Patents
Literature
161 results about "Universal subscriber identity module" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
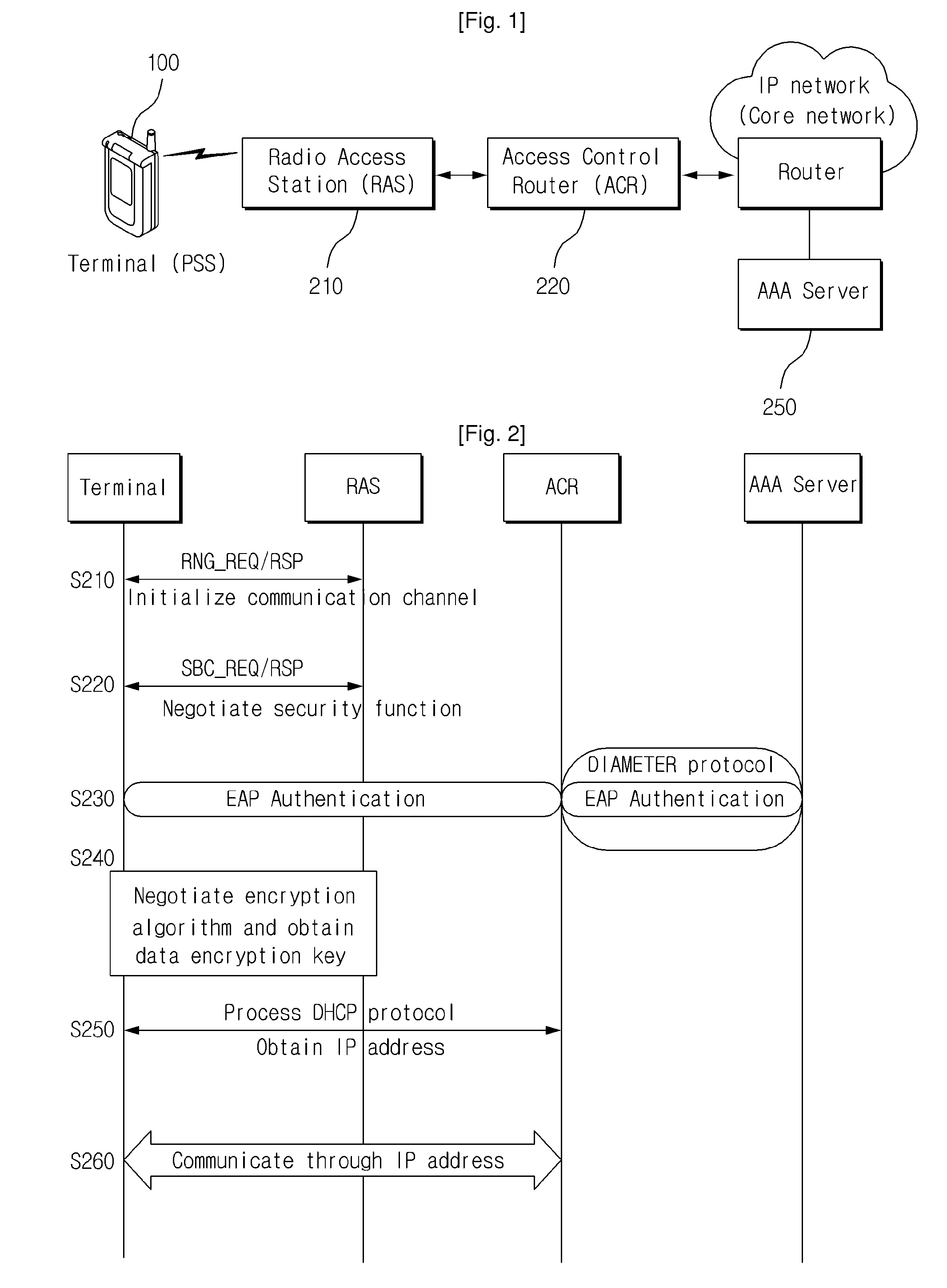
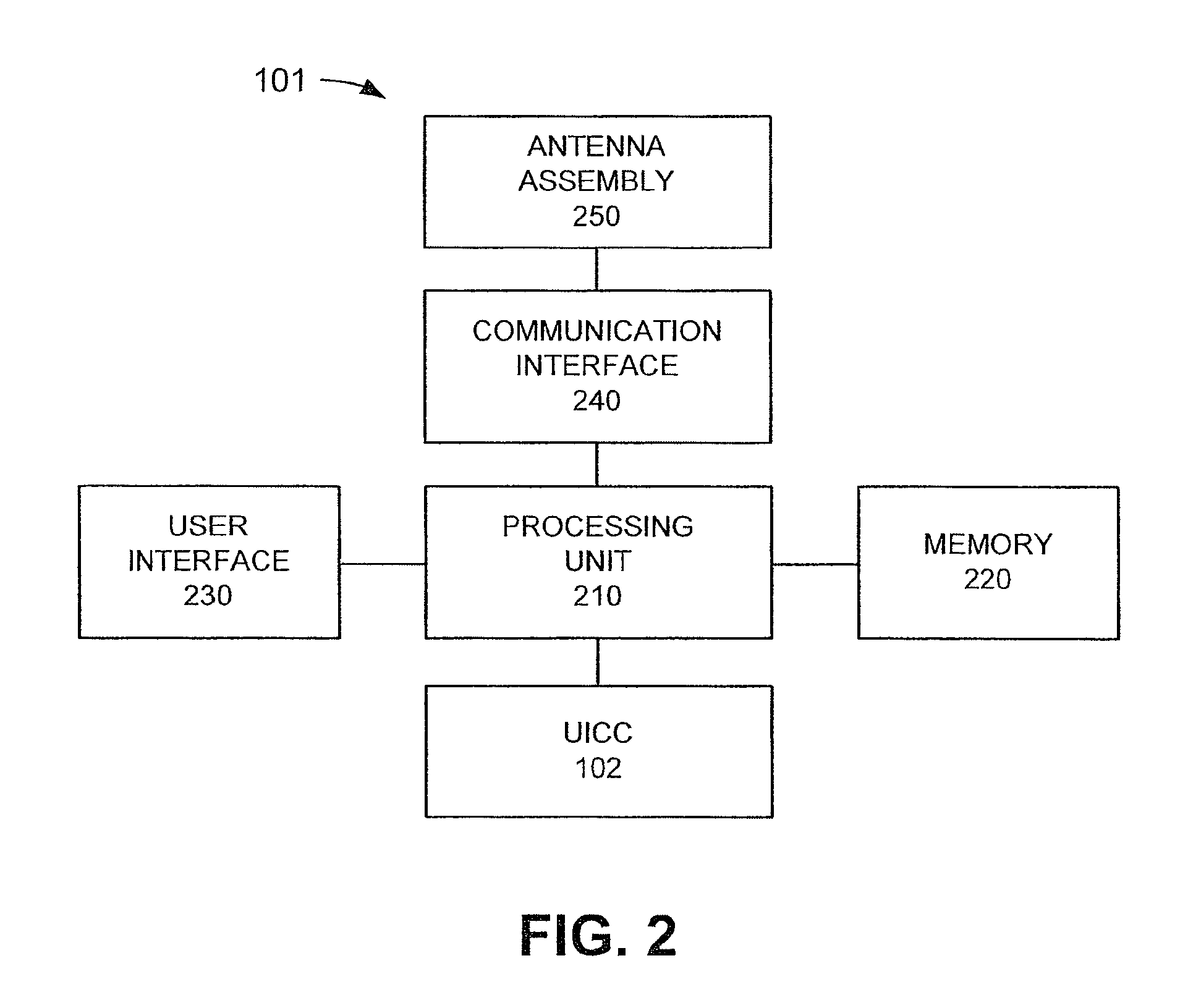
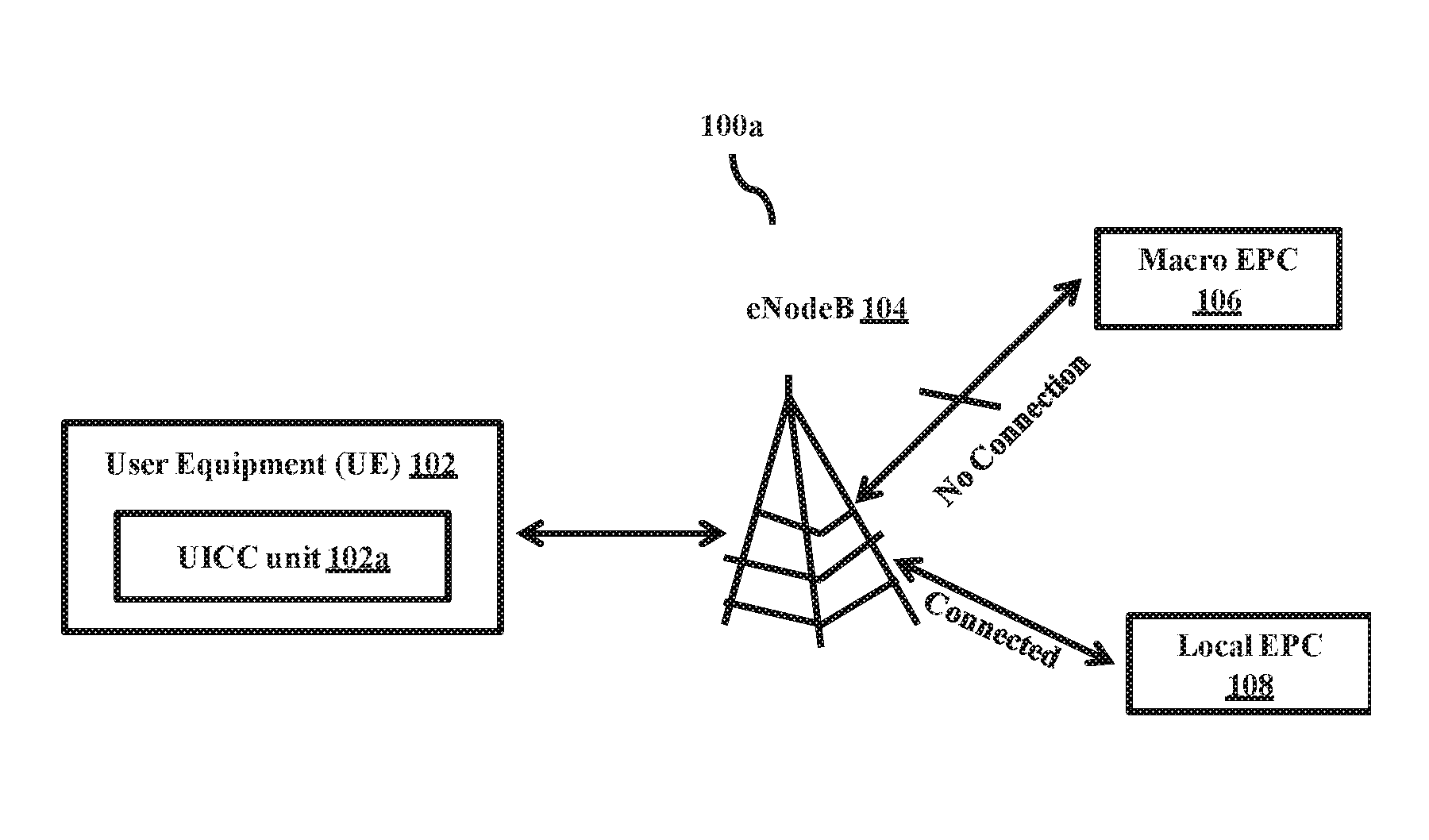
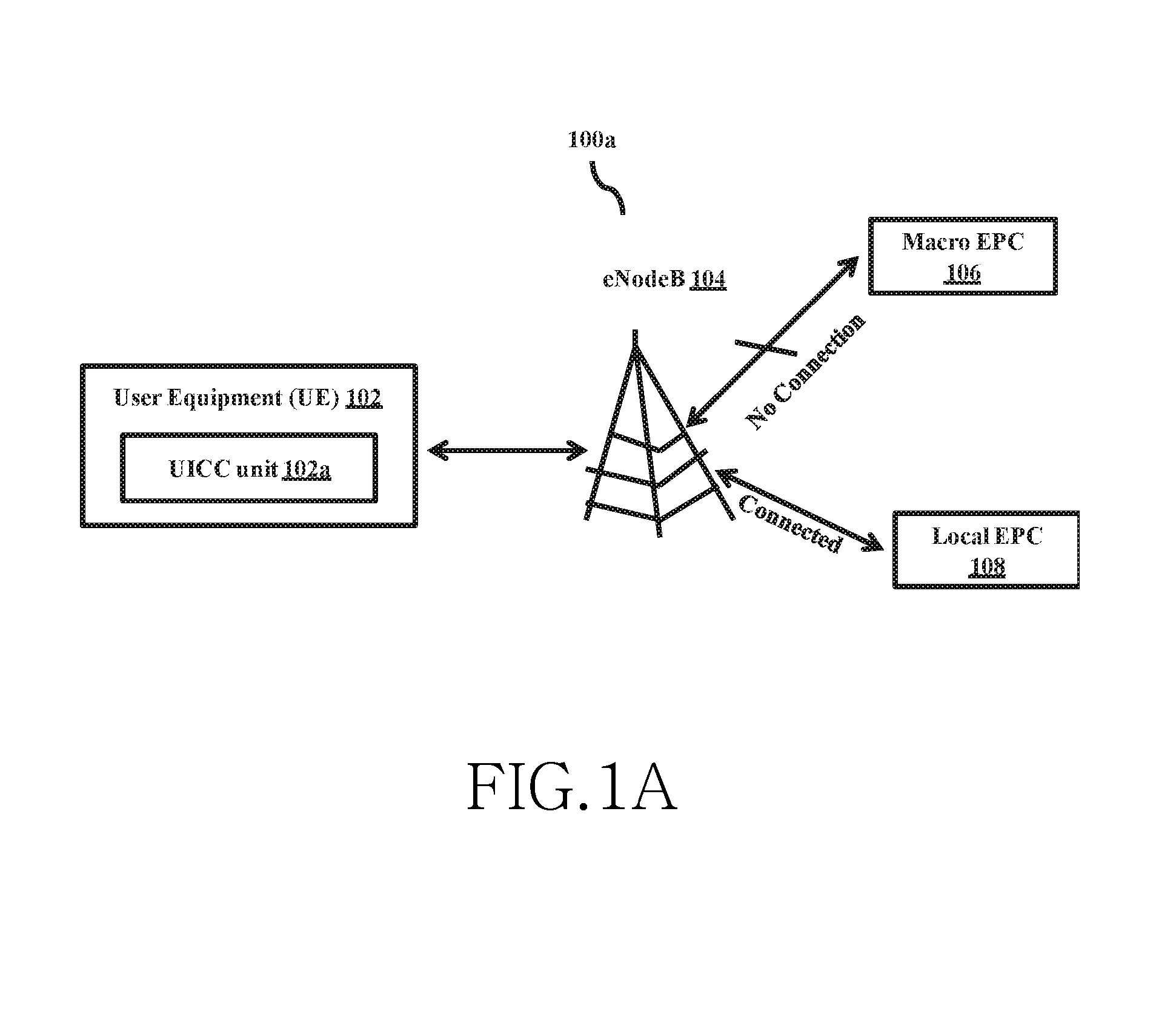
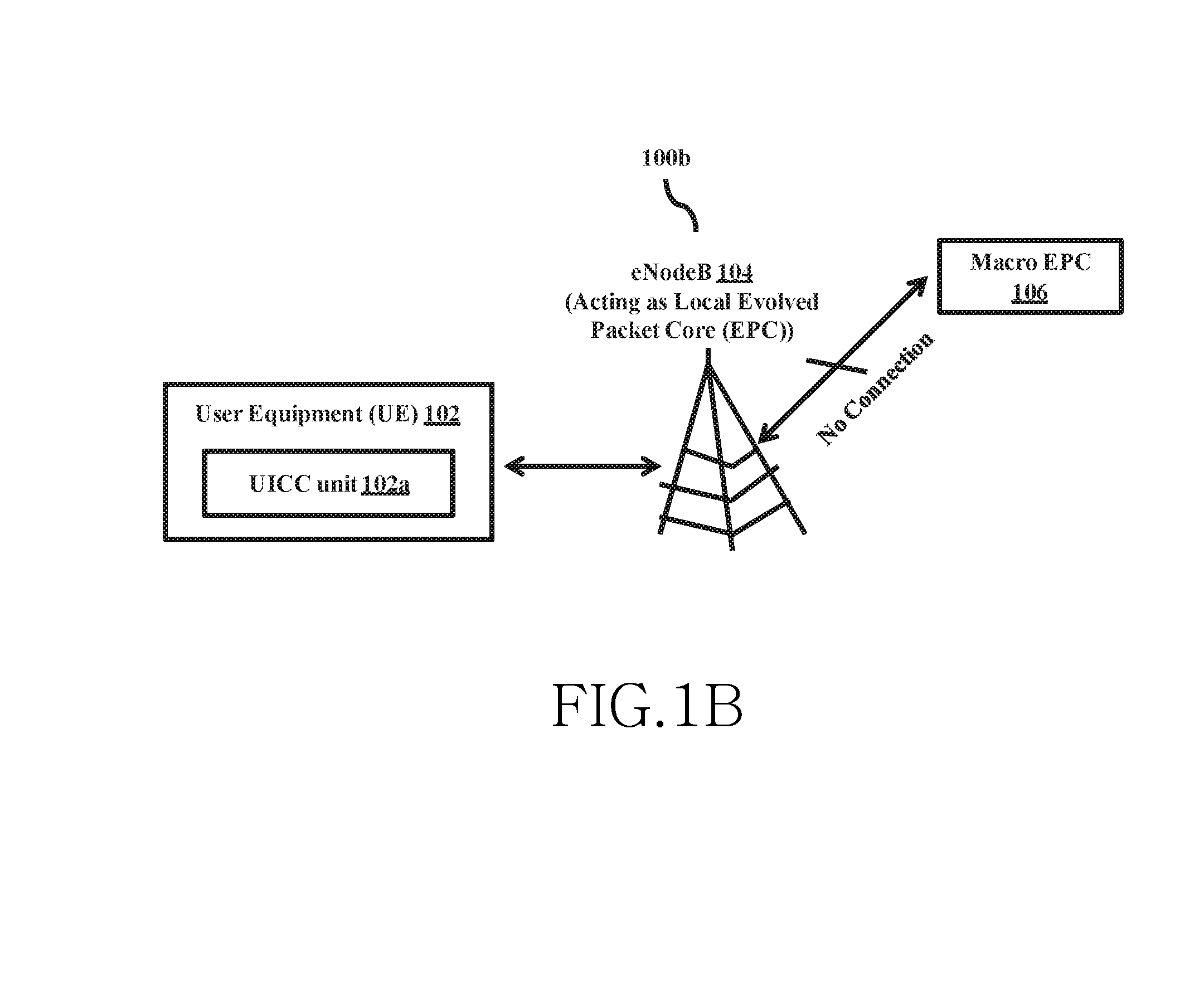
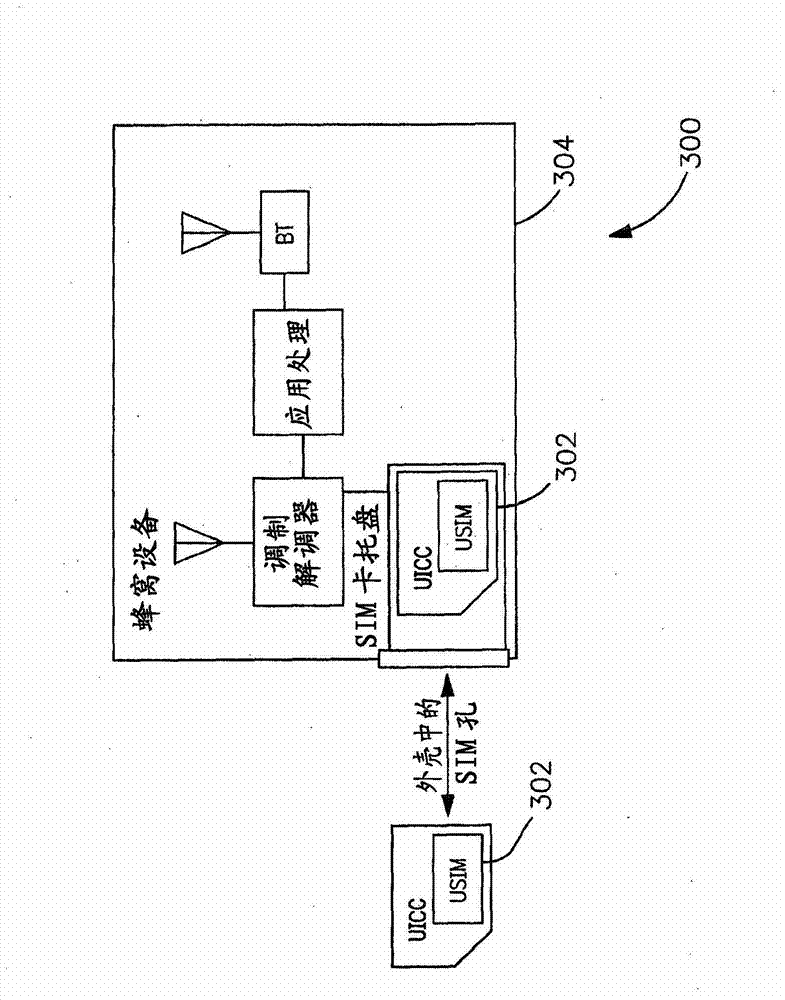
Universal subscriber identity module provisioning for machine-to-machine communications
InactiveUS20090191857A1Automatic exchangesWireless commuication servicesSubscriber identity moduleSafety Connect
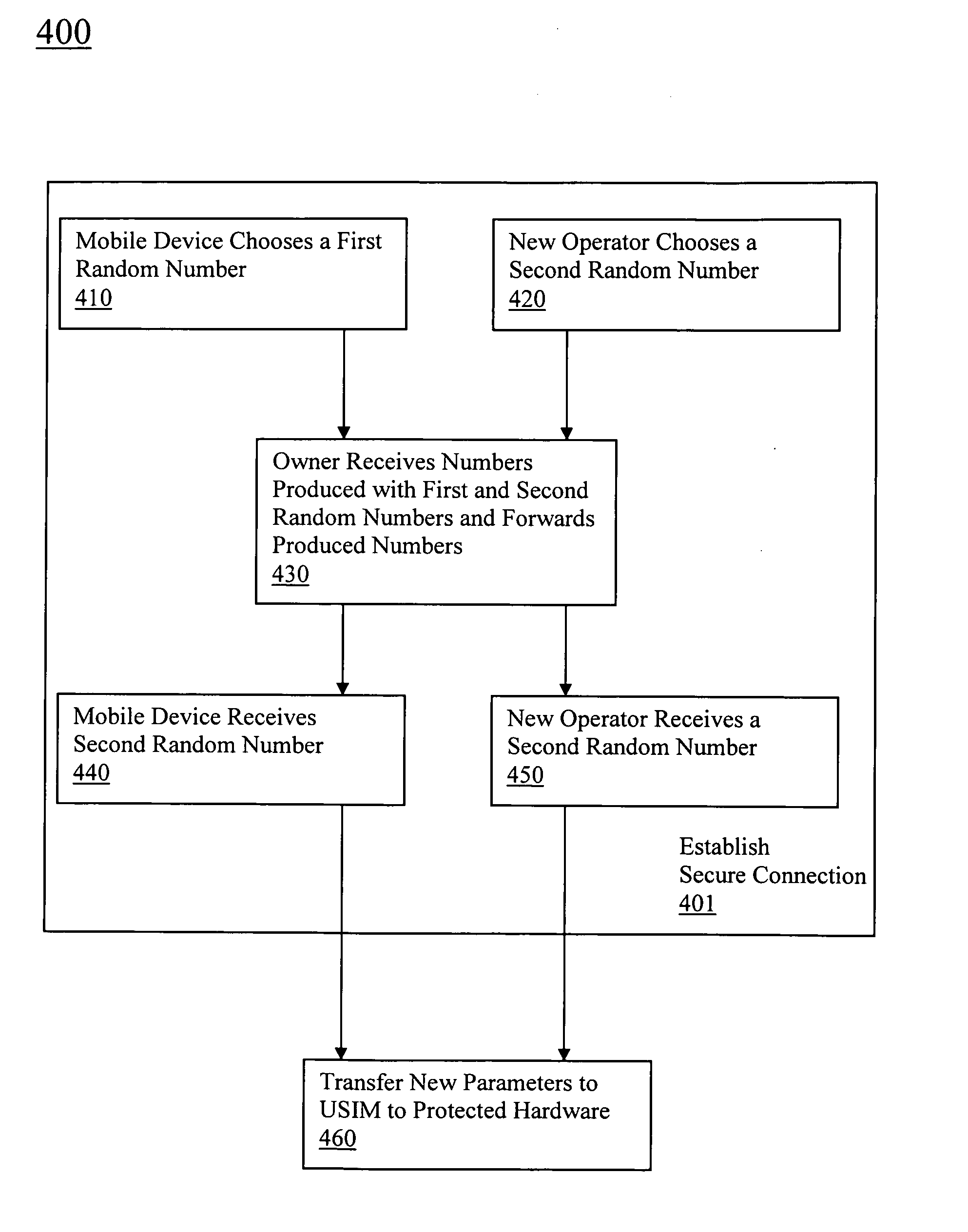
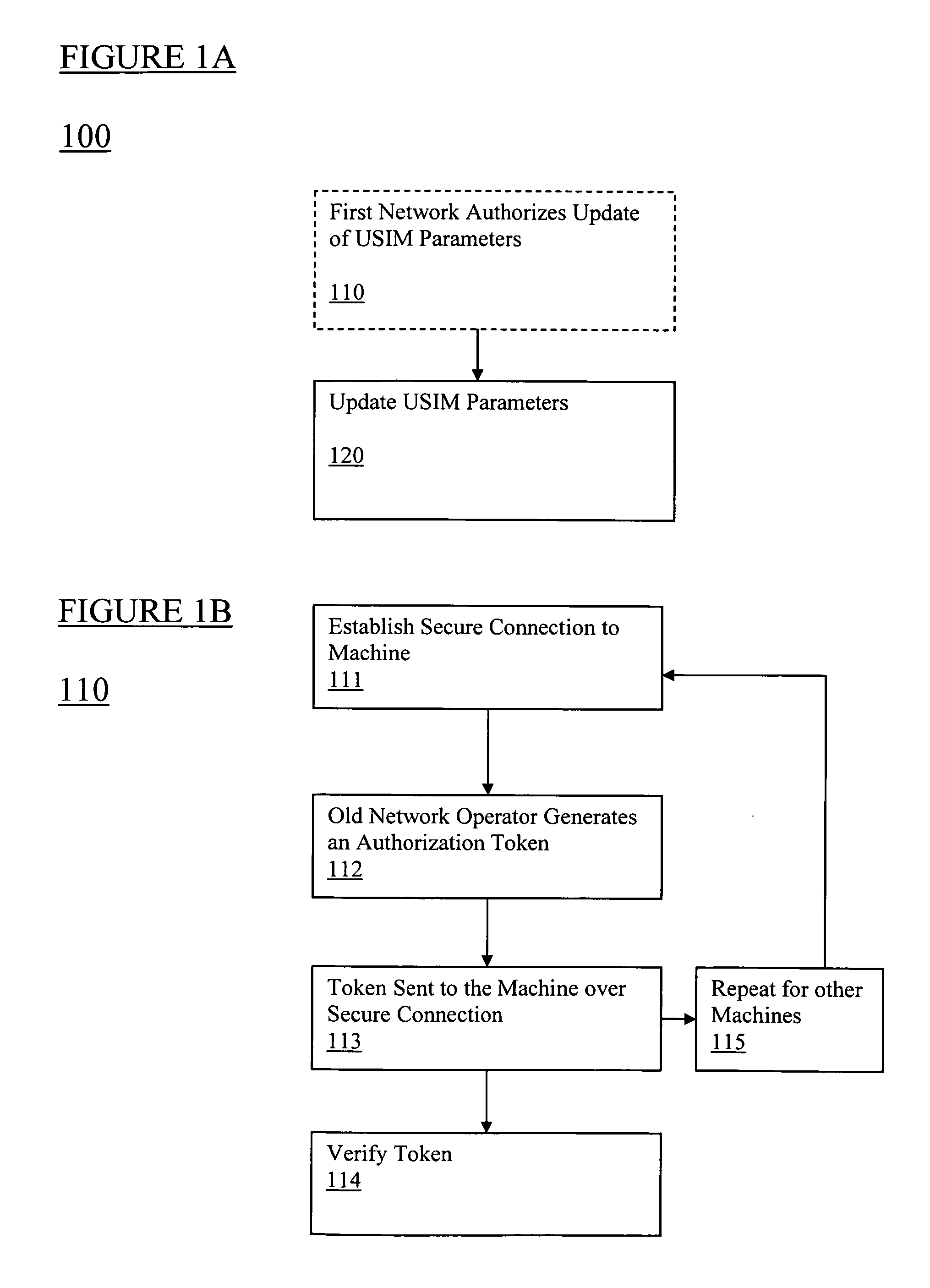
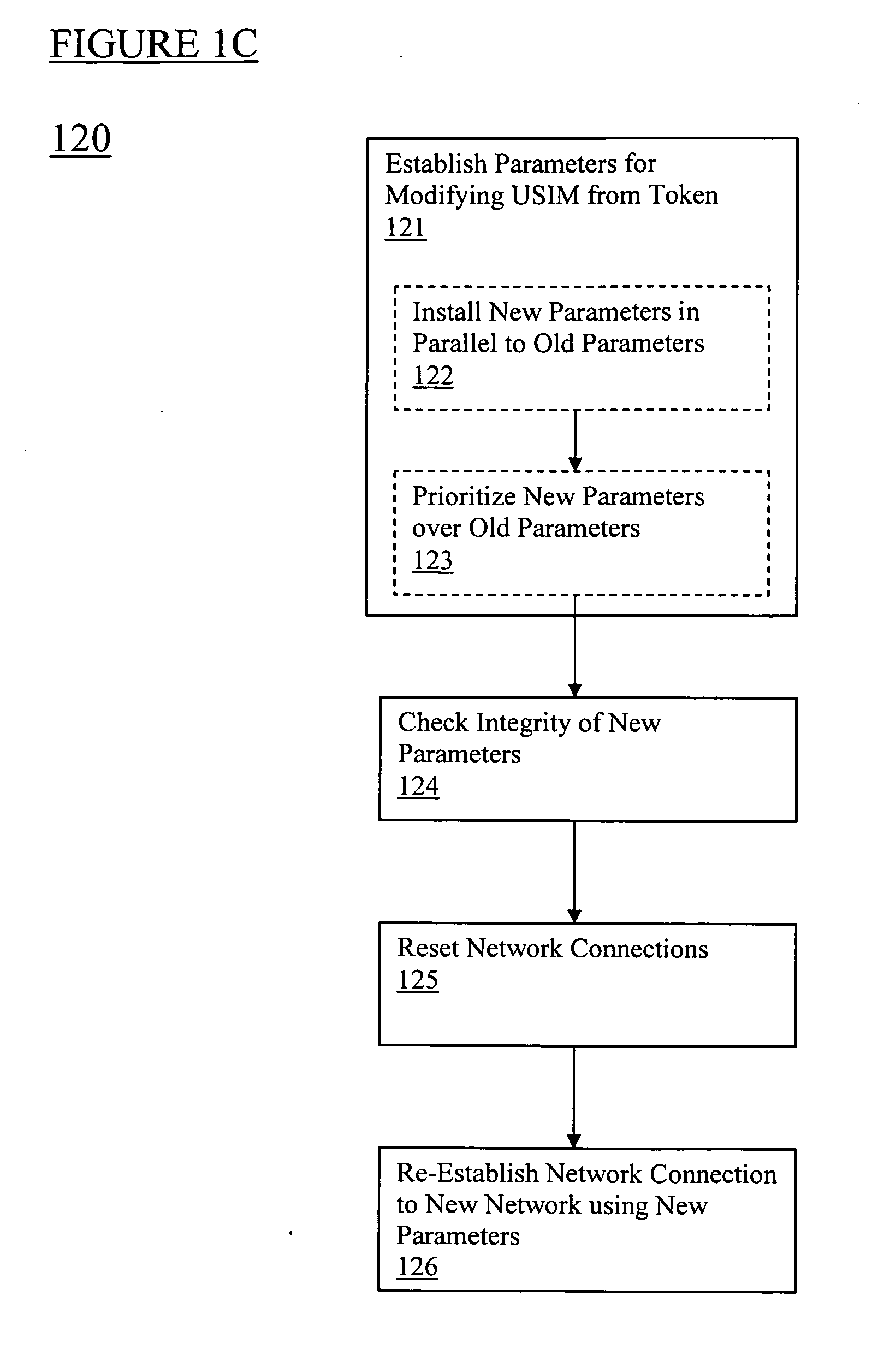
The present invention relates to remotely provisioning subscriber identification parameters in a device on a wireless network. A secure connection is established with the device, and a token containing the new subscriber identification parameters is forwarded over the secure connection. The device may verify the received token. In one embodiment, the subscriber identification parameters are updated to change network operators. The secure connection can be with the old network operator or the new network operator. The device on the wireless network may be a machine-to-machine device. The provisioned subscriber identification may be part of a universal subscriber identification module.
