Patents
Literature
2683 results about "Web environment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
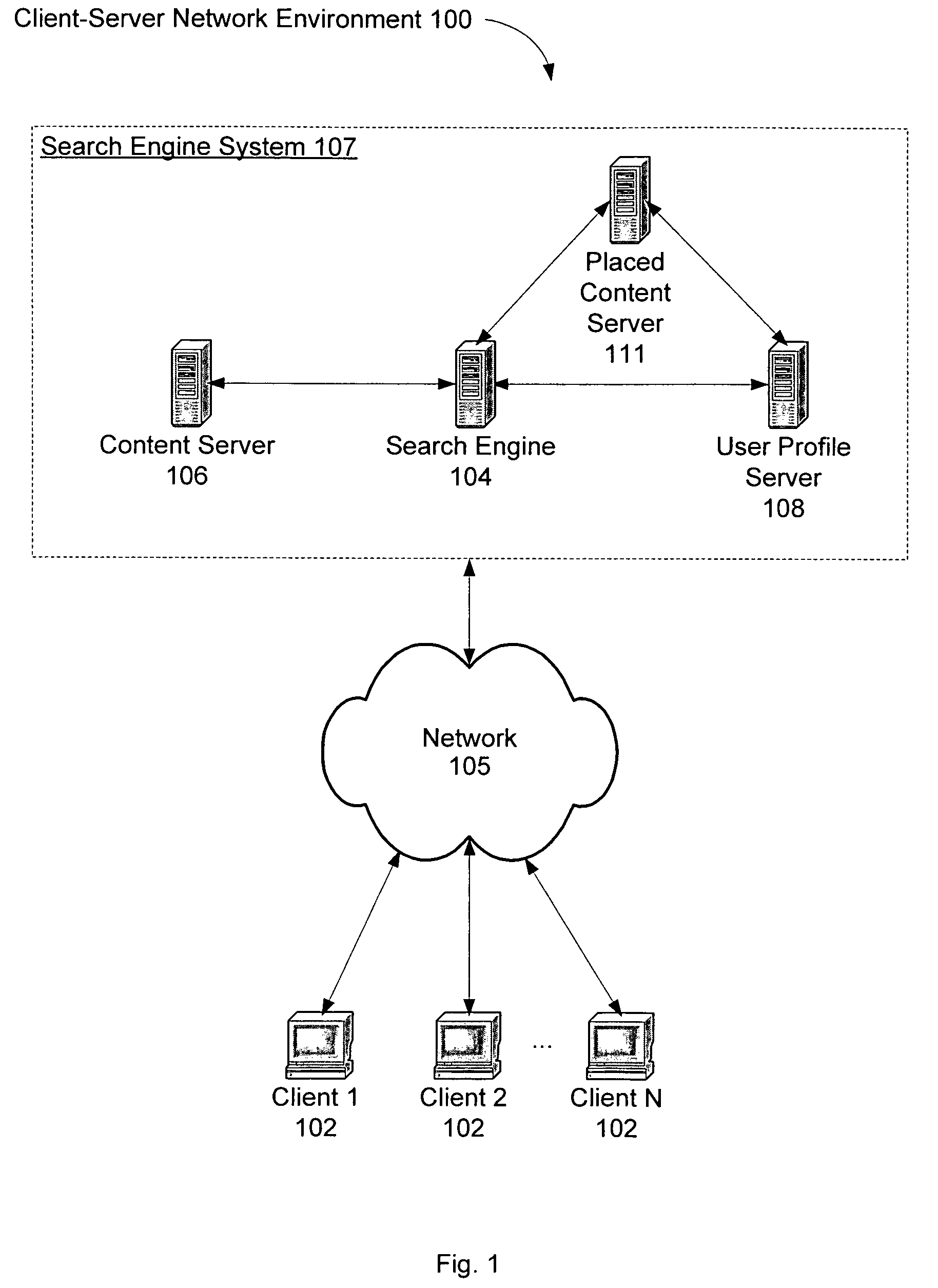
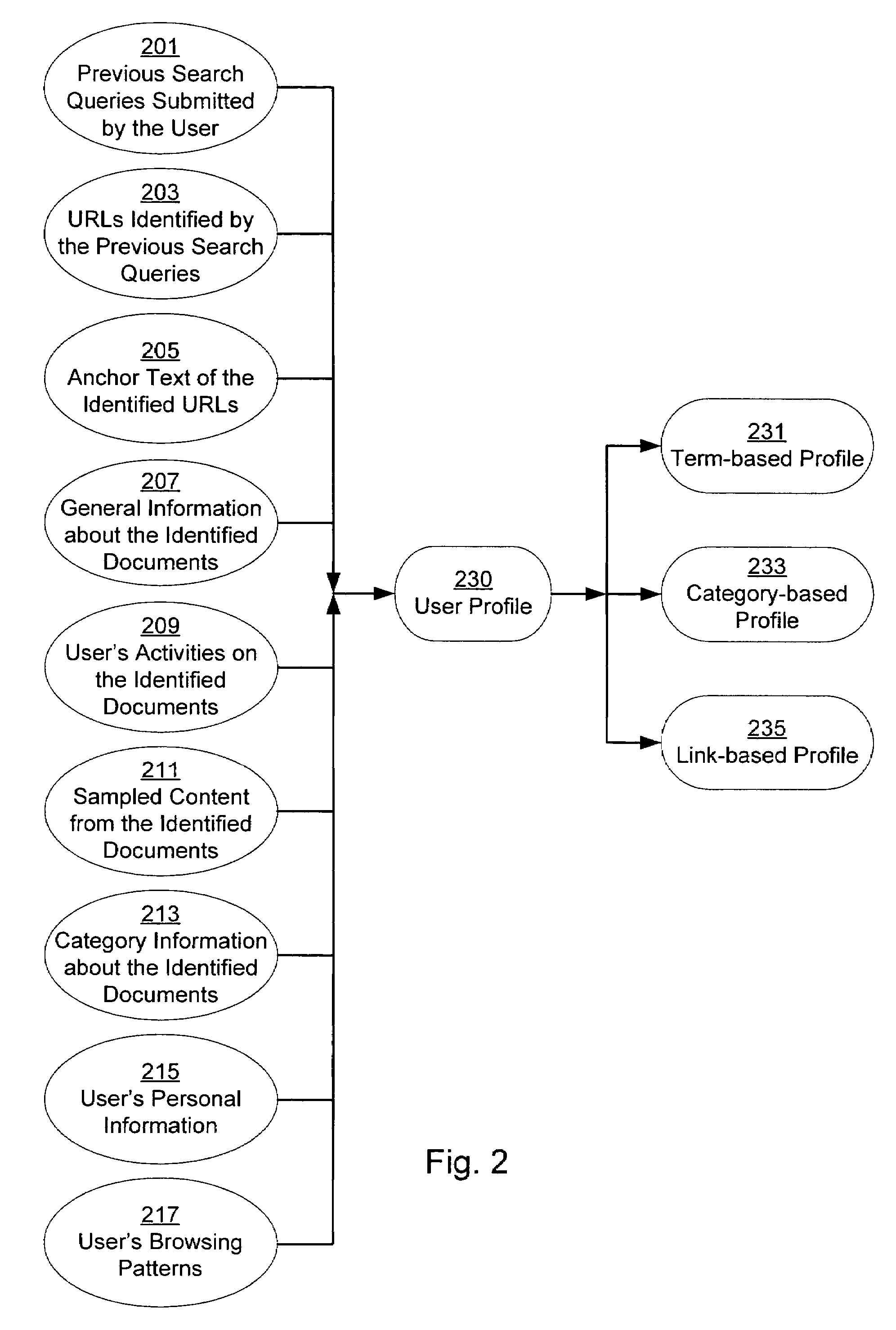
Personalization of web search
InactiveUS20050071328A1Web data retrievalSpecial data processing applicationsPersonalizationPaper document
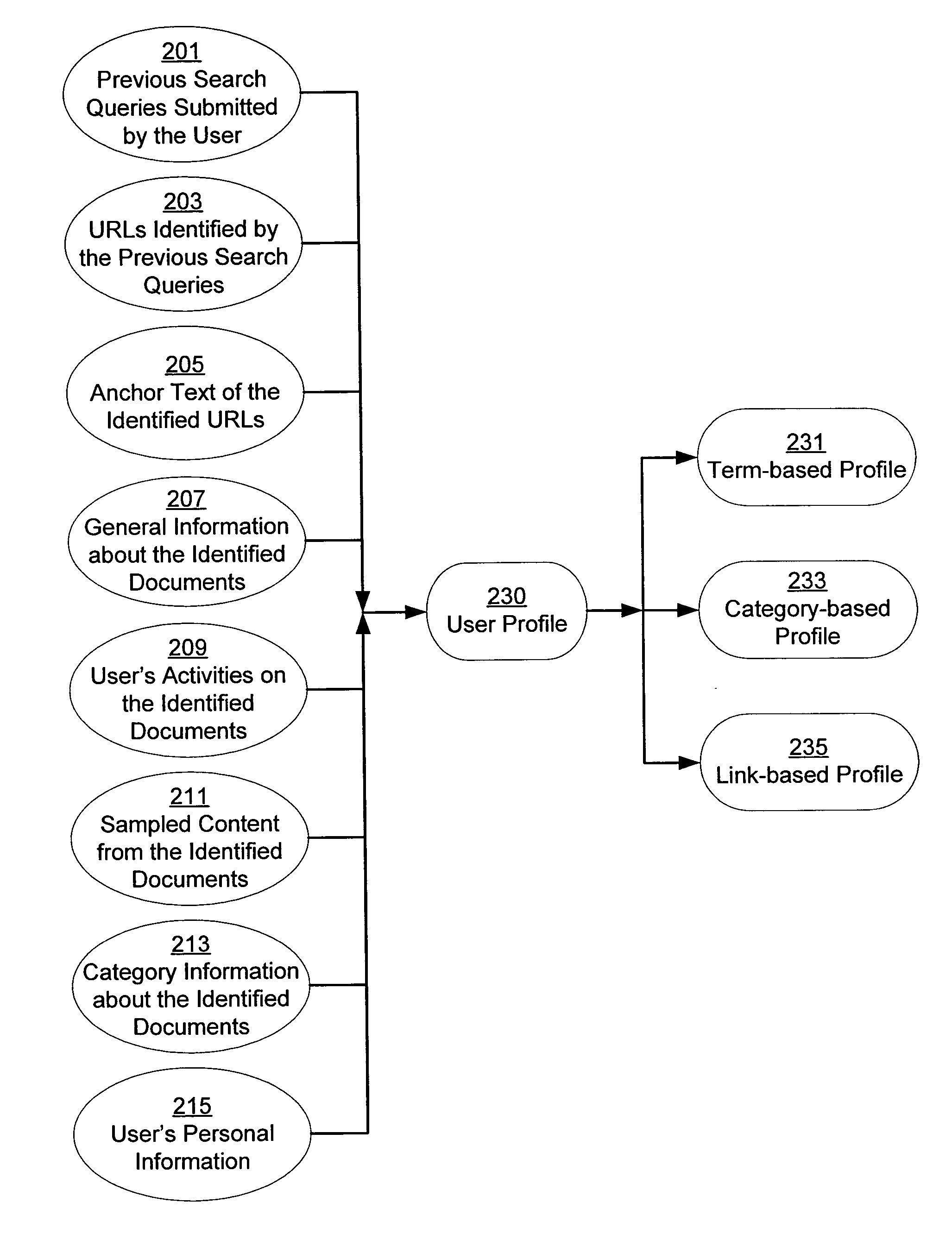
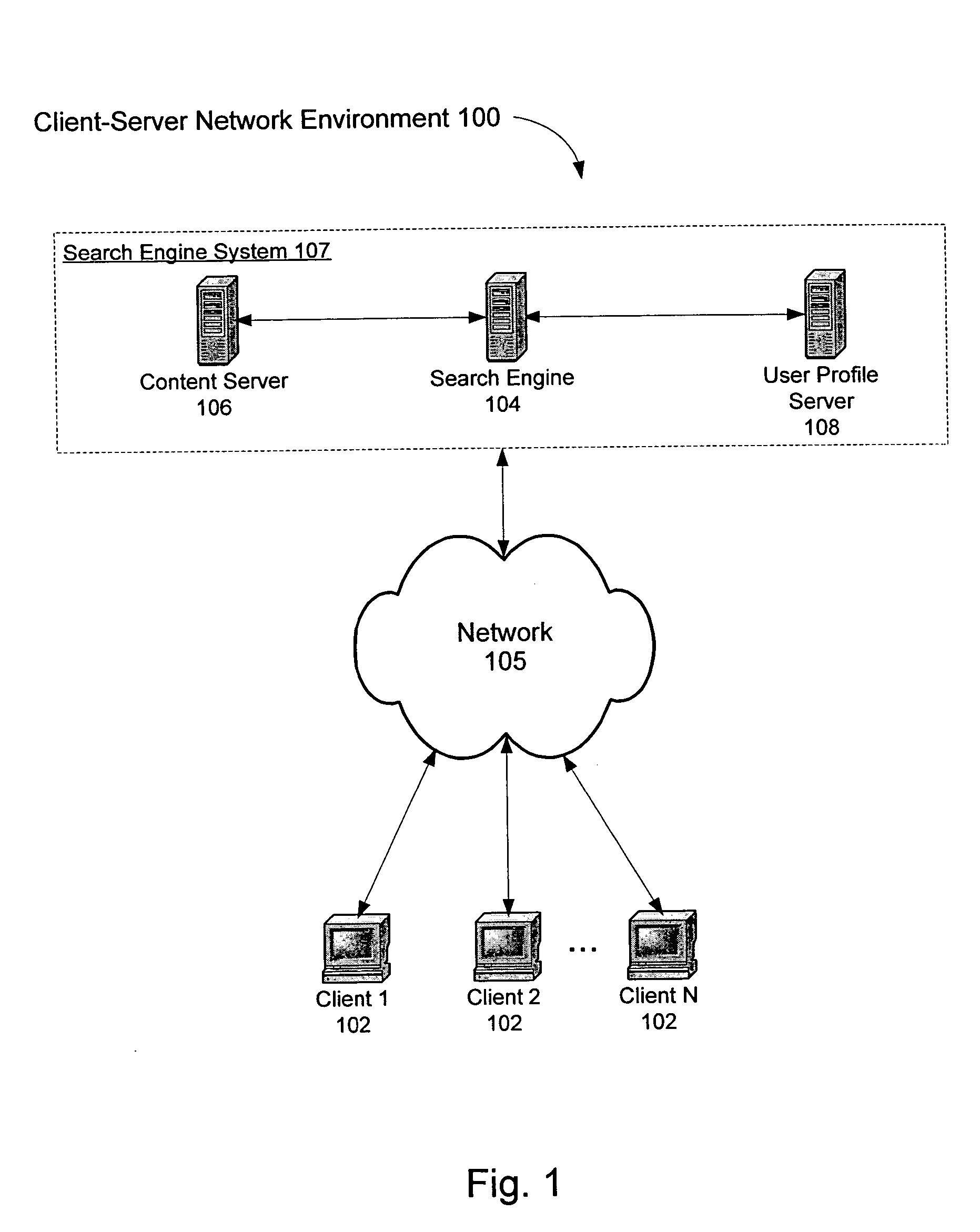
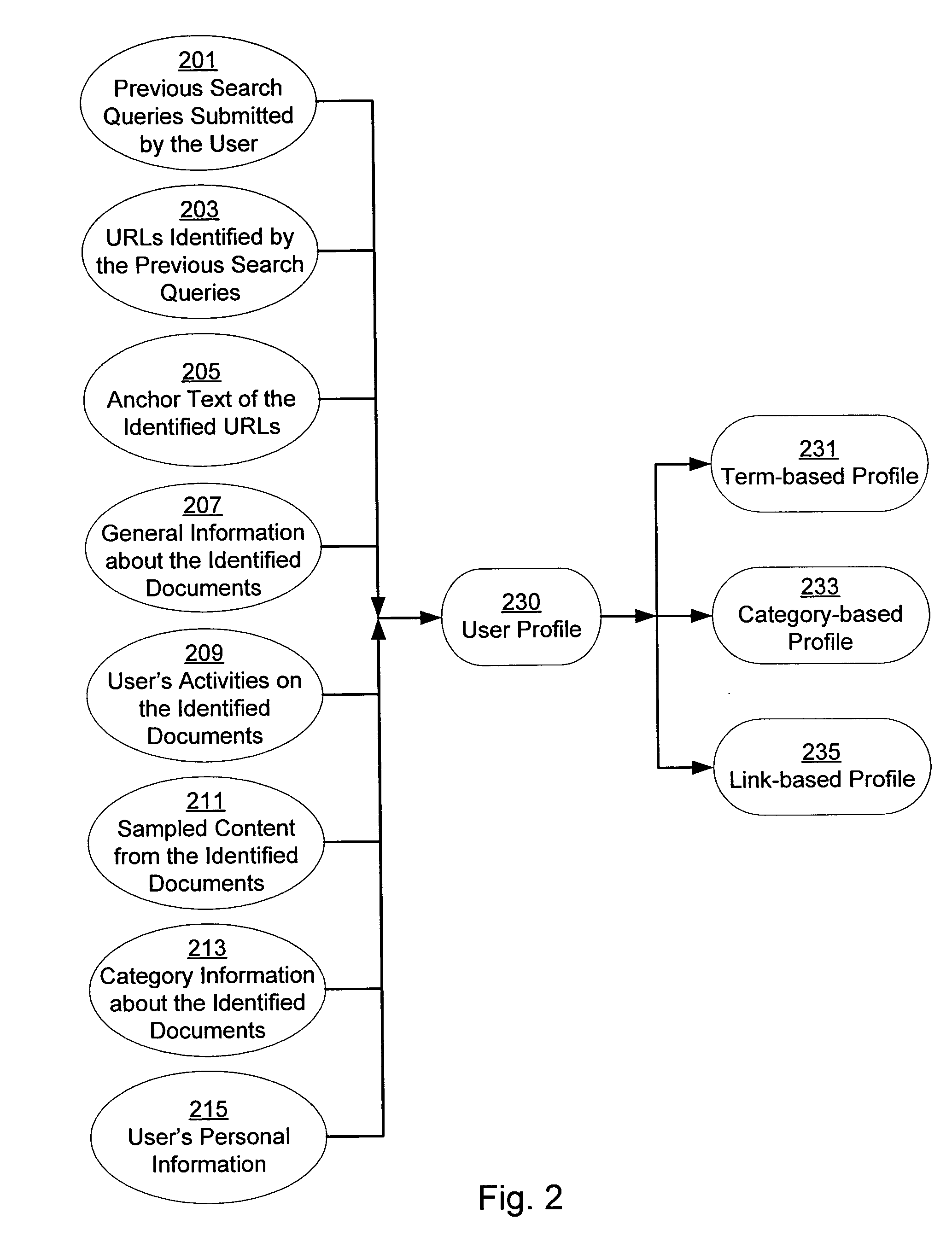
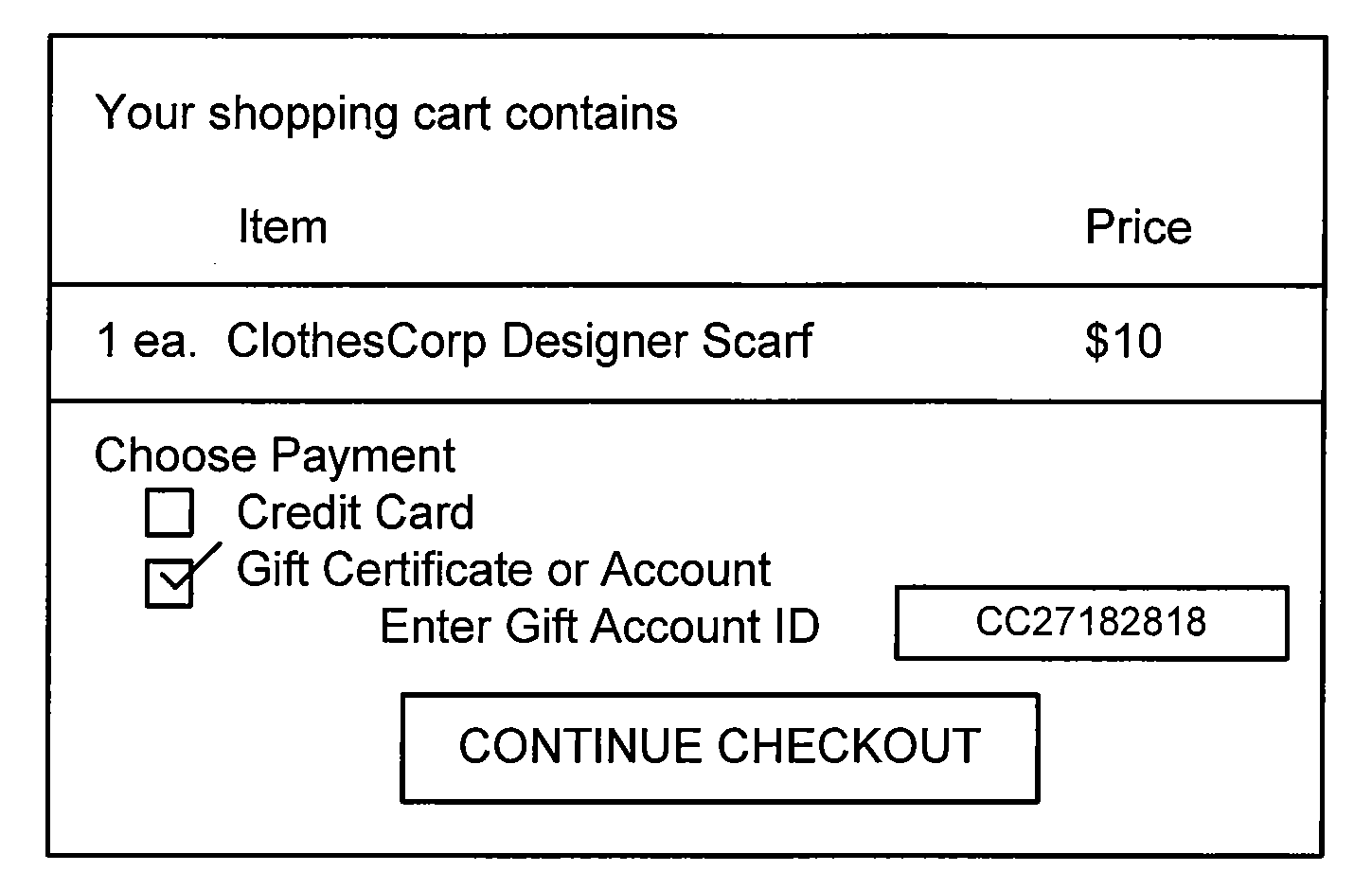
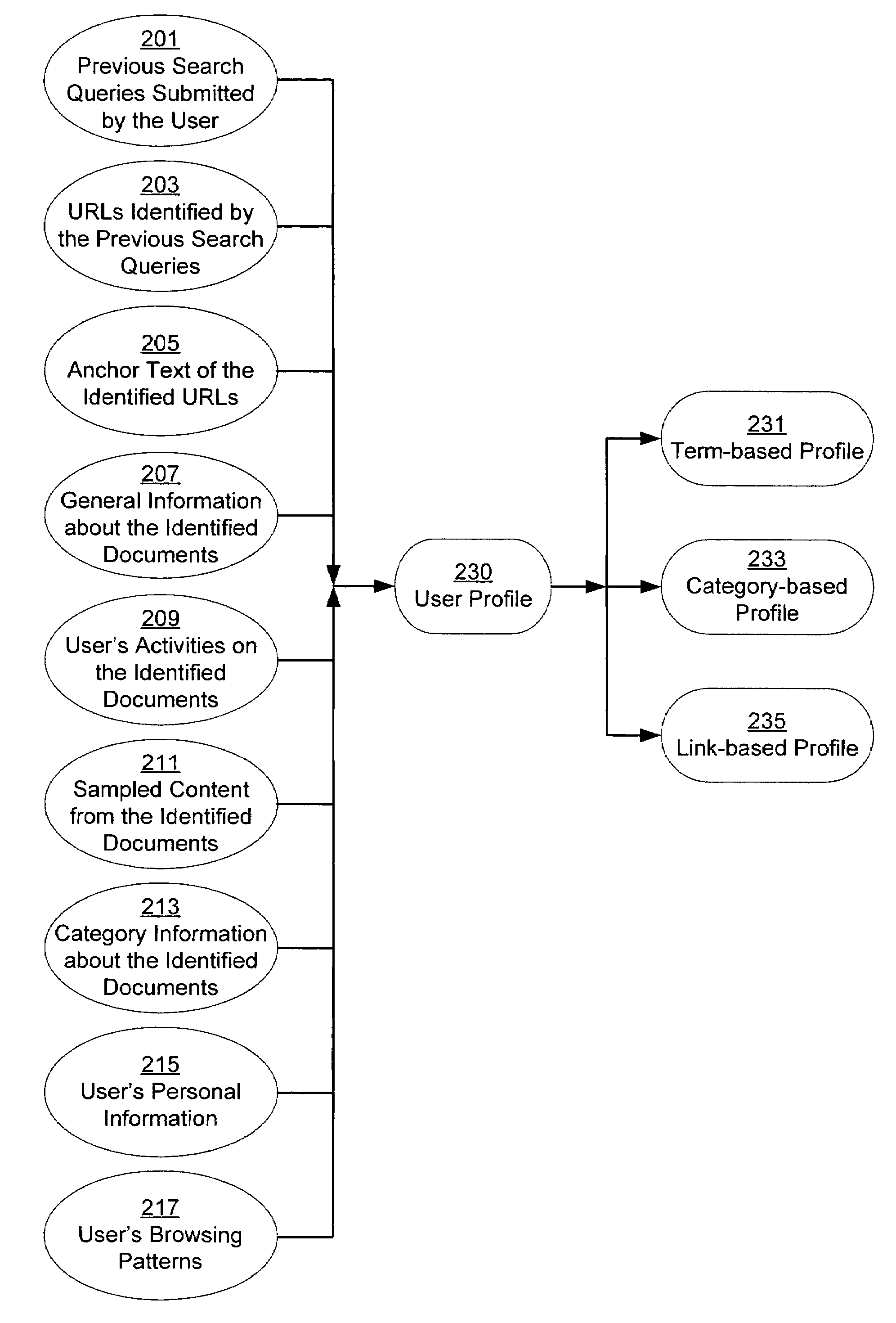
A system and method for creating a user profile and for using the user profile to order search results returned by a search engine. The user profile is based on search queries submitted by a user, the user's specific interaction with the documents identified by the search engine and personal information provided by the user. Generic scores associated with the search results are modulated by the user profile to measure their relevance to a user's preference and interest. The search results are re-ordered accordingly so that the most relevant results appear on the top of the list. User profiles can be created and / or stored on the client side or server side of a client-server network environment.
