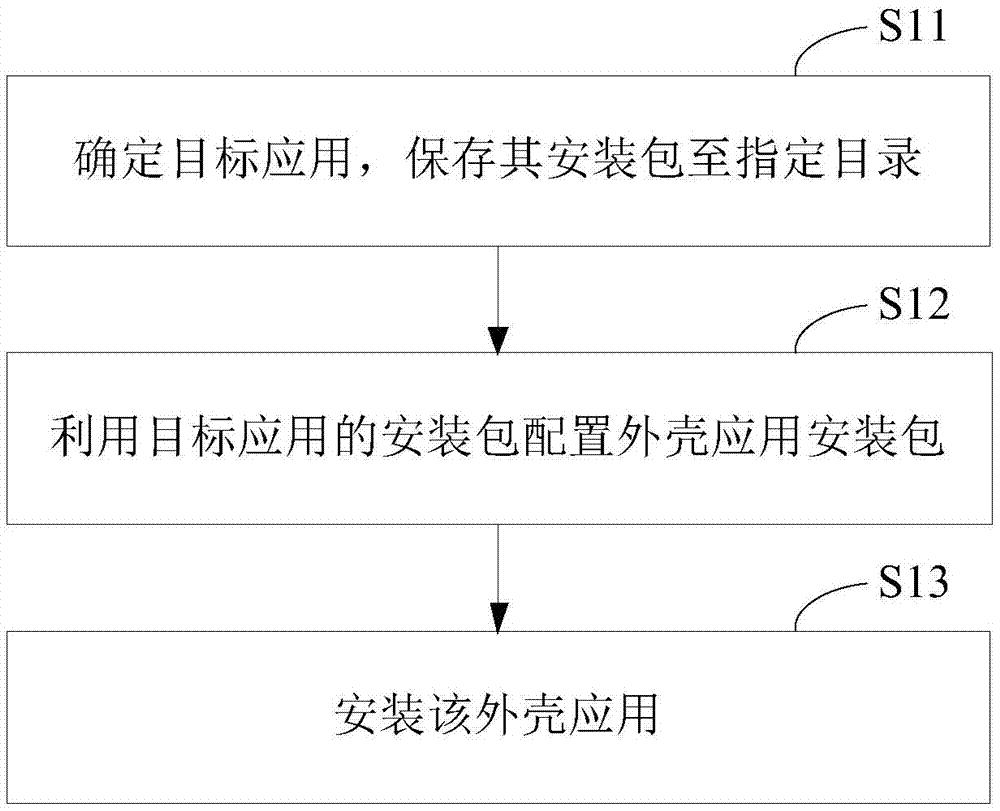
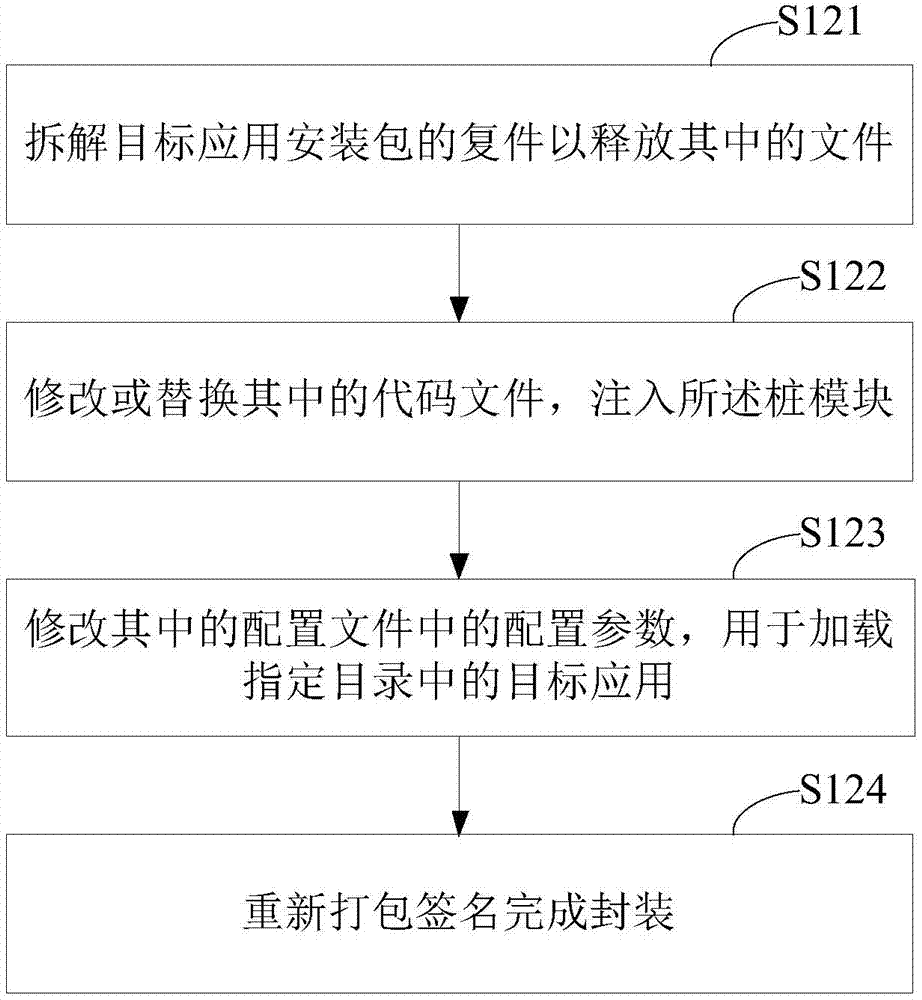
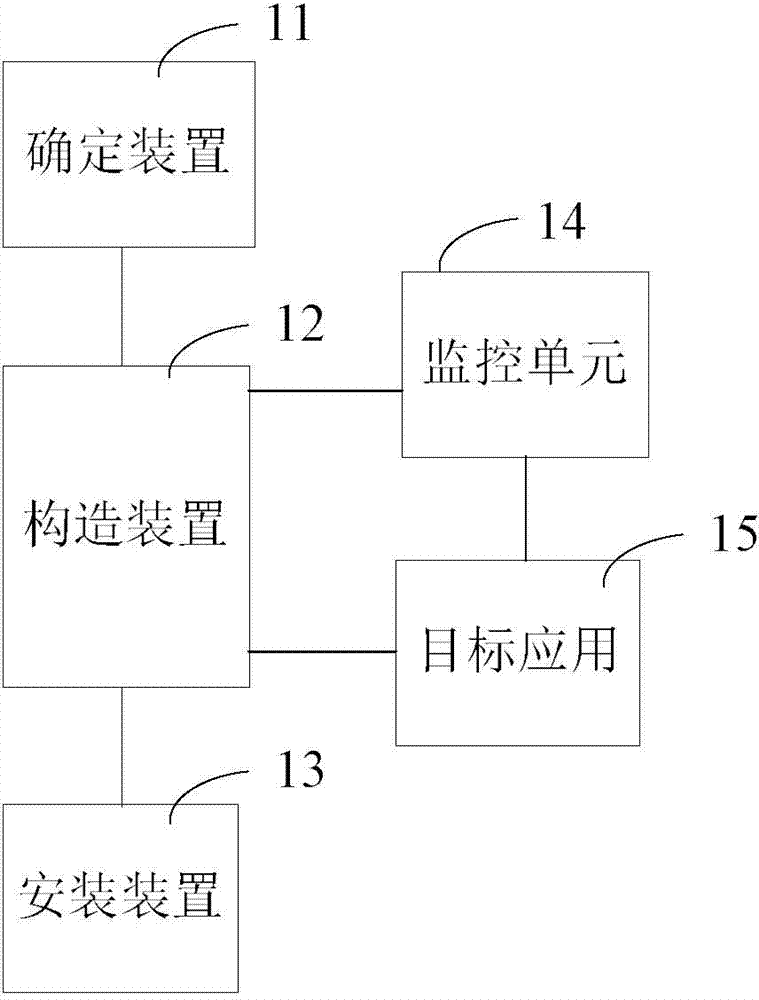
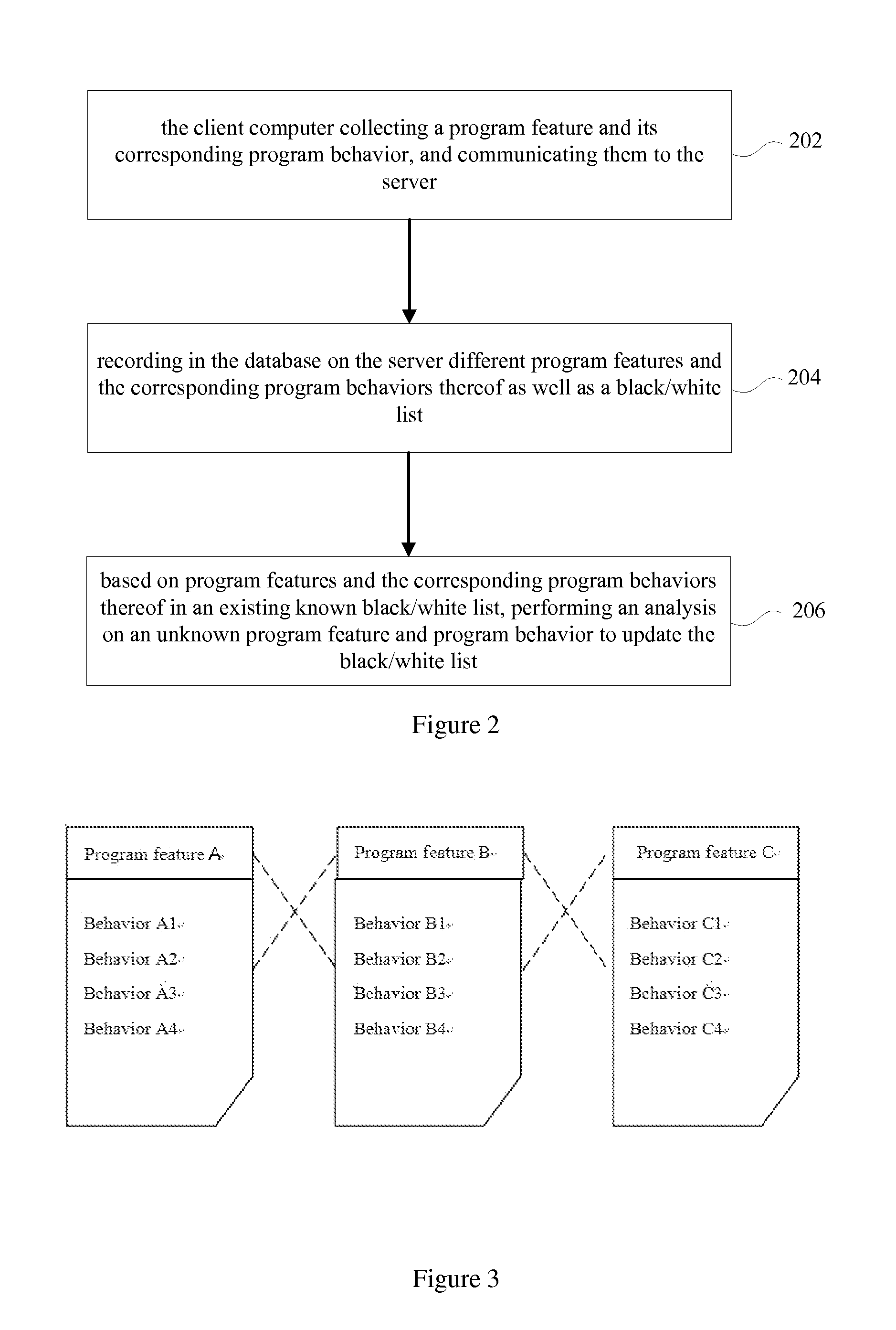
Patents
Literature
502 results about "Active Defense" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Active defense. The employment of limited offensive action and counterattacks to deny a contested area or position to the enemy. See also passive defense.
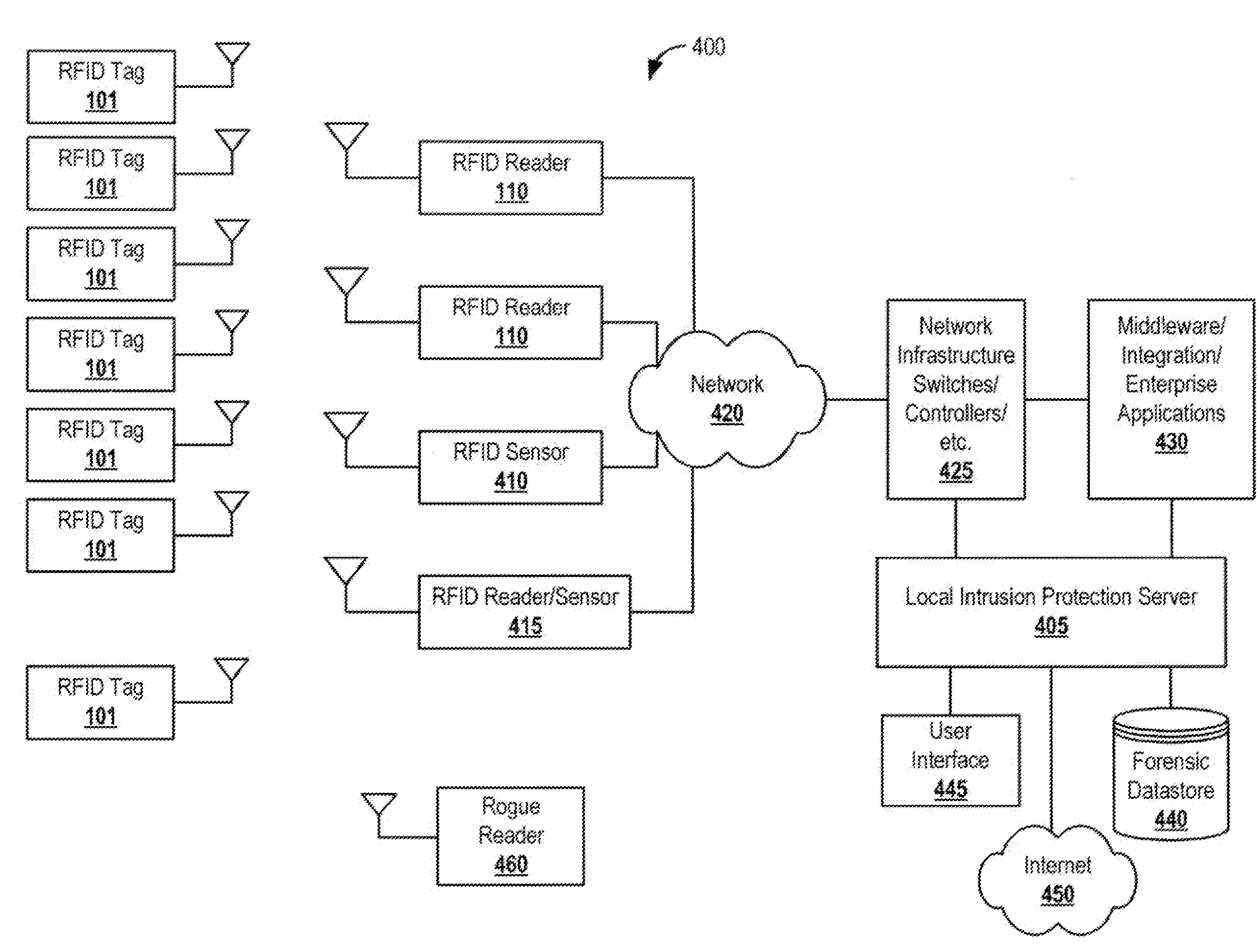
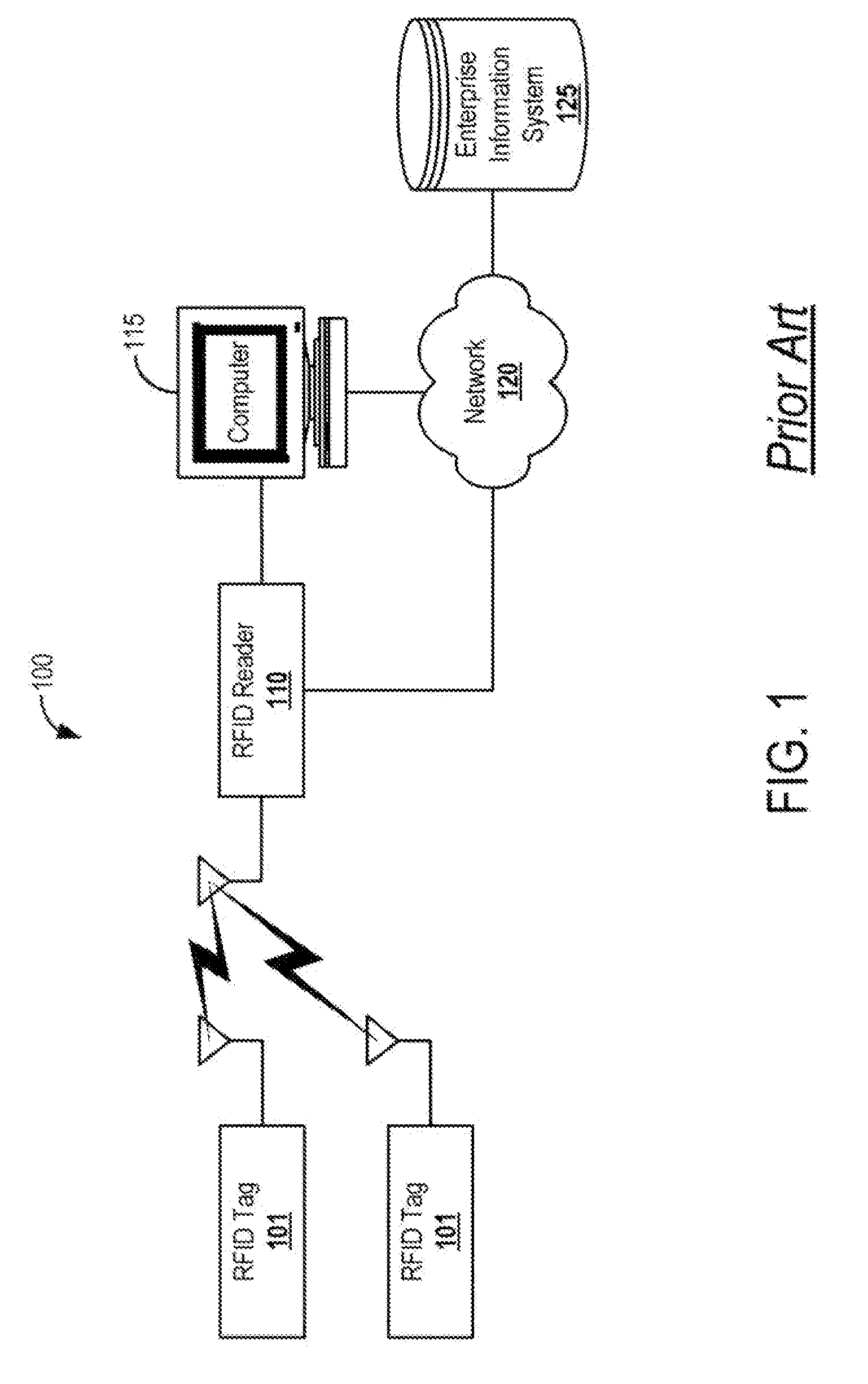
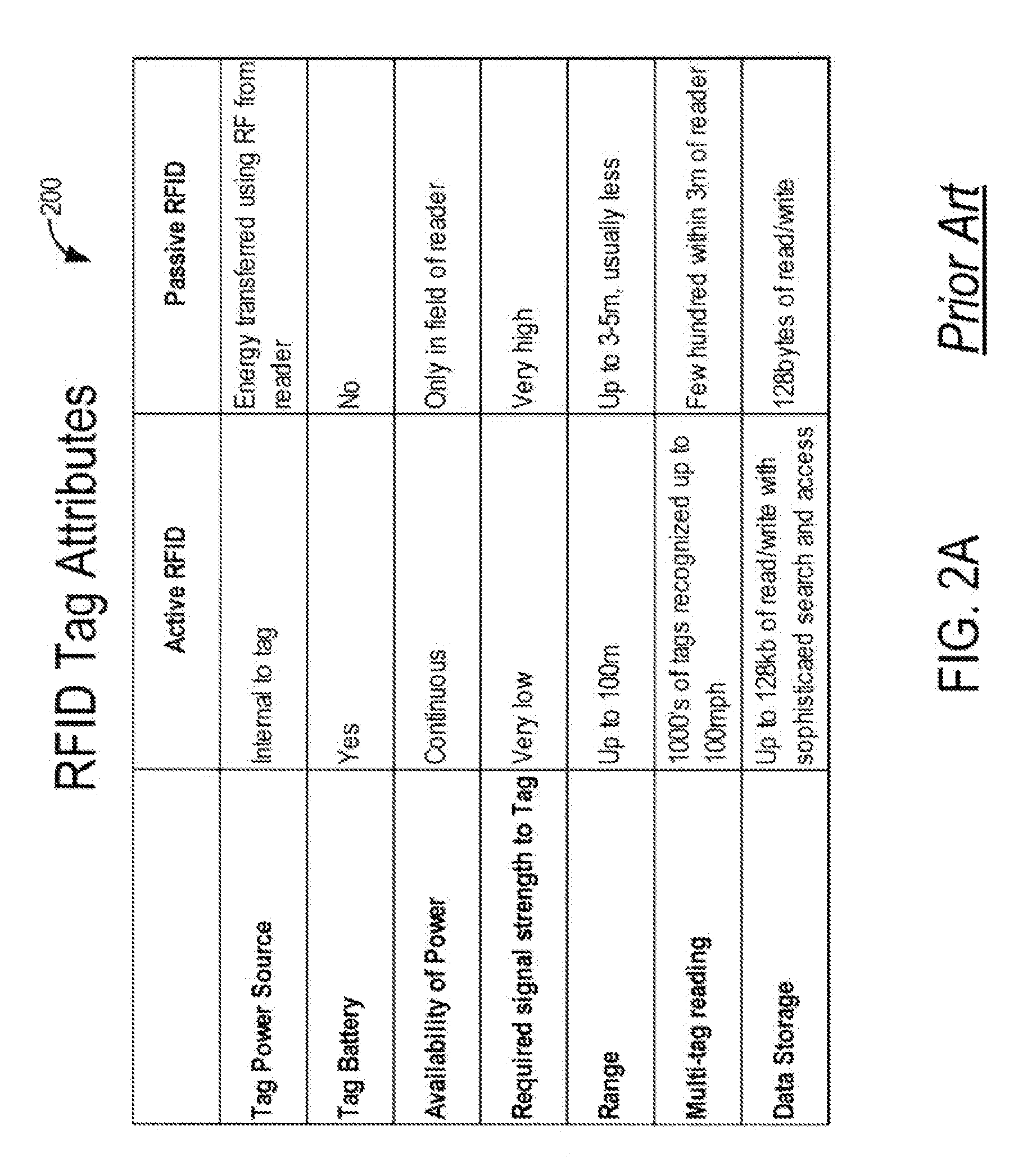
RFID Intrusion Protection System and Methods
InactiveUS20090021343A1Infiltrate the supply chainElectric signal transmission systemsMultiple keys/algorithms usageSystem usageProtection system
Systems and methods for RFID intrusion protection are defined. The system uses RFID sensors coupled with one or more servers to detect unauthorized scanning or programming of RFID tags. The system has active defense mechanisms to block unauthorized communications between a rogue RFID reader and one or more tags. Special IPS tags implement active defenses and log activity for tags that are not within the protected perimeter or in transit.
Owner:AIRDEFENSE INC
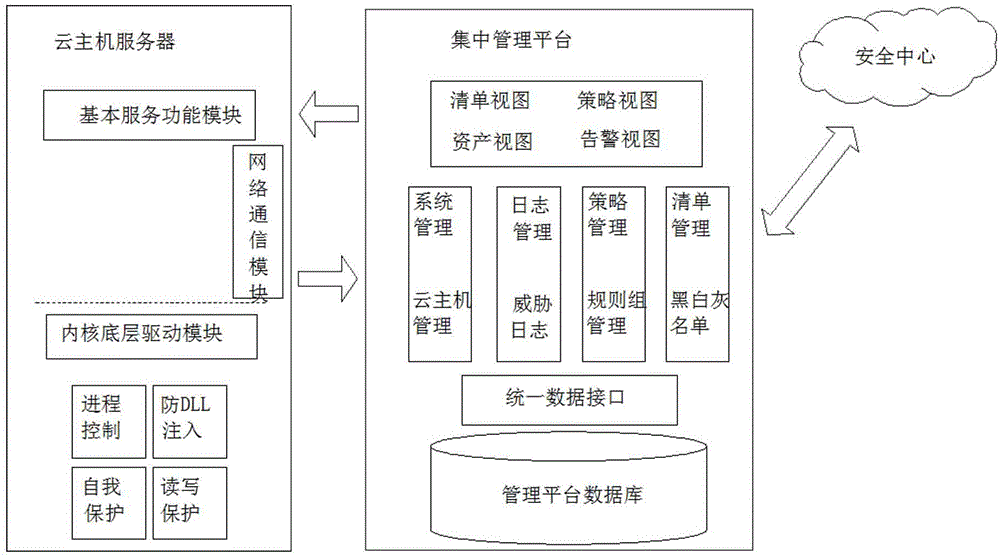
Active defense method based on cloud platform
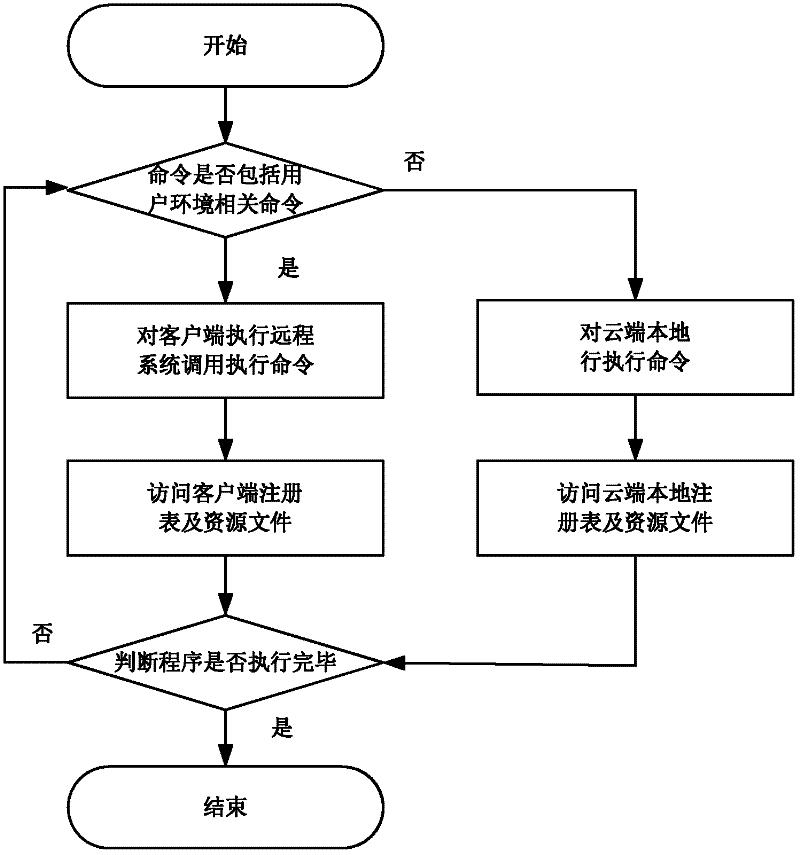
The invention discloses an active defense method based on a cloud platform. The active defense method comprises the following steps of: intercepting progress establishment by a client to acquire a program file route of a progress; calculating a characteristic value of a program file according to the program file route; judging whether the characteristic value of the program file exists in a local database; if the characteristic value of the program file does not exist in the local database, sending the characteristic value of the program file to a cloud end; judging whether the characteristic value of the program file exists in a database of the cloud end; if the characteristic value of the program file does not exist in the database of the cloud end, judging whether cloud end analysis is required to be performed on the program file; if the cloud end analysis is required to be performed on the program file, sending the program file to the cloud end; executing a command in the program file by the cloud end; judging whether the residual commands in the program file do not comprise commands related to a user environment; if the residual commands in the program file do not comprise commands related to the user environment, executing the residual commands; and detecting the security of the program file according to a behavior record of the program file, and returning a detection result back to the client.
