Patents
Literature
72313 results about "Information processing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Information processing is the change (processing) of information in any manner detectable by an observer. As such, it is a process that describes everything that happens (changes) in the universe, from the falling of a rock (a change in position) to the printing of a text file from a digital computer system. In the latter case, an information processor (the printer) is changing the form of presentation of that text file (from bytes to glyphs).
Data security system and method for separation of user communities
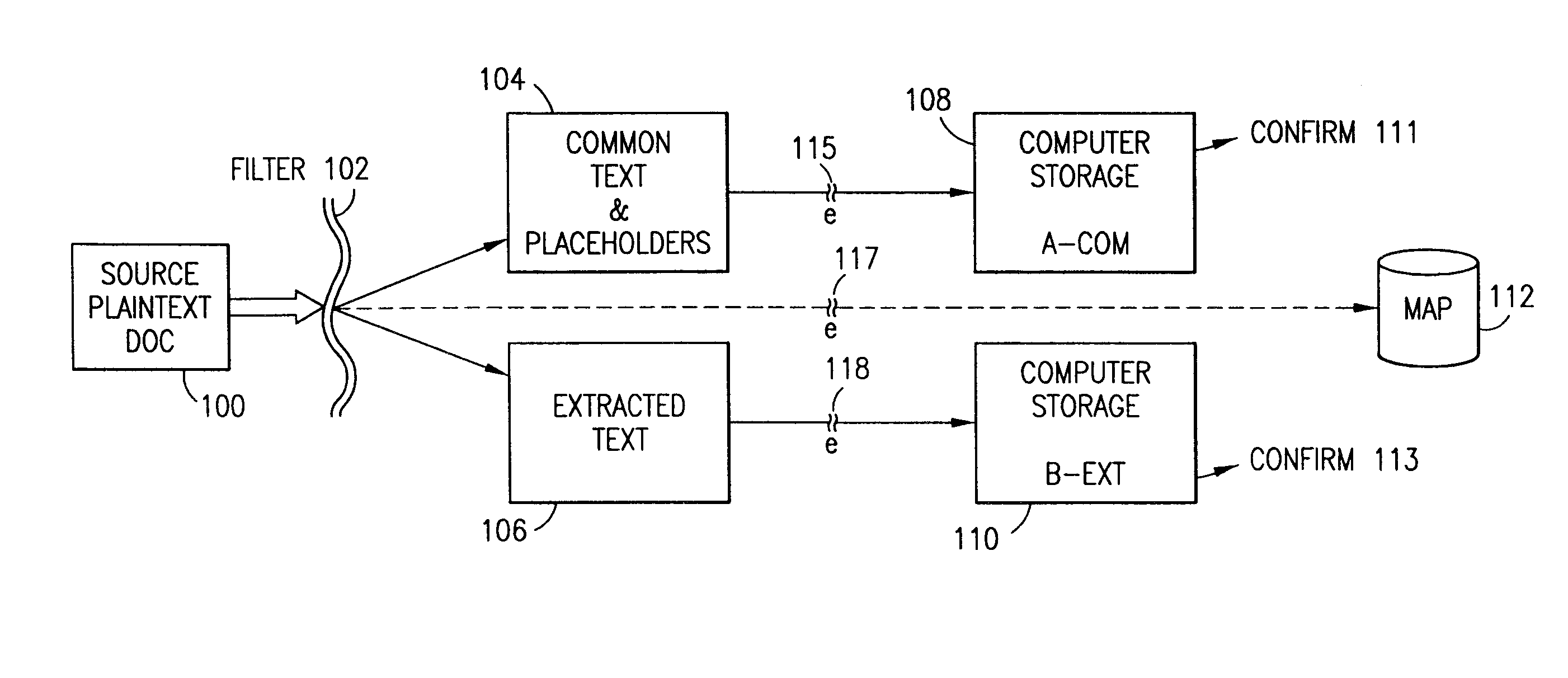
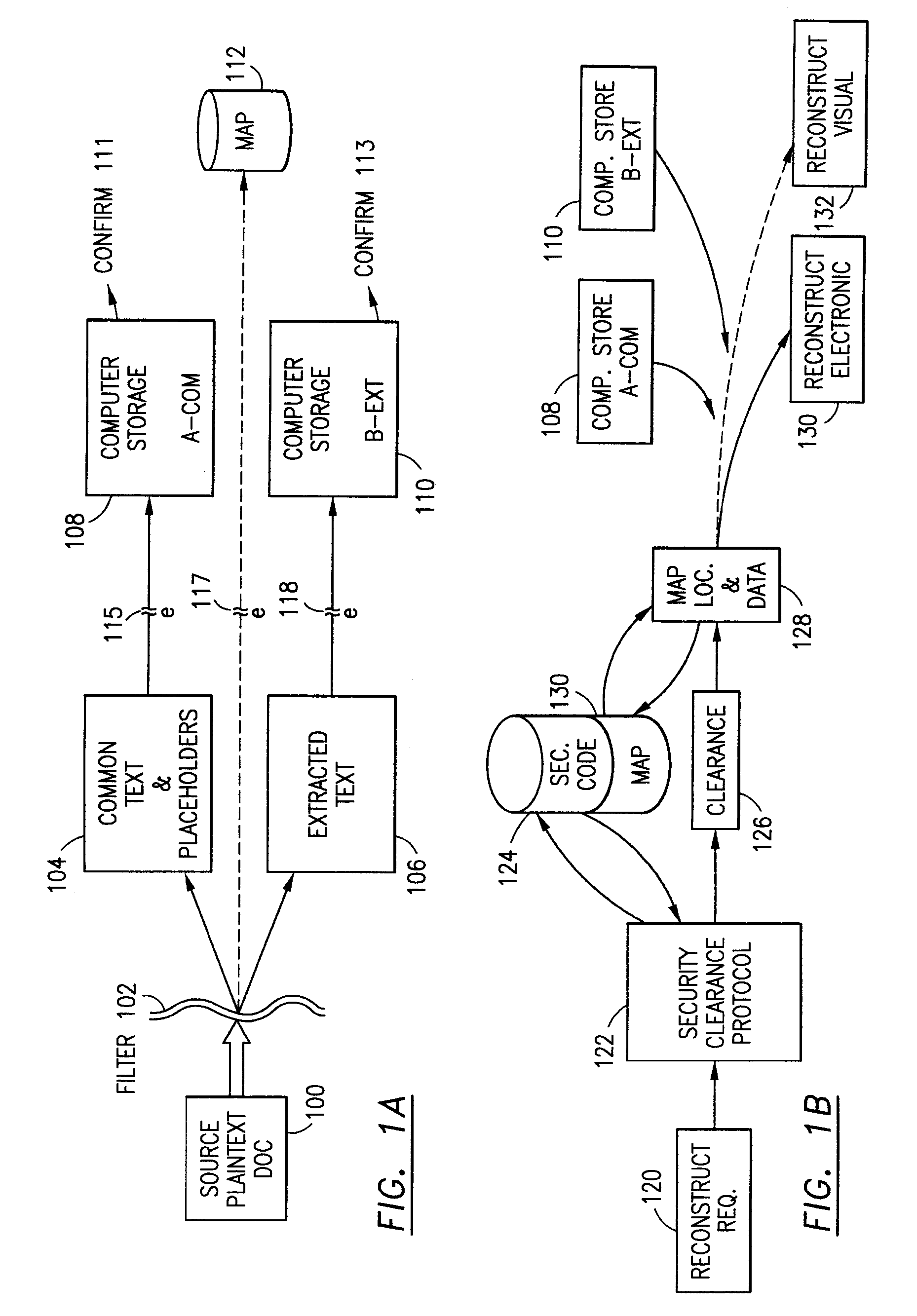
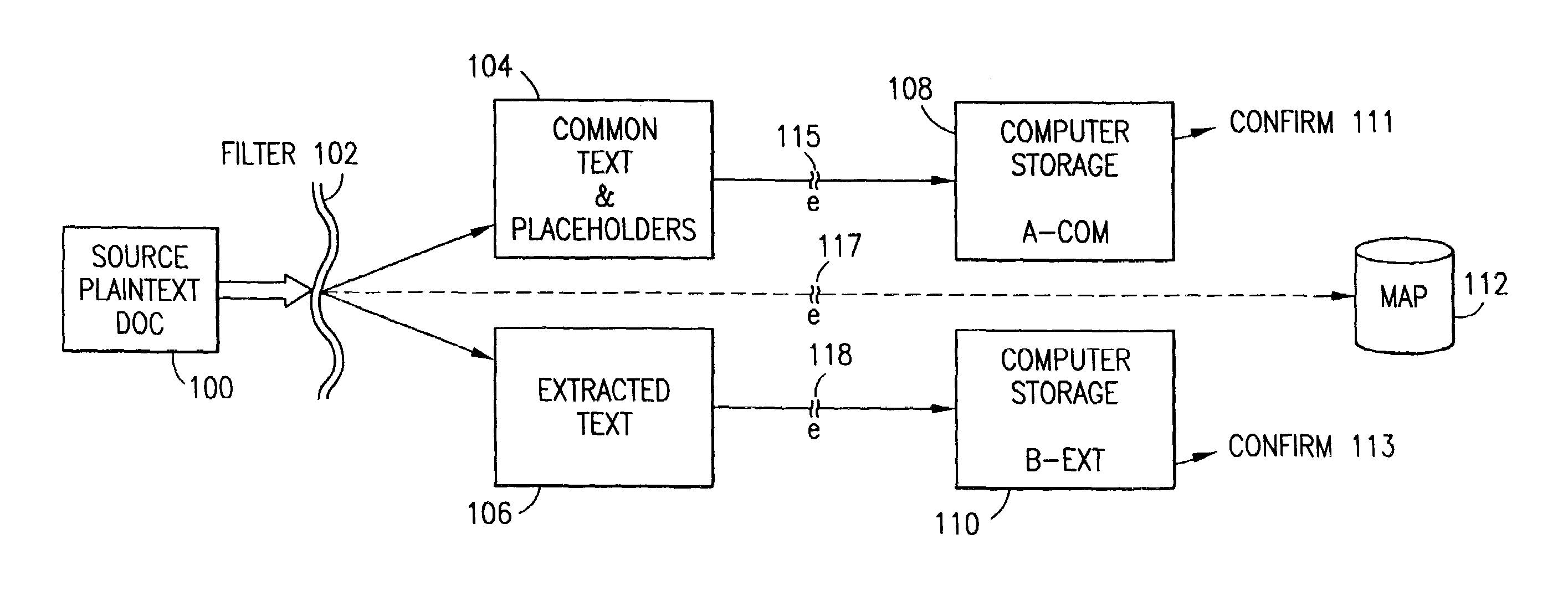
InactiveUS7140044B2Multiple keys/algorithms usageDigital data processing detailsInformation processingPlaintext
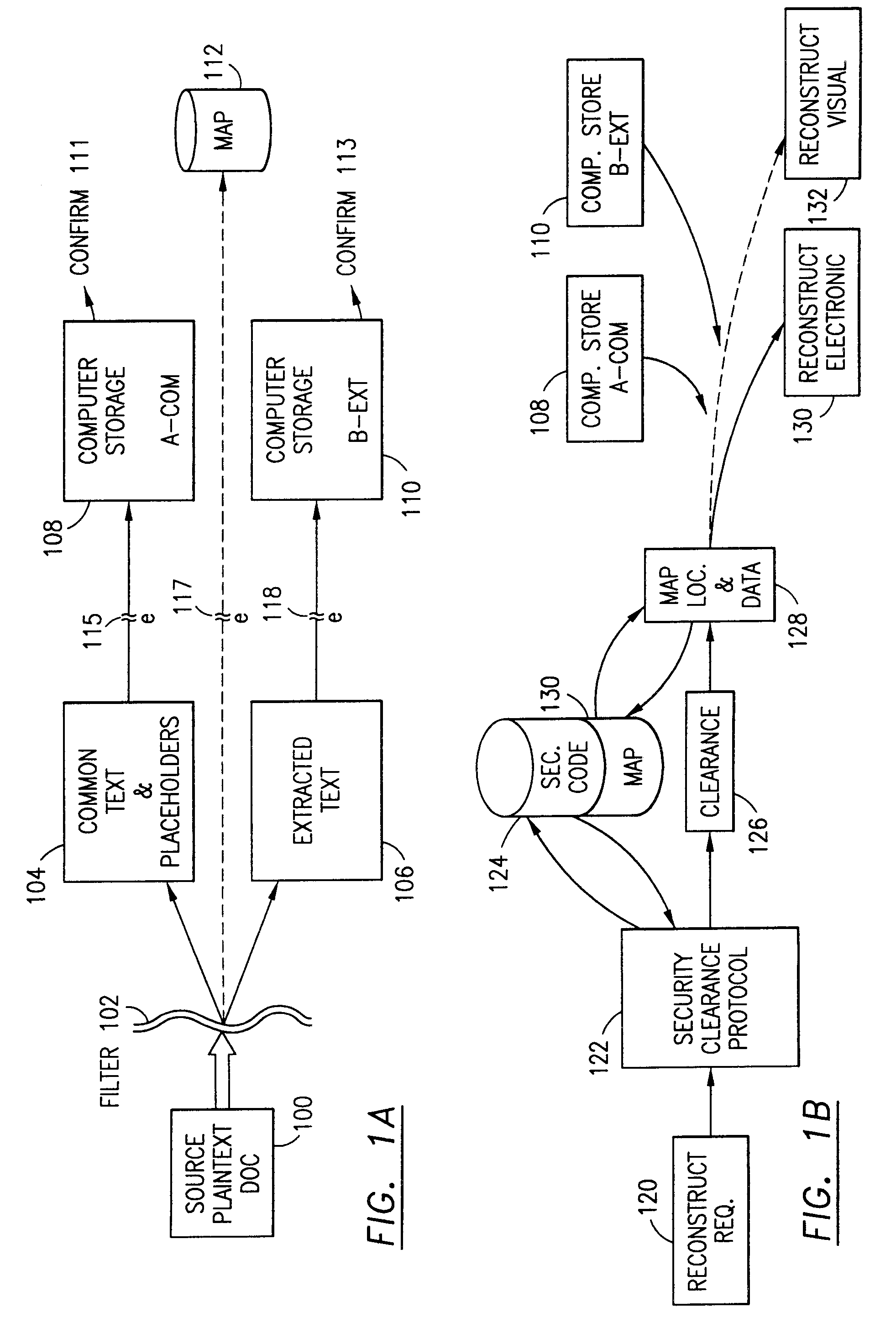
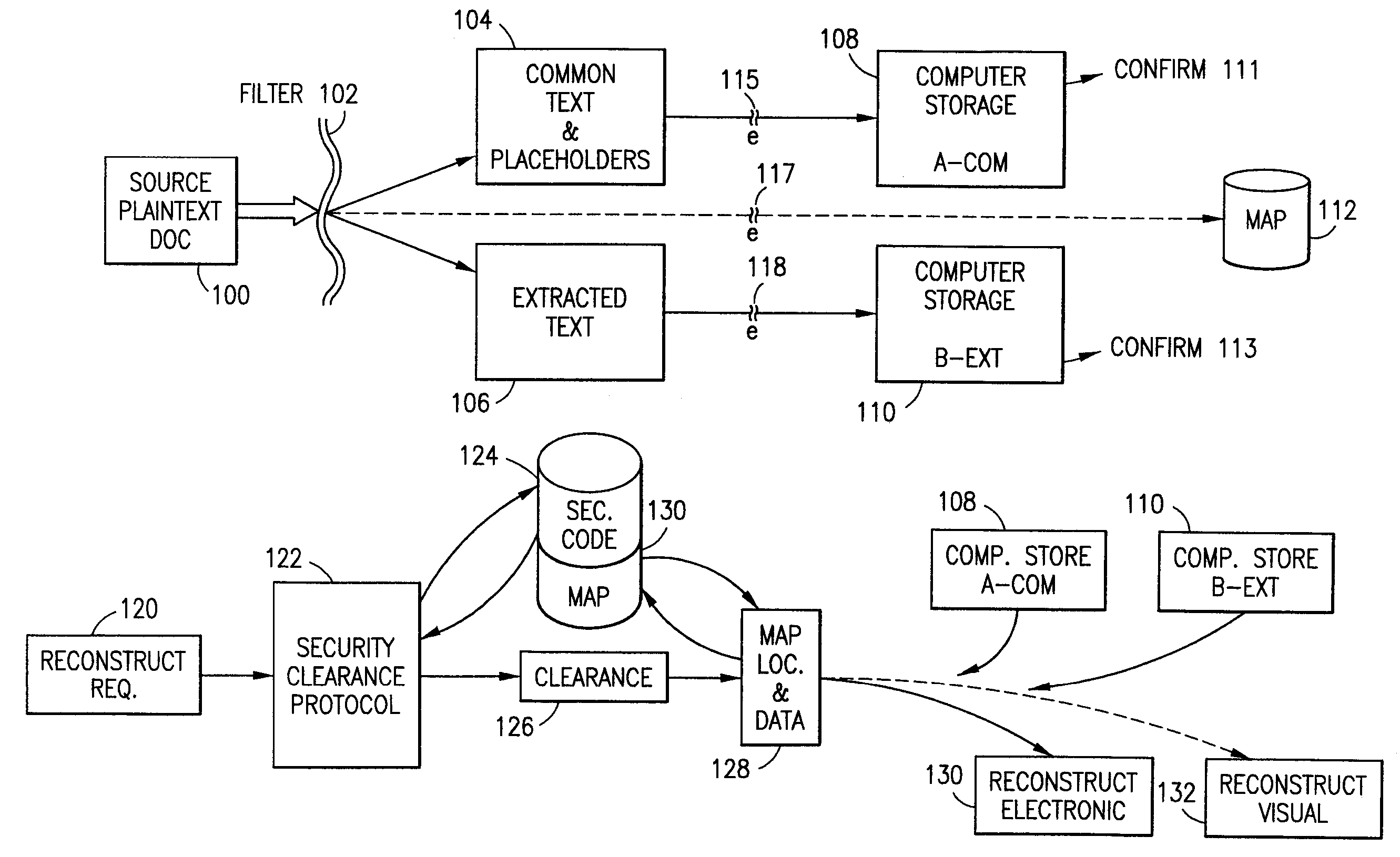
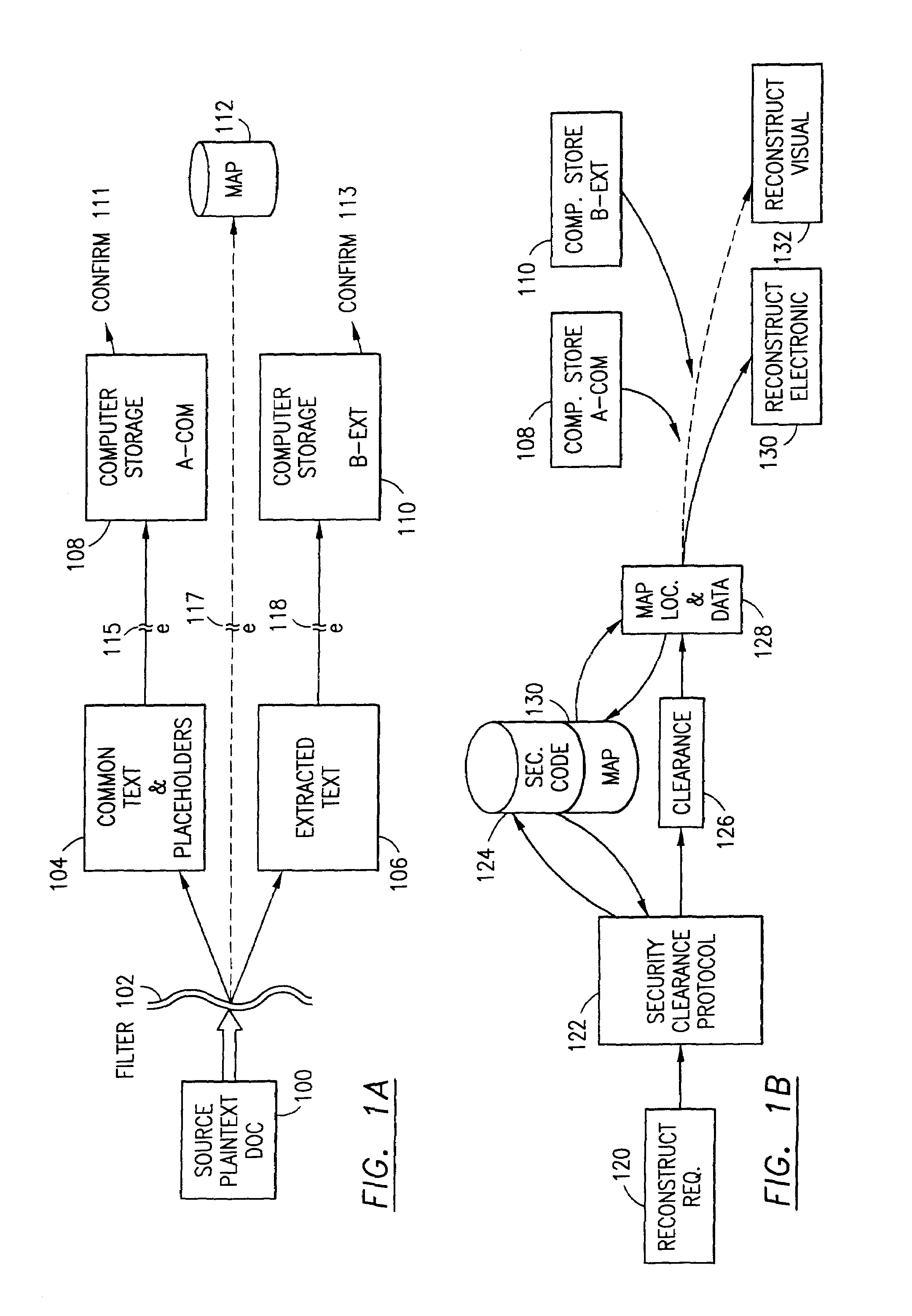
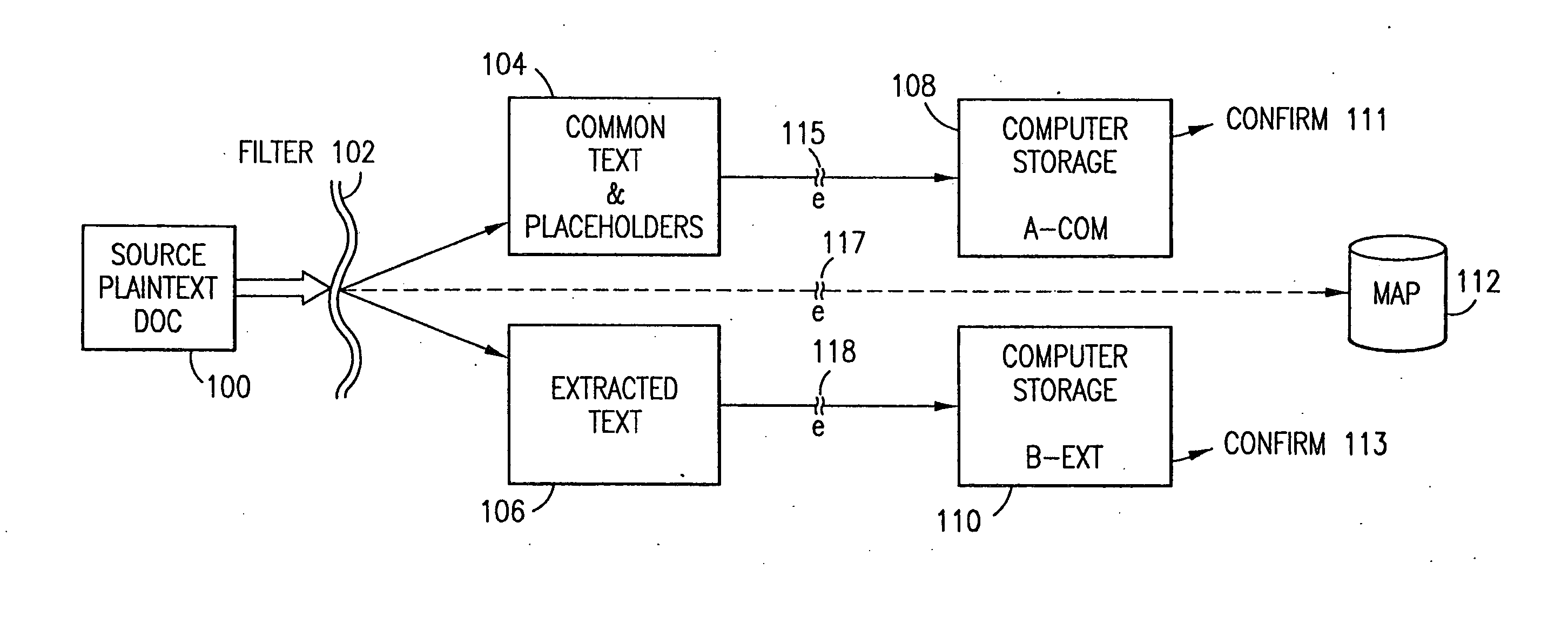
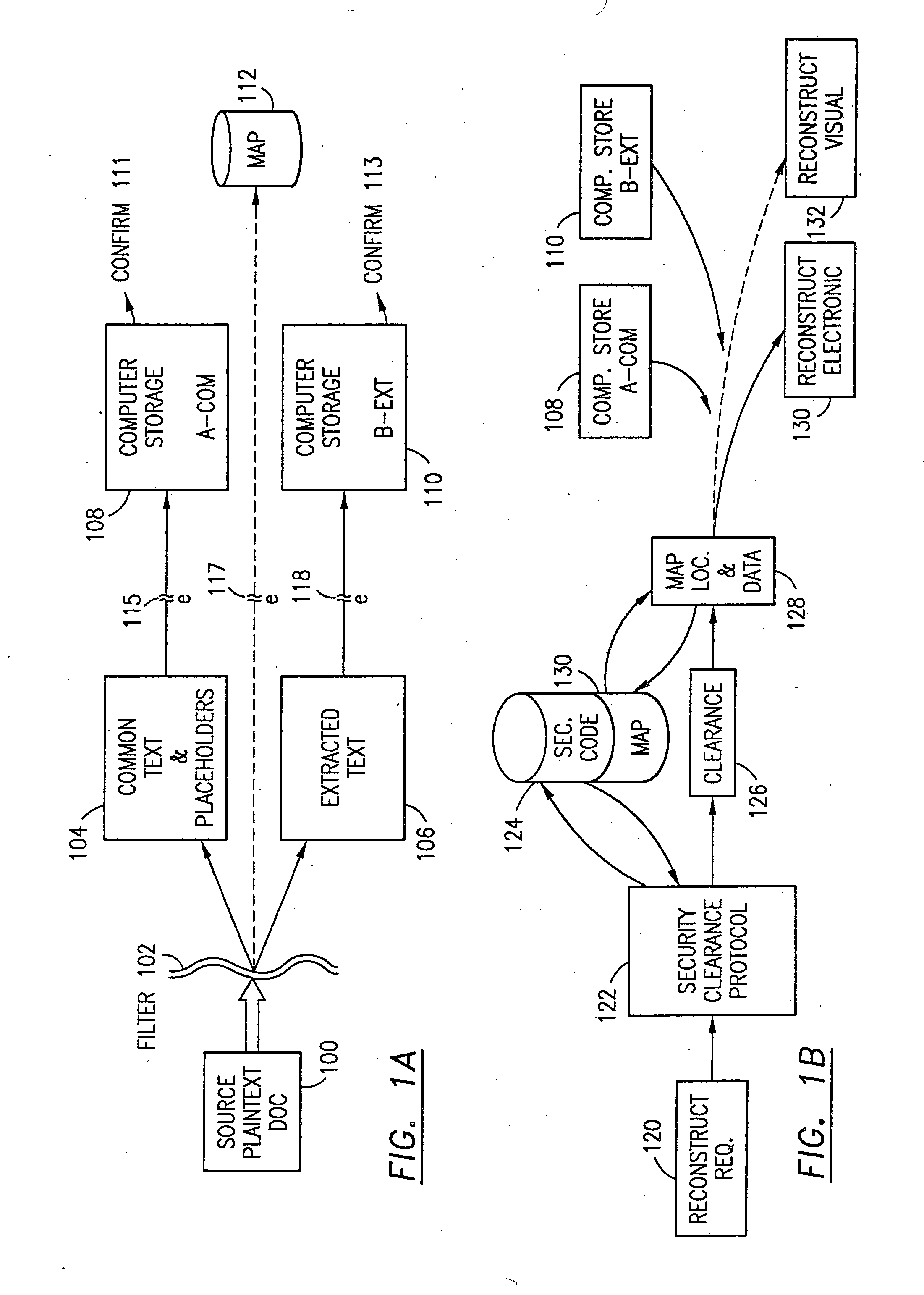
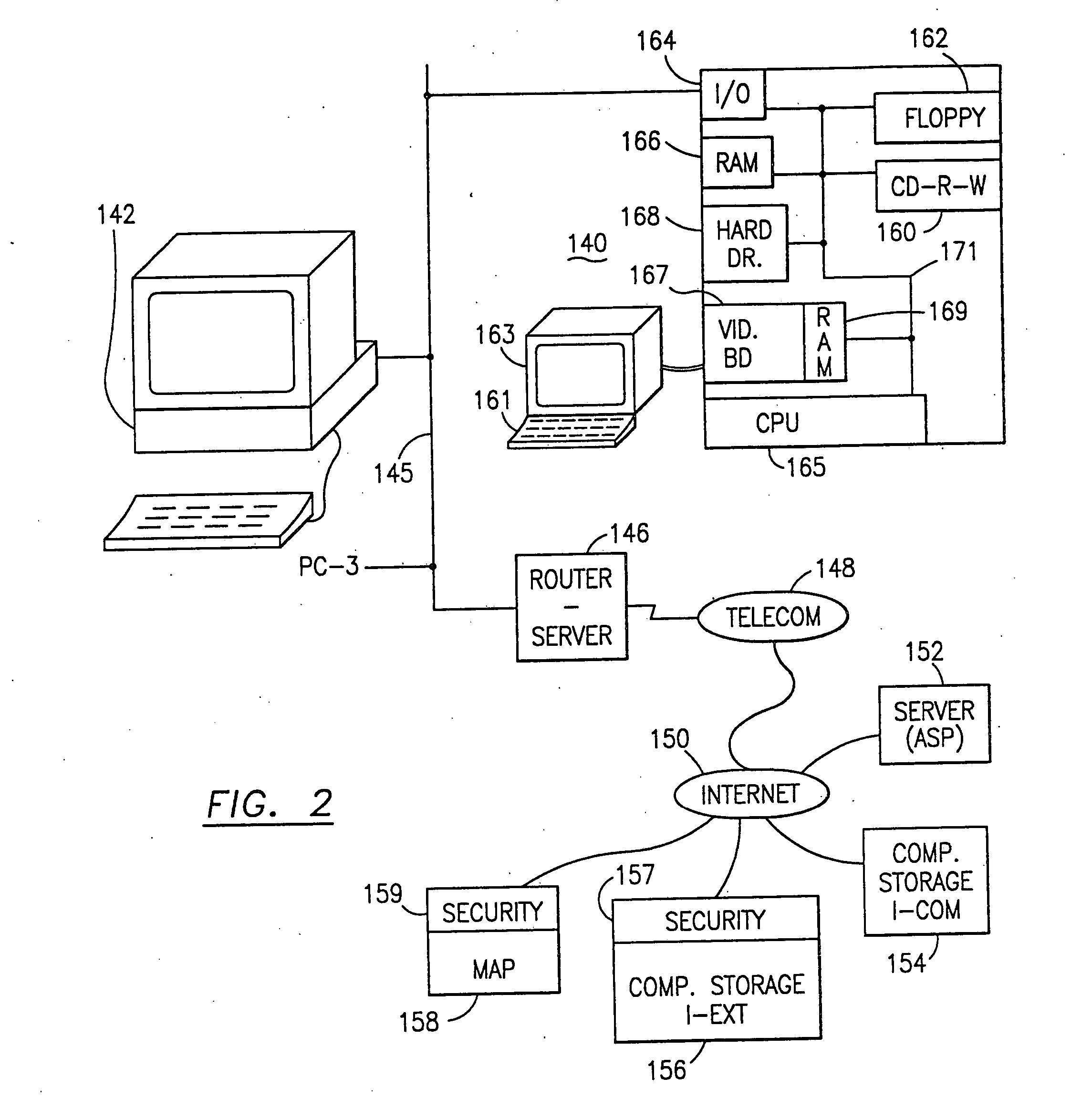
Data is secured in a computer network to transparently establish and manage a separation of user-based communities of interest based upon crypto-graphically separated, need to know, security levels. Data from a source document, data object or data stream is filtered to form subsets of extracted data and remainder data based upon security levels for the communities. Extracts are stored in assigned memories. Full or partial plaintext reconstruction is permitted only in the presence of assigned security clearance for the community of the inquiring party. Encryption, corresponding to security levels, establishes separation of secured data. The information processing system uses a data filter to extract security sensitive words, data objects, etc., a distributed storage system and a compiler is used to reconstruct plaintext based on security clearance. Multiple level encryption in one document is also available.
Owner:DIGITAL DOORS
Data security system and method
ActiveUS7103915B2Memory loss protectionDigital data processing detailsPlaintextInformation processing
The method for securing data includes establishing a group of security sensitive items, filtering data and extracting and separating the security items from remainder data. The filtered data are separately stored (locally on a PC or on another computer in a LAN or WAN or on the Internet.) A map may be generated. The filter and / or map may be destroyed or stored. The data input, extracted data and remainder data may be deleted from the originating computer. Encryption may be utilized to enhance security (including transfers of data, filter and map). Reconstruction of the data is permitted only in the presence of a predetermined security clearance. A plurality of security clearances may be used to enable a corresponding plurality of partial, reconstructed views of the plaintext (omitting higher security words). A computer readable medium containing programming instructions and an information processing system is encompassed.
Owner:DIGITAL DOORS
Data security system and method responsive to electronic attacks
ActiveUS7146644B2Ease overhead performanceHigh overhead performanceMemory loss protectionMultiple keys/algorithms usageInformation processingSelf adaptive
An adaptive method, system and program for securing data against a plurality of electronic and environmental events directed at computers utilizes a hacking monitor which generates attack warnings (such as a hacking warning) dependent upon the severity of the attack. Based upon these warnings, data is filtered to extract security sensitive words etc. and the extract and remainder data (if necessary) is stored in assigned memory. Full or partial reconstruction is permitted, manually or automatically, with a security clearance. Encryption is typically used dependent upon the warning. The information processing system includes a filter which is adjusted based upon the degree of attack warning to extract security sensitive words. A storage system stores extracted data and remainder data (if necessary) based upon the level of the warning and a compiler is used to reconstruct the data in the presence of the appropriate security clearance level.
