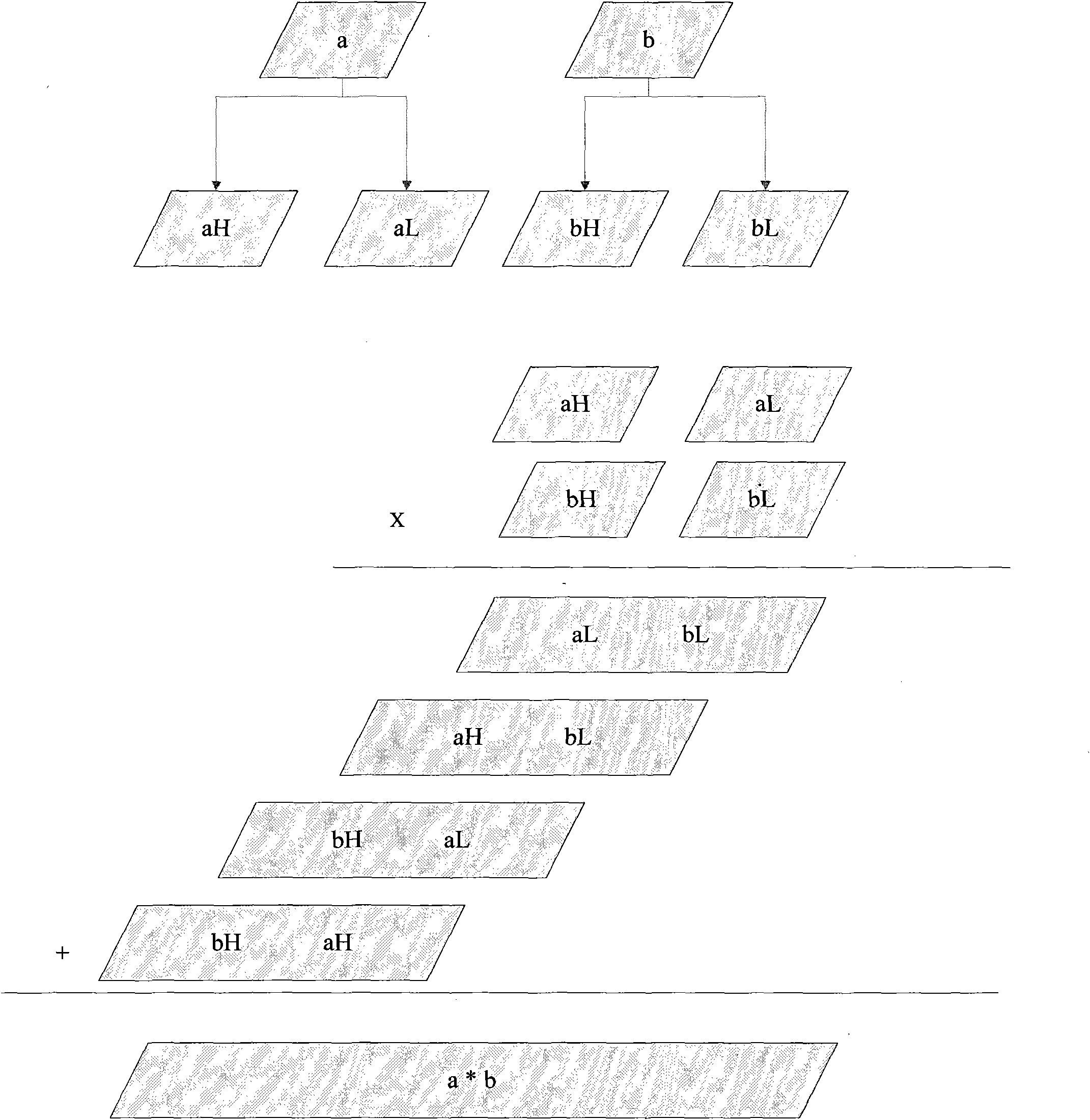Patents
Literature
78 results about "Smart card security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
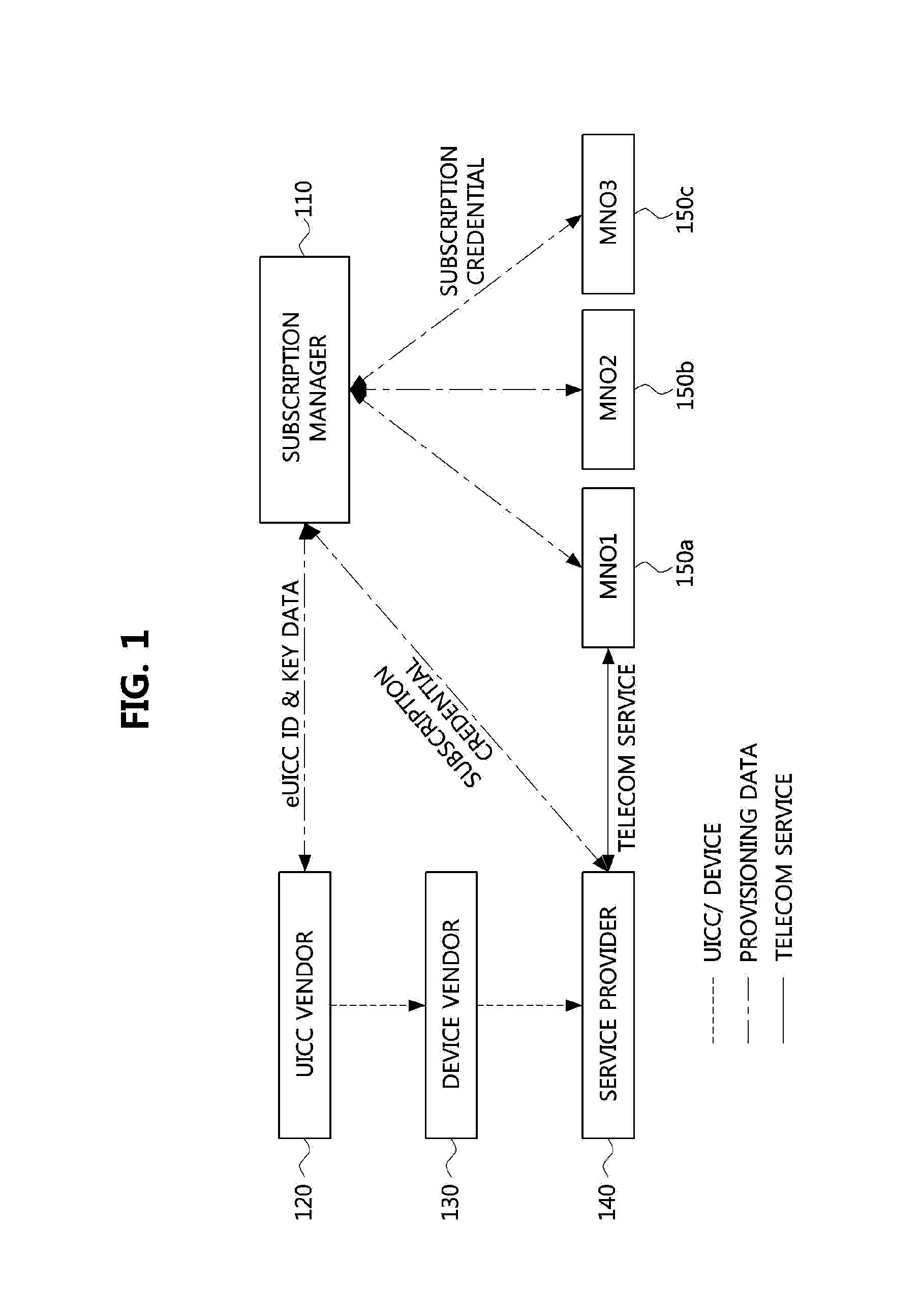
The security of a smart card system consists of the front-end enforcement, front-end and back-end verification, back-end audit and system fraud damage control. Security is addressed at the system level. Technically Mifare cards can be emulated. However if the system security design is correct, fraud is only possible with a collaborating cardholder or merchant. It is improbable that a merchant would accept a payment with the cardholder carrying a big emulator to pay for the transaction.
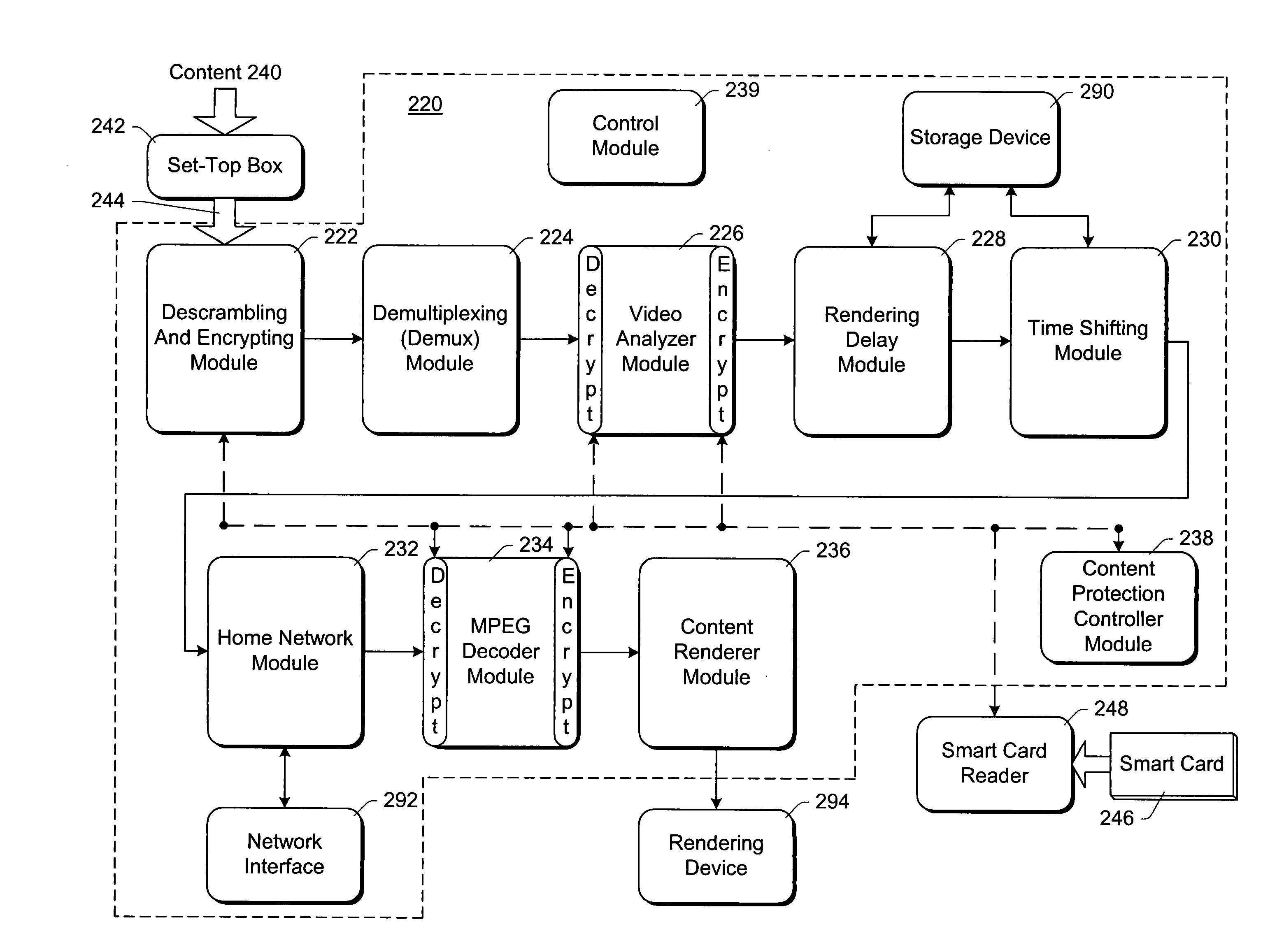
Enhancing smart card usage for associating media content with households
InactiveUS7124938B1Improve privacyEasy to changeAcutation objectsPayment architectureUser privacySmart card security
Various enhancements are made to using smart cards that are associated with (or to be associated with) a household. In one embodiment, data that is expected to be of value to a user (e.g., electronic money) is attached to that user's smart card(s), thereby providing an incentive for the user to keep his or her smart card(s) secure. In another embodiment, the smart cards are used for parental control (e.g., by restricting the children's access to one or more of the smart cards). In yet another embodiment, smart cards are used to enhance user privacy by maintaining user-specific information on the smart cards (which can be de-coupled from the computing device whenever the user desires). In another embodiment, the boundaries of a network of computing devices are defined by multiple smart cards—any computing device to which a smart card is coupled is part of the network.
Owner:MICROSOFT TECH LICENSING LLC
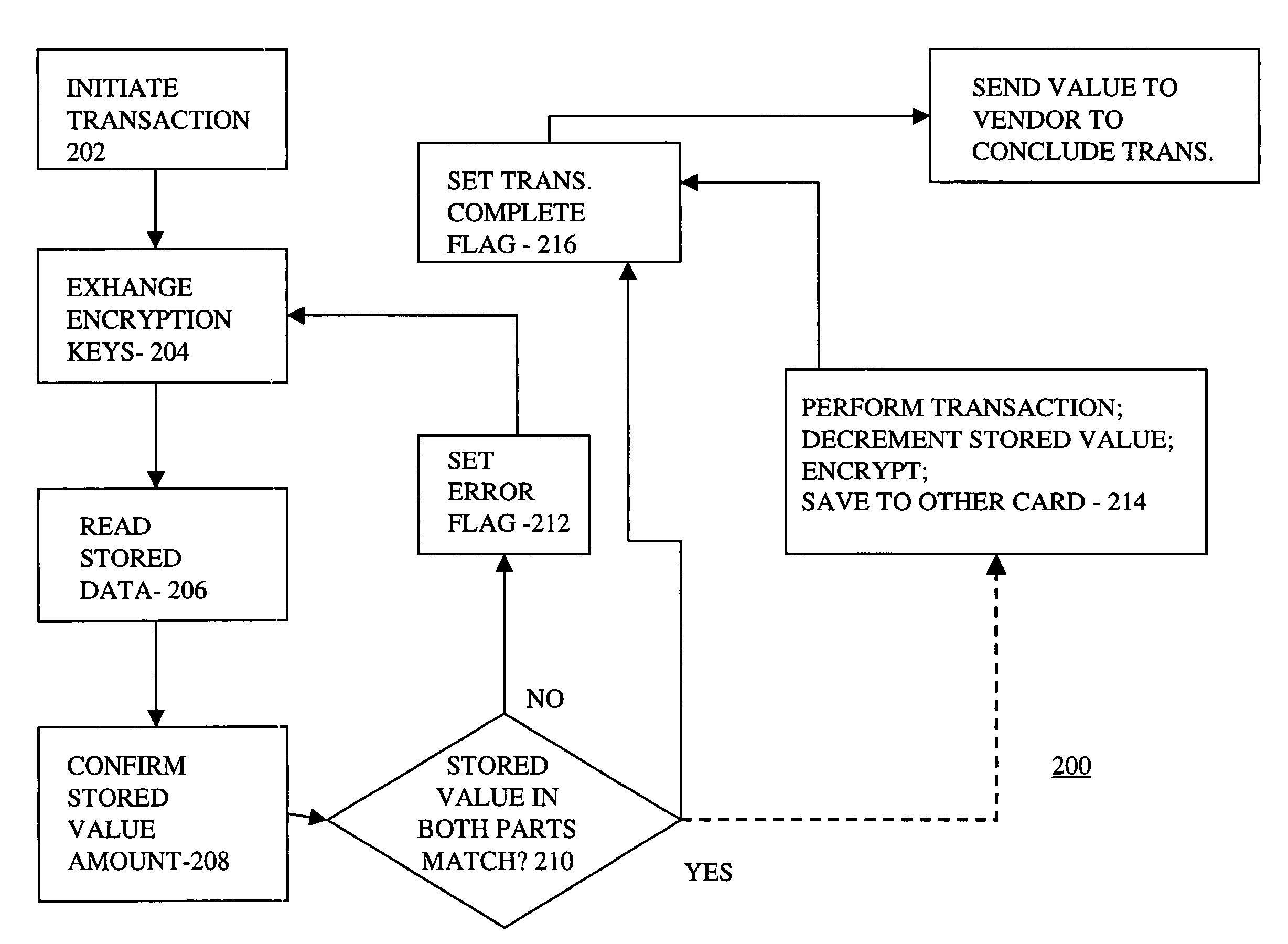
Smart card with back up
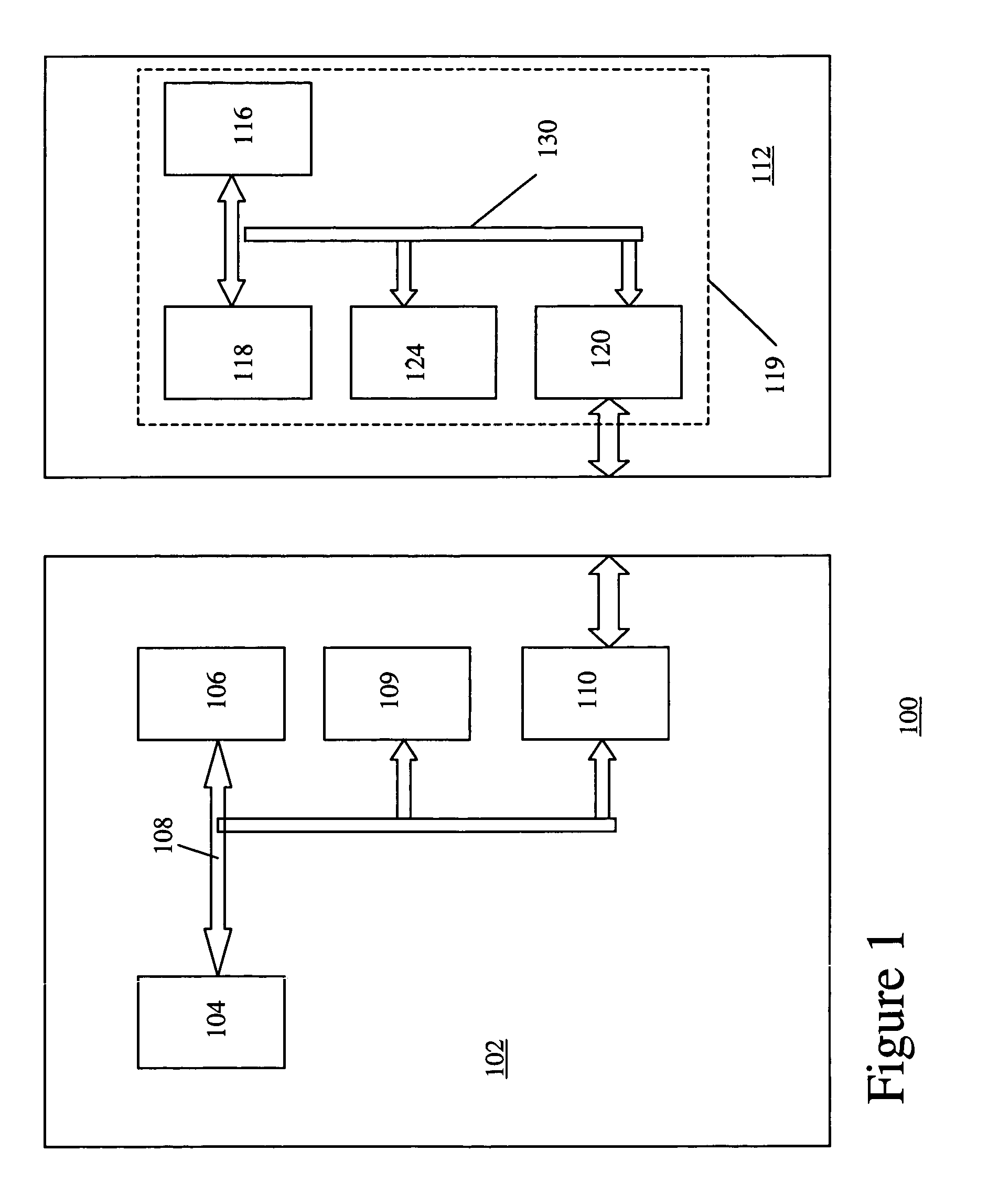
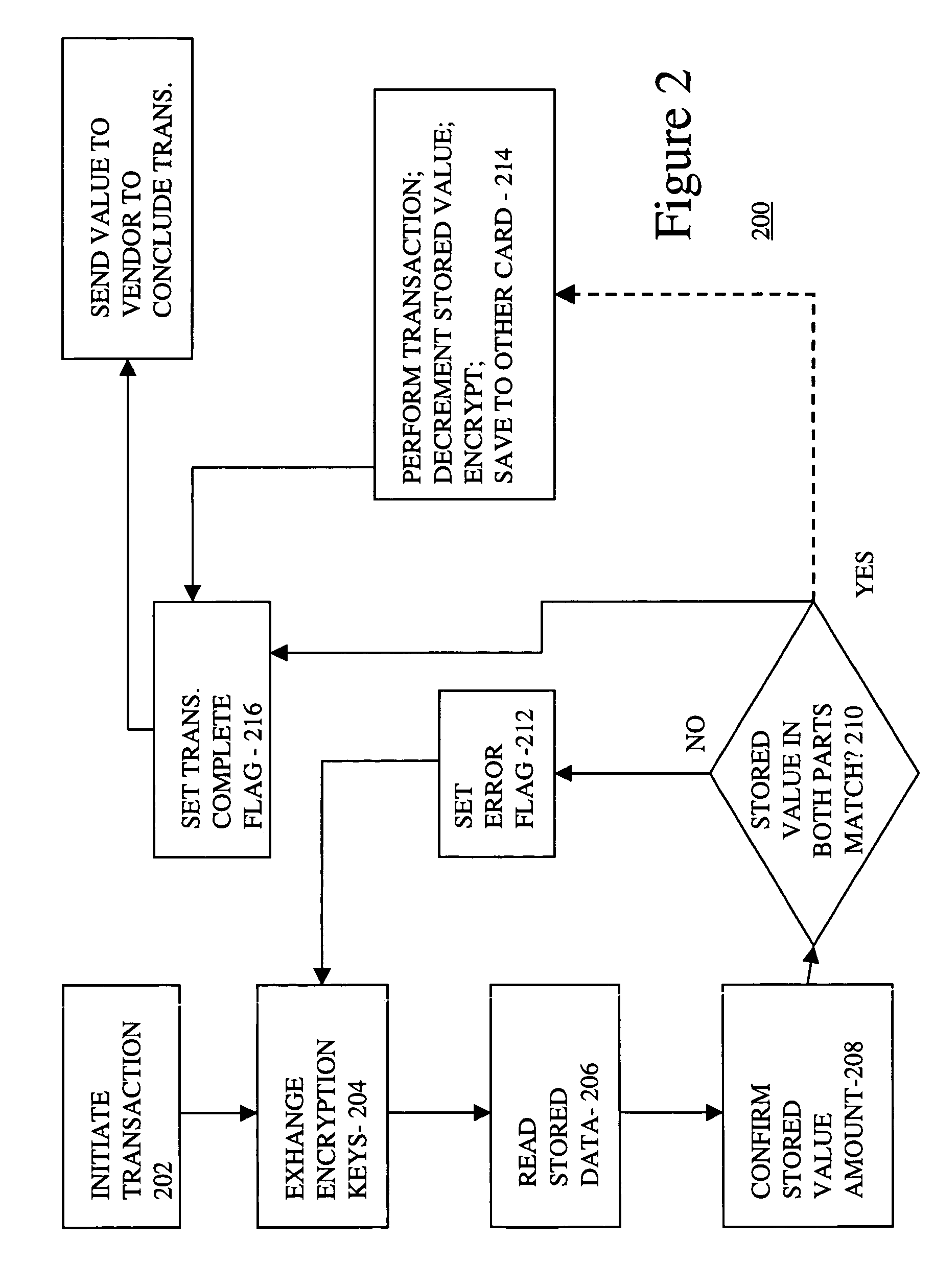
InactiveUS7206847B1Data SecurityImprove securityComplete banking machinesAcutation objectsProgram instructionSmart card security
Smart card security is enhanced by making the smart card a two-piece device. Both parts of the smart card contain copies of user data and a processor, which executes program instructions stored in the smart card half so as to give each part of the two-part smart card security and intelligence. Both parts must be in communication with each other for the data in either card to be accessible and useable. By separating the two pieces, data compromise is virtually impossible.