Owner:GOOGLE LLC
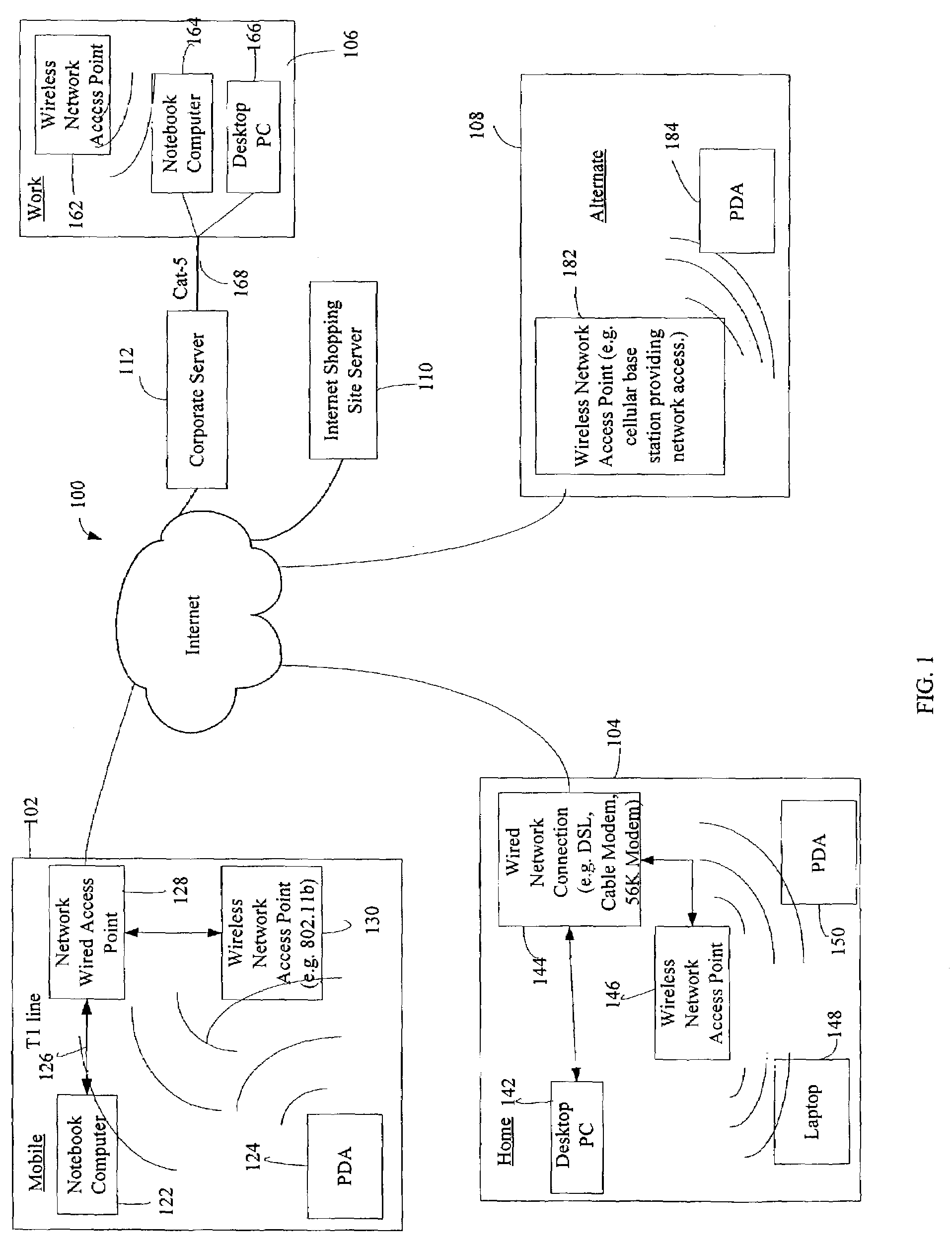
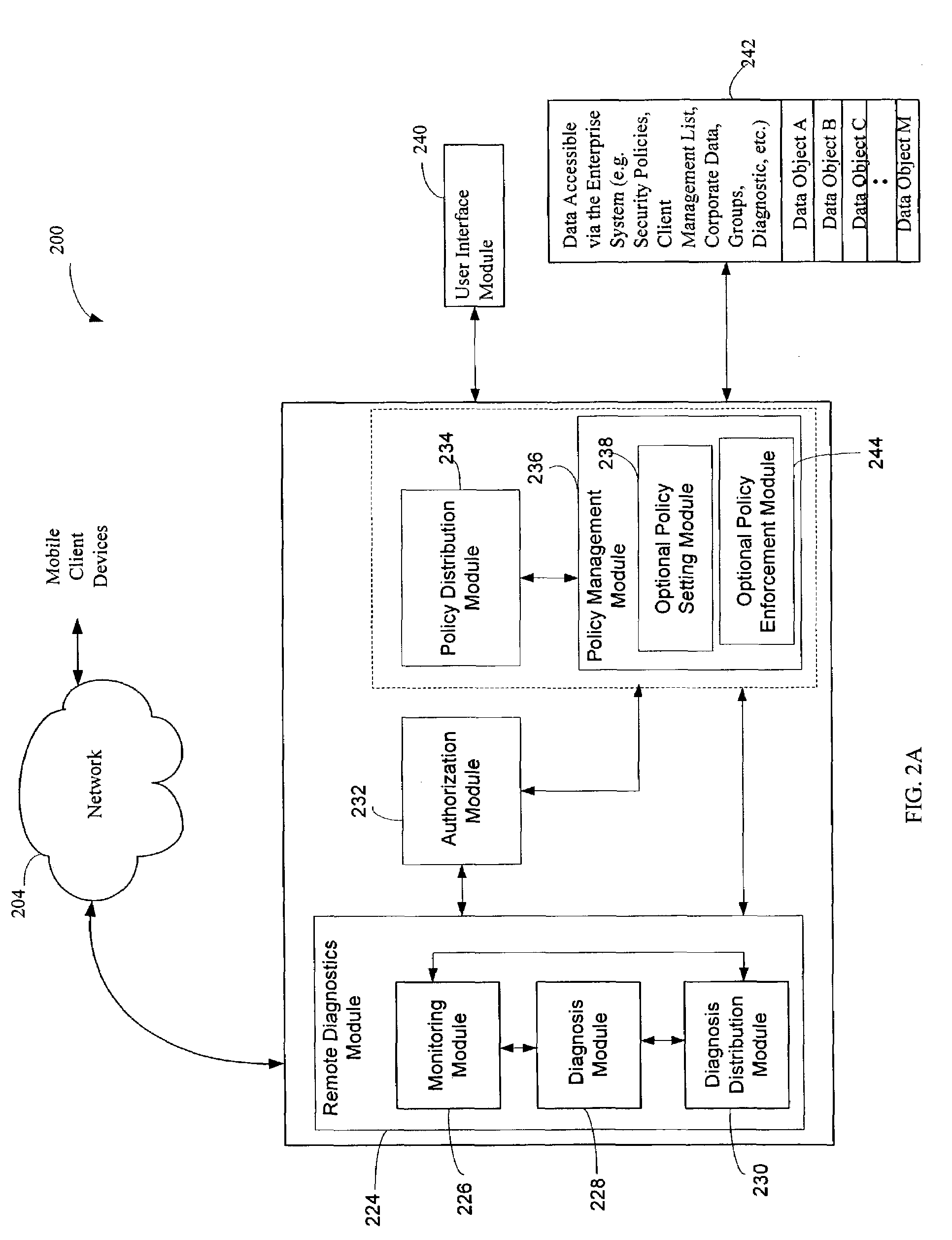
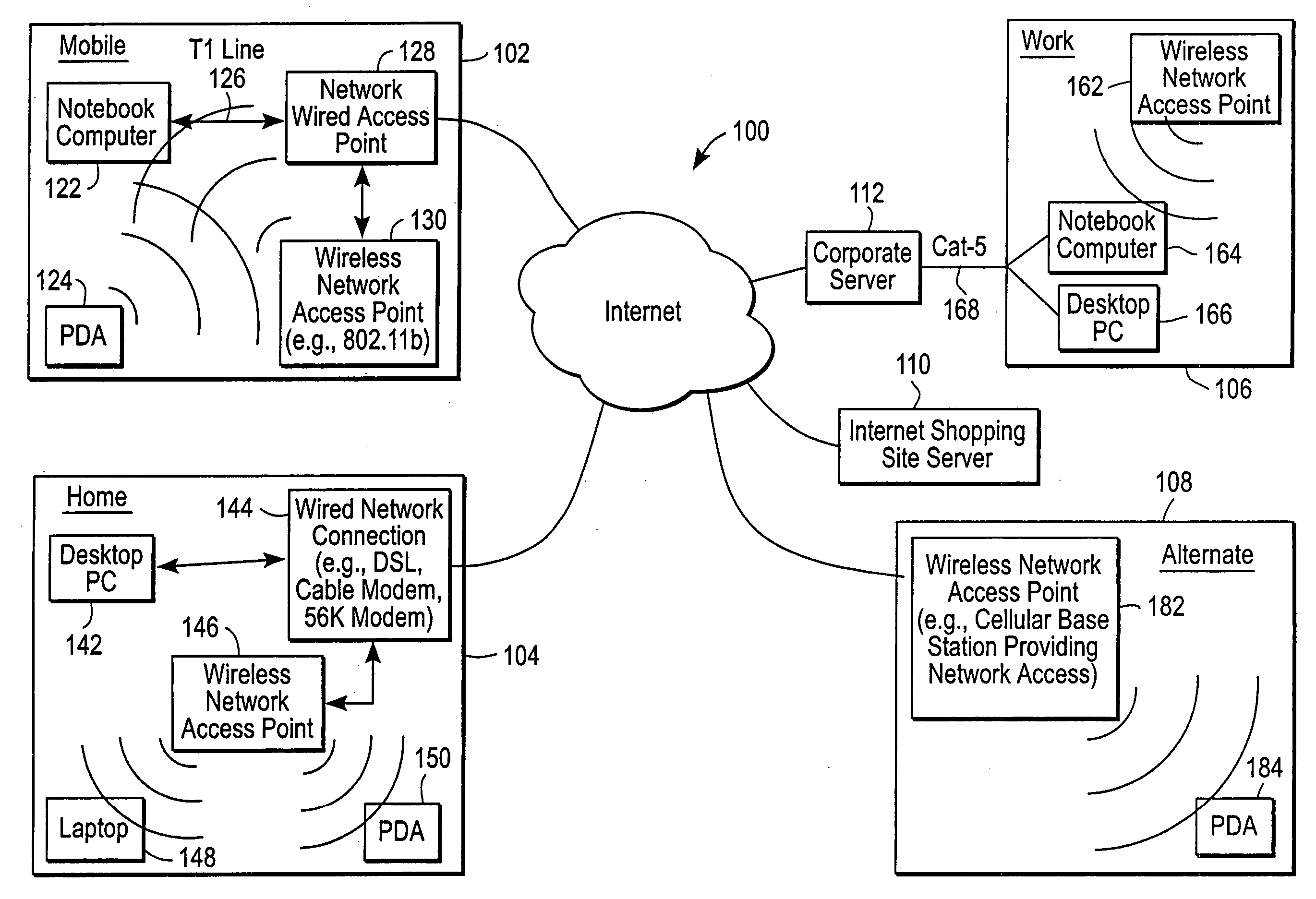
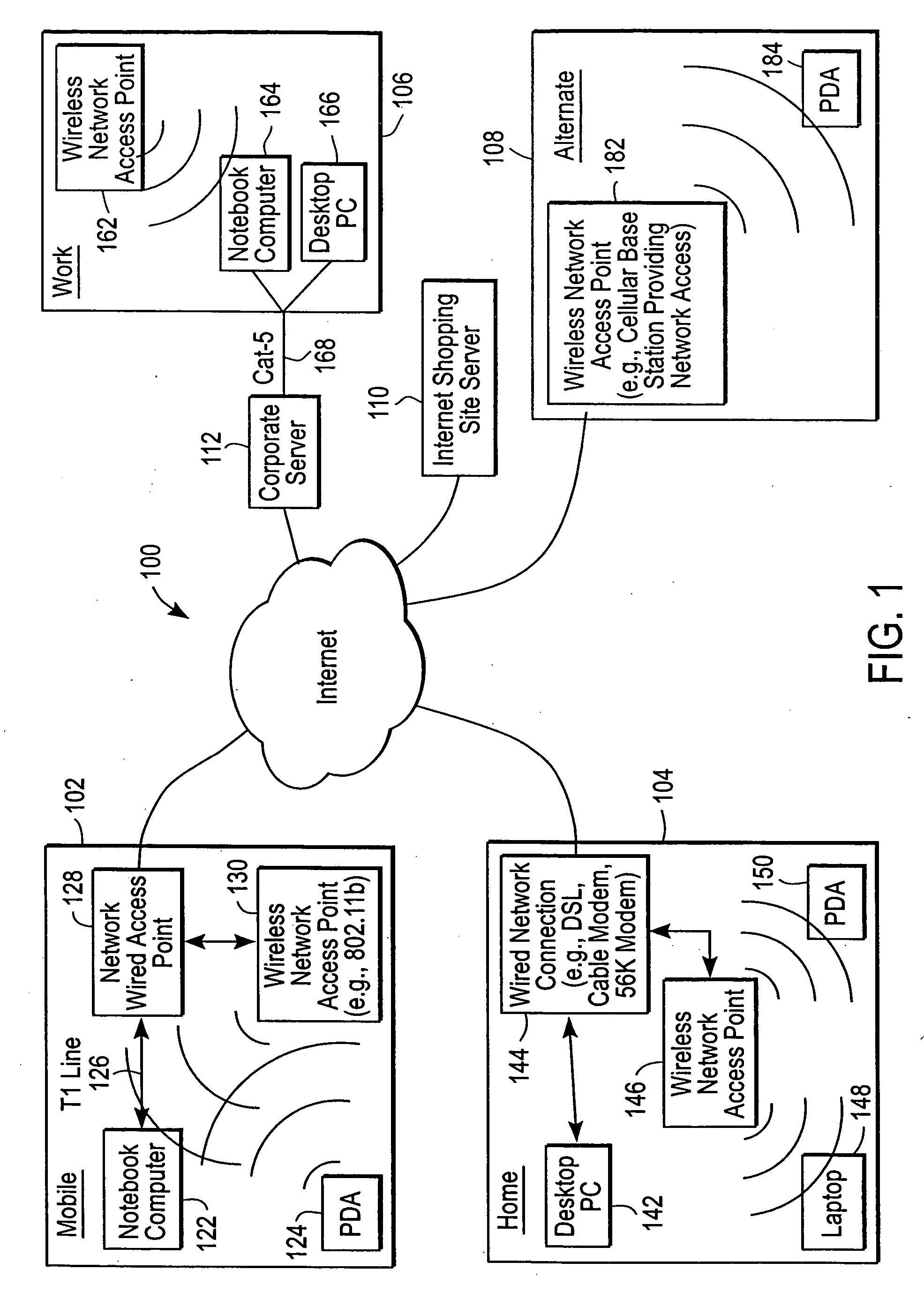
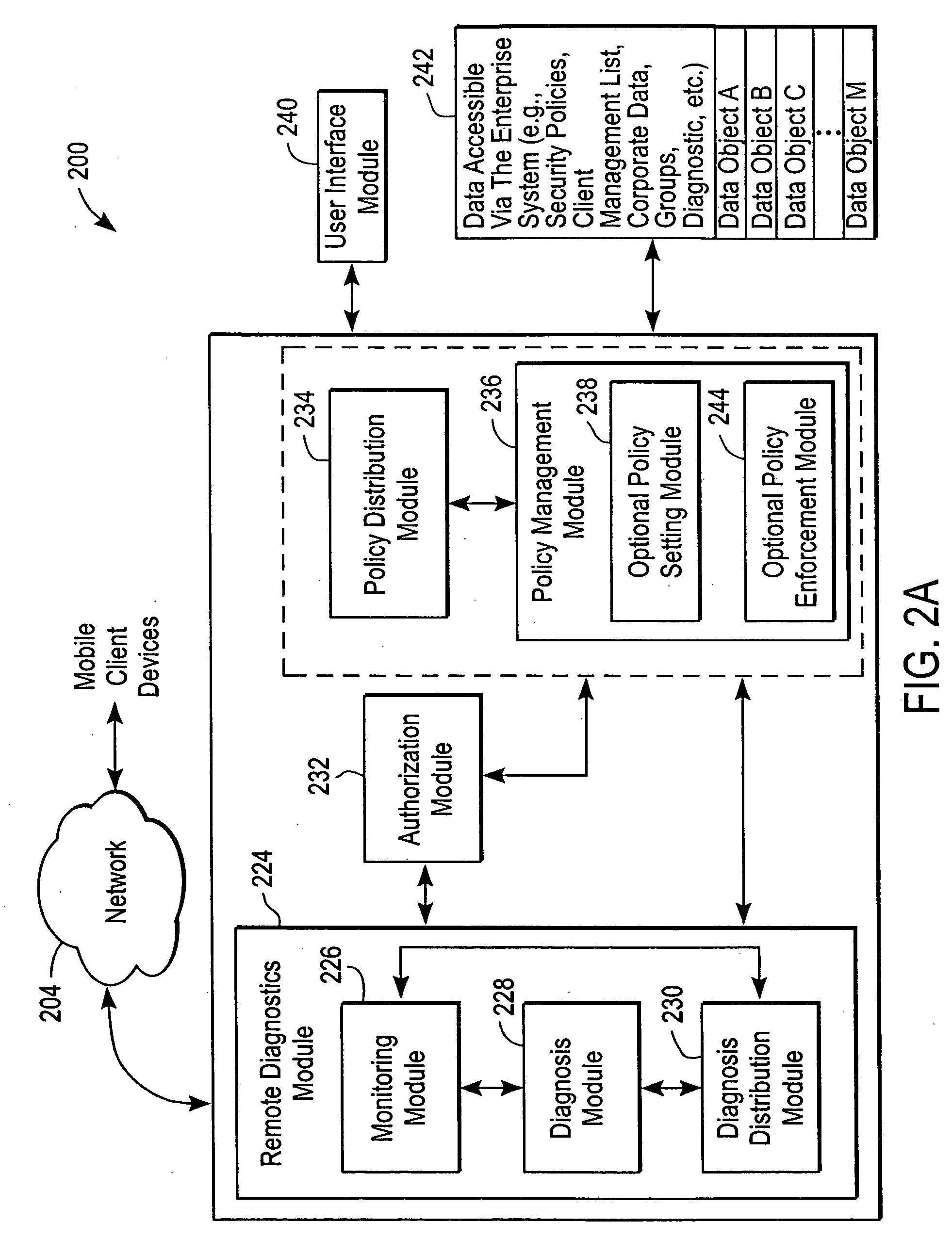
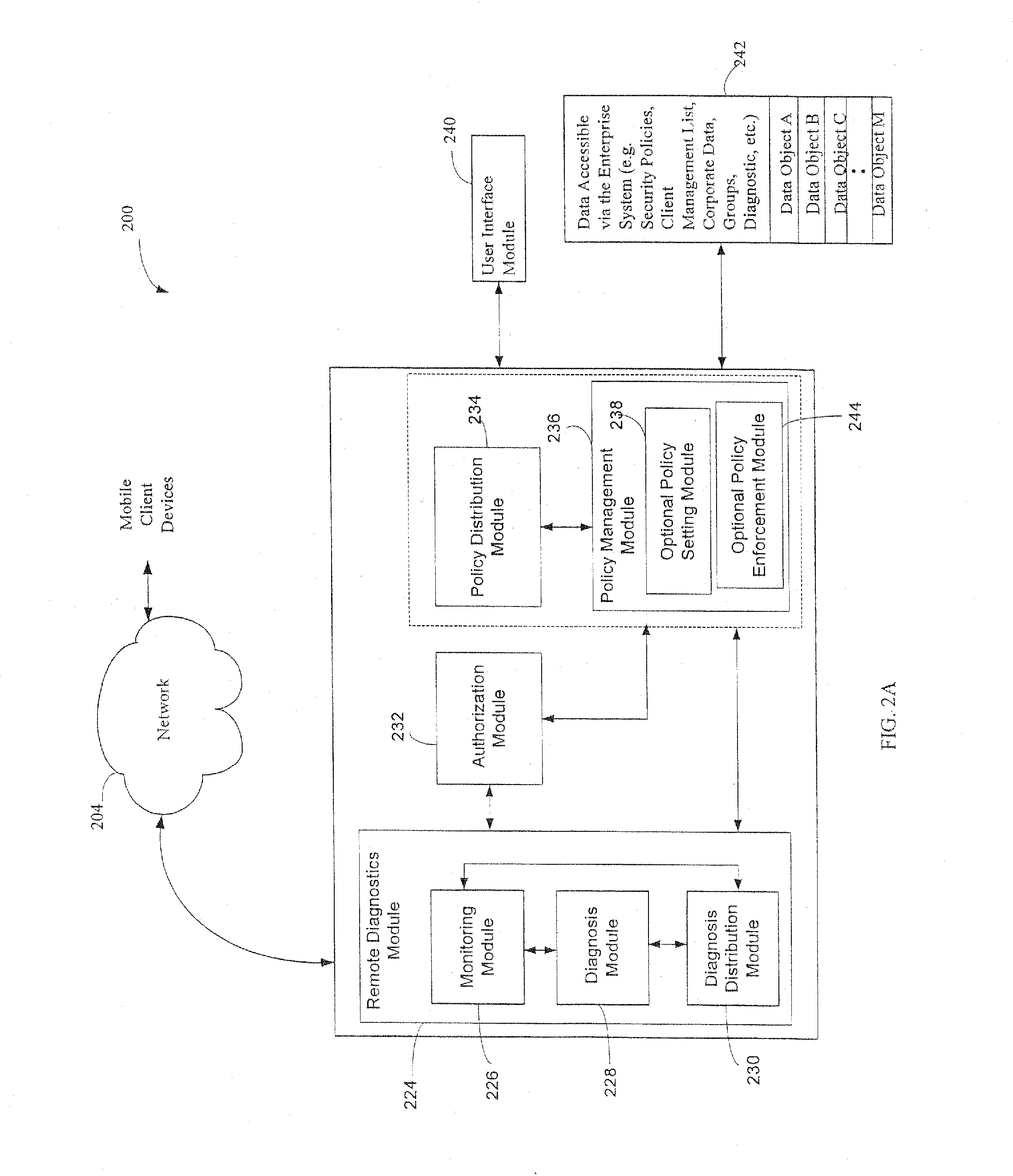
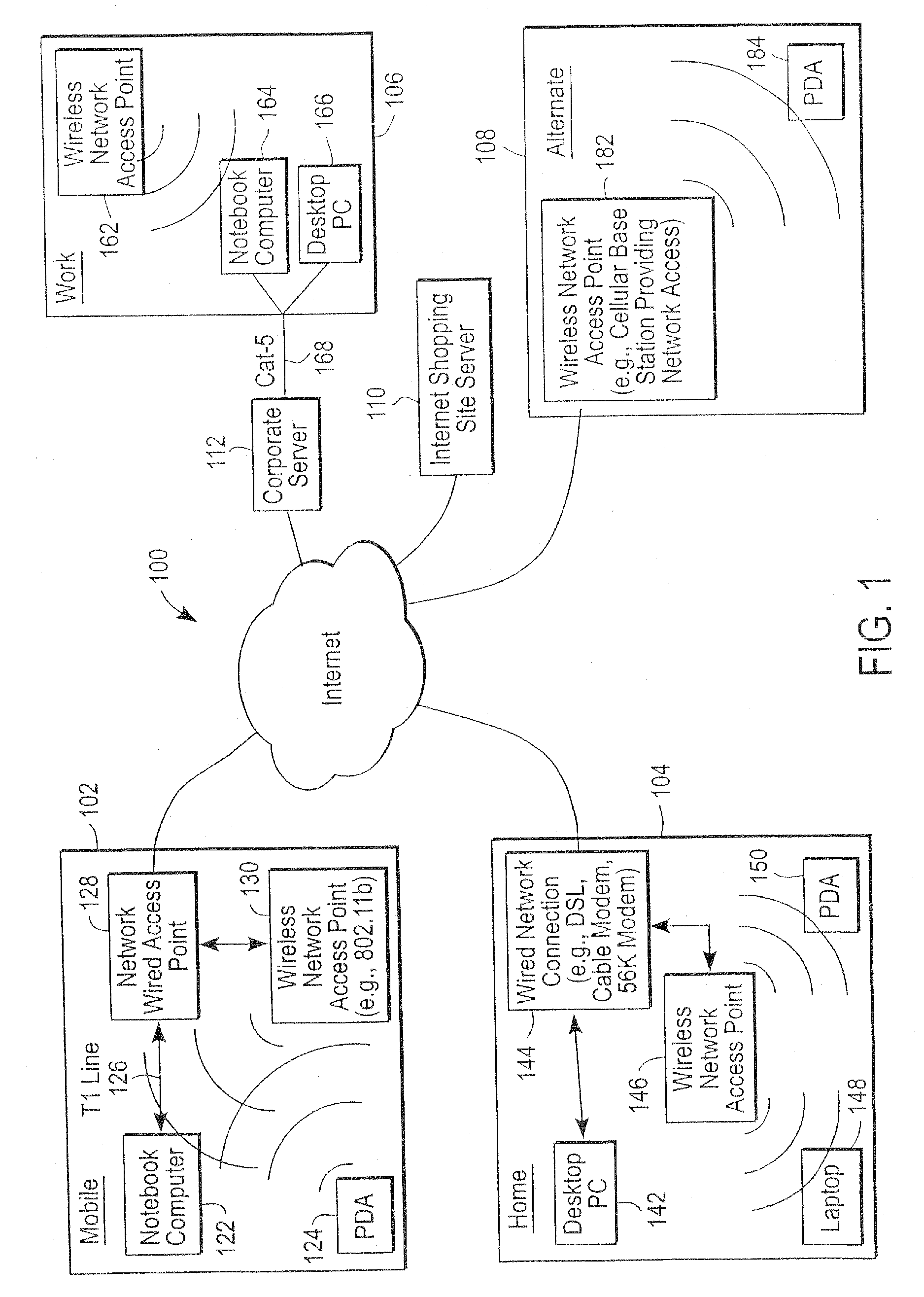
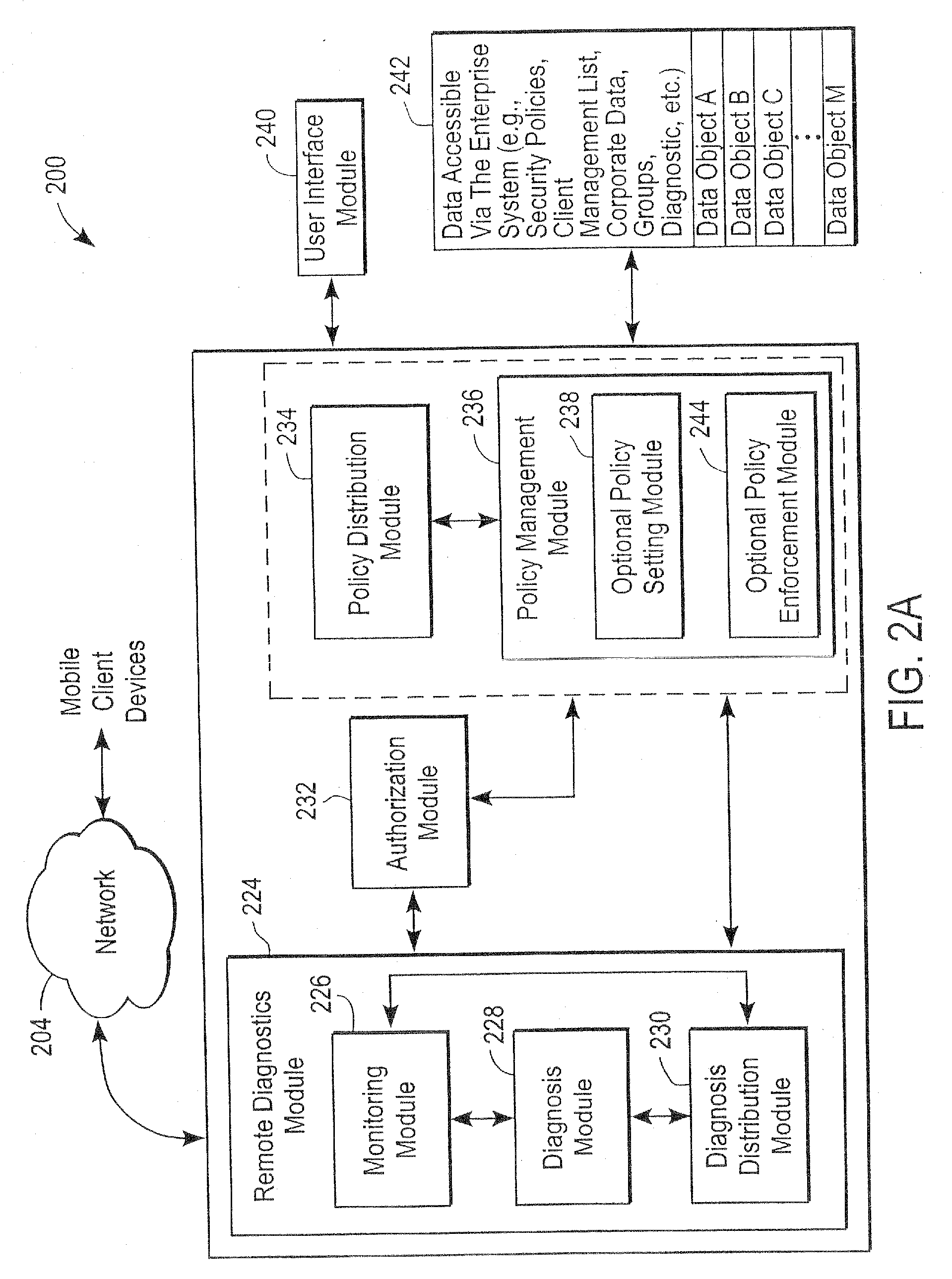
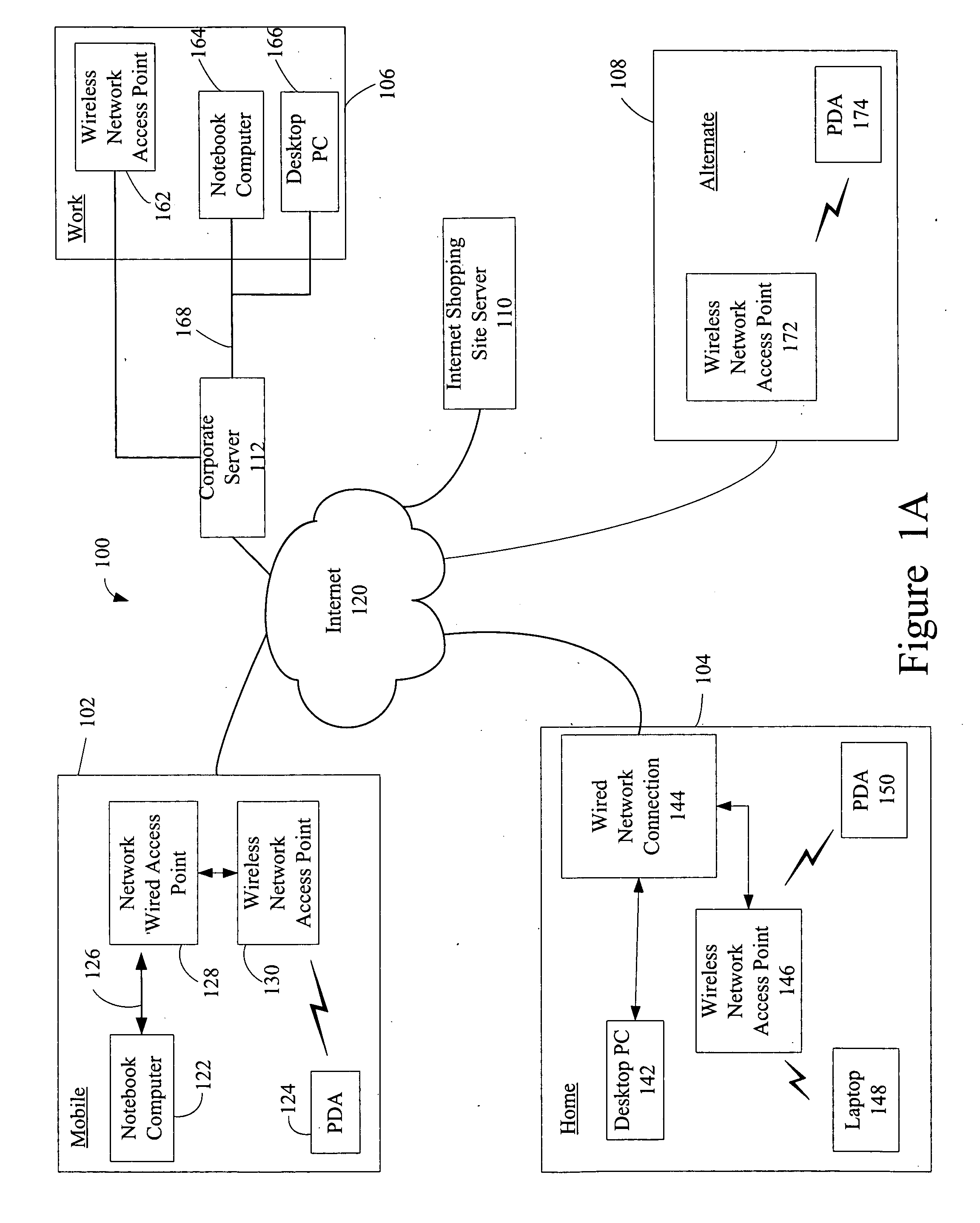
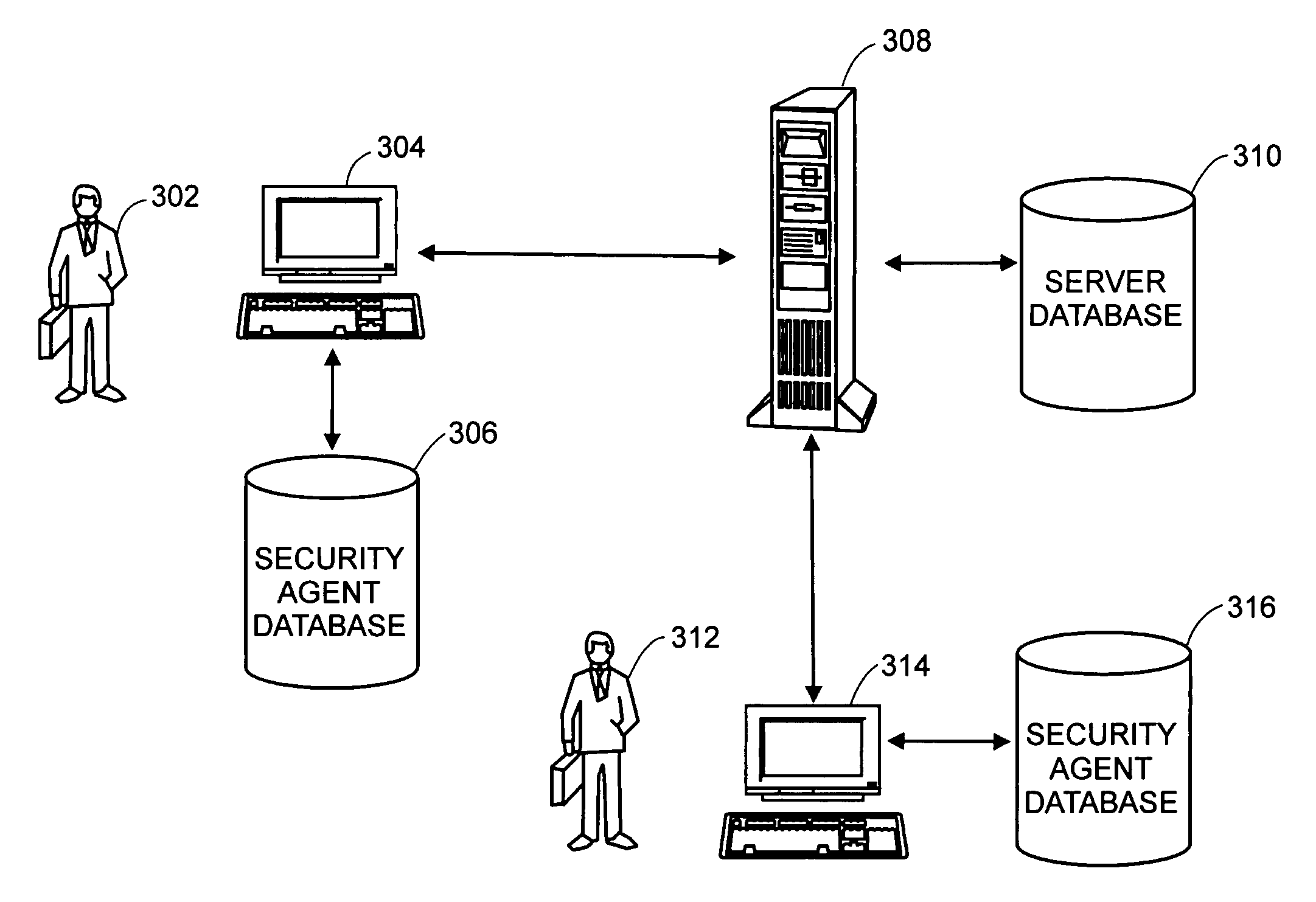
Administration of protection of data accessible by a mobile device
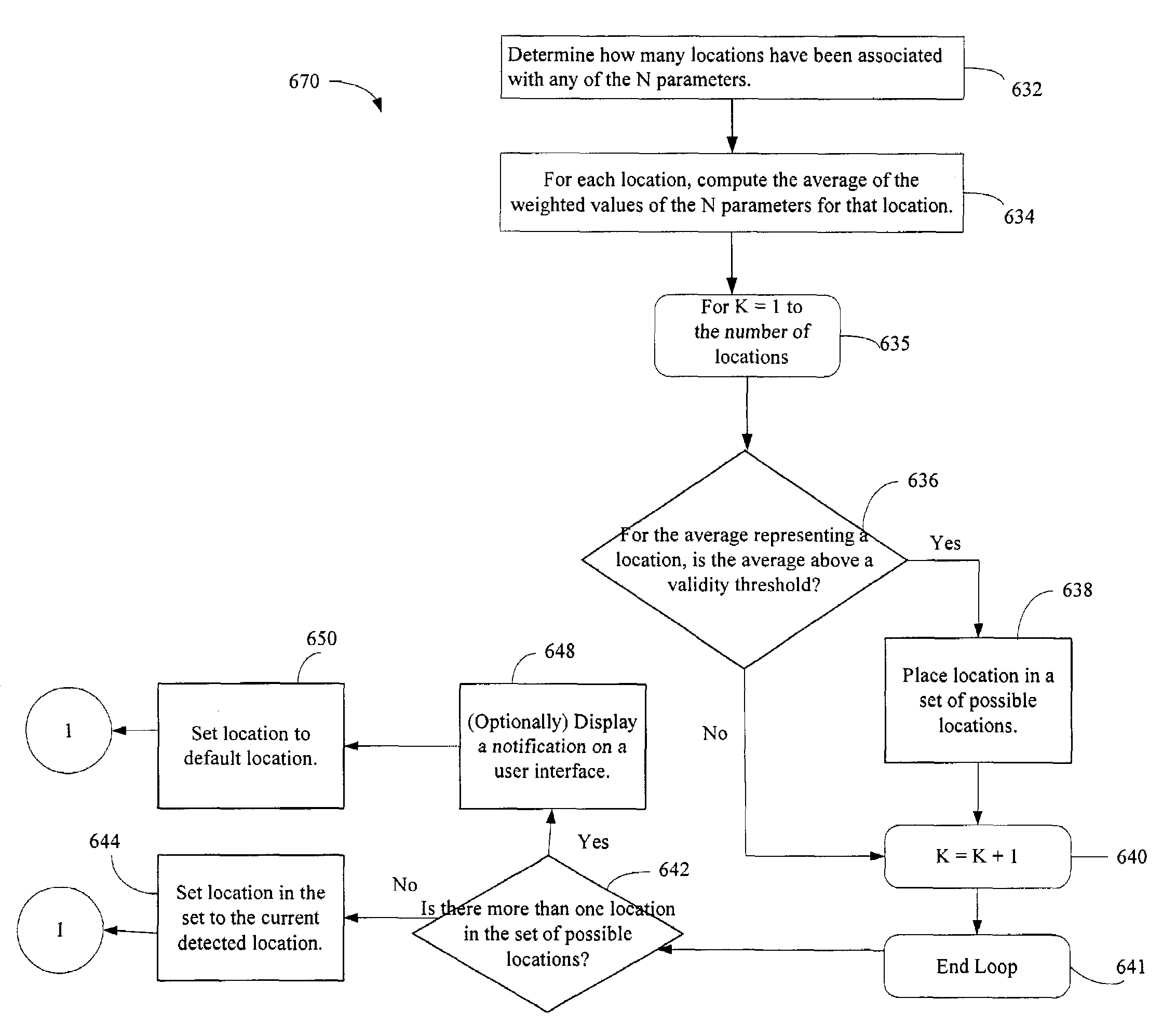
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Administration of protection of data accessible by a mobile device
ActiveUS20050055578A1Digital data processing detailsMultiple digital computer combinationsAnti virusEnterprise networking
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Administration of protection of data accessible by a mobile device
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
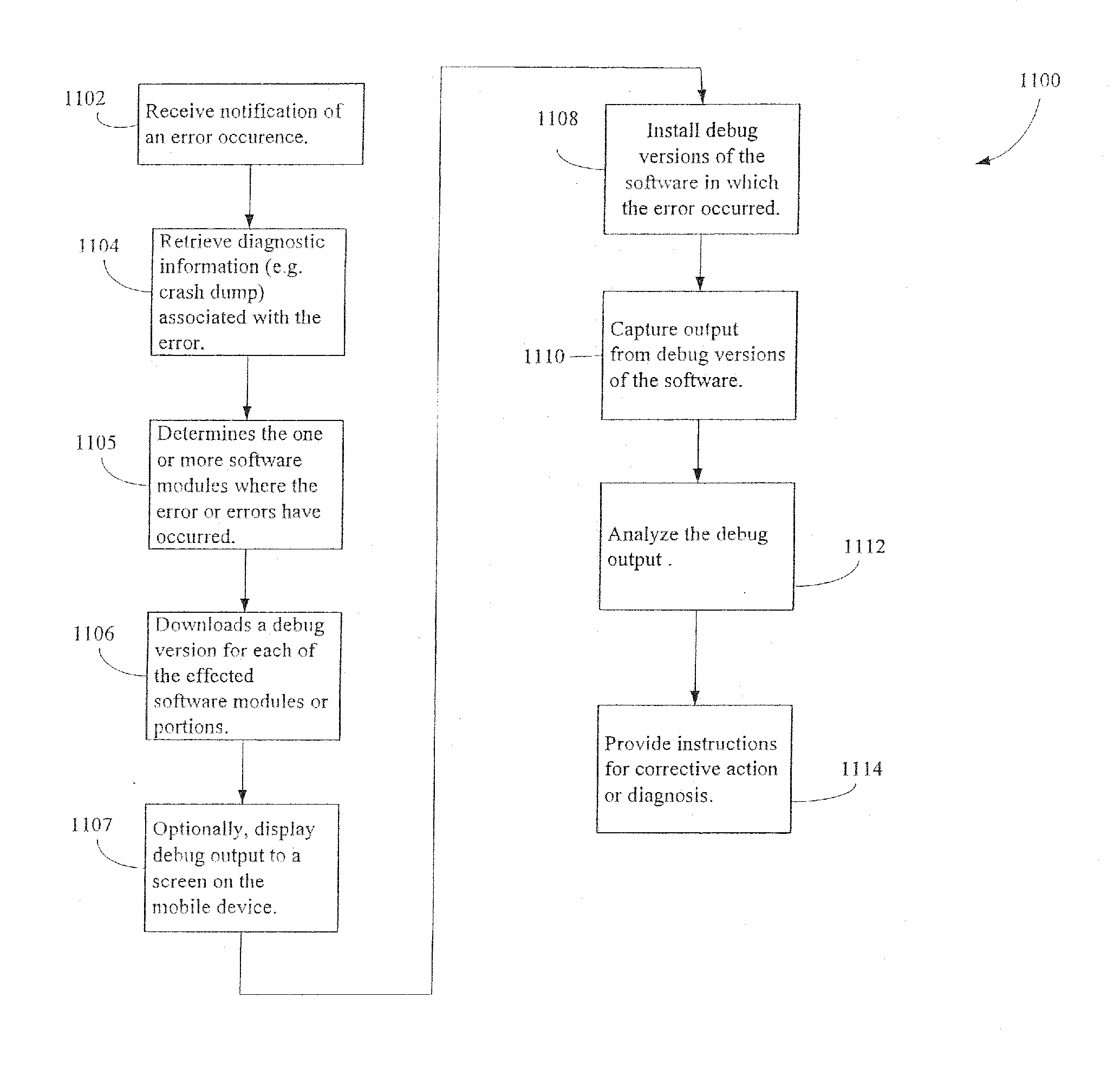
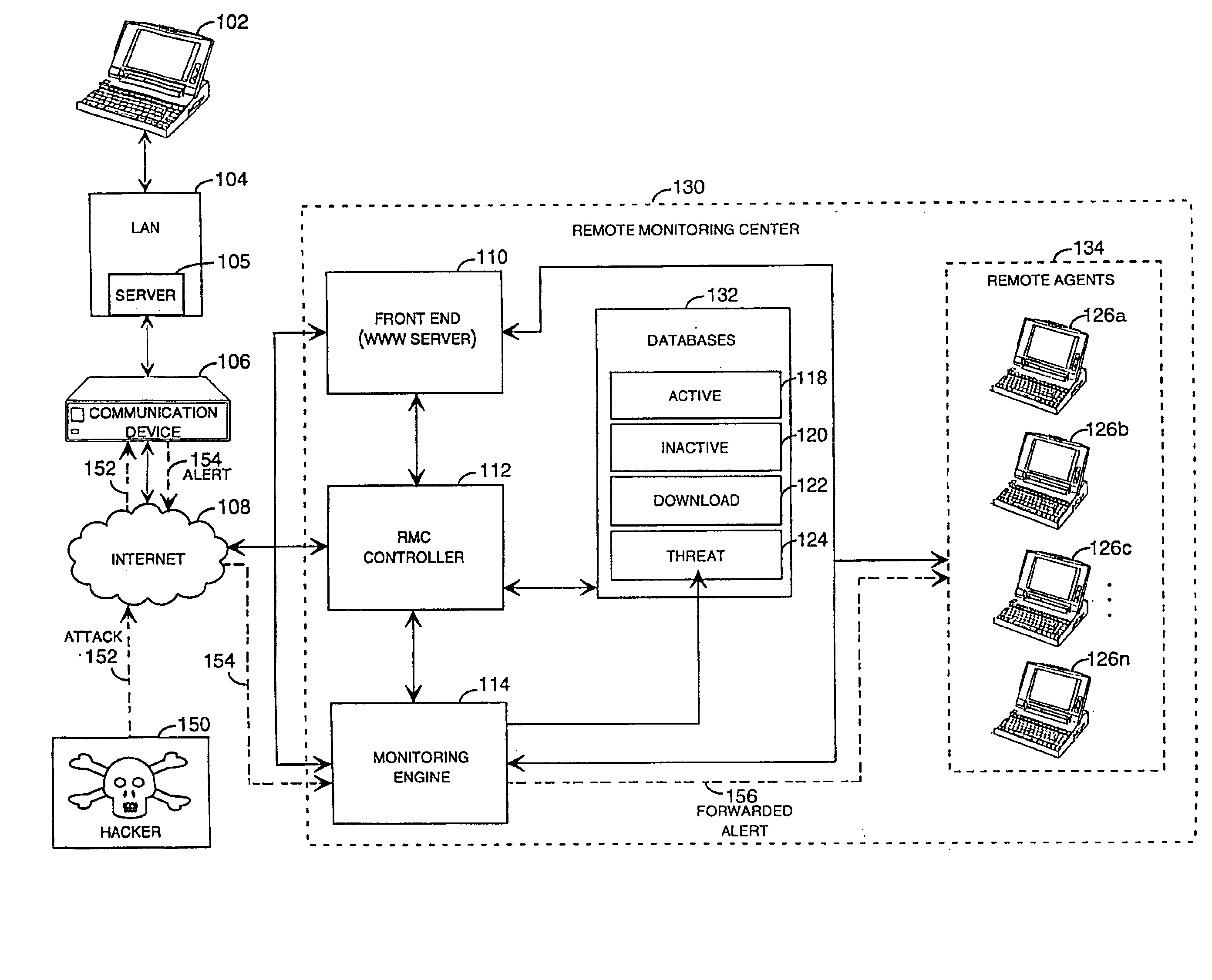
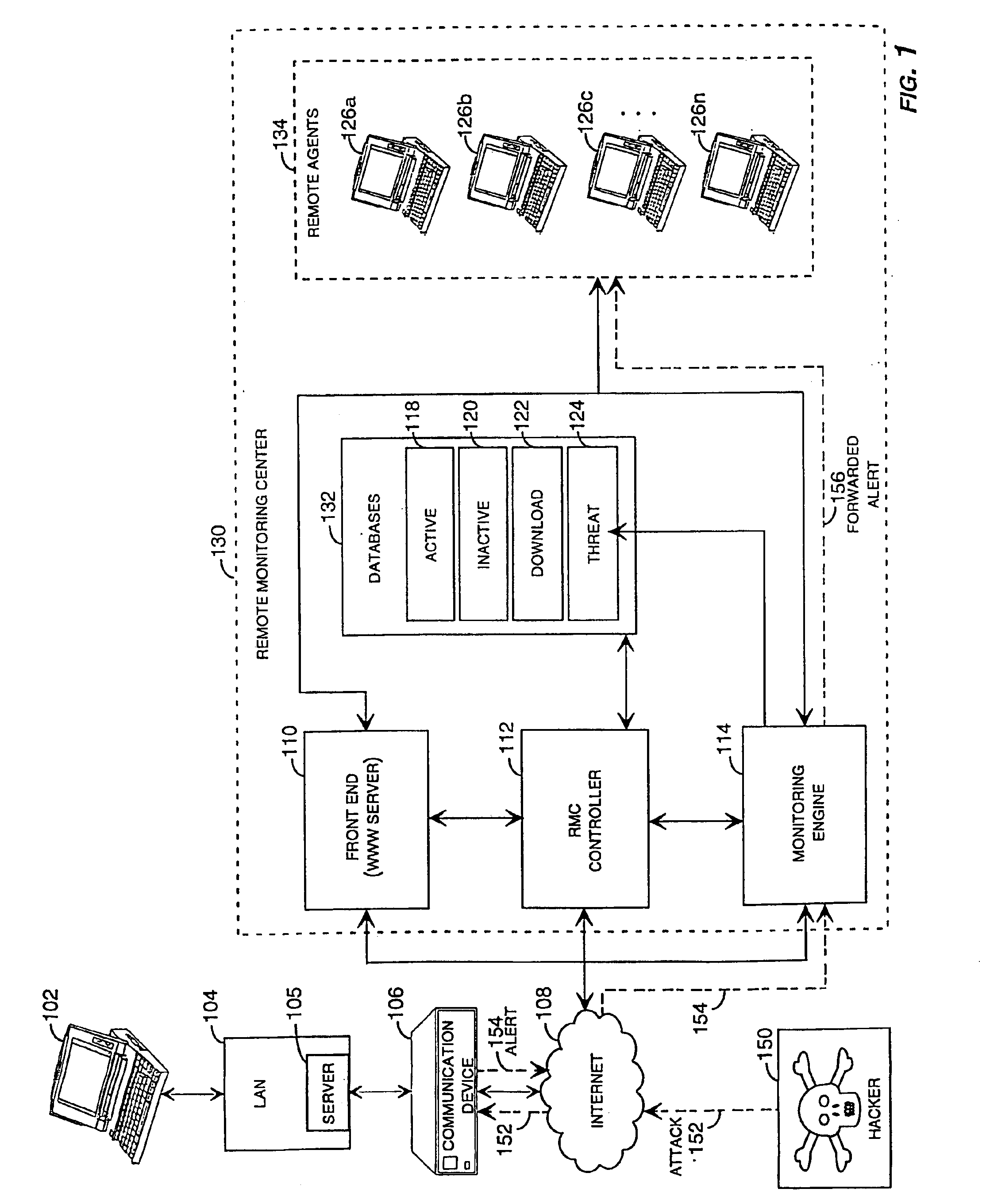
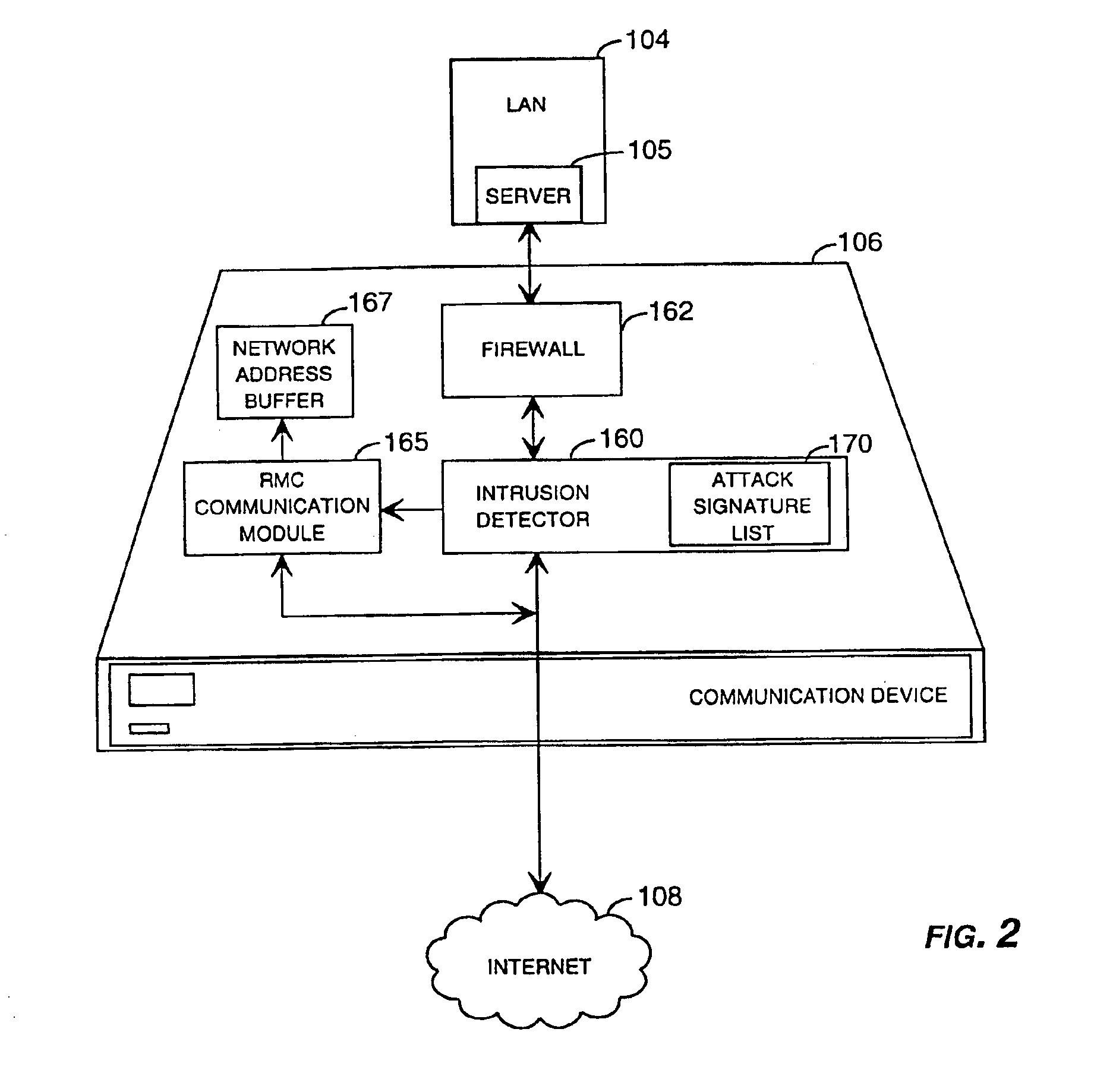
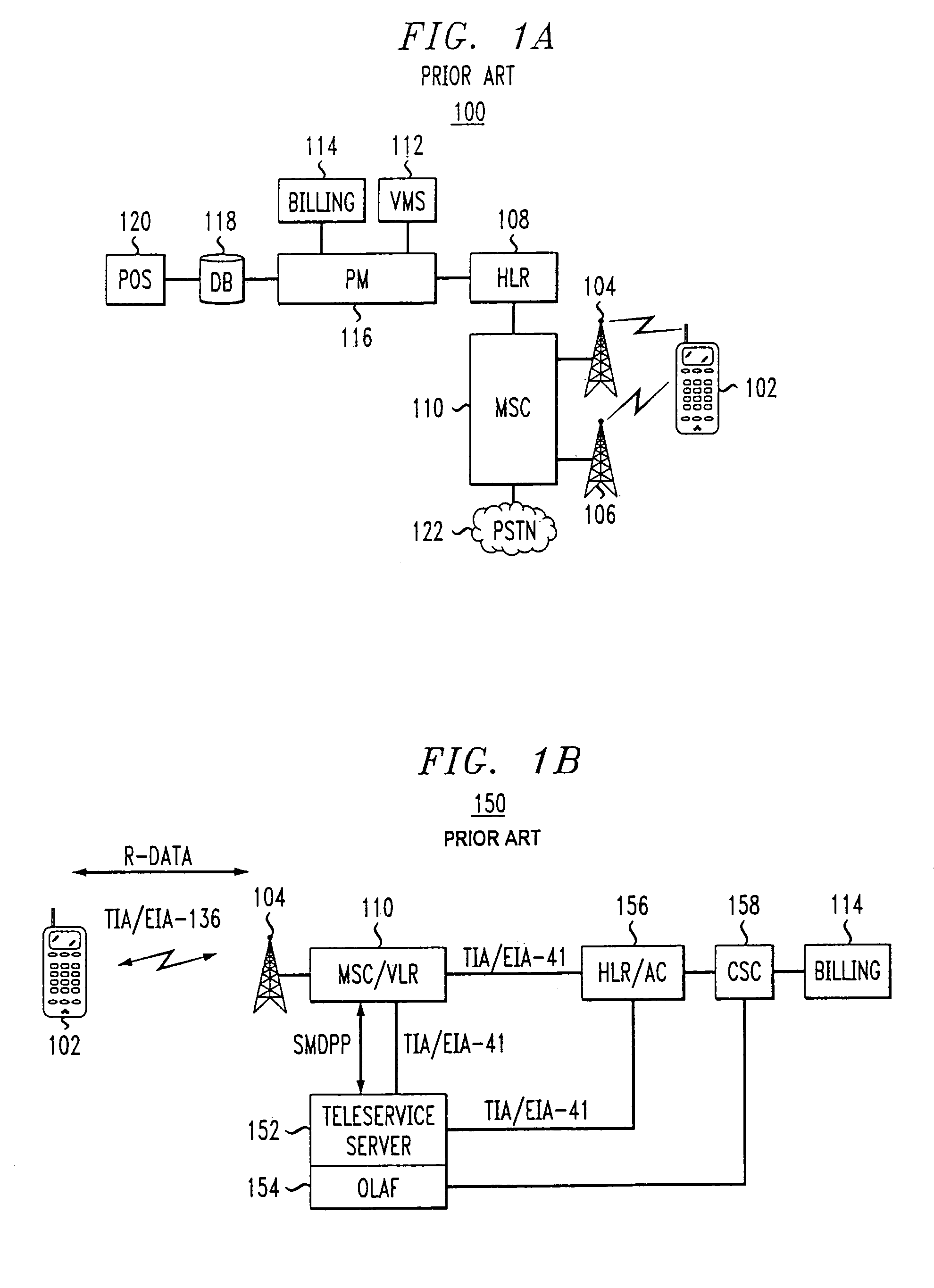
Method and system for remotely configuring and monitoring a communication device
InactiveUS6990591B1Rapid responseMemory loss protectionUnauthorized memory use protectionImage resolutionThe Internet
Owner:SECUREWORKS
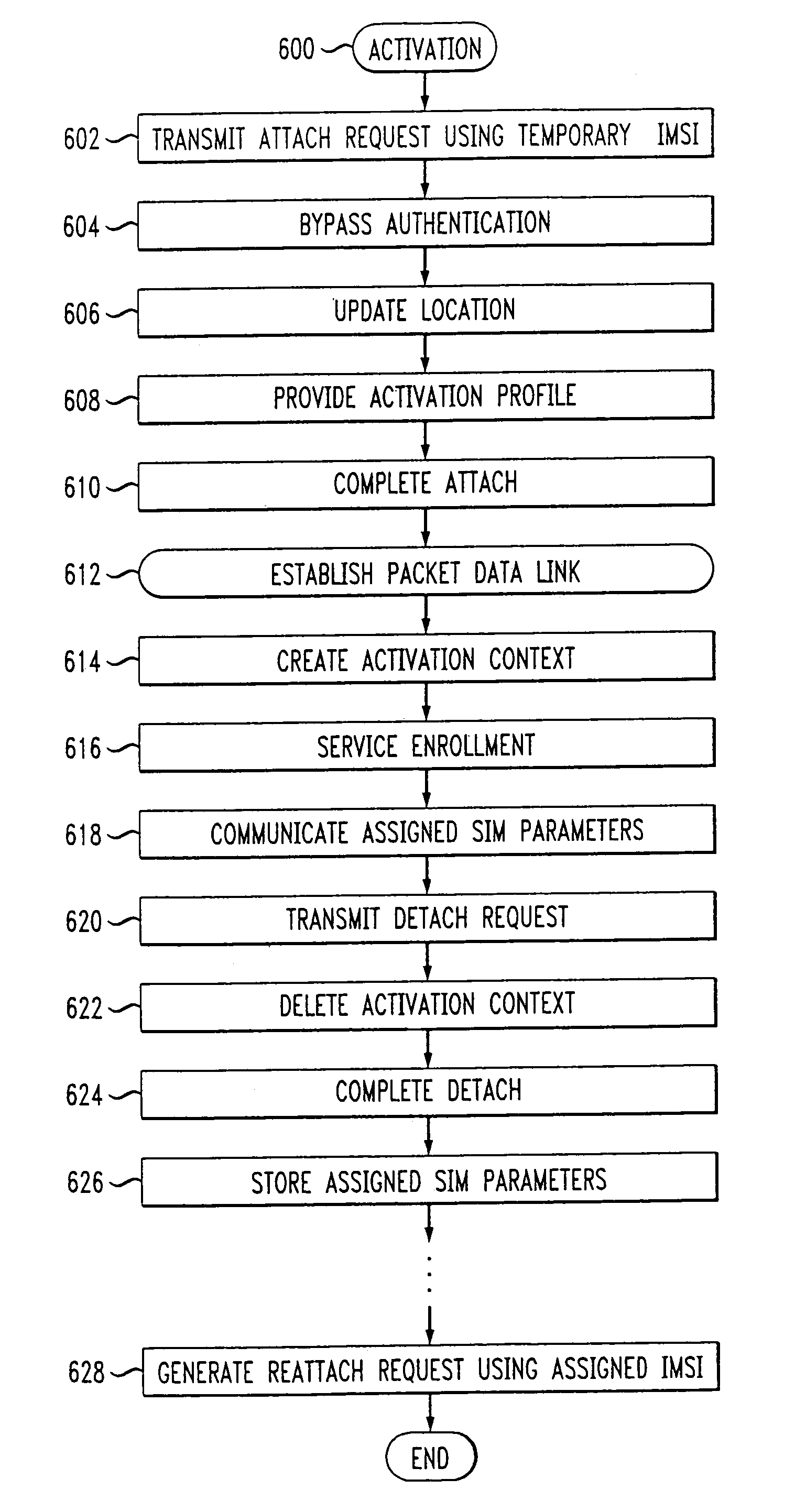
Activation and remote modification of wireless services in a packet network context
InactiveUS7266371B1The process is convenient and fastConvenient and quick mobile device activationRadio/inductive link selection arrangementsSubstation equipmentTerms of serviceThird generation
A third generation (3G) mobile communication system supports an over-the-air activation scheme utilizing a wireless packet data protocol. A subscriber identity module (SIM) is preloaded with temporary operating parameters such as a temporary international mobile subscriber identity (IMSI) that is used for