Patents
Literature
826 results about "Network administrator" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
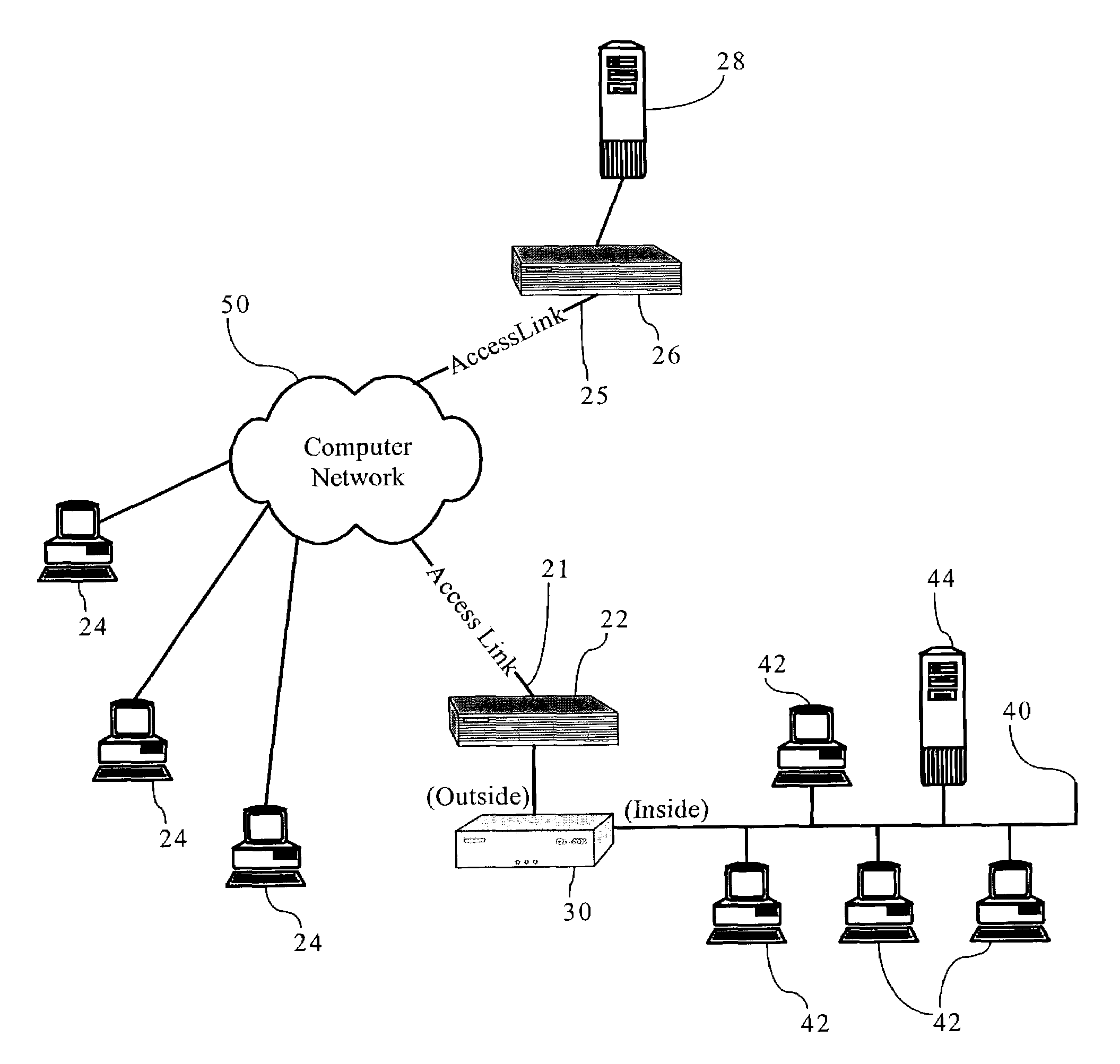
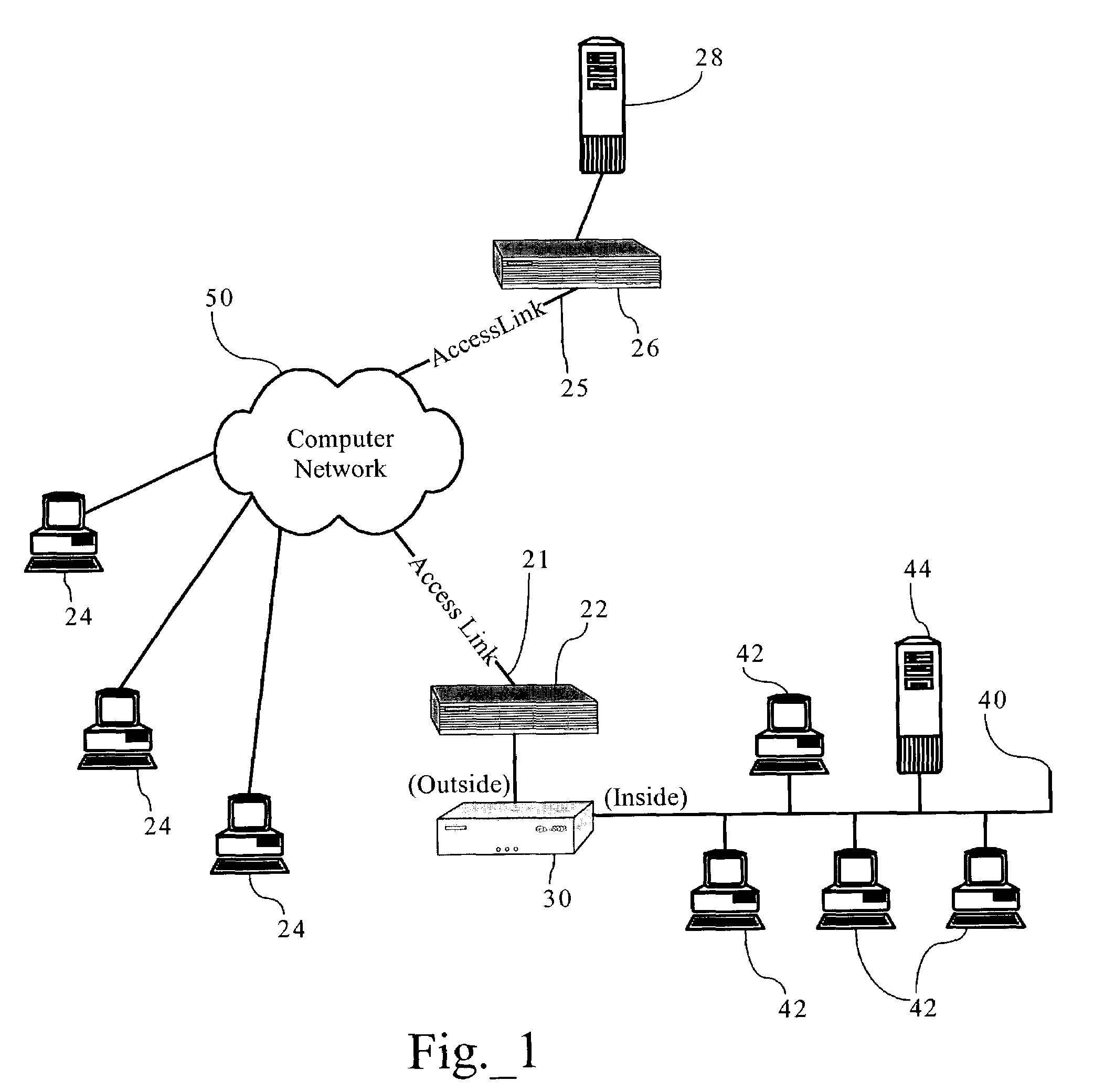
A network administrator is the person designated in an organization whose responsibility includes maintaining computer infrastructures with emphasis on networking. Responsibilities may vary between organizations, but on-site servers, software-network interactions as well as network integrity/resilience are the key areas of focus.
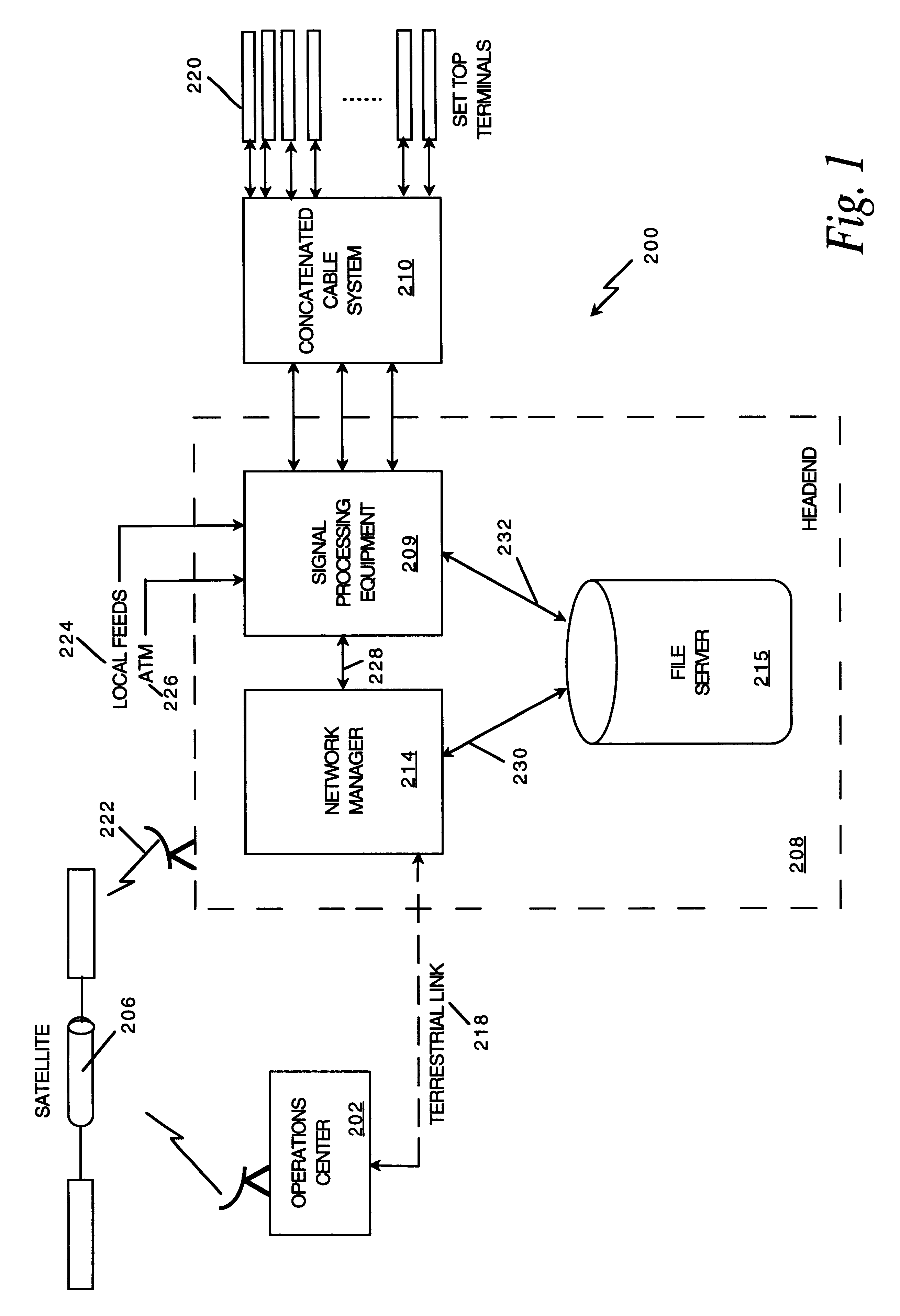
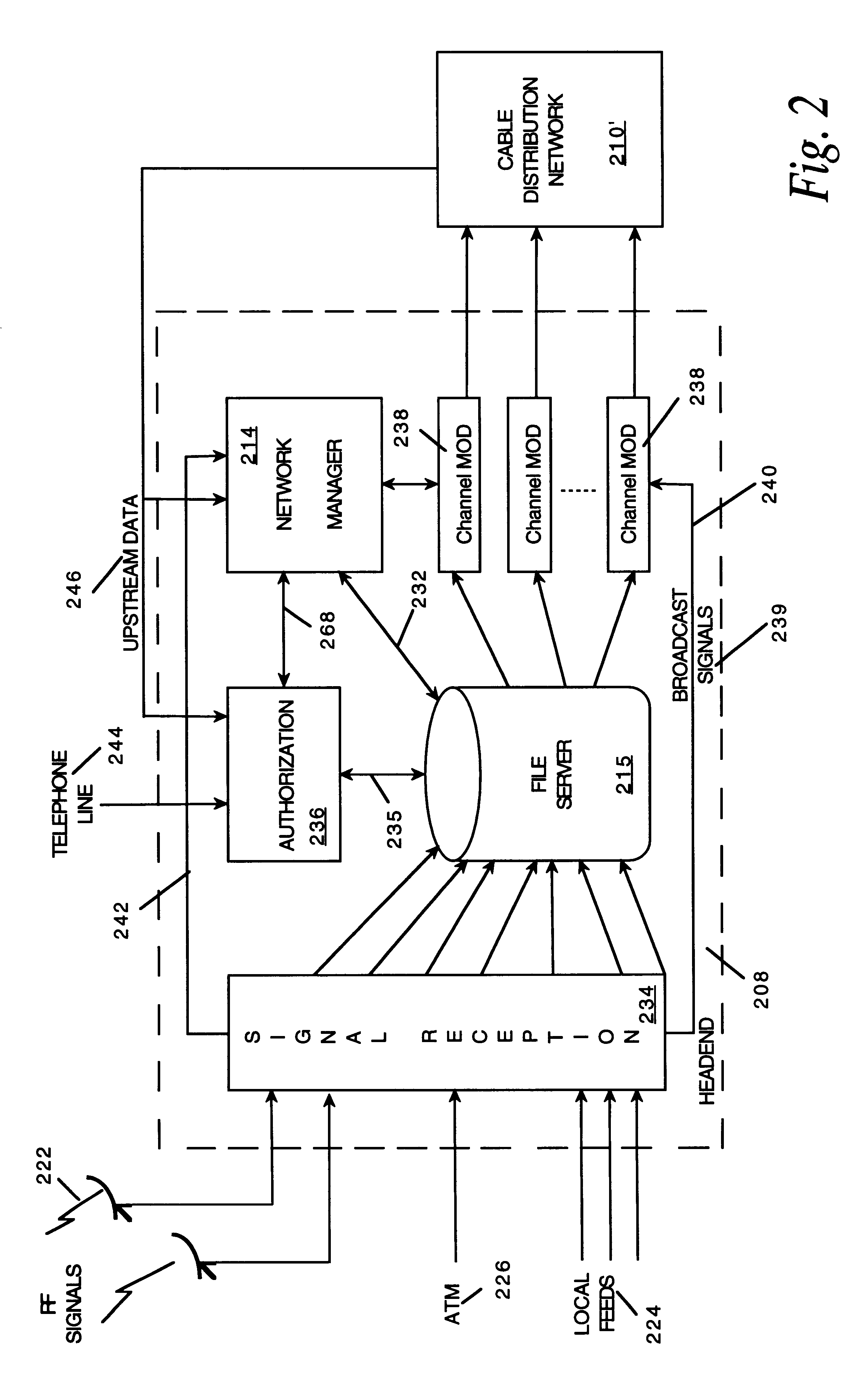
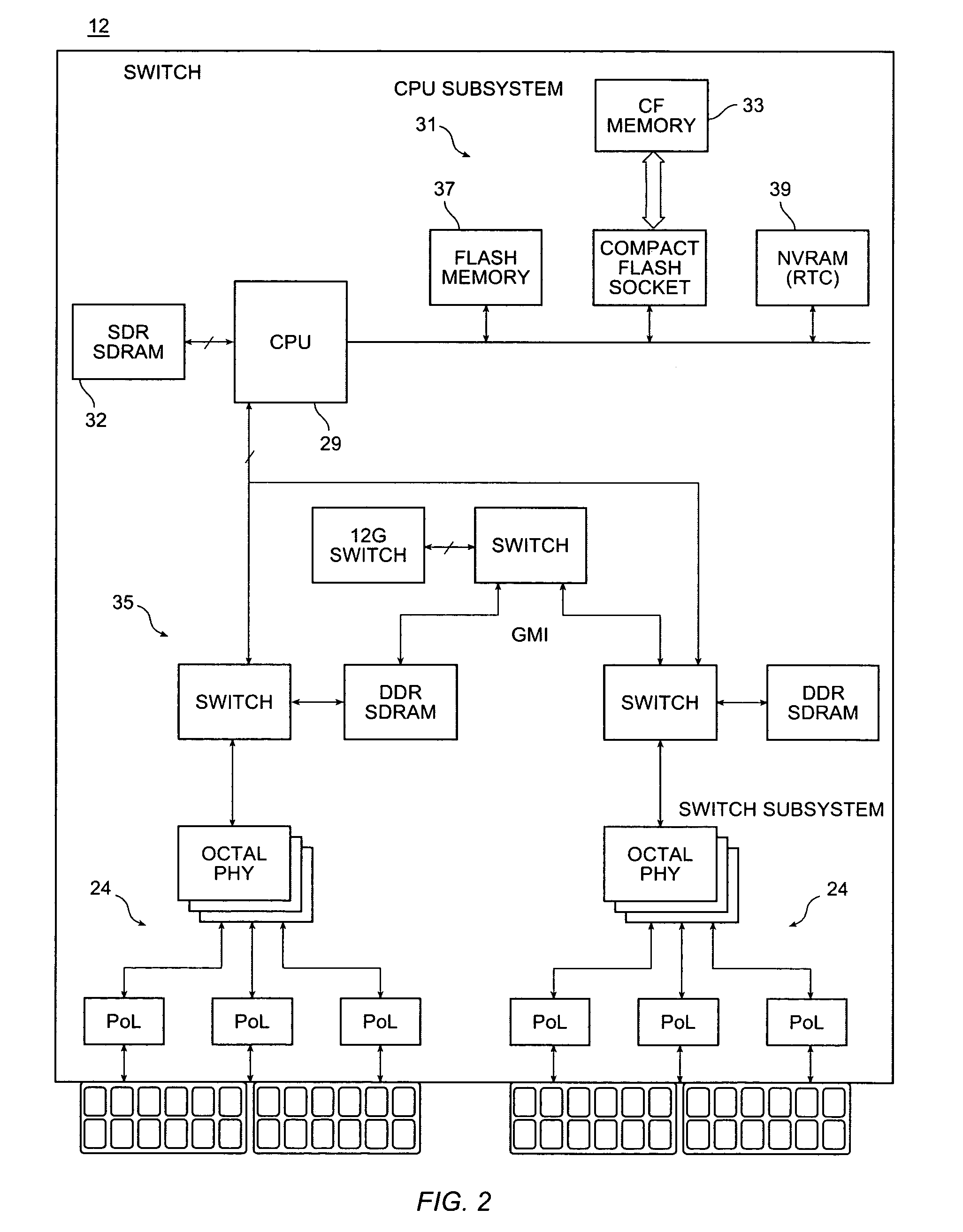
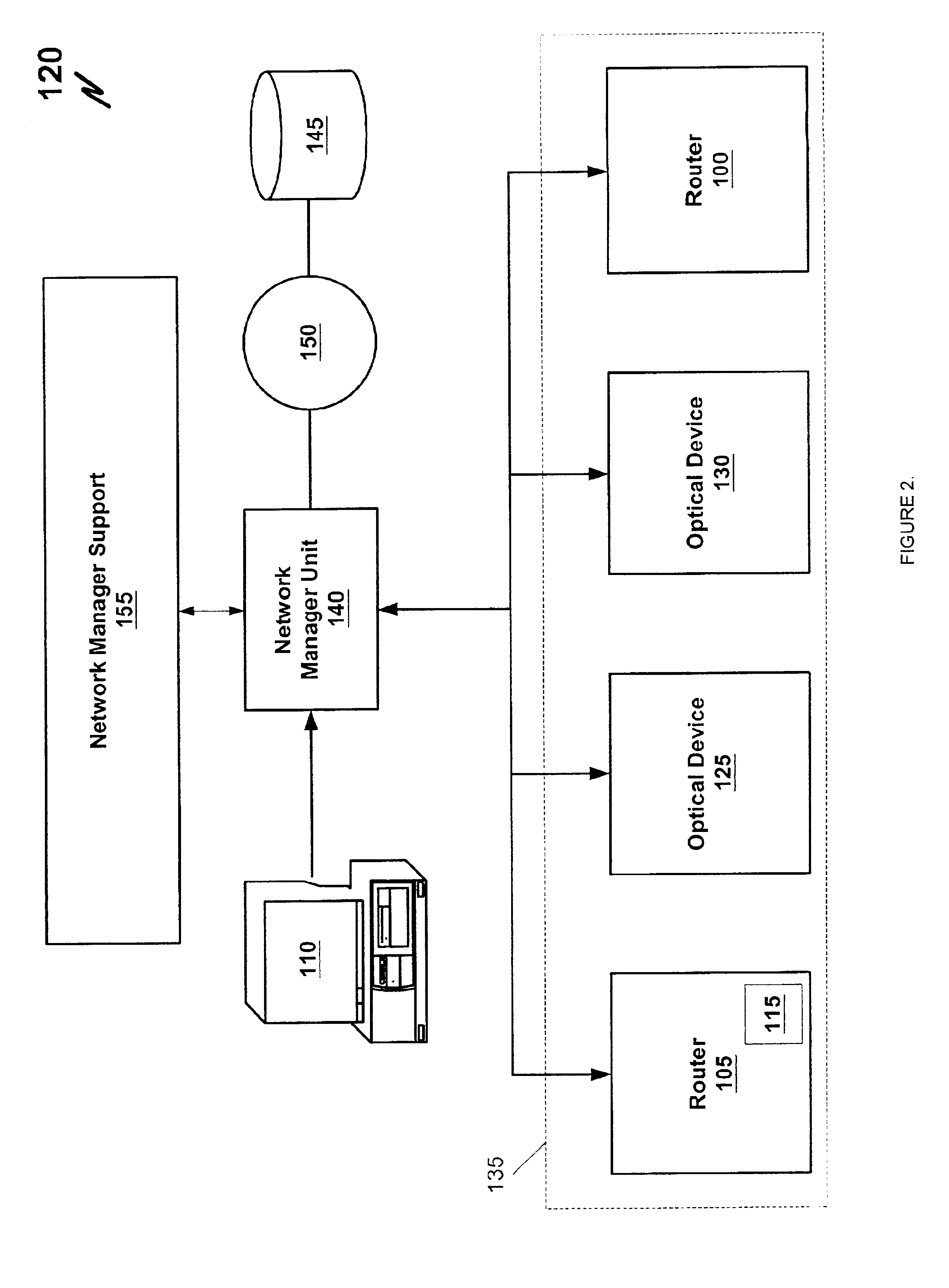
Network manager for cable television system headends
InactiveUS6201536B1Increase flexibilityImprove rendering capabilitiesTelevision system detailsPulse modulation television signal transmissionInformation processingInstruction memory
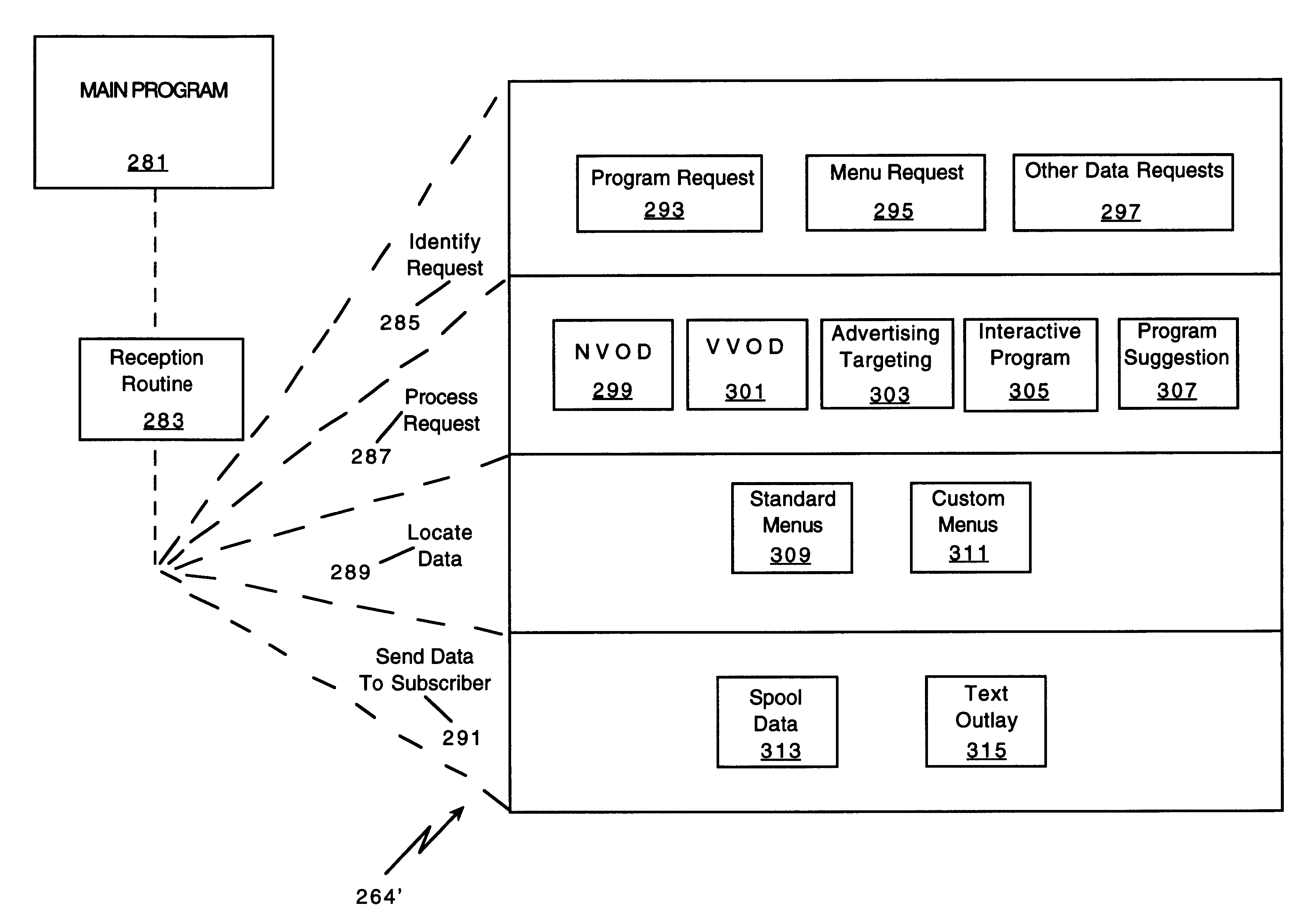
A novel network manager for use with a cable television system headend capable of monitoring and managing headend components and set top terminals in a television delivery system is described. The invention relates to methods and apparatus that manage and coordinate the reception of various programming and control signals at a headend. The invention manages and coordinates the storage of such signals for intelligent selection and distribution to set top terminals. The invention makes use of a receiver or set of receivers, a work station, a program control information processing component, a network management CPU, databases, control software and an instruction memory. The invention uses these components to manage and monitor certain headend components, such as signal reception equipment, an authorization component, a file server, MPEG decoders, a digital buffer with frame repeat and channel modulators. The invention is particularly useful in processing and responding to upstream information and subscriber communications received from set top terminals. In so doing, the invention accommodates various system services, including (1) near video on demand (NVOD), (2) virtual video on demand (VVOD), (3) video on demand (VOD), (4) interactive program services, (5) program suggestion features, (6) advertisement targeting, (7) generation of standard and custom menus, and (8) data spooling and text overlaying.
Owner:COMCAST IP HLDG I
Method and apparatus for displaying health status of network devices
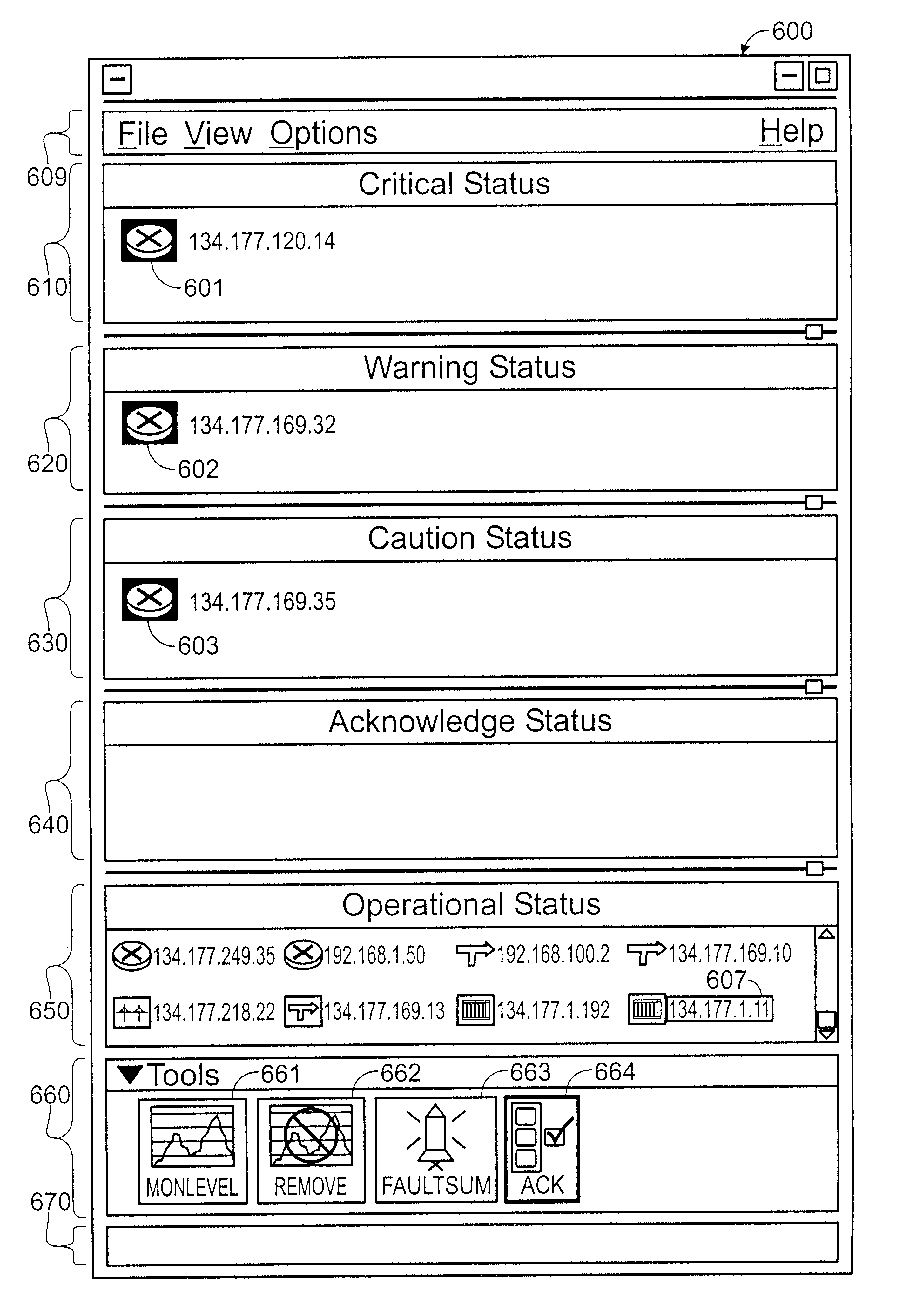
A method and apparatus for concurrently displaying from a single window on a network management station the health status of all network devices and objects of a computer network. The network devices may be categorized according to state or device type, as determined by the network manager. The method and apparatus provides a network manager with the ability to determine the current state of network devices and objects within an enterprise network and invoke further actions such as configuration, performance, fault, and security management tasks. The network manager can drag and drop icons from one network management system application window to another network management system application window to obtain fault information about network devices and objects, thus allowing multiple network management system applications to run concurrently on the same network management station. The network manager is further able to add new network devices and objects by dragging site, folder or device icons from one network management system application window to a second network management system application window for displaying the health status of the new devices. The dragged-in devices are added to the appropriate status panes within the second window according to the method of the present invention.
