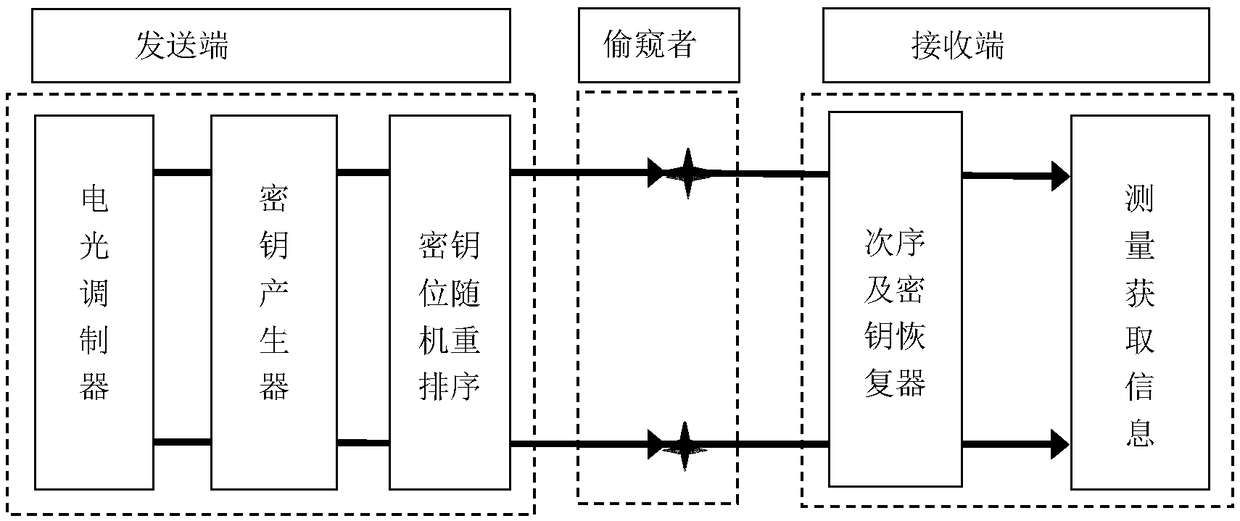
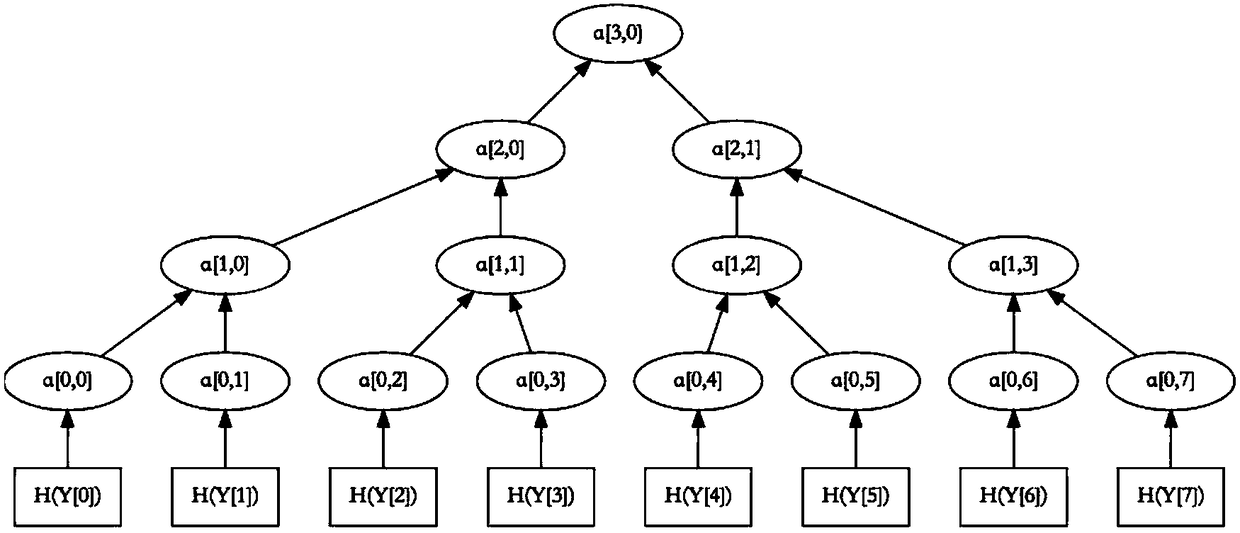
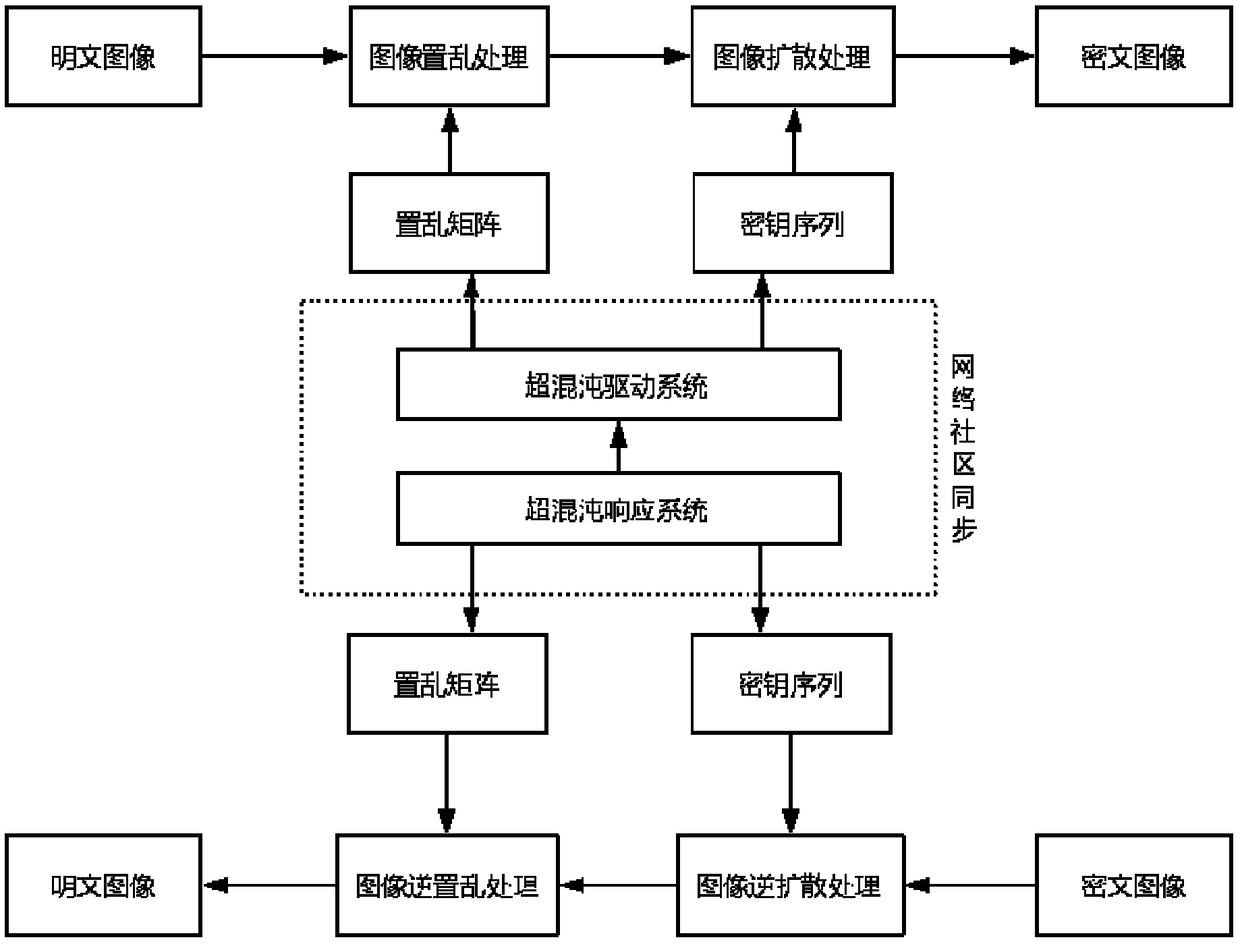
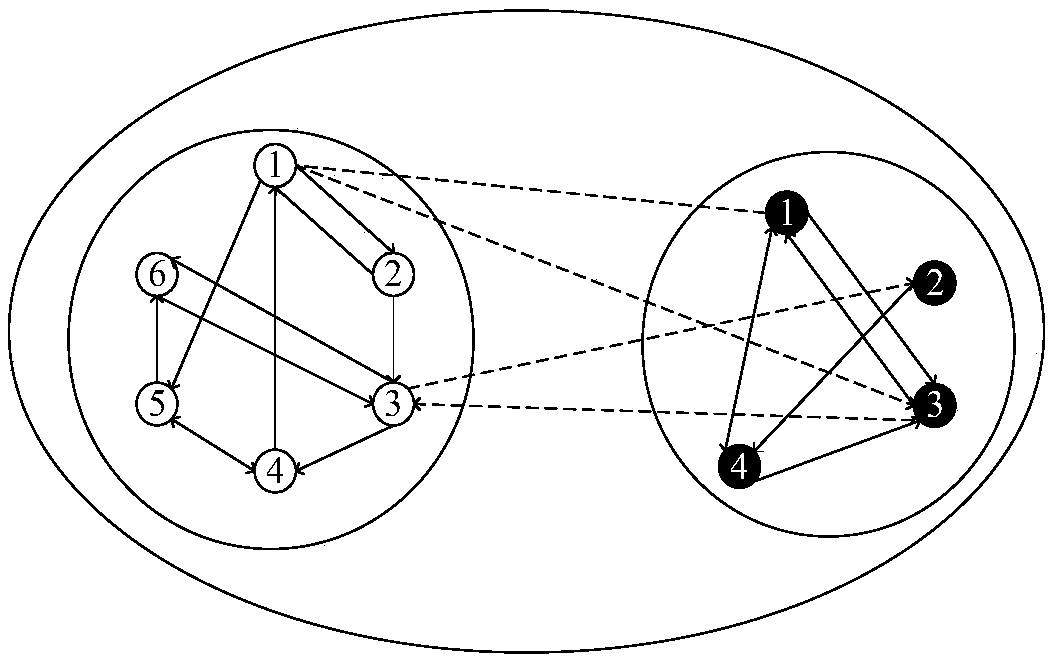
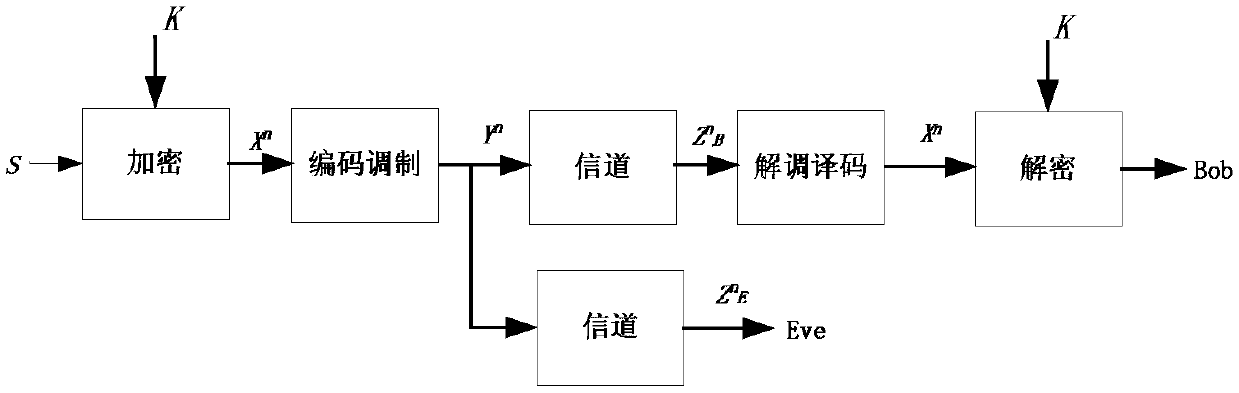
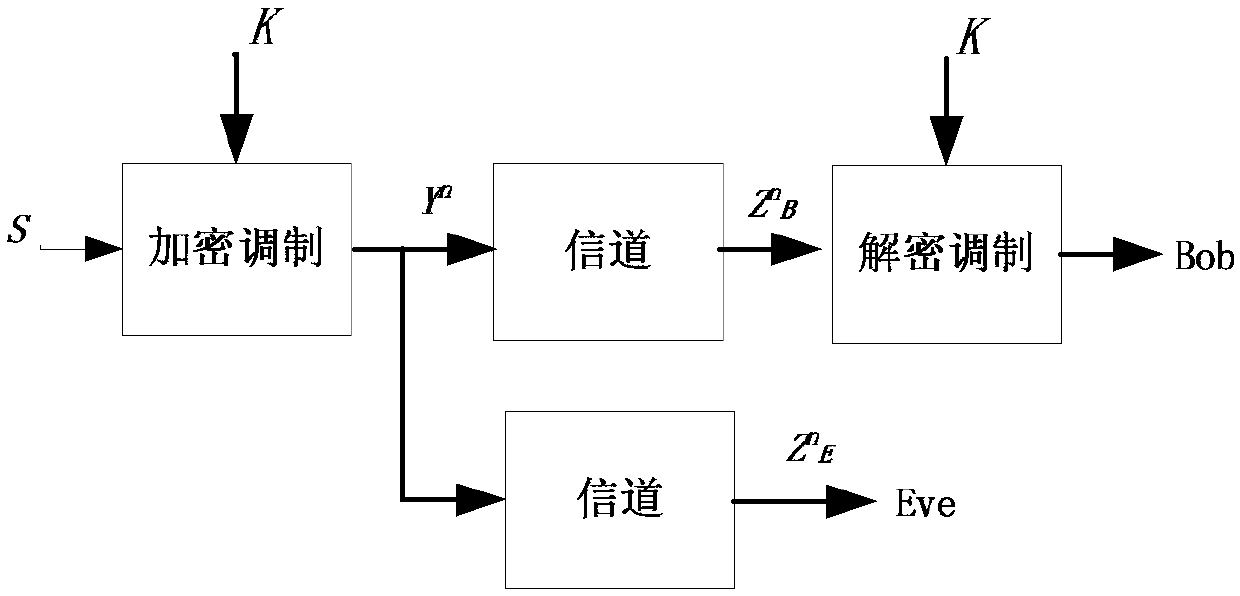
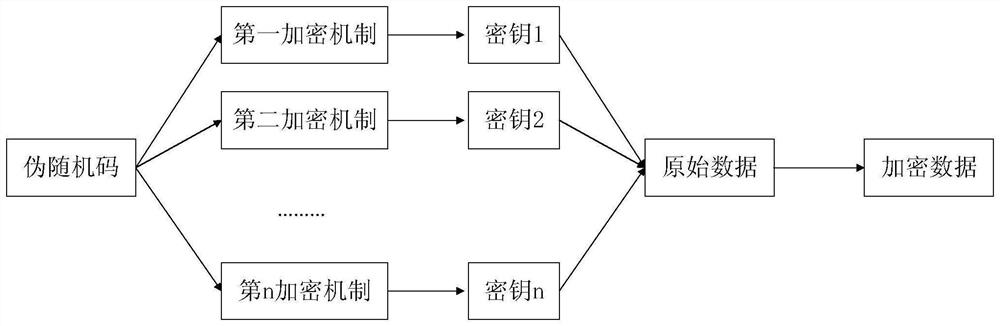
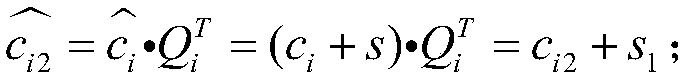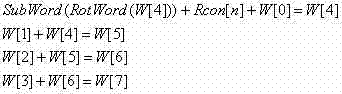Patents
Literature
123results about How to "Increase the difficulty of deciphering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
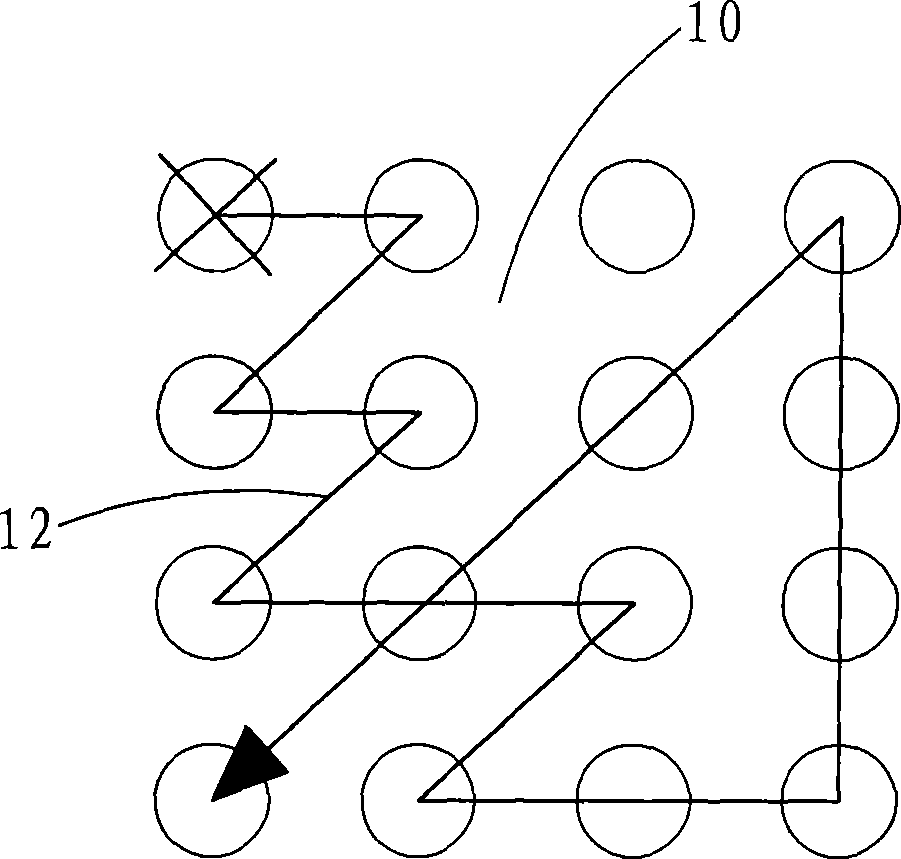
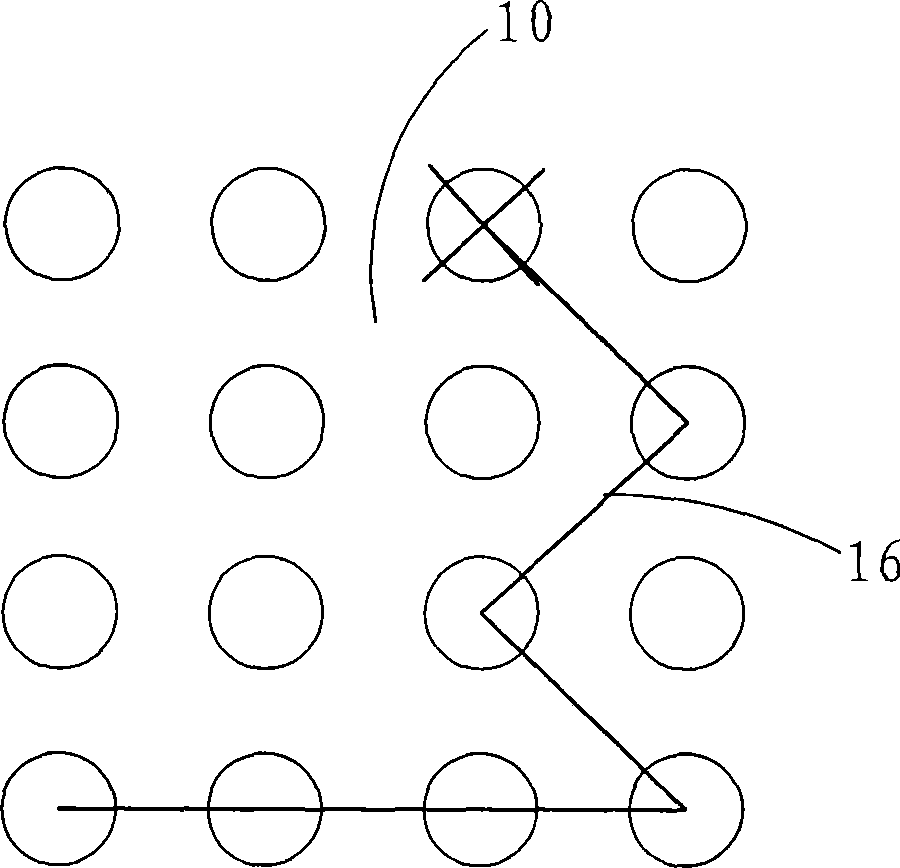
Path password input method based on contacts
ActiveCN101251884AFast typingStrong passwordInternal/peripheral component protectionUser needsPassword
The invention relates to a path password input method based on touch spots, which is as follows: an input device displays a password input matrix on the display screen of the input device; users lay off a path from the password input matrix as a password through a mouse or a touch screen and other input devices, the password input information is transferred to a processor in the input device; the processor of the input device transforms the path password information into letters or figures, then compares the letters or the figures with the pre-stored password in the processor, if matching, the password validation is passed, and if not, the users need to return to re-input the password. The path password input method based on touch spots has the advantages that: the users orderly pass each spot of the password input matrix to form the path as the password, which ensures the password input becomes easy and rapid, improves the memorability of the password and high intensity of the setting,; and the path password does not have any relations with the personal profile, which is not easy to form the password dictionary. The path password input method based on touch spots not only can be used for password input, but also can be used as a short cut for starting a certain program or can be used as a shortcut key of a certain function of the program.
Owner:FUJIAN ETIM INFORMATION & TECH
Security control methods for date transmission process of software protection device and device thereof
ActiveCN101008972AProtection securityIncrease the difficulty of decipheringComputer security arrangementsSecuring communicationInterference (communication)Software engineering
This invention relates to one software protection device data transmission process safety control method, which comprises the following steps: sending the data between computer and software protection device by code form to make the whole process data without clear data in the communication circuit; due to random interference type and coding process of data, it makes each same order sent from protection software into software protection device and the feedback order from software protection device is variable.
