Patents
Literature
290 results about "Safety Connect" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
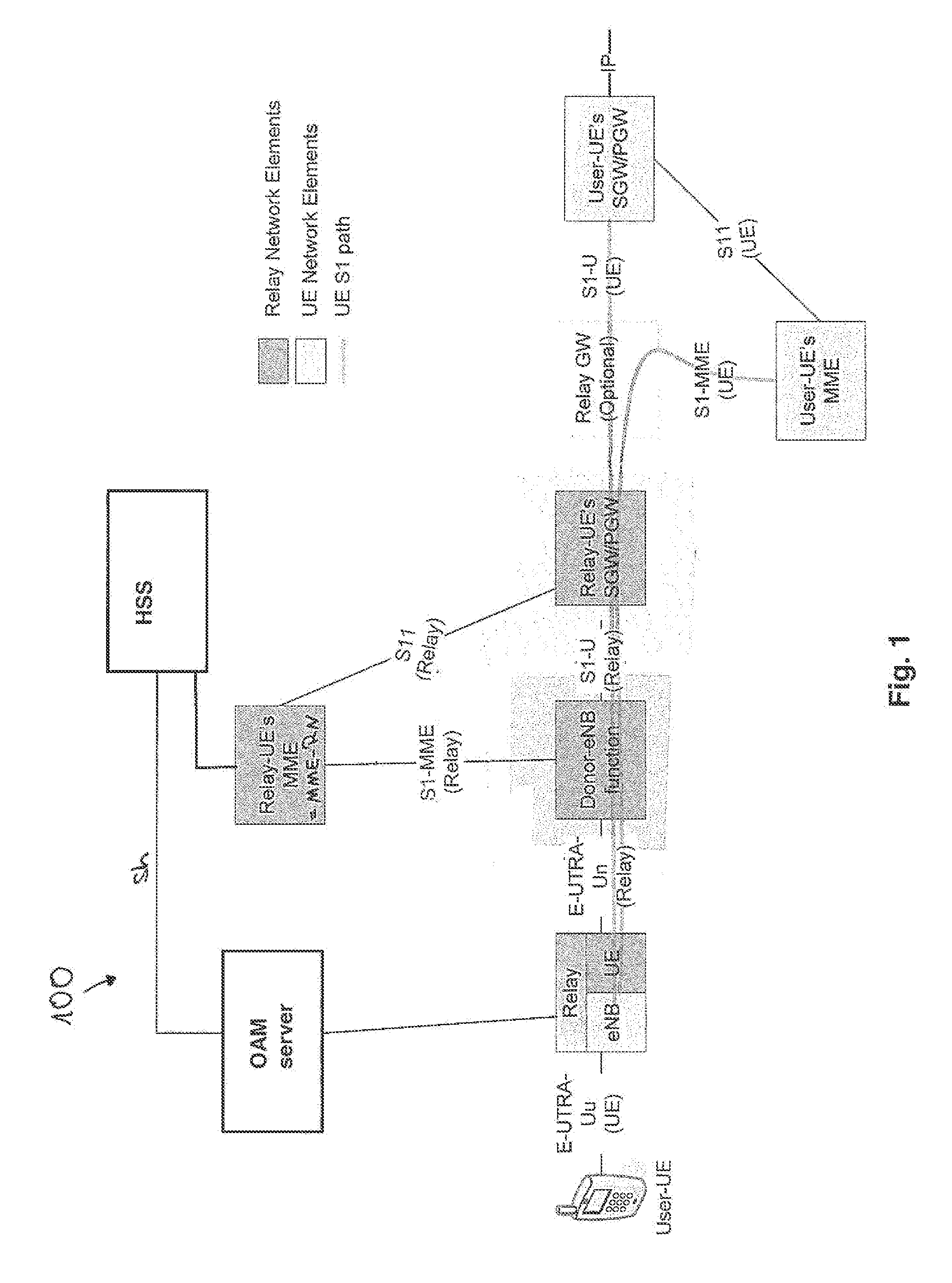
Safety Connect is a subscription-based telematics system introduced by Toyota Motor Corporation in 2009 for its Toyota-branded and Lexus models. The system provides communications, roadside assistance, car safety, remote diagnostics, and other services. Unlike the earlier Lexus Link service offered on Lexus models, the Safety Connect system is proprietary and not licensed from GM's OnStar service. Safety Connect began to be offered on vehicles in the middle of 2009. For Toyota vehicles, the Safety Connect service is offered including the aforementioned features as part of the Toyota Entune telematics package, while Lexus models receive the Lexus Enform telematics system with Safety Connect, adding hands free calling, and destination assistance services.
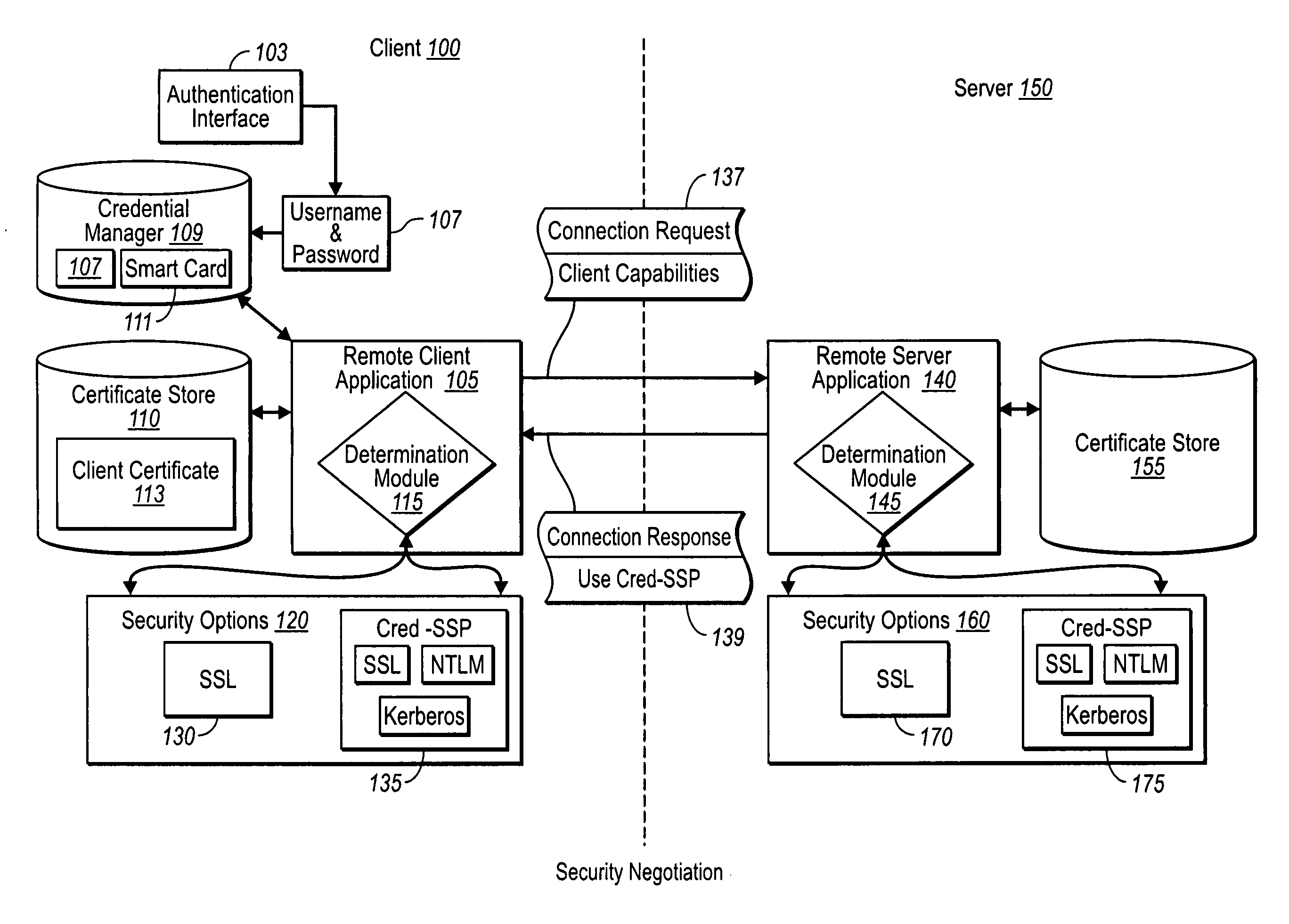
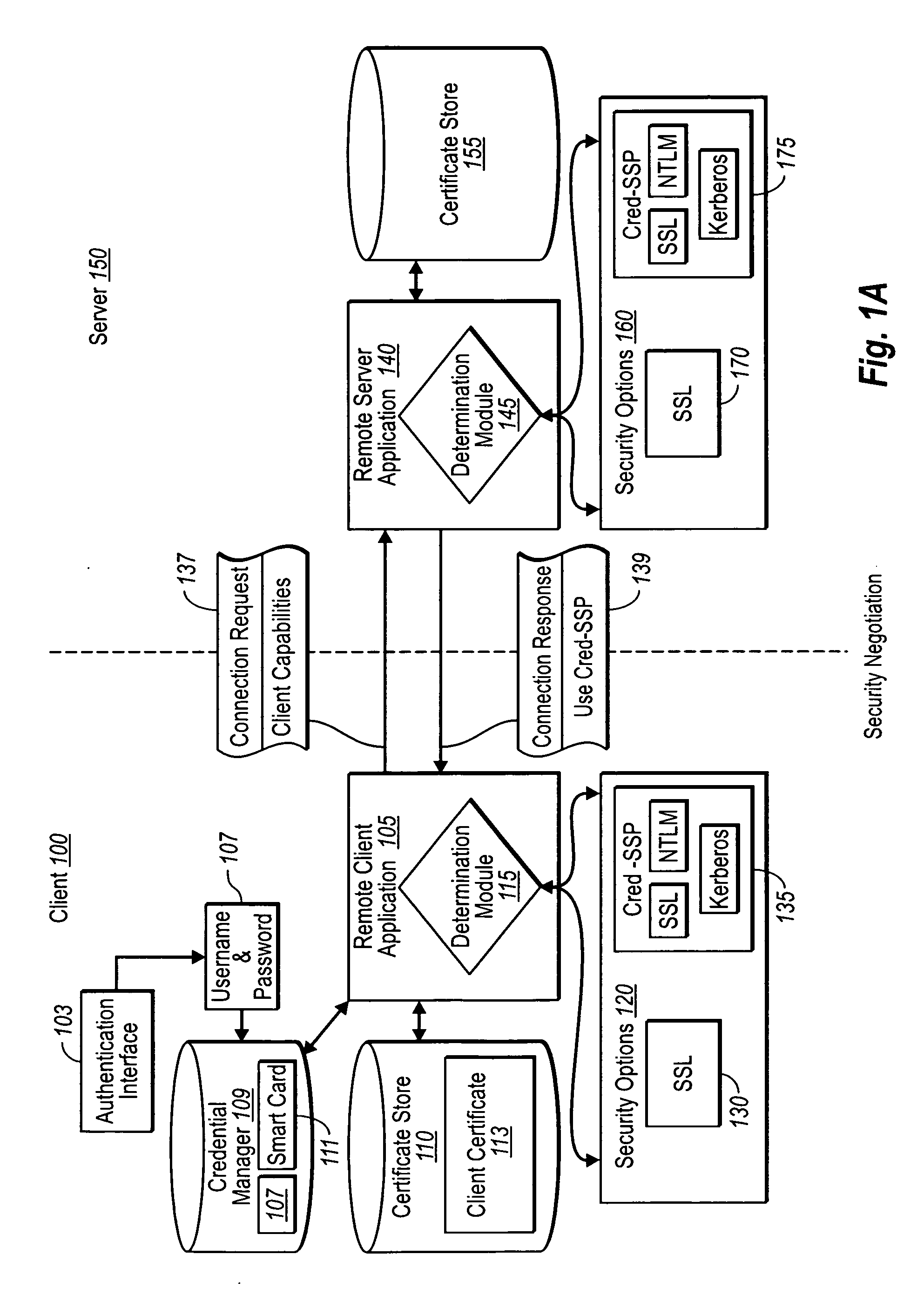
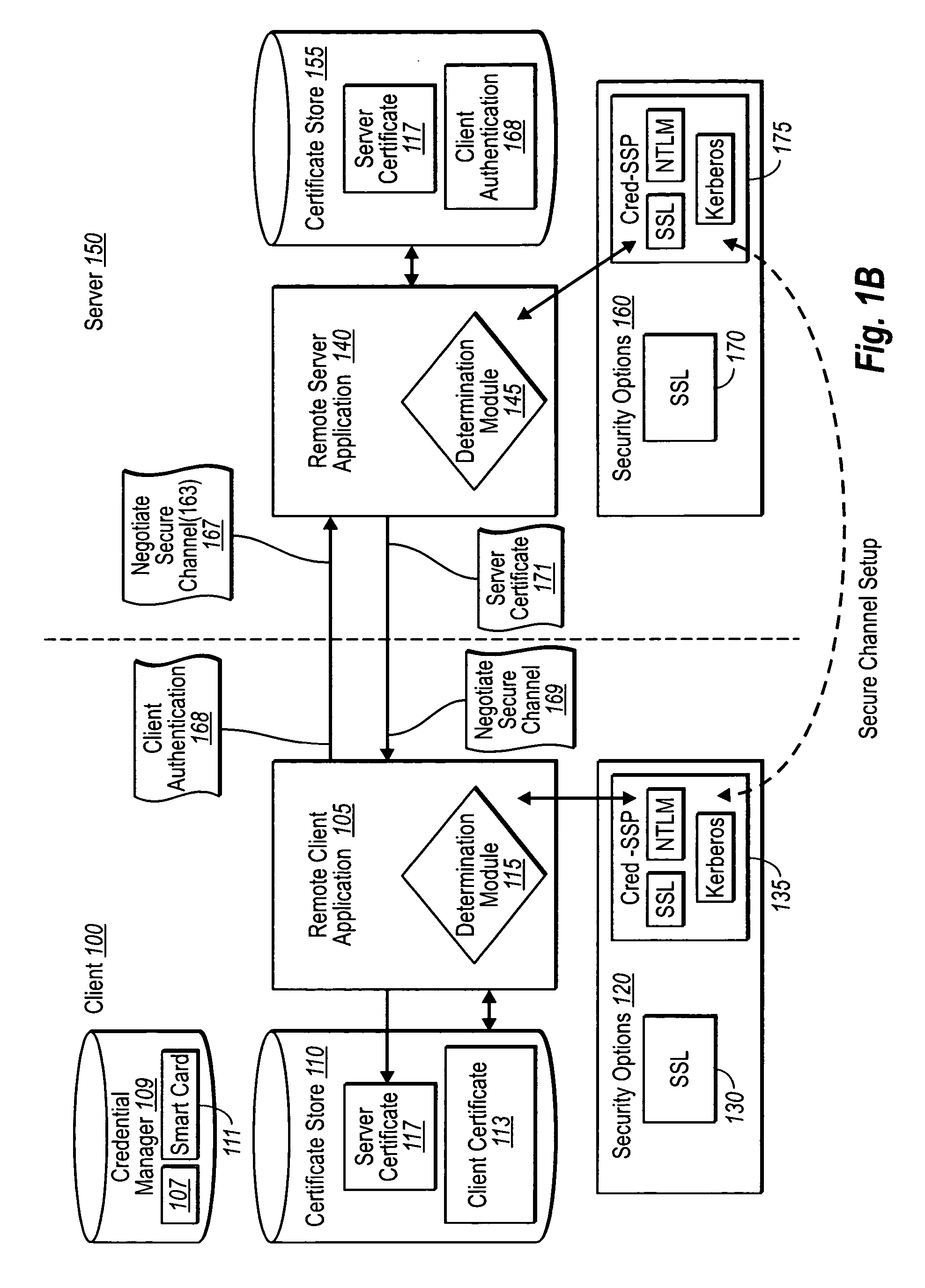
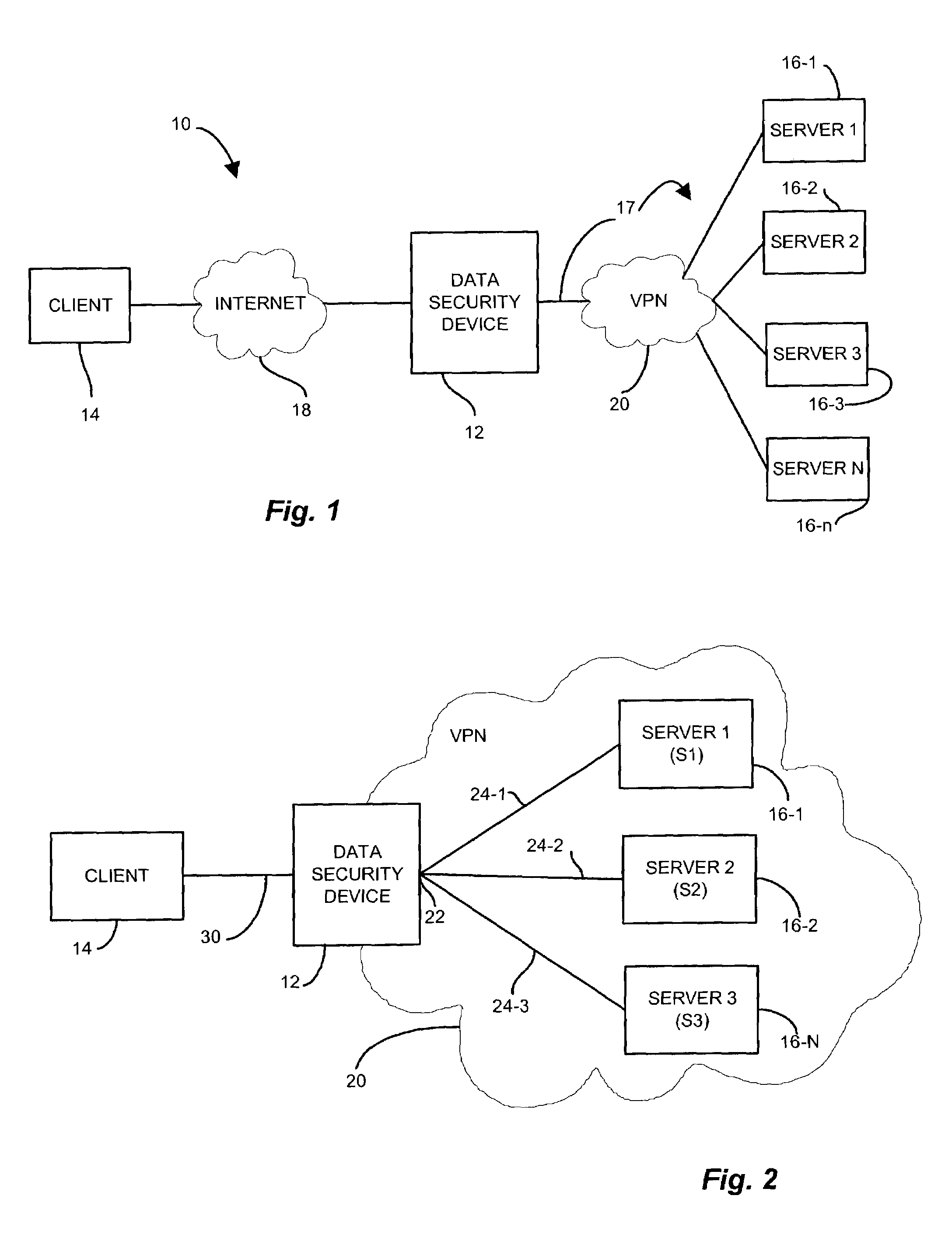
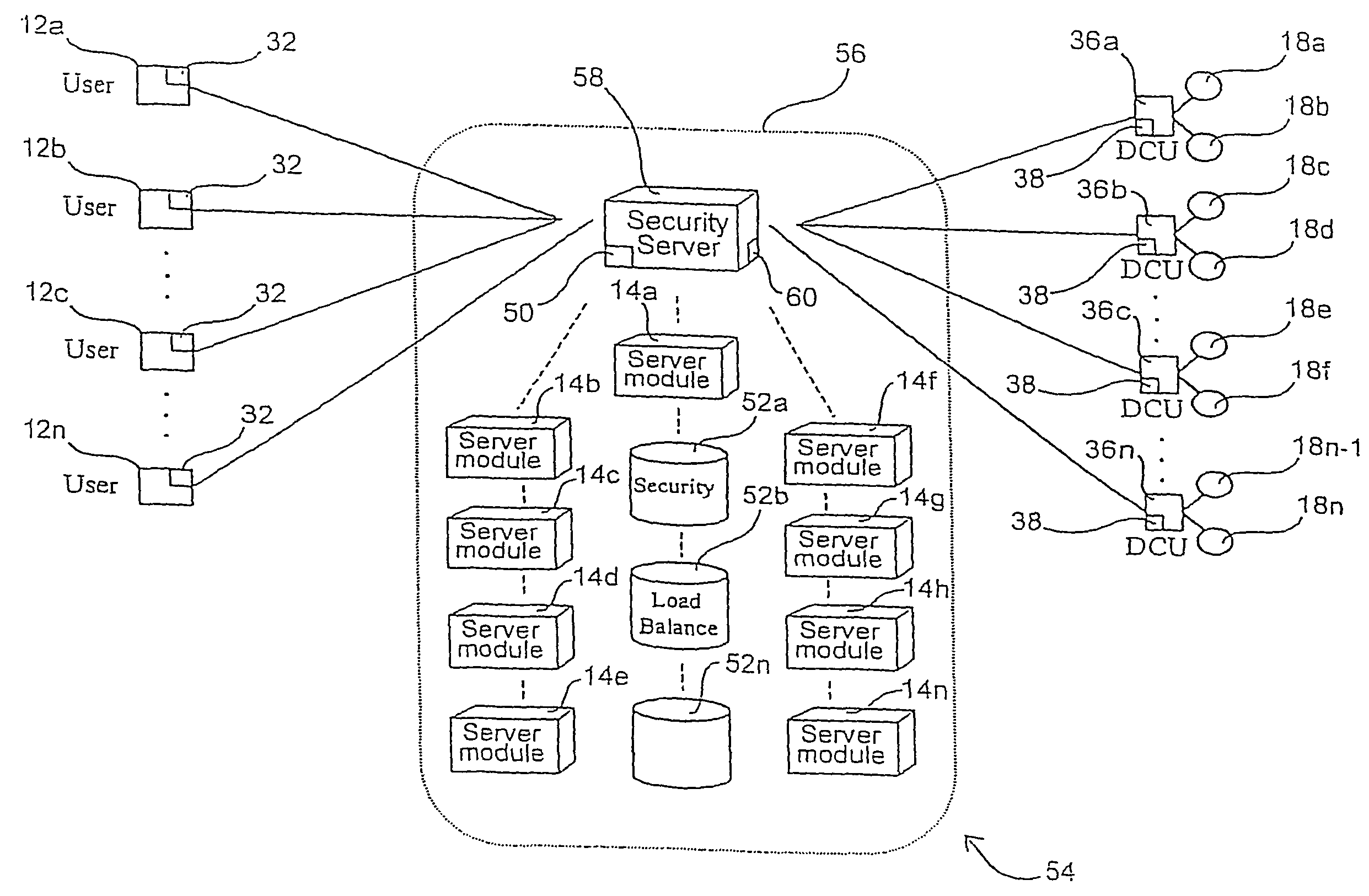
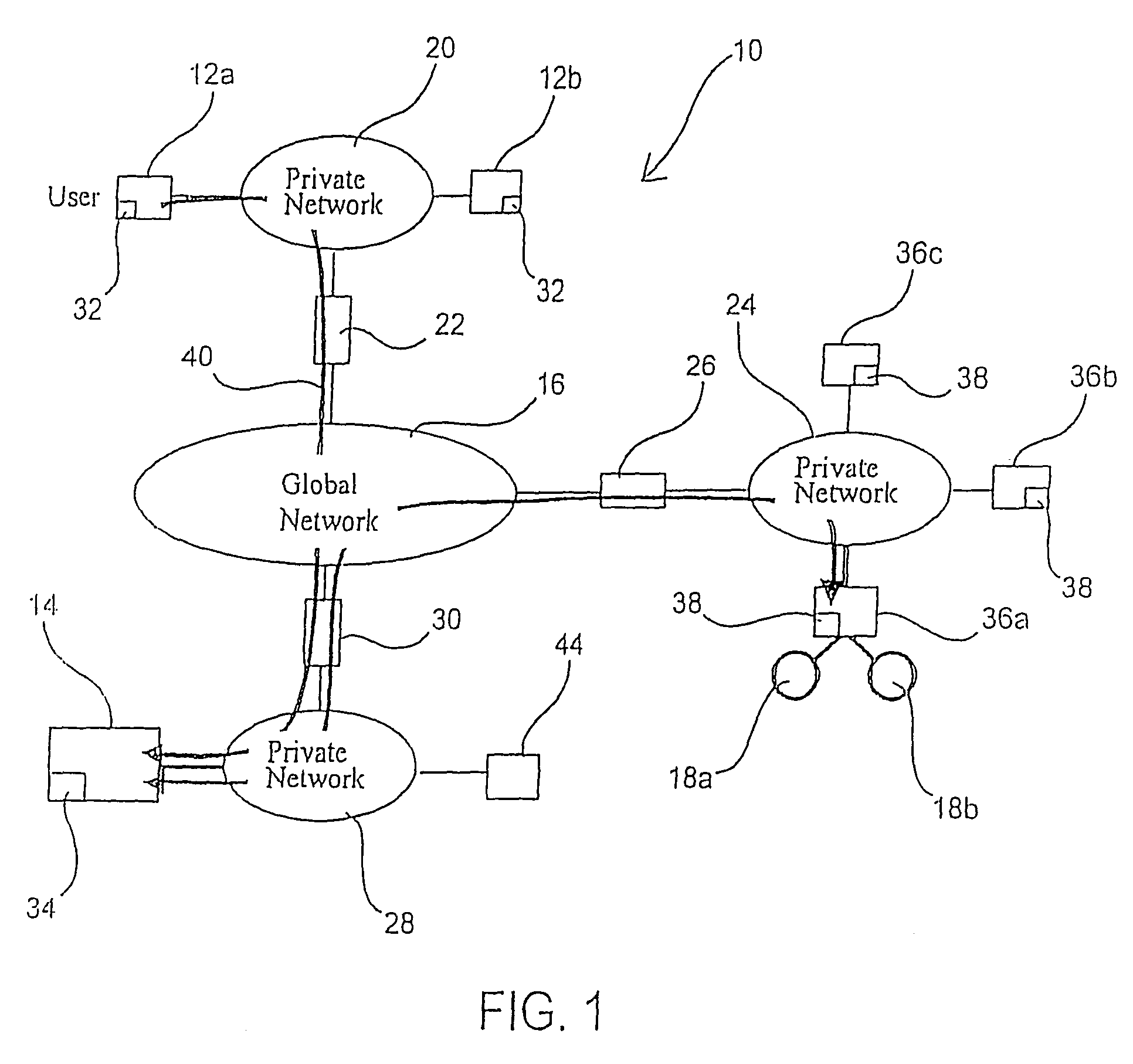
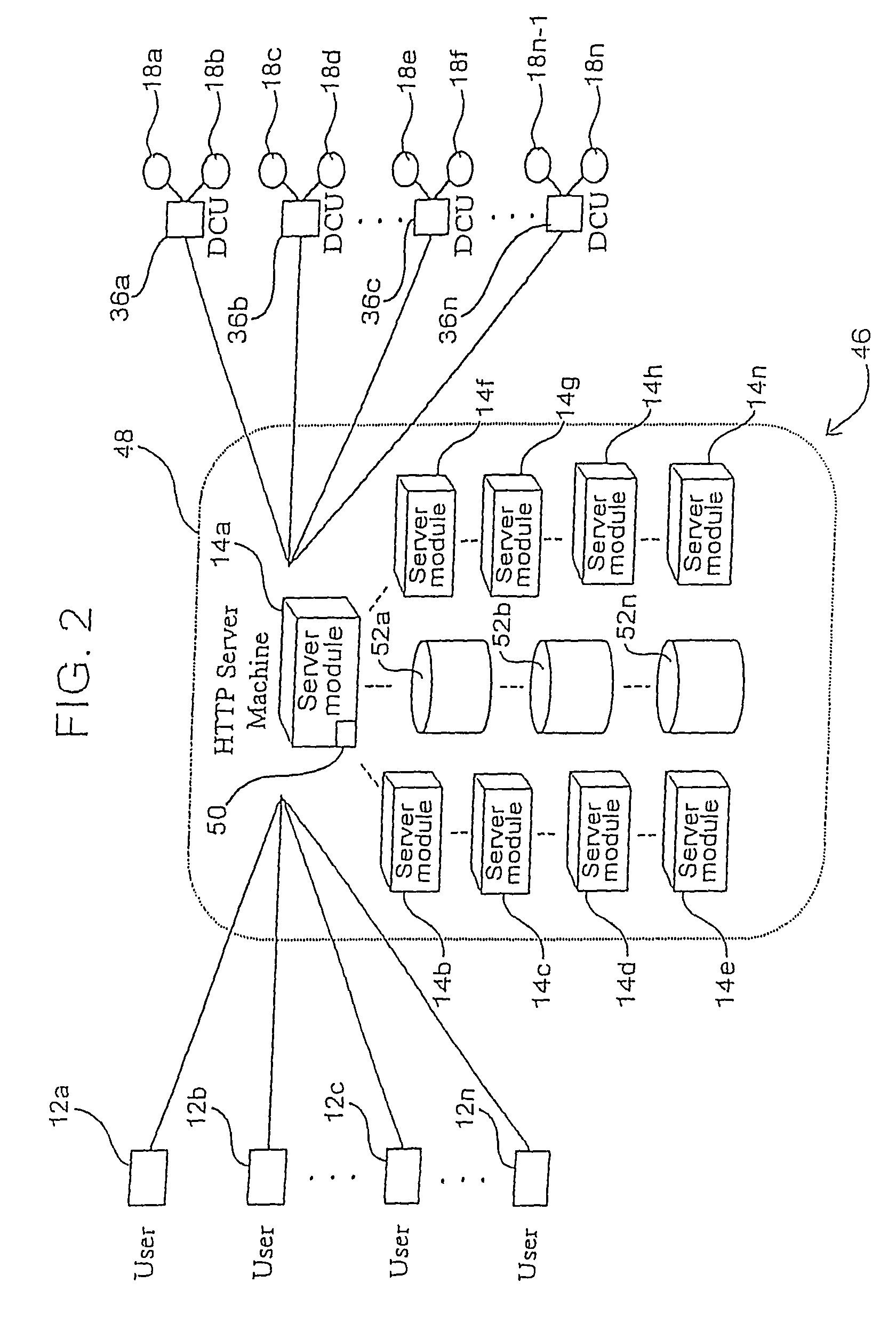
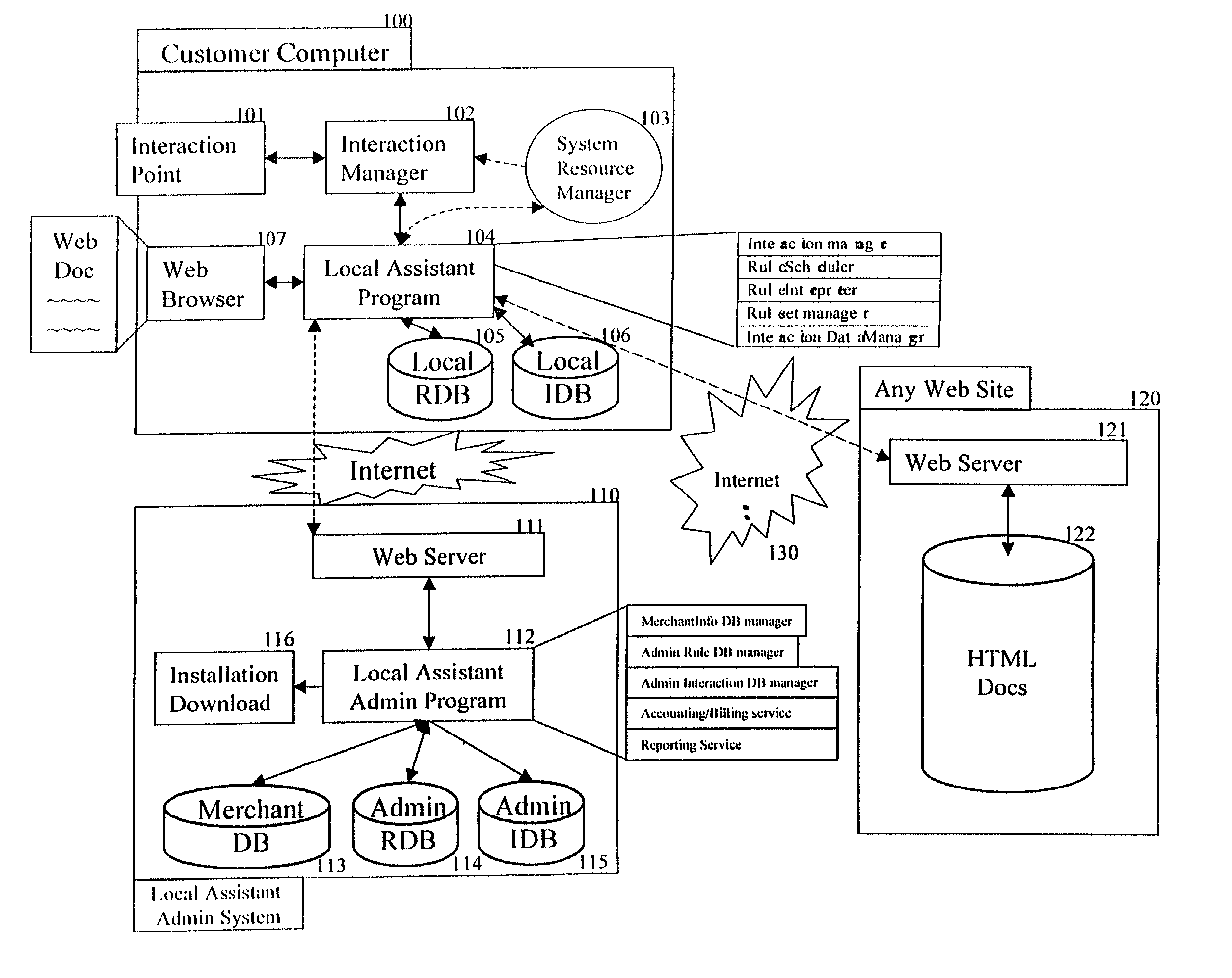
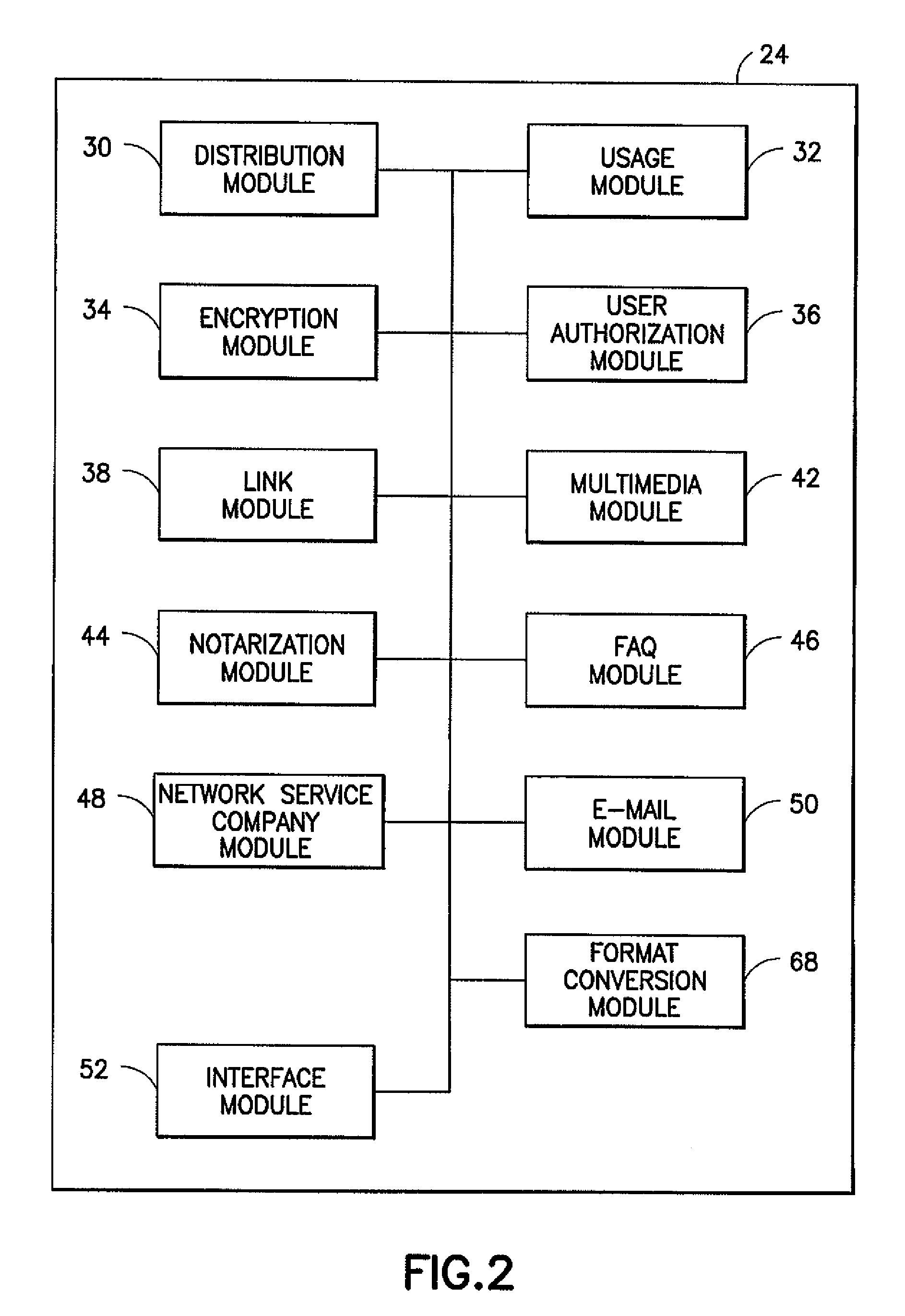
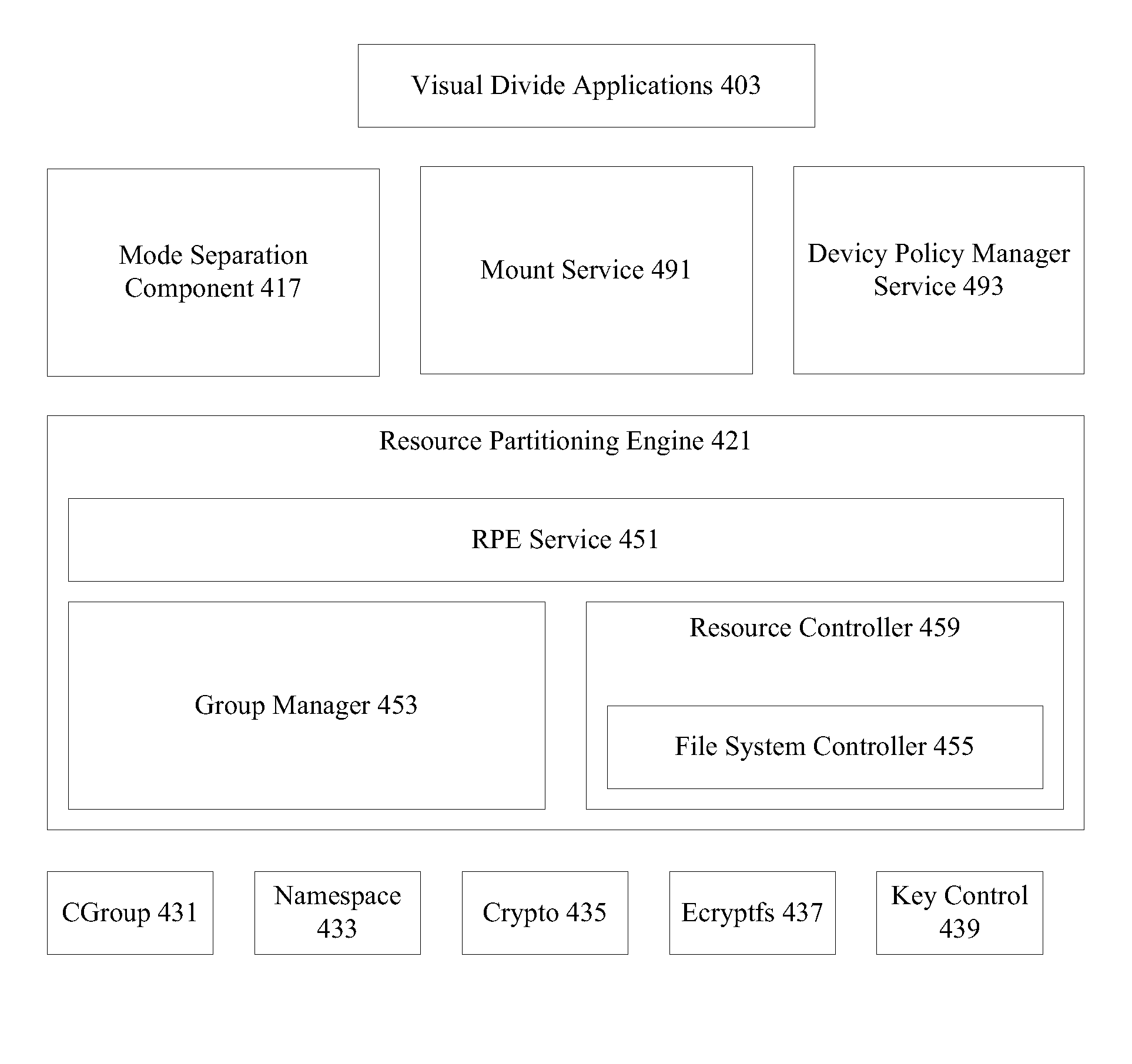
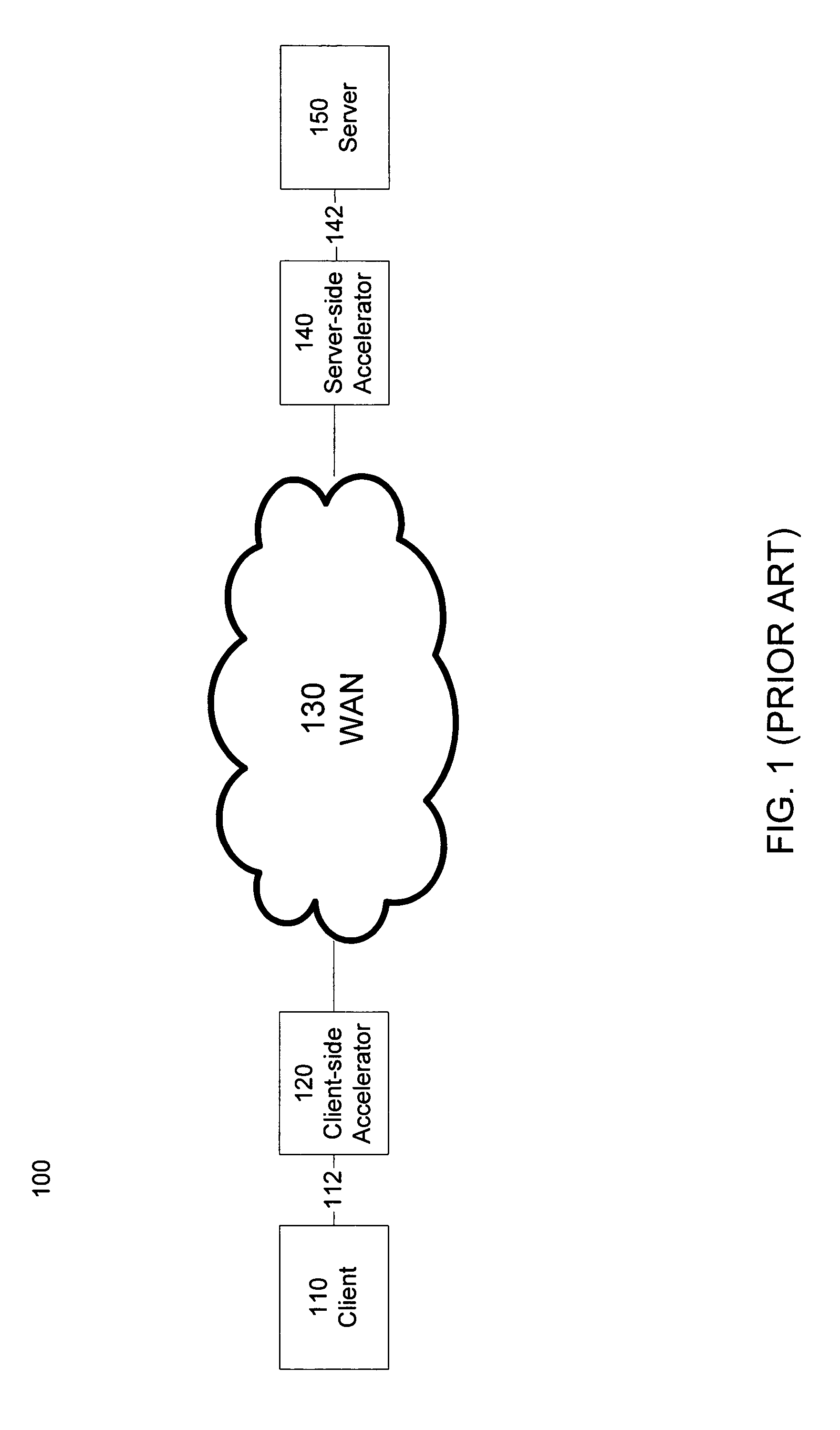
Creating secure interactive connections with remote resources
ActiveUS20070061878A1Easy to adaptDigital data processing detailsUser identity/authority verificationSecure communicationClient-side
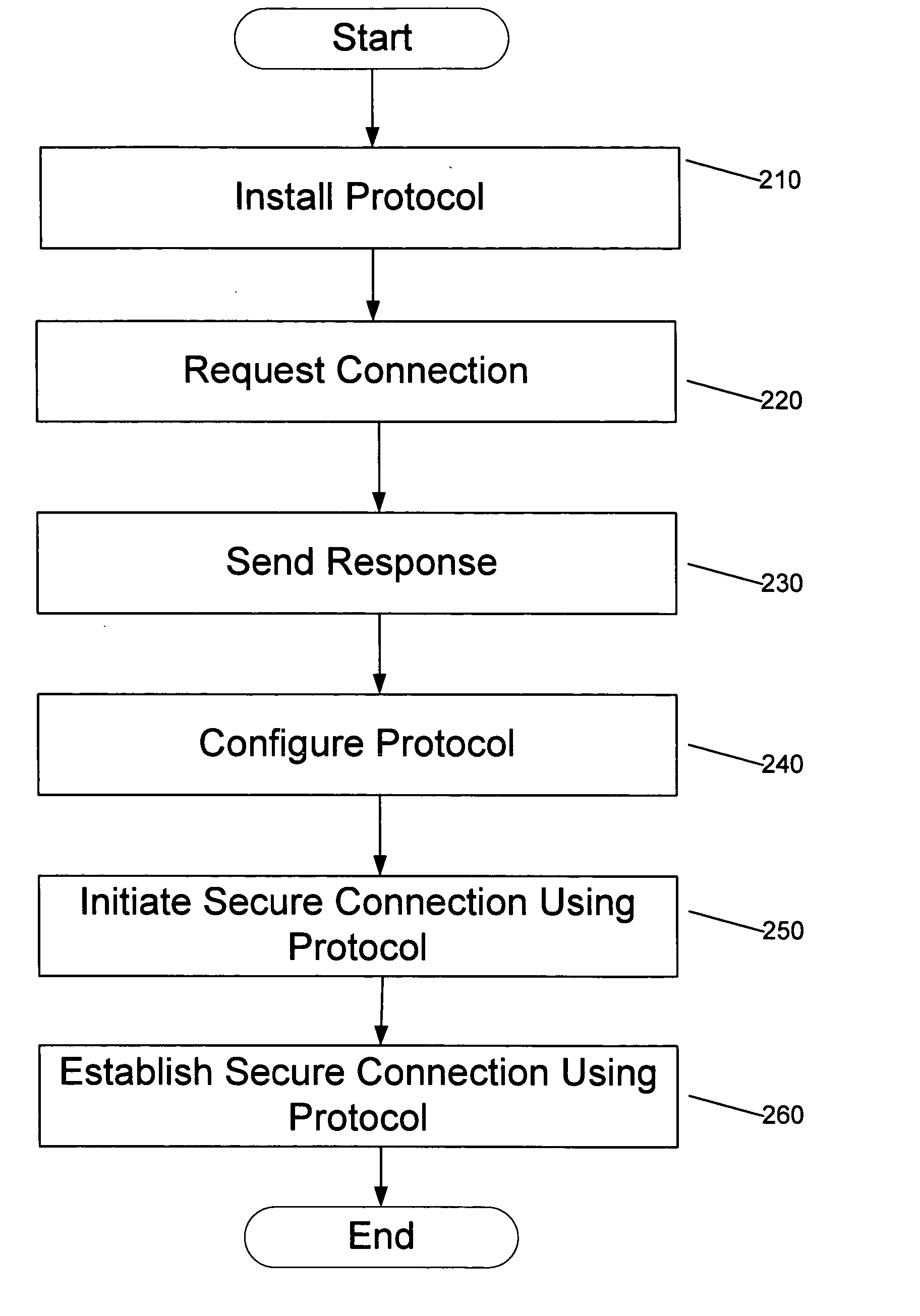
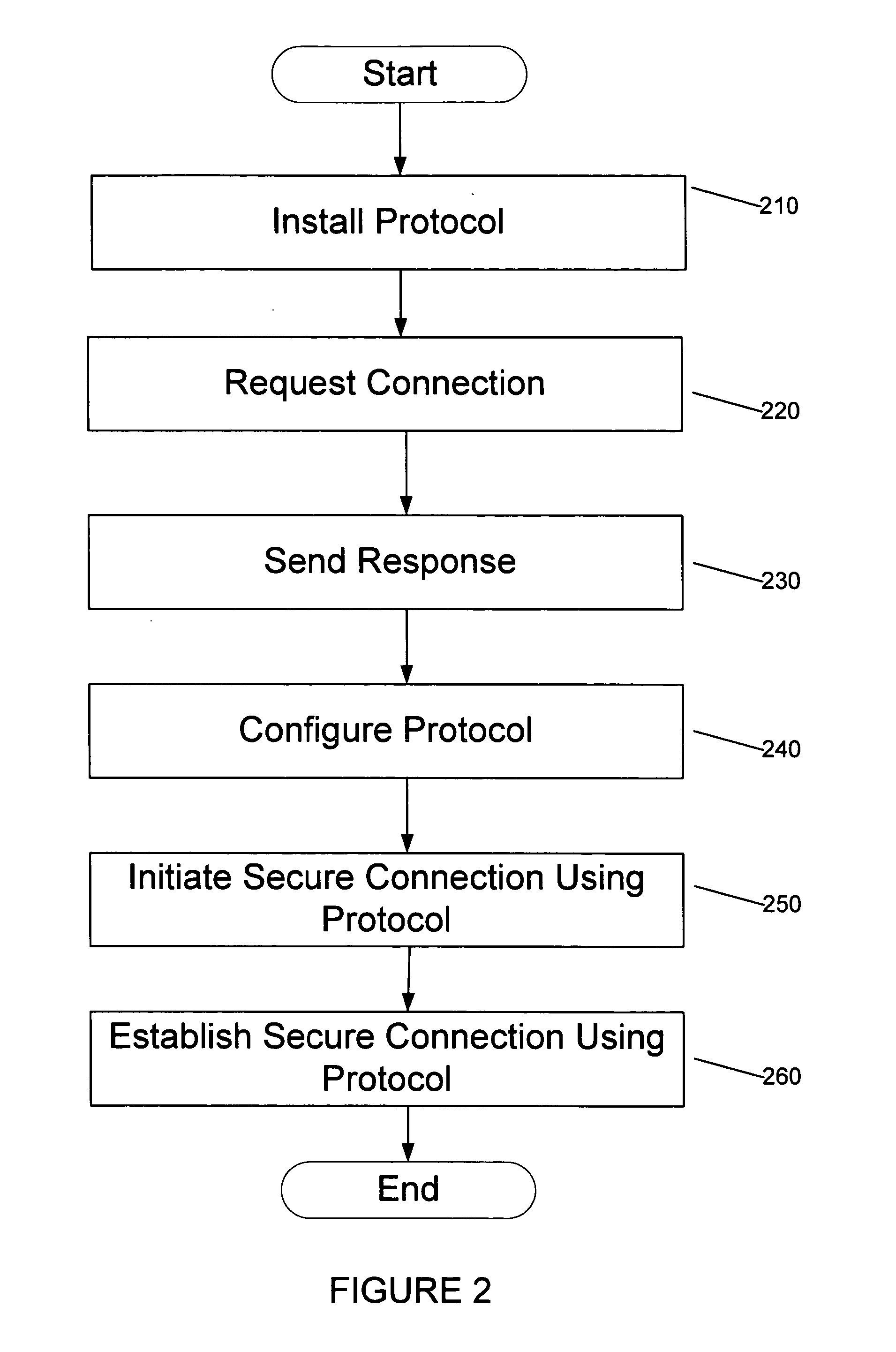
Implementations of the present invention efficiently establish secure connections between a client and server, at least in part by authenticating the client and server early on in the connection setup phases. A client initiating a connection with a server identifies the secure communication protocols enabled at the client, and identifies these protocols in a connection request it sends to the server. The server processes the message and responds with a communication protocol it deems appropriate for the connection. The client and server then exchange appropriate authentication information, and then establish a connection session that implements the chosen communication protocol, and encrypts messages using the negotiated communication protocol. Additional implementations relate to reestablishing dropped connections behind virtual Internet Protocol addresses, without necessarily having to recommit much connection resource overhead.