Owner:HUAZHONG UNIV OF SCI & TECH
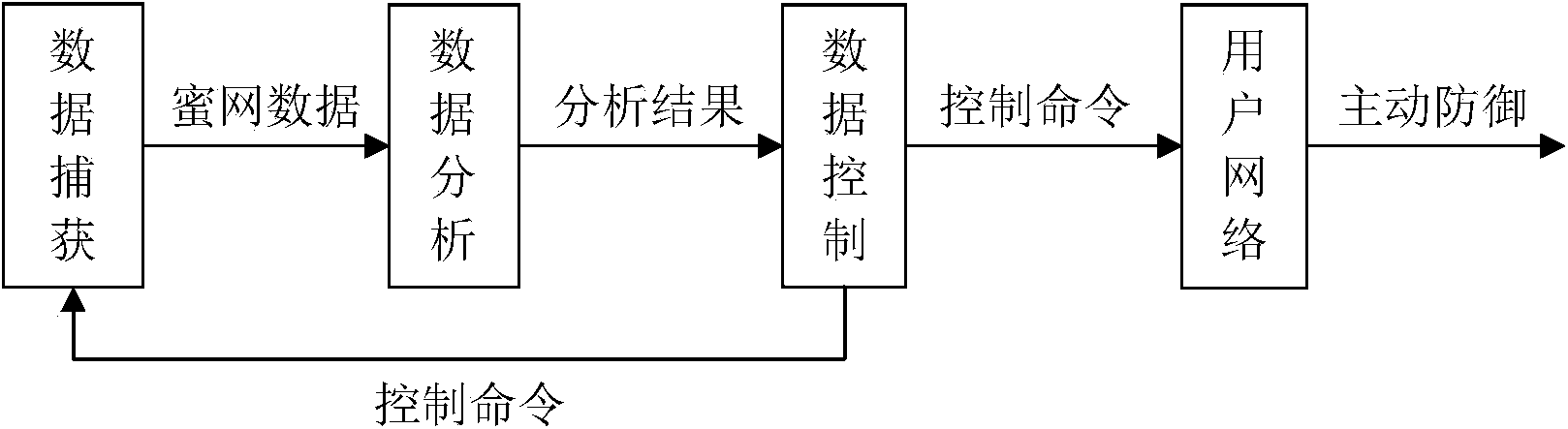
Cooperative type active defense system based on honey nets
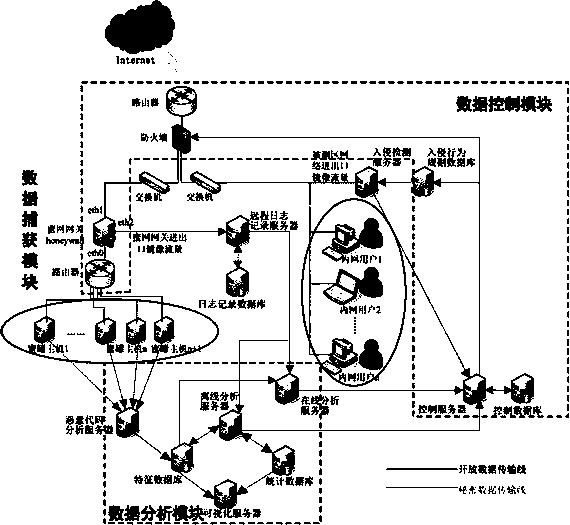
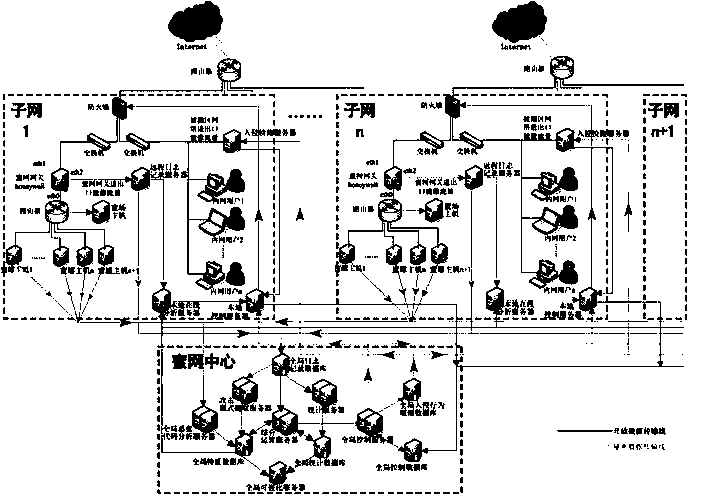
The invention provides a cooperative type active defense system based on honey nets. The cooperative type active defense system comprises a data capture module, a data analysis module and a data control module and is characterized in that the data capture module, the data analysis module and the data control module are arranged at the center of one honey net and a plurality of sub nets in a distributed mode. The cooperative type active defense system depends on a honey net technology, a cooperative type active defense thought is adopted, attacker information captured by the different honey nets is shared in real time, active defensiveness of a network layer is achieved, defensive initiative and real-time performance are improved, and the cooperative type active defense system is suitable for large-scale enterprise networks. The cooperative type active defense system built through the method is high in defense rate, hit rate and robustness, and time delay from the time that attackers are firstly found to the time that all network deployment and control is achieved is greatly reduced.
Owner:XI AN JIAOTONG UNIV
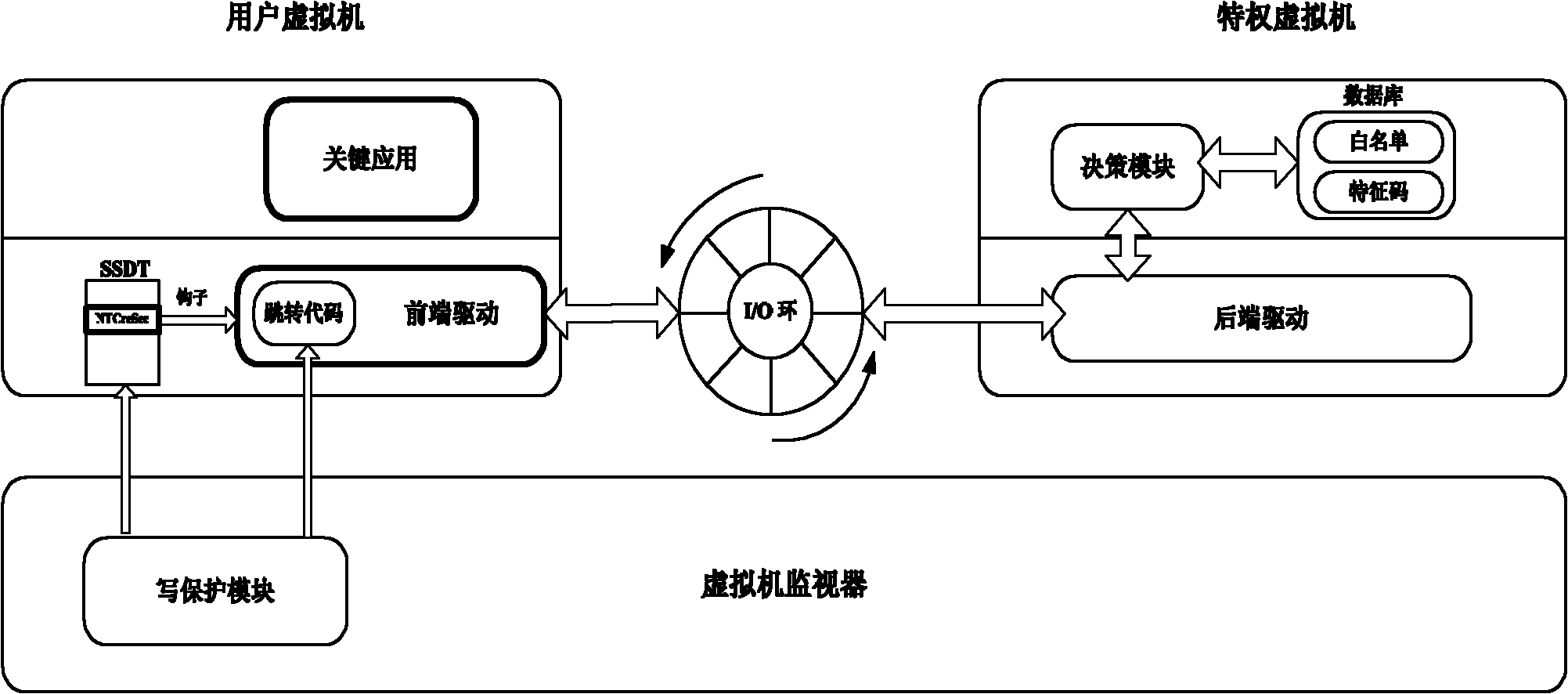
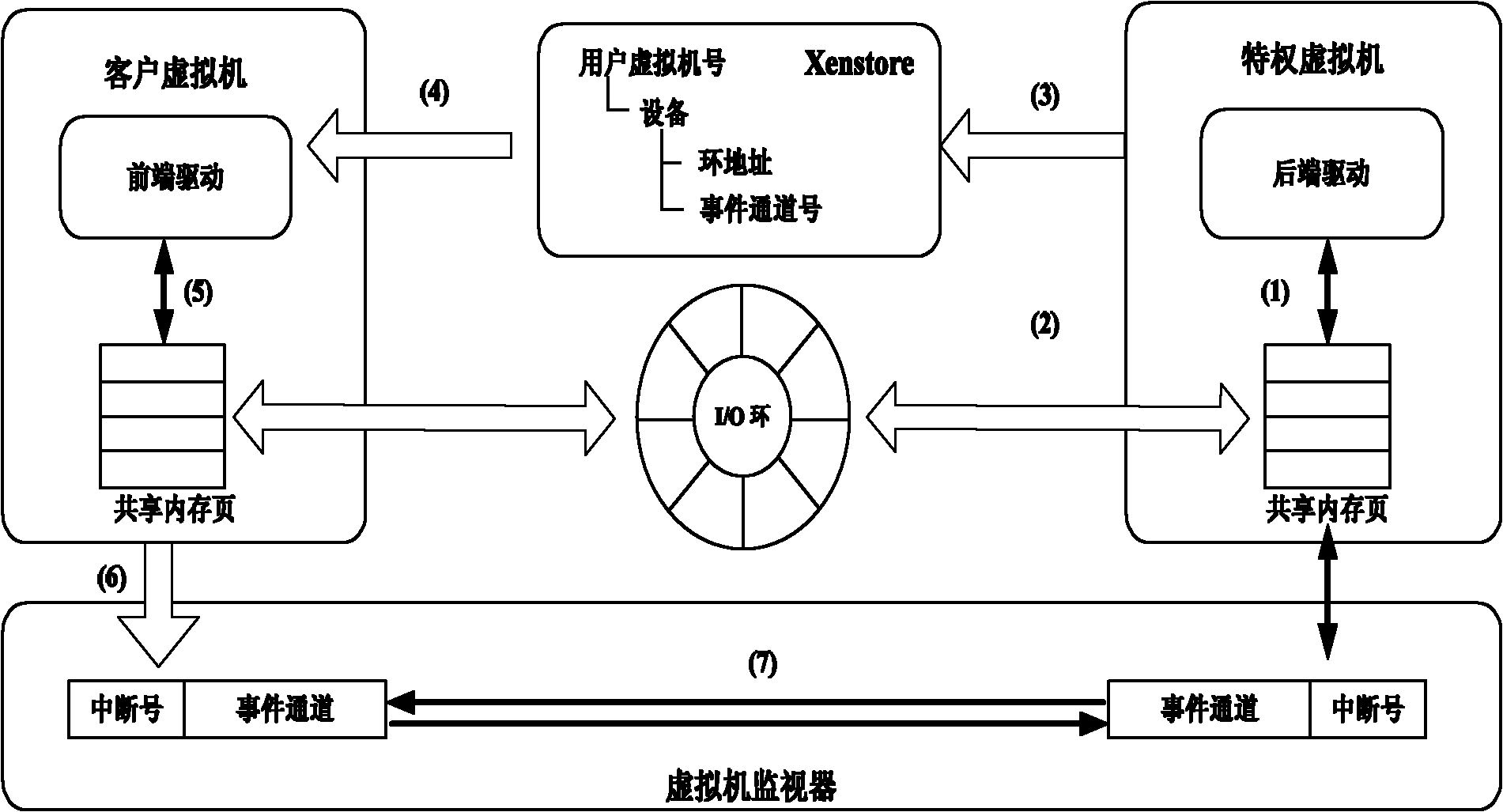
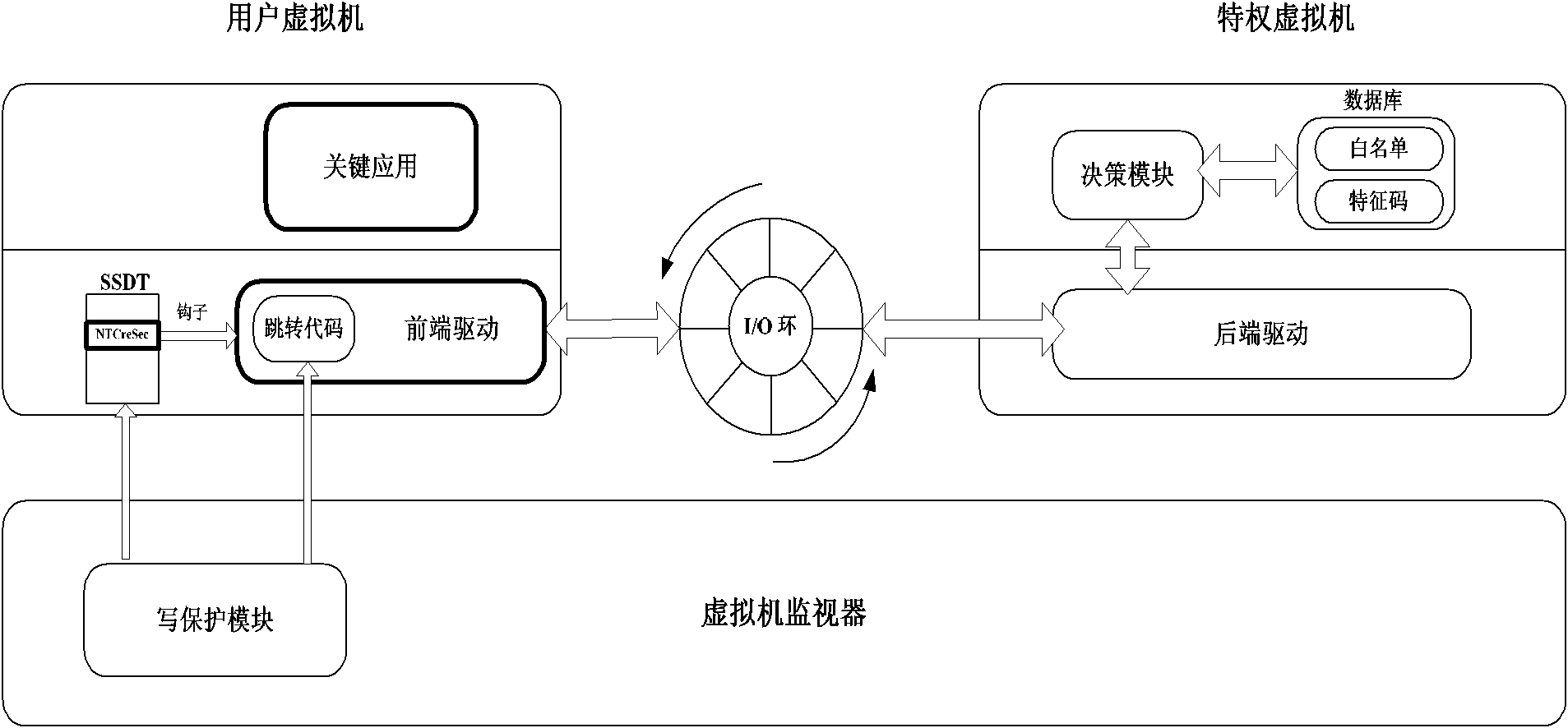
Xen-based active defense method
The invention discloses a virtual machine Xen-based active defense method, which comprises the following steps of: generating a virtual machine for a user by using Xen, and making the user perform operation in the virtual machine; simultaneously removing conventional security programs required to be installed in the virtual machine and arranging the removed security programs outside the virtual machine of a system, so that kernel modules of the security programs are invisible for rogue programs; in addition, setting a front-end drive in the virtual machine of the user to make the security modules outside the virtual machine can scan and intervene in the operation in the virtual machine, and simultaneously protecting the front-end drive by using a memory protection module in a monitor layer of the virtual machine to prevent the front-end drive from being attacked by the rogue programs. In the method, the kernel modules are arranged outside the virtual machine, and are invisible for therogue programs, thereby achieving security higher than that of a conventional security program deployment method; in addition, a para-virtualization front / rear-end drive communication way is introduced to greatly reduce system overhead caused by virtualization and make the method highly practicable.
Owner:BEIJING UNIV OF TECH
White list based realization method for active defense of cloud host
ActiveCN105138901APrecise managementStop runningPlatform integrity maintainanceMalwareZero-day attack
The invention discloses a white list based realization method for active defense of a cloud host. The method involves a centralized management platform of a server and a client, and the client is mounted on each cloud host needed to be protected. The specific realization process is as follows: all binary files in the protected cloud host are scanned through server software; a cloud security center identifies out trust ratings of the scanned files and adds a graded file list library into a white list library, a black list library and a gray list library separately; and at the client, only trusted application programs in a white list are allowed to run for preventing loading of a dynamic-link library file in a kernel. Compared with the prior art, the white list based realization method for active defense of the cloud host can completely prevent potential unwanted application programs and codes and prevent advanced threats, is free of feature code update, and can consistently enable known good software, prevent known or unknown bad software, correctly manage new software and effectively prevent unknown malicious software and zero-day attacks.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
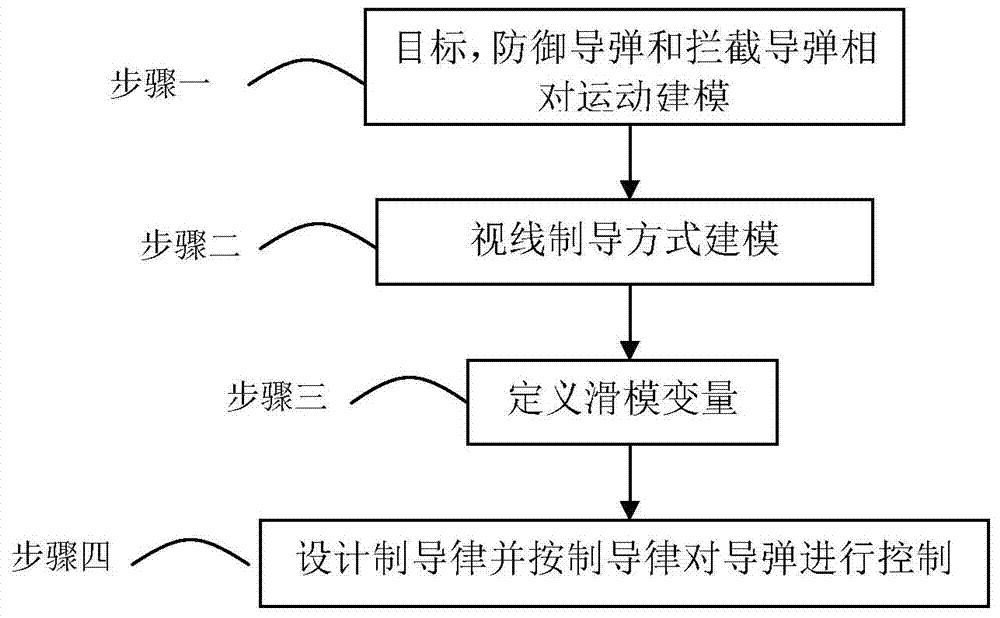
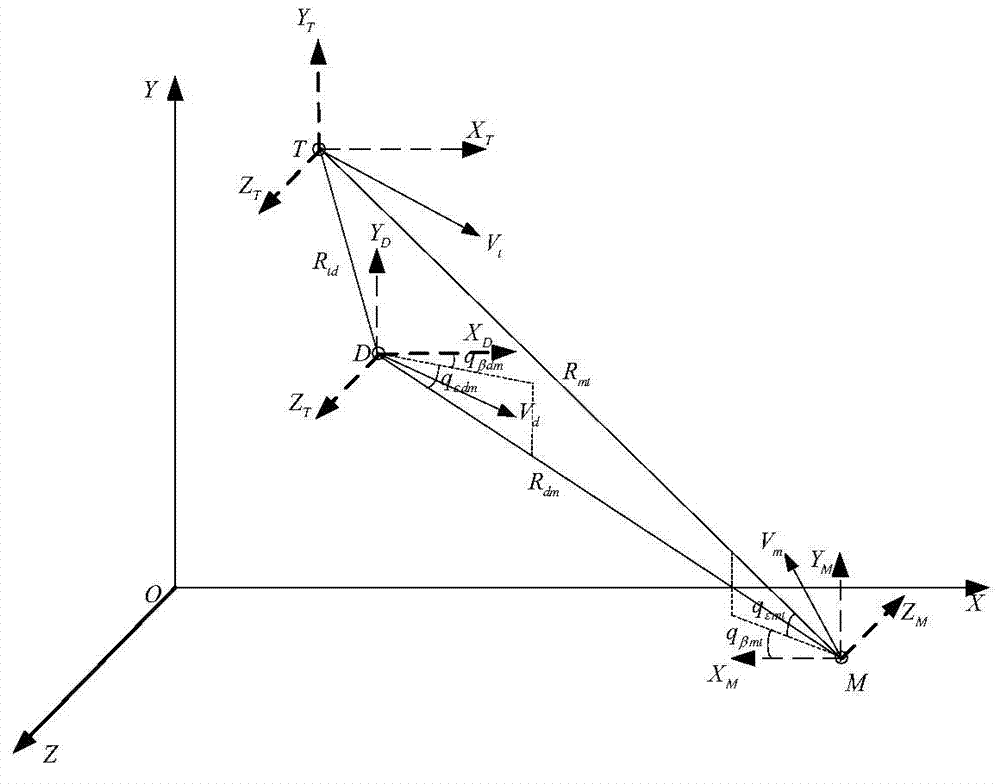
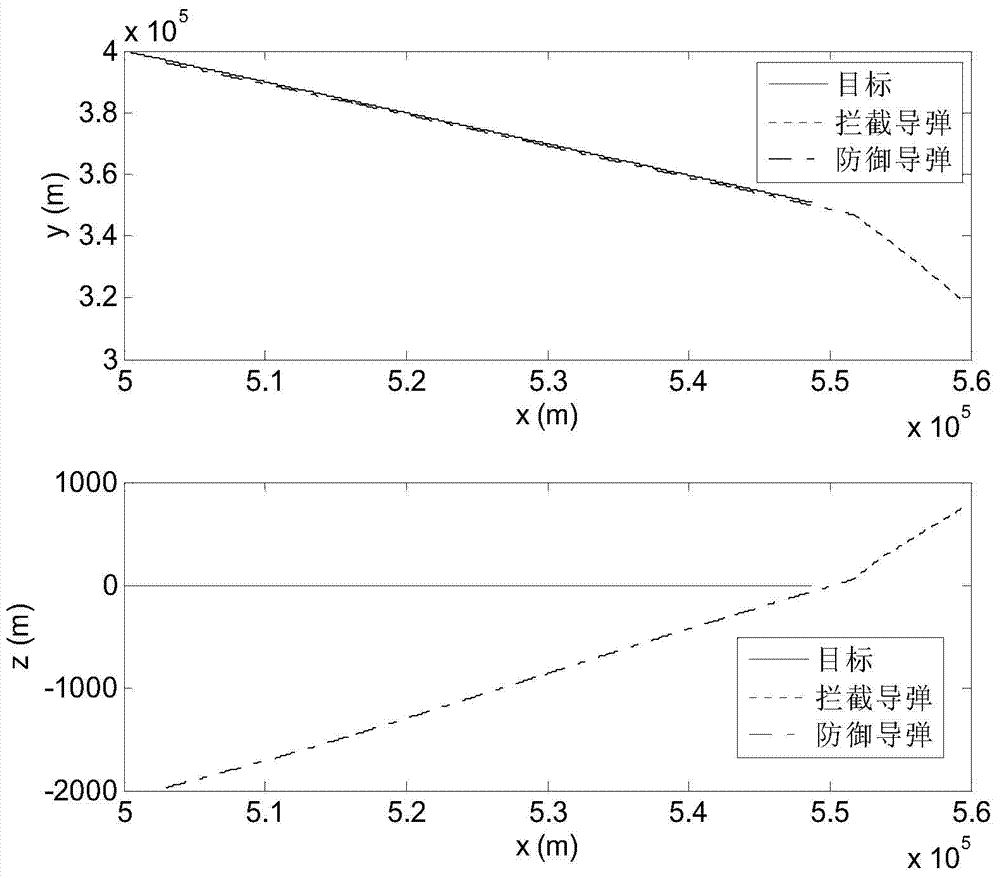
Sight line based finite time convergence active defense guidance control method
ActiveCN104266546AReduce demand overloadDirection controllersSpecial data processing applicationsLongitudinal planeGuidance control
The invention provides a sight line based finite time convergence active defense guidance control method, relates to a guidance control method, in particular to an active defense guidance control method, and aims at solving the problem that a defensive missile is limited in overload capacity. The sight line based finite time convergence active defense guidance control method comprises the steps of firstly modeling relative motions of a target, the defensive missile and an intercept missile, adopting a sight line guidance mode to design a guidance rule for the defensive missile, then adopting a nonsingular terminal sliding mode to control the designed guidance rule, respectively defining sliding mode variables (shown in the description) of a longitudinal plane and a lateral plane, performing derivation on the sliding mode variables, substituting relative motion equations of the target, the defensive missile and the intercept missile into the variables and obtaining the guidance rule (shown in the description) of the longitudinal plane and the guidance rule (shown in the description) of the lateral plane through compilation, and controlling the missiles according to the guidance rules. By means of the sight line based finite time convergence active defense guidance control method, overload needed by the defensive missile can be effectively reduced. The sight line based finite time convergence active defense guidance control method is suitable for active defense guidance control.
