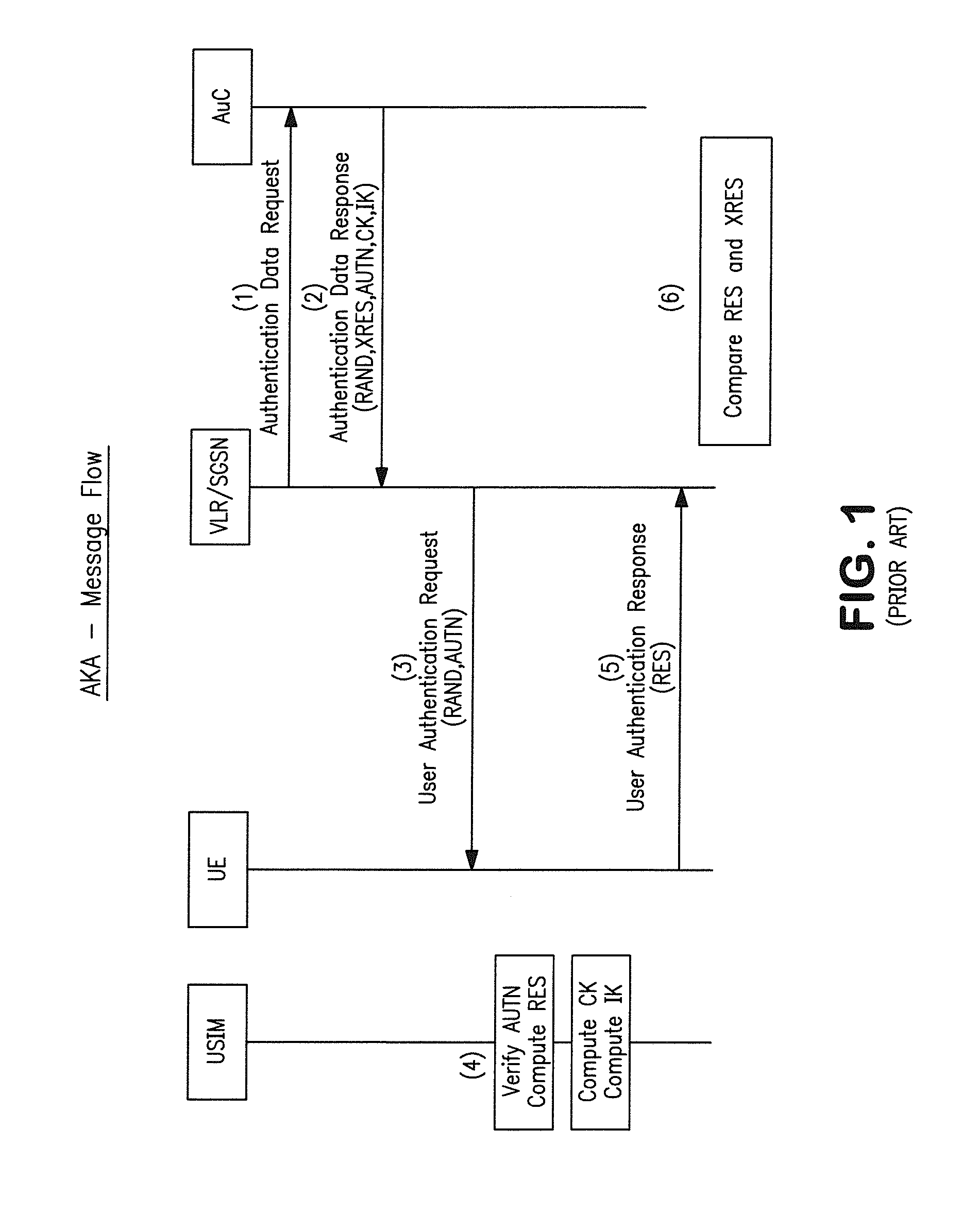
Patents
Literature
3316 results about "Subscriber identity module" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
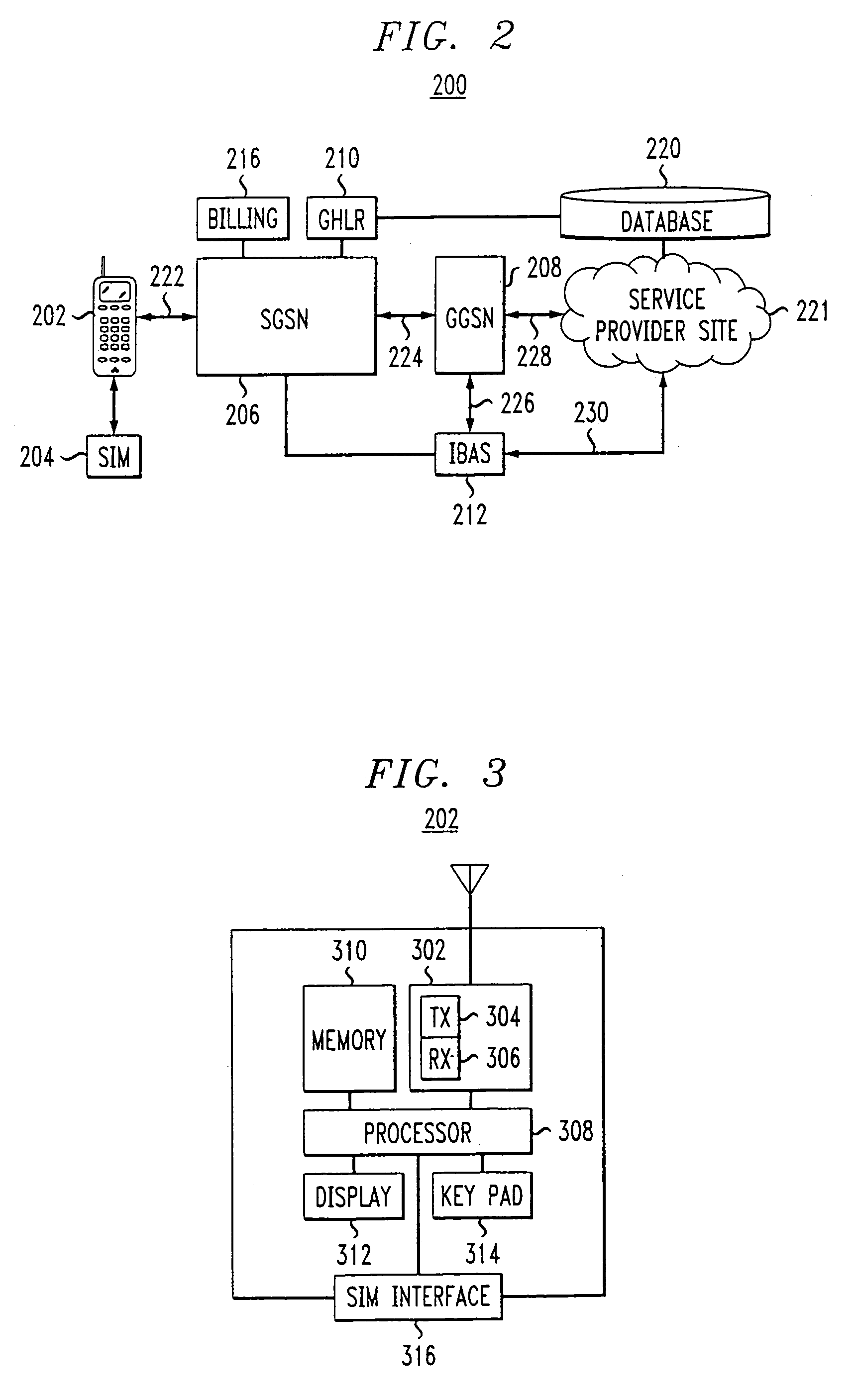
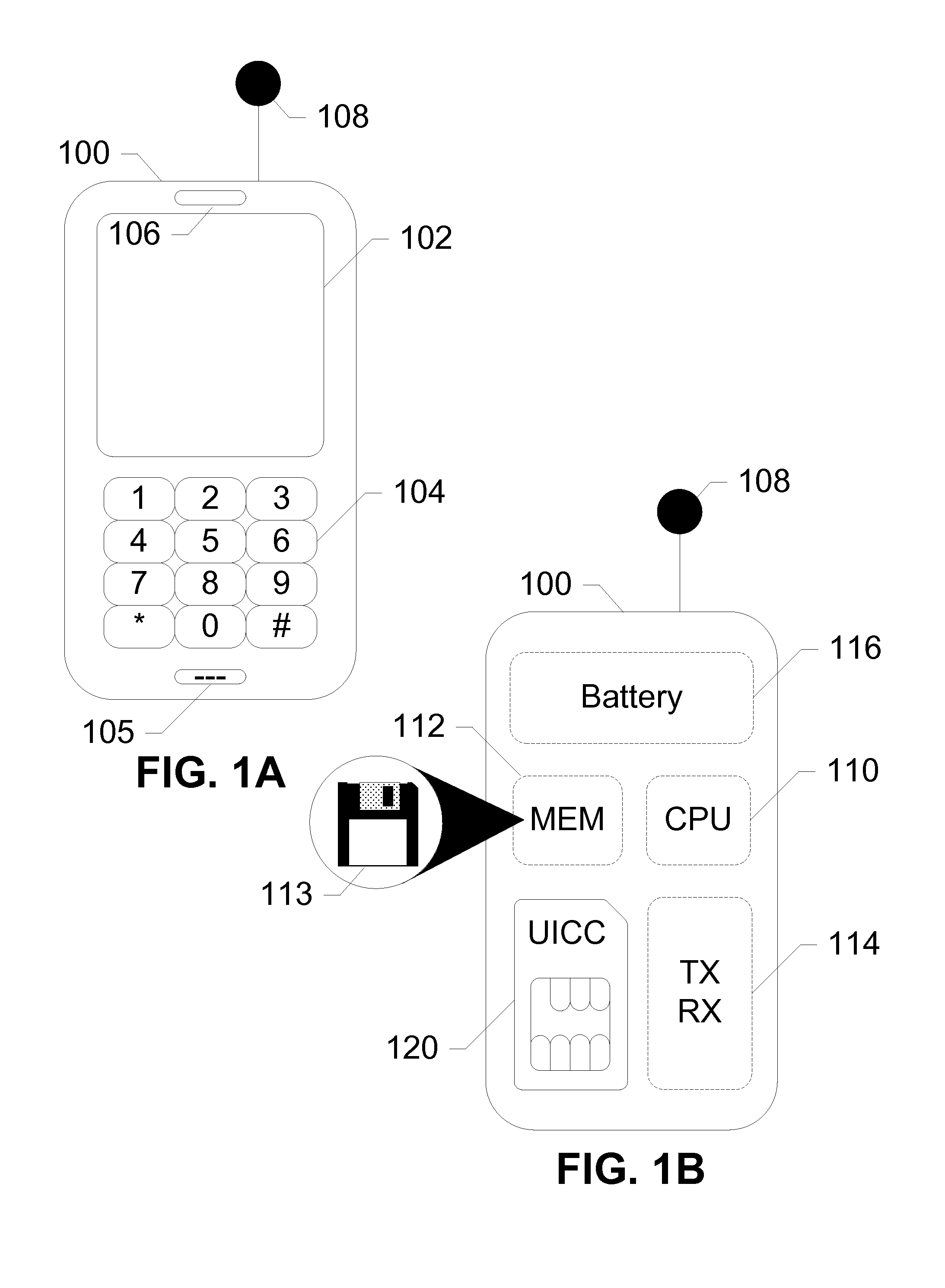
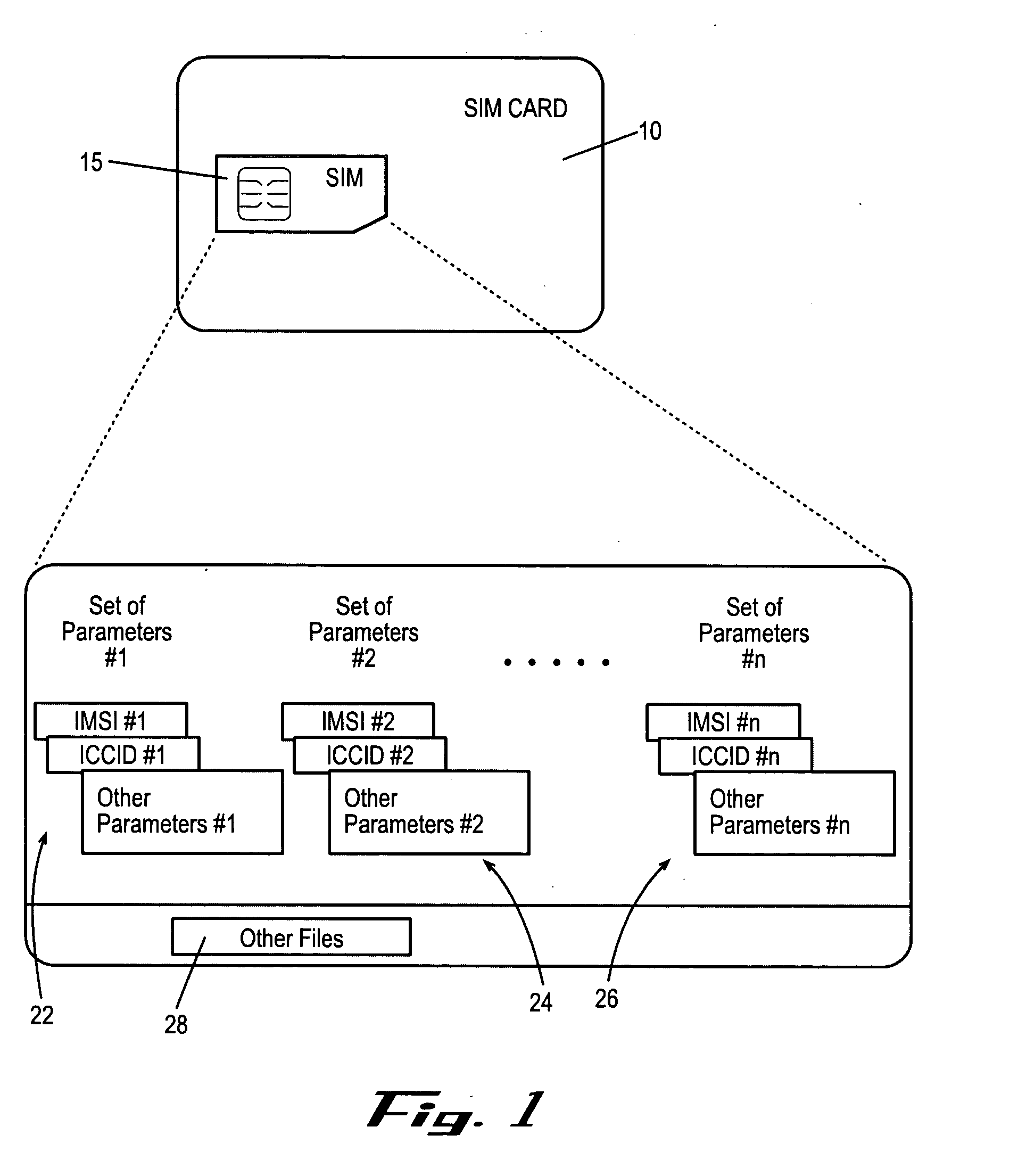
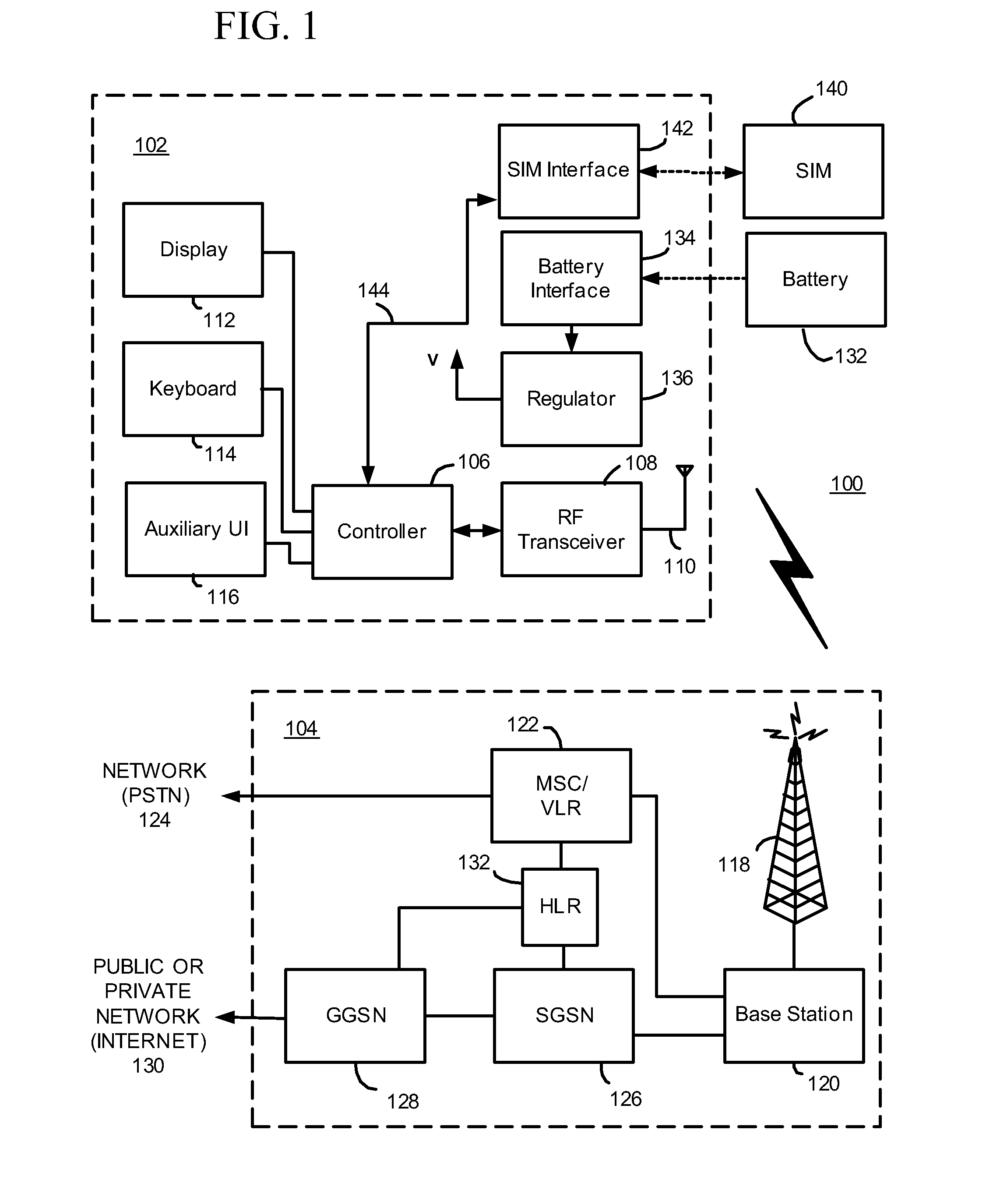
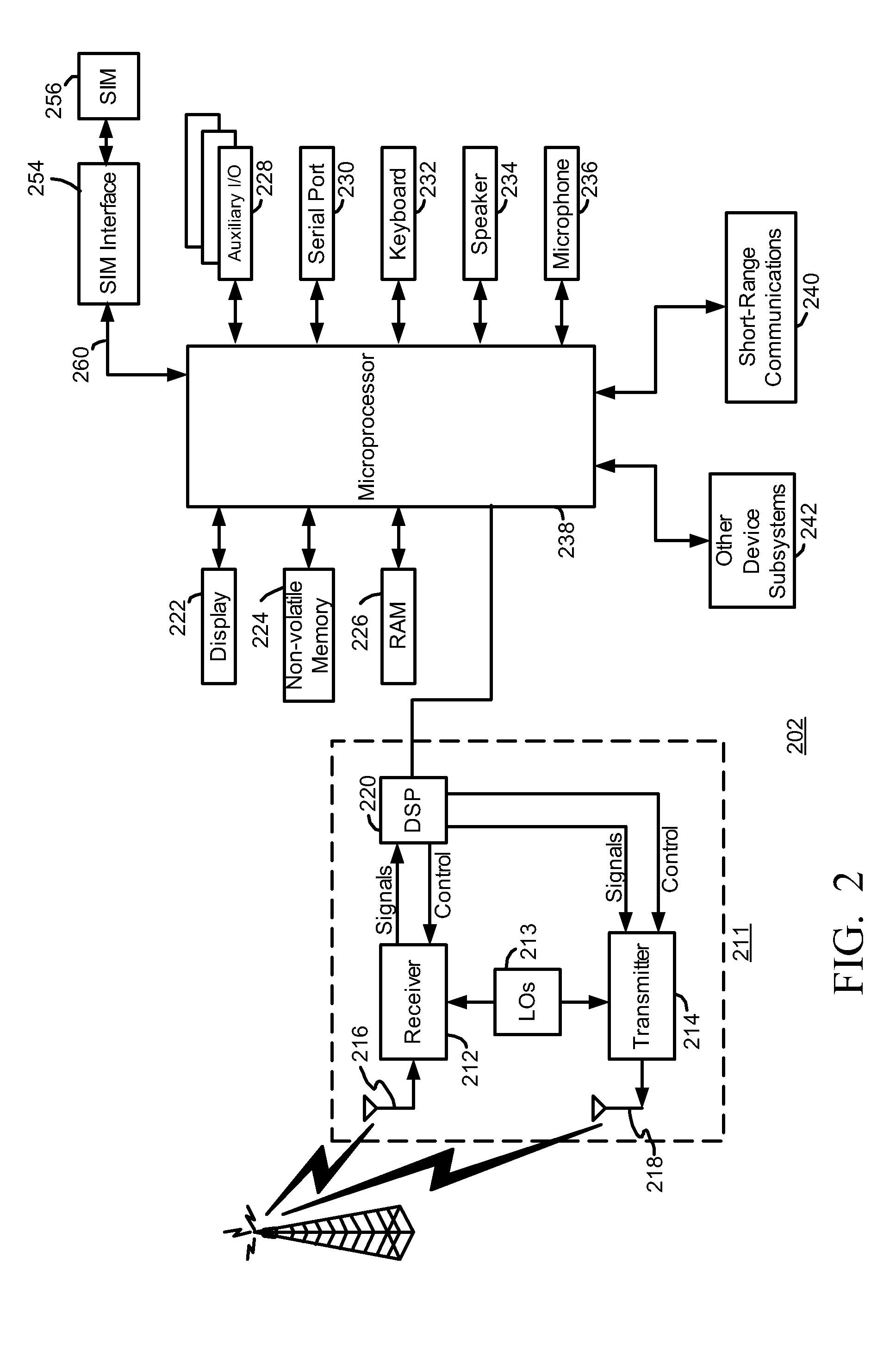
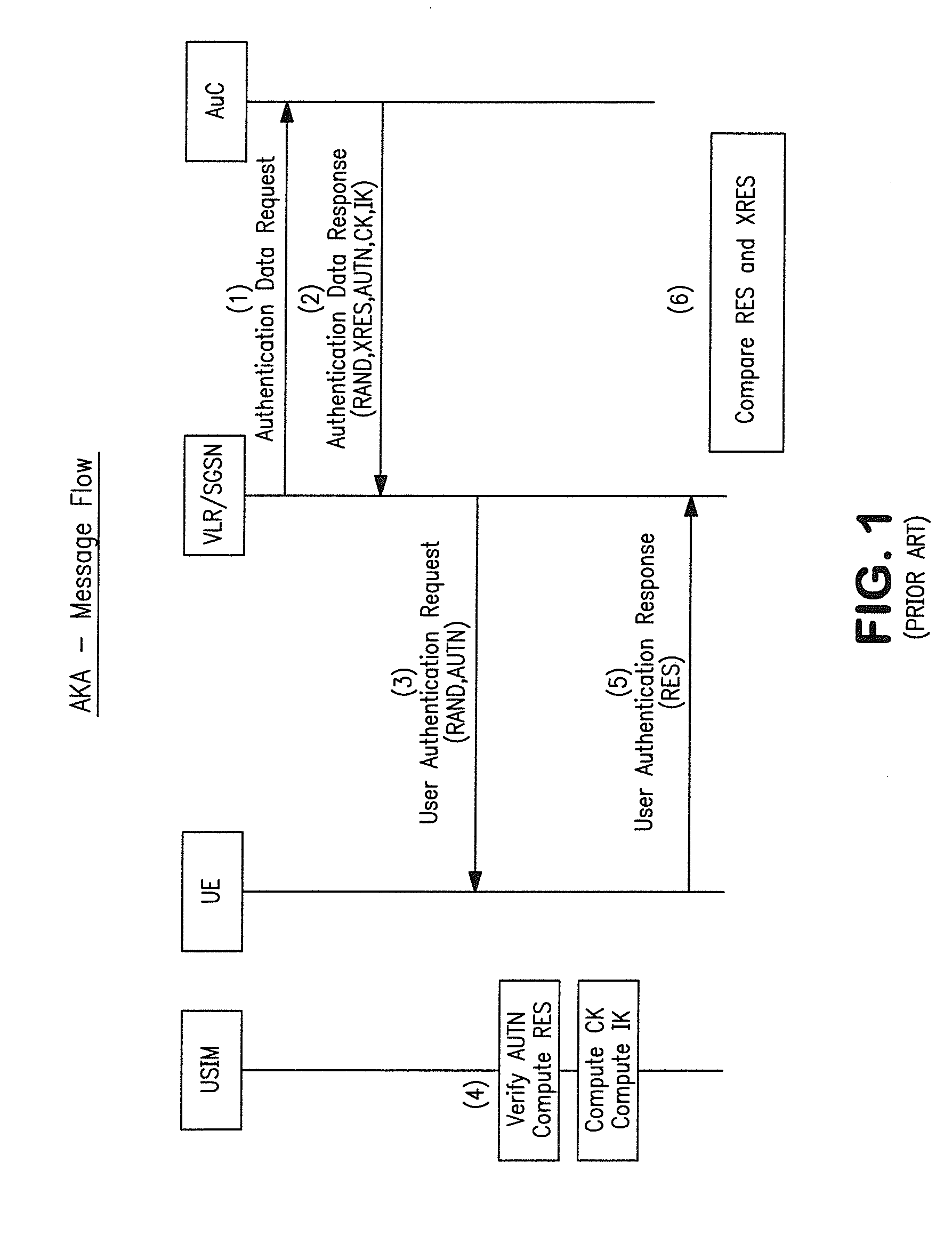
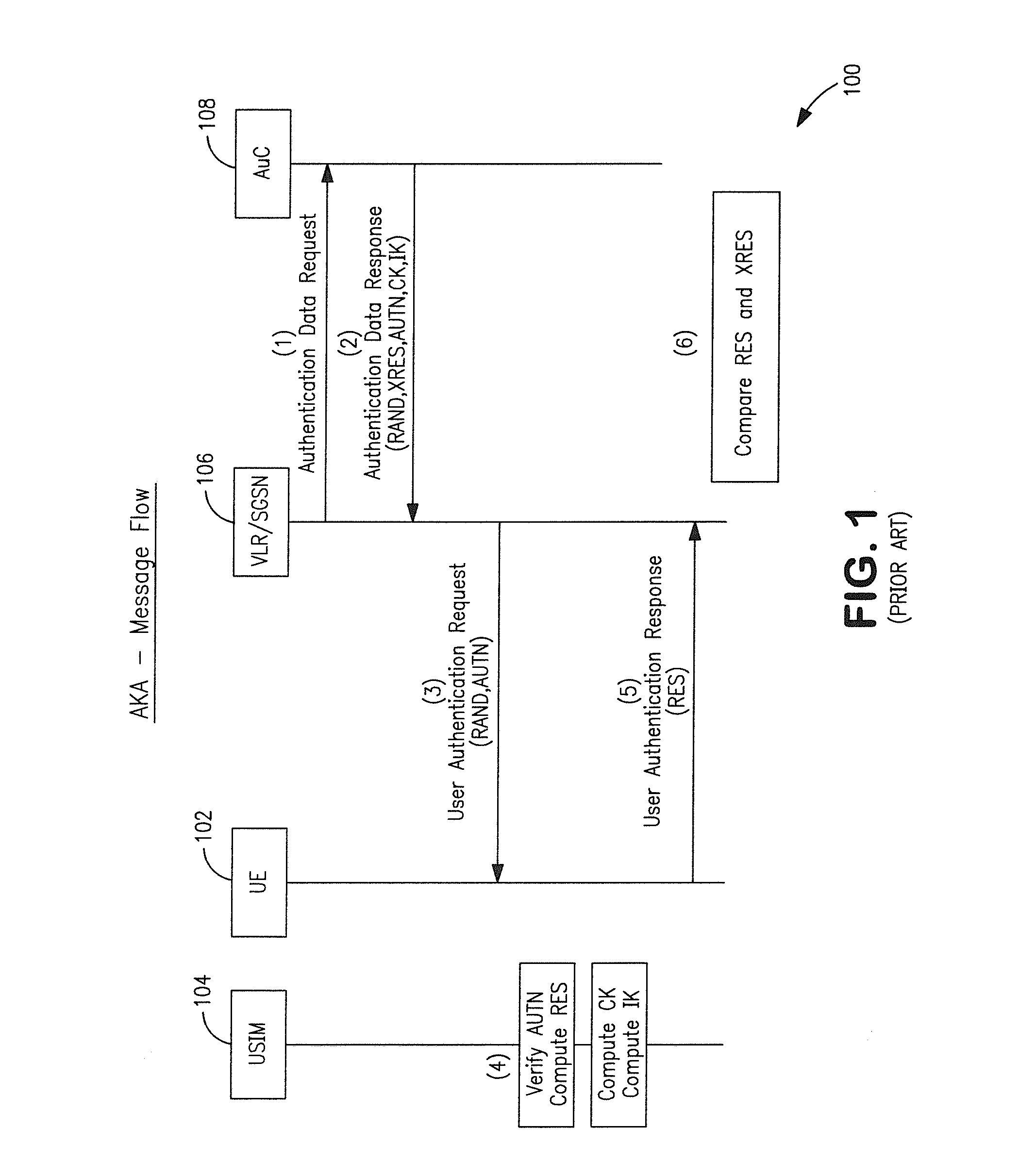
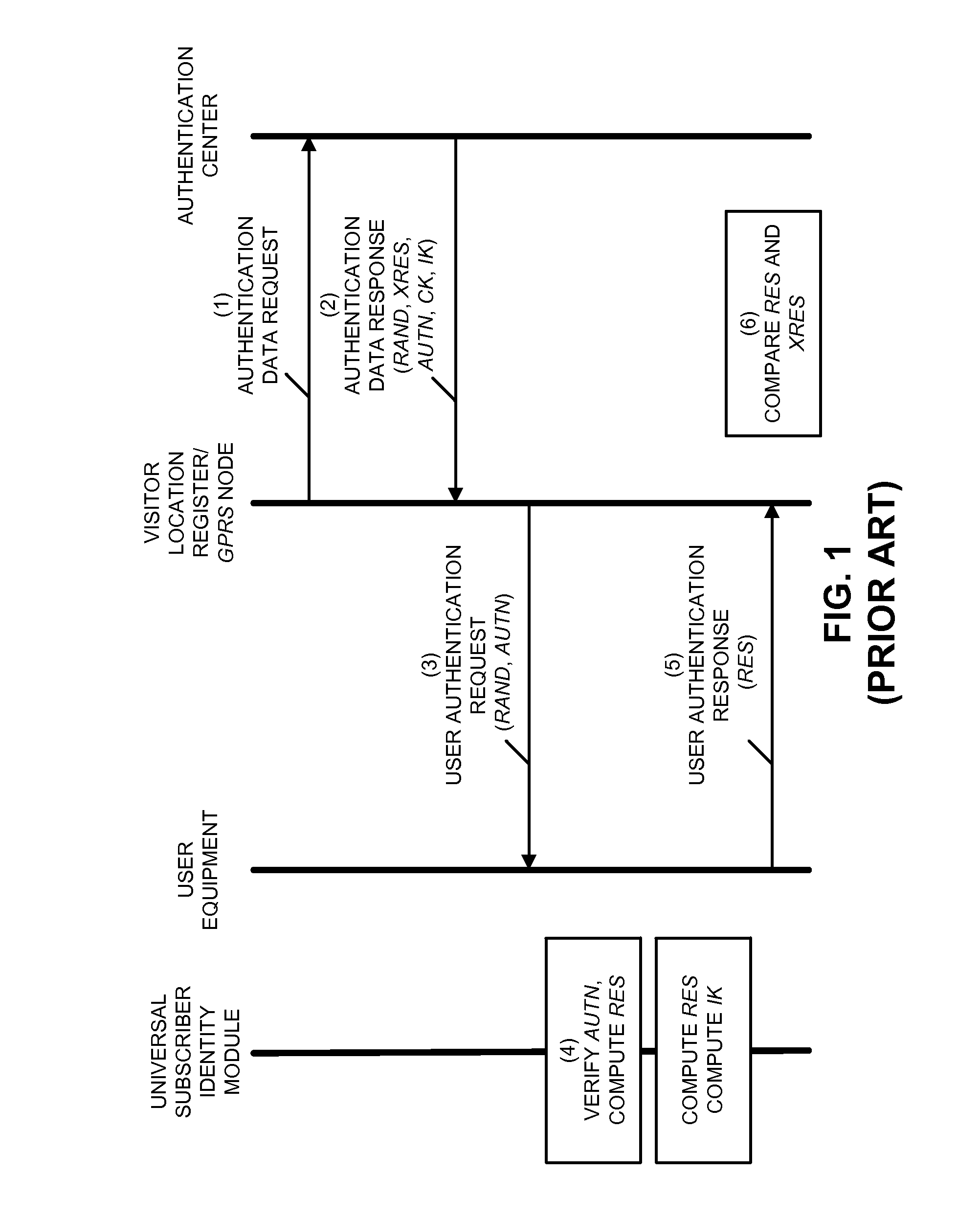
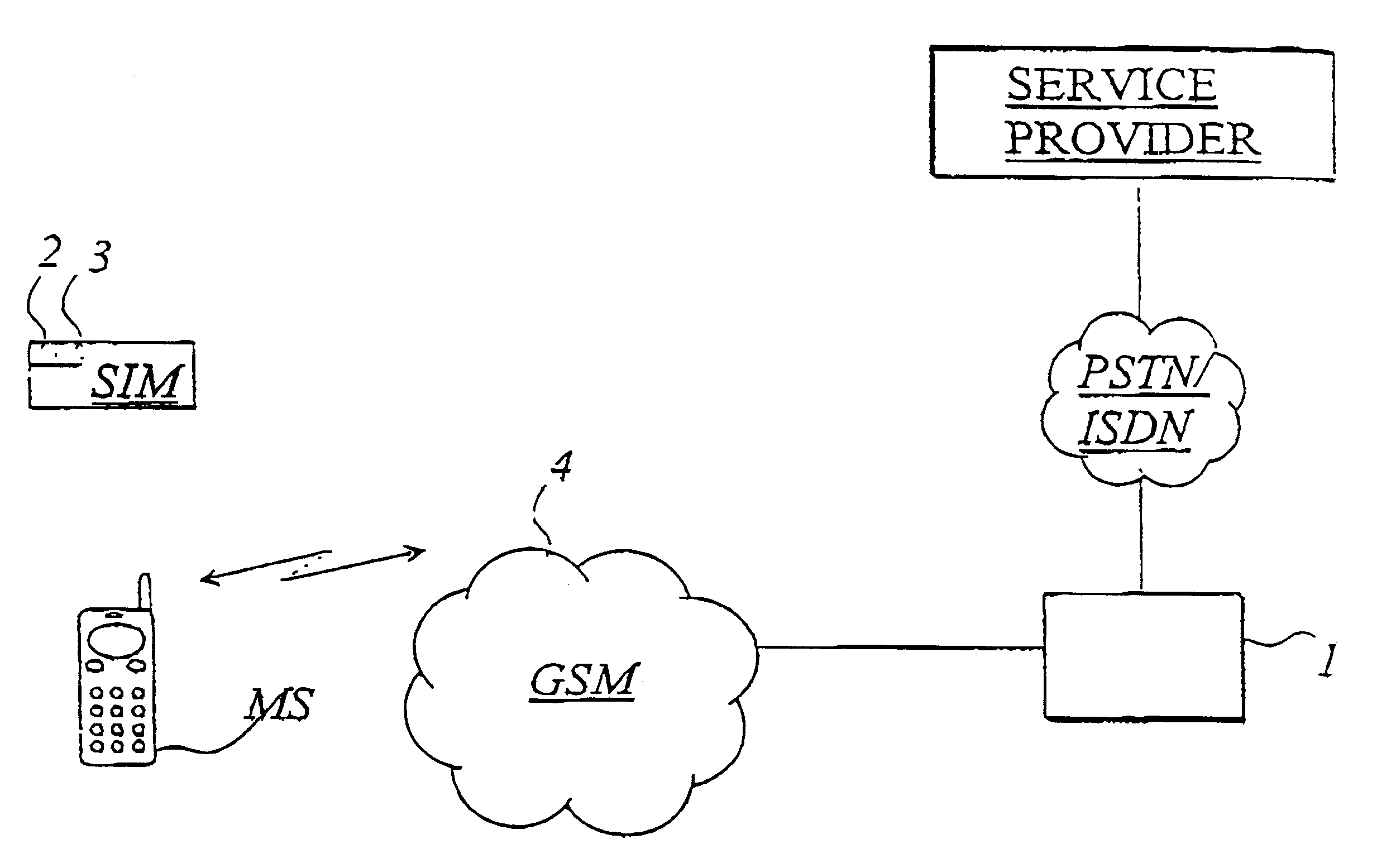
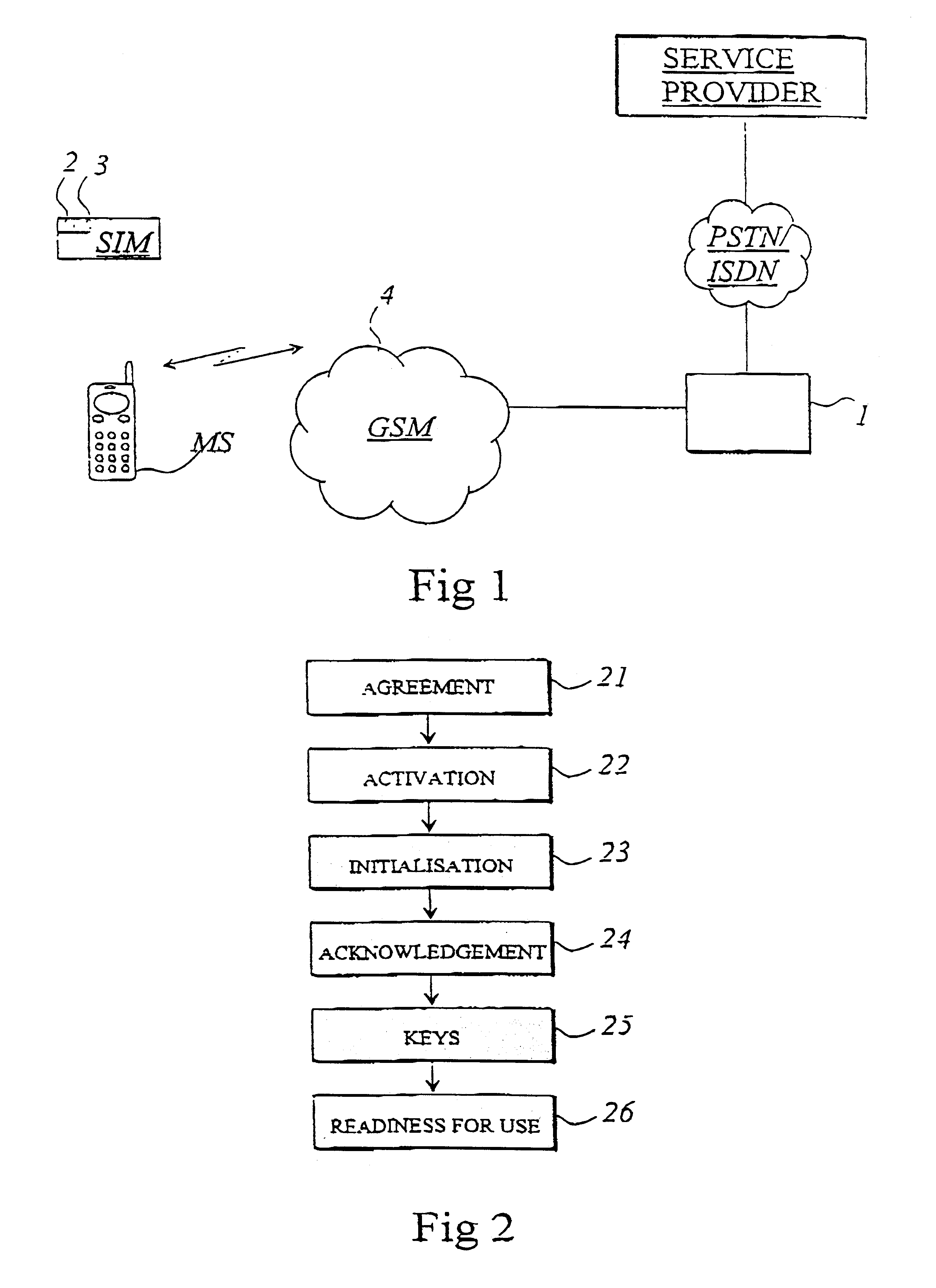
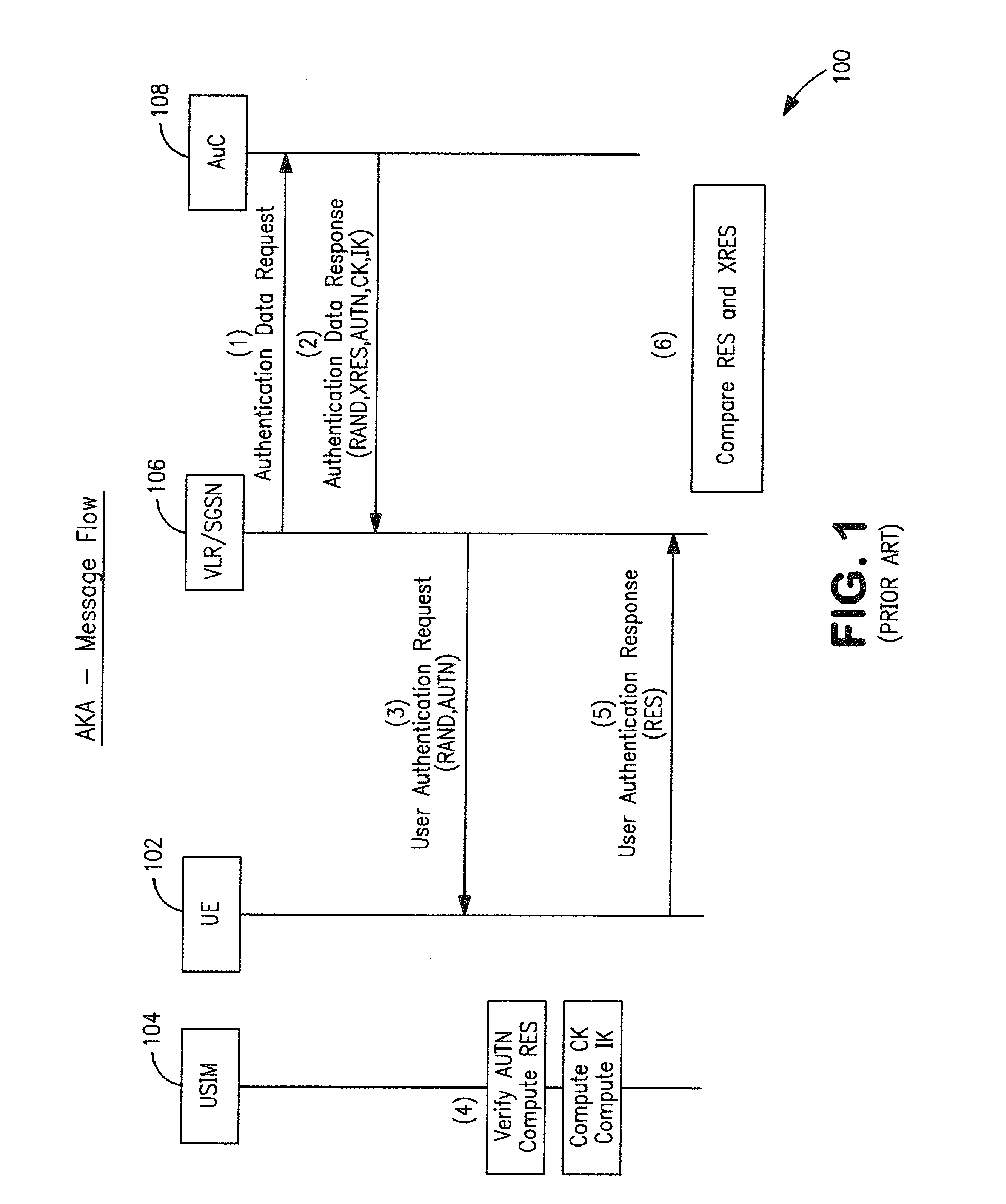
A subscriber identity module or subscriber identification module (SIM), widely known as a SIM card, is an integrated circuit that is intended to securely store the international mobile subscriber identity (IMSI) number and its related key, which are used to identify and authenticate subscribers on mobile telephony devices (such as mobile phones and computers). It is also possible to store contact information on many SIM cards. SIM cards are always used on GSM phones; for CDMA phones, they are only needed for newer LTE-capable handsets. SIM cards can also be used in satellite phones, smart watches, computers, or cameras.
