Patents
Literature
10244 results about "Workstation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
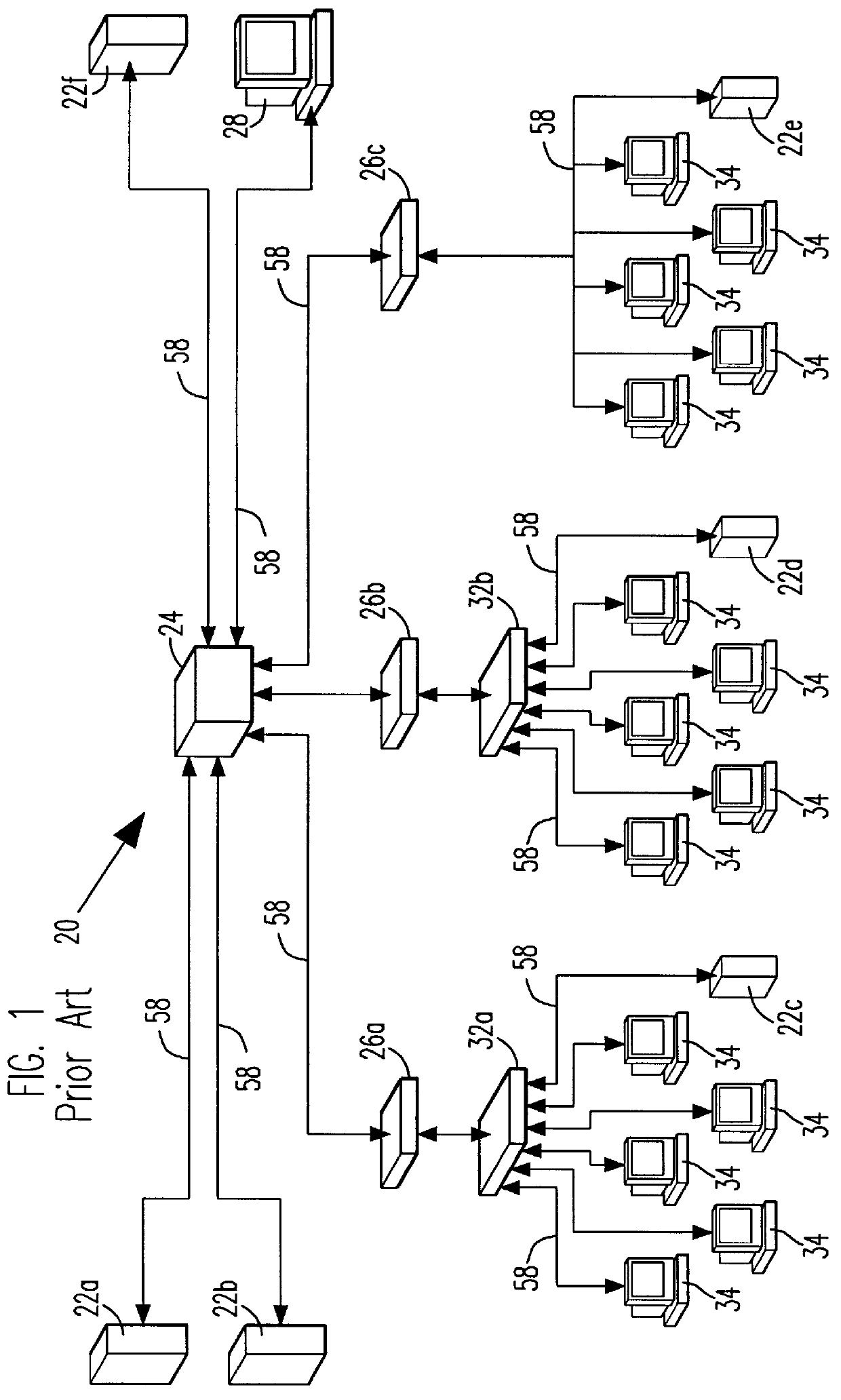
A workstation is a special computer designed for technical or scientific applications. Intended primarily to be used by one person at a time, they are commonly connected to a local area network and run multi-user operating systems. The term workstation has also been used loosely to refer to everything from a mainframe computer terminal to a PC connected to a network, but the most common form refers to the group of hardware offered by several current and defunct companies such as Sun Microsystems, Silicon Graphics, Apollo Computer, DEC, HP, NeXT and IBM which opened the door for the 3D graphics animation revolution of the late 1990s.
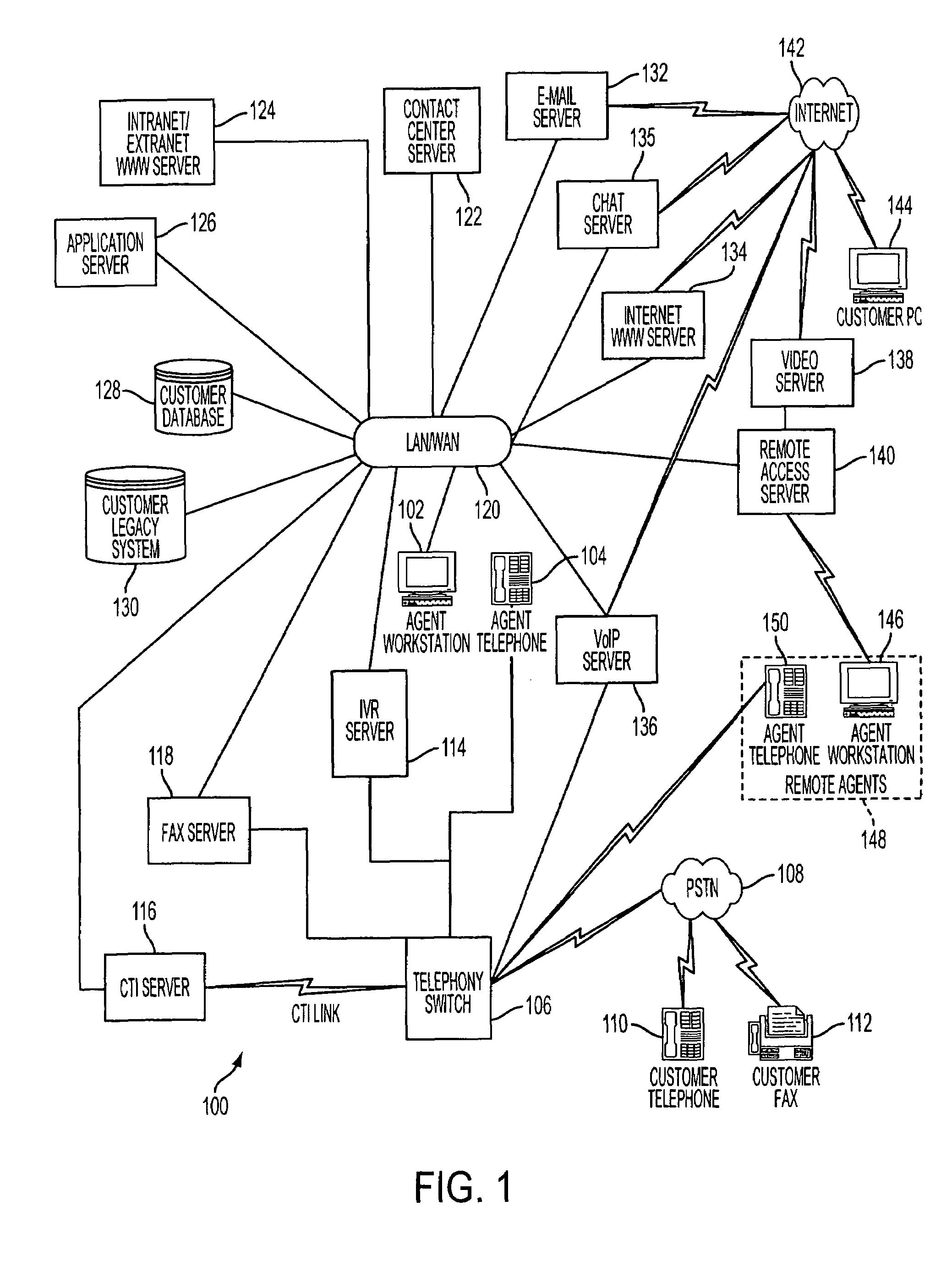
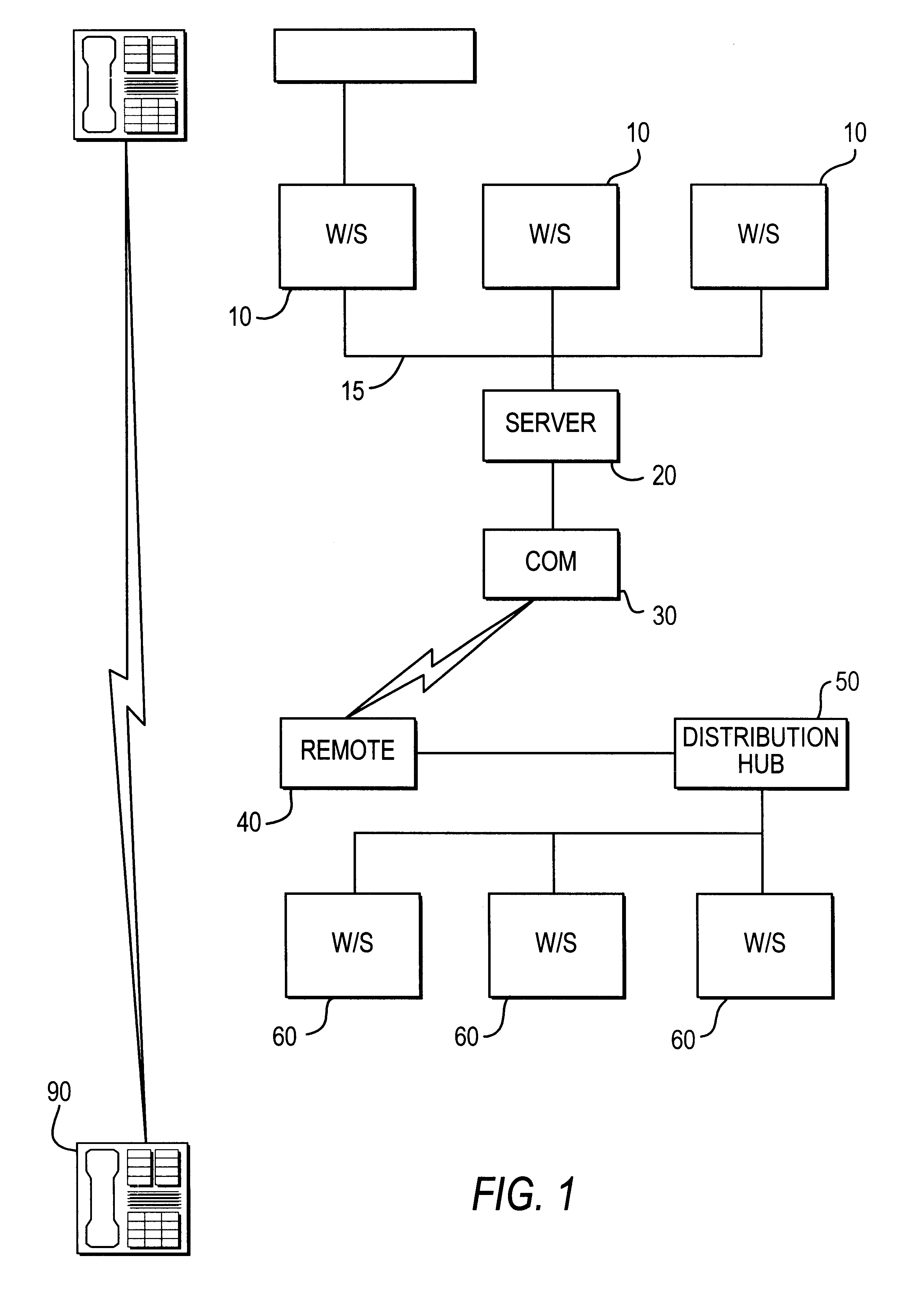
Multimedia surveillance and monitoring system including network configuration
InactiveUS6970183B1High bandwidthSignalling system detailsColor television detailsVideo monitoringStructure of Management Information
A comprehensive, wireless multimedia surveillance and monitoring system provides a combination of megapixel digital camera capability with full motion video surveillance with a network, including network components and appliances such as wiring, workstations, and servers with the option of geographical distribution with various wide area carriers. The full service, multi-media surveillance system is capable of a wide range of monitoring techniques utilizing digital network architecture and is adapted for transmitting event data, video and / or image monitoring information, audio signals and other sensor and detector data over significant distances using digital data transmission over a LAN, wireless LAN, Intranet or Internet for automatic assessment and response including dispatch of response personnel. Both wired and wireless appliance and sensor systems may be employed. GPS dispatching is used to locate and alert personnel as well as to indicate the location of an event. Automatic mapping and dispatch permits rapid response. The wireless LAN connectivity permits local distribution of audio, video and image data over a relatively high bandwidth without requirement of a license and without relying on a common carrier and the fees associated therewith. The surveillance system may be interfaced with a WAN (wide area Network) or the Internet for providing a worldwide, low cost surveillance system with virtually unlimited geographic application. Centralized monitoring stations have access to all of the surveillance data from various remote locations via the Internet or the WAN. A server provides a centralized location for data collection, alarm detection and processing, access control, dispatch processing, logging functions and other specialized functions. The server may be inserted virtually anywhere in the Intranet / Internet network. The topology of the network will be established by the geographic situation of the installation. Appropriate firewalls may be set up as desired. The server based system permits a security provider to have access to the appliance and sensor and surveillance data or to configure or reconfigure the system for any station on the network.
Owner:PR NEWSWIRE
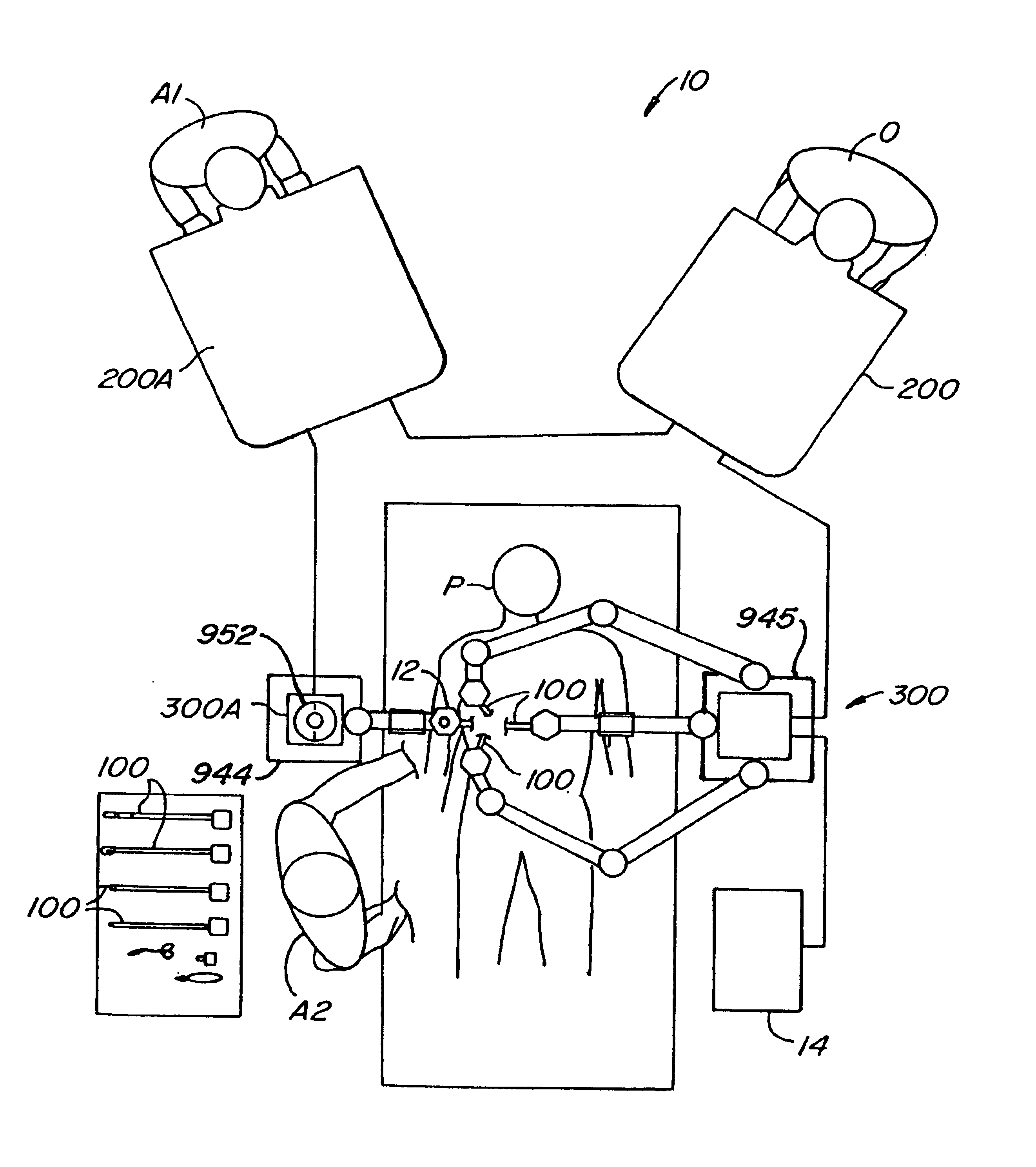
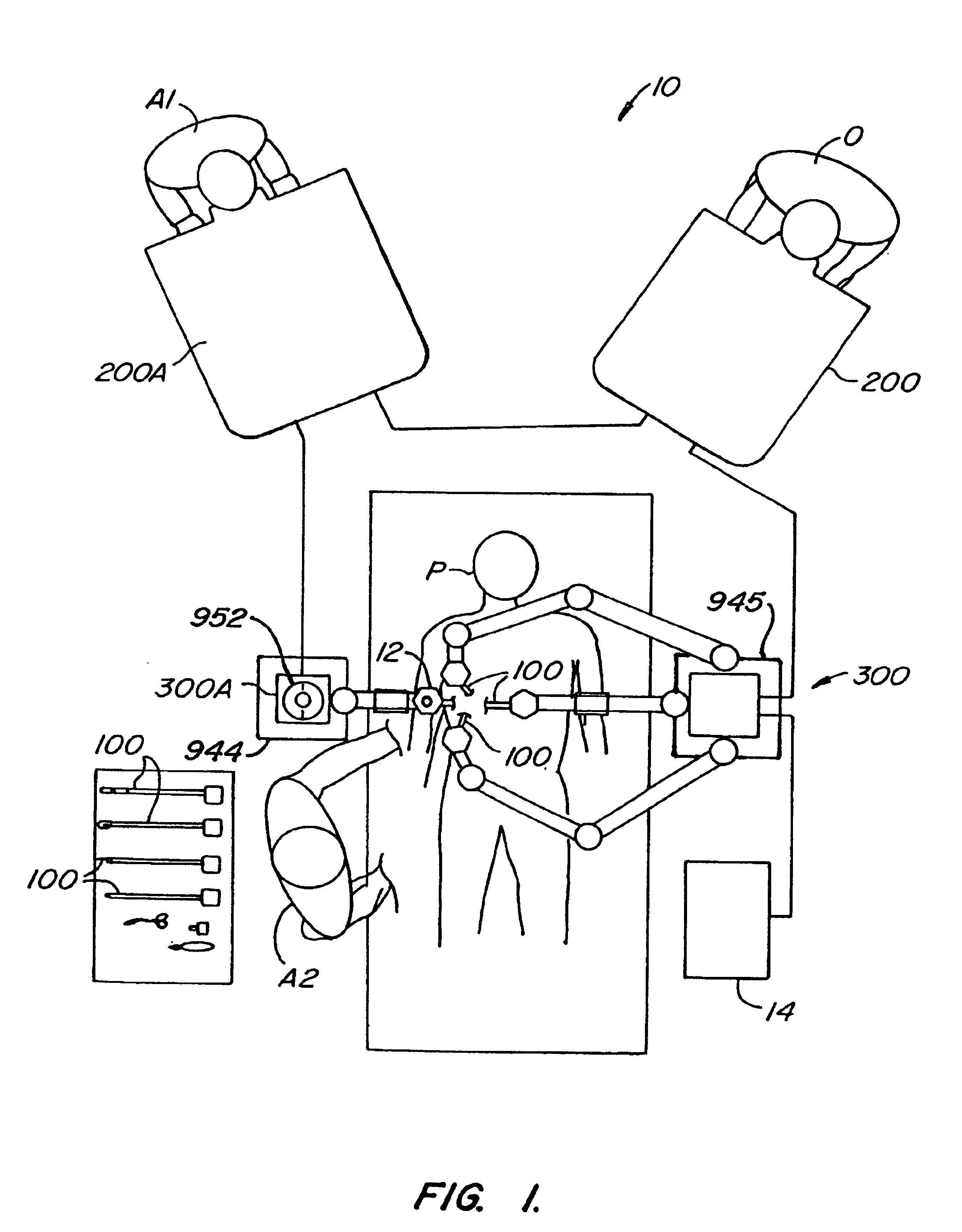
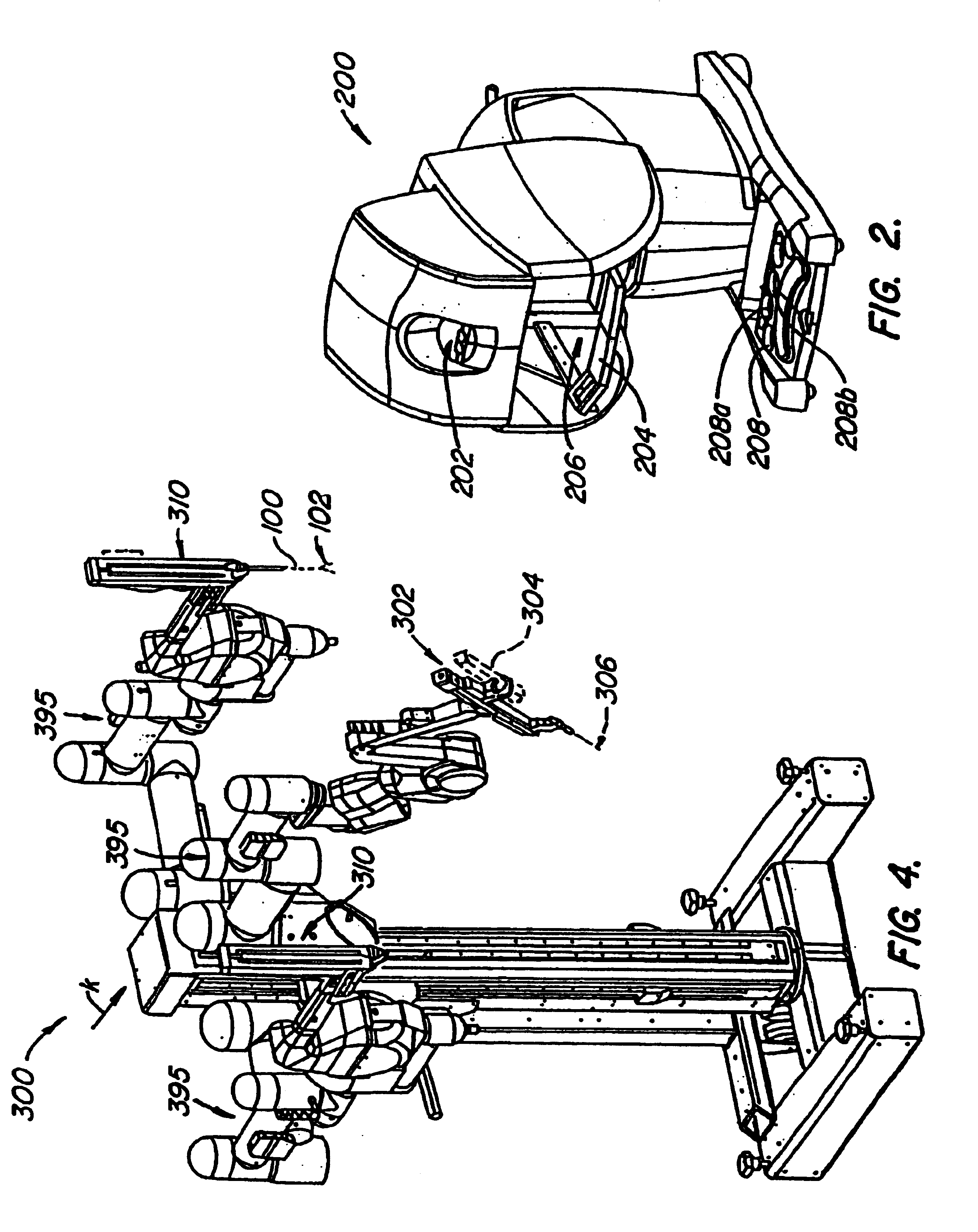
Arm cart for telerobotic surgical system
InactiveUS6837883B2Clear accessEasy to controlMechanical/radiation/invasive therapiesDiagnosticsSurgical operationRobotic arm
Improved robotic surgical systems, devices, and methods often include a first assembly with a surgical end effector supported and manipulated relative to a first base by a first robotic linkage, while a second surgical end effector manipulated and supported relative to a second, independent base by a second robotic linkage. One or more of these robotic assemblies may be moved relative to the other. To coordinate the end effector movements with those of input devices being manipulated by a surgeon relative to a display of a surgical worksite, the processor deriving the commands for movement of the robotic linkages may make use of a signal indicating a relative orientation of the bases of the robotic arm assemblies. Surprisingly, the robotic arm assemblies may not transmit signals to the processor indicating a relative translational position of the bases.
Owner:INTUITIVE SURGICAL OPERATIONS INC
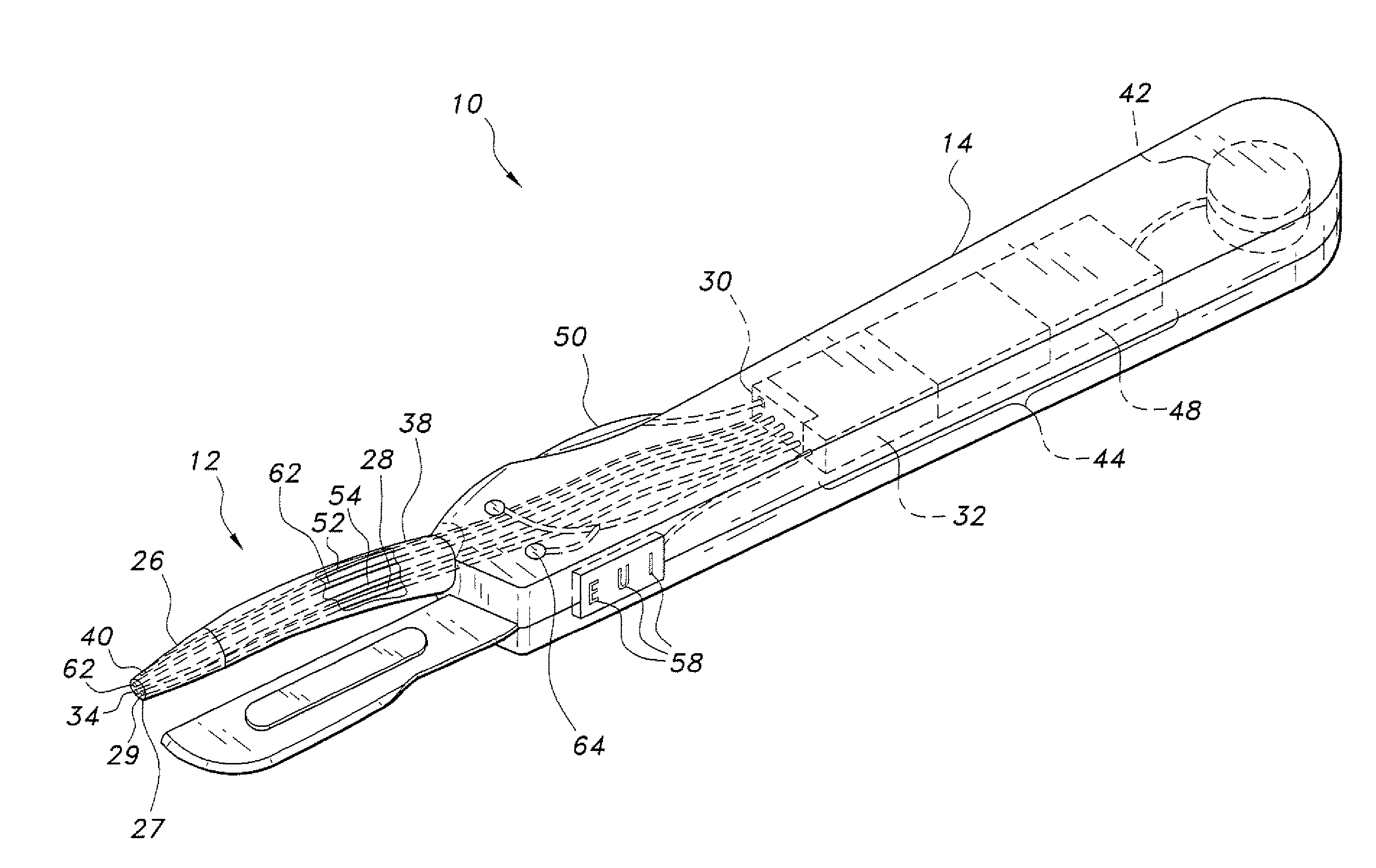
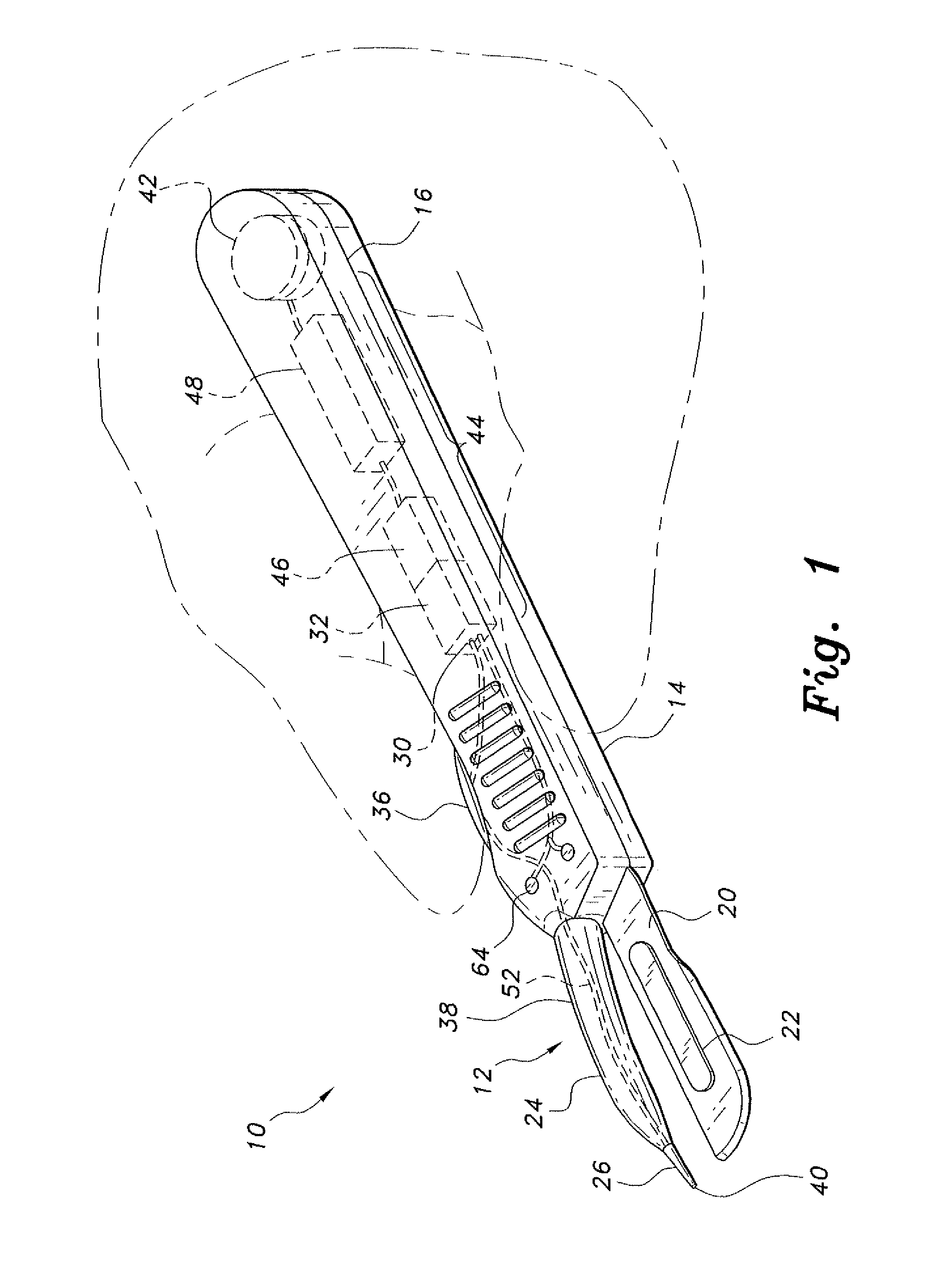
Tissue-identifying surgical instrument
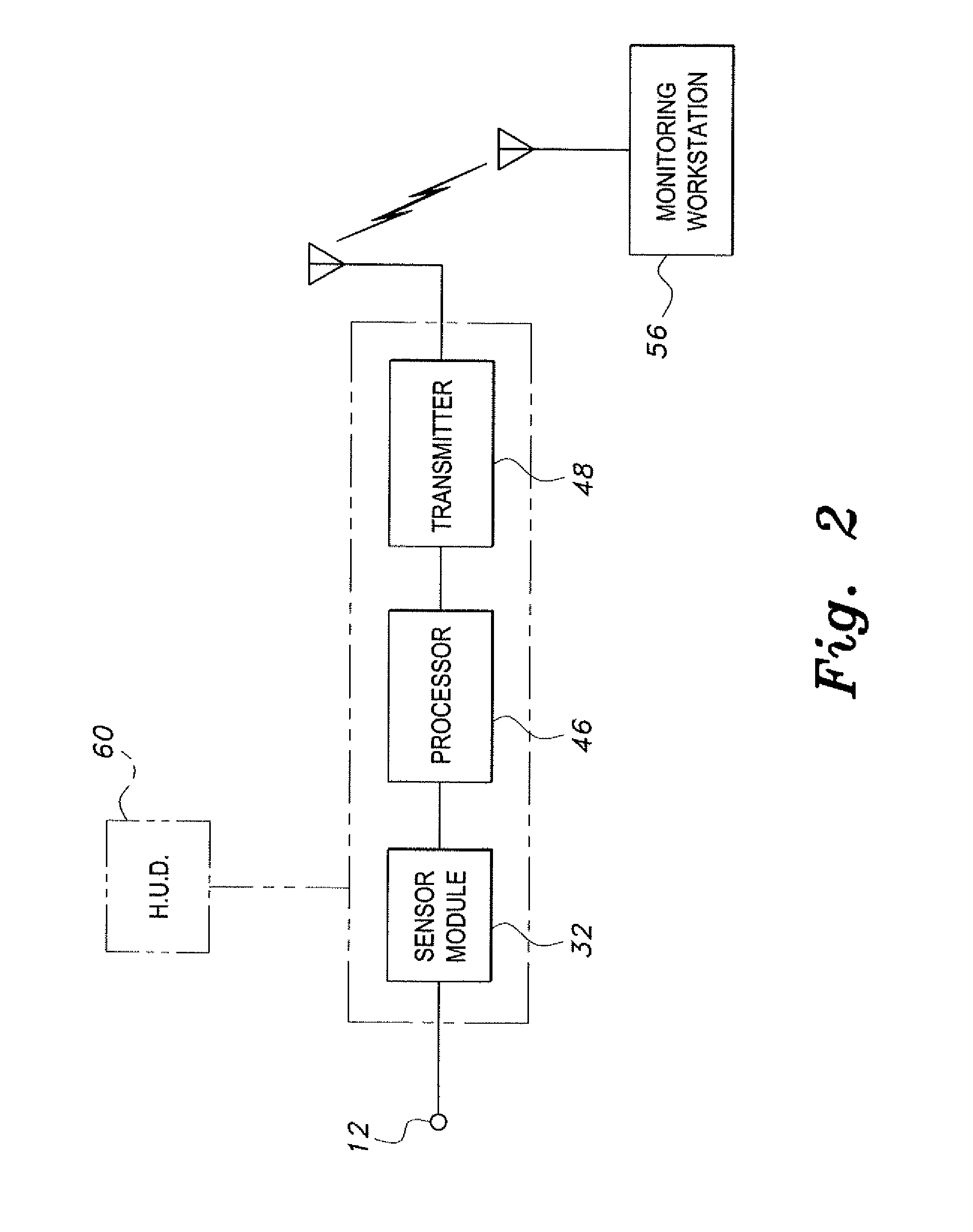
The tissue-identifying surgical instrument includes a surgical instrument having a handle and an integral probe operatively connected to the handle. The probe senses a tissue of interest to identify the type of tissue, e.g., nerve, muscle, vein or other. The interior of the handle includes a control assembly connected to a power source for operation of the tissue identification function. The control assembly displays and wirelessly transmits tissue identification data to a monitoring workstation to inform the surgeon of the type of tissue contacted by the probe.