Owner:MICROSOFT TECH LICENSING LLC
Managed peer-to-peer applications, systems and methods for distributed data access and storage
InactiveUS20050149481A1Reduce bandwidth requirementsDigital data processing detailsMultiple digital computer combinationsData accessRemote computer
Applications, systems and methods for efficiently accessing and controlling data of devices among multiple computers over a network. Peer-to-peer exchanges of data between private computers is made possible while providing seamless, firewall-compliant connectivity. Such functionality is available even among private users over a public network, and even when multiple firewalls must be passed through. A firewall compliant connection may be established between a local computer and at least one remote computer; at least one file on a storage device associated with one of the computers is selected, and securely sent to at least one other computer over the secure connections. Computers may be connected over a wide area network with or without a connection server, with or without a VPN.
Owner:WESTERN DIGITAL TECH INC
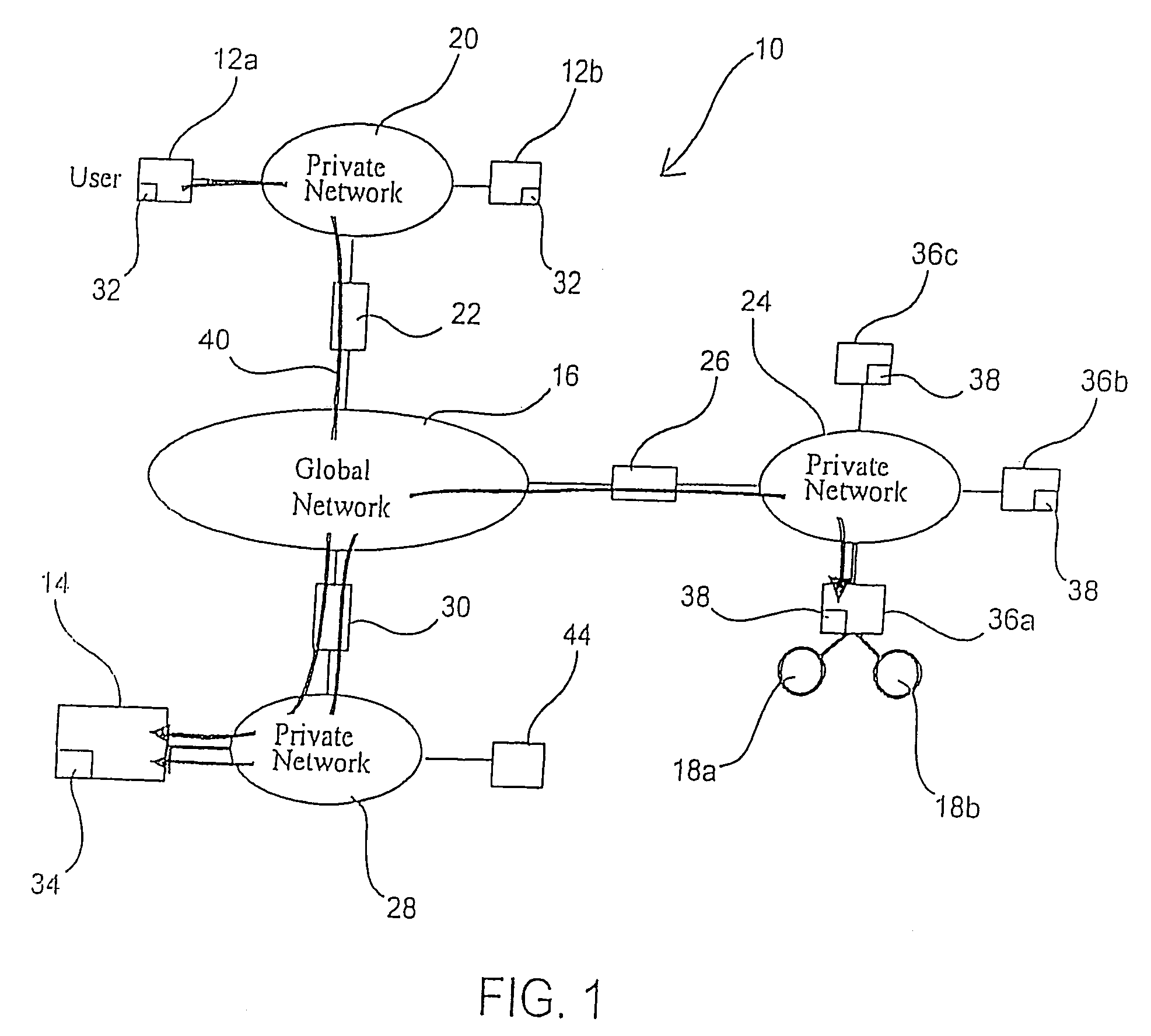
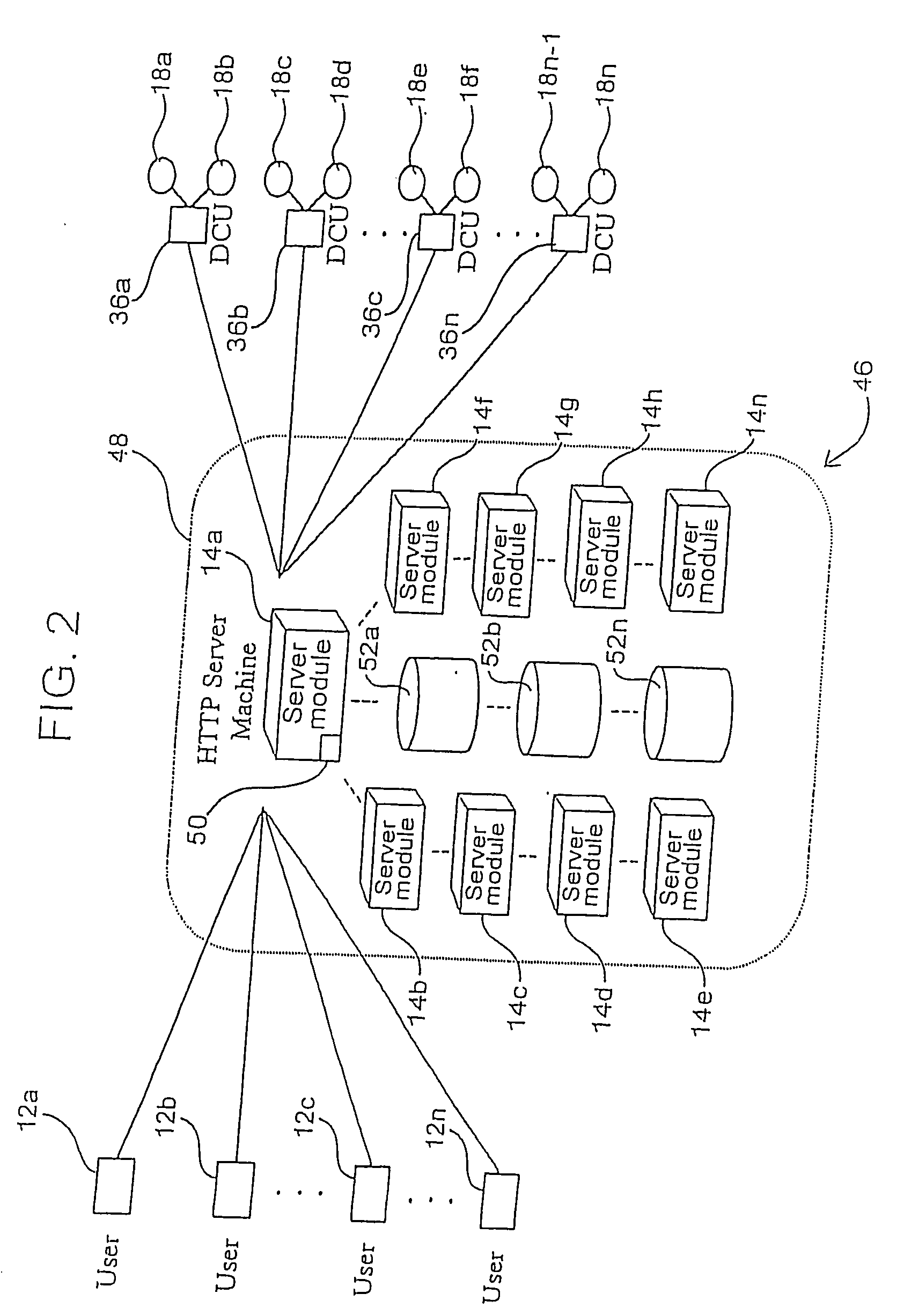
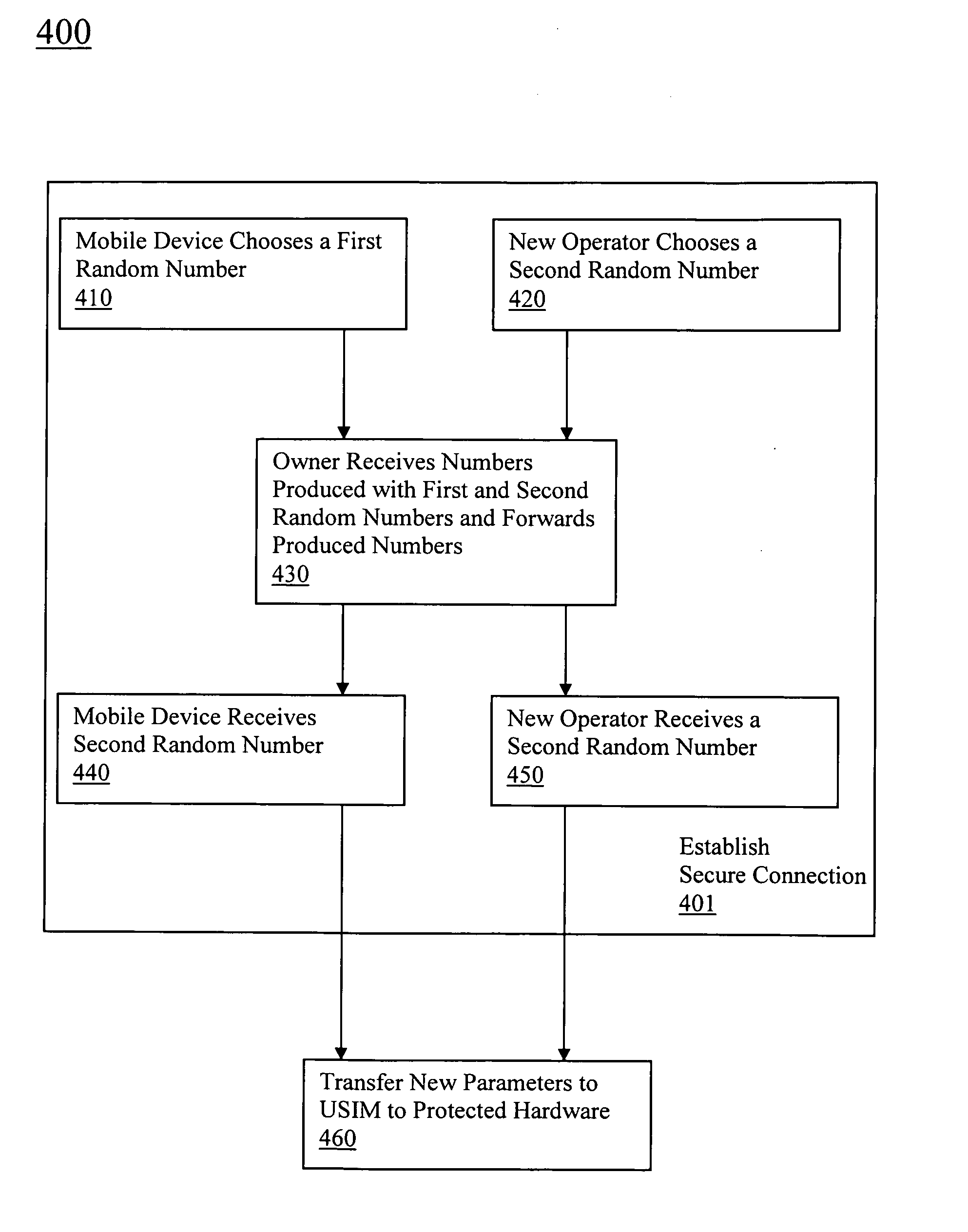
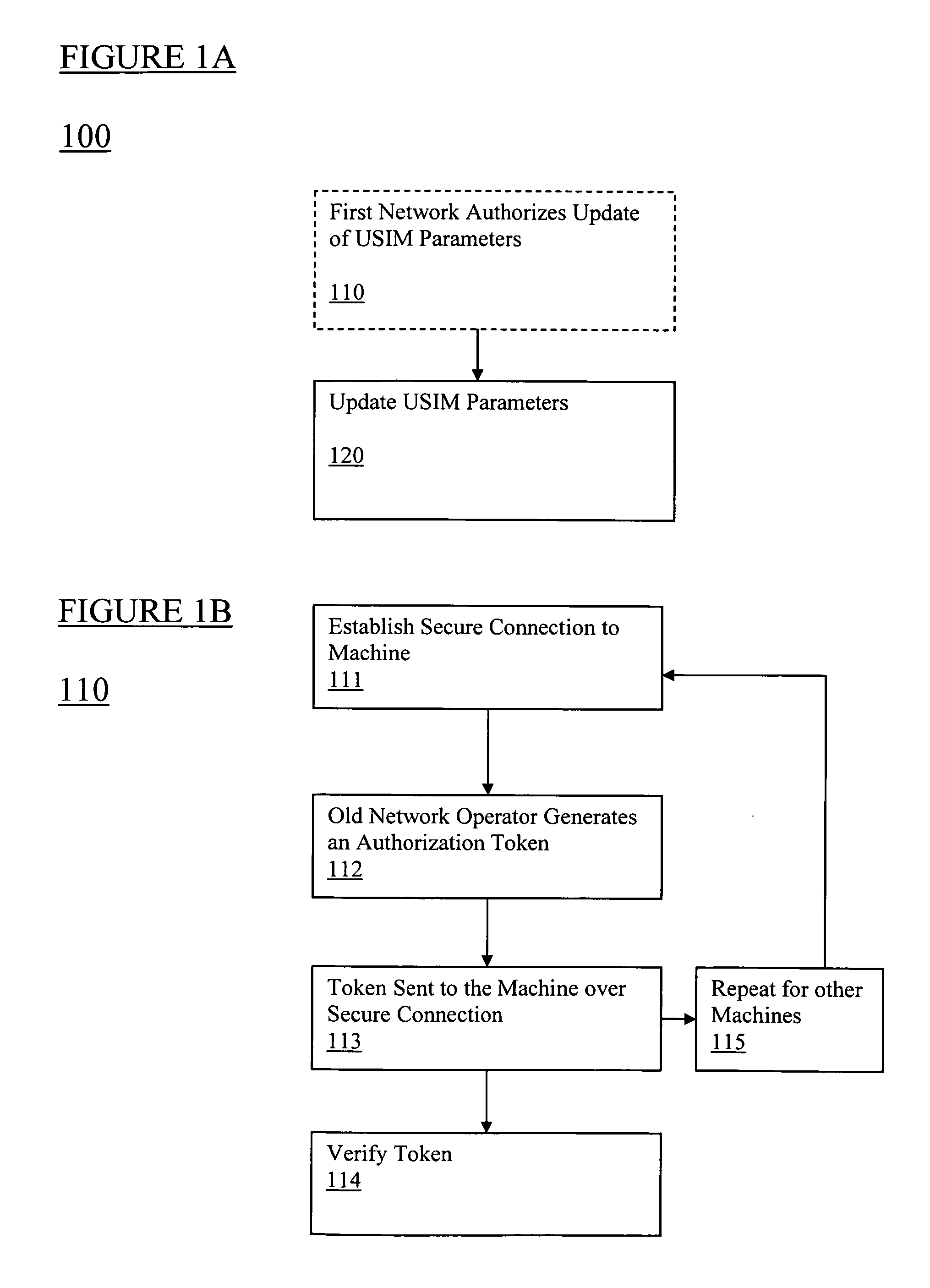
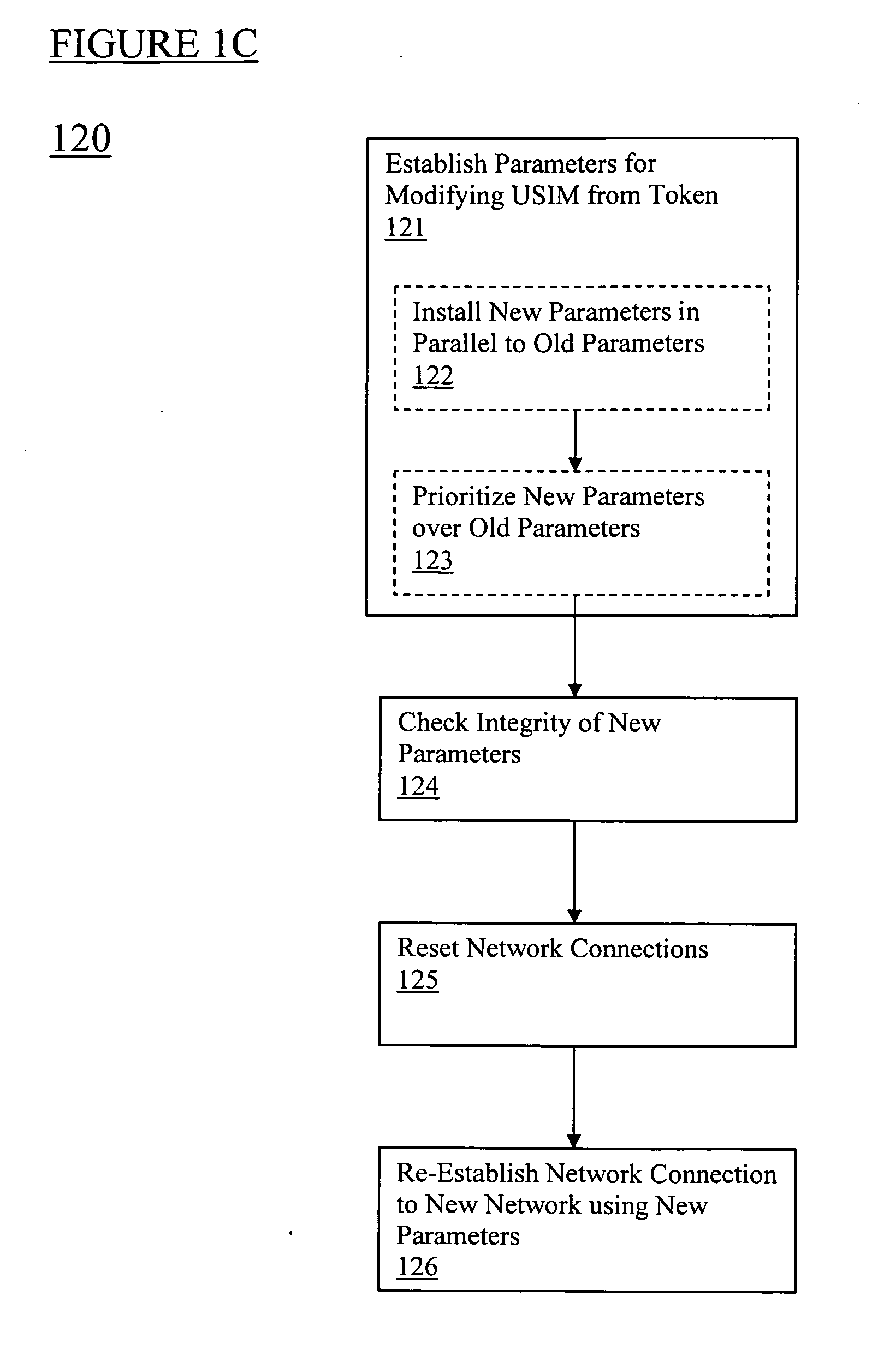
Universal subscriber identity module provisioning for machine-to-machine communications
InactiveUS20090191857A1Automatic exchangesWireless commuication servicesSubscriber identity moduleSafety Connect
The present invention relates to remotely provisioning subscriber identification parameters in a device on a wireless network. A secure connection is established with the device, and a token containing the new subscriber identification parameters is forwarded over the secure connection. The device may verify the received token. In one embodiment, the subscriber identification parameters are updated to change network operators. The secure connection can be with the old network operator or the new network operator. The device on the wireless network may be a machine-to-machine device. The provisioned subscriber identification may be part of a universal subscriber identification module.
