Patents
Literature
2158results about How to "Improve privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
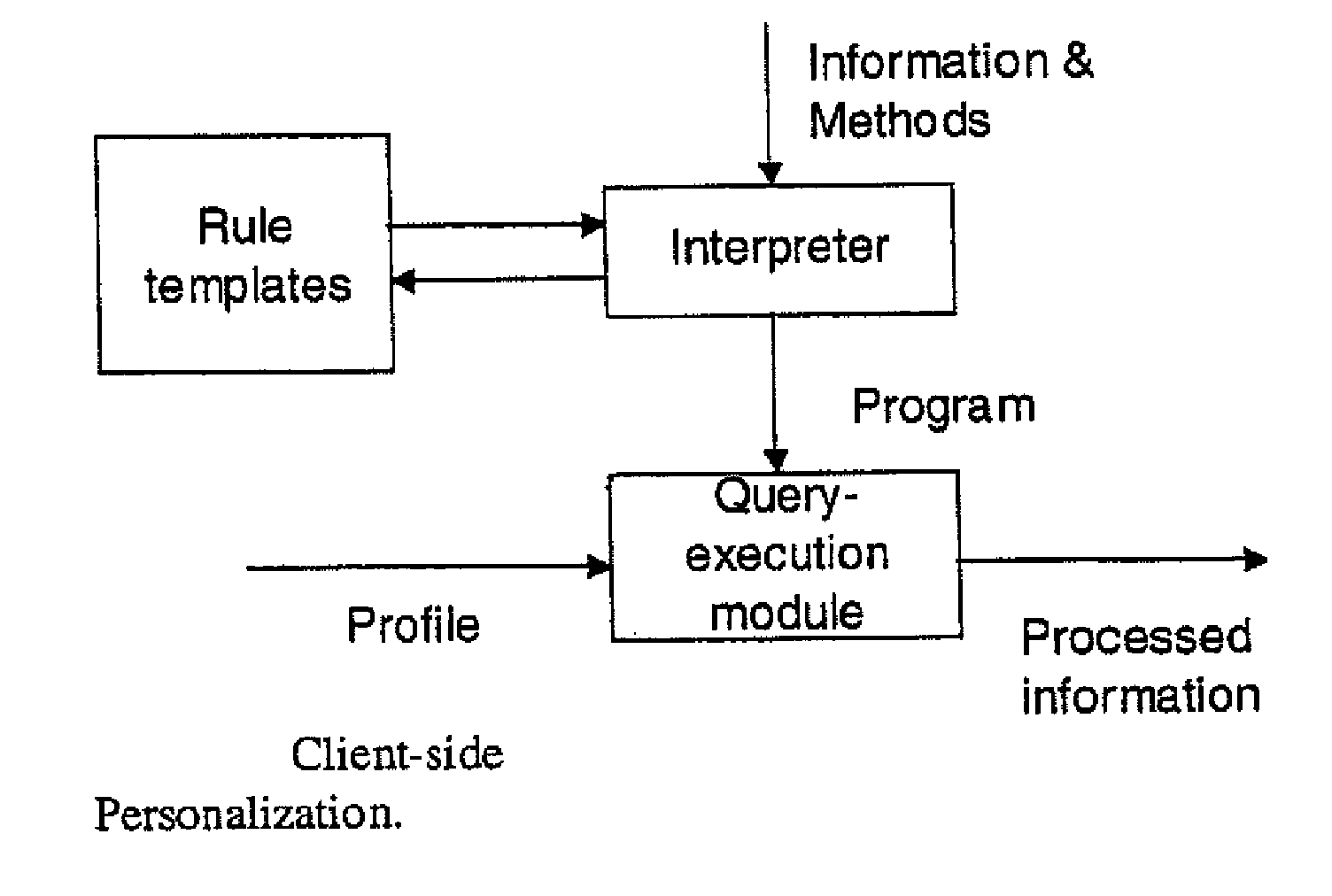
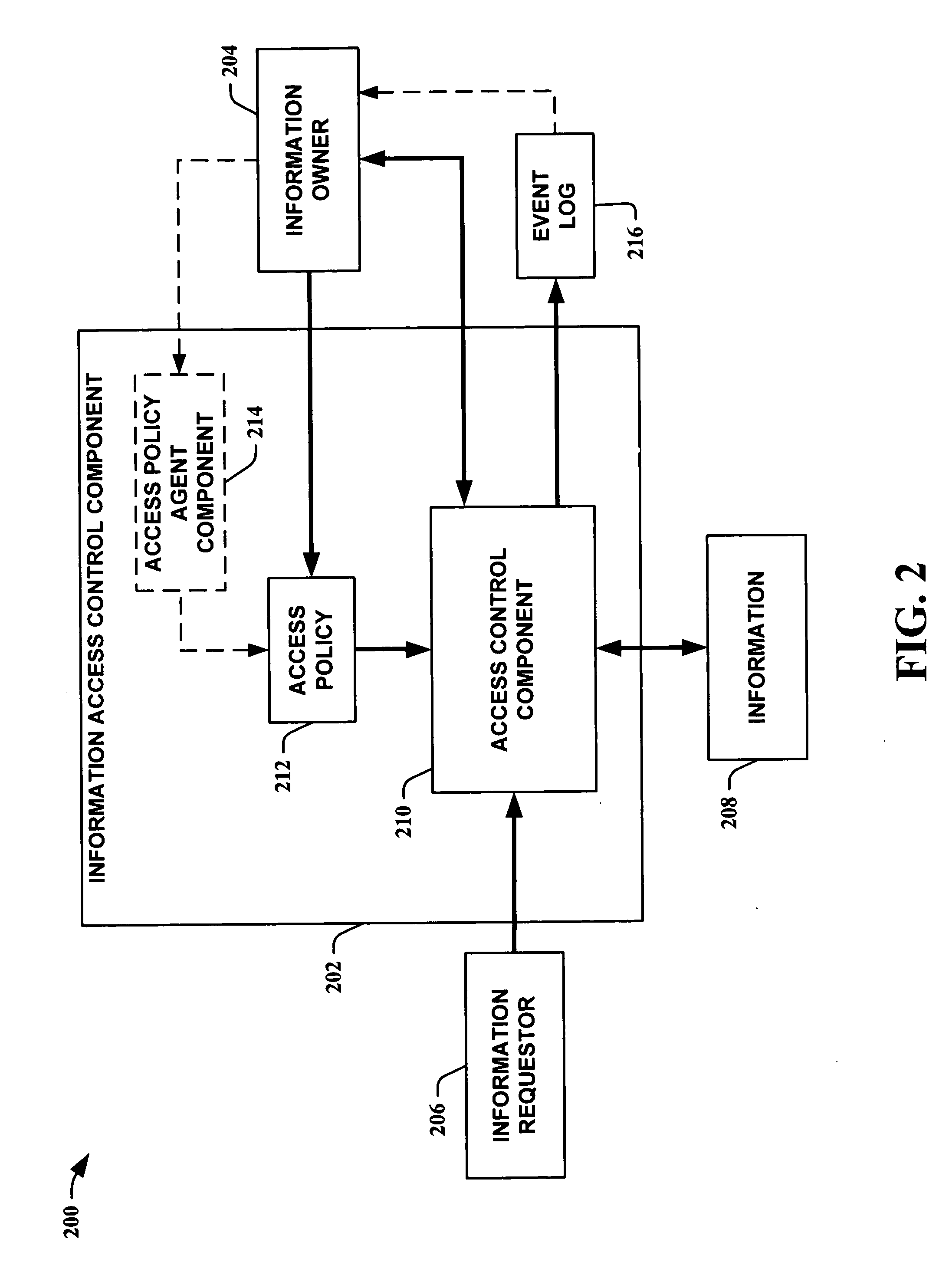
Secure data interchange
InactiveUS20090254971A1Improve privacyLimited accessDigital data processing detailsAnalogue secracy/subscription systemsInformation accessData interchange
A secure data interchange system enables information about bilateral and multilateral interactions between multiple persistent parties to be exchanged and leveraged within an environment that uses a combination of techniques to control access to information, release of information, and matching of information back to parties. Access to data records can be controlled using an associated price rule. A data owner can specify a price for different types and amounts of information access.
Owner:STRIPE INC
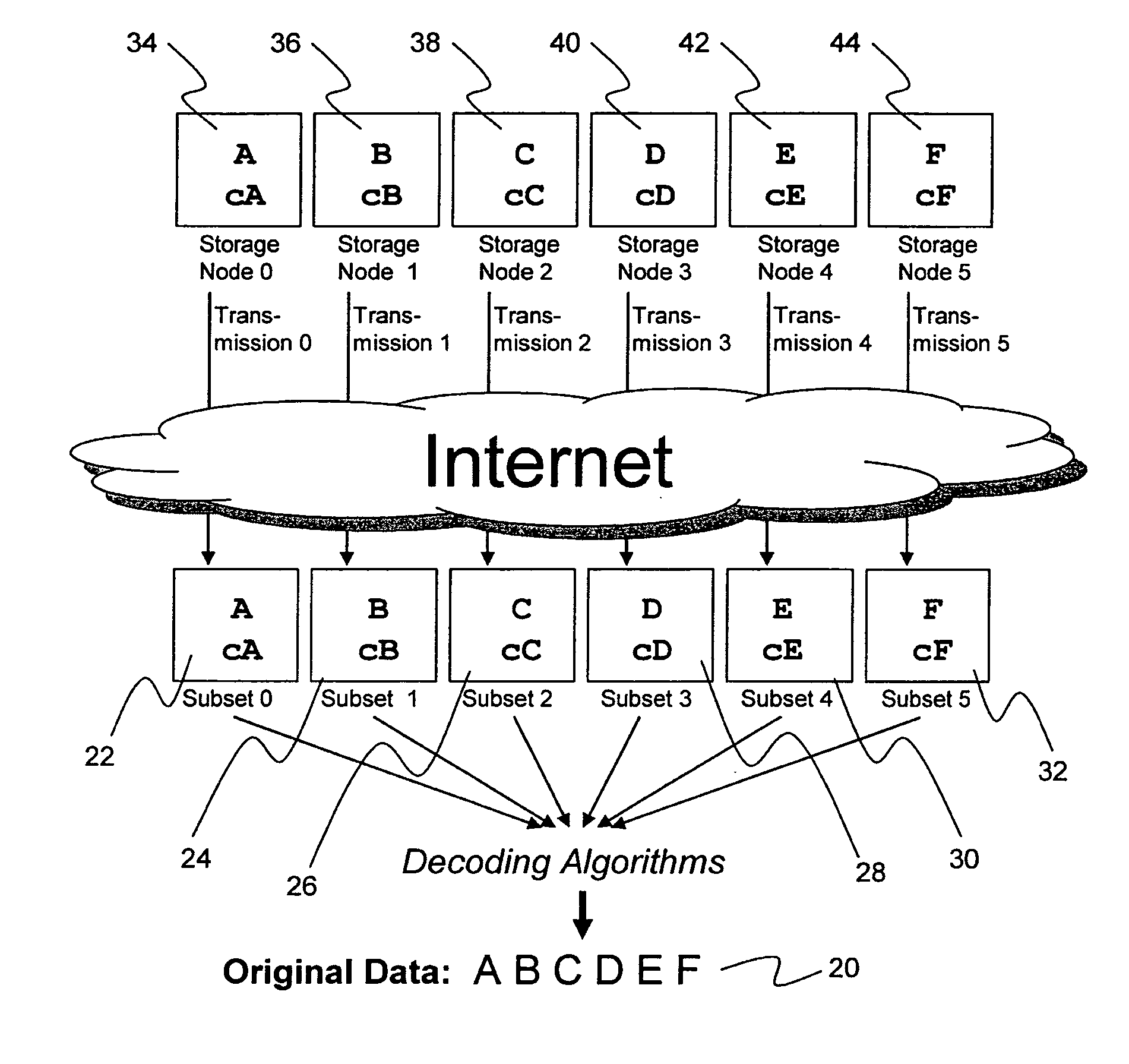
System for rebuilding dispersed data
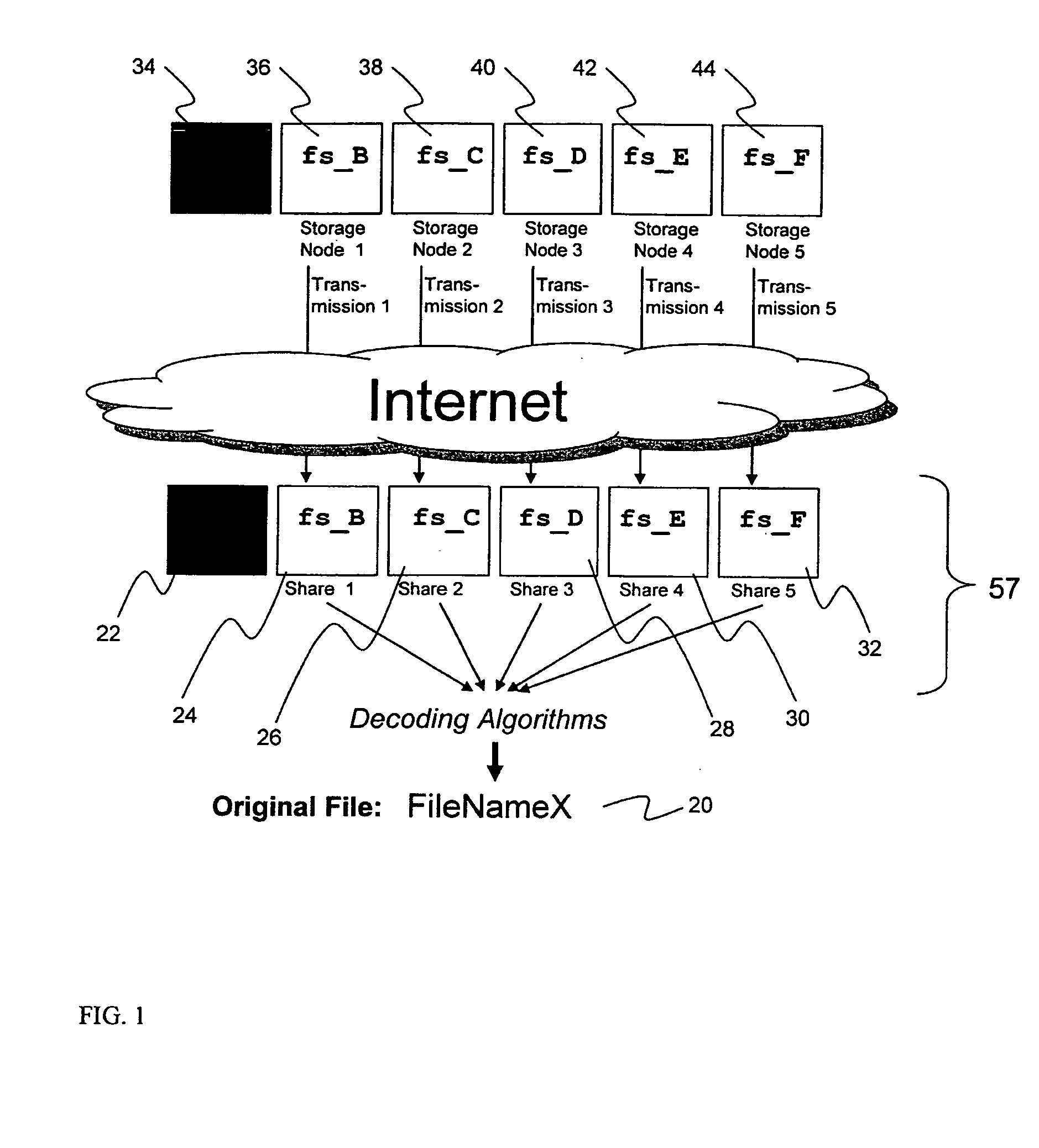
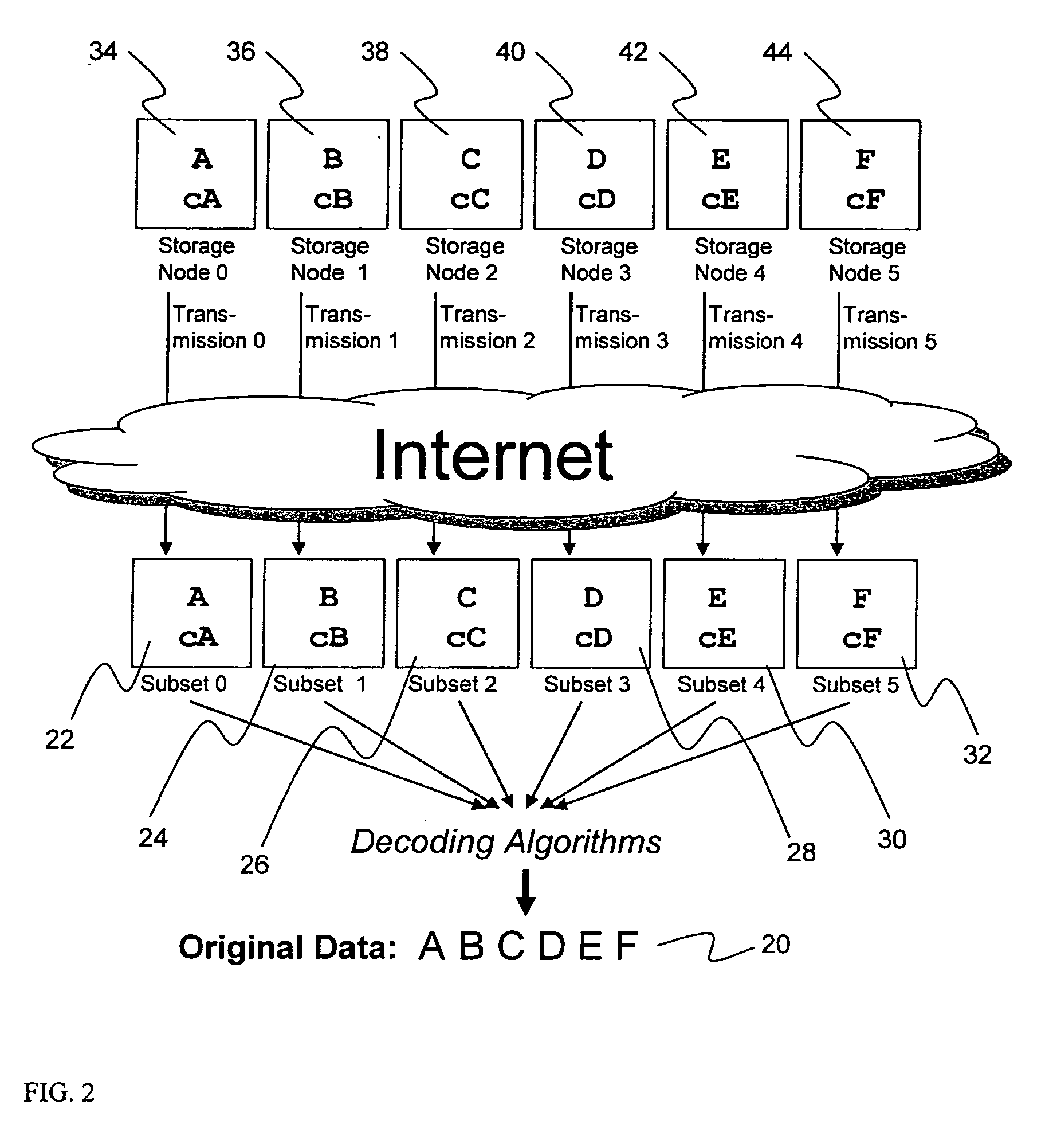
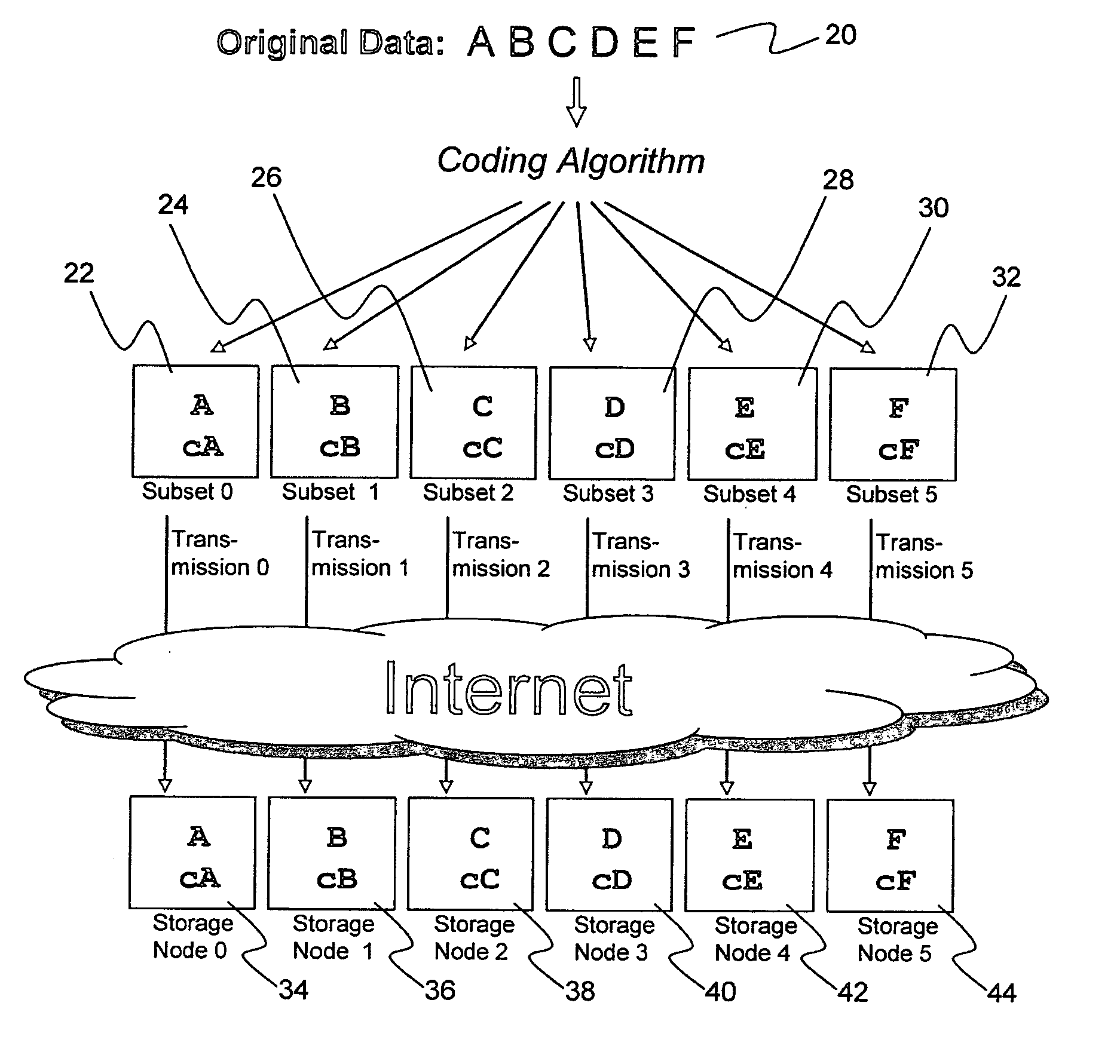
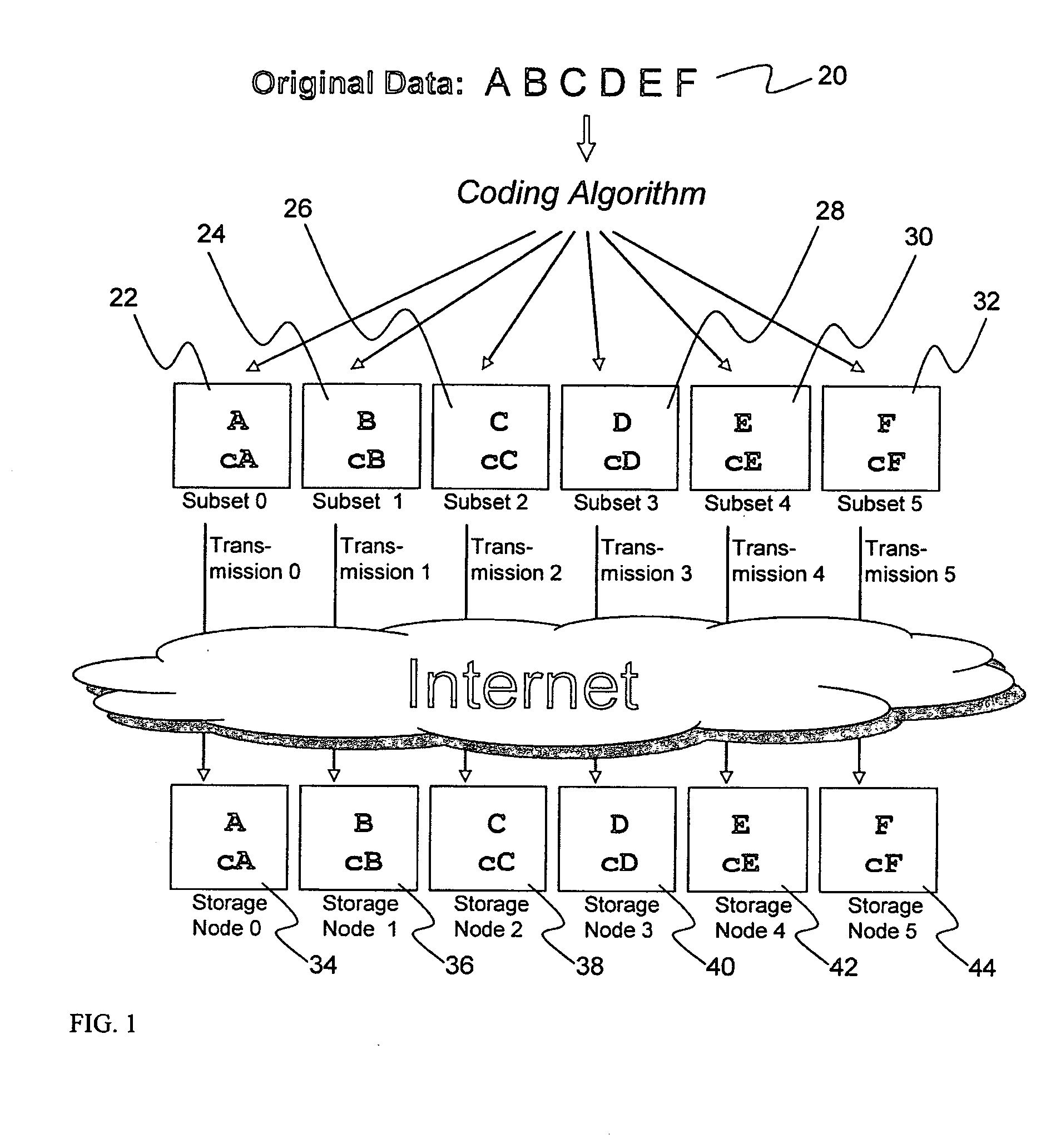
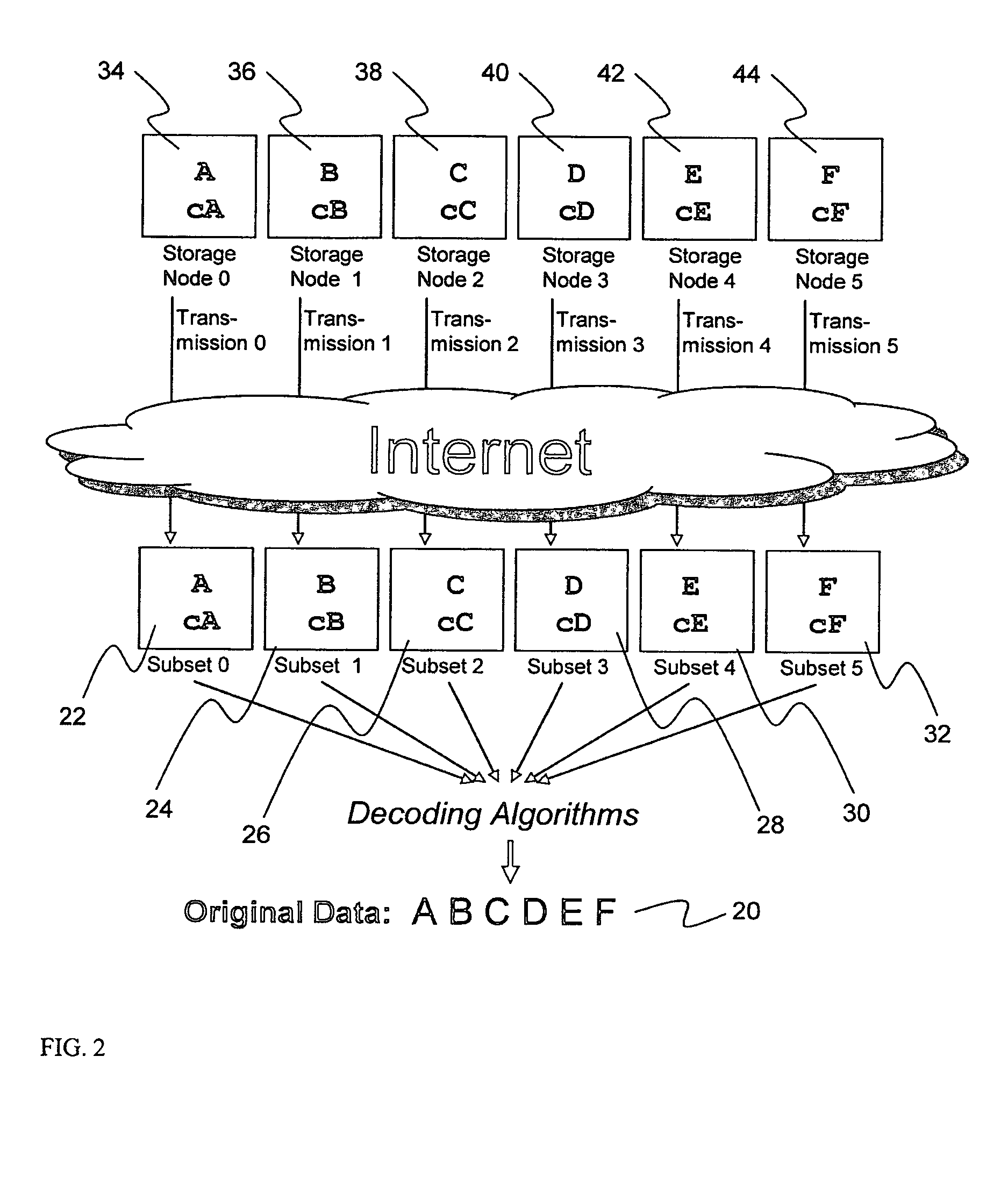
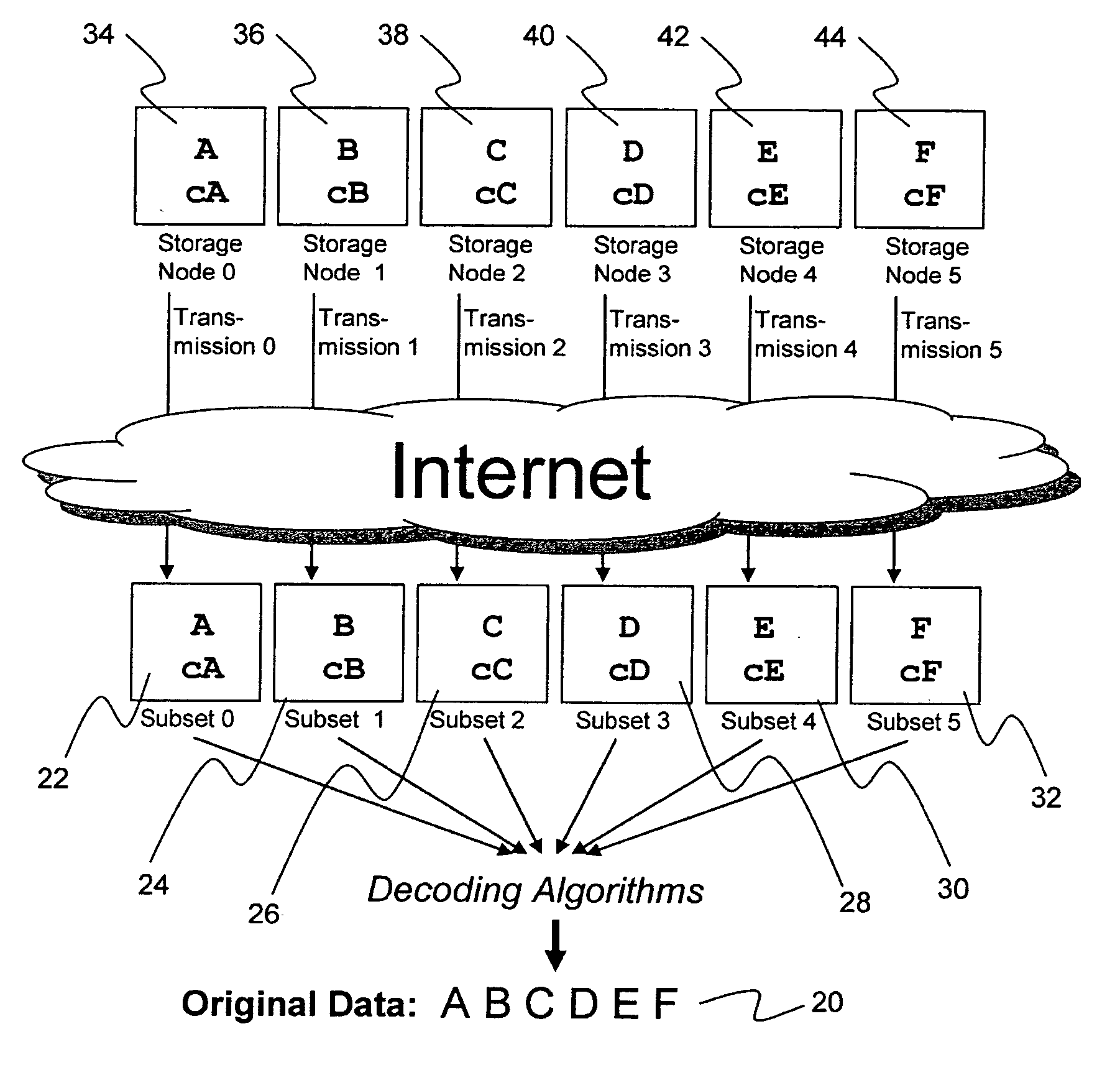
ActiveUS20070079082A1Reliably and securely protectImprove privacyError detection/correctionDigital data protectionGrid resourcesInformation dispersal
A digital data file storage system is disclosed in which original data files to be stored are dispersed using some form of information dispersal algorithm into a number of file “slices” or subsets in such a manner that the data in each file share is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other file shares. These file shares are stored on separate digital data storage devices as a way of increasing privacy and security. As dispersed file shares are being transferred to or stored on a grid of distributed storage locations, various grid resources may become non-operational or may operate below at a less than optimal level. When dispersed file shares are being written to a dispersed storage grid which not available, the grid clients designates the dispersed data shares that could not be written at that time on a Rebuild List. In addition when grid resources already storing dispersed data become non-available, a process within the dispersed storage grid designates the dispersed data shares that need to be recreated on the Rebuild List. At other points in time a separate process reads the set of Rebuild Lists used to create the corresponding dispersed data and stores that data on available grid resources.