Owner:GOOGLE TECH HLDG LLC
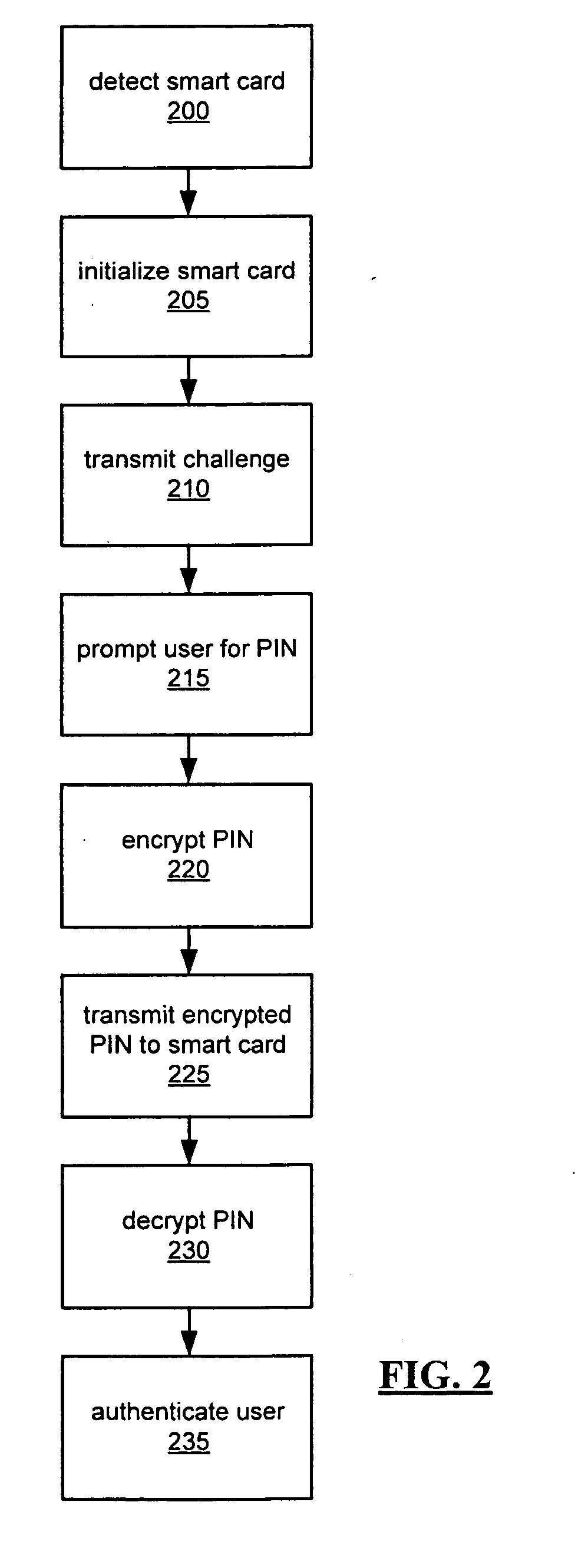
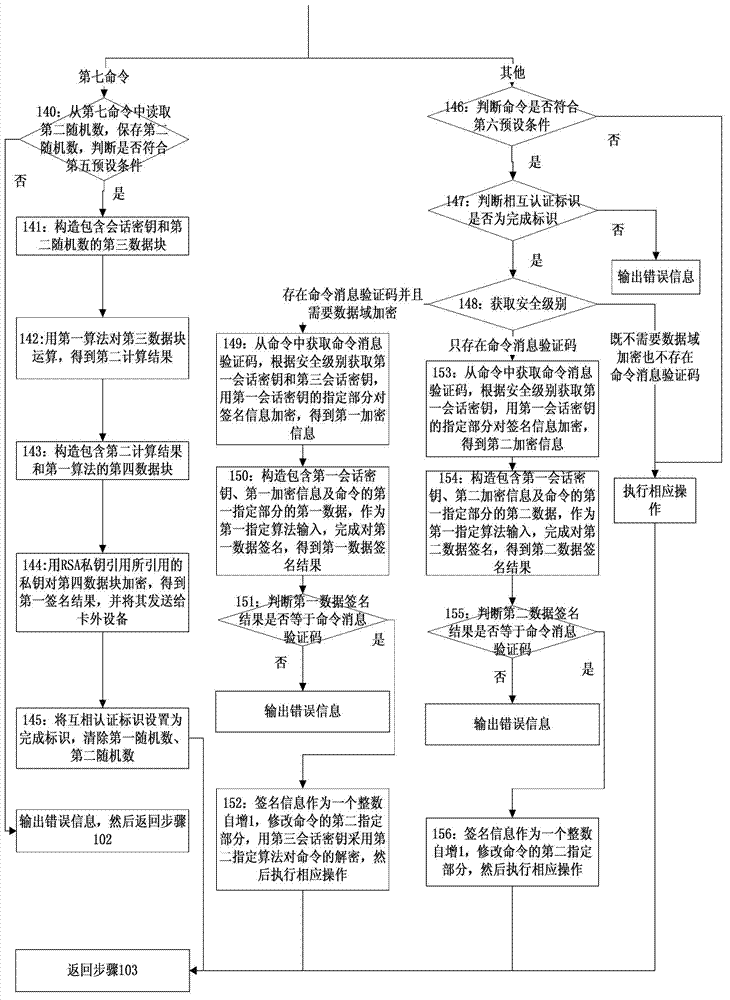
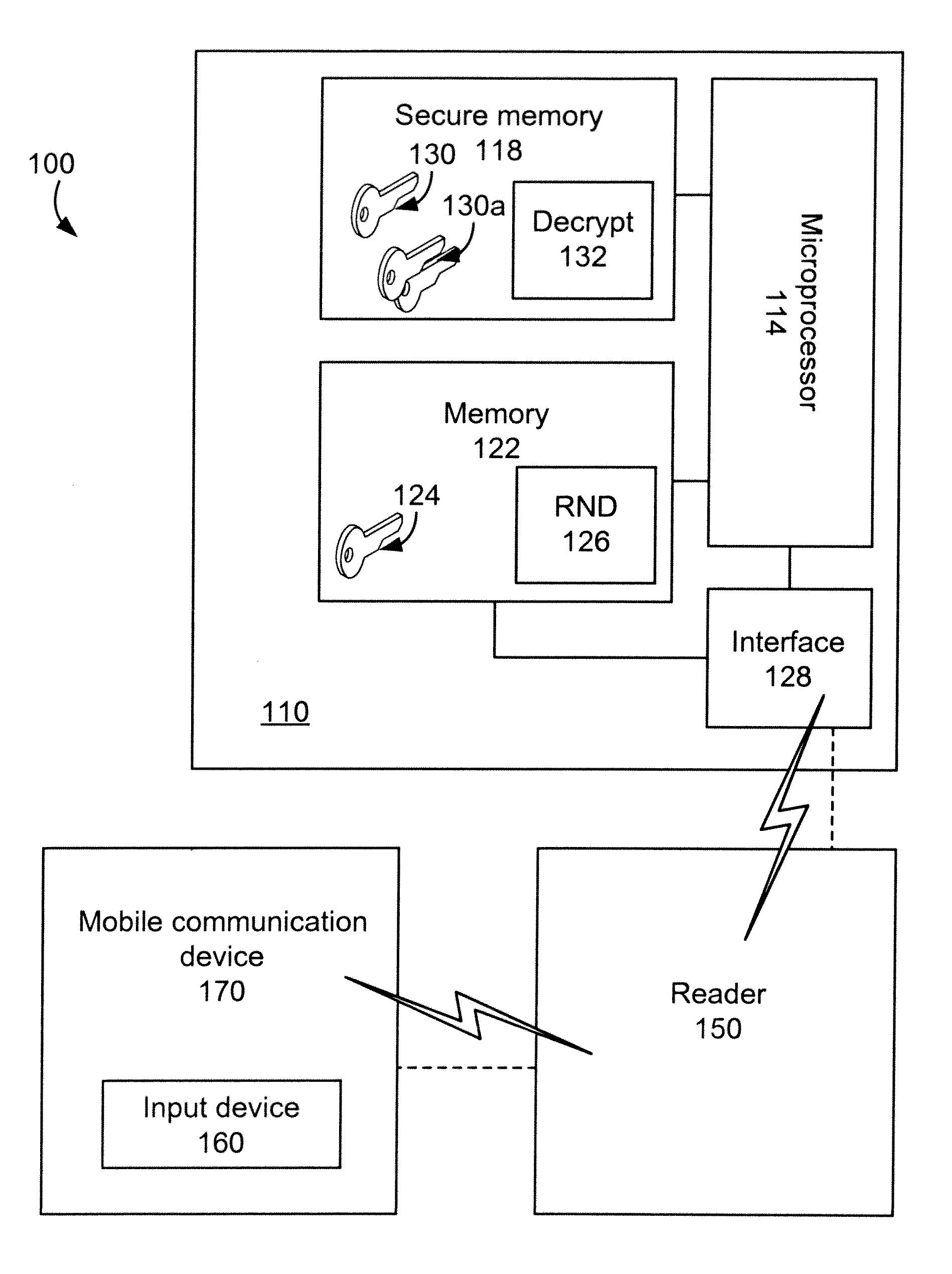
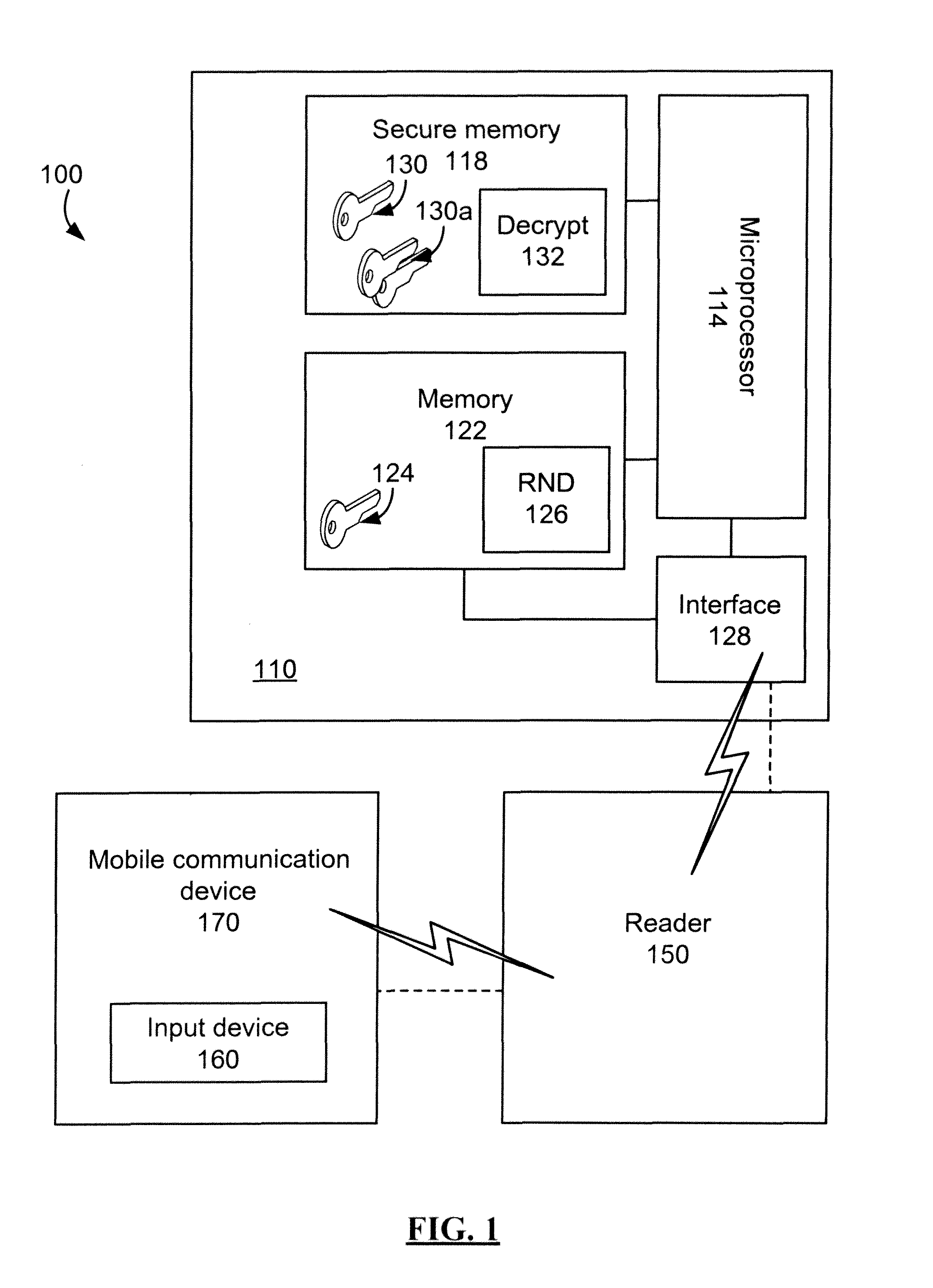
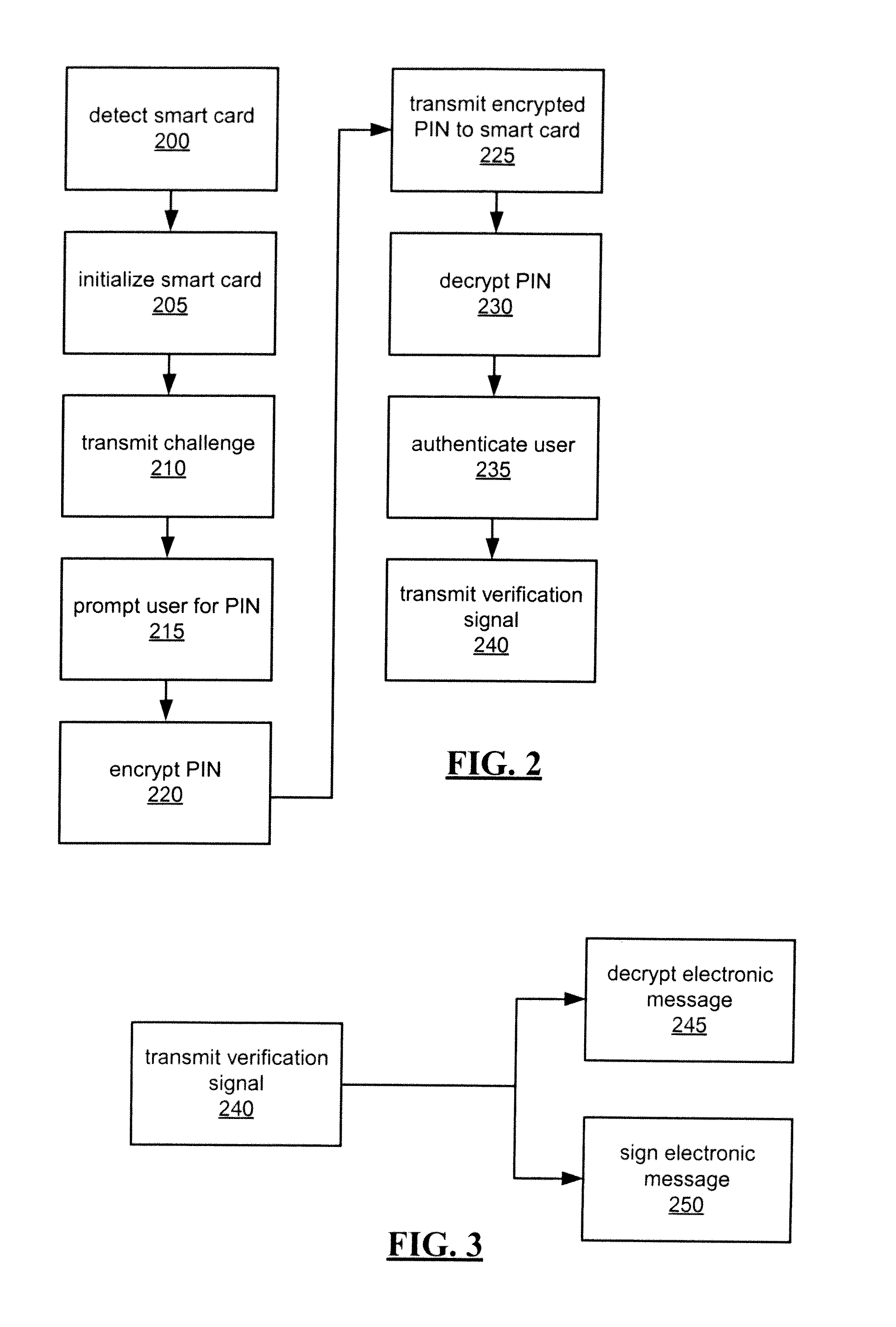
System and method for encrypted smart card pin entry
A smart card, system, and method for securely authorizing a user or user device using the smart card is provided. The smart card is configured to provide, upon initialization or a request for authentication, a public key to the user input device such that the PIN or password entered by the user is encrypted before transmission to the smart card via a smart card reader. The smart card then decrypts the PIN or password to authorize the user. Preferably, the smart card is configured to provide both a public key and a nonce to the user input device, which then encrypts a concatenation or other combination of the nonce and the user-input PIN or password before transmission to the smart card. The smart card reader thus never receives a copy of the PIN or password in the clear, allowing the smart card to be used with untrusted smart card readers.
Owner:MALIKIE INNOVATIONS LTD
Smart card security information configuration and recovery system
InactiveUS6981152B2None of methods is secureEasy to createUser identity/authority verificationUnauthorized memory use protectionWeb siteCMOS
A smart card security information configuration and recovery system provides a secure Web site and server that allows smart card users to easily create and obtain smart cards and passwords. The client program accesses the smart card inserted into the client computer and retrieves the smart card's ID and other user and system information and sends them to the server which creates an access key. The access key and the smart card ID are stored in the client computer's CMOS or non-volatile memory for boot-up access. The client computer will boot only if the proper smart card is installed or the proper access key is entered when the smart card is unavailable. If the user loses his smart card, then he must gain access to his computer through the access key which the server issues after the user logs in. When the user wants to get a new smart card issued, he logs onto the server which is sent the new smart card's ID that replaces the previous smart card's ID and the server generates a new access key and stores it. The new access key and the smart card's ID are stored in the client computer's CMOS or non-volatile memory for boot access.
Owner:O2 MICRO INT LTD
Method, apparatus and computer program product for providing smart card security
ActiveUS20100095364A1Detection and prevention of useImprove securityUnauthorised/fraudulent call preventionDigital data processing detailsSmart card securitySmart card
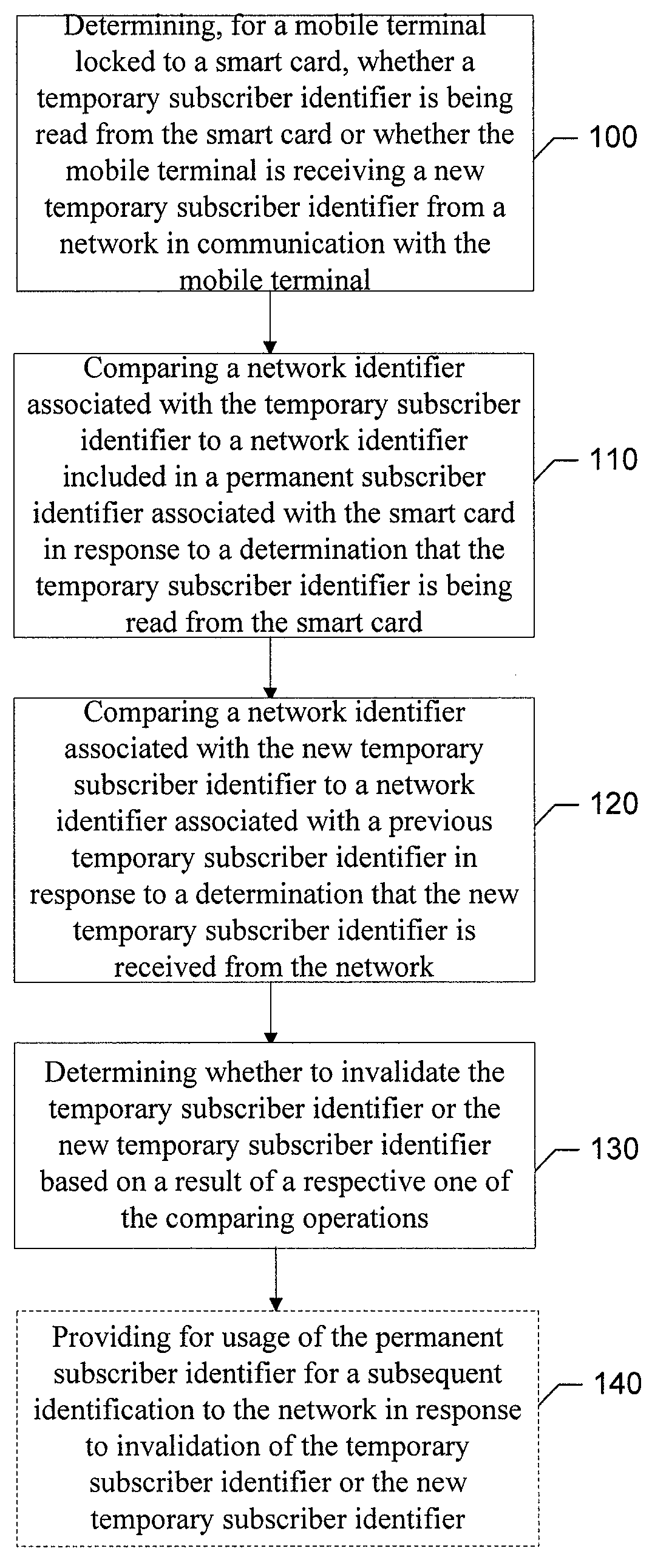
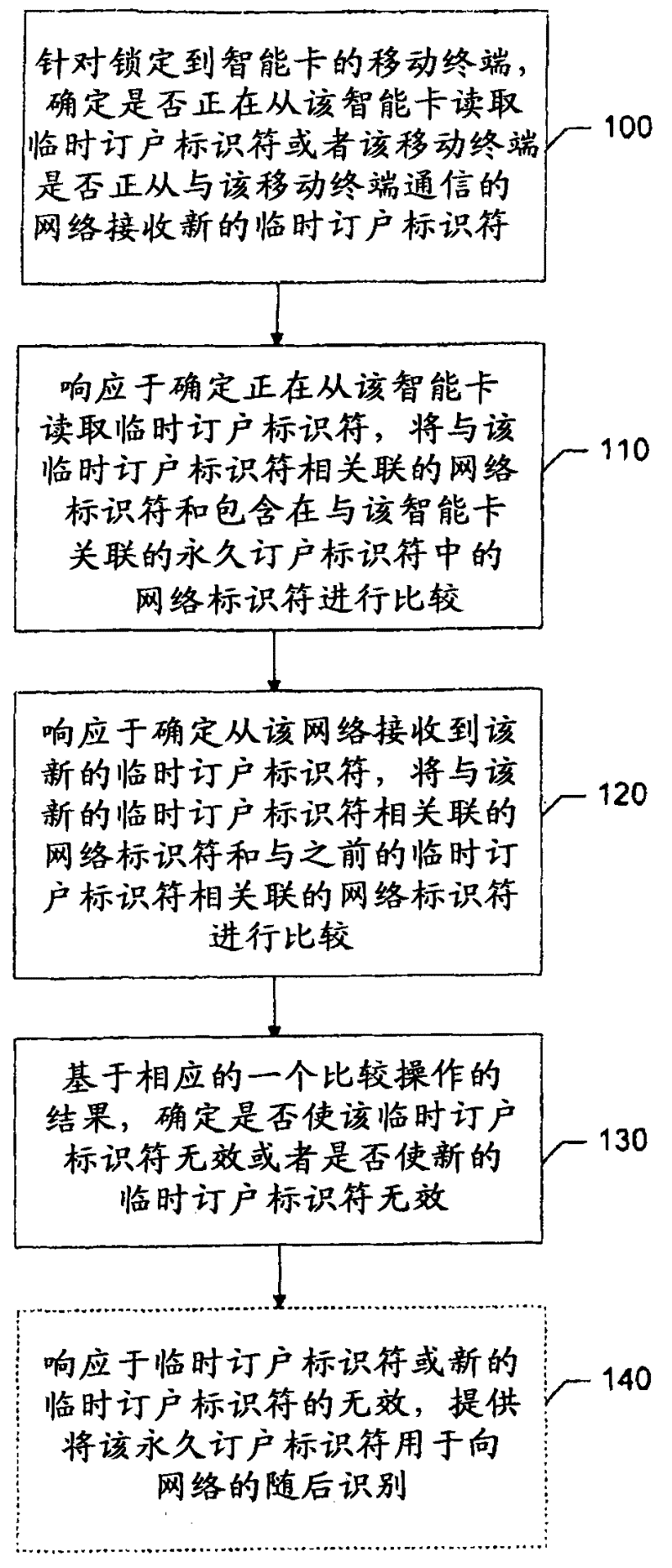
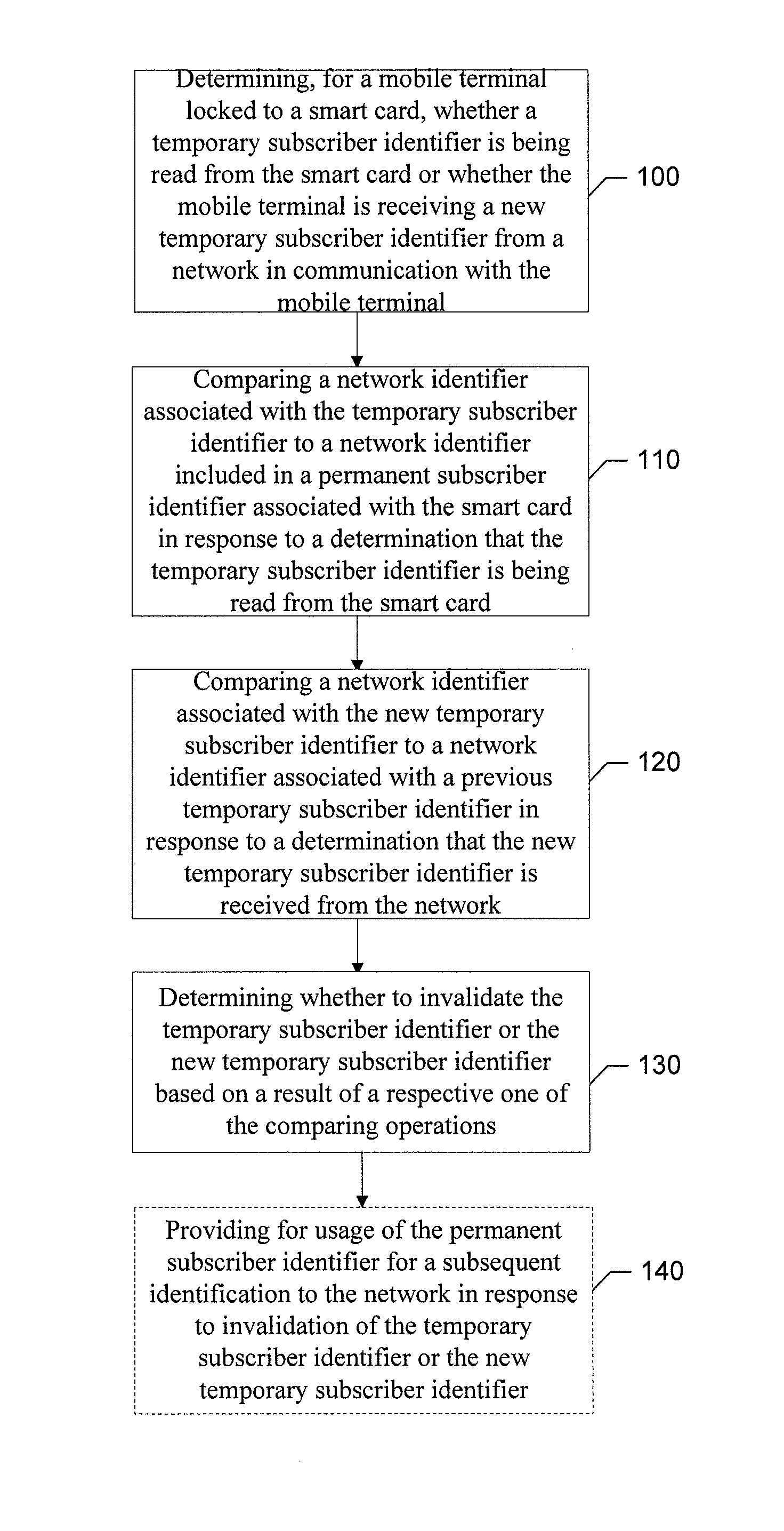
An apparatus for providing smart card security may include a processor. The processor may be configured to determine, for a mobile terminal locked to a smart card, whether a temporary subscriber identifier is being read from the smart card or whether the mobile terminal is receiving a new temporary subscriber identifier from a network in communication with the mobile terminal, compare a network identifier associated with the temporary subscriber identifier to a network identifier included in a permanent subscriber identifier associated with the smart card in response to a determination that the temporary subscriber identifier is being read from the smart card, compare a network identifier associated with the new temporary subscriber identifier to a network identifier associated with a previous temporary subscriber identifier in response to a determination that the new temporary subscriber identifier is received from the network, and determine whether to invalidate the temporary subscriber identifier or the new temporary subscriber identifier based on a result of a respective one of the comparing operations.