Owner:SOLOMON CLIFFORD T +1
Multi server, interactive, video-on-demand television system utilizing a direct-access-on-demand workgroup
InactiveUS6049823ABroadcast transmission systemsMultiple digital computer combinationsWorkstationPeer-to-peer
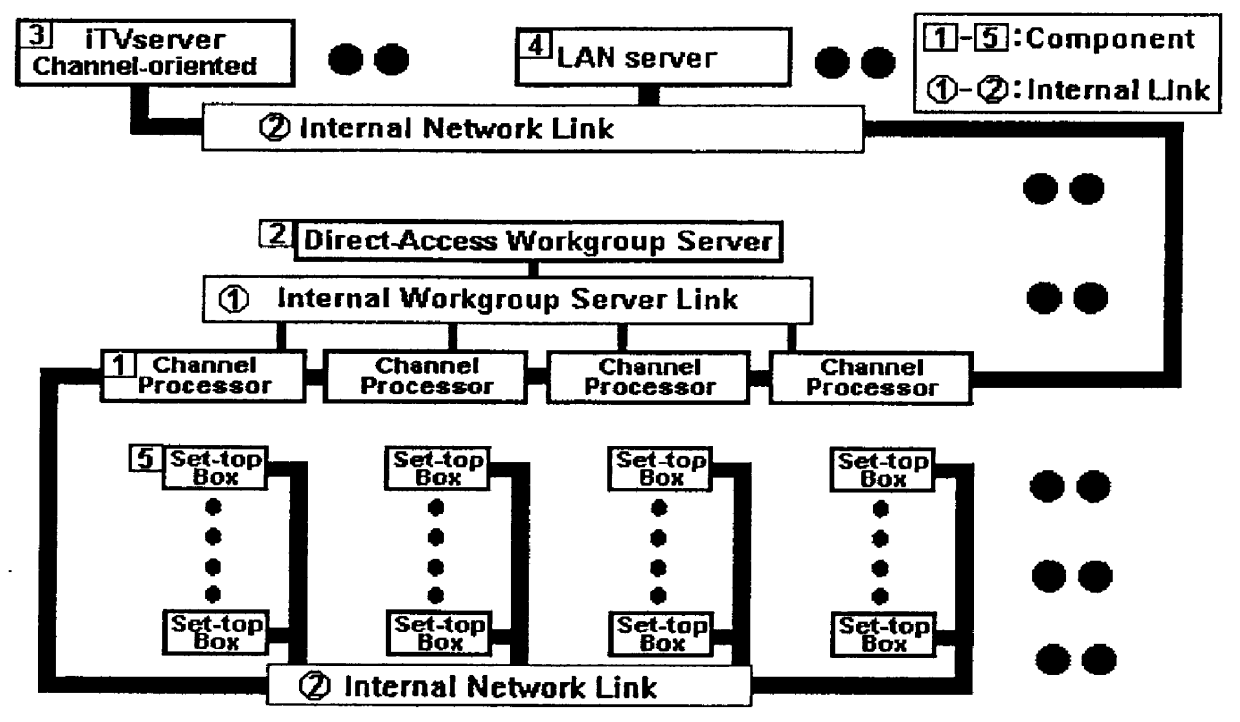
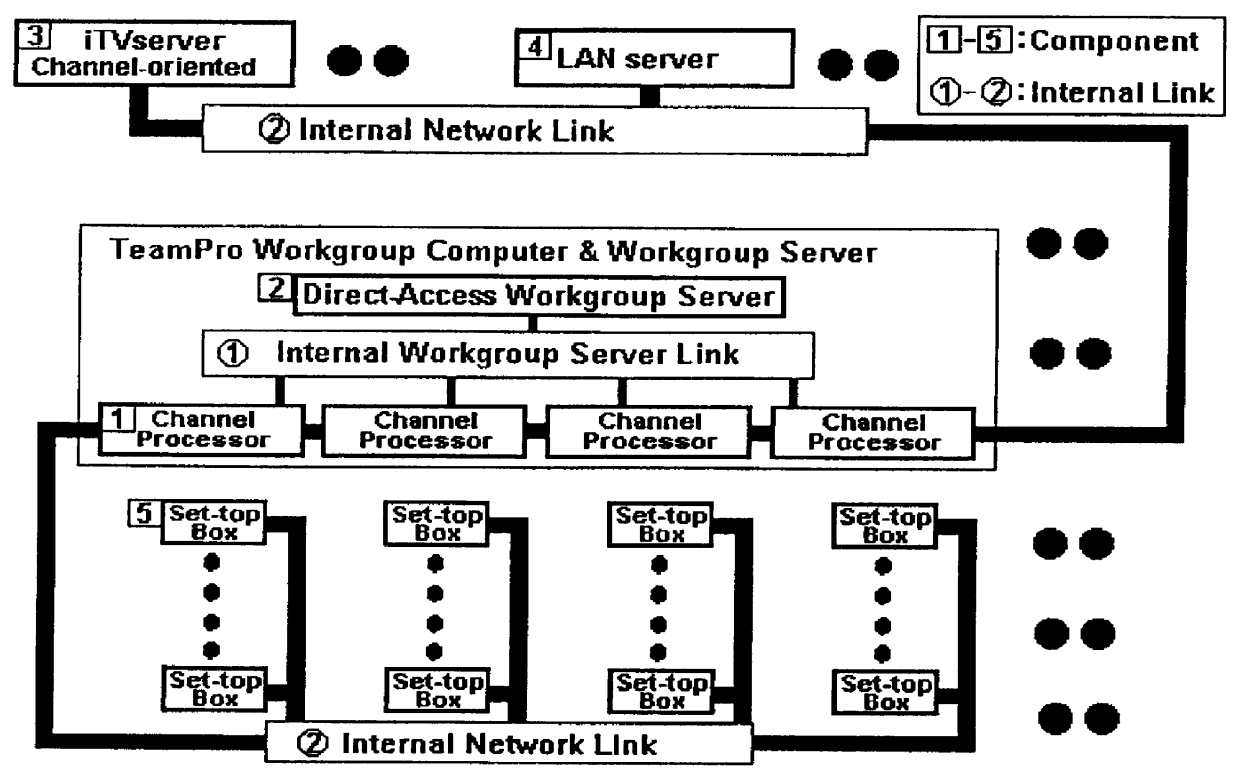
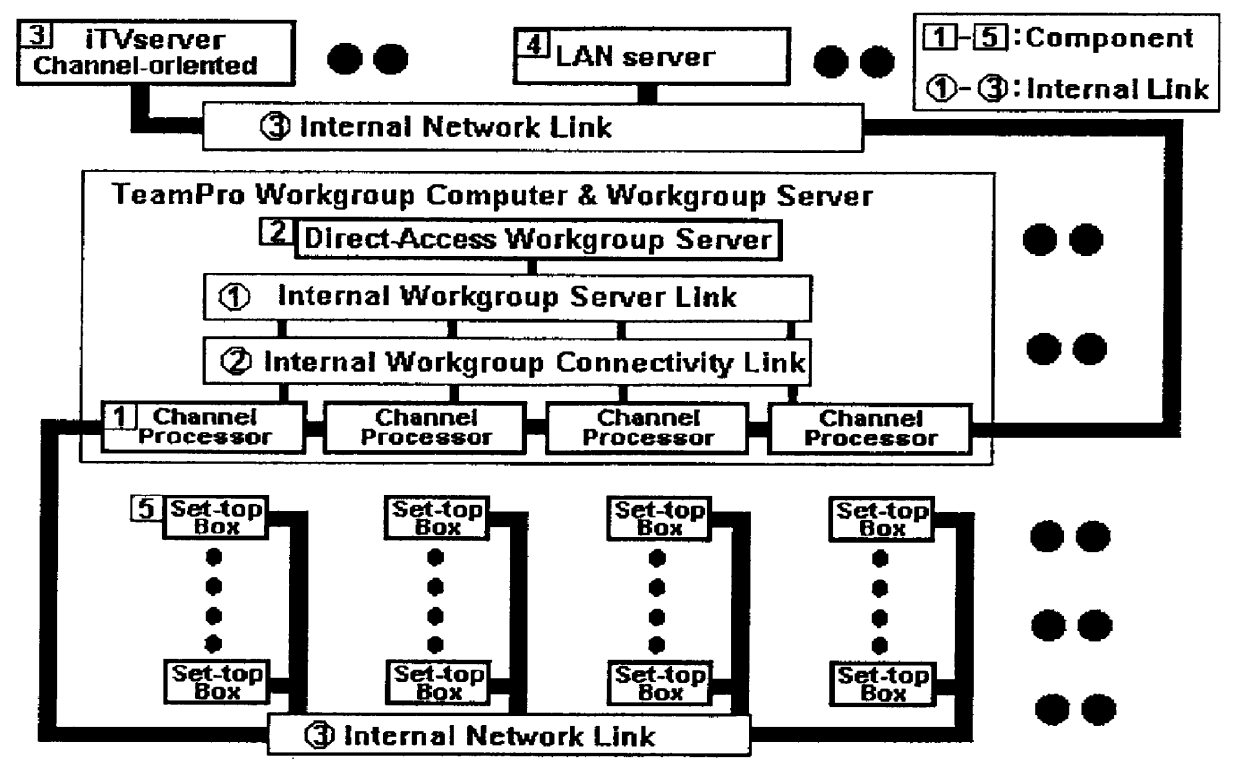
An interactive television system that renders on-demand interactive multimedia services for a community of users. The interactive multimedia is delivered to each user on a TV or on a LAN-node (Local-Area-Network) computer through an "interactive TV channel" created and controlled by a Channel-processor, which can be implemented as either a PC or a high-end workstation. The system employs a direct-access on-demand workgroup server. It is equipped with the primary on-demand multimedia data base stored on a hard disk subsystem that is connected directly to the Channel-processors through an internal workgroup link. Using a no-overhead server technology, the connected workgrouped Channel-processors can all concurrently retrieve and process the data directly from the hard disk subsystem without resorting to a stand-alone server system for data retrieving and downloading. The system also employs peer-to-peer workgroup connectivity, so that all of the workgrouped Channel-processors that are connected to the workgroup server through the internal workgroup link, can communicate with one another.
Owner:HWANG IVAN CHUNG SHUNG
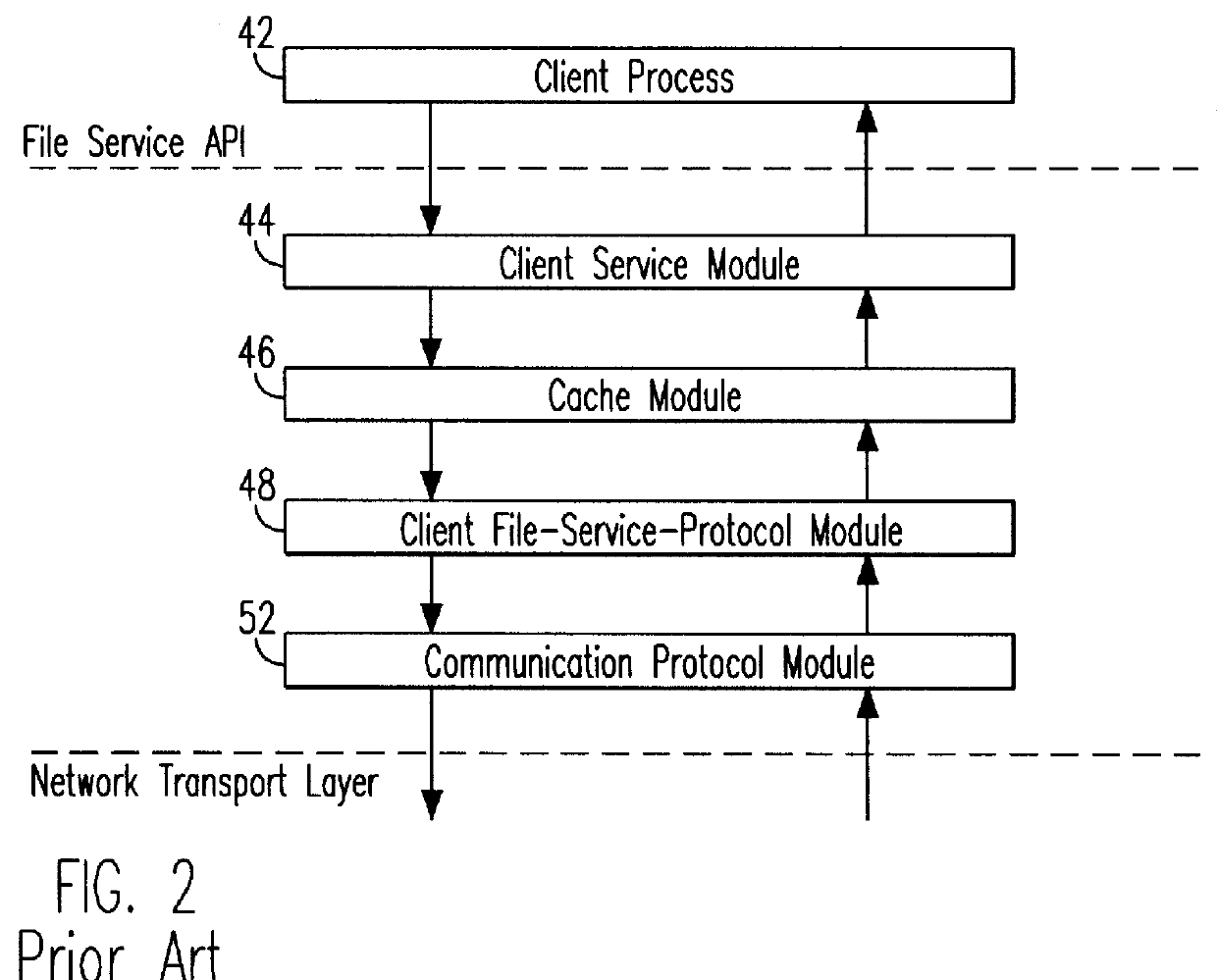
Remote file services network-infrastructure cache
InactiveUS6085234AMultiple digital computer combinationsMemory systemsService protocolSchema for Object-Oriented XML
A network-infrastructure cache ("NI Cache") transparently provides proxy file services to a plurality of client workstations concurrently requesting access to file data stored on a server. The NI Cache includes a network interface that connects to a digital computer network. A file-request service-module of the NI Cache receives and responds to network-file-services-protocol requests from workstations through the network interface. A cache, also included in the NI Cache, stores data that is transmitted back to the workstations. A file-request generation-module, also included in the NI Cache, transmits requests for data to the server, and receives responses from the server that include data missing from the cache.
Owner:MOSAID TECH +1
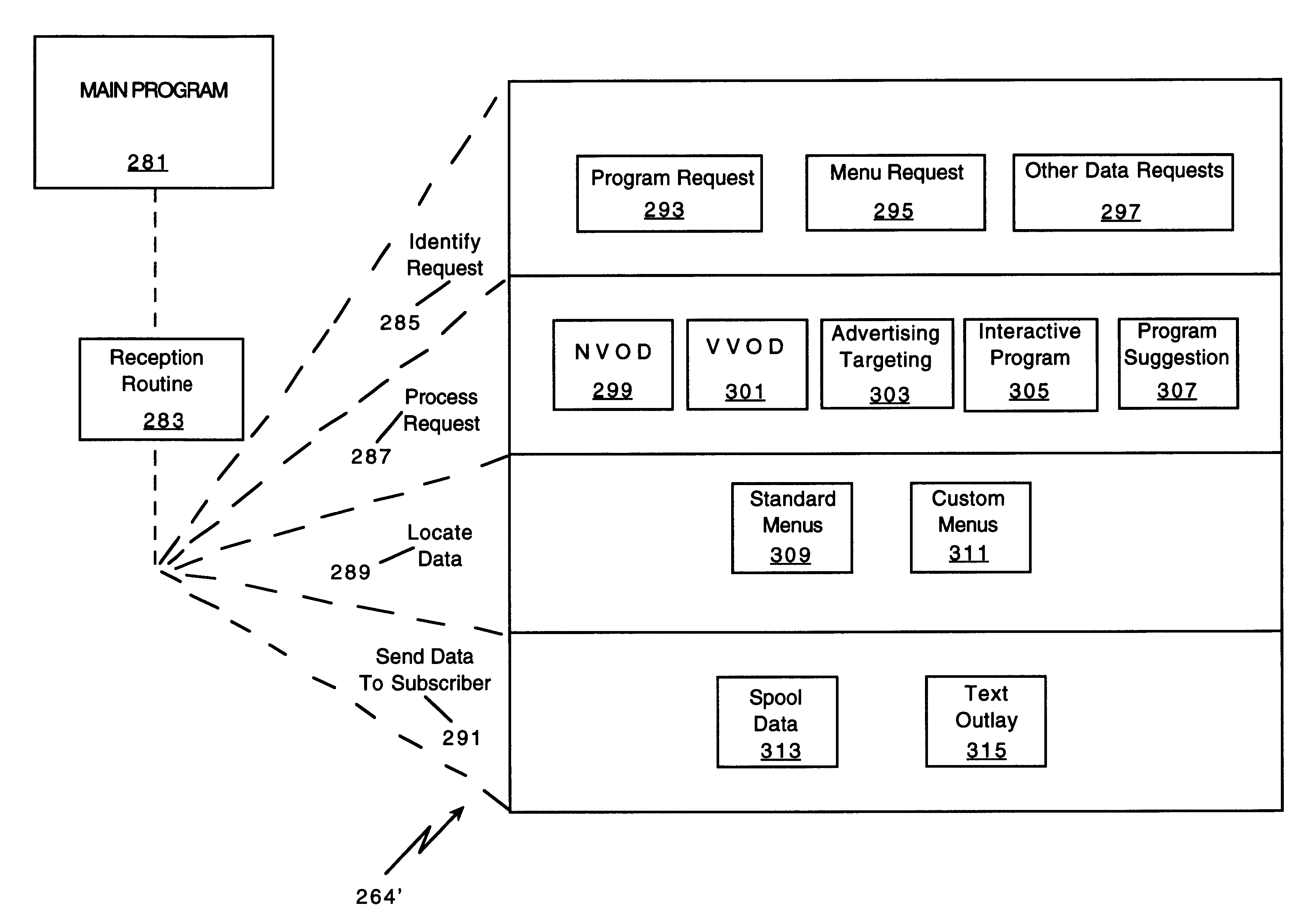
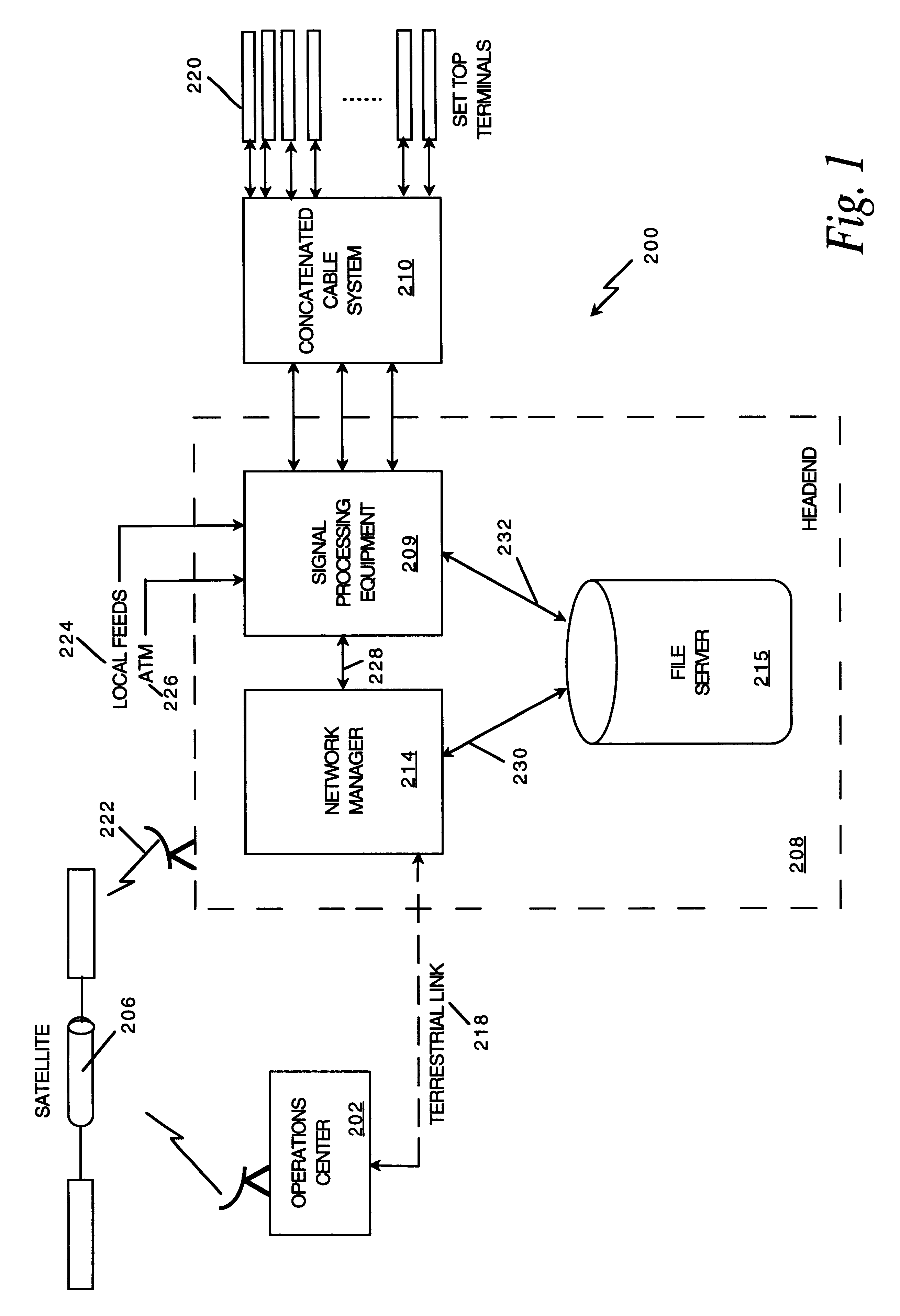
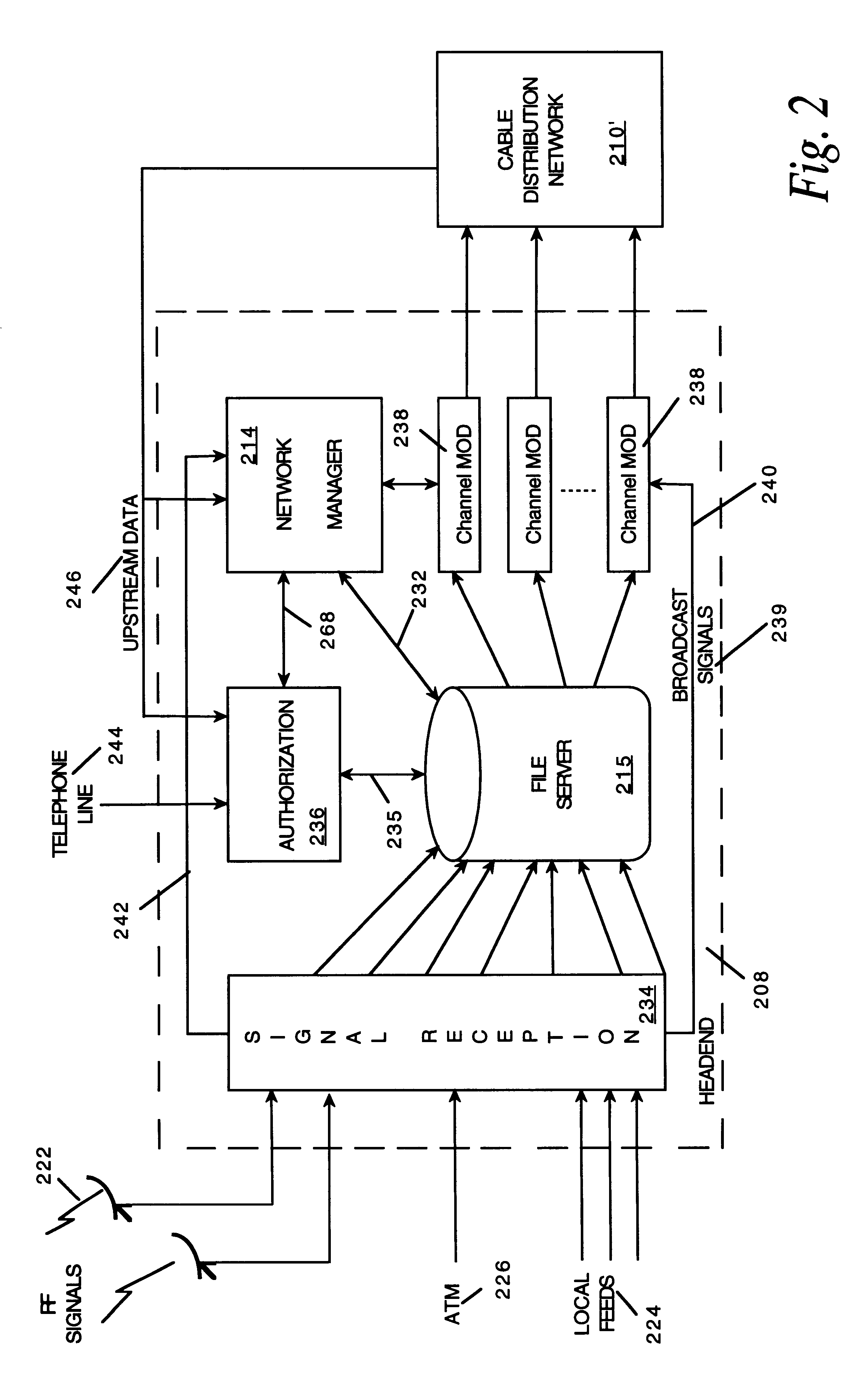
Network manager for cable television system headends
InactiveUS6201536B1Increase flexibilityImprove rendering capabilitiesTelevision system detailsPulse modulation television signal transmissionInformation processingInstruction memory
A novel network manager for use with a cable television system headend capable of monitoring and managing headend components and set top terminals in a television delivery system is described. The invention relates to methods and apparatus that manage and coordinate the reception of various programming and control signals at a headend. The invention manages and coordinates the storage of such signals for intelligent selection and distribution to set top terminals. The invention makes use of a receiver or set of receivers, a work station, a program control information processing component, a network management CPU, databases, control software and an instruction memory. The invention uses these components to manage and monitor certain headend components, such as signal reception equipment, an authorization component, a file server, MPEG decoders, a digital buffer with frame repeat and channel modulators. The invention is particularly useful in processing and responding to upstream information and subscriber communications received from set top terminals. In so doing, the invention accommodates various system services, including (1) near video on demand (NVOD), (2) virtual video on demand (VVOD), (3) video on demand (VOD), (4) interactive program services, (5) program suggestion features, (6) advertisement targeting, (7) generation of standard and custom menus, and (8) data spooling and text overlaying.