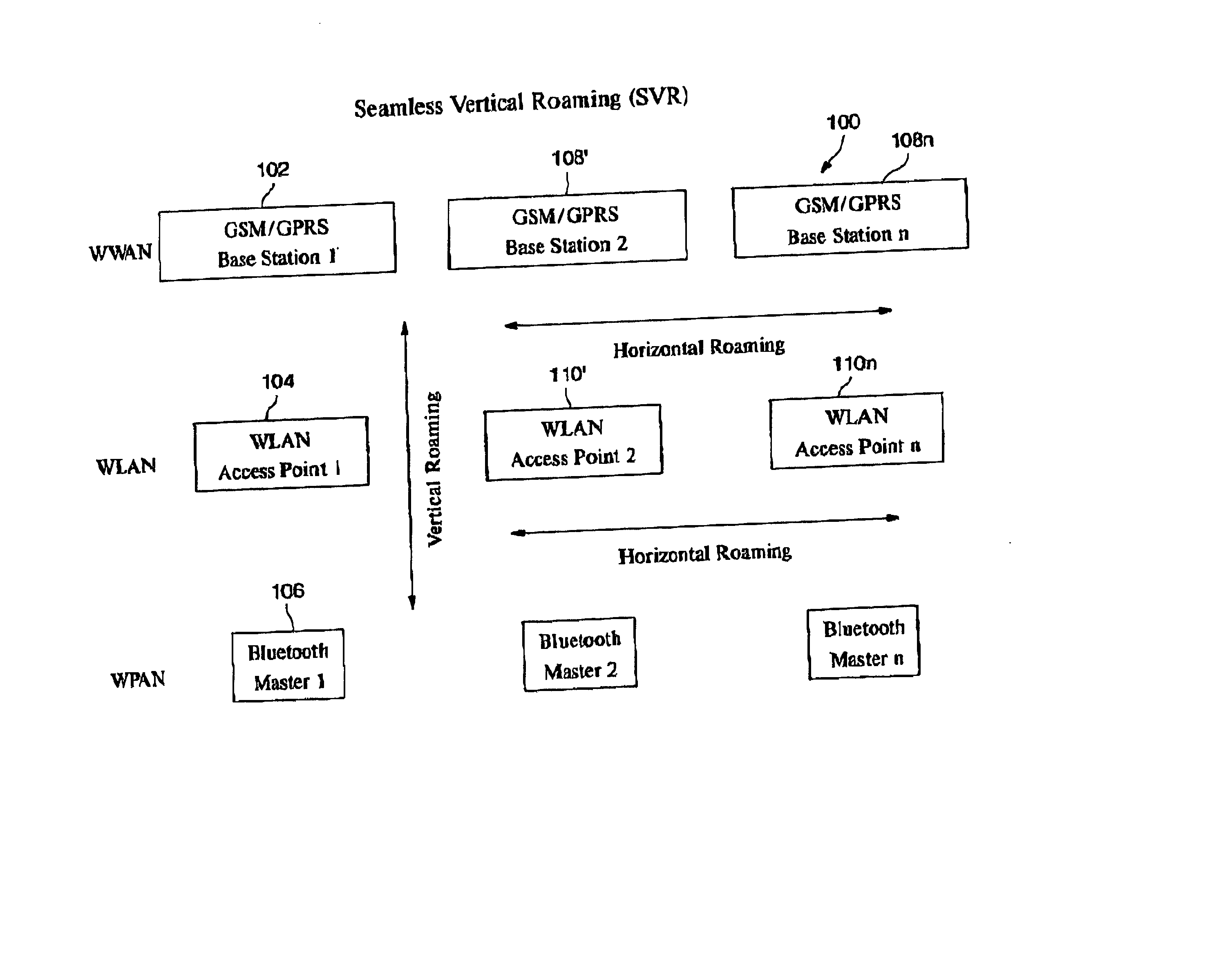
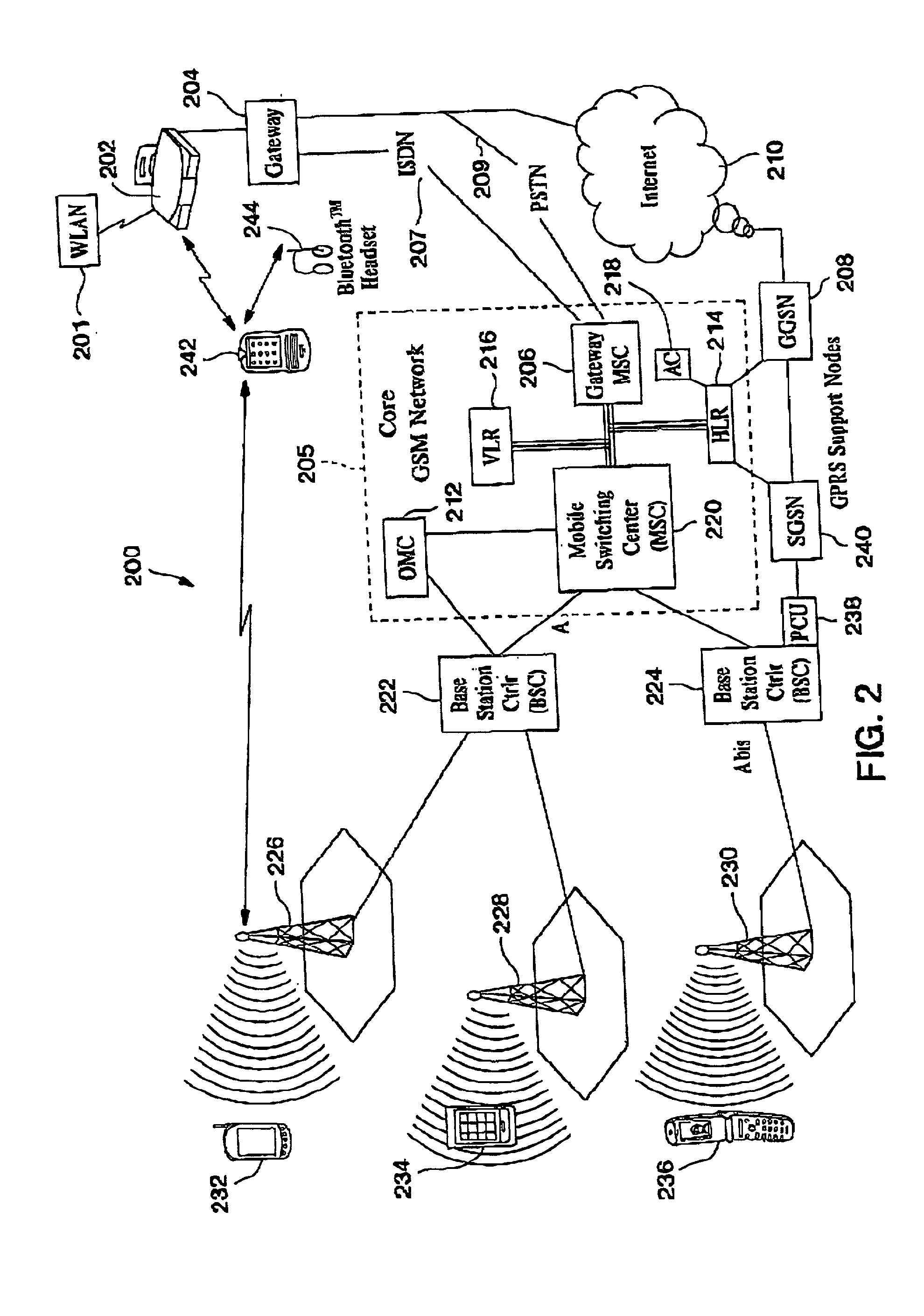
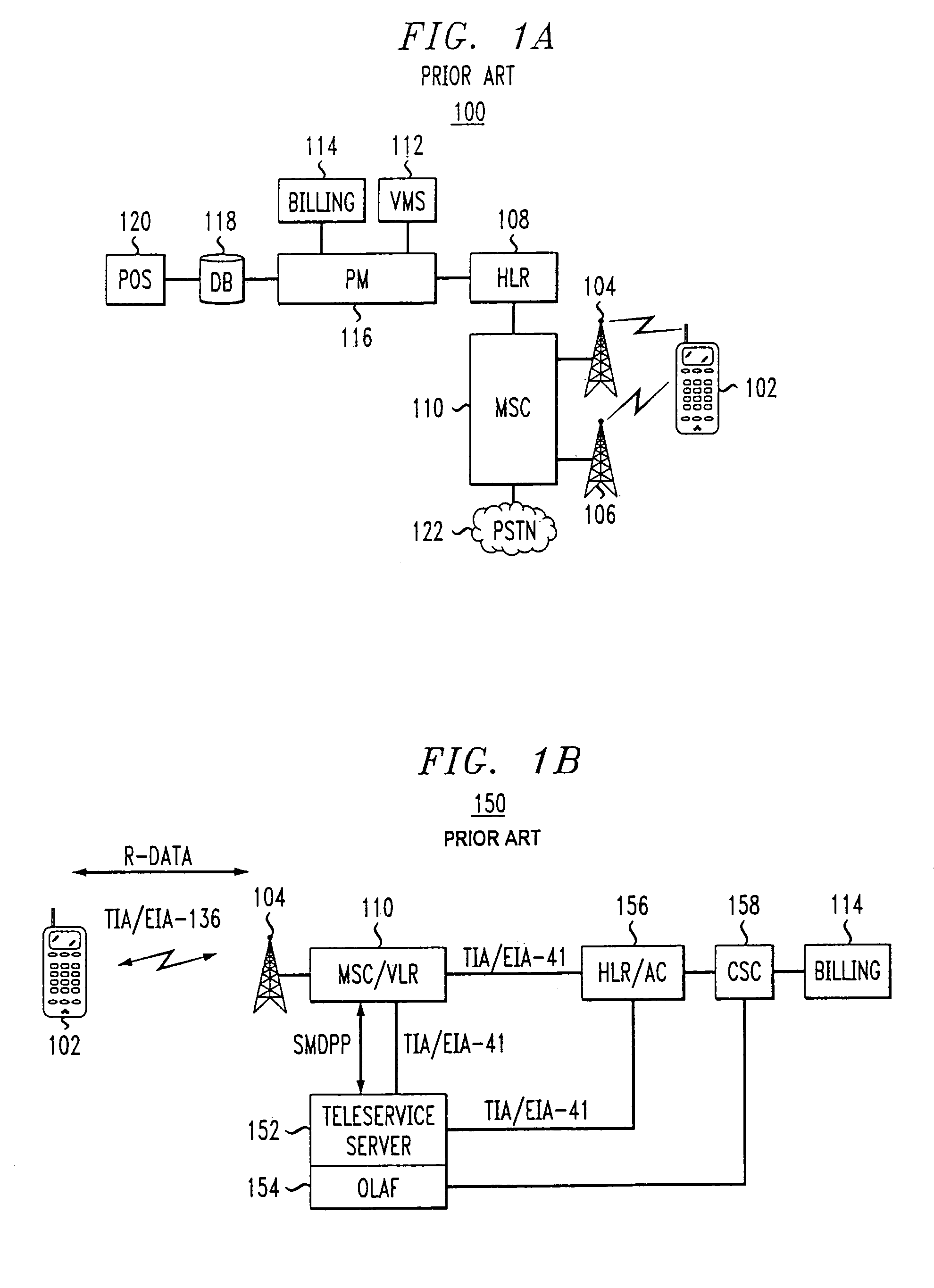
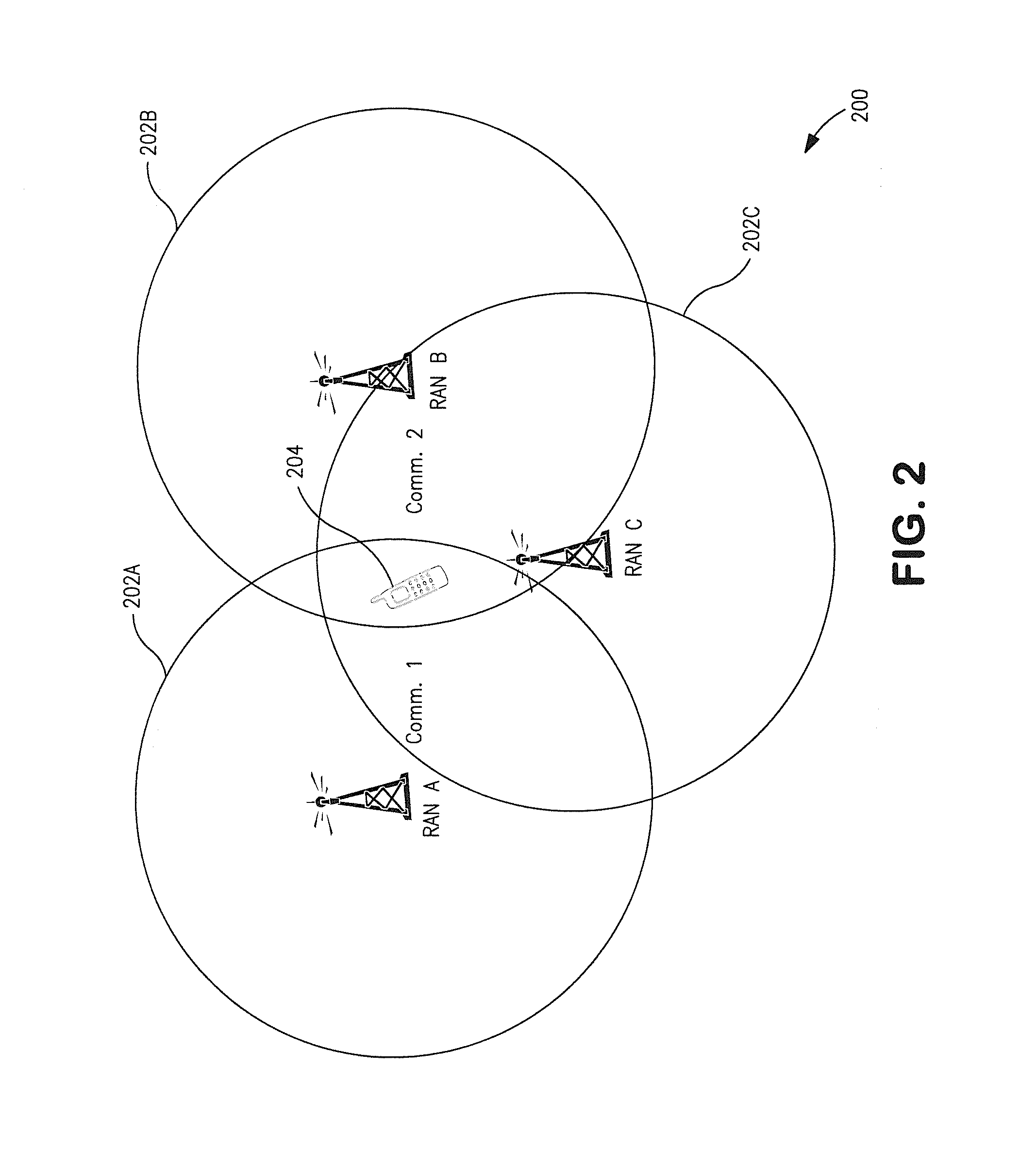
Automatic and seamless vertical roaming between wireless local area network (WLAN) and wireless wide area network (WWAN) while maintaining an active voice or streaming data connection: systems, methods and program products
ActiveUS20020085516A1Data switching by path configurationRadio/inductive link selection arrangementsData connectionUser verification
A Mobile Station (MS) is able to vertically roam in either direction between two different network, i.e. WWAN and WLAN. The MS is equipped with a dual mode Radio for WWAN and WLAN transmissions. The WLAN Radio is linked to a WLAN Enterprise Gateway Controller (EGC) via a first air link and the WWAN Radio is linked to a WWAN Base Transceiver Station (BTS) via a second air link. The EGC is connected to a Mobile Switching Center (MSC) which is in turn connected to the BTS. An outgoing VoIP call from the WLAN Radio to a remote party on the WWAN will transition or seamlessly switch over to a WWAN connection when the MS detects packet error rates, frequent scale back or consistent signal degradation. Upon such conditions, the WLAN Radio requests the EGC to request an Explicit Call Transfer via the MSC to the MS integrated WWAN Radio portion which automatically accepts the call based on referenced information stored in the user's subscriber identification module (SIM). Once the WWAN Radio is confirmed connected to the remote party on the WWAN, the WLAN Radio drops the WLAN connection. An incoming call between the MS and a remote user via the WWAN will transition to the WLAN Radio when the MS enters WLAN coverage. The MS issues an ECT to the WLAN. After user verification by the WLAN Radio and the EGC signals acceptance of the call, the WWAN Radio connection is dropped and the call is now established between the WLAN Radio and the remote party on the WWAN.
Owner:SYMBOL TECH LLC
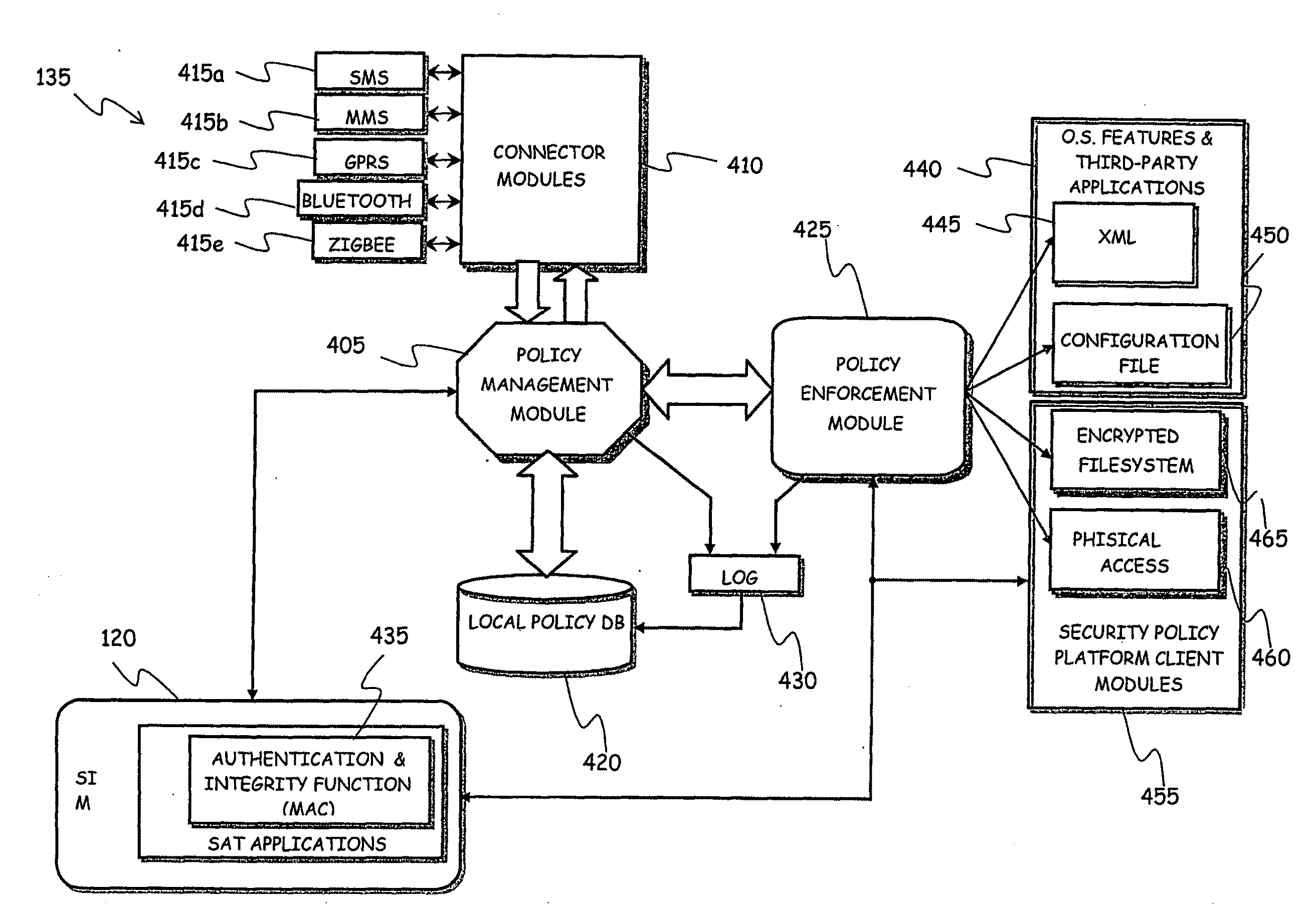
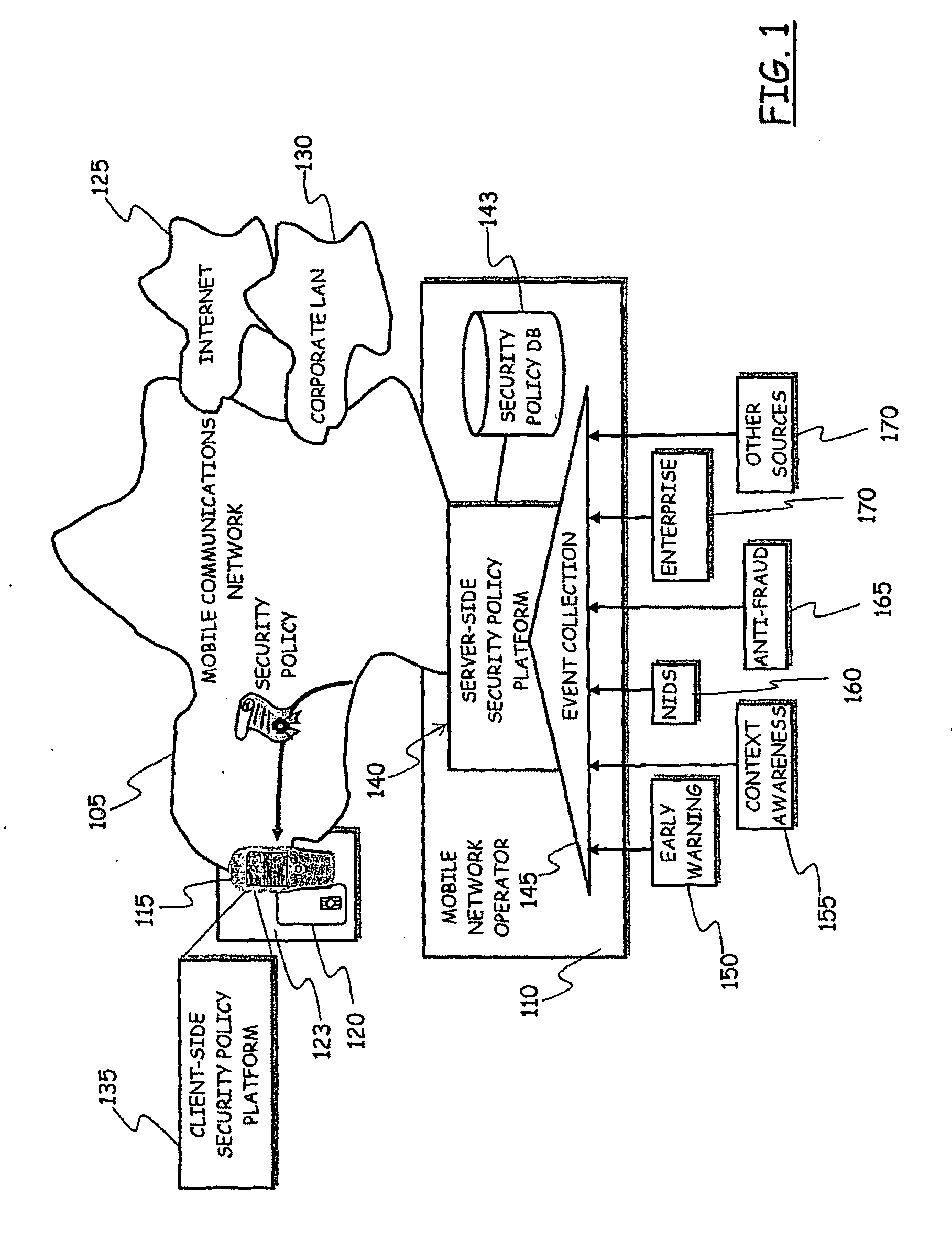
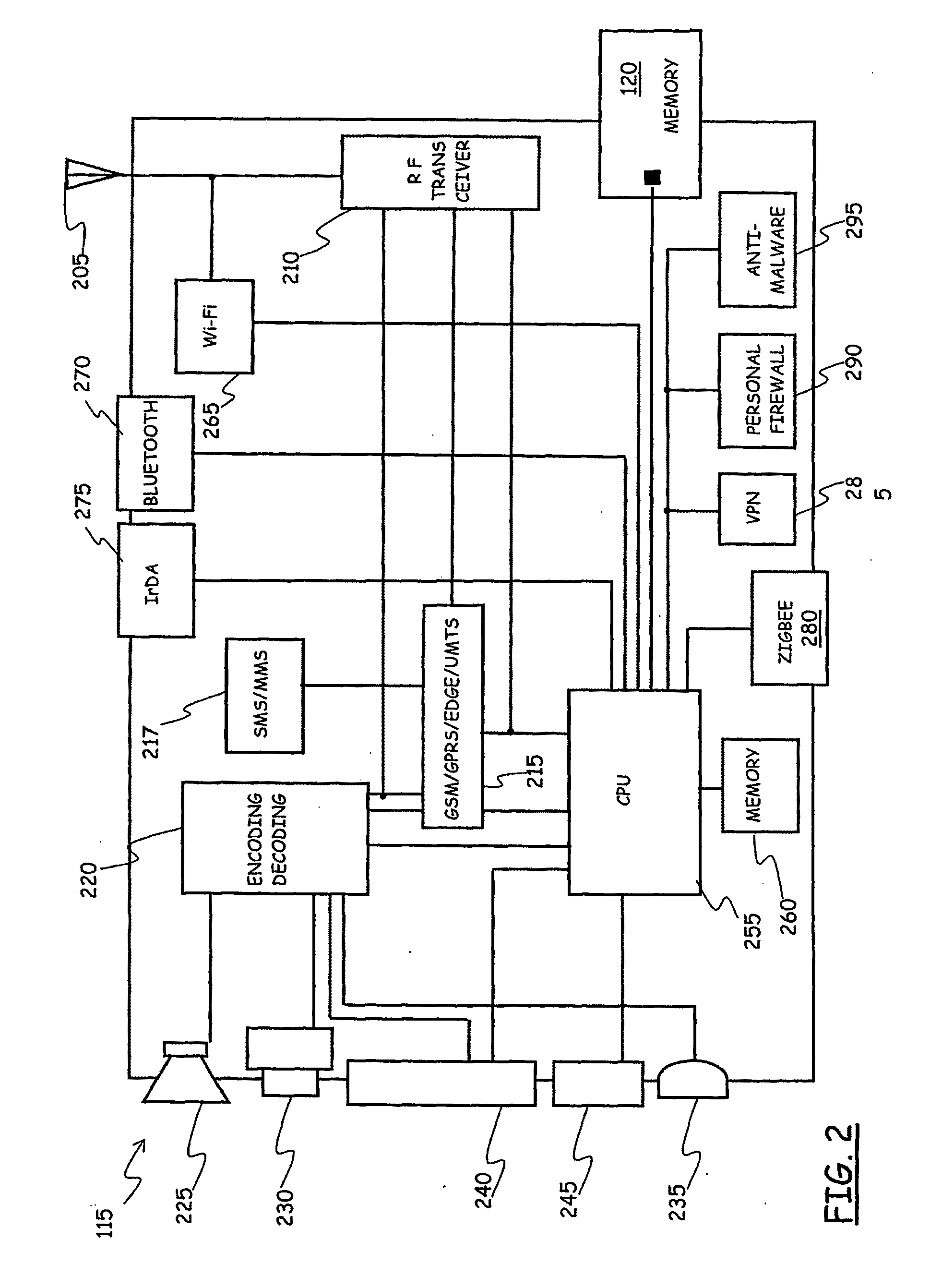
System for Enforcing Security Policies on Mobile Communications Devices
A system for enforcing security policies on mobile communications devices is adapted to be used in a mobile communications network in operative association with a subscriber identity module. The system having a client-server architecture includes a server operated by a mobile communications network operator and a client resident on a mobile communications device on which security policies are to be enforced. The server is adapted to determine security policies to be applied on said mobile communications device, and to send thereto a security policy to be applied. The client is adapted to receive the security policy to be applied from the server, and to apply the received security policy. The server includes a server authentication function adapted to authenticate the security policy to be sent to the mobile communications device; the client is further adapted to assess authenticity of the security policy received from the server by exploiting a client authentication function resident on the subscriber identity module.