Owner:FEITIAN TECHNOLOGIES
User identity protection method based on public-key mechanism
ActiveCN102026178AIncrease the difficulty of decipheringIntegrity guaranteedSecurity arrangementInternet privacyEngineering
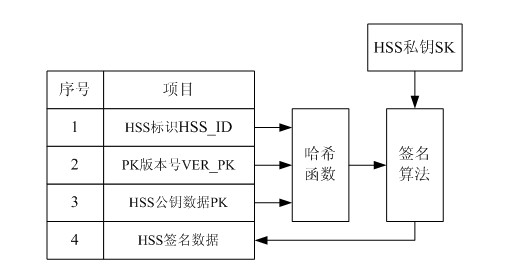
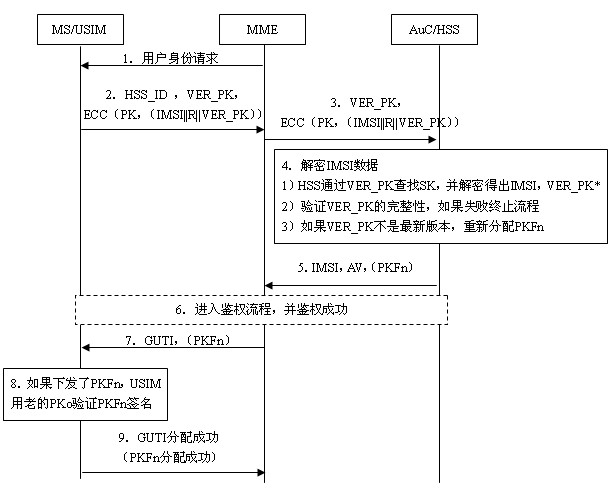
The invention relates to the secret communication field of mobile communication technologies, and discloses a user identity protection method based on a public-key mechanism. The method comprises the following steps: an HSS (hierarchical service system) produces a pair of keys, namely, a public key PK and a secret key SK, then the public key PK is preset to a USIM (universal subscriber identity module) card of UE (user equipment) belonging to the public key PK in the form of a public key file PKF, and the secret key SK is stored in the HSS; a mobile phone sends the following information to anMME (mobility management entity), including HSS identification: HSS_ID, public-key PK version number: VER_PK; and data (IMSI || R|| VER_PK) encrypted by using an asymmetric encryption algorithm; after receiving the information, the MME sends the VER_PK and the (IMSI || R|| VER_PK) to the HSS according to the HSS_ID; and the HSS decrypts the VER_PK and the (IMSI || R|| VER_PK) by using the secret key SK. Because attackers do not know the secret key SK of the HSS, the attackers can not decrypt the (IMSI || R|| VER_PK).
Owner:成都三零瑞通移动通信有限公司
ELF file protection method and system based on ARM instruction virtualization
InactiveCN105608346AOrganizational forms are ever-changingSimple and flexible implementationProgram/content distribution protectionVirtualizationProcessor register
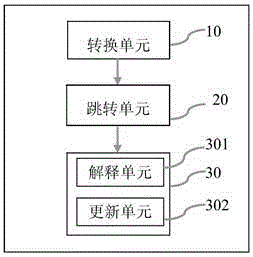
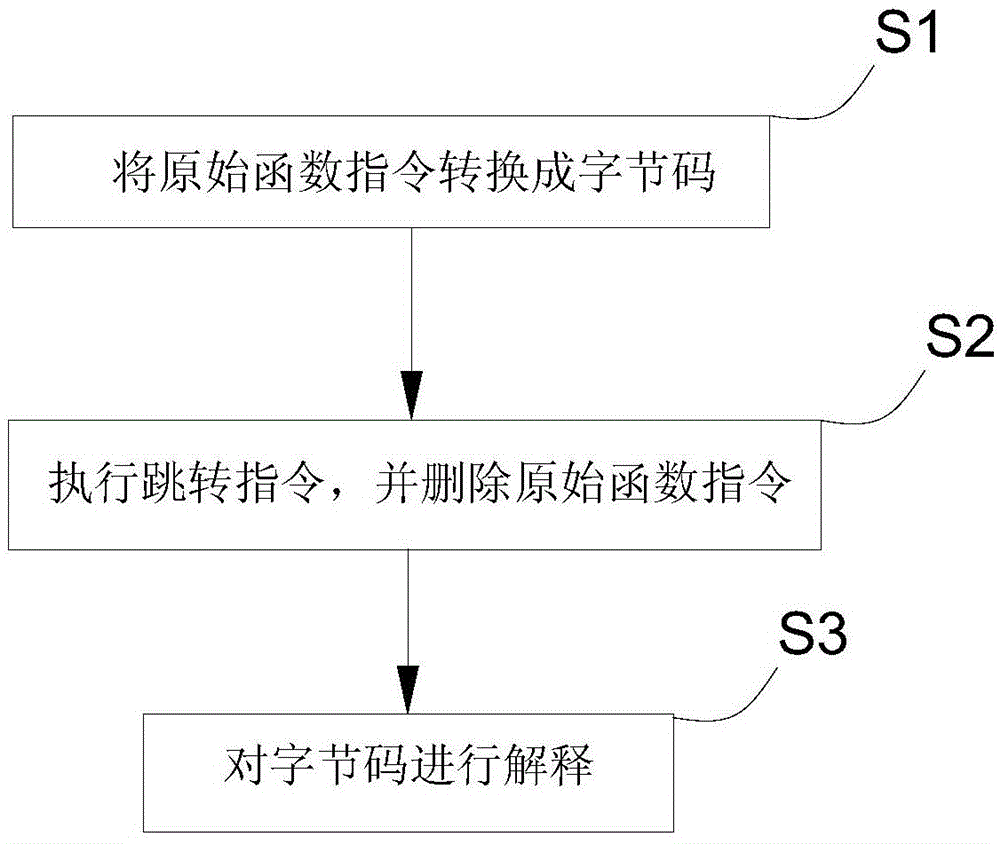
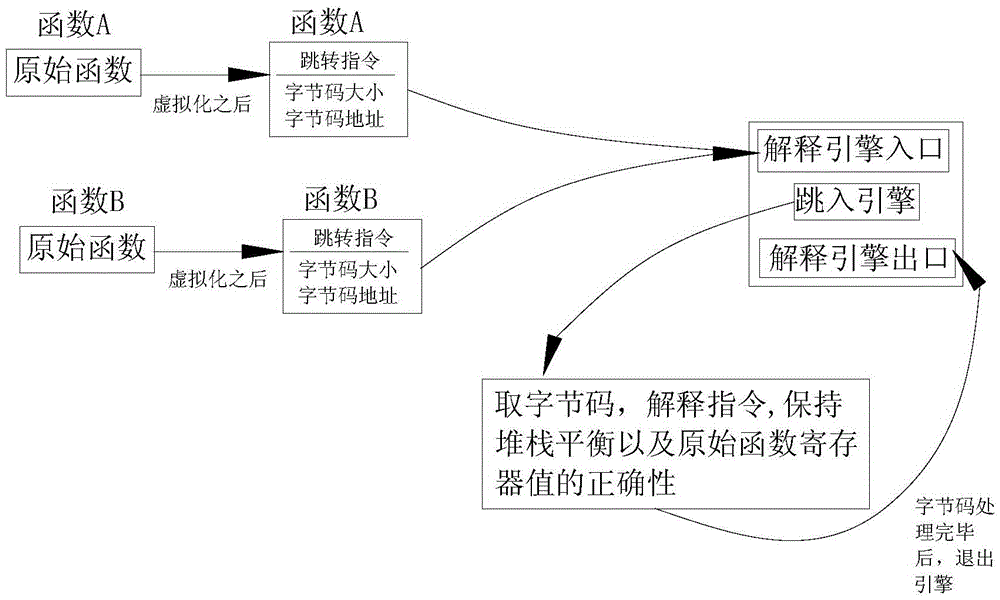
The invention discloses an ELF file protection method and system based on ARM instruction virtualization. The method includes the steps that an original function instruction is converted into bytecodes; a register and stack information of an original function are stored, a jump instruction is added, and other instructions are deleted; the jump instruction is executed, and the bytecodes are interpreted by jumping to an interpreting engine. In this way, the original function instruction is converted into the bytecodes in a virtualization mode, the difficulty of a cracker is increased, and the file protection strength is improved.
