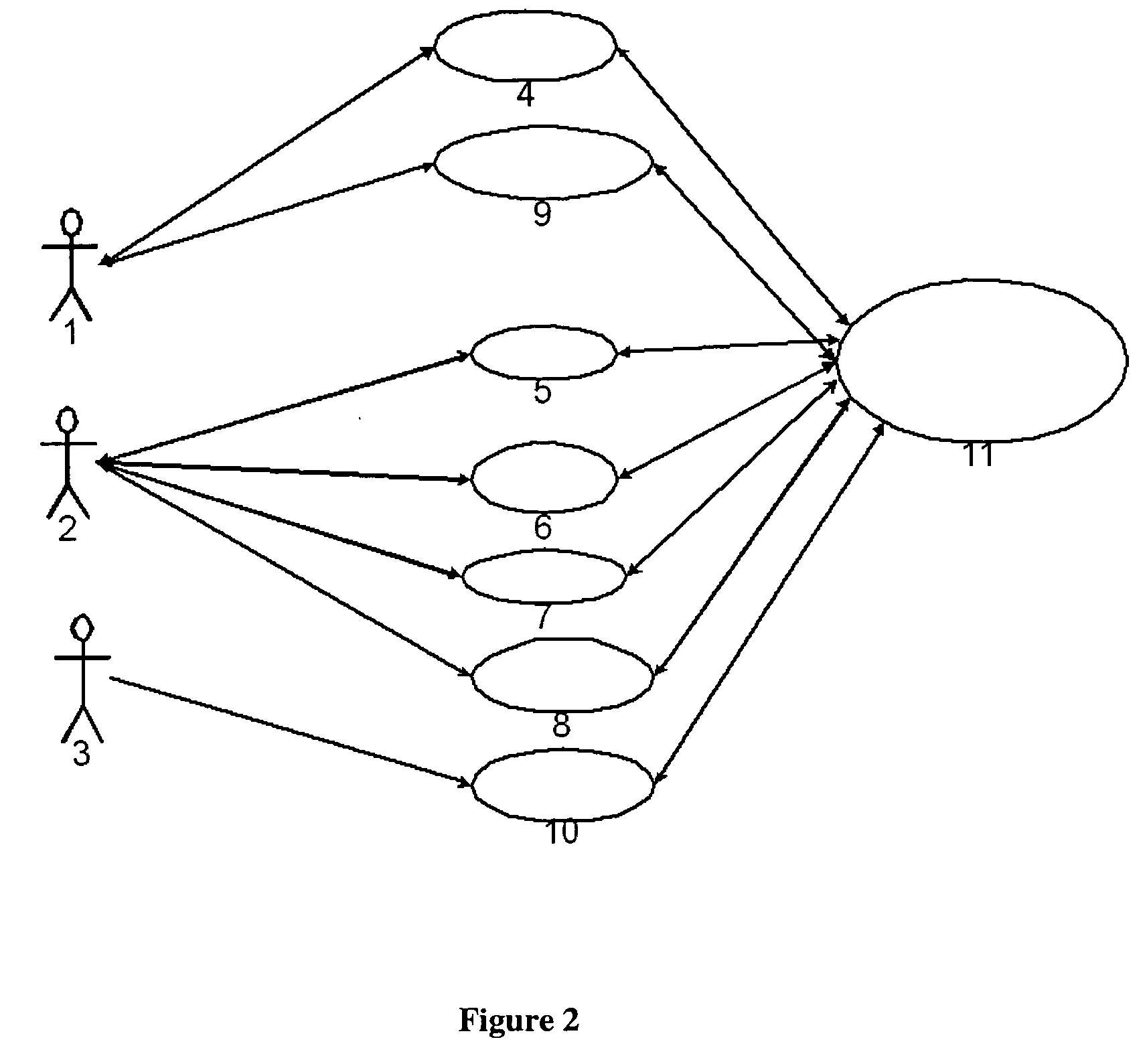
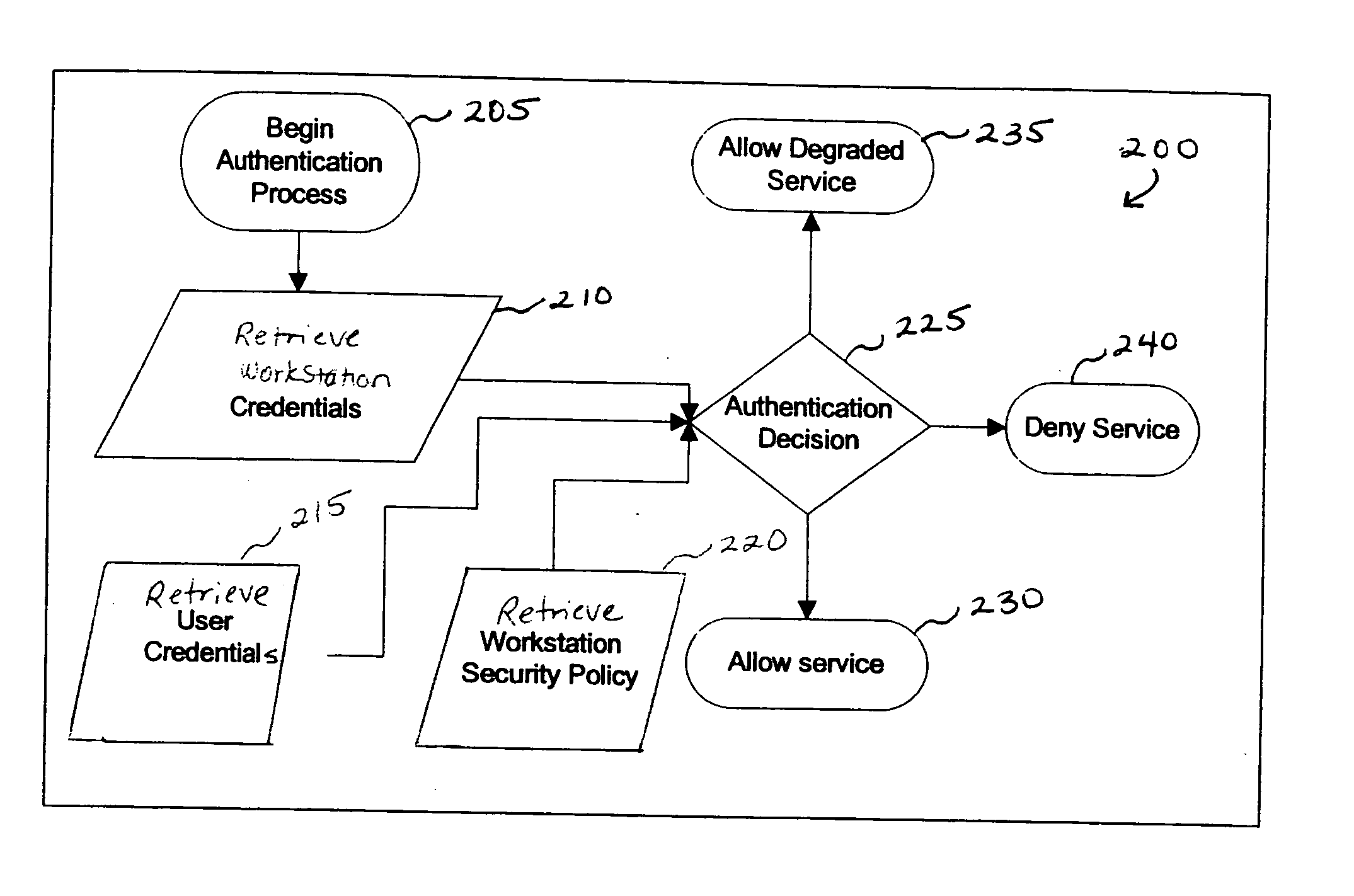
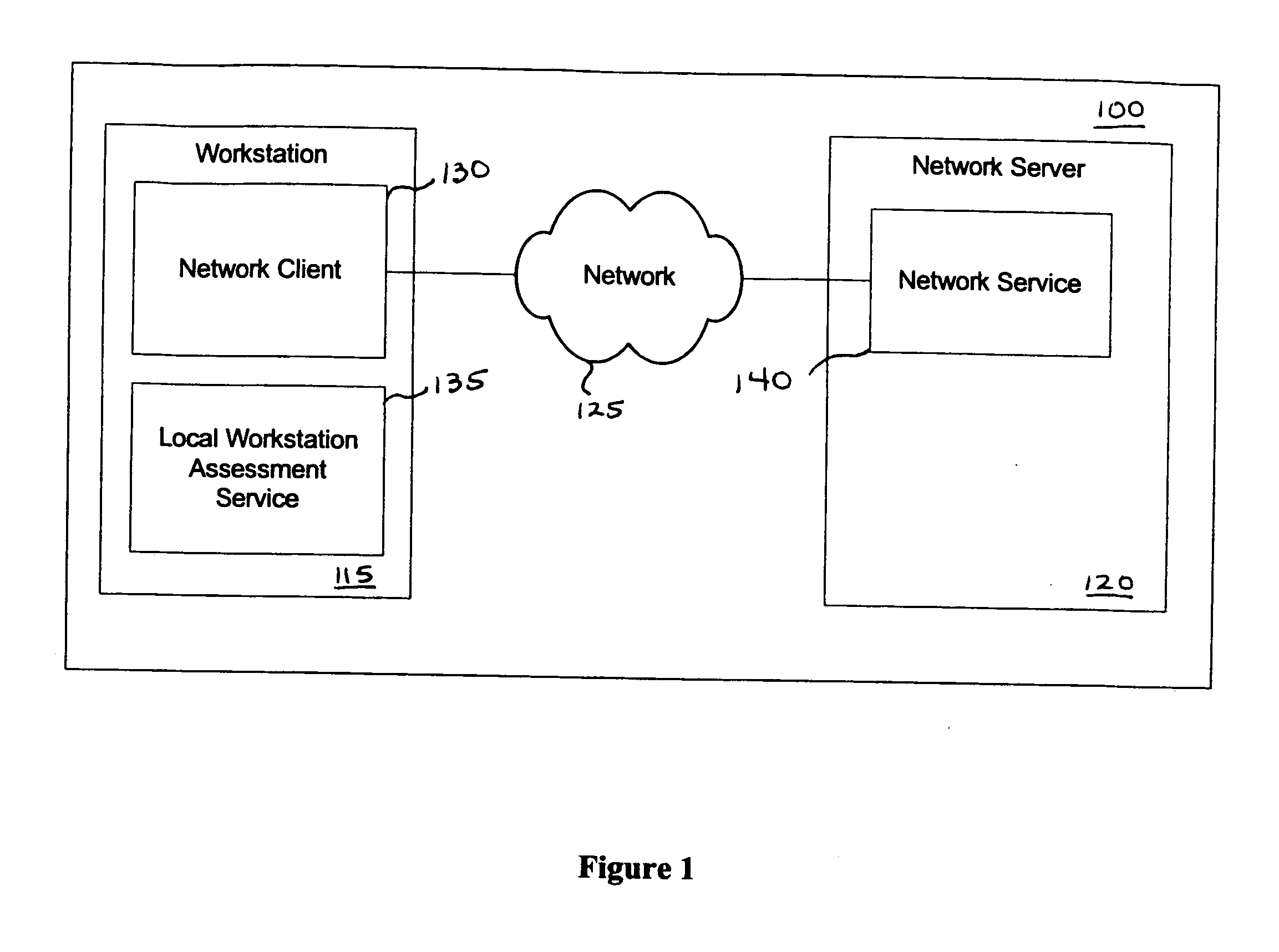
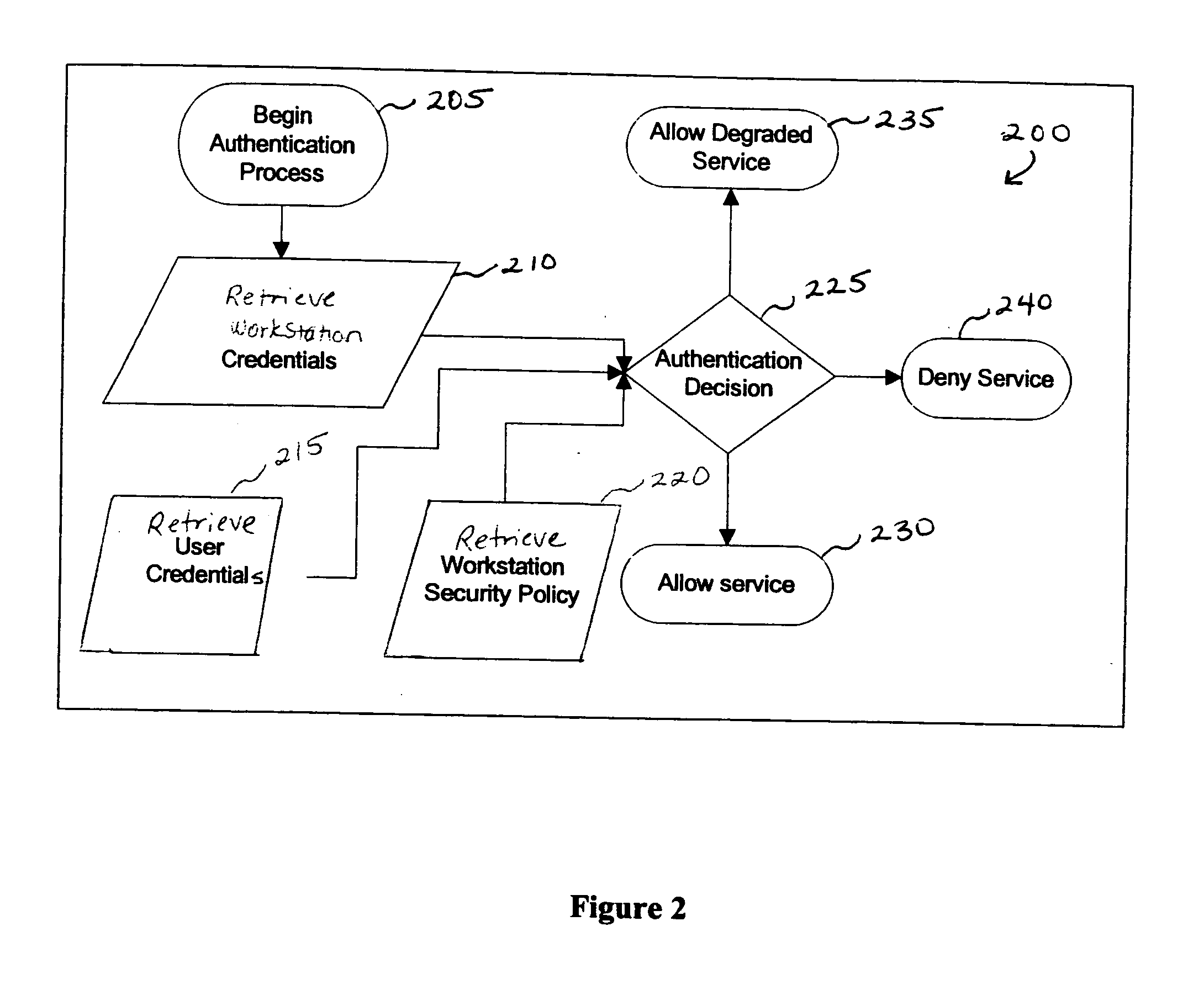
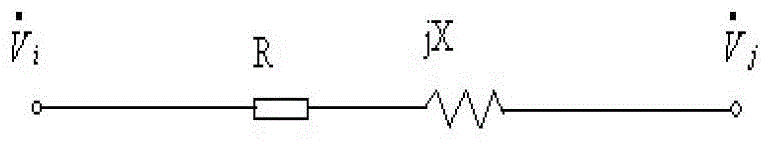Patents
Literature
122 results about "Vulnerability assessment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
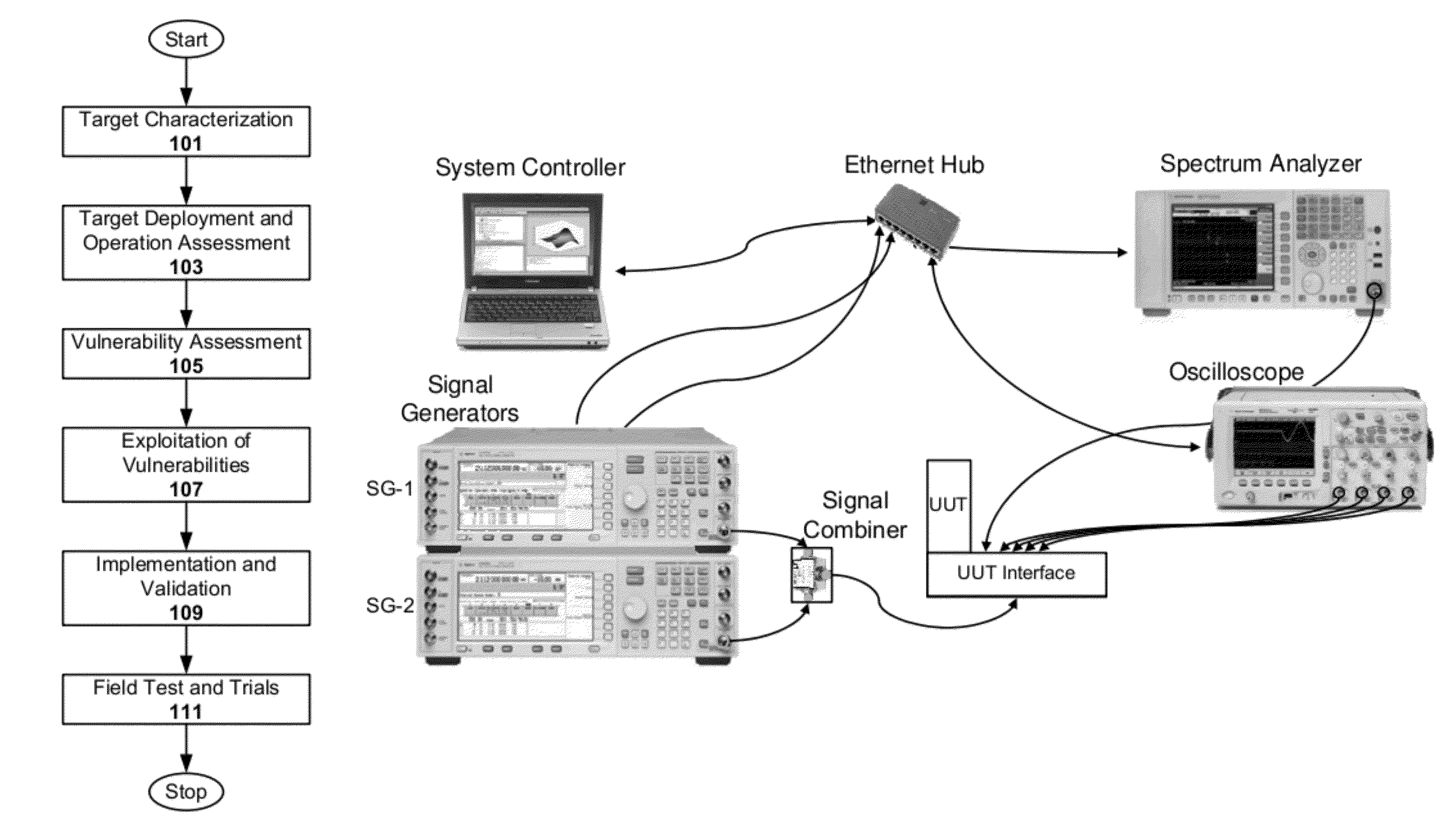
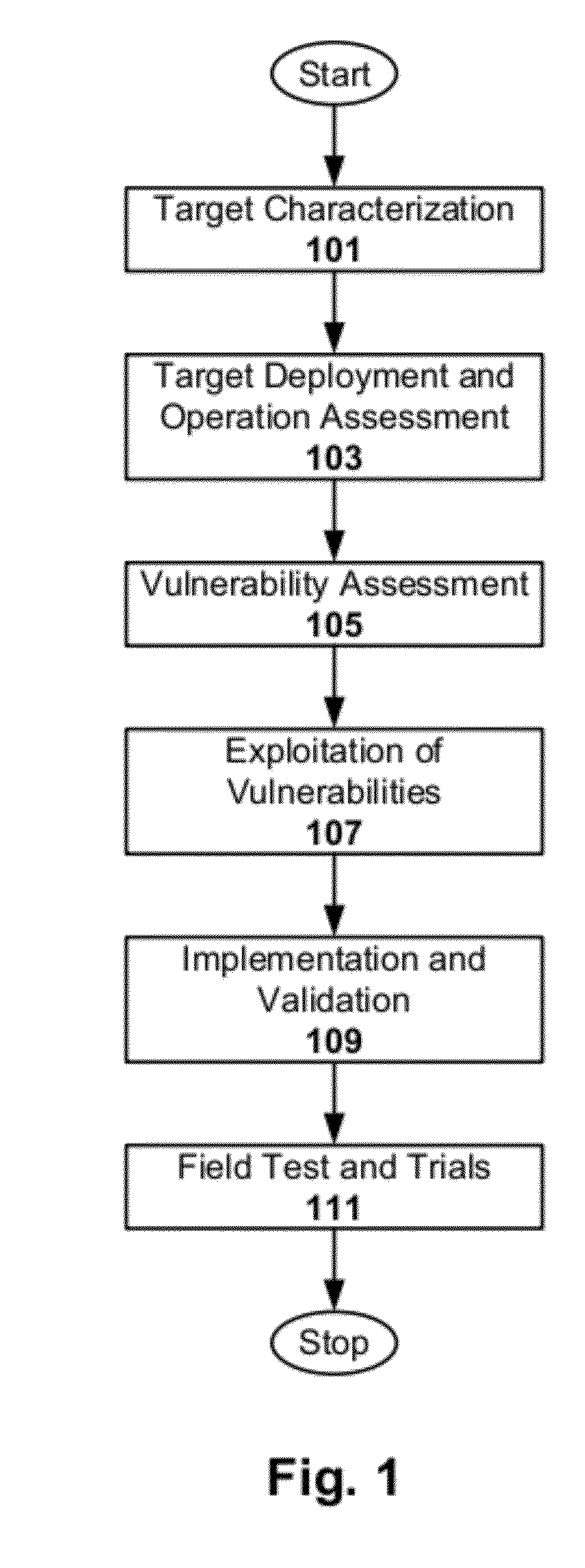
A vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Examples of systems for which vulnerability assessments are performed include, but are not limited to, information technology systems, energy supply systems, water supply systems, transportation systems, and communication systems. Such assessments may be conducted on behalf of a range of different organizations, from small businesses up to large regional infrastructures. Vulnerability from the perspective of disaster management means assessing the threats from potential hazards to the population and to infrastructure. It may be conducted in the political, social, economic or environmental fields.
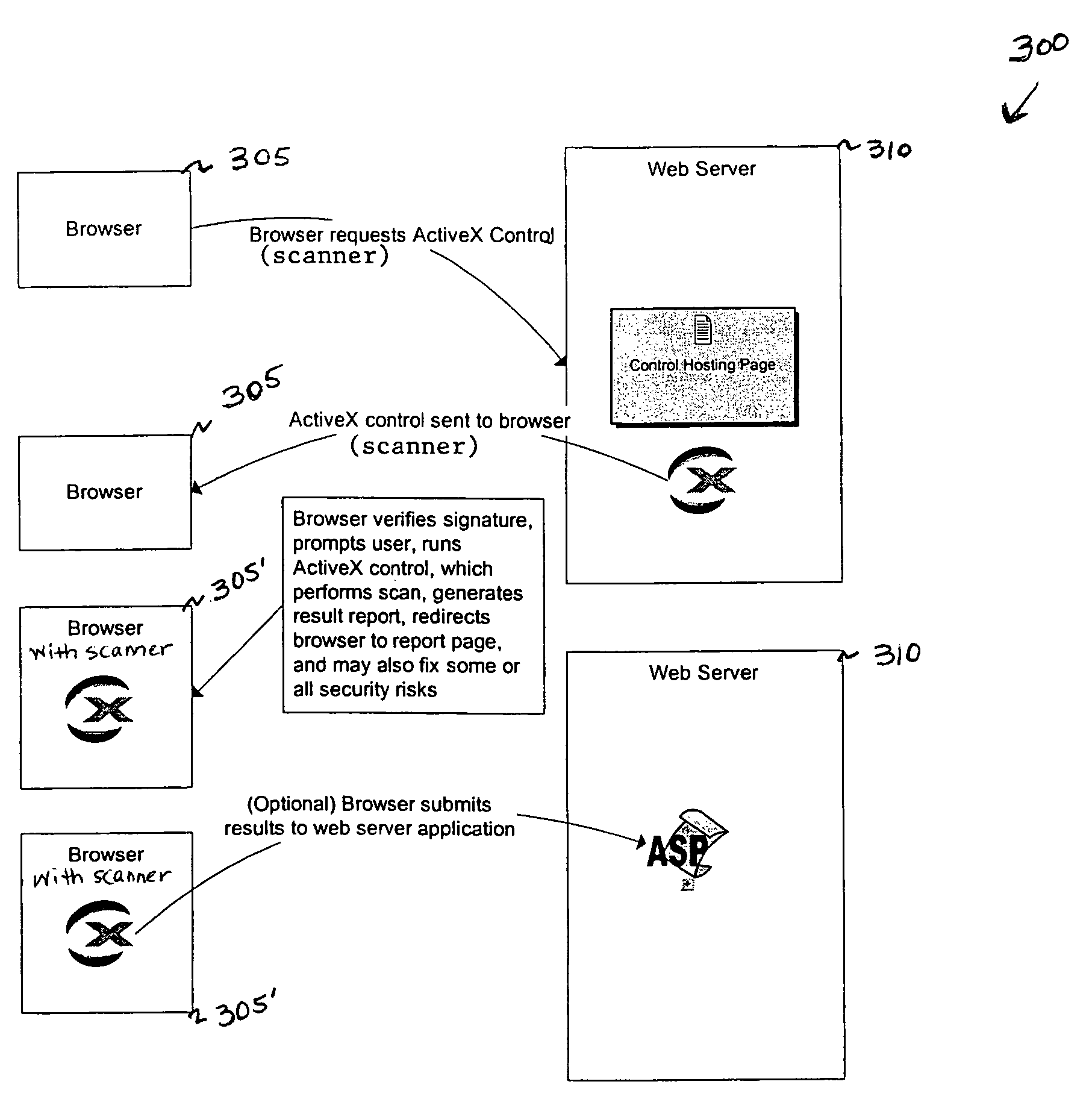
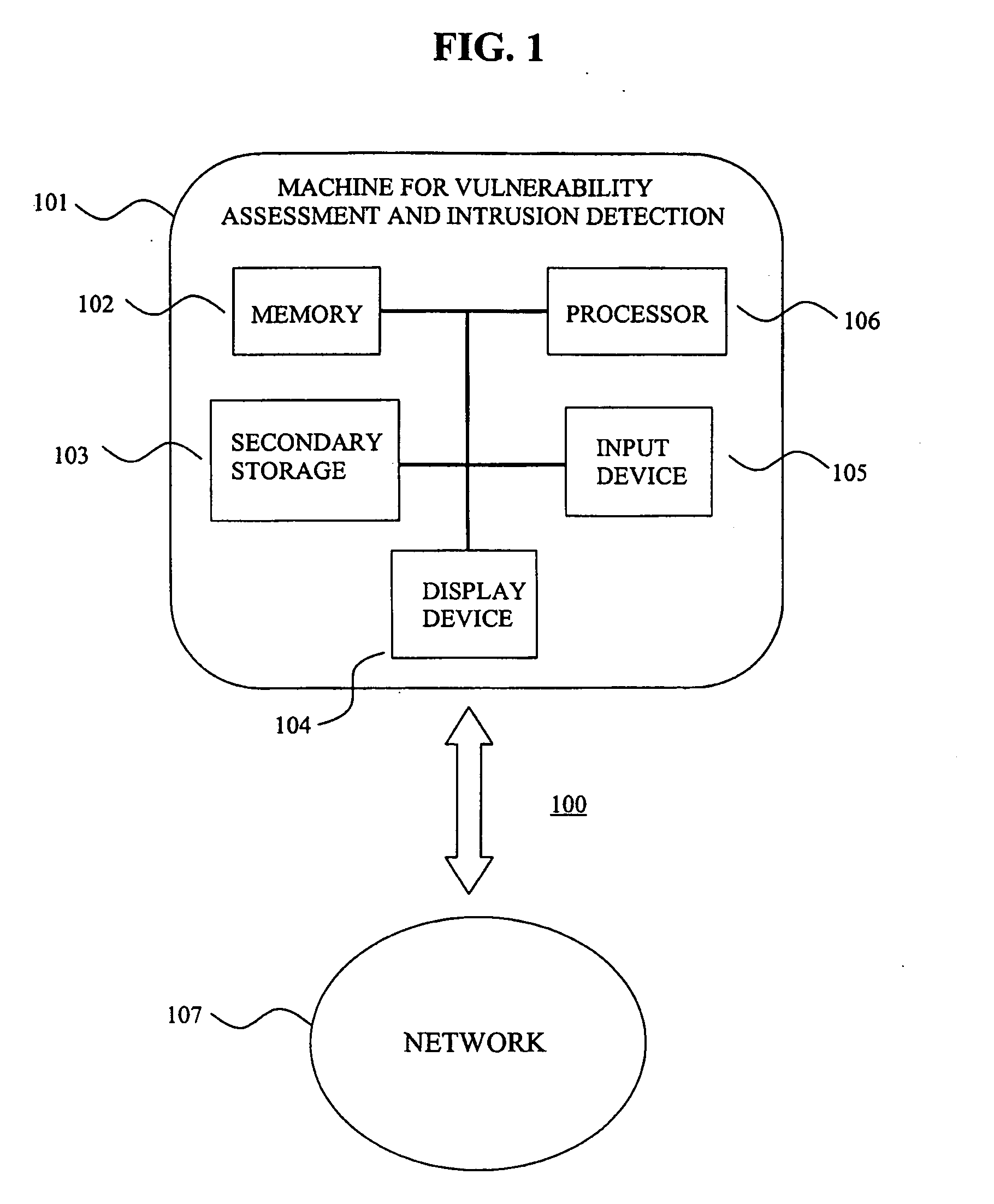
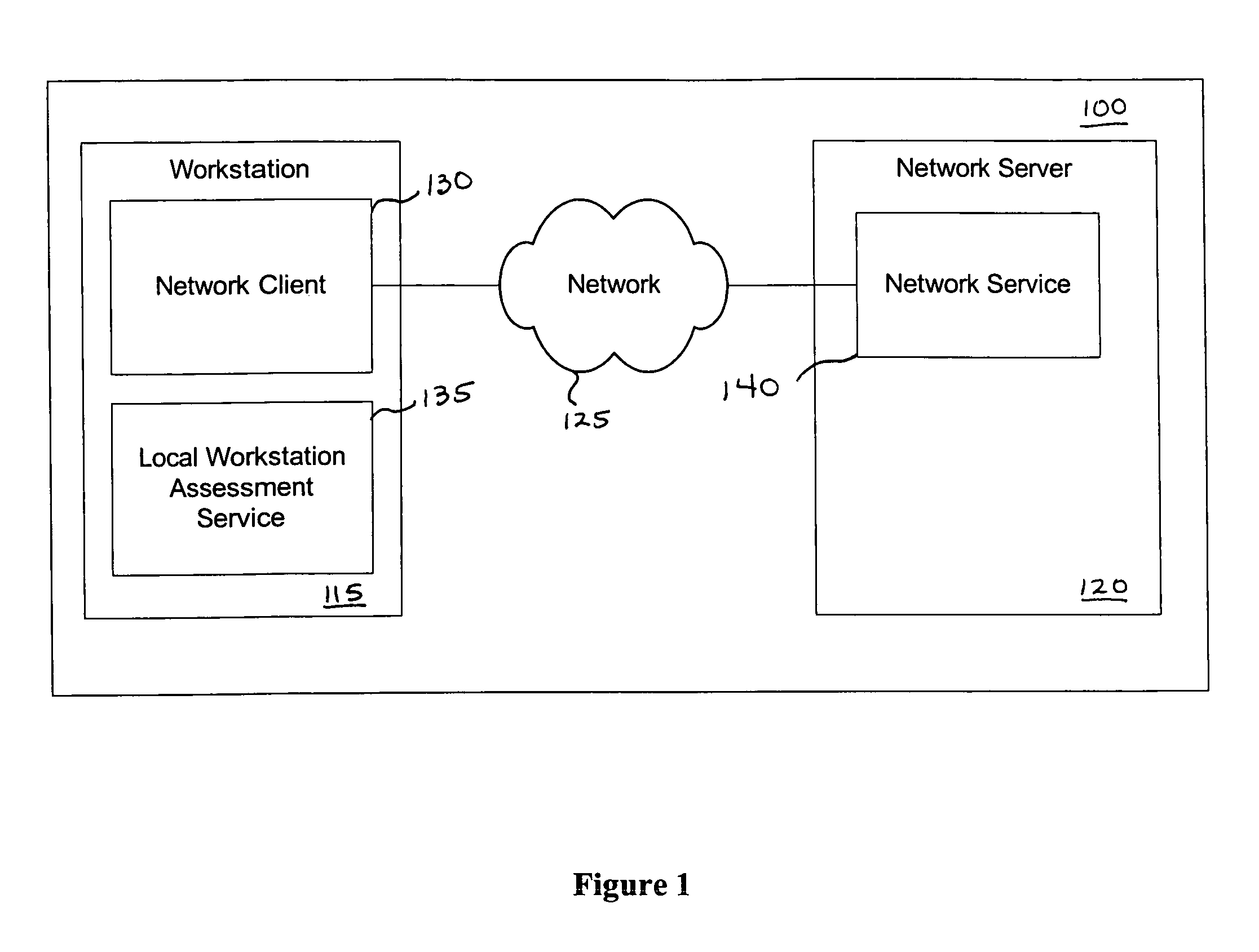
Vulnerability assessment and authentication of a computer by a local scanner
InactiveUS7178166B1Overcome disadvantagesMemory loss protectionDigital data processing detailsWorkstationNetwork service
Providing a user with assurance that a computer is secure based on a vulnerability assessment completed by a browser-compatible scanner operating on the computer. If the scanner finds a vulnerability, the scanner can inform the user that the machine is or may be compromised, or repair the vulnerability. For example, the scanner may be able to repair the vulnerability of the workstation. In the alternative, the scanner can provide the scan results to a network server. If the vulnerability assessment shows that the workstation is compromised, or if the possibility of remote compromise is high, the network server can decline to provide network services to the workstation.
