Patents
Literature
54 results about "Moving target defense" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
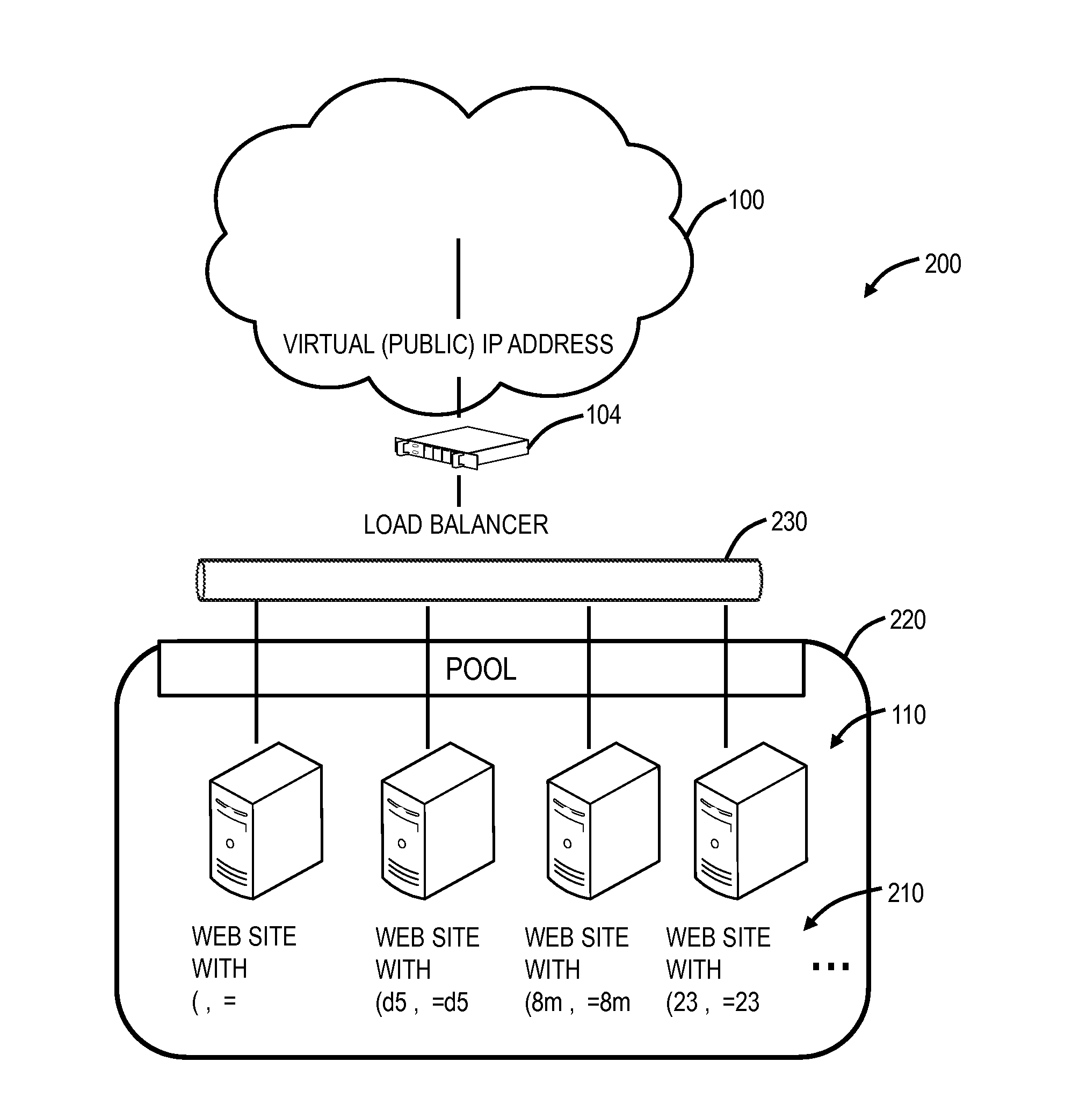
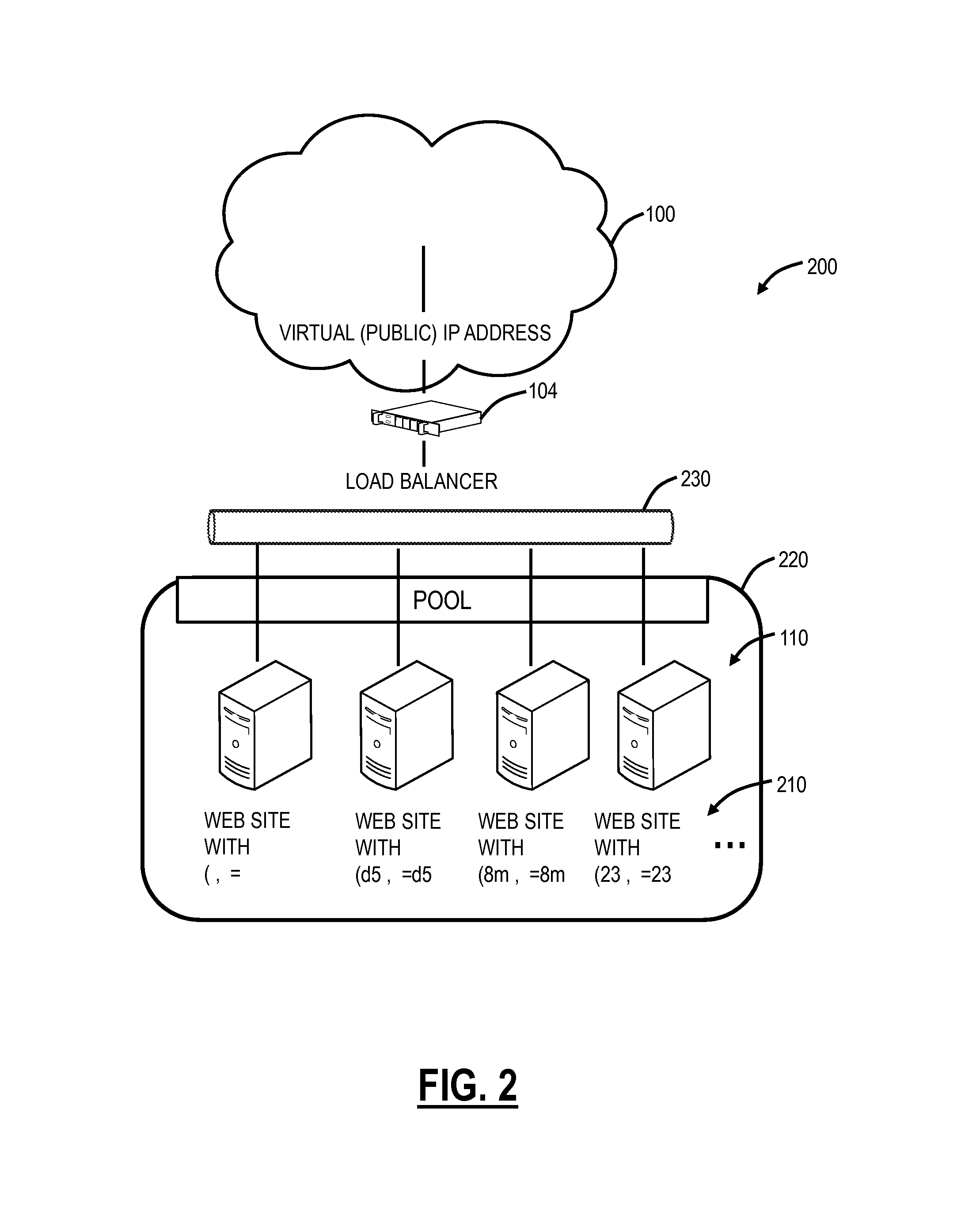
Moving target defense system and moving target defense method for SDN (self-defending network)
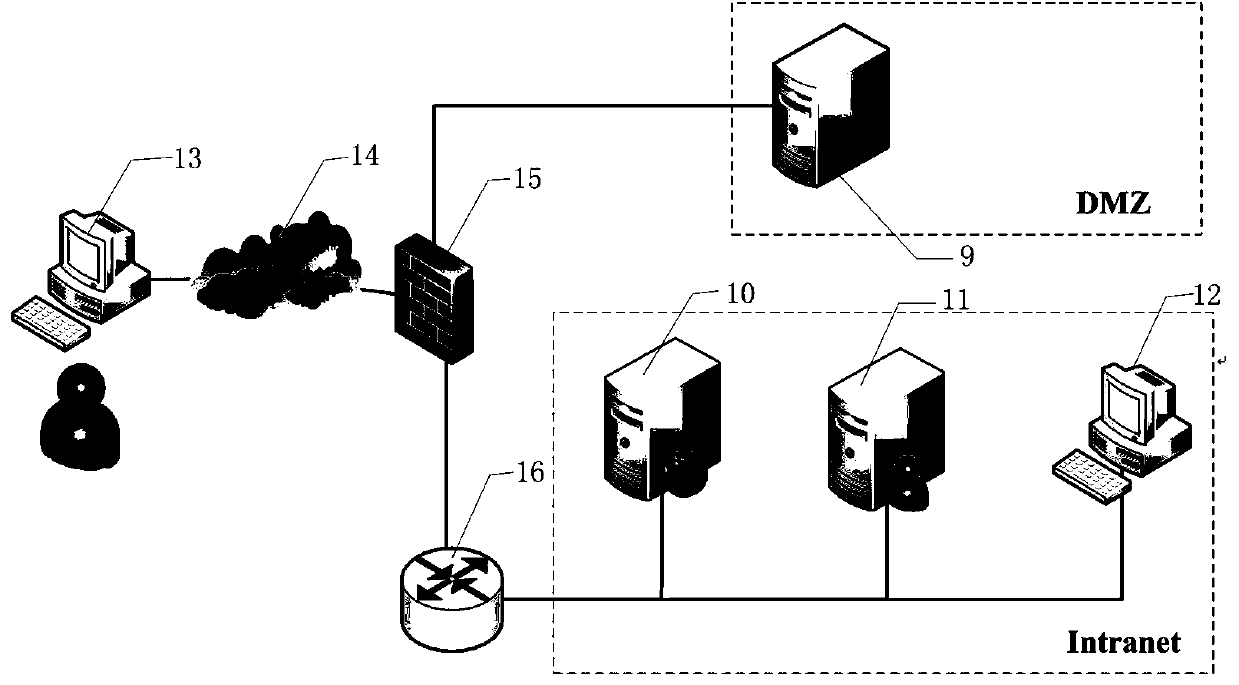
InactiveCN104506511AProtection securityIncrease the difficultyTransmissionTraffic flow analysisSafety Communications
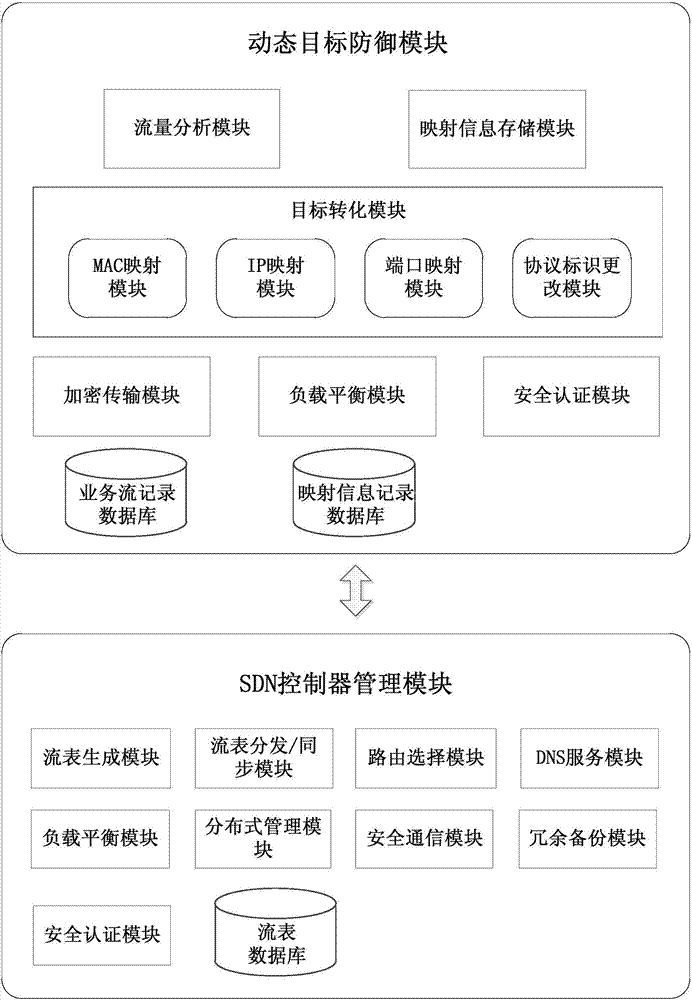
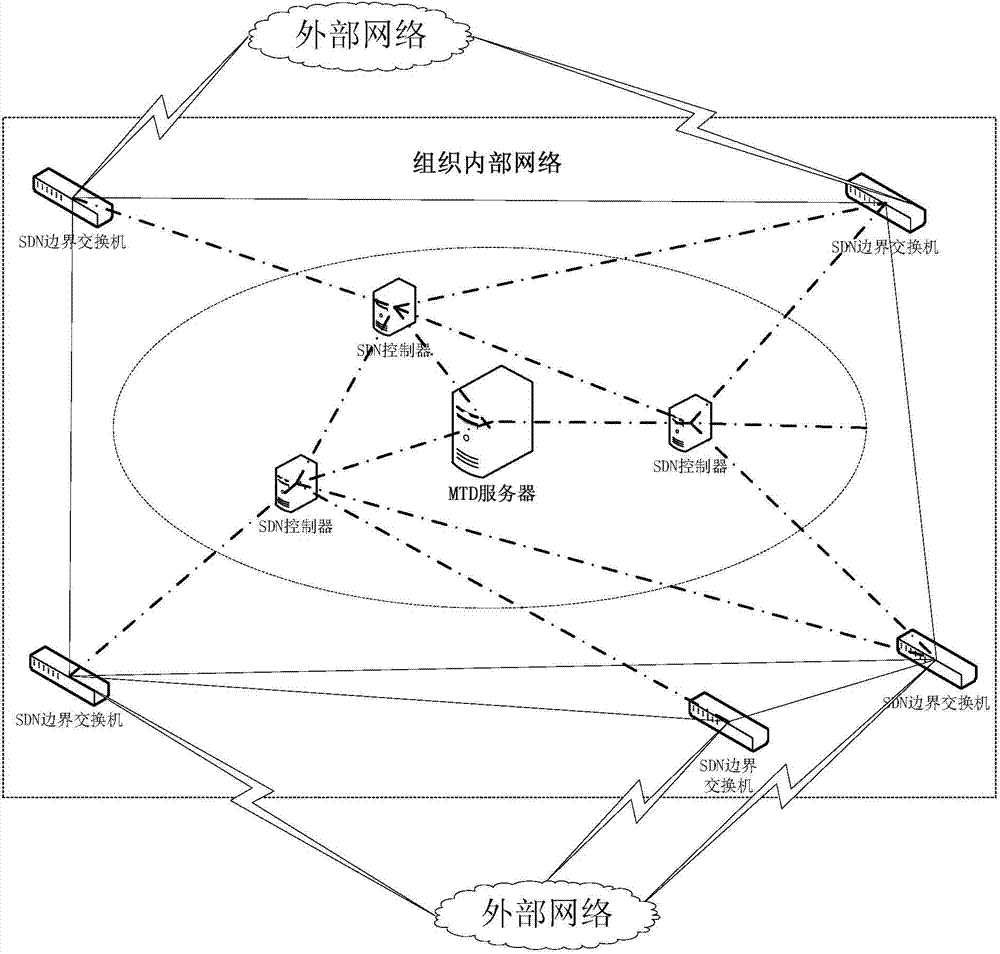
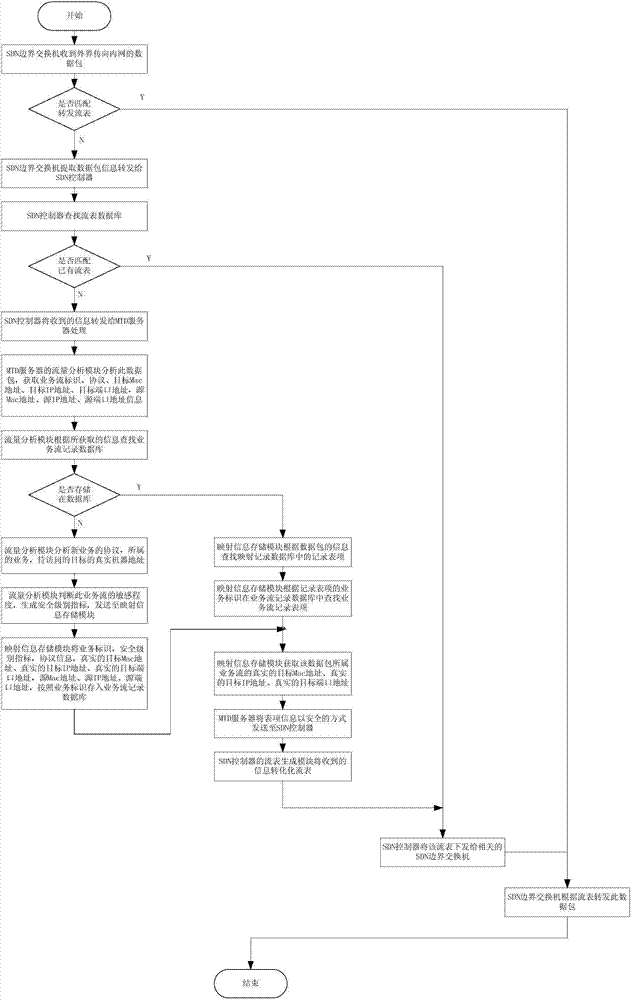
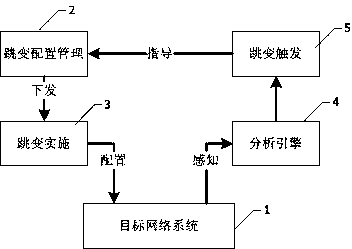
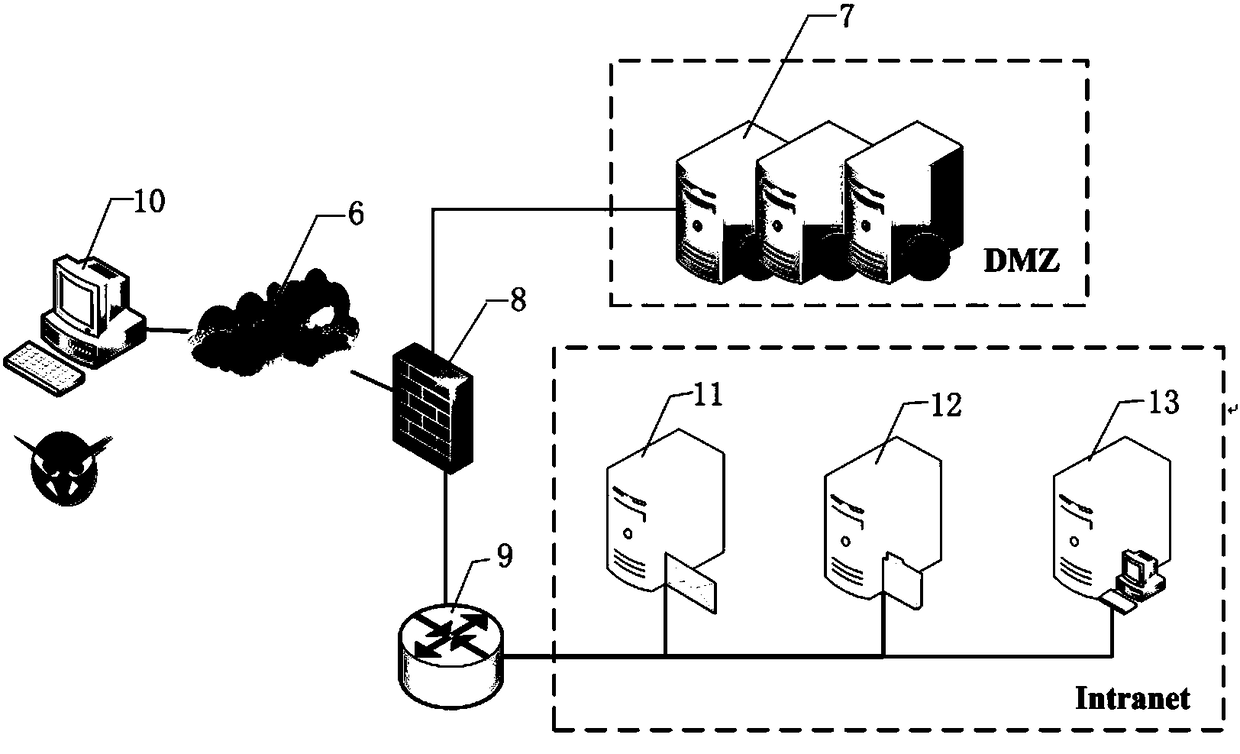
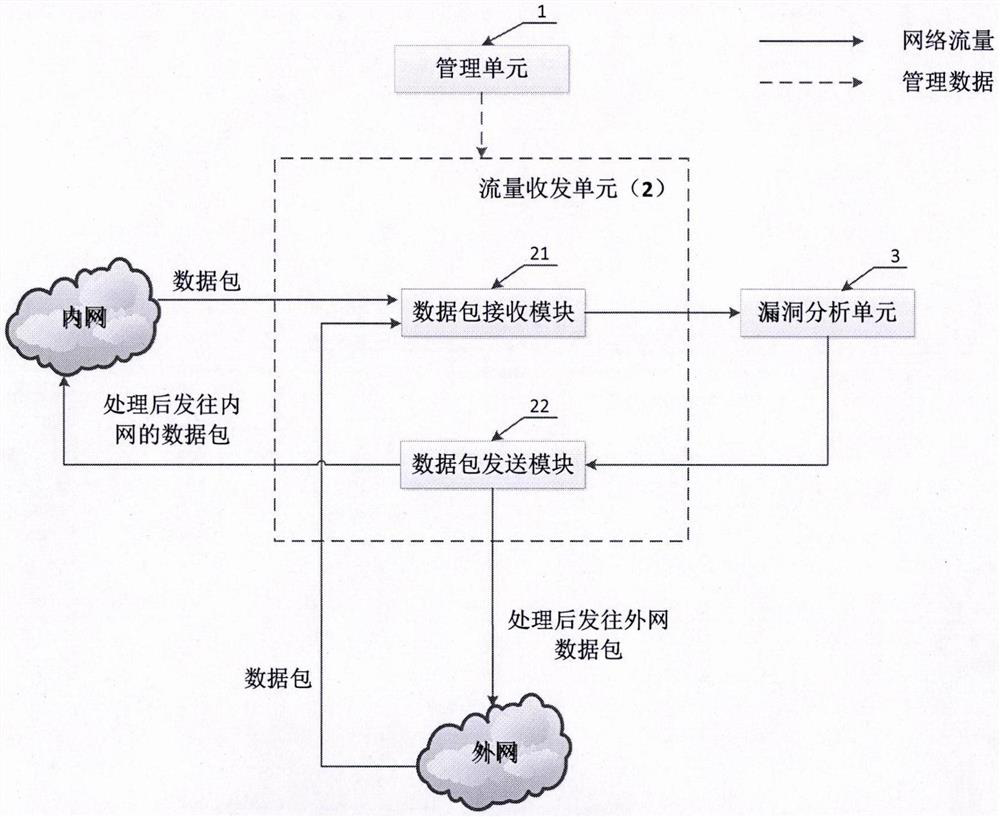
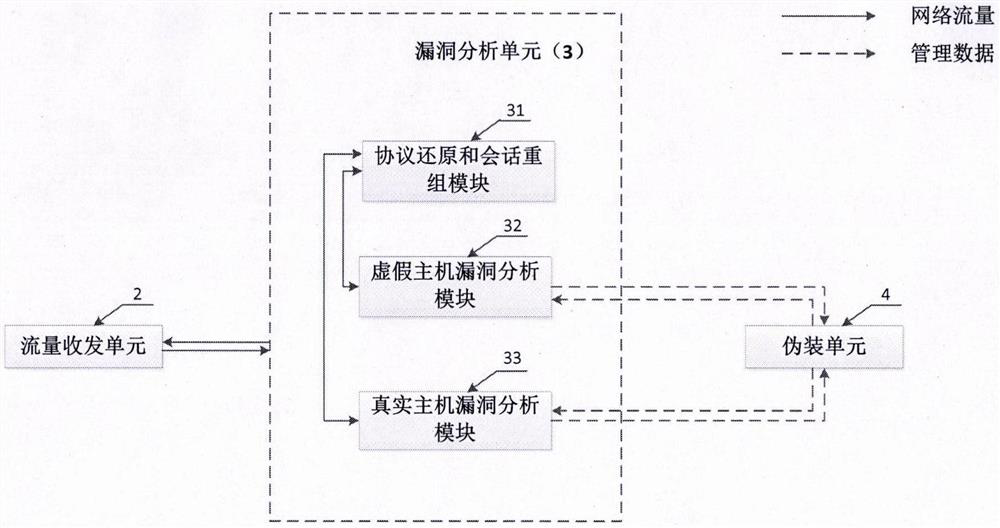
The invention discloses a moving target defense system for an SDN (self-defending network). The system consists of a moving target defense module and an SDN controller management module; the moving target defense module comprises a flow analysis module, a mapping information storage module, a target conversion module, an encryption transmission module, a load balance module, a safety authentication module, a business flow recording database and a mapping information recording database; the SDN controller management module comprises a flow table generation module, a flow table distribution / synchronization module, a route selection module, a DNS service module, a load balance module, a distributed management module, a safety communication module, a redundant backup module, a safety authentication module and a flow table database; furthermore, the invention also discloses a moving target defense method for the SDN. Through the moving target defense system and the moving target defense method disclosed by the invention, the difficulty of an attacker to detect a target is increased further, and therefore the safety of an intranet is comprehensively protected.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
A two-layer defense method against spurious data injection attack in power system
ActiveCN108989330ADefense against injection attacksTransmissionInformation technology support systemEstimation methodsElectric power system
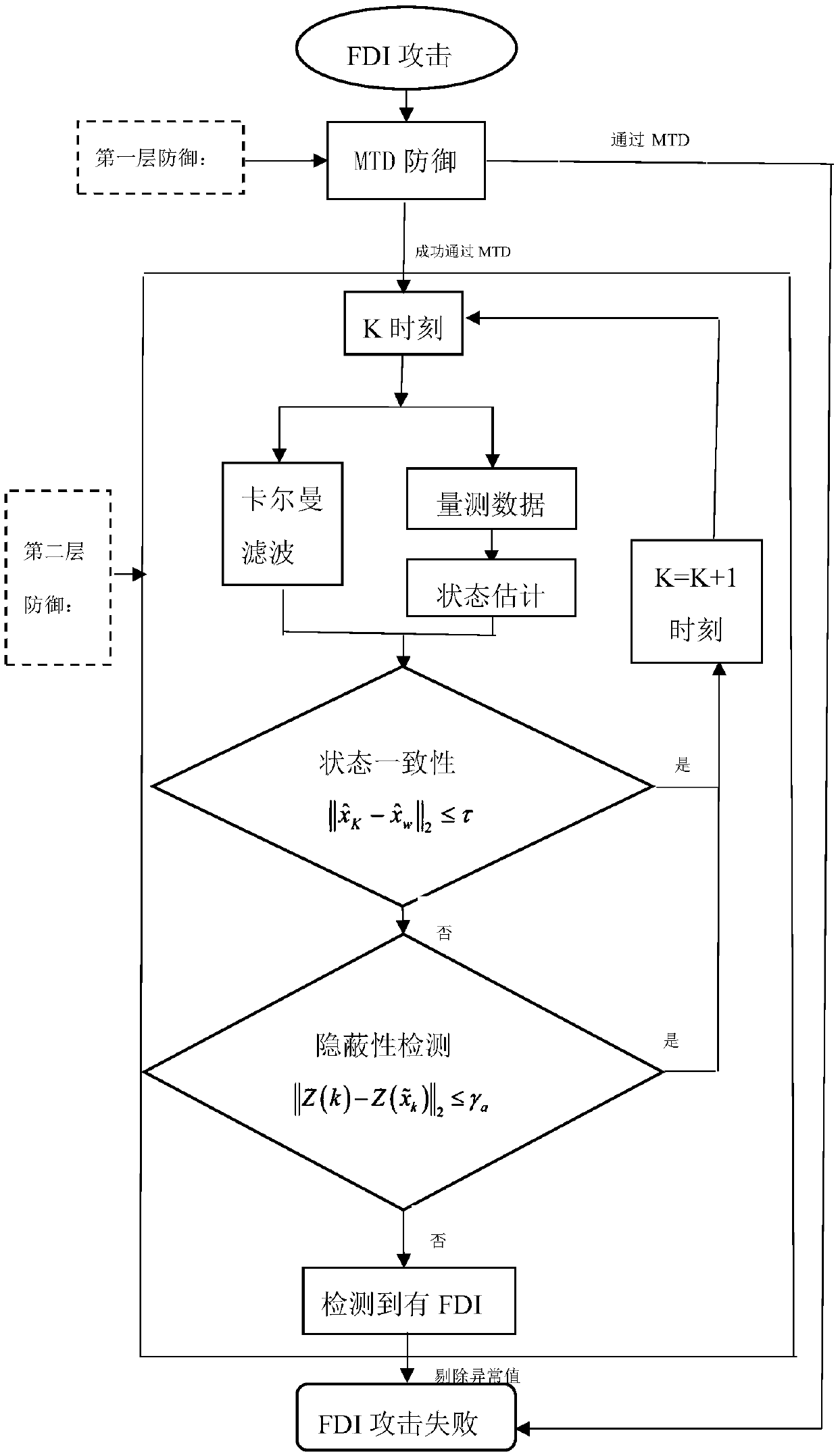
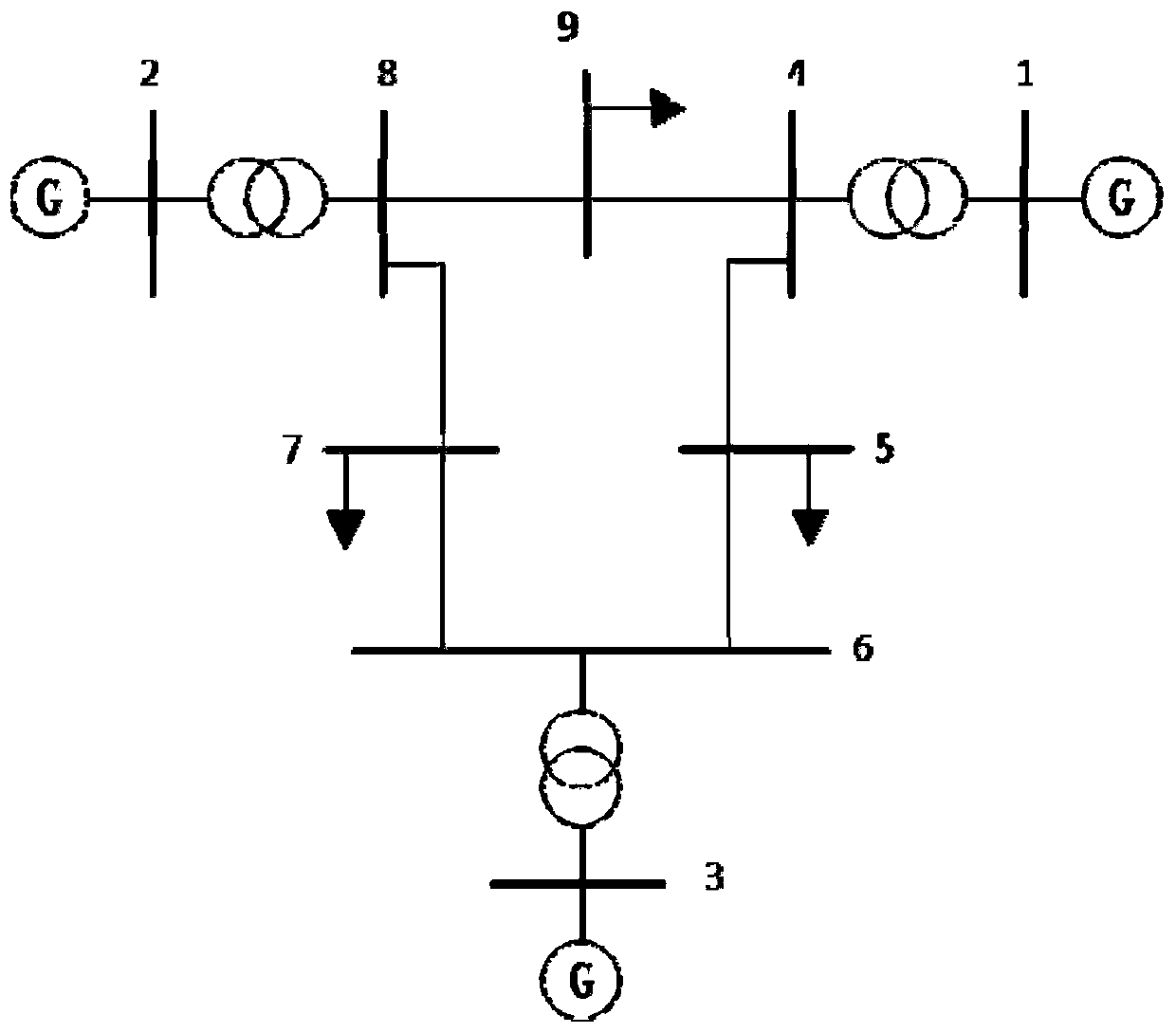
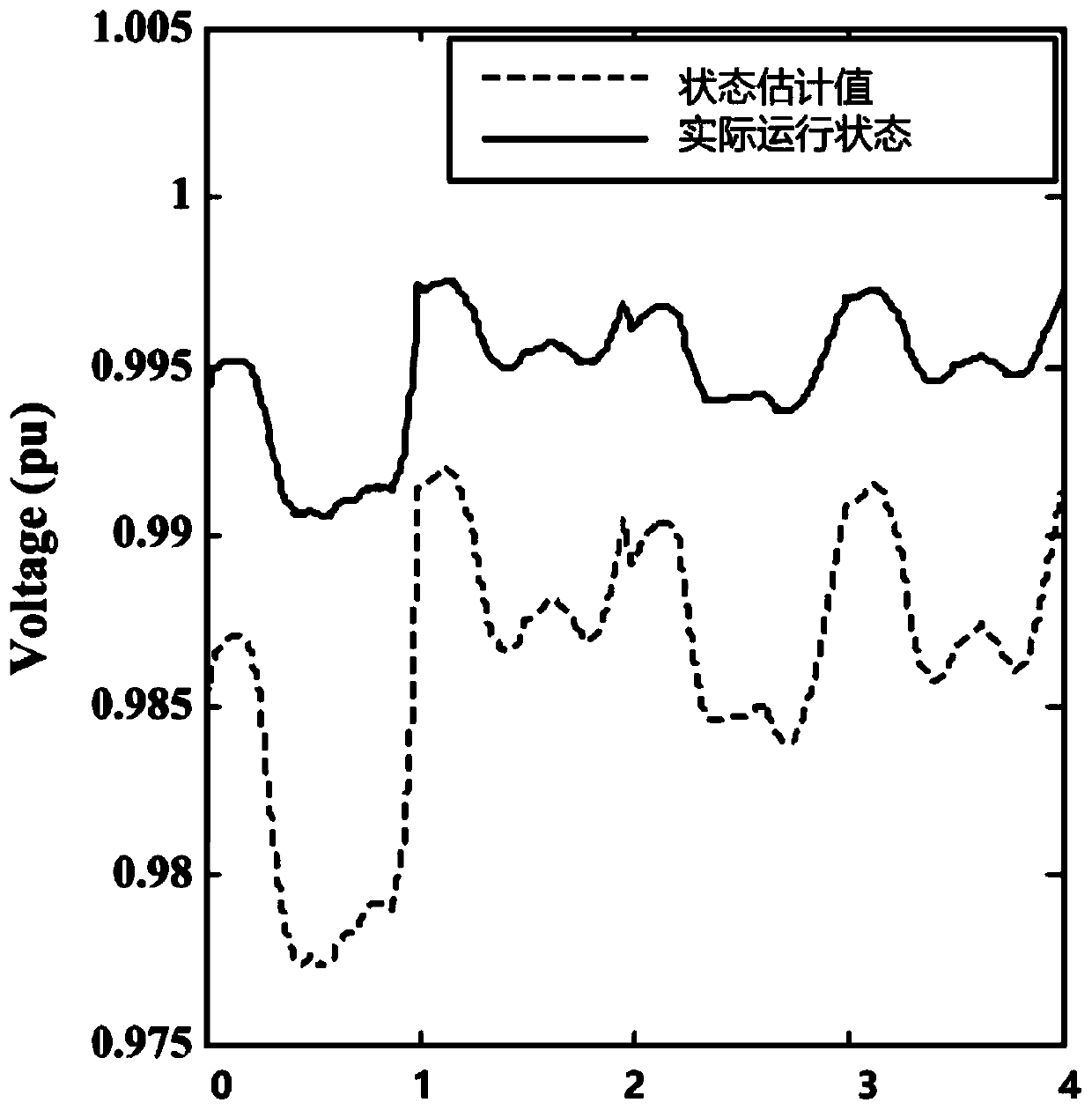
The invention discloses a two-layer defense method for false data injection attack in a power system, comprising a two-layer defense strategy. The first layer adopts moving target defense to defend the false data injection attack from the source, and the second layer adopts Kalman filter state estimation method to eliminate the false data injection attack after moving target defense. The inventionadopts a double-layer defense strategy, which makes up for the deficiency of using only the moving target defense, so as to maintain the normal operation of the electric power system.
Owner:GUANGDONG UNIV OF TECH
Moving target defense against cross-site scripting
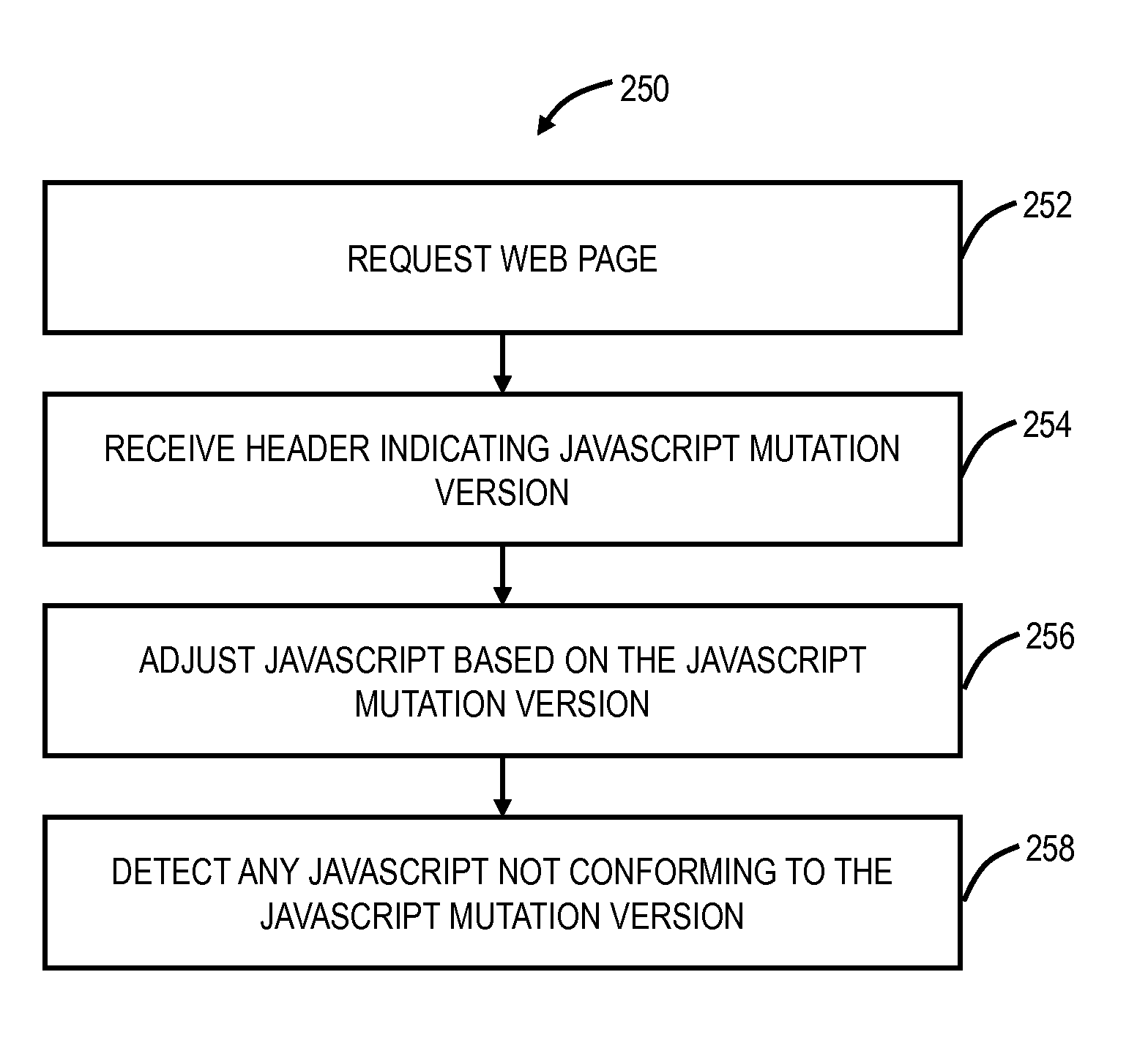
ActiveUS20150222657A1Avoid running timeMemory loss protectionError detection/correctionClient-sideWeb page