Owner:BEIJING QIHOO TECH CO LTD +1
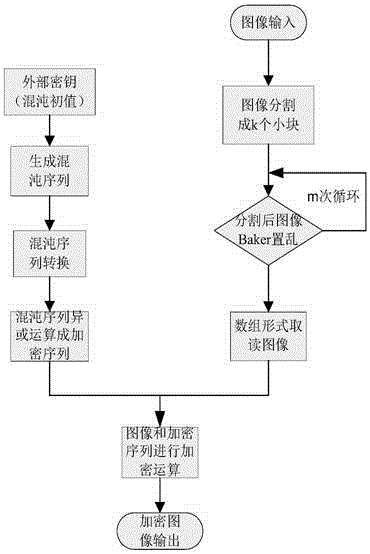
Chaotic key-based data encryption transmission card
InactiveCN101714917AEasy selectionIncrease the difficulty of decipheringSecuring communicationTransceiverData transmission
The invention aims to provide a chaotic key-based data encryption transmission card in which a chaotic key sequence is applied to the data encryption transmission card and which has high secrecy performance, high computing speed and high integration level of an encryption chip. The chaotic key-based data encryption transmission card consists of a standard RS-232 transceiver and an FPGA encryption chip; standard serial data sent by a serial port of a PC is demodulated into standard TTL level through the standard RS-232 transceiver, is sent to the I / O port of the FPGA encryption chip, is encrypted by the FPGA encryption chip and then is modulated into standard 232 level through the standard RS-232 transceiver and sent to a communication channel. A hardware-based chaos algorithm is applied to the data encryption transmission card to form the chaotic key-based data encryption transmission card with high secrecy performance. The chaotic key-based data encryption transmission card is suitable for vital departments such as banks, enterprises and the like, implements point-to-point encryption on information transmitted by important secret departments, and ensures the security of data transmission.
Owner:HEILONGJIANG UNIV +1
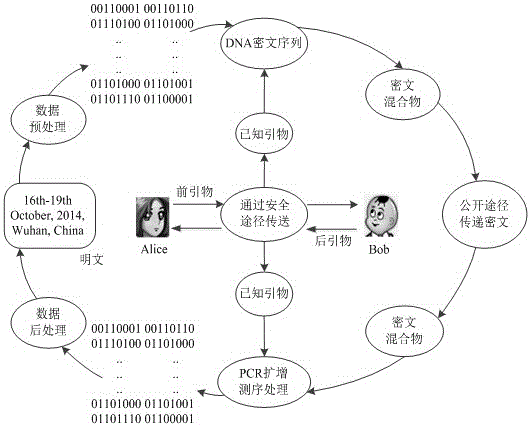
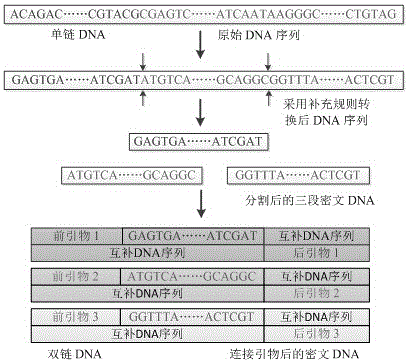
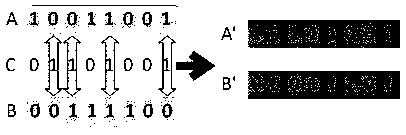
DNA coding based encryption system and encryption method
InactiveCN105119717AIncrease the difficulty of decipheringIncrease the difficulty of crackingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesInformation transmissionPassword
The invention belongs to the technical field of information security in communication transmission, and particularly relates to a DNA encryption system and an encryption method. The system comprises an encryption key, an information conversion portion, an information encryption portion, an information transmission portion, a decryption key and an information decryption portion, wherein the encryption key and the decryption key are primer sequences; and information encryption refers to that information is converted and coded and then corresponds to A, T, C, G bases in DNA in a one-to-one mode according to a predetermined rule. The encryption system and the encryption method provided by the invention can realize automatic operation of corresponding code conversion, encryption and decryption by depending on biological problem setting and biological technology development and by being matched with development of corresponding computer information technologies at the same time, have the characteristics of good compatibility with other encryption methods, high automation degree, simple key, high password cracking difficulty, safer information transmission and the like, has good application values, and can provide better reference for other new encryption systems at the same time.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
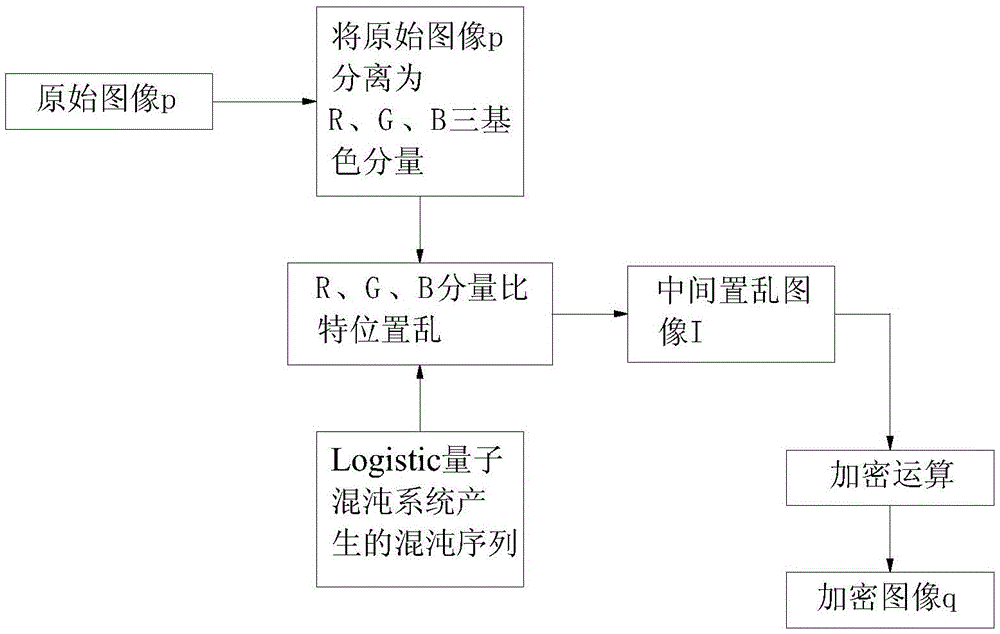
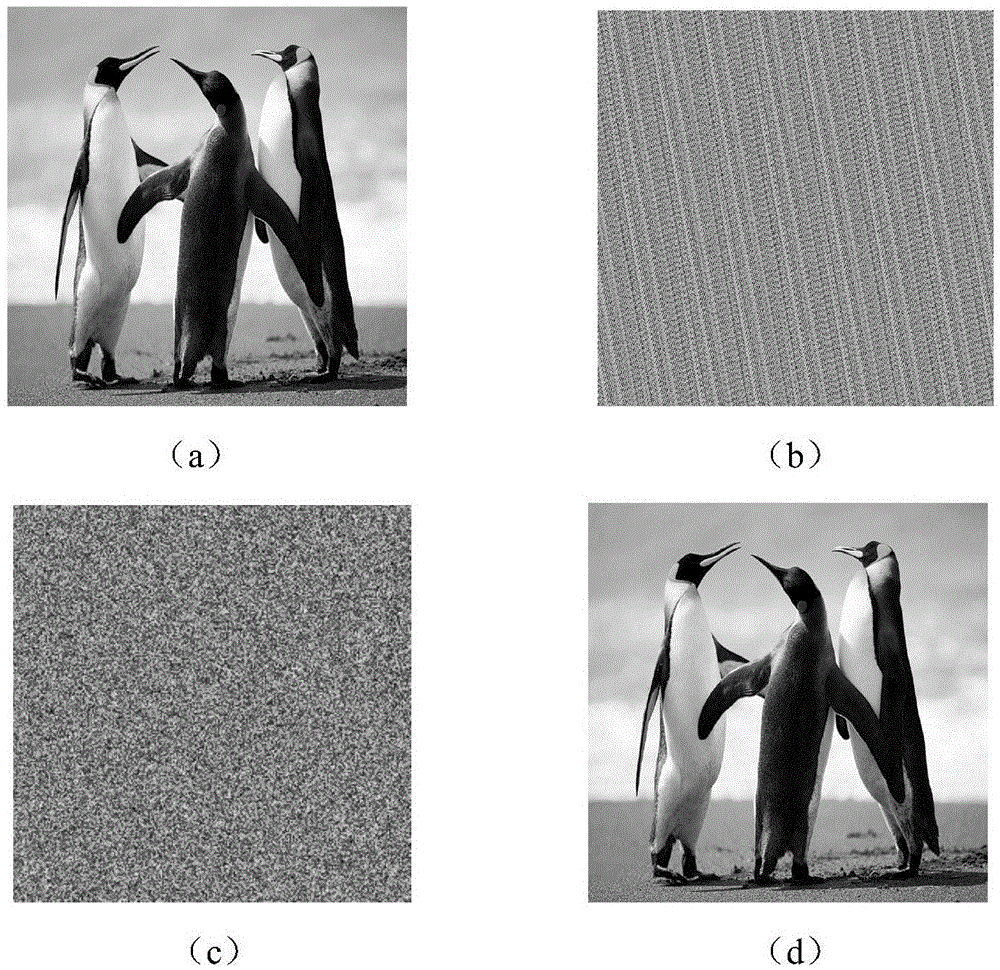
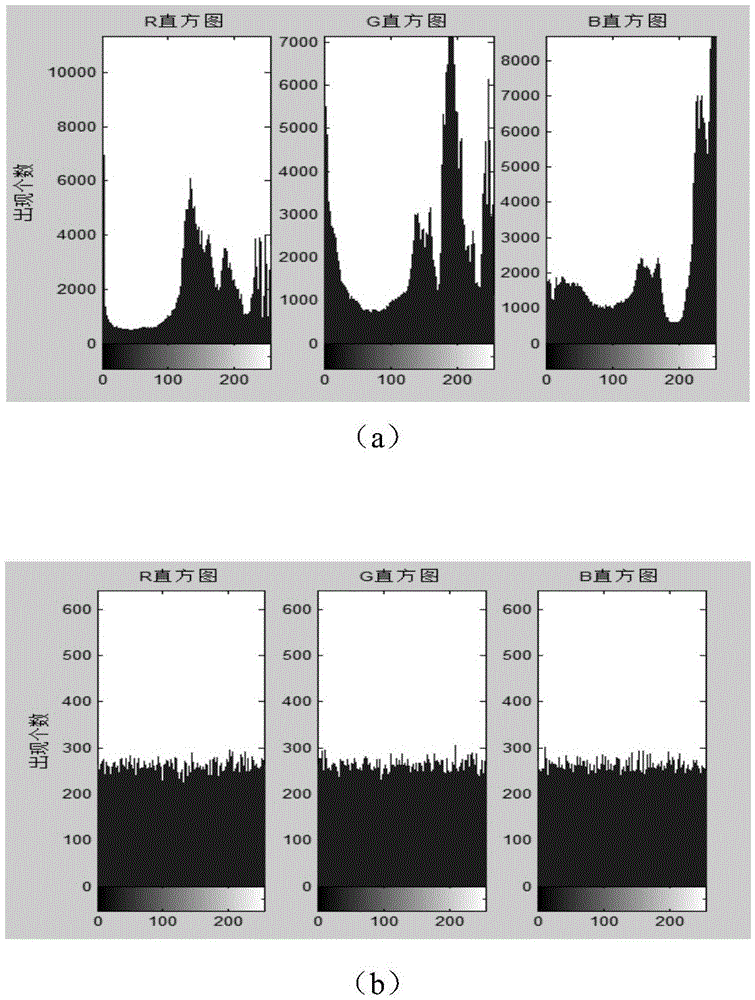
Quantum chaotic image encryption method based on bit scrambling
ActiveCN105631796ASimple physical structureResolve Loss of PrecisionImage data processing detailsComputer hardwareChaotic systems
The invention discloses a quantum chaotic image encryption method based on bit scrambling. The method comprises steps: a Logistic quantum chaotic system is used for generating a chaotic sequence, bit scrambling is carried out on R, G and B three-primary color component pixel values of an original image p, and a middle scrambling image I is obtained; and then, encryption operation is carried out on the middle scrambling image I, and a final encryption image q is obtained. The encryption method of the invention greatly increases the secret key space, the safety, the encryption effect and the secret key sensitivity are higher, the anti-attack ability is stronger, and the deciphering difficulty is greatly improved.