Owner:HARBIN INST OF TECH
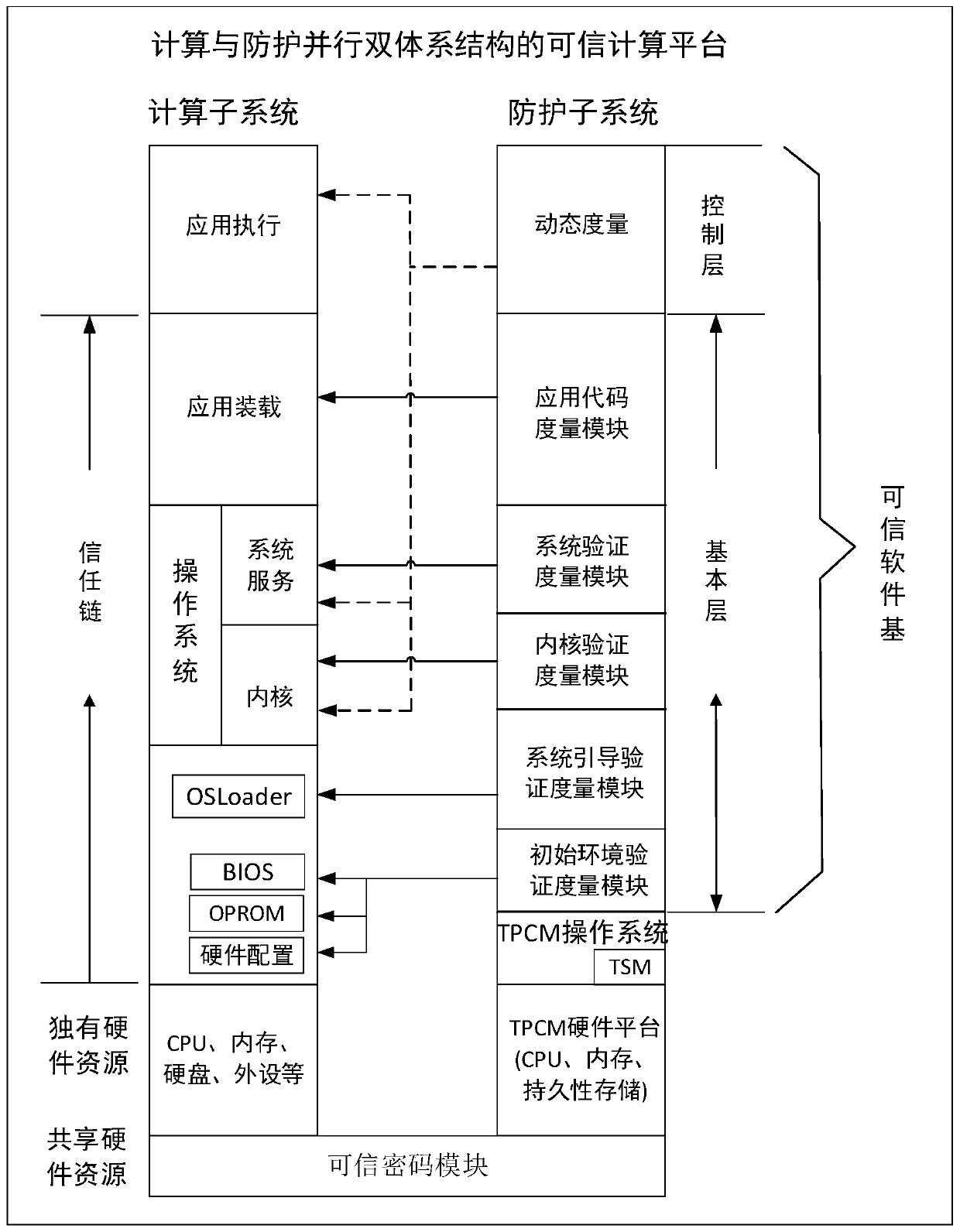
Trusted computing platform of a computing and protection parallel double-system structure
ActiveCN109871695AComputable, measurable and controllableRealize active security protectionPlatform integrity maintainanceActive safetyTrusted Computing
The invention discloses a trusted computing platform of a computing and protection parallel double-system structure. wherein the trusted computing platform comprises a computing subsystem and a protection subsystem which are parallel, the computing subsystem is used for completing a computing task, and the protection subsystem is used for carrying out active measurement and active control on the computing subsystem according to a trusted strategy through a trusted platform control module; And the protection subsystem is specifically used for respectively carrying out static measurement and dynamic measurement on the computing subsystem through the trusted software base. According to the trusted computing platform provided by the invention, active safety protection is realized while computing is realized through the computing subsystem and the protection subsystem which are parallel to each other. In addition to establishing a static trust chain which takes a trusted platform control module as a trust root for step-by-step measurement, a dynamic measurement mechanism based on a security trusted strategy is also designed, and active defense on the whole computer system in the starting and operating processes of the computer is realized.
Owner:北京自主可信科技有限公司
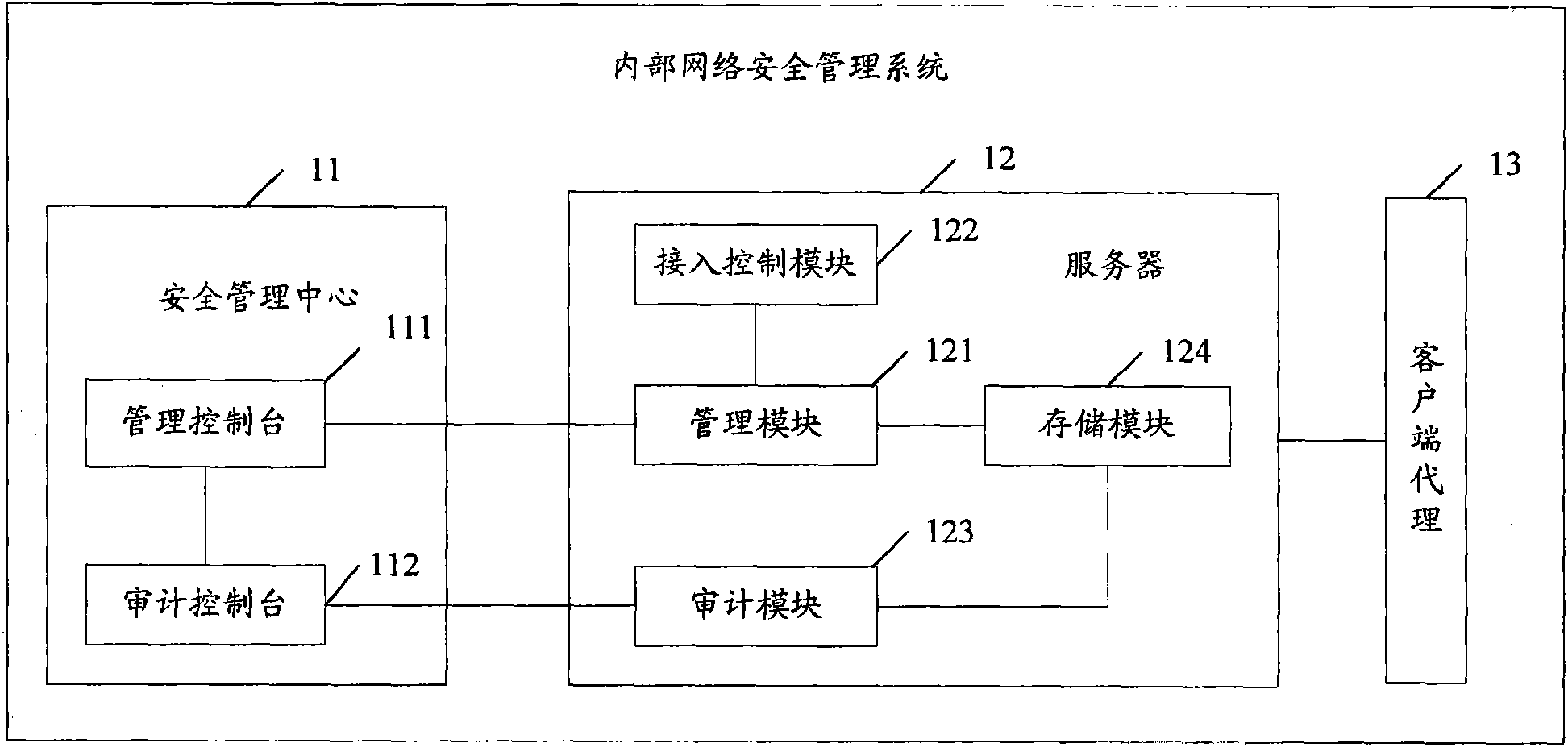
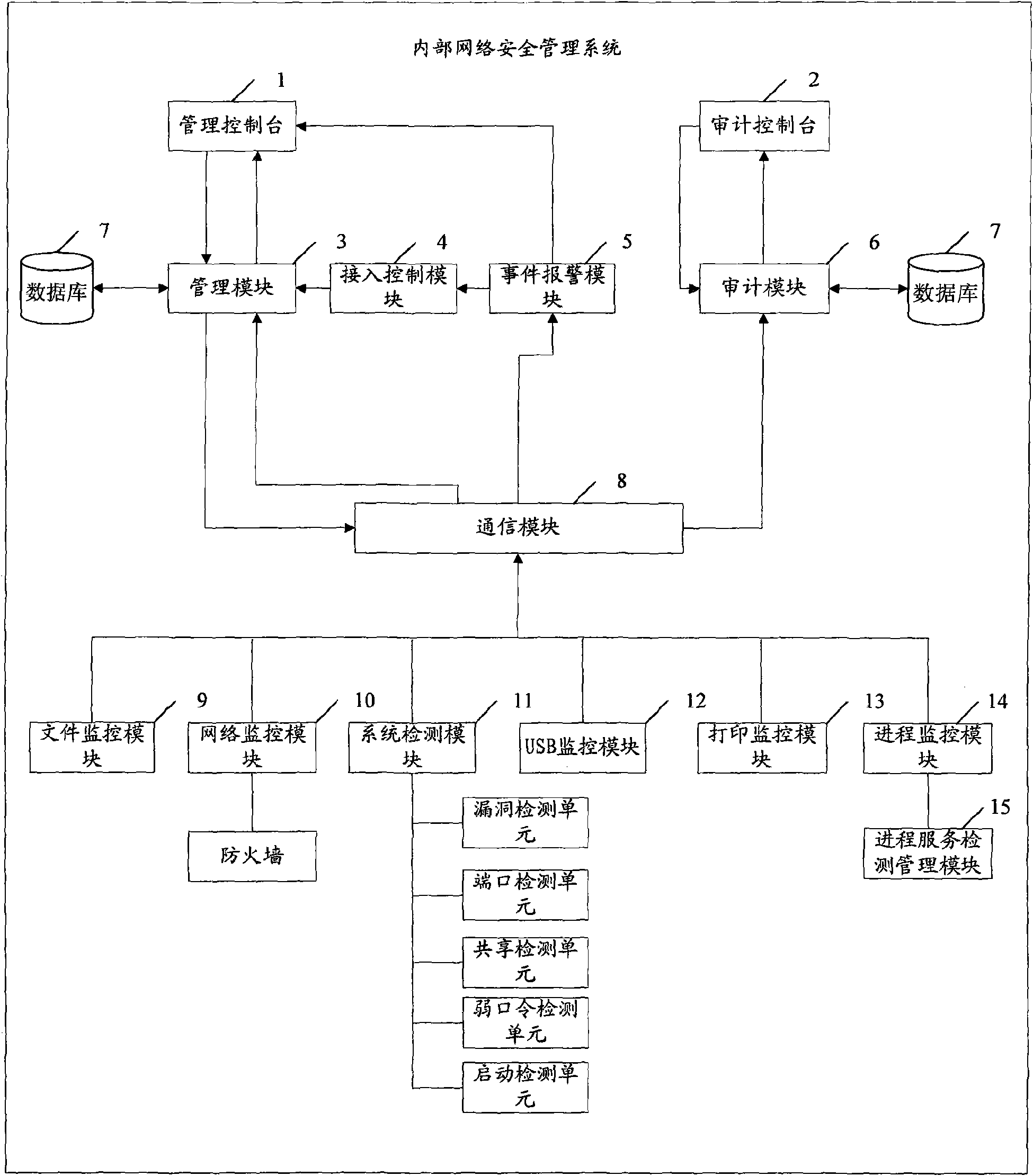
Associated equipment and method for internal network security management
InactiveCN101588360AIntegrity guaranteedAvoid abuseData switching by path configurationTerminal equipmentNetwork isolation
The invention provides associated equipment and method for internal network security management, wherein, through generating and maintaining a security management strategy and an audit strategy; the invention ensures that all the terminals accessible to internal network submit to the strategies; with respect to an piece of equipment unqualified to the strategies, the system processes the equipment as follows: providing a network isolation and locking device, and sending an warning, with the purpose of ensuring that the equipment does not bring the whole network with bad influence on the security and management. The invention not only implements an active defense mechanism of the system, but also effectively prevents some malicious acts of validated user, such as misapplication of network resource, information theft, and active attack by means of internal computers.
Owner:SHENZHEN CITY ANLUODACHENG TECH
Network security defensive system, method and security management server
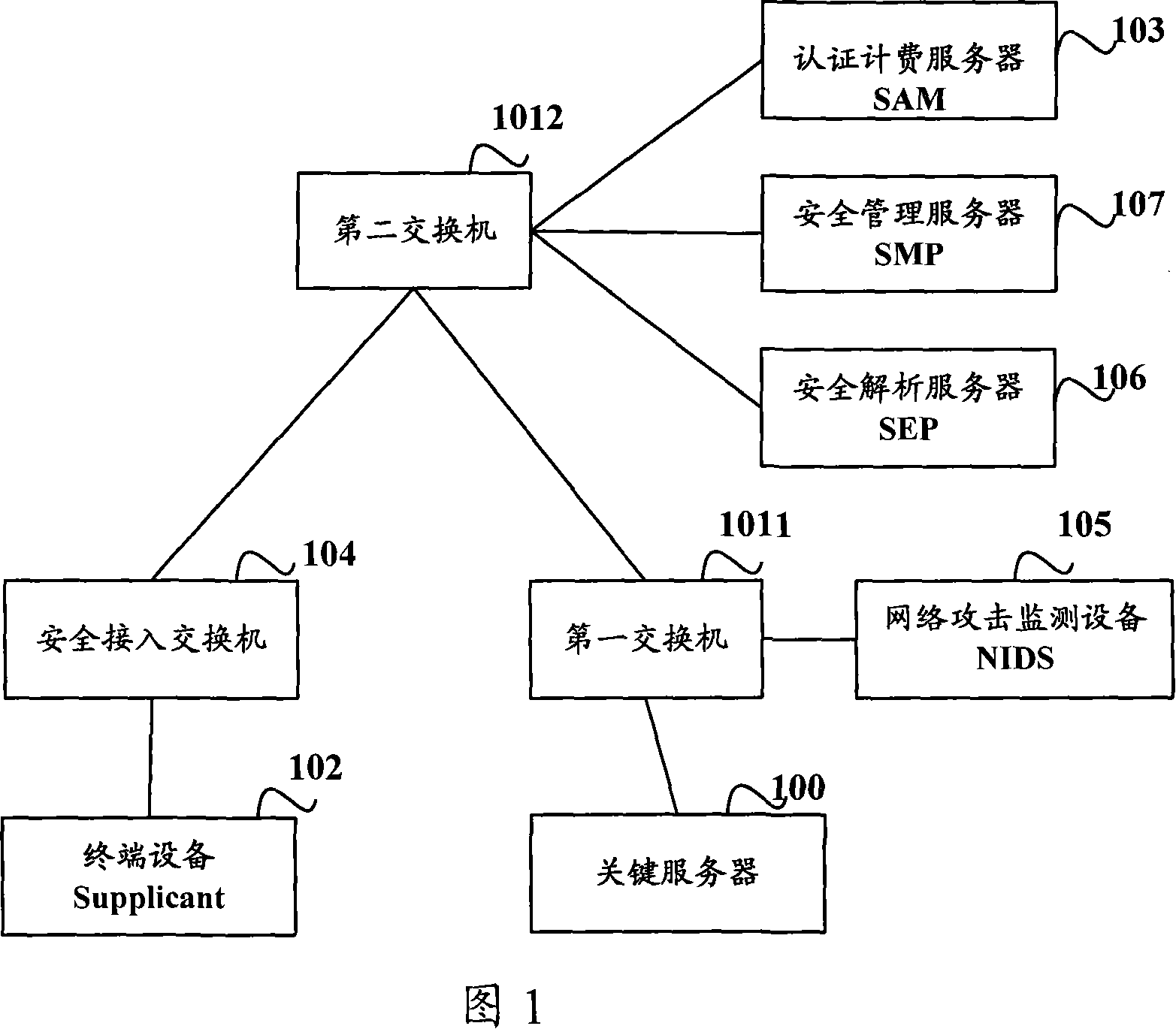
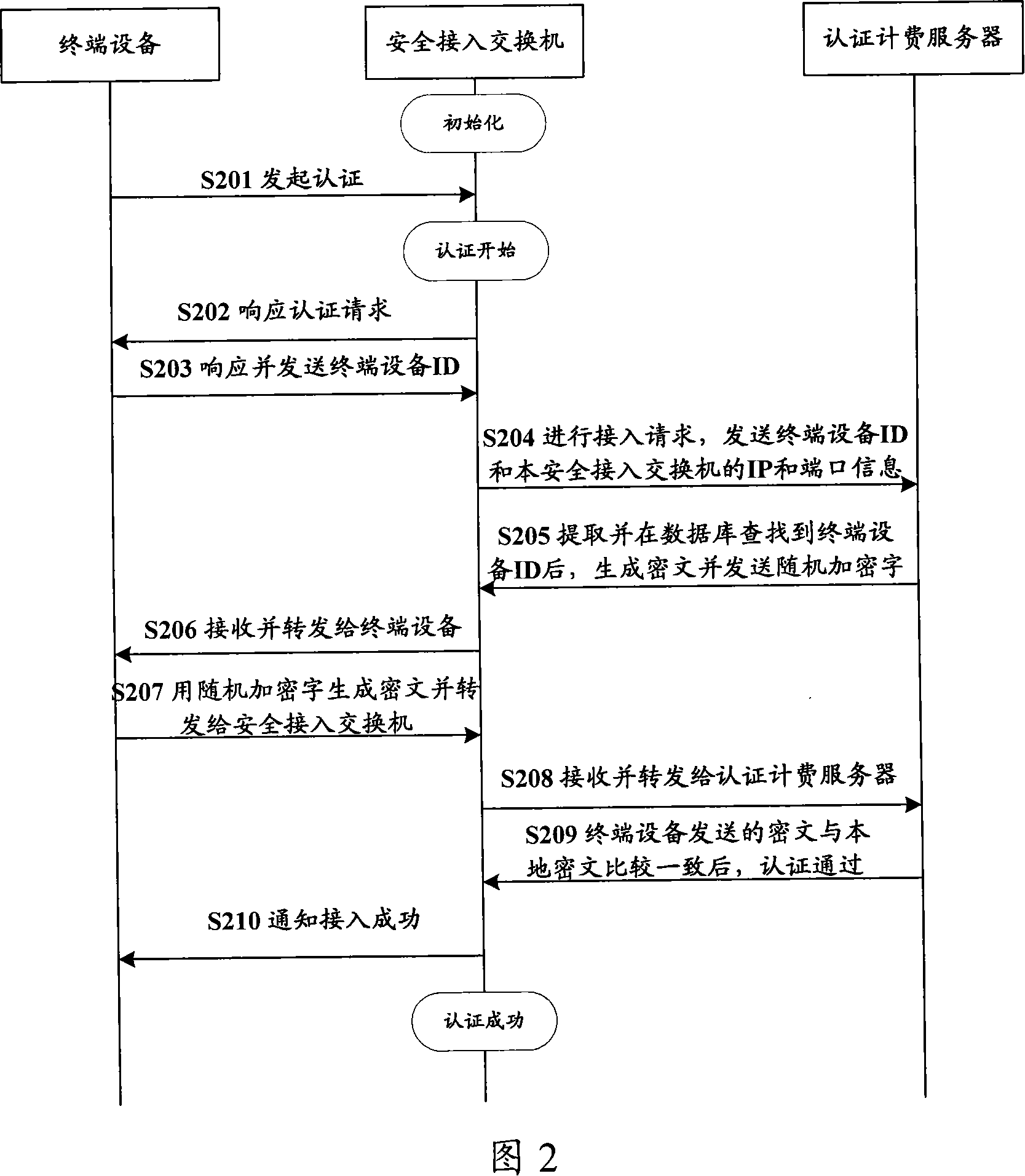
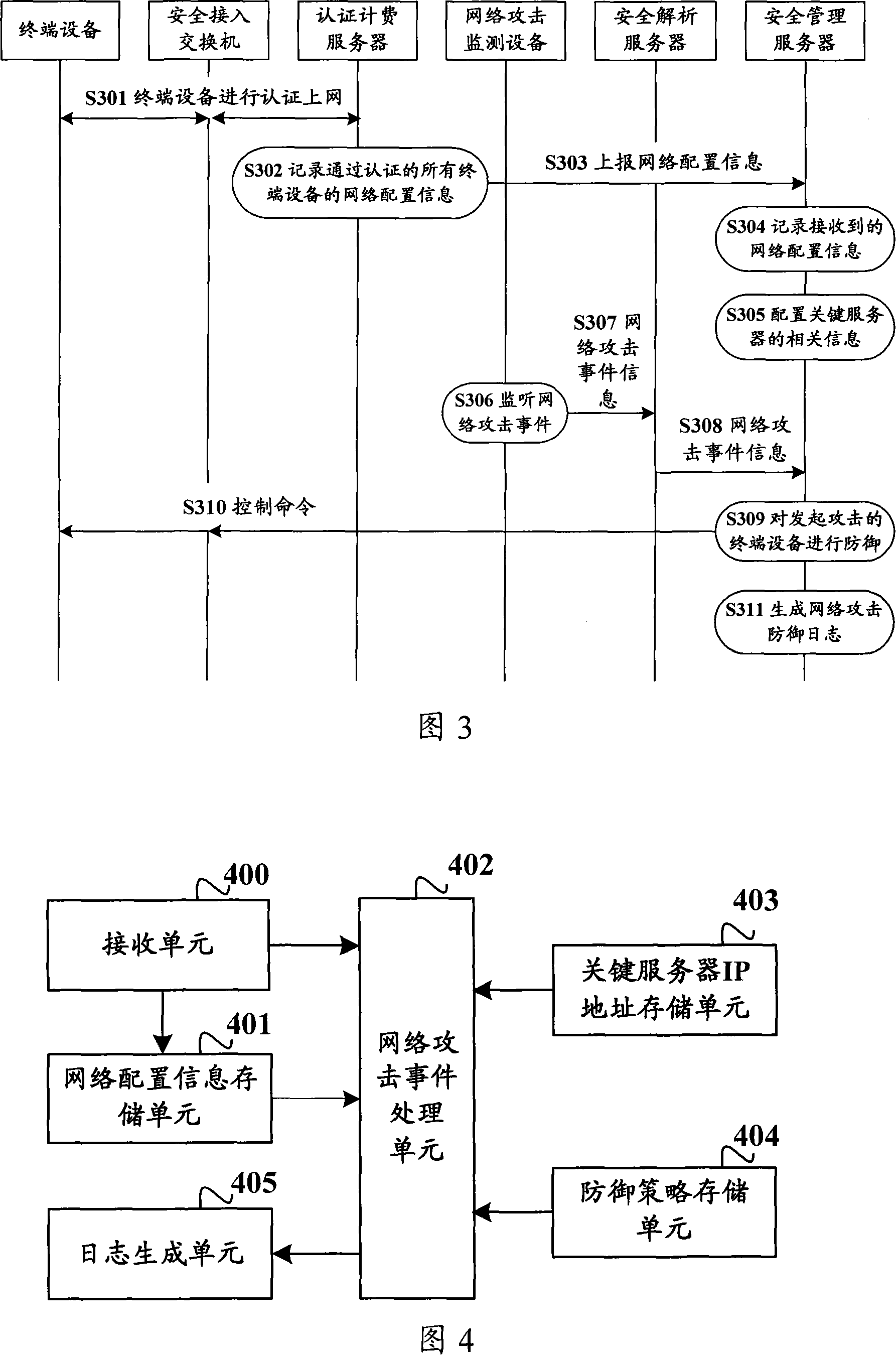
ActiveCN101141305AAvoid spreadingUser identity/authority verificationData switching networksTerminal equipmentNetwork attack
The utility model relates to a data communication network safety technology, more particularly, provides a network security defense system and the method as well as a safety management server, so as to conduct the active defense against the terminal equipment which attacks the severs in the network. The network security defense system comprises a safety certification client, a safety access exchanger, a certification charging server, a network attack monitoring unit and a safety management server. The network security defense mechanism provided can ascertain the terminal equipment which attacks the network and assume the active defense against such terminal equipment, so as to effectively guard against the continuous diffuseness of network attach incident.