Owner:NORTEL NETWORKS LTD
Systems and Methods for Providing Dynamic Spillover of Virtual Servers Based on Bandwidth
The present solution provides a spillover management technique for virtual servers of an appliance based on bandwidth. A network administrator may configure a bandwidth threshold for one or more virtual servers, such as virtual servers providing acceleration or load balancing for one or more services. The bandwidth threshold may be specified as a number of bytes transferred via the virtual server. The bandwidth threshold may also be specified as a round trip time or derivative thereof. A user may specify the bandwidth threshold via a configuration interface. Otherwise, the appliance may establish the bandwidth threshold. The appliance monitors the bandwidth used by a first virtual server. In response to detecting the bandwidth reaching or exceeding the bandwidth threshold, the appliance dynamically directs client requests to a second virtual server.
Owner:CITRIX SYST INC
Method and apparatus for defining and implementing high-level quality of service policies in computer networks
InactiveUS7185073B1Multiple digital computer combinationsData switching networksNetwork strategyNetwork administrator
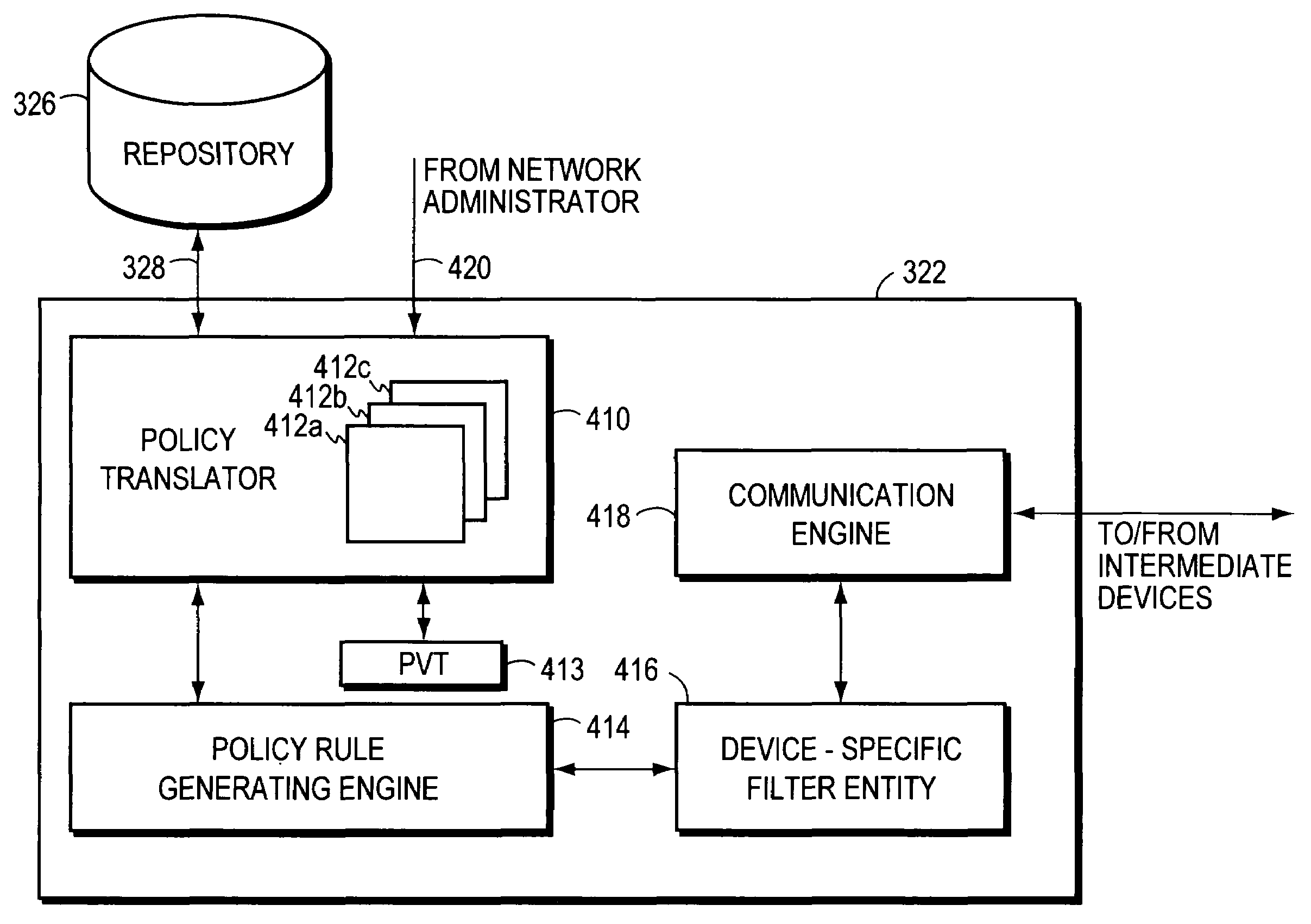
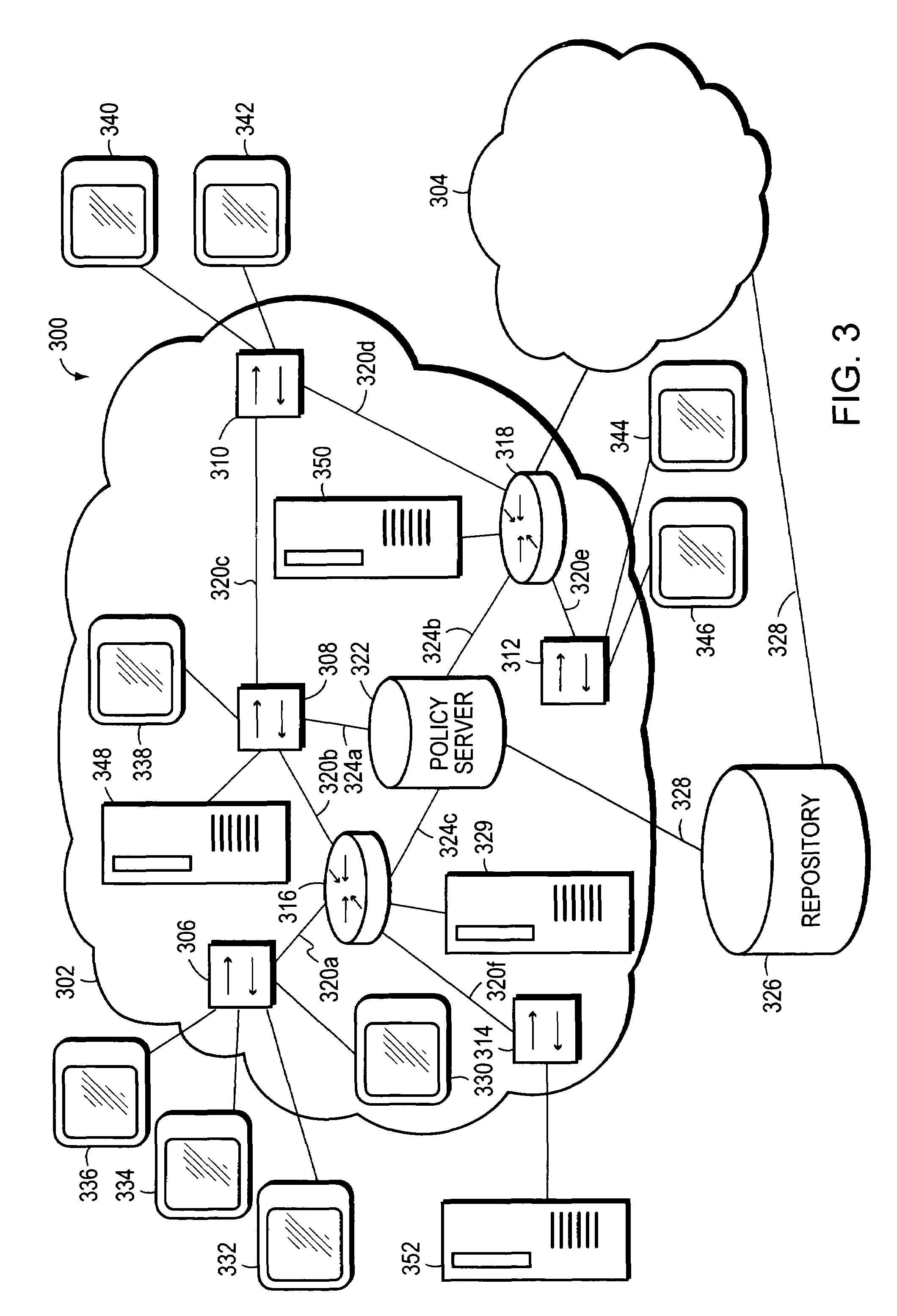
A computer network having multiple, dissimilar network devices includes a system for implementing high-level, network policies. The high-level policies, which are generally device-independent, are translated by one or more policy servers into a set of rules that can be put into effect by specific network devices. Preferably, a network administrator selects an overall traffic template for a given domain and may assign various applications and / or users to the corresponding traffic types of the template. Location-specific policies may also be established by the network administrator. The policy server translates the high-level policies inherent in the selected traffic template and location-specific policies into a set of rules, which may include one or more access control lists, and may combine several related rules into a single transaction. Intermediate network devices, which may have one or more roles assigned to their interfaces, are configured to request traffic management information from the policy server which replies with a particular set of transactions and rules. The rules, which may correspond to the particular roles assigned to the interfaces, are then utilized by the intermediate devices to configure their particular services and traffic management mechanisms. Other rules are utilized by the intermediate devices to classify packets with a particular priority and / or service value and to treat classified packets in a particular manner so as to realize the selected high-level policies within the domain.
Owner:CISCO TECH INC
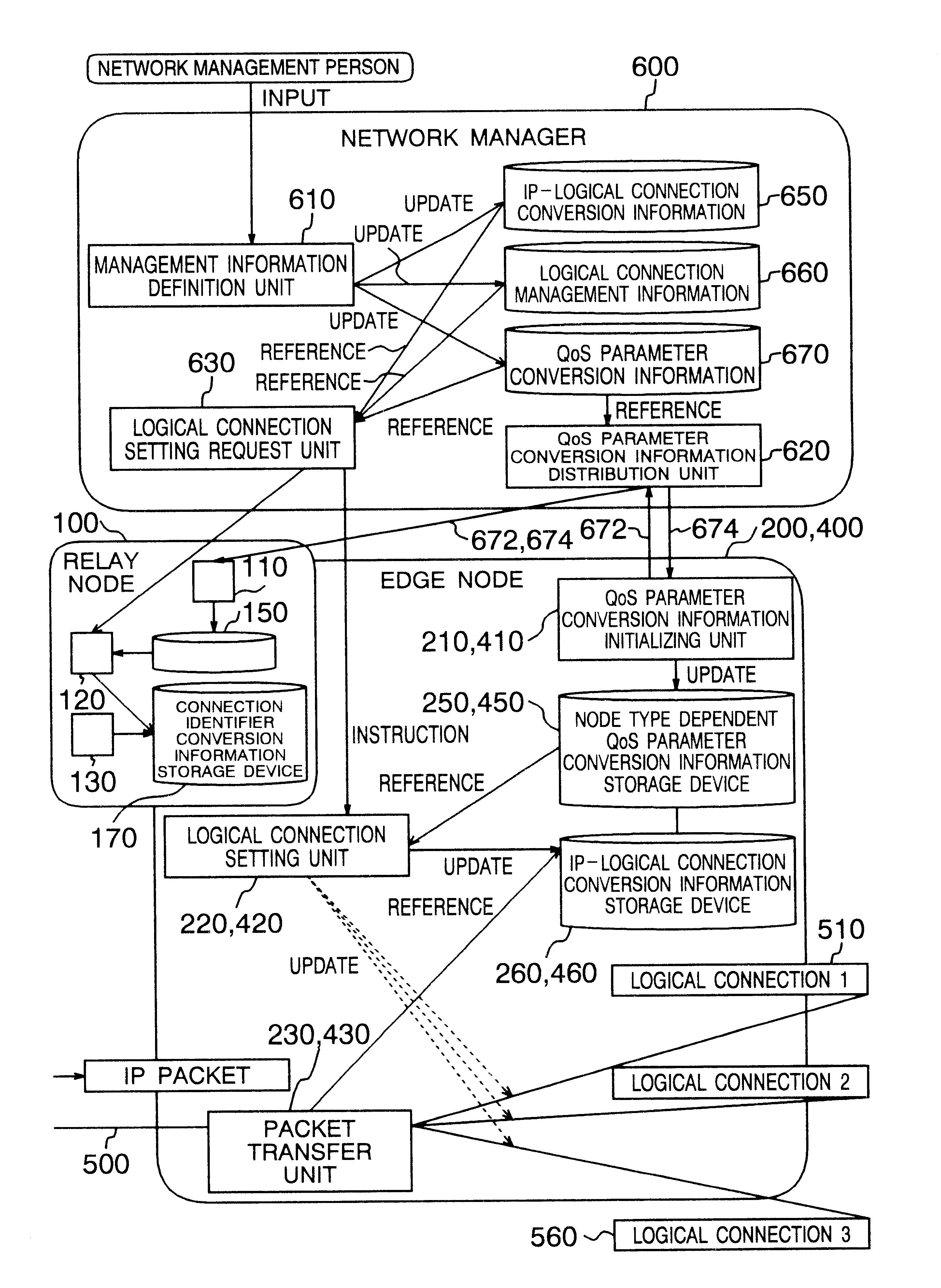
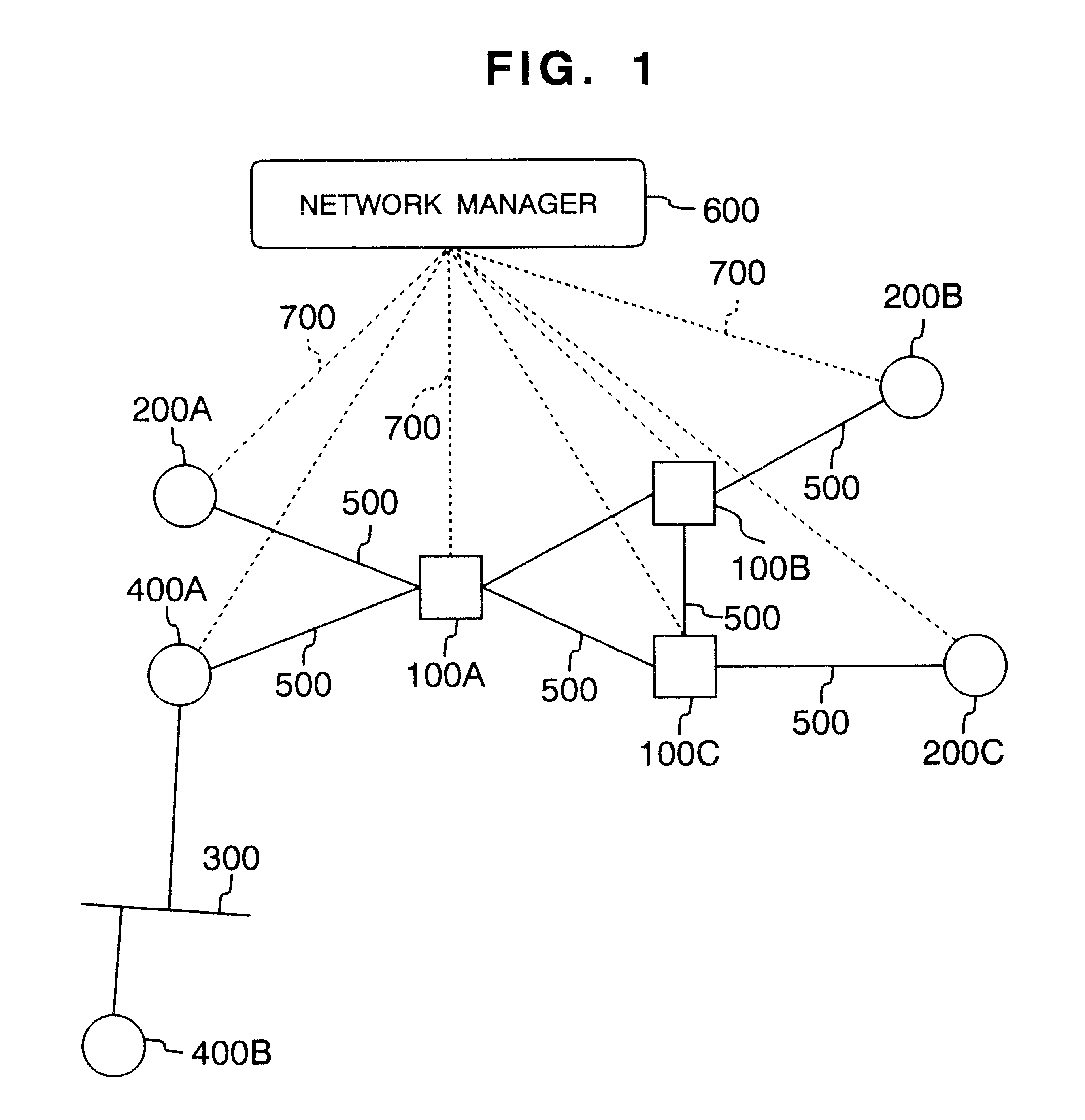
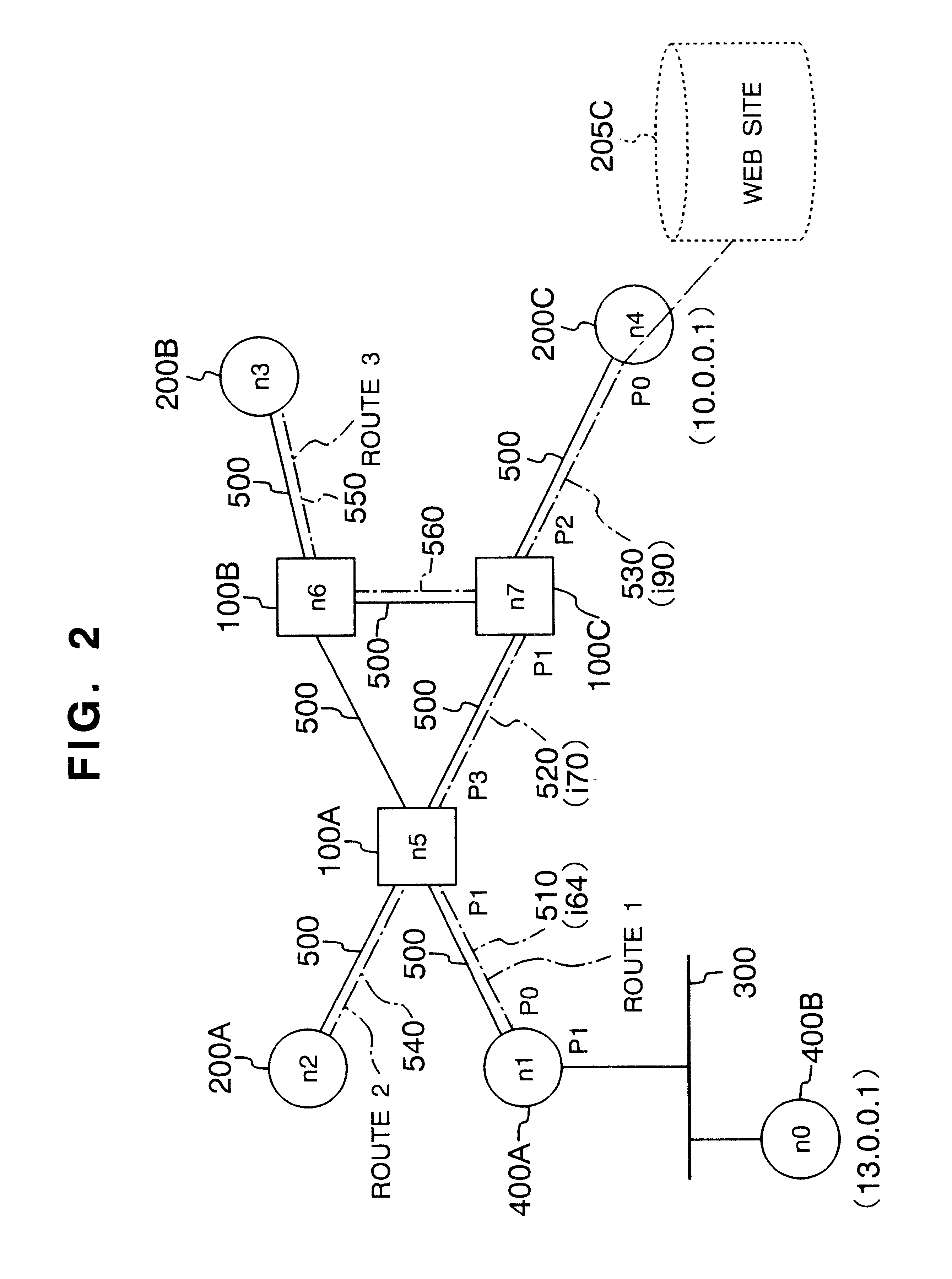
Network manager, nodes and network management system
In a communication network constituted of relay nodes and edge nodes interconnected by communication lines and a network manager, the network manager manages relay nodes and edge nodes connected to the network manager by operation management communication lines. The network manager requests to set a logical connection between an ingress and an egress of the connection, and in response to this request, relay nodes and edge nodes set a logical connection specifying at least one of a transmission source and a destination.
Owner:HITACHI LTD
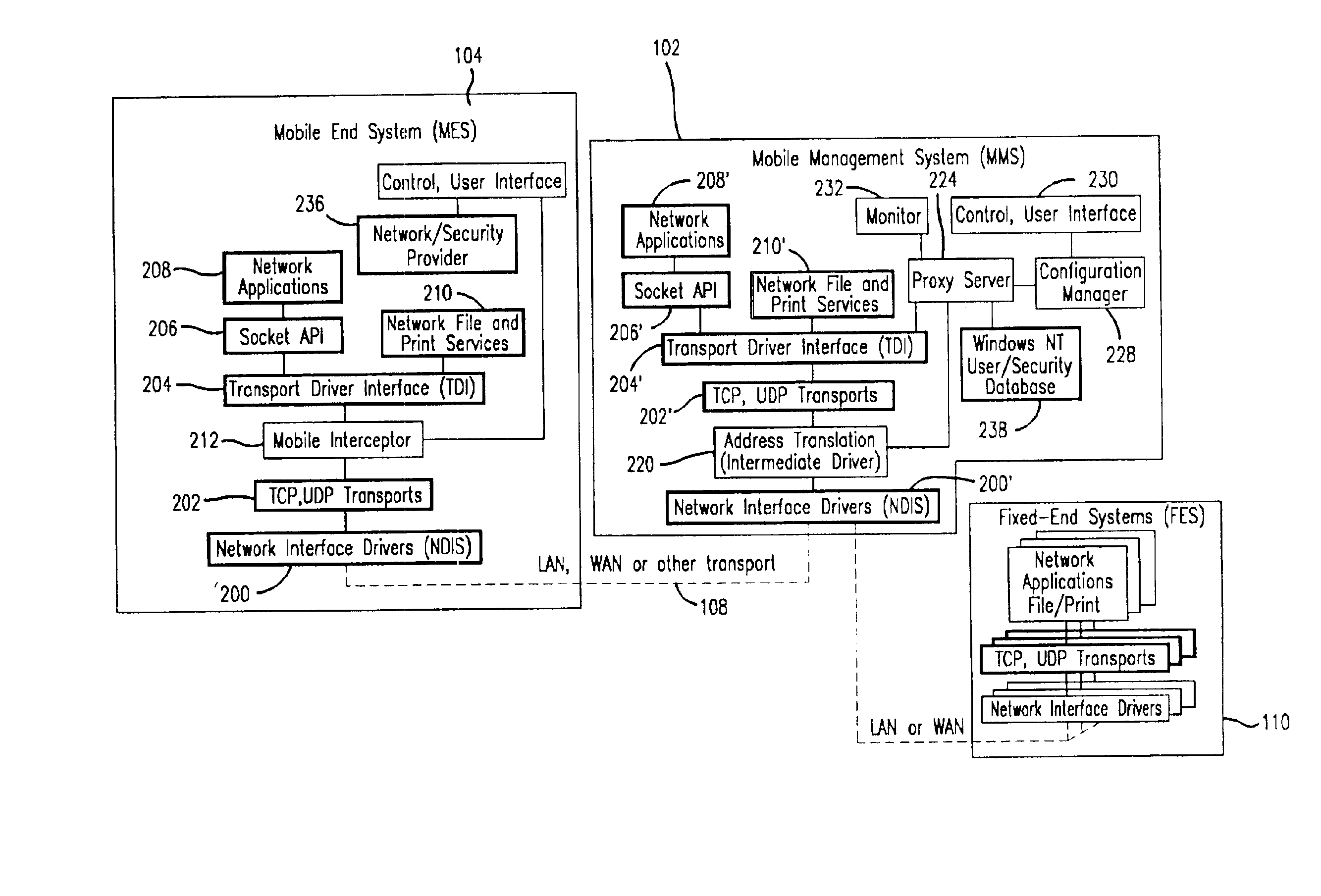
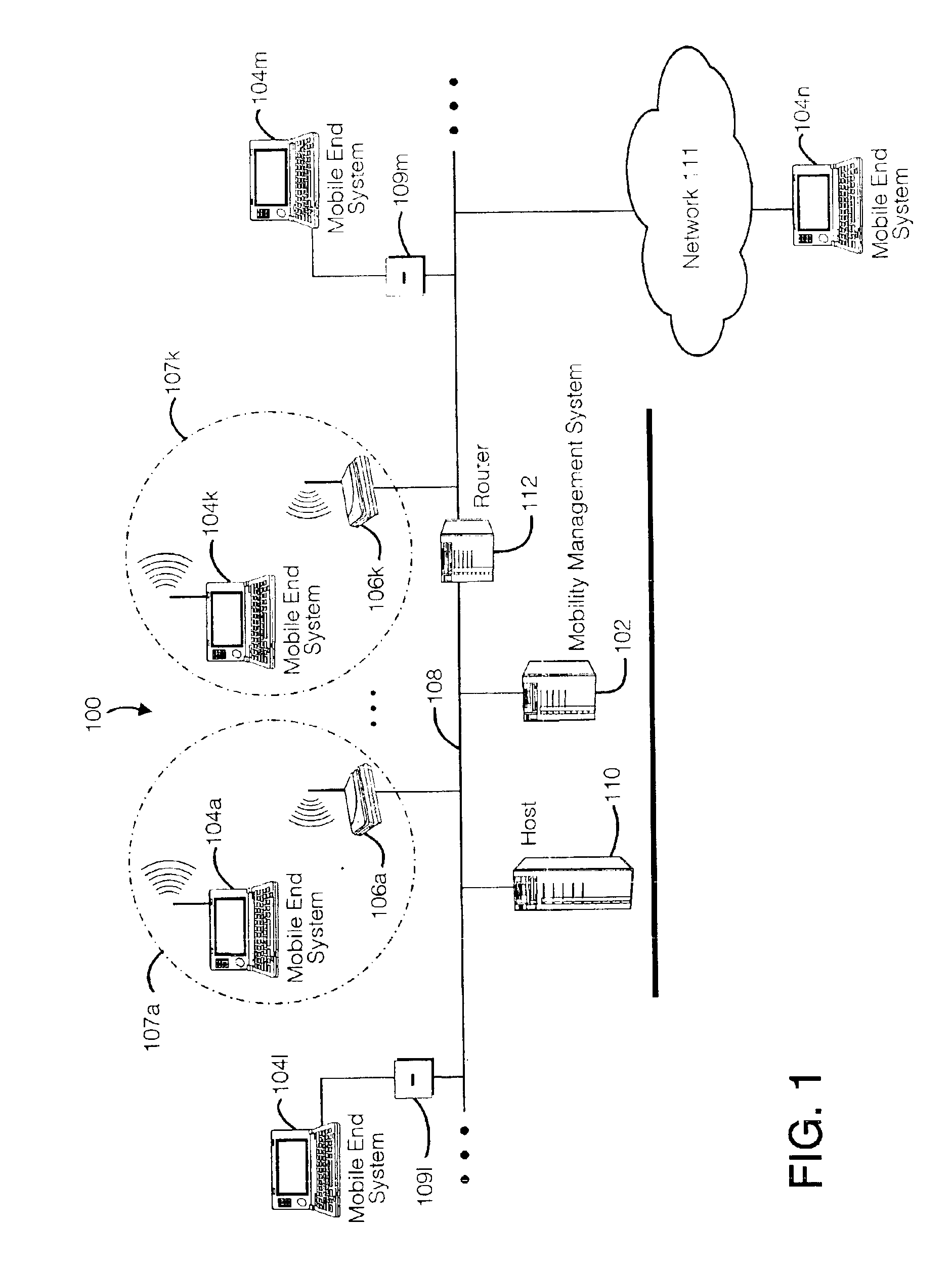
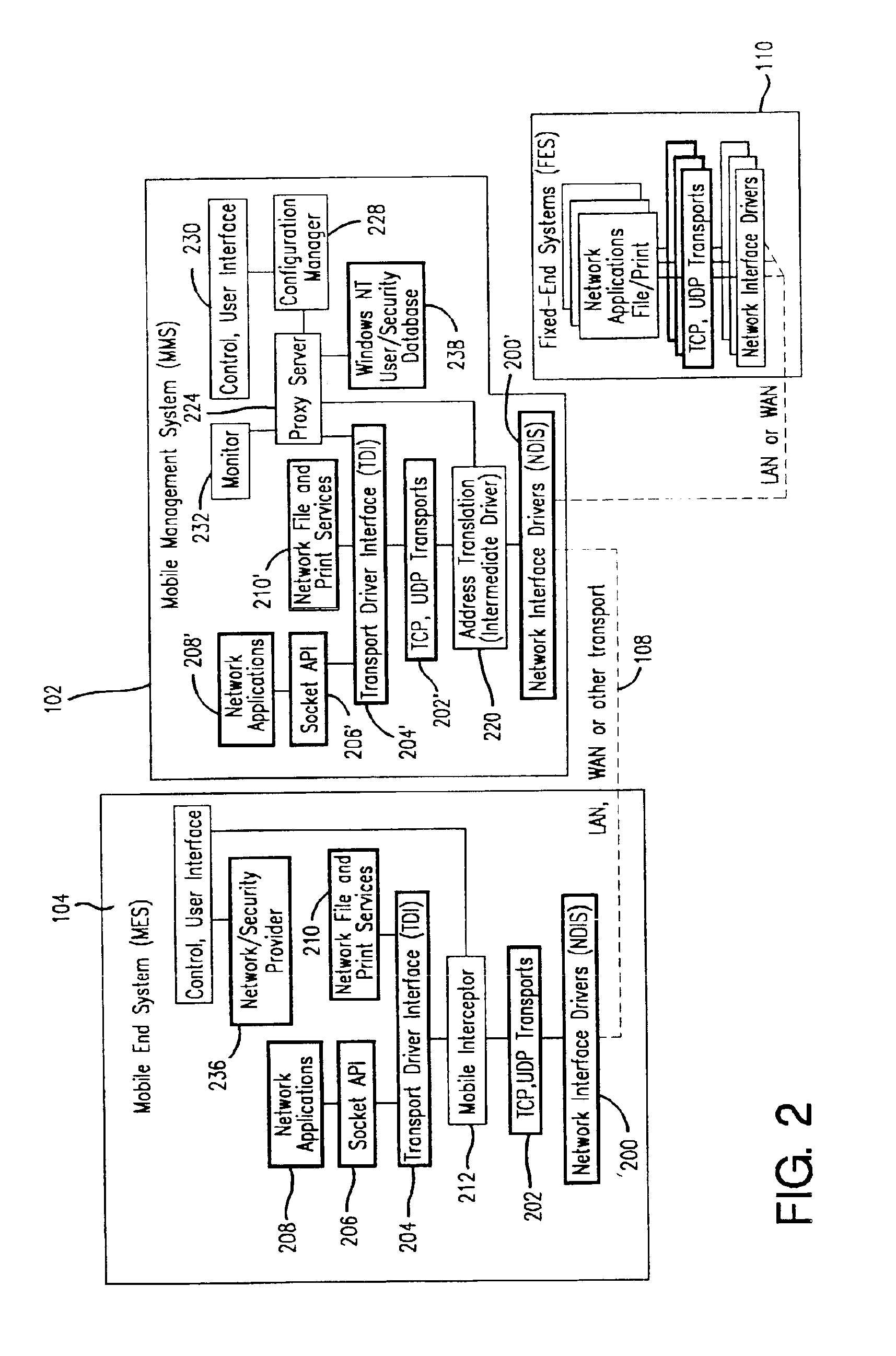
Method and apparatus for providing mobile and other intermittent connectivity in a computing environment
InactiveUS6981047B2Error prevention/detection by using return channelData switching by path configurationMobile endNetwork address
A seamless solution transparently addresses the characteristics of nomadic systems, and enables existing network applications to run reliably in mobile environments. The solution extends the enterprise network, letting network managers provide mobile users with easy access to the same applications as stationary users without sacrificing reliability or centralized management. The solution combines advantages of existing wire-line network standards with emerging mobile standards to create a solution that works with existing network applications. A Mobility Management Server coupled to the mobile network maintains the state of each of any number of Mobile End Systems and handles the complex session management required to maintain persistent connections to the network and to other peer processes. If a Mobile End System becomes unreachable, suspends, or changes network address (e.g., due to roaming from one network interconnect to another), the Mobility Management Server maintains the connection to the associated peer task—allowing the Mobile End System to maintain a continuous connection even though it may temporarily lose contact with its network medium. In one example, Mobility Management Server communicates with Mobile End Systems using Remote Procedure Call and Internet Mobility Protocols.