Owner:TELECOM ITALIA SPA
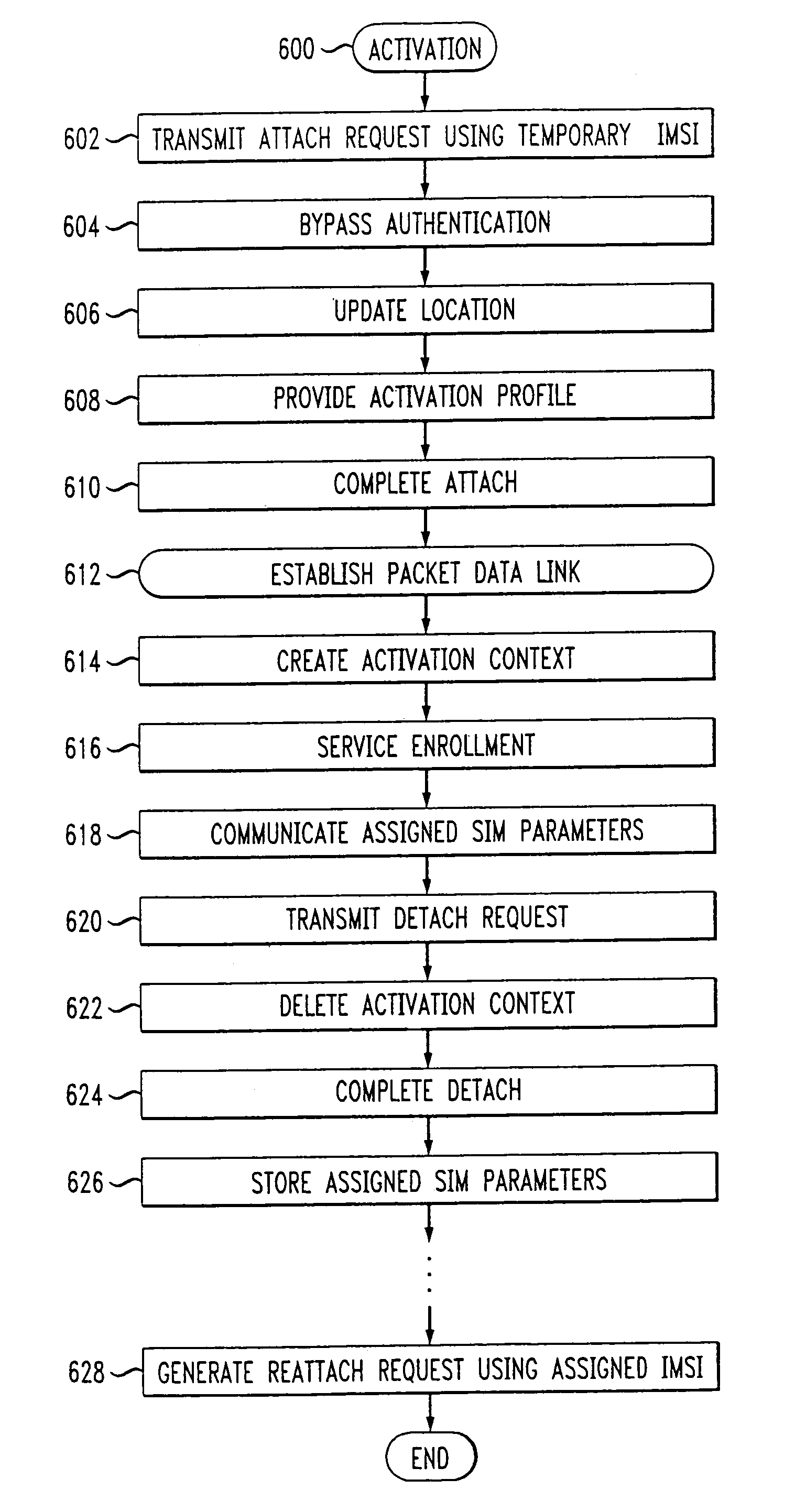
Activation and remote modification of wireless services in a packet network context
InactiveUS7266371B1The process is convenient and fastConvenient and quick mobile device activationRadio/inductive link selection arrangementsSubstation equipmentTerms of serviceThird generation
A third generation (3G) mobile communication system supports an over-the-air activation scheme utilizing a wireless packet data protocol. A subscriber identity module (SIM) is preloaded with temporary operating parameters such as a temporary international mobile subscriber identity (IMSI) that is used for initial access to a network. Once a packet data protocol communication link is established between the mobile device and a network support node, the user may remotely subscribe to a number of service terms using the mobile device. In addition, an activation procedure is carried out to assign permanent operating parameters, e.g., a permanent IMSI, to the SIM. After activation, the user can remotely modify existing terms or remotely enroll in additional service features via a wireless IP link between the mobile device and a network support node.
Owner:AT&T WIRELESS SERVICES
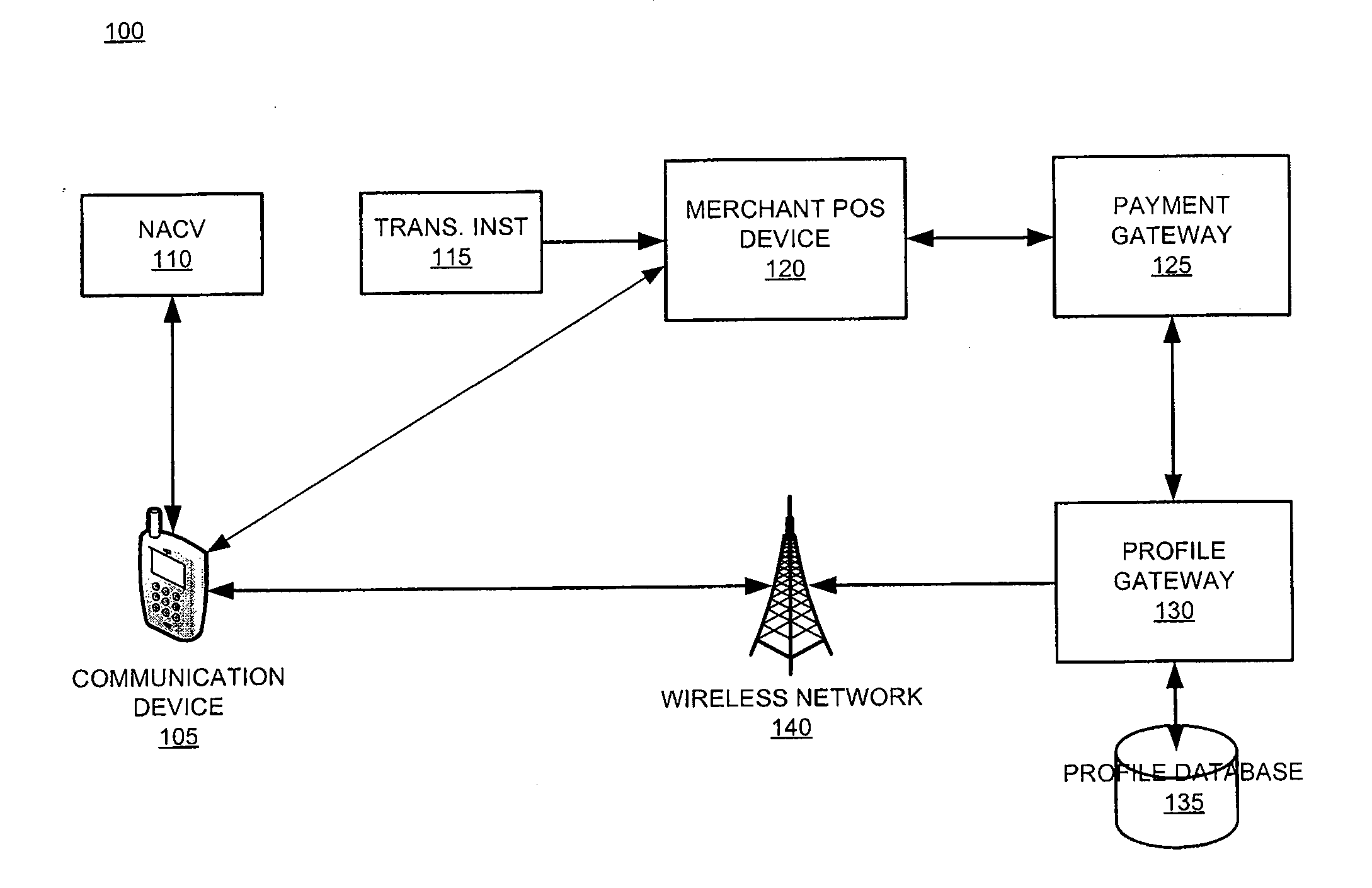
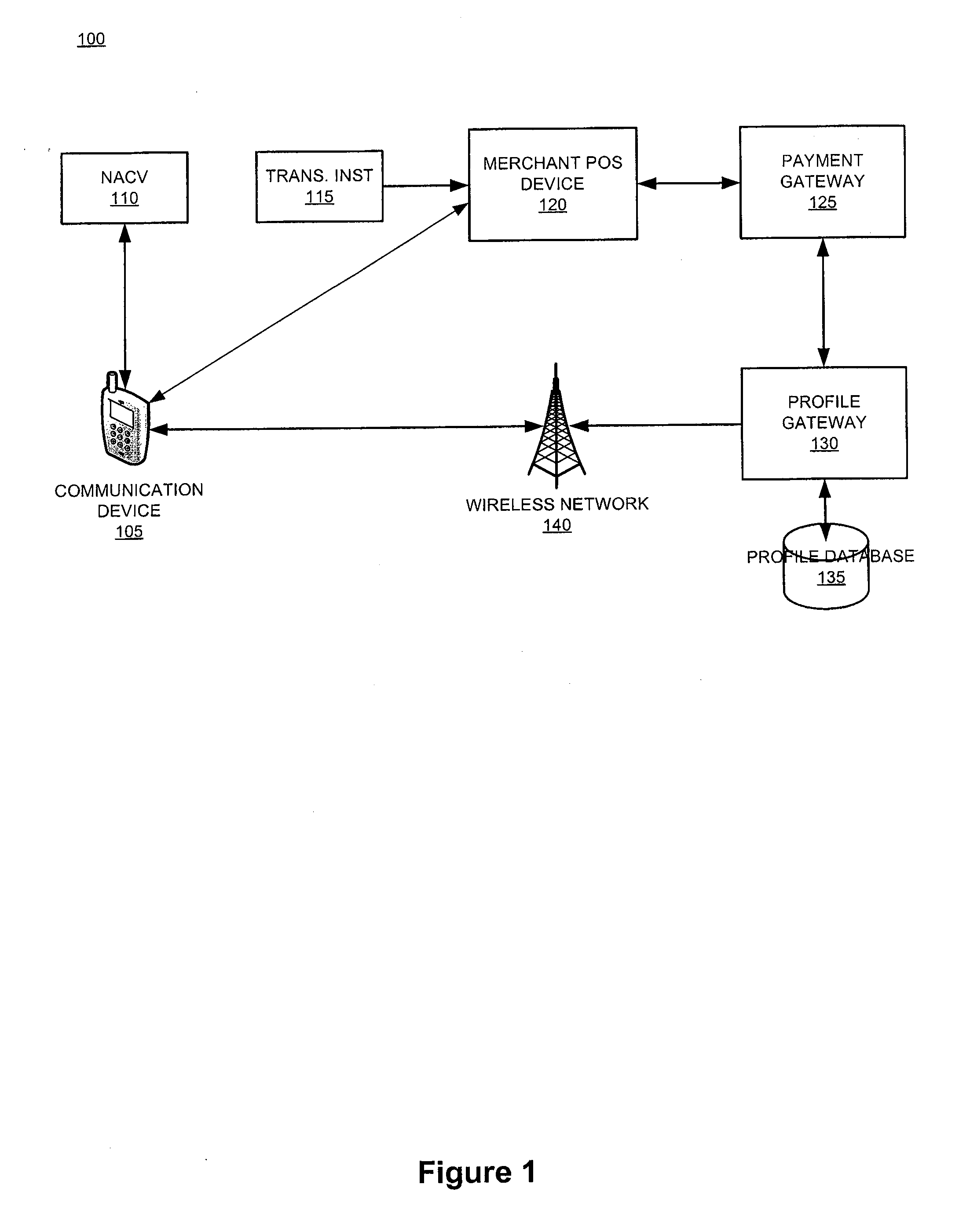
System and device for facilitating a transaction by consolidating sim, personal token, and associated applications for electronic wallet transactions
InactiveUS20120231844A1Increase dependenceFacilitating secure and convenient electronic transactionsPayment architectureSubstation equipmentPayment transactionSmart card
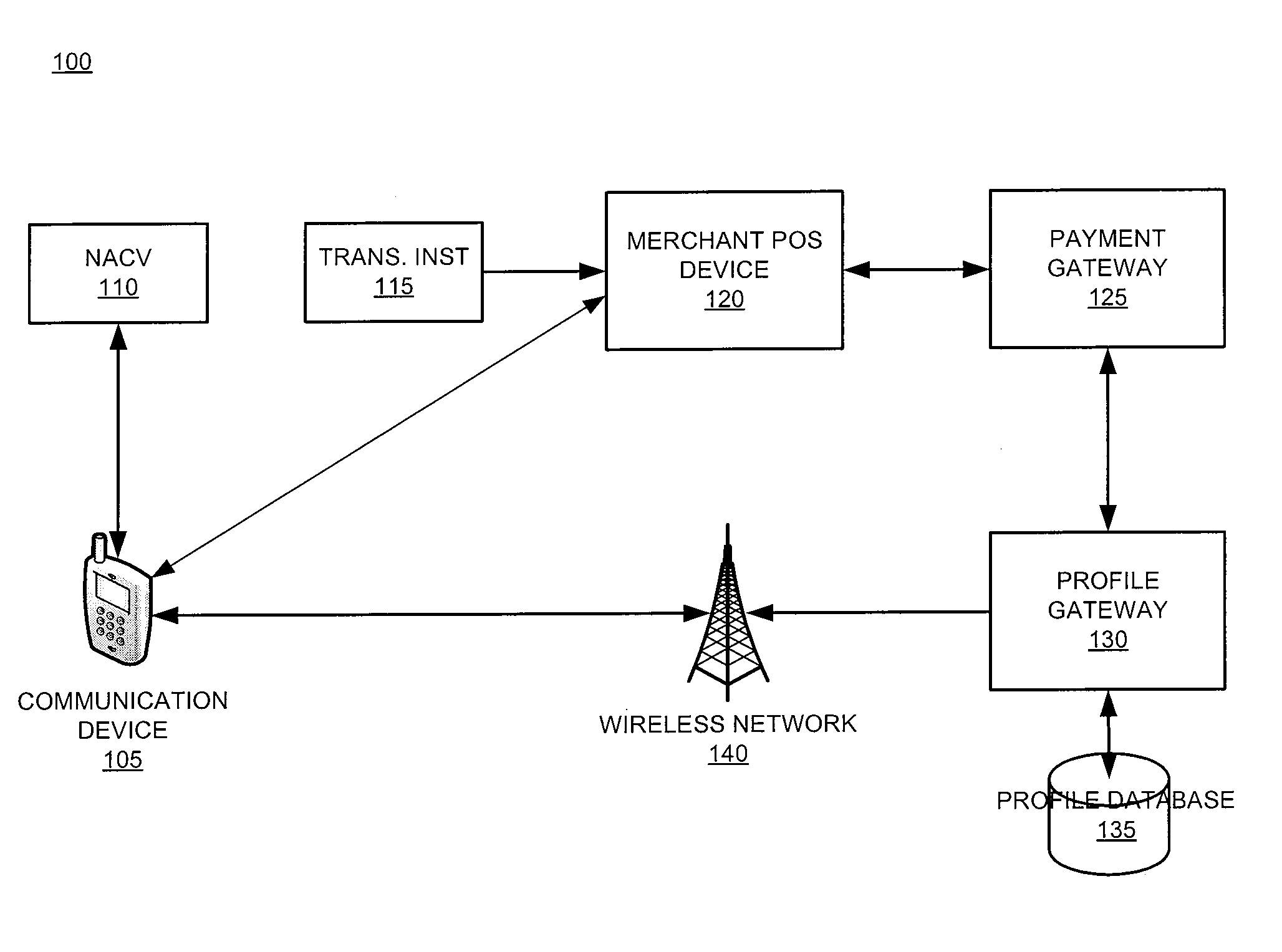
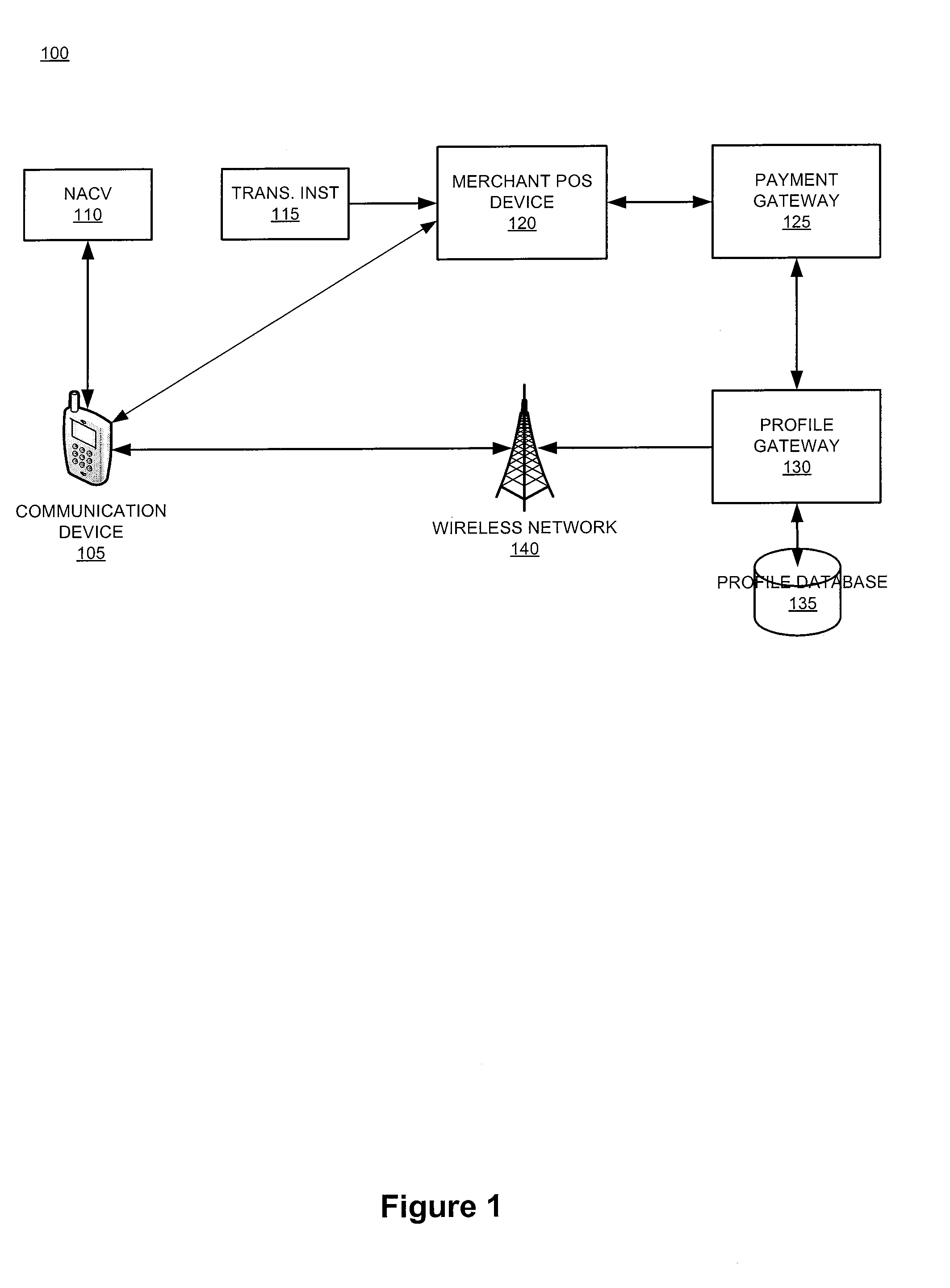
The invention relates generally to a smart card device that is configured to facilitate wireless network access and credential verification. Specifically, the device is configured to meet the physical and electrical specification for commercially available mobile devices utilizing a standard Subscriber Identity Module (SIM) for network access. The device combines the features of the SIM with Common Access Card or Personal Identity Verification card features to allow a network subscriber to invoke secure payment transactions over a carrier's network. The system includes data storage for maintaining a plurality of network and transaction instrument profiles and a profile gateway for receiving transaction information from a payment gateway, sending an authorization request to a user's mobile device, receiving a transaction authorization from the mobile device, and sending transaction information to a payment gateway to finalize the payment transaction.
Owner:APRIVA
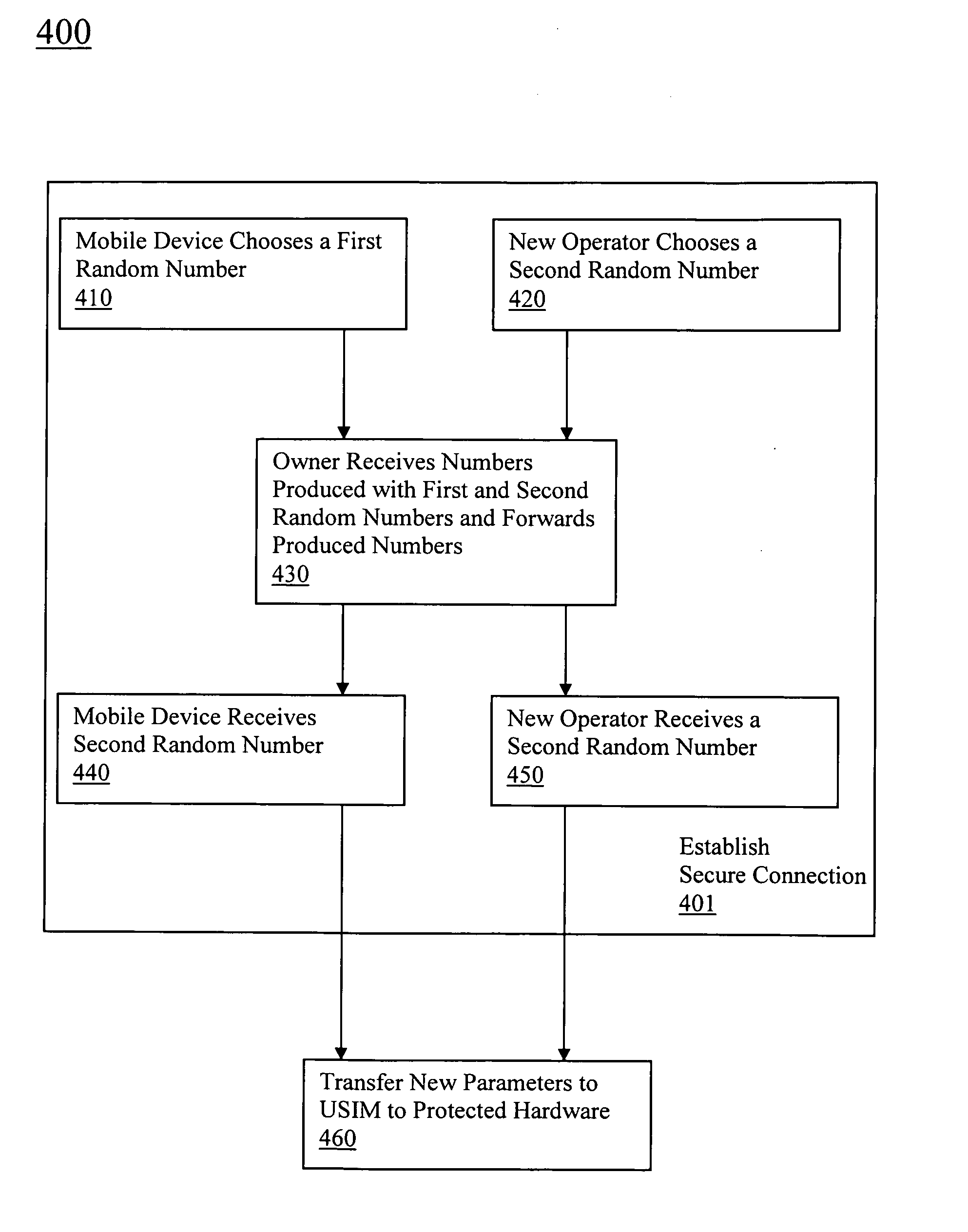
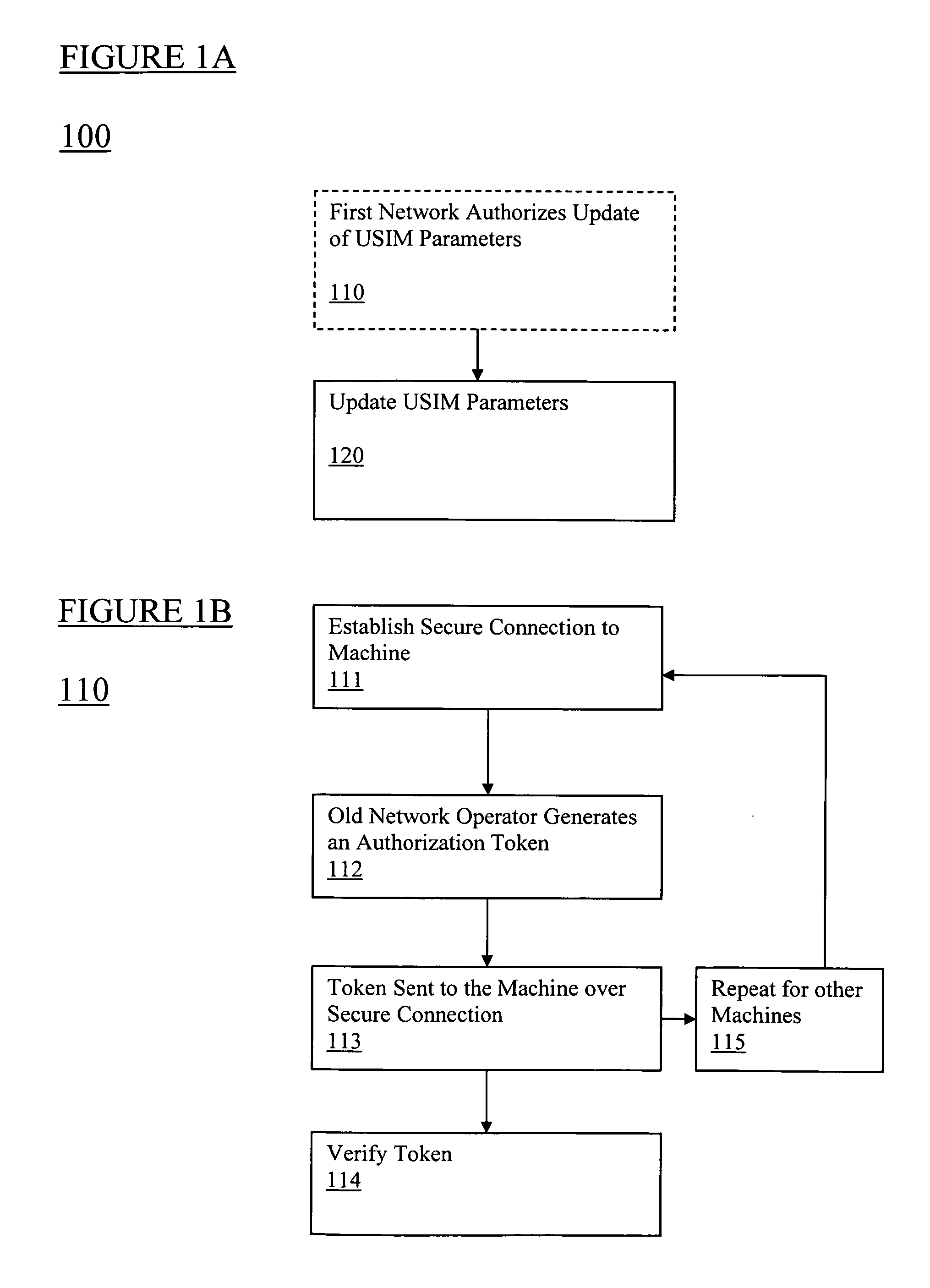
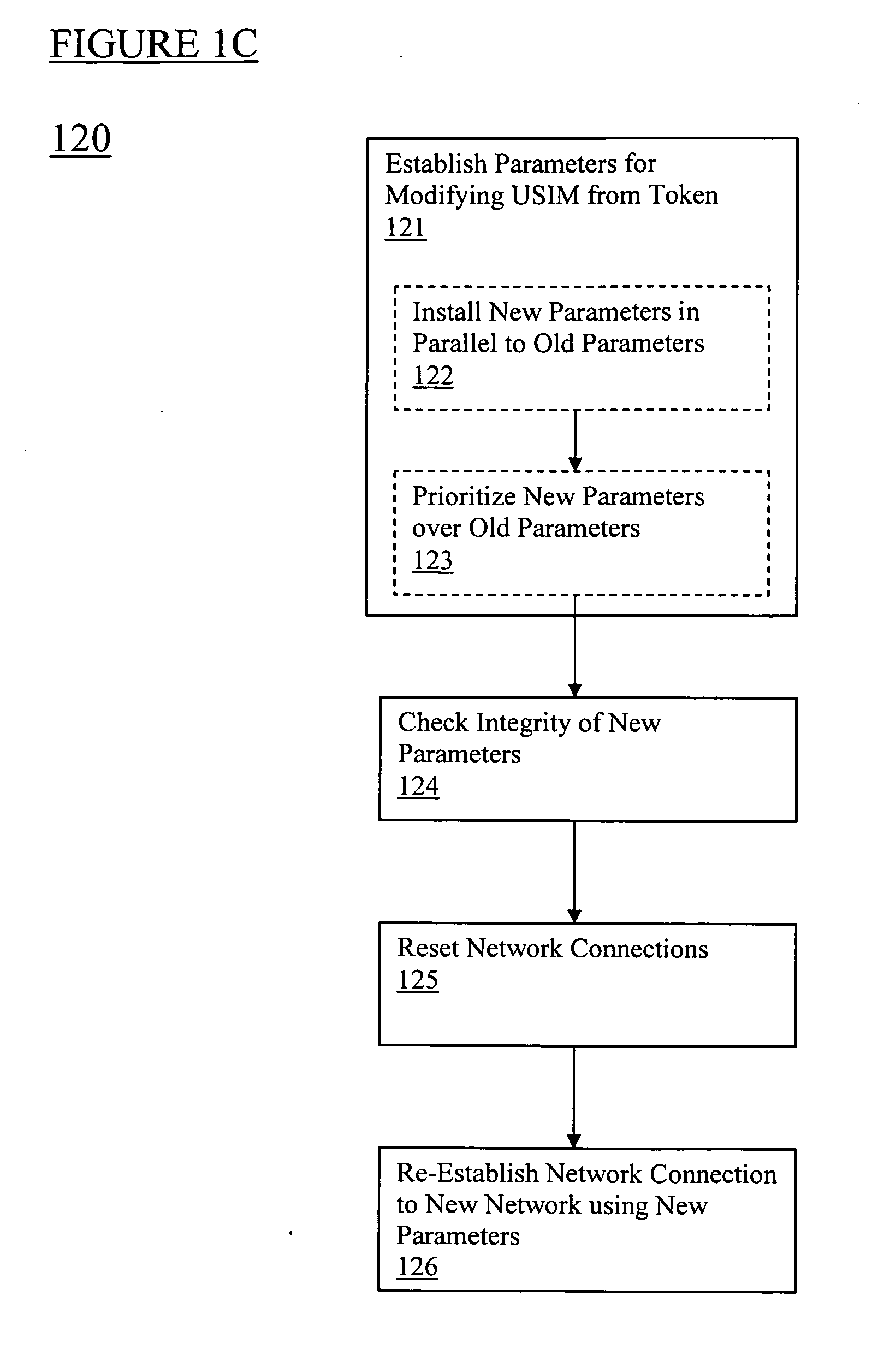
Universal subscriber identity module provisioning for machine-to-machine communications
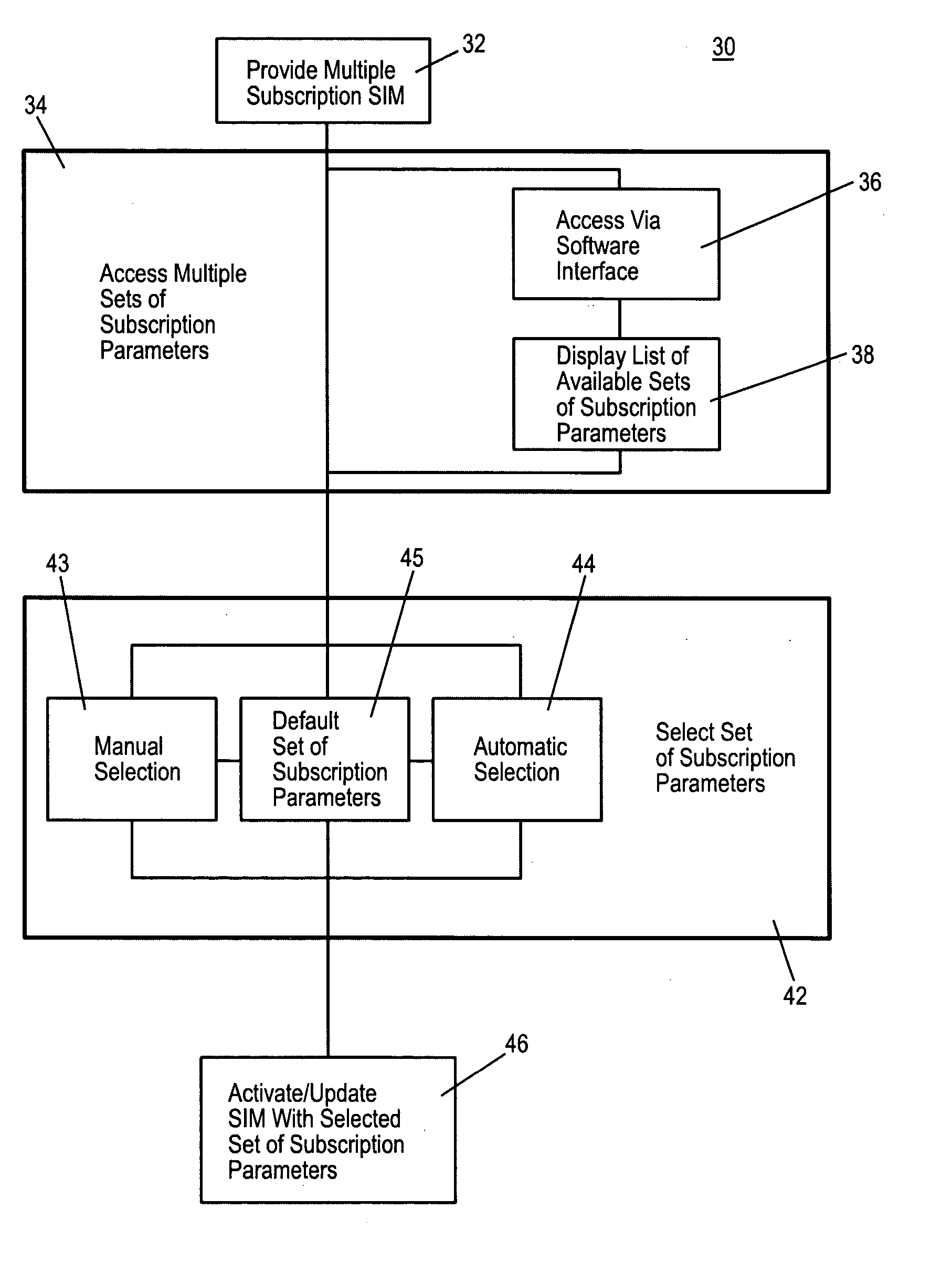
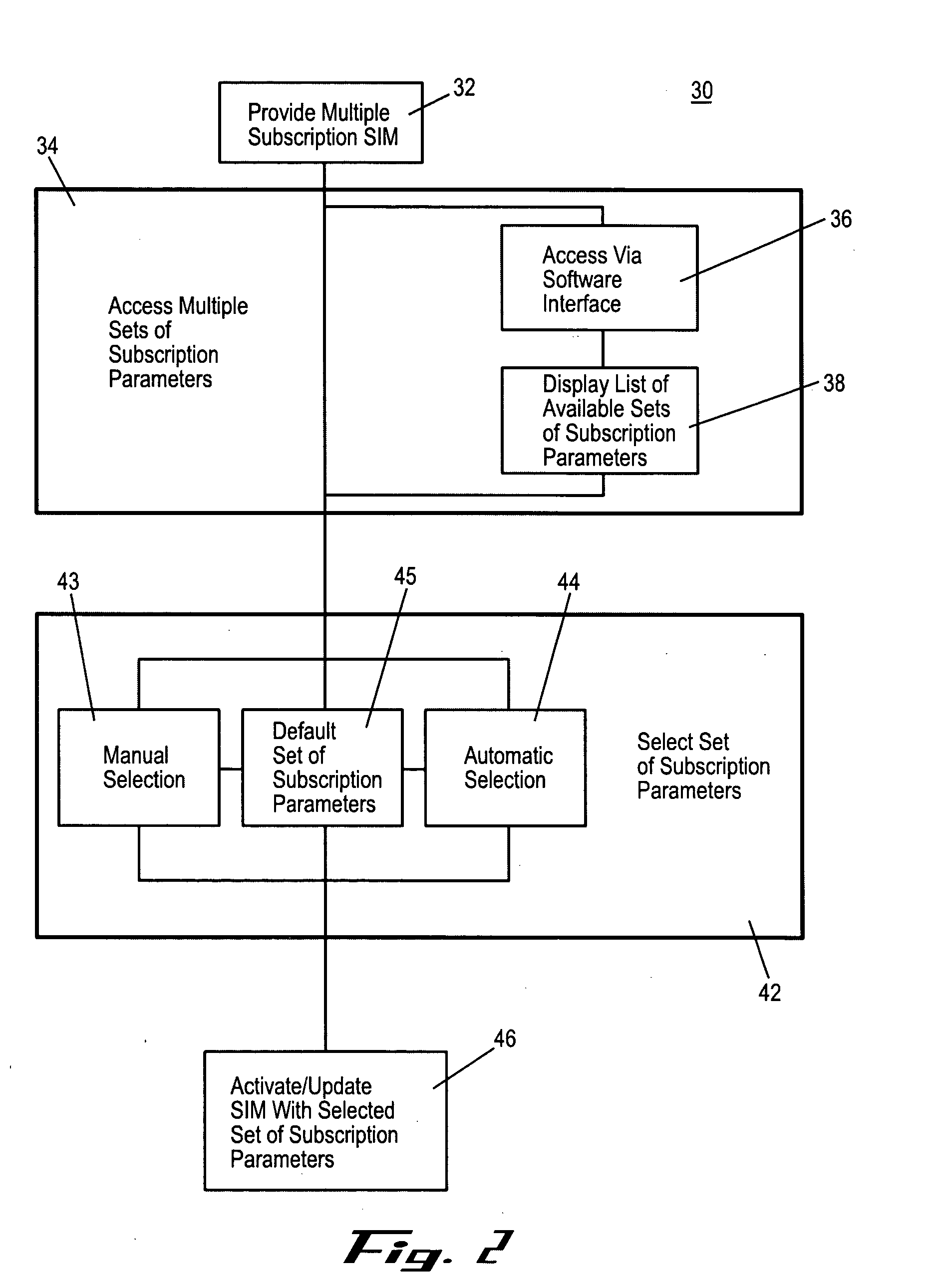
InactiveUS20090191857A1Automatic exchangesWireless commuication servicesSubscriber identity moduleSafety Connect
The present invention relates to remotely provisioning subscriber identification parameters in a device on a wireless network. A secure connection is established with the device, and a token containing the new subscriber identification parameters is forwarded over the secure connection. The device may verify the received token. In one embodiment, the subscriber identification parameters are updated to change network operators. The secure connection can be with the old network operator or the new network operator. The device on the wireless network may be a machine-to-machine device. The provisioned subscriber identification may be part of a universal subscriber identification module.
