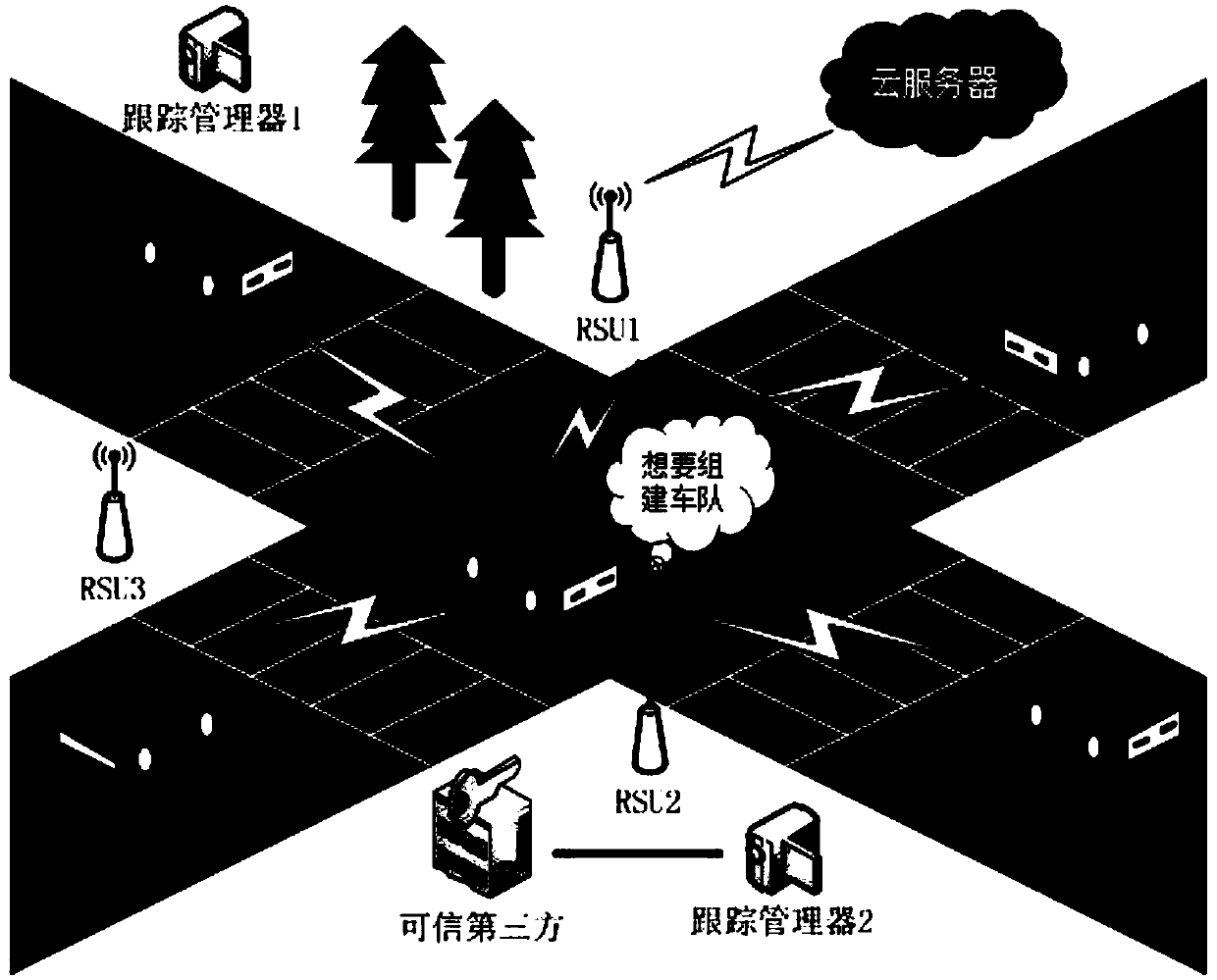
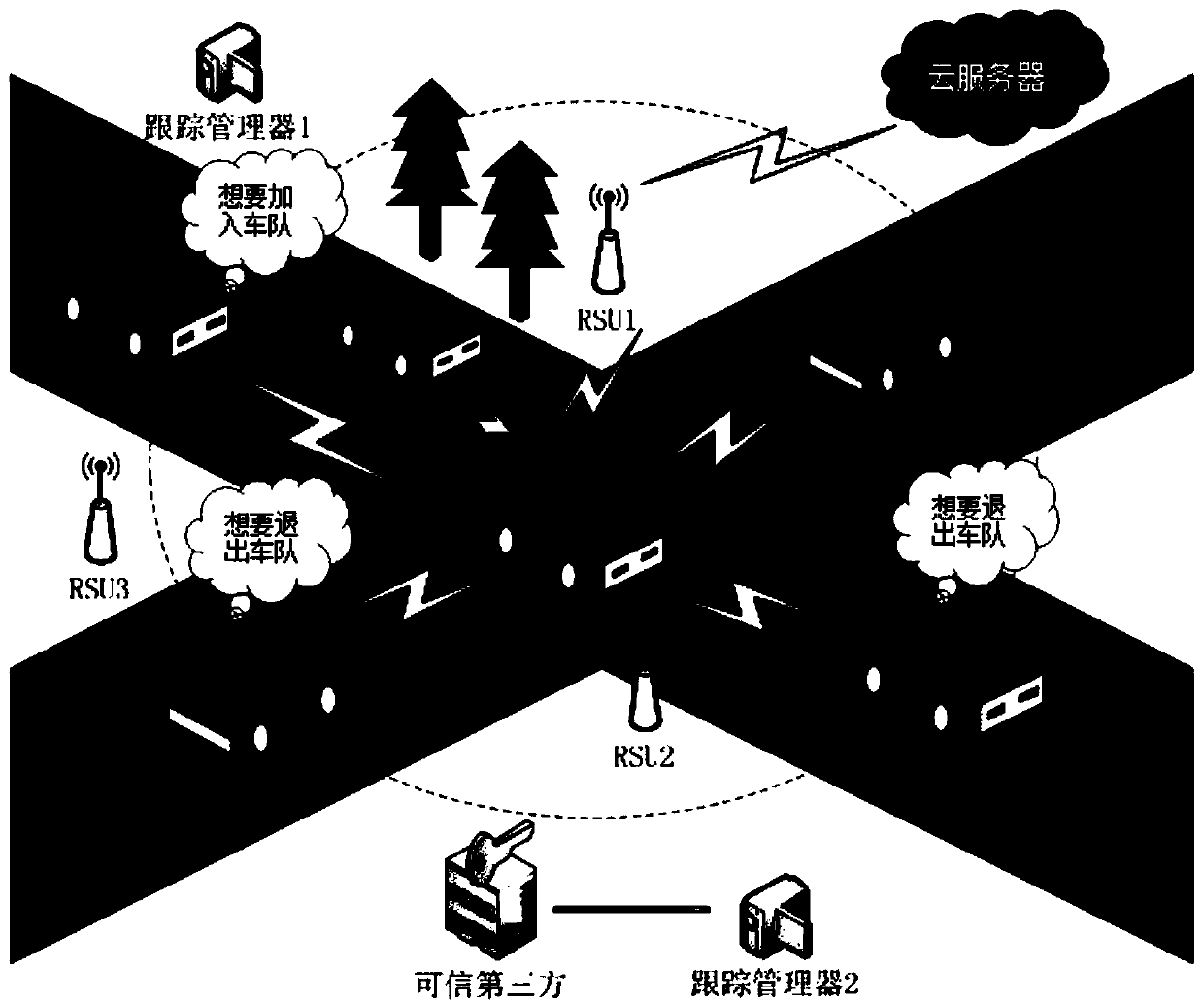
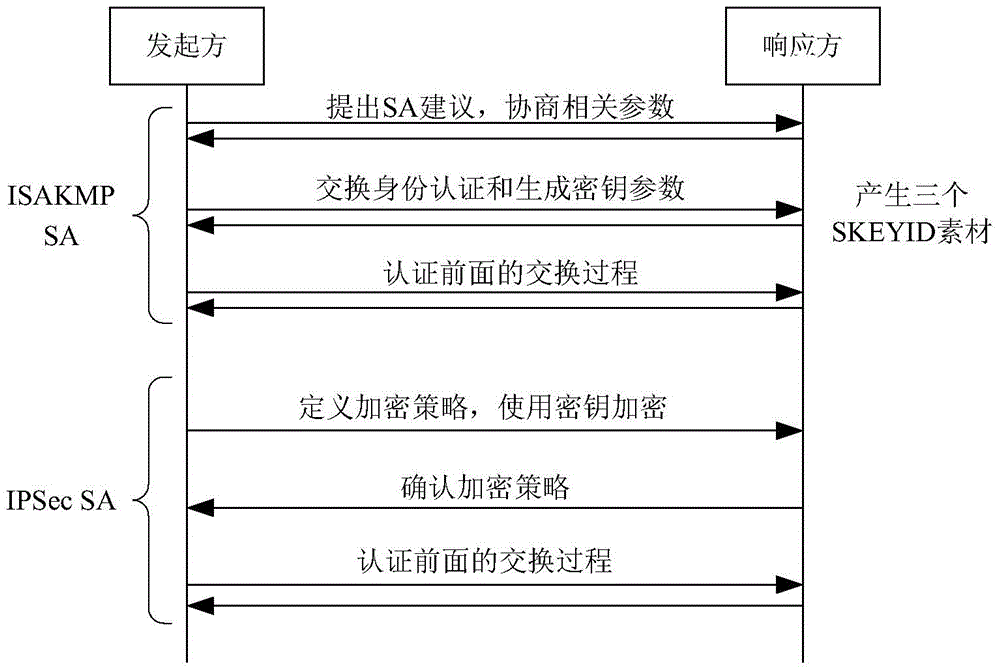
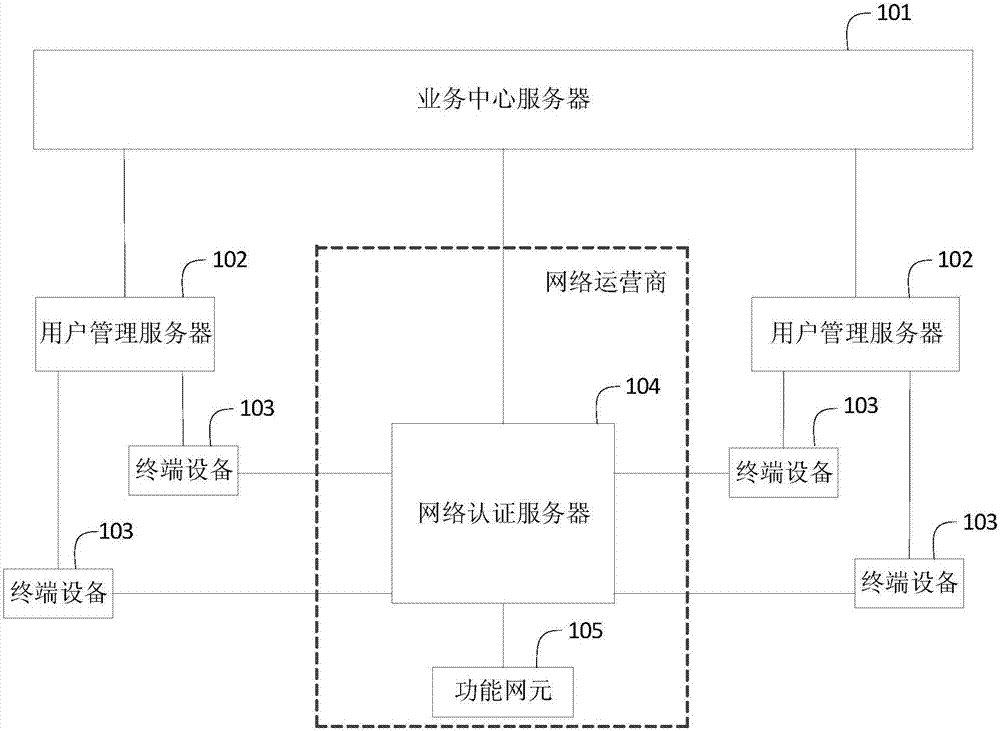
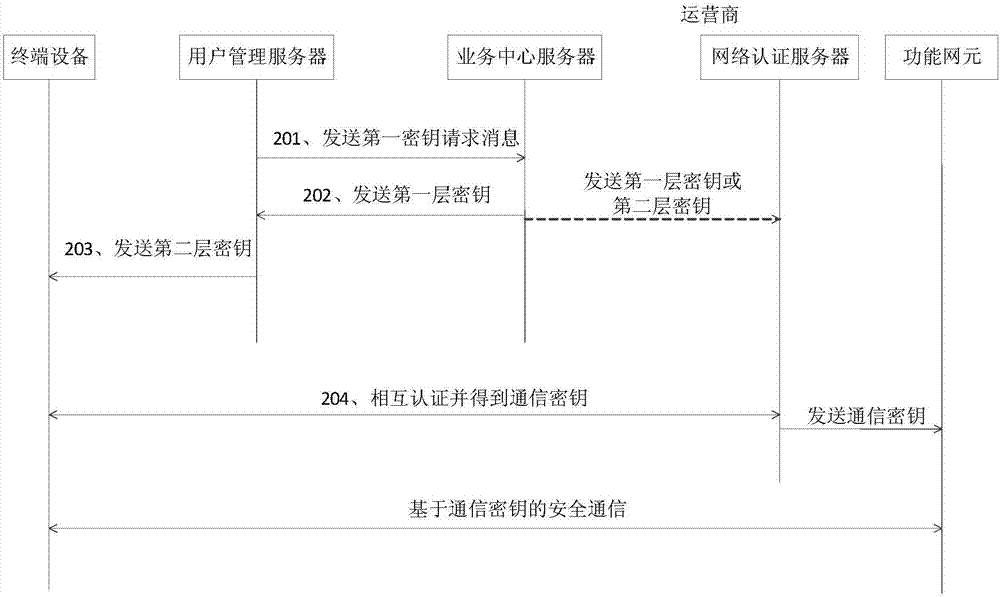
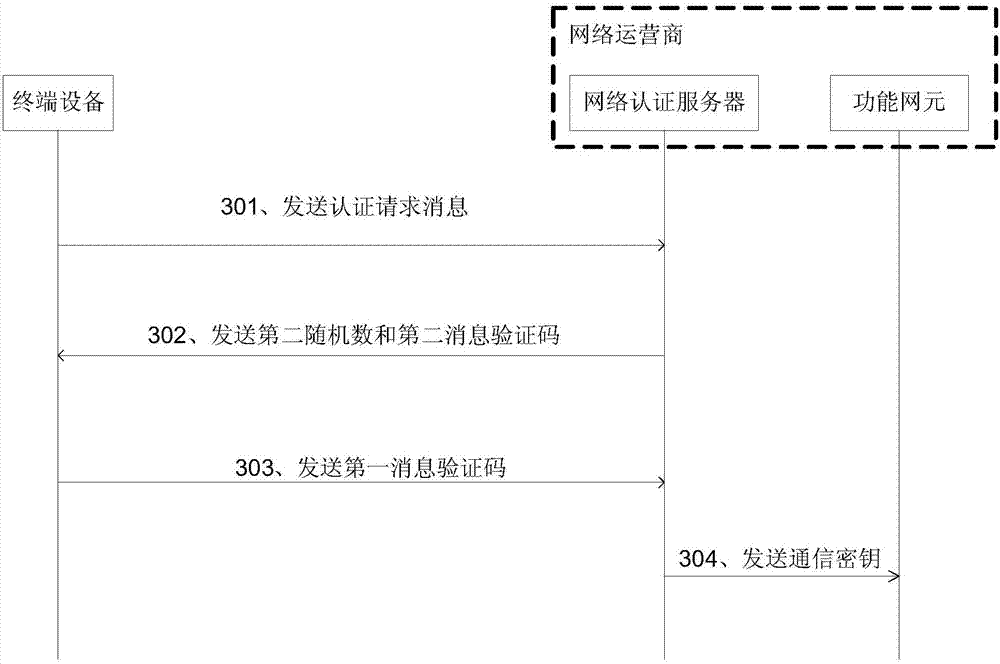
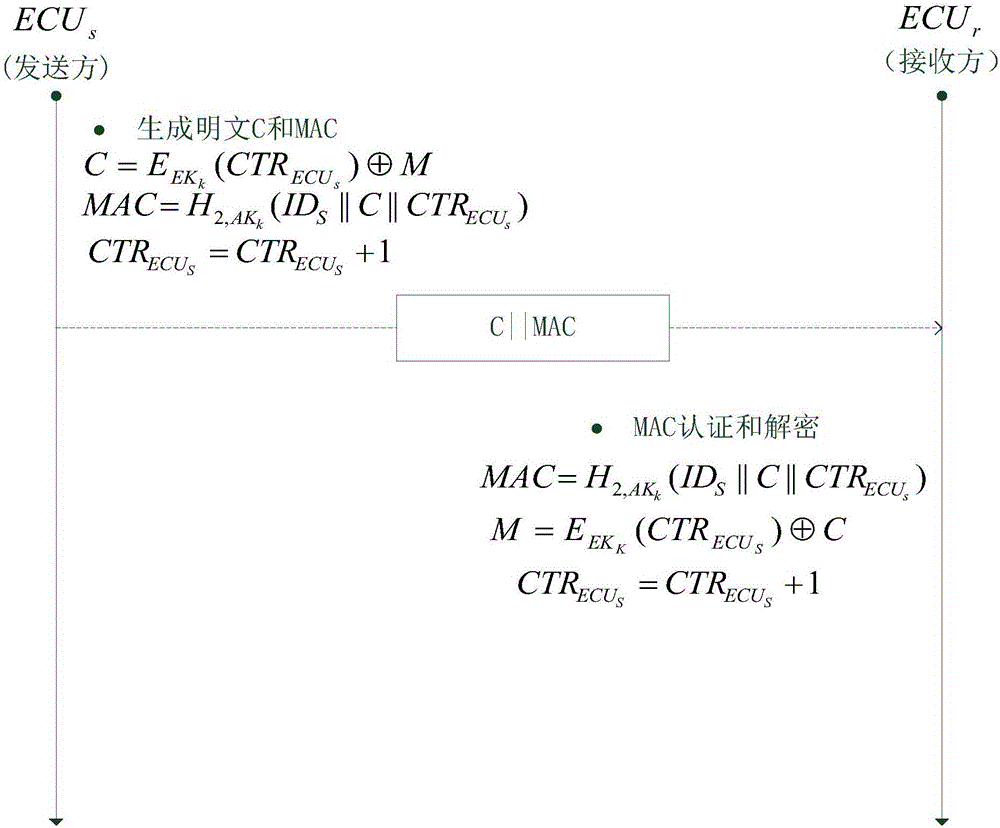Patents
Literature
895 results about "Safety Communications" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
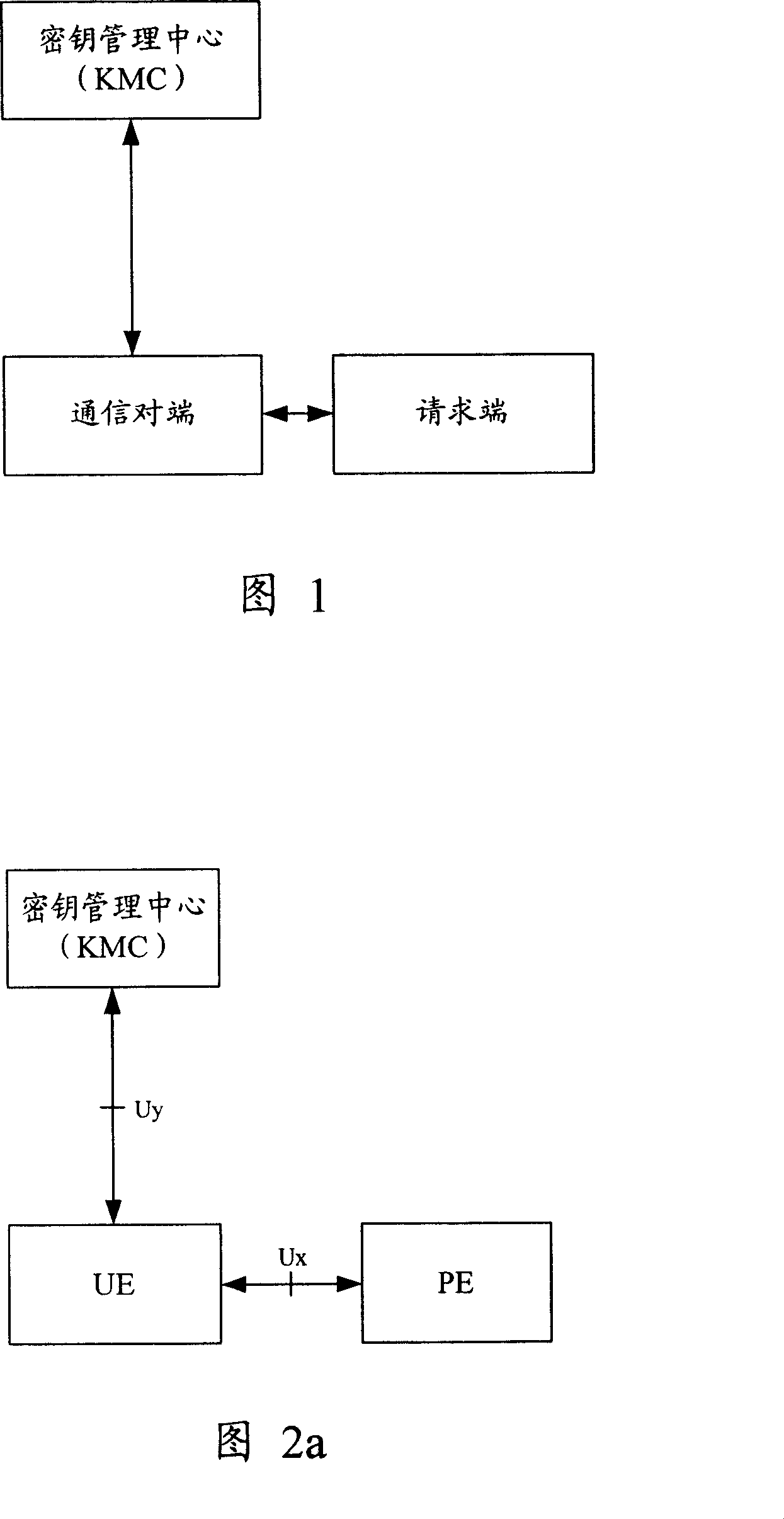
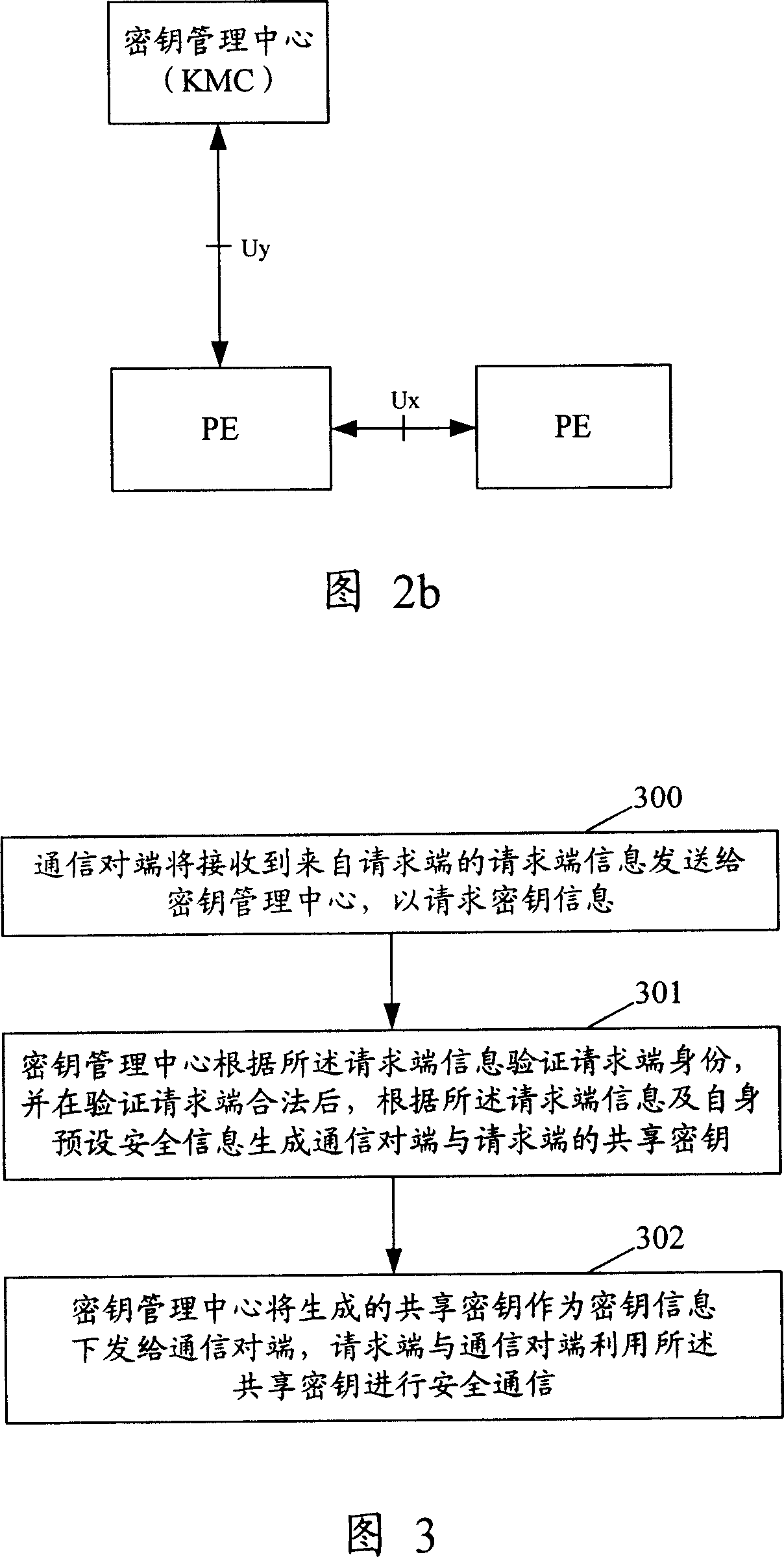
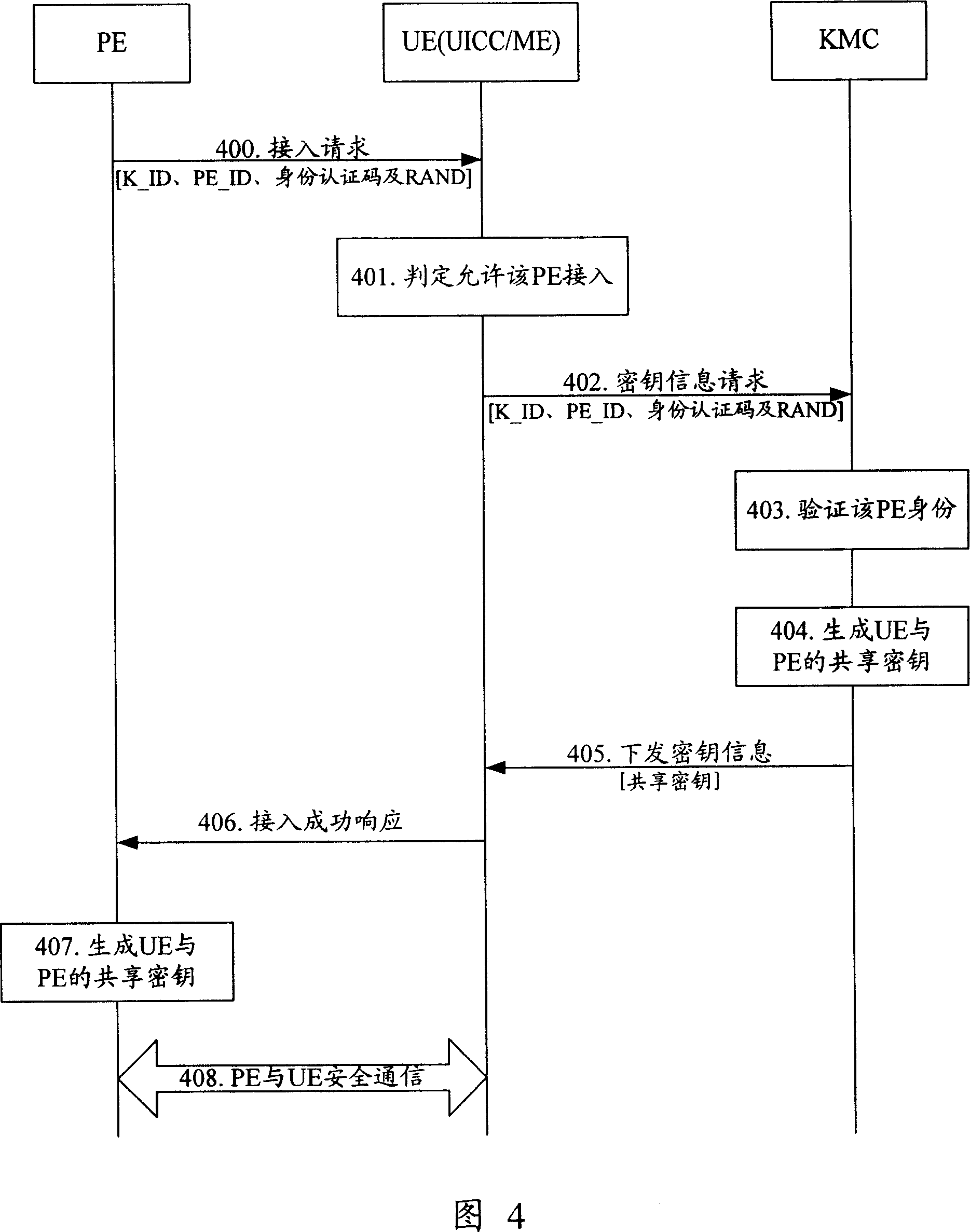
Method and device for realizing safety communication between terminal devices
ActiveCN101005359AEnsure secure communicationStable deliveryKey distribution for secure communicationUser identity/authority verificationSecure communicationTerminal equipment
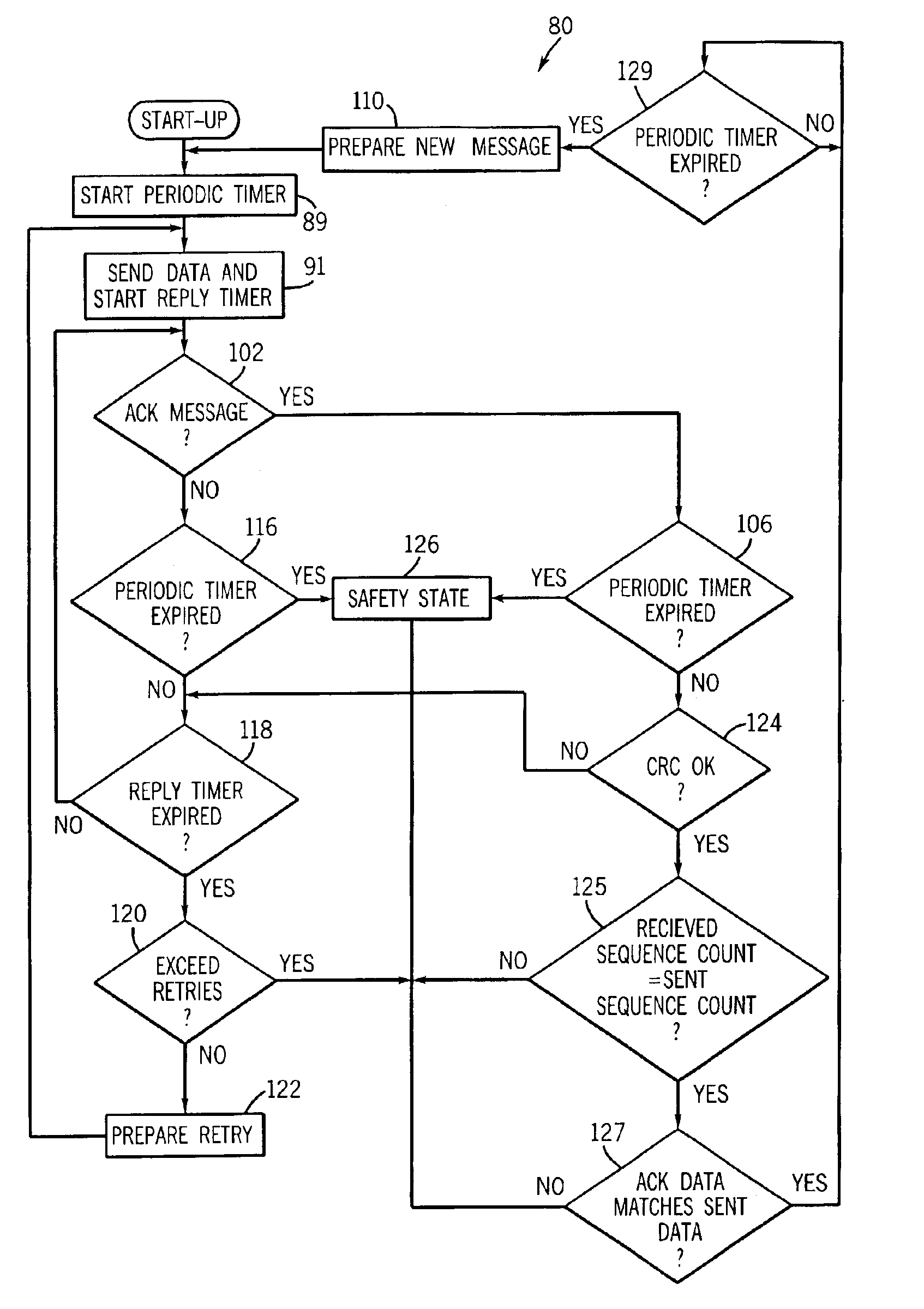
The method includes steps: communication opposite terminal (COT) sends the request end information received from the request end to the key management center (KMC); based on the request end information, KMC validates ID of the request end; after validating validity of the request end, KMC creates shared cipher key for COT and the request end based on the request end information, and self prearranged security information; KMC down sends the created shared cipher key as information of cipher key to COT; using the said shared cipher key, the request end and COT carry out security communication. The invention also discloses device for security communication between terminal devices. Guaranteeing security communication between terminal devices, the invention especially guarantees security communication between ME / UICC / PE and PE.