Owner:MOBILE SONIC INC
Unified, configurable, adaptive, network architecture
ActiveUS7310664B1Reduce the burden onReduce operating costsDigital computer detailsTransmissionAdaptive managementNetwork architecture
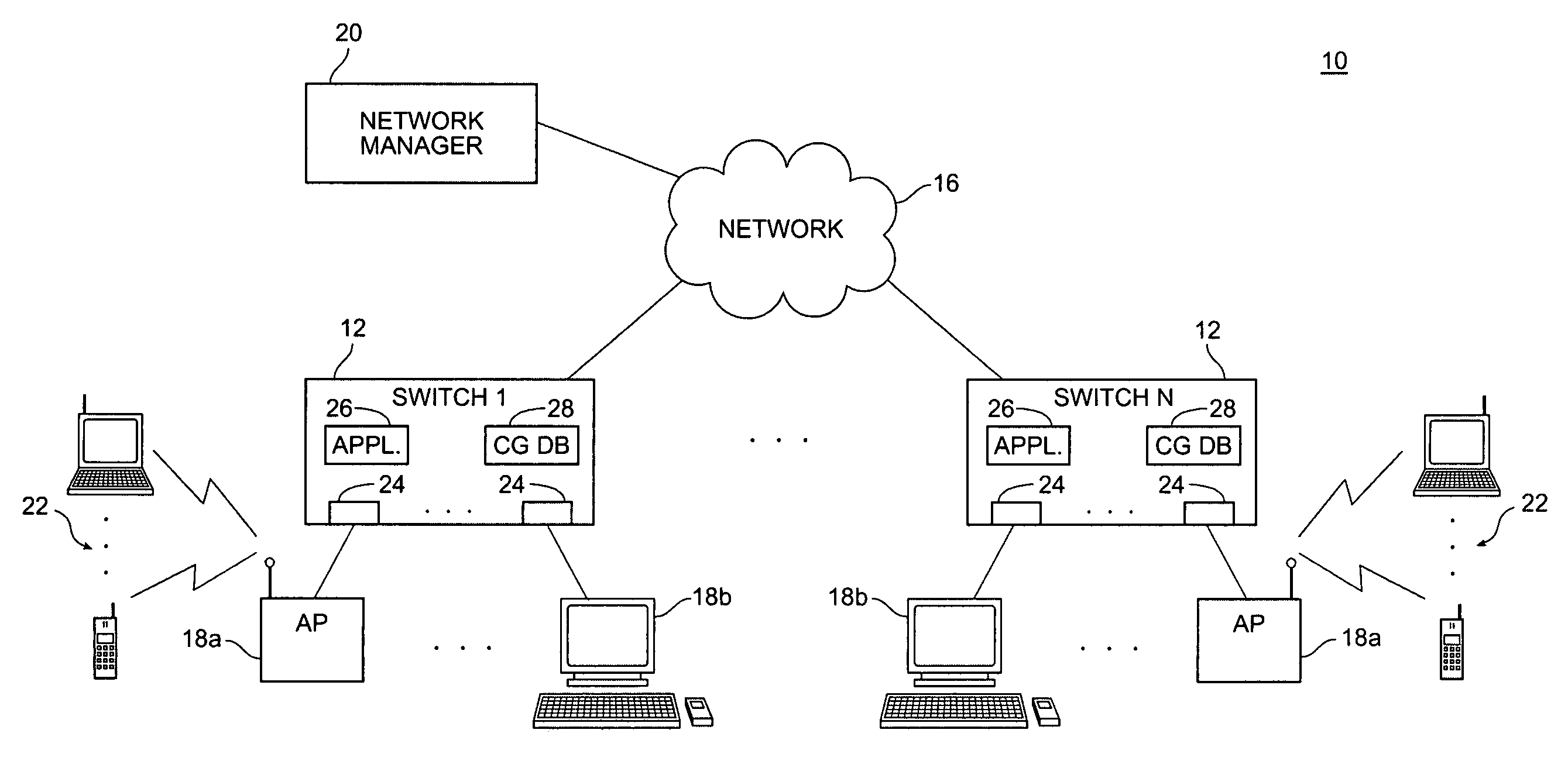
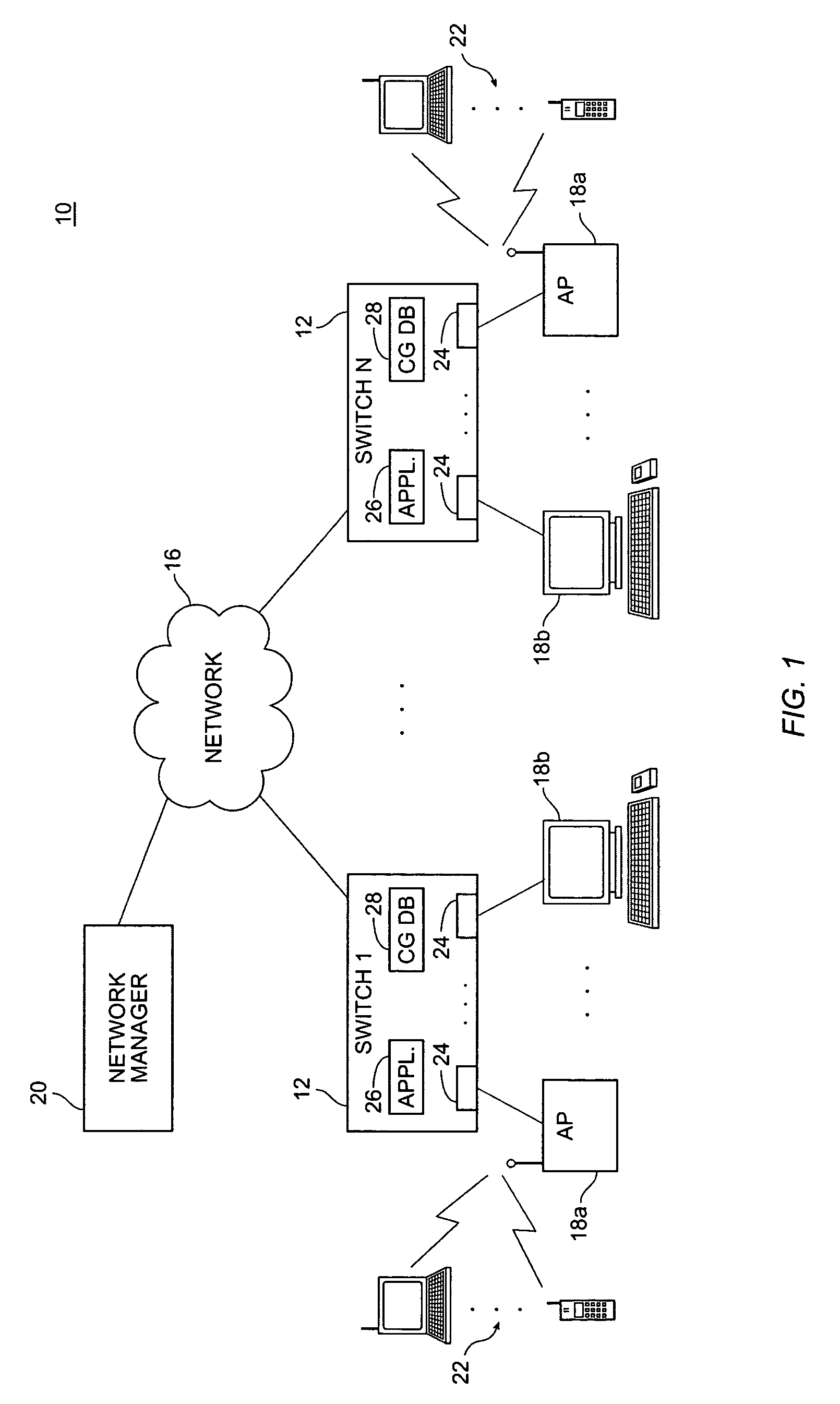
A network switch having a unified, adaptive management paradigm for wireless network devices is disclosed. The switch includes configurable ports for connecting devices. A software application running on the switch allows a network administrator to selectively configure each port to support either a wired device or wireless device. Configuration information and software images that are needed for operation of the wireless device are associated with the port. When a wireless device is first plugged into the switch port, it downloads its configuration directly from the switch port. By storing the configuration information and images at the switch and automatically downloading them to the wireless devices, the task of configuring the devices is greatly simplified for the network administrator. This is particularly advantageous in heterogeneous network environments that support both wired and wireless devices, and where wireless device are readily moved to different ports.
Owner:EXTREME NETWORKS INC
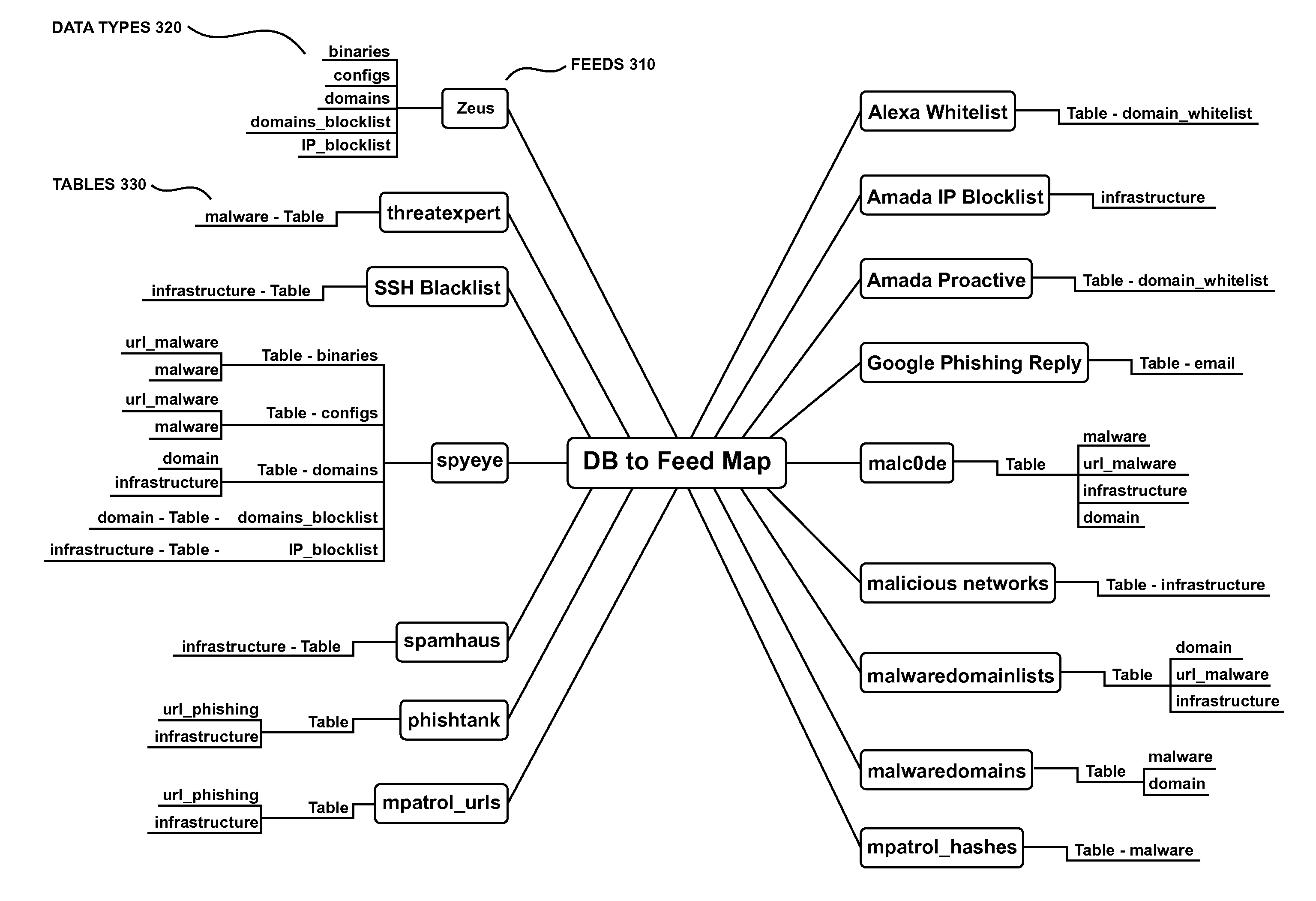
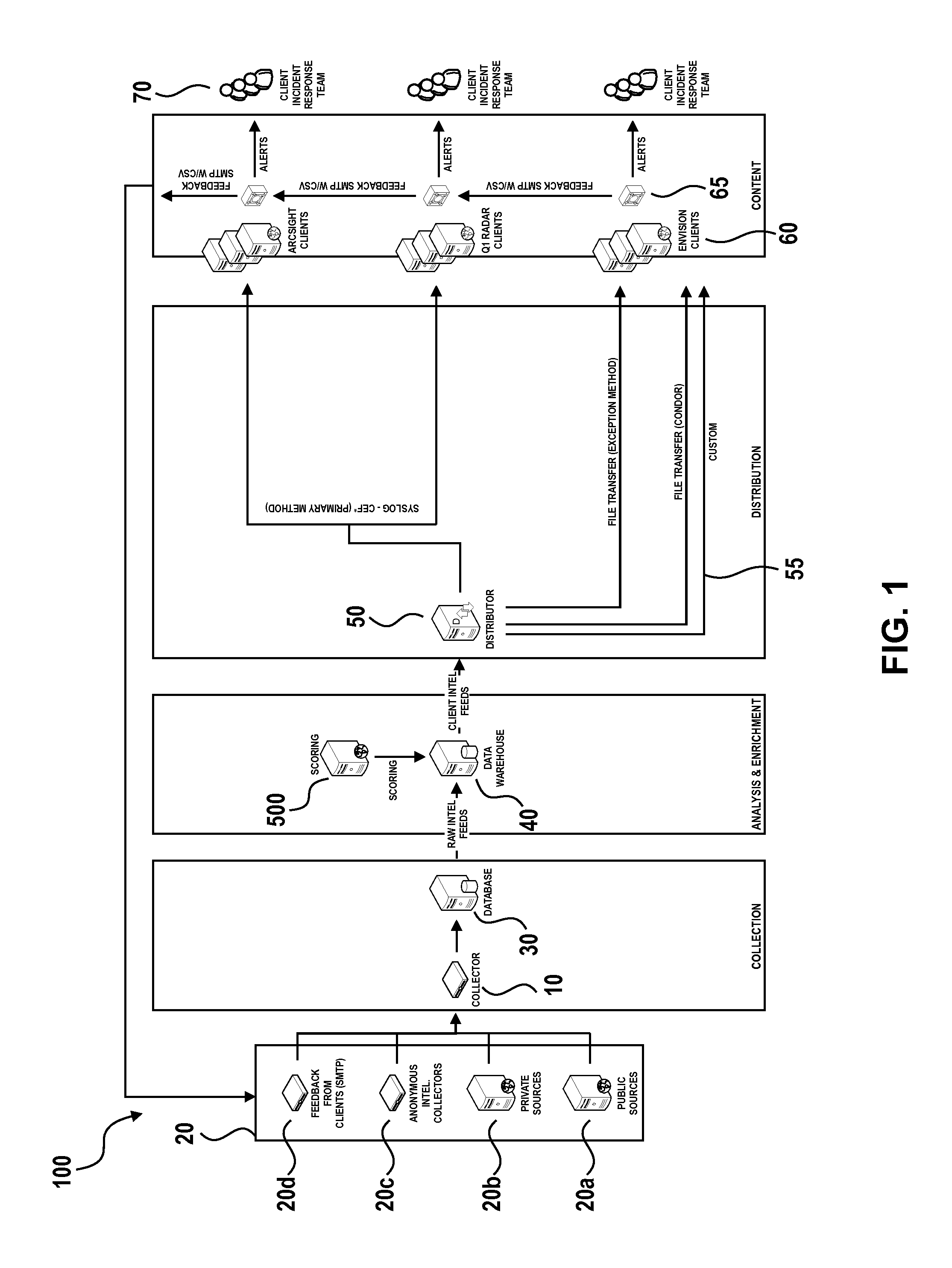
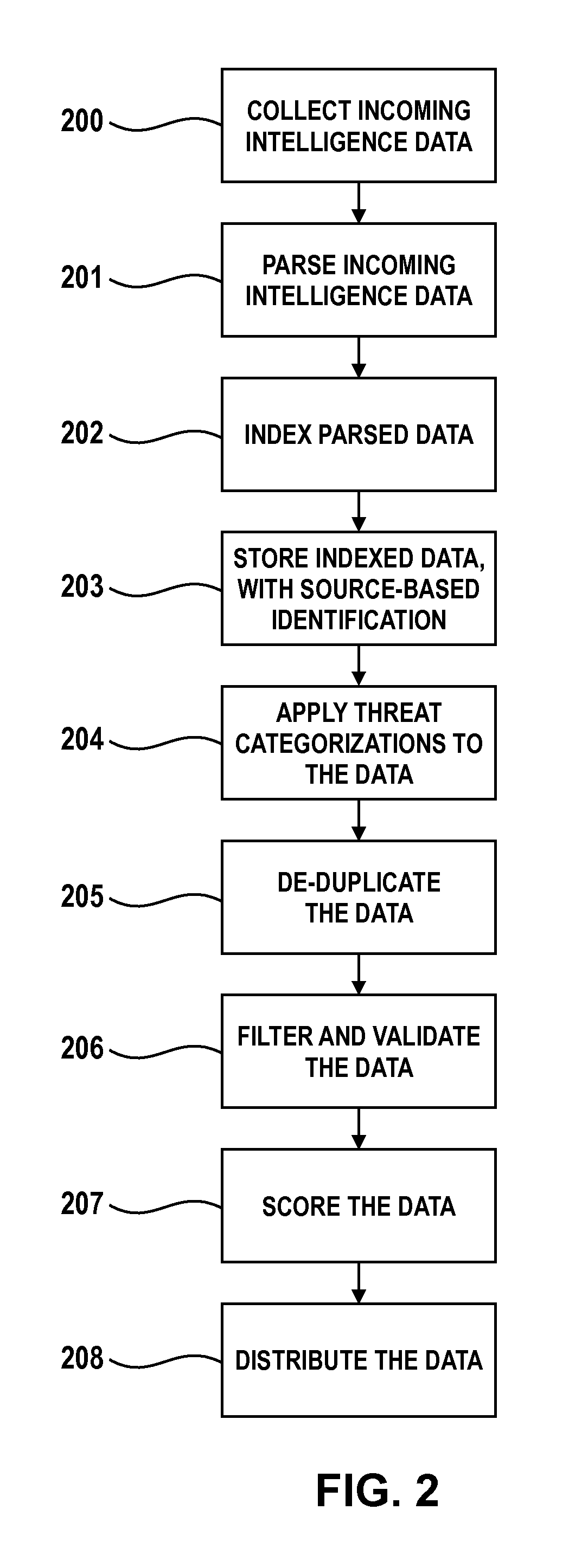
Collective Threat Intelligence Gathering System
ActiveUS20140007238A1Quality improvementImprove information qualityMemory loss protectionError detection/correctionIp addressInformation networks
Threat intelligence is collected from a variety of different sources. The threat intelligence information is aggregated, normalized, filtered and scored to identify threats to an information network. Threats are categorized by type, maliciousness and confidence level. Threats are reported to network administrators in a plurality of threat feeds, including for example malicious domains, malicious IP addresses, malicious e-mail addresses, malicious URLs and malicious software files.
Owner:DELOITTE DEV
System and method for detecting unauthorized wireless access points
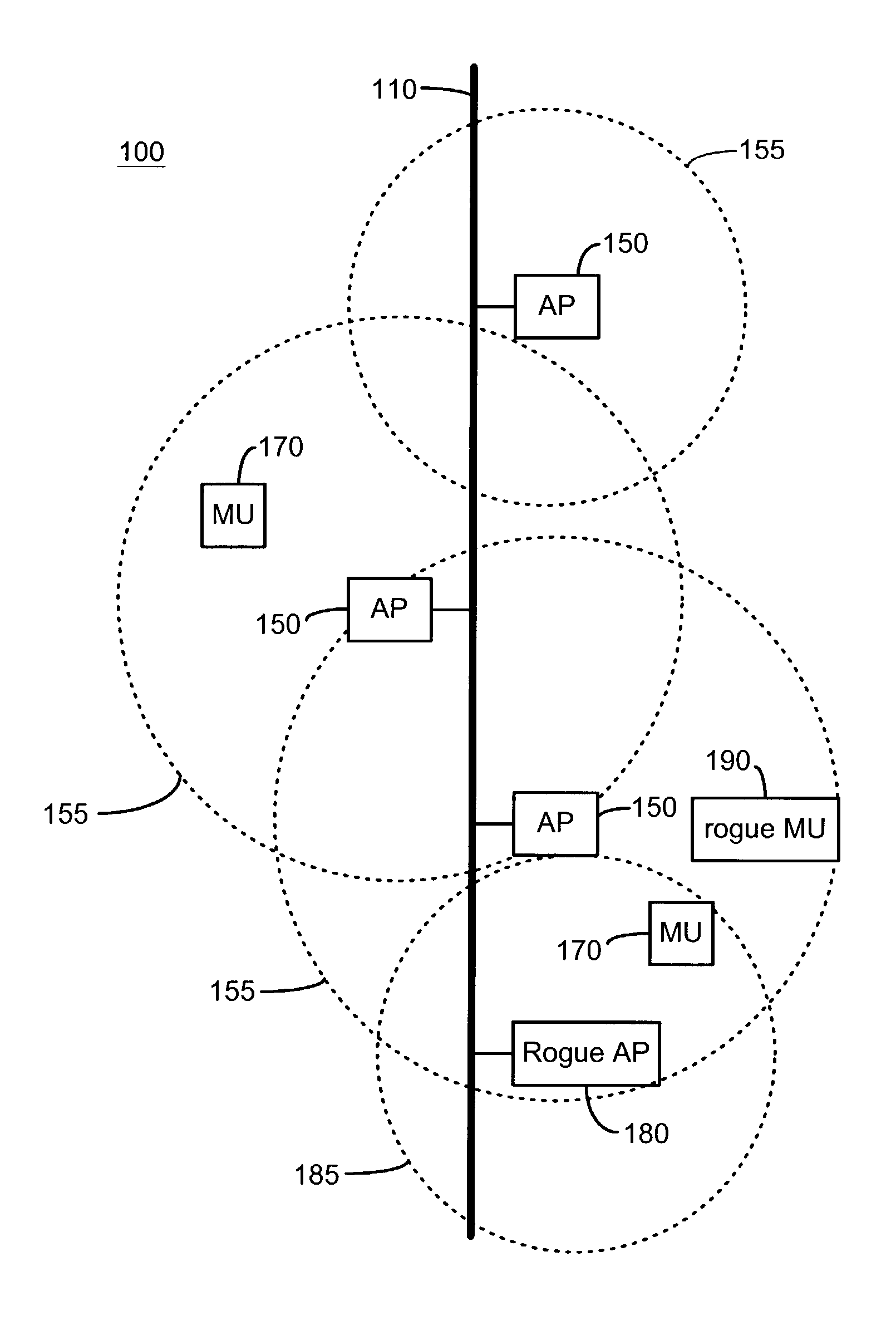
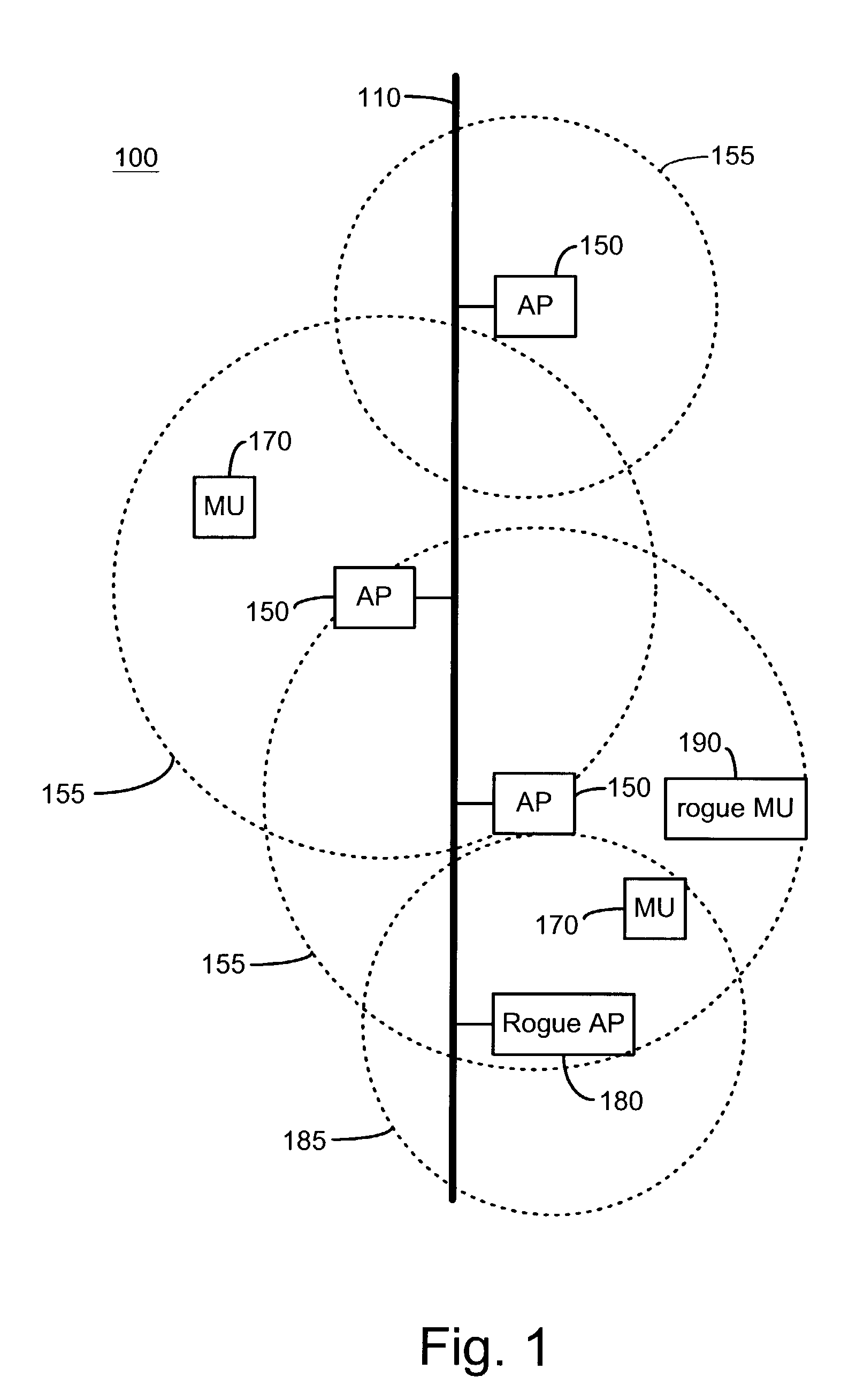
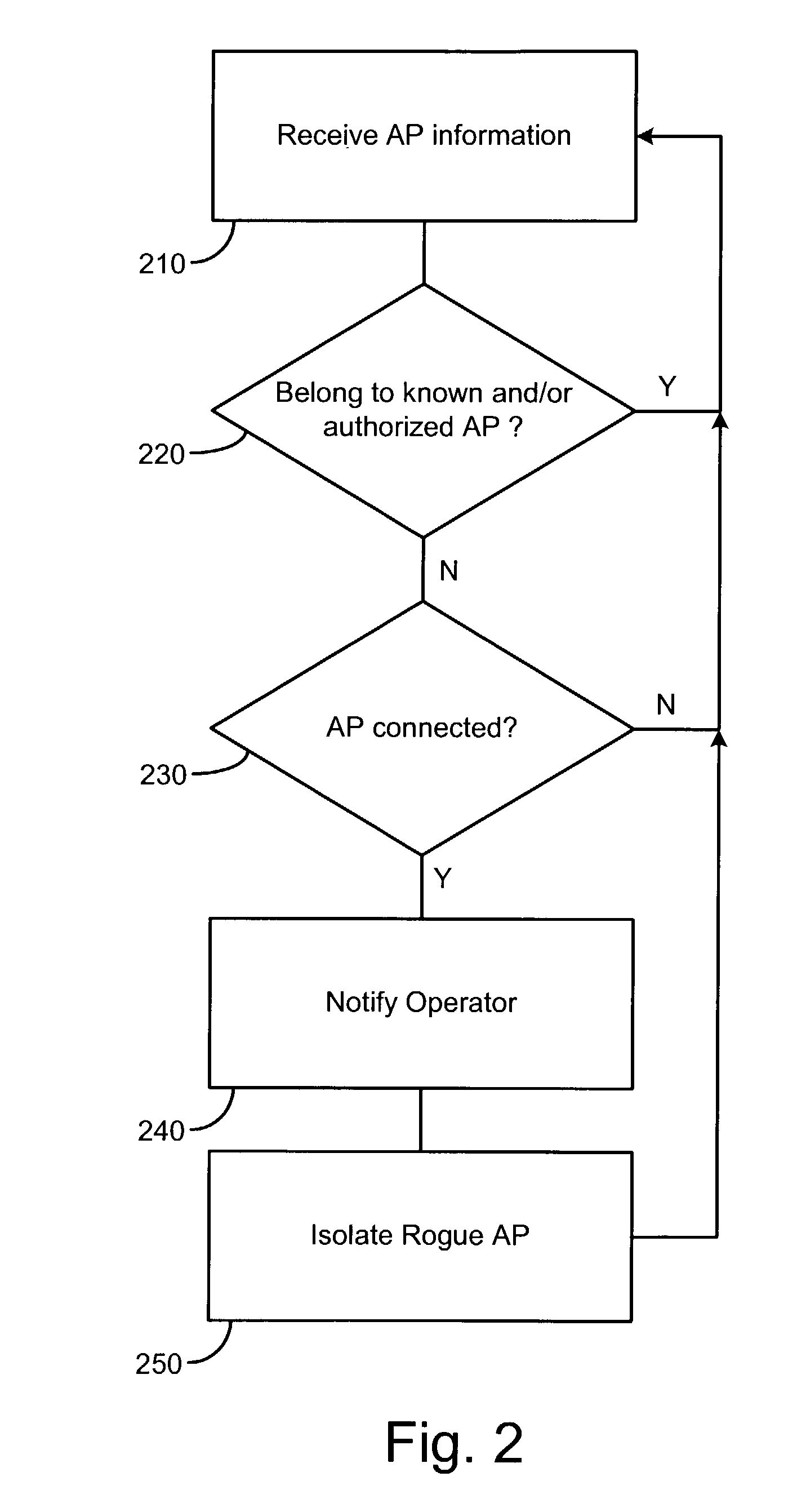
InactiveUS7965842B2Data switching by path configurationSecret communicationCyber operationsInternet privacy
Unauthorized wireless access points are detected by configuring authorized access points and mobile units to listen to all wireless traffic in its cell and report all detected wireless devices to a monitor. The monitor checks the reported devices against a list of authorized network devices. If the reported wireless device is not an authorized device, the monitor determines if the reported device is connected to the network. If the reported device is connected to the network and is not an authorized device, the monitor alerts the network operator or network manager of a rogue device connected to the network and attempts to locate and isolate the rogue device.