Owner:NOKIA TECHNOLOGLES OY
Ticket buying and checking method and movie ticket service system
ActiveCN102819911ARealize self-service ticket purchaseEasy accessApparatus for meter-controlled dispensingPaymentSmart card security
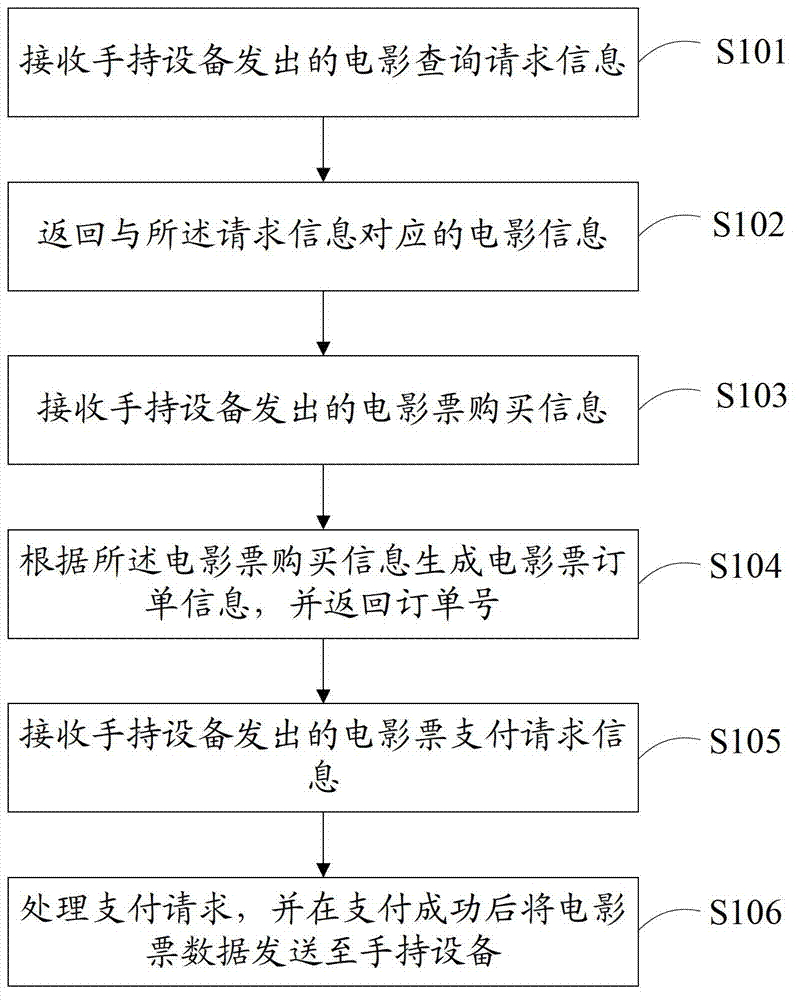
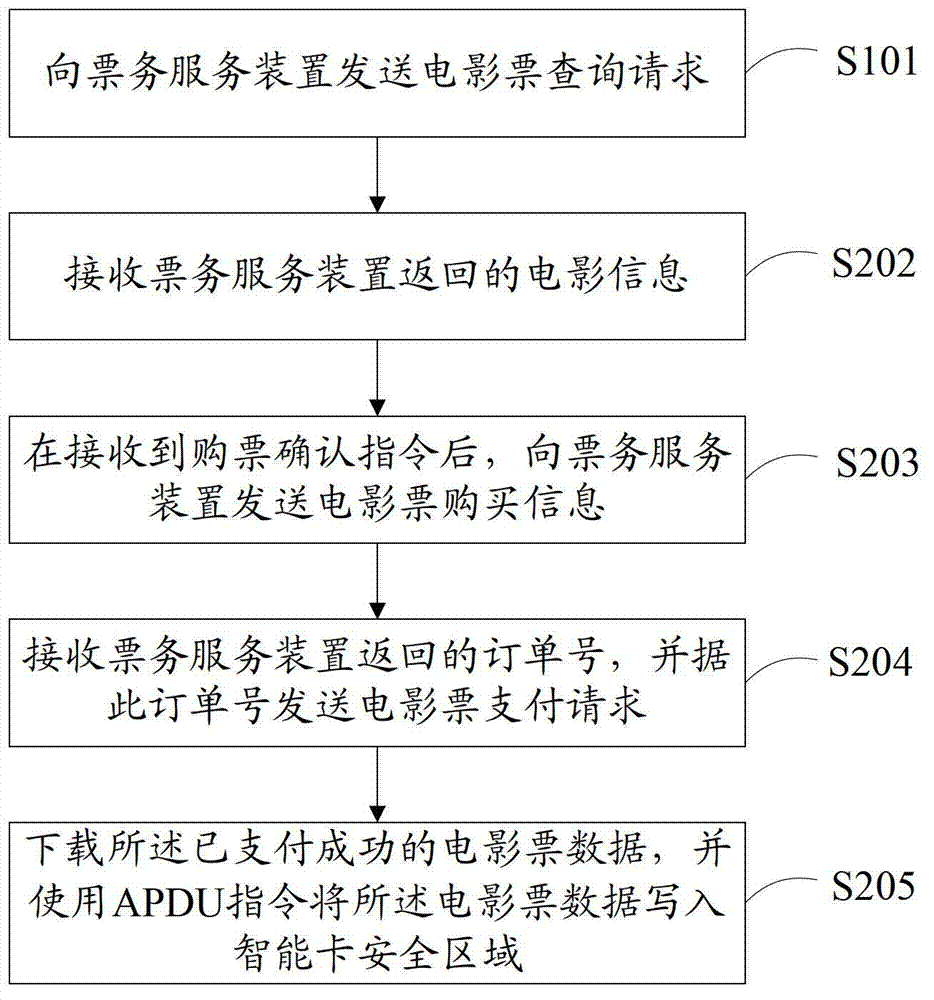
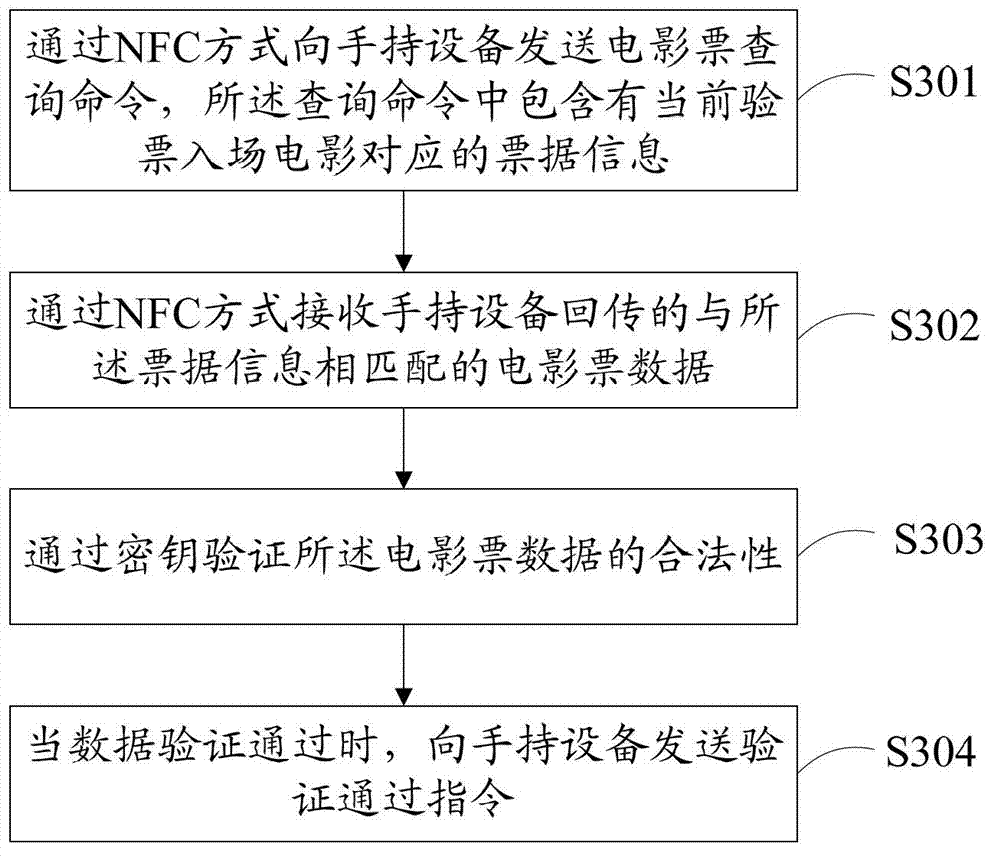
The invention provides a ticket buying and checking method and a movie ticket service system, belonging to the field of NFC (near field communication) technology application, wherein the ticket buying method comprises the following steps: receiving movie inquiring request information sent by a handheld device; returning movie information corresponding to the request information; receiving movie ticket buying information sent by the handheld device; generating movie ticket order information according to the movie ticket buying information and returning an order number; receiving movie ticket paying request information sent by the handheld device; and treating the paying request and sending movie ticket data to the handheld device after payment. Compared with the traditional ticket buying and checking method, the ticket buying and checking method provided by the invention can very conveniently buy and check a ticket so as to effectively save time, moreover, the movie ticket data are stored in a smart card safety zone, so that the data are ensured to be whole and are prevented from being distorted or copied, and the safety of the system can be enhanced.
Owner:WUHAN TIANYU INFORMATION IND
Intelligent card safety communication method
ActiveCN103095460AKey distribution for secure communicationPublic key for secure communicationSecure communicationSmart card security
Owner:FEITIAN TECHNOLOGIES
System and method for encrypted smart card PIN entry
Owner:MALIKIE INNOVATIONS LTD
Smart card security session system
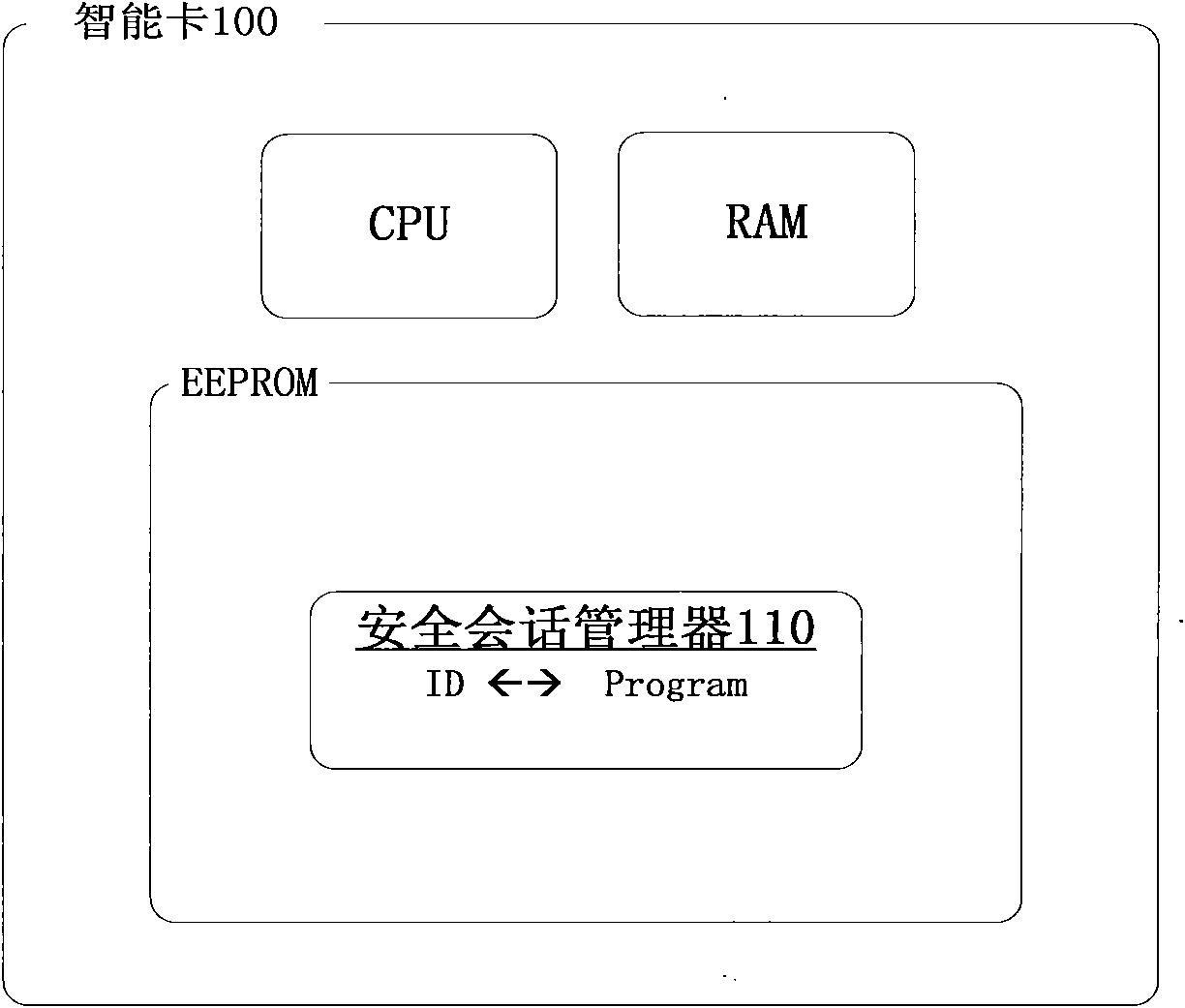
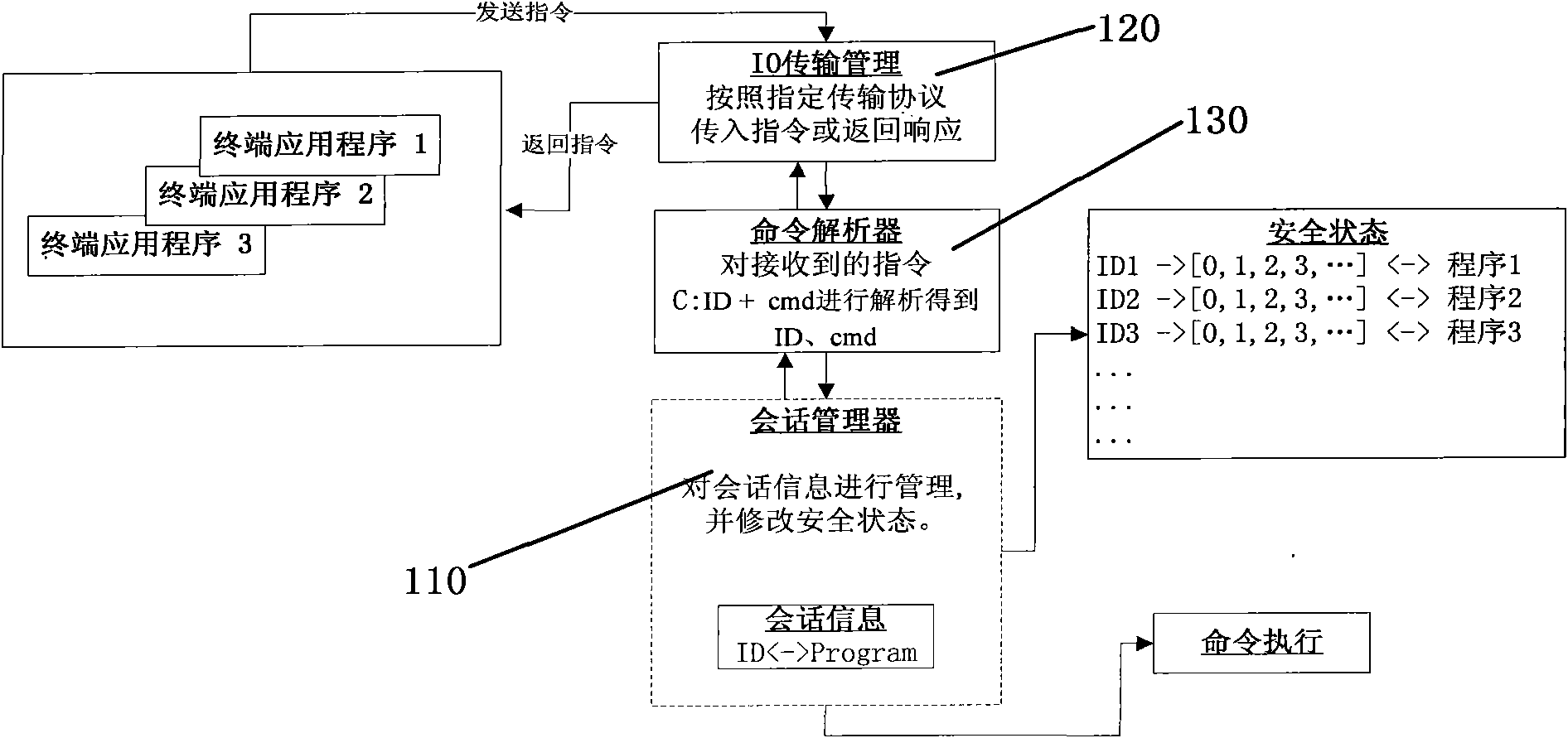
InactiveCN101894235AEnsure consistencyUnderstand clearlyPublic key for secure communicationUser identity/authority verificationSession managementSmart card security
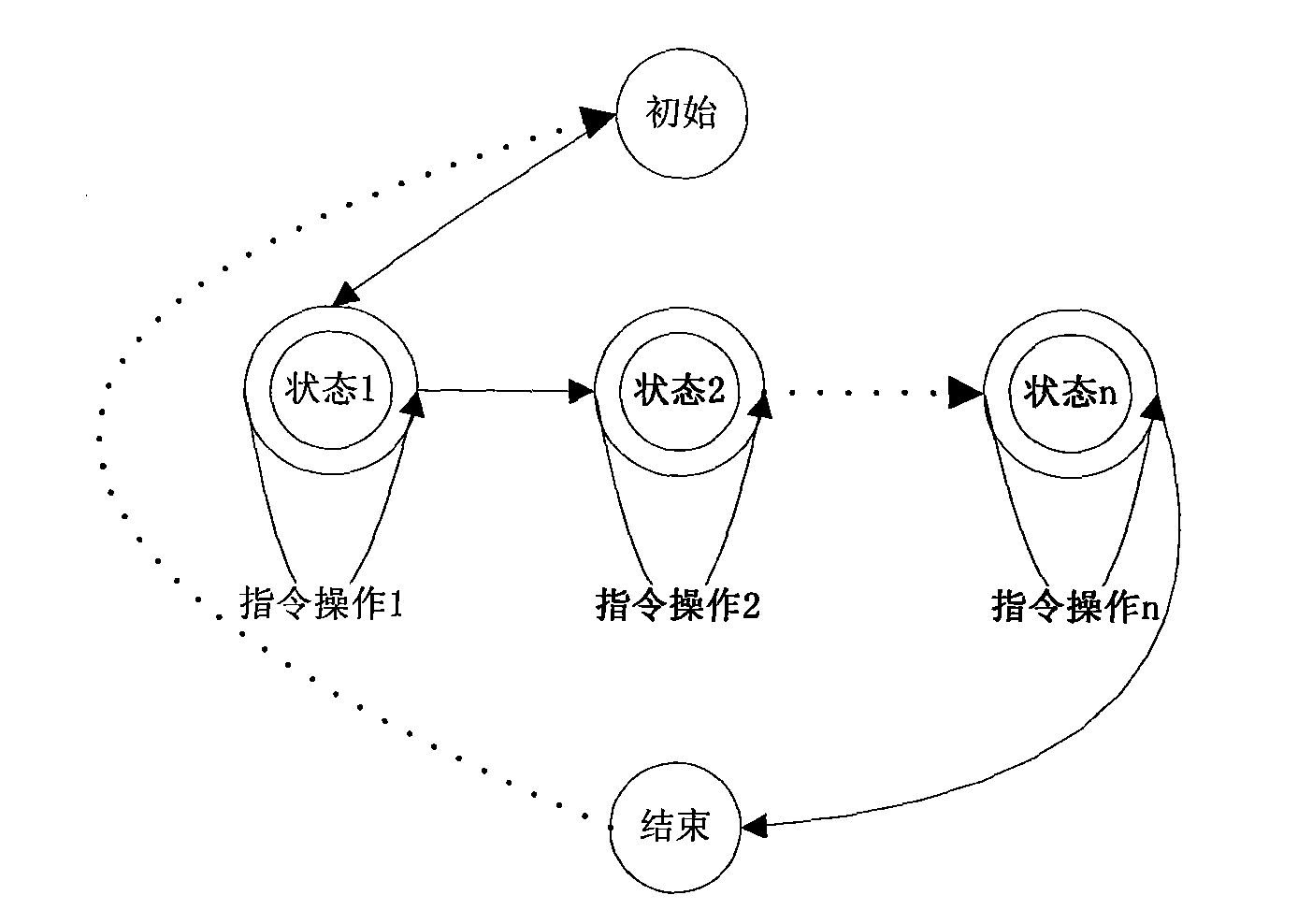
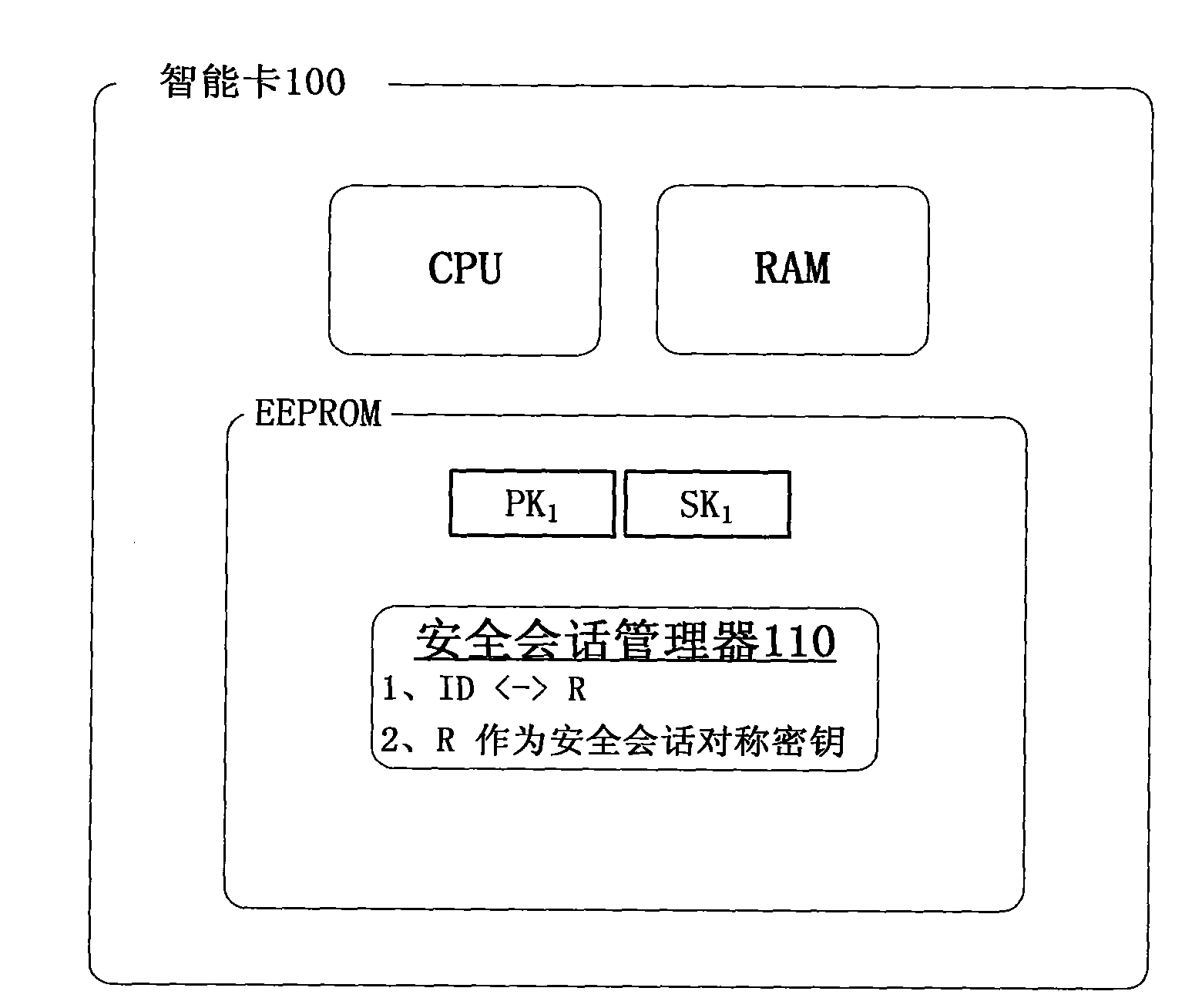
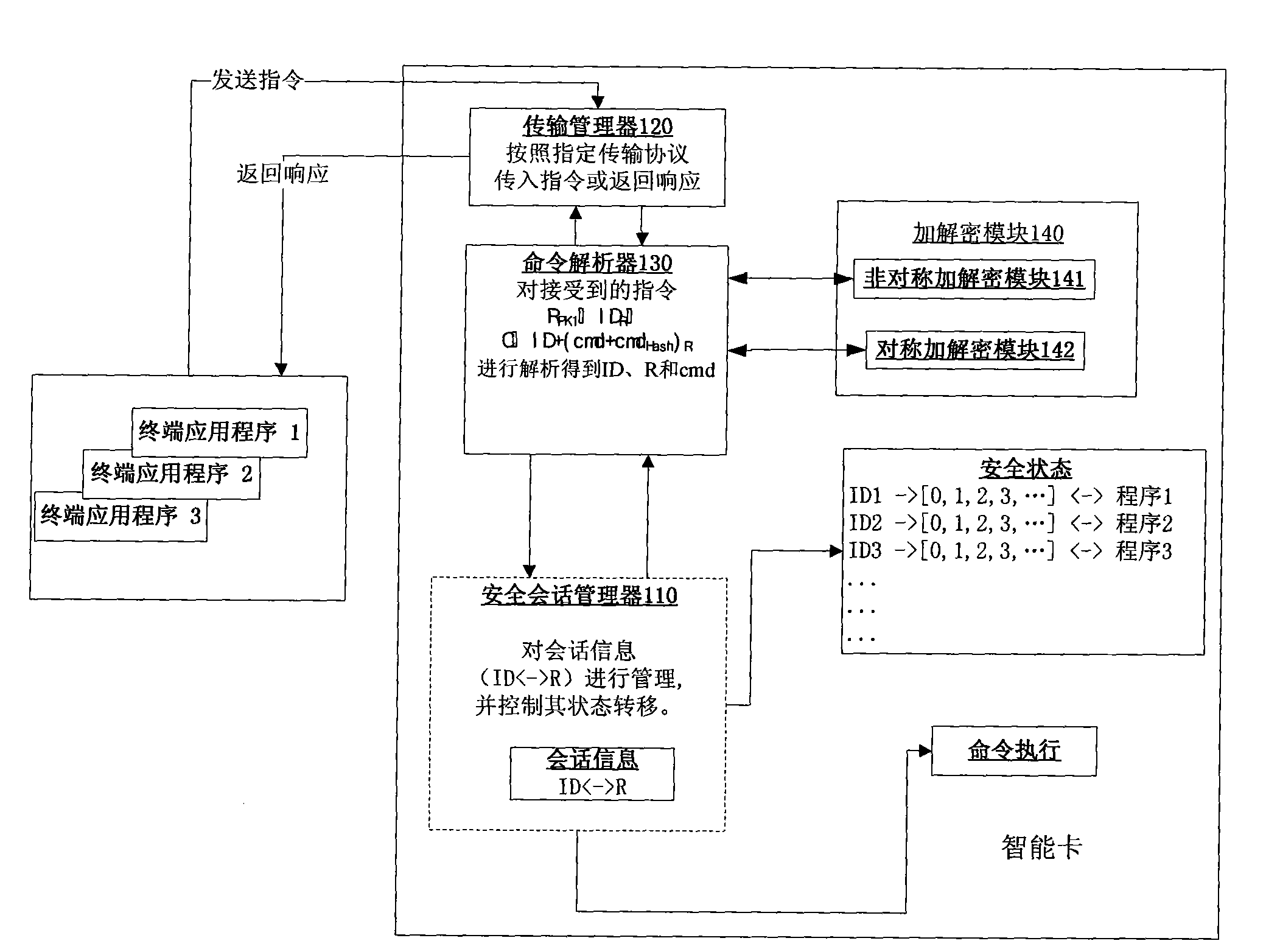
The invention aims to disclose a smart card security session system. The system comprises a smart card, wherein the smart card consists of a security session manager, a transmission manager, a command analyzer and an encryption and decryption module; the security session manager, the transmission manager and the command analyzer are connected one another; the encryption and decryption module is connected with the command analyzer; in the conventional smart card security system, the concept of security session is introduced, and the application program is associated with a request initiated per se by adopting a semi-permanent interactive information switching method with automatic recovery mechanism, which is established between the smart card and a terminal application program in a certain period, so as to ensure that the security sessions of different application programs are independent from one another; and in addition, once established, the security session exists all the time until the operation of the application program is finished or other conditions for stopping the security session occur; and the security of the session is protected by security session symmetric keys and a security session public and private key pair.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
Methods and systems for conducting smart card transactions
ActiveUS8990572B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsSmart card securitySmart card
A method for conducting smart card transactions is provided that includes causing a computer to recognize communications from a mobile device as communications from a smart card reader containing a smart card, and conducting a smart card transaction in accordance with smart card security techniques with the mobile device.