Owner:RUIJIE NETWORKS CO LTD
Network security monitoring method for industrial control system
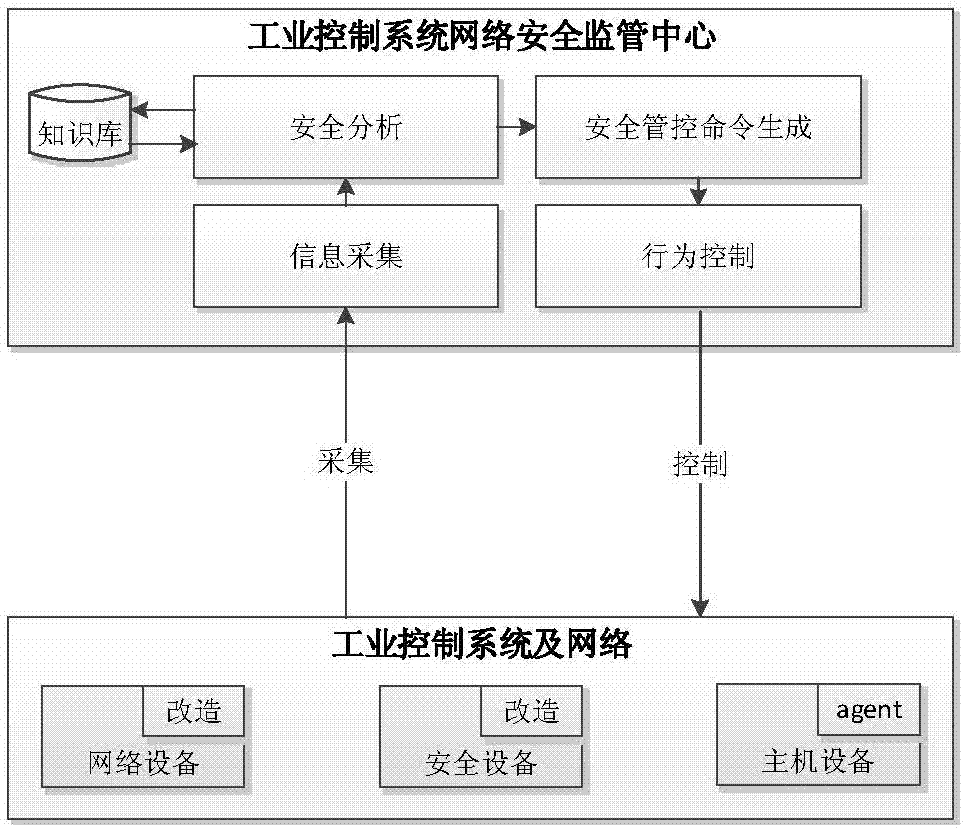
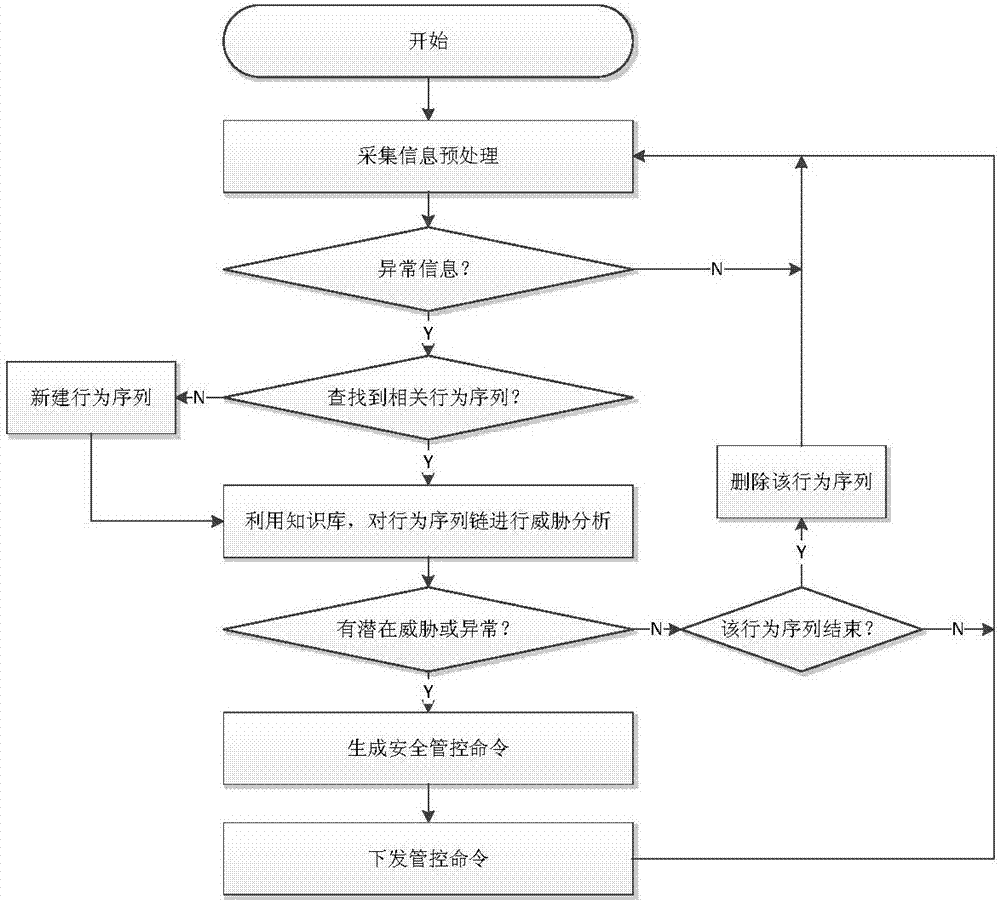
ActiveCN107493265ARealize real-time monitoringRealize active defenseData switching networksRelevant informationIndustrial systems
The invention discloses a network security monitoring method for an industrial control system. The method comprises the following steps: collecting relevant information of an internal monitoring object of the industrial control system; performing security analysis on the collected relevant information; and when potential abnormal behavior is found through analysis, generating a relevant safety control order, and issuing the order to the relevant monitoring object for execution so as to block the abnormal behavior. According to the invention, real-time monitoring on major hidden security dangers of the industrial control system such as peripheral access, personnel operation, network external connection and the like is realized through abundant data acquisition of core networking equipment of the industrial control system. At the same time, through analysis processing on various behavior, the abnormal behavior is found and blocked timely, and thus real active defense of the industrial system is realized. For the current difficulty of effectively applying traditional security protection measures to the industrial control system, the major security threats to the industrial control system at present are well solved from the perspective of monitoring early warning.
Owner:NANJING NARI GROUP CORP +2
Secondary loop panoramic state monitoring system for electric operating mechanism of circuit breaker
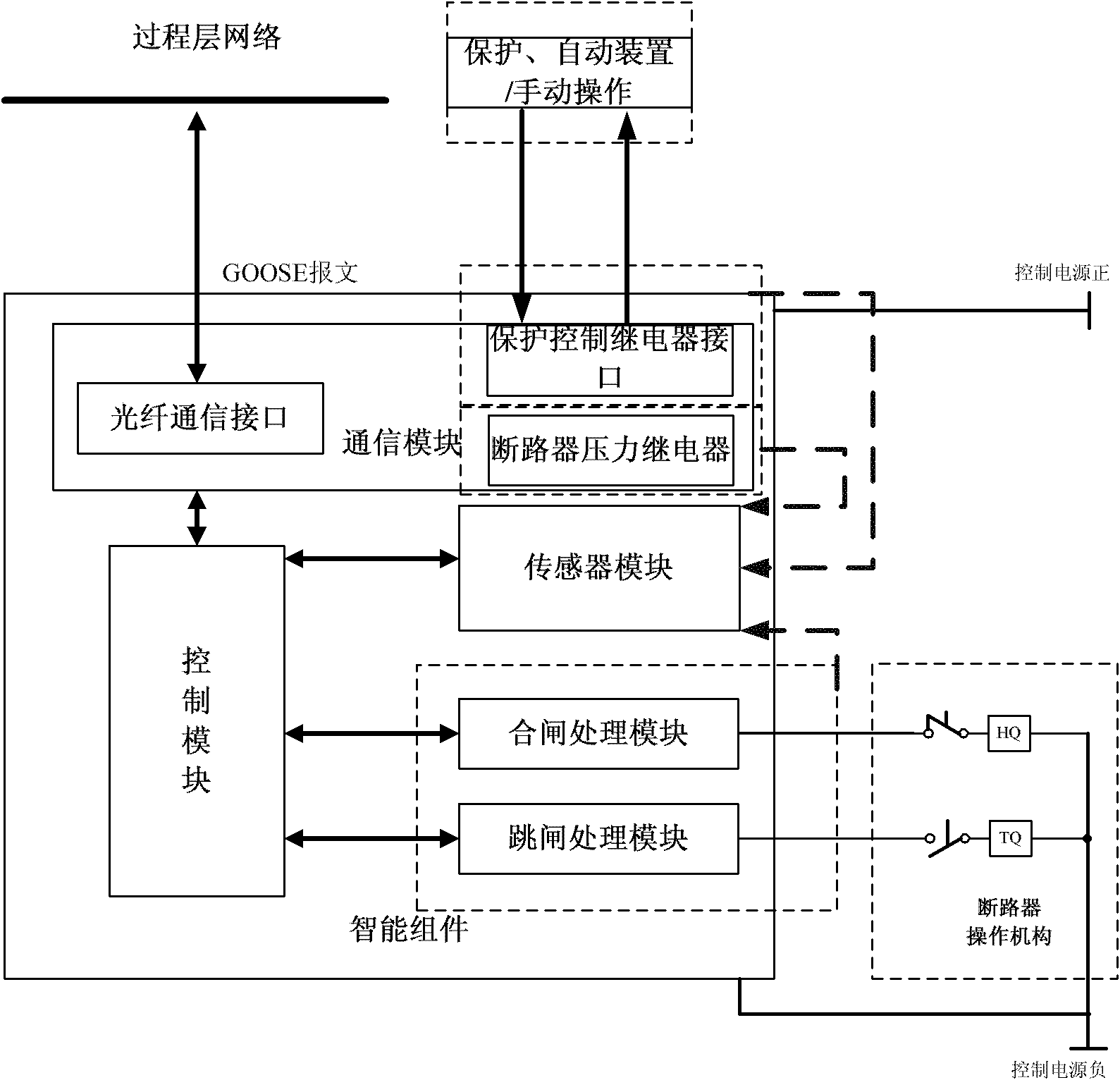
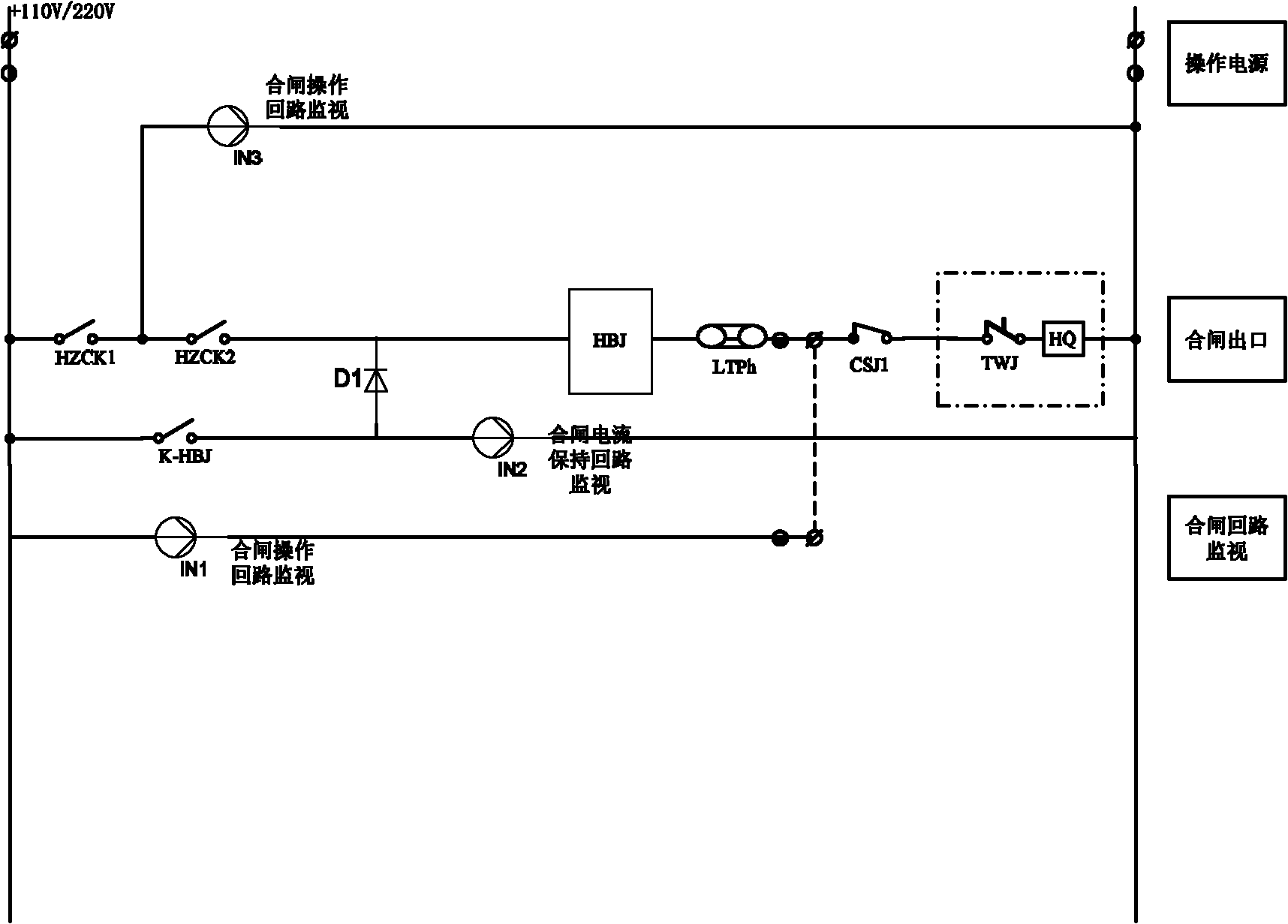
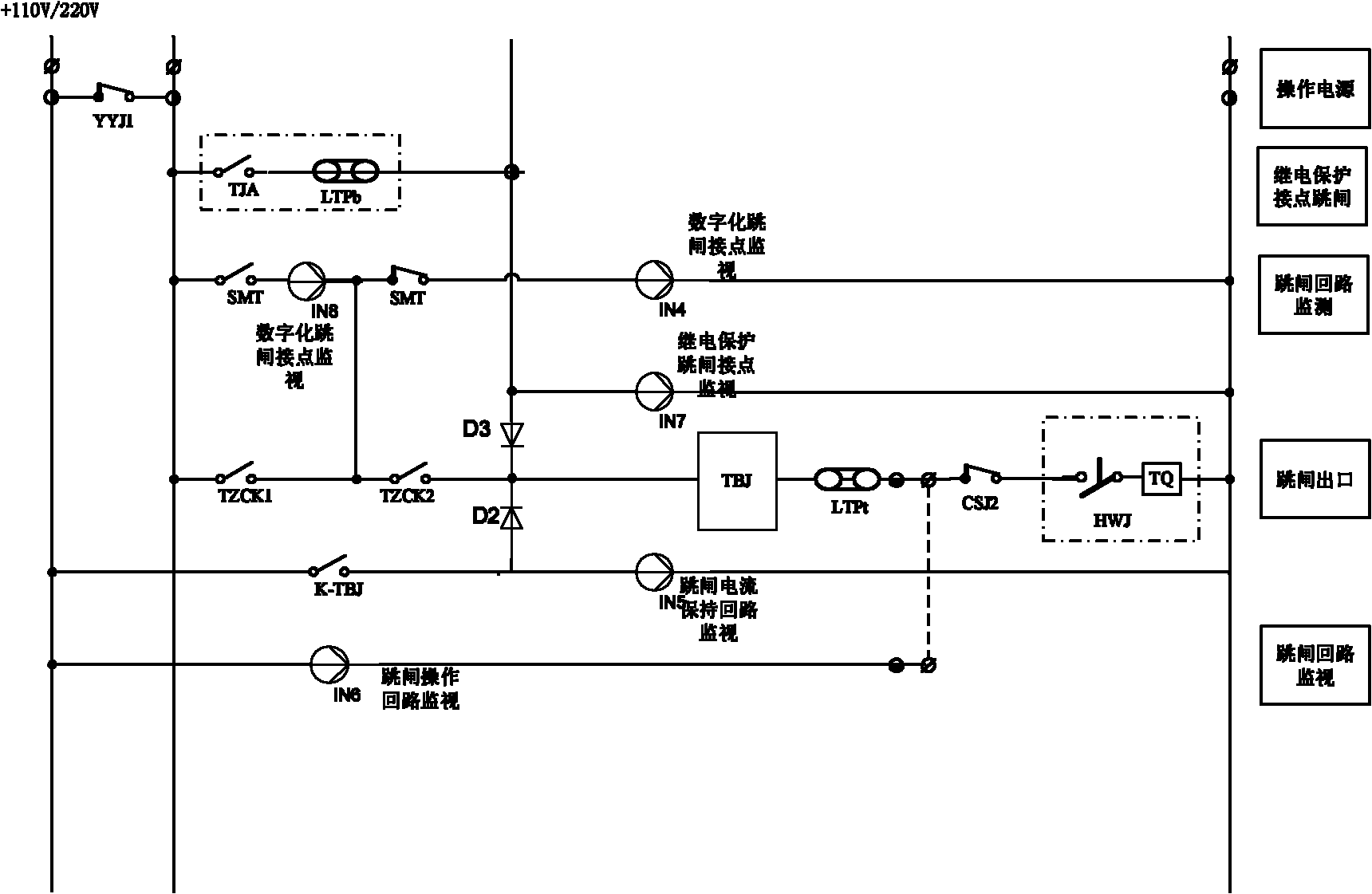
ActiveCN101944771ASimple designImprove reliabilityNon-electrical signal transmission systemsCircuit arrangementsProcess moduleElectric power system
The invention discloses a secondary loop panoramic state monitoring system for an operating mechanism of a circuit breaker in the technical field of power systems. The system comprises a communication module, a control module, a sensor module, a switch-on processing module and a trip processing module. The system can perform on-line monitoring per se on the integrity of an operating loop, a monitoring loop and loop elements in various working states of the circuit breaker such as switch-off, switch-on and the like, realizes state monitoring of trip and switch-on loops in a full state, and has active defense function. Compared with the prior art, the system simplifies the tripping and closing operation loops, improves the integral reliability of the system, provides necessary conditions for state overhauling of the intelligent circuit breaker, ensures safe operation of the high-voltage circuit breaker, and improves the power supply reliability of the power system.
Owner:上海思源弘瑞自动化有限公司
Method and device for actively defending rogue program
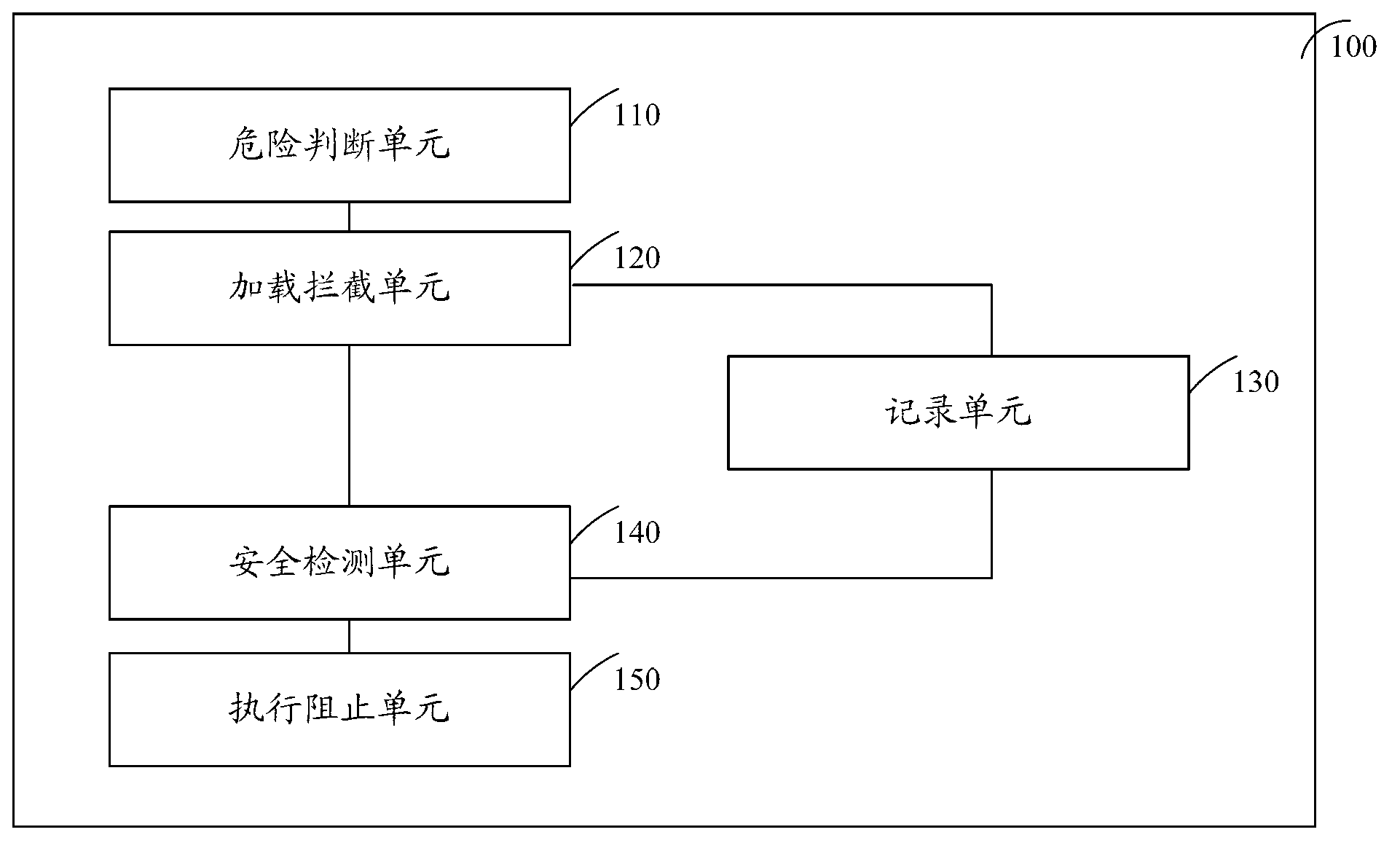
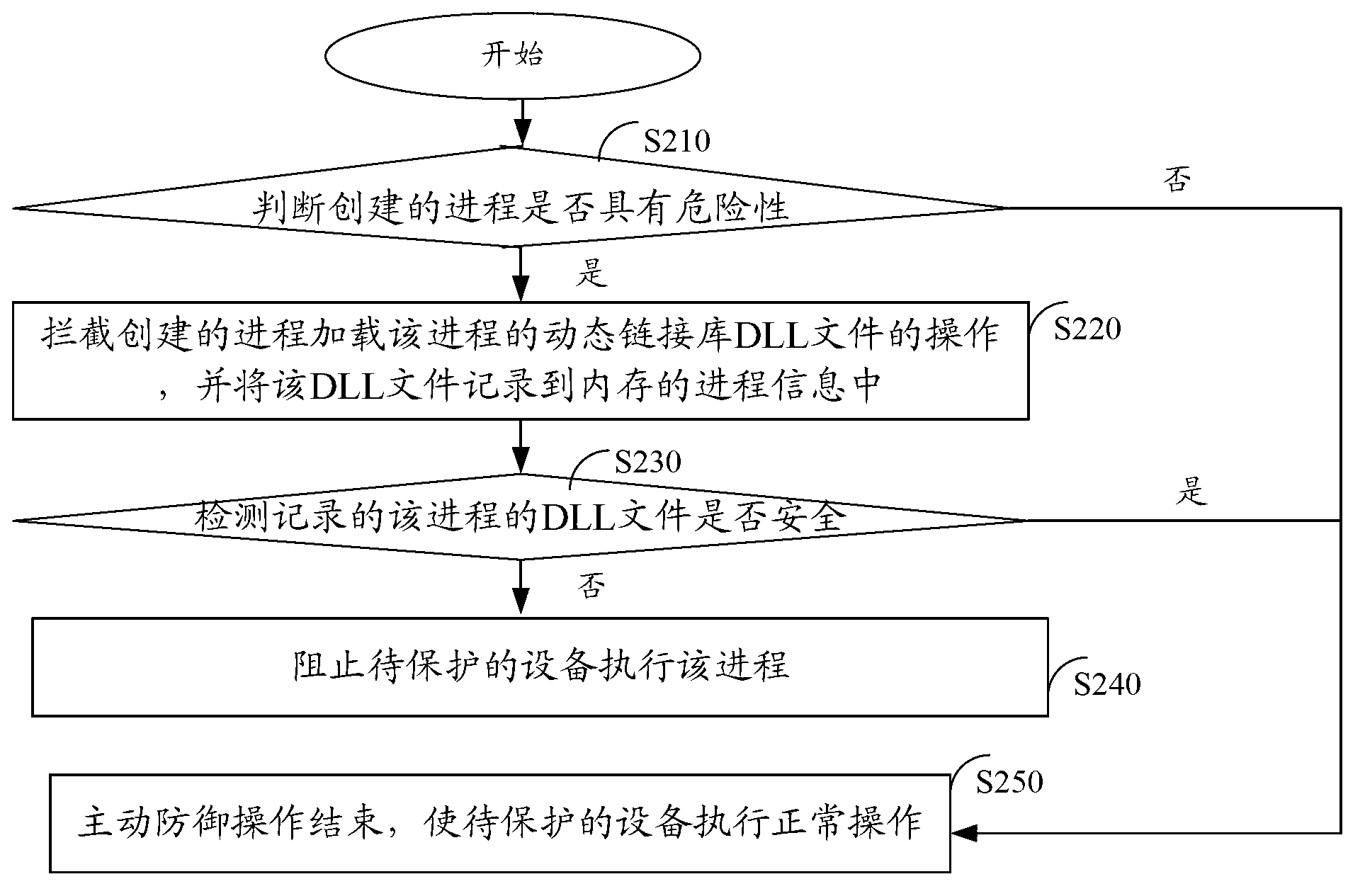
ActiveCN103077353AExecution blockReduce the probability of detectionPlatform integrity maintainanceInternal memoryProcess information
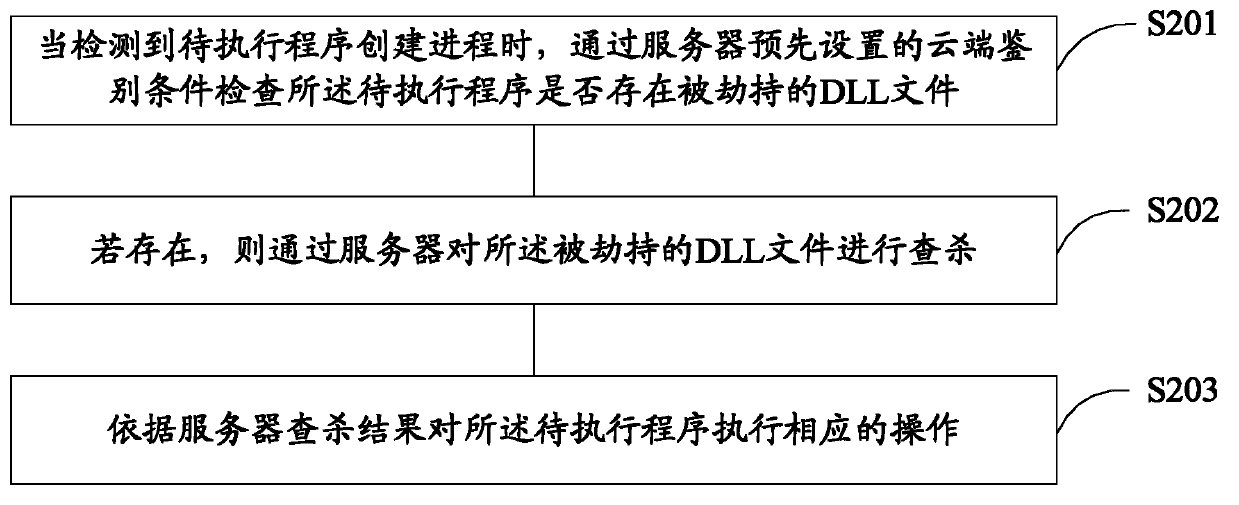
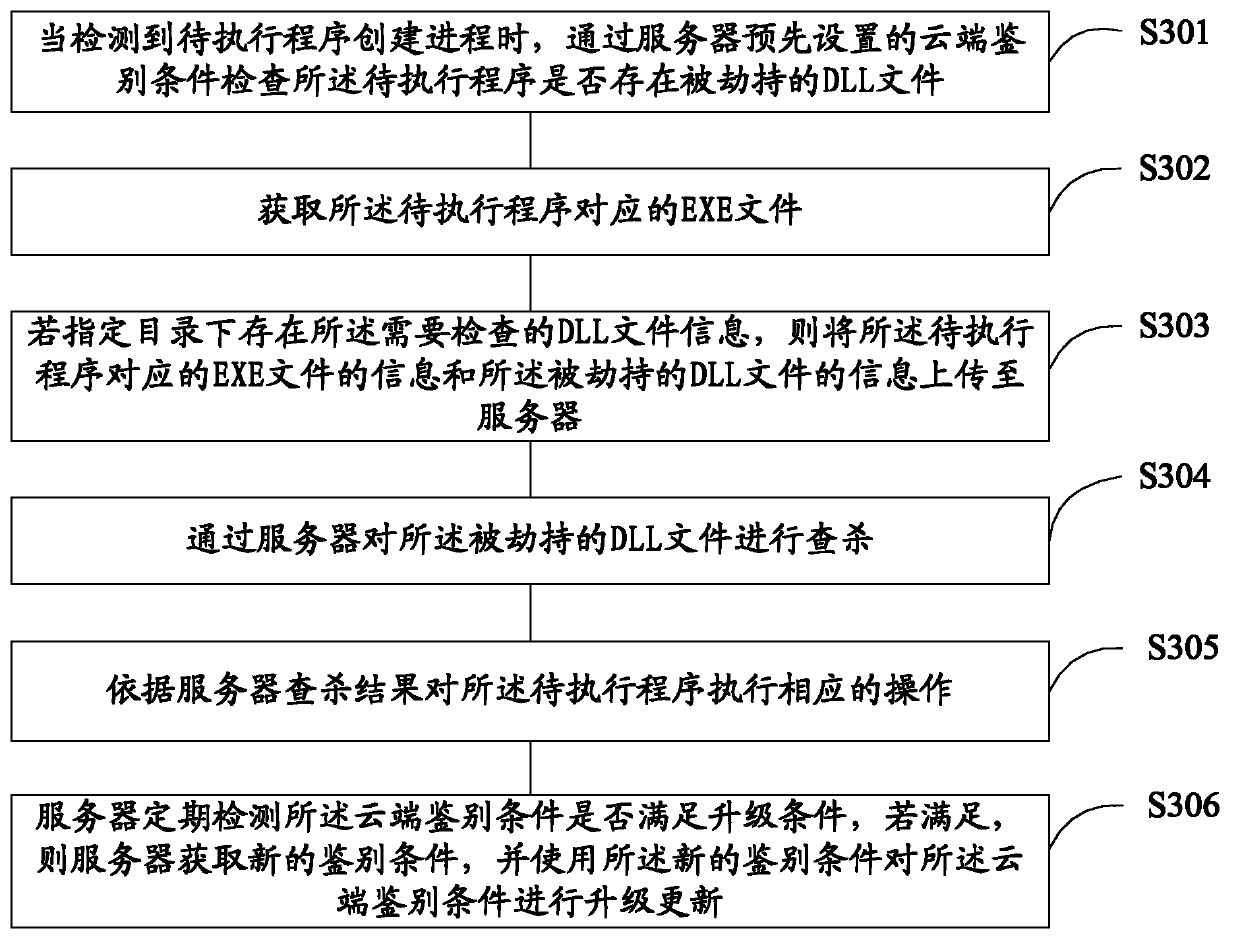
The invention relates to the field of computer network safety and discloses a method and a device for actively defending a rogue program. The method comprises the following steps of: when to-be-protected equipment creates a process, judging whether a created process has risk or not according to process files related to the created process, if yes, intercepting an operation of loading DLL (Dynamic Link Library) files of the process by the created process, and recording the DLL files into the process information of an internal memory; and after the to-be-protected equipment starts the process, if the operated executed by the process is a dangerous operation, detecting whether the recorded DLL files of the process are safe or not, if the recorded DLL files are unsafe, preventing the to-be-protected equipment from executing the operation of the process. The method and the device can be used for solving the technical problem that the rogue program packs rogue DLL files and trusty white programs together, when the white programs are executed, the rogue DLL files are loaded, and thus the active defense is broken through.