Owner:GUANGDONG UNIV OF TECH
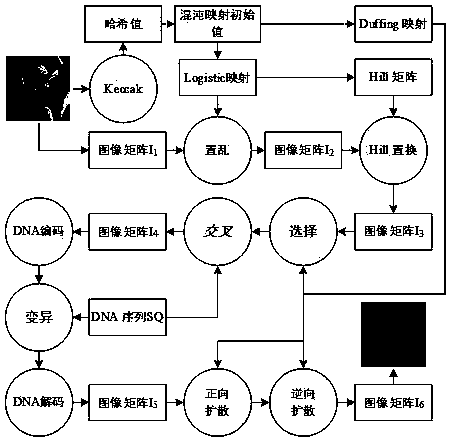
An image encryption method based on Duffing mapping and genetic operation
ActiveCN109376540AIncreased sensitivityIncrease the difficulty of decipheringDigital data protectionPlaintextExclusive or
The invention provides an image encryption method based on Duffing mapping and genetic operation. The hash value of a plaintext image is calculated by using a Keccak algorithm as an initial value input key of a chaotic system; the sensitivity and pseudo-randomness of the chaotic map to the initial conditions are used, the pseudo-random sequence is obtained by iterating the Logistic map and the Hill encryption matrix is generated to scramble and replace the image matrix. Combined with Duffing map and DNA coding technology, pixel selection, crossover and mutation are realized by genetic operation to achieve pixel diffusion and scrambling, and bidirectional exclusive OR operation with chaotic sequence to enhance its confusion and diffusion characteristics. The invention utilizes the pseudo-randomness of Duffing mapping and Logistic mapping, ergodicity and the crossover mutation operation of genetic algorithm, has strong sensitivity to key, can effectively resist statistical attack and differential attack, etc., has good security and application potential, and the image encryption effect and performance are remarkably improved.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
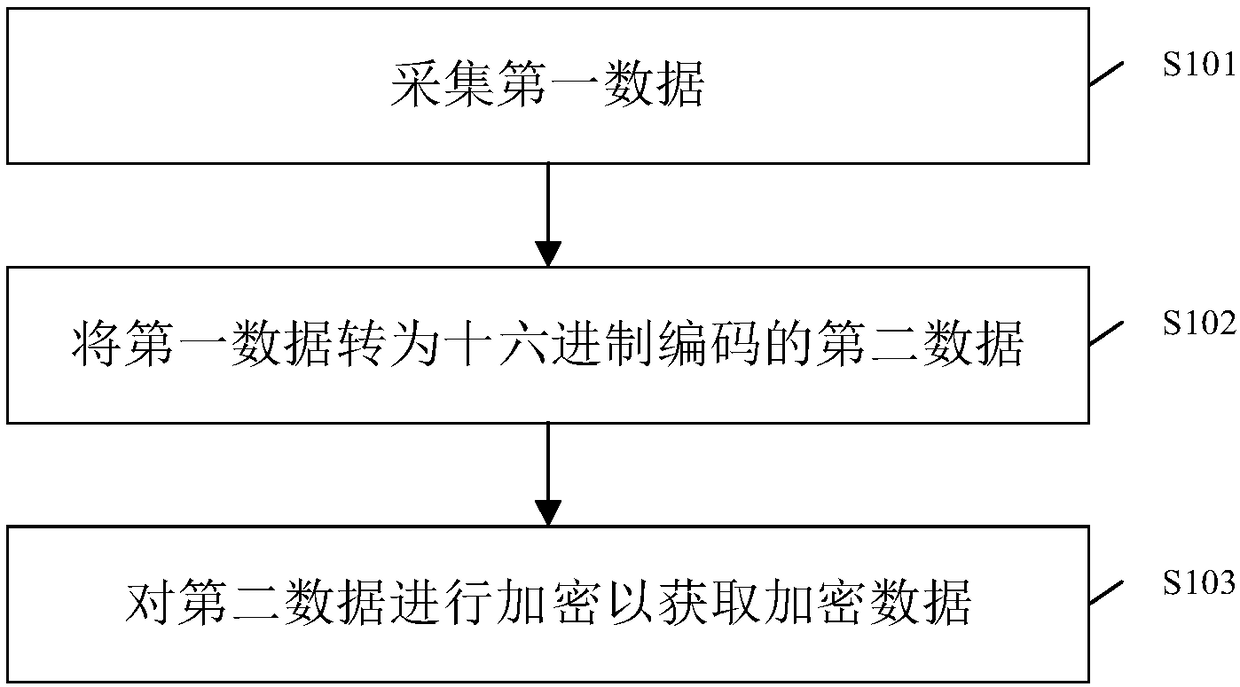
Data encryption method
InactiveCN108429735AEnsure safetyIncrease the difficultyKey distribution for secure communicationMultiple keys/algorithms usageIntel HEXComputer hardware
The invention provides a data encryption method. The data encryption method comprises the following steps that first data is acquired, wherein the first data is fingerprint data, identity card data, adigital cipher and / or MF card data; the first data is converted into hexadecimal coded second data; and the second data is subjected to a hardware encryption mechanism and a software encryption mechanism to acquire encrypted data. According to the data encryption method, by means of the process that the first data is acquired and converted into the hexadecimal coded second data, and then the second data is encrypted to acquire the encrypted data, the security of the data can be guaranteed.
Owner:陈柱
A chaotic image encryption method based on complex network synchronization
ActiveCN109104544AHigh actual use valueImprove securityPictoral communicationCiphertextComputer science
The invention provides a chaotic image encryption method based on complex network synchronization, which relates to the technical field of network encryption. A chaotic image encryption method based on complex network synchronization is disclosed. Firstly, the complex network is synchronized. Then the plaintext image is quantized and used as the current image. The current image is preprocessed byhyperchaos driving system, and the current image is scrambled and diffused to get the ciphertext image. Finally, the obtained ciphertext image is quantized, and the ciphertext image is taken as the current image to be processed, and the scrambling sequence is generated synchronously by using the super-mixing response system, and the current ciphertext image to be processed is processed by inversediffusion and inverse scrambling, so as to obtain the plaintext image. The chaotic image encryption method based on complex network synchronization provided by the invention makes the ciphertext imageconcealment strong, greatly increases the difficulty of deciphering, and enables the encryption algorithm to resist various statistical attacks, violent attacks and differential attacks.