Owner:IVANTI INC
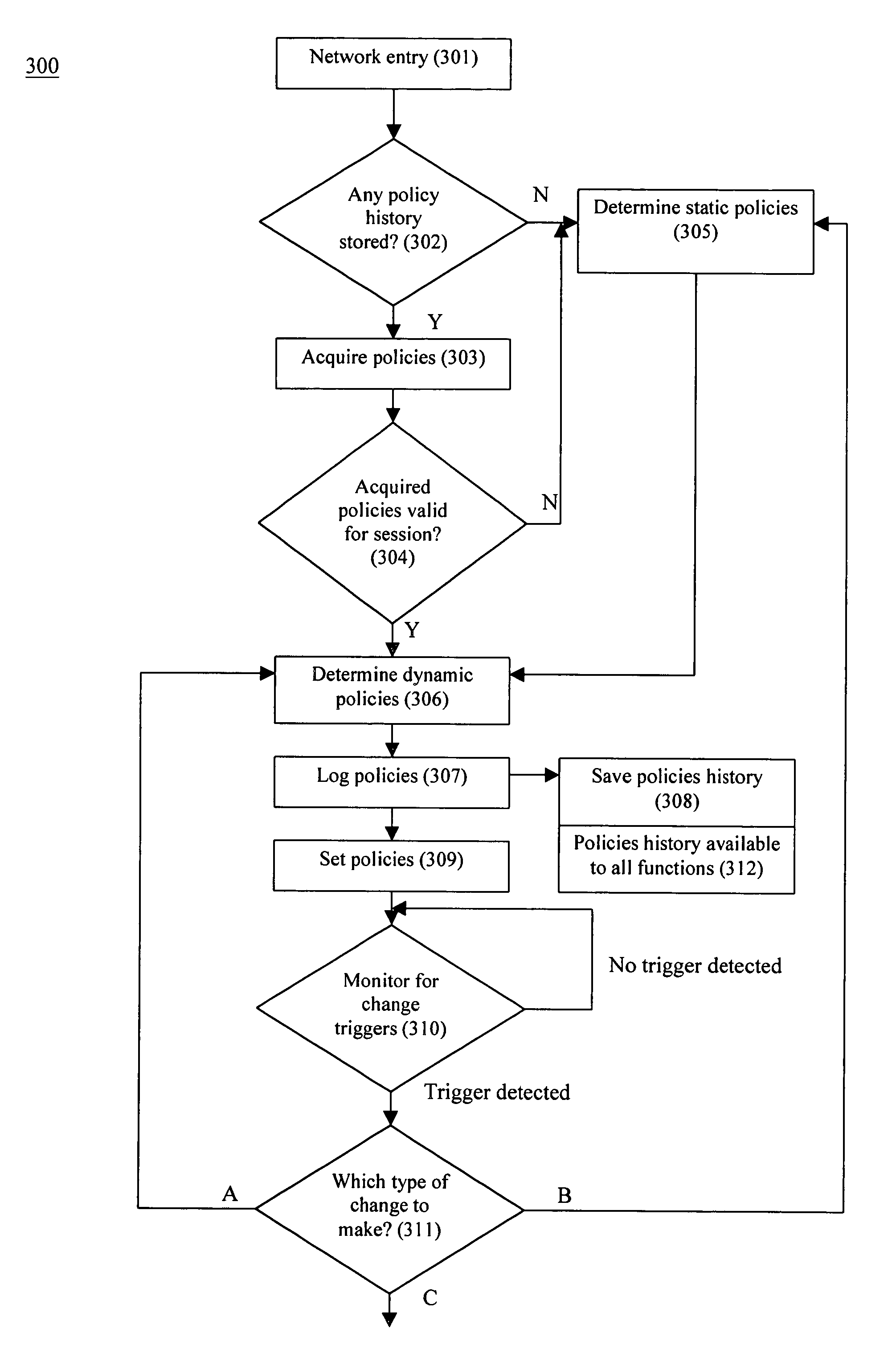
System and method for dynamic network policy management
InactiveUS7526541B2Improve accuracyImprove allocationDigital data protectionMultiple digital computer combinationsNetwork serviceNetwork administrator
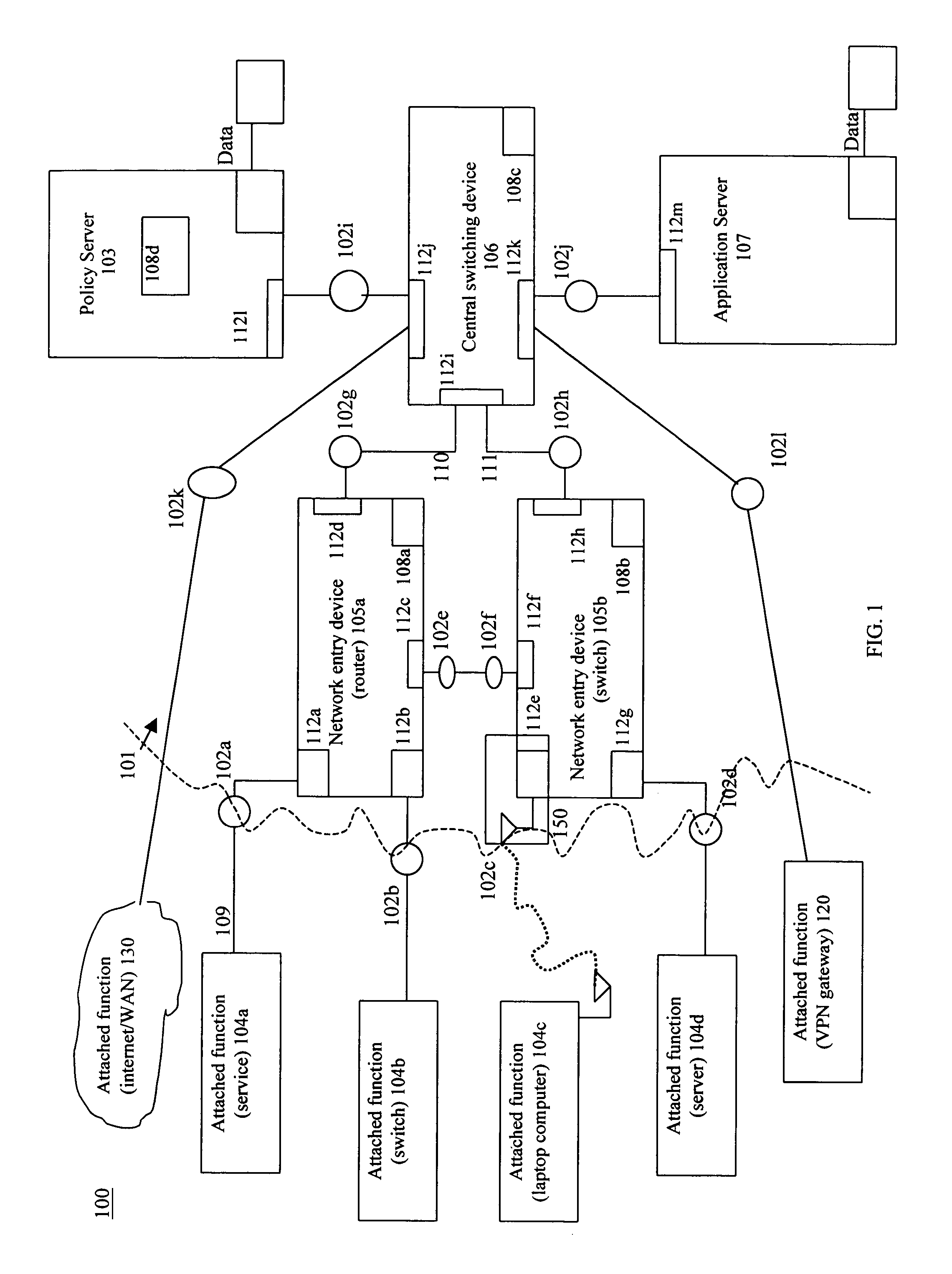
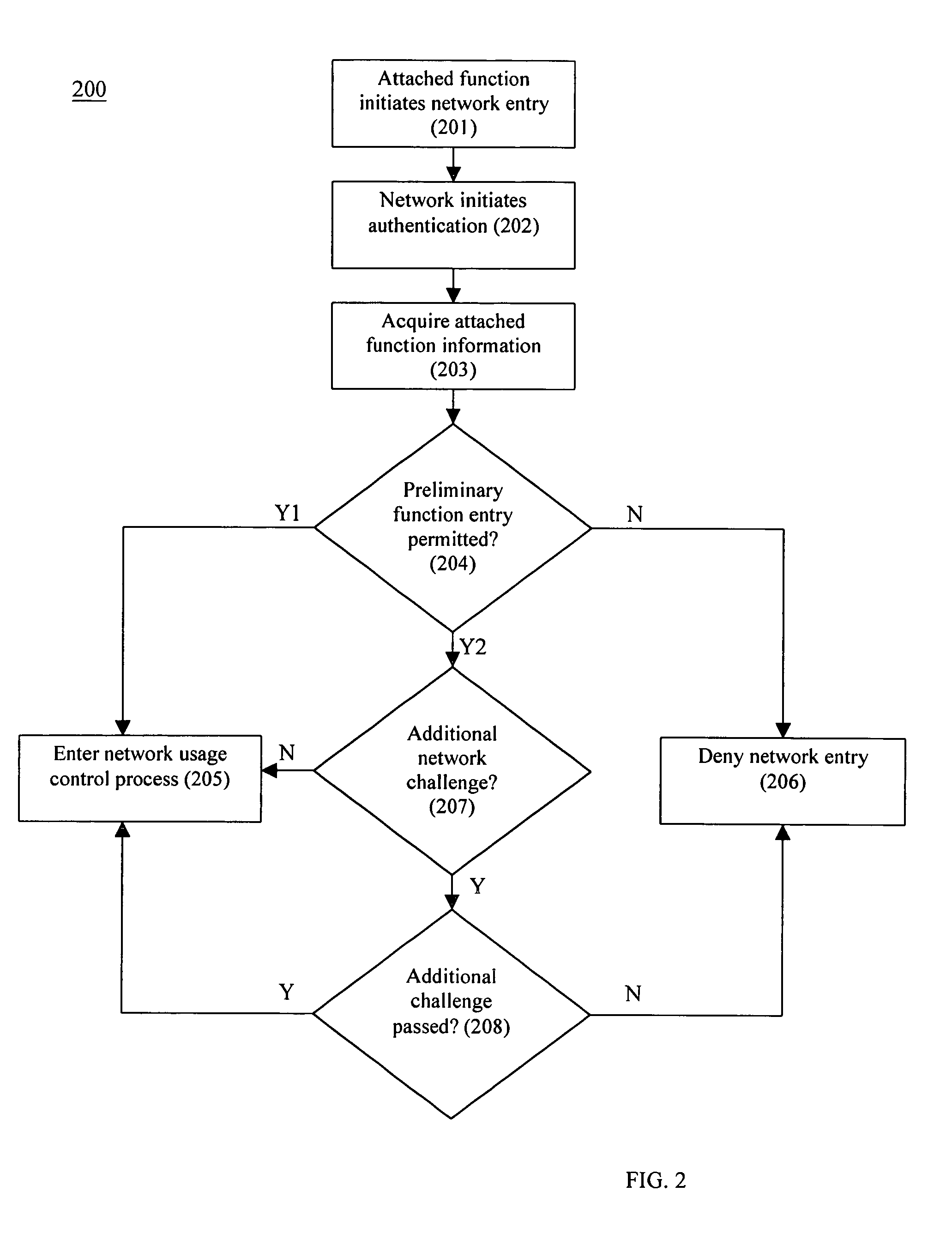
A system and method that provides dynamic network policy management. The system enables a network administrator to regulate usage of network services upon initiation of and throughout network sessions. The system employs a method of identifying selectable characteristics of attached functions to establish static and dynamic policies, which policies may be amended before, during and after any session throughout the network based on the monitored detection of any of a number of specified triggering events or activities. Particular policies associated with a particular identified attached function in prior sessions may be cached or saved and employed in subsequent sessions to provide network usage permissions more rapidly in such subsequent sessions. The cached or saved policy information may also be used to identify network usage, control, and security. The system and method of the present invention provides static and dynamic policy allocation for network usage provisioning.
Owner:EXTREME NETWORKS INC
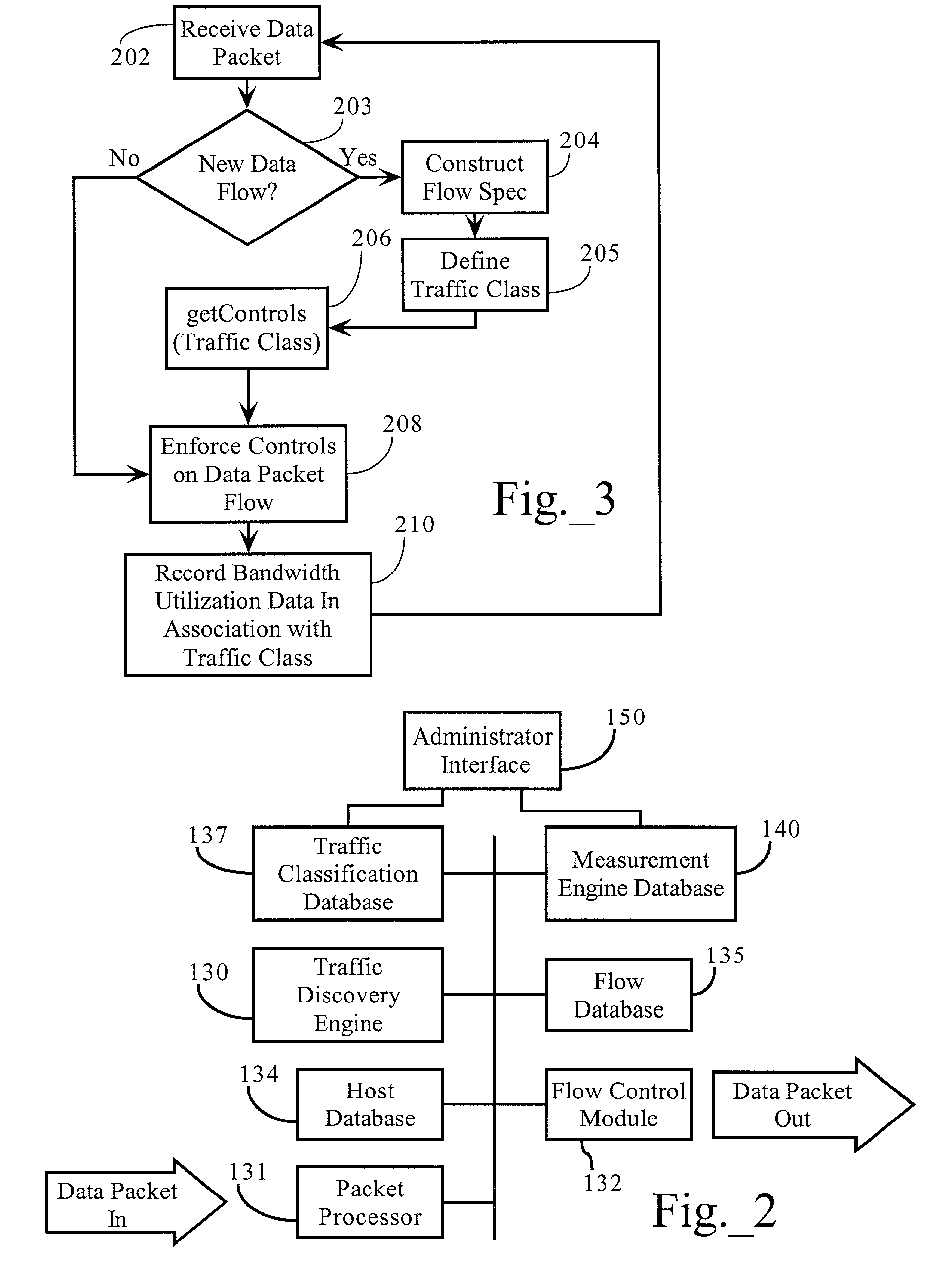
Interface facilitating configuration of network resource utilization
ActiveUS7203169B1OptimizationQuickly easily configureError preventionFrequency-division multiplex detailsResource utilizationParameter control
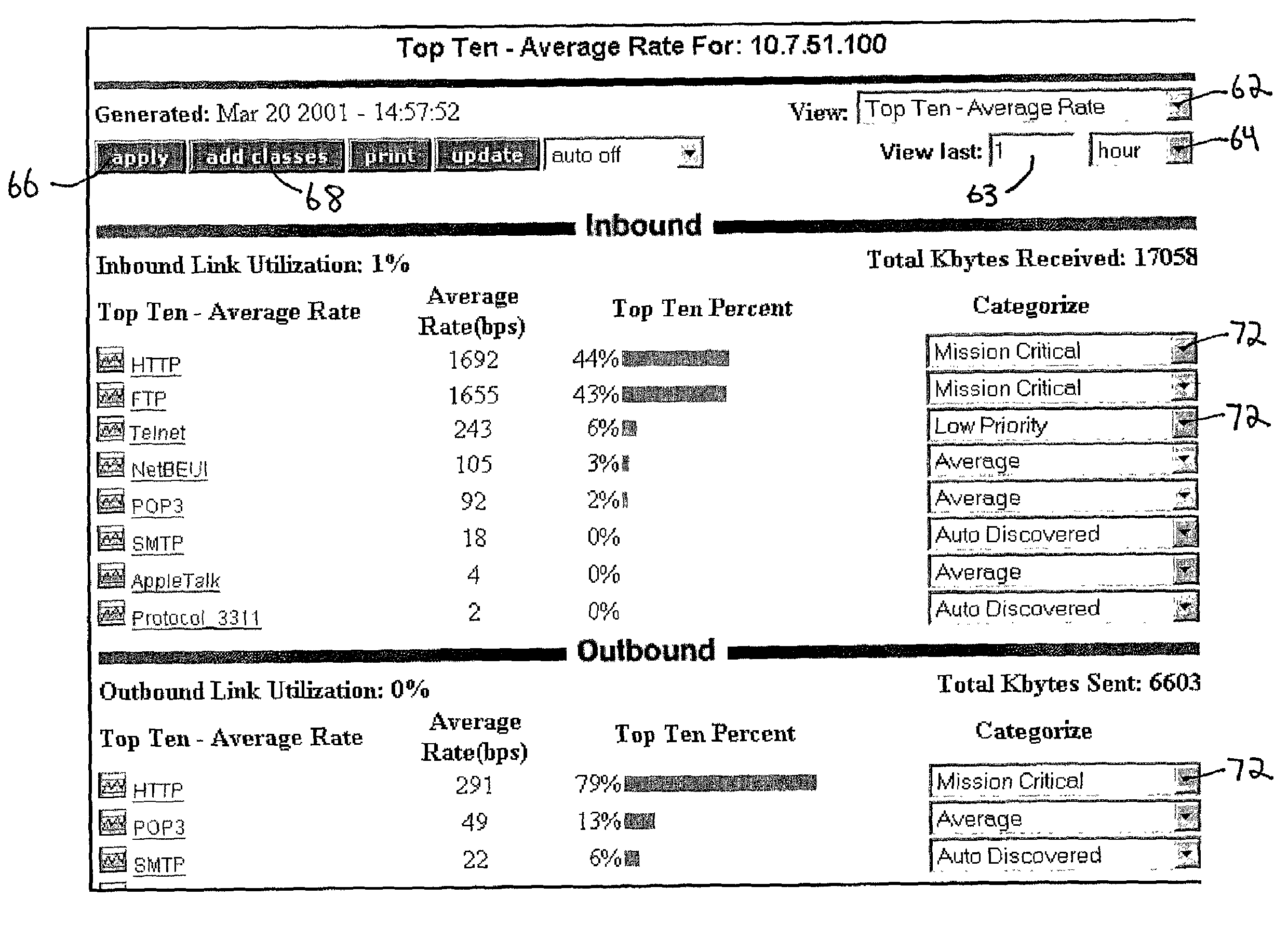
Methods, apparatuses and systems facilitating the configuration of parameters controlling utilization of a network resource. In one embodiment, the present invention allows a network administrator to quickly and easily configure effective bandwidth utilization controls and observe the results of applying them. According to one embodiment, a network administrator is presented with an interface displaying the most significant traffic types with respect to a bandwidth utilization or other network statistic and allowing for the association of bandwidth utilization controls to these traffic types.
Owner:CA TECH INC
Systems and methods for providing dynamic spillover of virtual servers based on bandwidth
Owner:CITRIX SYST INC
Selective tunneling of streaming data
InactiveUS6189039B1Spread the wordImprove bandwidth utilizationSpecial service provision for substationMultiple digital computer combinationsStreaming dataData stream
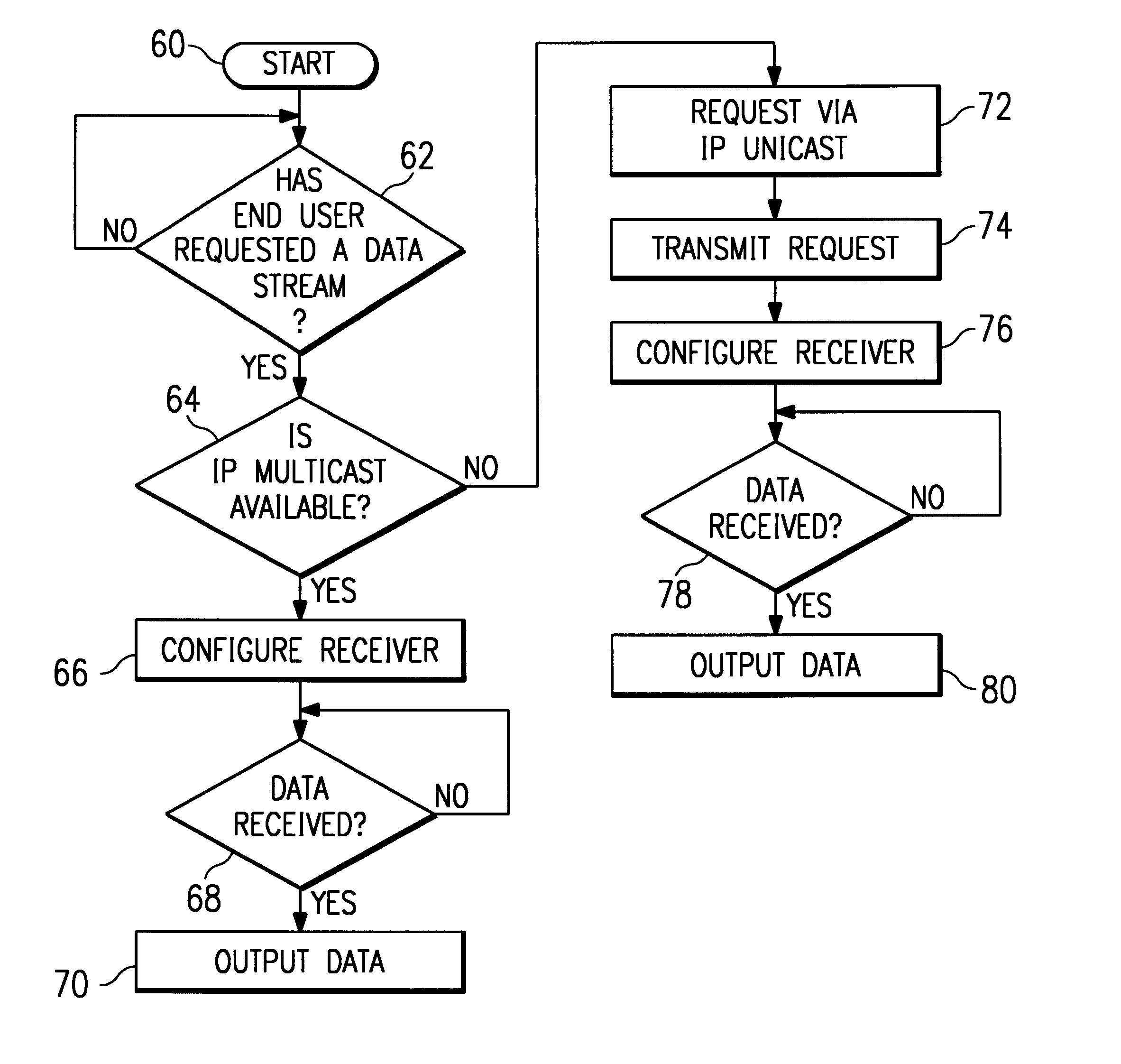
A method and system for "selective" tunneling of streaming data from a server to a client in a computer network having one or more network segments. The server has a tunneler utility, and the client has a receiver utility. The receiver utility first attempts to detect if a given data stream is available via IP multicast on the network segment supporting the client. If not, then the receiver utility issues a request for a IP unicast stream. This request is serviced by the tunneler utility. The tunneler utility re-broadcasts the IP multicast feed using IP unicast to send the data stream directly to the requesting user and / or to a repeater utility. The receiver utility then receives and processes the data stream for output to the end user. Alternatively, the receiver application, or a network administrator, launches the repeater utility, which then converts the IP unicast stream back to IP multicast format for re-broadcast over the network segment to other clients.
