Network security defensive system, method and security management server
A defense system and security management technology, applied in the field of network security defense, can solve the problems of scattered security defense mechanism, inability to carry out unified management and technical statistics, and proliferation of network security problems, and achieve the effect of preventing continued proliferation and spread
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
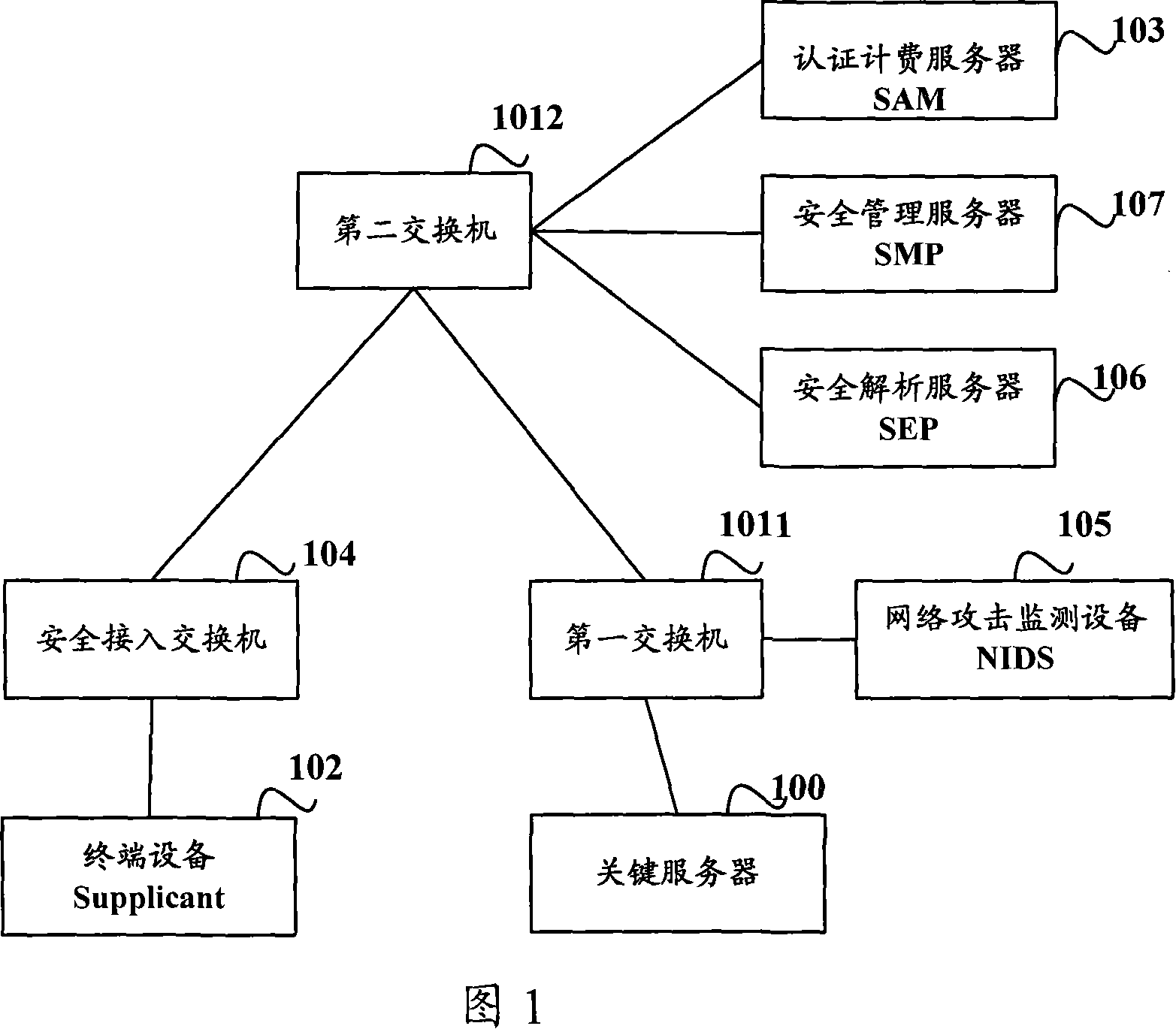
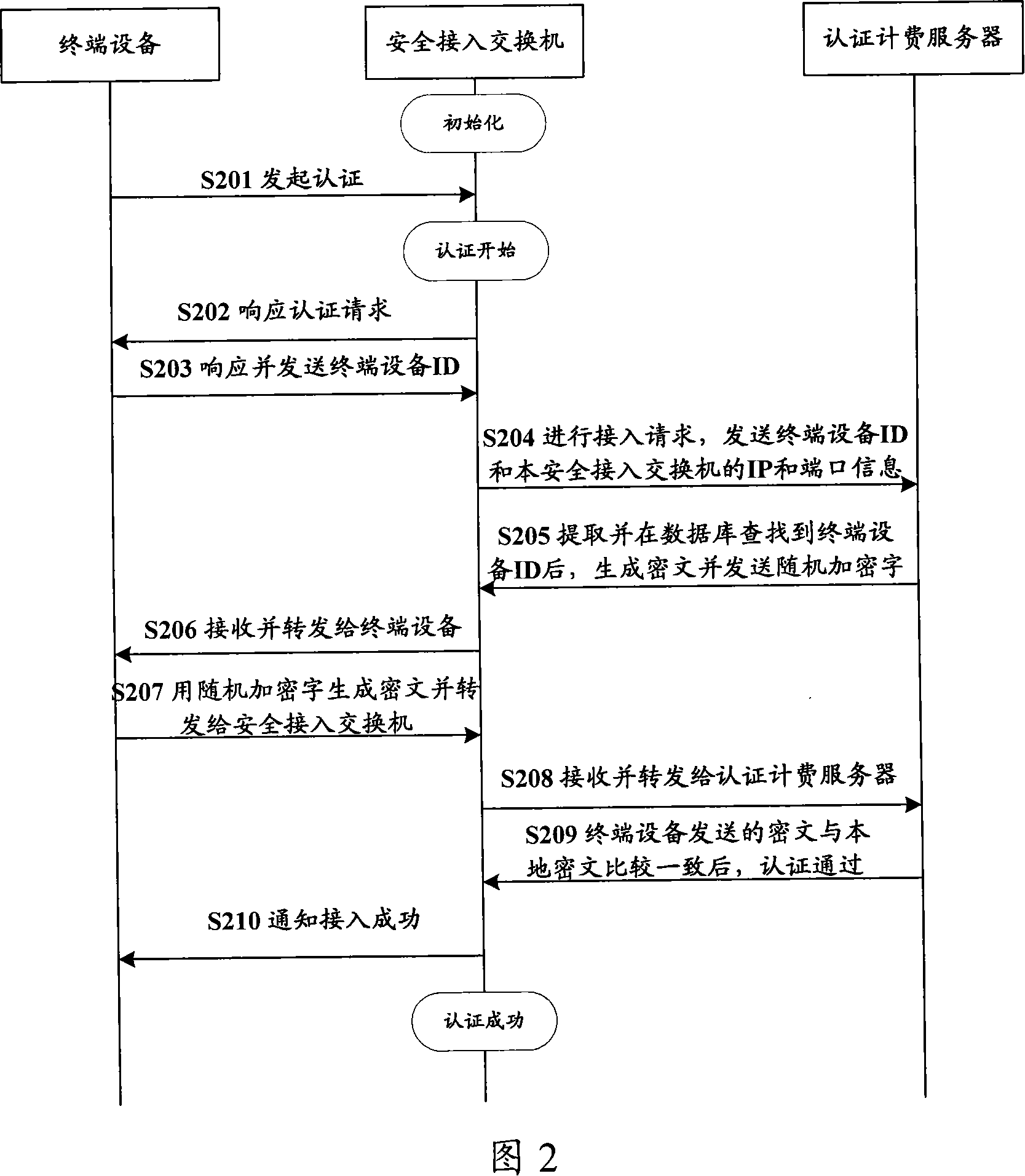