Owner:NORTHEASTERN UNIV
Cloud storage data confidentiality protection method
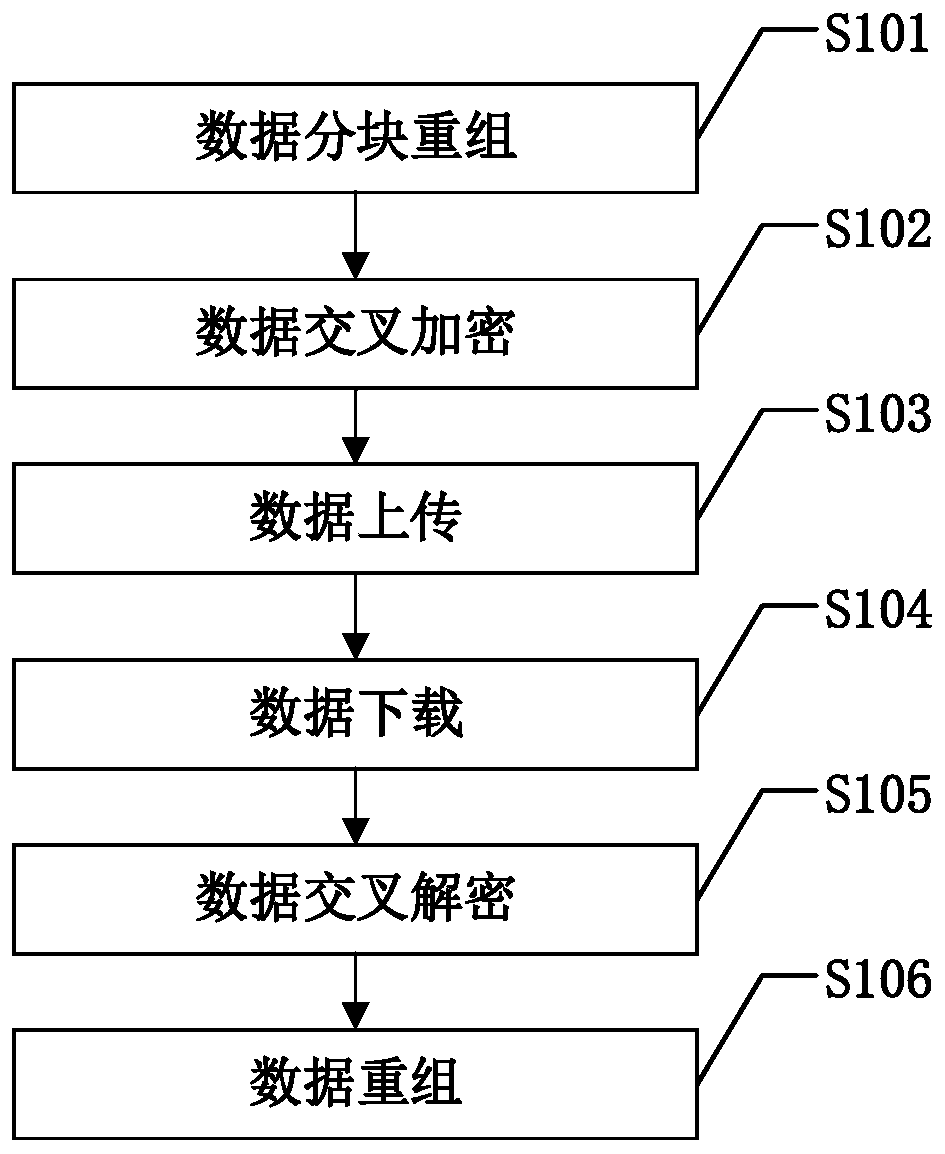
ActiveCN110213354AIncrease the difficulty of decipheringImprove confidentialityDigital data protectionTransmissionData fileCloud storage
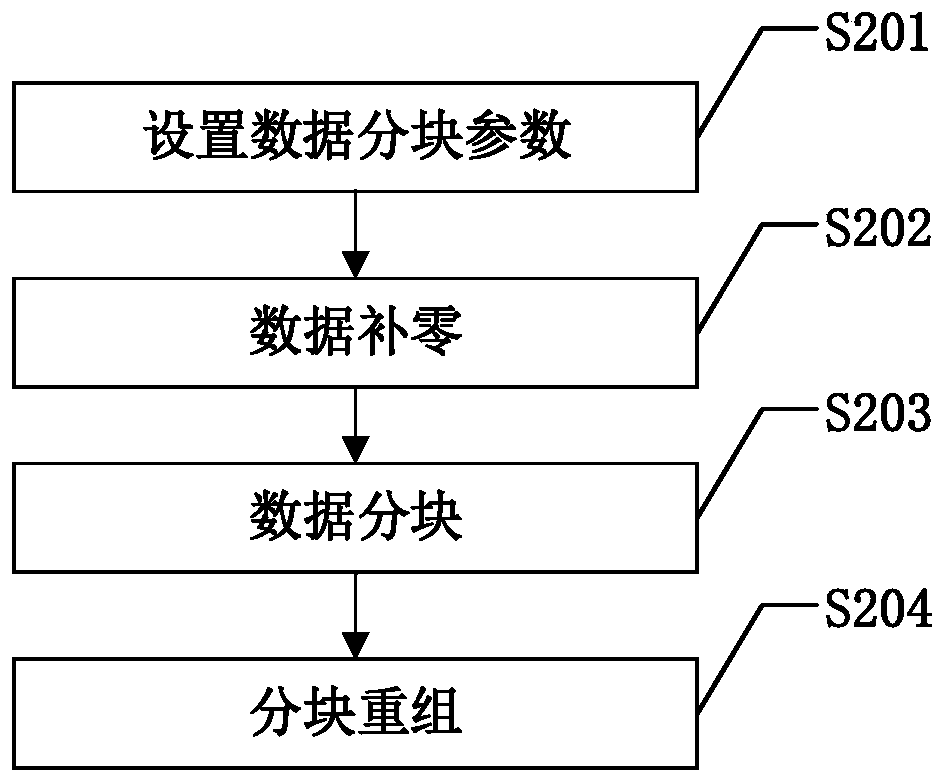
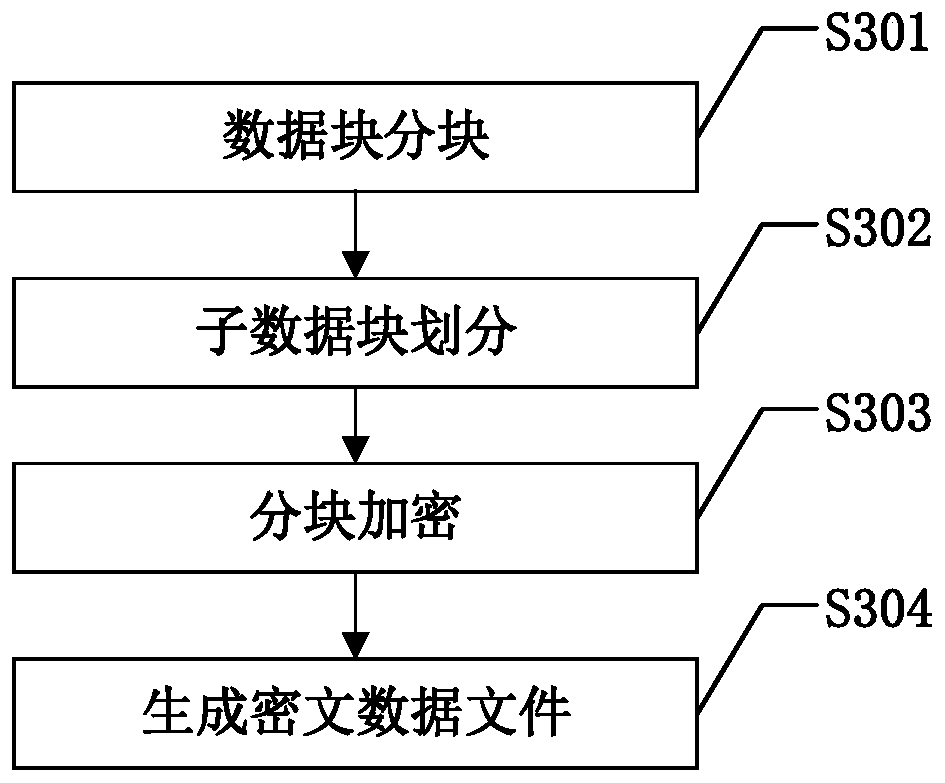
The invention discloses a cloud storage data confidentiality protection method. The method comprises: partitioning the data file to be uploaded to the cloud storage server by adopting the following method; then, obtaining a plurality of data blocks through scrambling and sequential recombination; dividing each data block into sub-data blocks; dividing the sub-data blocks into two parts; encryptingeach part by adopting different encryption algorithms; recombining the obtained ciphertext data blocks to obtain a ciphertext data file; uploading the data to a cloud storage server for storage; whendata needs to be used, the data can be used, downloading the ciphertext data file from the cloud storage server, dividing the ciphertext data file according to the inverse process of ciphertext datablock recombination during uploading, decrypting different parts by adopting different decryption algorithms, and recombining the decrypted data blocks according to the inverse process of data block recombination during uploading to recover the data file. According to the method, data block recombination and cross encryption are adopted, so that the security of storing the user data on the cloud storage server is improved.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
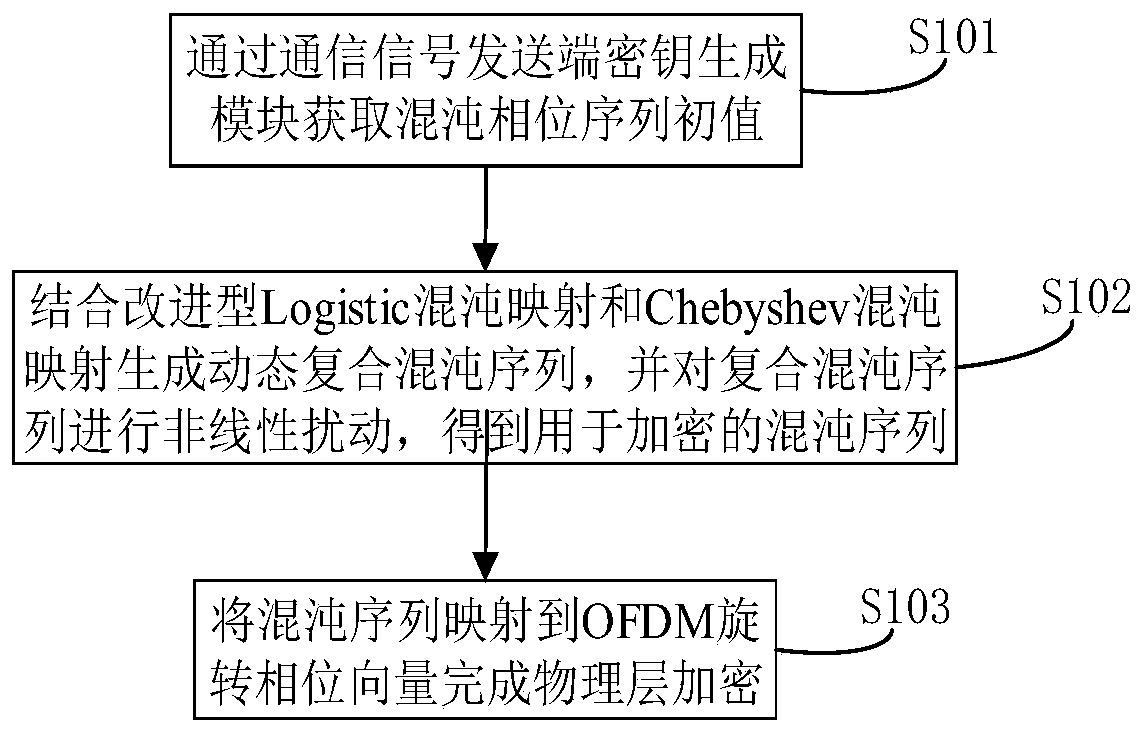
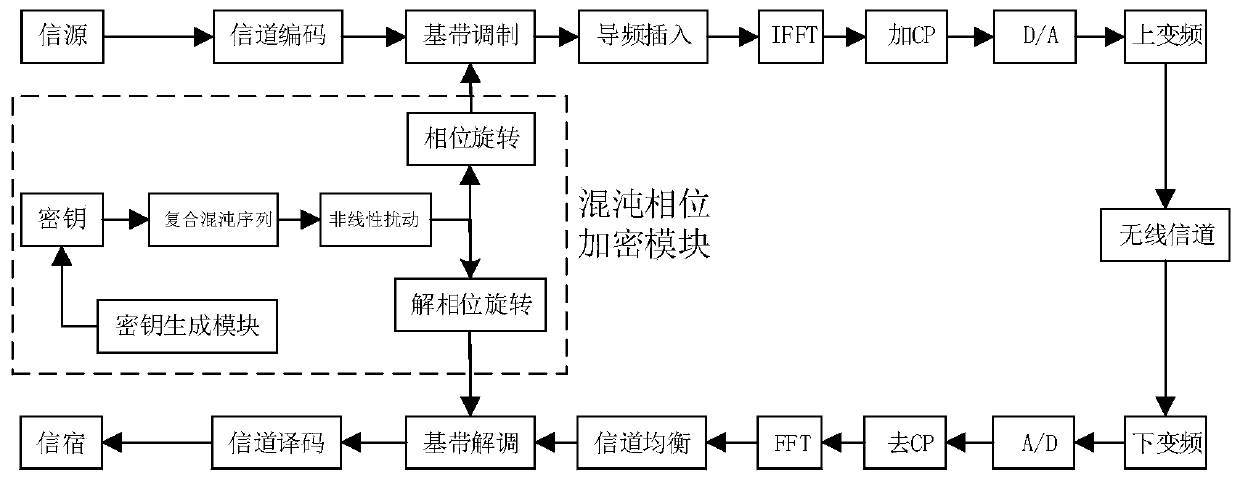
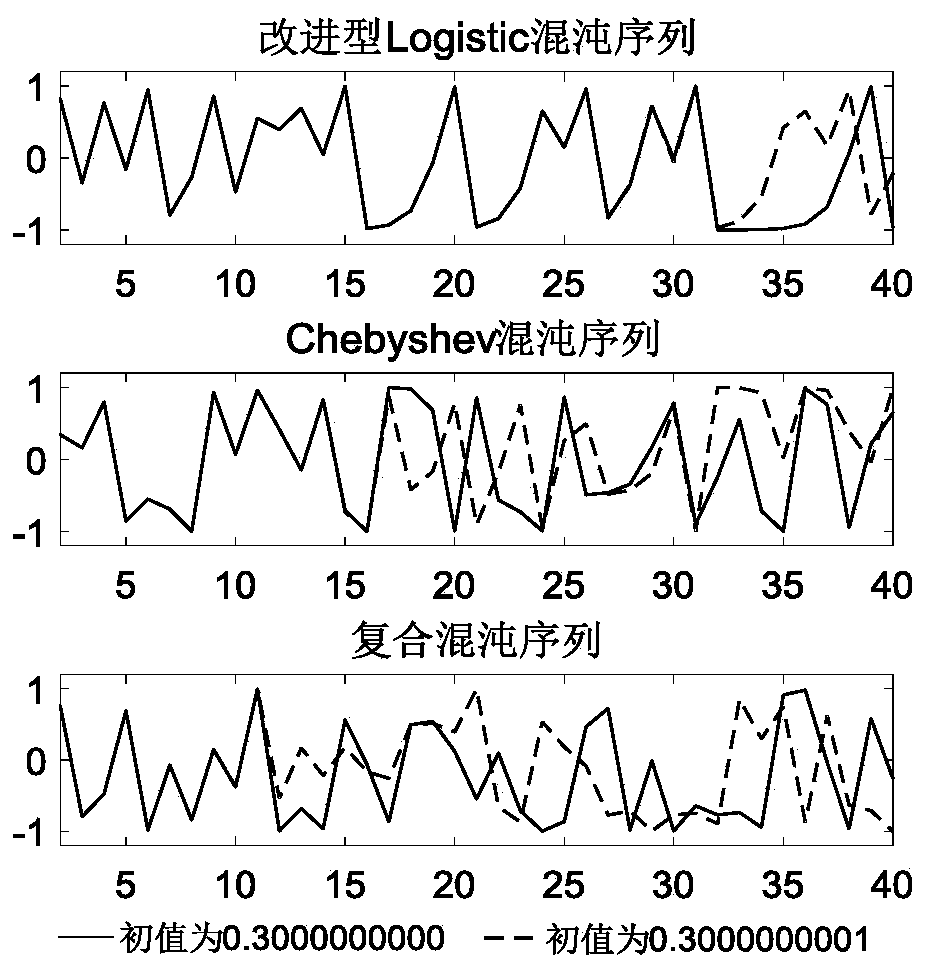
OFDM communication signal physical layer encryption method and device
ActiveCN110601821AIncrease randomnessImprove securityKey distribution for secure communicationSecuring communication by chaotic signalsCommunications securityPhysical layer
The invention belongs to the technical field of communication security, and particularly relates to an OFDM communication signal physical layer encryption method and device, and the method comprises the steps: carrying out the symbol-by-symbol switching of a chaotic phase sequence initial value through a communication signal transmitting end secret key generation module; generating a dynamic composite chaotic sequence by combining the improved Logistic chaotic mapping and the Chebyshev chaotic mapping, and performing nonlinear disturbance on the composite chaotic sequence to obtain a chaotic sequence for encryption; and mapping the chaotic sequence to an OFDM rotation phase vector to complete physical layer encryption. According to the invention, symbol-by-symbol switching of chaotic sequence initial values is carried out; then, generating a composite chaotic sequence by combining the improved Logistic chaotic mapping and the Chebyshev chaotic mapping; the sequence randomness is improved through nonlinear disturbance, the initial value sensitivity of chaotic mapping is fully utilized, the decoding difficulty is further increased, compared with a traditional chaotic phase encryptionscheme, the operand is greatly reduced, the communication safety performance is greatly enhanced while the encryption chaotic performance is improved, and good application value is achieved.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