Owner:BEIJING QIHOO TECH CO LTD
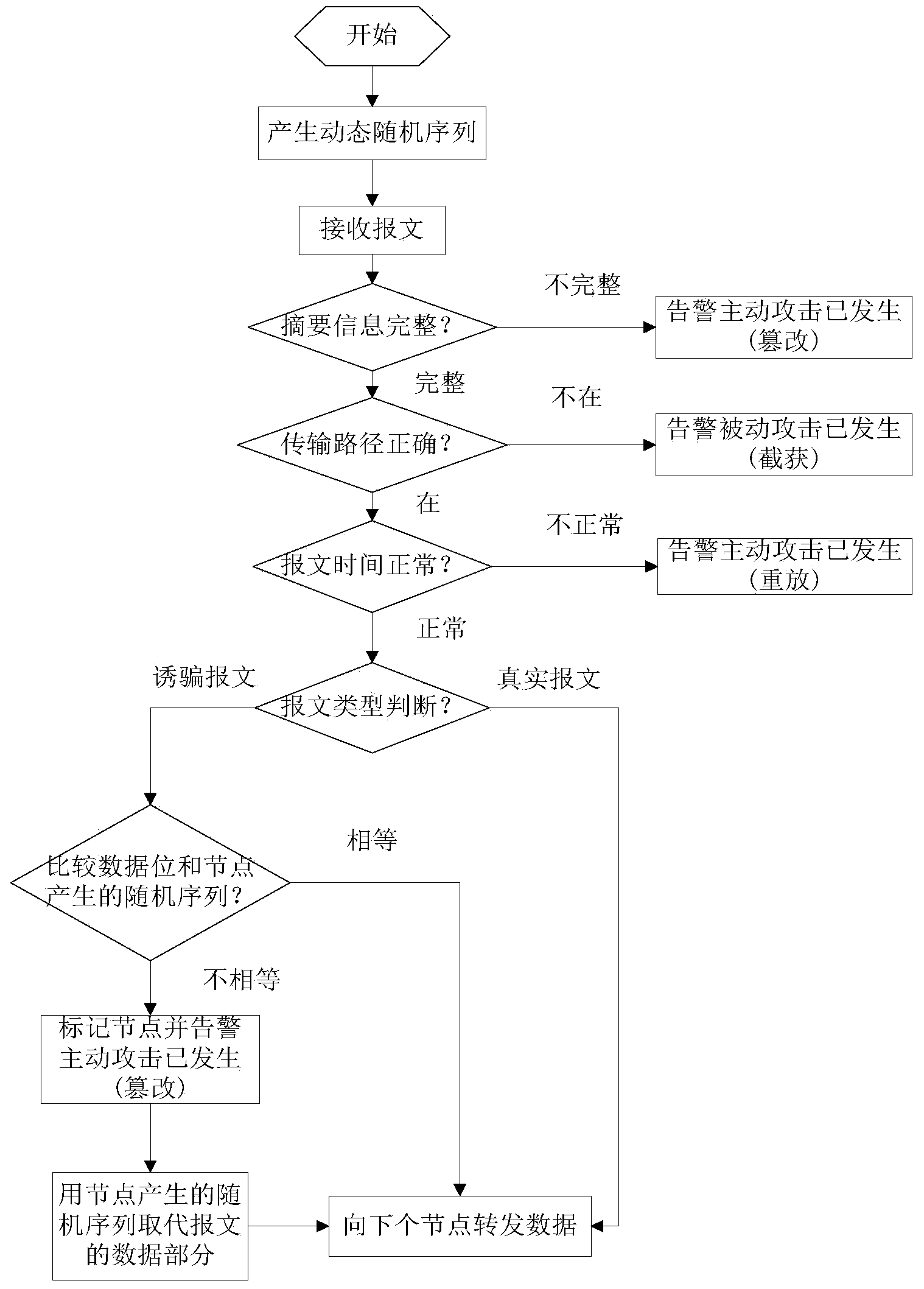
Active defense method for network trick and counter attack
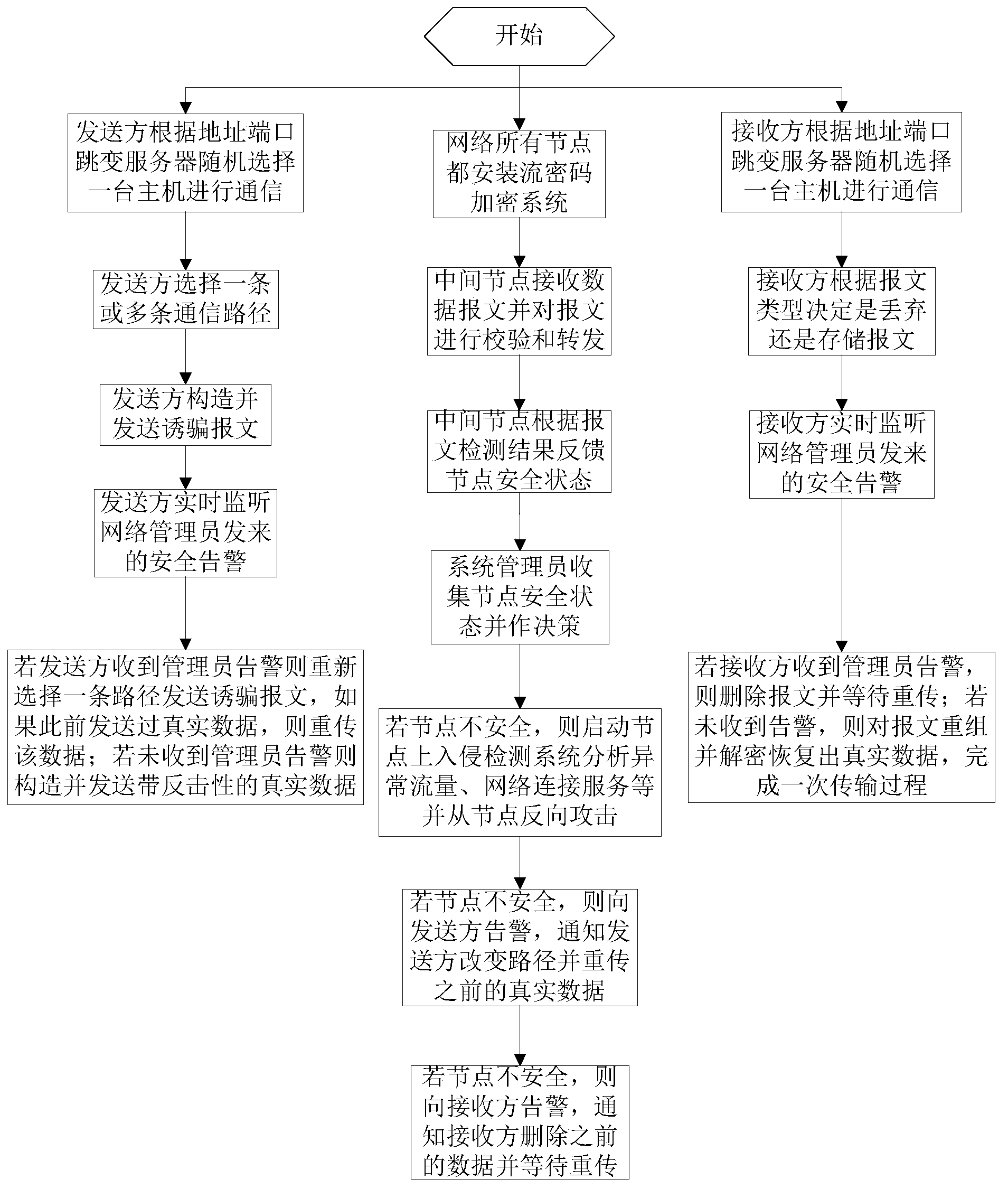
InactiveCN103457931AGuaranteed dynamic performanceReduce the chance of attackData switching networksNetwork communicationDefensive measure
The invention discloses an active defense method for a network trick and a counter attack. The method comprises the following steps that two communication sides set a plurality of host computers for data sending and receiving, and one host computer is dynamically and randomly selected as a communication host computer through an address and port hopping server; a sender selects one or more transmission links to send a trick message to detect the safety and the channel quality of the transmission links, wherein if the links are safe, true data with the counter attack are constructed and sent, and meanwhile the sender continues to send the trick message to detect the links; an intermediate node takes in charge of detecting and feeding the safety situation of the transmission links back to a network administrator; the network administrator updates a transmission path according to the safety situation of the node and takes the defensive measure. The active defense method can effectively prevent and detect common safety attack in the network communication and carry out certain counter attack on an attacker.
Owner:HUAZHONG UNIV OF SCI & TECH
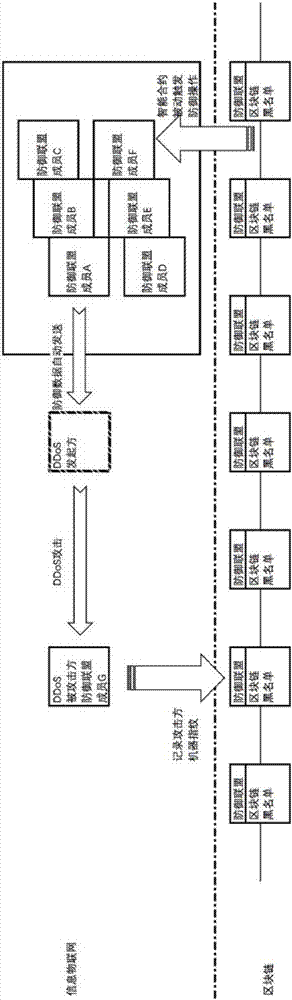
Active defense method based on block chain intelligent contract, and node
InactiveCN107172085APrevent malicious tamperingAvoid misjudgmentTransmissionNetwork packetThe Internet
The invention provides an active defense method based on a block chain intelligent contract, and the method comprises the following steps: enabling one defensive alliance member to judge whether a flow is an abnormal flow or not after the defensive alliance member is attacked: recording the attack side machine fingerprint if the flow is the abnormal flow, and notifying one of the remaining defensive alliance members or more of the abnormal flow, and requiring for the defense; executing a second intelligent contract after the remaining defensive alliance members receives the notification of defense requiring, i.e., transmitting a data package to an attack side, and quitting the active defense till a set quitting condition is met. According to the invention, equipment which supports the block chain intelligent contract is deployed on the Internet, and the intelligent contract will be automatically started after one server is attacked, and a data package is actively transmitted to the attack side, thereby enabling the attack side not to continue to attack, and achieving the purpose of protecting the server.
Owner:浙江华信区块链科技服务有限公司
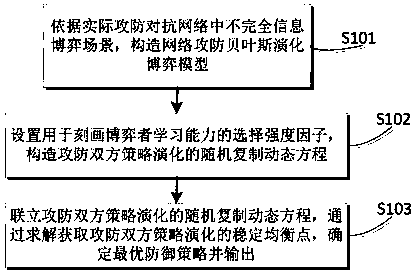
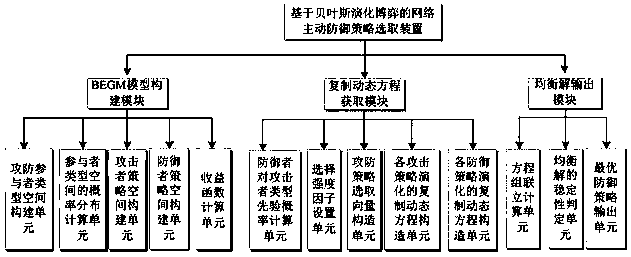
Network active defense policy selection method and device based on Bayesian evolutionary game
InactiveCN108833401APractical applicationImprove versatilityData switching networksDynamic equationInformation networks
The invention belongs to the technical field of the network security, and especially relates to a network active defense policy selection method and device based on Bayesian evolutionary game. The method comprises the following steps: constructing a network attack Bayesian evolutionary game model according to an incomplete information game scene in an actual attack-defense adversarial network; setting a selection strength factor for describing gamer learning capacity, and constructing a random replicate dynamic equation about the attacker-defender policy evolution; combining the random replicate dynamic equations about the attacker-defender policy evolution, solving to acquire a stable balance point of the attacker-defender policy evolution, and determining and outputting an optimal defense policy. From the limited intellectual visual angle of the participant, a replicate dynamic equation about the participant decision process is constructed and solved by means of the replicate dynamicmechanism for describing the biological evolution, the method is suitable for incomplete information network attack-defense adversarial network and more suitable for the actual application, the generality and operability in the network decision implementation process are enhanced, and the effective guidance is provided for selecting the active defense policy.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
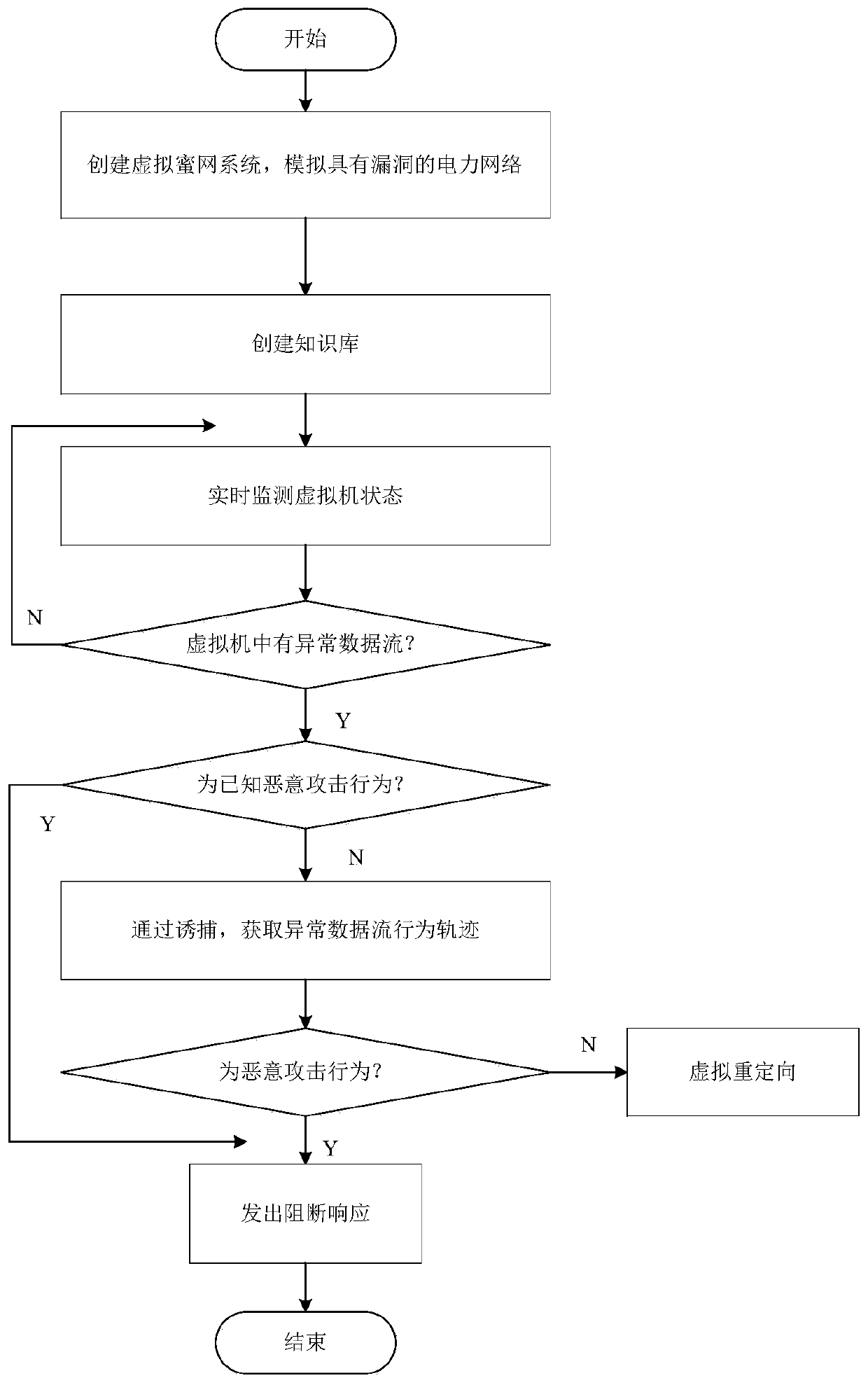
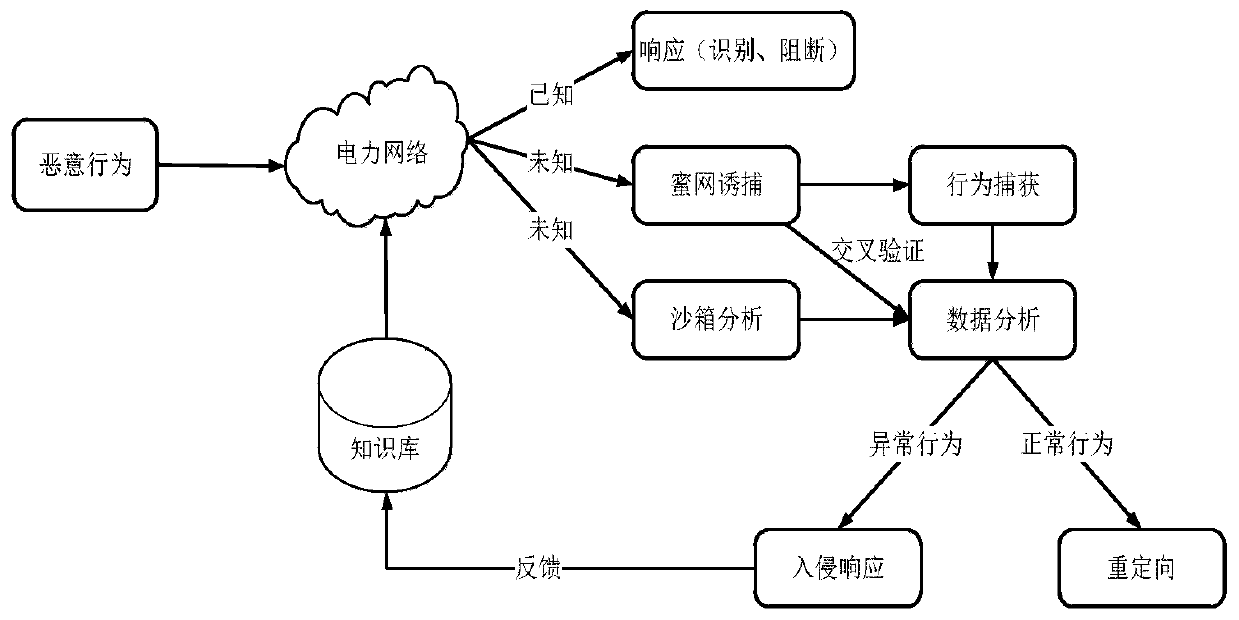
Power monitoring active defense method and system based on virtualization dynamic deployment
InactiveCN110784476AImprove securityReduce the likelihood of being detectedTransmissionVirtualizationData stream
The invention relates to a power monitoring active defense method and system based on virtualization dynamic deployment, and the method comprises the steps: (1), building a virtual honeynet system, and simulating a real business system of a power network; (2) monitoring the state of the virtual machine in real time, and carrying out honeynet trapping to obtain an abnormal behavior track when an abnormal data flow is monitored; and (3) analyzing whether the behavior is a malicious attack behavior or not, and carrying out blocking response. The active defense system adopting the honeypot and sandbox technology can reduce the possibility that a real service network of the power system is detected, increase the attack cost difficulty and timeliness of attackers, and effectively complement passive protection measures existing in the power system.