Owner:DIGITAL DOORS
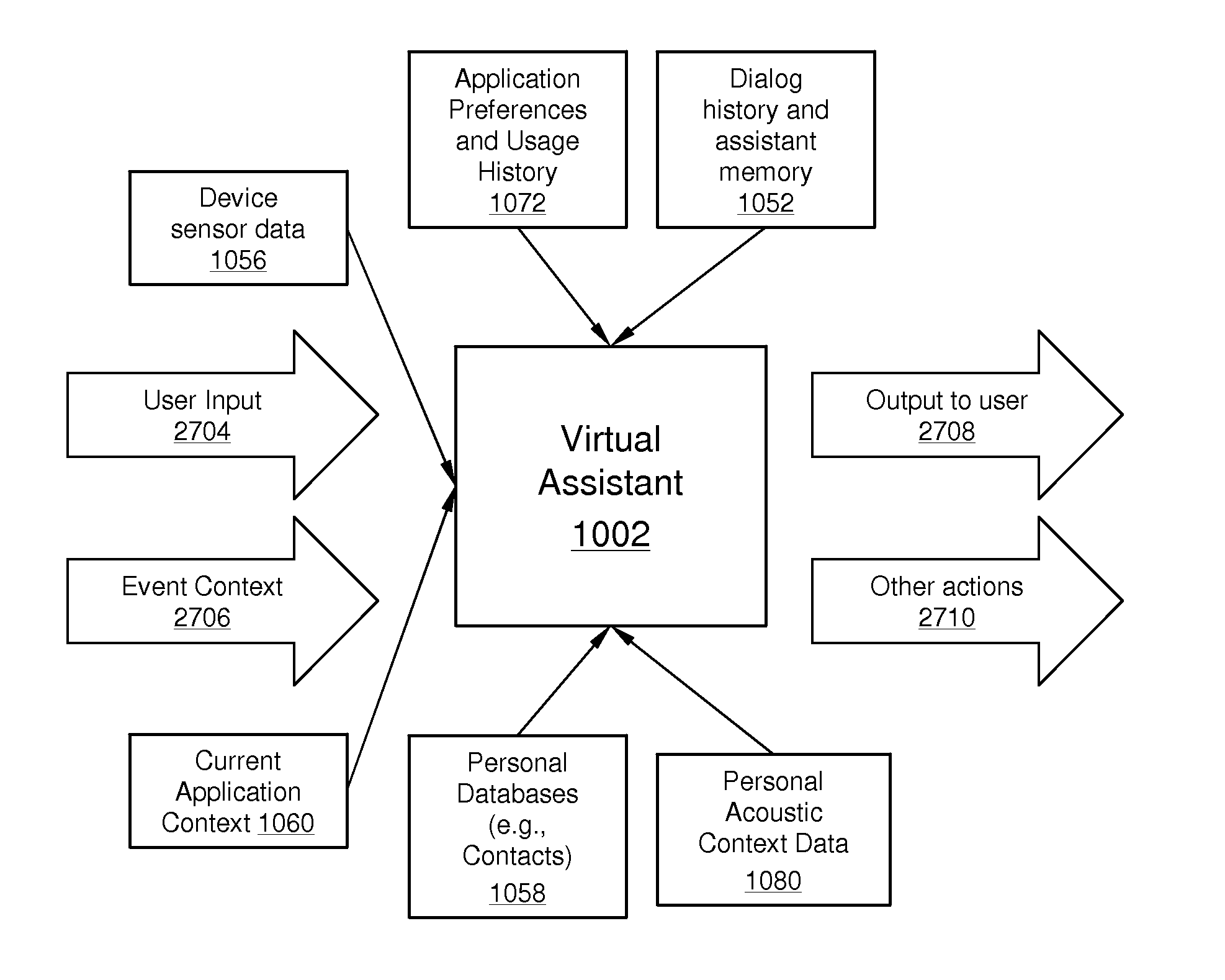
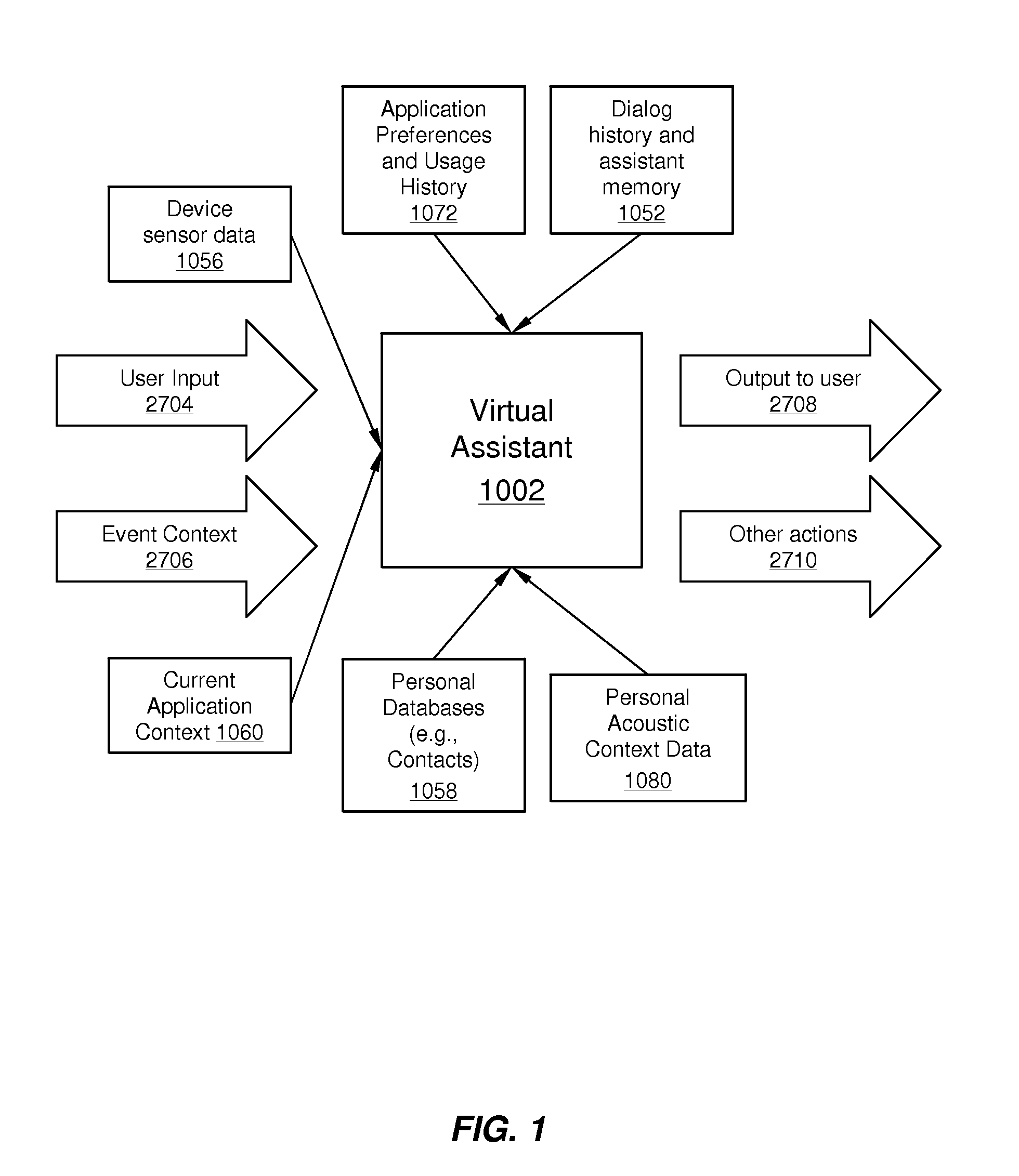
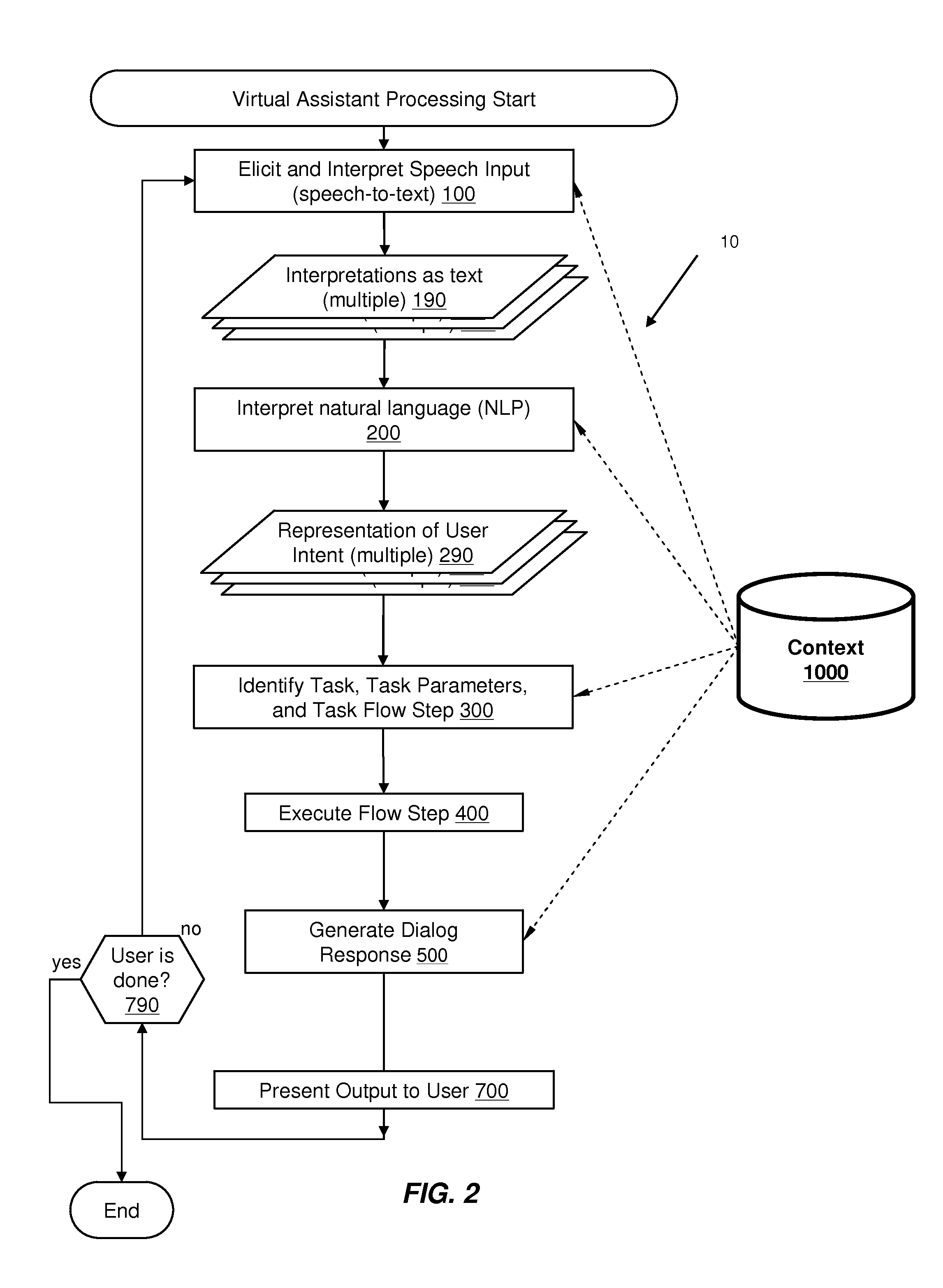
Using Context Information To Facilitate Processing Of Commands In A Virtual Assistant
ActiveUS20120265528A1Clarify userReduce in quantityNatural language data processingSpeech recognitionPersonalizationInformation processing
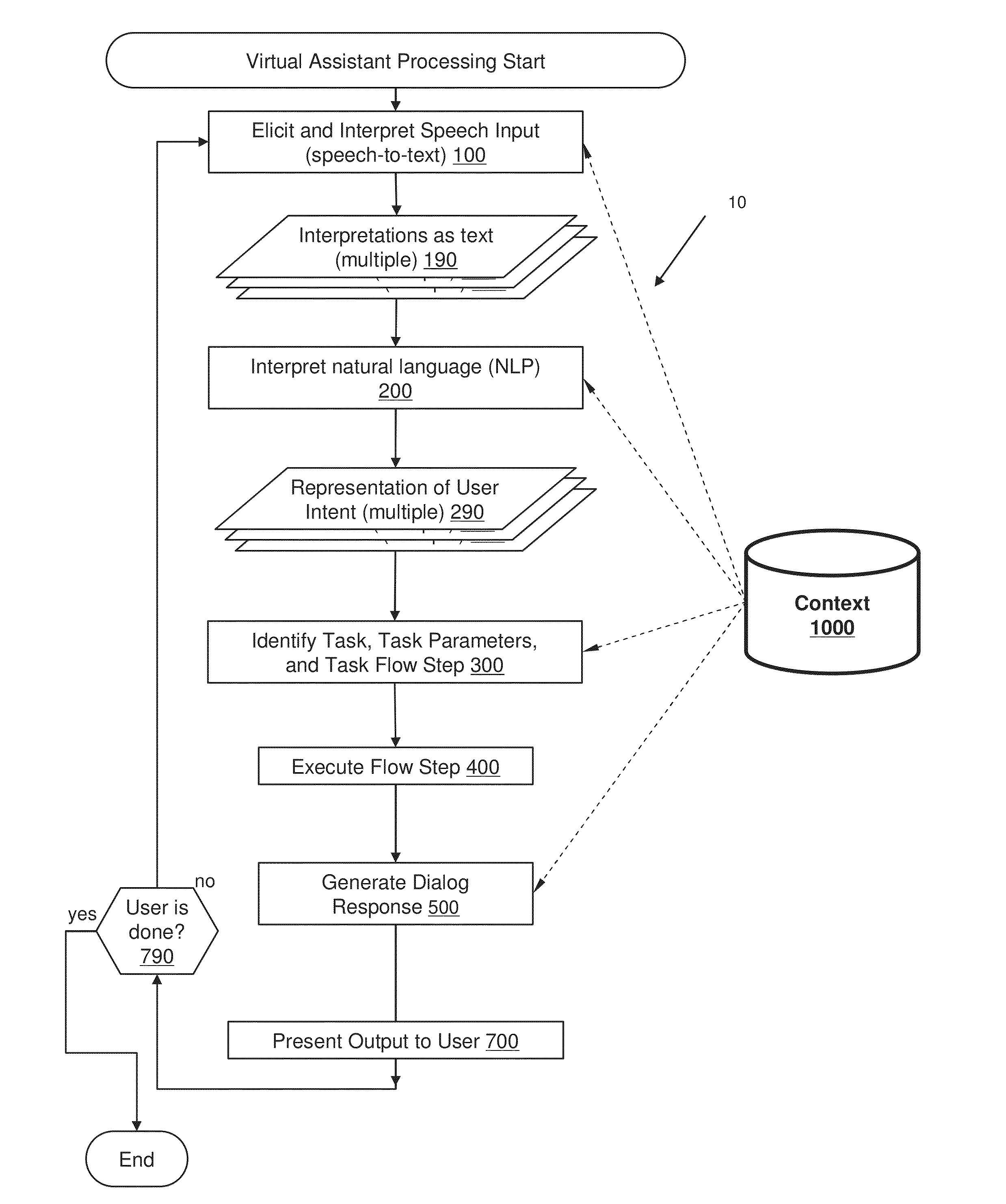
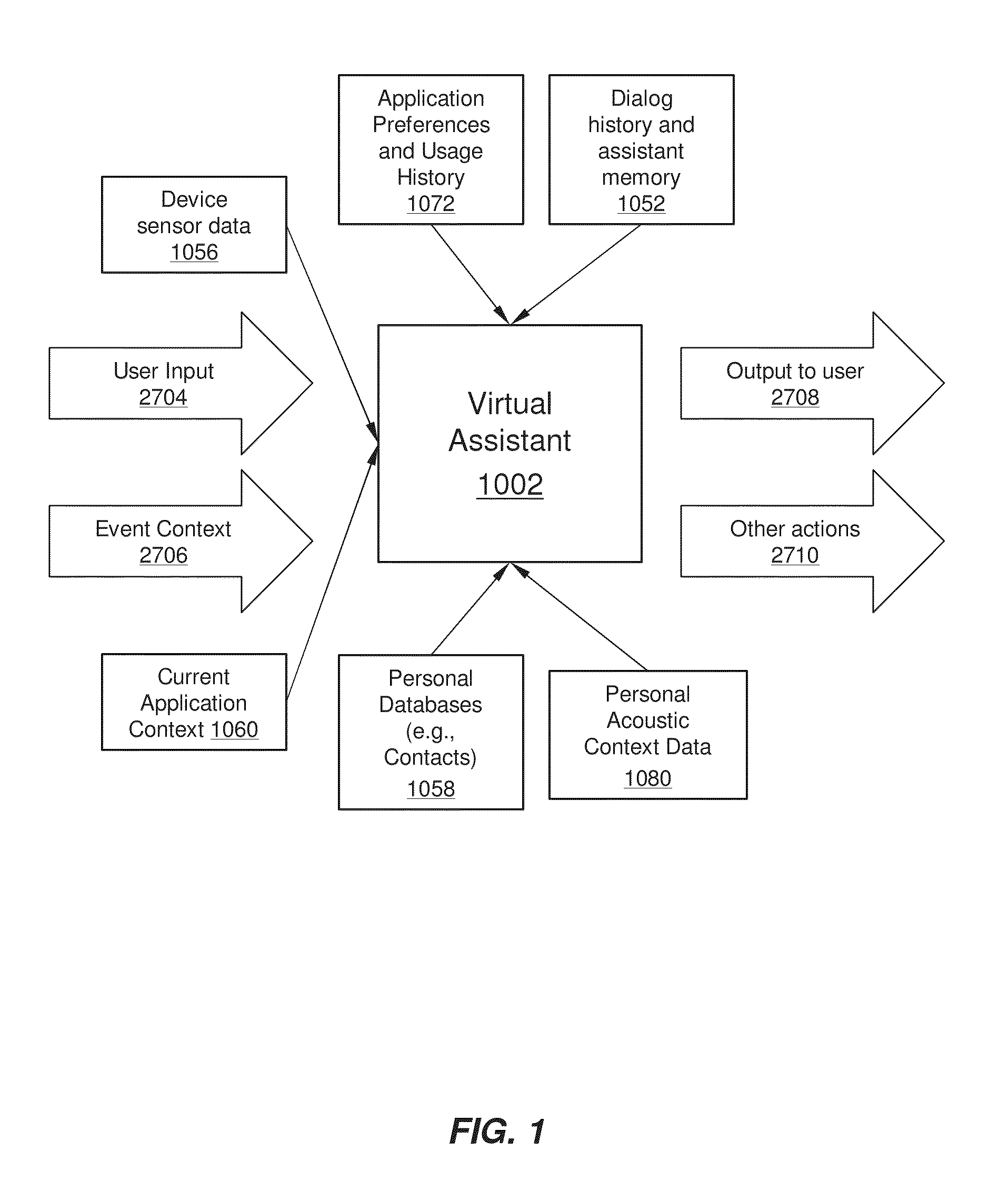
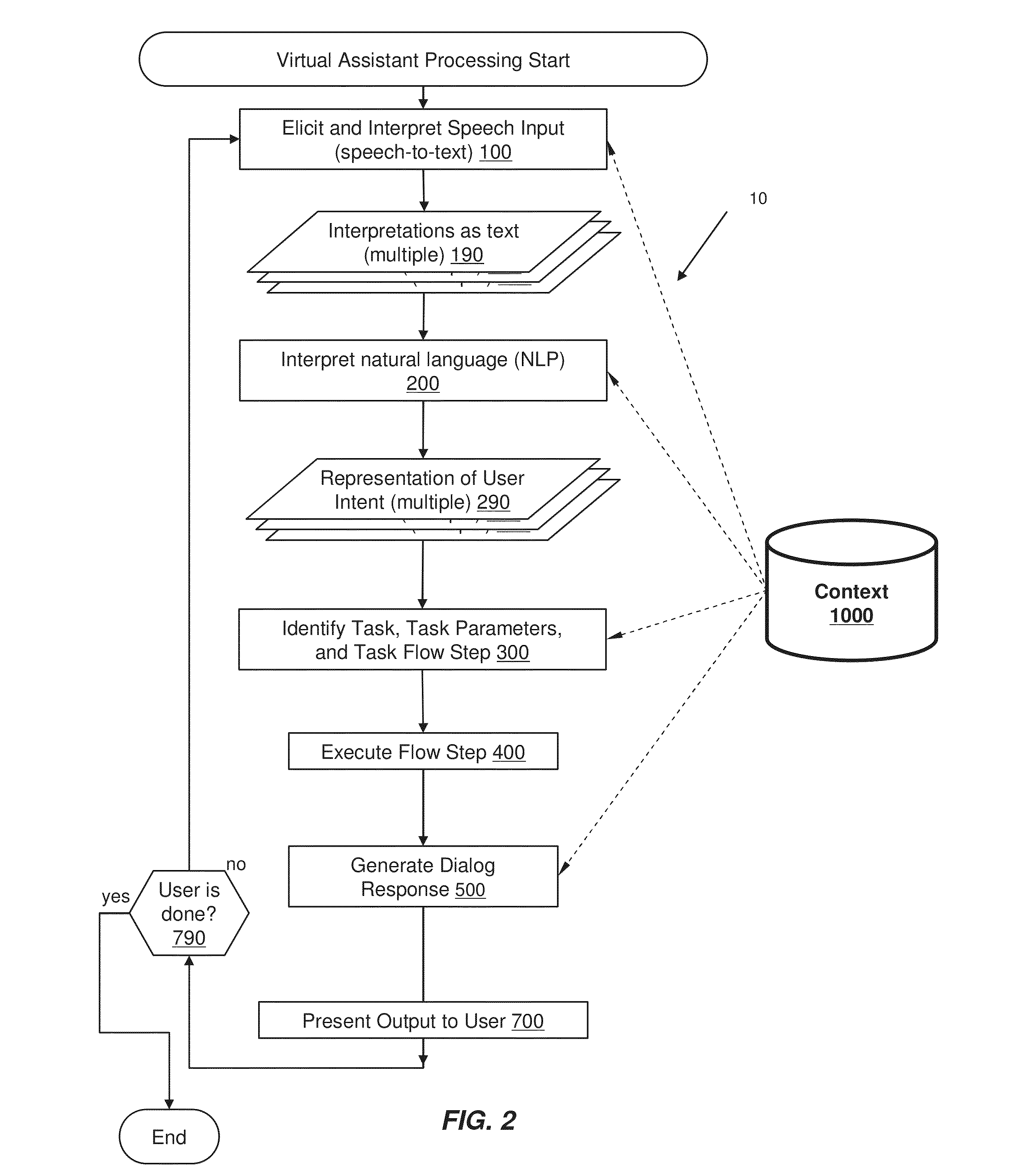
A virtual assistant uses context information to supplement natural language or gestural input from a user. Context helps to clarify the user's intent and to reduce the number of candidate interpretations of the user's input, and reduces the need for the user to provide excessive clarification input. Context can include any available information that is usable by the assistant to supplement explicit user input to constrain an information-processing problem and / or to personalize results. Context can be used to constrain solutions during various phases of processing, including, for example, speech recognition, natural language processing, task flow processing, and dialog generation.
Owner:APPLE INC
Mobile systems and methods for responding to natural language speech utterance
ActiveUS20100145700A1Promotes feeling of naturalOvercome deficienciesVehicle testingInstruments for road network navigationInformation processingRemote system
Owner:DIALECT LLC
Method and apparatus to dynamically create a customized user interface based on a document type definition
InactiveUS20020152244A1Natural language data processingSpecial data processing applicationsInformation processingSERCOS interface
A method on an information processing unit performing steps for creating a user interface (UI) to assemble a document that conforms to a particular document type definition. The method hides the specific syntax of document type definitions such as DTDs and schemas from the user. The method begins with a selection from a user for a document type or an existing document. Once the document type is selected or determined from the existing document the document type definitions are retrieved. The document type definitions include one or more elements. The method parses the elements which are subsequently mapped to one or more interface controls such as icons, pull-down menus, buttons, selection boxes, progress indicators, on-off checkmarks, scroll bars, windows, window edges for resizing the window, toggle buttons, forms, and UI widgets. UI can be GUIs or interactive voice response systems. A UI editor is presented by assembling the one or more interface controls without presenting specific document type definition syntax to a user. The UI editor permits the user to create and edit the content objects that are associated with the interface controls. The content objects are aggregated in an XML compatible format and ready to be checked in for further processing. The method permits specific UI interfaces to be created for specific publishing environments and at the same time permit the creation of reusable content objects.
Owner:IBM CORP
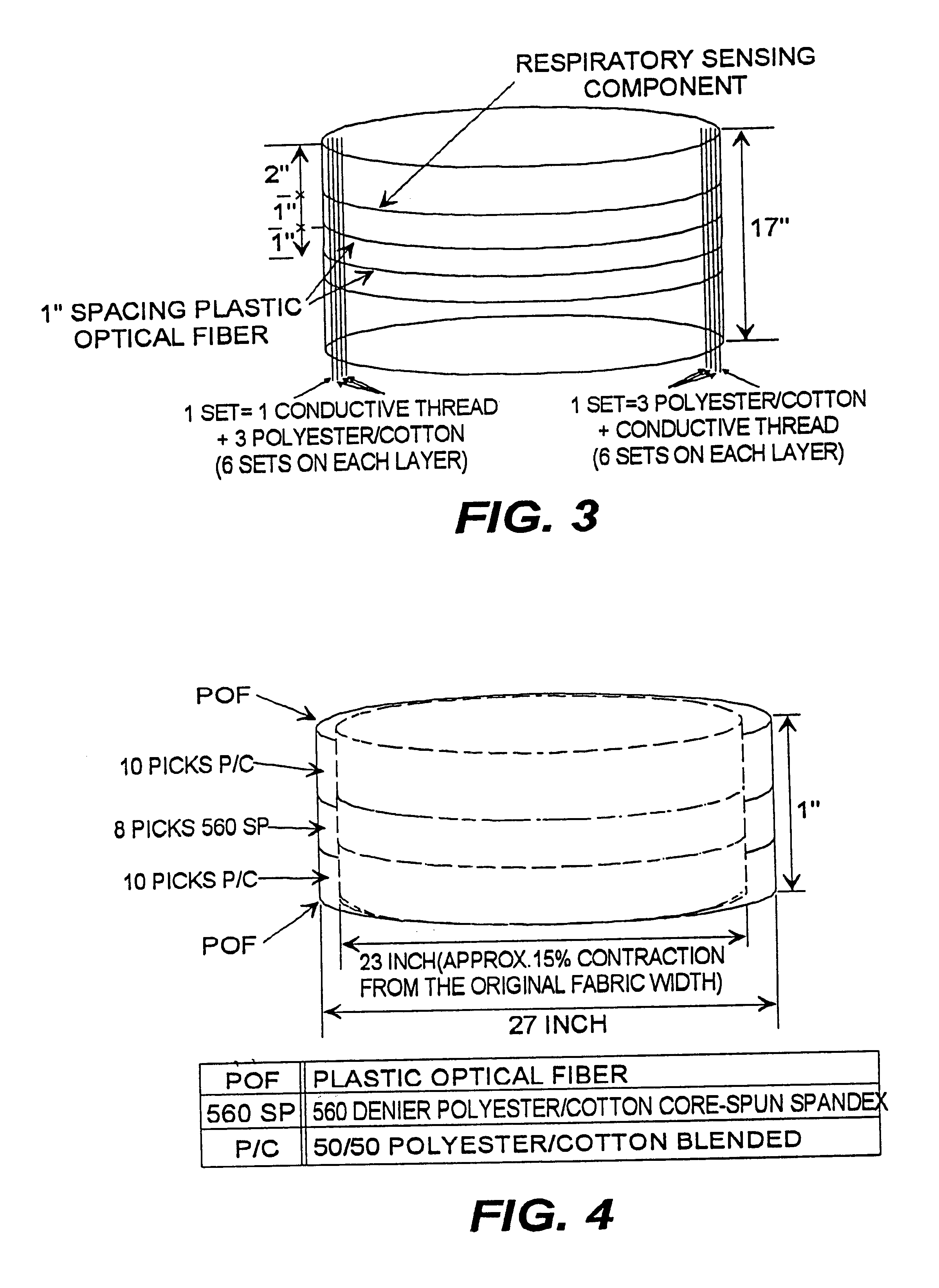
Fabric or garment with integrated flexible information infrastructure
InactiveUS6381482B1Raise the ratioImprove high temperature stabilityWeft knittingOrnamental textile articlesInformation processingEngineering
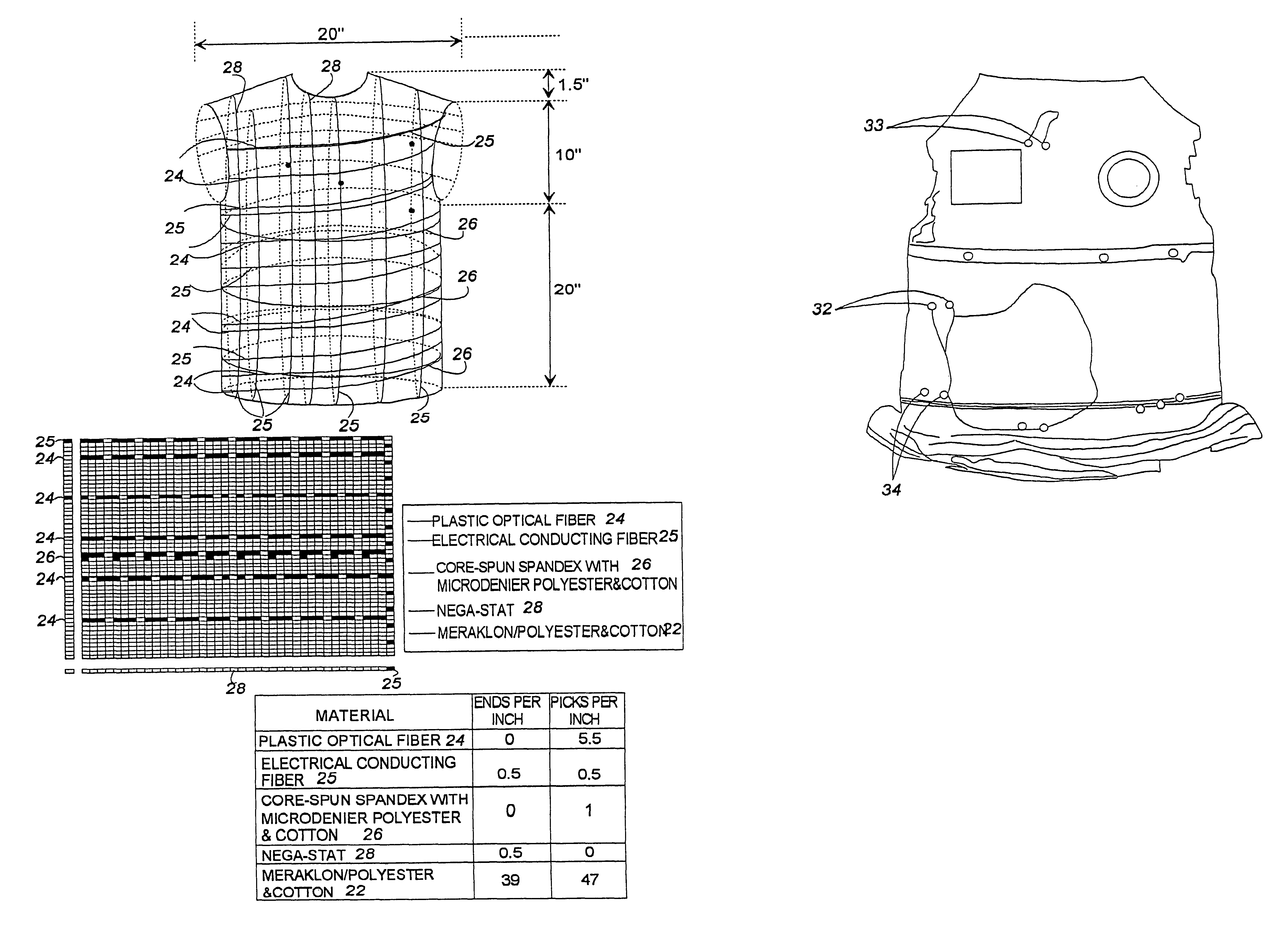
A fabric, in the form of a woven or knitted fabric or garment, including a flexible information infrastructure integrated within the fabric for collecting, processing, transmitting and receiving information concerning-but not limited to-a wearer of the fabric. The fabric allows a new way to customize information processing devices to "fit" the wearer by selecting and plugging in (or removing) chips / sensors from the fabric thus creating a wearable, mobile information infrastructure that can operate in a stand-alone or networked mode. The fabric can be provided with sensors for monitoring physical aspects of the wearer, for example body vital signs, such as heart rate, EKG, pulse, respiration rate, temperature, voice, and allergic reaction, as well as penetration of the fabric. The fabric consists of a base fabric ("comfort component"), and an information infrastructure component which can consist of a penetration detection component, or an electrical conductive component, or both. The preferred penetration detection component is a sheathed optical fiber. The information infrastructure component can include, in addition to an electrically conductive textile yarn, a sensor or a connector for a sensor. A process is provided for making an electrical interconnection between intersecting electrically conductive yarns. Furthermore, a process is established for sheathing the plastic optical fiber and protecting it.
