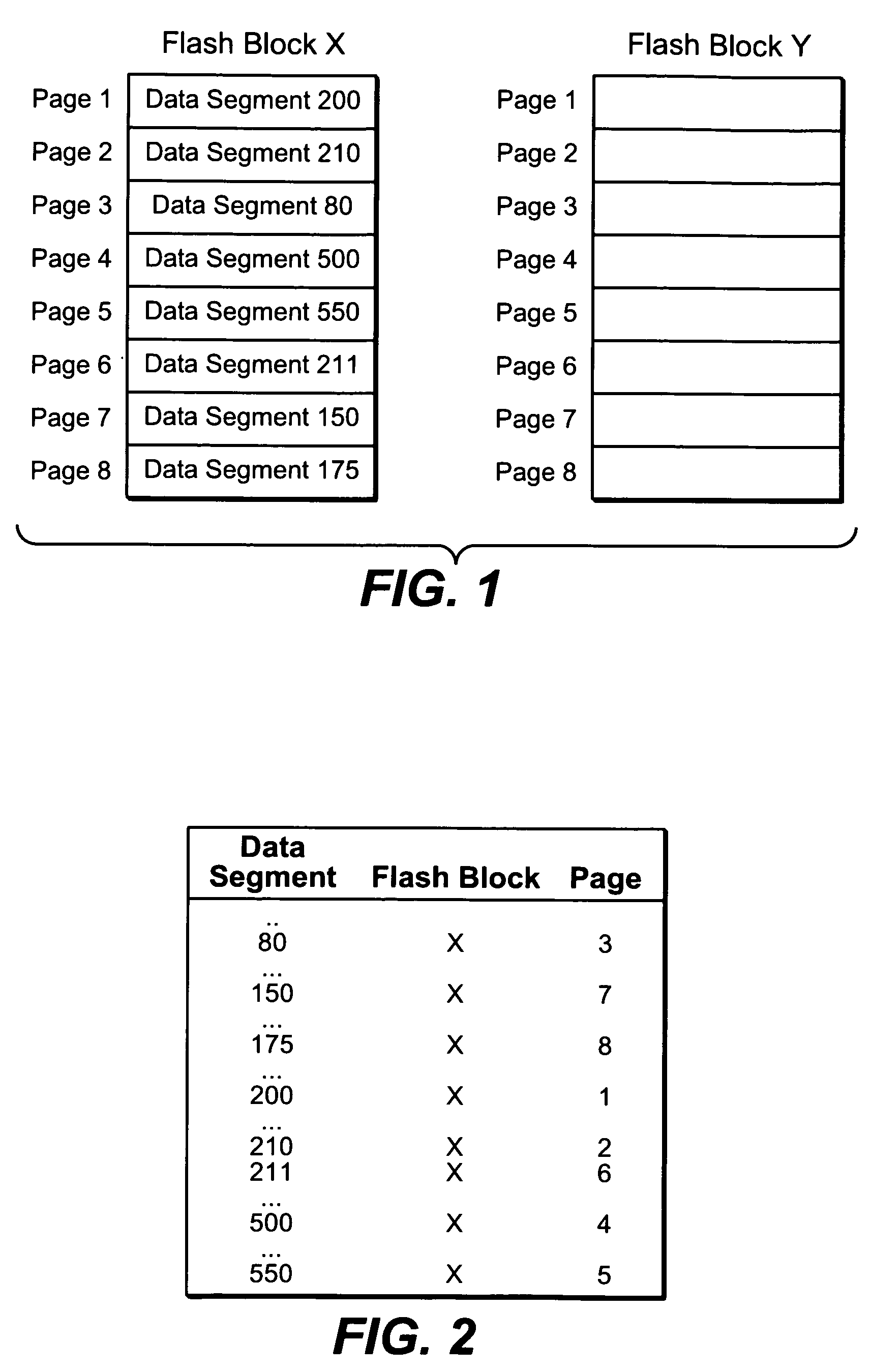
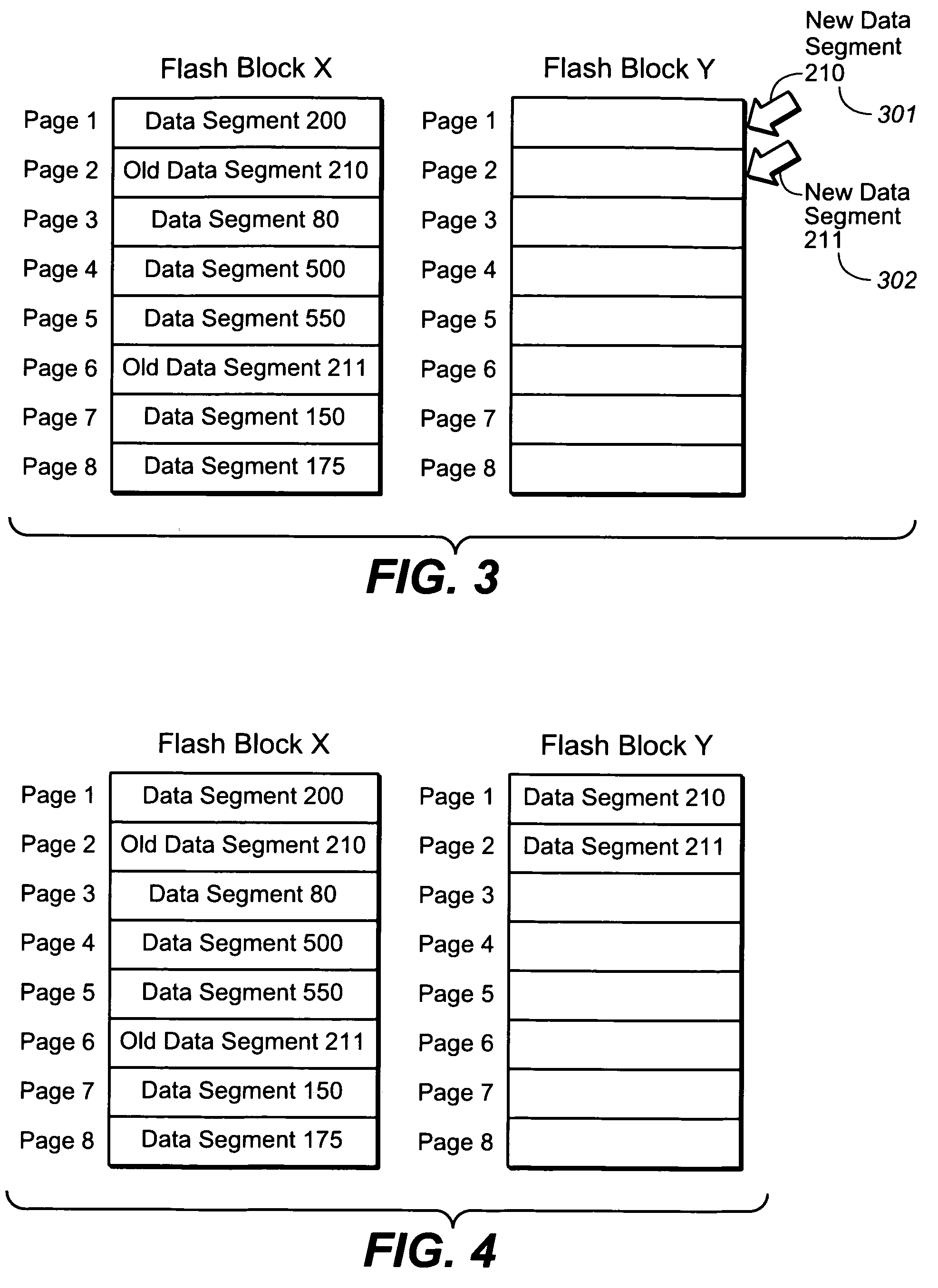
A method and apparatus for taking a snapshot of a storage system employing a solid state disk (SSD). A plurality of mapping tables in the SSD store data needed to create a one or more point in time snapshots and a current view of the SSD. In response to a write command, the SSD executes its normal write process and updates its mapping tables to indicate the current view of the SSD and additionally retains the original data in a table of pointers to the original data, as the snapshot of an earlier state of the SSD. In the preferred embodiment, the innate ability of SSDs to write data to a new location is used to perform a point-in-time copy with little or no loss in performance in performing the snapshot.