Owner:NOKIA SOLUTIONS & NETWORKS OY
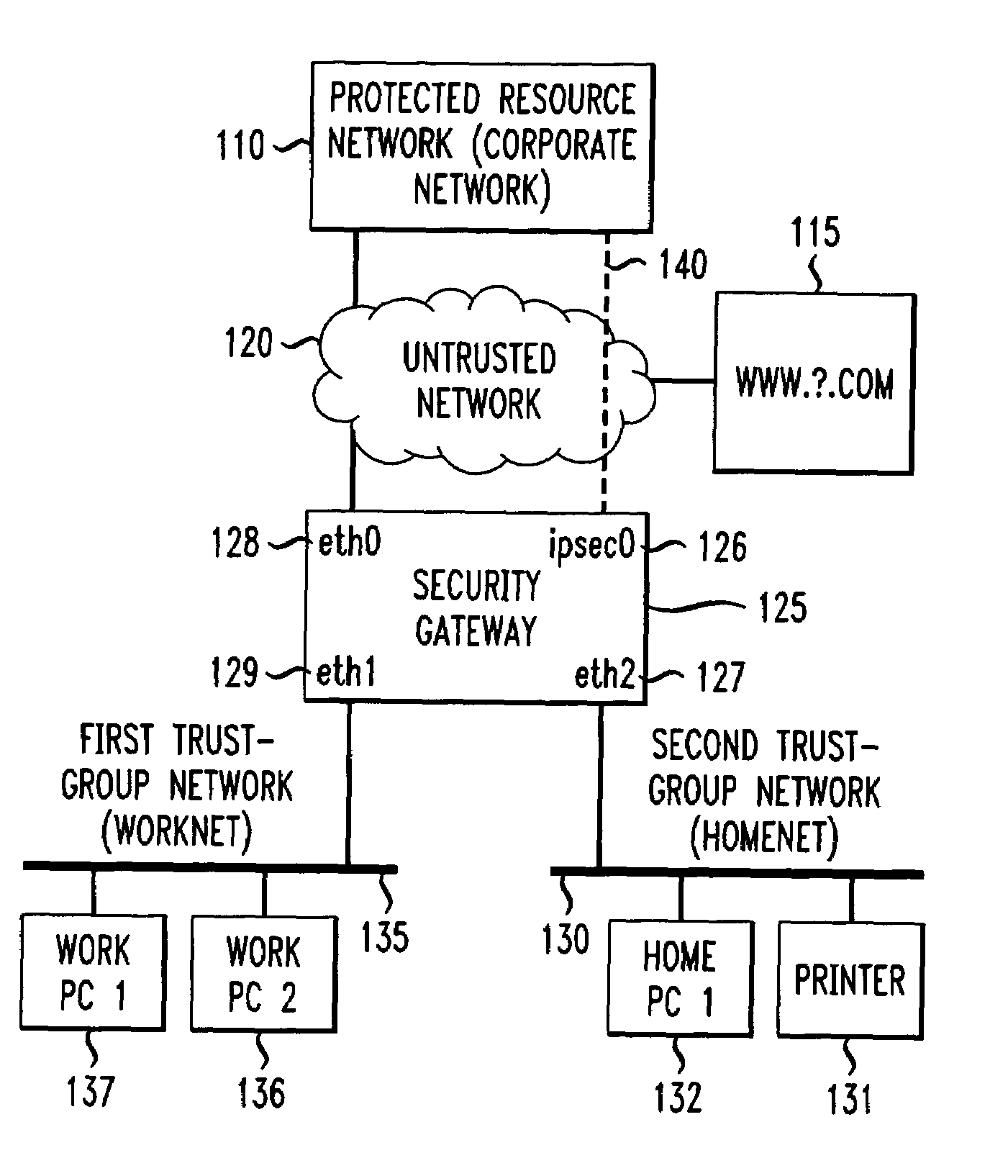
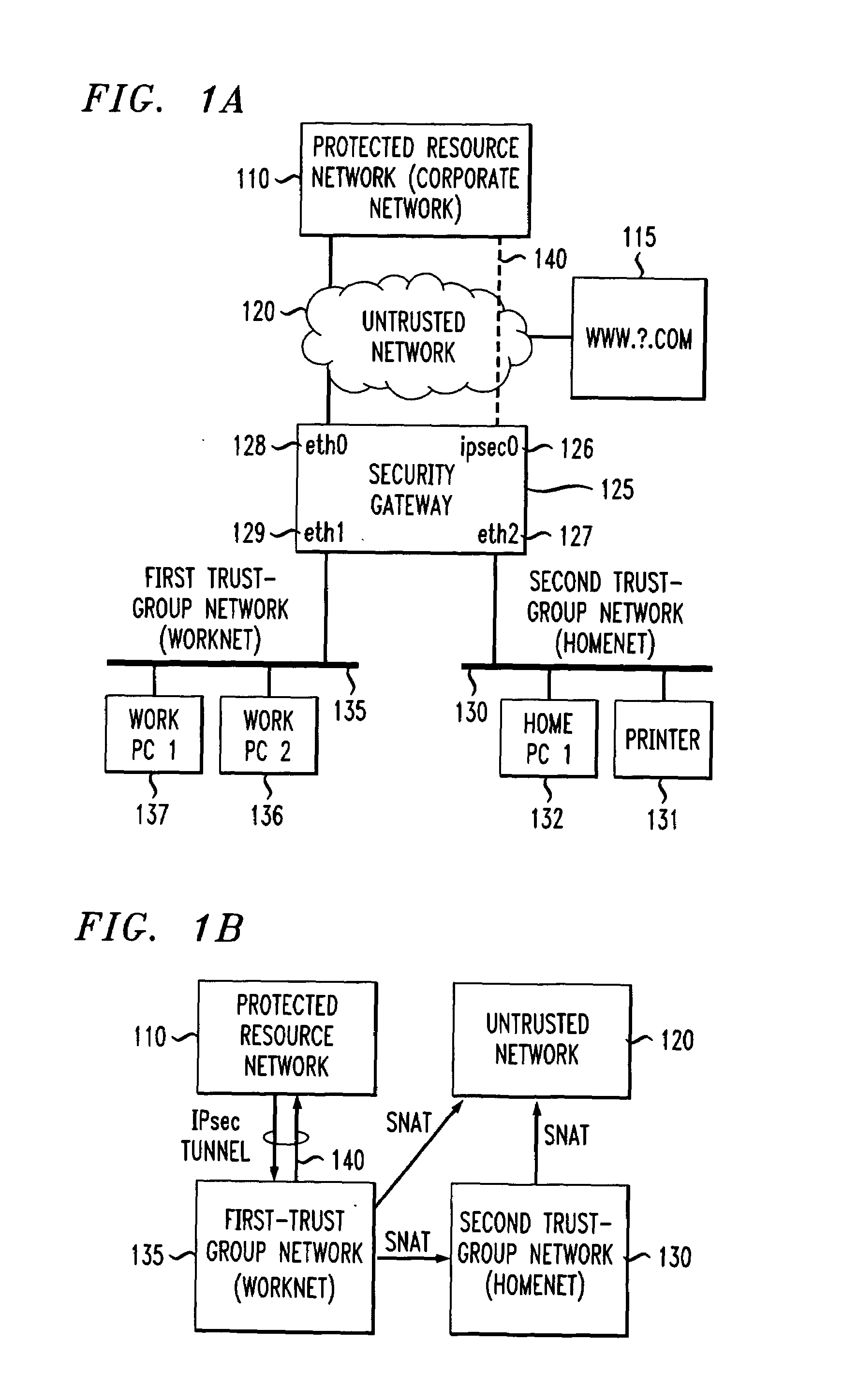
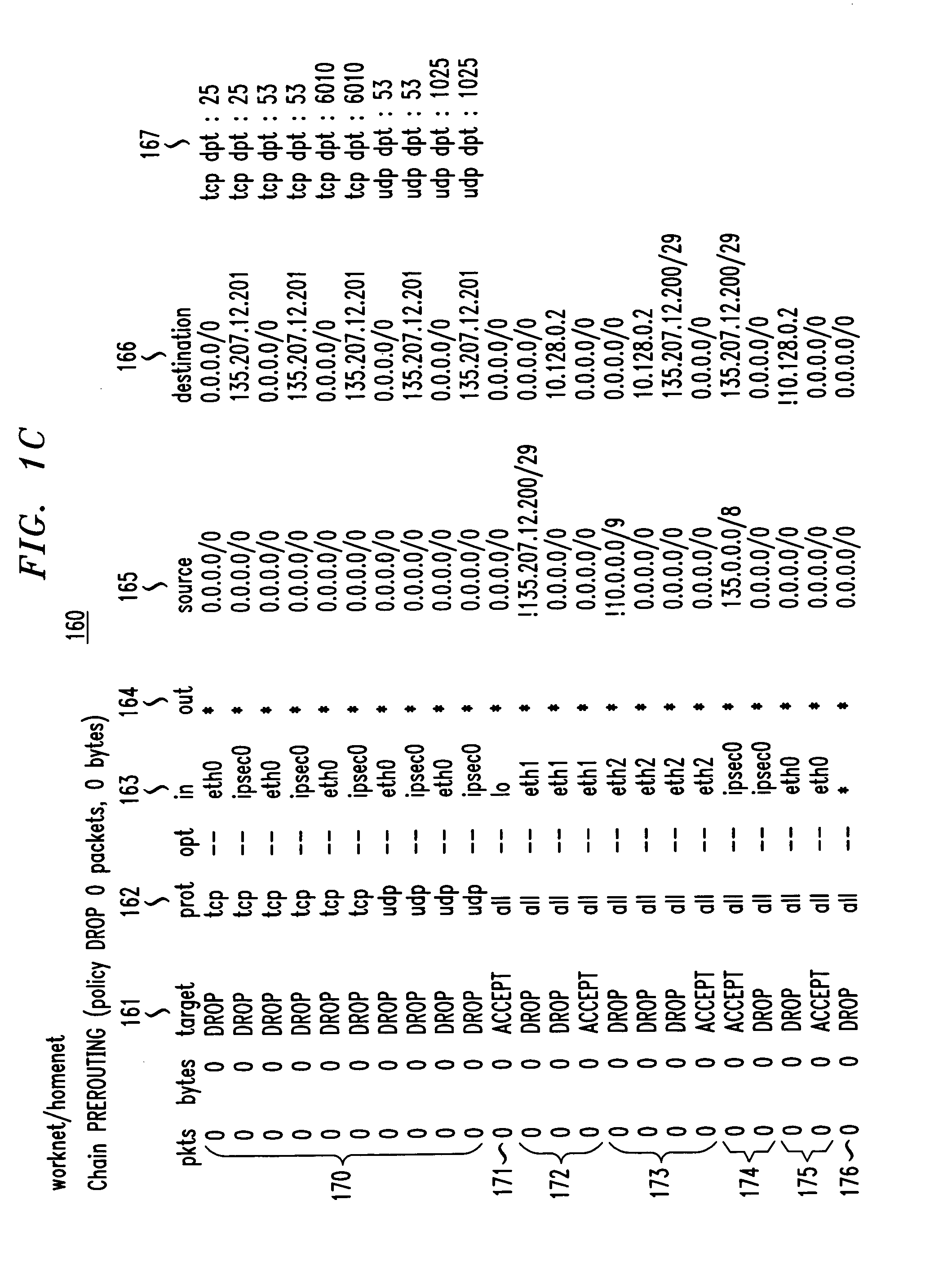
Method and apparatus for securely connecting a plurality of trust-group networks, a protected resource network and an untrusted network
InactiveUS7131141B1Improve securityMultiple digital computer combinationsProgram controlPrivate networkIp address
A security gateway provides a secure connection among one or more networks and a protected resource network. One of the local networks may be connected to the remote private network via a VPN IPsec tunnel. The networks may be local networks that share resources without compromising the security of the protected resource network. The local networks may have access to an untrusted network such as the Internet, sharing a single connection through the security gateway. Dynamic source network address translation is used to permit access from the network connected to the protected resource network to other, less trusted networks while concealing the actual IP addresses of hosts within that network.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
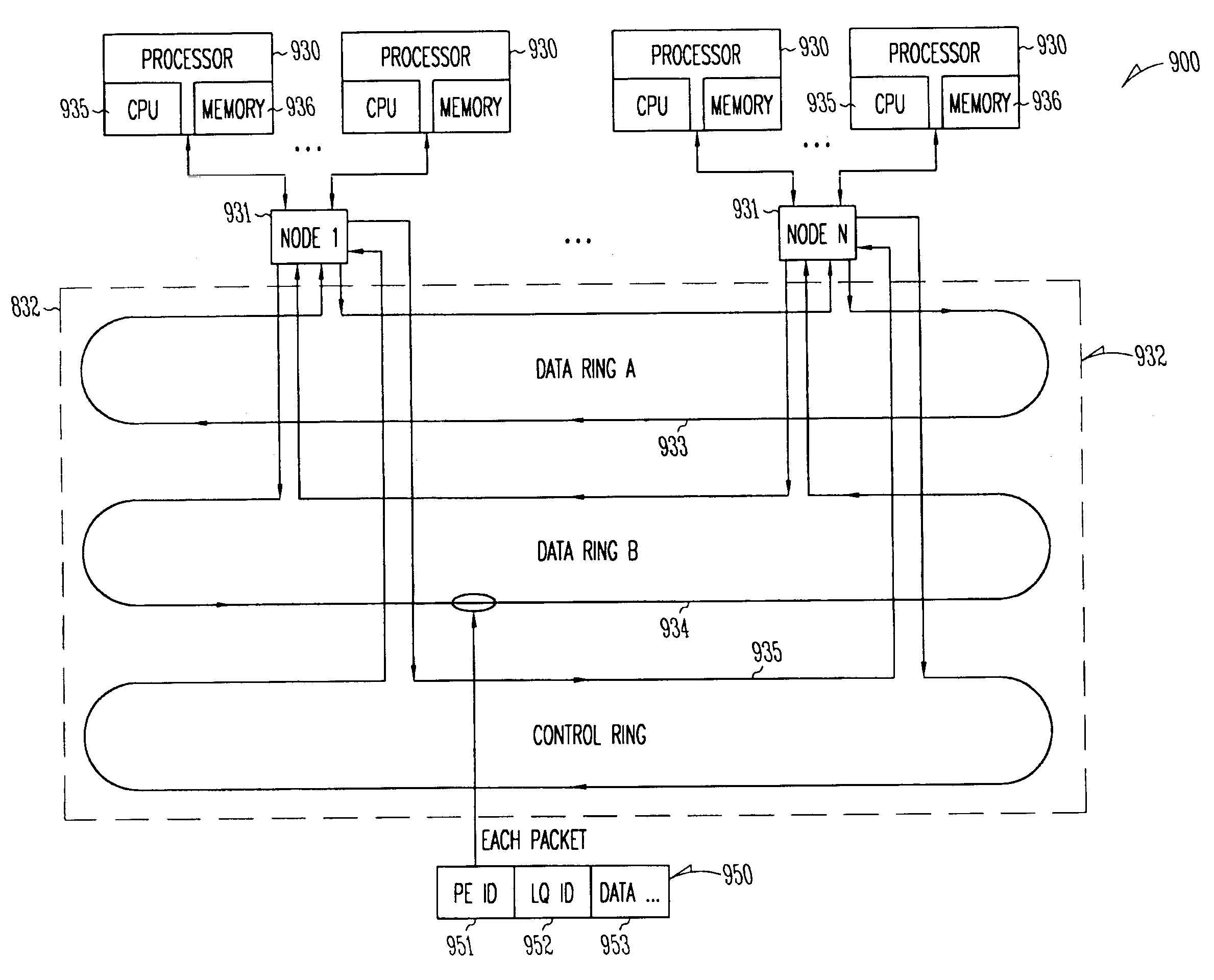
Packet routing system and method
InactiveUS7111072B1Multiple digital computer combinationsLoop networksComputer hardwarePrivate network
A flexible, scalable hardware and software platform that allows a service provider to easily provide internet services, virtual private network services, firewall services, etc., to a plurality of customers. One aspect provides a method and system for delivering security services. This includes connecting a plurality of processors in a ring configuration within a first processing system, establishing a secure connection between the processors in the ring configuration across an internet protocol (IP) connection to a second processing system to form a tunnel, and providing both router services and host services for a customer using the plurality of processors in the ring configuration and using the second processing system. a packet routing system and method is described that includes a processor identifier in each packet to route the packets to a physical processor, and a logical queue identifier to route the packets to the destination object within that processor.
Owner:FORTINET
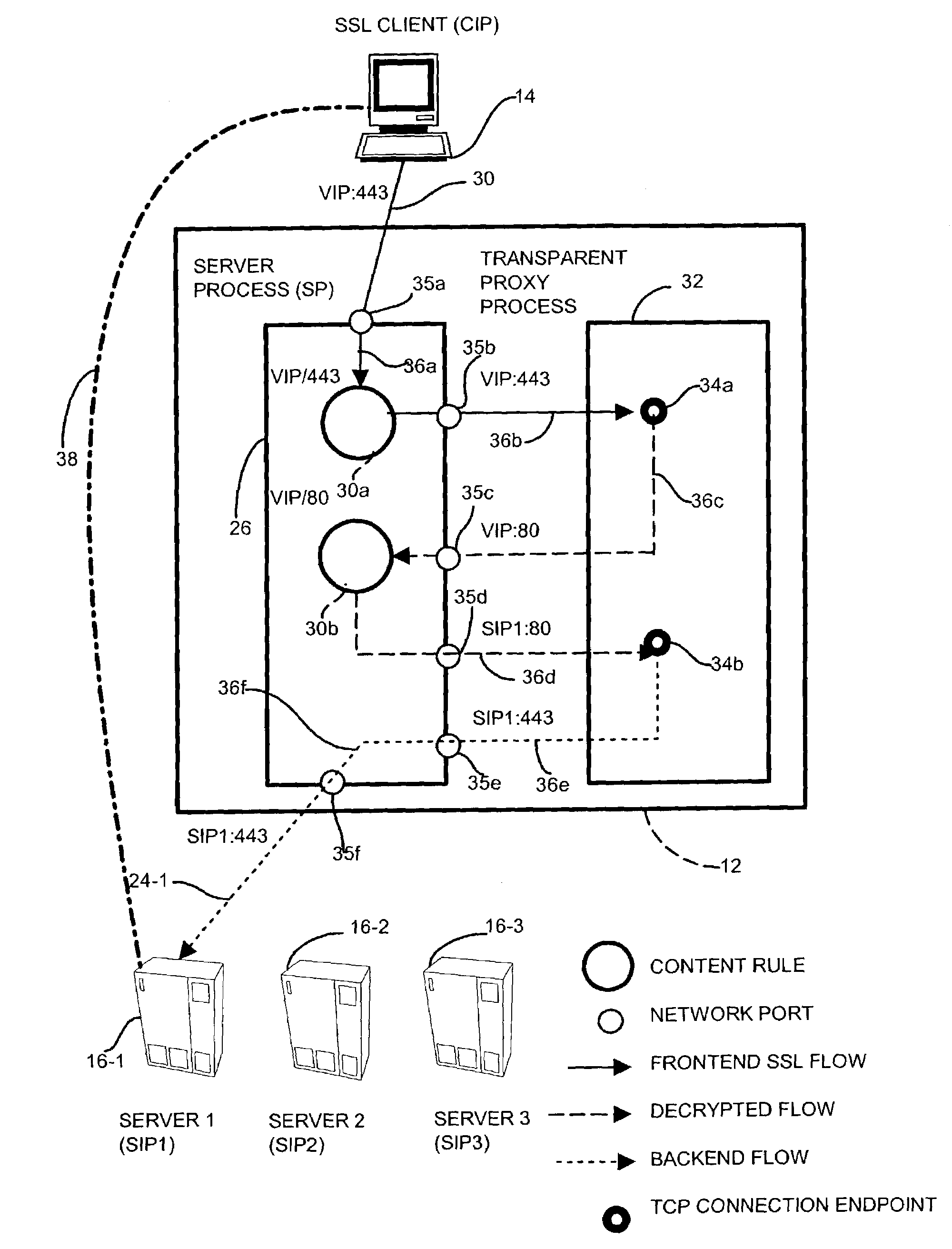
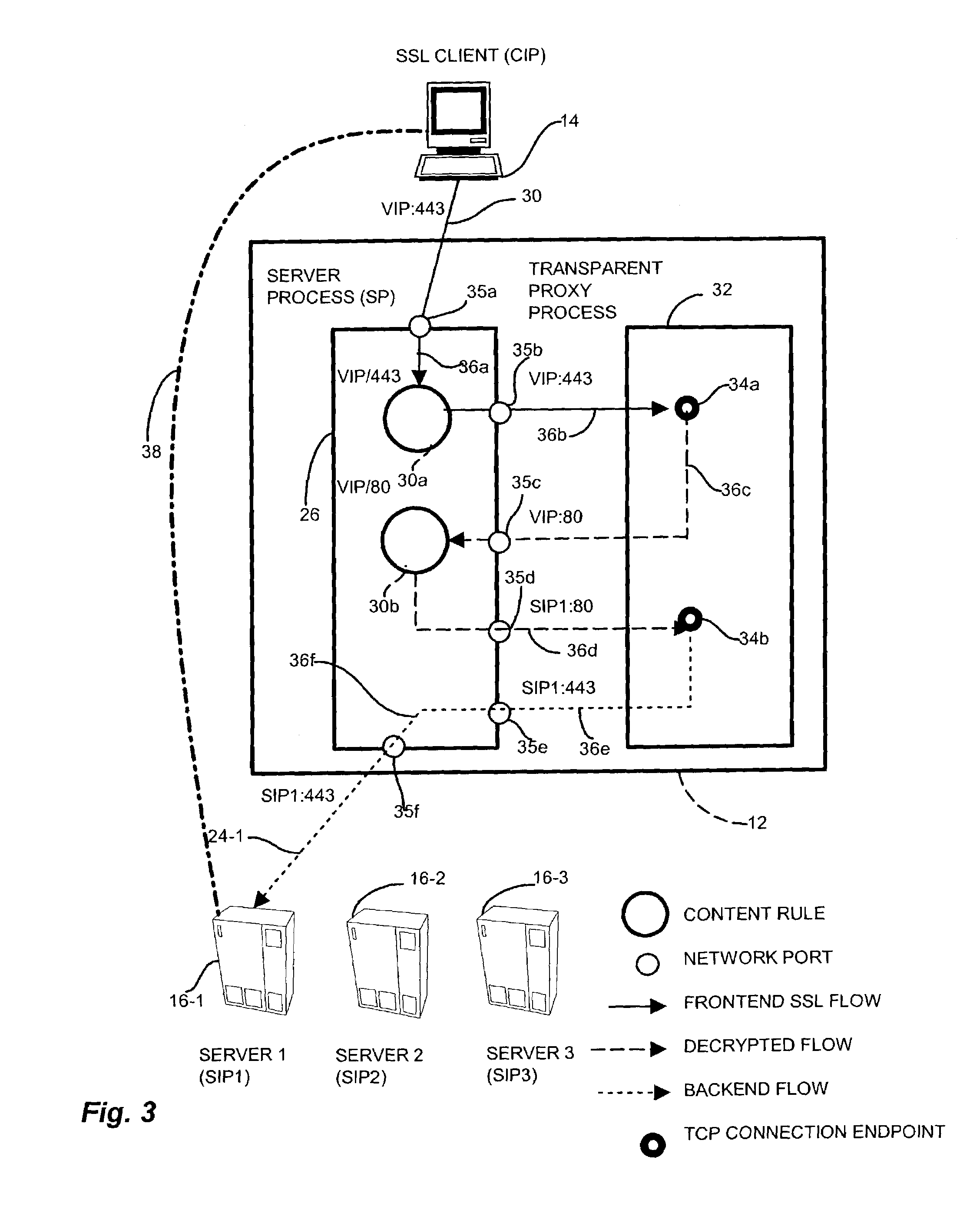
Methods and apparatus for network communications via a transparent security proxy
InactiveUS7506368B1Reduce encryption overheadPerformance degradation can be preventedMultiple keys/algorithms usageUser identity/authority verificationSecure communicationNetwork communication
A data security device for providing a network transport connection via a transparent network proxy that employs different encryption security mediums along a communications session between two endpoints by emulating one of the endpoints at an intermediate node such that the communication session appears as an atomic, secure connection to the endpoints yet provides appropriate security over the end-to-end connection. A sender node sends a connection request to establish a secure communication session with an intended receiver node. A transparent proxy on an intermediate node receives the request and establishes the link employing an encryption mechanism. The transparent proxy establishes a second link with the intended receiver, and applies a second, less expensive encryption mechanism. The transparent proxy combines the two links to form the trusted, secure connection but incurring only the mitigated expense over the second link.
Owner:CISCO TECH INC
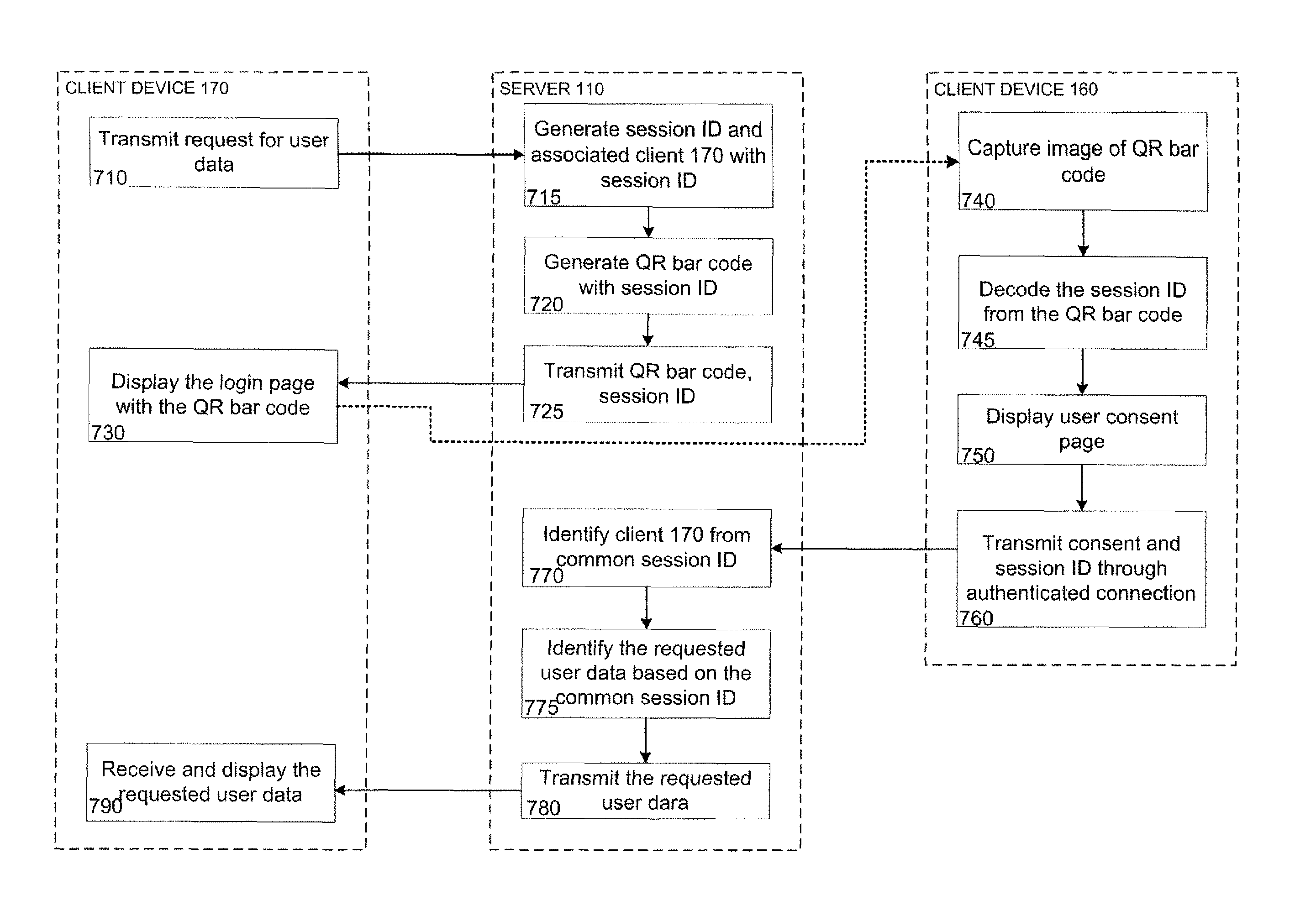
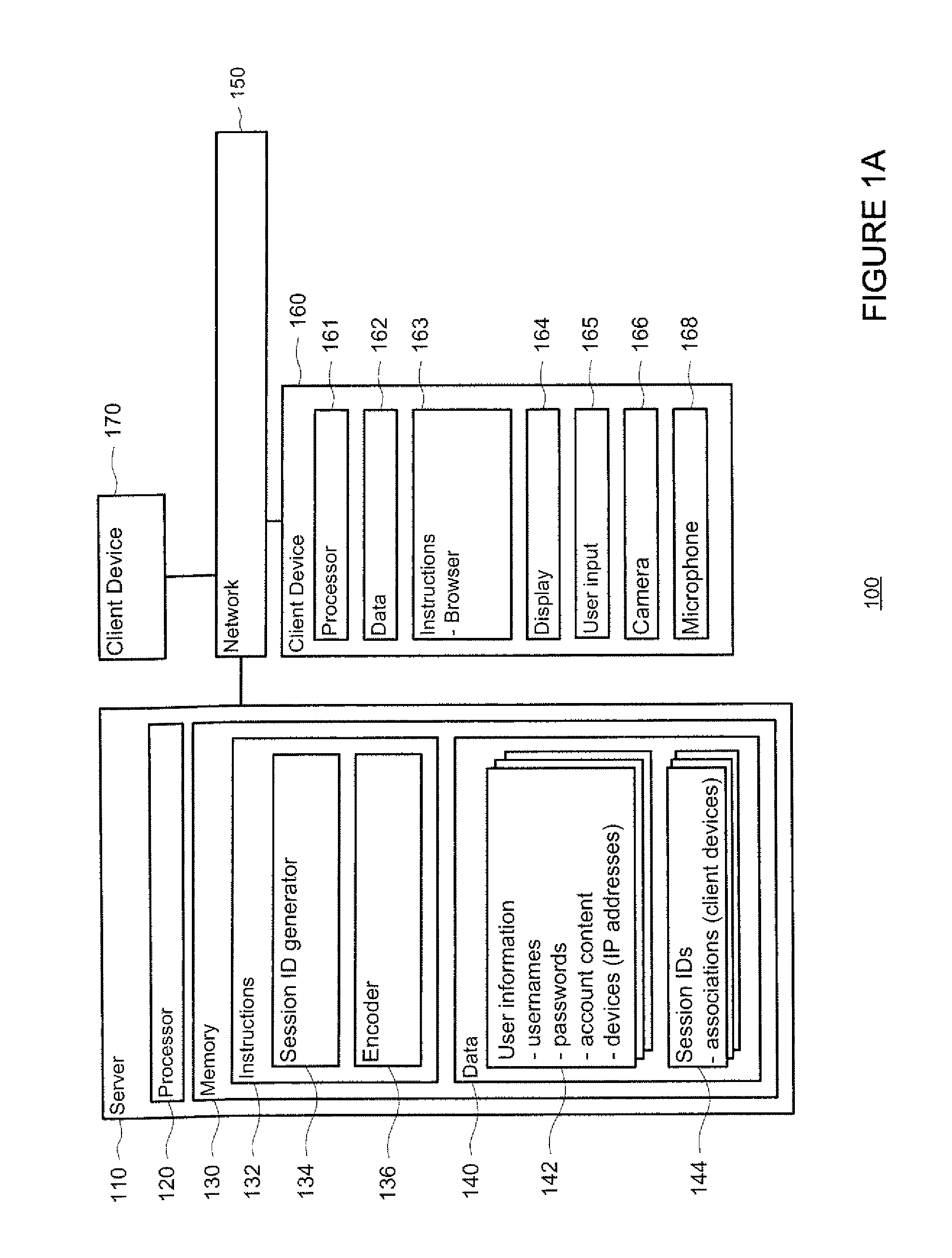
Out-of band authentication of browser sessions
Systems and methods provide a user with secure access to a web site at a first client device without having to enter login information, such as a username and password, at that device. For example, the first device may request access to user information from a server system. The server may generate a session ID, associate it with the first device, and encode it into a bar code that is displayed at the first device. Using camera functions, a second client device may identify and decode the bar code to determine the session ID. The login information may be entered into the second device in order to establish a secure connection with the server. The second device may transmit the session ID to the server system. The server may identify the first client device based on the common session ID and transmit the requested user information to the first device.