Owner:DAON TECH
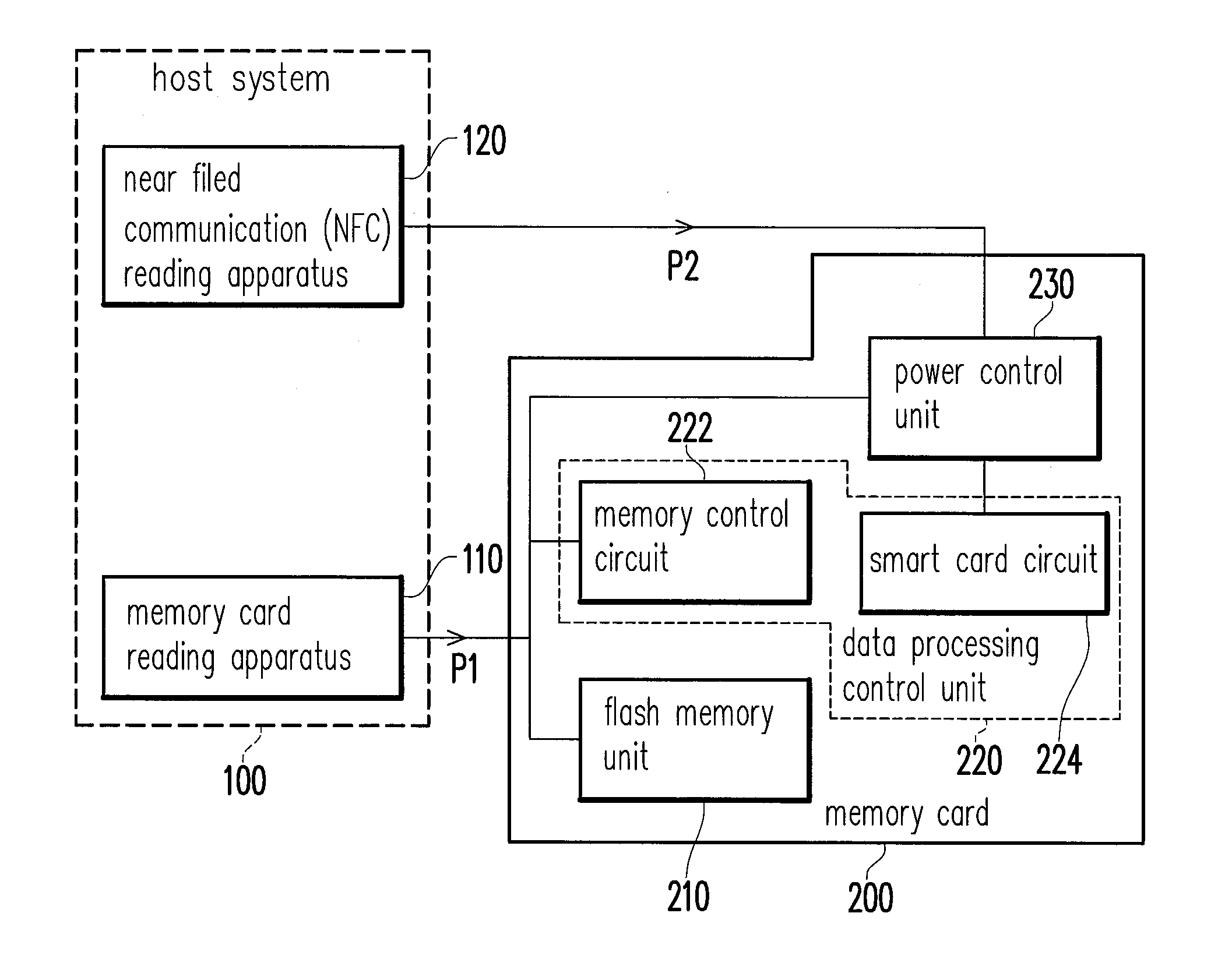
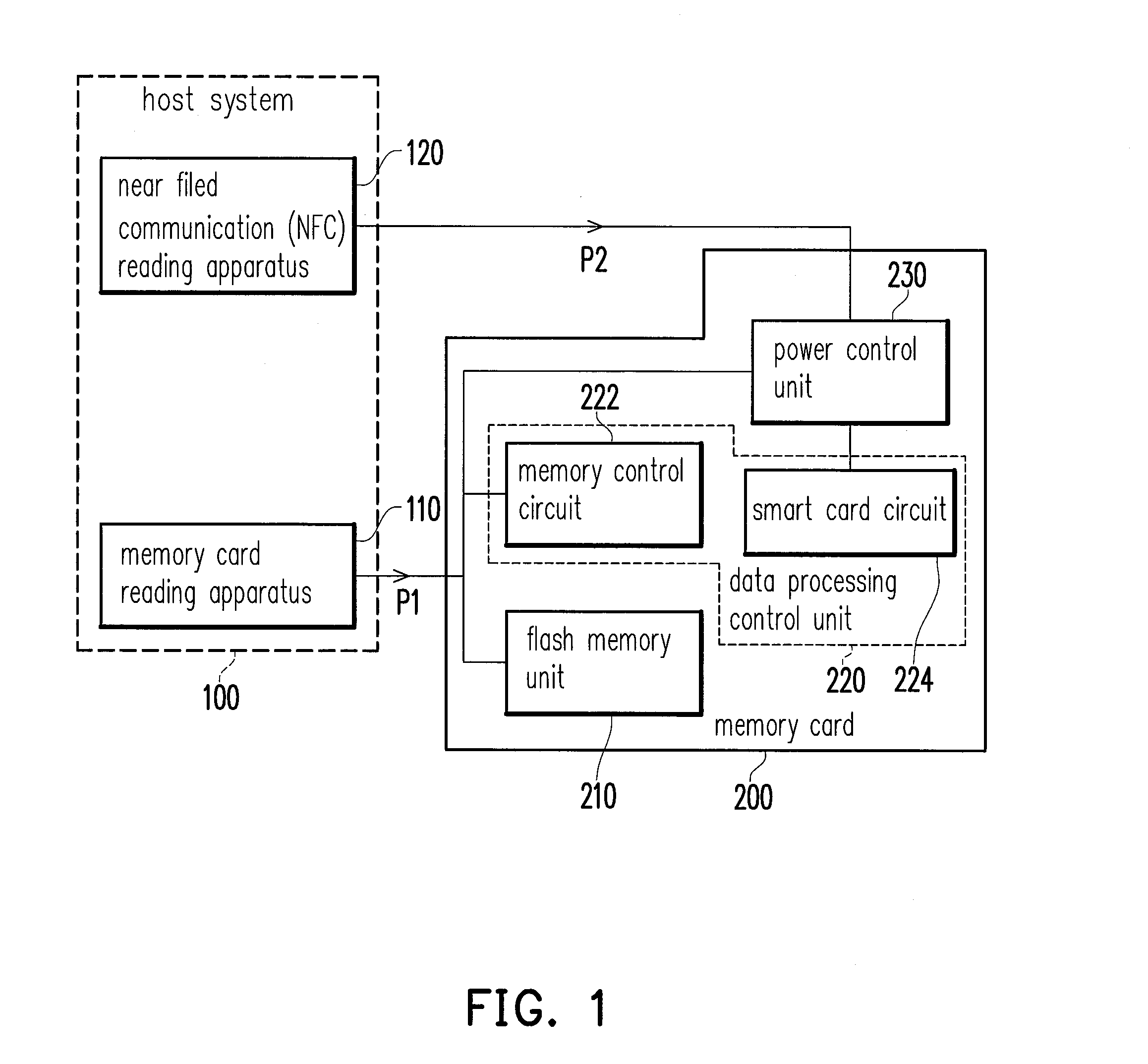
Memory card with smart card function and power control method and power control circuit thereof
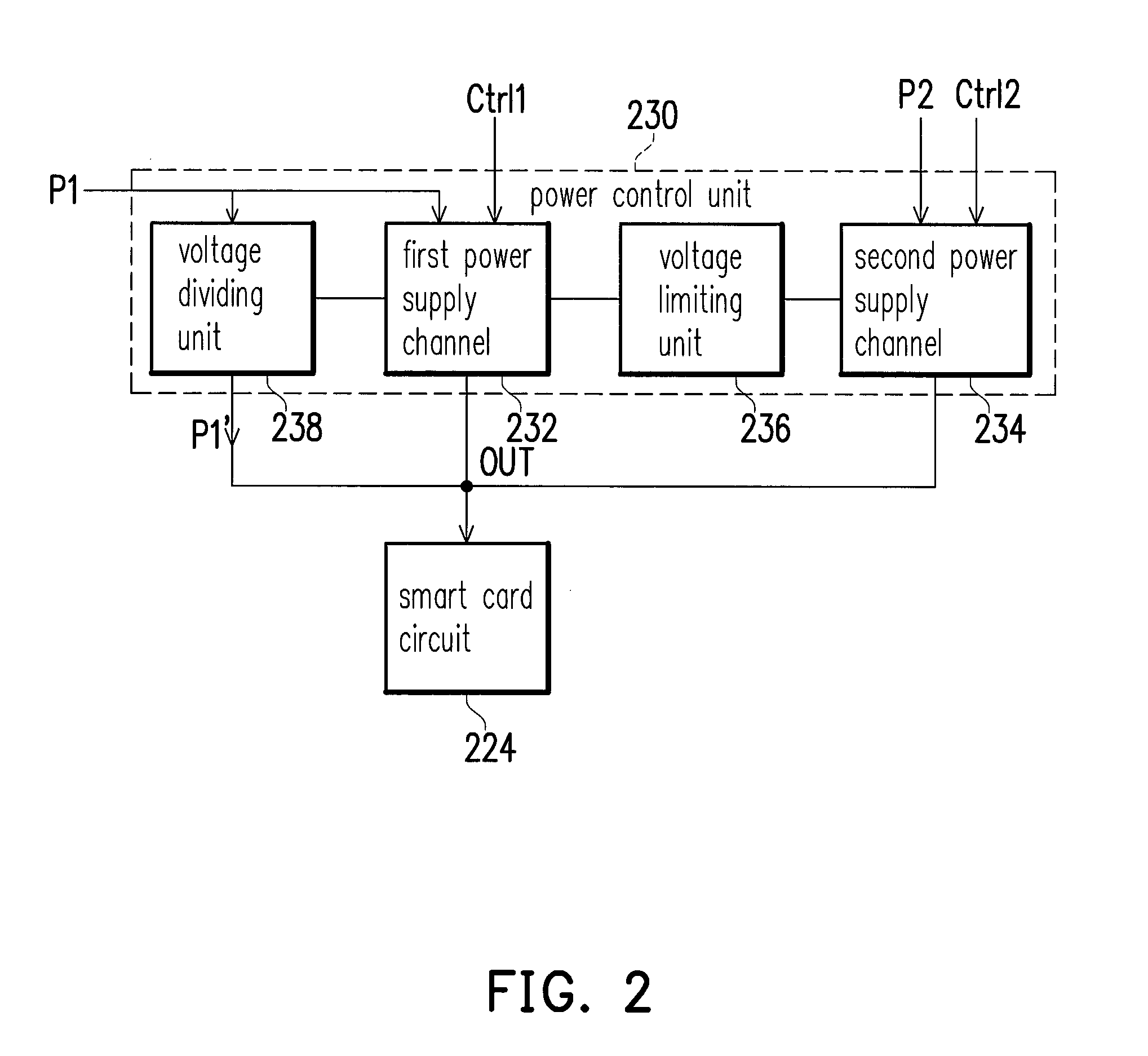
ActiveUS20130238910A1Volume/mass flow measurementMemory adressing/allocation/relocationControl powerControl signal
A memory card with a smart card function including a flash memory unit, a data processing control unit, and a power control unit is provided. The data processing control unit is coupled to the flash memory unit. The data processing control unit controls the flash memory unit and encrypts, decrypts and stores smart card security data. The power control unit receives at least one of a first power input and a second power input. The power control unit selects the first power input or the second power input and provides the selected one to the data processing control unit according to at least one control signal. An output terminal of the power control unit is coupled to the first power input. Furthermore, a power control method and a power control circuit of the forgoing memory card are also provided.
Owner:PHISON ELECTRONICS
Methods and systems for conducting smart card transactions
ActiveUS20130281055A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsSmart card securitySmart card
A method for conducting smart card transactions is provided that includes causing a computer to recognize communications from a mobile device as communications from a smart card reader containing a smart card, and conducting a smart card transaction in accordance with smart card security techniques with the mobile device.
Owner:DAON TECH
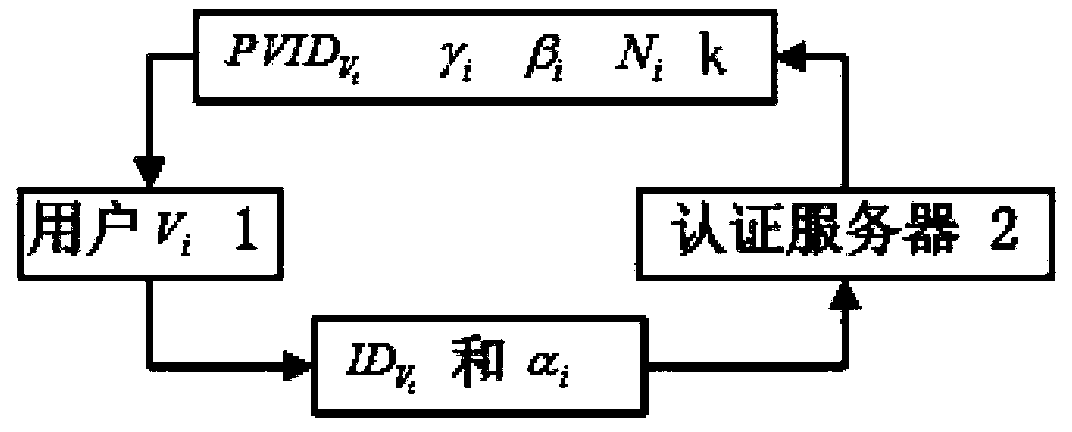
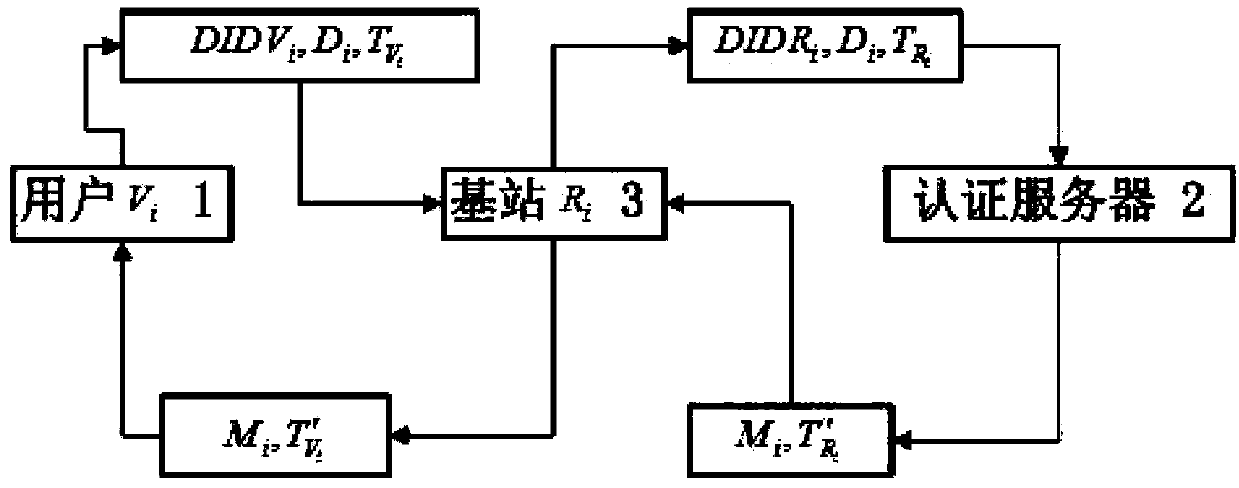
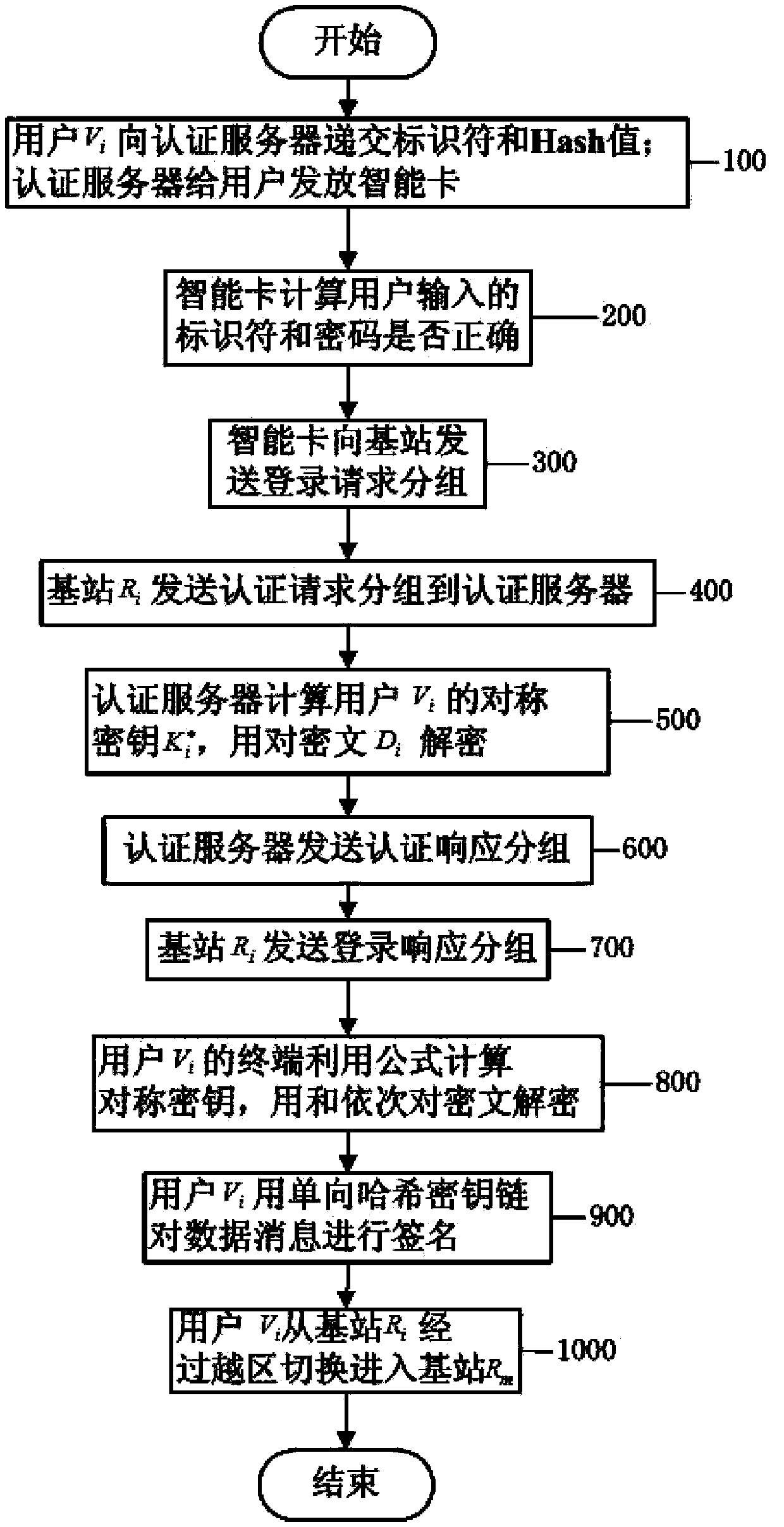
Safety certification method of vehicular adhoc network based on intelligent card
InactiveCN103415011AResistance to loss attacksReduce computational overheadNetwork topologiesSecurity arrangementHash functionPassword
The invention discloses a safety certification method of a vehicular adhoc network based on an intelligent card. The user identity certification method is based on a one-way hash function and a simple bitwise XOR operation, and is small in calculation amount and suitable for achieving the intelligent card. The method is used for verifying the identity legality of a vehicle user. The method has the advantages of being capable of resisting the attack from the losing of the intelligent card, resisting the attack of off-line password guessing, resisting replay attacks, resisting the attack of base station capturing, and being low in calculation cost and communication cost.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
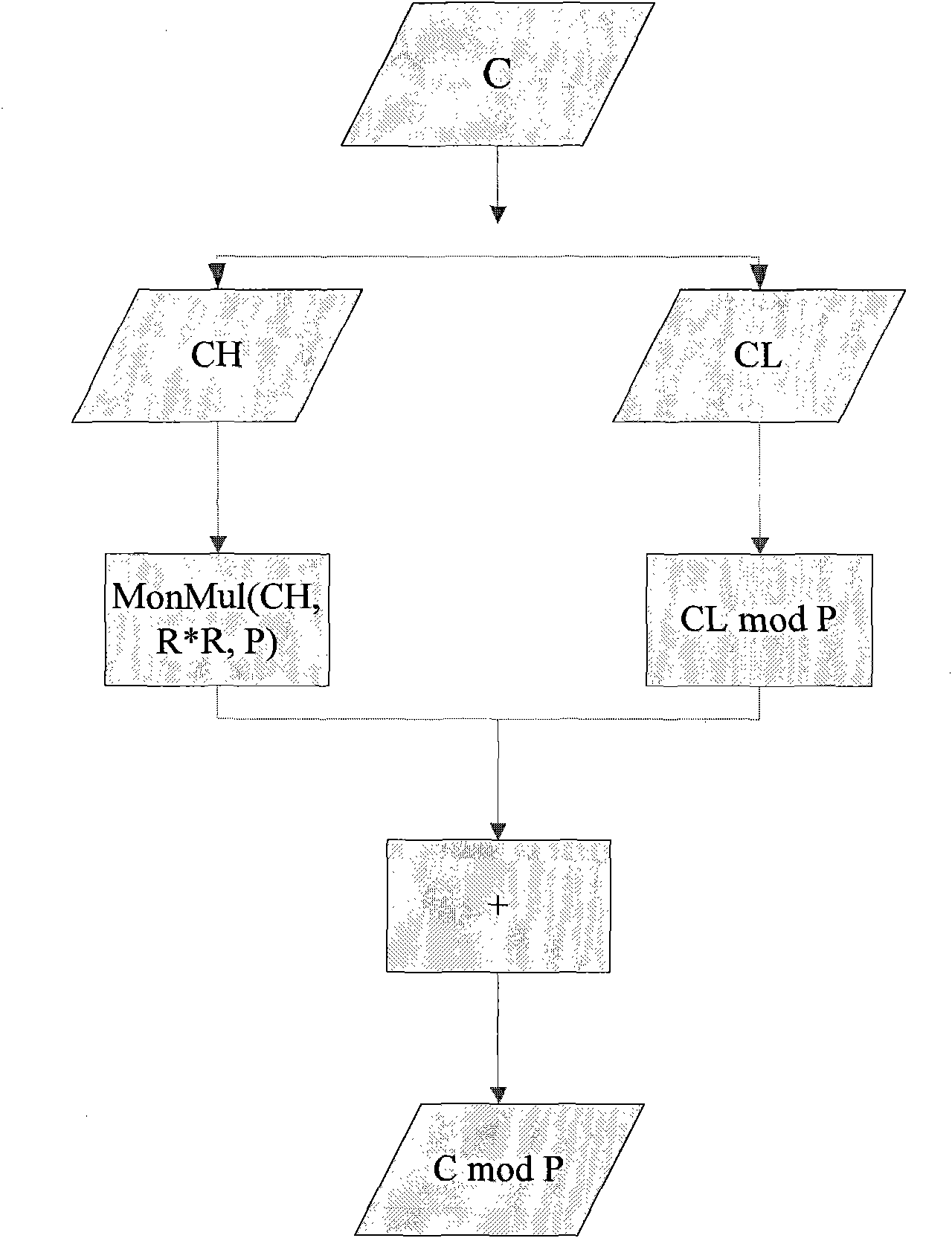
RSA (Ron Rivest, Adi Shamir and Leonard Adleman) algorithm digital signature method
ActiveCN102571342ALow costFast to marketKey distribution for secure communicationUser identity/authority verificationCoprocessorDigital signature
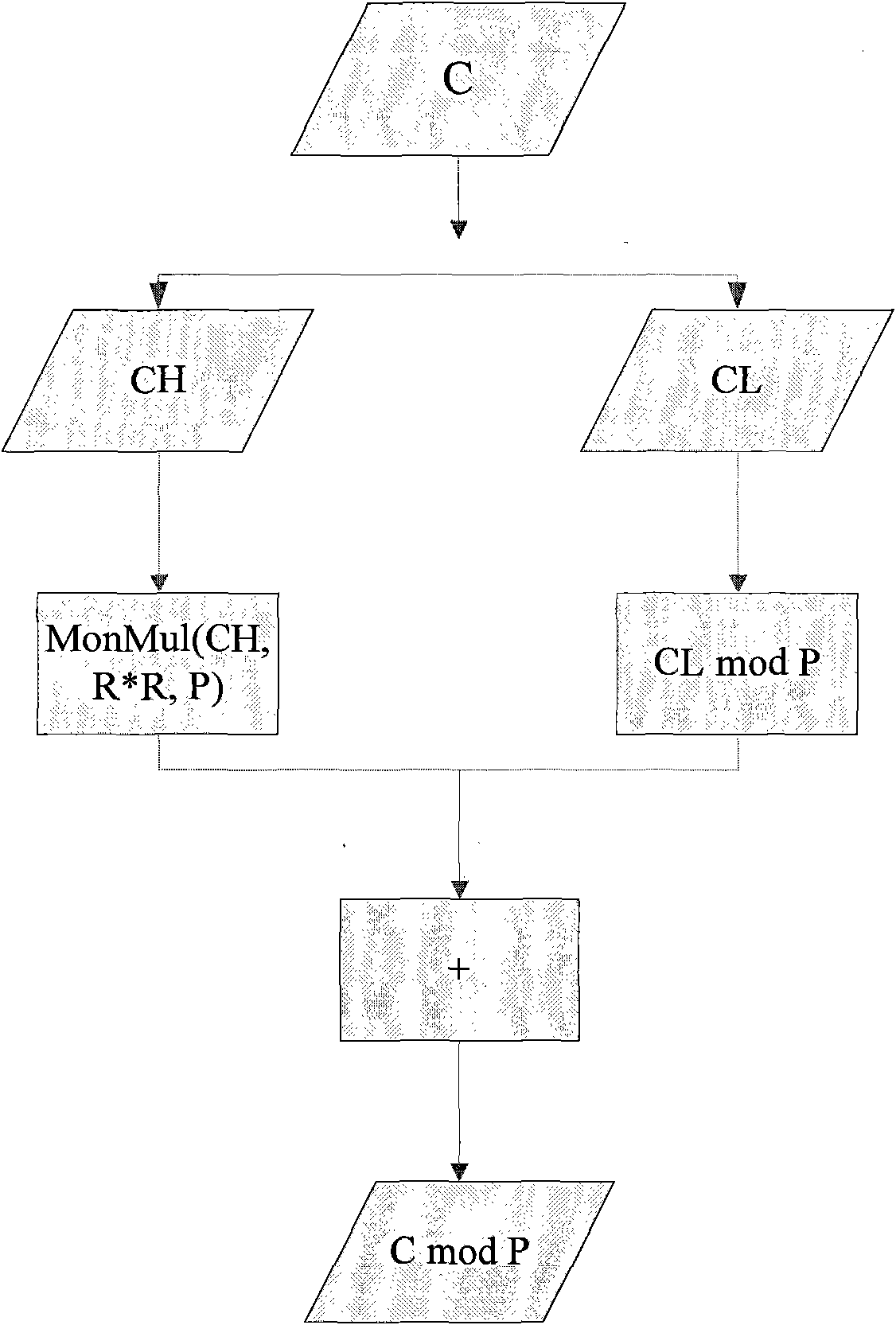
The invention designs an RSA (Ron Rivest, Adi Shamir and Leonard Adleman) algorithm digital signature method which realizes a 1408-bit RSA private key operation technology based on a 1024-bit hardware coprocessor and is mainly applied to the field of safety calculation of smart cards. A parameter in a large-bit-length RSA private key operation is calculated by utilizing a modular multiplier with small bit length, for example, a parameter in 1408-bit or 2048-bit RSA private key operation is calculated by utilizing a modular multiplier of 1024 bits. The RSA private key operation utilizes a Chinese remainder theorem and can be used for reducing the operation length of a main operation-modular exponentiation, but an operation of a key parameter, such as C mod P, C mod Q and a multiply operation, wherein the C represents a plain text, the length of the C is double the lengths of the P and the Q; and the multiply operation is accelerated by utilizing the modular multiplier, and a final result is also over the calculation capability of the modular multiplier. In the technology of the invention, the C is split into two numbers with the small bit lengths to calculate the C mod P by mainly utilizing the algorithm deformation of modular arithmetic; and the multiply operation larger than the length of the modular multiplier is calculated through a quarter multiply operation.