A method, in a server, implementing a moving target defense against cross-site scripting includes receiving a request for a web page, wherein the server has N versions of the web page each with a mutated version of JavaScript; selecting a web page of the N versions; and sending an indication of the mutated version of JavaScript associated with the web page in response to the request. Another method, in a client device, using a moving target defense against cross-site scripting includes requesting a web page; receiving an indication of a mutated version of JavaScript for the web page; and adjusting a JavaScript interpreter based on the mutated version of JavaScript for the web page.
Owner:THE UNIV OF NORTH CAROLINA AT CHAPEL HILL
Moving target defense against cross-site scripting
ActiveUS20150096006A1Avoid running timeDigital data processing detailsComputer security arrangementsWeb pageJavaScript
A method, in a server, implementing a moving target defense against cross-site scripting includes receiving a request for a web page, wherein the server has N versions of the web page each with a mutated version of JavaScript; selecting a web page of the N versions; and sending an indication of the mutated version of JavaScript associated with the web page in response to the request. Another method, in a client device, using a moving target defense against cross-site scripting includes requesting a web page; receiving an indication of a mutated version of JavaScript for the web page; and adjusting a JavaScript interpreter based on the mutated version of JavaScript for the web page.
Owner:THE UNIV OF NORTH CAROLINA AT CHAPEL HILL
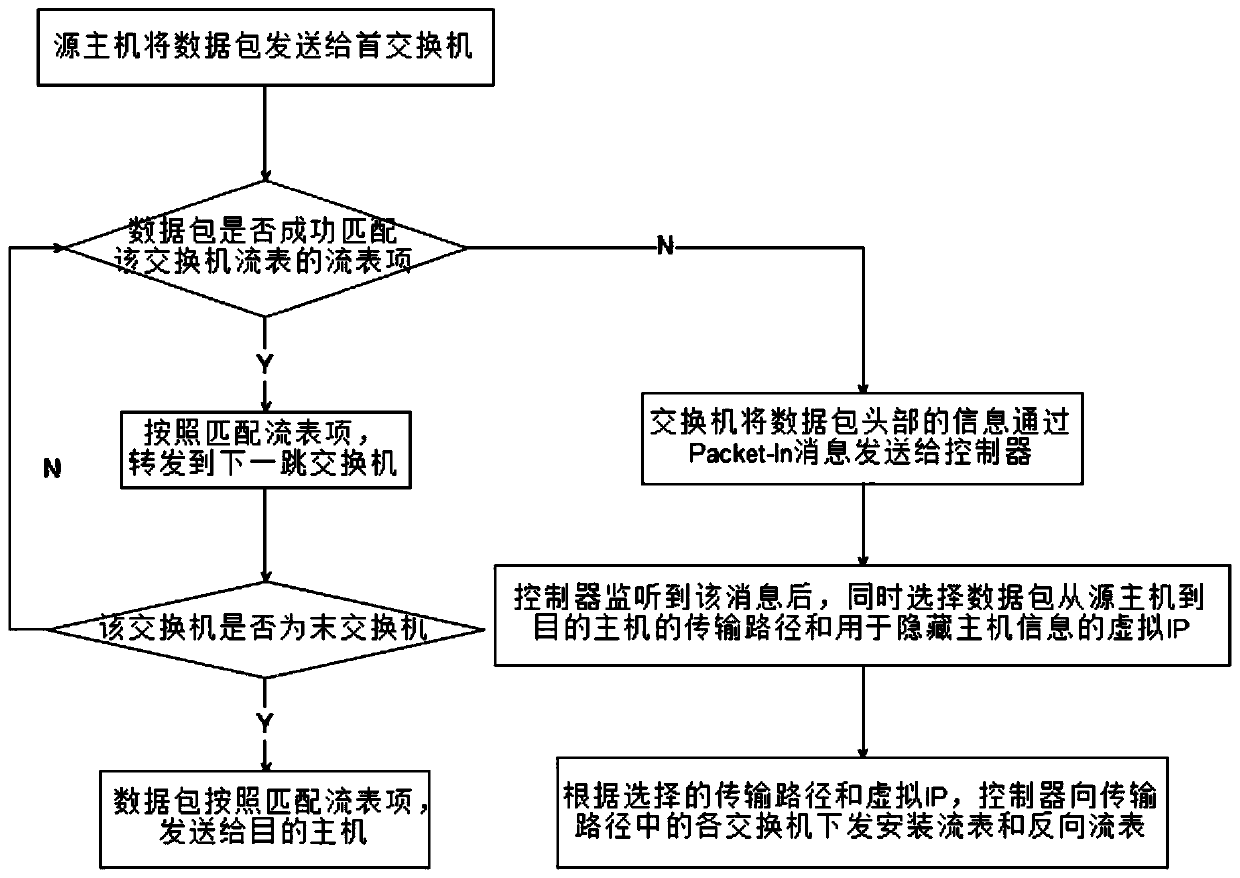
Active defense method based on path and IP address hopping in SDN network
InactiveCN110198270AIncrease the difficultyReduced availabilityData switching networksControl layerIp address
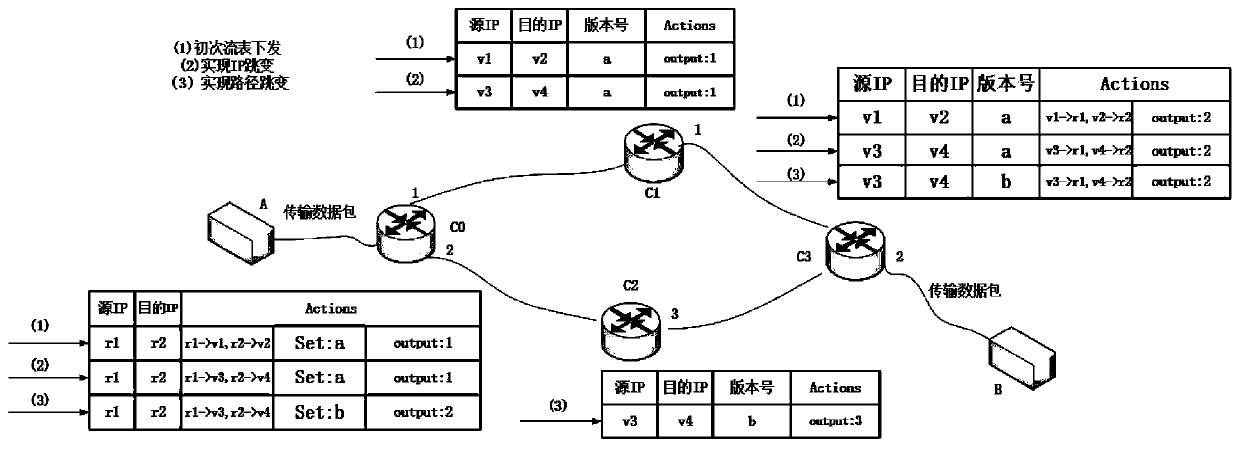
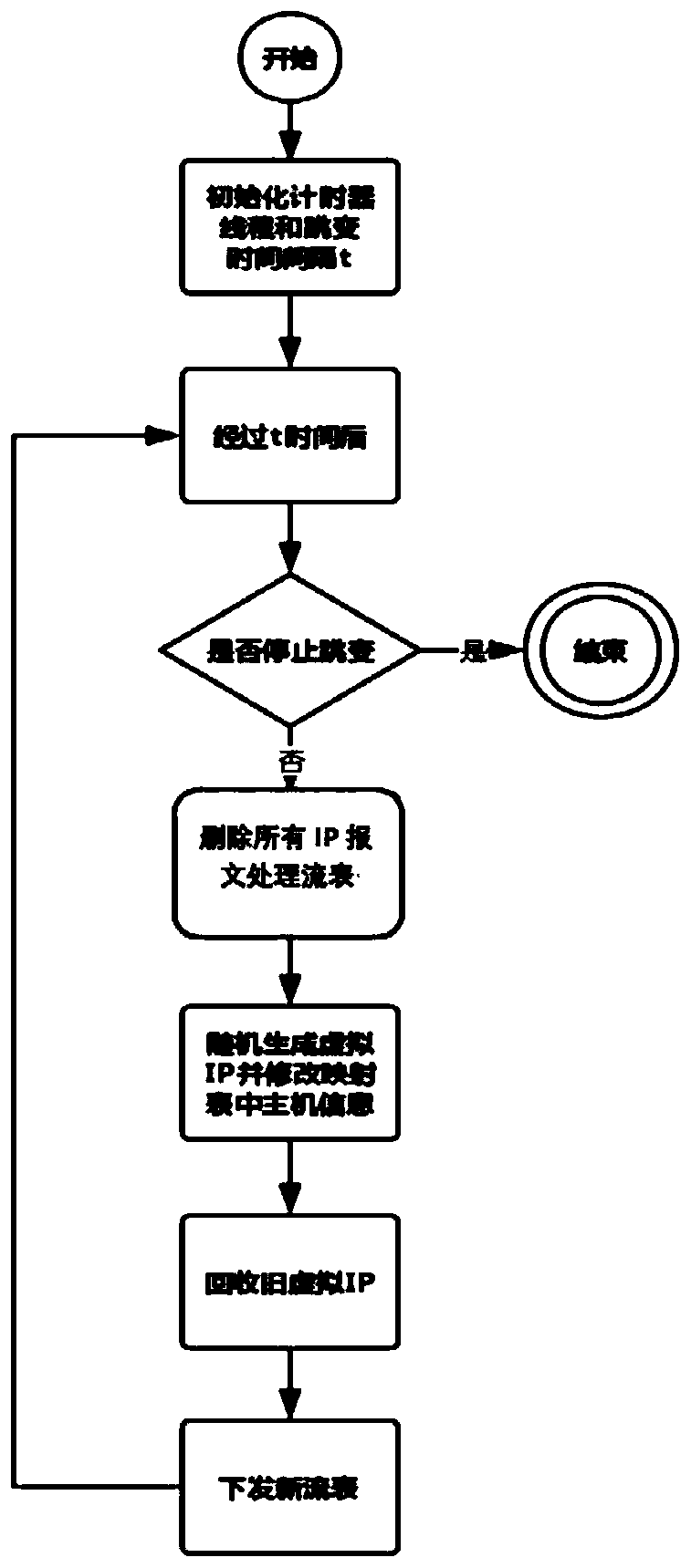
The invention discloses an active defense method based on path and address hopping in an SDN network, and belongs to the field of mobile target defense. The method comprises the following steps: S1, asource host sending a data packet to a first switch; S2, judging whether the data packet is successfully matched with the flow table item or not, if yes, forwarding the data packet to a next hop switch, and entering a step S5; otherwise, the switch sending the Packet-In message to the controller, and executing the step S3; S3, the controller selecting a data packet transmission path and a virtualIP at the same time; S4, the controller generating a flow table rule according to the selected transmission path and the virtual IP, and issuing a flow table and a reverse flow table to each switch;and S5, judging whether the switch is a final switch or not, if yes, sending the data packet to a target host, and otherwise, entering the step S2. By utilizing the separation characteristic of the SDN network data layer and the control layer and the idea of active operation change in the MTD, the IP and the transmission path of the data packet are changed on the premise of not influencing the normal communication of the network, and the difficulty of an attacker in acquiring information is increased, so that the active defense capability of the system is improved.