Owner:KYNDRYL INC
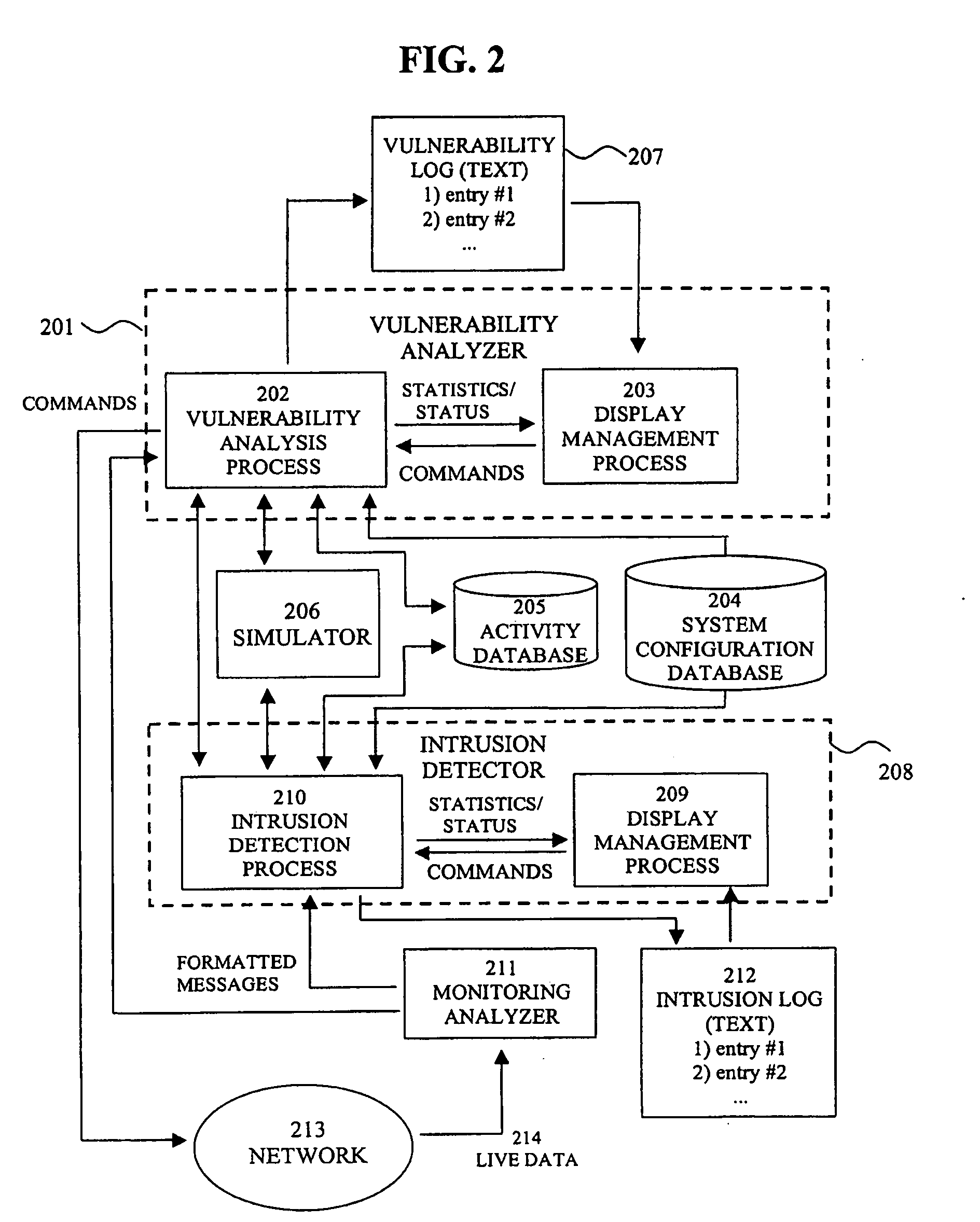
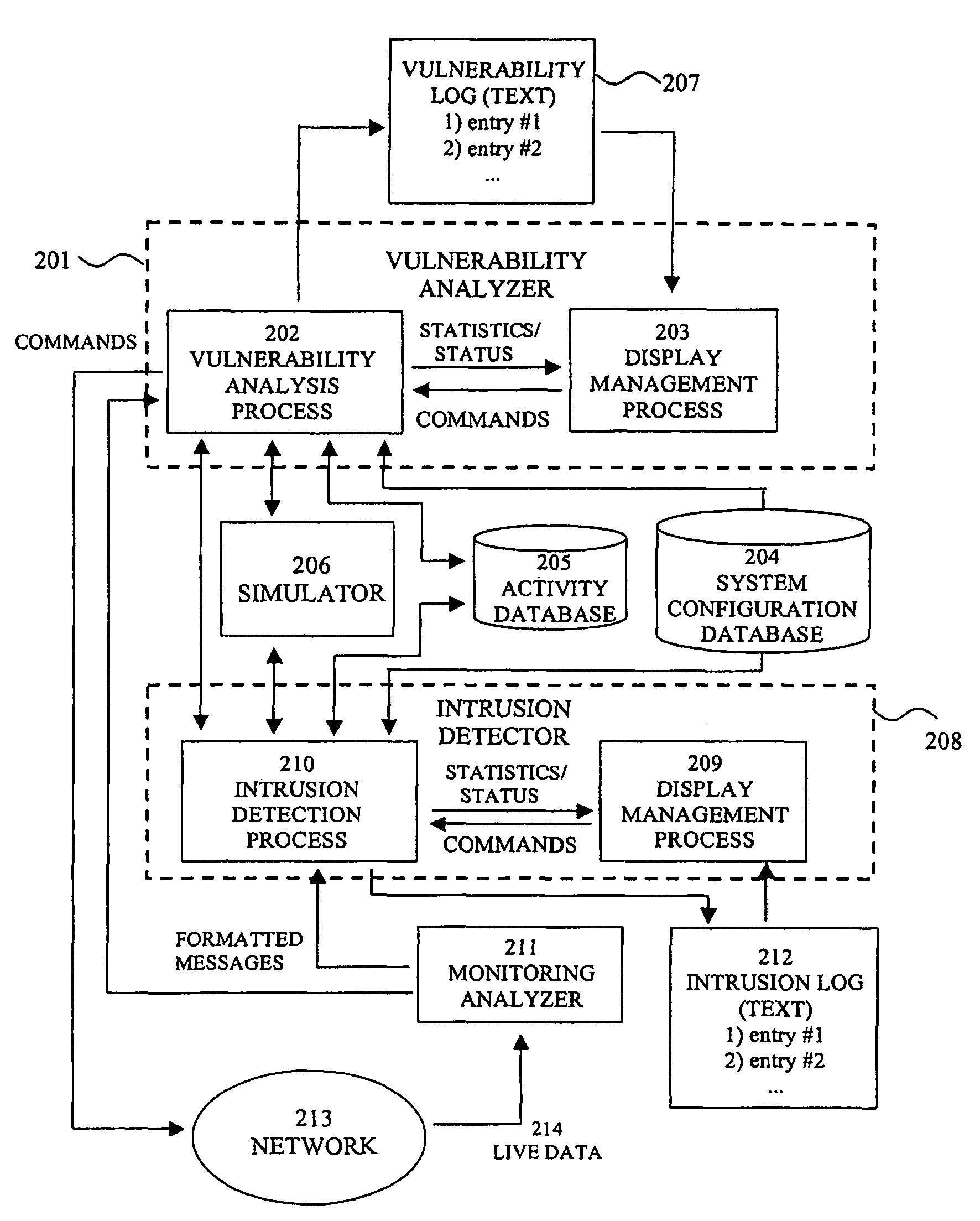
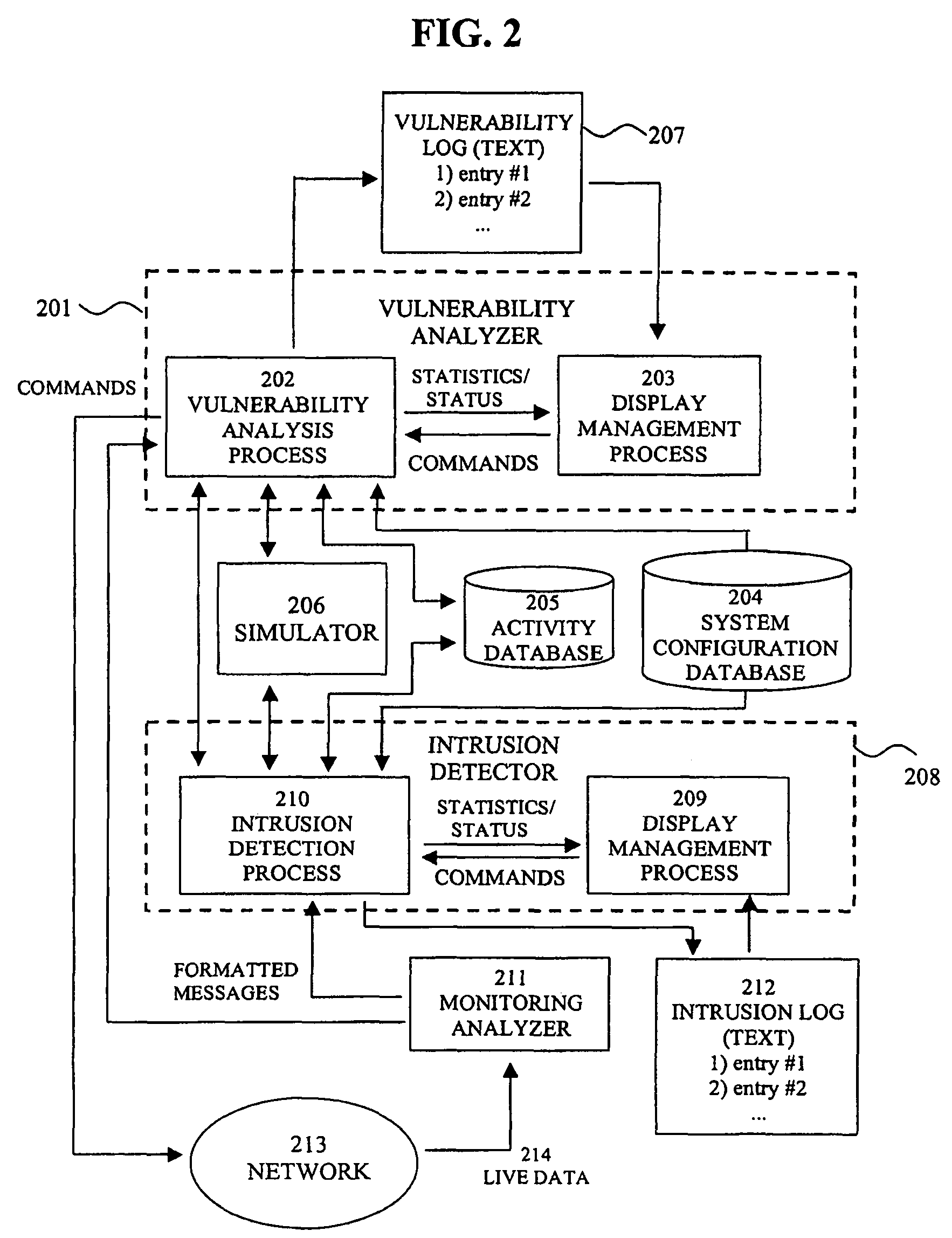
System for intrusion detection and vulnerability assessment in a computer network using simulation and machine learning
InactiveUS20060191010A1Memory loss protectionError detection/correctionComputer configurationData transmission
The present invention provides a system and method for predicting and preventing unauthorized intrusion in a computer configuration. Preferably, the invention comprises a communication network to which at least two computing devices connect, wherein at least one of the computing devices is operable to receive data transmitted by the other computing device. The invention further comprises a database that is accessible over the network and operable to store information related to the network. A vulnerability assessment component is provided that is operable to execute a command over the communication network, and a data monitoring utility operates to monitor data transmitted over the communication network as the vulnerability assessment component executes commands. Also, an intrusion detection component is included that is operable to provide a simulated copy of the network, to generate a first data transmission on the simulated copy of the network that represents a second data transmission on the communication network, and to compare the first data transmission with a second data transmission. The vulnerability assessment component preferably interfaces with the intrusion detection component to define rules associated with the first and second data transmissions, to store the rules in the database, and to retrieve the rules from the database in order to predict and prevent unauthorized intrusion in the computer configuration.
Owner:PACE UNIVERSITY
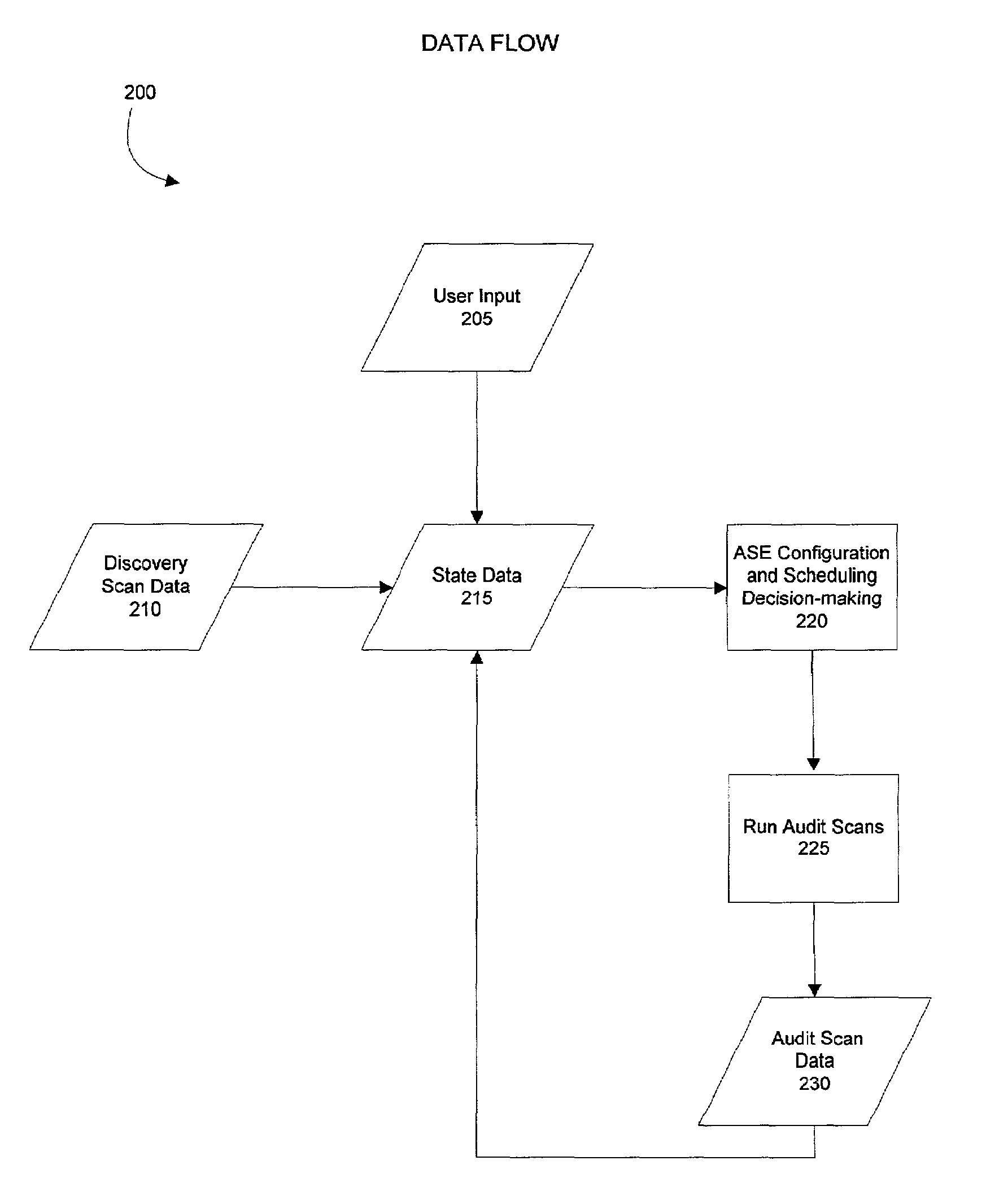
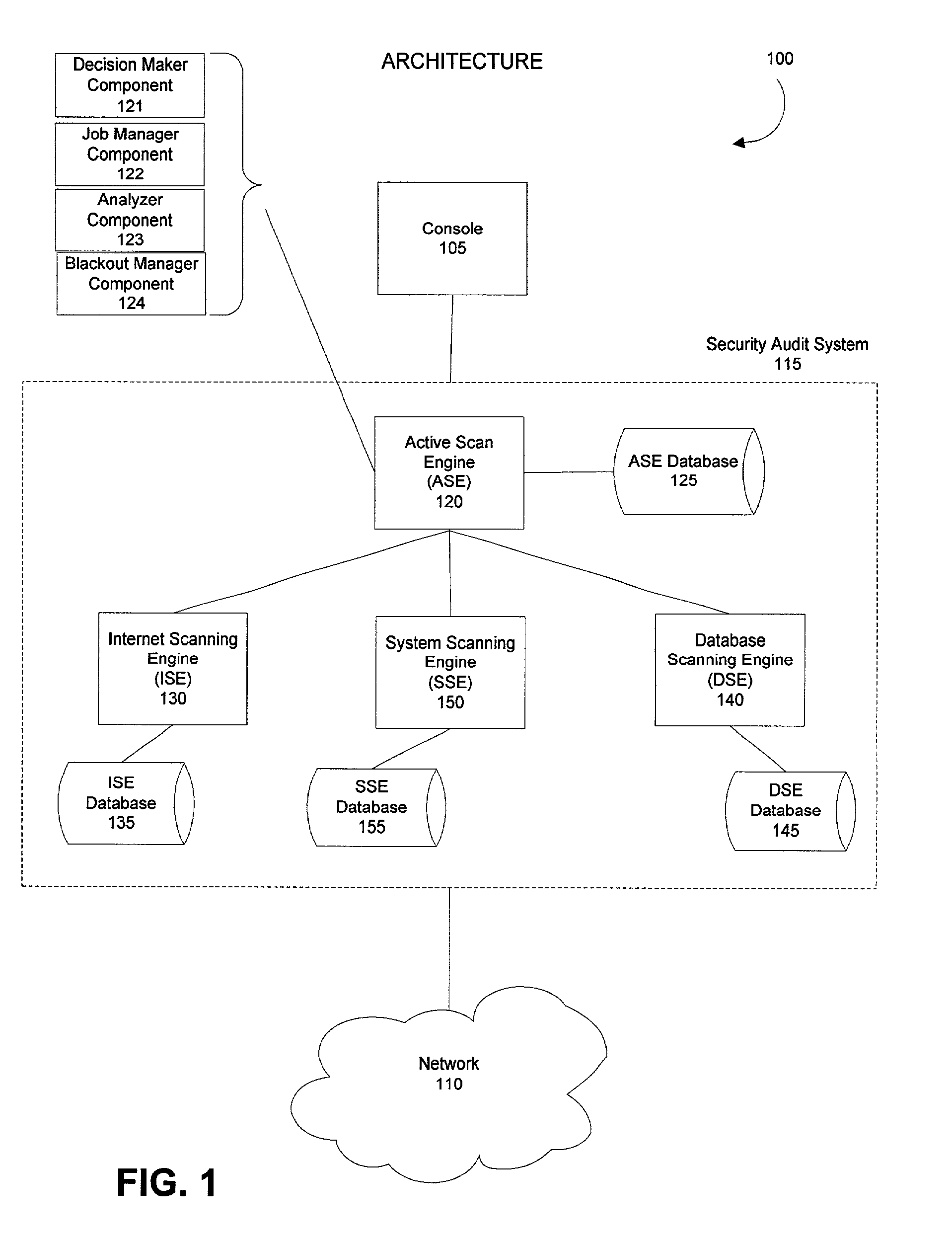
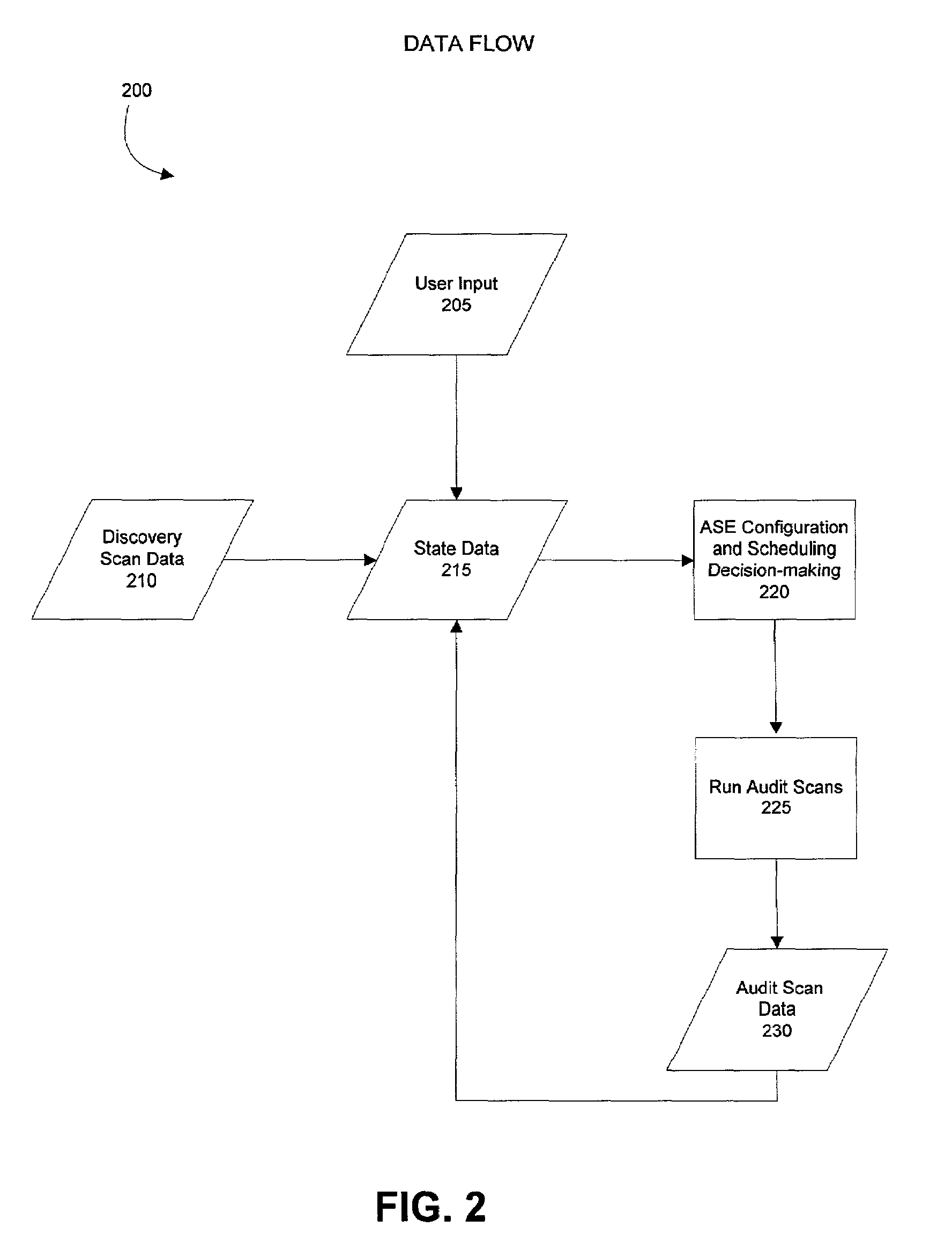
Method and system for configuring and scheduling security audits of a computer network
ActiveUS7340776B2Improves existing network security techniquesNetwork security issueMemory loss protectionDigital data processing detailsOperational systemVulnerability assessment
Managing the selection and scheduling of security audits run on a computing network. The computer network is surveyed by a security audit system to determine the function and relative importance of the elements in the network. Based on function and priority, a more thorough type of security audit is selected to run against each of the network elements by the security audit system. The security audit can also be automatically scheduled based on the information gathered from the survey. Once the system runs the security audit, a vulnerability assessment can be calculated for each element in the network. The vulnerability assessment can be presented in a format that facilitates interpretation and response by someone operating the system. The vulnerability assessment can also be used to configure and schedule future security audits.
Owner:FINJAN BLUE INC
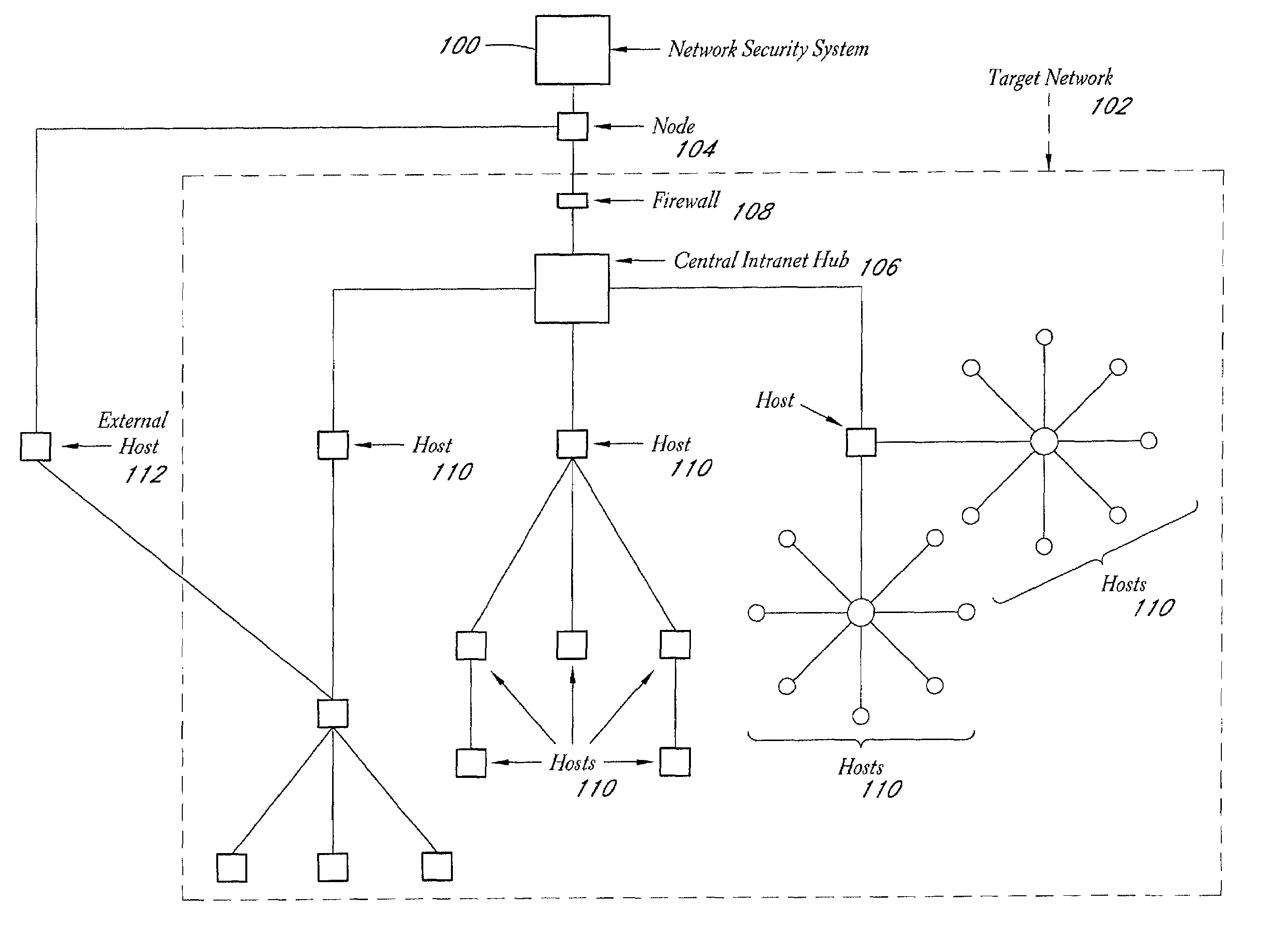
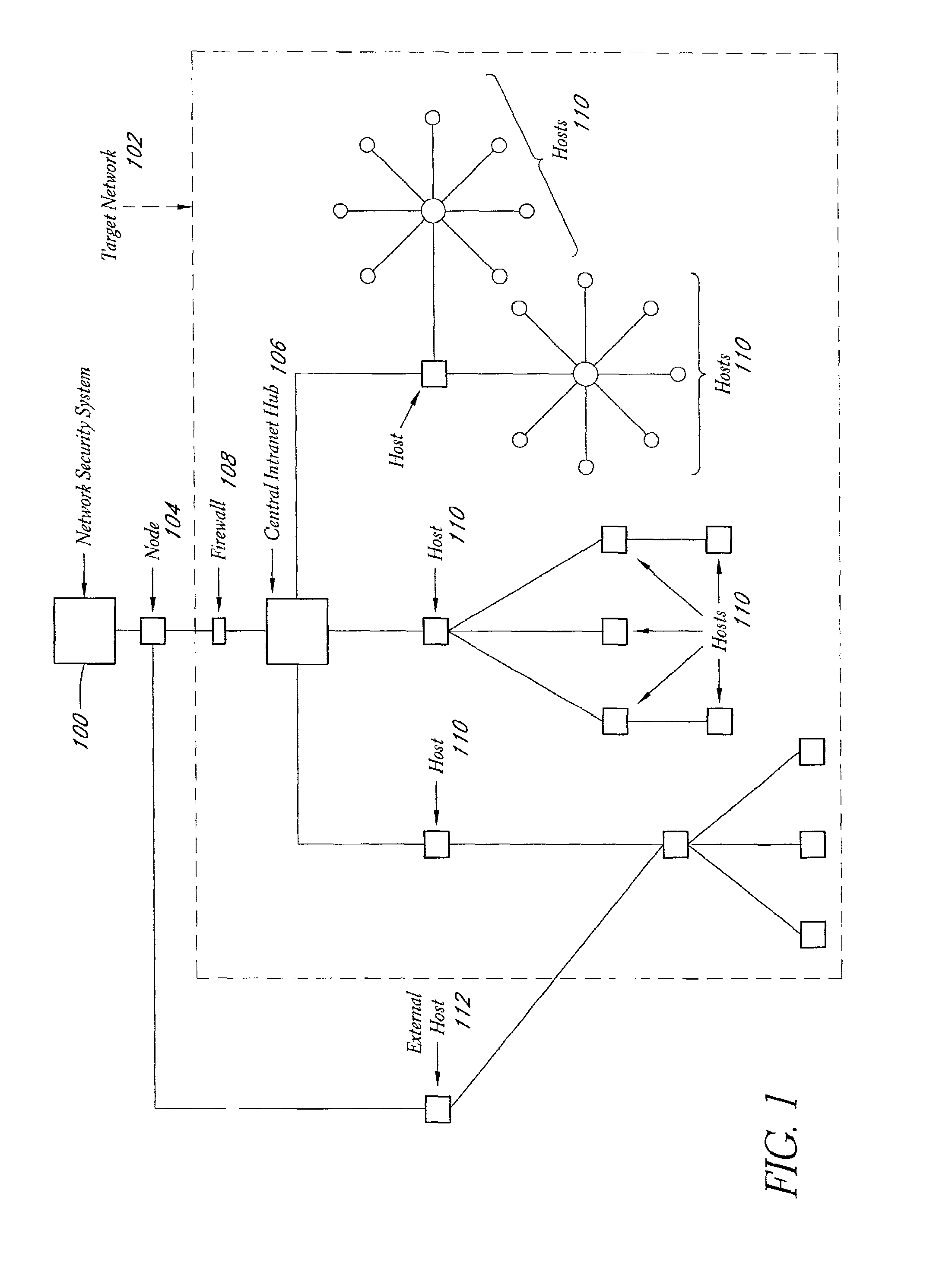
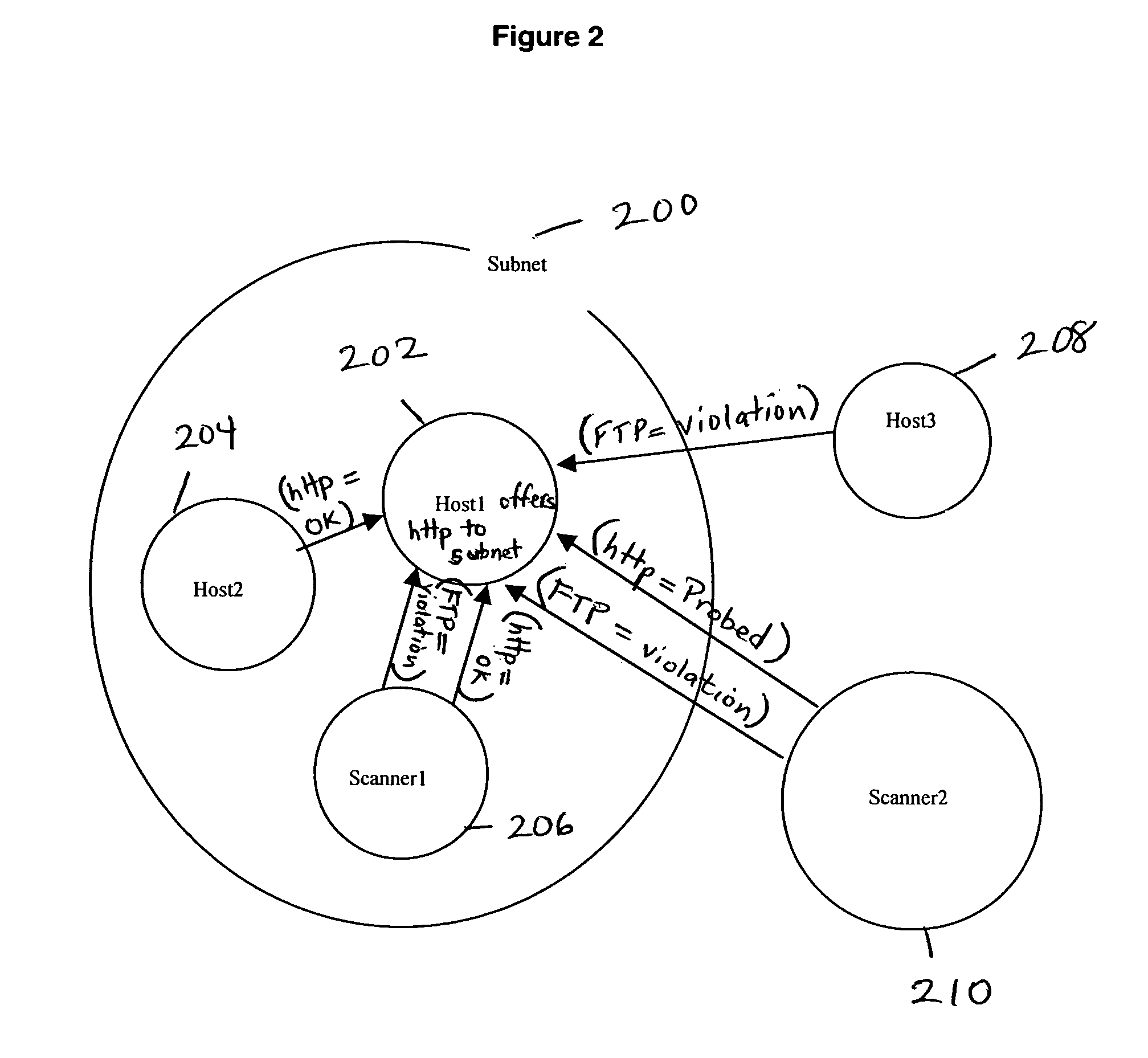
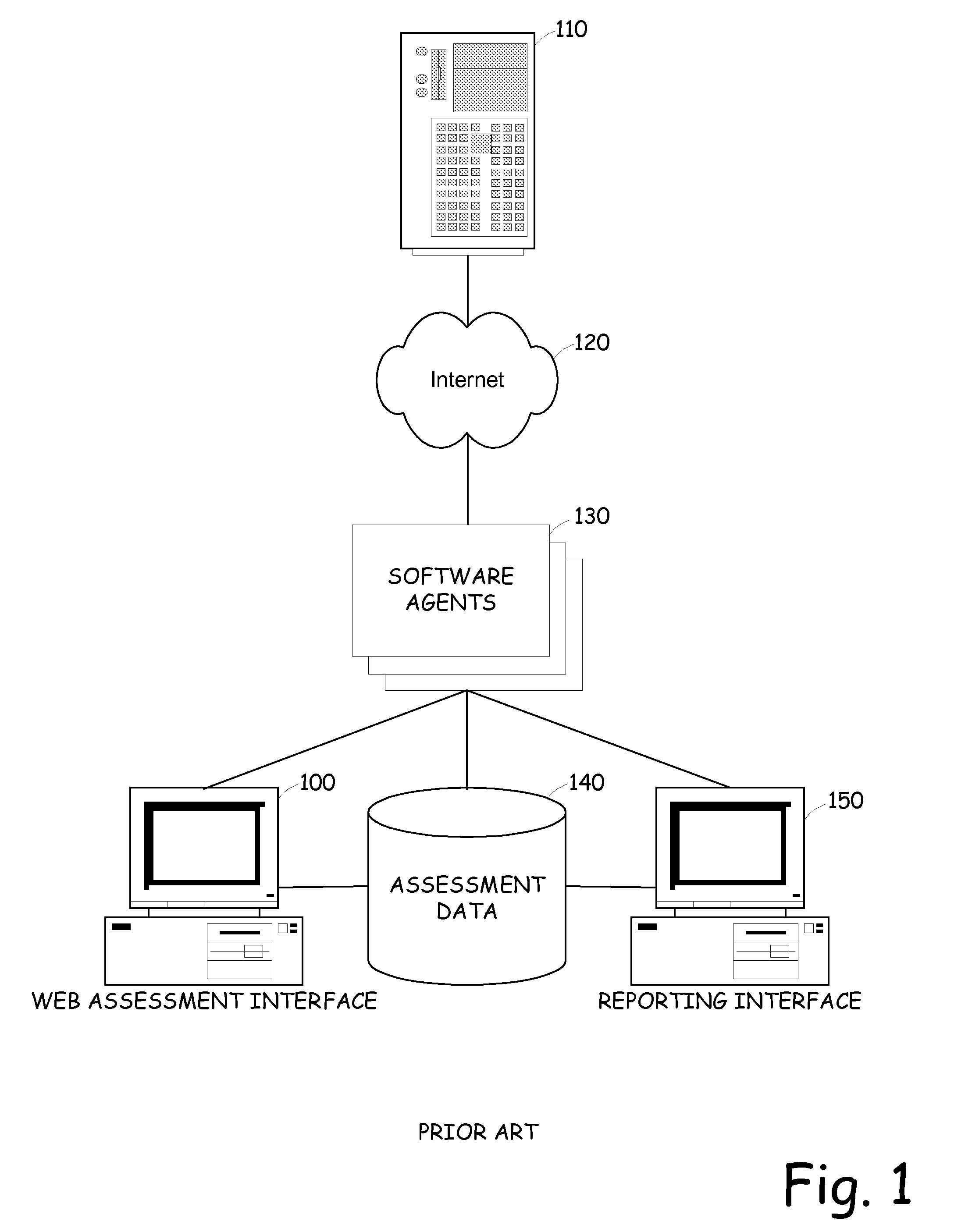
System and method for network vulnerability detection and reporting
ActiveUS7152105B2Easy to useReliably determinedElectric signal transmission systemsImage analysisGraphicsOperational system
A system and method provide comprehensive and highly automated testing of vulnerabilities to intrusion on a target network, including identification of operating system, identification of target network topology and target computers, identification of open target ports, assessment of vulnerabilities on target ports, active assessment of vulnerabilities based on information acquired from target computers, quantitative assessment of target network security and vulnerability, and hierarchical graphical representation of the target network, target computers, and vulnerabilities in a test report. The system and method employ minimally obtrusive techniques to avoid interference with or damage to the target network during or after testing.