Owner:BEIJING CEC HUADA ELECTRONIC DESIGN CO LTD
Method for generating secrete key of smart card
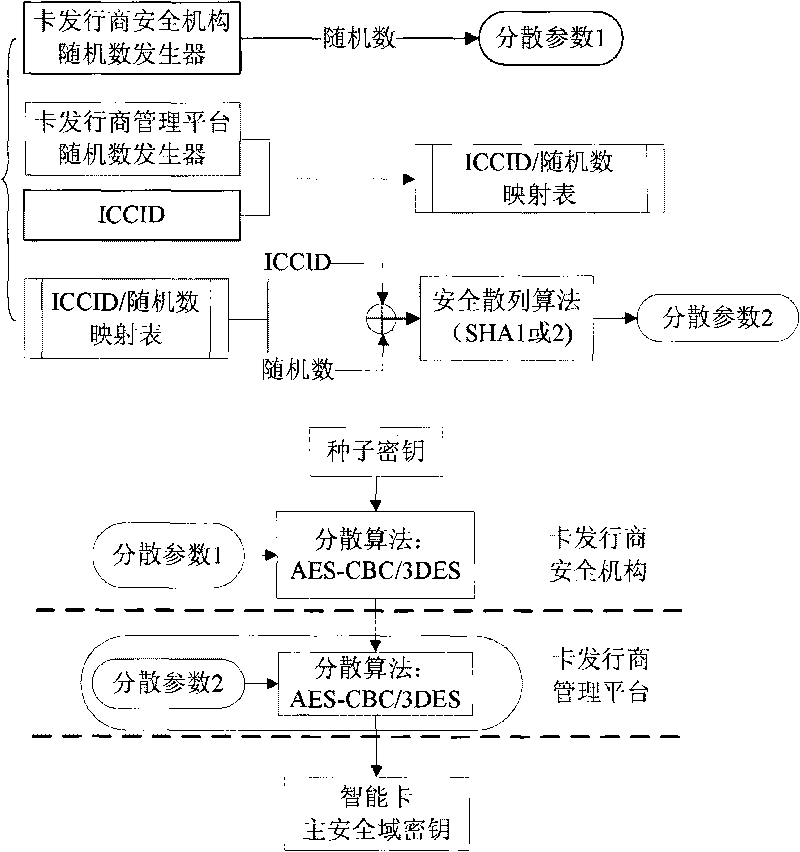
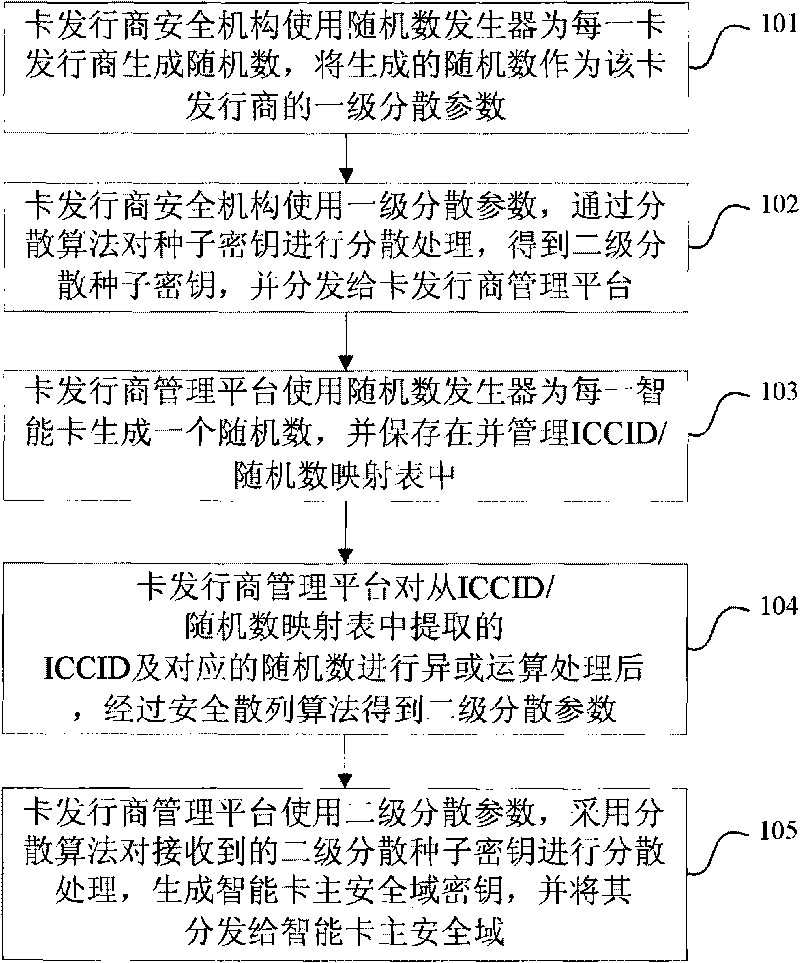
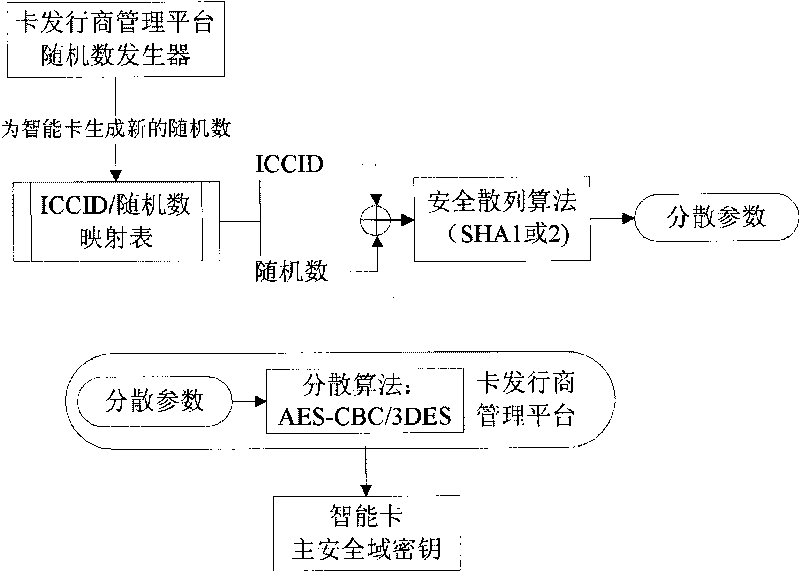
InactiveCN101739756ASolve the problem that the key is not easy to updateSecuring communicationCoded identity card or credit card actuationSmart card securitySecurity domain
The invention discloses a method for generating a secrete key of a smart card. When the secrete key of a security domain of the smart card is generated, a management platform generates random numbers for the security domain of the smart card and generates the distributed parameters of the security domain of the smart card by using the random numbers; and the distributed parameters and seed keys of the management platform are used as the parameters of a decentralized algorithm, so the secrete key of the security domain of the smart card is generated by using the decentralized algorithm. The method for generating the secrete key of the smart card solves the problem that the secrete key of the security domain of the smart card is difficult to update.
Owner:ZTE CORP
Method for realizing secure communication between set-top box and intelligent card
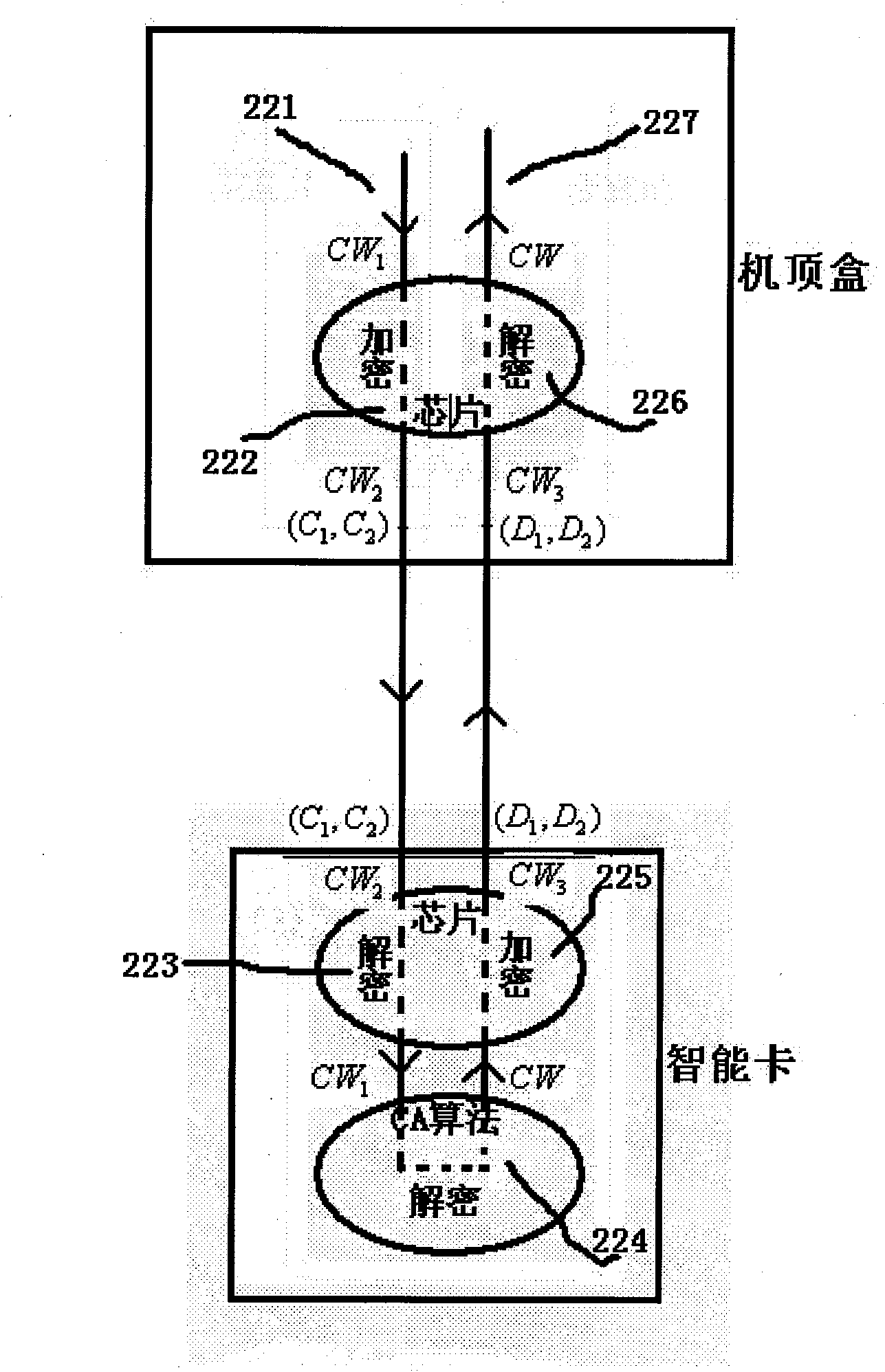
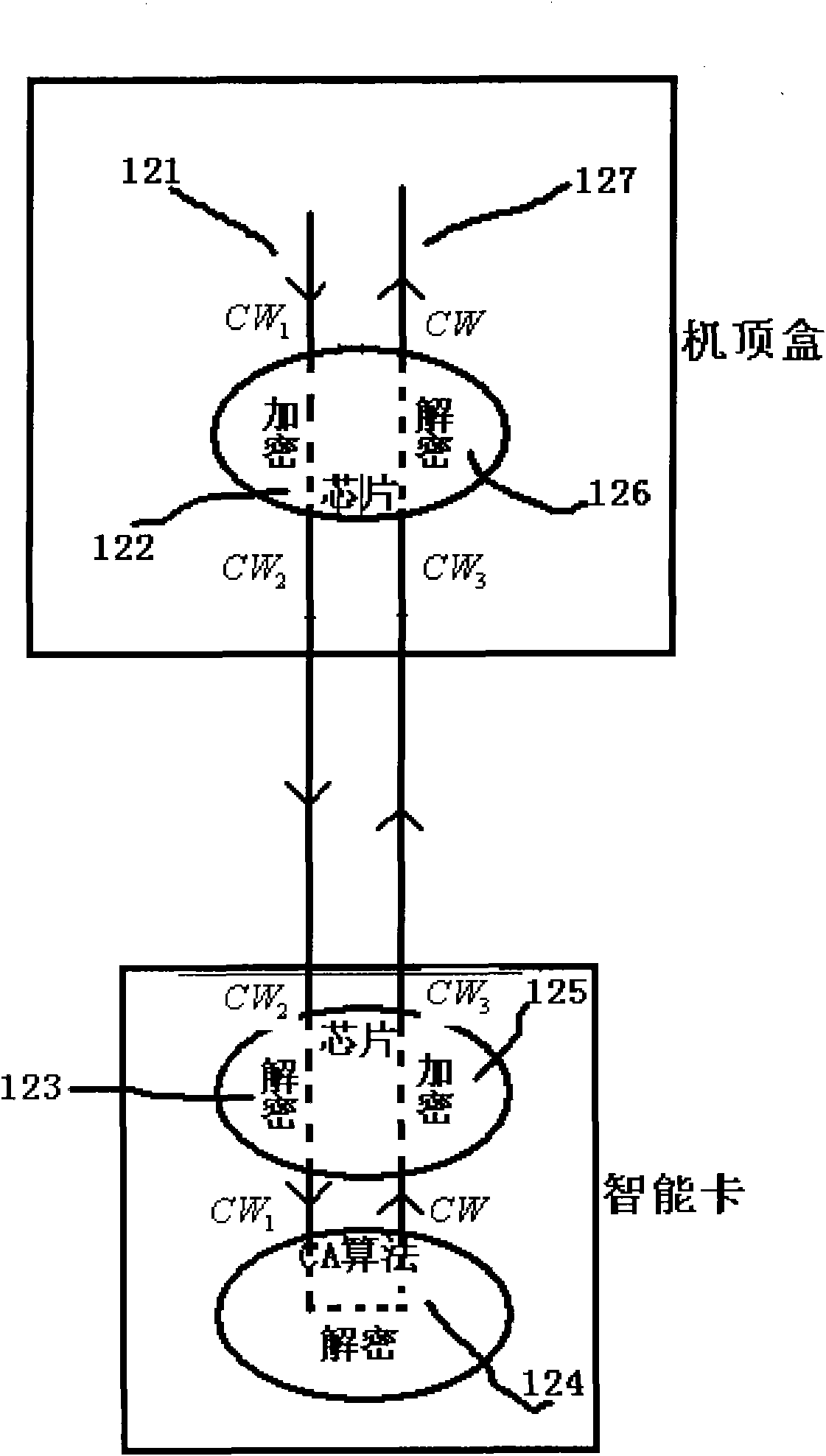
InactiveCN102075802AEnsure safetySecurity exchangePublic key for secure communicationUser identity/authority verificationSecure communicationSmart card security
The invention discloses a method for realizing secure communication between a set-top box and an intelligent card. The method comprises the following steps that: both the set-top box and the intelligent card have a pair of asymmetric keys; and the set-top box and the intelligent card are matched with each other in pair. The set-top box and the intelligent card are mutually authenticated before exchanging a control word; after the authentication, the exchanged information is encrypted by using the public keys of the opposite parties and then transmitted; and the receiving parties can decipher the information by using the own private keys. Through the mutual authentication mechanism between the set-top box and the intelligent card, the communication between an illegal set-top box (or an illegal intelligent card) and a legal intelligent card (or a legal set-top box) can be prevented so as not to exchange the keys. By encrypting the information exchanged through the communication between the set-top box and the intelligent card, the connection between the set-top box and the intelligent card can be effectively prevented from being attacked, so that the security of the exchange processis guaranteed.
Owner:中山爱科数字家庭产业孵化基地有限公司
Access method, device and system for intelligent card
InactiveCN103617005AImprove securityImplement real-time mount controlInput/output to record carriersInternal/peripheral component protectionAccess methodSmart card security
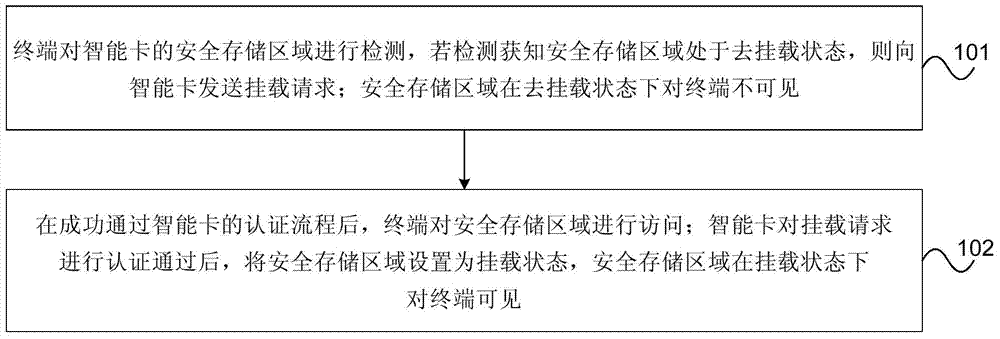
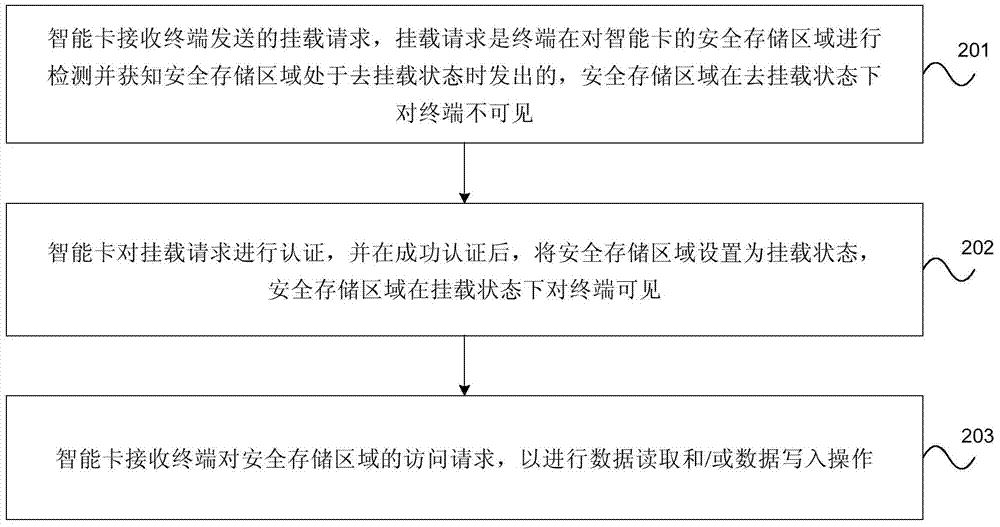
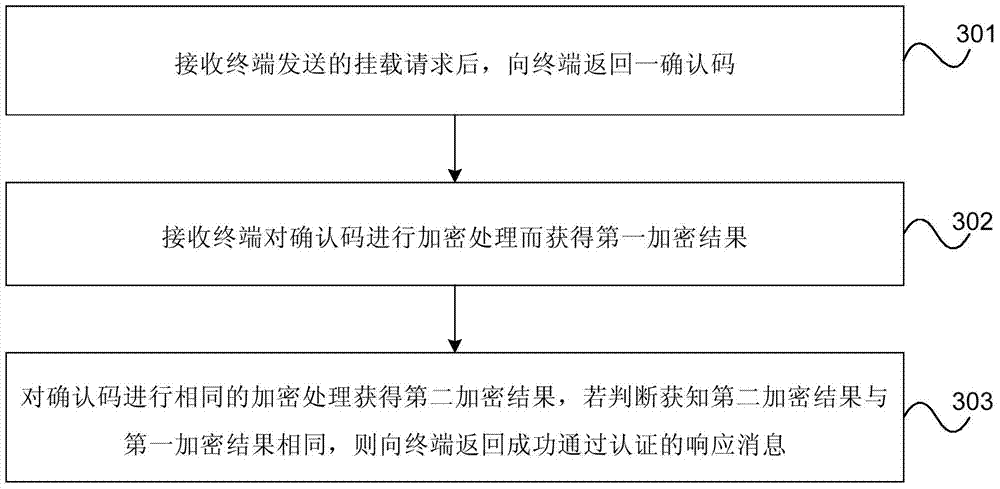
The invention provides an access method, device and system for an intelligent card. The access method for the intelligent card comprises the steps that a terminal detects a secure storage region of the intelligent card, and if the terminal detects and is informed that the secure storage region is in the dismounting status, the terminal sends a mounting request to the intelligent card; the secure storage region is invisible in the dismounting status for the terminal; after the terminal successfully passes through the authentication process of the intelligent card, the terminal has access to the secure storage region; after the intelligent card conducts authentication on the mounting request, and the mounting request passes through the authentication of the intelligent card, the secure storage region is set to be in the mounting status, and the secure storage region is visible in the mounting status for the terminal. According to the access method, device and system for the intelligent card, the real-time mounting control over the secure storage region of the intelligent card is achieved, and safety of access of the intelligent card is improved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Smart card SM4 calculation based DPA attack and secret key restoring method and DPA attack and secret key restoring system
ActiveCN103546277AGood attackImprove defenseKey distribution for secure communicationEncryption apparatus with shift registers/memoriesSmart card securitySmart card
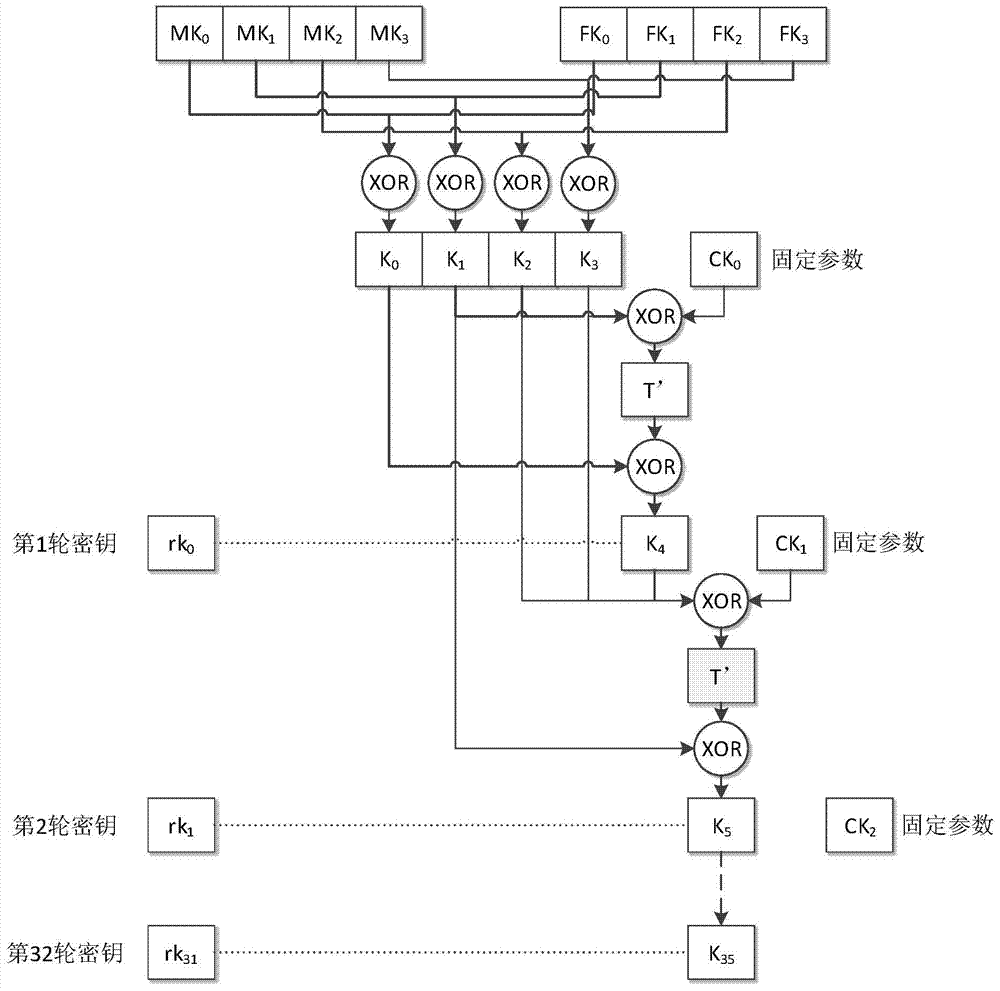
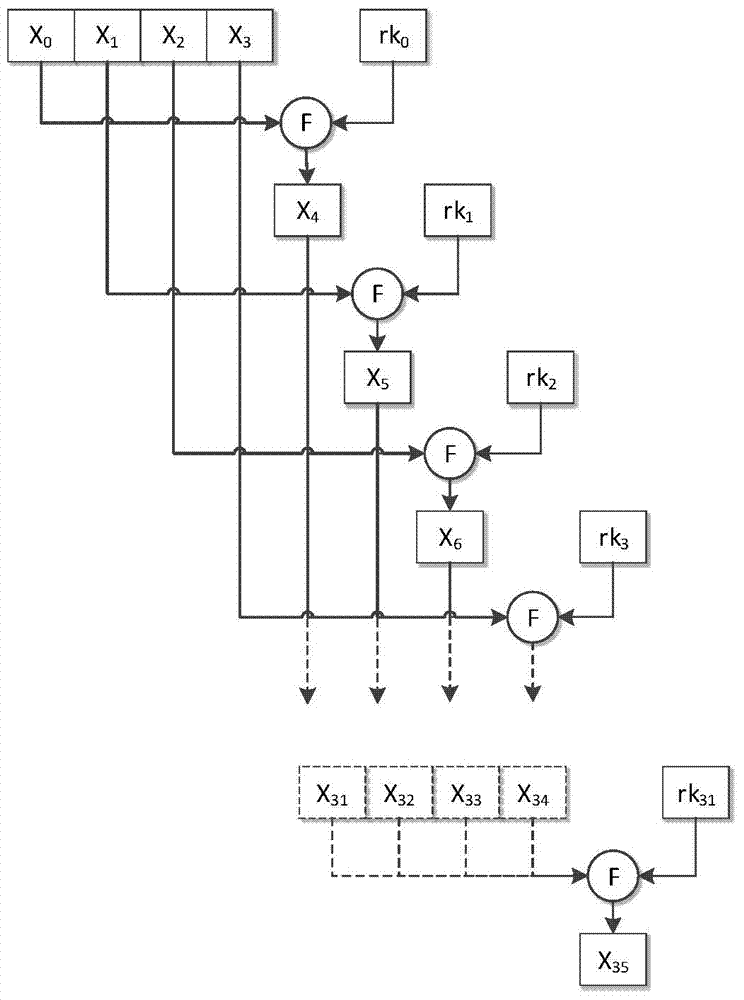
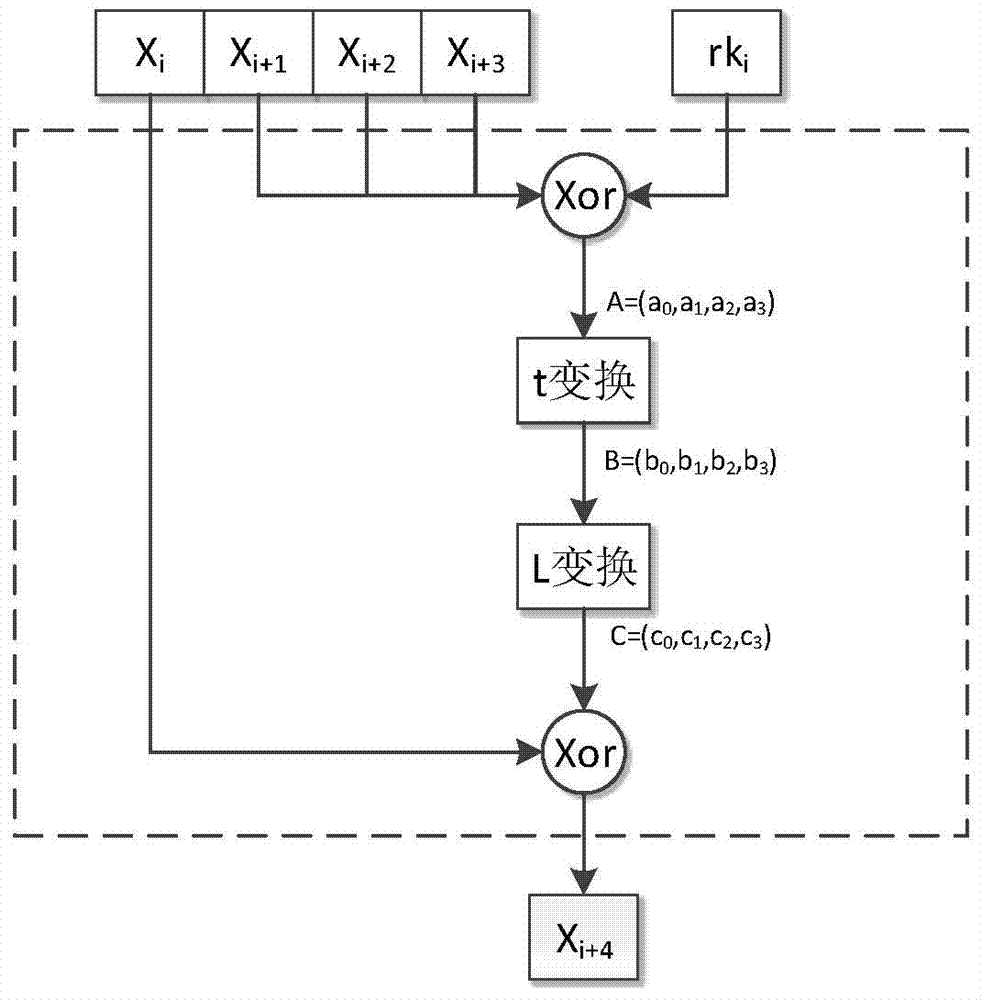
The invention relates to a smart card SM4 calculation based DPA attack and secret key restoring method and a smart card SM4 calculation based DPA attack and secret key restoring system, and belongs to the field of smart card safety. The smart card SM4 calculation based DPA attack and secret key restoring method includes, step 1, performing DPA attack to the first four rounds in SM4 calculation encrypting process to acquire sub keys of the first four rounds; step 2, utilizing the acquired sub keys of the first four rounds to restore SM4 secret keys. With the DPA attack and secret key restoring method and the DPA attack and secret key restoring system, DPA attack to the SM4 calculation of smart cards, restoration of SM4 encrypted secret keys and verification of anti-attack capacity of SM4 calculation of smart cards can be realized.