initial access to a network. Once a packet data protocol communication link is established between the mobile device and a network support node, the user may remotely subscribe to a number of service terms using the mobile device. In addition, an activation procedure is carried out to assign permanent operating parameters, e.g., a permanent IMSI, to the SIM. After activation, the user can remotely modify existing terms or remotely enroll in additional service features via a wireless IP link between the mobile device and a network support node.
Owner:AT&T WIRELESS SERVICES
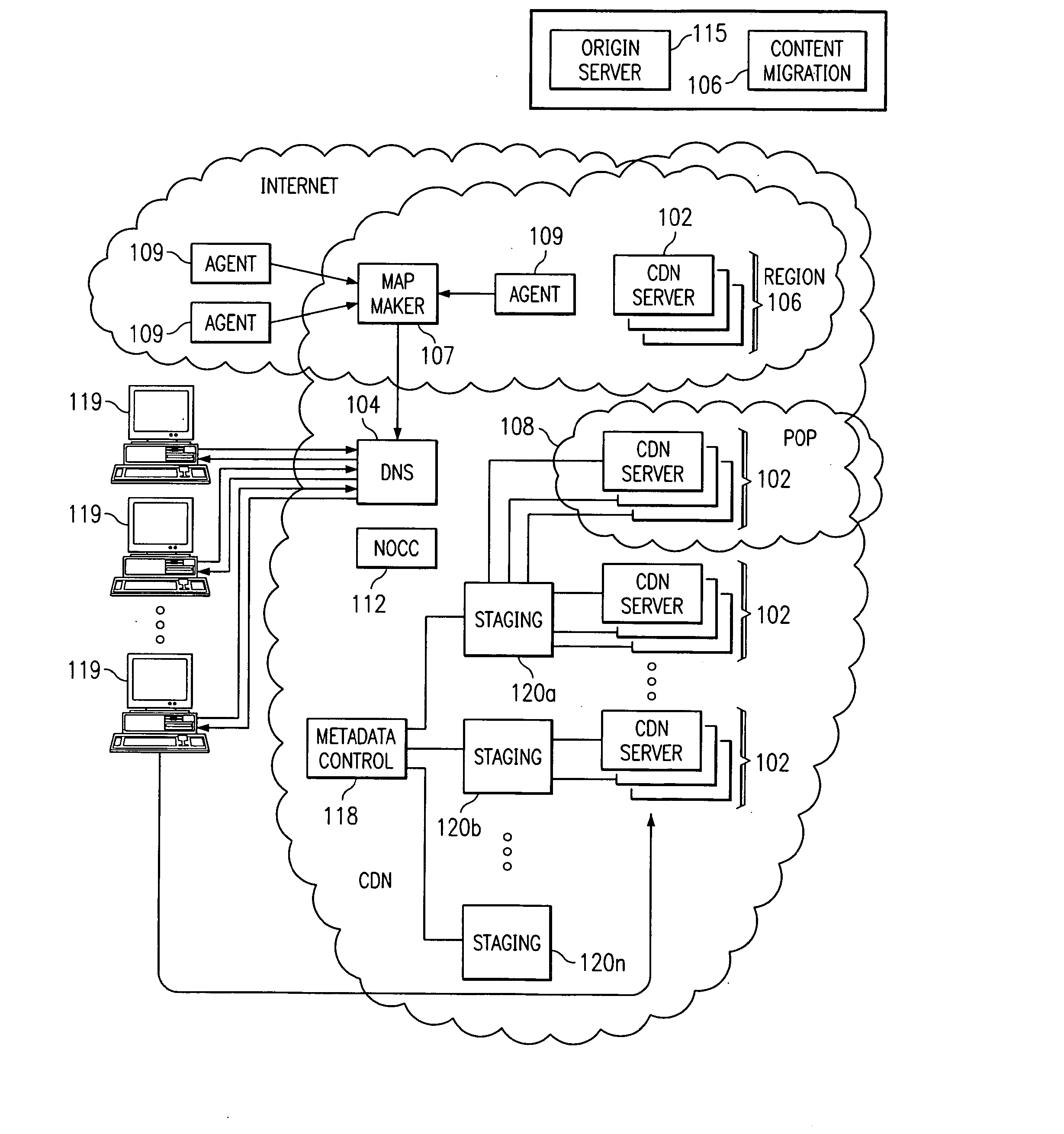
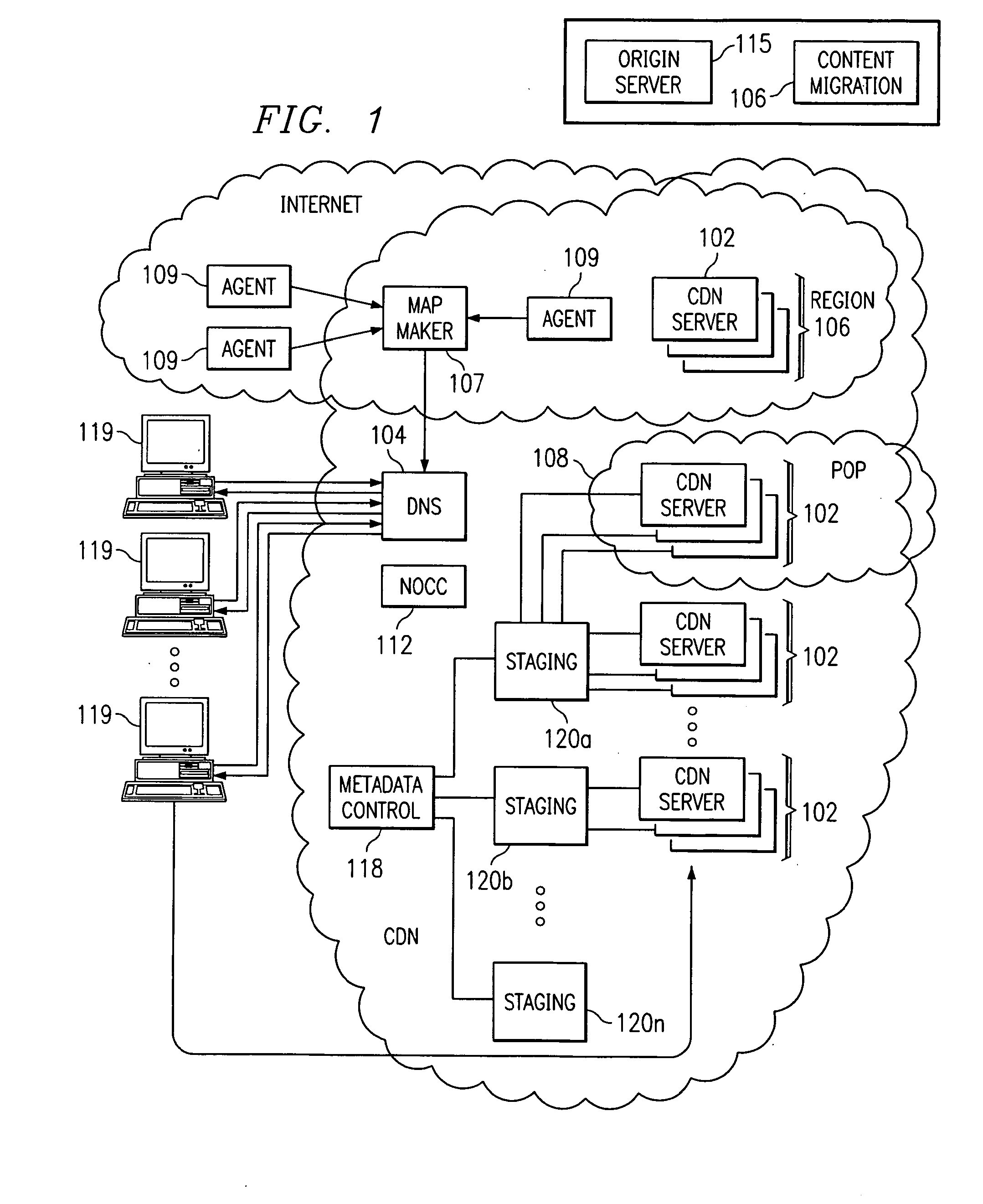
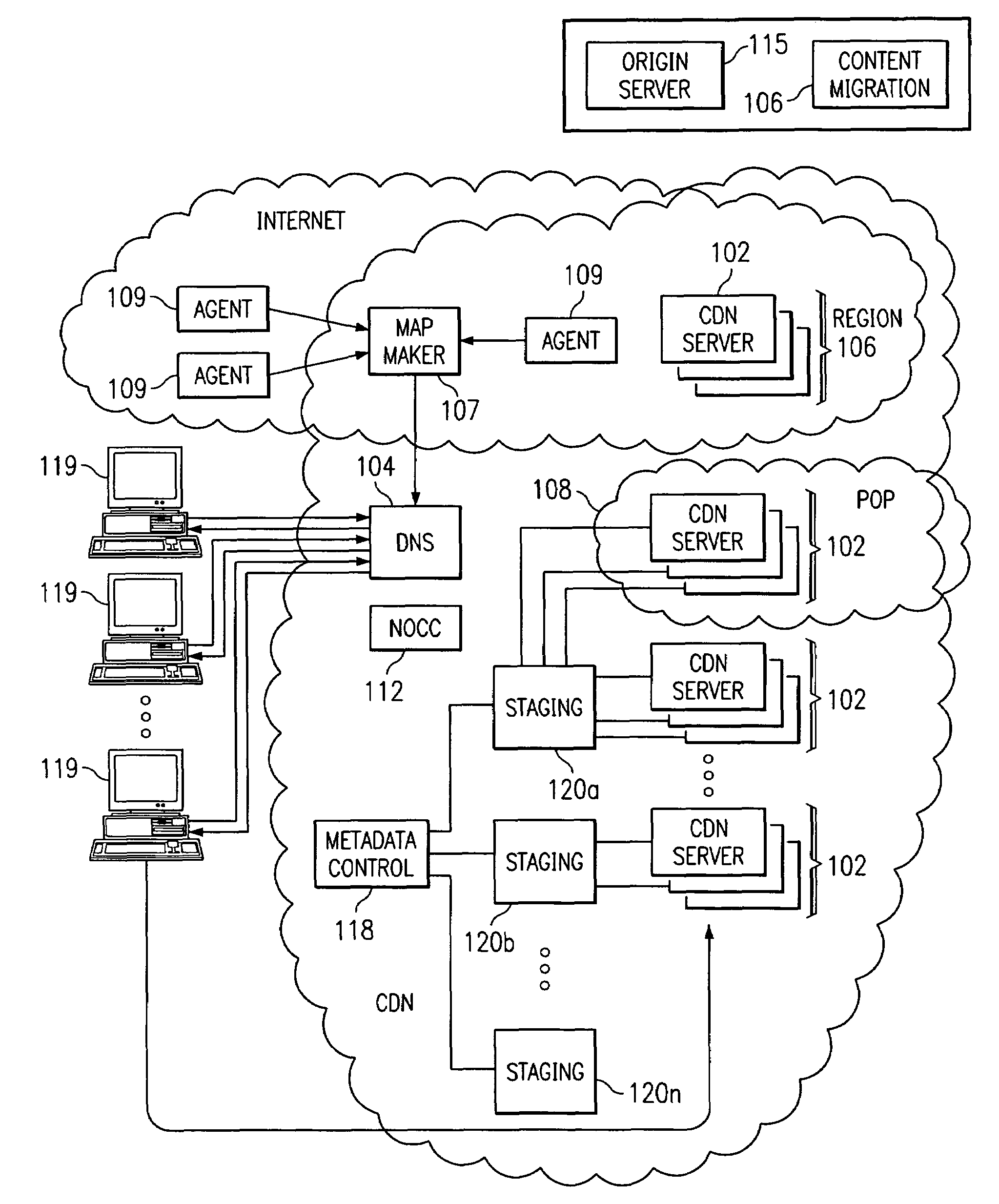
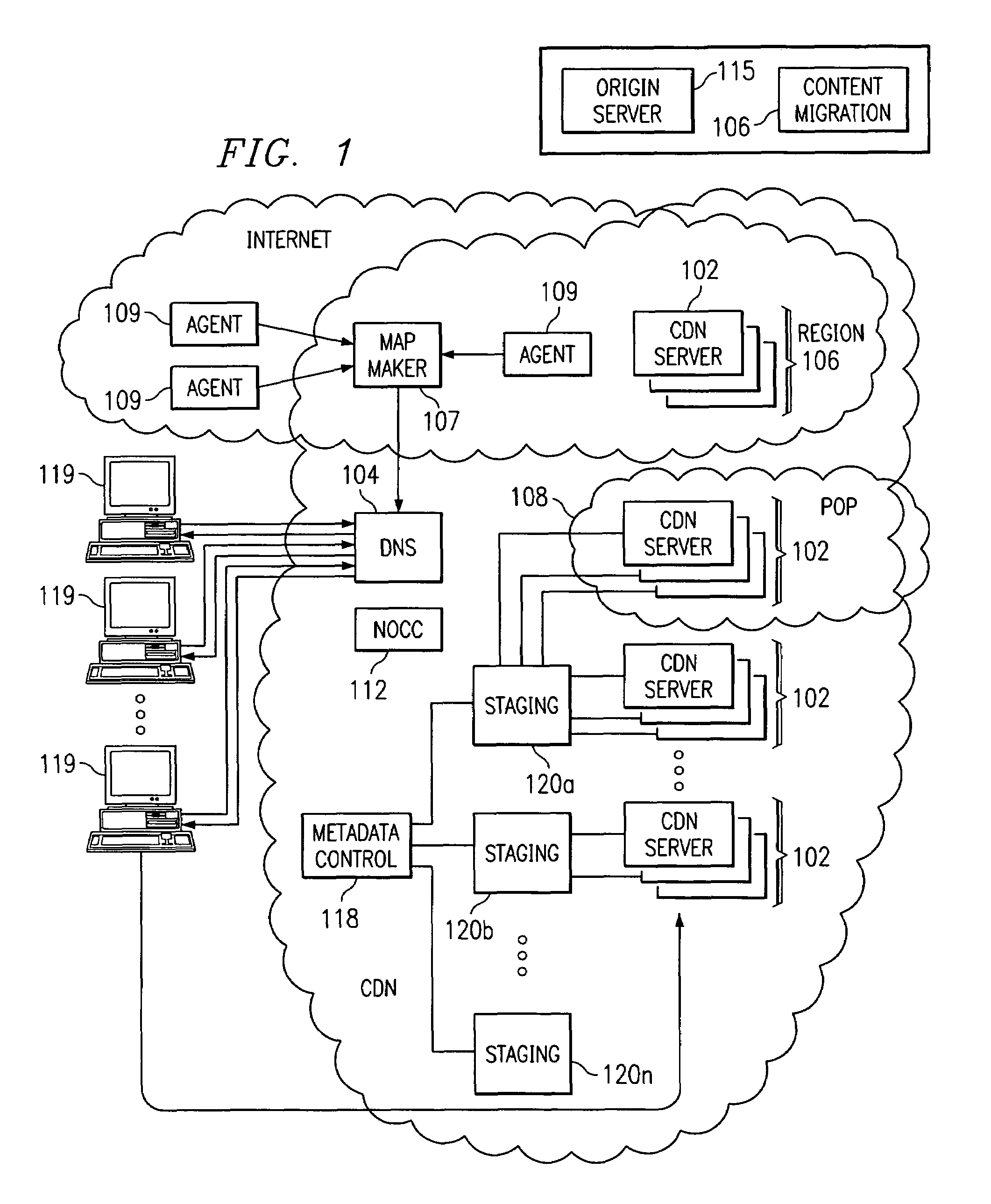
Optimal route selection in a content delivery network
InactiveUS20080008089A1Improve speed and reliabilityRetrieve content (cacheableError preventionTransmission systemsFile area networkPeer-to-peer
A routing mechanism, service or system operable in a distributed networking environment. One preferred environment is a content delivery network (CDN) wherein the present invention provides improved connectivity back to an origin server, especially for HTTP traffic. In a CDN, edge servers are typically organized into regions, with each region comprising a set of content servers that preferably operate in a peer-to-peer manner and share data across a common backbone such as a local area network (LAN). The inventive routing technique enables an edge server operating within a given CDN region to retrieve content (cacheable, non-cacheable and the like) from an origin server more efficiently by selectively routing through the CDN's own nodes, thereby avoiding network congestion and hot spots. The invention enables an edge server to fetch content from an origin server through an intermediate CDN server or, more generally, enables an edge server within a given first region to fetch content from the origin server through an intermediate CDN region.