Owner:GOOGLE LLC
System and method for securely providing a configuration file over and open network
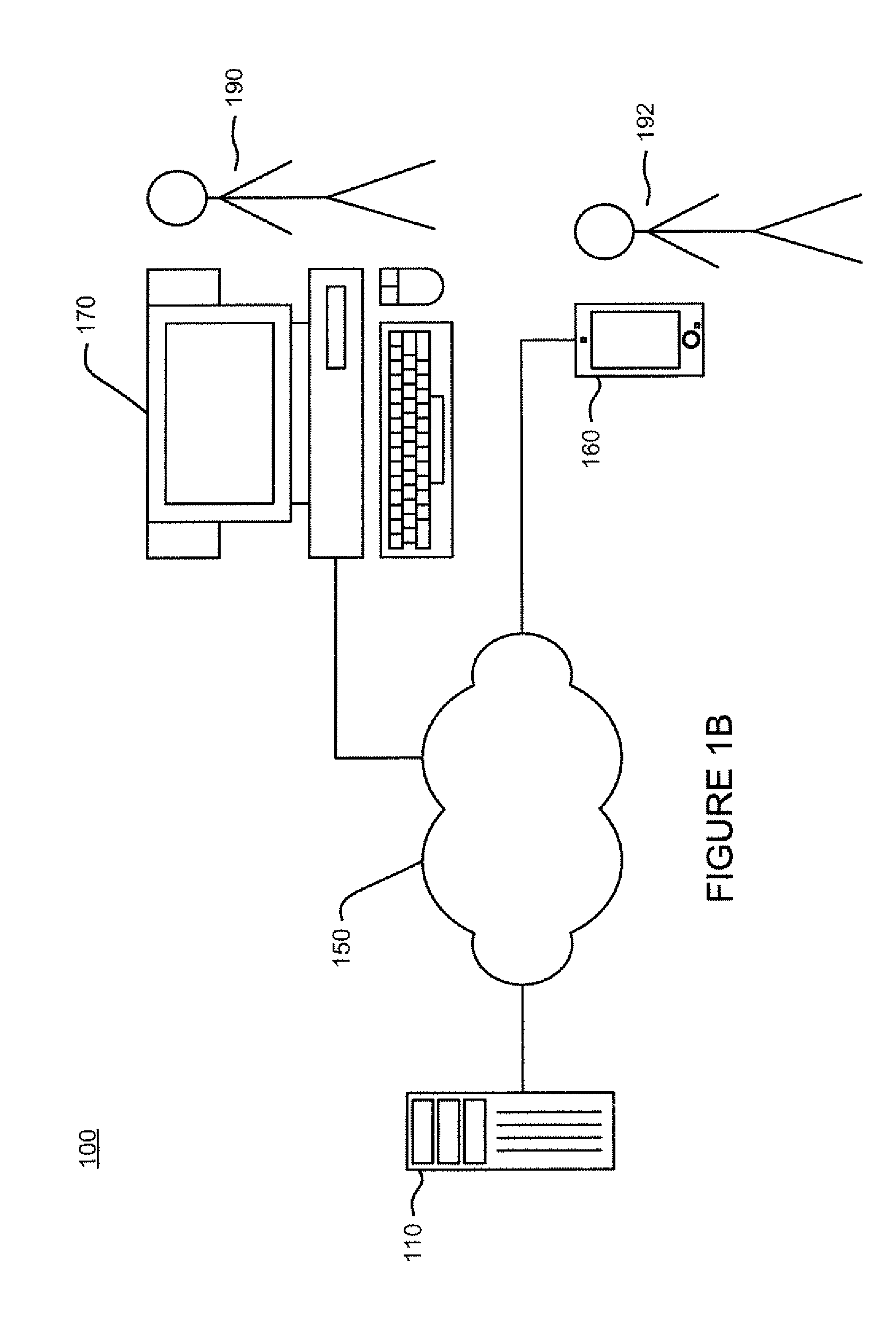
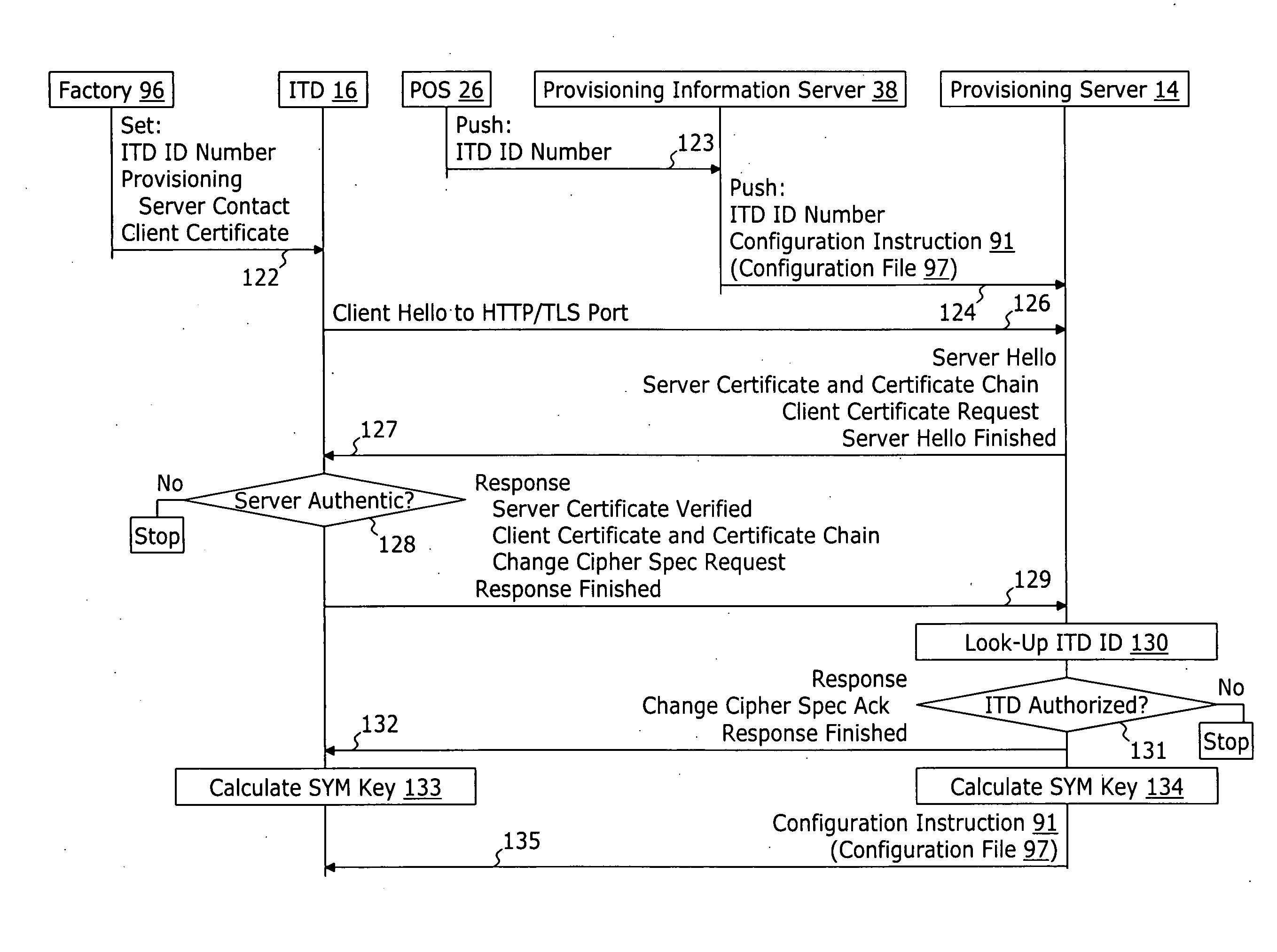
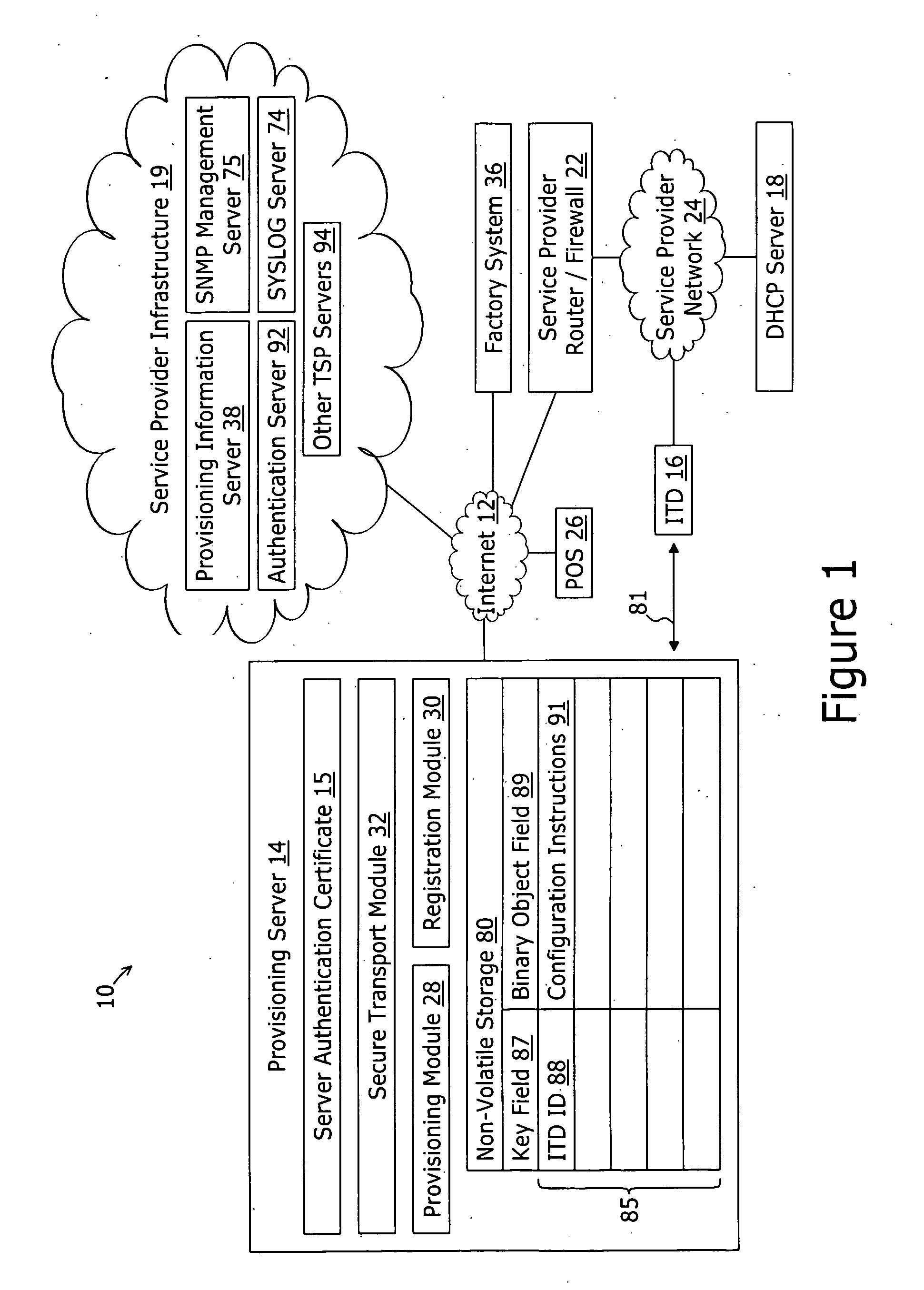
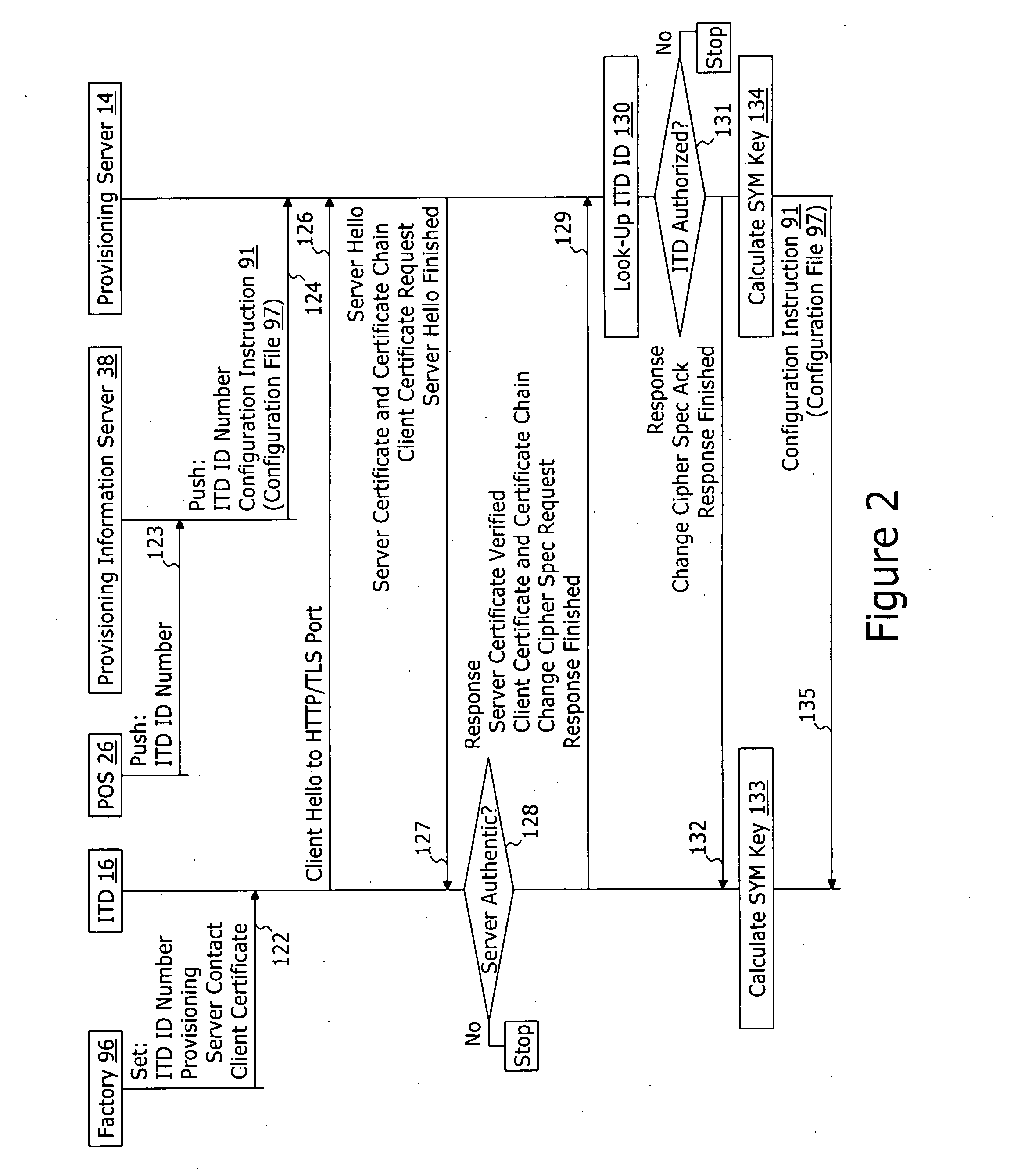
ActiveUS20060174018A1User identity/authority verificationUnauthorized memory use protectionDomain nameNetwork connection
A method for securely provisioning a device for operation within a service provider infrastructure over an open network comprises the device establishing physical and data link layer network connections for communication on at least a subnet of the open network and obtaining a network configuration data such as an IP address and a subnet mask from a provisioning server that responds to a network configuration broadcast request. A device establishes a secure hypertext transport protocol connection to a first provisioning server that corresponds to one of: i) and IP address and port number; and ii) a fully qualified domain name stored in a non-volatile memory of the device. After mutual authentication, the first provisioning server provides at least one of: i) a configuration file; and ii) identification of a second provisioning server and a cipher key through the secure connection. If the first provisioning server provided identification of a second provisioning server, the device establishes a transport connection to the identified second provisioning server. The second provisioning server provides an encrypted file which, when decrypted using the cipher key yields the configuration information needed by the device for operation with the service provider infrastructure.
Owner:INOMEDIA
Managed peer-to-peer applications, systems and methods for distributed data access and storage
InactiveUS7917628B2Reduce bandwidth requirementsDigital data processing detailsMultiple digital computer combinationsData accessRemote computer
Applications, systems and methods for efficiently accessing and controlling data of devices among multiple computers over a network. Peer-to-peer exchanges of data between private computers is made possible while providing seamless, firewall-compliant connectivity. Such functionality is available even among private users over a public network, and even when multiple firewalls must be passed through. A firewall compliant connection may be established between a local computer and at least one remote computer; at least one file on a storage device associated with one of the computers is selected, and securely sent to at least one other computer over the secure connections. Computers may be connected over a wide area network with or without a connection server, with or without a VPN.
Owner:WESTERN DIGITAL TECH INC
Method and system for modifying and transmitting data between a portable computer and a network
InactiveUS7035828B2Facilitate communicationAccurate displayComputer security arrangementsOffice automationInternet accessClient-side
A system for assisting a mobile client interact with associated computers includes a mobile device, a broker, a mini-server and a personal agent. The mobile device transmits requests which include identification information and security information. The requests are transmitted to the mini-server either directly or through the broker. The requests may also be transmitted to the personal agent. Public and restricted requests are transmitted to the mini-server which responds to the requests by providing information accessible through the internet. Private requests are transmitted to the personal agent. Secure connections between the mobile device, broker, mini-server and personal agent are used if required by the security level of the request. The mini-server or personal agent obtains the requested information and formats the requested information according to the requirements of the mobile client identification. The requested information is transmitted to the mobile client in a format which accounts for the visual display limitations of the mobile client.
Owner:WEBLOYALTY COM INC
Computerized method and system for managing the exchange and distribution of confidential documents
A method and system for sending, receiving and managing the exchange of messages between an intranet and multiple external users using a secure server as an intermediary interface for Internet communications. In one form, the secure server operates in a replication mode with a Lotus Domino server wherein secure transmissions are designated by an @secure URL. In another form, secure transmissions are implemented by establishing a secure connection to the secure server using a browser addressing the server URL. The server operating system interfaces with the intranet so that the intranet user can use standard groupware, such as Lotus Notes, to create, send and receive secure documents. External users are notified by normal e-mail of the presence of secure documents at the server and must connect to the server in a secure mode to retrieve documents. Responses to documents are automatically returned to the sender's e-mail server using secure transmission.
Owner:FLEET NAT BANK
System and method for providing a secure connection between networked computers
ActiveUS20050044350A1Improve privacyConnection securityDigital data processing detailsHardware monitoringAuto-configurationOperational system
Owner:RPX CORP
Enabling an on-premises resource to be exposed to a public cloud application securely and seamlessly
InactiveUS20160241633A1Easy accessFacilitating quick connection setupResource allocationData switching networksData setIp address
An application deployed in a public cloud is enabled to access an on-premises resource securely and without requiring additional ports on a firewall. A pair of security gateways is instantiated, one at the cloud, and another located on-premises. Each gateway can access information that is necessary to locate and establish a secure connection to the on-premises resource. In response to a determination that the application needs to access the on-premises resource, the data set is used to locate the resource. A communication request is then issued from the cloud gateway to the on-premises gateway over a socket-based communication channel established between the gateways. The communication request is sent over an HTTP-based protocol such that the application is able to access the on-premises resource without requiring an additional IP address / port to be defined at the firewall. Proxied connectivity is then enabled from the application to the on-premises resource.
Owner:IBM CORP
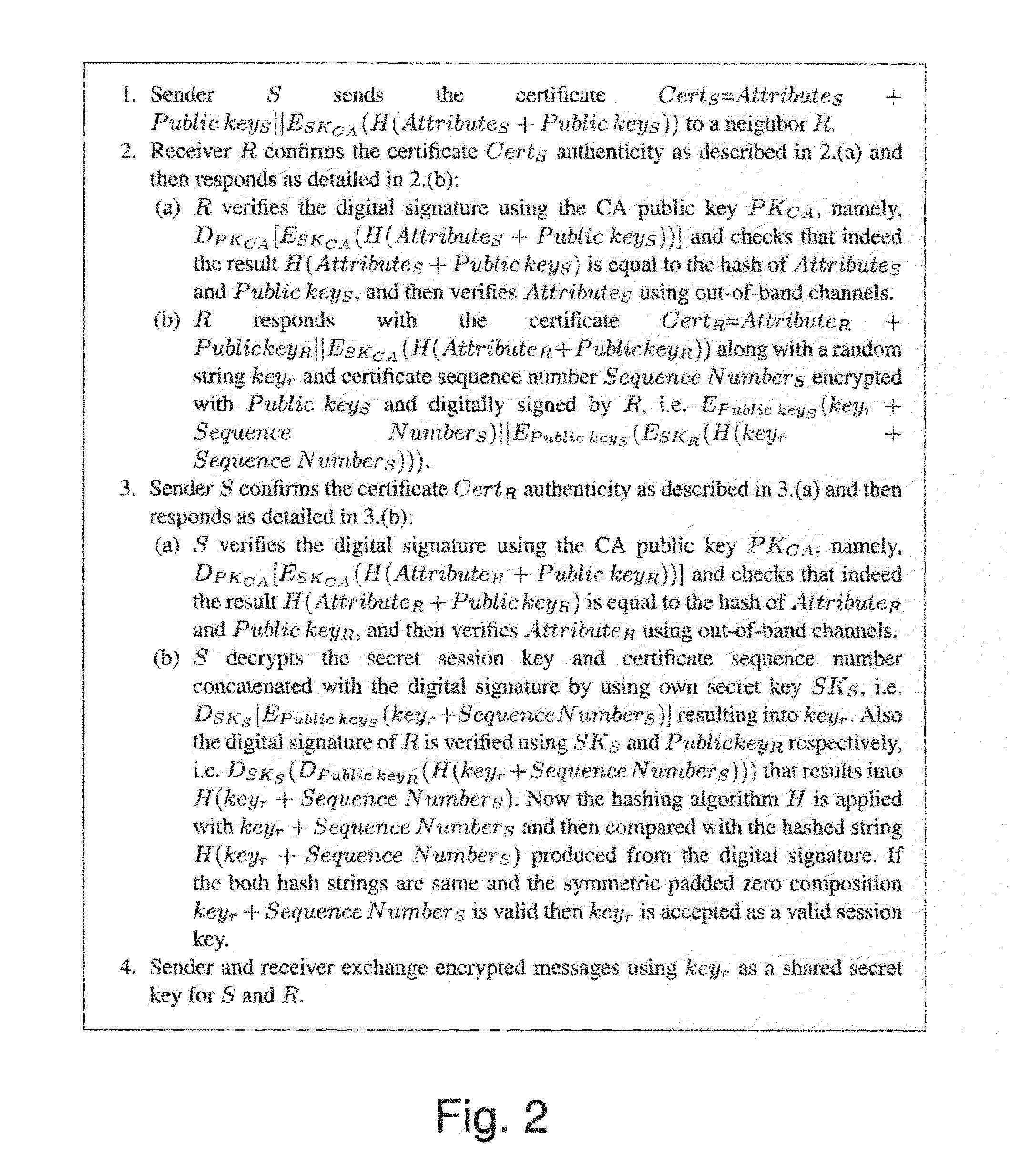
Certificating vehicle public key with vehicle attributes
ActiveUS20150052352A1Public key for secure communicationUser identity/authority verificationImaging processingDigital signature
A method for providing secure connection between vehicles over channels of a wireless communication network, according to which, a first unique pair of digitally signed public key and private key is provided to each vehicle, along with additional vehicle-related data including a visually static collection of attributes of the vehicle. A unique certificate number is generated for each vehicle and monolithic data consisting of the public key, the certificate number and the attributes is signed by a trusted certificate generating authority. Prior to wireless communication between a first vehicle and a second vehicle, a verification step is performed during which the first vehicle sends its unique certificate number to a second vehicle over a communication channel; the second vehicle verifies the authenticity of received unique certificate number of the first vehicle and attributes by a camera that captures attributes which are visible, using image processing means. If the attributes are verified successfully, the second vehicle sends its unique certificate number to the first vehicle over a communication channel, along with a secret session key, which is valid for the current session only. Then the first vehicle verifies the authenticity of received unique certificate number of the second vehicle and attributes by a camera that captures attributes of the second vehicle which are visible, using signal processing means and both vehicles are allowed to securely exchange message or data using the secret session key.
Owner:DOLEV SHLOMI +3
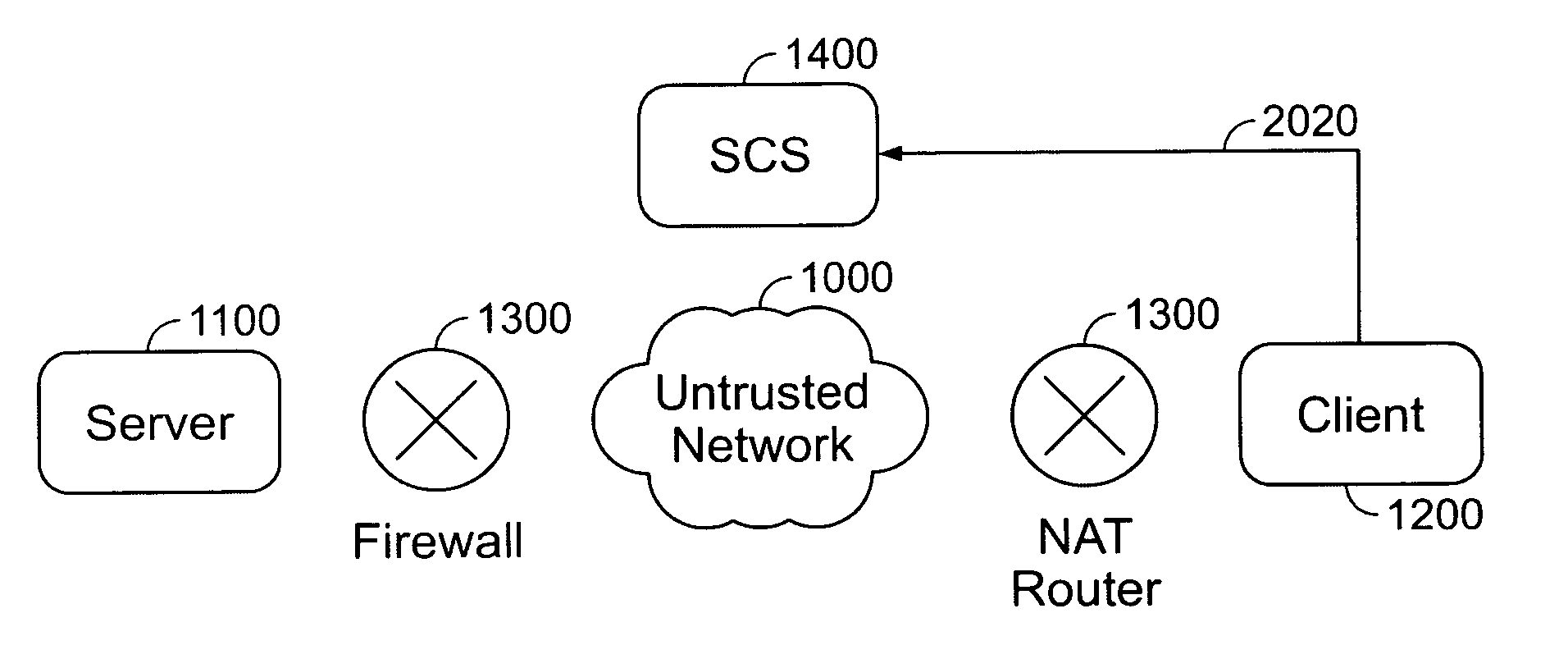
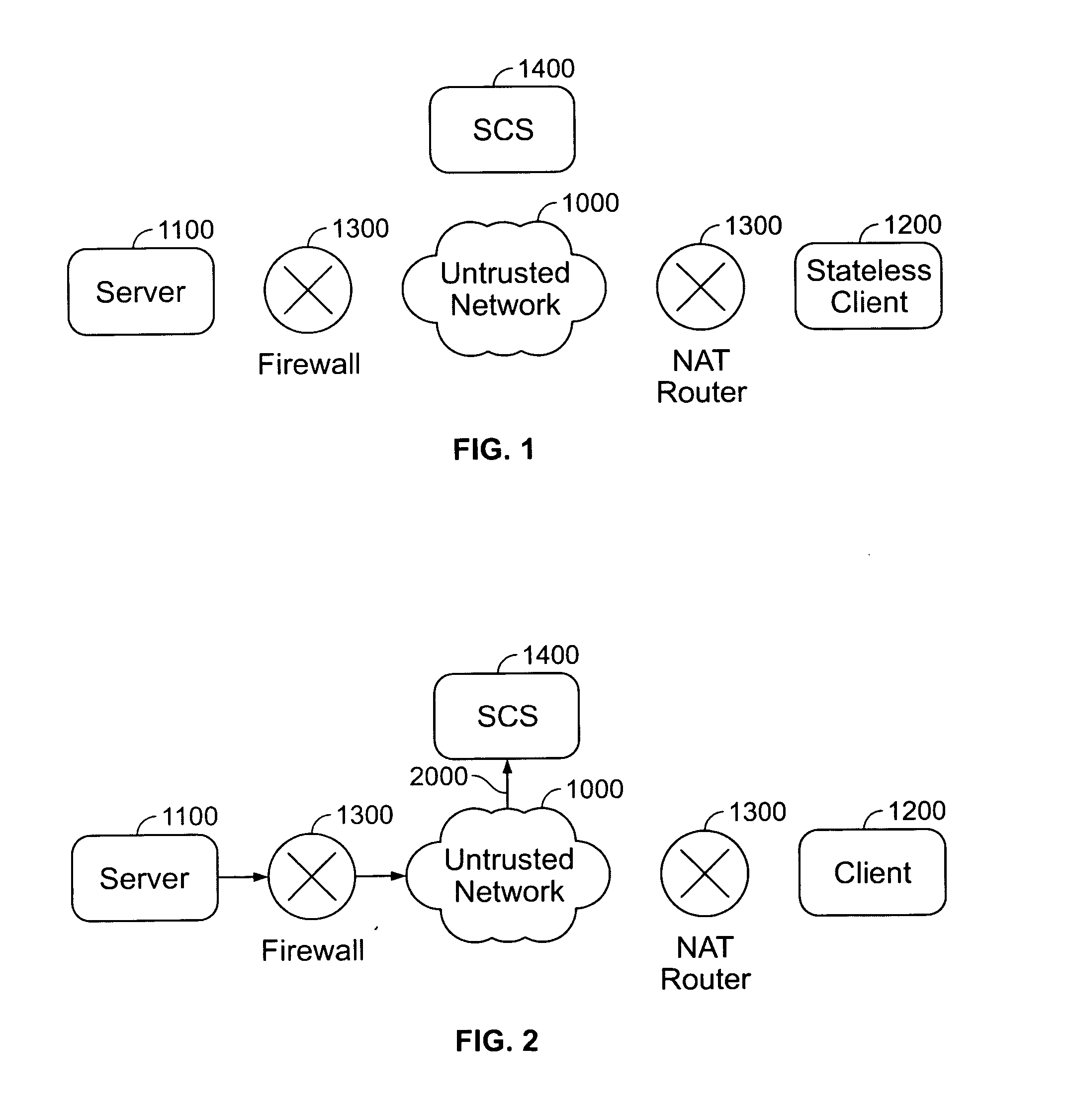
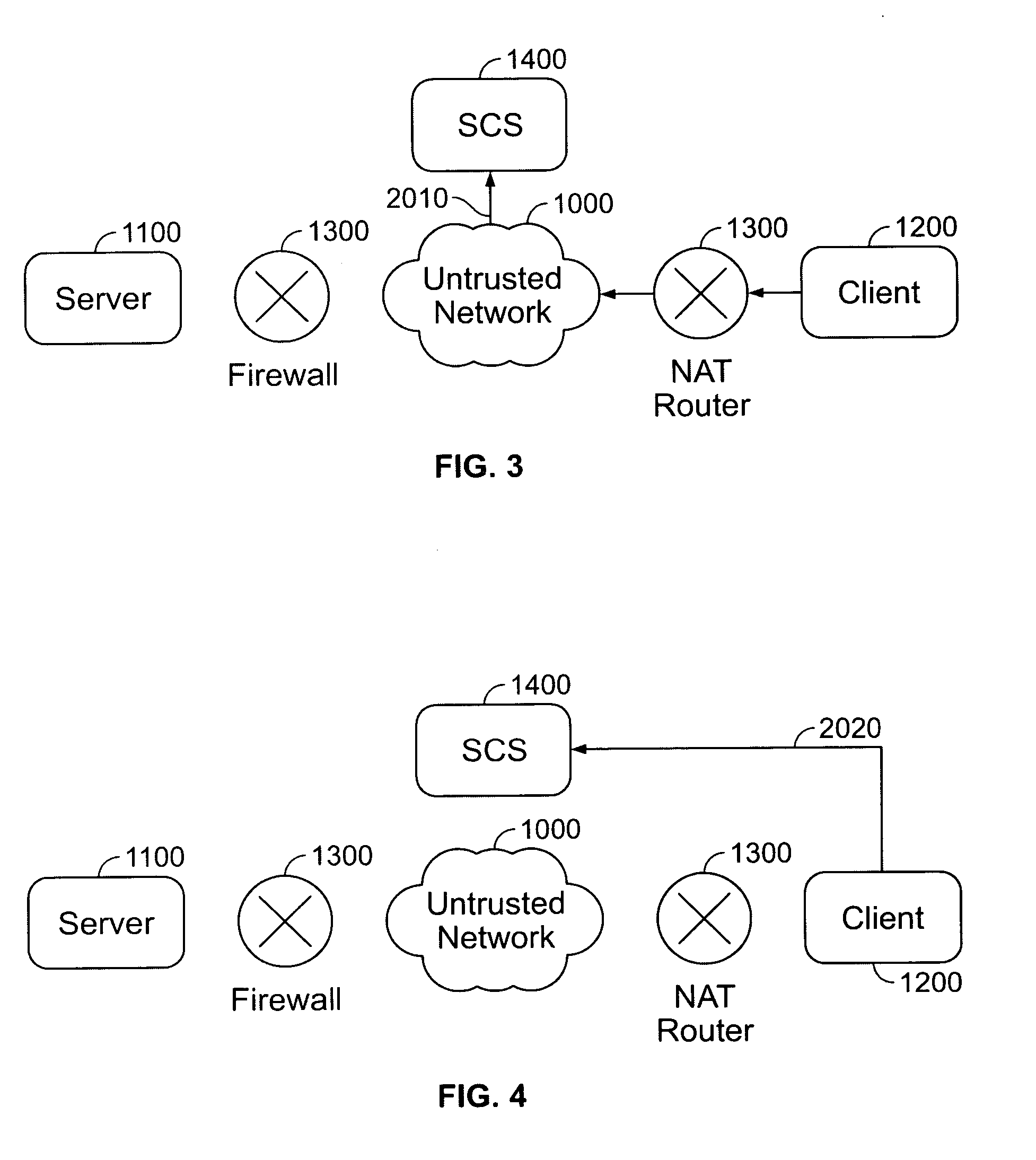
System and method for automatically initiating and dynamically establishing secure internet connections between a fire-walled server and a fire-walled client
InactiveUS20050238034A1Unprecedented ease to useConnection securityData taking preventionData switching by path configurationSession controlThe Internet
A system and method for automatically and dynamically initiating and establishing secure connections between a Server and a Client using a session control server (SCS). Both the Server and the Client are connected to an untrusted network (such as the Internet) through a Network Address Translator or Translation (NAT) router or a firewall. The SCS, independently trusted by both the Server and the Client, brokers the required connection parameters to establish a secure connection between the Server and the Client. The system and method does not require any user configuration on the Client and eliminates the need for the Server to accept explicit connection requests or packets from the Client, thereby allowing the Server firewall to always remain closed to all inbound traffic.