Owner:LEVEL 3 COMM LLC
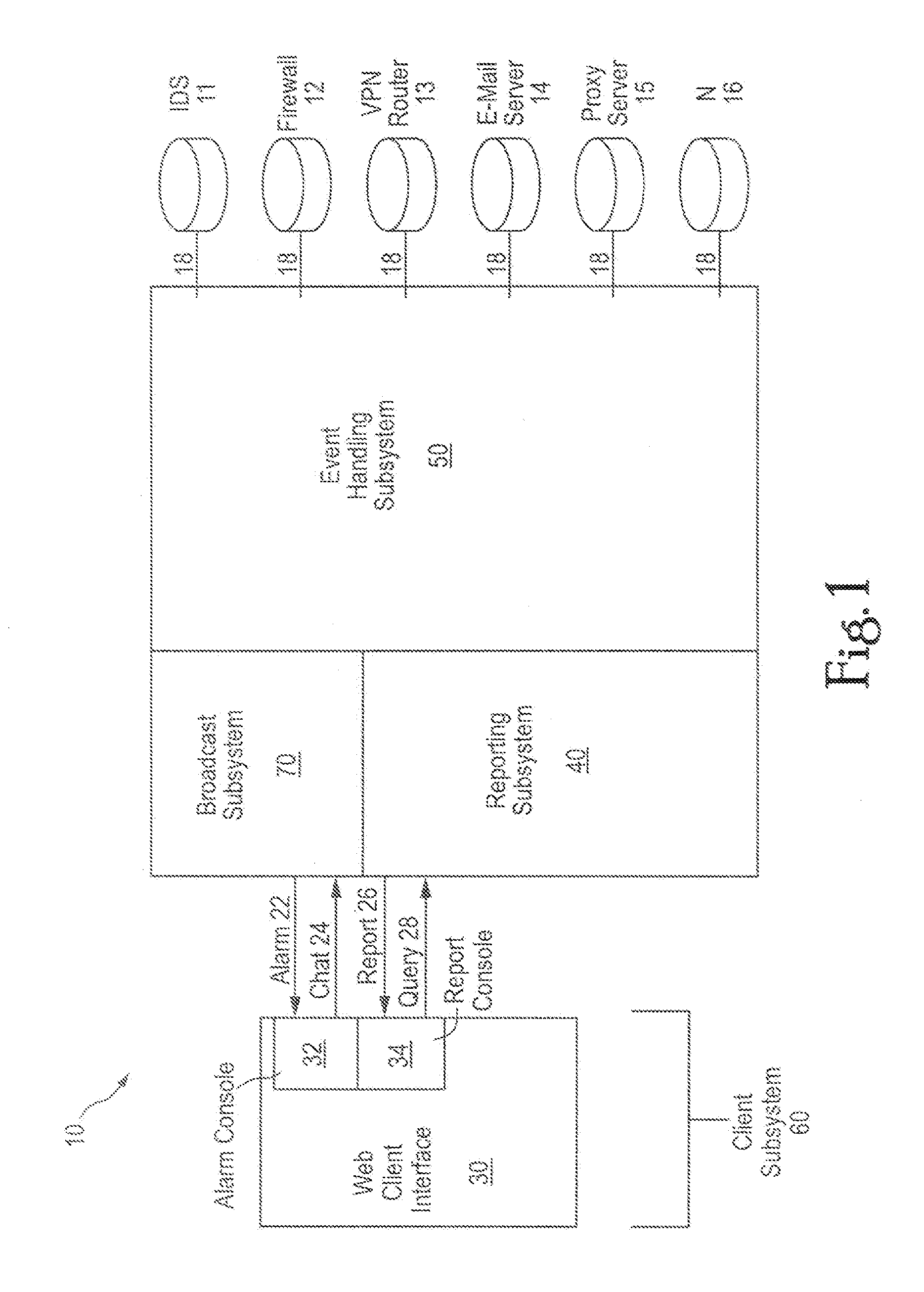
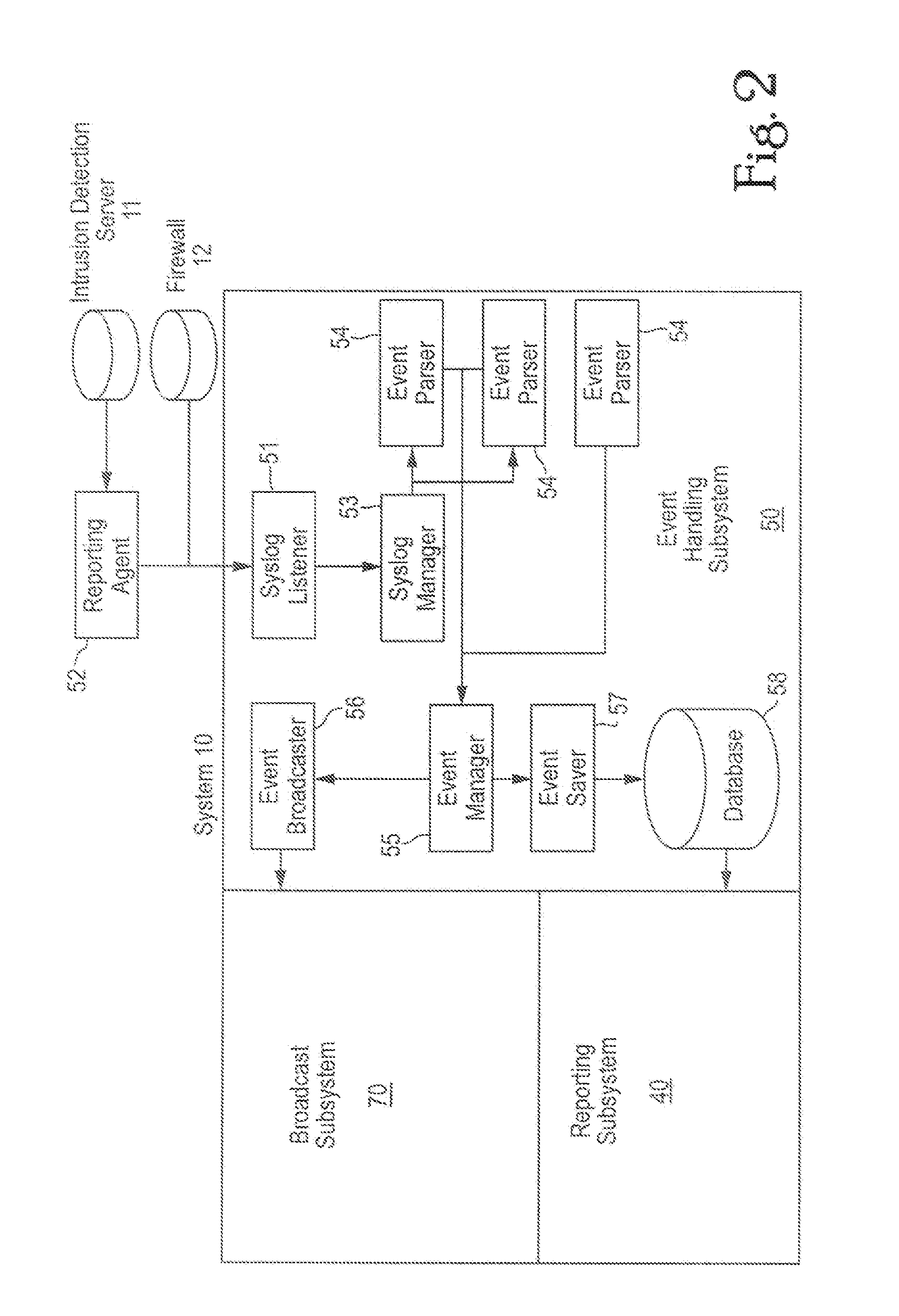
Comprehensive security structure platform for network managers
InactiveUS7127743B1Convenient reviewMemory loss protectionError detection/correctionComputerized systemNetwork service
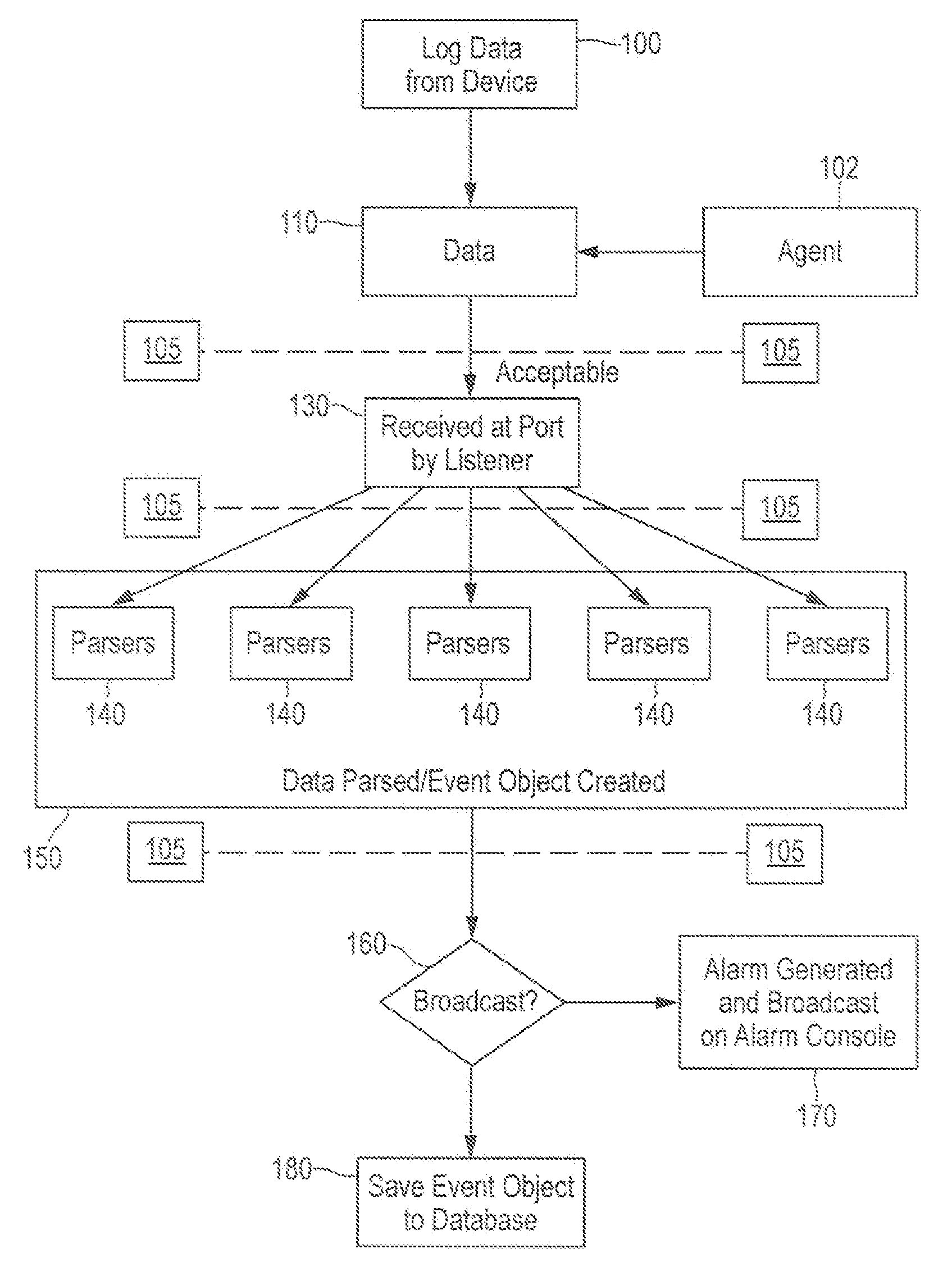
An embodiment includes a computer system for detecting and monitoring network intrusion events from log data received from network service devices in a computer network. An embodiment may include an event parser in communication with multiple network service devices. The event parser may parse information to create corresponding event objects concerning intrusion events. The system may include an event manager in communication with the event parser. The event manager may be configured to evaluate the event objects according to at least one predetermined threshold condition. The system may include an event broadcaster in communication with the event manager for receiving event objects designated by the event manager for broadcast. The event broadcaster may be able to transmit the event objects in real time. The system may also include means for alerting the user that a network intrusion event has occurred.
Owner:BLACKSTRATUS
Brink of failure and breach of security detection and recovery system
ActiveUS20050050377A1Reduce the impactAvoid power outagesError detection/correctionTransmissionTelecommunications linkProgram planning
A method and apparatus for managing a network includes detecting occurrence of a network event associated with a new network condition including unplanned and planned macro-events associated with network elements and communication links of the network. The network event is classified as being associated with at least one of a network element failure, communications link failure, and a security breach. In response to the network event exceeding a network degradation threshold, the network event is identified as a network degradation event, and an alert is sent to a network administrator to normalize the network degradation event.
Owner:ALCATEL-LUCENT USA INC +1
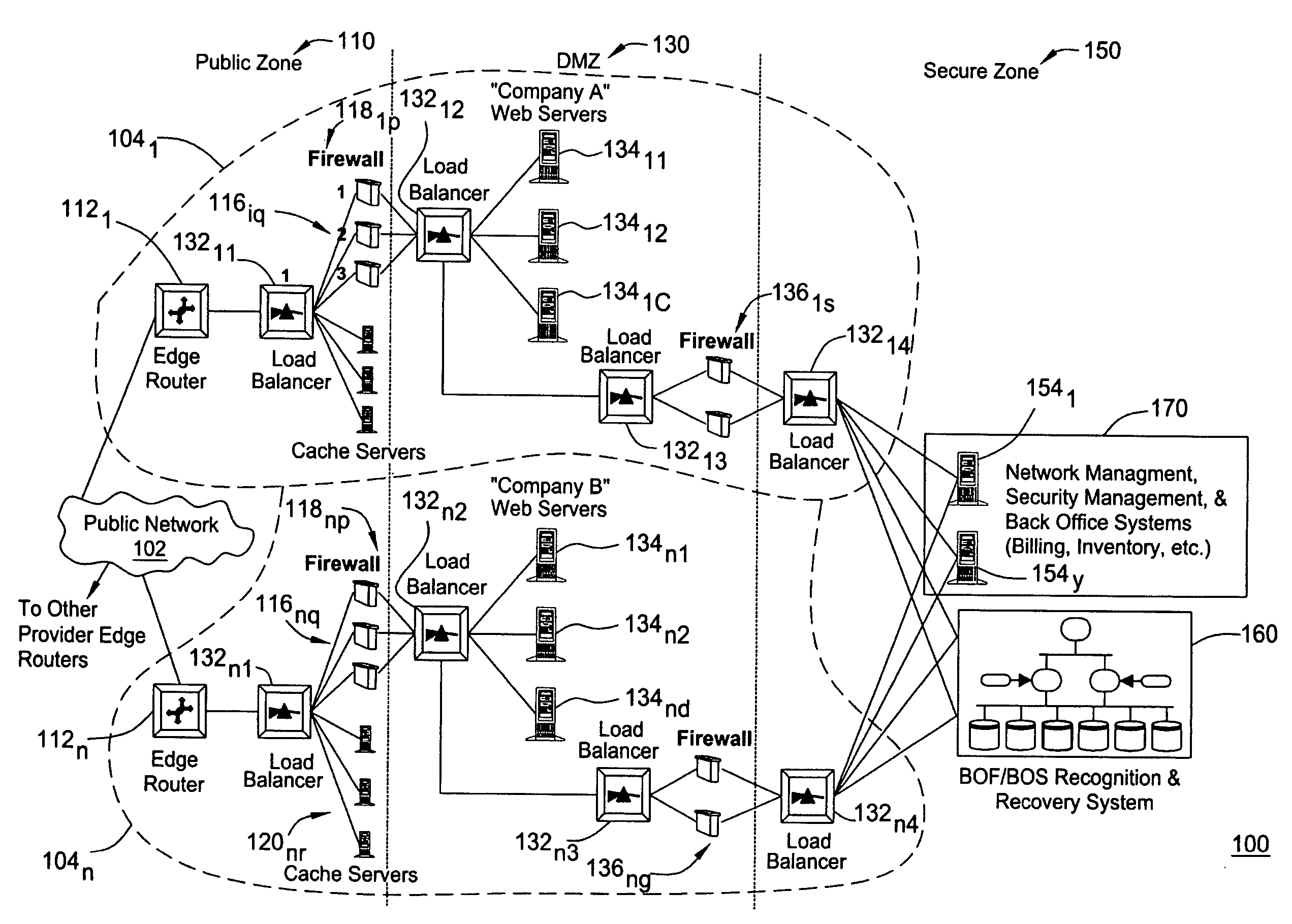
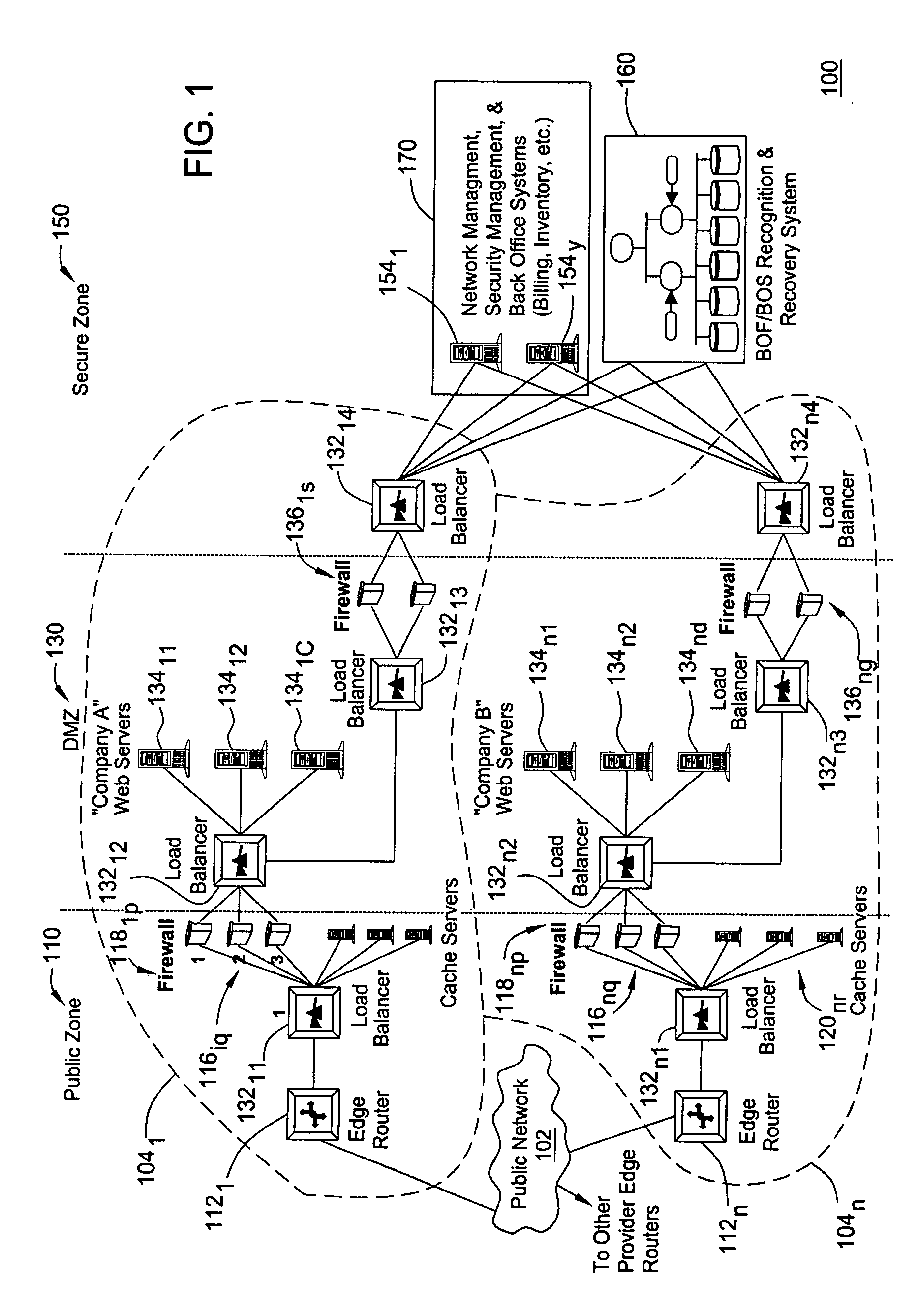
Financial services network and associated processes
InactiveUS20060015450A1Quickly and easily requestQuickly and easily and provideFinancePayment architectureComputer compatibilityTransport network
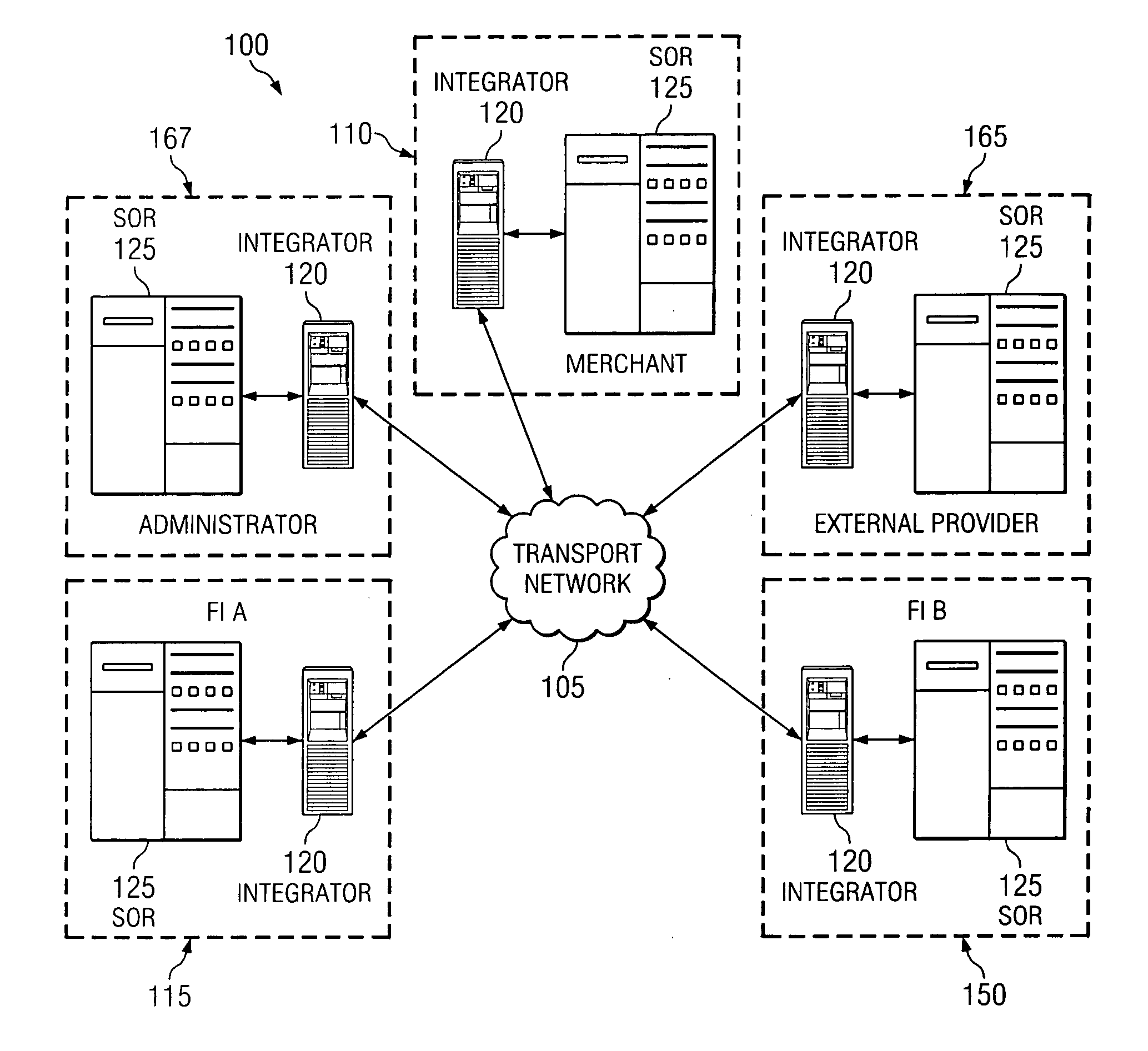
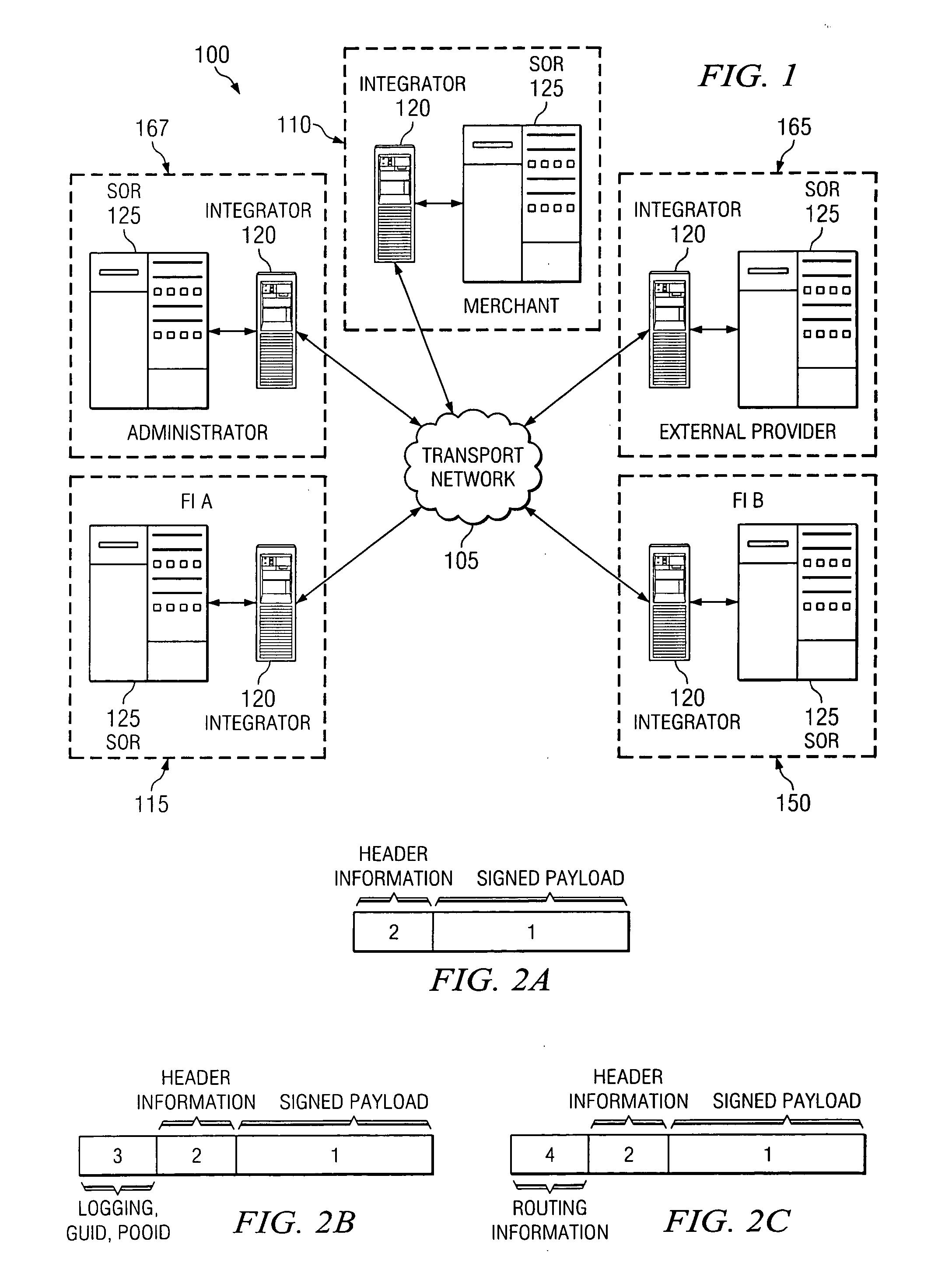
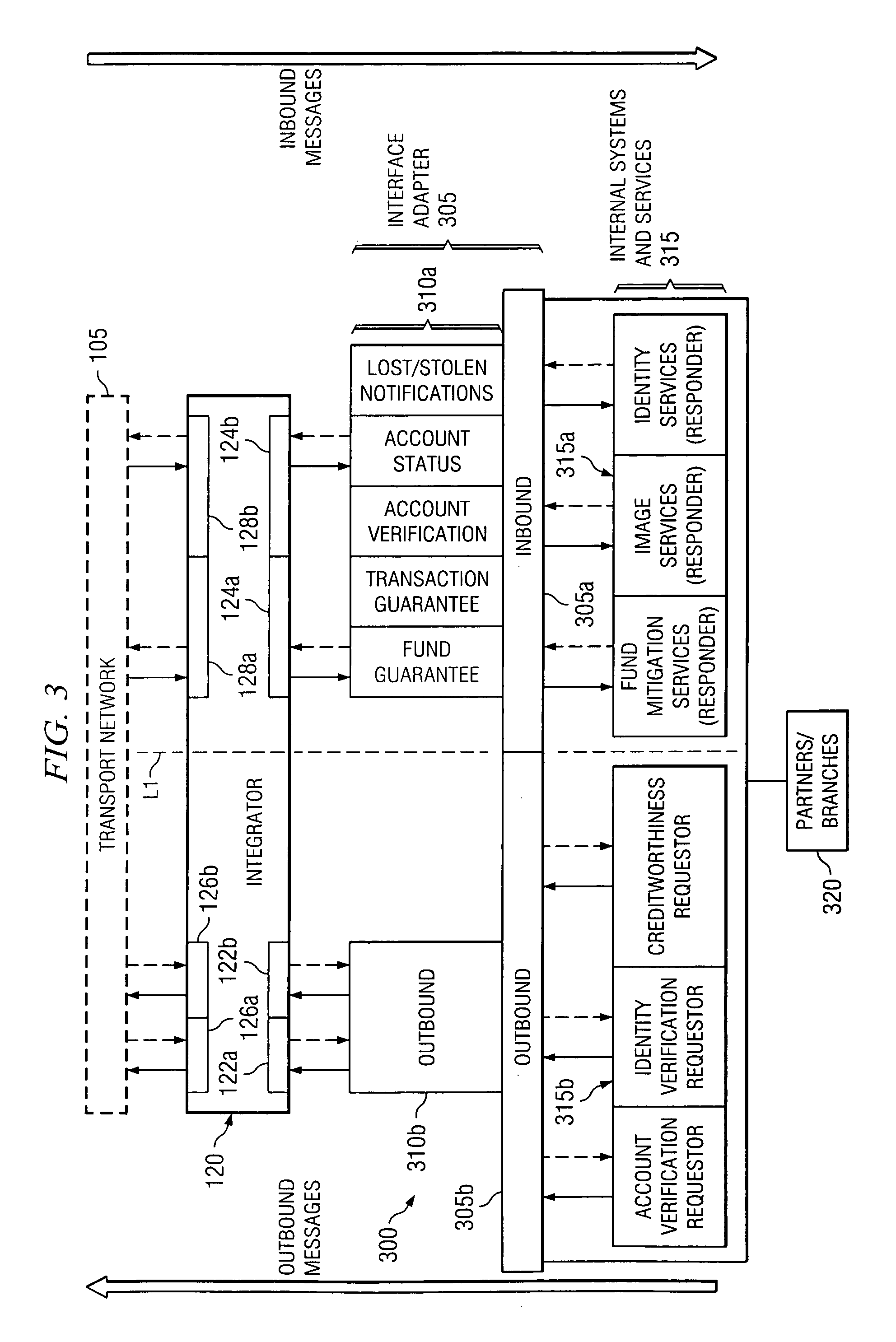
Disclosed herein are a financial services network and associated processes for providing interactive transmissions between network participants. The financial services network includes a private and secure transport network that allows for any number of financial services to be conducted between participants and other entities associated with the network. Each participant can operate as a requestor or responder. The system also includes a network administrator that is configured to govern the flow of messages directly between participants. By interconnecting participants to an unlimited number of information providers, all participants can obtain information and verifications on an interactive basis. Also, by employing a single network having a standardized message format and protocol, all participants can quickly and easily interactively request or provide information and verify to any other participant without the concern of incompatibility between system, transmission, or even message formats or protocols.