Owner:NOKIA SOLUTIONS & NETWORKS OY
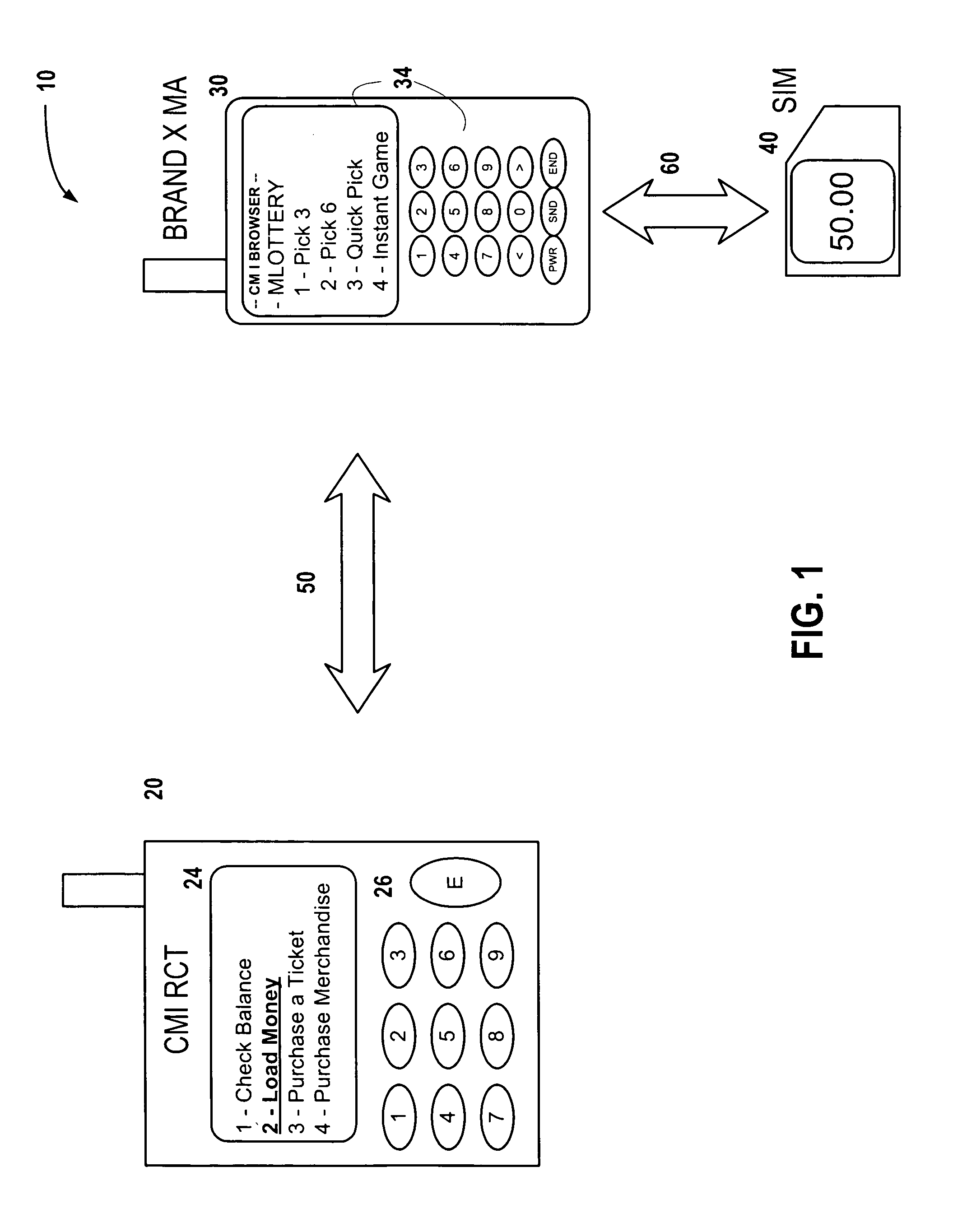
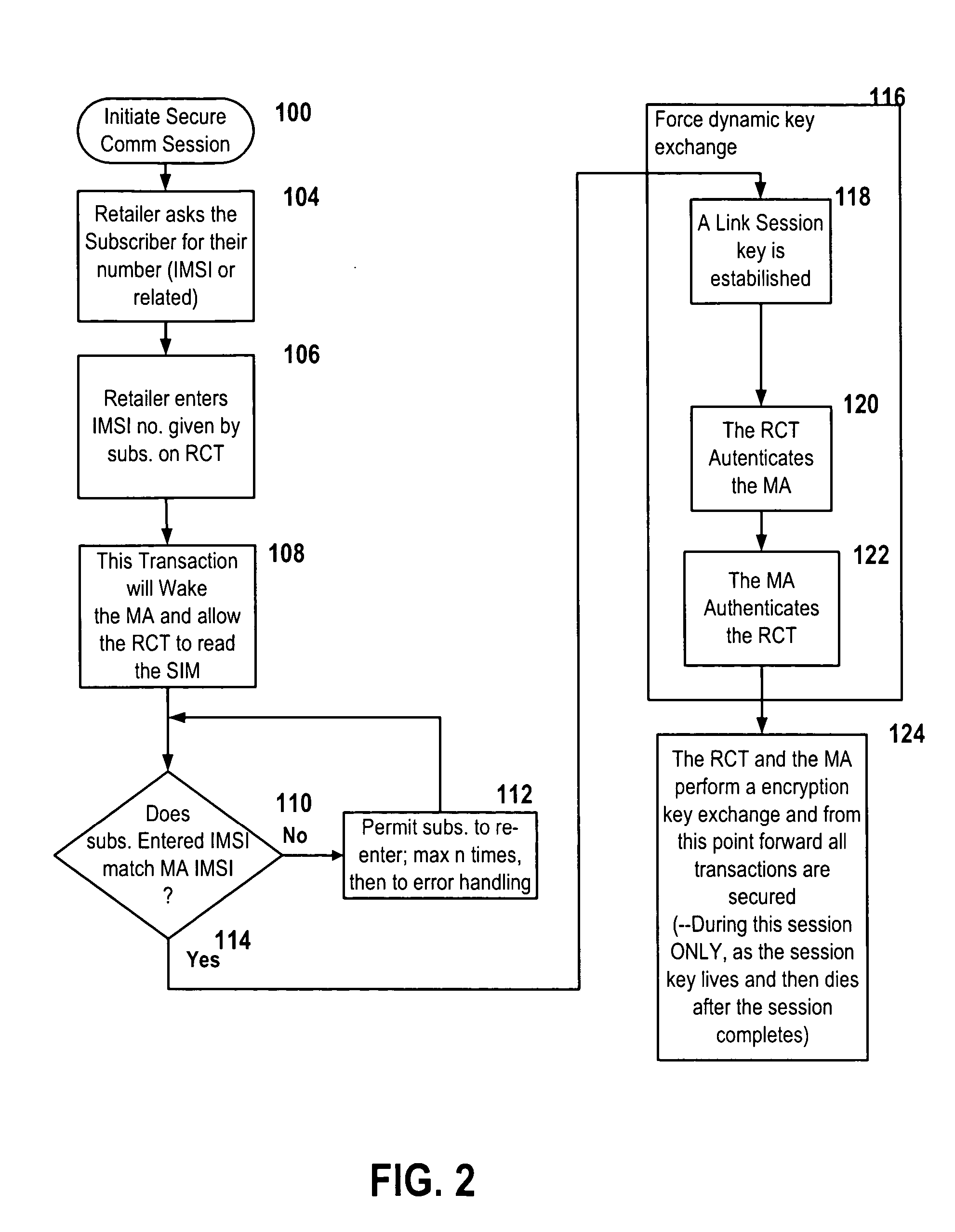
Mobile lottery, gaming and wagering system and method
InactiveUS20050181875A1Credit registering devices actuationTelephonic communicationPagerElectronic cash
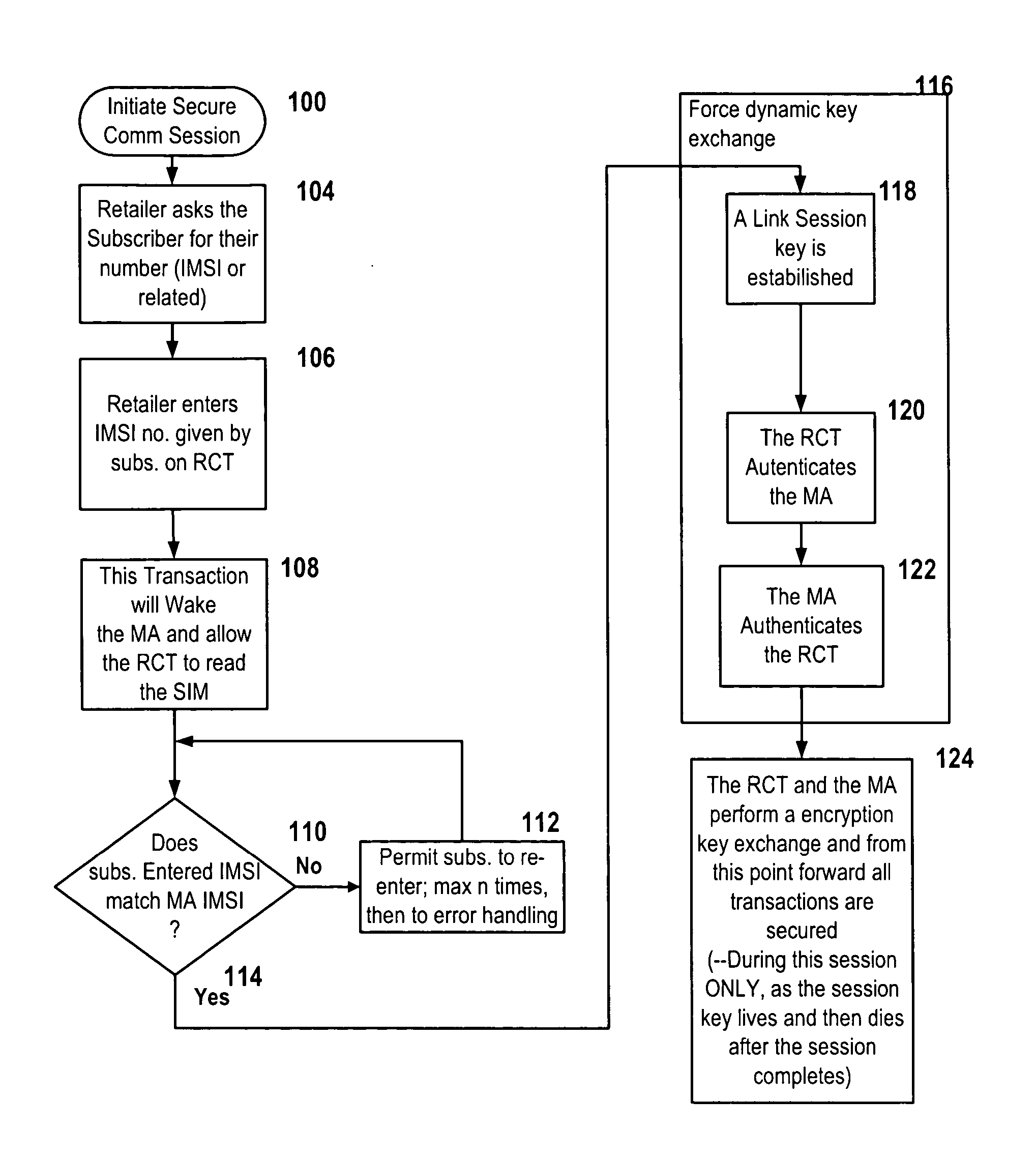
An apparatus or method to allow the secure downloading of an operating system, file management system and or state machine to a Miniature Smart Card (MSC) such as a Subscriber Identity Module (SIM), Universal Subscriber Identity Module (USIM), Removable User Identity Module (RUIM) or Universal Integrated Chip Card (UICC) in a mobile appliance (MA), such as but not limited to a mobile phone, personal digital assistant (PDA), pager or a proprietary device. This would in turn allow an E-purse applet as well as Lottery, Wagering and Gaming applets to be downloaded to the same Miniature Smart Card (MSC) and further allow the downloading of e-cash to be used to remotely play the Lottery, Wagering or Gaming applets as well as make retail purchases.
Owner:COIN MECHANISMS
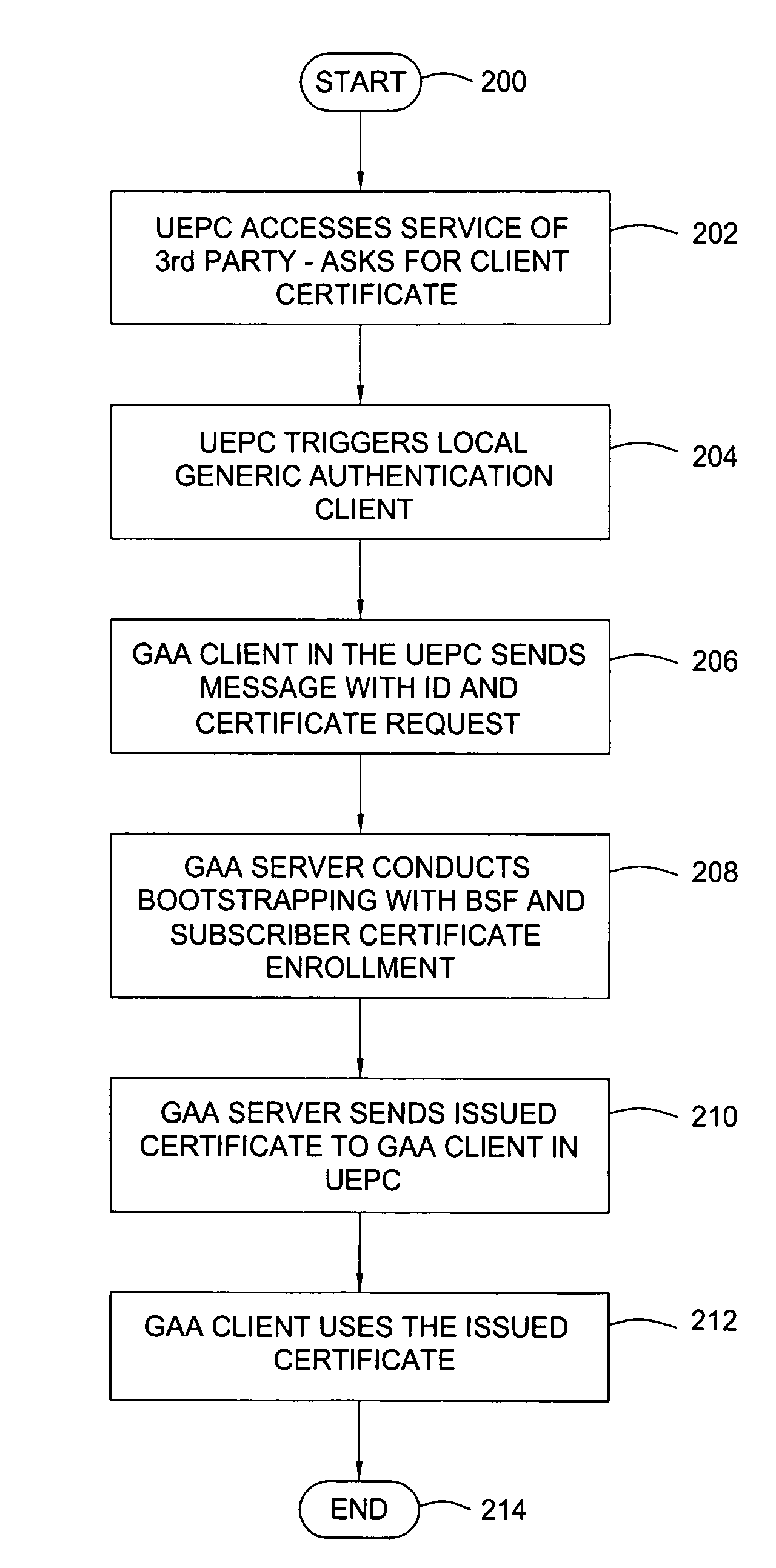
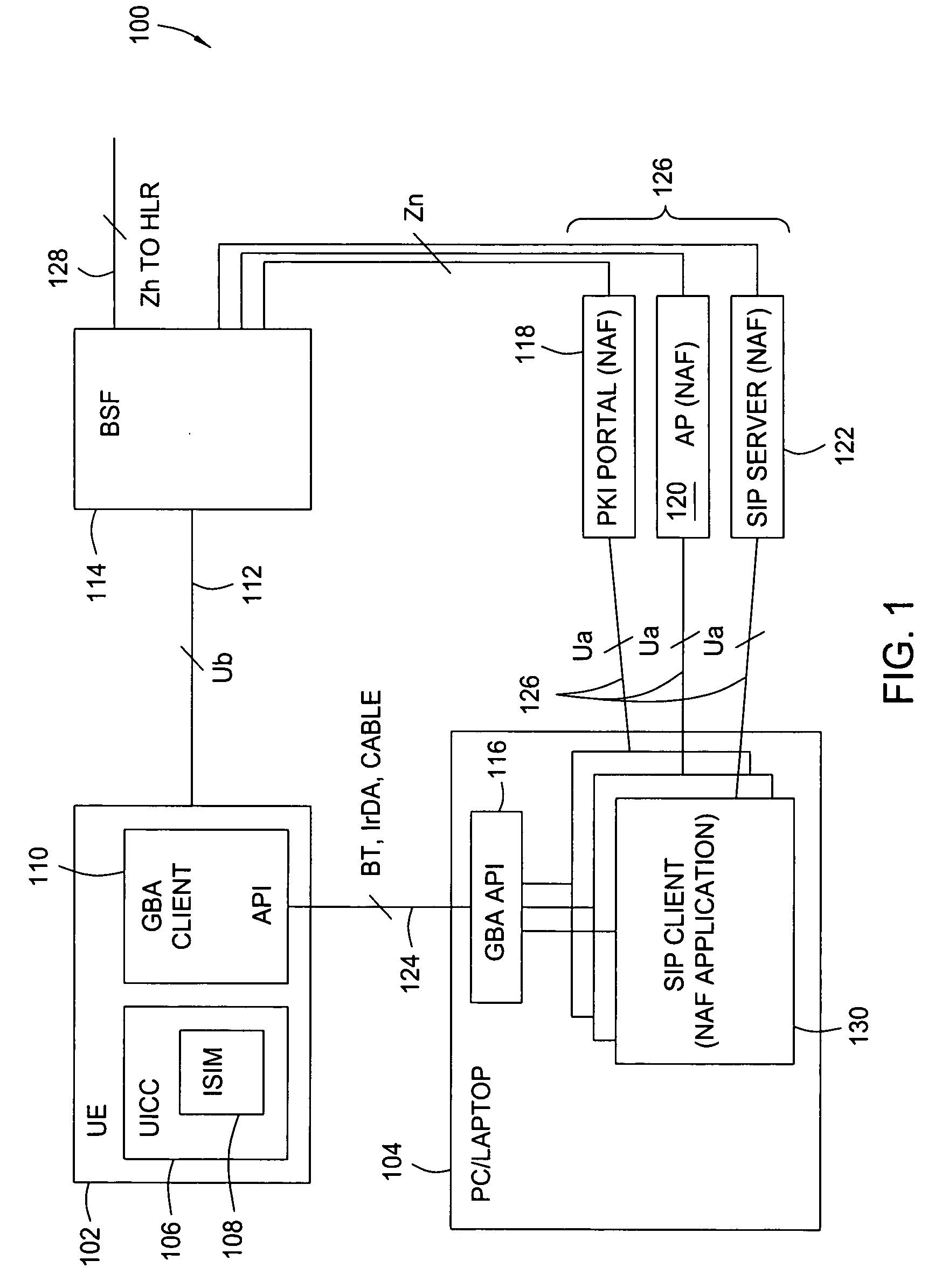
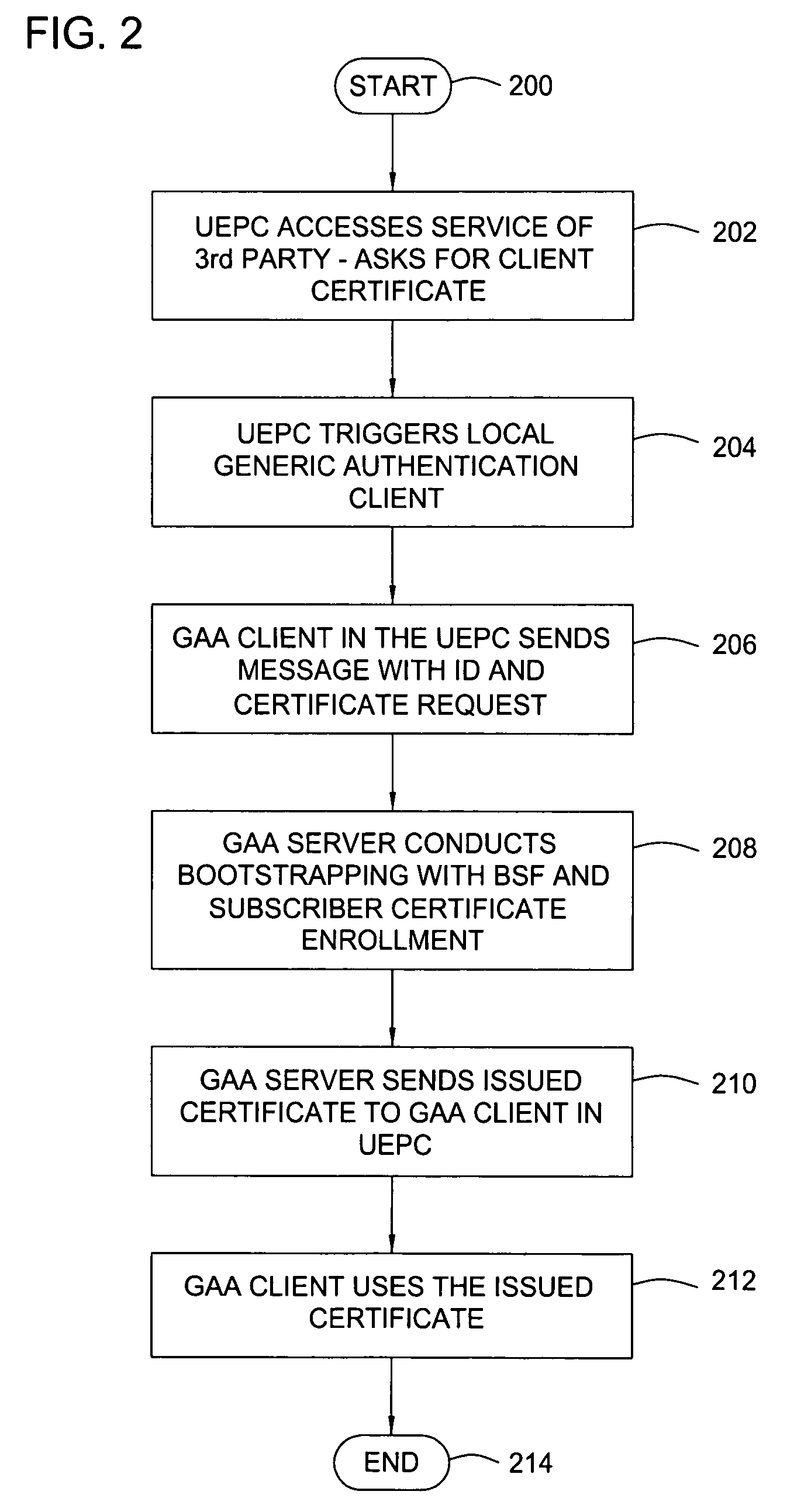
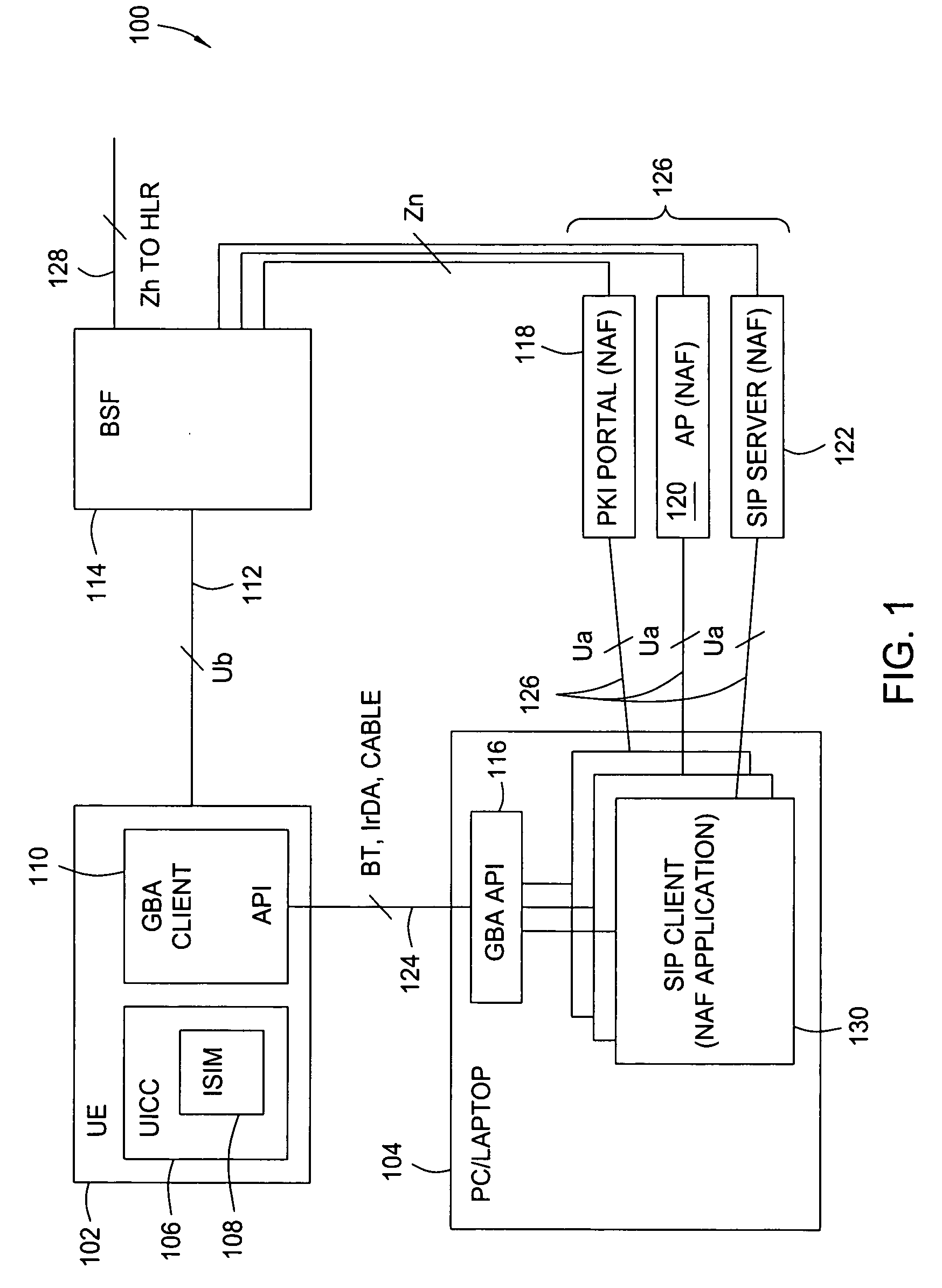
Method and apparatus for using generic authentication architecture procedures in personal computers
ActiveUS8543814B2Digital data processing detailsUser identity/authority verificationThird partyService provision
A method and apparatus for authenticating to a third party service provider from a personal computer. The method includes authenticating, with a mobile terminal, to the service provider with a universal subscriber identity module associated with the mobile terminal to obtain credentials specific to the service provider, transferring the credentials specific to the service provider from the mobile terminal to the personal computer, and accessing the service provider with the personal computer using the credentials transferred from the mobile terminal. The apparatus includes a mobile terminal, a computing device, a bootstrapping security module, and a network application function that cooperatively work to allow the computing device to access the network application function using a security credential from the mobile terminal.