Owner:SIMTONE CORP (US)
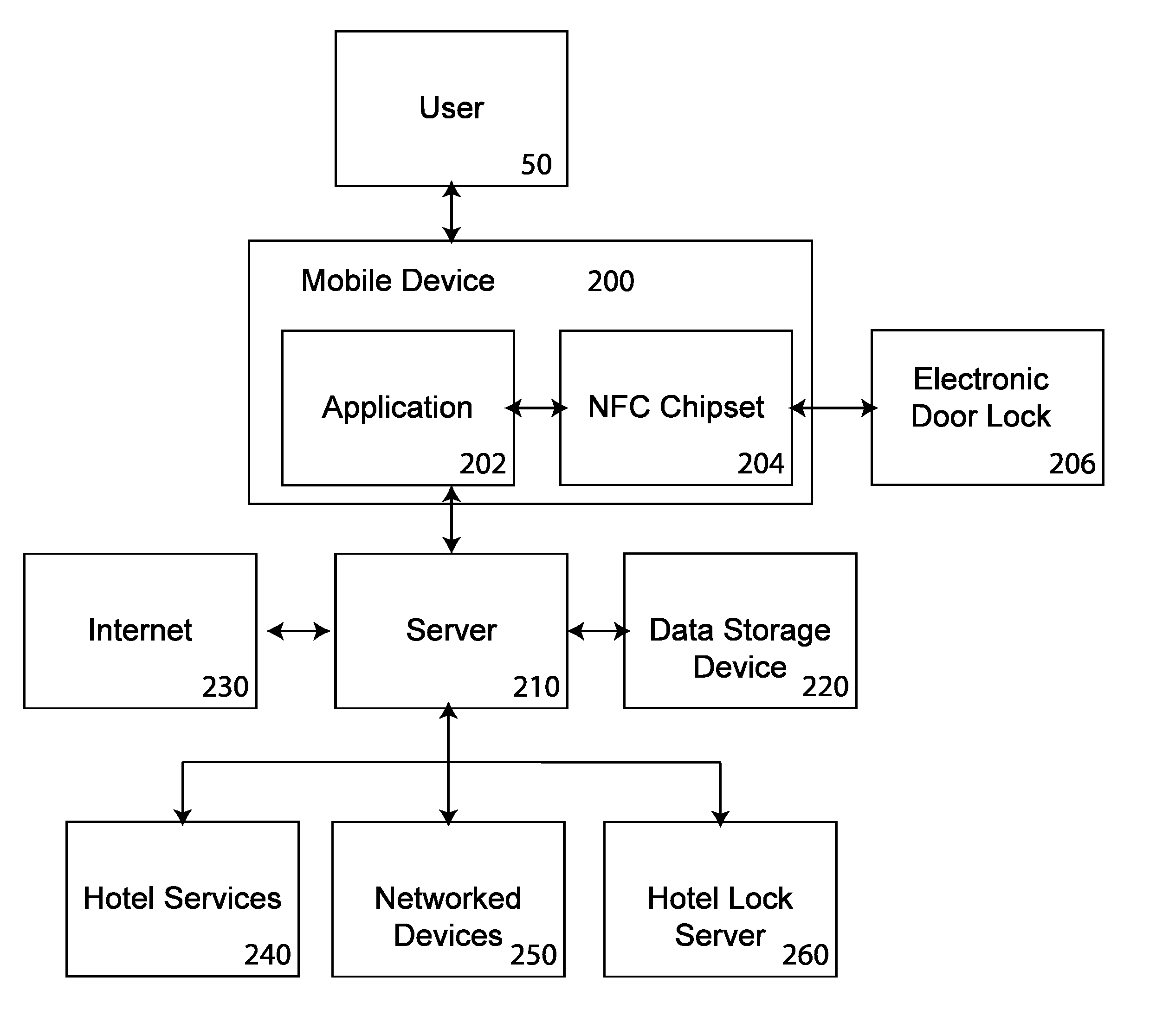
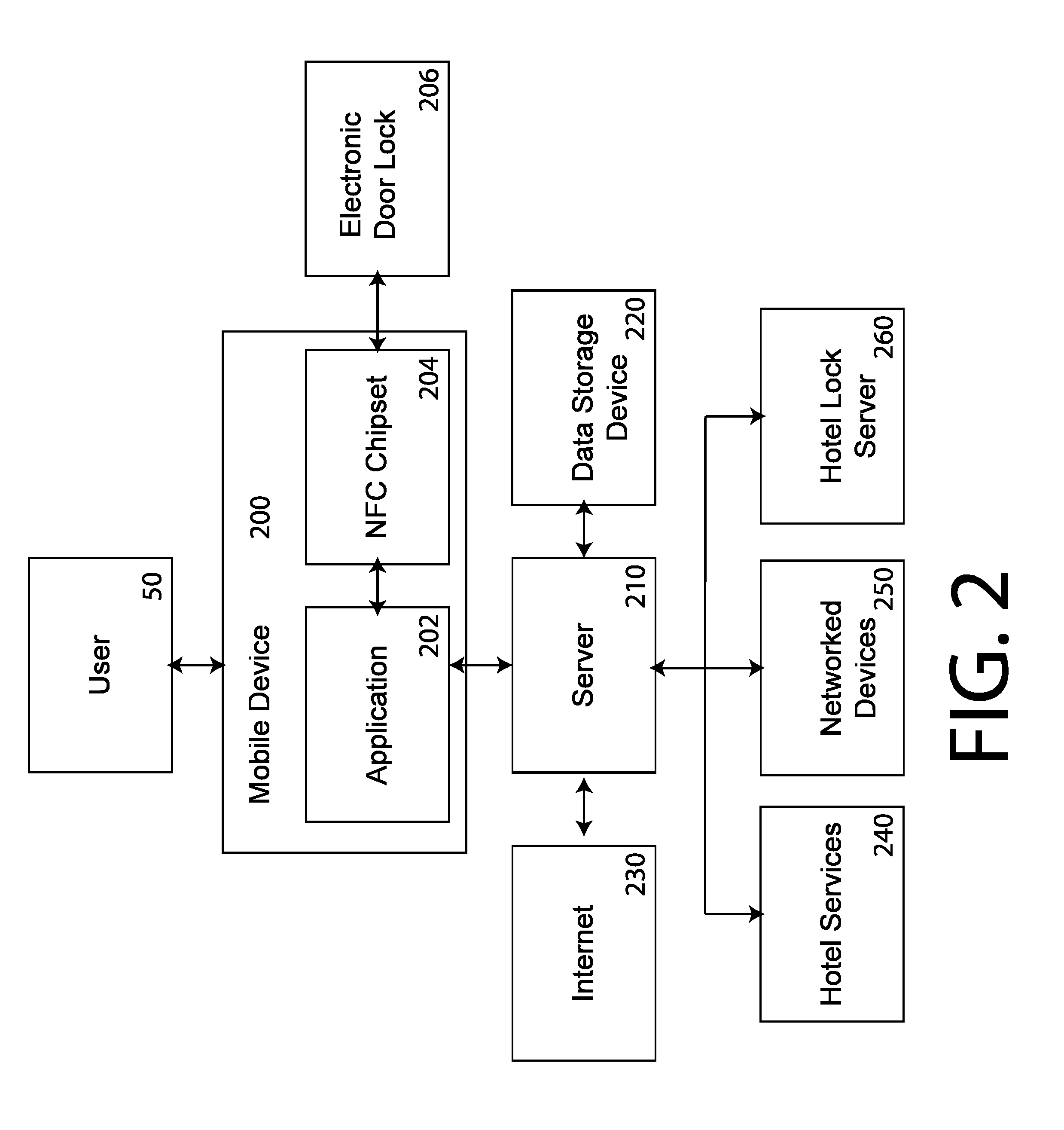
Entry lock control and operation system
InactiveUS20150170448A1Programme controlElectric signal transmission systemsOperational systemEngineering
A system for hotel and residential properties to allow guests and residents security access using electronic devices already in the possession of the user. The system would allow hotel and residential properties to provide guests and residents with an inexpensive near field communication (NFC) tag to affix to their mobile device. Such an NFC tag could be registered by the hotel front desk upon check-in, or at the first reader the guest encounters at the hotel, in conjunction with their mobile device. Additionally, the system allows for the use of peer-to-peer (P2P) NFC to create a secure connection and allow data transfer between a NFC enabled door lock and a mobile device, allowing for an encrypted door code to be used.
Owner:ALTERNATIVE STRATEGY PARTNERS PTE LTD
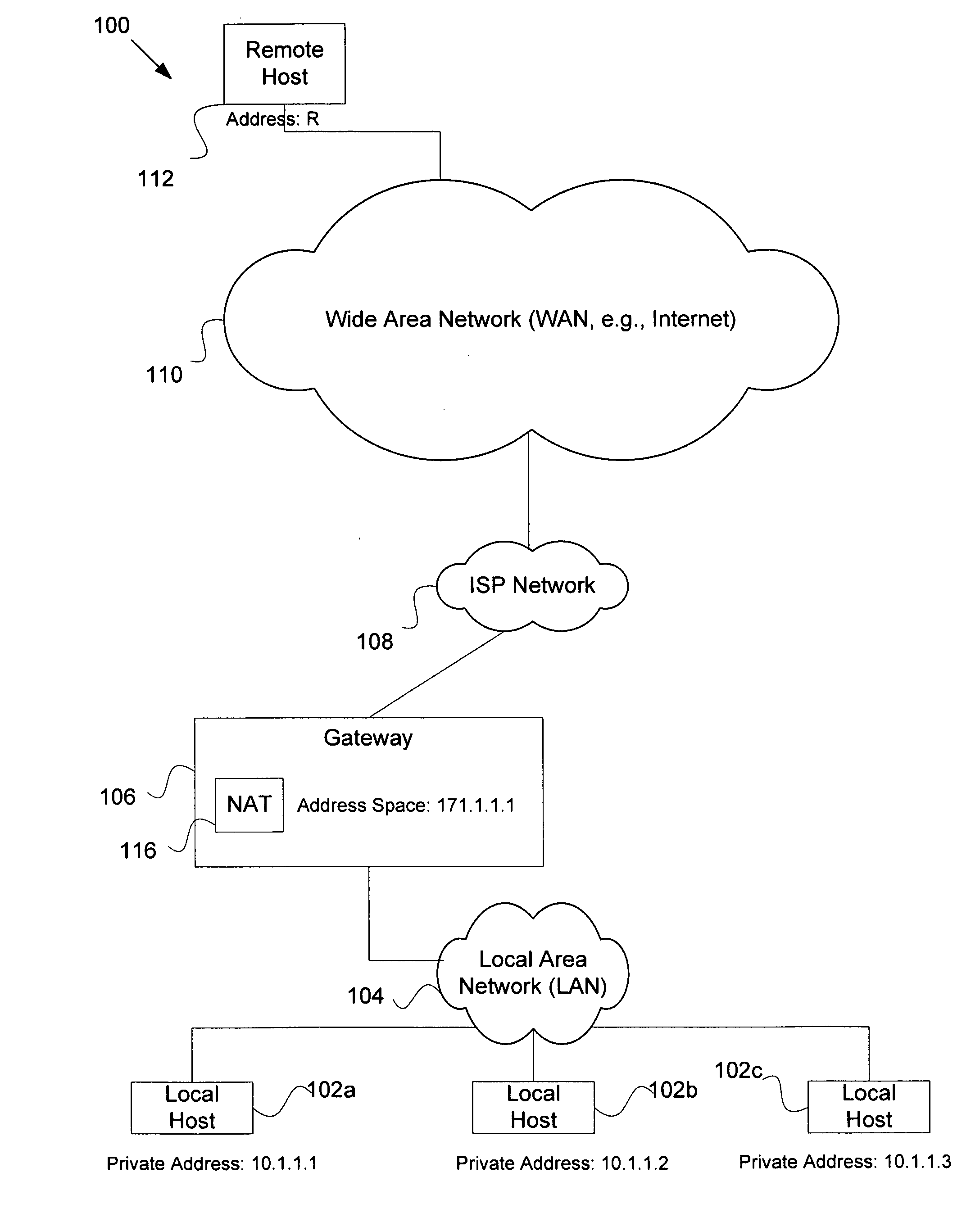
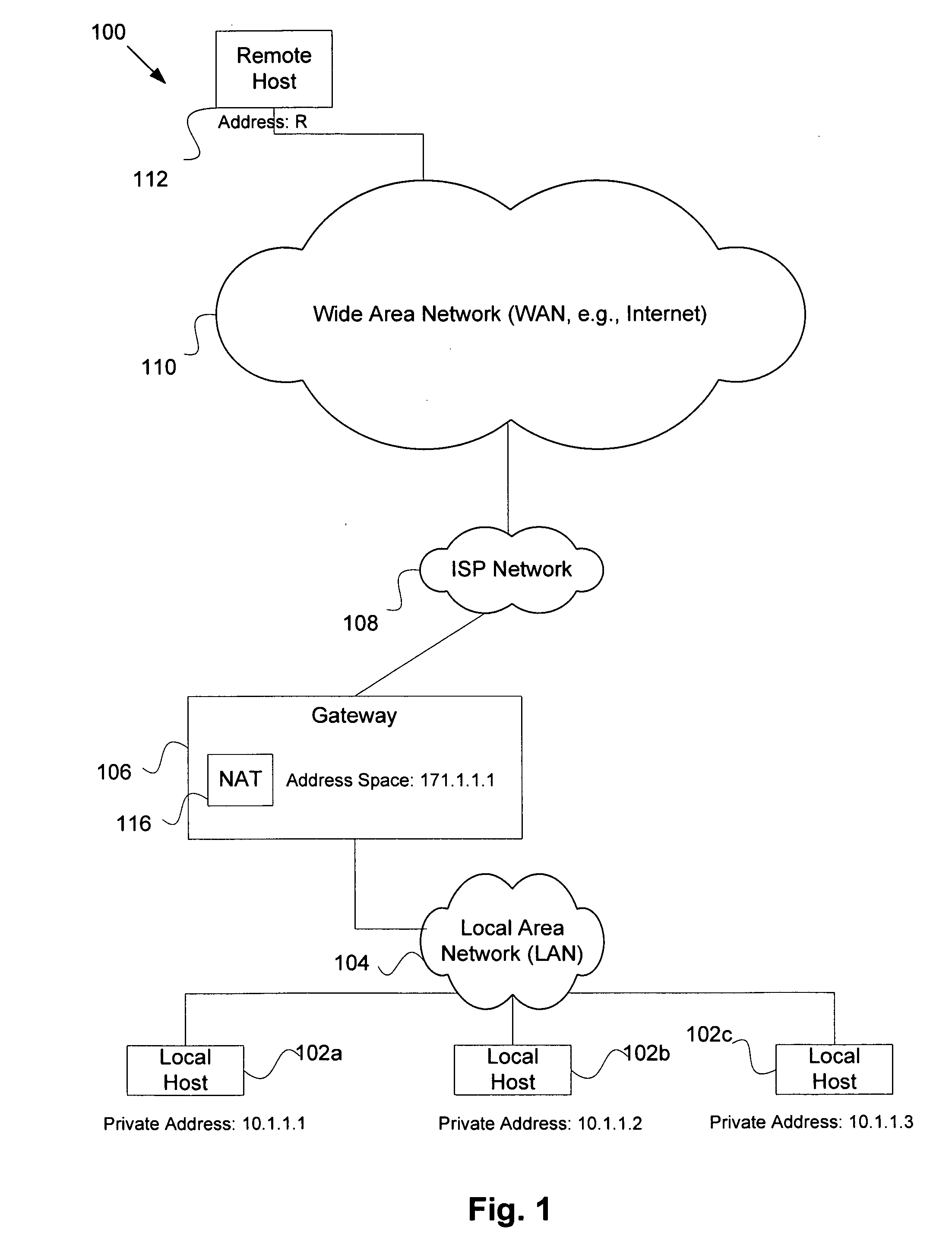
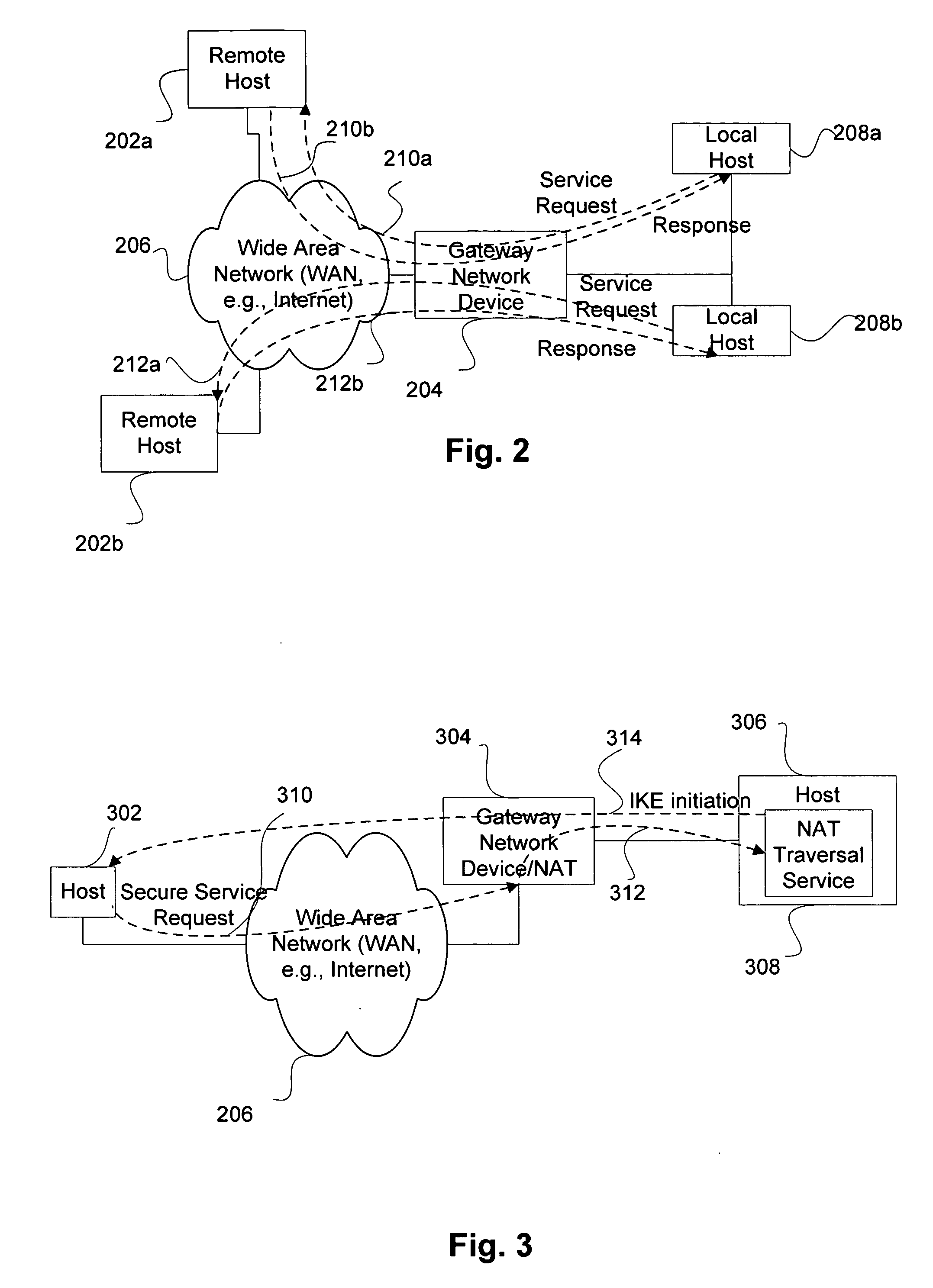
Service for NAT traversal using IPSEC
Disclosed are methods and apparatus for methods and apparatus for facilitating a secure connection between a first and a second node in a computer network where one or both of the nodes may or may not reside behind a network address translation (NAT) enabled gateway. Embodiments of the present invention provide a seamless integration by providing a uniform solution for establishing secure connections, such as IPSEC, between two nodes irrespective of whether they are behind a NAT-enabled gateway or not. In general, a gateway is operable to receive a request from a remote host for a secure connection to a local host that within the home network of the gateway. The gateway then forwards this received request to a NAT traversal service. The NAT traversal service receives the request and then automatically sends an initiation message to set up a secure session, e.g., performing authentication and exchanging keys. In a specific aspect, the setup data utilizes an IKE (Internet Key Exchange) initiation message that is sent to the originator of the request via the gateway. Upon receipt of this initiation message, the gateway is then able to set up a two way connection to allow other setup data to flow between the remote and local hosts to complete the setup session and then secure data to flow between the remote and local hosts in a secure communication session, such as in IPSec or VPN session.
Owner:CISCO TECH INC
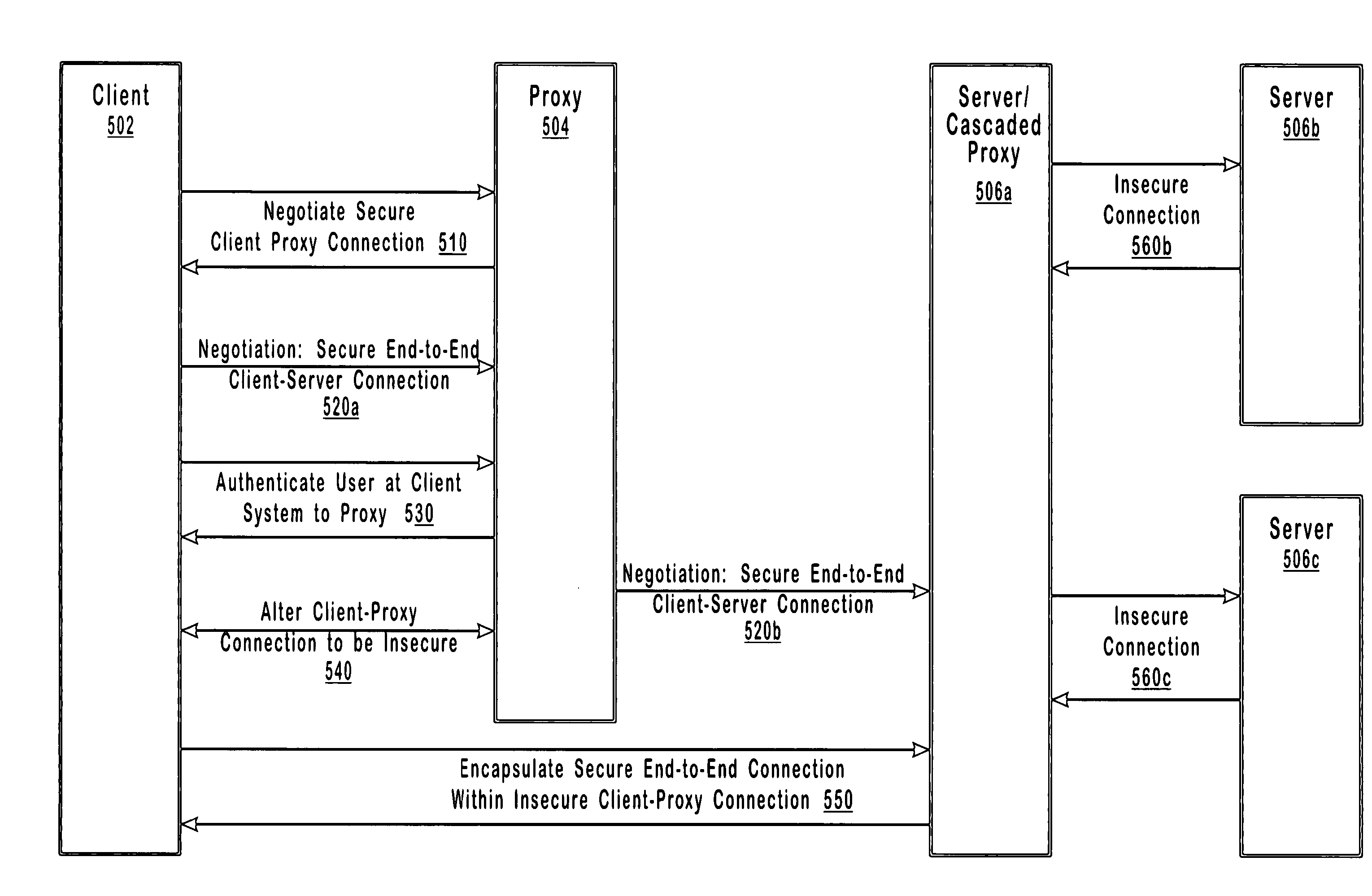
Negotiating secure connections through a proxy server
Owner:MICROSOFT TECH LICENSING LLC
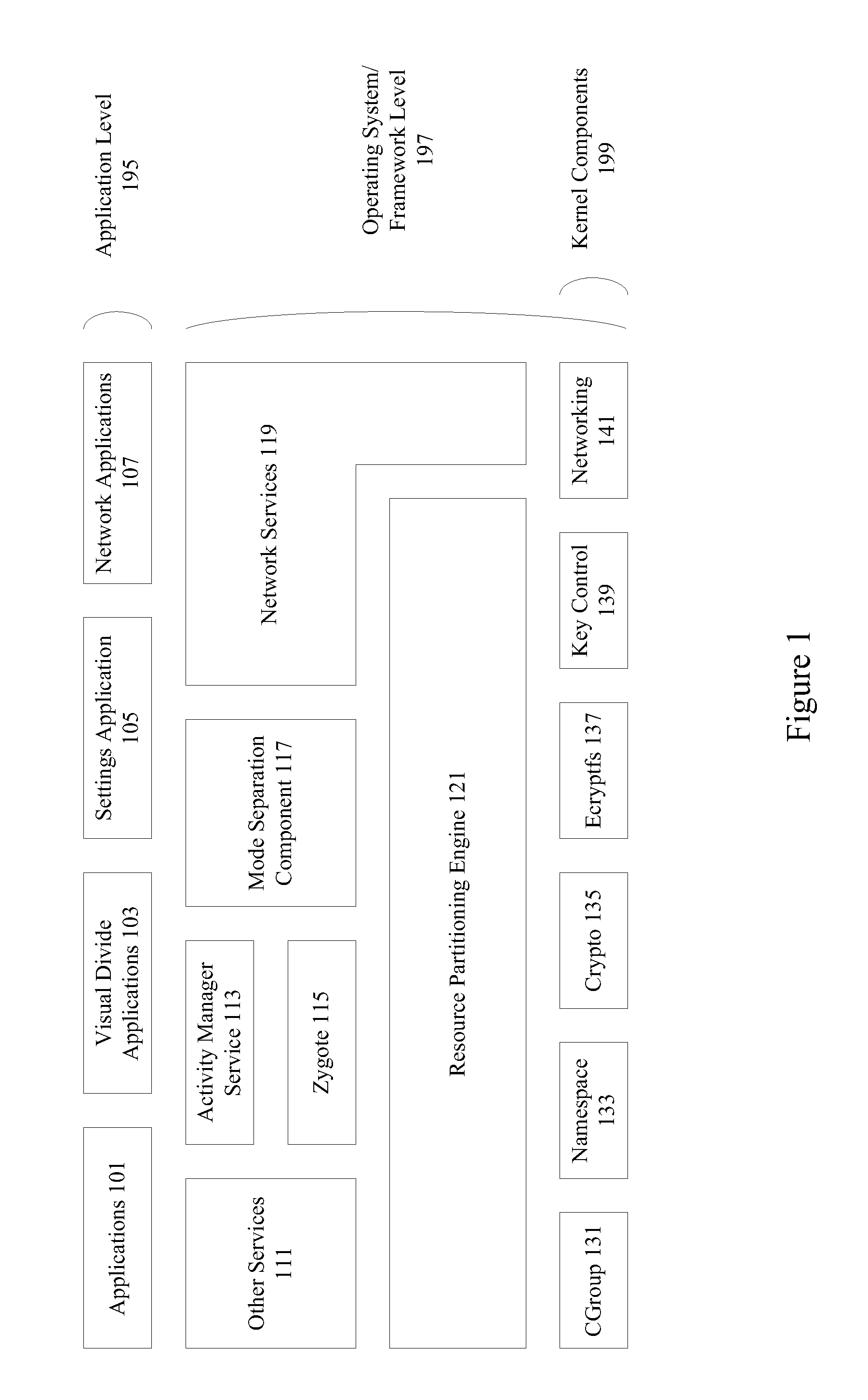
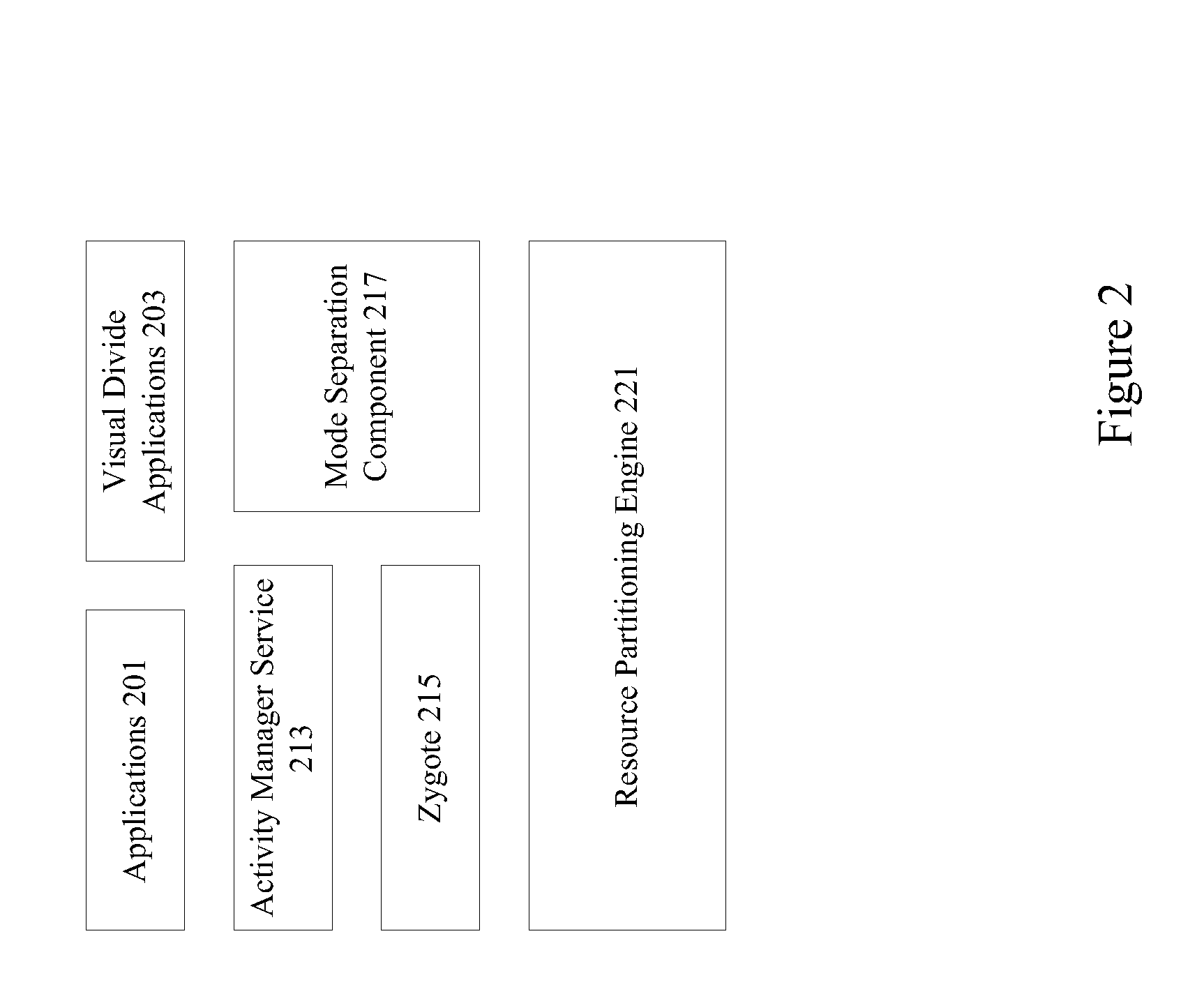
Mode sensitive networking
Mode sensitive networking is provided to allow mode specific communications using a mobile device. If a device has an established secured connection and an application is running in work mode, packets are routed through the secure connection. If the device has an established secured connection but an application is running in personal mode, packets are routed through an alternate connection. Secured connections may be established by using privileged applications. A device and associated applications may have access to different servers, sites, and destinations based on a current mode.