Owner:PURE STORAGE
Metadata management system for an information dispersed storage system
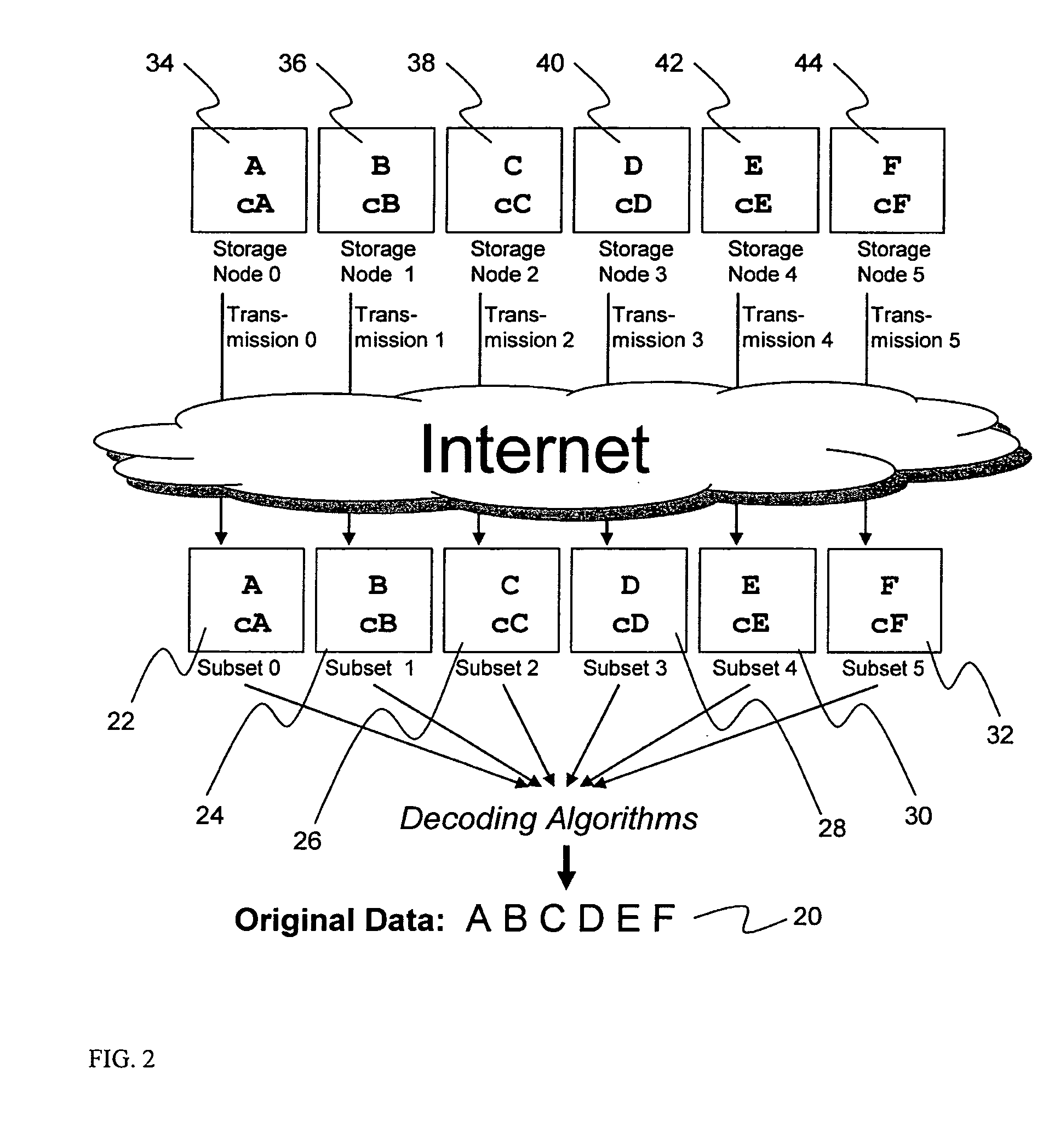
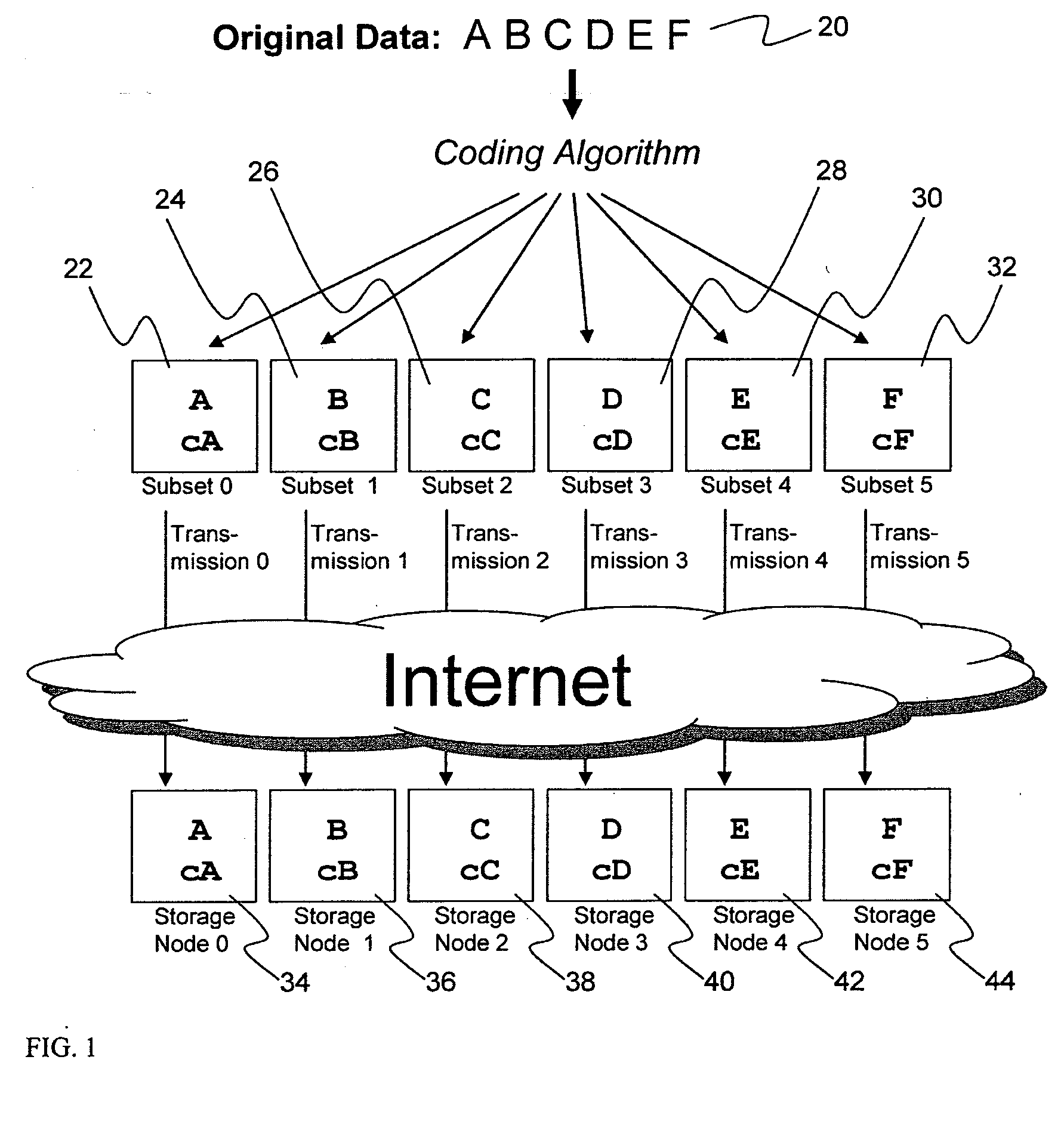
ActiveUS20070079083A1Less usableImprove privacyComputer security arrangementsMemory systemsInformation dispersalMetadata management
Briefly, the present invention relates to an information dispersal sytem in which original data to be stored is separated into a number of data “slices” in such a manner that the data in each subset is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other data subsets. These data subsets are stored on separate storage devices as a way of increasing privacy and security. In accordance with an important aspect of the invention, a metadata management system stores and indexes user files across all of the storage nodes. A number of applications run on the servers supporting these storage nodes and are responsible for controlling the metadata. Metadata is the information about the data, the data slices or data subsets and the way in which these data subsets are dispersed among different storage nodes running over the network. As used herein, metadata includes data source names, their size, last modification date, authentication information etc. This information is required to keep track of dispersed data subsets among all the nodes in the system. Every time new data subsets are stored and old ones are removed from the storage nodes, the metadata is updated. In accordance with an important aspect of the invention, the metadata management system stores metadata for dispersed data where: The dispersed data is in several pieces. The metadata is in a separate dataspace from the dispersed data. Accordingly, the metadata management system is able to manage the metadata in a manner that is computationally efficient relative to known systems in order to enable broad use of the invention using the types of computers generally used by businesses, consumers and other organizations currently.
Owner:PURE STORAGE
Billing system for information dispersal system
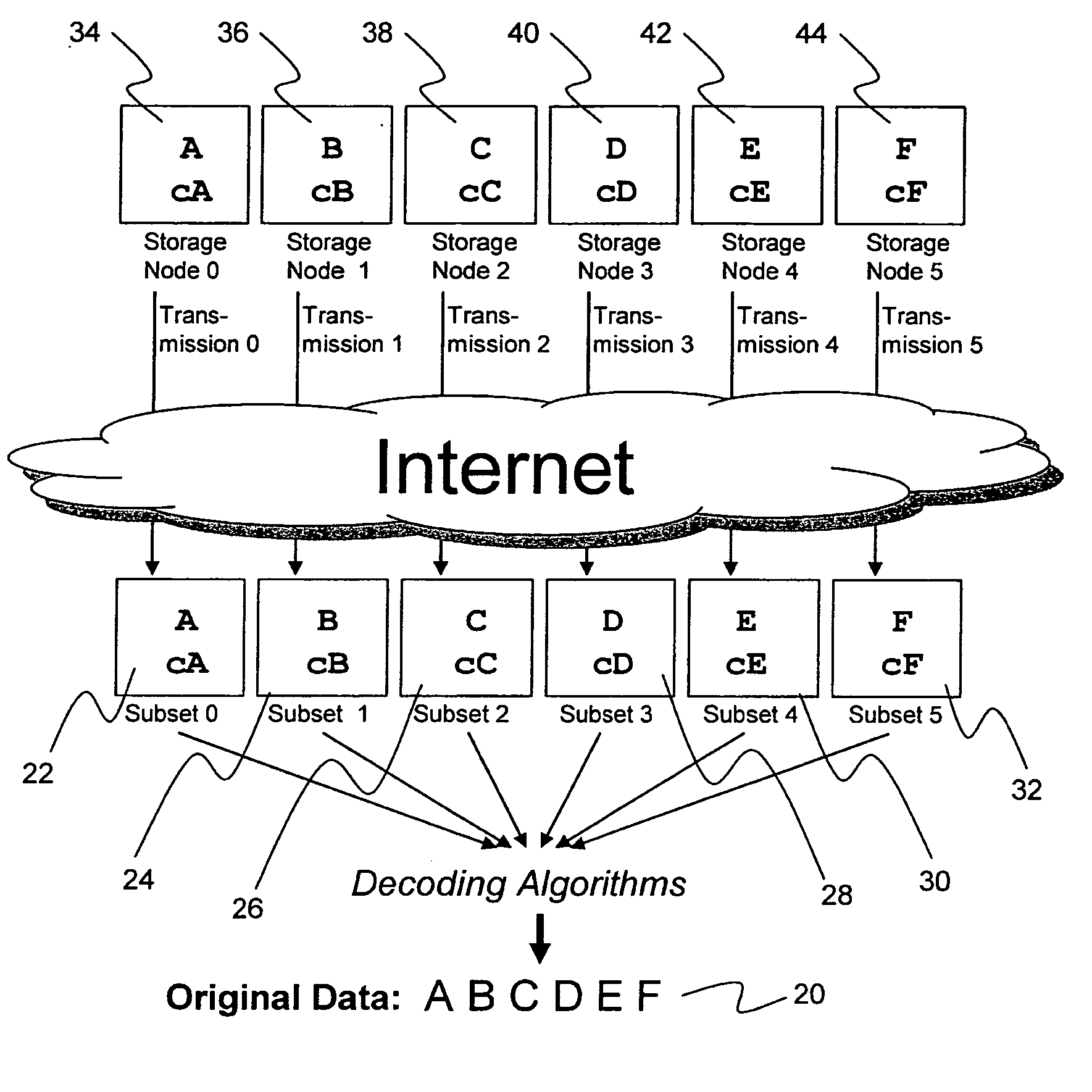
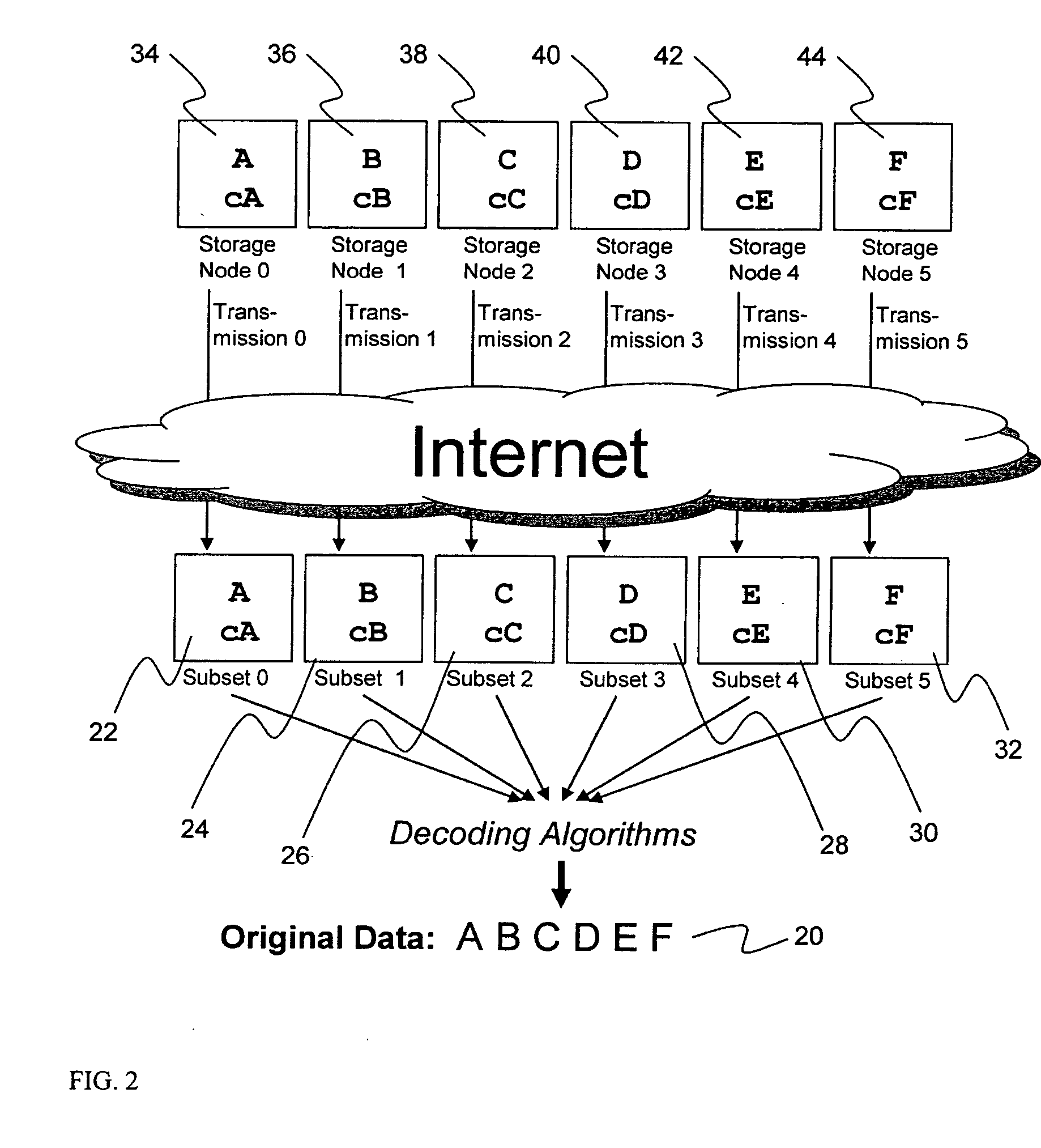
ActiveUS20070174192A1Less usableLess recognizableFinanceComputer security arrangementsInformation dispersalOriginal data
A billing process is disclosed for a information dispersal system or digital data storage system. In one embodiment of the invention, the original data to be stored is separated into a number of data “slices” or shares in such a manner that the data in each subset is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other data subsets. These data subsets are stored on separate digital data storage devices as a way of increasing privacy and security. As dispersed file shares are being stored or removed from a grid of distributed storage locations, a set of metadata tables are created, separate from the dispersed file share storage, to maintain information about the original data size of each block, file or set of file shares dispersed on the grid. The original data size information in these separate metadata tables is used to determine usage information based upon the original file size even though the file has been dispersed onto a storage grid that contains file slices who size may not relate to the original file size and the file slices may have been compressed by the system in order to reduce storage space or improve transmission time. As such, the billing process is able to enable a broad range of commercial billing options for billing for commercial data services on an information dispersal grid.
Owner:PURE STORAGE
Digital data storage system
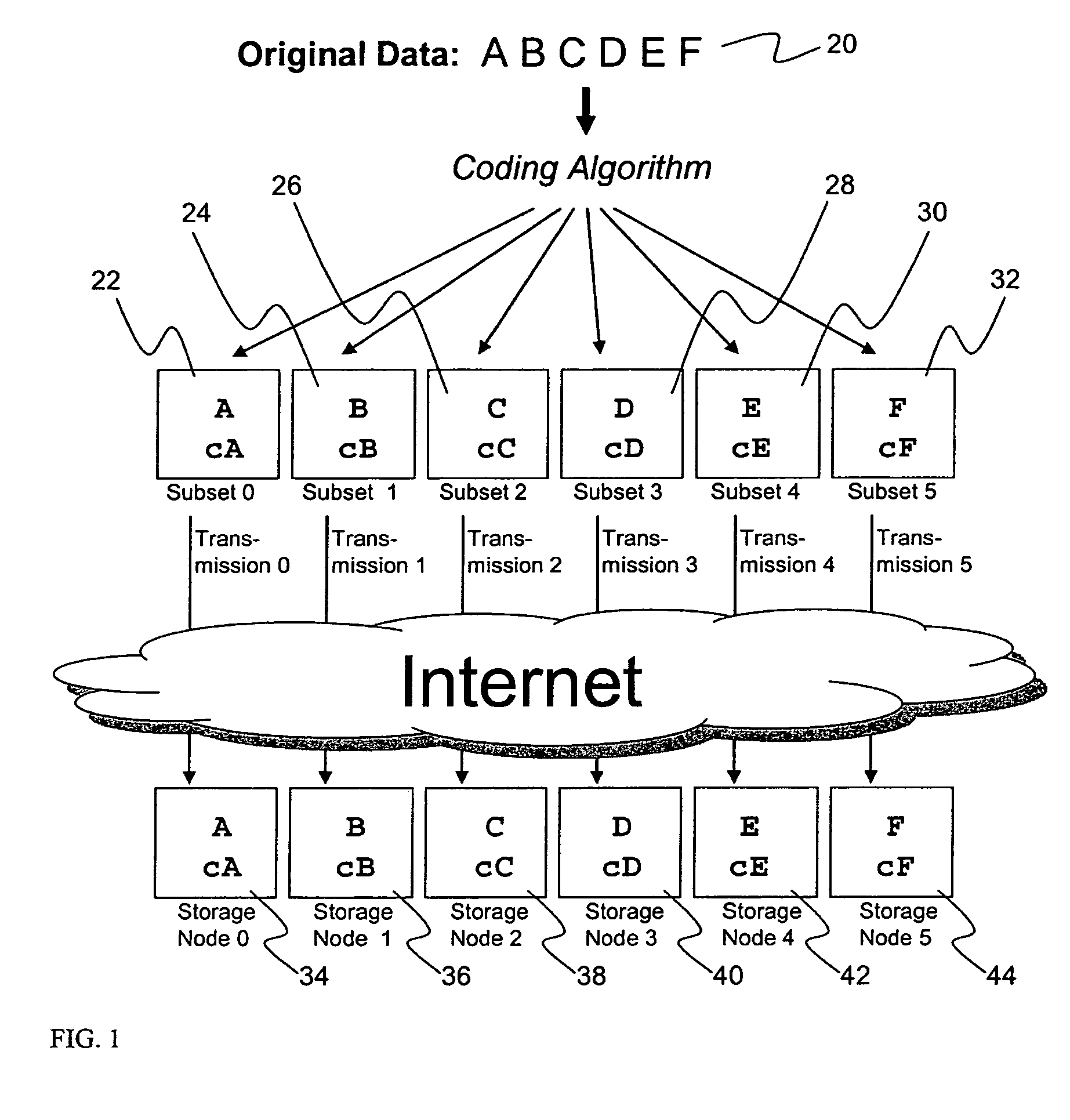
ActiveUS20070079081A1Less usableImprove privacyComputer security arrangementsMemory systemsOriginal dataSmall data
An efficient method for breaking source data into smaller data subsets and storing those subsets along with coded information about some of the other data subsets on different storage nodes such that the original data can be recreated from a portion of those data subsets in an efficient manner.