Owner:HUAWEI TECH CO LTD
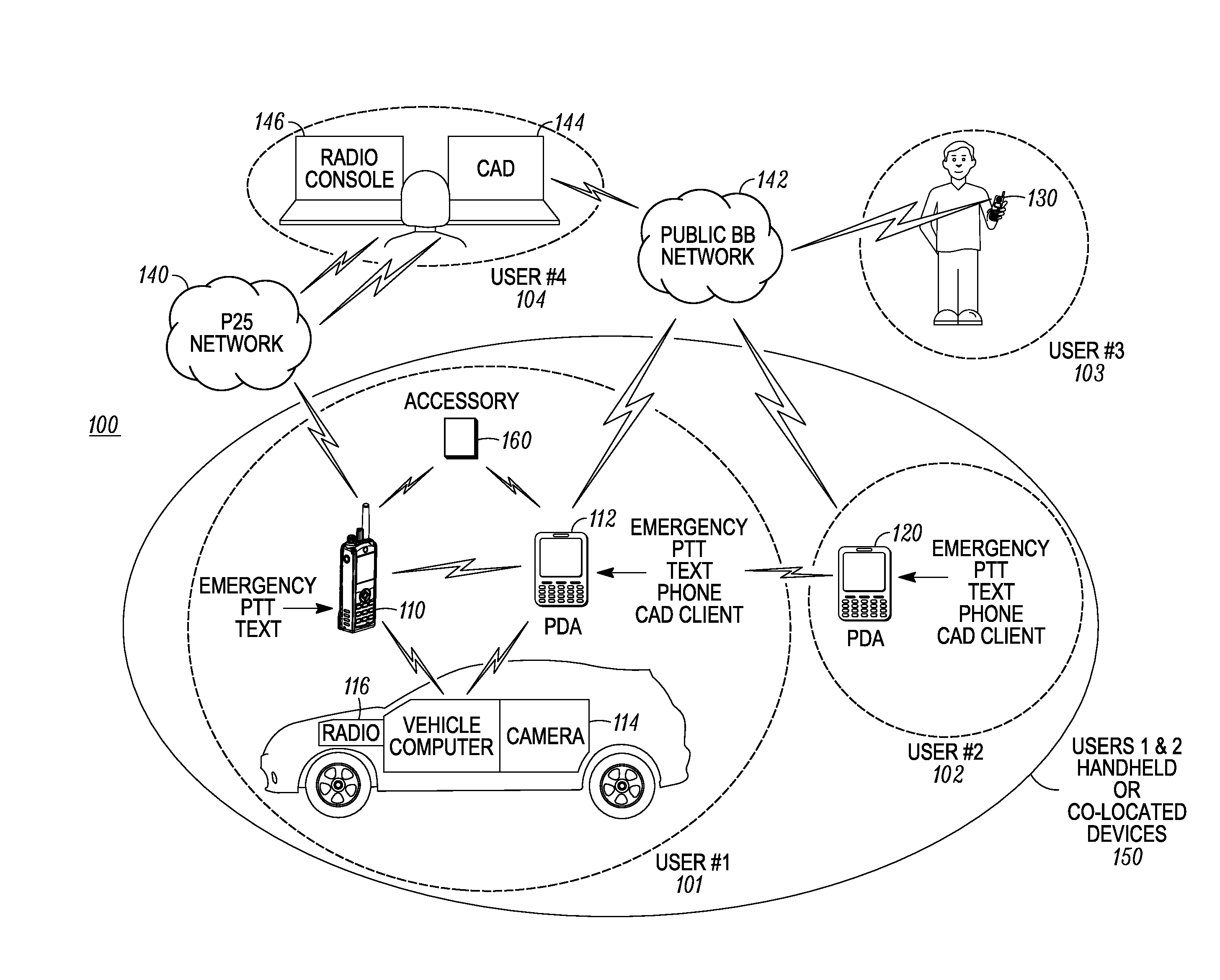
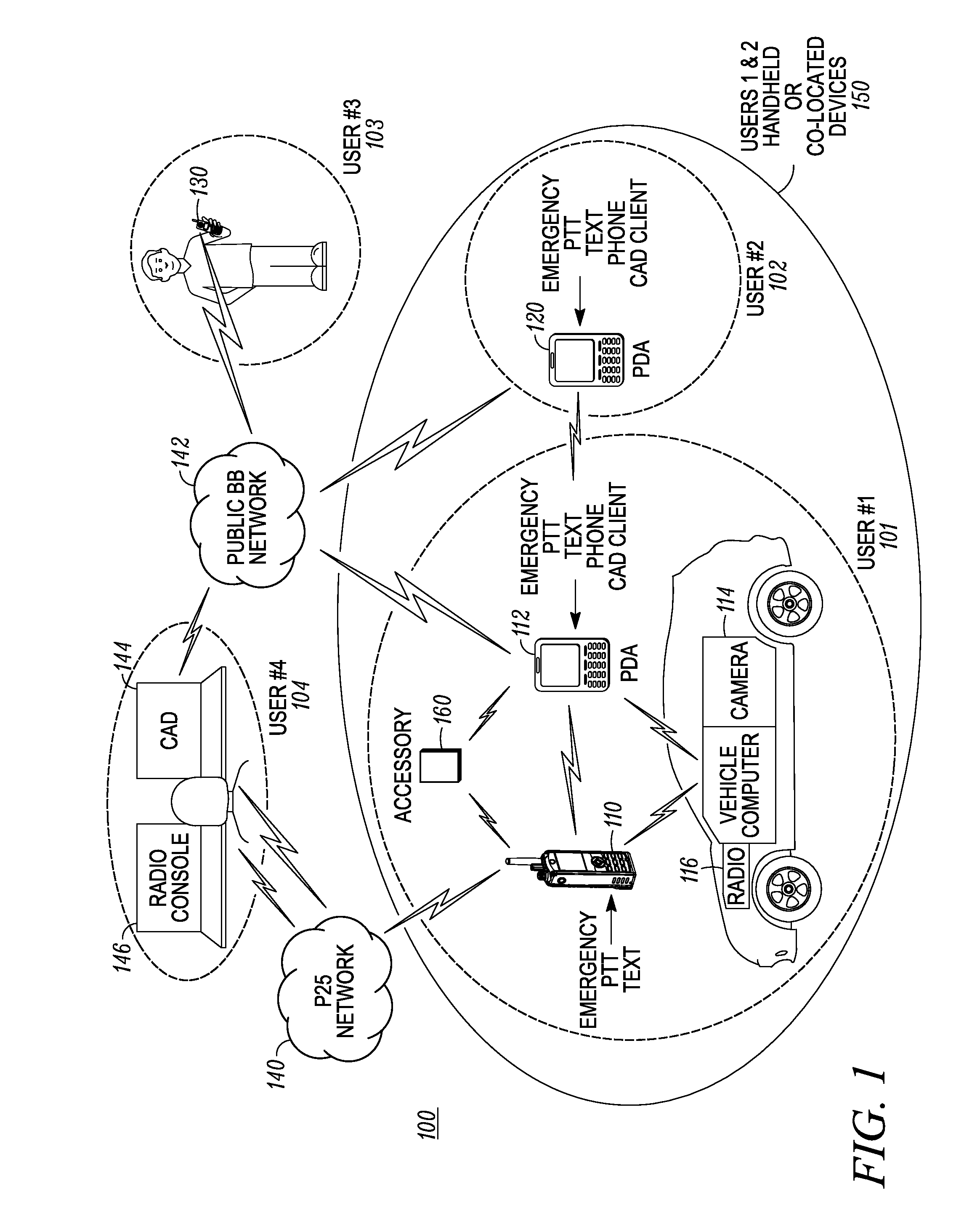
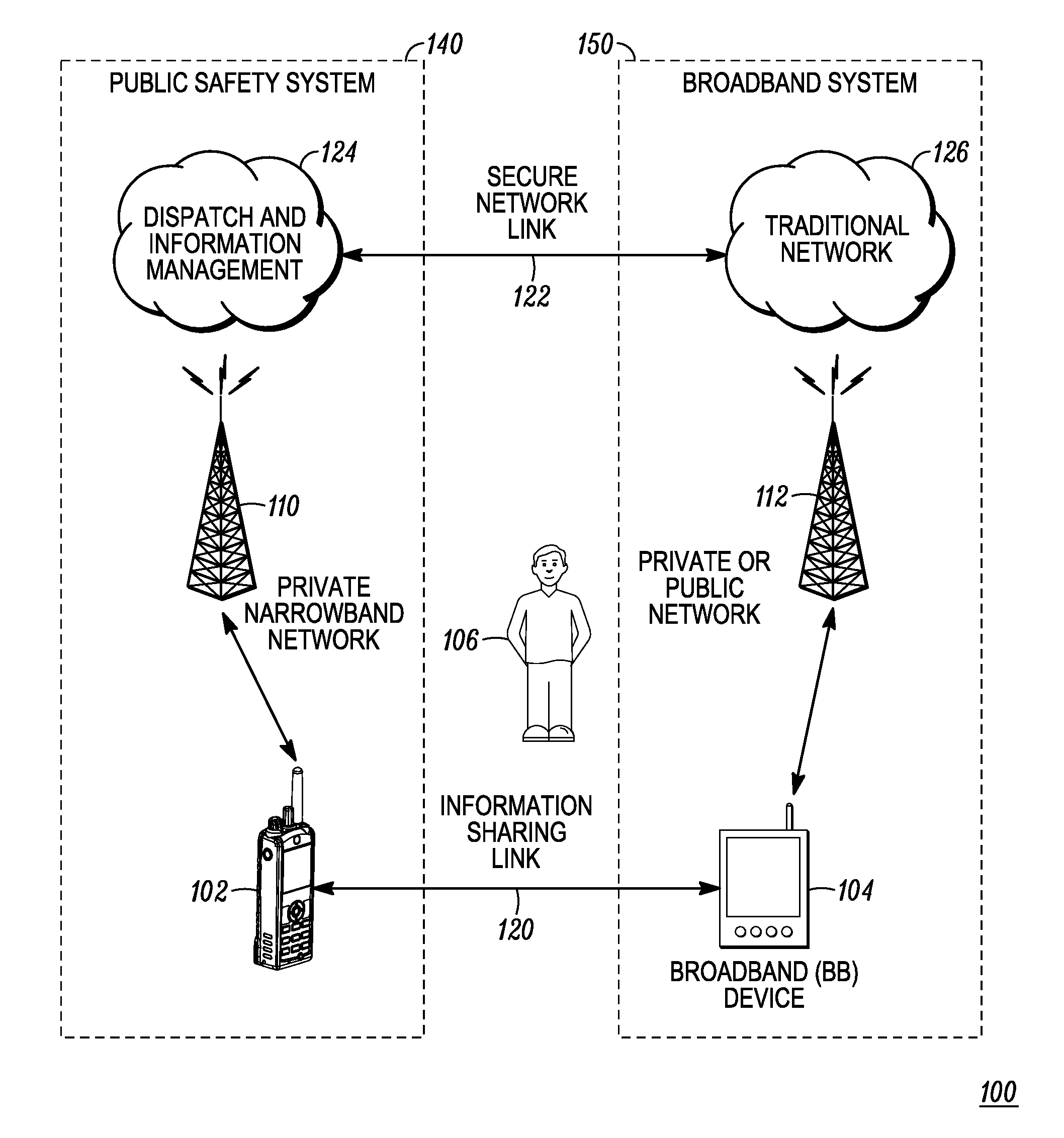
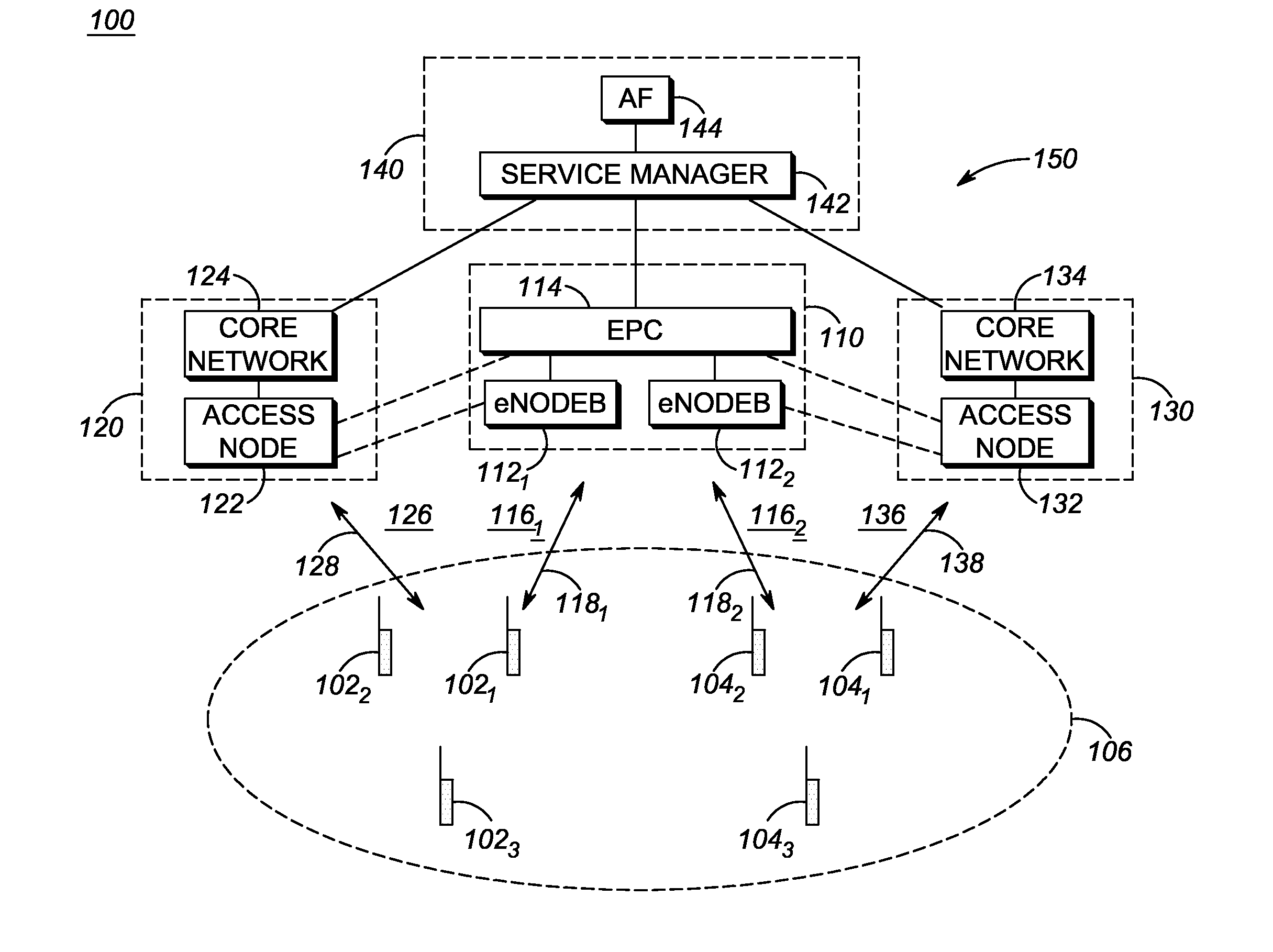
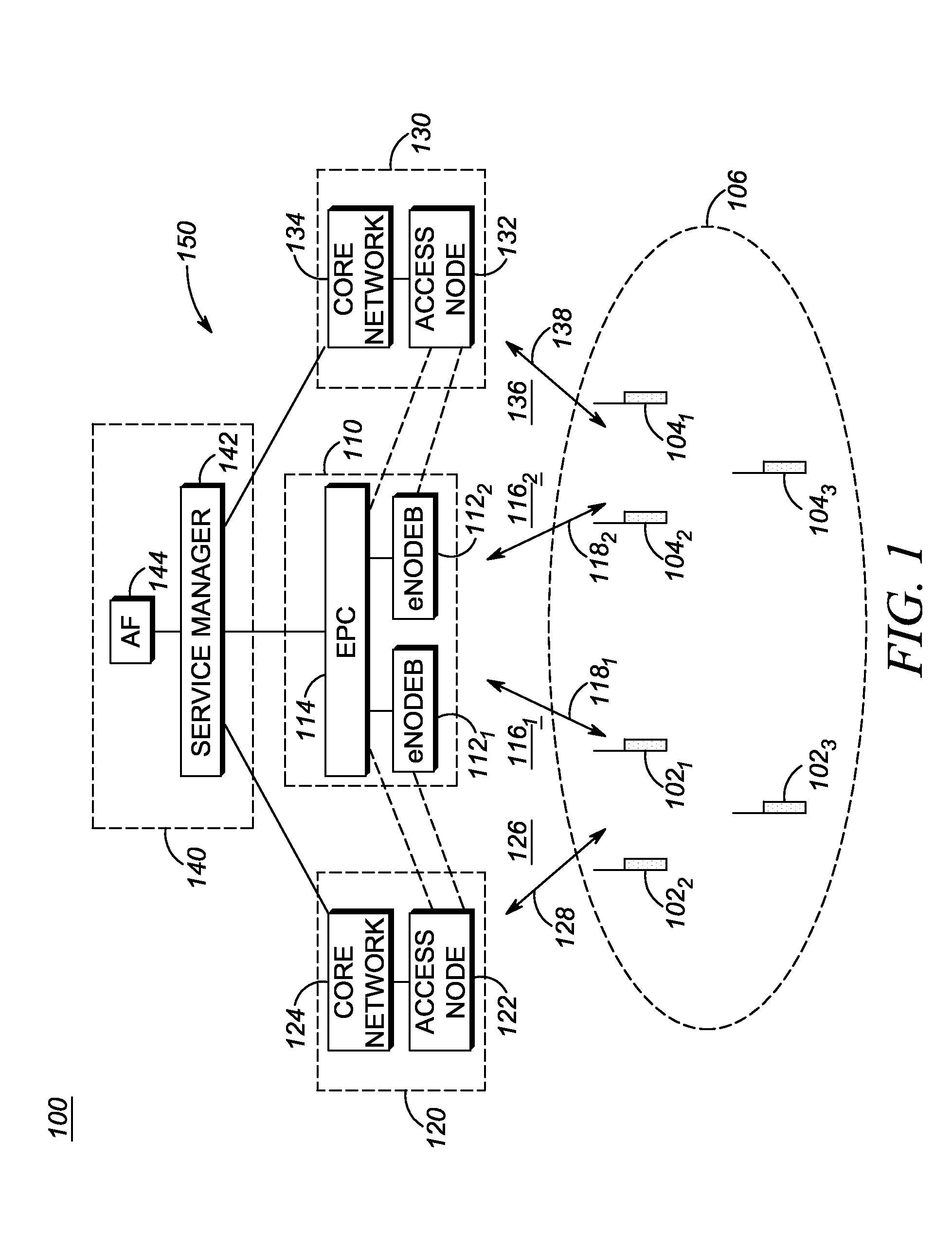
Enhanced public safety communication system
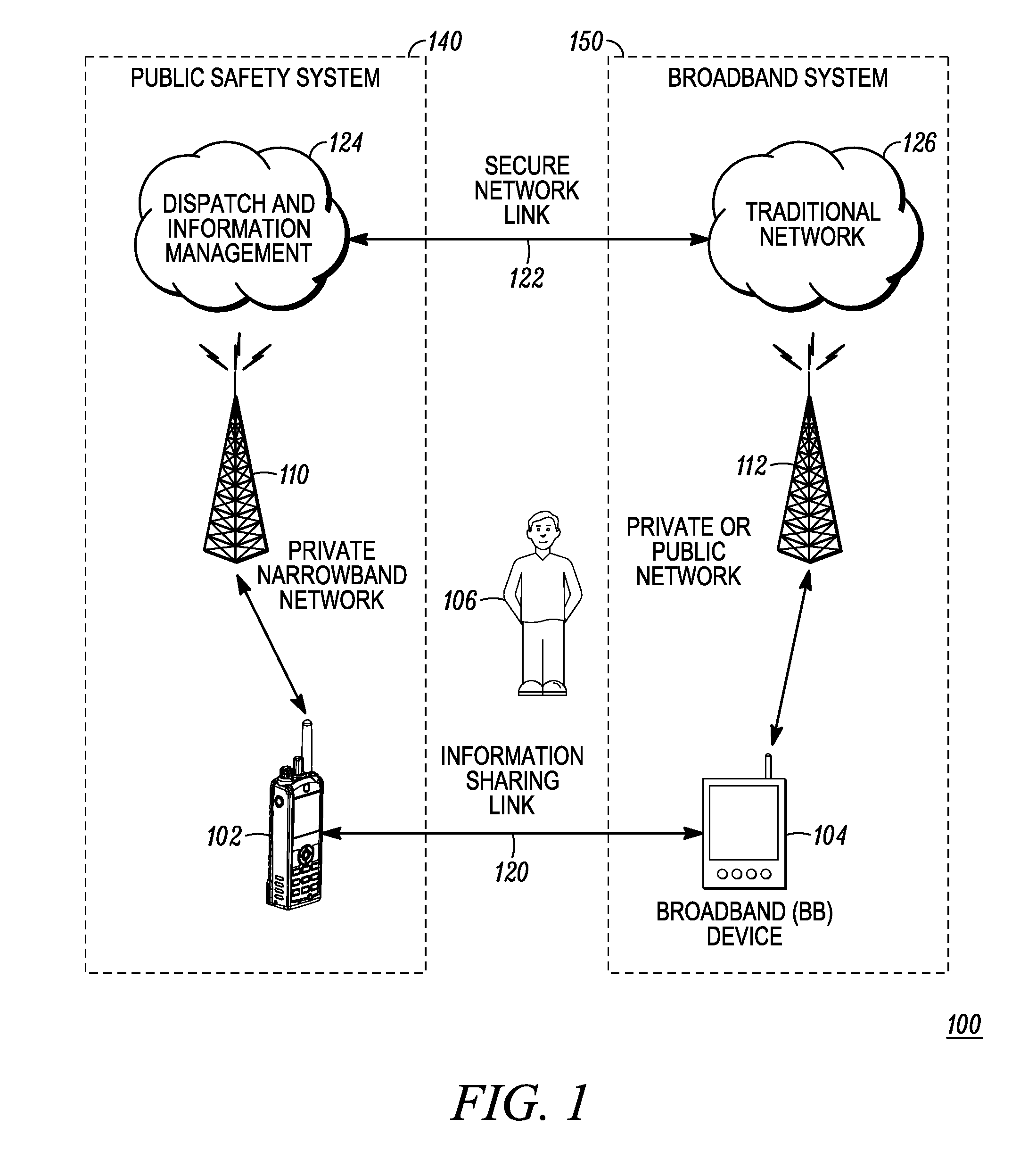
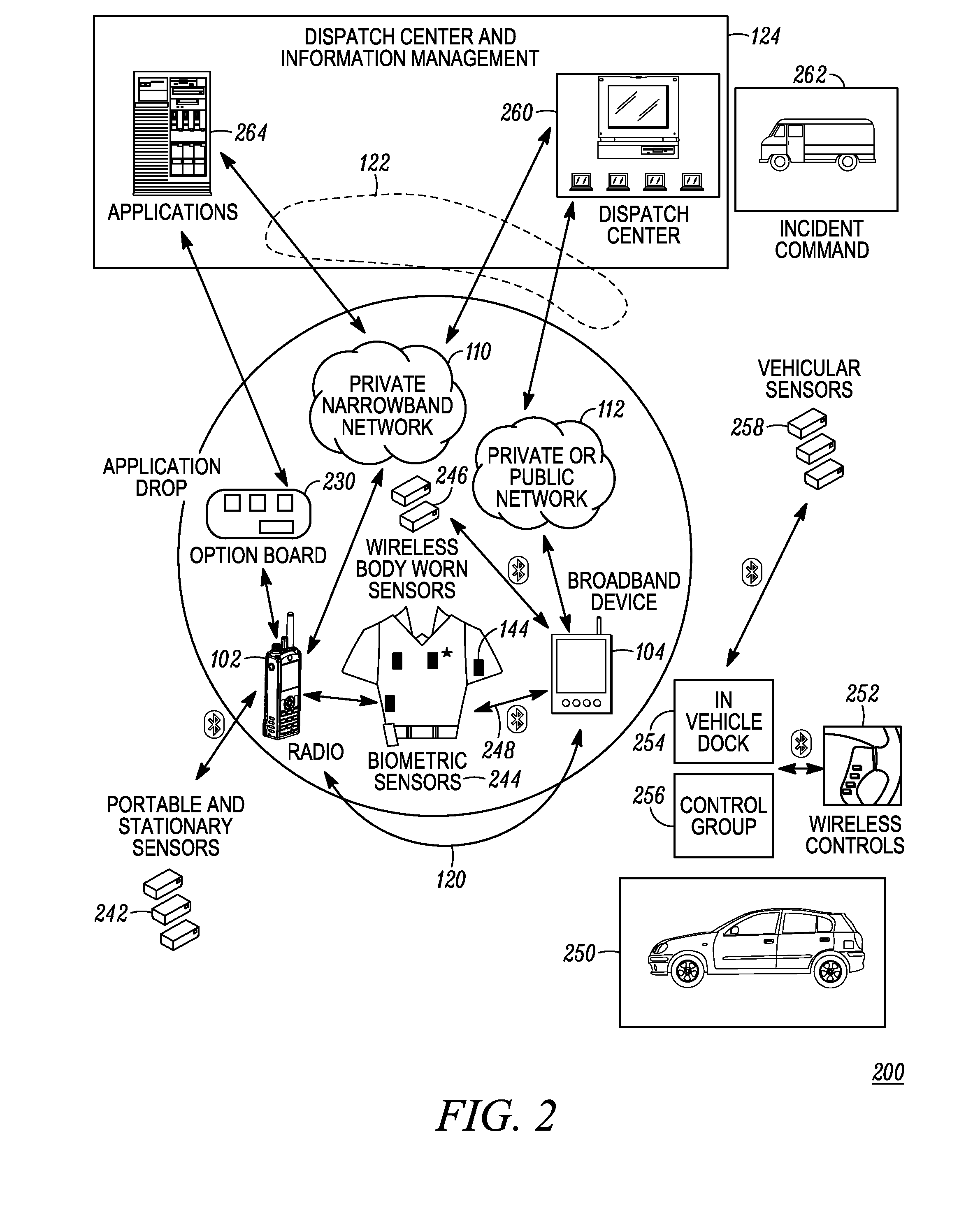
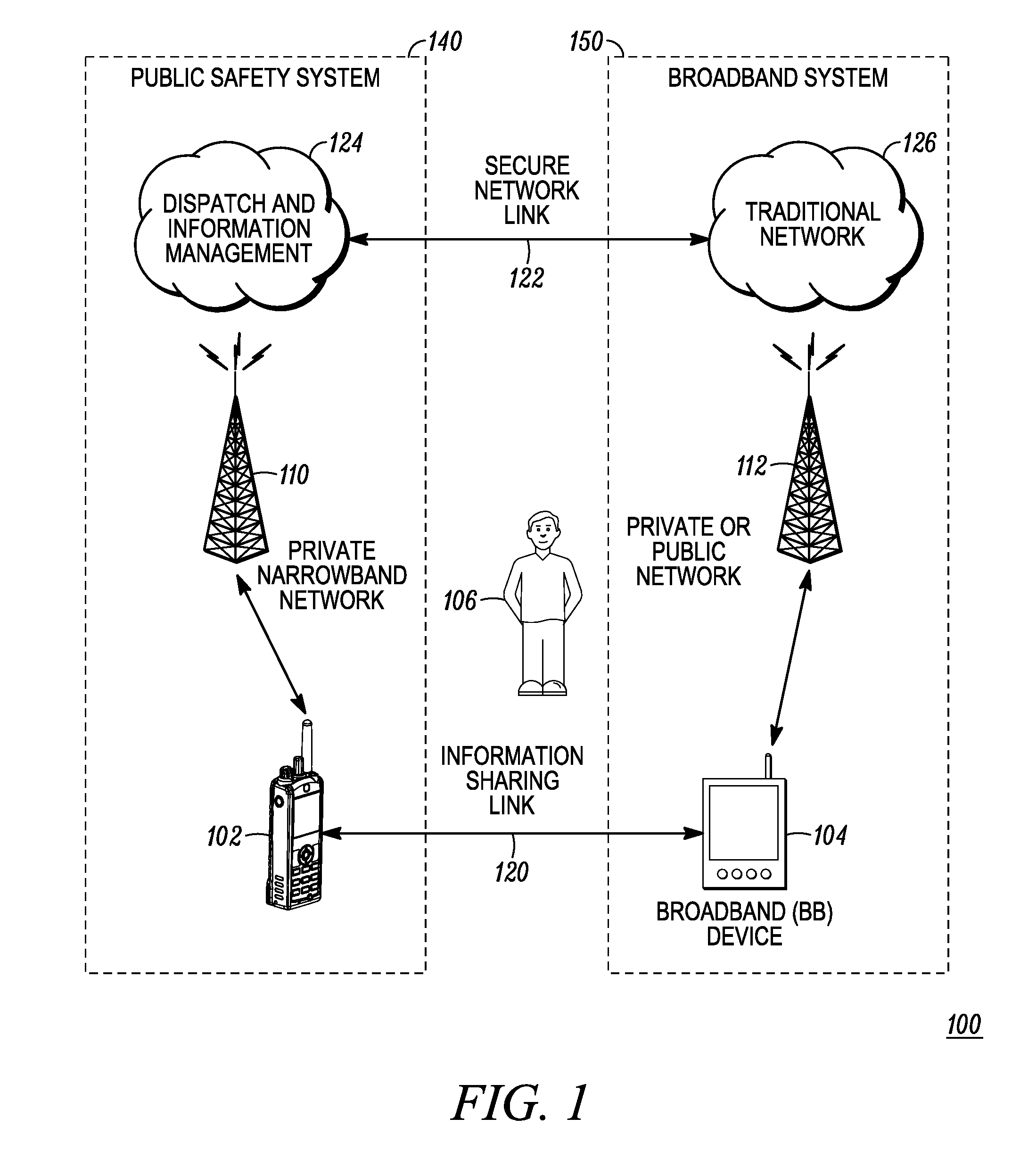
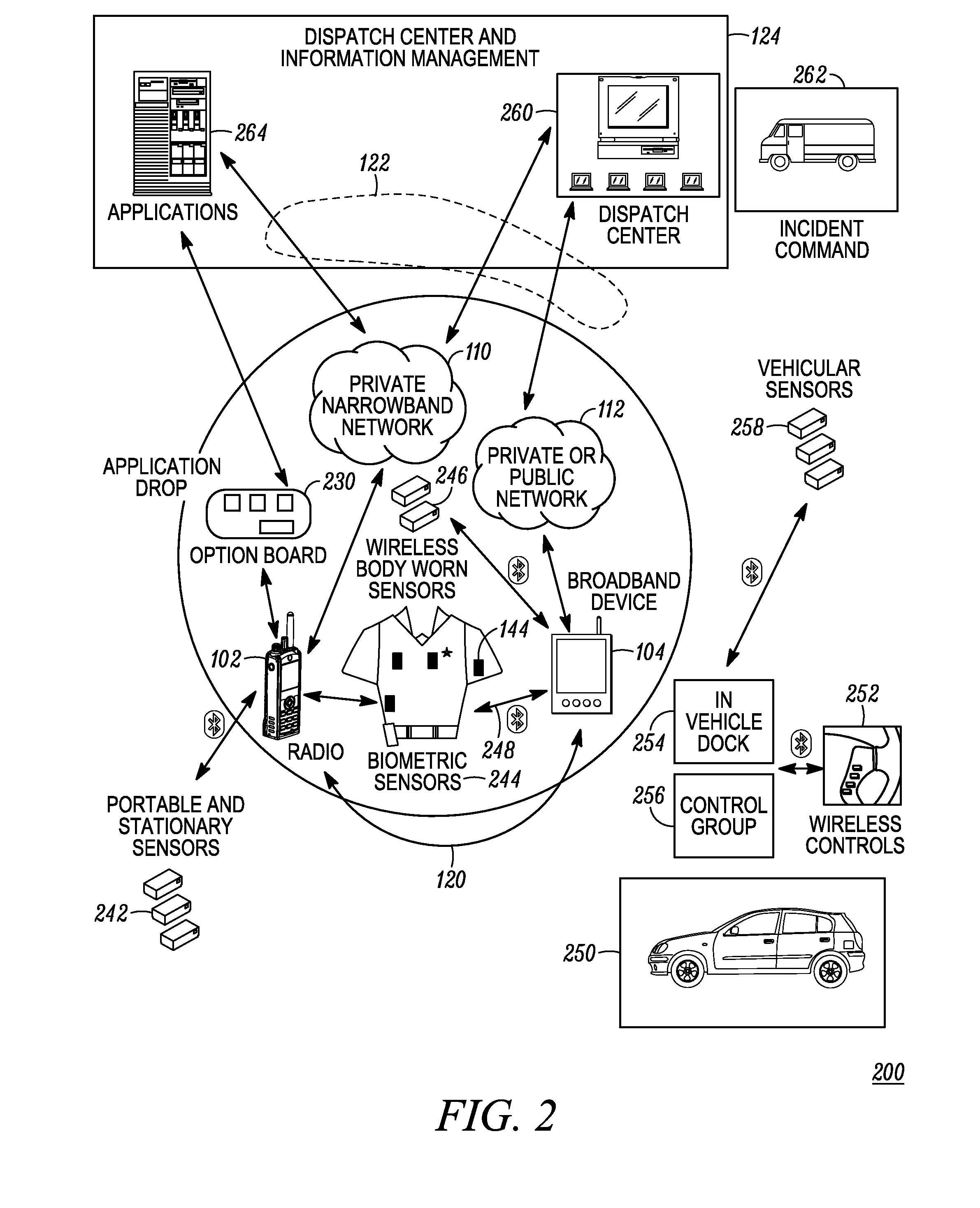
ActiveUS20110237287A1Emergency connection handlingNetwork topologiesCommunication deviceBroadband communication
A communication system (100) provides collaboration between narrowband communication devices (102) and broadband communication devices (104) operating over different networks. The communication devices (102, 104) are linked to provide peer-to-peer communication that supports the dissemination of public safety information to a public safety personnel user utilizing the devices. Applications within the devices (102, 104) automatically control features amongst the plurality of devices for redundancy of critical information, removal of non-critical information and power management. Context information can also be examined and shared between amongst the devices.