Owner:HUAZHONG UNIV OF SCI & TECH +1
Chaos moving target defense method based on SDN and system thereof
ActiveCN105141641ALow need for protectionReduce the cost of confusionTransmissionStructure of Management InformationConfusion
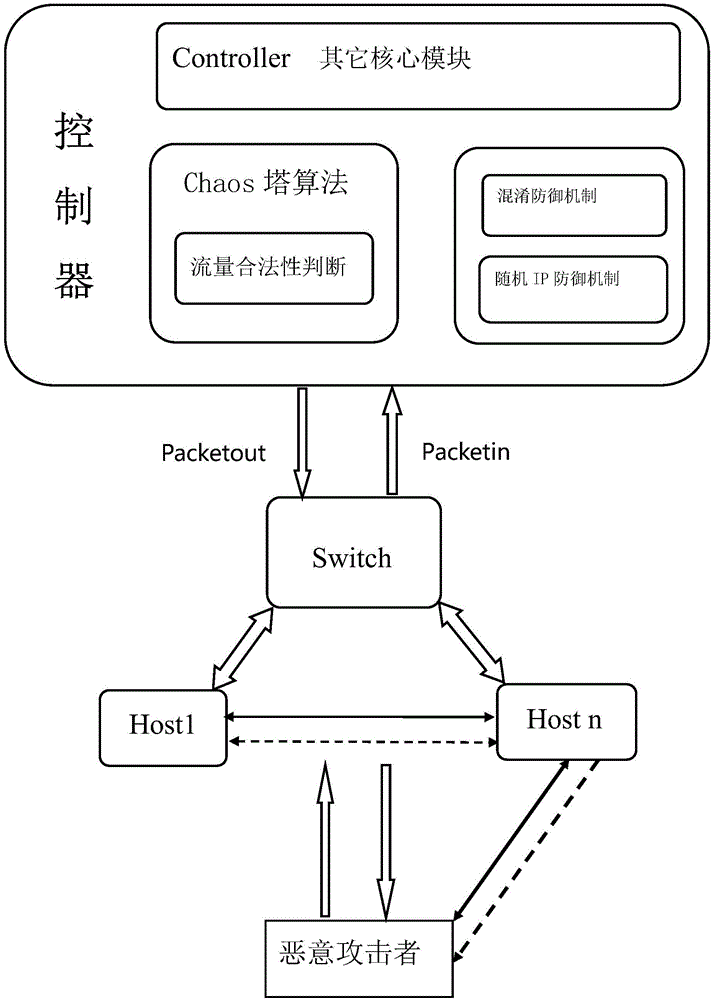
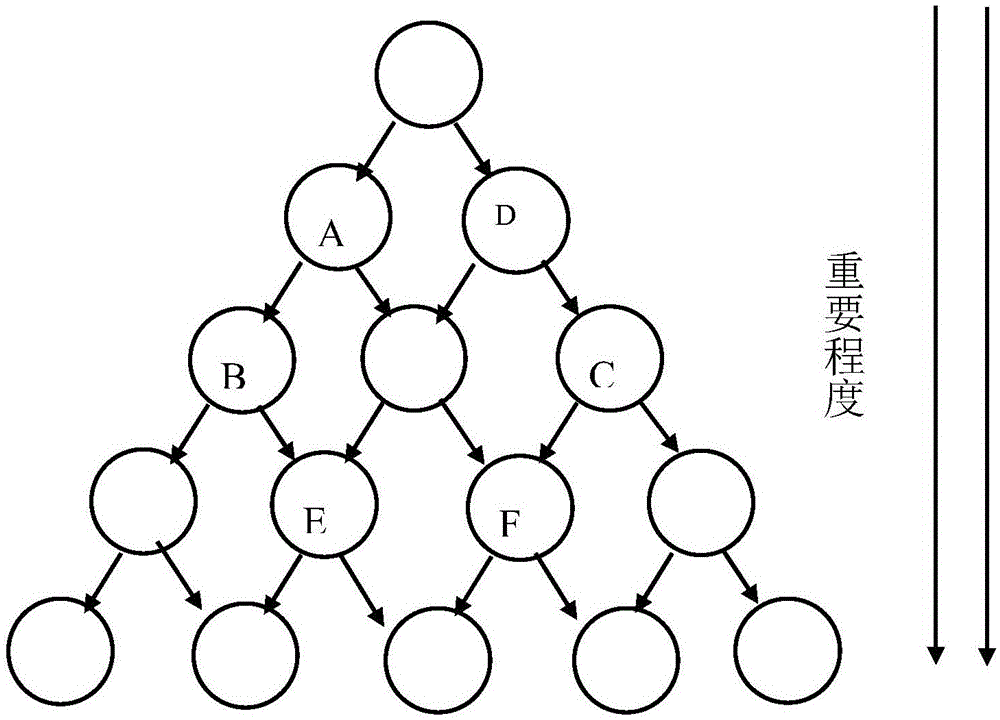
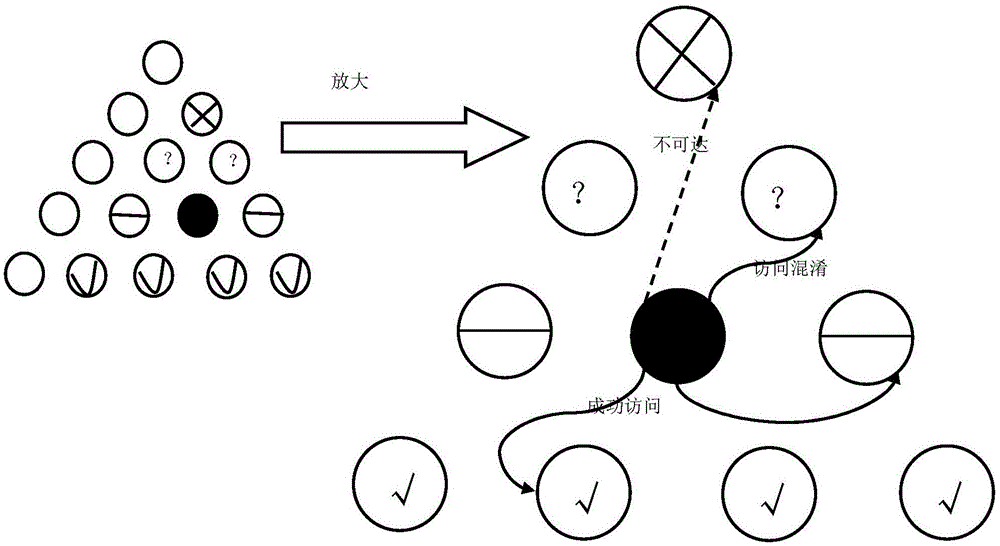
The invention discloses a Chaos moving target defense method based on an SDN and a system thereof. Confusion and dynamic change functions of a network system for requesters can be realized by utilizing a Chaos tower algorithm, a confusion defense method and a random IP defense method. Therefore, a Chaos tower structure is designed by the system to grade the hosts of the network according to degree of importance. Confusion defense performs grade confusion on illegal access, and confusion of return information is performed according to the confusion index so that attackers are enabled to receive false information; and when the confusion index excessively high, communication is directly blocked out. Random IP defense is performed on legal flow network access, and flow tables are periodically issued via a controller to perform IP random conversion on legal communication in an intranet environment. Network equipment in the area has extremely high anonymity and fluctuation under the condition of guaranteeing normal information exchange efficiency so that probing of intruders can be defended, attack range is widened and attack cost is increased.
Owner:WUHAN UNIV
Unknown threat-oriented dynamic network change decision method and system
The invention relates to the technical field of network security, and in particular relates to an unknown threat-oriented dynamic network change decision method and system. The method comprises the steps of: constructing the type space of a player according to the current network state; judging the type of the opposite side by the player according to the prior belief, and obtaining a selectable offensive and defensive strategy set according to the type; obtaining the system state transition probability according to the network state and the offensive and defensive strategy set; obtaining earnings of both offensive and defensive game sides for the selected offensive and defensive strategy, and, in combination with the system state transition probability, constructing a moving target defencemodel based on an incomplete information Markov game; and equivalently converting the solution of the moving target defence model into a target function, so that the optimal moving target defence strategy is obtained. By means of the unknown threat-oriented dynamic network change decision method and system in the invention, the unknown threat-oriented optimal defence strategy can be selected based on limited network resources; and thus, the technical effect that the network performance overhead and MTD defence earnings are balanced can be realized.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Multiple operating system rotation environment moving target defense
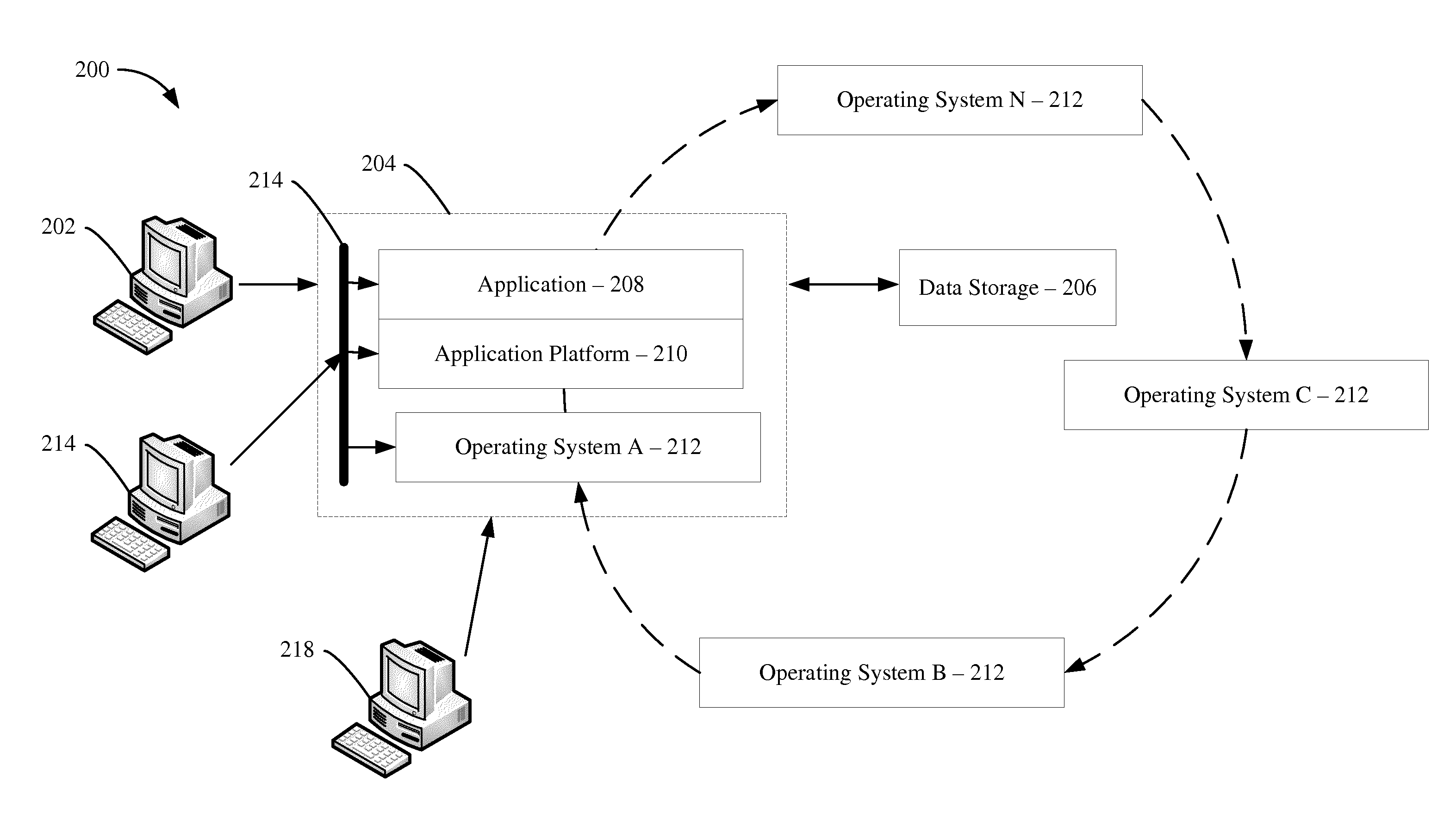
ActiveUS20160065612A1Memory loss protectionError detection/correctionOperational systemComputerized system
Systems and methods for providing a multiple operating system rotation environment (“MORE”) moving target defense (“MTD”) computing system are described. The MORE-MTD system provides enhanced computer system security through a rotation of multiple operating systems. The MORE-MTD system increases attacker uncertainty, increases the cost of attacking the system, reduces the likelihood of an attacker locating a vulnerability, and reduces the exposure time of any located vulnerability. The MORE-MTD environment is effectuated by rotation of the operating systems at a given interval. The rotating operating systems create a consistently changing attack surface for remote attackers.