Owner:PURE STORAGE
Software-based method for gaining privacy by affecting the screen of a computing device
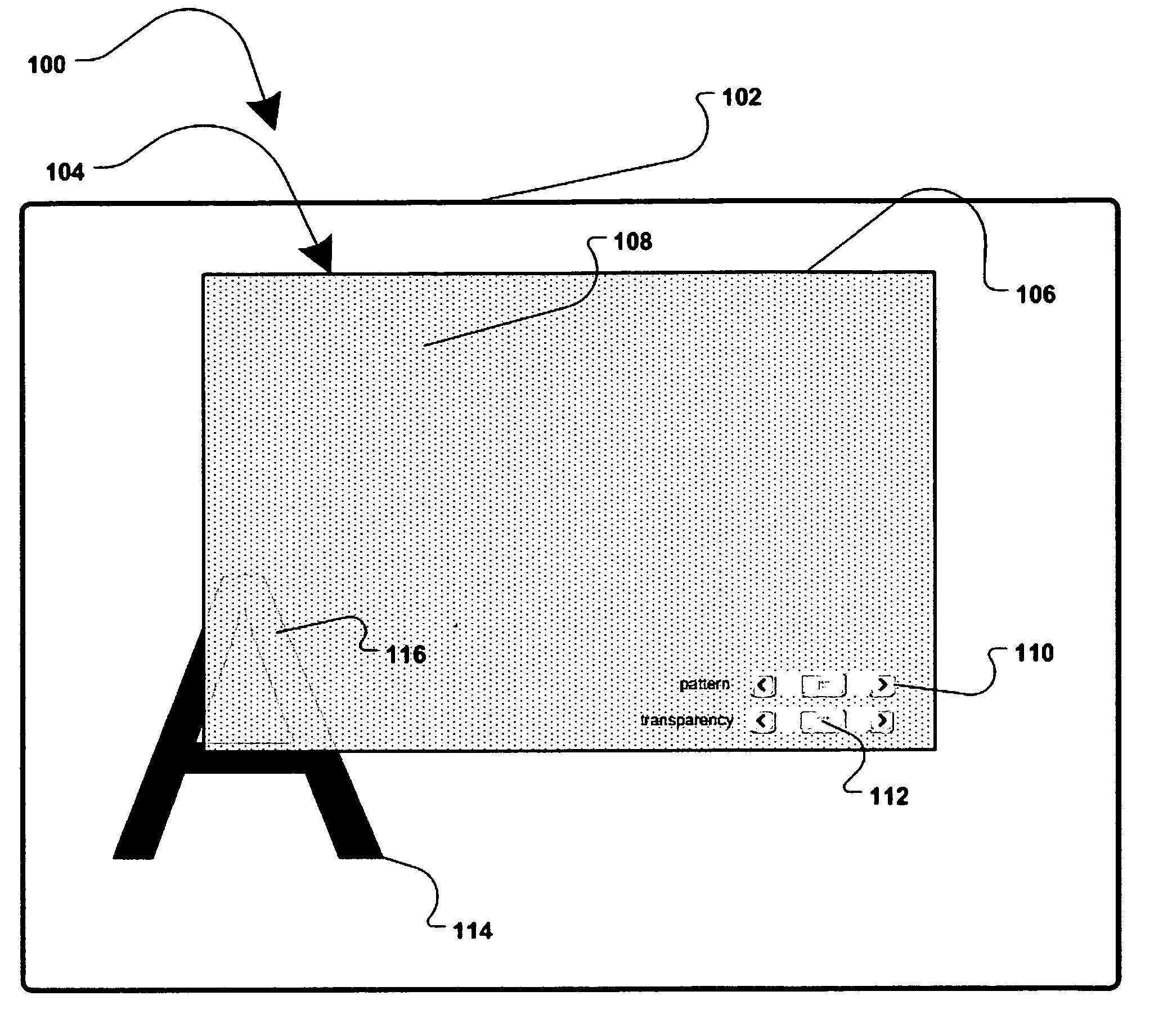
InactiveUS7779475B2Improve privacyMinimal impactDigital data processing detailsUnauthorized memory use protectionGraphicsInternet privacy
A method and apparatus for allowing the user of an electronic device to enhance privacy over a display with the use of software, are disclosed. A security window including a translucent graphical effects region may be displayed on the electronic device such that it overlays content the user may choose to protect. The security window allows the protected content to remain discernable for the user of the device yet substantially indiscernible to a person at a further distance and / or greater viewing angle from the screen of the device. One or more security windows, each of which may be of any size, shape, texture, translucency level and any other graphical or behavioral properties may be displayed on the display associated with the electronic device. The user may control the size, shape, texture, translucency level and any other graphical or behavioral properties of the security window and graphical effects region. The user may invoke or terminate a security window with the single click of a button. Security windows may automatically attach to applications in focus, or be attached in response to a user command, and allow uninterrupted usability of those applications.
Owner:PETNOTE
Analyte monitoring device alarm augmentation system
InactiveUS6553244B2Improve efficiencyReduces and eliminates transportSensorsTelemetric patient monitoringAnalyteAugmentation system
The present invention relates to a device for augmenting an alarm signal generated by an analyte monitoring device, e.g., the GlucoWatch(R) (Cygnus, Inc., Redwood City, Calif.) biographer glucose monitoring device, for improving the alarm signal's effectiveness in alerting the user, and / or for communicating the signal to a person or person(s) other than the user, or to a trained assistance animal.
Owner:LIFESCAN IP HLDG LLC +1
Analyte monitoring device alarm augmentation system
InactiveUS20020065453A1Maximize effectivenessImprove efficiencyMicrobiological testing/measurementSensorsAnalyteEngineering
The present invention relates to a device for augmenting an alarm signal generated by an analyte monitoring device, e.g., the GlucoWatch(R) (Cygnus, Inc., Redwood City, Calif.) biographer glucose monitoring device, for improving the alarm signal's effectiveness in alerting the user, and / or for communicating the signal to a person or person(s) other than the user, or to a trained assistance animal.
Owner:LIFESCAN IP HLDG LLC +1
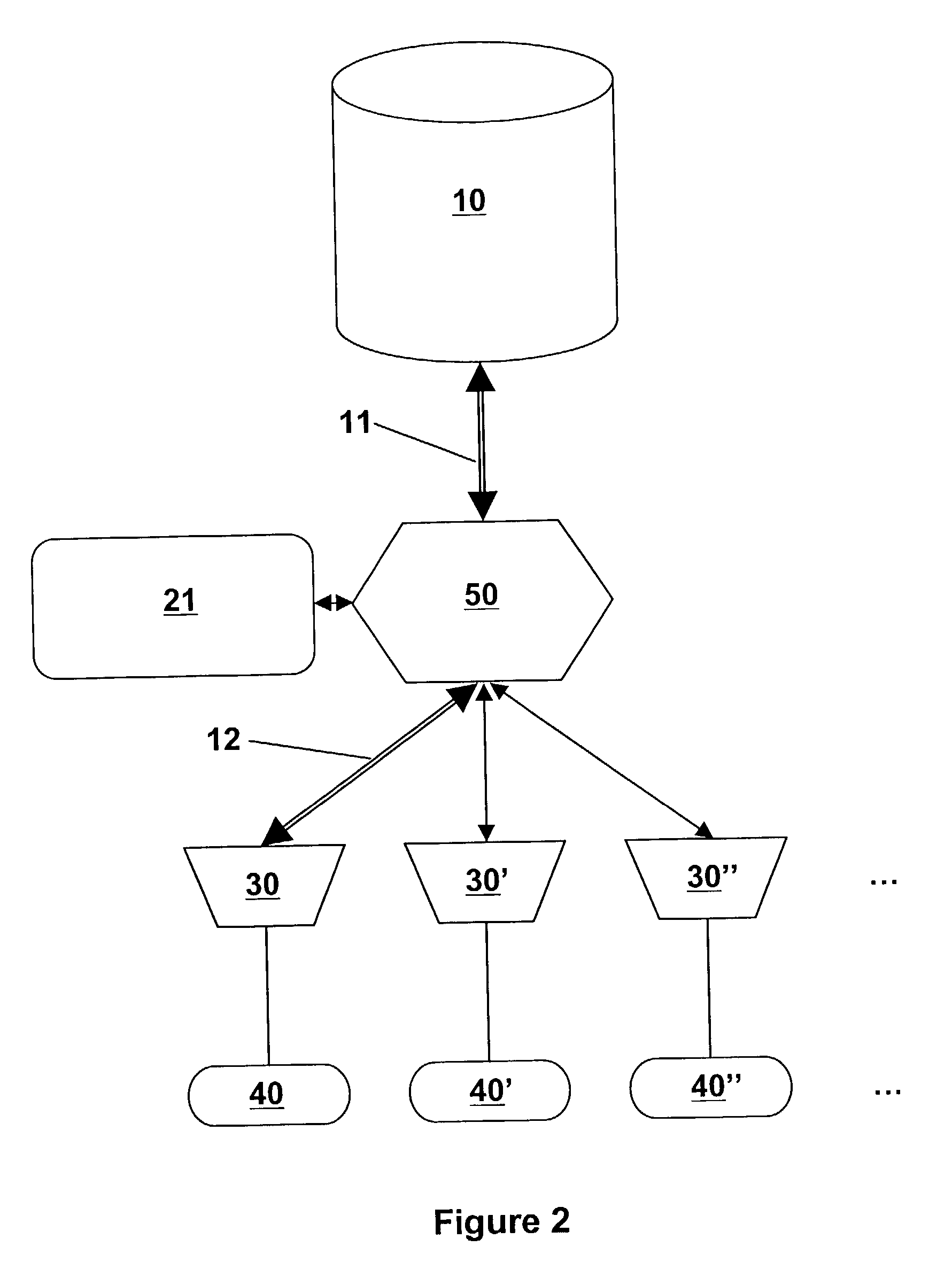
Method and apparatus for online advertising
InactiveUS20050086605A1Increase individual privacyFacilitate group interactionProgram controlSpecial data processing applicationsComputer usersUser interface
A method of online advertising allows a plurality of computer users to communicate via a set of interconnected terminals allows for shared online experiences. A plurality of terminals, each having a user interface, connect to a server or network through a portal rather than directly to the server. On occasion and when initiated by the users, one terminal serves as a leader terminal, and each terminal has an interface that provides access to the terminal. Each terminal connects to the portal so that it can send and receive data and commands between each of the plurality of terminals and the portal through the portal, and display advertising messages generated at the portal. The portal then connects to a server using a telecommunications connection to provide the informational content resident thereon desired by the user.
Owner:FERRER MIGUEL +1
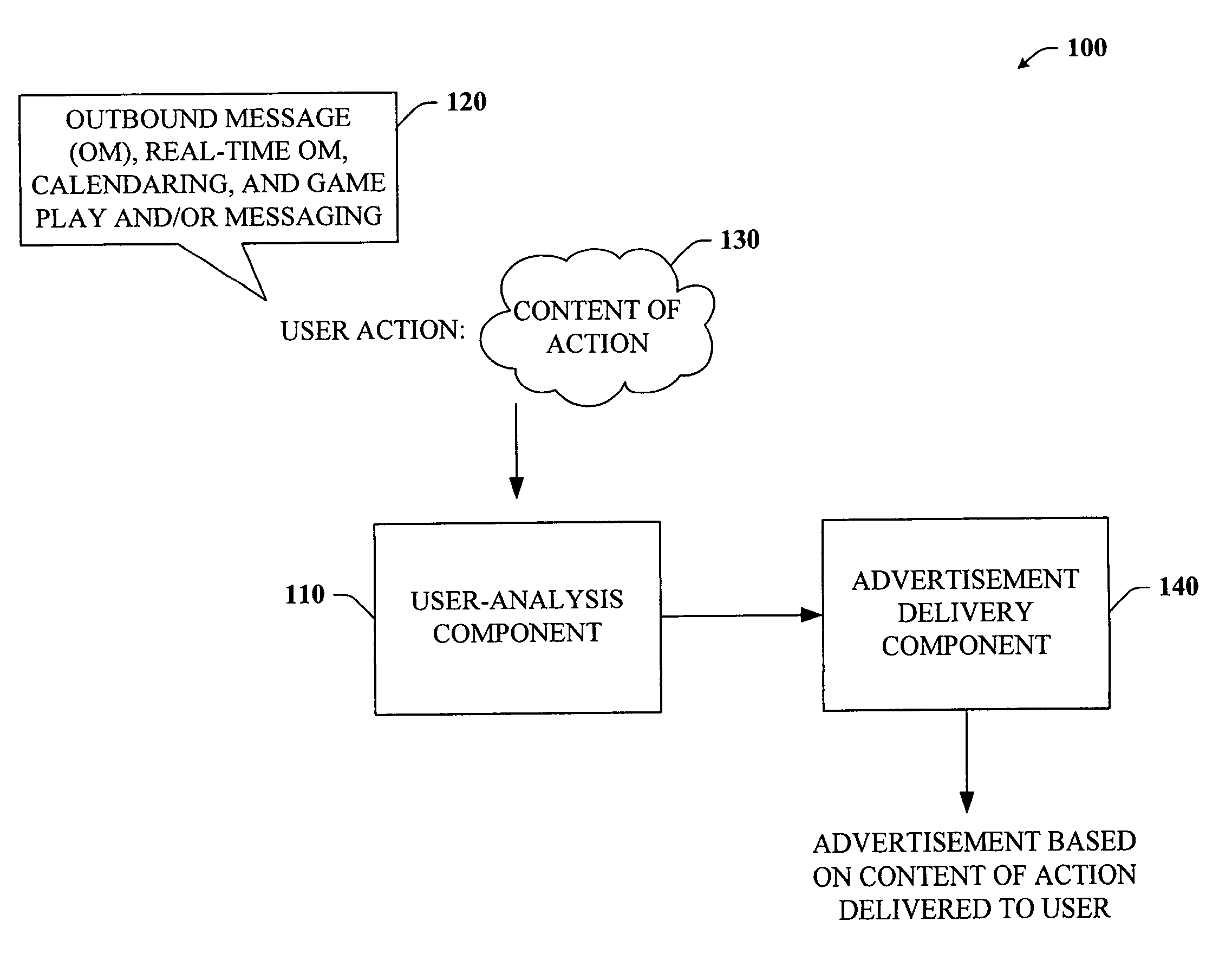
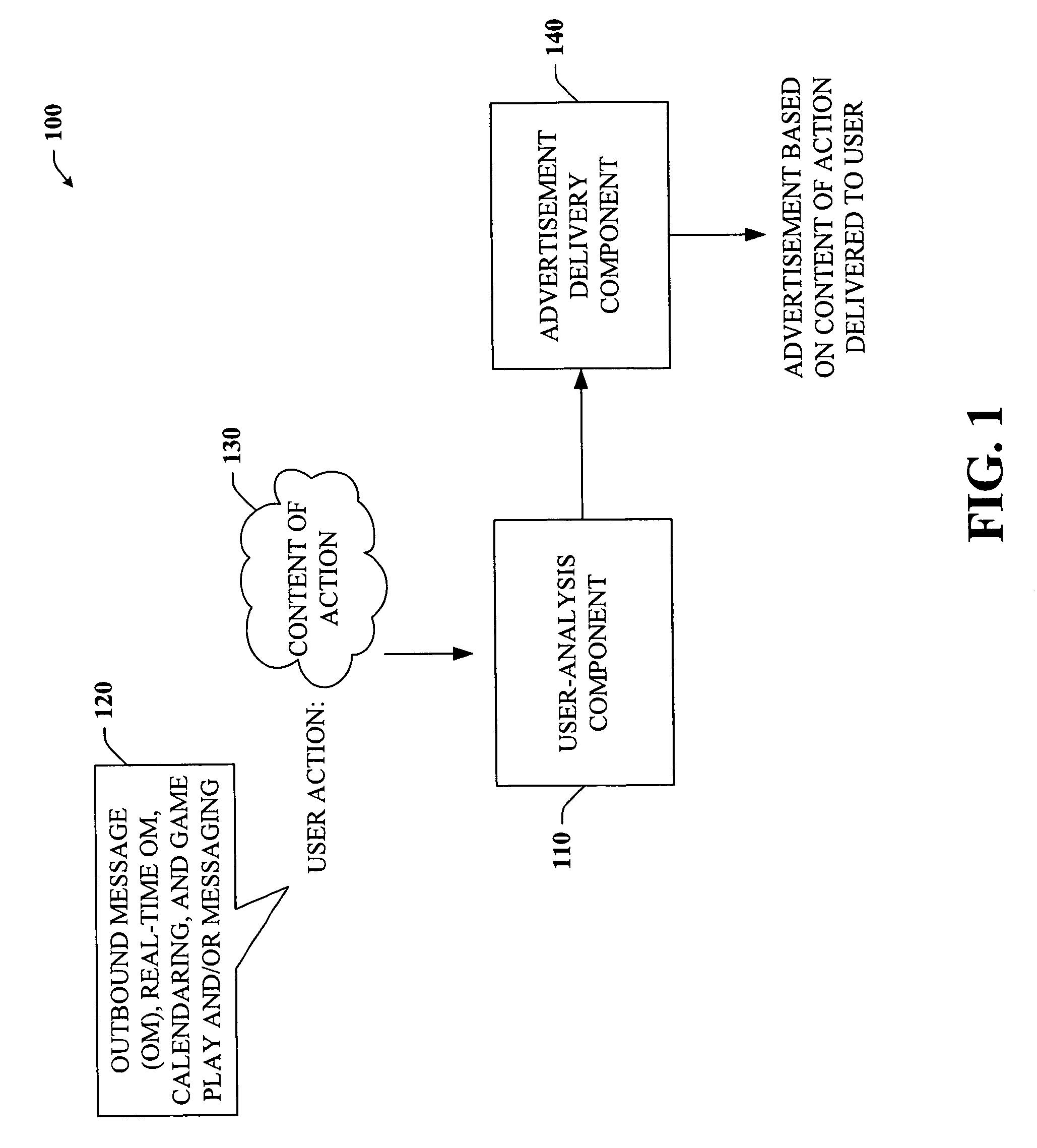
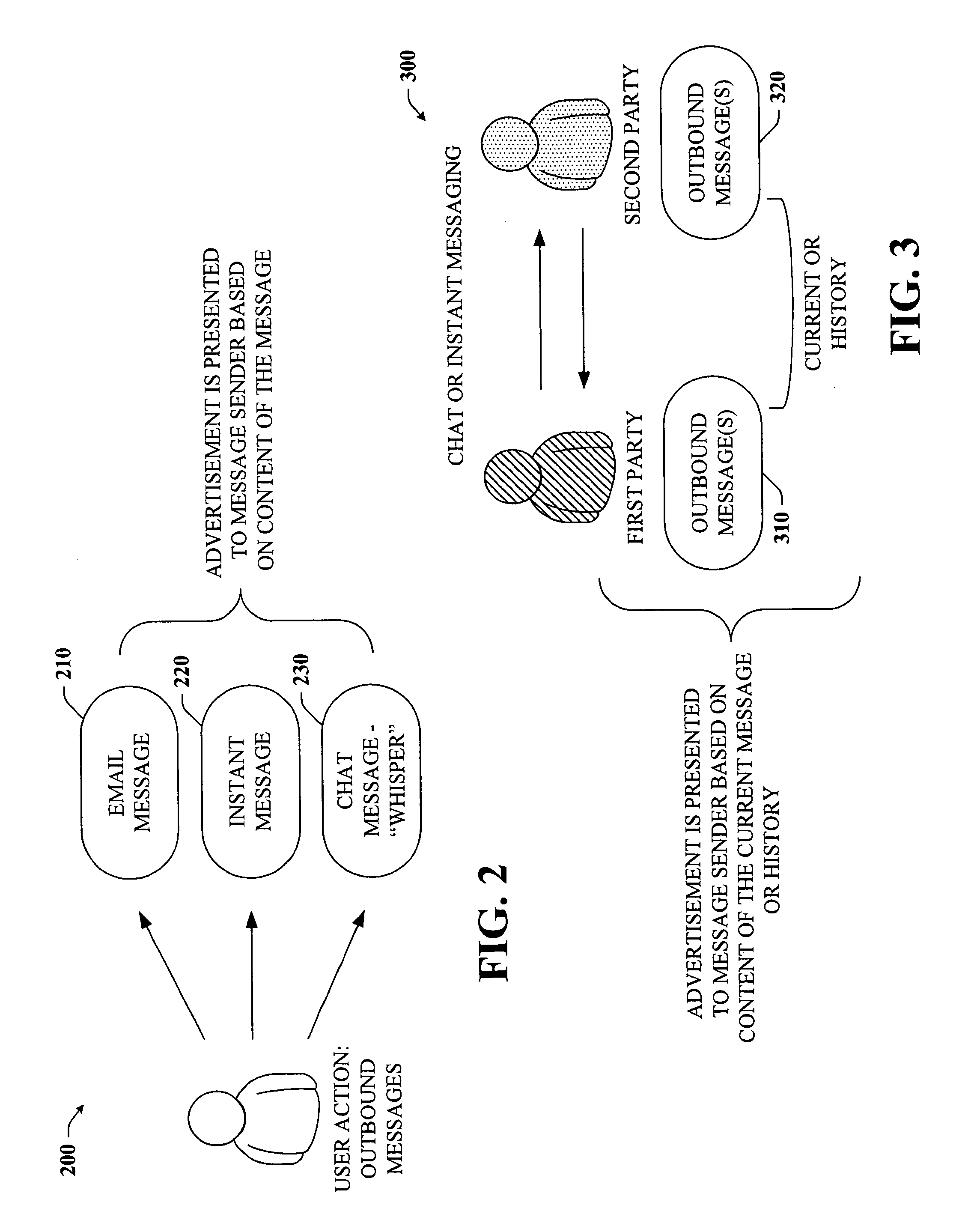
Content-targeted advertising for interactive computer-based applications
InactiveUS20060167747A1Reduce user experienceUser privacy is enhancedMarketingUser privacyContent analytics
The subject invention provides a unique system and method that facilitates providing content-targeted advertising to a user based at least in part on the content of a user action. The user action can be performed in connection with an outbound messaging system, a real-time messaging system such as a chat or instant messaging, a game environment, and / or calendaring system. The system and method analyze at the least the content of an outbound message and then present a content-targeted advertisement based on the content of the message. The same can be done with respect to calendar entries. However, outbound and inbound calendar entries, invitations, and responses to invitations can be analyzed for content and have content-targeted advertisements presented to the sender or receiver of such items. User privacy can be maintained and / or increased by allowing a user to opt out of content-targeting advertisements. Reasons for being targeted can also be provided to the user.
Owner:MICROSOFT TECH LICENSING LLC
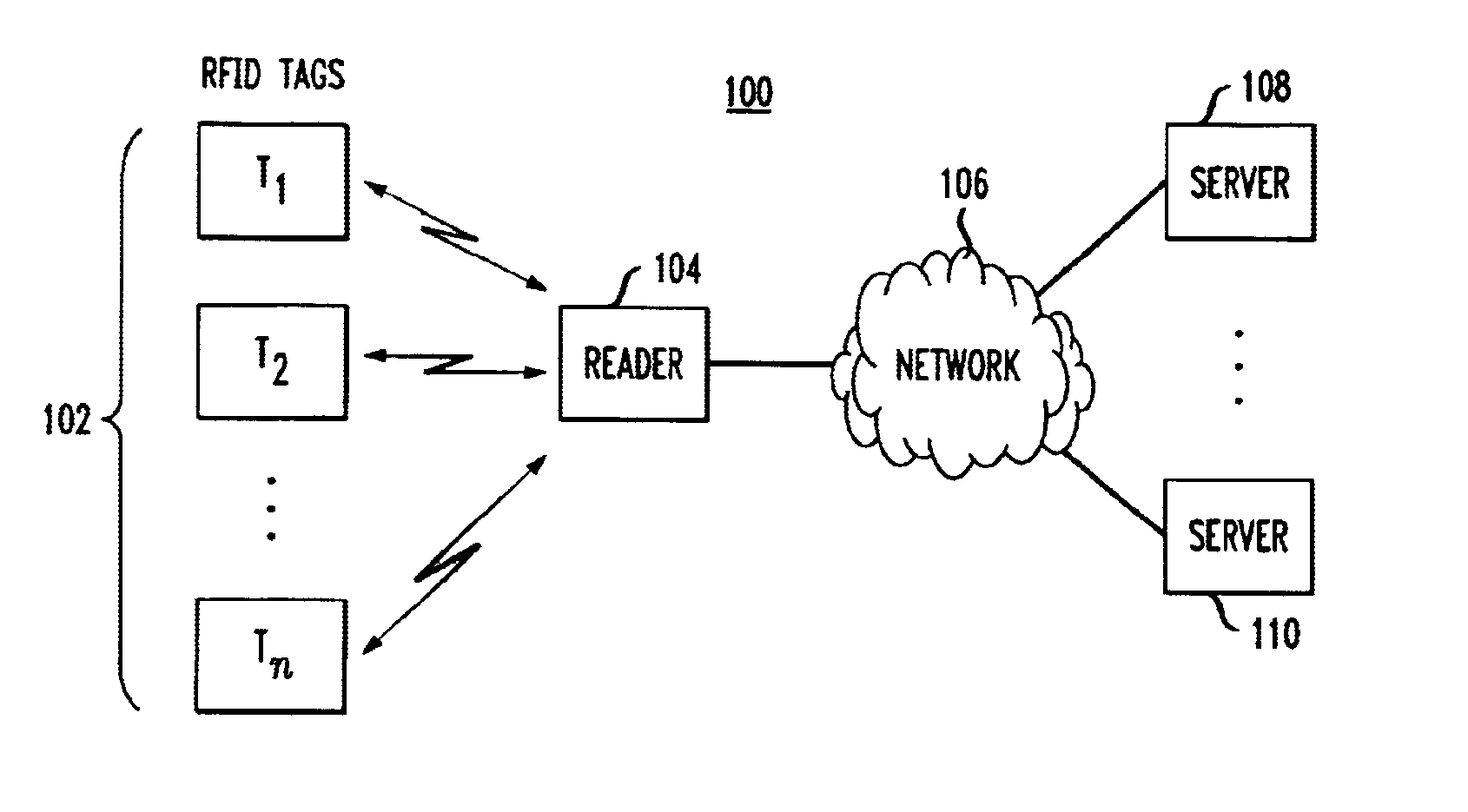
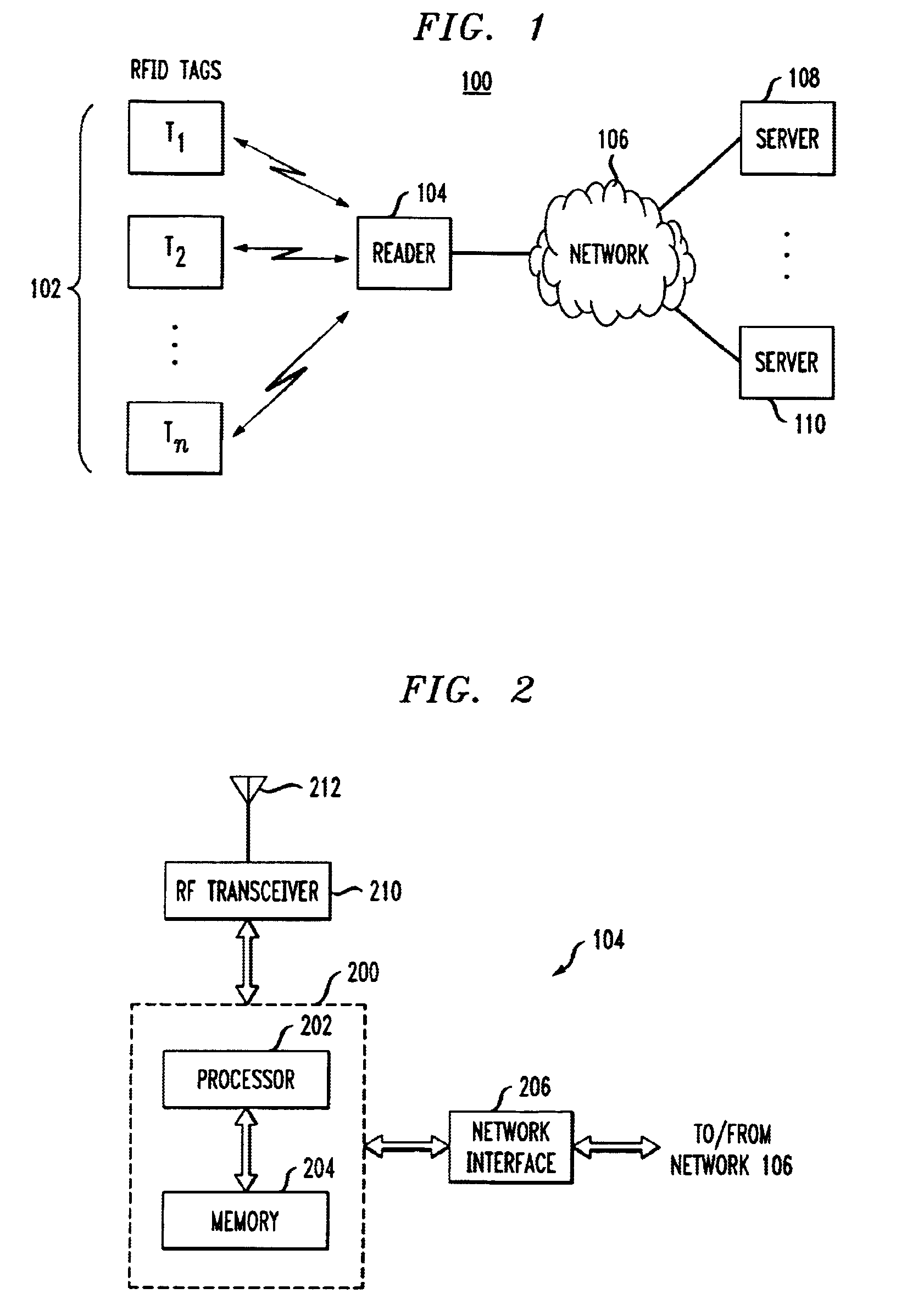
Method and apparatus for selective blocking of radio frequency identification devices
ActiveUS6970070B2Enhanced consumer privacyIncreased complexityMemory record carrier reading problemsTime-division multiplexComputer hardwareRadio-frequency identification
Techniques are disclosed for providing enhanced privacy in an RFID system comprising a plurality of RFID devices, each having an associated identifier, and at least one reader which communicates with one or more of the devices. A blocker device is operative to receive a communication directed from the reader to one or more of the RFID devices, and to generate, possibly based on information in the received communication, an output transmittable to the reader. The output simulates one or more responses from at least one of the RFID devices in a manner which prevents the reader from determining at least a portion of the identifier of at least one of the RFID devices. The blocker device may itself comprise one of the RFID devices. In an illustrative embodiment, the output generated by the blocker device interferes with the normal operation of a singulation algorithm implemented by the reader.