Owner:MCAFEE LLC
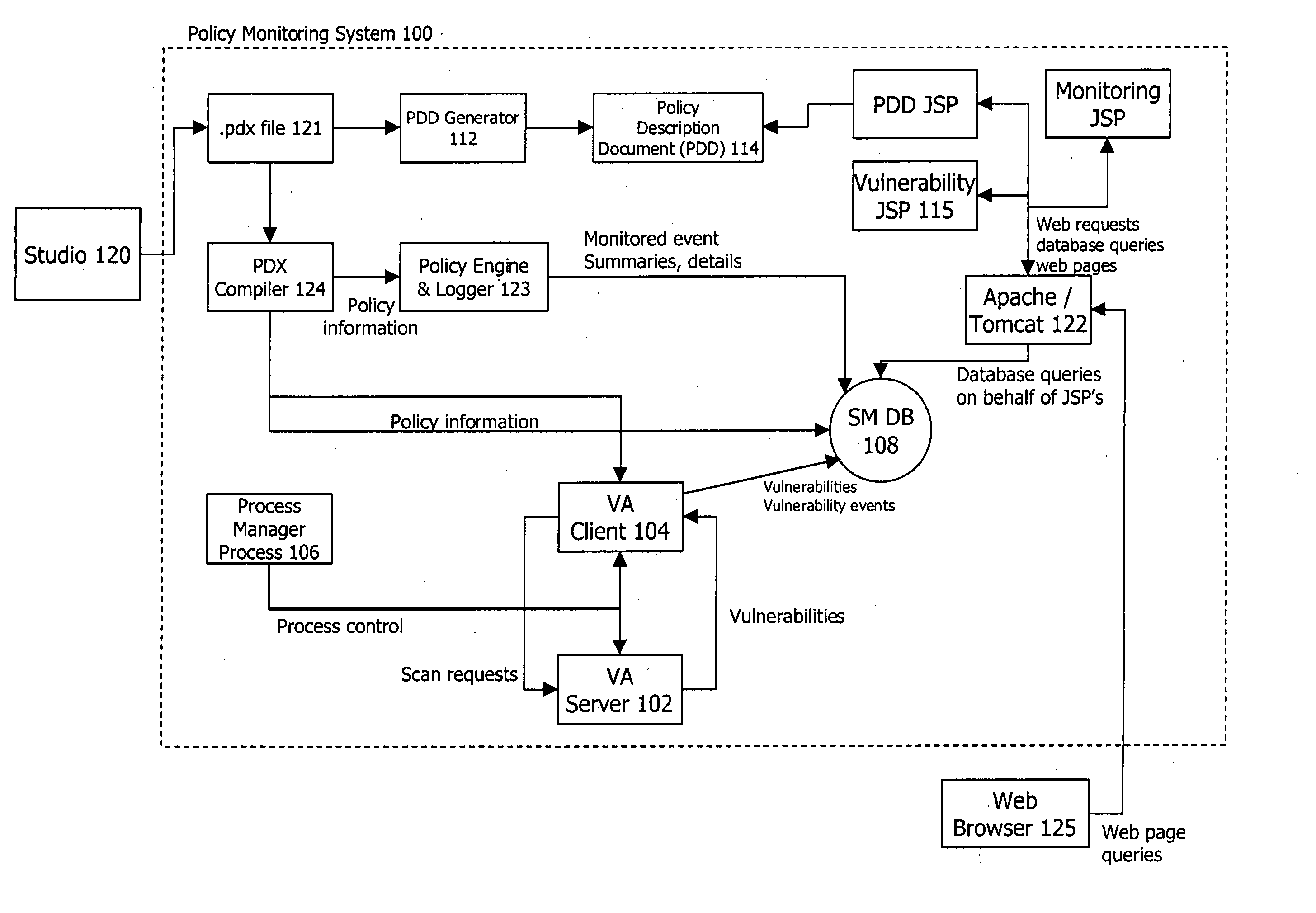
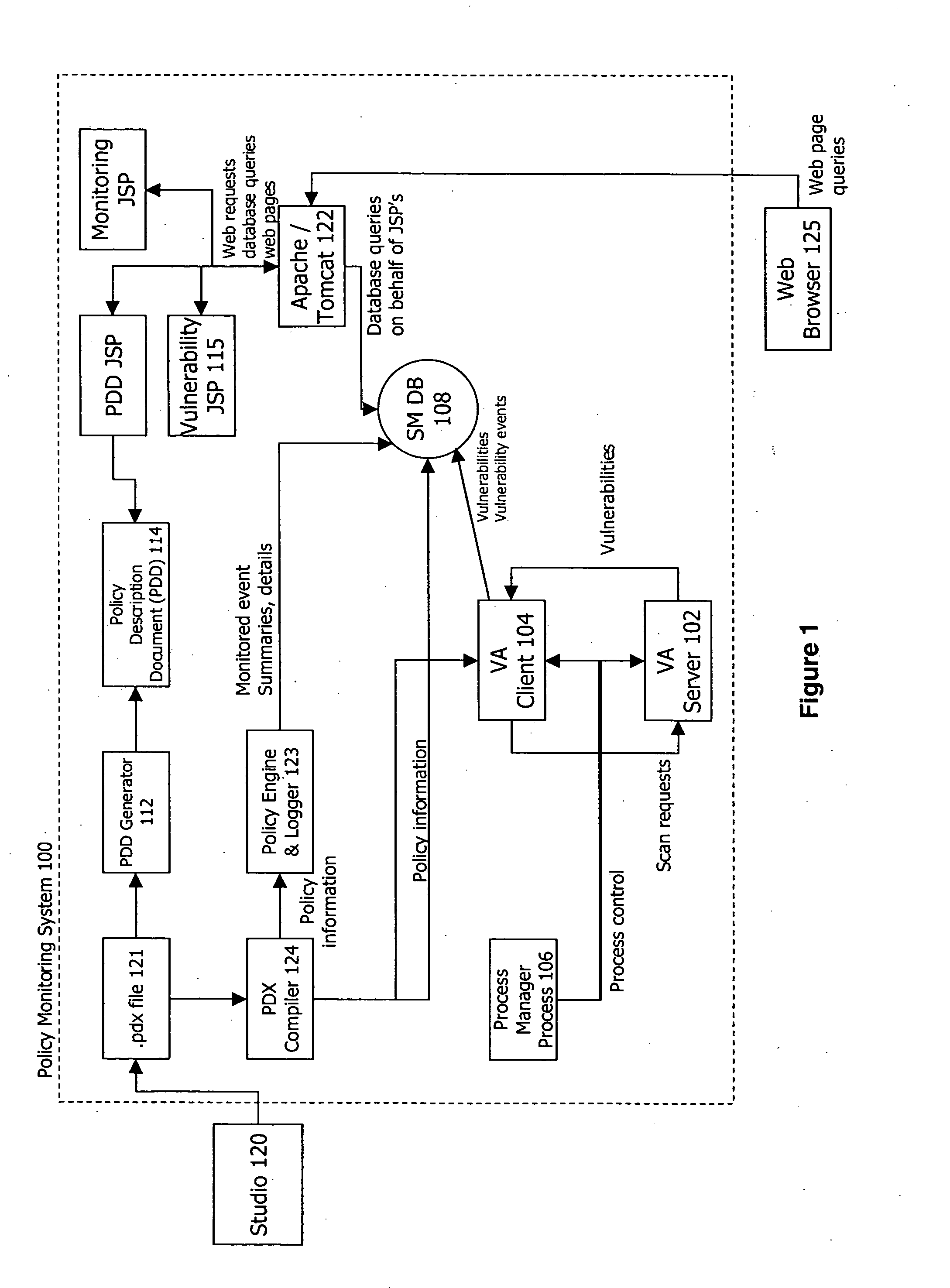
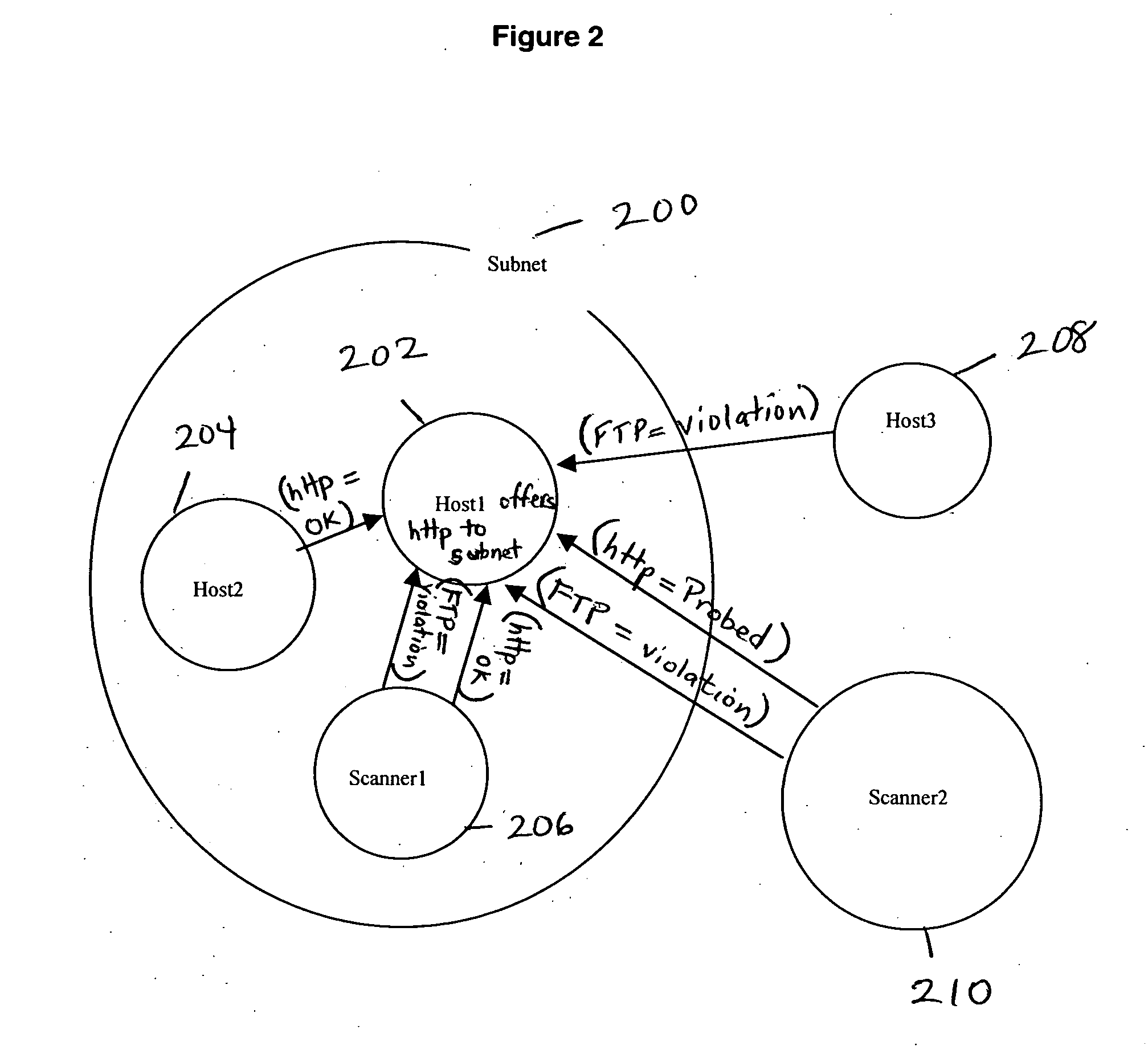
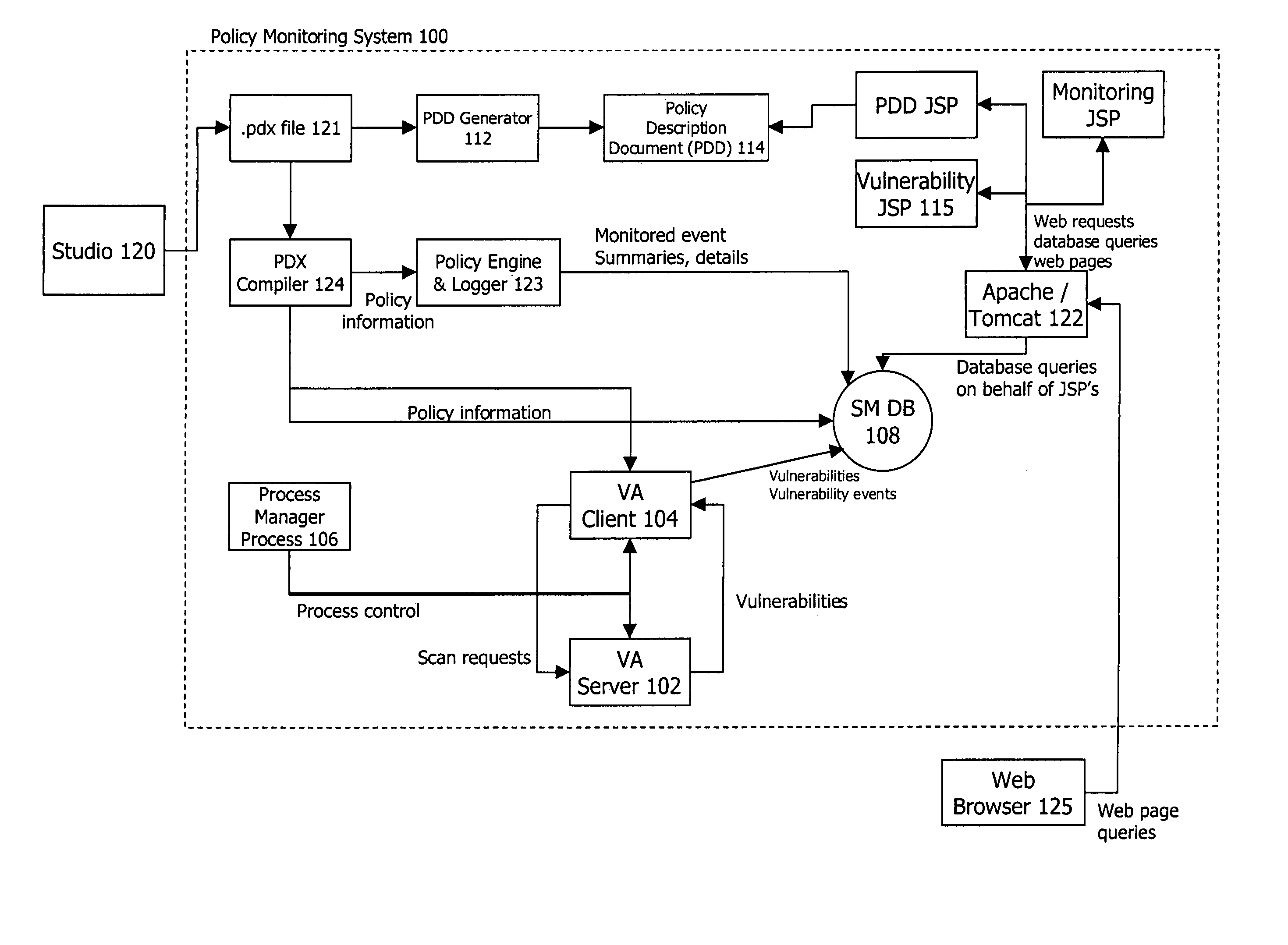
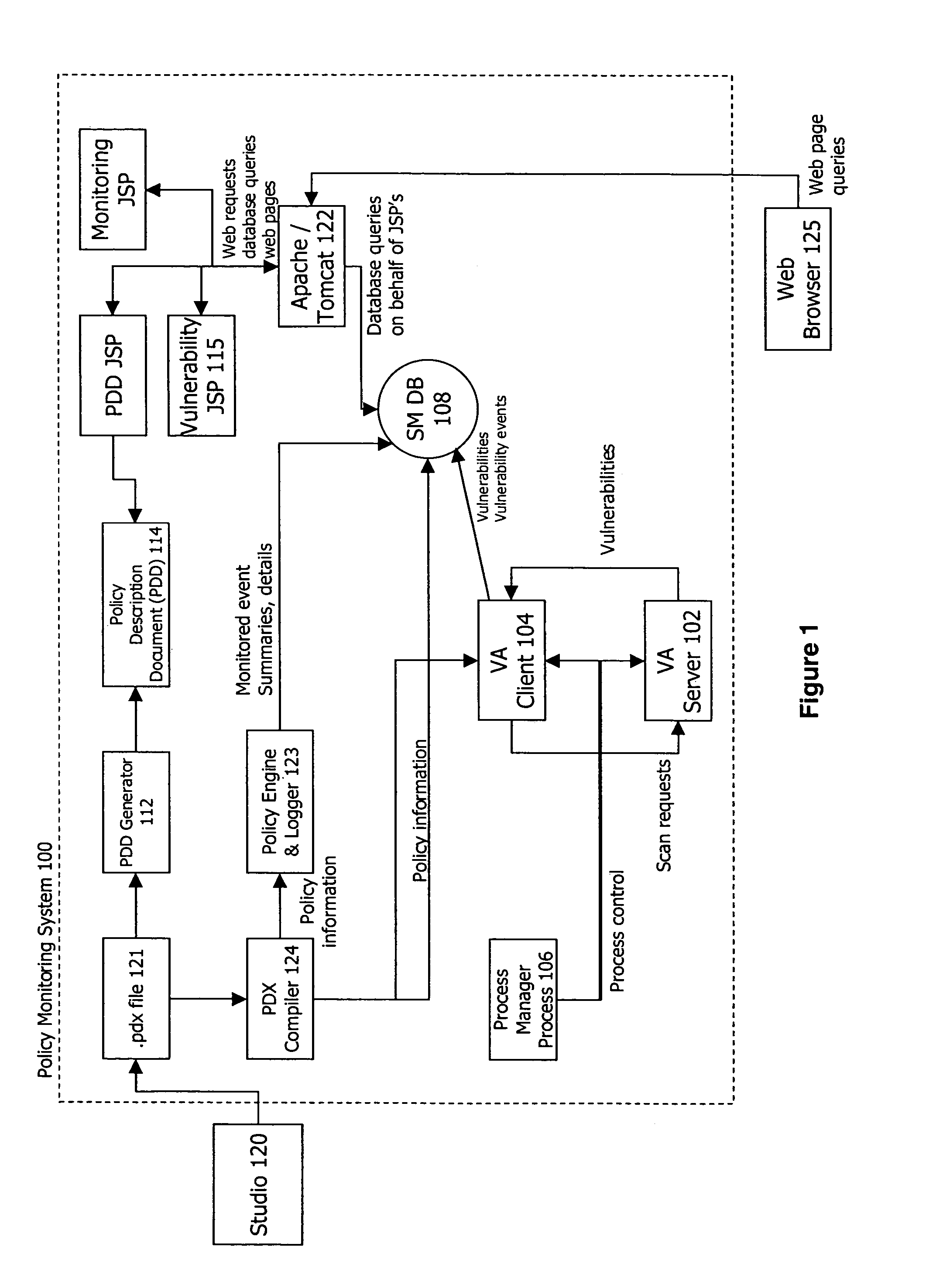
Policy-based vulnerability assessment
ActiveUS20050010821A1Reduce information overloadRemove redundant informationMemory loss protectionError detection/correctionOperating systemVulnerability assessment
A system and method for a vulnerability assessment mechanism that serves to actively scan for vulnerabilities on a continuous basis and interpret the resulting traffic in context of policy is provided. Vulnerability information is presented within an enterprise manager system enabling the user to access vulnerability information, recommended remediation procedures, and associated network traffic. A studio mechanism is used to add scanners to the appropriate policies and control the scope and distribution of scans within the target network.
Owner:MUSARUBRA US LLC
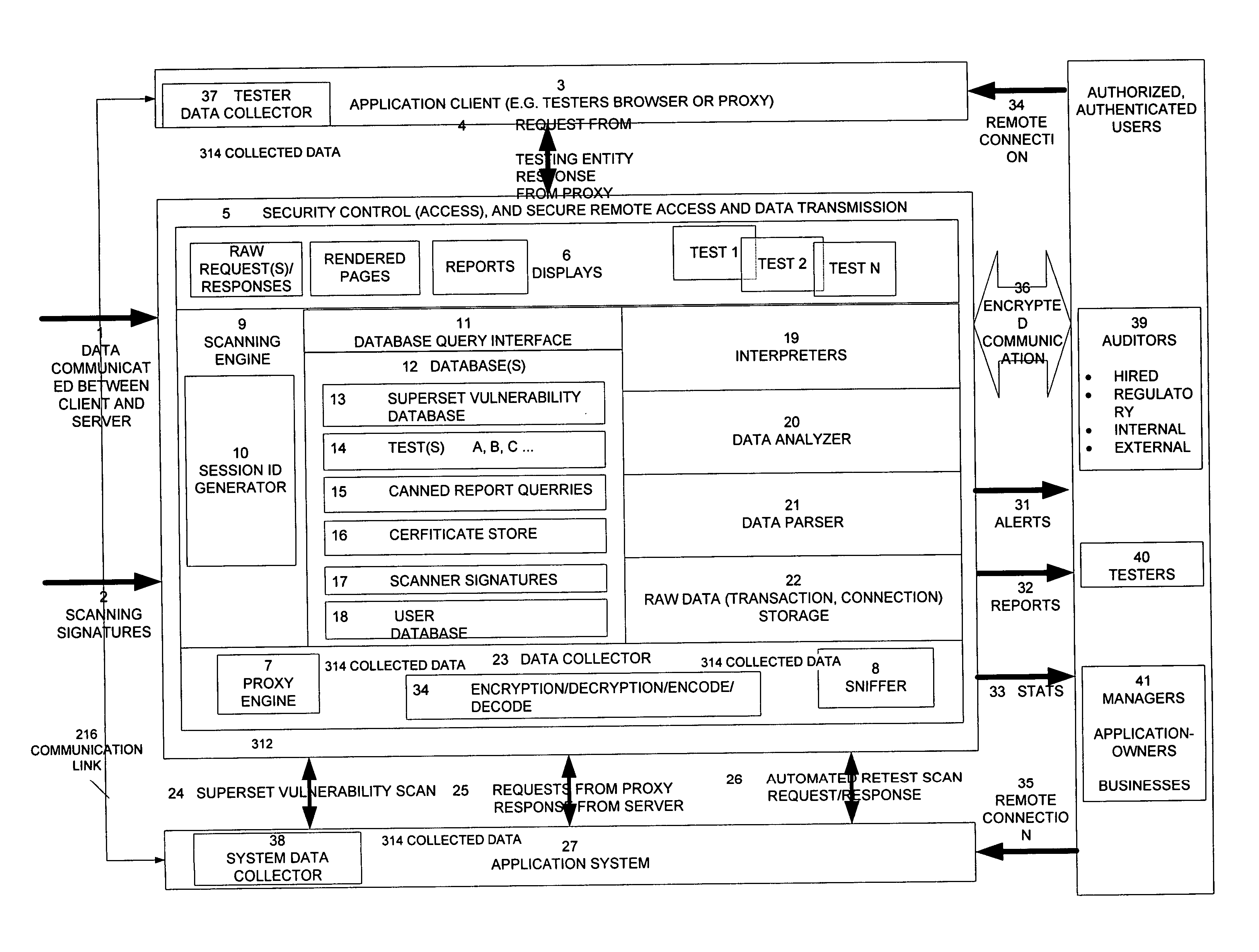
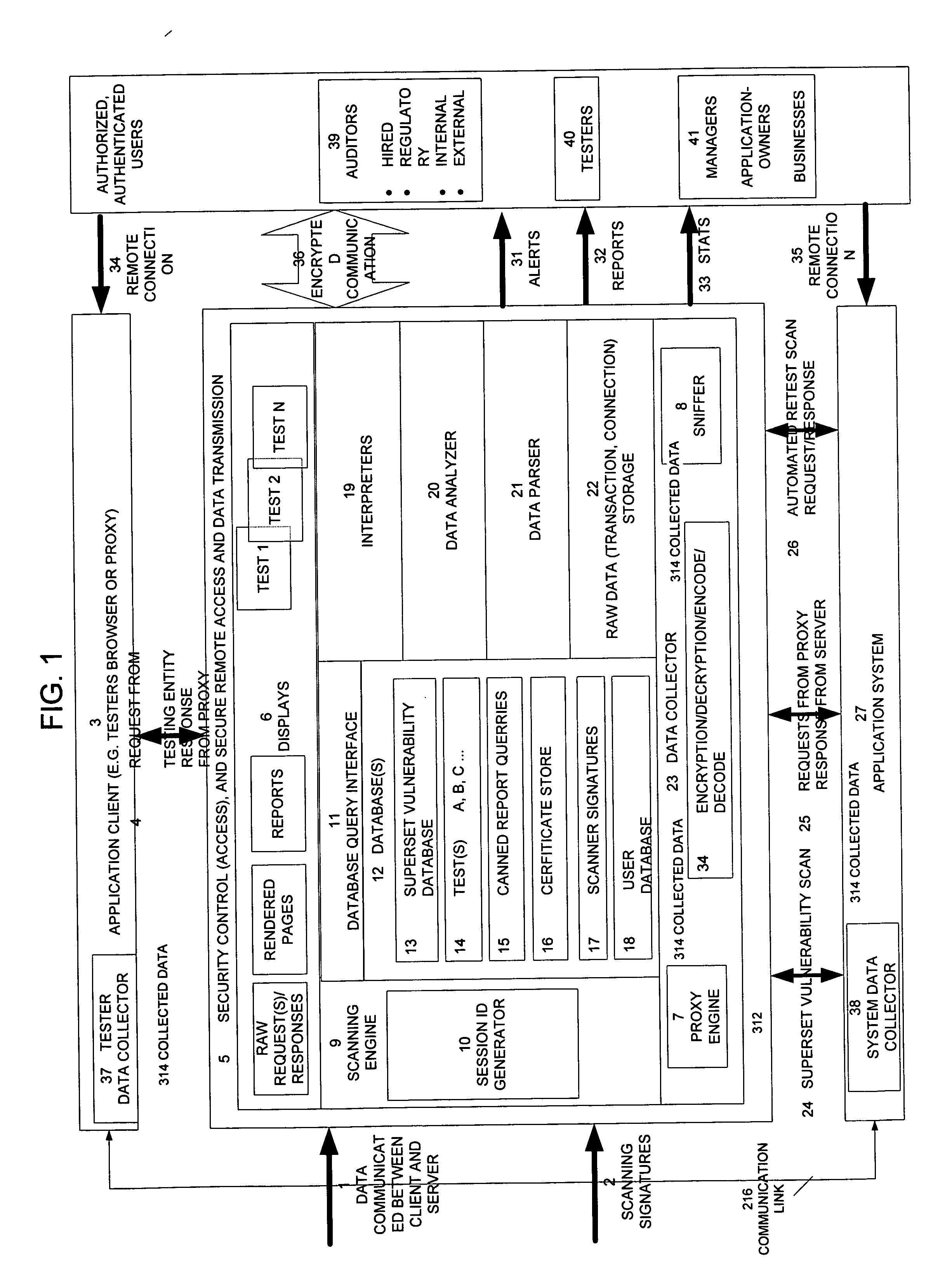
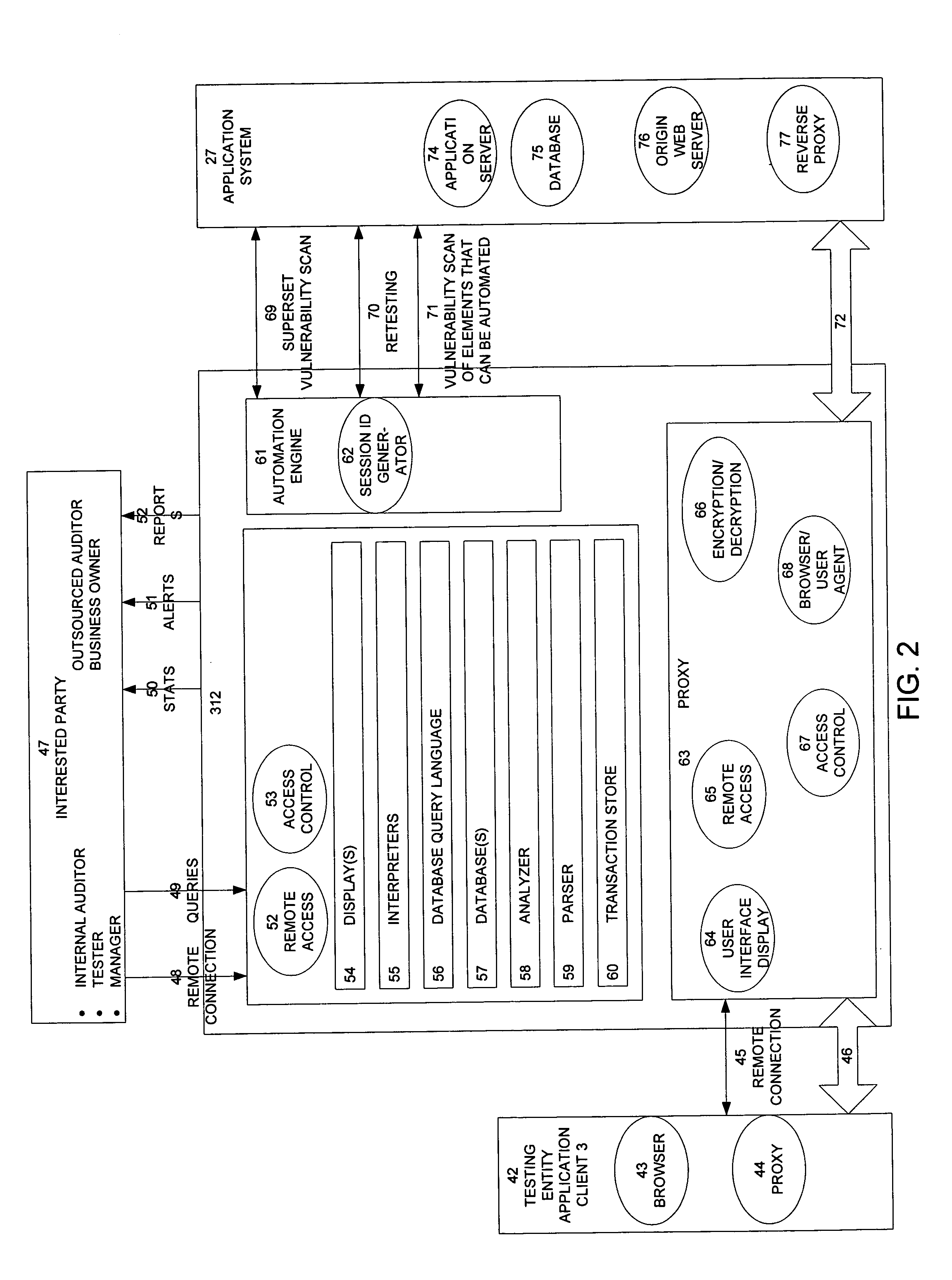
Method, system, and apparatus for managing, monitoring, auditing, cataloging, scoring, and improving vulnerability assessment tests, as well as automating retesting efforts and elements of tests
InactiveUS20050138426A1Streamline and improve test effortImprove consistencyDigital data processing detailsHardware monitoringAnalysis dataWeb application
A scalable method, system, and apparatus for non-intrusively auditing and improving security assessments includes capturing, storing, presenting, displaying, inspecting, monitoring, and analyzing data flow in client-server security assessments and / or network / infrastructure security assessments. The invention provides interested parties with a mechanism to non-intrusively audit in real-time the vulnerability test effort, as well as review, replay, and analyze all aspects of the security assessment during and after the test. For web application assessments, the data capture includes one of the following or some combination: an intermediary with all data passing through the intermediary; a sniffer that can passively extract all data being communicated between the application and tester; and a plurality of computing modules (e.g., software, appliances, etc.) installed in the tester environment or within the application system environment (e.g., software installed on the tester's computer, or on the computer where the intermediary is running, or software installed on the application systems proxy or web server, or an appliance in either environment) for storing, processing, analyzing, reporting, and displaying the data.