Owner:COMCAST IP HLDG I
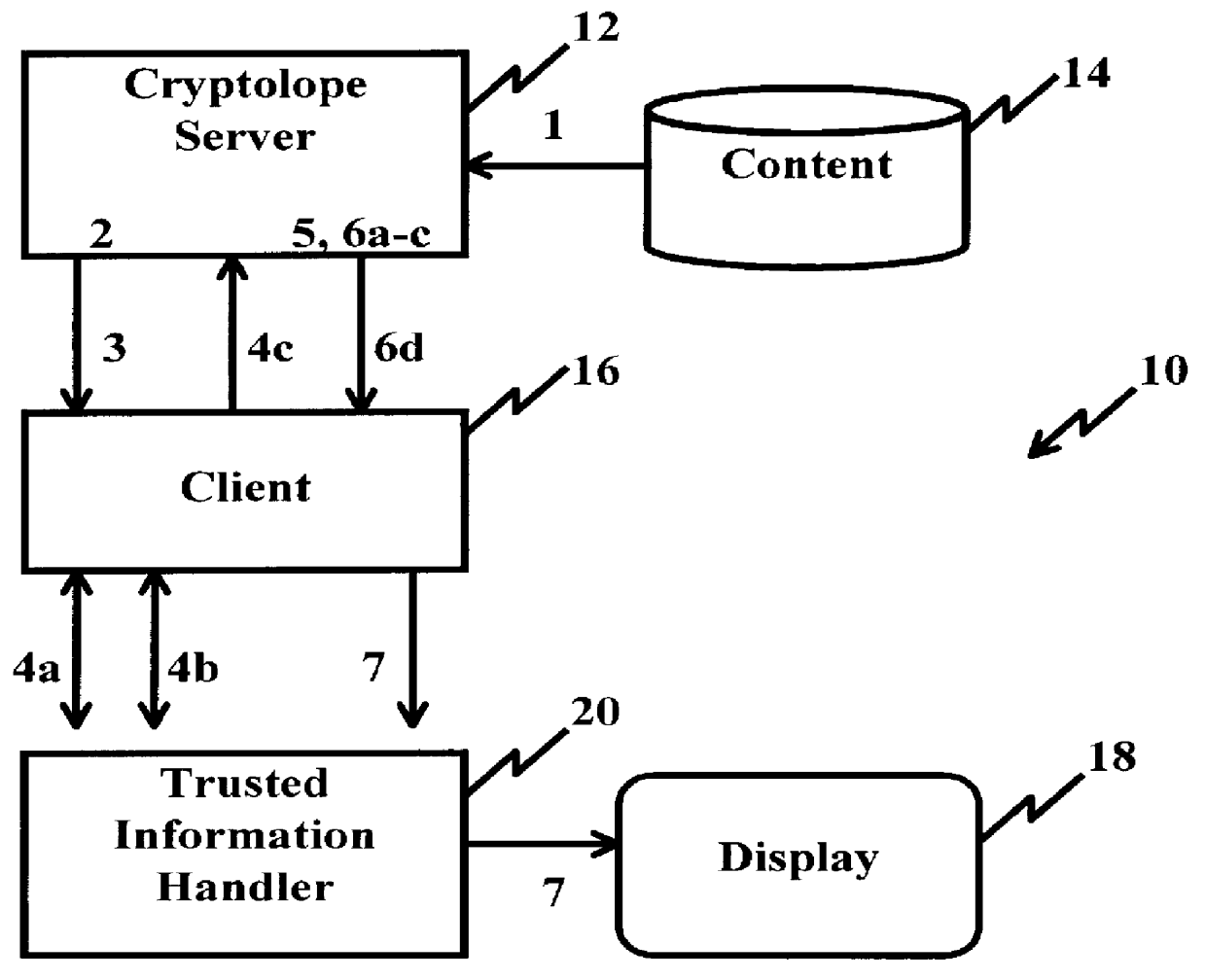
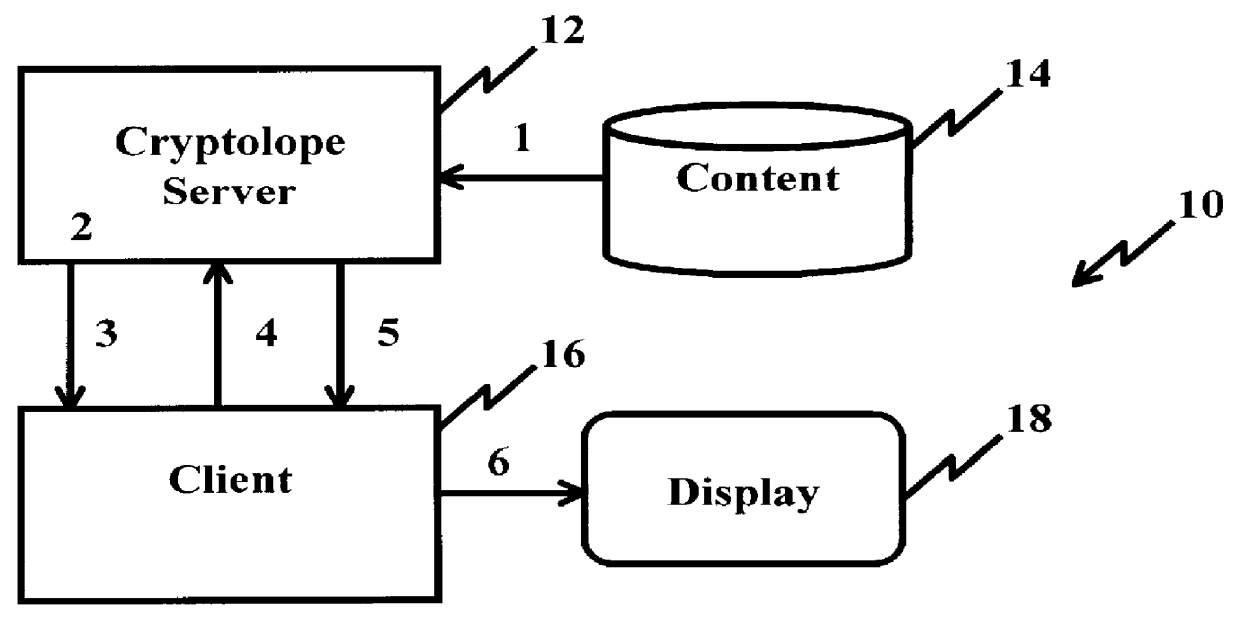
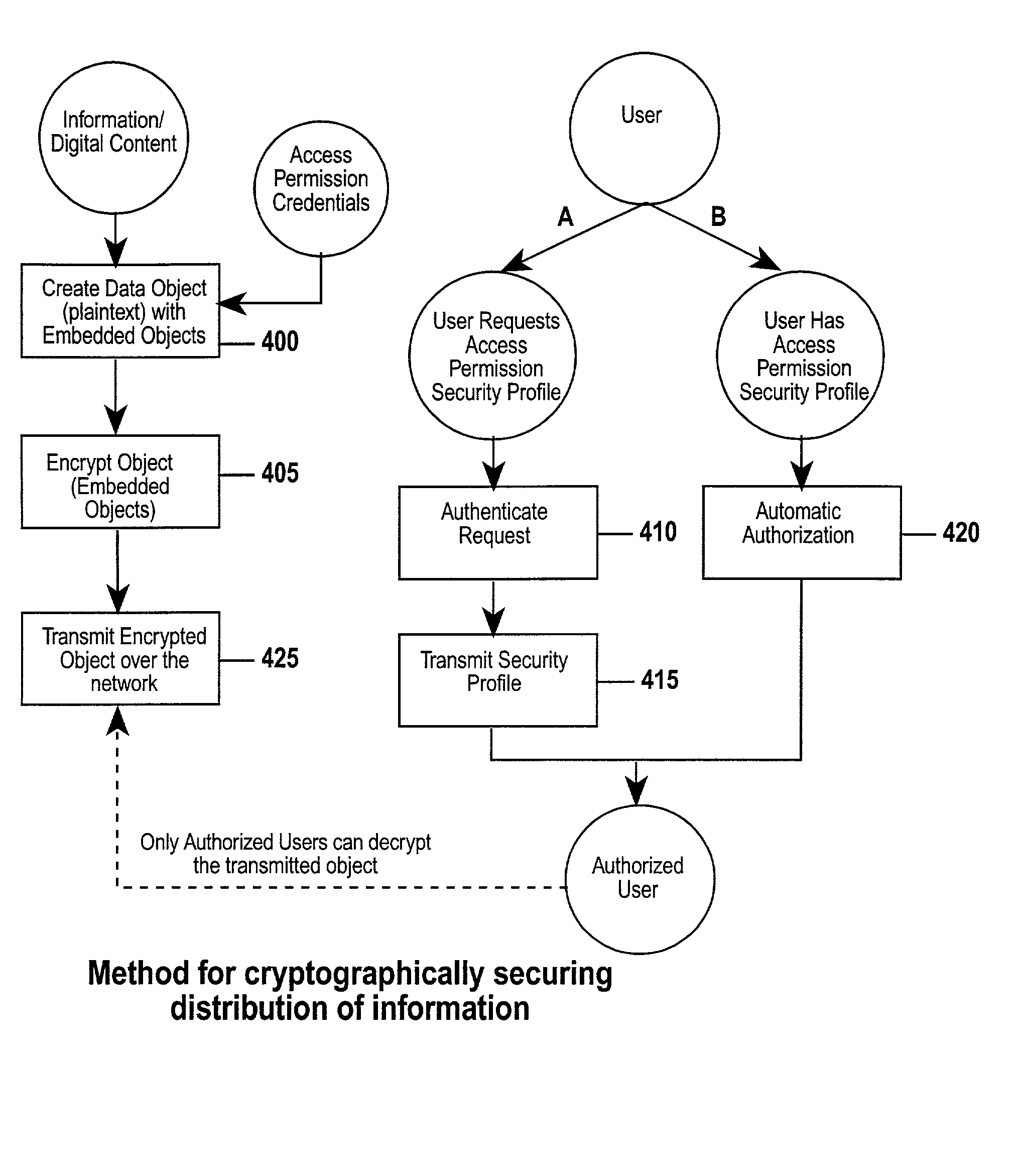
System and method for controlling access rights to and security of digital content in a distributed information system, e.g., Internet
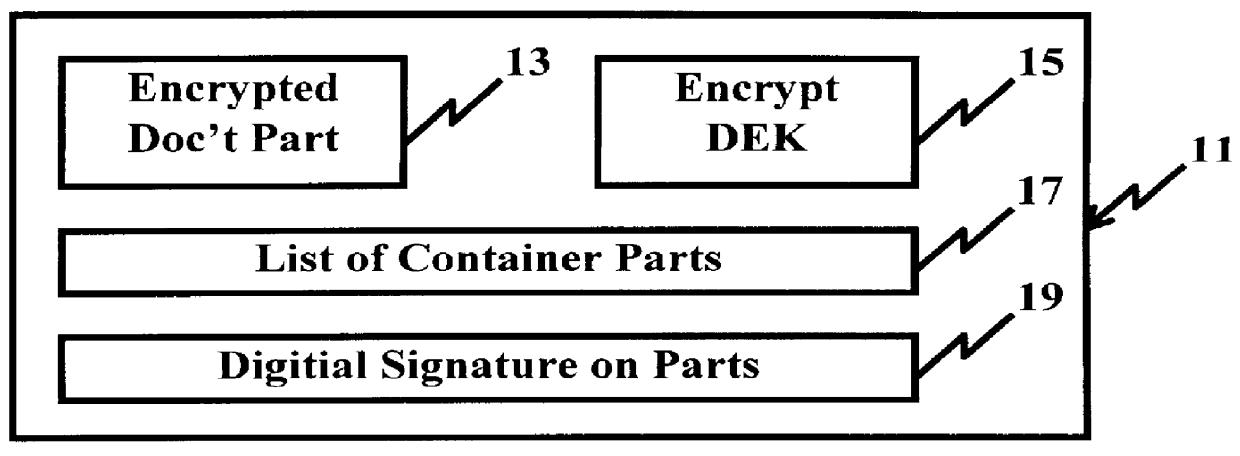
InactiveUS6098056AKey distribution for secure communicationPublic key for secure communicationPersonalizationThe Internet
A system and method for limiting access to and preventing unauthorized use of an owner's digital content stored in an information network and available to clients under authorized conditions. The network includes at least one server coupled to a storage device for storing the limited access digital content encrypted using a random-generated key, known as a Document Encryption Key (DEK). The DEK is further encrypted with the server's public key, using a public / private key pair algorithm and placed in a digital container stored in a storage device and including as a part of the meta-information which is in the container. The client's workstation is coupled to the server for acquiring the limited access digital content under the authorized condition. A Trusted Information Handler (TIH) is validated by the server after the handler provides a data signature and type of signing algorithm to transaction data descriptive of the purchase agreement between the client and the owner. After the handler has authenticated, the server decrypts the encrypted DEK with its private key and re-encrypts the DEK with the handler's public key ensuring that only the information handler can process the information. The encrypted DEK is further encrypted with the client's public key personalizing the digital content to the client. The client's program decrypts the DEK with his private key and passes it along with the encrypted content to the handler which decrypts the DEK with his private key and proceeds to decrypt the content for displaying to the client.
Owner:ACTIVISION PUBLISHING
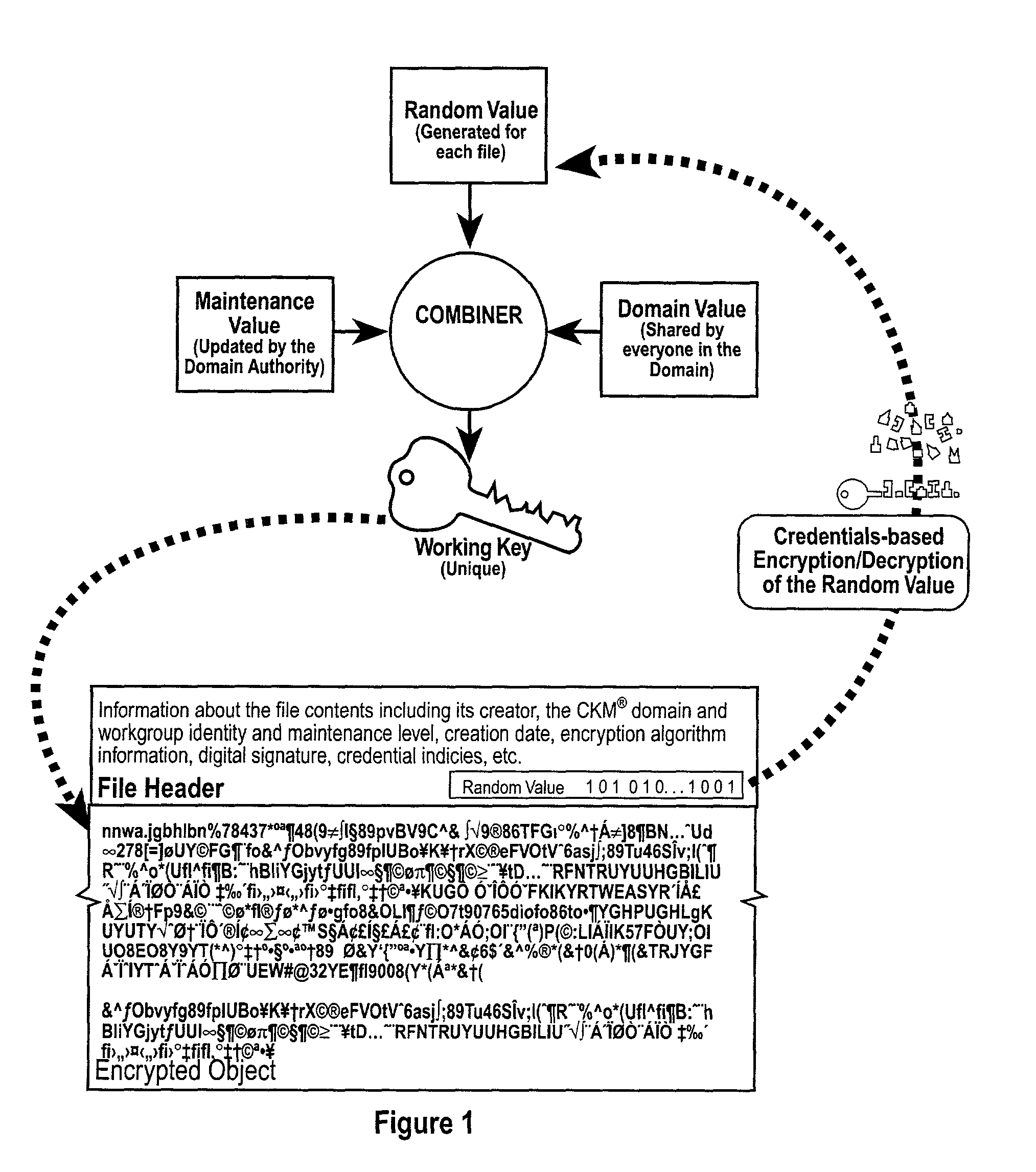
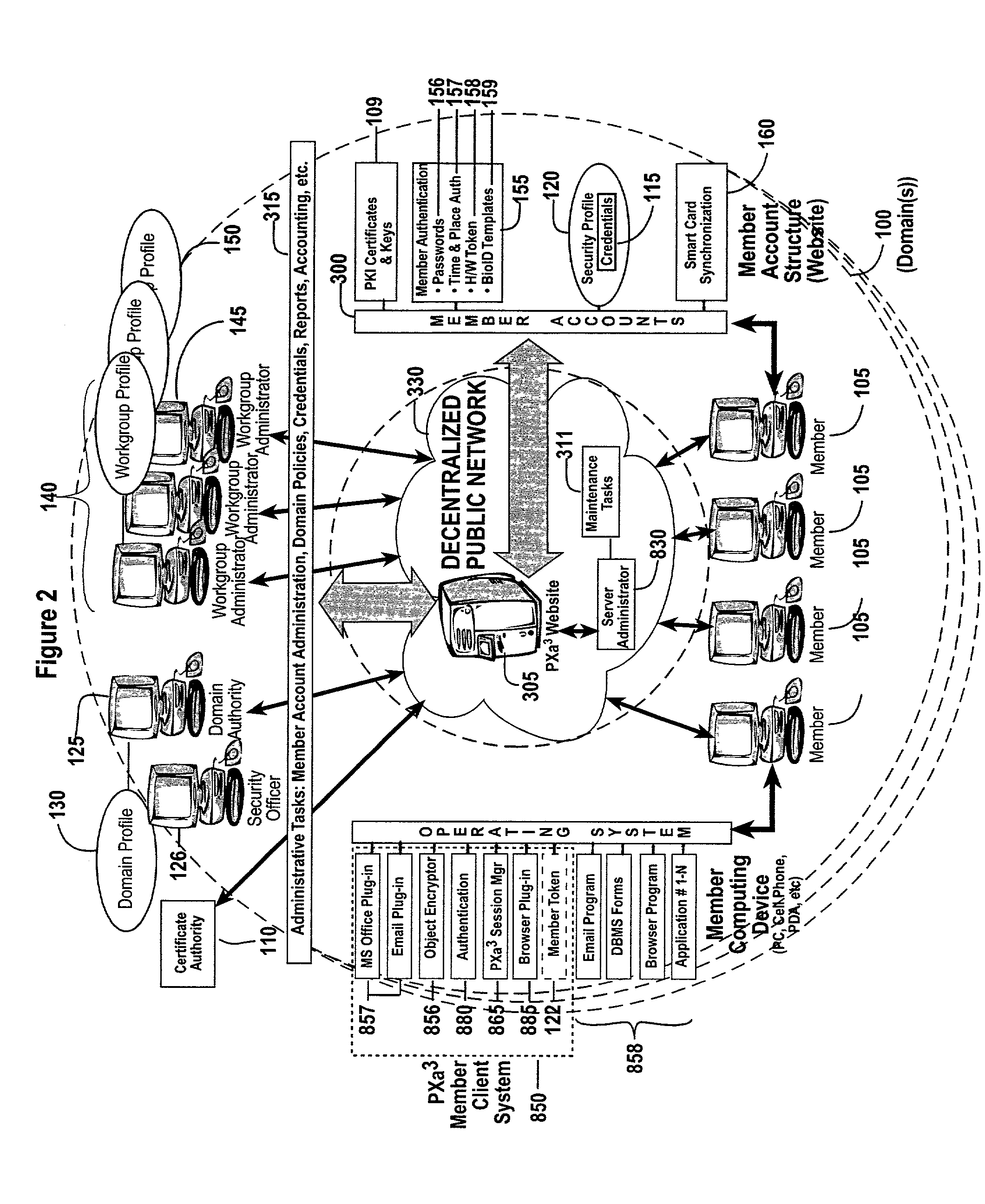
Method and apparatus for a web-based application service model for security management
The invention combines cryptographic key management technology with various authentication options and the use of a companion PKI system in a web-centric cryptographic key management security method and apparatus called PXa3(TM) (Precise eXtensible Authentication, Authorization and Administration). The PXa3 model uses a security profile unique to a network user and the member domain(s) he / she belongs to. A PXa3 server holds all private keys and certificates, the user's security profile, including credentials and the optional authentication enrollment data. The server maintains a security profile for each user, and administrators simply transmitted credential updates and other periodic maintenance updates to users via their PXa3 server-based member accounts. Domain and workgroup administrators also perform administrative chores via a connection to the PXa3 web site, rather than on a local workstation. A member's security profile, containing algorithm access permissions, credentials, domain and maintenance values, a file header encrypting key, optional biometric templates, and domain-specific policies is contained in one of two places: either on a removable cryptographic token (e.g., a smart card), or on a central server-based profile maintained for each member and available as a downloadable "soft token" over any Internet connection.
Owner:SIVAULT INC
Data security system and method with multiple independent levels of security
InactiveUS20050138110A1Ease overhead performanceHigh overhead performancePeptide/protein ingredientsNGF/TNF-superfamilyInformation processingWorkstation
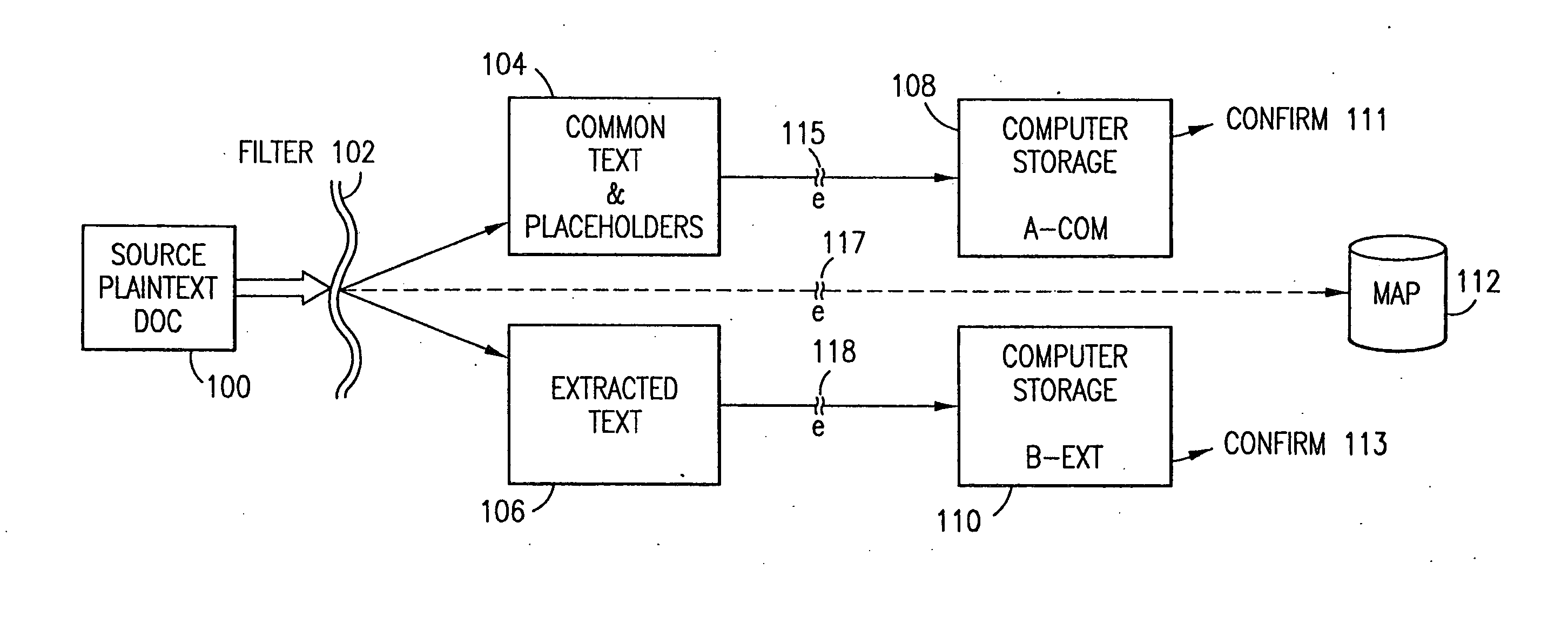
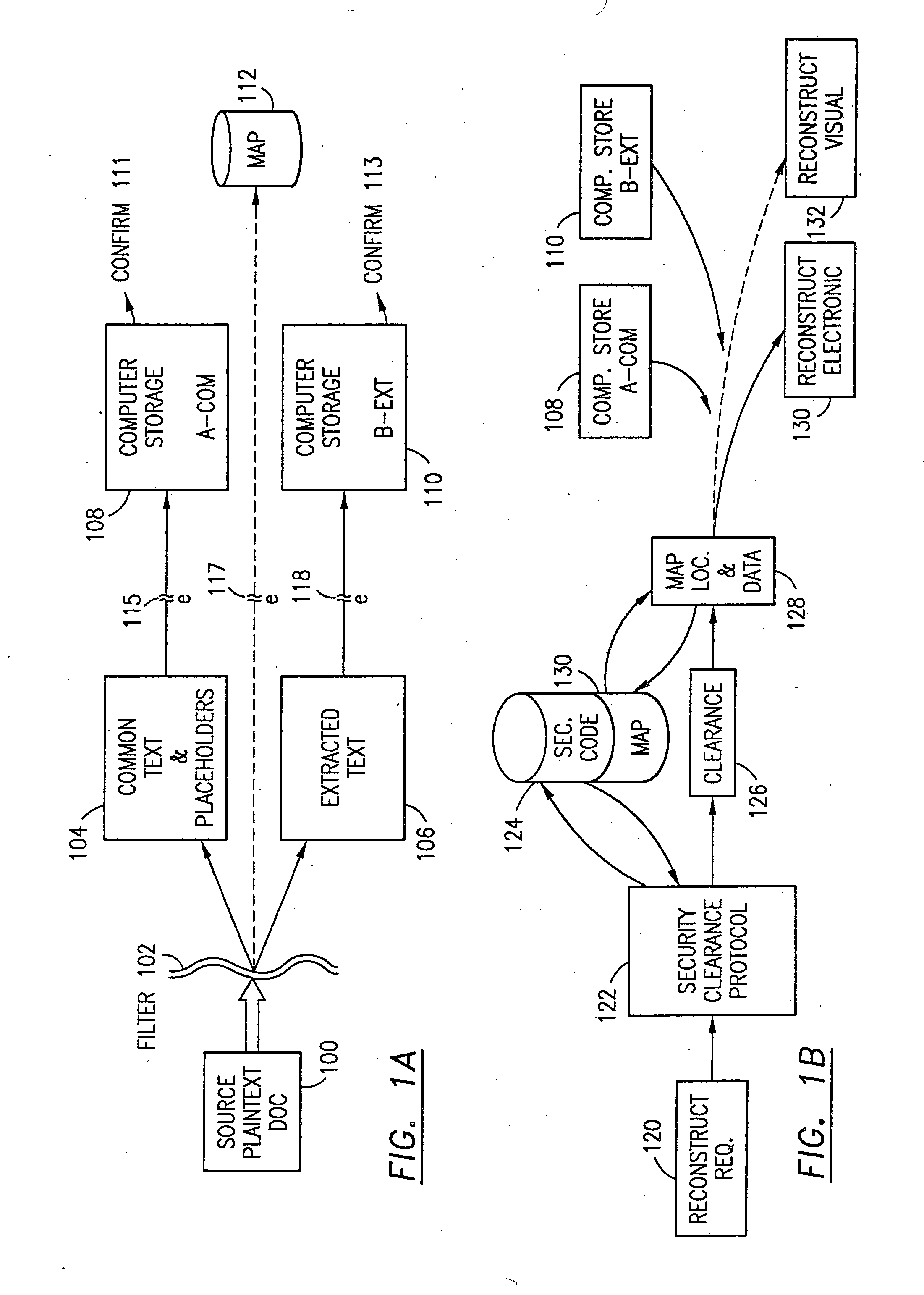
The method, program and information processing system secures data, and particularly security sensitive words, characters or data objects in the data, in a computer system with multiple independent levels of security (MILS). Each level of MILS has a computer sub-network with networked workstations. The MILS sub-networks are connected together via security guard computer(s) and each guard computer has separate memories for each level (TS, S, C, UC(or remainder)). The method extracts the security sensitive words / data (a granular action), from the source document for each MILS level, stores the extracted data in a corresponding extract store for each level and permits reconstruction / reassembly of the dispersed data via said extracted data at each said level of said multiple security levels and remainder data only in the presence of a predetermined security clearance commensurate with each MILS level.