Owner:MOTOROLA SOLUTIONS INC
Public safety communications network using asymmetric receive/transmit channels
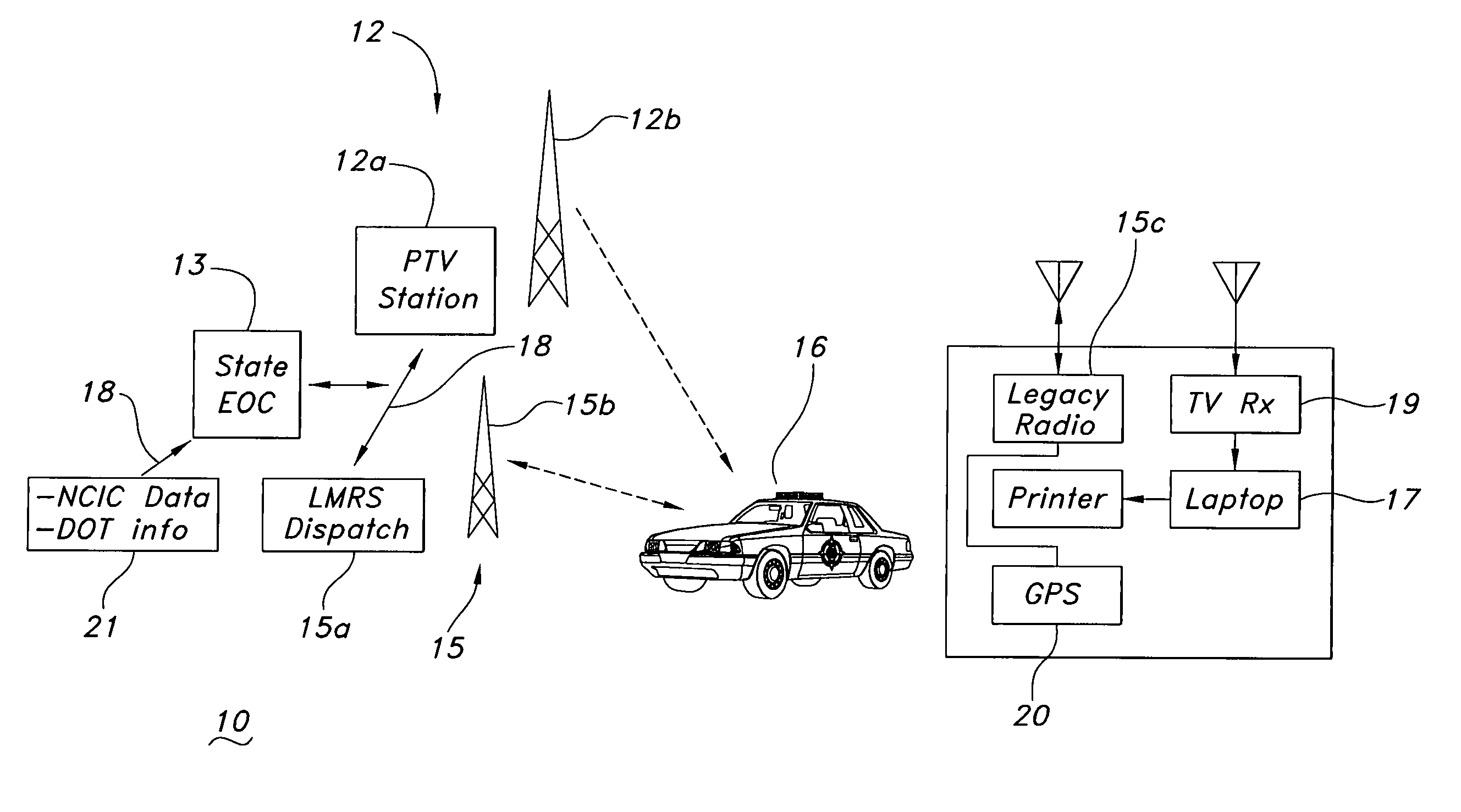
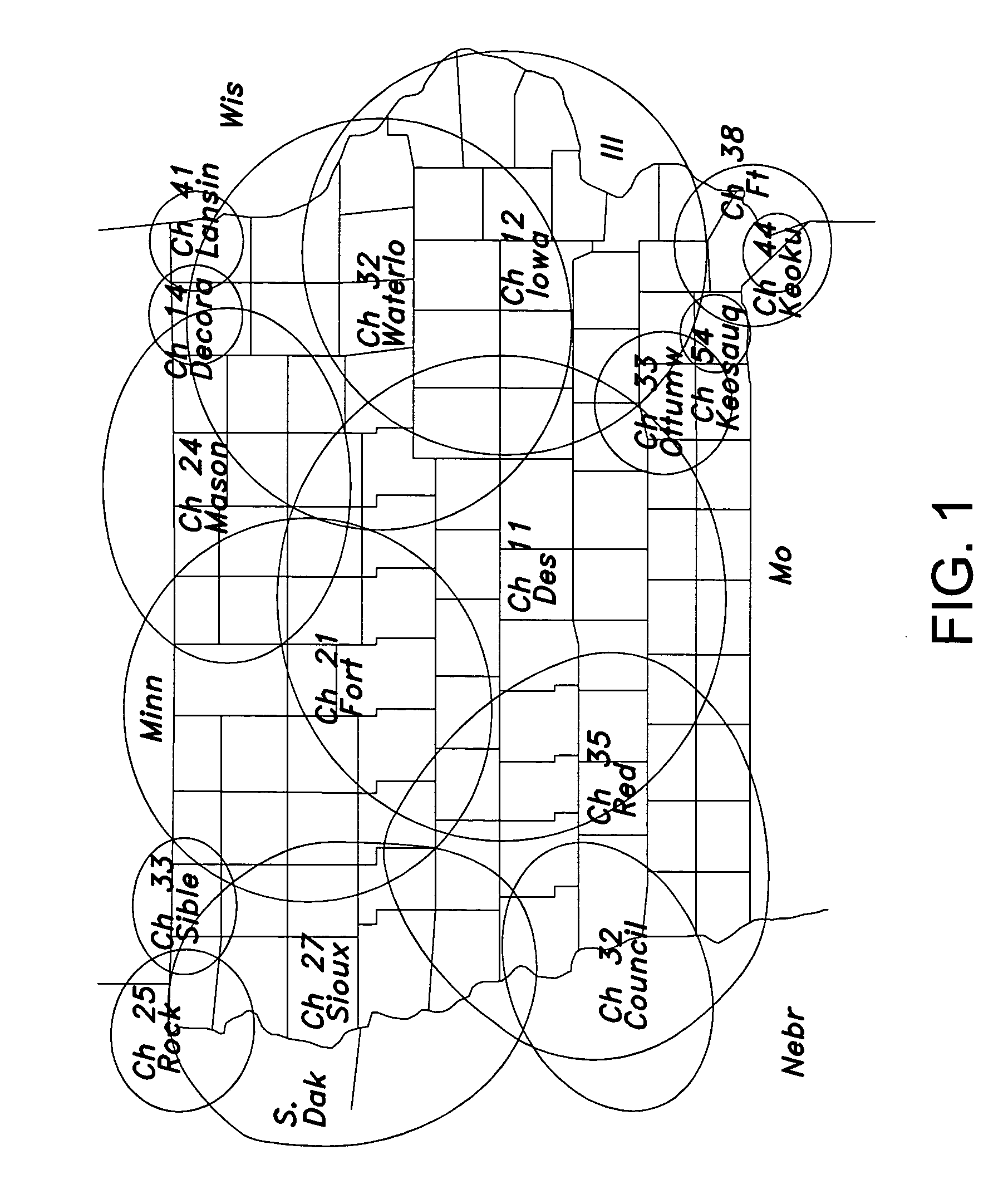
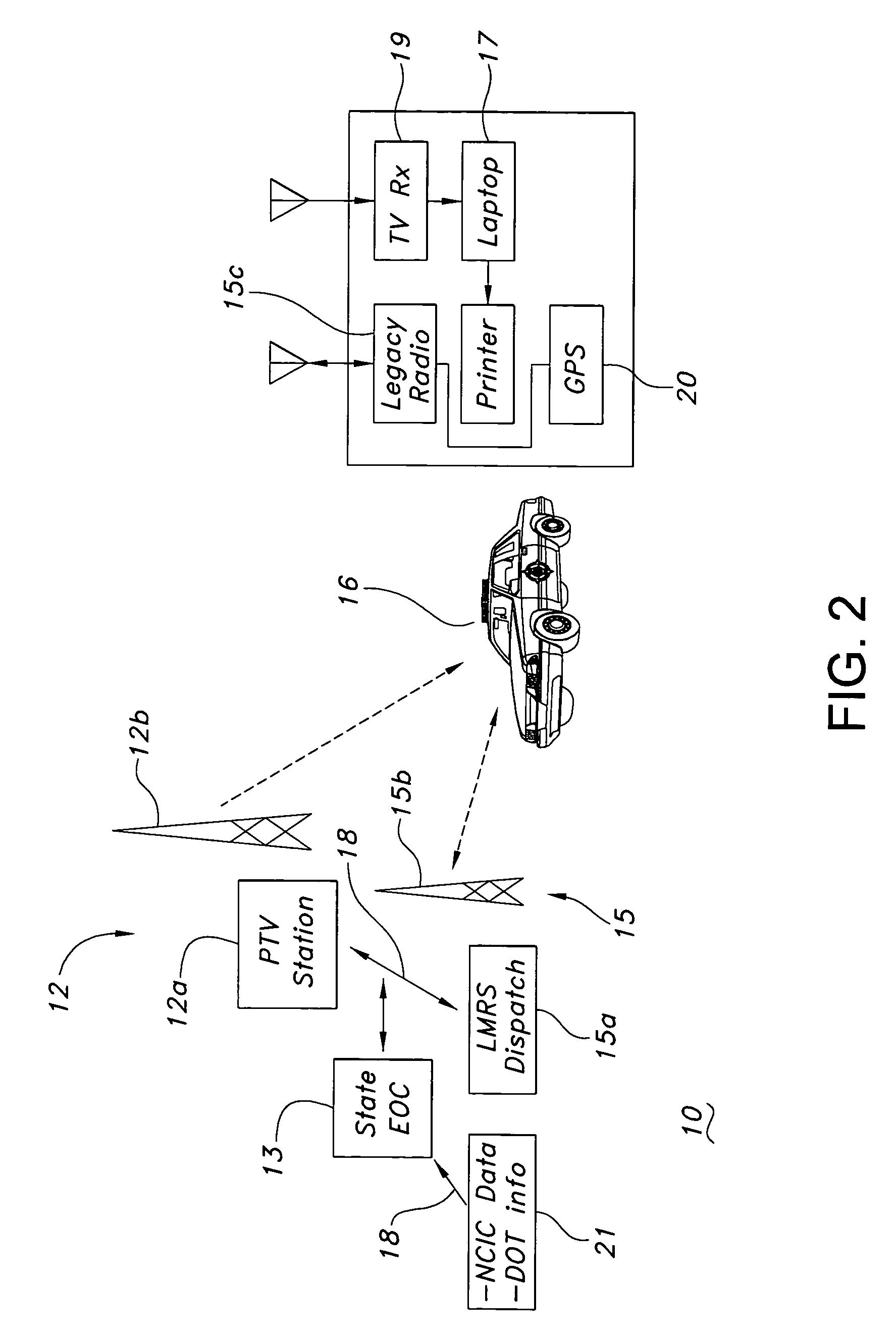
ActiveUS7783316B1Increase data rateQuality improvementTelevision system detailsError preventionGeolocationLand mobile radio system
A public safety communications network uses asymmetric channels for receiving requests for data from a mobile client over a narrowband land mobile radio system (LMRS) channel and delivering wideband data over a digital television (DTV) network channel to a DTV datacast receiver with the mobile client. An emergency operations center connected to the LMRS receives and processes the data requests and forwards the requested data. DTV network stations have a data multiplex insertion system for inserting the requested data into a DTV signal. The DTV network may be a public television network. An addressing system identifies unique mobile client addresses and unique mobile client group addresses and selects a DTV transmitter for delivering response messages in accordance with the addresses. A forward error correction (FEC) regulation system is used in transmitting requested data with FEC strength regulated as a function of historical bit-error-rate or receive power for a geographical location.
Owner:ROCKWELL COLLINS INC
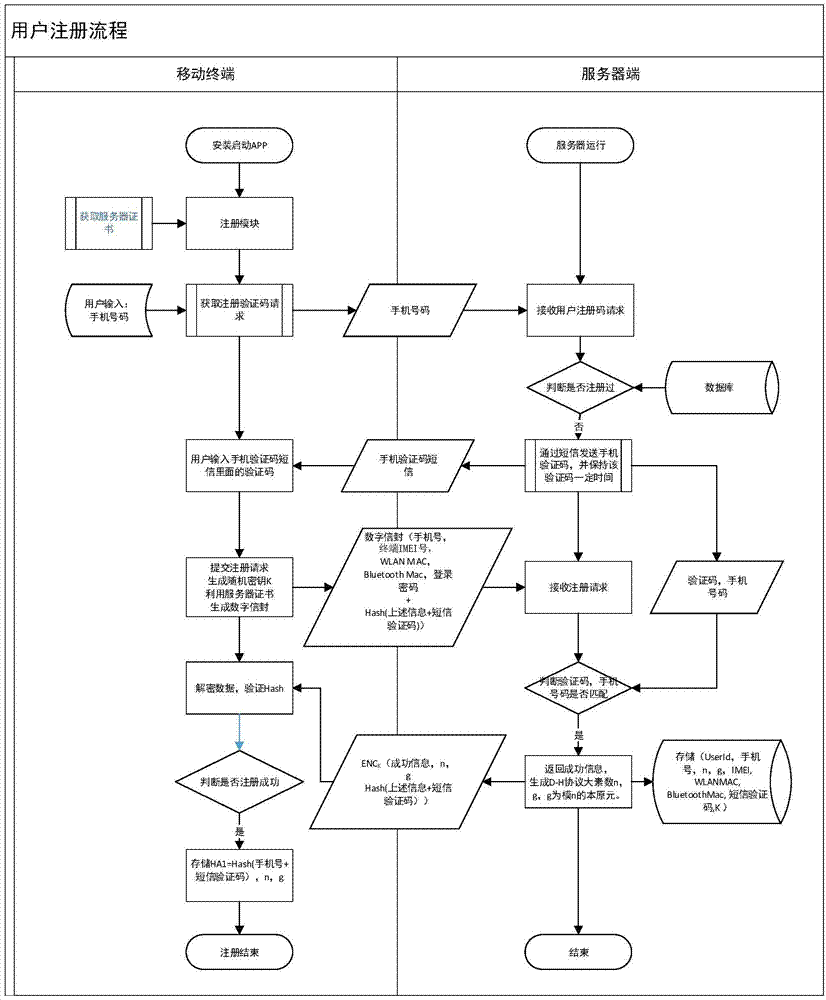
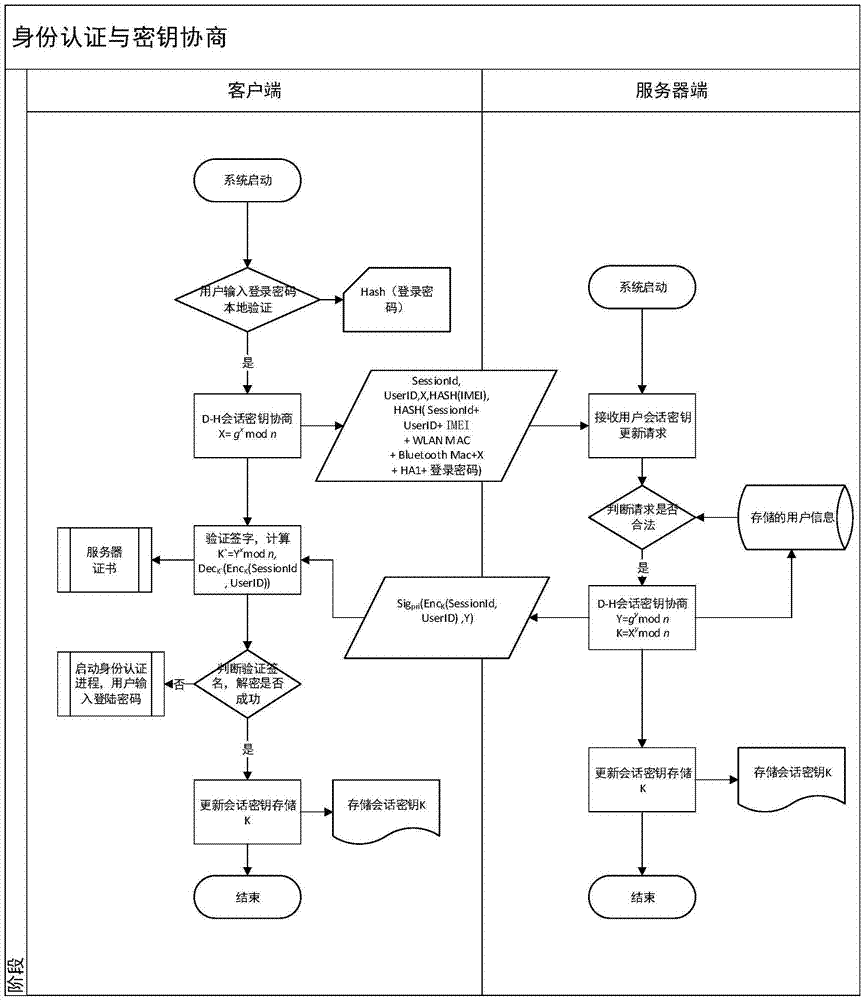
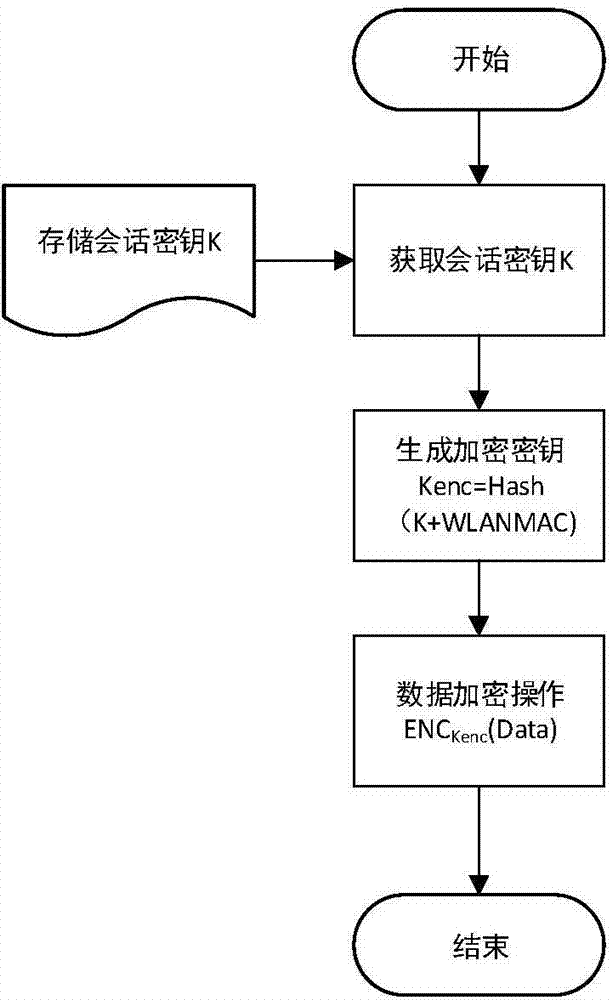
Safety communication secret key negotiation interaction scheme
ActiveCN104506534AGuarantee authenticityEnsure communication securityKey distribution for secure communicationUser identity/authority verificationThe InternetNetwork service
The invention provides a method for safety communication between an application on a mobile terminal and a network server. Shared secrets of a user and a server are overlapped and bound with an identification code of mobile intelligent terminal equipment and a mobile phone number of the user by utilizing a cryptology; then the obtained product is applied to an identity authentication system to implement authentication on a client side; a digital certificate and a digital signature mechanism are utilized to implement authentication on the server; a session key is established with a network server by utilizing a Differ-Hellman secret key negotiation protocol so as to carry out safety data communication. The method is characterized in that the shared secrets are overlapped and bound with identification code of the machine and the mobile phone number of the user and the shared secrets are updated regularly; even though information is stolen by an attacker, a system still cannot be influenced. The user not only needs to provide a login password, but also needs to use the system on designated equipment. The method can ensure that the user carries out safety communication with the server on internet by the mobile equipment.