Owner:GEORGIA TECH RES CORP
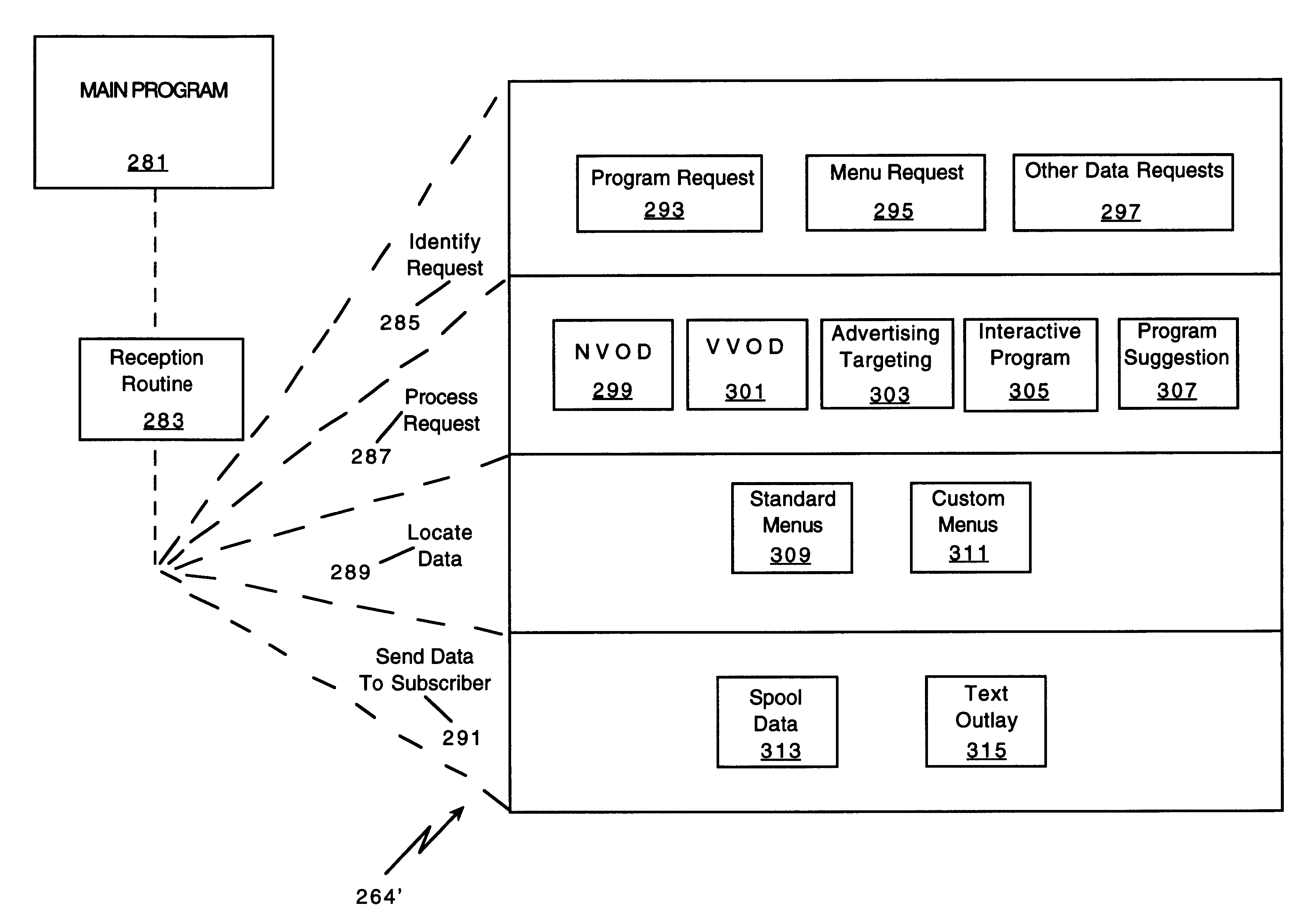
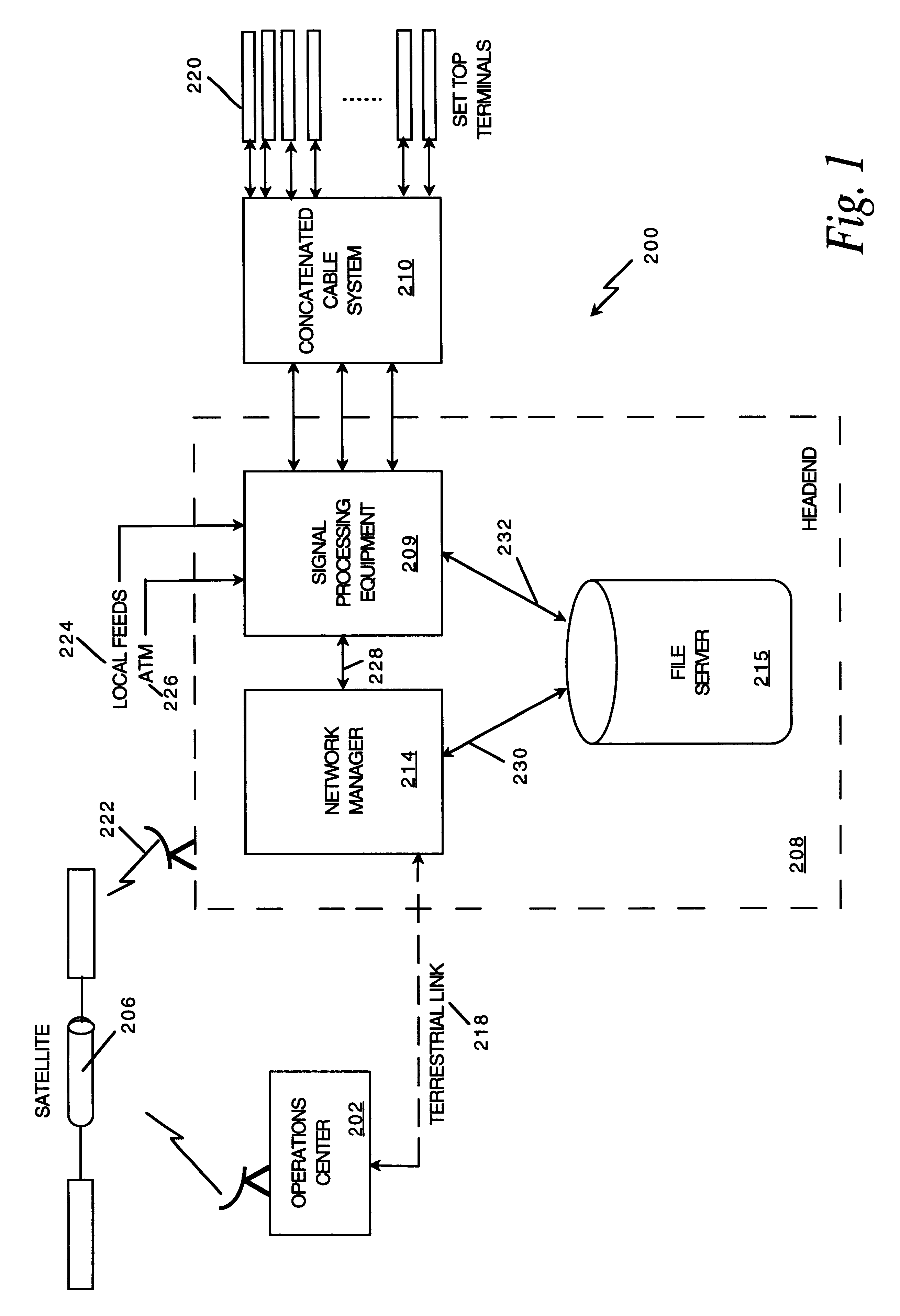
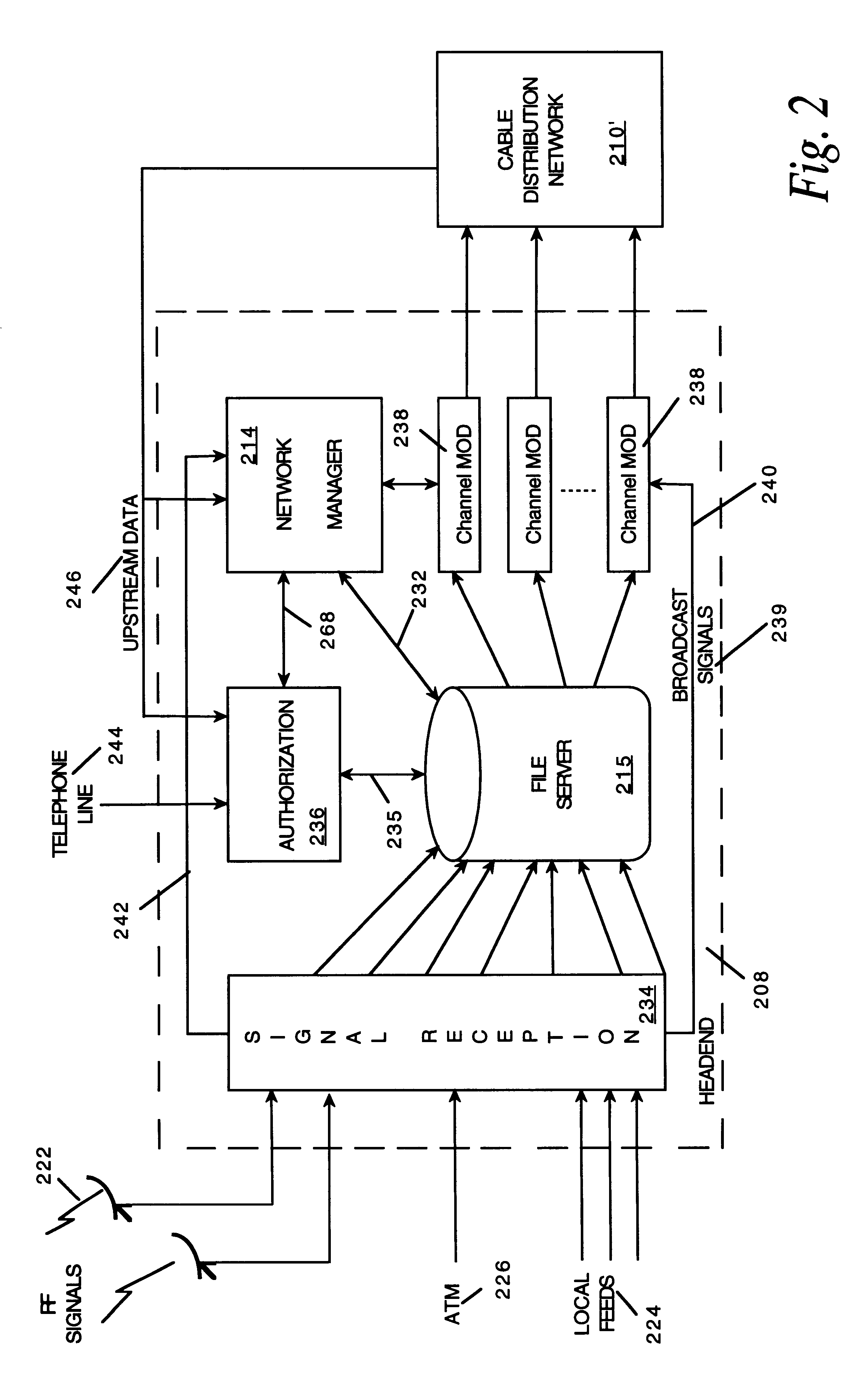
Network manager for cable television system headends
InactiveUS6201536B1Increase flexibilityImprove rendering capabilitiesTelevision system detailsPulse modulation television signal transmissionInformation processingInstruction memory
A novel network manager for use with a cable television system headend capable of monitoring and managing headend components and set top terminals in a television delivery system is described. The invention relates to methods and apparatus that manage and coordinate the reception of various programming and control signals at a headend. The invention manages and coordinates the storage of such signals for intelligent selection and distribution to set top terminals. The invention makes use of a receiver or set of receivers, a work station, a program control information processing component, a network management CPU, databases, control software and an instruction memory. The invention uses these components to manage and monitor certain headend components, such as signal reception equipment, an authorization component, a file server, MPEG decoders, a digital buffer with frame repeat and channel modulators. The invention is particularly useful in processing and responding to upstream information and subscriber communications received from set top terminals. In so doing, the invention accommodates various system services, including (1) near video on demand (NVOD), (2) virtual video on demand (VVOD), (3) video on demand (VOD), (4) interactive program services, (5) program suggestion features, (6) advertisement targeting, (7) generation of standard and custom menus, and (8) data spooling and text overlaying.
Owner:COMCAST IP HLDG I
System and method for controlling access rights to and security of digital content in a distributed information system, e.g., Internet
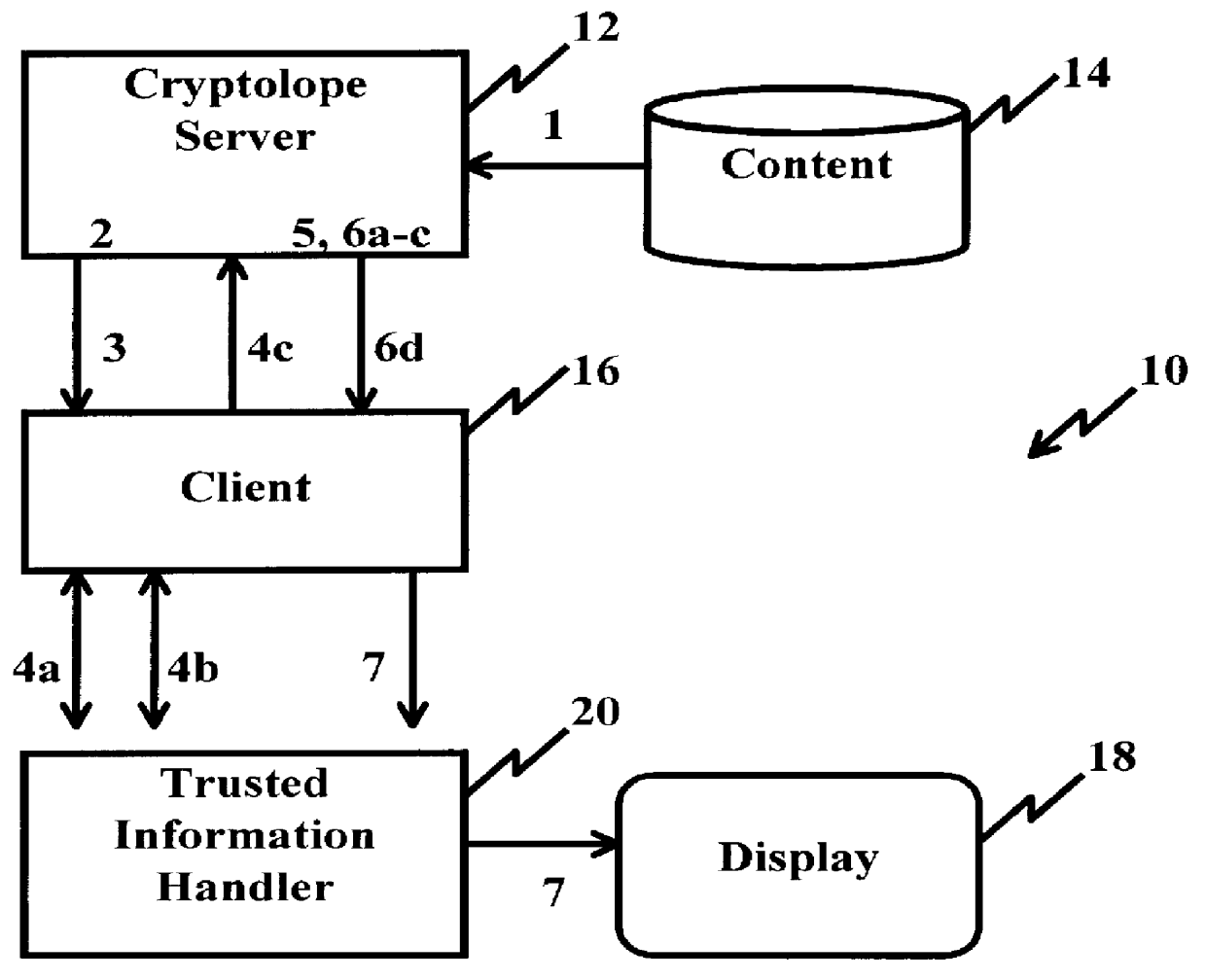
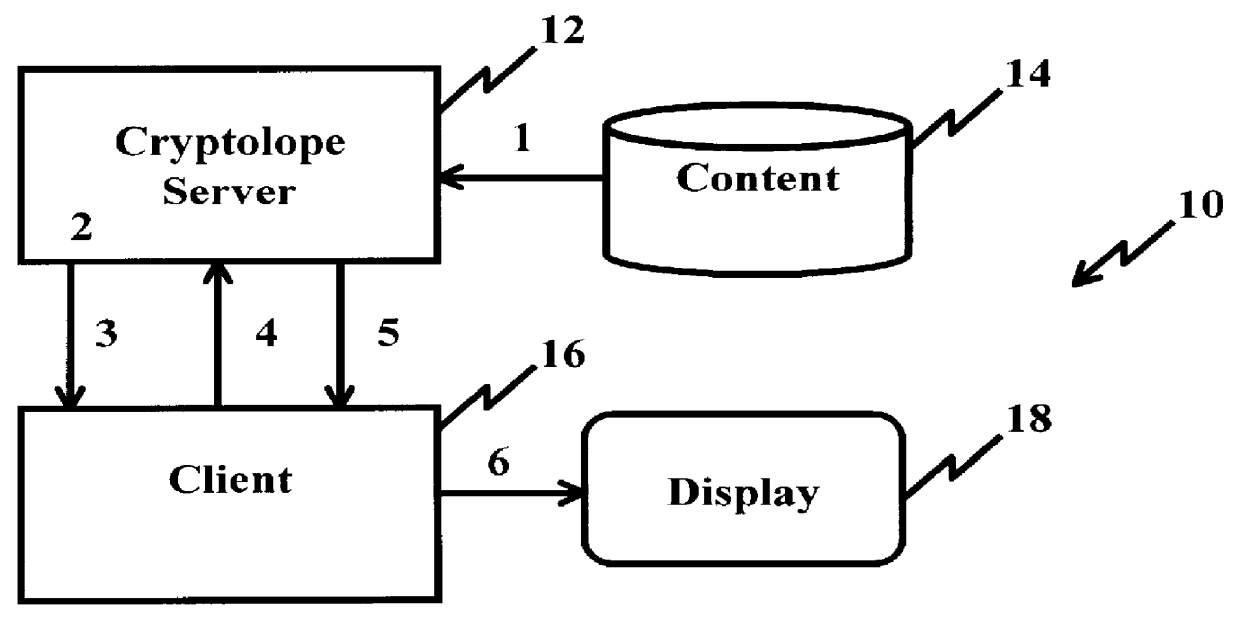
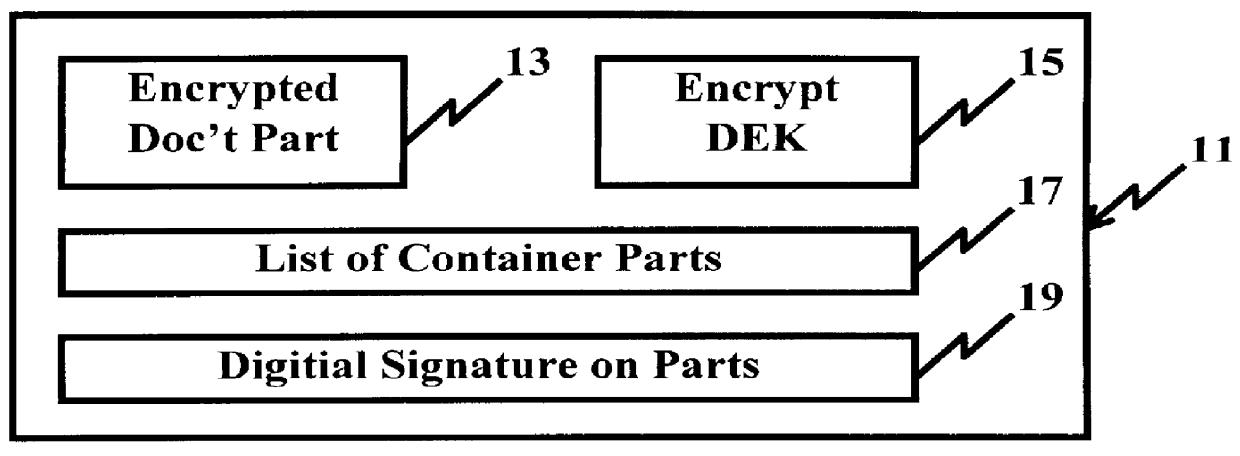
InactiveUS6098056AKey distribution for secure communicationPublic key for secure communicationPersonalizationThe Internet
A system and method for limiting access to and preventing unauthorized use of an owner's digital content stored in an information network and available to clients under authorized conditions. The network includes at least one server coupled to a storage device for storing the limited access digital content encrypted using a random-generated key, known as a Document Encryption Key (DEK). The DEK is further encrypted with the server's public key, using a public / private key pair algorithm and placed in a digital container stored in a storage device and including as a part of the meta-information which is in the container. The client's workstation is coupled to the server for acquiring the limited access digital content under the authorized condition. A Trusted Information Handler (TIH) is validated by the server after the handler provides a data signature and type of signing algorithm to transaction data descriptive of the purchase agreement between the client and the owner. After the handler has authenticated, the server decrypts the encrypted DEK with its private key and re-encrypts the DEK with the handler's public key ensuring that only the information handler can process the information. The encrypted DEK is further encrypted with the client's public key personalizing the digital content to the client. The client's program decrypts the DEK with his private key and passes it along with the encrypted content to the handler which decrypts the DEK with his private key and proceeds to decrypt the content for displaying to the client.
Owner:ACTIVISION PUBLISHING
Multi-window management apparatus and program, storage medium and information processing apparatus
InactiveUS20100088634A1Easy to understandFacilitates user operationCathode-ray tube indicatorsInput/output processes for data processingInformation processingComputer hardware
Owner:SHARP KK
Operation indication outputting device for giving operation indication according to type of user's action
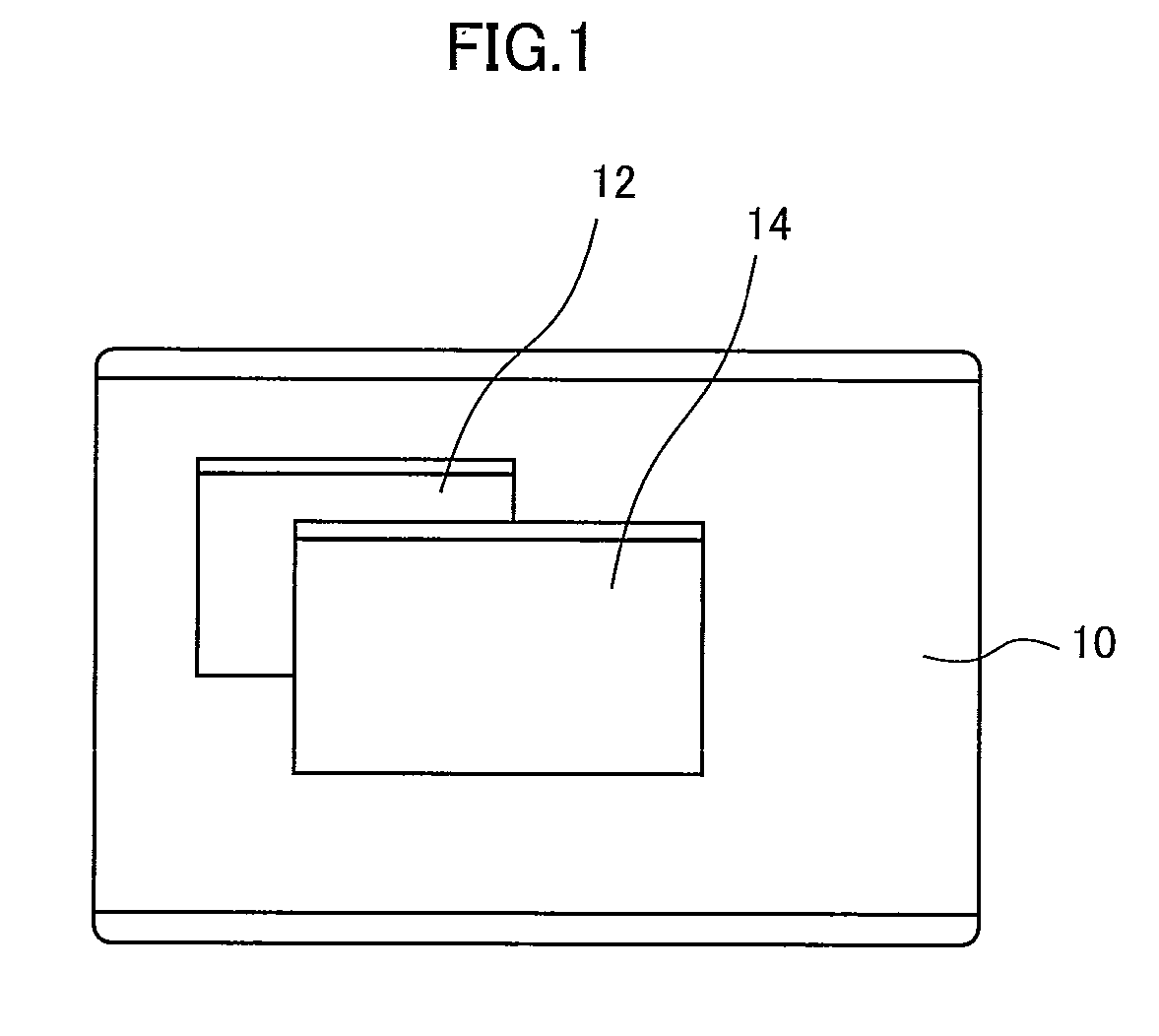
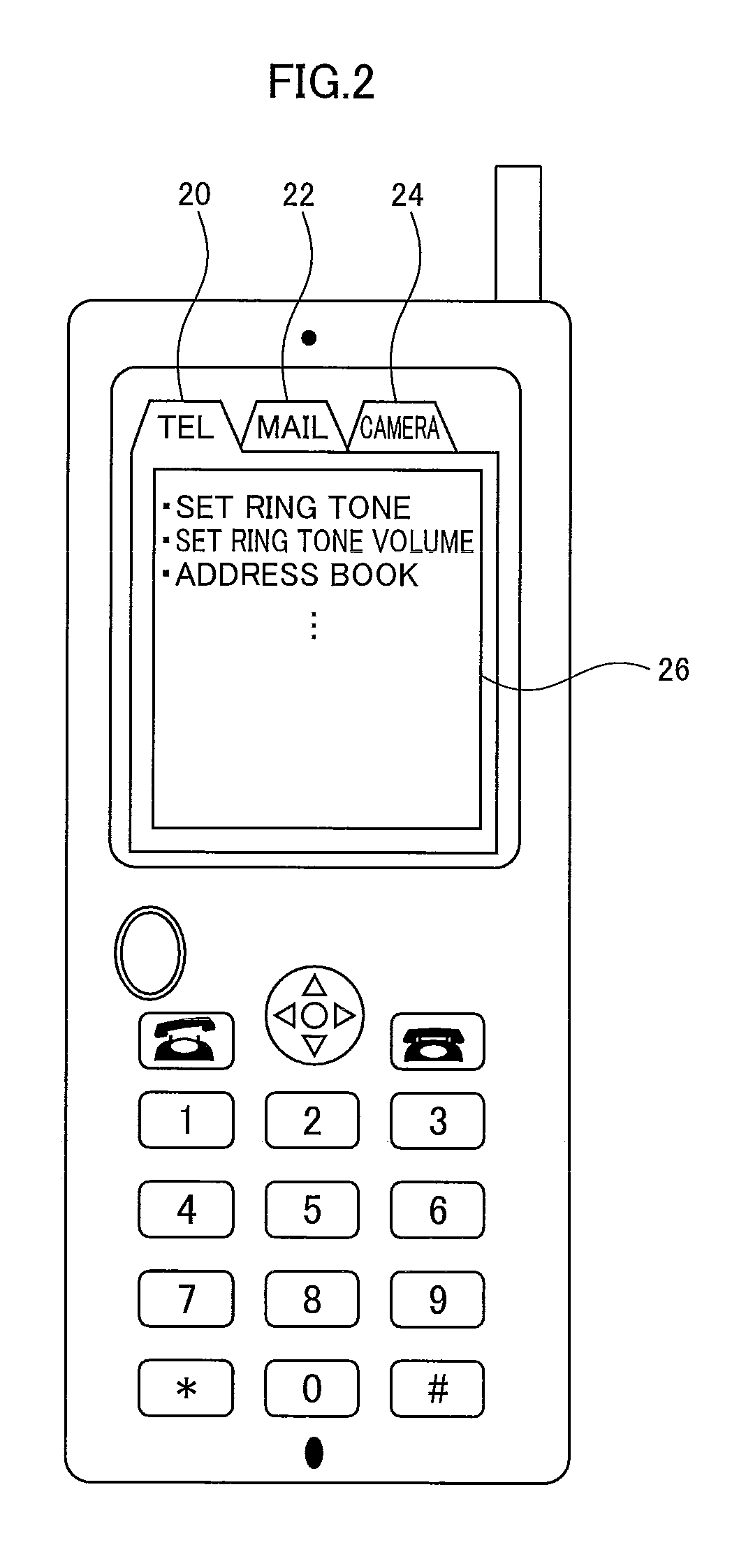
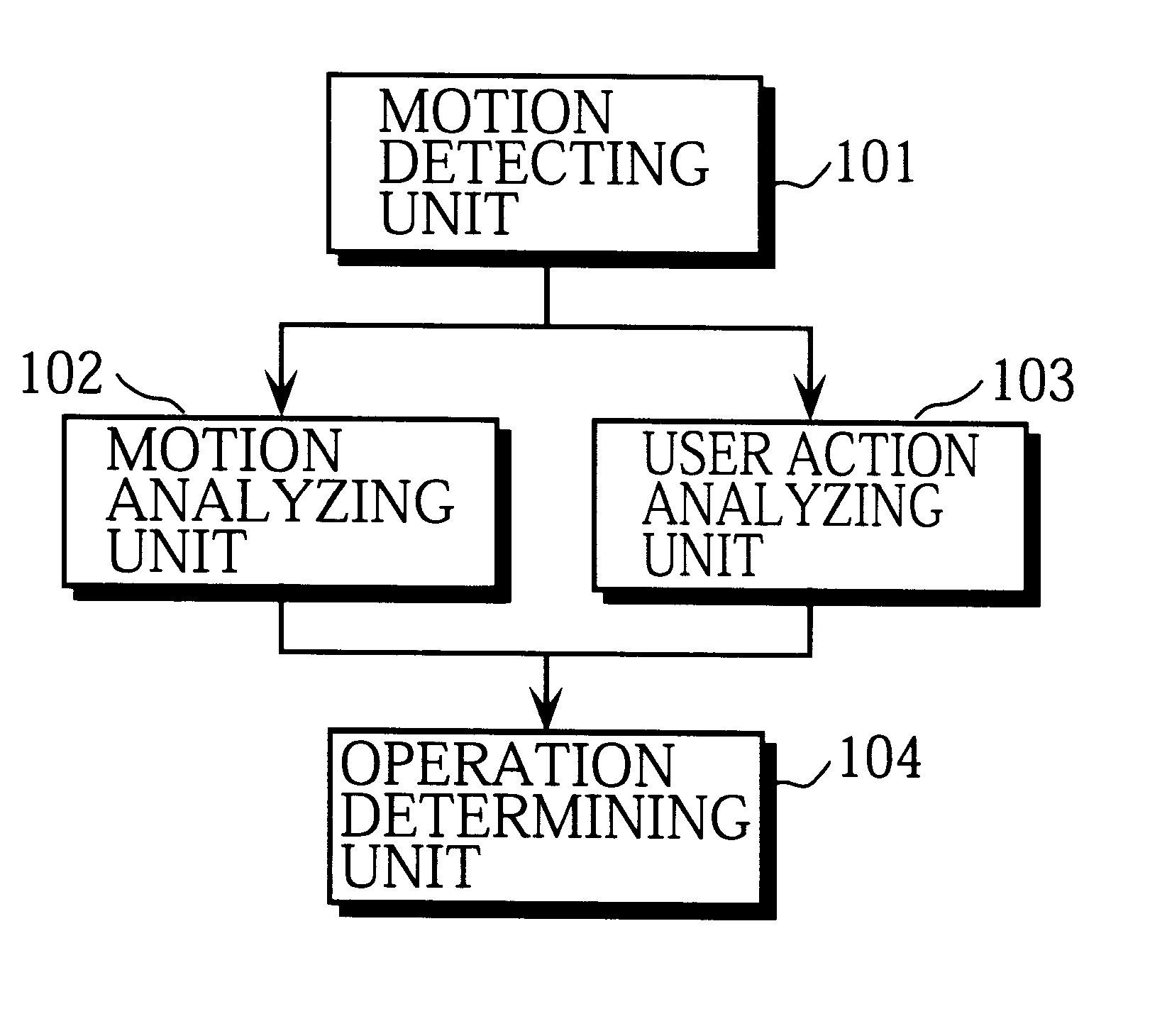
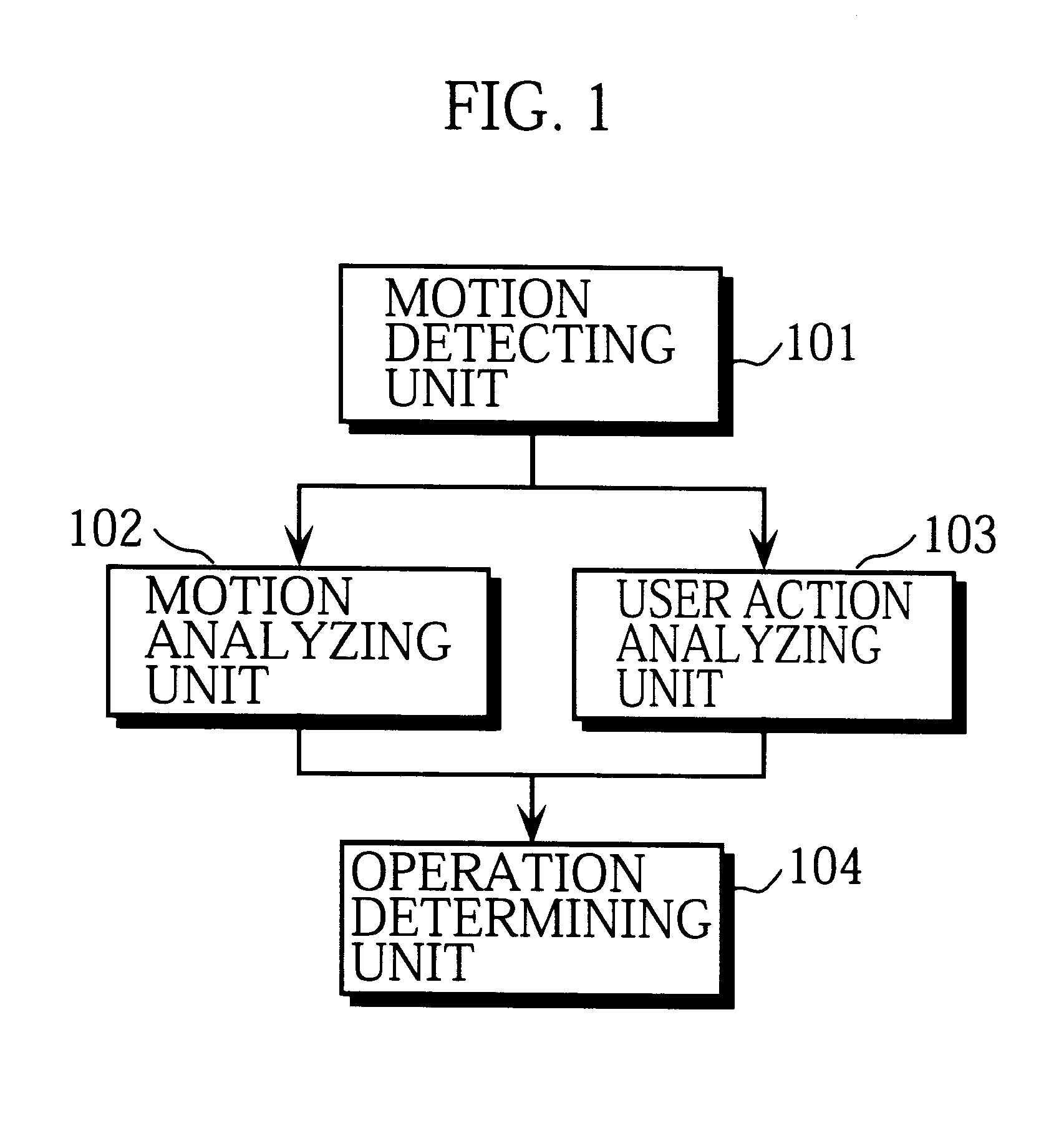
InactiveUS6369794B1Simple procedureLow priceInput/output for user-computer interactionInterconnection arrangementsInformation processingOutput device
A motion detecting unit detects a motion of an operation indication outputting device. A motion analyzing unit analyzes a direction, strength, and number of occurrence of the detected motion. A user action analyzing unit analyzes a type of a user's action by obtaining a frequency distribution from the detected motion. An operation determining unit includes a storing unit which stores operation indications that each correspond to a type of the user's action and a direction and other attributes of a motion of the operation indication outputting device caused by the user's action, and outputs an operation indication corresponding to the analysis results by the motion analyzing unit and user action analyzing unit to an information processing apparatus.
Owner:INTERTRUST TECH CORP
Data security system and method with multiple independent levels of security
InactiveUS20050138110A1Ease overhead performanceHigh overhead performancePeptide/protein ingredientsNGF/TNF-superfamilyInformation processingWorkstation
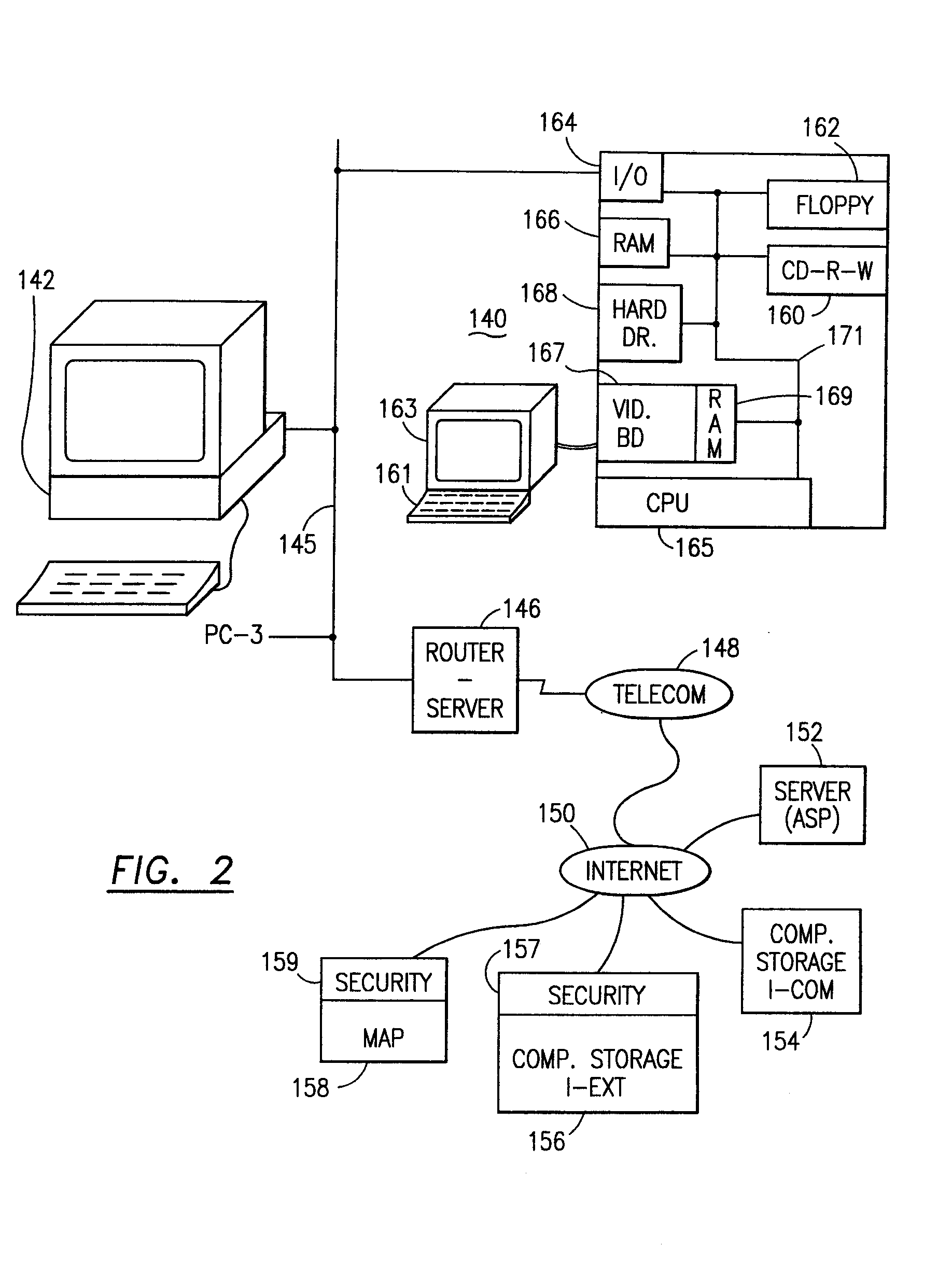
The method, program and information processing system secures data, and particularly security sensitive words, characters or data objects in the data, in a computer system with multiple independent levels of security (MILS). Each level of MILS has a computer sub-network with networked workstations. The MILS sub-networks are connected together via security guard computer(s) and each guard computer has separate memories for each level (TS, S, C, UC(or remainder)). The method extracts the security sensitive words / data (a granular action), from the source document for each MILS level, stores the extracted data in a corresponding extract store for each level and permits reconstruction / reassembly of the dispersed data via said extracted data at each said level of said multiple security levels and remainder data only in the presence of a predetermined security clearance commensurate with each MILS level.