Owner:STATE GRID HENAN ELECTRIC POWER ELECTRIC POWER SCI RES INST +2
Network safety protective method for preventing reject service attack event
InactiveCN1822593AEasy to handleTo achieve the protective effectData switching networksTime segmentNetwork packet
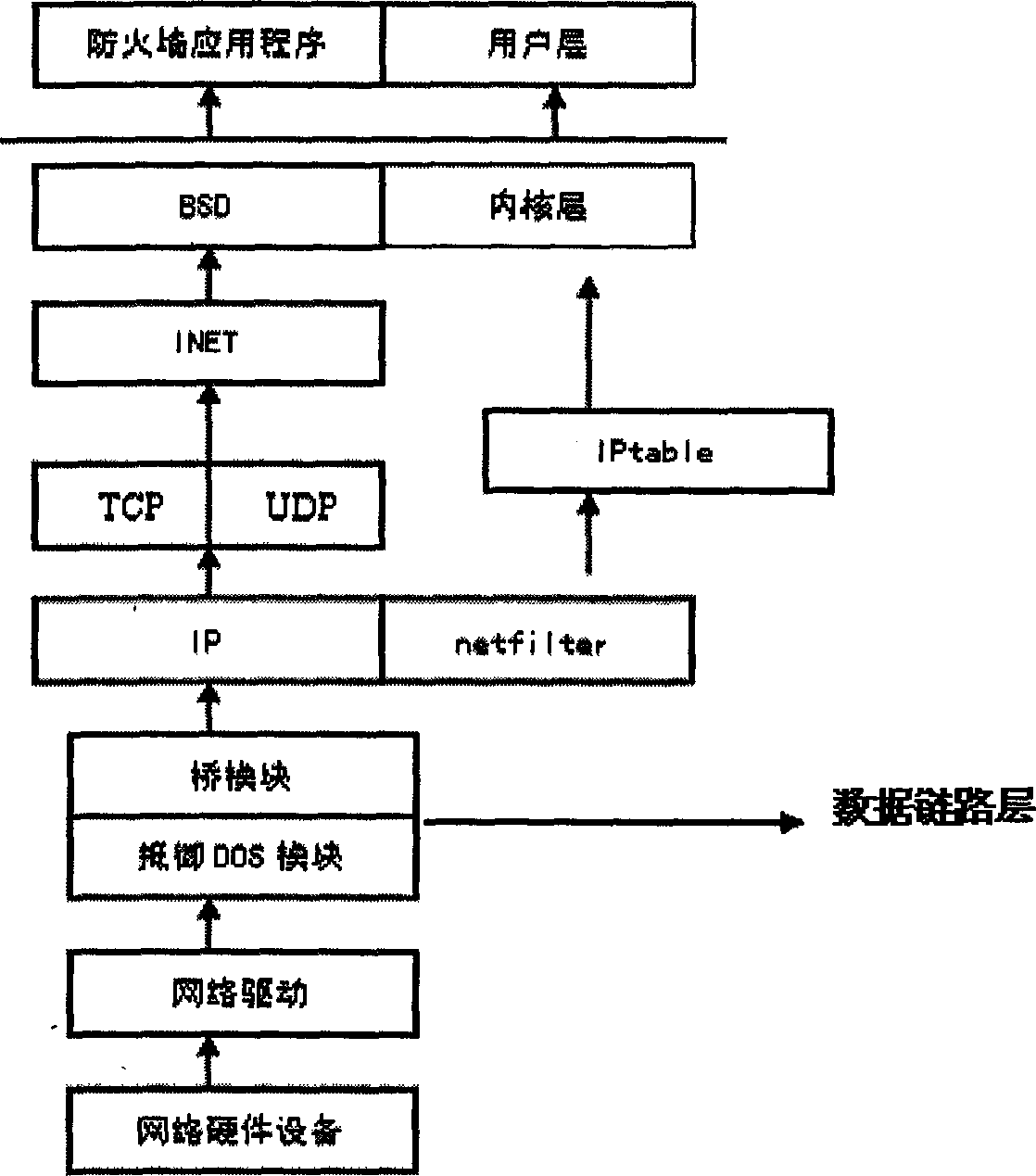
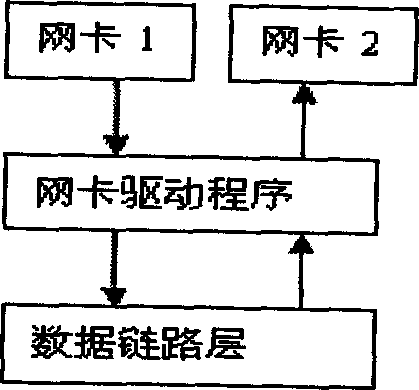
A network security protection method withstanding denial of service attack event designs defence module in data link layer. Said method judges TCP request packet received from different kinds of IP address to realize to denial of service offensive filtering. Said method includes following steps : fire wall capturing outer network client-side sent TCP data package to inner network server, to realize first layer protective treatment, the TCP data package passing first layer protection entering second layer protective treatment, checking whether said received TCP categorical data having matched item in legal IP address chaining recording list, if having matched item, then regarding as normal data package capable of directly handing inner core processing, otherwise to proceed package flow rate statistics in period of time. Said invention can active defense denial of service attack from any kind of attack tool and realize inner core active defense protection effect.
Owner:赵洪宇
Mobile terminal, security defense device thereof and security defense method thereof
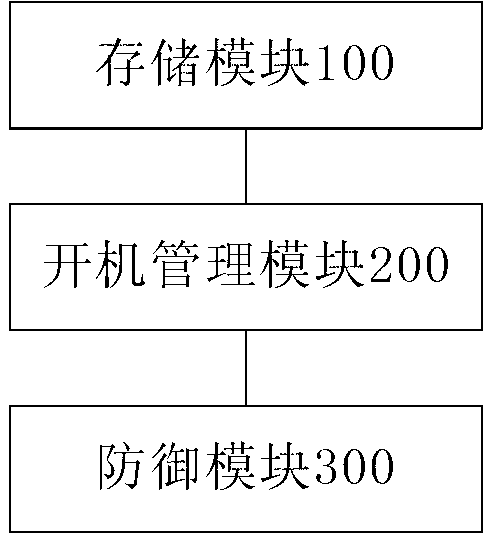
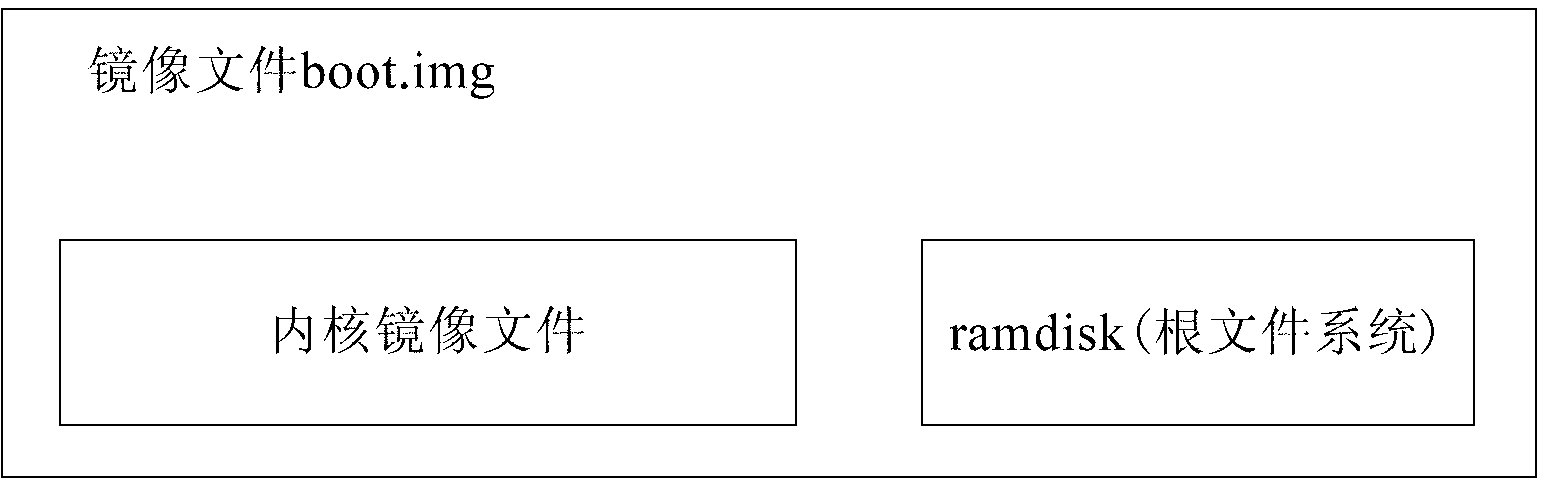
ActiveCN103324887ASecurity Defense GuaranteeImplement non-uninstallable featuresPlatform integrity maintainanceFile systemComputer terminal
The invention provides a mobile terminal, a security defense device thereof and a security defense method thereof. The security defense device comprises a storage module, a start-up management module and a defense module. The storage module is arranged in a root file system of the mobile terminal and used for storing an executable file in the defense module. The start-up management module is used for acquiring and operating the executable file according to a configuration file in the mobile terminal during starting-up of the mobile terminal. The defense module is used for generating a permanent defense progress according to the operating executable file. The defense progress is used for monitoring abnormal behaviors of the mobile terminal and taking active defense according to the abnormal behaviors. By the security defense device, incapability of uninstalling of a safety protection program, and permanent memory operation and automatic start-up management of a safety protection progress are realized, all-around monitoring and protection as well as self-repairing, performed by the safety protection progress, on an application layer and a service layer of an operating system of the mobile terminal are guaranteed, and safety protection of the operating system can be effectively guaranteed.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
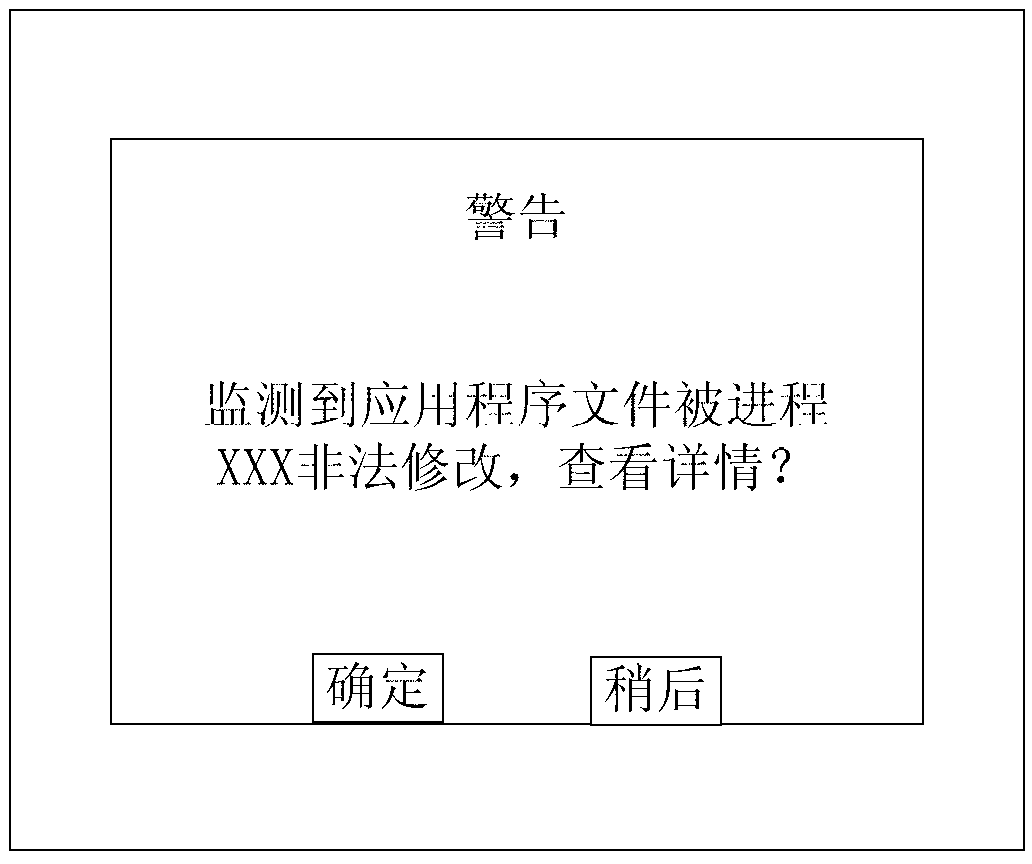
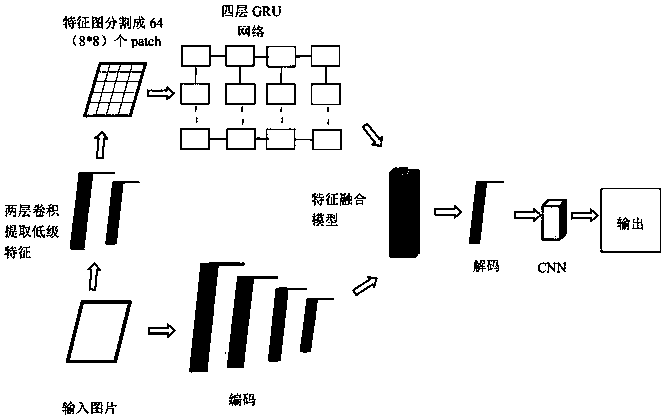
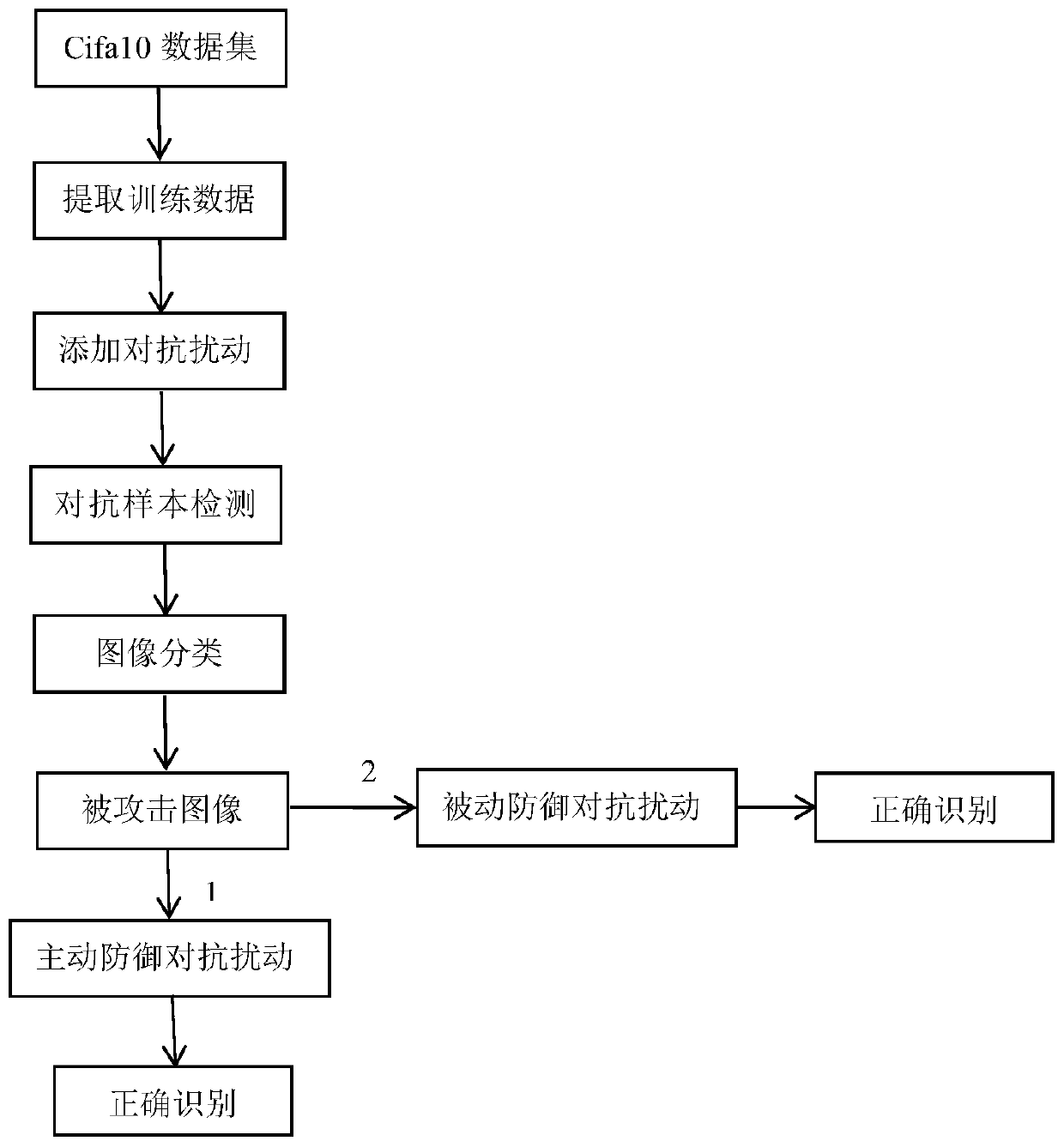
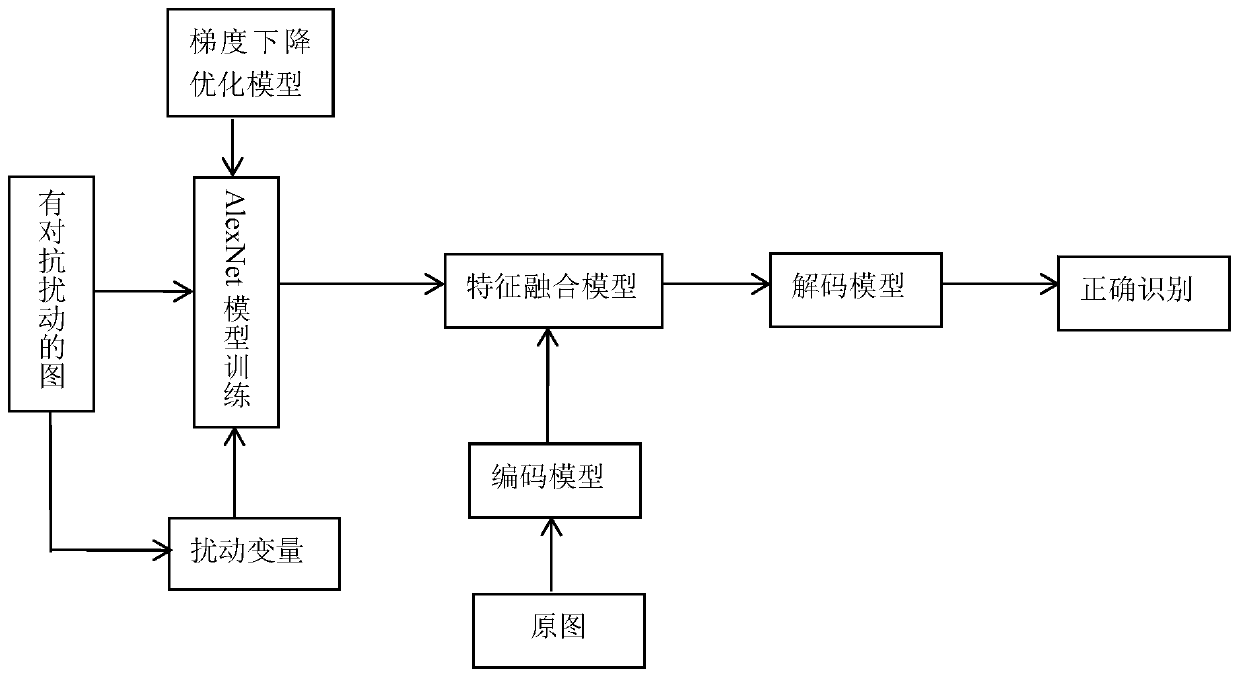
Mimicry defense method for deep learning model confrontation attack
ActiveCN110647918AReduce training timeImprove defenseCharacter and pattern recognitionPlatform integrity maintainanceFeature extractionEngineering
The invention discloses a mimicry defense method for deep learning model confrontation attack. The method comprises the following steps: 1) preparing a confrontation sample; 2) training a confrontation sample detector; 3) detecting the confrontation sample; 4) defensing confrontation disturbance, specifically actively defensing confrontation disturbance and deactively defensing confrontation disturbance. According to the method, the defects of manual feature extraction and pixel block division are avoided, the process is simplified, the training efficiency is improved, the data updating speedand accuracy are improved, and the data processing efficiency is improved.
Owner:ZHEJIANG UNIV OF TECH
Program processing method and program processing system
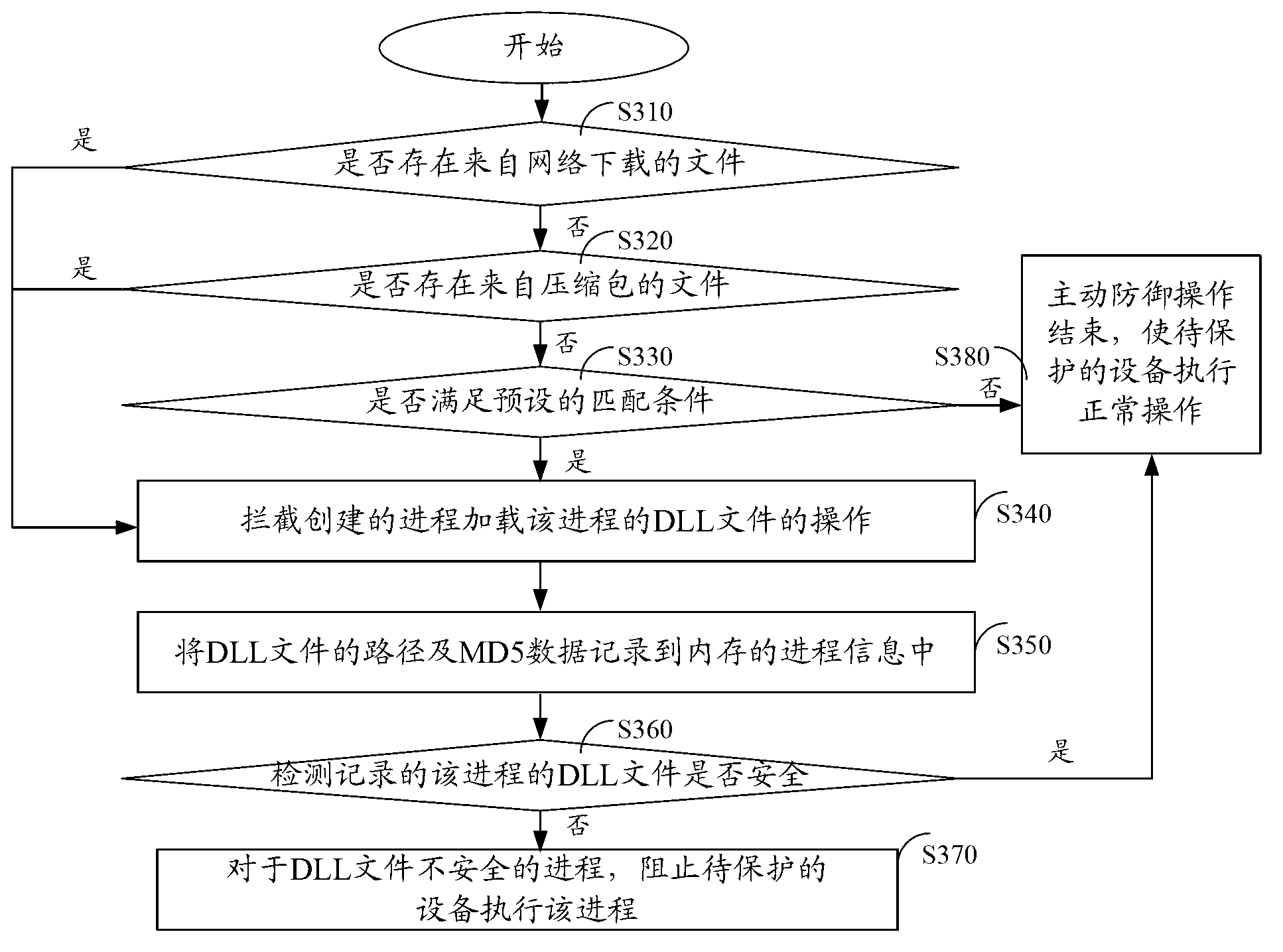
ActiveCN103001947AEffective interceptionAvoid lostPlatform integrity maintainanceProgram loading/initiatingProgram treatmentComputer engineering
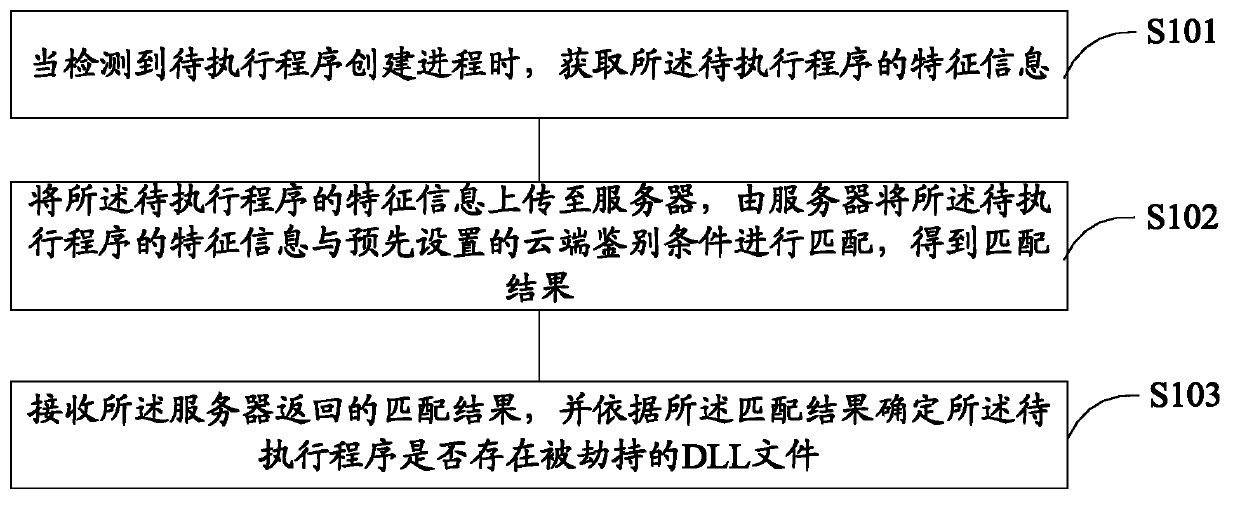
An embodiment of the invention discloses a program processing method and a program processing system, and aims to solve the problem that active defense cannot normally intercept a malicious program since the malicious program utilizes a credible program in a white list to load malicious DLL (dynamic link library) files. The program processing method includes: acquiring feature information of the program to be executed when the program to be executed is detected to create courses; uploading the feature information of the program to be executed to a server, and matching the feature information of the program to be executed with a preset cloud-end identifying condition by the server to obtain a matching result; receiving the matching result returned by the server, and determining whether intercepted DLL files exist in the program to be executed or not according to the matching result. By the aid of the program processing method and the program processing system in the embodiment, malicious programs can be intercepted more effectively.