Owner:DIGITAL DOORS
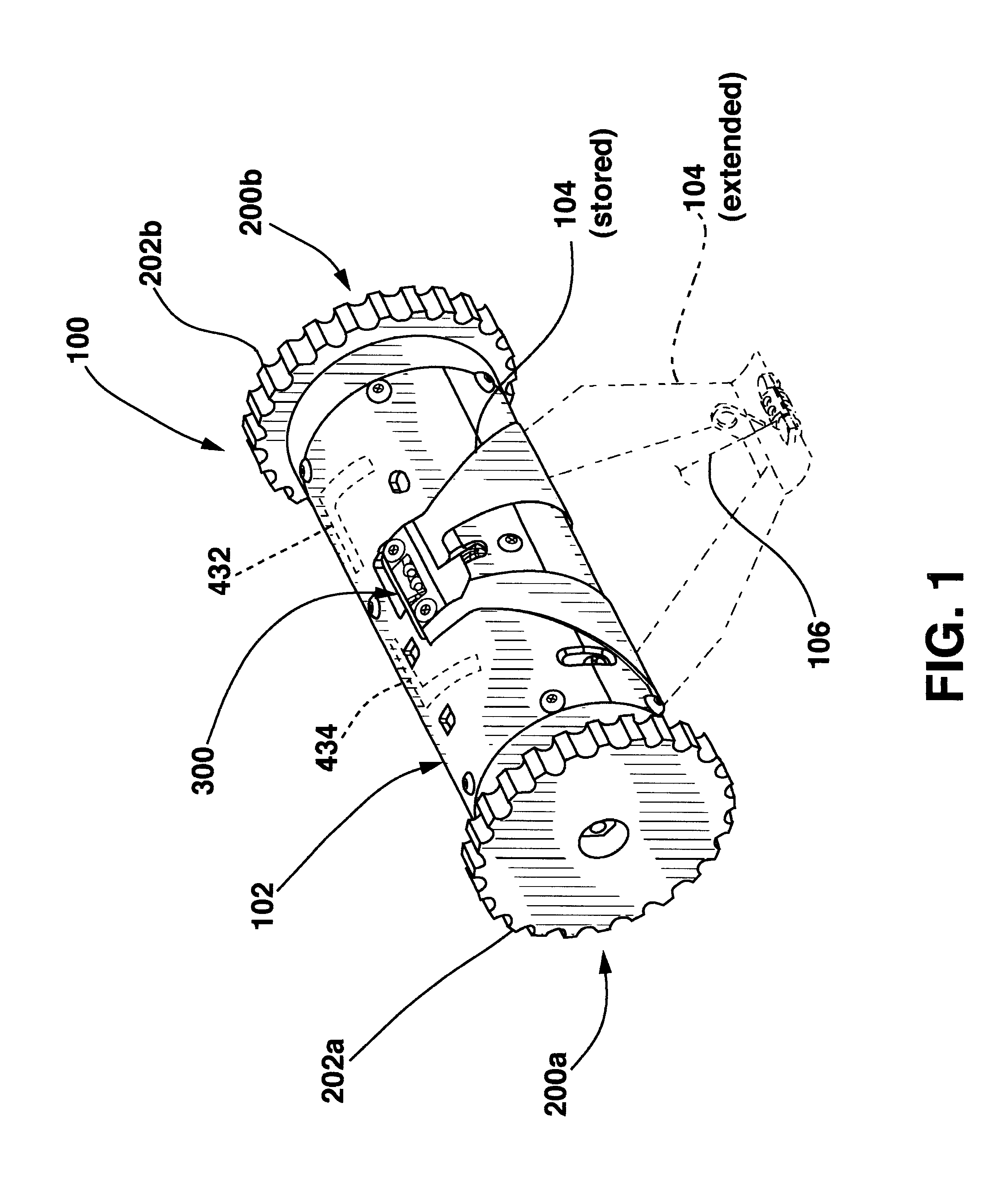
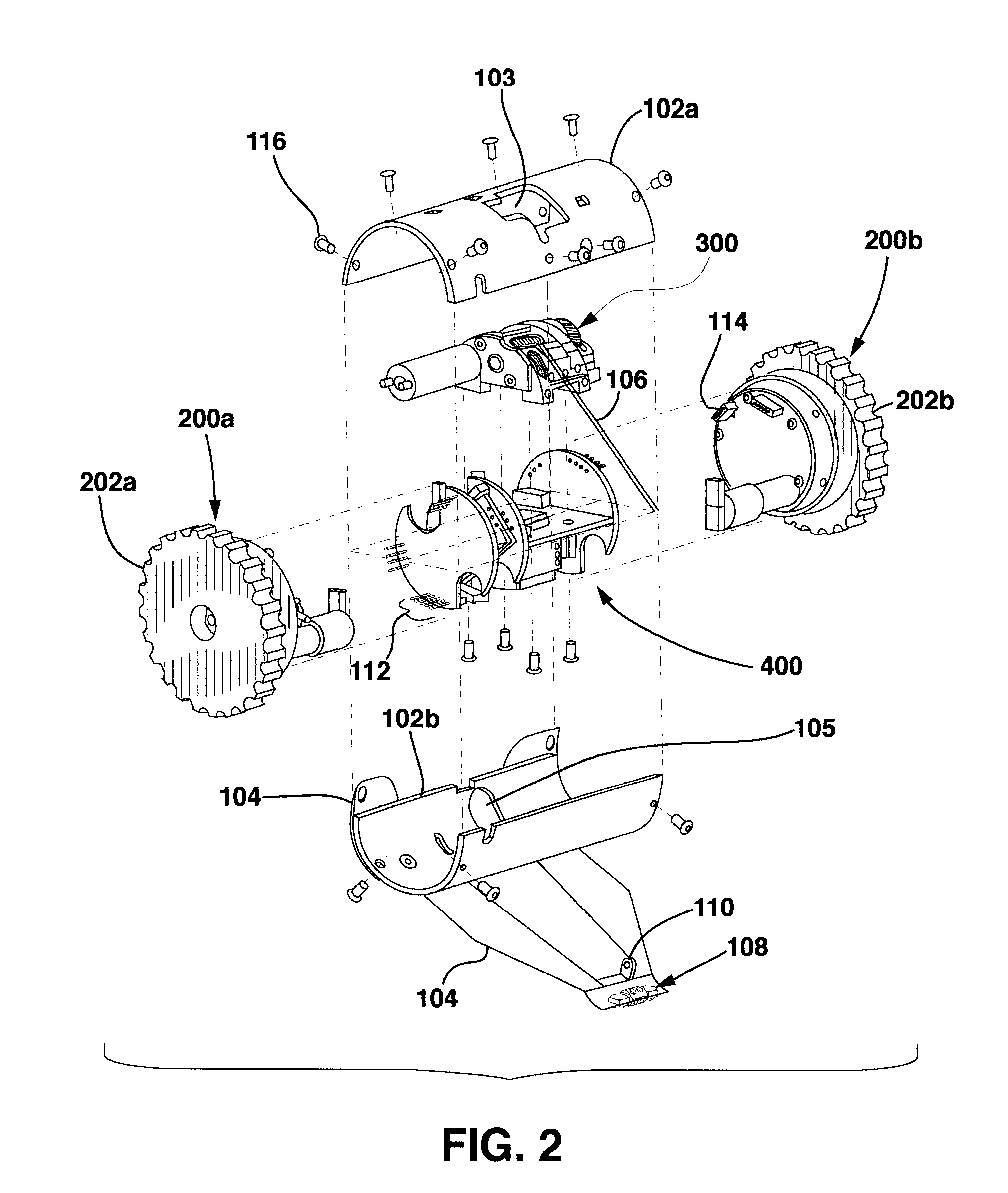
Miniature robotic vehicles and methods of controlling same
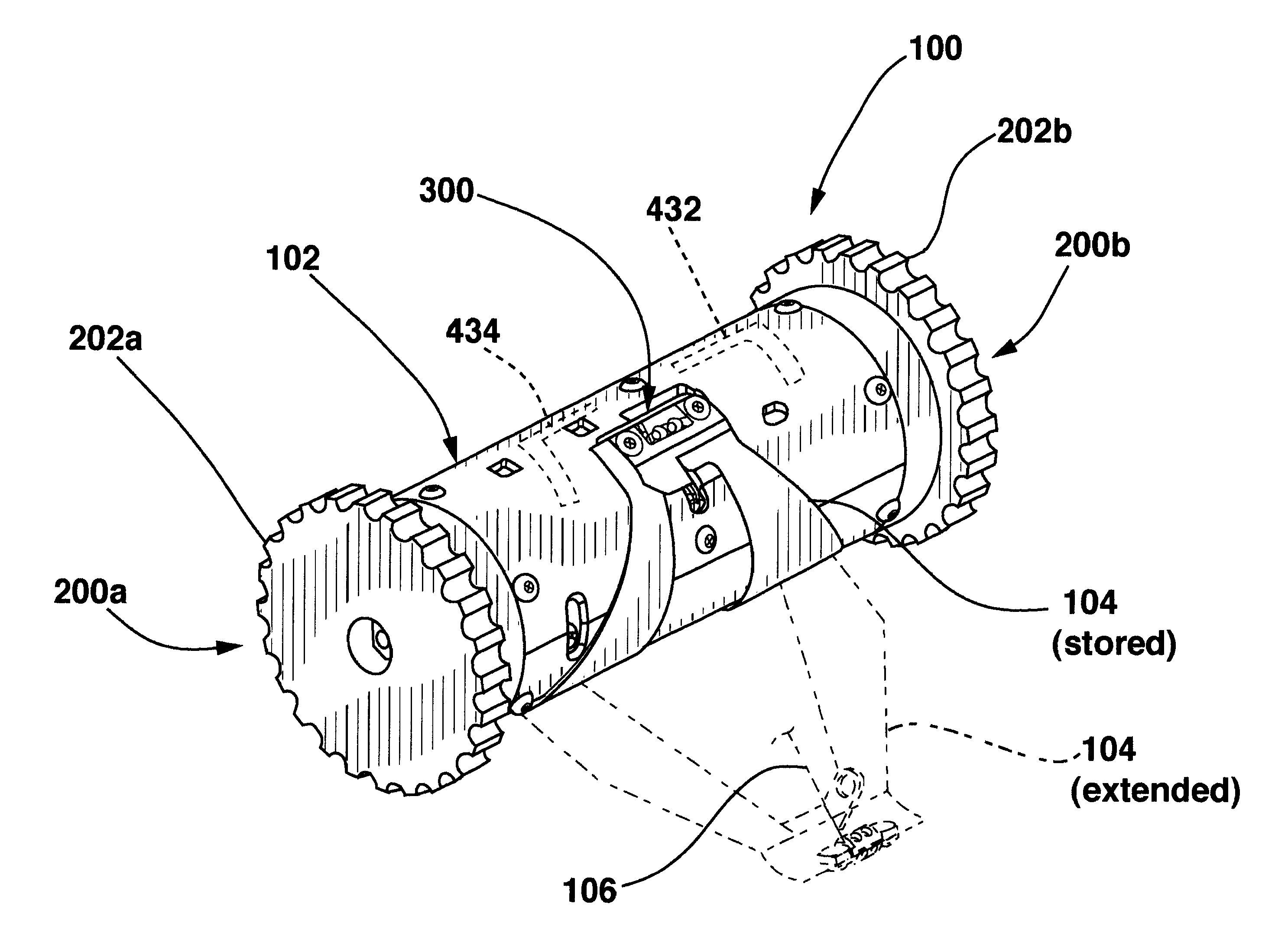
A robotic vehicle capable of traveling over various terrain and traversing obstacles. In one embodiment, the vehicle includes a cylindrical body having two or more drive wheels coupled to the ends thereof. The wheels are selectively powered to propel the vehicle. The vehicle may further include a spring member which may be deflected to a first, stored position from a second, extended position. The spring member may be quickly released from the first, stored position such that it strikes the terrain with sufficient force to lift and propel the vehicle over or onto a proximate obstacle or object. Robotic vehicles of the present invention may also include one or more sensing devices operable to collect information. Electronics may further permit autonomous, semi-autonomous, and / or remote control of the vehicle. In still other embodiments, the robotic vehicle forms part of a multi-robot surveillance team. The robotic vehicles may be delivered to the desired location through the use of a deployment and communication apparatus which, in one embodiment, is a larger robotic vehicle. The deployment and communication apparatus may form part of the communication system between the robotic vehicles and a remote workstation.
Owner:MINNESOTA RGT UNIV OF A CORP OF MN +1
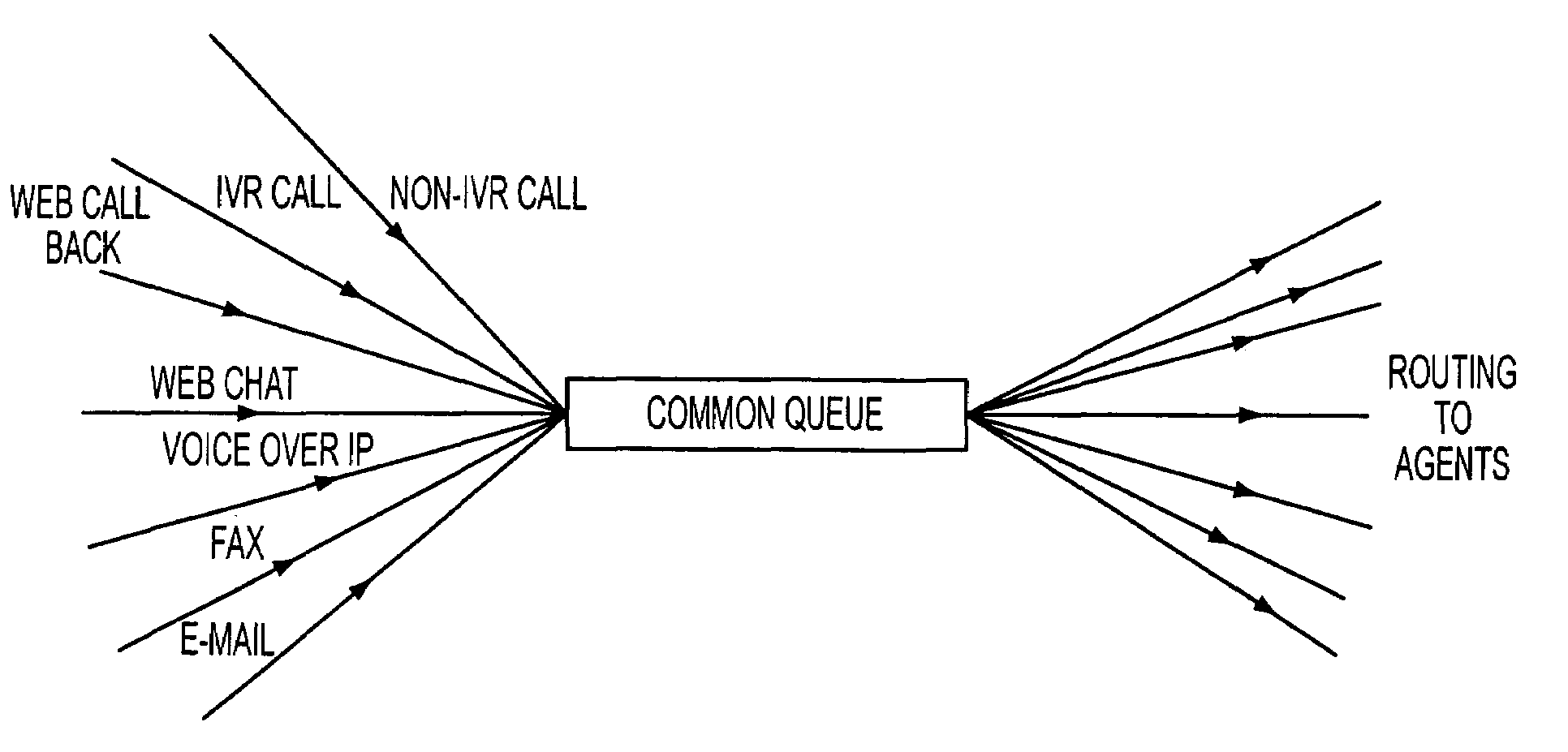
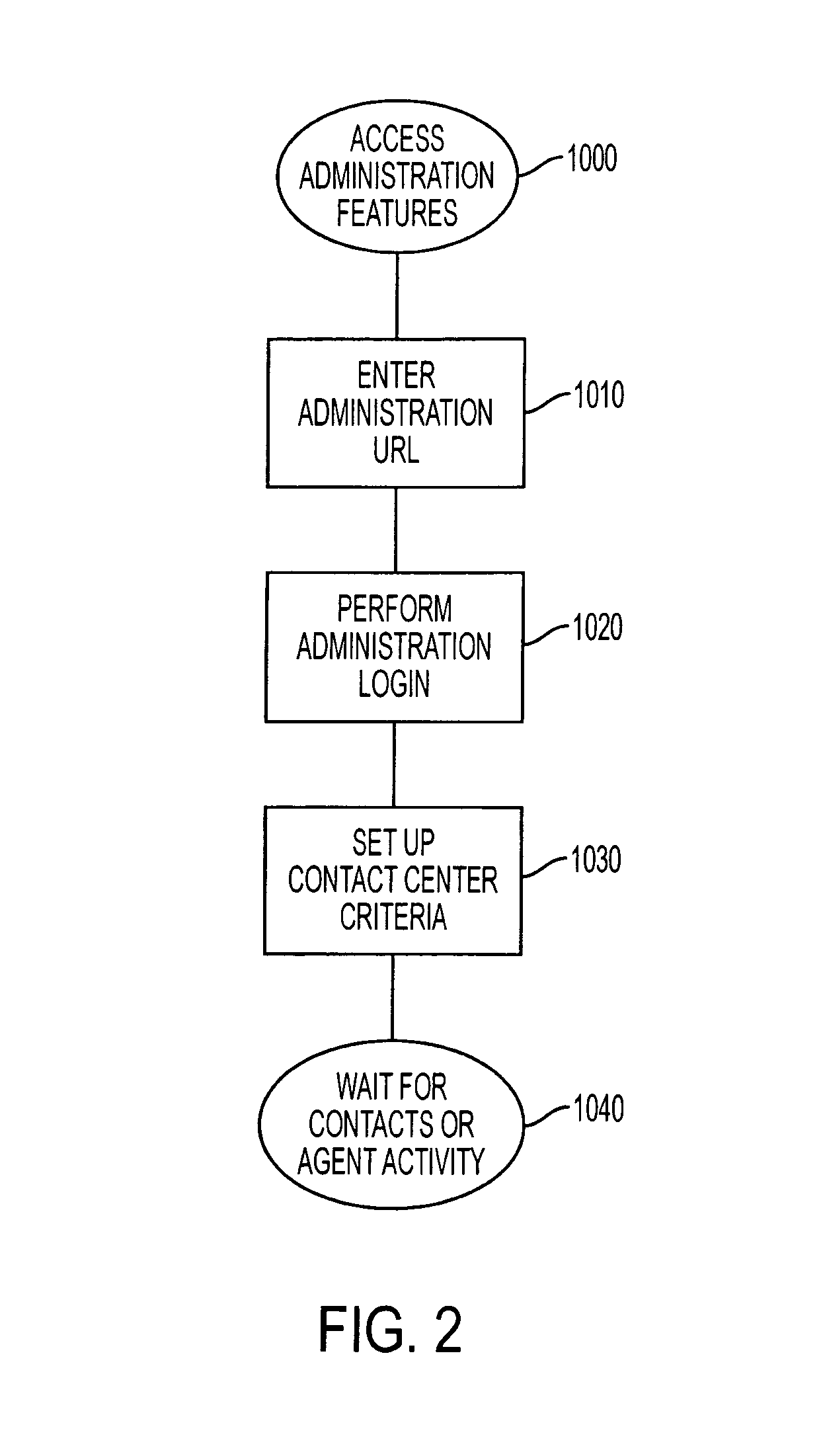
Contact center system capable of handling multiple media types of contacts and method for using the same
InactiveUS7092509B1Efficiently and effectively handlingManual exchangesAutomatic exchangesMedia typeContact center
A contact center system and method employing a plurality of agent workstations, and which includes a queuing component, capable of receiving contacts of different media-types, such as telephone calls, e-mails, facsimiles, web chat, voice over internet protocol, and so on, and maintaining the different media types contacts in a common queue while awaiting routing to the agent workstations. The system further comprises a routing component which routes the queued contacts to the agents based on criteria of the contacts, criteria of the agents, or both. A media changing component of the system is capable of changing a media-type of any of the media-type contacts to generate a changed media-type contact, while the queuing component is capable of entering the changed media-type contact in the common queue, and the routing component is capable of routting the queued changed media-type contact to at least one of the workstations. A contact handling component initiates an event at any of the workstations in response to the contact being routed to the workstation, so that an agent at the workstation can handle the contact as appropriate.
Owner:MICROLOG
Method and apparatus for the management of data files
InactiveUS6263330B1Easy retrievalEasy accessData processing applicationsTelemedicineMedical recordData file
The present invention provides a network system for storage of medical records. The records are stored in a database on a server. Each record includes two main parts, namely a collection of data elements containing information of medical nature for the certain individual, and a plurality of pointers providing addresses or remote locations where reside other medical data for that particular individual. Each record also includes a data element indicative of the basic type of medical data found at the location pointed to by a particular pointer. This arrangement permits a client workstation to download the record along with the set of pointers which link the client to the remotely stored files. The identification of the basic type of information that each pointer points to allows the physician to select the ones of interest and thus avoid downloading massive amounts of data where only part of that data is needed at that time. In addition, this record structure allows statistical queries to be effected without the necessity of accessing the data behind the pointers. For instance, a query can be built based on keys, one of which is the type of data that a pointer points to. The query can thus be performed solely on the basis of the pointers and the remaining information held in the record.
Owner:BESSETTE LUC
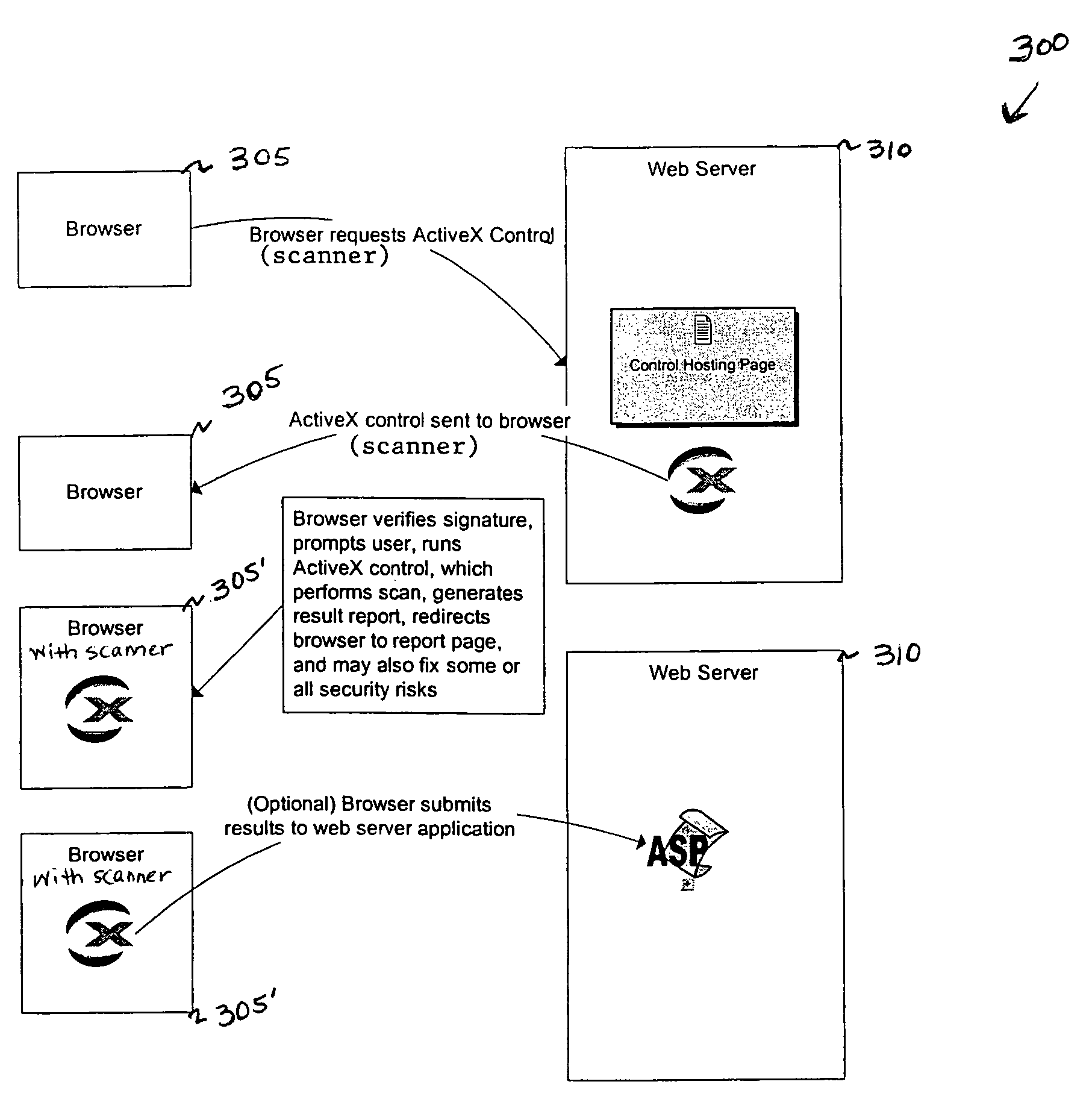
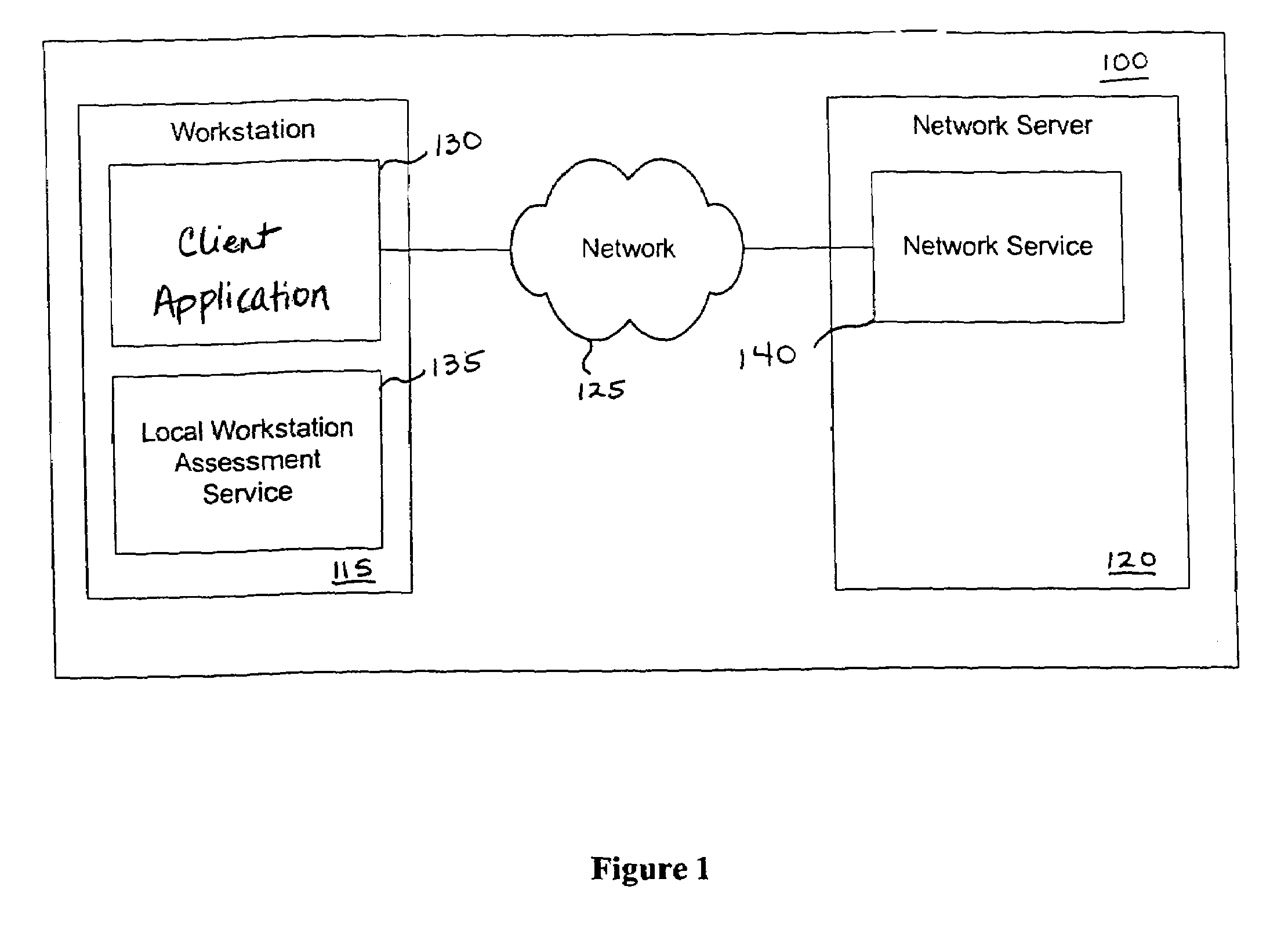
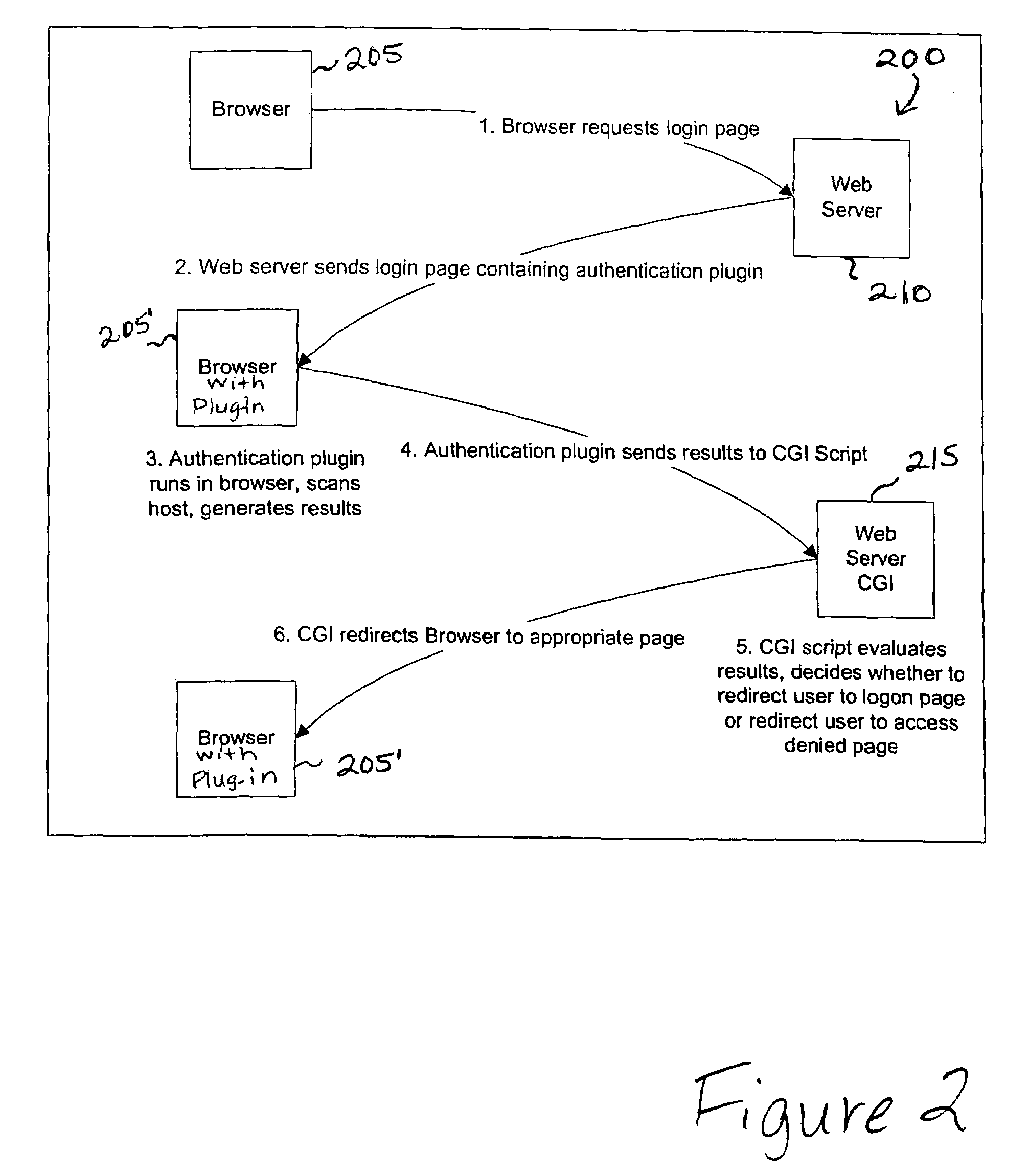
Vulnerability assessment and authentication of a computer by a local scanner
InactiveUS7178166B1Overcome disadvantagesMemory loss protectionDigital data processing detailsWorkstationNetwork service
Providing a user with assurance that a computer is secure based on a vulnerability assessment completed by a browser-compatible scanner operating on the computer. If the scanner finds a vulnerability, the scanner can inform the user that the machine is or may be compromised, or repair the vulnerability. For example, the scanner may be able to repair the vulnerability of the workstation. In the alternative, the scanner can provide the scan results to a network server. If the vulnerability assessment shows that the workstation is compromised, or if the possibility of remote compromise is high, the network server can decline to provide network services to the workstation.
Owner:KYNDRYL INC
Simulation gridding method and apparatus including a structured areal gridder adapted for use by a reservoir simulator
InactiveUS6106561AHigh simulationSimulation results are accurateElectric/magnetic detection for well-loggingComputation using non-denominational number representationHorizonTriangulation
A Flogrid Simulation Gridding Program includes a Flogrid structured gridder. The structured gridder includes a structured areal gridder and a block gridder. The structured areal gridder will build an areal grid on an uppermost horizon of an earth formation by performing the following steps: (1) building a boundary enclosing one or more fault intersection lines on the horizon, and building a triangulation that absorbs the boundary and the faults; (2) building a vector field on the triangulation; (3) building a web of control lines and additional lines inside the boundary which have a direction that corresponds to the direction of the vector field on the triangulation, thereby producing an areal grid; and (4) post-processing the areal grid so that the control lines and additional lines are equi-spaced or smoothly distributed. The block gridder of the structured gridder will drop coordinate lines down from the nodes of the areal grid to complete the construction of a three dimensional structured grid. A reservoir simulator will receive the structured grid and generate a set of simulation results which are displayed on a 3D Viewer for observation by a workstation operator.