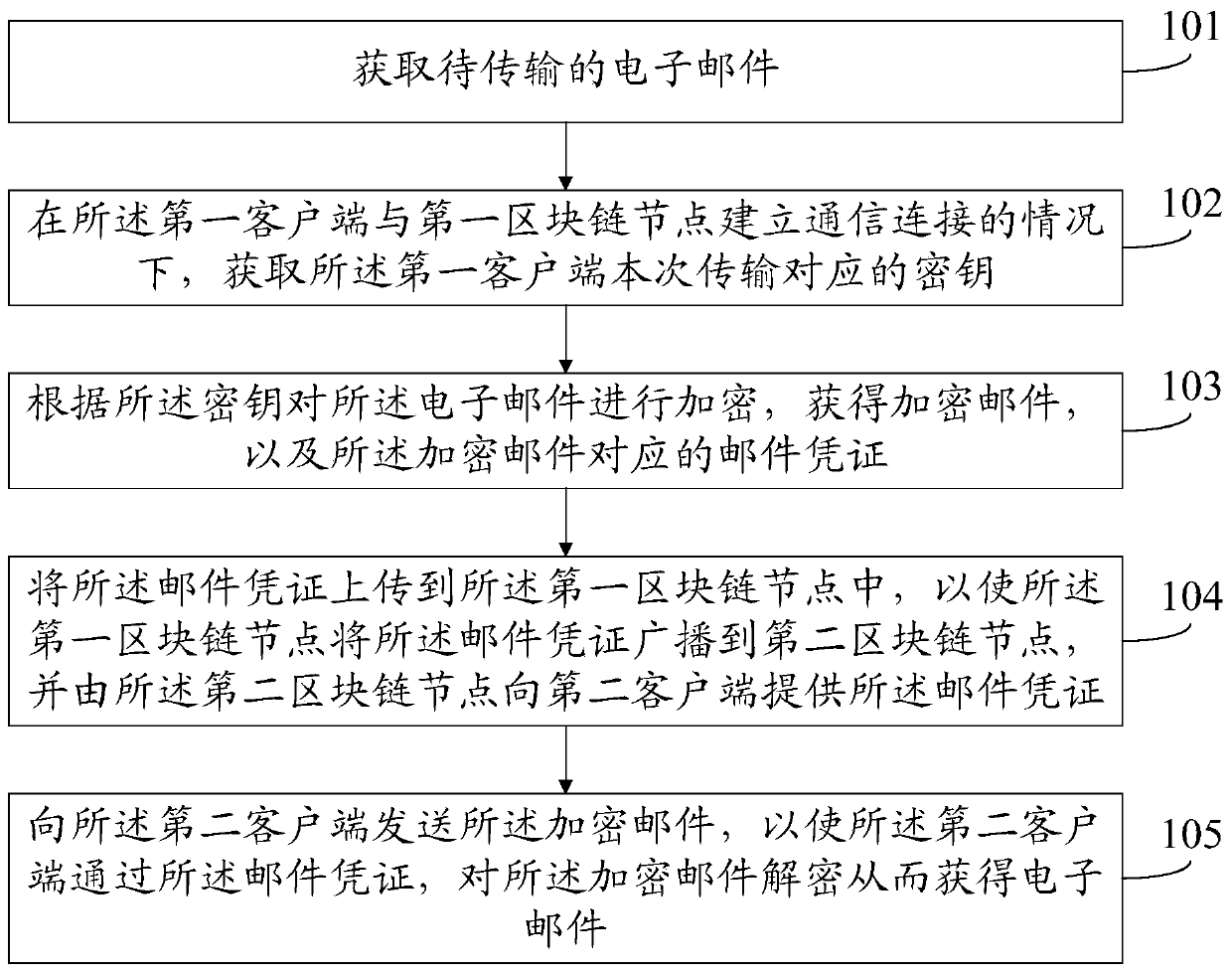
E-mail encryption method, first client and blockchain system
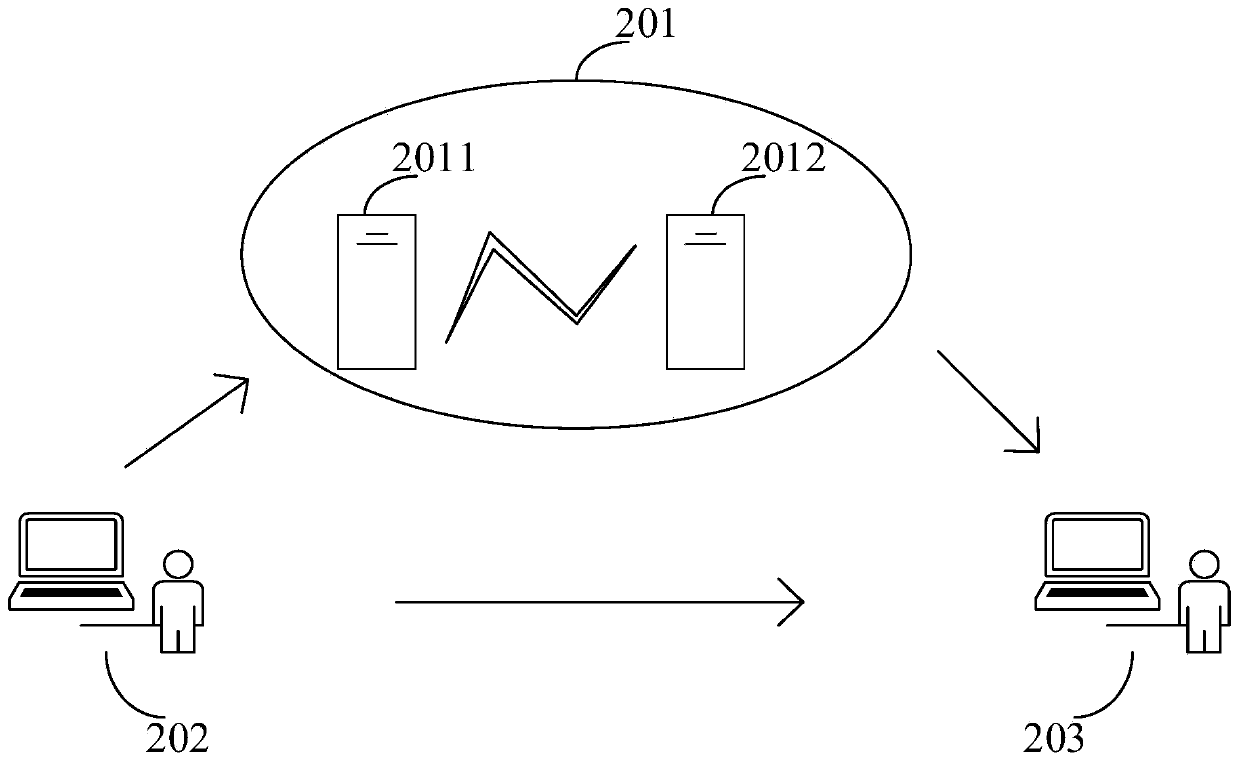
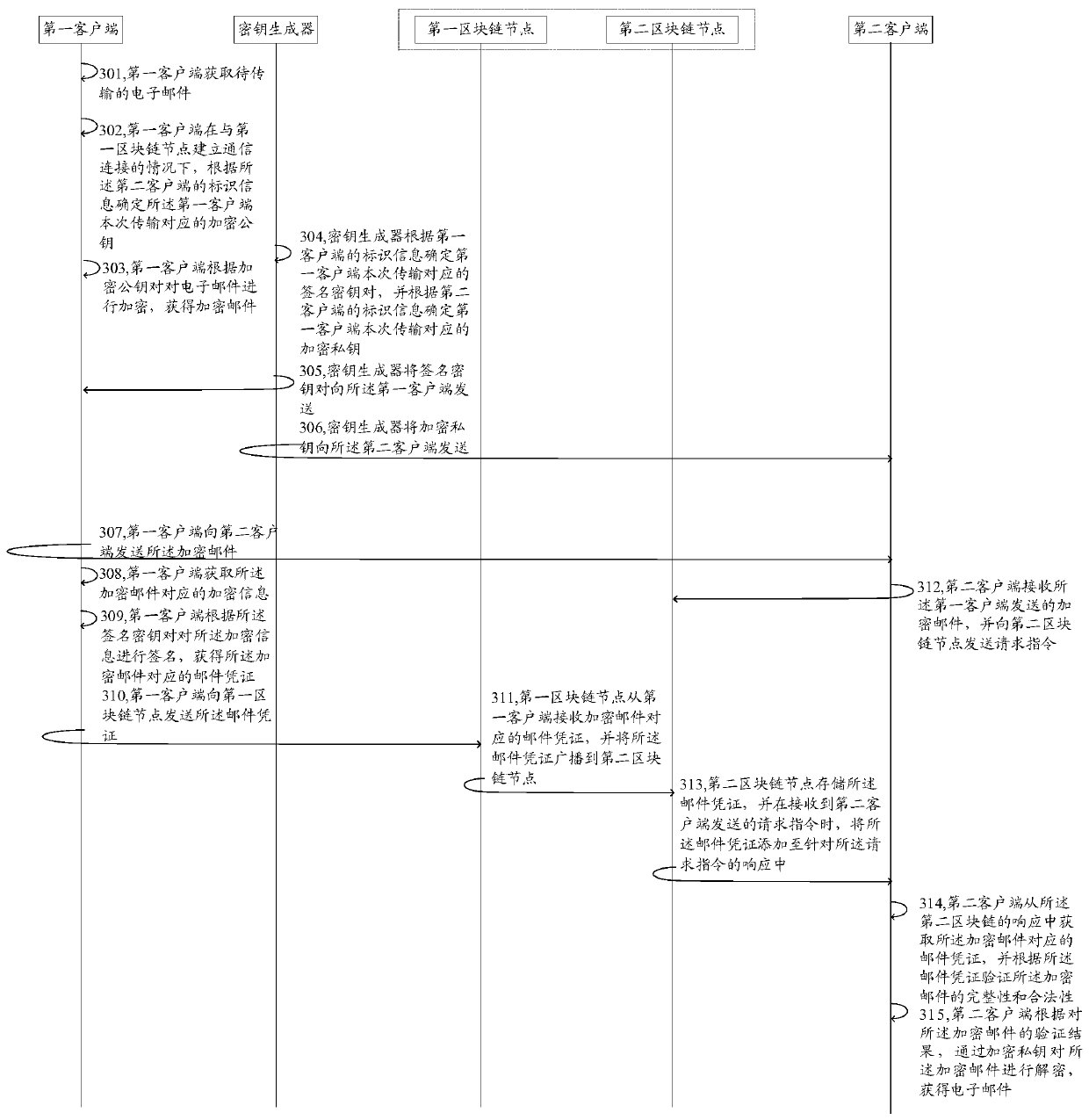
InactiveCN111464494AIncrease the difficulty of decipheringImprove securityUser identity/authority verificationData switching networksInternet privacyData transport
The invention provides an e-mail encryption method, a first client and a blockchain system. The method comprises the following steps: acquiring an e-mail to-be-transmitted; under the condition that afirst client establishes a communication connection with a first blockchain node, obtaining a key corresponding to the current transmission of the first client; encrypting the e-mail according to thesecret key to obtain an encrypted e-mail and an e-mail certificate; uploading the mail voucher to the first blockchain node so that the first blockchain node broadcasts the mail voucher to a second blockchain node and provides the mail voucher to a second client; and sending the encrypted email to the second client so that the second client decrypts the encrypted email through the email certificate to obtain the e-mail. On the basis of an original mail transmission path, only the mail certificate is transmitted through the blockchain, the property that the blockchain is suitable for small-volume data transmission is met, and the reconstruction, operation and maintenance cost of a mail system is reduced while mail encryption is achieved.
Owner:北京十安赛恩科技有限公司
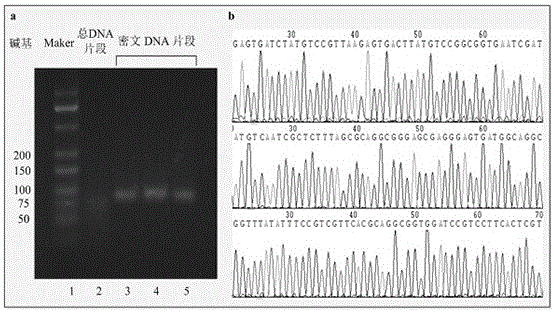
DNA chip based cipher system
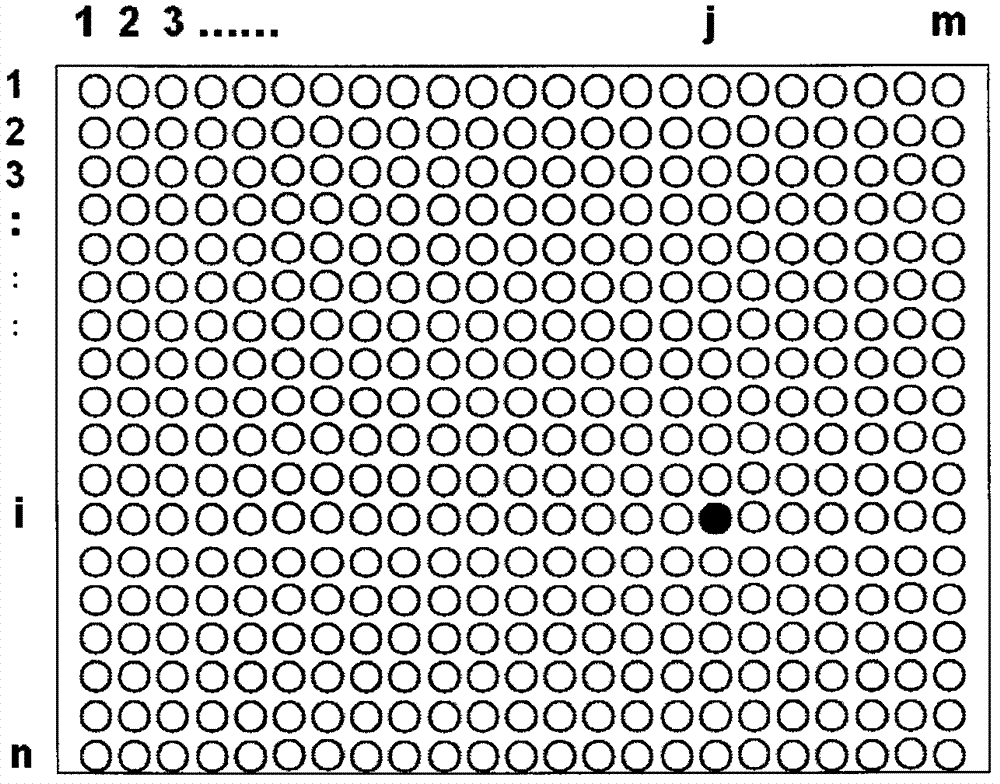
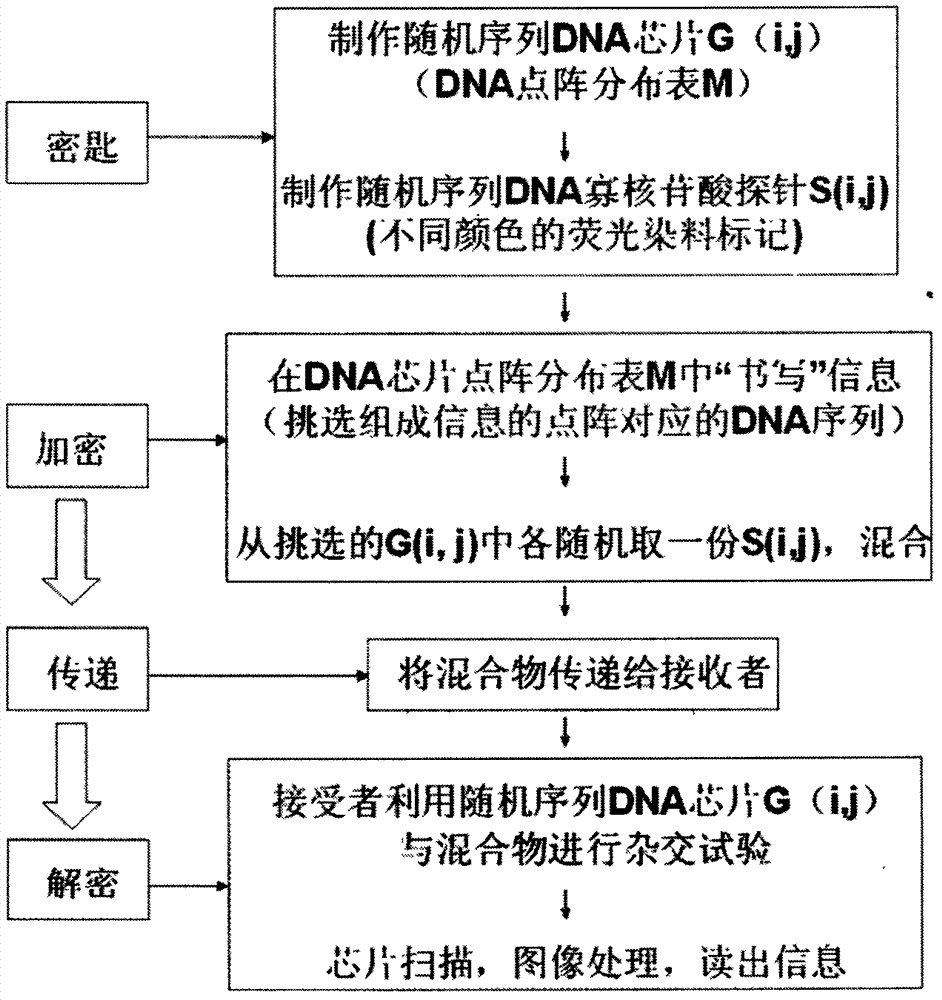
InactiveCN103114127AClear messageIncrease costMicrobiological testing/measurementFluorescence/phosphorescenceOligonucleotideDna microchips
The invention provides a DNA chip based cipher system. The DNA of the DNA chip of the cipher system is a random sequence G (i, j). Oligonucleotide probes S (i, j) are oligonucleotide fragments obtained through artificially synthesizing the reverse complement sequences of a small-segment DNA sequence randomly intercepted from the random DNA sequence G (i, j) corresponding to the lattices of the DNA chip, and the uniqueness of the small-segment DNA sequence in the DNA chip is determined through using BLAST. Information encryption is that a DNA chip lattice distribution map M is marked with different G (i, j) to represent plaintext information, and then the oligonucleotide probes S (i, j) corresponding to the G (i, j) are mixed; and information decryption is that the oligonucleotide probes S (i, j) are hybridized with the random sequence DNA sequence. The encryption of same plaintext information can be realized through a large amount of different S (i, j) probe mixture combinations and can be admixed with any unlabeled DNA at will. The S (i, j) probes are composed of the random DNA sequence, and plaintext information related information is not coded in the DNA sequences of the mixtures of the S (i, j) probes, so the system cannot be decoded.