Owner:NOKIA SOLUTIONS & NETWORKS OY
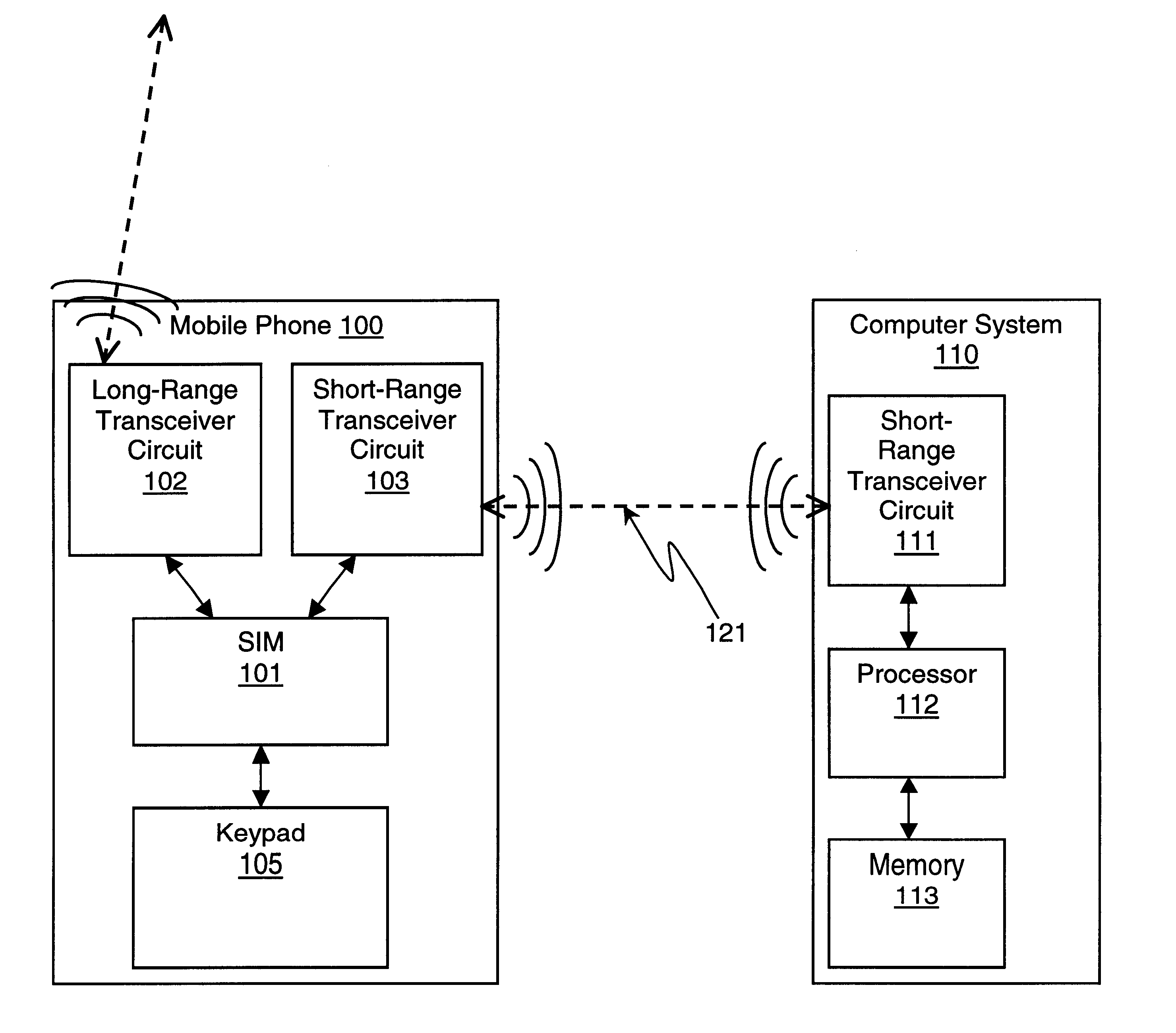
Method and apparatus for controlling access to a computer system
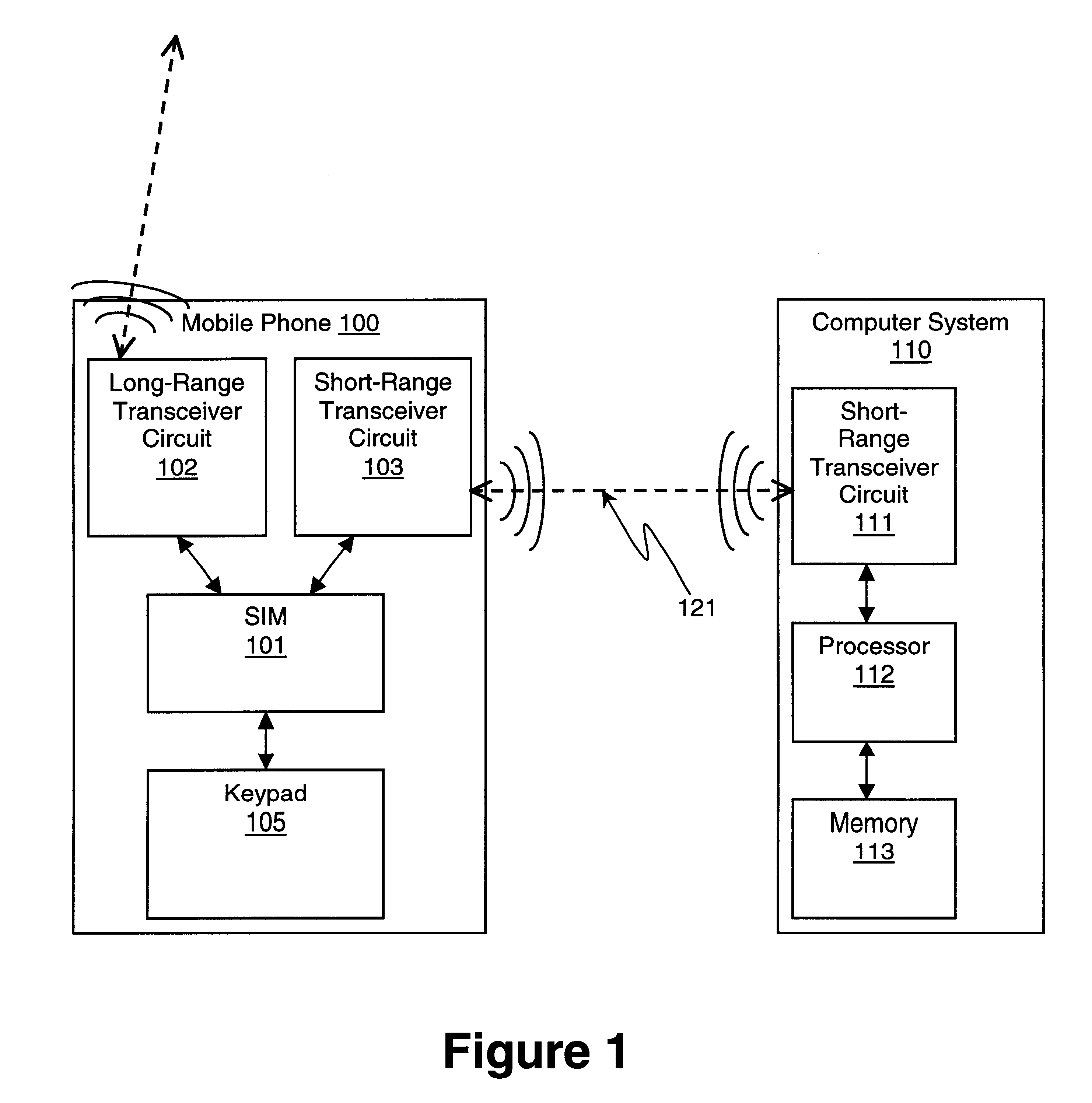
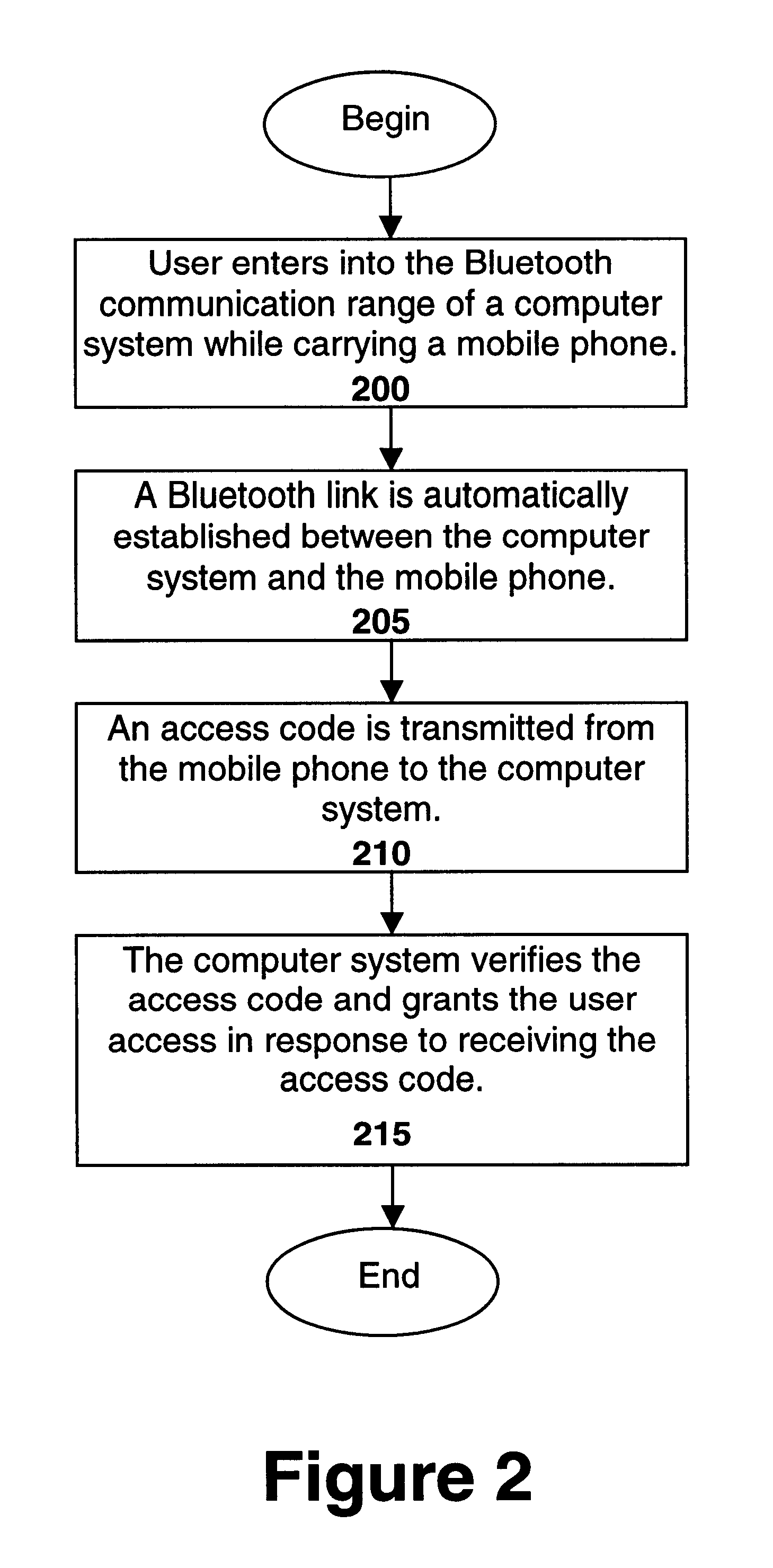
InactiveUS6871063B1Cordless telephonesUnauthorised/fraudulent call preventionTelecommunications linkComputer module
For one embodiment, a short-range, wireless communication link, such as a Bluetooth link, is established between a mobile phone and a computer system. The mobile phone transmits an access code via the link to the computer system. The access code is generated using data stored in the subscriber identity module (SIM) in the mobile phone. Access to the computer system is granted in response to receiving the access code. In this manner, the SIM is used not only to identify the user during cellular phone calls (or other long-range, wireless communication) but also to authenticate the user and to gain access to a computer system.
Owner:INTEL CORP
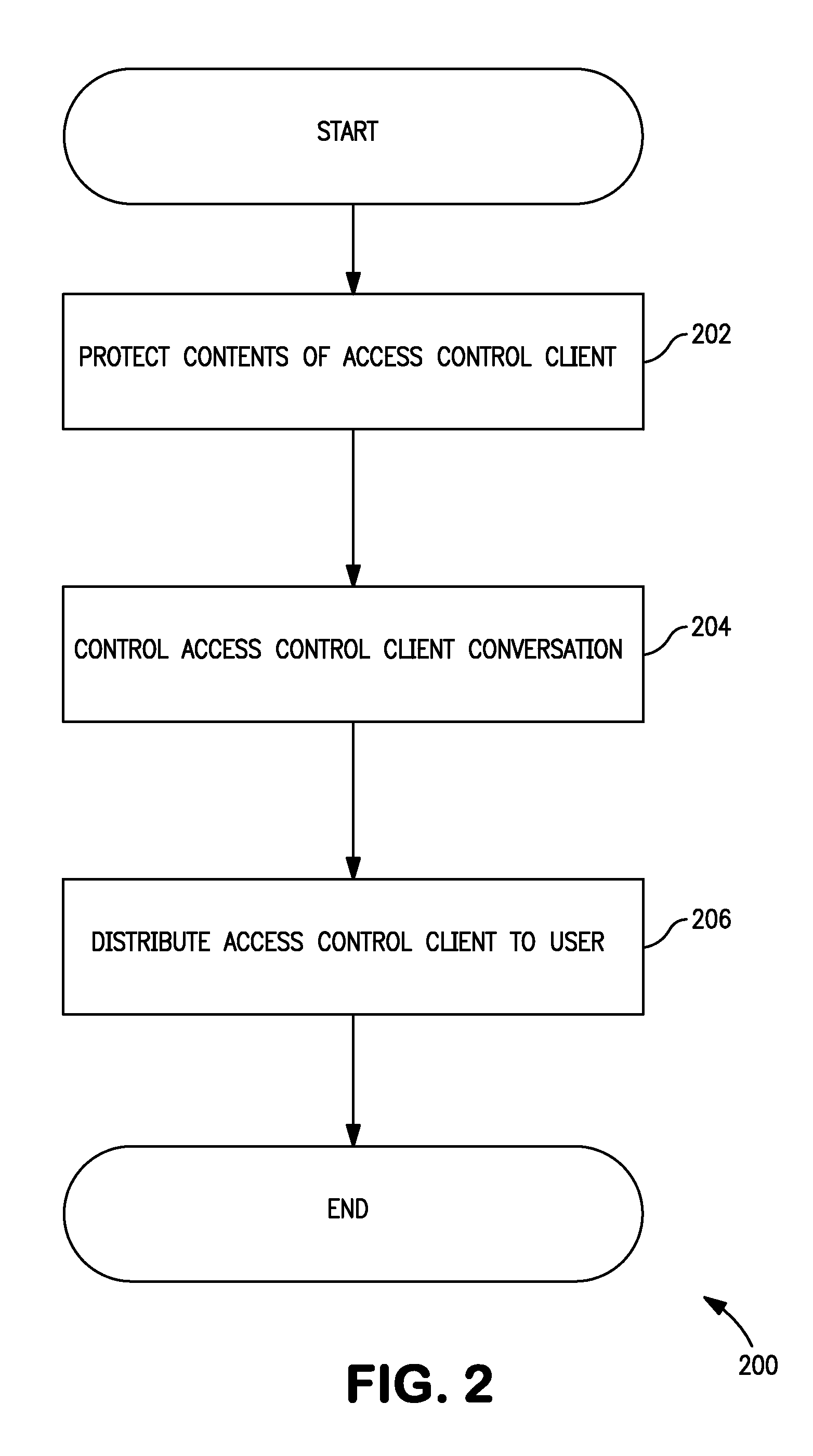
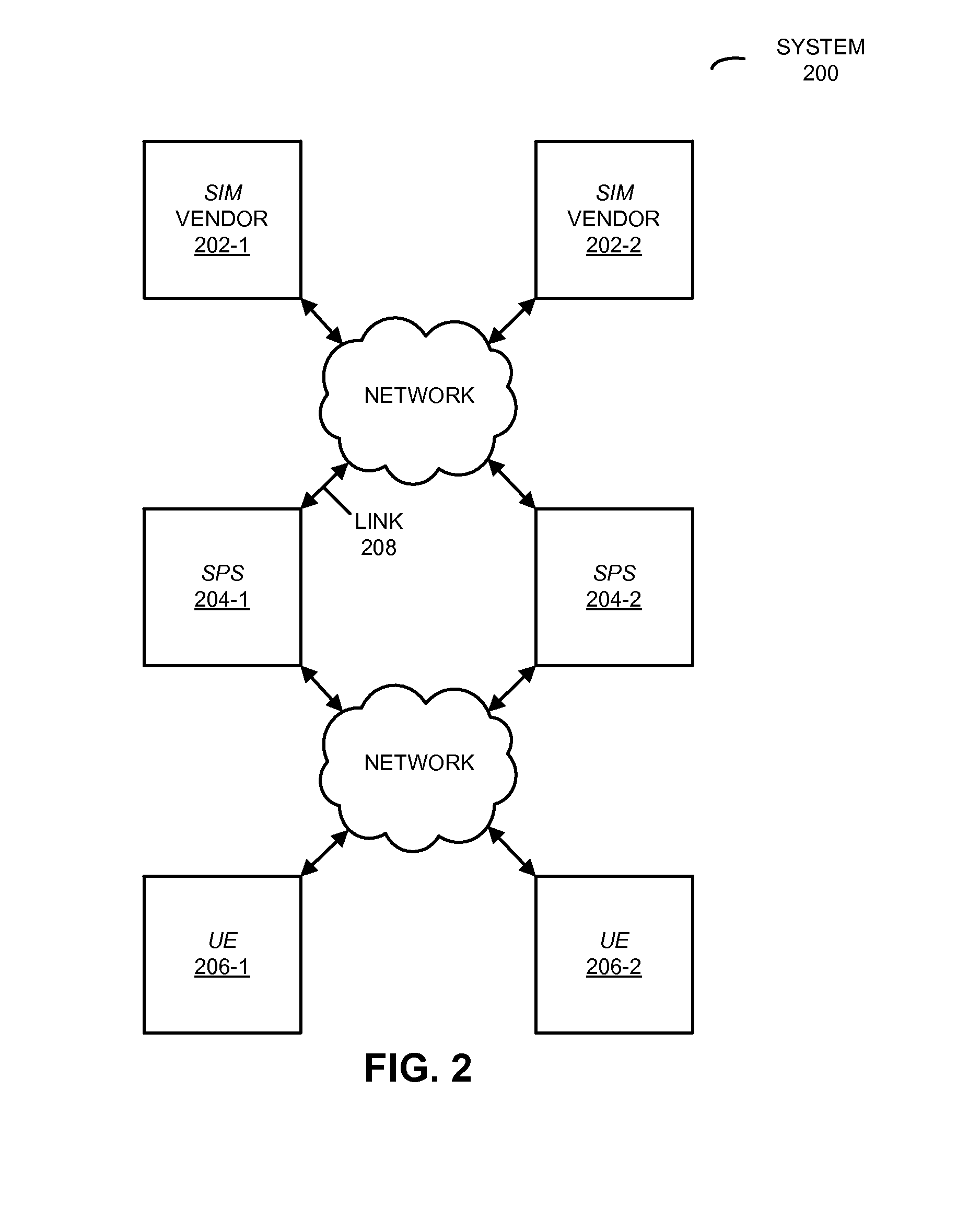
Methods and apparatus for large scale distribution of electronic access clients
ActiveUS20130227646A1Large distributionDigital data processing detailsMultiple digital computer combinationsElectronic accessSecurity software
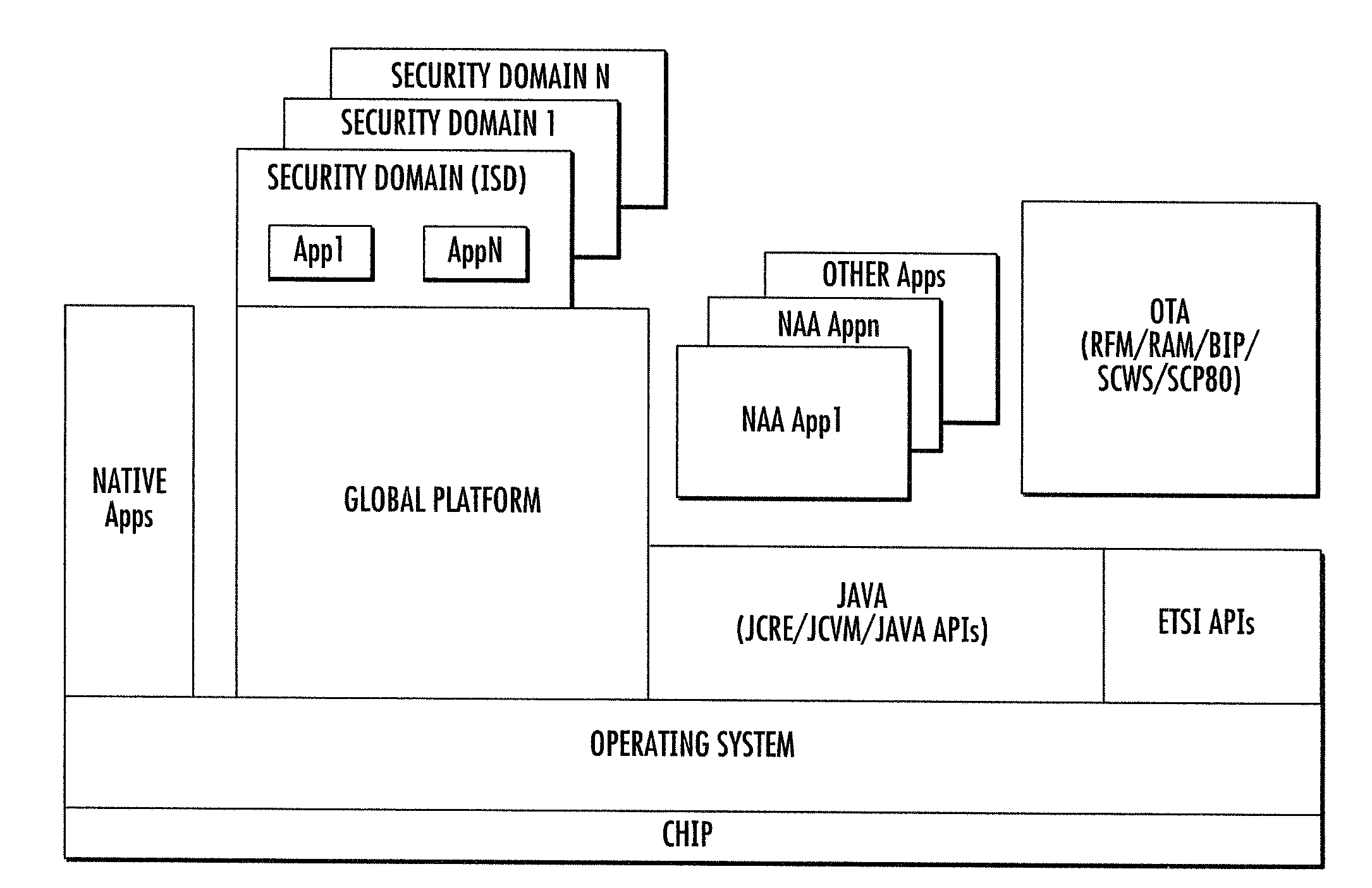
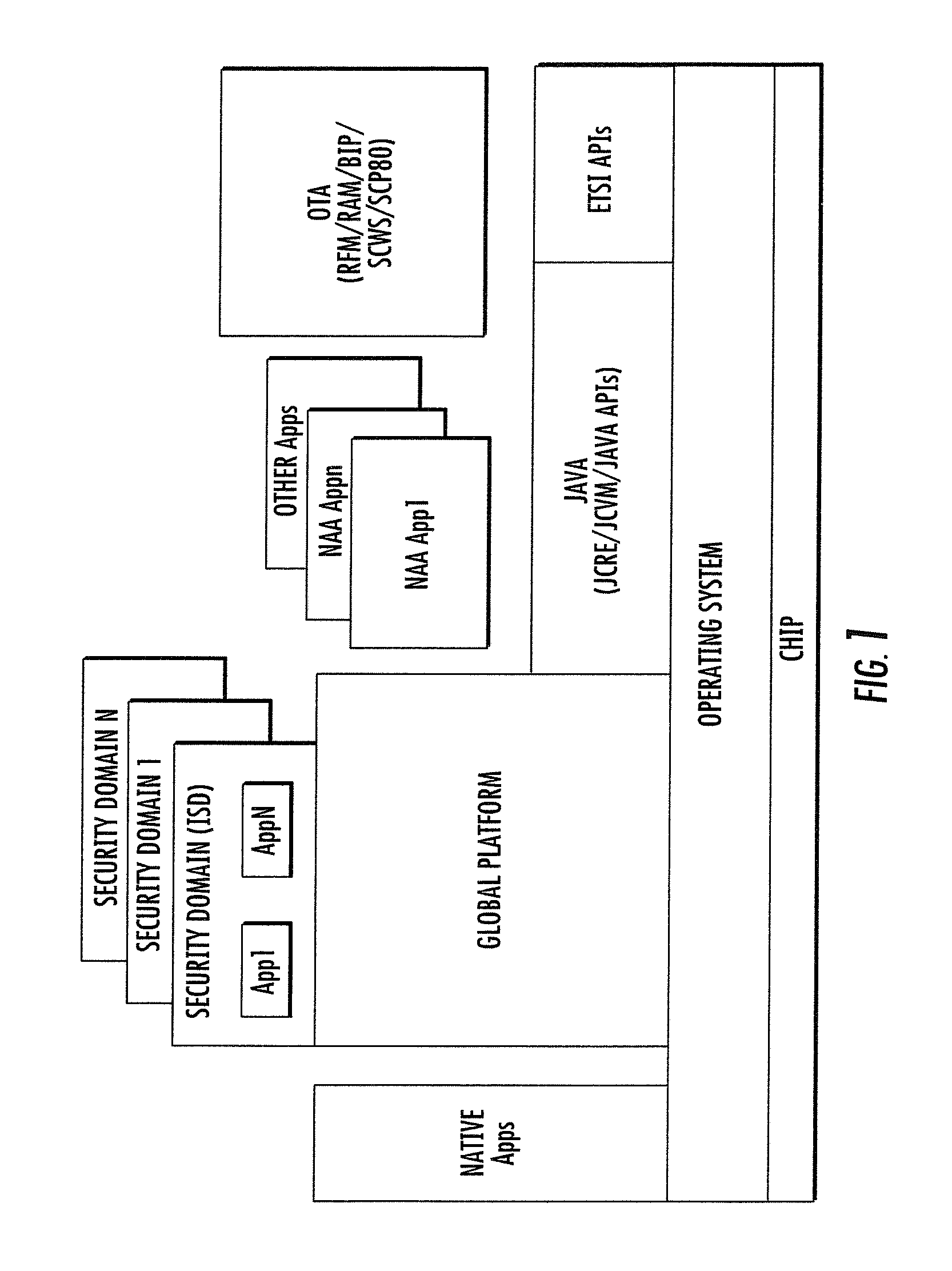
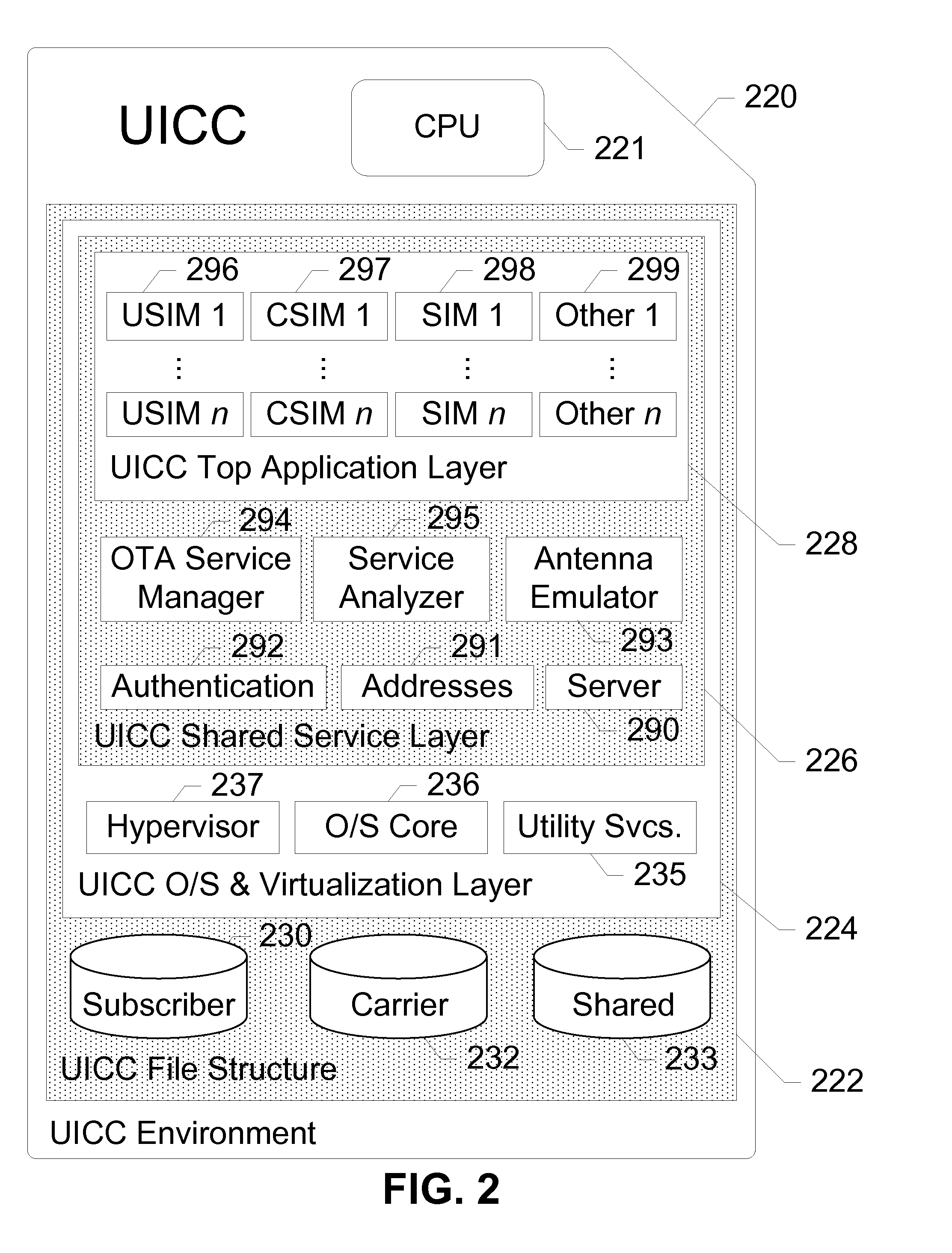
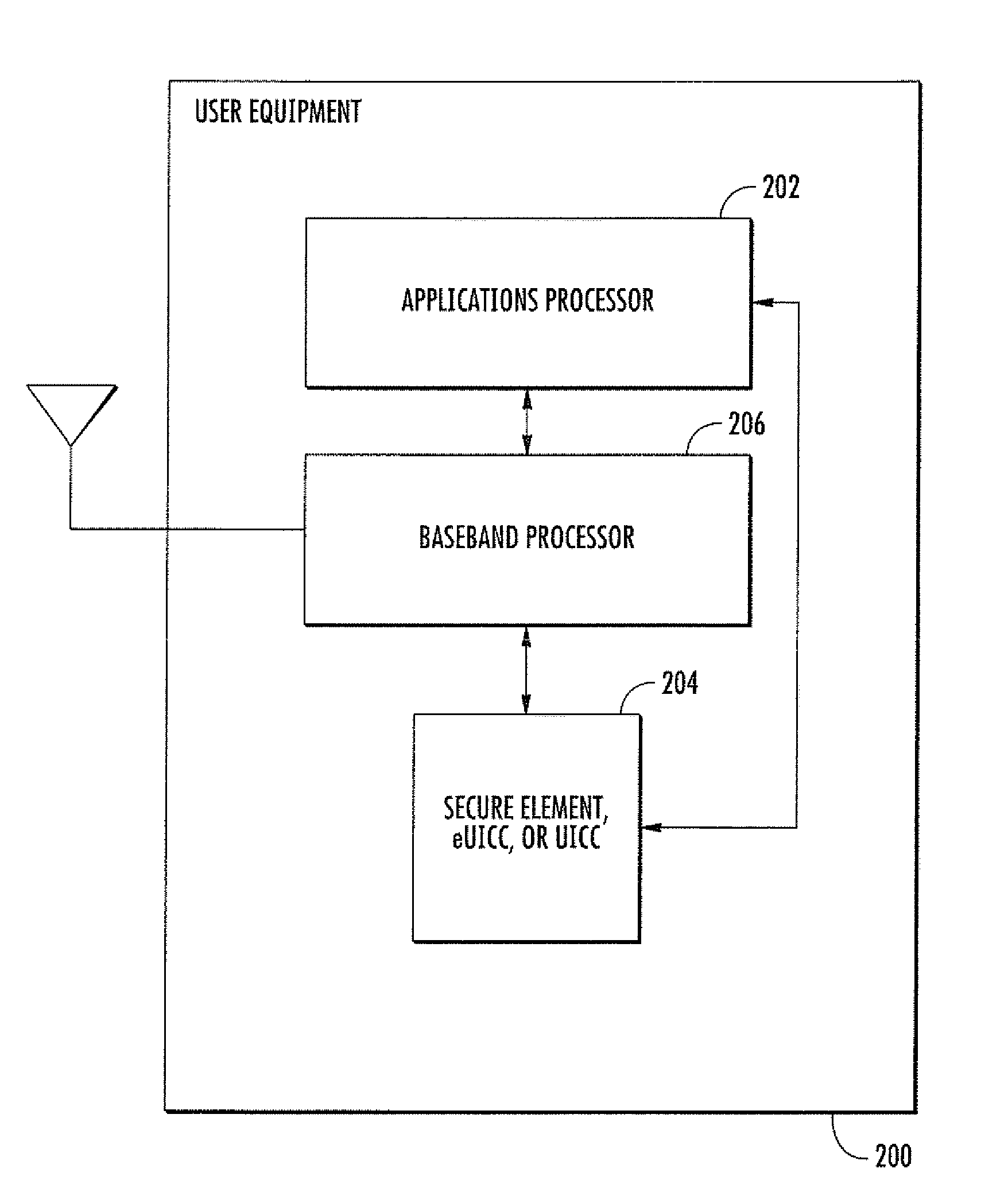
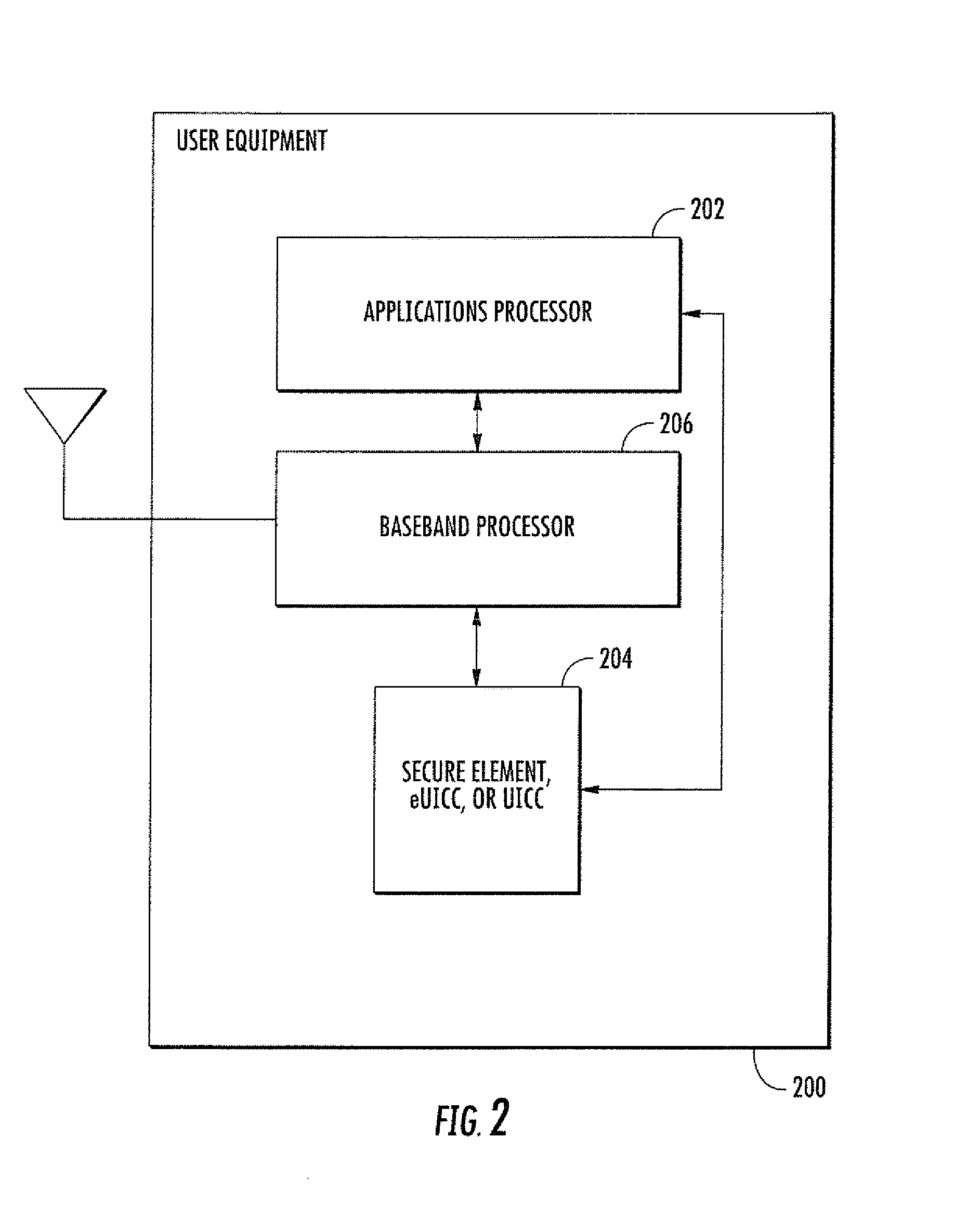
Methods and apparatus for large scale distribution of electronic access control clients. In one aspect, a tiered security software protocol is disclosed. In one exemplary embodiment, a server electronic Universal Integrated Circuit Card (eUICC) and client eUICC software comprise a so-called “stack” of software layers. Each software layer is responsible for a set of hierarchical functions which are negotiated with its corresponding peer software layer. The tiered security software protocol is configured for large scale distribution of electronic Subscriber Identity Modules (eSIMs)
Owner:APPLE INC
UICC Carrier Switching Via Over-The-Air Technology
ActiveUS20130023235A1Eliminate needService provisioningUnauthorised/fraudulent call preventionVirtual userCarrier signal
Devices, systems, and methods are disclosed which relate to provisioning a universal integrated circuit card (UICC) with multiple services. The UICC enables a wireless communication device to communicate through multiple carriers by using a unique virtual subscriber identity module (SIM) to register with each carrier. The unique virtual SIM is one of a plurality of virtual SIMs stored on and managed by the UICC. A carrier network includes a server for provisioning a new virtual SIM on a UICC over-the-air (OTA) when a new customer requests a service such as voice, data, or other type of service. These UICCs may also include logic to automatically select the best carrier for a voice call depending on the user settings.