Owner:QINGDAO WEIZHIHUI INFORMATION
Safety communication on a single backplane
InactiveUS6909923B2Safety arrangmentsComputer controlProgrammable logic controllerProgrammable Interrupt Controller
Owner:ROCKWELL AUTOMATION TECH
Internet of Vehicles safety communication method, vehicle-mounted terminal, server and system
ActiveCN106453269AImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesTransmission protocolThe Internet
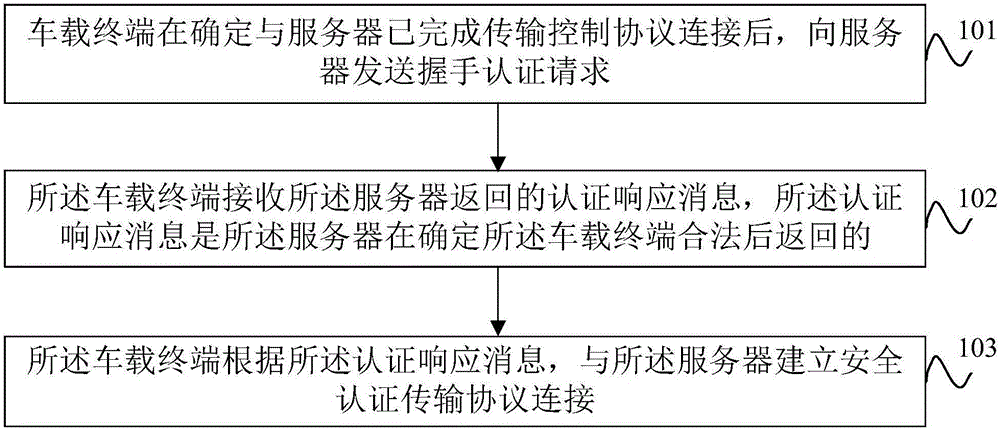
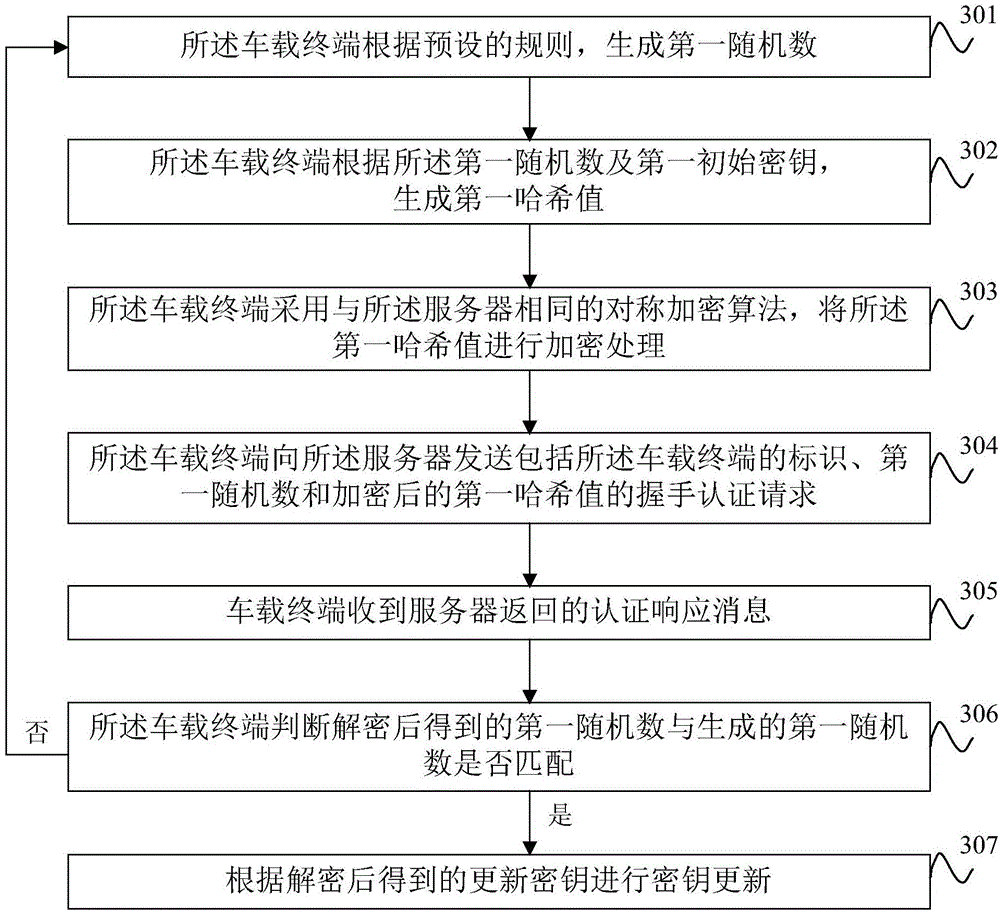
The application provides an Internet of Vehicles safety communication method, a vehicle-mounted terminal, a server and a system. The Internet of Vehicles safety communication method is characterized by comprising the following steps: the vehicle-mounted terminal sends a handshake authentication request to a server after determining that the transmission control protocol connection with the server has been finished, wherein the handshake authentication request comprises an identifier of the vehicle-mounted terminal and a first Hash value encrypted by use of a symmetrical encryption algorithm same as that adopted by the server; the vehicle-mounted terminal receives an authentication response message returned by the server, wherein the authentication response message is returned by the server after determining that the vehicle-mounted terminal is legal; and the vehicle-mounted terminal establishes a safety authentication transmission protocol connection with the server according to the authentication response message. A lightweight safety authentication transmission protocol is established between the vehicle-mounted terminal and the server by use of less resource, and the security of the data transmission between the vehicle-mounted terminal and the server is improved.
Owner:NEUSOFT CORP
IP address jump safety communication method based on SDN framework
InactiveCN105429957AIncrease attack difficultyRealize IP hoppingData switching networksDomain nameSafety Communications
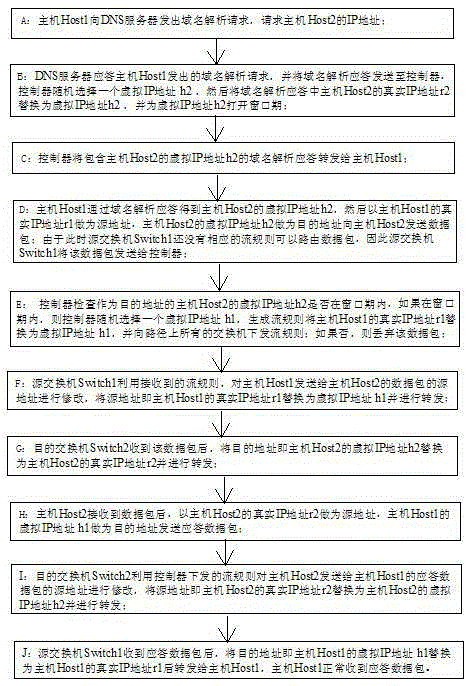
The invention discloses an IP address jump safety communication method based on an SDN framework. The method comprises steps that A, an IP address of a Host2 is requested by a Host1; B, a real IP address r2 of the Host2 is replaced by a virtual IP address h2 through a controller; C, a domain analysis response is forwarded by the controller to the Host1; D, an r1 is taken as a source address and the h2 is taken as a target address by the Host1 to send a data packet to the Host2; E, a flow rule is generated by the controller to replace the r1 by a virtual IP address h1, and the flow rule is issued; F, the r1 is replaced by the h1 through the source switch, and forwarding is carried out; G, the h2 is replaced by the r2 through the target switch, and forwarding is carried out; H, the r2 is taken as a source address and the h1 is taken as a target address by the Host2 to send a response data packet; I, the r2 is replaced by the h2 through the target switch, and forwarding is carried out; J, the h1 is replaced by the r1 through the source switch, and forwarding to the Host1 is carried out. Through the method, jump IPs can be dynamically distributed to a host computer in the IPH network, one-time one-change access to the host computer IP is transparently realized, attack based on scanning and DDoS attach can be effectively fought against.
Owner:芦斌
Internet of Things smart home security gateway system
ActiveCN104580233AEnhanced defense against attacksRealize free decouplingUser identity/authority verificationNetwork connectionsThe InternetSecure authentication
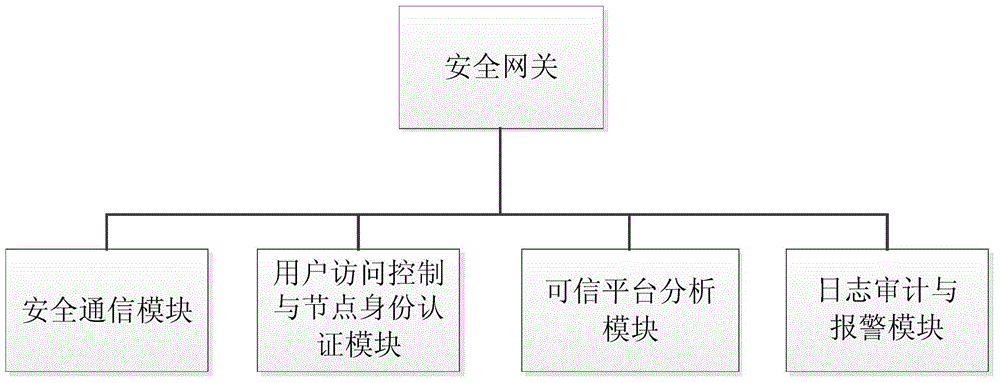
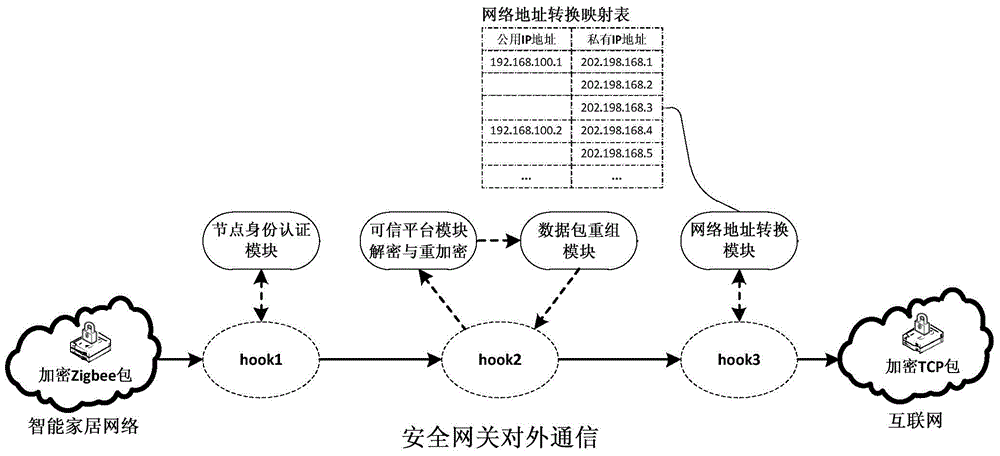
The invention relates to an Internet of Things smart home security gateway system. The system comprises a user side, a security gateway and a terminal node. The user side and the terminal node each comprise a data encrypting / decrypting module used for encrypting / decrypting a sent control order and received data through a preset encrypting program on a remote client side or the terminal node; the security gateway comprises a safety communication module, a user access control and node identity authentication module, a credible platform module and a log audit and alarm module; the safety communication module achieves data safety filtering, reconstructing and forwarding and guarantees safety of the bi-direction transmission; the credible platform module is used for achieving system safety authentication, user behavior credibility analysis, data sealing storage and free decoupling and can be independently maintained and upgraded; the log audit and alarm module is used for recording user access and node authentication behaviors, carrying out safety audit on the operation of viewing logs and giving a timely alarm for an abnormal phenomenon found in the gateway system safety monitoring process. By means of the Internet of Things smart home security gateway system, the safety performance of a smart home system and the running efficiency of a gateway can be improved, and a safety guarantee is provided for Internet of Things smart home.
Owner:重庆中邮信科集团股份有限公司
Method and apparatus for enhanced safety in a public safety communication system
ActiveUS20110237217A1Multiplex system selection arrangementsSpecial service provision for substationCommunications systemEngineering
A communication system (100) provides collaboration amongst a plurality of communication devices (110, 112, 114, 116, 120) during emergency conditions. Emergency trigger(s) are used to detect an emergency condition. Emergency information is collected and can be shared and appended amongst the communication devices prior to the emergency information being transferred in a redundant manner across a plurality communication systems (140, 142) to a plurality of external devices (130, 144, 146).
Owner:MOTOROLA SOLUTIONS INC
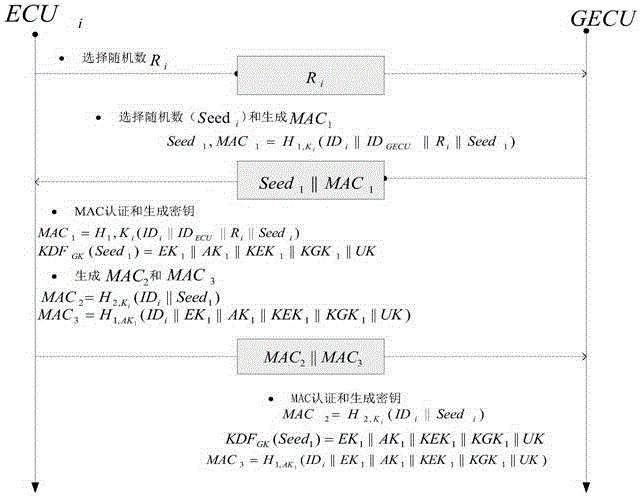
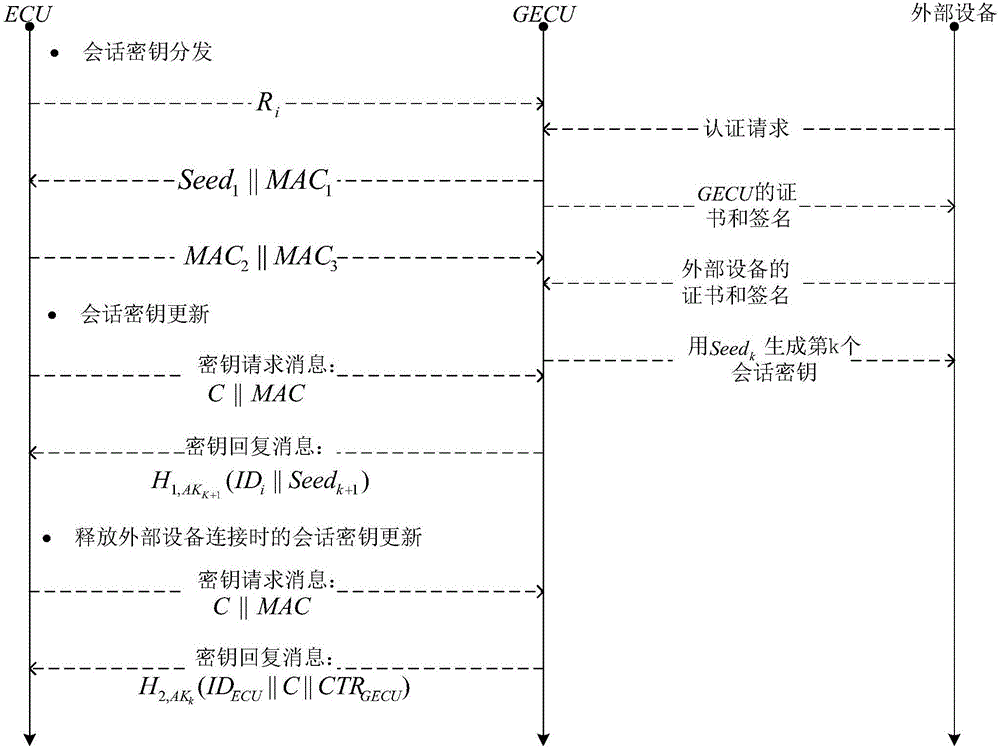
Method for safety communication of ECUs (Electronic Control Unit) in CAN (controller area network) bus
ActiveCN106790053AReduce computing costImprove efficiencyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesArea networkKey generation
The invention discloses a method for safety communication of ECUs (Electronic Control Unit) in a CAN (controller area network) bus, which comprises the steps that: 1, a system model is established; 2, an GECU (Gateway Electronic Control Unit) loads a session key into a safety storage of the GECU; 3, the GECU carries out session key distribution on each ECU in the CAN bus; 4, a receiver ECUr carries out authentication on an encrypted data frame sent by a sender ECUs; 5, the GECU updates an encryption key and an authentication key which are used for communication, wherein update is mainly divided into two stages of in-vehicle ECU key update and key update when a connection of external equipment is released; and 6, when a vehicle is connected with the external equipment, designing an additional authentication and key distribution method so as to ensure legality of the accessed external equipment. According to the method disclosed by the invention, calculation cost can be obviously reduced, and a load of the CAN bus is reduced; and optimization is carried out for a key distribution protocol in the in-vehicle CAN bus, a key update problem generated when the external equipment is connected and released is considered, a counter is used for generating a random number to change a parameter for key generation, and a relay attack is effectively prevented.
Owner:JIANGSU UNIV
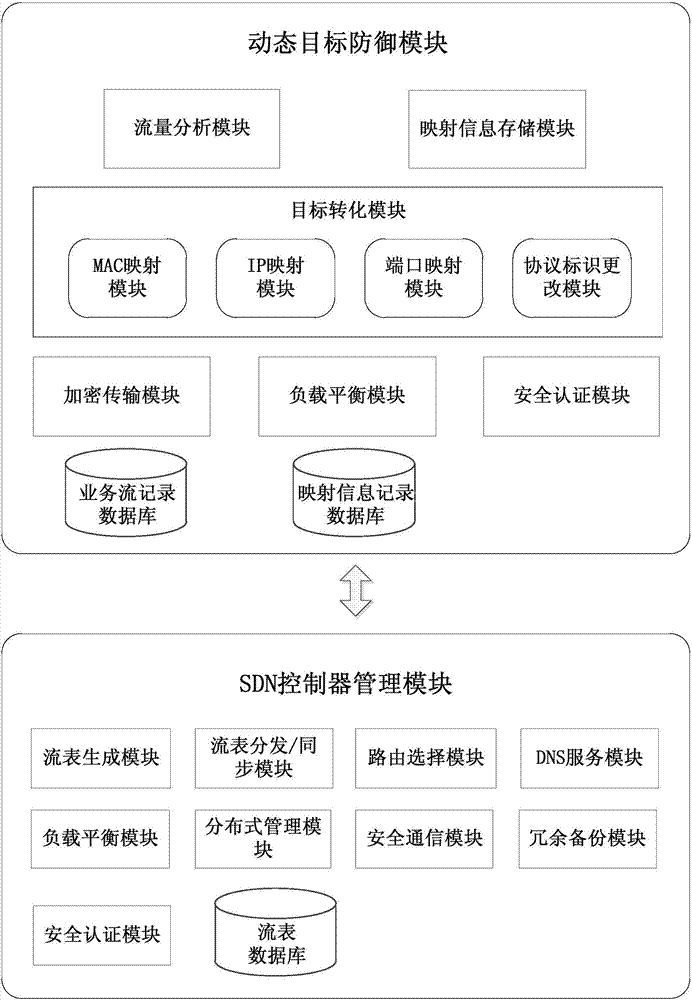
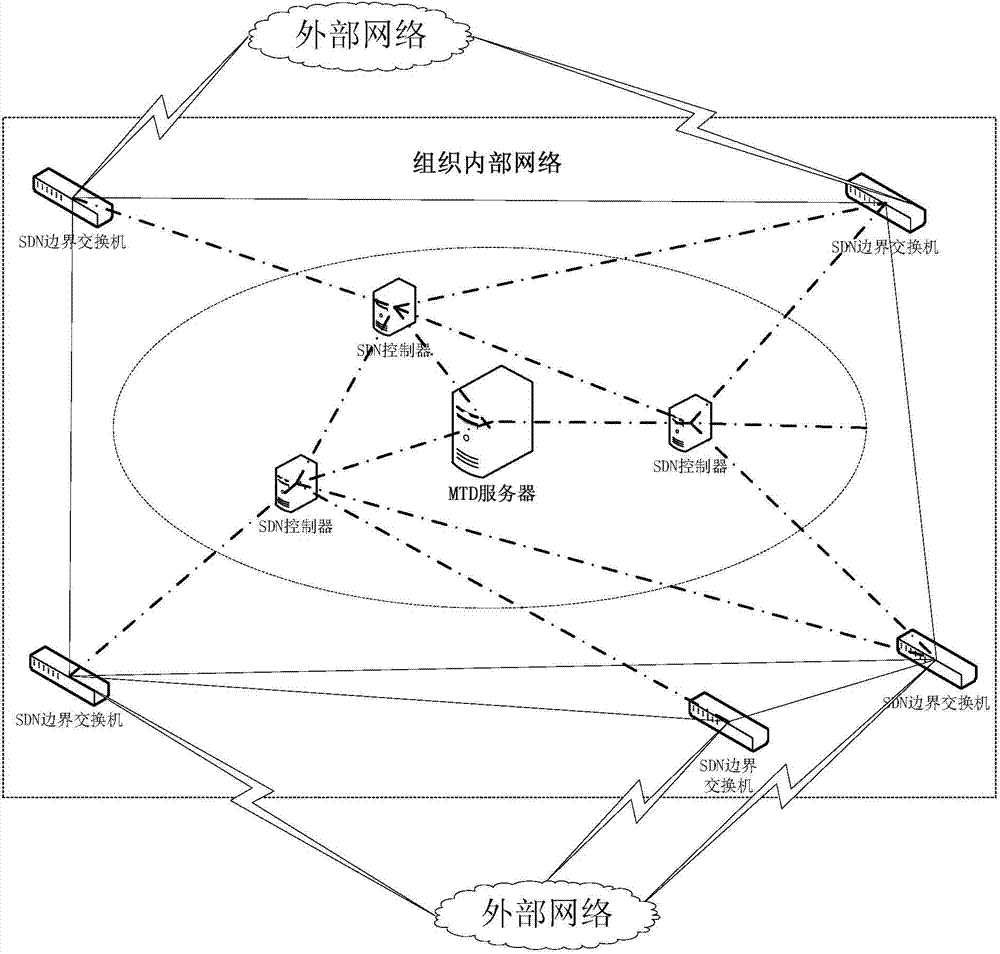
Moving target defense system and moving target defense method for SDN (self-defending network)
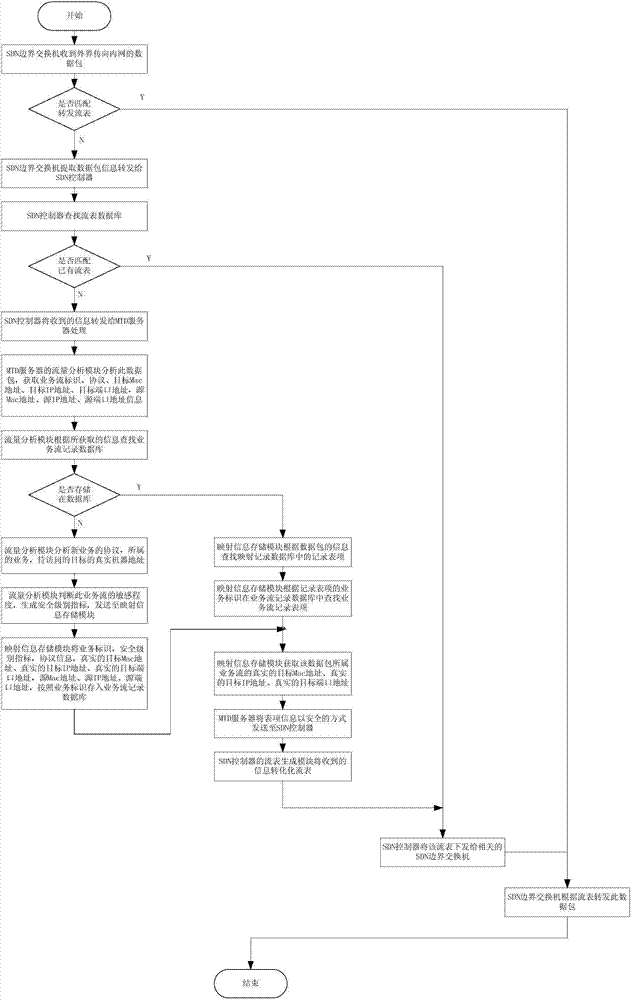
InactiveCN104506511AProtection securityIncrease the difficultyTransmissionTraffic flow analysisSafety Communications
The invention discloses a moving target defense system for an SDN (self-defending network). The system consists of a moving target defense module and an SDN controller management module; the moving target defense module comprises a flow analysis module, a mapping information storage module, a target conversion module, an encryption transmission module, a load balance module, a safety authentication module, a business flow recording database and a mapping information recording database; the SDN controller management module comprises a flow table generation module, a flow table distribution / synchronization module, a route selection module, a DNS service module, a load balance module, a distributed management module, a safety communication module, a redundant backup module, a safety authentication module and a flow table database; furthermore, the invention also discloses a moving target defense method for the SDN. Through the moving target defense system and the moving target defense method disclosed by the invention, the difficulty of an attacker to detect a target is increased further, and therefore the safety of an intranet is comprehensively protected.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
Intelligent transport system for urban railway based on safety communication
InactiveCN103386994AEasy to unifyOvercome the influence of "network storm"Automatic systemsNetwork connectionThe Internet
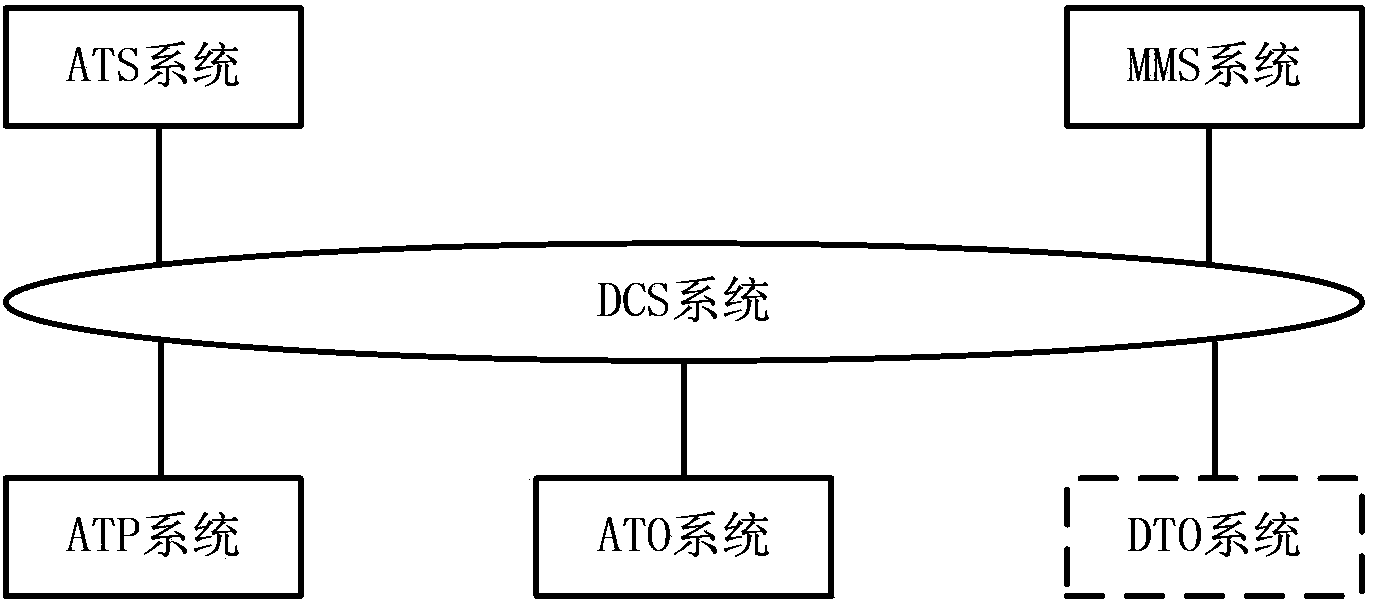
The invention discloses an intelligent transport system for an urban railway based on safety communication. The intelligent transport system for the urban railway comprises a DCS (data communication system), an ATS (automatic train supervision), an ATP (automatic train protection), an ATO (automatic train operation), a DTO (driverless train operation) and a MMS (maintenance management system), wherein the ATS, the ATP, the ATO, the DTO and the MMS realize the network connection through the DCS. The intelligent transport system for the urban railway has the advantages that the proper Internet storm influence of a CBTC (communication based train control) is favorably overcome, the safety problem of the train-ground wireless communication is favorably solved, the man-machine interface of the CBTC is favorably unified, the linkage efficiency among the systems under the emergency condition is improved, the ease maintenance of the system is enhanced, and the complete network operation scheme is provided.