Owner:STYSLINGER BRIAN
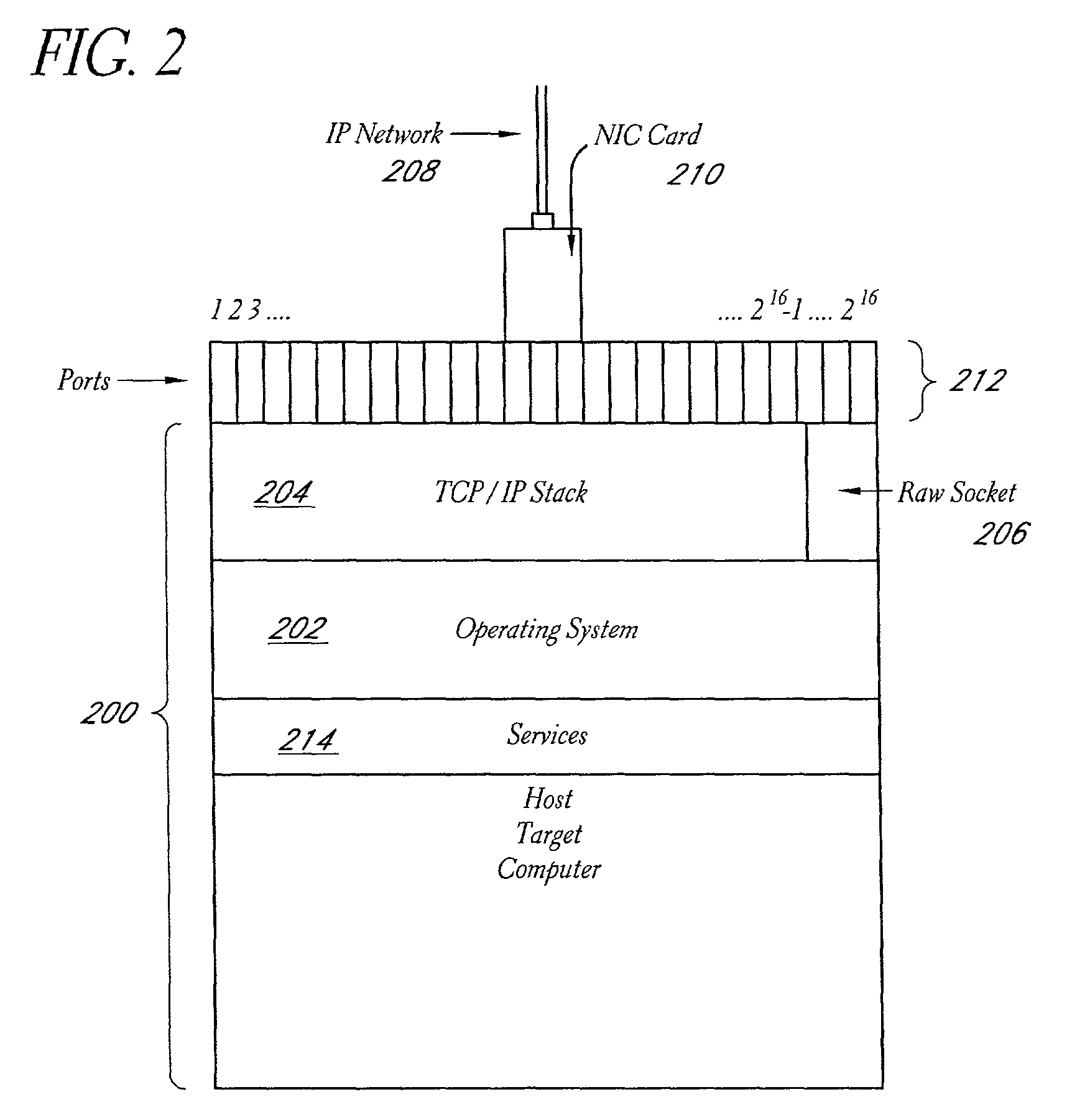
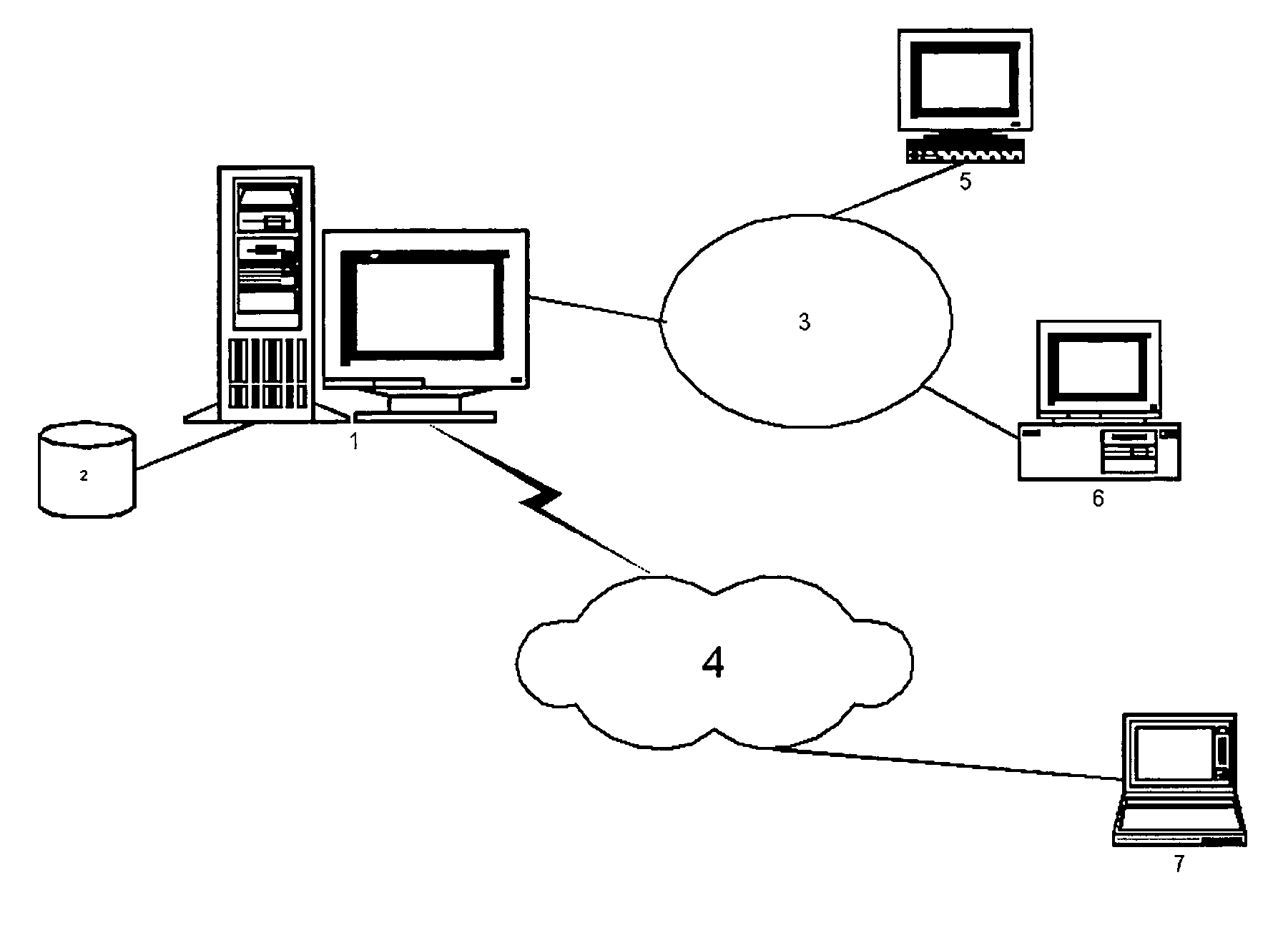
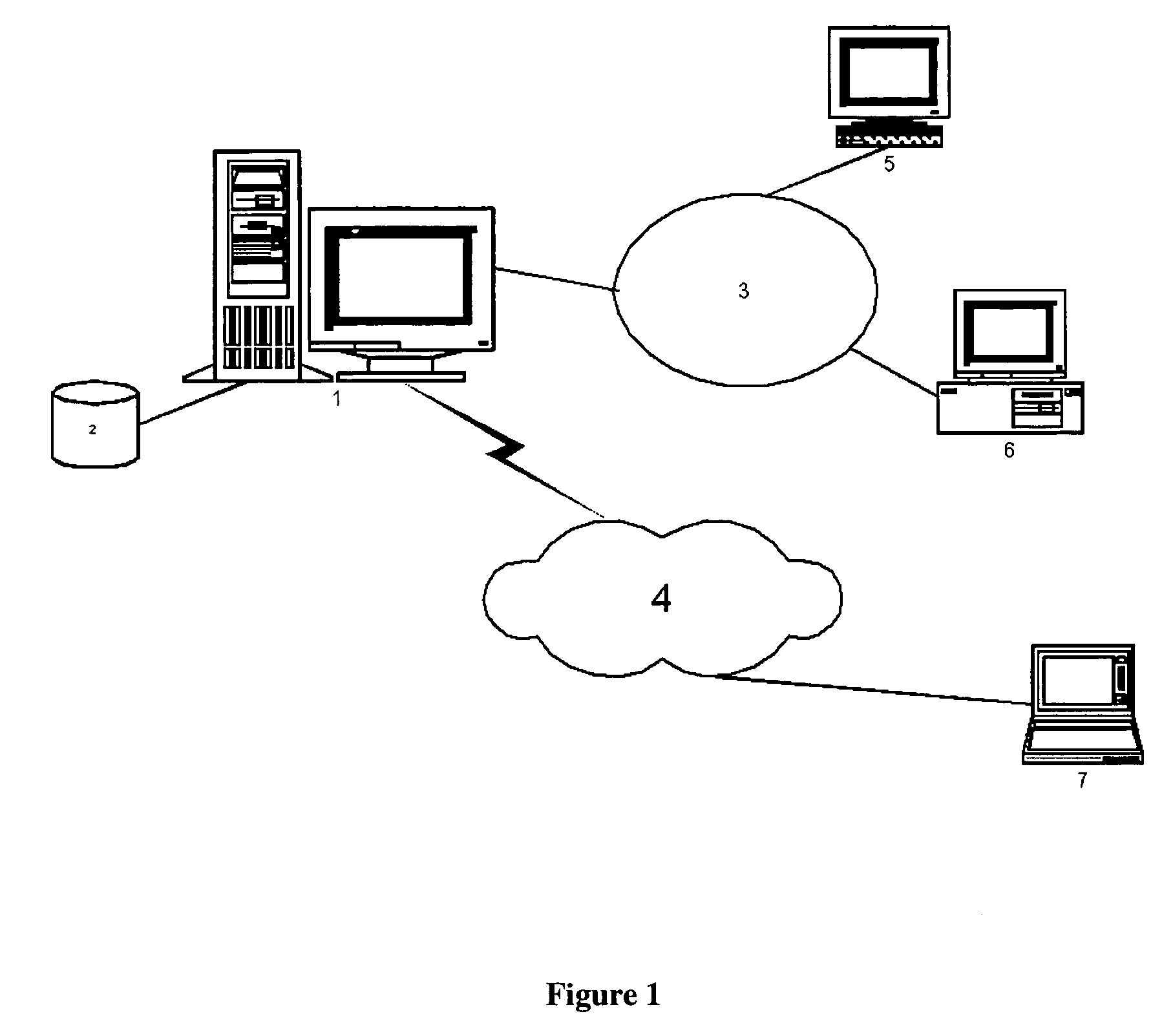
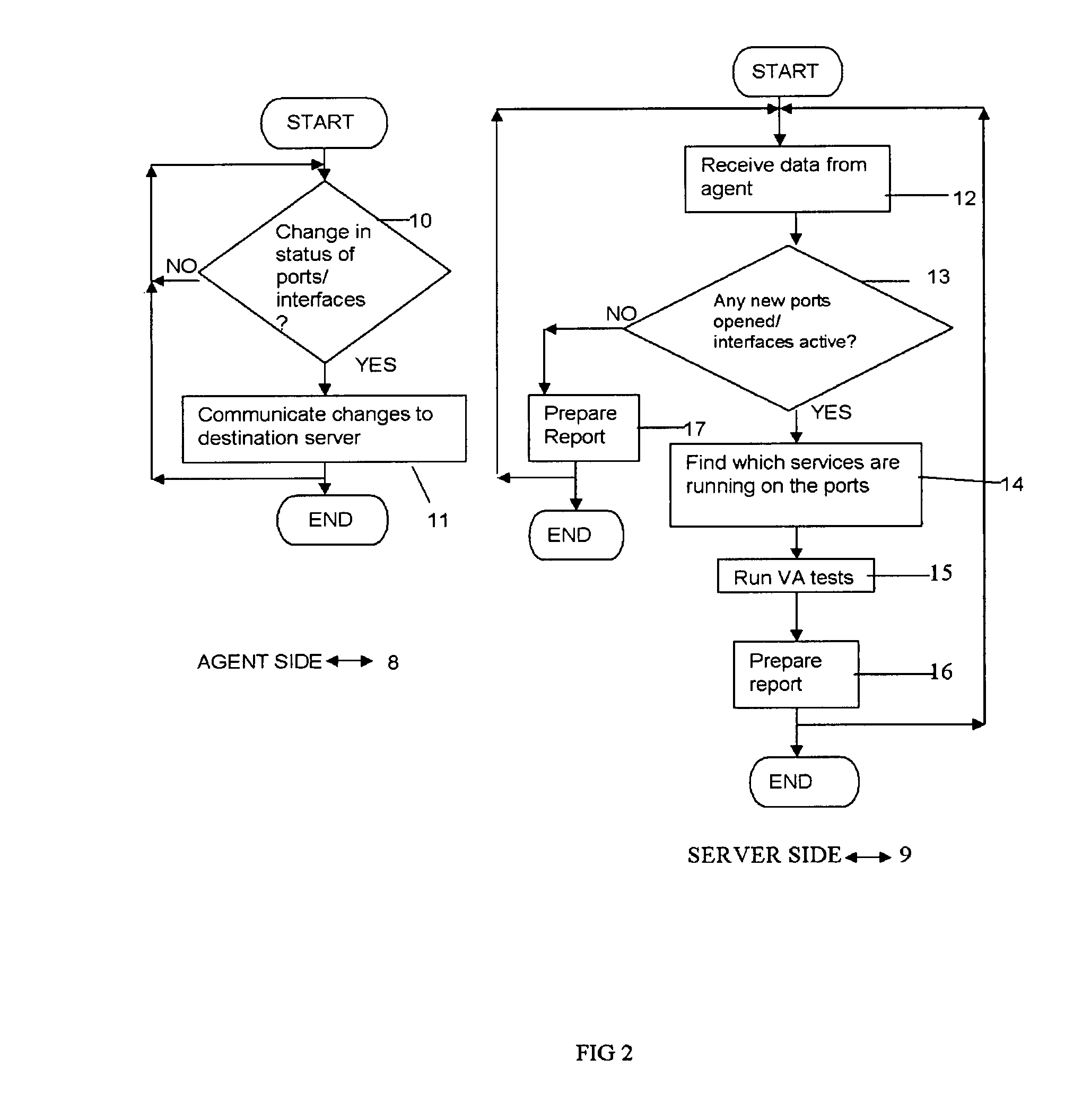
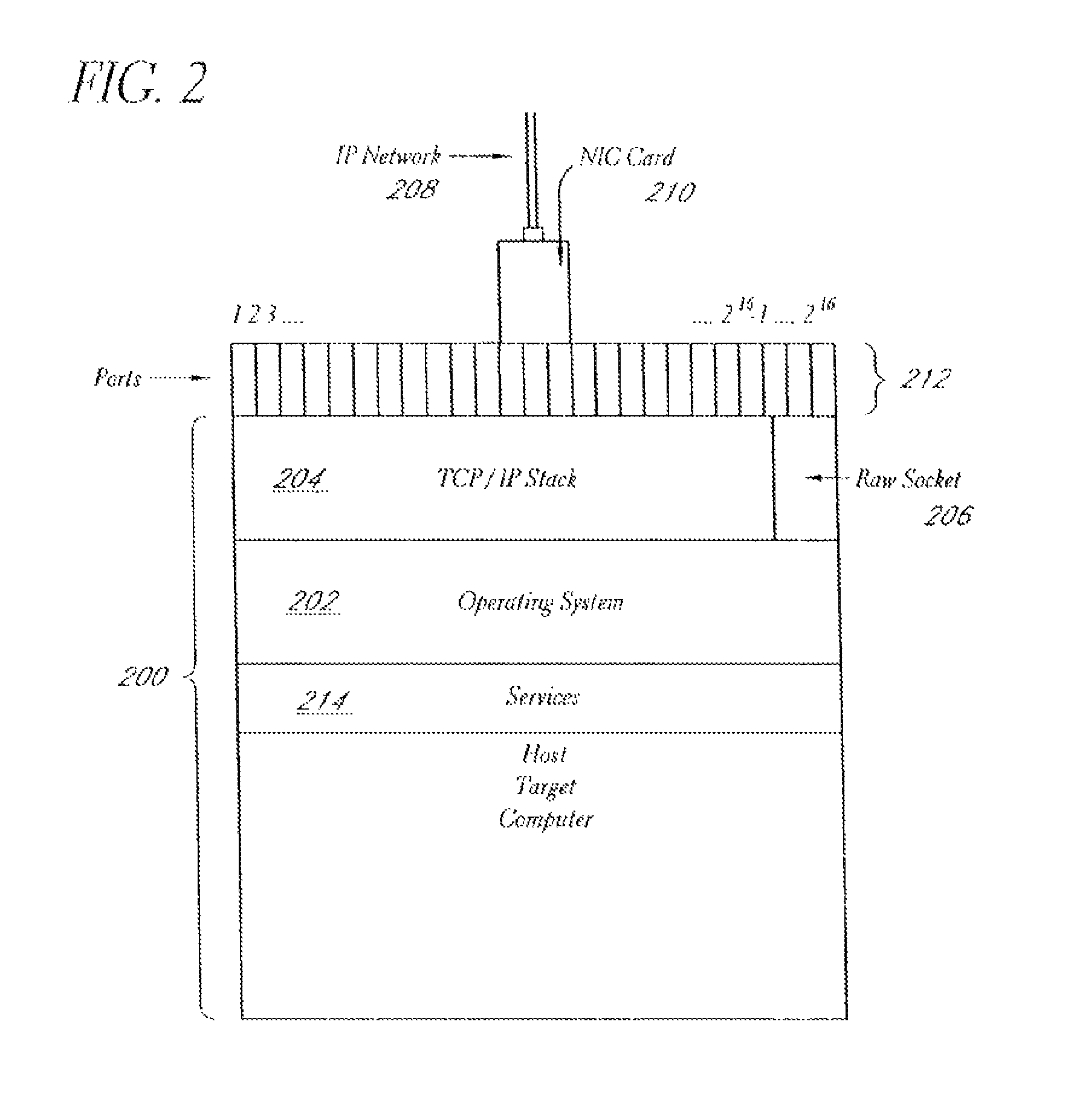
System for real-time network-based vulnerability assessment of a host/device via real-time tracking, vulnerability assessment of services and a method thereof
ActiveUS20050005169A1Not consuming high bandwidth and other resourceError preventionFrequency-division multiplex detailsComputer hardwareState variation
A system for real-time vulnerability assessment of a host / device, said system comprising an agent running on the host / device. The agent includes a a first data structure for storing the status of interfaces and ports on the interfaces of the host / device. An n executable agent module is coupled to the first data structure to track the status of interfaces and ports on the interfaces of the host / device and to store the information, as entries in said first data structure. The executable agent module compares the entries to determine a change in the status of interfaces and / or of ports on the interfaces of the host / device. A remote destination server is provided that includes a second data structure for storing the status of interfaces and the ports on the interfaces of the host / device. An executable server module is coupled to the second data structure to receive the information communicated by the agent executable module of the agent on the host / device. The executable server module stores the received information as entries in the second data structure wherein the entries indicate the state of each of the ports on each of the active interfaces of the host / device as received. The executable server module compares the entries in said data structures to determine the change in the status of interfaces and ports on the interfaces of the host / device. The executable server module runs vulnerability assessment tests on the host / device in the event of a change in the status of interface / ports.
Owner:RPX CORP
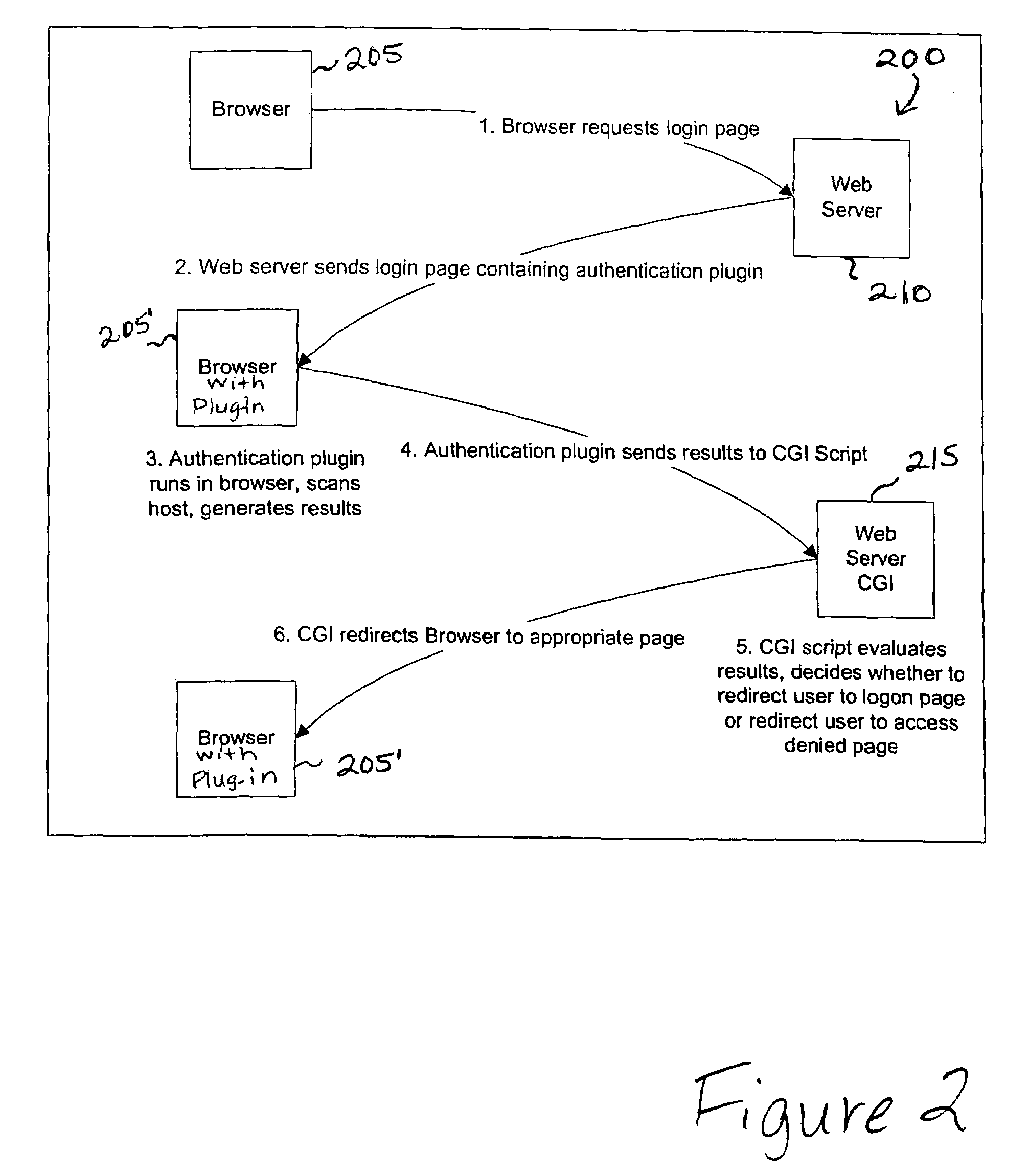
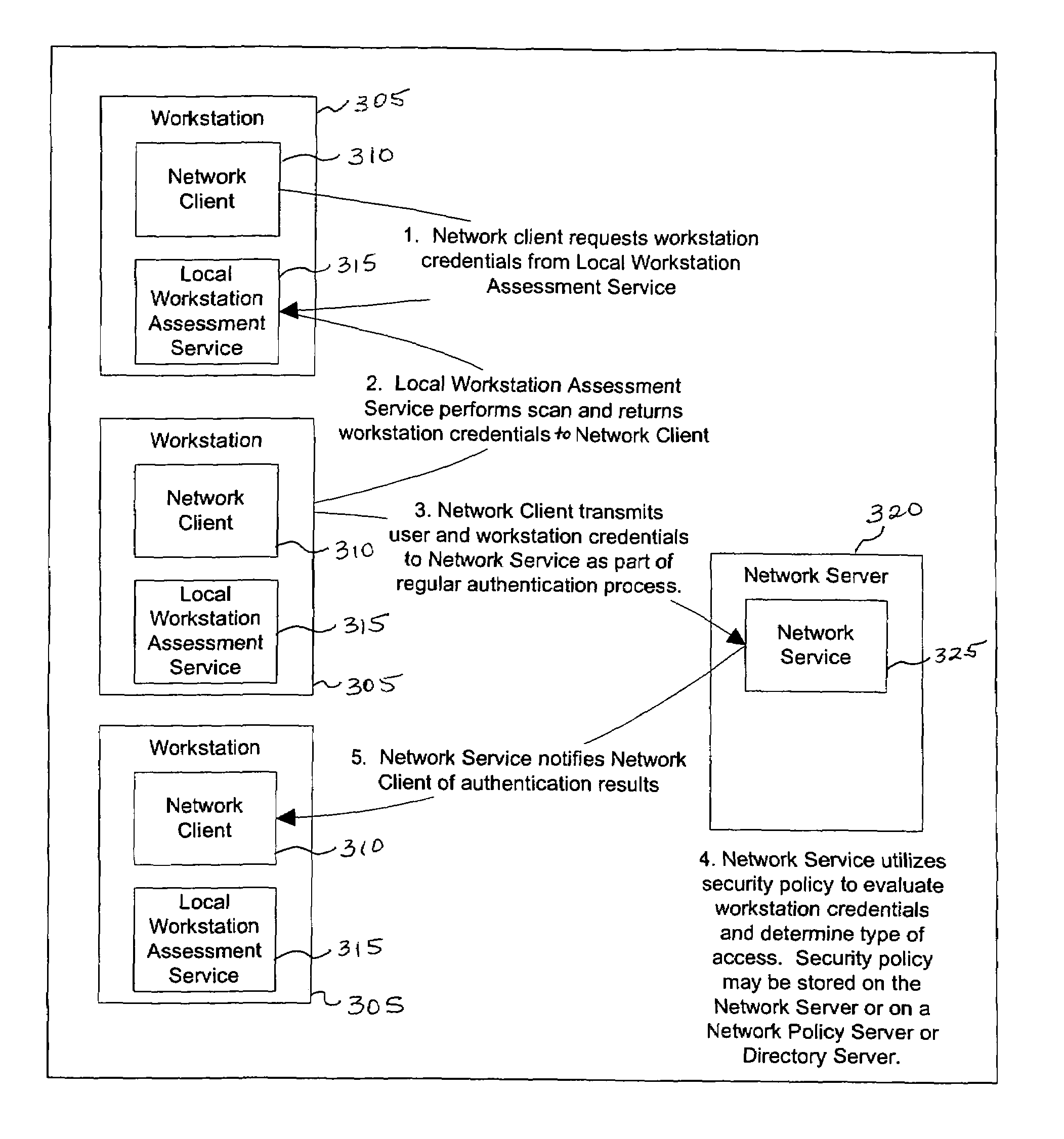
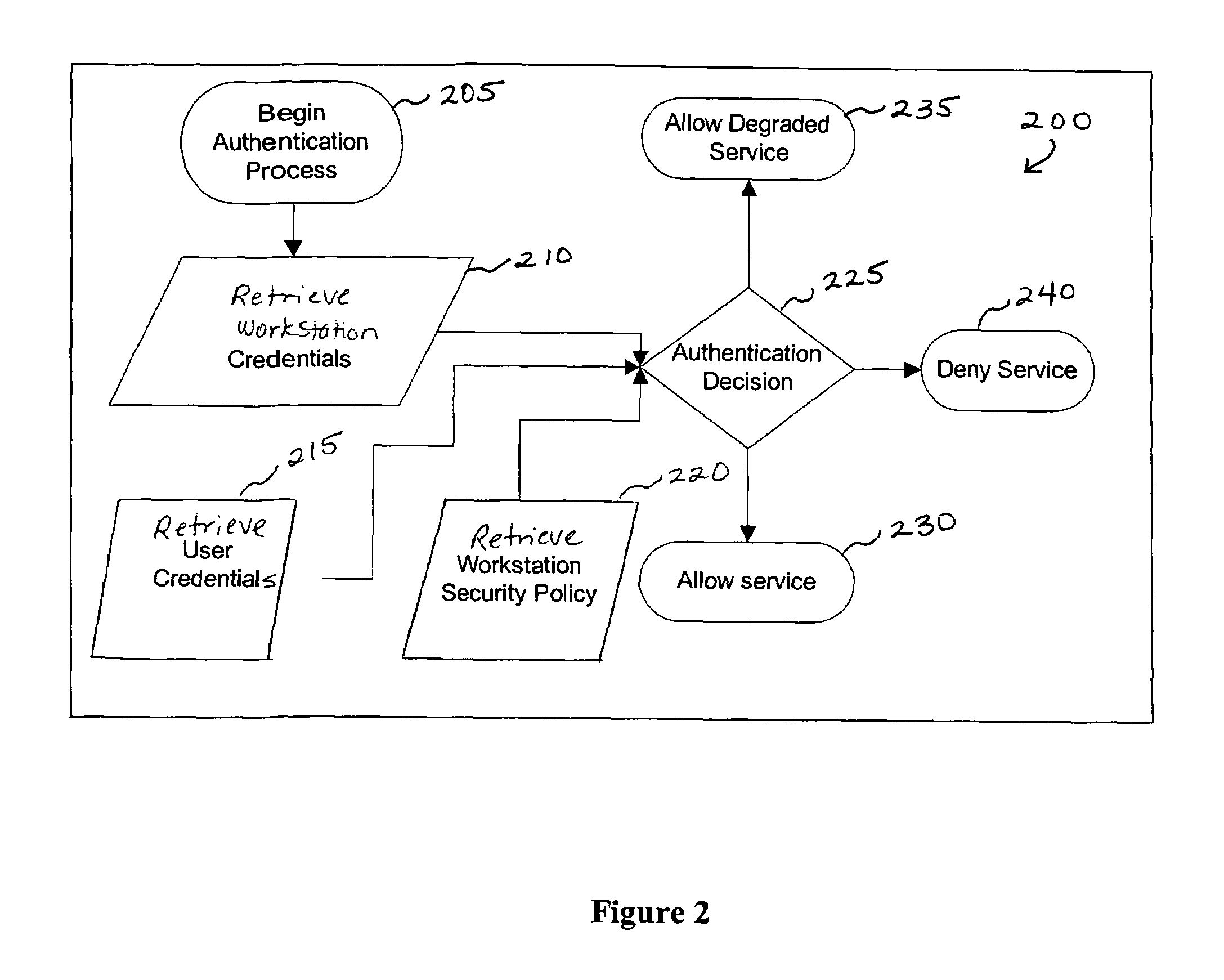
Method and apparatus for network assessment and authentication
InactiveUS20060272011A1Prevent overly frequent reassessmentImprove securityDigital data processing detailsUser identity/authority verificationWorkstationNetwork service
Providing a user with assurance that a networked computer is secure, typically before completion of the log-in operation. This can be accomplished by extending the local log-in process to perform a host assessment of the workstation prior to requesting the user's credentials. If the assessment finds a vulnerability, the log-in process can inform the user that the machine is or may be compromised, or repair the vulnerability, prior to completion of the log-in operation. By performing vulnerability assessment at the level of the workstation, a network server is able to determine whether the workstation is a “trusted” platform from which to accept authentication requests. If the vulnerability assessment shows that the workstation is compromised, or if the possibility of remote compromise is high, the network server can elect to fail the authentication on the grounds that the workstation cannot be trusted. Optionally, a vulnerability assessment tool may be able to repair the vulnerability of the workstation, and then allow the authentication to proceed.