Owner:UCHICAGO ARGONNE LLC
Mobile target defense decision selection method, device and system based on Markov time game
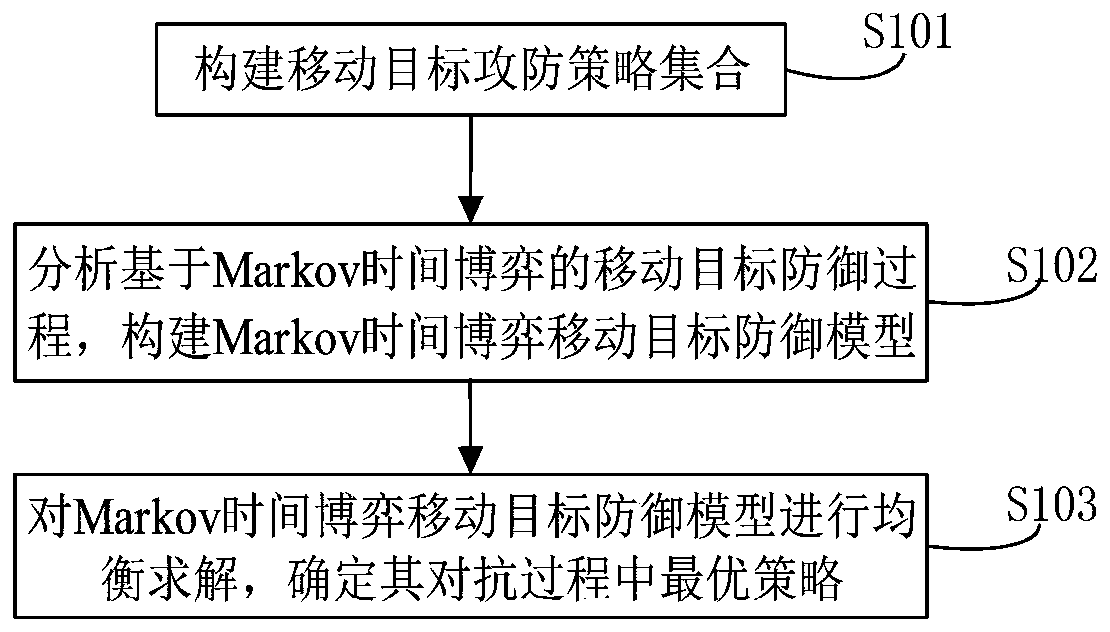
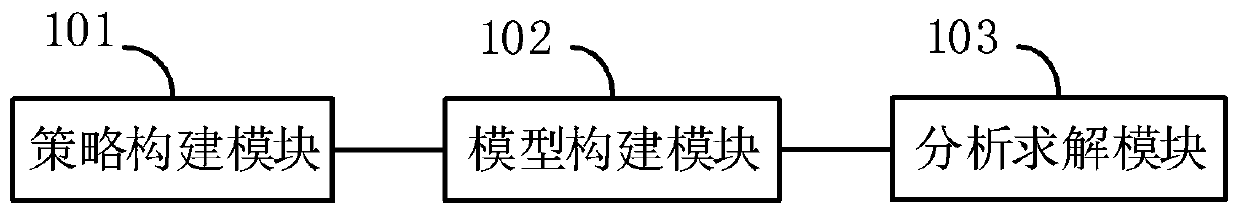
ActiveCN110300106ARealize quantitative analysisFacilitate decision-makingTransmissionExperimental researchAlgorithm
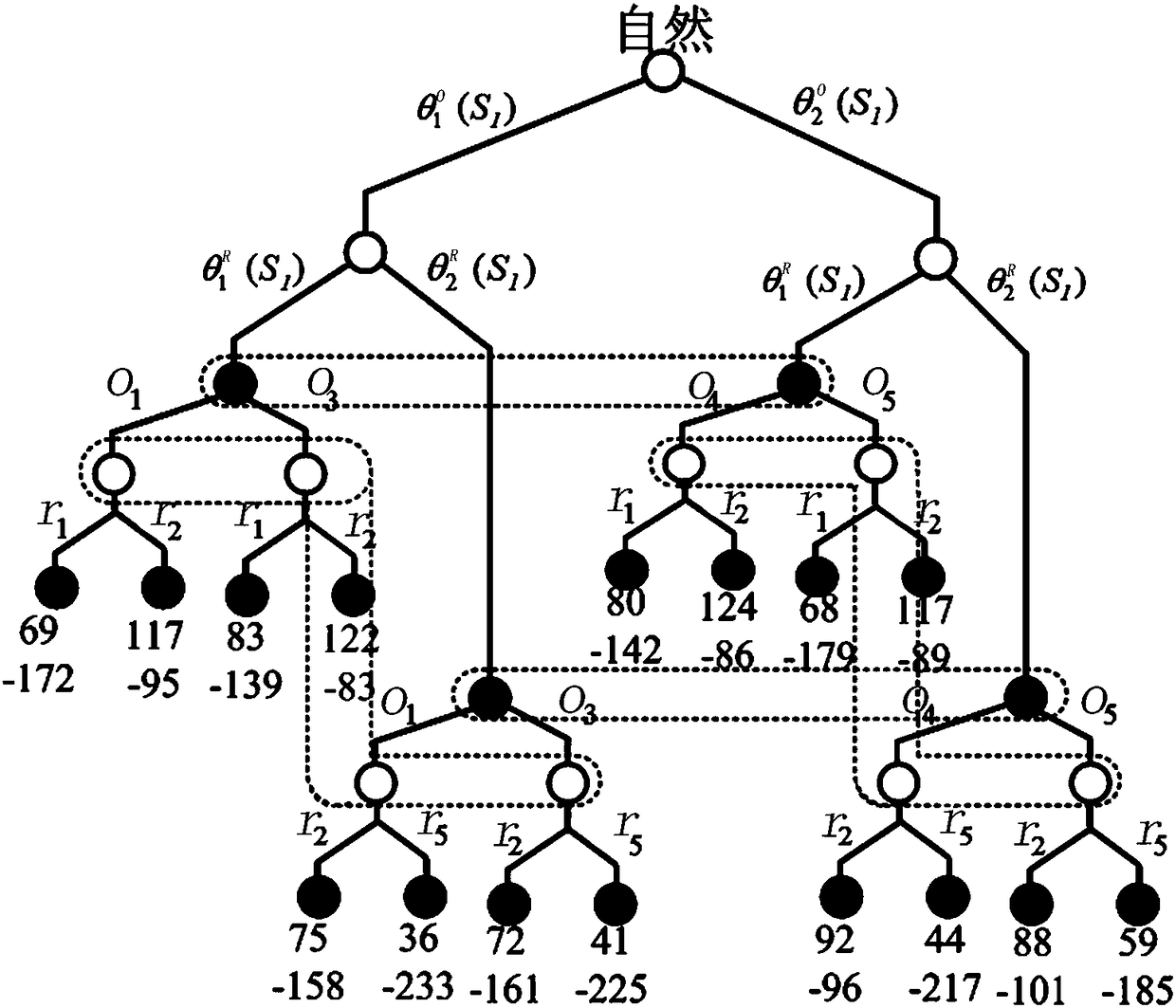
The invention belongs to the technical field of network security, and particularly relates to a moving target defense decision selection method, device and system based on a Markov time game, and themethod comprises the steps: building a moving target attack and defense strategy set; analyzing a moving target defense process based on the Markov time game, and constructing a Markov time game moving target defense model; and carrying out equilibrium solution on the Markov time game moving target defense model, and determining an optimal strategy in the confrontation process of the Markov time game moving target defense model. On the basis of analyzing a moving target attack and defense process, a Markov time game model is constructed, a target criterion function of a moving target defense game is designed based on discount total revenue, and multi-stage attack and defense game quantitative analysis is realized; designing a multi-stage optimal defense strategy selection algorithm based on nonlinear programming multi-stage game equilibrium calculation; further, experimental research results show that the confrontation process can be effectively described, the optimal strategy can be correctly selected, the implementation accuracy of moving target defense can be ensured, and network security management personnel can be helped to make a better decision.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
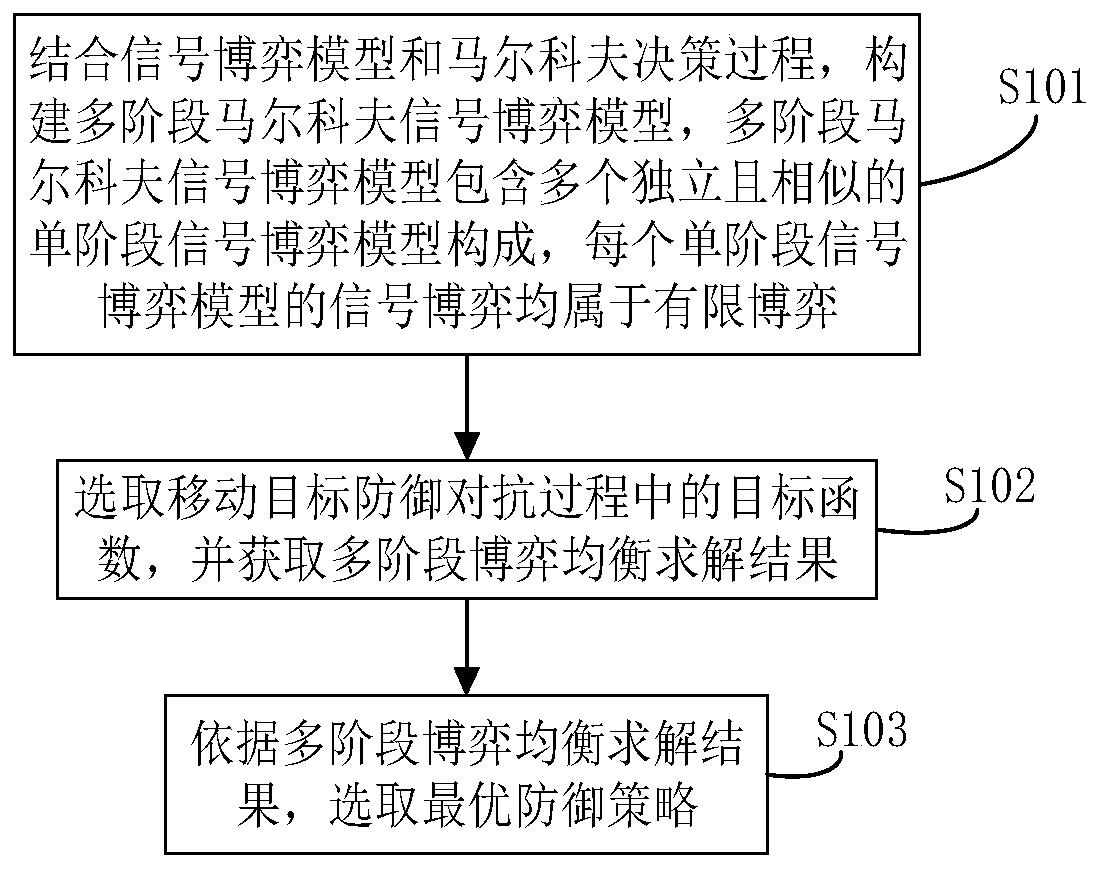
Markov signal game-based moving target defense strategy selection method and equipment
ActiveCN110460572AGood for real researchVerify validityTransmissionSingle stagePhases of clinical research
The invention belongs to the technical field of network security, in particular to a Markov signal game-based moving target defense strategy selection method and device. The method comprises the stepsthat a signal game model and a Markov decision process are combined, a multi-stage Markov signal game model is constructed, the multi-stage Markov signal game model comprises a plurality of independent and similar single-stage signal game models, and the signal game of each single-stage signal game model belongs to a limited game; a target function is selected in the defense and confrontation process of the moving target, and a multi-stage game equilibrium solving result is obtained; and an optimal defense strategy is selected according to a multi-stage game equilibrium solving result. The dynamic confrontation process between the attacker and the defender is analyzed, multi-stage game equilibrium is solved, the optimal defense strategy is selected, the defects of passive defense in the field of network space security are overcome, the timeliness, objectivity and accuracy of system defense are improved, and the active defense capacity of network security is enhanced.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Moving target defense opportunity selection method and device based on covert confrontation
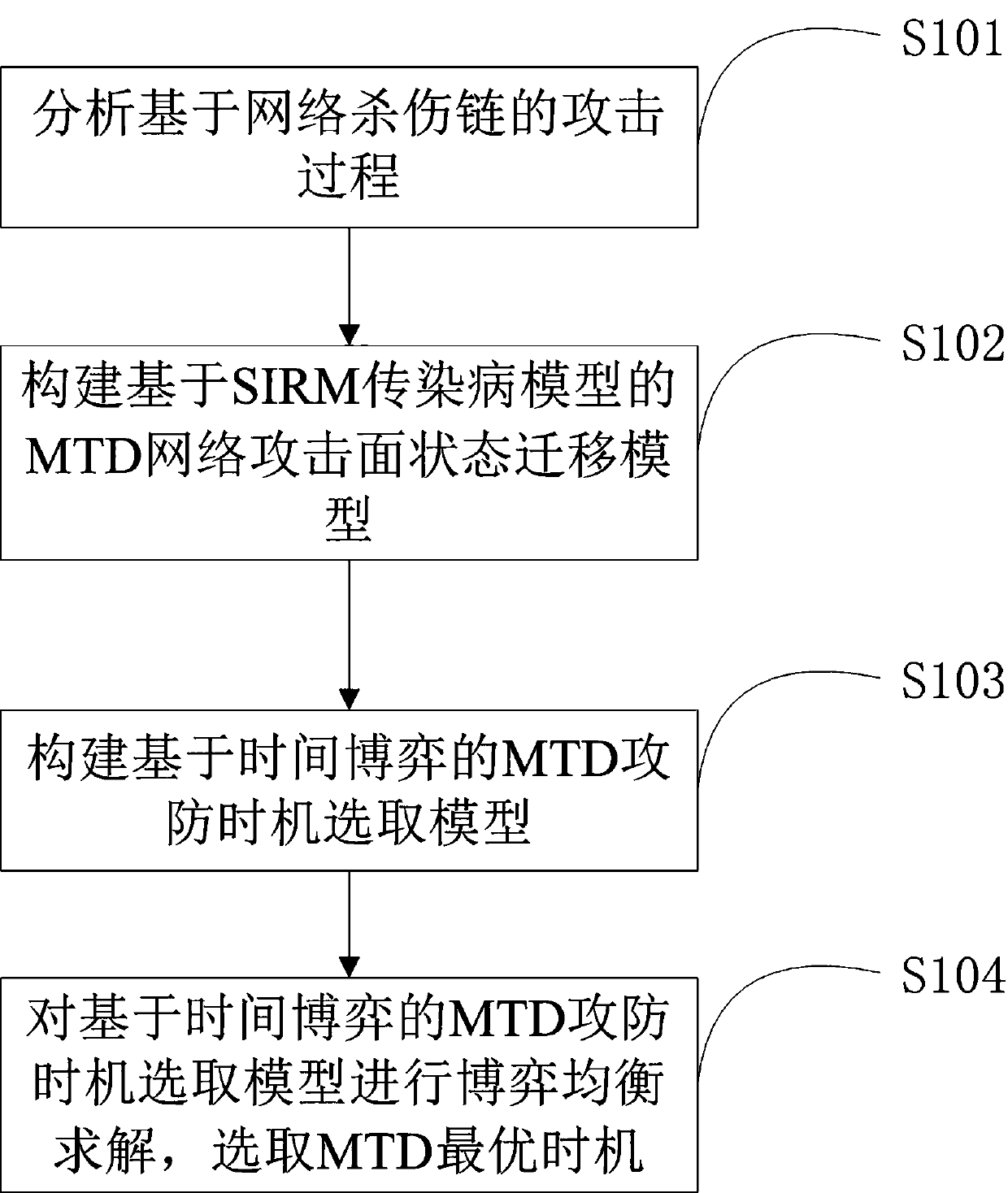
ActiveCN111385288APractical guidance is of good valueGame equilibrium solutionData switching networksQuality of serviceAttack