Owner:DELL PROD LP
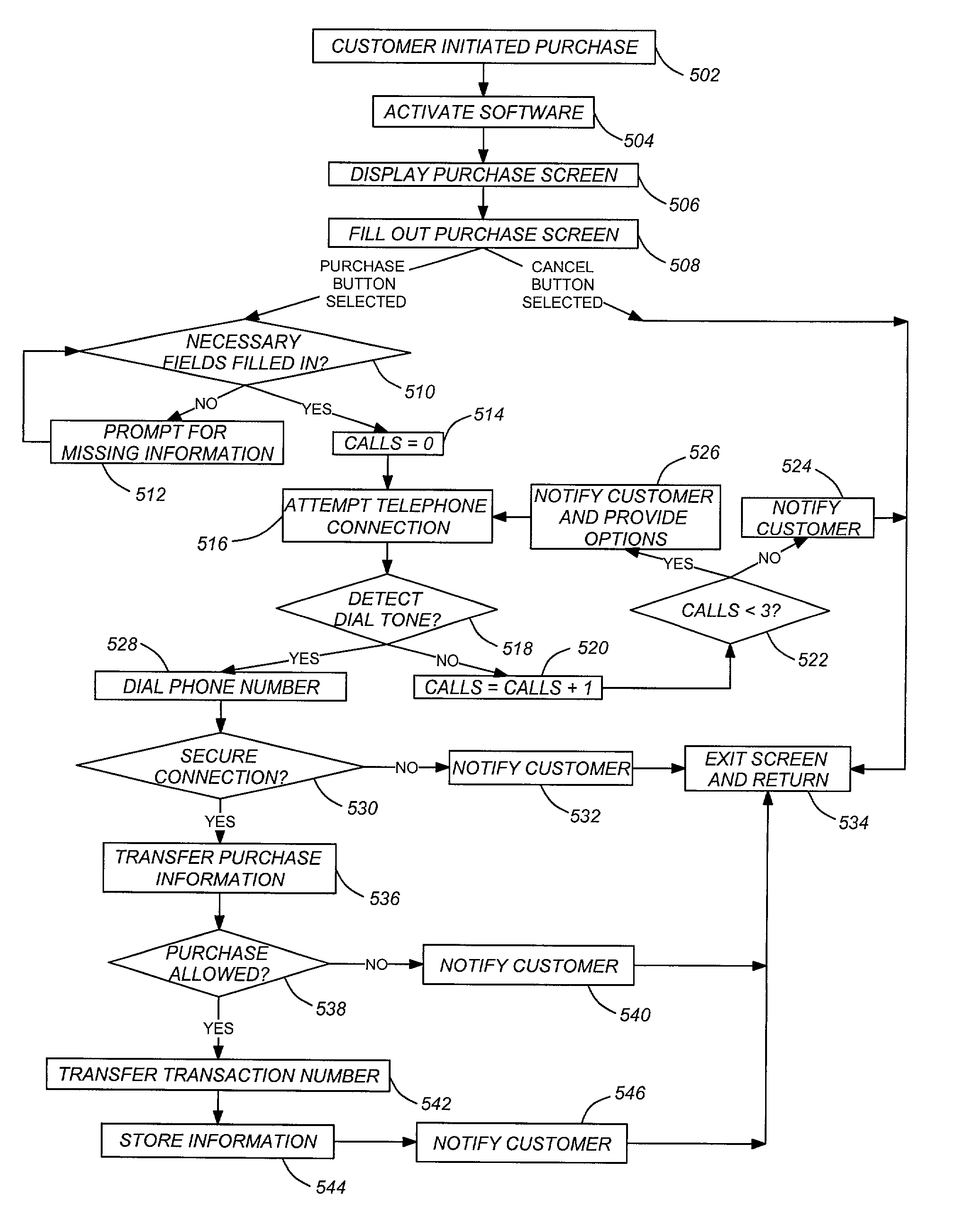
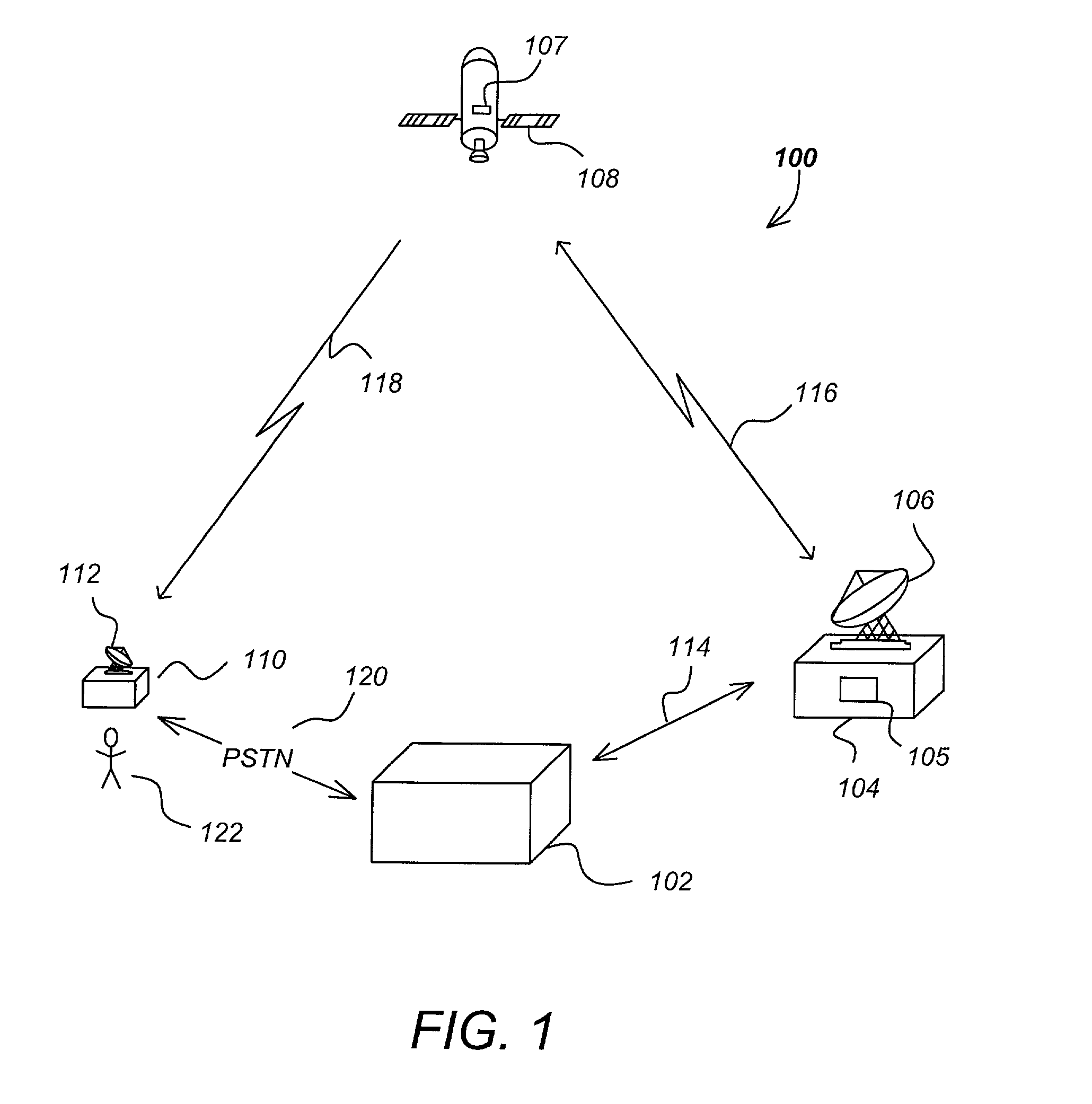
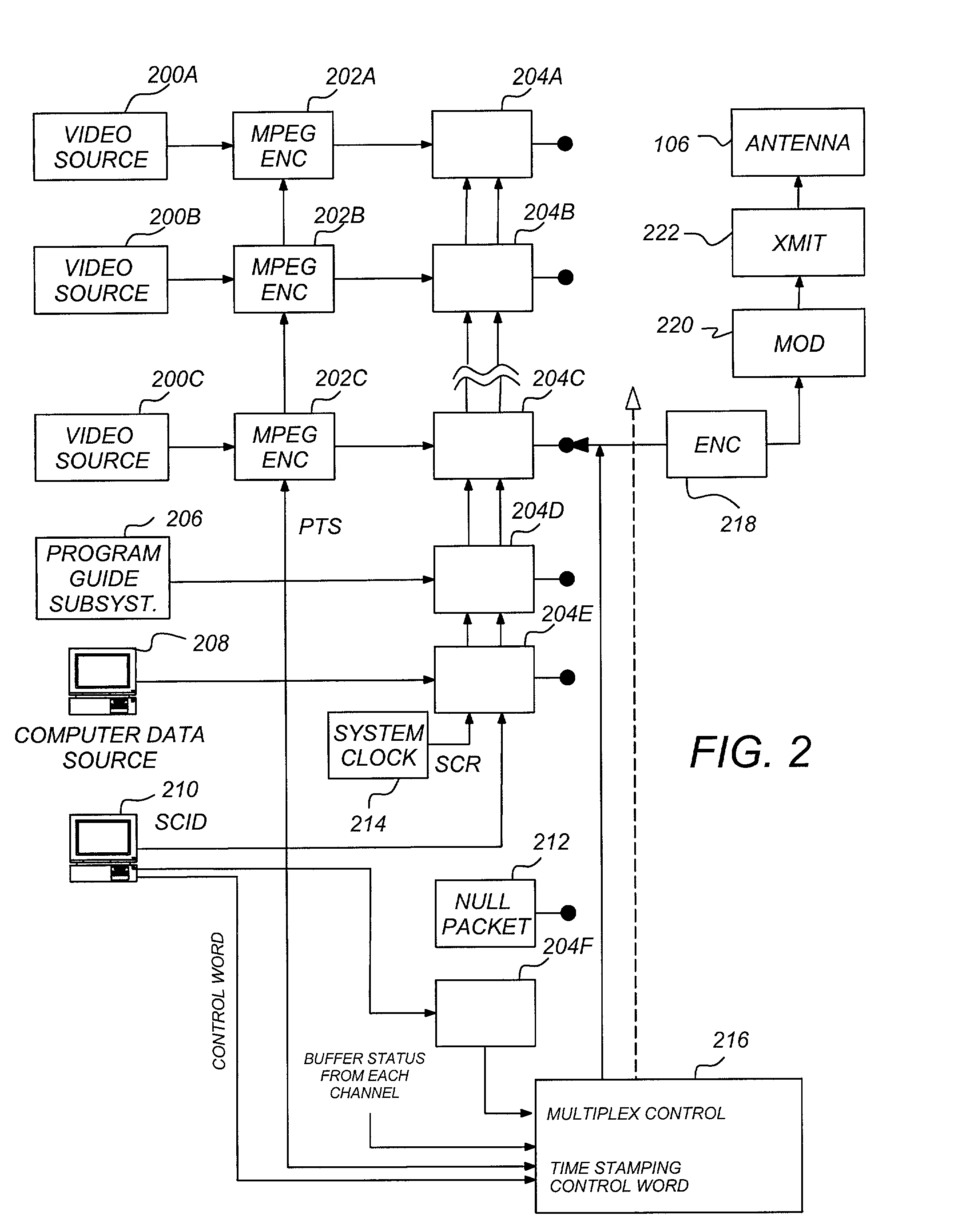
Pay-TV billing, system activation, and E-commerce using a pay-TV receiver
InactiveUS6993499B2Reduce in quantityTelevision system detailsDigital computer detailsCredit cardModem device
One or more embodiments of the invention utilize a receiver as a terminal to enable commercial transactions to take place that may or may not be coupled with programming that is being broadcast and to provide customers with the option of having their pay-TV bills charged directly to a credit card. The pay-TV provider could allow the customer to activate their pay-TV systems, with the programming package of their choice, without having to call the pay-TV customer service. Utilizing the fact that receivers may have built in modems that are connected to phone lines, connections can be made through that phone line to initiate, transfer, and purchase services and merchandise. If the receiver can successfully establish a secure connection with the pay-TV service provider, vendor, or credit card provider and the billing information is successfully transferred, then the merchandise can be shipped or the appropriate signals can be sent to the receiver to activate the service that the customer has selected. This would have the potential of significantly reducing the number of customer service calls to the pay-TV service provider. Instead of the pay-TV service provider being responsible for billing, debt collection, etc. this now becomes the responsibility of the credit card company.
Owner:HUGHES ELECTRONICS
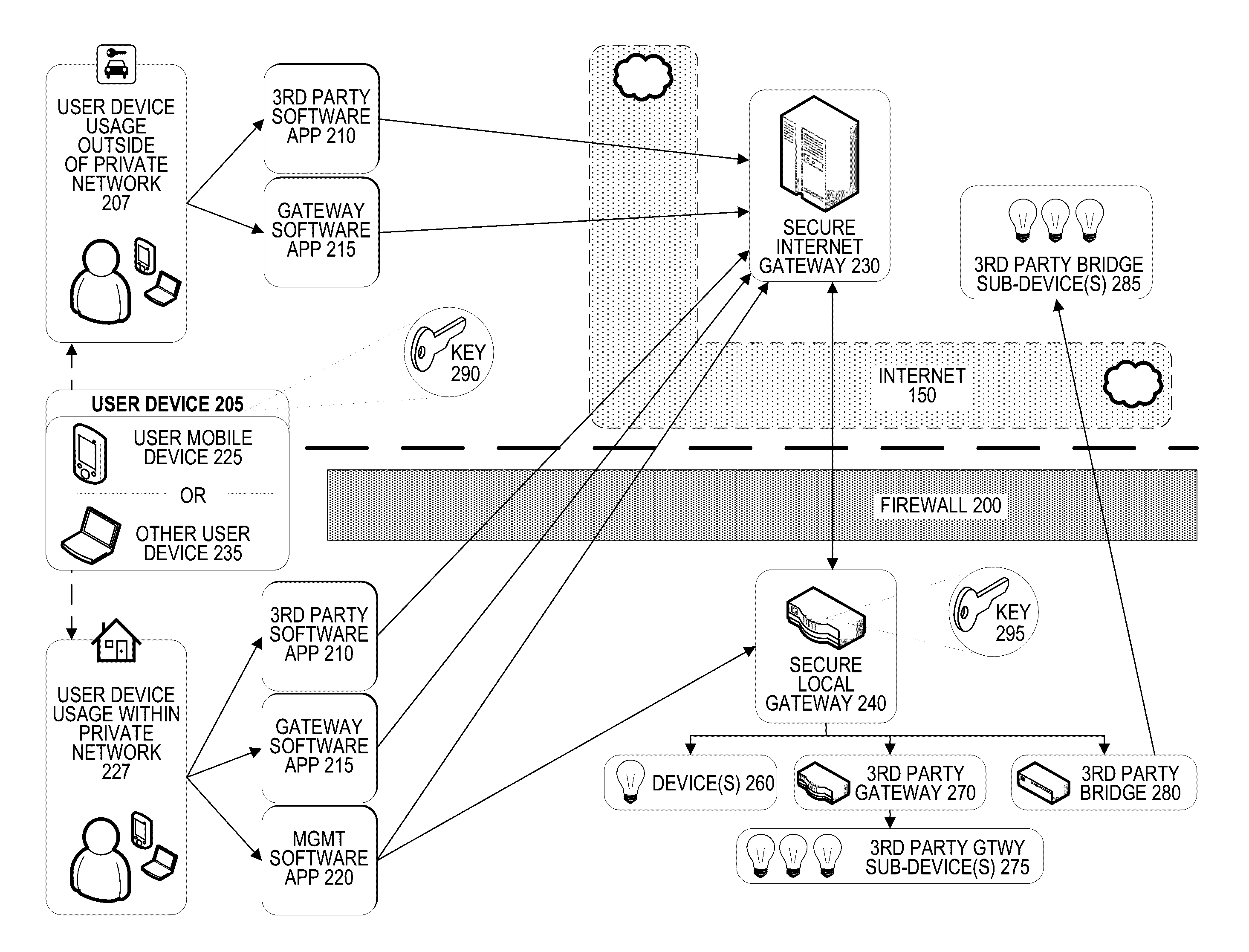
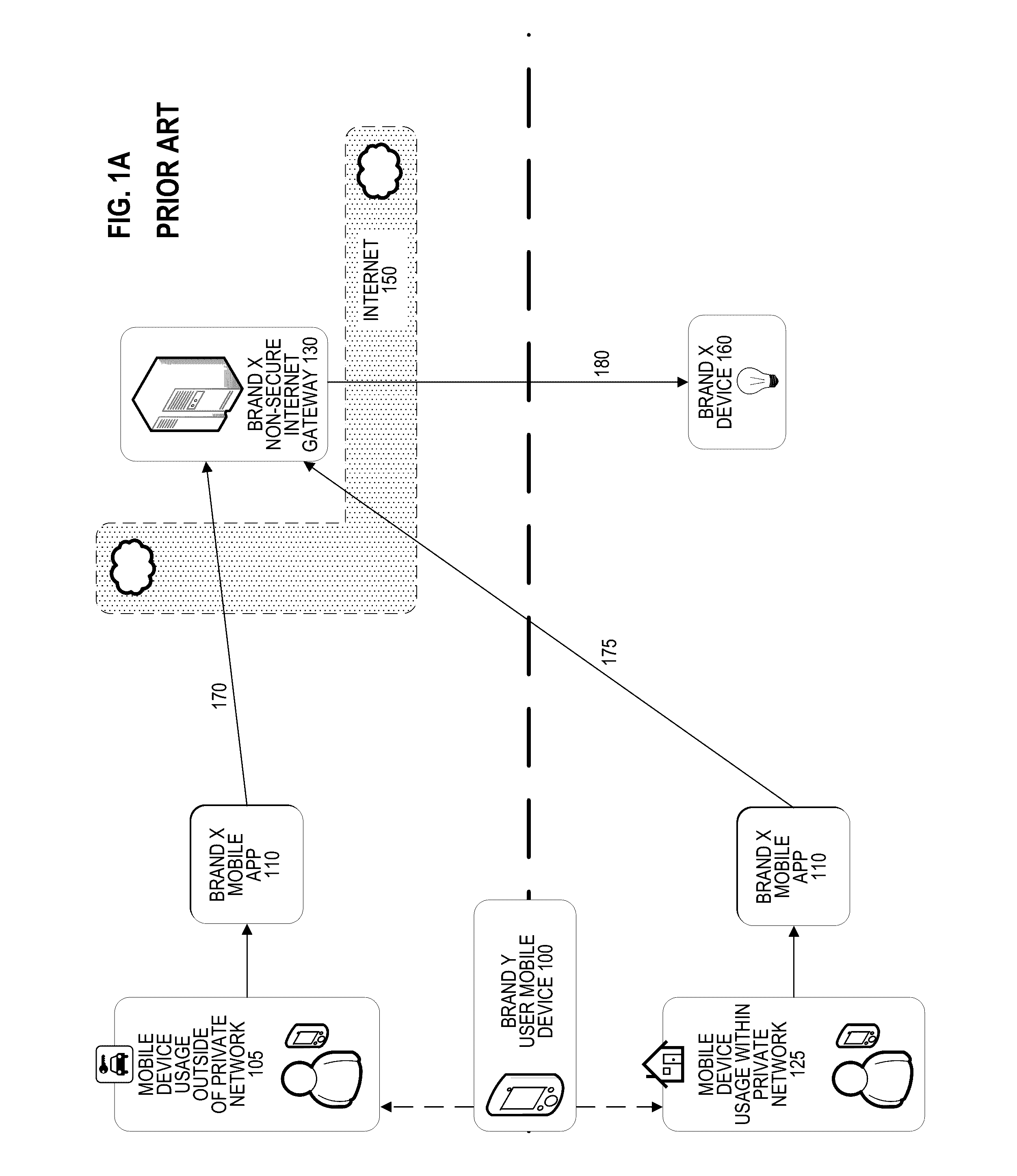
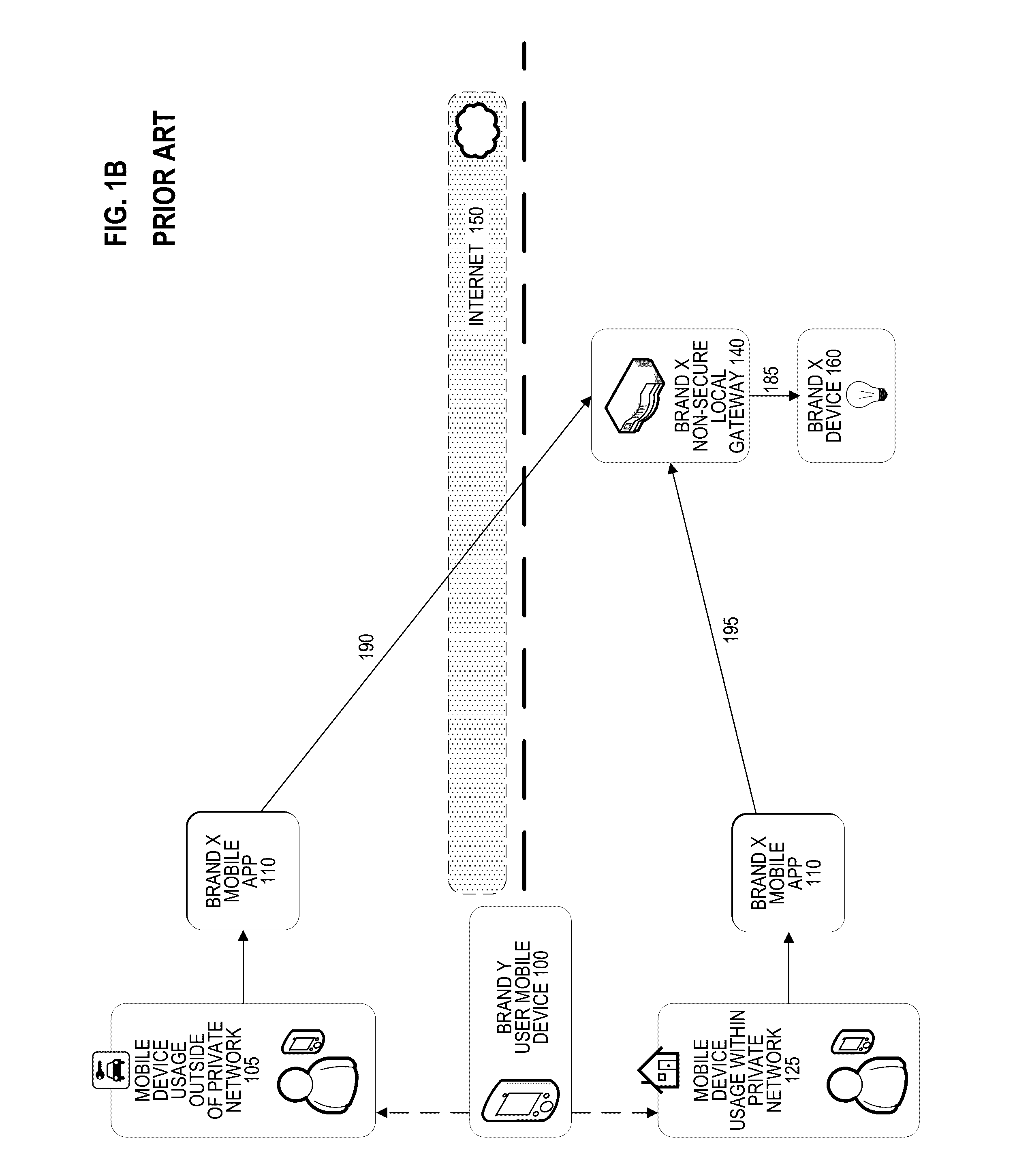
Securing internet of things communications across multiple vendors
A secure connection between a user mobile device and a “Internet-of-Things” network-connected device (e.g., a home appliance or a vehicle) may be provided using an internet gateway residing in the public internet and a local gateway residing in a private network behind a firewall. The user device may receive an input through a software application and may generate an electronic instruction based on the input. The user device may then encrypt the electronic instruction and send the encrypted electronic instruction to the internet gateway over a secure connection (e.g., SSH, TLS). The internet gateway then sends the encrypted electronic instruction to the local gateway, which decrypts the encrypted electronic instruction, interprets it, and generates and transmits a device instruction to communicate with the network-connected device, either directly or through an intermediary device such as a third-party bridge or hub. Only the user device and local gateway have encryption / decryption keys.
Owner:SONICWALL US HLDG INC +1
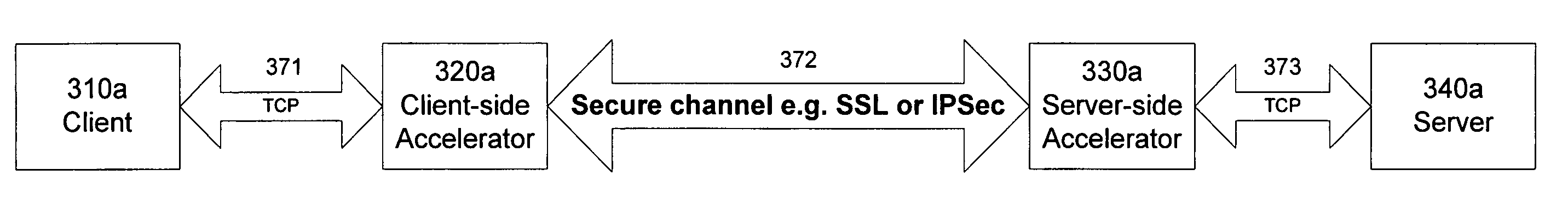
Split termination for secure communication protocols
ActiveUS8613071B2Avoid problemsDigital data processing detailsComputer security arrangementsSecure communicationClient-side
Owner:RIVERBED TECH LLC
Wireless LAN safety connecting-in control method
InactiveCN1455556AReduce hardware complexityImprove security strengthMultiple keys/algorithms usageUser identity/authority verificationTelecommunicationsThree stage
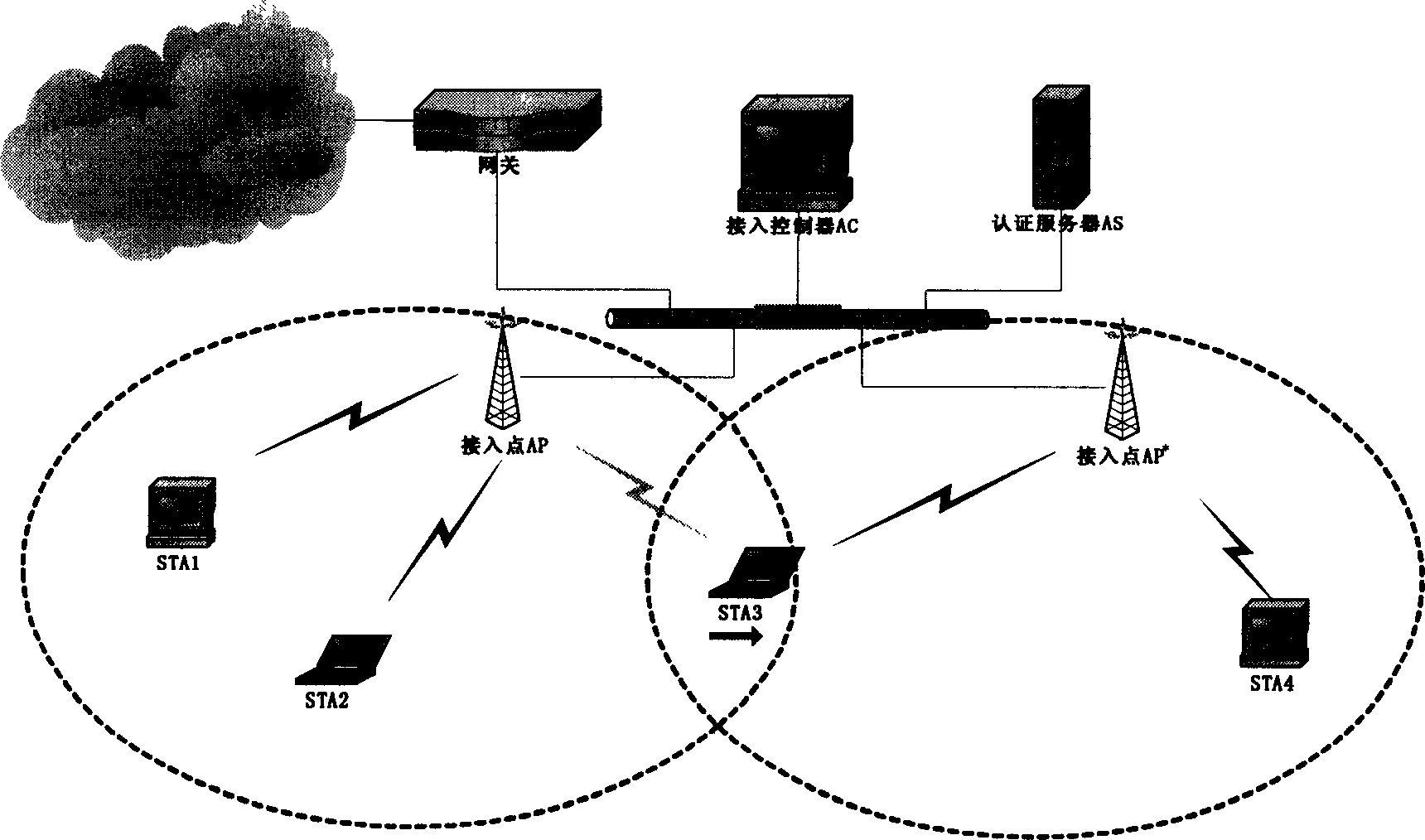
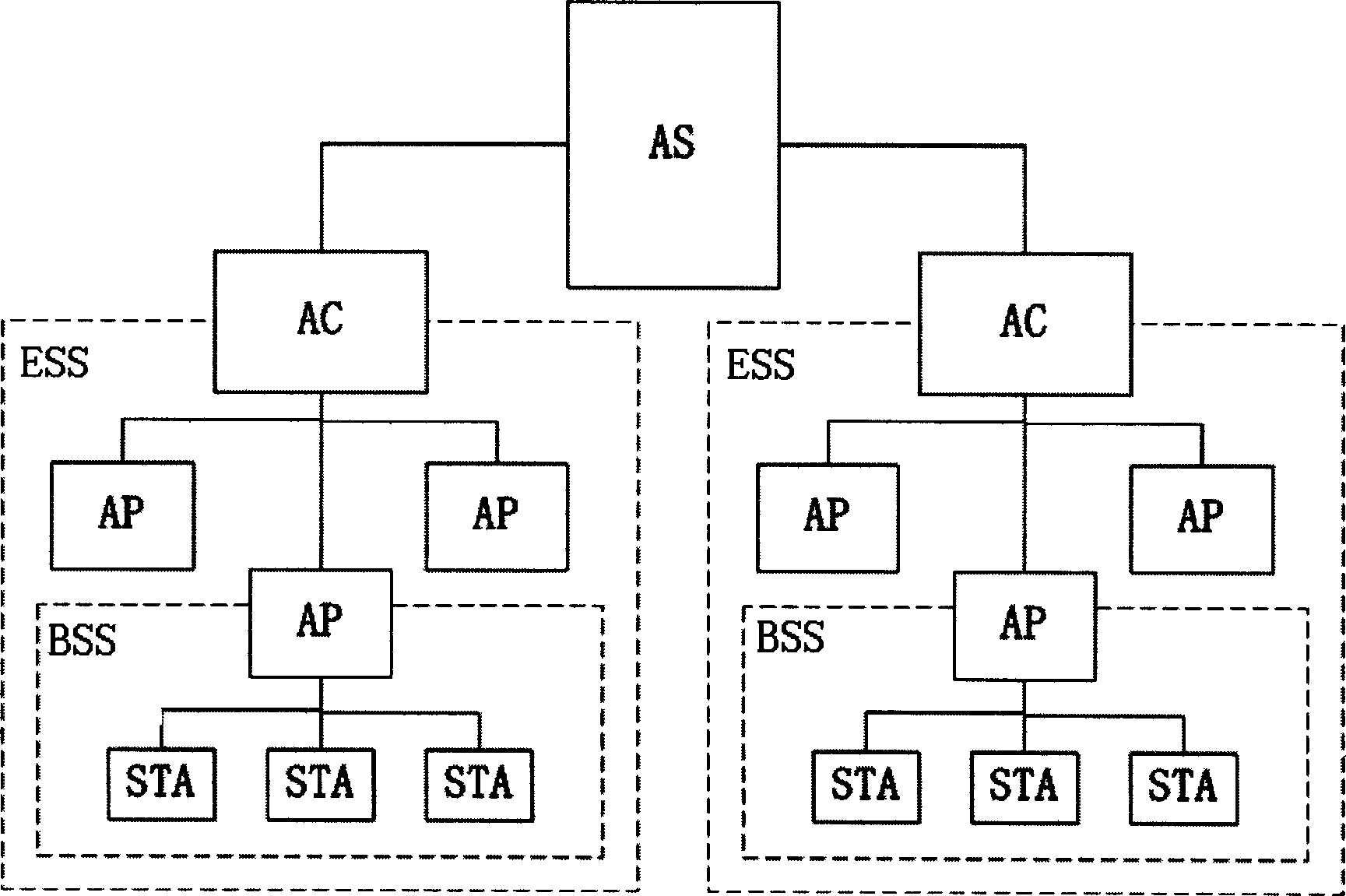
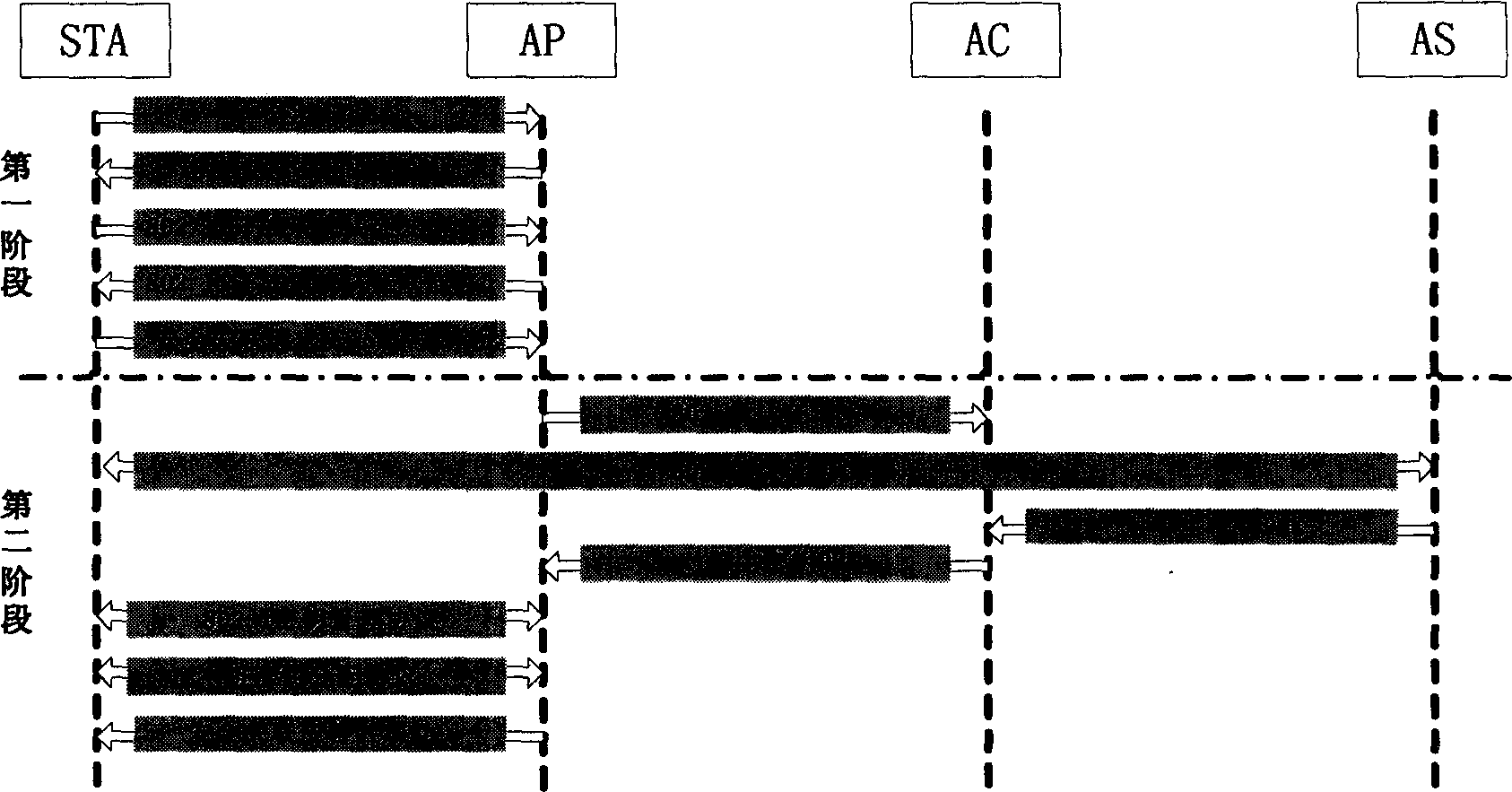
The control course includes three stages: setting up connection and safety performance bargin as broadcasting connection request by STA and all AP at the area to send connection response message declaring all data protective method to STA; setting up safe correlation a sending 802.1x authentication request message to AC by AP after STA safe correlation request received to request AC to use 802.1x authentication protocol to make authentication for STA by AS; resetting up safe correlation as switching the correlative switch in point from one area to another by STA as well as setting up connection and bargaining safety performance by STA and AP* as per steps in the first stage under the roaming condition with AP* service range being entered by STA.