Owner:EMC IP HLDG CO LLC
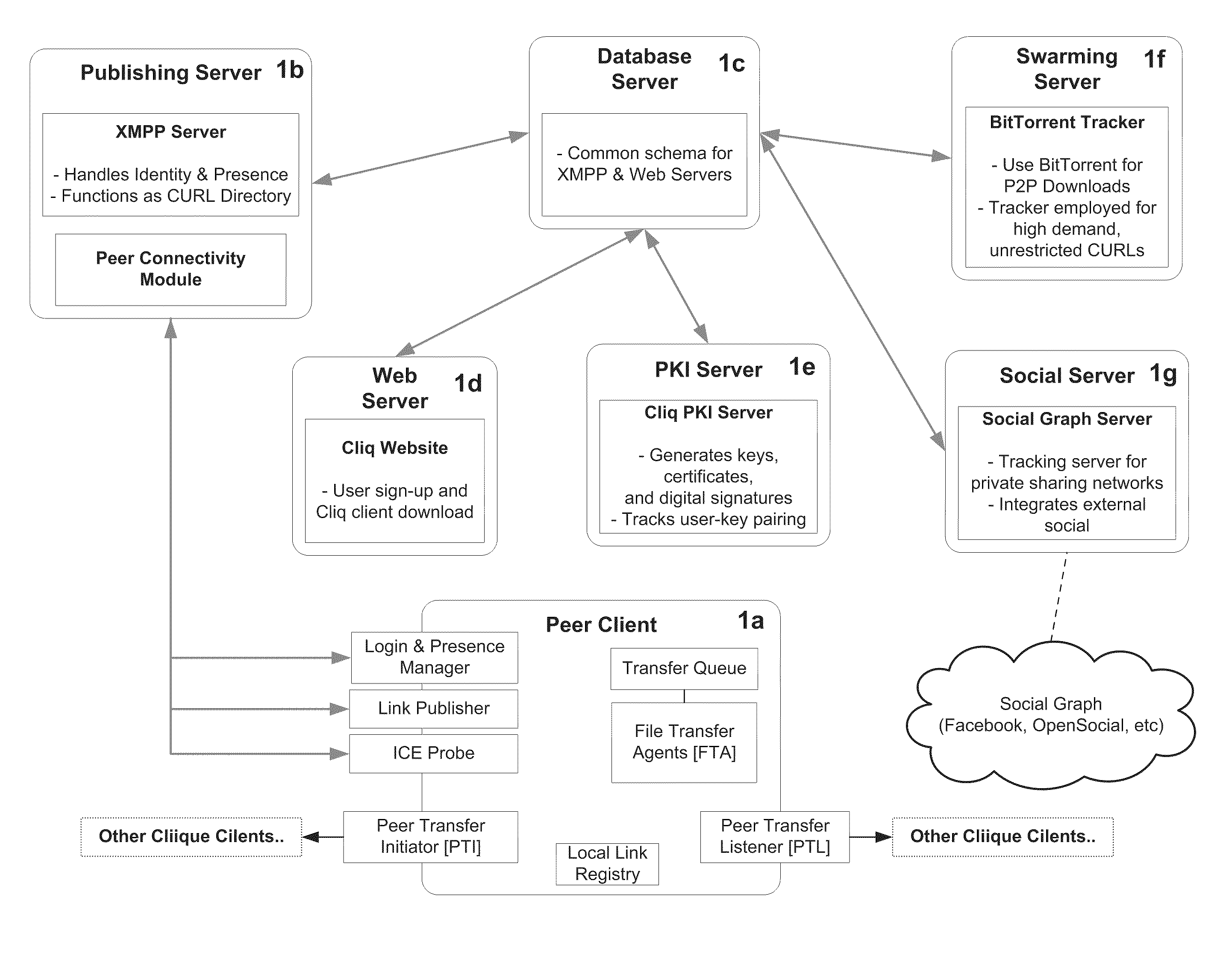
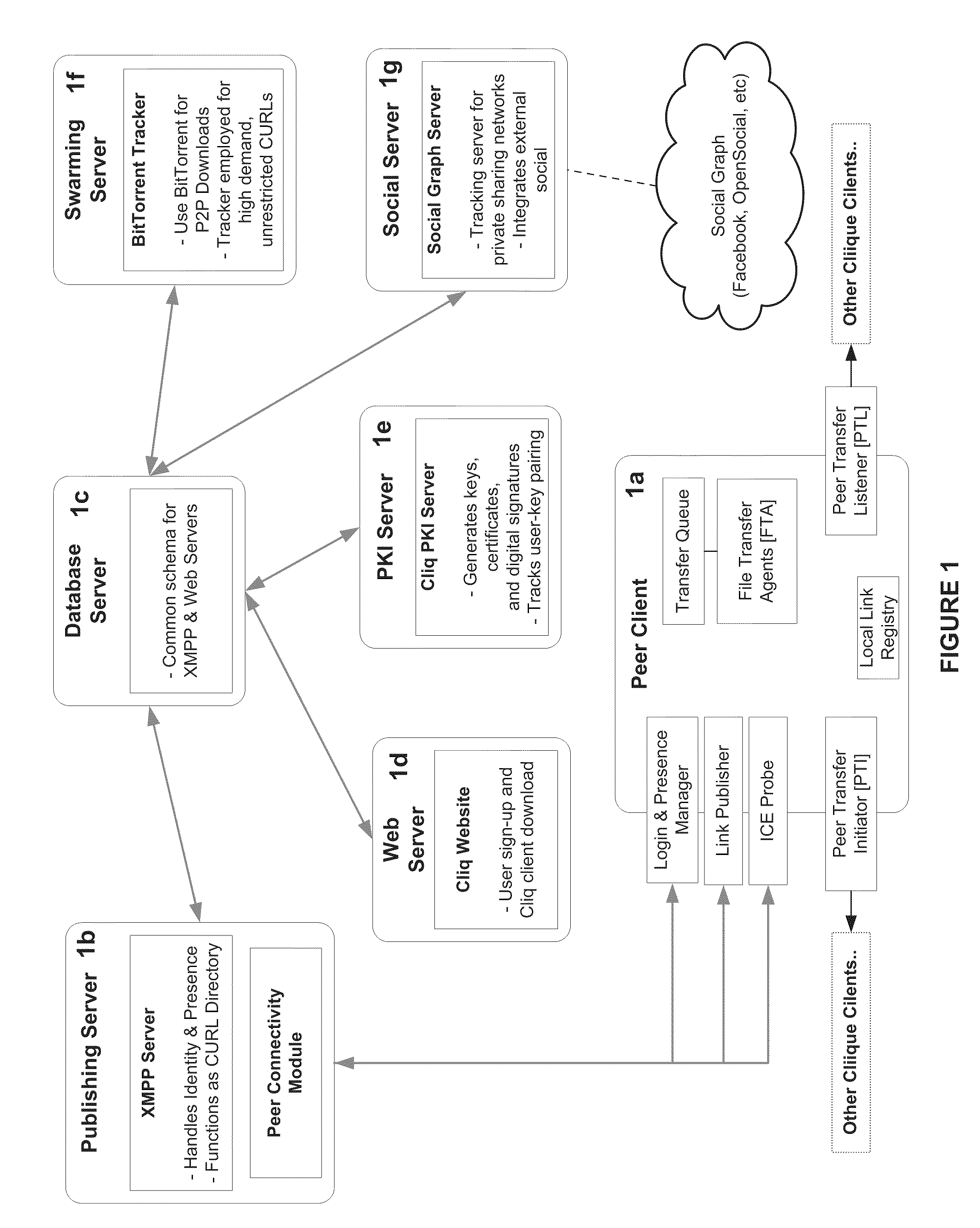
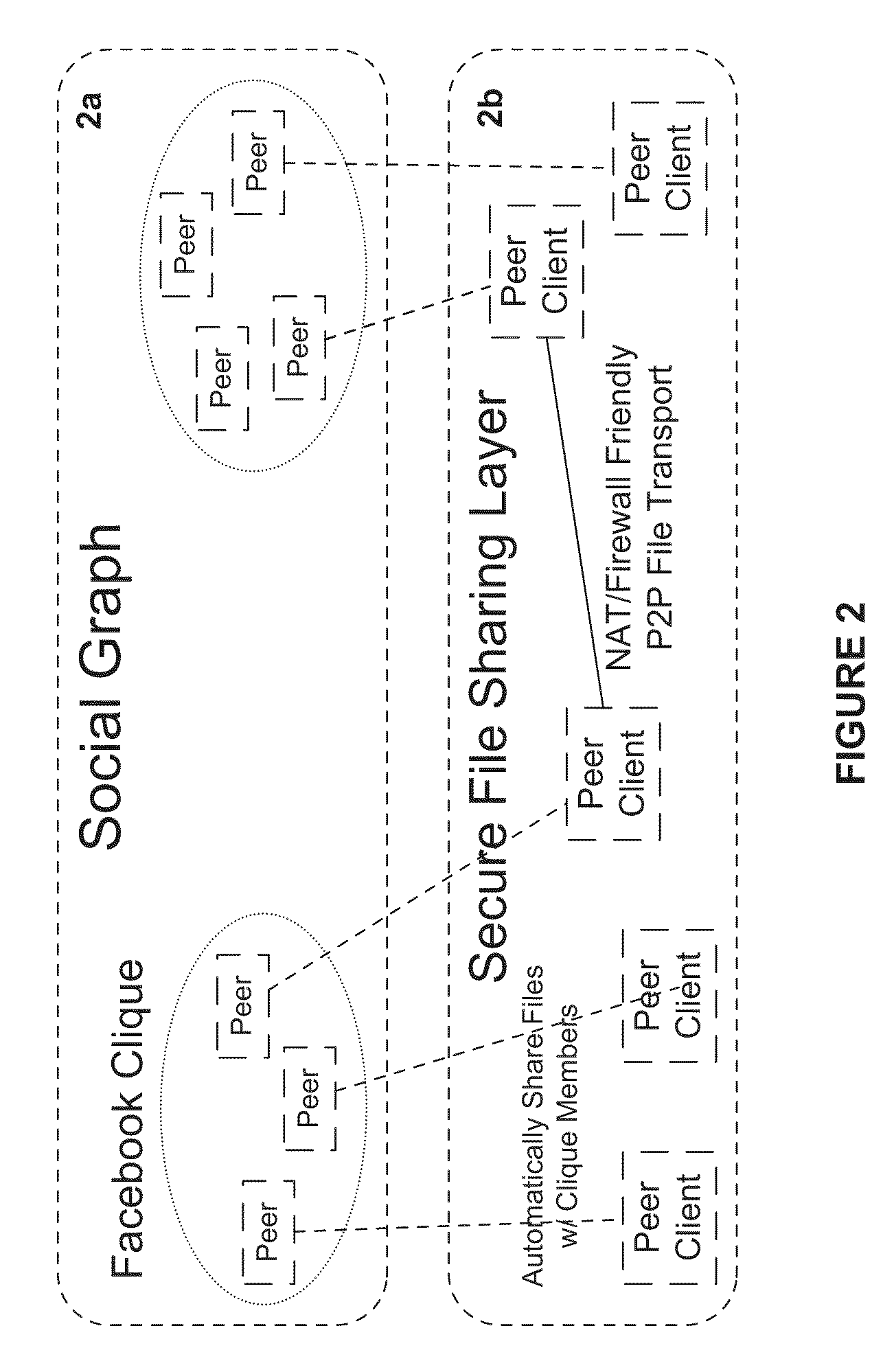
System and Method for Anonymous Addressing of Content on Network Peers and for Private Peer-to-Peer File Sharing
ActiveUS20110035503A1Efficient and privateEfficient and private peer-to-peer file sharingMultiple digital computer combinationsTransmissionPeer to peer file sharingPeer-to-peer
A system and method for efficient and private peer-to-peer file sharing consists of ascribing a uniquely identified and anonymous link (an“edgelink”) to any file or set of files on a peer computer. The link is registered with a publishing server along with continuously updated connectivity information about the peer without registering any identifying information about the file. A peer recipient is able to access the link, receive connectivity information about the publishing peer from the server, and then receive the file from the publishing peer without file content passing through the server, mediating any intermediary NAT devices without requiring any manual or automatic device reconfiguration.
Owner:ZAID SAM
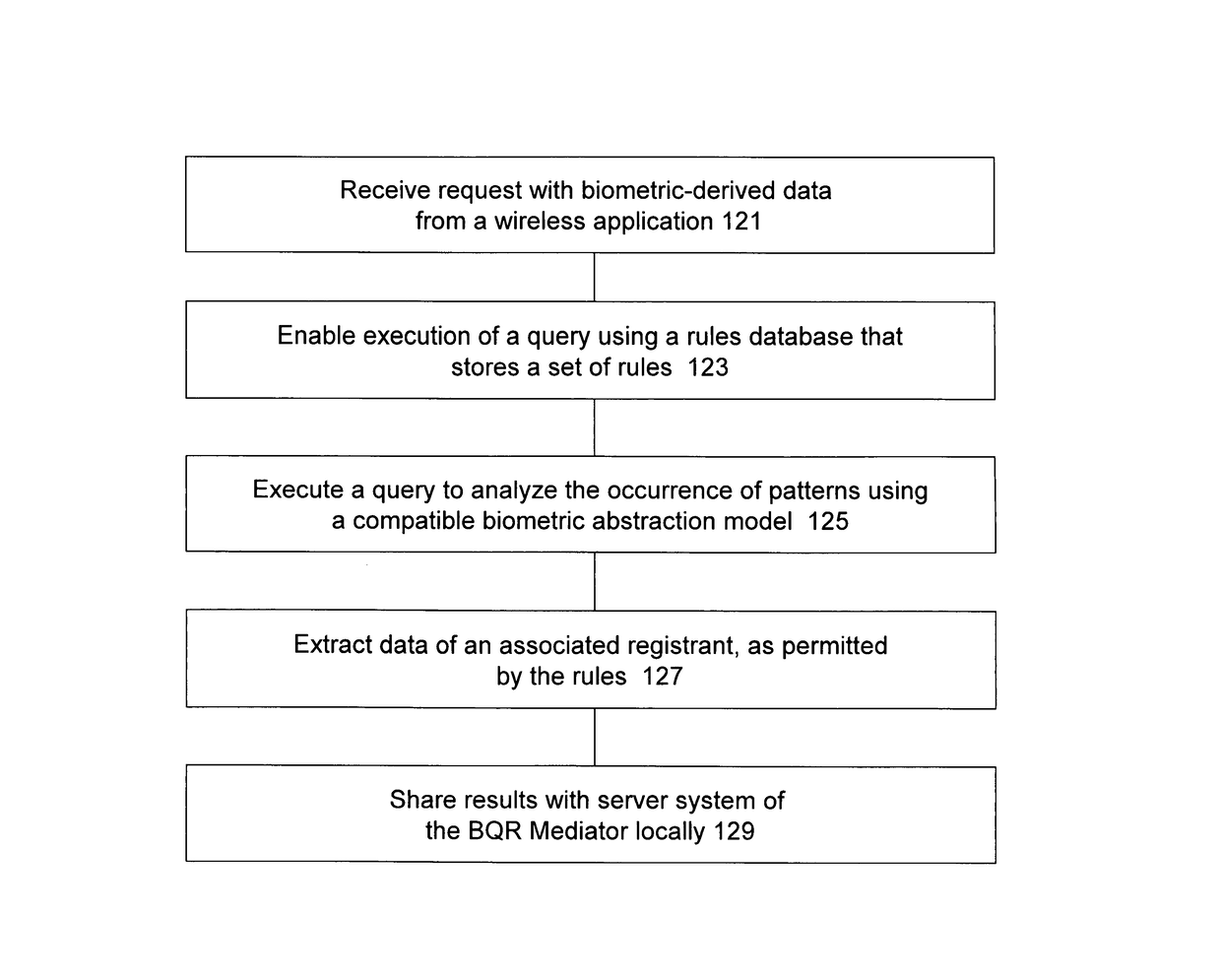
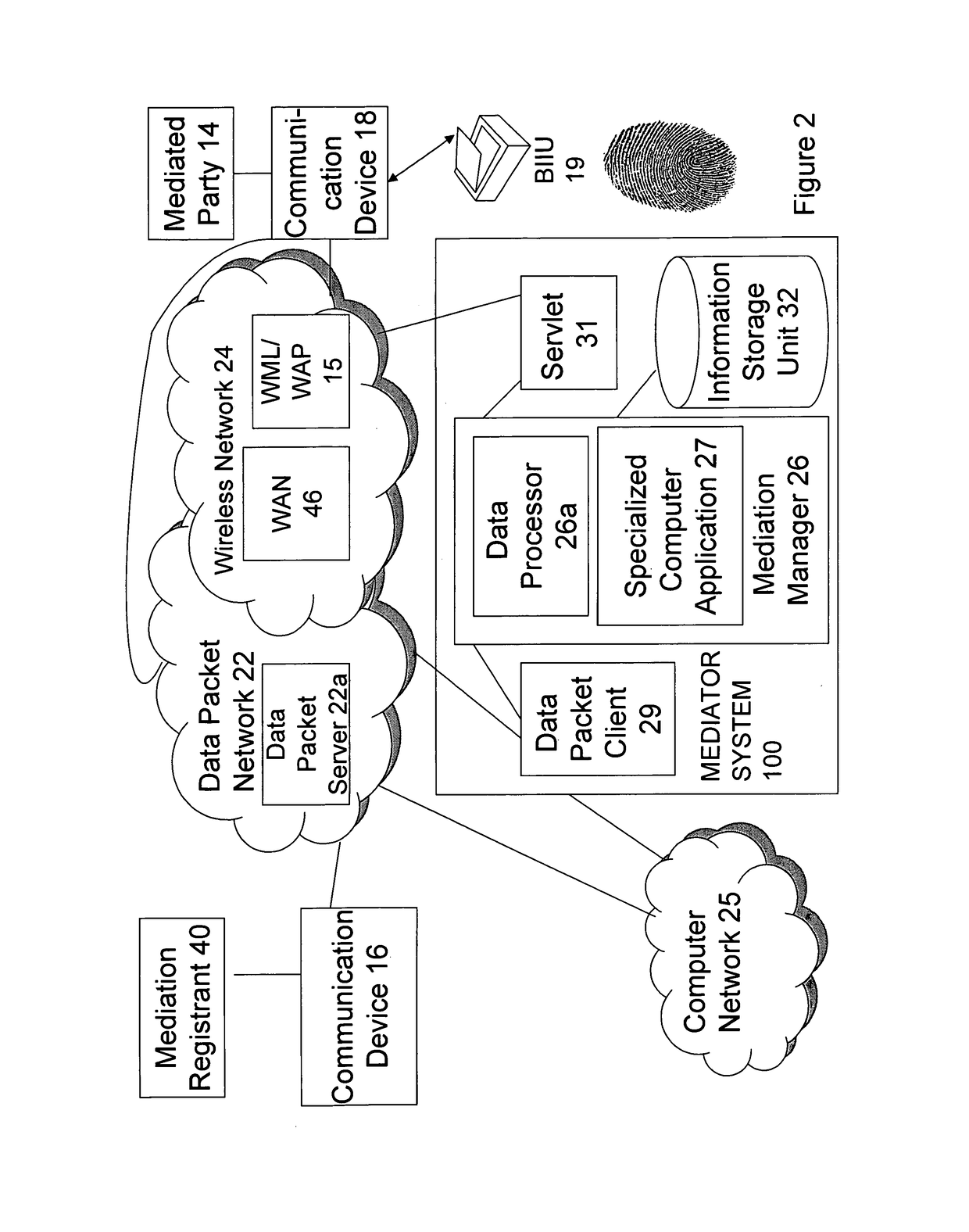
Methods using mediation software for rapid health care support over a secured wireless network; methods of composition; and computer program products therefor
ActiveUS9928379B1Increased riskImprove privacyMedical data miningWeb data indexingBiometric dataPrivacy rule
Some of these new methods harness distributed computing capabilities to integrate biometric abstraction processes, wireless network connectivity, and specialized software for mediation, to produce a unified result set. A mediator that enables rapid health care support is used in a computer system having a database of information to be shared with authorized requesters, under privacy rules or other pre-defined constraints. The methods, using specialized software for mediation, are preferably enabled to process a securely transmitted remote data request as a query to verify or identify an individual, whether it is sent via a network that is wireless in any part, or not. Upon receiving a remote request, typically sent by a requesting application other than one operated by the individual who is the subject of the request, the mediator uses the individual's transformed biometric data of the request to rapidly advance query resolution, under all query preprocessing rules, and query results post-processing rules, that apply.