Owner:AKAMAI TECH INC
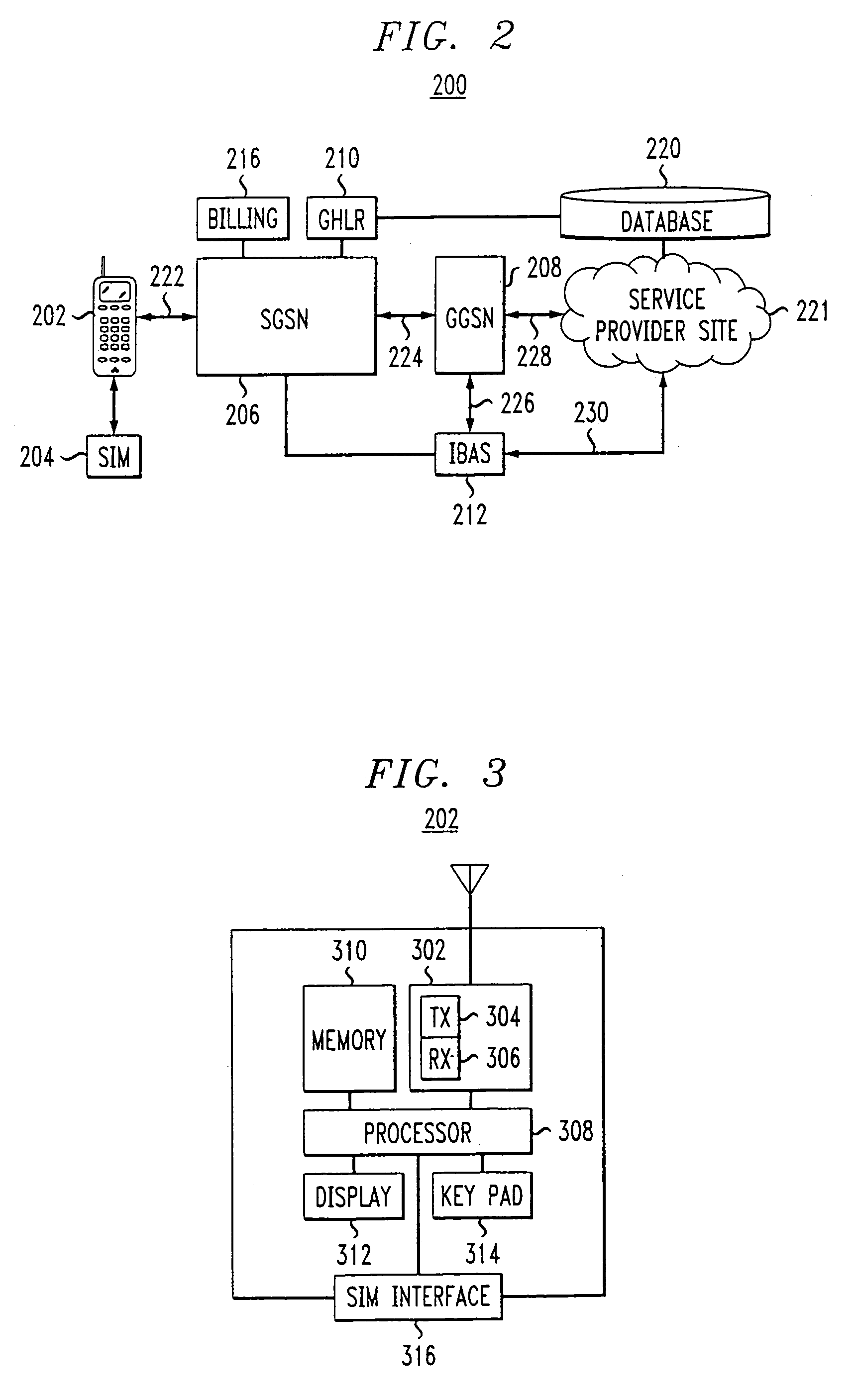
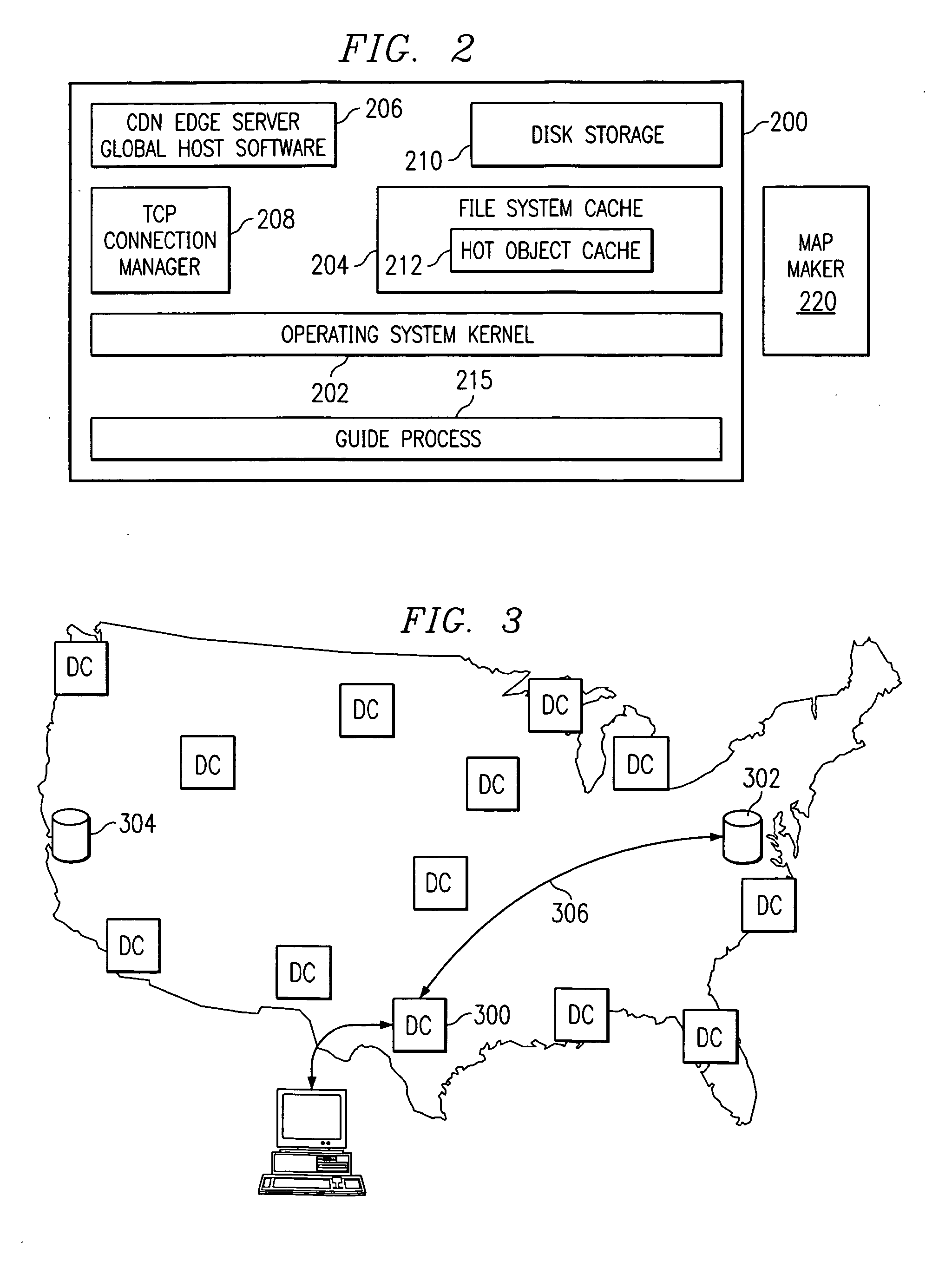
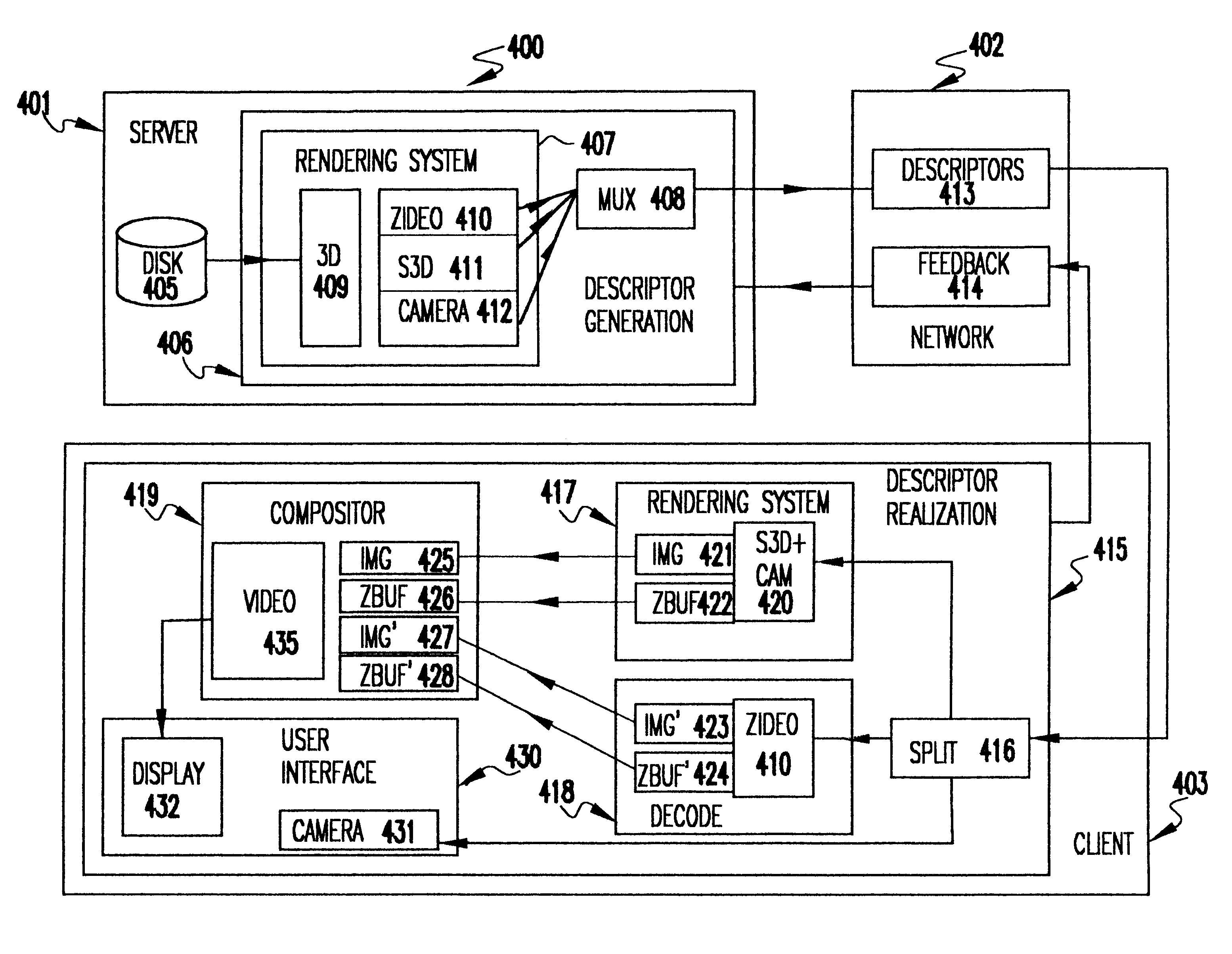
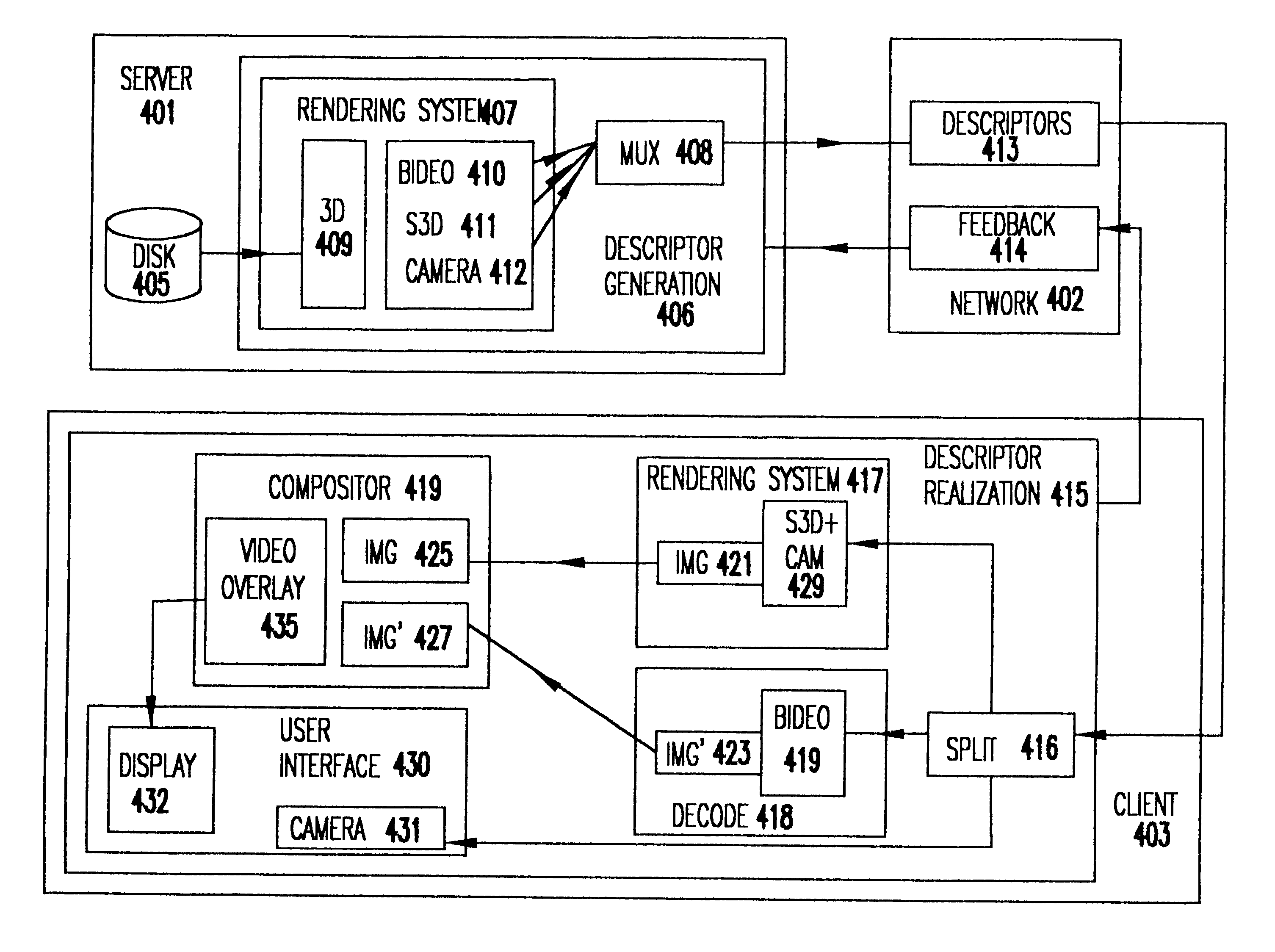
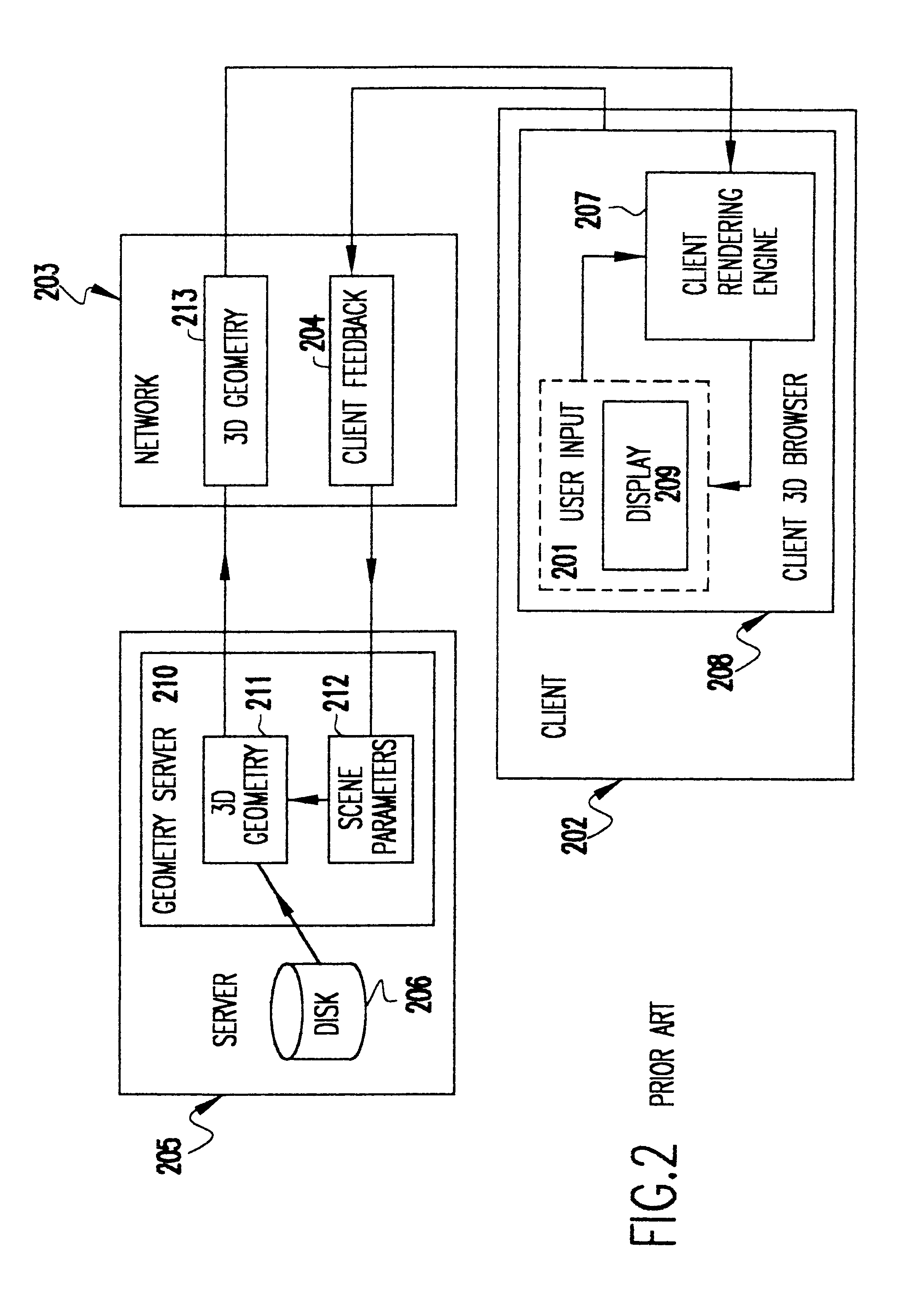
Methods and apparatus for delivering 3D graphics in a networked environment
InactiveUS6377257B1Pulse modulation television signal transmissionSelective content distributionImage resolutionThree dimensional graphics
A system and method for seamlessly combining client-only rendering techniques with server-only rendering techniques. The approach uses a composite stream containing three distinct streams. Two of the streams are synchronized and transmit camera definition, video of server-rendered objects, and a time dependent depth map for the server-rendered object. The third stream is available to send geometry from the server to the client, for local rendering if appropriate. The invention can satisfy a number of viewing applications. For example, initially the most relevant geometry can stream to the client for high quality local rendering while the server delivers renderings of less relevant geometry at lower resolutions. After the most relevant geometry has been delivered to the client, the less important geometry can be optionally streamed to the client to increase the fidelity of the entire scene. In the limit, all of the geometry is transferred to the client and the situation corresponds to client-only rendering system where local graphics hardware is used to improve fidelity and reduce bandwidth. Alternatively, if a client does not have local three-dimensional graphics capability then the server can transmit only the video of the server-rendered object and drop the other two streams. In either case, the approach also permits for a progressive improvement in the server-rendered image whenever the scene becomes static. Bandwidth that was previously used to represent changing images is allocated to improving the fidelity of the server-rendered image whenever the scene becomes static.
Owner:LENOVO (SINGAPORE) PTE LTD
Optimal route selection in a content delivery network
ActiveUS7274658B2Improve speed and reliabilityRetrieve content (cacheableError preventionTransmission systemsFile area networkPeer-to-peer
A routing mechanism, service or system operable in a distributed networking environment. One preferred environment is a content delivery network (CDN) wherein the present invention provides improved connectivity back to an origin server, especially for HTTP traffic. In a CDN, edge servers are typically organized into regions, with each region comprising a set of content servers that preferably operate in a peer-to-peer manner and share data across a common backbone such as a local area network (LAN). The inventive routing technique enables an edge server operating within a given CDN region to retrieve content (cacheable, non-cacheable and the like) from an origin server more efficiently by selectively routing through the CDN's own nodes, thereby avoiding network congestion and hot spots. The invention enables an edge server to fetch content from an origin server through an intermediate CDN server or, more generally, enables an edge server within a given first region to fetch content from the origin server through an intermediate CDN region. As used herein, this routing through an intermediate server, node or region is sometimes referred to as “tunneling.”
Owner:AKAMAI TECH INC
Administration of protection of data accessible by a mobile device
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
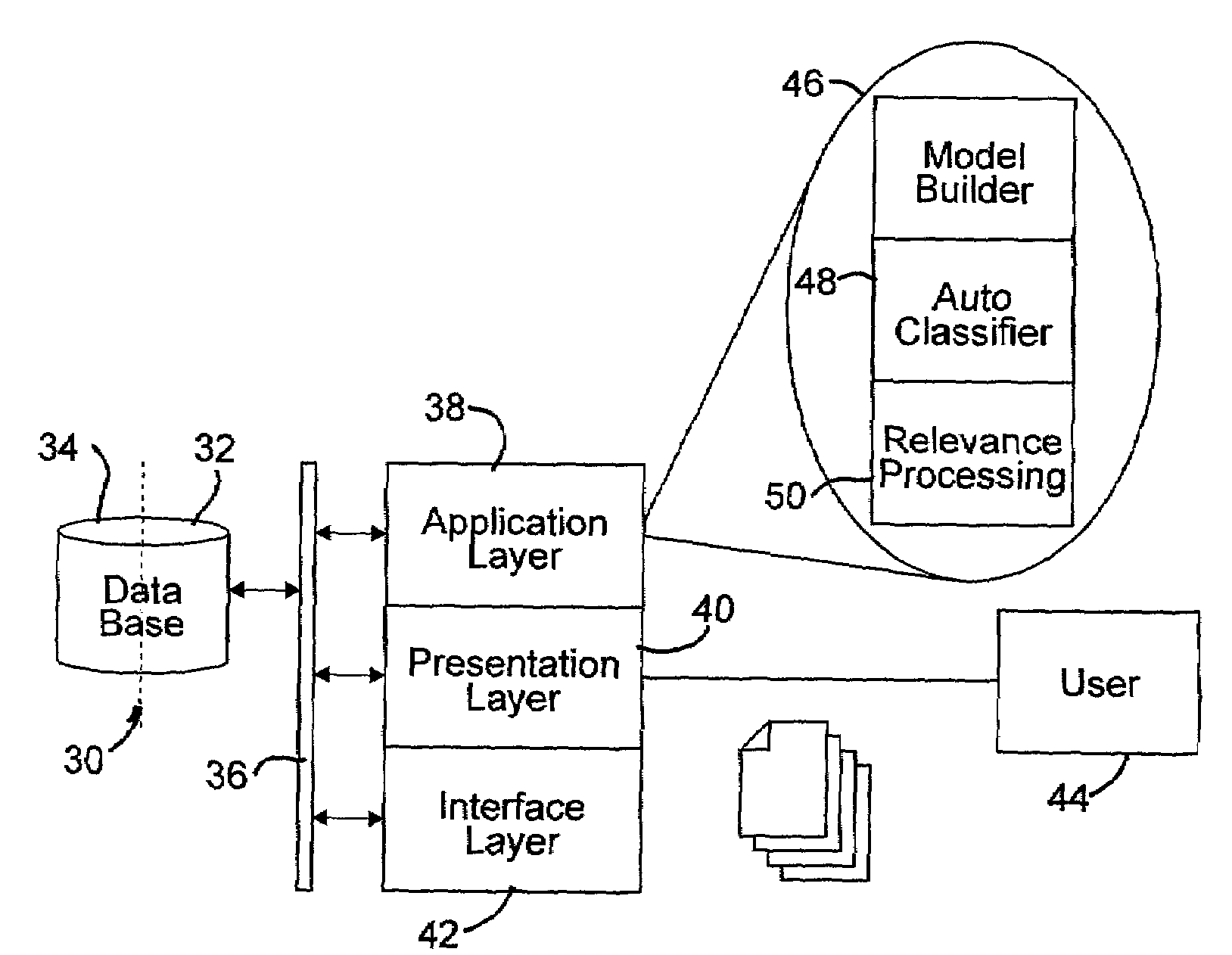
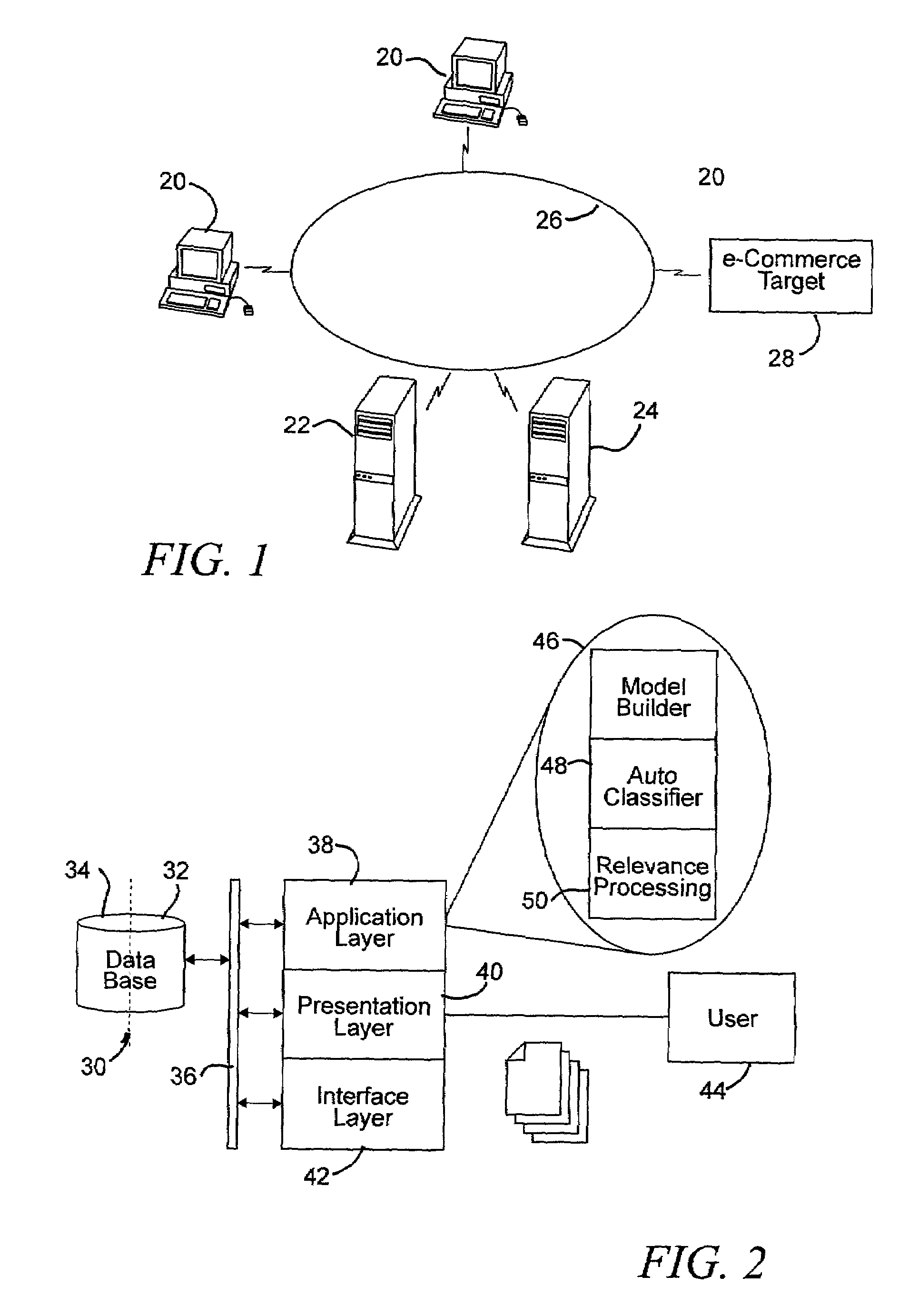
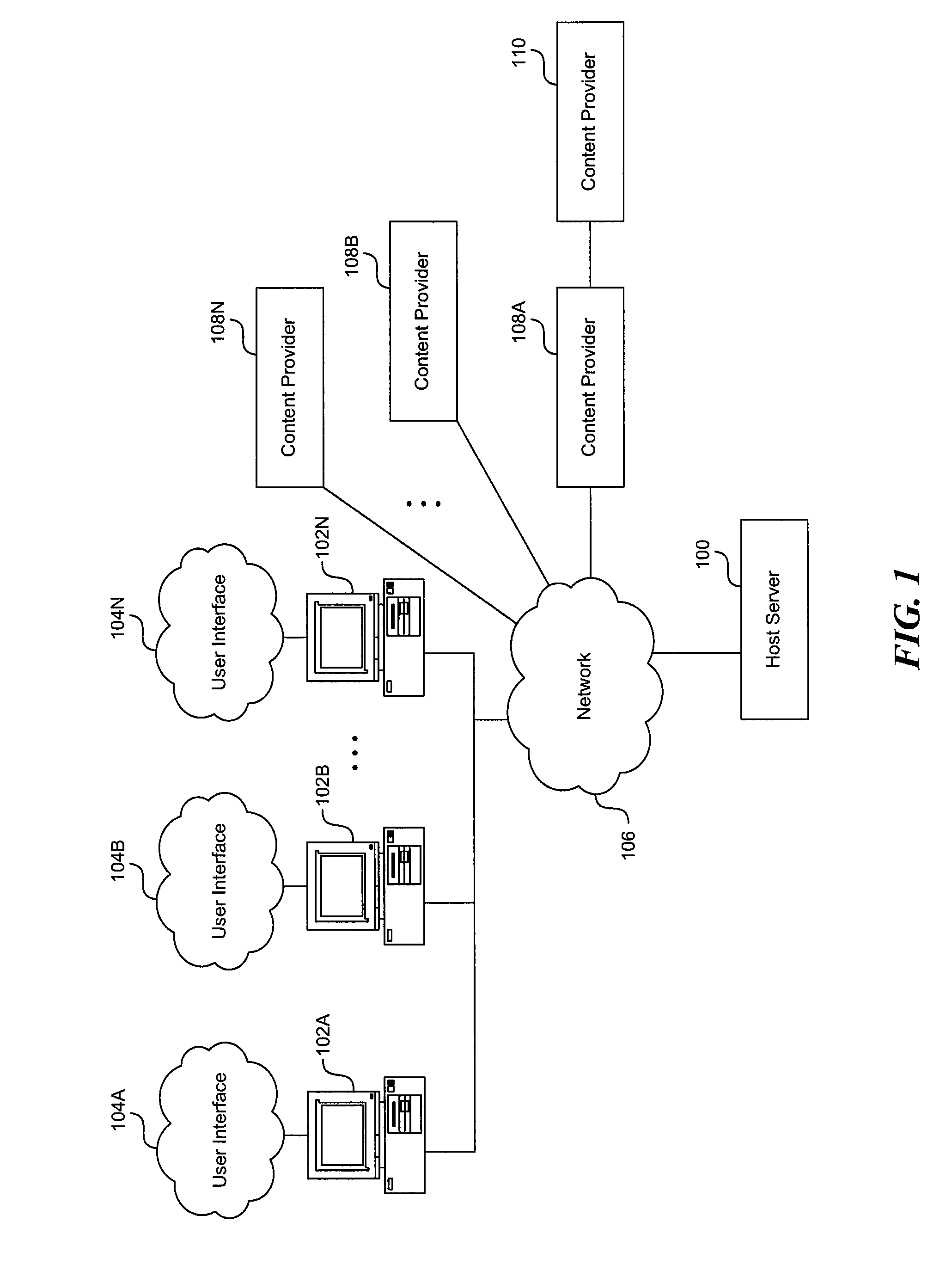
Interface and system for providing persistent contextual relevance for commerce activities in a networked environment
InactiveUS7089237B2Improve experienceImprove user interactionData processing applicationsDigital data information retrievalObject basedSubject matter
A search and recommendation system employs the preferences and profiles of individual users and groups within a community of users, as well as information derived from categorically organized content pointers, to augment electronic commerce related searches, re-rank search results, and provide recommendations for commerce related objects based on an initial subject-matter query and an interaction history of a user. The search and recommendation system operates in the context of a content pointer manager, which stores individual users' content pointers (some of which may be published or shared for group use) on a centralized content pointer database connected to a network. The shared content pointer manager is implemented as a distributed program, portions of which operate on users' terminals and other portions of which operate on the centralized content pointer database. A user's content pointers are organized in accordance with a local topical categorical hierarchy. The hierarchical organization is used to define a relevance context within which returned objects are evaluated and ordered.