The invention belongs to the field of network security, and particularly relates to a moving target defense opportunity selection method and a moving target defense opportunity selection device basedon covert confrontation. The moving target defense opportunity selection method comprises the steps of: analyzing an attack process based on a cyber kill chain; constructing an MTD network attack surface state migration model based on a SIRM infectious disease model; constructing an MTD attack and defense opportunity selection model based on time game; and performing game equilibrium solution on the MTD attack and defense opportunity selection model based on the time game, and selecting the optimal opportunity of the MTD. According to the moving target defense opportunity selection method, theoptimal equilibrium point of strategy implementation opportunities of an attacker and a defender is analyzed in a time game theory framework in accordance with a real network attack and defense scene, so that the MTD implementation opportunity is guided for the defender, and the SDN service quality and MTD decision income are balanced.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
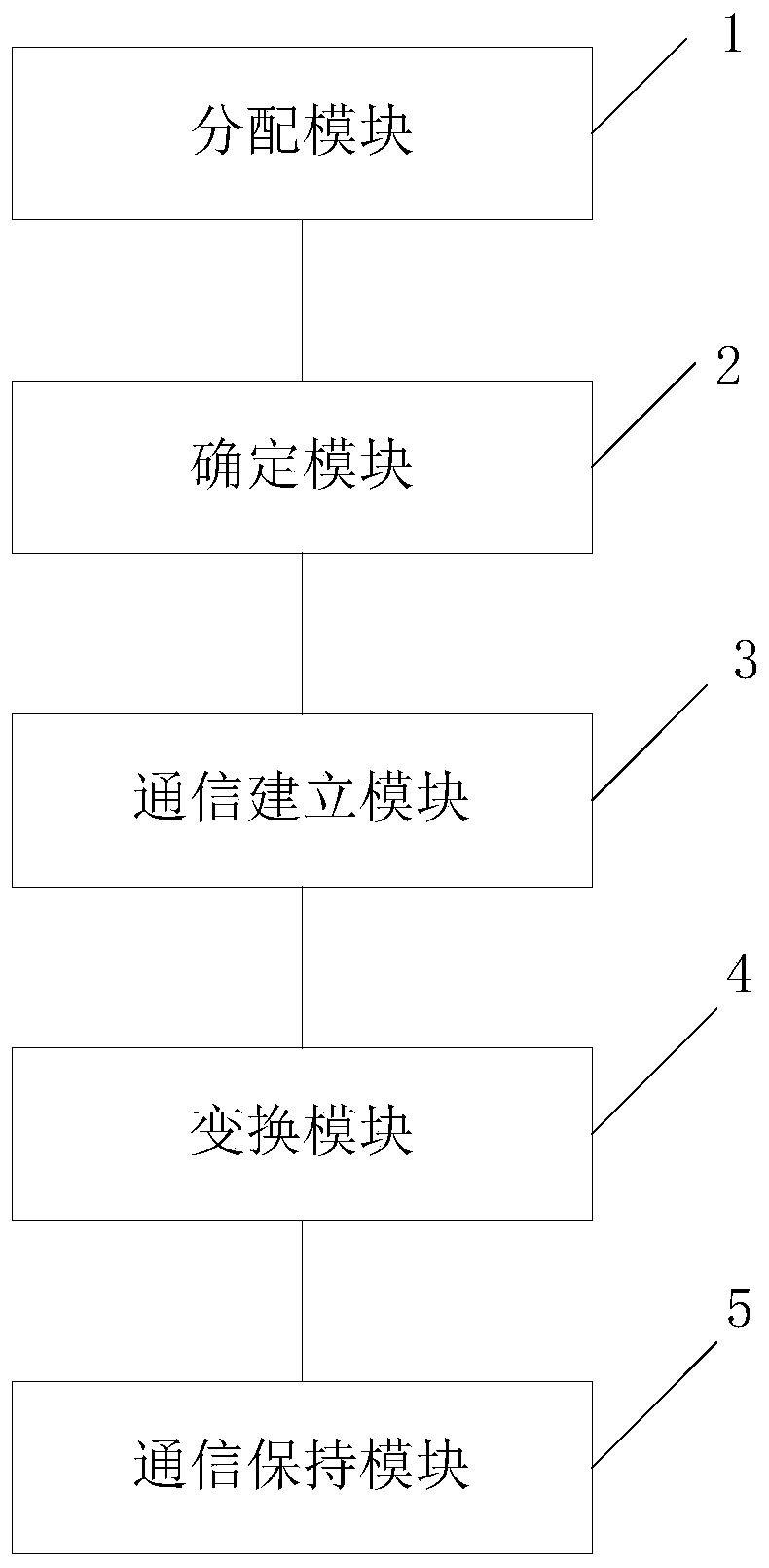
Local area network communication method and device based on moving target defense
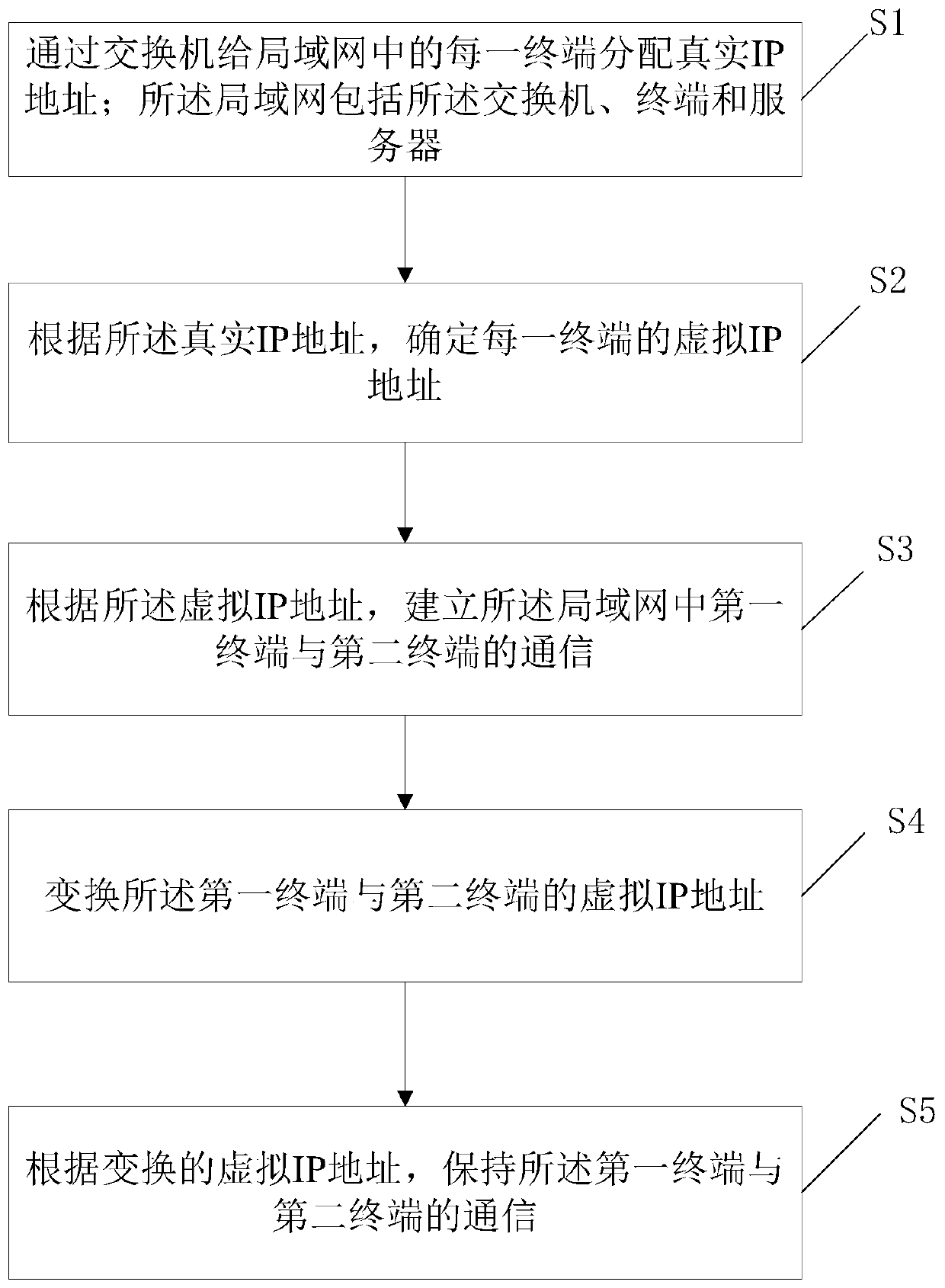
InactiveCN110611671AEnsure normal communicationRealize communicationTransmissionComputer terminalInformation security
The invention discloses a local area network communication method and a device based on moving target defense. The method comprises the following steps: allocating a real IP address to each terminal in a local area network through a switch; the local area network comprises the switch, a terminal and a server; determining a virtual IP address of each terminal according to the real IP address; establishing communication between a first terminal and a second terminal in the local area network according to the virtual IP address; converting the virtual IP addresses of the first terminal and the second terminal; and maintaining communication between the first terminal and the second terminal according to the converted virtual IP address, thereby realizing local area network communication and protecting information security in a local area network communication process under the condition of not changing an original switch of the local area network and not needing manual configuration.
Owner:BEIJING UNIV OF POSTS & TELECOMM +1
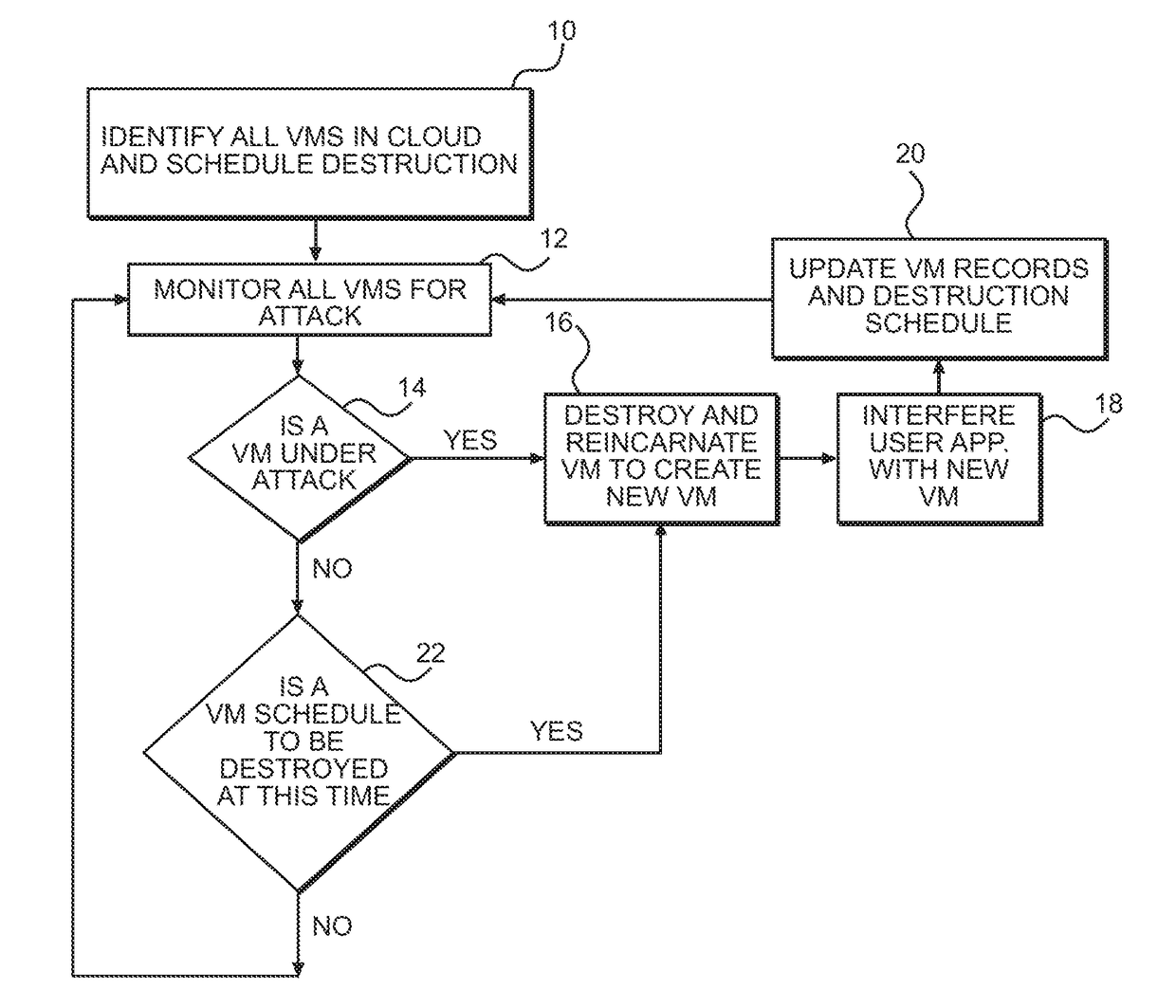
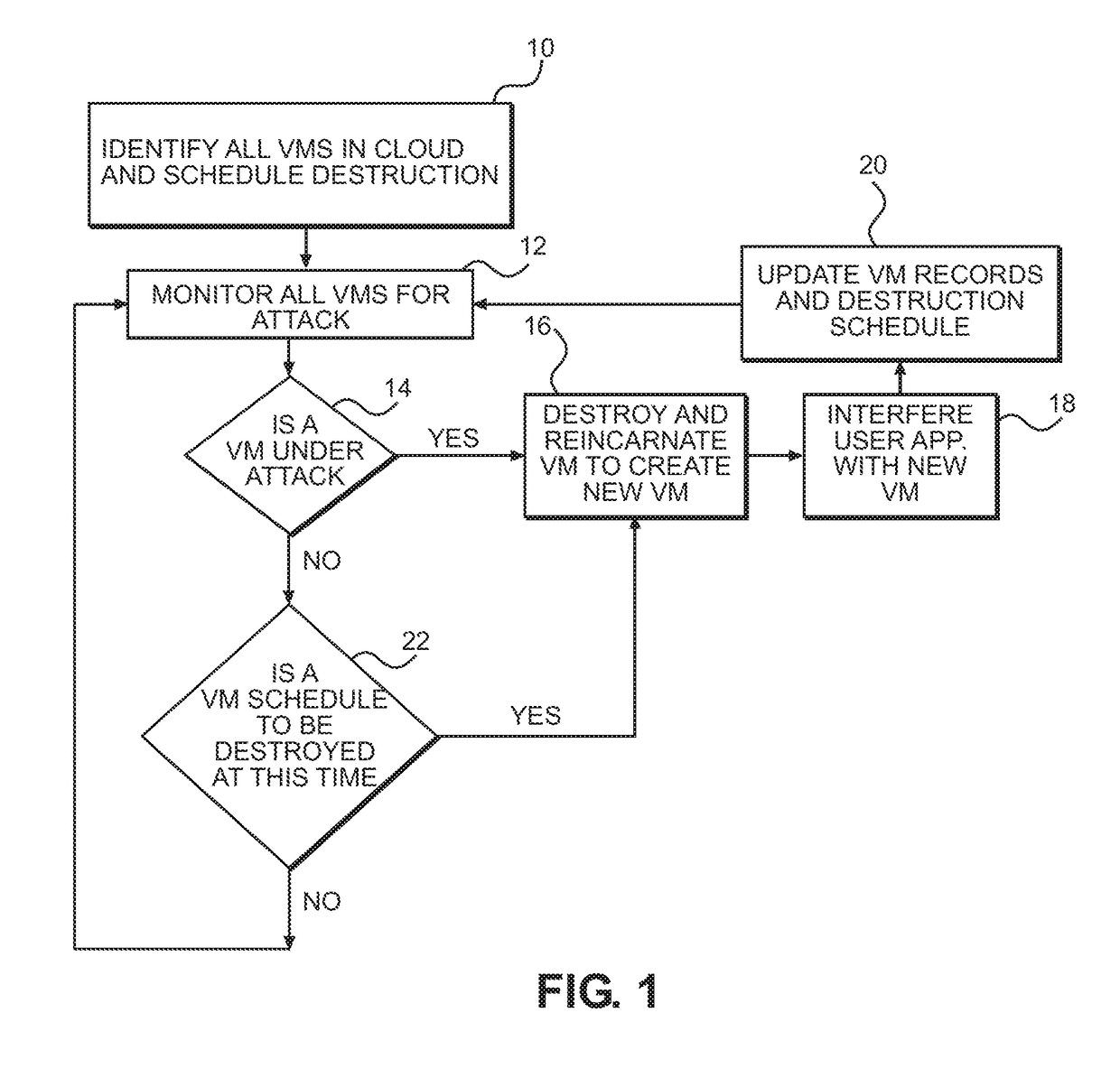
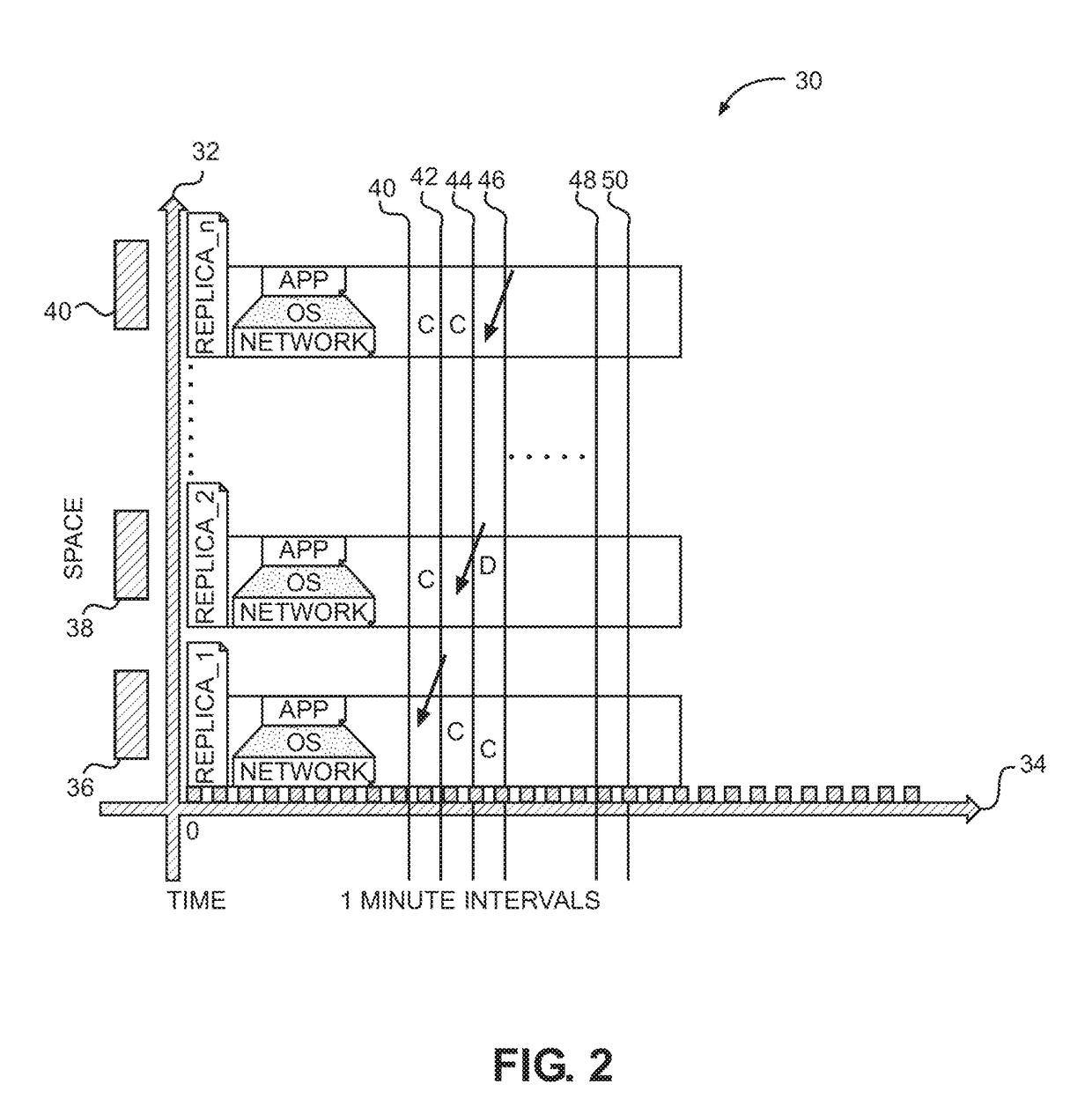
Moving Target Defense for Distributed Systems
InactiveUS20180332073A1Maximizing costMinimizing probability of successfulProgram initiation/switchingTransmissionOperational systemRobin Sequence
An apparatus and method defends against computer attacks by destroying virtual machines on a schedule of destruction in which virtual machines are destroyed in either a random sequence or a round-robin sequence with wait times between the destruction of the virtual machines. Also, each virtual machine is assigned a lifetime and is destroyed at the end of its lifetime, if not earlier destroyed. Destroyed virtual machines are reincarnated by providing a substitute virtual machine and, if needed, transferring the state to the substitute virtual machine. User applications are migrated from the destroyed machine to the replacement machine. All virtual machines are monitored for an attack at a hypervisor level of cloud software using Virtual Machine Introspection, and if an attack is detected, the attacked virtual machine is destroyed and reincarnated ahead of schedule to create a new replacement machine on a different hardware platform using a different operating system.