Owner:BEIJING WATCH DATA SYST
Smart card safety protection circuit and smart card safety protection method
InactiveCN102567774AImprove stabilityImprove reliabilityInternal/peripheral component protectionRecord carriers used with machinesProcessor registerSmart card security
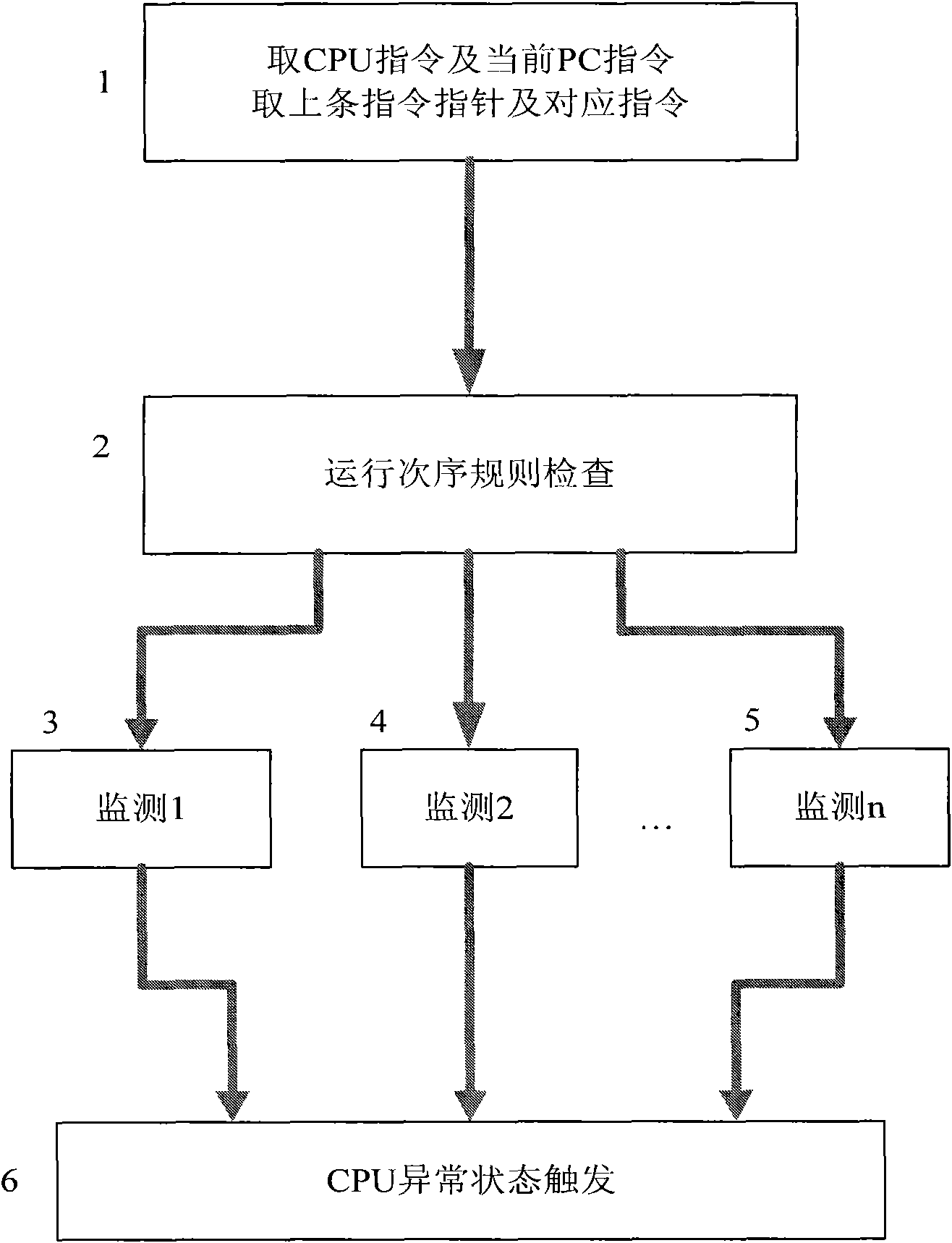
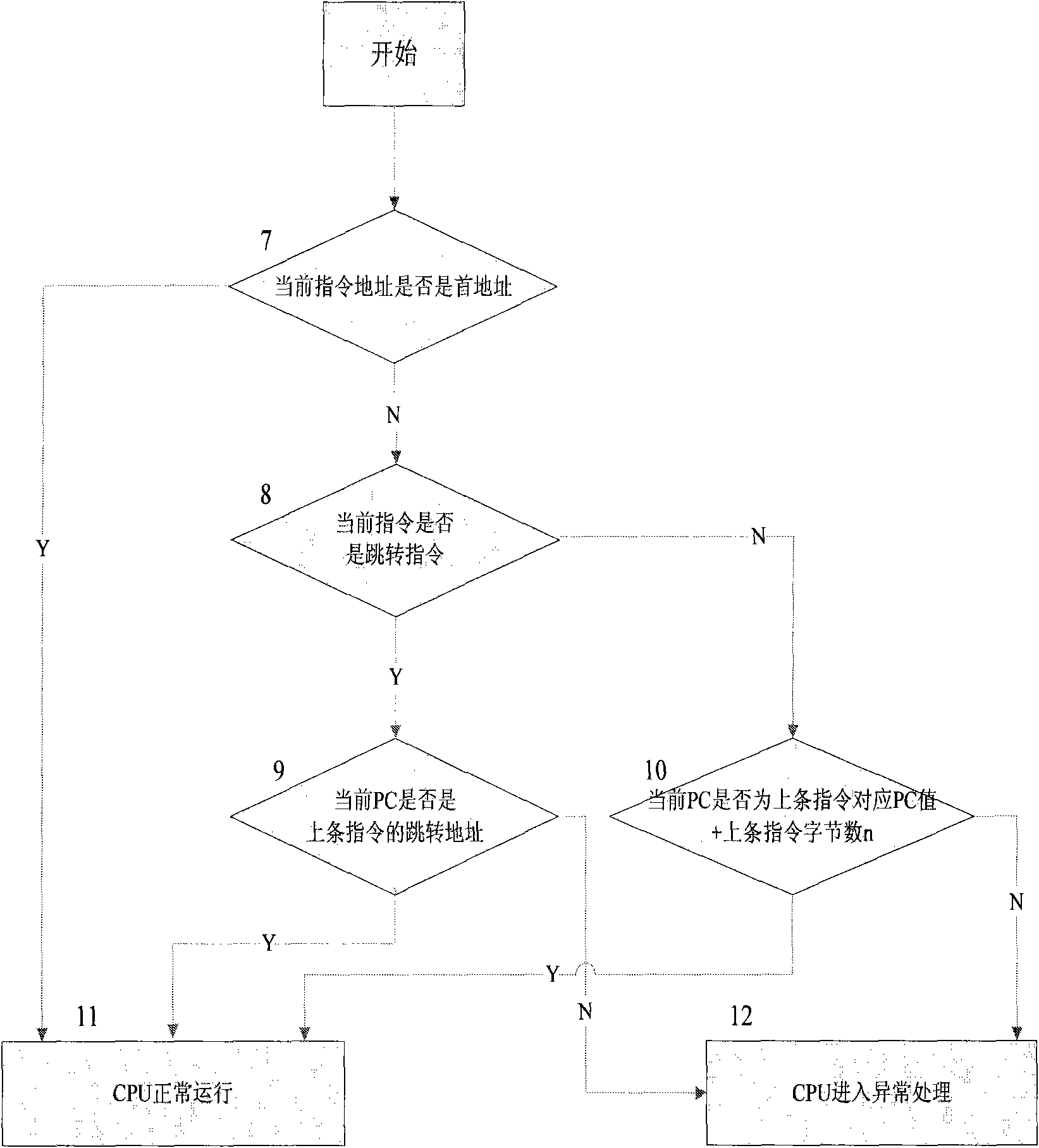
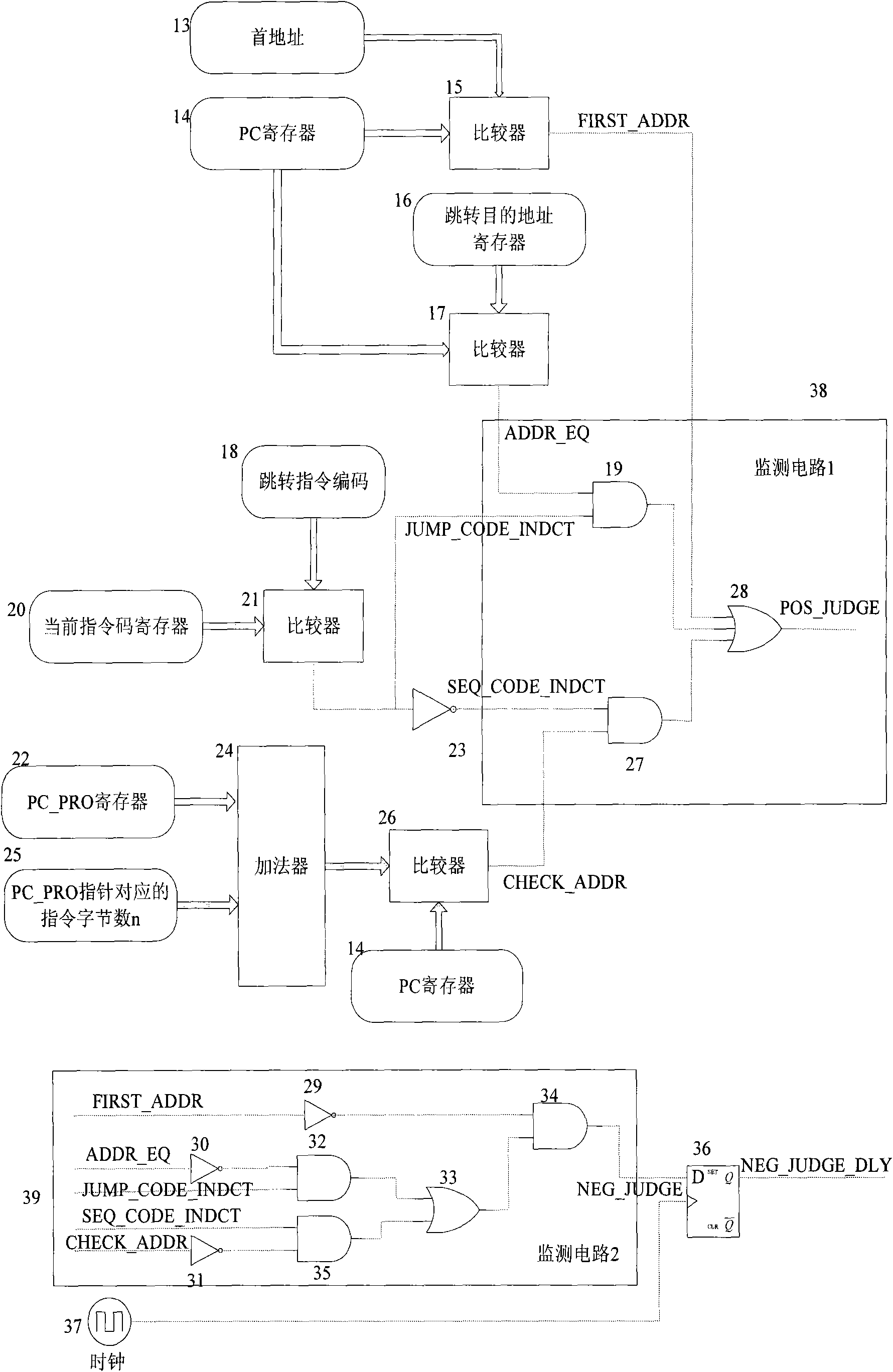
The invention discloses a smart card safety protection method. The method is used for monitoring a running order rule of a CPU (Central Processing Unit) in real time in a time-sharing and distributed manner, and detecting whether the running of the CPU meets the running order rule; once the error of the program running order is detected, the program with error is stopped, and a chip is trigged to deal with the exception so as to ensure the execution of the program according to the correct running order and prevent program fleet; and effective safety protection is provided when the chip of the smart card is influenced by external attacks or the runtime environment is unsteady. The invention also discloses a circuit for realizing the method. The circuit comprises a current instruction code register (20), a jumping destination address register (16), a PC (Personal Computer) register (14), a PC-PRO register (22), an adding device (24), a comparator (15), a comparator (17), a comparator (26), a comparator (21), a monitoring circuit 1 (38) and a monitoring circuit 2 (39). The circuit monitors the running order of the CPU by the monitoring circuit 1 and the monitoring circuit 2, and if the CPU runs exceptionally, the circuit triggers the chip of the smart card at different time to deal with the exception so as to prevent the chip from exception.
Owner:BEIJING CEC HUADA ELECTRONIC DESIGN CO LTD
Smart card secure online checkout
ActiveUS20180181956A1Convenient paymentFacilitate multi-factor authentication and secure electronic checkoutWeb data indexingCommercePaymentWeb site
Wireless communication technologies, a dynamic transaction card, and a mobile application may be utilized to facilitate multi-factor authentication and secure electronic checkout of any website. A wireless connection between a dynamic transaction card and a user device may be utilized to authenticate a user. A user device application may be triggered to call, via an application programming interface (API), an account provider system, and this unique pairing may automatically facilitate payment to a merchant system associated with the electronic check out page. The account provider system may send a push notification to a browser extension associated with the checkout page to prompt the browser extension to populate fields on the electronic checkout page using user account information transmitted from the account provider system, providing a novel digital authentication framework that utilizes digital authentication techniques enables by user devices and dynamic transaction cards to seamlessly facilitate electronic checkout.
Owner:CAPITAL ONE SERVICES
Method for generating security file system of smart card
ActiveCN104573571AMeet the management needs of different application functionsImprove securityInternal/peripheral component protectionRedundant data error correctionFile systemSmart card security
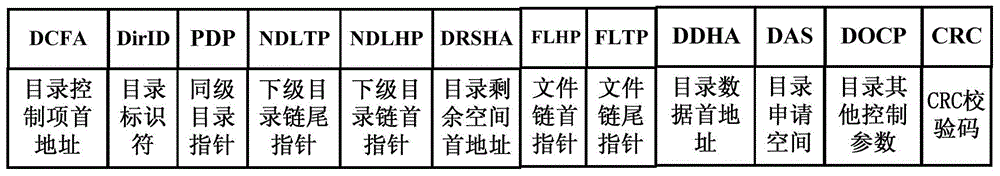
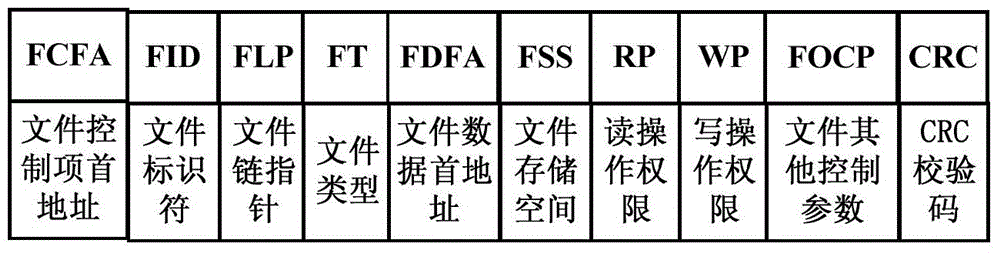
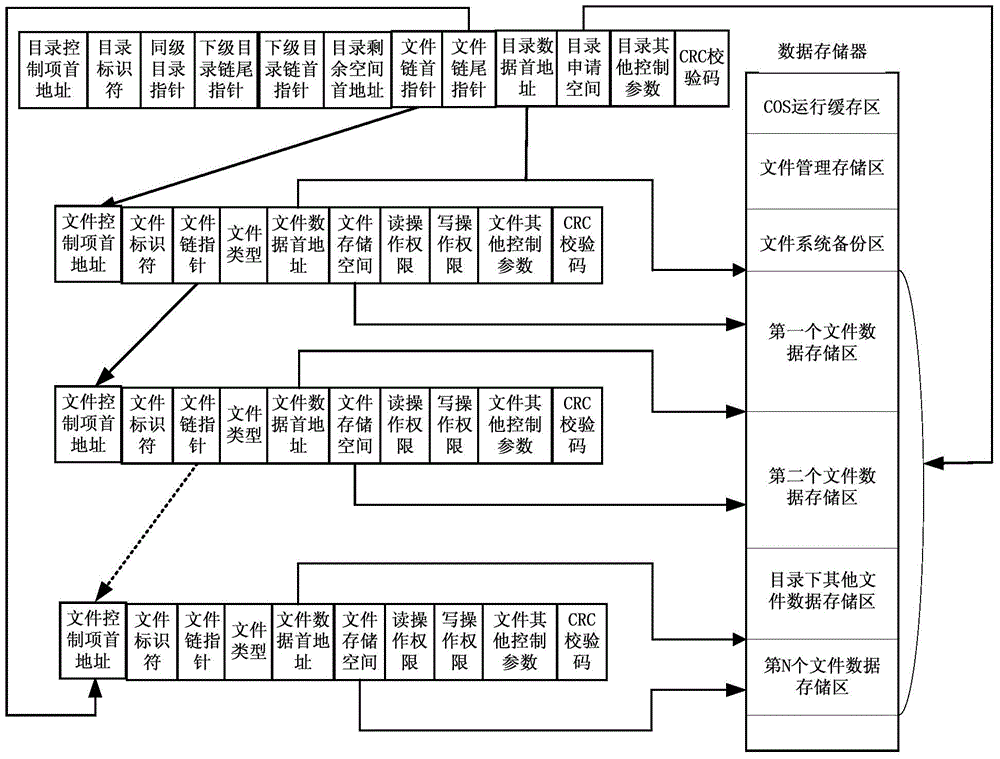
The invention relates to a method for generating a security file system of a smart card. The method comprises the following steps: 1, after the smart card receives a pre-initializing command, performing initial checking on a smart card data storage unit area, and determining the numbers of to-be-created directory control items and file control items according to parameters of the command; 2, creating the relative numbers of empty directory control items and empty file control items, and constructing independent empty directory control item chain tables and empty file control item chain tables; 3, based on the empty directory control item chain tables and the empty file control item chain tables, creating directories and files, constructing a membership relation between a directory and another directory and a relationship that the files are subordinate to the directories, and constructing specifically applied directory control item chain tables and file control item chain tables; and 4, performing corresponding directory and file selection and cancel. According to the method for generating the security file system of the smart card, the utilization rate of a data storage unit and the access control speed of the file system are increased, and meanwhile, the safety and the robustness of the file system are enhanced.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Method for providing smart card (SIM) security by checking a temporary subscriber identifier (TMSI)
ActiveCN102177740AFunction increaseLow costUser identity/authority verificationDigital data authenticationSmart card securitySmart card
An apparatus for providing smart card security may include a processor. The processor may be configured to determine, for a mobile terminal locked to a smart card, whether a temporary subscriber identifier is being read from the smart card or whether the mobile terminal is receiving a new temporary subscriber identifier from a network in communication with the mobile terminal, compare a network identifier associated with the temporary subscriber identifier to a network identifier included in a permanent subscriber identifier associated with the smart card in response to a determination that the temporary subscriber identifier is being read from the smart card, compare a network identifier associated with the new temporary subscriber identifier to a network identifier associated with a previous temporary subscriber identifier in response to a determination that the new temporary subscriber identifier is received from the network, and determine whether to invalidate the temporary subscriber identifier or the new temporary subscriber identifier based on a result of a respective one of the comparing operations.
Owner:NOKIA TECH OY
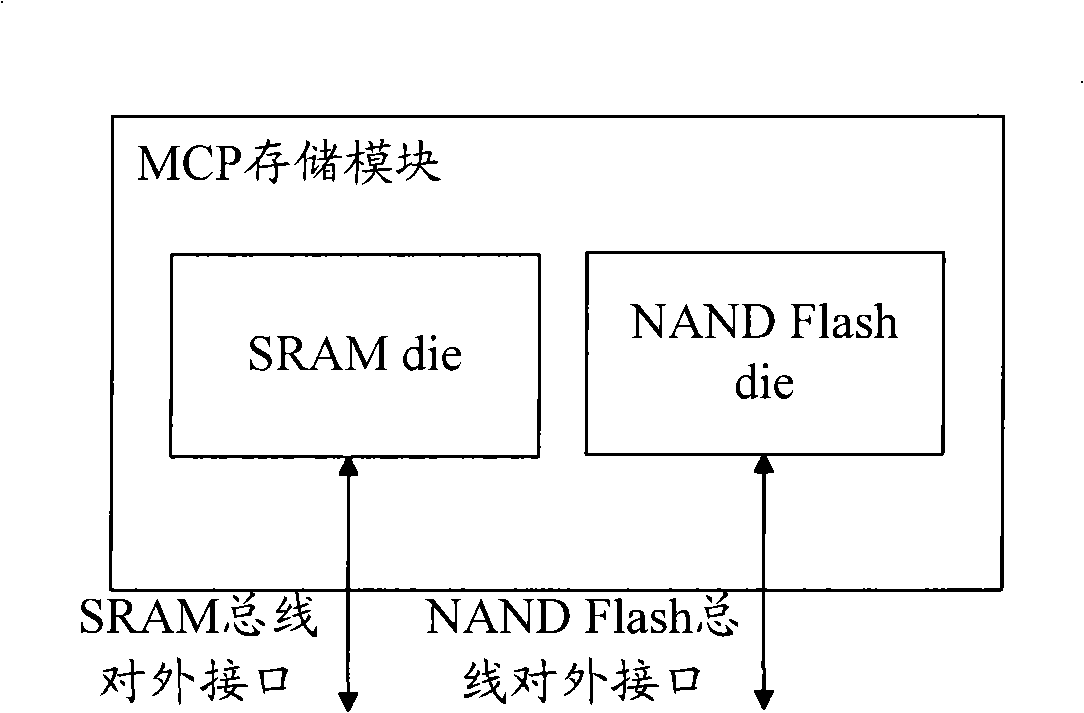
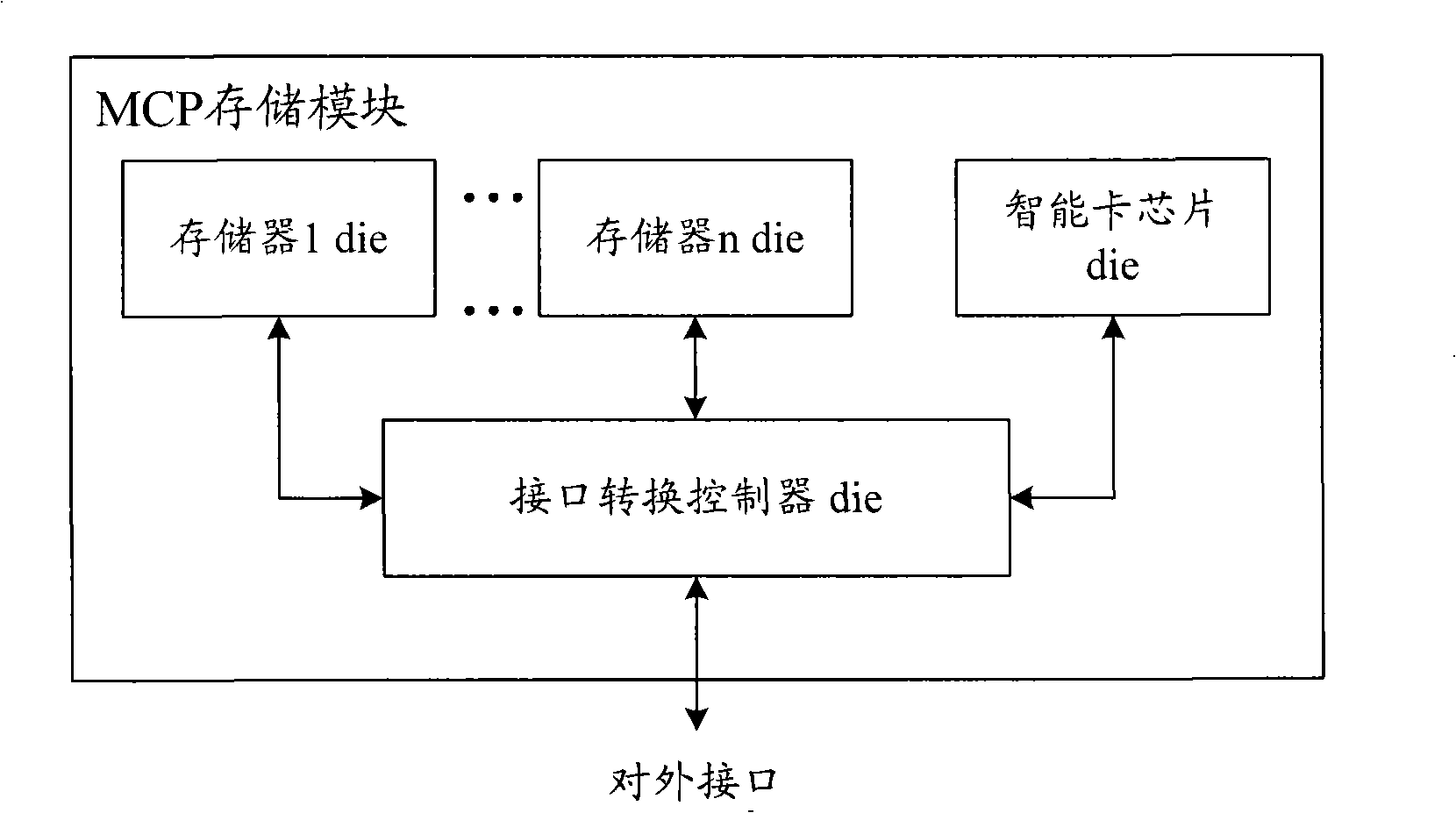
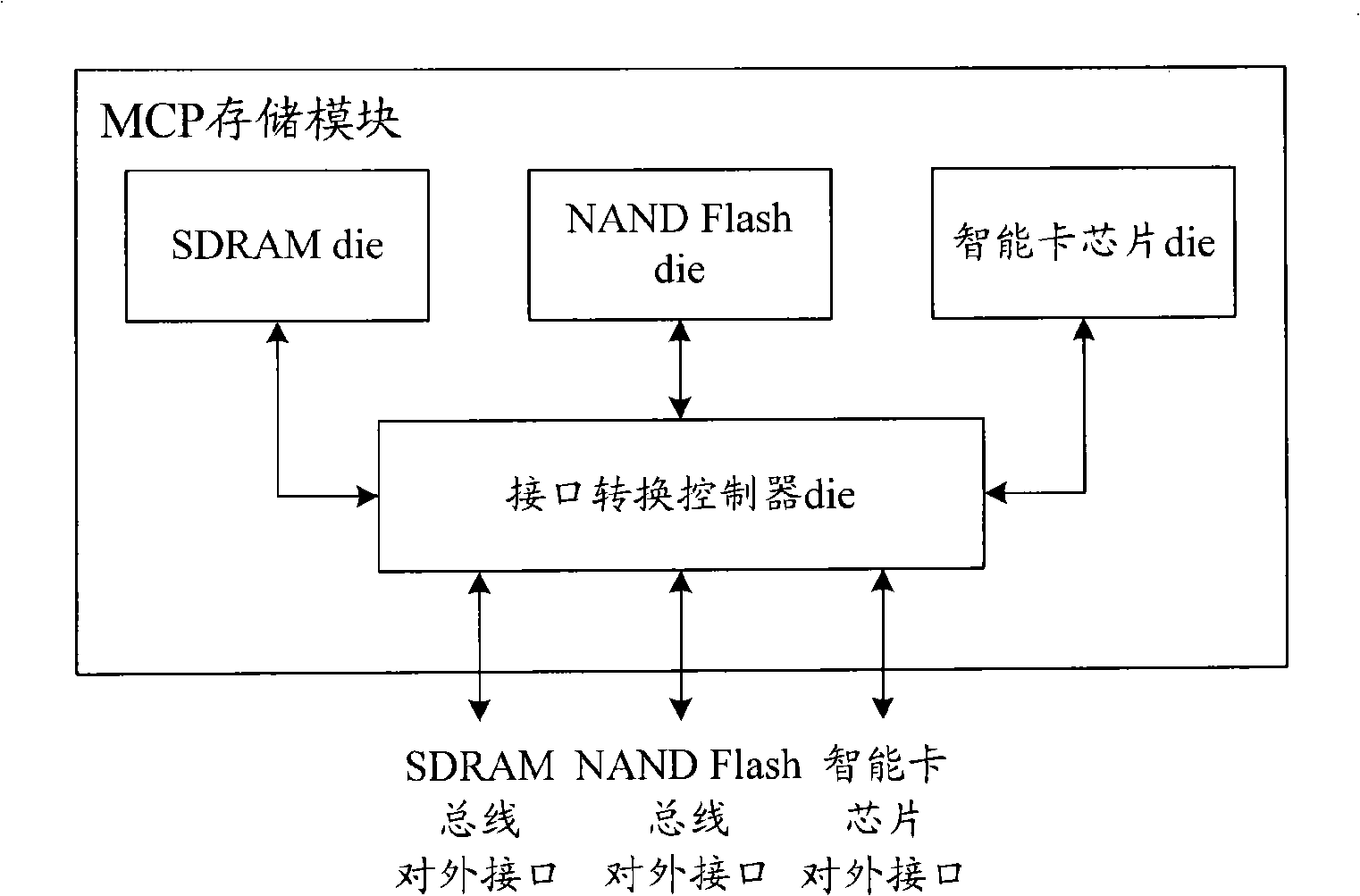
Multi-chip encapsulation storage module
InactiveCN101303885ARealize function extensionReduce in quantityDigital storageSmart card securityComputer module
The invention discloses a multi-chip packaging (MCP) memory module. The MCP memory module of the invention not only packages a plurality of types of memorizers for memory but also packages an interface conversion controller and a smart card chip; wherein, the smart card chip can realize relevant safety business of the smart card chip; the interface conversion controller can realize interface specification conversion when the outer part interacts with a plurality of types of memorizers and the smart card chip through an external interface so that the MCP memory module is not limited to the memory function but realizes functional extension. Moreover, the interface conversion controller can realize interface specification conversion, so the external interface arranged on the MCP memory module of the invention can correspond to a plurality of types of memorizers and the smart card chip one by one. Preferably, less external interfaces are needed, e.g. one or two, so that the number of external interface pins of the MCP memory module can be reduced.