Owner:AT&T INTPROP I L P
System and device for facilitating a transaction through use of a proxy account code
InactiveUS20110246317A1Increase dependenceFacilitating secure and convenient electronic transactionsFinancePoint-of-sale network systemsPayment transactionSmart card
The present invention relates generally to a smart card device that is configured to facilitate wireless network access and credential verification. Specifically, the device is configured to meet the physical and electrical specification for commercially available mobile devices utilizing a standard Subscriber Identity Module (SIM) for network access. The device combines the features of the SIM with Common Access Card or Personal Identity Verification card features to allow a network subscriber to invoke secure payment transactions over a carrier's network. The system includes data storage for maintaining a plurality of network and transaction instrument profiles and a profile gateway for receiving transaction information from a payment gateway, sending an authorization request to a user's mobile device, receiving a transaction authorization from the mobile device, and sending transaction information to a payment gateway to finalize the payment transaction.
Owner:APRIVA
Methods and apparatus for storage and execution of access control clients
ActiveUS20120108205A1Service provisioningUnauthorised/fraudulent call preventionPersonalizationThird party
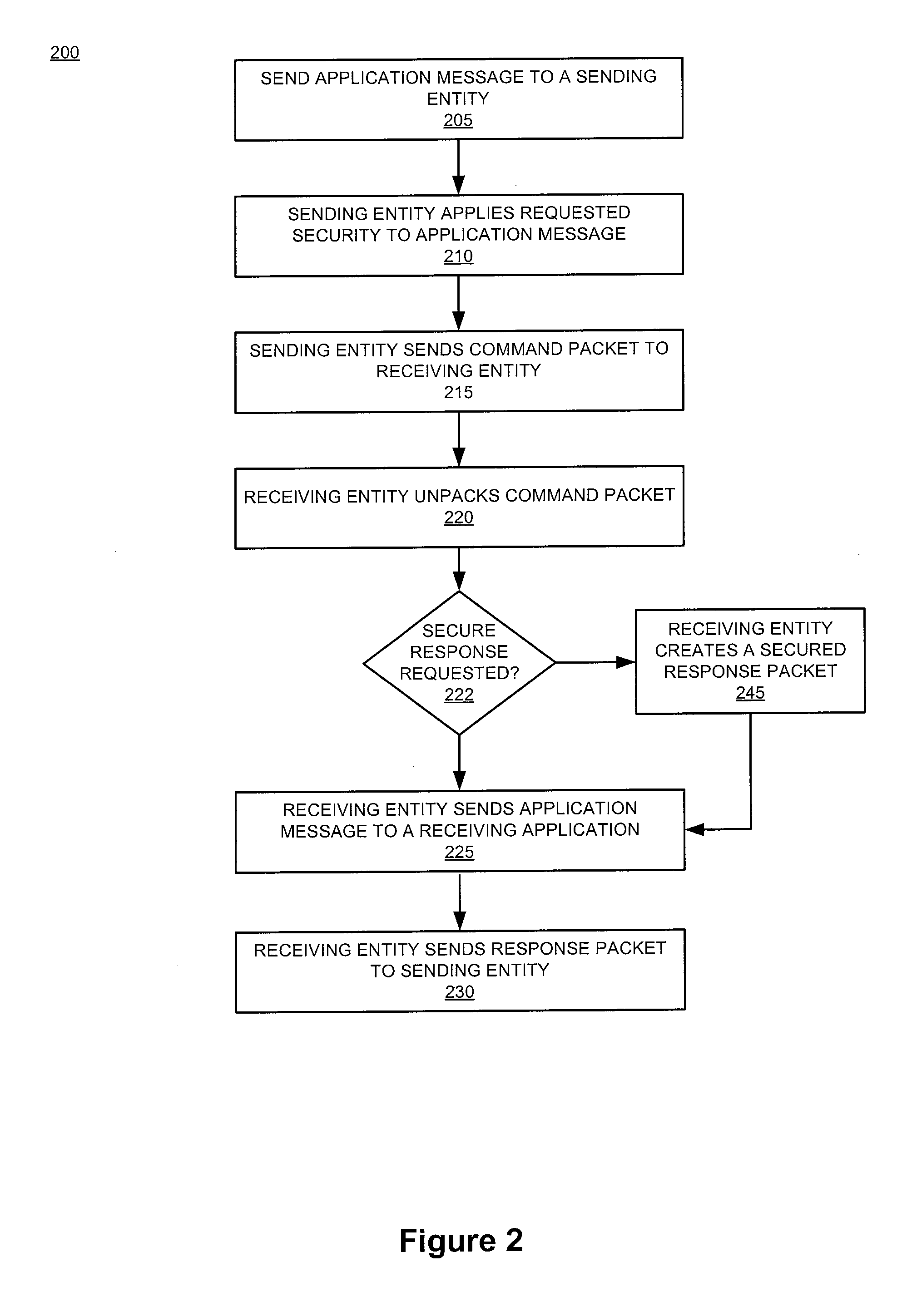
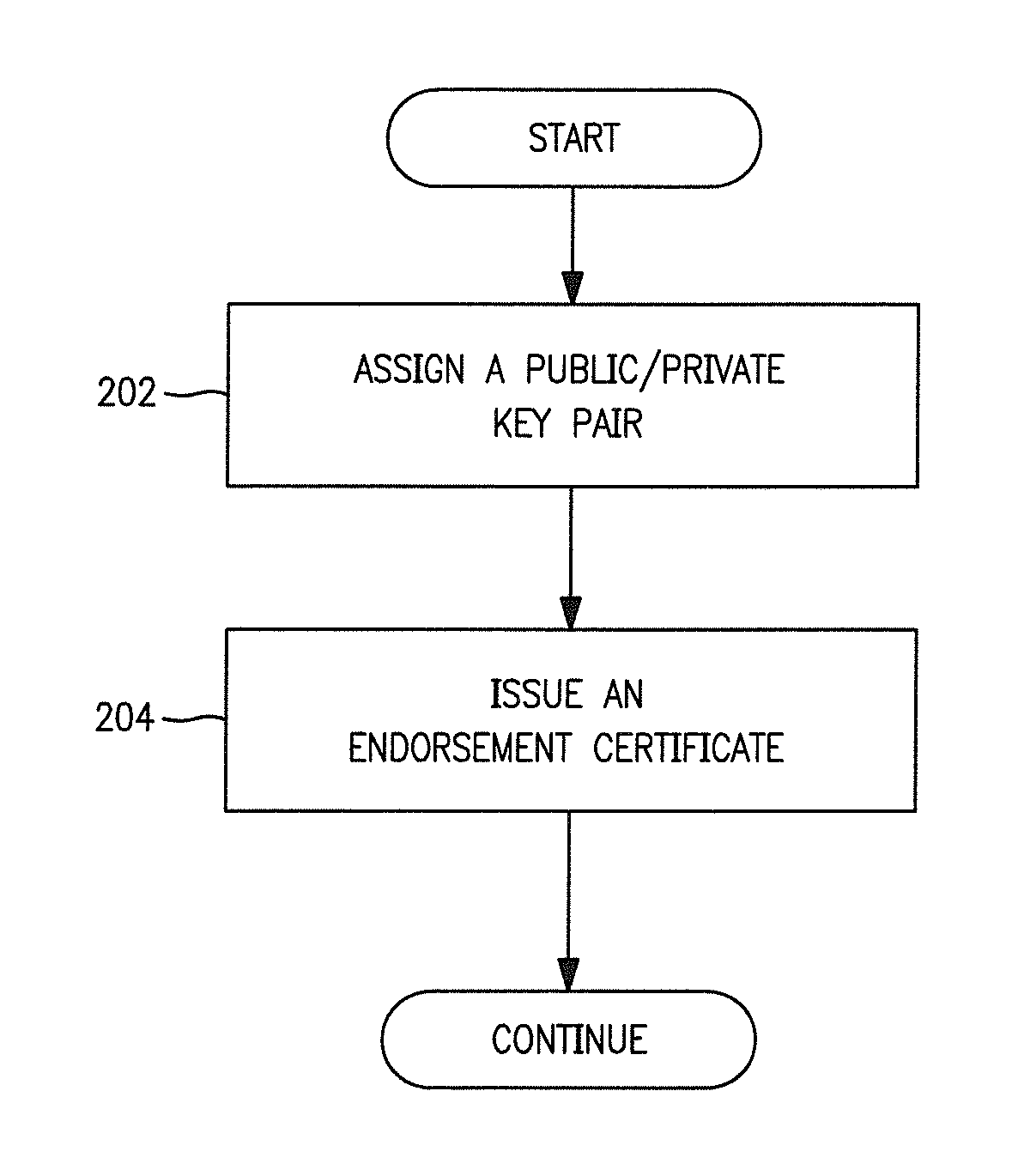
Methods and apparatus for secure provision of access control entities (such as electronic or virtual Subscriber Identity Module (eSIM) components) post-deployment of the host device on which the access control entity will be used. In one embodiment, wireless (e.g., cellular) user equipment is given a unique device key and endorsement certificate which can be used to provide updates or new eSIMs to the user equipment in the “field”. The user equipment can trust eSIM material delivered by an unknown third-party eSIM vendor, based on a secure certificate transmission with the device key. In another aspect, an operating system (OS) is partitioned into various portions or “sandboxes”. During operation, the user device can activate and execute the operating system in the sandbox corresponding to the current wireless network. Personalization packages received while connected to the network only apply to that sandbox. Similarly, when loading an eSIM, the OS need only load the list of software necessary for the current run-time environment. Unused software can be subsequently activated.
Owner:APPLE INC
Mobile Telephone Gateway Apparatus, Communication System, and Gateway Operating System
InactiveUS20060291483A1Facilitates proper initializationImprove coordinationDevices with wireless LAN interfaceData switching by path configurationOperational systemWireless data
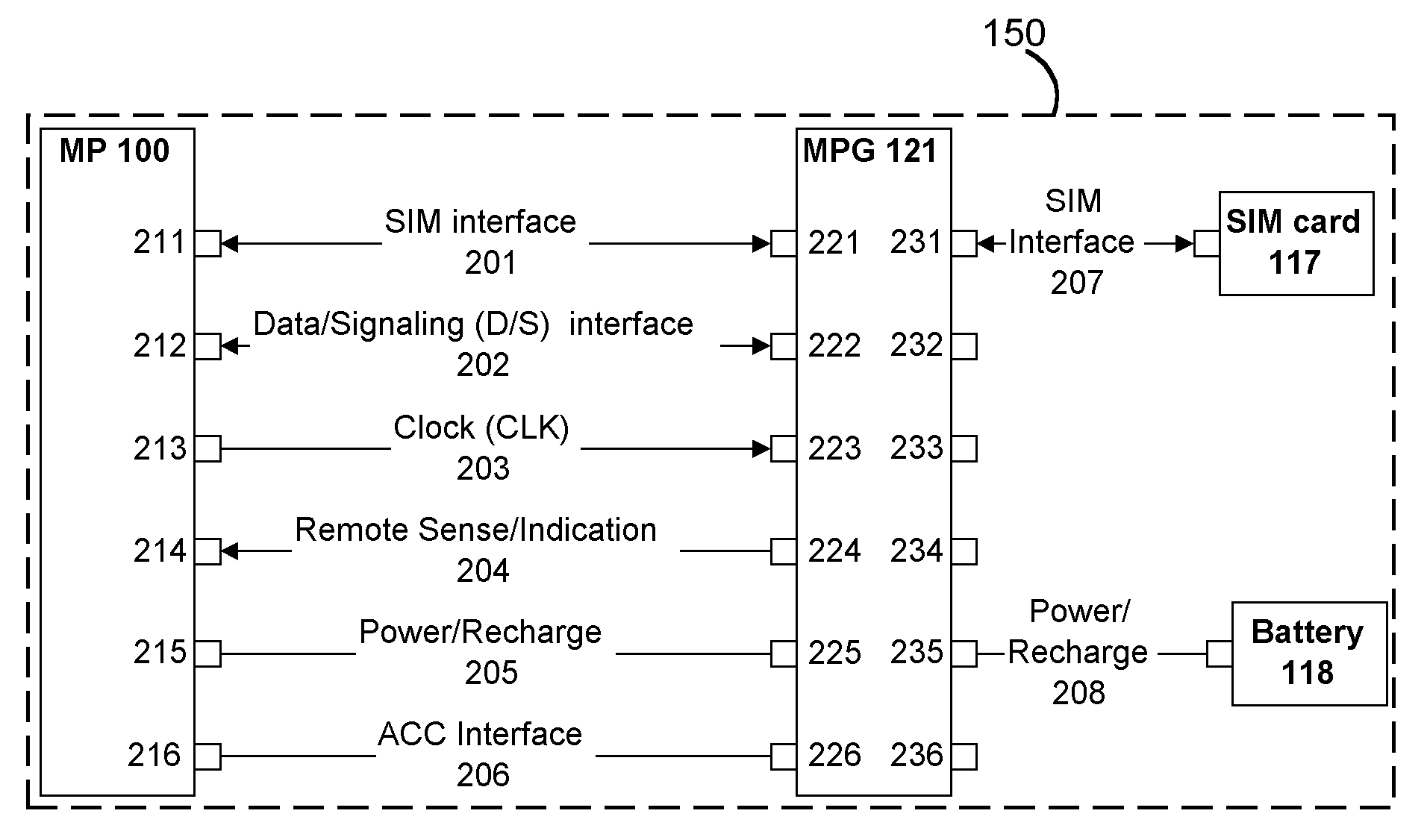
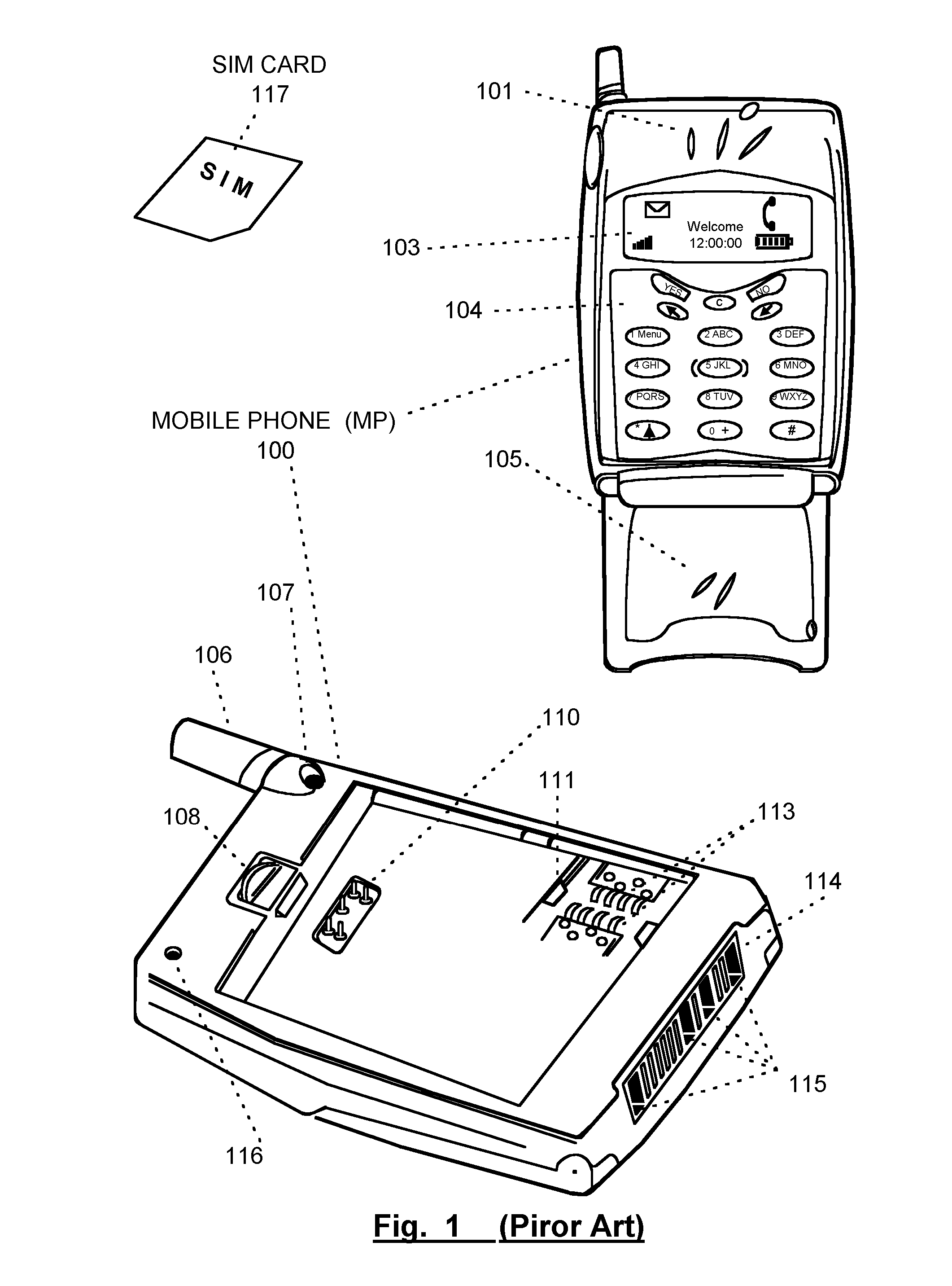
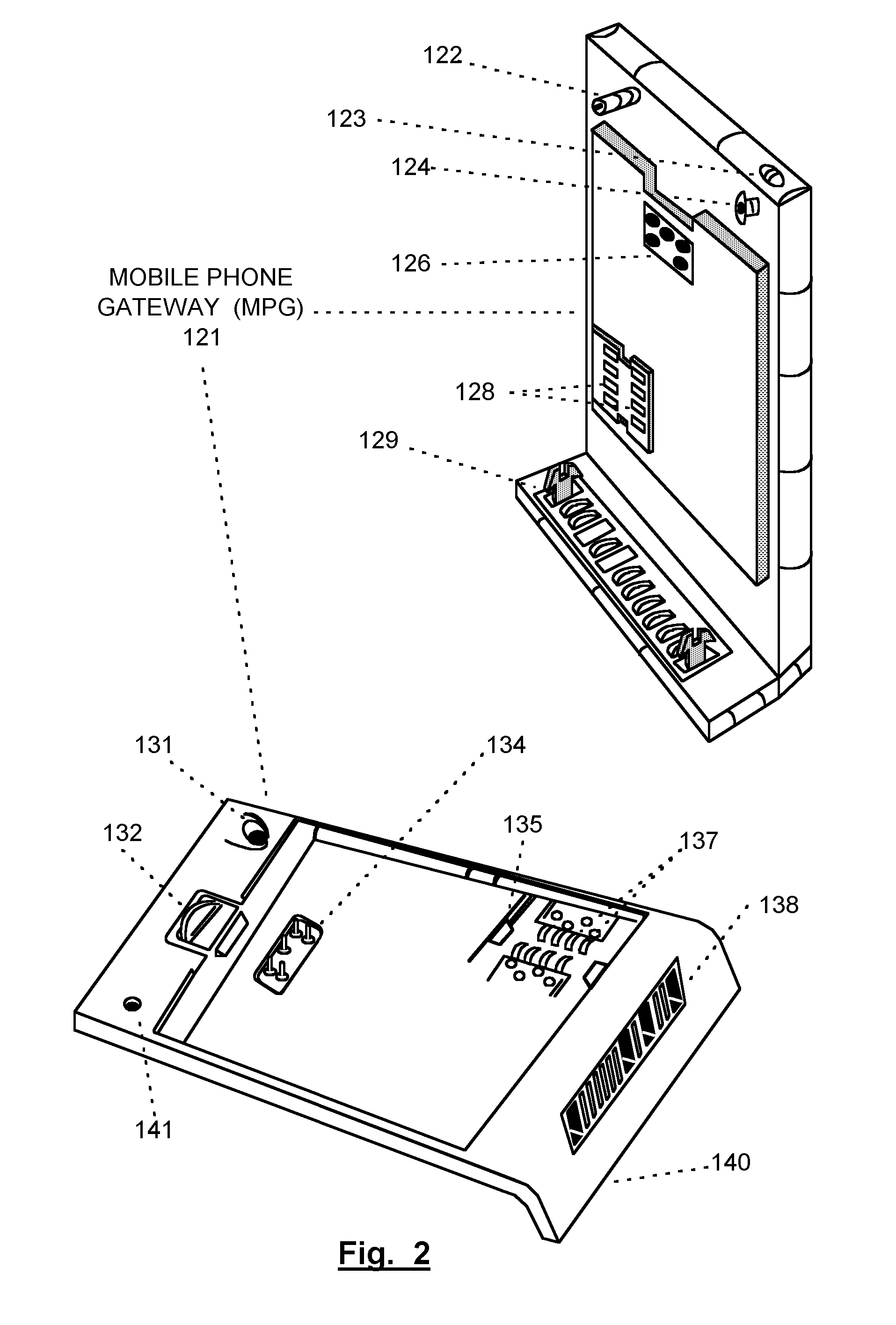
A mobile telephone gateway and communication routing device (MPG) (121) disclosed by the present invention is coupled through an electrical signaling transmission medium with a mobile telephone (100) operative on a first communication network in accordance with a first communication protocol, for adding communication capabilities through at least a second communication network in accordance with a second communication protocol. A mobile communication system (150) is disclosed, comprising MPG (121) placed in-between mobile phone (100) and battery (118) and Subscriber Identification Module (SIM) card (117). MPG connects to the SIM interface of mobile phone (100), using which it wraps SIM functionalities and controls call management. It connects to the data / signaling interface of mobile phone (100), using which it communicates with it, while communicating with the second network using another communication means. It may optionally connects to an accessory device interface of mobile phone (100) such as a Terminal Adapter / Terminal Equipment (TA / TE) or a USB OTG interface, thereby enabling communication between the mobile phone and wireless data terminals of the second network. In a preferred embodiment of the present invention, a MPG is provided for use with a mobile phone operative on a mobile communication network such as GSM, adding communication capabilities through a wireless communication network such as Bluetooth or Wi-Fi. Furthermore, gateway applications are provided to facilitate or support communication through at least the second network in accordance with mobile web protocols and technologies such as Mobile IP, mobile SIP, and mobile VoIP.
Owner:SELA YOSSY
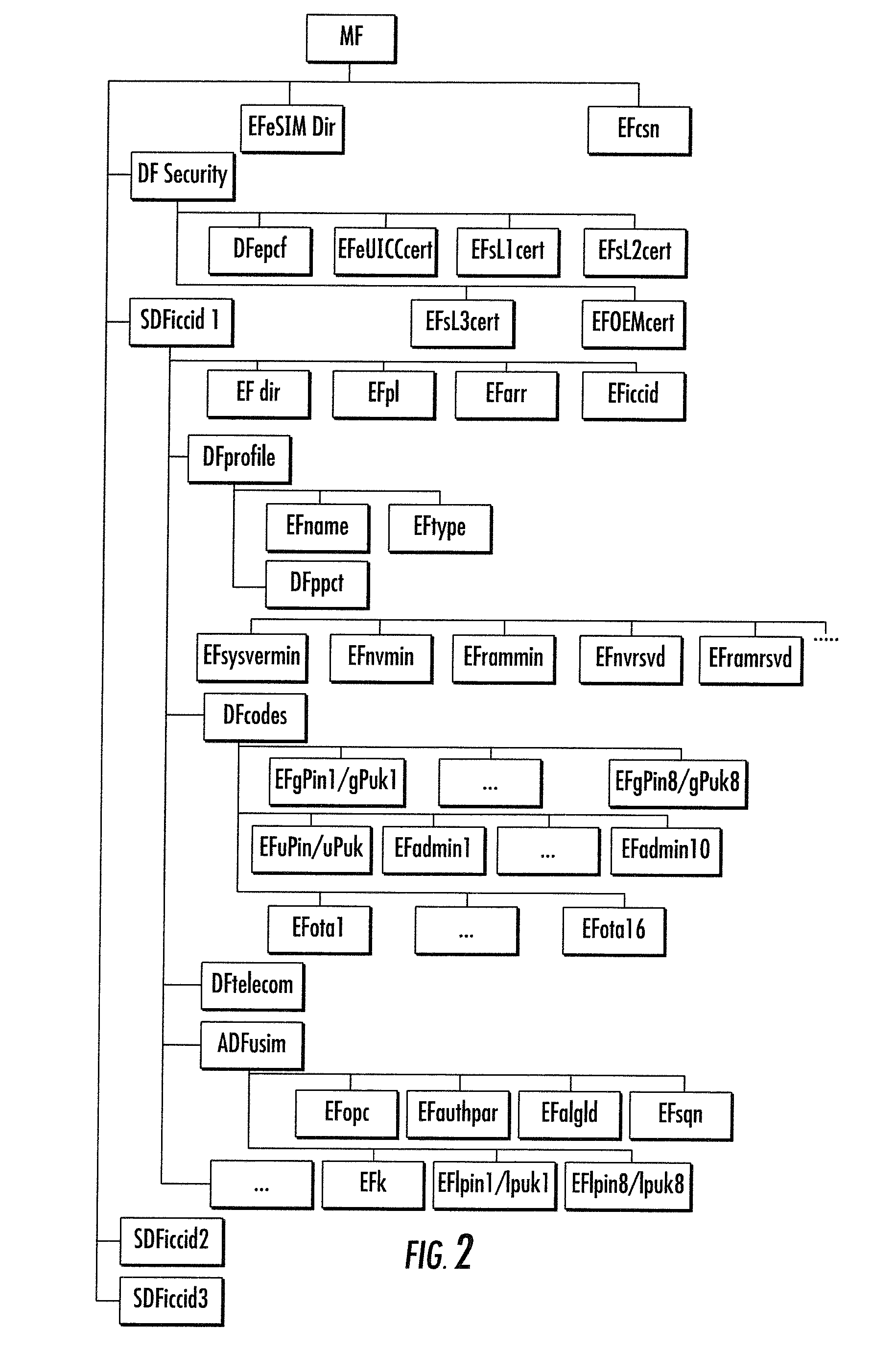
Subscriber Identity Module
InactiveUS20080051142A1Substation equipmentSensing record carriersSecure communicationComputer module
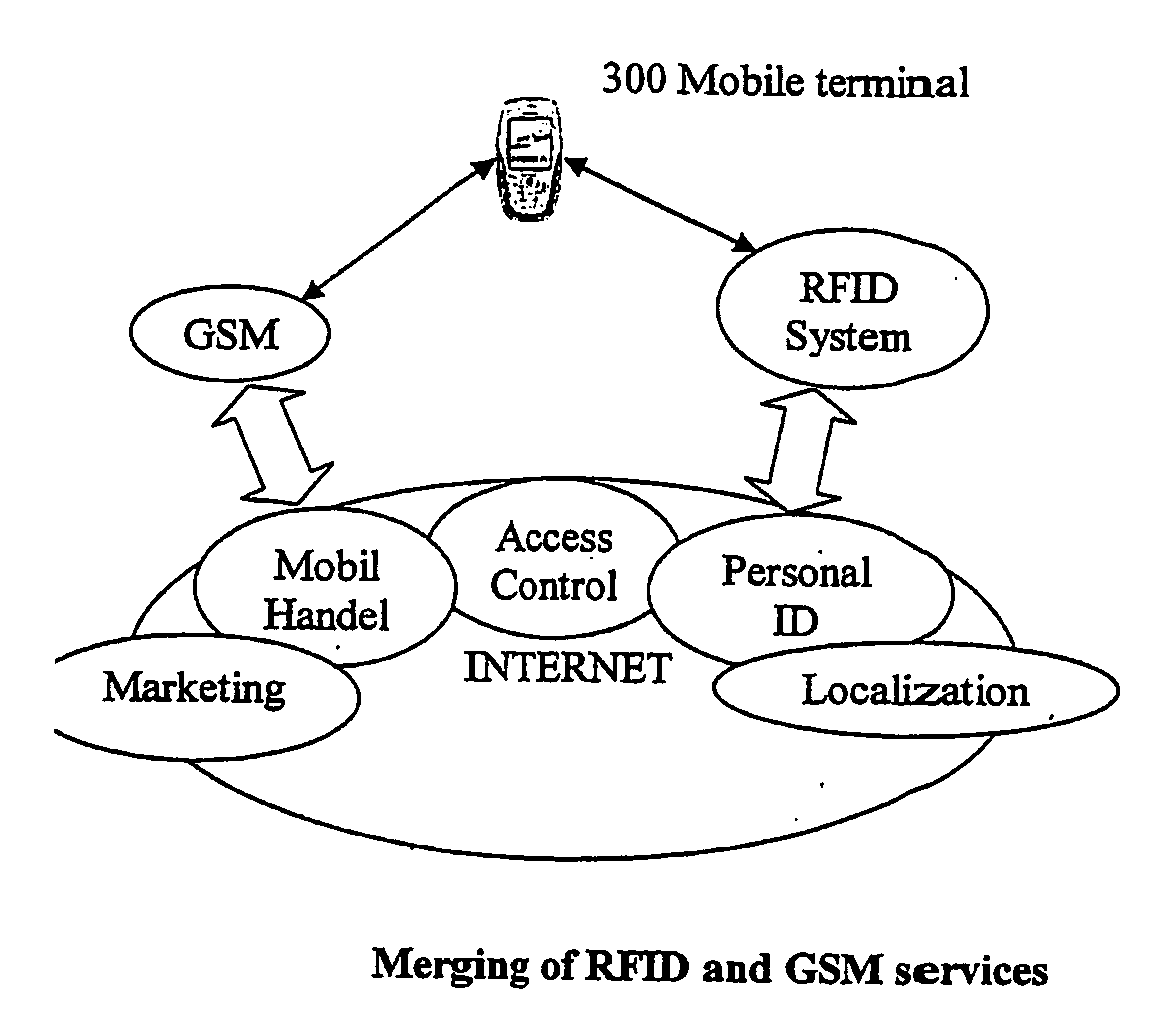
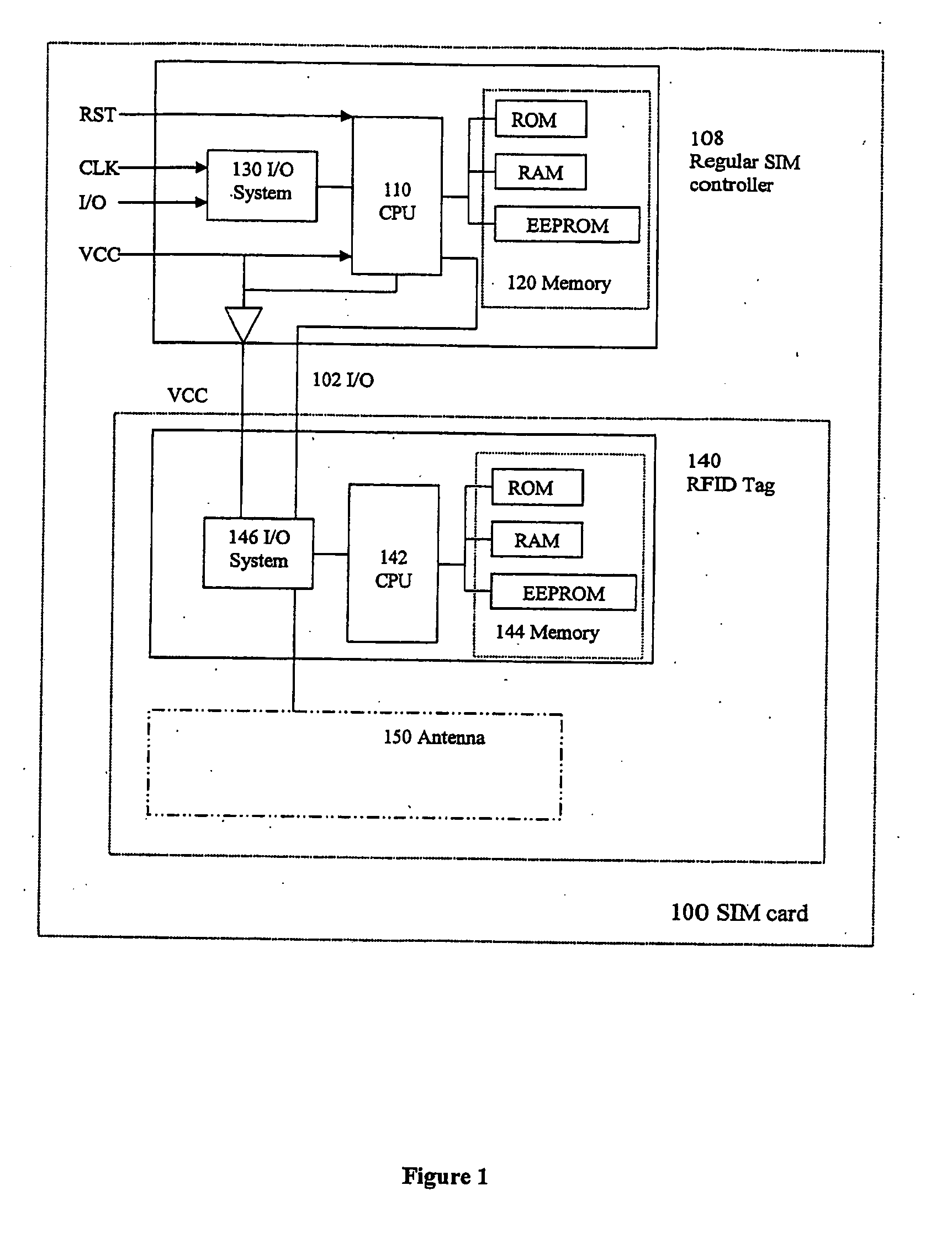
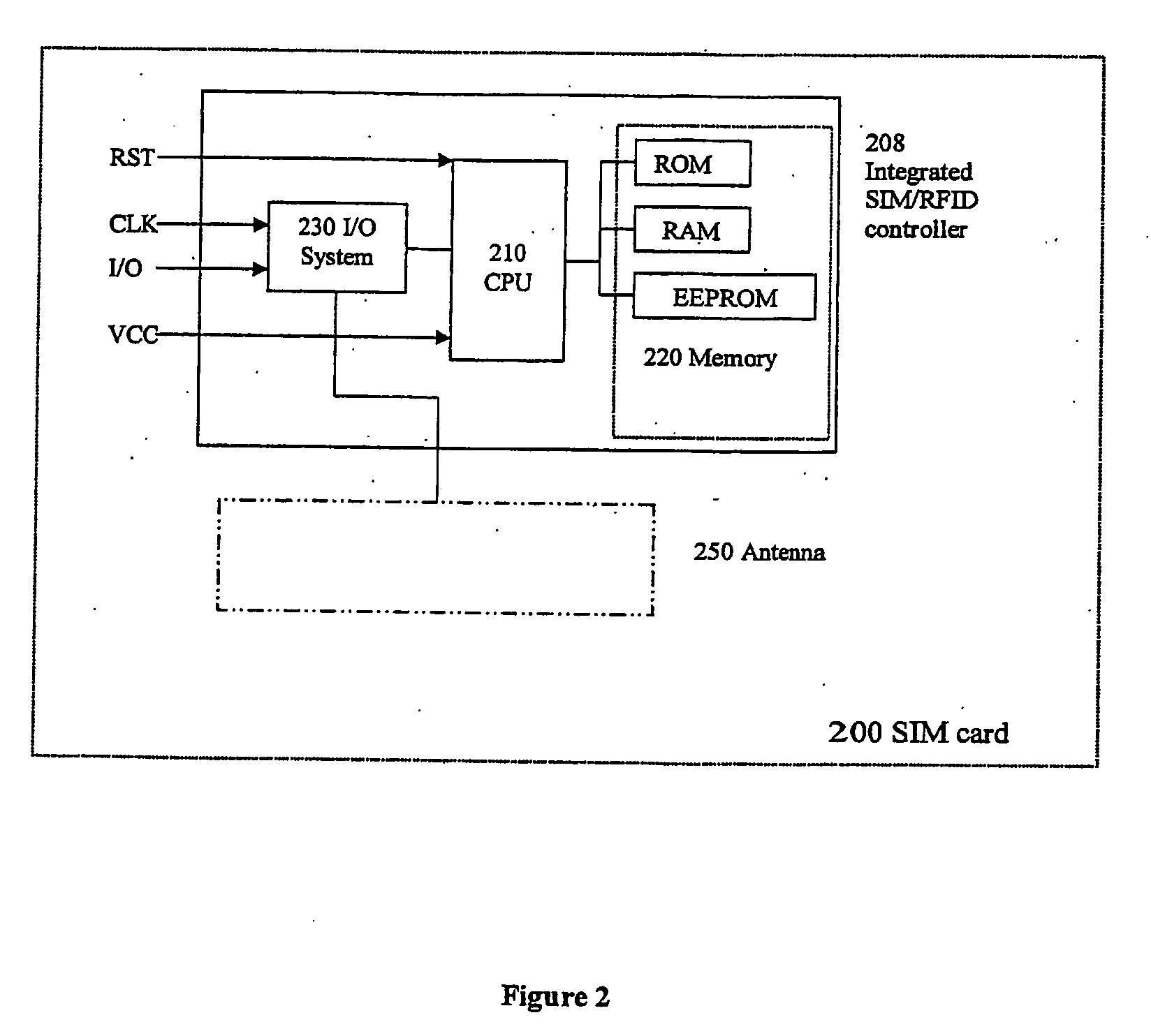
The invention relates to a subscriber identity module for a mobile communication terminal, comprising a processing device, a memory device, an I / O device and a wireless communication device, in particular an interrogatable transponder such as an RFID transponder. The RFID transponder is operatively controllable by said processing device, and comprises a memory which contains identification data, configurable by the processing device. The RFID-enabled subscriber identification module may be used as an authentication token. A method for providing secure communications between the subscriber identification module and an RFID interrogating device is also provided.