Owner:RPX CORP
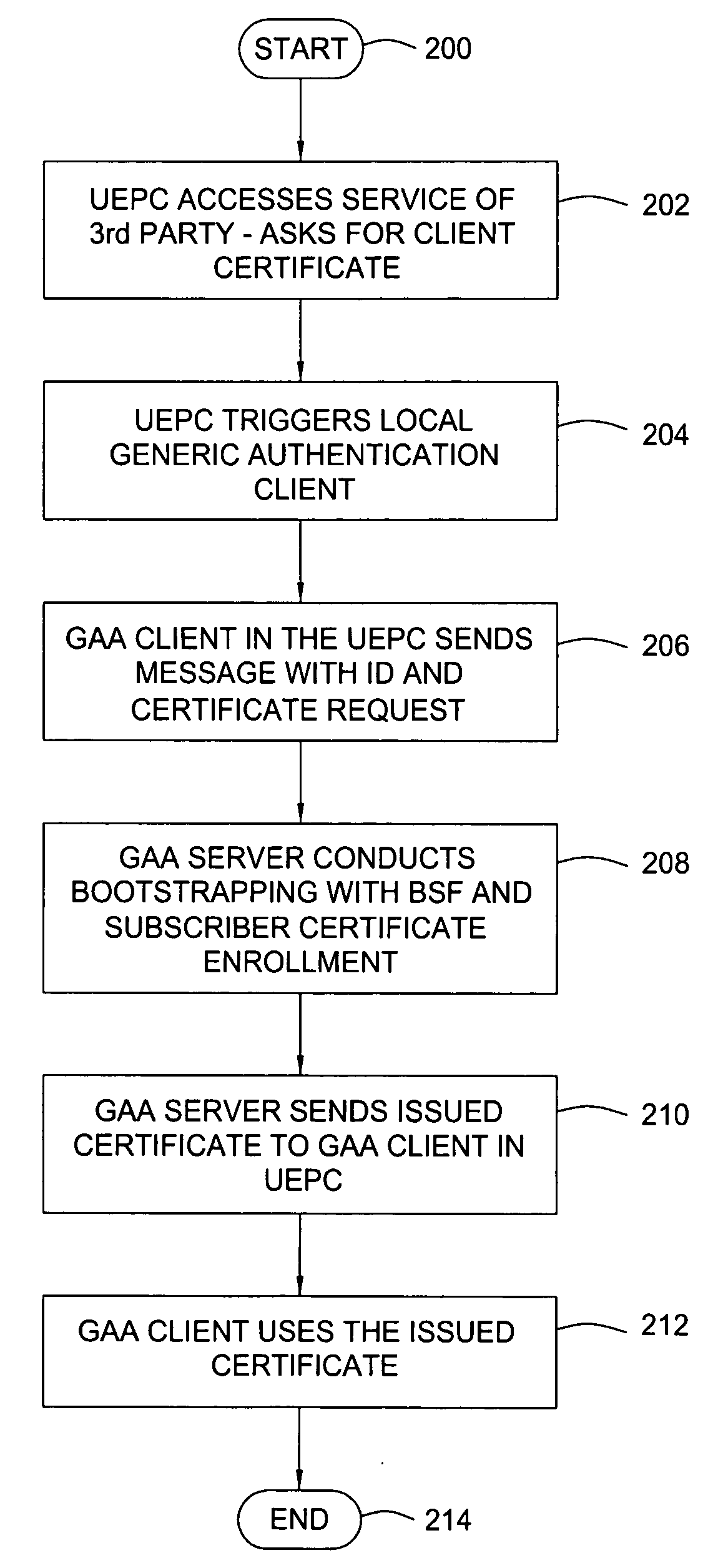
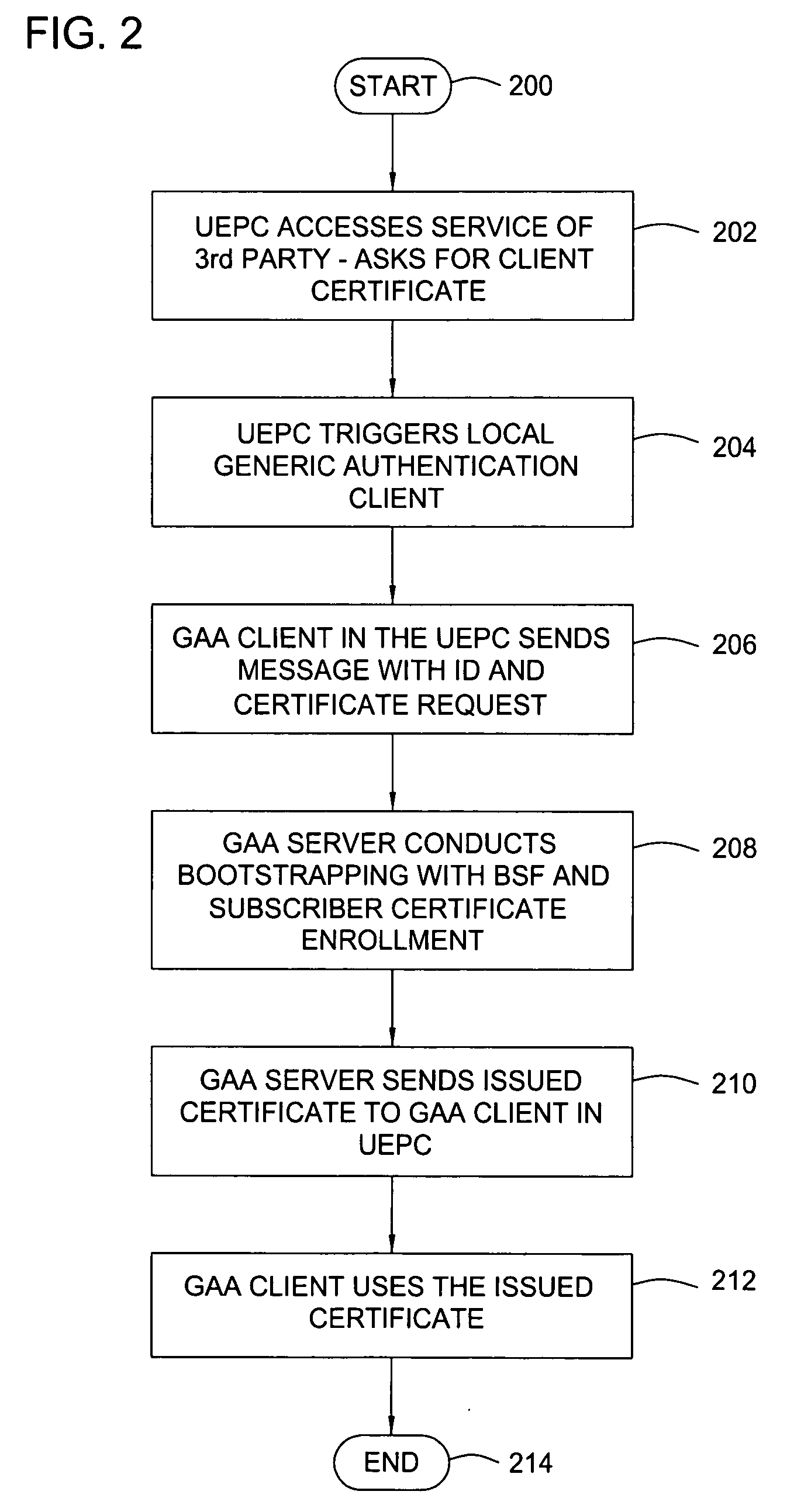
Method and apparatus for using generic authentication architecture procedures in personal computers
ActiveUS20060218396A1Digital data processing detailsUser identity/authority verificationThird partyPersonal computer
A method and apparatus for authenticating to a third party service provider from a personal computer. The method includes authenticating, with a mobile terminal, to the service provider with a universal subscriber identity module associated with the mobile terminal to obtain credentials specific to the service provider, transferring the credentials specific to the service provider from the mobile terminal to the personal computer, and accessing the service provider with the personal computer using the credentials transferred from the mobile terminal. The apparatus includes a mobile terminal, a computing device, a bootstrapping security module, and a network application function that cooperatively work to allow the computing device to access the network application function using a security credential from the mobile terminal.
Owner:RPX CORP
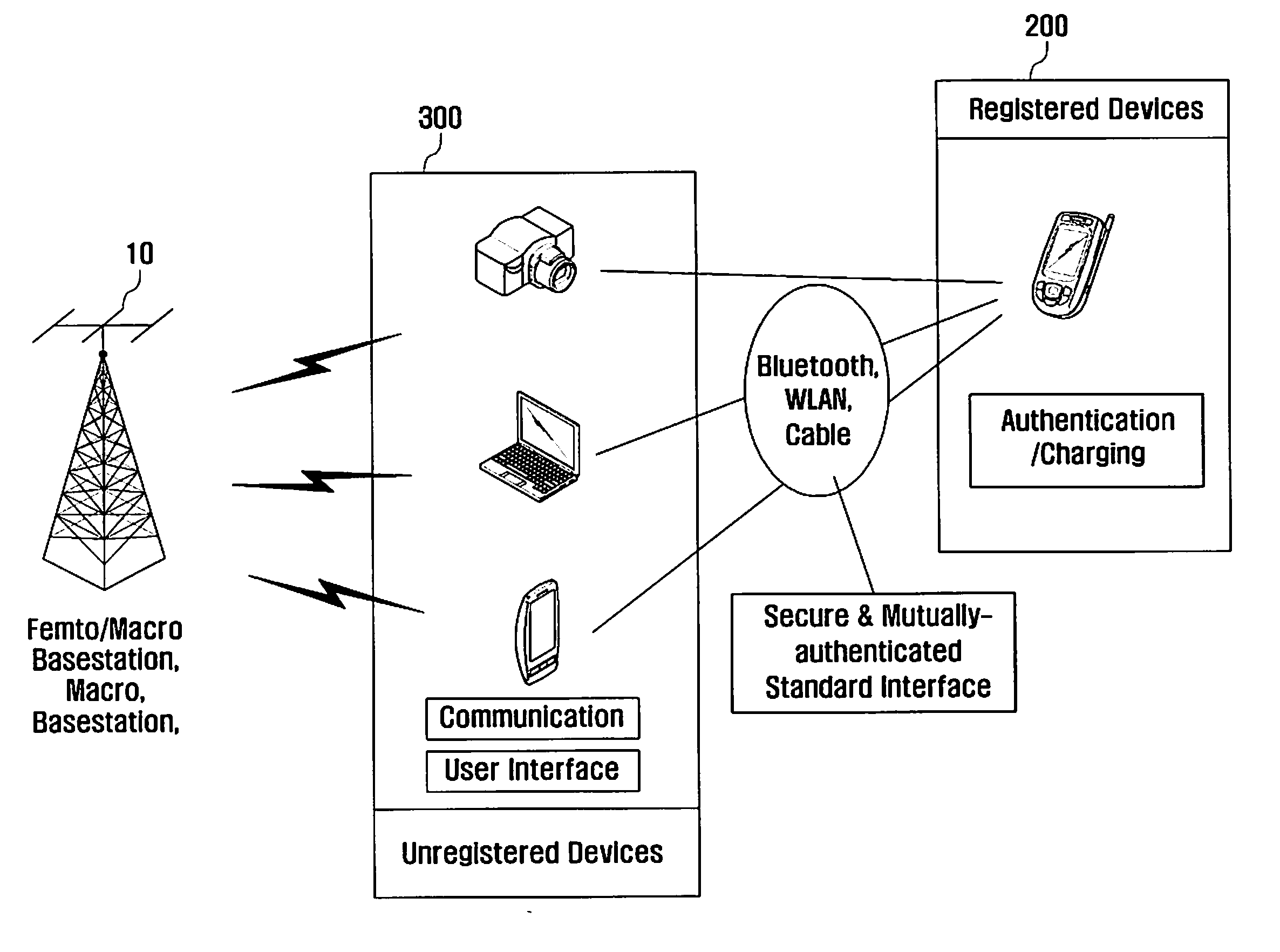
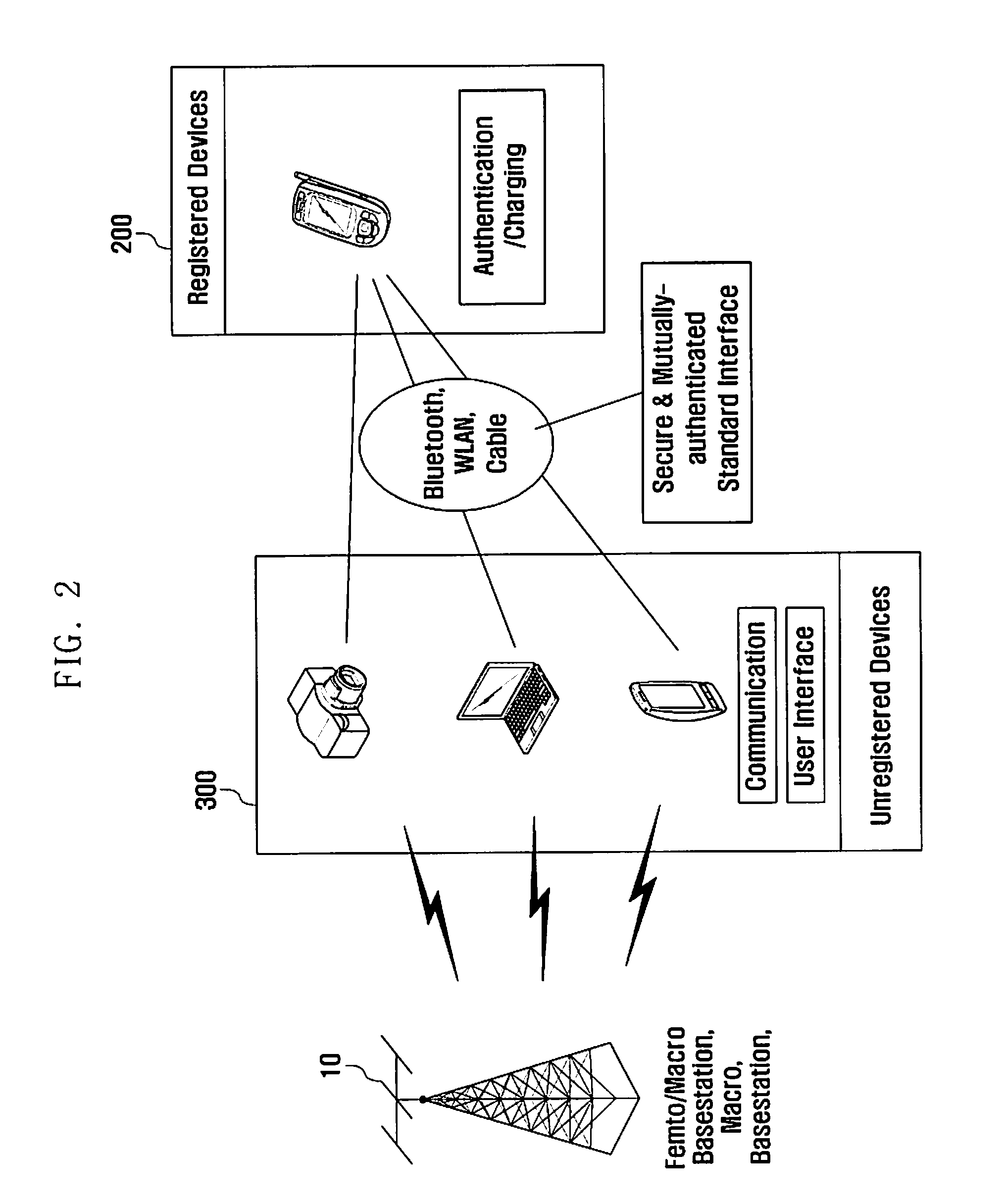
System for managing unregistered terminals with shared authentication information and method thereof
ActiveUS20110028126A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer scienceAuthentication information
Provided are a system and method for managing unregistered devices with authentication information sharing. The method includes receiving an authentication information duplication request from the unregistered device by the registered device, obtaining authentication information from a Universal Subscriber Identity Module (USIM) by the registered device when the registered device receives the authentication information duplication request, and transmitting the obtained authentication information to the unregistered device by the registered device.
Owner:SAMSUNG ELECTRONICS CO LTD +1
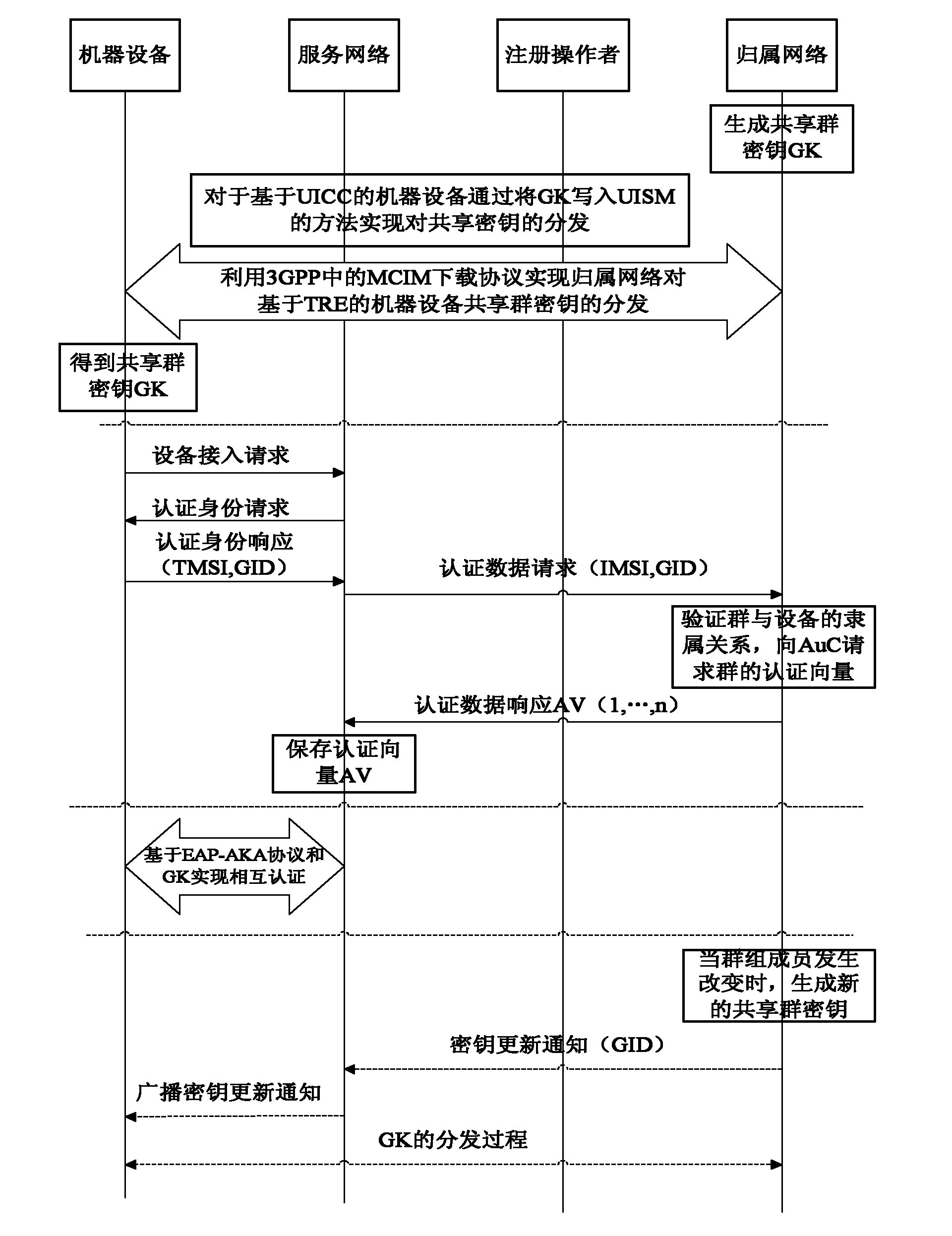
Authentication method based on shared group key in machine type communication (MTC)
ActiveCN102137397AOptimizing Signaling DataReduce congestionSecurity arrangementBroadcastingService networks
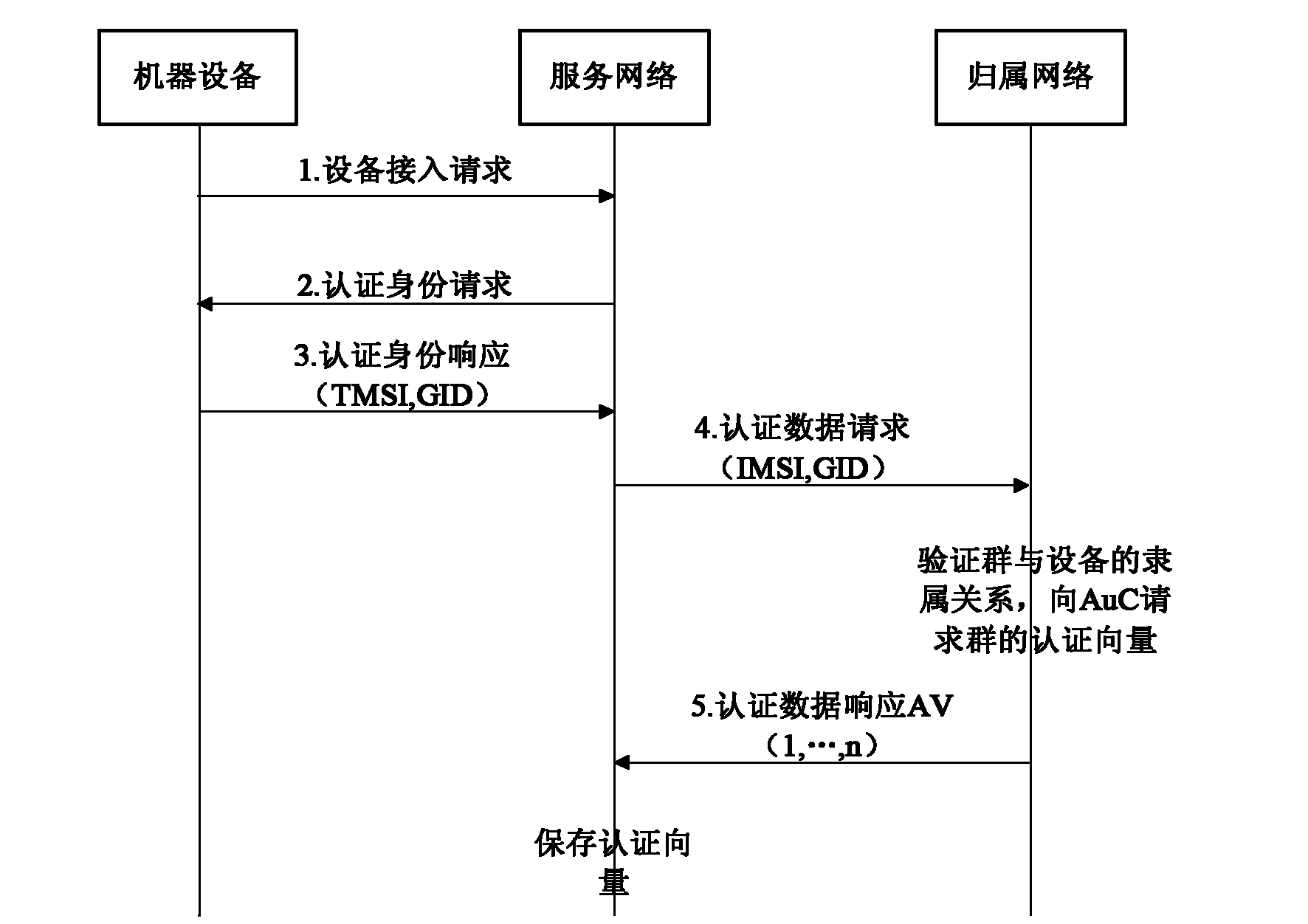
The invention discloses an authentication method based on a shared group key in machine type communication (MTC), mainly solving the defect of lack of an authentication mechanism based on an MTC group in the existing standard. The authentication process comprises the following steps that: (1) a home network (HN) generates a shared group key (GK), and writes the generated GK into a universal subscriber identity module (USIM) or distributes the generated GK as part of a machine to machine (M2M) communication identity module (MCIM) to all machinery equipment (ME) in the group; (2) the HN sends authentication data generated based on the GK to a service network (SN); (3) the SN performs mutual authentication on the ME in the group by using the obtained authentication data; and (4) when the relation among the group members is changed, the HN broadcasts a key updating notification message to all the ME belonging to the group, and realizes update of the shared GK between the HN and the ME according to the step (1). The authentication method optimizes the signal data generated by authentication between the SN and the HN, reduces congestion of a link between the SN and the HN, and is safe, fast and suitable for fast access authentication of an ME group in MTC.
Owner:XIDIAN UNIV
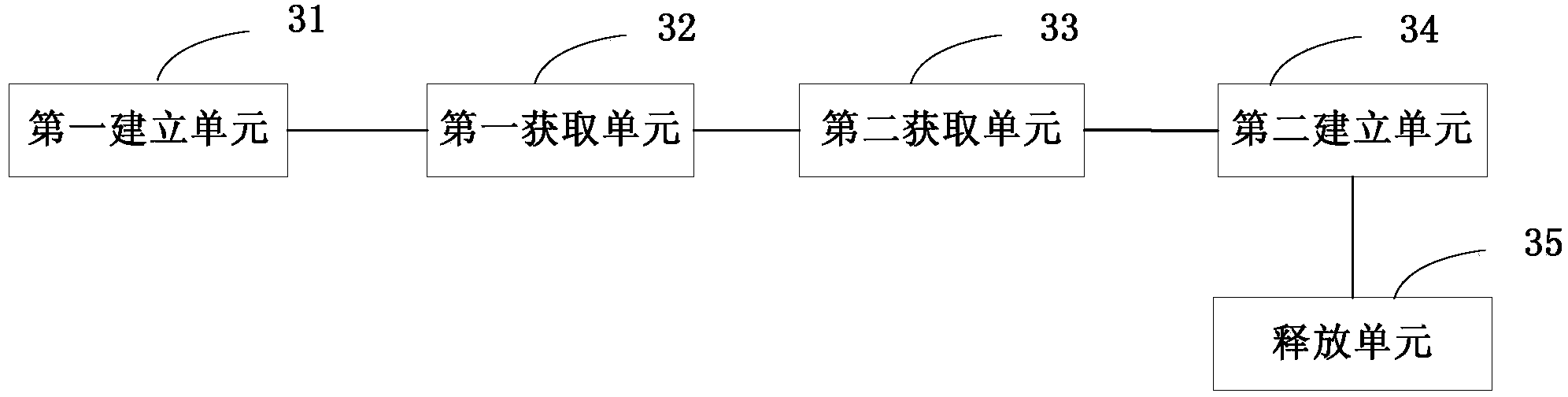
Establishment method and establishment device of communication links
InactiveCN104394522AImprove usabilityThe problem of saving high roaming chargesConnection managementNetwork data managementTelecommunications linkTelecommunications
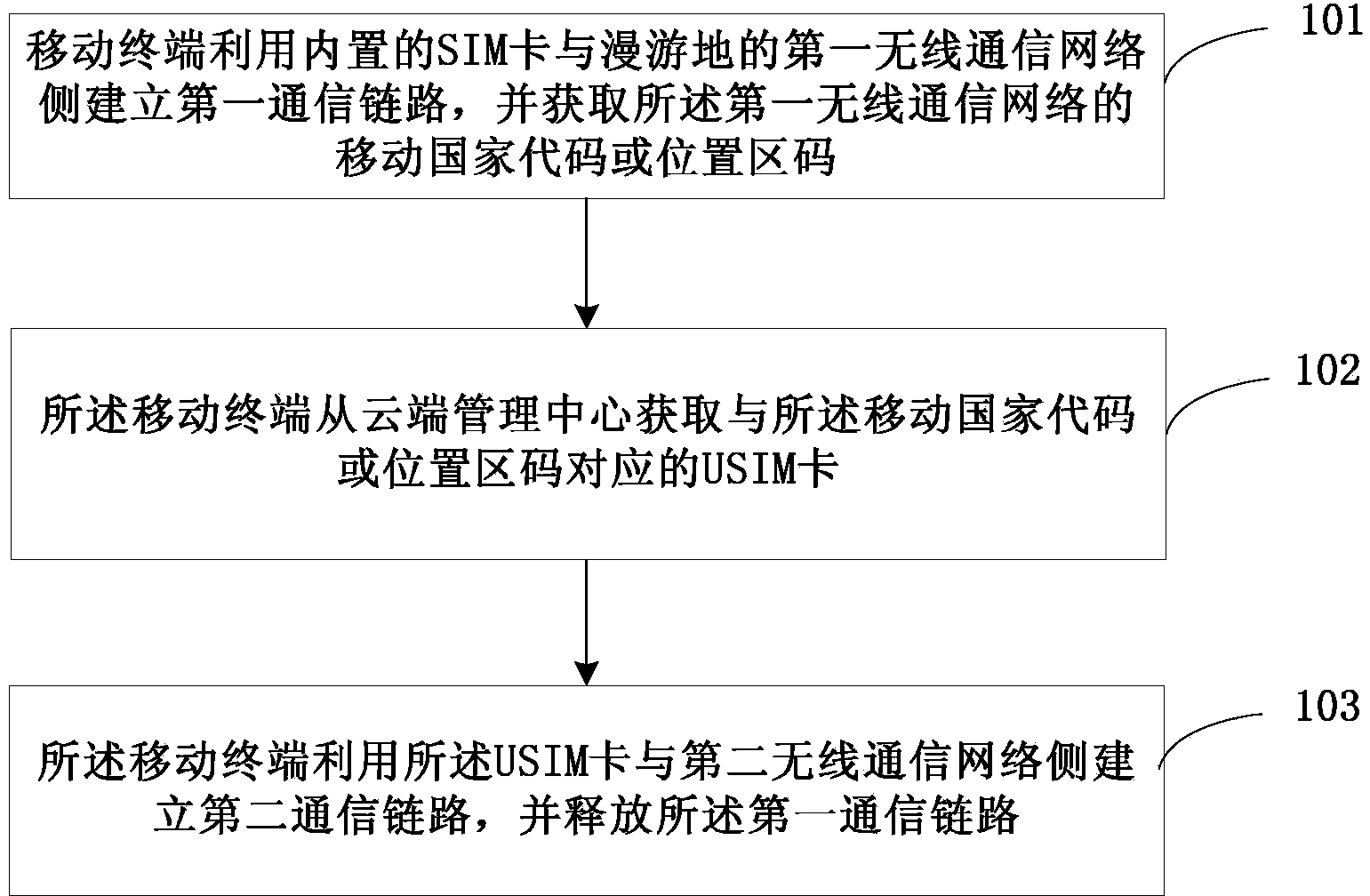
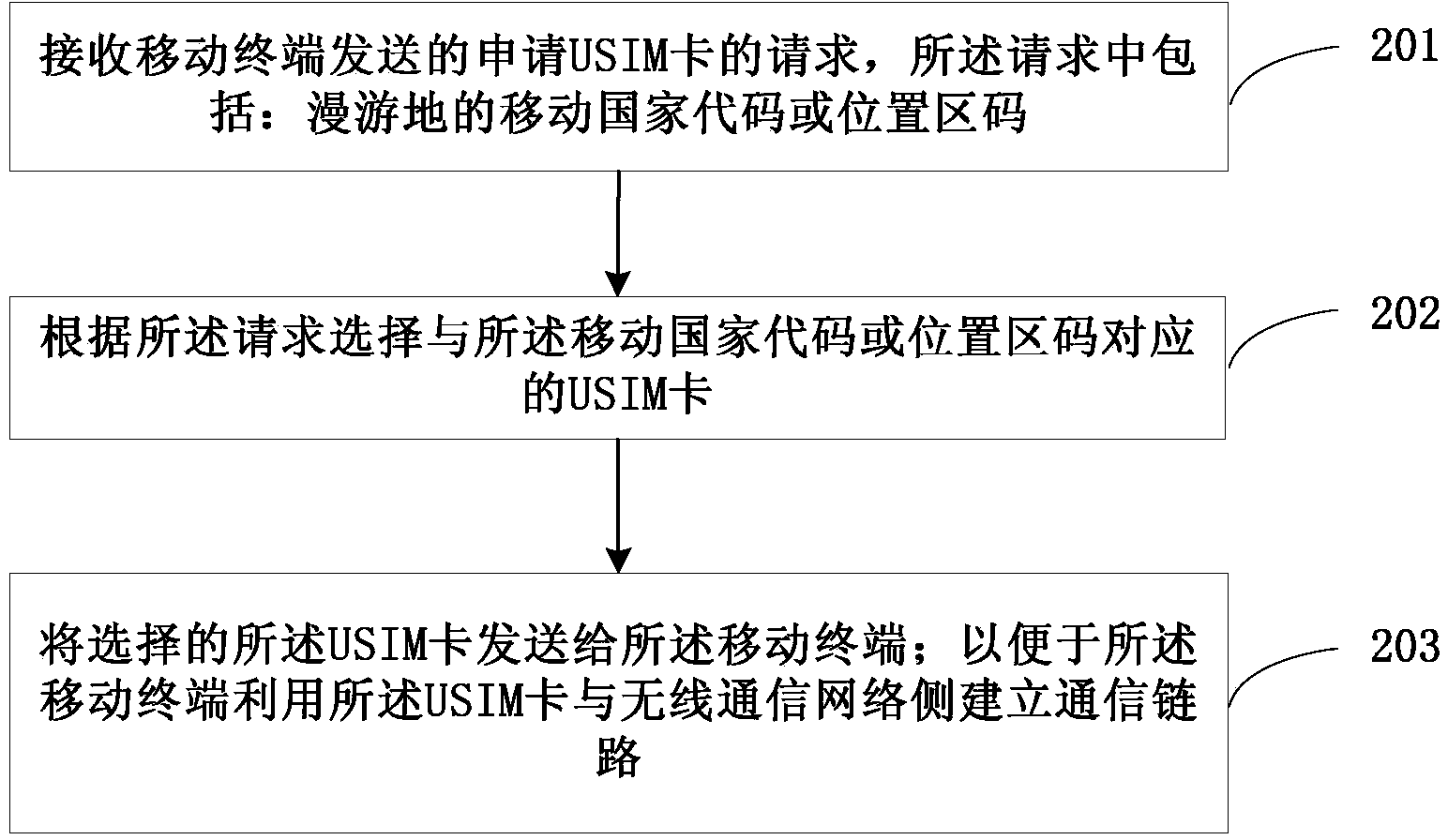
The embodiment of the invention discloses an establishment method and an establishment device of communication links. The method comprises the steps of allowing a mobile terminal to establish the first communication link with a first wireless communication network side in a roaming place by utilizing a built-in SIM (Subscriber Identity Module) card and to obtain a mobile country code or a location area code of a first wireless communication network, allowing the mobile terminal to obtain a USIM (Universal Subscriber Identity Module) card corresponding to the mobile country code or the location area code from a cloud management center, and allowing the mobile terminal to establish the second communication link with a second wireless communication network side by utilizing the USIM card and to release the first communication link. In the method, the mobile terminal utilizes the built-in SIM card to obtain the USIM card from the cloud management center and then utilizes the USIM card to establish connection with equipment on the wireless communication network side in the roaming place, so that high roaming charges of a roaming subscriber caused by using roaming data flow in the roaming place are saved, the usability of the mobile terminal is improved, and the operating cost is lowered.