Owner:GOOGLE LLC
Method and apparatus for content protection in a personal digital network environment
InactiveUS20050144468A1Easy to disassembleReliable lockingTelevision system detailsUser identity/authority verificationGraphicsVideo processing
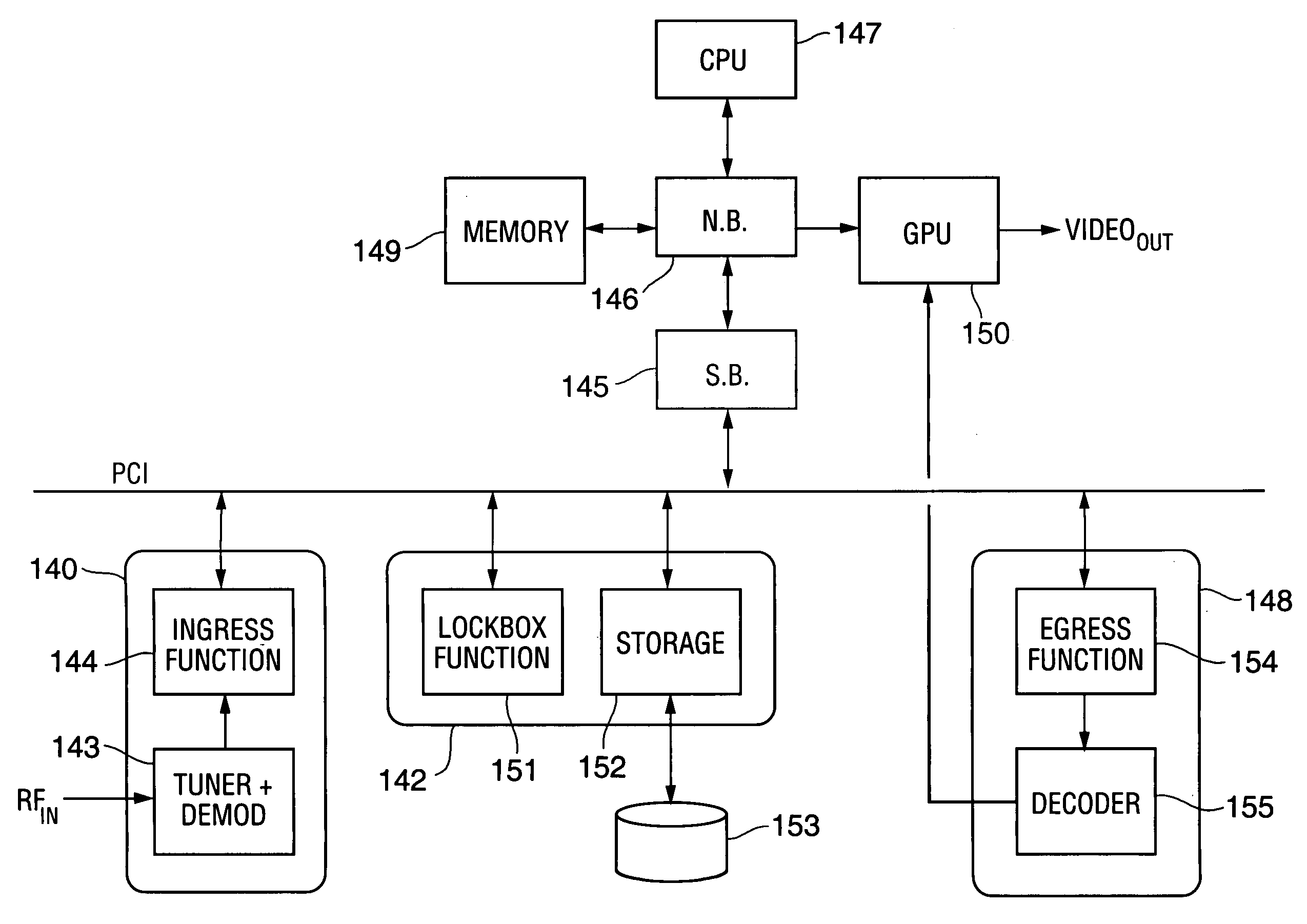
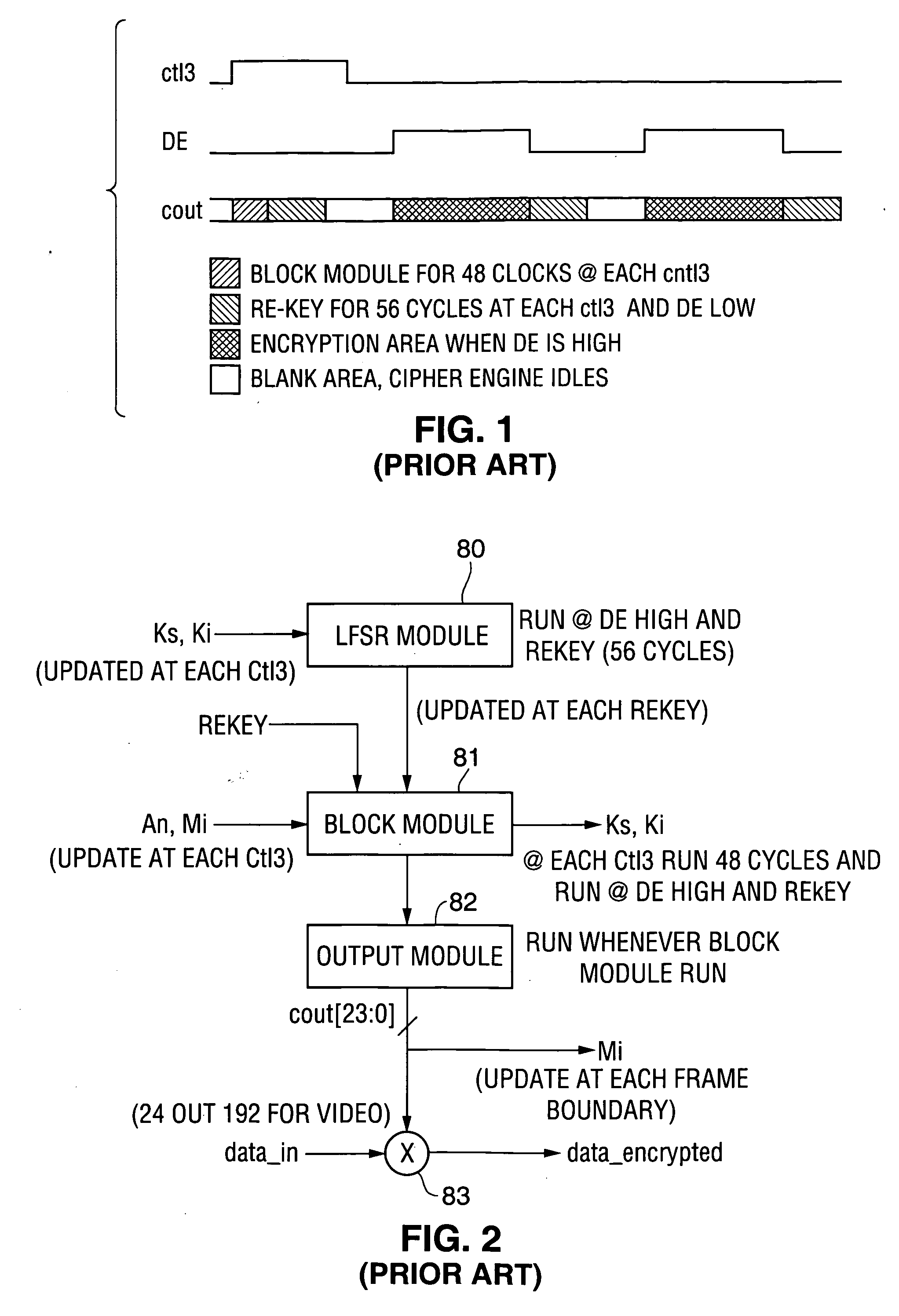
In some embodiments, the invention is a personal digital network (“PDN”) including hardware (sometimes referred to as Ingress circuitry) configured to transcrypt encrypted content that enters the PDN. Typically, the transcryption (decryption followed by re-encryption) is performed in hardware within the Ingress circuitry and the re-encryption occurs before the decrypted content is accessible by hardware or software external to the Ingress circuitry. Typically, transcrypted content that leaves the Ingress circuitry remains in re-encrypted form within the PDN whenever it is transferred between integrated circuits or is otherwise easily accessible by software, until it is decrypted within hardware (sometimes referred to as Egress circuitry) for display or playback or output from the PDN. Typically, the PDN is implemented so that no secret in Ingress or Egress circuitry (for use or transfer by the Ingress or Egress circuitry) is accessible in unencrypted form to software or firmware within the PDN or to any entity external to the PDN. Other aspects of the invention are methods for protecting content in a PDN (e.g., an open computing system) and devices (e.g., multimedia graphics cards, set top boxes, or video processors) for use in a PDN.
Owner:OPTIMUM CONTENT PROTECTION
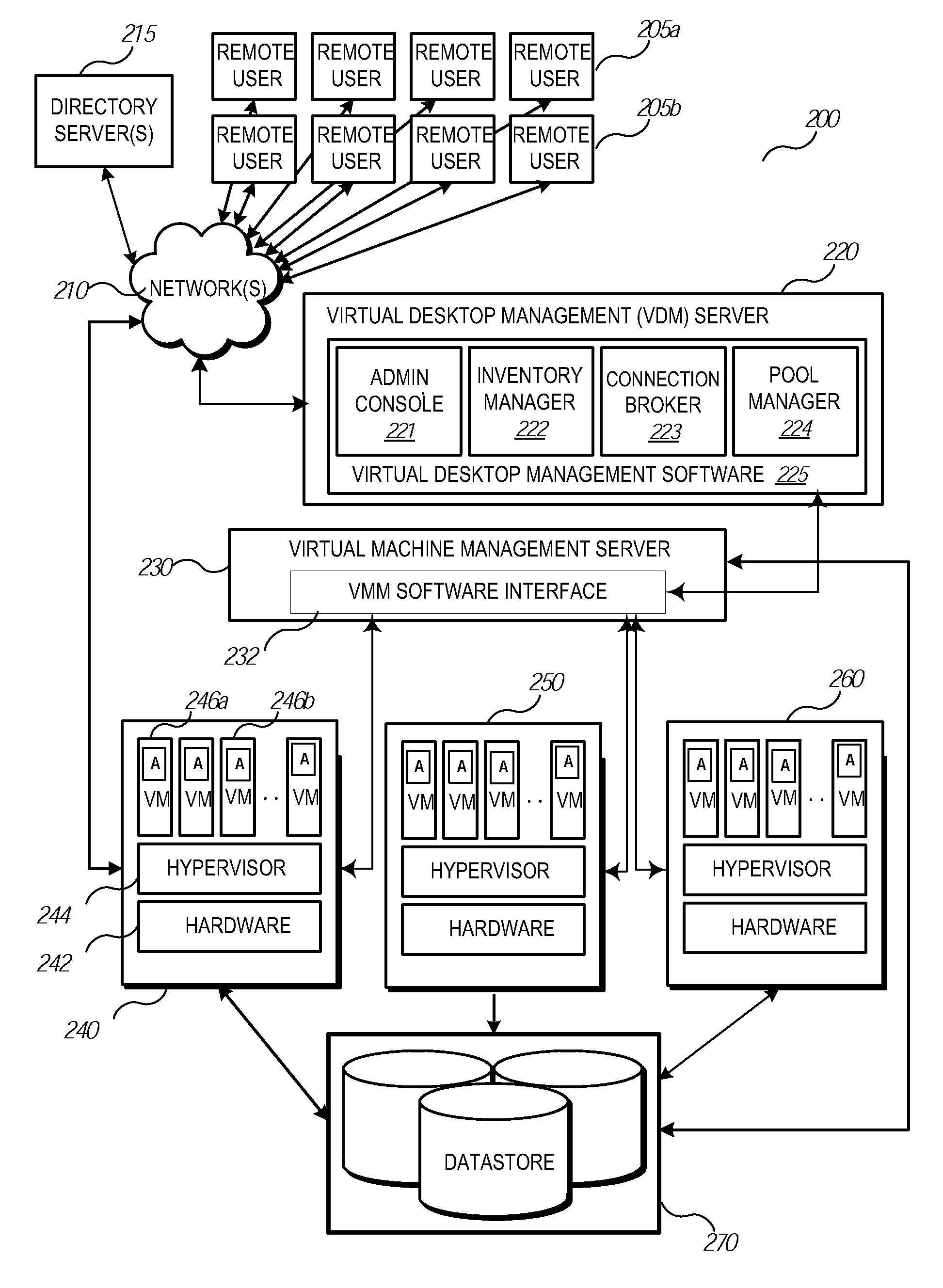
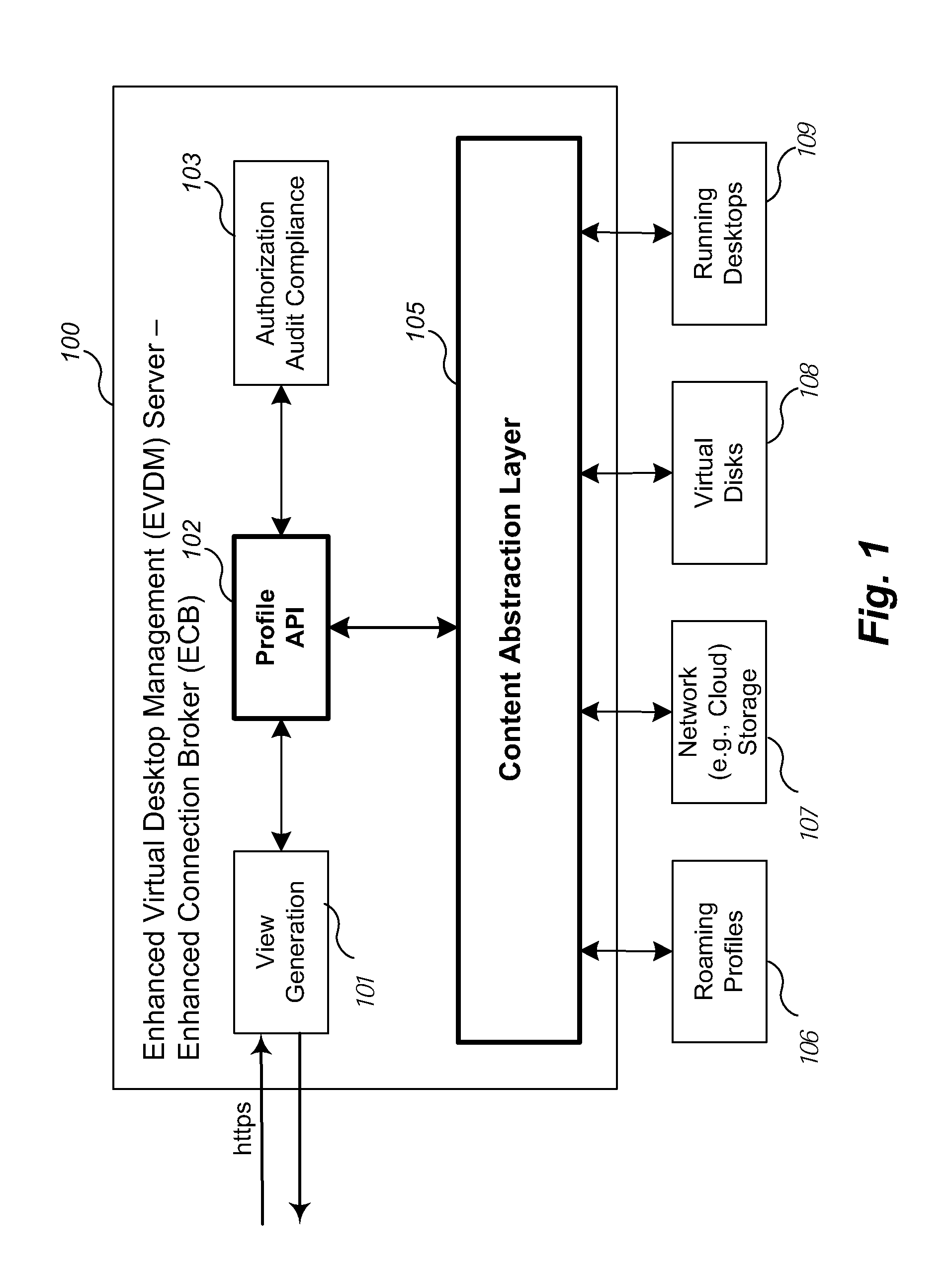
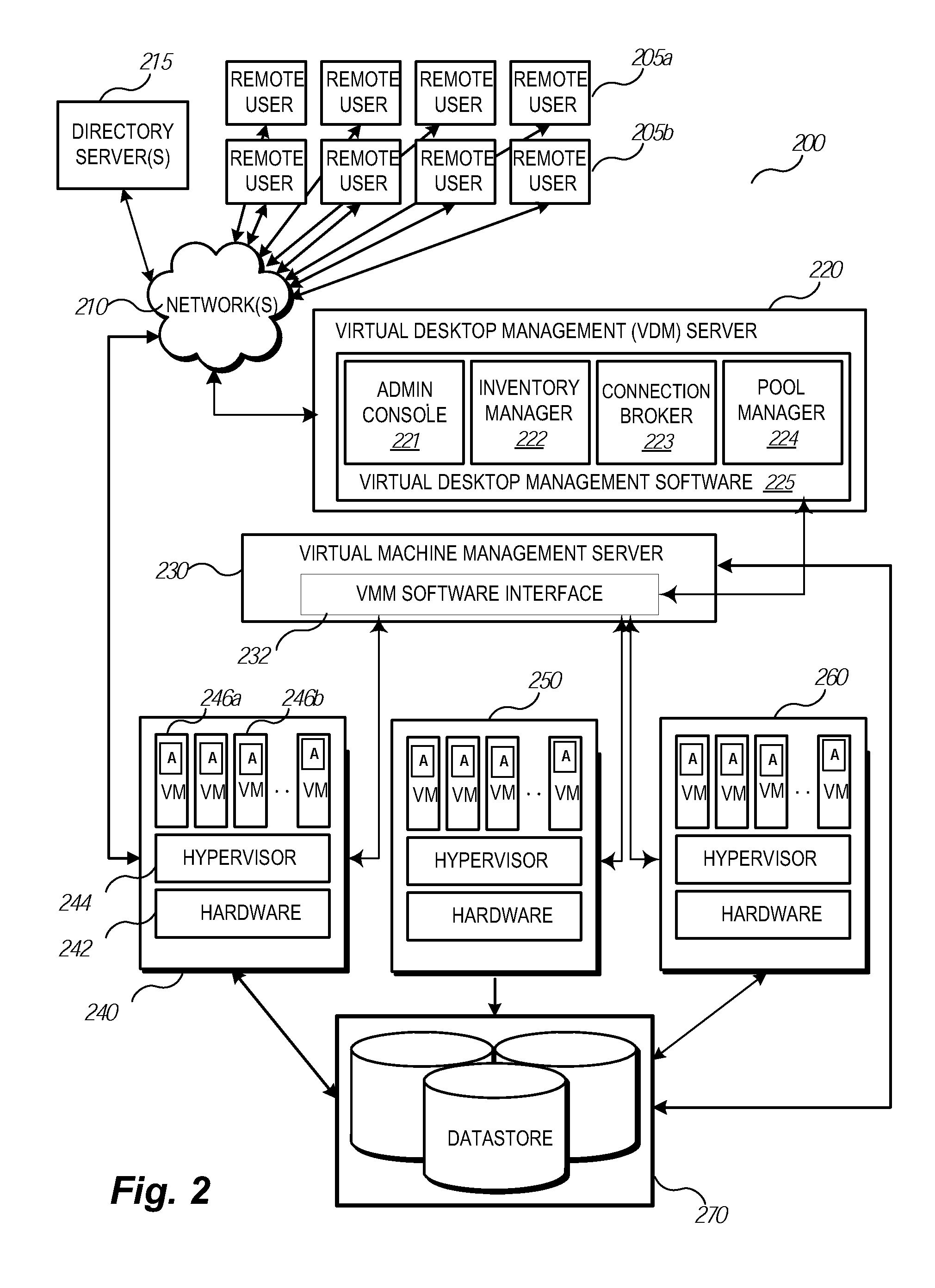
Accessing Virtual Disk Content of a Virtual Machine Without Running a Virtual Desktop
ActiveUS20110185355A1Multiprogramming arrangementsMultiple digital computer combinationsAbstraction layerData center
Methods, systems, and techniques for facilitating access to content stored remotely, for example, as part of a virtual machine infrastructure or elsewhere in a networked environment, using a uniform mechanism are provided. Example embodiments provide an Enhanced Virtual Desktop Management Server / System with a Content Abstraction Layer which enables users to access their data stored as part of a virtual machine environment, or replicated otherwise on a network, using a generic API. The API can be incorporated into a web browser or other third party interface to provide access to the users' data without needing to remote a bitmap representation of a virtual desktop display. Accordingly, users can access their data, applications, and settings regardless of the type of access device and regardless of whether the corresponding virtual desktop is running in the data center, provisioned in the datacenter but running on a client device, or not running at all.
Owner:VMWARE INC
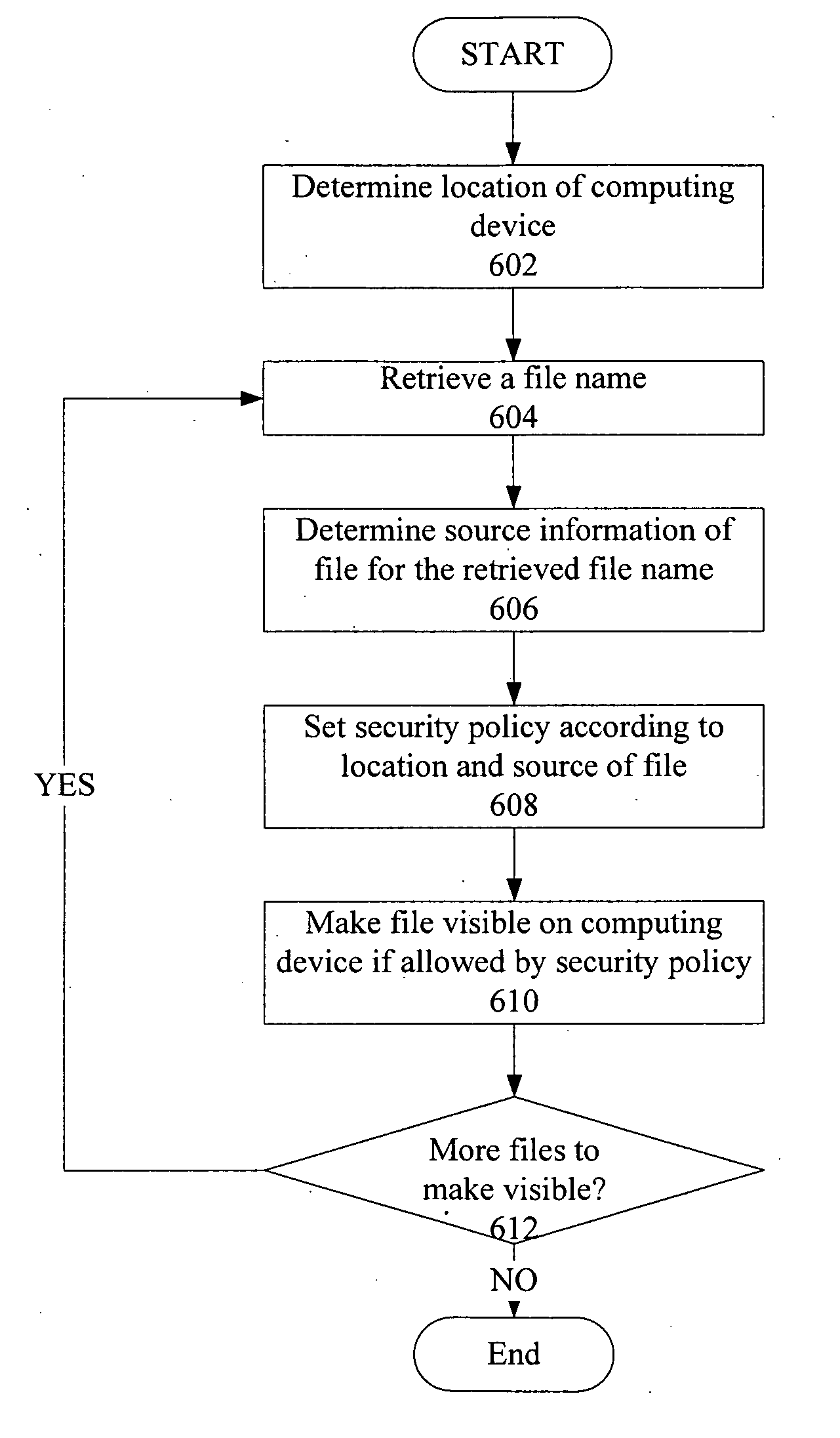
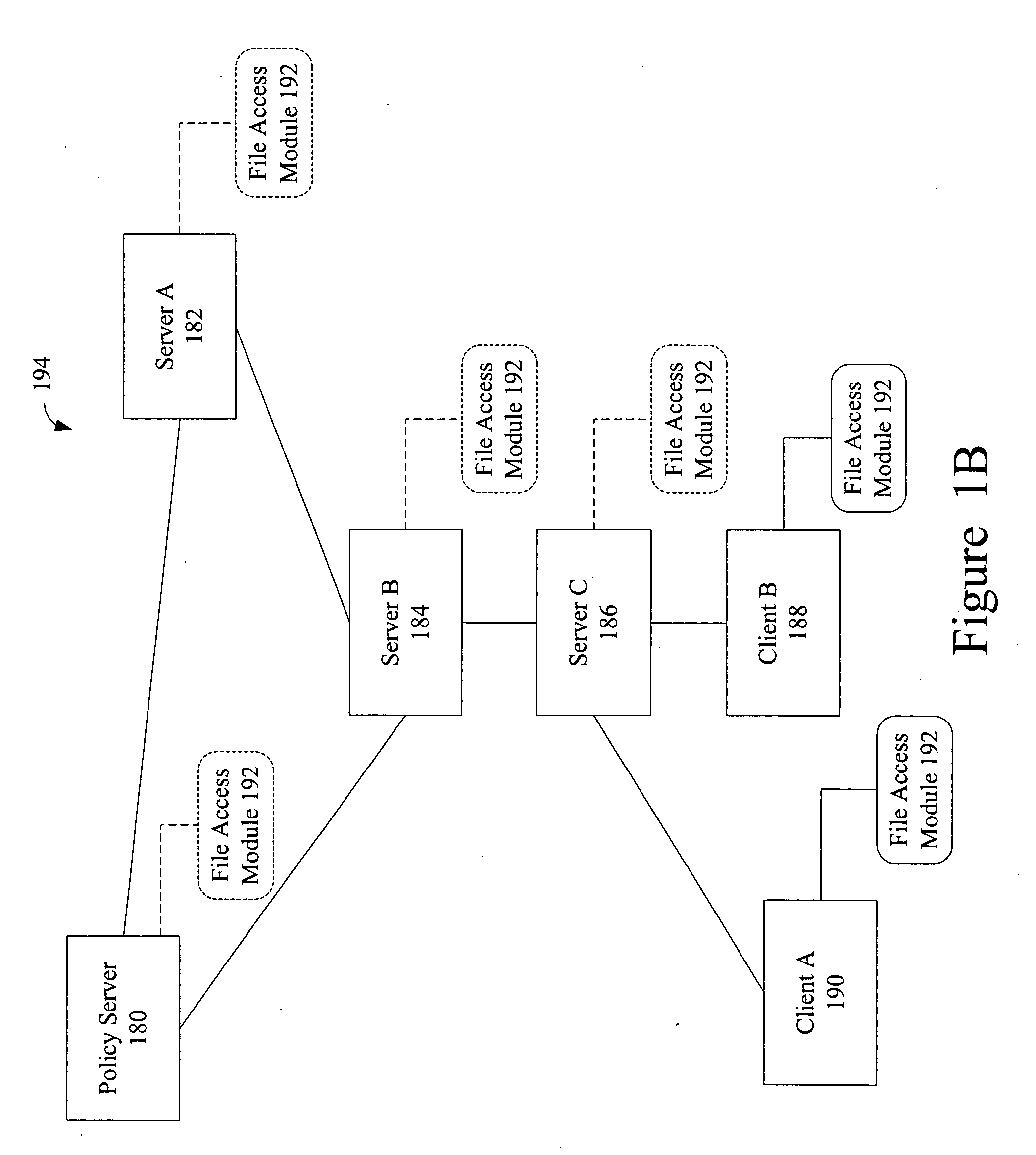
Access control to files based on source information
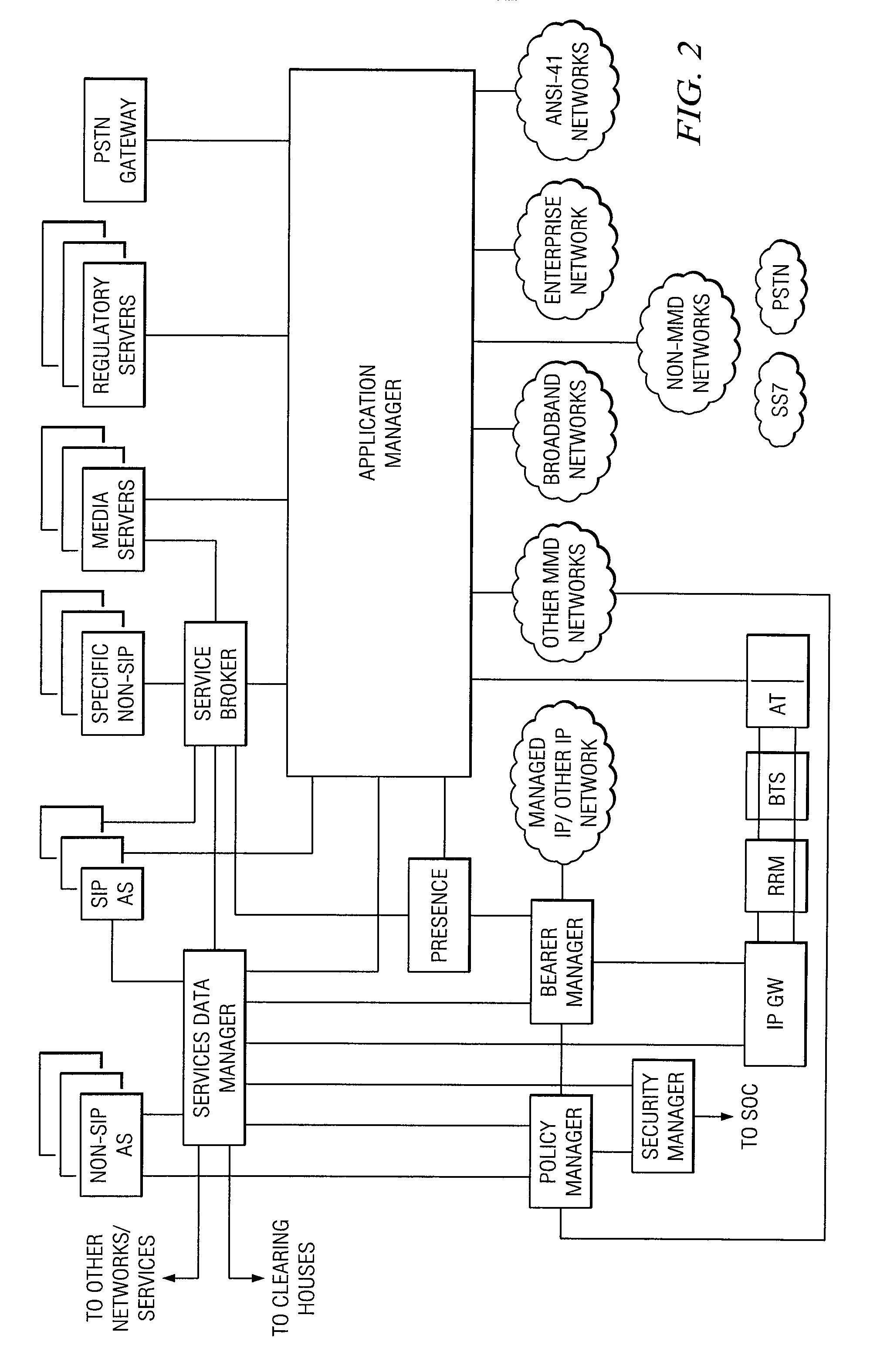
ActiveUS20060120526A1Digital data processing detailsUser identity/authority verificationWeb environmentSecurity policy
The present invention is a security tool for protection of data on a mobile computing device. The security tool provides a plurality of security policies to be enforced based on source information for the data and a location associated with a network environment in which a mobile device is operating. The security tool may be either located at the mobile computing device or at the server. The security tool includes a file access module for determining whether files are visible or accessible. The file access module comprises a tag generator, an association module, and a policy enforcement module. The tag generator creates source information for the file being accessed and the policy enforcement module determines what actions, if any, can be performed on the file and under what conditions such as location and network environment, type of file and other factors.
Owner:NOVELL INC
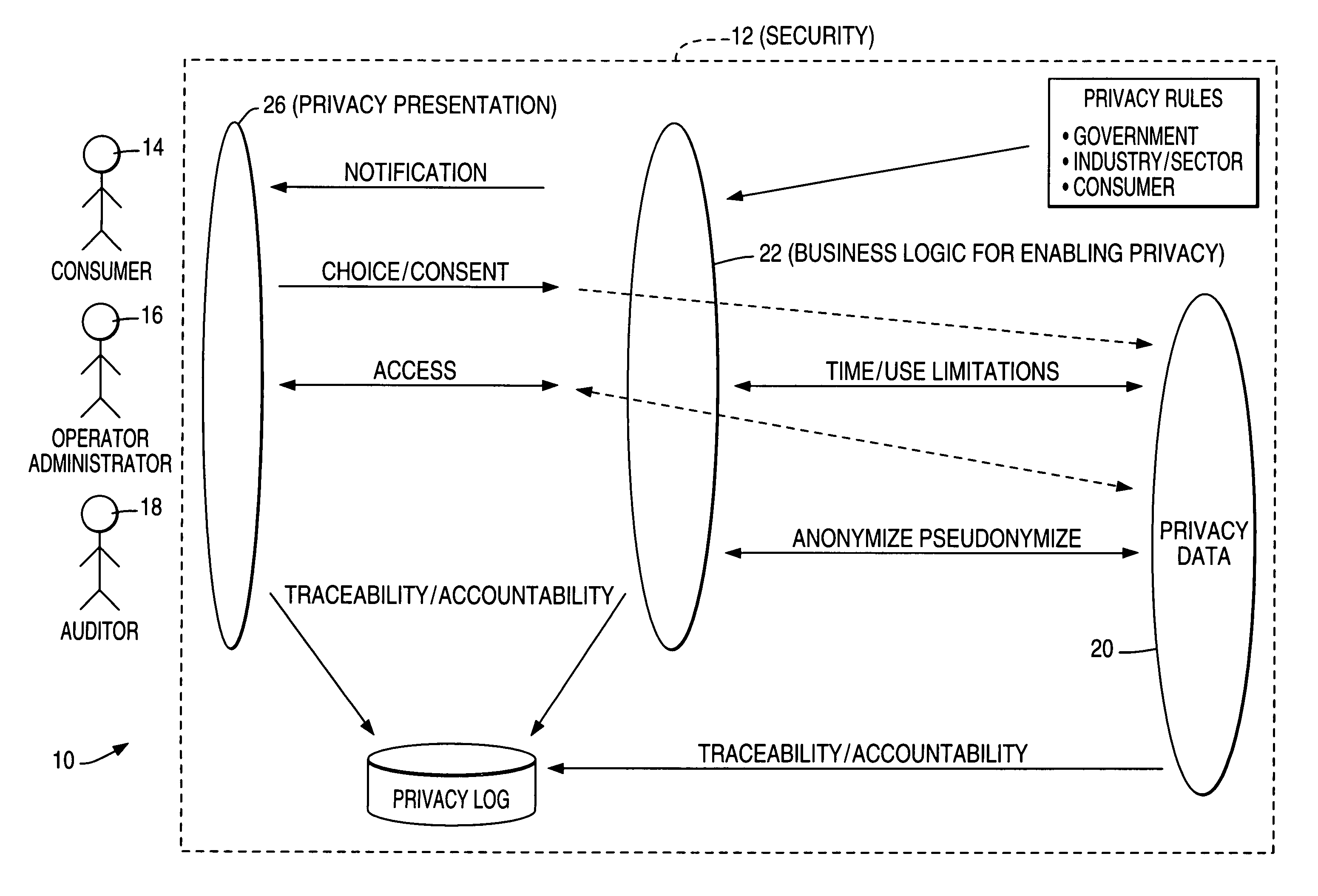
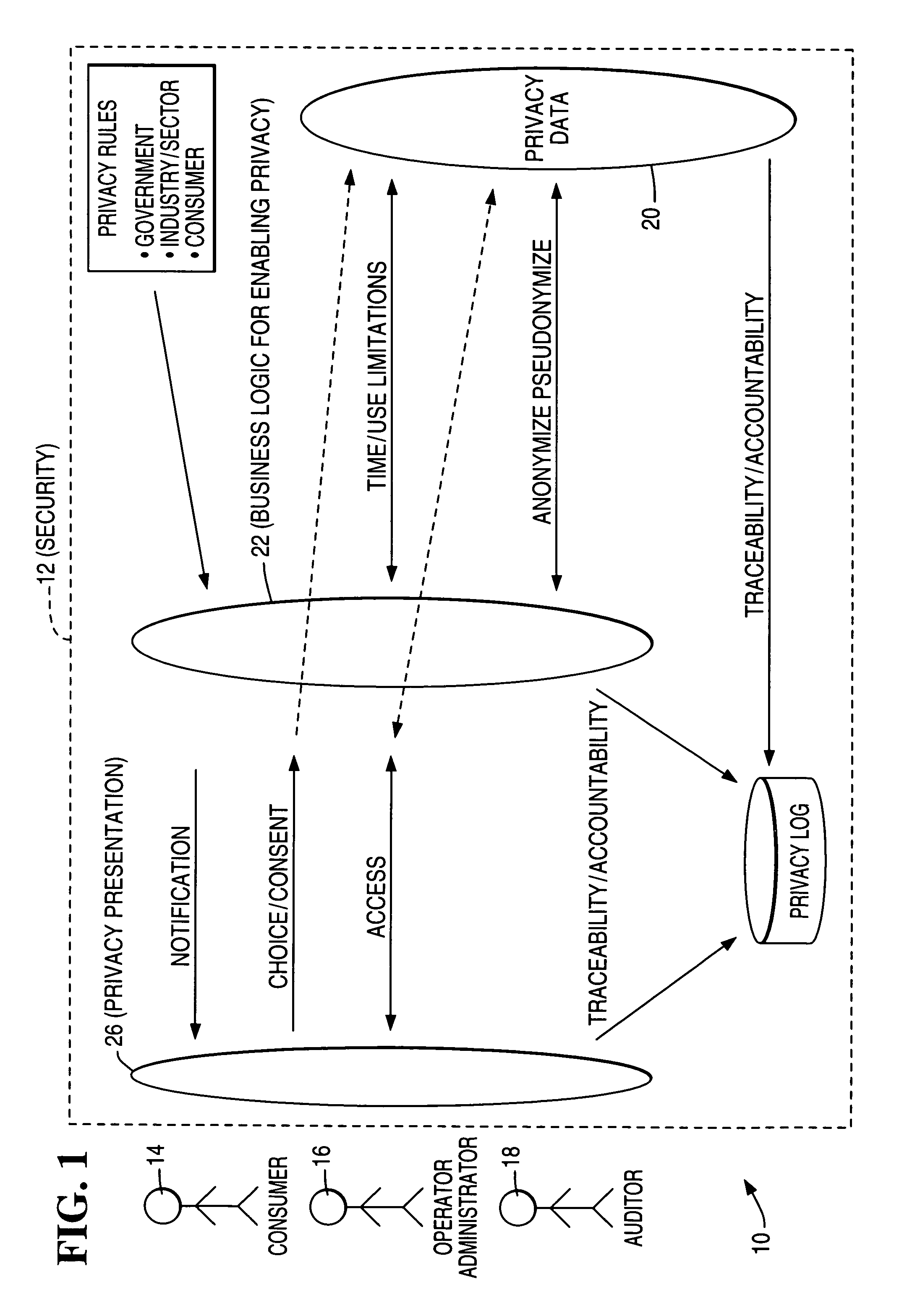
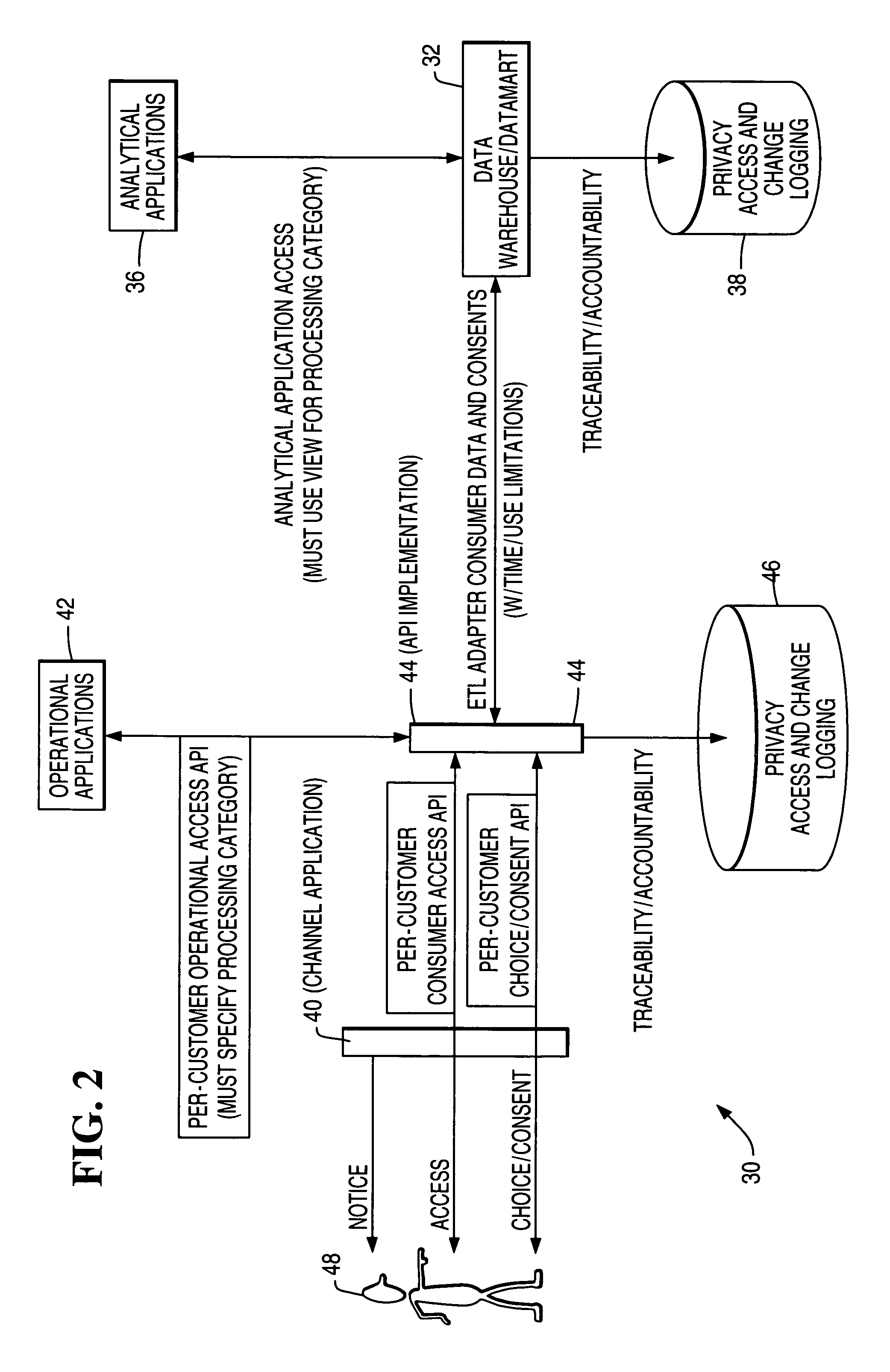
Architecture and method for operational privacy in business services
Consent-based application programming interfaces (APIs) are used to provide privacy access controls to operational systems for business services accomplished particularly in an electronic and / or networked environment. An API implementation device or host provides a link between a channel application, configured to provide an interface with a customer, and privacy data as used by operational applications and obtained from databases such as data warehouses. The privacy APIs provide per-customer choice / consent to obtaining and / or retrieval of privacy information / data and per-customer access thereto. In one form, the privacy APIs are used in business initiated self service applications wherein an activity or event triggers business to customer initiation.