Owner:WELLS FARGO BANK NA
Methods, apparatuses, and systems allowing for bandwidth management schemes responsive to utilization characteristics associated with individual users
ActiveUS7296288B1Digital data processing detailsUnauthorized memory use protectionHTTP tunnelData stream
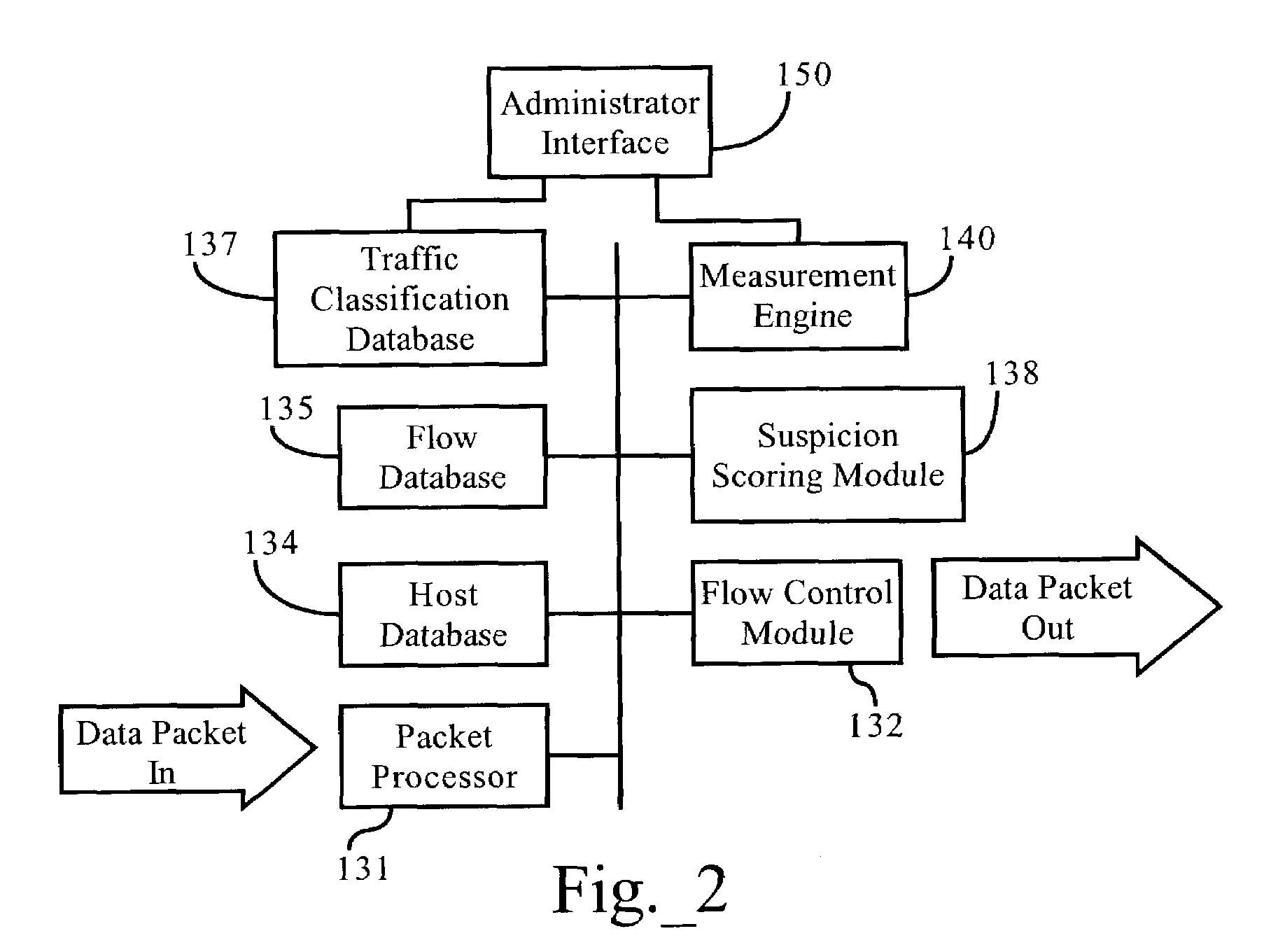
Methods, apparatuses and systems allowing for bandwidth management schemes responsive to utilization characteristics associated with individual users. In one embodiment, the present invention allows network administrators to penalize users who carry out specific questionable or suspicious activities, such as the use of proxy tunnels to disguise the true nature of the data flows in order to evade classification and control by bandwidth management devices. In one embodiment, each individual user may be accorded an initial suspicion score. Each time the user is associated with a questionable or suspicious activity (for example, detecting the set up of a connection to an outside HTTP tunnel, or peer-to-peer application flow), his or her suspicion score is downgraded. Data flows corresponding to users with sufficiently low suspicion scores, in one embodiment, can be treated in a different manner from data flows associated with other users. For example, different or more rigorous classification rules and policies can be applied to the data flows associated with suspicious users.
Owner:CA TECH INC
System and method for PE-node protection
ActiveUS20070121486A1Fast reroute (FRR)Quickly and efficiently reroutingError preventionFrequency-division multiplex detailsNetwork ConvergenceNetwork packet
A novel fast reroute (FRR) technique is provided for quickly and efficiently rerouting selected types of network traffic in response to a node or link failure at the edge of a computer network. According to the technique, the network includes first and second edge devices that function as “FRR mates,” such that network traffic originally destined for one FRR mate may be quickly rerouted to the other without having to wait for conventional network convergence. When an edge device receives rerouted packets originally destined for its FRR mate, the device responds by forwarding only those rerouted packets matching the selected traffic types; rerouted packets that do not match the selected traffic types are dropped or otherwise discarded. The first and second edge devices may be statically configured as FRR mates, e.g., by a network administrator, or they may be configured to automatically detect their compatibility as FRR mates.
Owner:CISCO TECH INC
System and method for configuring a network device
A system and method for communicating with network devices without regard to the device type and / or manufacturer is described. In one embodiment, the present invention provides a global graphical user interface (GUI) for communicating with various network devices. The global GUI includes an intuitive interface driven by a template library. For each device type and each device manufacturer, this template library can store both the attribute fields required for device configuration and the format for communicating those attribute fields. When a network administrator wants to communicate with a particular network device, the template associated with that device can be retrieved from the template library. The network administrator can then populate the attribute fields of that template with the appropriate data. This attribute data can be formatted and provided to the network device.
Owner:FOCUS GLOBAL SOLUTIONS LLC
Method and system for path identification in packet networks
ActiveUS20050025059A1Simple methodColor television with pulse code modulationError preventionEntry pointSource area
A method and system for extracting and building end-to-end route information in a multi-area Internet protocol (IP) autonomous system (AS) is disclosed. The method and system enable a user, such as a network administrator, to explicitly identify a full set of paths (links and routers) that a given IP packet would potentially traverse from its entry point in the source area of the AS where it originates until its exit point in its intended destination area.
Owner:SONS OF INNOVATION LLC
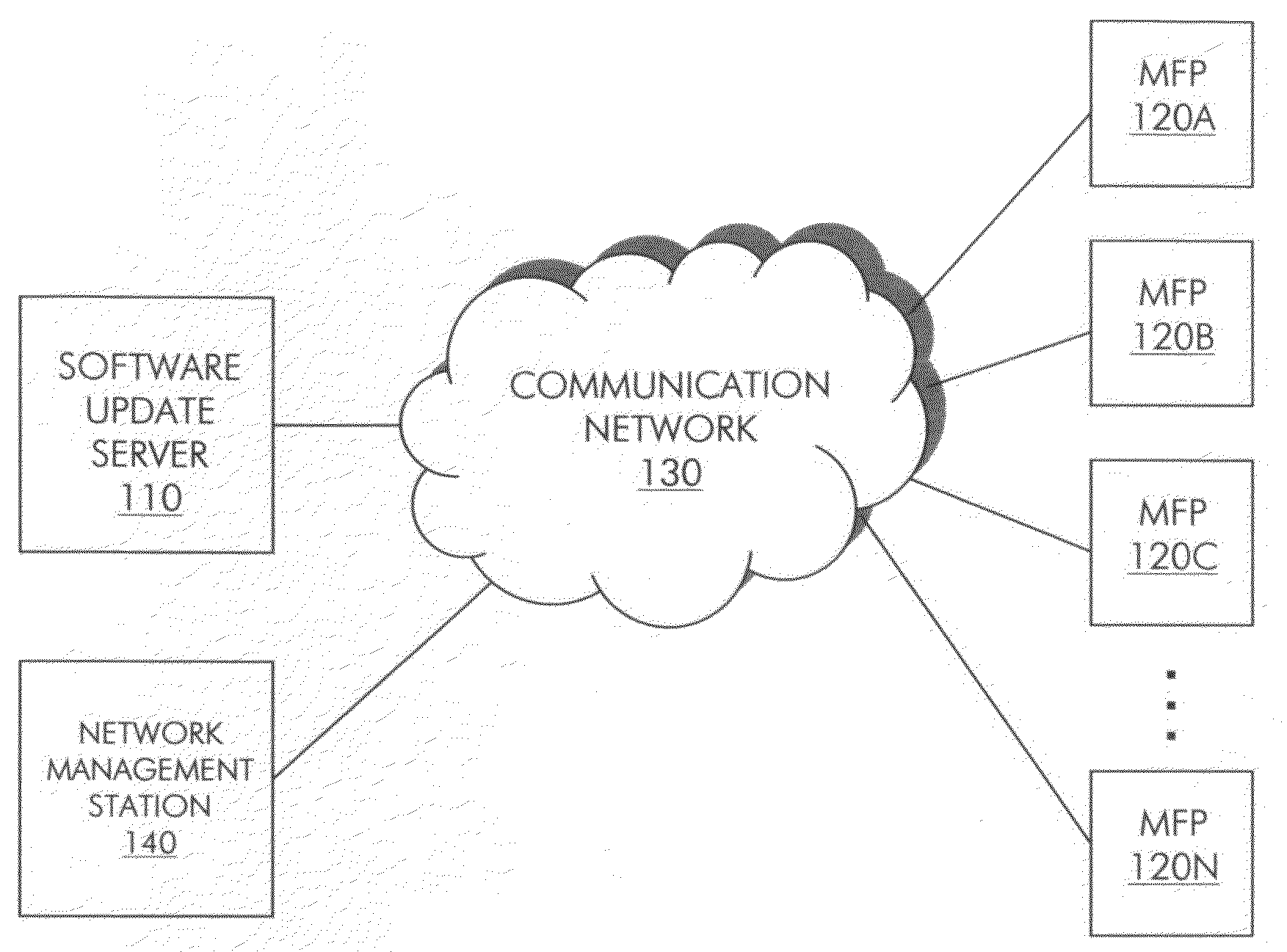
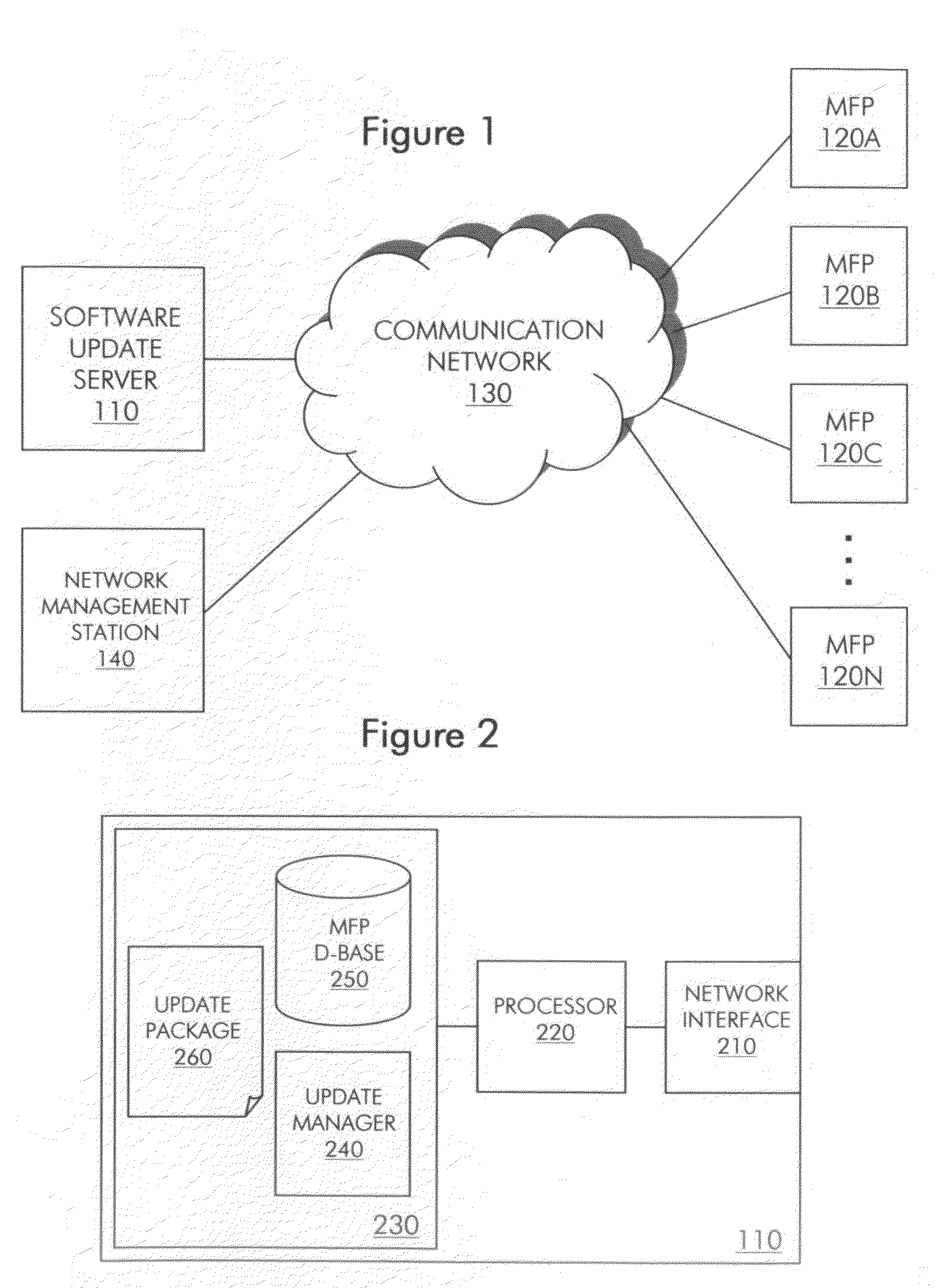
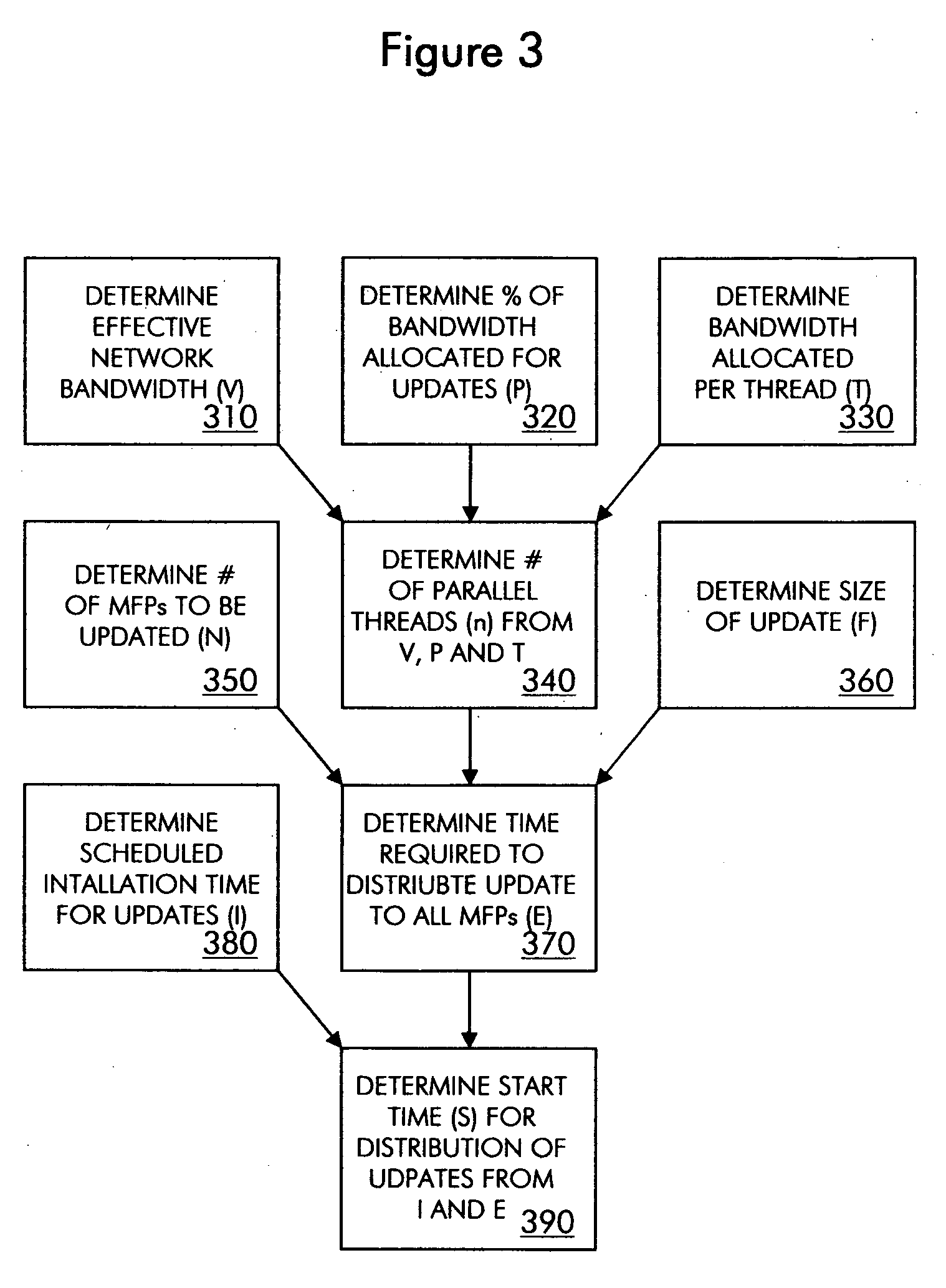
Method and system for updating the software of multiple network nodes
ActiveUS20090150878A1Improve network performanceHigh degreeMultiple digital computer combinationsSpecific program execution arrangementsCompletion timeStart time
A method and system for updating a group of network nodes, such as a group of MFPs, with replacement software in a manner that improves network performance and the predictability of a completion time for installation of the replacement software involves throttling distribution of a software update package to avoid resource oversubscription while time-bounding distribution so that installation of the software update on all of the network nodes can be completed by a certain time and, in some embodiments, further involves determining a start time for distribution of the software update package based at least in part on a scheduled installation time selected by a network administrator, which provides a high degree of confidence that installation of the software update across the entire group of network nodes will be completed around a scheduled time (e.g. during “off hours”) notwithstanding the staggered distribution of the software update package.
Owner:SHARP KK
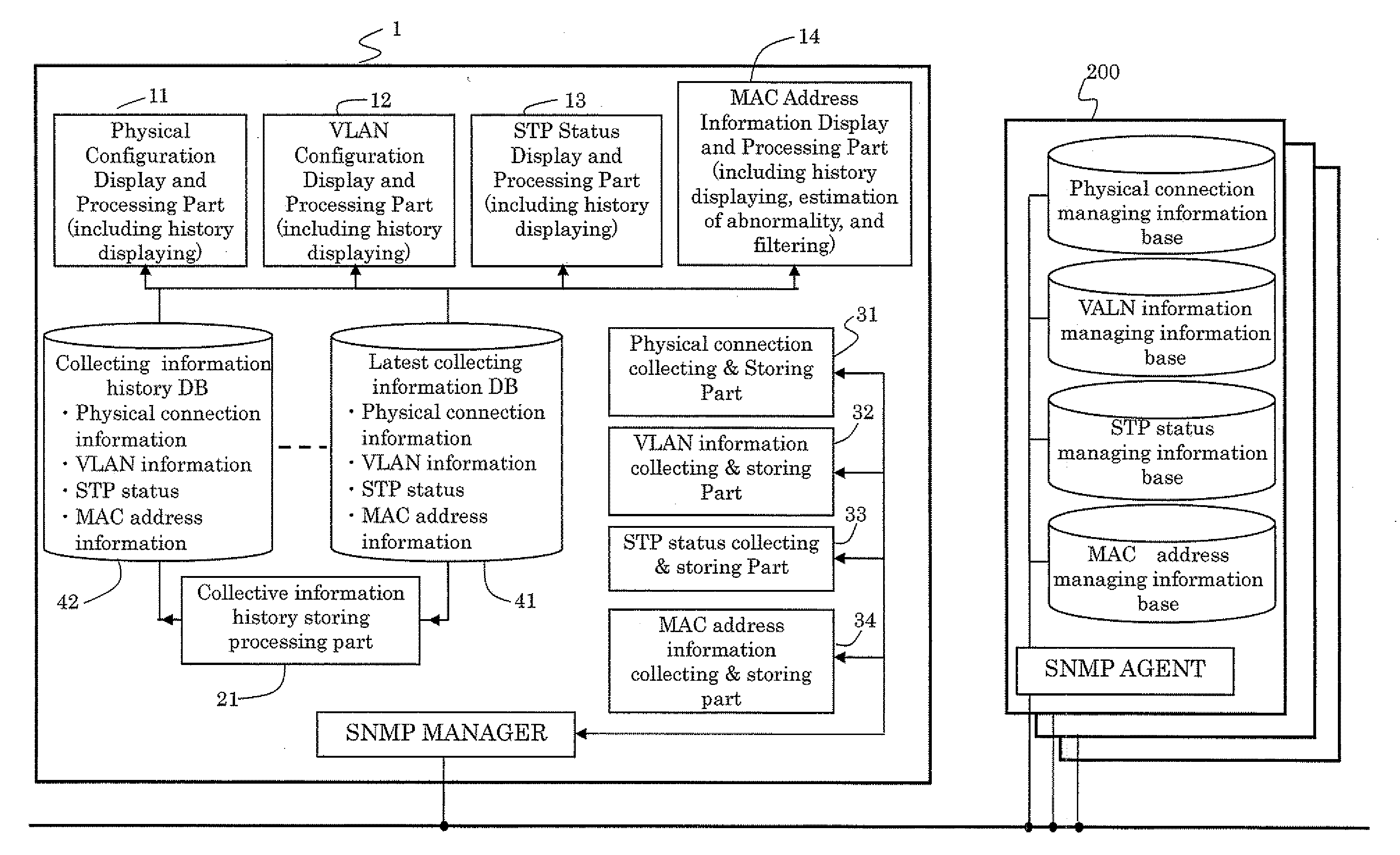
Network management method
InactiveUS20070274234A1Reliable monitoringGood estimateData switching by path configurationNetwork managementLogical network
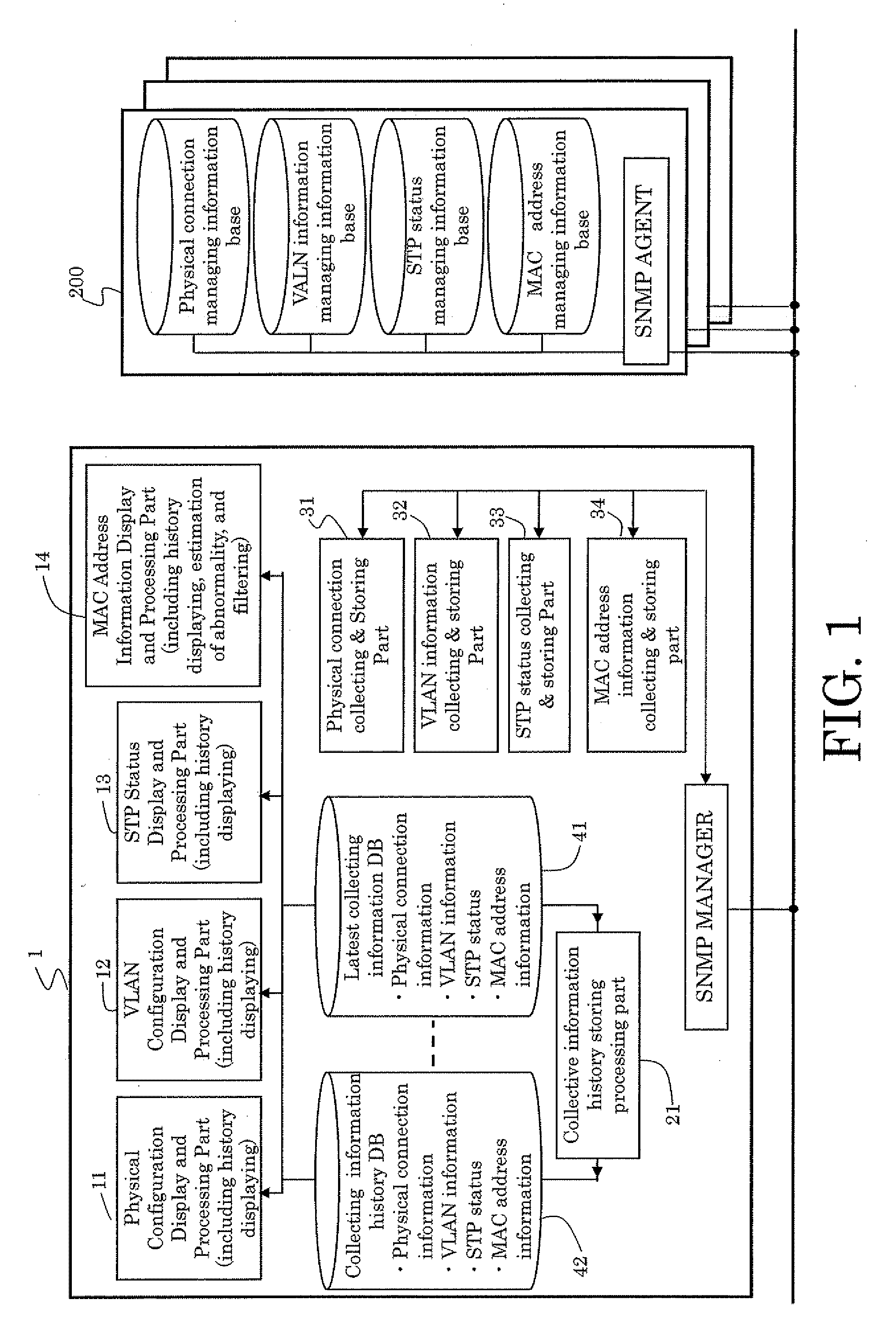
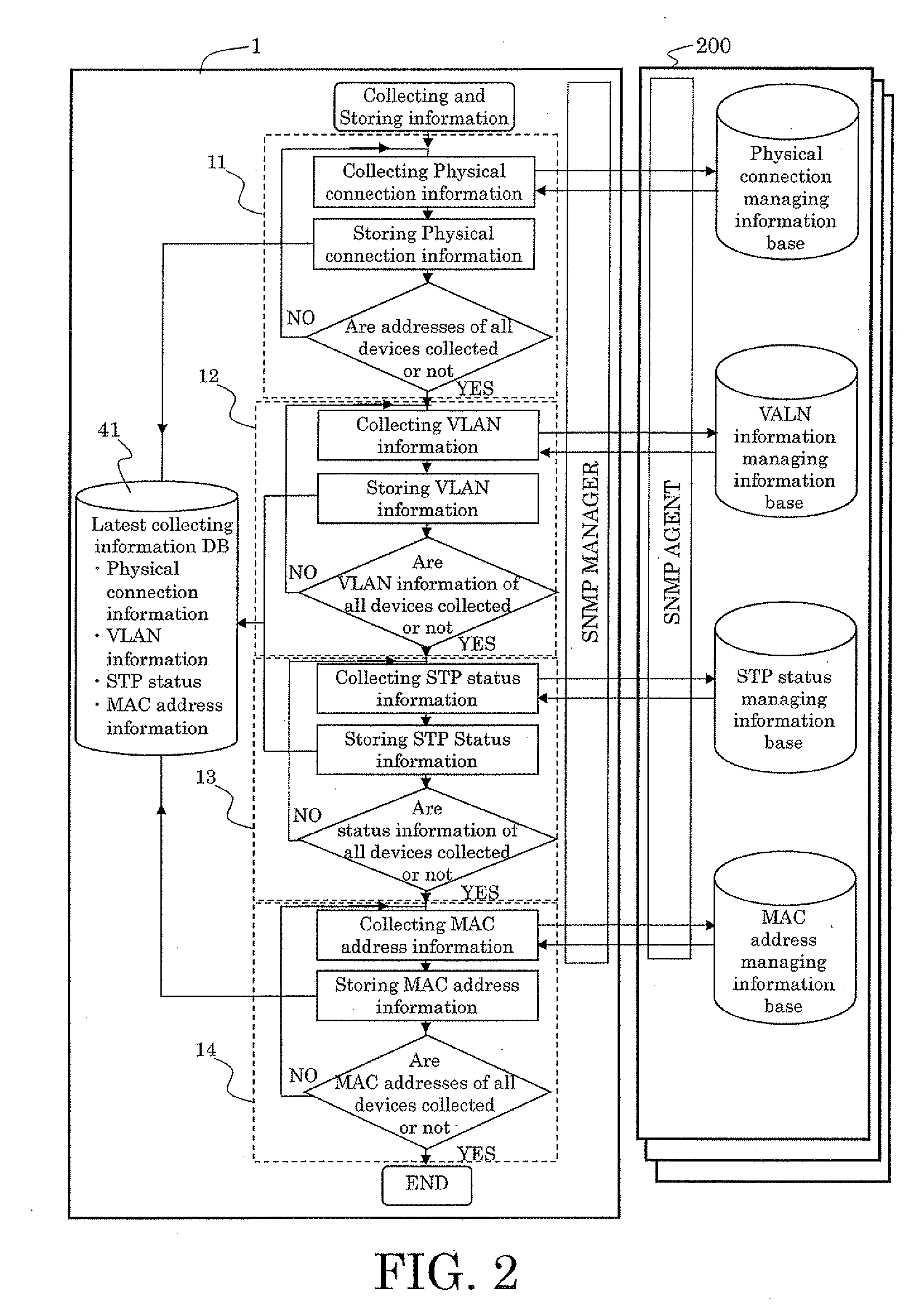
The present invention provides a method in which the physical connection information and the logical network configuration information are kinked to the status of spanning tree, and the status of spanning tree is displayed with the physical connection and the logical network configurations. The method can provide the better recognition about not only intended the physical and logical configurations but the status of spanning tree to a network administrator. Therefore, the network administrator can integrally recognize the status of the network and the failure in the network will be analyzed easily to recover the network to normal state in shorter time.