Owner:TELENOR AS
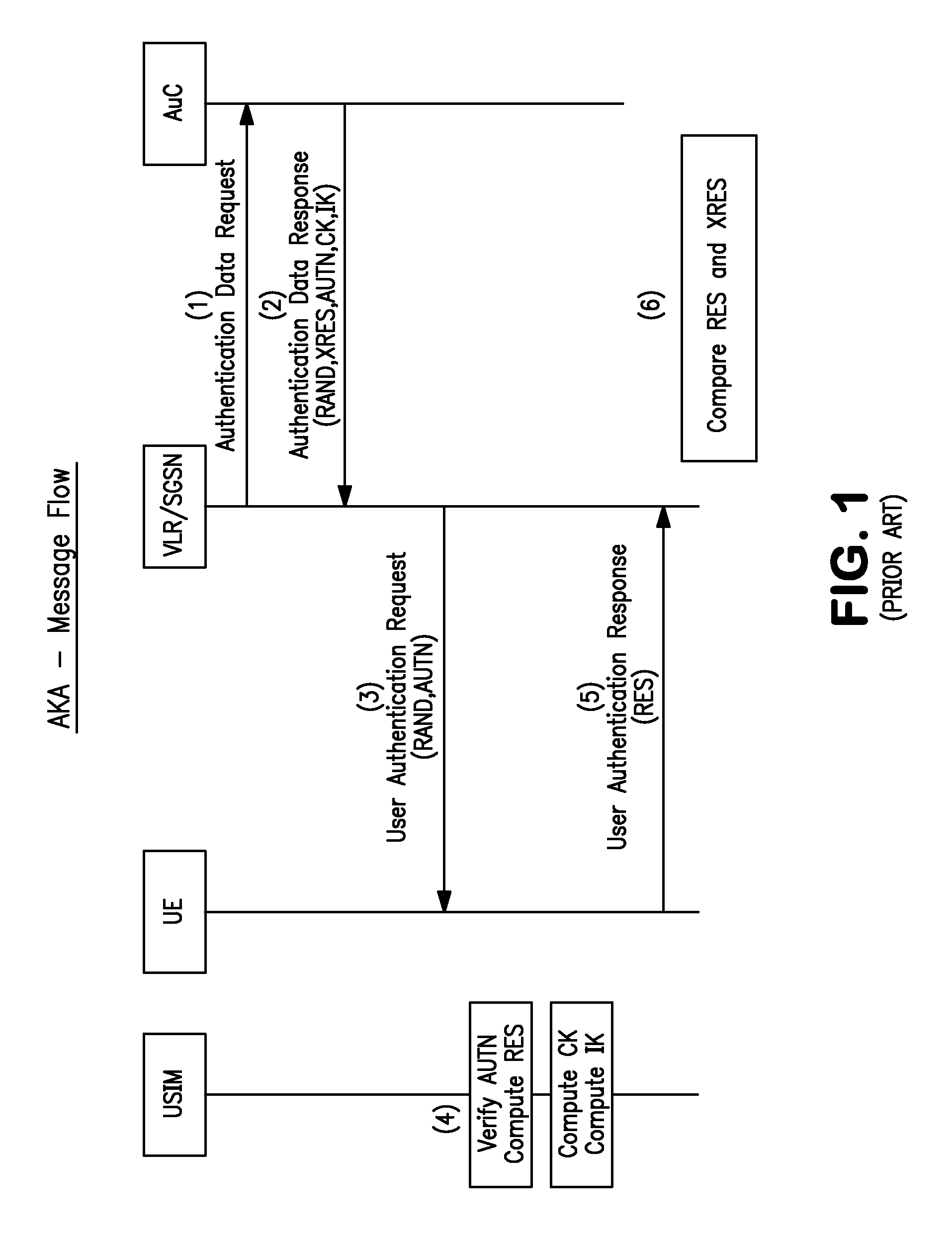
Techniques for secure channelization between uicc and a terminal
InactiveUS20090209232A1Improve integrityReduce needUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunications systemThird generation
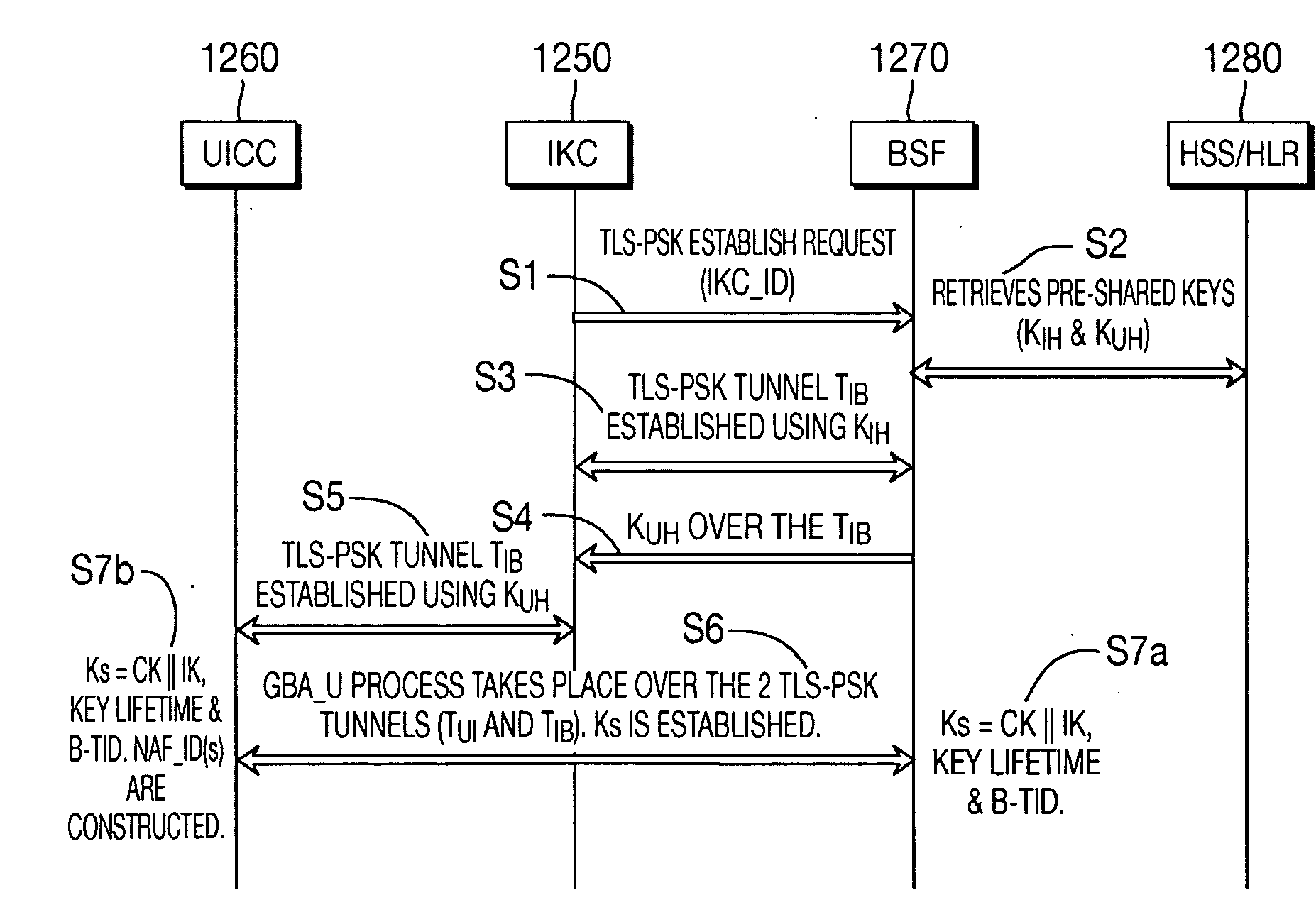
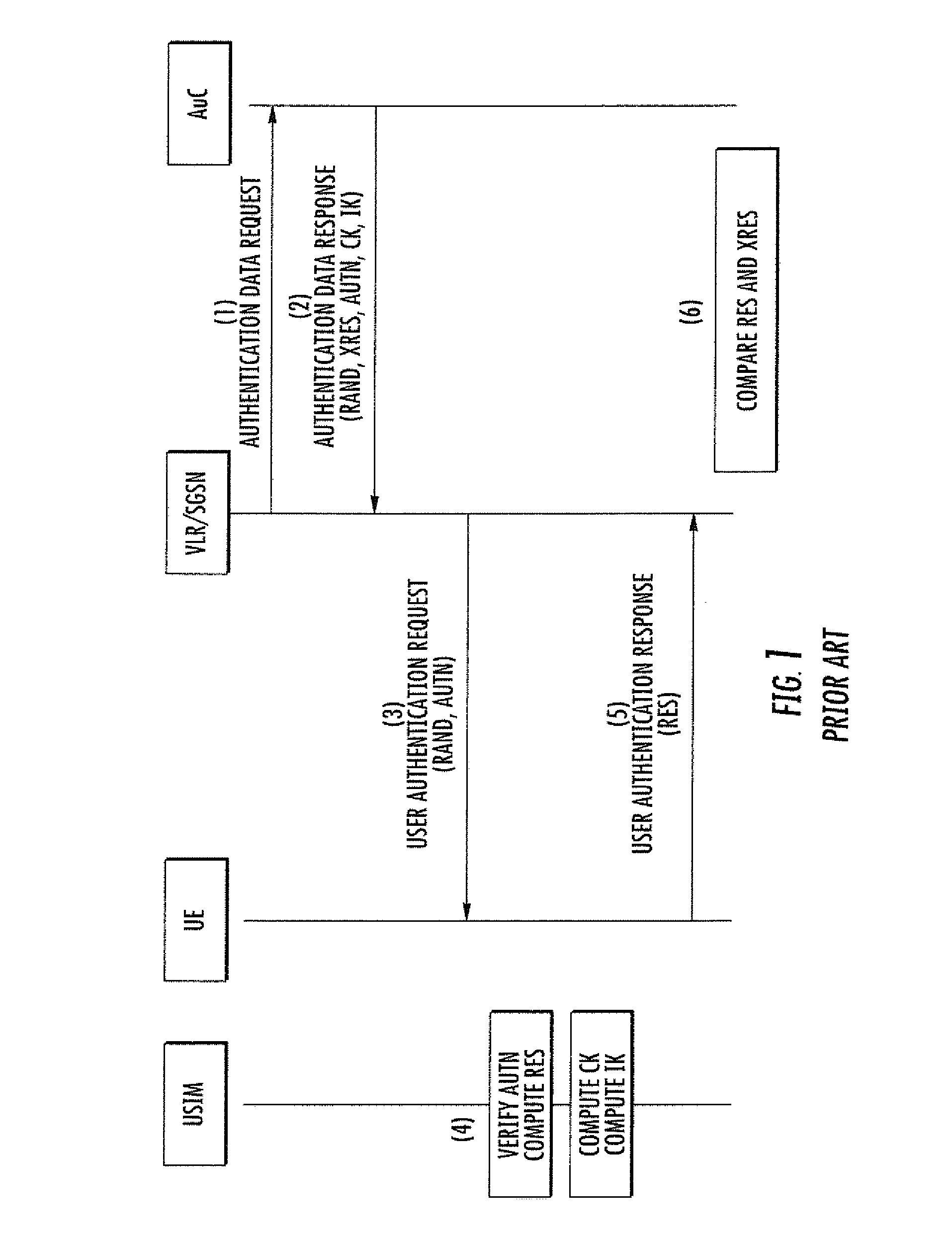
The present invention is related to a wireless communication system. 3G UMTS mobile phone systems rely on a protected smart card called the UMTS integrated circuit card (UICC) that provides UMTS subscriber identity module (USIM) applications as a basis or root of various security measures protecting the communication path between the 3G mobile terminal and the UMTS wireless network (or UTRAN). Disclosed is a method by which the UICC exchanges information with a terminal, such as an Internal Key Center (IKC 1250) and a Bootstrapping Server Function (BSF 1270) enables a procedure where multiple local keys specific to applications and Network Application Functions (NAFs) (Ks_local) are used for authentication and to encrypt and decrypt messages.
Owner:INTERDIGITAL TECH CORP
Mobile terminal with user identification card including personal finance-related information and method of using a value-added mobile service through said mobile terminal
ActiveUS20050097038A1Labor savingShorten the timeBatteries circuit arrangementsCredit registering devices actuationPaymentRelevant information
The present invention enables a user to receive a financial service anywhere through a mobile terminal equipped with a UIM (User Identification Module) electronic card. In the present invention, a user enters his or her password to a mobile terminal with a UIM card including subscriber telephone number, finance, authorization, and personal information, then, if the entered password is correct, authorization is processed with a remote authorizing server based on the authorization information. After authorization, user's requesting service, e.g., payment service, transaction particulars inquiry service, prepaid card recharging service is conducted through a mobile network.
Owner:SK PLANET CO LTD
Mobile Telephone Firewall and Compliance Enforcement System and Method
ActiveUS20090325615A1Improve protectionSubstation equipmentMessaging/mailboxes/announcementsComputer softwareSubscriber identity module
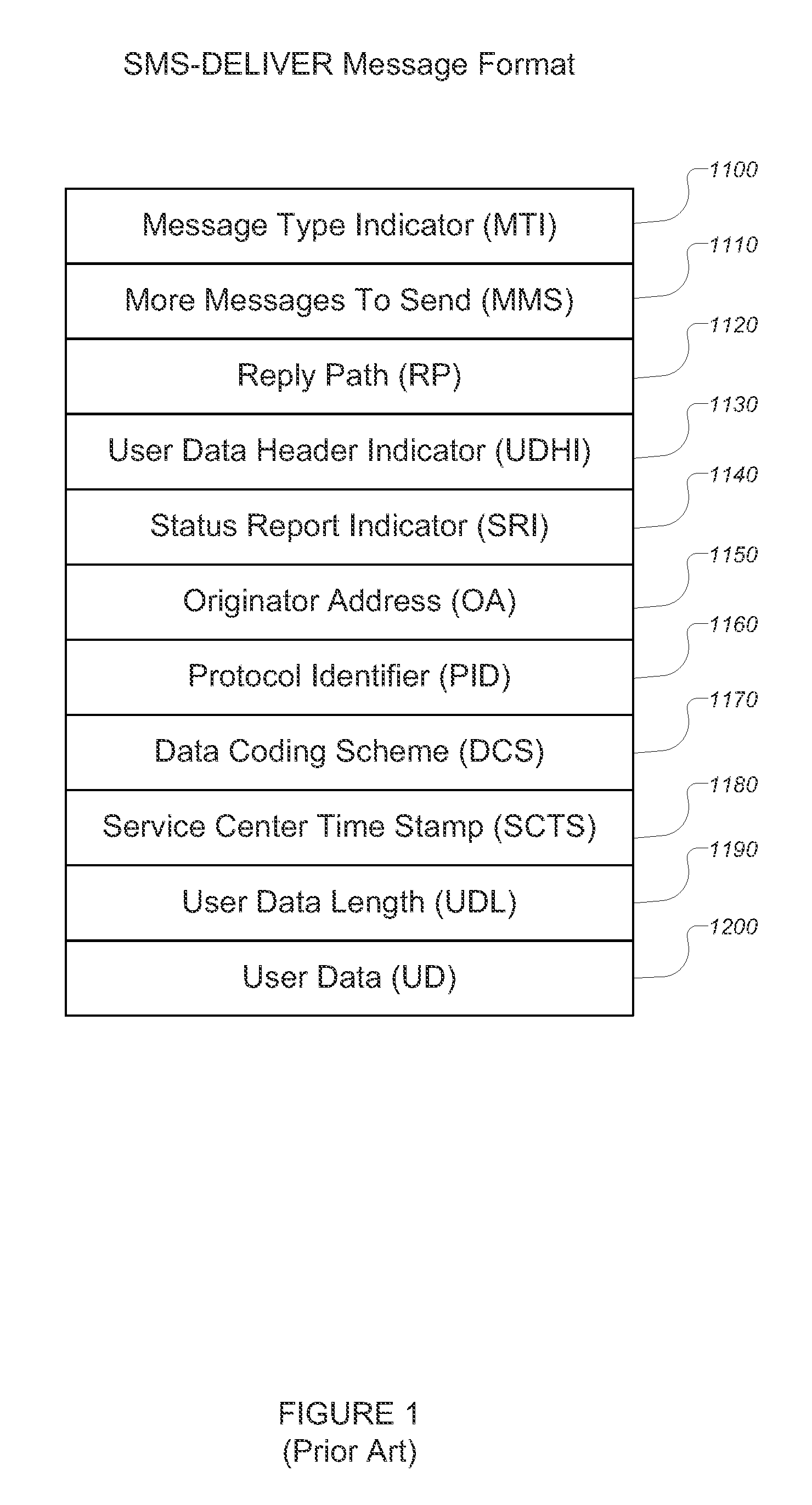
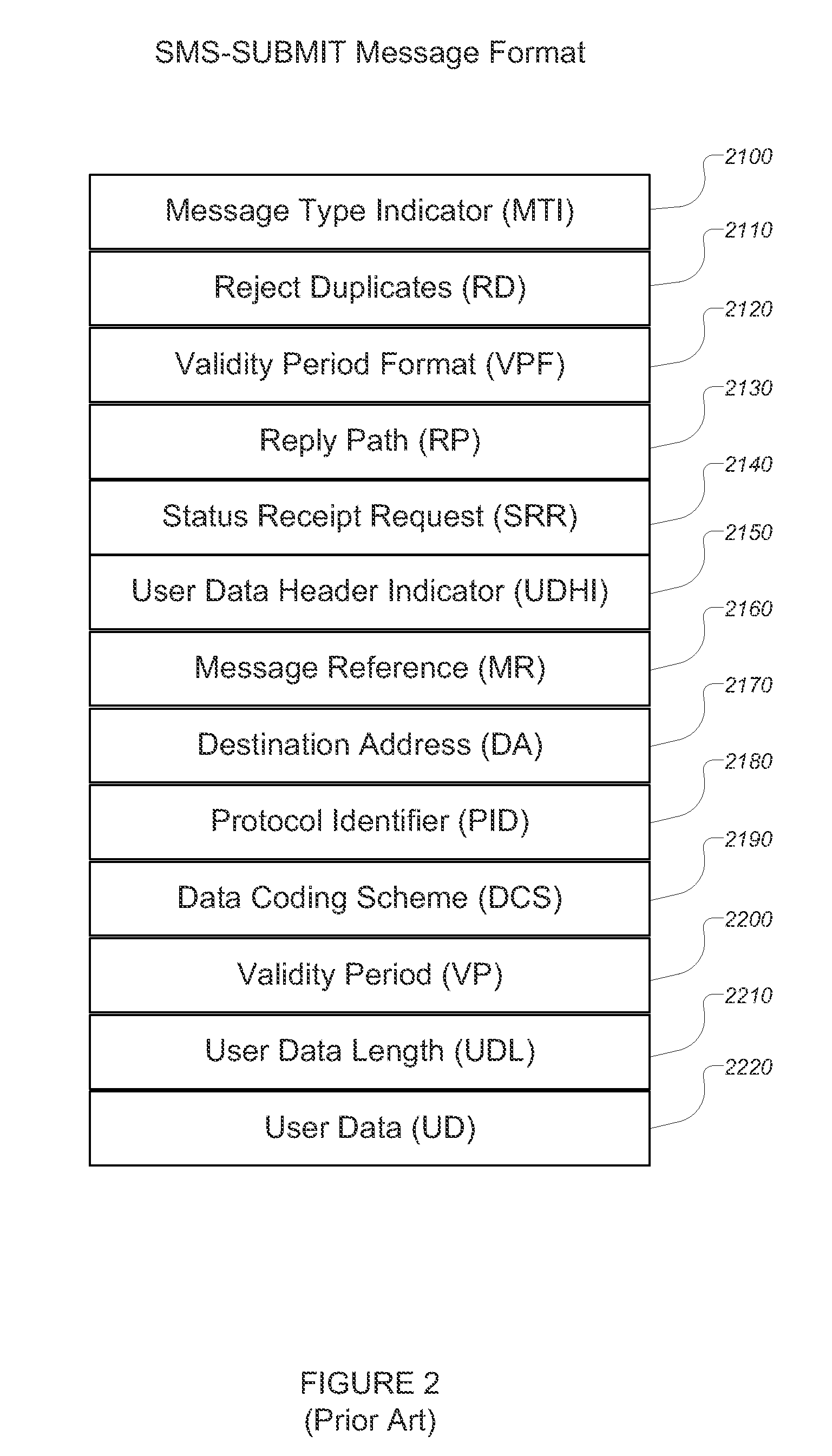
Methods, systems, and software for mediating SMS messages, and especially type 0 SMS messages, in a wireless mobile communications device configured to send and receive data using a GSM protocol and including a subscriber identity module (“SIM”) including electronic hardware and computer software executed by the hardware such that the SIM is configured to send, receive, and process messages using a Short Message System (“SMS”) between the wireless mobile communications device and a communications network. One aspect includes a method for mediating SMS messages comprising: configuring electronic hardware on the wireless mobile communications device to implement a firewall on the wireless mobile communications device, the firewall configured to identify and optionally mediate infrastructure SMS messages.
Owner:MANTECH ADVANCED SYST INT
Multiple subscription subscriber identity module (SIM) card
ActiveUS20050164737A1Substation equipmentTransmissionSubscriber identity moduleInternational mobile subscriber identity
Embodiments of the invention include a multiple subscription subscriber identity module (SIM) card. The SIM card includes a plurality of sets of subscription parameters from which to select and activate a single set of parameters. The sets of subscription parameters each contain various information, e.g., information such as an Integrated Circuit Card Identifier (ICCID) and an International Mobile Subscriber Identity (IMSI), and are based on various criteria, e.g., different service regions of use for the electronic device on which the SIM card is installed. A set of subscription parameters is selected for a particular region of use either manually or automatically. The SIM card, which can include a software interface that provides a list of available sets of subscription parameters, is activated by updating the selected set of subscription parameters. Alternatively, a default set of subscription parameters is selected unless a different set of subscription parameters is selected manually from among the plurality of sets of subscription parameters. According to alternative embodiments of the invention, the selected set of subscription parameters can be deactivated and a different set of subscription parameters can be selected and updated to in the SIM card.
Owner:CINGULAR WIRELESS II LLC
Methods And Apparatus For Providing Manual Selection Of A Communication Network For A Mobile Station
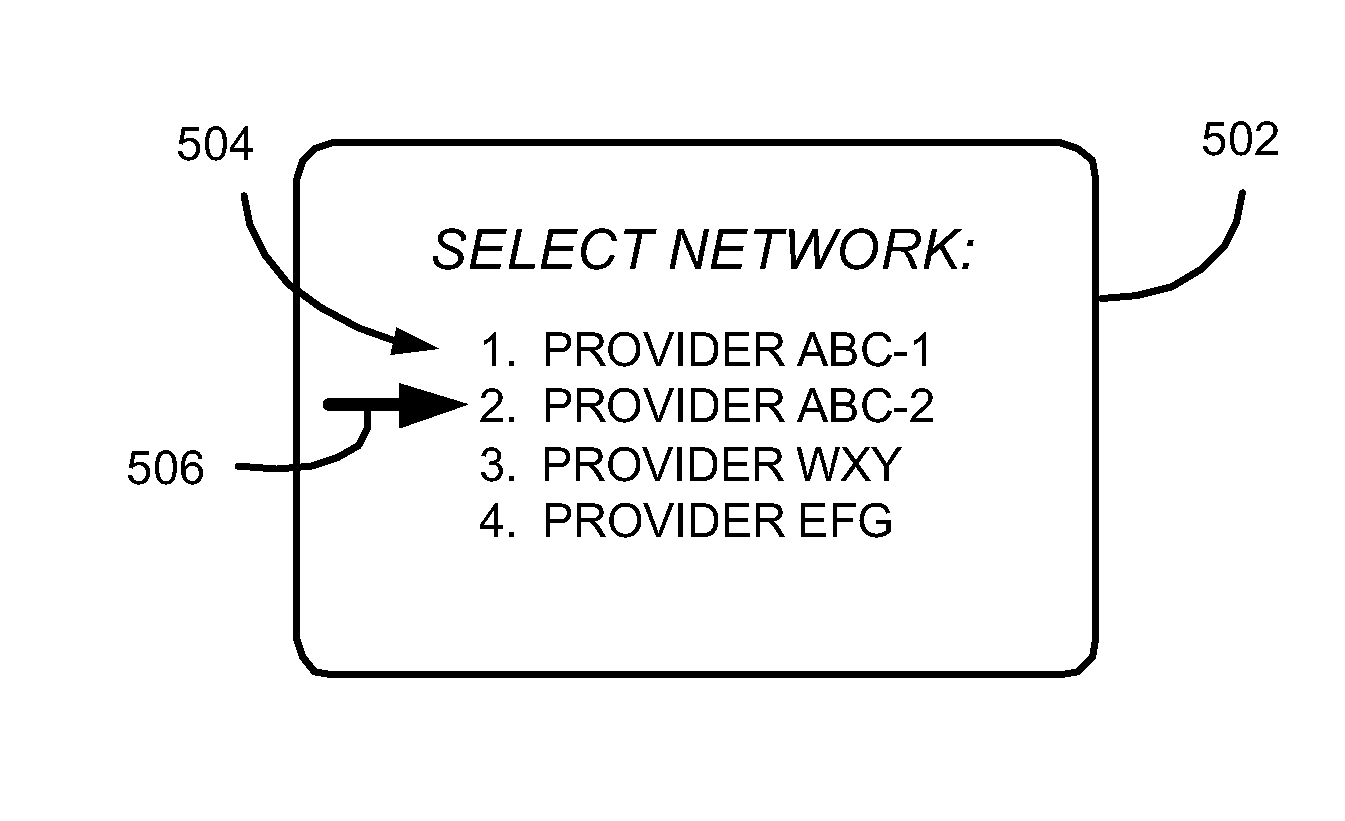
ActiveUS20080096559A1Assess restrictionRadio/inductive link selection arrangementsMobile network codeTelecommunications
Methods and apparatus for providing manual selection of a communication network for a mobile station are described. A plurality of communication networks are identified by scanning a coverage area within which the mobile station is operating. A plurality of network identifiers corresponding to the plurality of communication networks are then retrieved from memory of a Subscriber Identity Module (SIM) in accordance with an Enhanced Operator Name String (EONS) protocol. Preferably, each network identifier is retrieved based on a Mobile Country Code (MCC), a Mobile Network Code (MNC), and a Location Area Code (LAC). The plurality of network identifiers are visually displayed for user selection, and at least two of the network identifiers may be substantially the same. The user selected communication network is registered with and the network identifier associated with this network is visually displayed.
Owner:LEPATENT (BEIJING) CONSULTING CORP LTD
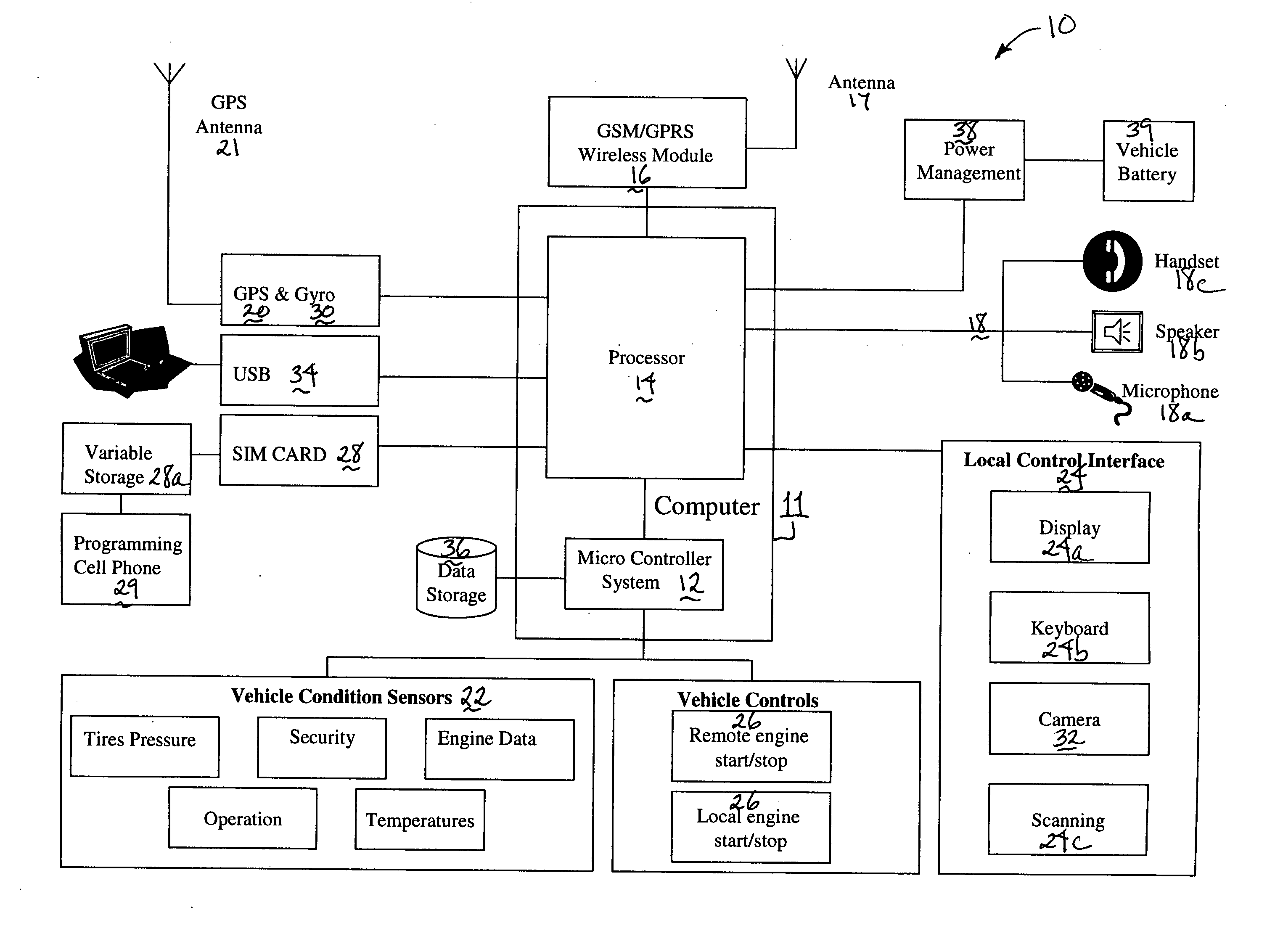
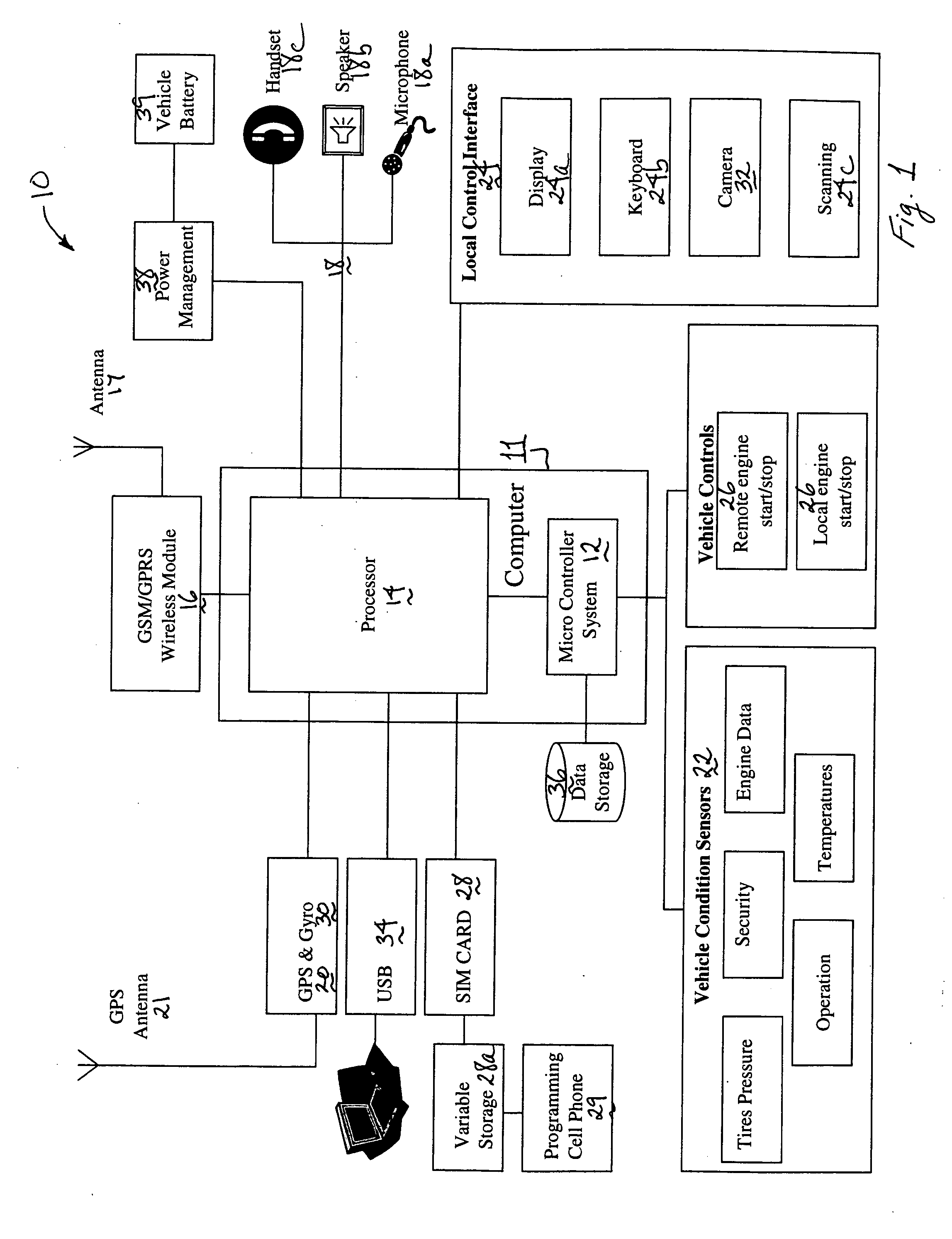
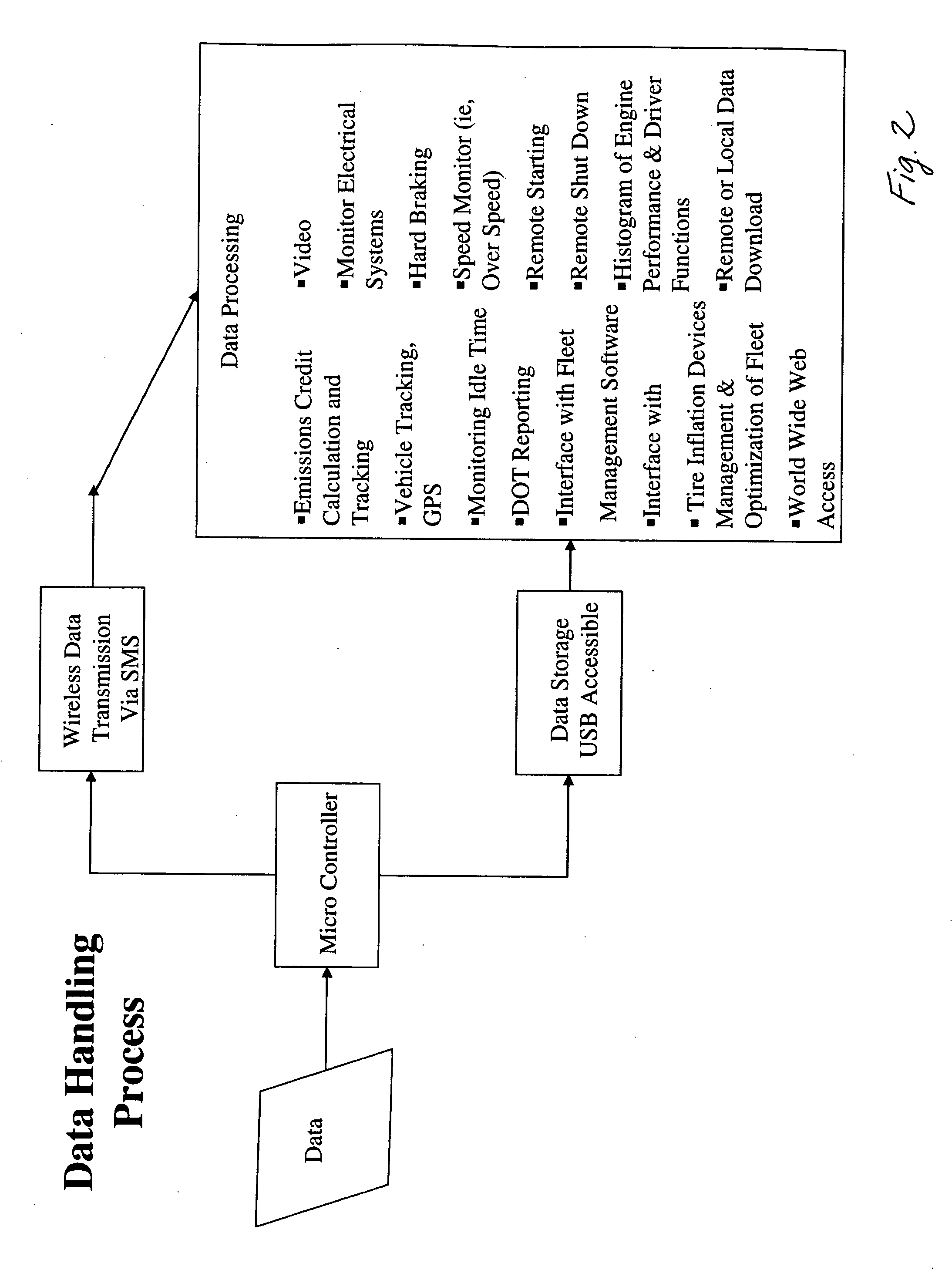
Systems and methods for remote vehicle management
InactiveUS20060271246A1Registering/indicating working of vehiclesDigital data processing detailsGyroscopeGps receiver
A system is provided that is adapted to be operably connected to a vehicle for use in management of the vehicle. The system includes: a computer; a wireless communication module operably connected to the computer; an audio interface operably connected to the computer; a GPS receiver module operably connected to the computer; at least one vehicle condition sensor operably connected to the computer; and a local control interface operably connected to the computer. According to a first aspect of the invention, the system further includes an engine start / stop controller operably connected to the computer. According to a second aspect of the invention, the system further includes a subscriber identity module (“SIM”) operably connected to the computer. According to a third aspect of the invention, the system further includes a gyroscope module operably connected to the GPS receiver module. According to yet another aspect of the invention, a method is provided for controlling the engine idle time of a vehicle. The method includes the steps of: operatively connecting at least one temperature sensor to measure the temperature of at least one part of the vehicle; operatively connecting the at least one temperature sensor to a computer; operatively connecting an engine start / stop controller to the engine of the vehicle; operatively connecting the engine start / stop controller to the computer; using the computer to start the engine when the at least one temperature sensor reports a temperature that is outside of a settable temperature range; and using the computer to stop the engine when the at least one temperature sensor reports a temperature that is within a settable temperature range.