Owner:NETWORK APPLIANCE INC
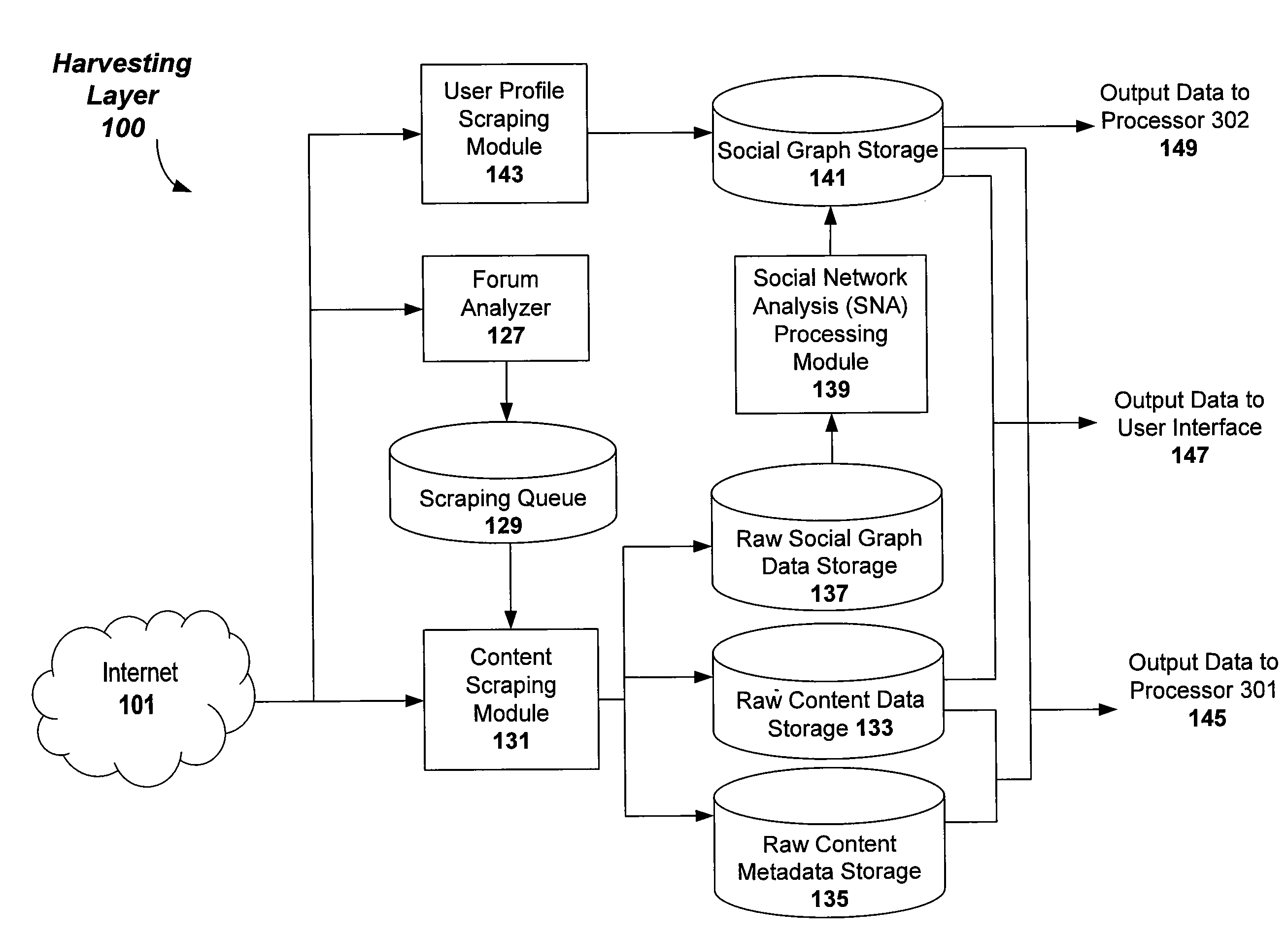
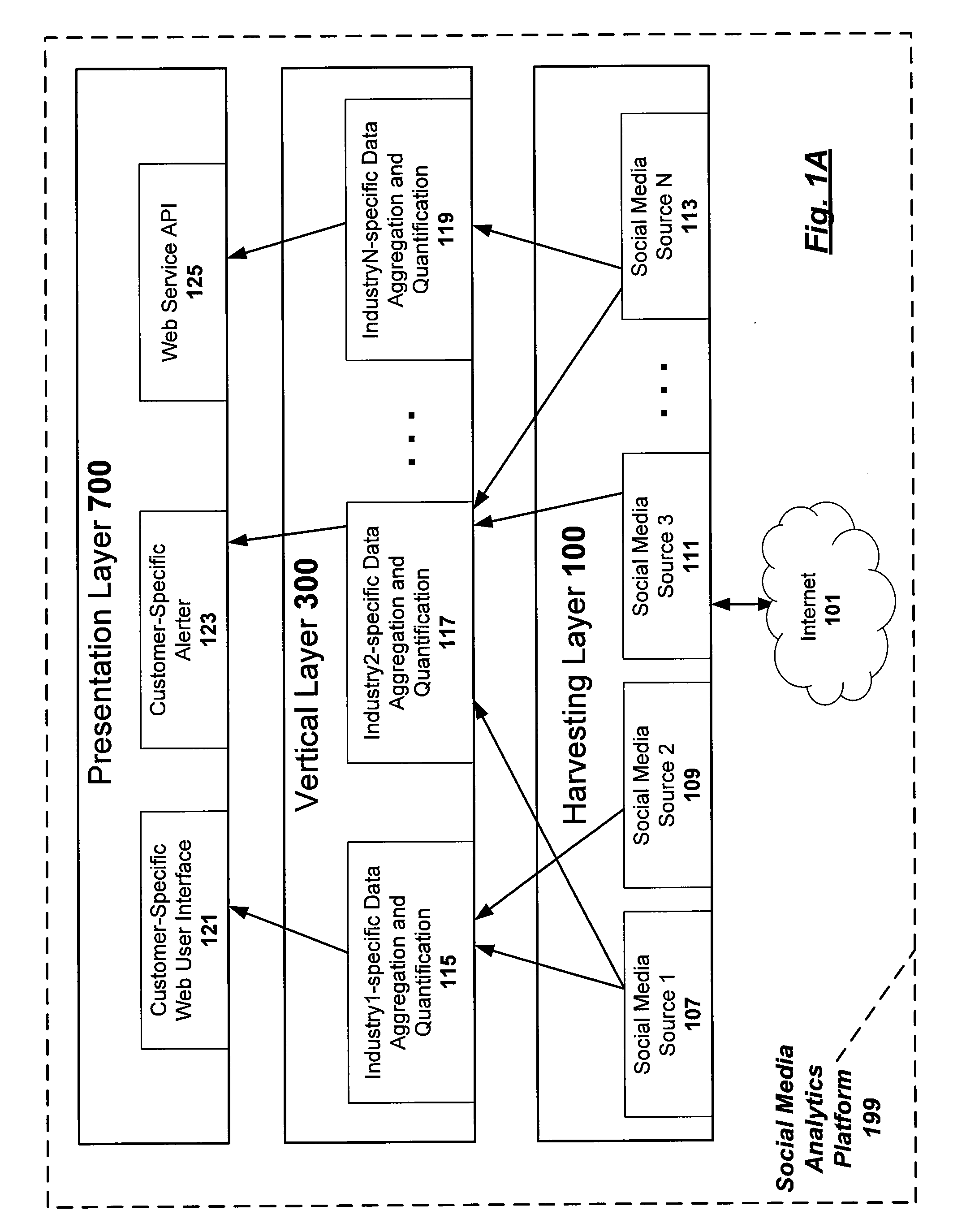
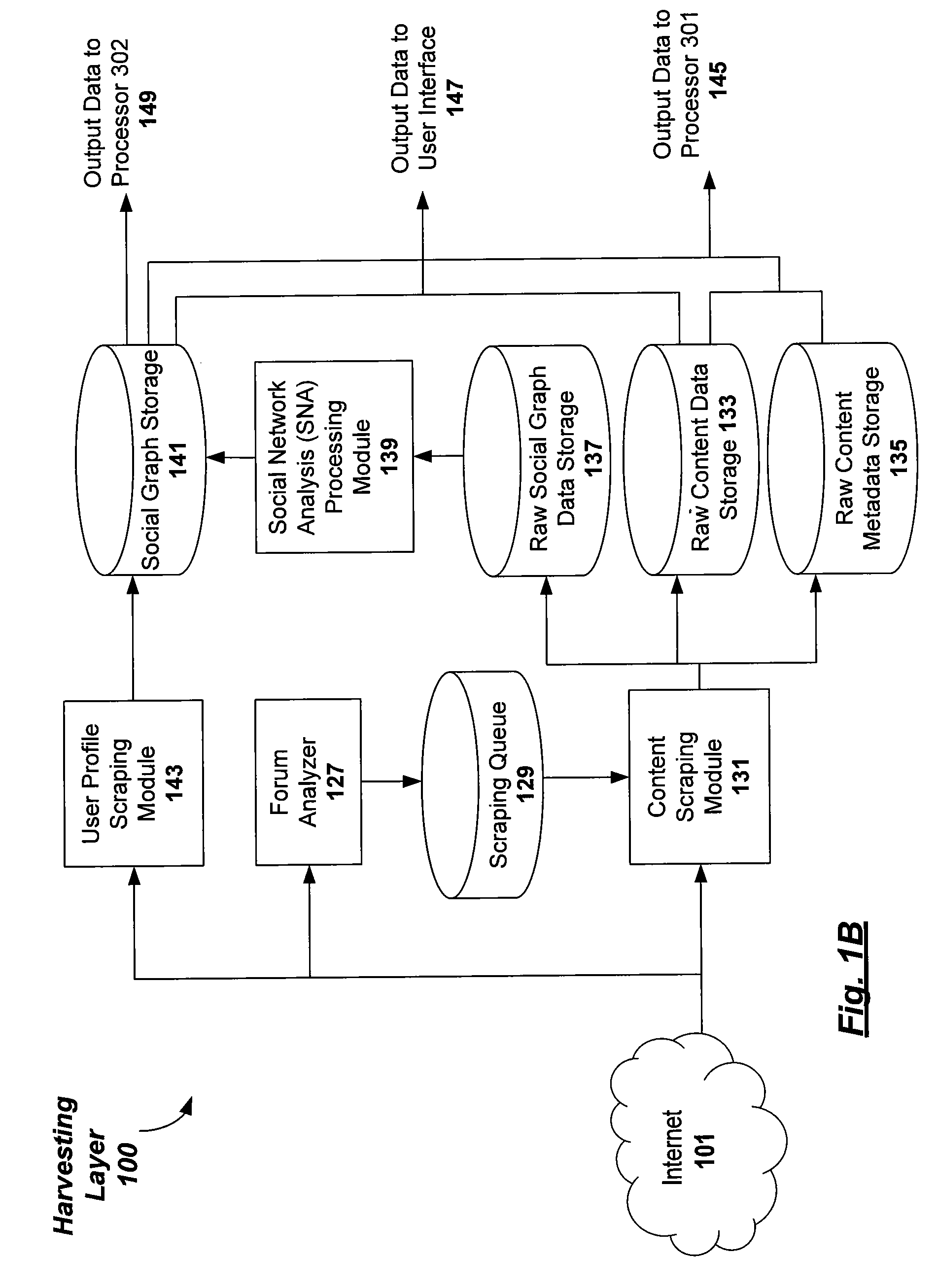
Modeling social networks using analytic measurements of online social media content
Methods, apparatuses, and computer-readable media for generating a social network graph to model one or more social networks of related authors of online social media and their corresponding posts of online social media conversations relevant to subject matter of interest in a category. Embodiments are configured to harvest and aggregate posts of online social media conversations from one or more online social media sources; to perform content scraping on the posts of online social media conversations to obtain raw data that includes user-profile information of a social media author corresponding to each individual post of online social media conversations; and performing social network analysis processing on the raw data to obtain the social network graph.
Owner:BUZZIENT
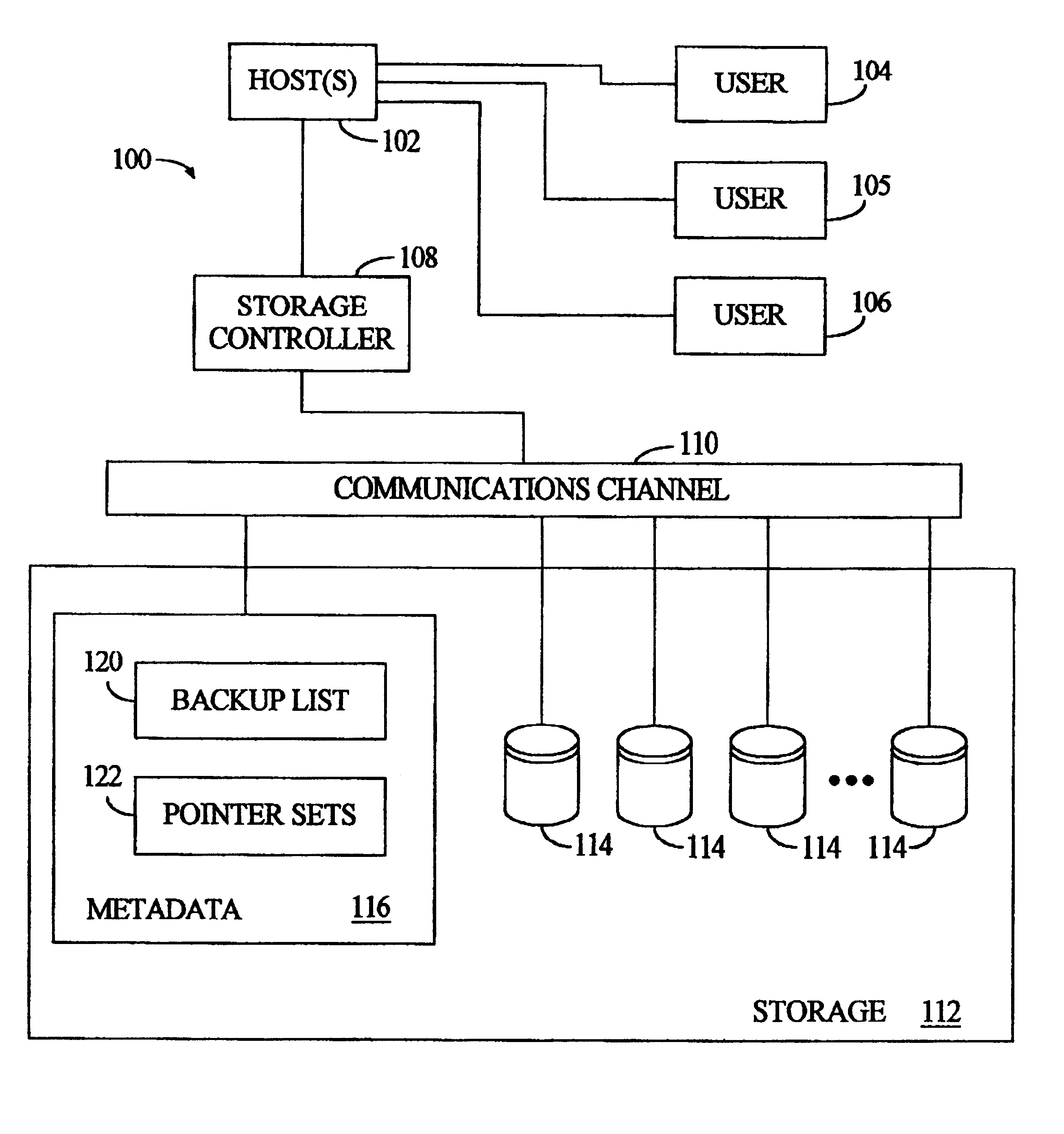
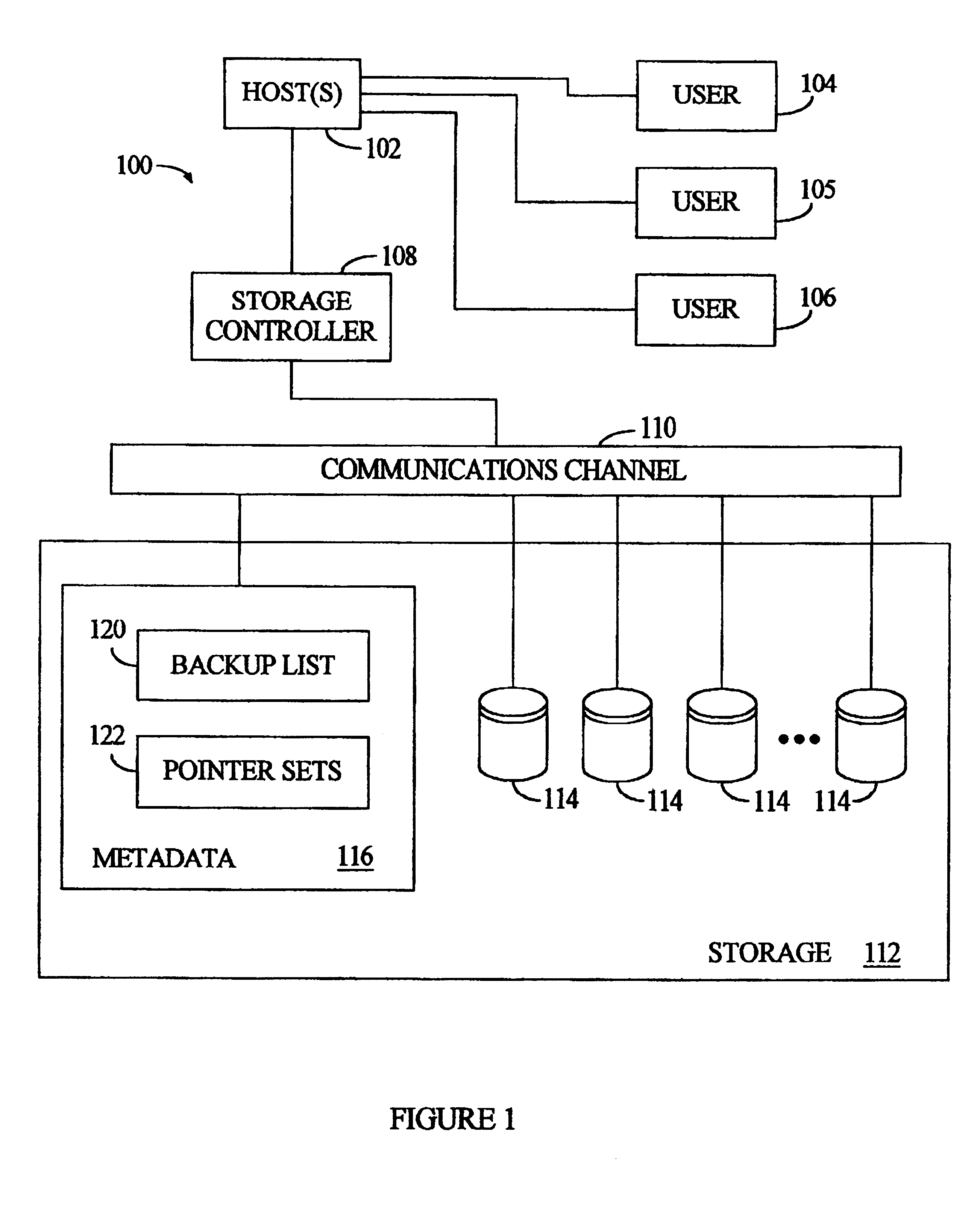
Method and apparatus for immediate data backup by duplicating pointers and freezing pointer/data counterparts