Owner:IBM CORP
Policy-based vulnerability assessment
ActiveUS7451488B2Reduce information overloadRemove redundant informationMemory loss protectionDigital data processing detailsTraffic capacityOperating system
Owner:MUSARUBRA US LLC
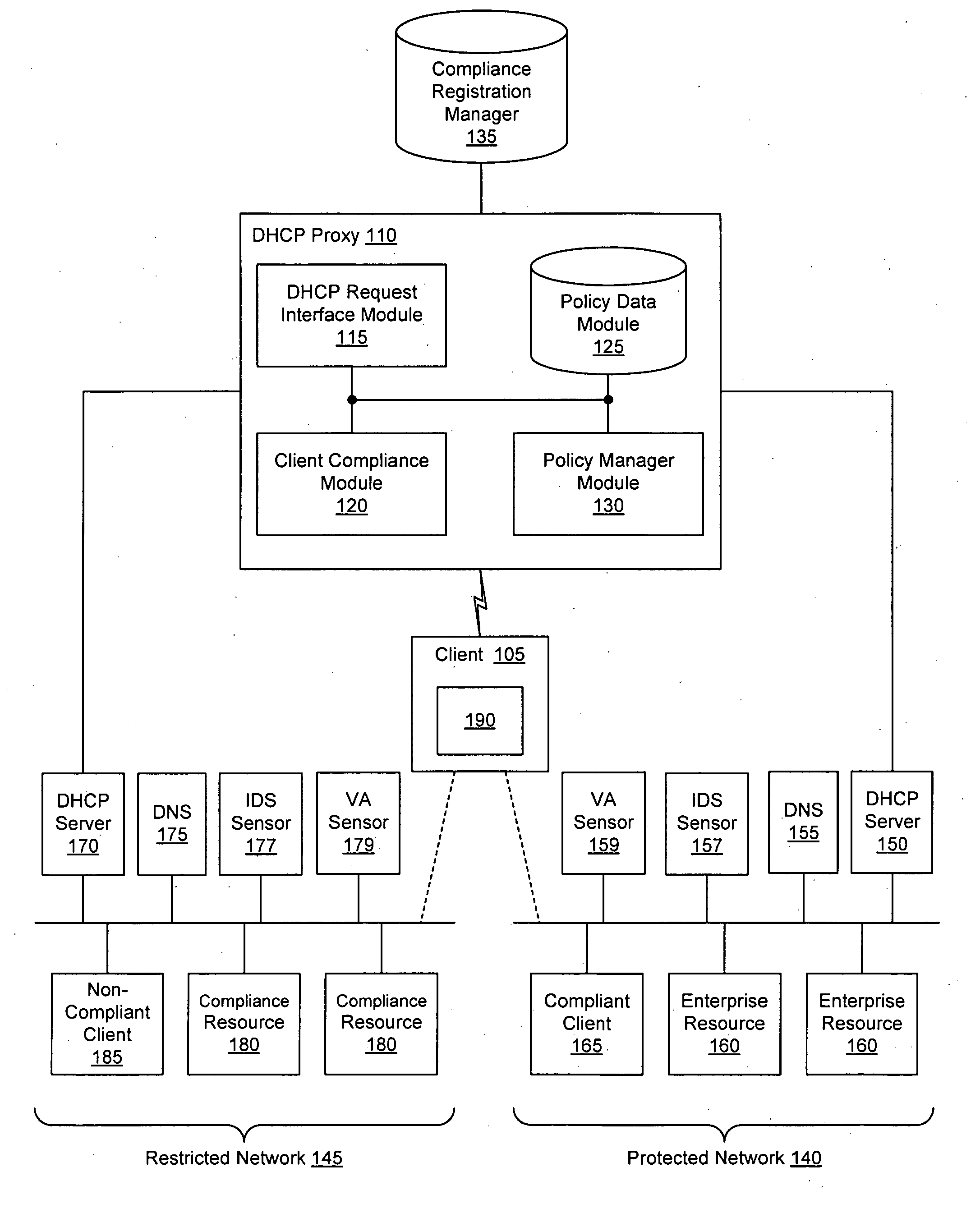
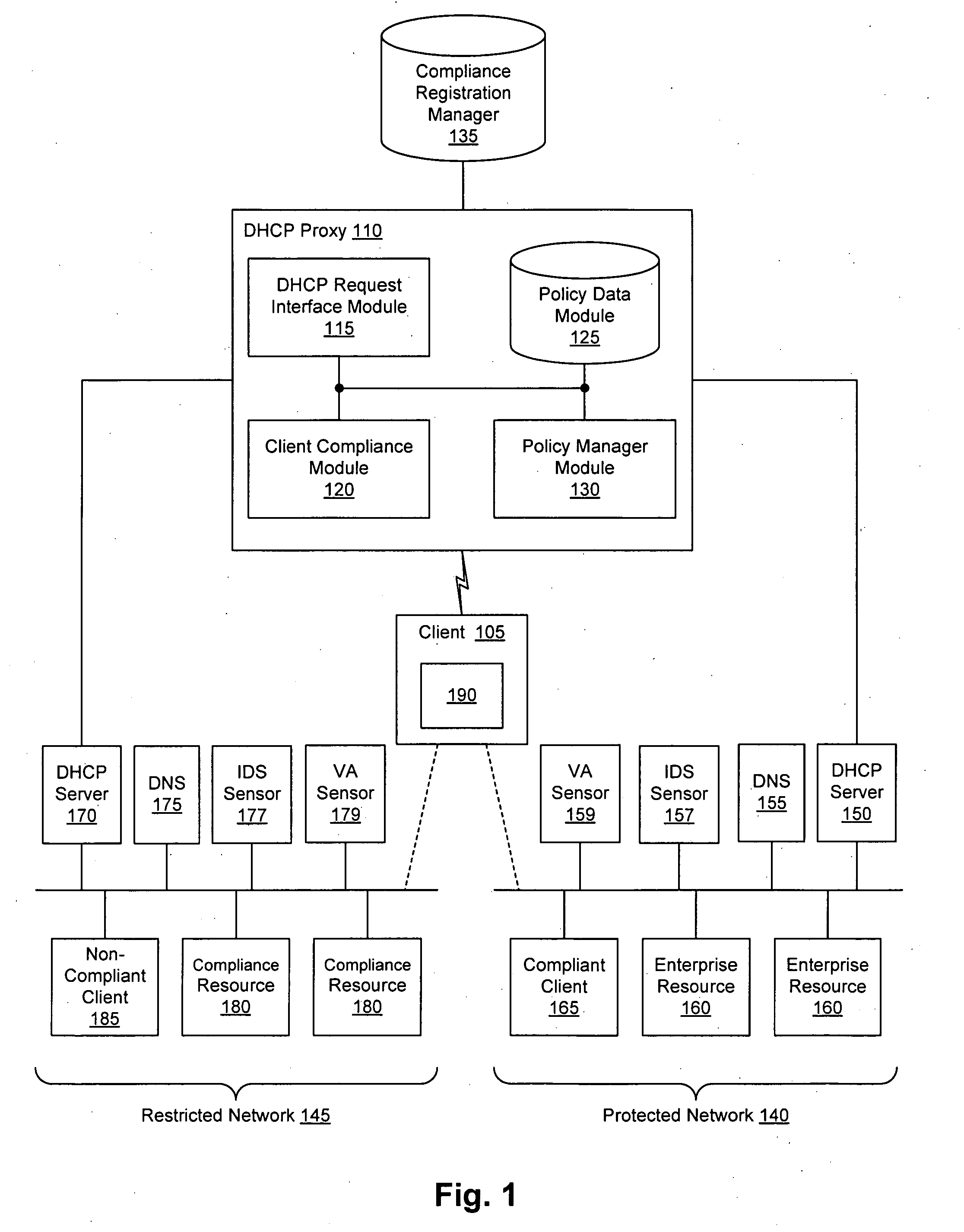
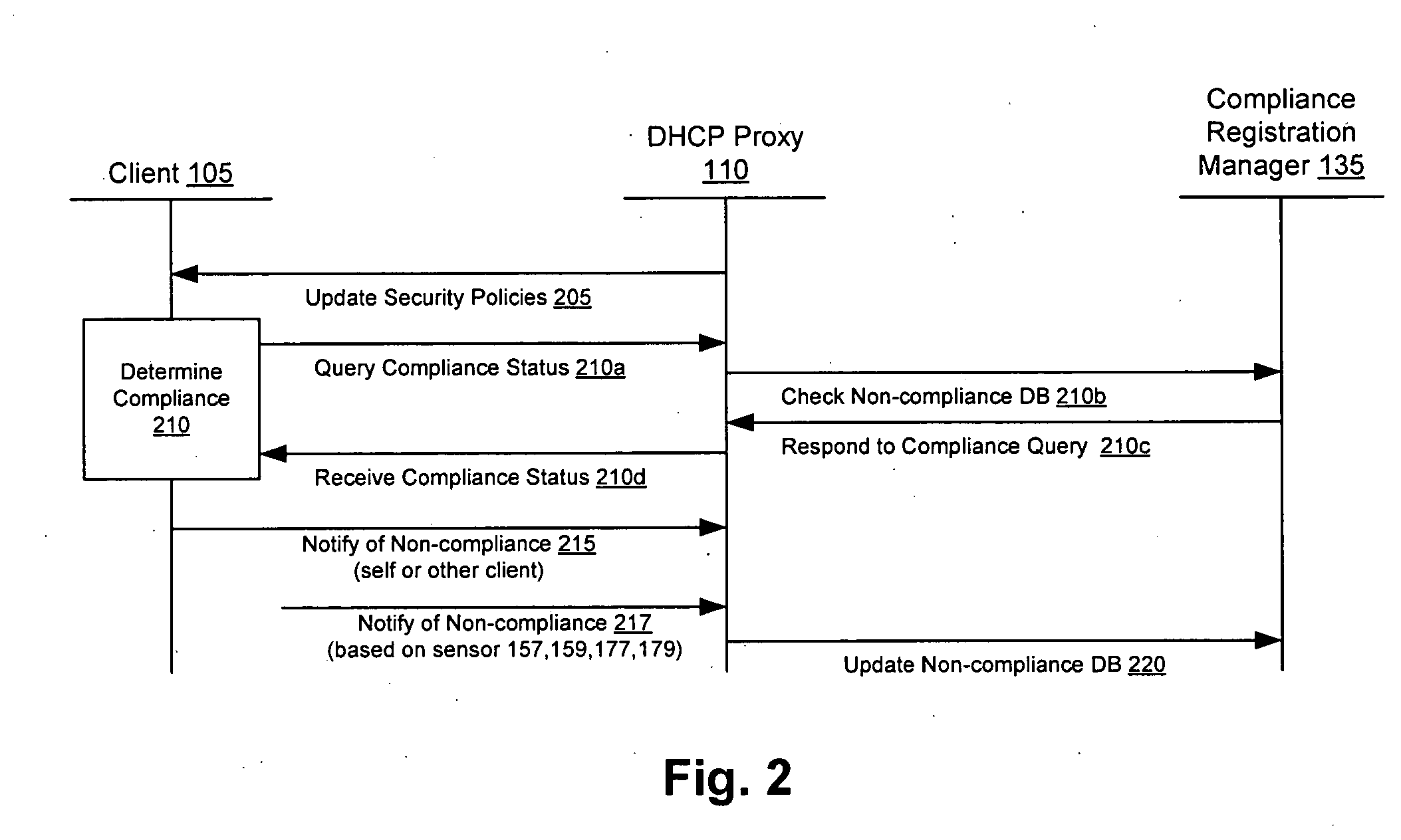
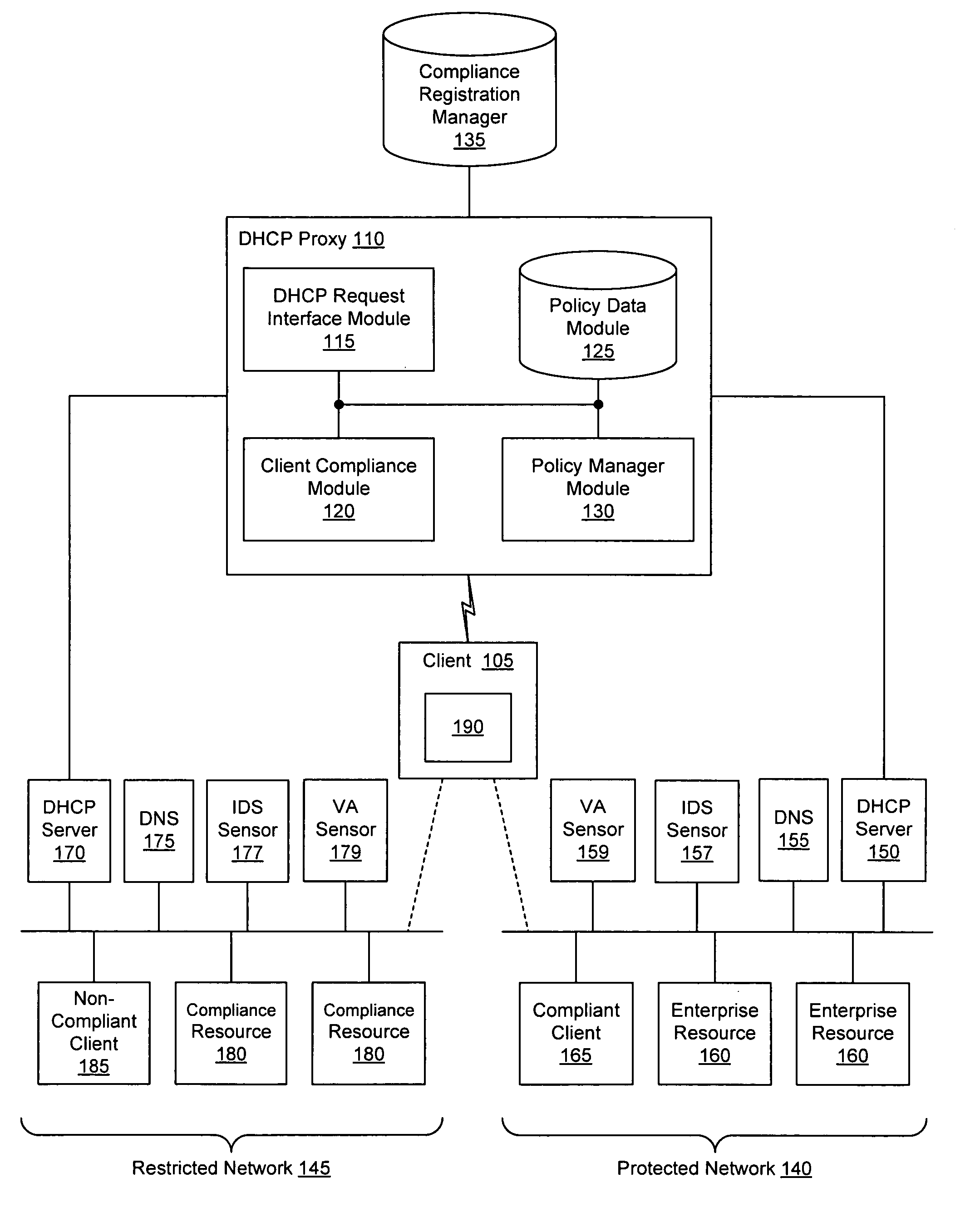
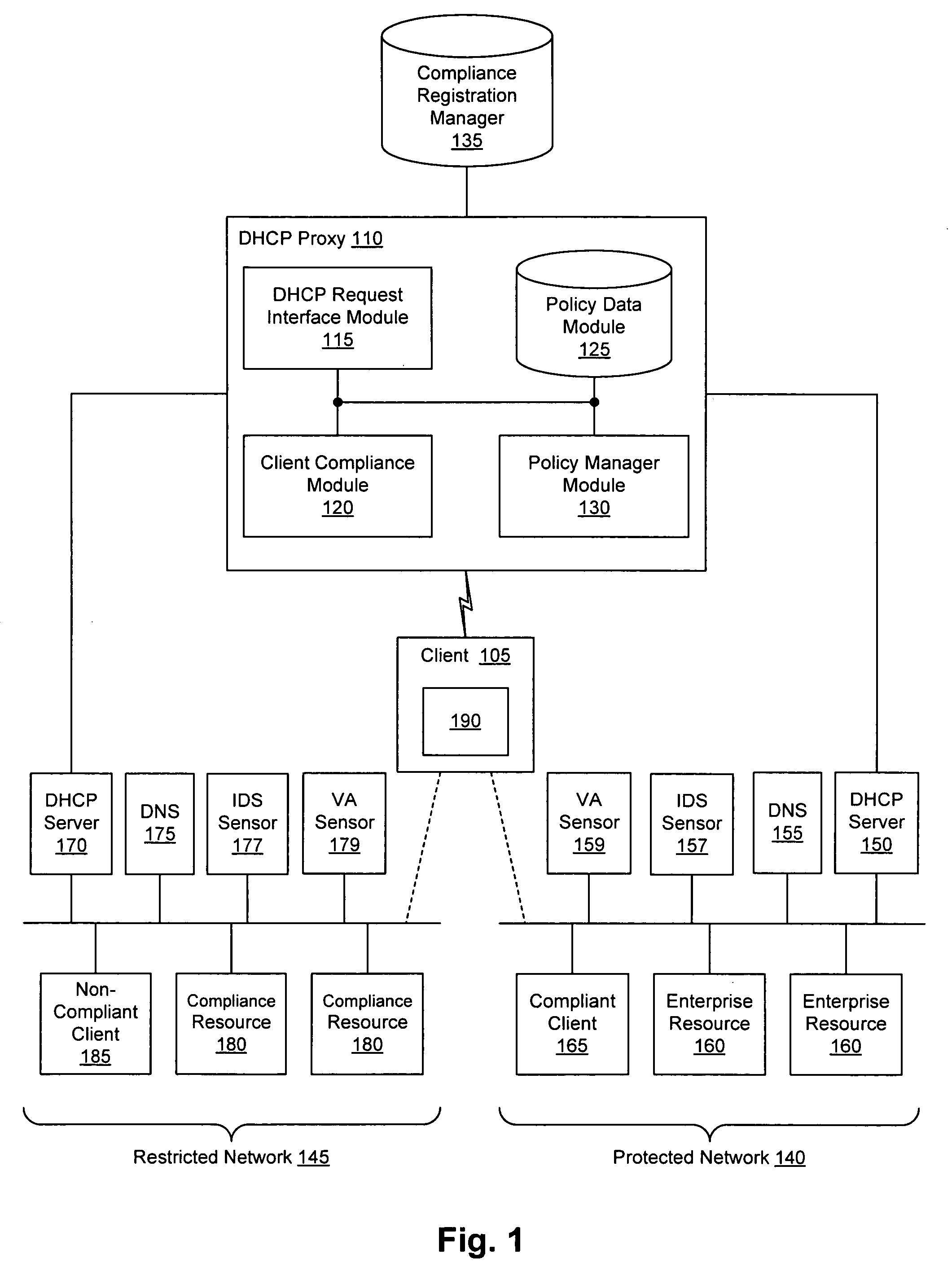
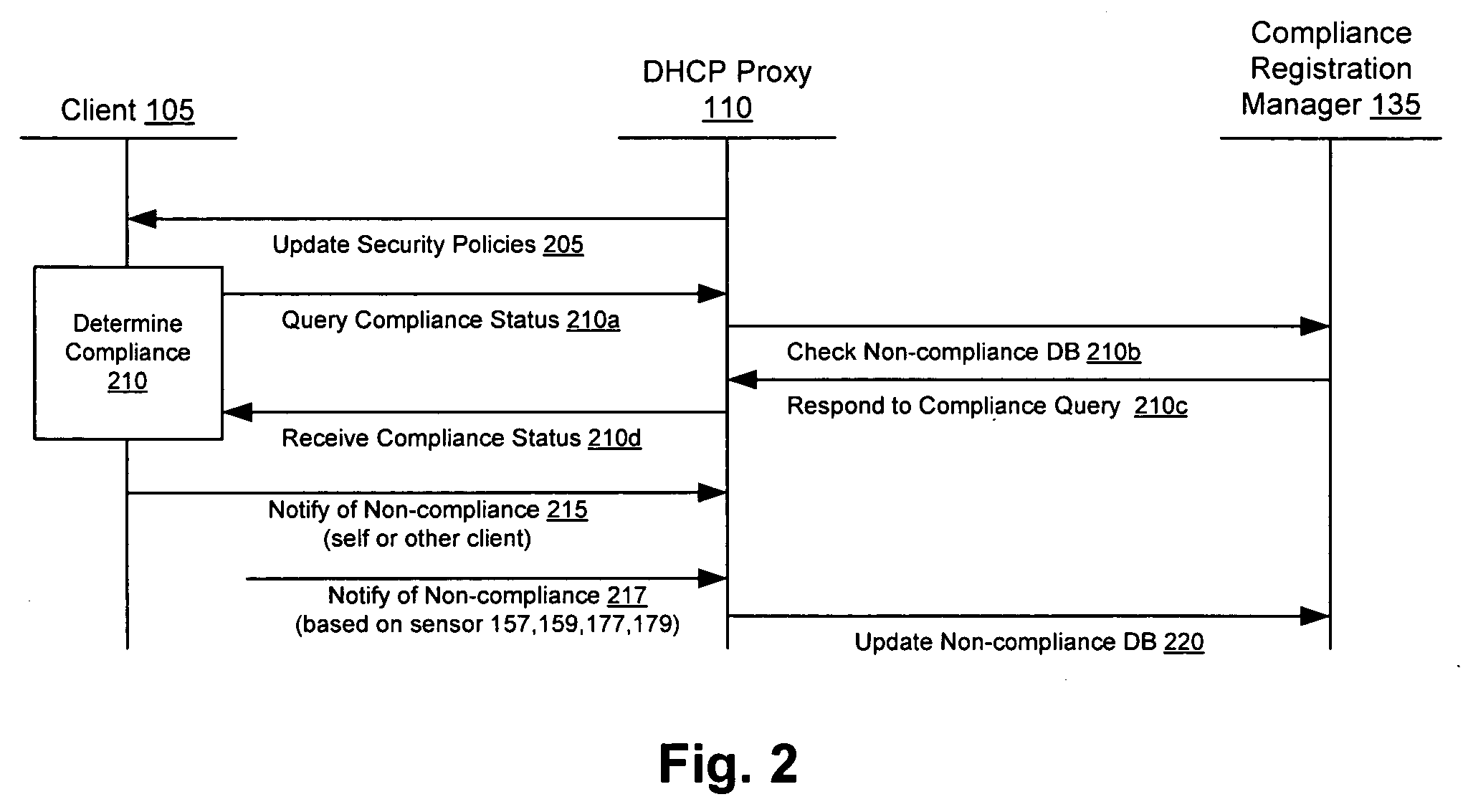
Client compliancy with self-policing clients
InactiveUS20060130139A1Memory loss protectionDigital data processing detailsNon complianceClient compliance
Security sensor data from intrusion detection system (IDS) sensors, vulnerability assessment (VA) sensors, and / or other security sensors is used to enhance the compliancy determination in a client compliancy system. A database is used to store the security sensor data. In one particular embodiment, a list of device compliance statuses indexed by corresponding identifiers (e.g., IP / MAC addresses) combined from IDS, VA, and / or other security sensing technologies is made available as a non-compliance database for query, so that clients and other compliancy authentication elements can tell that a particular client appears to be out of compliance. A client-side self-policing compliance system is enabled, and can be used in conjunction with automated endpoint compliance policy configuration to reduce system administrator burden.
Owner:CA TECH INC
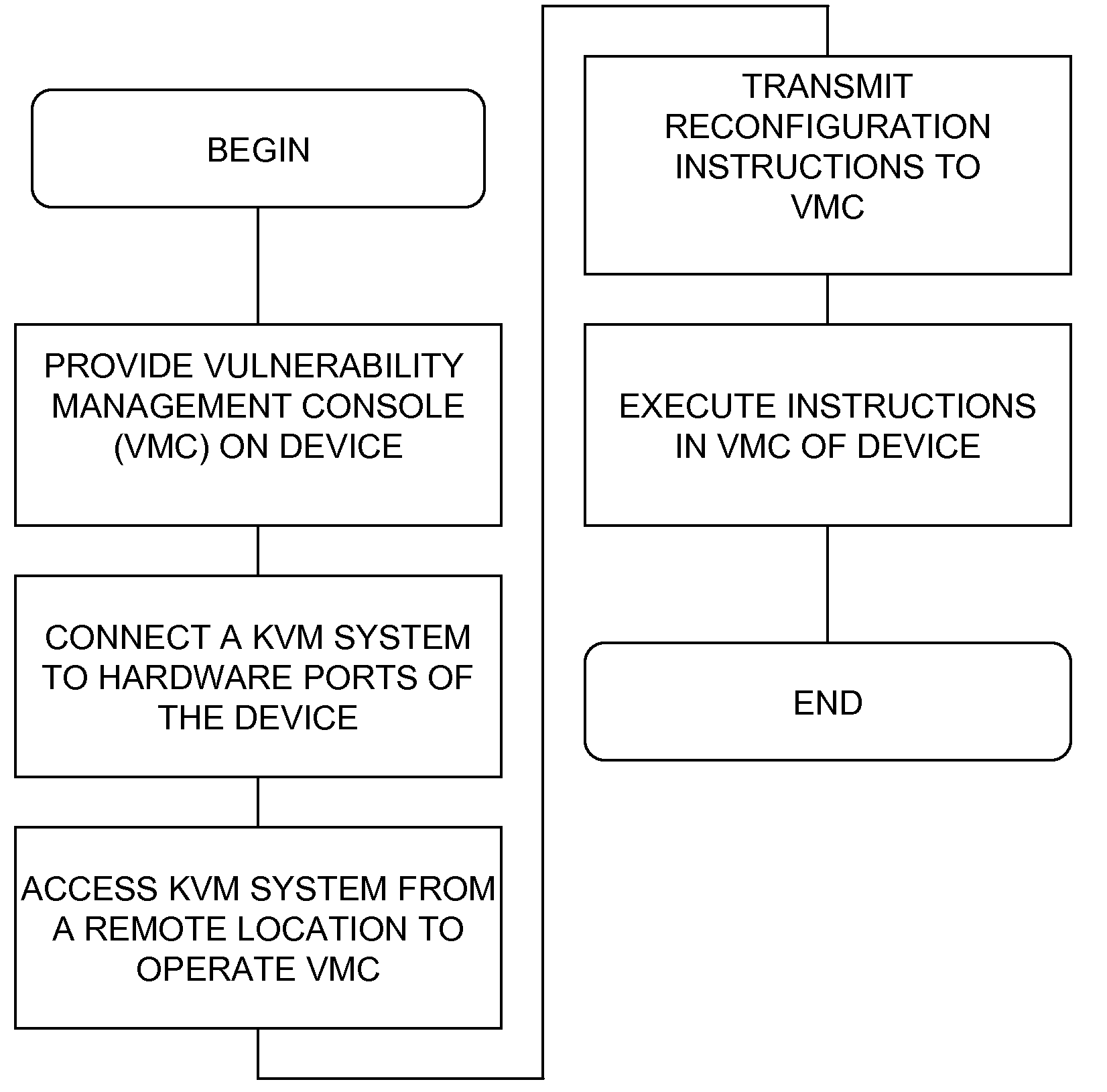
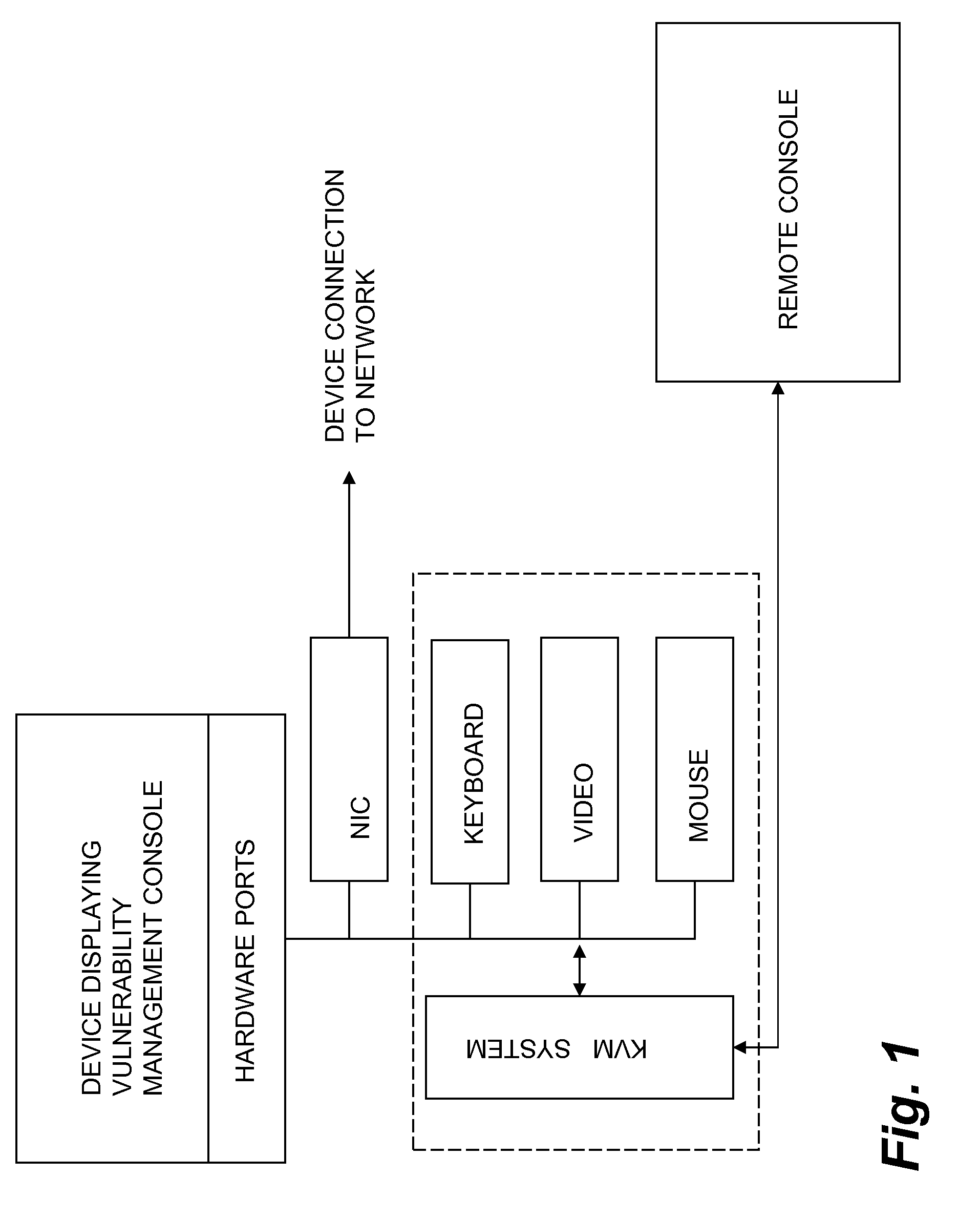
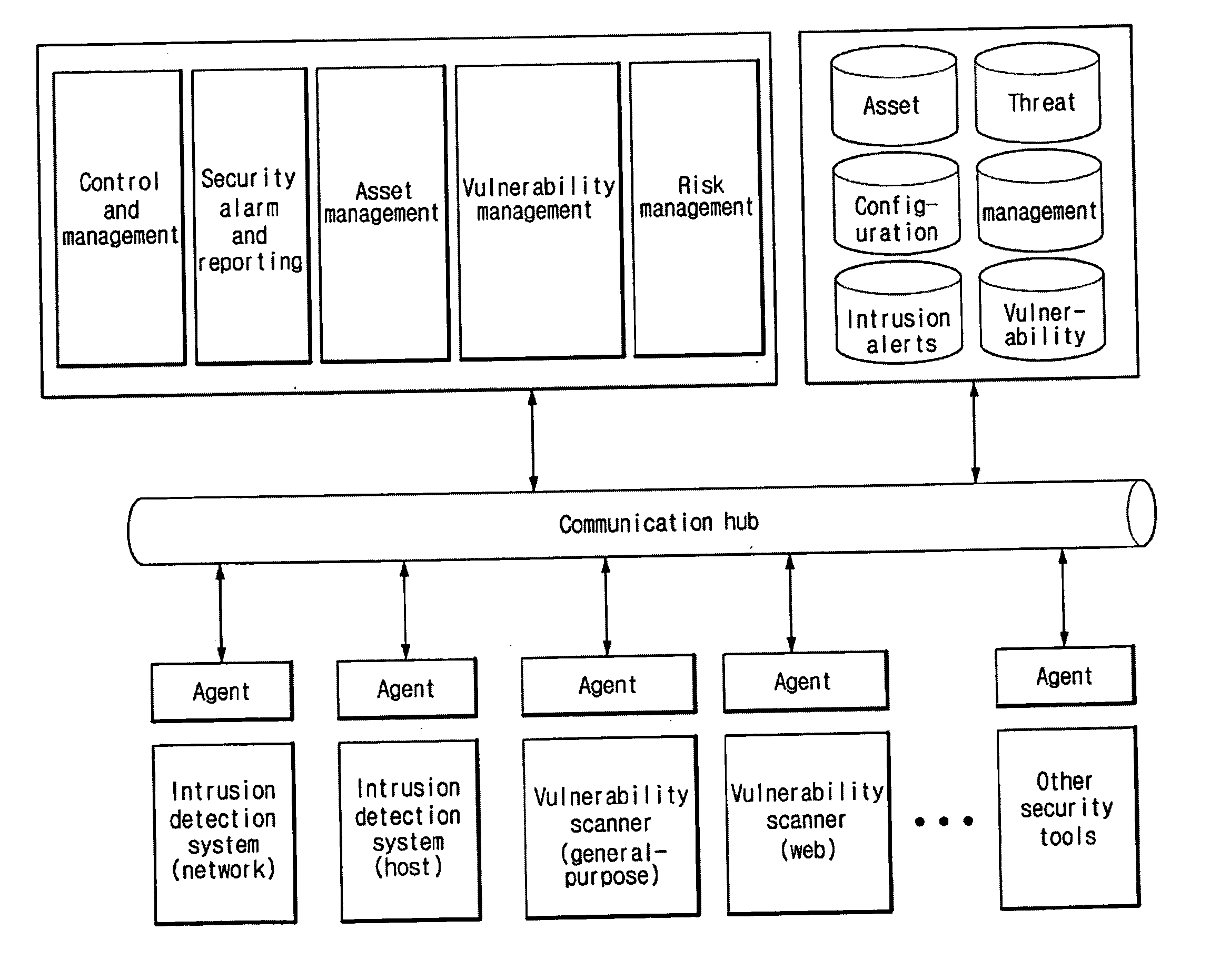
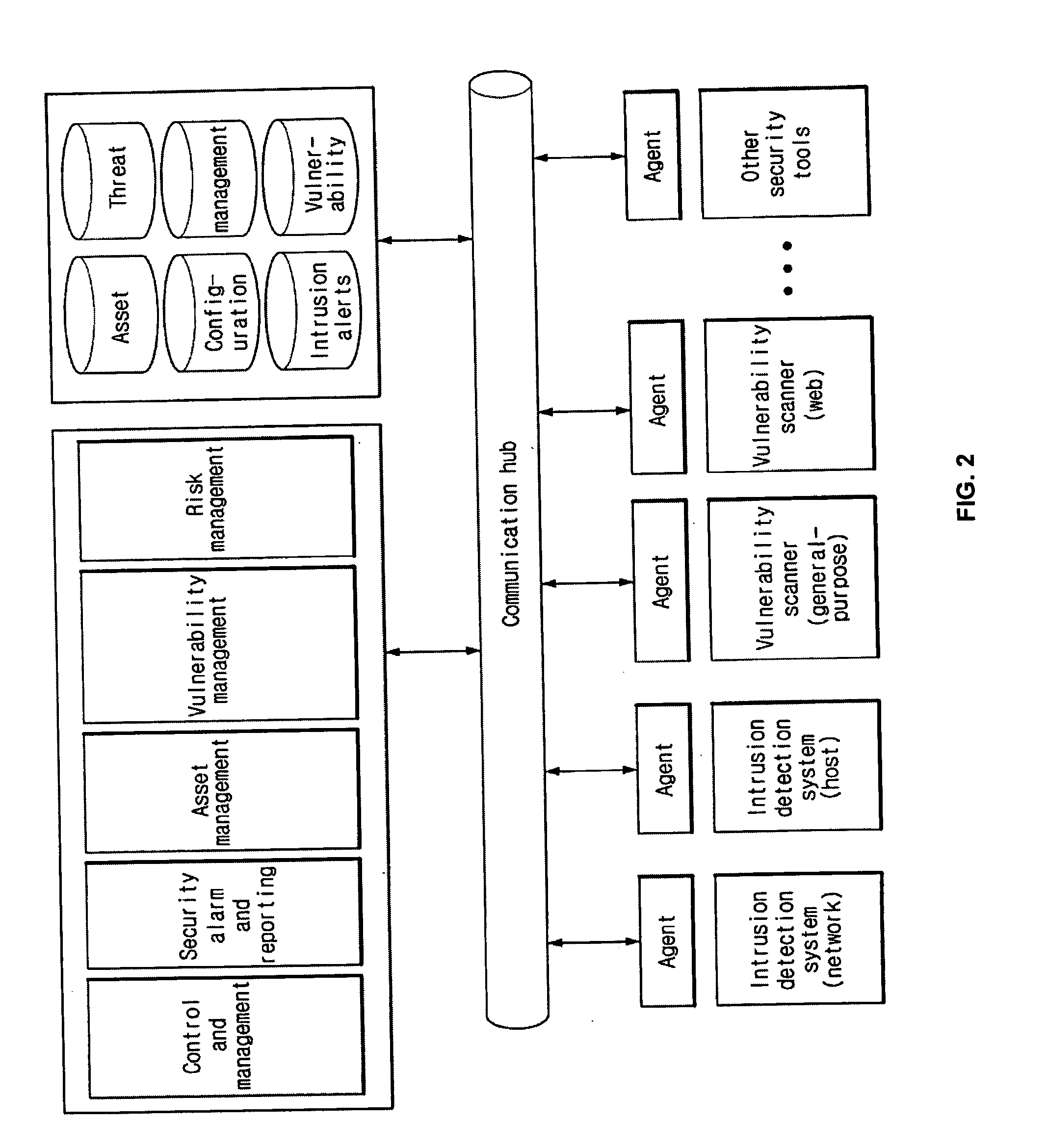
Enterprise security management for network equipment
InactiveUS20090199298A1Eliminate the problemMemory loss protectionUnauthorized memory use protectionEnterprise security managementDashboard
The inventive device includes a dashboard or graphical user interface (GUI), a security access control (AUTH) and secure communications sub-system (SEC-COMM), network and asset discover and mapping system (NAADAMS), an asset management engine (AME), vulnerability assessment engine (CVE-DISCOVERY), vulnerability remediation engine (CVE-REMEDY), a reporting system (REPORTS), a subscription, updates and licensing system (SULS), a countermeasure communications system (COUNTERMEASURE-COMM), a logging system (LOGS), a database integration engine (DBIE), a scheduling and configuration engine (SCHED-CONFIG), a wireless and mobile devices / asset detection and management engine (WIRELESS-MOBILE), a notification engine (NOTIFY), a regulatory compliance reviewing and reporting system (REG-COMPLY), client-side (KVM-CLIENT) integration with KVM over IP or similar network management equipment, authentication-services (KVM-AUTH) integration with KVM over IP or similar network management equipment and server-side (KVM-SERVER) integration with KVM over IP or similar network management equipment.
Owner:NETCLARITY
Network security testing
ActiveUS7325252B2Improve viewing effectShort working hoursMemory loss protectionError detection/correctionSecurity solutionWork period
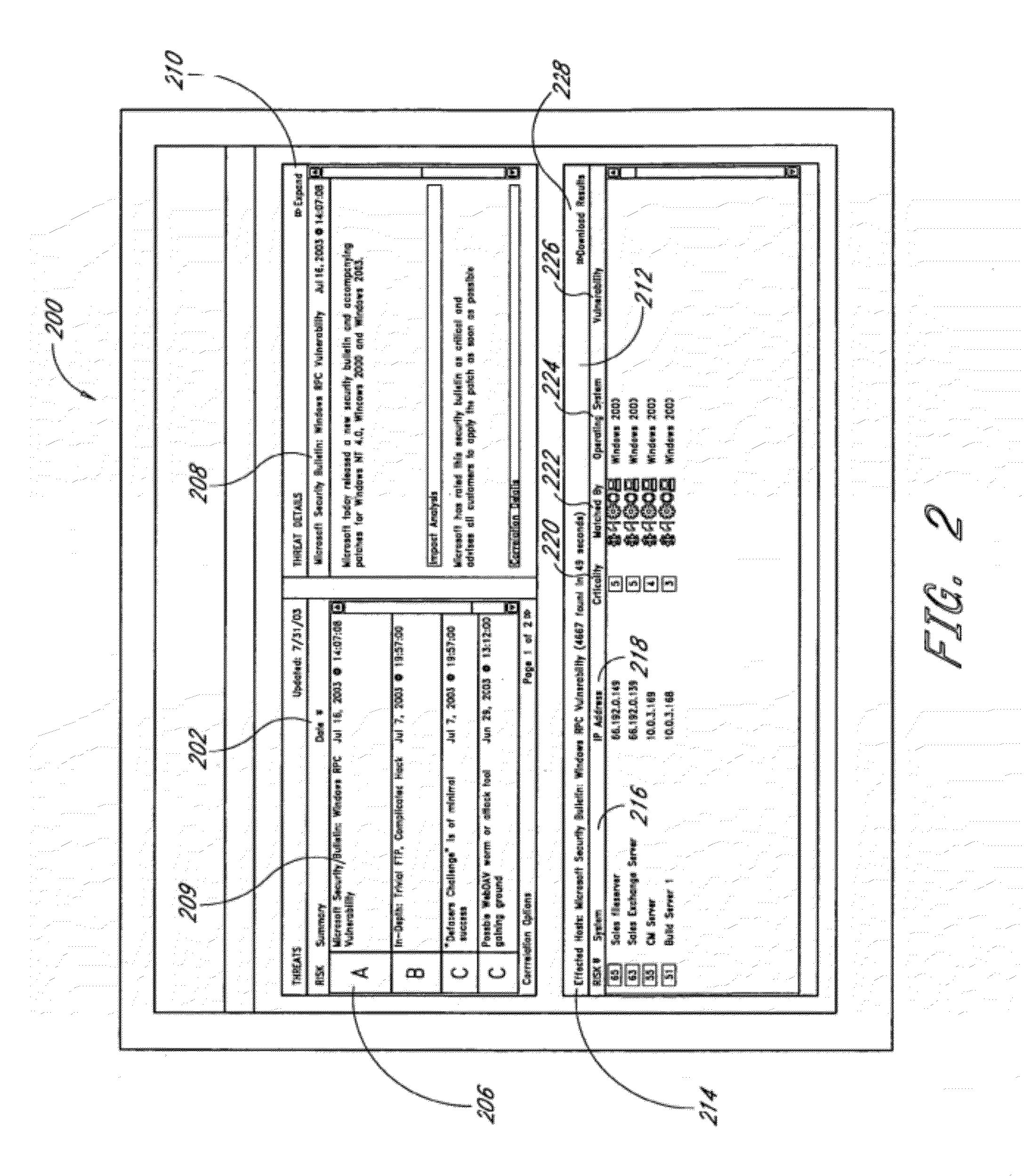
To answer the security needs of the market, a preferred embodiment was developed. A preferred embodiment provides real-time network security vulnerability assessment tests, possibly complete with recommended security solutions. External vulnerability assessment tests can emulate hacker methodology in a safe way and enable study of a network for security openings, thereby gaining a true view of risk level without affecting customer operations. Because this assessment can be performed over the Internet, both domestic and worldwide corporations benefit. A preferred embodiment's physical subsystems combine to form a scalable holistic system that can be able to conduct tests for thousands of customers any place in the world. The security skills of experts can be embedded into a preferred embodiment systems and automated the test process to enable the security vulnerability test to be conducted on a continuous basis for multiple customers at the same time. A preferred embodiment can reduce the work time required for security practices of companies from three weeks to less than a day, as well as significantly increase their capacity. Component subsystems typically include a Database, Command Engine, Gateway, multiple Testers, Report Generator, and an RMCT.
Owner:ALERT LOGIC
Method and apparatus for network assessment and authentication
InactiveUS7162649B1Improve securityAugments authentication and authorization processHardware monitoringMultiple digital computer combinationsWorkstationNetwork service
Providing a user with assurance that a networked computer is secure, typically before completion of the log-in operation. This can be accomplished by extending the local log-in process to perform a host assessment of the workstation prior to requesting the user's credentials. If the assessment finds a vulnerability, the log-in process can inform the user that the machine is or may be compromised, or repair the vulnerability, prior to completion of the log-in operation. By performing vulnerability assessment at the level of the workstation, a network server is able to determine whether the workstation is a “trusted” platform from which to accept authentication requests. If the vulnerability assessment shows that the workstation is compromised, or if the possibility of remote compromise is high, the network server can elect to fail the authentication on the grounds that the workstation cannot be trusted. Optionally, a vulnerability assessment tool may be able to repair the vulnerability of the workstation, and then allow the authentication to proceed.