Owner:SHANGHAI FUXIN INTELLIGENT TRANSPORTATION SOLUTIONS
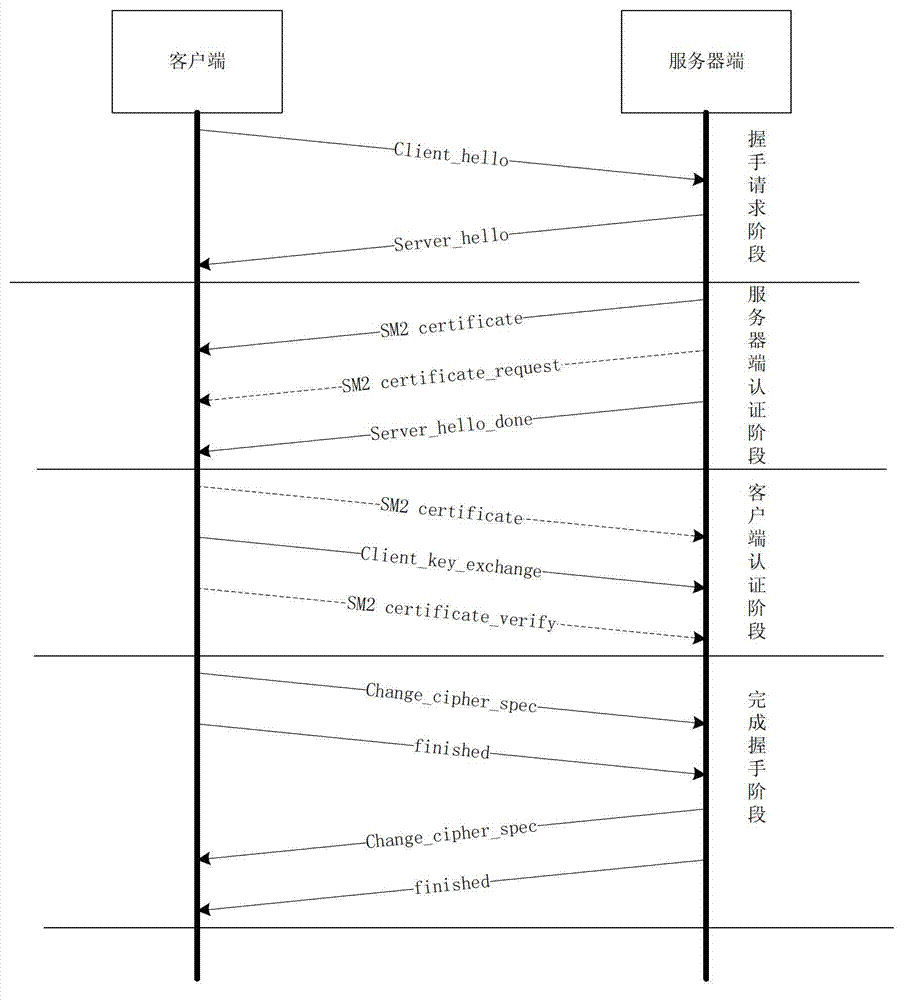
Transport layer security (TLS) channel constructing method based on cryptographic algorithm
The invention relates to the technical field of network safety and provides a transport layer security (TLS) channel constructing method based on a cryptographic algorithm. The TLS channel constructing method includes steps that: a server side launches a request and a client side respond to a hello message, or the client side launches the hello message; the server side responds to the hello message of the server side; the server side transmits an SM2 certificate to the server side and then transmits a hello completing message; the client side receives the hello completing message and then transmits a secret key exchange message; the client side transmits a cipher suite change message and a finishing message, and the server side transmits the cipher suite change message and the finishing message after receiving the finishing message of the client side; and the server side and the client side perform data safe transmission according to the agreed safety parameters after receiving the finishing messages of each other and passing verification. According to the TLS channel constructing method, the cryptographic algorithm is blended into a TLS protocol to perform safety communication, the signature speed is obviously superior to that of a remote signaling alarm (RSA) algorithm by aid of short secret key length, and the TLS channel constructing method is a data safety method with the 2048-bit safety level of the RSA algorithm.
Owner:CHINA FINANCIAL CERTIFICATION AUTHORITY
Public safety warning network
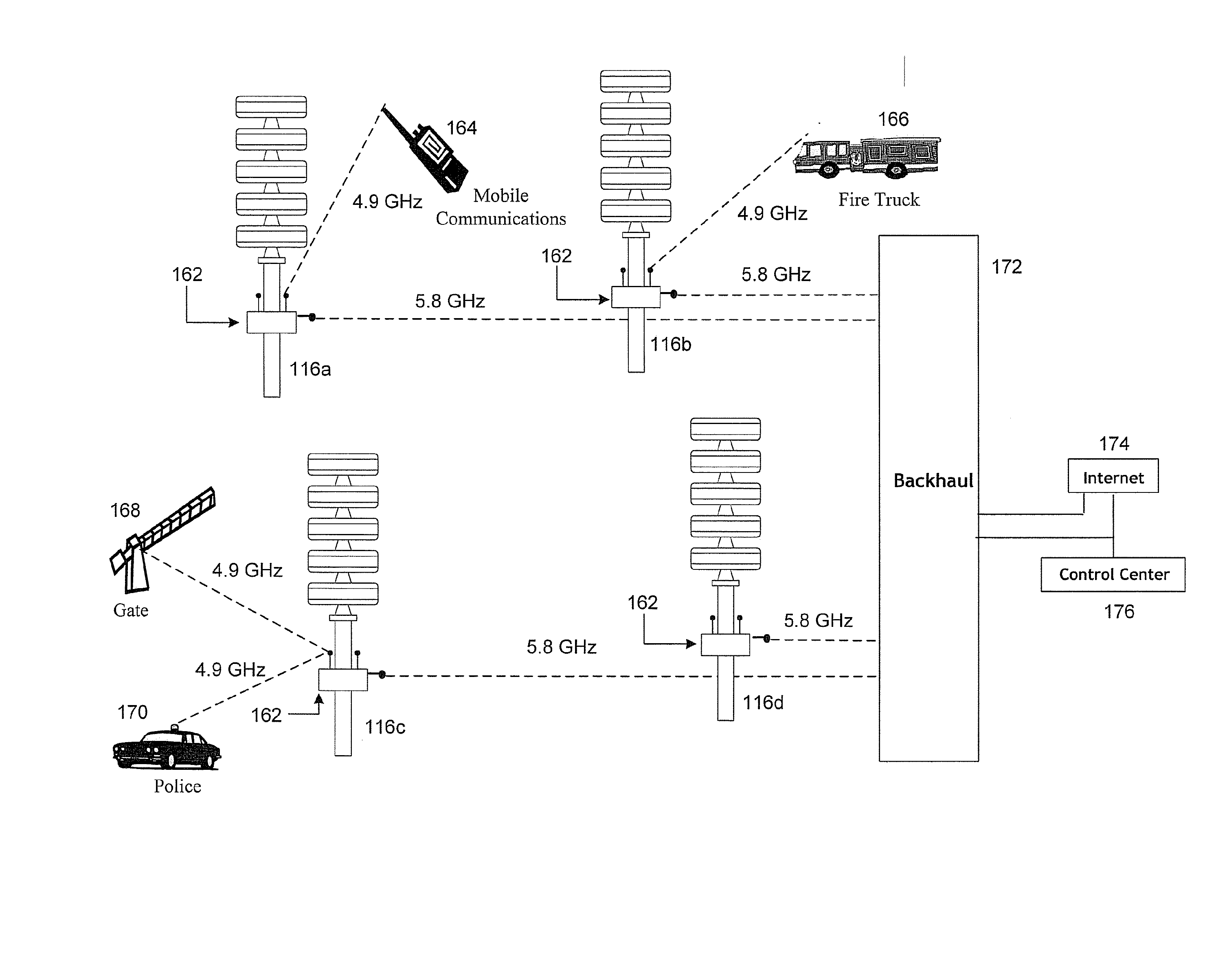
A communications infrastructure is upgraded to a public safety network that supports wireless communications of emergency information. Communities have installed public safety communications systems such as community warning siren systems that rely on point-to-point communications systems. Each site in the system is upgraded to a node in a wireless network that provides the communications infrastructure for a network-enabled public safety communications system that enables trusted resources such as warning sirens to access the network and communicate with other trusted resources across the network. Additionally, the public safety network may be patched using mobile transceivers to form an ad hoc network in the event part of the infrastructure supporting the emergency response network is lost. Additionally, the upgrading of the communications system may include a public access network that relies on at least some of the same communications sites or nodes employed by the public safety network.
Owner:FEDERAL SIGNAL CORPORATION
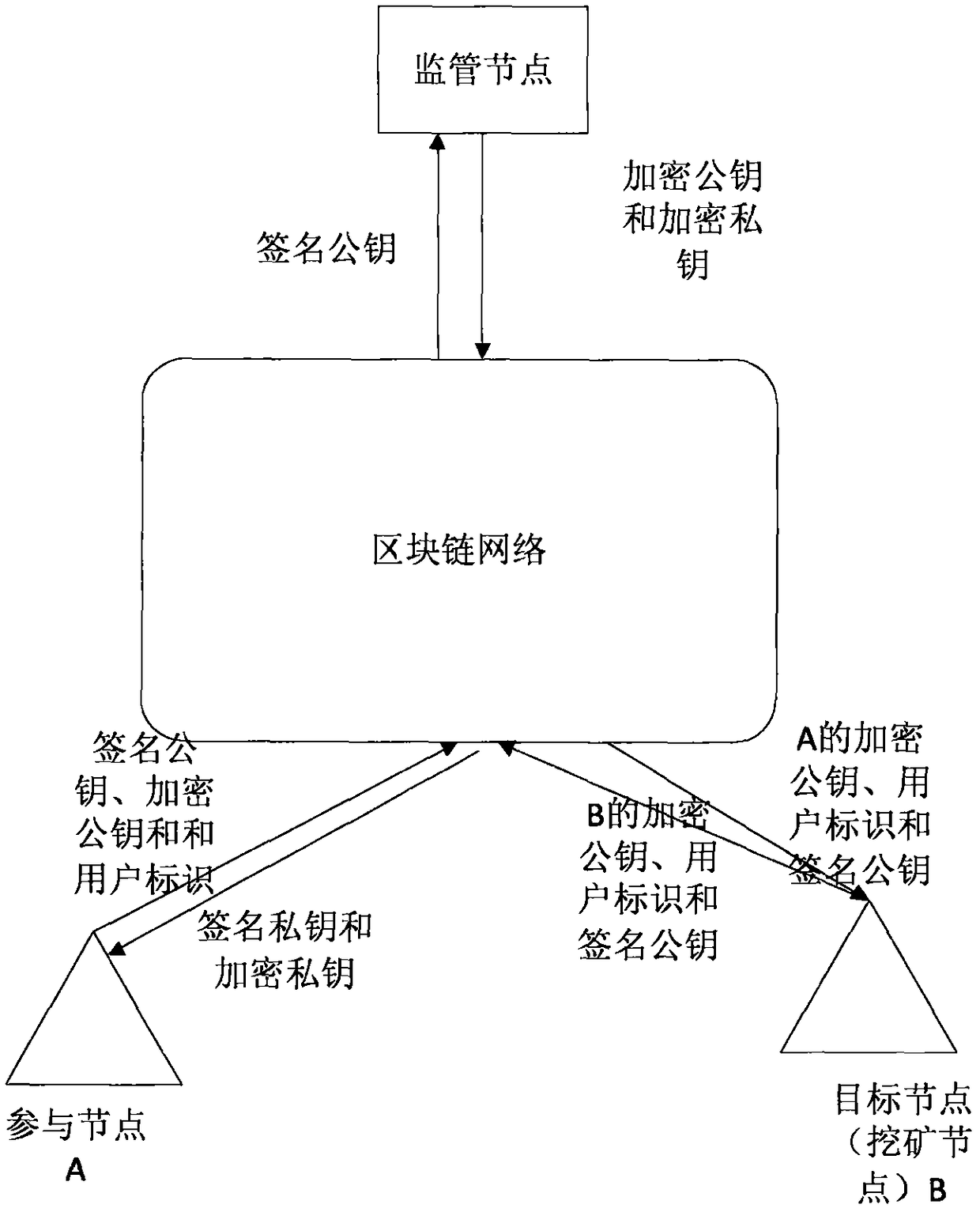
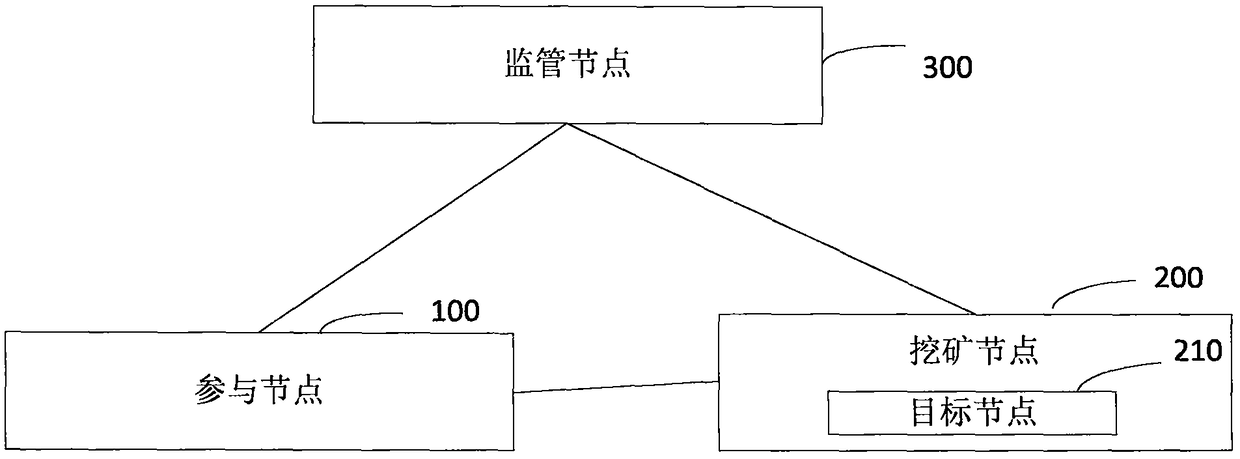
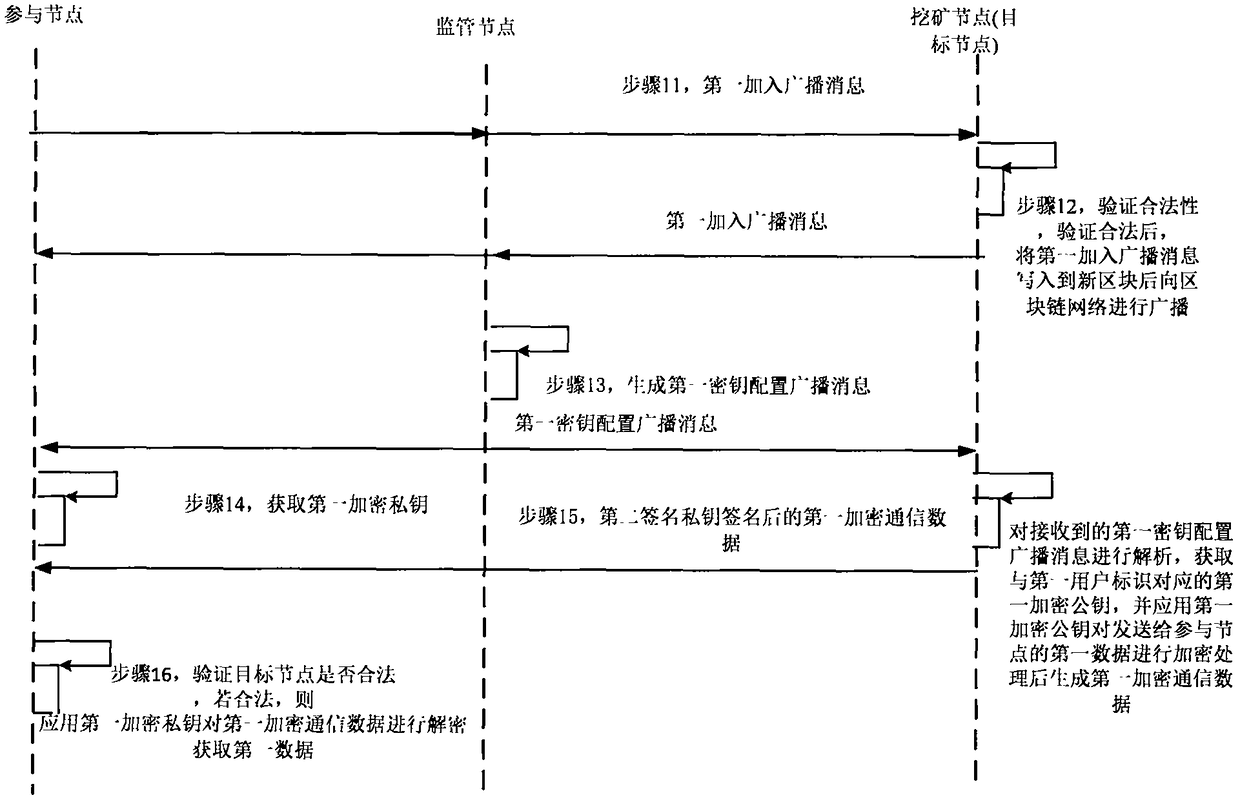
Encrypted communication method and system of block chain node
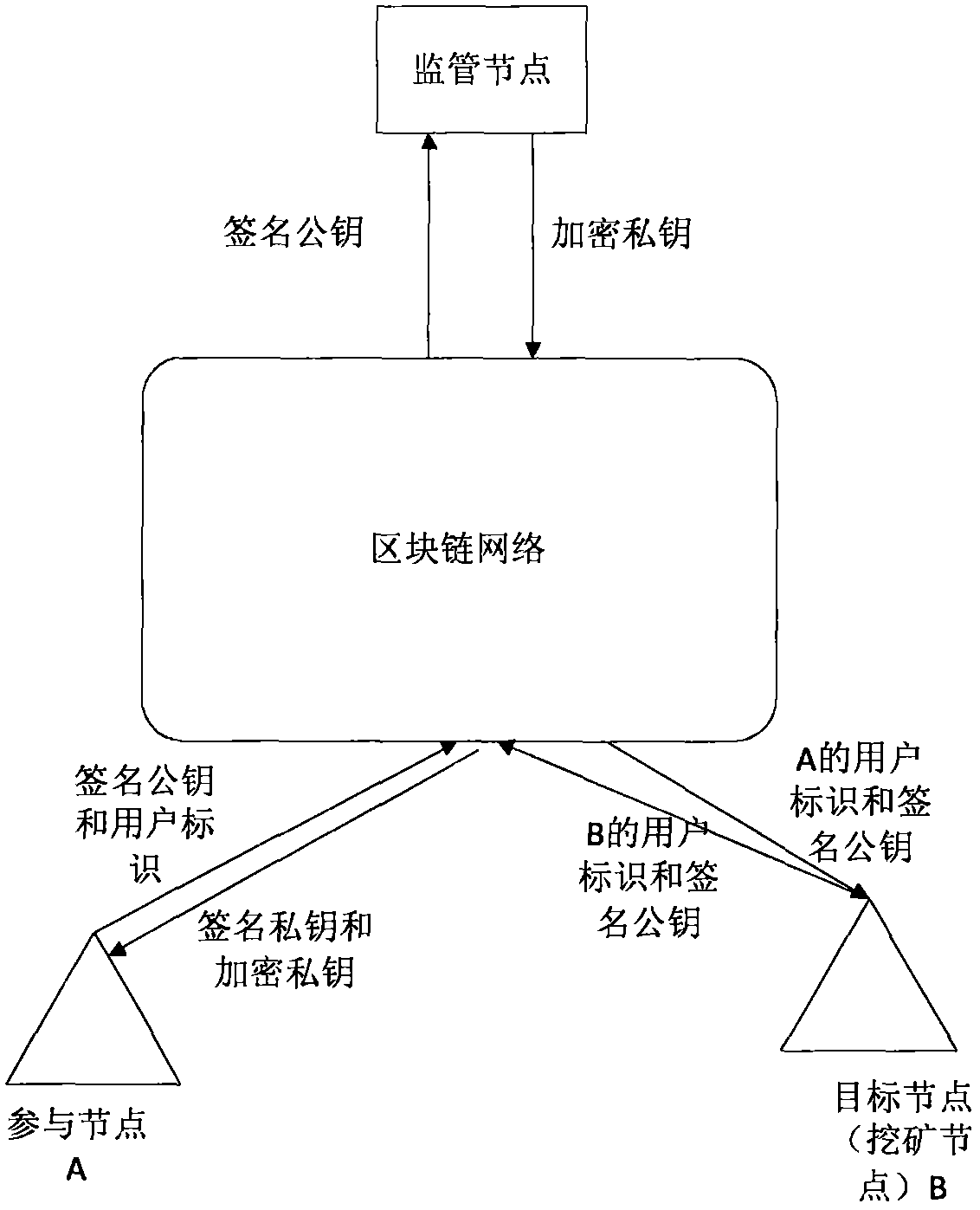
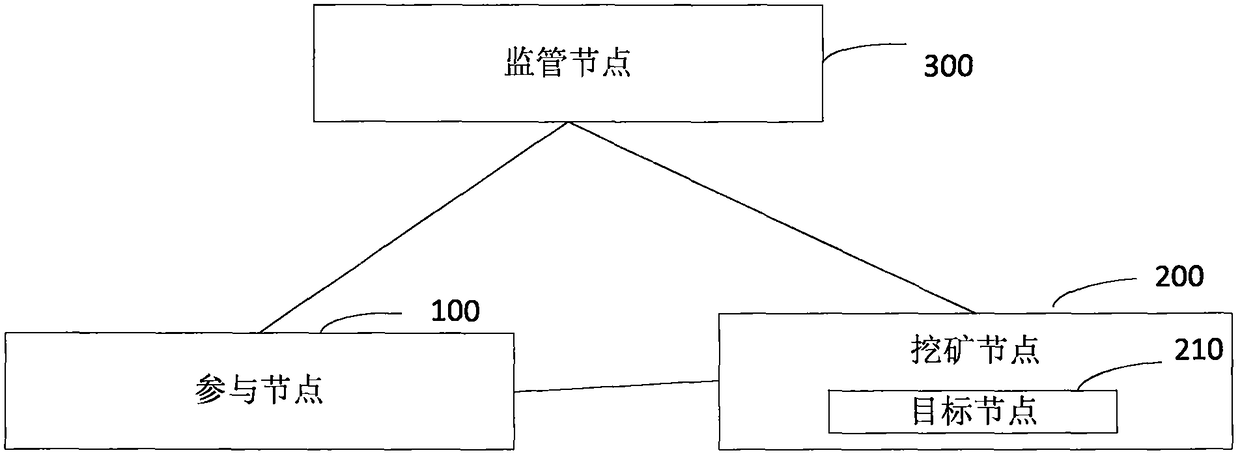
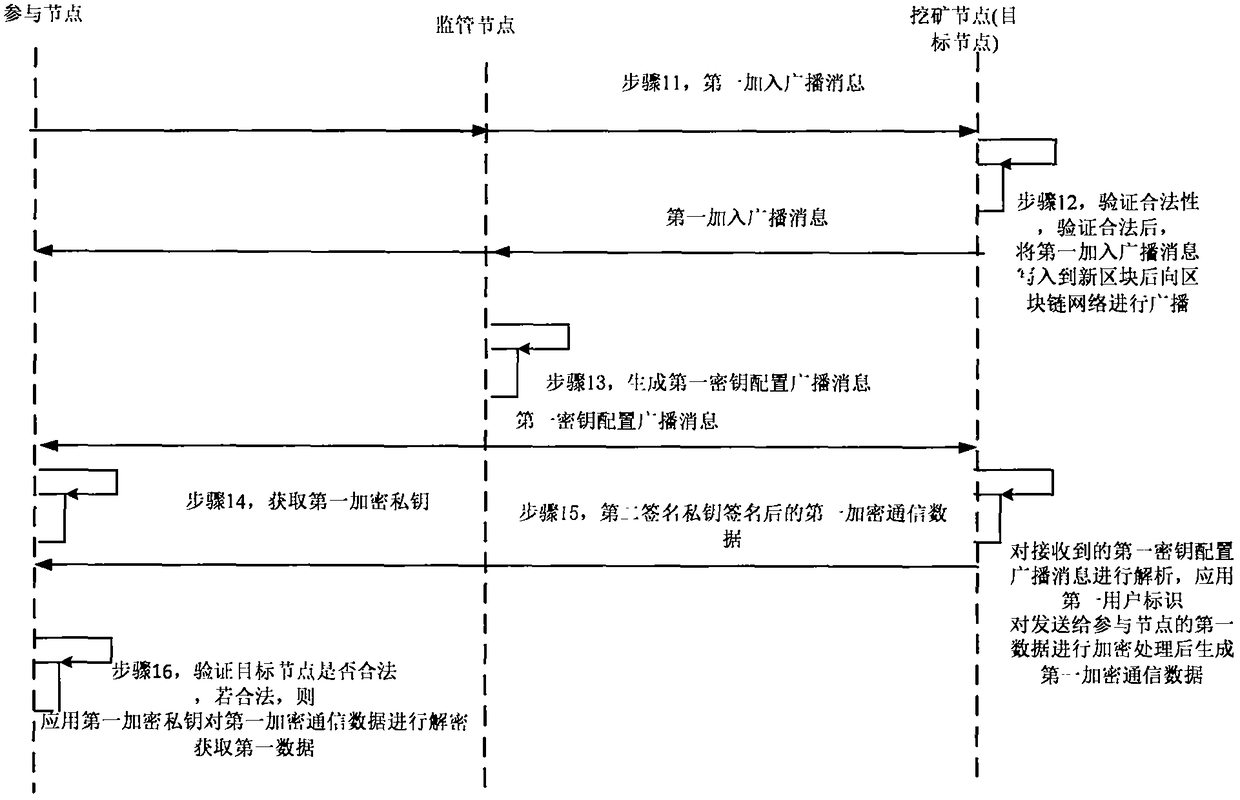
InactiveCN108737430AEnsure communication securityAvoid accessSpecial service provision for substationKey distribution for secure communicationSecure communicationCommunications security
The invention provides an encrypted communication method and system of a block chain node. The method comprises the following steps: for a participating node firstly added in a block chain network, afirst user identifier and a first signature private key of the participating node are signed by using a first signature private key of the participating node, and a first adding broadcast message is sent by the block chain network after the timestamp is stamped thereon through a timestamp server; a mining node analyzes the first adding broadcast message to acquire the first user identifier and thefirst signature public key, and performs the legality verification on the participating node according to the first signature public key; a supervision node generates and distributes the first encryption public key and the first encryption private key corresponding to the first user identifier according to the first signature public key; the participating node perform safety communication with the target node based on the first encryption public key and the first encryption private key. Therefore, the public key certificate scheme is combined with the block chain network to guarantee the communication security of the block chain network.
Owner:全链通有限公司
Enhanced public safety communication system
ActiveUS8504090B2Emergency connection handlingTransmission systemsDisseminationBroadband communication
A communication system (100) provides collaboration between narrowband communication devices (102) and broadband communication devices (104) operating over different networks. The communication devices (102, 104) are linked to provide peer-to-peer communication that supports the dissemination of public safety information to a public safety personnel user utilizing the devices. Applications within the devices (102, 104) automatically control features amongst the plurality of devices for redundancy of critical information, removal of non-critical information and power management. Context information can also be examined and shared between amongst the devices.
Owner:MOTOROLA SOLUTIONS INC
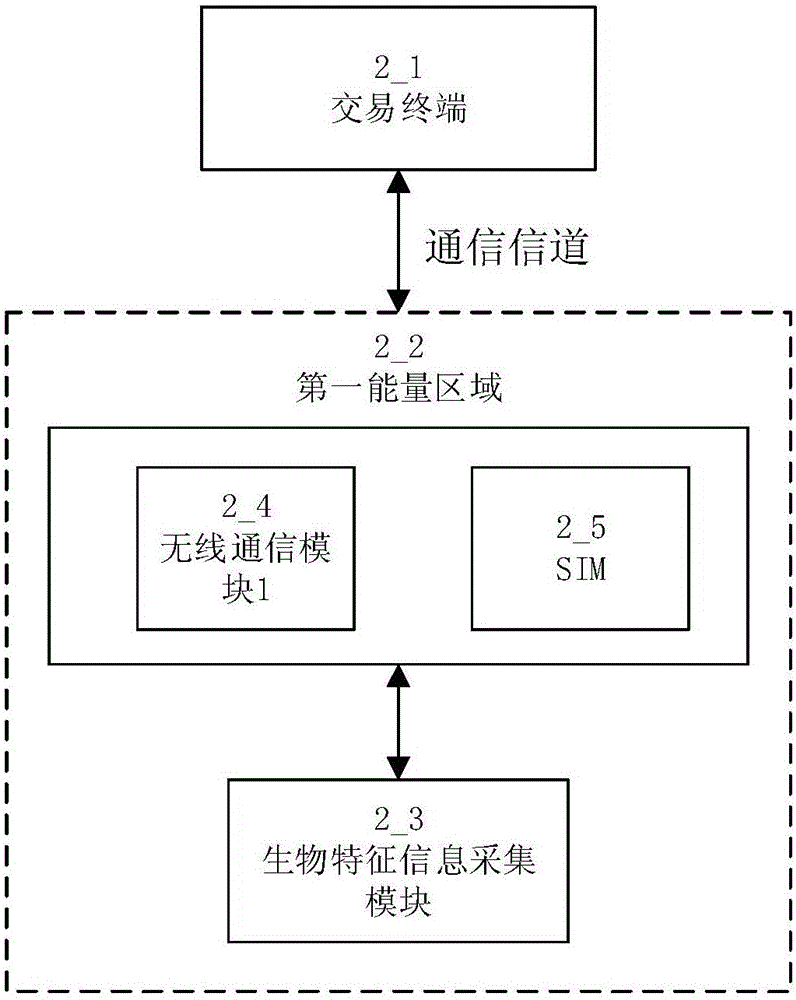
Mobile-terminal ultra-low power consumption and high safety communication method
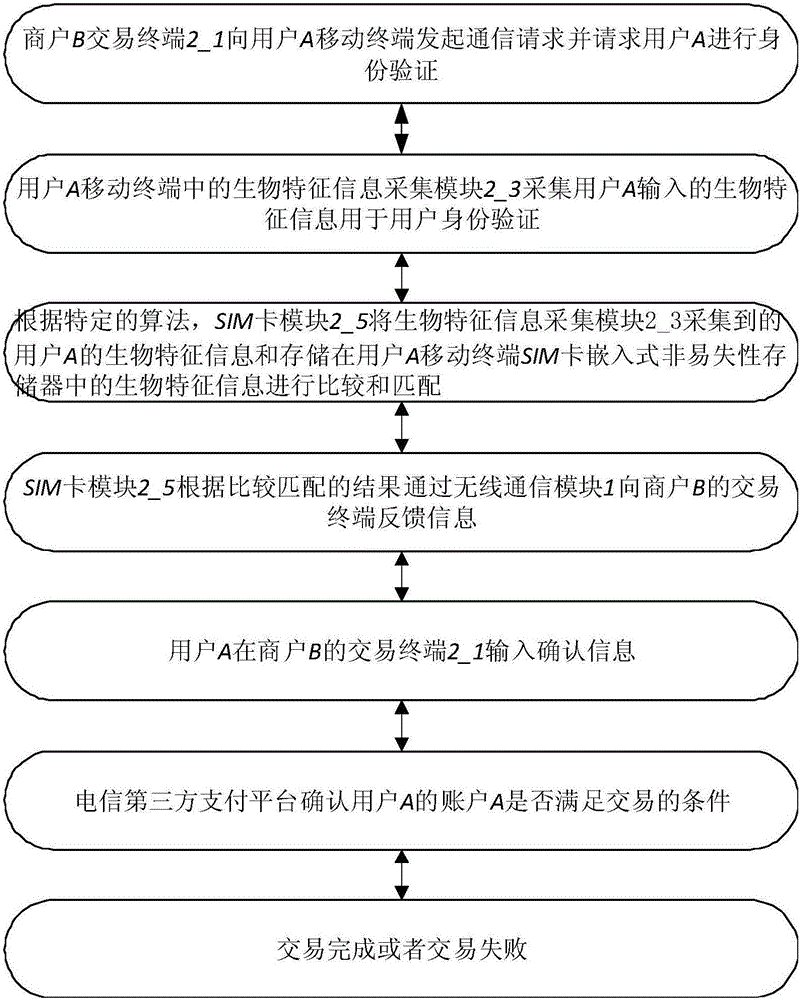
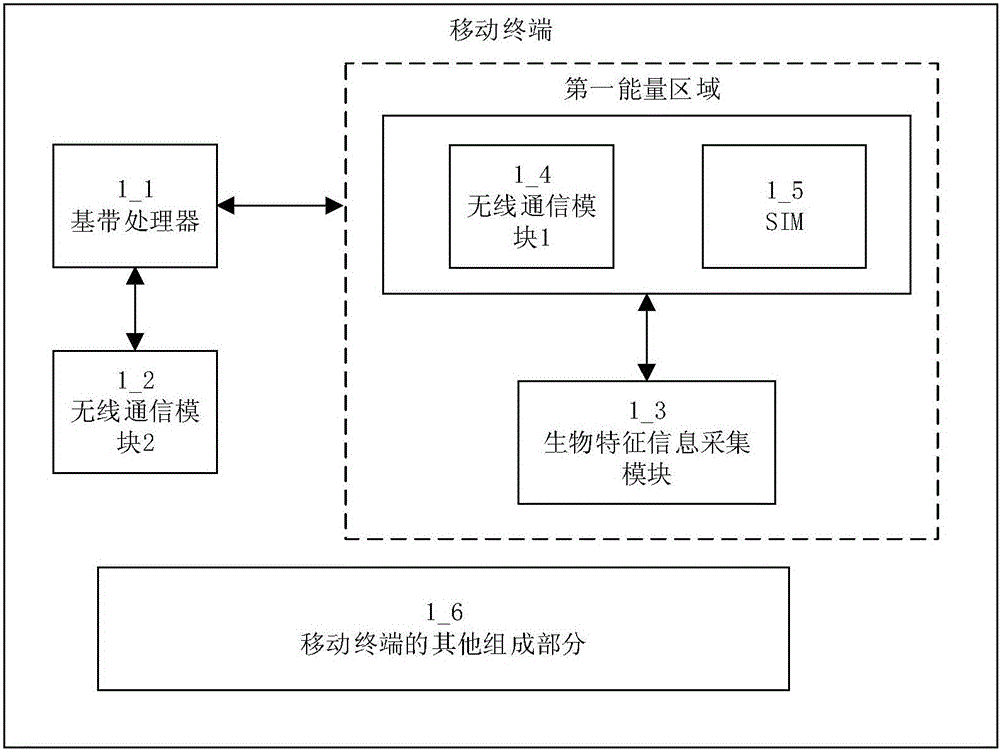
InactiveCN105844468AImprove securityPrevent theftProtocol authorisationComputer terminalSafety Communications
The invention relates to the data communication technology field and especially relates to a mobile-terminal ultra-low power consumption and high safety communication method and a high-safety online payment method. The mobile-terminal ultra-low power consumption and high safety communication method comprises the following steps that a standard verification information of a user is prefabricated in a SIM unit of a mobile terminal; when a first communication module in the mobile terminal receives an identity verification request, an identity information acquisition module of the mobile terminal acquires identity information of a current user; whether the identity information matches with the standard verification information is determined, and a determination result is formed and output.