Owner:GOVERNMENT OF THE UNITED STATES AS REPRESENTED BY THE SEC OF THE AIR FORCE
WEB dynamic adaptive defense system and defense method based on false response
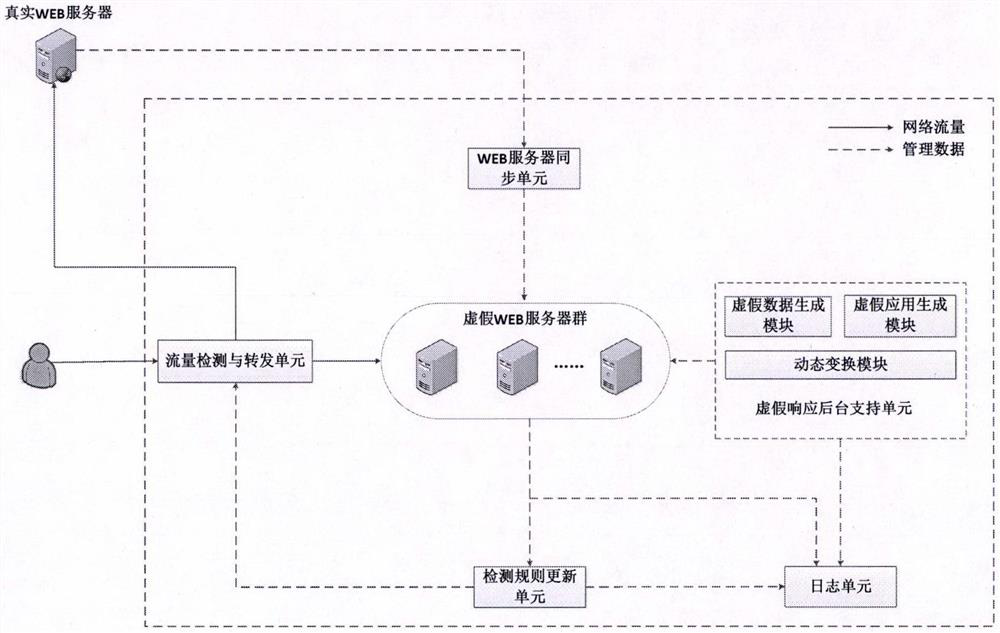
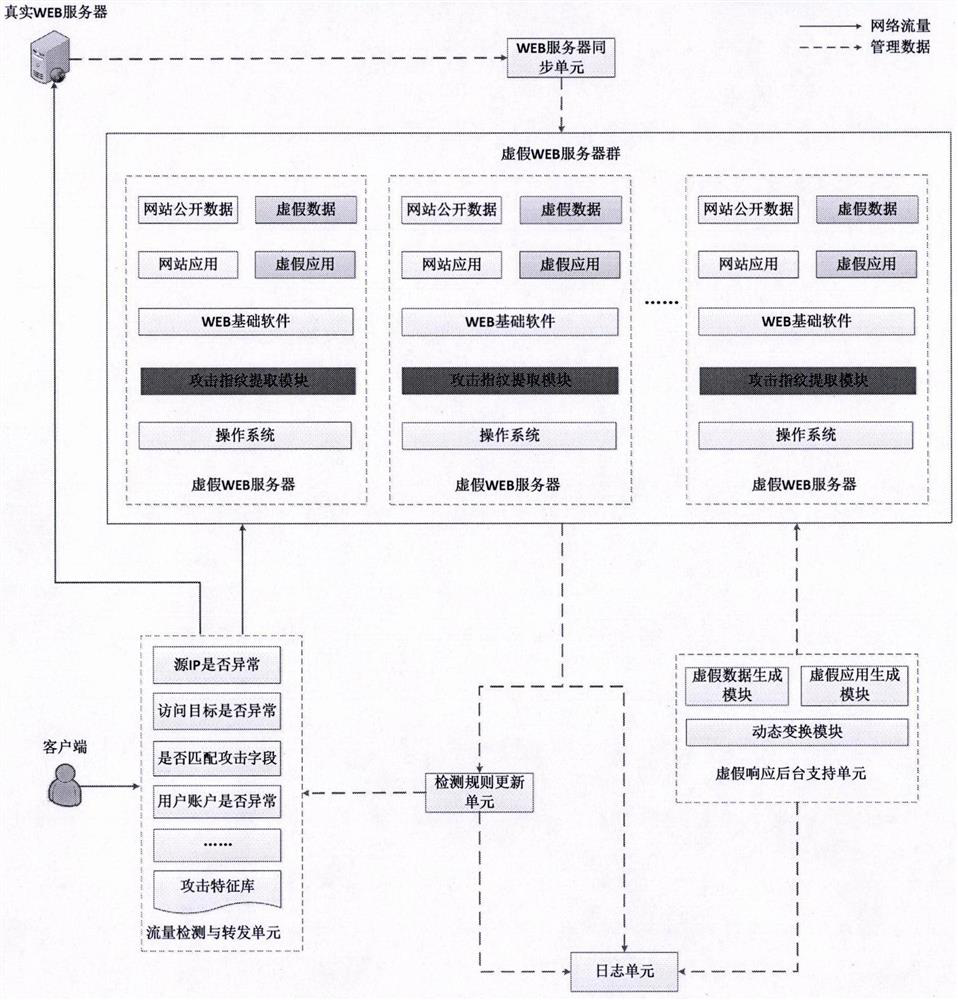
The invention provides a WEB dynamic adaptive defense system and defense method based on false response. Based on the concept of moving target defense, a plurality of false WEB servers capable of being dynamically transformed is constructed around a protected WEB server, false sensitive data, false applications, false vulnerabilities and the like are constructed on the false WEB servers, and cheating hackers attack the false WEB servers. When a known attack or a suspicious behavior is identified, the known attack or the suspicious behavior is introduced into the false WEB server, and an attacker enters the false environment and then executes a subsequent attack action in the false environment until the attack is finished, so that multiple attempt attacks of the attacker are effectively defended, and meanwhile, the method has a relatively good defending capability on an unknown WEB attack. Besides, by continuously observing attack behaviors in a false environment, WEB attack features can be automatically extracted, attack detection rules are dynamically and adaptively adjusted, and the dynamic adaptive capacity of a defense system is improved.
Owner:张长河
Safe operation method and system of mimicry voter
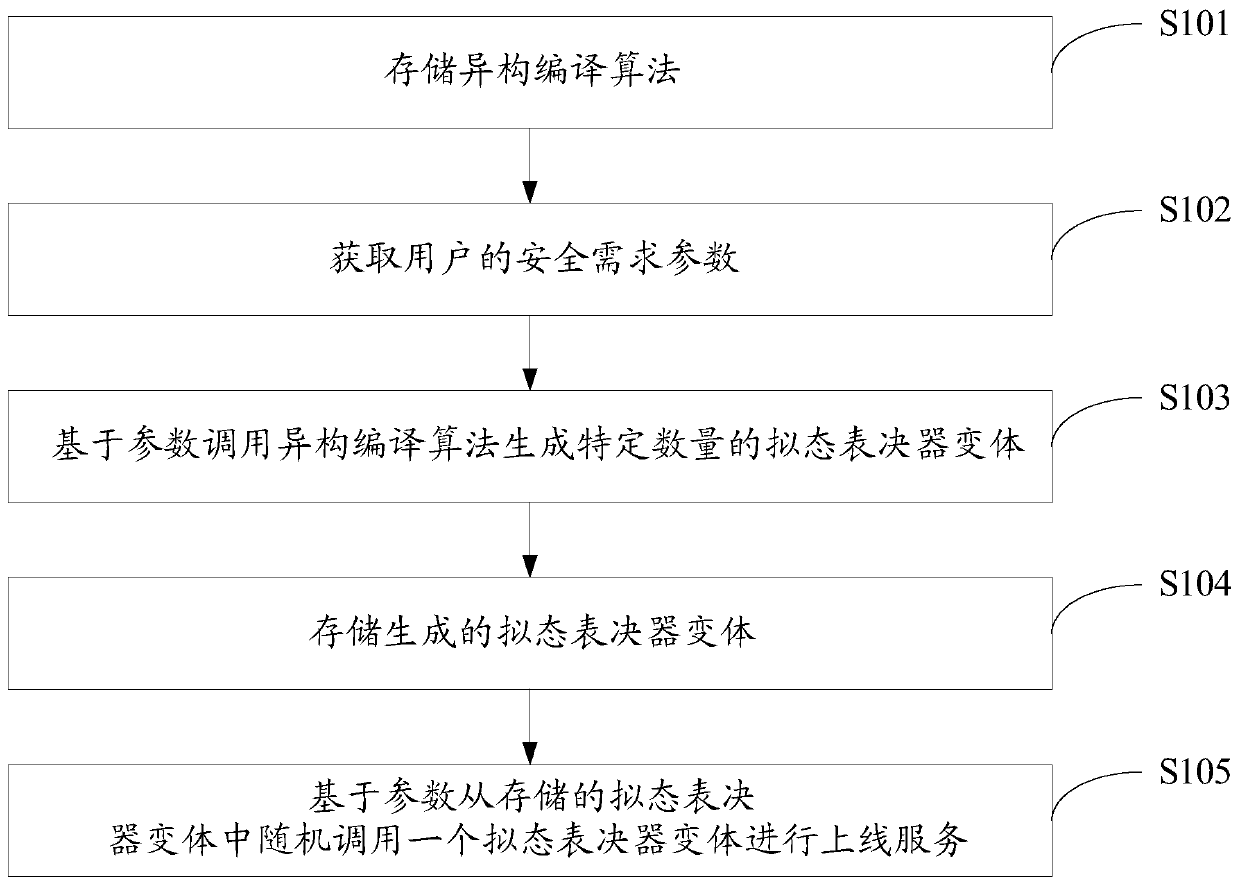
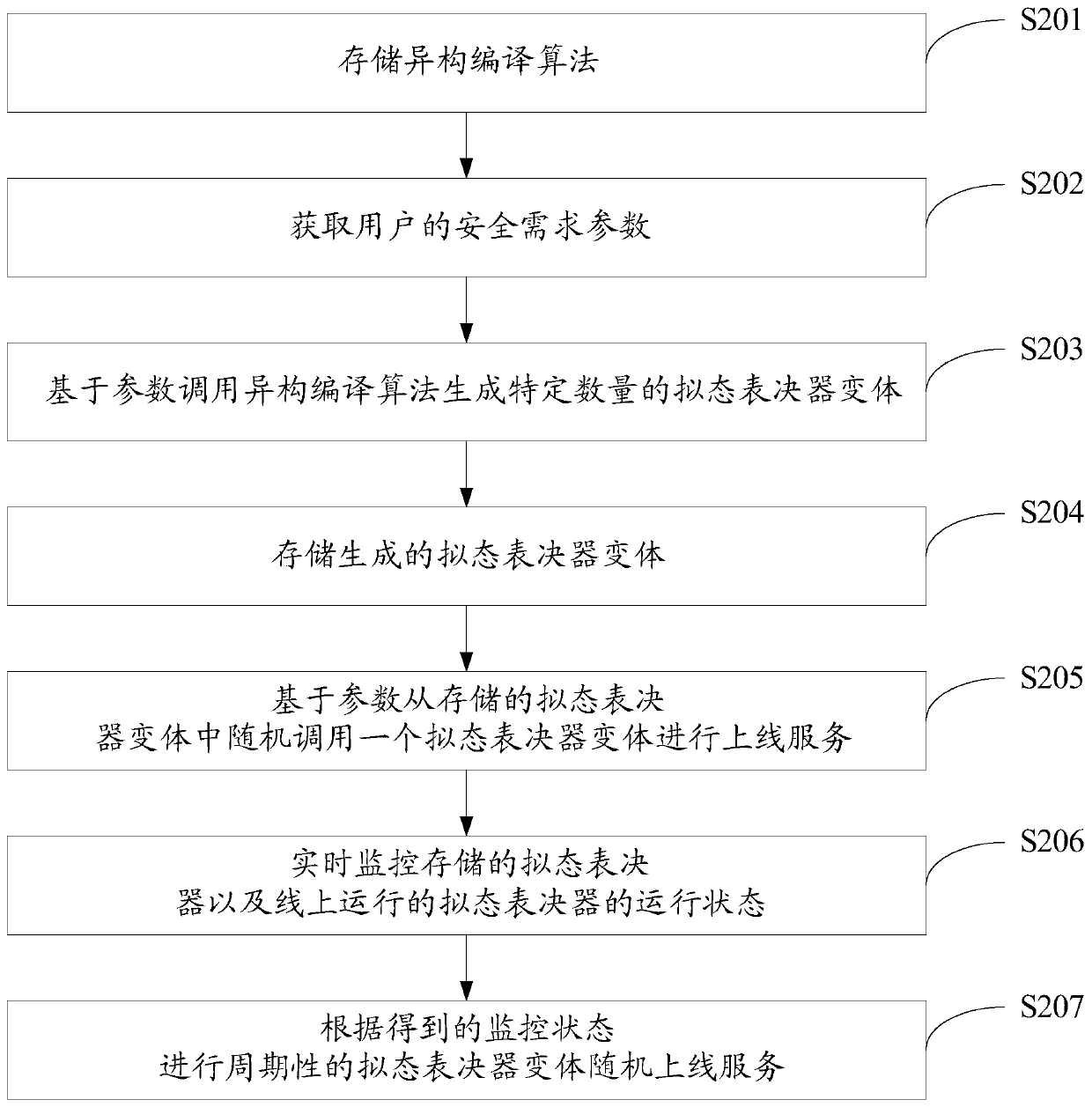
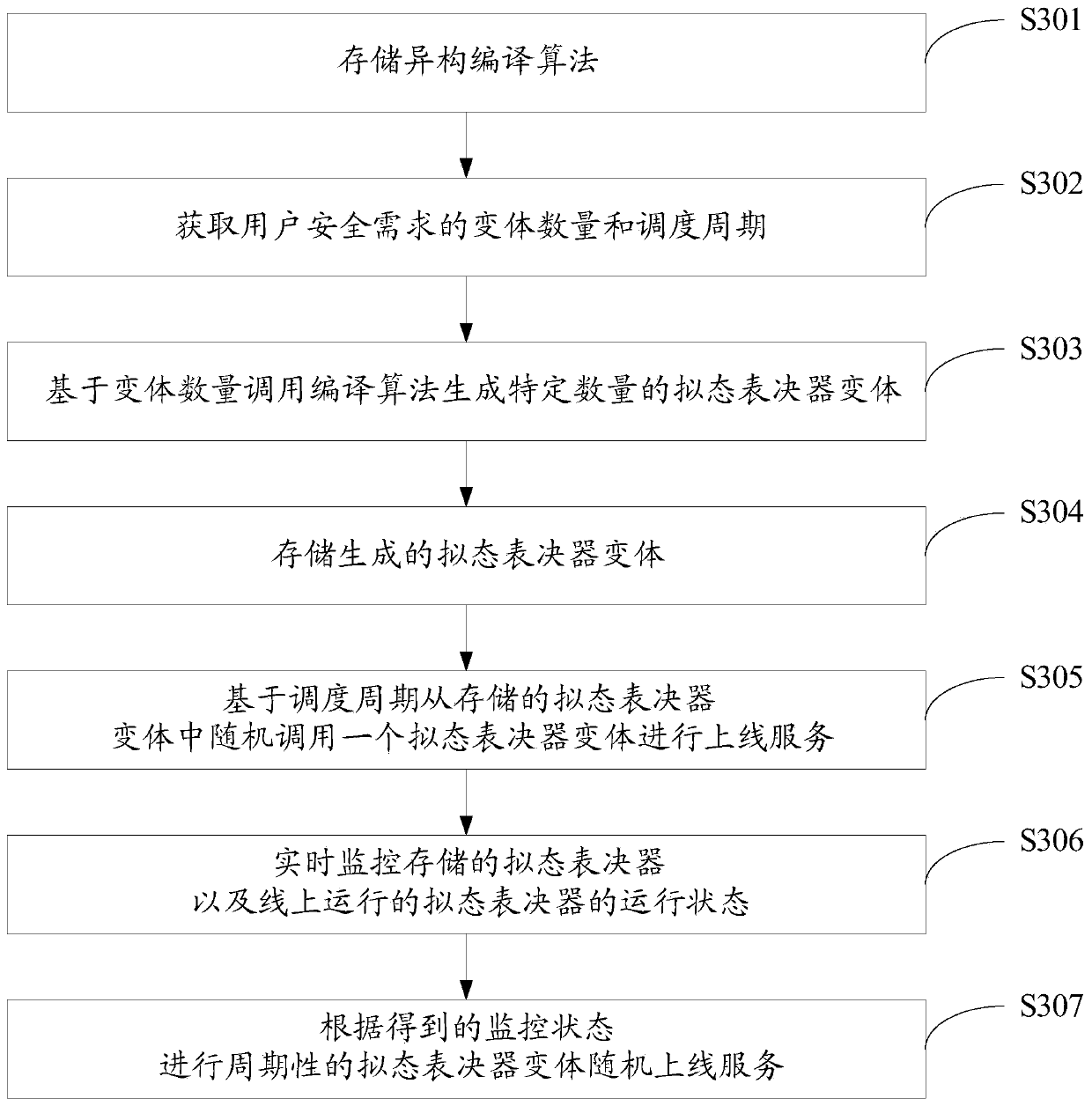
ActiveCN111475805AEnsure safetyIncrease uncertaintyPlatform integrity maintainanceSpecial data processing applicationsUser needsSafe operation
The invention discloses a safe operation method and system for a mimicry voter, and the method comprises the steps: storing a heterogeneous compiling algorithm, and obtaining a safety demand parameterof a user; calling a heterogeneous compiling algorithm based on the parameters to generate a specific number of mimicry voter variants, and storing the generated mimicry voter variants; and randomlycalling one mimicry voter variant from the stored mimicry voter variants based on the parameters to perform online service. According to the invention, the mimicry voter software can be isomerized andcompiled on the basis of software diversification and moving target defense thought, and meanwhile, the voter variants are periodically and randomly scheduled according to user requirements, so the uncertainty of voter service is increased, the attack difficulty of attackers is improved, and the safety of the mimicry voter is guaranteed.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU +1
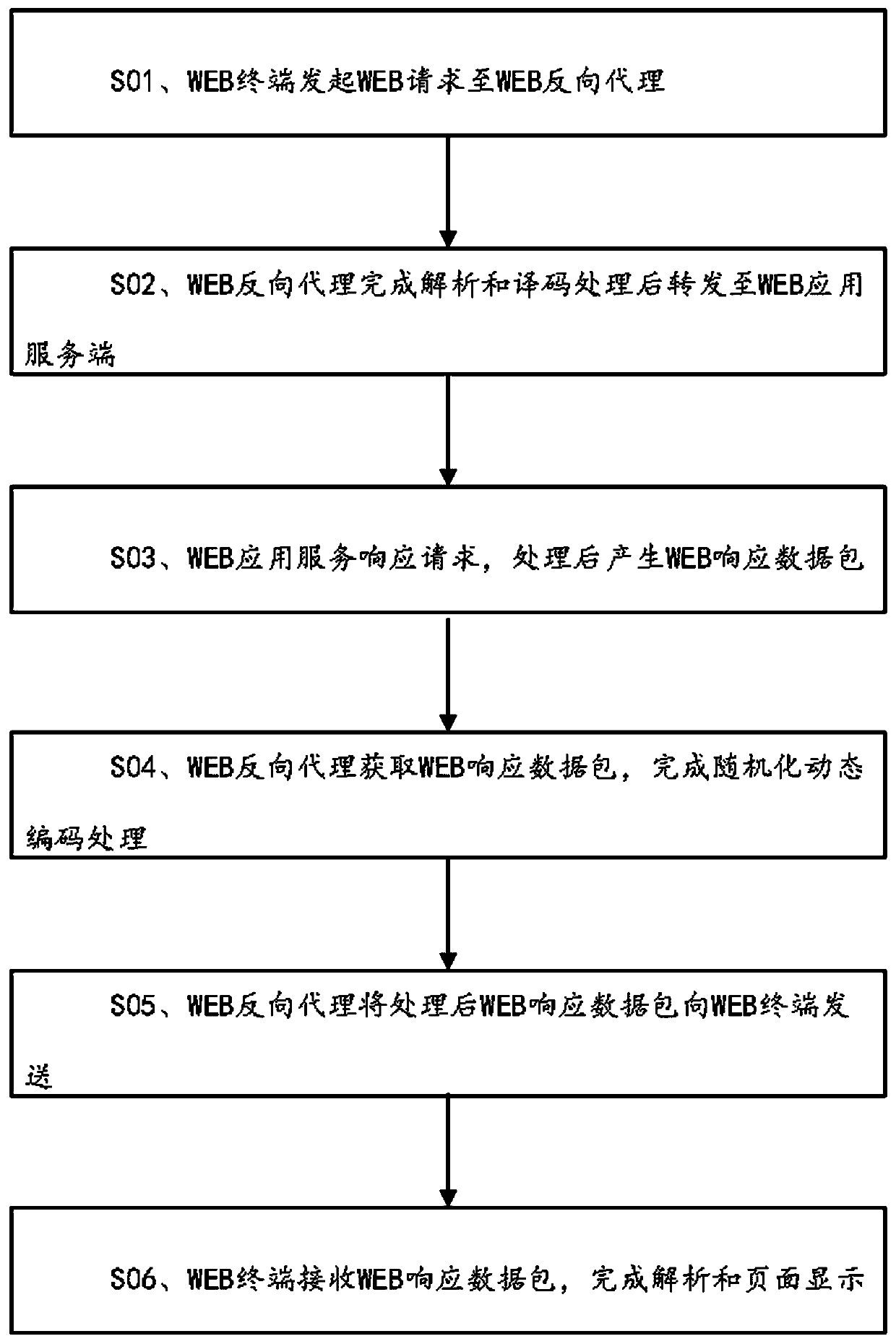
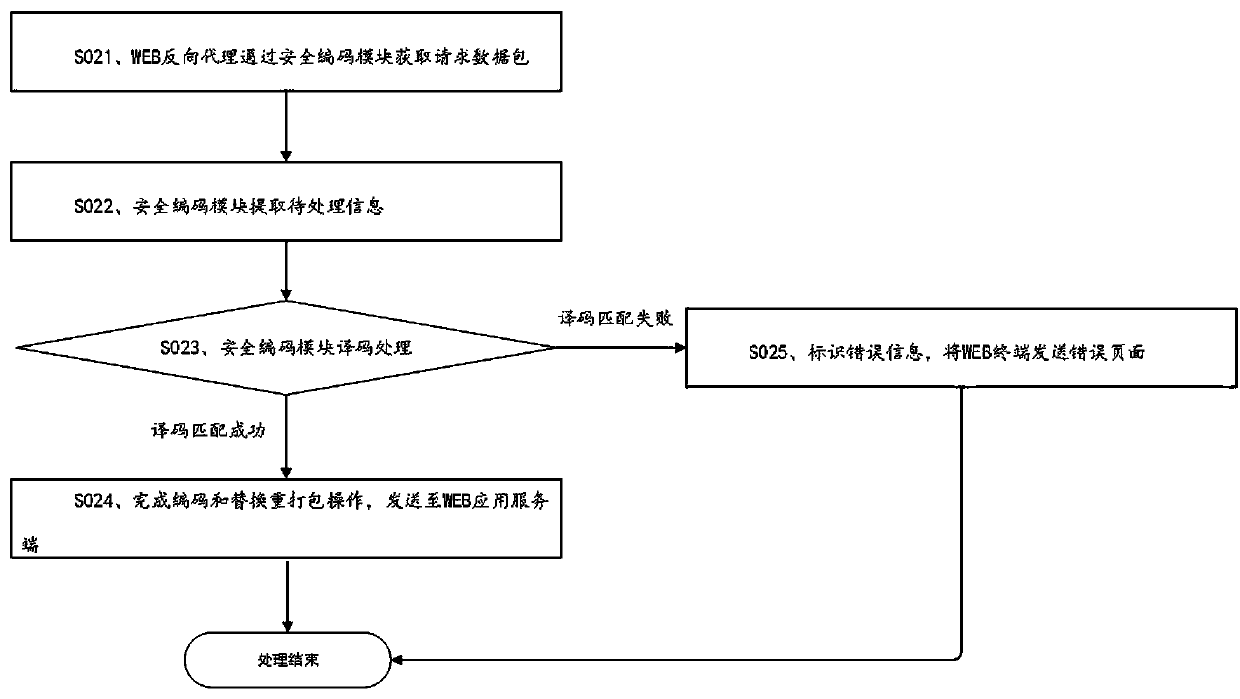
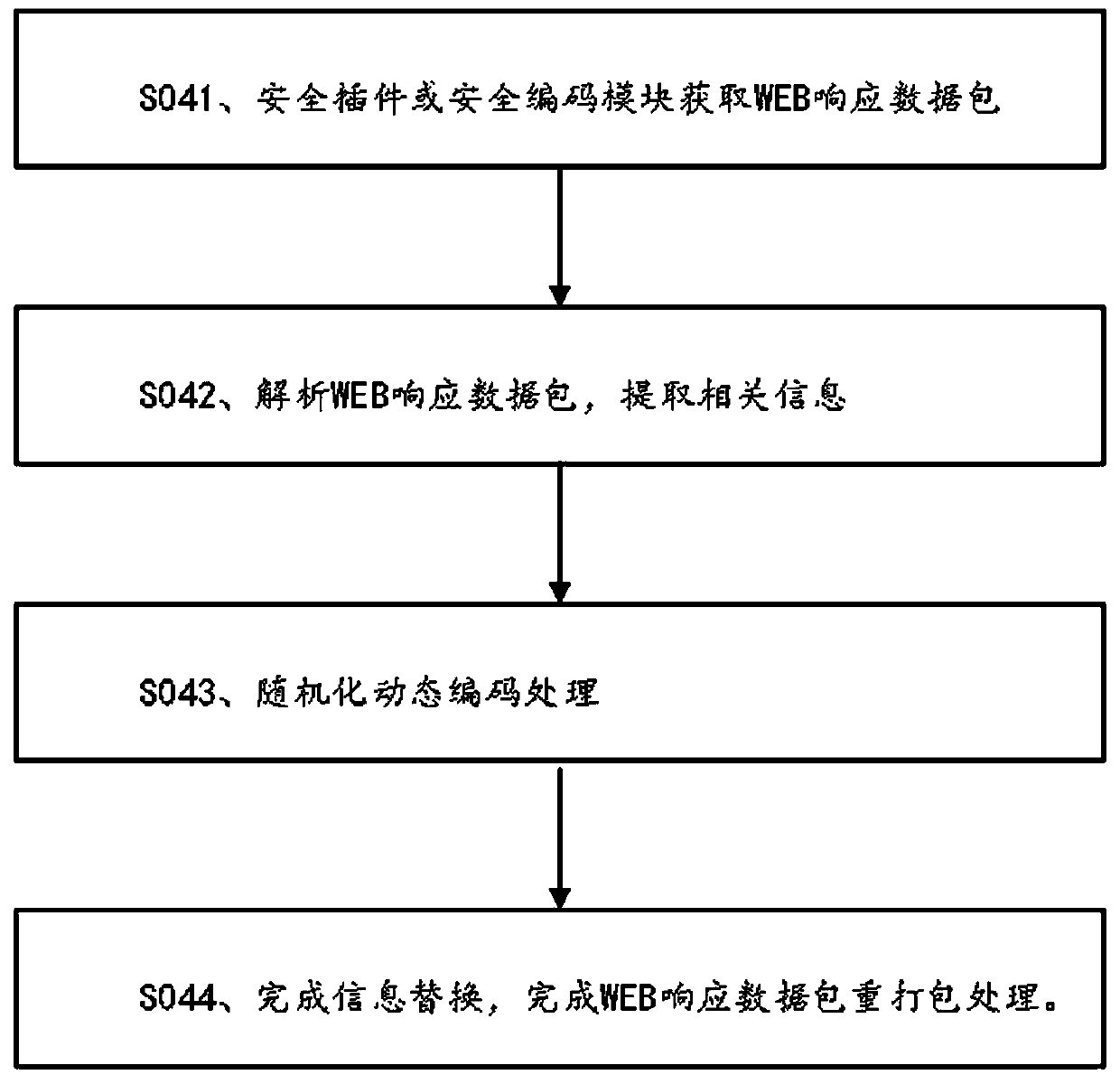
WEB dynamic security defense method and system
InactiveCN110381049AImplement virtualizationImplement one-shot transcodingTransmissionWeb applicationWeb service
The invention discloses a WEB dynamic security defense method and system. The method is based on a moving target defense technical thought. The invention provides an active dynamic defense mechanism for a WEB service system. When the protected WEB application service system is not attacked, the service entry or the resource address is actively transformed, so that the information of the backgroundof the server is effectively hidden and protected, the dynamics and uncertainty of the attacked surface of the system are realized in a randomized dynamic coding technical mode, the difficulty of network attack implementation is improved, and the anti-attack capability of the WEB application service system is effectively enhanced.
Owner:浙江智贝信息科技有限公司
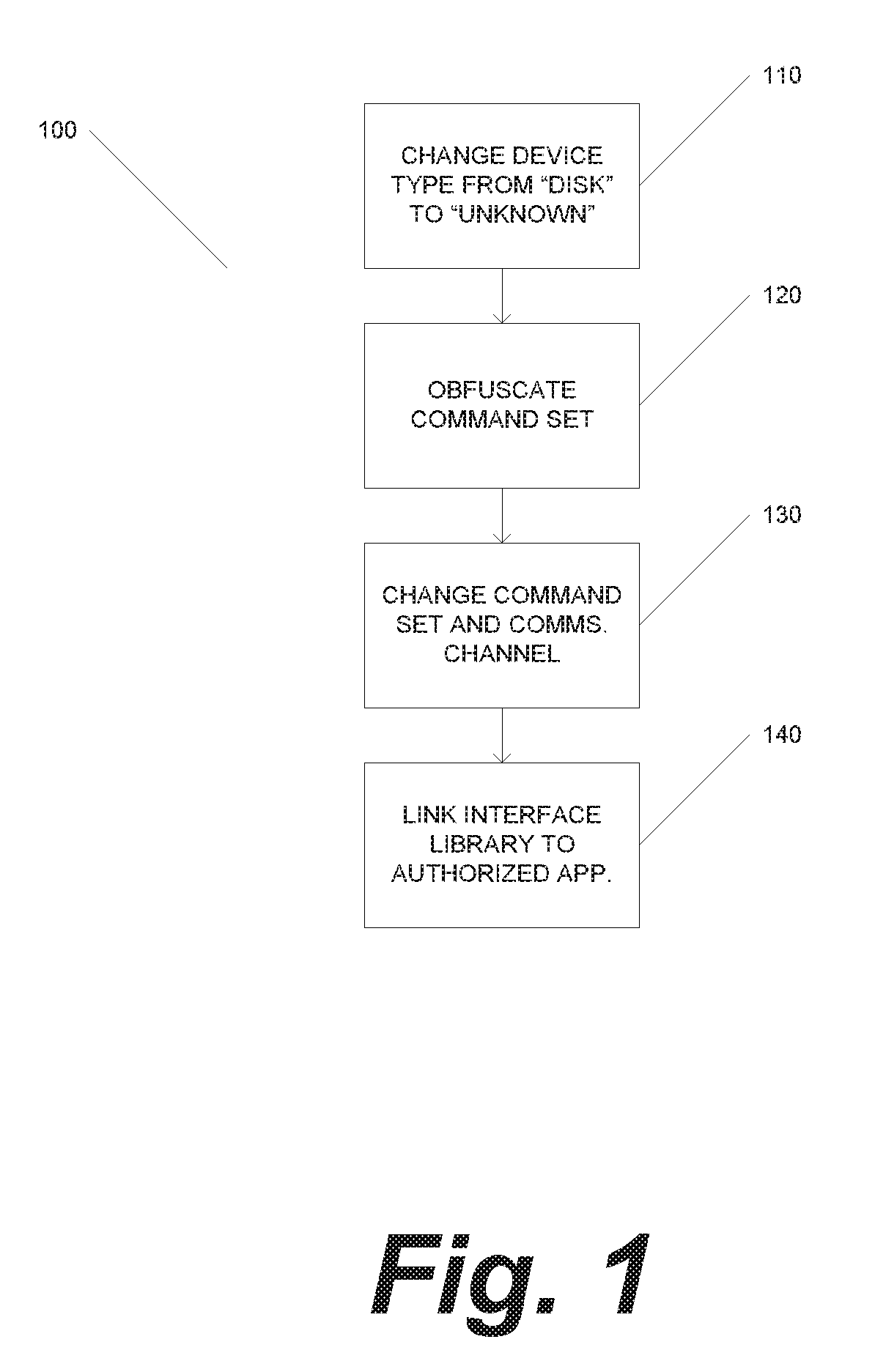
Moving target defenses for data storage devices
ActiveUS20190042742A1Internal/peripheral component protectionPlatform integrity maintainanceData virtualizationNetwork virtualization
Systems and methods for actively securing data storage devices utilize the technique of storage virtualization. In embodiments, would-be cyberattackers are presented with many possible “ports” or “channels” by which to communicate over a network with a data storage device. Unknown to the attacker, at any given time, only one of these ports or channels is the “correct,” or “active,” port; all of the other ports are dummies that do not permit communication with the storage device. The active port is dynamically, randomly, and / or continually reconfigured, seriously impeding the ability of the attacker to access the data storage device through the active port.
Owner:NEXITECH INC
Decision method for dynamic network transformation under full information conditions and system thereof
InactiveCN109379322AEfficient analysisAccurately describe the offensive and defensive confrontation processData switching networksAttack strategyData mining
The invention belongs to the technical field of network safety and specifically relates to a decision method for dynamic network transformation under full information conditions and a system thereof.The decision method comprises the following steps: obtaining state transition probability according to the network state, an attack strategy and a defense strategy; using a game theory to describe gains of both sides of the offensive and defensive game during moving target defense; constructing a moving target defense model based on a Markov game in combination with the state transition probability; transforming the solution of the moving target defense model into an equivalent of a target function and obtaining an optimal moving target defense strategy. According to the method and the systemin the invention, the moving target defense model based on the Markov game is constructed according to the state transition probability and both the sides of the offensive and defensive game; furthermore, the optimal moving target defense strategy is obtained by solving so as to realize balance of network performance overheads and moving target defense gains and solve the technical problem of howto select the optimal defense strategy based on limited network resources.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
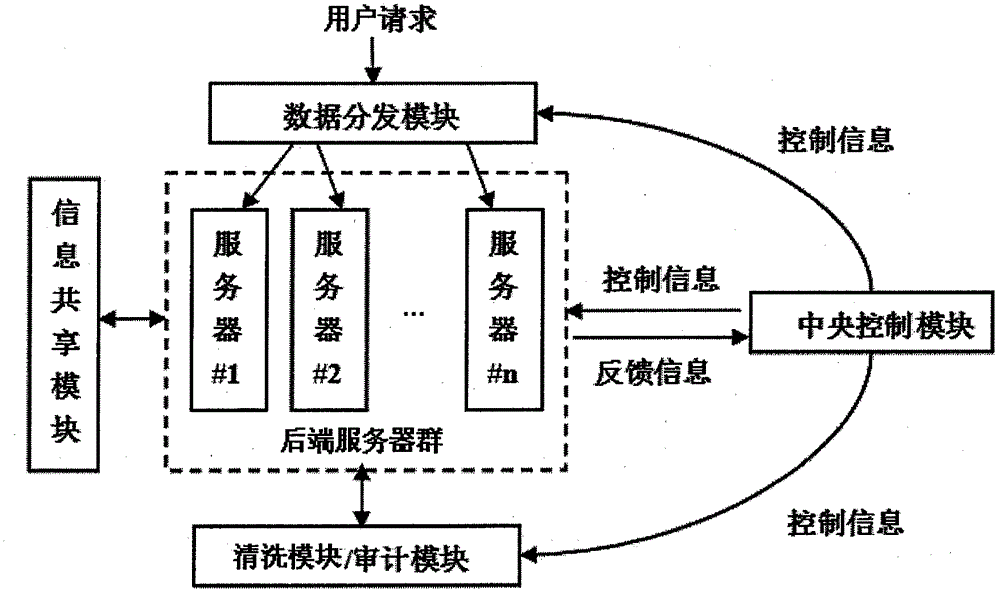
SCIT-based mobile target defensive system
The invention belongs to the technical field of internets, and discloses a SCIT-based mobile target defensive system. The system comprises a back-end server group, a data distribution module, a central control module, a cleaning module, an auditing module and an information sharing module; the central control module controls the data distribution module to forward an access request of a user to a server in the running state in the back-end server group to process, after a period of time, the central processor selects a clean server from the server group in a ready state according to a scheduling algorithm when the switching time arrives, the state of the clean server is switched to the running state, and the central processor notifies the data distribution module to forward the request from the user to the new server in the running state, and the primary server enters an offline cleaning state. The technical scheme disclosed by the invention is based on the switching and cleaning of the server, the critical infrastructure servers are mechanized to improve the security through the introduction of the diversity of the software and the randomness and the unpredictability of the system.