Owner:FUJITSU LTD
System and methods for providing network quarantine
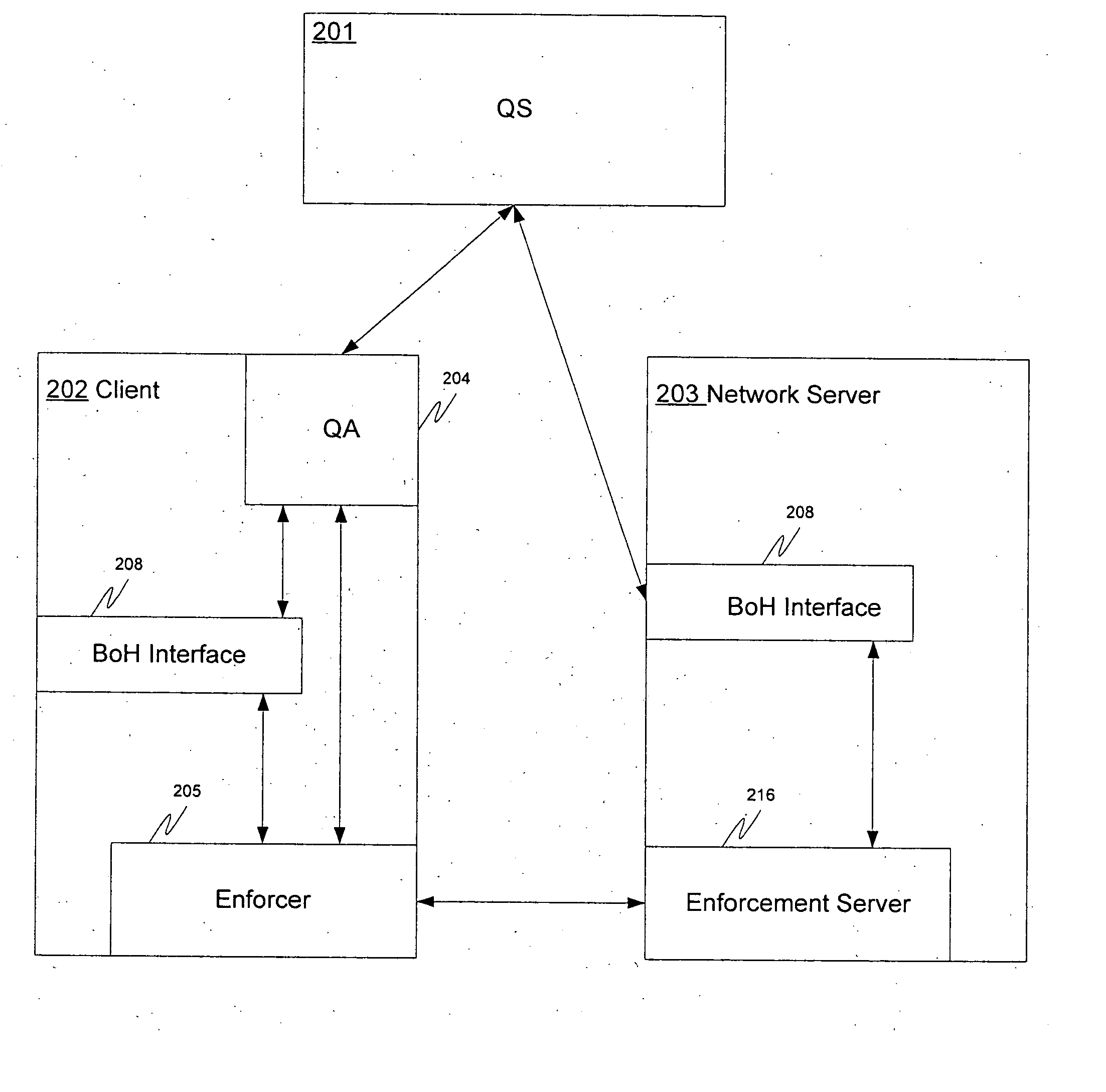
InactiveUS20050131997A1Network resource is limitedMemory loss protectionDigital data processing detailsAccess networkSecure state
A system and method for ensuring that machines having invalid or corrupt states are restricted from accessing network resources are provided. A quarantine server located on a trusted machine in a network provides a bill of health to a quarantine agent located on a client computer that wishes to gain access to network resources administered by an organization. The quarantine agent requests bill of health from the quarantine server, and receives a manifest of checks that the client computer must perform. The quarantine agent then sends a status report on the checks back to the quarantine server. If the client computer is in a valid security state, the bill of health is issued to the client. If the client computer is in an invalid state, the client is directed to install the appropriate software / patches to achieve a valid state. When a client requests the use of network resources from a network administrator, the network administrator requests the client's bill of health. If the bill of health is valid, the client is admitted to the network. If the bill of health is invalid, or if the client does not have a quarantine agent, the client is placed in quarantine, in which the only network resources accessible to the client are those necessary to install the quarantine agent and requisite software / patches to achieve a valid state.
Owner:MICROSOFT TECH LICENSING LLC
System, method and computer program product for diagnostic supervision of internet connections
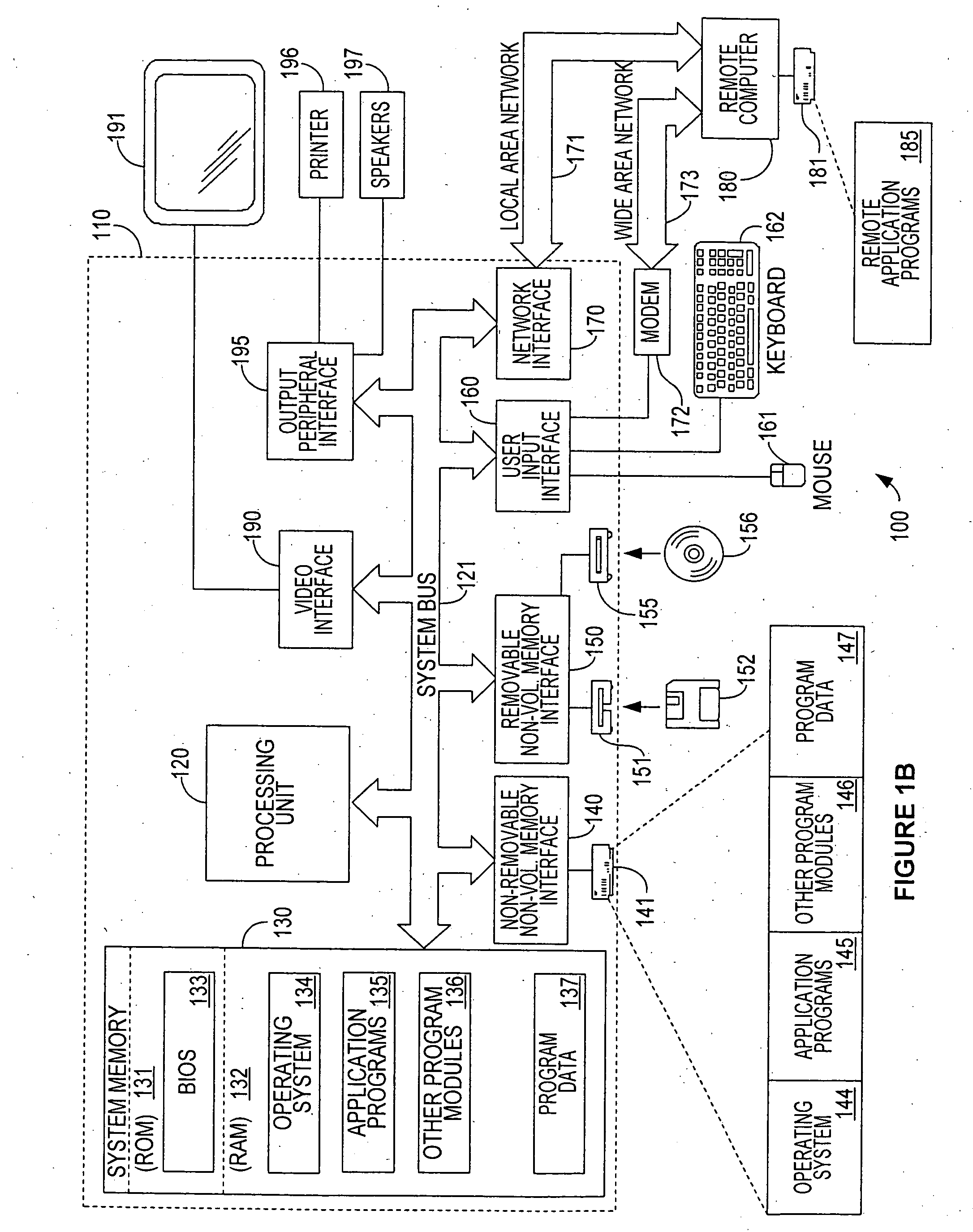
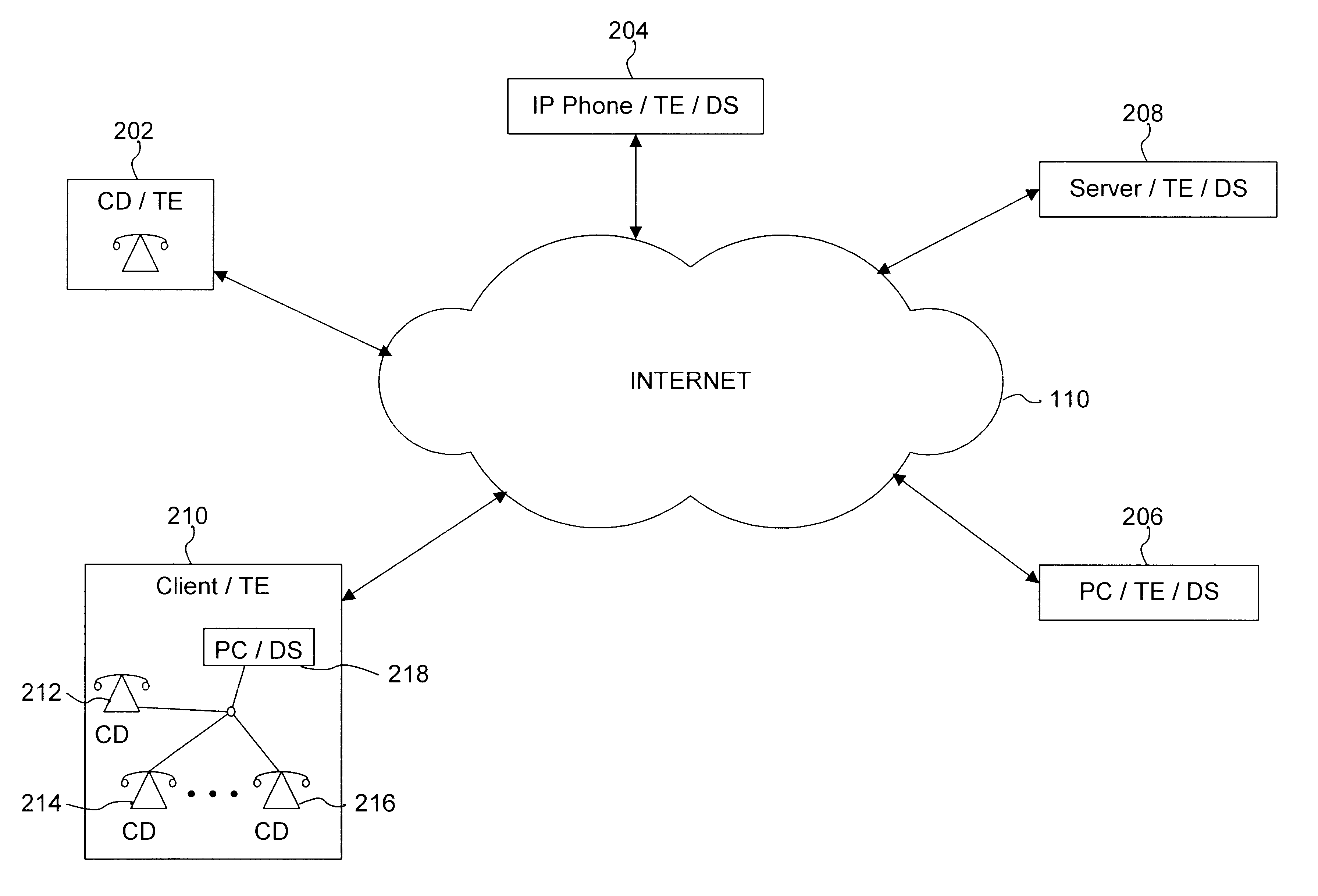
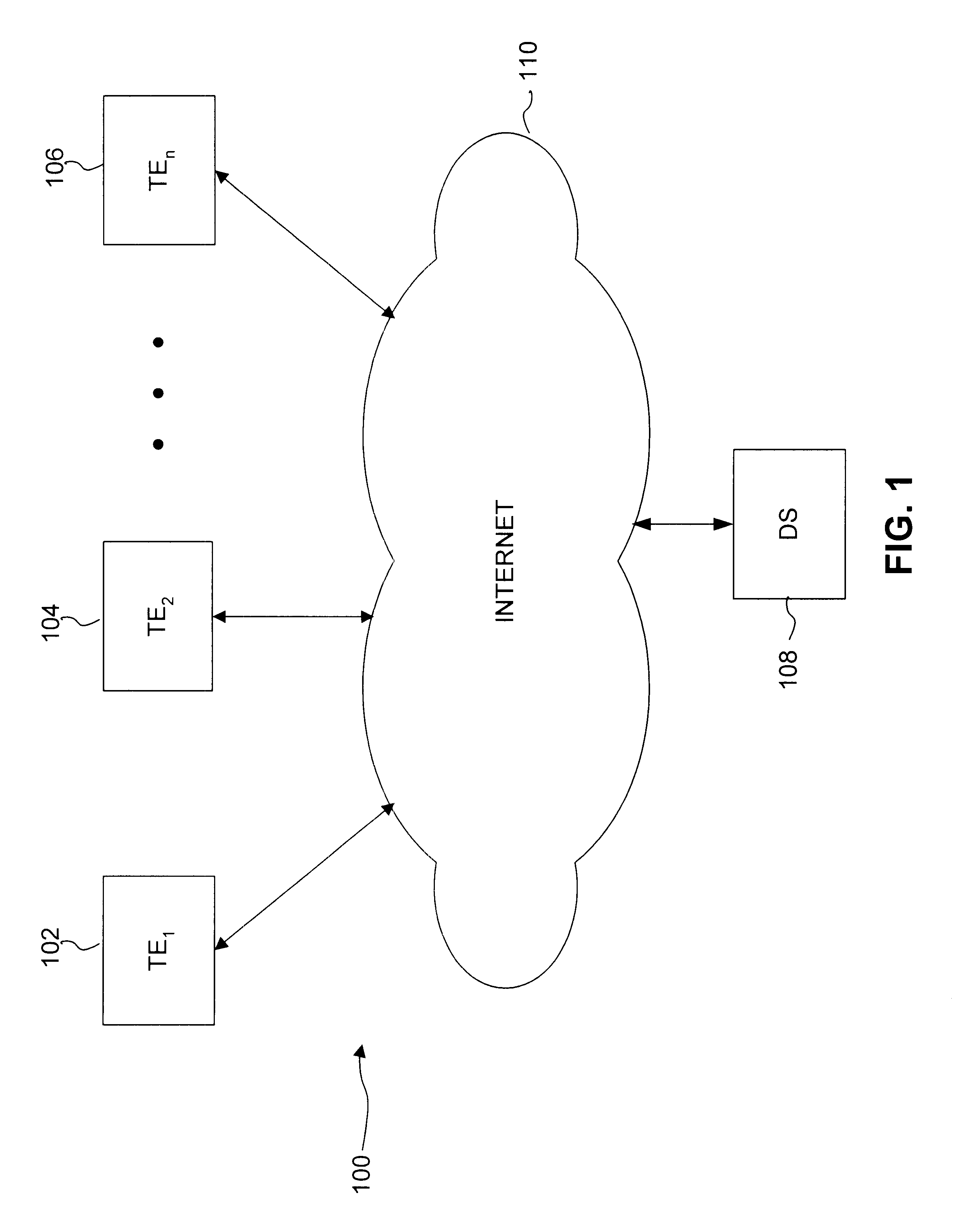
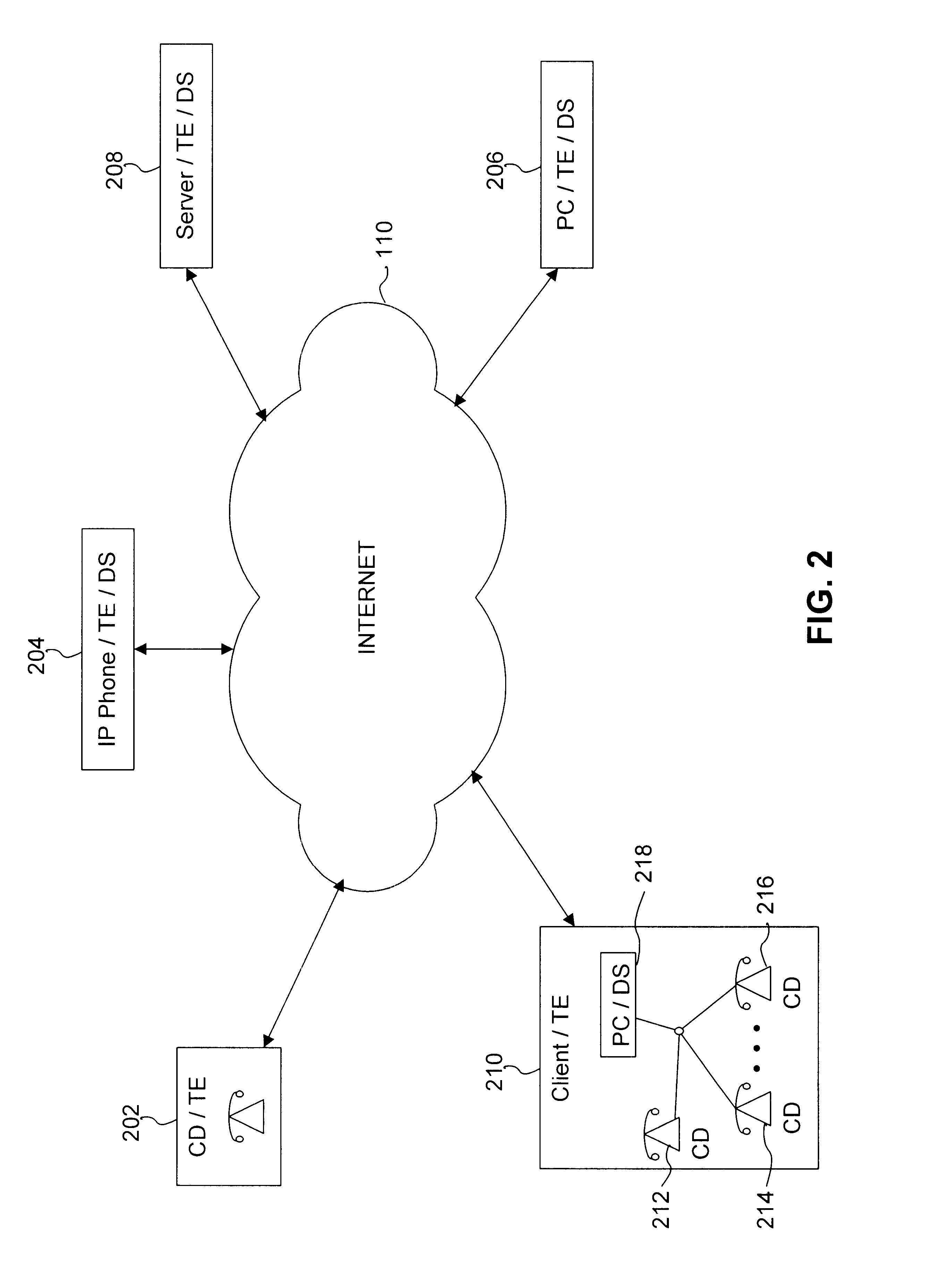
InactiveUS6553515B1Error detection/correctionDigital computer detailsModem deviceCommunications system
A system, method and computer program product for managing diagnostic and performance information for communications system terminal endpoints (TEs) communicating over an Internet Protocol (IP) network. The TEs communicate by connections that are voice, modem, facsimile, video, data transmissions, or the like. A Diagnostic Supervisor (DS) transmits Diagnostic Configuration Messages (DCMs) to the TEs. The TE's generate Diagnostic Messages (DMs) based on diagnostic information, including error statistics, voice statistics, facsimile statistics, video statistics, data statistics, or the like, concerning IP network connections in which the TEs participate. The DCMs instructs the TEs how to format and when to transmit DMs. The DMs are transmitted by the TEs to the DS. In a system with more that one DS, the TEs can transmit DMs to the plural DSs, other TEs or any network devices. The DS can be programmed locally or remotely to send various types of DCMs. The DS can also be programmed locally or remotely to provide diagnostic reports based on DMs to network users or to the network administrator. Diagnostic information is used for disconnect supervision, answer detection, attendant supervision, billing management, rerouting of IP connections to the PSTN, and the like.
Owner:CHEMTRON RES
System and method of assigning and reclaiming static addresses through the dynamic host configuration protocol
InactiveUS6957276B1Reduce probabilityData resettingMultiple digital computer combinationsIp addressFree state
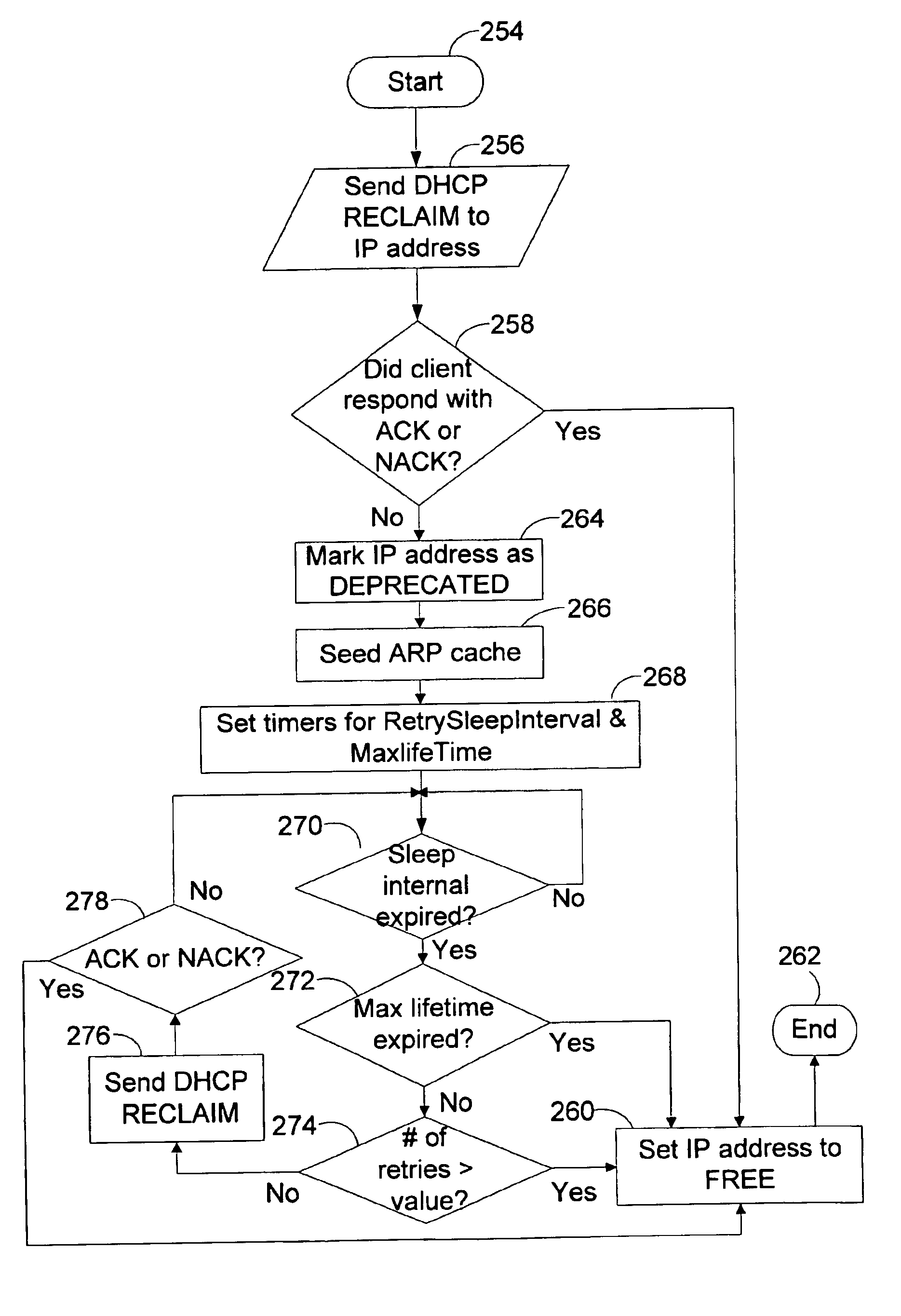
Presented is a system and method for providing centralized address management of static IP addresses through the dynamic host control protocol. Static or permanent IP addresses are those addresses assigned by DHCP having an infinite lease time. The assignment of such static IP addresses follows the conventional DHCP mechanism for the assignment of other IP addresses. However, the centralized reclamation of a statically or permanently assigned IP address by a network administrator through the DHCP server presents novel aspects of the invention heretofore unknown. Specifically, through the system and method of the present invention, the DHCP server is capable of reclaiming at any point in time, a statically or permanently assigned IP address by transmitting a DHCP RECLAIM command to the DHCP client, or through its relay agent. In the normal situation, the DHCP client acknowledges the RECLAIM command, allowing the IP address to be placed in the FREE state. If, however, the DHCP client does not respond or the responses are not received by the DHCP server, the DHCP server marks the state of the IP address as DEPRECATED. The state of the IP address will be changed from DEPRECATED to FREE once a number of retries of the RECLAIM process has been completed, or a maximum period of time has passed. Security mechanisms to prevent a malicious attacker from reclaiming static IP address from DHCP clients are also presented.
Owner:MICROSOFT TECH LICENSING LLC
Method to detect application execution hijacking using memory protection
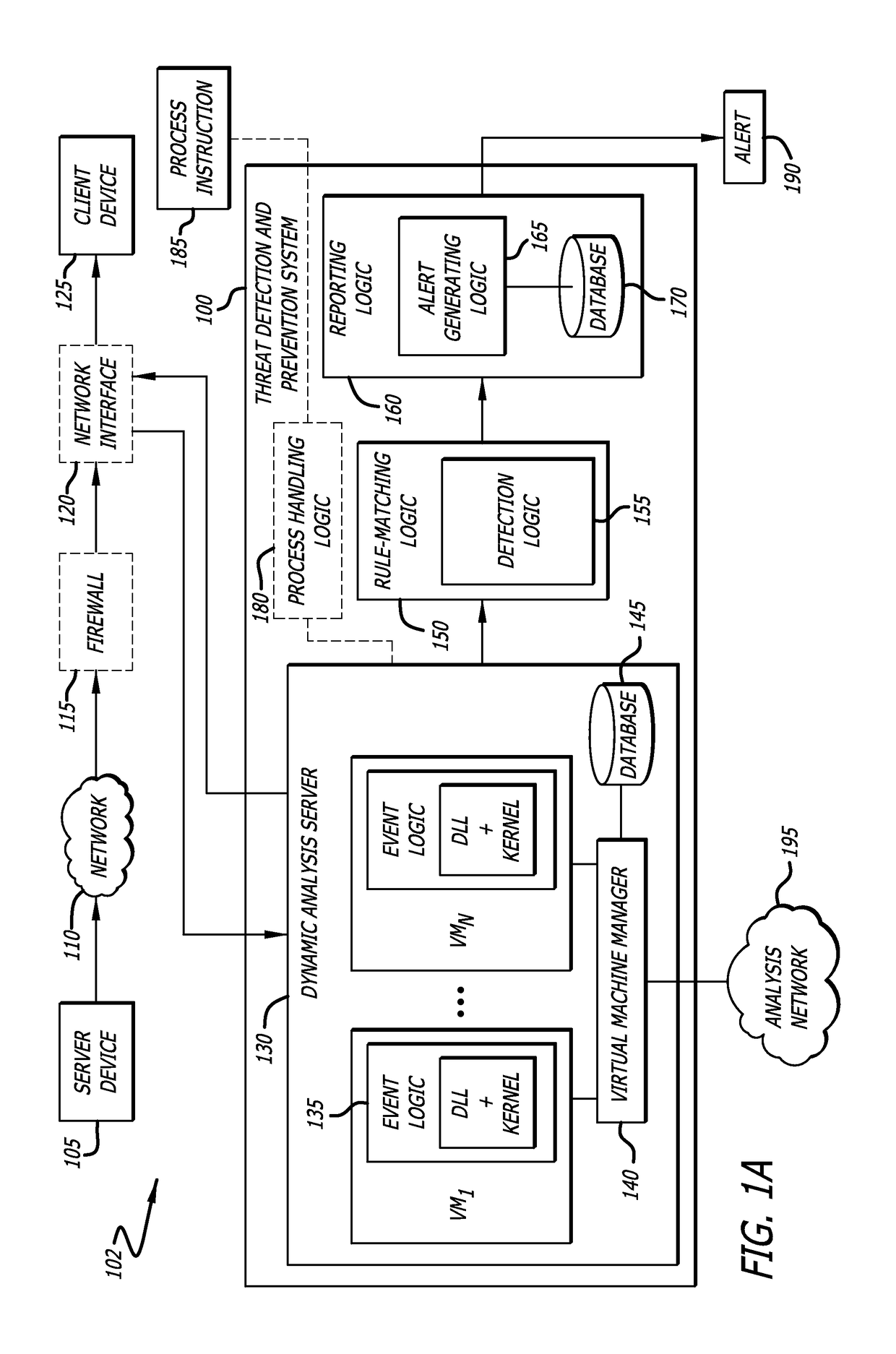
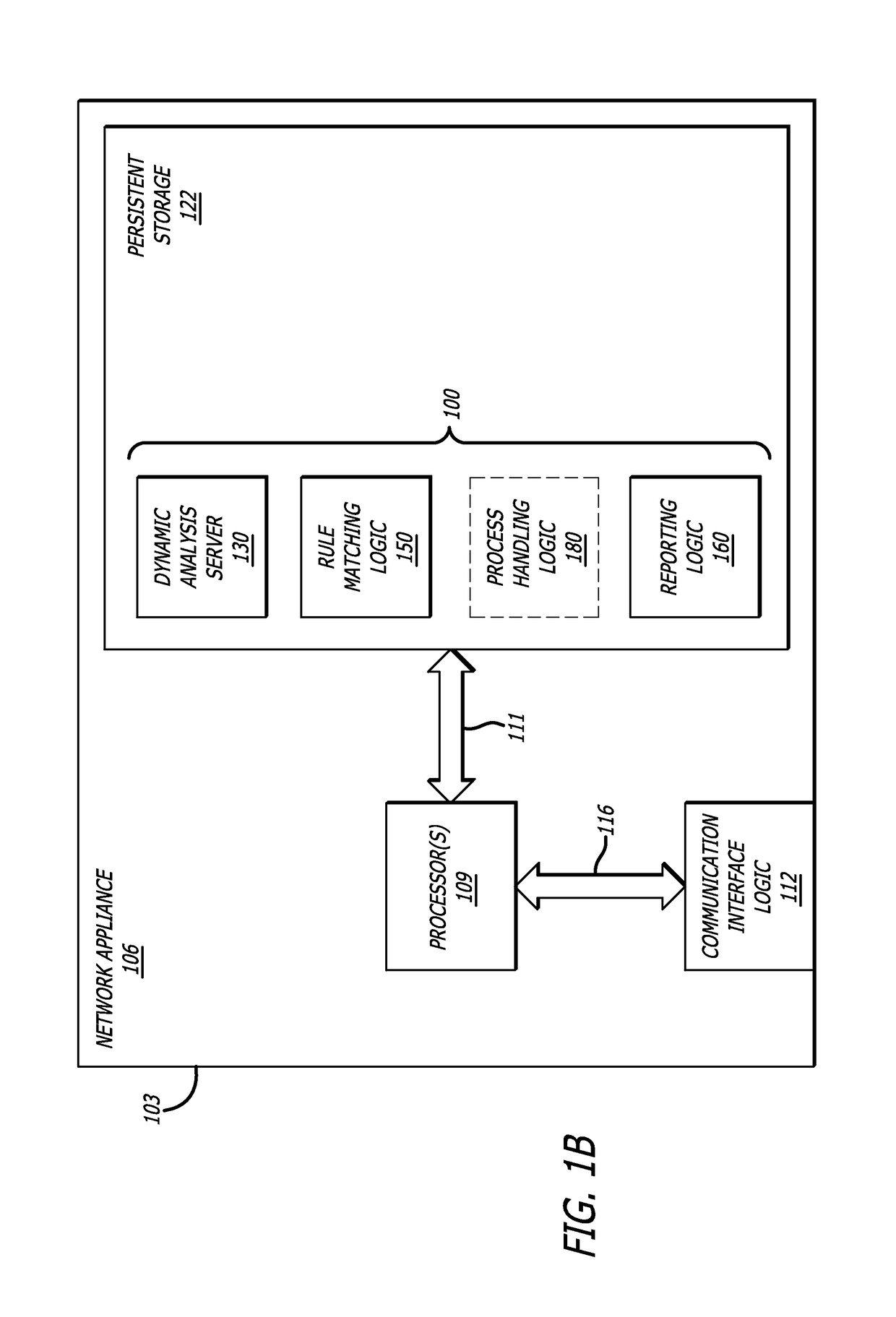
According to one embodiment, a system comprising a dynamic analysis server comprising one or more virtual machines is disclosed, wherein the one or more virtual machines may be configured to execute certain event logic with respect to a loaded module. The virtual machines may be communicatively coupled to a virtual machine manager and a database; and rule-matching logic comprising detection logic, wherein the detection logic is configured to determine (1) whether an access source is attempting to access a protected region such as a page guarded area; and (2) determine whether the access source is from the heap. The system further comprises reporting logic that is configured to generate an alert so as to notify a user and / or network administrator of a probable application-execution hijacking attack.