Owner:TIANJIN ROAMWIFI TECH
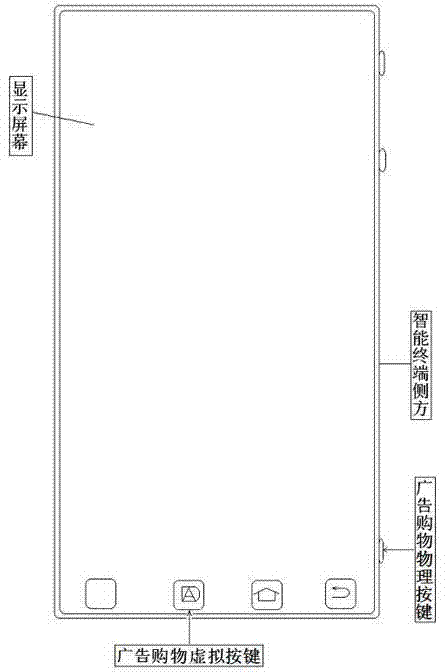
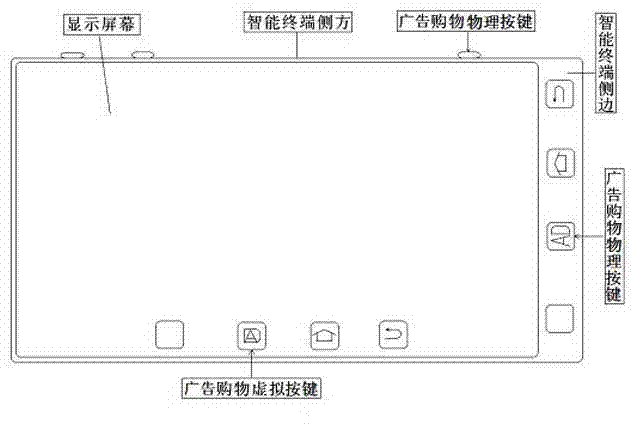
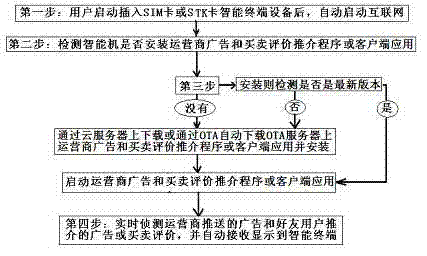
Intelligent terminal for intelligent push of advertisements and buying and selling comments
ActiveCN103401923AFree trafficFree shoppingAccounting/billing servicesSubstation equipmentTablet computerComputer hardware
The invention discloses an intelligent terminal for intelligent push of advertisements and buying and selling comments. The intelligent terminal comprises a terminal, wherein a physical advertisement shopping key is added beside or on the side edge of the terminal; a virtual advertisement shopping virtual key is added on the display interface of the terminal to construct the intelligent terminal; and the terminal comprises a mobile phone using a USIM (Universal Subscriber Identity Module) or STK (SIM Card Tool Kit) mobile phone card, a tablet computer, a notebook computer, a desktop computer, a television and a telephone. According to the intelligent terminal, intelligent push of advertisements and buying and selling comments is performed during voice and information communication of the Internet or mobile Internet, so that the dreams and goals of making telephone calls for free, sending short messages for free, using flow for free, surfing the Internet for free, even shopping for free and earning money are achieved.
Owner:张先锋
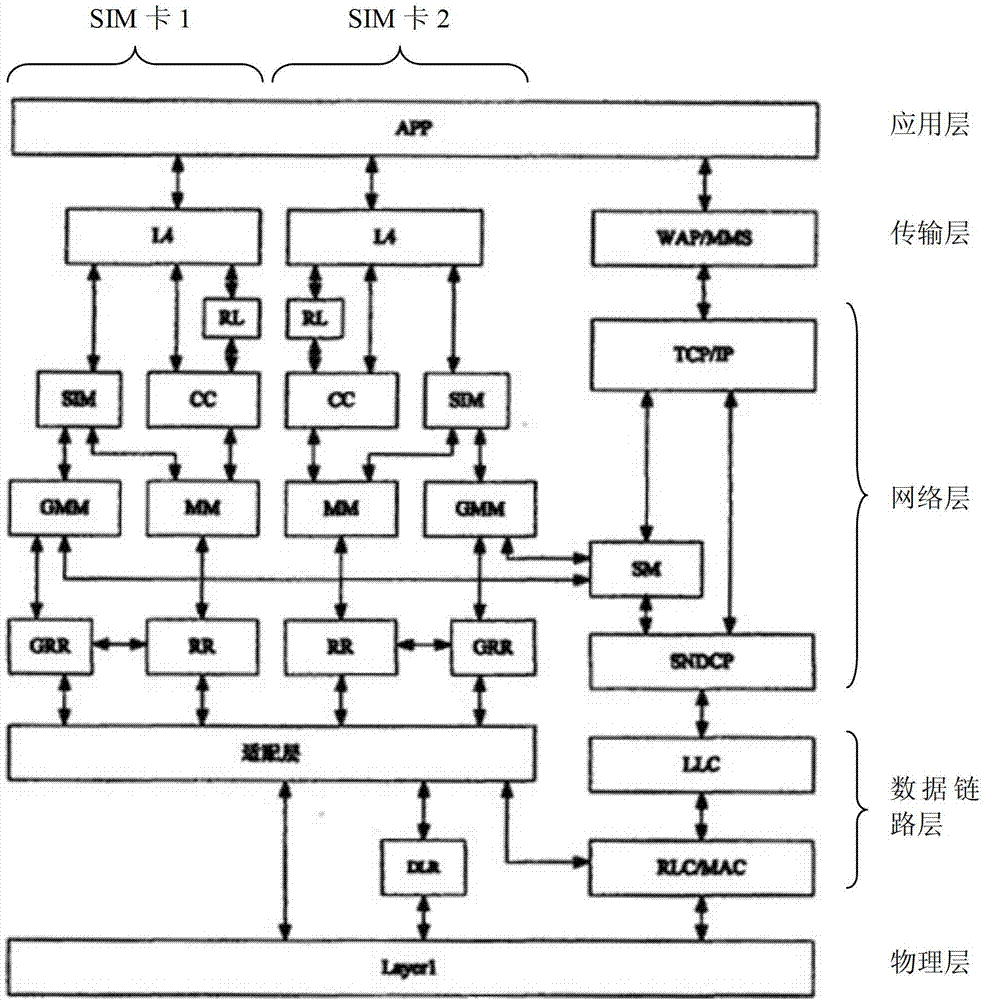
Single-card dual-mode terminal and communication method thereof
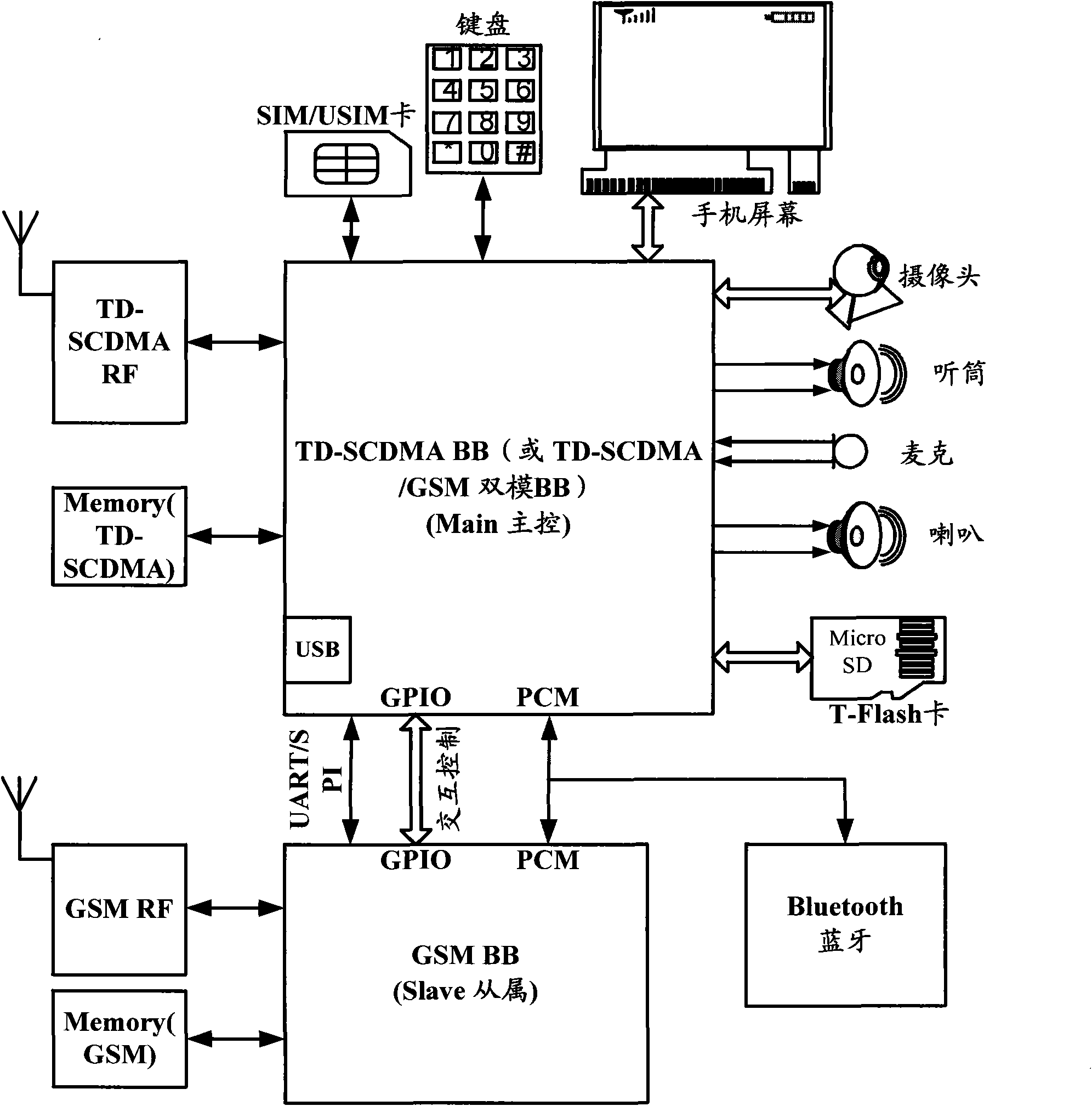
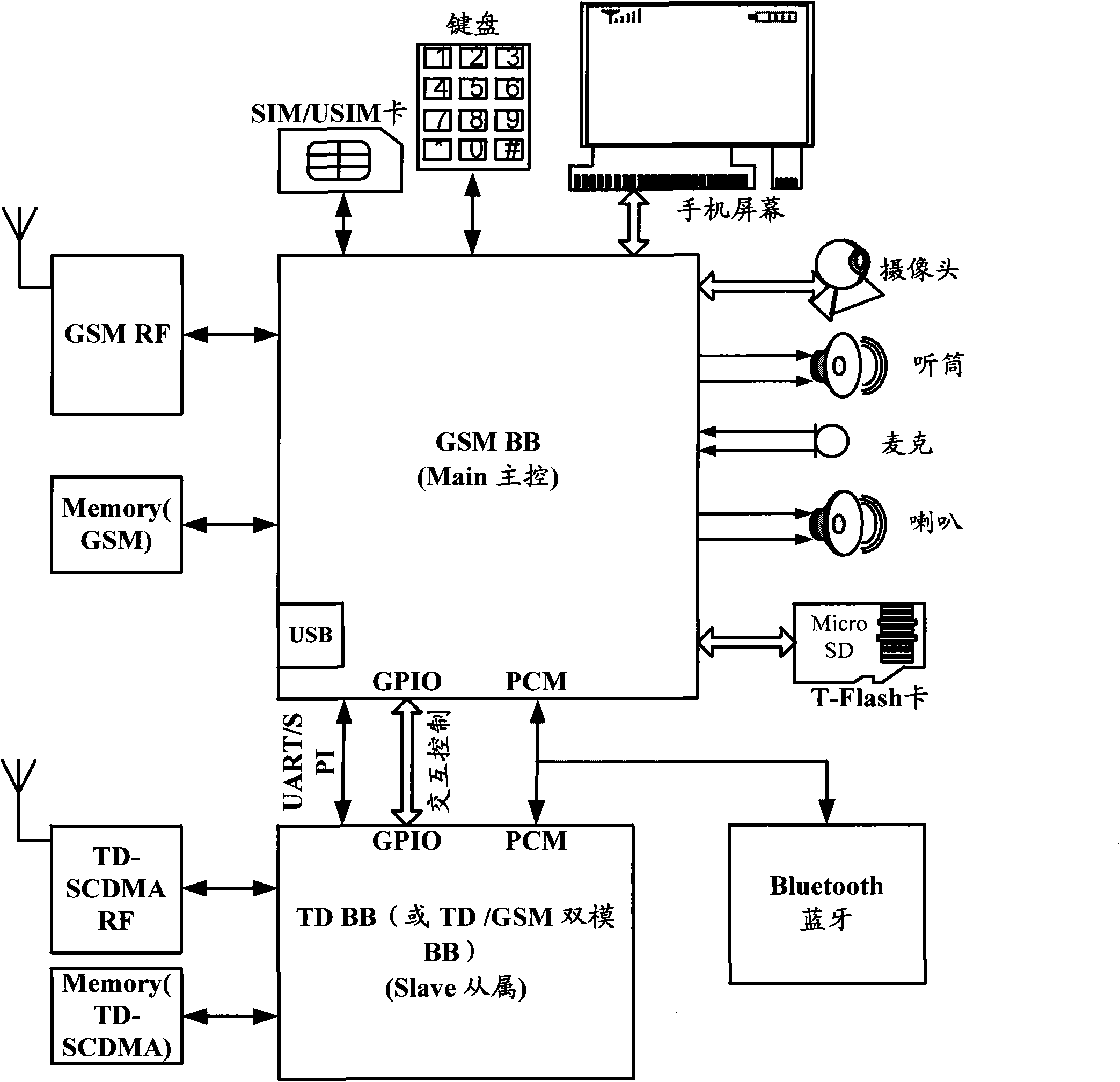
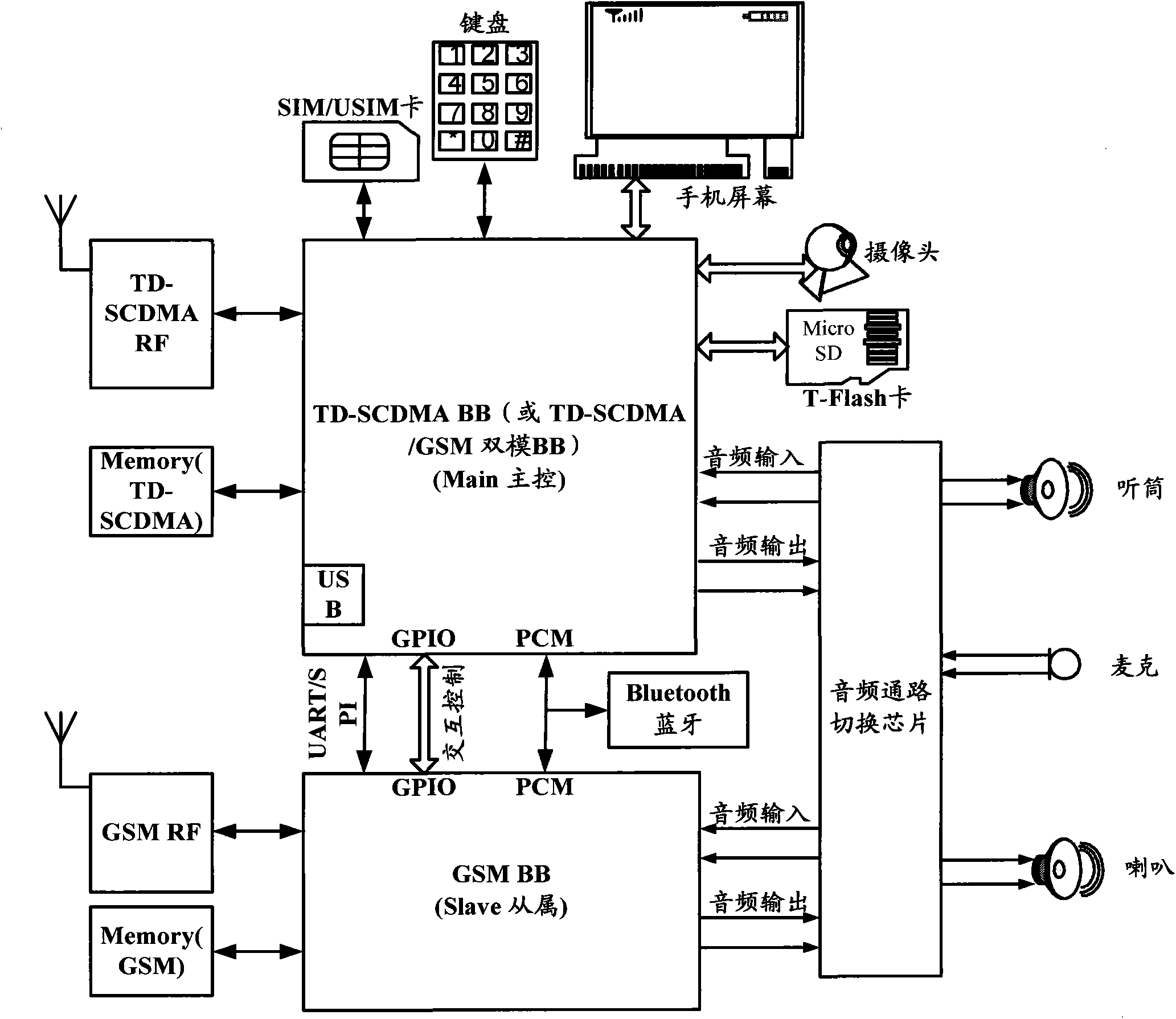
The invention relates to the field of communication, in particular to a single-card dual-mode terminal and a communication method thereof. In the invention, services in a first network mode and services in a second network mode are respectively dispatched and processed through a main control module and a slave module, and the main control module also takes the action of a passage among the slave module, an SIM (Subscriber Identity Module) / USIM (Universal Subscriber Identity Module) card and peripheral devices. Accordingly, the dual-standby function can be realized by simultaneously residing one SIM card or USIM card in two different network modes so as to realize a single-card dual-mode and dual-standby terminal. The invention not only avoids the load of a single-card user for additionally purchasing other cards, but also can likewise realize the concurrency of a CS (Circuit Switch) service and a PS (Postscript Switch) service through the single SIM / USIM card. In addition, the whole power consumption is smaller than that of a traditional dual-card dual-mode and dual-standby terminal.
Owner:SPREADTRUM COMM (SHANGHAI) CO LTD
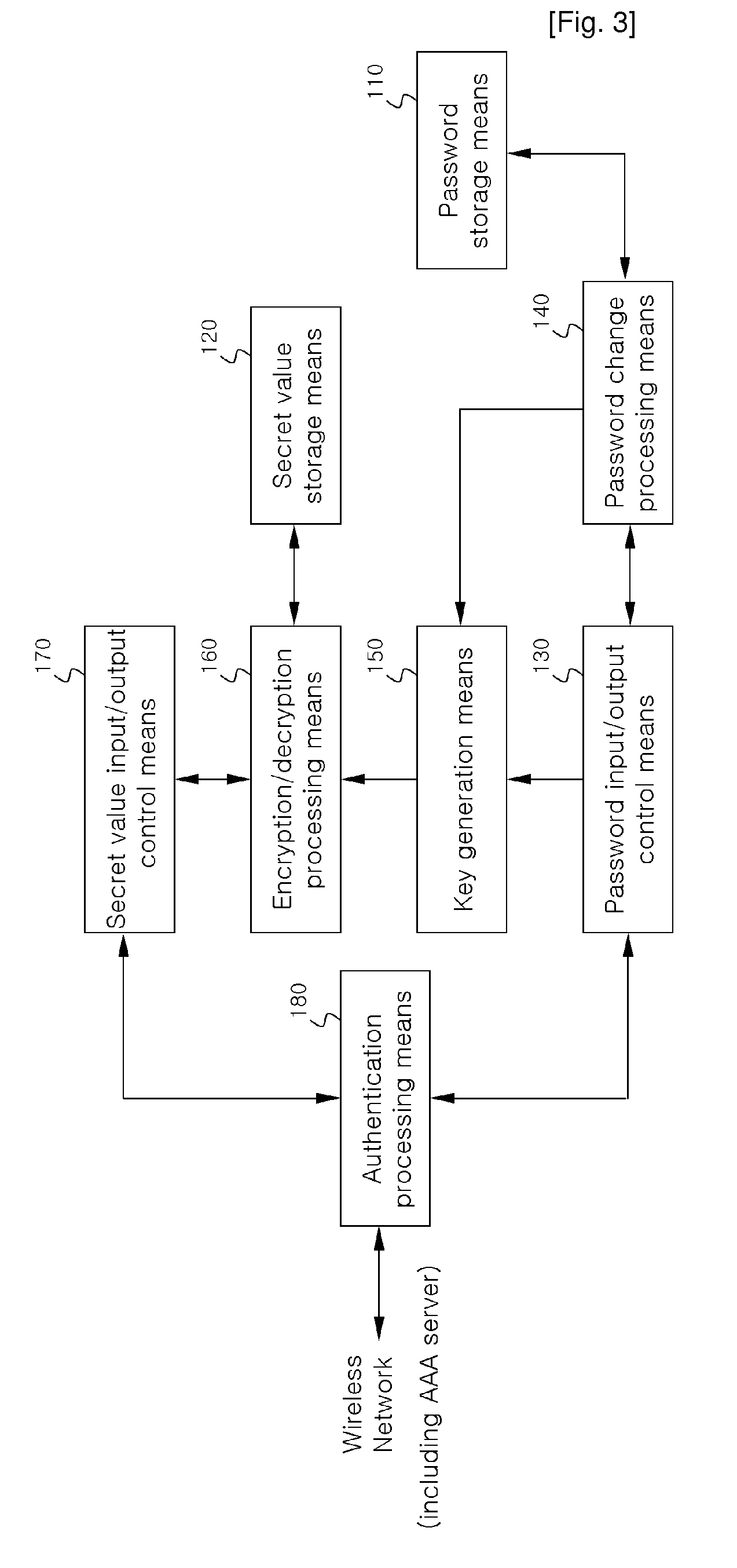
Apparatus and Method for Processing Eap-Aka Authentication in the Non-Usim Terminal
InactiveUS20080317247A1Key distribution for secure communicationUser identity/authority verificationComputer hardwarePassword
Disclosed are an apparatus and a method for processing authentication using Extensible Authentication Protocol-Authentication and Key Agreement (EAP-AKA) in a non-Universal Subscriber Identity Module (USIM) terminal without a USIM card.According to the present invention, although the USIM card used for user authentication function is absent, the secret value that used to be stored in the USIM card for user authentication is directly stored in the non-USIM terminal. Therefore, both a user password and a secret value are applied for EAP-AKA authentication of the terminal and the user and user authentication problems caused by lack of the USIM card can be overcome.
Owner:POS DATA CO LTD
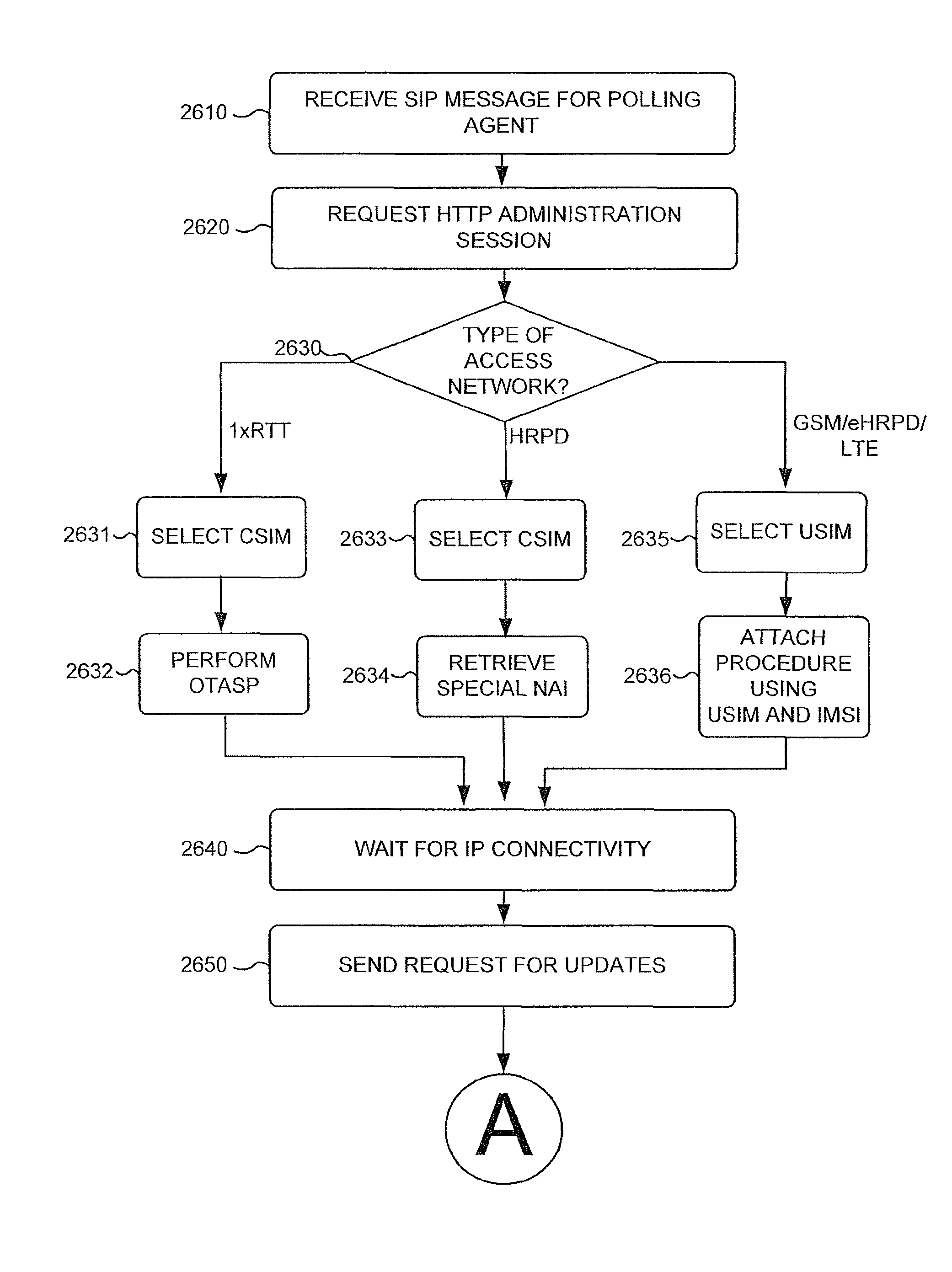
Universal integrated circuit card updates in a hybrid network
A universal integrated circuit card (UICC) may include a universal subscriber identity module (USIM); a code division multiple access (CDMA) subscriber identity module (CSIM); a memory to store instructions; and a processor. The processor may execute instructions to determine a type of wireless access network available to a user equipment (UE) associated with the UICC; perform updates of the UICC using the USIM, in response to detecting a CDMA enhanced High Rate Packet Data (eHRPD) network, a Global System for Mobile Communication (GSM) access network, or a Long Term Evolution (LTE) access network; and perform updates of the UICC using the CSIM, in response to detecting an available CDMA access network other than a CDMA eHRPD access network.