Owner:ANHUI XINHUA UNIV
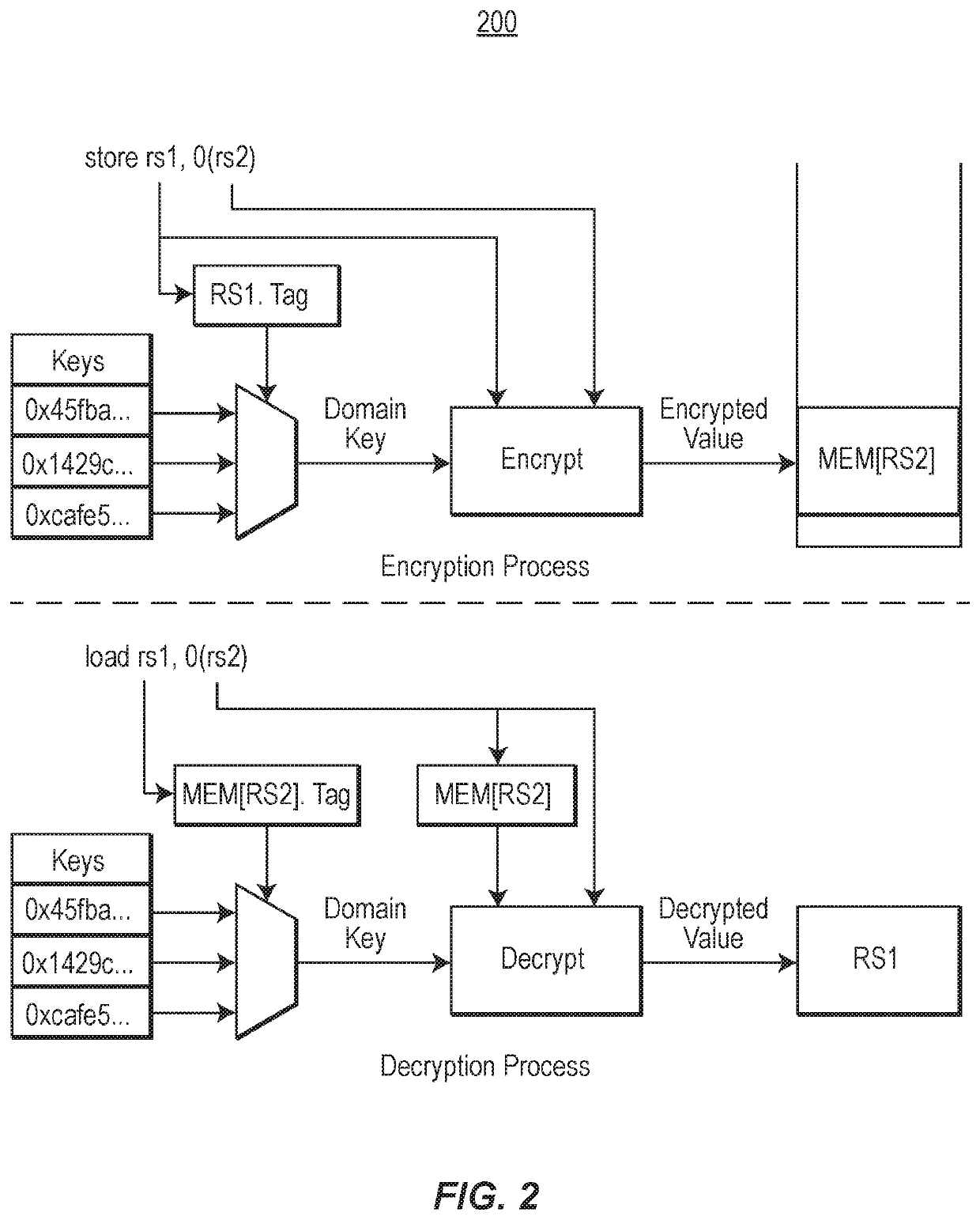
Computer system with moving target defenses against vulnerability attacks
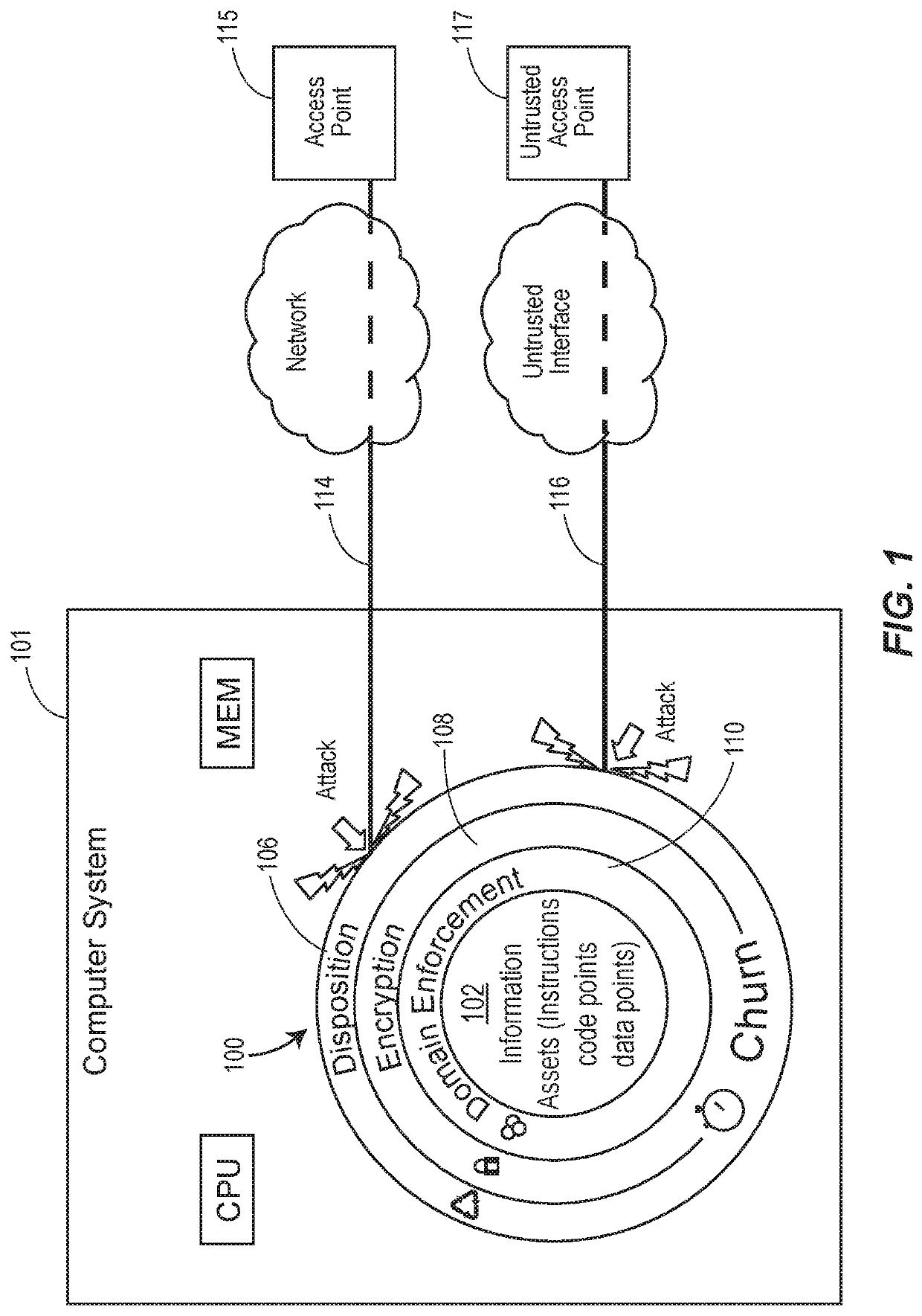
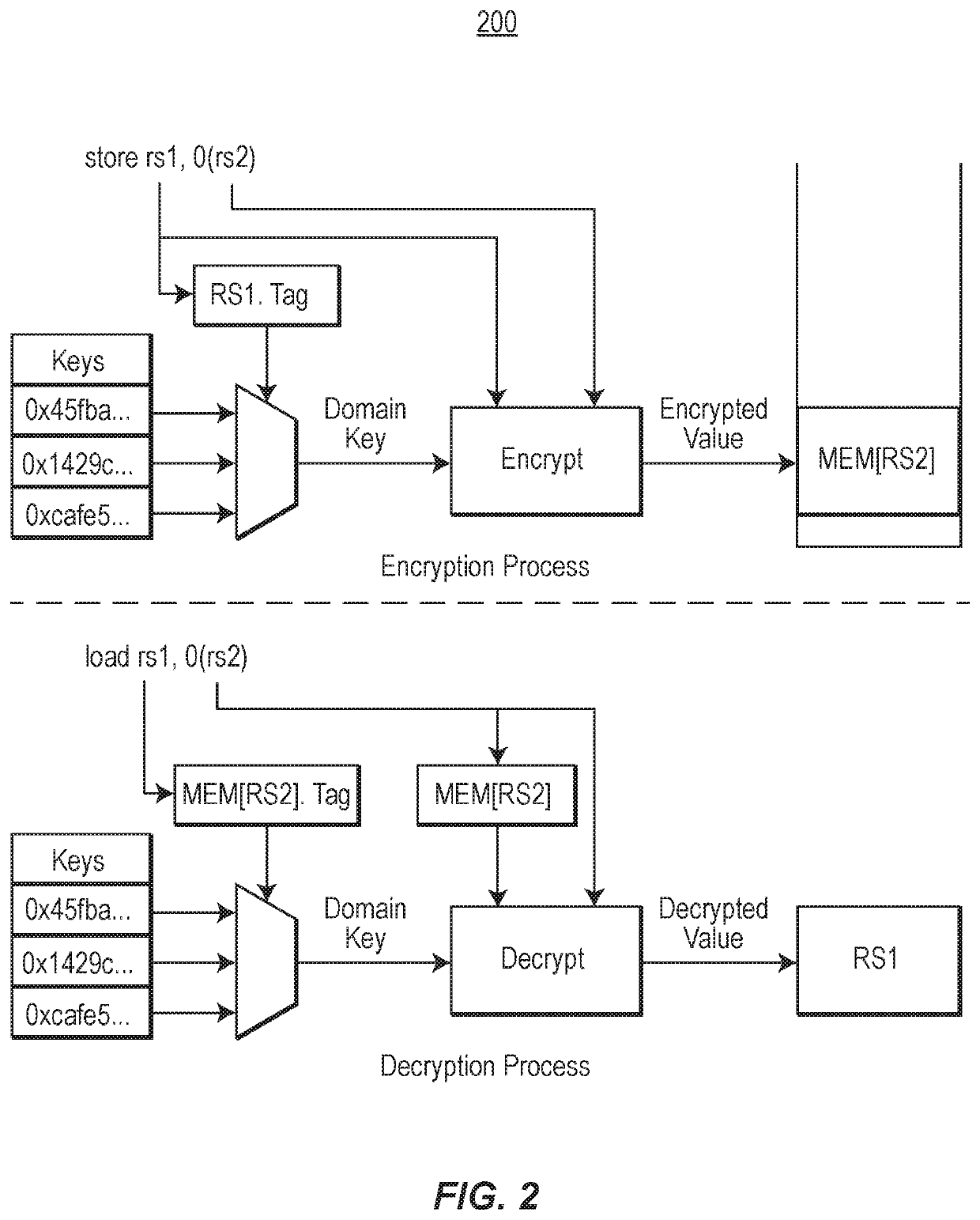
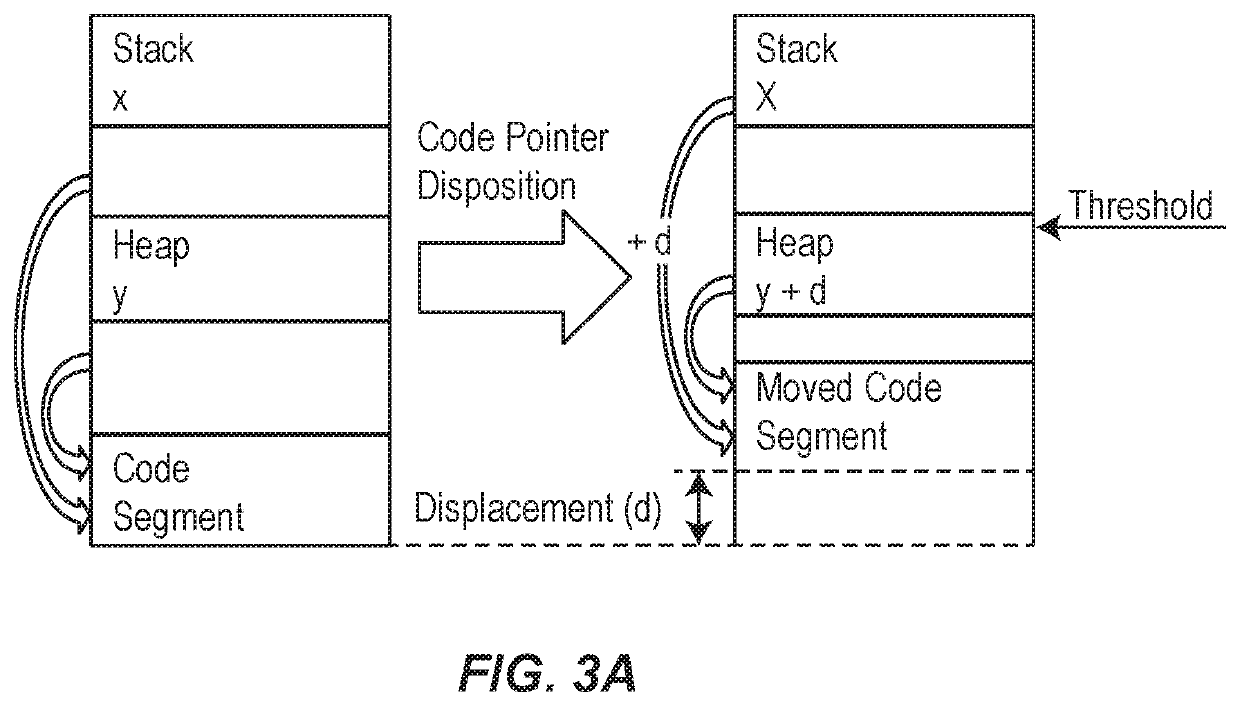
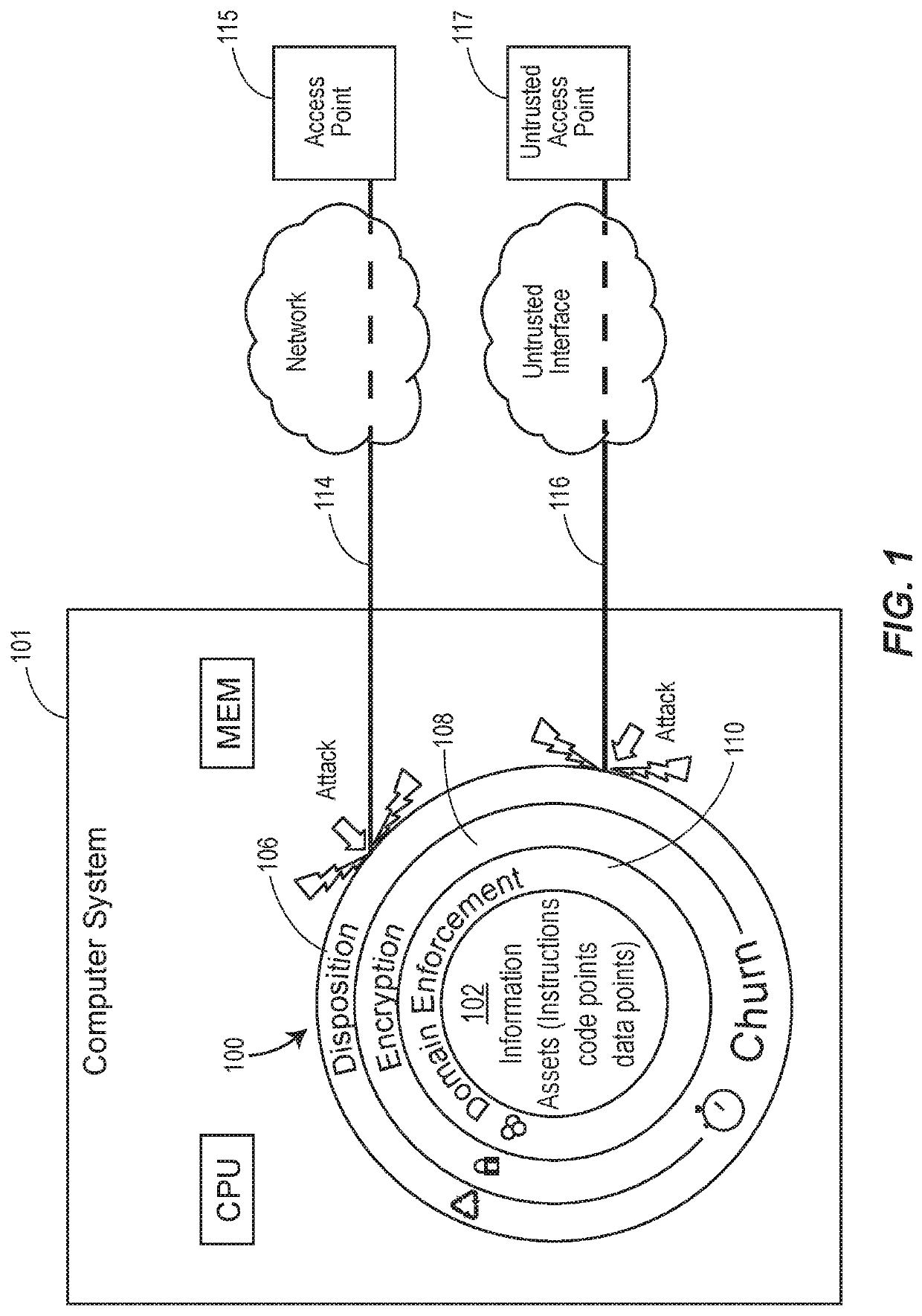
ActiveUS20200110884A1High protection levelImprove protectionKey distribution for secure communicationDigital data protectionAttackEngineering
A computer system includes an ensemble moving target defense architecture that protects the computer system against attack using a plurality of composable protection layers that change each churn cycle, thereby requiring an attacker to acquire information needed for an attack (e.g., code and pointers) and successfully deploy the attack, before the layers have changed state. Each layer may deploy a different attack information asset protection providing multiple different attack protections each churn cycle.
Owner:RGT UNIV OF MICHIGAN
Moving target defense response method guided by economic and security requirements
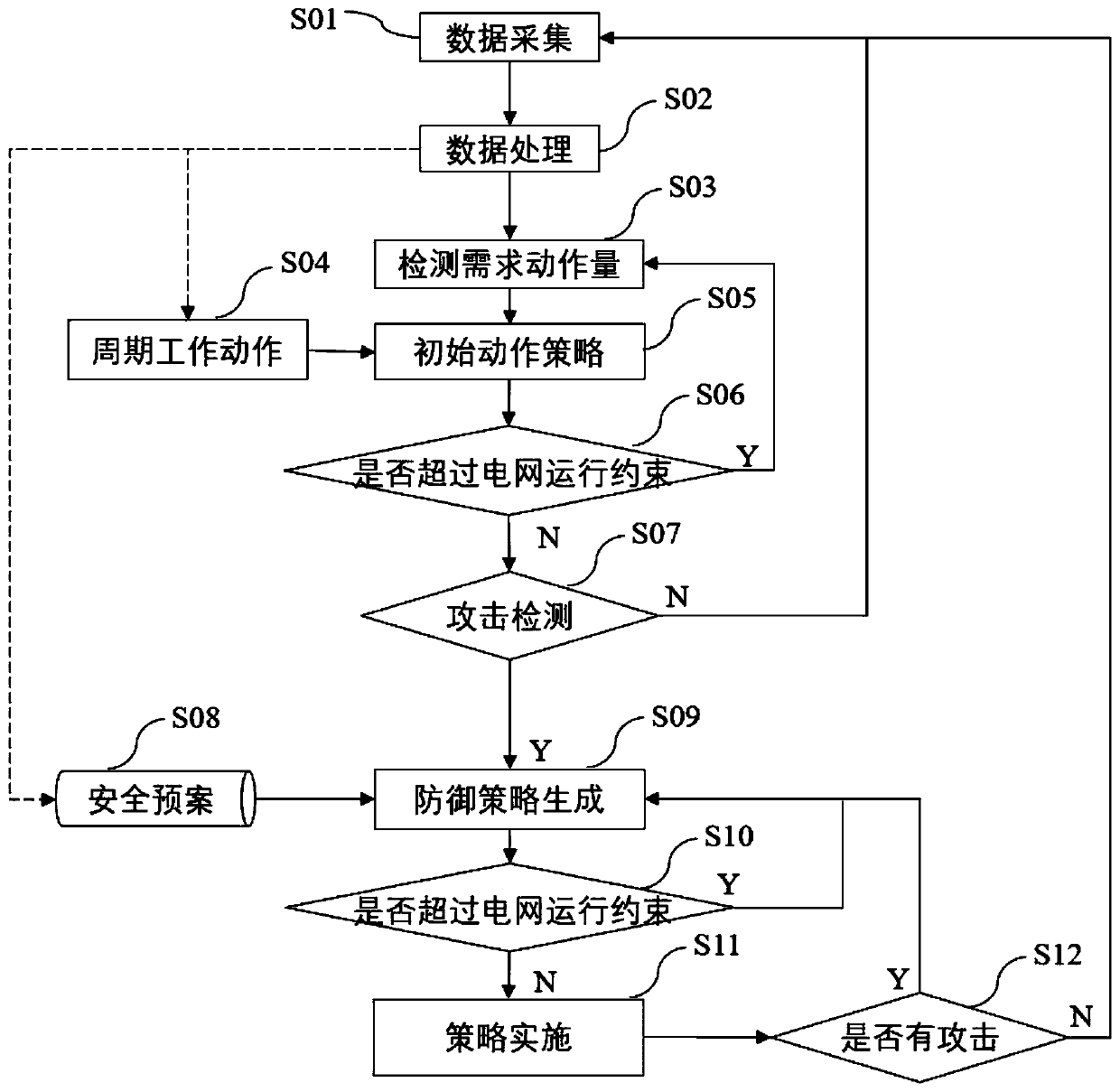
ActiveCN111262856AGuaranteed monitoring effectLower economic budgetData processing applicationsTransmissionPower flowAttack
The invention discloses a moving target defense response method guided by economic and security requirements. The method is characterized in that the method comprises the steps of S01 collecting maindata of a system; S02 preprocessing the acquired data; S03 detecting the required action quantity; S04 periodically working; S05 carrying out an initial action strategy; S06 checking a detection strategy; S07 detecting attack quantity; S08 carrying out a safety plan; S09 generating a defense strategy; S10 carrying out power grid operation constraint detection; S11 implementing a strategy; and S12carrying out attack quantity detection. According to the method, the security requirement is added into periodic power flow adjustment of the D-FACTS equipment due to the economic requirement of thepower grid; under the condition that the operation state of the power grid is not influenced, line parameters related to fragile nodes are properly changed to detect bad data; when abnormal data are detected, the D-FACTS equipment is enabled to enter a more comprehensive and larger-amplitude response state according to the safety plan; and whether FDI attacks exist in the system can be rapidly andeffectively judged on the premise of ensuring economy.
Owner:STATE GRID SHAANXI ELECTRIC POWER RES INST +2
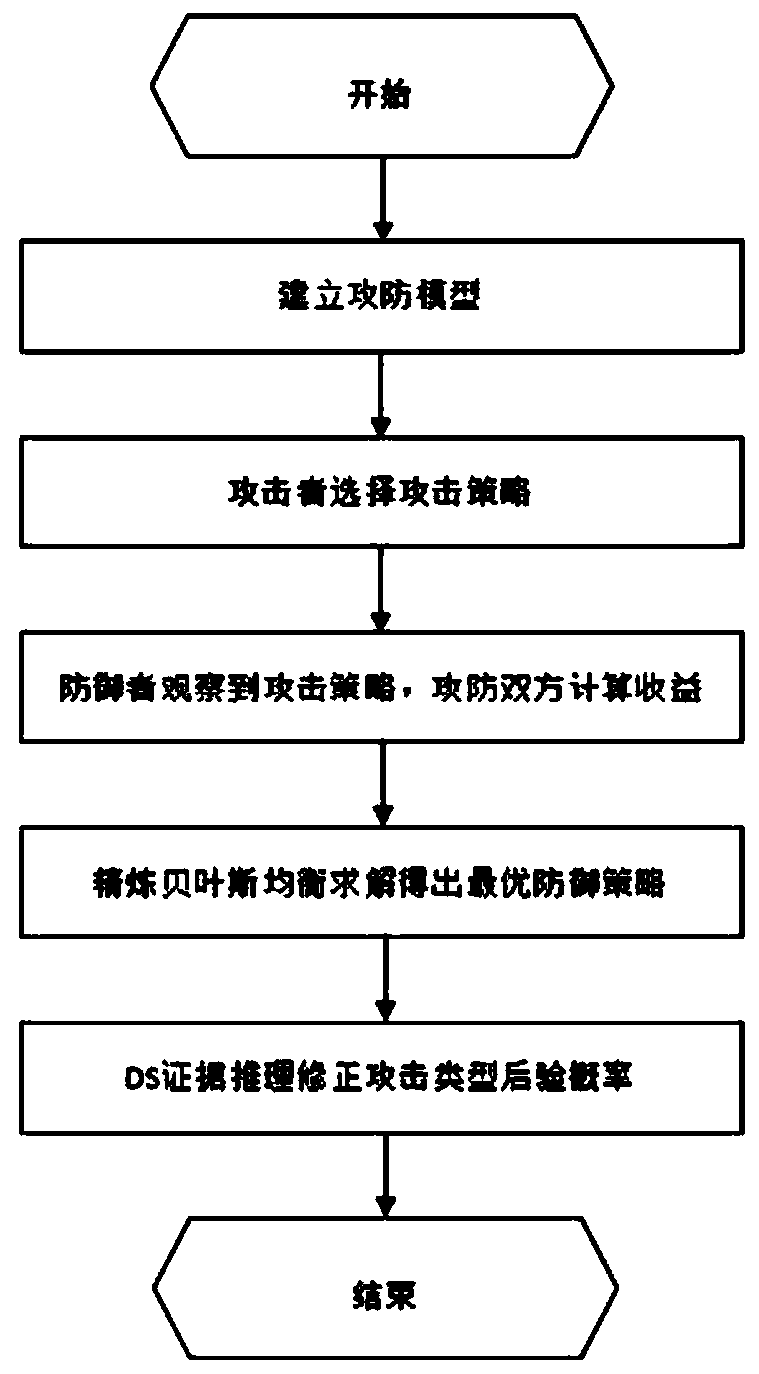
Method for selecting moving target defense optimal strategy based on DS evidence reasoning
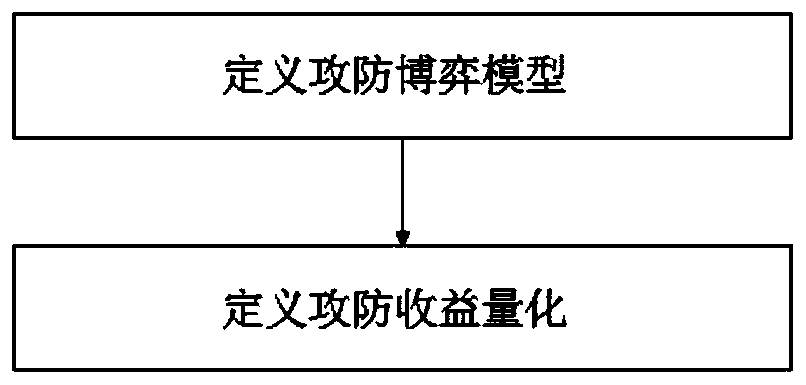
ActiveCN110166437AReasonable defense success rateDefense success rate increasedData switching networksEvidence reasoningDecision table
The invention discloses a method for selecting a moving target defense optimal strategy based on DS evidence reasoning. The method comprises the following steps: establishing an attack and defense game model; enabling an attacker to select an attack strategy; enabling a defender to observe the attack strategy, and enabling the attacker and the defender to calculate benefits; refining Bayesian equilibrium solution to obtain an optimal defense strategy; and enabling the defender to correct the type posterior probability of the attacker through DS evidence reasoning. The establishment of the attack and defense game model comprises the steps of defining the attack and defense game model; defining attack and defense revenue quantification. The income calculation step of the attacker and the defender comprises the steps that the defender calculates a posterior probability according to an observed attack strategy; the attacking and defending parties calculate respective revenues; an attack type reasoning decision table is formed according to the characteristic attributes of the previous attack records; and a basic probability assignment of the attack evidence is determined according to the decision table. According to the method, the defect of the prior probability in the existing model is overcome, the profit of the defense strategy is more reasonable, and the defense success rate ofthe early stage of the system is improved.
Owner:HANGZHOU DIANZI UNIV
IPv6 address hopping active defense method based on a sliding time window
ActiveCN108540461ADisruptive snoopingDisturbance analysisData switching networksSliding time windowEvent trigger
The invention relates to an IPv6 address hopping active defense method based on a sliding time window. A communication process based on IPv6 address hopping is executed on the basis of the negotiationof parameters such as sliding window size, hopping interval and the like between an IPv6 communication initiator and an IPv6 communication receiver. A time window adaptive adjustment algorithm is introduced, so that communication between IPv6 nodes presents the characteristics of randomization and dynamics, and can adapt to more complex network environments. Specific to the problems of high synchronization delay, difficulty in event triggering and low communication efficiency in an IPv6 network node address hopping process, the IPv6 address hopping active defense method based on the sliding time window is proposed according to a mobile target defense technical thought, thereby ensuring the overall efficiency of communication between end nodes, increasing the cost of attacker detection, and improve the security of IPv6 internode communication.