Owner:DIGITAL DOORS
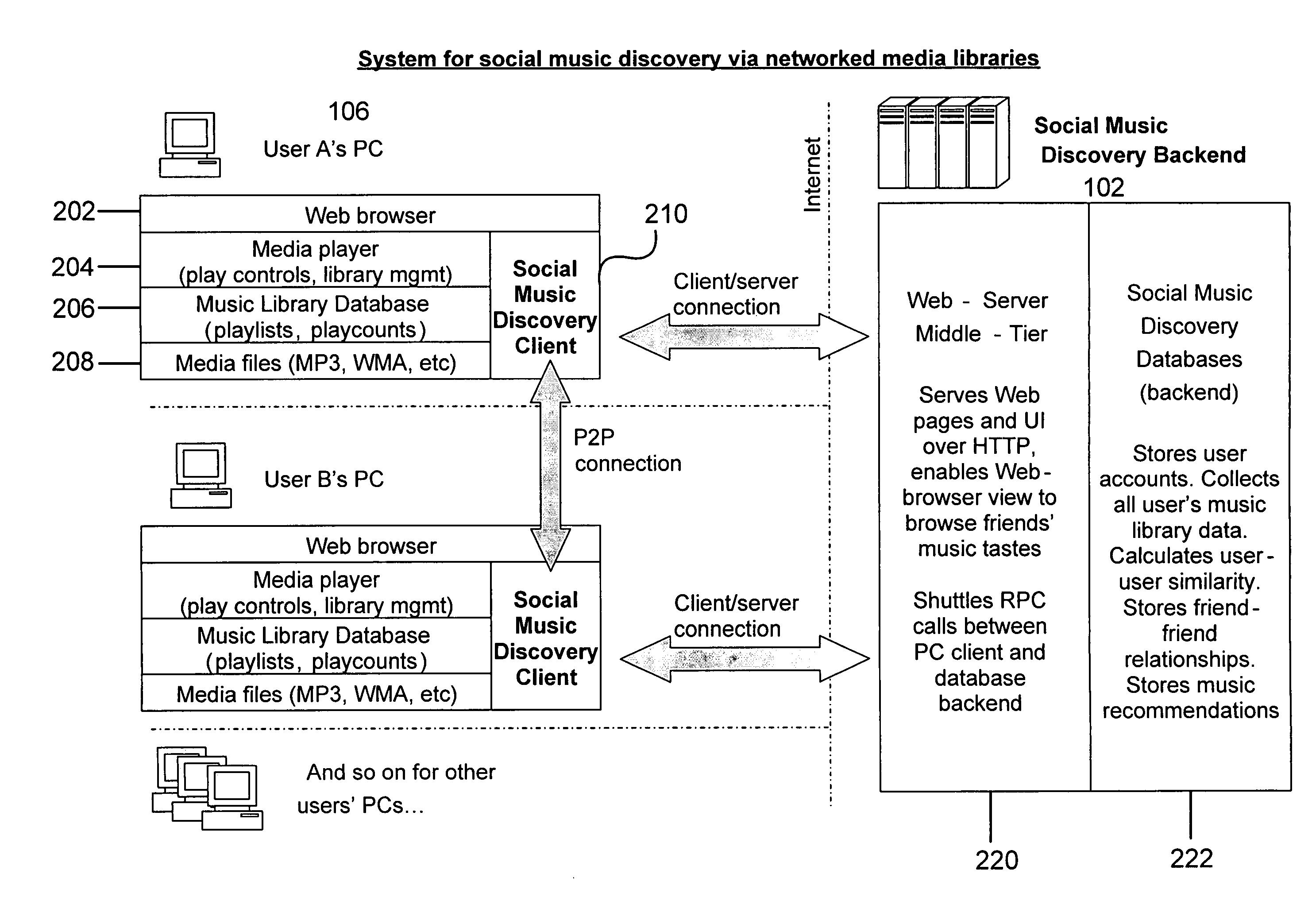
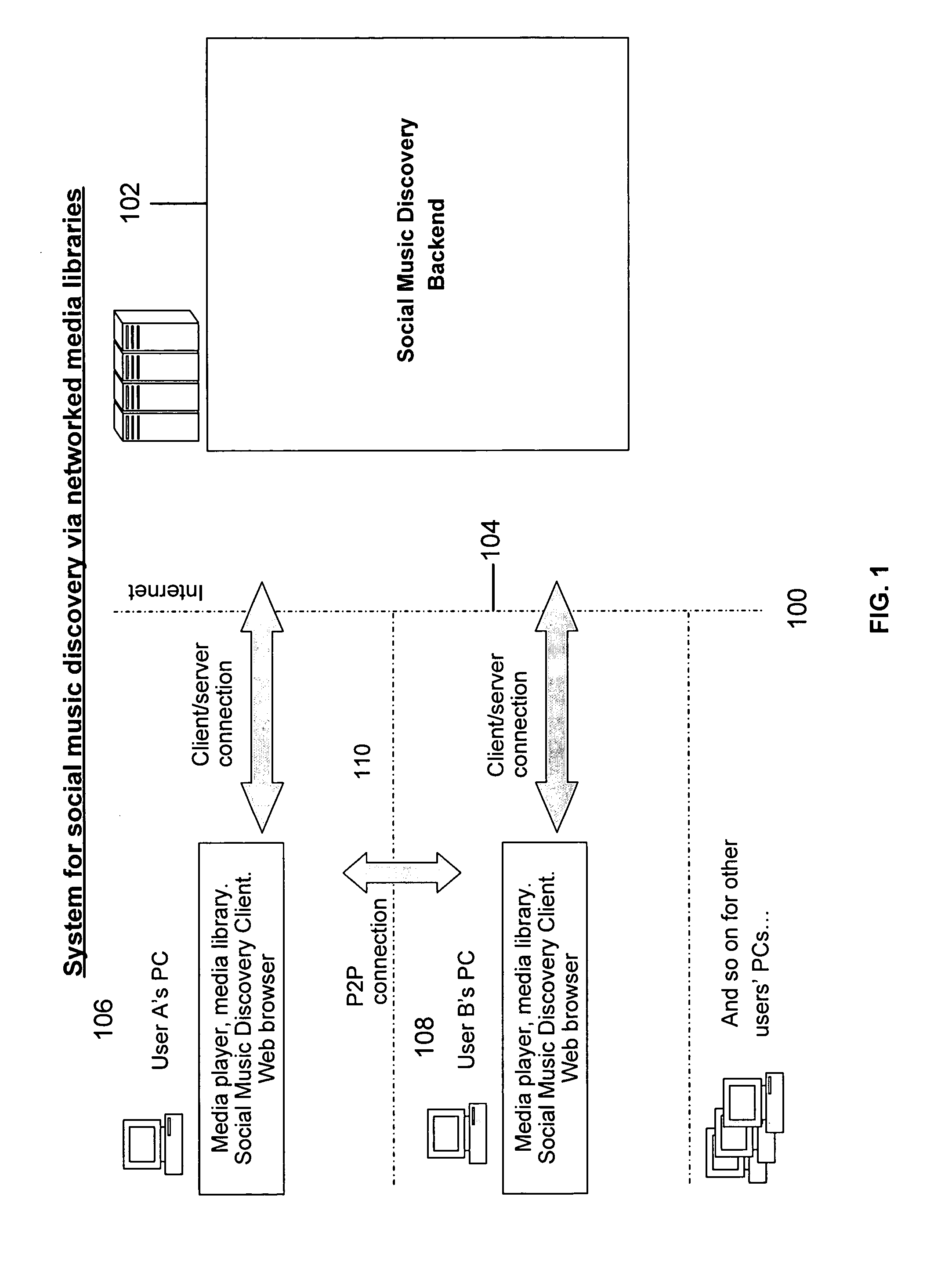
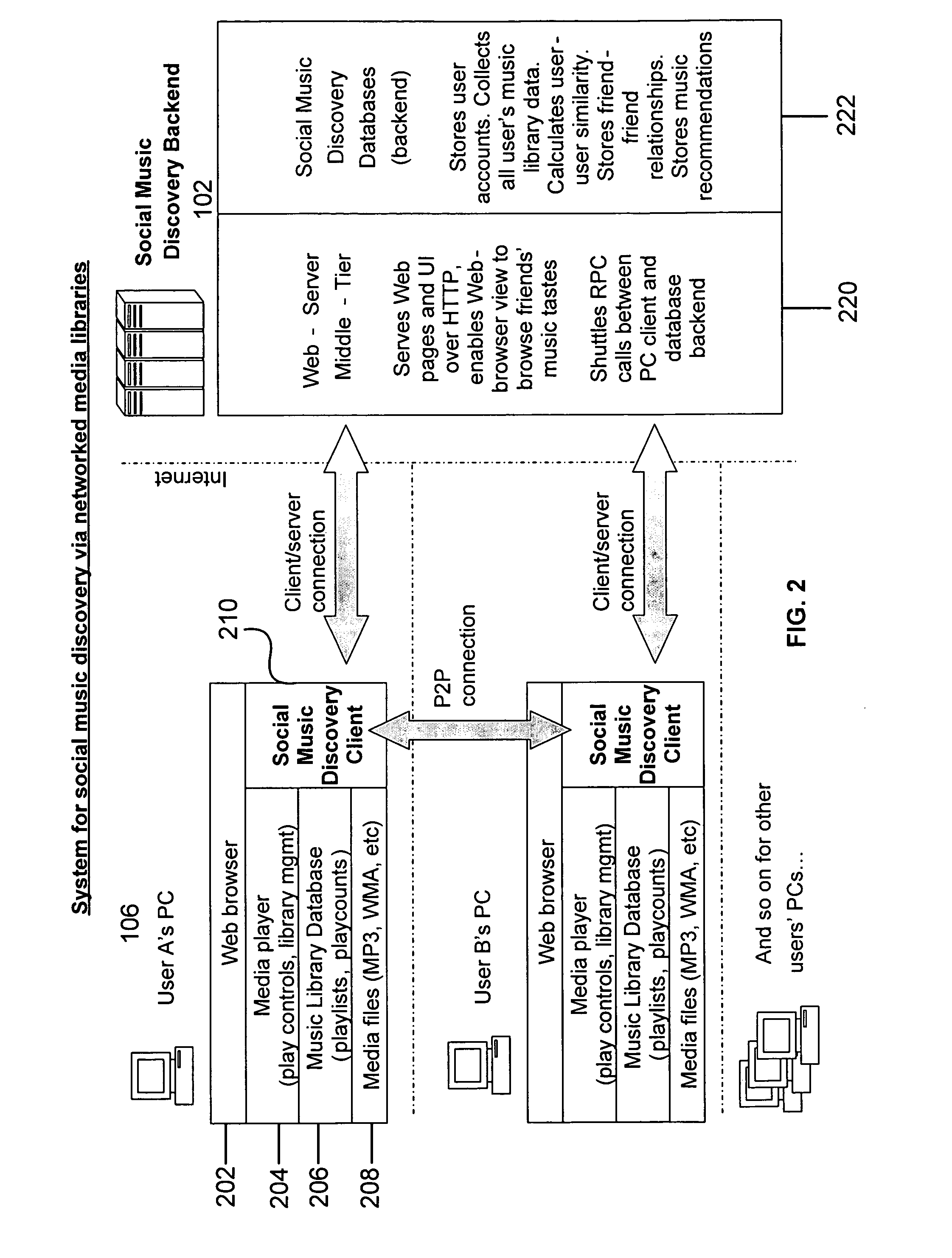
System, apparatus and method for discovery of music within a social network
ActiveUS20080052371A1Easy to findMultiple digital computer combinationsOffice automationInformation processingSocial web
A system, apparatus, and method to assist in the discovery of music or other content by members of a social network. The present invention permits network members to network together and share information about their music collections and listening habits with a processing platform and with each other. The processing platform processes music library content and playback related data to produce similarity and compatibility measures between artists (that is, an artist-to-artist measure) and between network members (that is, a network member-to-network member measure). By combining the content and playback related data with filtering mechanisms, recommendation techniques (which may be based on the calculated measures), and set membership concepts, the present invention provides network members of the network with tools to discover artists and / or songs that are likely to be of interest to them.
Owner:MYSPACE LLC
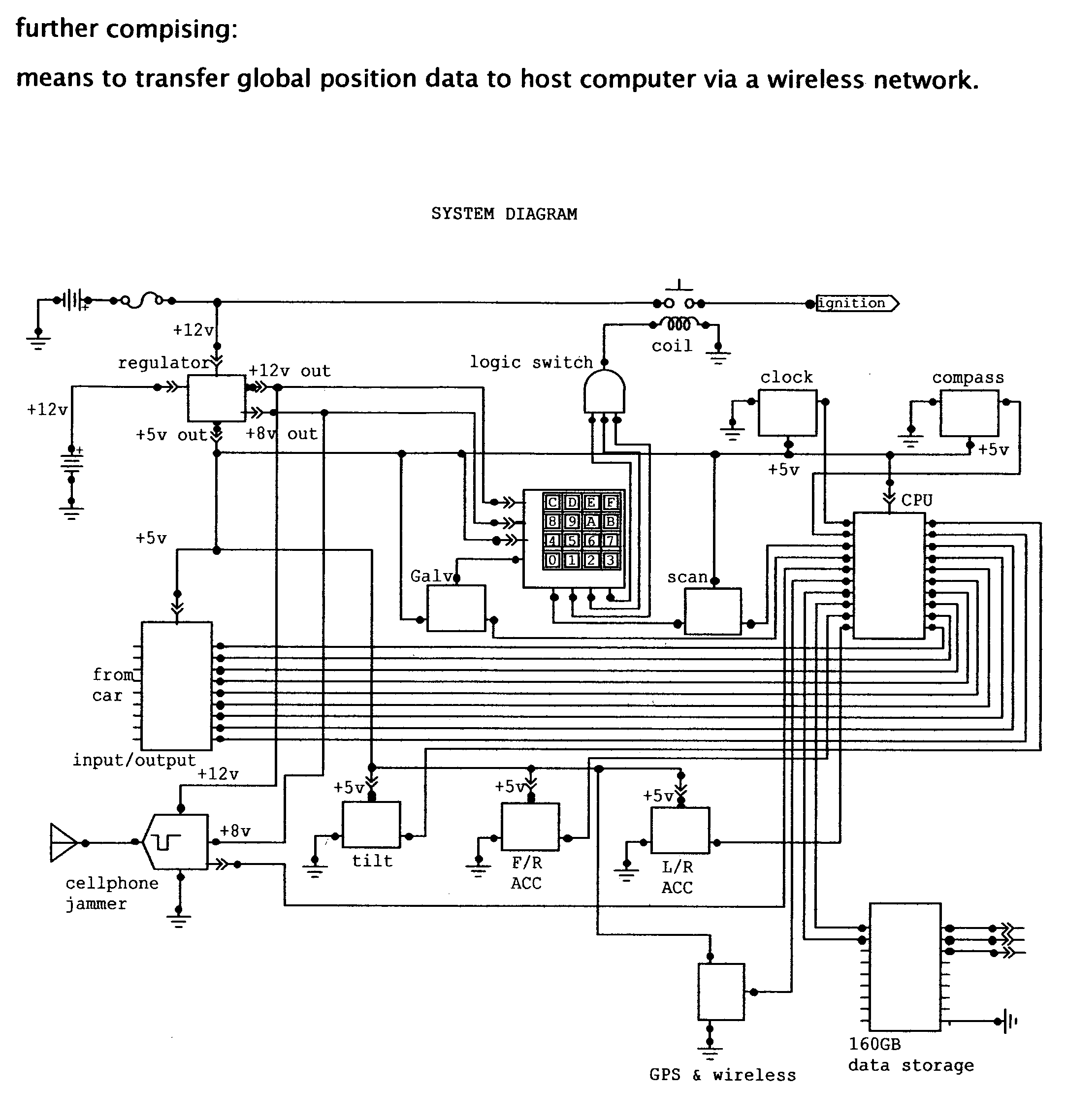
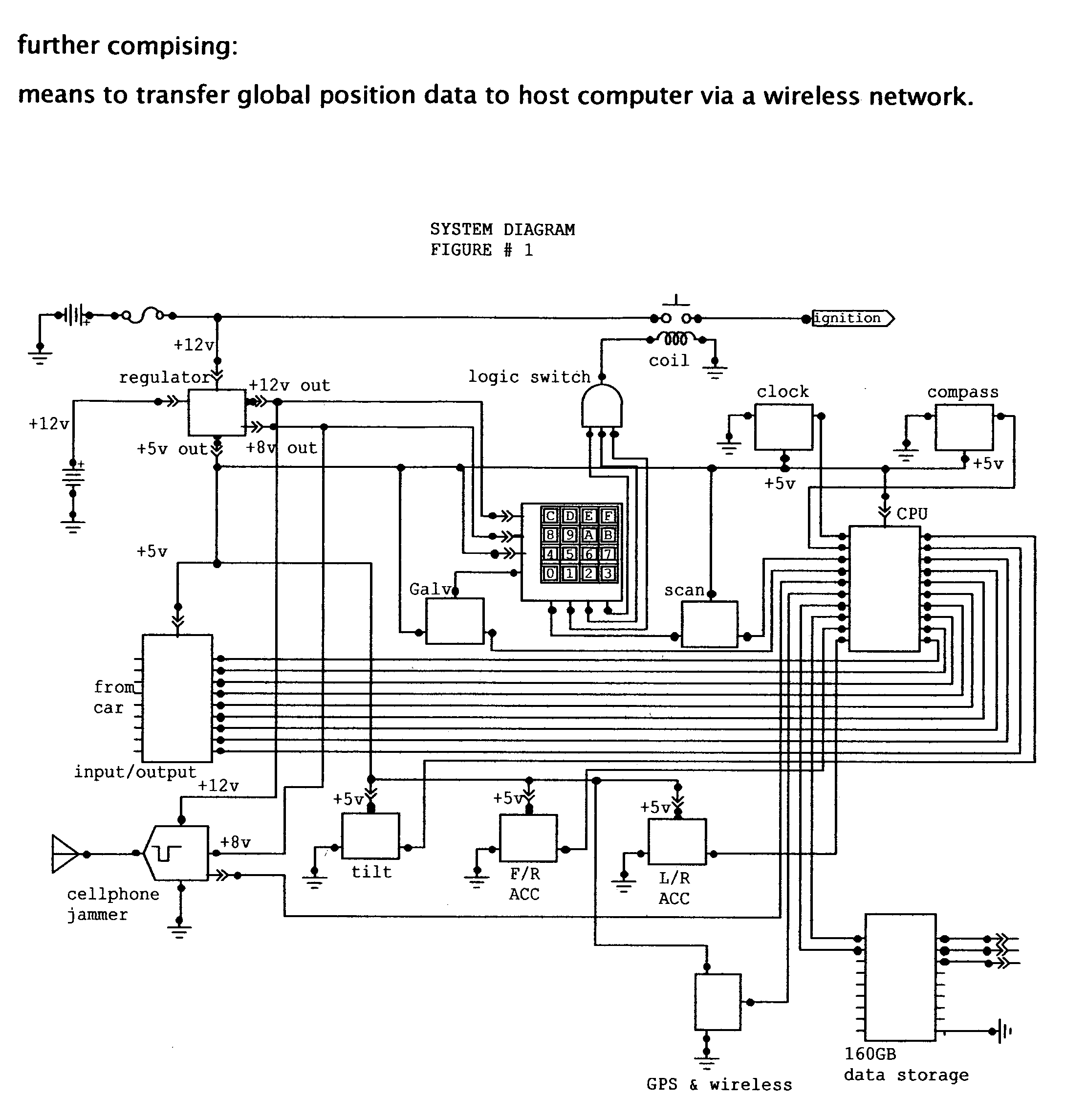
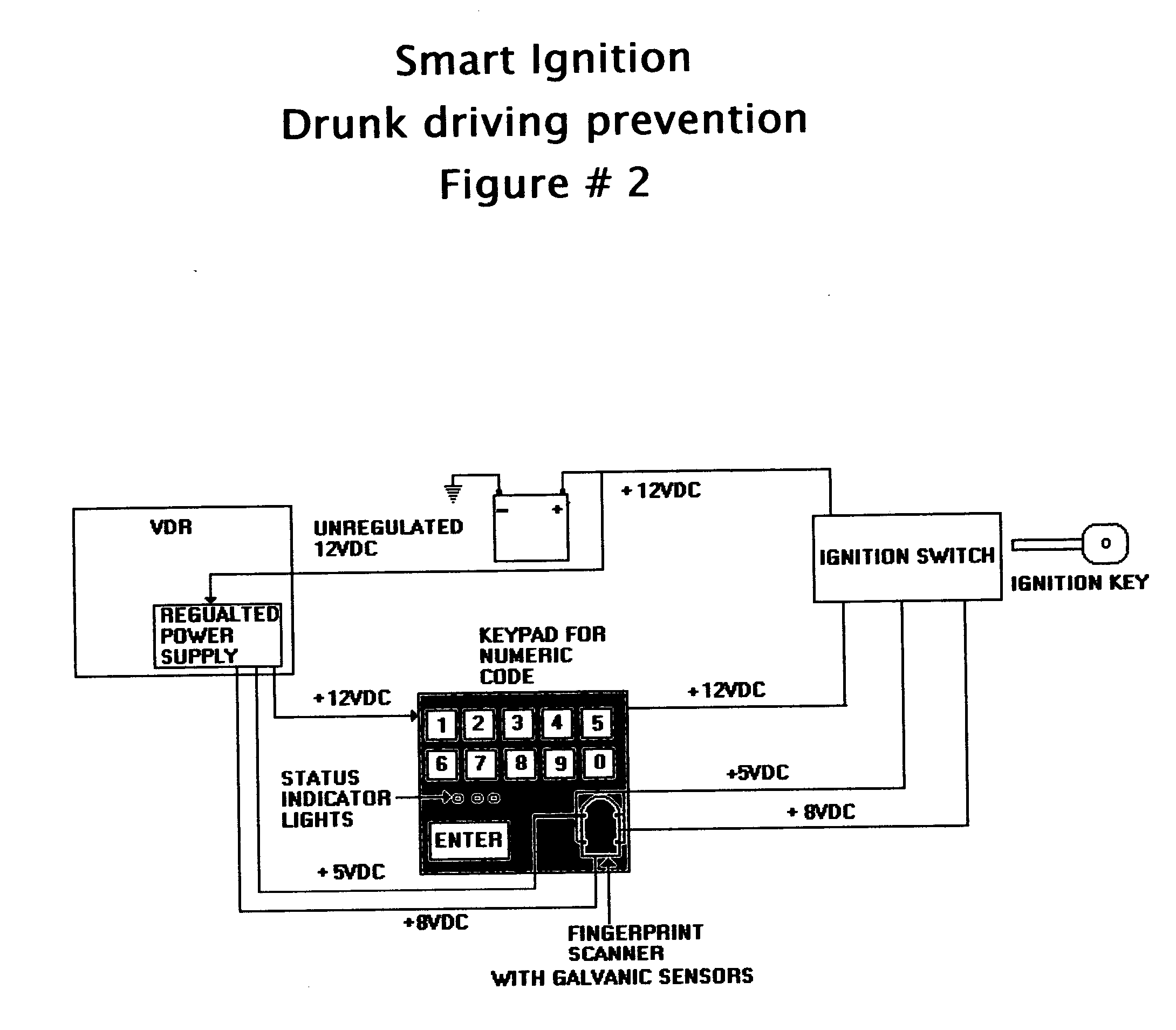
Vehicle data recorder and telematic device
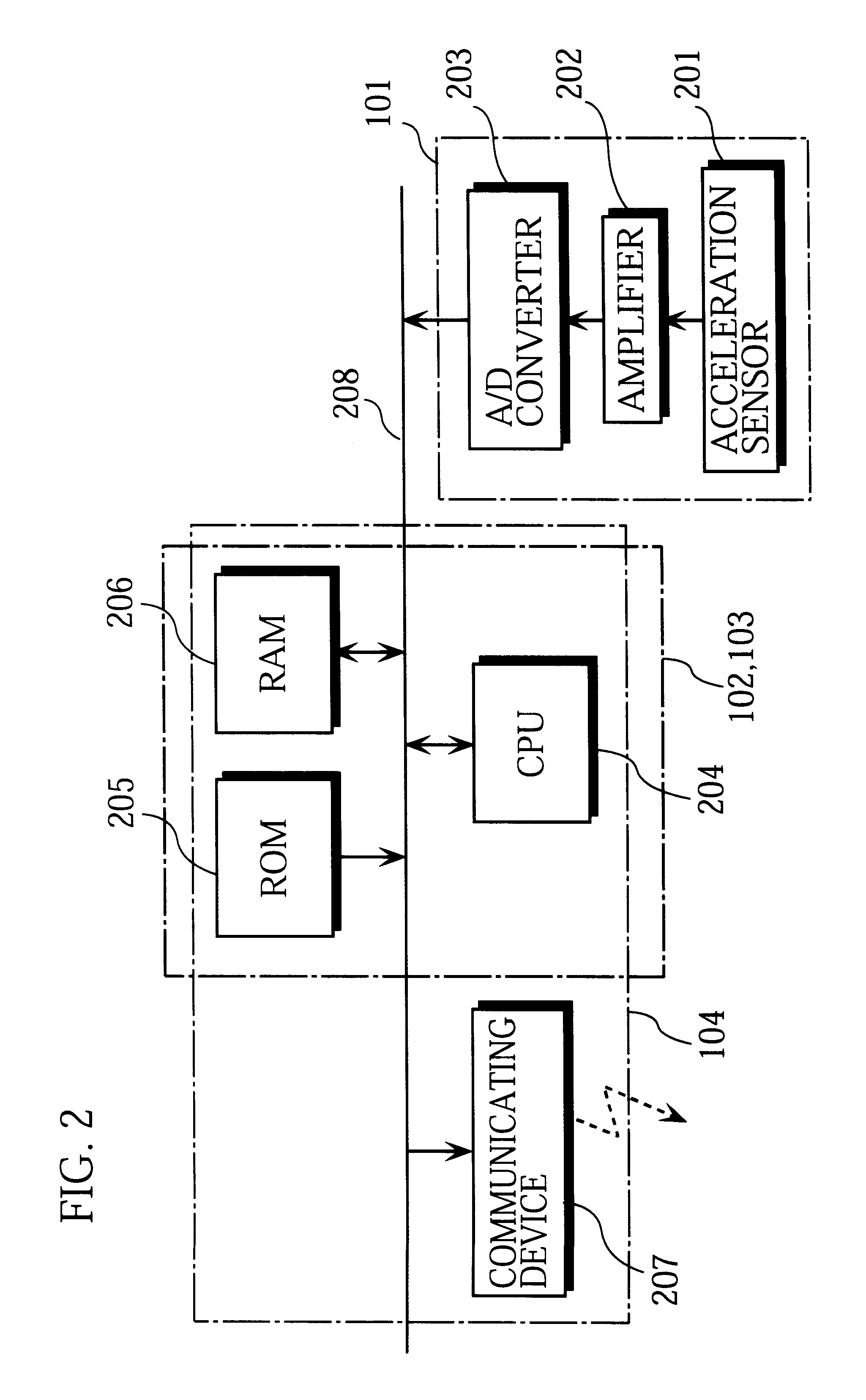
InactiveUS20060212195A1Reduce drunk drivingReduce automobile theftVehicle testingRegistering/indicating working of vehiclesPersonalizationInformation processing
This invention is a vehicle data recorder with the capability to continuously record and store selected data on both driver and vehicle performance that will include but not be limited to, miles driven, speed, acceleration / deceleration, brake activation, seatbelt usage, vehicle direction, steering anomalies, global position, impact forces and direction, transmission status, and alcohol usage. Specifically, this recorder will have extended data storage capacity, a drunk driver prevention smart ignition, real-time GPS data, low-power cell phone jamming, and internal wireless communication capabilities. It uses microprocessor controlled electronics to record, store, and transmit both driver and vehicle performance data in a date and time stamped file which can be utilized to establish personalized insurance rates, assess road tax and use fees, locate “Amber alert” victims or stolen vehicles, and with it's on scene access, provide critical mechanism of injury information to emergency responders.
Owner:VEITH GREGORY W +1
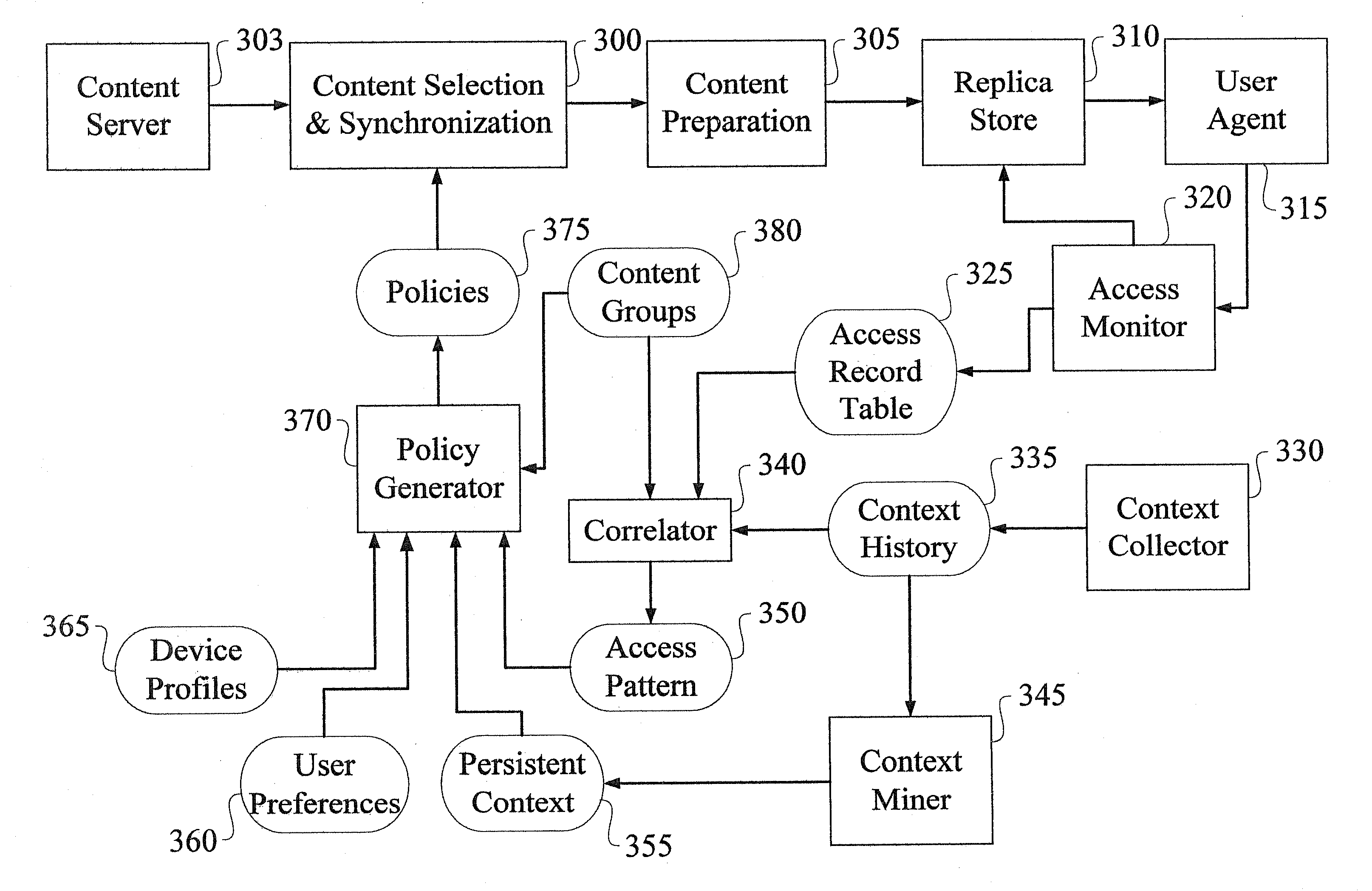
Method and Apparatus for Content Pre-Fetching and Preparation
InactiveUS20090287750A1Improve responsivenessMemory adressing/allocation/relocationInformation formatInformation processingProgram planning
A method of pre-fetching and preparing content in an information processing system is provided. The method includes the steps of generating at least one content pre-fetching policy and at least one content preparation policy, wherein each of the policies are at least in part a function of context information associated with a user. The content is pre-fetched based on information contained within the at least one content pre-fetching policy. Once the content has been pre-fetched, it is prepared based on information contained within the at least one content preparation policy. The context information associated with the user includes at least one of the user's usage patterns, current location, future plans and preferences.
Owner:IBM CORP
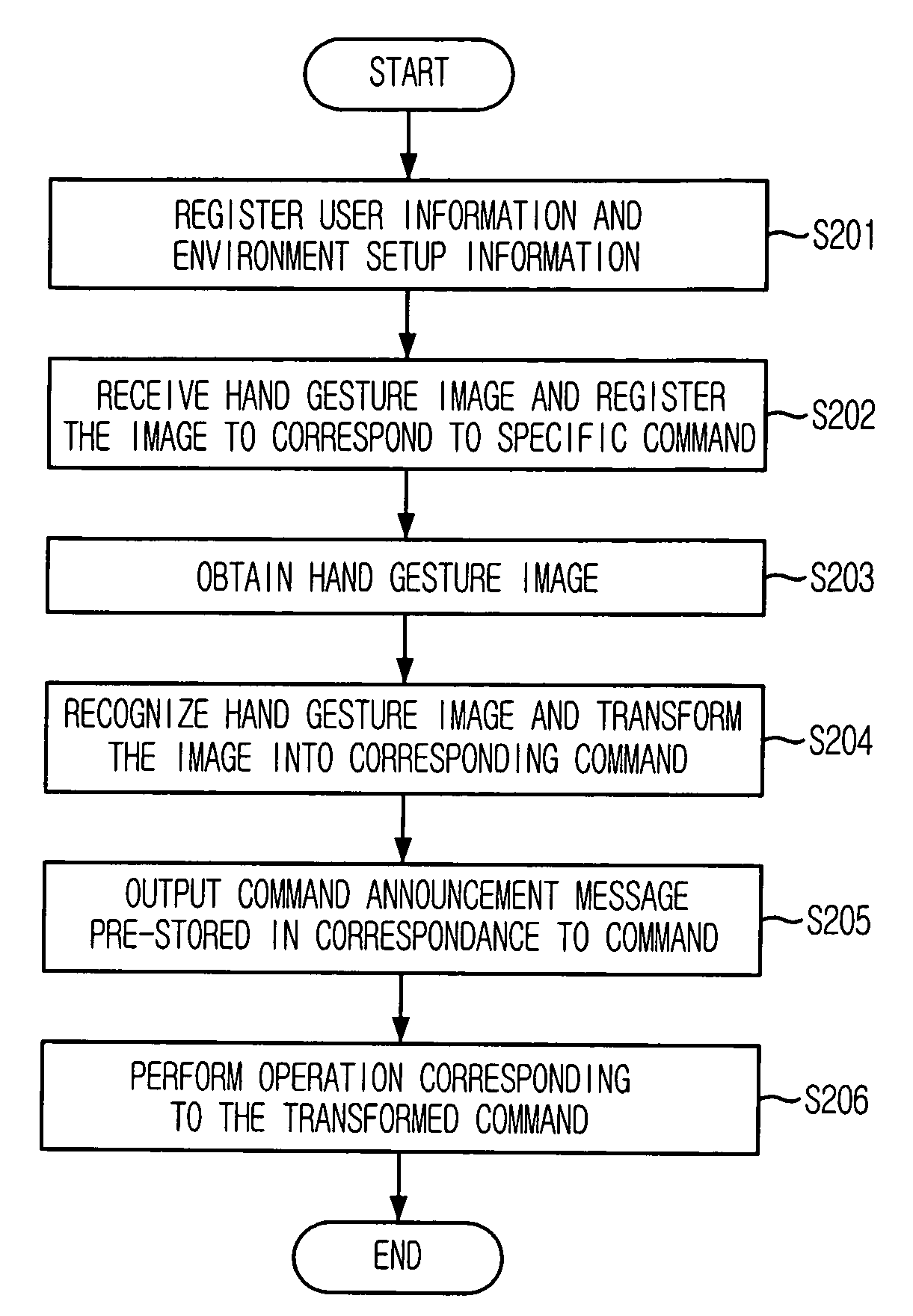
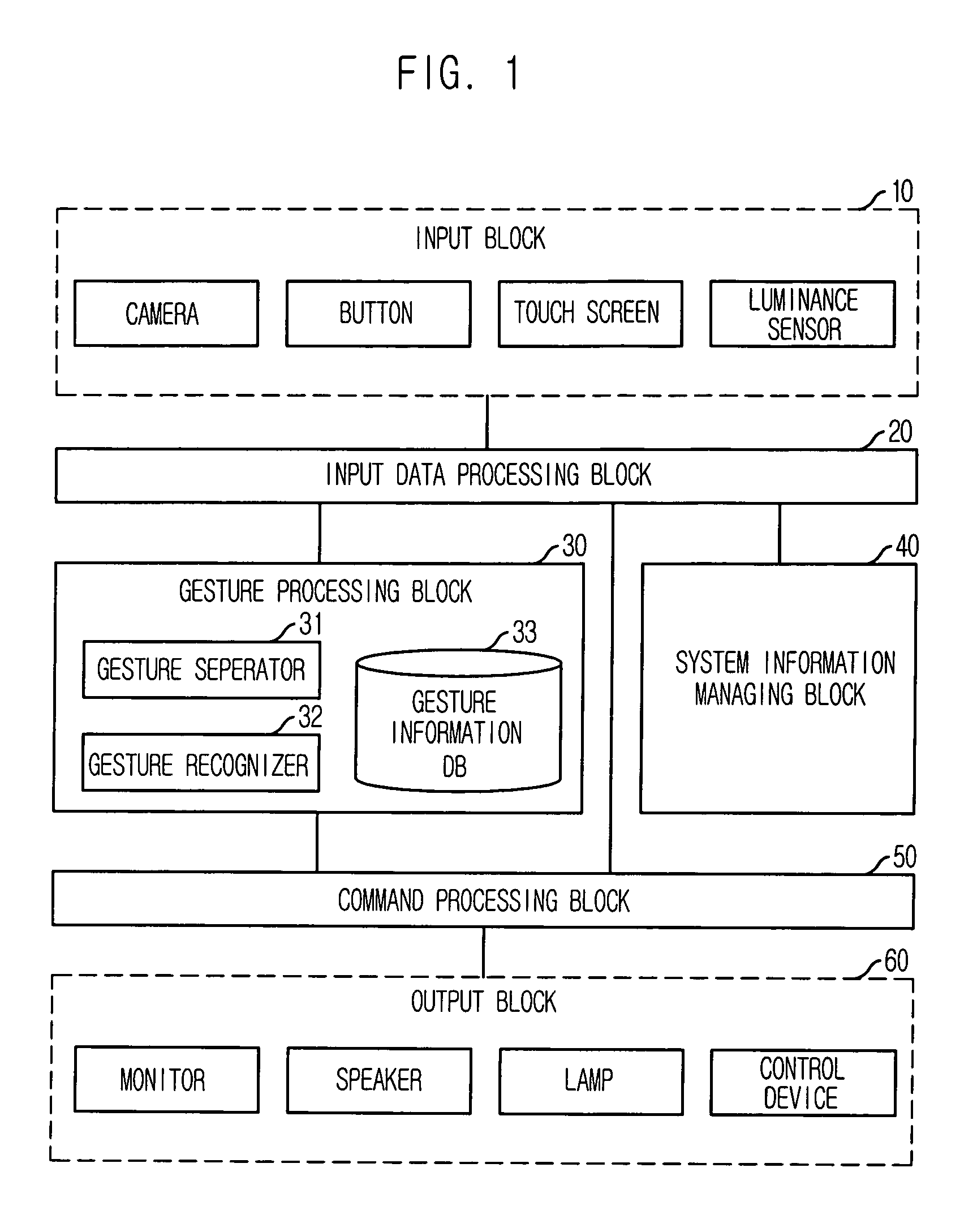
User interface apparatus using hand gesture recognition and method thereof
ActiveUS7702130B2Control process safetyEasily embodiedInput/output for user-computer interactionCharacter and pattern recognitionControl signalComputer terminal
Provided is a user interface apparatus that can control a telematics terminal safely and comfortably while driving, by recognizing a hand gesture image received through a camera in the telematics terminal as a corresponding control signal, and a method thereof. The interface apparatus using a hand gesture recognition, includes: an input receiving block for receiving a command registration request signal and a command selection signal; a hand gesture recognizing block for storing the hand gesture image in connection with a specific command, and transforming the hand gesture image into the corresponding command by recognizing the hand gesture image from the image obtained in the image obtaining block; and a command performing block for performing an operation corresponding to a command transformed in the hand gesture recognizing block.