InactiveUS6226759B1Data processing applicationsMemory adressing/allocation/relocationData setOriginal data
An expedited data backup is performed by creating a duplicate set of pointers to a current dataset already identified by an original pointer set, then designating the dataset as a backup dataset, and thereafter preventing changes to the pointed-to-data and the duplicate pointers, where changes to the current dataset are nonetheless effected by storing new data and modifying the original pointer set alone. More specifically, the backup involves an original dataset having multiple subparts residing at various original storage locations, which are pointed-to by a primary set of pointers. A virtual backup copy is created by duplicating the primary set of pointers to create a backup set of pointers. The backup set of pointers are entered in a backup list, in association with the virtual backup copy and the original dataset. To preserve the backup copy, the system prevents changes to the original dataset and the backup set of pointers. When any changes are directed to subparts of the original dataset, the system creates a changed dataset by storing the changes at one or more change storage locations and updating the primary set of pointers to identify the change storage locations along with any original storage locations still containing unchanged subparts of the original dataset. In addition to expediting data backups, fast data recovery is possible by updating the primary set of pointers to duplicate the backup set of pointers.
Owner:IBM CORP
Flash memory device and system with randomizing for suppressing errors
ActiveUS20080151618A1Reduce data sizeError detection/correctionMemory adressing/allocation/relocationOriginal dataData store
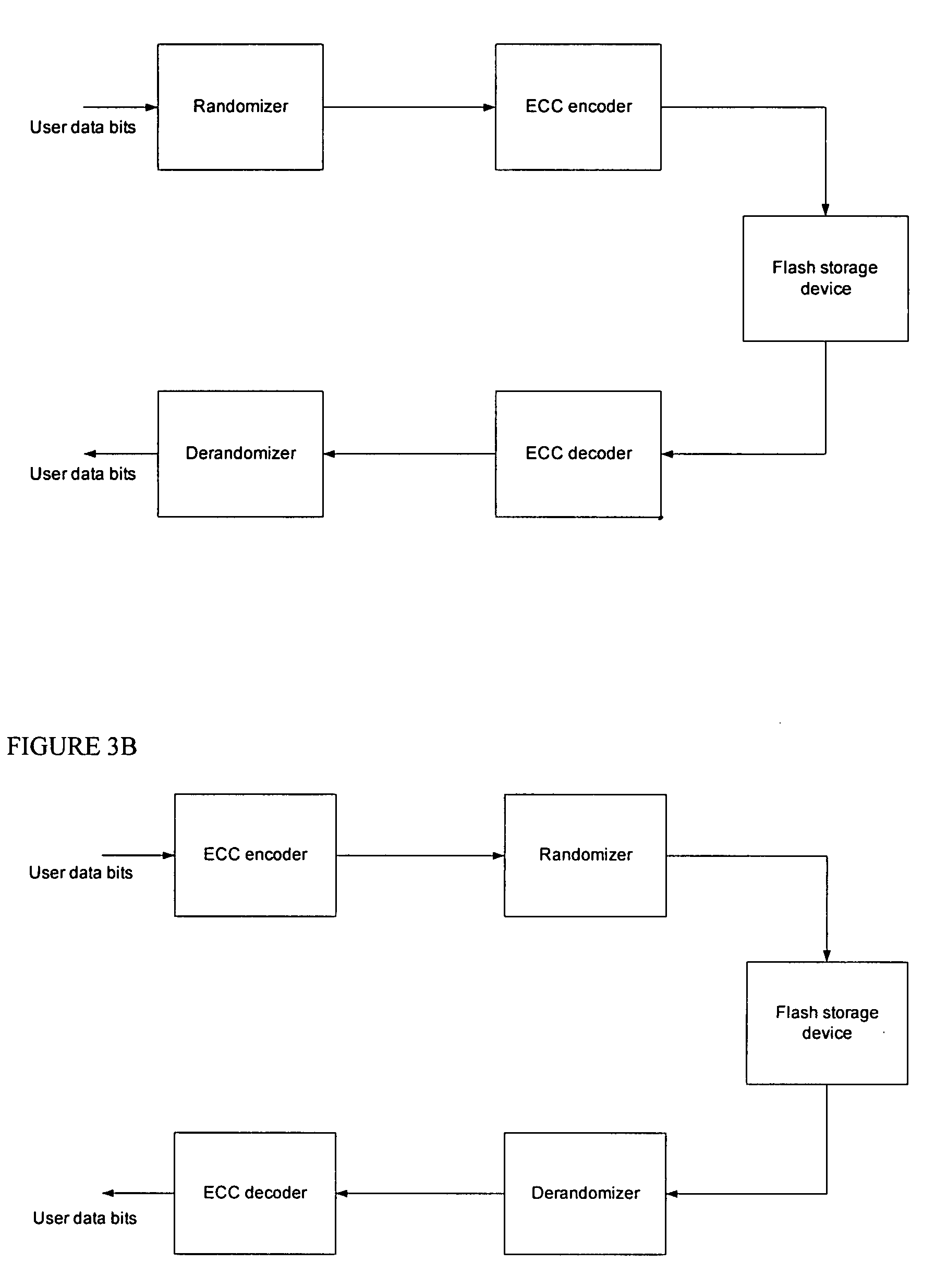
A device for storing data includes a nonvolatile memory and a controller and / or circuitry that randomize original data to be stored in the memory while preserving the size of the original data, that store the original data in the memory, and that, in response to a request for the original data, retrieve, derandomize and export the original data without authenticating the requesting entity. A system for storing data includes a first nonvolatile memory and a processor that similarly stores data in the first nonvolatile memory by executing driver code stored in a second nonvolatile memory. ECC encoding is applied either before or after randomizing; correspondingly, ECC decoding is applied either after or before derandomizing.