Owner:SCHLUMBERGER TECH CORP
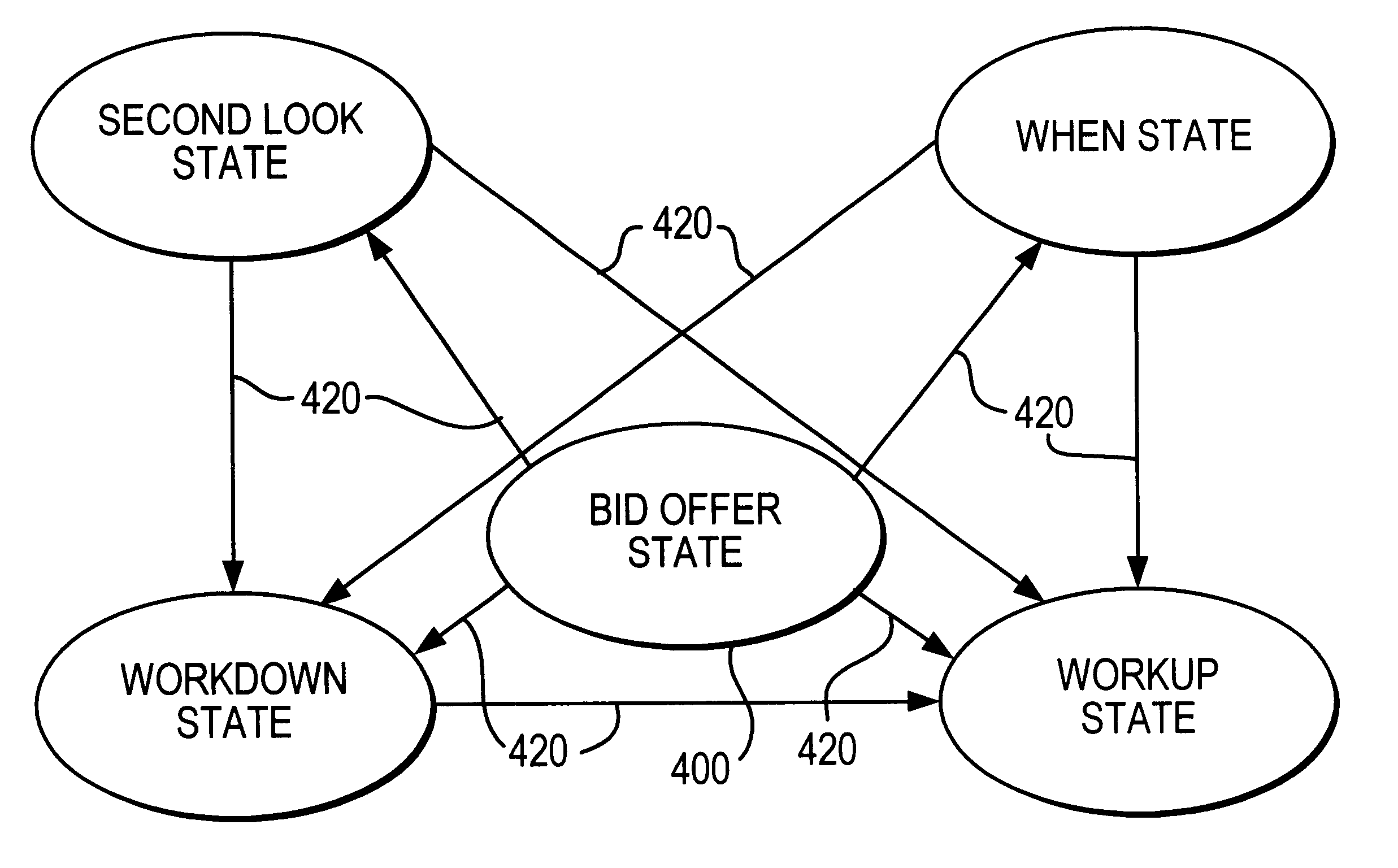
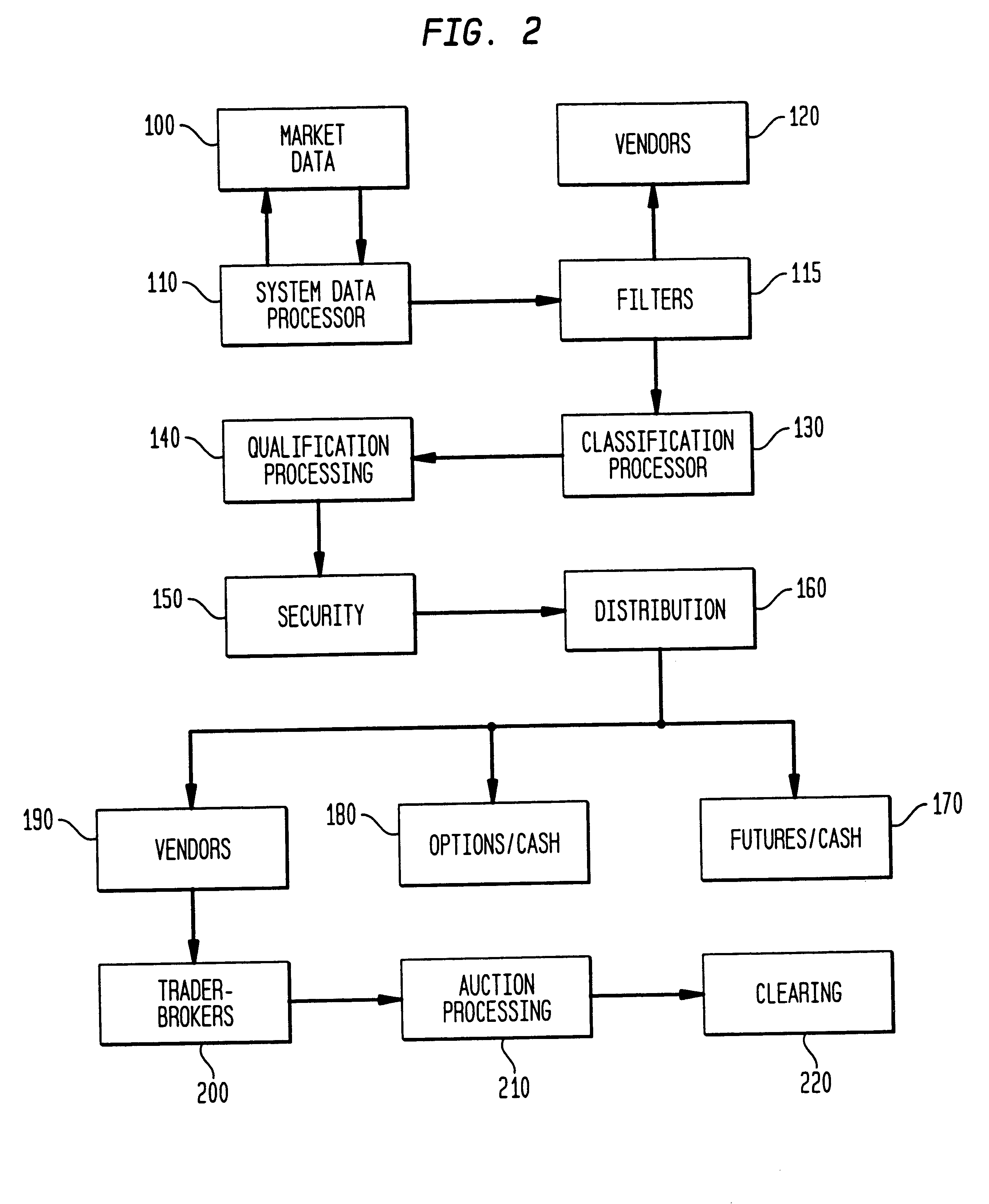
Automated price improvement protocol processor
InactiveUS6850907B2Distribute quicklyFast exchangeFinanceBuying/selling/leasing transactionsData processing systemProtocol processing
A data processing system for implementing transaction management of auction-based trading for specialized items such as fixed income instruments. The data processing system provides a highly structured trading protocol implemented through a sequence of trading paradigms. The system employs a distributed computer processing network linking together a plurality of commonly configured program controlled workstations. The protocol and its program controlling logic enhances trading efficiency, rewards market Makers, and fairly distributes market opportunity to system users.
Owner:CANTOR FITZGERALD LP +1
Method and economical direct connected apparatus for deploying and tracking computers
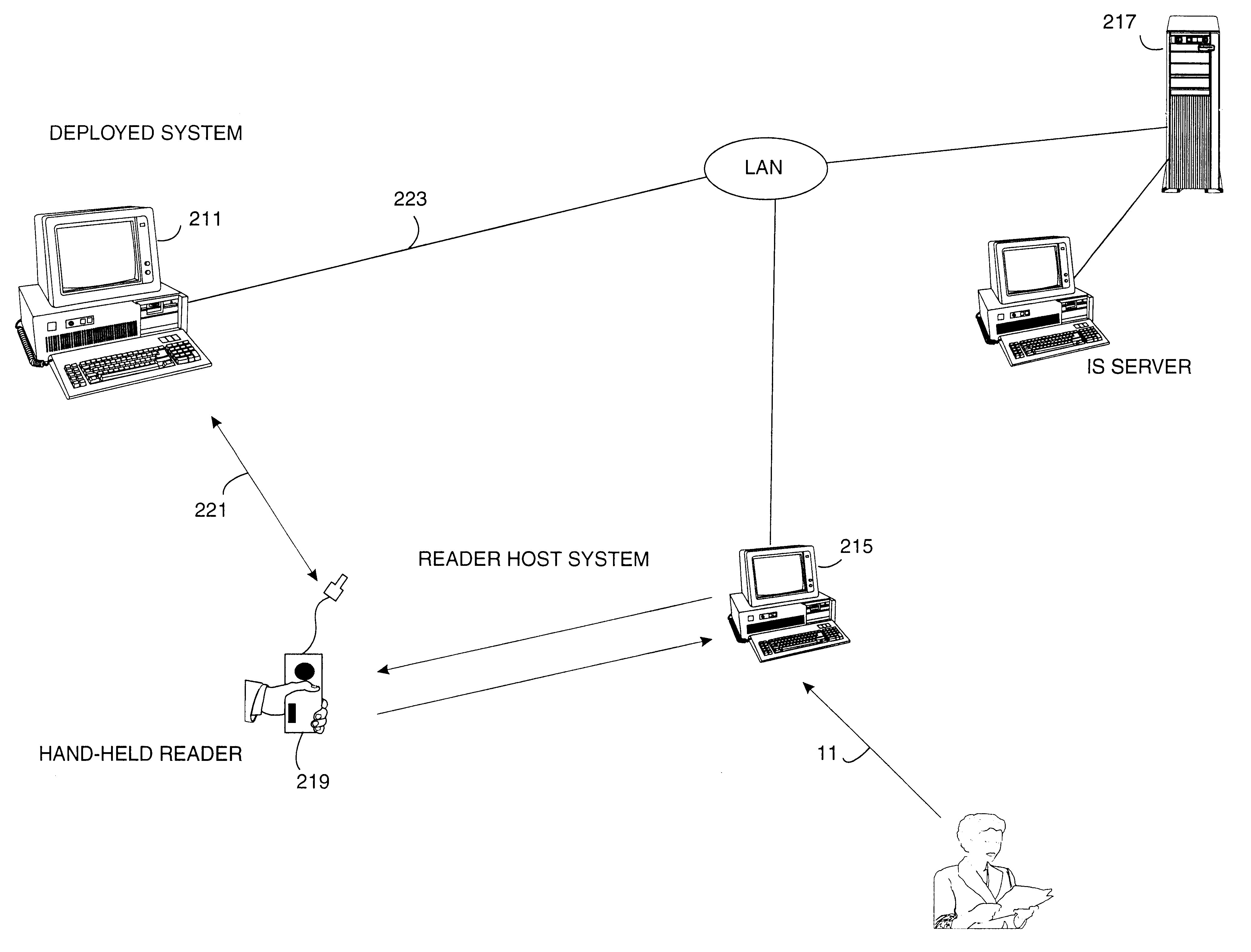
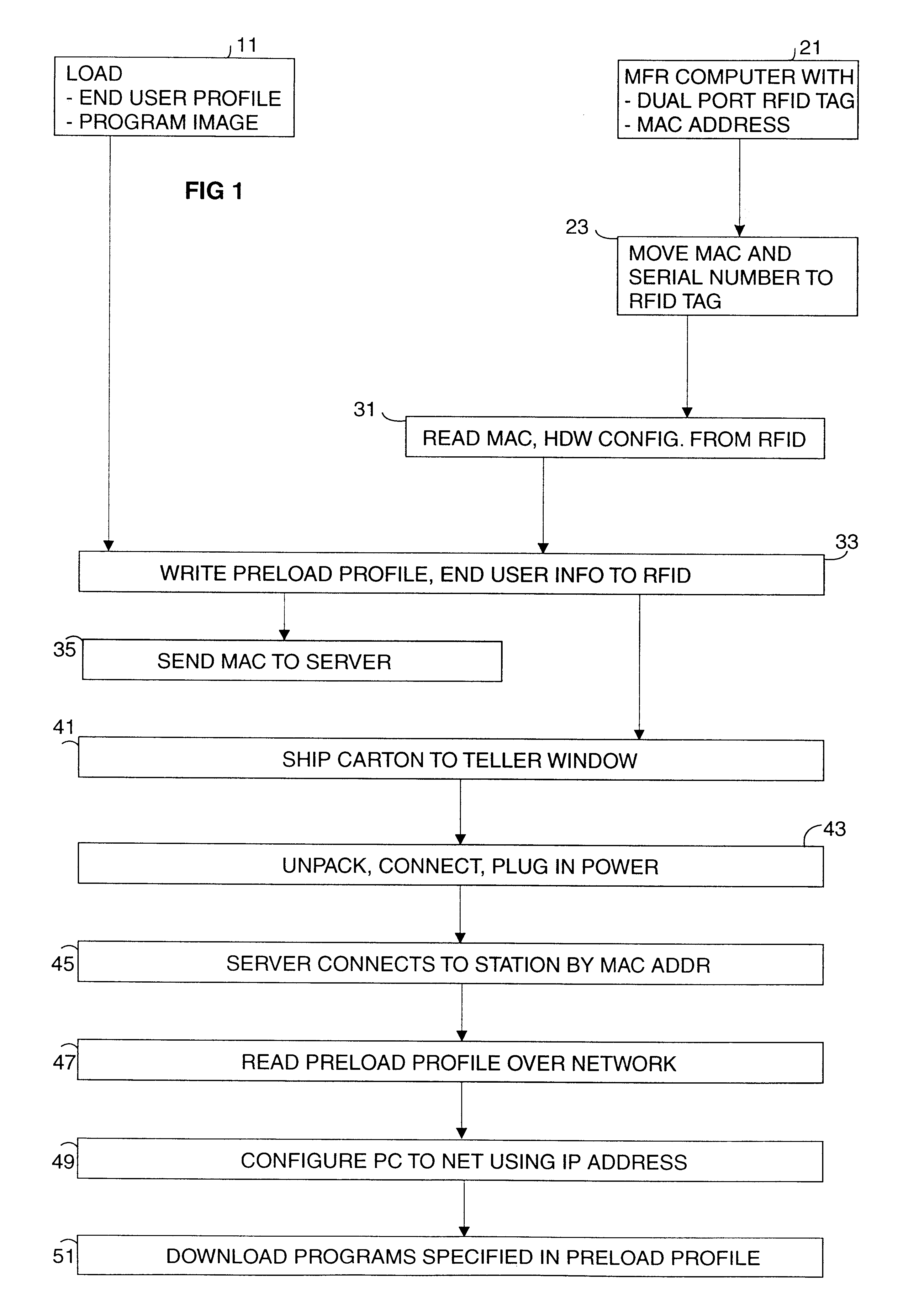
A method of asset control and workstation computer deployment that utilizes a dual port electronic memory identification RFID tag to hold serial number and hardware and software configuration profiles as well as user information. The RFID tag is mapped into the workstation computer memory space and can also be read and written by radio frequency signalling through a wired plug and access flap in a shipping carton. Serial numbers and MAC address is stored on the tag by the manufacturer. User information, workstation profile and software image information is stored onto the tag while the computer is being received for forwarding to the final workstation destination without the need to unpack and power up the computer. The information stored on the tag is used to allow automated system configuration and software downloading to the computer.
Owner:IBM CORP
Mobile provisioning tool system
ActiveUS20050075115A1Simple processLimited accessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile businessWorkstation
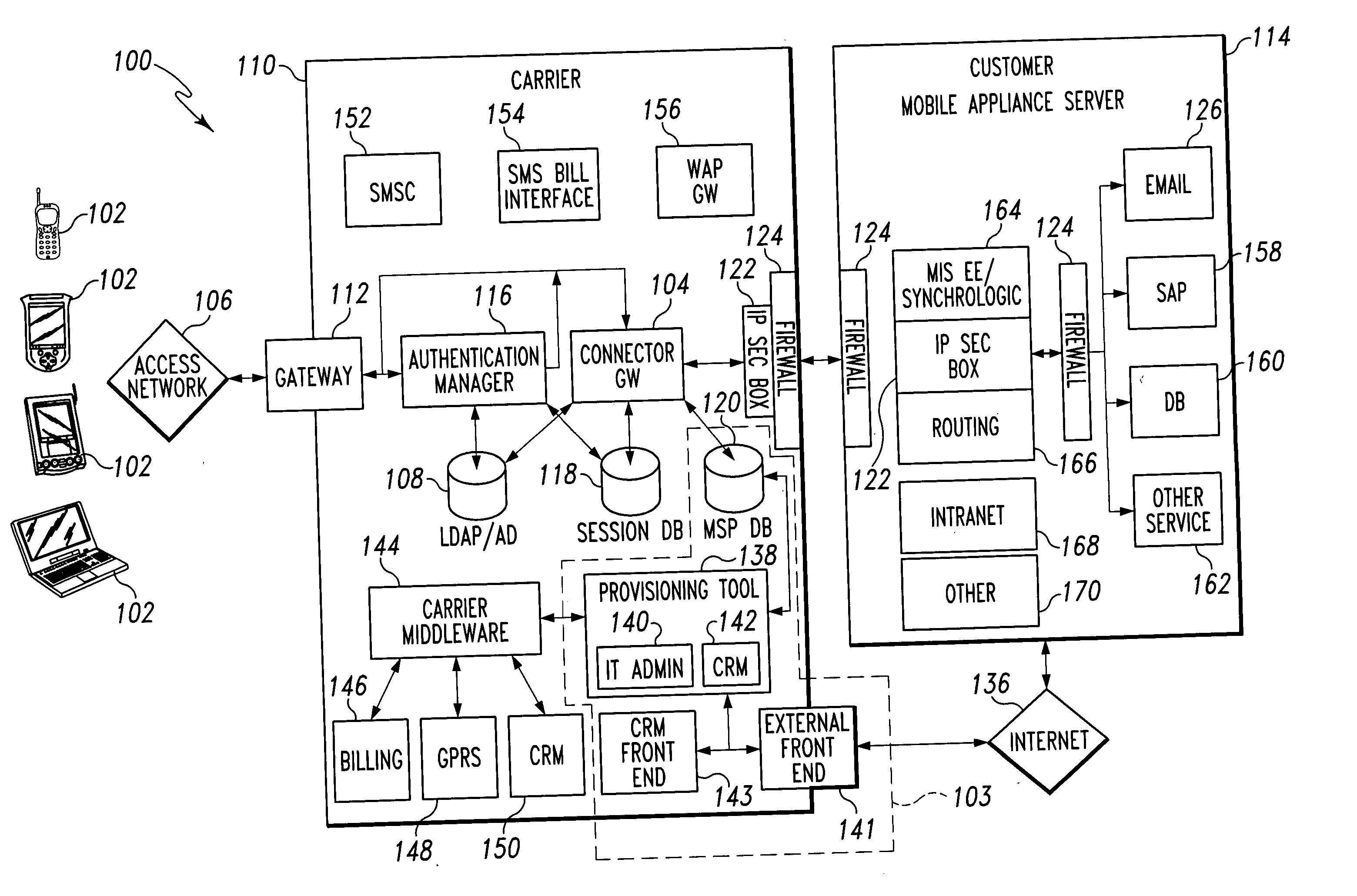
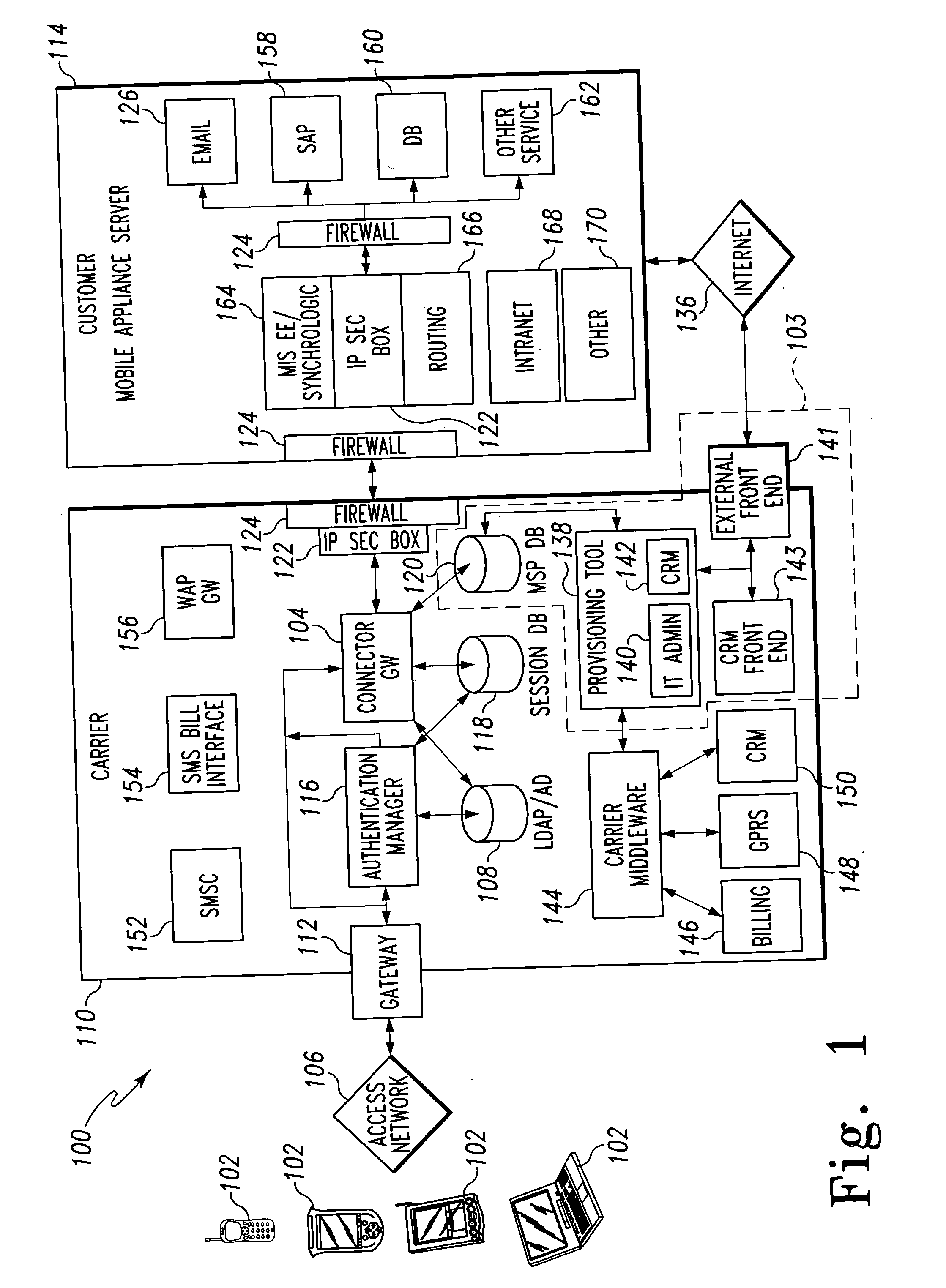
A mobile provisioning tool system including a software provisioning tool application. The mobile provisioning tool system includes mobile devices capable of conducting wireless communication with wireless access points. A carrier network is connected with the wireless access points and a customer network that includes at least one business application. A provisioning tool application is located on a provisioning server. The provisioning tool application includes a CRM Rep component and an IT Admin component. A software provisioning tool application allows the provisioning workstation to automatically install mobile business services and configure network configuration settings on the mobile device.
Owner:ACCENTURE GLOBAL SERVICES LTD
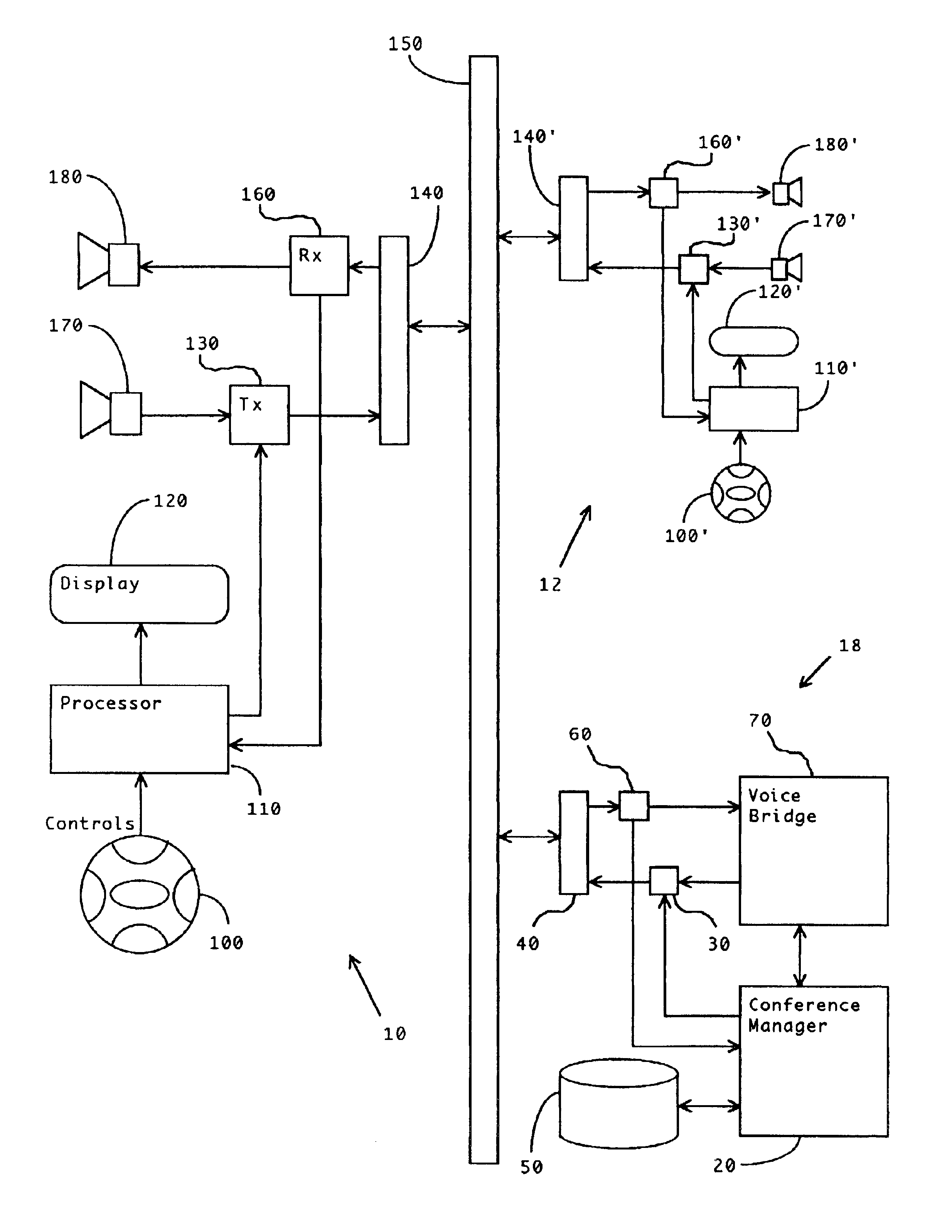
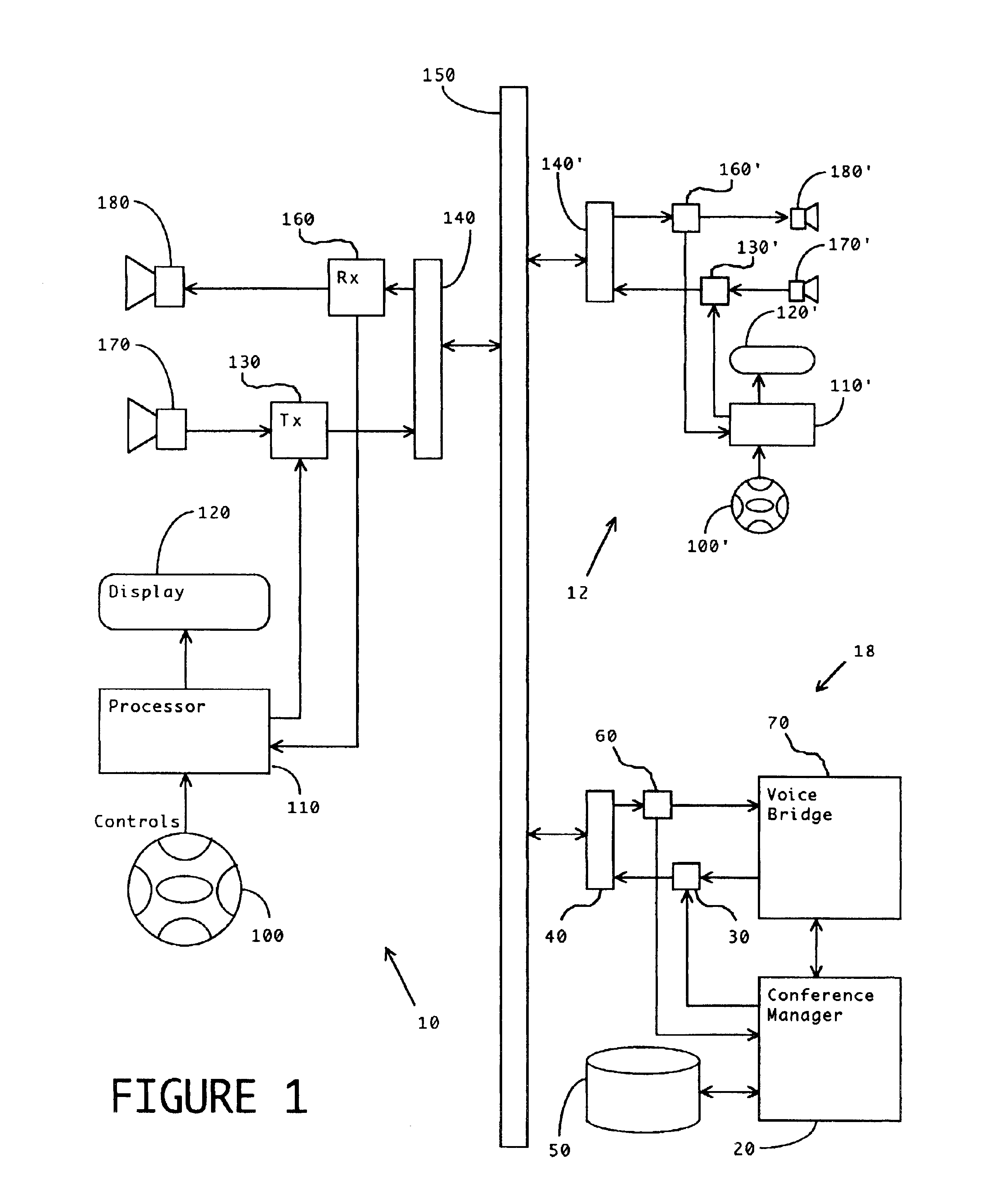
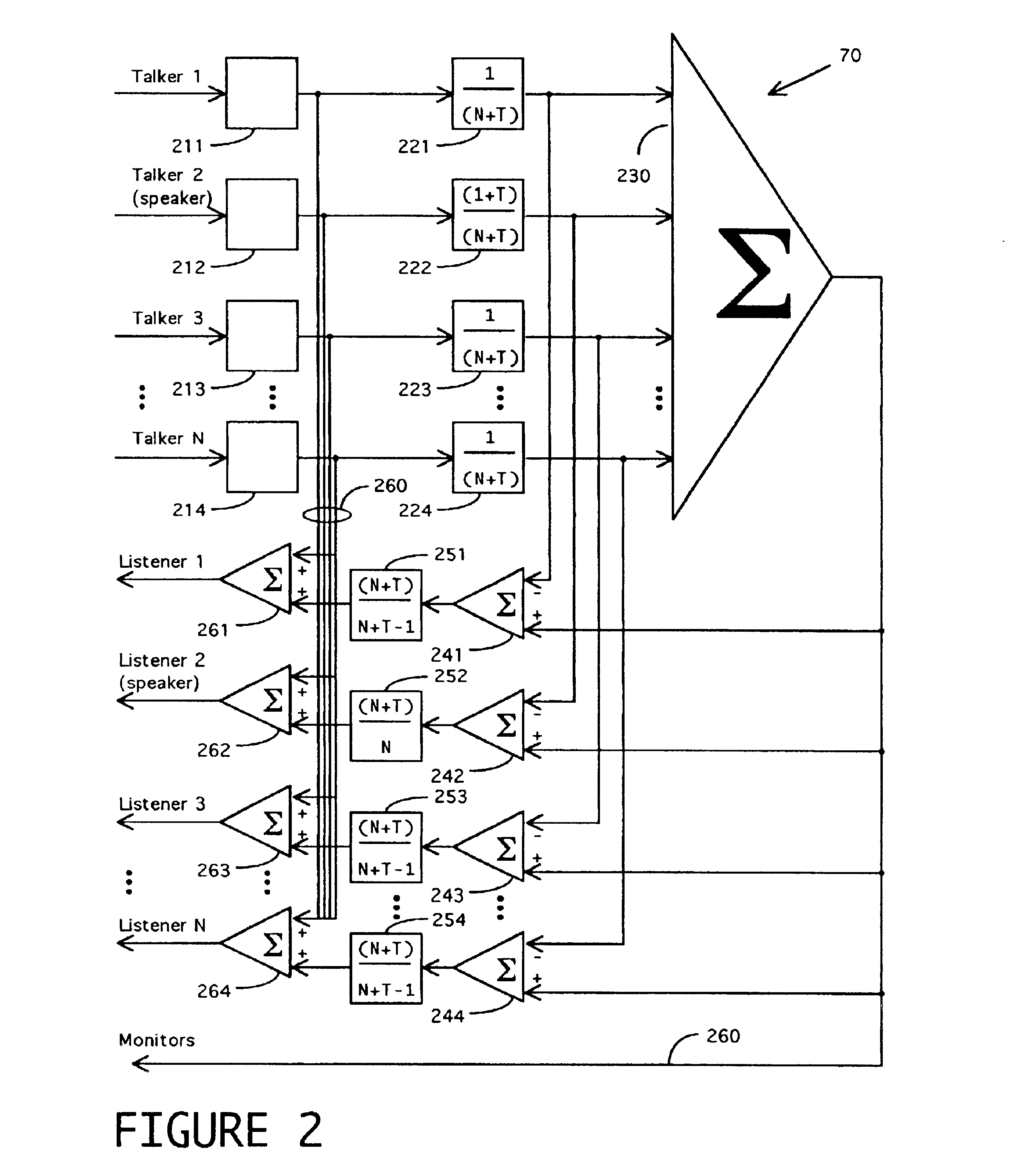
Method and apparatus for improved conference call management
InactiveUS6839417B2Exposure was also limitedIncrease exposureSpecial service for subscribersWireless networksOrganizational controlWorkstation
A method and apparatus are disclosed to allow individuals to initiate, join, manage, and participant in a conference call. Members of a community can meet and collaborate over telephones, especially cellular telephones, or computer workstations, in a way that is freeform or prescribed, automatic or moderated, spontaneous or scheduled, unassisted, and selectably anonymous. The invention provides broadly customizable degrees of collective and individual organizational control, and provides social safeguards to minimize disruptions by unruly participants.