Owner:CELLCO PARTNERSHIP INC +1
Method and apparatus for creating security context and managing communication in mobile communication network
ActiveUS20120129500A1Near-field transmissionUnauthorised/fraudulent call preventionComputer moduleSecurity context
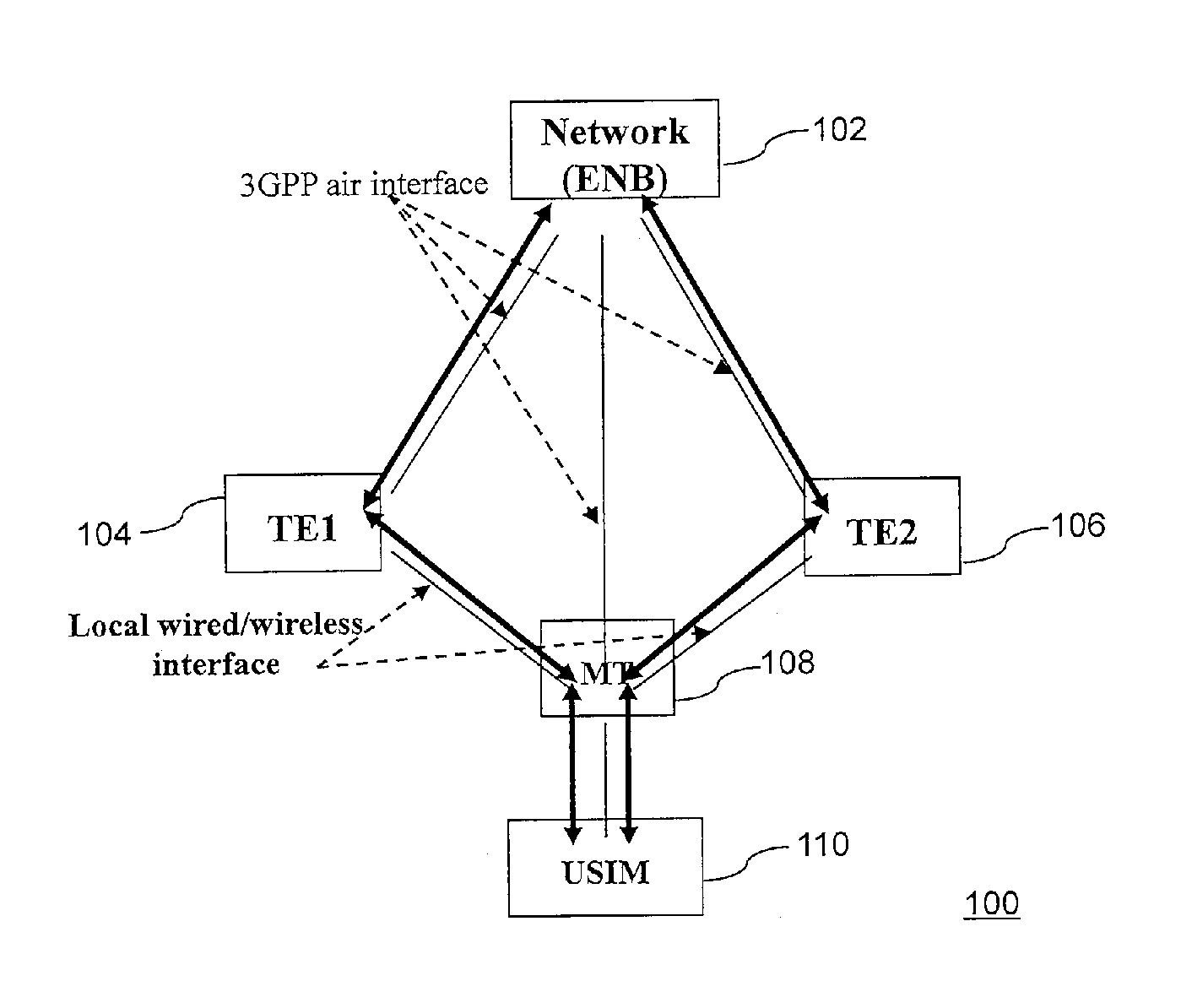
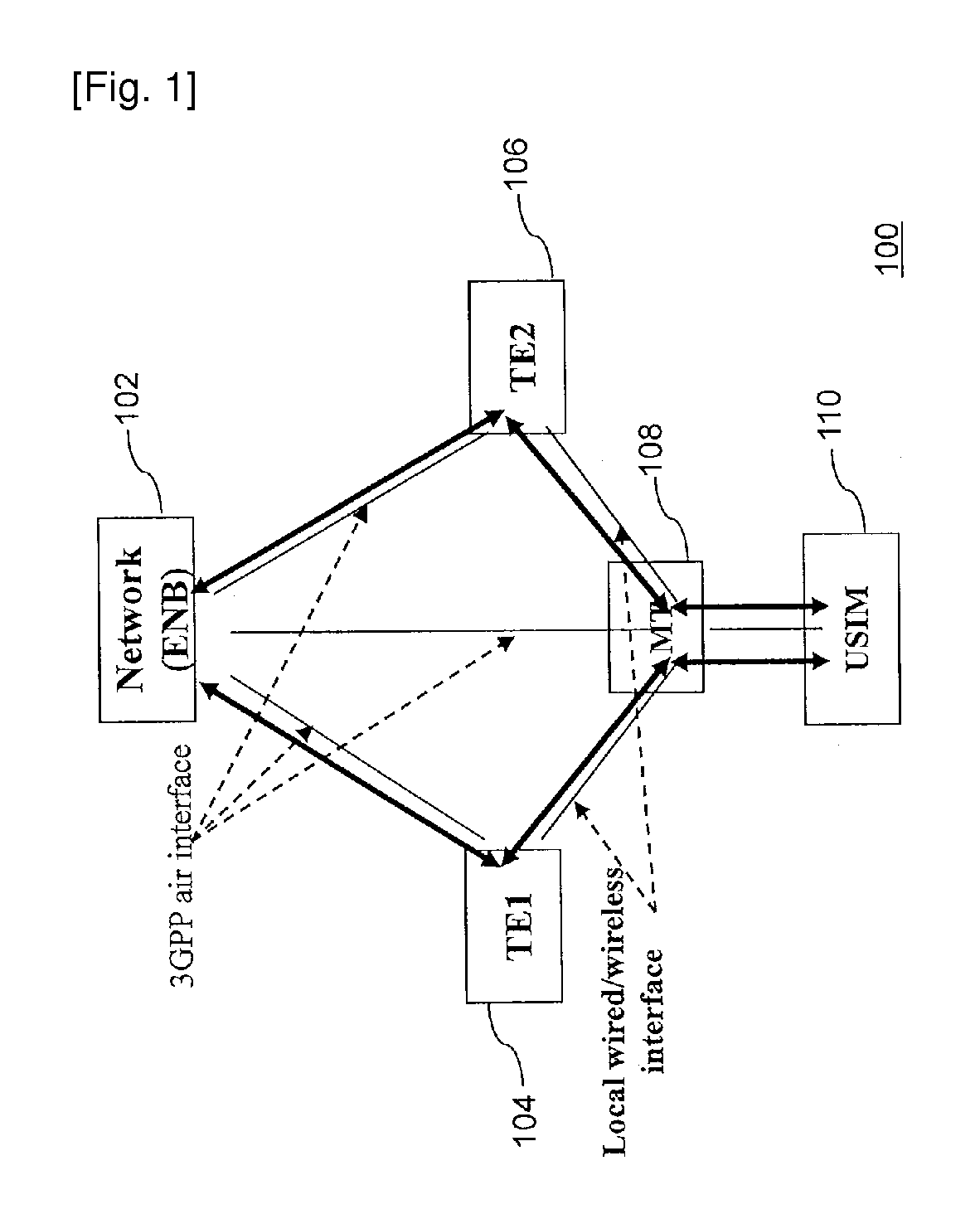
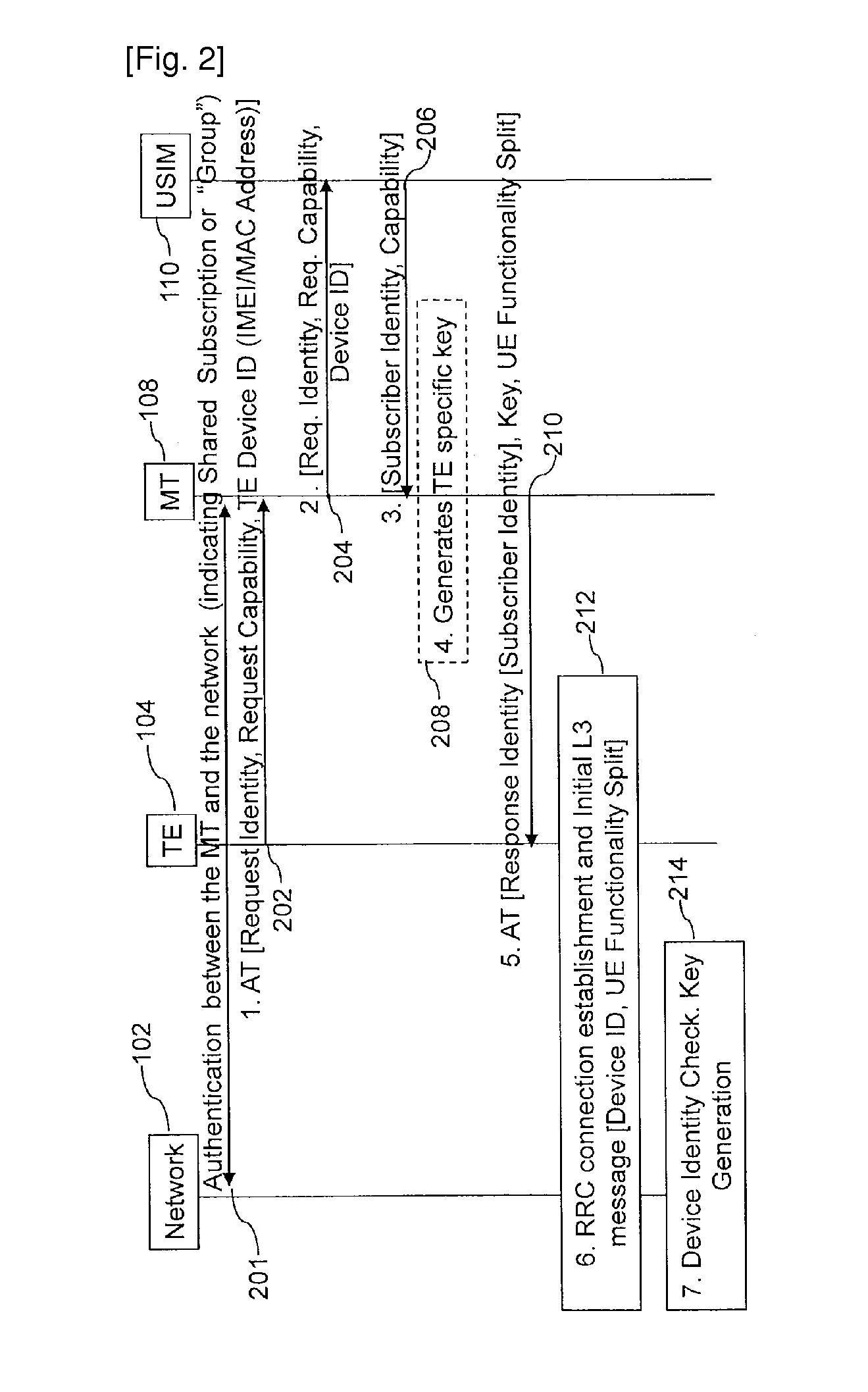
A method and apparatus for establishing communication between a plurality of communication devices and a communication network using a single subscription is provided. The method receives a first request from a second communication device to get a subscription identity and capabilities of subscription for accessing the communication network using subscription of the first communication device. The method then sends the first request to a Universal Subscriber Identity Module (USIM) associated with the first communication device. Thereafter, the method receives a response from the USIM including subscription identity, access protection keys and capabilities of the subscription. Then the method generates unique key for the second communication device based on the response received from the USIM. The method then sends the response along with the generated unique key to the second communication device to establish communication between the second communication device and the communication network using the subscription of first communication device.
Owner:SAMSUNG ELECTRONICS CO LTD
User identity protection method based on public-key mechanism
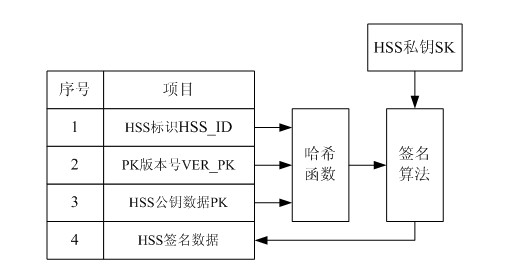
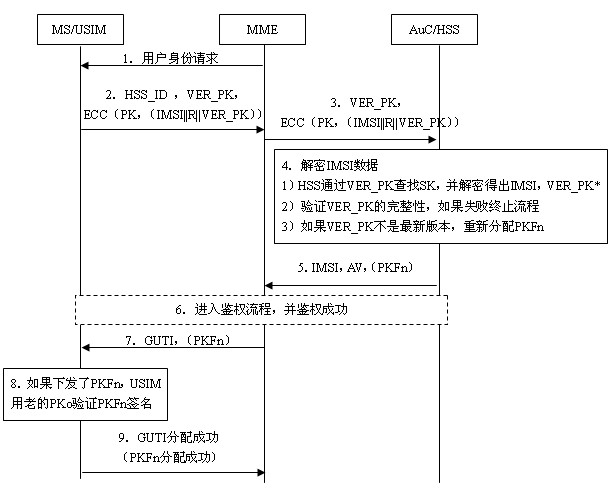
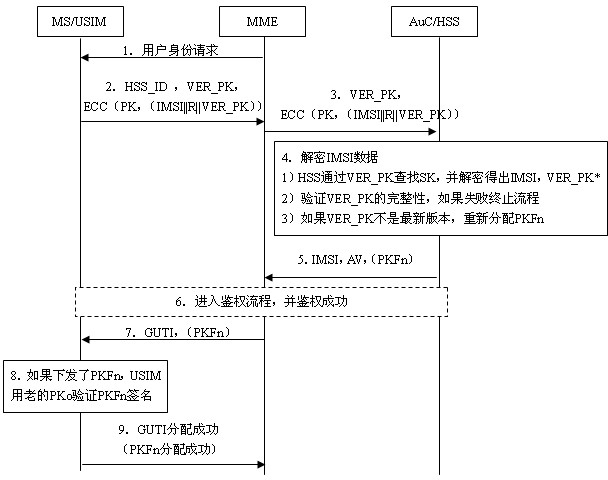
ActiveCN102026178AIncrease the difficulty of decipheringIntegrity guaranteedSecurity arrangementInternet privacyEngineering
The invention relates to the secret communication field of mobile communication technologies, and discloses a user identity protection method based on a public-key mechanism. The method comprises the following steps: an HSS (hierarchical service system) produces a pair of keys, namely, a public key PK and a secret key SK, then the public key PK is preset to a USIM (universal subscriber identity module) card of UE (user equipment) belonging to the public key PK in the form of a public key file PKF, and the secret key SK is stored in the HSS; a mobile phone sends the following information to anMME (mobility management entity), including HSS identification: HSS_ID, public-key PK version number: VER_PK; and data (IMSI || R|| VER_PK) encrypted by using an asymmetric encryption algorithm; after receiving the information, the MME sends the VER_PK and the (IMSI || R|| VER_PK) to the HSS according to the HSS_ID; and the HSS decrypts the VER_PK and the (IMSI || R|| VER_PK) by using the secret key SK. Because attackers do not know the secret key SK of the HSS, the attackers can not decrypt the (IMSI || R|| VER_PK).
Owner:成都三零瑞通移动通信有限公司
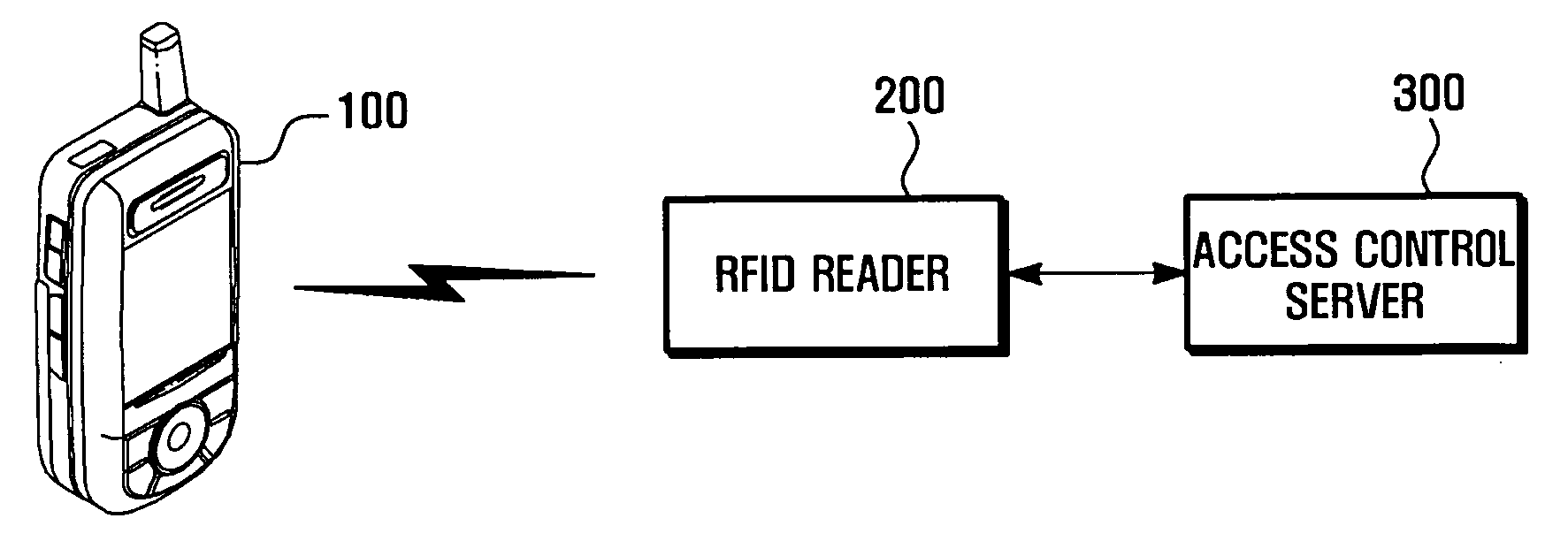
Method and system for setting security of a portable terminal
InactiveUS20100066486A1Limited functionNear-field transmissionElectric signal transmission systemsComputer hardwareThird generation
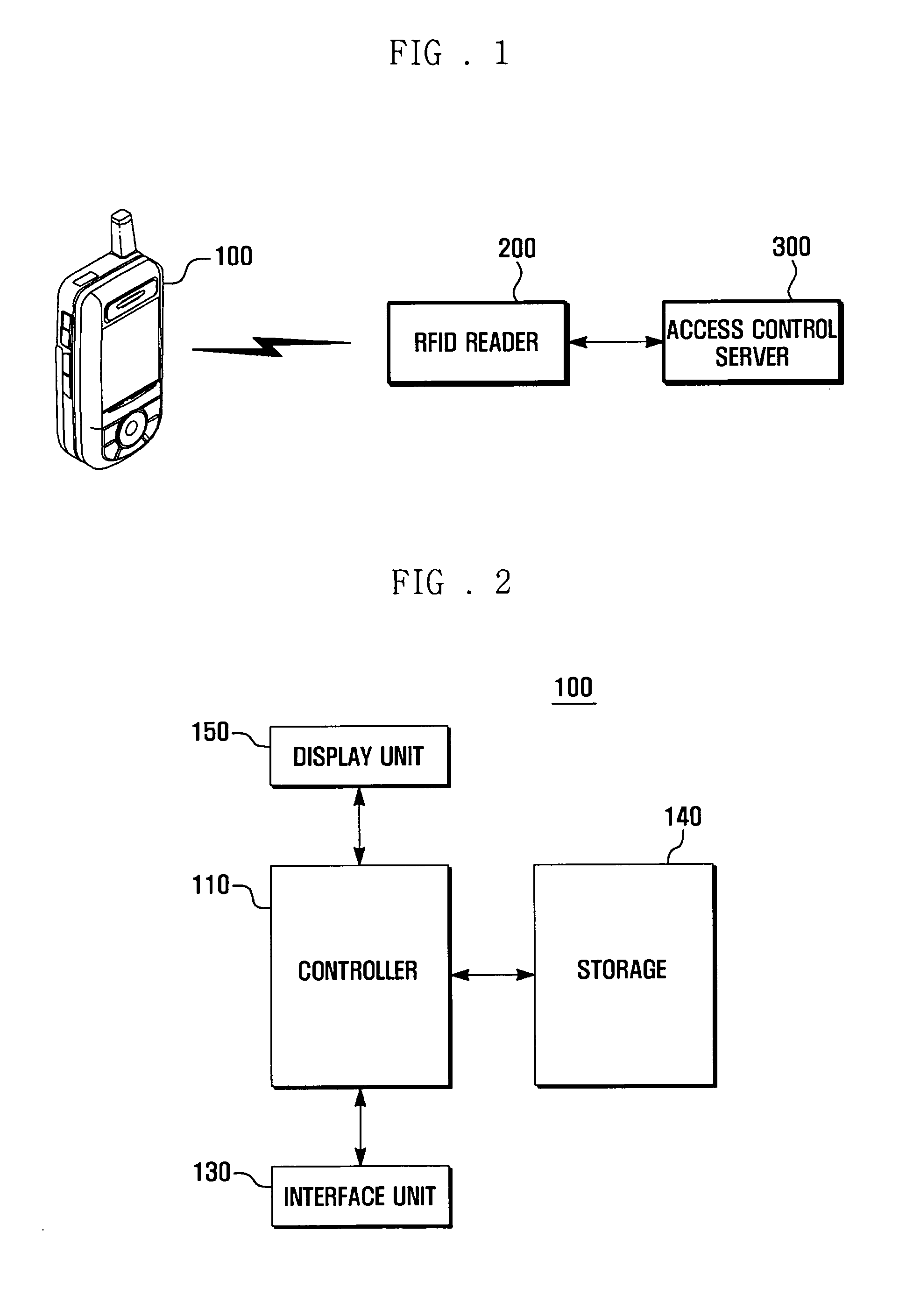
The present invention relates to a method and system for setting security of a portable terminal by utilizing an RFID (Radio Frequency Identification) function of a USIM (Universal Subscriber Identity Module) card used in Third Generation portable terminals. For this, USIM card information is registered in an access control server, and the USIM card information of the portable terminal is sensed through a RFID reader installed at a point of entry of a secure area, and the security setting of the portable terminal is automatically performed according to the registration of USIM card information in the access control server.
Owner:SAMSUNG ELECTRONICS CO LTD
Method, system and device for identifying terminal
InactiveCN102083212AImprove work efficiencySecurity arrangementNetwork data managementIntegrated Services Digital NetworkSubscriber identity module
The embodiment of the invention relates to a wireless communication technology, particularly a method, system and device for identifying a terminal. The invention is used for solving the problem of failure to identify a great deal of MTC (Machine-Type Communication) equipment in the 3GPP (3rd Generation Partnership Project) system in the prior art. The method provided by the embodiment of the invention comprises steps as follows: a network node determines an equipment identification, and determines the corresponding MTC equipment according to the equipment identification, wherein the equipment identification comprises an IMEI (International Mobile Equipment Identity) corresponding to the MTC equipment, and an IMSI (International Mobile Subscriber Identity) corresponding to an SIM (Subscriber Identity Module) or USIM (Universal Subscriber Identity Module) in the MTC equipment. In the method provided by the embodiment of the invention, since the IMSI and the IMEI are bound together to identify one MTC equipment and also identify the MTC equipment contract, the MTC equipment can be identified in the 3GPP system. The embodiment of the invention can also use the IMSI to identify an MTC subscriber contract, and use an MSISDN (Mobile Station-Integrated Services Digital Network) number to identify an MTC group composed of the MTC equipment in the MTC subscriber contract.
Owner:DATANG MOBILE COMM EQUIP CO LTD
System, method and equipment for changing signature data
ActiveCN102076124AEasy to changeQuick changeWireless communicationSubscriber identity moduleIntegrated circuit
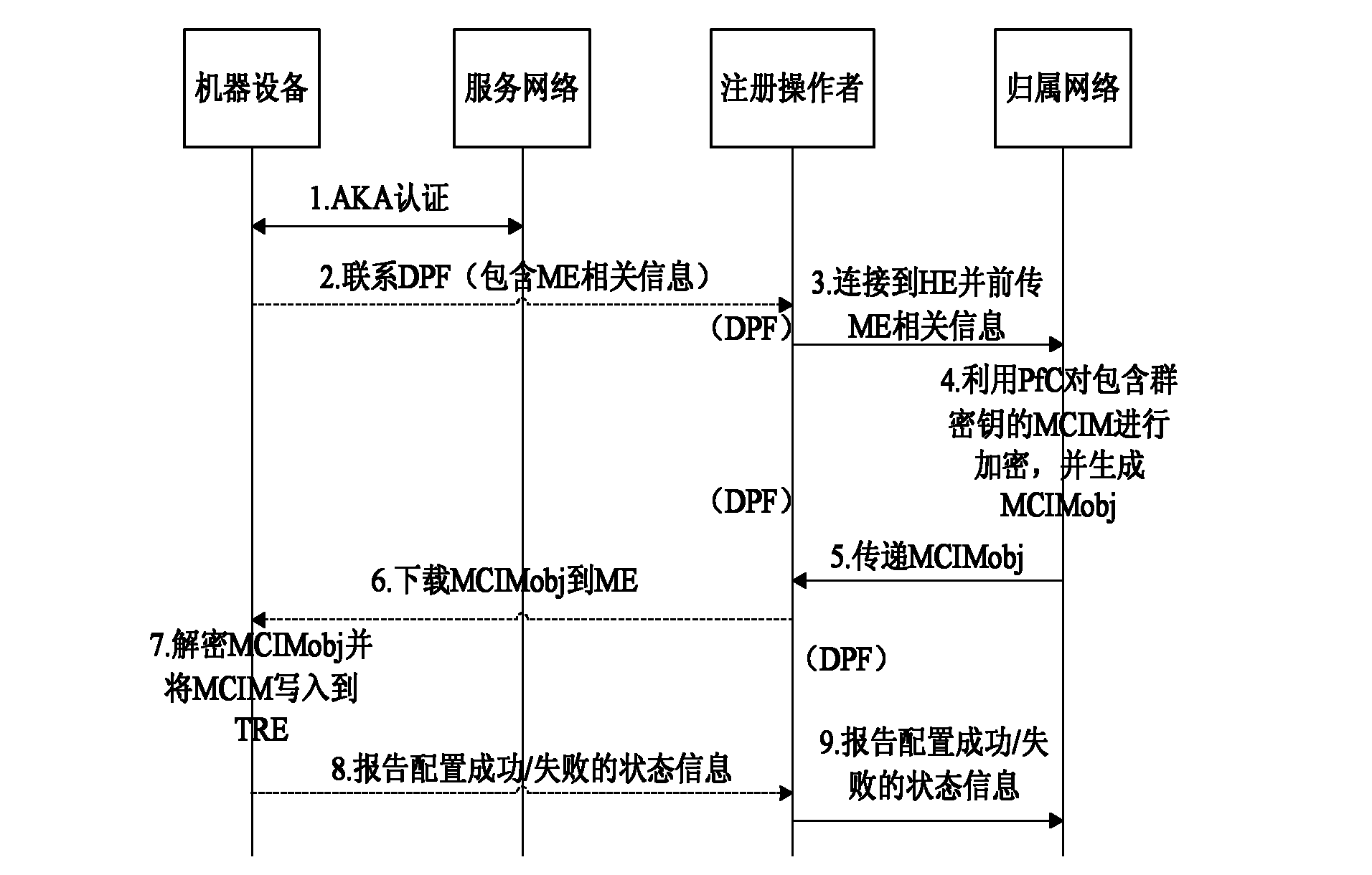
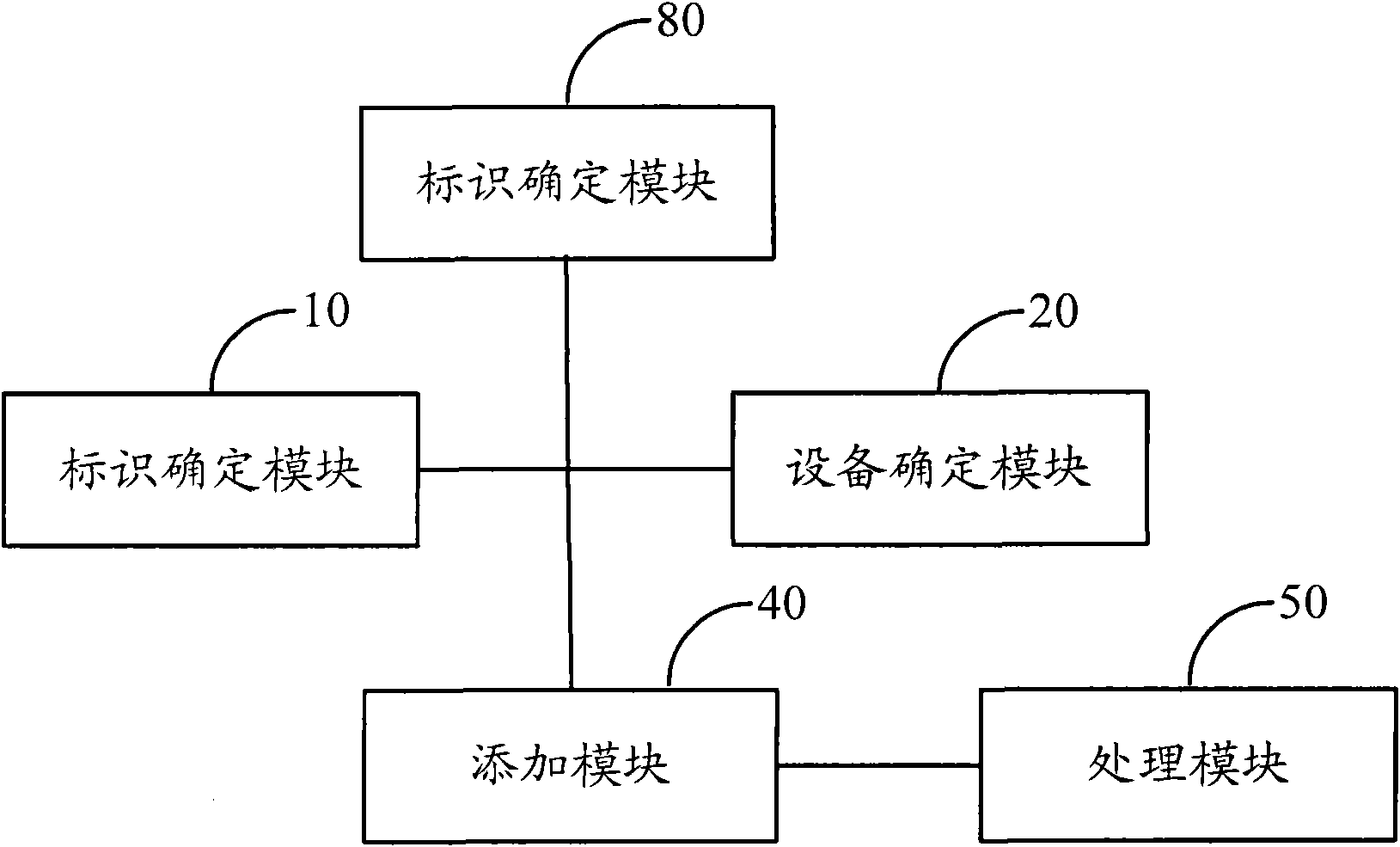
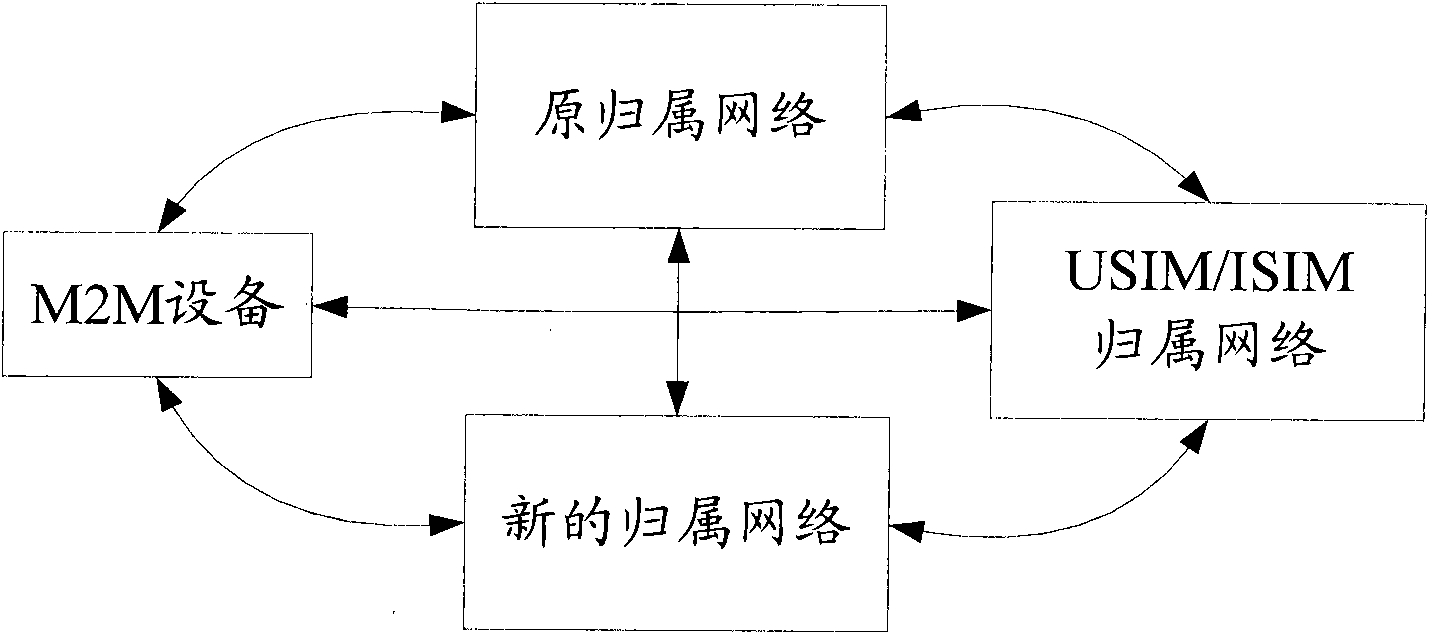
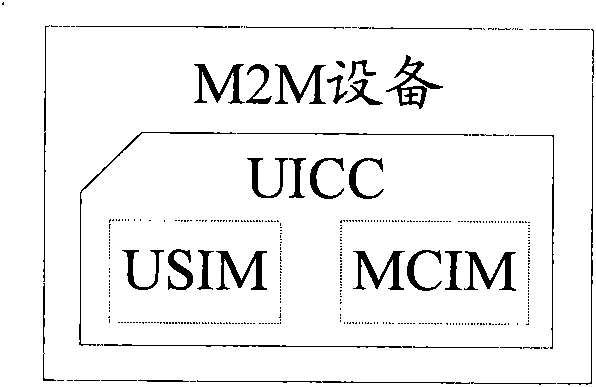
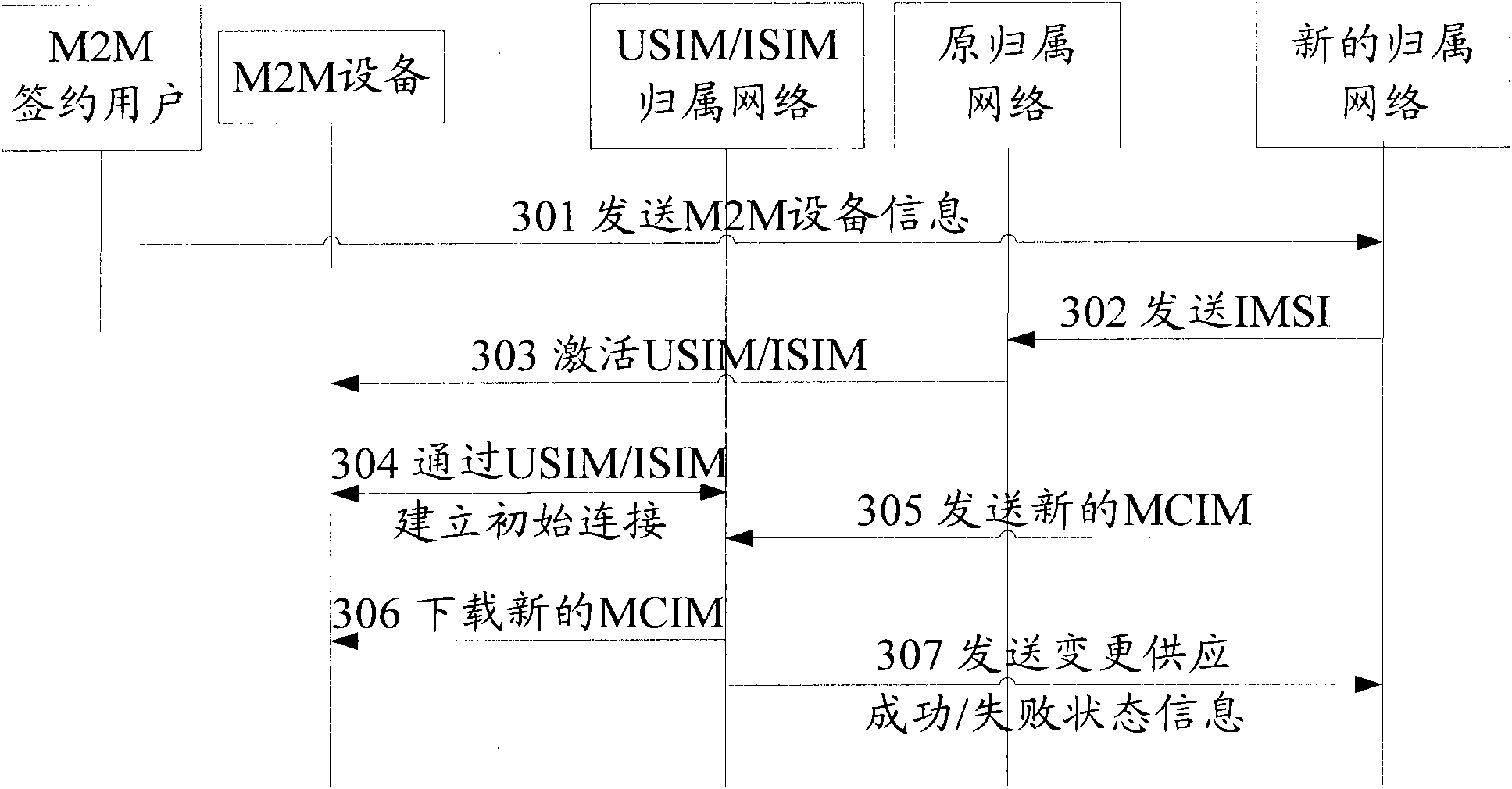
The invention discloses a system, a method and equipment for changing signature data. Based on the technical scheme, when M2M (Machine to Machine) equipment needs to change the signature data, after a USIM (Universal Subscriber Identity Module) / ISIM (International Subscriber Identity Module) of a UICC (Universal Integrated Circuit Board) is activated, initial connection is established through the USIM / ISIM and a USIM / ISIM home network; the change of an MCIM (Machine Communication Identity Module) is realized by receiving new signature data sent by a new home network with the initial connection; according to the technical scheme of the invention, the new signature data is transferred through the USIM / ISIM home network without transferring the new signature data among networks of different operators, thereby strengthening the safety of the signature data and conveniently and rapidly finishing the change of the signature data. In addition, aiming to the condition that the USIM / ISIM of the MCIM and the USIM / ISIM of the UICC are arranged in a same UICC, the UICC is not needed changing, thereby lowering the cost. Therefore, the invention safely and conveniently realizes the change of the signature data of the M2M equipment.