Owner:SANDISK TECH LLC
Storage system snapshot assisted by SSD technology
ActiveUS8200922B2Memory architecture accessing/allocationMemory loss protectionOriginal dataData needs
A method and apparatus for taking a snapshot of a storage system employing a solid state disk (SSD). A plurality of mapping tables in the SSD store data needed to create a one or more point in time snapshots and a current view of the SSD. In response to a write command, the SSD executes its normal write process and updates its mapping tables to indicate the current view of the SSD and additionally retains the original data in a table of pointers to the original data, as the snapshot of an earlier state of the SSD. In the preferred embodiment, the innate ability of SSDs to write data to a new location is used to perform a point-in-time copy with little or no loss in performance in performing the snapshot.
Owner:NETWORK APPLIANCE INC
Commonality factoring for removable media
Systems and methods for commonality factoring for storing data on removable storage media are described. The systems and methods allow for highly compressed data, e.g., data compressed using archiving or backup methods including de-duplication, to be stored in an efficient manner on portable memory devices such as removable storage cartridges. The methods include breaking data, e.g., data files for backup, into unique chunks and calculating identifiers, e.g., hash identifiers, based on the unique chunks. Redundant chunks can be identified by calculating identifiers and comparing identifiers of other chunks to the identifiers of unique chunks previously calculated. When a redundant chunk is identified, a reference to the existing unique chunk is generated such that the chunk can be reconstituted in relation to other chunks in order to recreate the original data. The method further includes storing one or more of the unique chunks, the identifiers and / or the references on the removable storage medium.
Owner:IMATION
System and method for using external references to validate a data object's classification / consolidation
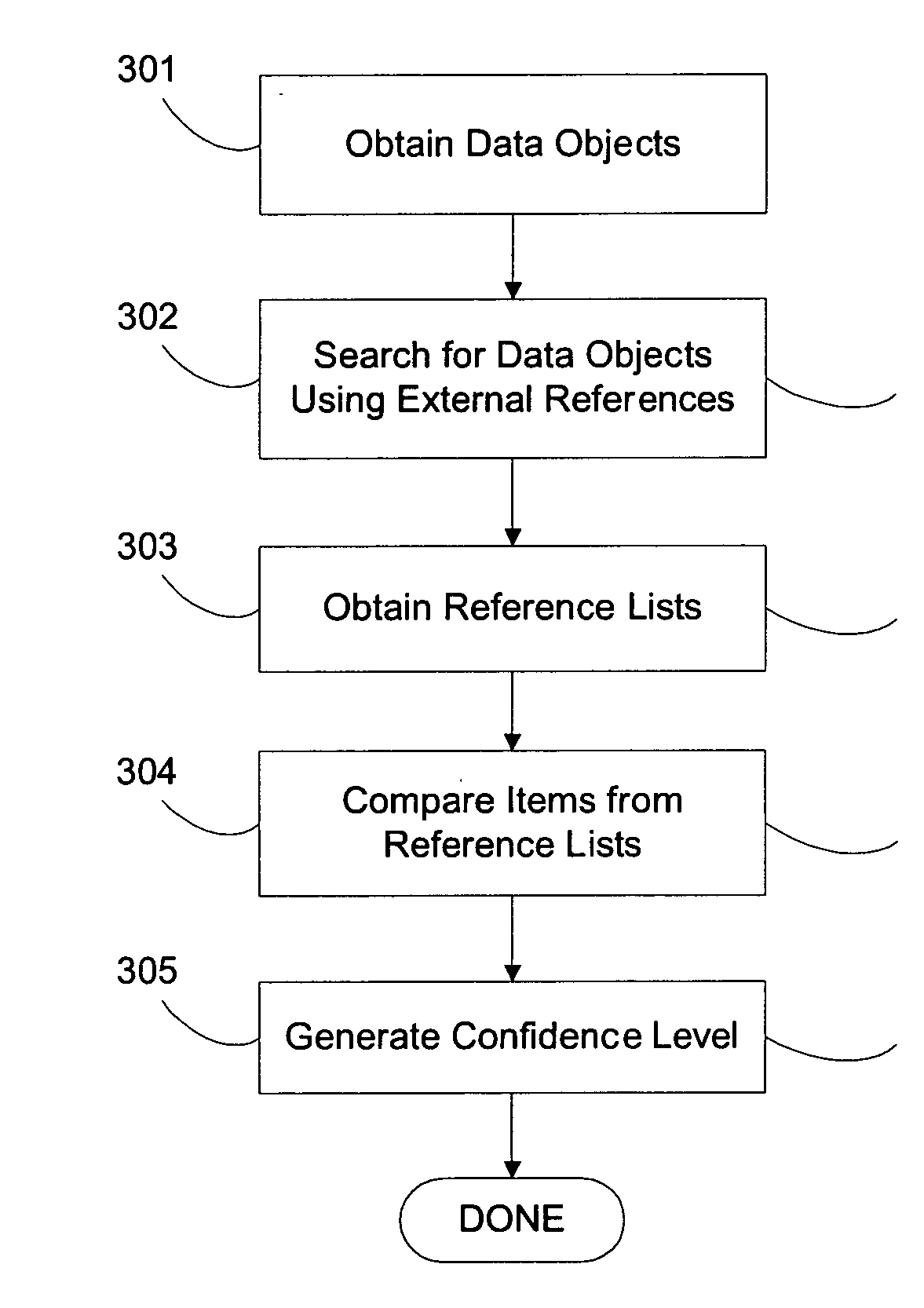
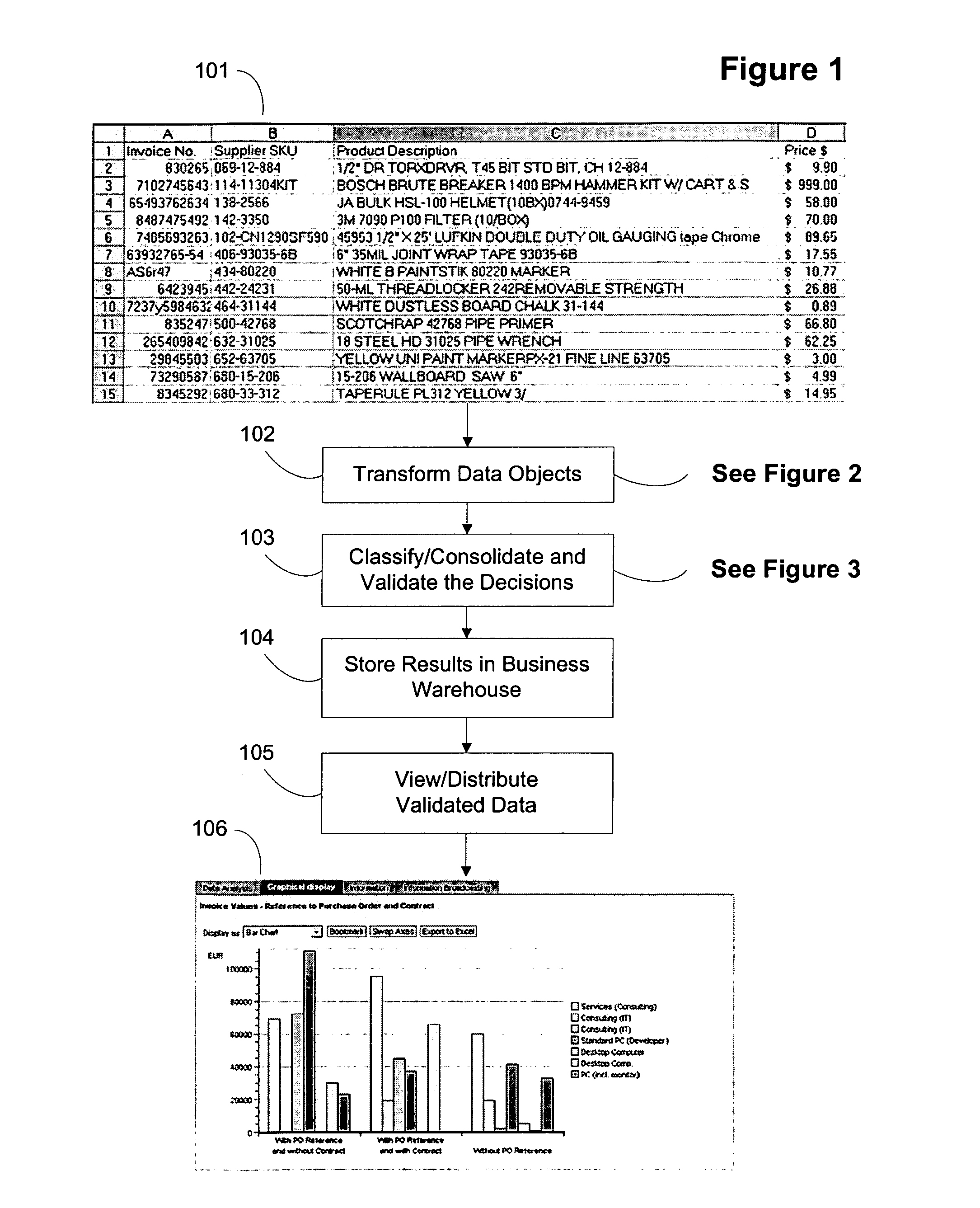
ActiveUS20070162414A1Improve trustTake substantial amountDigital data information retrievalDigital data processing detailsOriginal dataExternal reference
A computer system and method for validating data object classification and consolidation using external references. The external references may be web pages, product catalogs, external databases, URLs, search results provided by a search engine or subsets or combinations of any of these to validate a classification or consolidation of records. Embodiments validate a data object classification or consolidation decision by searching external data sources, such as databases, the Internet etc. for references to the transactional data object and determining a confidence level based on the original data object and the unstructured information reference, URL, or search result for example. Decisions may be verified or denied based on the comparison of the external references related to each data object. Embodiments of the invention save substantial labor in validating business data objects and make data more reliable across enterprise systems.