Owner:BUFFALO PATENTS LLC
Transmission control protocol/internet protocol (TCP/IP) packet-centric wireless point to multi-point (PTMP) transmission system architecture
InactiveUS6862622B2Special service provision for substationError detection/prevention using signal quality detectorTransport systemWorkstation
A packet-centric wireless point to multi-point telecommunications system includes: a wireless base station communicating via a packet-centric protocol to a first data network; one or more host workstations communicating via the packet-centric protocol to the first data network; one or more subscriber customer premise equipment (CPE) stations coupled with the wireless base station over a shared bandwidth via the packet-centric protocol over a wireless medium; and one or more subscriber workstations coupled via the packet-centric protocol to each of the subscriber CPE stations over a second network. The packet-centric protocol can be transmission control protocol / internet protocol (TCP / IP). The packet-centric protocol can be a user datagram protocol / internet protocol (UDP / IP). The system can include a resource allocation means for allocating shared bandwidth among the subscriber CPE stations. The resource allocation is performed to optimize end-user quality of service (QoS). The wireless communication medium can include at least one of: a radio frequency (RF) communications medium; a cable communications medium; and a satellite communications medium. The wireless communication medium can further include a telecommunications access method including at least one of: a time division multiple access (TDMA) access method; a time division multiple access / time division duplex (TDMA / TDD) access method; a code division multiple access (CDMA) access method; and a frequency division multiple access (FDMA) access method.The first data network includes at least one of: a wireline network; a wireless network; a local area network (LAN); and a wide area network (WAN). The second network includes at least one of: a wireline network; a wireless network; a local area network (LAN); and a wide area network (WAN).
Owner:INTELLECTUAL VENTURES I LLC
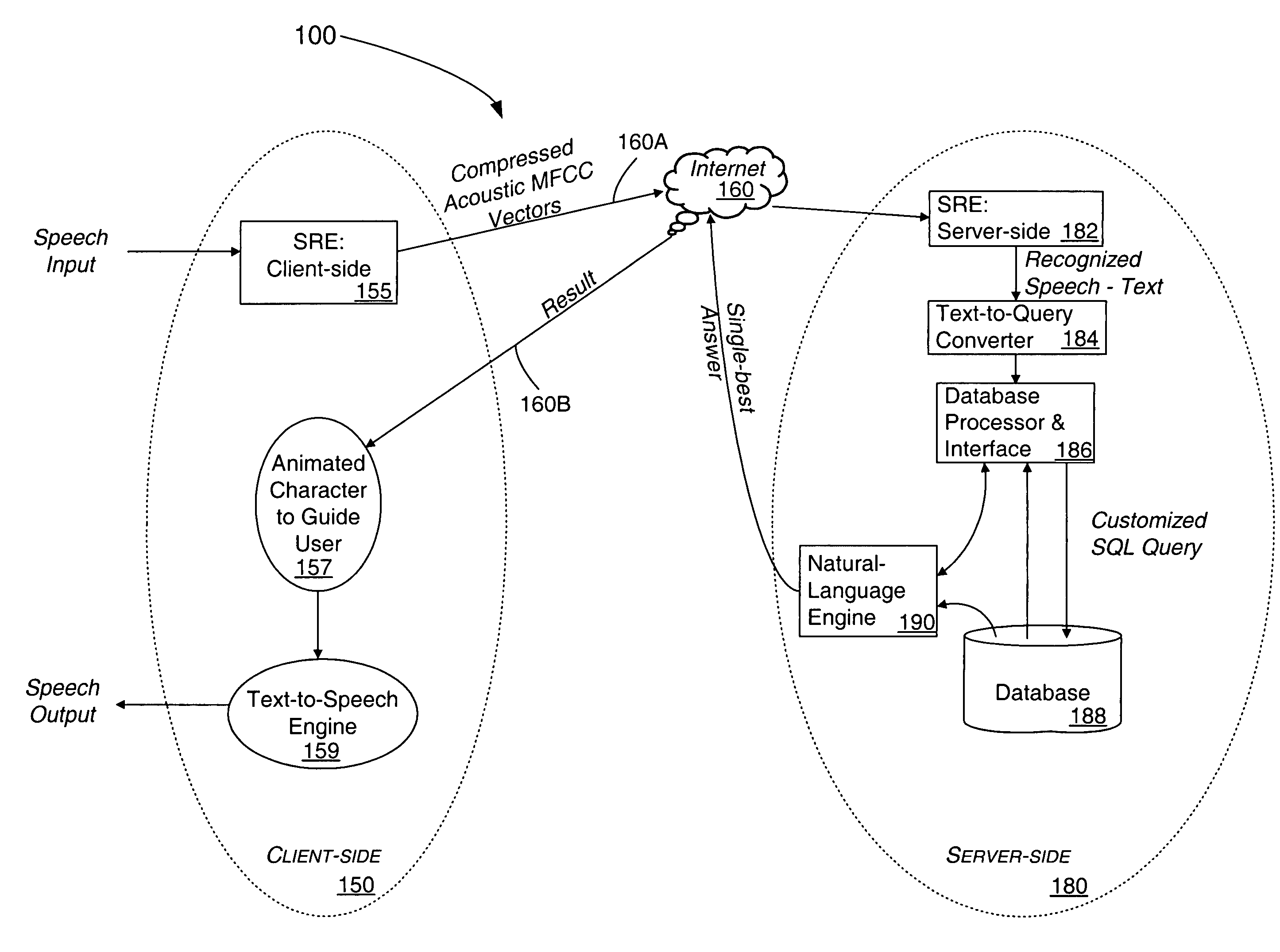
Method for processing speech signal features for streaming transport
InactiveUS7376556B2Flexibly and optimally distributedImprove accuracyNatural language translationData processing applicationsNetwork onClient server systems
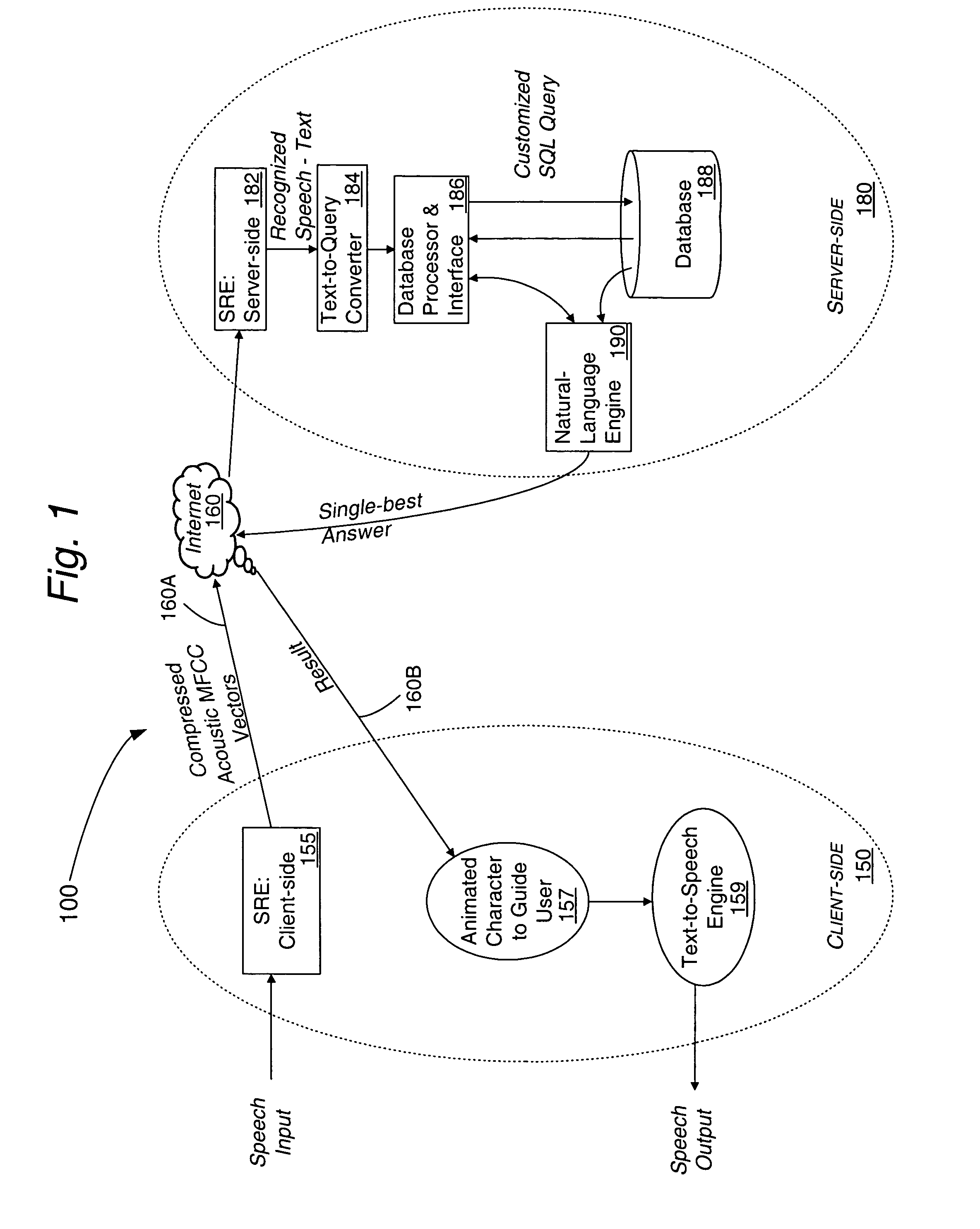
Speech signal information is formatted, processed and transported in accordance with a format adapted for TCP / IP protocols used on the Internet and other communications networks. NULL characters are used for indicating the end of a voice segment. The method is useful for distributed speech recognition systems such as a client-server system, typically implemented on an intranet or over the Internet based on user queries at his / her computer, a PDA, or a workstation using a speech input interface.
Owner:NUANCE COMM INC
Integrated customer web station for web based call management
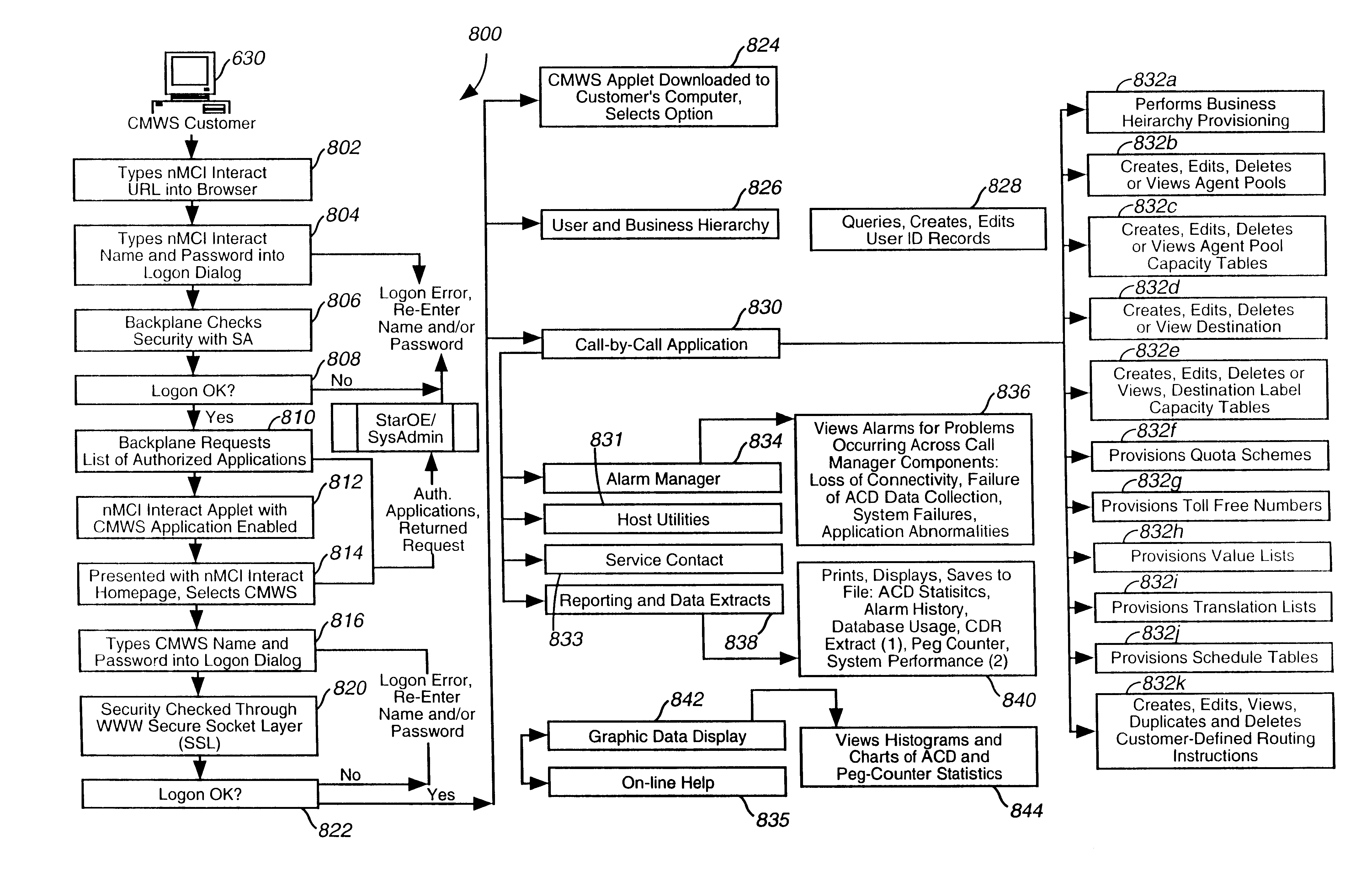
A Web-based call routing management workstation application which allows authorized customers to control toll free routing and monitor call center status. An architecture including one or more web servers located in a firewalled demilitarized zone (DMZ) as communications medium between the customer workstations at the customer sites and the enterprise back-end applications providing the call routing management services, provides a secure infrastructure for accessing the enterprise applications via the otherwise insecure public Internet. The present invention enables creation and management of call by call routing rules by a customer with a workstation having an Internet access and a supported Web browser. The customized rules may be tested and / or debugged via the Web-enabled workstation, using a debugger / tester which runs the routing rules under a simulated environment. In addition, customers may provision hierarchies for their business; create, modify or delete agent pools; manipulate capacity tables; and define quota schemes, value lists and schedule tables, all at the customer site via the Web-enabled workstation. The present invention also enables the customers to view near real-time displays of call center ACD statistics and peg counts based on routing rules, as well as, run provisioning and statistical reports on provisioning and statistical data and also to extract the data for further analysis. Additionally, the present invention supports foreign language and branding features on a graphical user interface. An infrastructure is provided which enables secure initiation, acquisition, and presentation of the call manager functionalities to customers from any computer workstation having a web browser and located anywhere in the world.
Owner:VERIZON PATENT & LICENSING INC
Smart instrument tray RFID reader
ActiveUS7362228B2Accurate and rapid trackingReduce processing costsSurgical furnitureDispensing apparatusEngineeringWorkstation
A radio frequency identification (RFID) workstation reader for RFID-enabled surgical instruments and surgical instrument trays and a method of using a RFID workstation reader to read RFID-enabled surgical instruments and surgical instrument trays is disclosed. The method, apparatus, and system enable individual instruments or a surgical instrument tray containing several surgical instruments to be quickly and efficiently inventoried and tracked. An instrument or instrument tray is placed on the workstation reader. An RF field generated by a plurality of antennae, causes RFID tags embedded in or attached to the instrument or instrument tray to emit a signal containing item specific identification information stored in the tags. The information is received by a control circuit and passed to a computer for data analysis. A status LED is illuminated on the workstation reader based on the results of the data analysis. The method, apparatus, and system can track, inspect, and verify inbound and outbound surgical instrument kits, and help to assess the surgical instruments' and trays' duty life cycle usage.
Owner:WARSAW ORTHOPEDIC INC
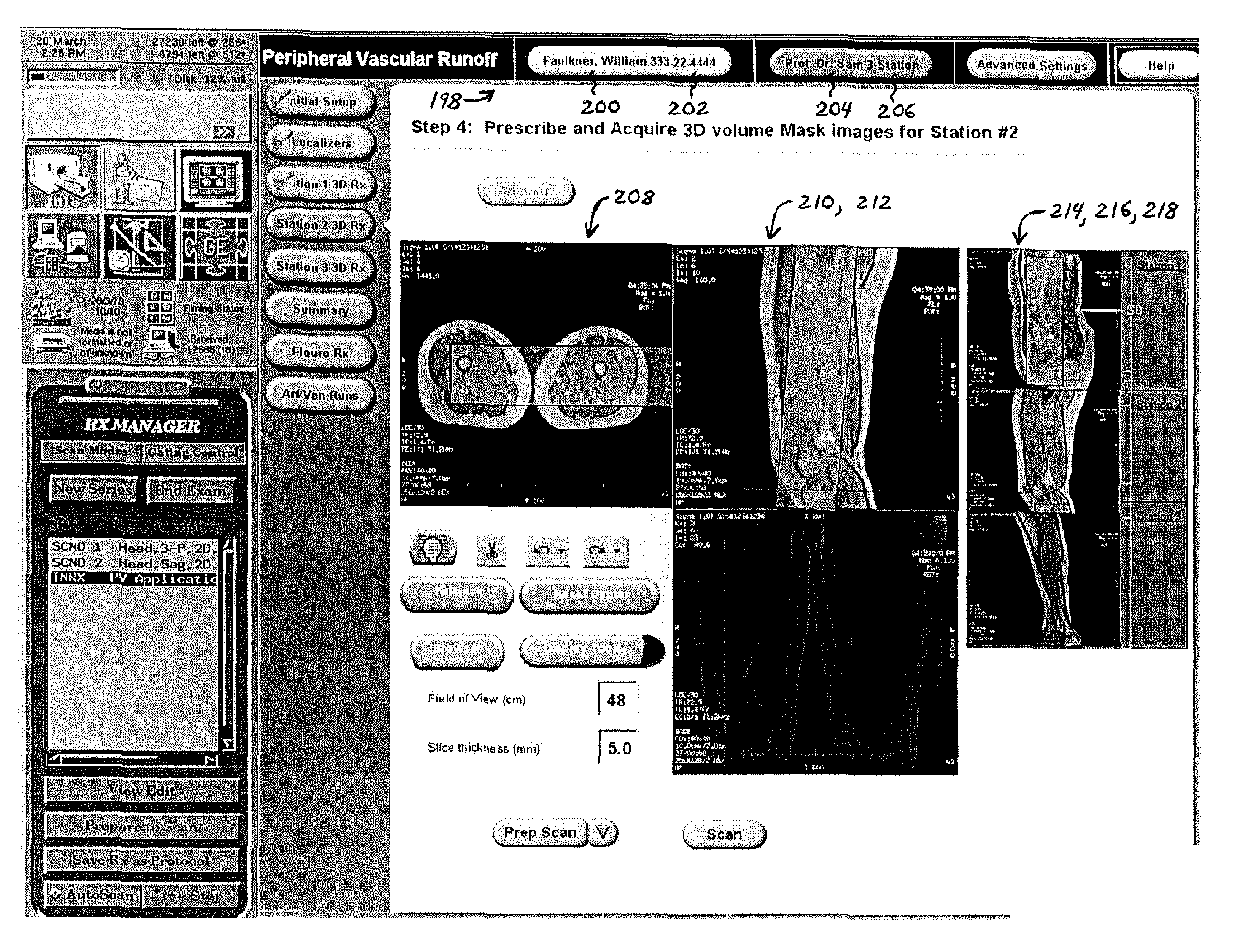
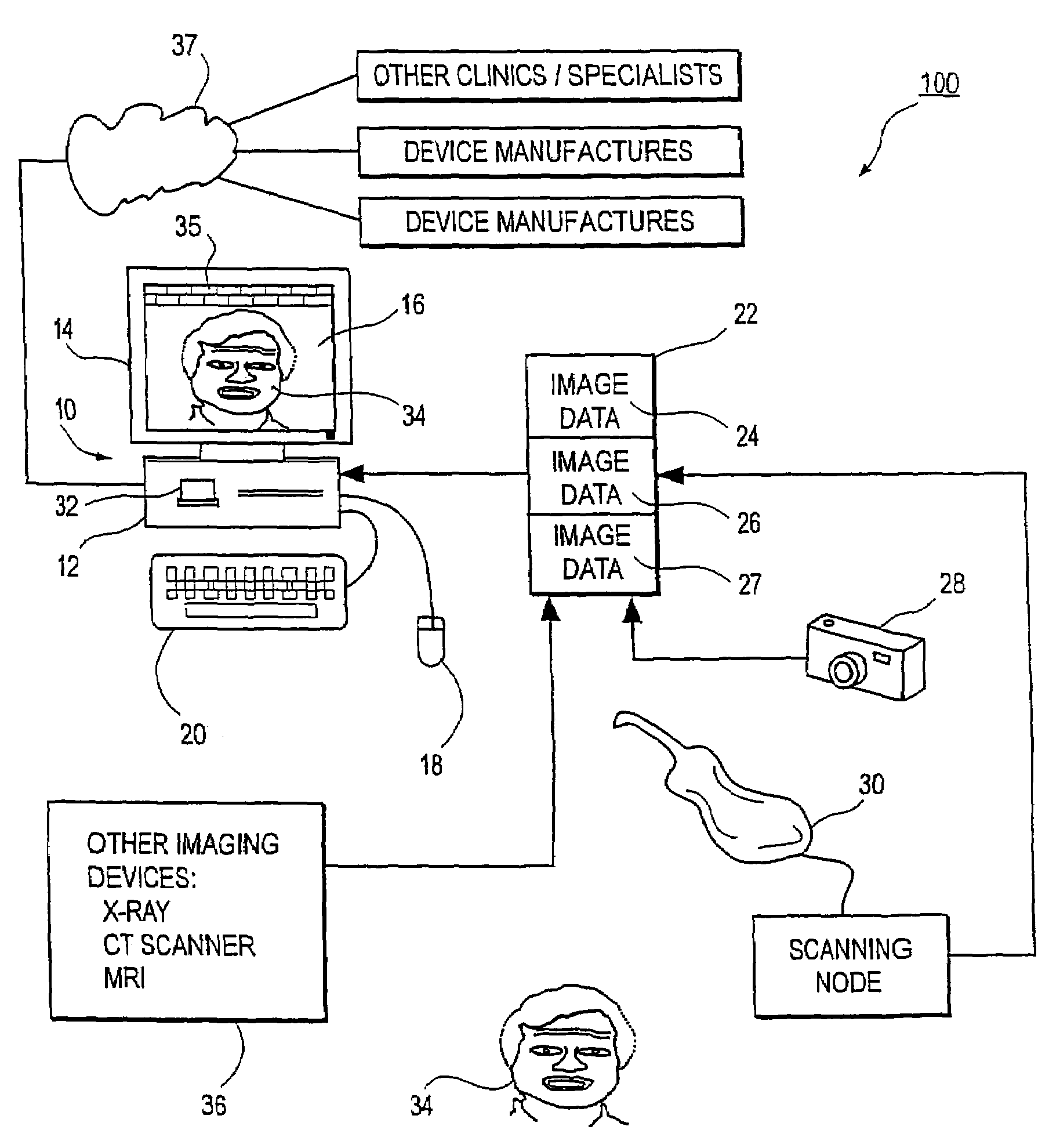
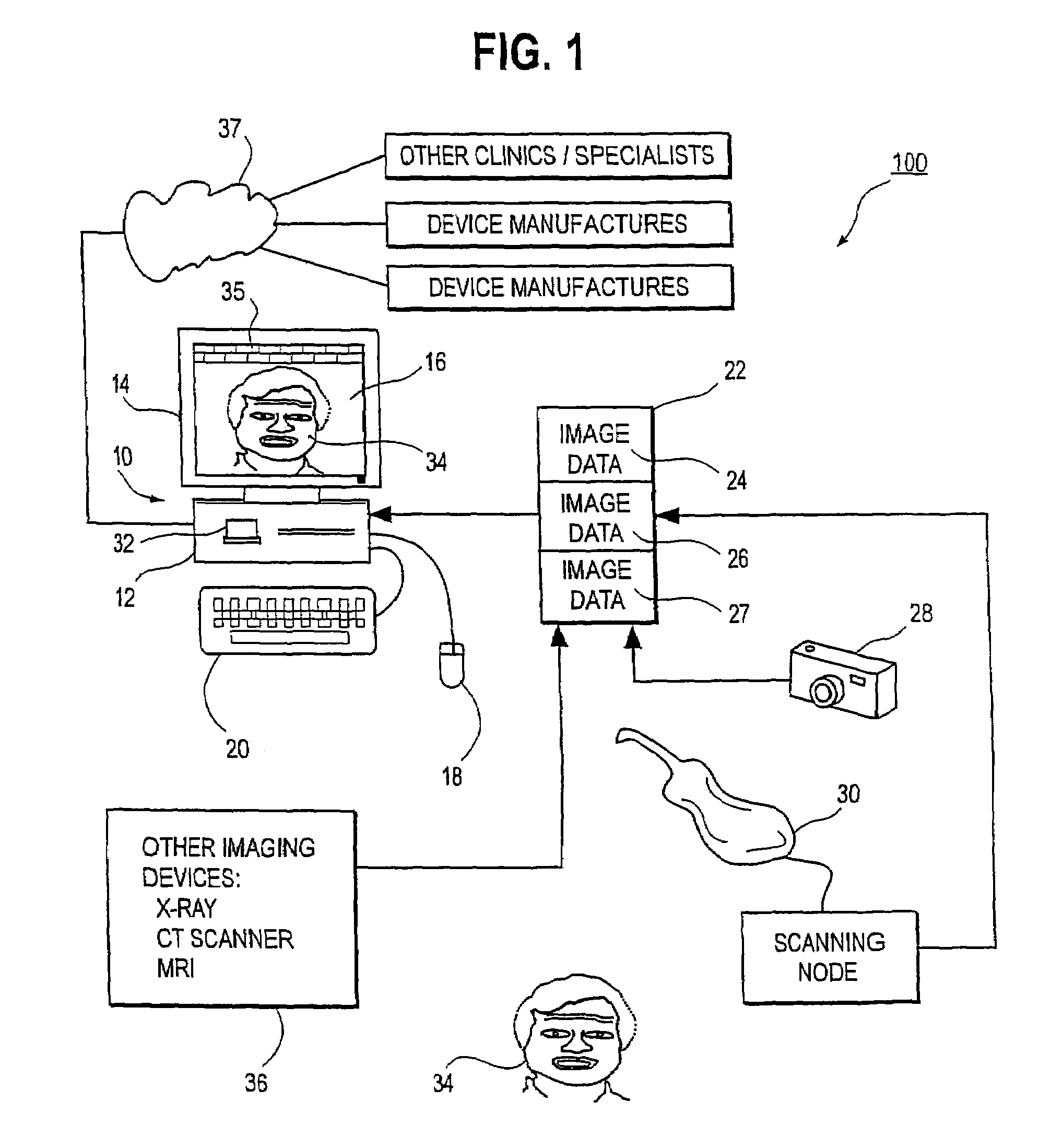
System and method for enabling a software developer to introduce informational attributes for selective inclusion within image headers for medical imaging apparatus applications
InactiveUS20050063575A1Character and pattern recognitionMedical imagesSoftware engineeringSoftware development
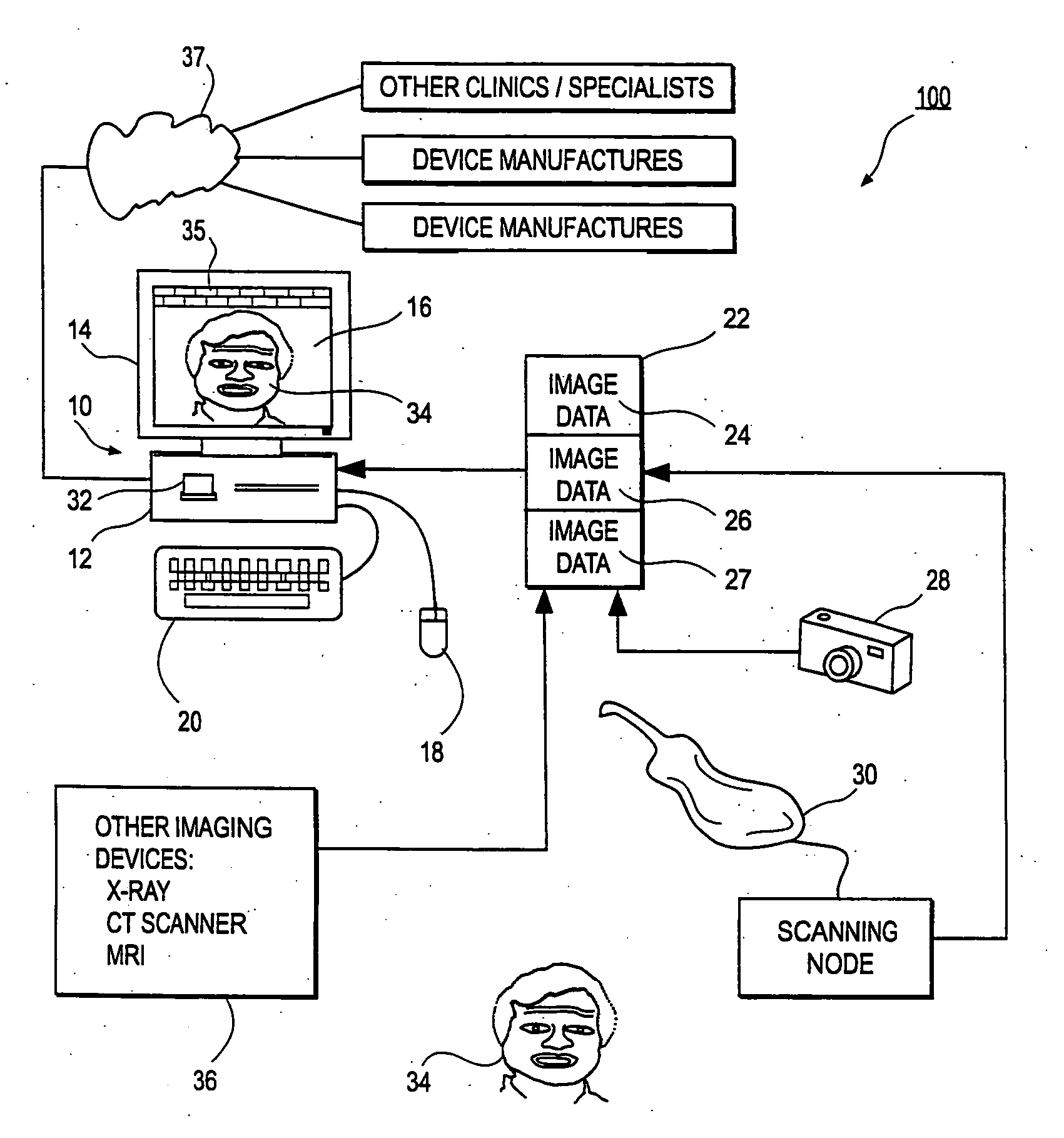
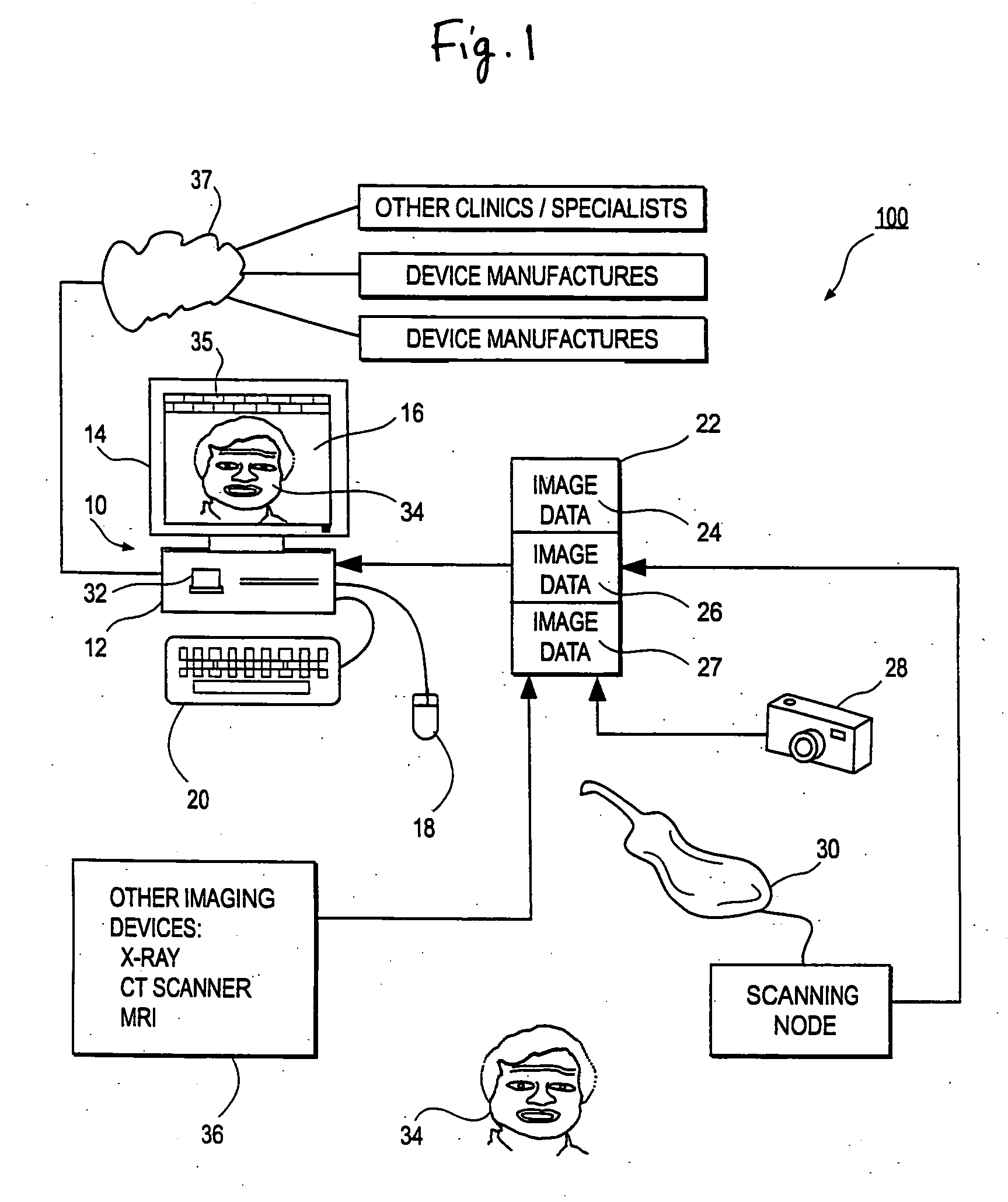
A system and method for enabling a developer to introduce informational attributes suitable for selective inclusion within image headers is disclosed herein. The image headers, along with their selectively included informational attributes, are displayable on a monitor screen together with associated digital images produced by an imaging apparatus. The image headers are also selectively storable in a database together with the pixel data of the associated digital images. The system includes an interactive workstation computer system having memory-stored software applications for operating the imaging apparatus, a memory-stored updatable table of defined informational attributes suited for selective inclusion within image headers, an interactive computer for generating software files of image header definitions from the table of defined informational attributes, and a means to transport the software files of image header definitions to the interactive workstation computer system.