Owner:产学研共同体(山东)科技成果转化有限公司
Mutual authentication between user equipment and an evolved packet core
ActiveUS20160205550A1Unauthorised/fraudulent call preventionAssess restrictionTelecommunicationsPublic land mobile network
A method of operating a User Equipment (UE) enabled isolated Evolved Universal Mobile Telecommunications System Terrestrial Radio Access Network (E-UTRAN) operation for public safety (IOPS) is provided. The method includes receiving, from an IOPS-capable eNodeB (eNB), a system information block (SIB) message including an IOPS public land mobile network (PLMN) identity; activating a dedicated IOPS universal subscriber identity module (USIM) application based on the IOPS PLMN identity; and authenticating the IOPS-capable eNB based on the dedicated IOPS USIM application.
Owner:SAMSUNG ELECTRONICS CO LTD
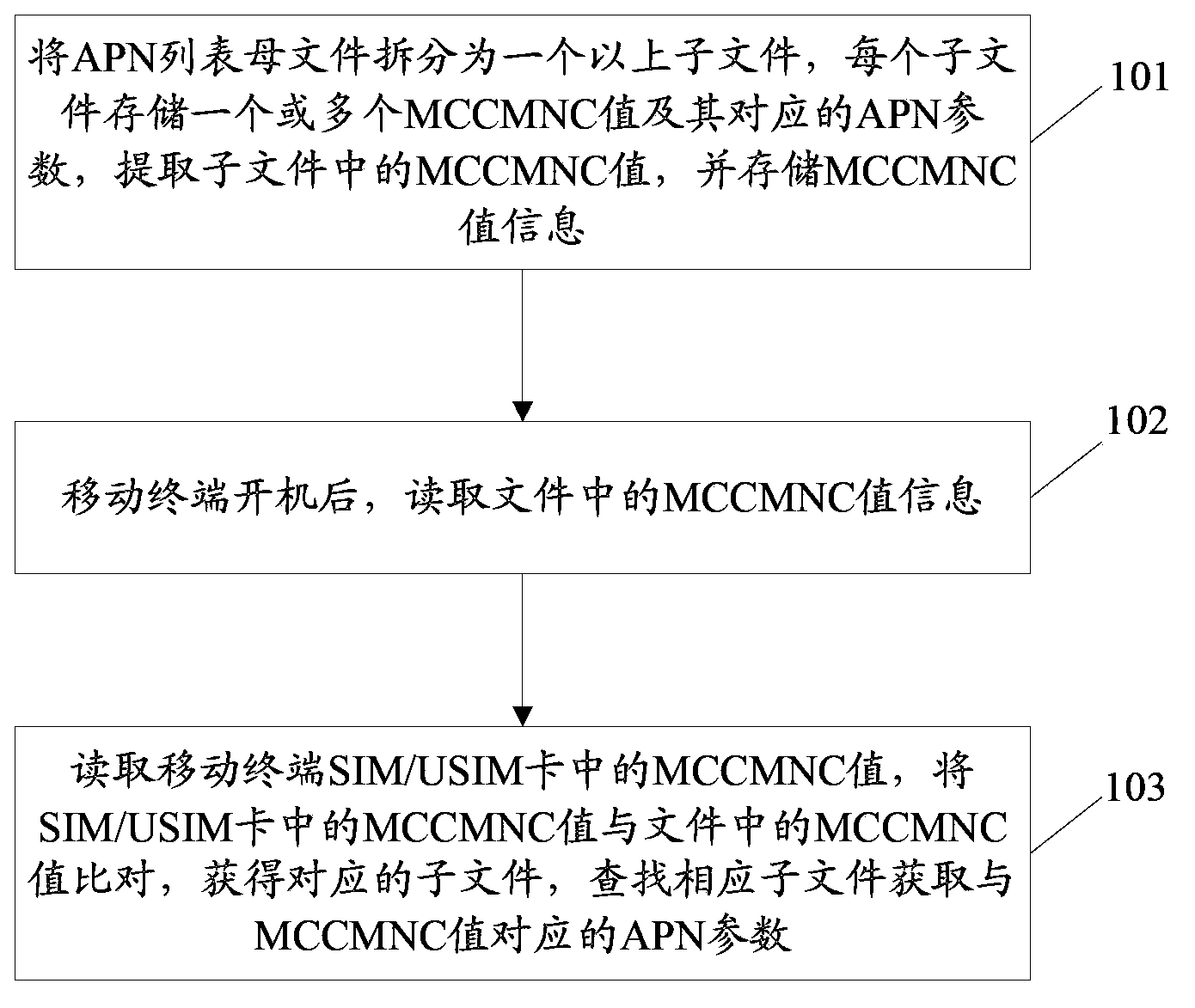
Method and device for automatically configuring and updating access point name parameters
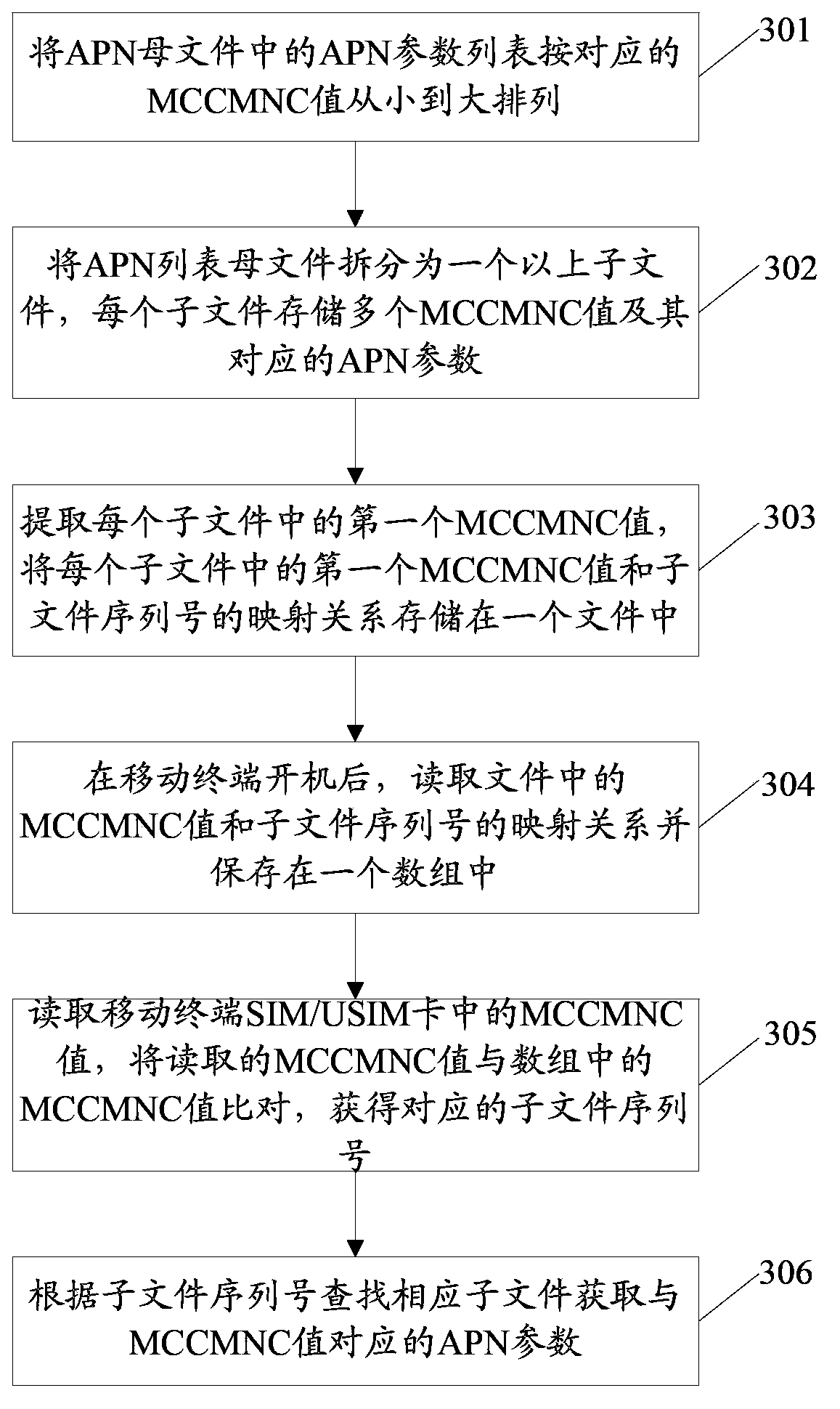
ActiveCN103813295AImprove auto-configurationImprove update speedNetwork data managementMobile network codeAuto-configuration
The invention discloses a method and a device for automatically configuring and updating APN (Access Point Name) parameters. The method comprises splitting an APN list parent file into more than one sub-file; storing one or more than one MCCMNC (Mobile Country Code and Mobile Network Code) value and the corresponding APN parameter in every sub-file; extracting the MCCMNC values stored in the sub-files and storing the MCCMNC value information; reading and comparing the stored MCCMNC values and MCCMNC values in an SIM / USIM (Subscriber Identity Module / Universal Subscriber Identity Module) card of a mobile terminal after startup of the mobile terminal to obtain the corresponding sub-files; searching the corresponding sub-files to obtain the APN parameters which are corresponding to the MCCMNC values. According to the technical scheme of the method and the device for automatically configuring and updating the APN parameters, the automatic configuration and update speed of the APN parameters is greatly improved and the user experience is improved.
Owner:ZTE CORP
Door lock apparatus for security identification using wireless communication device and method for the same
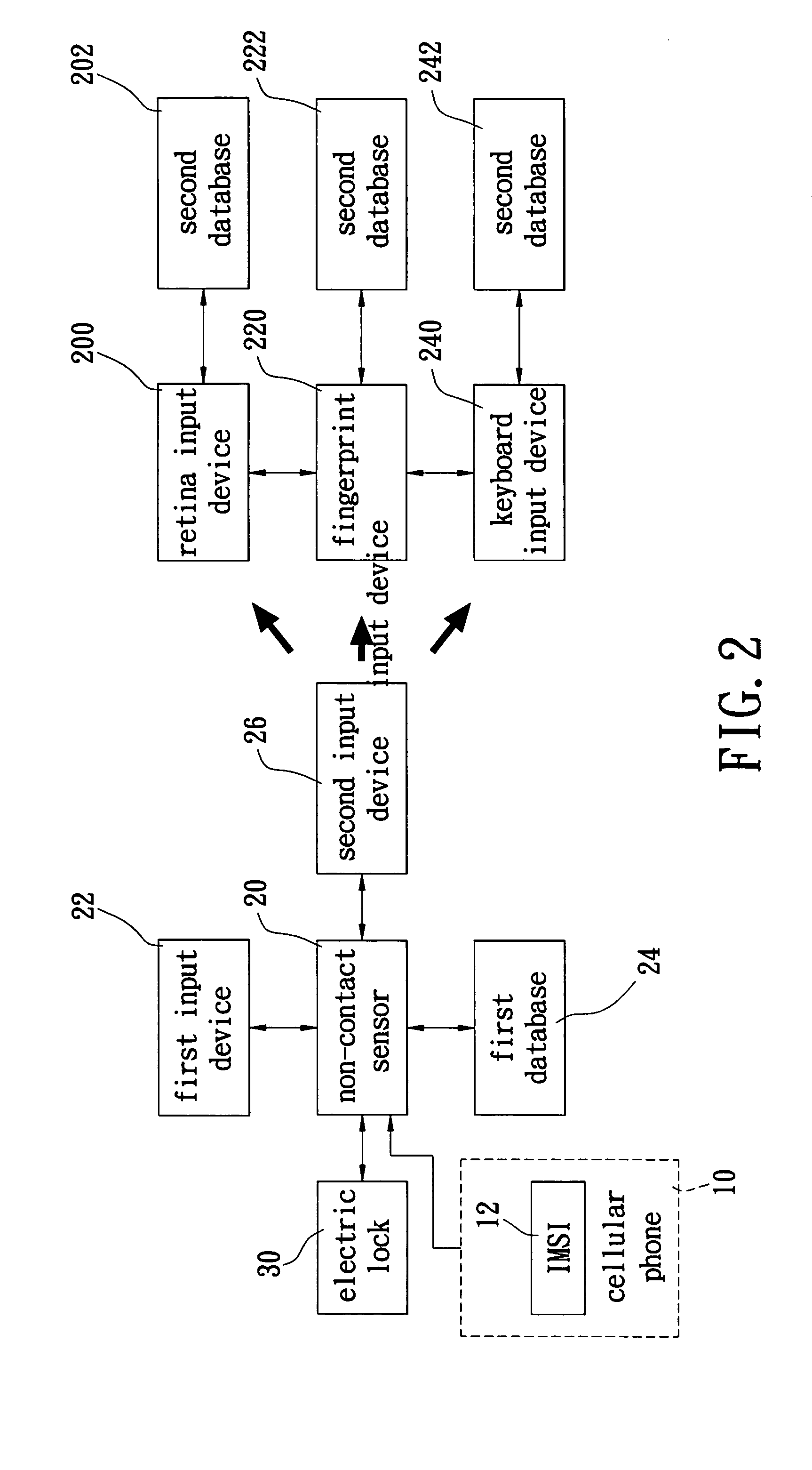
InactiveUS20050068159A1Optimization mechanismAvoid problemsAnti-theft devicesTelecommunicationsEngineering
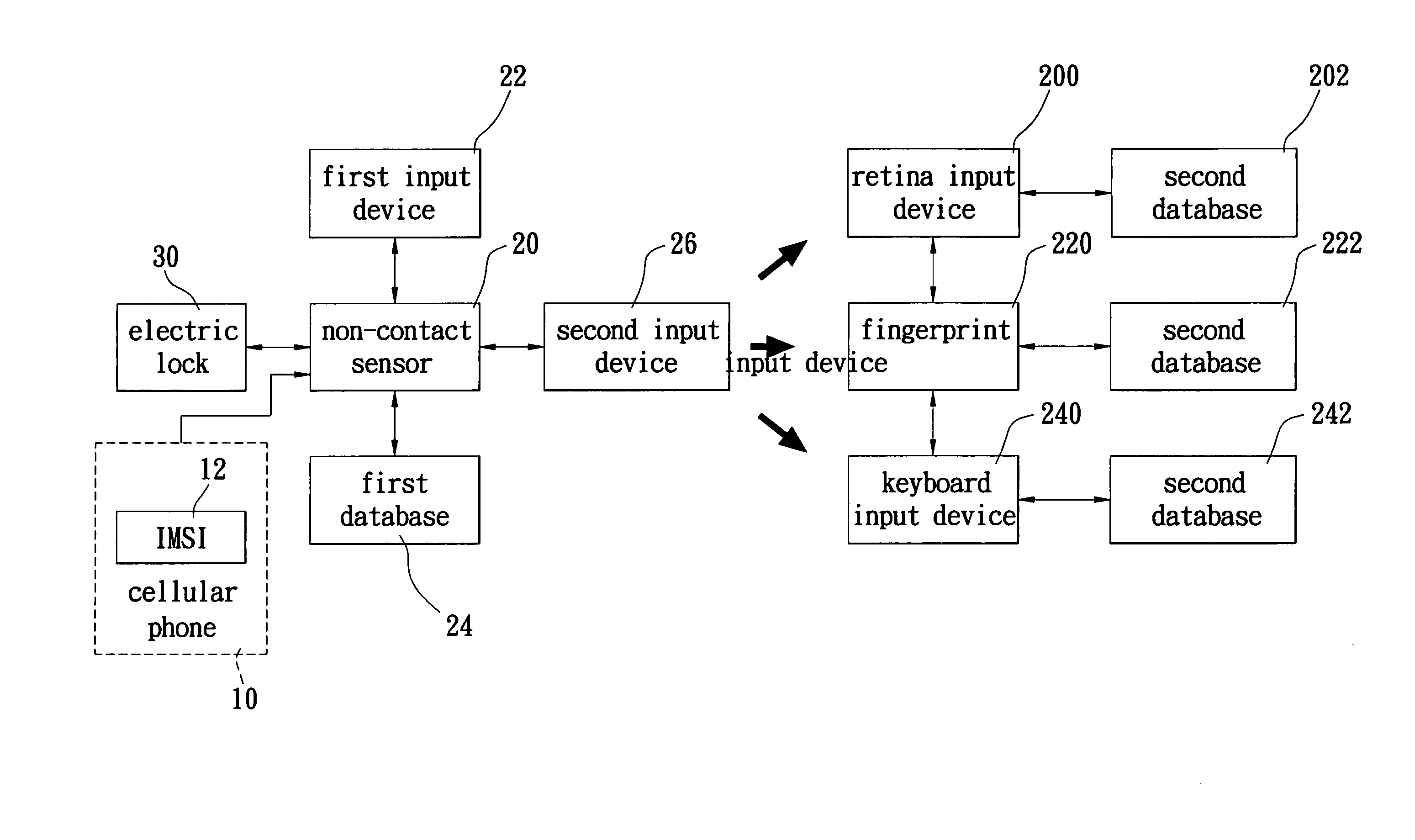
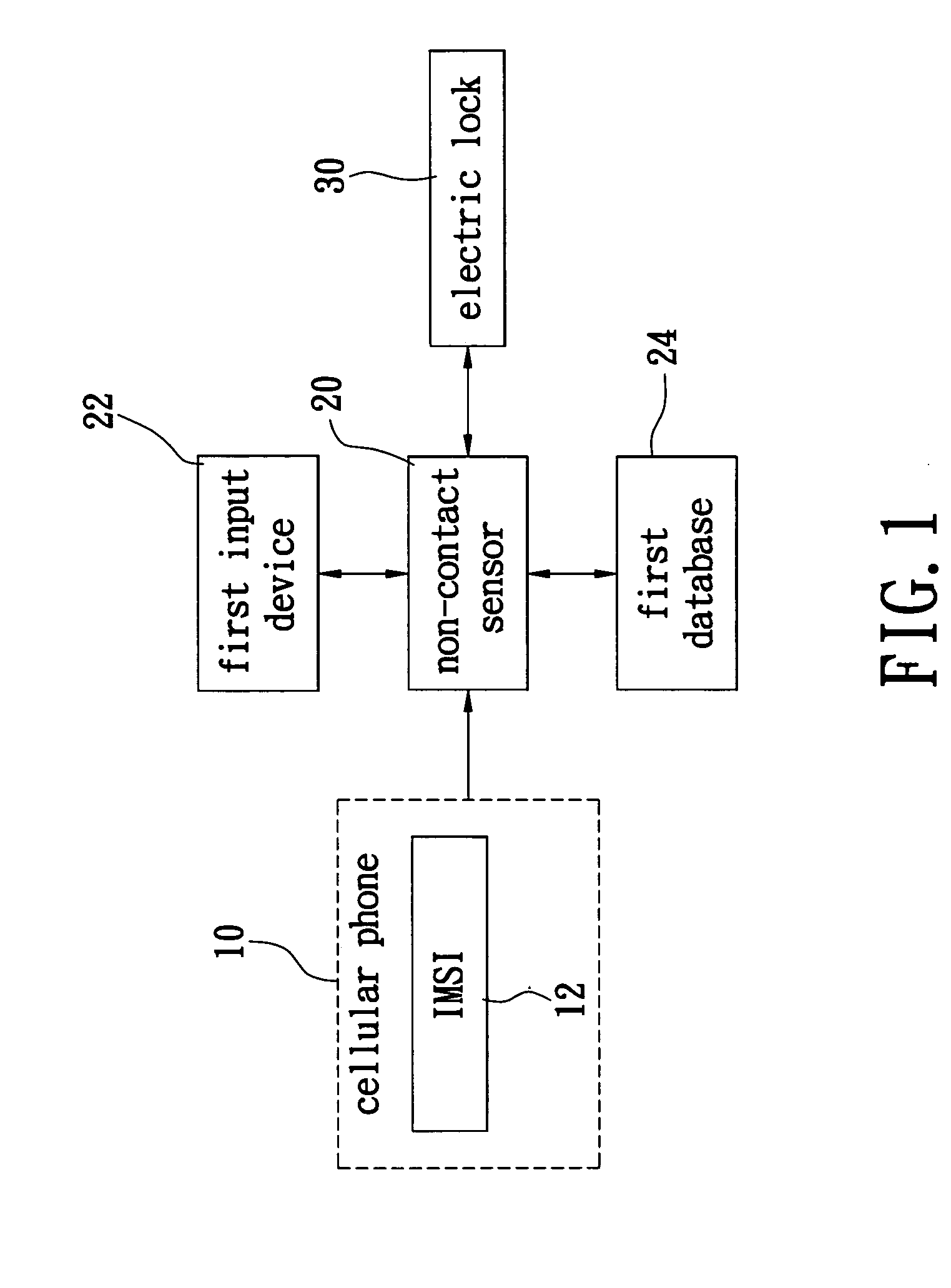
A door lock apparatus and method for security identification by using a wireless communication device are proposed. Due to the uniqueness of the IMSI (International Mobile Subscriber Identification Number) contained in a SIM (Universal Subscriber Identity Module, USIM) card of a wireless communication device, such as cellular phone, the present invention uses a non-contact sensor to read the IMSI for security identification and thereby determine whether an electric lock should be locked or unlocked. Since the IMSI is unique for each wireless device, the security of the entrance control can be improved considerably. By this way, the wireless communication device can be applied to the identification mechanism of entrance locks, car's door locks or car's actuation.
Owner:GUAN TECH
Personalized card writing method, system and device
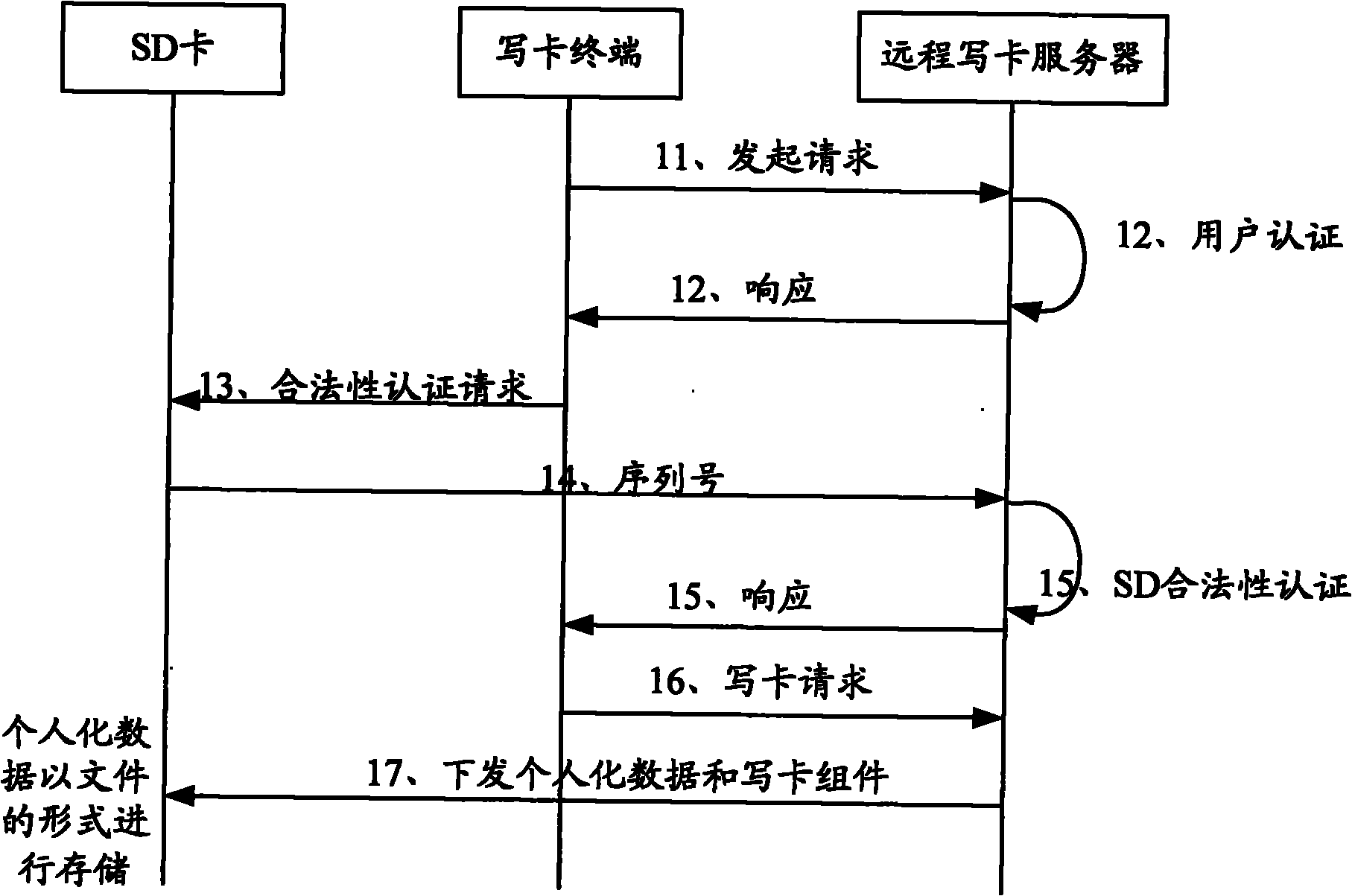
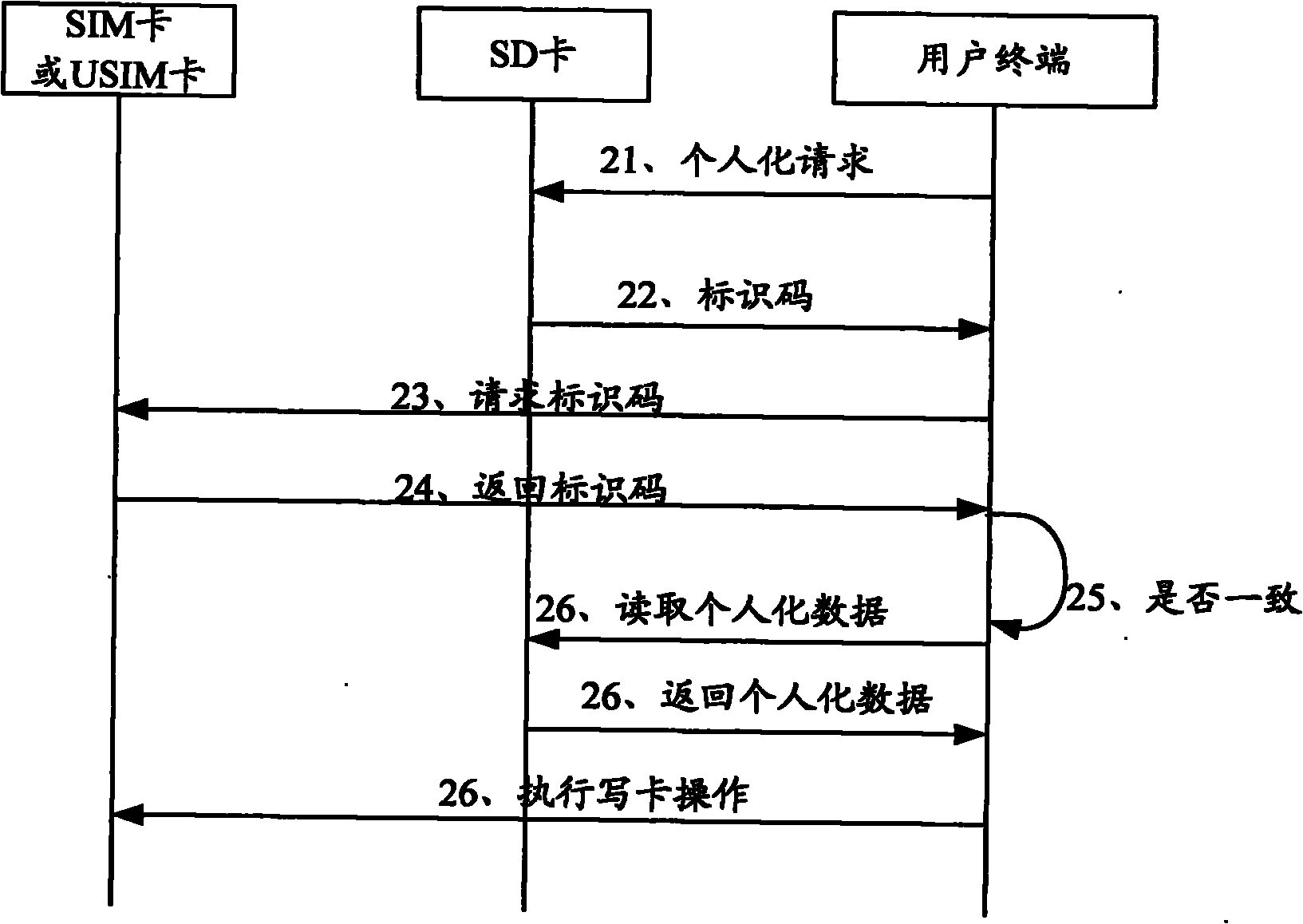
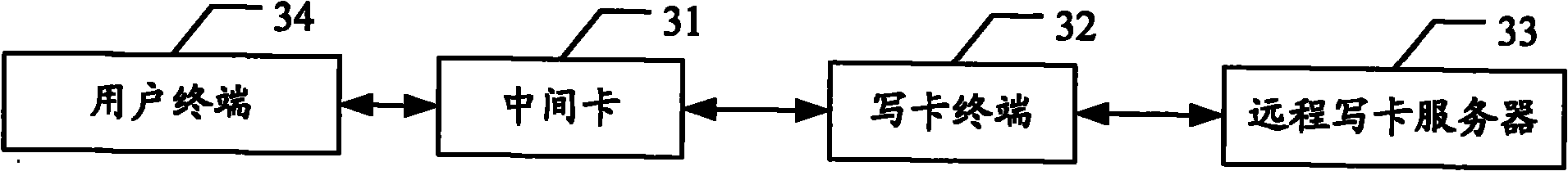
ActiveCN102149083APrevent leakageEnsure safetySecurity arrangementNetwork data managementService experienceComputer terminal
The invention discloses a personalized card writing method and system. The method comprises: a subscriber logs in a remote card writing server via a card writing terminal; the remote card writing server distributes personalized data and card writing components required by the subscriber to an intermediate card connected with the card writing terminal, and the intermediate card stores the personalized data and the card writing components; and the intermediate card is connected to a subscriber terminal used by the subscriber, and the subscriber terminal reads the personalized data in the intermediate card, and calls the card writing components in the intermediate card to write the personalized data to a subscriber identity module (SIM) or a universal subscriber identity module (USIM) in the subscriber terminal. The invention simultaneously discloses the remote card writing server, a subscriber card and the user terminal. By adopting the method, system and device provided by the invention, the safety of the service data can be ensured, the realization is simple and convenient, and the service experience of subscribers can be enhanced.