Owner:SAP AG
Electronic-medical-record sharing system based on block chain
InactiveCN107391944AAchieve tamper-proofAchieve rating reviewData processing applicationsSpecial data processing applicationsMedical recordOriginal data
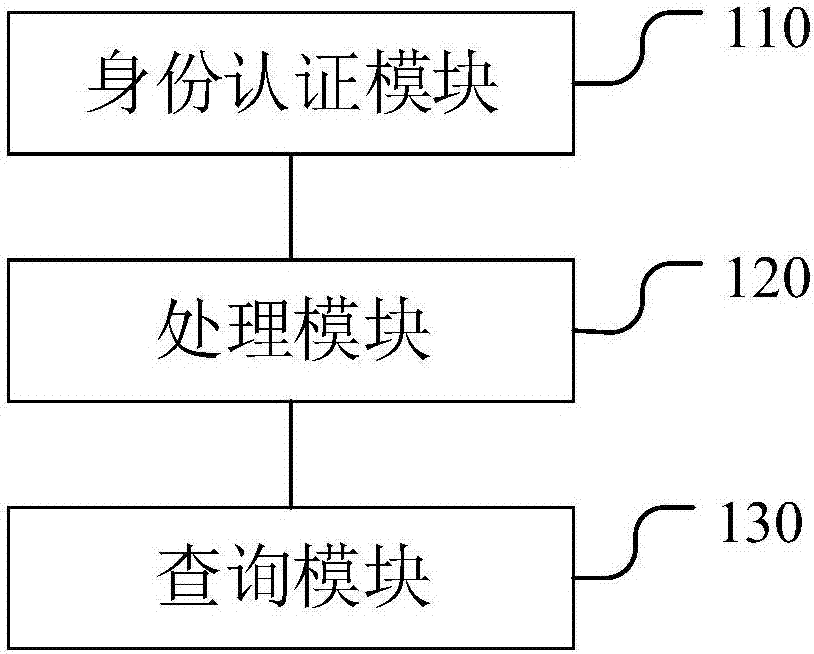
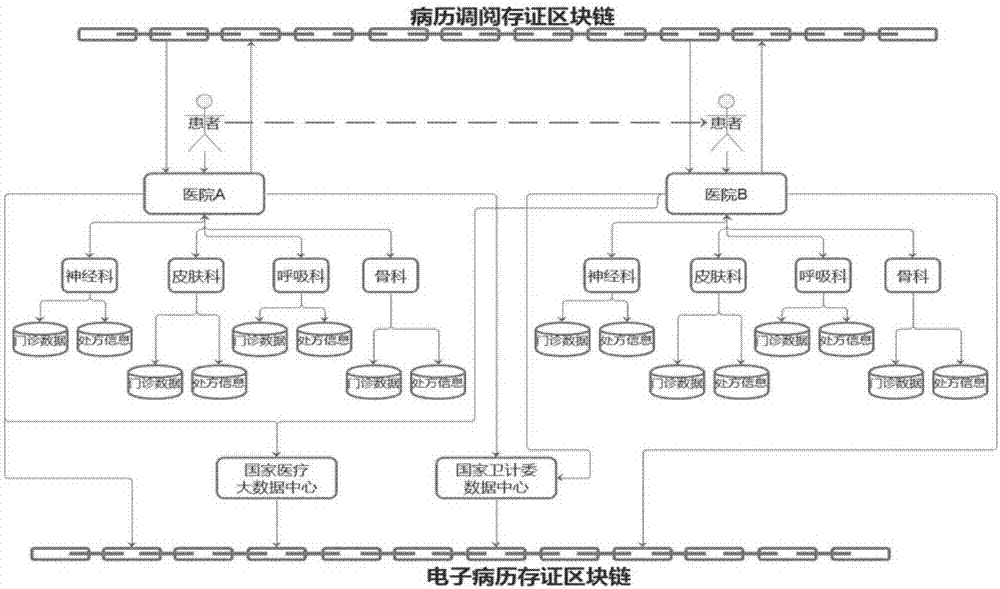
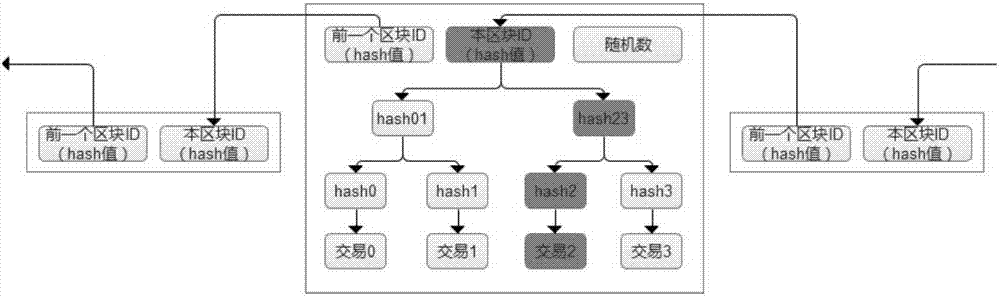
The embodiment of the invention discloses an electronic-medical-record sharing system based on a block chain. The electronic-medical-record sharing system comprises an identity verification module, a processing module and a querying module, wherein the identity verification module is used for receiving a logging-in account input by a user, identifying the logging-in account and configuring corresponding operating authorization for the logging-in account; the processing module is used for being connected with a pre-established block-chain database, wherein the block-chain database comprises a plurality of nodes, and each node corresponds to a hospital database; the querying module is used for receiving a querying order input by the user, obtaining a corresponding electronic medical record from the block-chain database according to the querying order and showing the obtained electronic medical record to the user. The electronic-medical-record sharing system is established based on the block chain technology in the embodiment, all data can be only preserved in a hospital server generated through original data, only data hash values are stored on the block-chain database so that the aims that data cannot be tampered, is looked up in a classified mode and is retrospective in consulting can be achieved, and the electronic-medical-record sharing system has the advantage that the data security is improved.