Owner:GE MEDICAL SYST GLOBAL TECH CO LLC
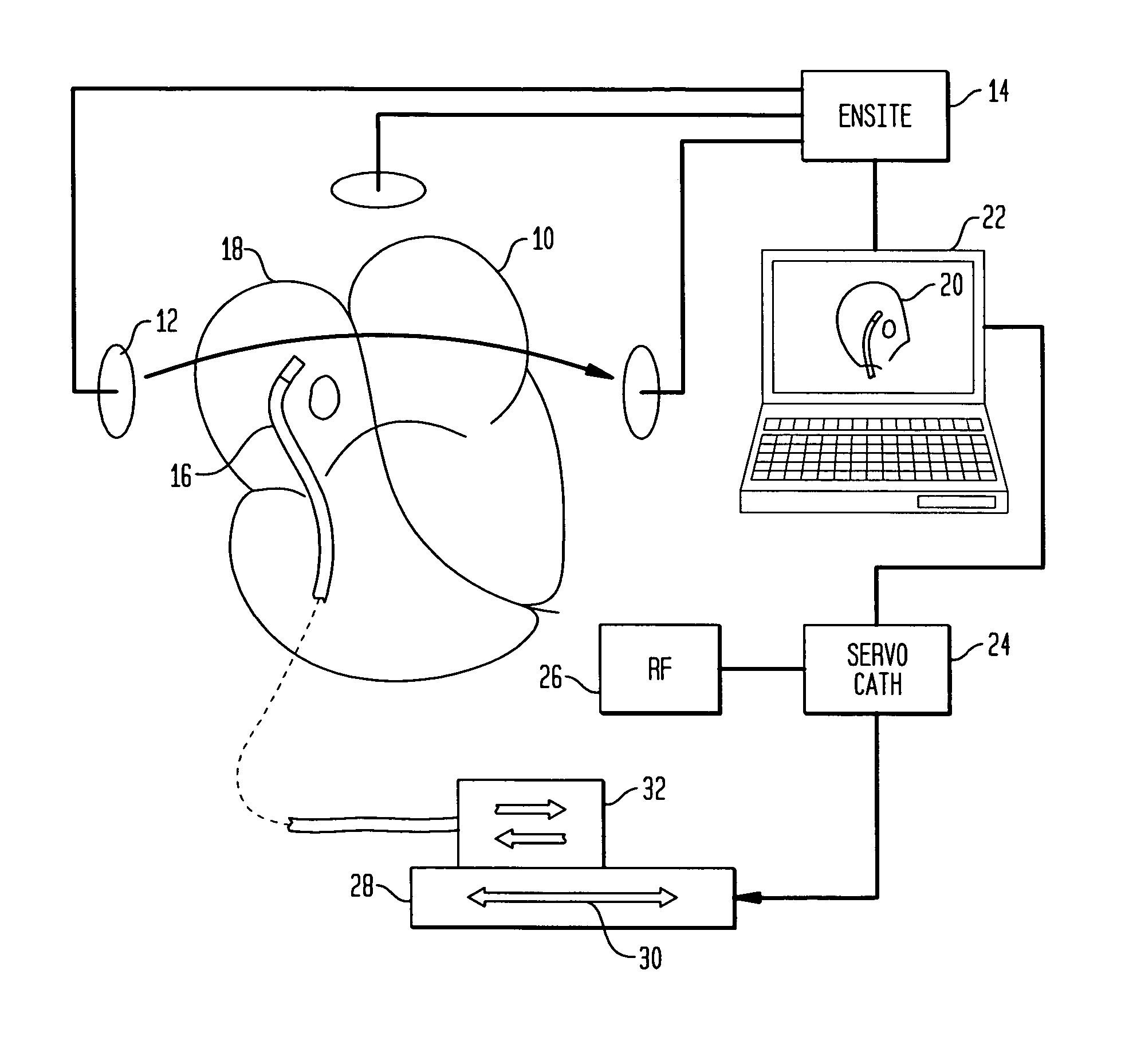
Radio frequency ablation servo catheter and method
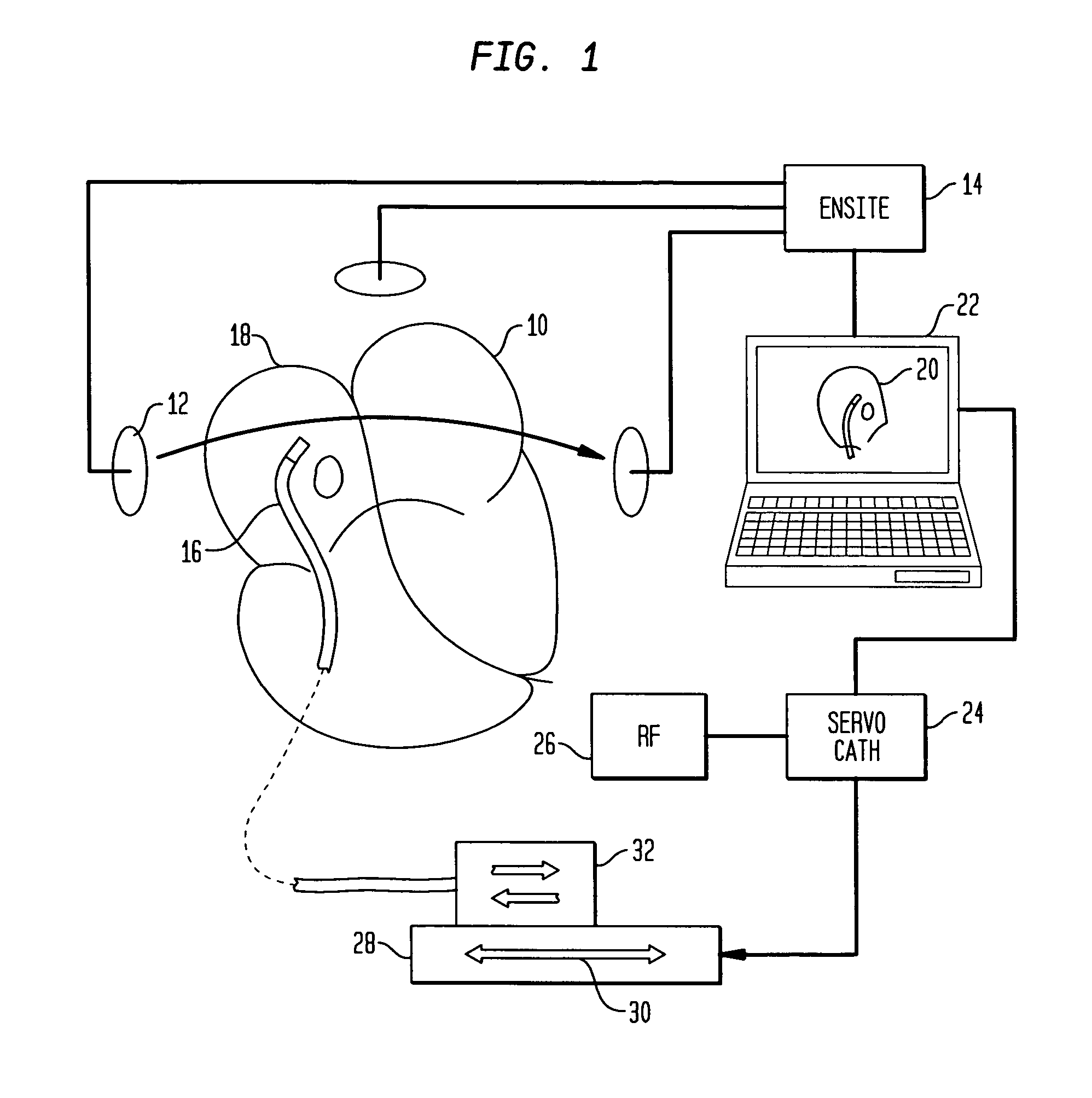
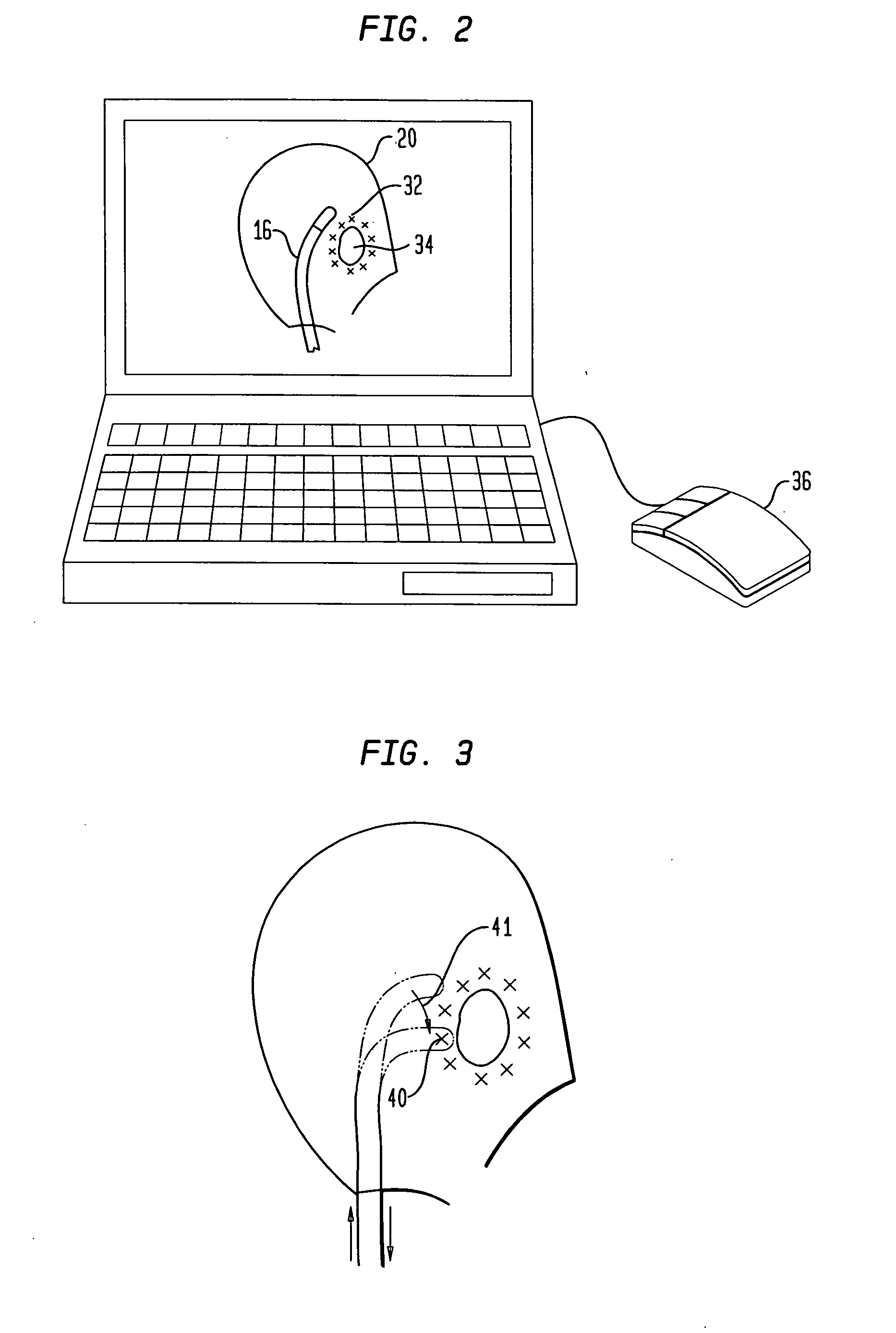
ActiveUS20060015096A1Surgical navigation systemsDiagnostic recording/measuringRf ablationWorkstation
A system that interfaces with a workstation endocardial mapping system allows for the rapid and successful ablation of cardiac tissue. The system allows a physician to see a representation of the physical location of a catheter in a representation of an anatomic model of the patient's heart. The workstation is the primary interface with the physician. A servo catheter having pull wires and pull rings for guidance and a servo catheter control system are interfaced with the workstation. Servo catheter control software may run on the workstation. The servo catheter is coupled to an RF generator. The physician locates a site for ablation therapy and confirms the location of the catheter. Once the catheter is located at the desired ablation site, the physician activates the RF generator to deliver the therapy.
Owner:ST JUDE MEDICAL ATRIAL FIBRILLATION DIV
Intranet-based medical data distribution system
InactiveUS6871211B2Low costRapid designMultiple digital computer combinationsAngiographyWeb servicePatient data
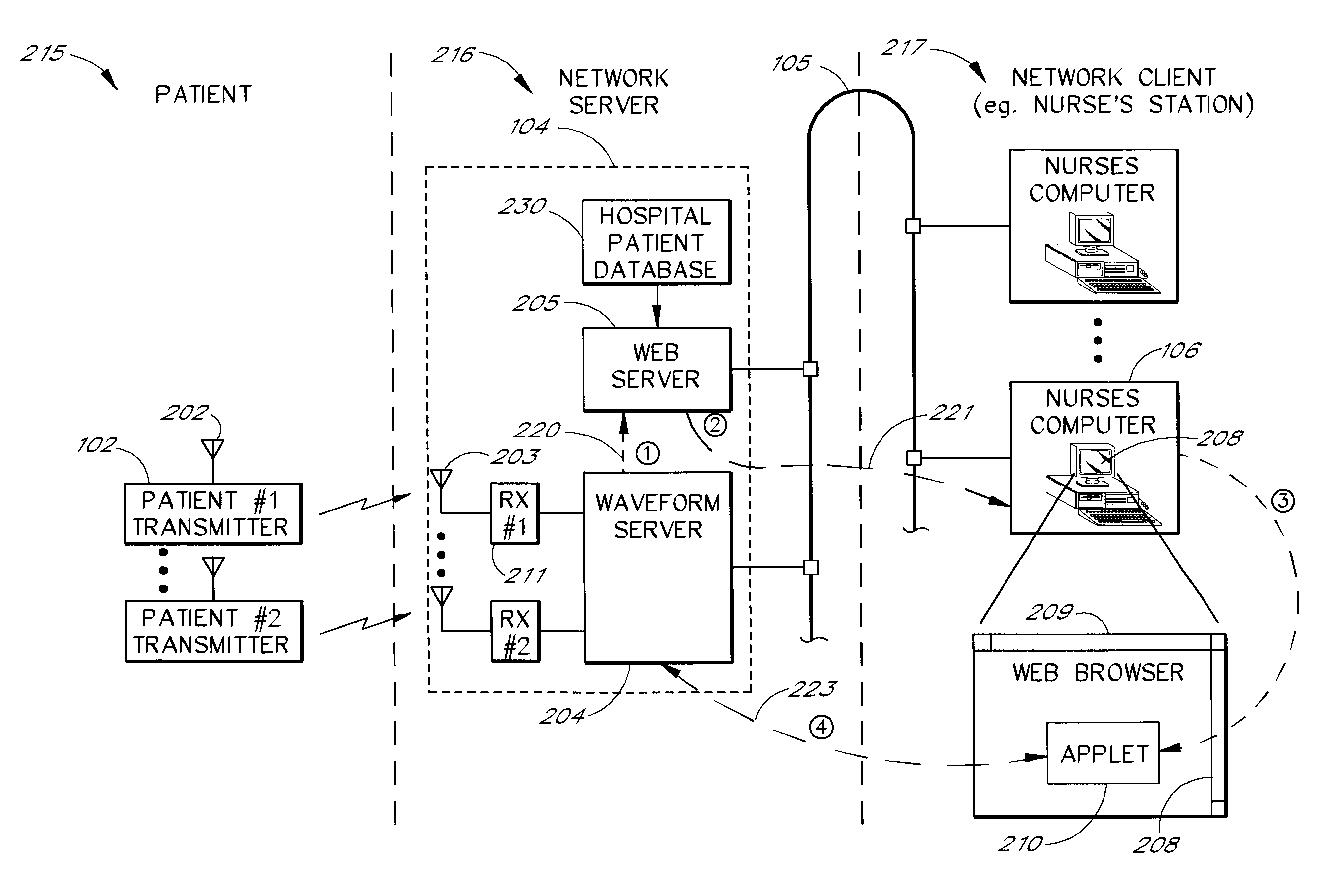
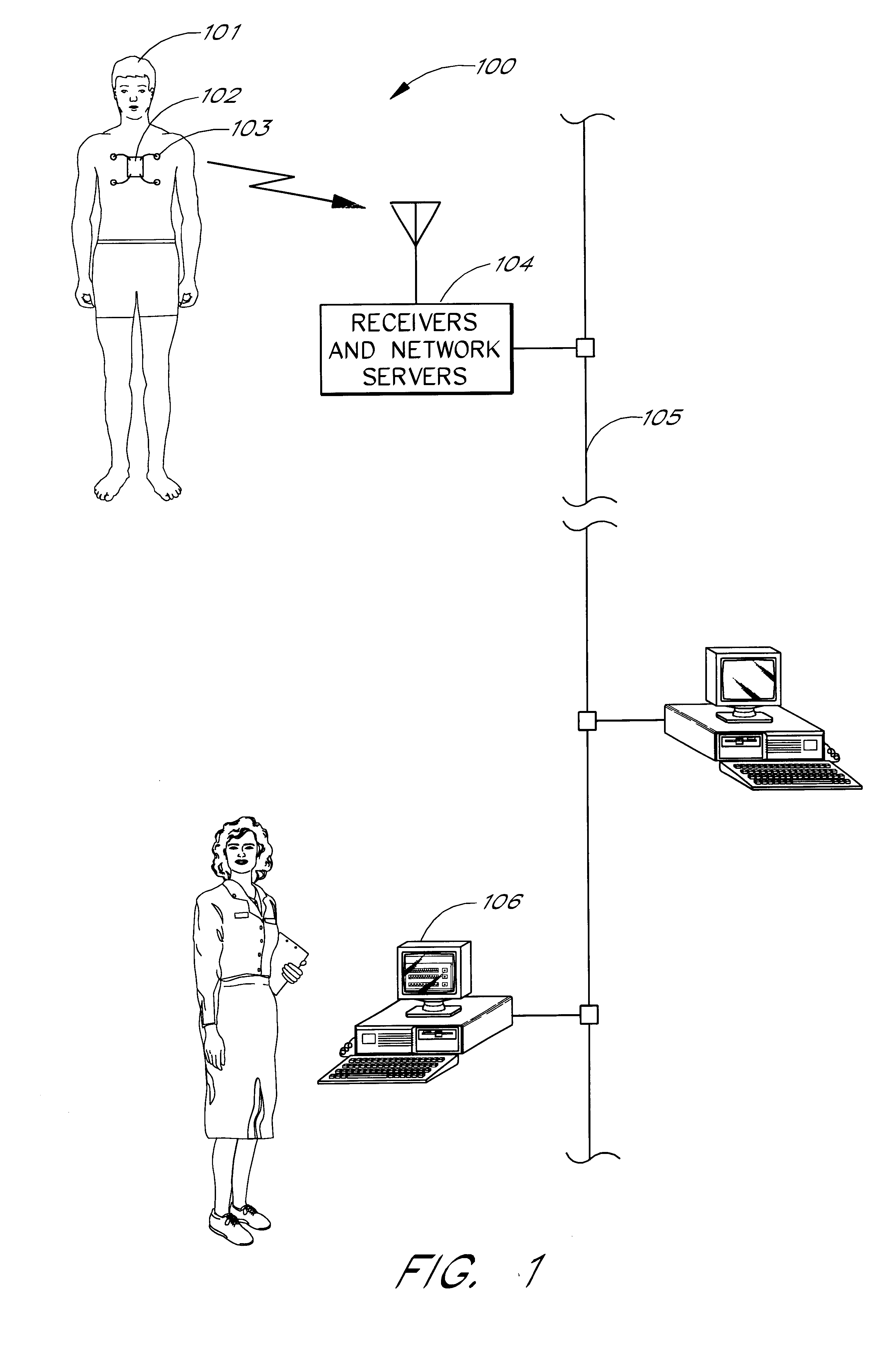
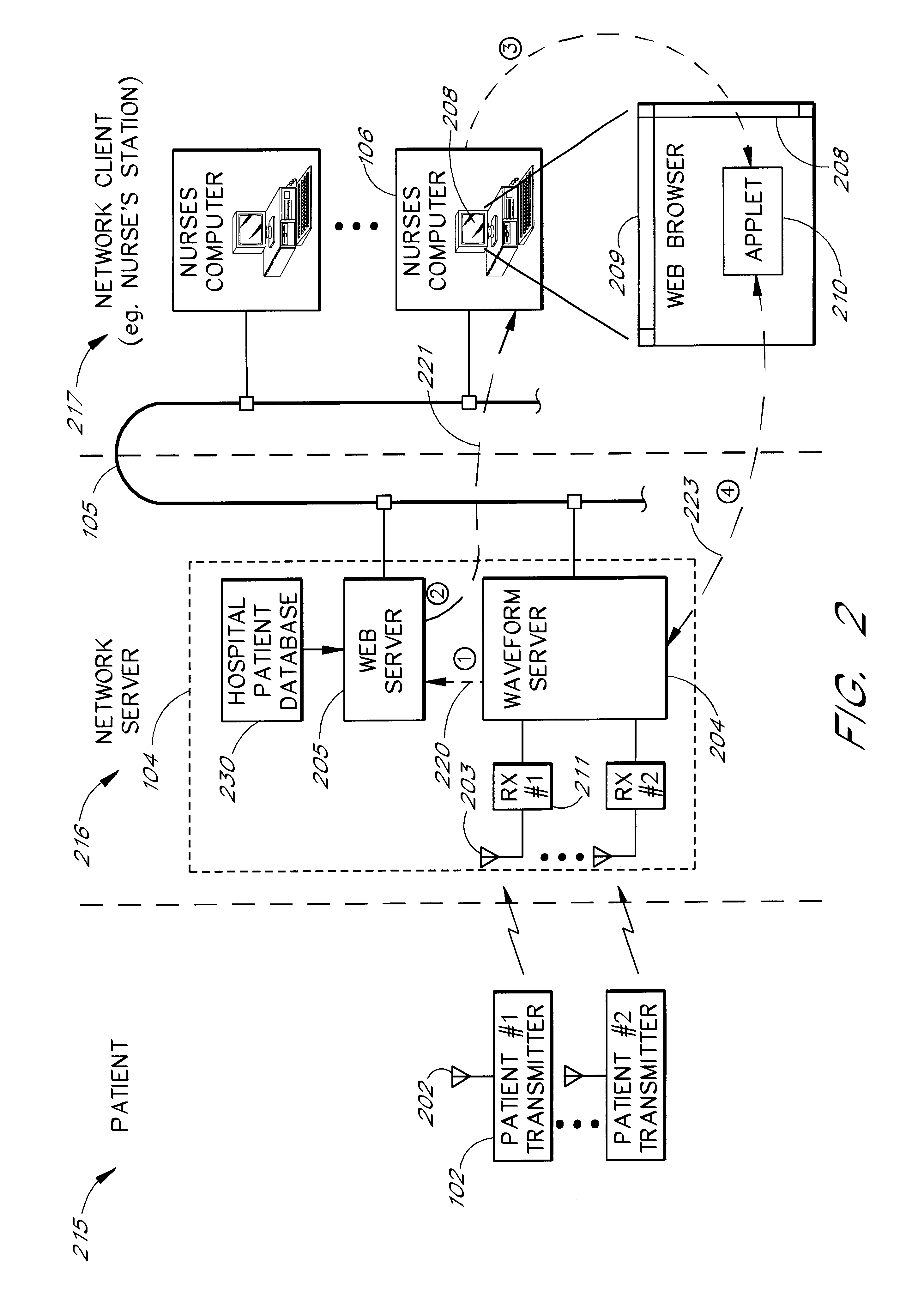
A network based medical telemetry system that uses, to the greatest extent possible, standard hardware and software components. The system allows clinicians using computers anywhere in a large hospital to view physiologic data from patients of the hospital. Each patient is fitted with a set of sensors that measure physiologic properties of the patient (e.g., EKG sensors). The sensors are connected to a transmitter that relays the physiologic data to a central server. The central server comprises a WEB server that supplies basic patient data such as the patient's name and medical history. The central server also comprises a waveform server which supplies the physiologic data, in real-time or near real-time. Workstation, used by a clinician receives the basic patient data from the Web server and the physiologic data from the waveform server, and produces a combined display. The combined display is continuously updated, showing, for example, the patient's EKG.
Owner:GE MEDICAL SYST INFORMATION TECH
Method and system for comprehensive evaluation of orthodontic care using unified workstation
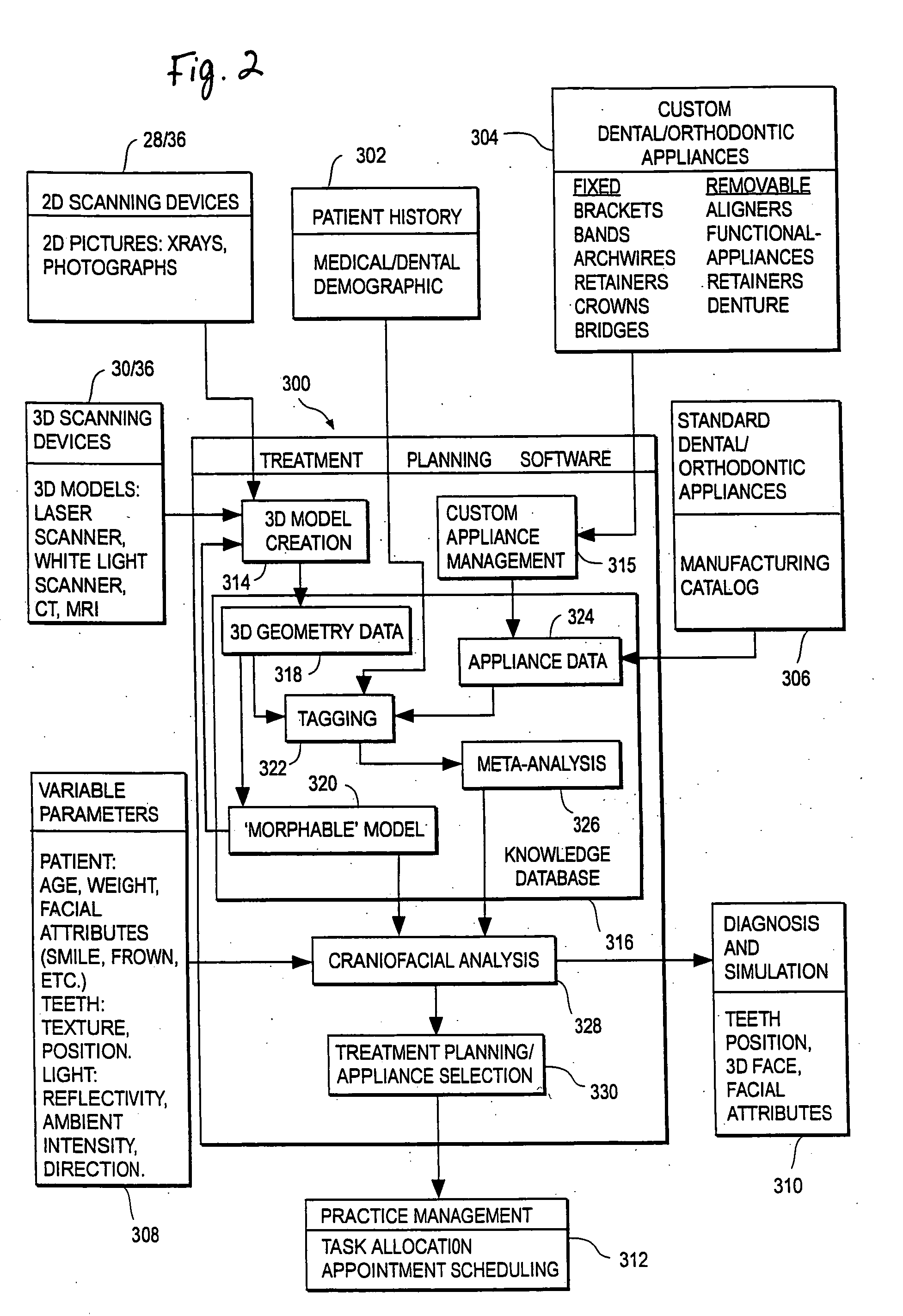
A method and system for orthodontic treatment planning, evaluation and quality measurement is provided comprising a workstation having computing platform, a graphical user interface, a processor and a computer storage medium containing digitized records pertaining to a patient. The digitized records include image and other types of data. The computer storage medium further includes a set of software instructions providing graphical user interface tools for providing a user with access to the digitized records for planning orthodontic treatment of a patient. Also provided are reference databases for aiding in the decision process during treatment selection, treatment planning and treatment delivery and progress monitoring and evaluation. Also provided are parameter or criteria measurement techniques and generally acceptable thresholds, which can be updated through learning process and through acquisition of patient data. Once the treatment is planned, the virtual dentition model of the patient in the proposed treatment set-up or the target state is evaluated using several virtual model evaluation features and criteria.