Owner:VEHICLE MANAGEMENT SYST
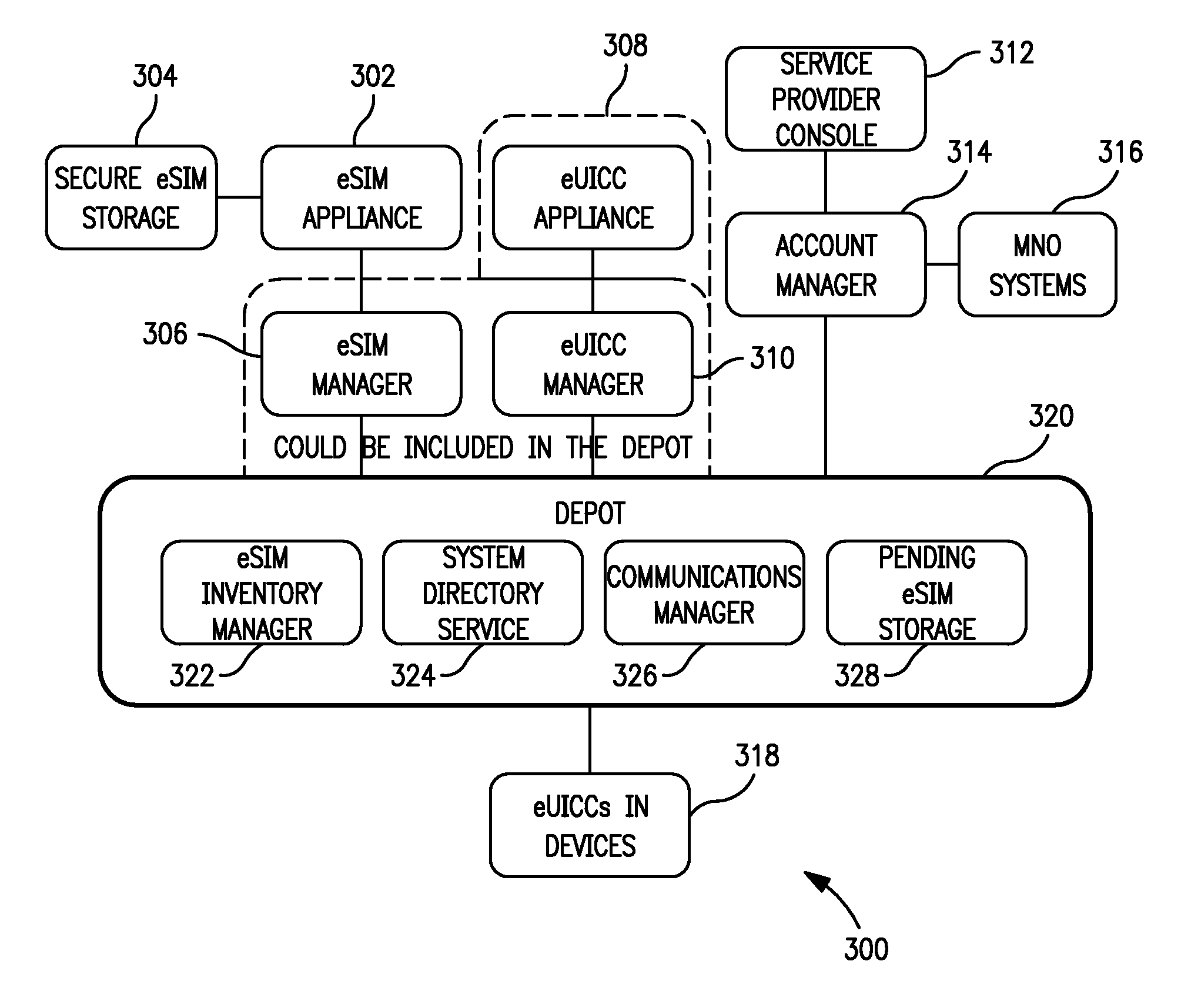
Electronic access client distribution apparatus and methods
ActiveUS20120331292A1Effective distributionEfficiently distributedDigital data processing detailsUser identity/authority verificationElectronic accessService provision
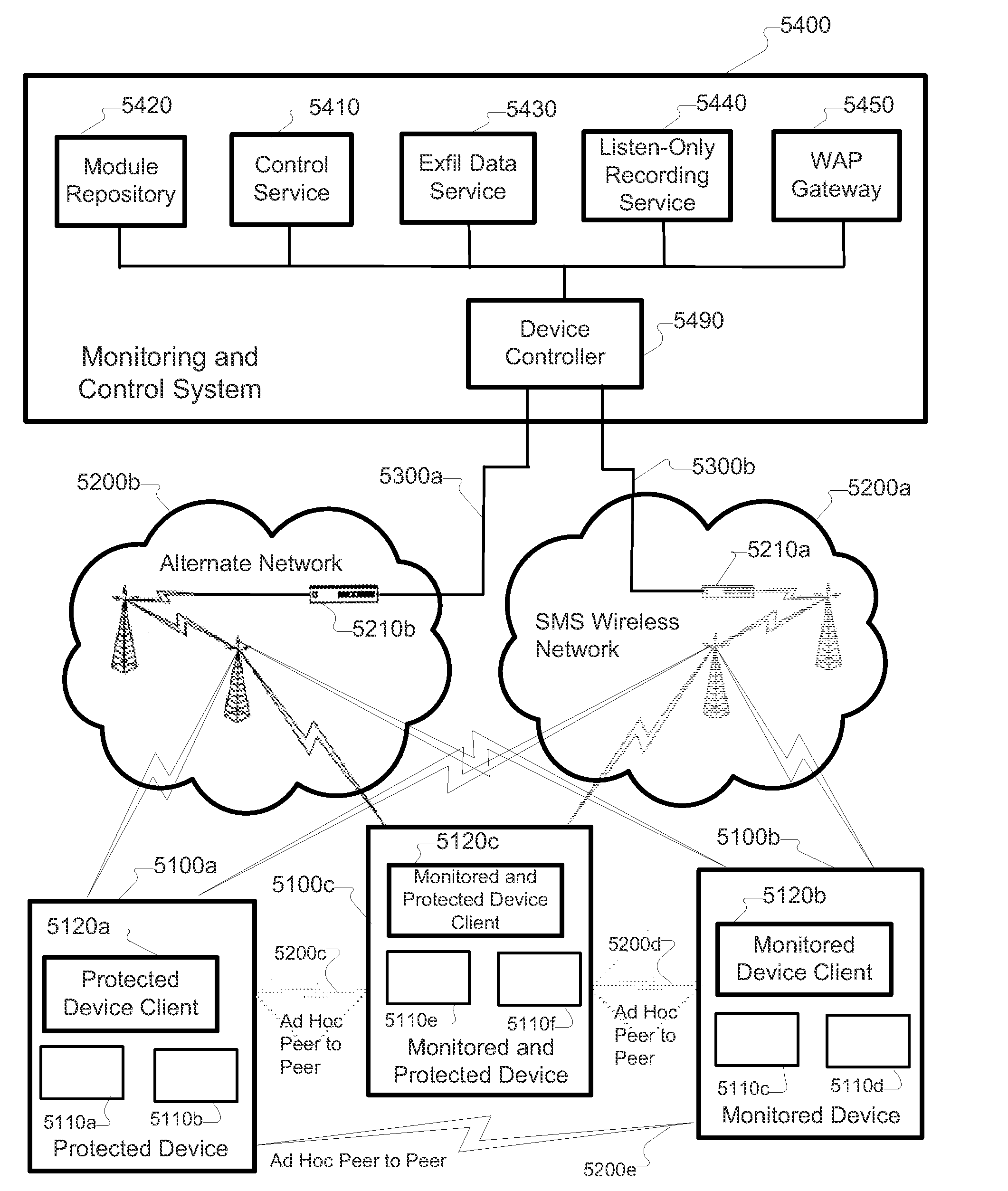
Apparatus and methods for distributing access control clients. In one exemplary embodiment, a network infrastructure is disclosed that enables delivery of electronic subscriber identity modules (eSIMs) to secure elements (e.g., electronic Universal Integrated Circuit Cards (eUICCs), etc.) The network architecture includes one or more of: (i) eSIM appliances, (ii) secure eSIM storages, (iii) eSIM managers, (iv) eUICC appliances, (v) eUICC managers, (vi) service provider consoles, (vii) account managers, (viii) Mobile Network Operator (MNO) systems, (ix) eUICCs that are local to one or more devices, and (x) depots. Moreover, each depot may include: (xi) eSIM inventory managers, (xii) system directory services, (xiii) communications managers, and / or (xiv) pending eSIM storages. Functions of the disclosed infrastructure can be flexibly partitioned and / or adapted such that individual parties can host portions of the infrastructure. Exemplary embodiments of the present invention can provide redundancy, thus ensuring maximal uptime for the overall network (or the portion thereof).
Owner:APPLE INC
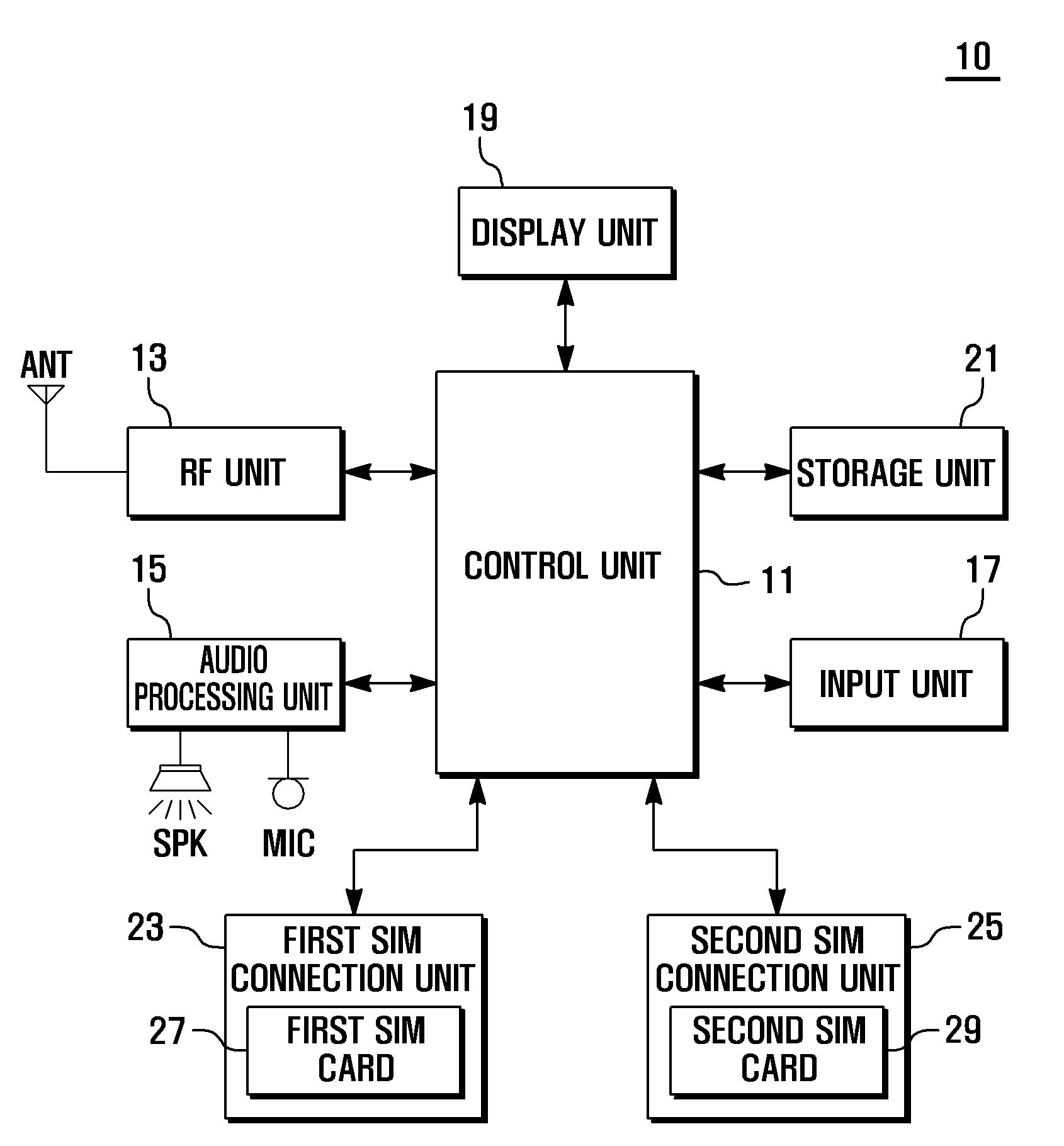
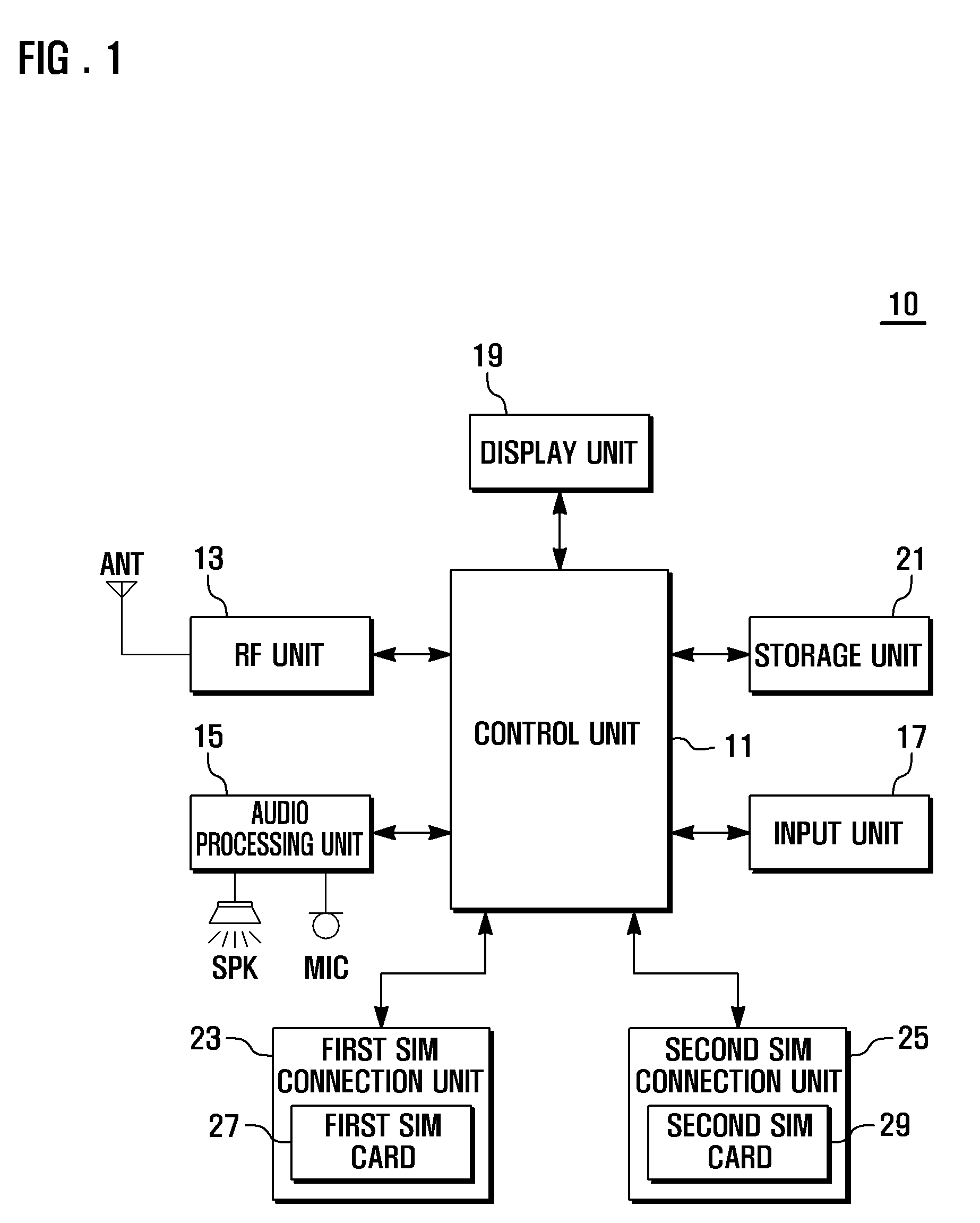
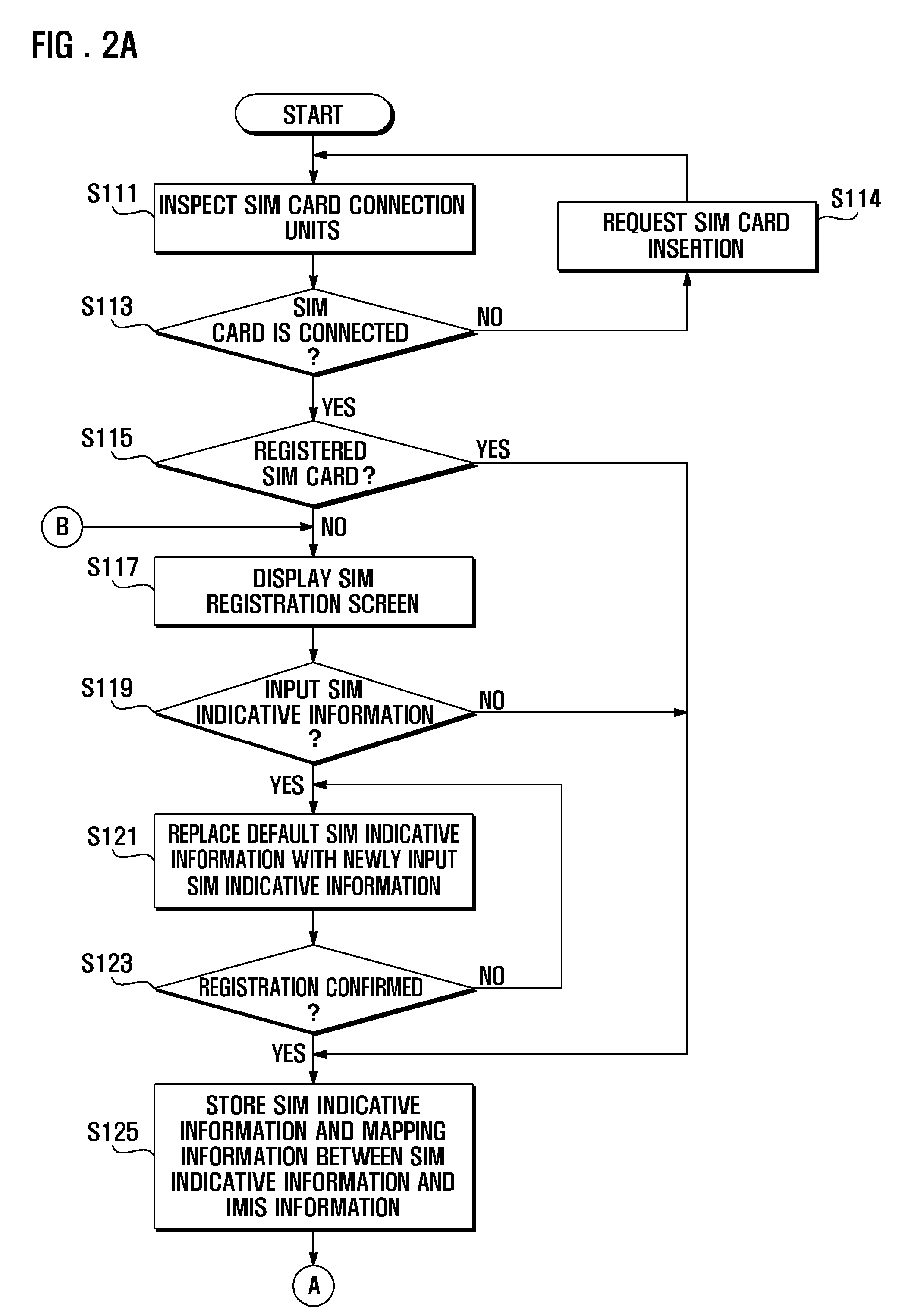
Mobile terminal and sim indicative information display method thereof
InactiveUS20090029736A1Improve usabilityTelephonic subscriber detailsSubstation equipmentSubscriber identity module
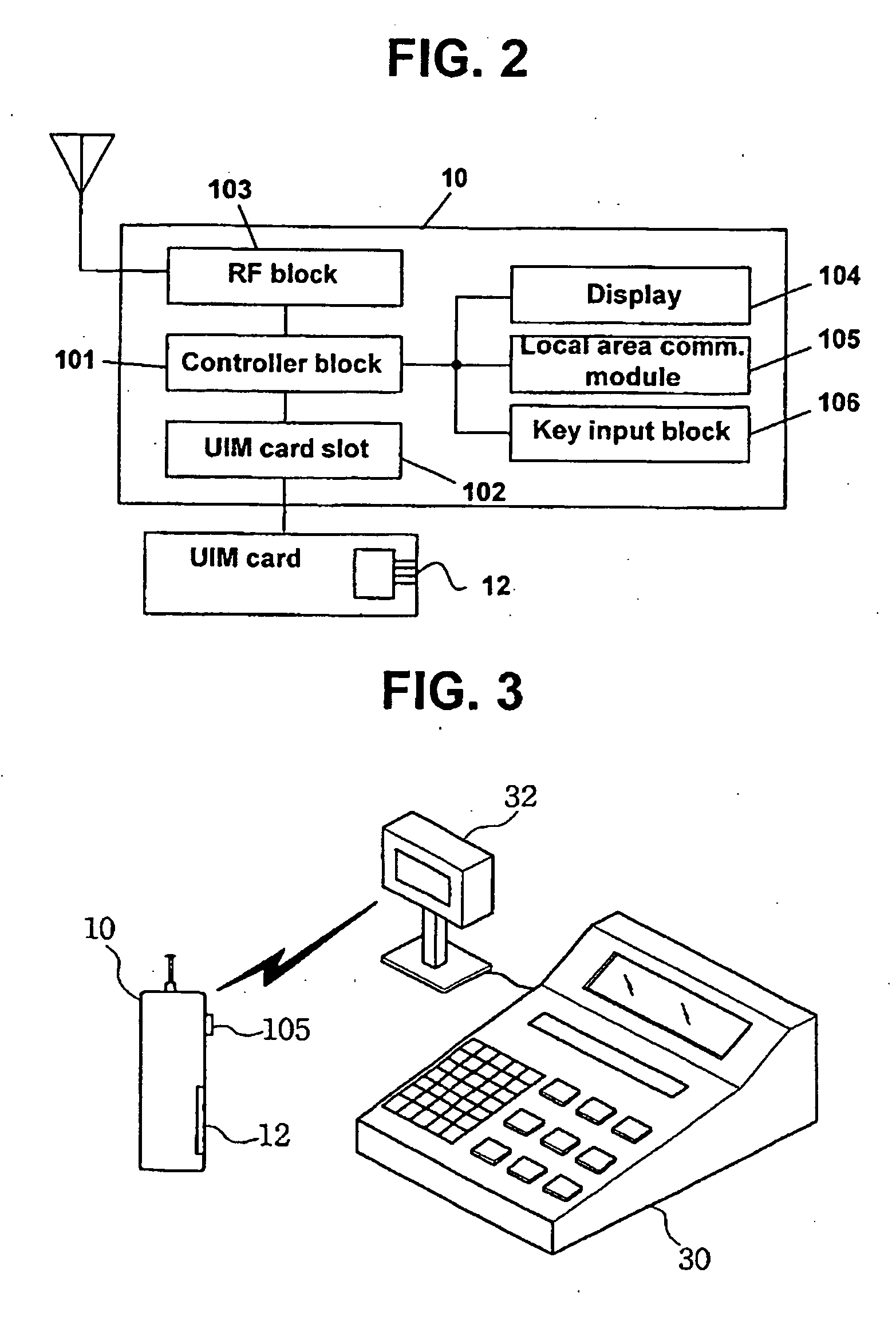
A subscriber identity module (SIM) indicative information display method of the present invention includes receiving SIM indicative information one of a SIM card detected in one of the SIM card slots, registering the SIM indicative information with a SIM identity of the SIM card, detecting a SIM indicative information request requesting the SIM indicative information of the SIM card, and displaying the SIM indicative information mapped to the SIM identity of the SIM card when a SIM indicative information request is detected.
Owner:SAMSUNG ELECTRONICS CO LTD
Management systems for multiple access control entities
ActiveUS20120108204A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsUser deviceFlight management system
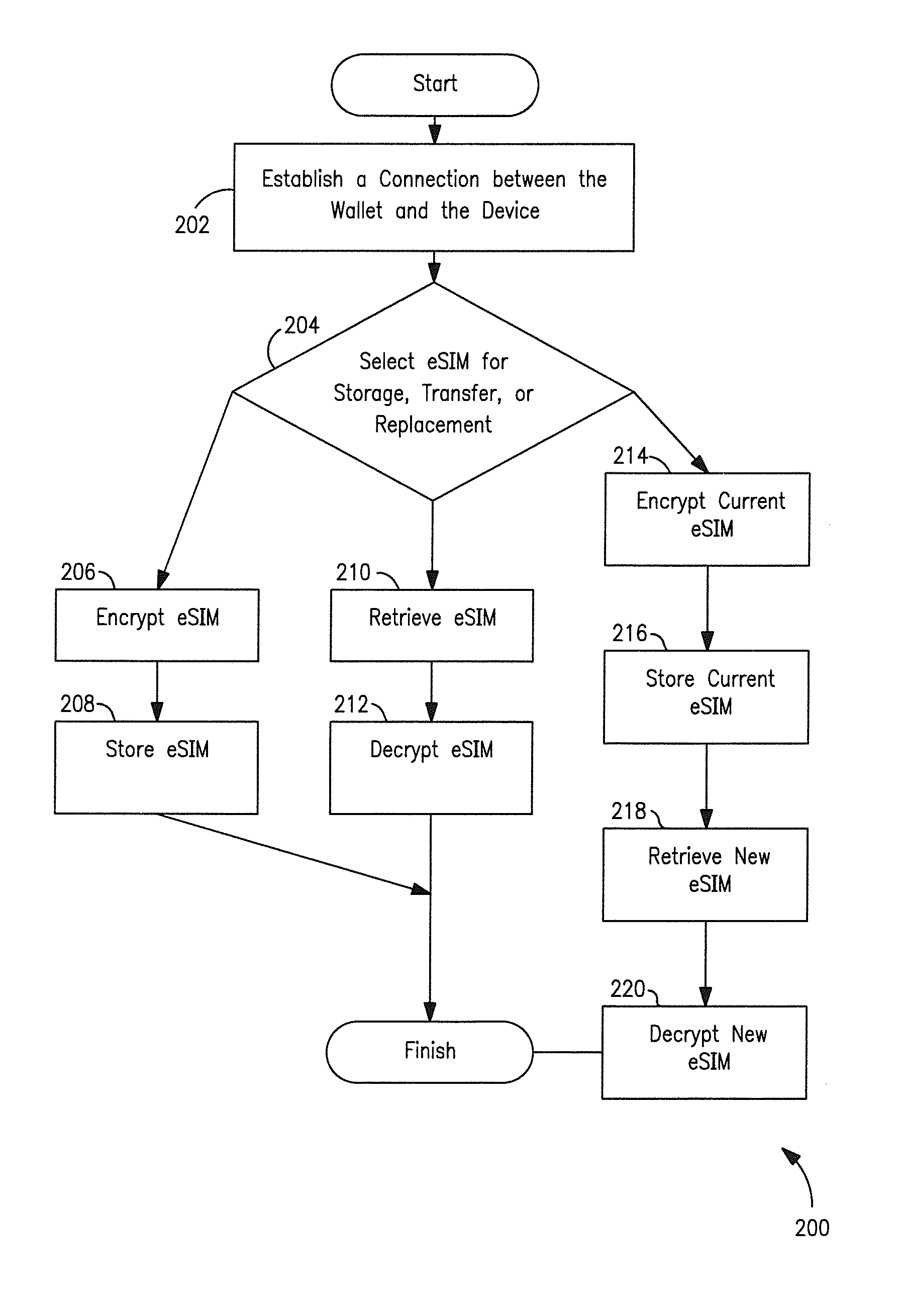
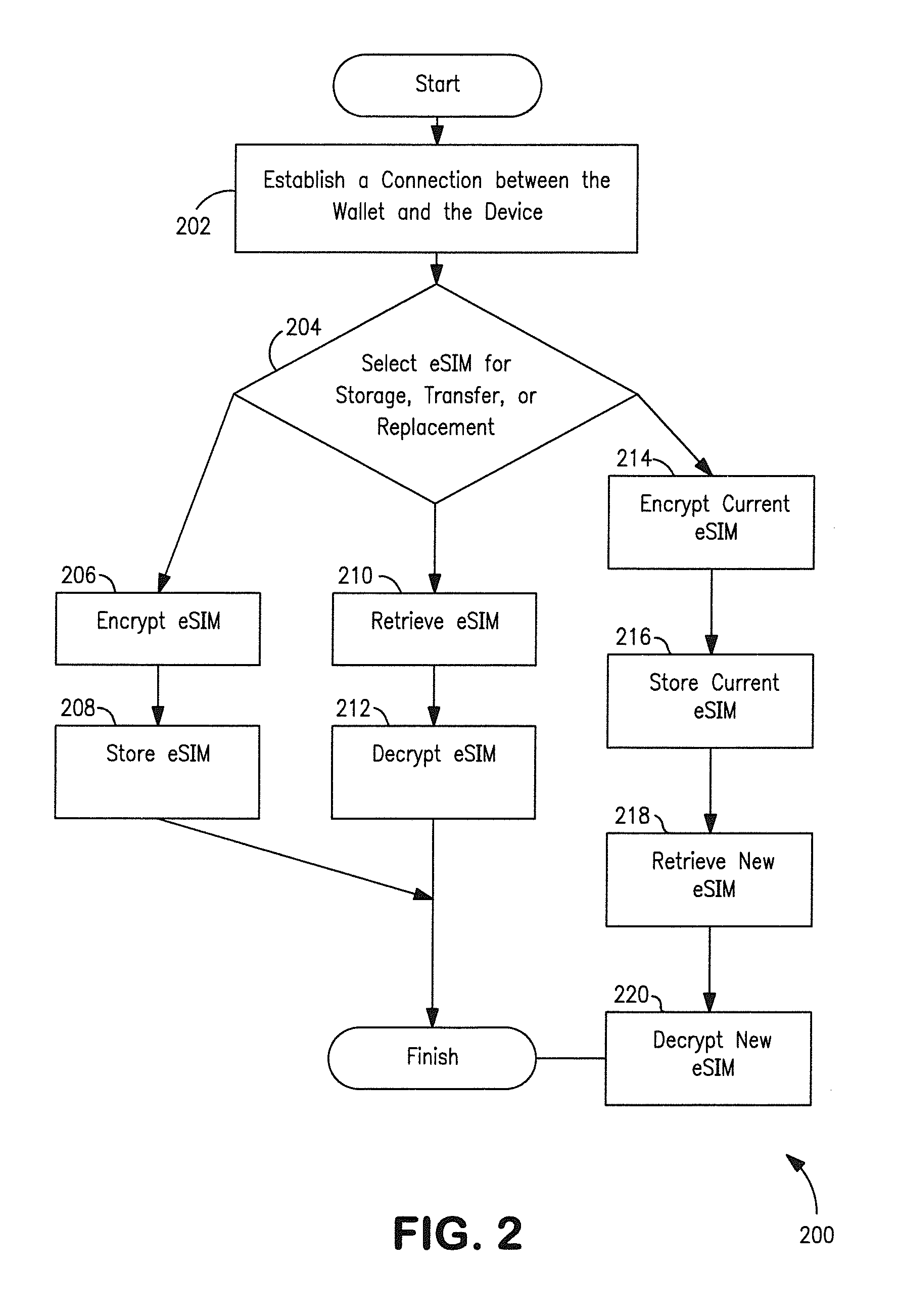
Methods and apparatus for managing multiple user access control entities or clients. For example, in one embodiment, a “wallet” of electronic subscriber identity modules (eSIMs) may be stored and used at a user device and / or distributed to other devices for use thereon. In another embodiment, a networked server may store and distribute eSIM to a plurality of user devices in communication therewith. A database of available eSIM is maintained at the wallet entity and / or at the network which enables request for a particular eSIM to be processed and various rules for the distribution thereof to be implemented. Security precautions are implemented to protect both user and network carrier specific data as the data is transmitted between networked entities. Solutions for eSIM backup and restoration are also described.