Owner:SOUTH CHINA BOTANICAL GARDEN CHINESE ACADEMY OF SCI
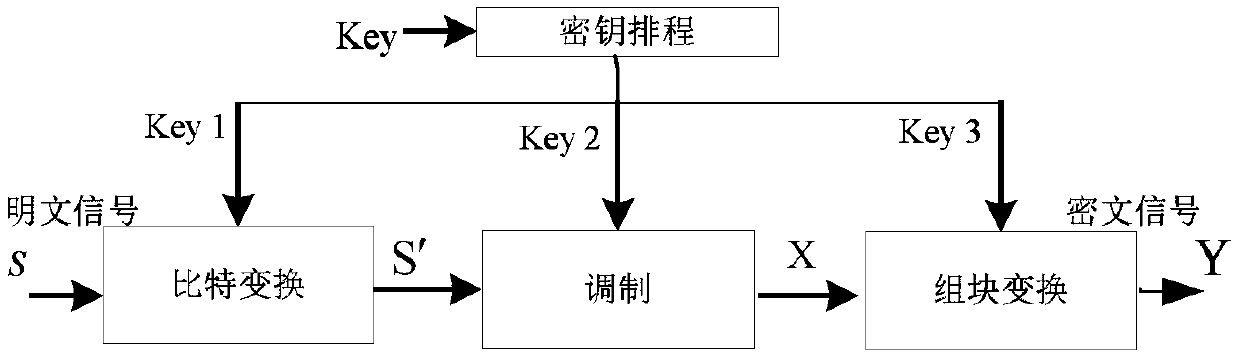
Packet physical layer encryption method based on matrix transformation
ActiveCN108833390AIncrease confusionImprove protectionKey distribution for secure communicationMulti-frequency code systemsComputer hardwarePhysical layer
The invention belongs to the field of communication signal encryption technology, and specifically designs a packet physical layer encryption method based on matrix transformation. The method comprises the following steps: (1) transforming plaintext signals S into an information sequence S' through bits; (2) modulating the information sequence S' to obtain modulation information X; and (3) performing block transformation on the modulation information X according to key information to output ciphertext signals Y. The invention also provides a packet physical layer encryption method of a block chaining mode, which adds a logical operation vector based on the matrix physical layer encryption method based on matrix transformation, so that each ciphertext block depends on all plaintext blocks in front. The method has larger ciphertext space and key space, increases the difficulty of deciphering, can resist known plaintext attacks and selective plaintext attacks, can protect training symbols, and has no loss on bit error rate performance but high constellation map chaos, and well protects constellation information.
Owner:NAT UNIV OF DEFENSE TECH
Anti-peeping display system based on rotary polaroids
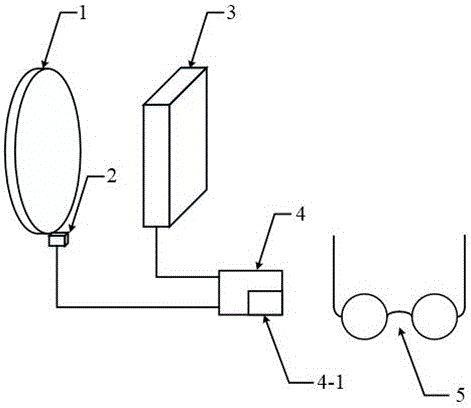
ActiveCN105911740AMinor changesReduce the difficulty of production technologyNon-linear opticsLiquid-crystal displayEngineering
The invention provides an anti-peeping display system based on rotary polaroids, relates to the technical field of liquid crystal display, and aims at solving the problems that in the anti-peeping display technology, the existing anti-peeping display technology is poor in anti-peeping performance and safety, large in technological difficulty and high in production cost. The system comprises the first polaroid, a first motor, a liquid crystal module, a first control module and polaroid glasses. The liquid crystal module comprises a TFT array plate, a liquid crystal box and a color filtering plate. A signal sending device is included in the first control module. The polaroid glasses comprise the second polaroid, the third polaroid, a first transmission rod, a second transmission rod, a second motor, a second control module and a polaroid manual adjusting knob. A signal receiving device is included in the second control module. The decoding difficulty of display content for a peeper is increased through the changes of the rotating speeds of the polaroids.
Owner:HARBIN UNIV OF SCI & TECH
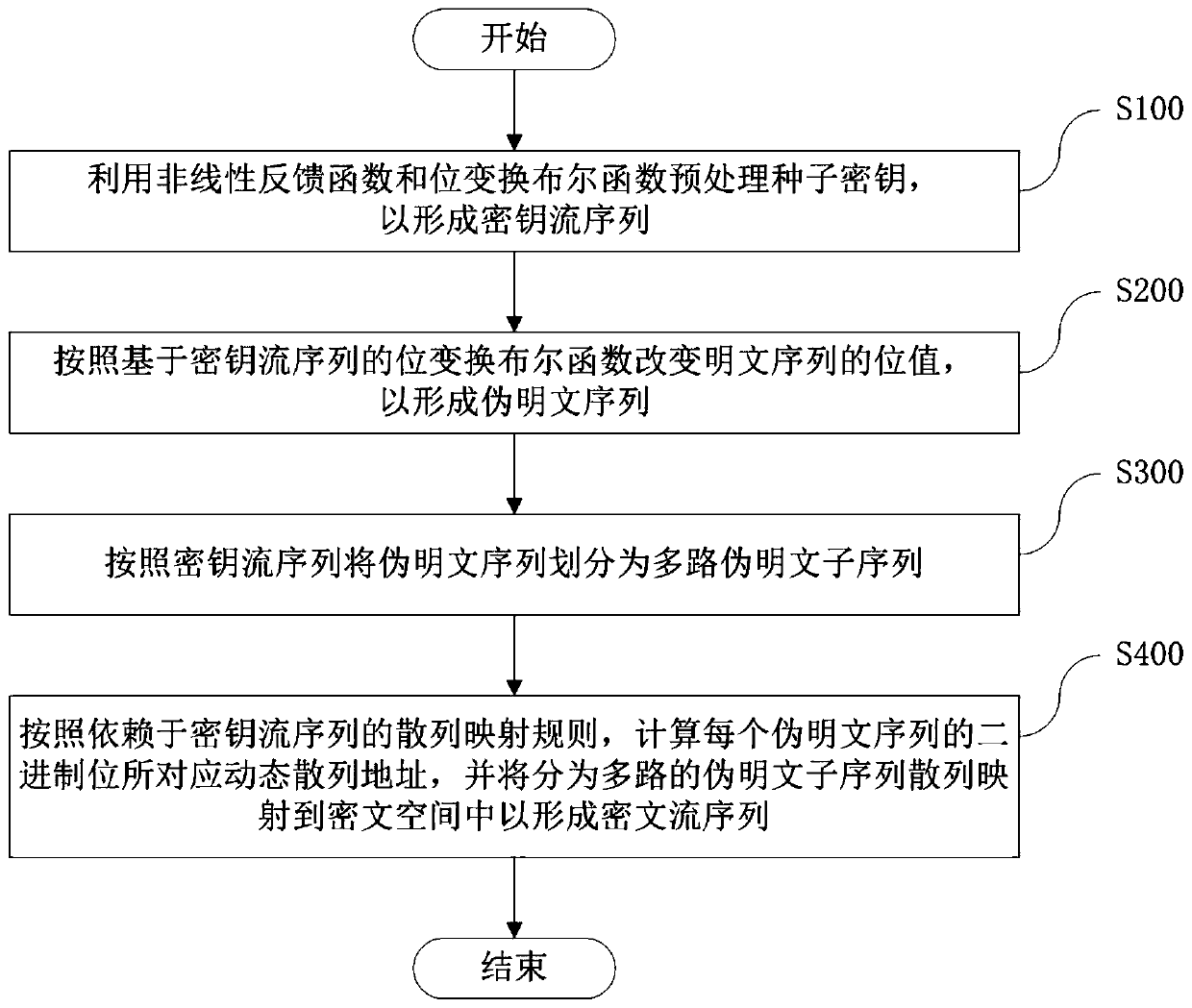
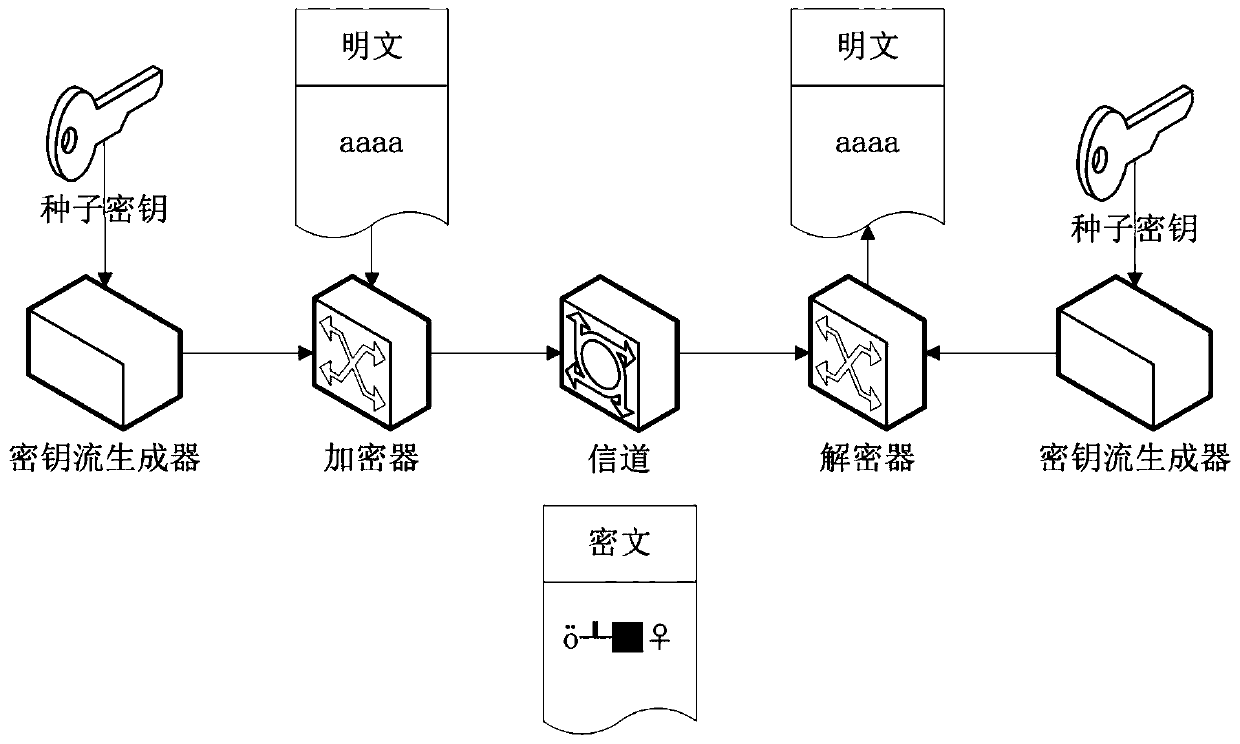
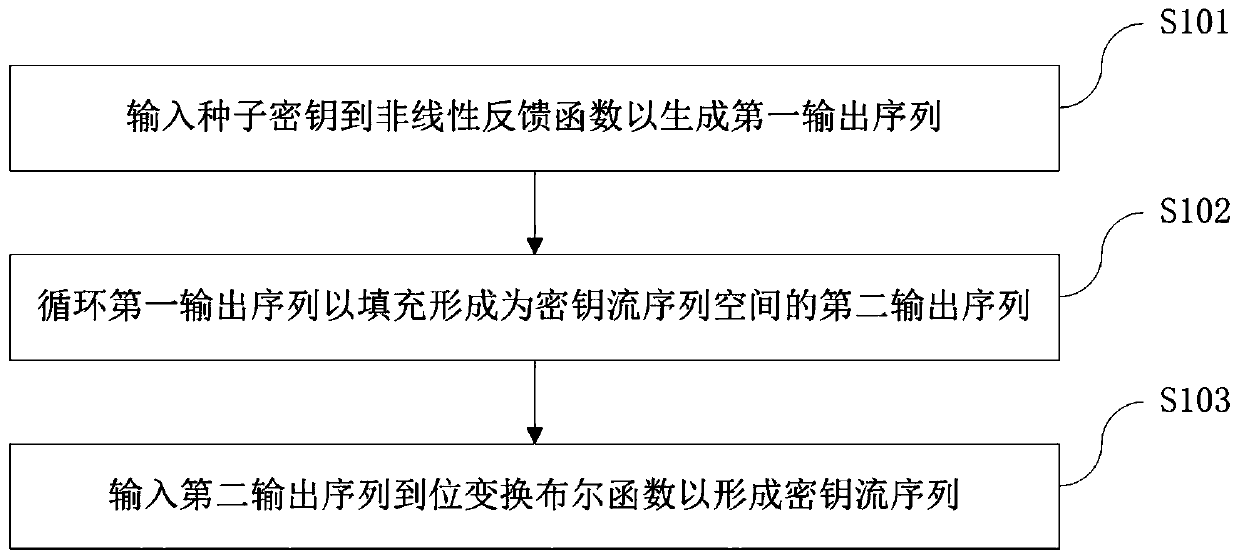
Encryption and decryption method and device based on zipper type dynamic hash and NLFSR
ActiveCN109981249AImprove uniformityLong cycleEncryption apparatus with shift registers/memoriesPlaintextShift register
An encryption and decryption method based on zipper type dynamic hashes and NLFSRs comprises the following steps that a nonlinear feedback function and a bit transformation Boolean function are used for preprocessing a seed secret key to form a secret key stream sequence; changing the bit value of the plaintext sequence according to the bit transformation Boolean function based on the key stream sequence to form a pseudo plaintext sequence; dividing the pseudo-plaintext sequence into a plurality of paths of pseudo-plaintext subsequences according to the key stream sequence; and calculating a dynamic hash address corresponding to the binary bit of each pseudo plaintext sequence according to a hash mapping rule depending on the key stream sequence, and mapping the pseudo plaintext subsequence hashes which are divided into multiple paths into a ciphertext space to form the ciphertext stream sequence. The method has the beneficial effects that the key stream generator not only uses a nonlinear feedback shift register, but also introduces a bit transformation Boolean function, so that the key stream with longer period and better randomness is obtained; and through a plaintext bit transformation rule and a zipper type dynamic hash mapping rule, the decoding difficulty of the ciphertext stream sequence is improved.