Owner:360 TECH GRP CO LTD
Safety protection method of electric power information for mobile Internet
ActiveCN104135475AAvoid security issuesPrevent malicious tamperingTransmissionElectricityEcological environment
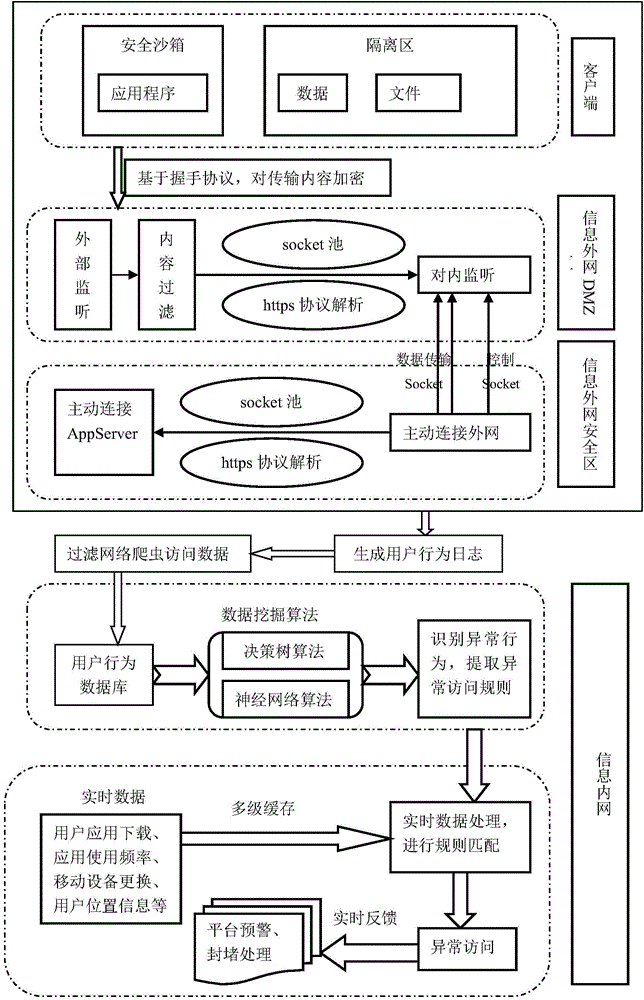
The invention discloses a safety protection method of electric power information for mobile Internet. The safety protection method is characterized in that safety protection is enhanced from two aspects: service resource safety protection and active defense, through utilizing safety protection mechanisms, such as a safety sandbox, an isolation region, a one-way access channel and a content filtering, data safety interaction of the mobile Internet is implemented, and the network security level is improved and perfected. According to the safety protection method, personal privacy of an electricity customer under the environment of the mobile Internet is effectively protected, the active defense is implemented based on a user behavior model, the integral level of mobile marketing service is improved, and a safe and reliable ecological environment for electricity service is built.
Owner:STATE GRID CORP OF CHINA +3
Identity authentication method and system, electronic equipment and computer readable storage medium
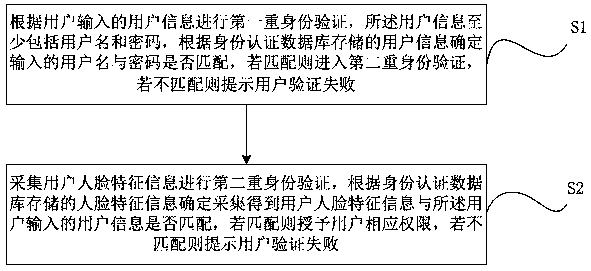
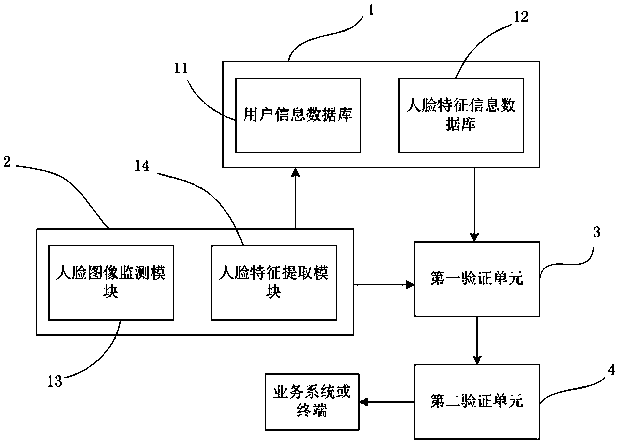
InactiveCN109815665ACharacter and pattern recognitionDigital data authenticationUser verificationUser input
The invention provides an identity authentication method and system, an electronic device, a computer readable storage medium. The method comprises the following steps that first identity verificationis conducted according to user information input by a user, the user information at least comprises a user name and a password, whether the input user name is matched with the password or not is determined according to the user information stored in a database, if yes, second identity verification is conducted, and if not, user verification fails is prompted; And collecting user face feature information to carry out second identity verification, determining whether the collected user face feature information is matched with user information input by the user according to the face feature information stored in the database, if so, granting a corresponding authority to the user, and if not, prompting that the user verification fails. The system, the electronic equipment and the computer readable storage medium are used for realizing the method. According to the invention, a safe, reliable and flexible integrated face recognition authentication service and early warning are provided foran enterprise, and the requirement of enterprise user identity information security active defense is better met.
Owner:SHENZHEN POWER SUPPLY BUREAU
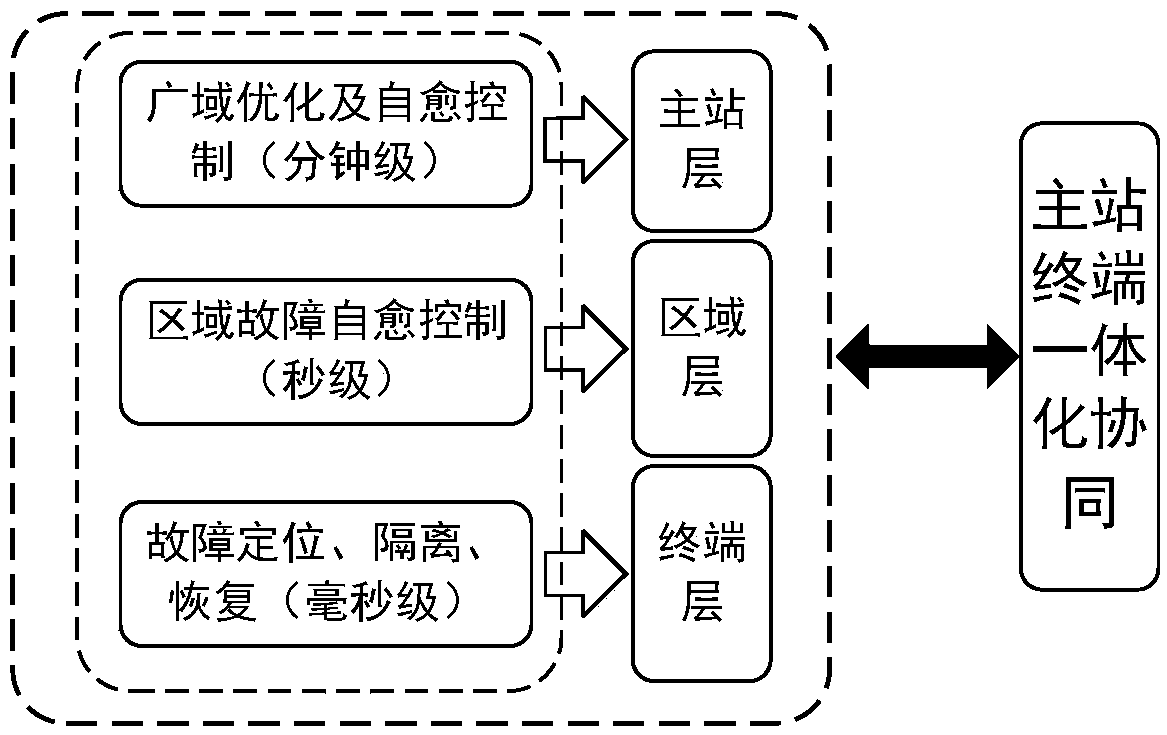
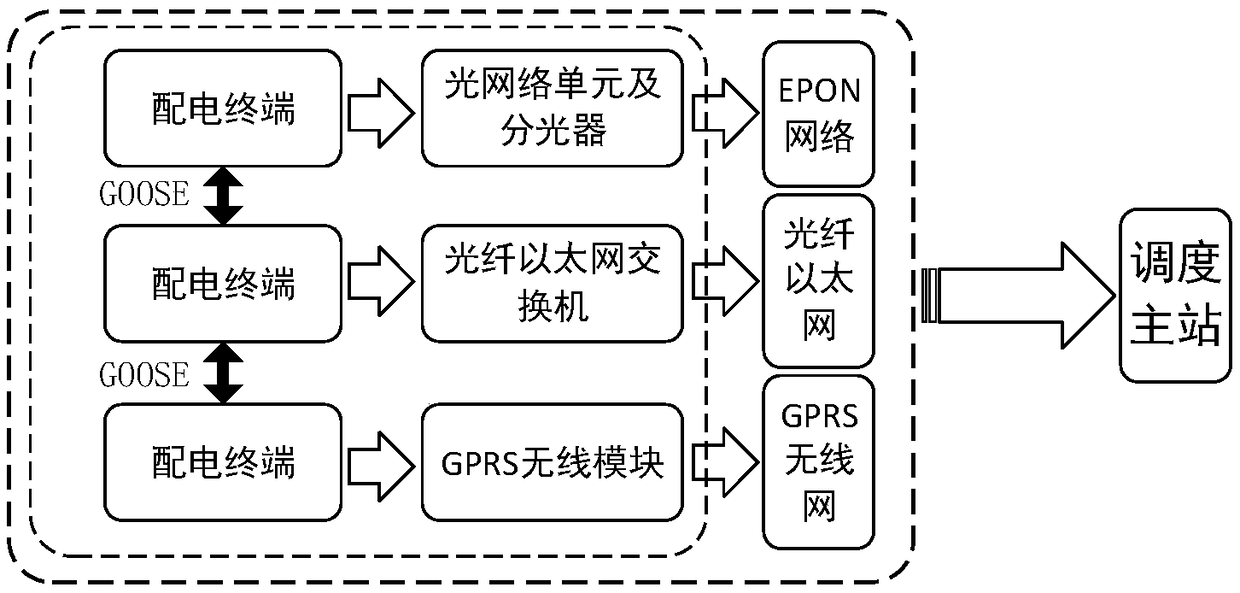
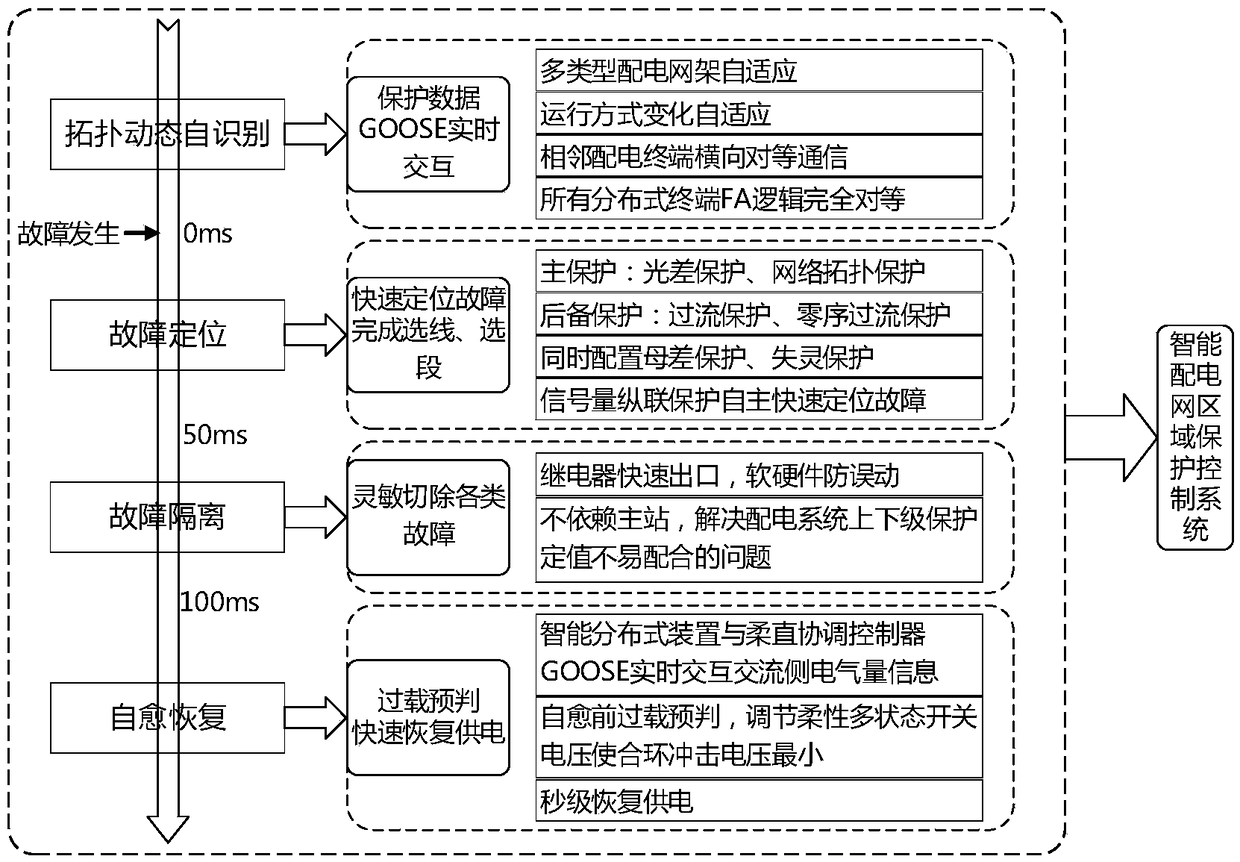
An intelligent distribution network area protection control system and a control method
ActiveCN109193582AEffectively respond to accessAchieve isolationEmergency protective circuit arrangementsTime informationControl system
The invention discloses an intelligent distribution network area protection control system and a control method. The system is mainly composed of intelligent distributed devices, a flexible and straight coordination controller. By exchanging GOOSE real-time information with each other, Under the fault condition, the active defense control, fault crossover control of flexible multi-state switches and the fault recovery control of cooperation between conventional contact switches and flexible multi-state switches can realize the fast location and isolation of distribution network faults and thefast transfer of non-fault sections, and improve the reliability of distribution network power supply.
Owner:CHINA SOUTHERN POWER GRID COMPANY +1
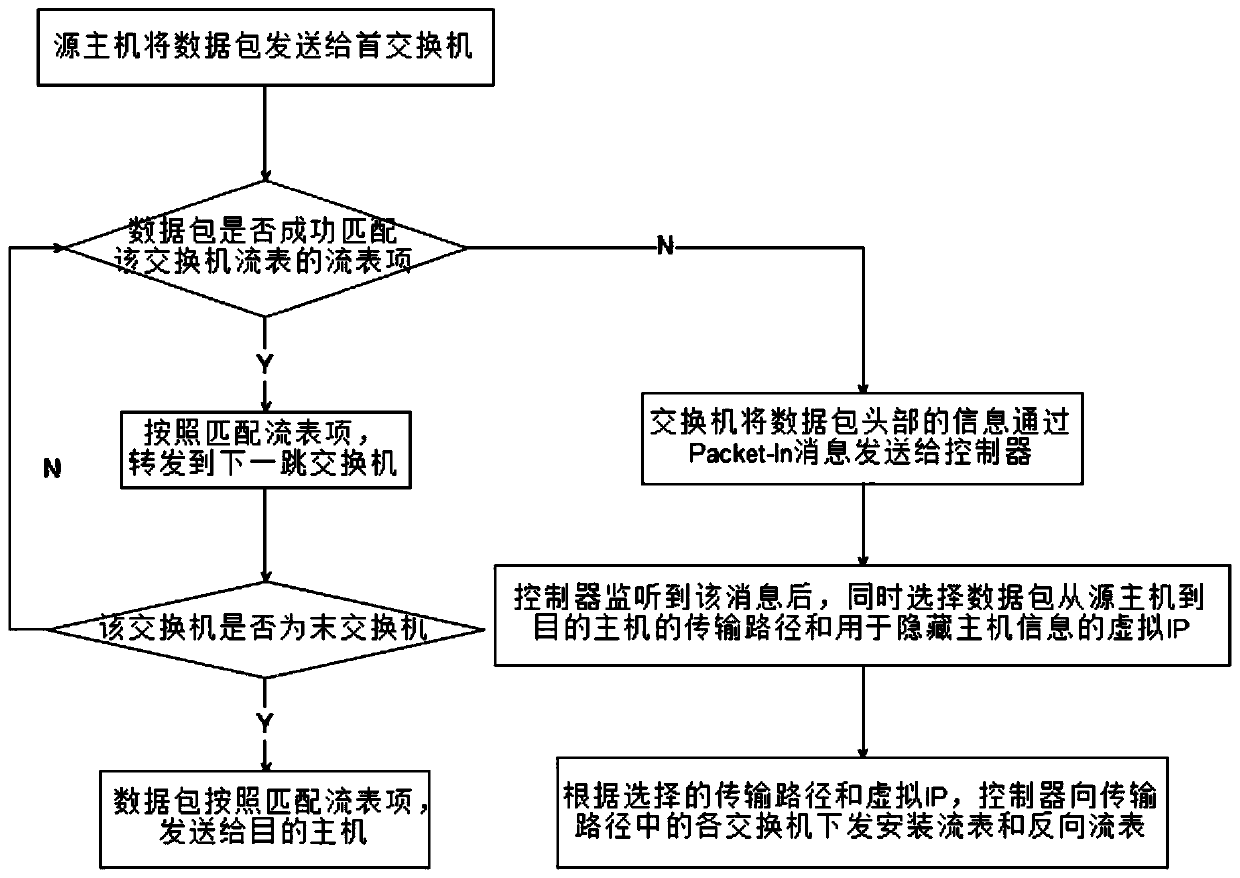
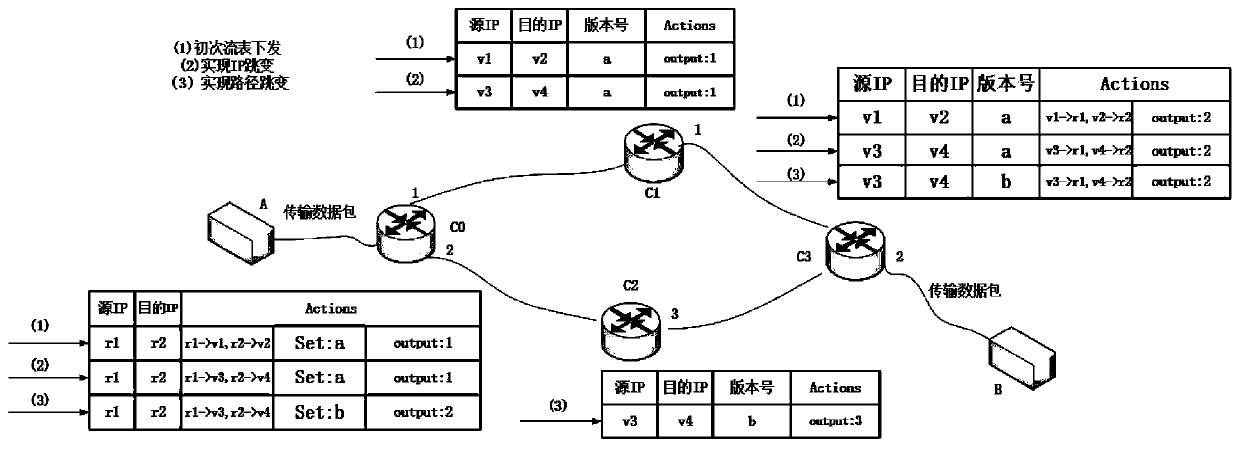
Active defense method based on path and IP address hopping in SDN network
InactiveCN110198270AIncrease the difficultyReduced availabilityData switching networksControl layerIp address
The invention discloses an active defense method based on path and address hopping in an SDN network, and belongs to the field of mobile target defense. The method comprises the following steps: S1, asource host sending a data packet to a first switch; S2, judging whether the data packet is successfully matched with the flow table item or not, if yes, forwarding the data packet to a next hop switch, and entering a step S5; otherwise, the switch sending the Packet-In message to the controller, and executing the step S3; S3, the controller selecting a data packet transmission path and a virtualIP at the same time; S4, the controller generating a flow table rule according to the selected transmission path and the virtual IP, and issuing a flow table and a reverse flow table to each switch;and S5, judging whether the switch is a final switch or not, if yes, sending the data packet to a target host, and otherwise, entering the step S2. By utilizing the separation characteristic of the SDN network data layer and the control layer and the idea of active operation change in the MTD, the IP and the transmission path of the data packet are changed on the premise of not influencing the normal communication of the network, and the difficulty of an attacker in acquiring information is increased, so that the active defense capability of the system is improved.