Owner:HOFFER STEVEN M
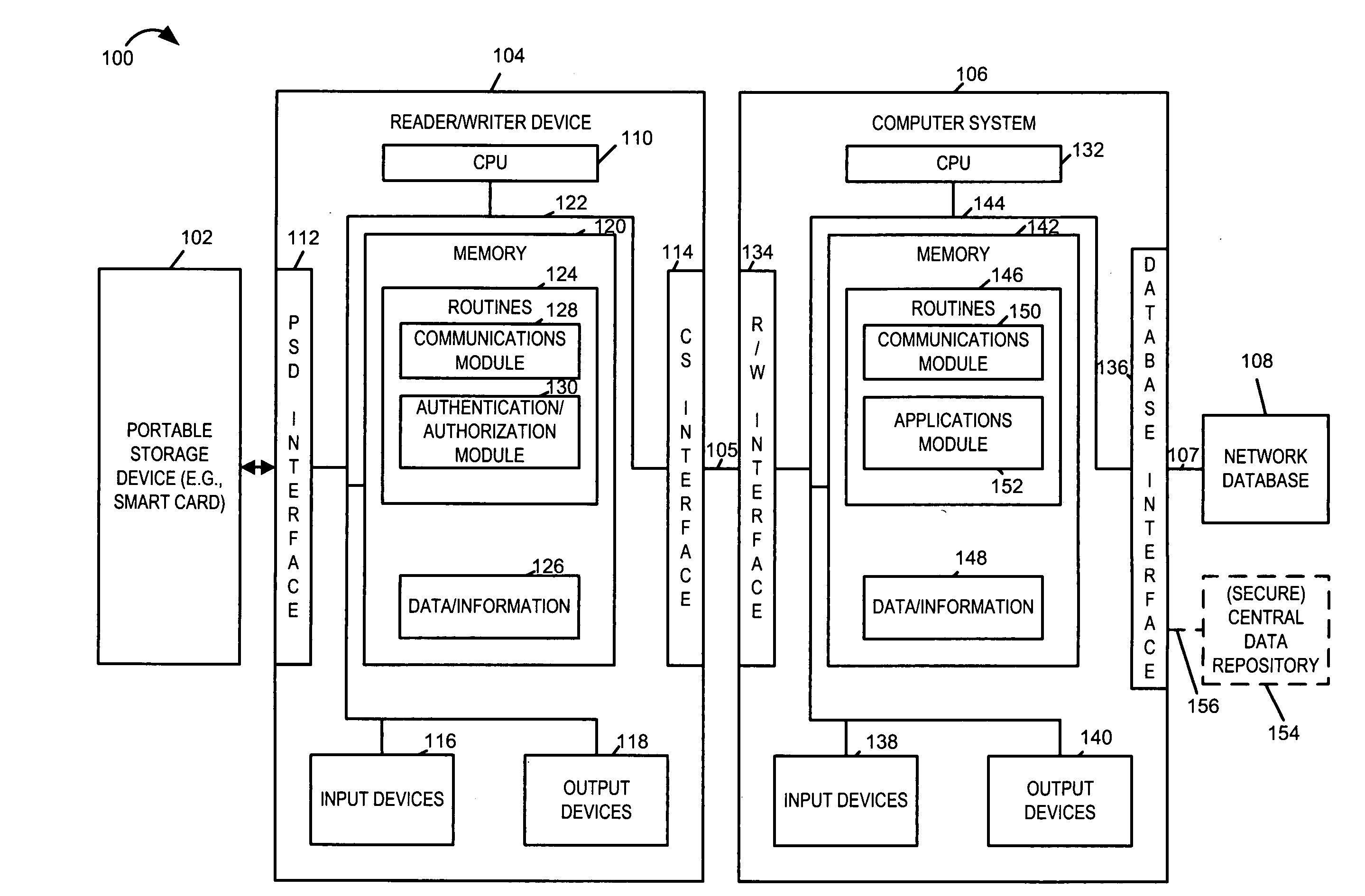
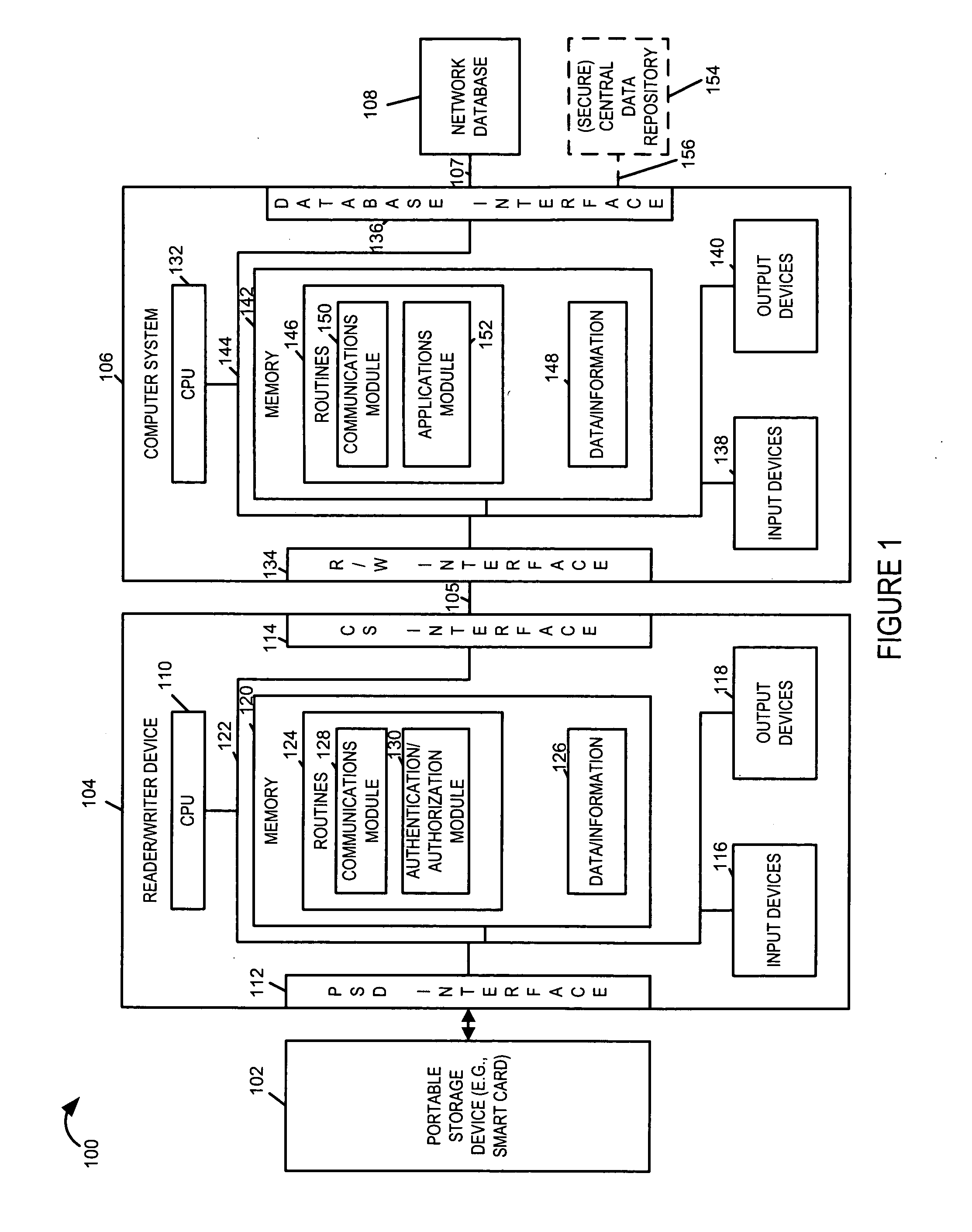
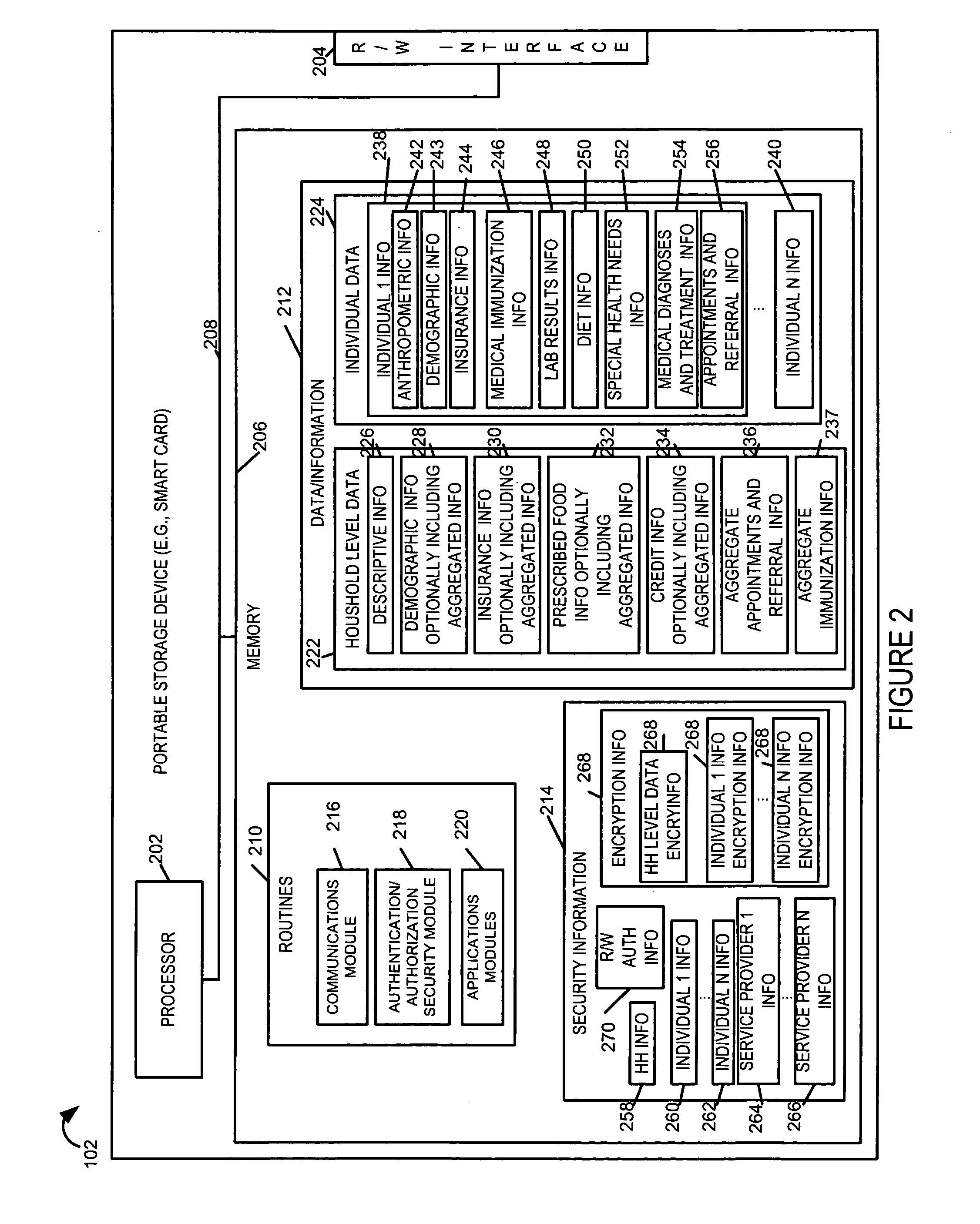
Portable electronic data storage and retreival system for group data
InactiveUS20050197859A1Improve efficiencyImprove privacyPatient personal data managementOffice automation
Methods and apparatus for providing and using a portable electronic data storage and information retrieval system for healthcare and / or other types of applications are described. Each portable storage device (PSD) (e.g., smart card) for a group, e.g., household, allows the storage and retrieval of household level information in addition to individual household member data / information. Data / information is stored corresponding to different applications. The PSD is accessed by a service provider's computer system. Access to the data / information is secured via authentication and / or various encryption techniques. Various service providers or types of service providers have access to different portions of the information stored on the portable storage device based upon pre-arranged agreements and / or service needs. Access is controlled through security information and / or security modules which are used to limit access. Service providers can update network based information databases and / or update the information on the PSD, e.g., to indicate a particular service or treatment.
Owner:HITACHI AMERICA
Method and apparatus for improved private messaging
InactiveUS20150096042A1Improve security and privacyImprove privacyDigital data processing detailsAnalogue secracy/subscription systemsComputer hardwareTime segment
An improved method and apparatus for private messaging is disclosed. In one embodiment, a first device transmits a message to a second device via a server. The message is displayed on the second device without any identification of the sender, and the message disappears after a predetermined time period and is permanently deleted from the first device, second device, and server. In another embodiment, the second device sends communications to the server indicating that the second device received the message, opened the message, and deleted the message, and the server sends those communications to the first device.
Owner:CRIPTEXT
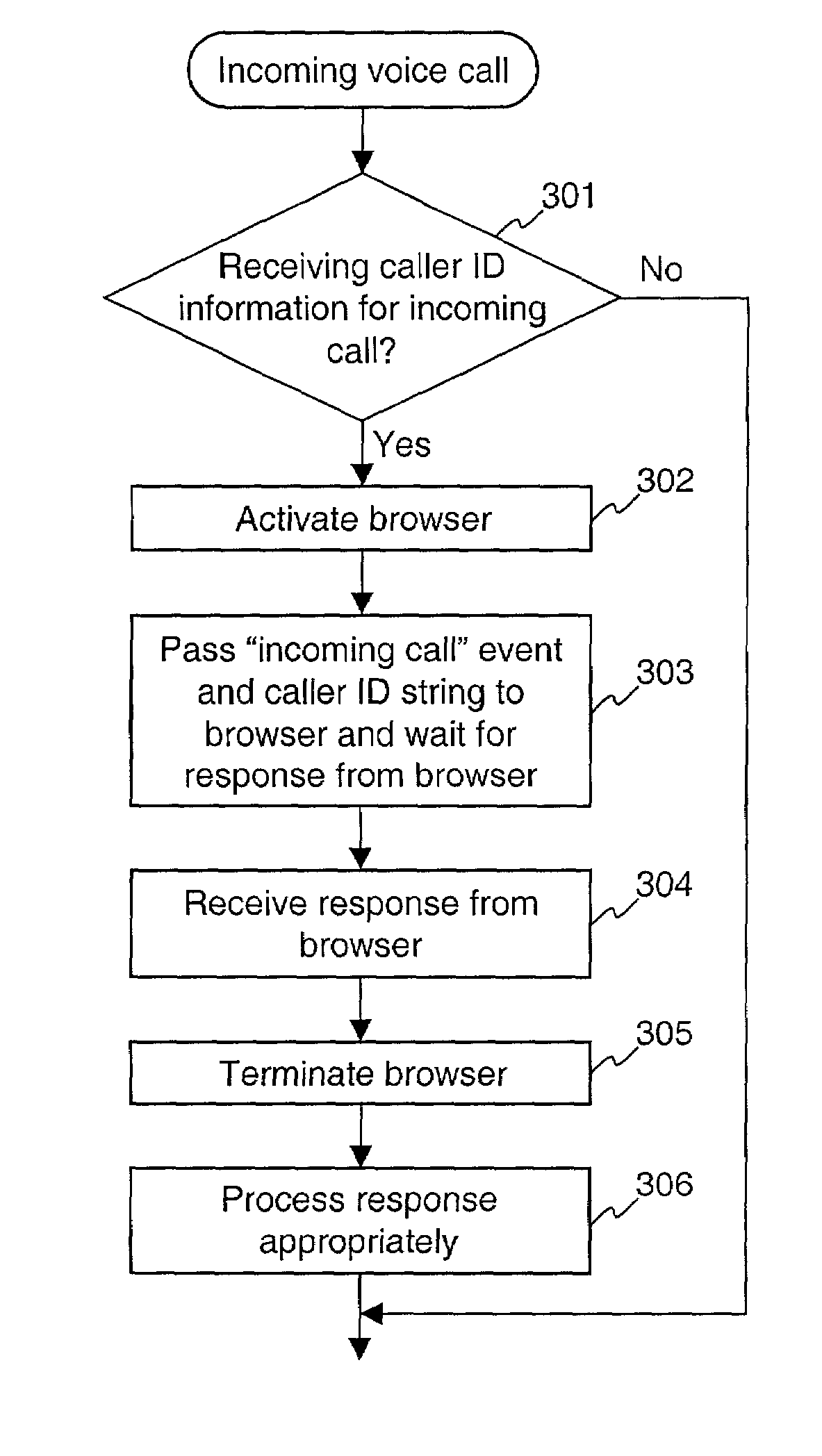
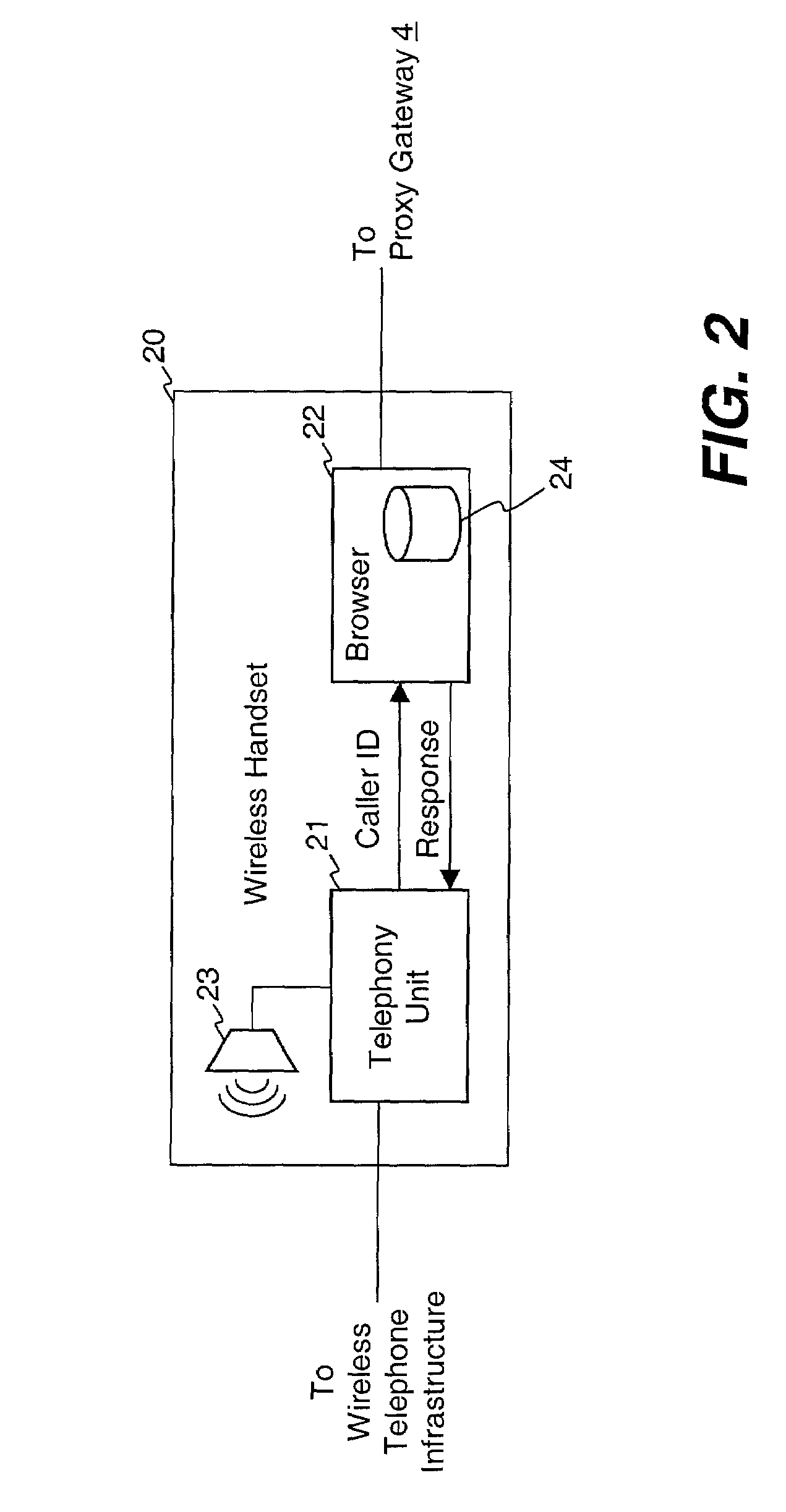
Method and apparatus for using Caller ID information in a browser of a mobile communication device
InactiveUS7127238B2Improve practicalityBetter privacy of userSpecial service for subscribersCalling susbscriber number recording/indicationCommunication deviceMobile telephony
A mobile telephone comprises a telephony unit to process wireless telephony signals and a browser to enable the user to navigate hypermedia information via a wireless network. The telephony unit receives a signal indicating an incoming telephone call with Caller-ID information. The telephony unit provides the Caller-ID information to the browser, which uses the Caller-ID information to identify an action or data previously associated with the Caller-ID information. In one embodiment, the browser looks up ring tone data associated with the Caller-ID information and provides the ring tone data to the telephony unit, which causes a ring tone to be generated based on the ring tone data. Distinctive ring tones may be associated with particular callers or groups of callers. The browser may request ring tone data from a remote server over the wireless network.
Owner:UNWIRED PLANET
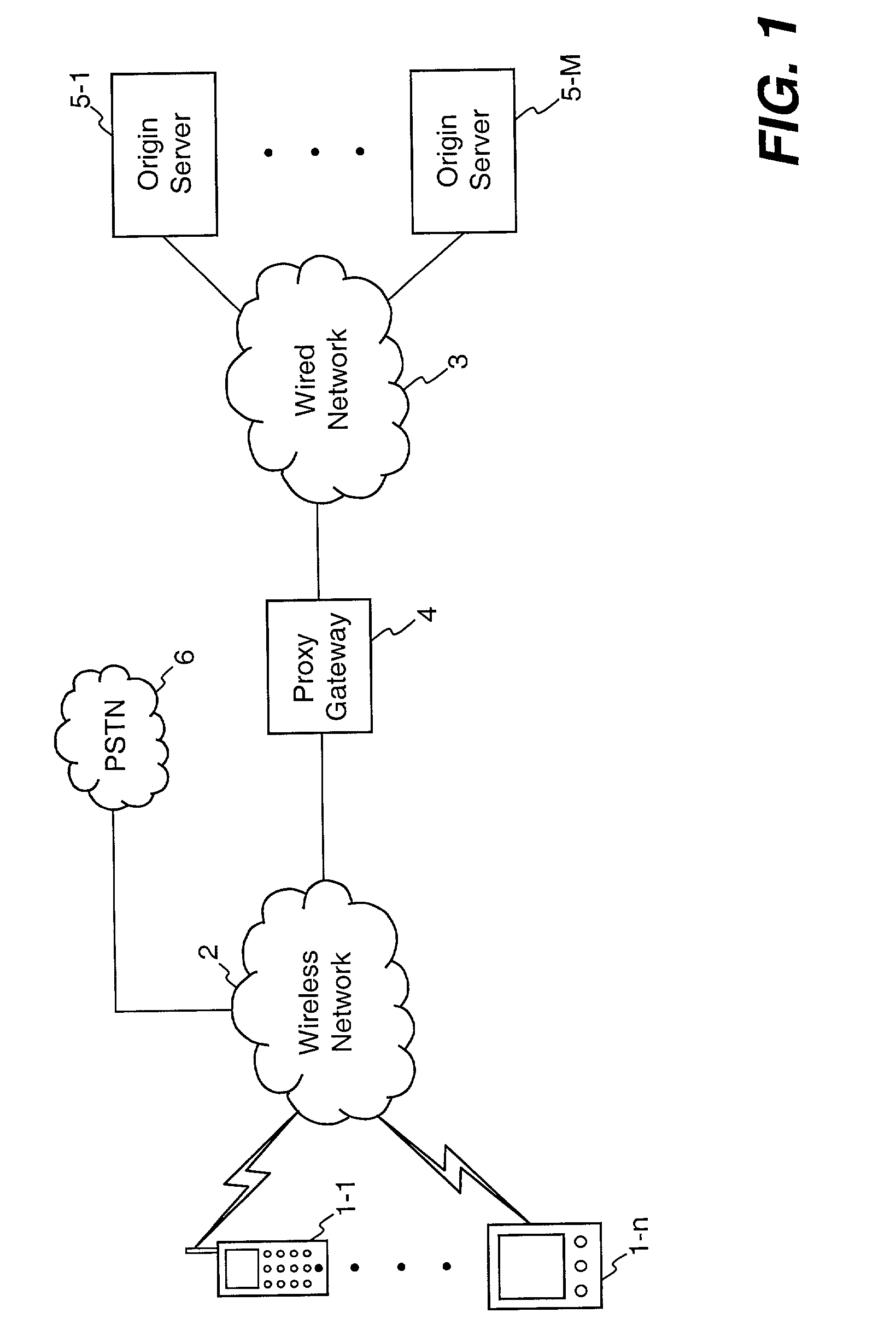
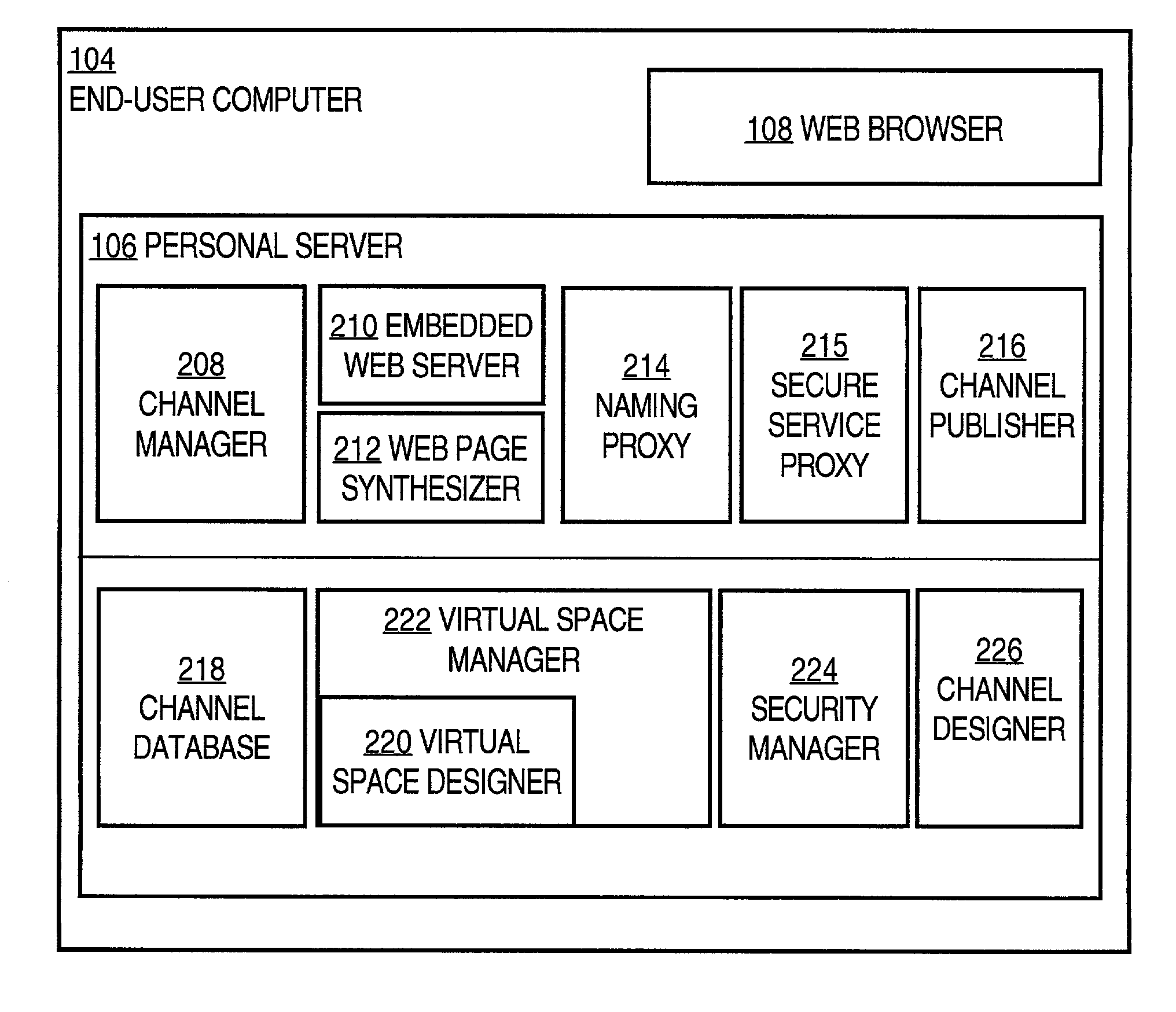
Method and apparatus for network content distribution using a personal server approach
InactiveUS7346649B1Increased complexityImprove sophisticationDigital data information retrievalMultiple digital computer combinationsContent distributionChannel data
A method and apparatus providing network content distribution using a personal server approach is disclosed. A receiving client is provided with a personal server that can select, aggregate, and organize one or more channels of content in a virtual display space of the client. Selection, aggregation, and organization information is stored only locally. Raw data representing content is stored at a logically separate server across a network. Periodically the personal server requests updated content from the server and stores the content in a local channel database. The personal server synthesizes or generates one or more electronic documents containing the content, based on user-defined virtual space specifications and page organization information. The personal server then presents the electronic documents to a browser or other client element. Unlike past approaches that involve distributing fully formatted content to clients, the personal server can receive raw data, replace tokens in the raw data with other content, obtain embedded channel data, and render pages locally, using a conventional browser, without requiring use of a proprietary viewer, and without sending channel selections and other personal information across the network to an untrusted server.
Owner:TAMIRAS PER PTE LTD LLC
Advertising based on widgets
ActiveUS20080010133A1Improve segmentationImprove protectionCommerceSpecial data processing applicationsUser inputElectronic information
Electronic advertisements and other types of electronic information are distributed based on user profiles and in particular, collections of widgets. User profiles may be generated based on a combination of user entered information and information inferred or derived from user behavior and interaction patterns. The use and collection of various widgets may also be recorded by a user profile to determine a user's preferences and interests. An advertisement may be distributed by segmenting a user population according to user profile information and one or more attributes of the advertisement. Users may further interact with the widgets in a variety of ways including requesting additional information about the advertised product or service and / or requesting communications with an advertiser without compromising their privacy.
Owner:NOKIA TECHNOLOGLES OY
Methods for matching, selecting, narrowcasting, and/or classifying based on rights management and/or other information
InactiveUS20030069748A1Difficult to navigateImprove privacyAdvertisementsRelational databasesRights managementUtility system
Rights management information is used at least in part in a matching, narrowcasting, classifying and / or selecting process. A matching and classification utility system comprising a kind of Commerce Utility System is used to perform the matching, narrowcasting, classifying and / or selecting. The matching and classification utility system may match, narrowcast, classify and / or select people and / or things, non-limiting examples of which include software objects. The Matching and Classification Utility system may use any pre-existing classification schemes, including at least some rights management information and / or other qualitative and / or parameter data indicating and / or defining classes, classification systems, class hierarchies, category schemes, class assignments, category assignments, and / or class membership. The Matching and Classification Utility may also use at least some rights management information together with any artificial intelligence, expert system, statistical, computational, manual, or any other means to define new classes, class hierarchies, classification systems, category schemes, and / or assign persons, things, and / or groups of persons and / or things to at least one class.
