Intelligent card safety communication method
A smart card and security technology, applied in the field of information security, can solve problems such as inability to prevent communication data from being monitored or intercepted, and imperfections
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
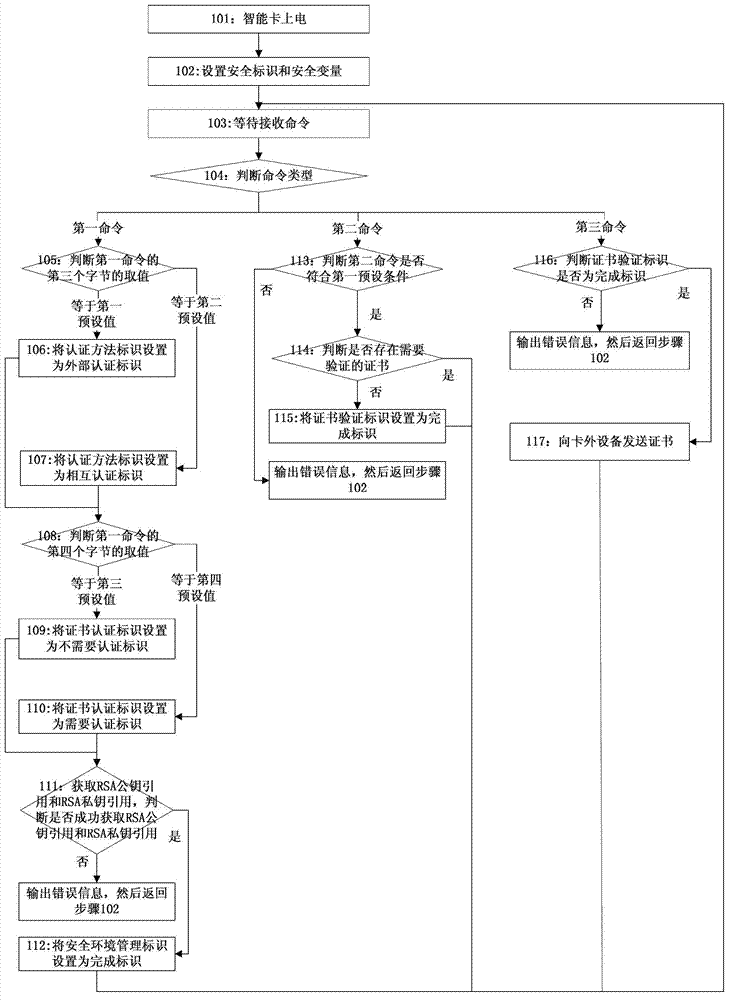
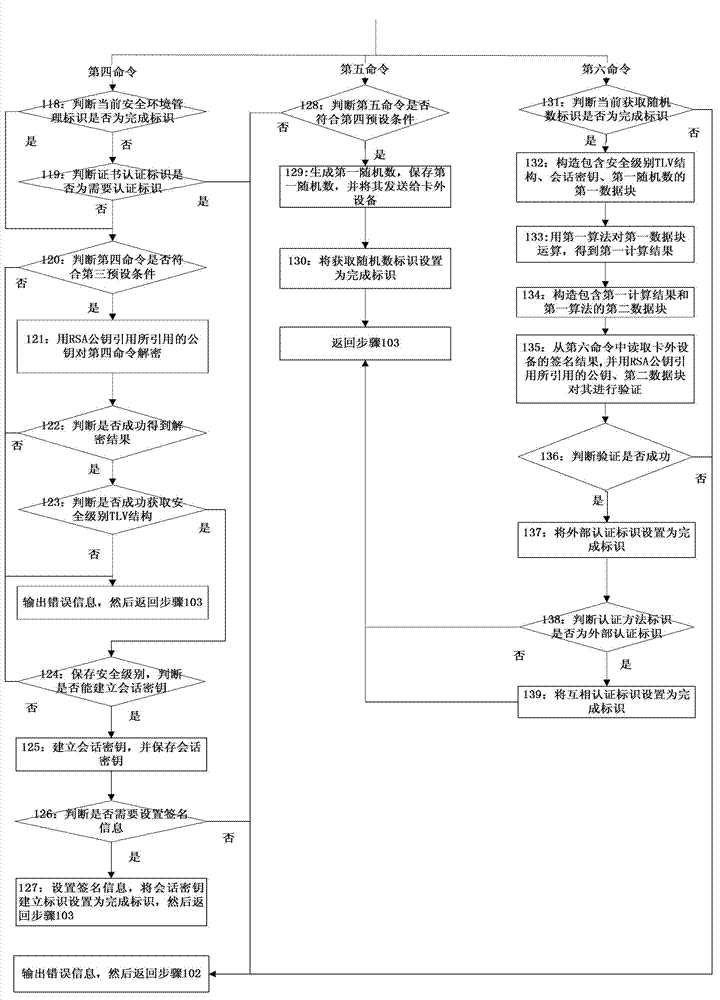
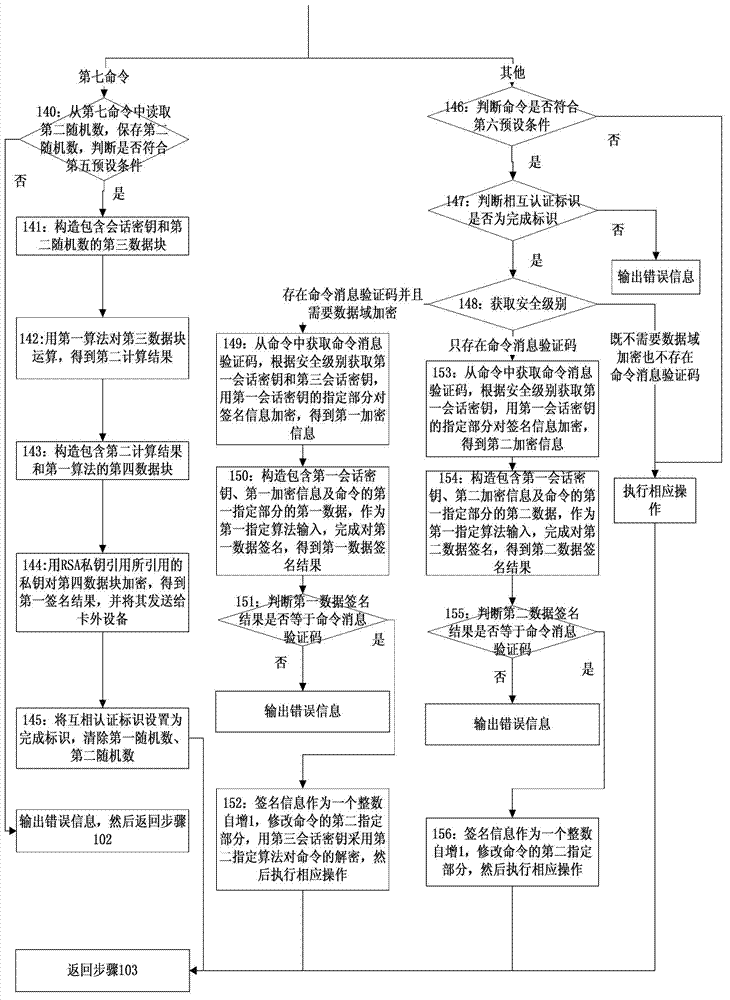
[0063] see Picture 1-1 , 1-2 and 1-3, Embodiment 1 provides a method for secure communication of a smart card, specifically including:
[0064] Step 101: power on the smart card;
[0065] Step 102: setting security identifiers and security variables;
[0066] In this embodiment, setting the security identifier specifically includes setting the security environment management identifier as an incomplete identifier, setting the initial state of the session security identifier as no security level, setting the certificate verification completion identifier as an incomplete identifier, and obtaining the random number Set ID to incomplete ID, set session key ID to not established ID, set external authentication ID to incomplete ID, set mutual authentication ID to incomplete ID;
[0067] In this embodiment, setting the security variable specifically includes, setting the RSA public key reference as PKV1, PKI1; setting the RSA private key reference as SKV1, SKI1; setting the first...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com