Owner:INT BUSINESS MASCH CORP
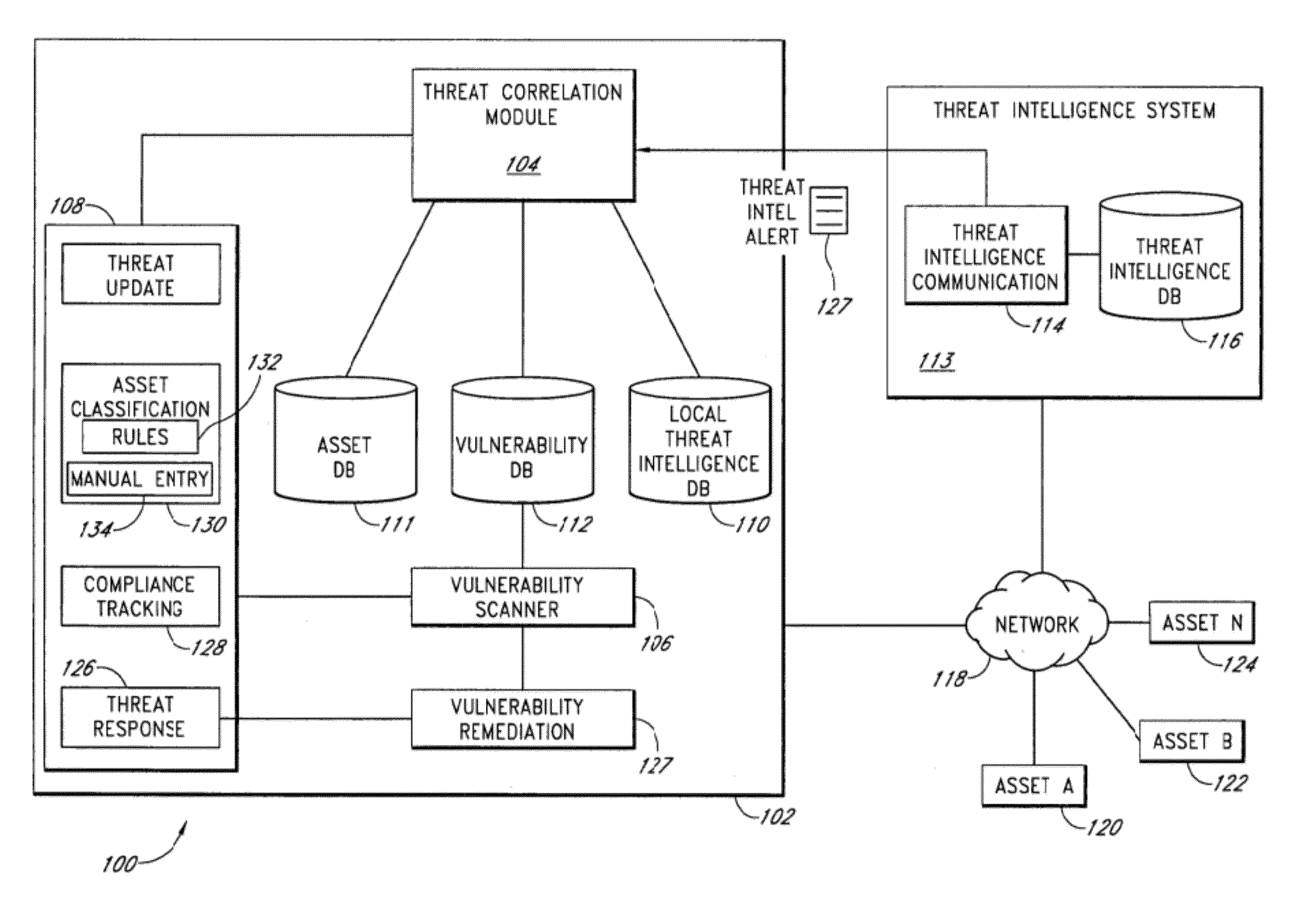
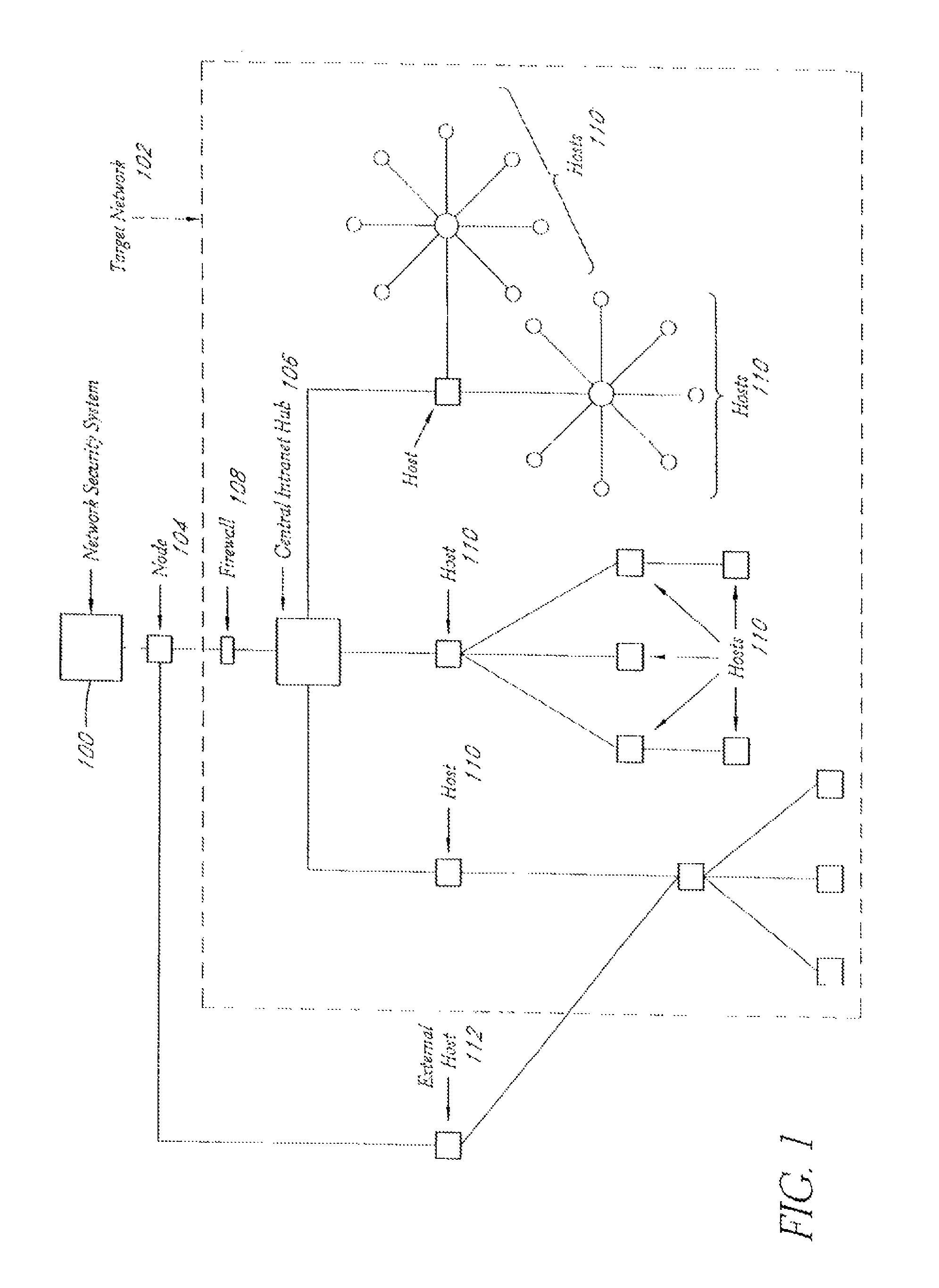
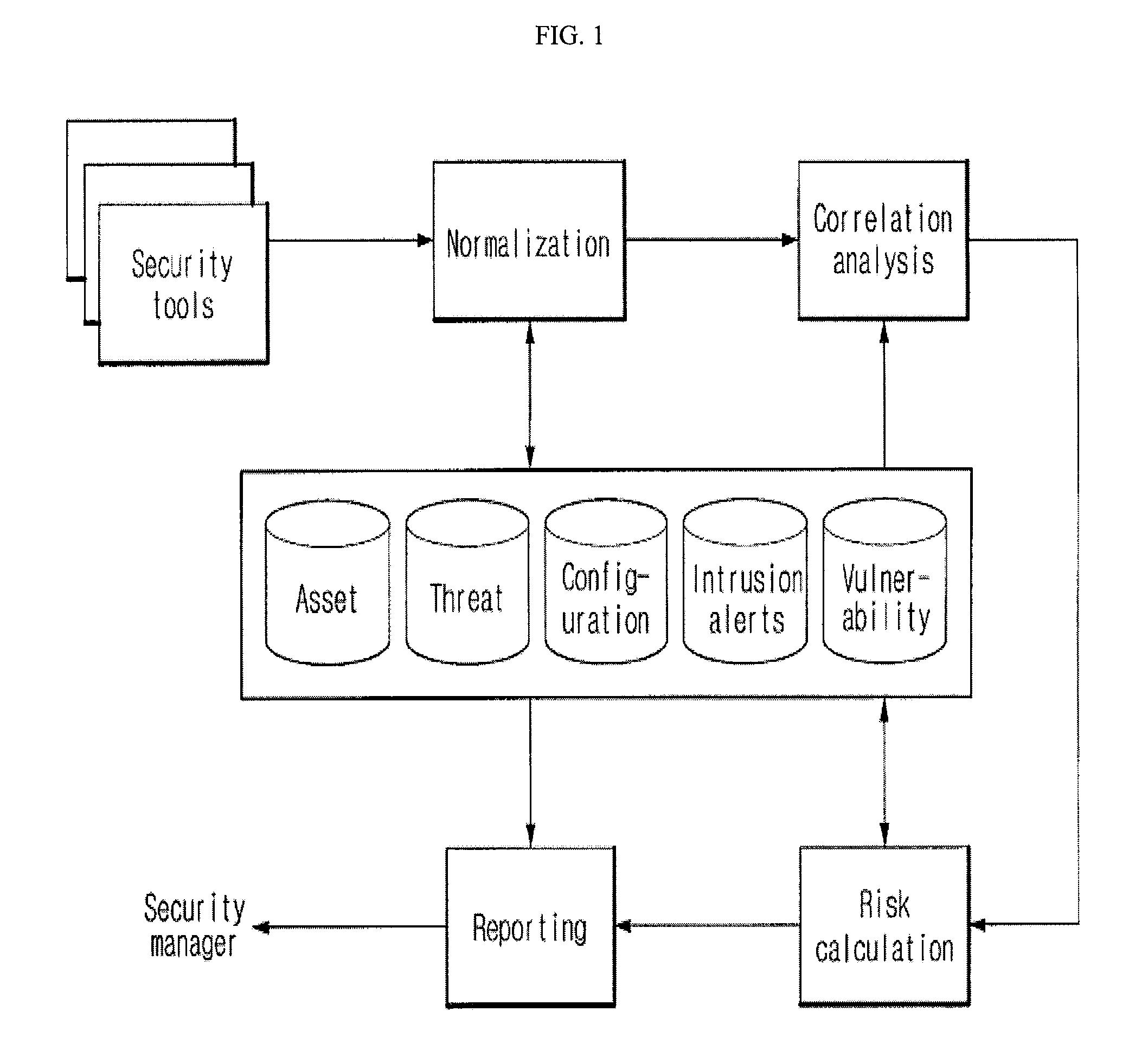
System and method of managing network security risks
InactiveUS20120185945A1Memory loss protectionError detection/correctionThreat intelligencePreventive action
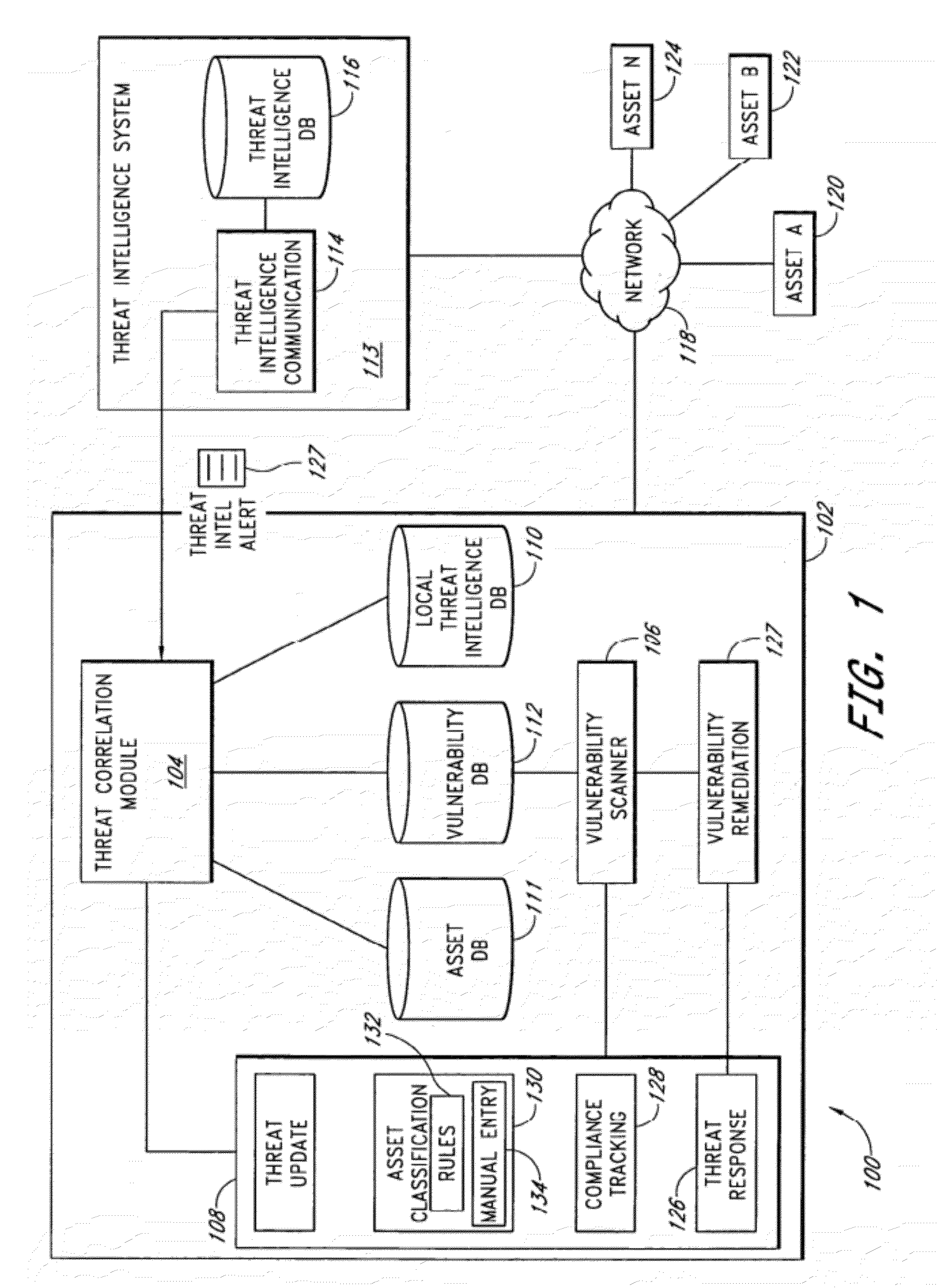
A security risk management system comprises a vulnerability database, an asset database, a local threat intelligence database and a threat correlation module. The vulnerability database comprises data about security vulnerabilities of assets on a network gathered using active or passive vulnerability assessment techniques. The asset database comprises data concerning attributes of each asset. The threat correlation module receives threat intelligence alerts that identify attributes and vulnerabilities associated with security threats that affect classes of assets. The threat correlation module compares asset attributes and vulnerabilities with threat attributes and vulnerabilities and displays a list of assets that are affected by a particular threat. The list can be sorted according to a calculated risk score, allowing an administrator to prioritize preventive action and respond first to threats that affect higher risk assets. The security risk management system provides tools for performing preventive action and for tracking the success of preventive action.
Owner:MCAFEE INC
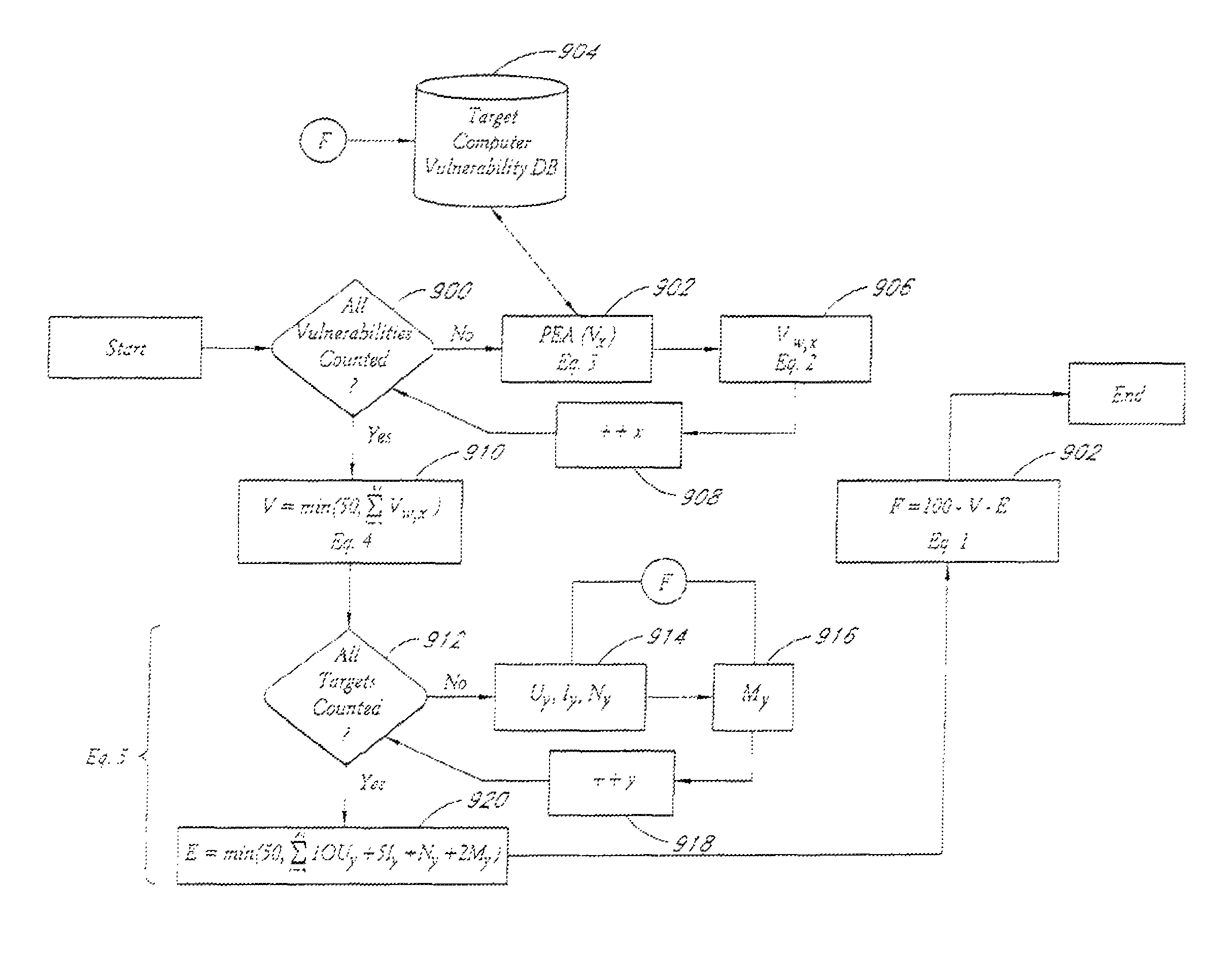
Method, apparatus and program storage device for providing automated tracking of security vulnerabilities
InactiveUS20050160480A1Memory loss protectionUnauthorized memory use protectionVulnerability factorOperating system
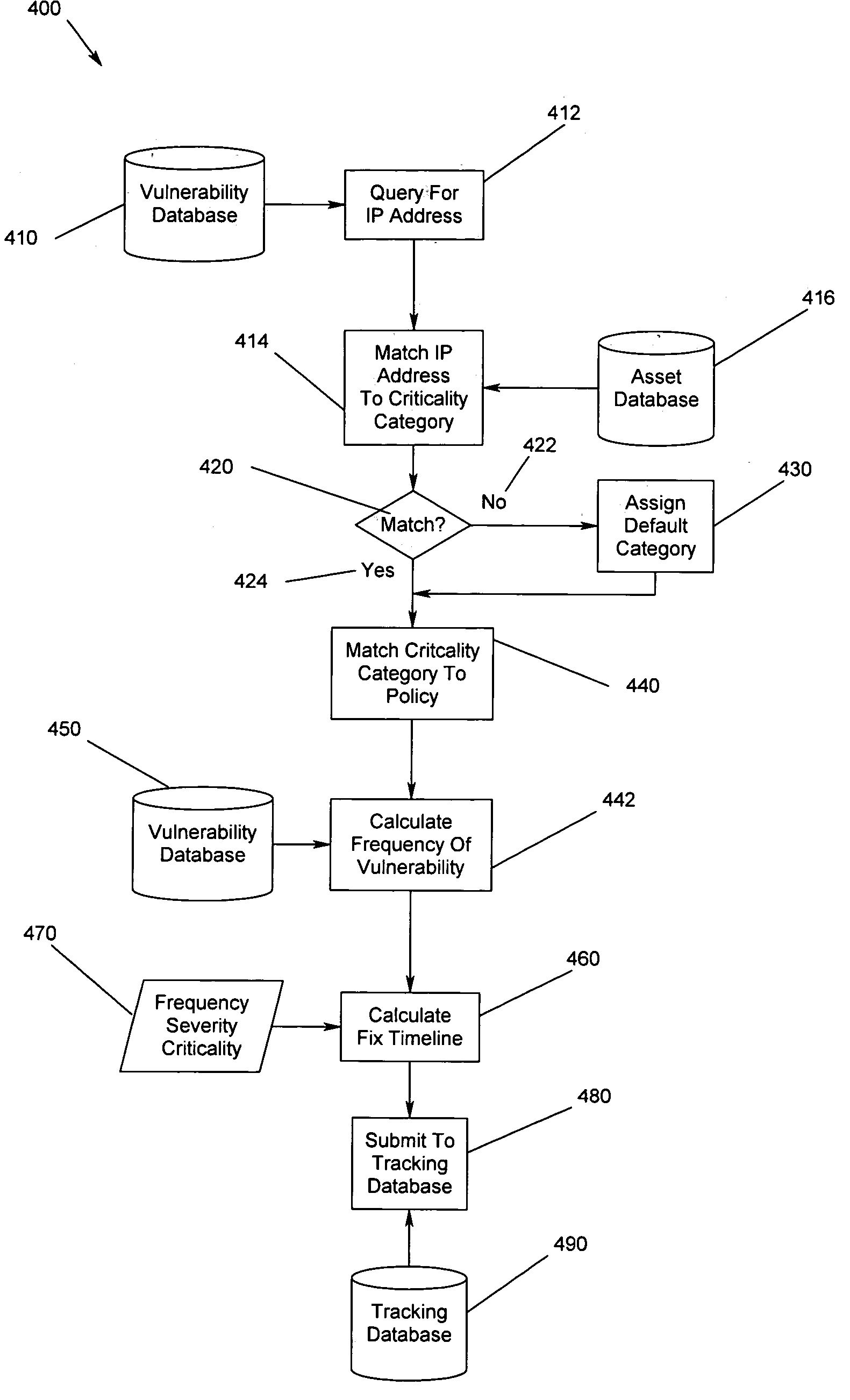
A method, apparatus and program storage device for providing automated tracking of security vulnerabilities is disclosed. Security problems are reported, aged and tracked. A time to fix the vulnerability identified by the vulnerability assessment of the system is based on the determined vulnerability score. The vulnerability factor is based upon consideration of a plurality of identified parameters.
Owner:IBM CORP
Enhanced client compliancy using database of security sensor data
InactiveUS20060070129A1Eliminate non-compliancyMemory loss protectionDigital data processing detailsNon complianceClient compliance
Security sensor data from intrusion detection system (IDS) sensors, vulnerability assessment (VA) sensors, and / or other security sensors is used to enhance the compliancy determination in a client compliancy system. A database is used to store the security sensor data. In one particular embodiment, a list of device compliance statuses indexed by corresponding identifiers (e.g., IP / MAC addresses) combined from IDS, VA, and / or other security sensing technologies is made available as a non-compliance database for query, so that clients and other compliancy authentication elements can tell that a particular client appears to be out of compliance. A client-side self-policing compliance system is enabled, and can be used in conjunction with automated endpoint compliance policy configuration to reduce system administrator burden.
Owner:CA TECH INC
Systems and methods for real-time network-based vulnerability assessment
A system for real-time vulnerability assessment of a host / device, said system comprising an agent running on the host / device. The agent includes a a first data structure for storing the status of interfaces and ports on the interfaces of the host / device. An n executable agent module is coupled to the first data structure to track the status of interfaces and ports on the interfaces of the host / device and to store the information, as entries in said first data structure. The executable agent module compares the entries to determine a change in the status of interfaces and / or of ports on the interfaces of the host / device. A remote destination server is provided that includes a second data structure for storing the status of interfaces and the ports on the interfaces of the host / device. An executable server module is coupled to the second data structure to receive the information communicated by the agent executable module of the agent on the host / device. The executable server module stores the received information as entries in the second data structure wherein the entries indicate the state of each of the ports on each of the active interfaces of the host / device as received. The executable server module compares the entries in said data structures to determine the change in the status of interfaces and ports on the interfaces of the host / device. The executable server module runs vulnerability assessment tests on the host / device in the event of a change in the status of interface / ports.
Owner:RPX CORP
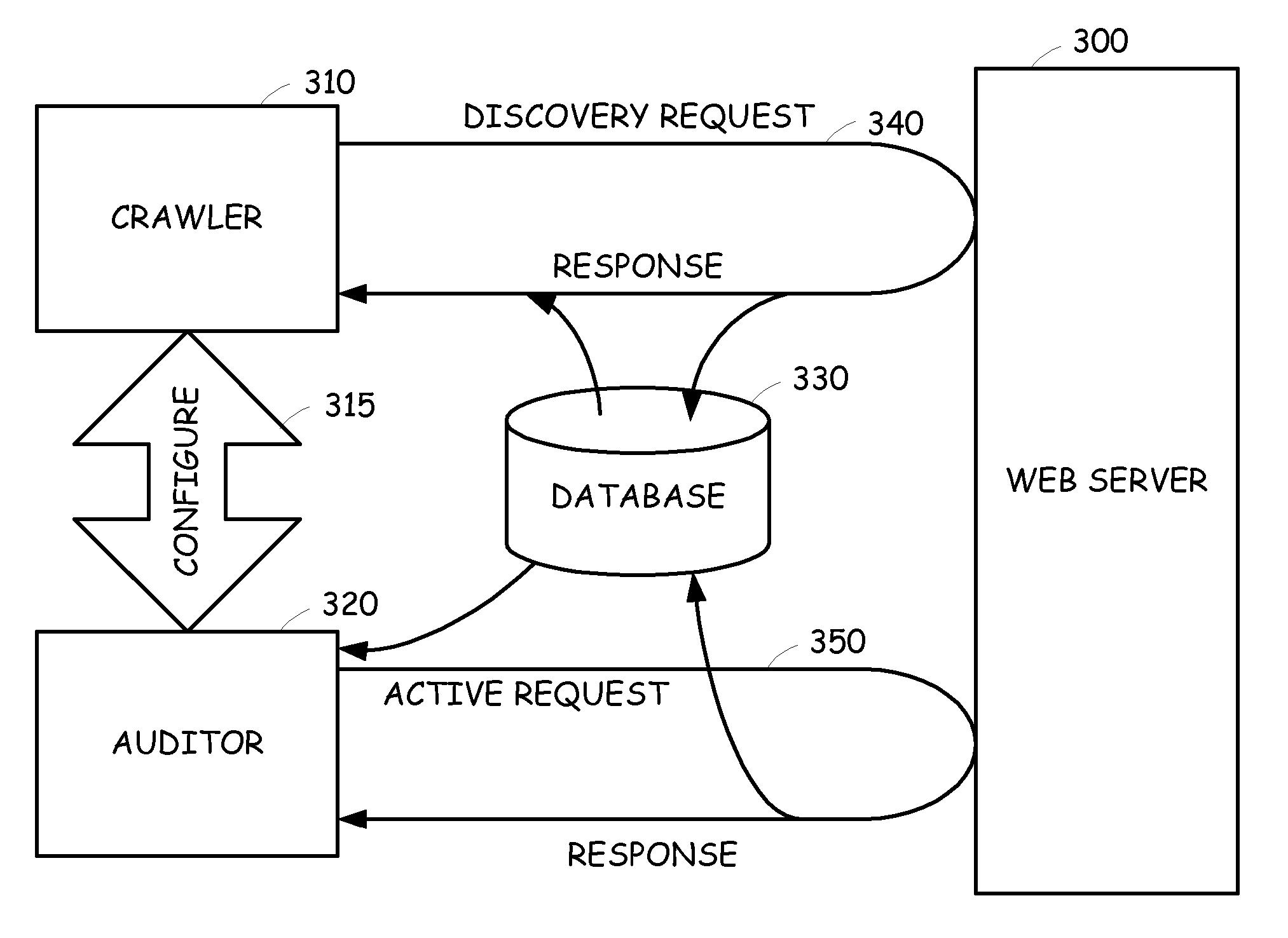
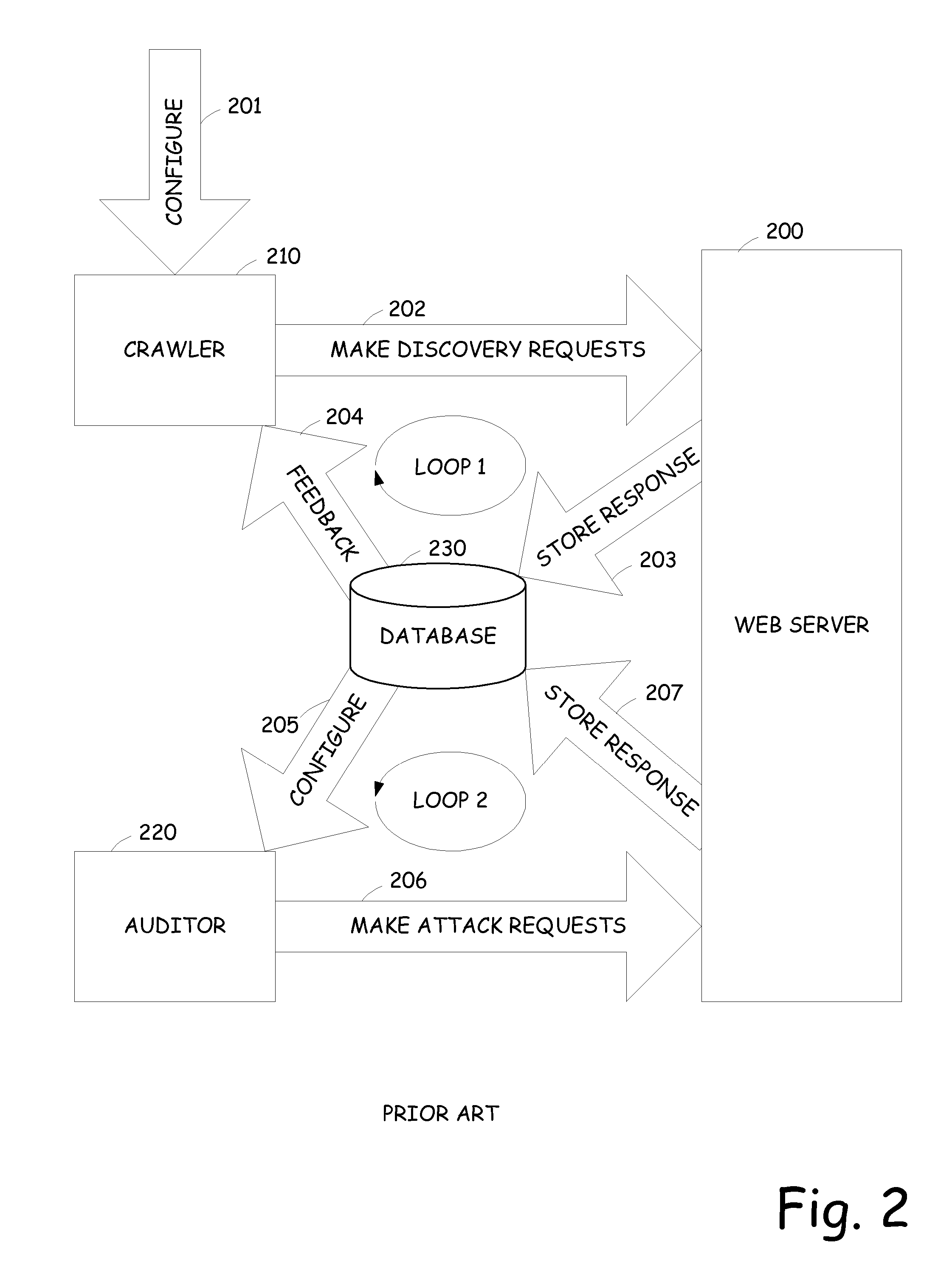
Integrated crawling and auditing of web applications and web content
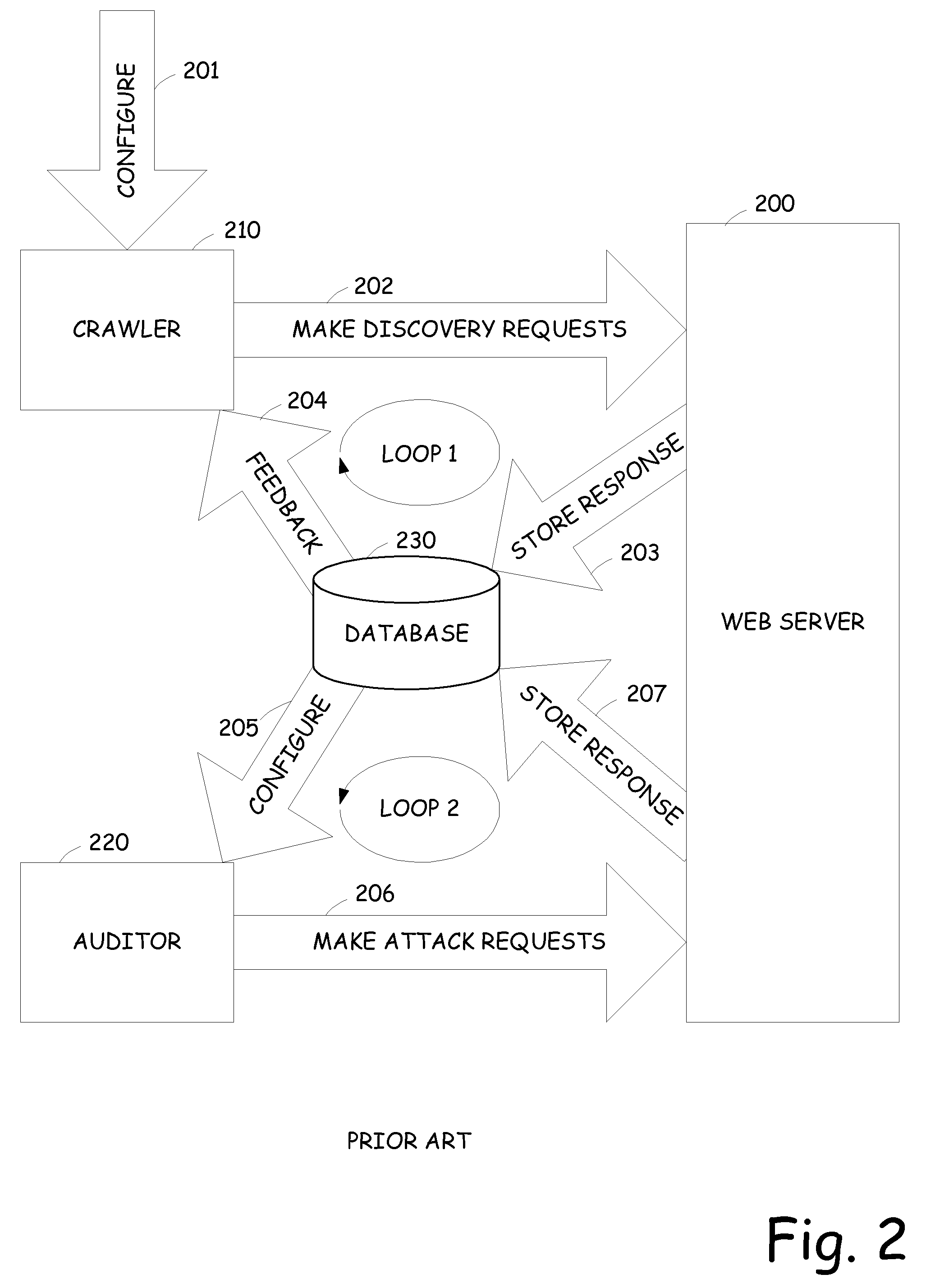
InactiveUS20070061877A1Easy to handleReduce processMemory loss protectionDigital data processing detailsWeb siteWeb application
A vulnerability assessment tool that is operative to analyze web sites by simultaneously operating a crawling process and an audit process. Once the crawling process is invoked, the results are provided to the audit process. The audit process, rather than waiting until the crawl process is completed, simultaneously audits the web site based on the already provided crawl results. The results of the audit are also fed back to the crawl process to further enhance the crawl.