Owner:TERADATA US
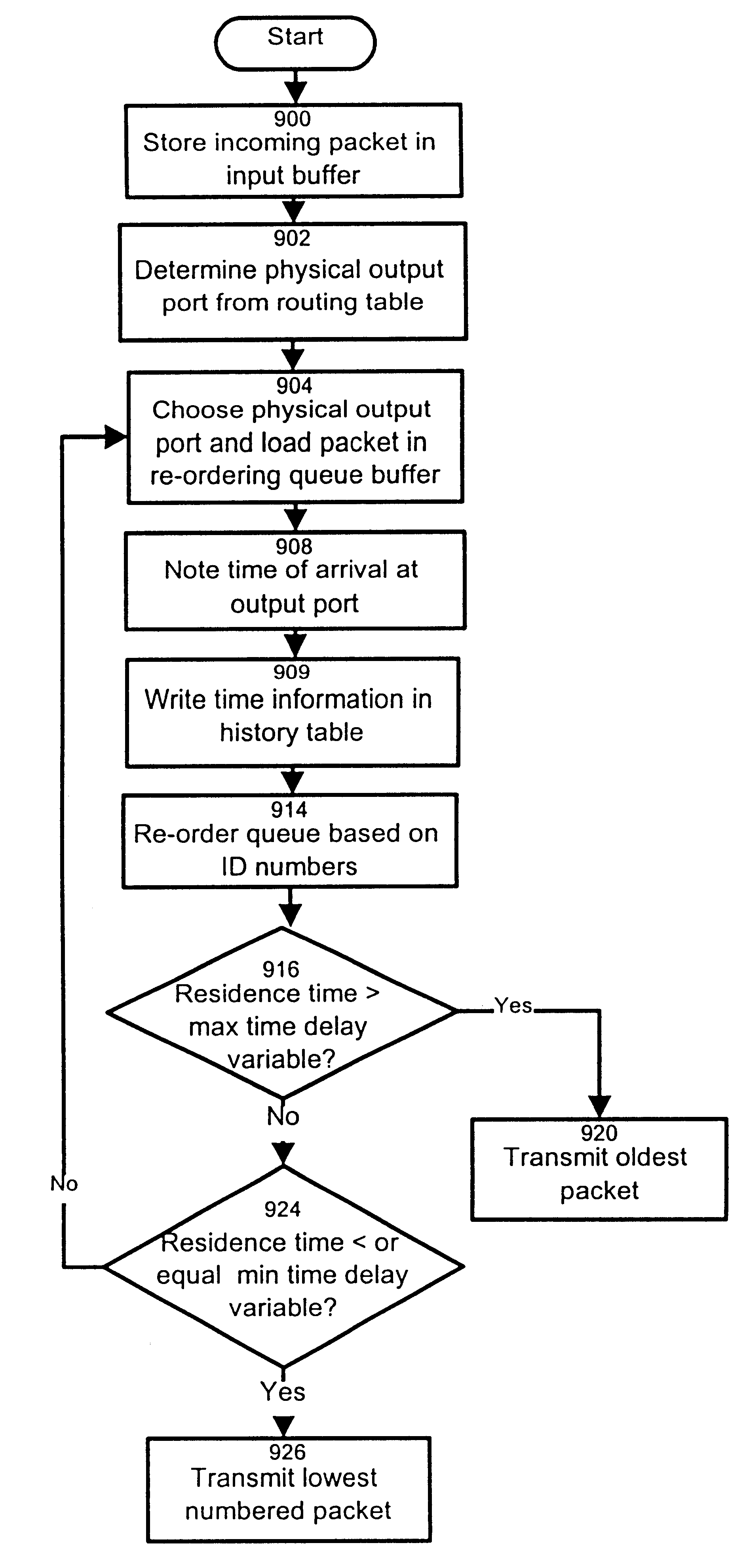
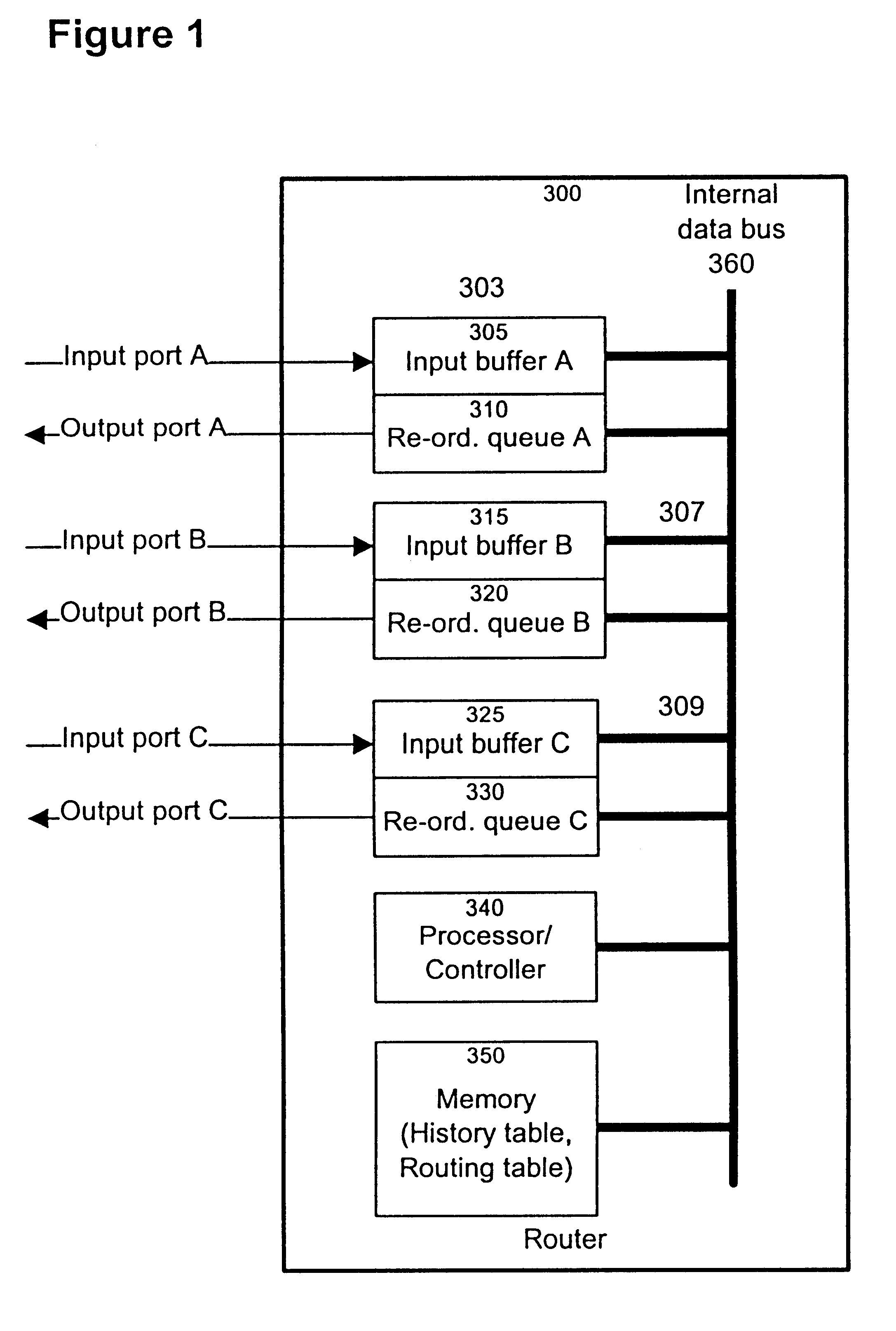
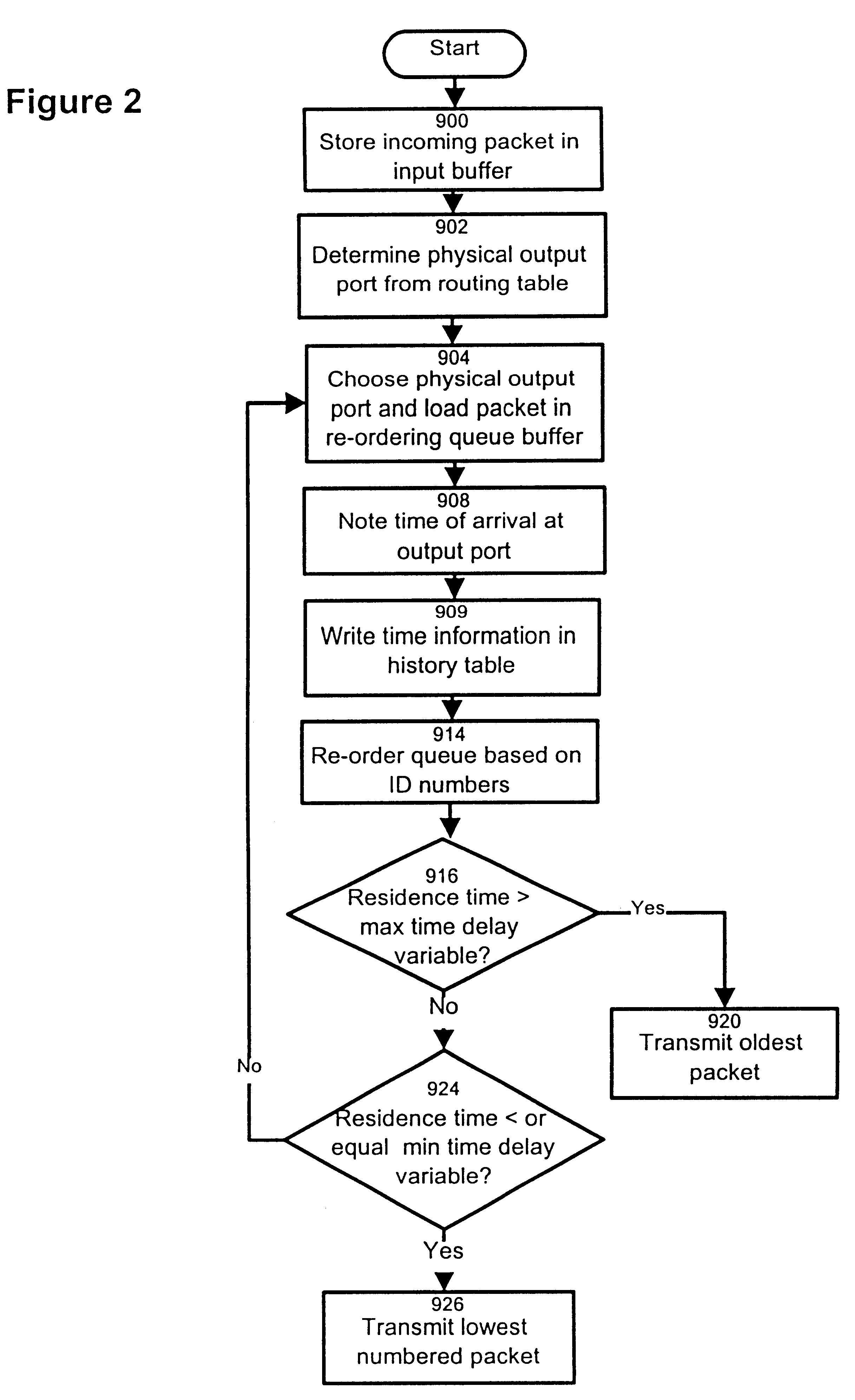
Method and apparatus for re-ordering data packets in a network environment
InactiveUS6246684B1Lower Level RequirementsAvoid changeMultiplex system selection arrangementsData switching by path configurationTime delaysNetwork packet
The invention provides a method and apparatus for re-ordering data traffic units, such as IP data packets, that may have been miss-ordered during a transmission over a multi-pathway link between a source node and a destination node in a network. The re-ordering apparatus includes a storage medium for intercepting the IP data packets and holding the IP data packets to allow IP data packets delayed on slower pathways to catch-up. The IP data packets in the storage medium are re-ordered based on their sequence number in an attempt to restore the original order of the IP data packets. A maximal time delay variable determines how long a certain IP data packet can be held in the storage medium. The TP data packet is released prior to the maximal time delay variable or as the maximal time delay variable is exceeded.
Owner:RPX CLEARINGHOUSE +1
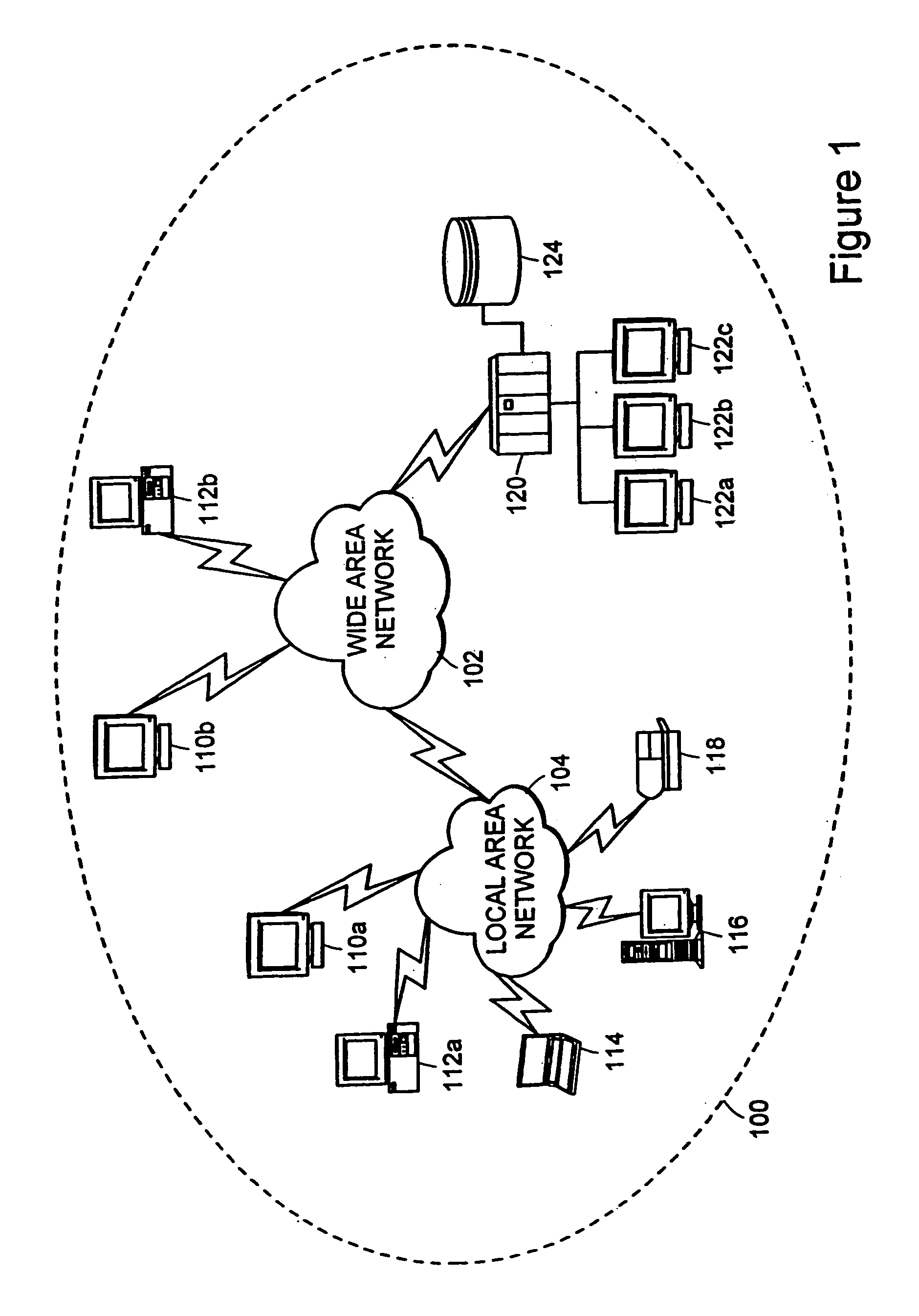
Method and system for distributing data in a network
InactiveUS20030101253A1Digital computer detailsData switching networksStreaming dataTopology information
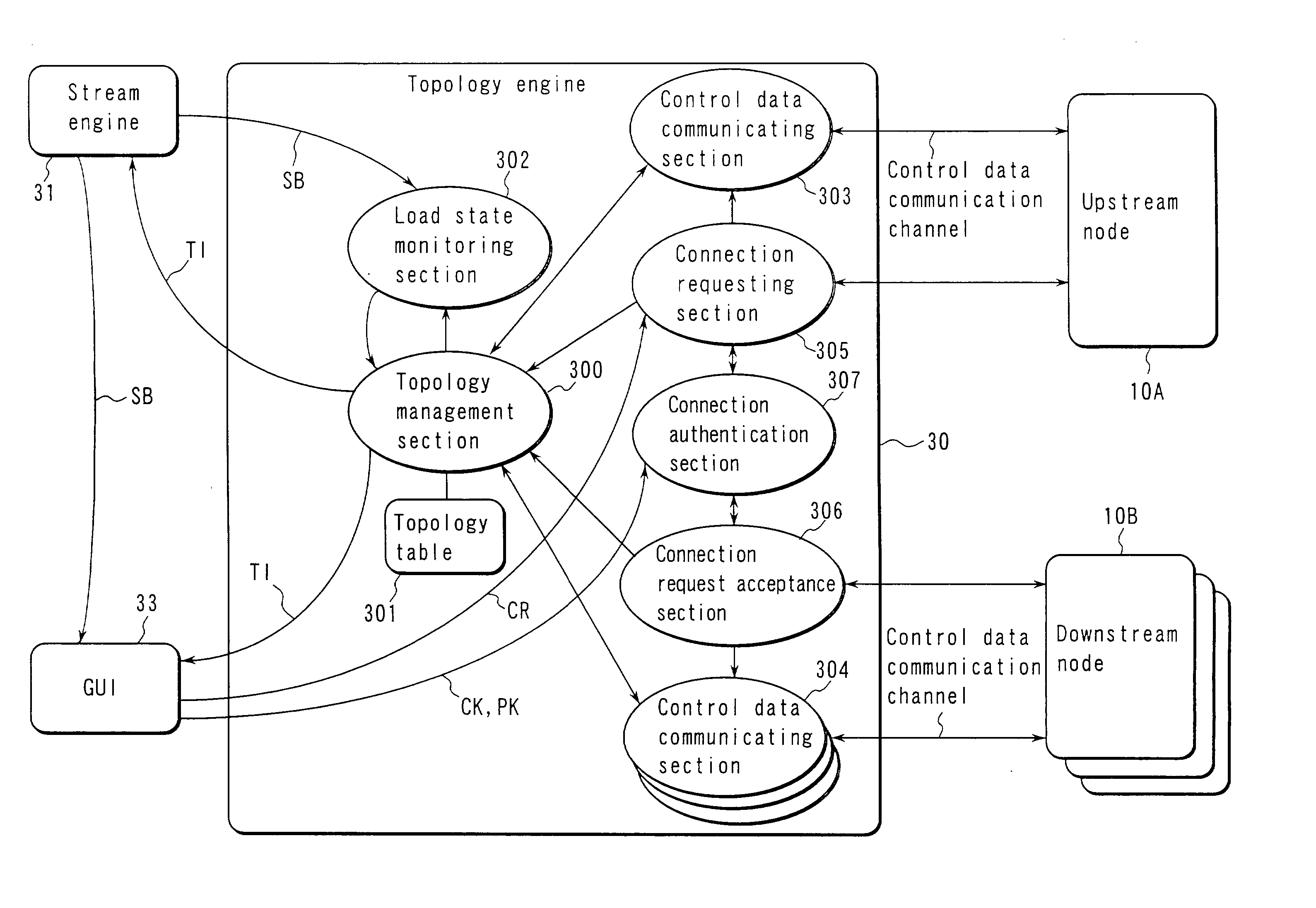
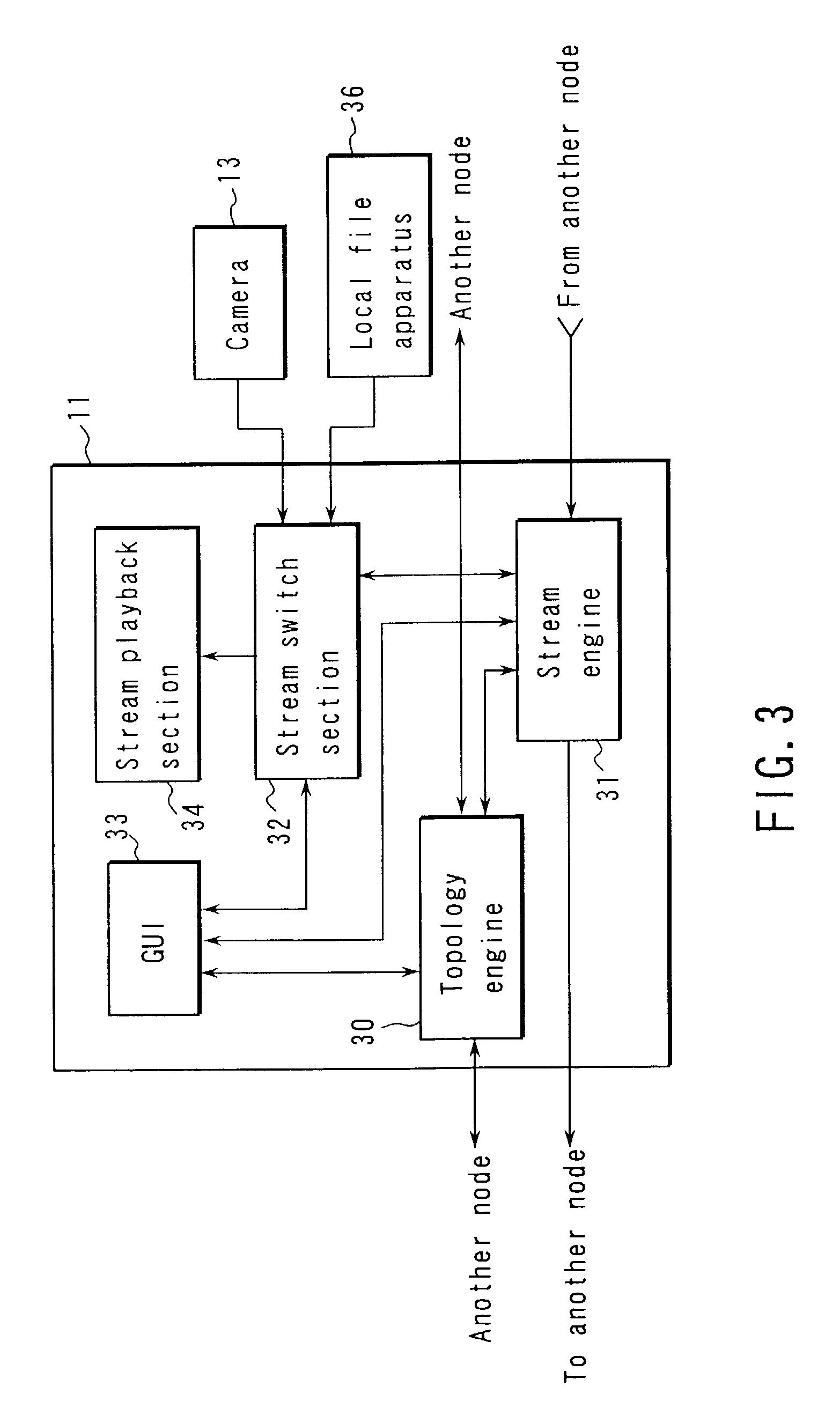
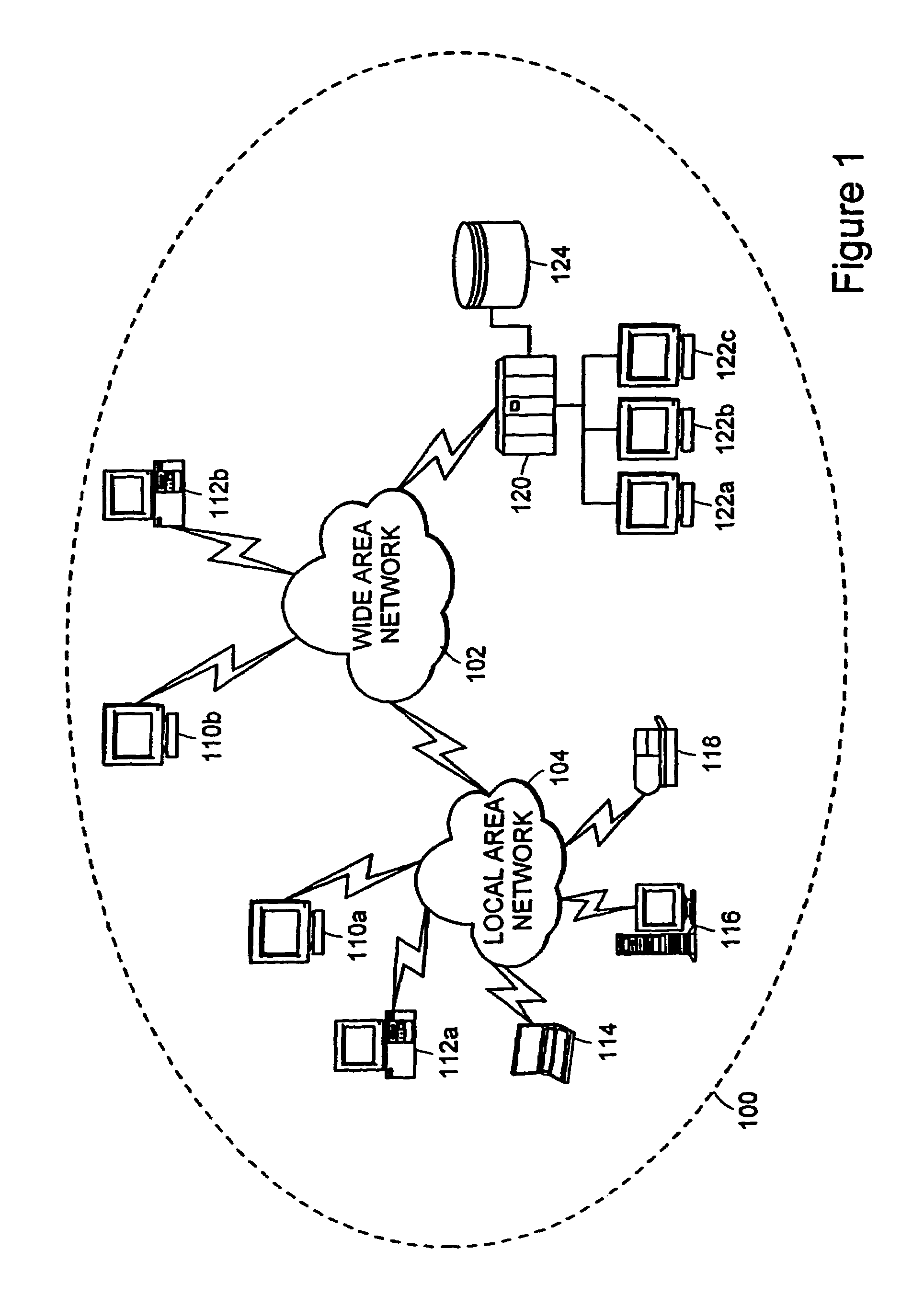
A data distribution method is disclosed which can realize autonomous or private data distribution between user terminals in a network environment such as the Internet. In this method, the respective nodes exchange topology information indicating a connection relationship between upstream nodes and downstream nodes, and relay stream data from the upstream nodes to the downstream nodes. Each node arbitrarily separates from the network and connects to an upstream node in accordance with a predetermined condition.