Owner:深圳市零伍贰陆科技有限公司
Network security vulnerability defense system based on dynamic camouflage
ActiveCN111835694ABreak the knowledge accumulation of loopholesMonitor communicationTransmissionHigh level techniquesInternet privacyEngineering
The invention provides a network security vulnerability defense system based on dynamic camouflage. According to basic technical idea of the system, a network dynamic environment is constructed basedon the concept of moving target defense, a large number of dynamic false hosts is constructed around a protected host by using a network spoofing technology, and a dynamic false vulnerability libraryis constructed to trap attackers; in addition, for a real host, a plurality of false vulnerability libraries can be randomly and dynamically generated for the real host. No matter a hacker performs vulnerability scanning on the target host by using a known or unknown vulnerability scanning tool, a false vulnerability in the virtual or real host is touched inescapably, an alarm of a defense systemcan be triggered when the false vulnerability is detected and utilized, and the defense system can automatically position an attacker in real time and cut off a first loop of a network attack chain, so that beforehand defense is realized and the threat of an unknown vulnerability is effectively reduced.
Owner:张长河
Moving target defense dynamic response strategy generation method based on abnormal traffic
ActiveCN111162531ALittle impact on operationTroubleshoot Dynamic Response StrategiesAc network circuit arrangementsData acquisitionPower grid
The invention provides a moving target defense dynamic response strategy generation method based on abnormal flow, and the method is specifically characterized in that the method comprises the steps:S01, data collection; S02, data processing; S03, node state estimation; S04, abnormal node detection; S05, inputting abnormal node data; S06, calculation of the adjustment capability of each line fordifferent nodes; S07, generation of a defense strategy; S08, checking of the defense strategy for the first time; S09, secondary inspection on the defense strategy; and S10, defense strategy output. For FDI attack, the detection capability of each line on abnormal data of different nodes is analyzed after deploying flexible alternating current transmission equipment (D-FACTS) equipment, accordingto the method, the real-time abnormal condition of the node flow is taken as the configuration weight of the detection capability, the dynamic configuration strategy which has the strongest detectioncapability on the current abnormal flow node data and has the minimum FACTS adjustment on the power grid operation is constructed, and the problem of the dynamic response strategy when the MTD technology is used for detecting the FDI attack is solved.
Owner:STATE GRID SHAANXI ELECTRIC POWER RES INST +2
Moving target defense method based on Internet of Things DDoS attack
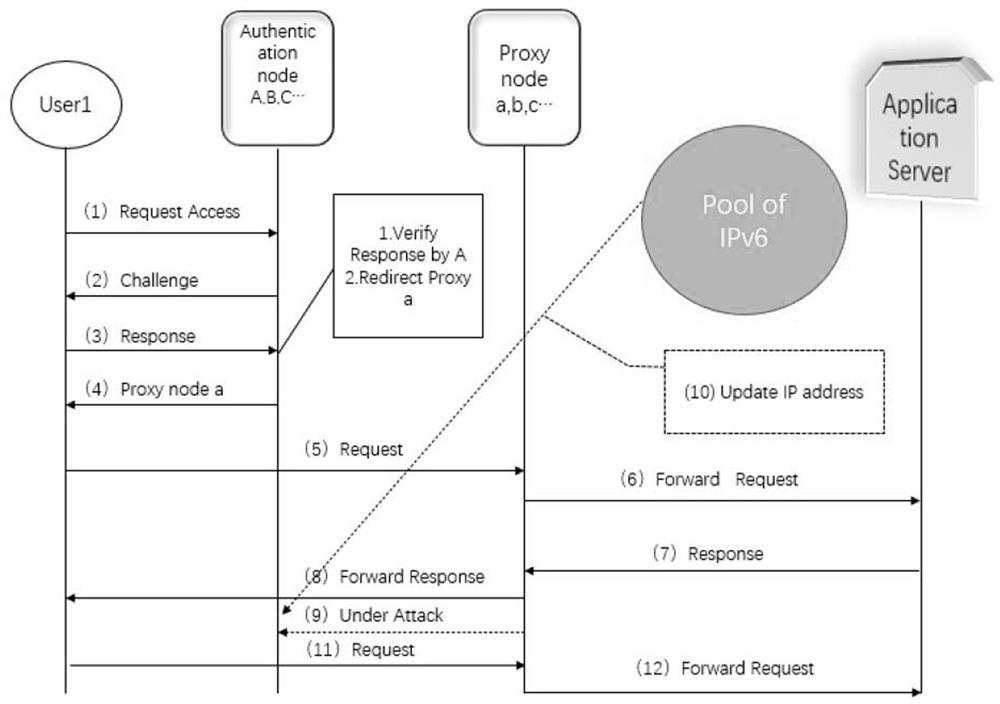
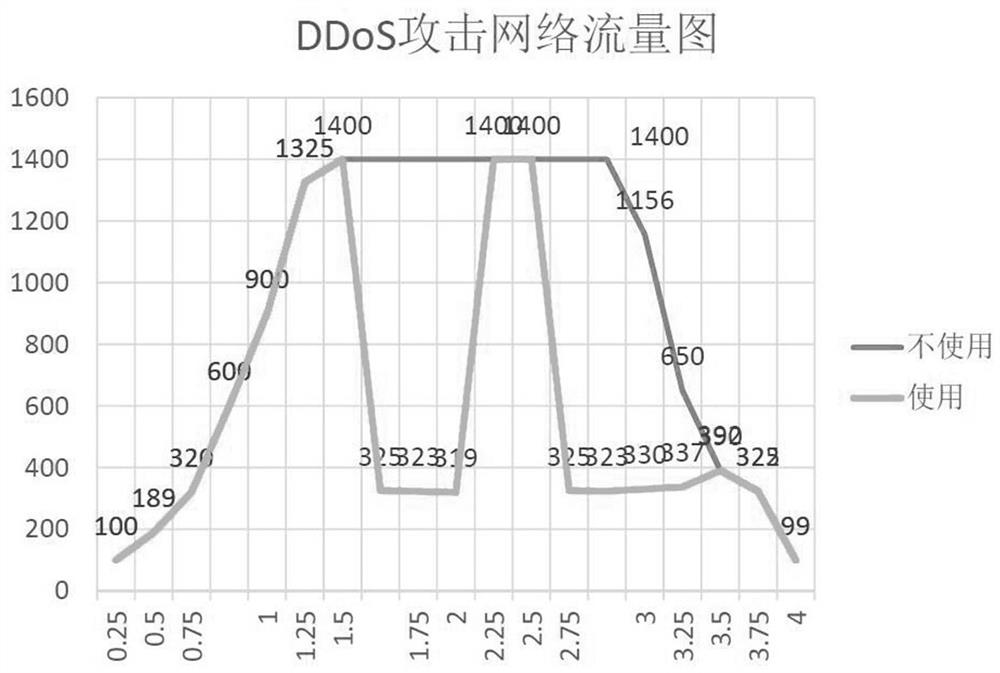
ActiveCN113206858AEasy accessEnsure normal communicationTransmissionSecurity arrangementNetwork connectionAttack
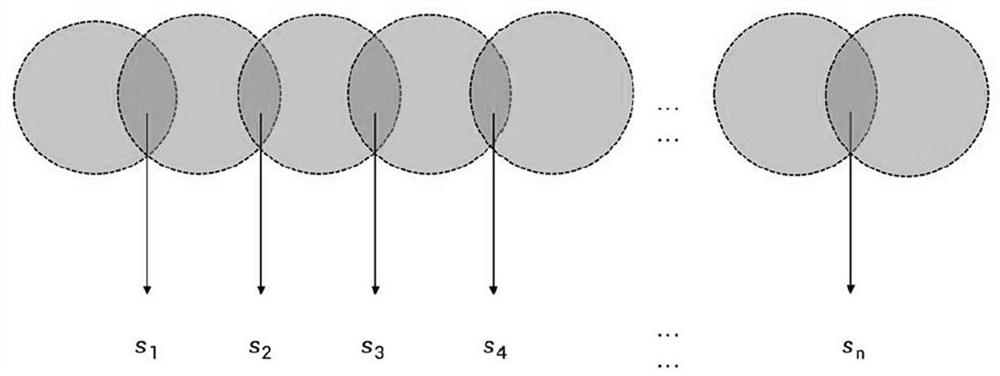
The invention provides a mobile target defense method based on an internet of things DDoS attack, and the method comprises the following steps: 1), deploying agent nodes which comprise an identity authentication node and a relay forwarding node; 2) deploying and operating a DDoS detection function at the proxy node; 3) under the condition of no DDoS attack, when a user client sends an access request, verifying the legality of the user, if the verification is passed, executing a jump protocol, jumping network connection to a relay forwarding node, and completing the access of the user to the server; 4) if the DDoS attack is detected, encrypting and switching the IPv6 addresses of all proxy nodes, and writing the encrypted IPv6 address of the identity authentication node into a domain name resolution system; 5) the identity authentication node executes a specific identity authentication method to exclude Internet of Things equipment, and 6) the real identity of an attacker is determined through the intersection of multiple times of login information. The Internet of Things DDoS attack can be resisted, and the real identity of the attacker can be determined.
Owner:NANJING UNIV OF POSTS & TELECOMM
Communication method, device and equipment and storage medium
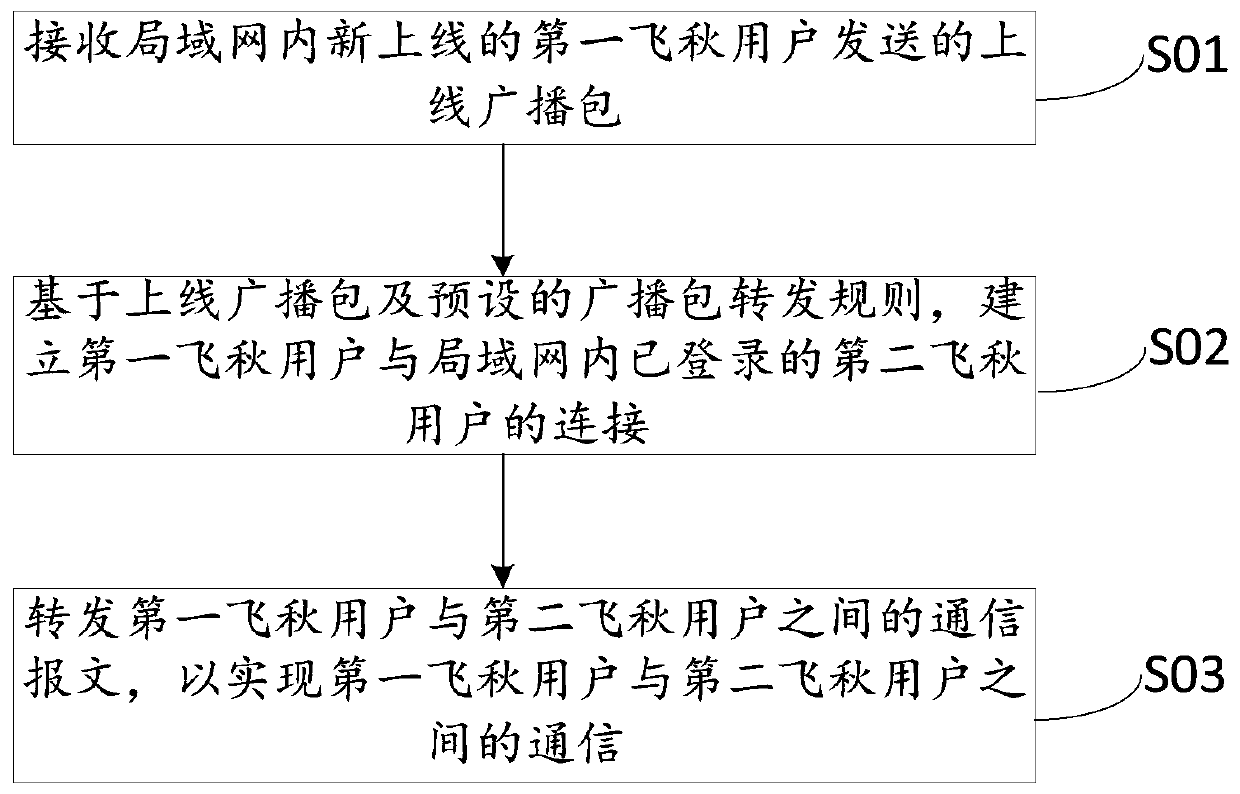
ActiveCN111405560ARealize communicationAssess restrictionConnection managementBroadcast packetTelecommunications
One or more embodiments of the invention provide a communication method, device and equipment, and a storage medium. The method comprises the steps of receiving an online broadcast packet sent by a newly online first flying autumn user in a local area network; wherein the local area network is a local area network based on mobile target defense; establishing connection between the first flying autumn user and a second flying autumn user logged in the local area network based on the online broadcast packet and a preset broadcast packet forwarding rule; and forwarding the communication message between the first flying autumn user and the second flying autumn user to realize communication between the first flying autumn user and the second flying autumn user; according to broadcast packets forwarding rules, sending the online broadcast packet of the first flying autumn user to other logged-in flying autumn users in the local area network to establish connection between the flying autumn users in the local area network based on the mobile target defense, and finally realizing communication between the flying autumn users, so that the local area network based on the mobile target defense can be compatible with local area network communication software.
Owner:BEIJING UNIV OF POSTS & TELECOMM +1
Autonomous elastic cloud system management method
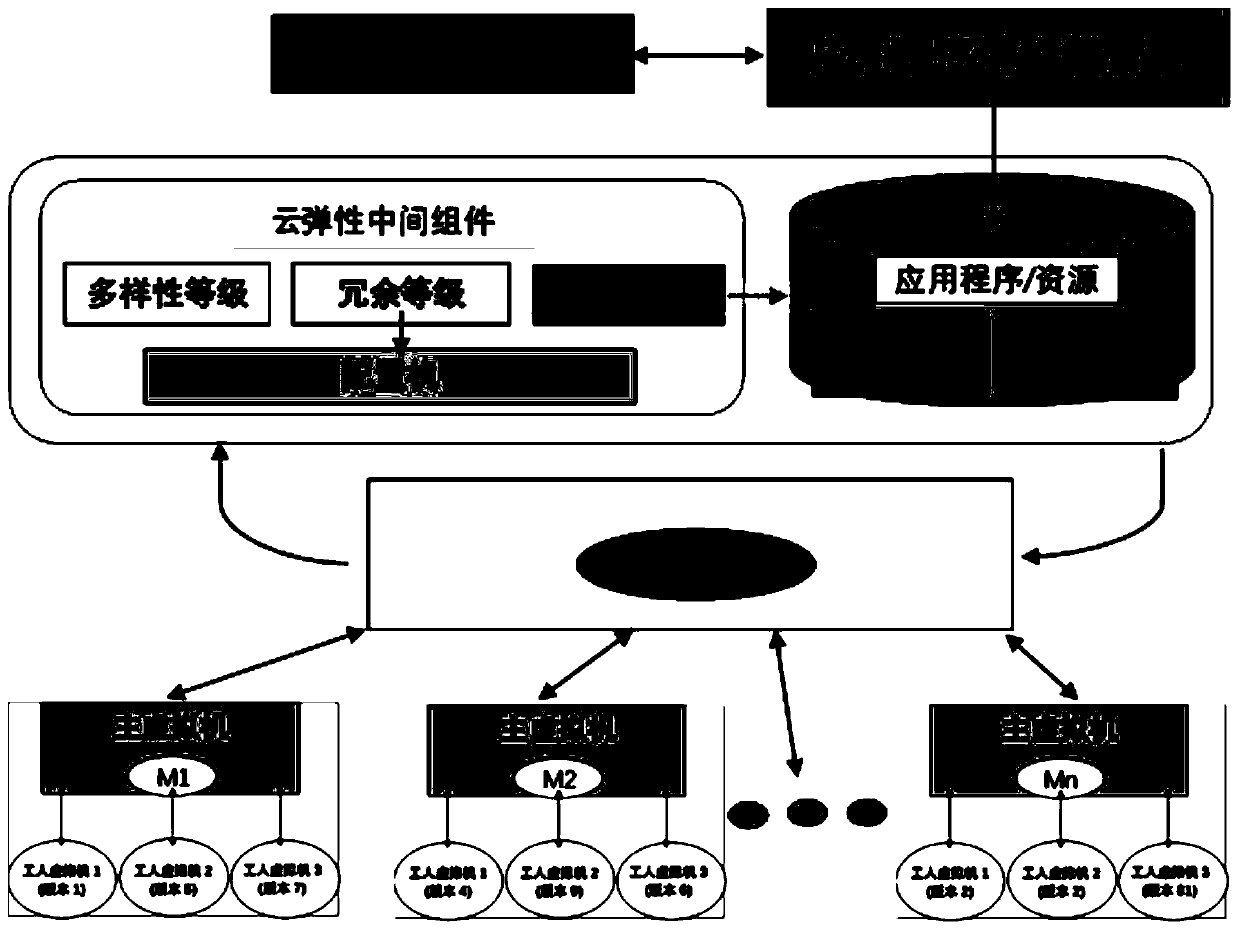
The invention discloses an autonomous elastic cloud system management method. The method comprises four modules, namely an application program elastic editor, a cloud elastic intermediate component, asupervised virtual machine and a main virtual machine. By continuously and randomly changing the cloud execution environment and the platform type, especially an internal attacker, the current execution environment and vulnerabilities existing in the current execution environment are difficult to find, so that the system can escape from attacks. According to the cloud service behavior fuzzy algorithm, the space-time behavior confusion and moving target defense are utilized, so that the active computing nodes and the internal resources thereof of the system are continuously changed, and therefore, attackers are avoided. In addition, diversity is achieved by using different execution of each software component, and the ARCM method is adopted, so that the normal operation of the cloud application program is difficult to interrupt by attacks. The dynamic changes in the execution environment can effectively hide potential vulnerabilities of the system, and an automatic management algorithmis adopted to provide a dynamically changing configuration capability and hide a cloud execution environment.
Owner:基本立子(北京)科技发展有限公司
Computer system with moving target defenses against vulnerability attacks
ActiveUS11232212B2High protection levelImprove protectionKey distribution for secure communicationDigital data protectionAttackEngineering
A computer system includes an ensemble moving target defense architecture that protects the computer system against attack using a plurality of composable protection layers that change each churn cycle, thereby requiring an attacker to acquire information needed for an attack (e.g., code and pointers) and successfully deploy the attack, before the layers have changed state. Each layer may deploy a different attack information asset protection providing multiple different attack protections each churn cycle.
Owner:RGT UNIV OF MICHIGAN
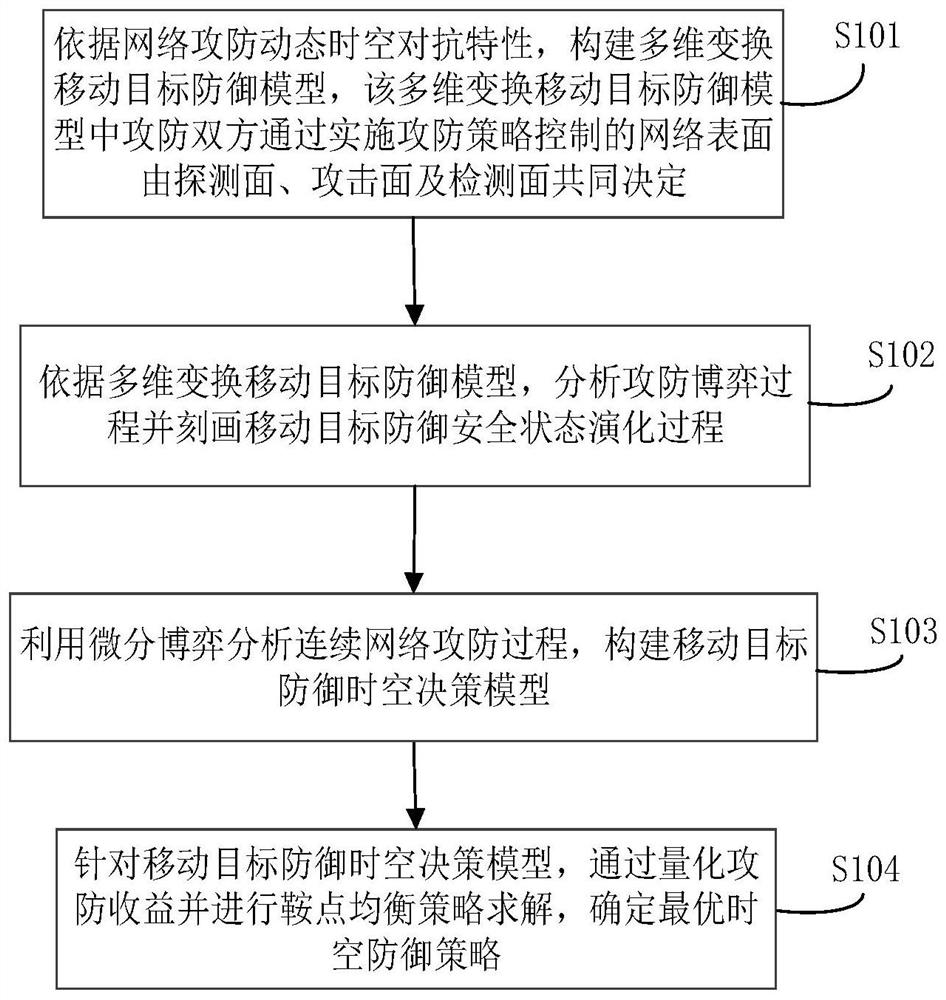
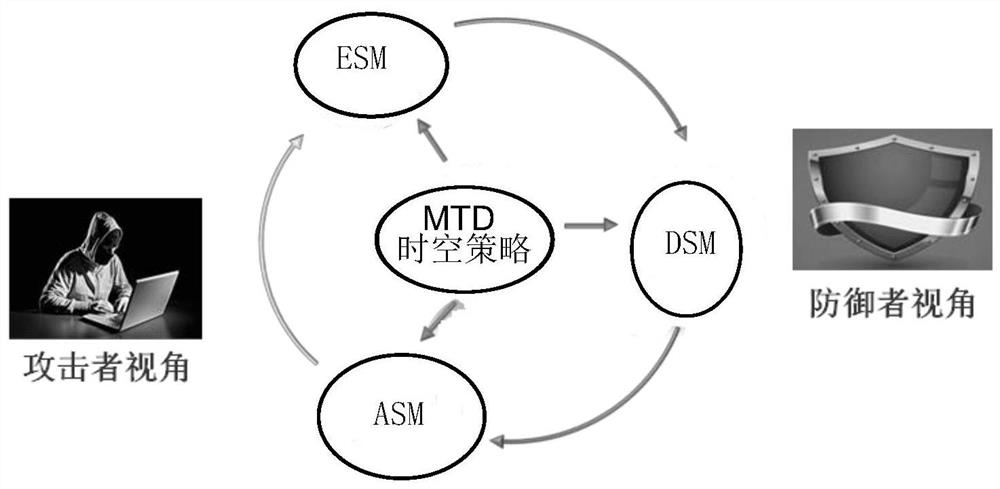
Network security dynamic defense decision-making method based on space-time game
ActiveCN112003854AImprove targetingImprove continuous decision-making abilityMachine learningTransmissionSimulationNetwork attack
The invention belongs to the technical field of network security, and relates to a network security dynamic defense decision-making method based on space-time game. The network security dynamic defense decision-making method comprises the steps of: constructing a multi-dimensional transformation moving target defense model according to network attack and defense dynamic space-time confrontation characteristics, wherein an attack party and a defense party in the multi-dimensional transformation moving target defense model are jointly determined by a detection surface, an attack surface and a detection surface through a network surface for implementing attack and defense strategy control; according to the multi-dimensional transformation moving target defense model, analyzing an attack and defense game process and describing a moving target defense security state evolution process; analyzing a continuous network attack and defense process by utilizing differential game, and constructinga moving target defense space-time decision-making model; and for the moving target defense space-time decision-making model, determining an optimal space-time defense strategy by quantifying attack and defense benefits and solving a saddle point equalization strategy. Based on the game model, the defense decision considering a space strategy and a time strategy is realized, the pertinence and timeliness of the network security defense decision are enhanced, and the network security defense efficiency is improved.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com