Owner:SOUTHEAST UNIV
Method for establishing a secure and authorized connection between a smart card and a device in a network
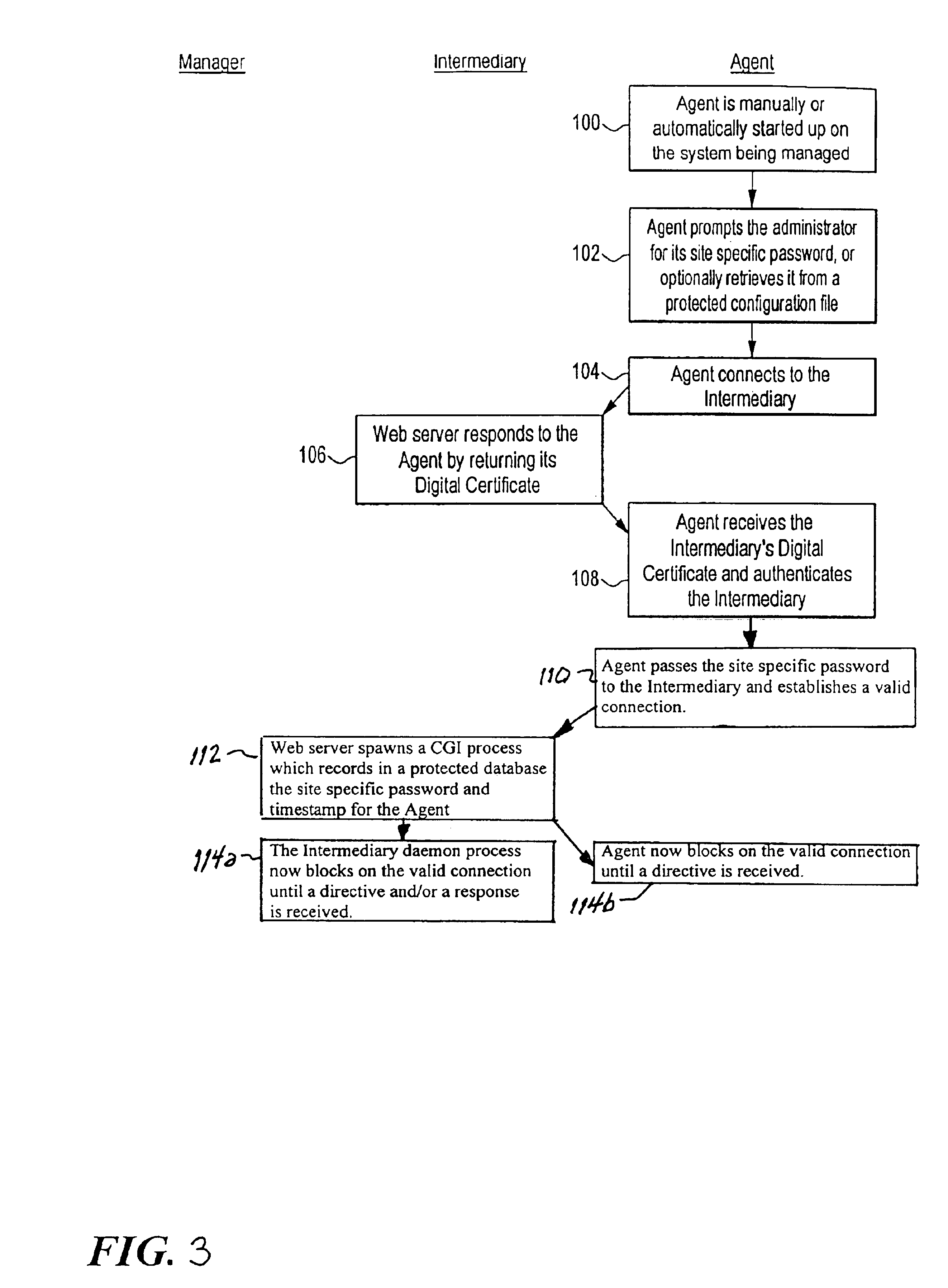
InactiveUS20130091556A1Protection interfaceSecure transmissionDigital data processing detailsMultiple digital computer combinationsSafety ConnectSmart card
It is provided a method a method for establishing a first secure and authorized connection between a smart card and a first device in a network, wherein the first device comprises a second secure connection to a second device, wherein the method comprises storing a first security data; transferring the first security data between the first device and the second device; providing the first security data at the first device; establishing a binding between the smart card and the first device via the first secure and authorized connection utilizing the first security data; authorizing the binding between the smart card and the first device; and sending a second security data from the smart card to the first device via the first secure and authorized connection whereas the second security data may be usable for authentication of the first device to the network.
Owner:NOKIA SOLUTIONS & NETWORKS OY
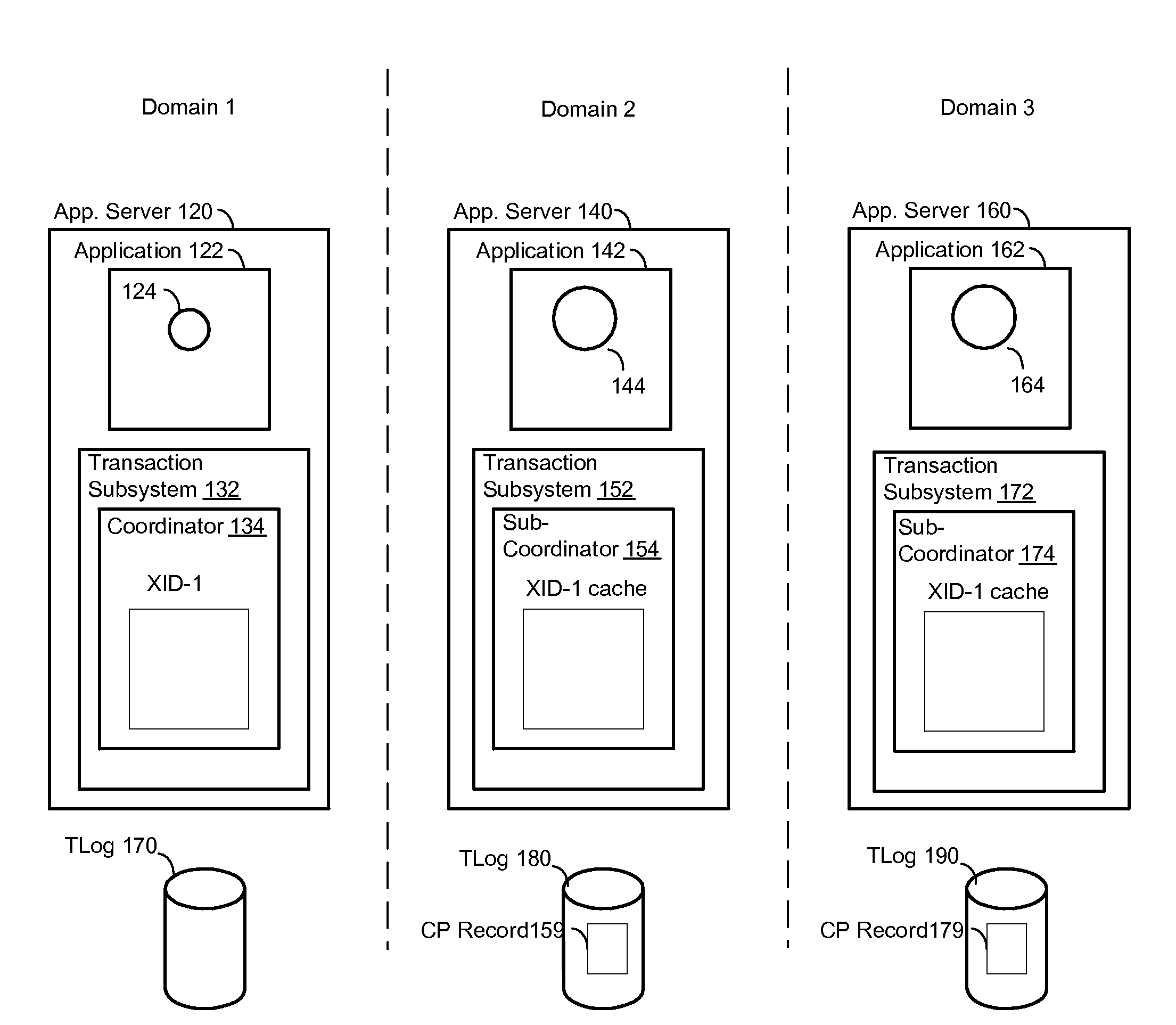
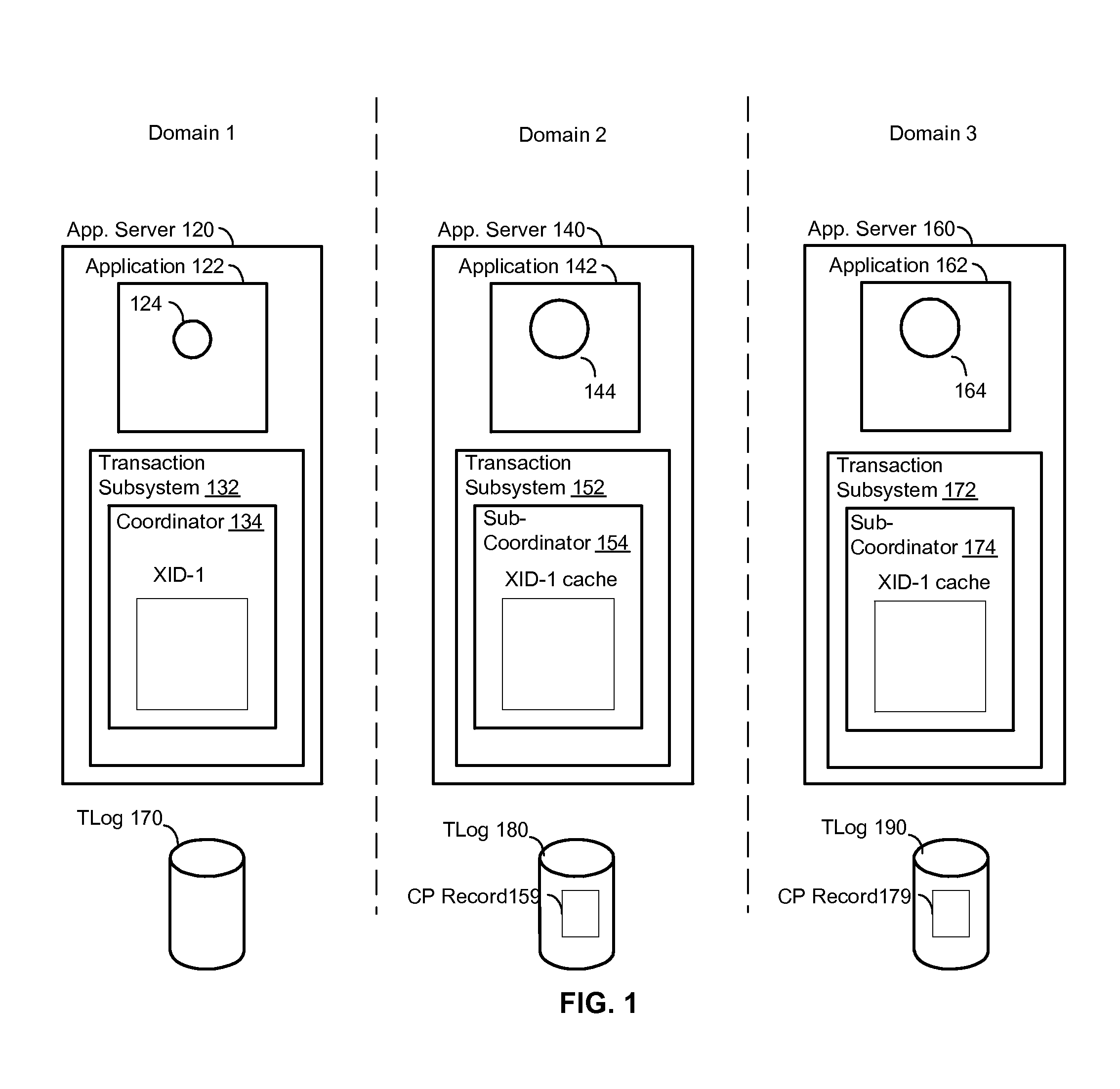
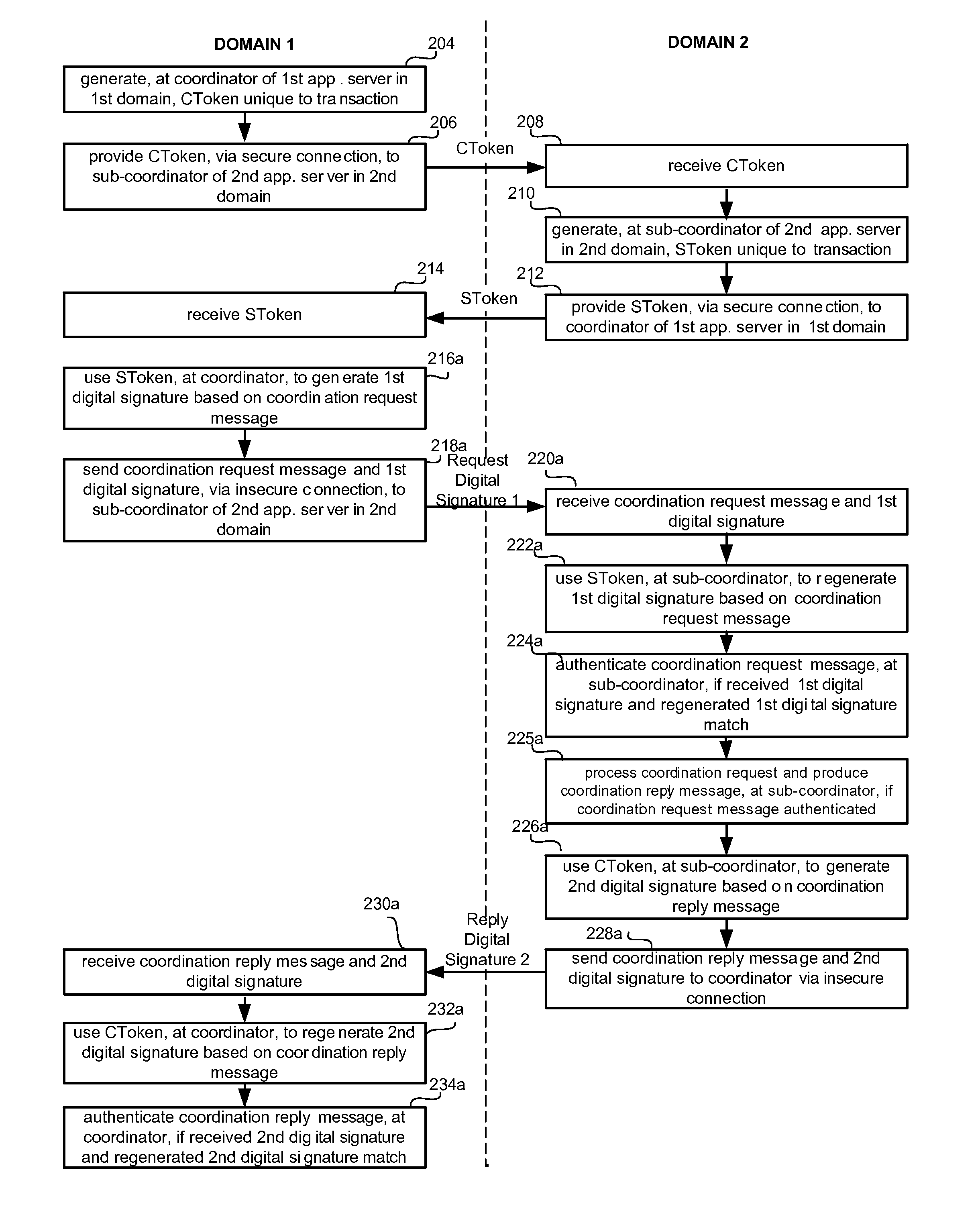
Systems and methods for mutually authenticated transaction coordination messages over insecure connections
ActiveUS20090024851A1Digital data processing detailsUser identity/authority verificationDistributed computingSafety Connect
Systems and methods are provided that enable authentication of transaction coordination messages sent via insecure connections. Also provided are systems and methods for controlling transaction coordination and recovery. In many embodiments, there is an exchange between a coordinator and a sub-coordinator, such that the coordinator provides the sub-coordinator with a coordinator token, and the sub-coordinator provides the coordinator with a sub-coordinator token. The coordinator and sub-coordinator tokens are used to authenticate transaction coordination messages sent over one or more insecure connections between the coordinator and the sub-coordinator.
Owner:ORACLE INT CORP
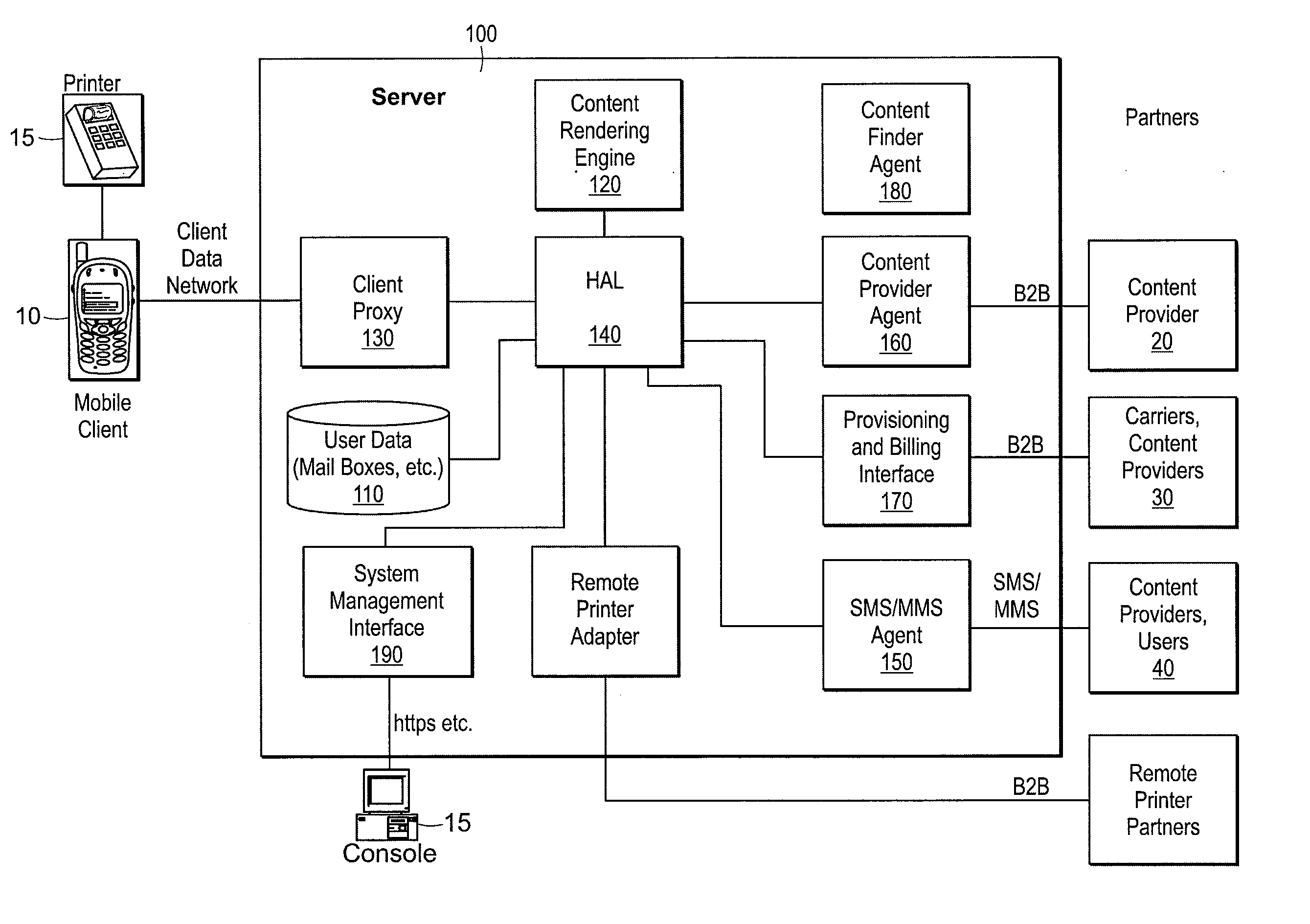
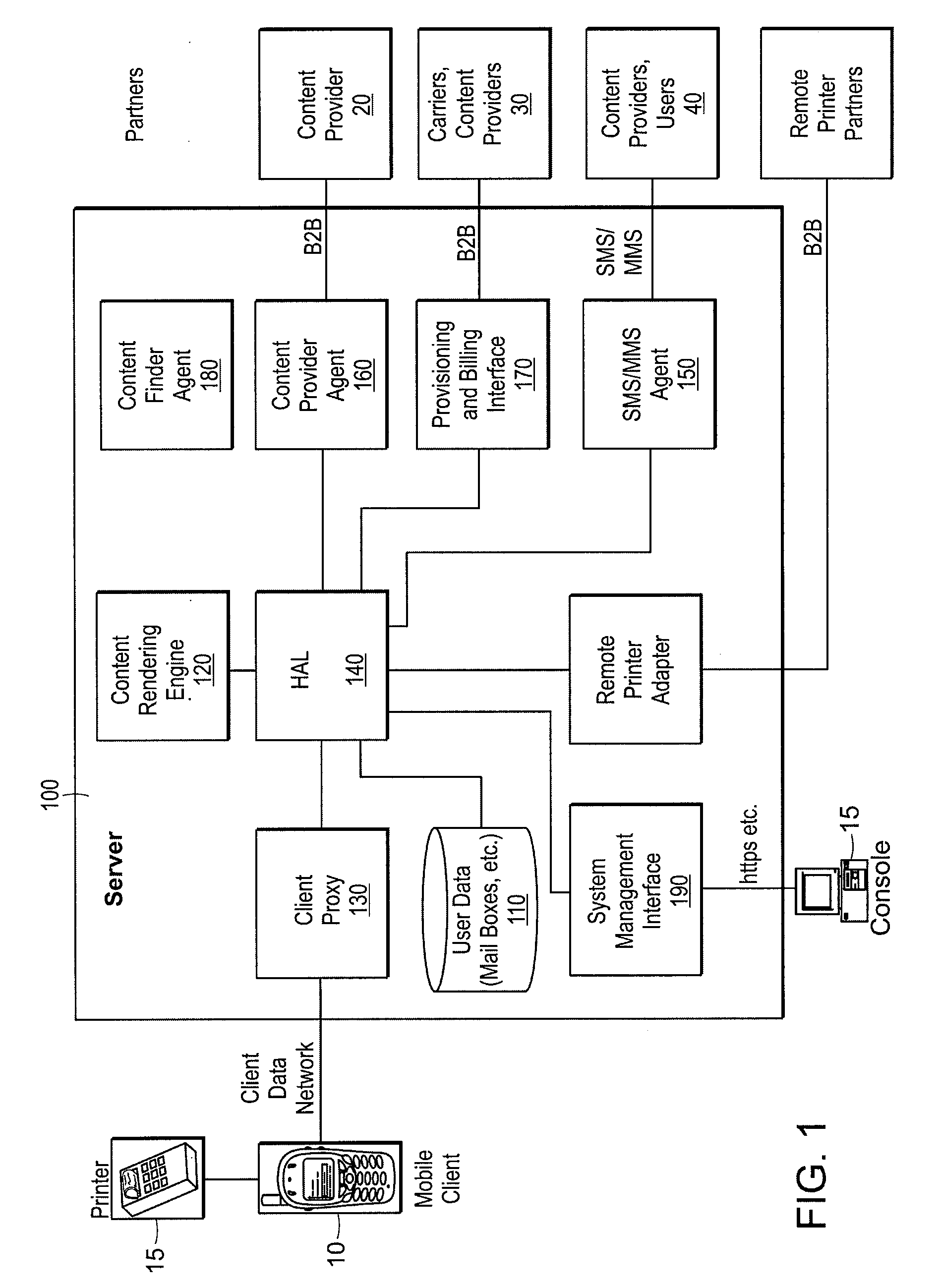
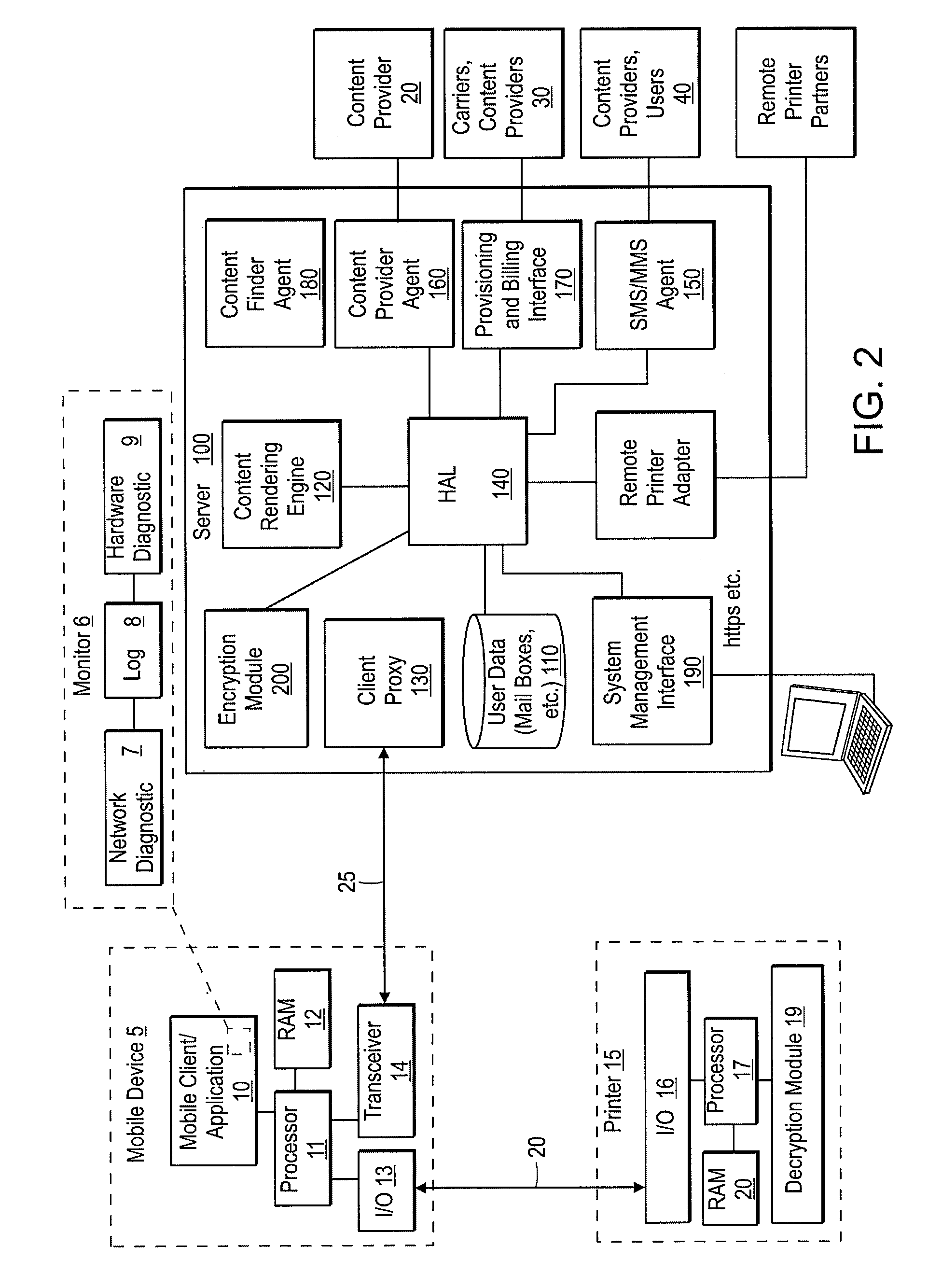
Quality of service methods and systems for mobile printing
InactiveUS20080084578A1Preventing the media from fallingDigital output to print unitsSecure communicationQuality of service
Systems and methods for secure, remote printing includes a mobile device (e.g., cell phone or PDA) establishing a secure communication connection with a mobile printer and a server, such a connection using one or more encryption protocols (e.g., SSL, TLS, etc.). The server encrypts the requested data and transmits it to the printer via the secure connection, whereon the printer decrypts and prints the data. The mobile device can, according to other aspects of the invention, logs operational performance characteristic of the printer, the server, and / or the communication connections therebetween. A media cartridge can be provided includes an enclosure having a substantially planar shape, wherein each of its length and width dimensions are greater than its height. An opening is disposed along a width-wise edge (e.g., a “front” of the enclosure), and one or more regions are also disposed on opposing length-wise edges (e.g., a “left side” and a “right side” of the enclosure). The regions permit a user to see and / or exert a force on sheet media (e.g., paper) contained within the enclosure.
Owner:AIRPRINT NETWORKS
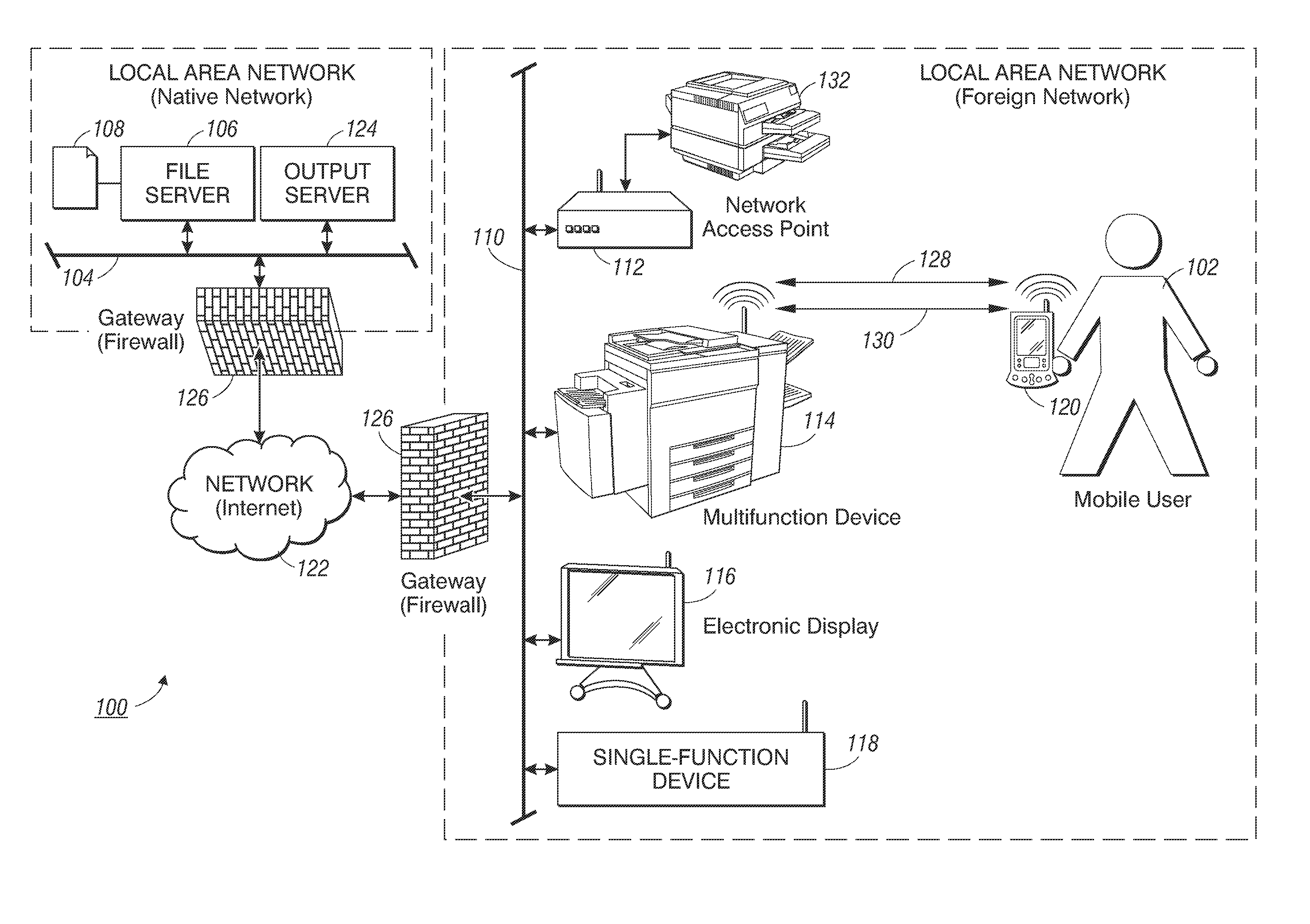
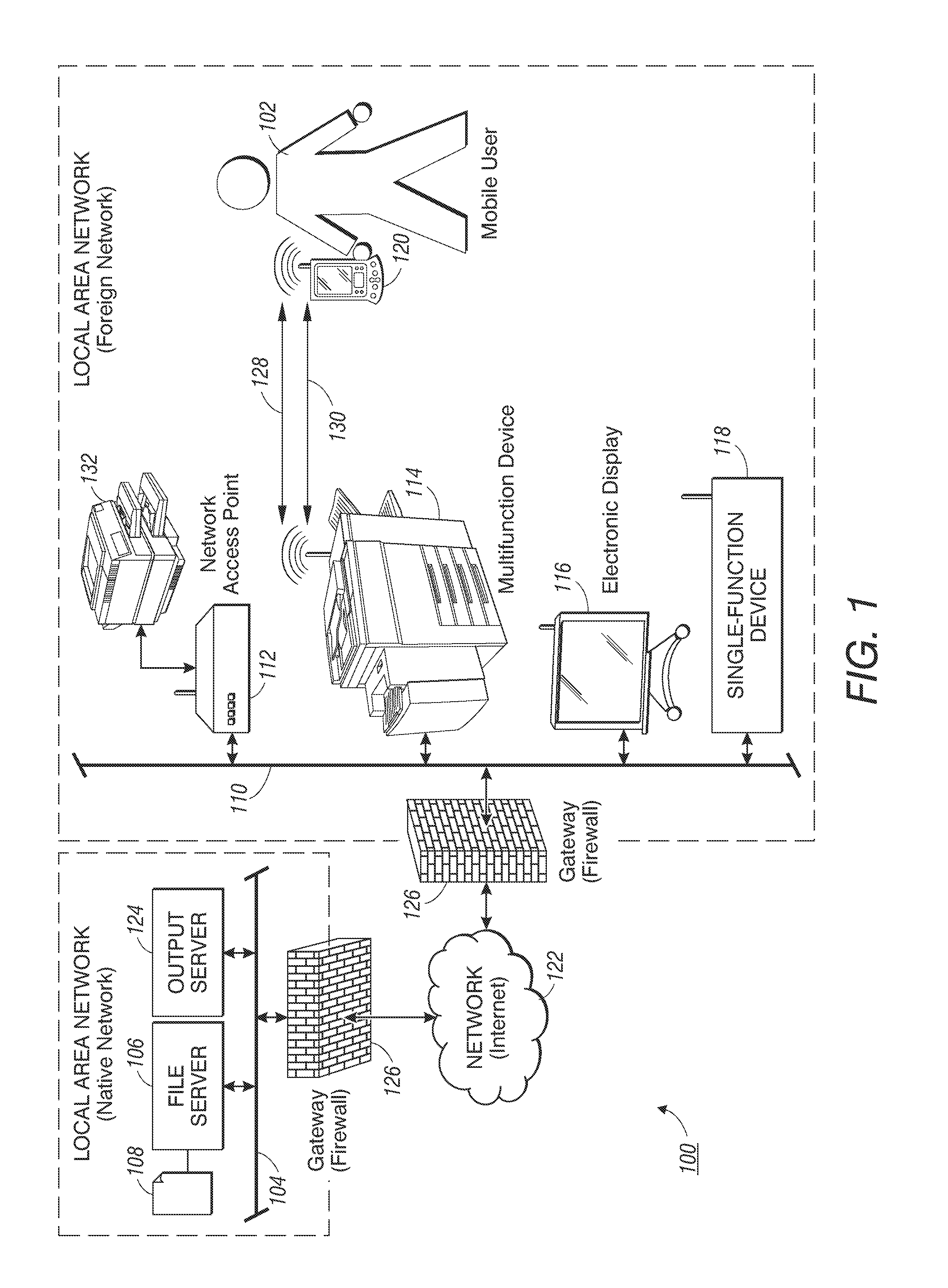
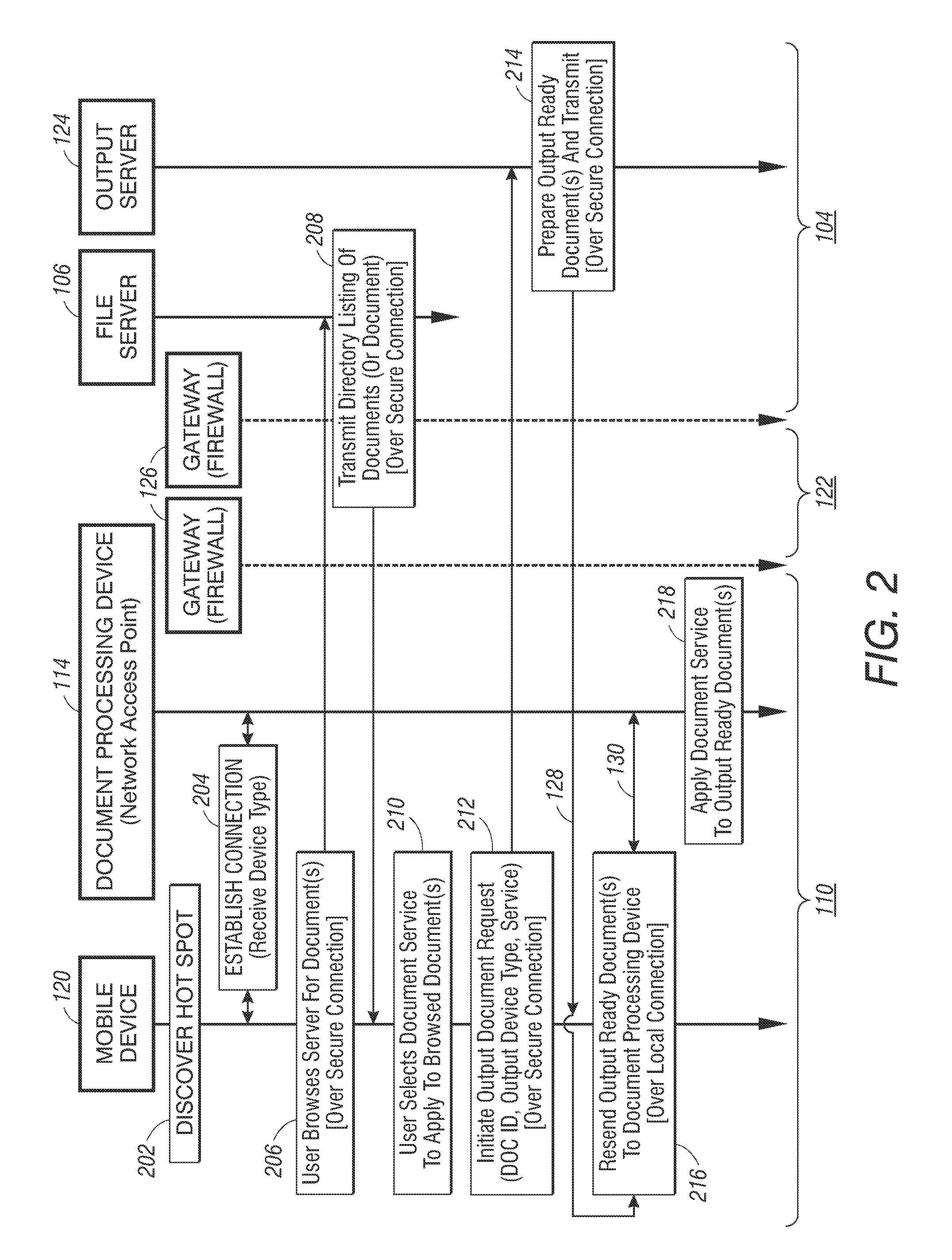
Method and apparatus for controlling document service requests from a mobile device
Methods for controlling a document service request involve defining a document service request workflow and redirecting document service requests from the mobile device. In one embodiment, through a short-range connection with a document processing device on a foreign network, a mobile device establishes a secure connection to the mobile device's native network to identify a document stored on a file server operating thereon. Once a document is identified, the mobile device over the secure connection initiates a document service request by requesting an output server operating on the native network to retrieve and convert the identified document into an output-ready format suitable for the document processing device. Upon receipt of the output-ready document, the mobile device resends the output-ready document over a local connection to the document processing device to carry out the document service request.