Owner:INTERTRUST TECH CORP
Umethod, system and program for managing relationships among entities to exchange encryption keys for use in providing access and authorization to resources
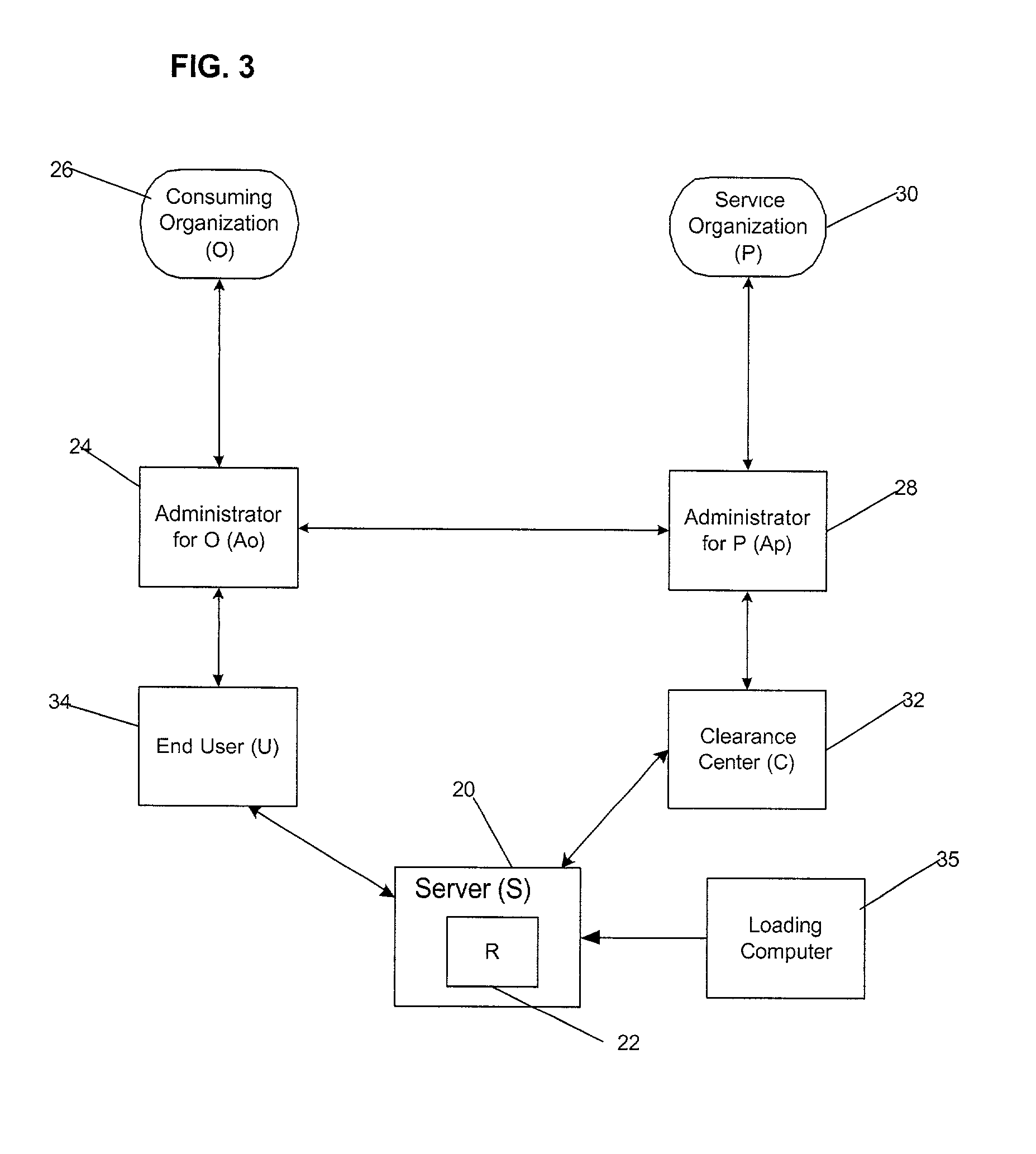
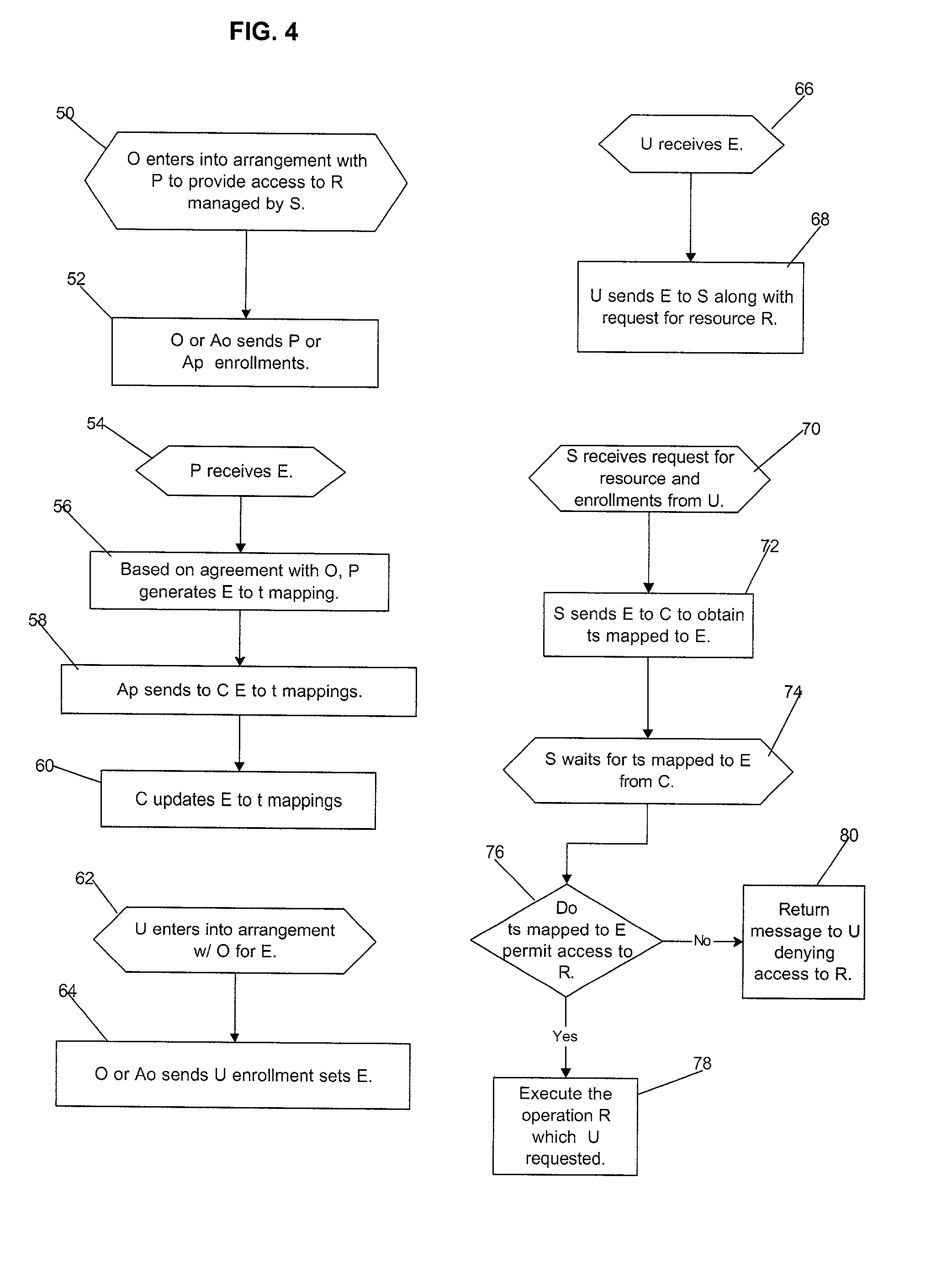
InactiveUS20010020228A1Strong level of assuranceMaintain privacyKey distribution for secure communicationUser identity/authority verificationAuthorizationComputer science
Provided is a method, system, and program for managing access to resources. Encryption keys are exchanged among a first entity, second entity, third entity, and a fourth entity. Each entity has one relationship with one other entity and the encryption keys are exchanged pursuant to the relationships. Electronic messages are encrypted with the encryption keys concerning digital enrollments to provide to the first entity. The digital enrollment is associated with at least one digital ticket that authorizes access to a resource managed by the fourth entity. Presentation of the digital enrollment causes the presentation of one digital ticket associated with the digital enrollment to authorize the first entity to access the resource.
Owner:IBM CORP
Abstractions and automation for enhanced sharing and collaboration
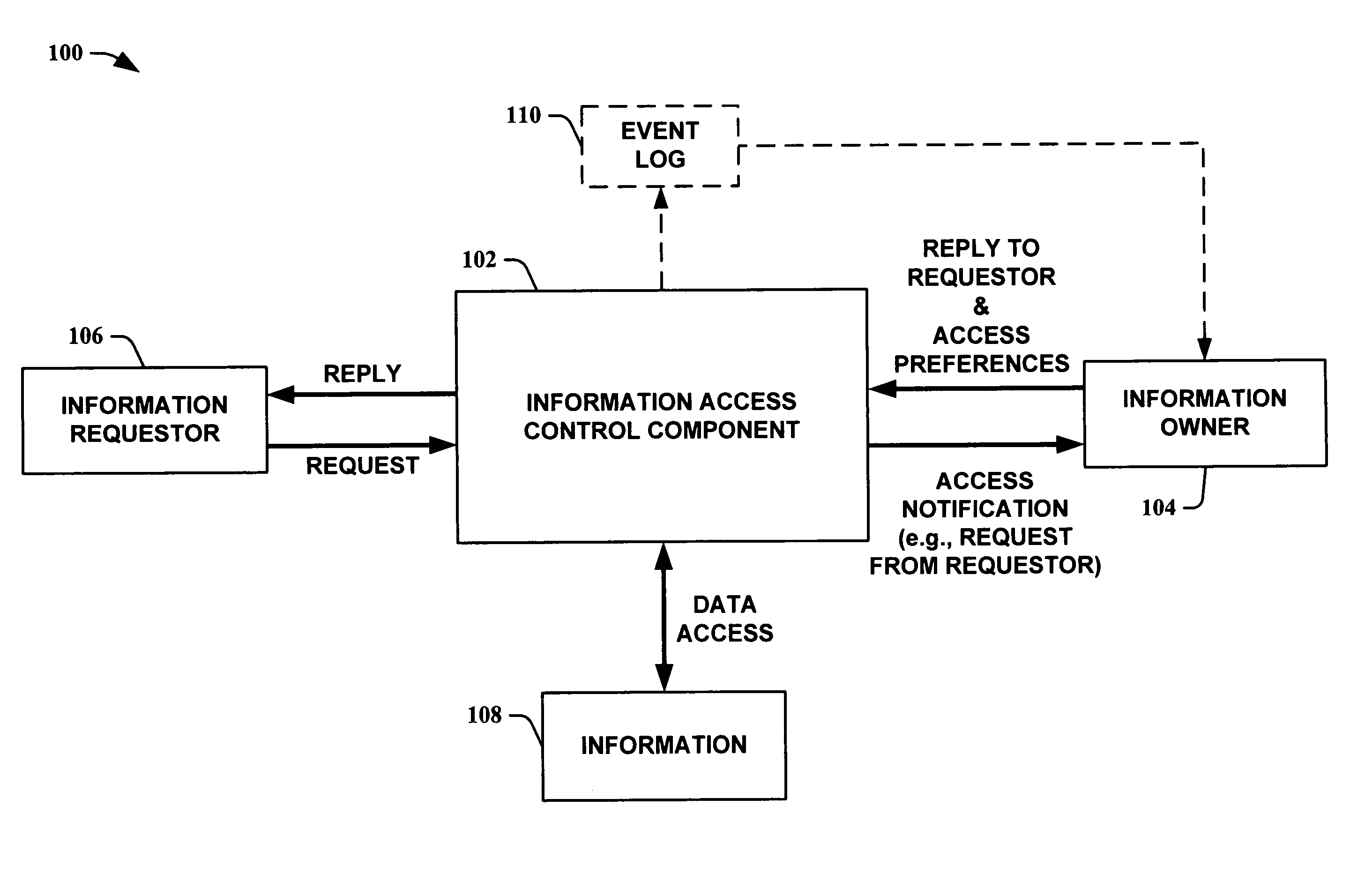
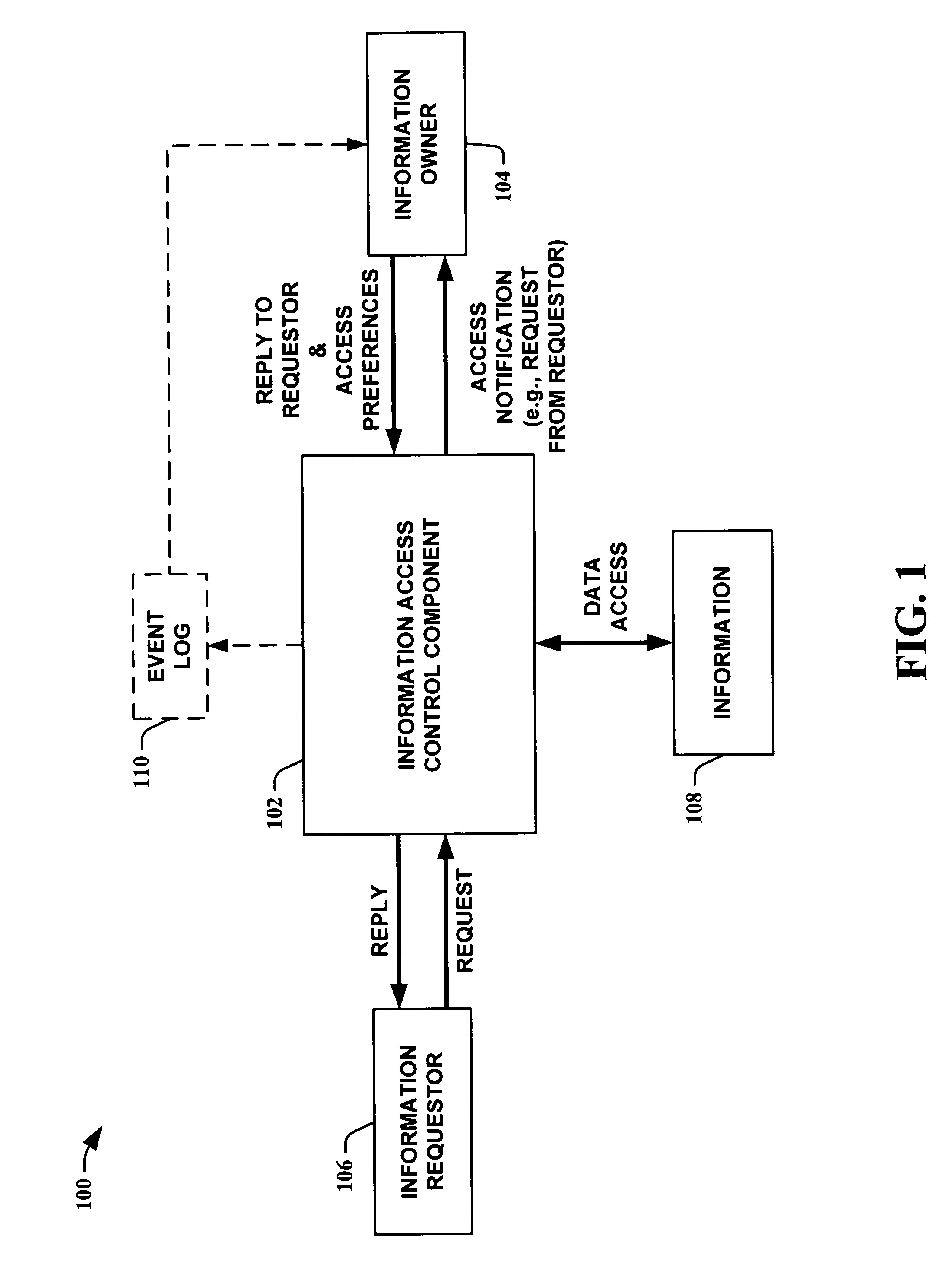
InactiveUS20050232423A1Optimal information privacyReduce the burden onDigital data processing detailsUser identity/authority verificationInformation sharingCrowds
The present invention provides methods for using abstractions of people, including dynamic and static groups of people, to enhance the efficiency of the specification and automation of policies for sharing information between users with a “need-to-know.” An instance of the present invention can also provide these users information based on a “time-to-know.” By providing access to information based on group affiliation and properties of the content of the information, the present invention maintains optimal information privacy while minimizing encumbrances to sharing data with appropriate users and even at appropriate times. The present invention can be integrated with other communication technologies to facilitate access to information in a time appropriate manner. Other instances of the present invention employ automated and semi-automated, mixed-initiative techniques, to make information-sharing decisions. Additional instances of the present invention include the employment of machine-learning techniques to facilitate construction of access policies from the actions or profile of a single user or a community of users, including the construction of automated sharing agents that work in an automated or mixed-initiative manner to respond to real-time requests for information.
Owner:MICROSOFT TECH LICENSING LLC
Enhancing smart card usage for associating media content with households
InactiveUS7124938B1Improve privacyEasy to changeAcutation objectsPayment architectureUser privacySmart card security
Various enhancements are made to using smart cards that are associated with (or to be associated with) a household. In one embodiment, data that is expected to be of value to a user (e.g., electronic money) is attached to that user's smart card(s), thereby providing an incentive for the user to keep his or her smart card(s) secure. In another embodiment, the smart cards are used for parental control (e.g., by restricting the children's access to one or more of the smart cards). In yet another embodiment, smart cards are used to enhance user privacy by maintaining user-specific information on the smart cards (which can be de-coupled from the computing device whenever the user desires). In another embodiment, the boundaries of a network of computing devices are defined by multiple smart cards—any computing device to which a smart card is coupled is part of the network.
Owner:MICROSOFT TECH LICENSING LLC
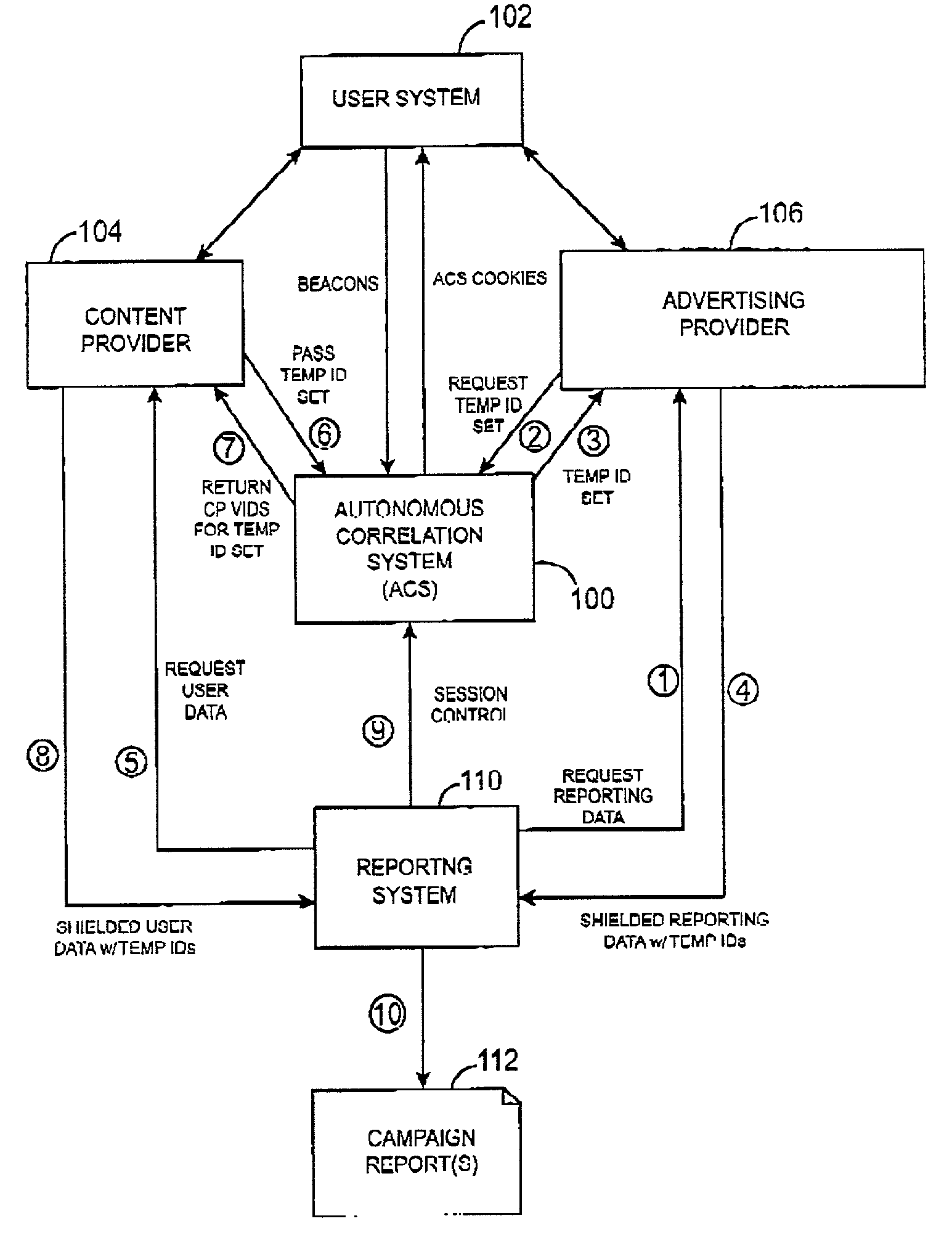
System and method for correlating user data from a content provider and user data from an advertising provider that is stored on autonomous systems
ActiveUS7257546B2Increase valueProtect user privacyAdvertisementsAnalogue secracy/subscription systemsReference databaseUser identifier
An autonomous correlation system correlates user data from a content provider and advertising view data from an advertising provider, wherein the user data is present on one autonomous system and the advertising view data is present on another autonomous system distinct from the one autonomous system, the systems being autonomous in that each is normally secured against unconstrained access by another. The autonomous correlation system comprises logic to accept a first message from a user, wherein the first message contains an indication of an object being presented to the user, the object being at least one of a content page and an advertisement, a first user identifier associated with the user by a presenter of the object; a reference database for storing an association between the first user identifier and the user; logic to accept a second message from the user, wherein the second message contains an indication of an object being presented to the user, the object being at least one of a content page and an advertisement, a second user identifier associated with the user by a presenter of the object; wherein the reference database stores an association between the second user identifier and the user.
Owner:PINTEREST
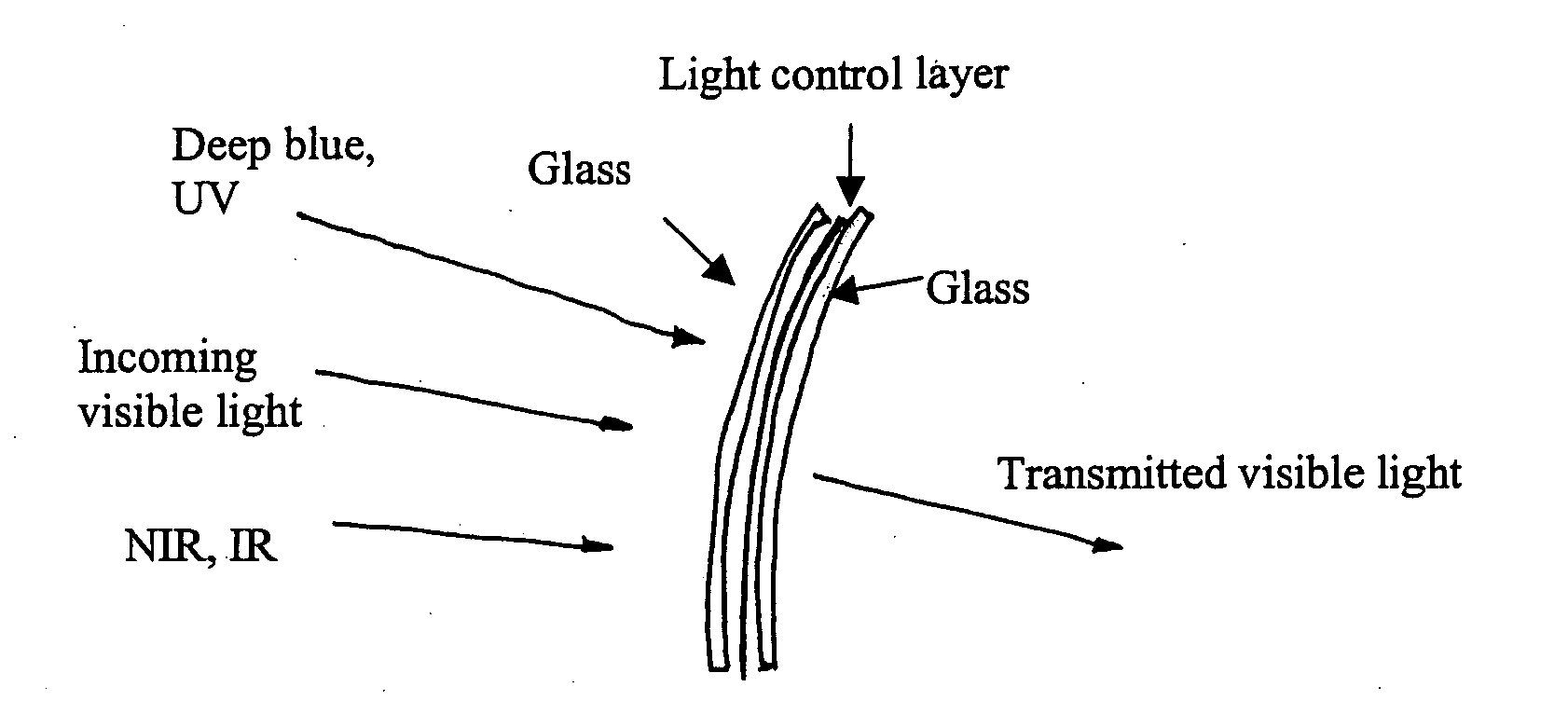
Adjustably opaque window
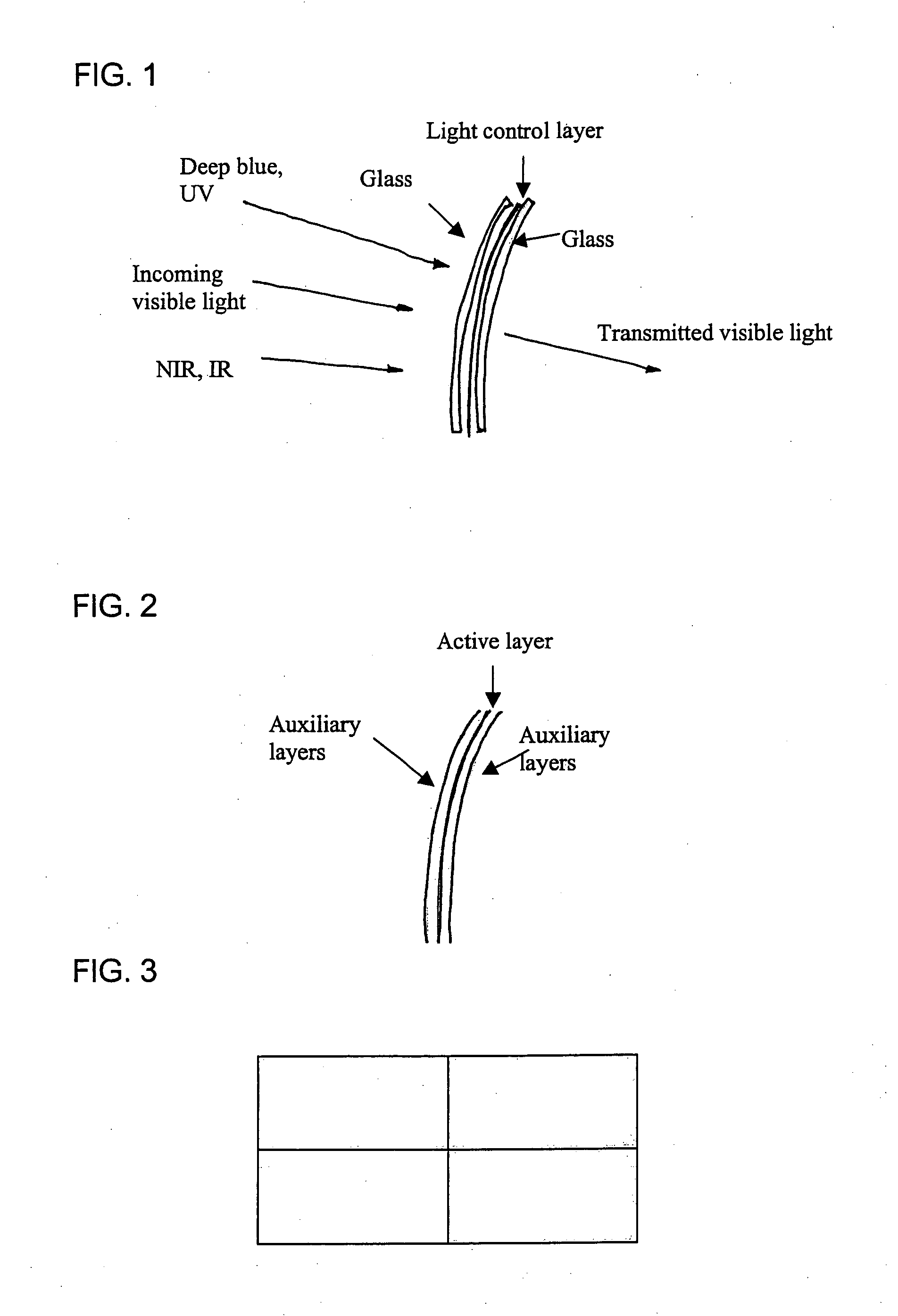
InactiveUS20050068629A1Reduce decreaseMinimized and eliminatedLight dependant control systemsAntiglare equipmentControl layerLight transmission
An adjustably opaque window including an external pane, an internal pane, a light transmission control layer and a shock-absorbing layer is provided. The external pane and the internal pane provide a cavity between them, and the light transmission control layer and the shock-absorbing layer are positioned in the cavity. The shock-absorbing layer is a flexible sheet that supports and protects the light transmission control layer. The light transmission layer consists of liquid crystal cells. The transmission ratio of the cells can be controlled variably.