Owner:ANCL +1
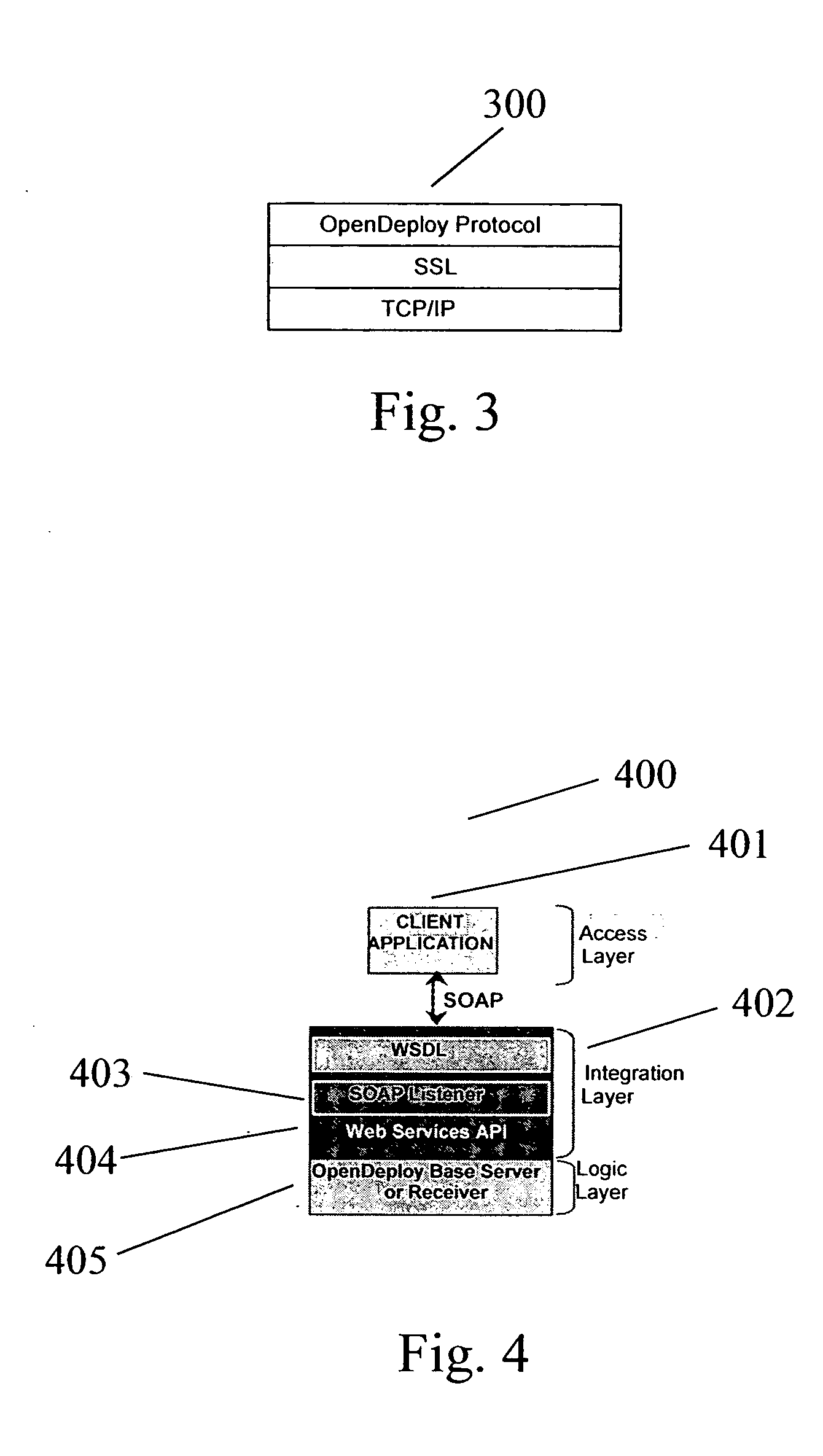
System for transactionally deploying content across multiple machines
InactiveUS20050080801A1Easy to deployDigital data processing detailsMultiple digital computer combinationsProgram planningBasic service
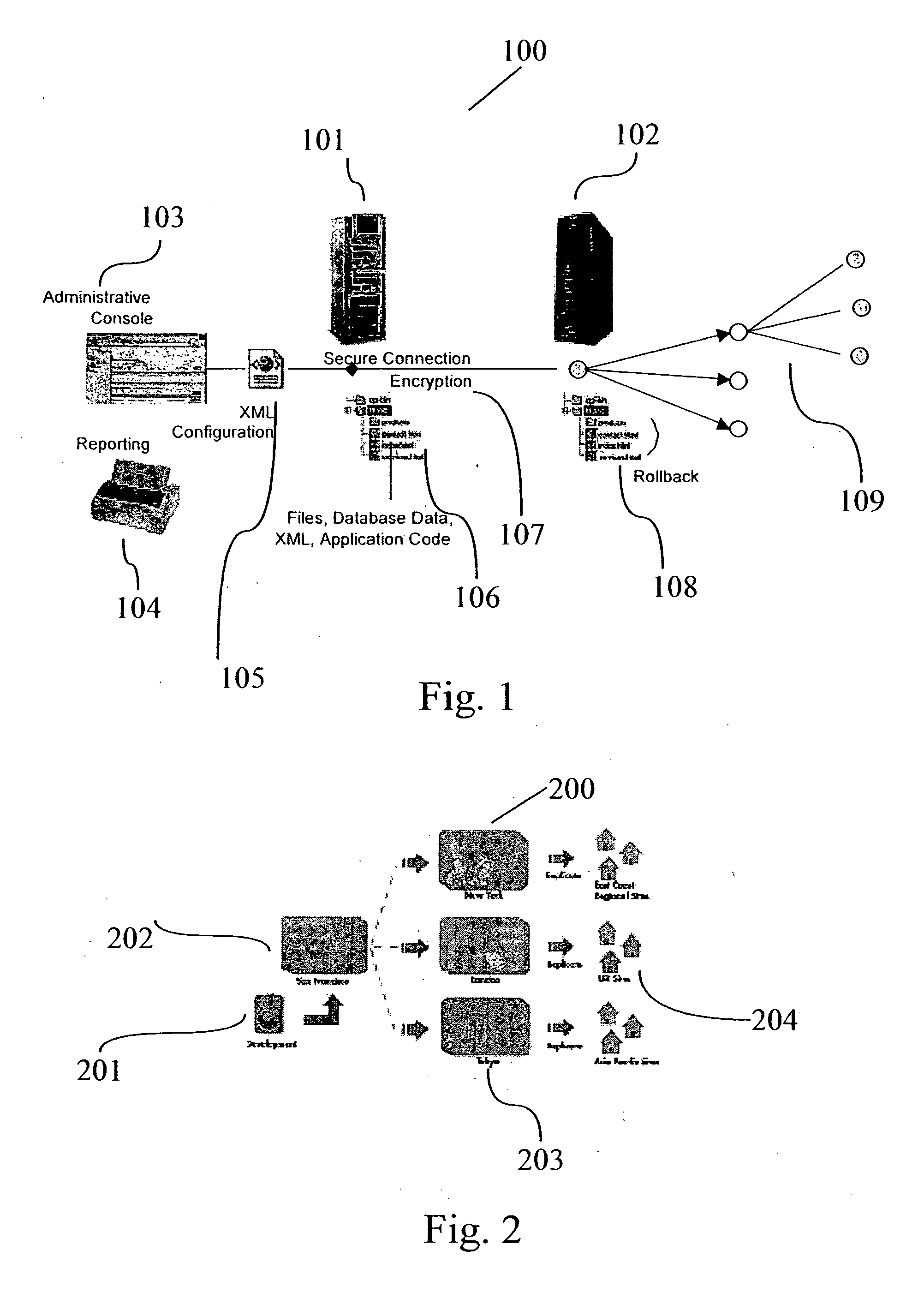
A system for transactionally deploying content across multiple machines in a network environment automates and synchronizes secure and reliable distribution of digital assets to multiple network locations, allowing controlled provisioning and synchronization of code and content updates to live applications. A distributed architecture includes at least one receiver—a secure listener configured to process incoming distribution jobs—and at least one base server—a sender that may also act as a receiver. An administration interface allows administrative and reporting services and deployment management. Using the administrative interface, users are enabled to launch, simulate, schedule and monitor activities for any network location at any time. The system provides fan-out and multi-tiered deployment topologies expandable to hundreds of servers. Each deployment is fully transactional, permitting rollback of the system to it “last known good” state in the case of failure.
Owner:OPEN TEXT CORPORATION
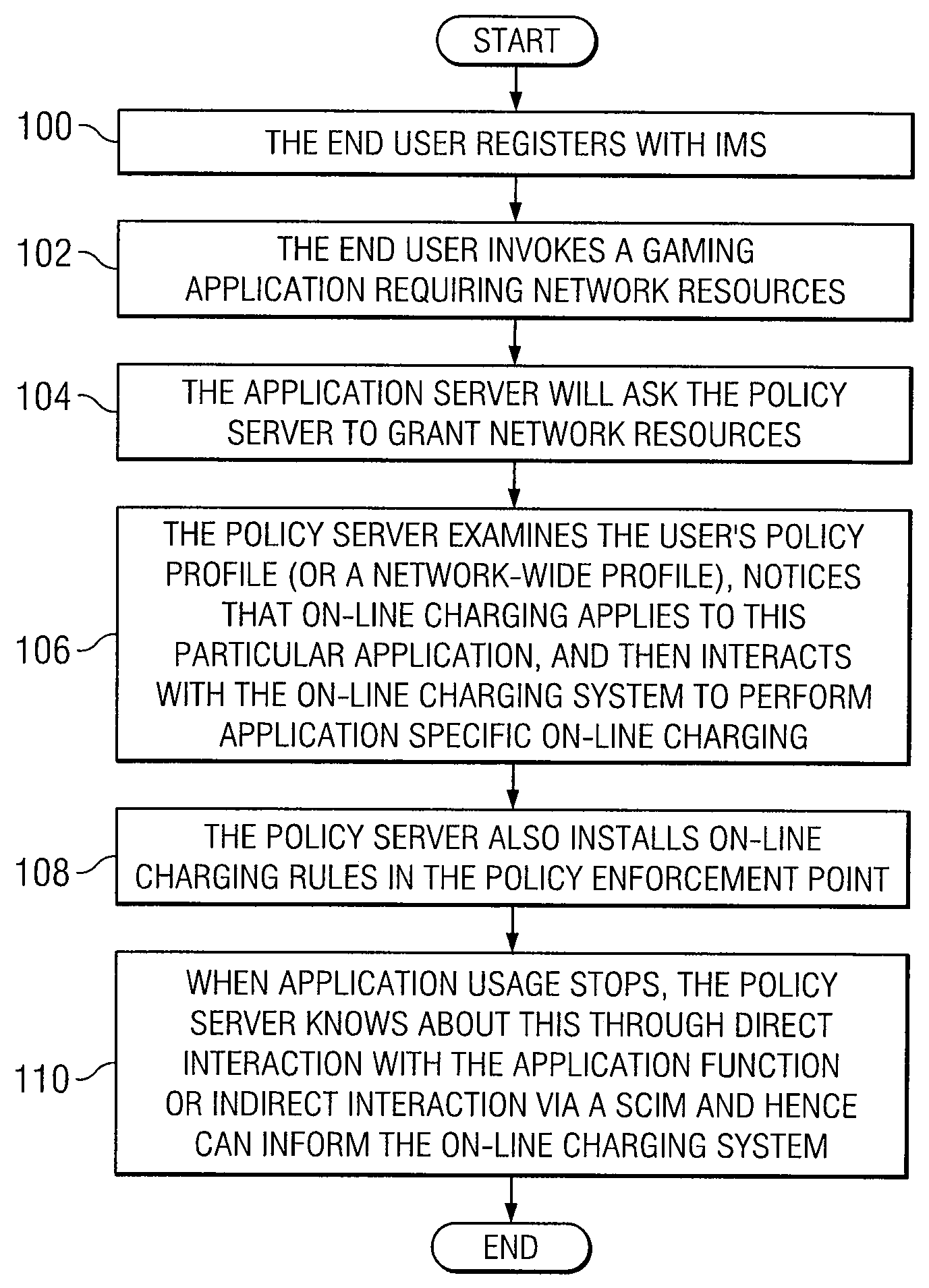
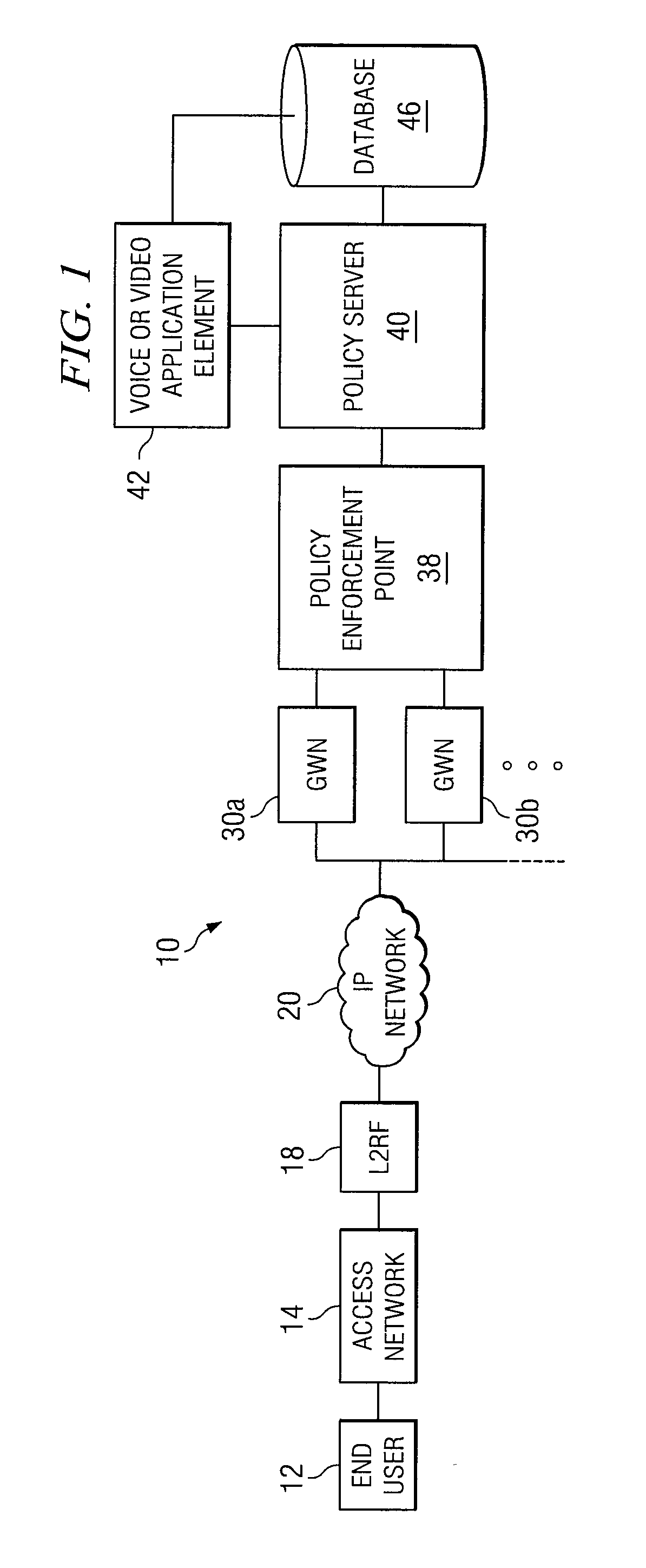
System and Method for Providing Application-Specific On-Line Charging in a Communications Environment
ActiveUS20080189760A1Optimal application configurationAccurate chargesDigital data processing detailsUser identity/authority verificationComputer networkApplication specific
An architecture for A method for providing on-line charging in a network environment is provided that includes interacting with an application that is selected by an end user, and with a policy enforcement point to install corresponding policies that are inclusive of charging rules. The method also includes performing, via a policy server, on-line charging interactions on behalf of the selected application itself such that application-specific on-line charging for the application is enabled. In more particular embodiments, the policy server understands which application is interacting with it by use of application tokens, source, or service identifiers. Also, the application element can query the policy server indirectly to grant network resources and the policy server examines an end user's policy profile or a network-wide profile (or both) and recognizes that on-line charging applies to the selected application.
Owner:CISCO TECH INC
End user risk management
ActiveUS7490356B2Respond effectivelyMemory loss protectionDigital data processing detailsReal time analysisSafety management systems
A flexible, efficient and easy-to-use computer security management system effectively evaluates and responds to informational risks on a wide variety of computing platforms and in a rapidly changing network environment. An individual computer system dynamically monitors its end user, without regard to network connectivity, in order to calculate a risk score and to ensure that the end user's behavior does not put corporate information or other assets at risk. Data regarding such risks and responses are analyzed and stored in real-time.
Owner:CITRIX SYST INC
End user risk management
ActiveUS20060020814A1Respond effectivelyMemory loss protectionDigital data processing detailsReal time analysisComputer science
A flexible, efficient and easy-to-use computer security management system effectively evaluates and responds to informational risks on a wide variety of computing platforms and in a rapidly changing network environment. An individual computer system dynamically monitors its end user, without regard to network connectivity, in order to calculate a risk score and to ensure that the end user's behavior does not put corporate information or other assets at risk. Data regarding such risks and responses are analyzed and stored in real-time.
Owner:CITRIX SYST INC
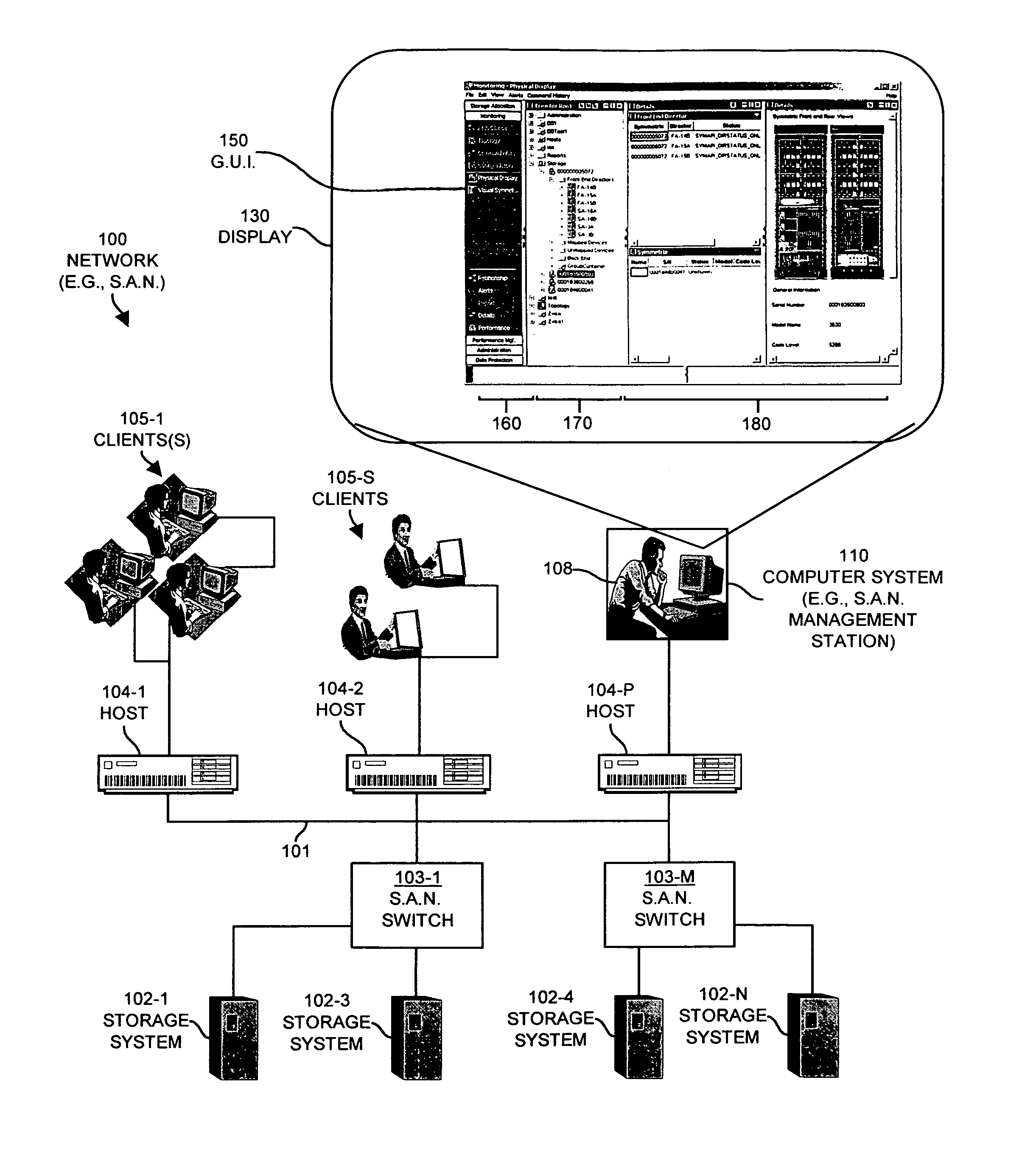
Methods and apparatus for graphically managing resources
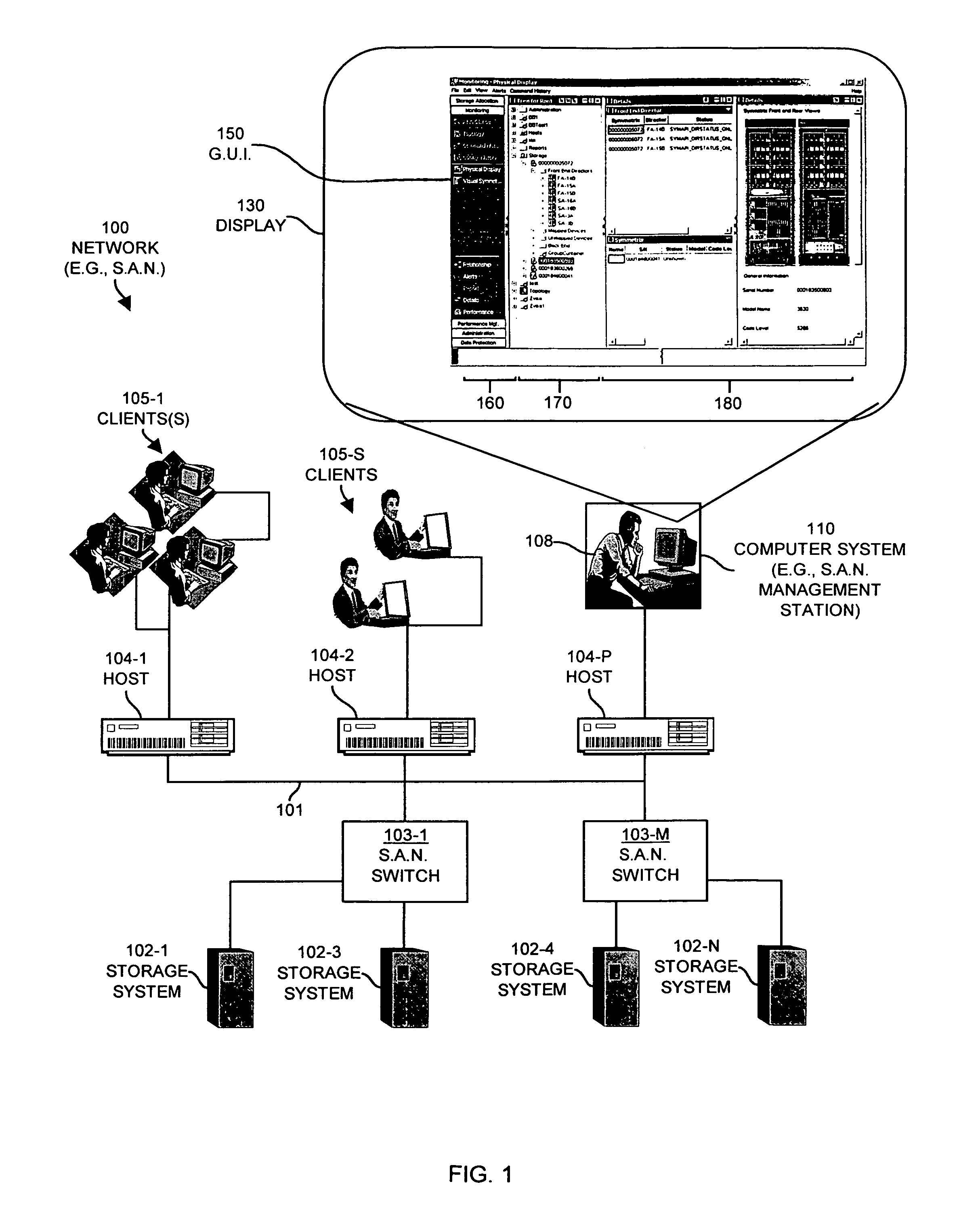
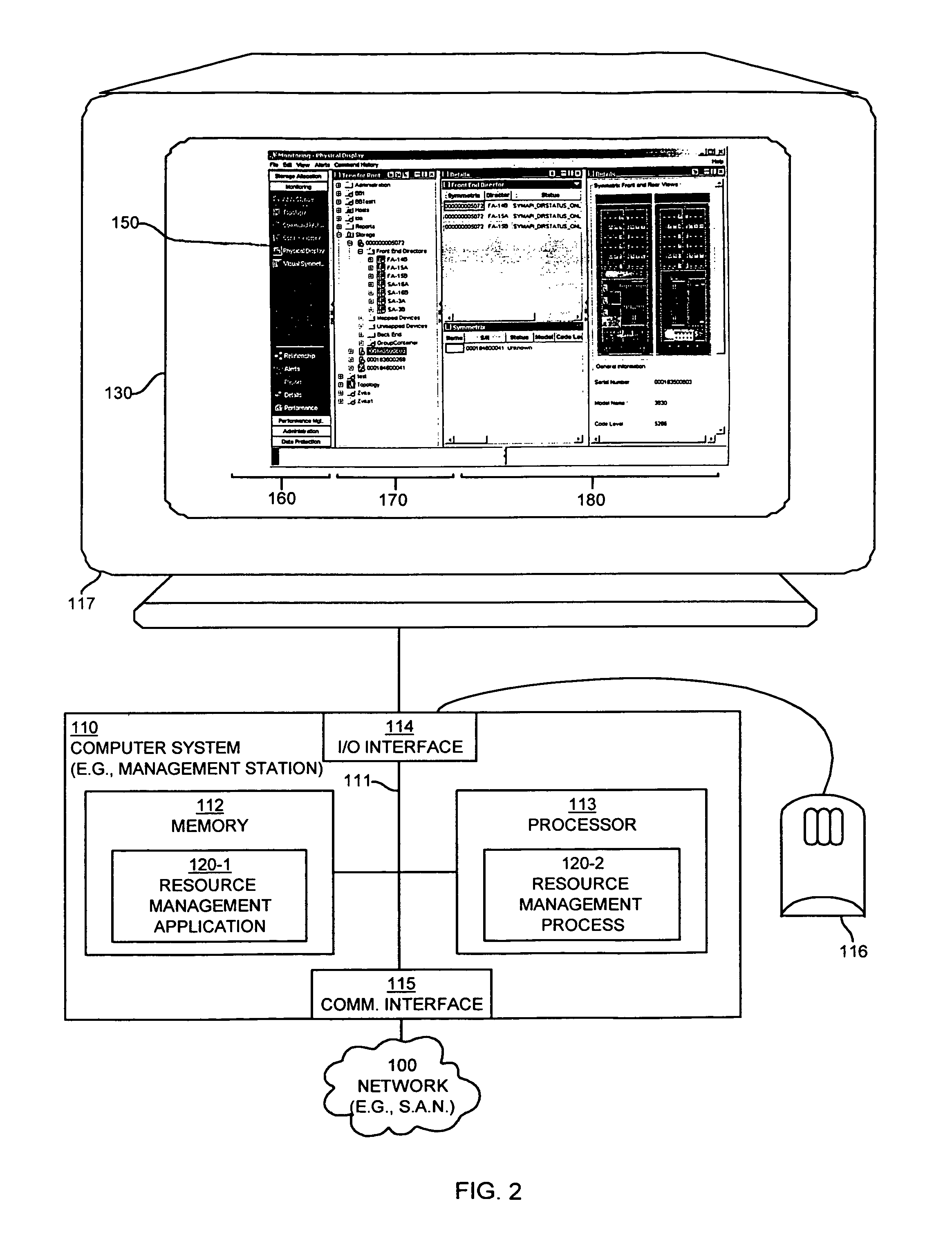
InactiveUS6966033B1Good choiceDigital computer detailsData switching networksGraphicsGraphical user interface
Mechanisms and techniques are disclosed that provide a graphical user interface and associated processing operations for performing management of resources in a network environment such as a storage area network. In one configuration, the system displays a plurality of resource tasks in a task display area on a graphical user interface and displays a plurality of resource objects in a resource display area on the graphical user interface. The system then receives a selection of one or more resource tasks identifying function(s) to apply to a selection of resource objects. The system then applies the function(s) associated with each selected resource task to the selection of resource objects to produce a set of resource information and displays the resource information for each resource object view panel(s) in an shared output display area for viewing by a user of the graphical user interface. This allows a user to apply multiple task functions to multiple selected resources and allows a user to display the results for all selected resource objects in a shared output display area.
Owner:EMC IP HLDG CO LLC
Manipulating association of data with a physical object
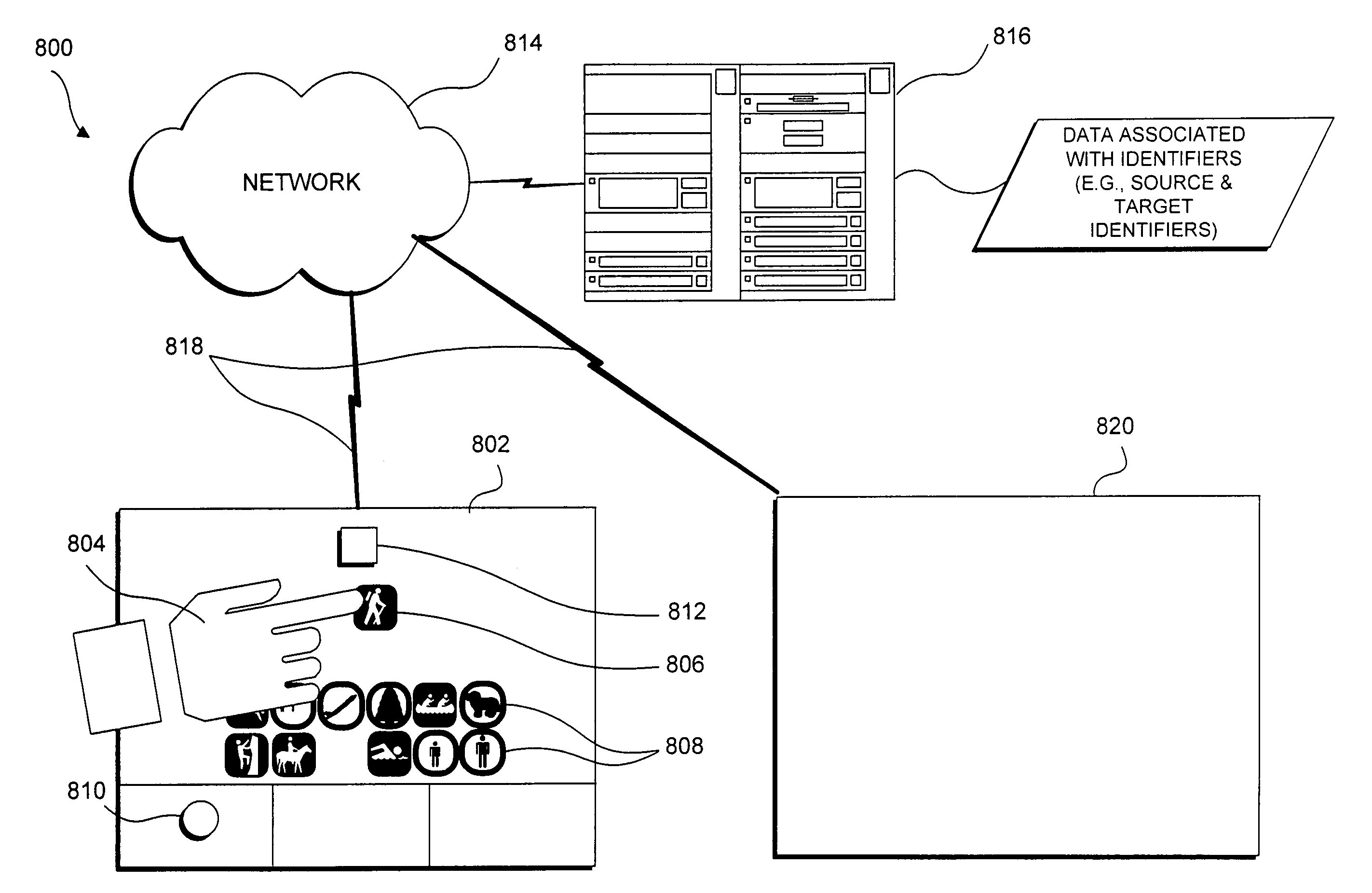
InactiveUS20050275636A1Easy retrievalSimple methodInput/output for user-computer interactionCathode-ray tube indicatorsWeb environmentComputing systems
Data elements stored in a computing system and associated with a physical object are reassociated with the same or another physical object. An identifying characteristic presented by the physical object, such as a reflective pattern applied to the object, is detected when the object is positioned adjacent to the interactive display surface. Images or other files associated with the identifying characteristic are accessed and displayed on the interactive display surface. A gesture by a user adjacent to the interactive display surface is detected to reassociate a selected representation. For example, the user can change where the selected element fits in a sequence of data elements, or reassociate the selected element with a second object placed on the interactive display surface. In a networked environment, the reassociated element can be stored on a server and subsequently accessed from a different interactive surface via the network using the second physical object.