Owner:INTELLECTUAL DISCOVERY CO LTD
Machine data web
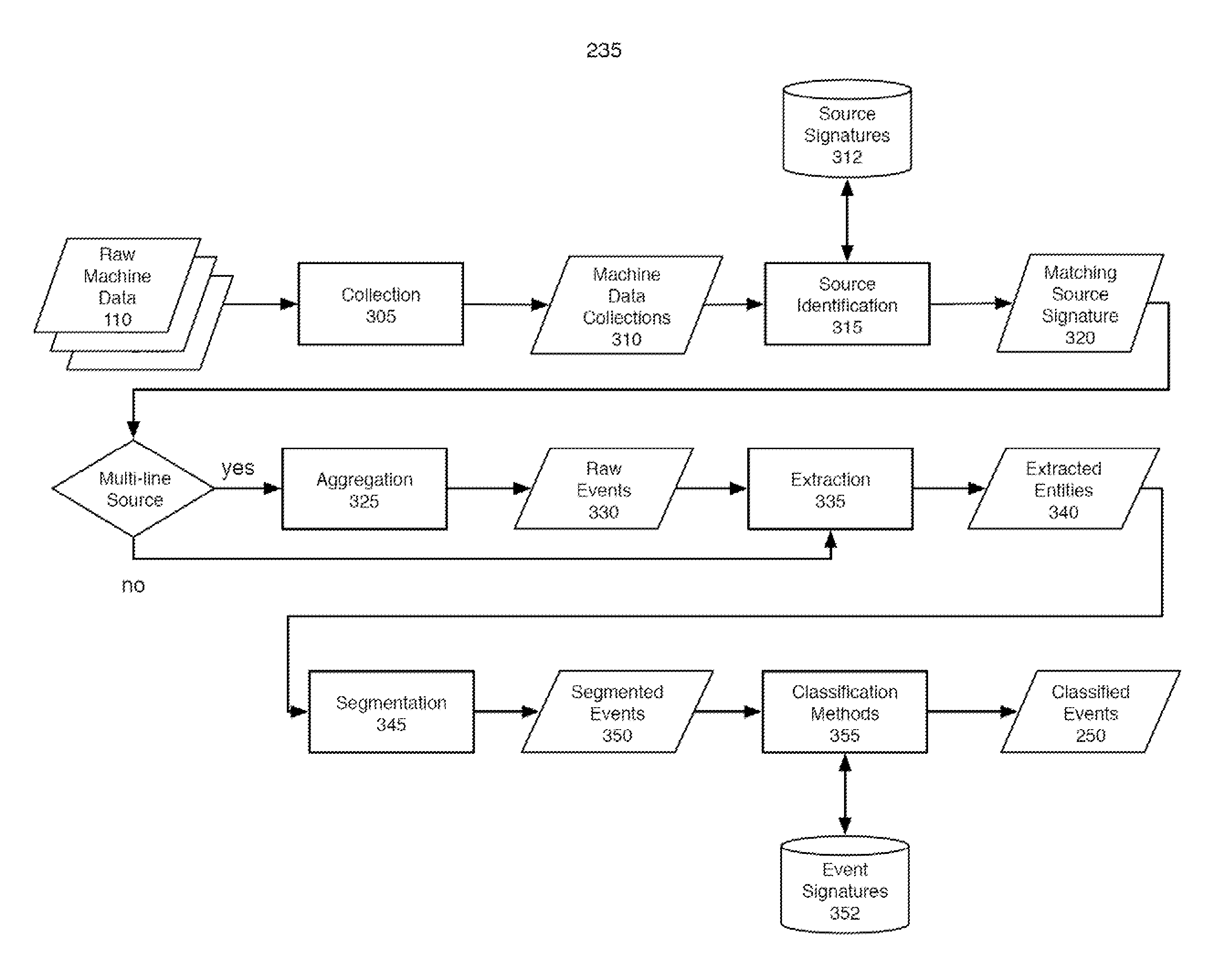
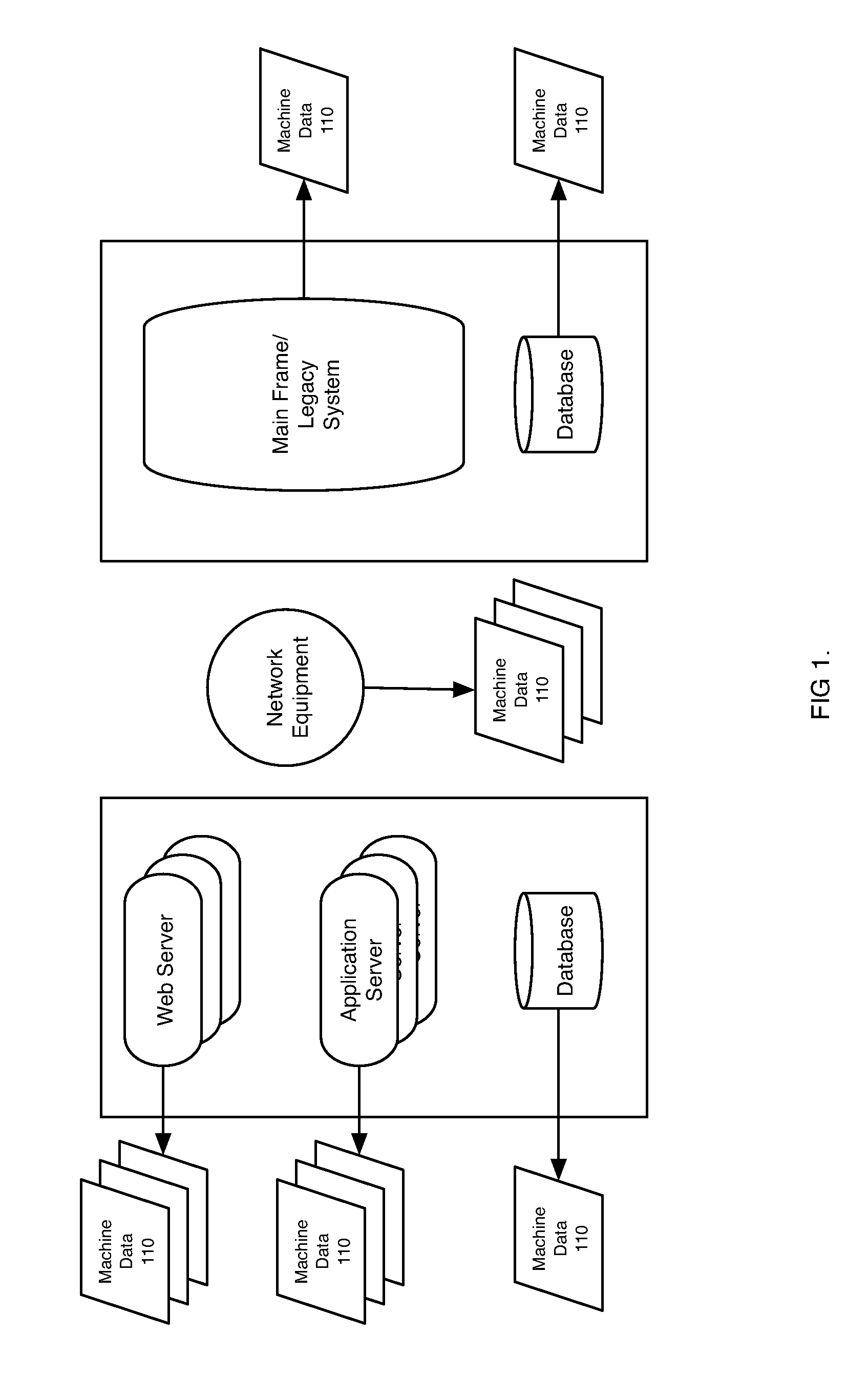
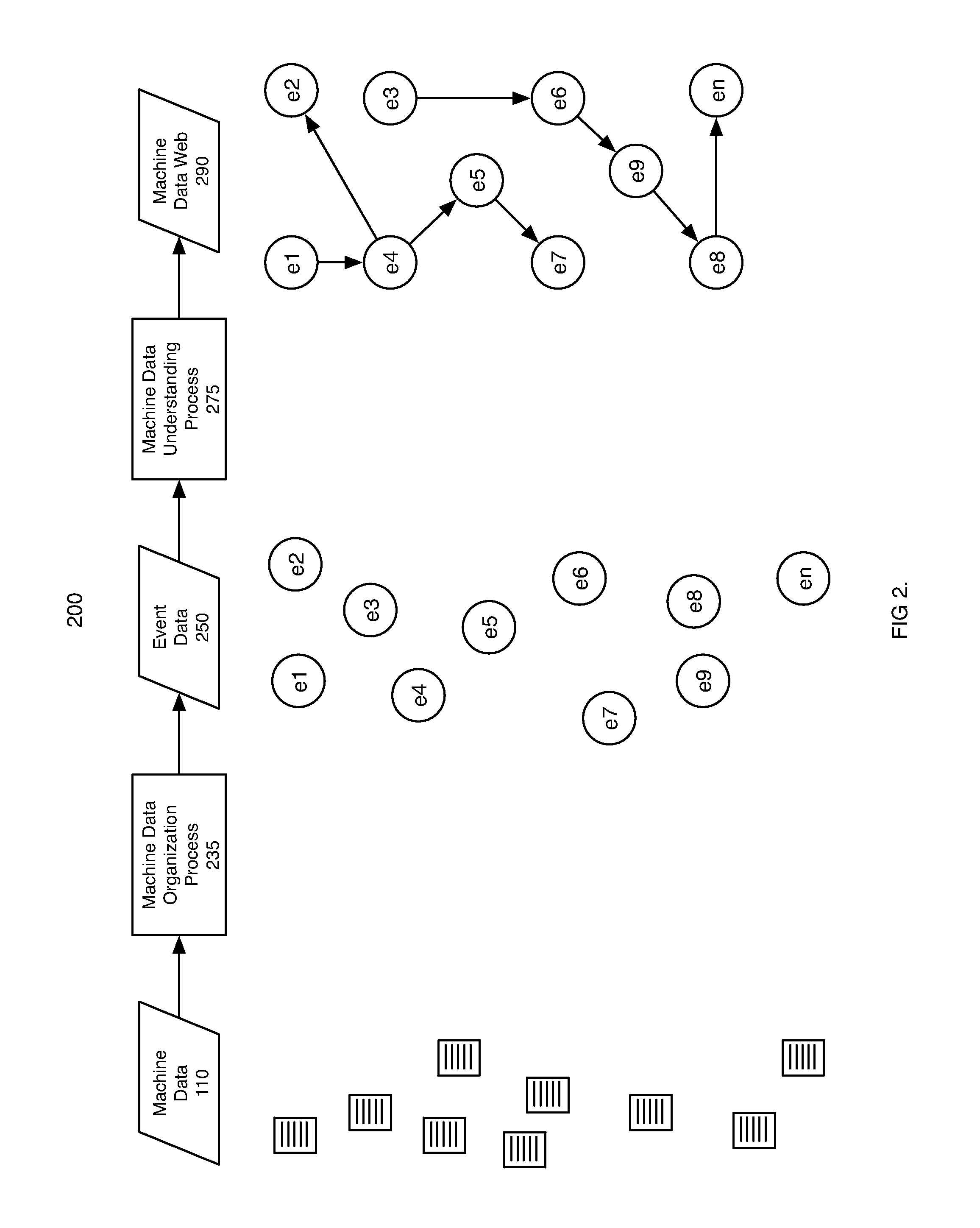
ActiveUS7937344B2Preserve integrityError detection/correctionInterprogram communicationInformation processingOriginal data
Methods and apparatus consistent with the invention provide the ability to organize and build understandings of machine data generated by a variety of information-processing environments. Machine data is a product of information-processing systems (e.g., activity logs, configuration files, messages, database records) and represents the evidence of particular events that have taken place and been recorded in raw data format. In one embodiment, machine data is turned into a machine data web by organizing machine data into events and then linking events together.
Owner:SPLUNK INC
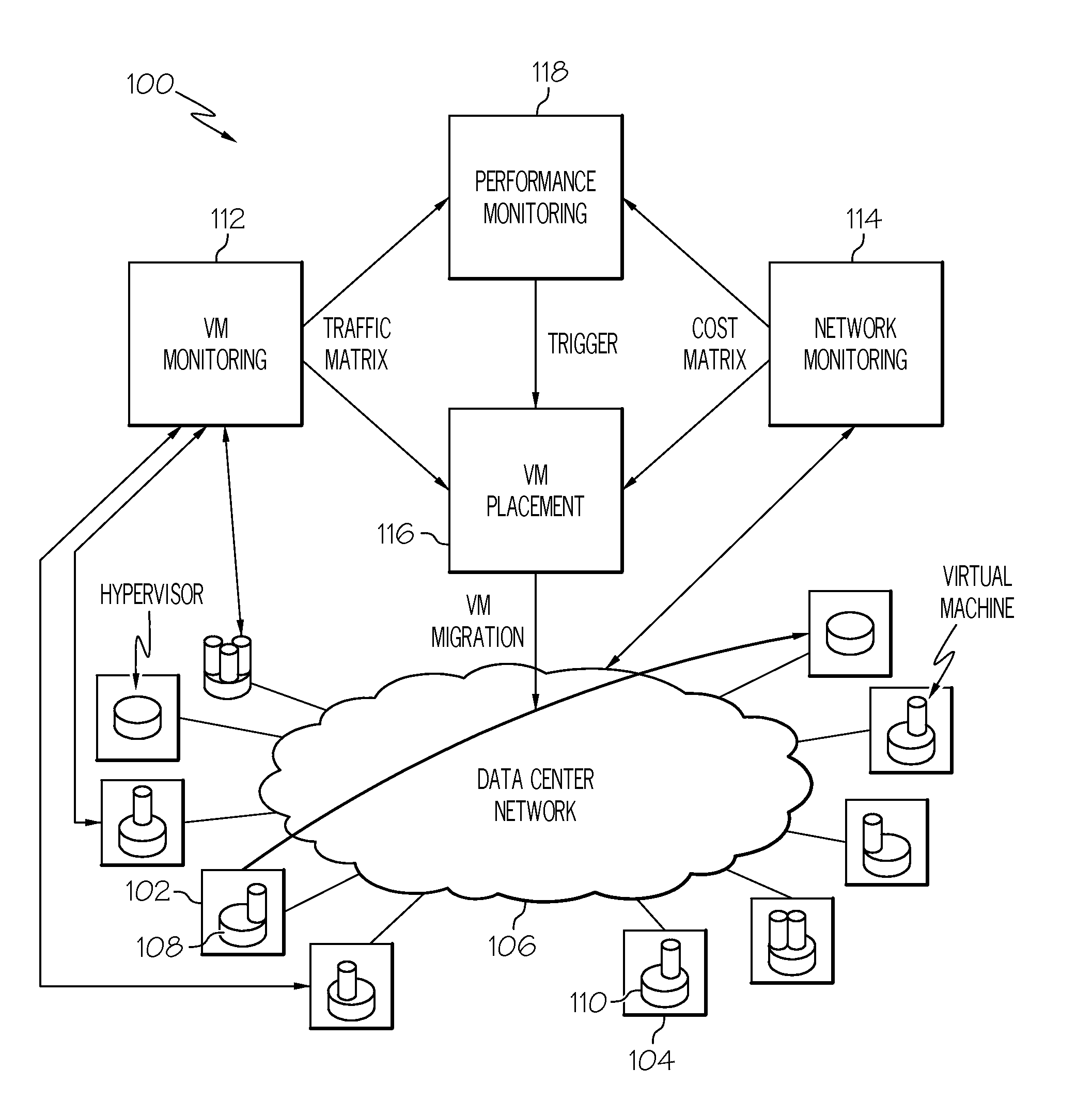
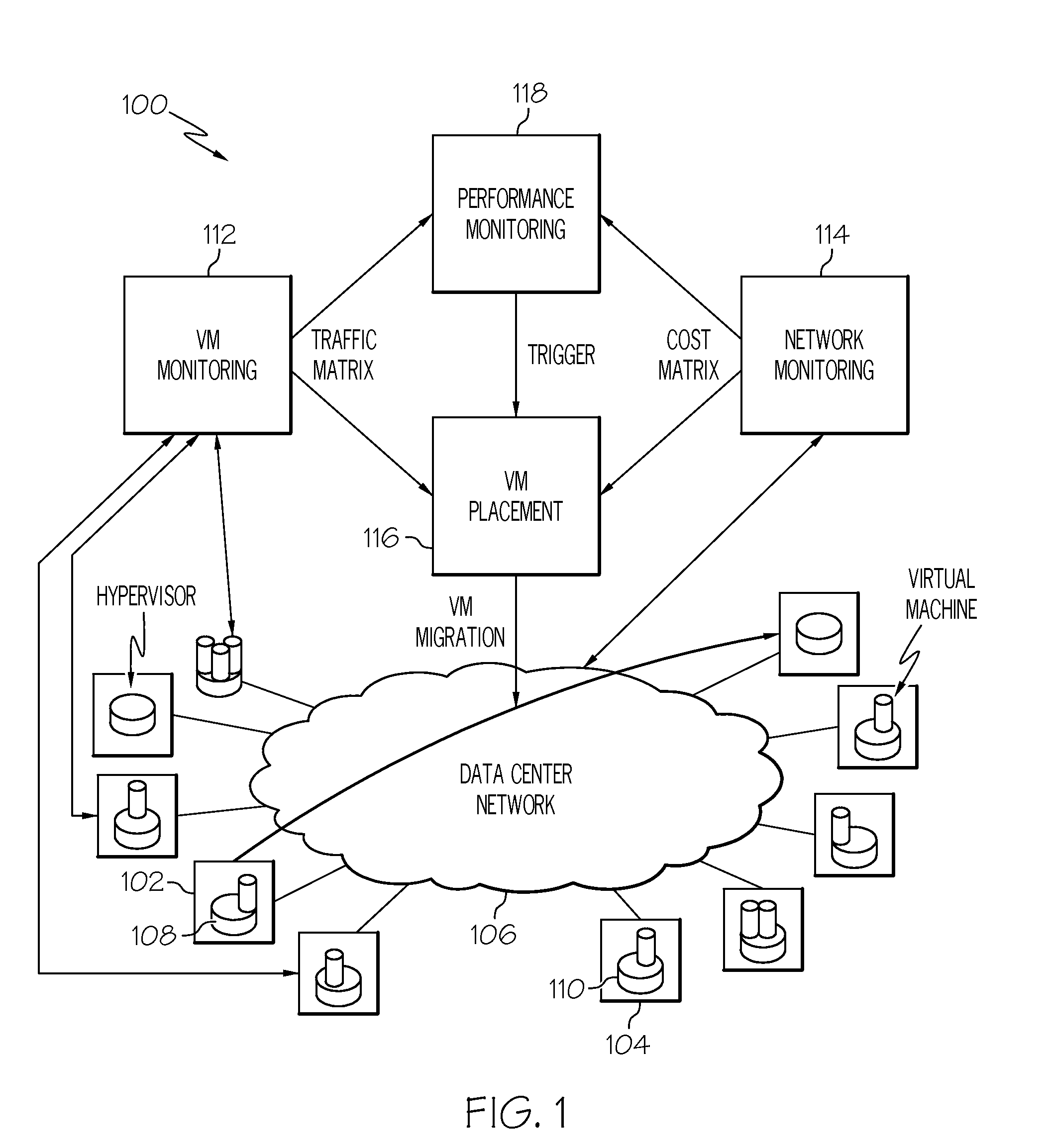
Placement of virtual machines based on server cost and network cost
InactiveUS20110225277A1Digital computer detailsMultiprogramming arrangementsInformation processingInformation handling system
A method, information processing system, and computer program product manage server placement of virtual machines in an operating environment. A mapping of each virtual machine in a plurality of virtual machines to at least one server in a set of servers is determined. The mapping substantially satisfies a set of primary constraints associated with the set of servers. A plurality of virtual machine clusters is created. Each virtual machine cluster includes a set of virtual machines from the plurality of virtual machines. A server placement of one virtual machine in a cluster is interchangeable with a server placement of another virtual machine in the same cluster while satisfying the set of primary constraints. A server placement of the set of virtual machines within each virtual machine on at least one mapped server is generated for each cluster. The server placement substantially satisfies a set of secondary constraints.
Owner:IBM CORP
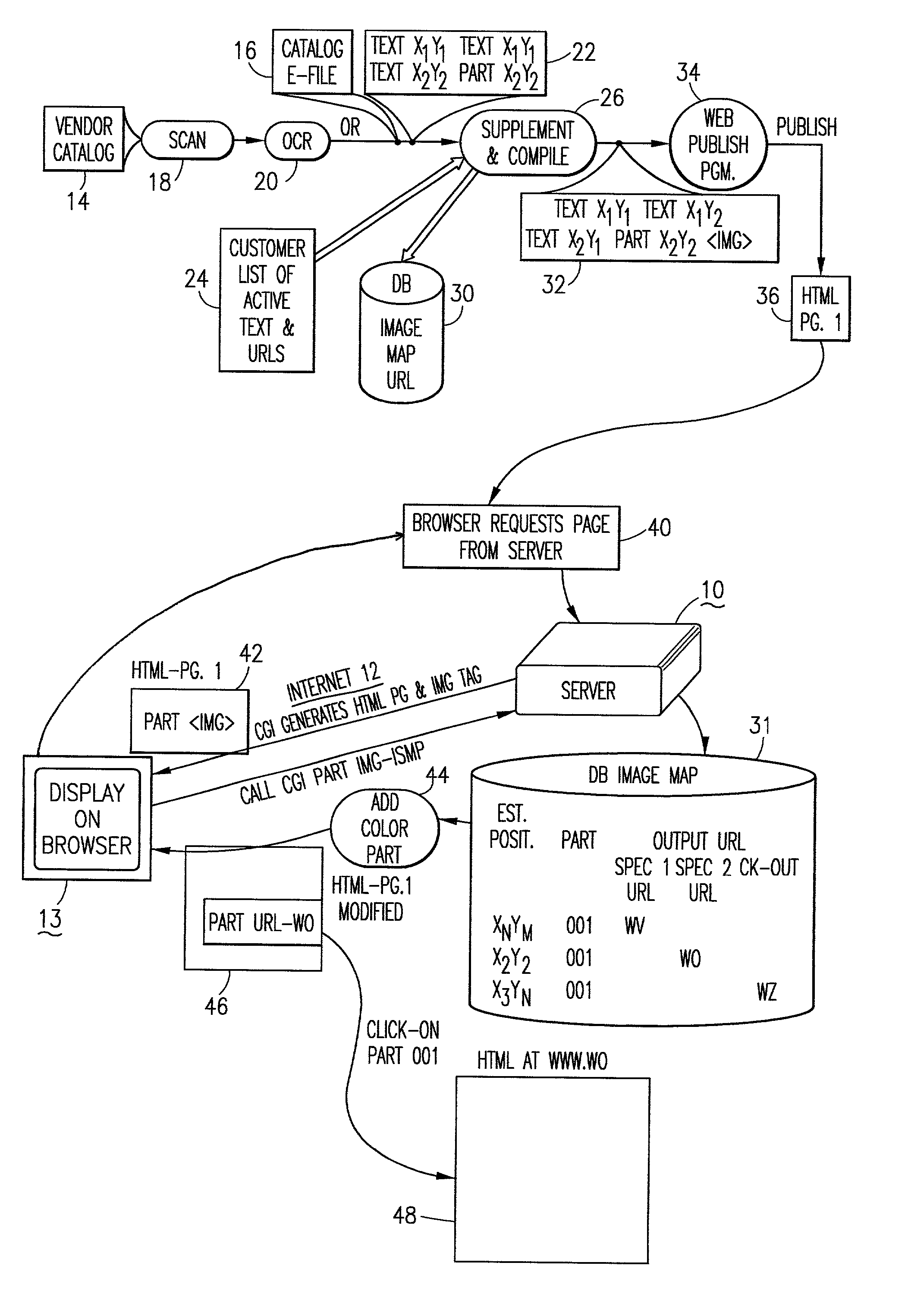
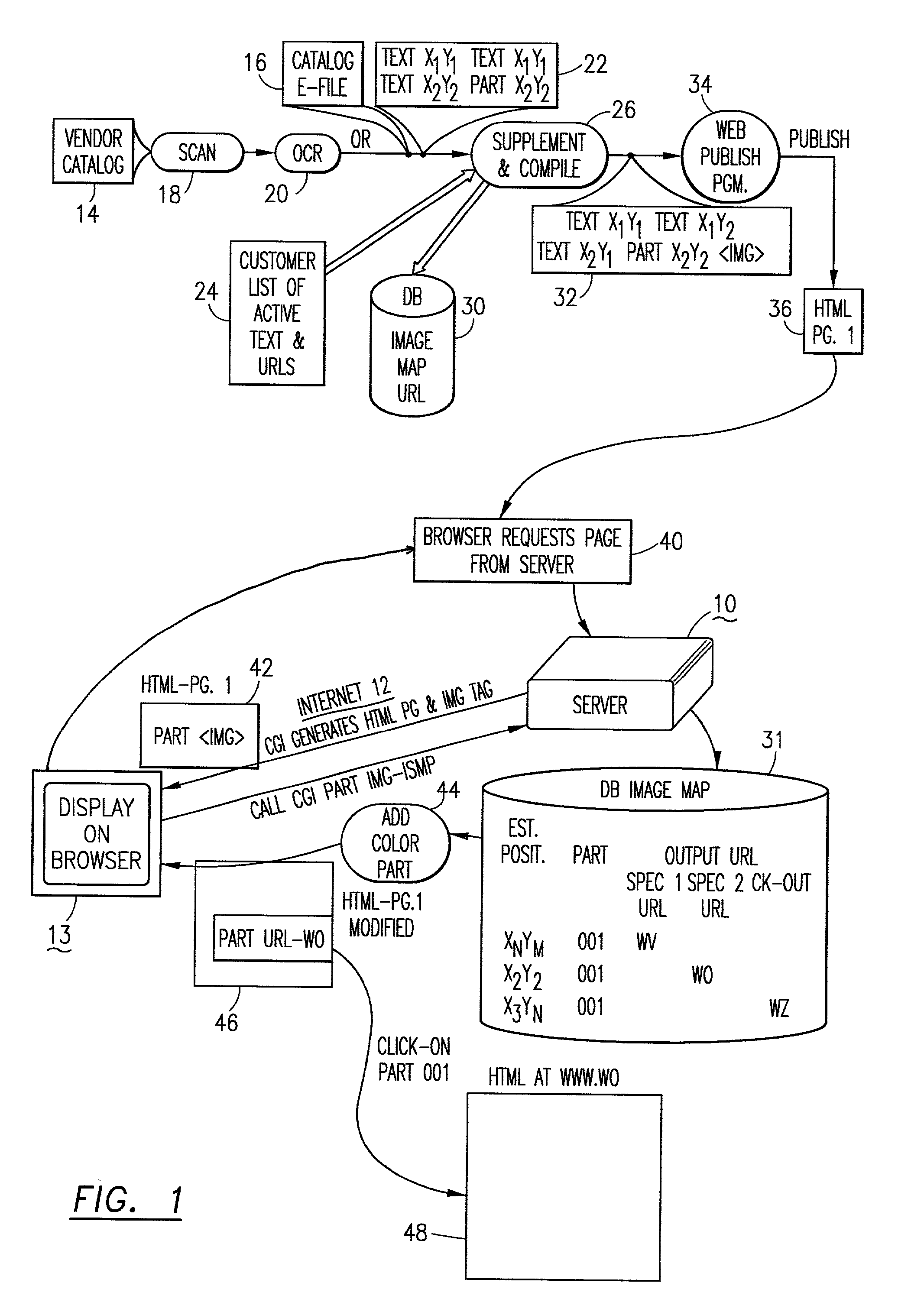
System and method for placing active tags in HTML document
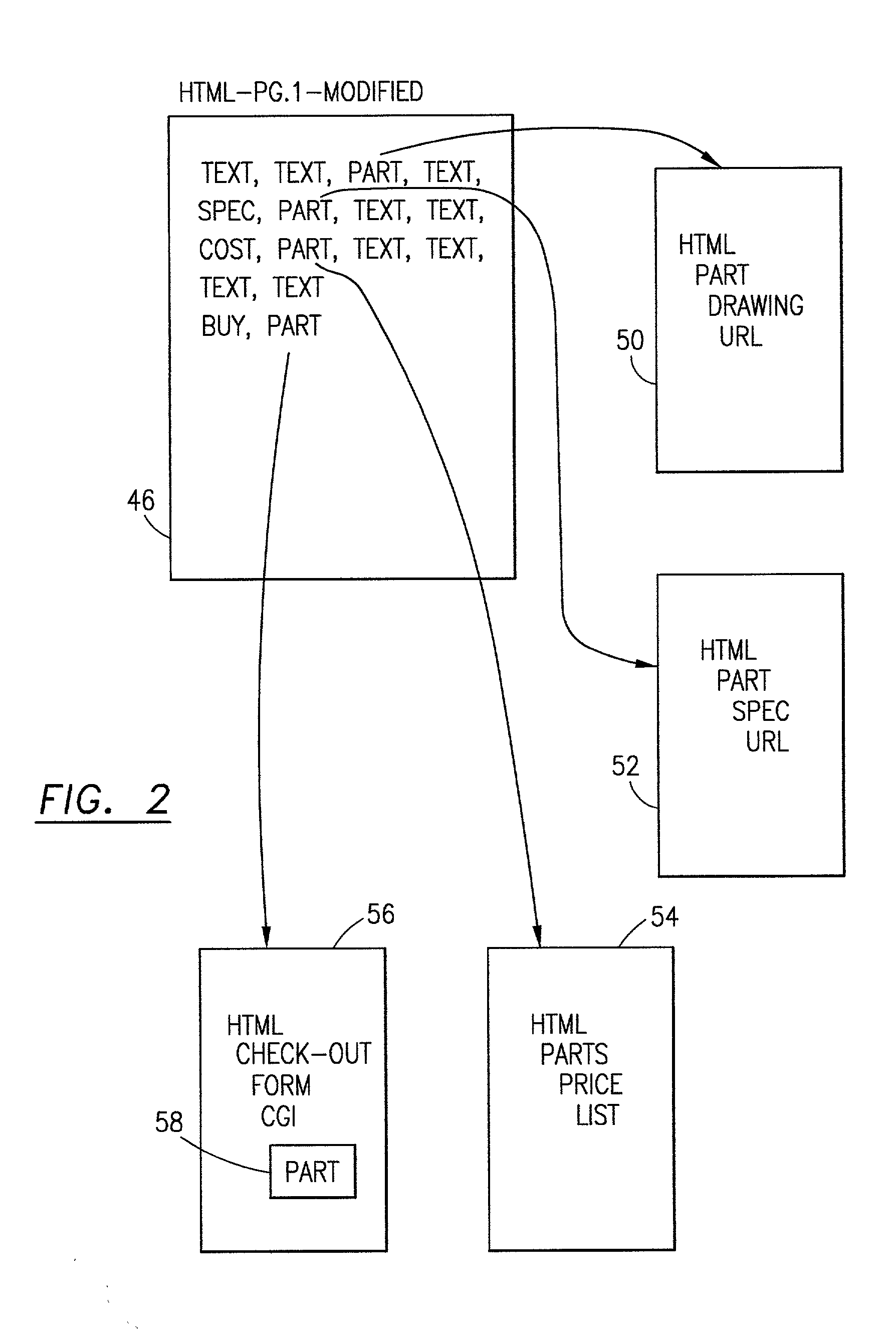
InactiveUS20020069222A1Quick conversionNatural language data processingSpecial data processing applicationsInformation processingDocument preparation
The method and the information processing system dynamically creates an HTML document with at least one embedded hyperlink code therein. The HTML document is based upon a source document provided by a manufacturer or a supplier of services. Typically, the system and the method is operable in a client-server computer environment. A database is provided on the server computer system which database associates location data of a plurality of data strings in the source document with hyperlink addresses. The location data in the database maps at least one predetermined data string in the source document. An HTML document, based upon the source document, is published with an image tag on, in or near the predetermined data string. As an example, the string may be a "part number" or a string of words "SONY PLAYSTATION II.". The published HTML document has an image tag on, at or near the part number and a map attribute command which supplies or generates an HTML location data unique to the image tag location in the HTML document when the browser calls the server's common gateway interface (CGI). The image tag URL points to the database on the server. The server, via the database provides a corresponding hyperlink address, associated with the unique location data correlated to the HTML location data, to the browser on the client computer system. The method and the system then publishes and embeds in the original or initial HTML document at, on or near the predetermined data string or part number an active hyperlink tag (an embedded code) with the corresponding hyperlink address obtained from the database.