Owner:SHANGHAI XINCHU INTEGRATED CIRCUIT
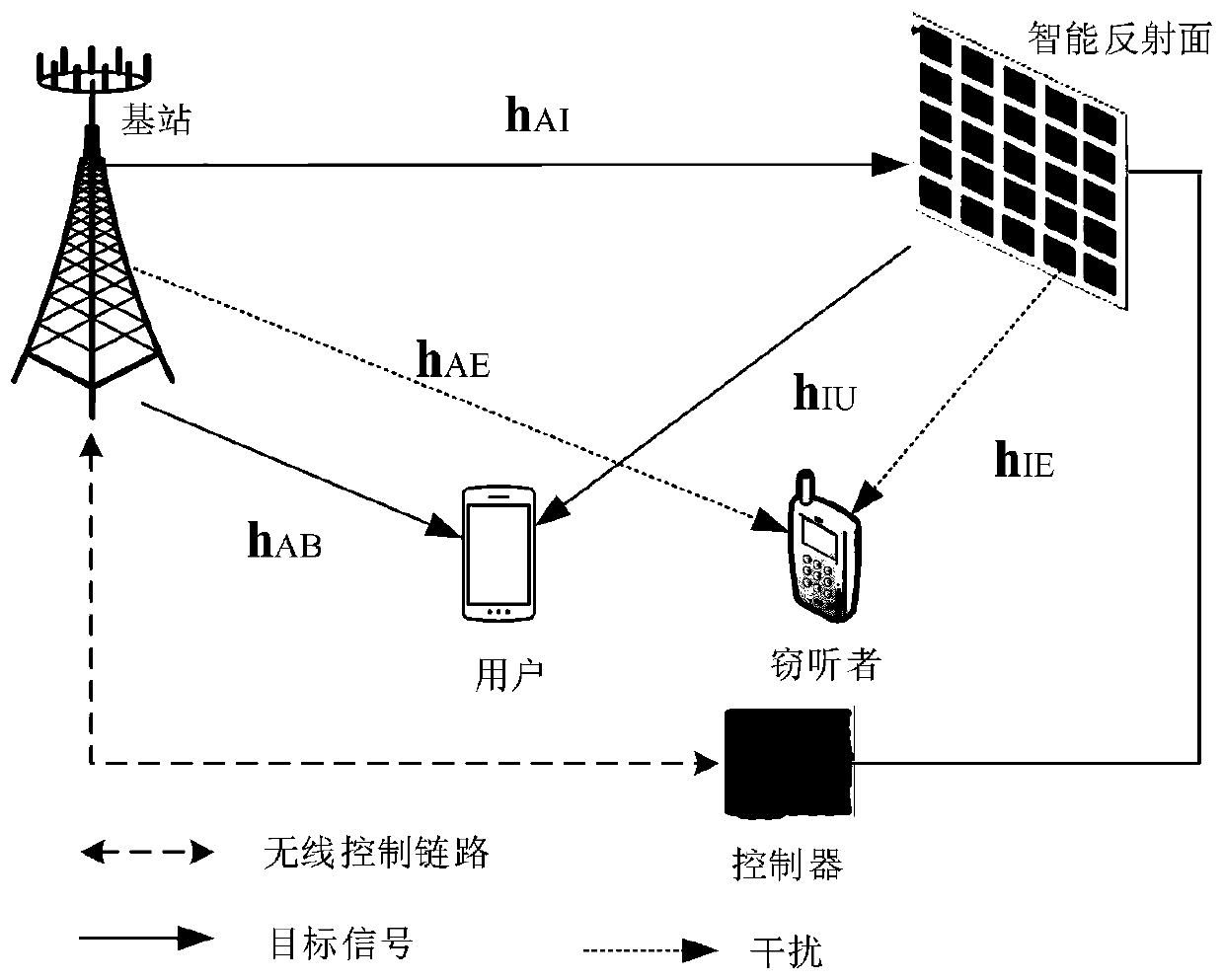
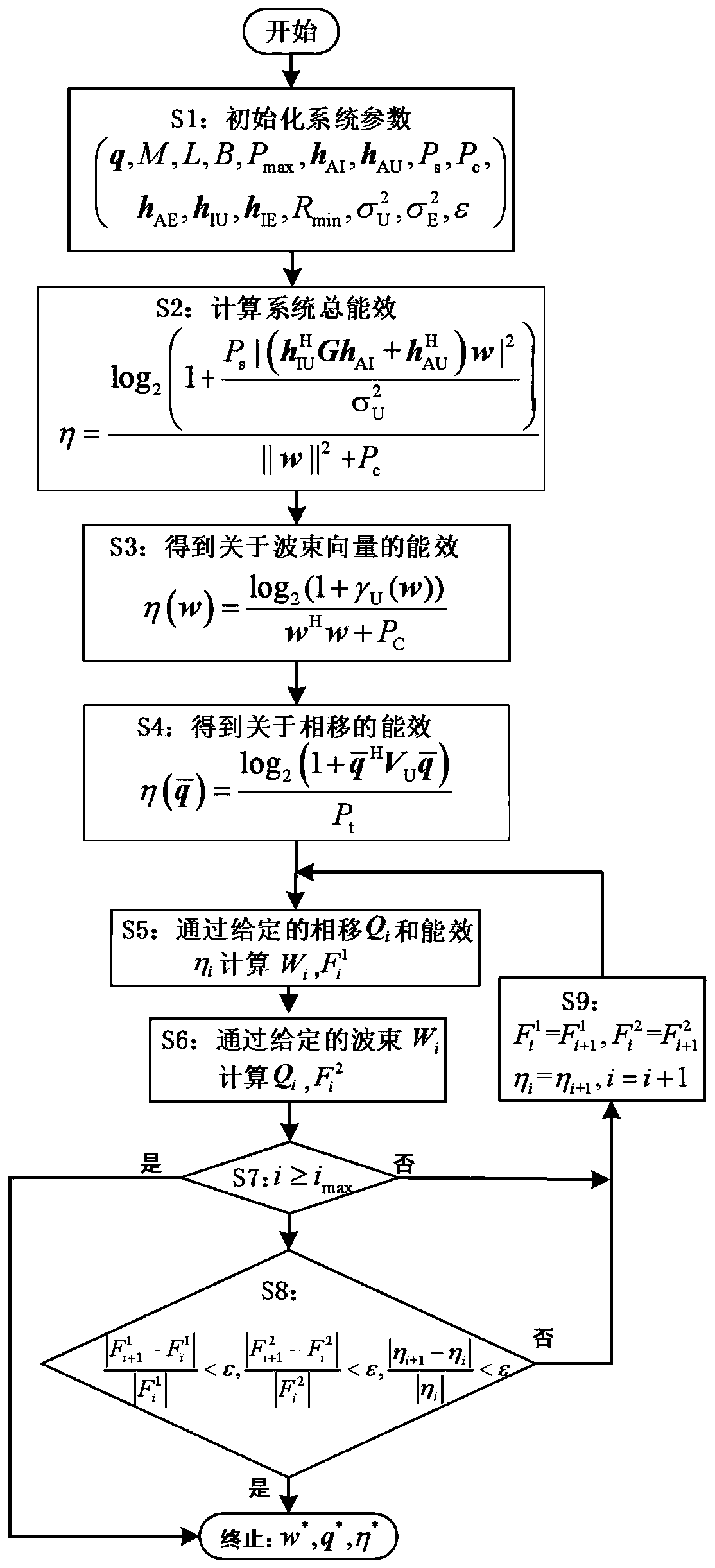
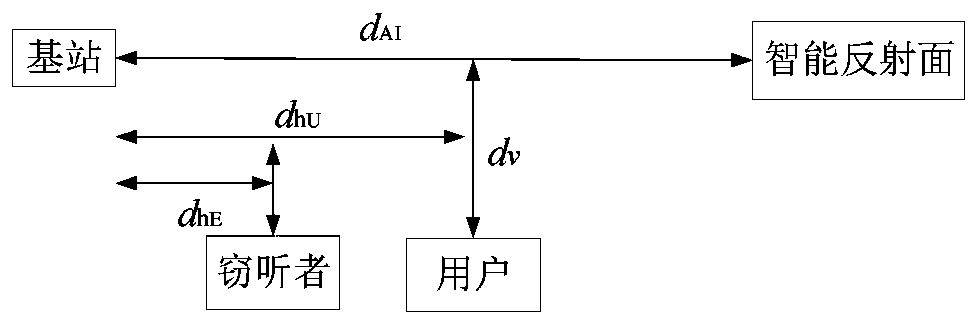
Intelligent reflecting surface energy efficiency maximum resource allocation method based on safety communication
ActiveCN111447618AImprove energy efficiencyImprove securitySecurity arrangementHigh level techniquesMulti inputSecure communication
The invention relates to an intelligent reflecting surface energy efficiency maximum resource allocation method based on safety communication, and belongs to the technical field of wireless communication. The method comprises the following steps: S1, constructing a multi-input single-output intelligent reflecting surface cellular communication system based on safety communication; s2, establishinga nonlinear and multivariable coupling resource allocation model taking maximization of the energy efficiency of the multi-input single-output cellular communication system as a target by consideringthe safety rate constraint of a user, the maximum transmitting power constraint of a base station and the continuous phase shift constraint; s3, converting a fractional objective function into an auxiliary variable parameter subtraction form by utilizing a Dinkelbach method, and then decoupling base station beam forming and reflection surface phase shift parameters according to an alternating iterative algorithm; and S4, converting the original non-convex problem into a standard semi-definite programming form, and carrying out solving by using a convex optimization tool. Simulation results show that the algorithm provided by the invention has higher energy efficiency and safety.
Owner:上海秉玉软件技术服务有限公司
Multilink safety communication method based on completion port model
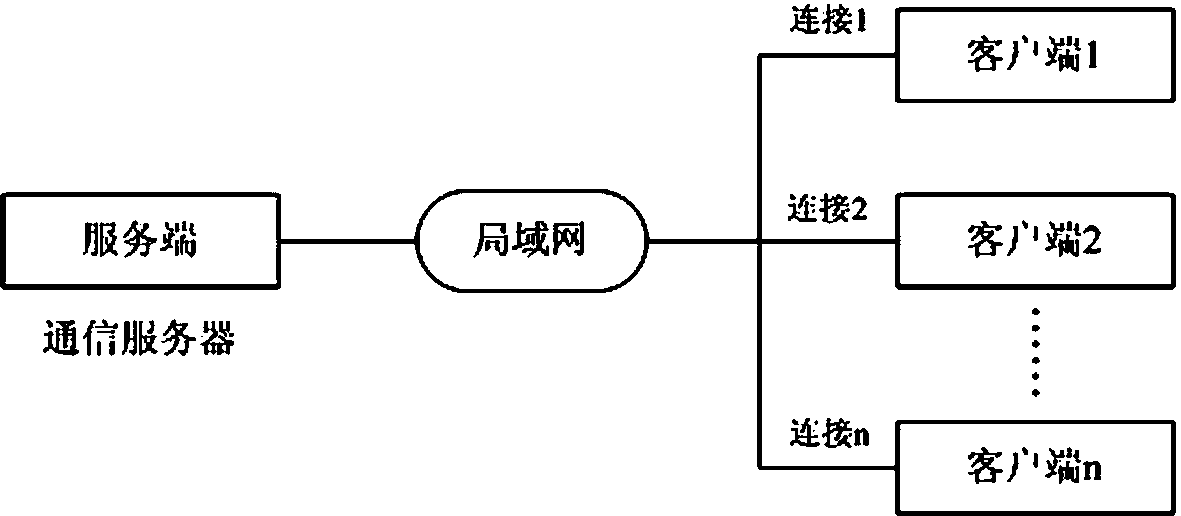
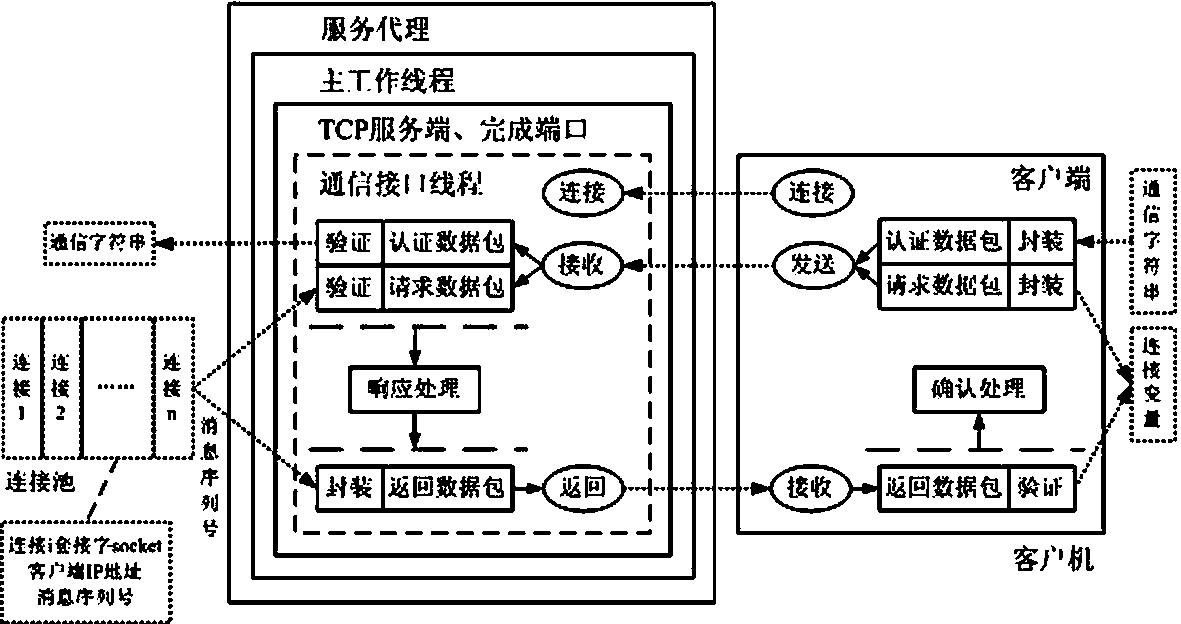
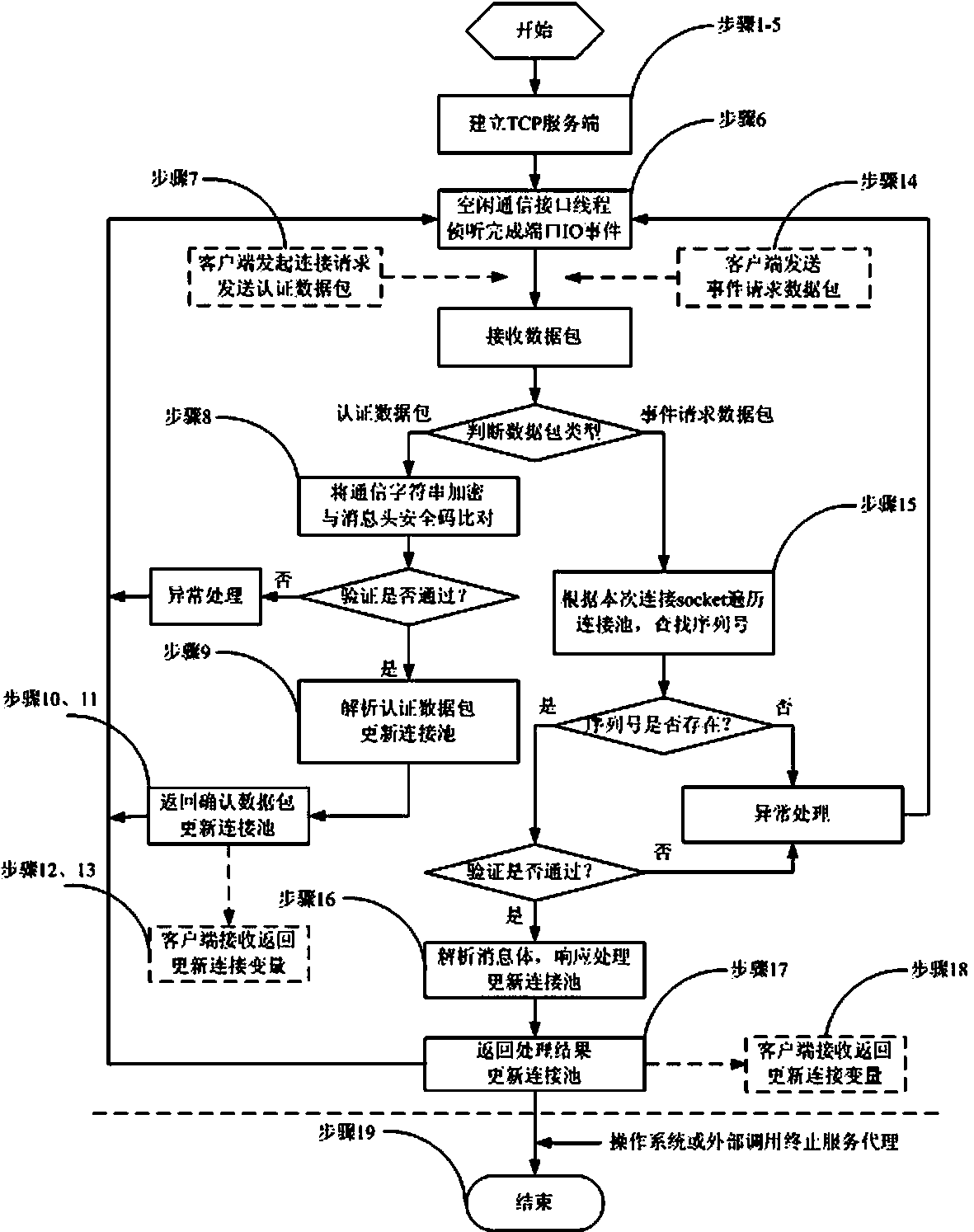
InactiveCN103391289AImprove scalabilityEasy to implementError preventionSecure communicationCommunication interface
The invention provides a method for supporting multilink concurrence safety communication between a server and multiple clients and relates to a multilink safety communication method based on a completion port model. The method includes that a main worker thread at a communication server is embedded into an application service of a Windows system to run, a transmission control protocol (TCP) communication server is built according to the completion port model, meanwhile a fixed number of communication interface threads are built to conduct communication with the clients in an asynchronous mode, and the parallel processing capability of the server is improved. In an interaction process, after any client builds the TCP connection, two communication parties must adopt a handshake mechanism to ensure connection legality and adopt connection pool queues or local variables to dynamically maintain message serial numbers in the following data receiving and transmitting process, data transmitted by any party on the legal connection are packaged again according to the data package structure definition, and the receiving party adopts a safety verification algorithm to verify the data packages and regroup the plurality of data packages according to the precedence order of the message serial numbers.
Owner:中船凌久高科(武汉)有限公司
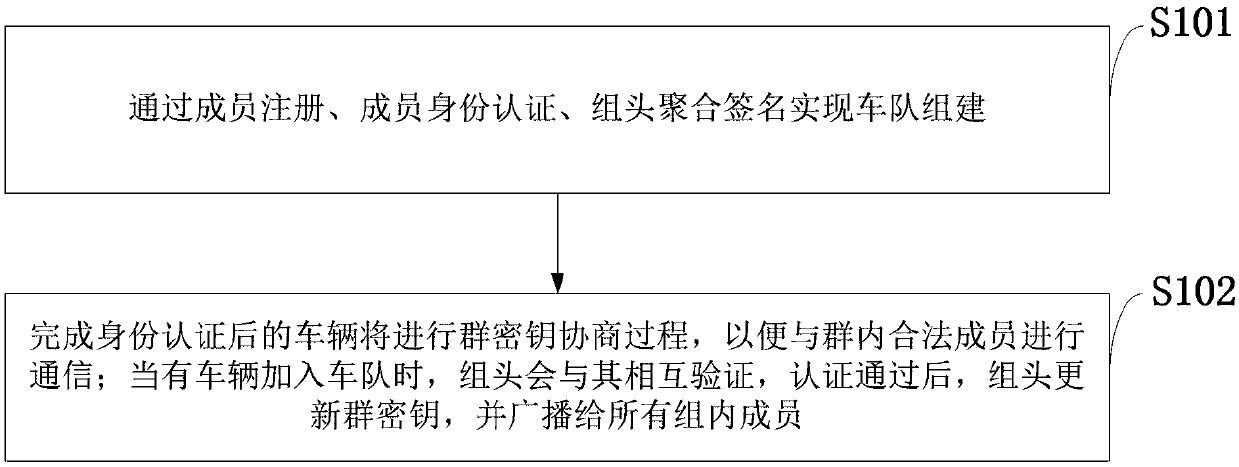
Motorcade establishment and management method and system based on block chain and PKI authentication mechanism
ActiveCN109687976ASolve authentication problemsTroubleshoot account management issuesKey distribution for secure communicationParticular environment based servicesSecure communicationThe Internet
The invention belongs to the technical field of safety communication between motorcades in Internet of Vehicles, and discloses a motorcade establishment and management method and system based on a block chain and a PKI authentication mechanism. The method is mainly divided into two parts of motorcade establishment and group key agreement and update; the motorcade establishment part comprises the following main processes of member registration, member identity authentication and group head aggregate signature; and the group key agreement and update part comprises the following main processes ofgroup key agreement and group key update for dynamic joining and exiting of a vehicle. According to the method and the system, the block chain is combined with the PKI authentication mechanism, a problem of identity authentication of the vehicle, a server and an RSU in the Internet of Vehicles is solved; the motorcade establishment is completed based on an elliptic curve, a bilinear pairing technology and an aggregate signature; and the group key agreement and update can be realized based on a DDH difficulty problem, the forward and backward safety is achieved, and the safety of member communication in the motorcade is ensured.
Owner:XIAN UNIV OF POSTS & TELECOMM
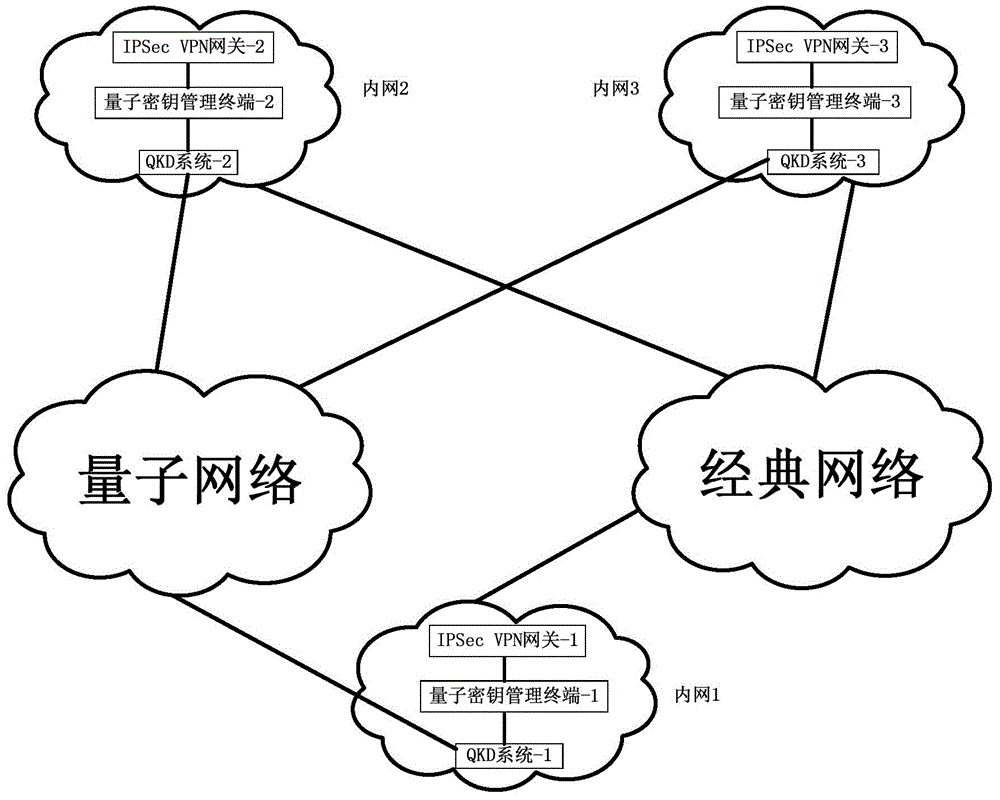
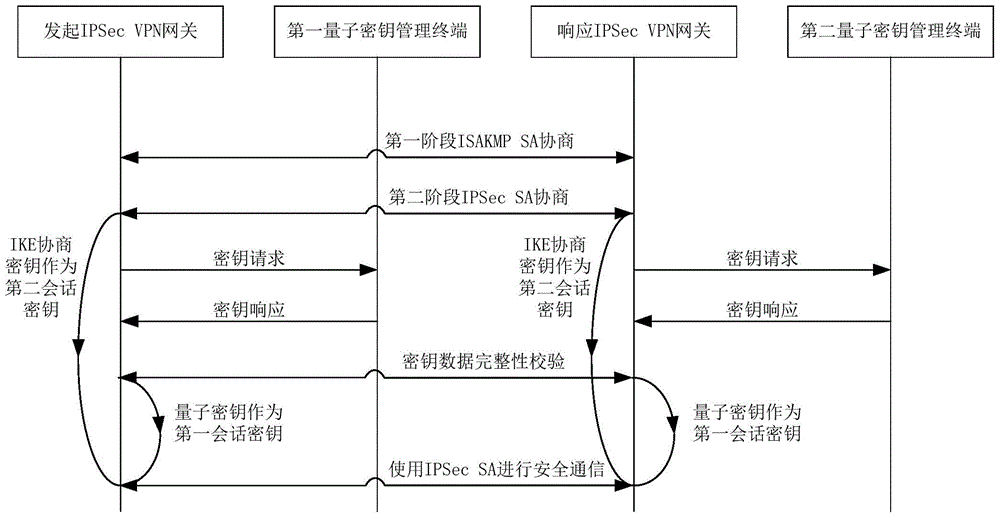
Method and system for extended use of quantum keys in IPSec VPN (internet protocol security-virtual private network)
ActiveCN104660603ANovel structureIncrease update frequencyKey distribution for secure communicationData switching networksSession keyKey management
The invention discloses a method and a system for extended use of quantum keys in an IPSec VPN (internet protocol security-virtual private network) system. The IPSec VPN system comprises at least two IPSec VPN gateways including an initiating IPSec VPN gateway and a responding IPSec VPN gateway as well as corresponding quantum key management terminals. The method comprises steps as follows: through parallel processing of negotiation of the quantum keys and IKE (internet key exchange) negotiated keys, the quantum keys are taken as first session keys for preferential use, and the IKE negotiated keys are taken as second session keys for safety communication. Besides, the invention further provides the corresponding IPSec VPN gateway, the quantum key management terminals and the IPSec VPN system. The quantum keys are taken as the session keys through extended use, so that the session key updating frequency is greatly increased and the safety communication performance of conventional IPSec VPN is guaranteed under the condition that an original IPSec VPN is compatible.