Owner:APPLE INC
Methods and apparatus for access control client assisted roaming
InactiveUS20120108206A1Expand coverageUnauthorised/fraudulent call preventionAssess restrictionCost effectivenessCode division multiple access
Methods and apparatus that allow a device to migrate wireless service across multiple wireless networks. In one exemplary embodiment, the present invention enables storing and switching between multiple Electronic Subscriber Identity Modules (eSIM), where each eSIM is specific to a different carrier network. By loading the appropriate eSIM, the user device can authenticate itself with the selected carrier, rather than roaming. During roaming operation, the user equipment can load one or more of the previously stored eSIMs. Selection of the eSIM can be done manually by the user or can be driven by the user equipment based on desired context; for example, based on carrier signal strength, cost-effectiveness, etc. Support for multiple radio technologies also allows universal connectivity for wireless devices, even spanning previously incompatible technologies such as GSM (Global Standard for Mobile Communications), CDMA (Code Division Multiple Access), etc.
Owner:APPLE INC
Policy-based techniques for managing access control
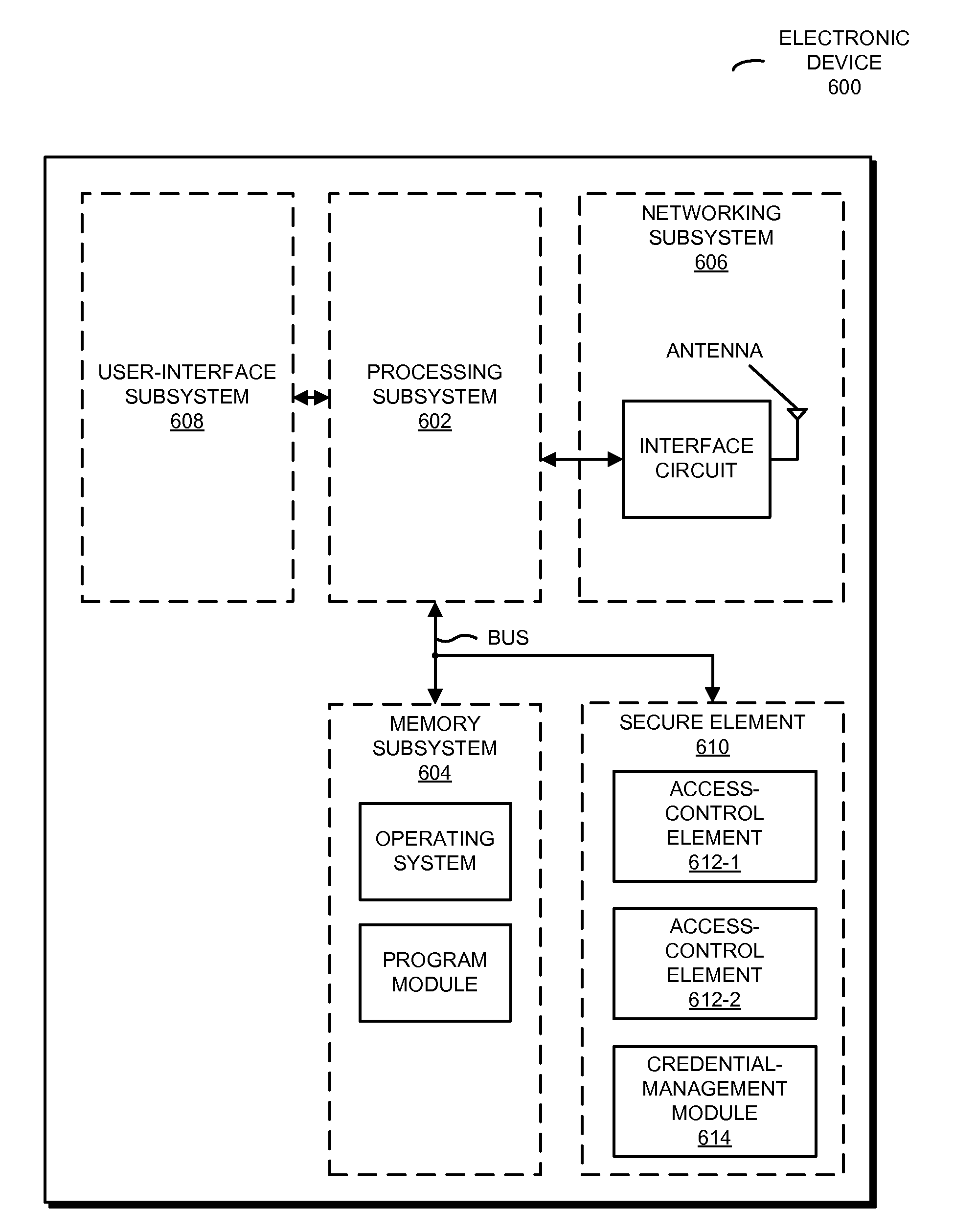
ActiveUS20140143826A1Facilitates secure communicationFacilitates privilegeDigital data protectionTransmissionCryptographic protocolMedia access control
A policy-based framework is described. This policy-based framework may be used to specify the privileges for logical entities to perform operations associated with an access-control element (such as an electronic Subscriber Identity Module) located within a secure element in an electronic device. Note that different logical entities may have different privileges for different operations associated with the same or different access-control elements. Moreover, the policy-based framework may specify types of credentials that are used by the logical entities during authentication, so that different types of credentials may be used for different operations and / or by different logical entities. Furthermore, the policy-based framework may specify the security protocols and security levels that are used by the logical entities during authentication, so that different security protocols and security levels may be used for different operations and / or by different logical entities.
Owner:APPLE INC
Procedure for the control of applications stored in a subscriber identity module
InactiveUS6711262B1Easy to implementHigh level of data securityKey distribution for secure communicationEavesdropping prevention circuitsCommunications systemComputer module
A procedure for the control of applications stored in a user's subscriber identity module (SIM) in a data communication system that includes a data communication network, a terminal device connected to the data communication network and to which the subscriber identity module is connected, and an application control server that is connected to the data communication network. The subscriber identity module contains a stored application that makes use of the data communication network and that is used by way of the terminal device. A key list comprising one or more application-specific keys is stored in the user's subscriber identity module, and a corresponding key list is also stored in the application control server which is operable to control applications stored in the subscriber identity modules of multiple users of the network. The application stored in the user's subscriber identity module is activated and / or closed through the transmission, verification and use of keys stored in the key lists at the subscriber identity module and at the application control server.
Owner:SONERA SMARTTRUST LTD
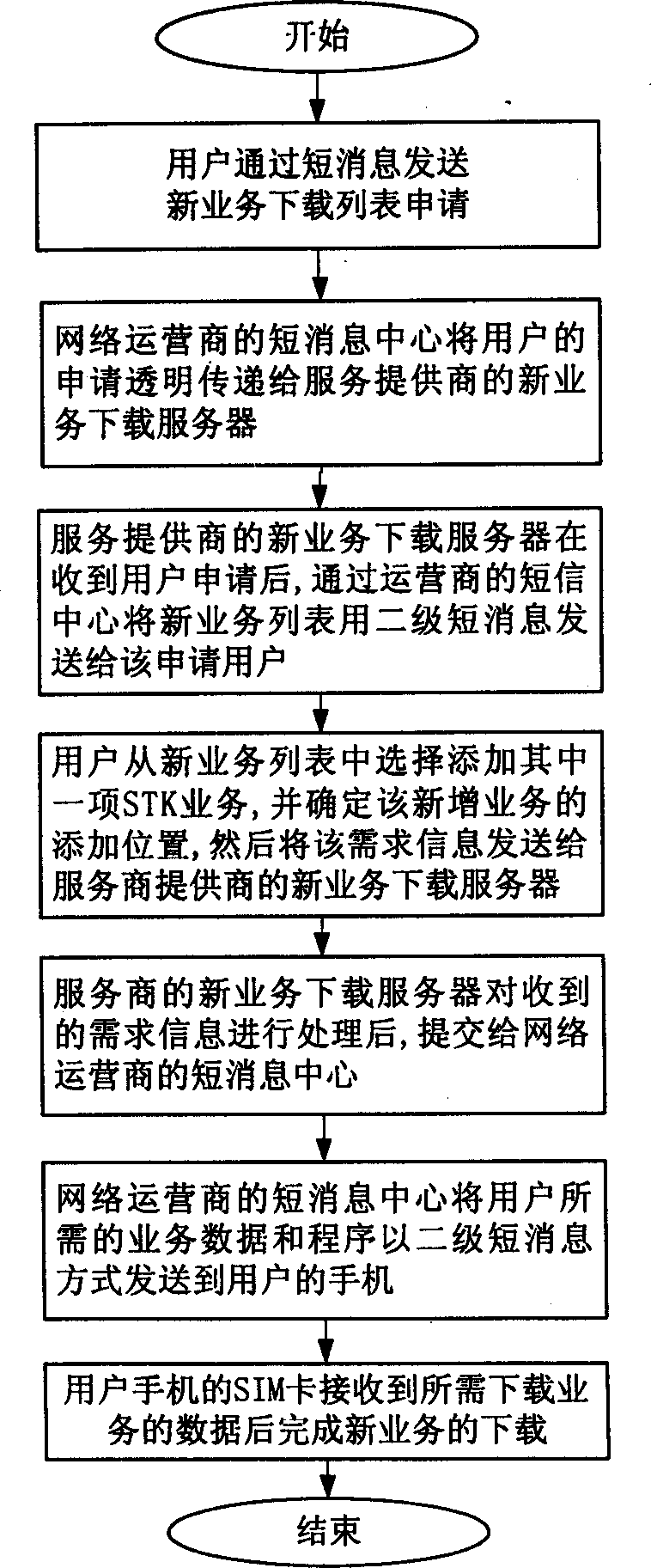
Air download method of increment business of user identifying module
InactiveCN1345154ALow costSolve limited capacityUnauthorised/fraudulent call preventionSpecial service for subscribersApplication softwareSubscriber identity module
The invnetion discloses a method used to download on-air a value added service to subscriber identification module (SIM) in digital mobile phone. The STK and application program is directly downloaded to subscriber's SIM card by using CLASS 2 SIM-specific message format. The STK menu data is provided for SIM card to add new service, and the application program is used for realizing STK application. The invented method takes full advantage of existing software and hardware facility, making user apply for new service without need to replace STK card, also without need going to appointed business hall.
Owner:DATANG MICROELECTRONICS TECH CO LTD
Methods and apparatus for managing data within a secure element
ActiveUS20140073375A1Satisfies needService provisioningSubstation equipmentComputer moduleApplication software
Apparatus and methods for managing and sharing data across multiple access control clients in devices. In one embodiment, the access control clients comprise electronic Subscriber Identity Modules (eSIMs) disposed on a embedded Universal Integrated Circuit Card (eUICC). Each eSIM contains its own data. An Advanced Subscriber Identity Toolkit application maintained within the eUICC facilitates managing and sharing multiple eSIMs' data for various purposes such as sharing phonebook contacts or facilitating automatic switch-over between the multiple eSIMs (such as based on user context).
Owner:APPLE INC
Methods and apparatus for delivering electronic identification components over a wireless network
ActiveUS20120108207A1Satisfies needService provisioningUnauthorised/fraudulent call preventionKey exchangeOperational system
Methods and apparatus enabling programming of electronic identification information of a wireless apparatus. In one embodiment, a previously purchased or deployed wireless apparatus is activated by a cellular network. The wireless apparatus connects to the cellular network using an access module to download operating system components and / or access control client components. The described methods and apparatus enable updates, additions and replacement of various components including Electronic Subscriber Identity Module (eSIM) data, OS components. One exemplary implementation of the invention utilizes a trusted key exchange between the device and the cellular network to maintain security.
Owner:APPLE INC
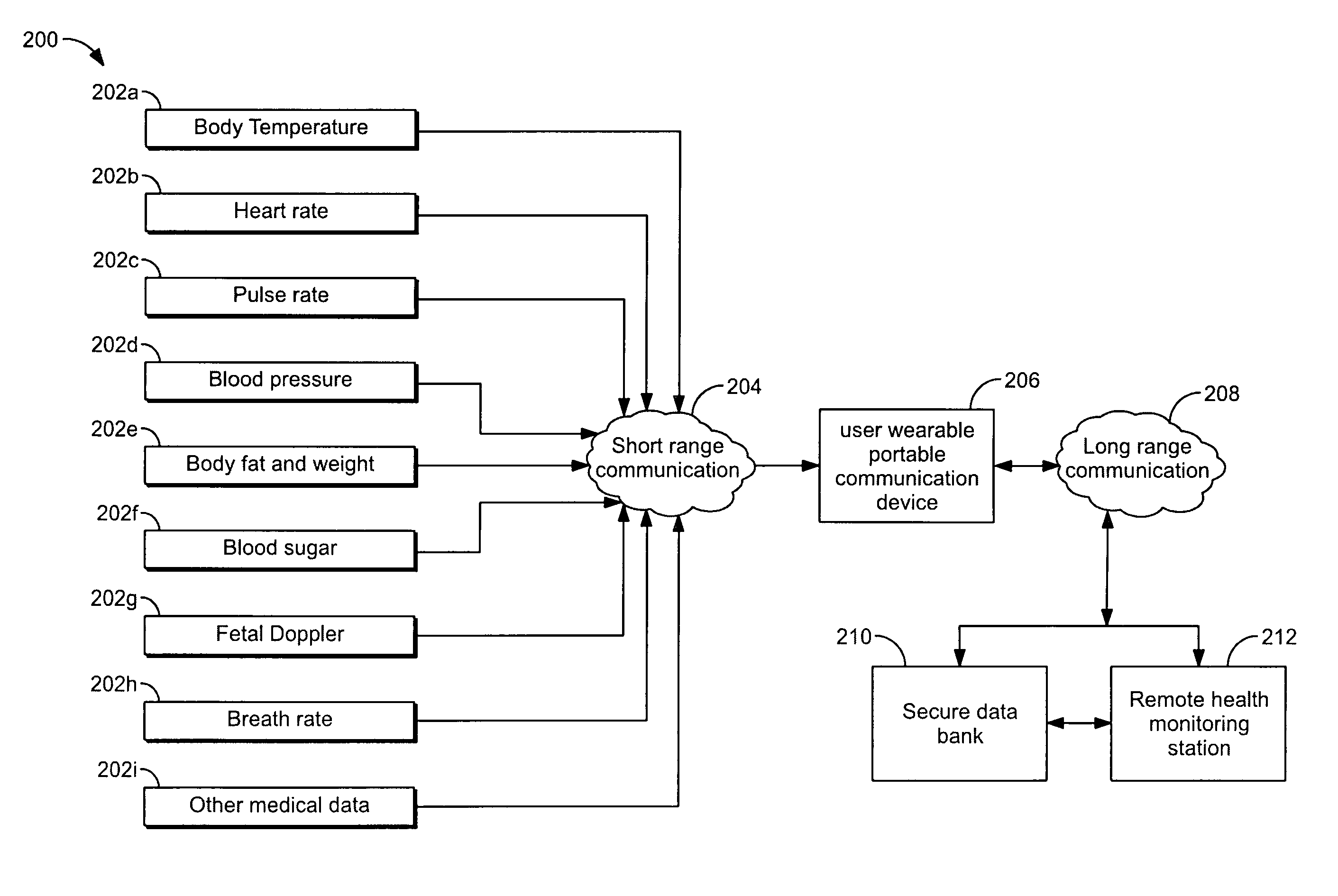
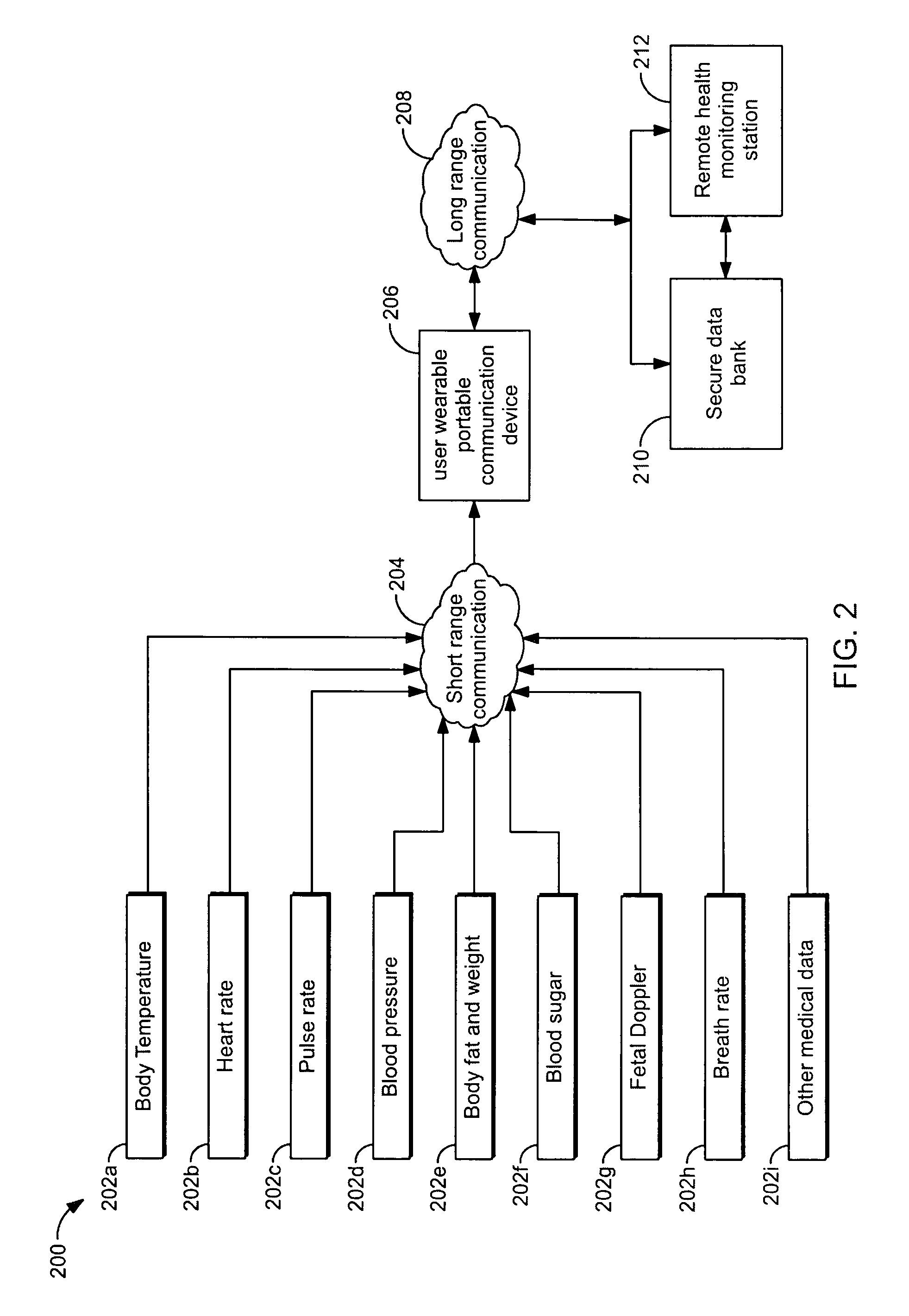
User wearable portable communication device for collection and transmission of physiological data
ActiveUS8568313B2Easy to operateFacilitate communicationUltrasonic/sonic/infrasonic diagnosticsMechanical apparatusFall detectionData collecting
A user wearable portable communication device and a method for collecting and transmitting a plurality of physiological parameters to a remote monitoring center are disclosed. The portable communication device includes a provision for enabling the user to establish a video conference, a fall detection module in conjunction with an accelerometer recognizes a placement of the portable communication device, a home automation module for enabling the user to remotely operate multiple electronic devices, an acknowledgment acceptance module for receiving the acknowledgment, a physiological data collecting module communicatively coupled to a fetal doppler module for monitoring and transmitting the physiological parameters associated with a child, multiple preprogrammed contact numbers for enabling the user to establish a communication, a subscriber identity module for enabling the user establish a communication and data transmission between the portable communication device and the remote monitoring center.
Owner:SADHU RAJENDRA PADMA
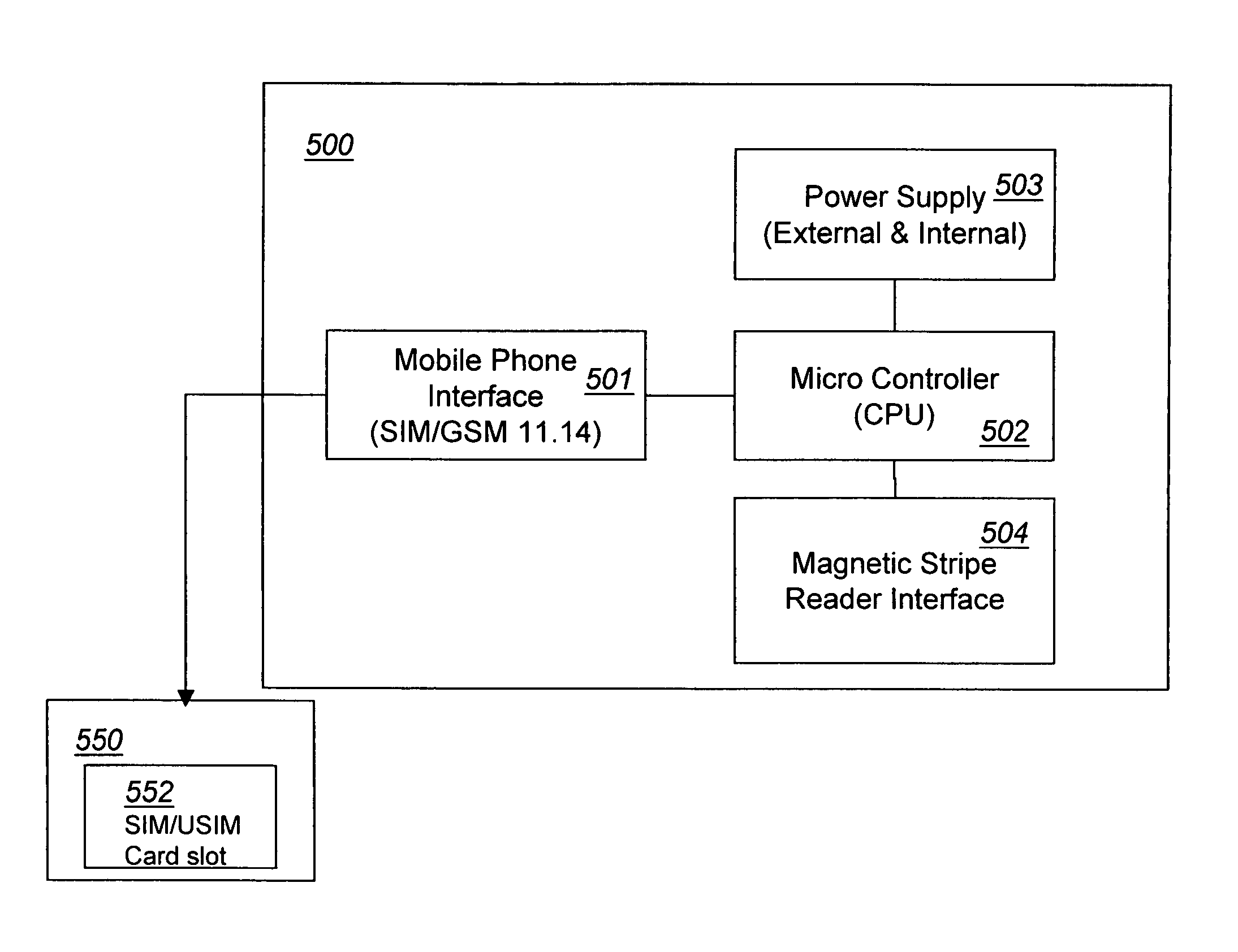
Mobile communication device equipped with a magnetic stripe reader
InactiveUS7336973B2Credit registering devices actuationAccounting/billing servicesElectricityComputer module
A wireless mobile device is adapted to access a wireless network and includes a subscriber identification module (SIM) card slot and a magnetic stripe reader module electrically connected to the SIM card slot and thereby to the wireless mobile phone. The magnetic stripe reader module is adapted to receive and read information stored in a magnetic stripe and transmit this information to an entity through the wireless mobile device and the wireless network. The wireless mobile device of this invention is used to conduct financial transactions using a payment card comprising a magnetic stripe. The financial transactions include face-to-face or remote purchases and payment with the payment card through a financial institution.
Owner:VERIFONE INC
Devices with multiple subscriptions that utilize a single baseband-radio frequency resource chain
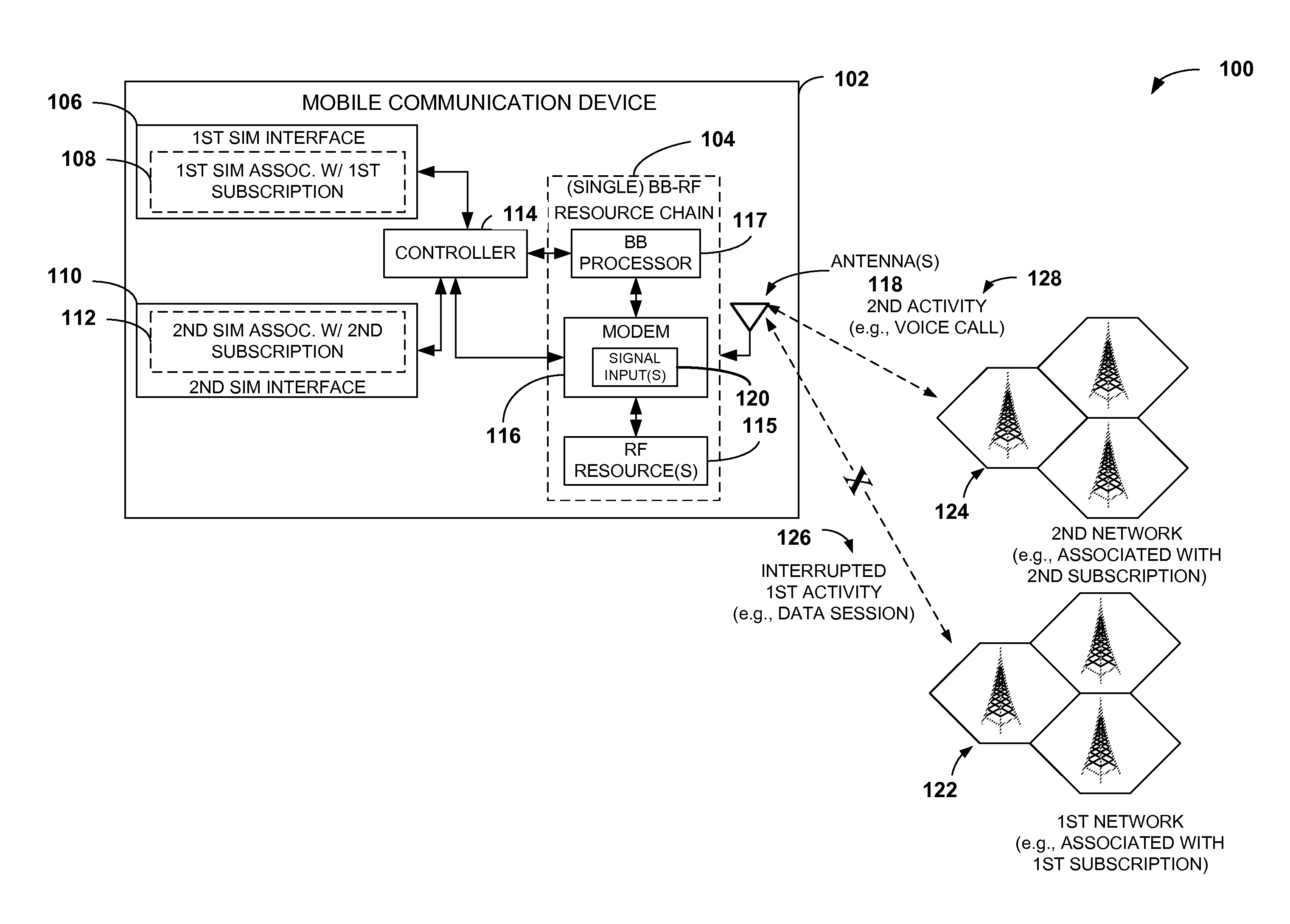
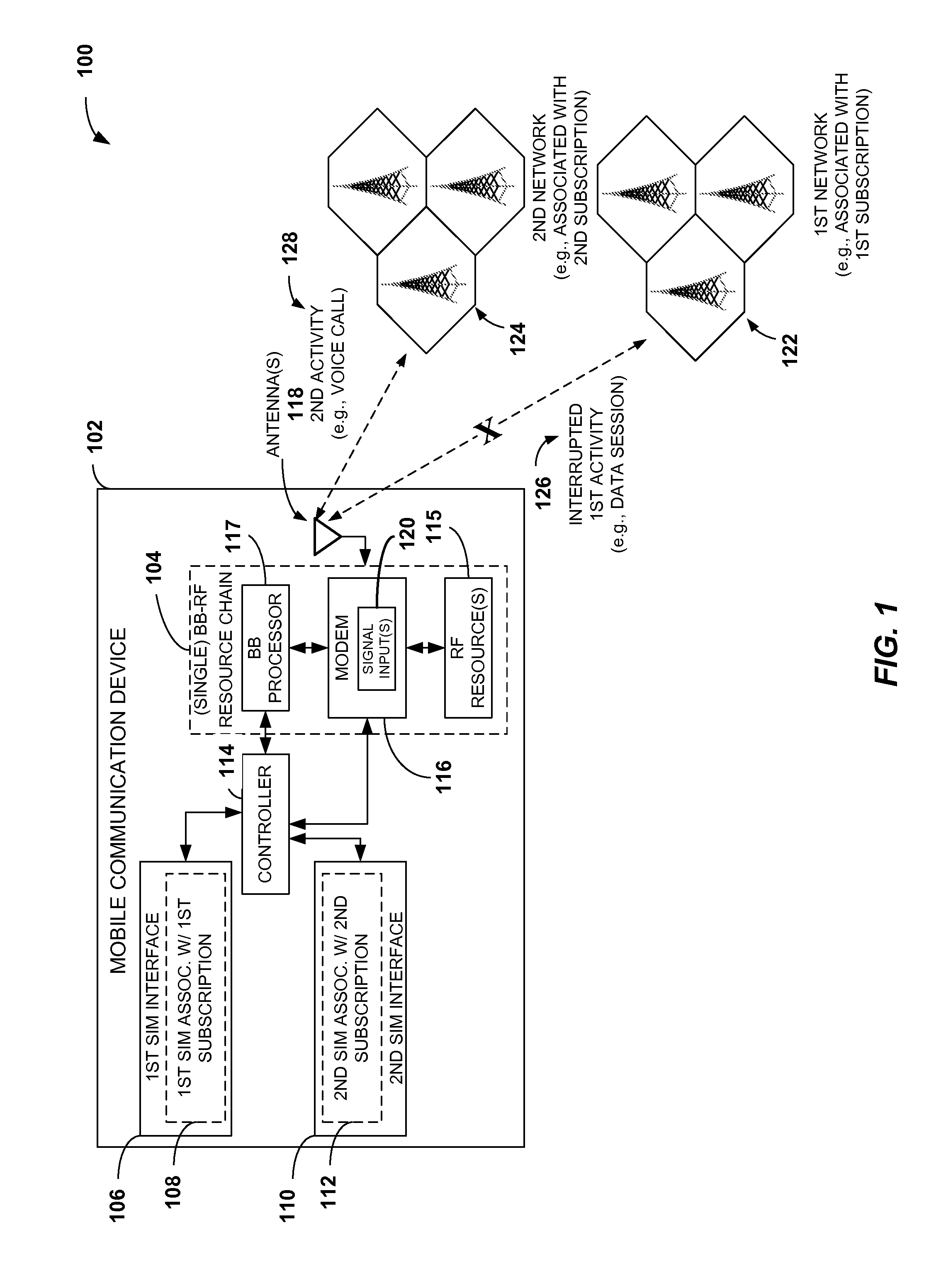
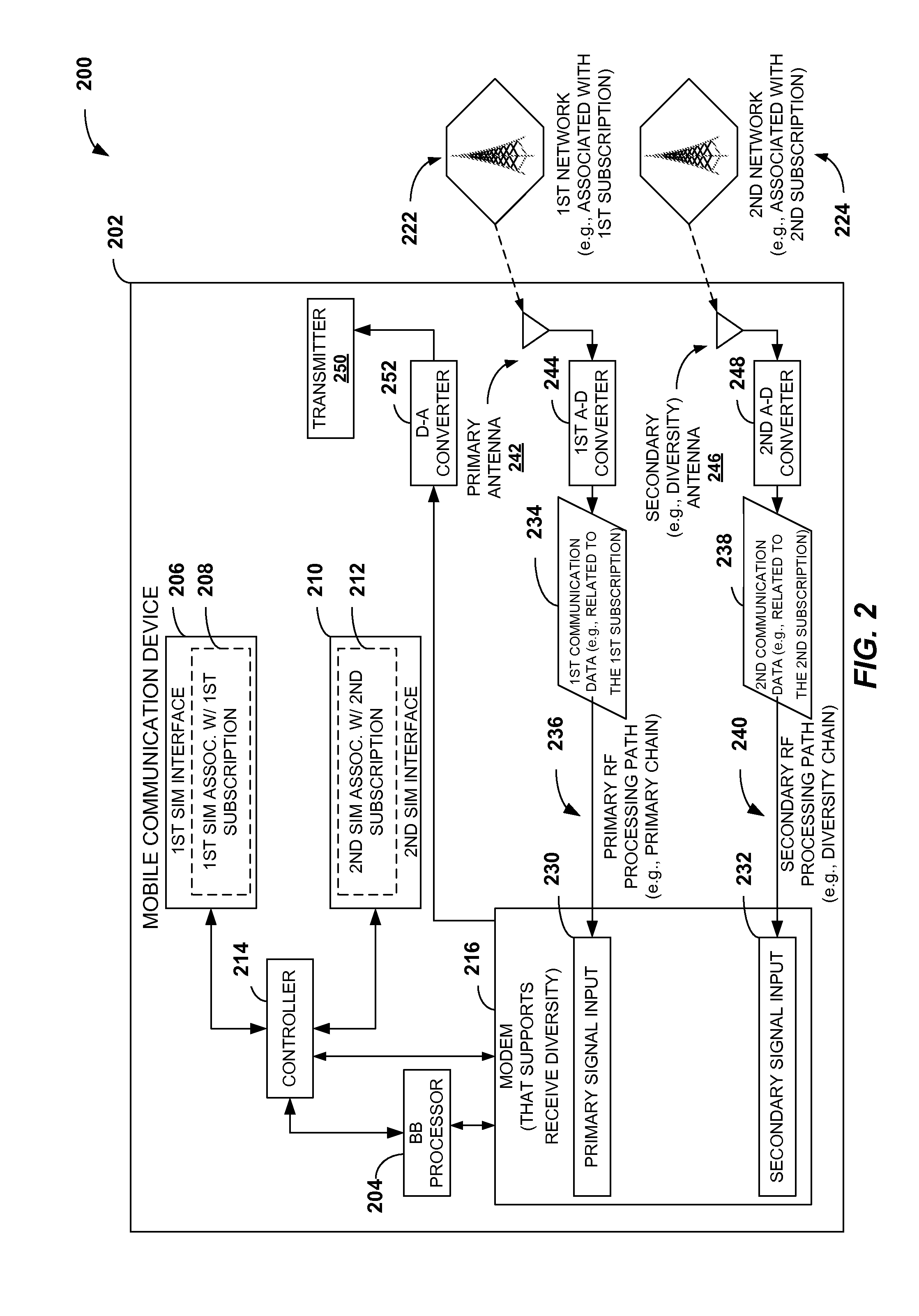
InactiveUS20110217969A1Improve performanceConnection managementWireless commuication servicesRadio frequencySubscriber identity module
A mobile communication device with multiple subscriptions includes a single baseband-radio frequency (BB-RF) resource chain. A first identity module, such as a subscriber identity module (SIM), a second identity module (e.g., a second SIM), and a controller are communicatively coupled to the single BB-RF resource chain. The first identity module is associated with a first subscription, and the second identity module is associated with a second subscription. The controller may be configured to arbitrate access to the single BB-RF resource chain to perform a first activity that corresponds to the first subscription or a second activity that corresponds to the second subscription. For example, the controller may interrupt a data session processed by the single BB-RF resource chain in response to receiving information indicating that a voice call is to be processed by the single BB-RF resource chain.
Owner:QUALCOMM INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com