Owner:MICRO FOCUS LLC
System and method for network vulnerability detection and reporting
InactiveUS8135823B2Reliably determinedSimple methodDigital computer detailsPolarising elementsGraphicsOperational system
Owner:MCAFEE LLC
Security risk evaluation method for effective threat management
InactiveUS20090106843A1Memory loss protectionError detection/correctionManagement environmentRisk assessment
Owner:KOREA INTERNET & SECURITY AGENCY
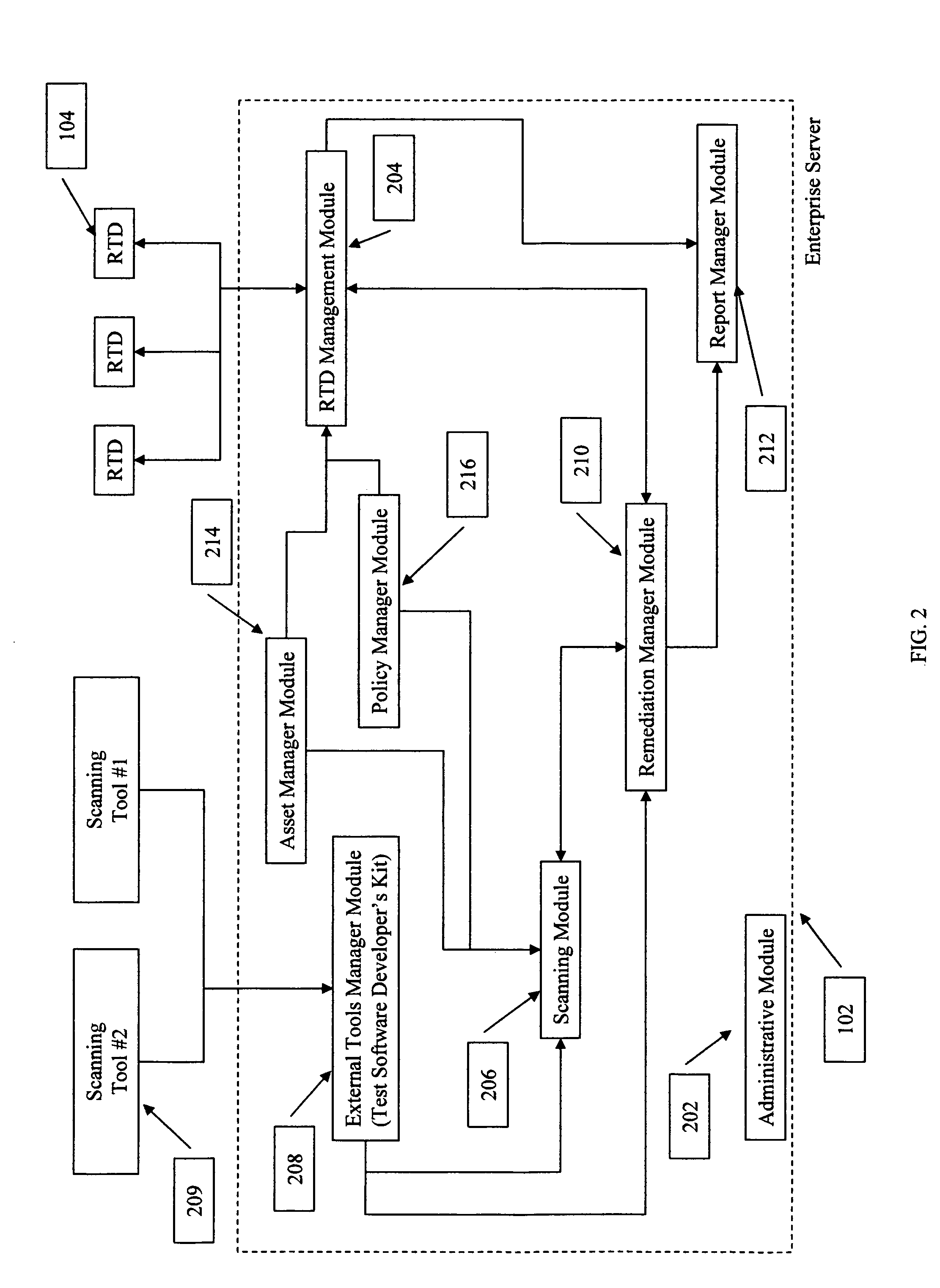
Method to provide customized vulnerability information to a plurality of organizations
InactiveUS20060101519A1Memory loss protectionError detection/correctionKnowledge managementWeb environment
The present invention provides a means of providing computer security vulnerability information to a plurality of organizations such that the vulnerability information provided to each organization is customized to its network environment. Each organization has an Enterprise Server. An asset management module in each organization's Enterprise Servers sends device configuration information to a system at a Co-Location Facility. The Co-Location Facility system aggregates this data. Information concerning vulnerabilities is also gathered from computer equipment vendors on an ongoing basis. This vulnerability information is compared to the aggregated data from the organizations' Enterprise Servers, and only the vulnerability information relevant to each organization is delivered back to that organization. The delivered information is then used to customize the vulnerability assessment and management activities, including scanning, for each organization such that their activities are limited to vulnerabilities that are directly related to their environment.
Owner:LASSWELL KEVIN W +2
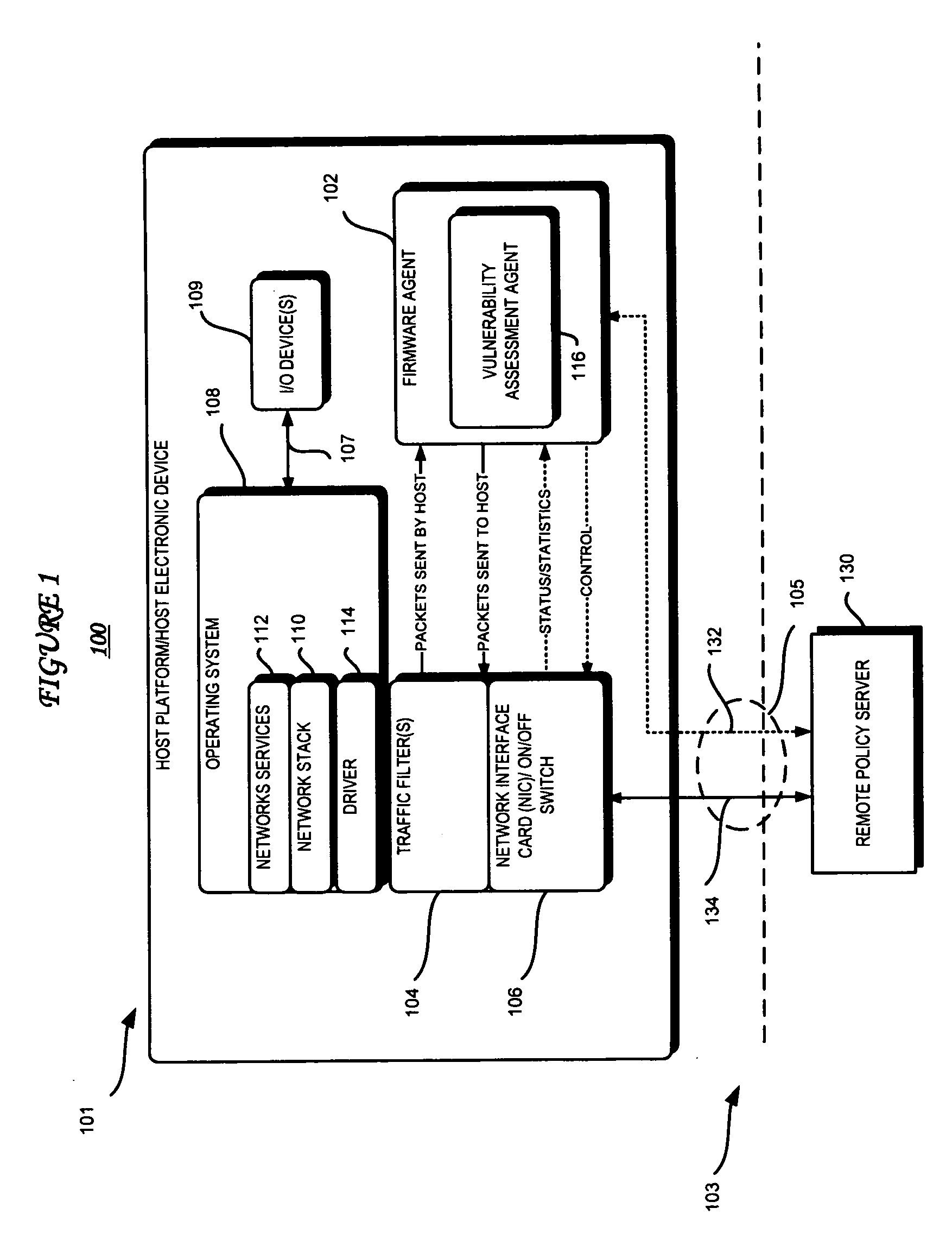
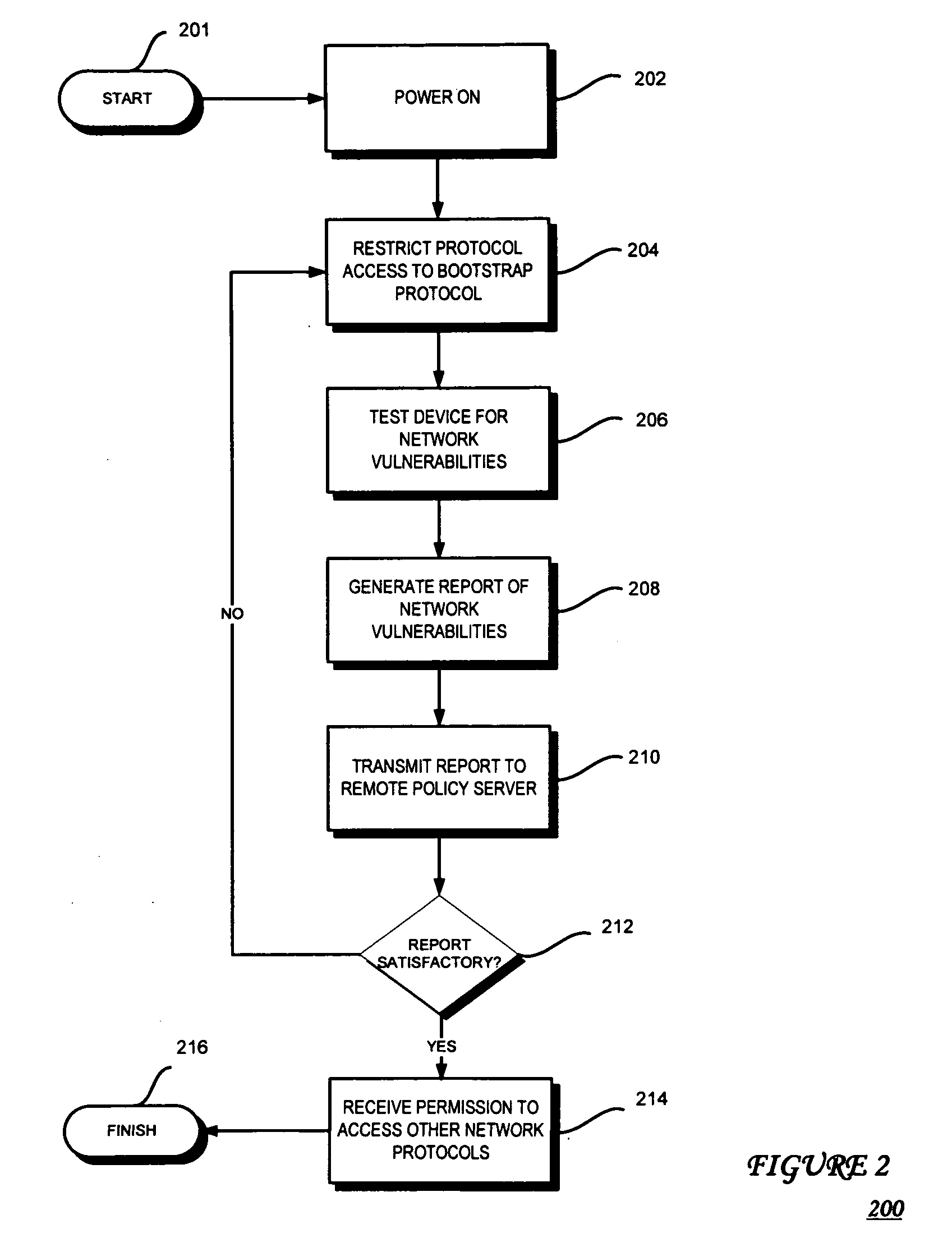
Network vulnerability assessment of a host platform from an isolated partition in the host platform
InactiveUS20070271360A1Memory loss protectionError detection/correctionTraffic capacityVulnerability assessment
According to embodiments of the present invention, host platform device includes an embedded firmware agent that may detect an attempt by the host platform device to fully connect to a network. The firmware agent may restrict traffic between the host platform device and the network to bootstrap traffic, test the device to determine device vulnerability, may temporarily stop access to other peripheral devices, and transmit a report of the device vulnerability to a remote policy server. After the test(s) are performed, the firmware agent may receive an indication from the remote policy server as to whether the device is permitted to fully connect to the network and, if so, whether there are any further restrictions on traffic flow, for example, and if the peripheral device access may be allowed.
Owner:INTEL CORP
System for intrusion detection and vulnerability assessment in a computer network using simulation and machine learning
InactiveUS7784099B2Memory loss protectionError detection/correctionComputer configurationData transmission
The present invention provides a system and method for predicting and preventing unauthorized intrusion in a computer configuration. Preferably, the invention comprises a communication network to which at least two computing devices connect, wherein at least one of the computing devices is operable to receive data transmitted by the other computing device. The invention further comprises a database that is accessible over the network and operable to store information related to the network. A vulnerability assessment component is provided that is operable to execute a command over the communication network, and a data monitoring utility operates to monitor data transmitted over the communication network as the vulnerability assessment component executes commands. Also, an intrusion detection component is included that is operable to provide a simulated copy of the network, to generate a first data transmission on the simulated copy of the network that represents a second data transmission on the communication network, and to compare the first data transmission with a second data transmission. The vulnerability assessment component preferably interfaces with the intrusion detection component to define rules associated with the first and second data transmissions, to store the rules in the database, and to retrieve the rules from the database in order to predict and prevent unauthorized intrusion in the computer configuration.
Owner:PACE UNIVERSITY
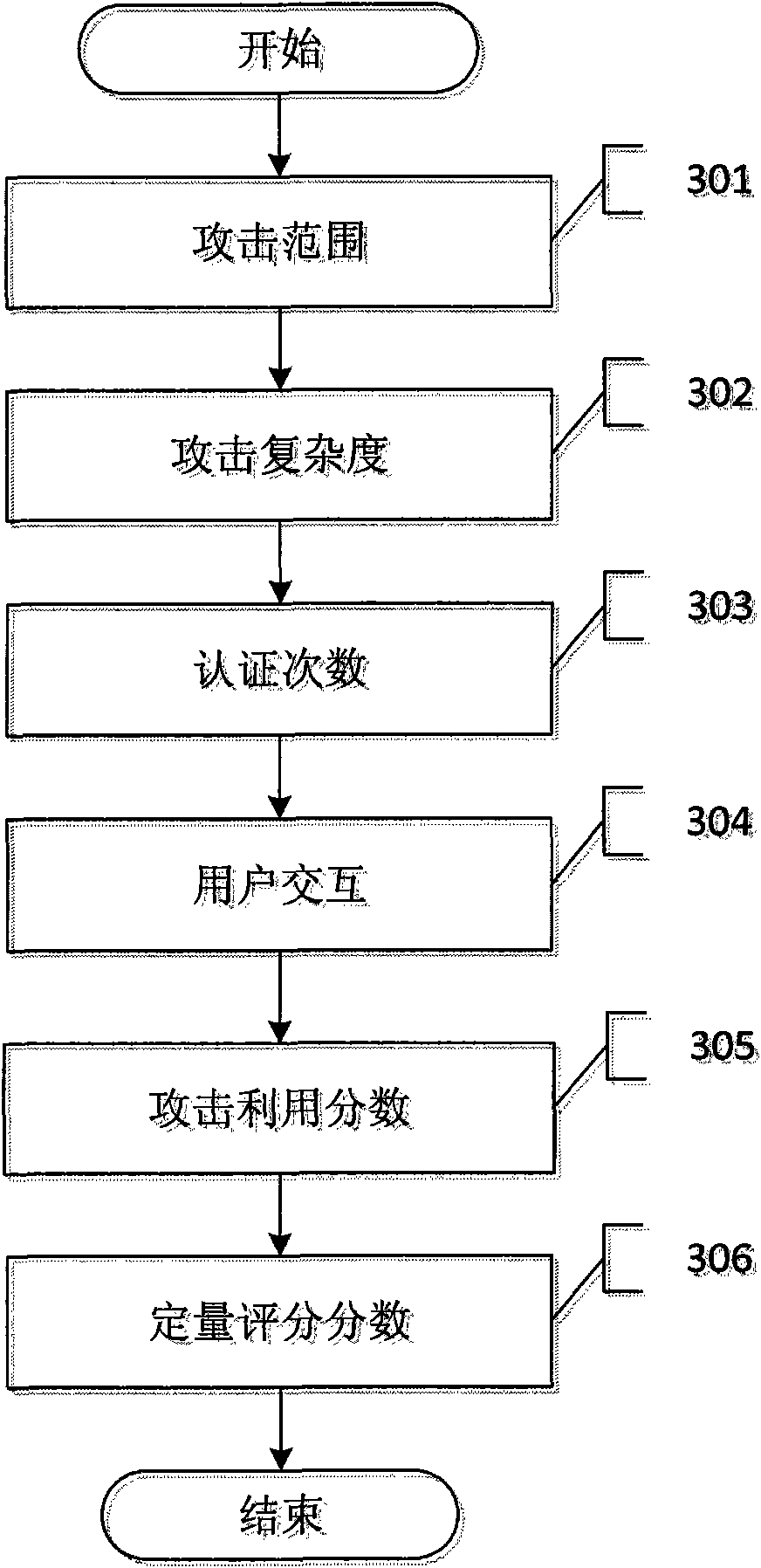
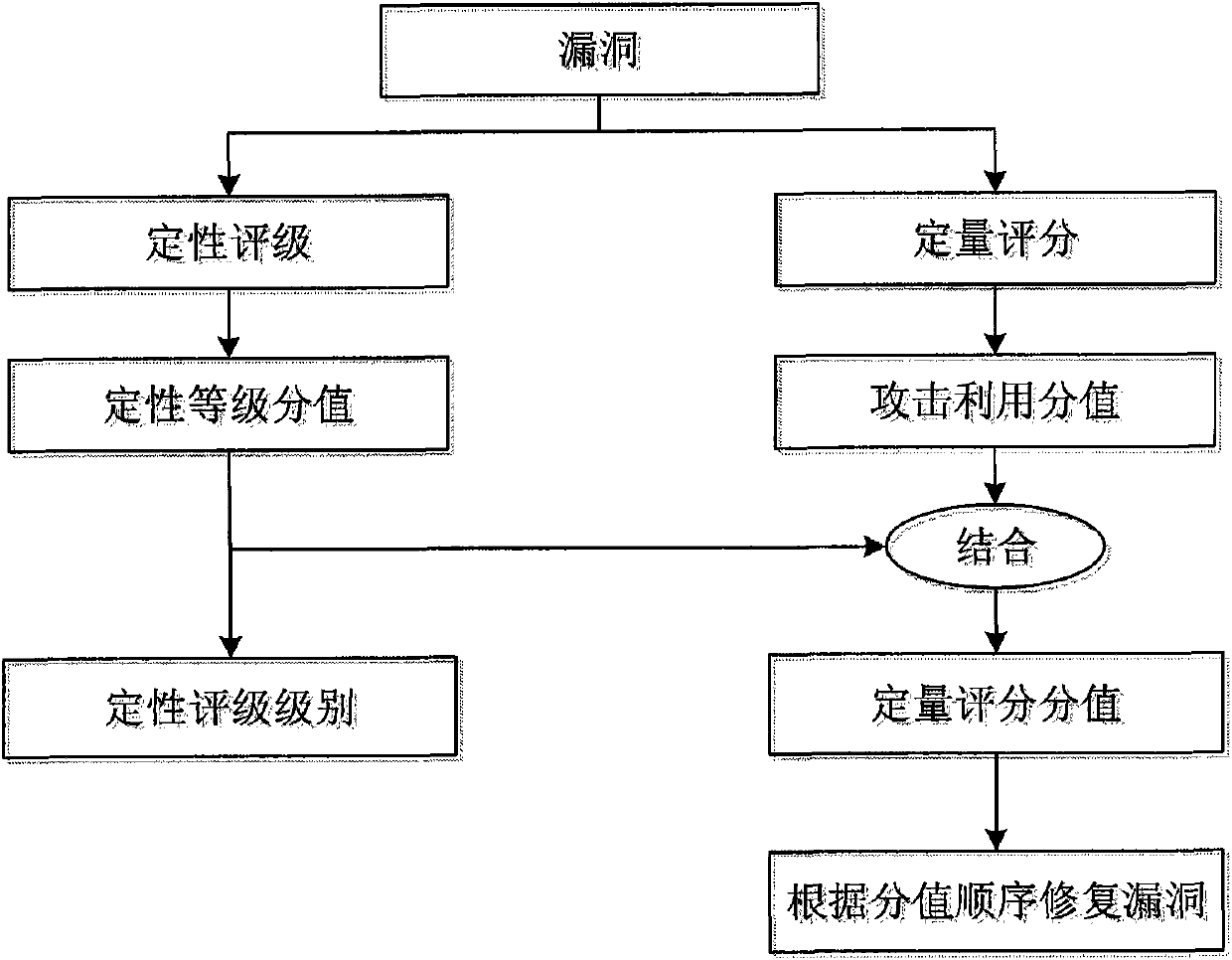
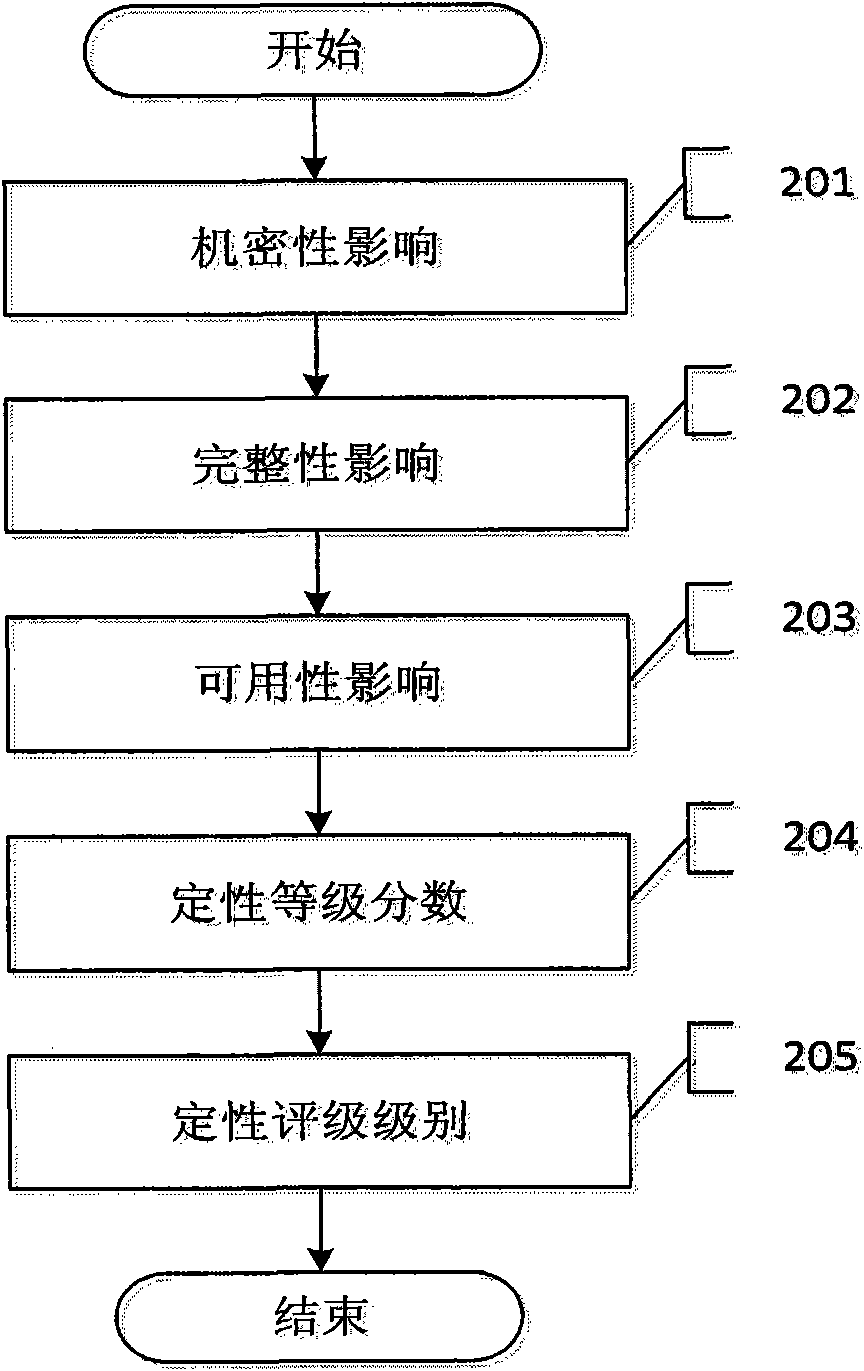
Bug repair method based on hierarchical bug threat assessment
The invention discloses a bug repair method based on hierarchical bug threat assessment. The method comprises the following steps: (1) extracting a plurality of information security attributes of the target system, a bug to be tested, and required attack conditions for the bug in the utilized process; (2) attacking the bug, and recording the value of the required attack conditions for the bug in the utilized process and the degree of damage after the bug is successfully utilized; (3) obtaining the qualitative grade score of the bug according to the degree of damage; (4) obtaining the attack utilization score of the bug according to the value of the required attack conditions; (5) obtaining the quantitative grade score according to the attack utilization value and the qualitative grade score; (6) and after determining the bug processing sequence according to the quantitative grade score of the bug to be tested, and repairing the bug. The method combines the advantages of qualitative and quantitative bug assessment methods, and divides the bugs as detailed as possible on the basis of visually giving out the bug threat degree, thereby helping the user to repair a great deal of bugs.
Owner:GRADUATE SCHOOL OF THE CHINESE ACAD OF SCI GSCAS
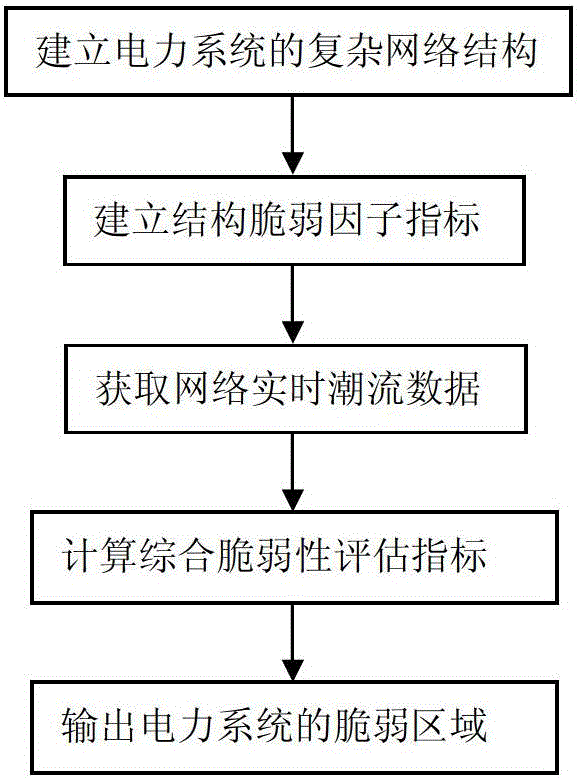
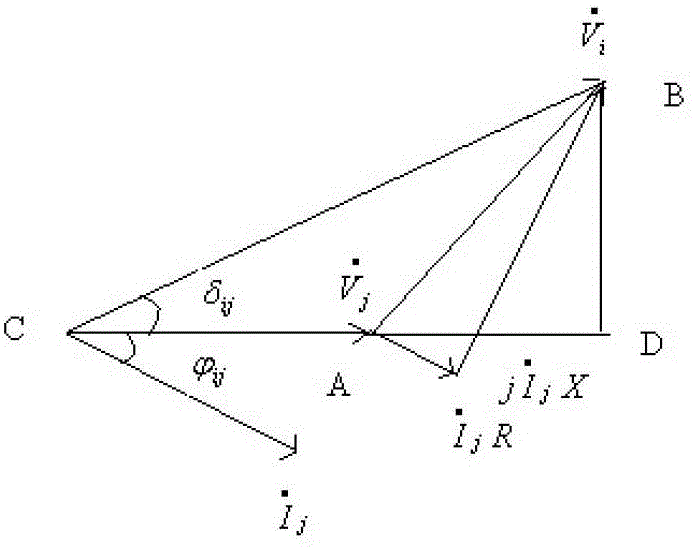
Electric power system vulnerability assessment method
InactiveCN104156769ACatastrophe preventionFully determinedData processing applicationsAc network circuit arrangementsStructural vulnerabilityEngineering
The invention discloses an electric power system vulnerability assessment method, and relates to the field of a power network safety analysis technology. The electric power system frangibility assessment method comprises the following steps: (1), establishing a complex network structure of an electric power system; (2), establishing a structure vulnerability factor indicator through electrical betweenness in the complex networks structure; (3), obtaining network real-time trend data through a static energy function method; (4), calculating a state vulnerability factor, and calculating to obtain an integrated vulnerability assessment indicator through combination with a structural vulnerability factor in step (2); and (5), outputting a vulnerable area of the electric power system. According to the invention, since the electric power system vulnerability assessment method analyzes vulnerable links which may exist in the electric power system from a global perspective, the vulnerable area in the operation of the electric power system can be comprehensively, accurately and effectively determined, the defects of a conventional single one-sided electric power system vulnerability assessment method and the like can be made up for, emphases are provided for prevention and control of safe operation of the electric power system, and collapse of the electric power system, caused by disturbance or accidents, is effectively prevented.
Owner:ELECTRIC POWER SCHEDULING CONTROL CENT OF GUIZHOU POWER GRID CO LTD +1
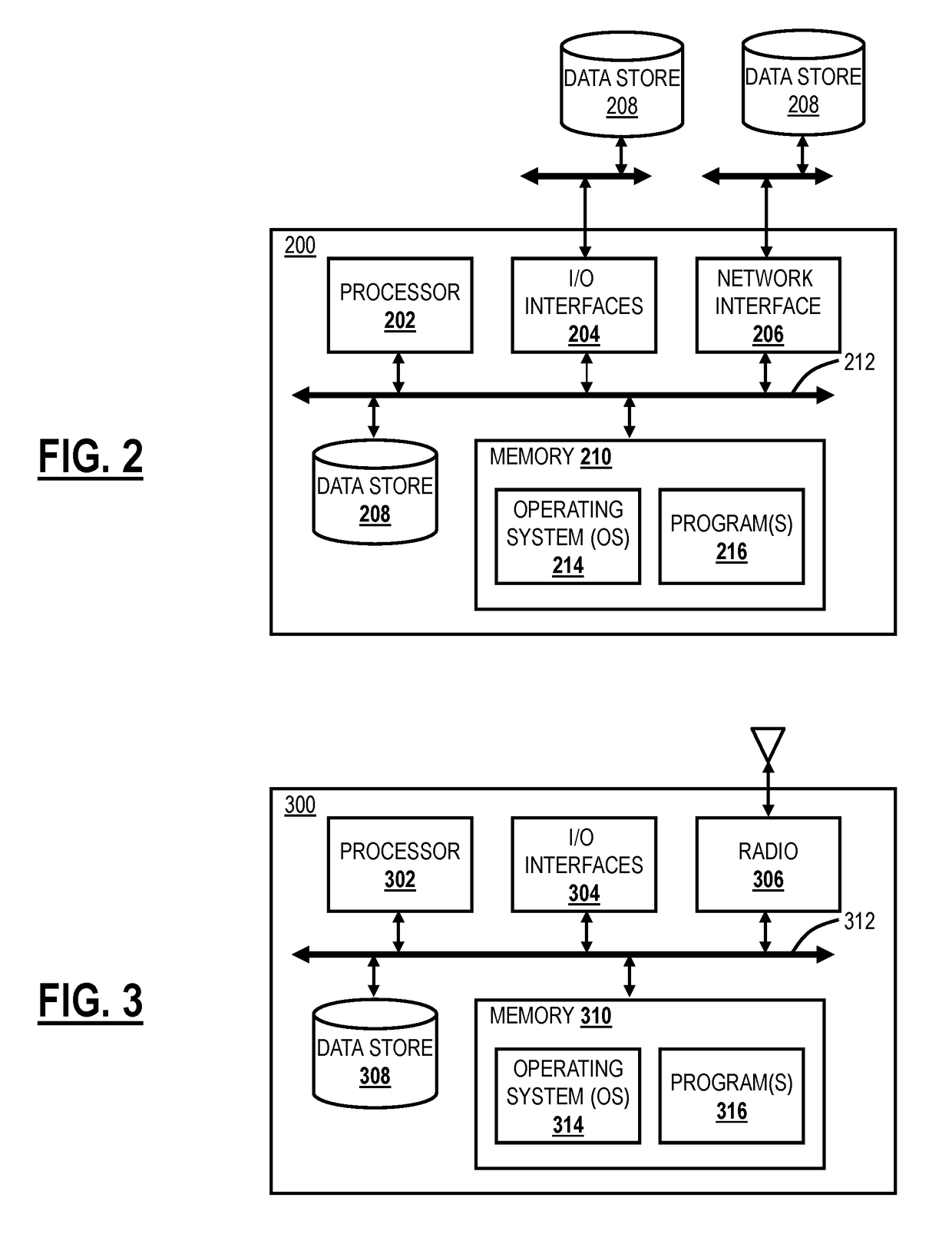
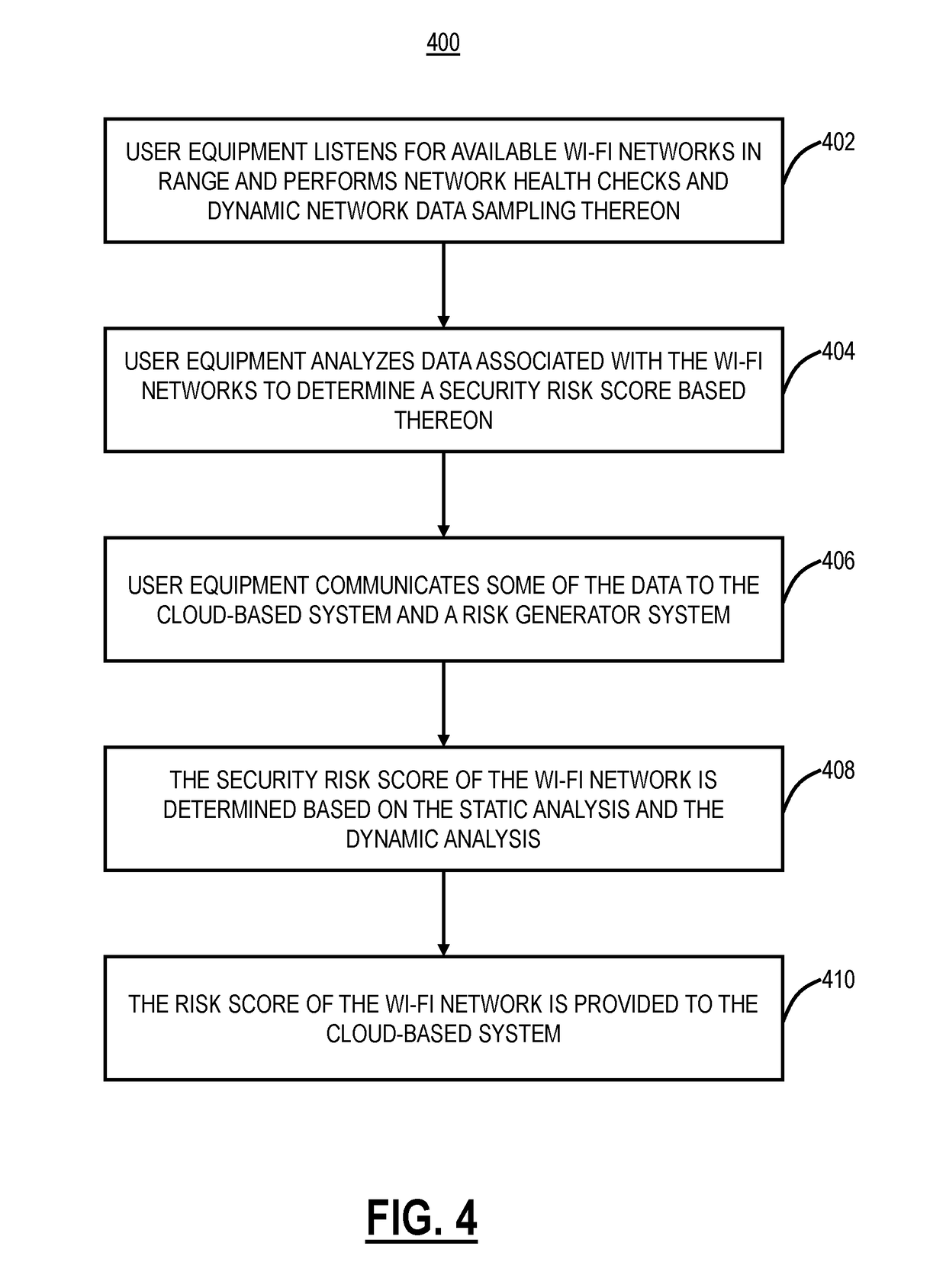
Systems and methods for network vulnerability assessment and protection of wi-fi networks using a cloud-based security system
ActiveUS20190081981A1Blocking in networkMany applicationsNetwork topologiesData switching networksWi-FiUser equipment
Systems and methods of assessing Wi-Fi network vulnerability and enforcing policy based thereon in a cloud-based security system include obtaining and storing security risk scores for a plurality of Wi-Fi networks based in part on analysis performed by user equipment in range of each of the plurality of Wi-Fi networks; detecting user equipment associated with the cloud-based security system either desiring to connect to or already connected to a Wi-Fi network; obtaining a security risk score of the Wi-Fi network; and enforcing policy for the user equipment based on the obtained security risk score of the Wi-Fi network.