Owner:POTEVIO INFORMATION TECH
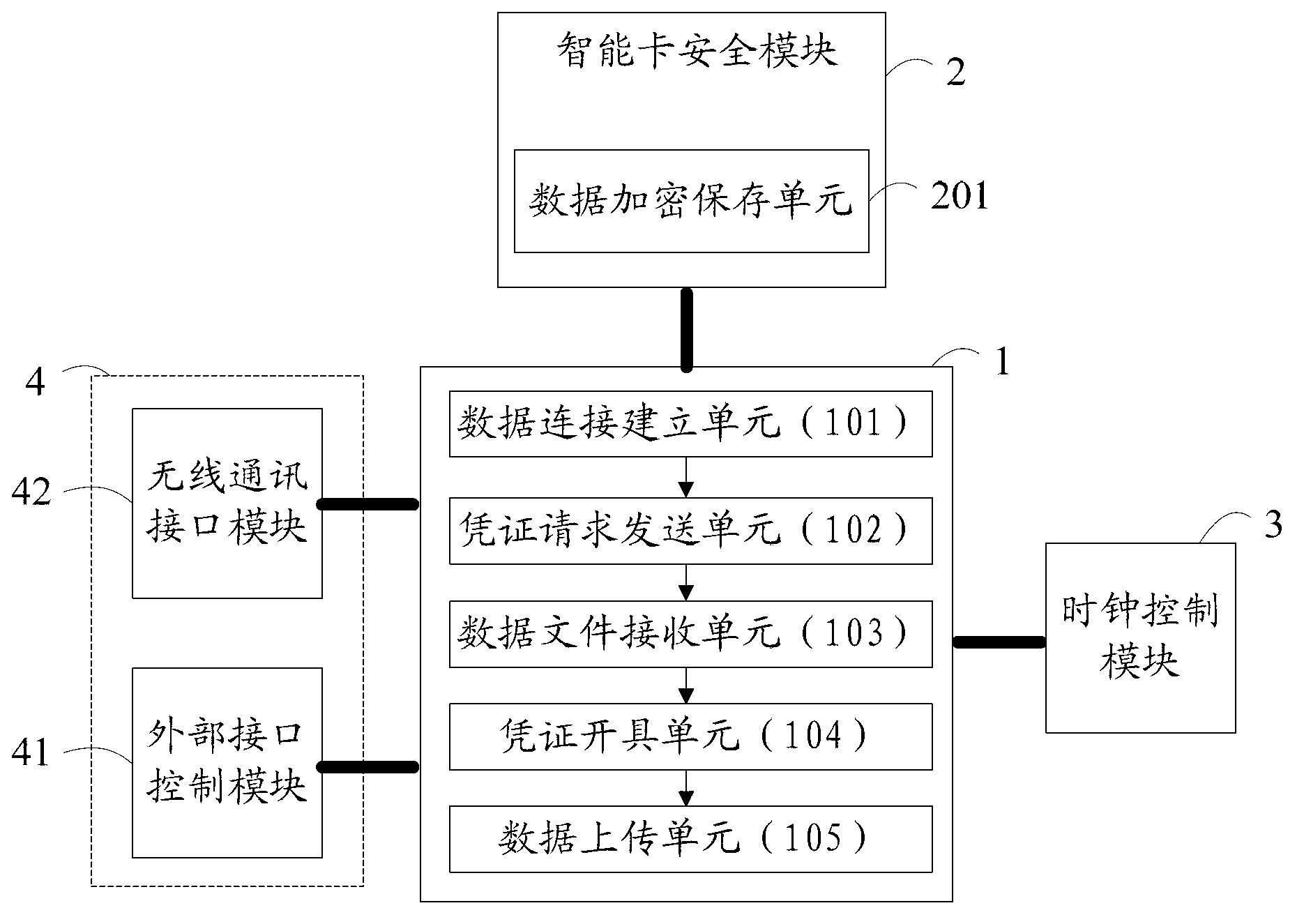
Electronic tax management terminal
The invention relates to the field of electronic tax services and provides an electronic tax management terminal. The electronic tax management terminal comprises a central processor, an intelligent card security module, a clock control module and an interface module, wherein the intelligent card security module comprises a data encryption storing unit, wherein the central processor comprises a data connection establishing unit, an evidence request transmitting unit, a data file receiving unit, an evidence making unit and a data uploading unit. With the adoption of the electronic tax management terminal provided by the invention, the function of making an electronic tax payment receipt is realized; and compared with a paper receipt, the tax evasion is prevented, the tax payment operation efficiency is improved, the tax payment can be managed uniformly, and a solving scheme for realizing invoice informatization, information tax management and reducing tax payment cost is provided.
Owner:WUHAN TIANYU INFORMATION IND
Smart card and safety protection method thereof
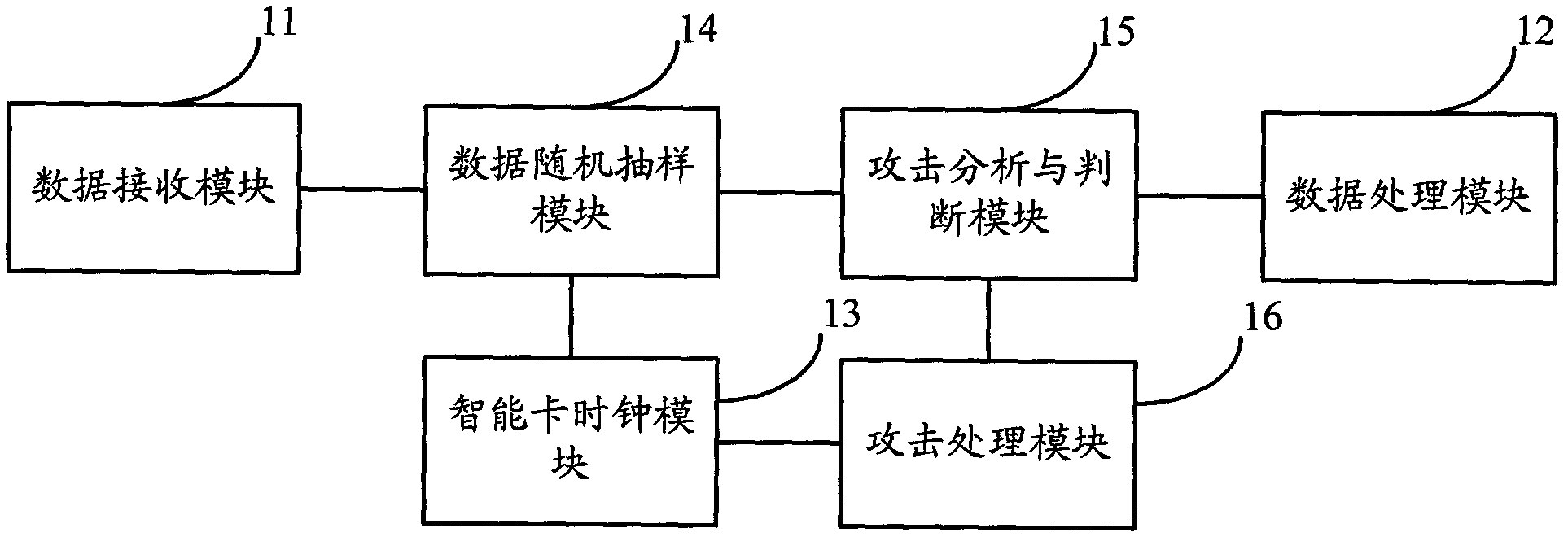
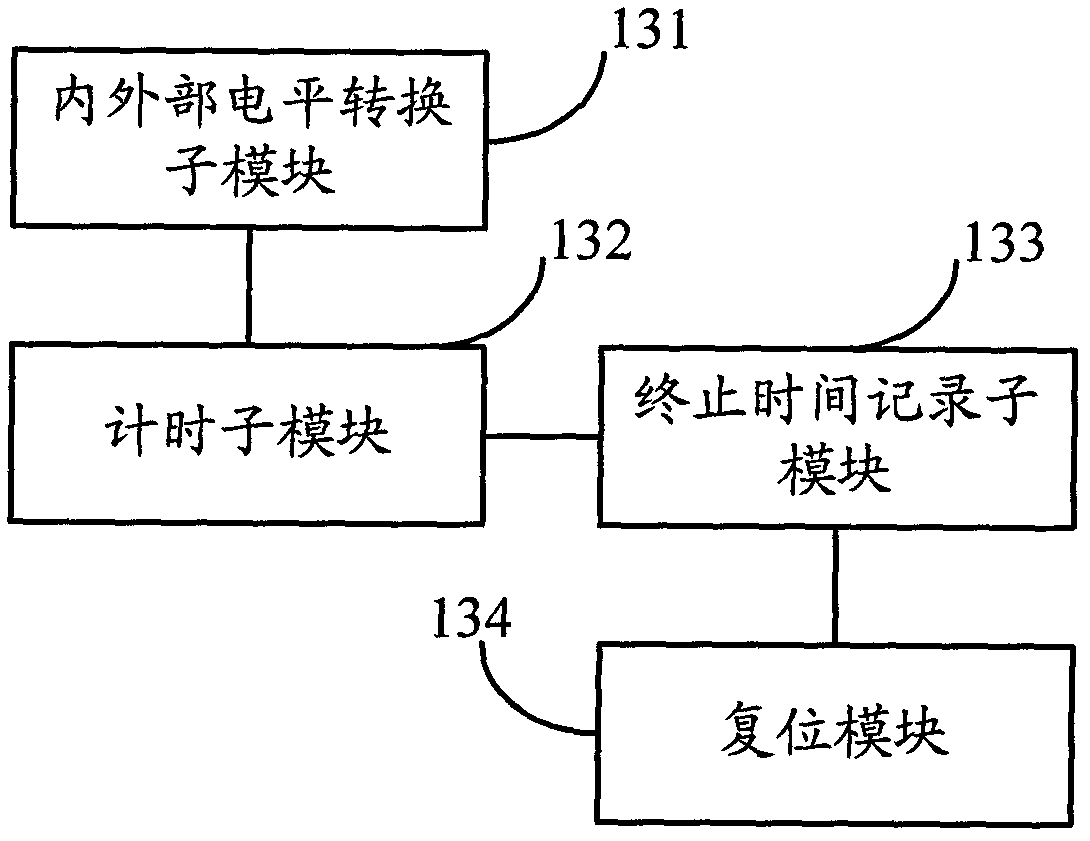
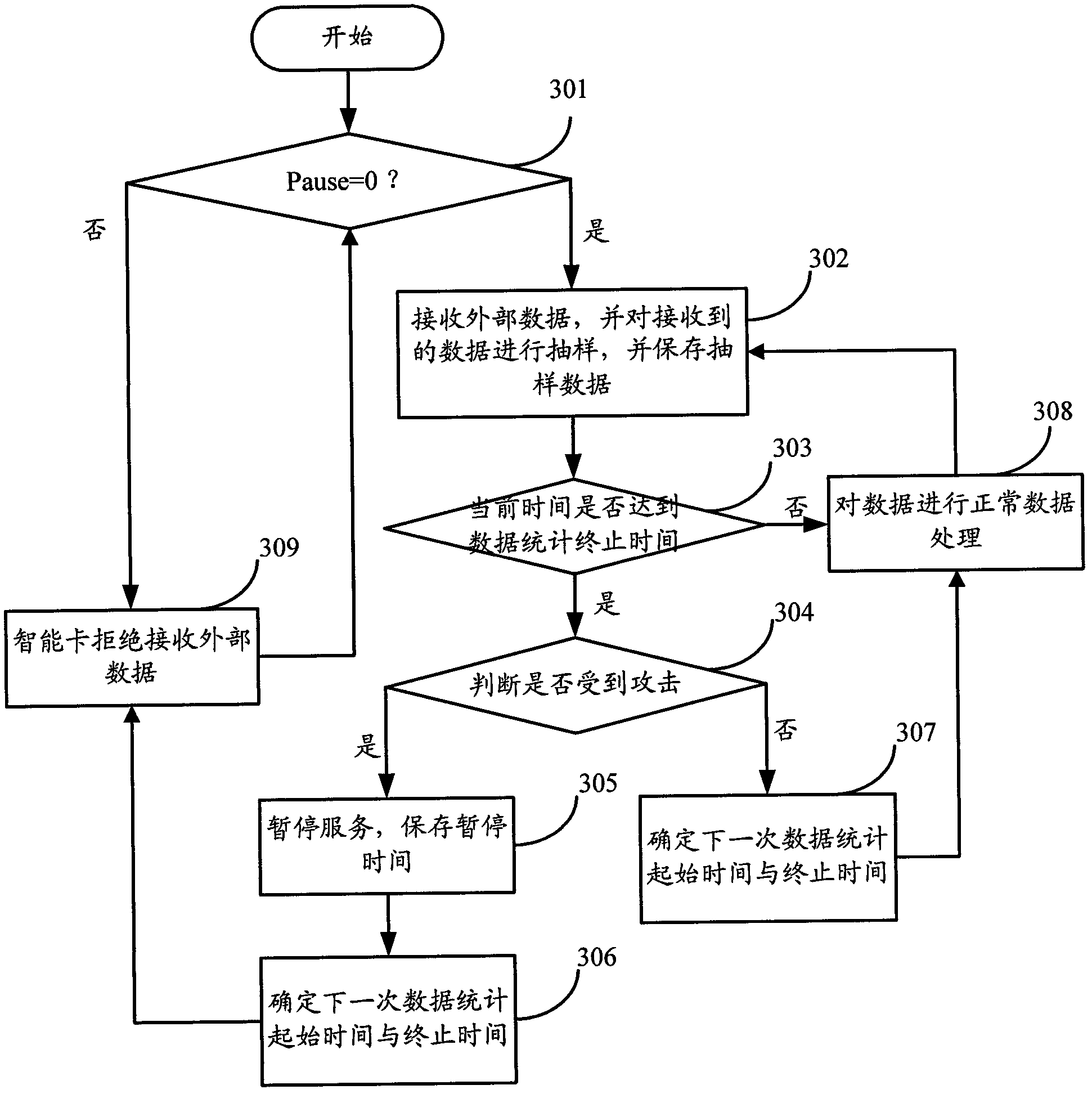
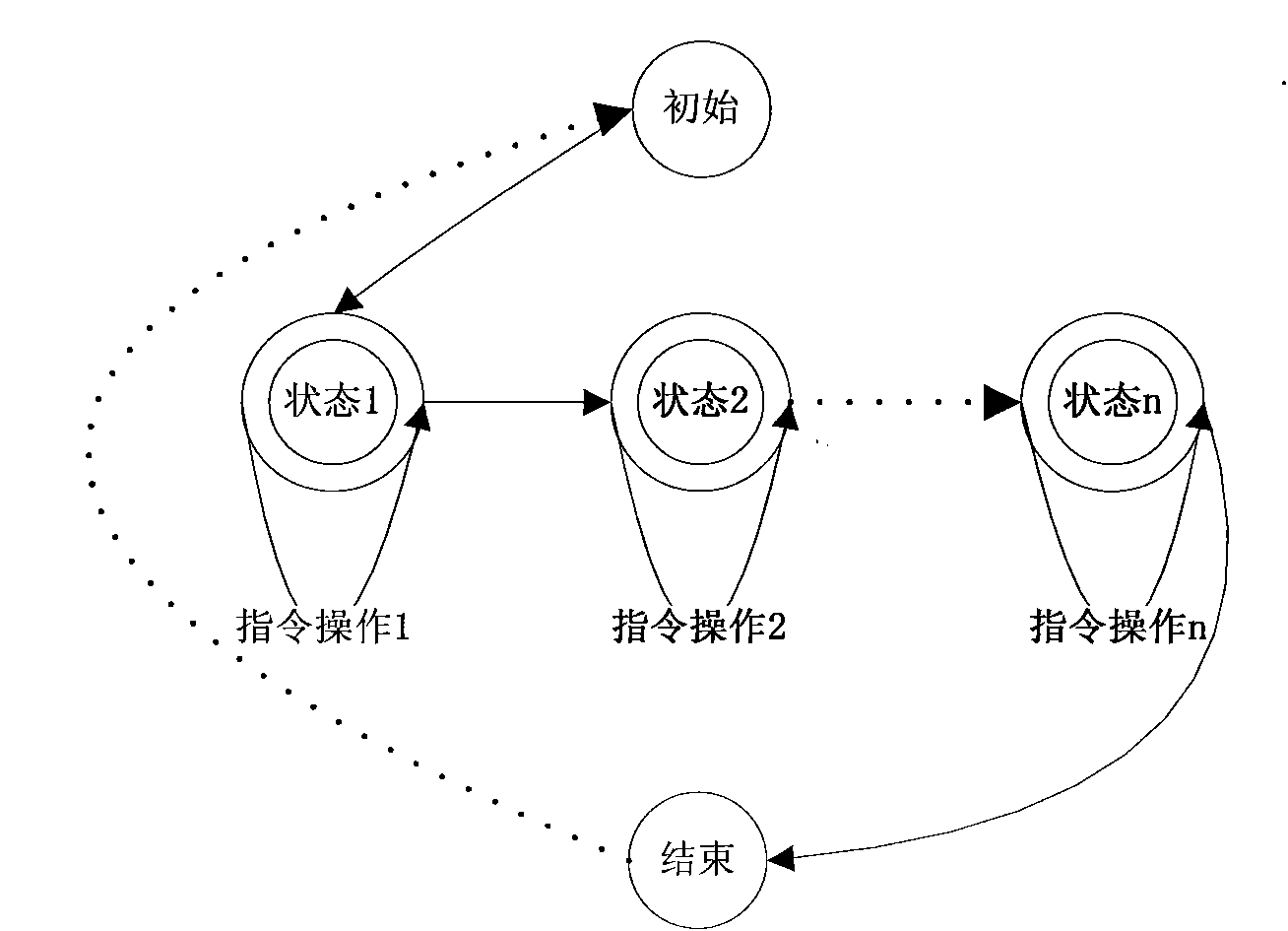
The invention discloses a smart card and a safety protection method of the smart card. The smart card comprises a smart card clock module, a data random sampling module, an attack analysis and judgment module and an attack processing module, wherein the smart card clock module is used for timing according to a received external level signal; the data random sampling module is used for determining the data statistics beginning time and the data statistics terminating time at random, and sampling the received data according to the data statistics beginning time and the data statistics terminating data; the attack analysis and judgment module is used for judging whether the smart card is attacked according to the obtained data sampled by the data random sampling module, and the corresponding data statistics beginning time and data statistics terminating time; and the attack processing module is used for carrying out anti-attack treatment when the attack analysis and judgment module judges the smart card is attacked. According to the safety protection method of the smart card, whether the smart card is attached can be more effectively judged.