Owner:CHINA MOBILE COMM GRP CO LTD
Re-option of public land mobile network
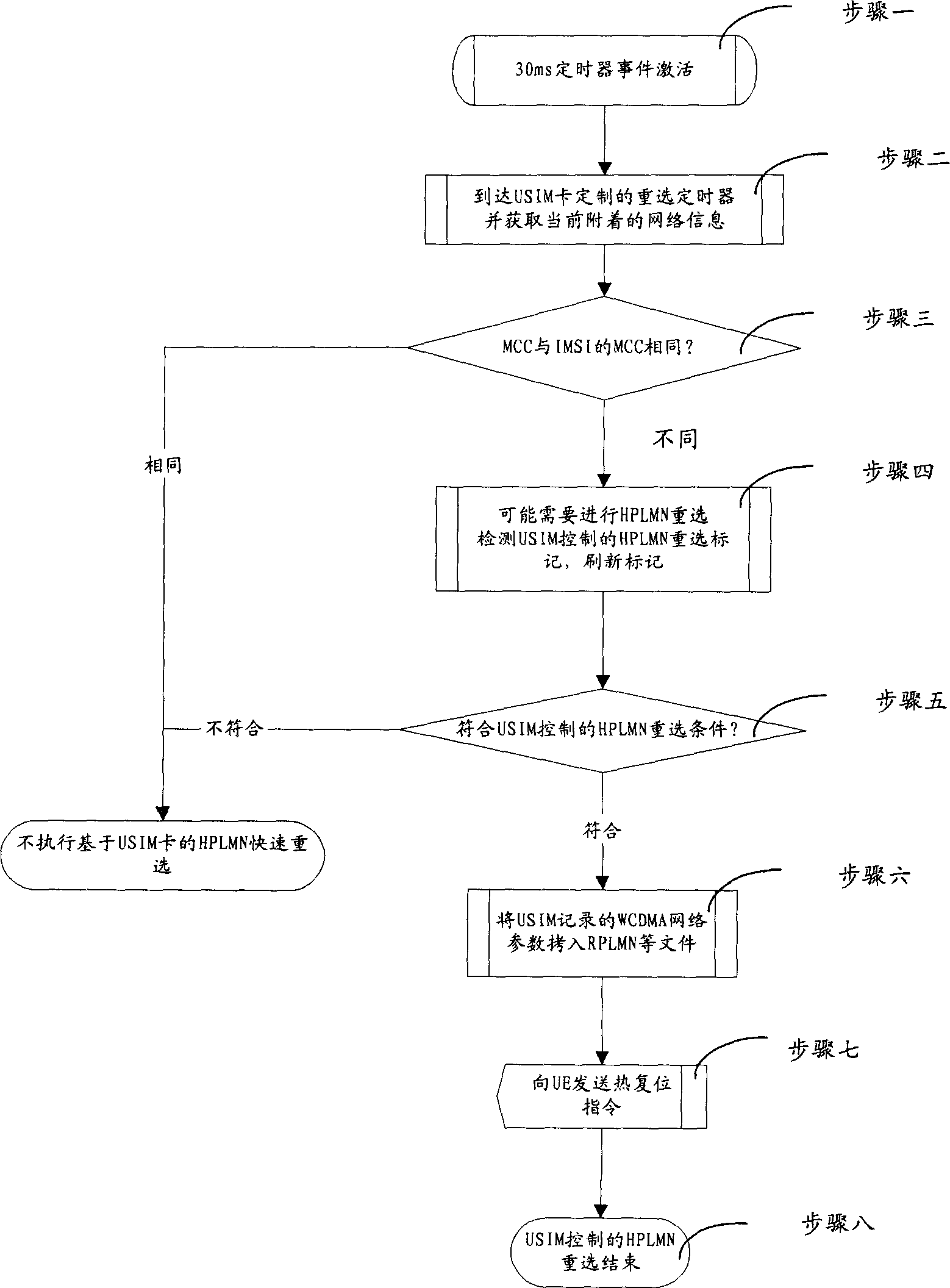
InactiveCN1780477AQuick reselect functionShorten access timeWireless communicationRelevant informationPublic land mobile network
The method includes following steps: records HPLMN (home public land mobile network) parameters of terminal in USIM (universal subscriber identity module); then sets timer in UDIM; when the preset time arrives, in term of interaction message between the terminal device and USIM, decides if current PLMN (public land mobile network) is identical; if not, in term of HPLMN parameter, returns to HPLMN where terminal is at. With setting timer in USIM, in term of time limit that can be accepted by terminal, resets a shorter searching period, and then in term of HPLMN relevant message saved in USIM, returns to HPLMN.
Owner:HUAWEI TECH CO LTD
Personalized service system based on smart card and method thereof, and smart card applied to the same
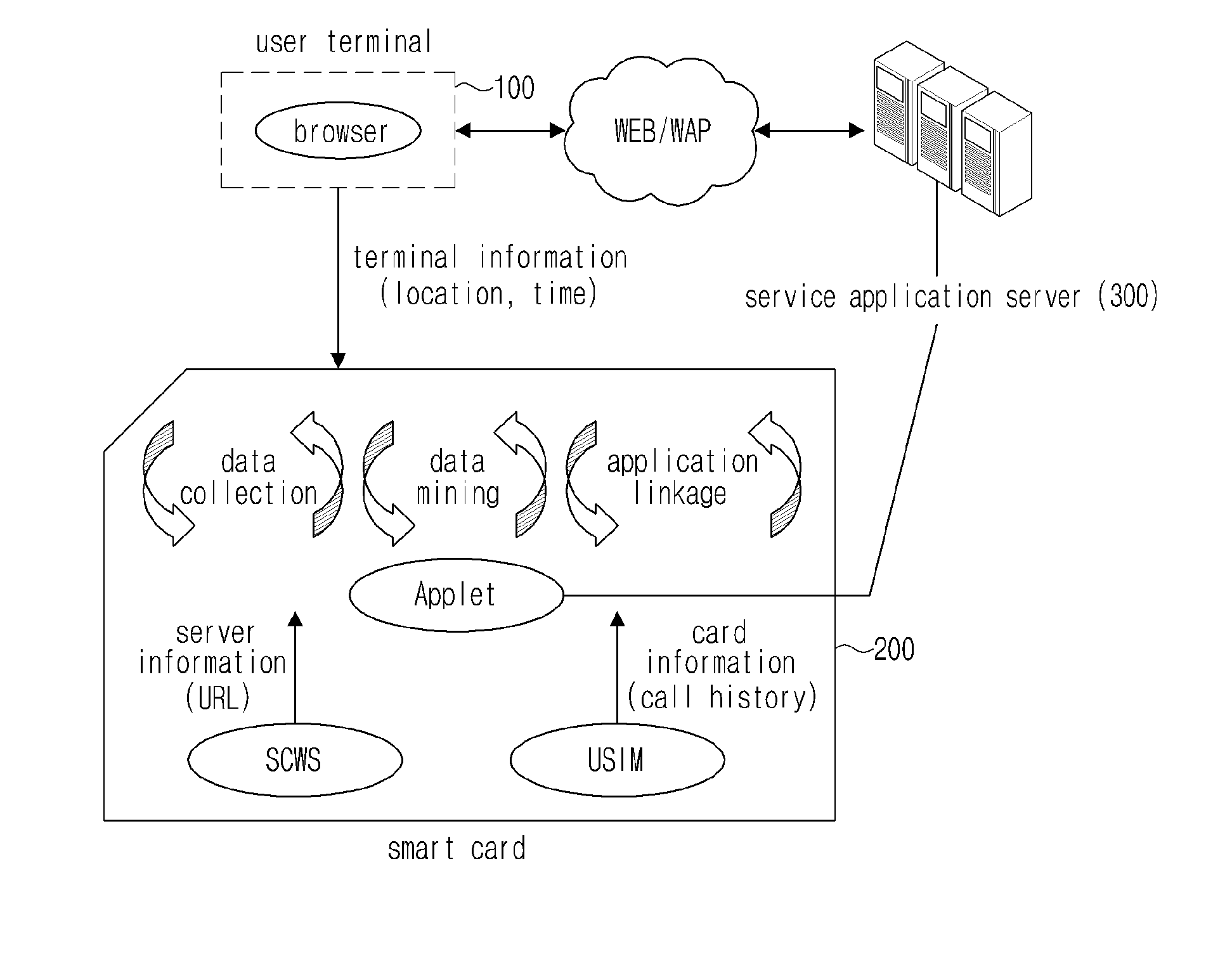
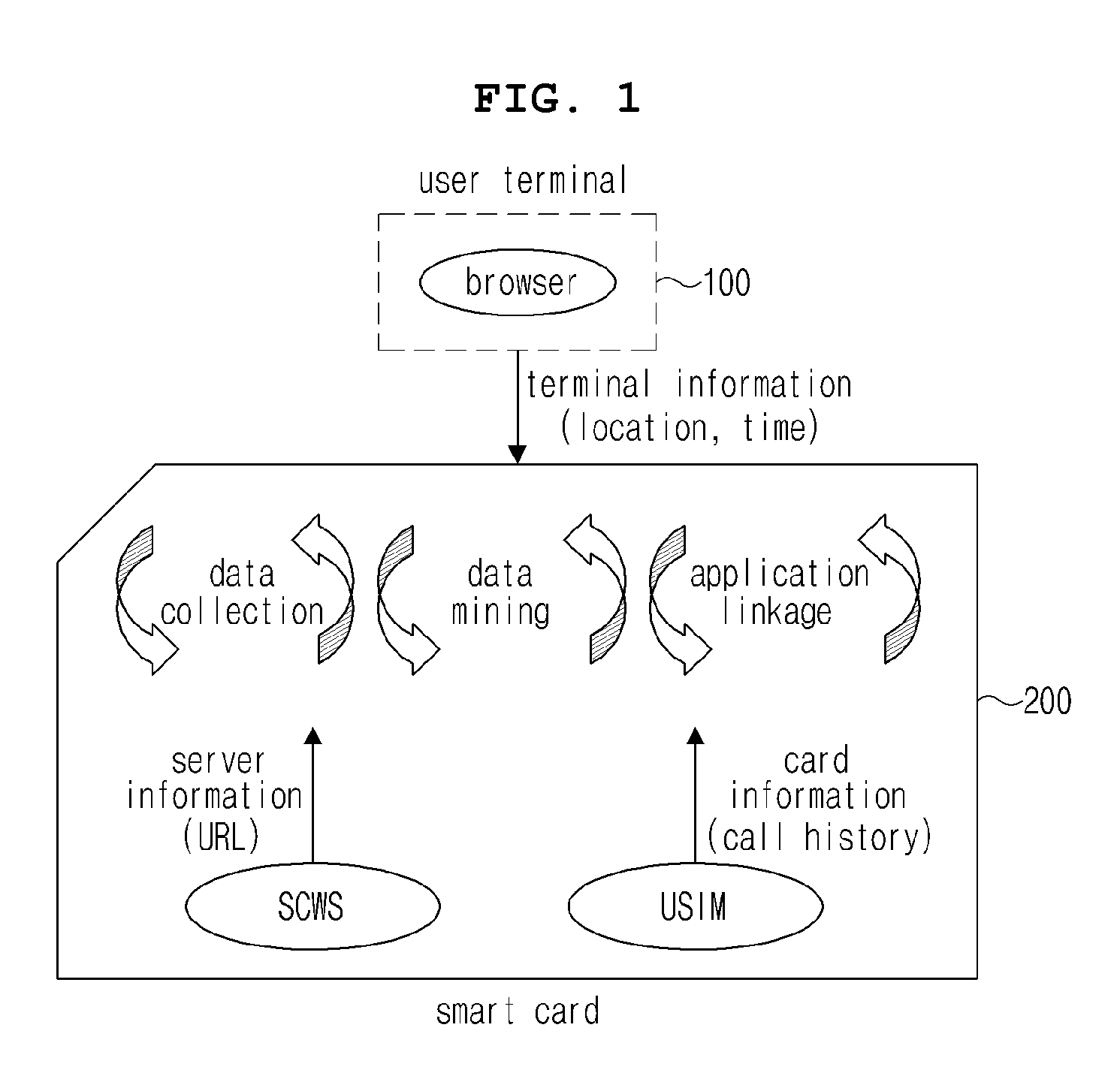
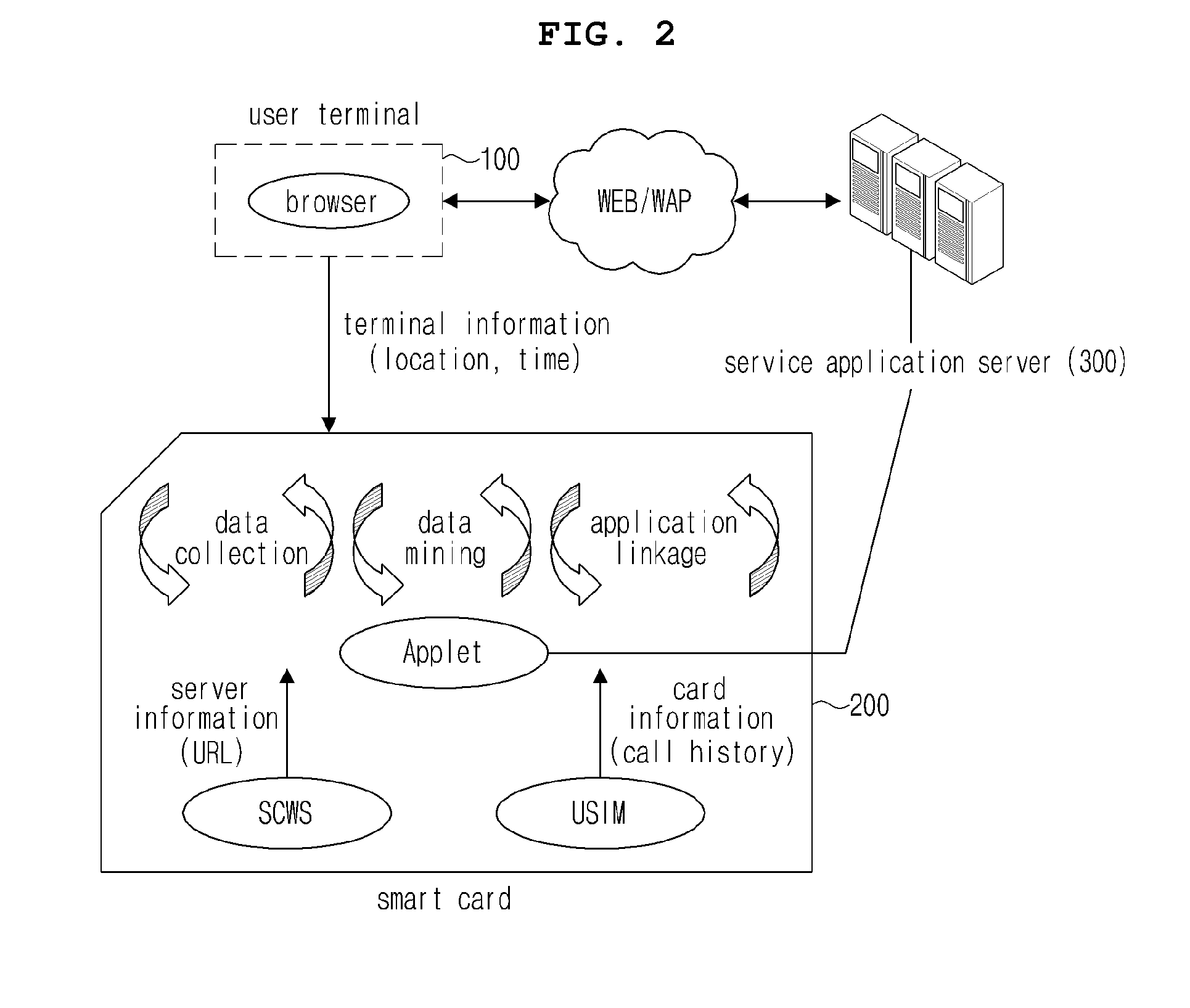
ActiveUS20100325269A1Easy to collectEasily utilizedDigital data information retrievalCo-operative working arrangementsUser inputAccess history
Disclosed are a personalized service system based on a smart card, a method thereof, and a smart card applied to the same. Personalized information is extracted through the data mining by collecting user input information stored based on an SCWS (smart card web server) function, access history information for a site requested by a user, call history information of a user terminal stored based on a USIM (universal subscriber identity module), and base station information received from the user terminal. Since the personalized information is obtained based on the SCWS function and the USIM installed in the smart card, various regulations related to personalized information are circumvented, enabling provision of various personalized services.
Owner:SK PLANET CO LTD
Apparatus and method for controlling functions of a mobile phone via NFC communication with an external RF reader
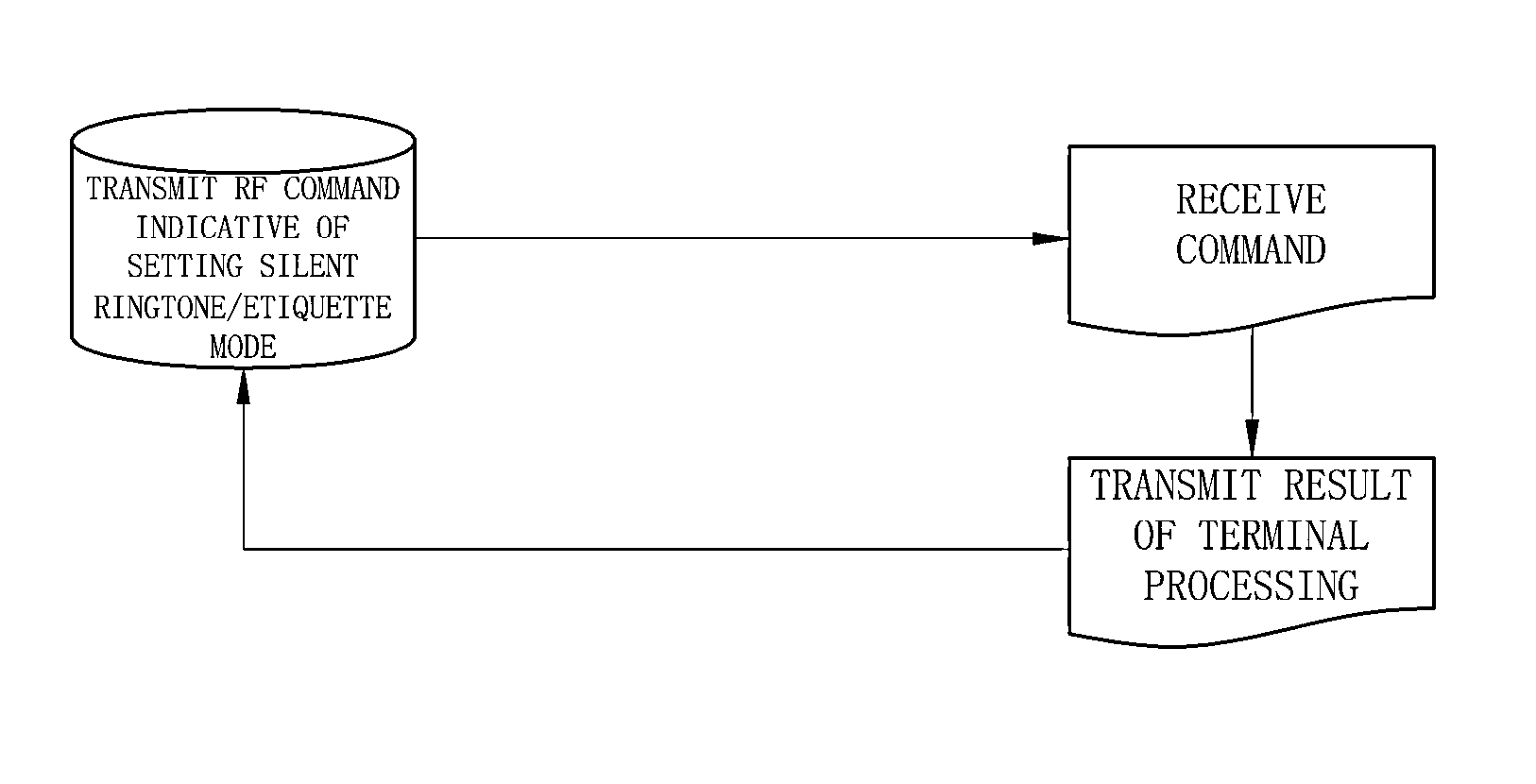
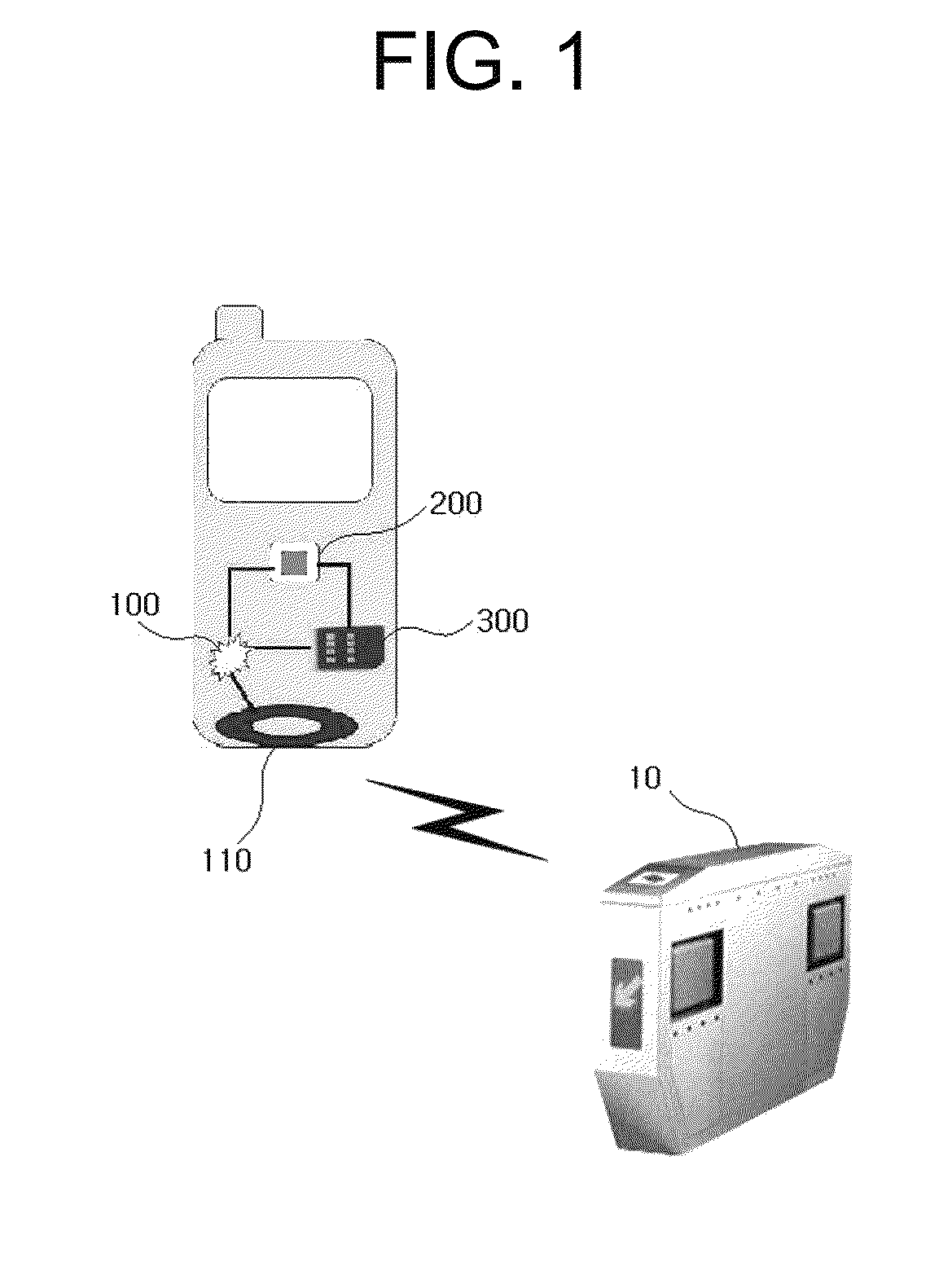
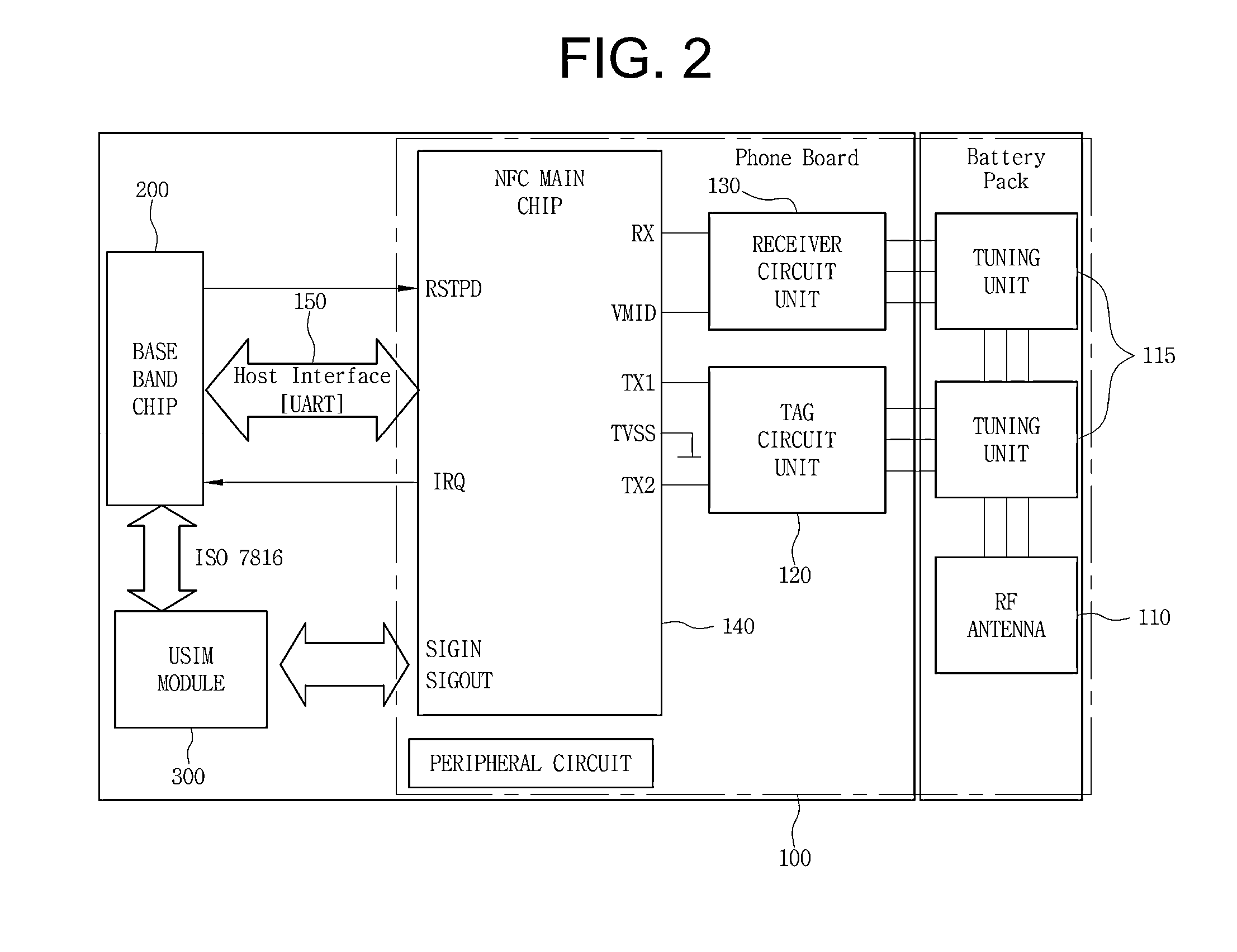
Disclosed herein is an apparatus for controlling the ringtone, camera, and communication functions of a mobile terminal using a Near Field Communication (NFC) chip module and an external Radio Frequency (RF) reader. The apparatus includes an NFC chip module, a base band chip, and a USIM card. The NFC chip module is electrically connected to the base band chip of a mobile terminal, allows a command data signal, received from an external RF reader via an RF antenna, to be transmitted to the base band chip or a Universal Subscriber Identity Module (USIM) card of the mobile terminal, and receives the result of terminal processing of the base band chip which operates in compliance with an external command, and transmits the result of the terminal processing to the external RF reader via the RF antenna.
Owner:AQ
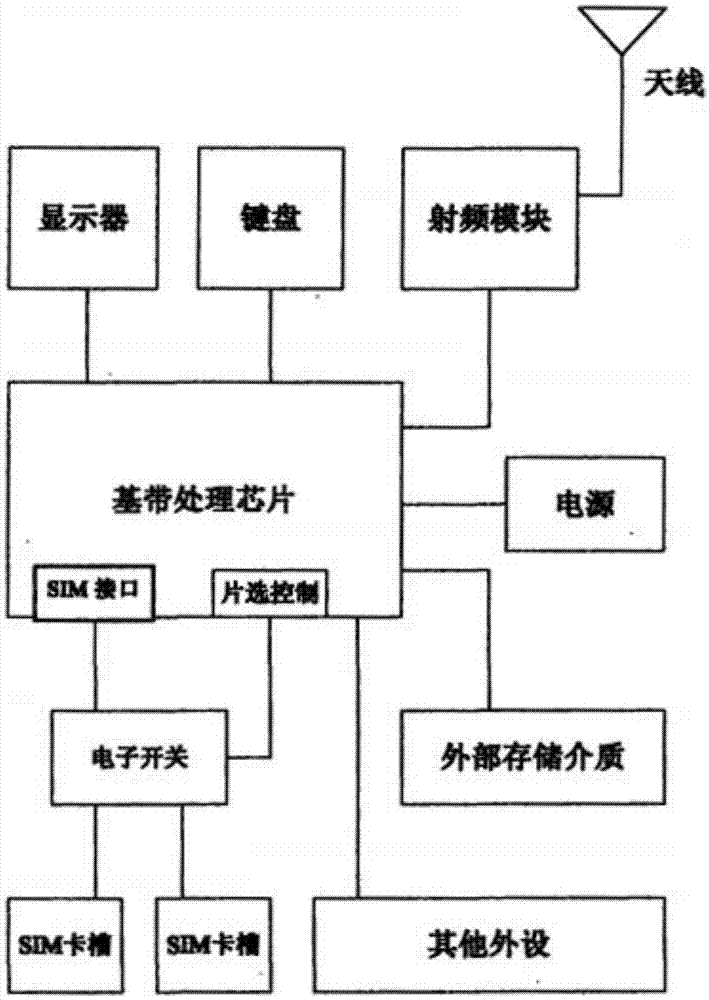
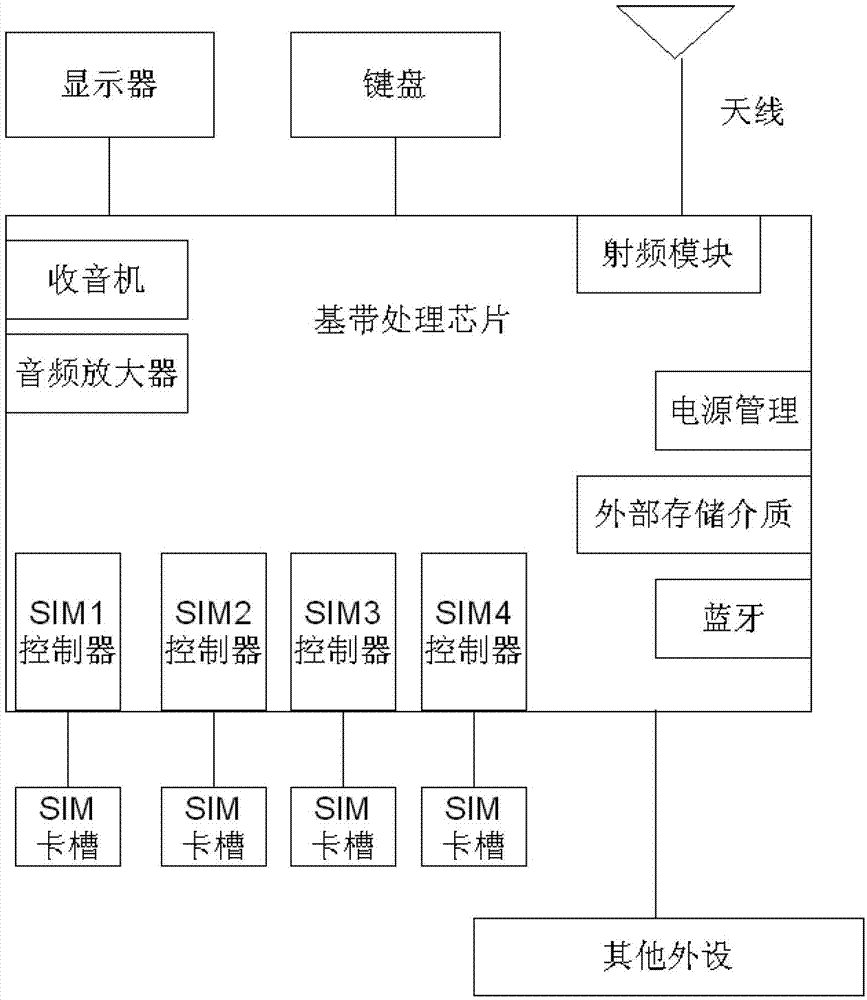
Single-chip, multi-card and multi-standby mobile phone as well as conflict resolution method thereof
ActiveCN102883471AHighly integratedReduce volumeEnergy efficient ICTTelephone set constructionsLow noiseComputer module
The invention discloses a single-chip, multi-card and multi-standby mobile phone. The mobile phone comprises a baseband processing chip and a plurality of card slots for installing a user identification module. A plurality of user identification controllers which are same with the card slots in number are integrated in the baseband processing chip; each user identification controller is connected to one card slot and the constant connection is kept; and one baseband processing controller integrated by the base band processing chip is only connected to one user identification controller at same time. The user identification module comprises an SIM (Subscriber Identity Module) card, a UIM (User Identify Module) card and a USIM (Universal Subscriber Identity Module) card; correspondingly the user identification controllers are an SIM controller, a UIM controller and a USIM controller. The mobile phone has the characteristics of high integration, small size and high reliability during change of multiple cards, and has the advantages of small interference and low noise. The invention further discloses a method for solving conflict of the single-chip, multi-card and multi-solution during reading-writing multiple cards and receiving service. The method has the characteristic of high efficiency and fast speed; and by adopting the method, unnecessary cell reselection operation can be avoided, and power consumption can be reduced.