Owner:LCT ENTERPRISES
Aircraft cabin seat configuration with enhanced ingress/egress
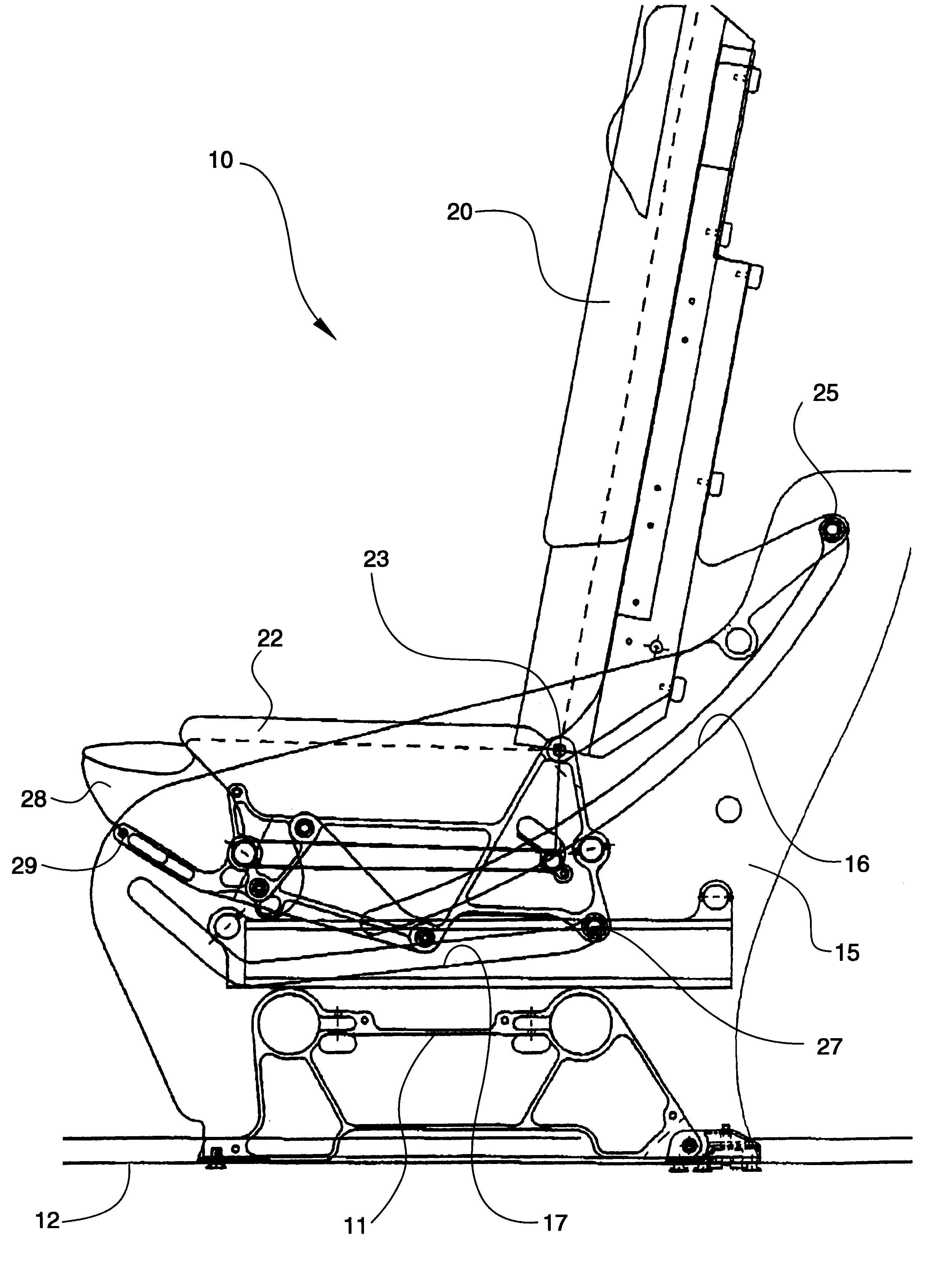
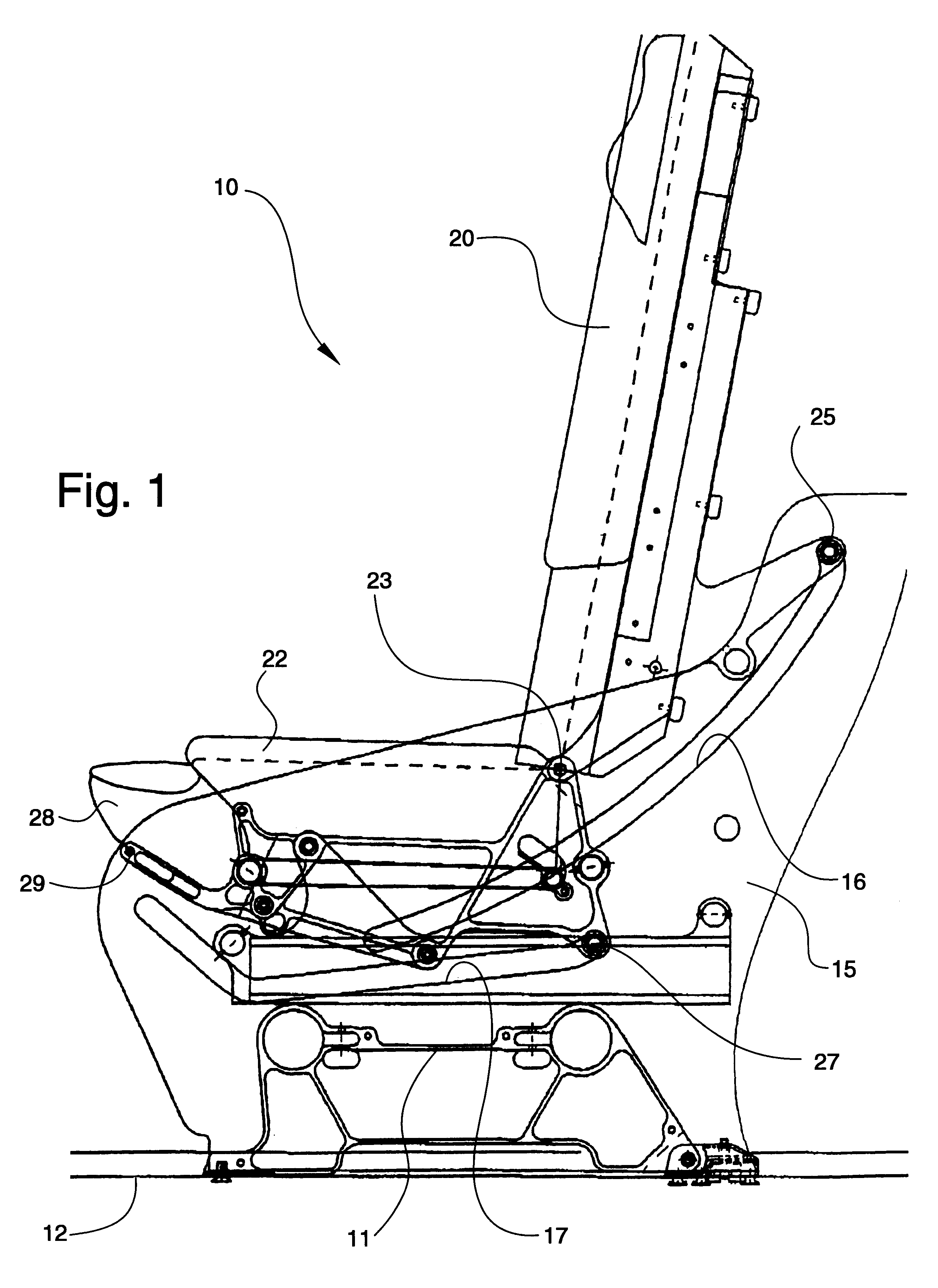
InactiveUS6305644B1Enhanced ingres and egressEnhanced and egressVehicle seatsSeating arrangementsAirplaneNacelle
A passenger seat configuration for an aircraft cabin having a fuselage wall with windows therein and an aisle for permitting movement within the cabin. The configuration includes an outboard seating unit for being positioned adjacent the fuselage wall of the aircraft, the outboard seating unit having a primary scat formed of a seat back and seat bottom, and a forwardly spaced-apart ottoman movable with respect to each other to define upright, semi-reclined and fully reclined positions. An inboard seating unit is provided for being positioned adjacent the at least one aisle and between the inboard seating unit and the aisle, the inboard seating unit having a primary seat formed of a seat back and a seat bottom, and a forwardly spaced-apart, free-standing ottoman movable with respect to each other to define upright, semi-reclined and fully reclined positions, the primary seat and ottoman of the inboard seating unit being positioned aft of the primary seat and ottoman of the outboard seating unit. The ottoman of the outboard seating unit and the ottoman of the inboard seating unit are independently movable relative to each other whereby the outboard ottoman is movable to a position relative to any position of the inboard ottoman to thereby provide space between the inboard ottoman and outboard ottoman for the outboard passenger to ingress to and egress from the outboard primary seat between the inboard ottoman and outboard ottoman and forward of the inboard ottoman to the aisle.
Owner:B E AEROSPCAE
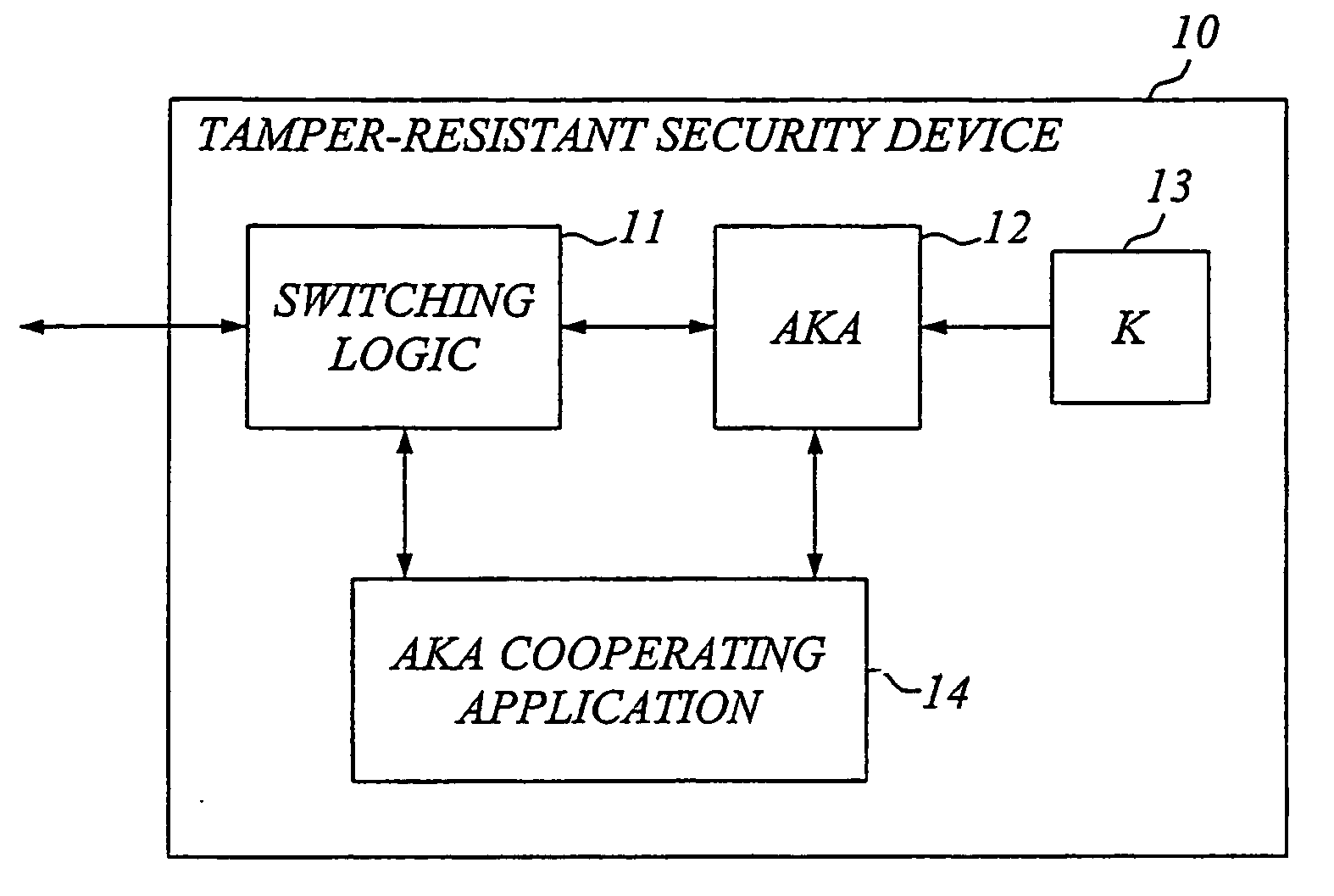
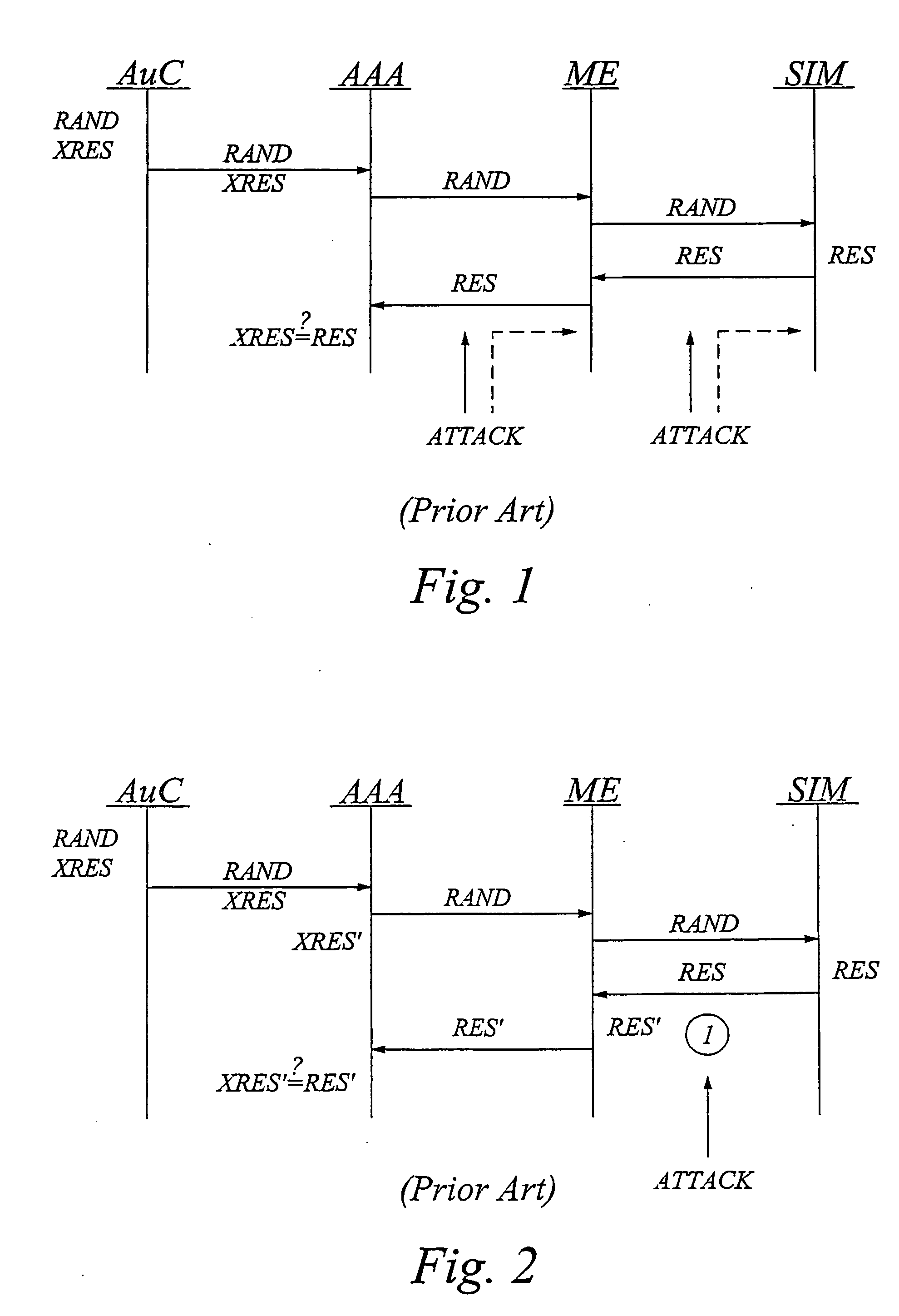
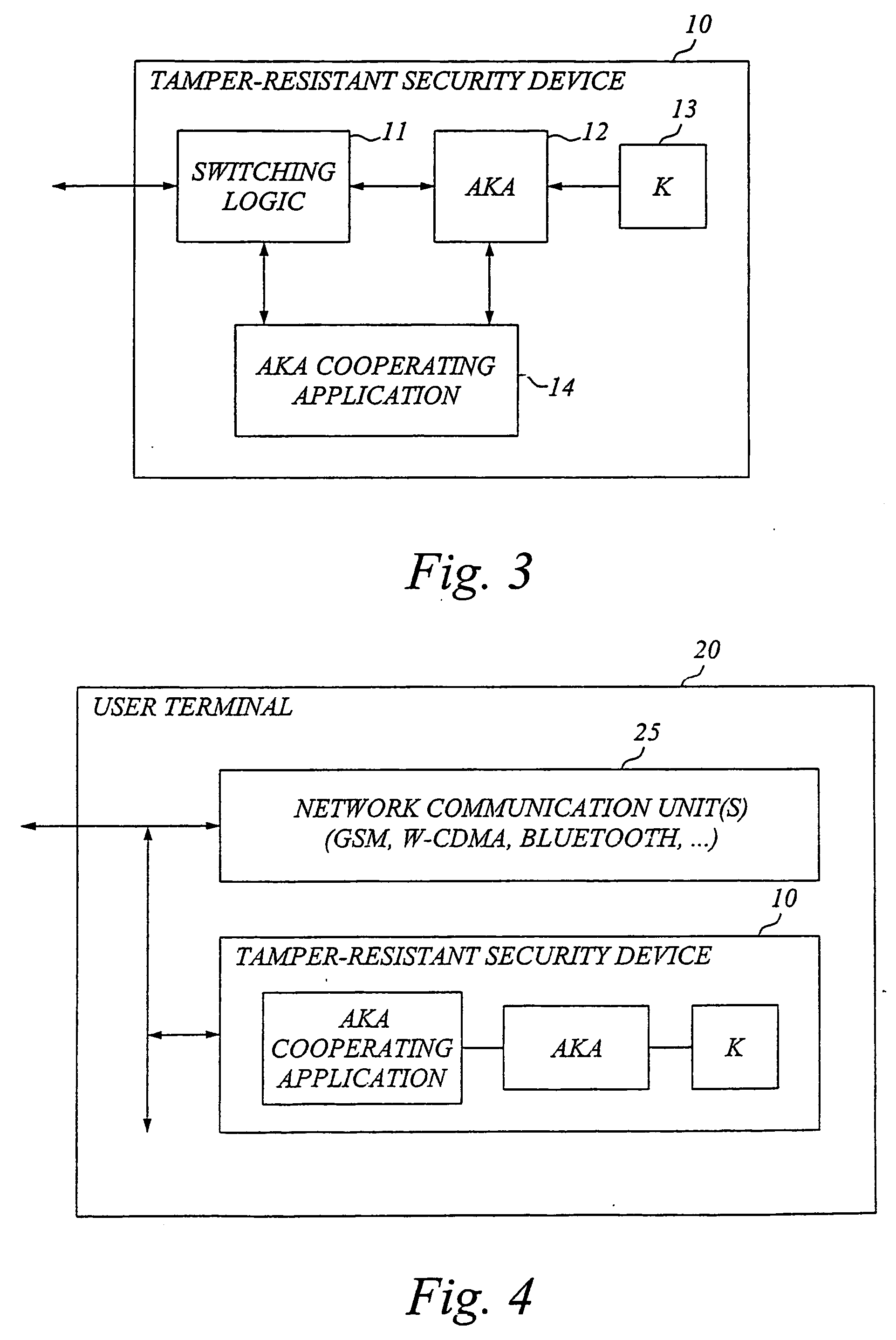
Security and privacy enhancements for security devices
InactiveUS20060288407A1Improve securityImprove privacyKey distribution for secure communicationPublic key for secure communicationInternet privacySubscriber identity module
The invention generally relates to a tamper-resistant security device, such as a subscriber identity module or equivalent, which has an AKA (Authentication and Key Agreement) module for performing an AKA process with a security key stored in the device, as well as means for external communication. The idea according to the invention is to provide the tamper-resistant security device with an application adapted for cooperating with the AKA module and means for interfacing the AKA module and the application. The application cooperating with the AKA module is preferably a security and / or privacy enhancing application. The application is advantageously a software application implemented in an application environment of the security device. For increased security, the security device may also be adapted to detect whether it is operated in its normal secure environment or a foreign less secure environment, and set access rights to resident files or commands that could expose the AKA process or corresponding parameters accordingly.
Owner:TELEFON AB LM ERICSSON (PUBL)
Systems and methods for communication protection
ActiveUS7236598B2High protection levelImprove privacyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile Telephone ServiceCommunications system
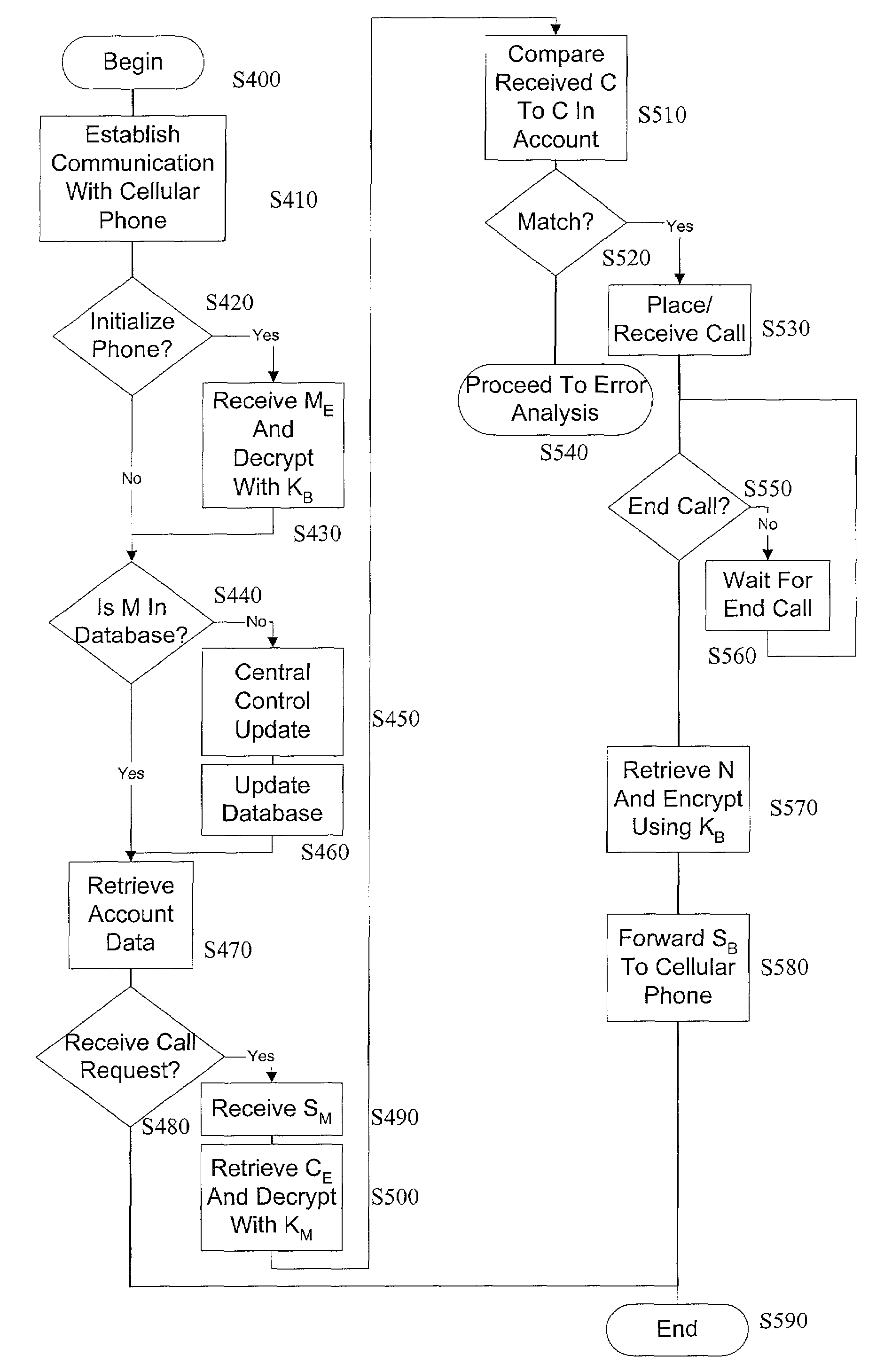
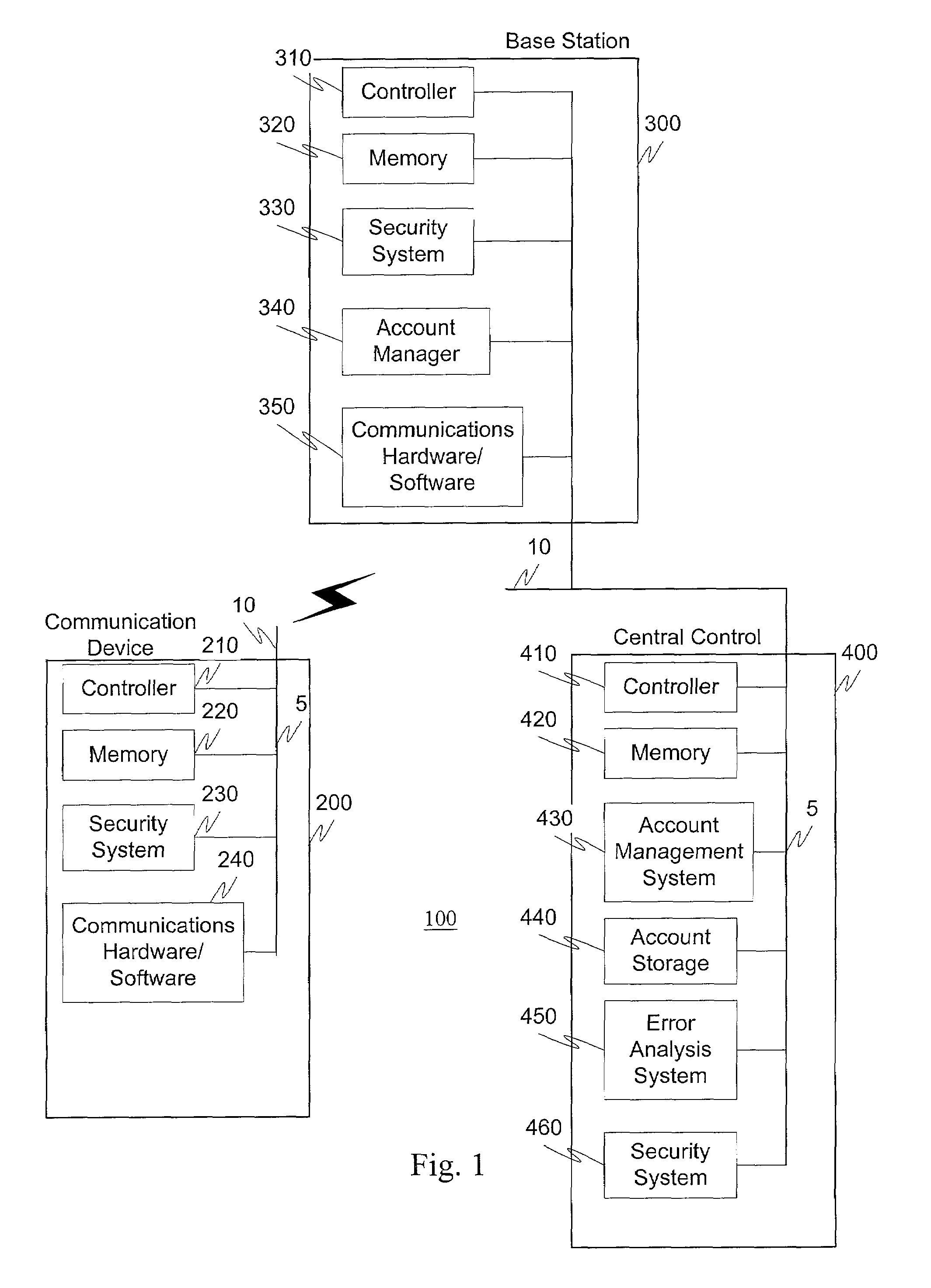
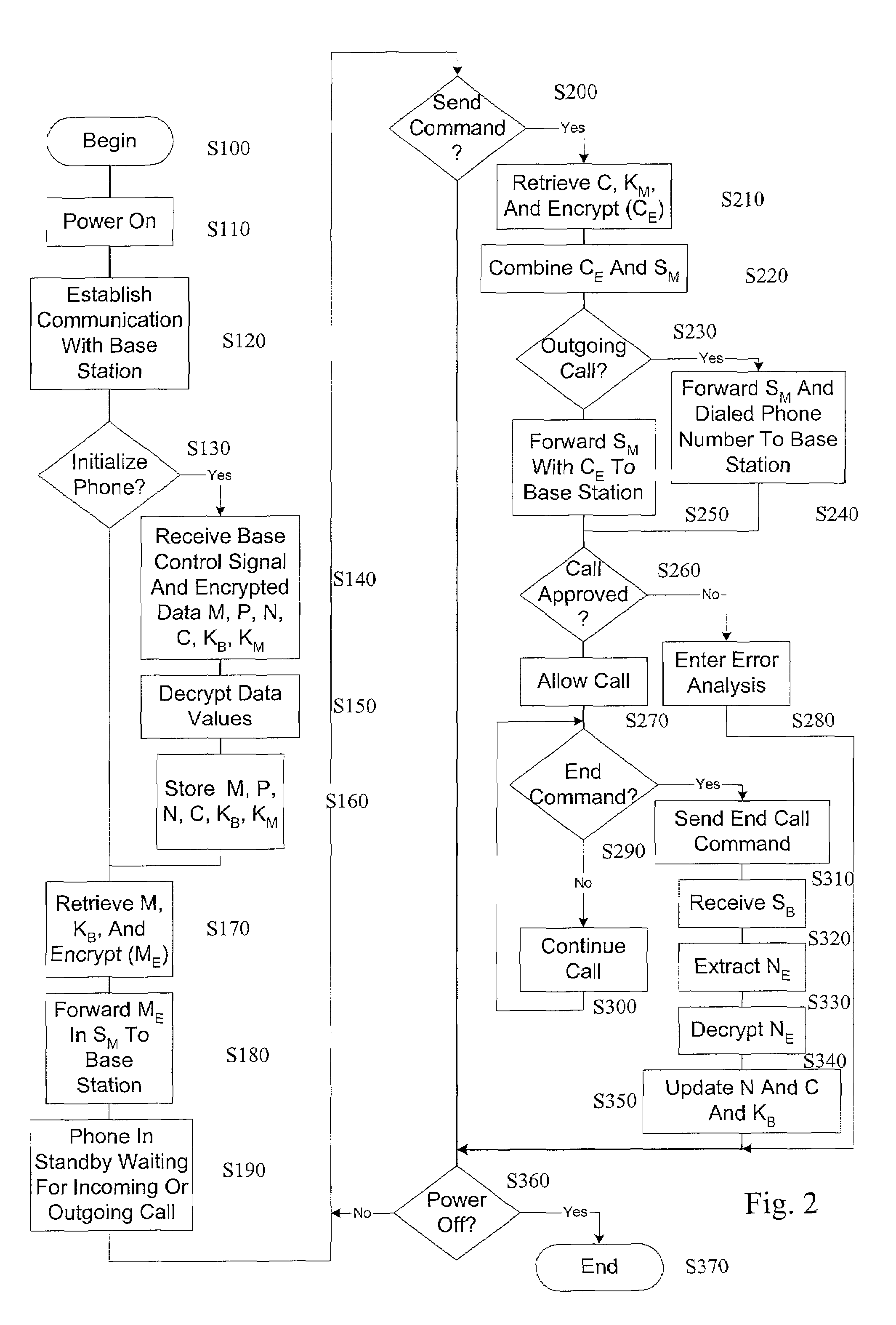
A communications system and method is provided to reliably protect communication systems, such as mobile phone systems, from unauthorized use, as well as to make the interception of wireless communication more difficult. Specifically, the static wireless phone number or other similar identifiers are not used for identification and authorization during communication between the mobile unit and a base station. Instead, a set of private identifiers is determined and is known only to the phone company and the base stations controlling the mobile phone calls. These private identifiers allow dynamic and continual updating of the mobile phone and base station directories with current valid identifiers that are used for communication between the devices.