Owner:SHANDONG INST OF QUANTUM SCI & TECH +1
Encryption communication method and system for blockchain node
ActiveCN108768630AAvoid accessEnsure communication efficiencySpecial service provision for substationKey distribution for secure communicationCommunications securitySecure communication
The invention provides an encryption communication method and system for a blockchain node, wherein the method comprises the following steps: firstly, joining a participating node of a blockchain network, using a first signature private key of the participating node to sign a first user identifier and a first signature public key of the participating node, transmitting a first joining broadcast message to the blockchain network after stamping a timestamp via a timestamp server; analyzing the first joining broadcast message to obtain the first user identifier and the first signature public keyvia a mining node; carrying out validity verification on the participating node according to the first signature public key; generating a first encryption private key of the participating node via a supervising node according to a main key, a public parameter and a first user identifier stored via the local node; and carrying out safety communication based on the first user identifier and the first encryption private key via the participating node and the target node. Thus, the communication efficiency is improved on the basis of ensuring the communication safety of the blockchain network.
Owner:全链通有限公司
Key distribution and authentication methods, devices and systems
ActiveCN107317789AReduce the burden onSolve the problem that it cannot be applied to smart devices that do not support USIM cardsKey distribution for secure communicationSecurity arrangementSecure communicationWeb authentication
Owner:HUAWEI TECH CO LTD
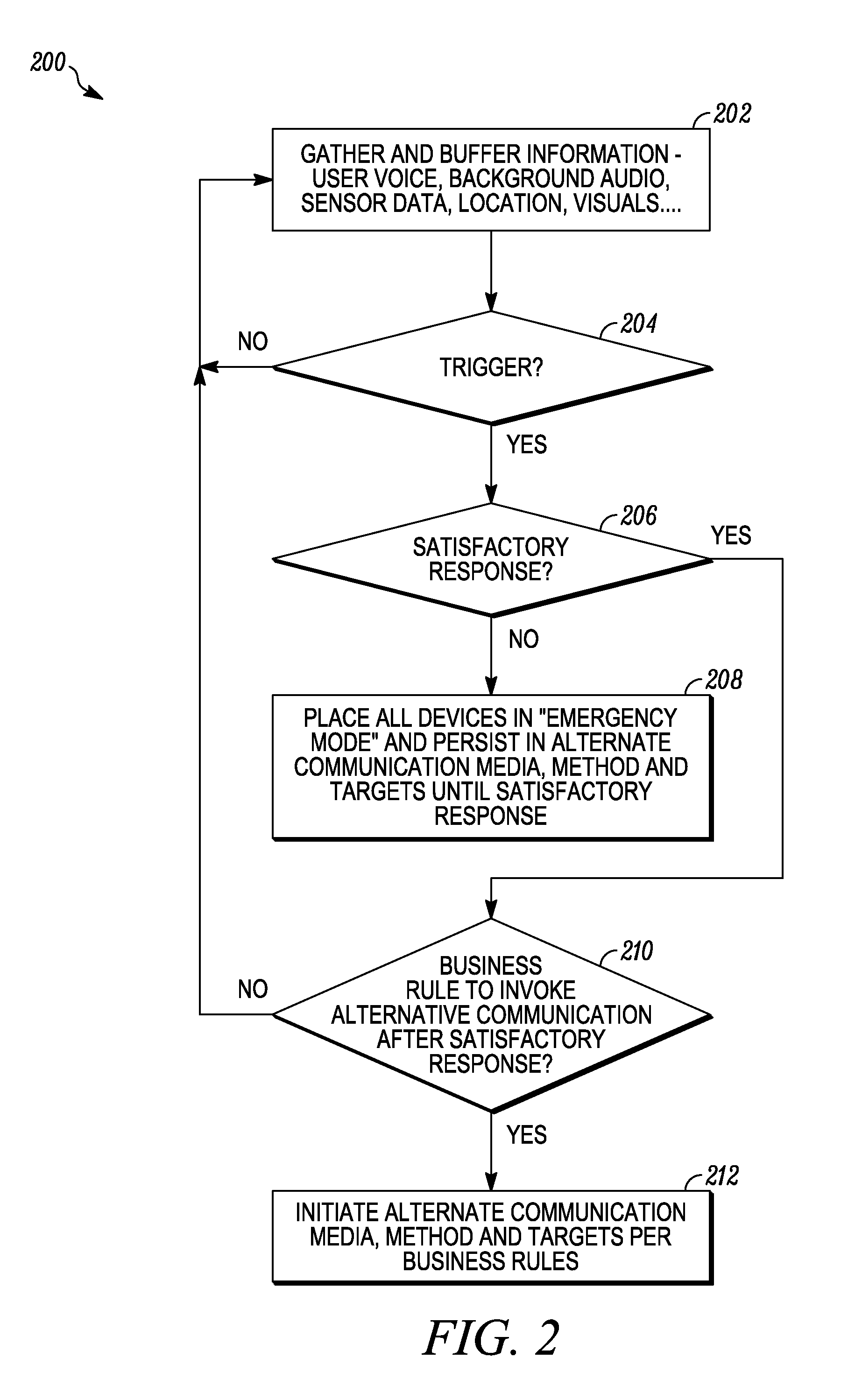
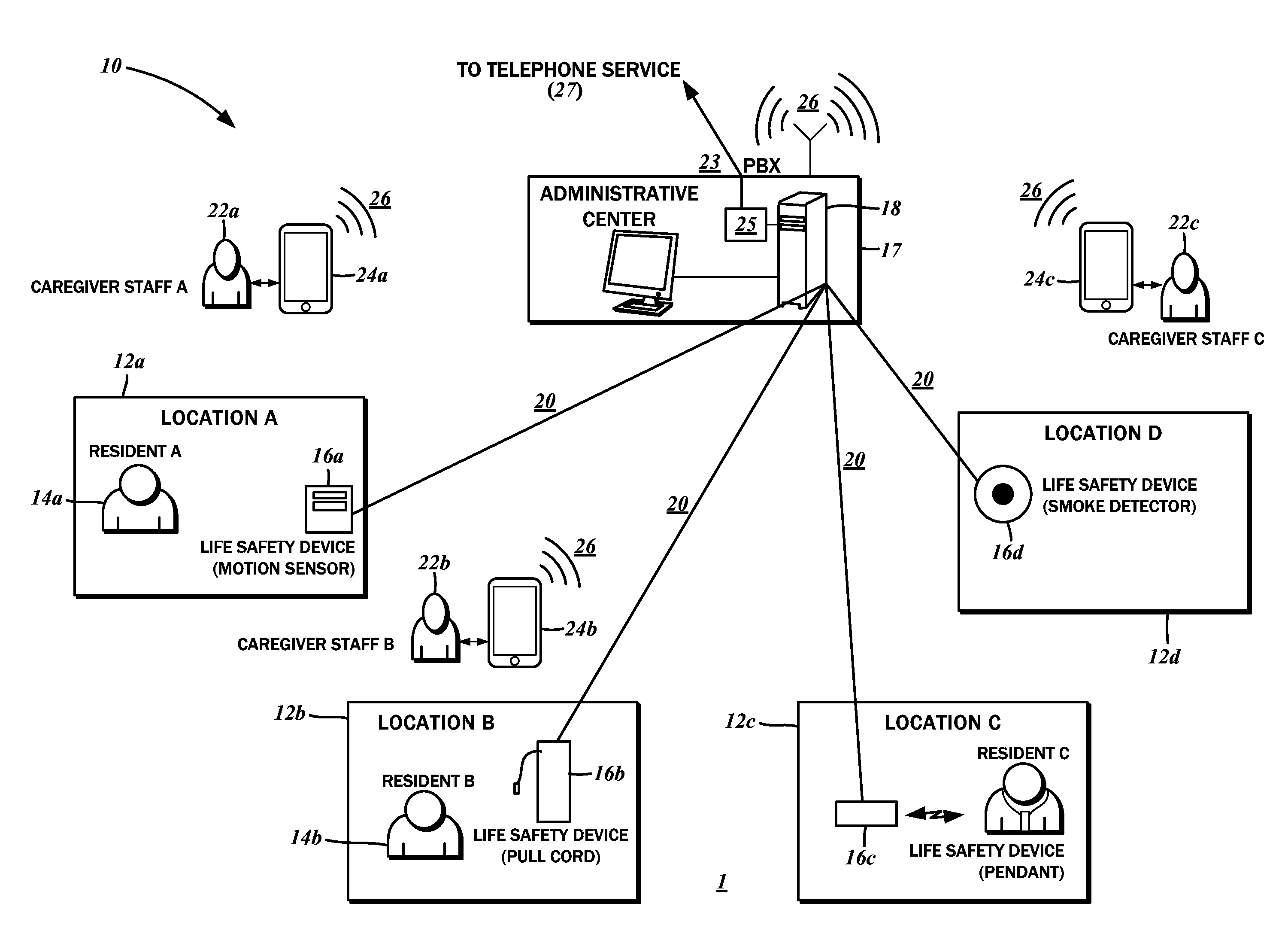
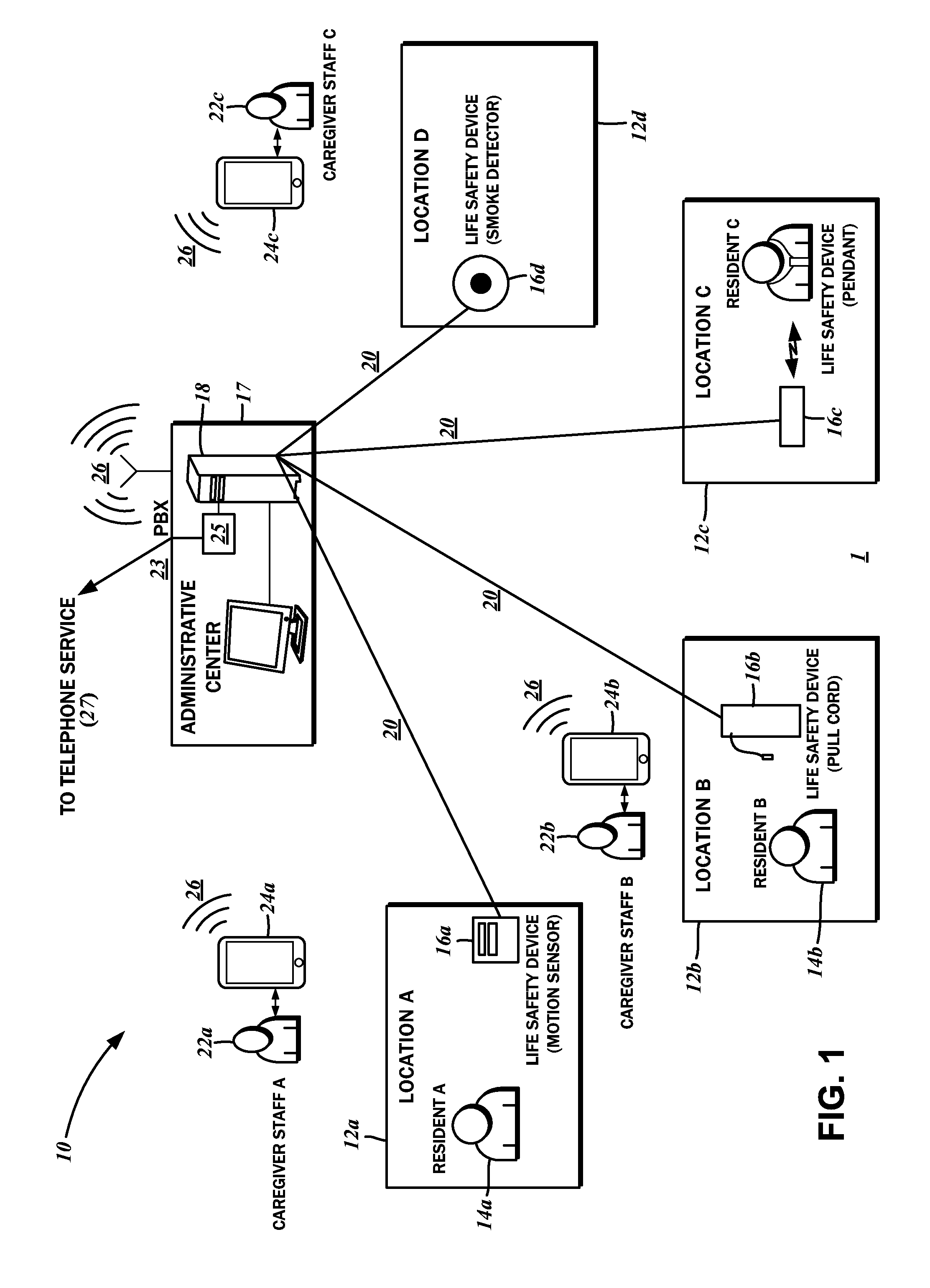
Interactive wireless life safety communications system
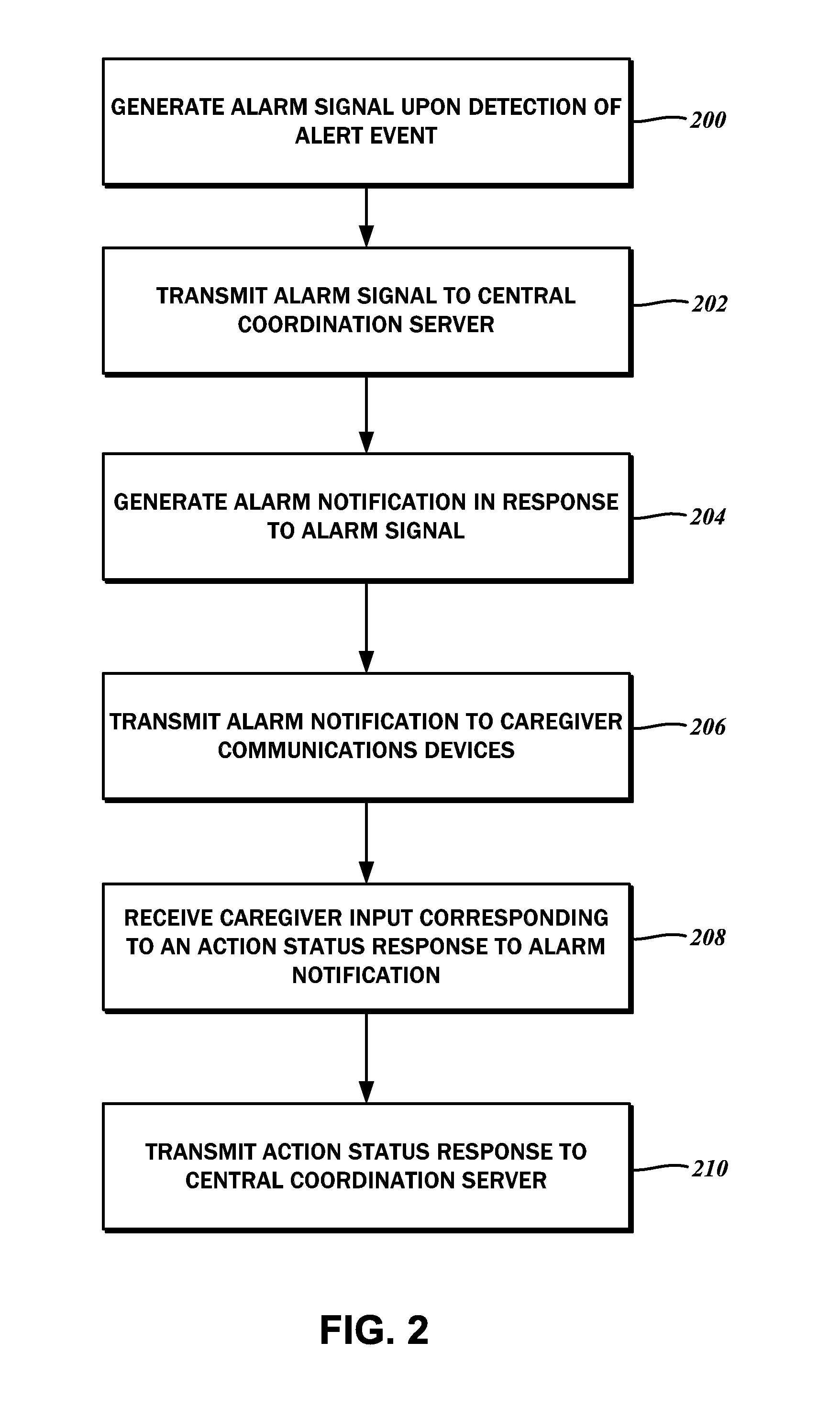
InactiveUS20140070939A1Improve efficiencyExtension of timeAlarmsElectric signalling detailsCommunications systemUser input
An interactive wireless life safety communications system is disclosed. A central coordination server is linked to a first network, over which there is a connection to at least one resident life safety device at a specific location or for specific resident. An alarm signal is generated by the resident life safety device upon detection of an alarm condition and transmitted to the central coordination server. A caregiver communications device is connected to the central coordination server over a second network, and is receptive to an alarm notification that is generated by the central coordination server in response to the alarm signal. The caregiver communications device is also receptive to a caregiver user input, from which an action status response is generated for transmission to the central coordination server.
Owner:RICMIC LLC
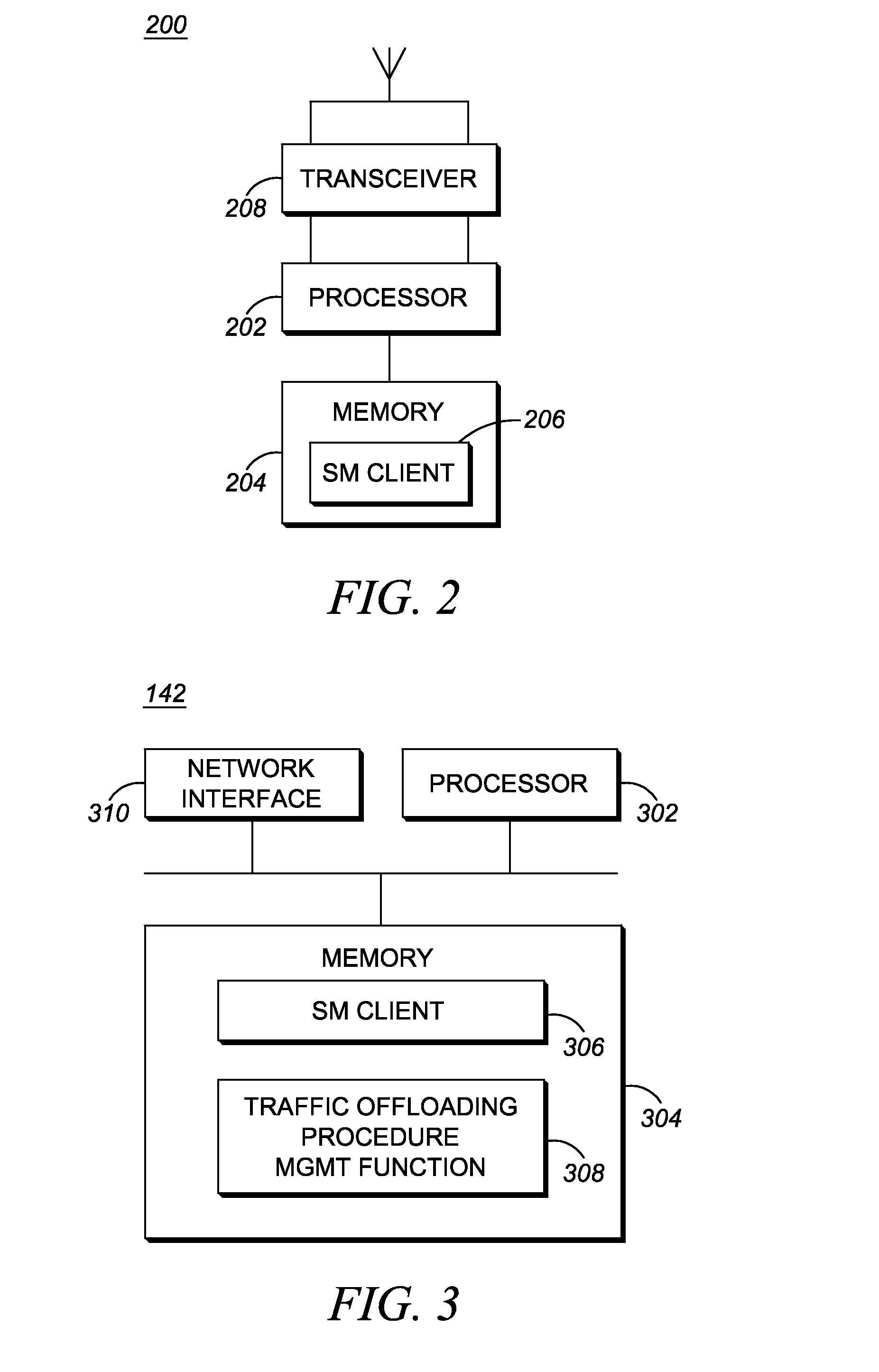
Method and apparatus for traffic offloading procedure management in a public safety communication system
ActiveUS20140370895A1Network traffic/resource managementConnection managementTraffic capacitySafety Communications
A system provides for traffic offloading in a Public Safety communication system. The system includes multiple user equipment (UEs), each a member of a same communications group, and a services network element configured to receive information comprising an identifier of the communications group, an identifier of each UE of the multiple UEs, and an identifier of a cell of a primary network where each UE resides; store, in association with each UE identifier, the communications group identifier and the primary network cell identifier; determine that a primary network cell is congested; responsive to determining that the cell is congested, determine a subset of the multiple UEs that are members of the communications group, reside in the congested cell, and are capable of being served by one or more secondary networks; and instruct the subset of UEs to offload their communications group traffic to the one or more secondary networks.
Owner:MOTOROLA SOLUTIONS INC
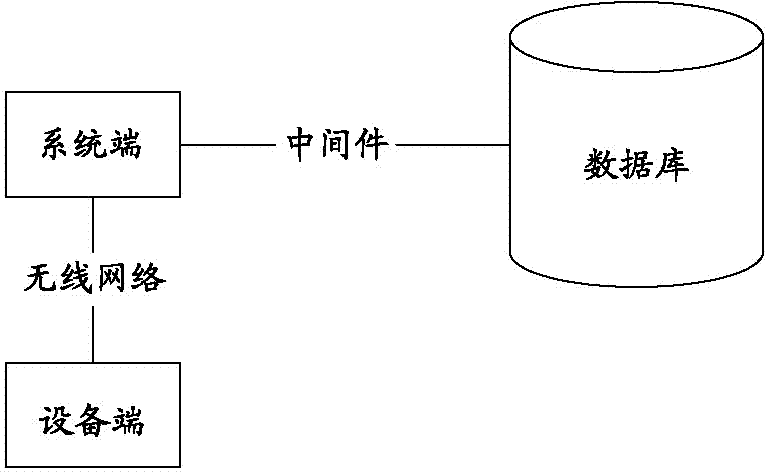
Method for safely transmitting data based on wireless network
ActiveCN102421096ATo achieve the purpose of safe transmissionEnsure secure communicationSecurity arrangementSecure communicationSecure transmission
The invention discloses a method for safely transmitting data based on a wireless network. A pair of key factors and a group of key sets are respectively arranged at a system end and an equipment end; during communication of the system end and the equipment end, a sender calculates a check sum of the data to be sent, calculates an authentication identifier (ID) by using the key factors and an equipment identifier, randomly selects a key from the key sets to encrypt the data to be sent, and sends the encrypted data and an adopted key code; and after receiving the data, the receiver acquires the corresponding key from the key sets through the key code, decrypts the data, calculates the authentication ID by using the equipment identifier and the key factors, judges whether the authentication ID accords with the authentication ID which is sent, and judges whether the check sum is accurate if the authentication ID accords with the authentication ID which is sent, so that the data can be safely transmitted. The method has the advantages that: the equipment identifier is fully utilized; functions of dynamic identity identification, data check and transmission encryption are integrated; safety communication of the data can be guaranteed; and presetting of an unrepeatable master key in each piece of equipment is not required.