Owner:RDA TECH
Method of Handling Manual Closed Subscriber Group Selection and Related Communication Device
InactiveUS20120064889A1Power managementAssess restrictionCommunications systemPublic land mobile network
A method of handling manual closed subscriber group (CSG) selection for a mobile device in a wireless communication system is disclosed. The method comprises storing a public land mobile network (PLMN) basis setting for indicating the mobile device to display all available CSG identities or only CSG identities present in an operator controlled list of allowed CSG identities, in a Subscriber Identity Module (SIM), an Universal Subscriber Identity Module (USIM) or a memory of the mobile device; and displaying CSG identities according to the PLMN basis setting during the manual CSG selection.
Owner:HTC CORP
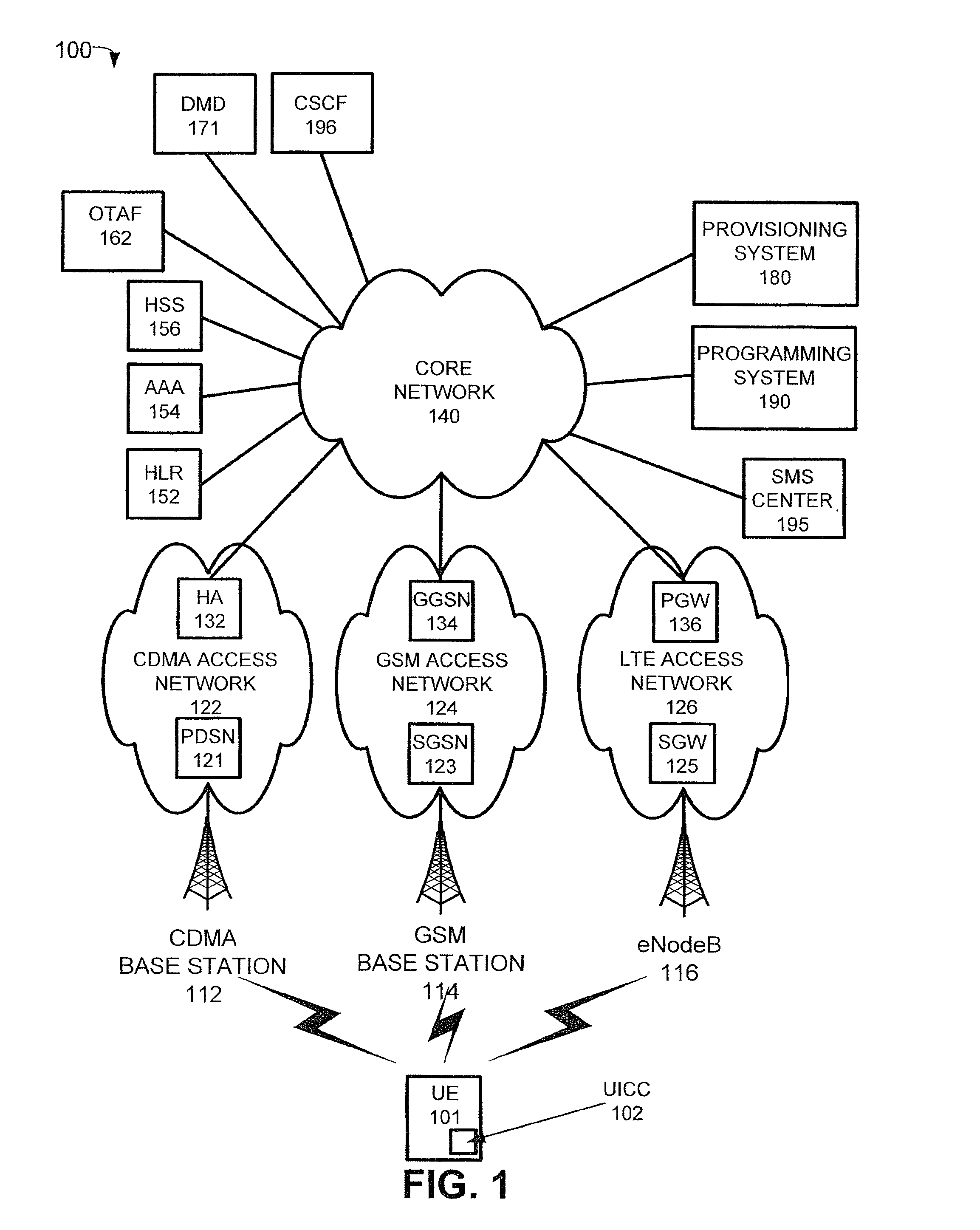
Universal integrated circuit card activation in a hybrid network
A universal integrated circuit card (UICC) may include a universal subscriber identity module (USIM); a code division multiple access (CDMA) subscriber identity module (CSIM); a memory to store instructions; and a processor. The processor may execute instructions to determine a type of wireless access network available to a user equipment (UE) associated with the UICC; perform activation of the UICC using the USIM, in response to detecting a CDMA enhanced High Rate Packet Data (eHRPD) network, a Global System for Mobile Communication (GSM) access network, or a Long Term Evolution (LTE) access network; and perform activation of the UICC using the CSIM, in response to detecting an available CDMA access network other than a CDMA eHRPD access network.
Owner:CELLCO PARTNERSHIP INC +1
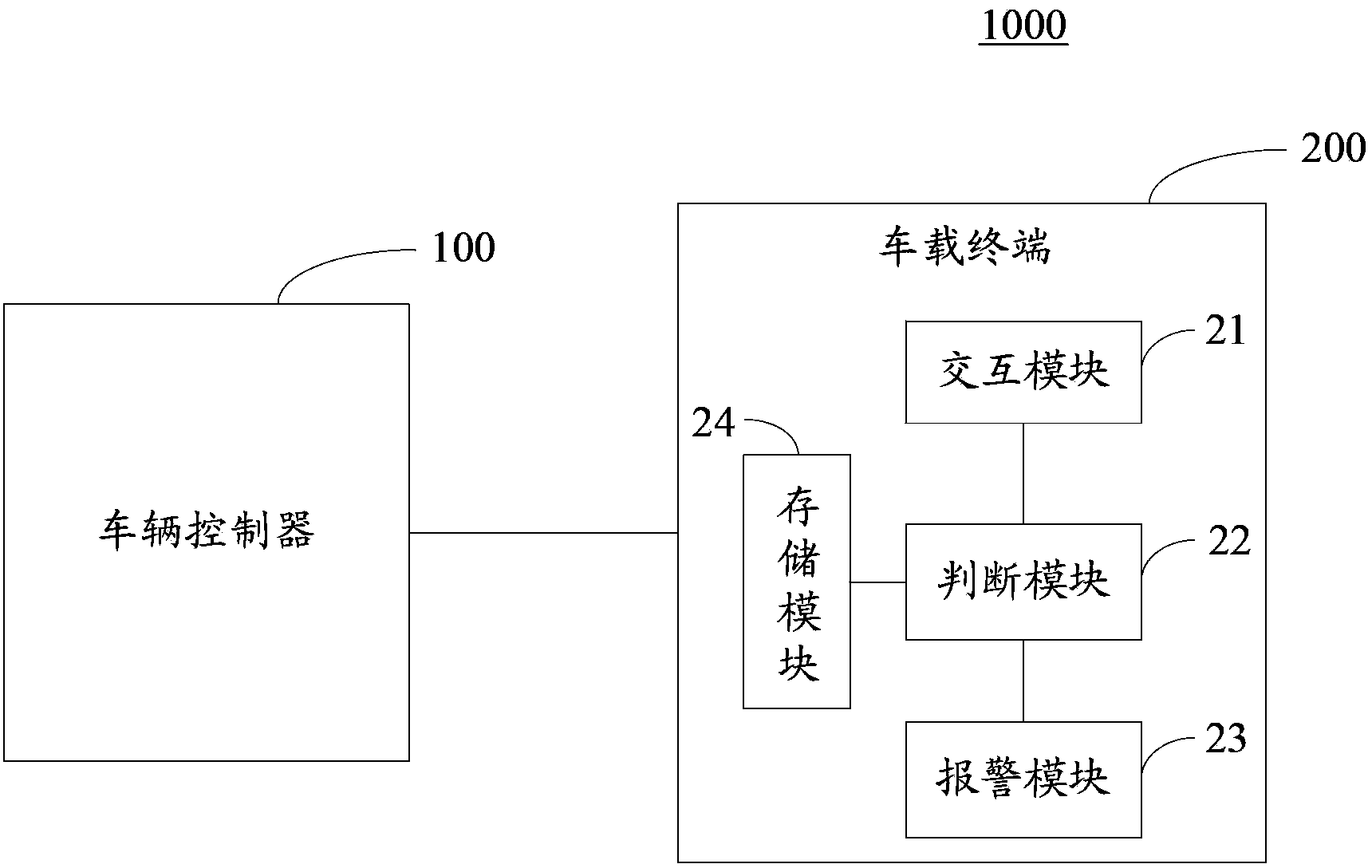
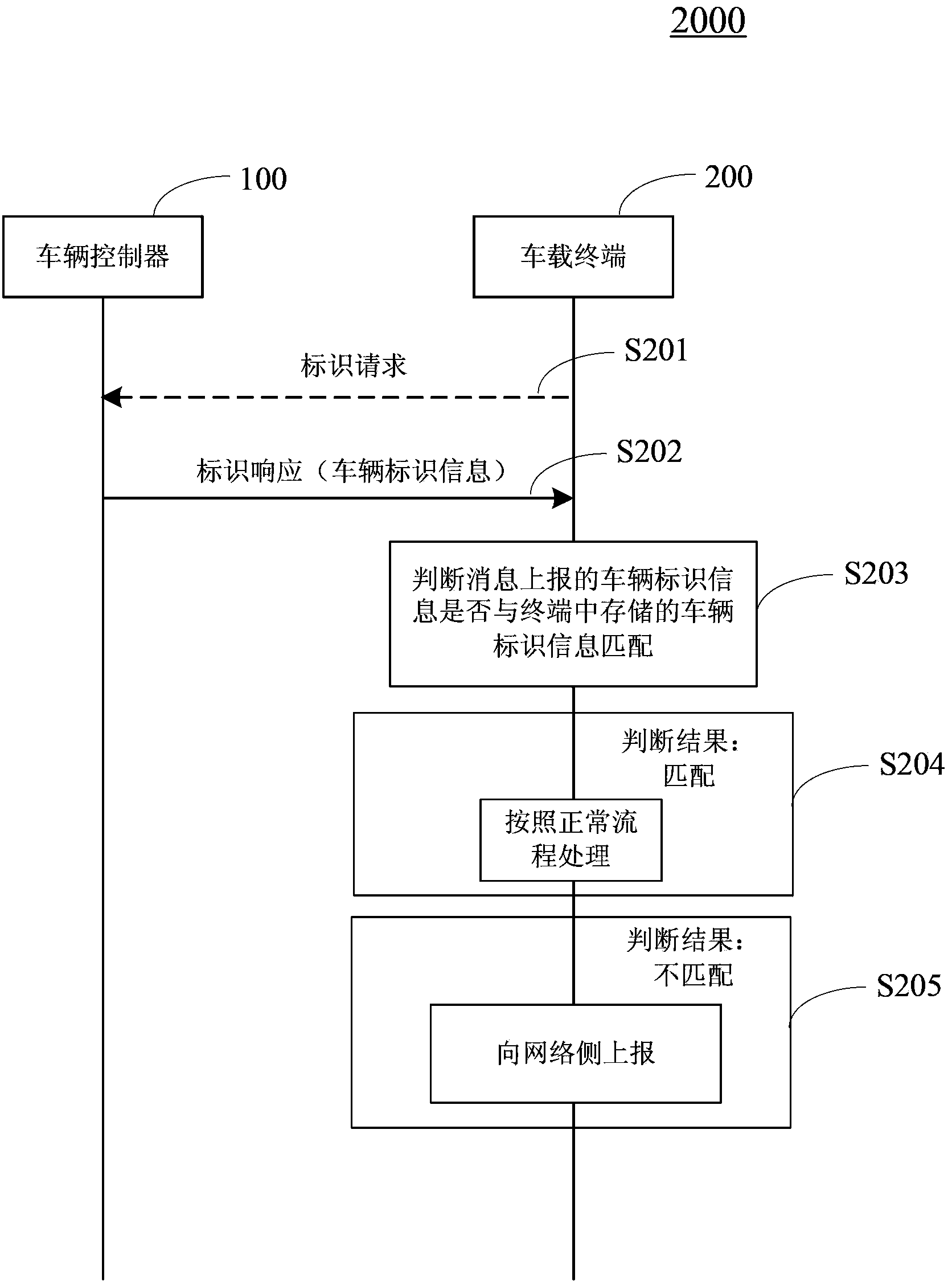
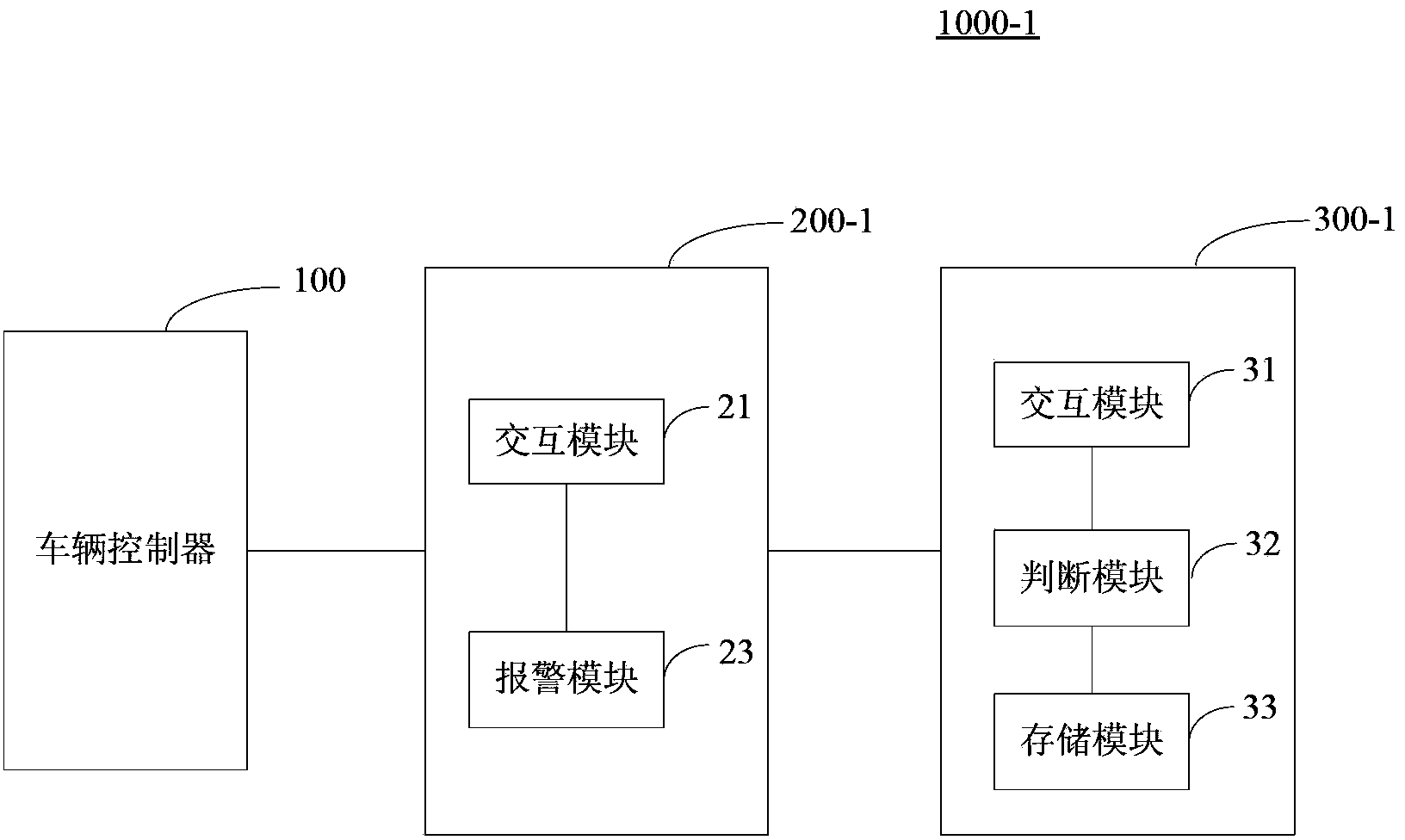
Method for detecting binding between vehicle-mounted terminal and vehicle, vehicle-mounted terminal and user identification unit
The invention provides a method for detecting binding between a vehicle-mounted terminal and a vehicle, the vehicle-mounted terminal and a user identification unit (such as a SIM (subscriber identity module) card or a USIM (universal subscriber identity module) card). The method for detecting the binding between the vehicle-mounted terminal and the vehicle on a terminal side can comprise the following steps of (a) determining a binding relationship between the vehicle and the vehicle-mounted terminal by pre-storing vehicle identification information on the terminal side; (b) performing interaction with a vehicle controller on the terminal side to acquire current vehicle identification information, determining whether the current vehicle identification information is matched with the pre-stored vehicle identification information or not, and if the current vehicle identification information is mismatched with the pre-stored vehicle identification information, transmitting alarming information through a network on the terminal side.
Owner:CHINA MOBILE COMM GRP CO LTD
Method for selecting network providing restricted local operator service in wireless communication system and apparatus thereof
ActiveUS20200084741A1Valid choiceAssess restrictionNetwork topologiesCommunications systemPublic land mobile network
A method for selecting, by a user equipment (UE), a public land mobile network (PLMN) in a wireless communication system is disclosed. The method includes attempting a registration on a PLMN selected by a user in a manual network selection mode, if the registration on the PLMN selected by the user cannot be achieved, finding one or more PLMNs offering access to restricted local operator service (RLOS), selecting a specific PLMN of the found one or more PLMNs among PLMNs contained in a RLOS PLMN list configured to a universal subscriber identity module (USIM) of the UE, and initiating a registration for an access to RLOS on the specific PLMN, thereby using RLOS with high quality and high security.
Owner:LG ELECTRONICS INC
Wireless network authentication apparatus and methods
Apparatus and methods for authenticating and granting a client device (e.g., cellular telephone) access to a network. In one embodiment, a network service provider such as a cellular telephone company may distribute user access (e.g., Universal Subscriber Identity Module or "USIM") credentials to a services manager via a USIM vendor. The services manager may maintain a list of authorized users. A user at a client may authenticate to the services manager. Once authenticated, the services manager may provide the user with a set of USIM credentials. When the user desires to use wireless network services, the user equipment may establish a wireless link between the user equipment and the network service provider. During authentication operations, the user equipment may use the USIM credentials to authenticate to the network service provider. Following successful authentication, the network service provider may provide the user equipment with wireless services.
Owner:APPLE INC
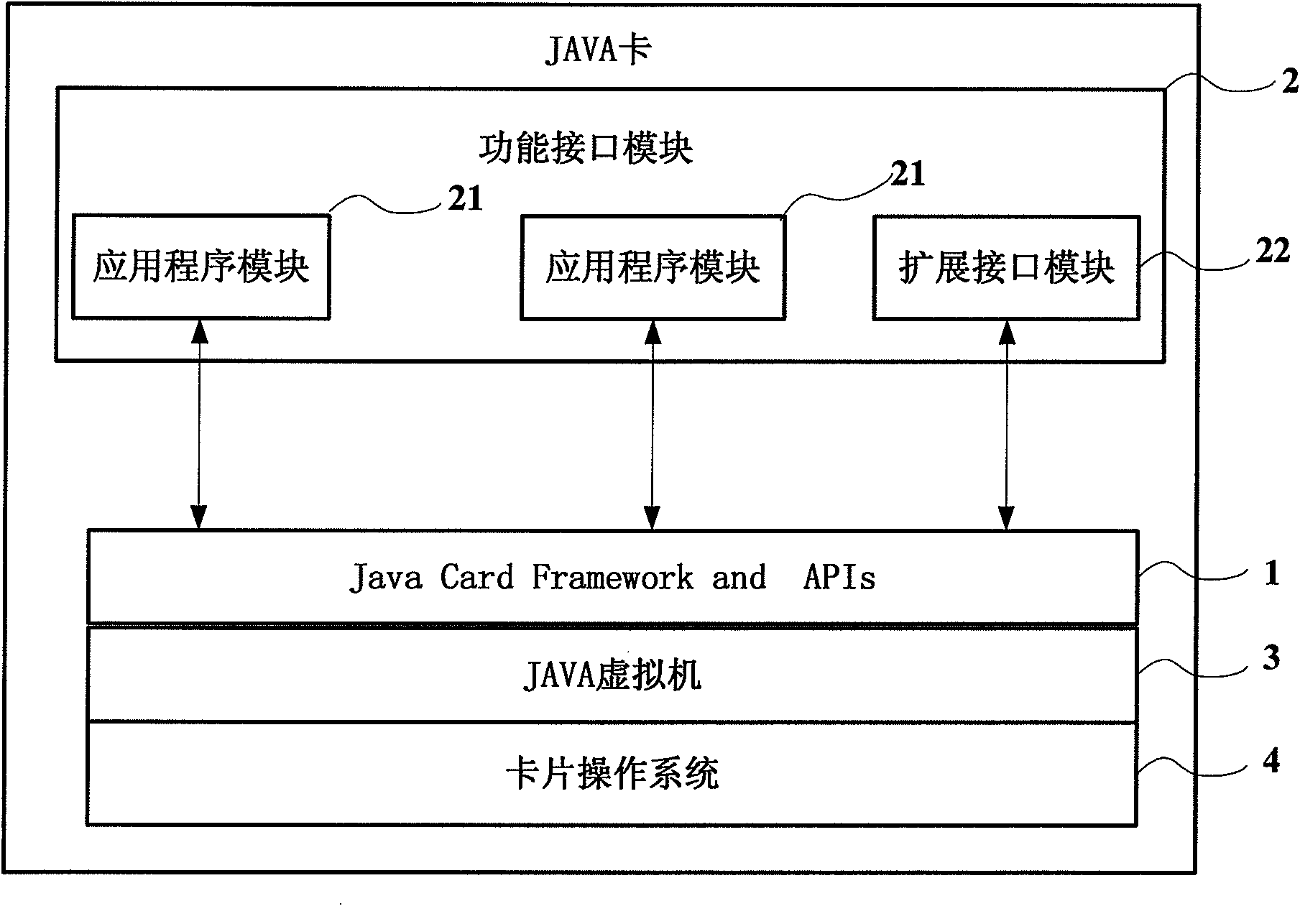
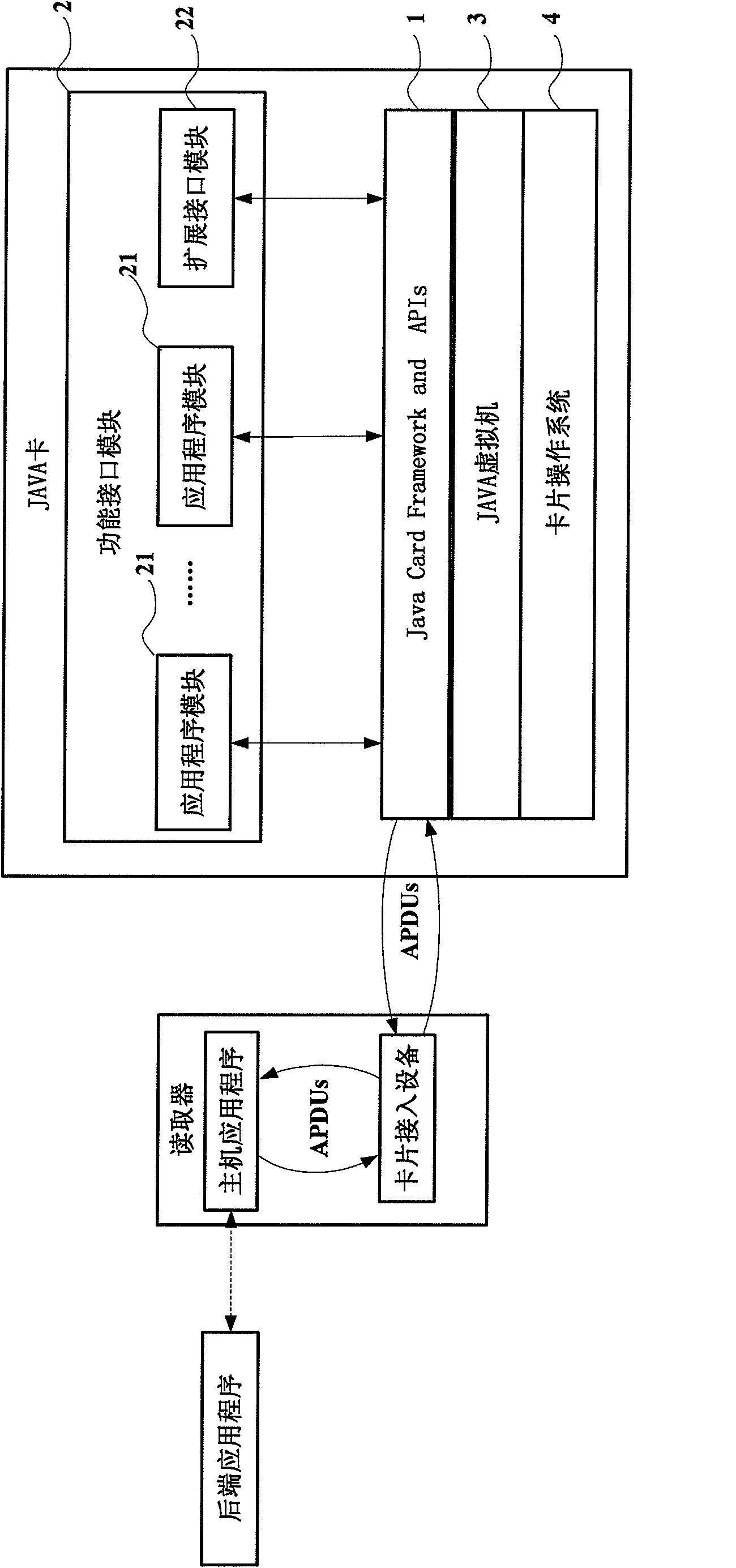
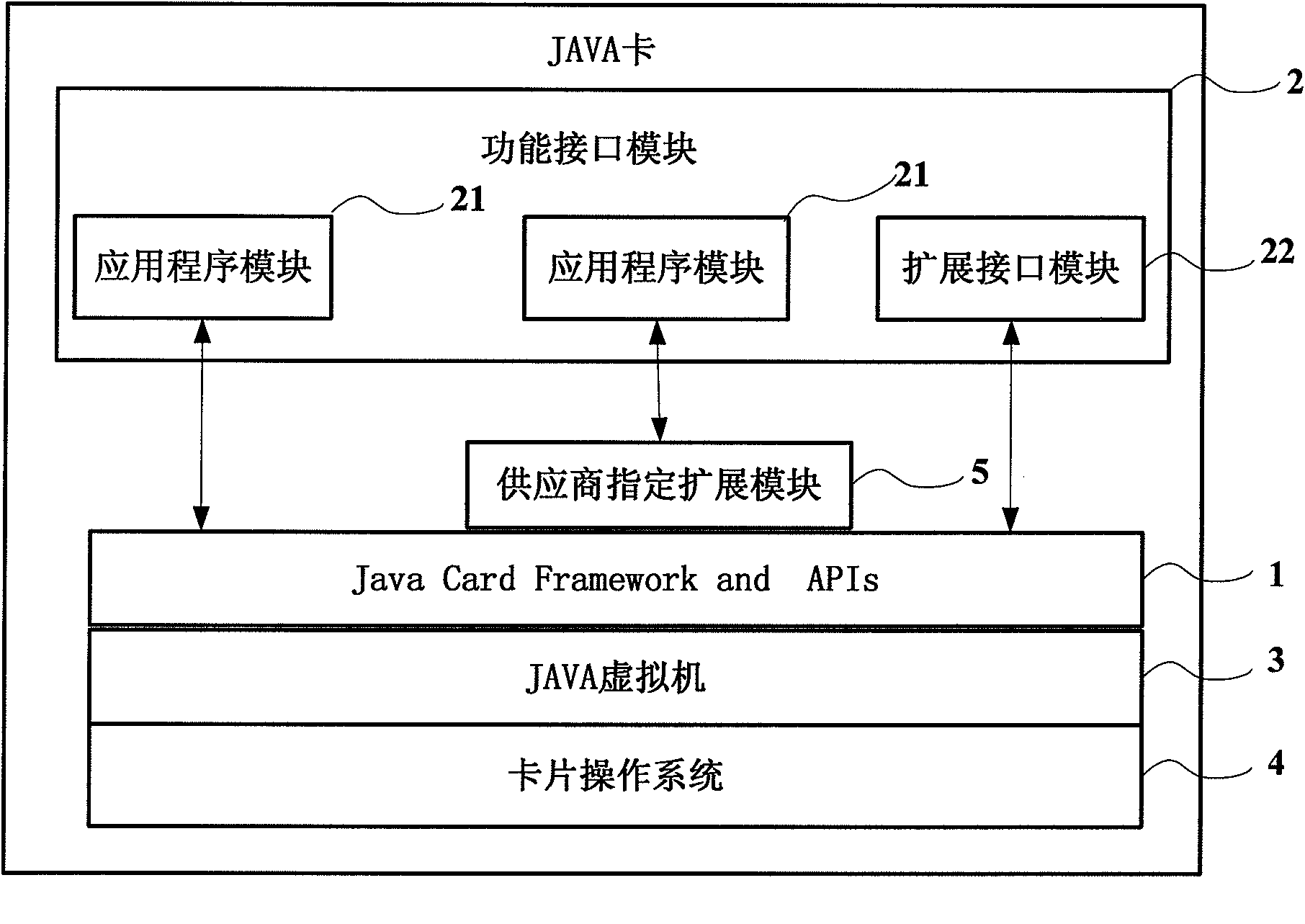
JAVA card
InactiveCN101986740ASpecific program execution arrangementsNetwork data managementOperational systemComputer module
The invention discloses a JAVA card, which aims to develop application of products with different functions on a USIM (universal subscriber identity module) smart card by utilizing a JAVACARD technology. The JAVA card comprises Java Card Framework and APIs, a functional interface module, a JAVA virtual machine and a card operation system, wherein the Java Card Framework and APIs is used for receiving APDU (application protocol data unit) transmitted by card access equipment and forwarding the APDU to the functional interface module; the functional interface module is connected with the Java Card Framework and APIs, and processes an APDU command to ensure that the processing result returns an APDU response through the Java Card Framework and APIs; the JAVA virtual machine is used to realize the uniformity of card interfaces and uniformity of programming language, including different technologies of various card suppliers on the card bottom; and the card operation system is responsible for processing of the lower layer.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com