Owner:BEIJING TAI CLOUD TECH LTD
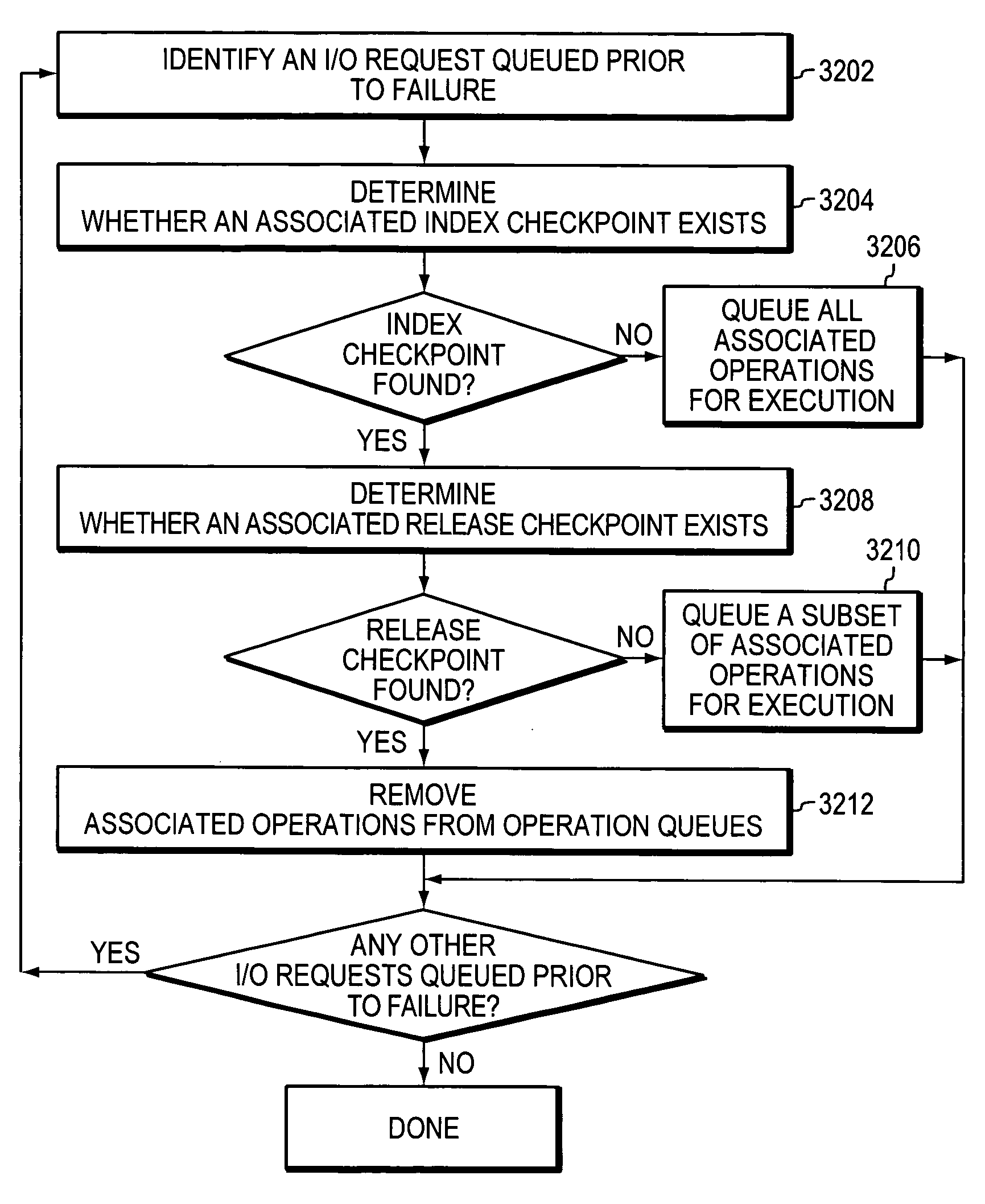
Recovering from storage transaction failures using checkpoints
ActiveUS20060047925A1Easy to useInformation can be usedMemory loss protectionError detection/correctionSuccessful completionOriginal data
The disclosed technology facilitates recovery from storage-related failures by checkpointing copy-on-write operation sequences. An operation sequence incorporating such checkpoints into a copy-on-write can include the following: receive a write request that identifies payload data to be written to a first data store, read original data associated with the first data store, copy the original data to a second data store, record transactional information associated with the write request, generate a first checkpoint to confirm the successful recordation of the transactional information and the successful copying of the original data to the second data store, write the payload data to the first data store, acknowledge a successful completion of the copy-on-write operation sequence, and generate a second checkpoint that confirms the successful completion of such