Owner:MICROSOFT TECH LICENSING LLC
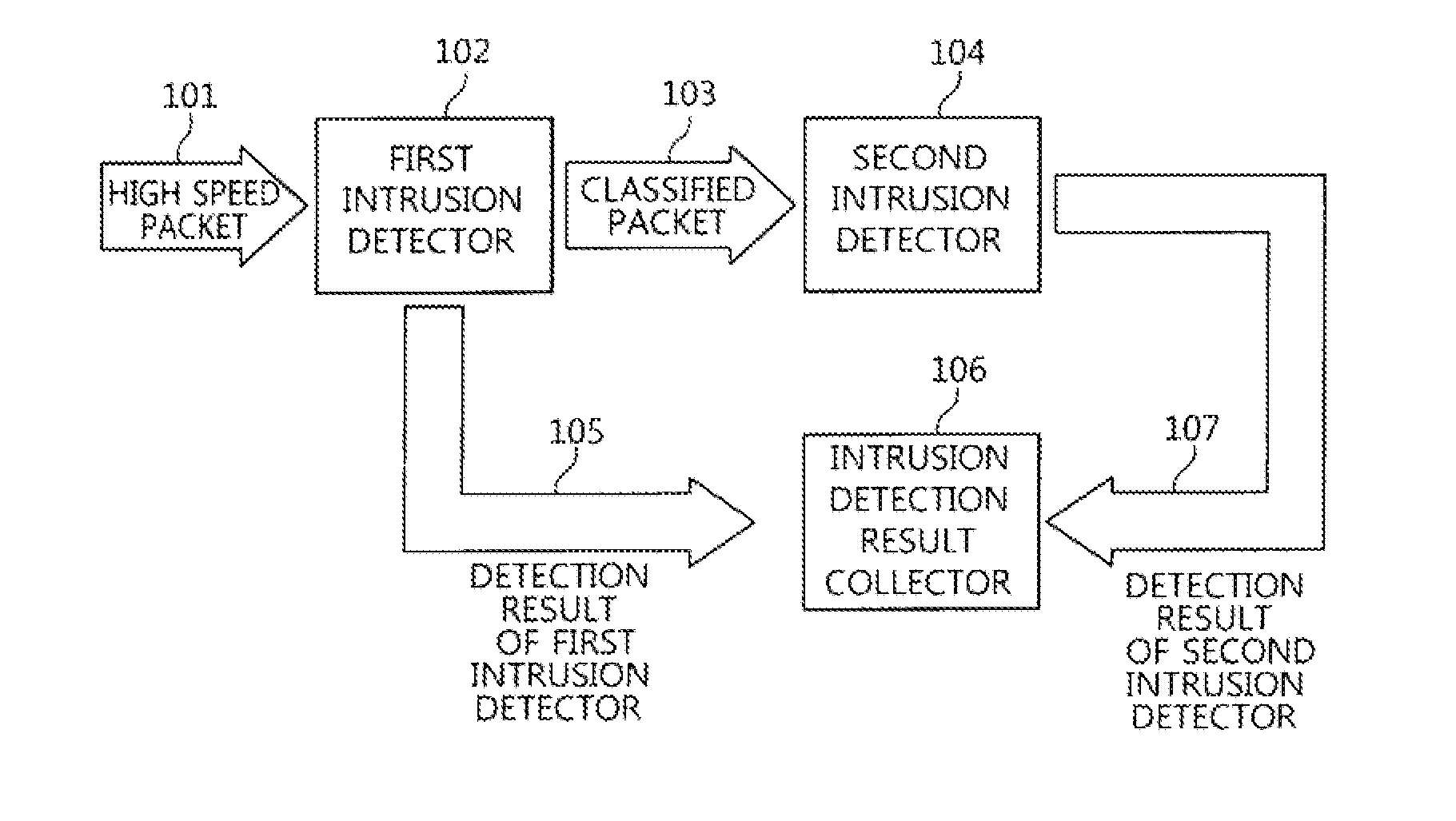
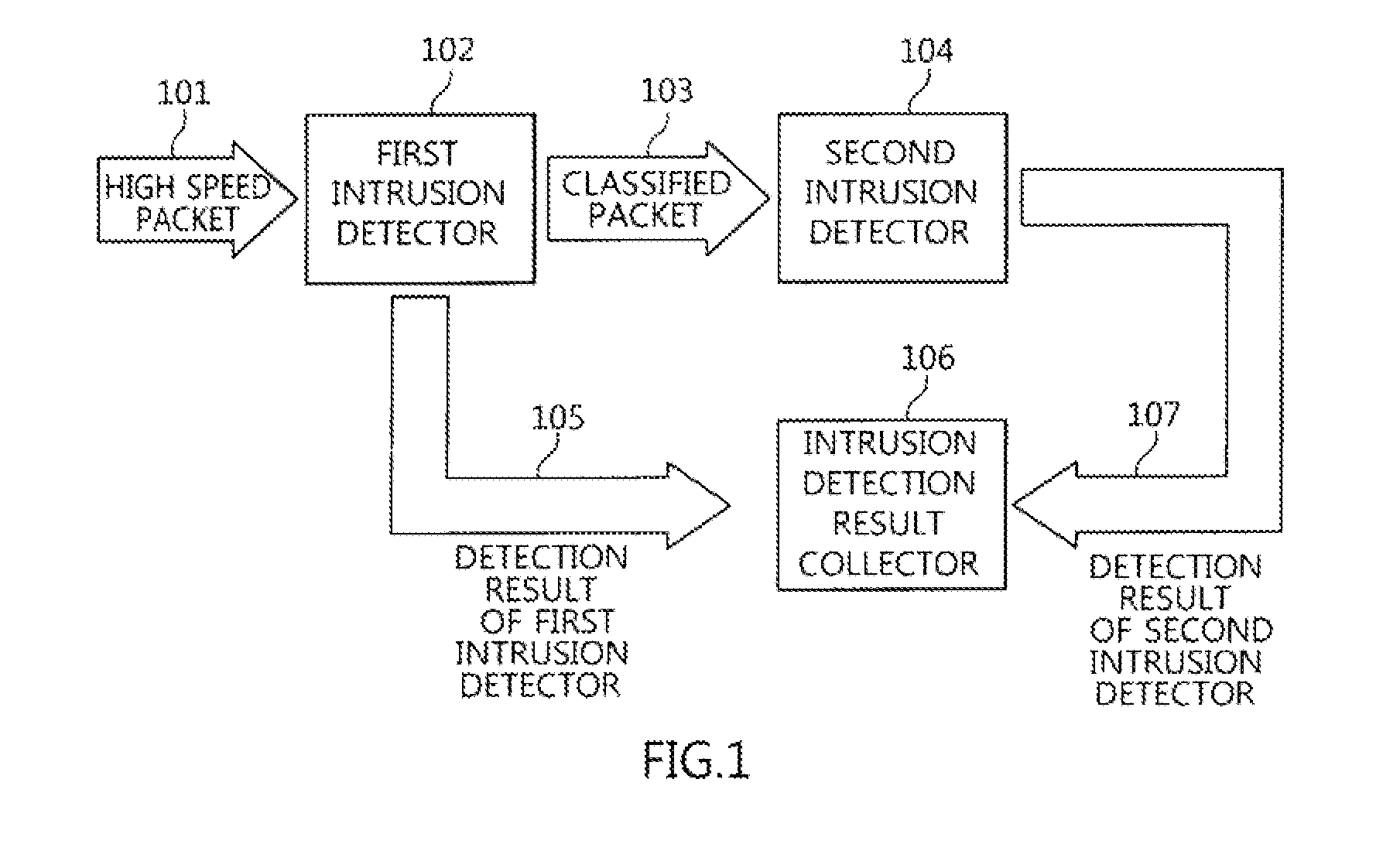
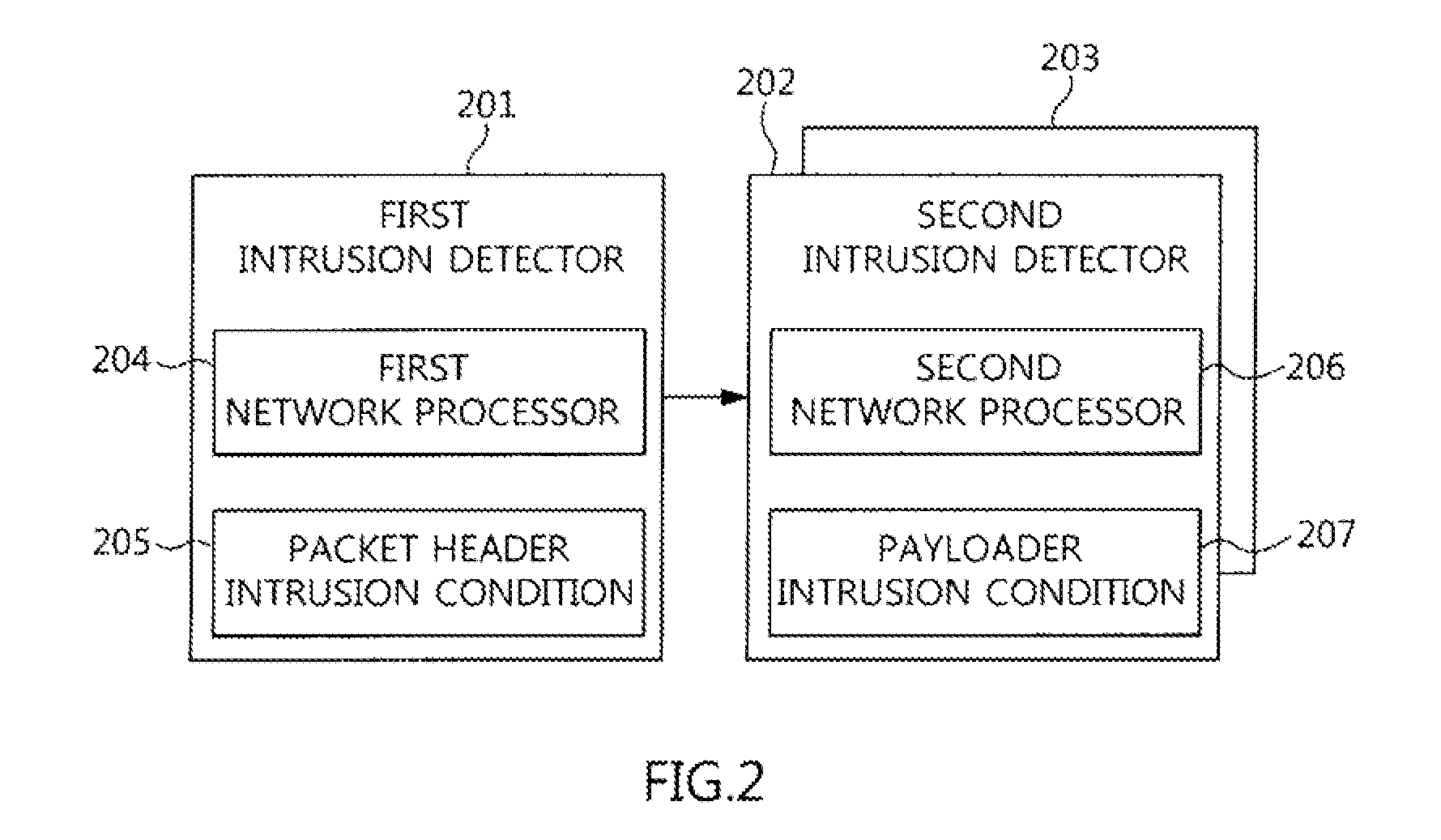
Two-stage intrusion detection system for high-speed packet processing using network processor and method thereof
ActiveUS20130160122A1Memory loss protectionData taking preventionNetwork processorDistributed computing
A system and method for detecting network intrusion by using a network processor are provided. The intrusion detection system includes: a first intrusion detector, configured to use a first network processor to perform intrusion detection on layer 3 and layer 4 of a protocol field among information included in a packet header of a packet transmitted to the intrusion detection system, and when no intrusion is detected, classify the packets according to stream and transmit the classified packets to a second intrusion detector; and a second intrusion detector, configured to use a second network processor to perform intrusion detection through deep packet inspection (DPI) for the packet payload of the packets transmitted from the first intrusion detector. Thereby, intrusion detection for high-speed packets can be performed in a network environment.
Owner:ELECTRONICS & TELECOMM RES INST
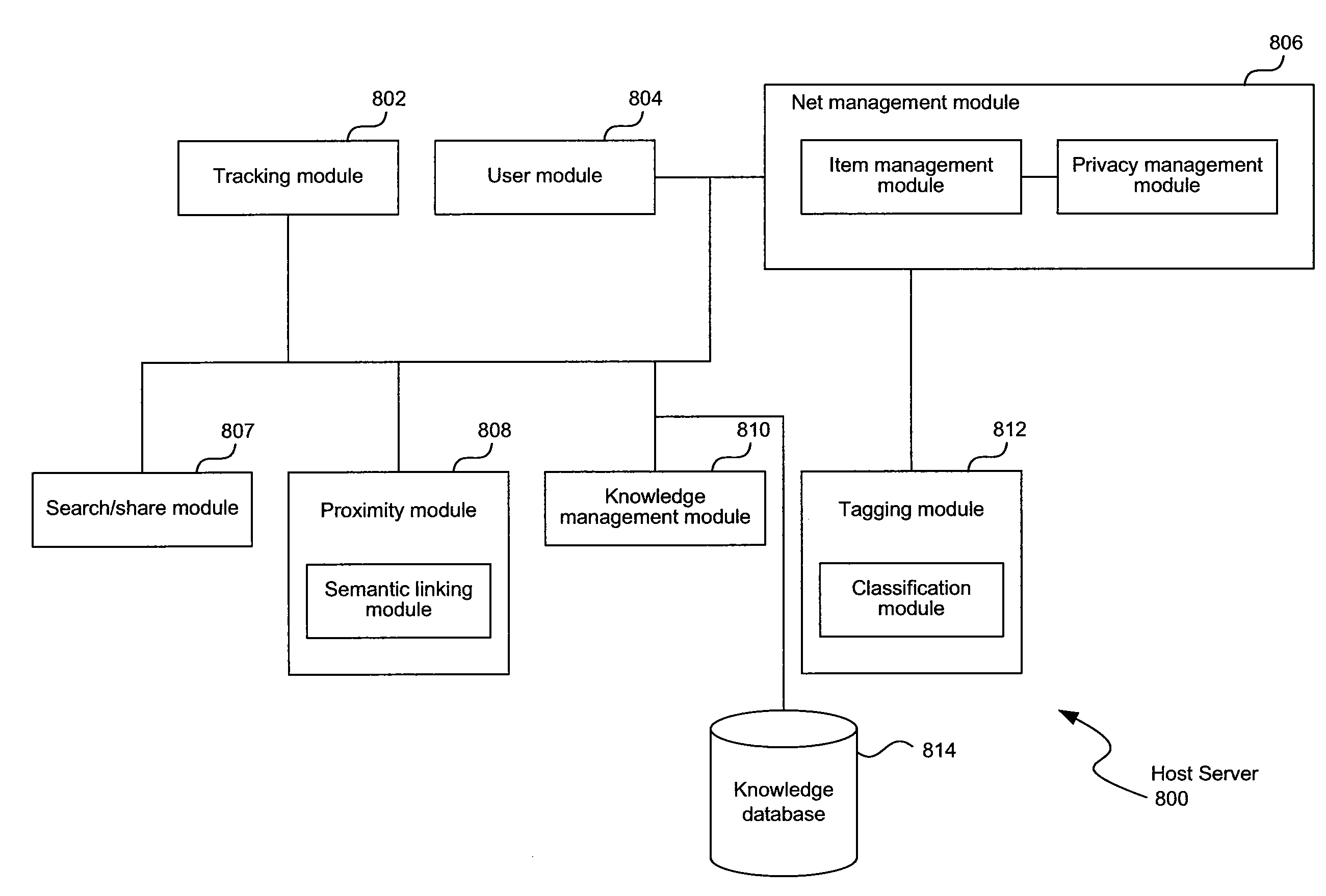
Systems and methods for stored-value exchange within social networking environments
Owner:FIRST DATA RESOURCES LLC
Personalization of placed content ordering in search results
ActiveUS7693827B2Digital data information retrievalData processing applicationsPersonalizationClient-side
A system and method for using a user profile to order placed content in search results returned by a search engine. The user profile is based on search queries submitted by a user, the user's specific interaction with the documents identified by the search engine and personal information provided by the user. Placed content is ranked by a score based at least in part on a similarity of a particular placed content to the user's profile. User profiles can be created and / or stored on the client side or server side of a client-server network environment.
Owner:GOOGLE LLC
Method of scheduling hosts for software updates in a distributed computer network
ActiveUS20040243996A1Digital computer detailsProgram loading/initiatingSoftware updateChange control
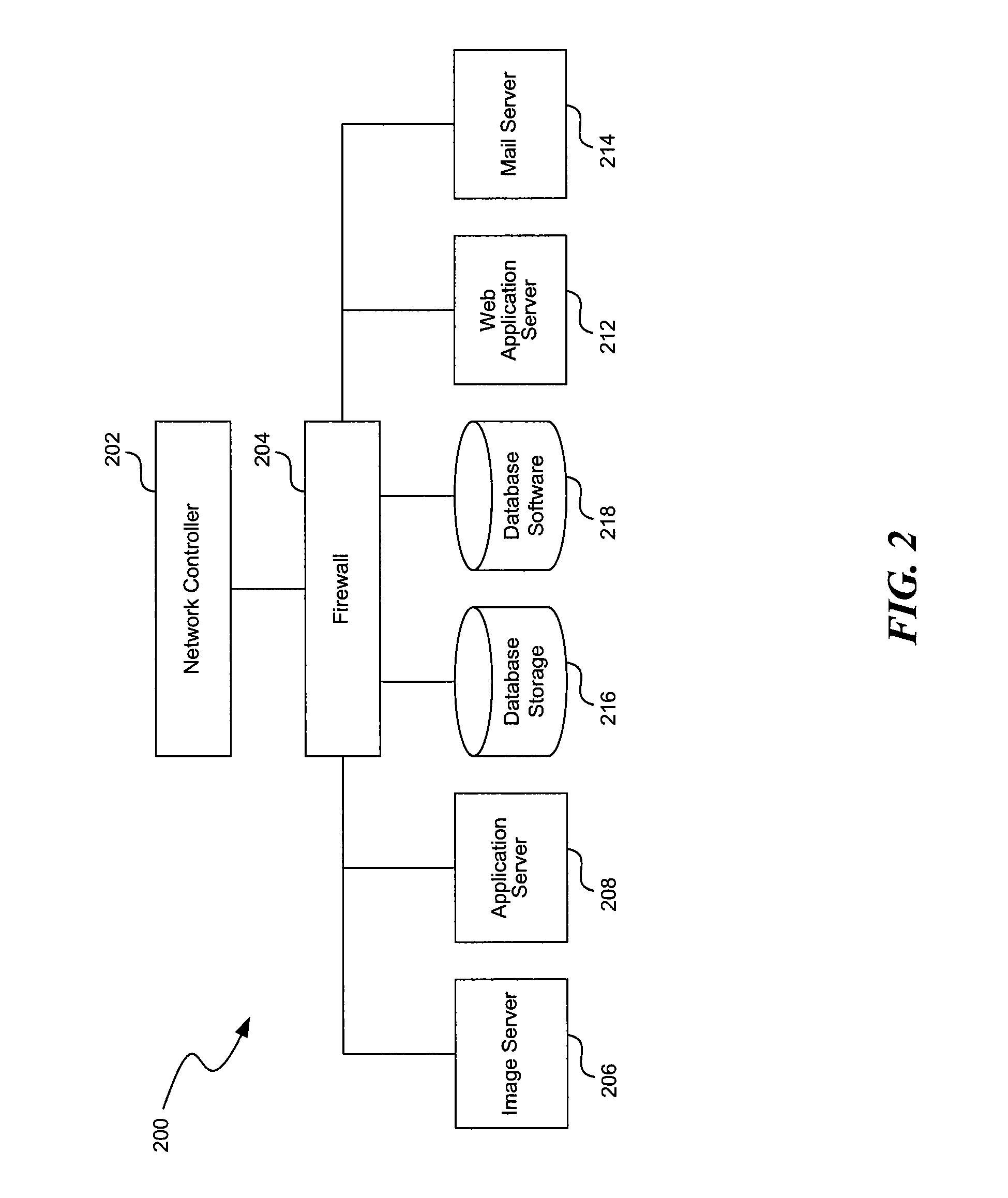
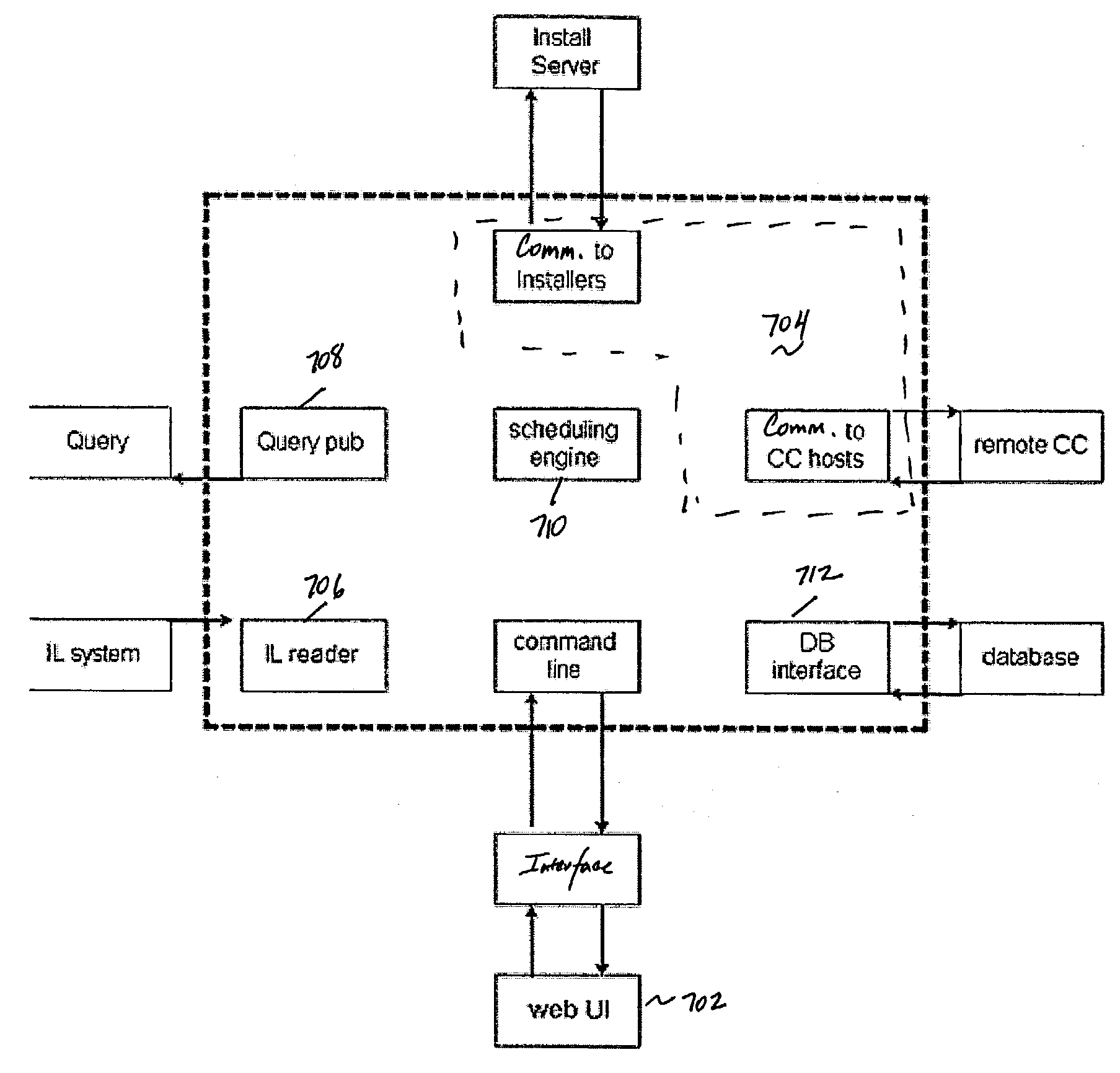
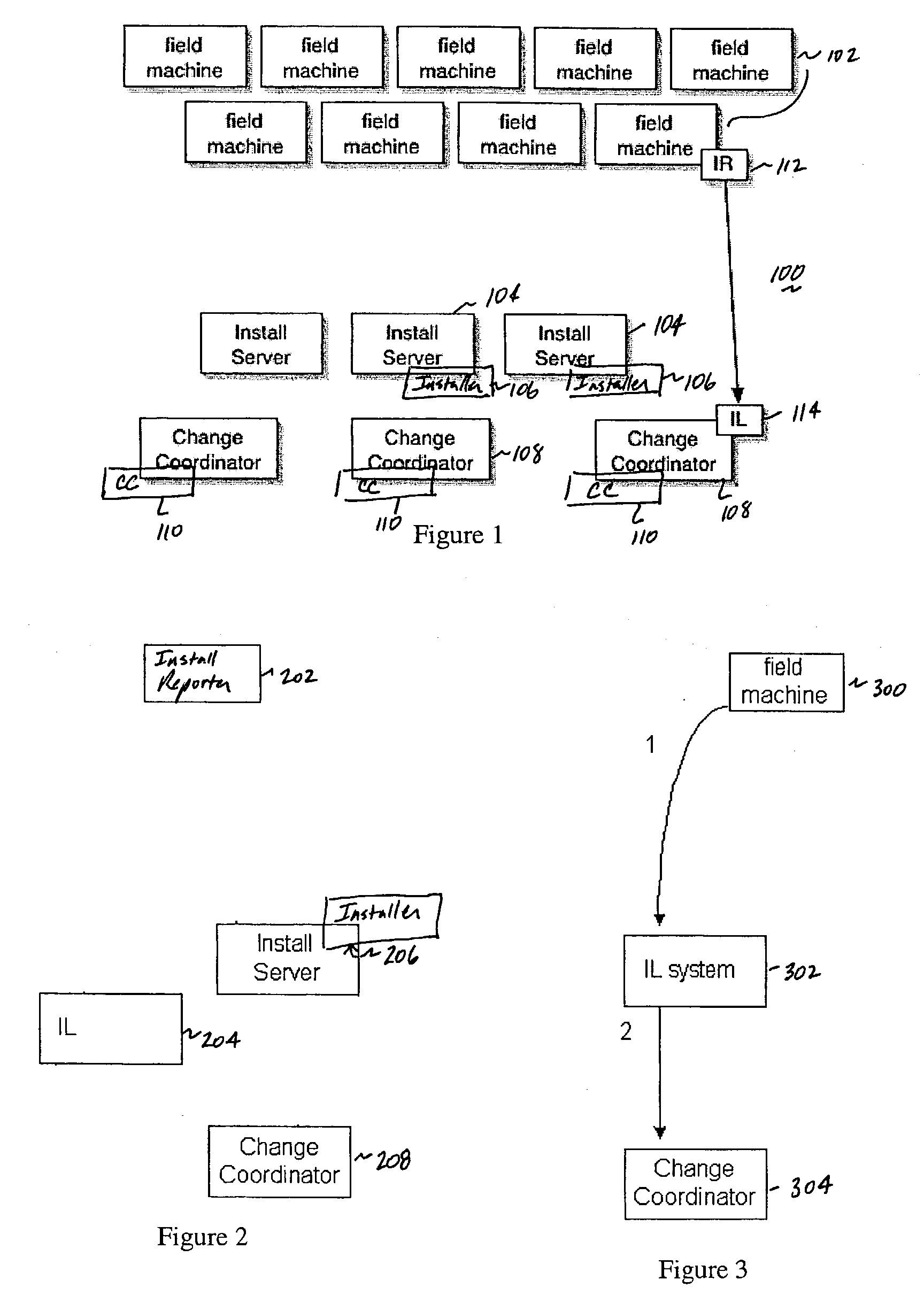
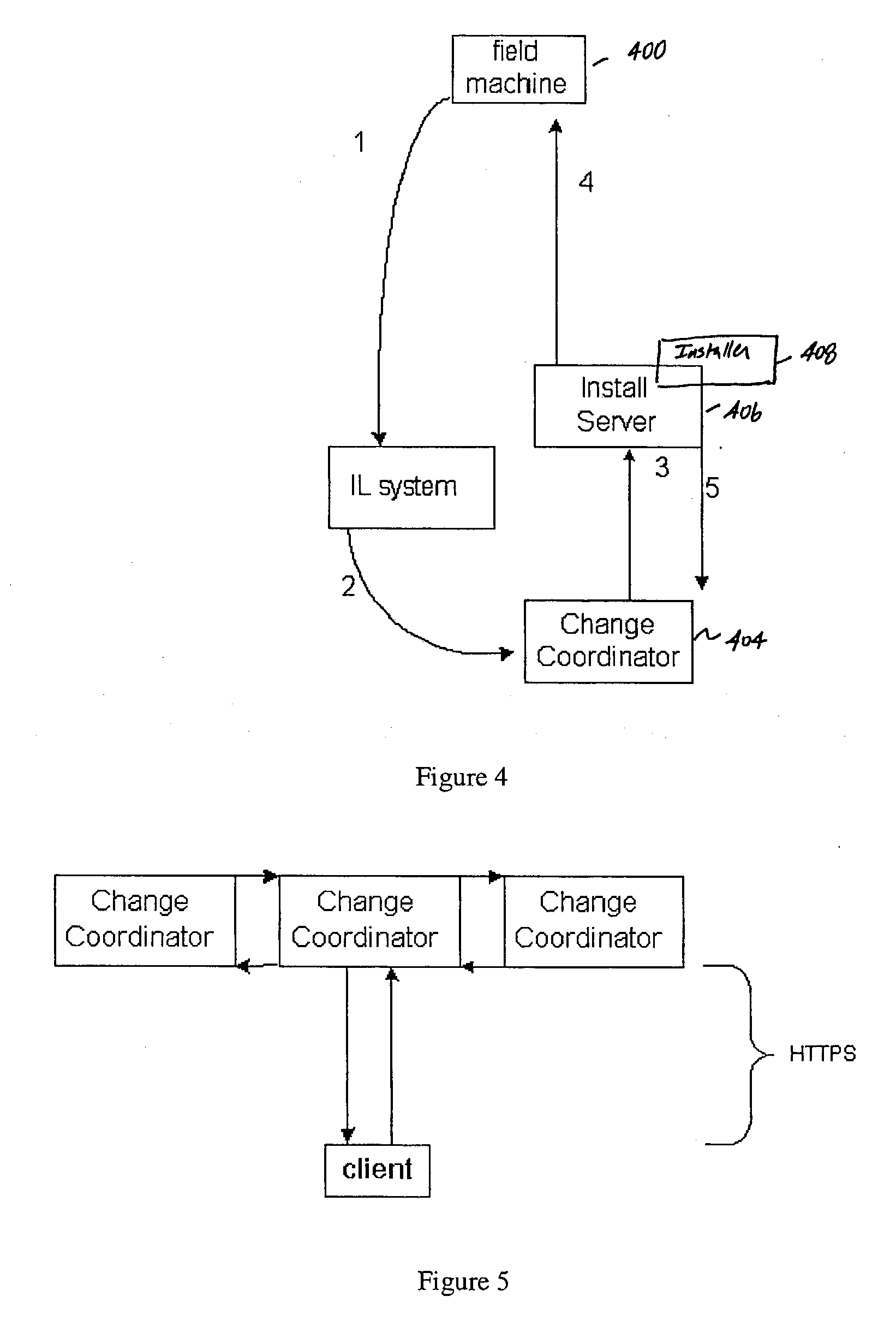
A method of and system for managing installs to a set of one or more field machines in a distributed network environment. In an illustrative embodiment, the system includes at least one change coordinator server that includes a database with data identifying a current state of each field machine, and a change controller routine for initiating a given control action to initiate an update to the current state on a given field machine. In particular, the change controller routine may include a scheduling algorithm that evaluates data from the database and identifies a set of field machines against which the given control action may be safely executed at a given time. At least one install server is responsive to the change controller routine initiating the given control action for invoking the update to the current state on the given field machine.
Owner:AKAMAI TECH INC
Method and apparatus for delivering 3D graphics in a networked environment using transparent video
InactiveUS6384821B1Pulse modulation television signal transmissionSelective content distributionImage resolutionThree dimensional graphics
A system and method for seamlessly combining client-only rendering techniques with server-only rendering techniques. The approach uses a composite stream containing three distinct streams. One stream is available to send geometry from the server to the client. Another stream contains video with transparent pixels that allow the client-rendered object to appear in the context of the server rendered objects. The third stream contains camera information. The invention can satisfy a number of viewing applications. For example, initially the most relevant geometry can stream to the client for high quality local rendering while the server delivers renderings of less relevant geometry at lower resolutions. After the most relevant geometry has been delivered to the client, the less important geometry can be optionally streamed to the client to increase the fidelity of the entire scene. In the limit, all of the geometry is transferred to the client and the situation corresponds to client-only rendering system where local graphics hardware is used to improve fidelity and reduce bandwidth. Alternatively, if a client does not have local three-dimensional graphics capability then the server can transmit only the video of the server-rendered object and drop the other two streams. In either case, the approach also permits for a progressive improvement in the server-rendered image whenever the scene becomes static. Bandwidth that was previously used to represent changing images is allocated to improving the fidelity of the server-rendered image whenever the scene becomes static.
Owner:NVIDIA CORP
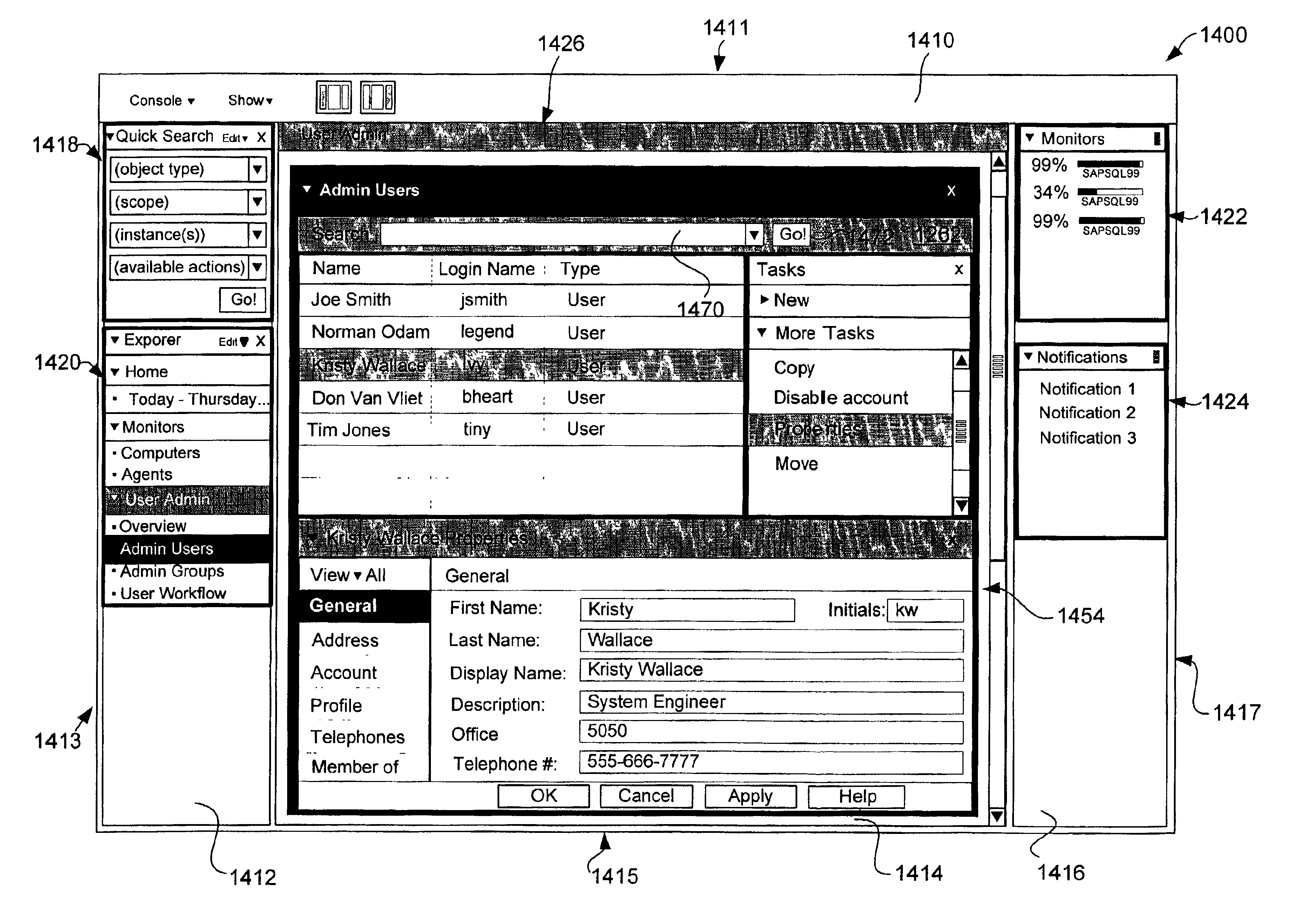
Navigation tool for accessing workspaces and modules in a graphical user interface
InactiveUS6950990B2Reduce overheadEasy and higher-level operation optionData processing applicationsResource allocationGraphicsGraphical user interface
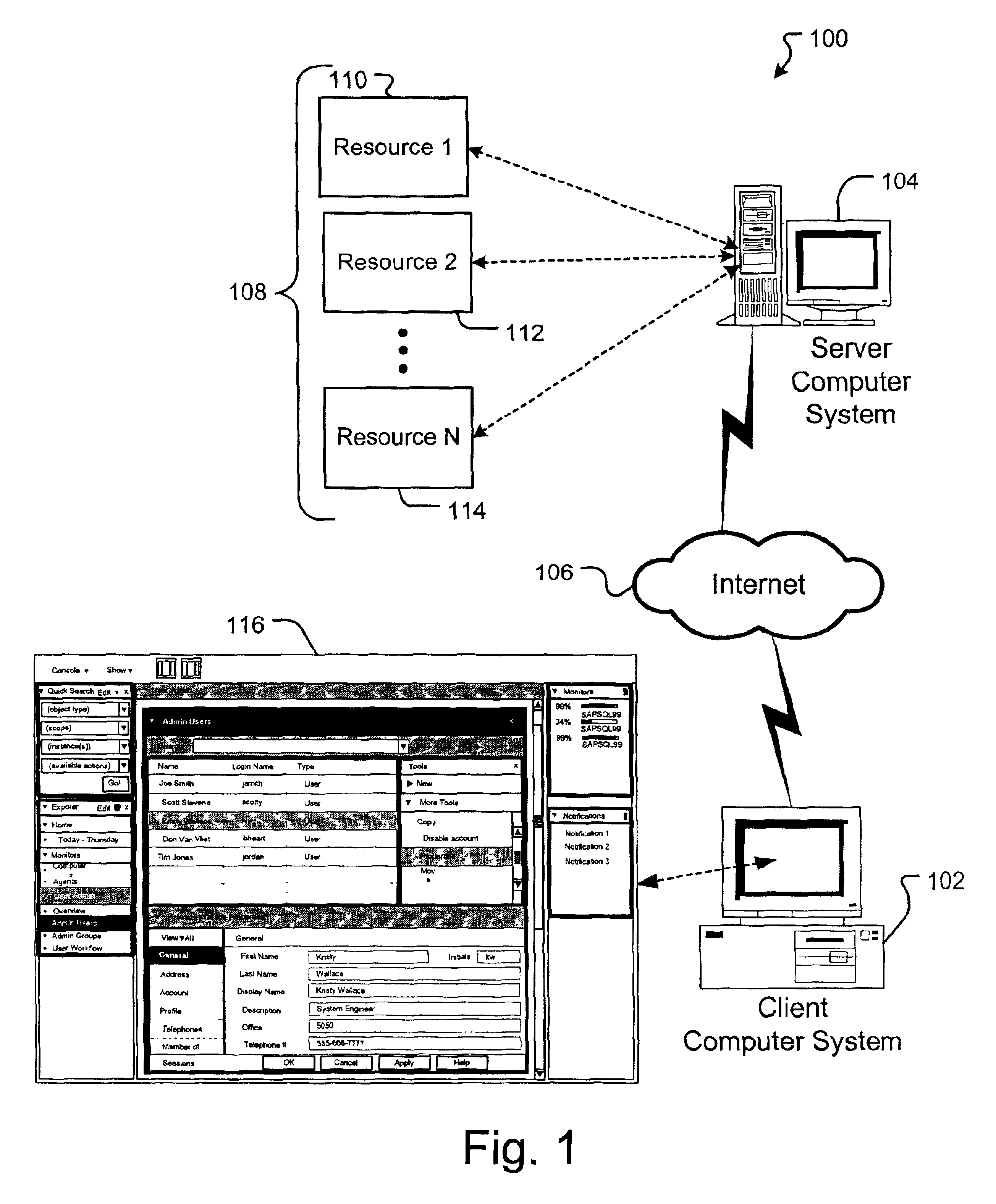
A method and system for displaying information related to a plurality of resources in a network environment. The system uses web technology to receive and store information related to back-end resources and to provide a framework by which client computer systems can manage the plurality of back-end resources in a uniform manner. In accordance with one embodiment, a method is employed in a computer system for selecting the visual arrangement of workspaces and modules in a network management console GUI. The console includes a first zone and a second zone. The method involves receiving a list of workspace names and, in response, displaying an explorer tool including the list of workspace names in the first zone. Upon indication from a user that a first workspace name from the list of workspace names has been selected, a first workspace associated with the first workspace name is displayed in the second zone.
Owner:SERVICENOW INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com