Owner:ZSCALER INC
RF communication receiver vulnerability assessment
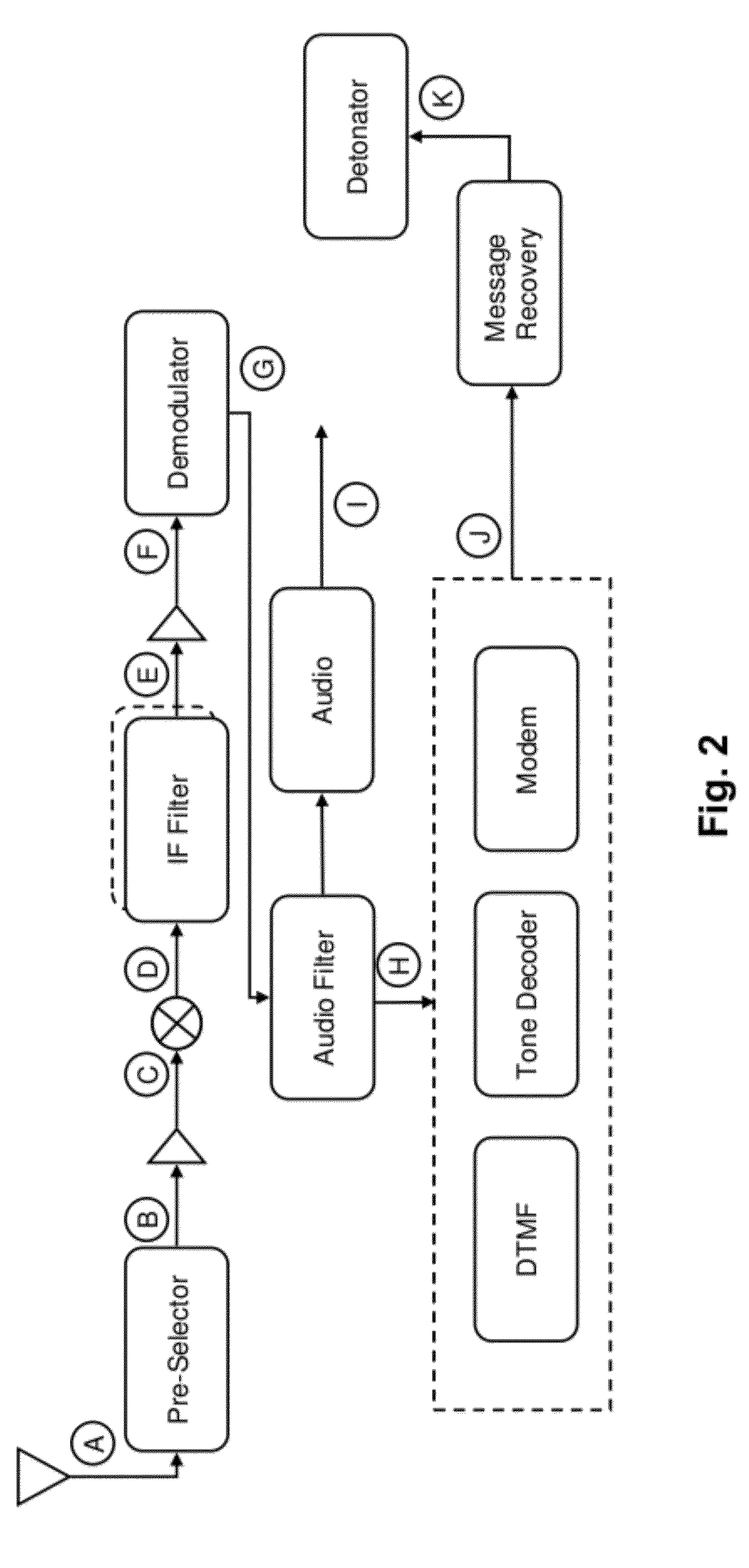
ActiveUS8229344B1Susceptibility to jammingReceivers monitoringCommunication jammingReporting parametersComputer science
Techniques are disclosed for analyzing a wireless communications device. The techniques include, for instance, assessing vulnerability of the device, including its susceptibility to jamming, by applying one or more interfering signals to the device and observing the device's response. The techniques further include identifying one or more vulnerabilities that can be exploited in defeating malicious behavior involving use of the device (e.g., such as using the device for remote detonation of explosives). Applying one or more interfering signals to the device may include, for instance, applying a trigger signal and a jamming signal to the device, and adjusting the jamming signal until the trigger signal is rendered ineffective in acting as a trigger signal. Identifying one or more vulnerabilities that can be exploited in defeating malicious behavior may include, for instance, reporting parameters of the one or more interfering signals that result in defeating the malicious behavior.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
Web application auditing based on sub-application identification
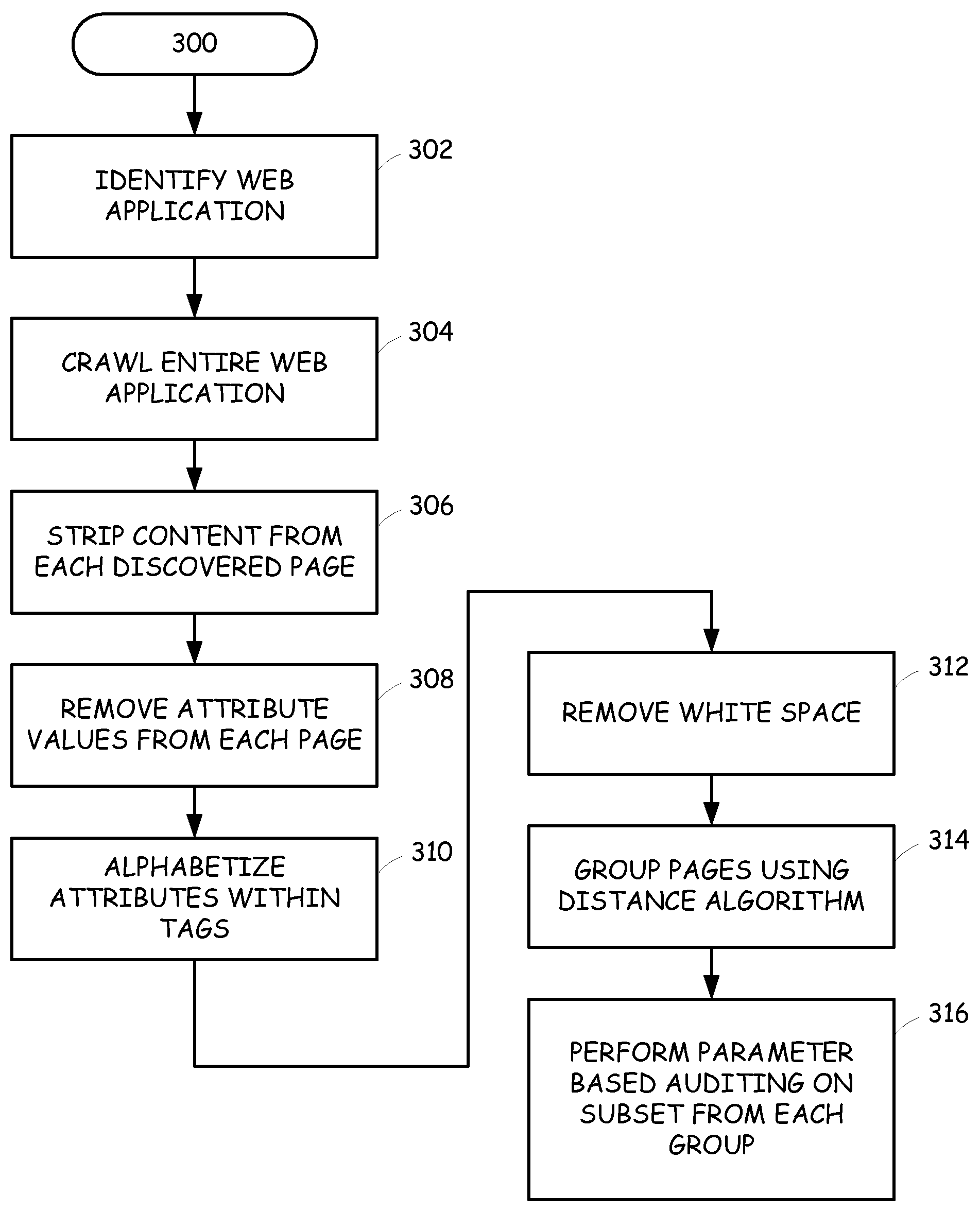
InactiveUS20080120305A1Limit scopeEasy to identifyWeb data indexingComputer security arrangementsWeb applicationWeb page
A web application is more efficiently analyzed by identifying the sub-applications used to generate the various web pages available at the web application and then limiting the vulnerability assessment to just a subset of the web pages generated by each sub-application. The sub-applications can be identified by detecting similarity between the web pages, based on the user interface presentation, the inputs required or allowed, or both. For the user interface presentation, the markup language used to generate the user interface is reduced to common markup language elements by removing content, attribute values and white space and then determining the edit distances between the various pages. Small edit distance values indicate similarity and thus, likely generated by a common sub-application.
Owner:HEWLETT PACKARD DEV CO LP
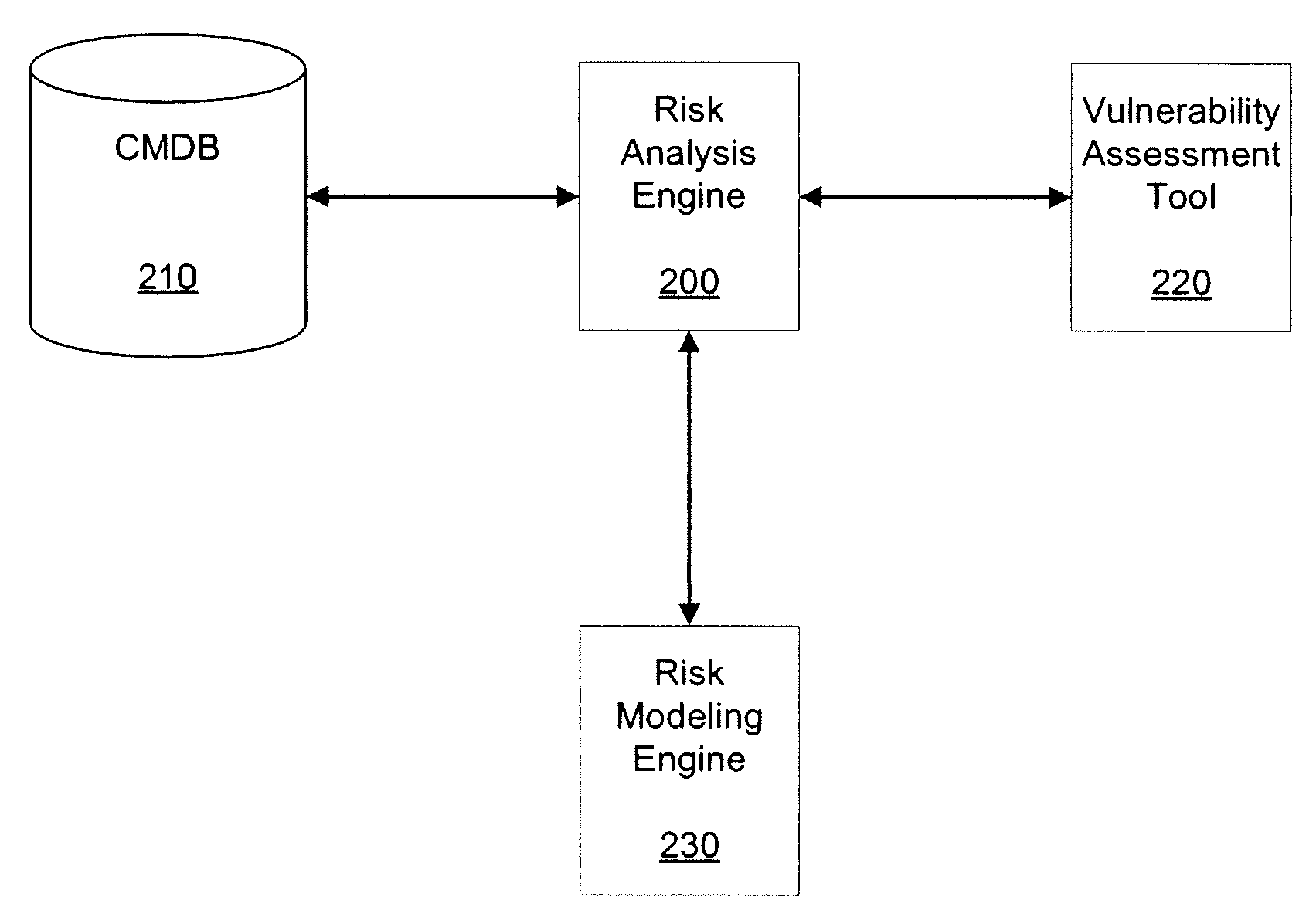
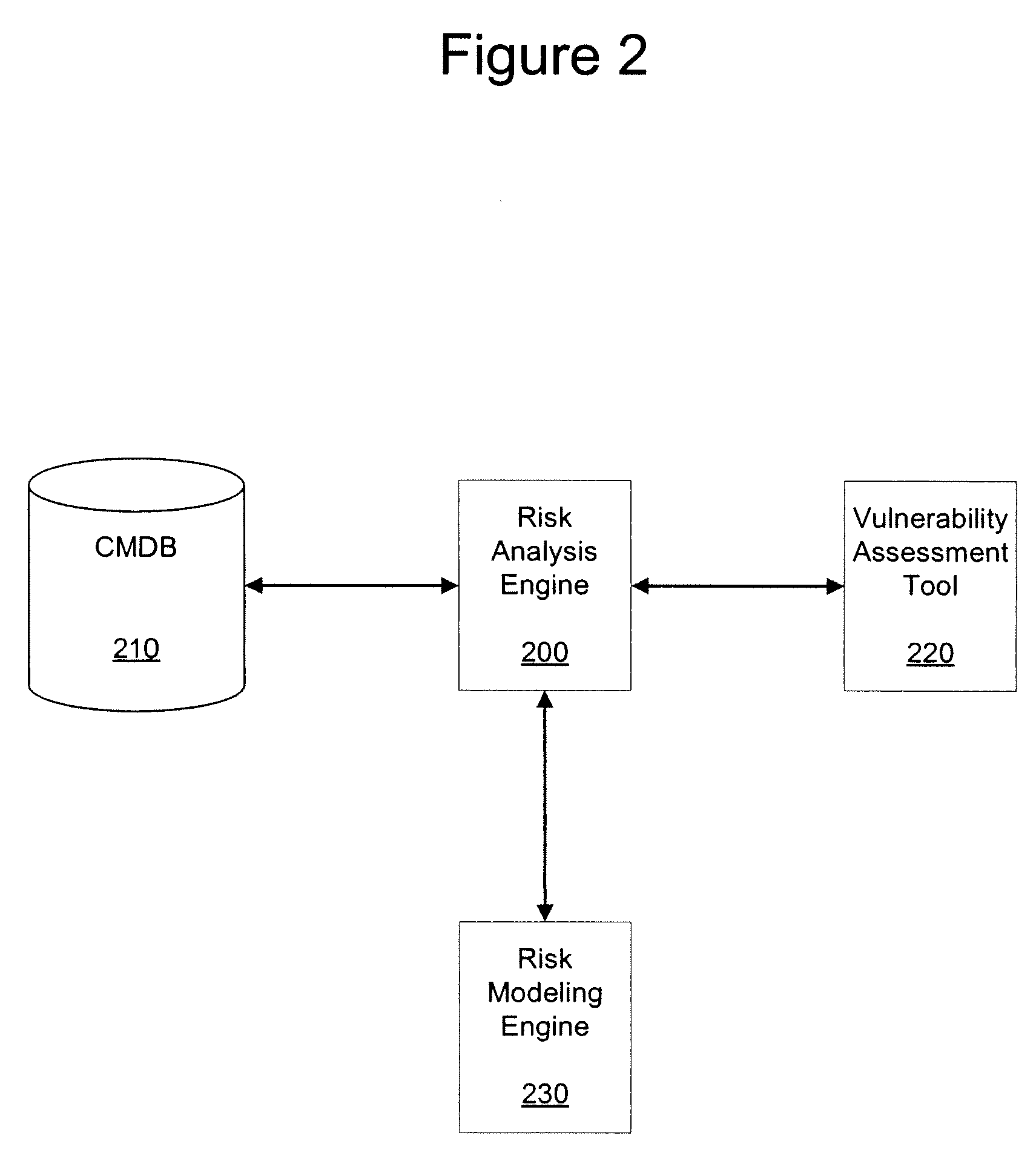
Device, method, and program product for determining an overall business service vulnerability score
A device, method, and program product are disclosed which are configured to receive, at a risk analysis engine, one or more business service models from a configuration management database, wherein the one or more business service models each comprises a set of configuration items, and wherein the one or more business service models each indicate a type of configuration item and a connectivity of the configuration item; send the set of configuration items to a vulnerability assessment tool; receive, from the vulnerability assessment tool, one or more vulnerability assessment scores for each configuration item within the set of configuration items; determine an overall business service vulnerability score for each of one or more business services based on the one or more business service models and the vulnerability assessment scores received from the vulnerability assessment tool; and output electronically the overall business service vulnerability score.
Owner:MARQETA
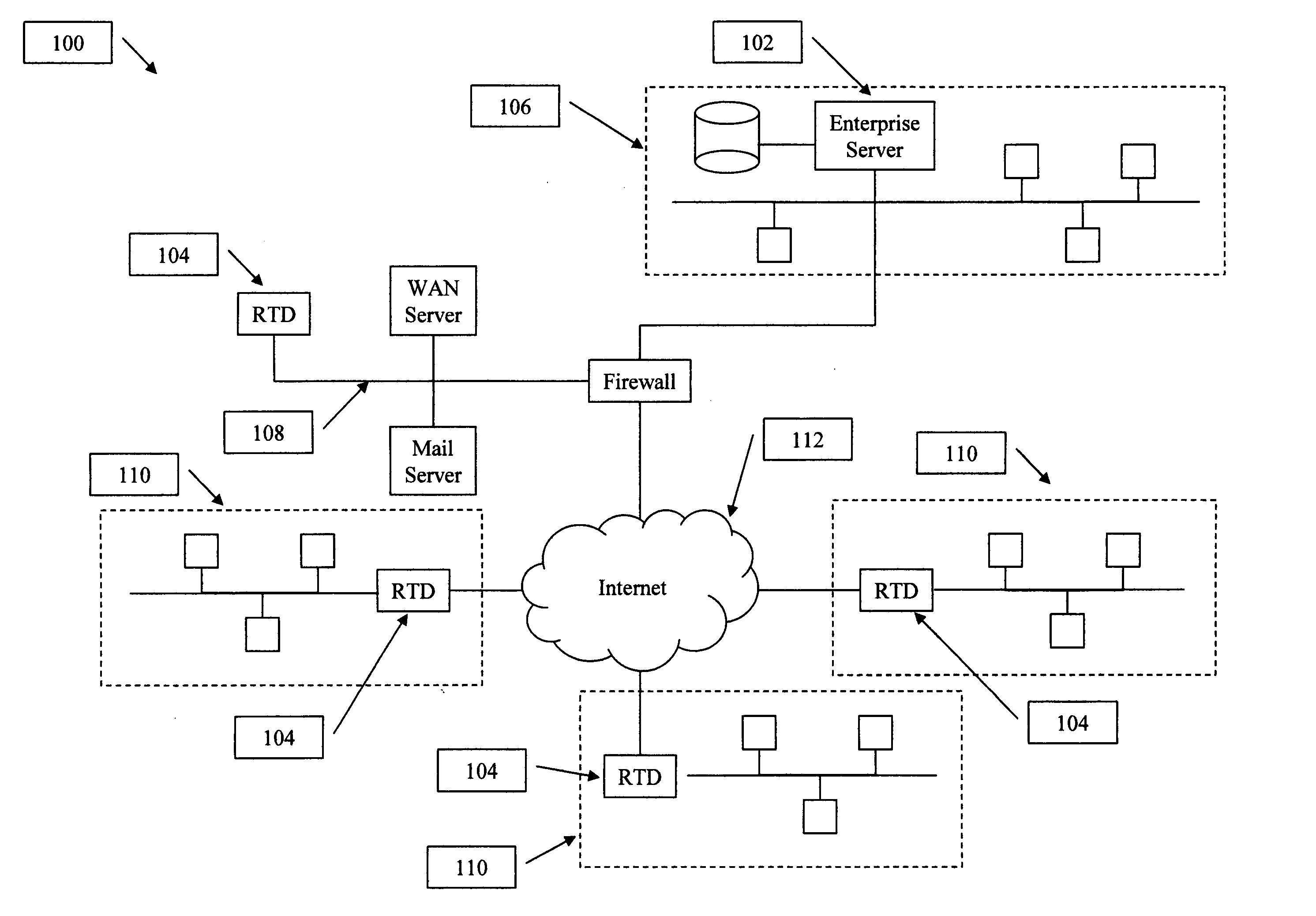
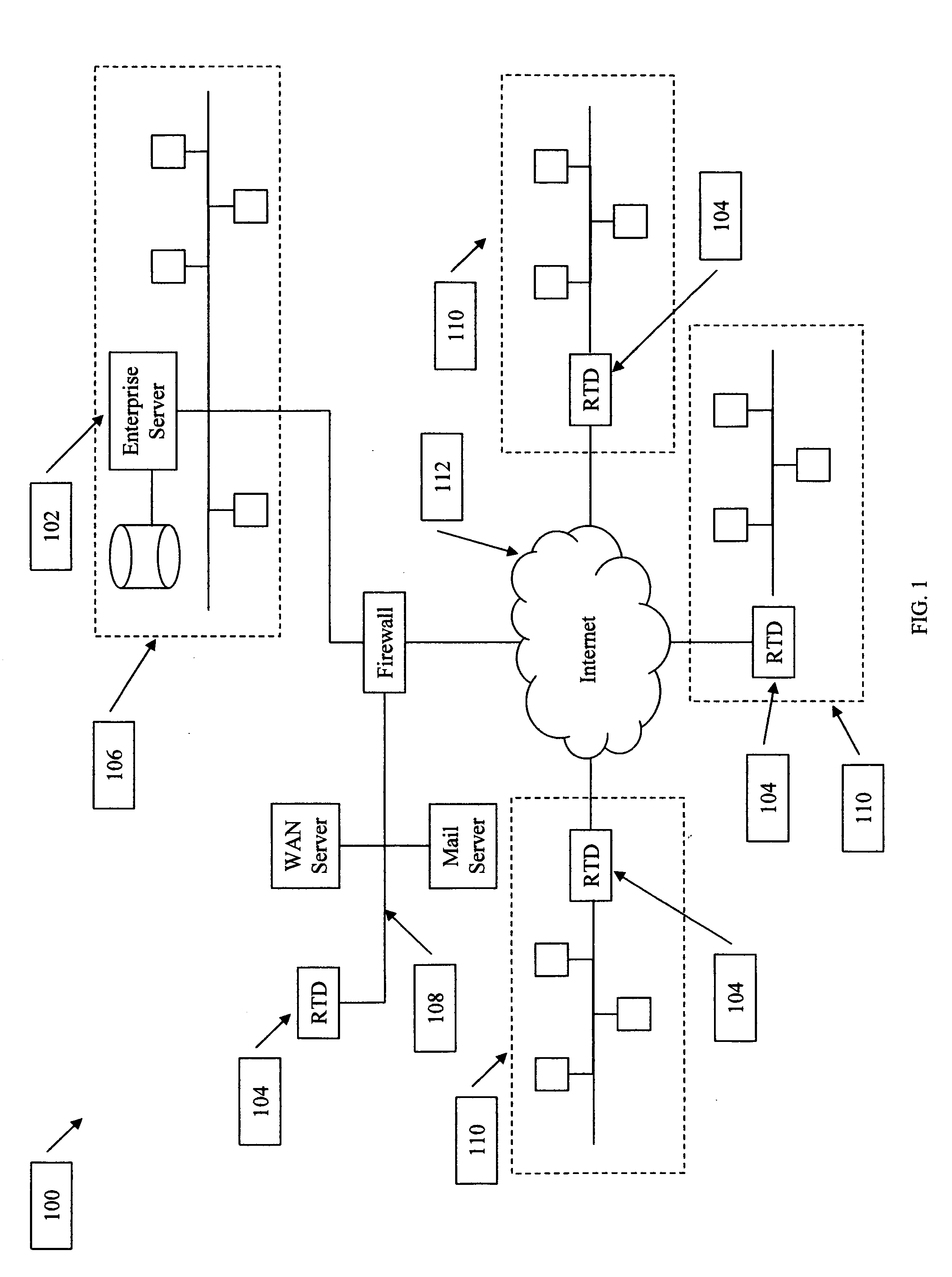
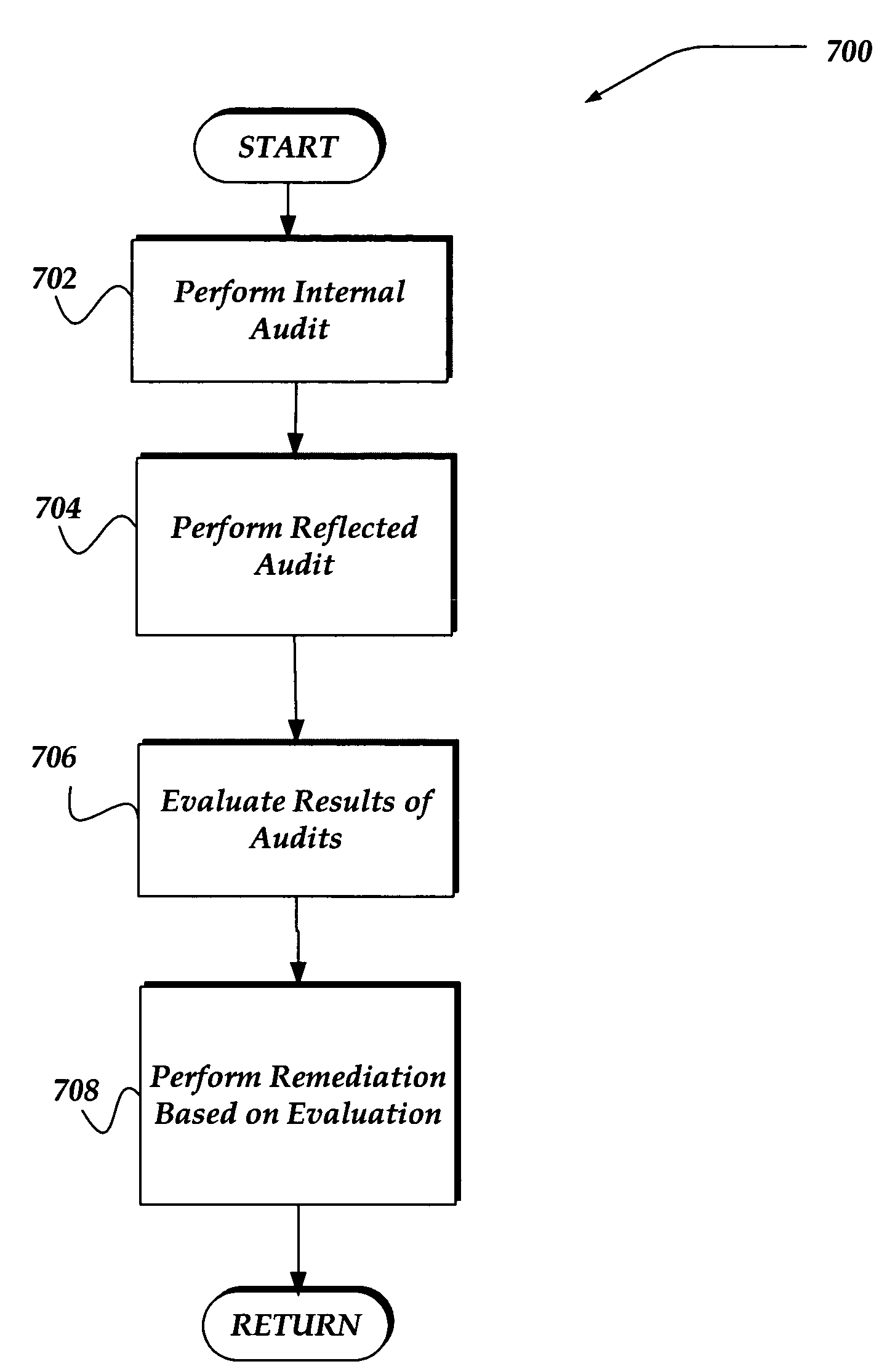
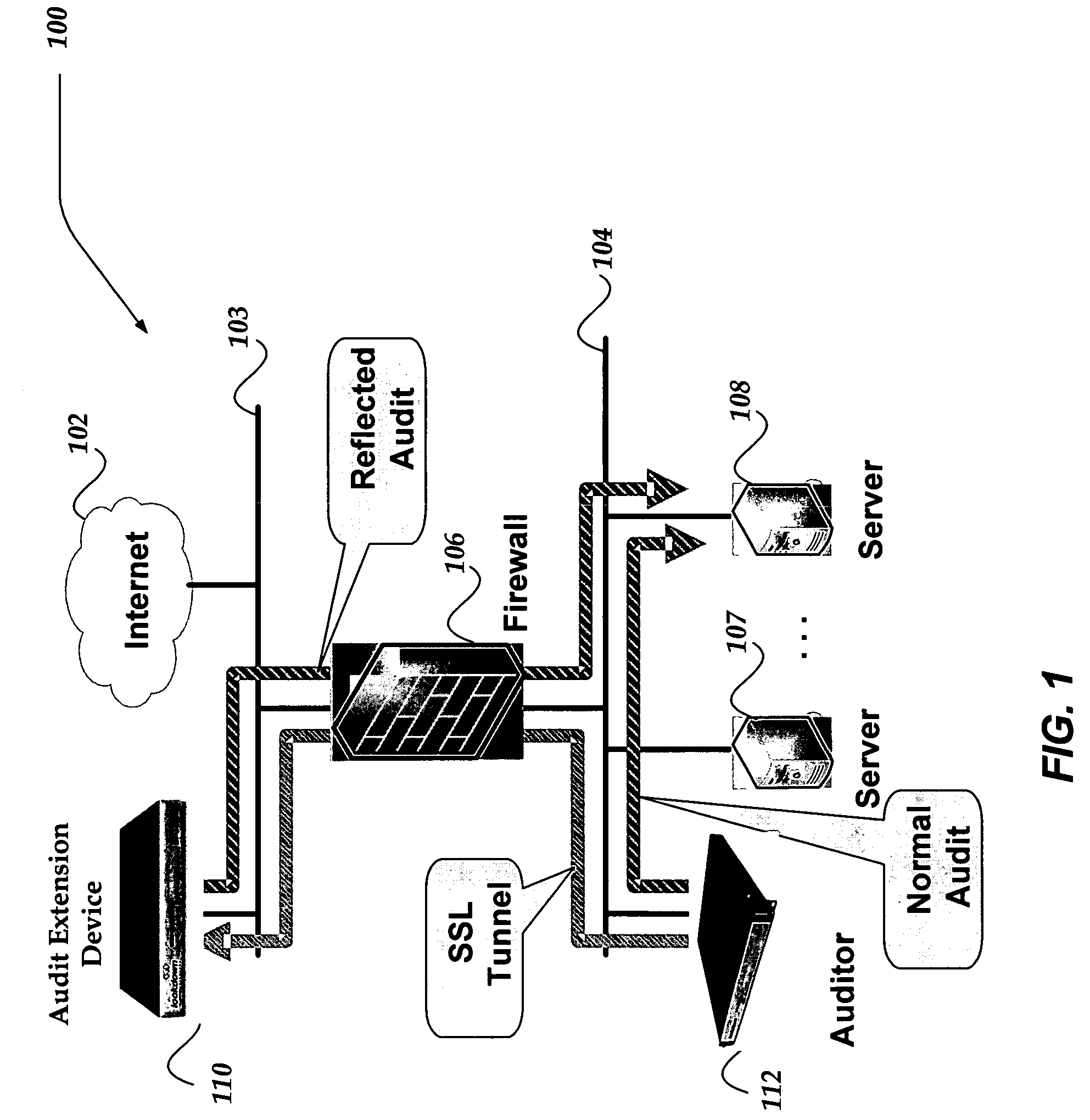
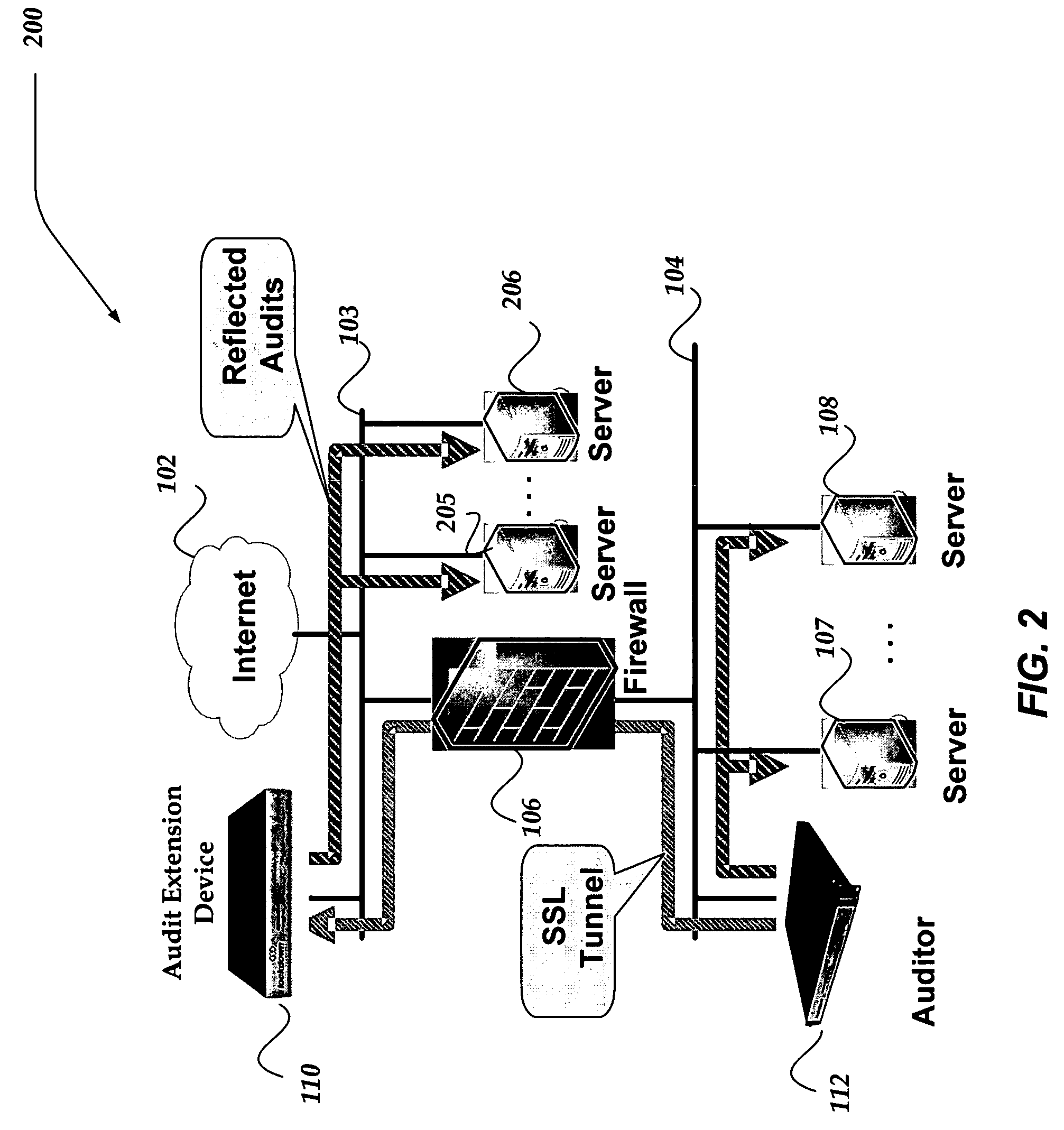
Network appliance for vulnerability assessment auditing over multiple networks
ActiveUS7310669B2Error preventionFrequency-division multiplex detailsComputer networkVulnerability assessment
An apparatus, system, and method are directed towards enabling auditing of network vulnerabilities from multiple network vantage points virtually simultaneously. Multiple network vantage points may include, but are not limited to, remote / branch enterprise sites, devices on an enterprise perimeter, on either side of a security perimeter, and even through the security perimeter. In one embodiment, an auditor performs reflected audits thereby extending auditing of network vulnerabilities to provide a comprehensive 360 degree audit of internal, external, and remote enterprise network sites. In one embodiment, the present invention may be implemented employing a single auditing device, and one or more audit extension devices that are configured to extend the auditing device's audit reach. The auditing device and one or more audit extension devices may communicate using an encrypted network channel through a security perimeter and / or across multiple networks.
Owner:CALLAHAN CELLULAR L L C
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com