Owner:CHINA MOBILE COMM GRP CO LTD
Method for identifying communication object of smart card
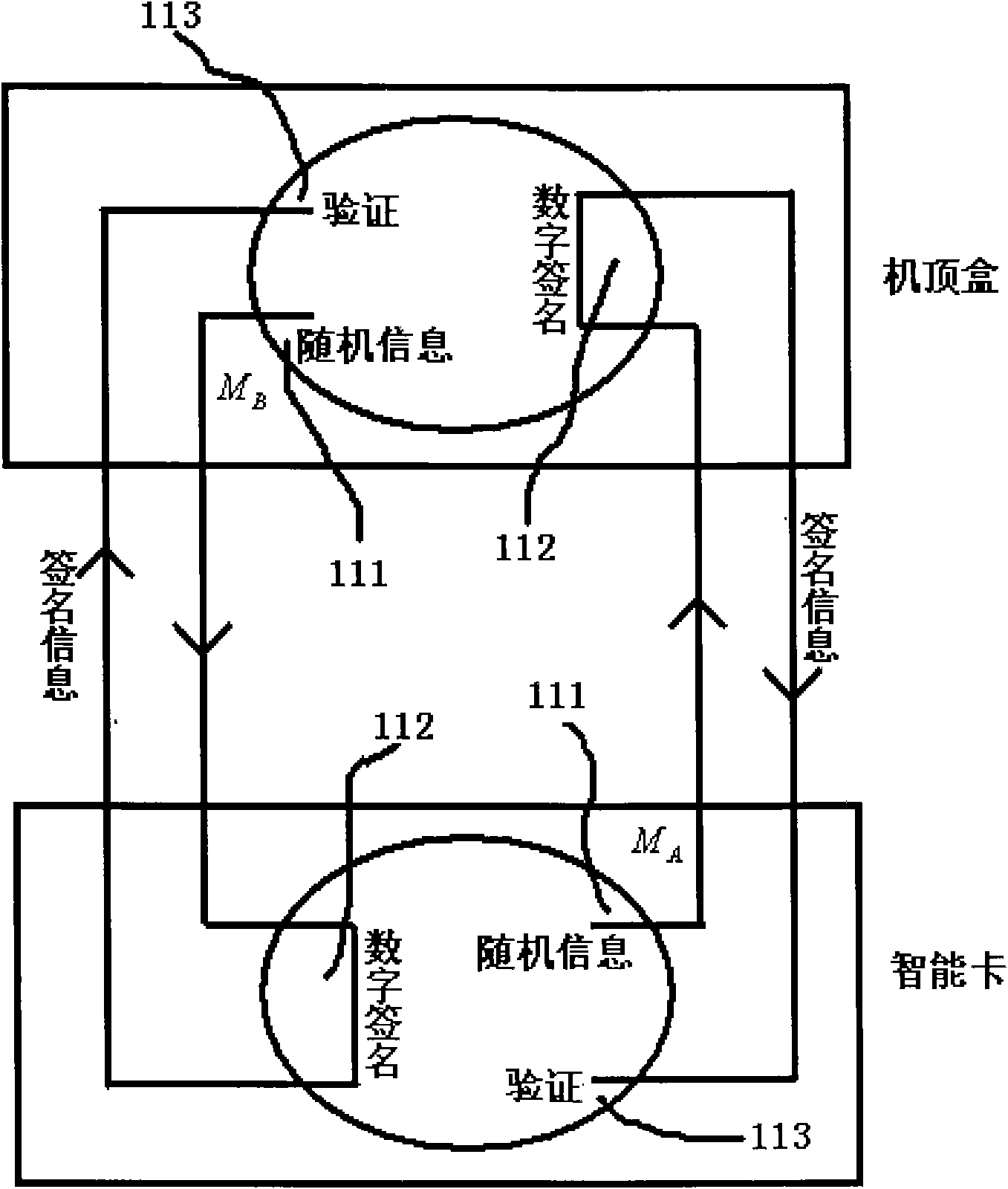
InactiveCN101930552AEnsure consistencyUnderstand clearlyCo-operative working arrangementsTransmissionSelf recoverySmart card security
The invention aims at disclosing a method for identifying a communication object of a smart card. By introducing a concept of secure conversation in the existing smart card security system, the invention associates application programs with requests transmitted thereby by using a semi-permanent and interactive communication object identification mode which is established between the smart card and terminal application programs within a certain time and has a self-recovery mechanism, thereby realizing that the smart card can simultaneously and securely communicate with multiple communication objects (such as the terminal application programs). In addition, once a secure conversation is established, the secure conversation exists all the time until the operation of the terminal application programs is completed or other conditions terminating the secure conversation appear; and the security of the conversation is protected by a secure conversation symmetric key and a secure conversation public / private key pair.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
Method for checking operating authority of smart card and smart card
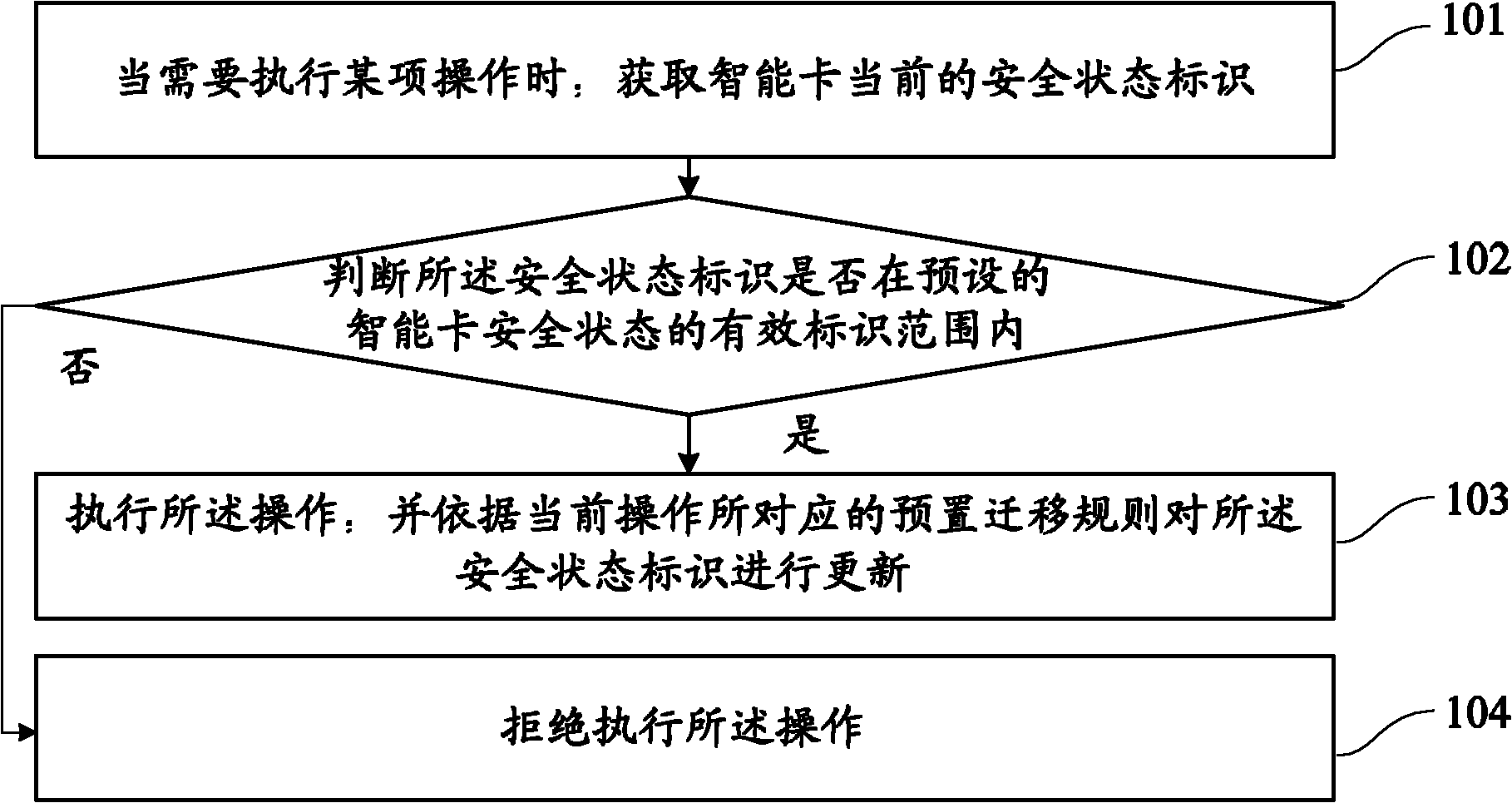
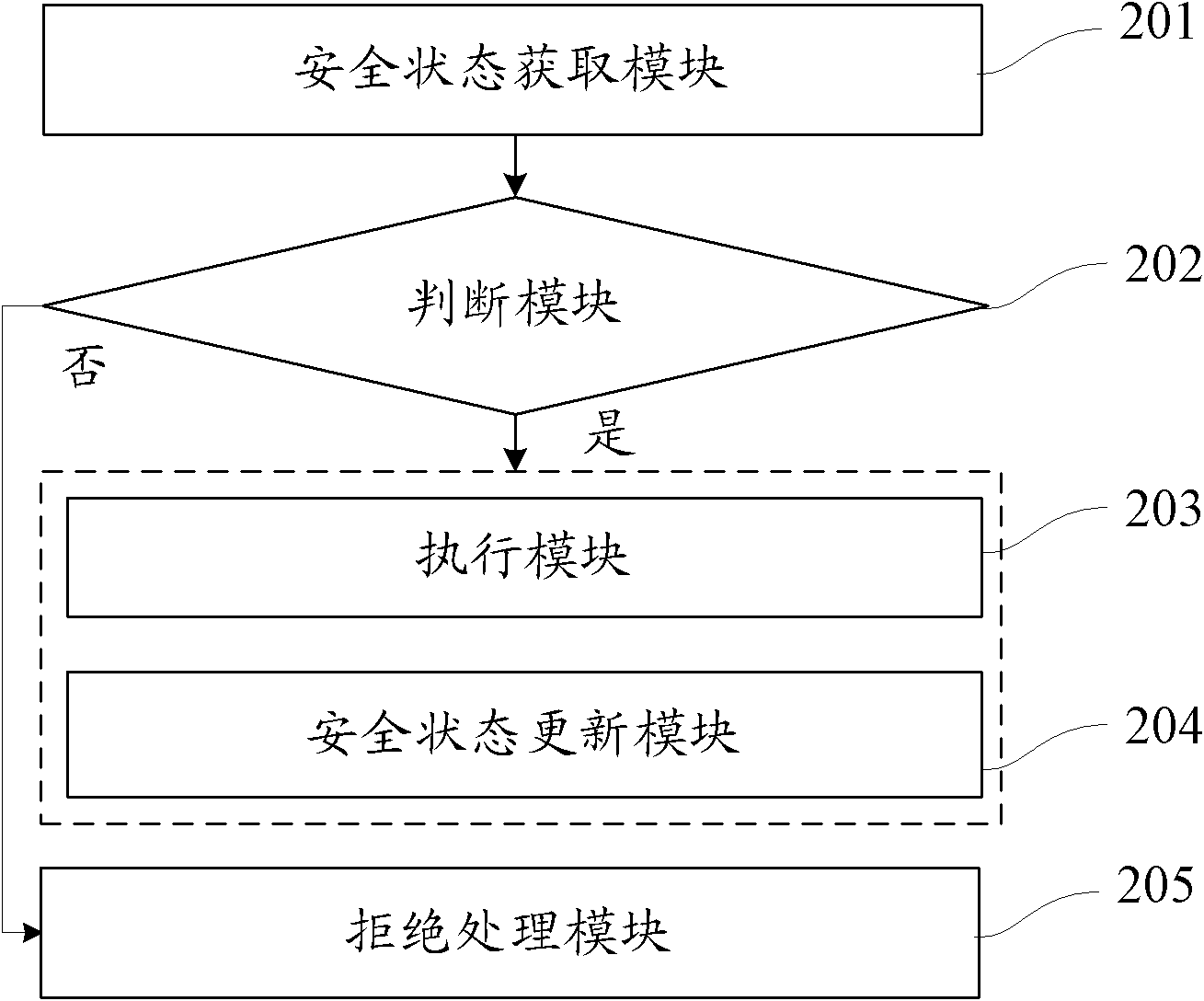
InactiveCN102110205ATo achieve the purpose of controlDigital data authenticationRecord carriers used with machinesSmart card securitySecure state
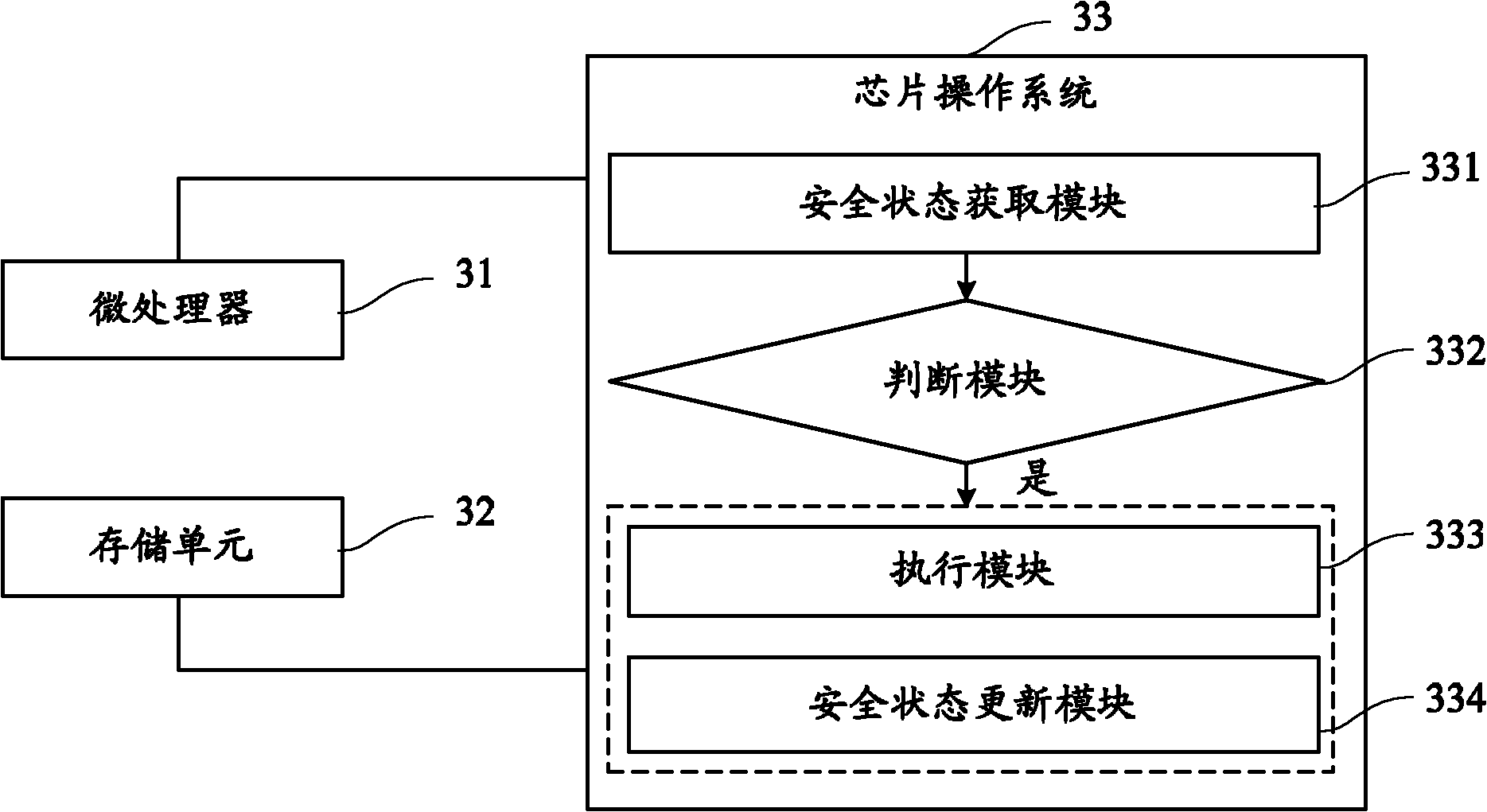
The invention provides a method for checking operating authority of a smart card. The method comprises steps as follows: when an operation of the smart card needs to be performed, current safety state identification of the smart card must be obtained and judged whether the safety state identification is within the valid identification range of the preset safety state of the smart card; if so, theoperation is executed, and the safety state identification is updated according to a preset transfer rule corresponding to the current operation. The invention can precisely and effectively control the safety state of the smart card, and improves the safety of the smart card.
Owner:BEIJING WATCH DATA SYST
Intelligent card safety authentication method and intelligent card safety authentication system on basis of data and short message technologies
ActiveCN107566413AAvoid attackAvoid interceptionMessaging/mailboxes/announcementsTransmissionSmart card securitySmart card
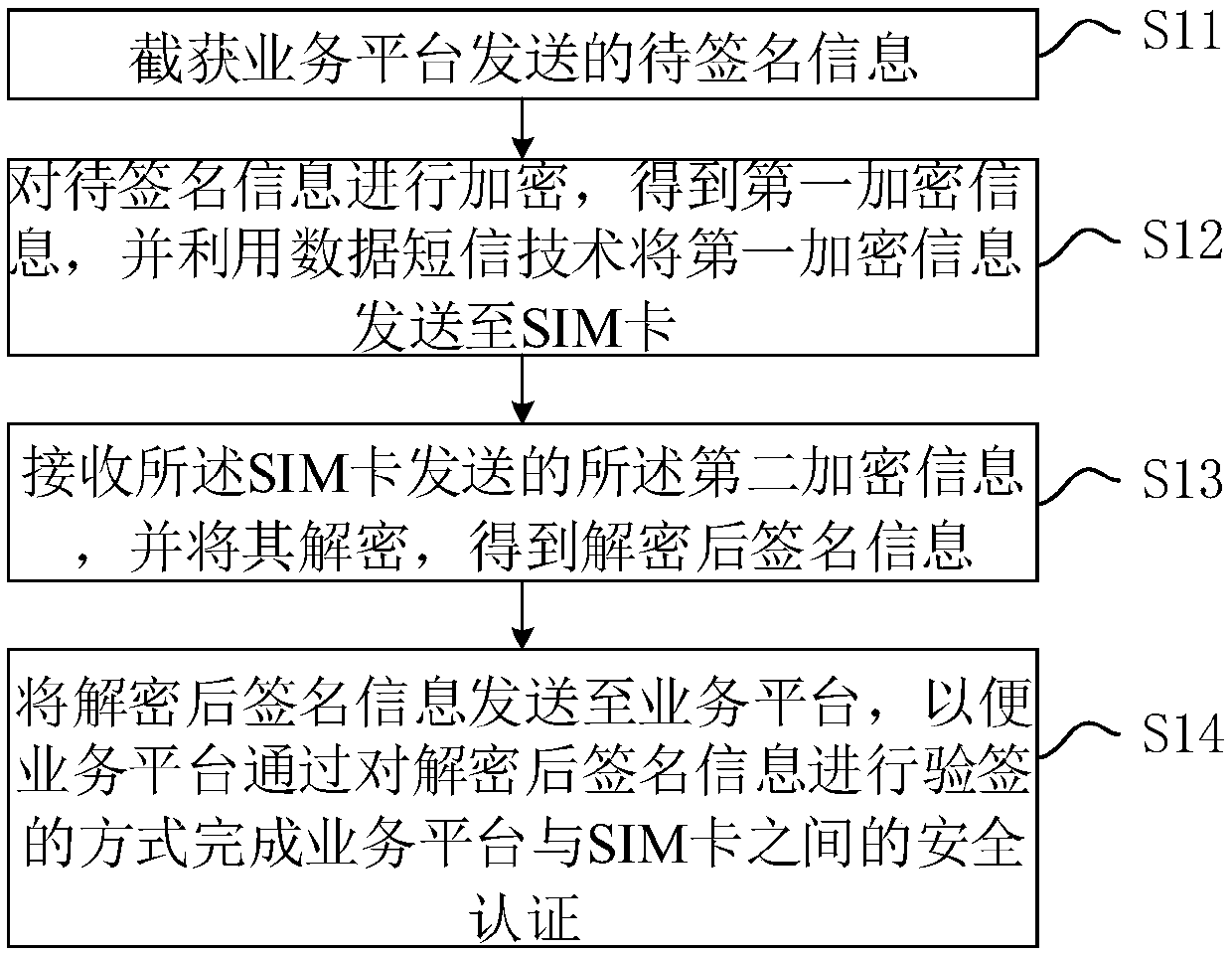
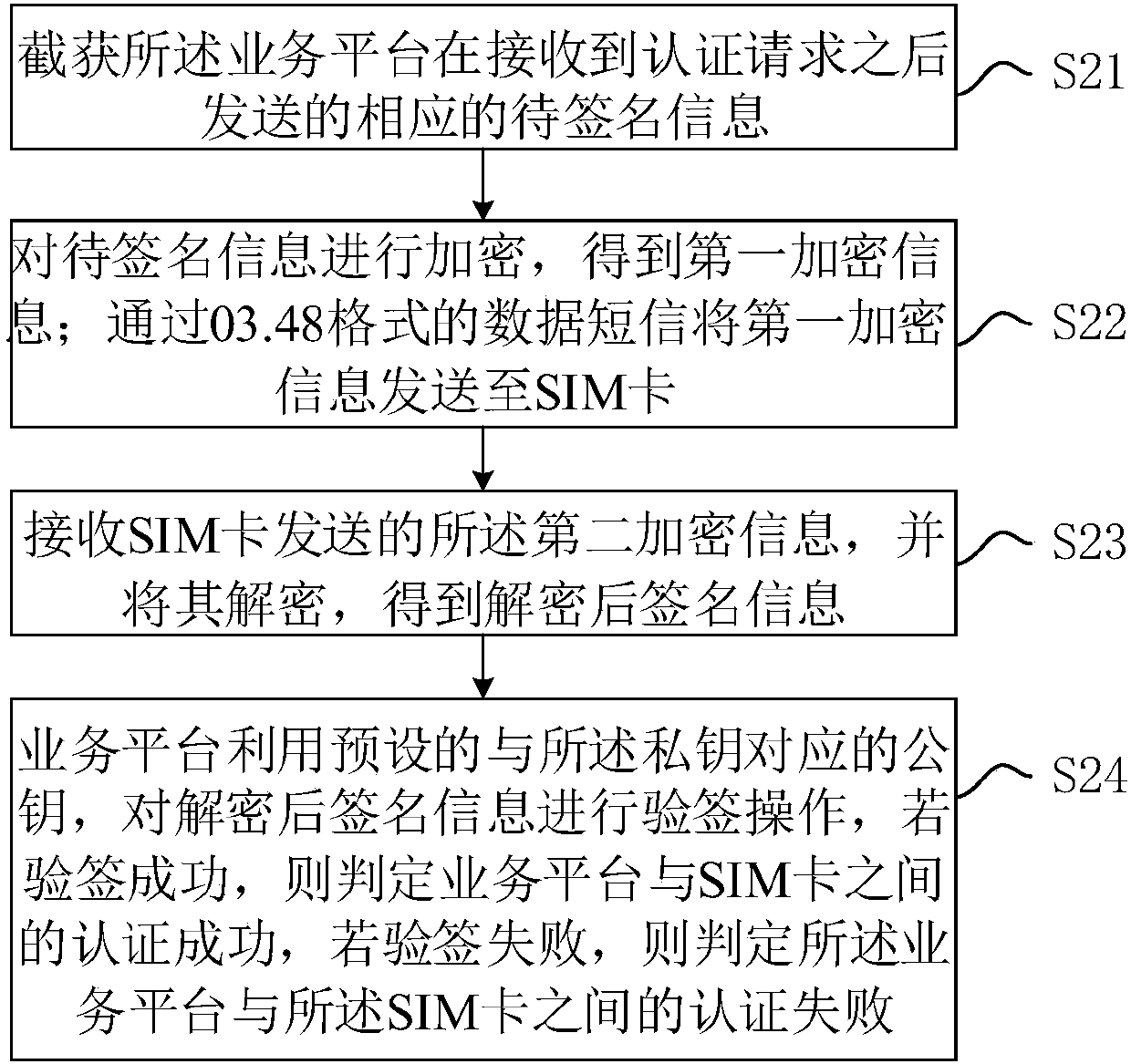
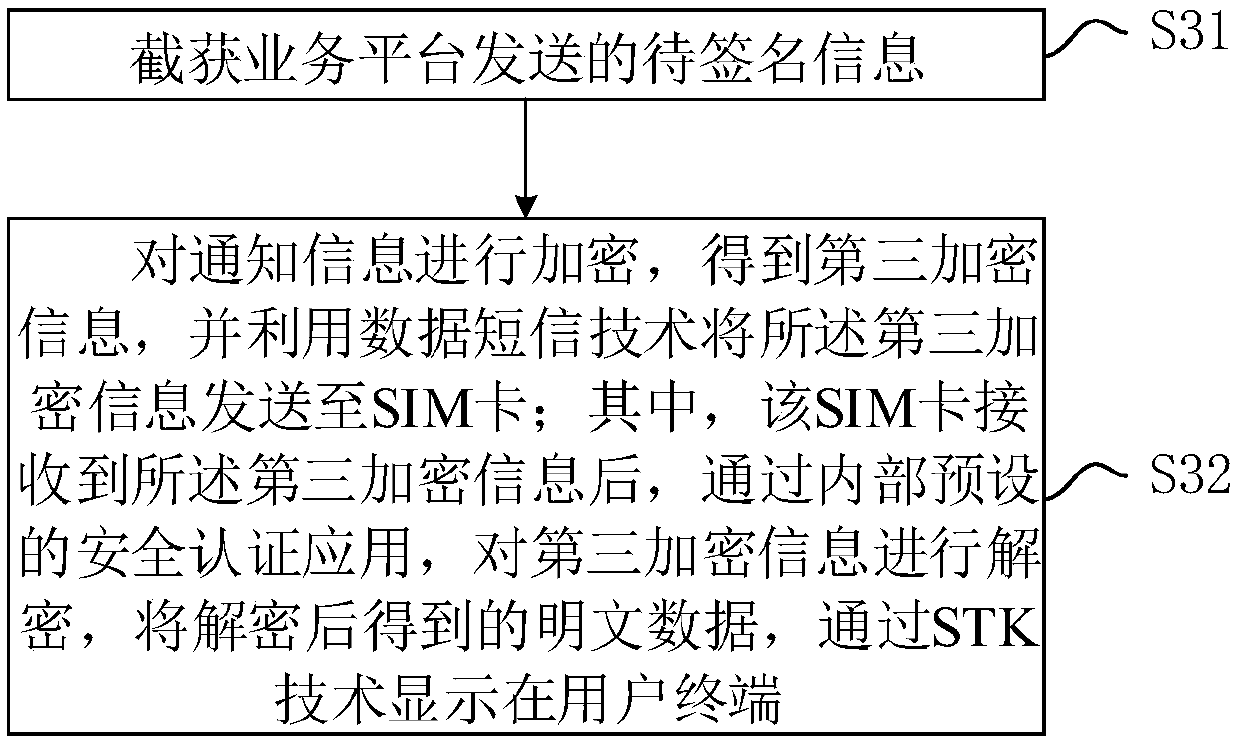
The invention discloses an intelligent card safety authentication method and an intelligent card safety authentication system on the basis of data and short message technologies. The intelligent cardsafety authentication method includes intercepting and capturing to-be-signed information transmitted by a business platform, encrypting the to-be-signed information to obtain first encrypted information and transmitting the first encrypted information to an SIM (subscriber identification module) card by the aid of the data and short message technologies; decrypting the first encrypted informationby the aid of safety authentication application after the first encrypted information is received by the SIM card, signing the decrypted to-be-signed information and encrypting obtained signed information to obtain second encrypted information; receiving the second encrypted information transmitted by the SIM card and decrypting the second encrypted information; transmitting the decrypted signedinformation to the business platform to allow the business platform to verify signature for the decrypted signed information so as to complete safety authentication. The intelligent card safety authentication method and the intelligent card safety authentication system have the advantages that the transmitted information is encrypted, and the safety authentication can be implemented between the business platform and the SIM card by the aid of signature functions of the safety authentication application and signature verification functions of the business platform.
Owner:EASTCOMPEACE TECH
Method, apparatus and computer program product for providing smart card security
ActiveUS8290474B2Detection and prevention of useImprove securityUnauthorised/fraudulent call preventionDigital data processing detailsSmart card securitySmart card
An apparatus for providing smart card security may include a processor. The processor may be configured to determine, for a mobile terminal locked to a smart card, whether a temporary subscriber identifier is being read from the smart card or whether the mobile terminal is receiving a new temporary subscriber identifier from a network in communication with the mobile terminal, compare a network identifier associated with the temporary subscriber identifier to a network identifier included in a permanent subscriber identifier associated with the smart card in response to a determination that the temporary subscriber identifier is being read from the smart card, compare a network identifier associated with the new temporary subscriber identifier to a network identifier associated with a previous temporary subscriber identifier in response to a determination that the new temporary subscriber identifier is received from the network, and determine whether to invalidate the temporary subscriber identifier or the new temporary subscriber identifier based on a result of a respective one of the comparing operations.
Owner:NOKIA TECHNOLOGLES OY
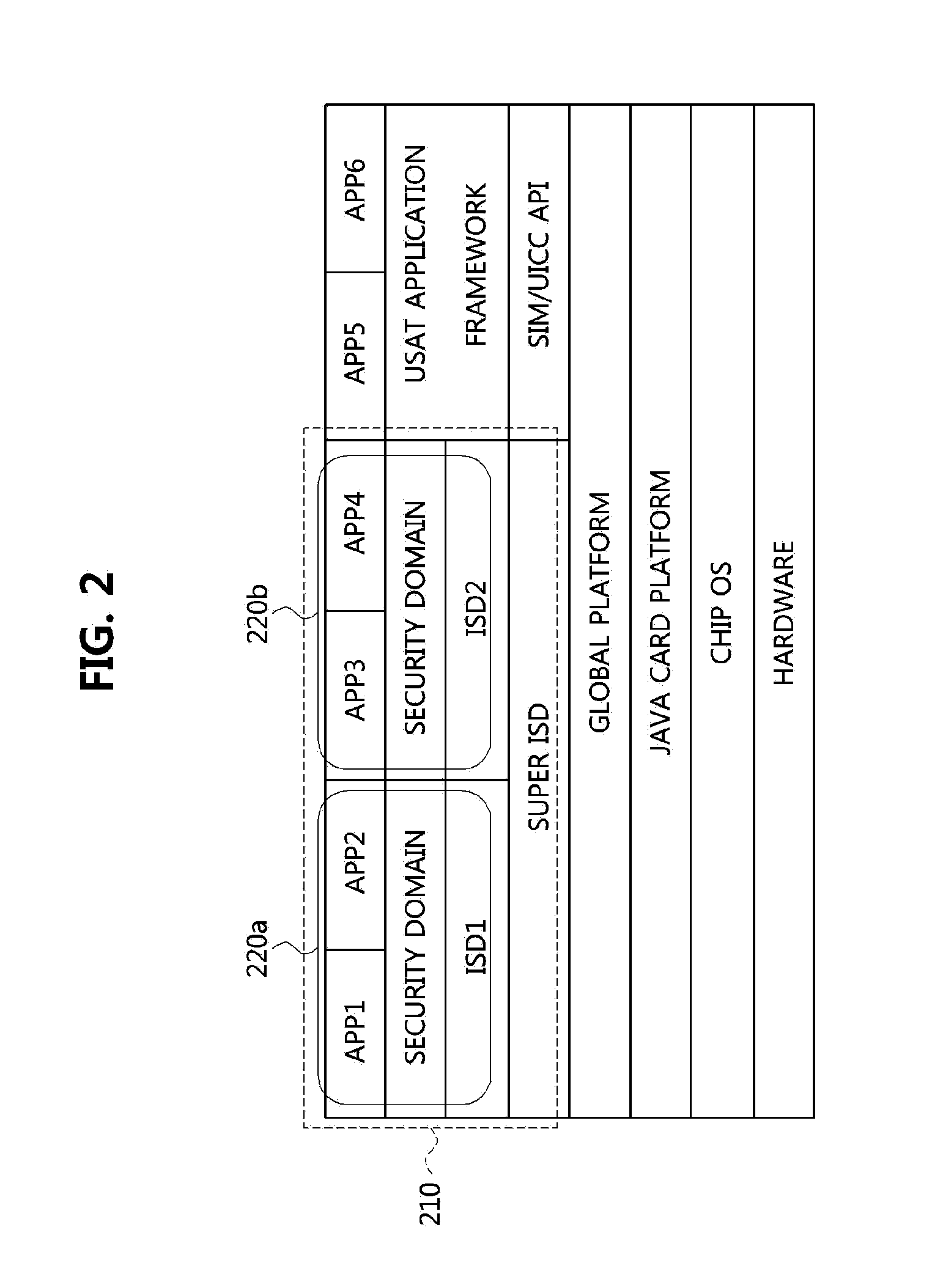
Method for modifying rights to security domain for smartcard, and server, smartcard, and terminal for same
ActiveUS20140325613A1Assess restrictionDigital data processing detailsSmart card securitySecurity domain
The present invention relates to modifying rights to a security domain for a smartcard, and more specifically, to a server for managing modification of rights to a security domain, a smartcard for modifying the rights to the security domain, a terminal which is loaded with the smartcard, and to a method for modifying the rights.
Owner:SAMSUNG ELECTRONICS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com