Owner:INVICTA NETWORKS INC
System and method for providing a secure connection between networked computers
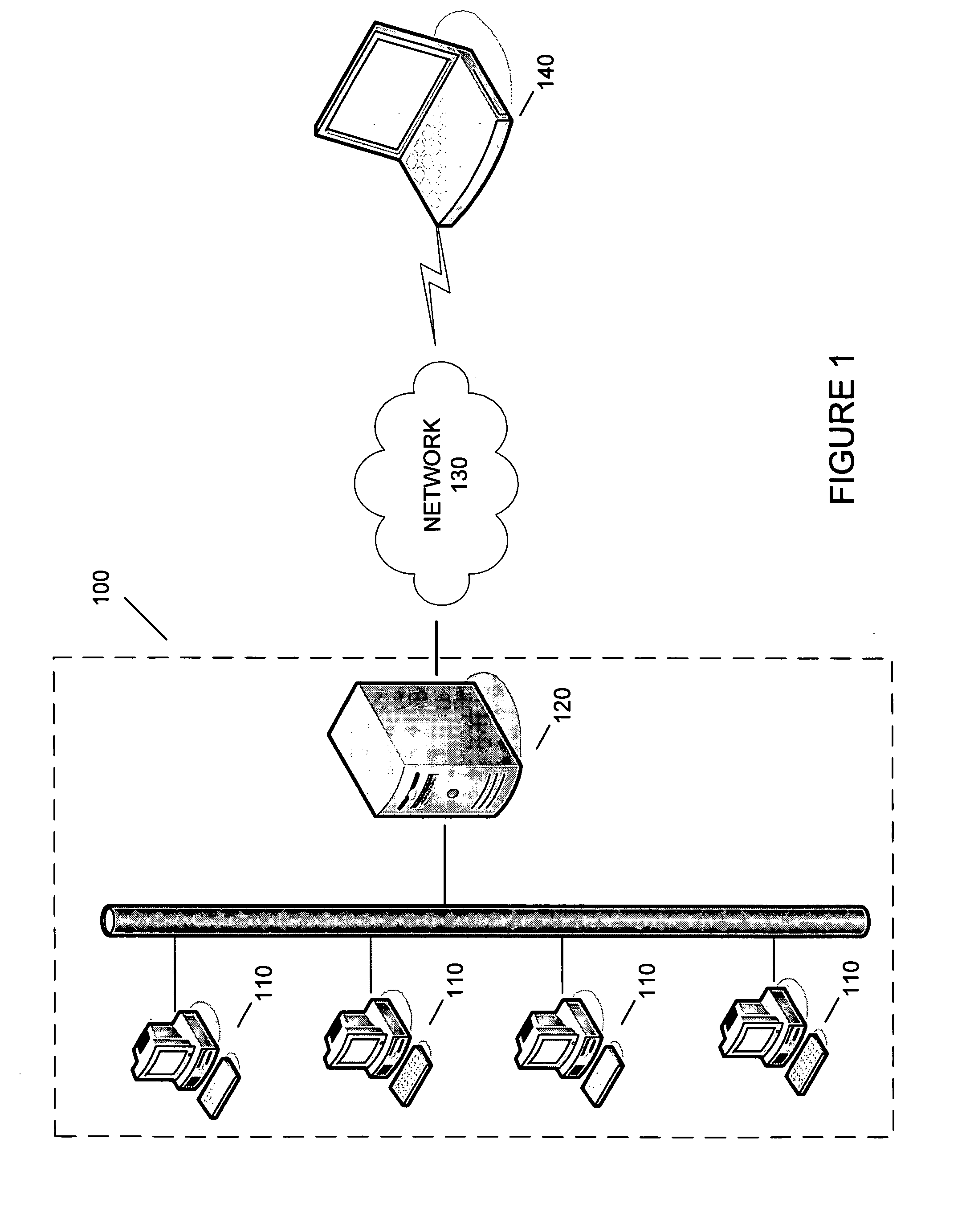
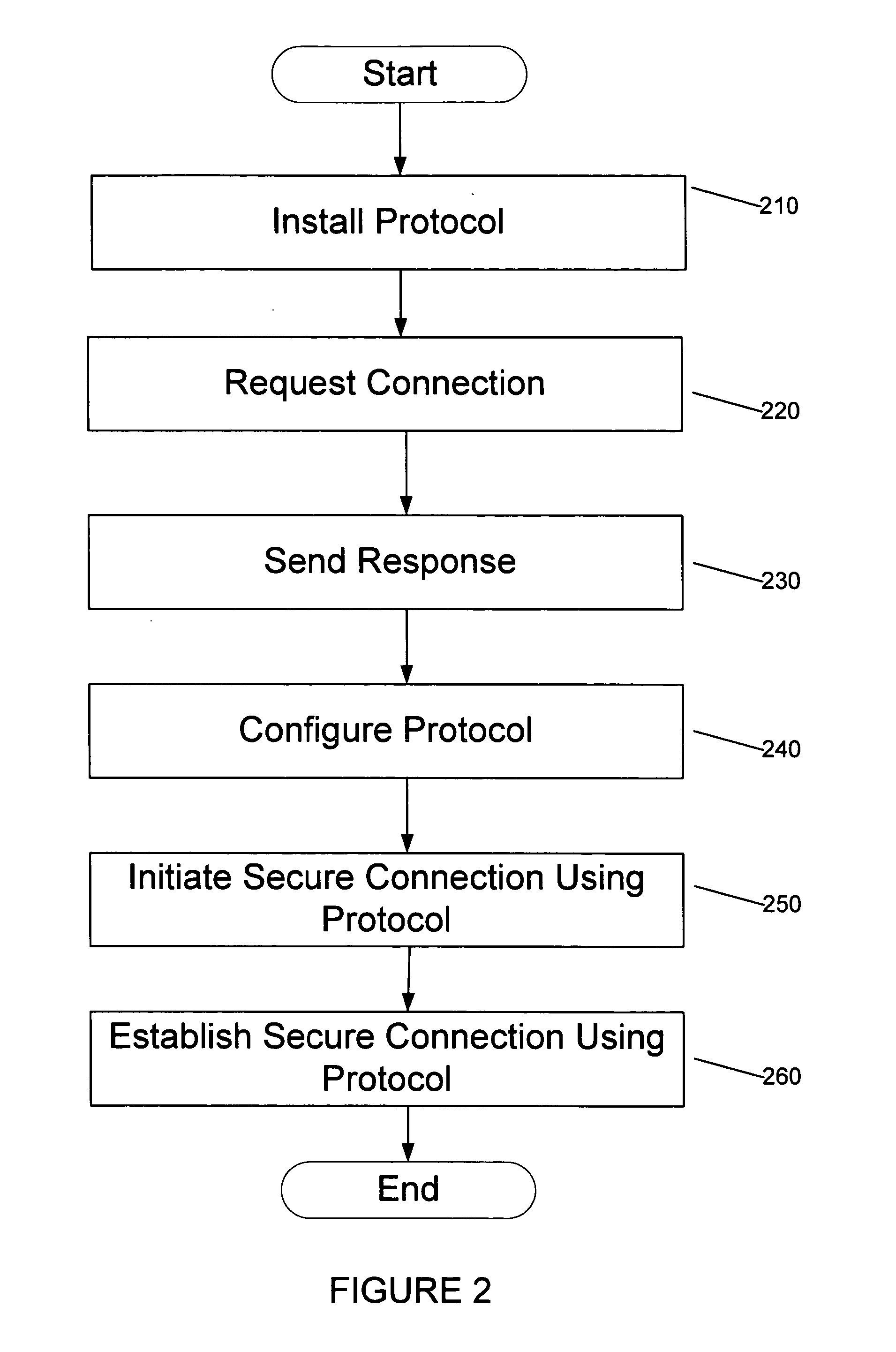
ActiveUS20050044350A1Improve privacyConnection securityDigital data processing detailsHardware monitoringAuto-configurationOperational system
Owner:RPX CORP
Mobile phone telephone and message anti-disturbance and private communication method and system
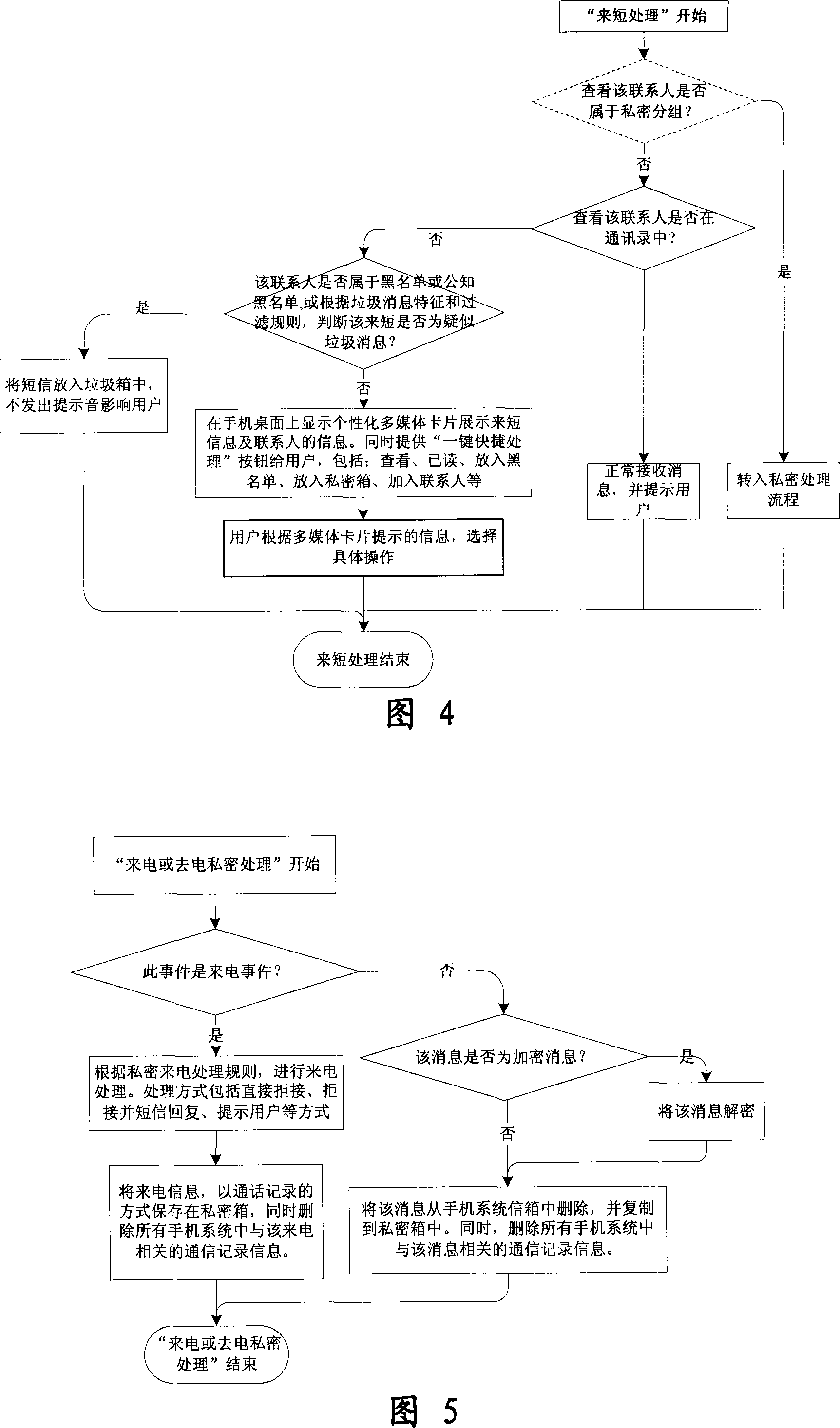
InactiveCN101184264AImprove filtering effectOptimize the effect of anti-harassmentRadio/inductive link selection arrangementsSubstation equipmentPrivate communicationSocial statistics
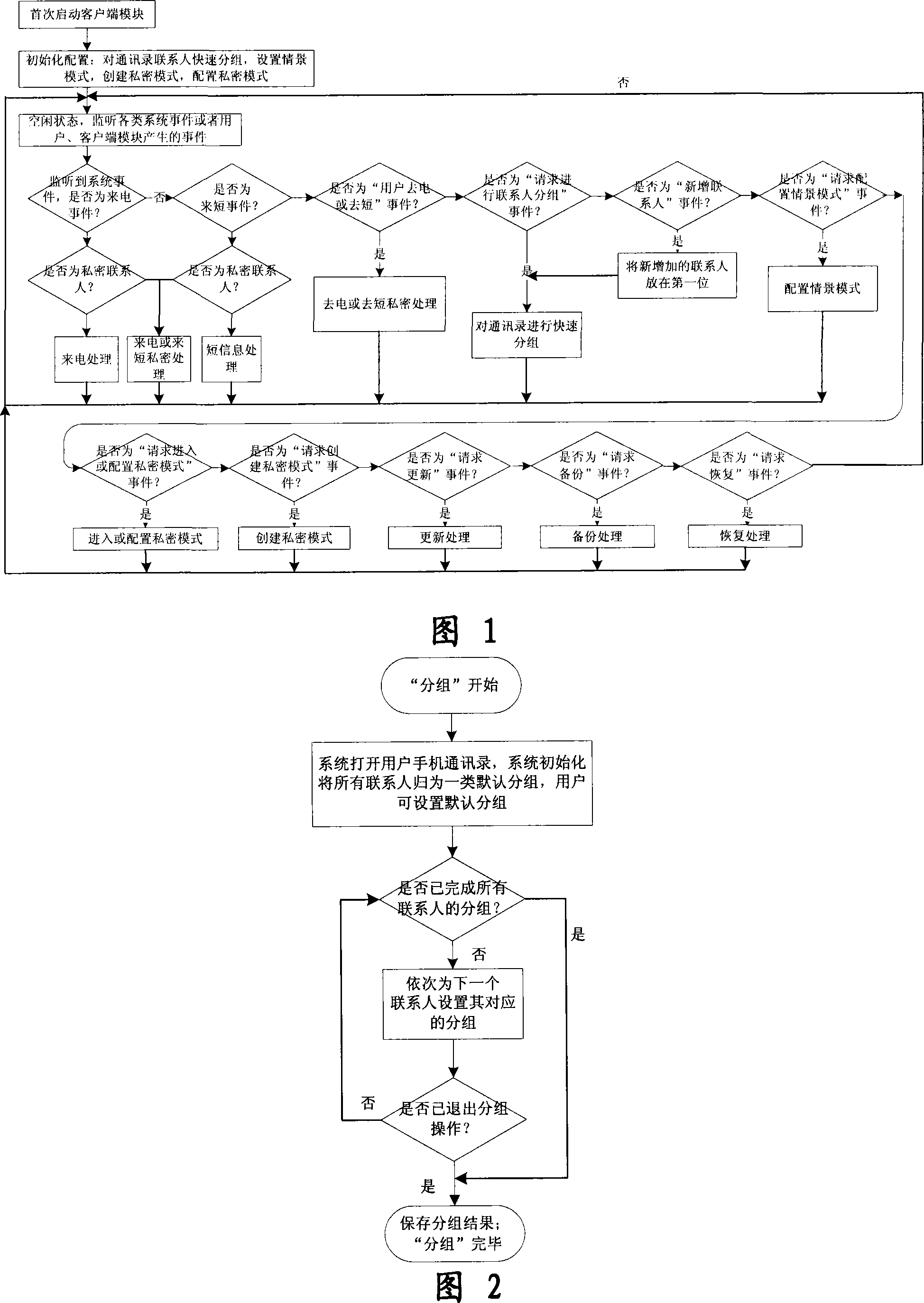
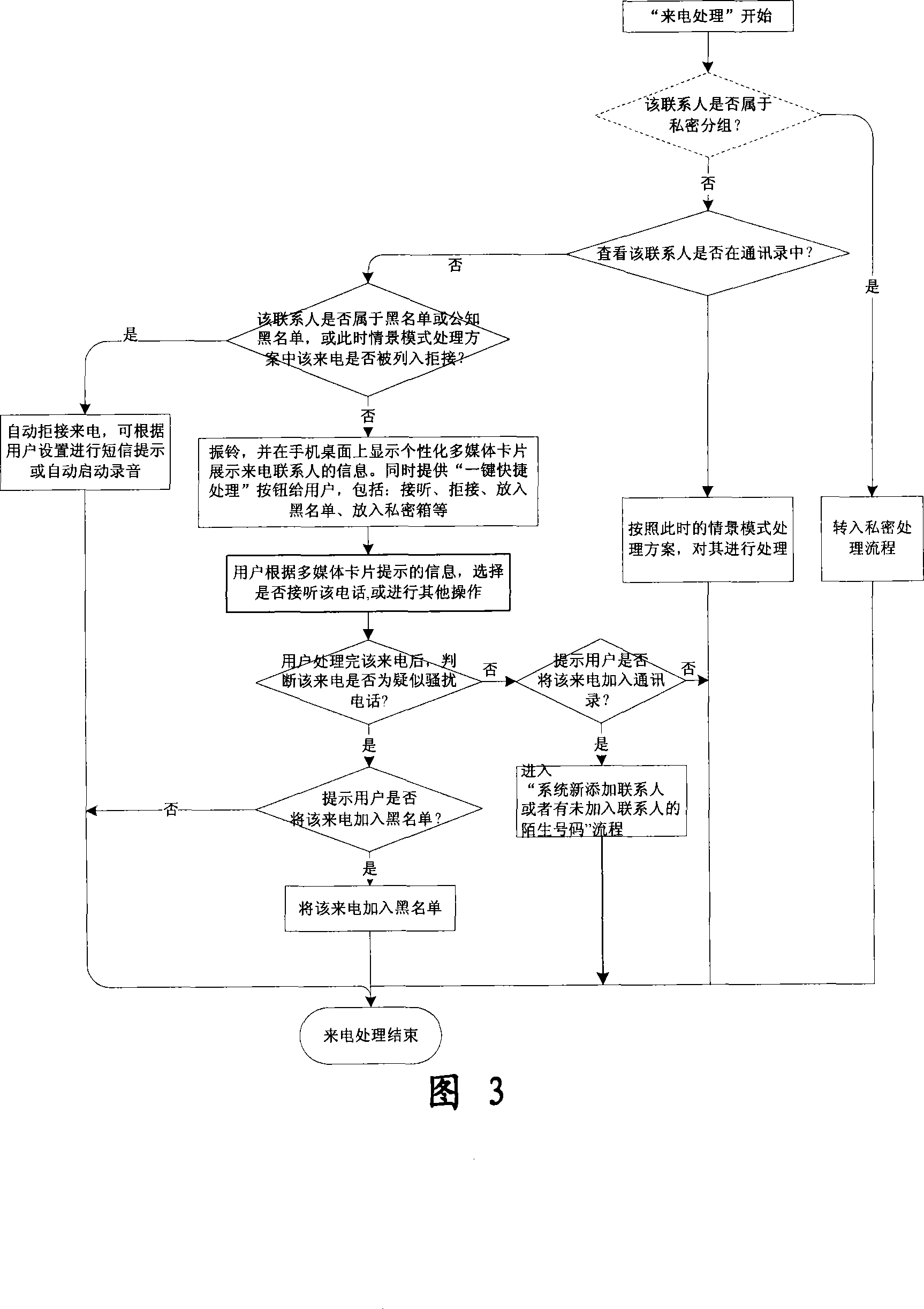
The invention relates to a processing method and the system of anti-harassment of mobile phone calls and messages and private communication, which is as follow: when grouping the contacts in the mobile phone address list according to different classes, a private group of private communicating contacts is added, and different scene modes of the user are set; when receiving a mobile phone call or a message (text message, multimedia message), depending on the grouping sort of the contact of the incoming call or the message or the multimedia message, and the current scene of the user, together with the behavior characteristics of the harassing call and the spam message with the database information of the public harassing message issued by the authoritative institution or obtained from social statistics, the corresponding process to the call, the message and the multimedia message of the mobile phone is executed to reduce harassment; meanwhile the communication records of incoming, dialed calls and message, multimedia message with the contacts in the private grouping are encrypted and preserved to protect the personal privacy of the user. The invention has the advantages of adopting the operating steps of uniform process, and resolving synthetically the harassment of calls, messages and multimedia messages for the mobile phone and the private protection.
Owner:BEIJING NETQIN TECH
Voice control method and system for electronic device
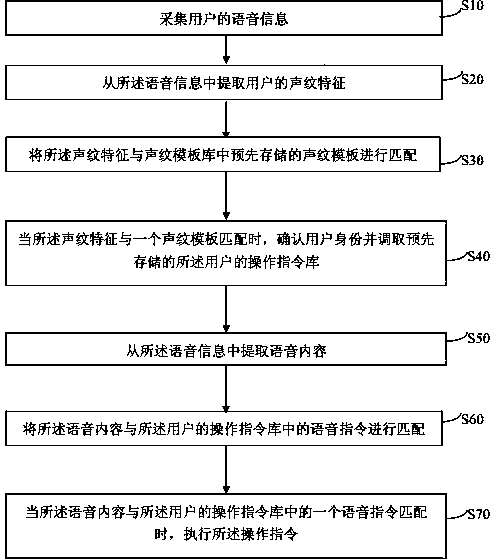
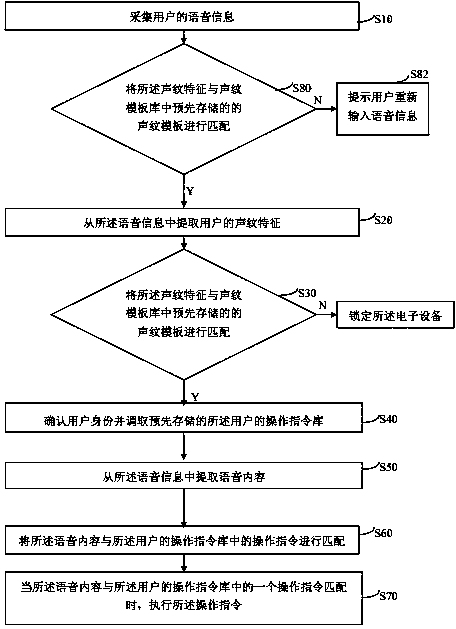
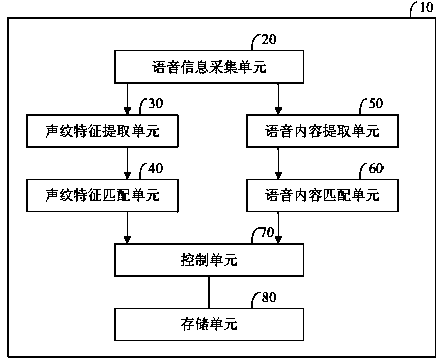
InactiveCN103730120AImprove securityImprove privacySpeech recognitionTemplate matchingTemplate based
The invention discloses a voice control method and system for an electronic device. The voice control method comprises the following steps: voice information of a user is acquired; a voice print feature of the user is extracted from the voice information; the voice print feature of the user is matched with voice print templates prestored in a voice print template base; when the voice print feature of the user is matched with one voice print template, the identity of the user is determined, and a prestored operation instruction base of the user is called; voice content is extracted from the voice information; the voice content is matched with operation instructions in the operation instruction base of the user; when the voice content is matched with one operation instruction in the operation instruction base of the user, the operation instruction is executed. According to the voice control method and system for the electronic device, the identity of a legal user of the electronic device is verified by matching the voice print feature of the user, so that illegal operation by illegal users is effectively prevented, and the safety and the privacy of the electronic device are improved; the operation instructions are executed by matching the voice content of the user, so that voice control is realized.
Owner:SHENZHEN ARATEK BIOMETRICS TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com