Owner:WIZNET
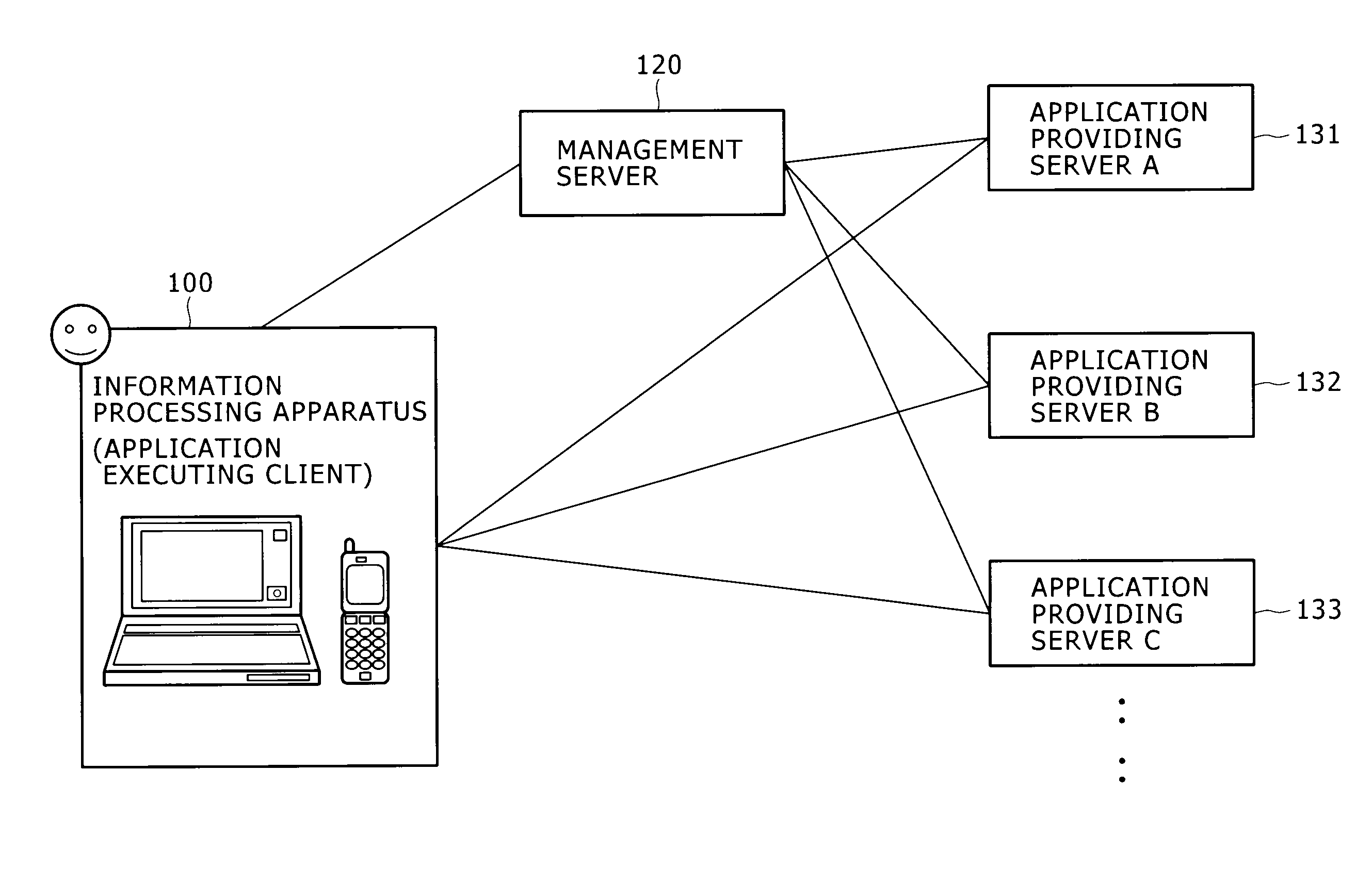
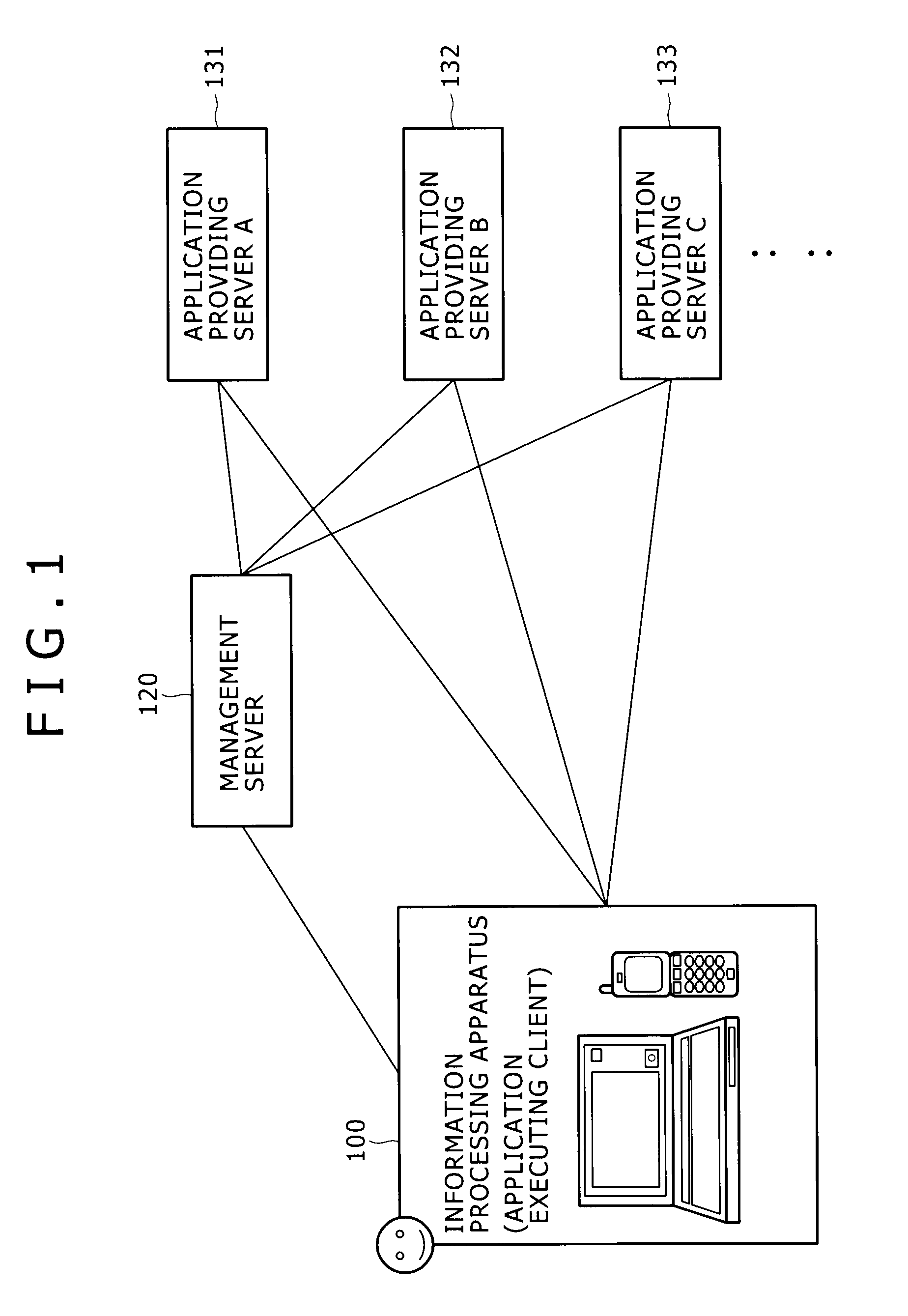
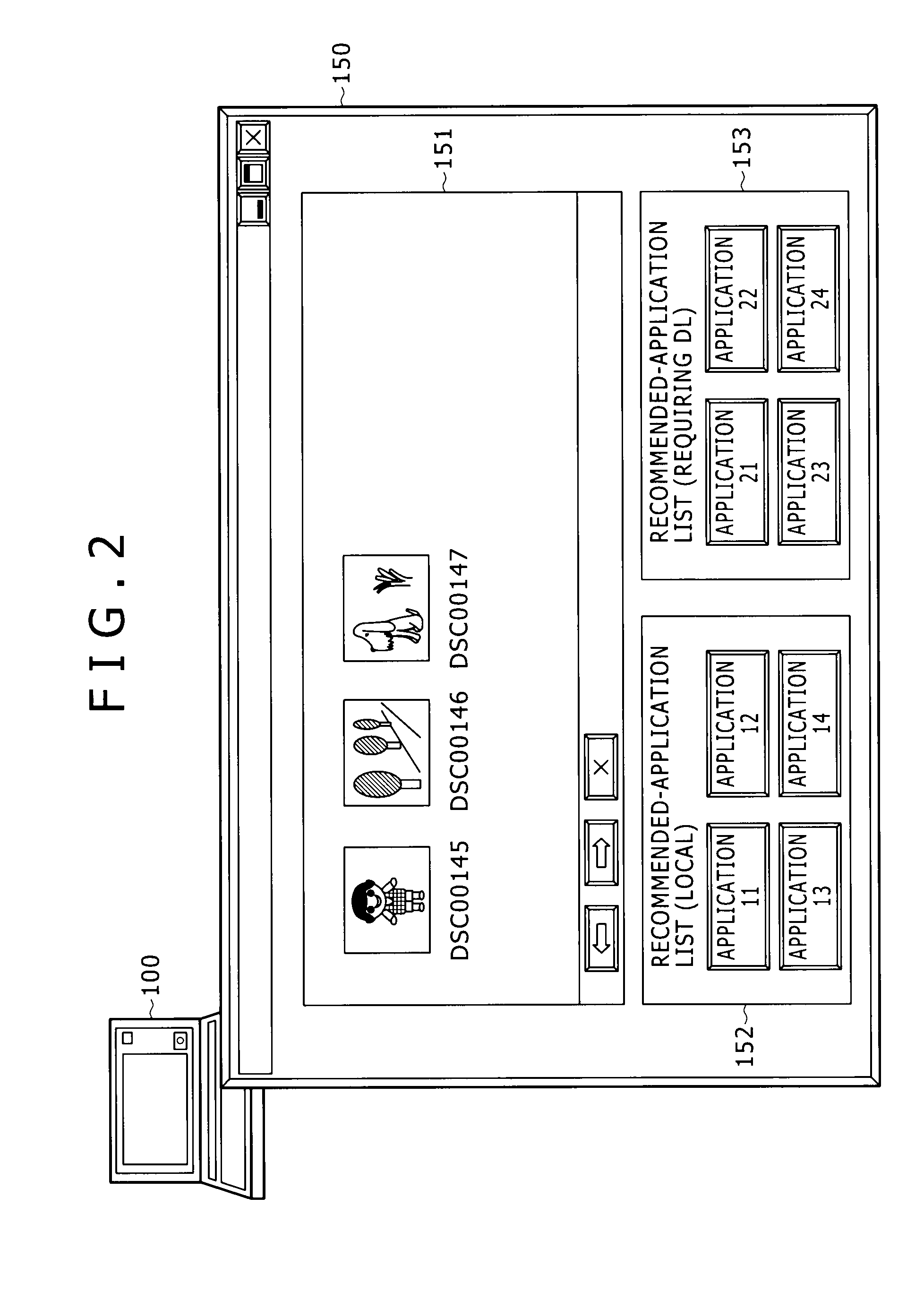
Information processing apparatus and information processing method
ActiveUS20100146442A1Easy to getMultiple digital computer combinationsOffice automationInformation processingRelevant information
Disclosed herein is an information processing apparatus including: a communication section configured to acquire application programs from external apparatus; a memory used for storing at least an application program and information relevant to the application program; an application execution section configured to execute the application program stored in the memory; and a control section configured to determine other application programs to be recommended in the course of execution of the application program in the application execution section, wherein information stored in the memory as the information relevant to the application program includes first relevant information and second relevant information which are used for determining the other application programs to be recommended in the course of execution of the application program in the application execution section
Owner:SONY CORP
Providing services for an information processing system using an audio interface
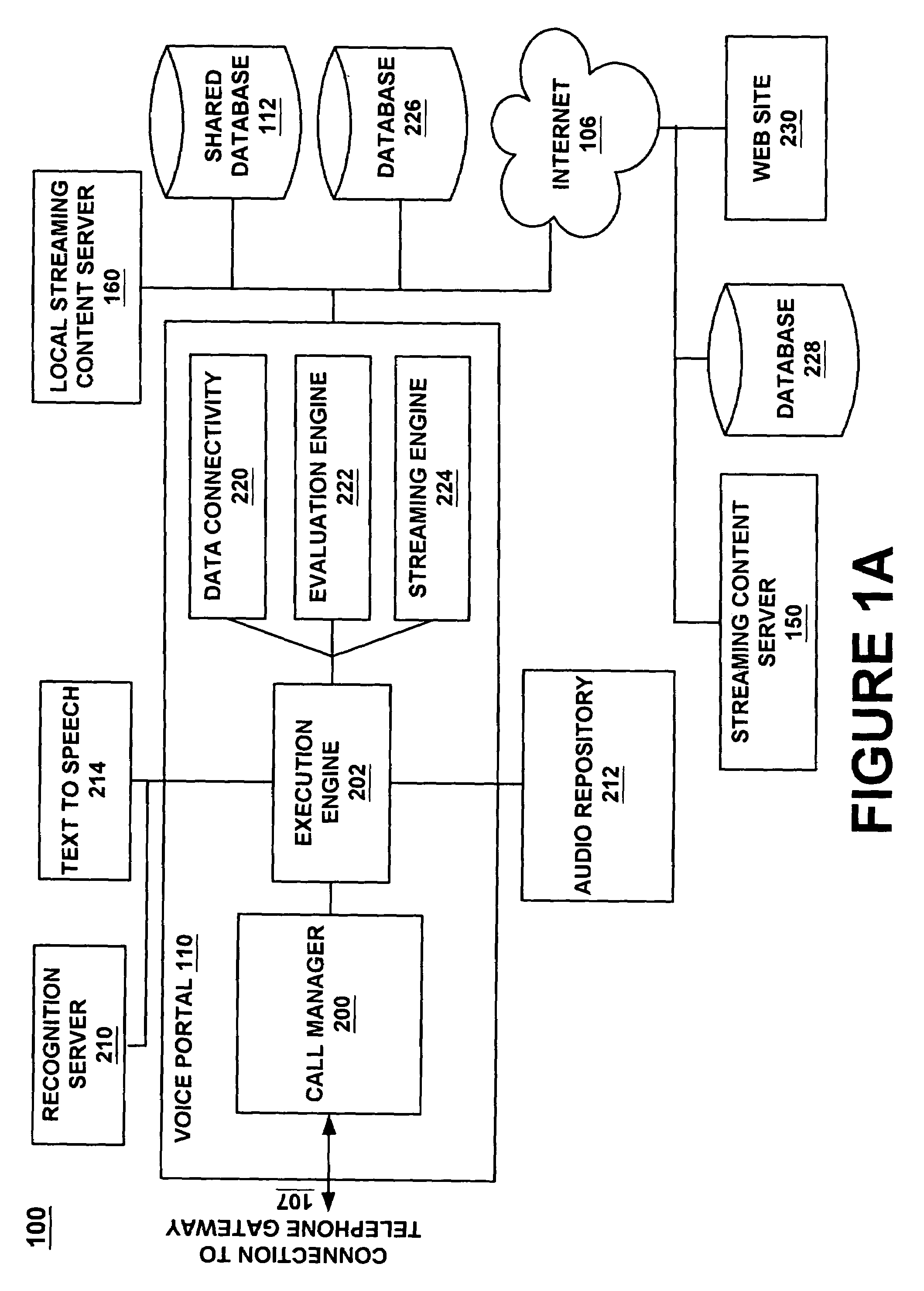
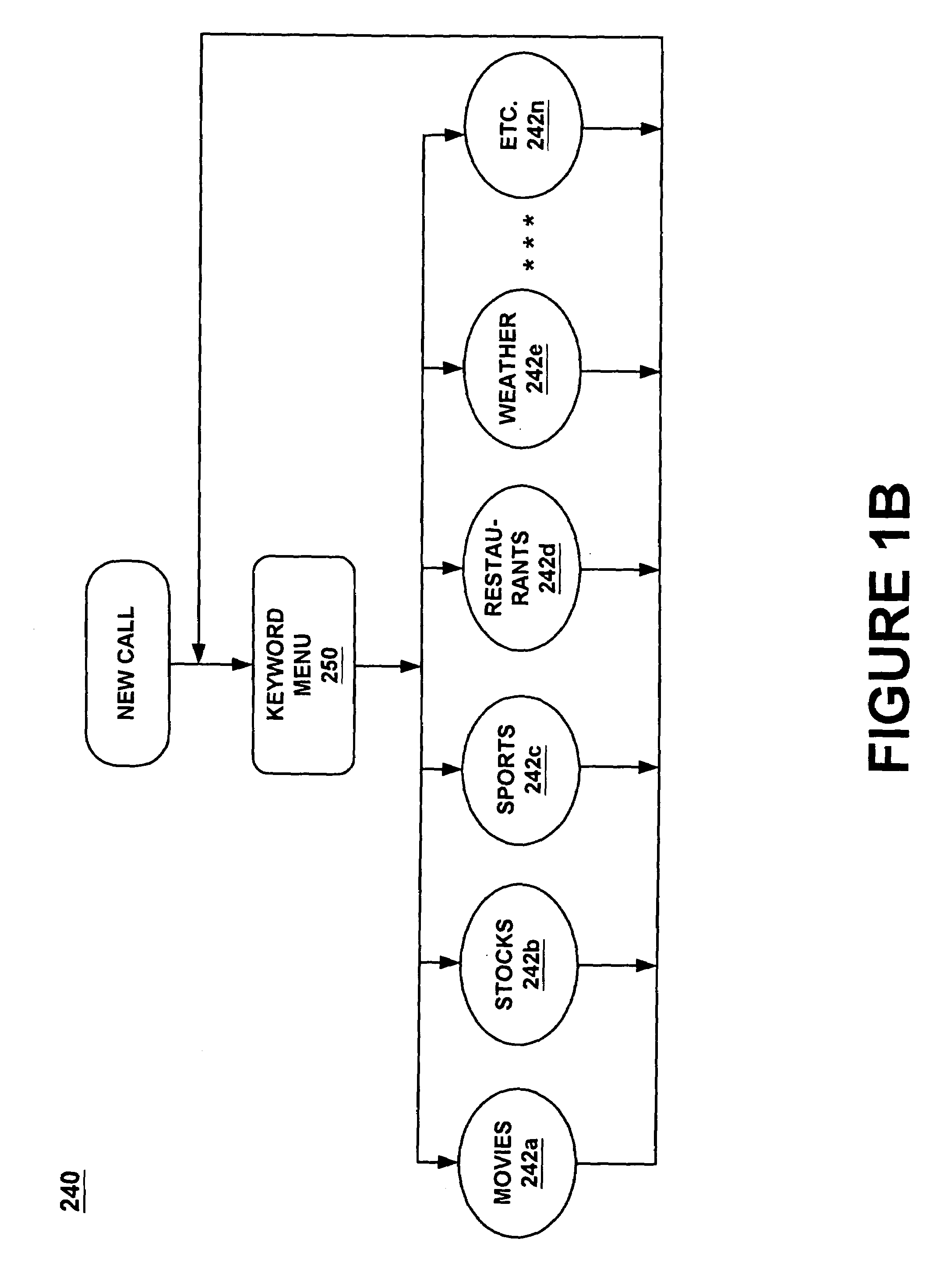
InactiveUS7308408B1Structured and efficient and effectiveEffectivelyAutomatic exchangesSpeech recognitionInformation processingSpeech identification
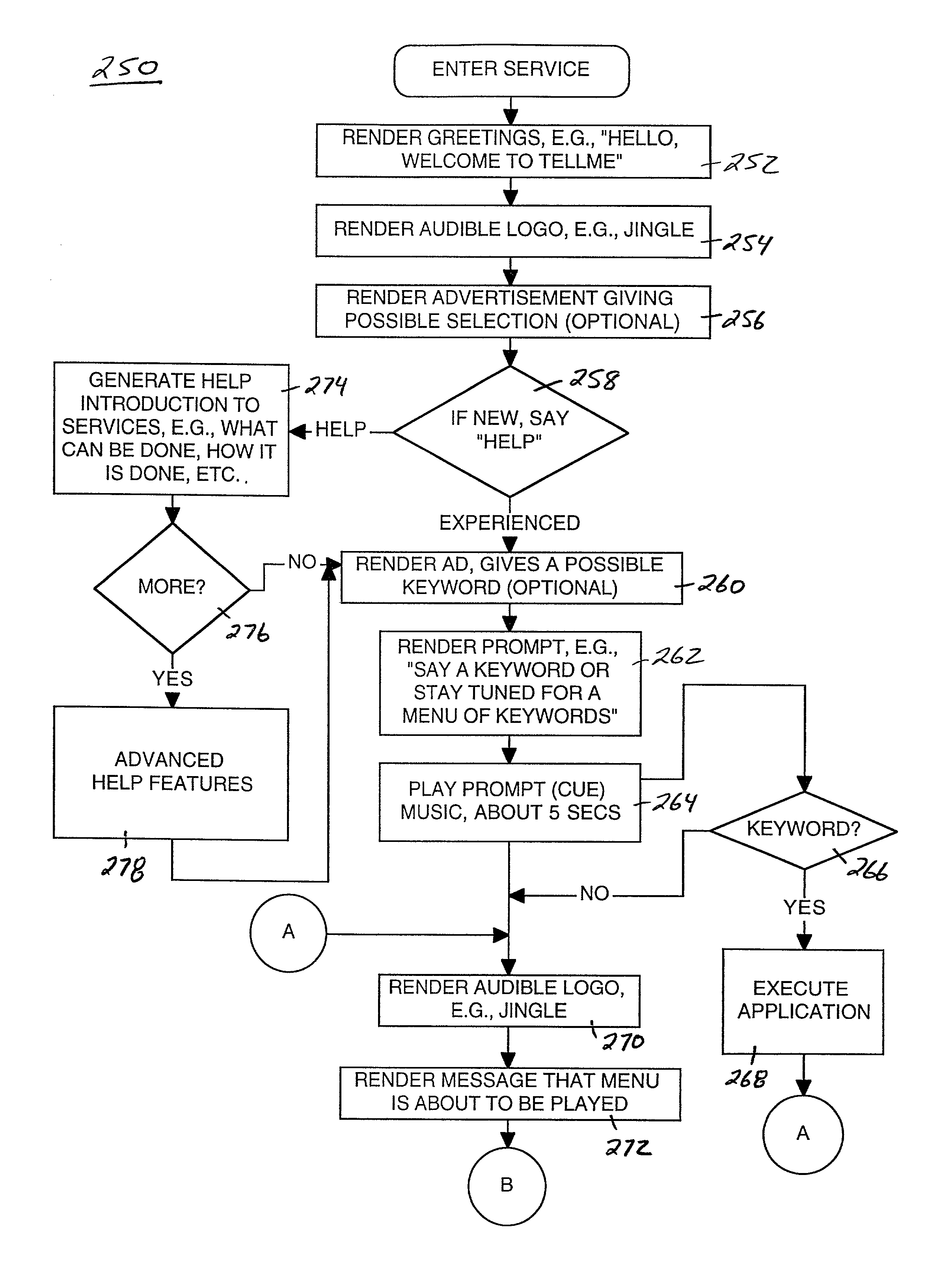
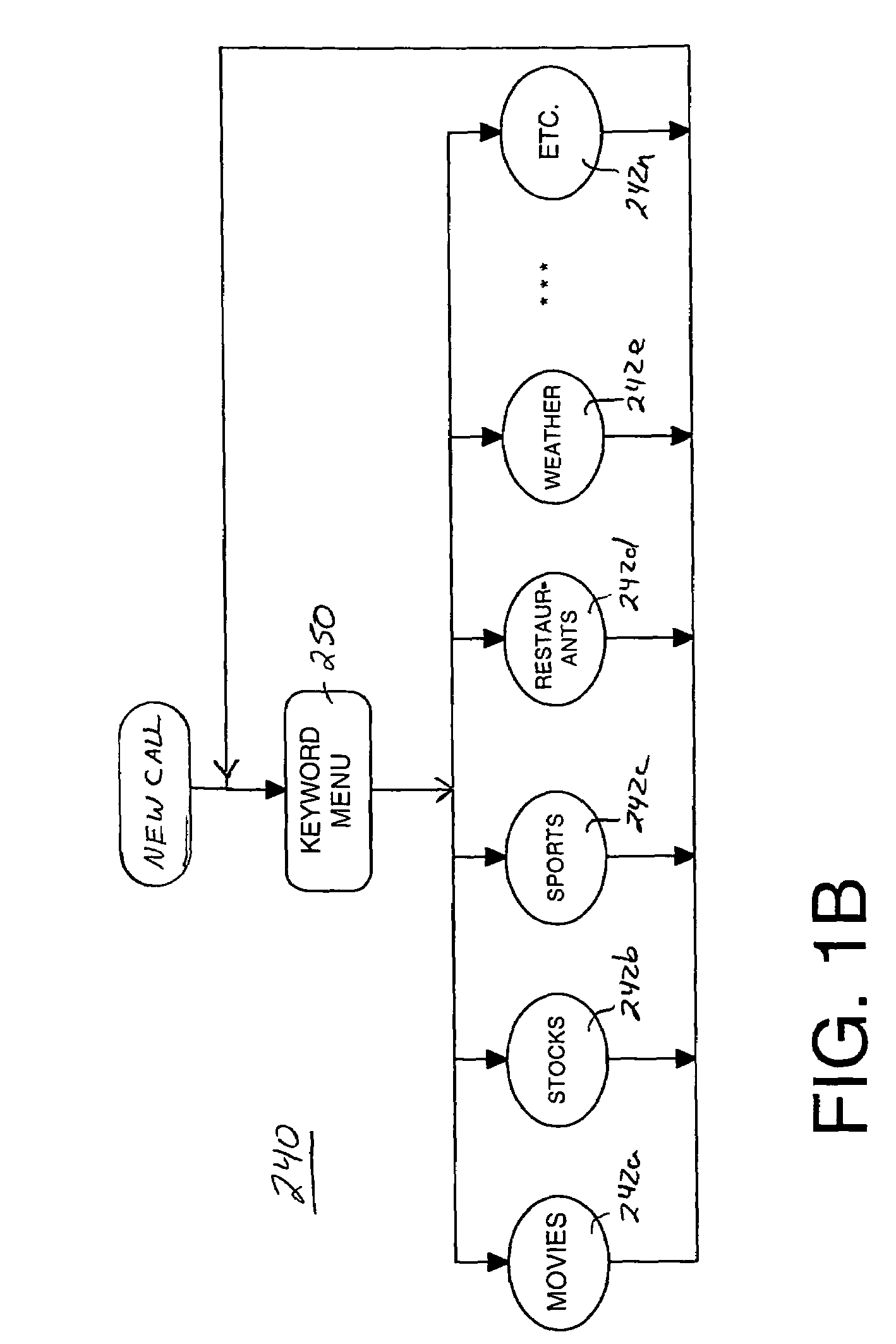
A method and system for providing efficient menu services for an information processing system that uses a telephone or other form of audio user interface. In one embodiment, the menu services provide effective support for novice users by providing a full listing of available keywords and rotating house advertisements which inform novice users of potential features and information. For experienced users, cues are rendered so that at any time the user can say a desired keyword to invoke the corresponding application. The menu is flat to facilitate its usage. Full keyword listings are rendered after the user is given a brief cue to say a keyword. Service messages rotate words and word prosody. When listening to receive information from the user, after the user has been cued, soft background music or other audible signals are rendered to inform the user that a response may now be spoken to the service. Other embodiments determine default cities, on which to report information, based on characteristics of the caller or based on cities that were previously selected by the caller. Other embodiments provide speech concatenation processes that have co-articulation and real-time subject-matter-based word selection which generate human sounding speech. Other embodiments reduce the occurrences of falsely triggered barge-ins during content delivery by only allowing interruption for certain special words. Other embodiments offer special services and modes for calls having voice recognition trouble. The special services are entered after predetermined criterion have been met by the call. Other embodiments provide special mechanisms for automatically recovering the address of a caller.