Owner:XEROX CORP
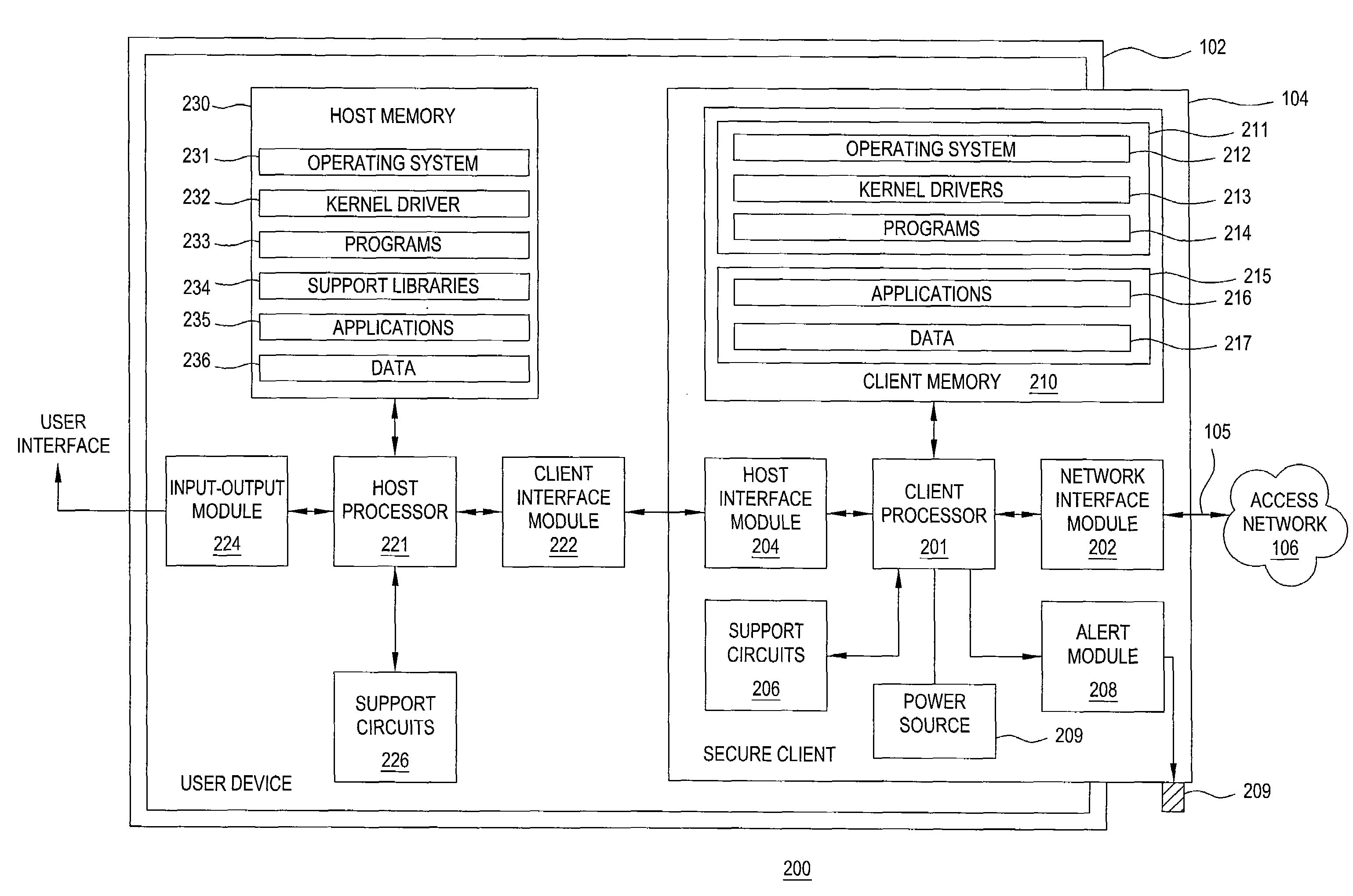
Method and apparatus for notification and delivery of messages to mobile PC users
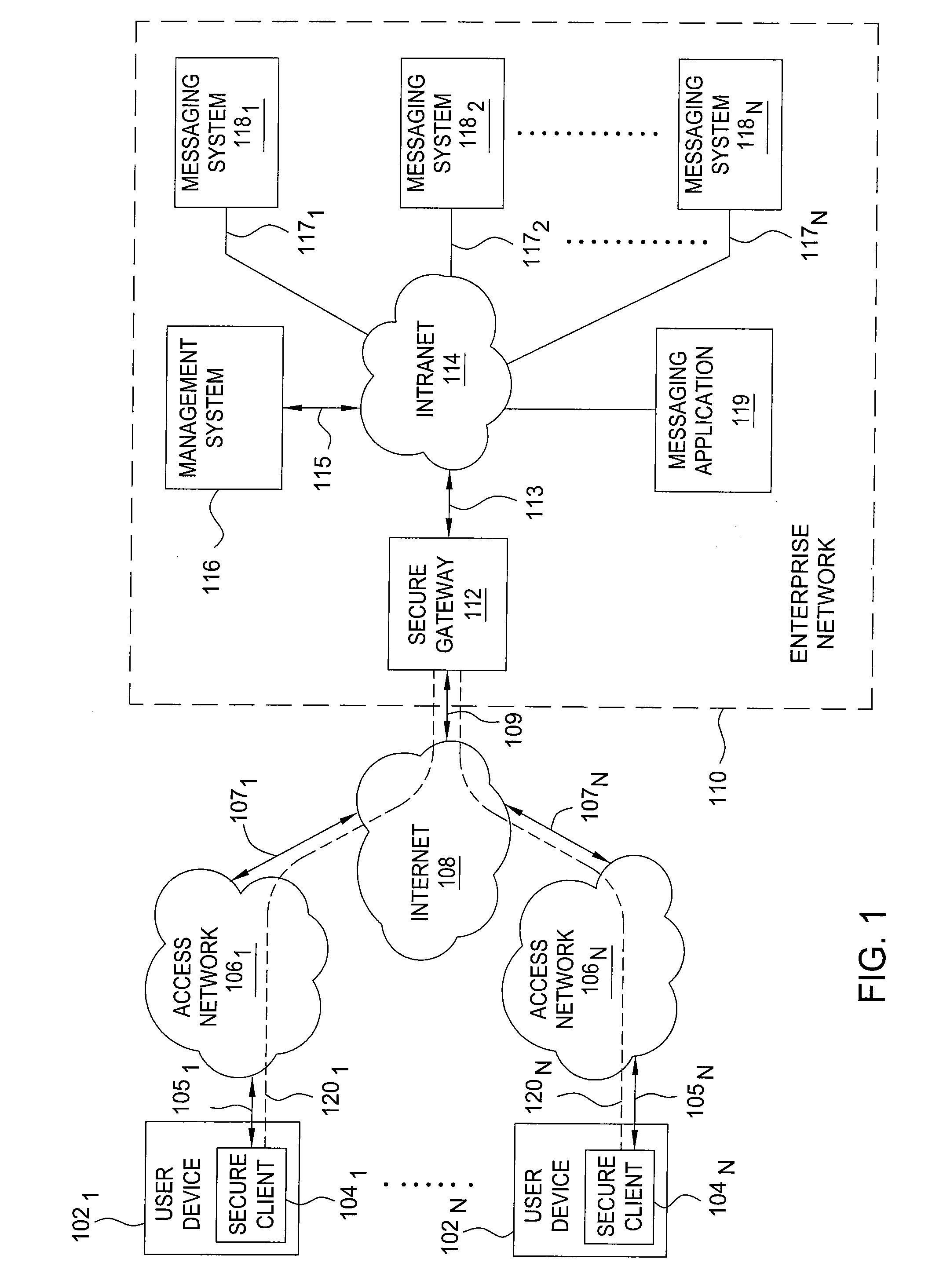
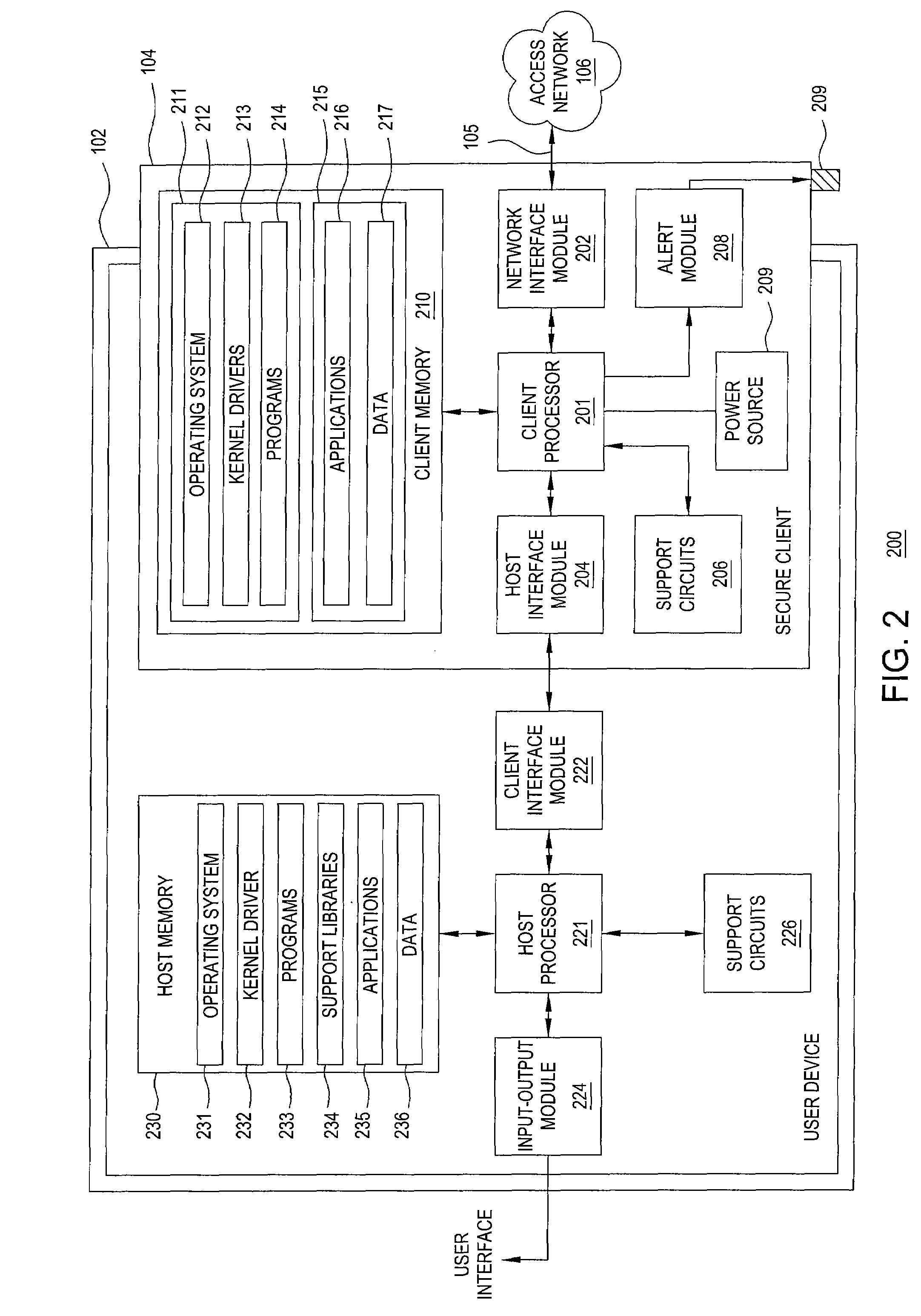
The invention includes a method and apparatus for notification and delivery of messages to mobile users using a secure client associated with a user device. The secure client includes a power module, a communication module, a storage module, and an alert module. The power module powers the client device independent of a power state of the user device. The communication module receives a wake-up message and responsively triggers the secure client to switch from an inactive state to an active state without changing the power state of the user device, initiates a secure connection with a secure gateway in response to the wake-up message, and requests and receives a user message from a messaging application using the secure connection. The storage module stores the received message independent of the power state of the user device. The alert module activates an alert to indicate that the message is available.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
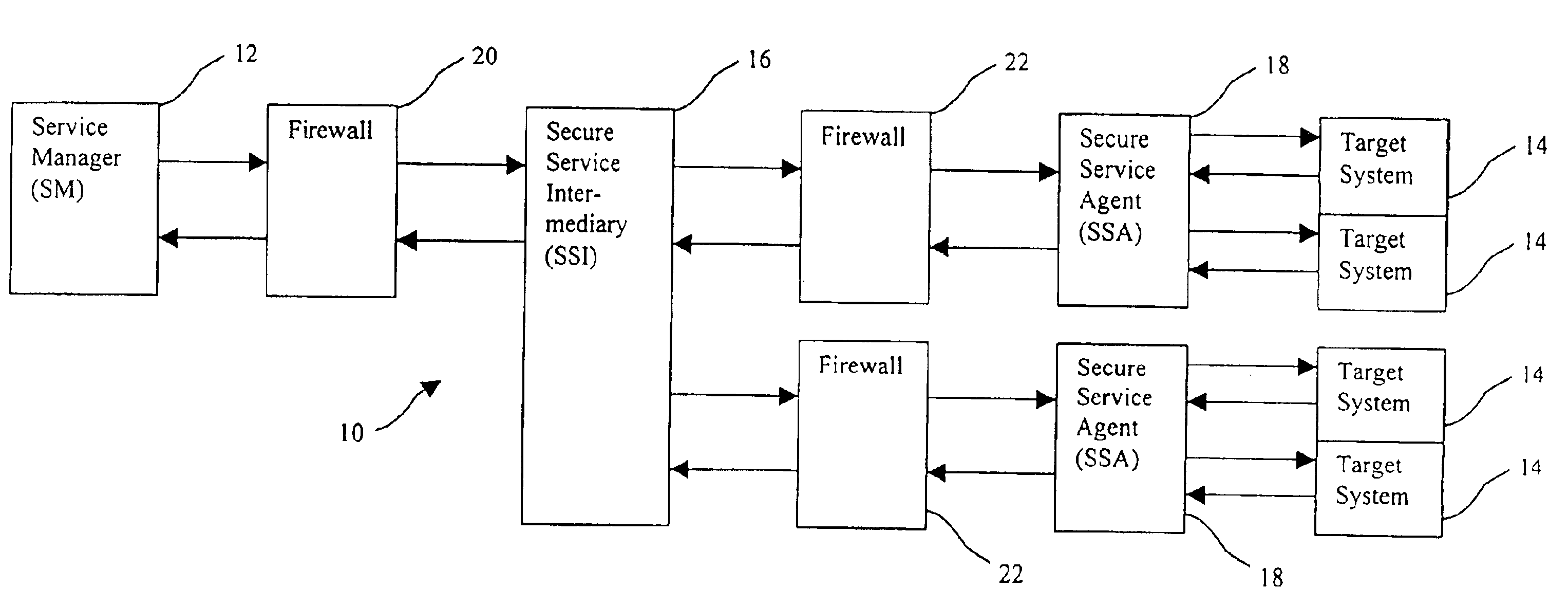
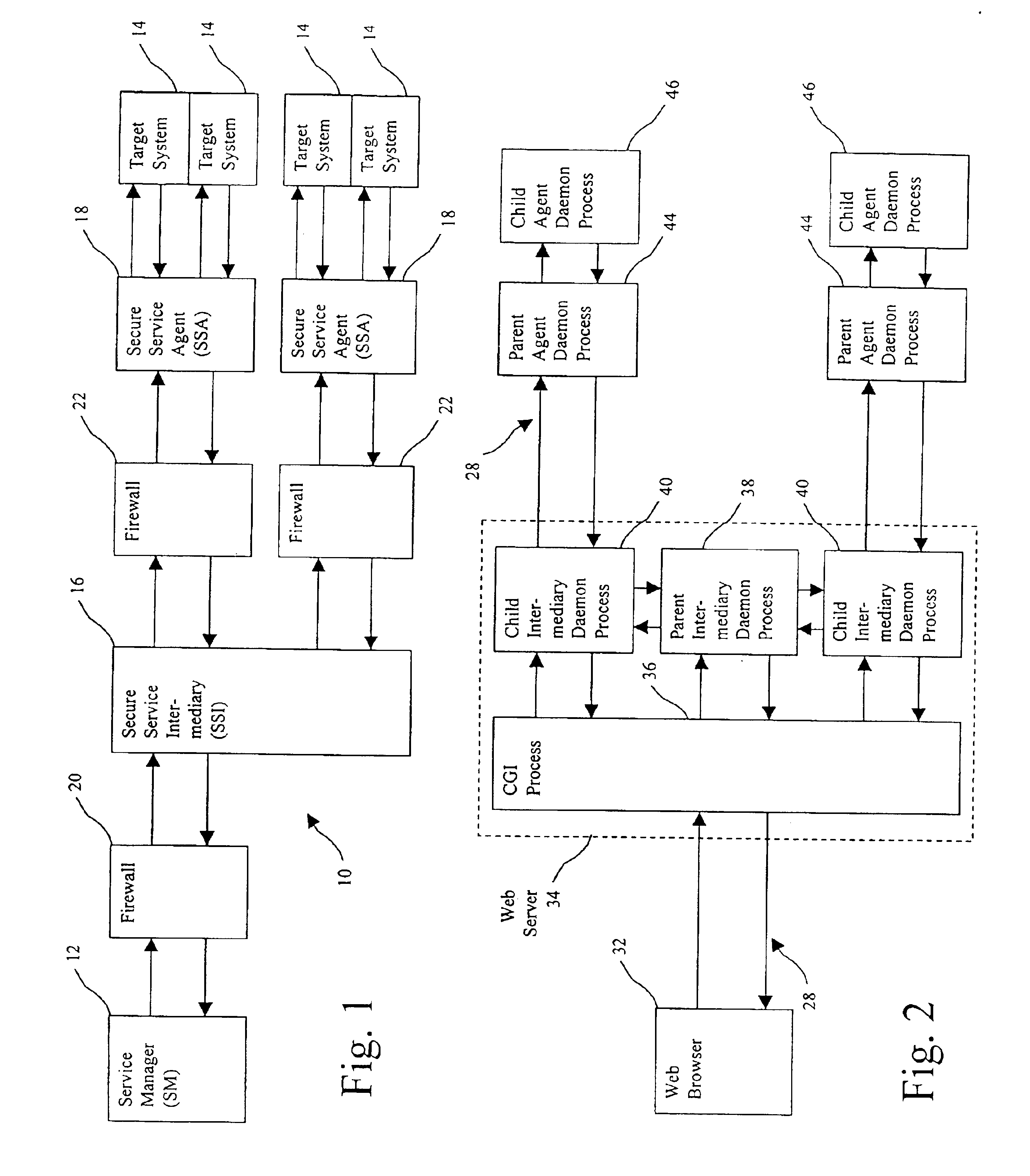
Secure remote servicing of a computer system over a computer network
InactiveUS6874088B1Digital data processing detailsUser identity/authority verificationSoftware modulesAuthentication
The remote servicing of a secure computer system employs an intermediate network entity accessible to both a remote service provider and to an agent running on the secure computer system to be serviced. A service provider's computer runs a manager software module, while the system being serviced, or an agent on its behalf, runs an agent software module. An intermediary software module runs on the intermediate network entity. The mutually accessible intermediate network entity may be located outside firewalls protecting the system to be serviced or inside such firewalls though with the firewalls configured to allow selected access. Access to the intermediate network entity is limited by secure access protocols. After authentication, the manager submits to the intermediary one or more directives to be executed by the agent. The intermediary then sends the directives to the agent over a secure connection to the agent. The agent then executes the directive(s) upon receipt and sends the response to the intermediary via the secure connection. The manager is then capable of accessing the results via the intermediary.
Owner:ANGELL ASSOC LLC +1
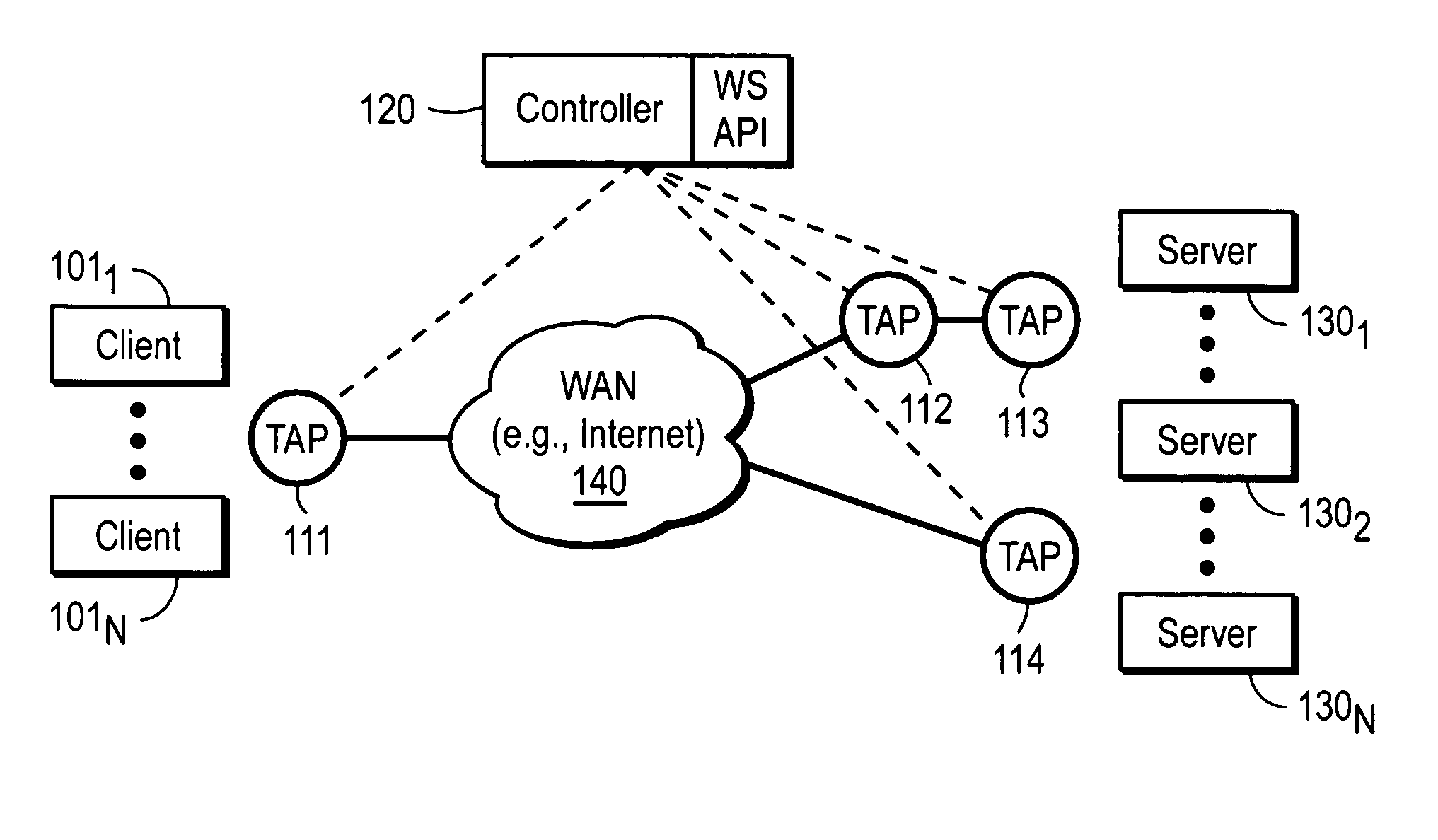
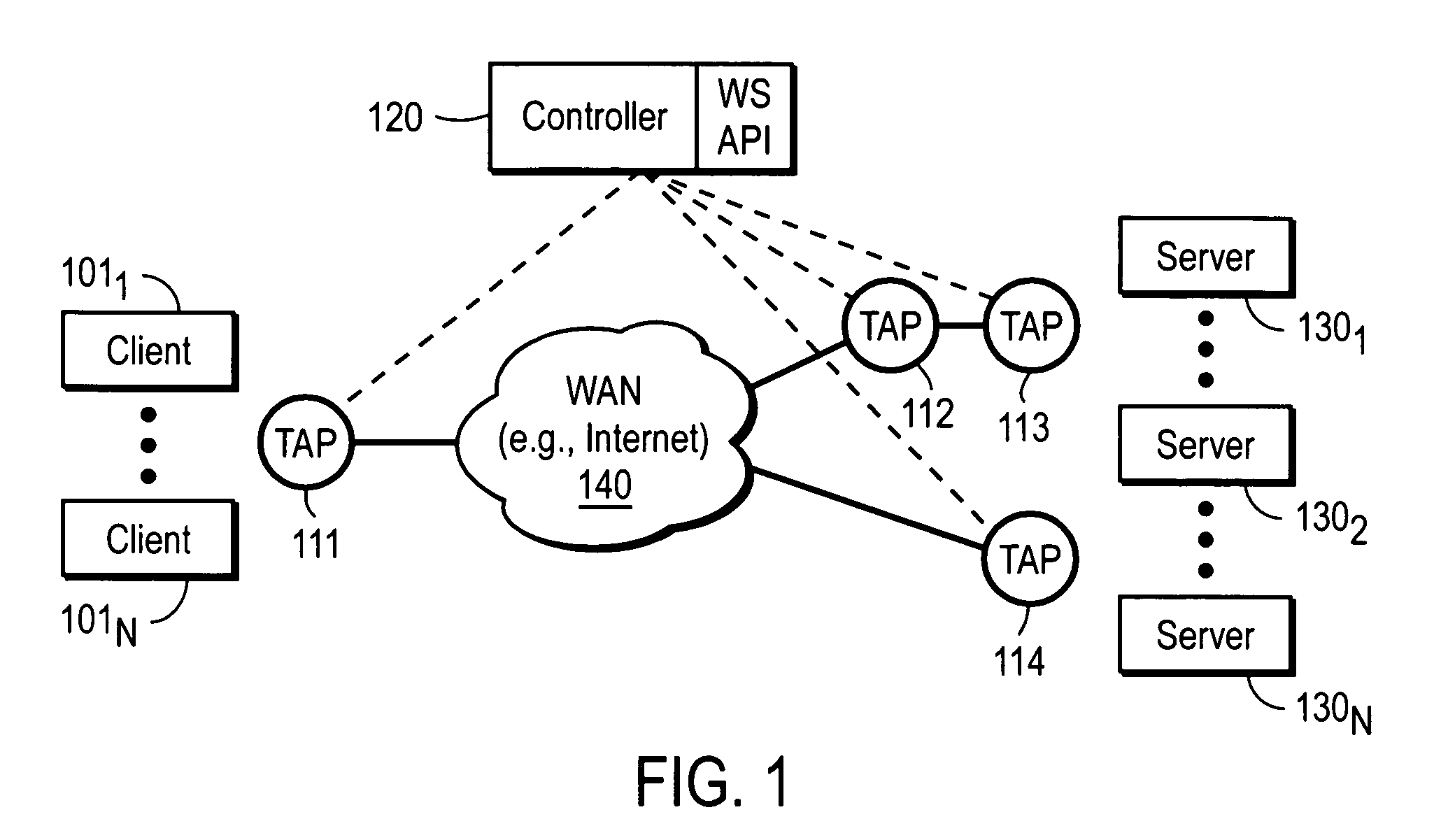
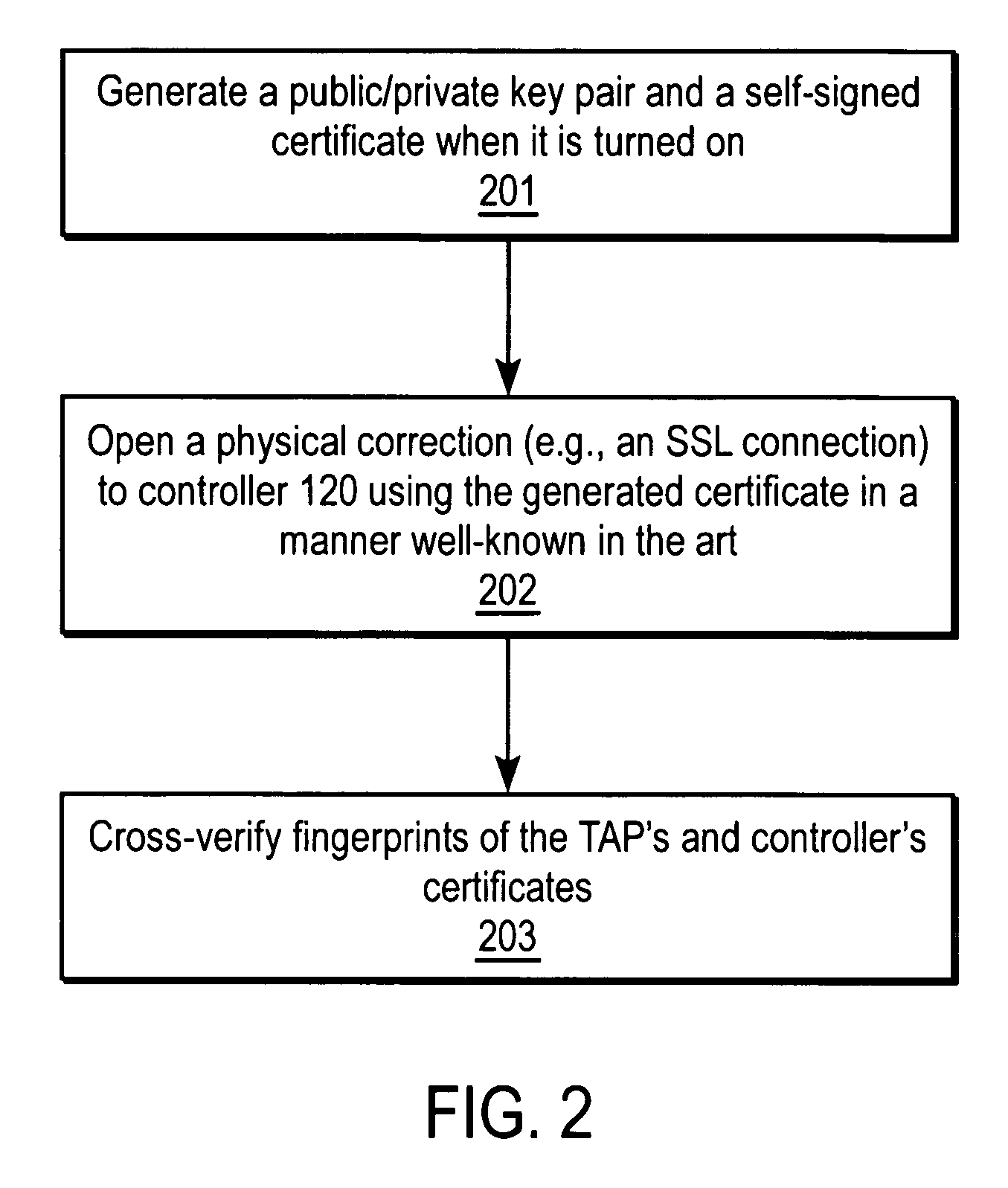
Overlay network infrastructure
A method and apparatus for processing an overlay network infrastructure. In one embodiment, the method comprises a plurality of transparent access points (TAPs). Each TAP is communicably coupled between one or more clients and servers and a wide area network (WAN) to enable the one or more clients to communicate with the one or more servers, and is coupled to other of the TAPs via permanently, established secure links. The overlay network also comprises a controller coupled to each of the TAPs via a secure connection to configure the TAPs with information to enable each TAP to know what services are available and from which of the TAPs each of the services can be accessed.
Owner:CITRIX SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com