Owner:FIREEYE SECURITY HLDG US LLC
Method and apparatus to manage network client logon scripts using a graphical management and administration tool
A GUI (Graphical User Interface) Manager is used by a network administrator to fill-in predefined templates. The administrator does not need to compile, debug or write a single line of scripting code. The GUI manager has a “select the box” and “point and click” and “fill-in the blank” approach for selecting computer settings. The predefined configuration and / or template(s) are used by a logon script program on a client system to manage the configuration of resources on at least one client. There are three levels of resources that can be managed. The first type of resource is an operating system. The second type of resource is an application resource. And the third type of resource is to redirect a resource on the client to a resource on a network such as a drive letter mapping. Resources include configurations from the group of configuration settings consisting of drive mappings, shell folders, printer deployment, proxy server access, application paths, service packs, anti-virus updates, policies and automatic mail profile creation. In another embodiment, validation logic is used on the clients' system during the execution of an application program that takes the template and applies the defined configuration settings in the template to the clients' system so as to automatically configure at least one configuration setting for a user if the combination of one or more predefined conditions for a selected group, a selected operating system and a selected connection method are met. In still another embodiment, an interpretive engine is used on the client's system to permit the administration of client resources with a template while also allowing network administrators to build their own custom logon scripts.
Owner:QUEST SOFTWARE INC
Method and system for providing a user-customized electronic book
InactiveUS7236966B1Precise positioningSatisfies needDigital data information retrievalData processing applicationsRelevant informationElectronic book
One embodiment of the present invention enables an individual to selectively choose an area(s) of interest and automatically scan a database to intelligently retrieve the relevant information and filter out the irrelevant information. Next, the relevant information may then be collated and made available in an electronic “book” format for ease of distribution. For example, a network administrator may go to his / her company's web page and utilize the present embodiment to download an electronic “book” pertaining to troubleshooting his / her particular network configuration. It is appreciated that the present embodiment may be utilized in a broad number of different areas since it covers any application where there may be a huge database of information and only a part of which may be of interest to selected parties. For example, the present embodiment may be quite useful in areas such as, but not limited to, pharmaceutical, manufacturing, medical, defense, and computer networking.
Owner:CISCO TECH INC
IP network vulnerability and policy compliance assessment by IP device analysis
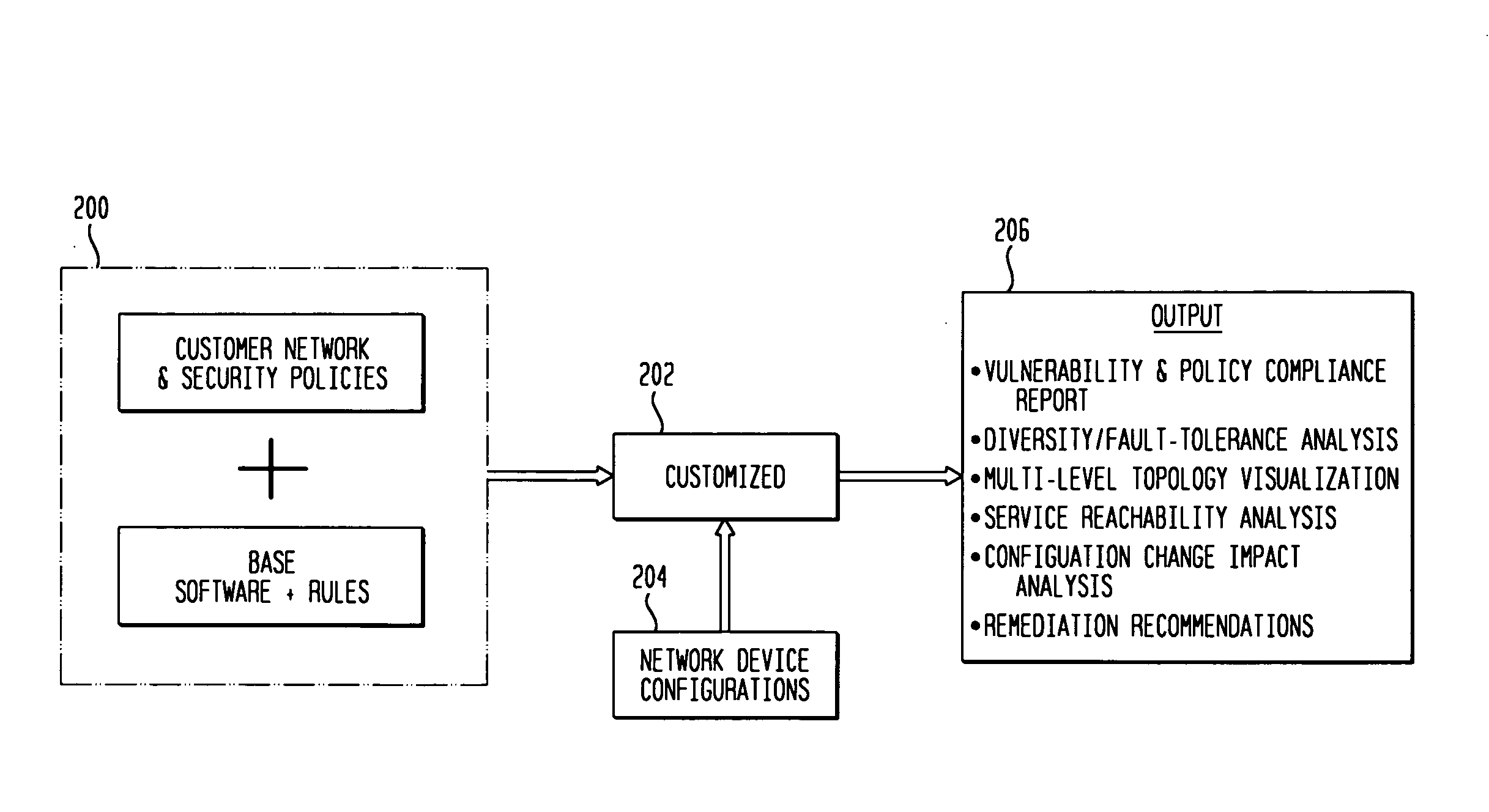
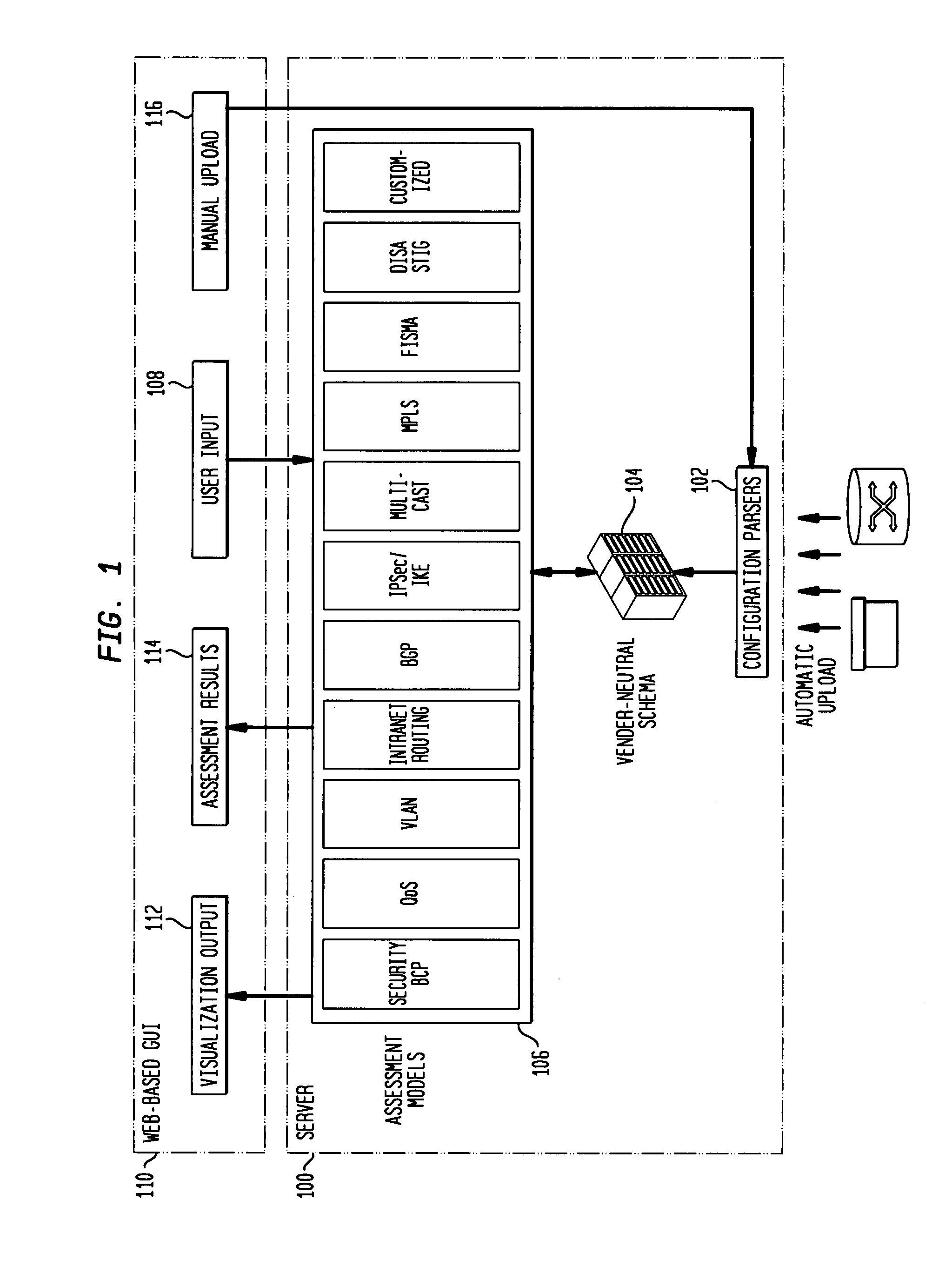
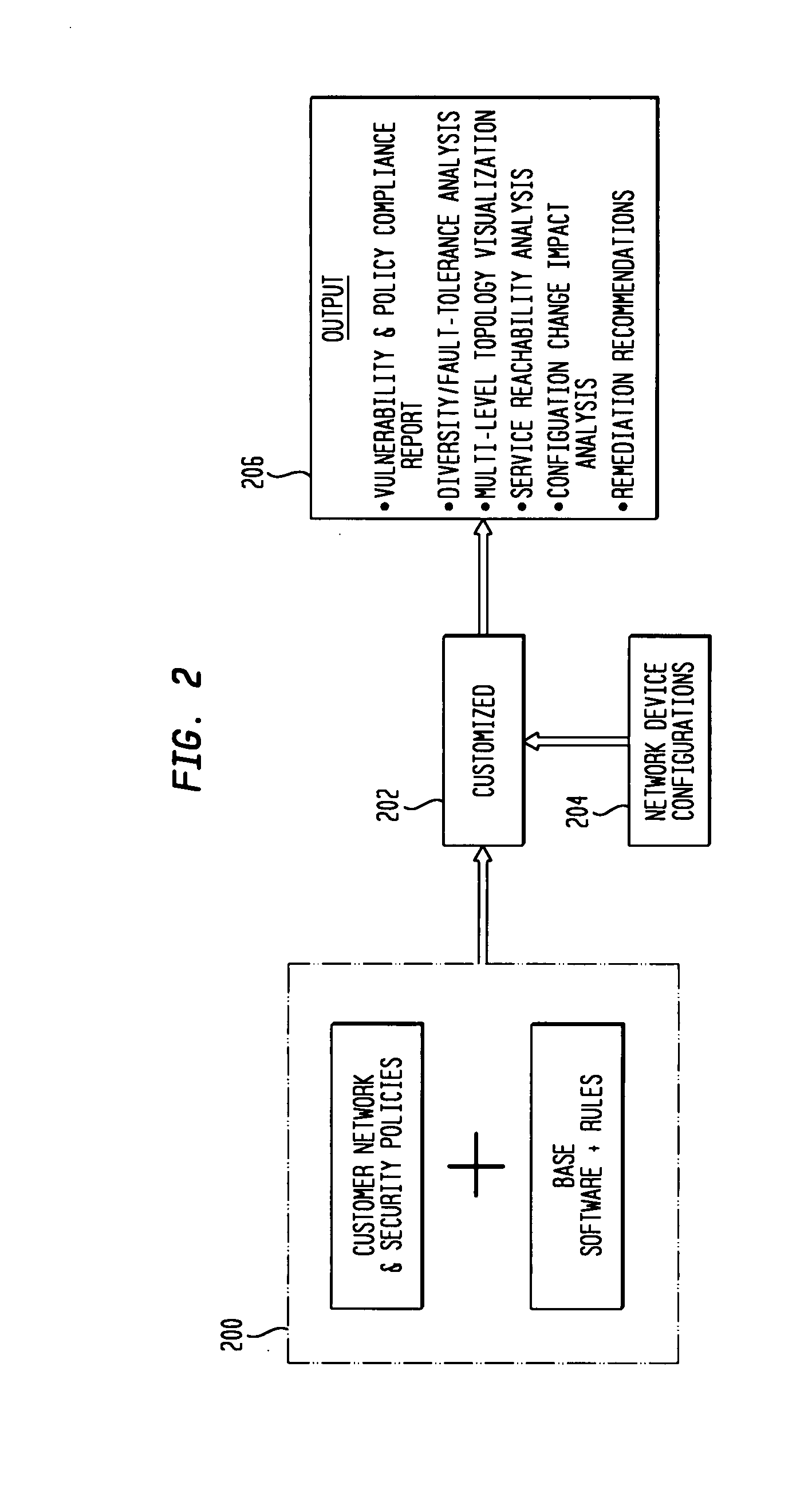
InactiveUS20080172716A1Reduce vulnerabilityImprove network securityTransmissionSpecial data processing applicationsNetwork security policyCompliance problem
Customizable software provides assurances about the ability of an IP network to satisfy security, regulatory and availability requirements by comprehensive vulnerability and compliance assessment of IP networks through automated analysis of configurations of devices such as routers, switches, and firewalls. The solution comprises three main approaches for testing of IP device configurations to eliminate errors that result in vulnerabilities or requirements compliance issues. The first two fall in to the “static constraint validation” category since they do not change significantly for each IP network, while the last approach involves incorporation of each specific IP network's policies / requirements. These approaches are complementary, and may be used together to satisfy all the properties described above. The first approach involves checking the configurations of devices for conformance to Best-Current-Practices provided by vendors (e.g. Cisco Network Security Policy) and organizations such as the NIST, NSA or CERT. Also this includes checks of compliance with regulations such as FISMA, SOX, HIPPA, PCI, etc. The second approach is where as one reads device configurations, one collects beliefs about network administrator intent. As each belief is collected, an inference engine checks whether the new belief is inconsistent with previously accumulated beliefs. The third approach addresses the multiple device / protocol issue by including an understanding of high-level service and security requirements about the specific IP network under test from the network administrators.
Owner:TT GOVERNMENT SOLUTIONS
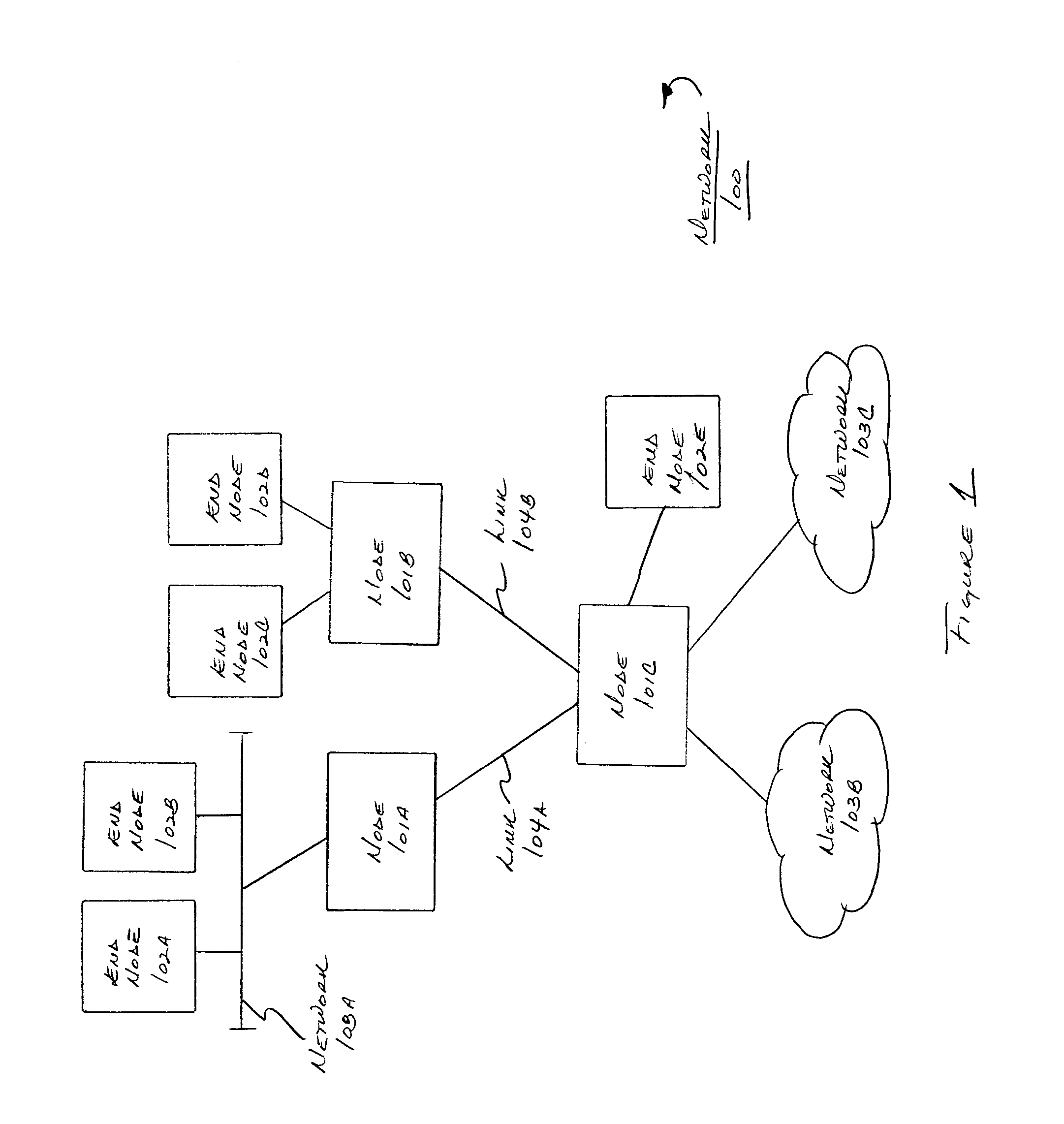
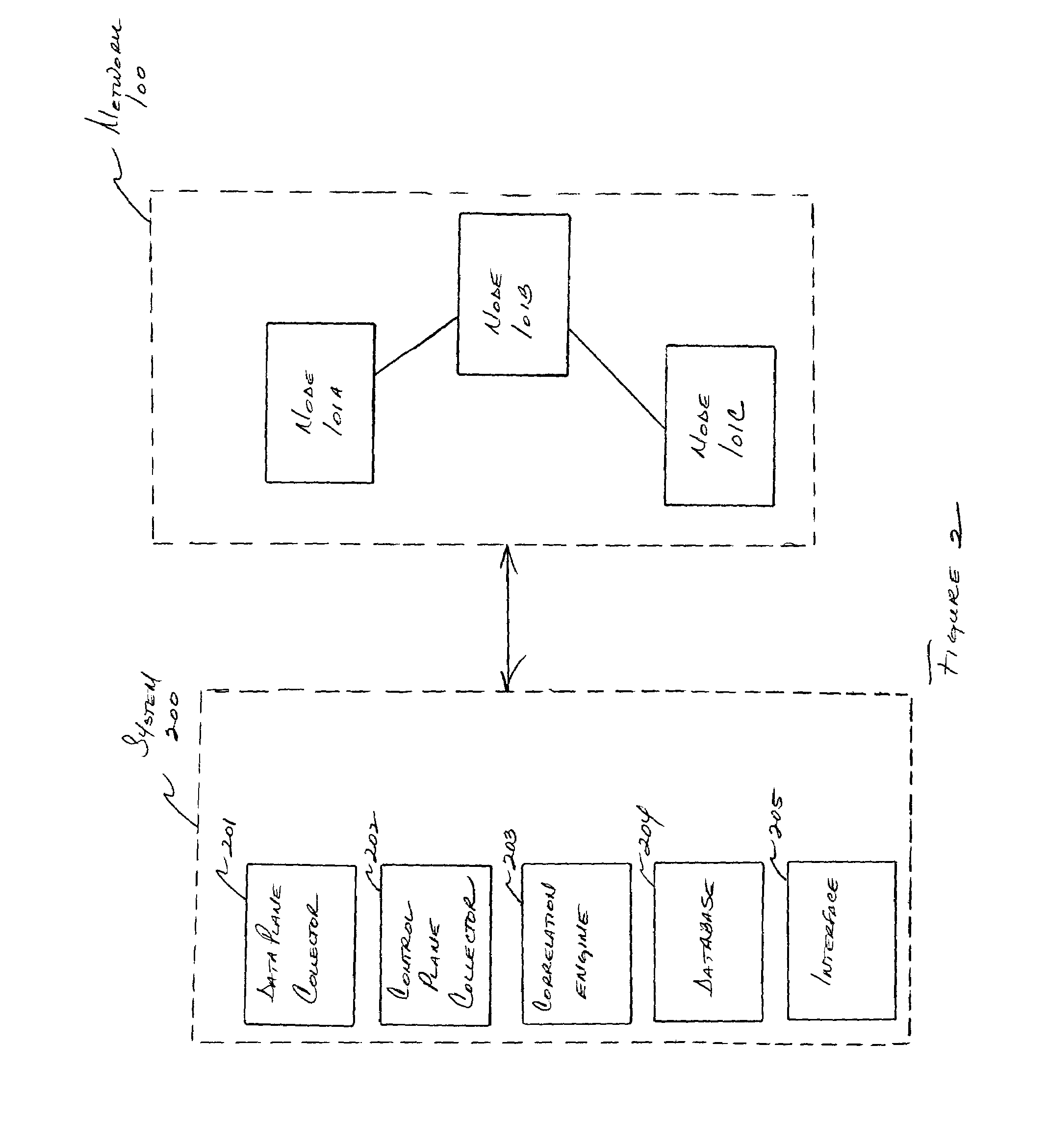
System and method for correlating traffic and routing information
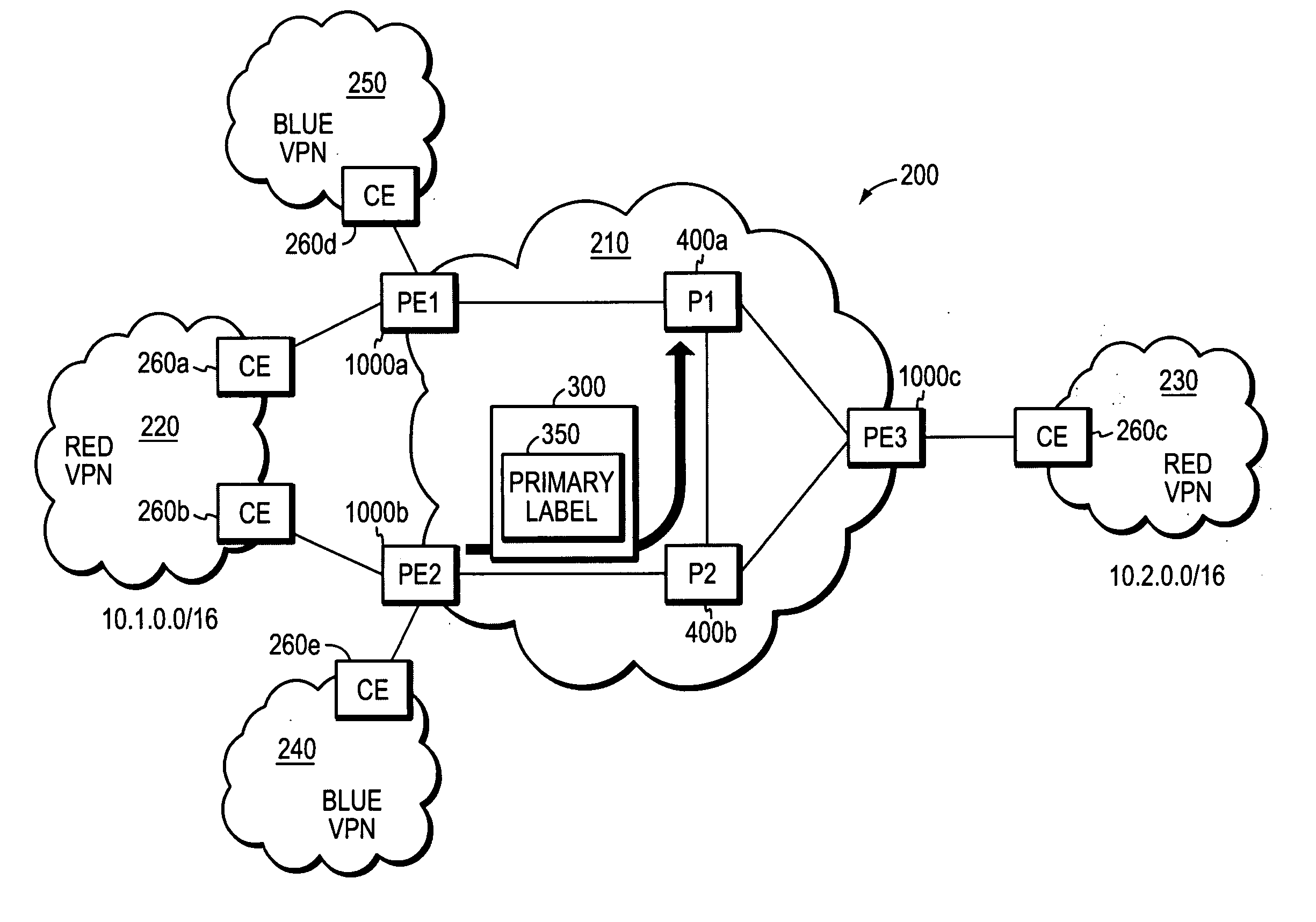
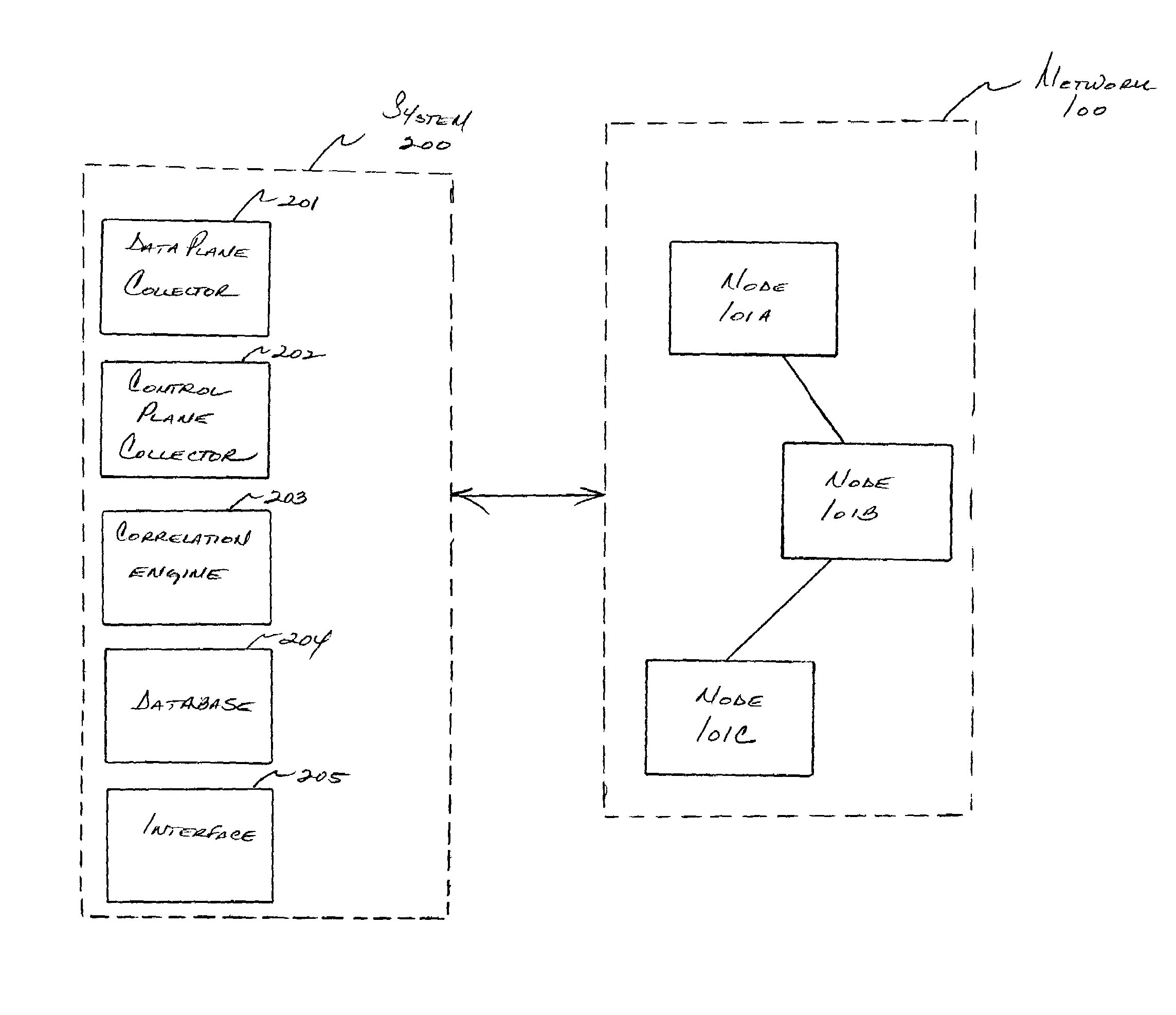
In one aspect, it is realized that changes in routing configuration (and therefore network topology) may have an effect on how data is forwarded in a communication network. More particularly, it is realized the changes in the control plane have a statistical effect on information tracked in the data plane, and this relation may be used by a network manager in monitoring the network and determining a control plane cause of a data plane forwarding effect. For instance, a change in BGP routing information (control plane information) may affect the data forwarded by a router based on the changed BGP routing information (e.g., next hop data may be forwarded to a different BGP router attached to another physical port). A system and method are provided that correlate control plane and data plane information to support root cause analysis functions.
Owner:ARBOR NETWORKS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com