Owner:MICROSOFT TECH LICENSING LLC
Hand-ear user interface for hand-held device
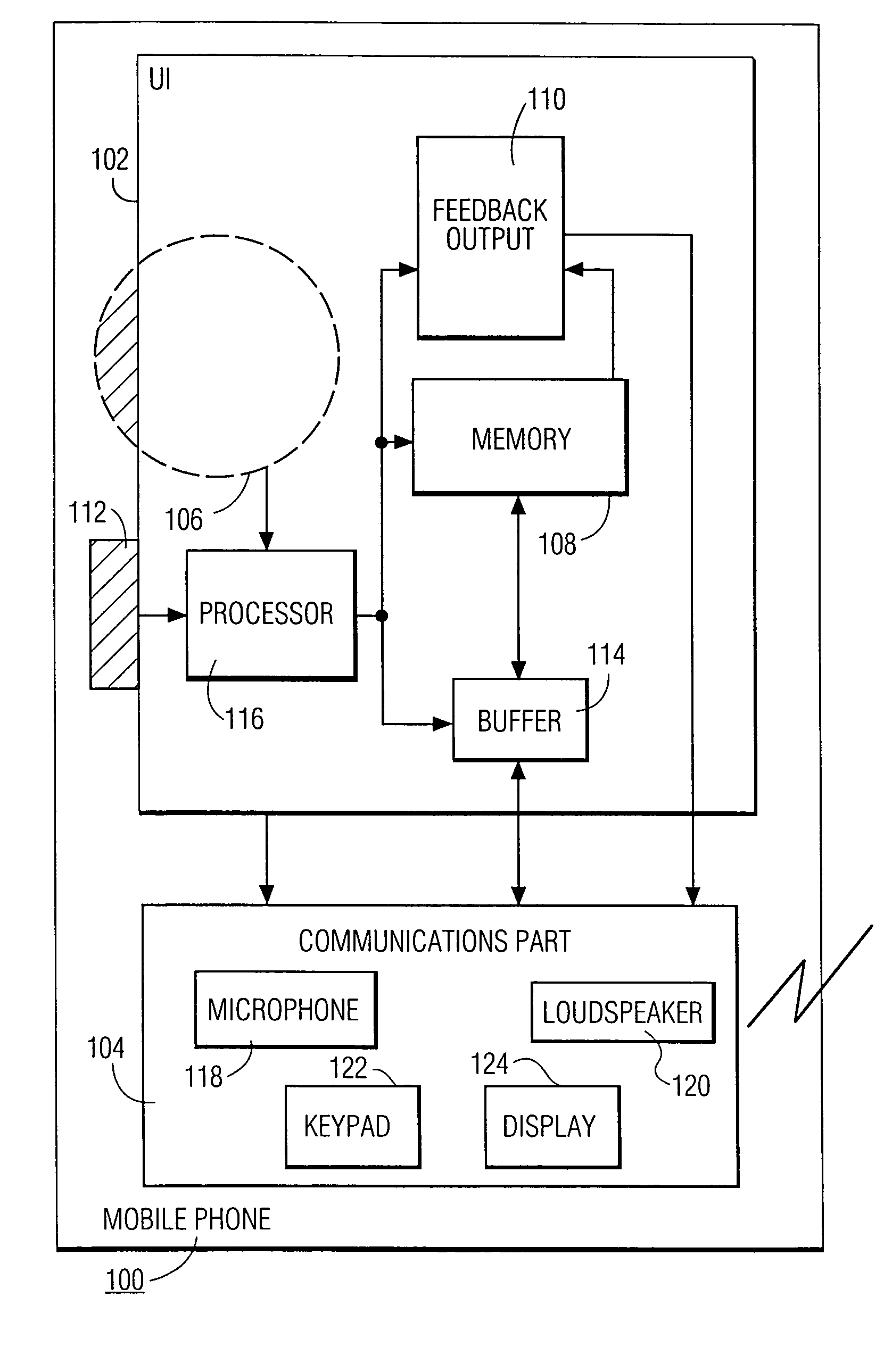
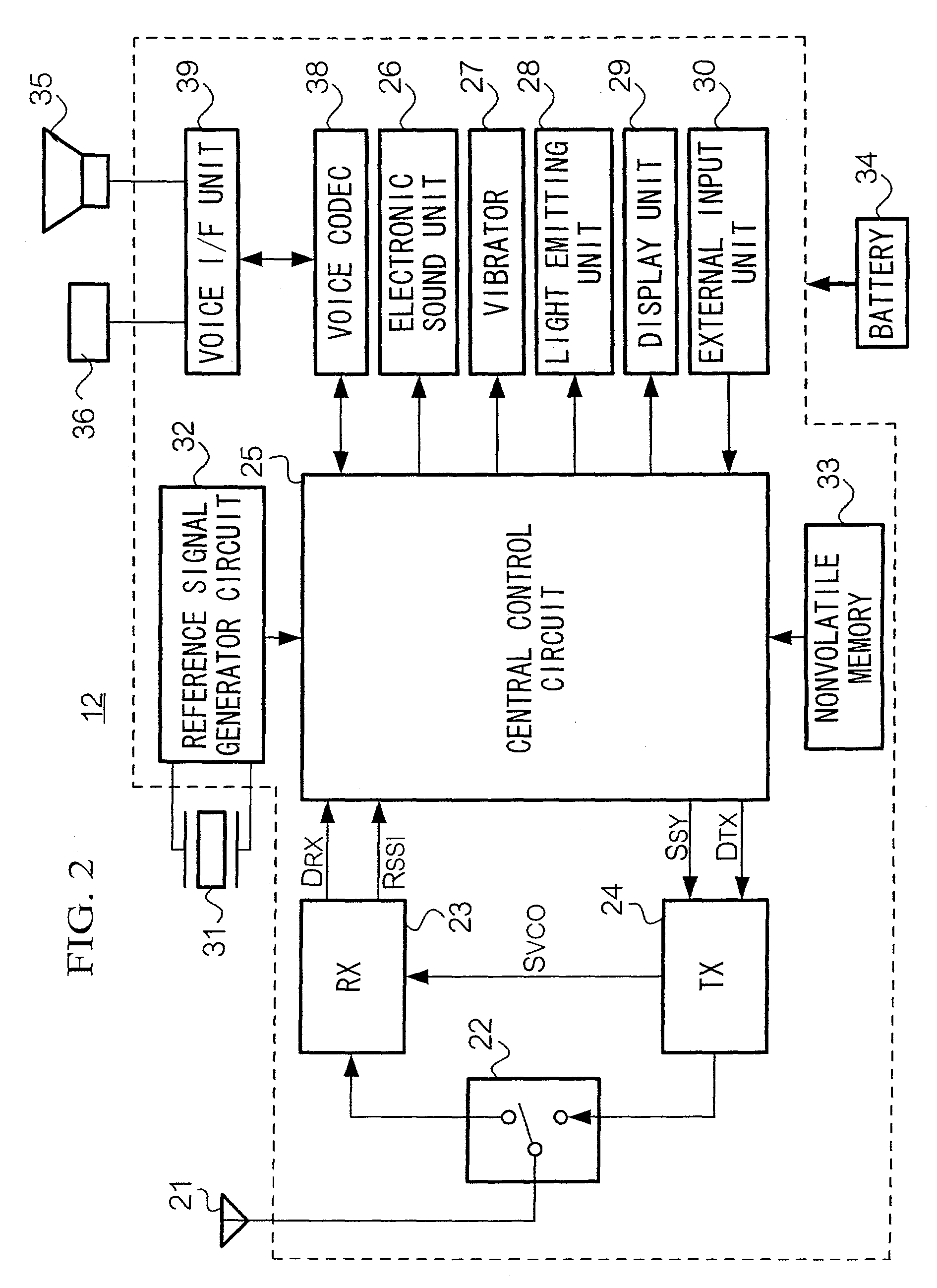
InactiveUS6978127B1Small sizeInput/output for user-computer interactionInterconnection arrangementsInformation processingPersonalization
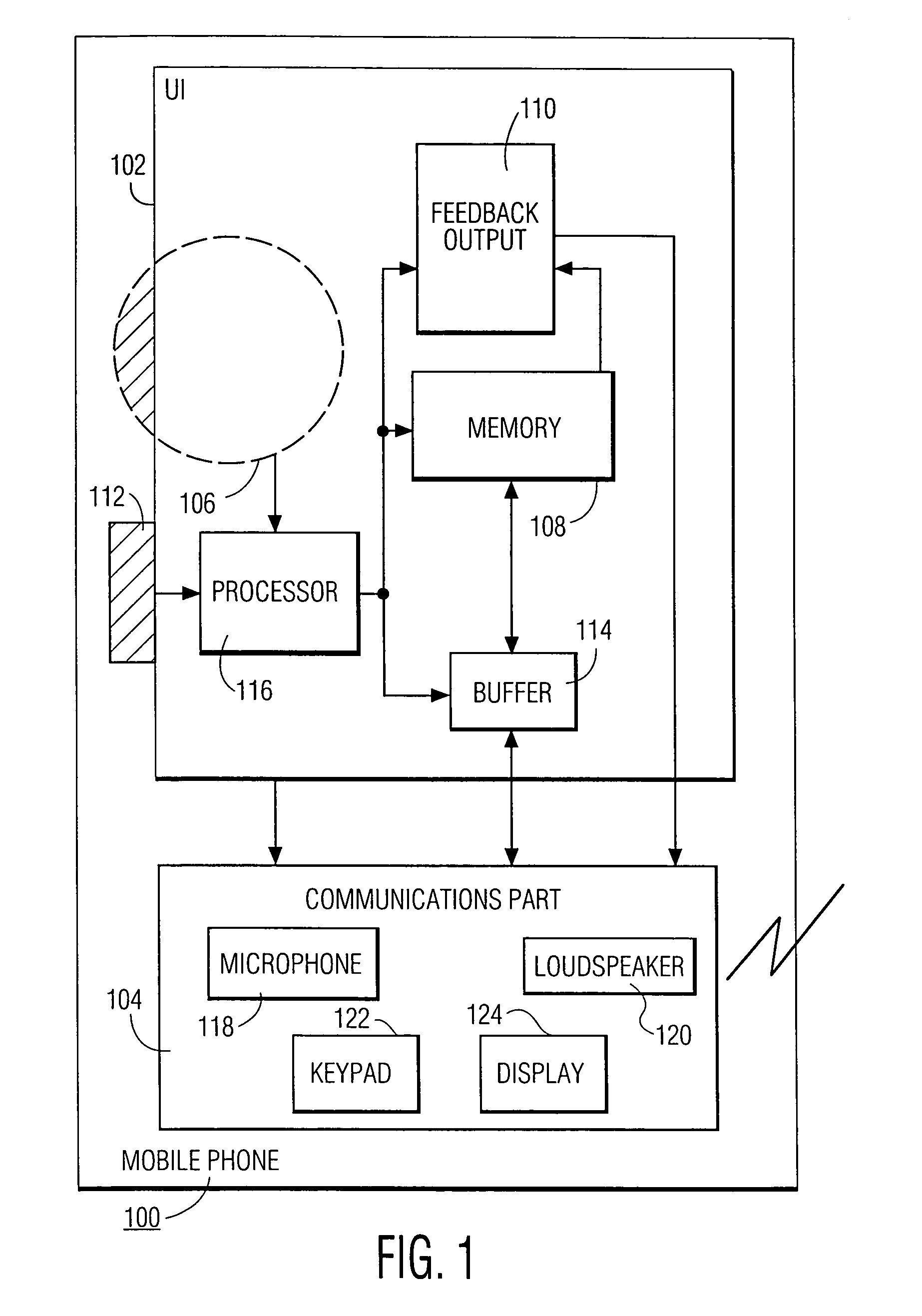
A hand-held information processing device, such as a mobile phone, has a thumb wheel that lets the user scan a circular array of options. Each respective one of the options is represented by a respective audio output that gets played out when the wheel is turned a notch up or down. This enables the user to select an option with one hand and without having to look at the device. It also allows for a form factor smaller than that of a conventional mobile phones since a keypad is not needed for entering digits to make a call from a personalized directory.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Methods and apparatus for downloading data between an information processing device and an external device via a wireless communications technique
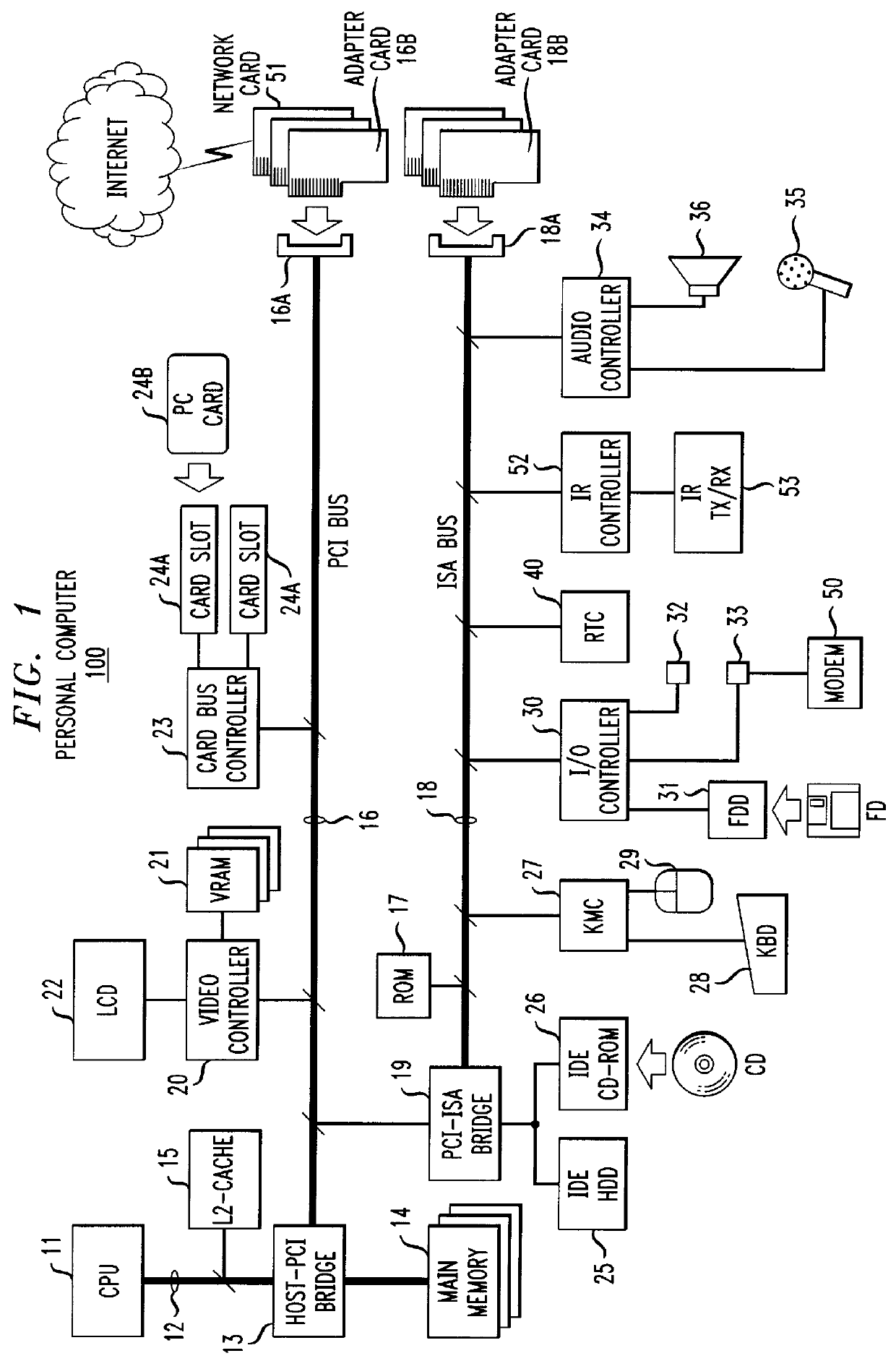
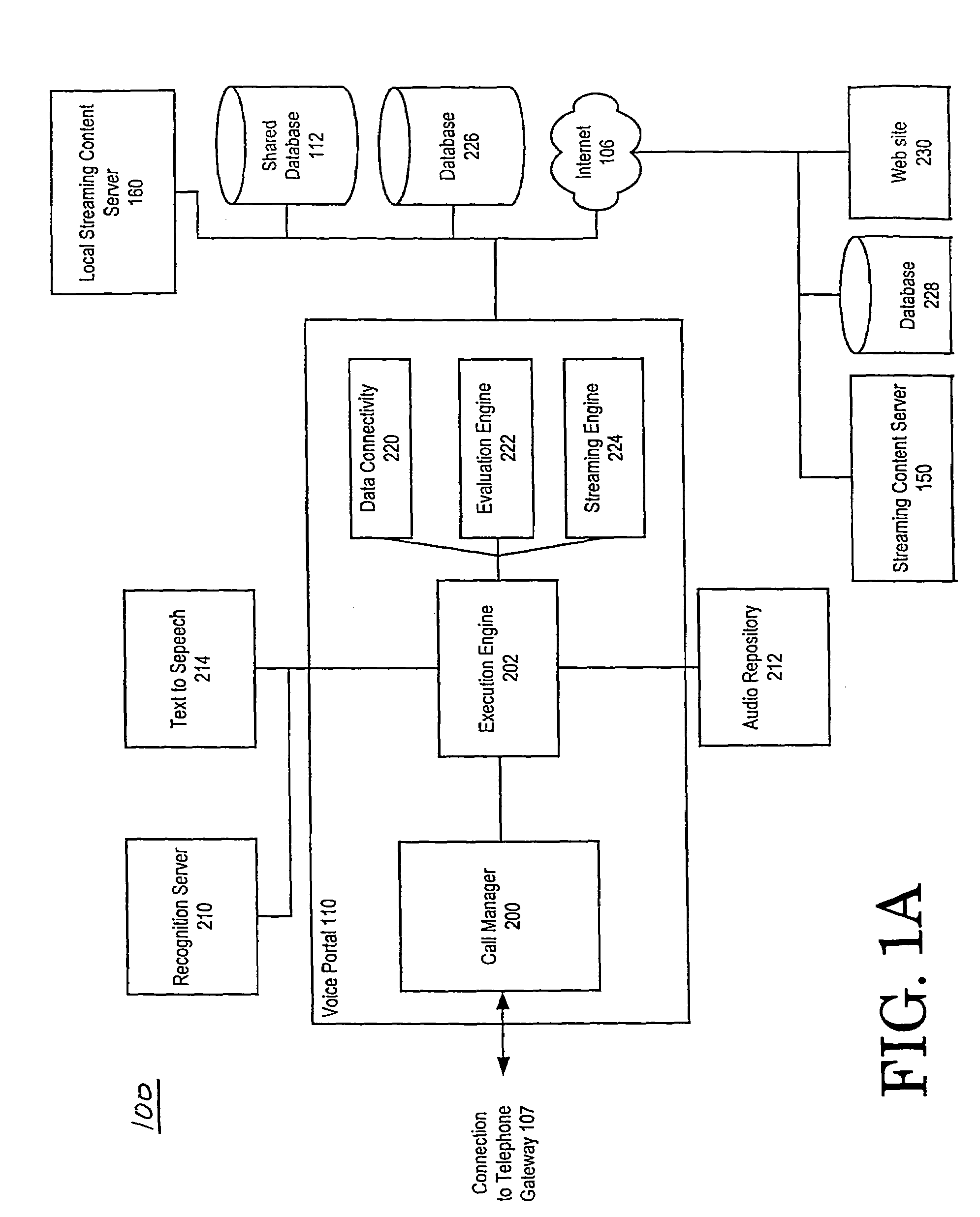
InactiveUS6088730AData smoothingImposing burdenDigital data processing detailsNetwork topologiesComputer hardwareInformation processing
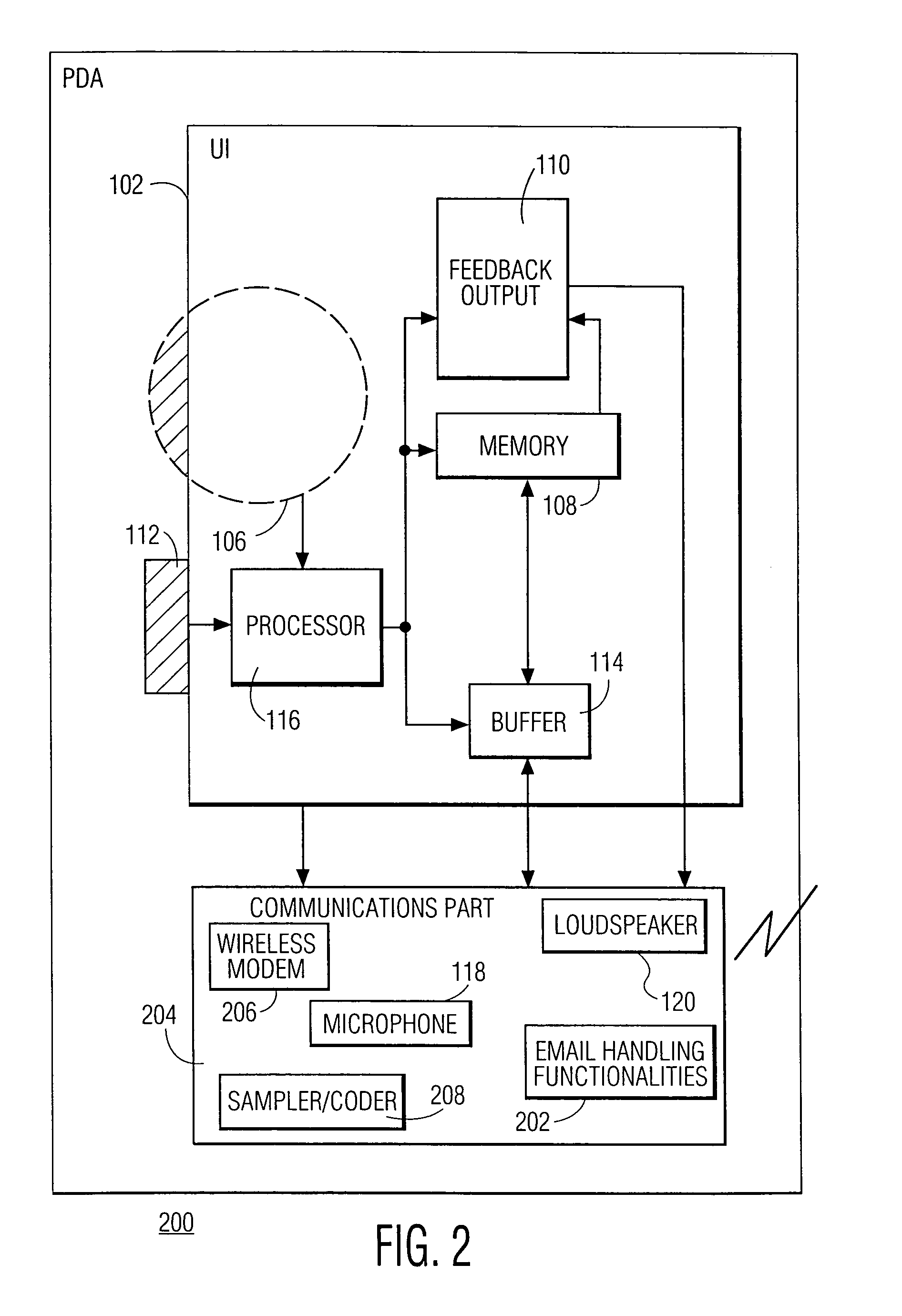
To provide an improved information processing apparatus and a method for controlling the same, which enables to smoothly transfer data, such as processed results obtained from execution of an application program, an HTML file acquired from a Web server in accordance with the TCP / IP protocol or the like, to an external device (PDA) by using an infrared communication function. The disclosed information processing apparatus periodically accesses a predetermined server machine (e.g., a Web server) to acquire a desired file (e.g., an HTML file). This file acquisition operation is carried out without the involvement of operations of an infrared transceiver. In other words, the information processing apparatus attempts to continually perform caching of the most recent download data. As a result, when the PDA as an external device is set into an infrared communication mode and a user simply holds the PDA to a station discoverable region of the information processing apparatus, a connection between them is established, thereby enabling the PDA to receive the most recent data.
Owner:IBM CORP
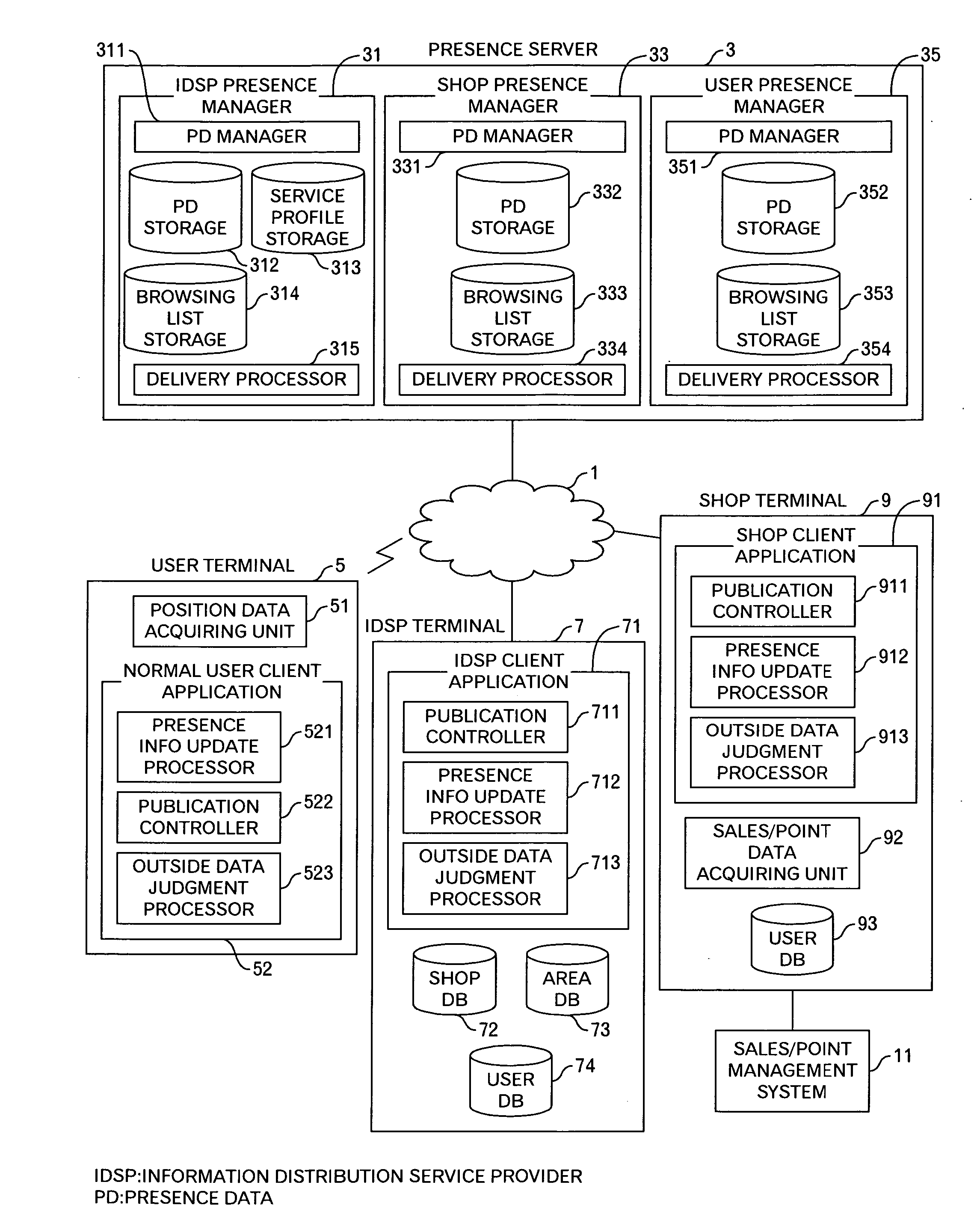
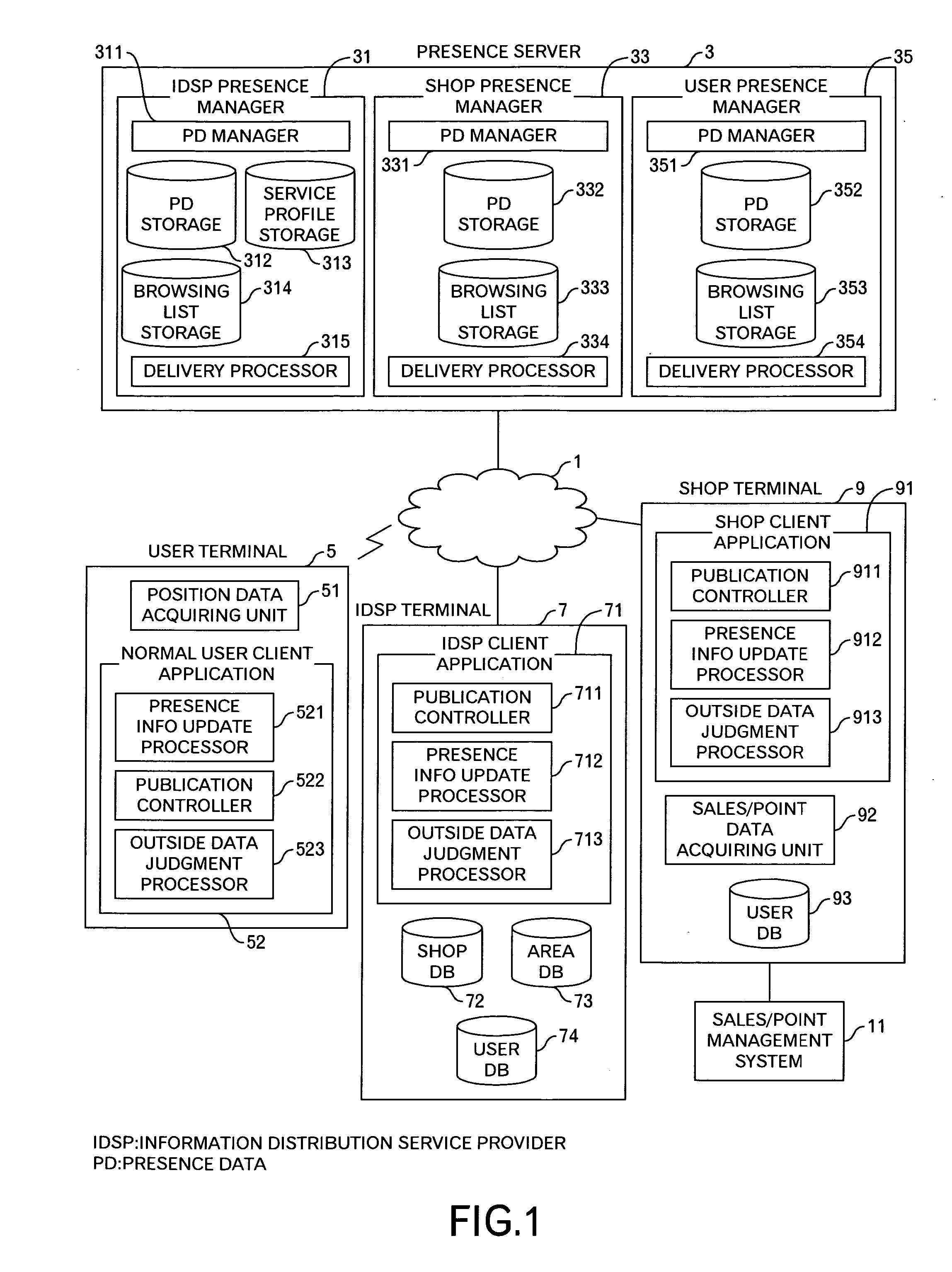
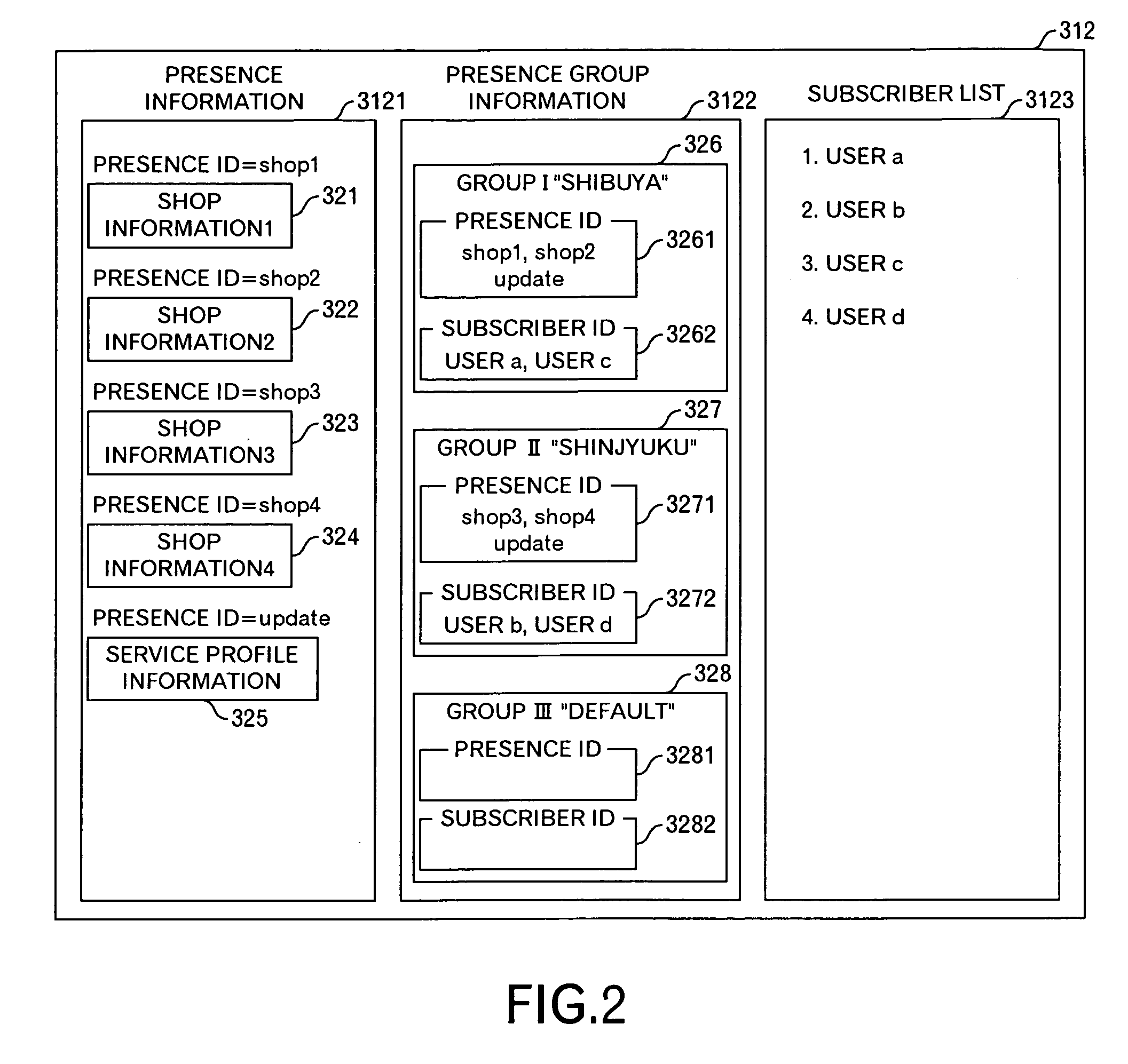
Presence information processing method and computer
InactiveUS20060242239A1Easy delivery settingSpecial service provision for substationMultiple digital computer combinationsInformation processingUser management
The presence information delivery system according to this invention manages, for each user, data of one or plural presence group so as to associate one or plural presence information items for the presence information to be delivered with an ID or IDs of one or plural delivery destination user of the presence information relating to the presence information item. With this configuration, by generating a new presence group associating the presence information item with the delivery destination user, by registering the presence information item to another presence group, and by registering the delivery destination user into another presence group, the flexible information delivery is enabled according to characteristics or the like of the delivery destination user and presence information.
Owner:FUJITSU LTD
RFID tag facility with access to external devices
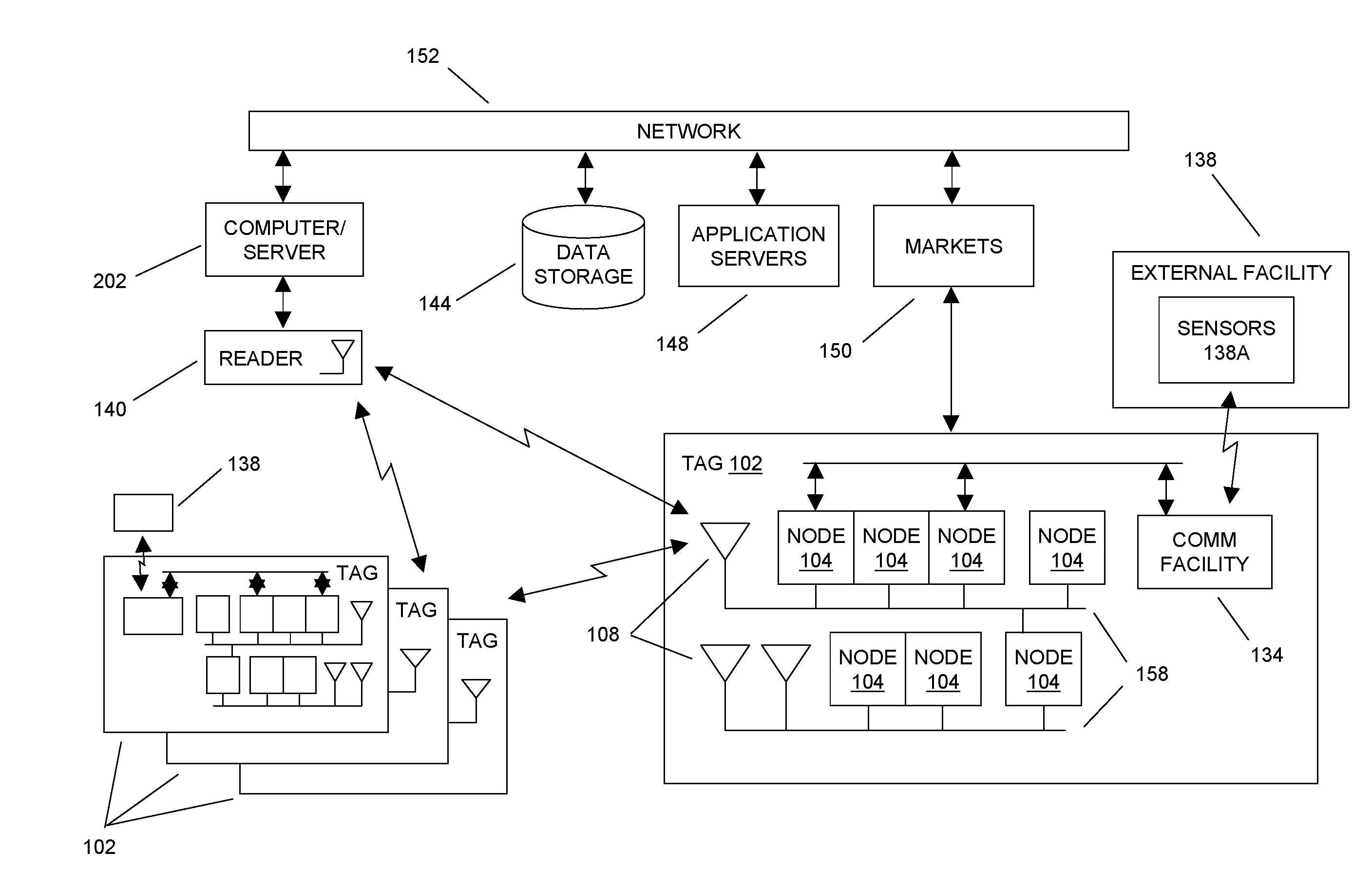
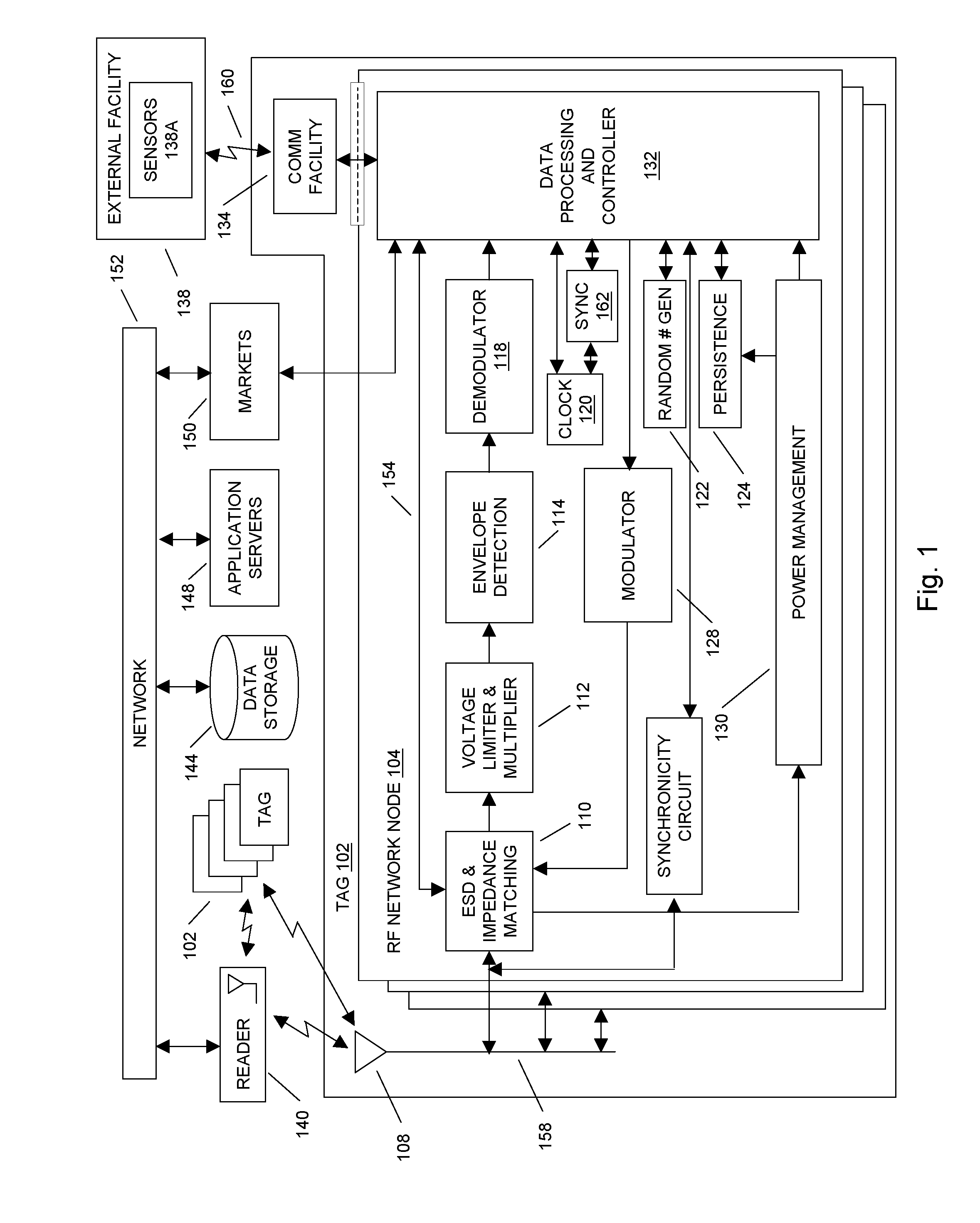
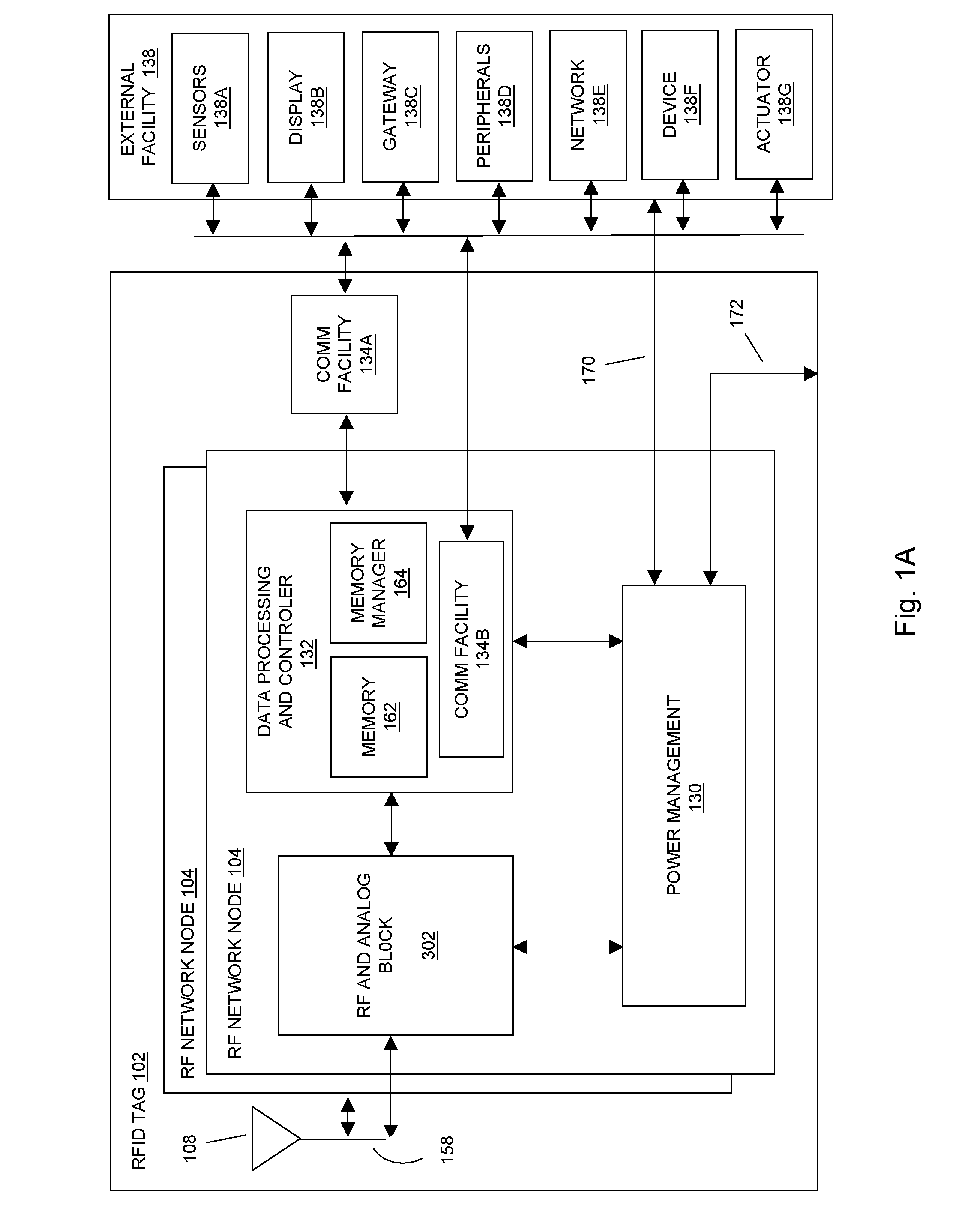
ActiveUS20100134257A1Memory record carrier reading problemsDigital storageInformation processingComputer hardware
In embodiments of the present invention improved capabilities are described for a passive radio frequency identification (RFID) tag, where the passive RFID tag contains an RF network node and communication facility. The RF network node includes an RF and analog block for receiving and transmitting an RFID reader signal, a data processing and controller block for digital information processing, a memory store, and a power management block for managing power requirements of the RF network node. The communication facility communicates at least in part with an external display facility. The distribution of power to the RF network node functional blocks is controlled using the power management block to select between an extended operational time and an increase in available functionality.