Owner:XIAMEN YAXON NETWORKS CO LTD
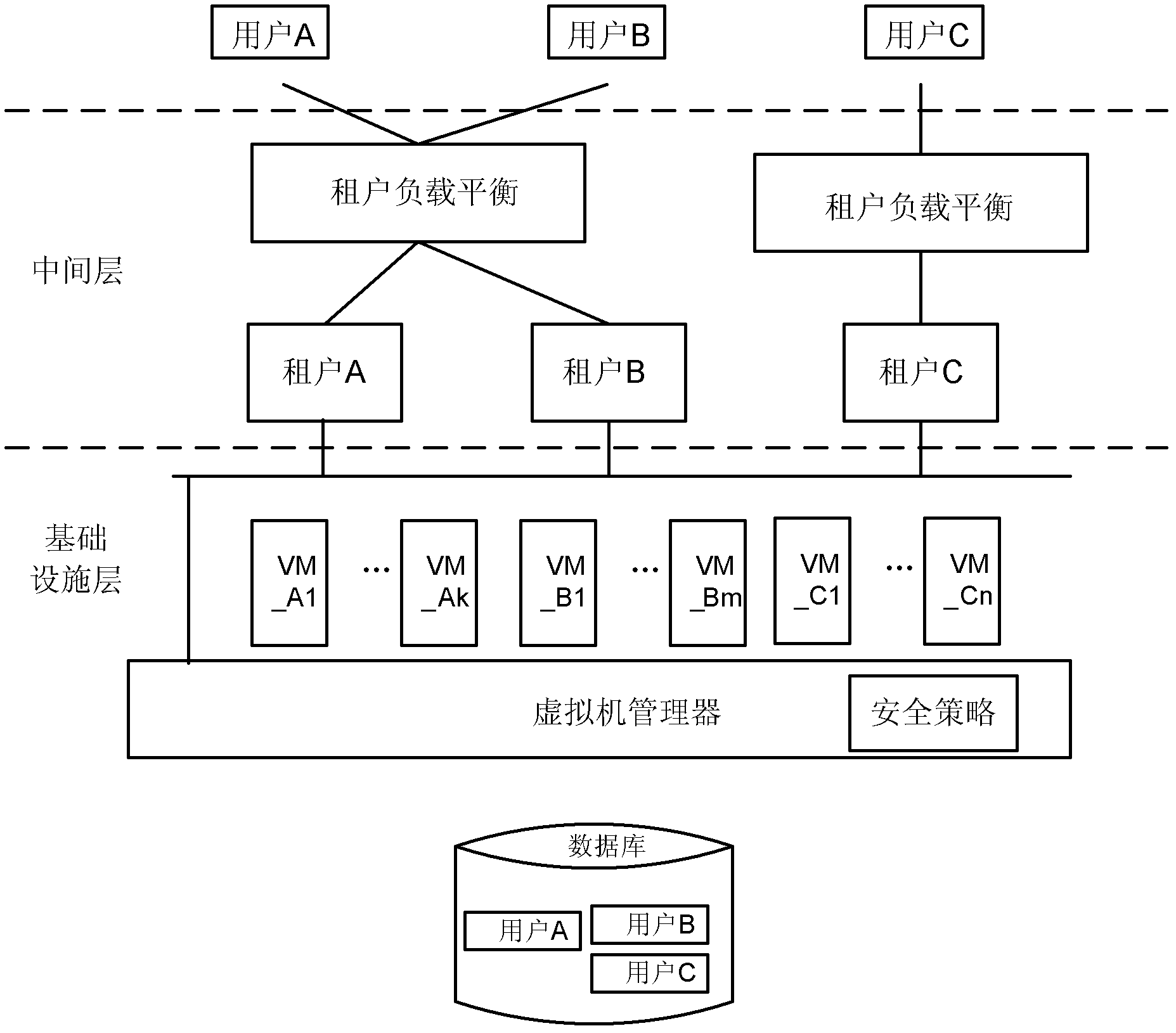
Safety communication among virtual machines in cloud computing framework
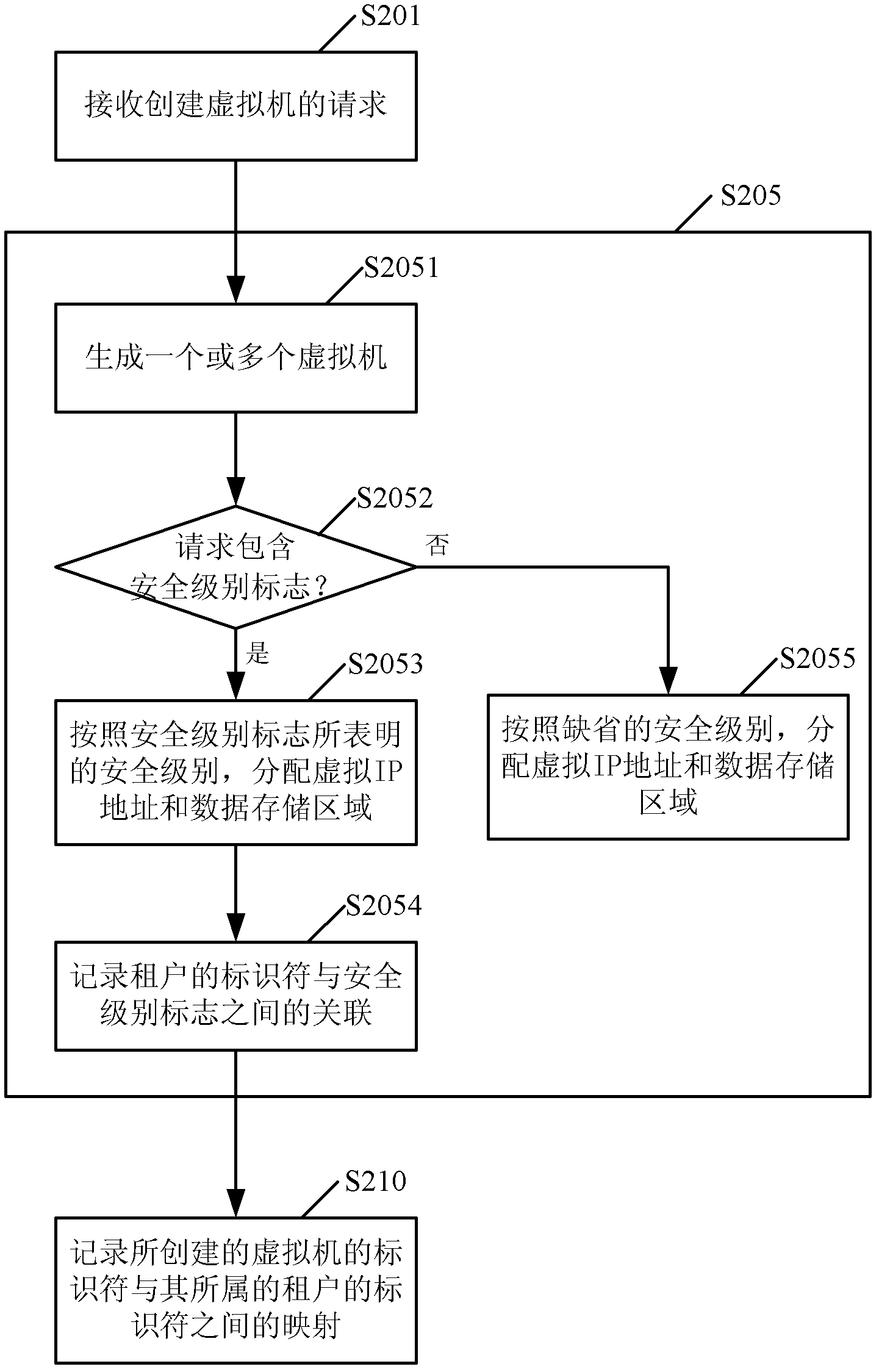
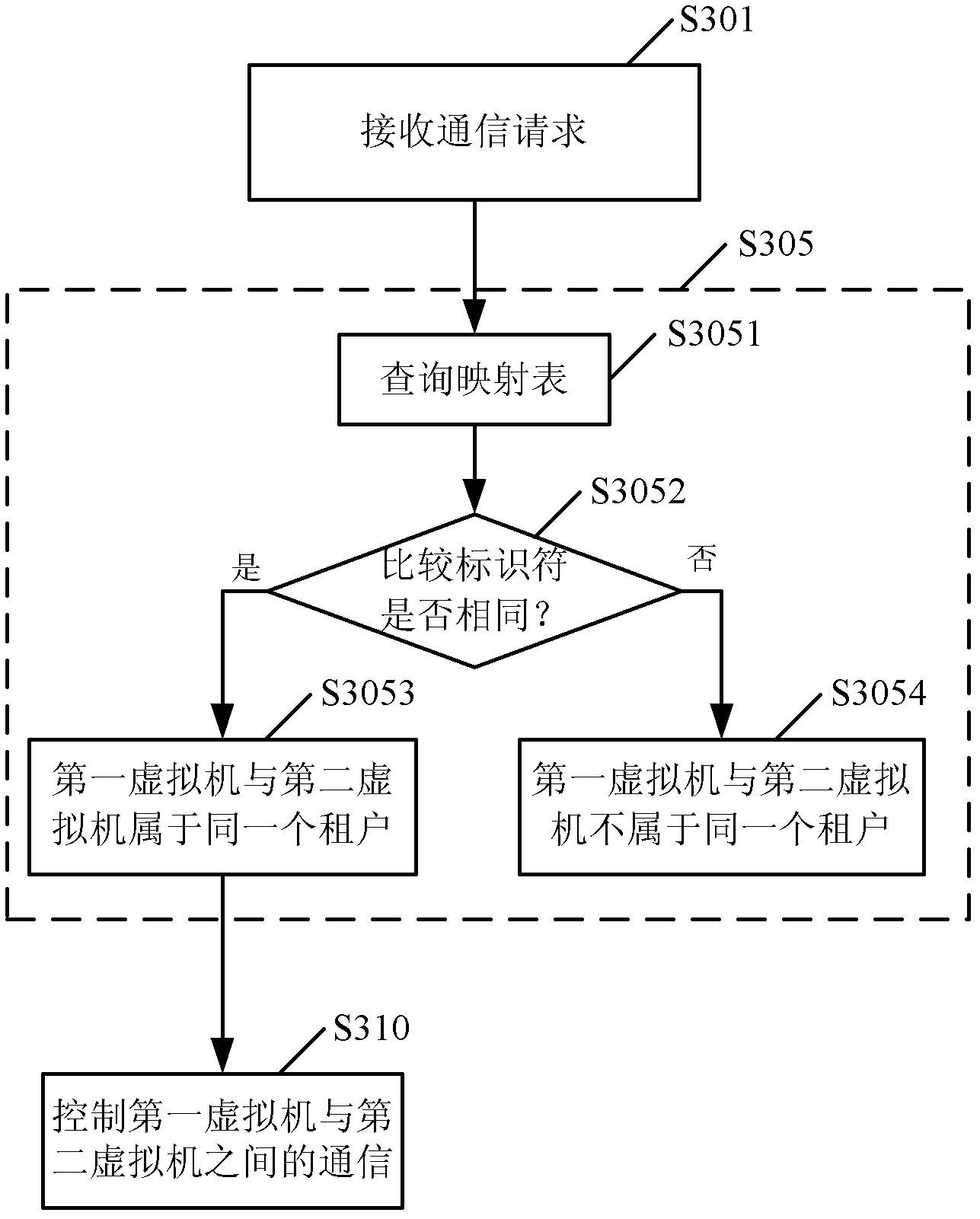
Provided is a method used for building a virtual machine of a user in a cloud computing framework. The method used for building the virtual machine of the user in the cloud computing framework comprises receiving a request for building the virtual machine from a tenant built by the user, responding to the request, and building the virtual machine of the user; and recording mapping between an identifier of the built virtual machine and a identifier of the tenant of the virtual machine in a mapping table. Due to the facts that the virtual machine is built, and the mapping between the identifier of the virtual machine and the identifier of the tenant of the virtual machine is recorded at the same time, relevance between the virtual machine and the tenant can be built, and safe communication among virtual machines can be provided. In addition, the invention further provides a corresponding device, and a method and a device used for controlling the safety communication among the virtual machines in the cloud computing framework.
Owner:ALCATEL LUCENT SHANGHAI BELL CO LTD
Remote industrial network monitoring method and system based on S-Link and VLAN (Virtual Local Area Network) technique
ActiveCN102096405AAchieve securityImprove integrityTransmissionProgramme total factory controlFrequency changerPlaintext
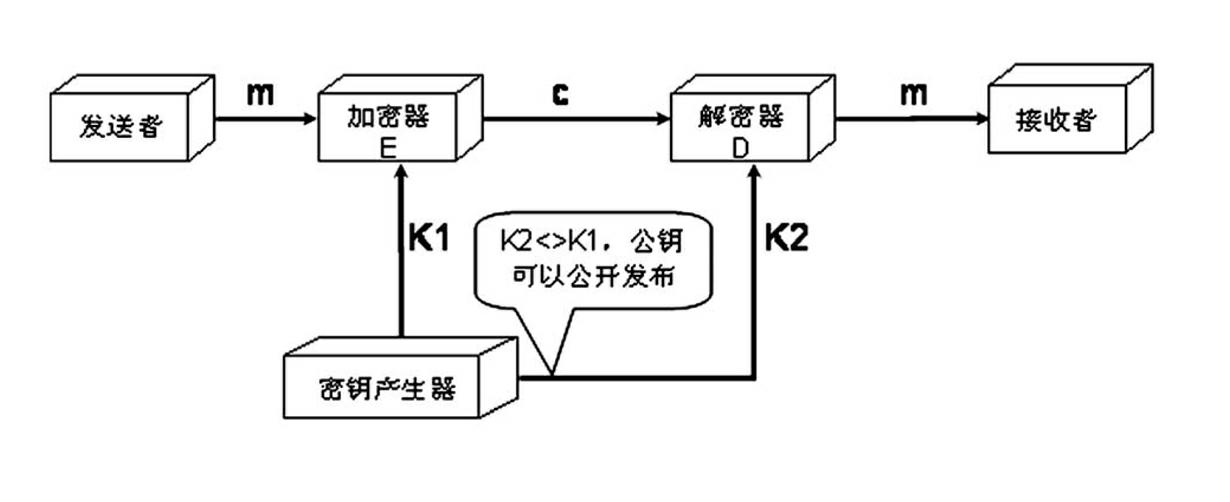
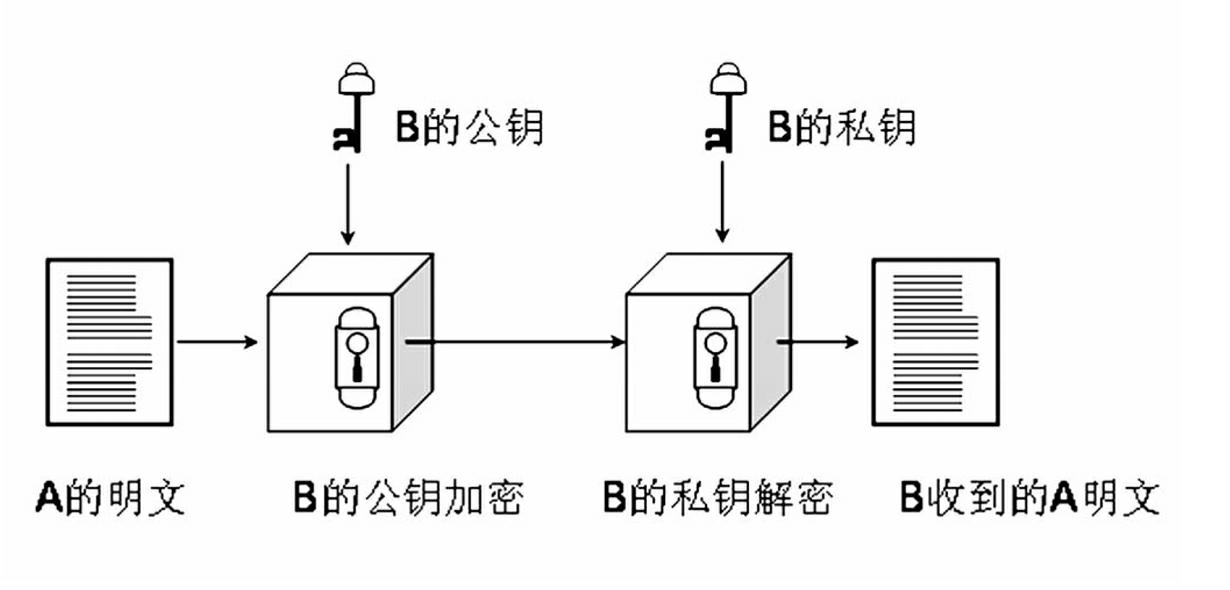
The invention relates to a remote industrial network monitoring method and system based on an S-Link and VLAN (Virtual Local Area Network) technique. An S-Link protocol and a VLAN are comprised in the method, wherein if A wants to send a plaintext to B through a double-key encrypting technique, and B has a pair of public key and private key, an encrypting and decrypting process is carried out as follows: B sends the public key to A; A uses the public key of B for encrypting information of A and then sends the encrypted information to B; B uses the private key to decrypte the information of A;conversely, if B wants to send the plaintext to A, the process is carried out as follows: A receives the plaintext of B; the private key of A is used for decryption; the public key of A is used for encryption; and B receives the plaintext of A. The system comprises a management computer, a server, a remote safety communication module, a 3G communication module, a PLC (Programmable Logic Controller) main station, a PLC auxiliary station, a camera, a frequency changer, a multifunctional panel HMI (Human Machine Interface) and an Internet.
Owner:SHENZHEN FUTURELOOKS AUTOMATION SYST
Method for realizing end-to-end communication among user equipment (UE), and UE
ActiveCN104066200AAchieve optimizationReduce overheadConnection managementSecurity arrangementSafety CommunicationsUser equipment
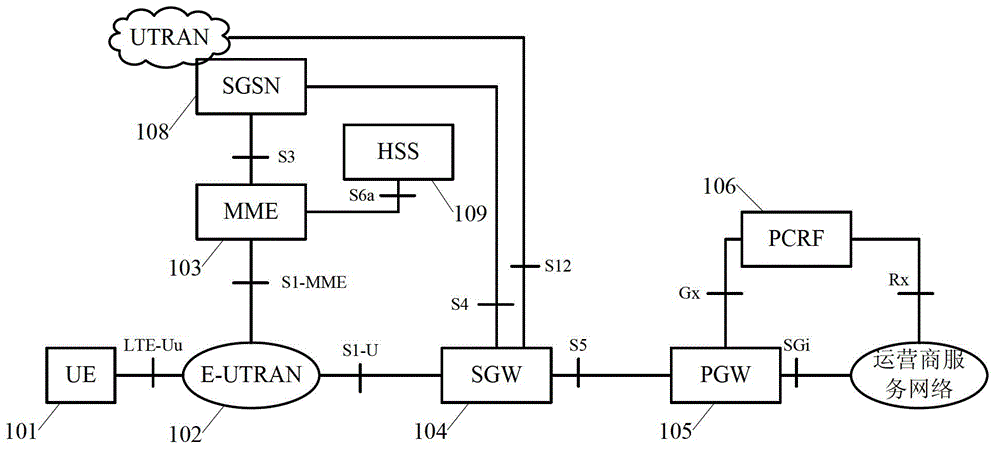
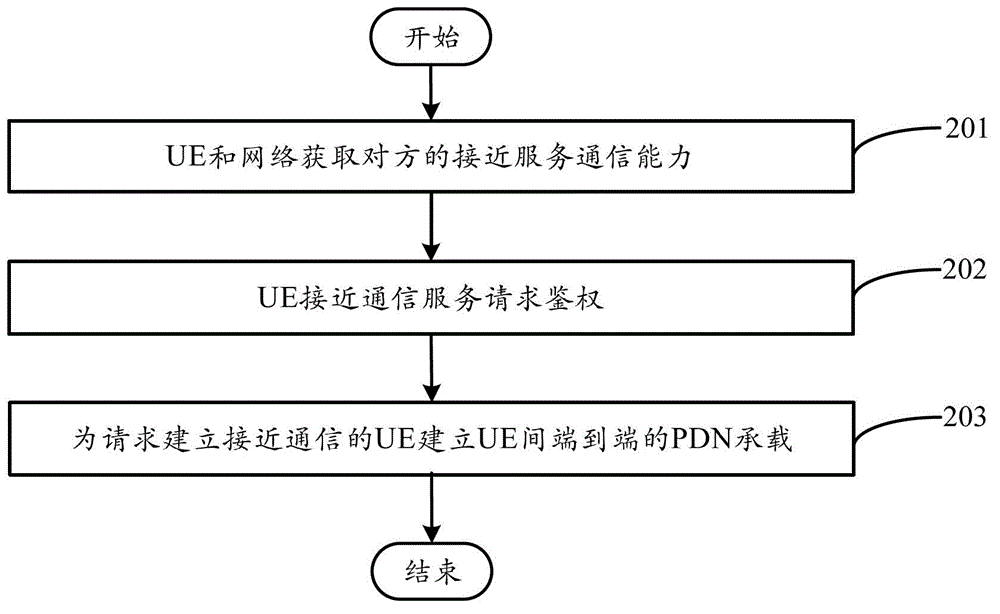
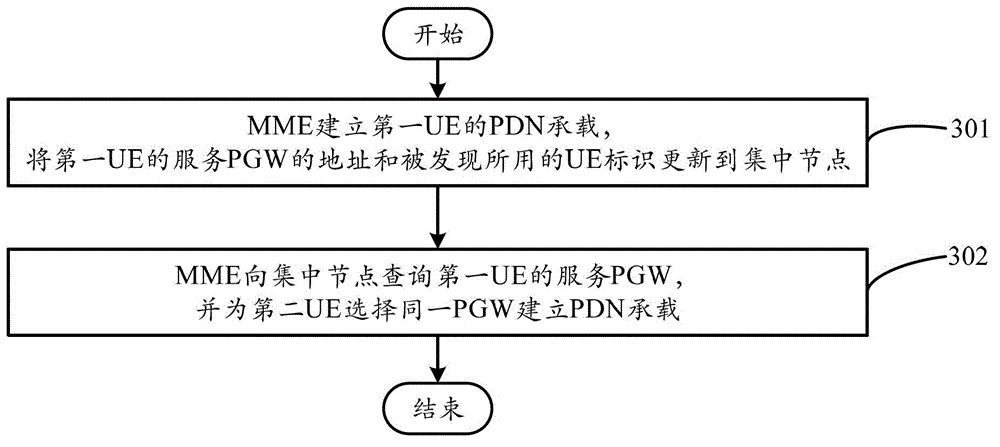
The present application provides a method for implementing a device to device (D2D) communication between UEs, wherein a UE and a network obtain each other's capability of Proximity Service (ProSe); the UE may activate the capability of ProSe that both the UE and the network support and initiates a request for a ProSe service with another UE to the network; the network authenticates the request for the ProSe service according to subscription information for the UE's device to device communication; and the network establishes a device to device PDN bearer between the two UEs for the request for the ProSe service passing the authentication. The present application further provides a user equipment. The present application is the basis for implementing the ProSe, the application thereof can satisfy service demands of public safety communication and realize network resource optimization configuration.
Owner:BEIJING SAMSUNG TELECOM R&D CENT +1
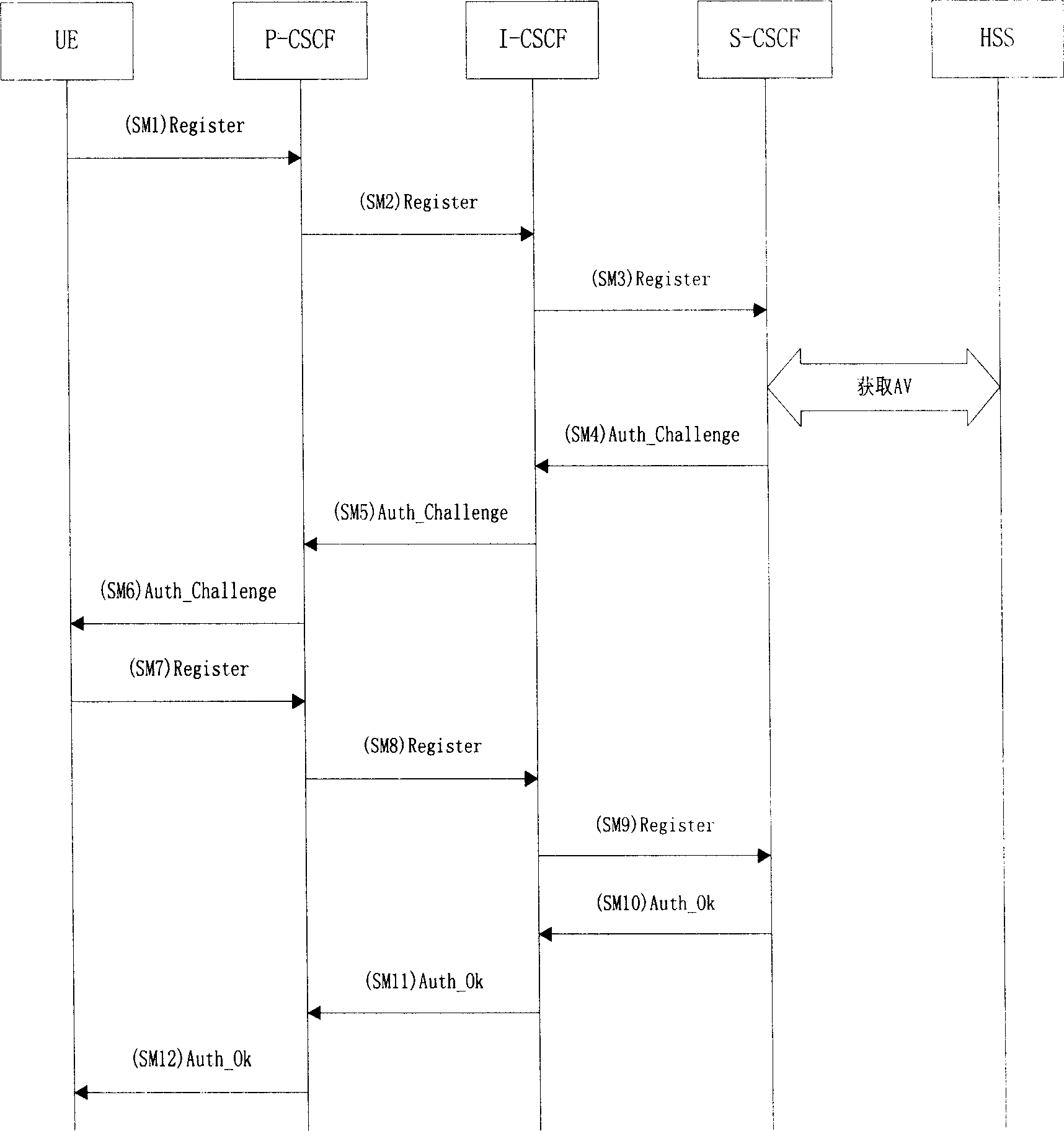
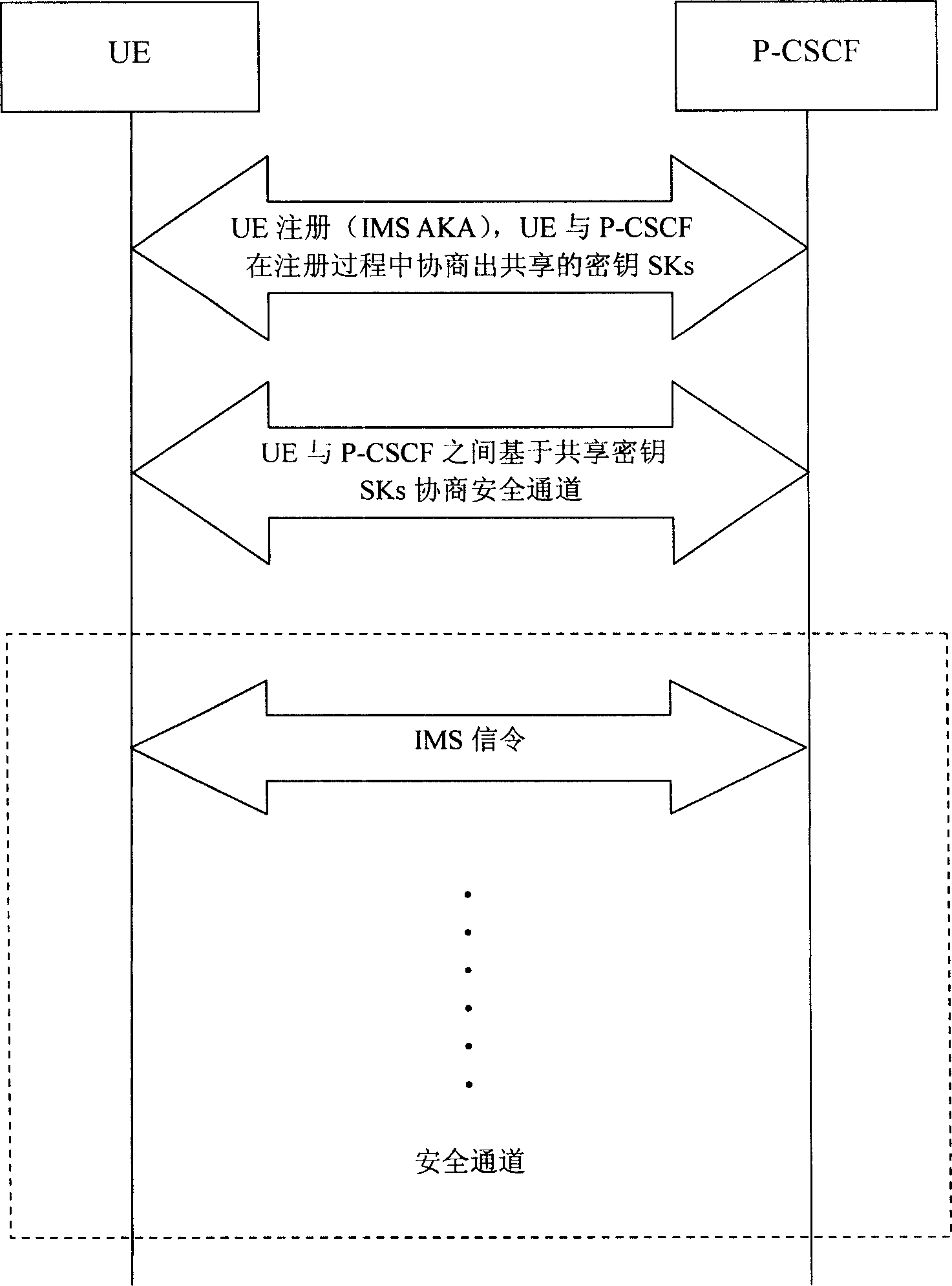
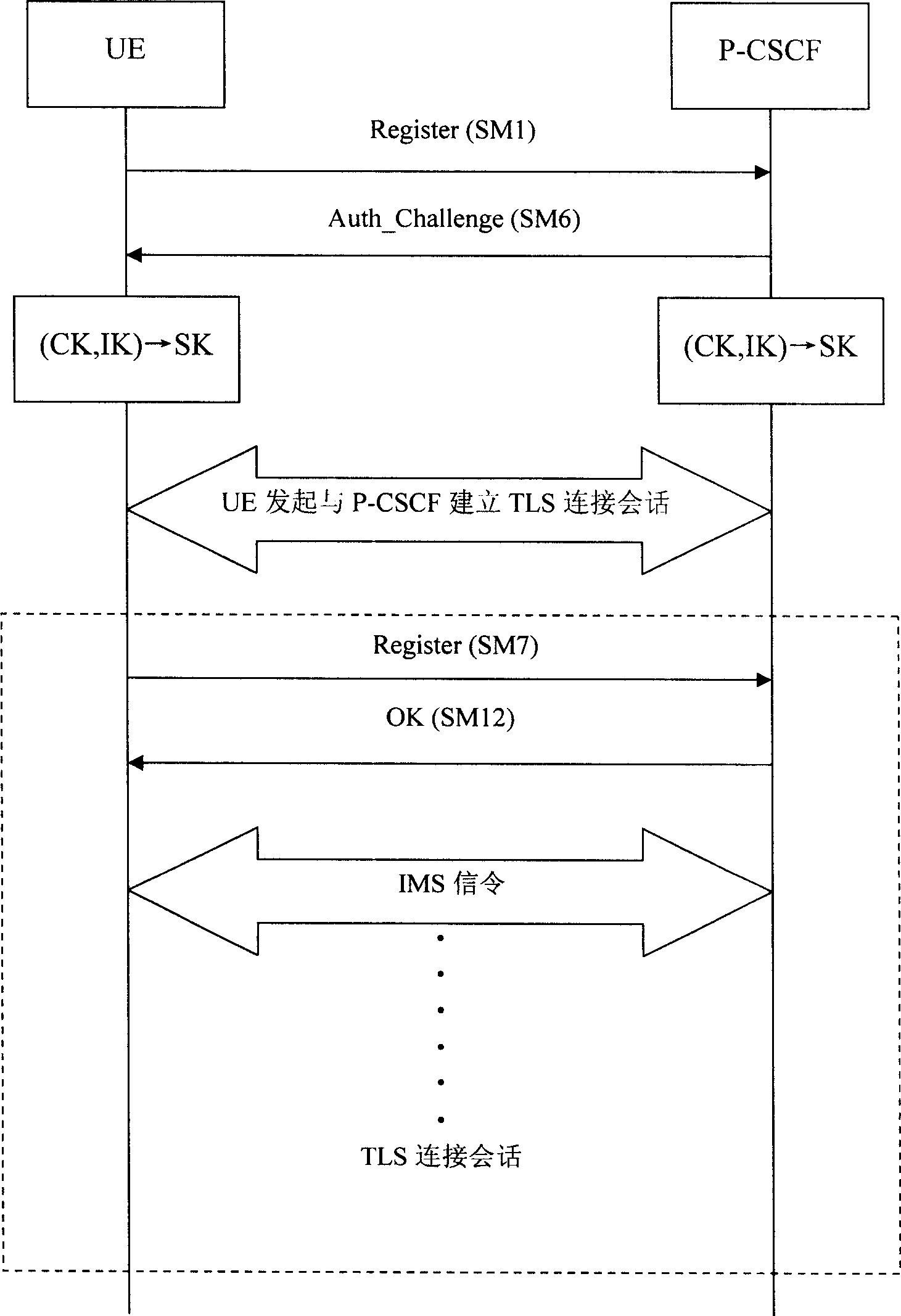
A protection method for access security of IP multimedia subsystem
ActiveCN1722689AEnsure access securityGuaranteed PenetrationSynchronising transmission/receiving encryption devicesData switching by path configurationMan-in-the-middle attackSafety Communications
This invention discloses a method for protecting the switch-in safety of the IP multimedia subsystem, characterized in that the UE and P-CSCF will negotiate a sharing code when the UE registering, setting up a safety communication channel based on the sharing code, making the IMS message transmitting between UE and P-CSCF safety, and the protected IMS message will penetrate the NAT transparently. The method combines the UE' registering process, safety channel negotiating process and the data coding process together, making sure the two-way identification between UE and P-CSCF; besides, the method also prevent the attacker attacking the go-between.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com