Owner:HUAZHONG UNIV OF SCI & TECH +1
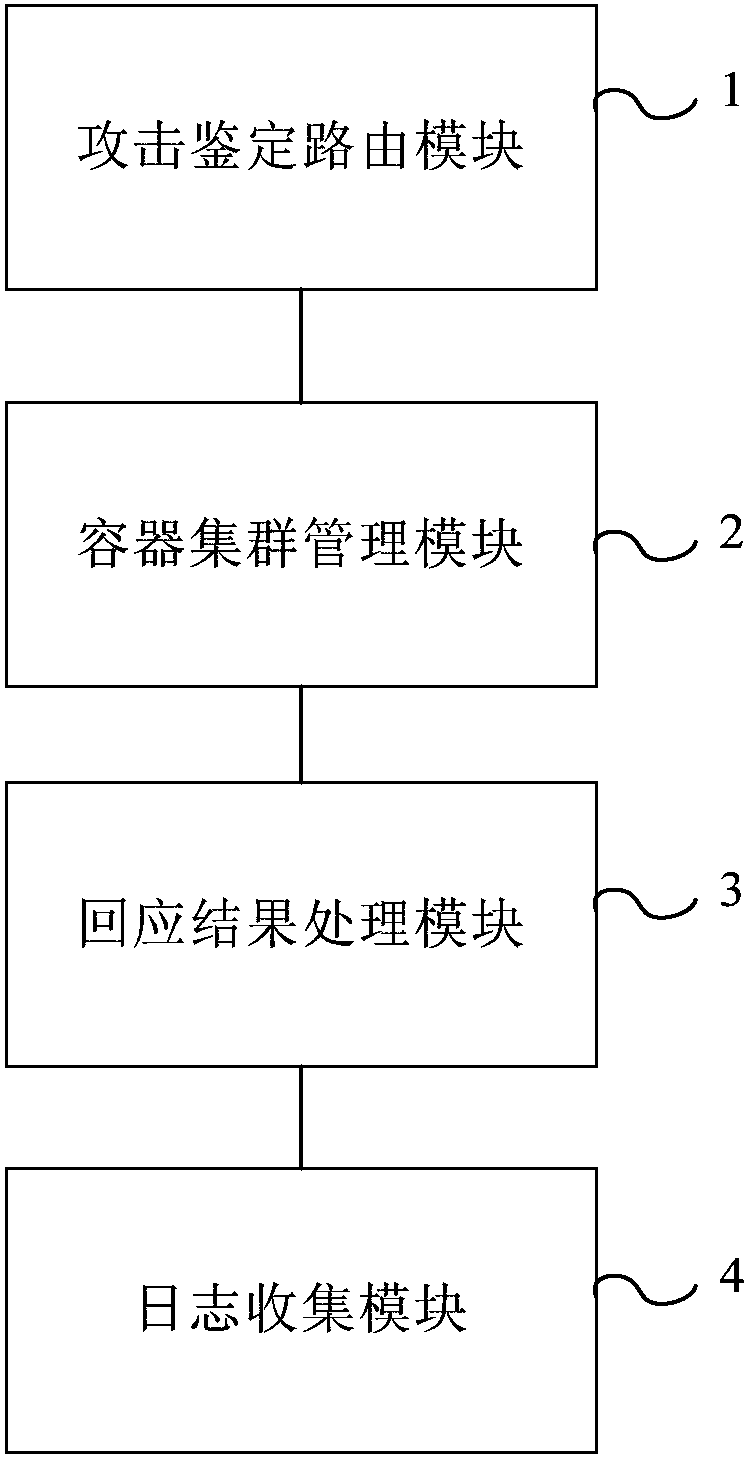
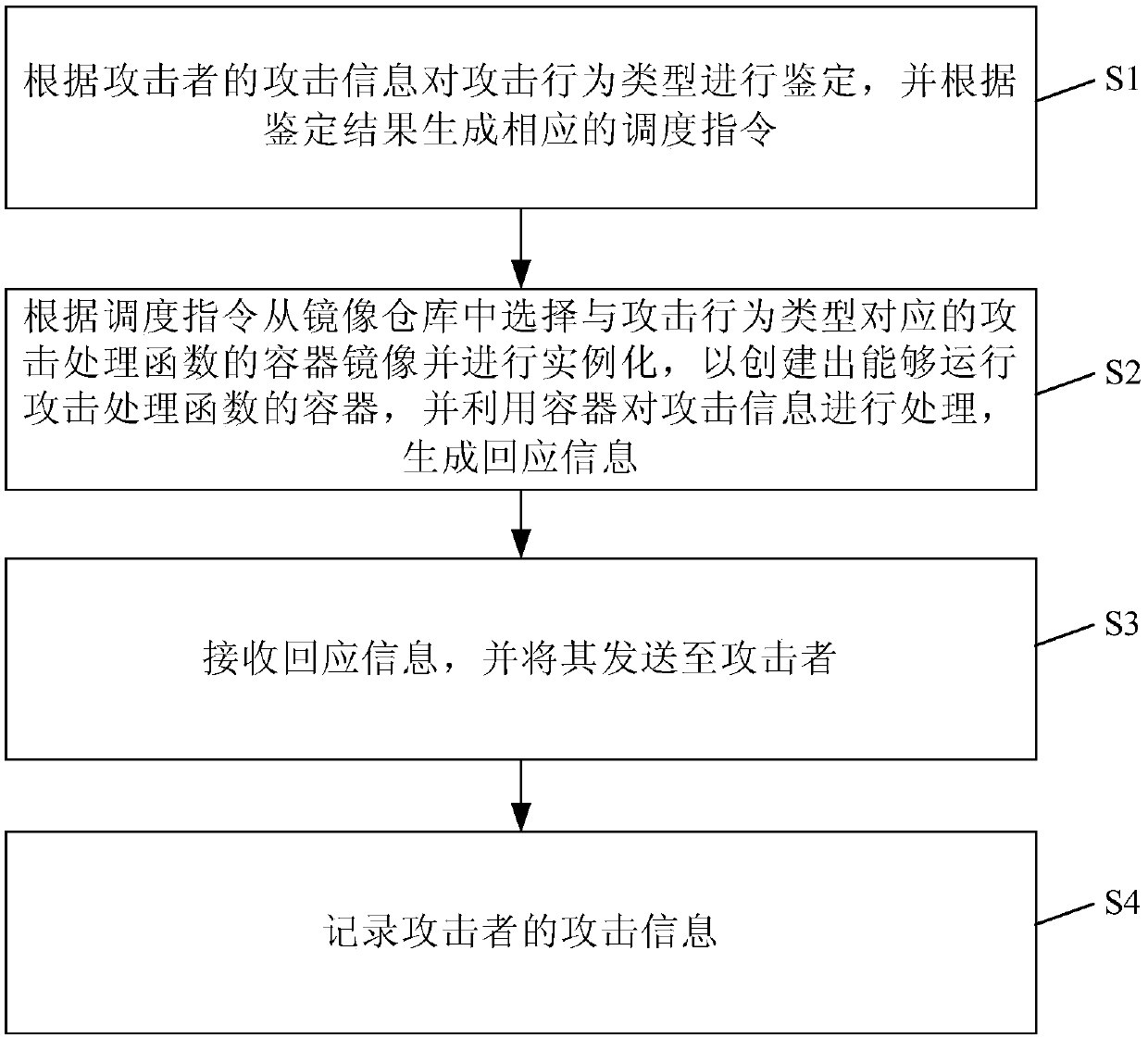
Honey pot active defense method and honey pot active defense system based on Serverless framework
The invention discloses a honey pot active defense method and a honey pot active defense system based on a Serverless framework. The honey pot active defense method comprises the steps: identifying anattack behavior type according to attack information of an attacker and generating a corresponding dispatching instruction according to an identifying result; choosing a container mirror image of anattach processing function corresponding to the attach behavior type from a mirror image warehouse according to the dispatching instruction, performing instantiation to establish a container which canoperate the attack processing function and utilizing the container to process of the attach information to generate response information; receiving the response information and sending the response information to the attacker. By means of the honey pot active defense method disclosed by the technical scheme of the invention, different types of attacks can be quickly responded; in addition, a honey pot is achieved by the container, a better environmental isolation effect is achieved, and that the attacker threatens the whole network environment through the honey pot environment is prevented tothe maximum extent.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Computer-system-based online handwriting authentication method
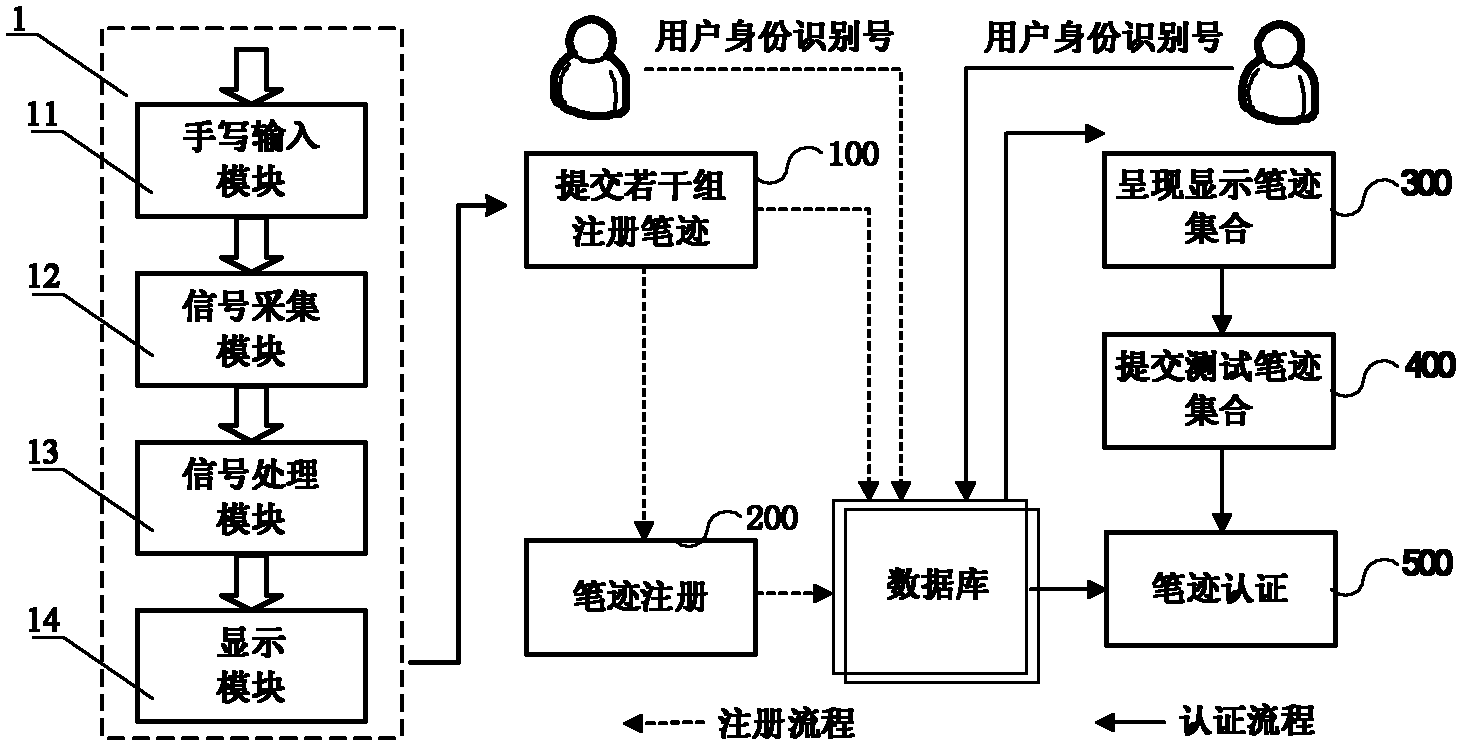
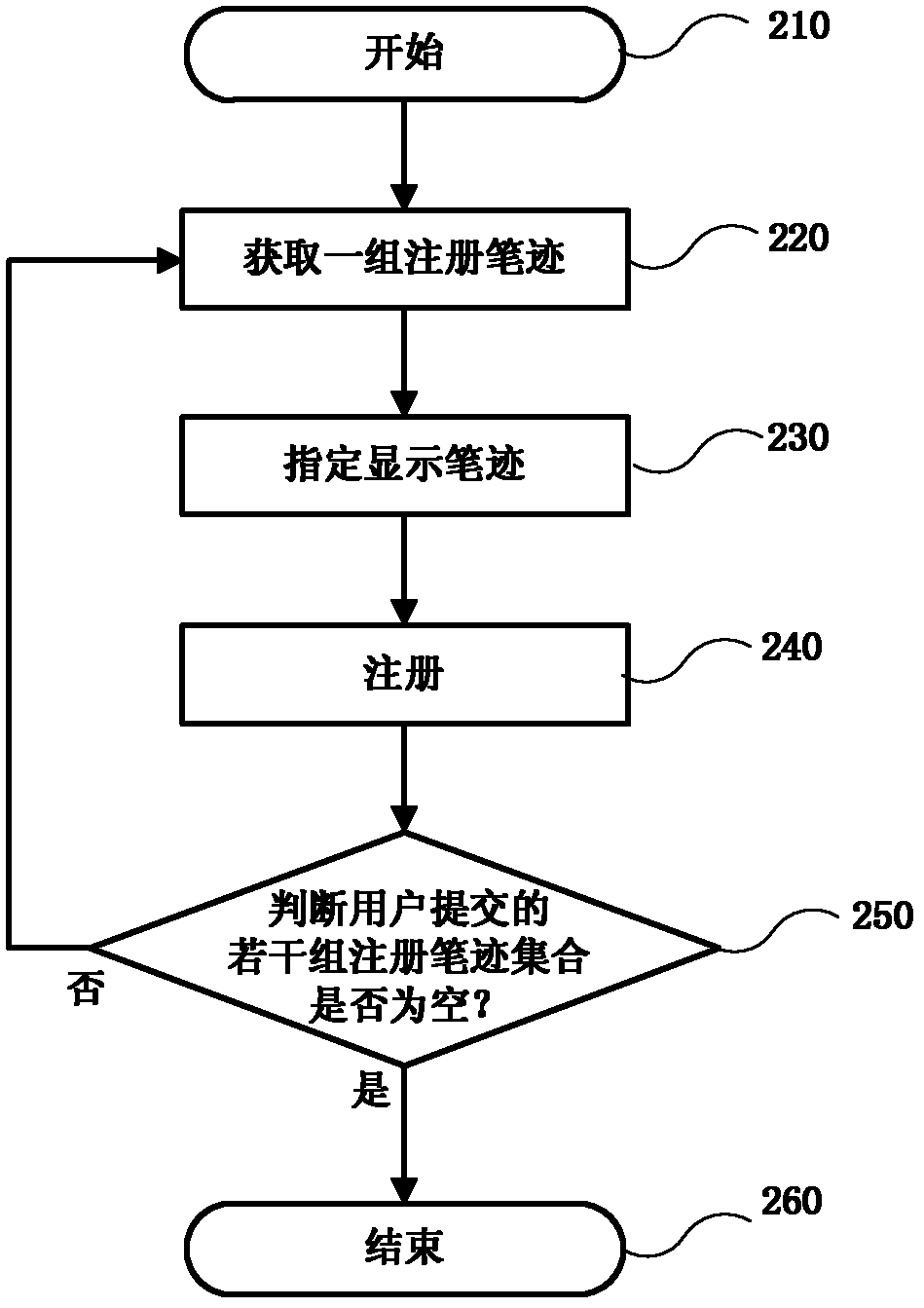
ActiveCN102592152AFull imitation of timeResist replay attacksCharacter and pattern recognitionHandwritingConfidentiality
The invention discloses a computer-system-based online handwriting authentication method, which comprises the following steps of: writing and submitting a plurality of groups of registered handwritings through handwriting input equipment by a user, storing the two-dimensional static character pattern position information of display handwritings corresponding to the registered handwritings into a database, and finishing handwriting registration according to the conventional online handwriting authentication method; in the test of a computer system, submitting a generated identification number by the user, randomly selecting a plurality of registered handwritings from the registered handwritings submitted by a corresponding user in a registration stage, and displaying the two-dimensional static character pattern position information of the display handwritings of the selected registered handwritings to the user; and submitting a corresponding test handwriting set at a time within a specified time by the user, finishing test handwriting authentication according to the computer-system-based online handwriting authentication method, and comprehensively making a decision to finish the authentication of the user. The method has the advantages of replay attack resistance, difficulty in the attack of an imitator and active defense; and the neglected shortcomings of dependence on handwriting confidentiality and high imitation rate neglected by the conventional online handwriting authentication method are effectively overcome.
Owner:HEFEI INSTITUTES OF PHYSICAL SCIENCE - CHINESE ACAD OF SCI
ROOT-free active defense configuration method and device
ActiveCN104239786ARealize active defenseRealize dynamic active defensePlatform integrity maintainanceEngineeringActive Defense
The invention provides a ROOT-free active defense configuration method and a corresponding device. The method comprises the following steps that a target application is determined, and an installation package of the target application is stored to a specified catalogue; an outer shell application installation package is configured through the installation package of the target application, a stub module for calling a monitoring unit is injected into the outer shell application installation package, configuration parameters in the pier module are modified to load the target application, and the monitoring unit is used for carrying out hooking monitoring on event behaviors from the target application; the outer shell application is installed. According to the active defense scheme, an existing system is modified a little, system compatibility cannot be influenced, and method and the device are easy to implement and efficient.
Owner:BEIJING QIHOO TECH CO LTD
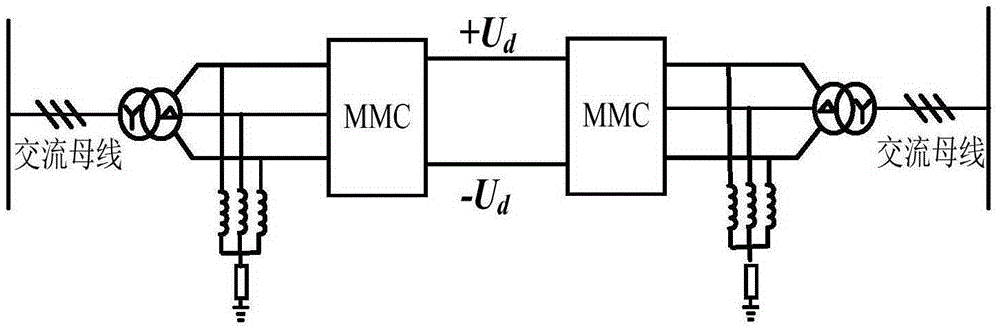
Asymmetric operational control method of direct current side monopolar grounding fault of MMC-HVDC system
ActiveCN105406500AEliminate overvoltageEliminate fault currentElectric power transfer ac networkContigency dealing ac circuit arrangementsEngineeringDirect current
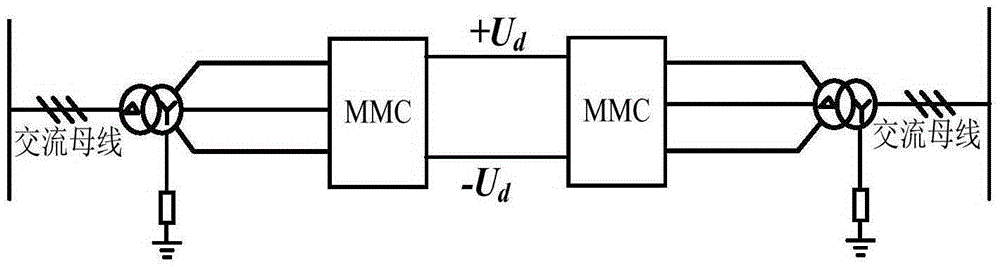
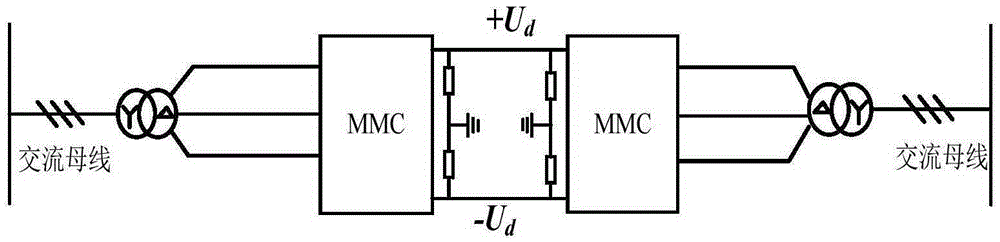
The invention discloses an asymmetric operational control method of the direct current side monopolar grounding fault of an MMC-HVDC system. For the MMC-HVDC system based on monopolar symmetric wiring, after a direct current side monopolar grounding fault occurs, over voltage and fault current at AC and DC sides can be rapidly eliminated by setting the DC component of the output voltage of a bridge arm of a fault pole without locking a current converter, and further the insulation threat to AC / DC systems can be eliminated. Through adjusting phase angles of alternating components of different bridge arm voltages, the system still can continue transmitting half of a rated active power and provide reactive power support for the AC system while isolating the direct current side monopolar grounding fault, which has positive significance for the stability of the connected AC / DC systems; during the fault period, the current converter does not need to exit from operating, the restore speed of the system is high, the current converter is in a controlled state in the whole process, and therefore the active defense capability of the MMC-HVDC system based on monopolar symmetric wiring against the direct current side monopolar grounding fault can be improved.
Owner:HUAZHONG UNIV OF SCI & TECH
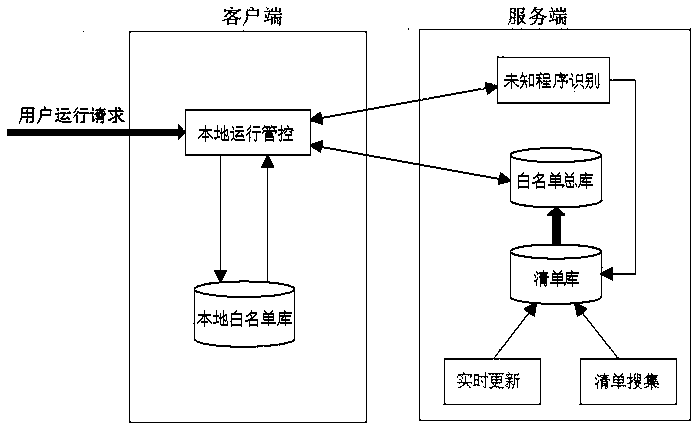
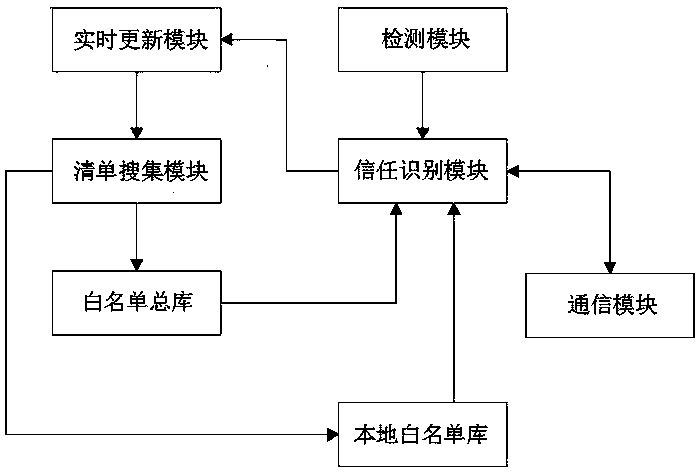
Active Defense Method on The Basis of Cloud Security
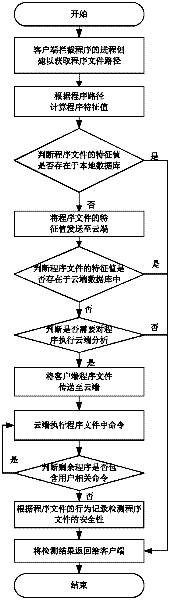
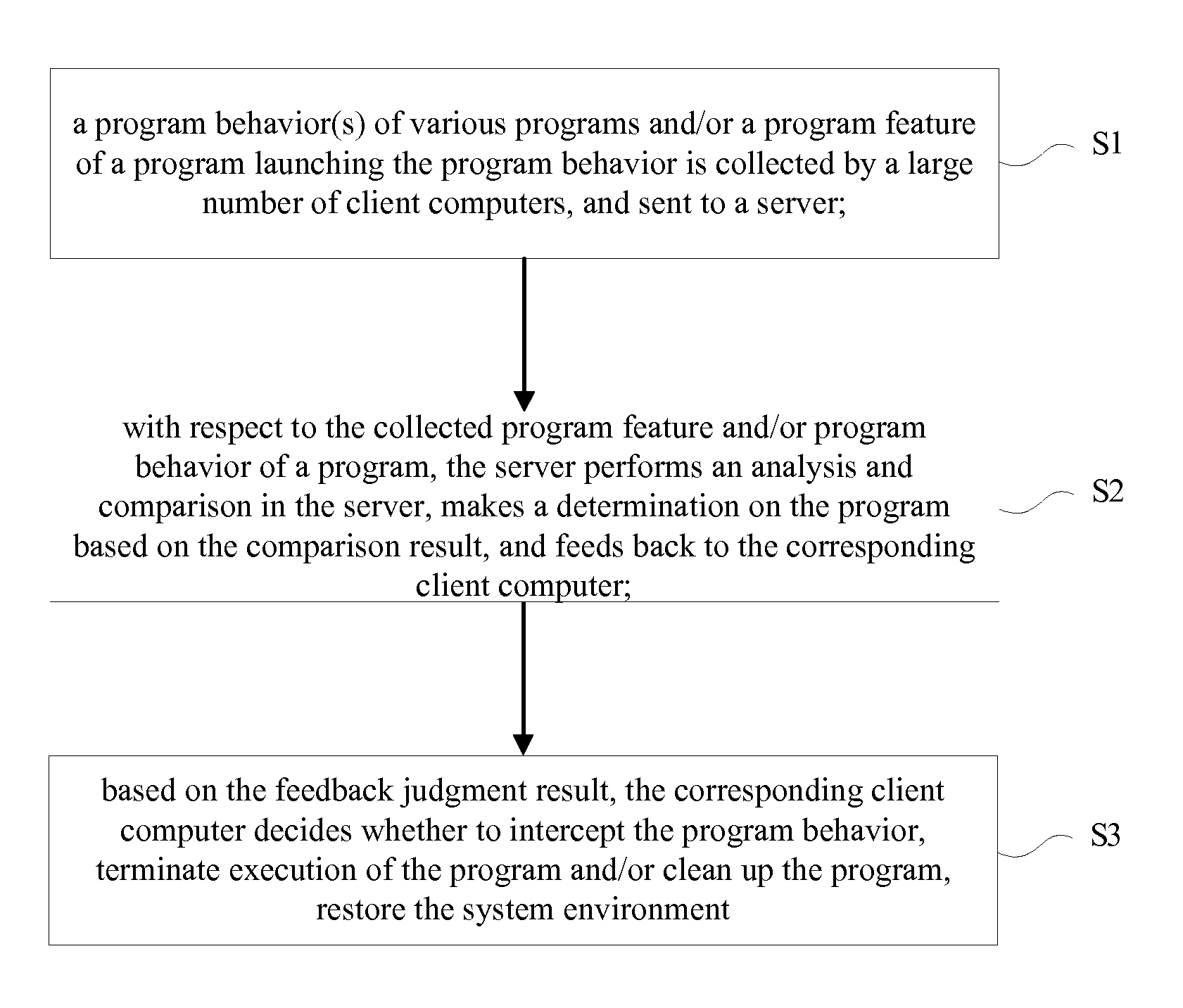
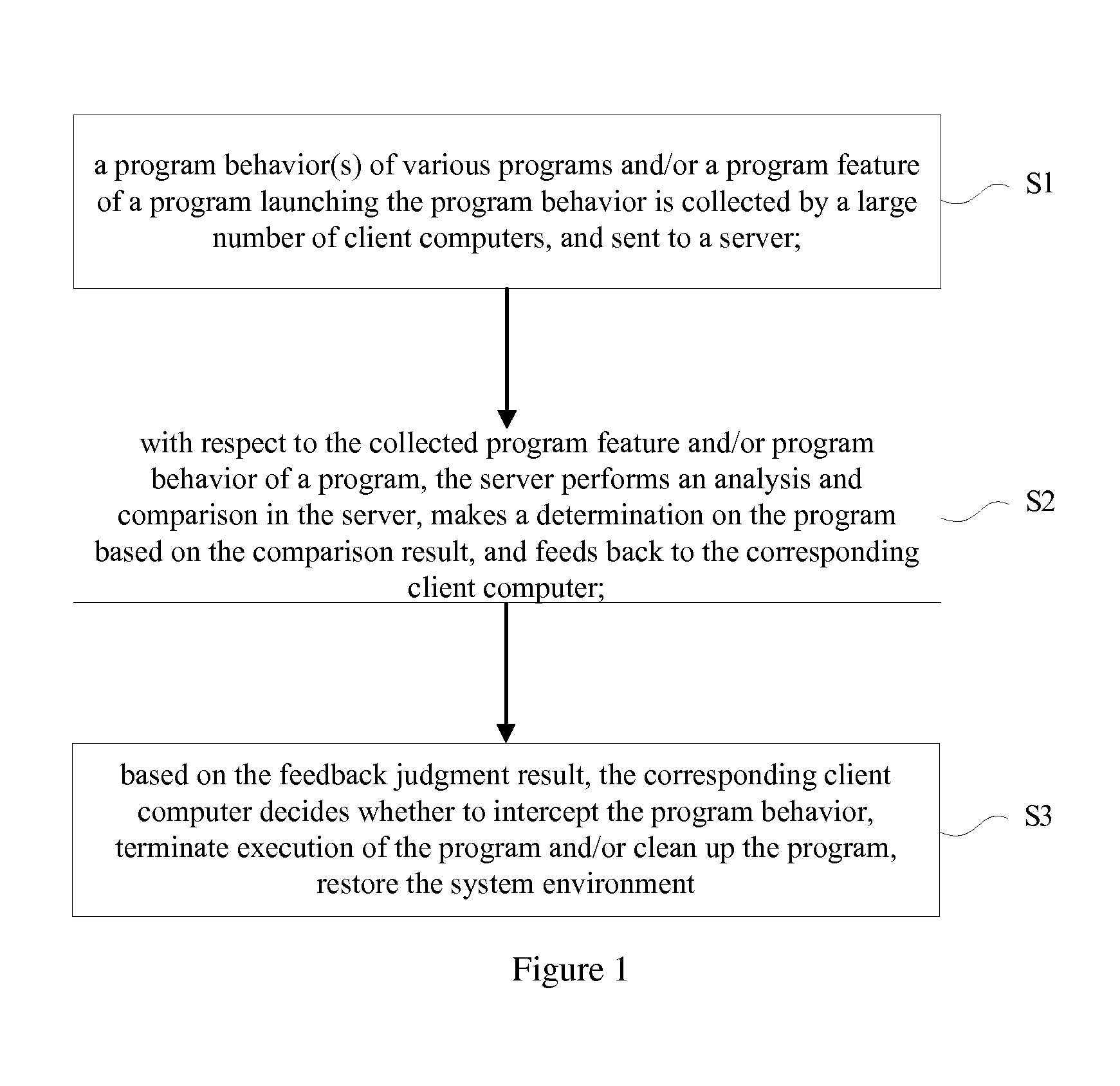
The present invention relates to an active defense method based on cloud security comprising: a client collecting and sending a program behavior launched by a program thereon and / or a program feature of the program launching the program behavior to a server; with respect to the program feature and / or the program behavior sent by the client, the server performing an analysis and comparison in its database, making a determination on the program based on the comparison result, and feeding back to the client; based on the feedback determination result, the client deciding whether to intercept the program behavior, terminate execution of the program and / or clean up the program, and restore the system environment. The invention introduces a cloud security architecture, and employs a behavior feature based on active defense to search and kill a malicious program, thereby ensuring network security.
Owner:BEIJING QIHOO TECH CO LTD +1
Design method of active defense system based on white list technology and system
InactiveCN107944232AGuarantee effectivenessGuaranteed recognition efficiencyPlatform integrity maintainanceProgram/content distribution protectionSystems designOperational system
The invention provides a design method of an active defense system based on white list technology and a system, belonging to the technical field of safety. According to the design method of the activedefense system, the reliability of a white list source is guaranteed through collecting the Hash value of a legal copy operation system mirror image; network visits are reduced through generating andcustomizing a local white list library for a customer, the recognition efficiency of a program is improved to some extent, and the starting speed of a run program is guaranteed; the pragmaticality and recognition efficiency of the white list are guaranteed through acquiring a patch updated by an operating system in real time; a recognition function is trusted through an unknown program, the resource requirement on traditional white list technology is solved, and the non-limitation of the white list is guaranteed. The method and the system can be used for effectively solving the problem whicha blacklist confronts, and are reliable, efficient, pragmatic and non-limited in the realization of the active defense system design of the white list.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com