Owner:ORAMETRIX
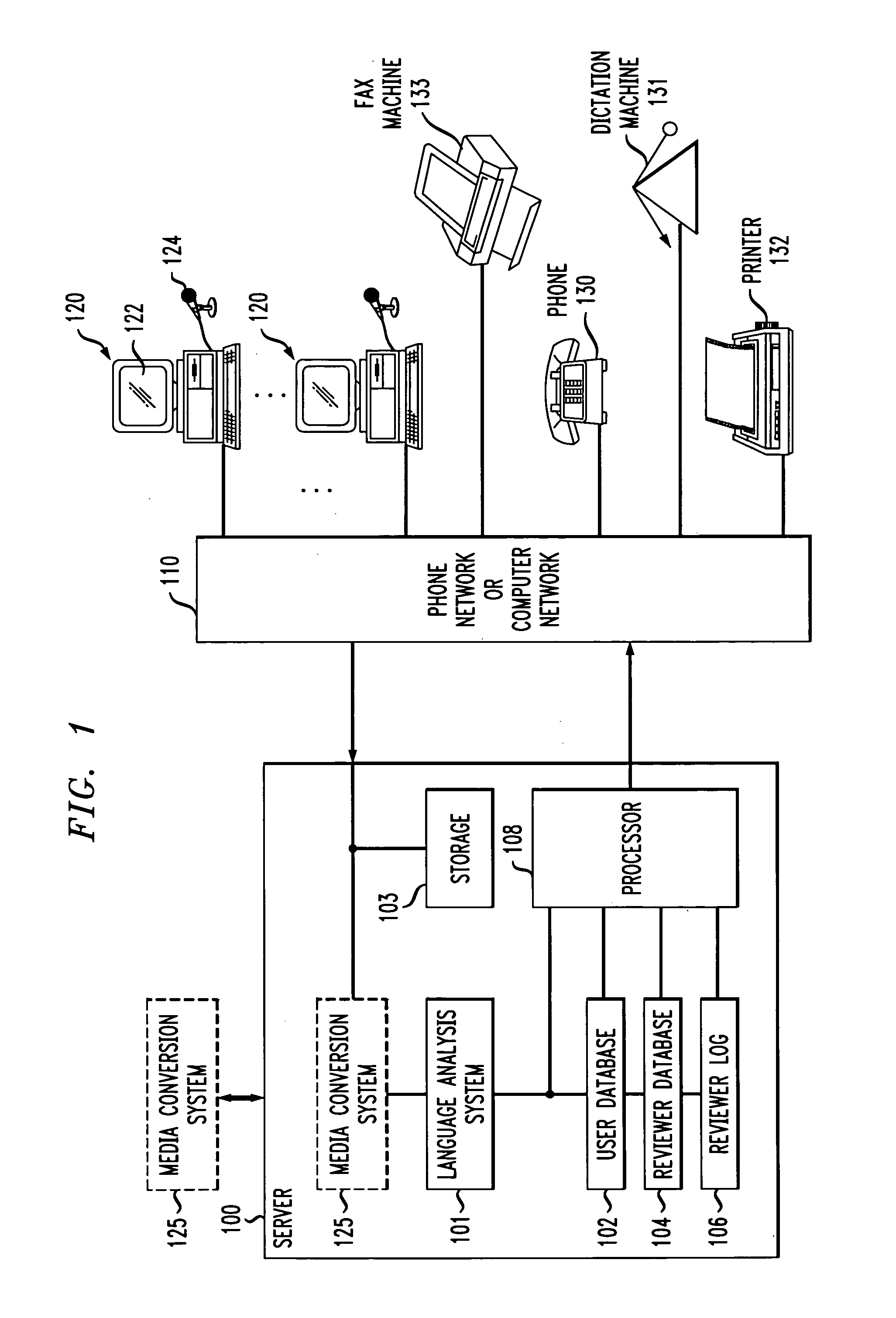
Method of and apparatus for improving productivity of human reviewers of automatically transcribed documents generated by media conversion systems
InactiveUS7236932B1Improve productivityPotential for errorSpeech recognitionDocumentation procedureFile system
An apparatus for improving productivity of human reviewers of transcribed documents generated by media conversion systems includes a server / client network of computers, memories and file systems. The server receives and stores voice files created by users of the system. The server is configured for coupling to a speech-to-text media conversion system to receive converted text files of the audio voice files. The server analyzes the converted text files and routes the converted files to the appropriate reviewers according to an adaptive algorithm. The converted files are displayed on the assigned reviewer's screen at the reviewer's workstation. To aid the reviewer in pinpointing potential errors, the workstation displays different segments of the converted files in different colors to reflect different confidence levels of transcription accuracy. Portions of the original voice message that correspond to the potential errors are played back for the reviewer. The reviewers' workstations also perform productivity enhancing functions such as spelling and grammar checking. After the reviewer has made all the necessary corrections, the reviewed files are transmitted back to the server to be stored and accessed by the users. A user database in the server is also updated to store recurrent user-specific errors corrected by the reviewer. A language analysis system is also disposed to adaptively correct user-specific errors in future reviews according to the information in the user database.
Owner:AVAYA INC
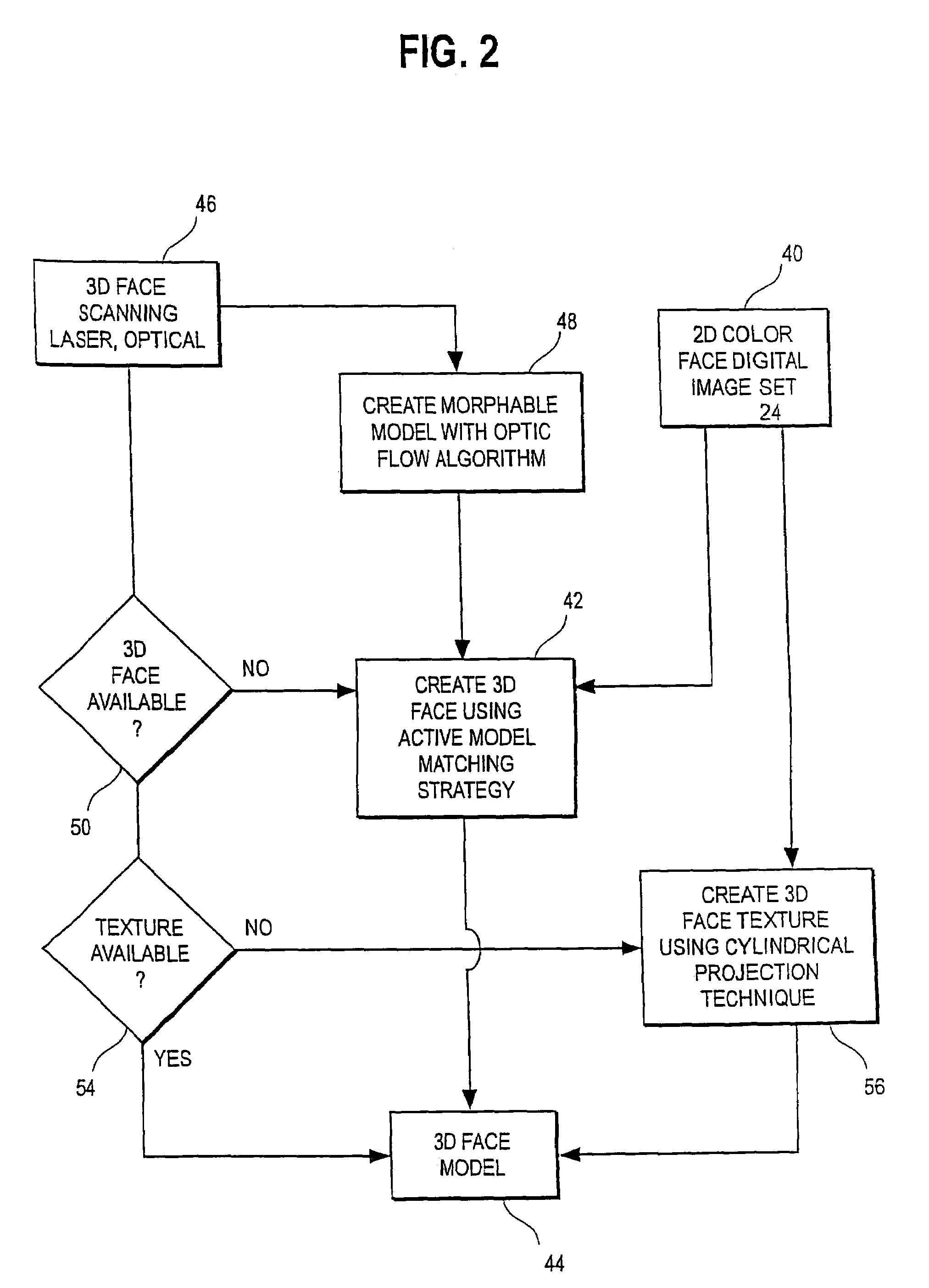
Unified workstation for virtual craniofacial diagnosis, treatment planning and therapeutics
InactiveUS7234937B2Quick analysisPowerful toolDental implantsImpression capsPlan treatmentPatient model
An integrated system is described in which digital image data of a patient, obtained from a variety of image sources, including CT scanner, X-Ray, 2D or 3D scanners and color photographs, are combined into a common coordinate system to create a virtual three-dimensional patient model. Software tools are provided for manipulating the virtual patient model to simulation changes in position or orientation of craniofacial structures (e.g., jaw or teeth) and simulate their affect on the appearance of the patient. The simulation (which may be pure simulations or may be so-called “morphing” type simulations) enables a comprehensive approach to planning treatment for the patient. In one embodiment, the treatment may encompass orthodontic treatment. Similarly, surgical treatment plans can be created. Data is extracted from the virtual patient model or simulations thereof for purposes of manufacture of customized therapeutic devices for any component of the craniofacial structures, e.g., orthodontic appliances.
Owner:ORAMETRIX
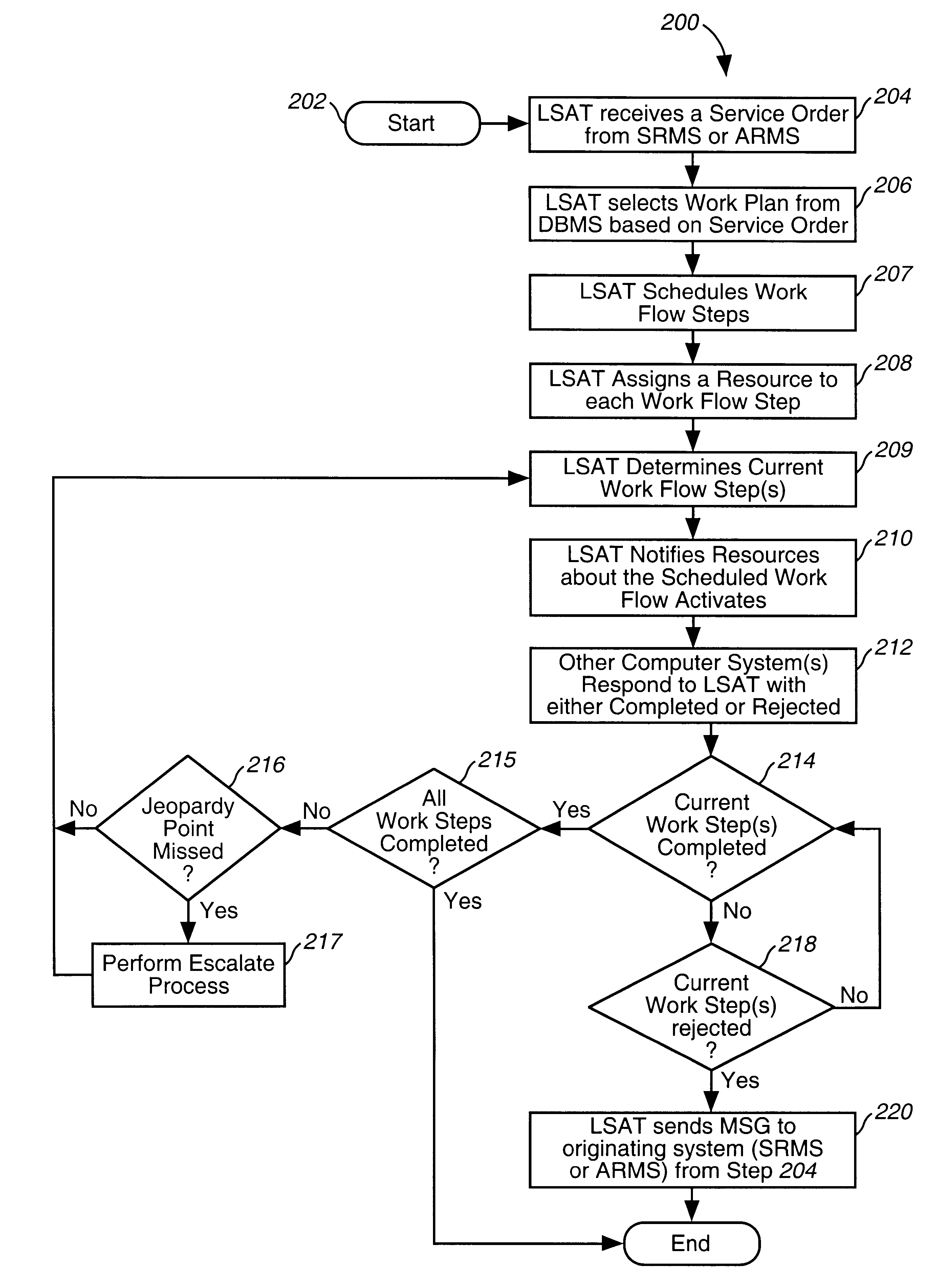
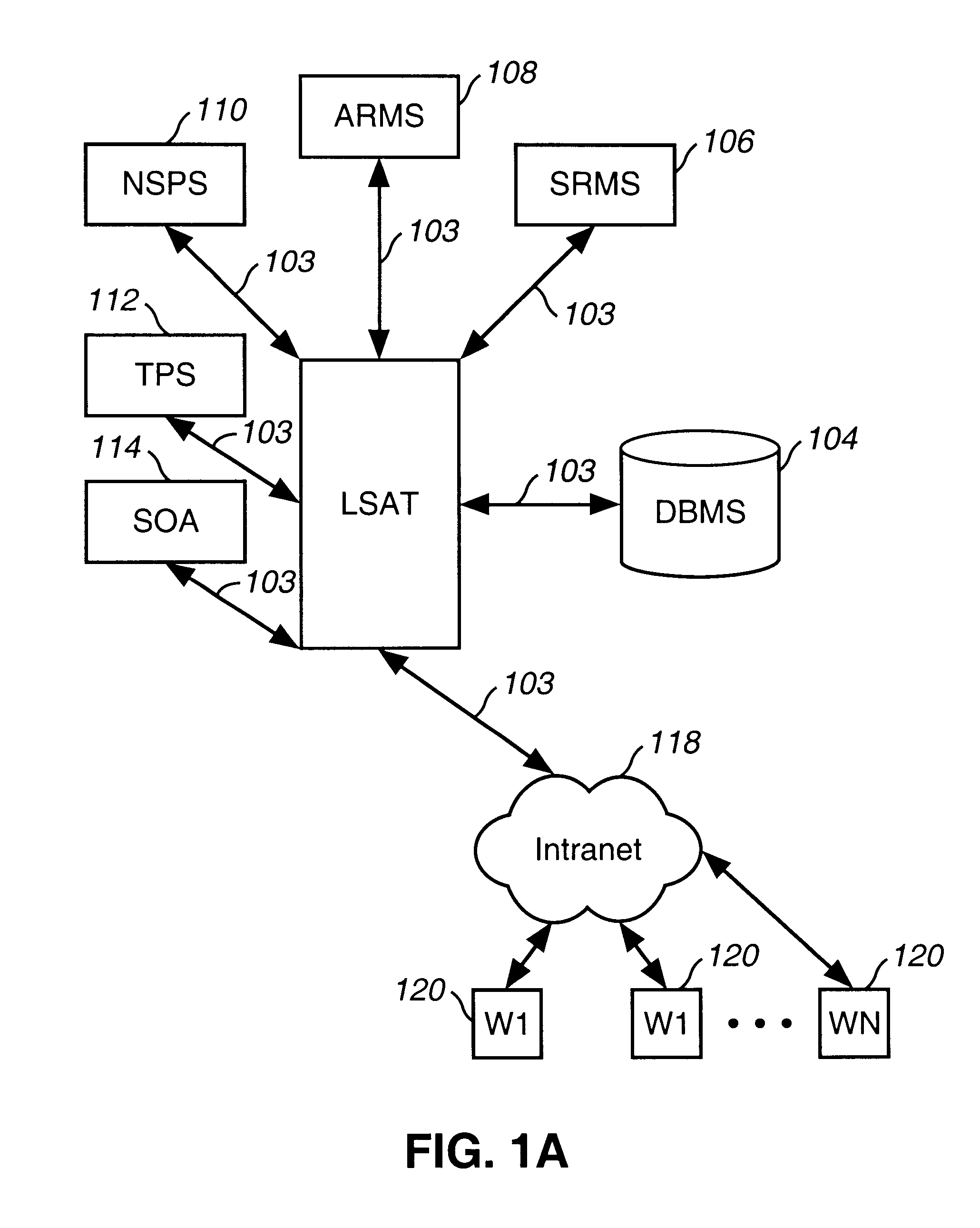
System and method for managing the workflow for processing service orders among a variety of organizations within a telecommunications company
A system and method for managing the workflow for processing Service Orders among a variety of organizations within a telecommunications company. The system and method coordinates all of the tasks and activities related to order processing among the various entities within the telecommunications company. Workflows are used to model business procedures used for processing Service Orders. Each workflow comprises a plurality of workflow steps. Business process models are depicted as workflow diagrams. Upon receipt of a Service Order, an appropriate Work Plan is selected based on information within the Service Order. Each workflow step is assigned a Resource and is scheduled for completion. The Workflow steps are then placed in In-boxes associated with the selected Resource. Once the processing steps have been scheduled, a current work step is calculated. Notification messages are sent to the appropriate systems to notify them to begin activity associated with the current work step. The system is automatically notified when the current work step is complete, so that the next work step can be processed in a similar fashion. Detailed statistical information is maintained for audit and reporting purposes. Users log-on to remote workstations coupled with a company-wide Intranet or the like. From the remote workstations, users from various organizations view their In-boxes and other detailed information about Service Orders according to selectable requests. Workflow steps can be transferred and re-assigned using the remote workstations. Detailed statistical information is maintained for audit and reporting purposes. Reports reflecting the effectiveness of workforce management and work administration is obtained.
Owner:VERIZON PATENT & LICENSING INC
Computer-aided system for 360º heads up display of safety/mission critical data
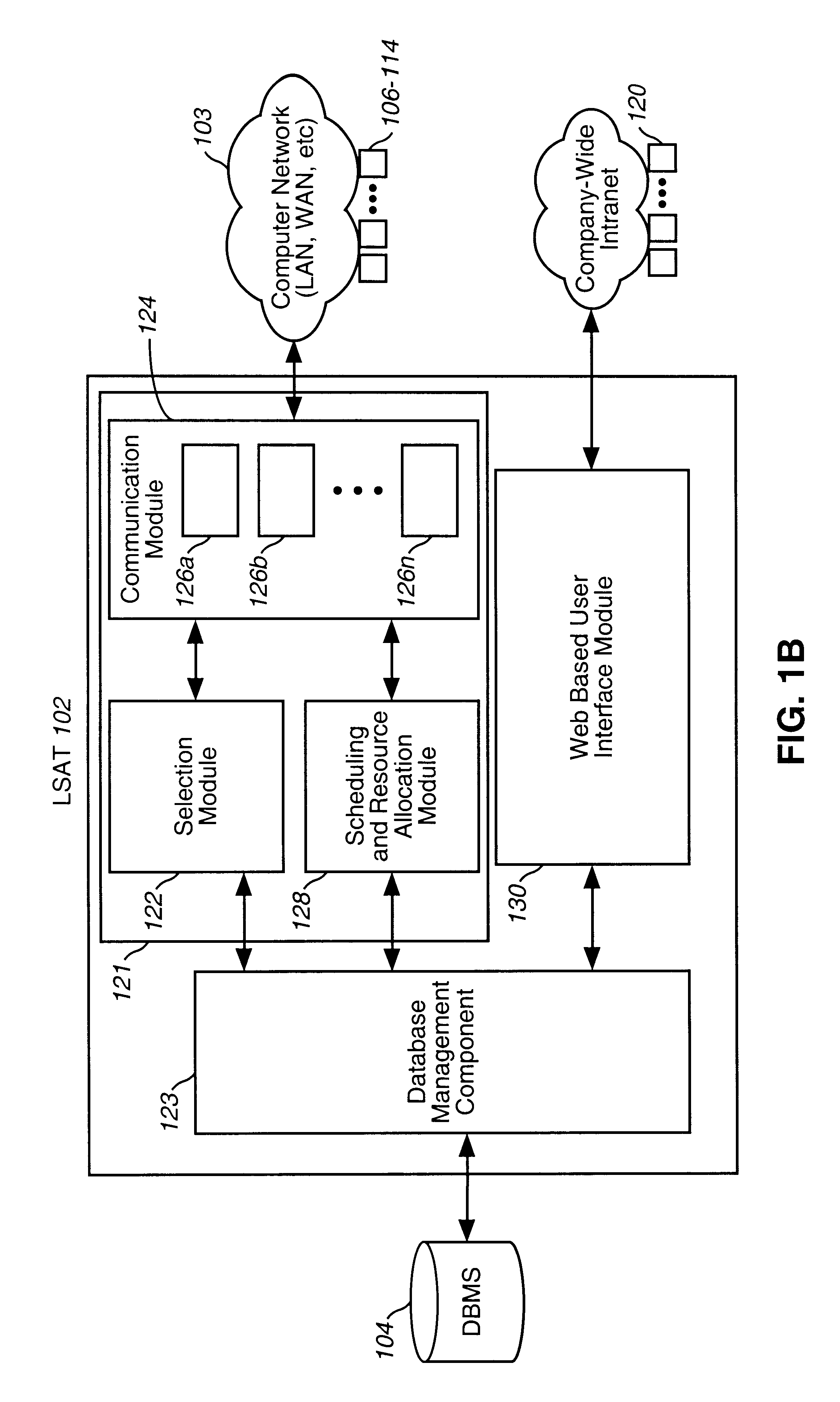
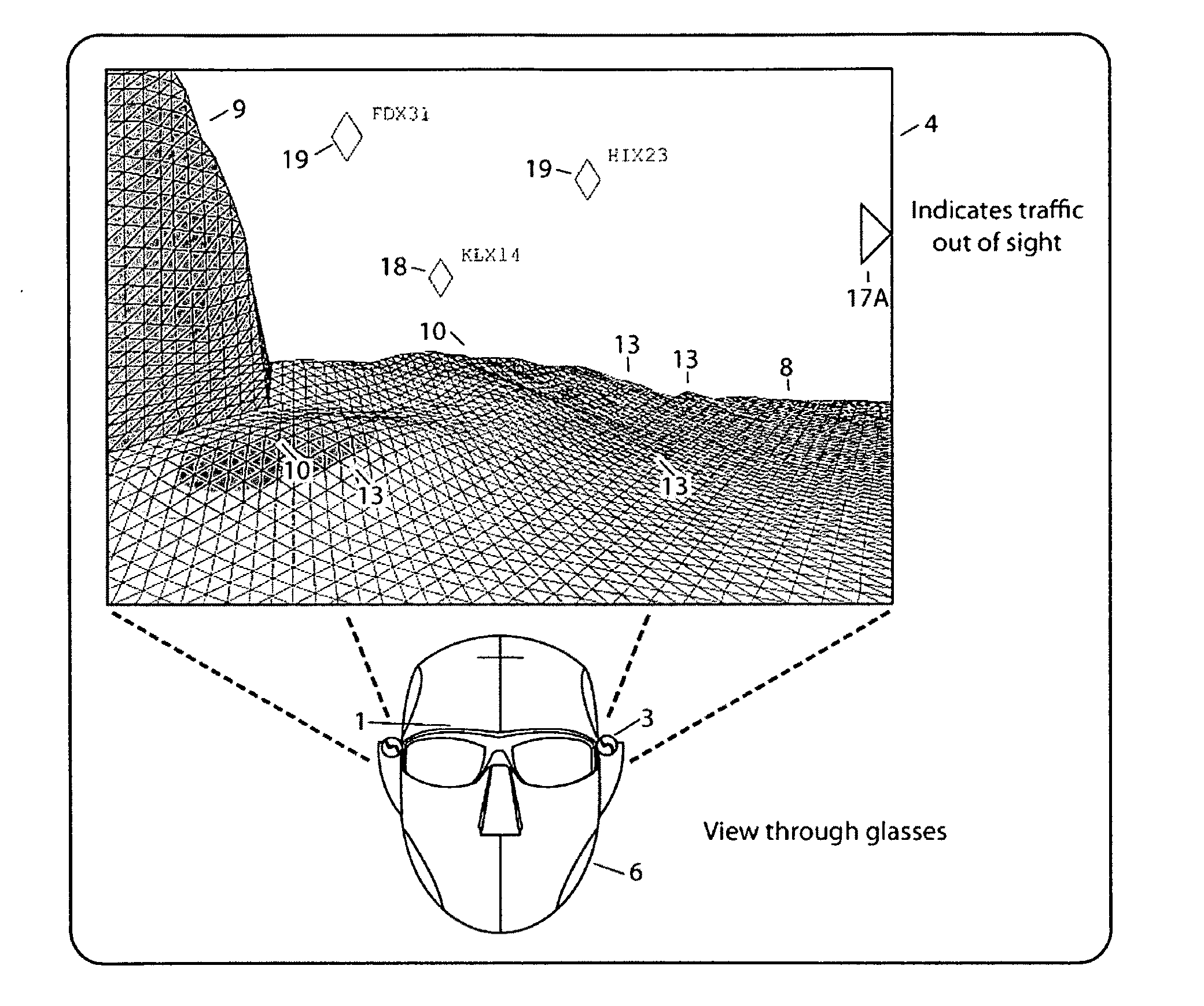
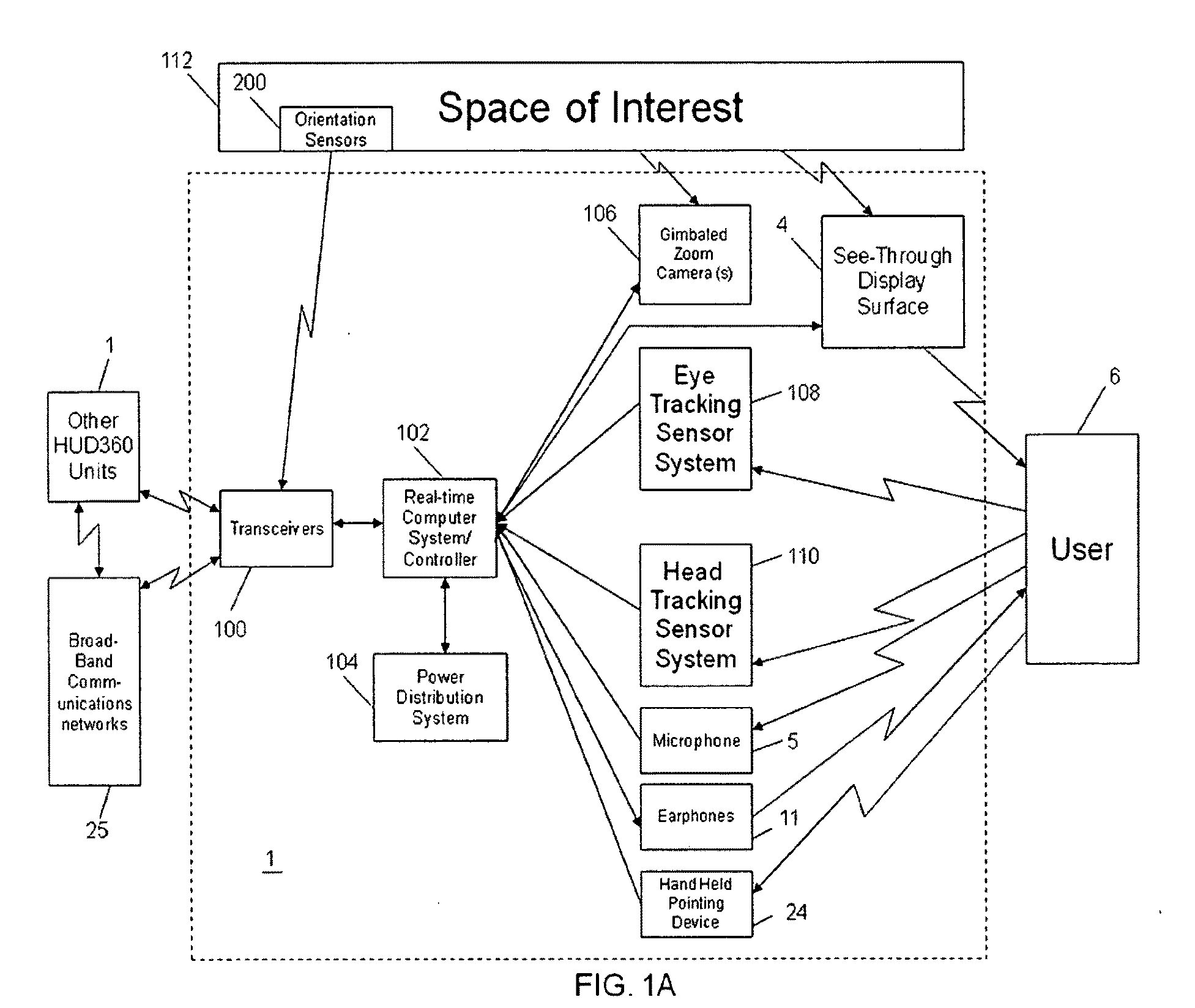
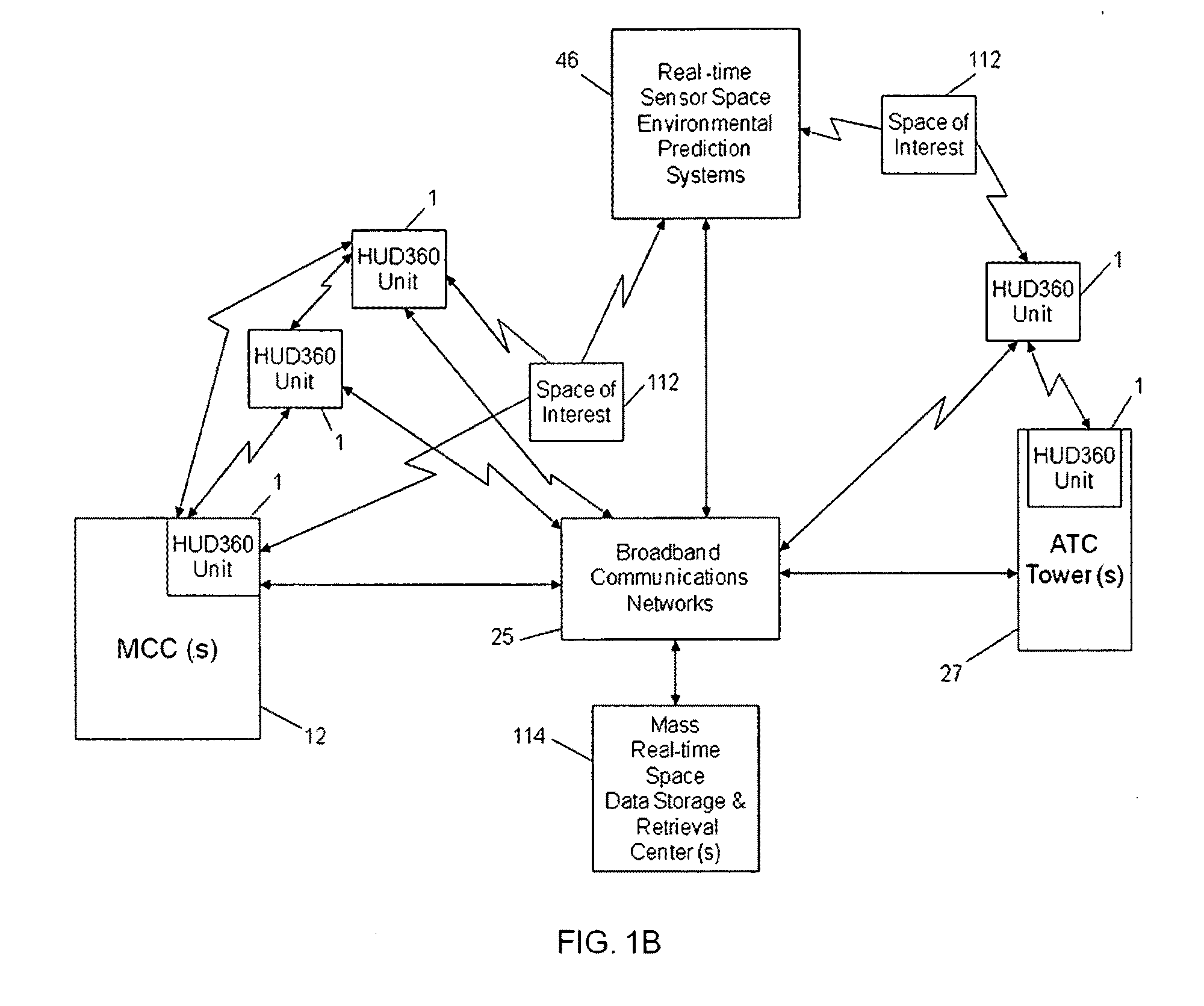
InactiveUS20100238161A1Improve assessmentSatisfy safety performance requirementsCathode-ray tube indicatorsInput/output processes for data processingHead-up displayDisplay device
A safety critical, time sensitive data system for projecting safety / mission critical data onto a display pair of Commercial Off The Shelf (COTS) light weight projection glasses or monocular creating a virtual 360° HUD (Heads Up Display) with 6 degrees of freedom movement. The system includes the display, the workstation, the application software, and inputs containing the safety / mission critical information (Current User Position, Total Collision Avoidance System—TCAS, Global Positioning System—GPS, Magnetic Resonance Imaging—MRI Images, CAT scan images, Weather data, Military troop data, real-time space type markings etc.). The workstation software processes the incoming safety / mission critical data and converts it into a three dimensional space for the user to view. Selecting any of the images may display available information about the selected item or may enhance the image. Predicted position vectors may be displayed as well as 3D terrain.
Owner:REALTIME
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com