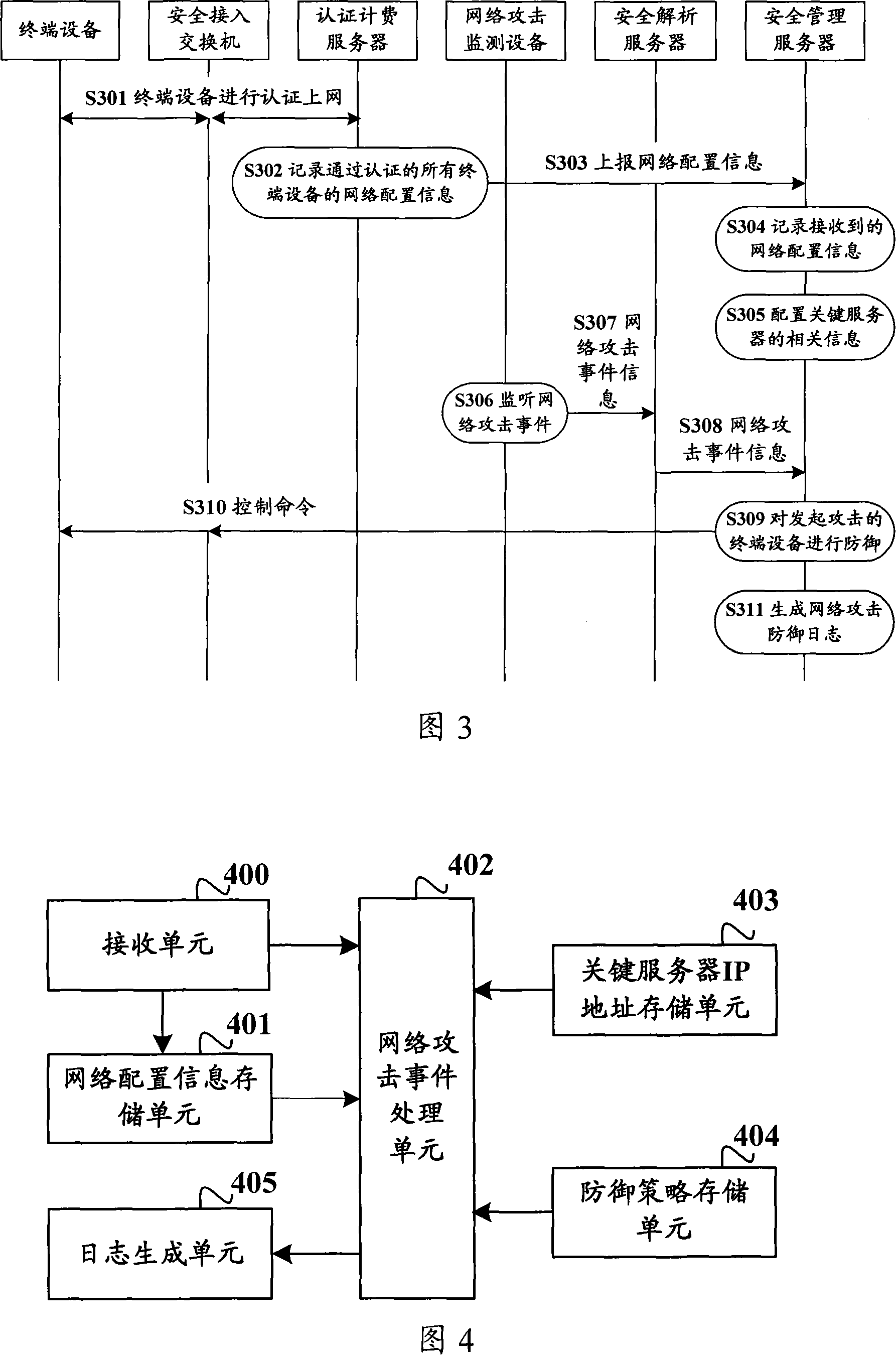
[0046] The embodiment of the present invention provides a method and system for security defense of servers in the network to solve the defects in the network security defense mechanism in the prior art, and is mainly used for active and efficient network security defense of key servers .
[0047]The embodiment of the present invention achieves the purpose of network security defense for servers, especially key servers, through the linkage and interaction of various security components, thereby effectively preventing malicious users from network attacks on servers, mainly involving the following security components: Authentication client (Supplicant), authentication and accounting management system (Security Accounting management System, SAM), security access functional components, security management platform (Security Manager Platform, SMP), security event parser (Security Event Parser, SEP), Network attack detection system (Net Intrusion Detection System, NIDS), in which: ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com