operation sequence. The first and second checkpoints are used to form a pre-failure representation of one or more storage units (or parts thereof). The checkpoints can be stored with other transactional information, to facilitate recovery in the event of a failure, and can be used to facilitate the use of optimizations to process I / O operations.
Owner:SYMANTEC OPERATING CORP
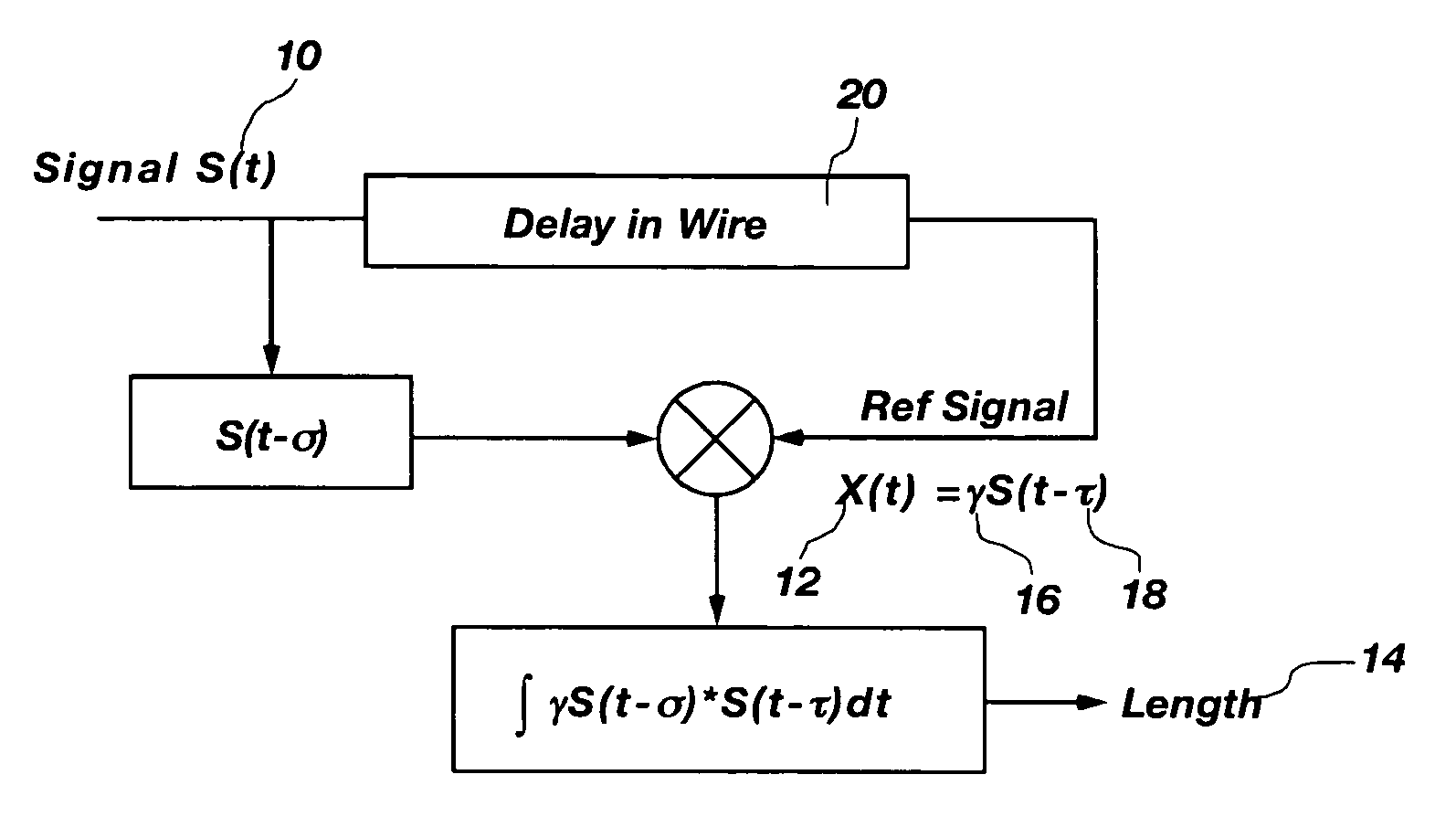
Digital spread spectrum methods and apparatus for testing aircraft wiring
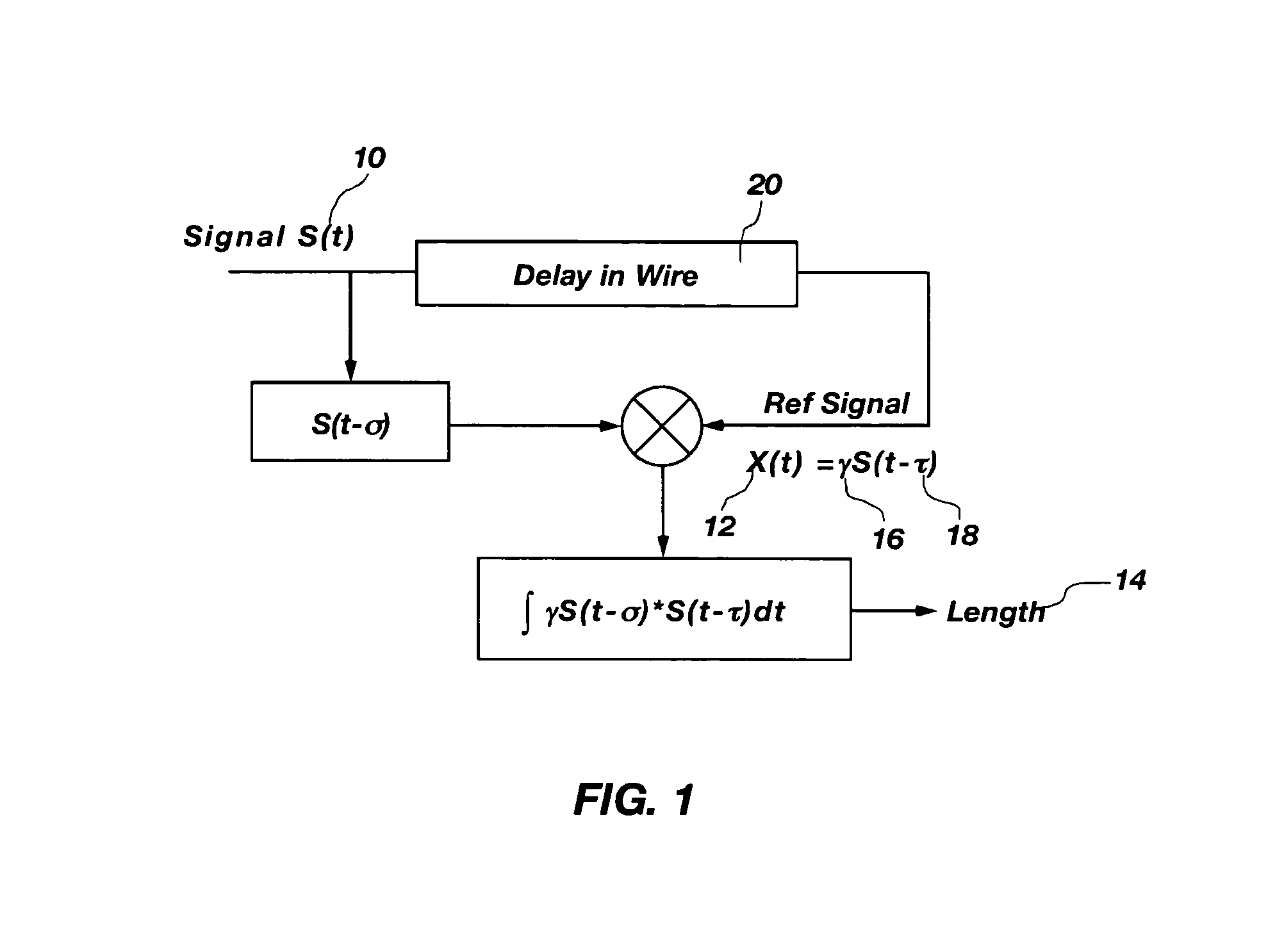
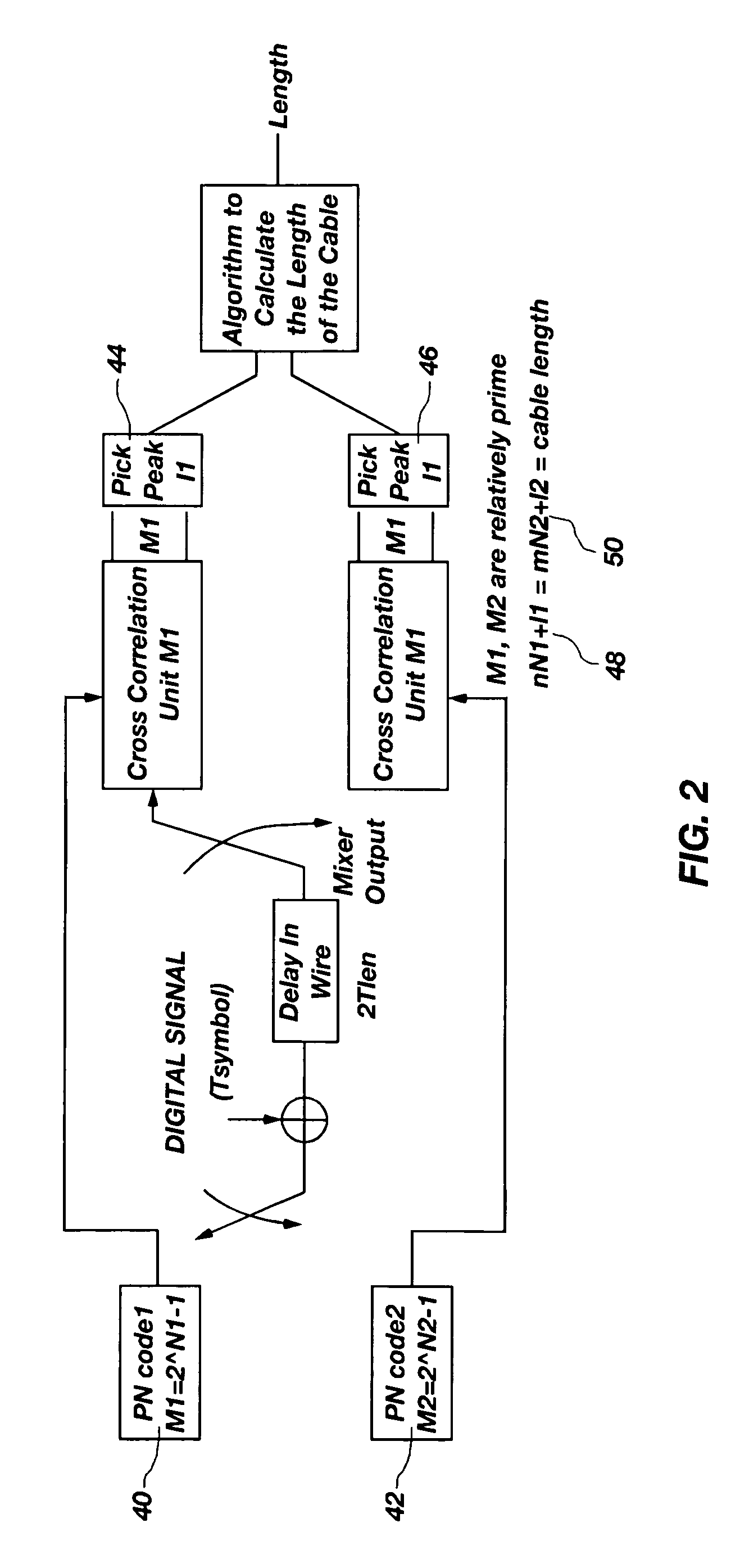
InactiveUS7069163B2Efficient implementationElectronic circuit testingTesting electric installations on transportOriginal dataData signal
A system and method that utilizes direct sequence spread spectrum signal (DSSS) encoding to enable testing of a live wire, wherein an original data signal is modified and then transmitted along the wire, and a reflected signal is collected and analyzed using correlation techniques to determine characteristics of the live wire, including the location of a fault.
Owner:UTAH STATE UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com