Owner:TEGO INC
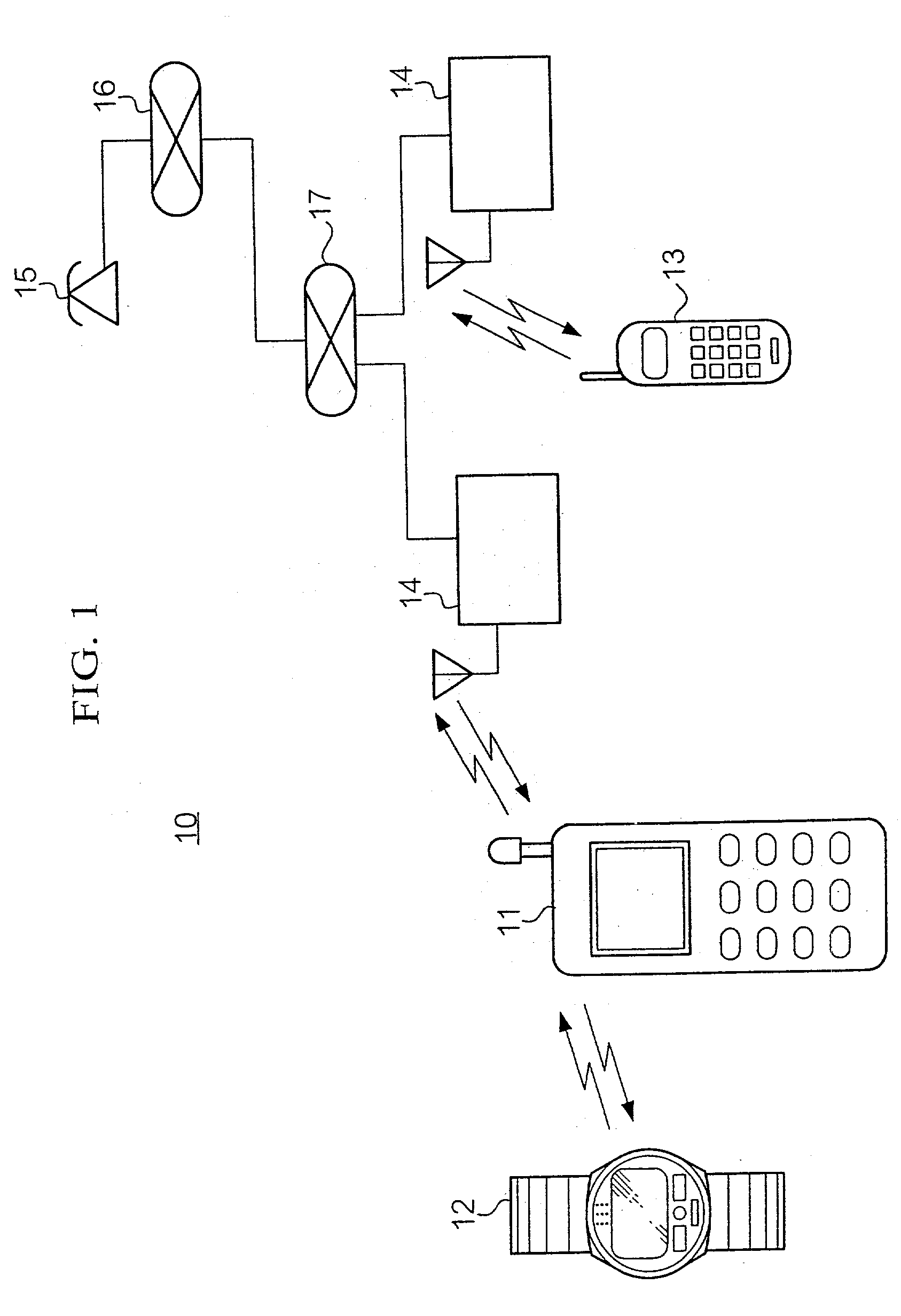
Mobile telephone and radio communication device cooperatively processing incoming call
InactiveUS20020115478A1Substation speech amplifiersAutomatic call-answering/message-recording/conversation-recordingInformation processingComputer science
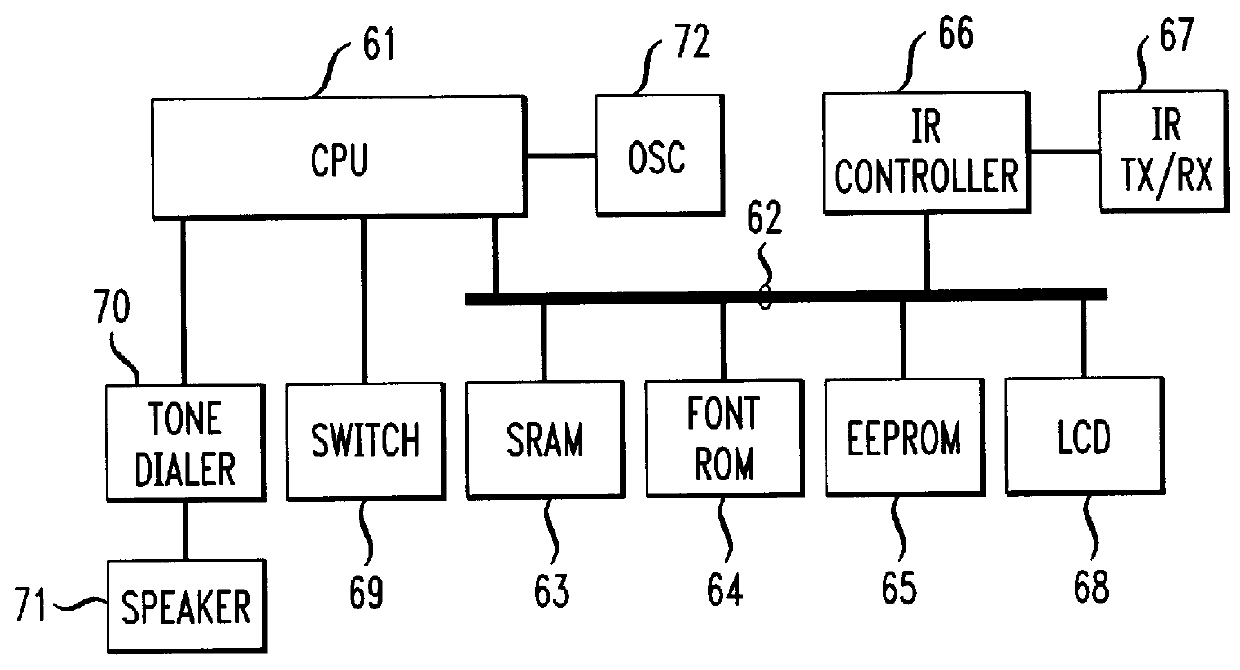
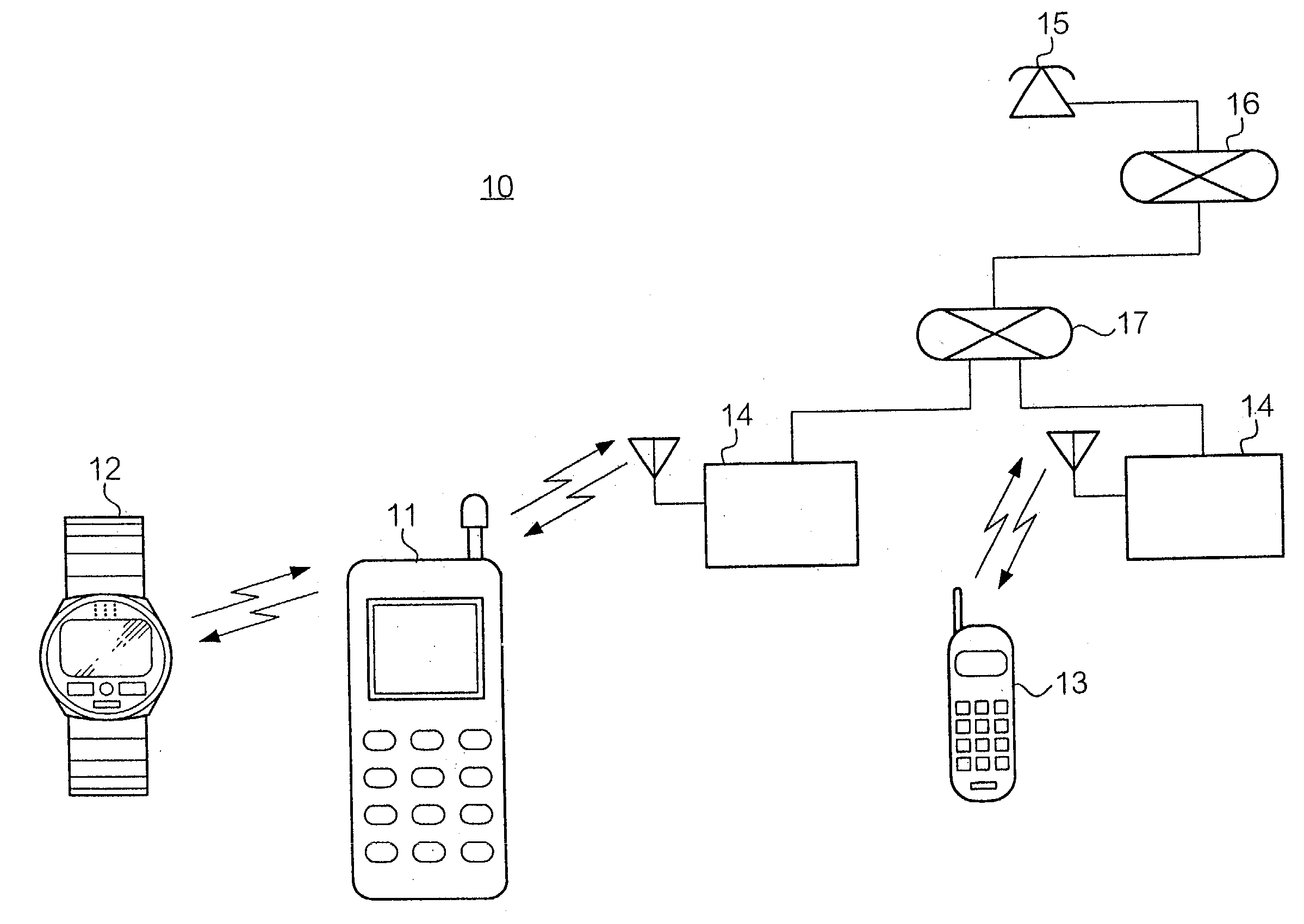
When there is an incoming call to a mobile telephone, it sends an incoming call notification signal to a watch-shaped information processing device. When the watch-shaped information processing device receives the incoming call notification signal, it notifies its user of the incoming call. The watch-shaped information processing device can also sends user's instructions to the mobile telephone. The instructions cause the mobile telephone to conduct processing for incoming call such as processing for asking the caller to wait, or asking the caller to leave a message.
Owner:SEIKO EPSON CORP
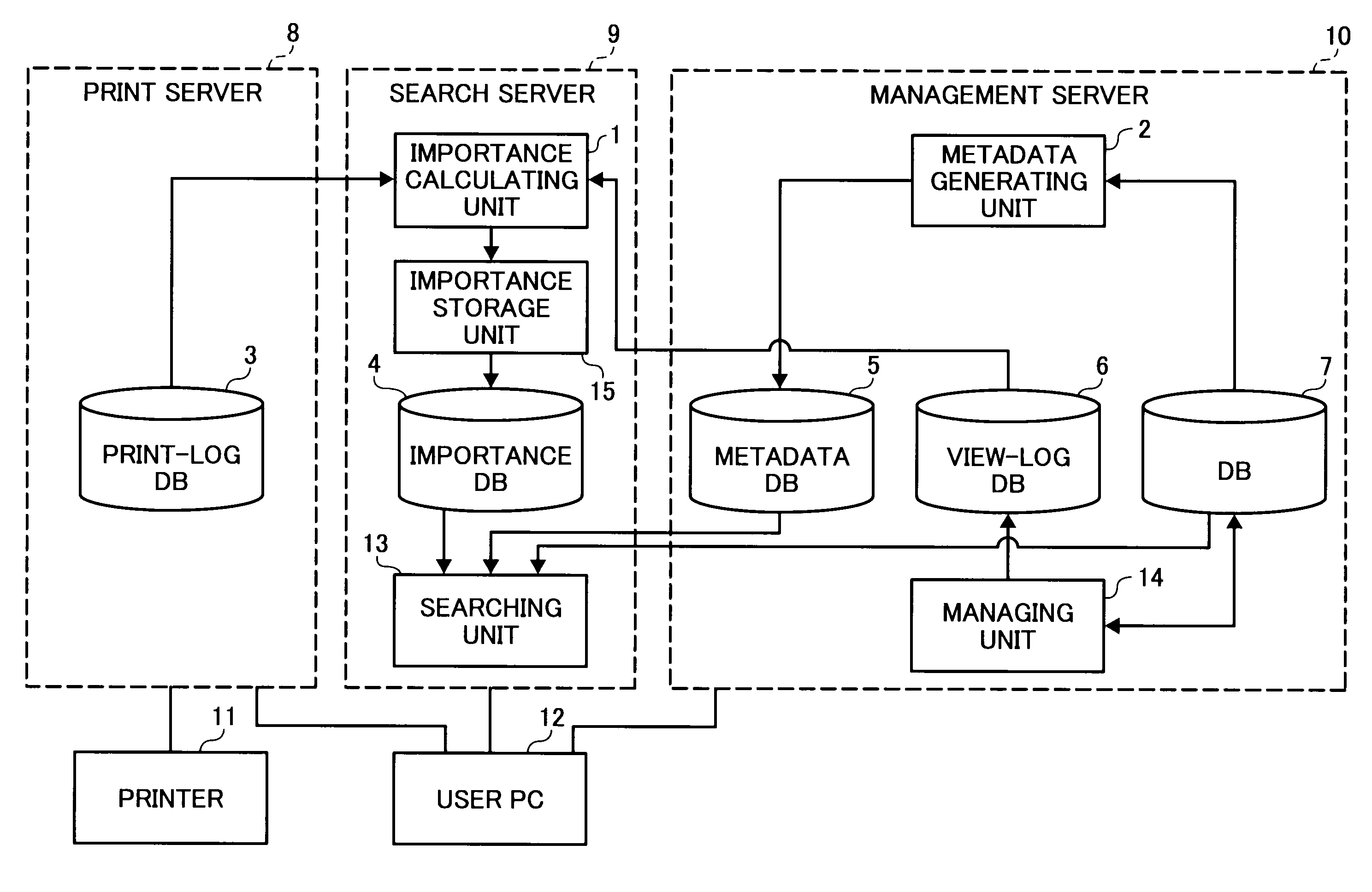
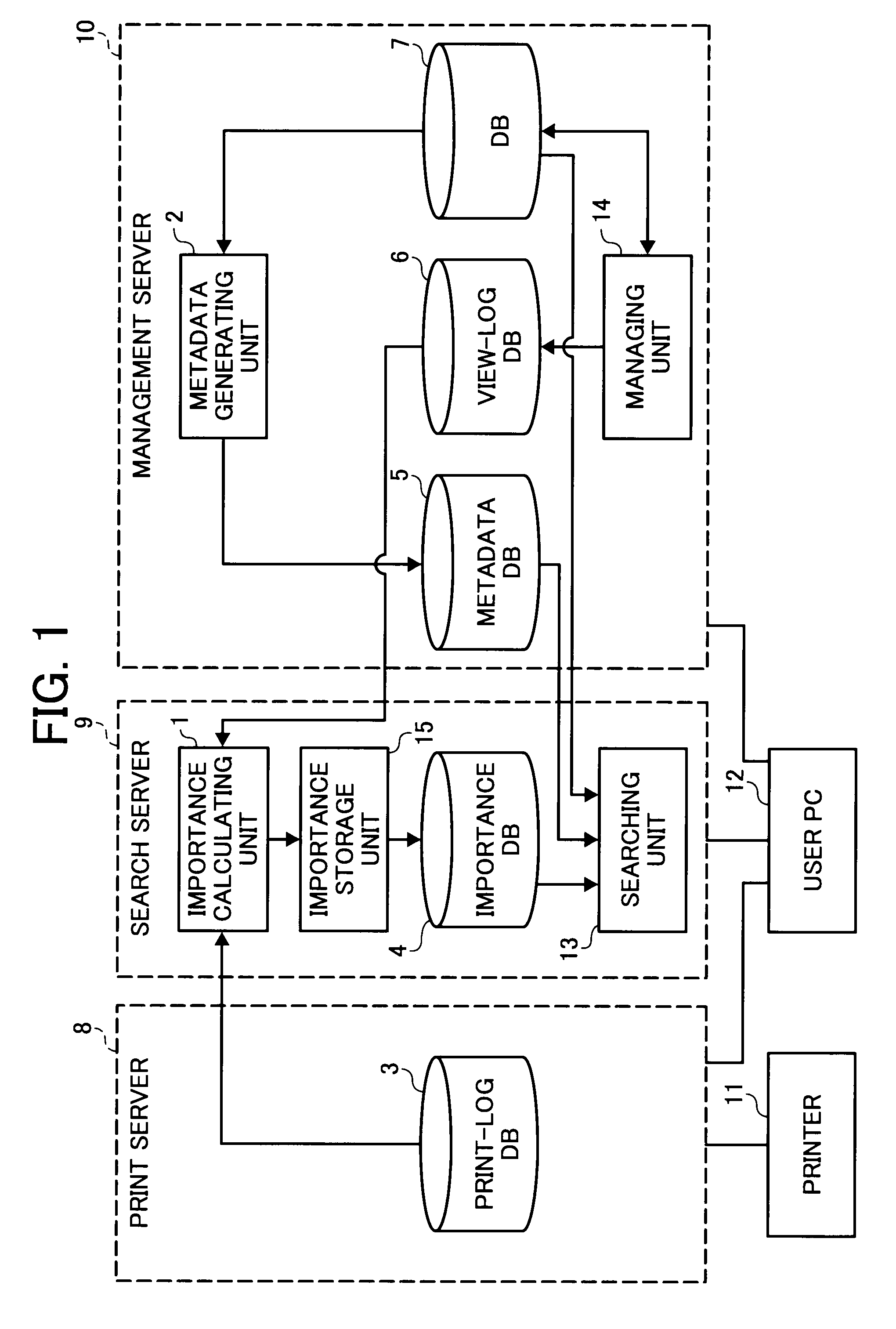
Information processing apparatus, information processing method, and computer program product
InactiveUS7986431B2Data processing applicationsDigital computer detailsInformation processingData mining
An information processing apparatus that calculates importance of data based on a print log. A print-log database stores therein a print log of data printed. A calculating unit refers to the print log to check the number of times of printing the data, and calculates importance of the data based on the number of times of printing. A storing unit stores the importance of the data in an importance database.
Owner:RICOH KK
Using context information to facilitate processing of commands in a virtual assistant
ActiveUS20140297284A1Clarify userReduce in quantityNatural language data processingSpeech recognitionPersonalizationInformation processing
A virtual assistant uses context information to supplement natural language or gestural input from a user. Context helps to clarify the user's intent and to reduce the number of candidate interpretations of the user's input, and reduces the need for the user to provide excessive clarification input. Context can include any available information that is usable by the assistant to supplement explicit user input to constrain an information-processing problem and / or to personalize results. Context can be used to constrain solutions during various phases of processing, including, for example, speech recognition, natural language processing, task flow processing, and dialog generation.
Owner:APPLE INC
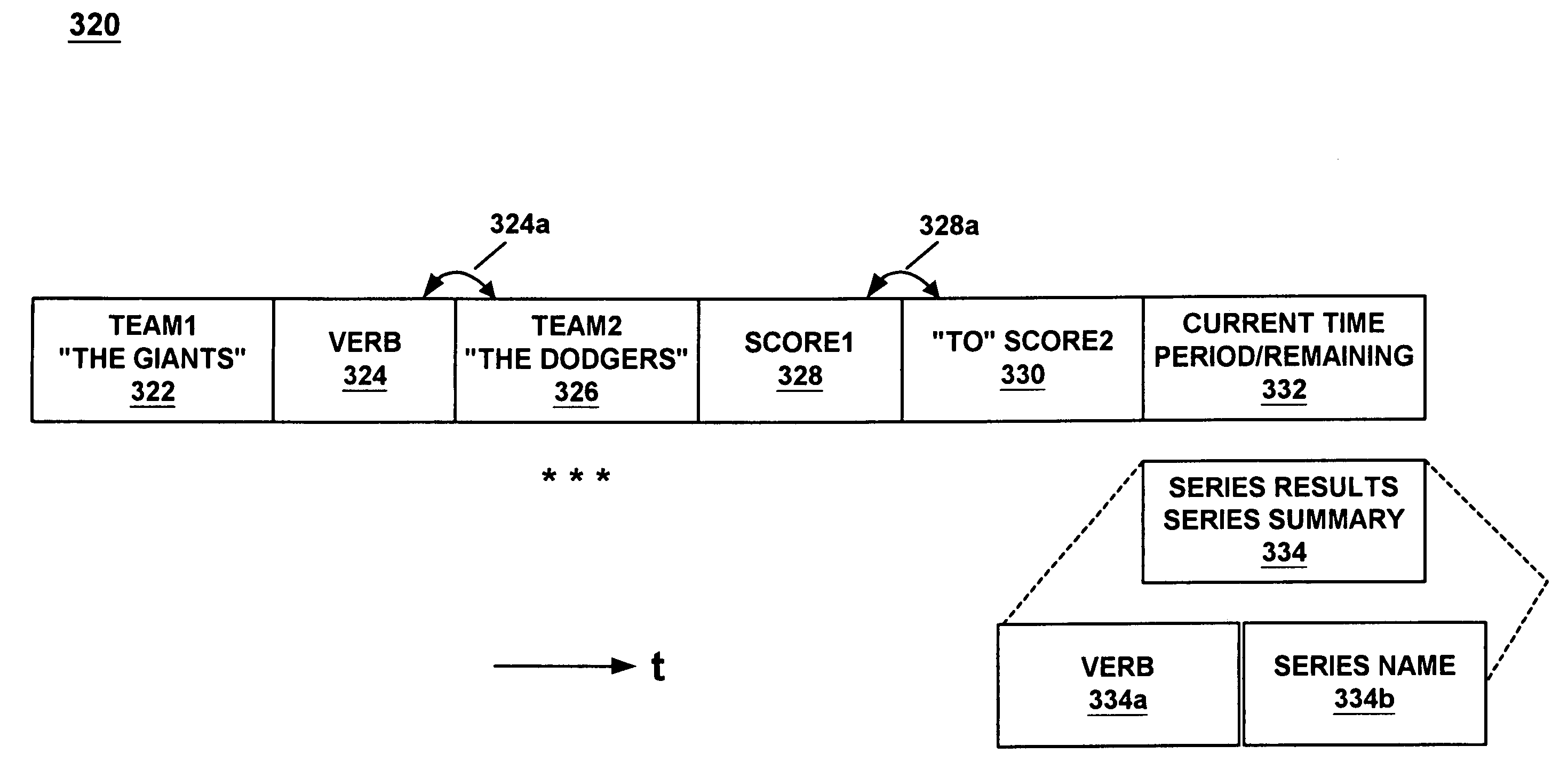
Providing menu and other services for an information processing system using a telephone or other audio interface
InactiveUS7143039B1Reduce generationStructured and efficient and effectiveAutomatic call-answering/message-recording/conversation-recordingAutomatic exchangesInformation processingWord selection
A method and system for providing efficient menu services for an information processing system that uses a telephone or other form of audio user interface. In one embodiment, the menu services provide effective support for novice users by providing a full listing of available keywords and rotating house advertisements which inform novice users of potential features and information. For experienced users, cues are rendered so that at any time the user can say a desired keyword to invoke the corresponding application. The menu is flat to facilitate its usage. Full keyword listings are rendered after the user is given a brief cue to say a keyword. Service messages rotate words and word prosody. When listening to receive information from the user, after the user has been cued, soft background music or other audible signals are rendered to inform the user that a response may now be spoken to the service. Other embodiments determine default cities, on which to report information, based on characteristics of the caller or based on cities that were previously selected by the caller. Other embodiments provide speech concatenation processes that have co-articulation and real-time subject-matter-based word selection which generate human sounding speech. Other embodiments reduce the occurrences of falsely triggered barge-ins during content delivery by only allowing interruption for certain special words. Other embodiments offer special services and modes for calls having voice recognition trouble. The special services are entered after predetermined criterion have been met by the call. Other embodiments provide special mechanisms for automatically recovering the address of a caller.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for managing and navigating within stacks of document pages
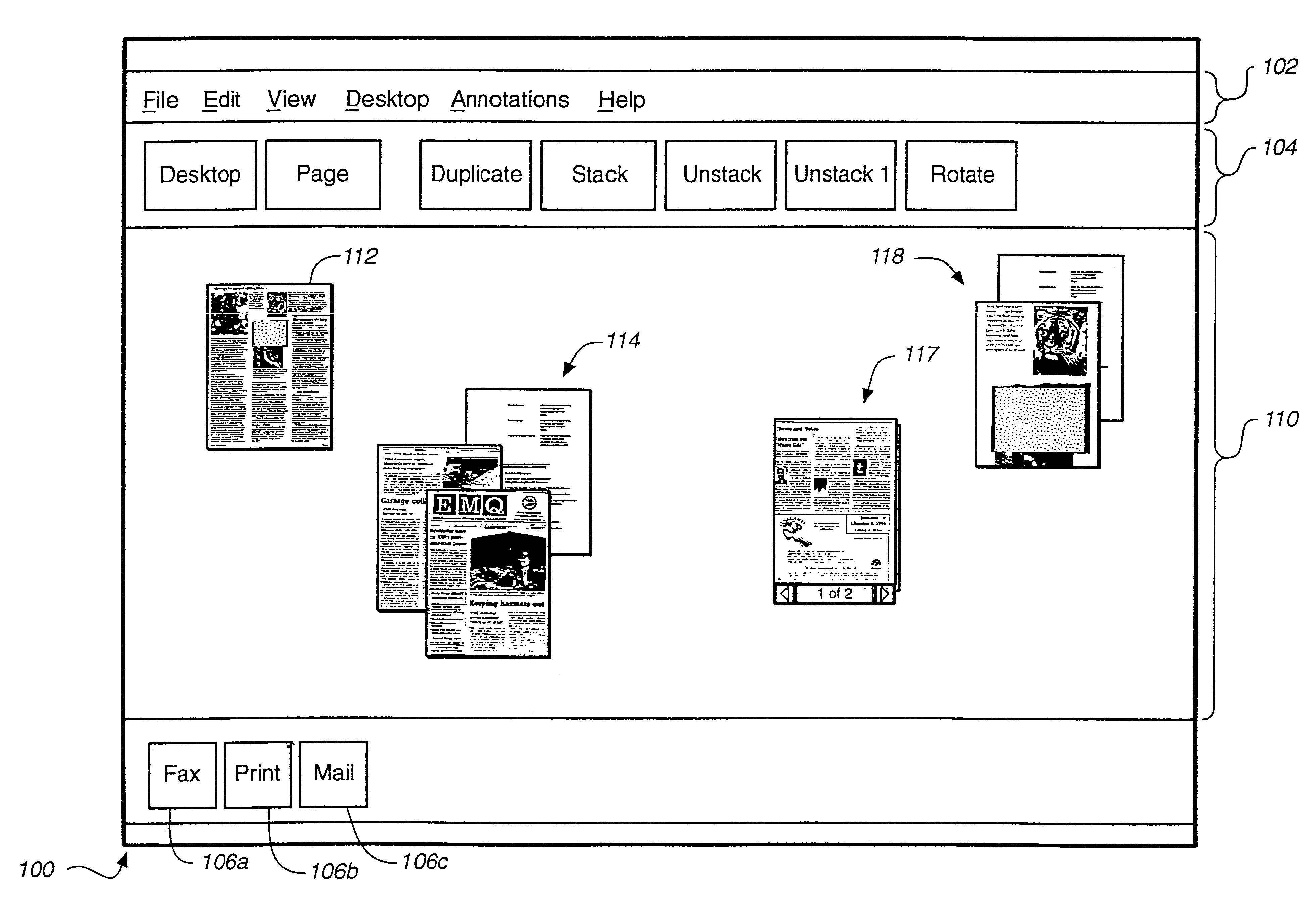
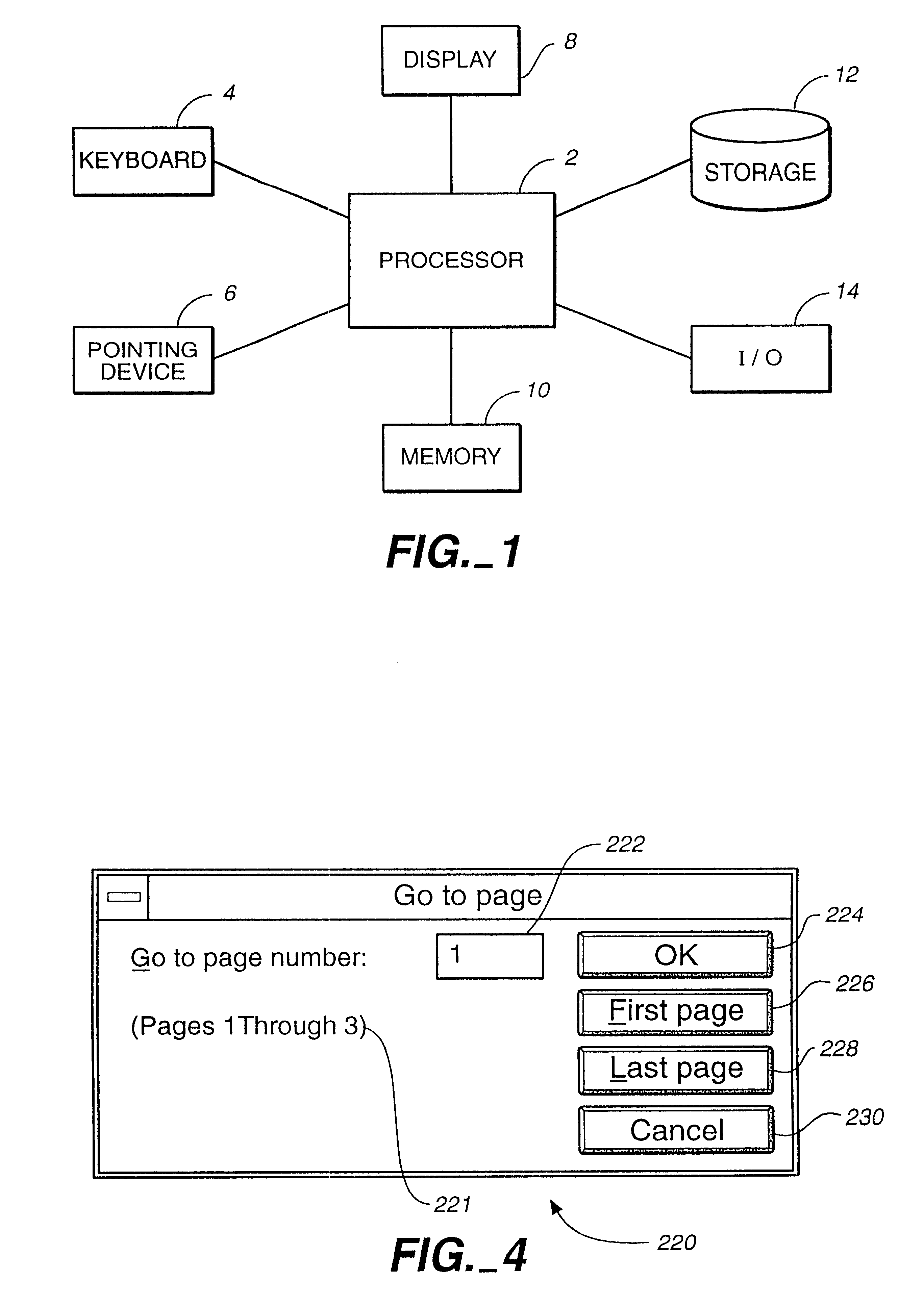
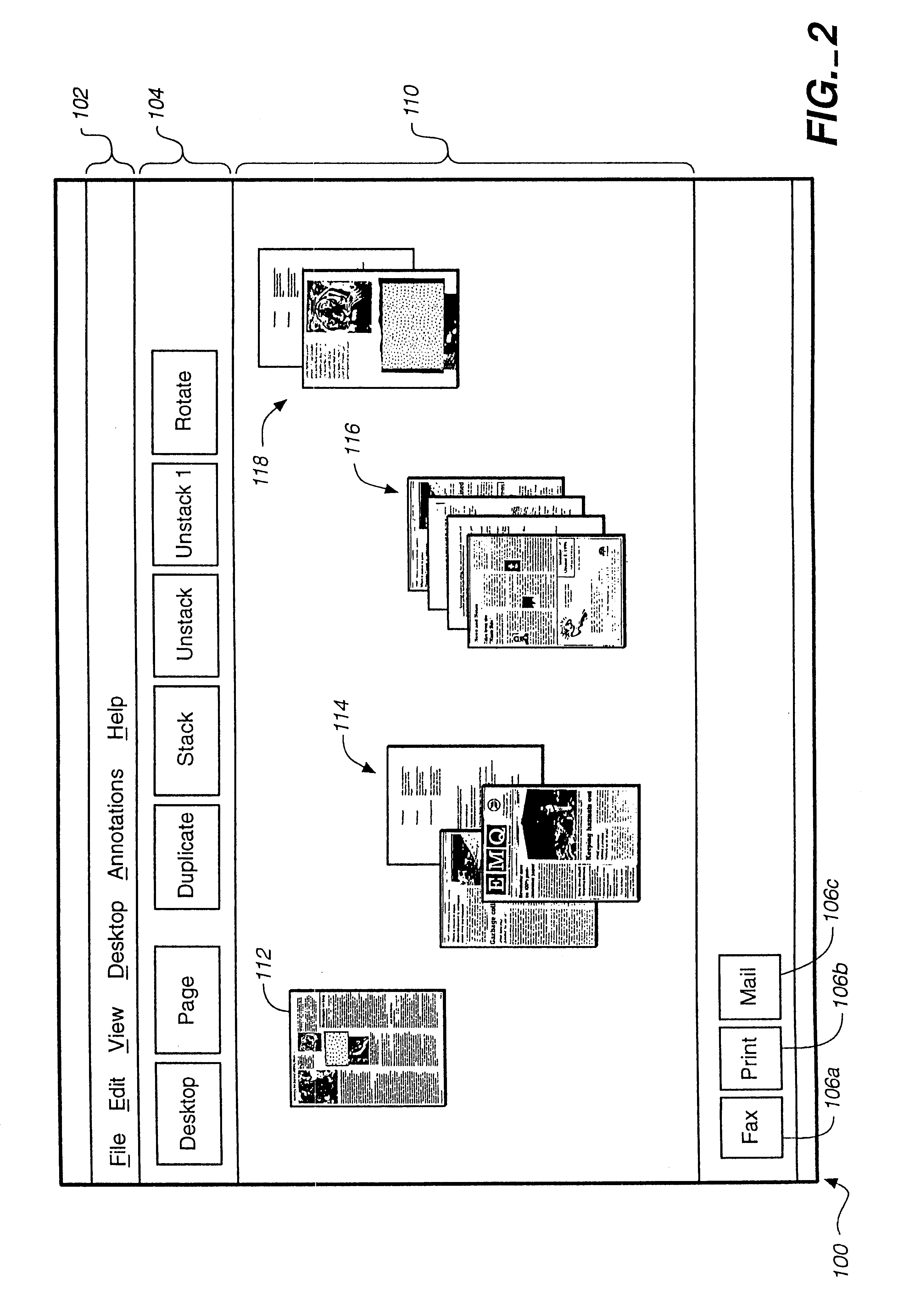
InactiveUS6262732B1Easy to operateSimplifies movingDigital data information retrievalDigital computer detailsInformation processingDocumentation procedure
An apparatus and method for an information processing system are disclosed for improved manipulation of documents consisting of multiple pages. In one embodiment, a multi-page document is depicted by a representation of a stack of pages and a request area through which an operator may navigate within the stack. In another embodiment, a multi-page document is depicted by static icon representing the stack and a dynamic miniature replica of a current page within the stack. Additional functions are disclosed such as adding one or more pages to a document, removing a page from a stack, rotating a page within a stack, and adding annotations to a page.
Owner:CANON KK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com