Owner:ZHUHAI COLLEGE OF JILIN UNIV +1
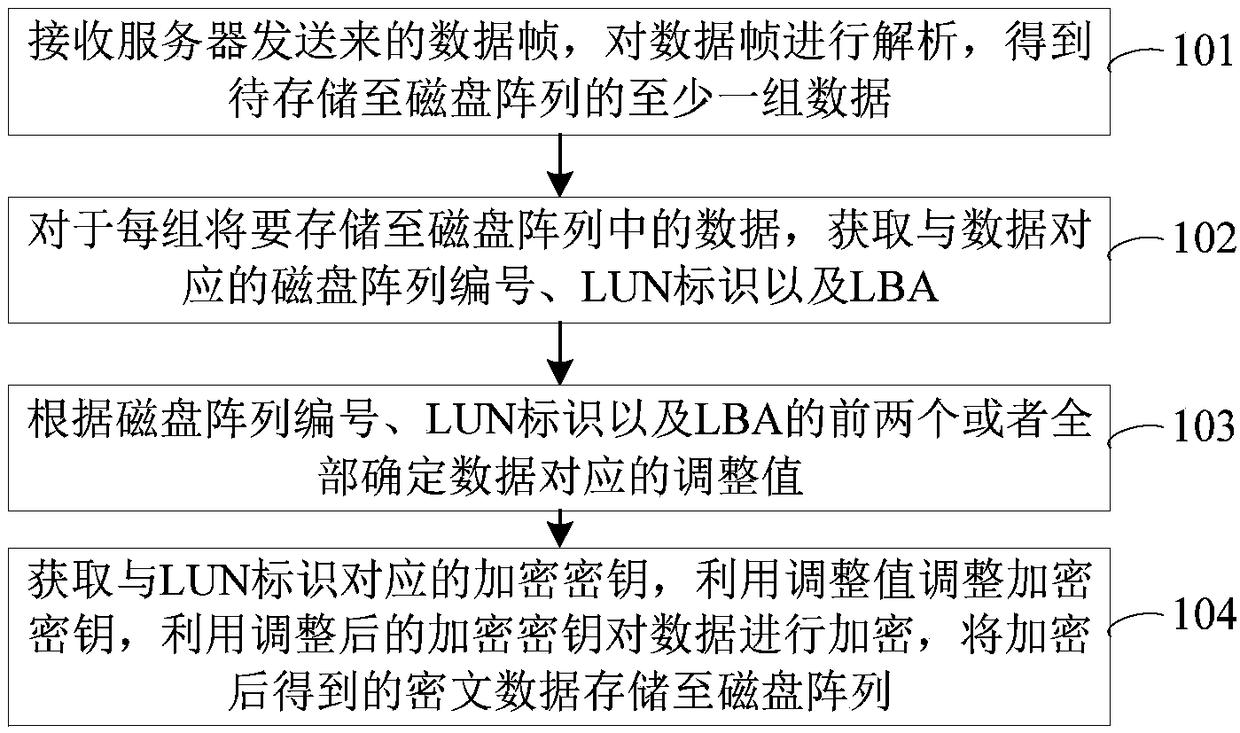
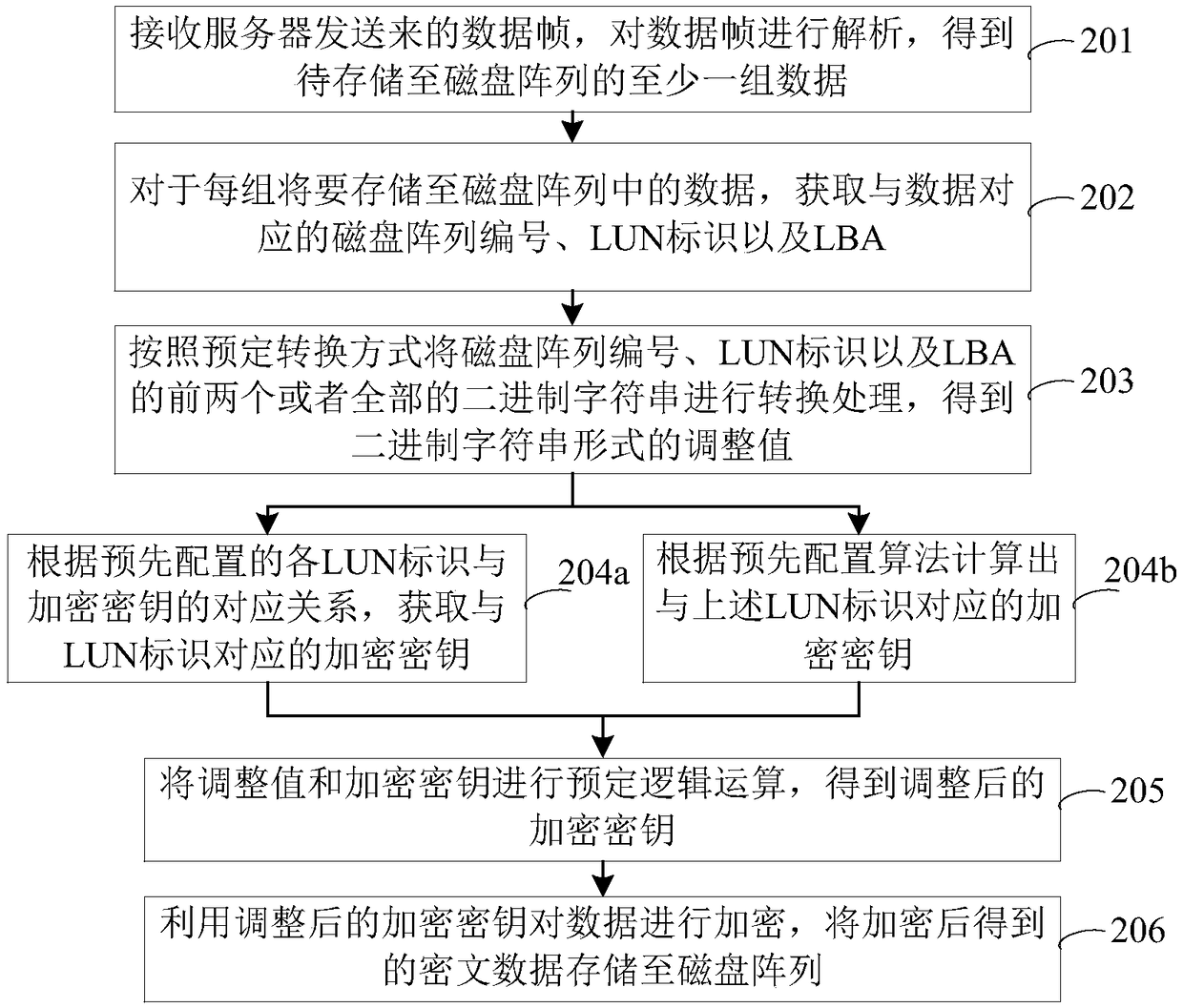
A method and apparatus for encrypting data stored in a disk array
InactiveCN109033849AIncrease the difficulty of decipheringEnsure safetyUnauthorized memory use protectionDigital data protectionDisk arrayCiphertext
A method and apparatus for encrypting data stored in a disk array belong to the field of storage encryption technology. The encryption method comprises the steps of receiving data frames sent from a server, analyzing the data frames, and obtaining at least one group of data to be stored in a disk array; for each set of data to be stored in the disk array, obtaining a disk array number, a LUN identification and an LBA corresponding to the data; determining adjustment values corresponding to data according to disk array numbers, LUN identification and the first two or all of LBA; obtaining theencryption key corresponding to the LUN identifier, adjusting the encryption key by the adjustment value, encrypting the data by the adjusted encryption key, and storing the encrypted ciphertext datain the disk array. The application enables each group of data stored in the LBA to have a unique encryption key, thereby increasing the difficulty of deciphering the ciphertext data and ensuring the security of the ciphertext data in the disk array.
Owner:WUXI ALEADER INTELLIGENT TECH
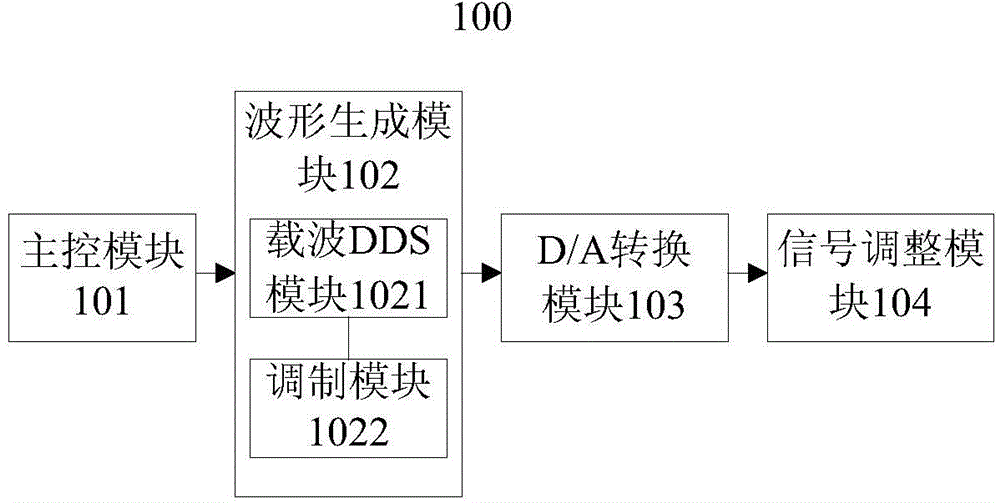
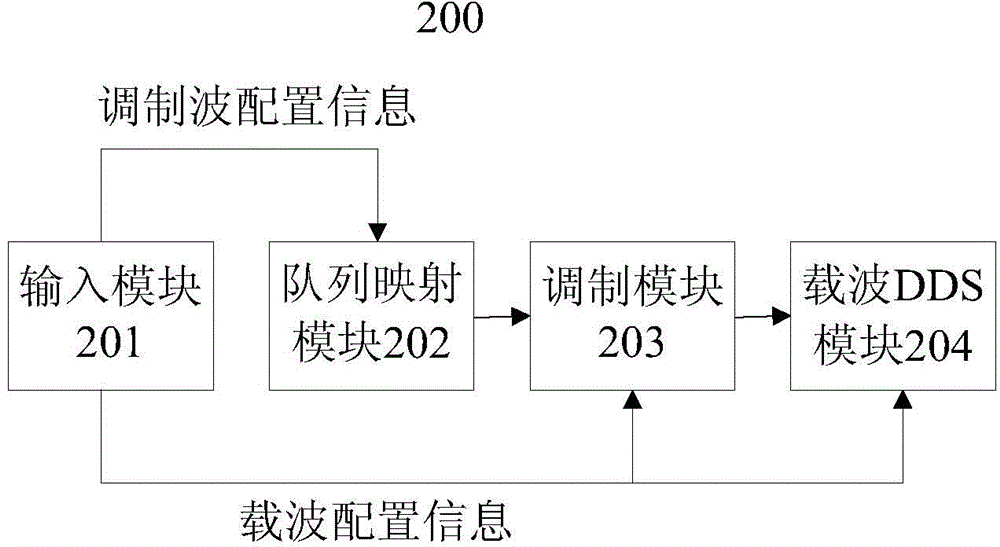
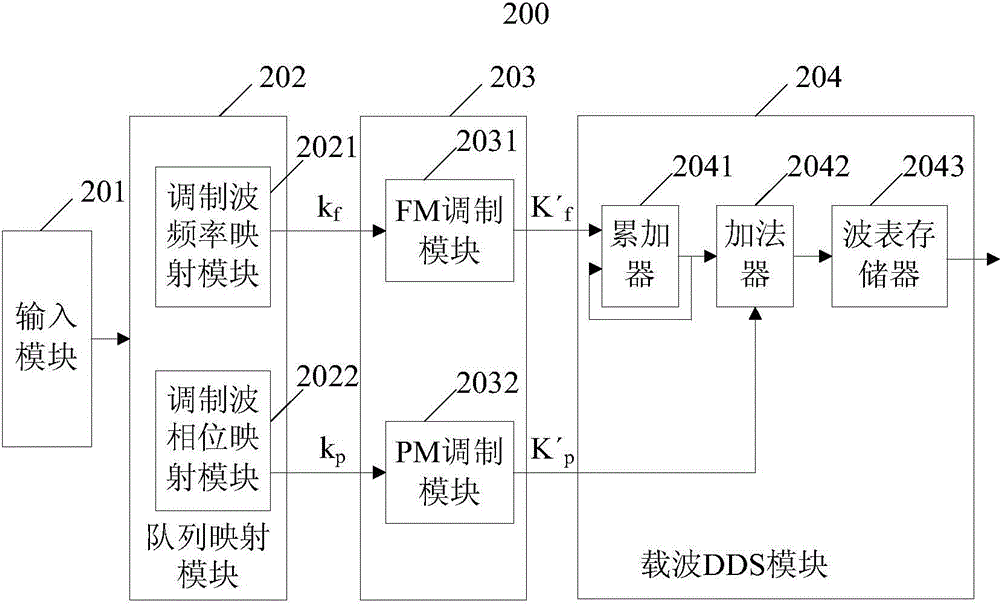
Signal generator capable of flexiblely modulating in segmentable mode
ActiveCN105871339AChange the speed of modulationIncrease the difficulty of decipheringSimultaneous amplitude and angle modulationUser inputCarrier signal
The invention provides a signal generator capable of flexiblely modulating in a segmentable mode. The signal generator comprises an input module used for receiving carrier wave configuration information and modulated wave configuration information input by a user; wherein the modulated wave configuration information comprises modulated wave configuration queues and corresponding time intervals; a queue mapping module used for transiting the modulated wave configuration queues to modulated wave control word queues; a modulation module used for storing the modulated wave control word queues, and taking each queue element in the modulated wave control word queues according to the time intervals, and generating multiple groups of regulate control parameters according to the carrier wave configuration information and each queue element; and a carrier wave DDS module used for generating multi-segment modulating signals according to the multiple groups of regulate control parameters and the carrier wave configuration information. The signal generator can realize the segmented regulation function of variable frequency, phase or amplitude of modulated signals, complexity of the generated modulated signal is high, and the modulated signal is difficultly intercepted and decoded, and is suitable for practical application occasions such as modulation-demodulation experiments.
Owner:SUZHOU RIGOL PRECISION ELECTRIC TECH
Identity verifying method, device and system
InactiveCN106686009ASimplify the verification processIncrease the difficulty of decipheringDigital data authenticationTransmissionTuring testThe Internet
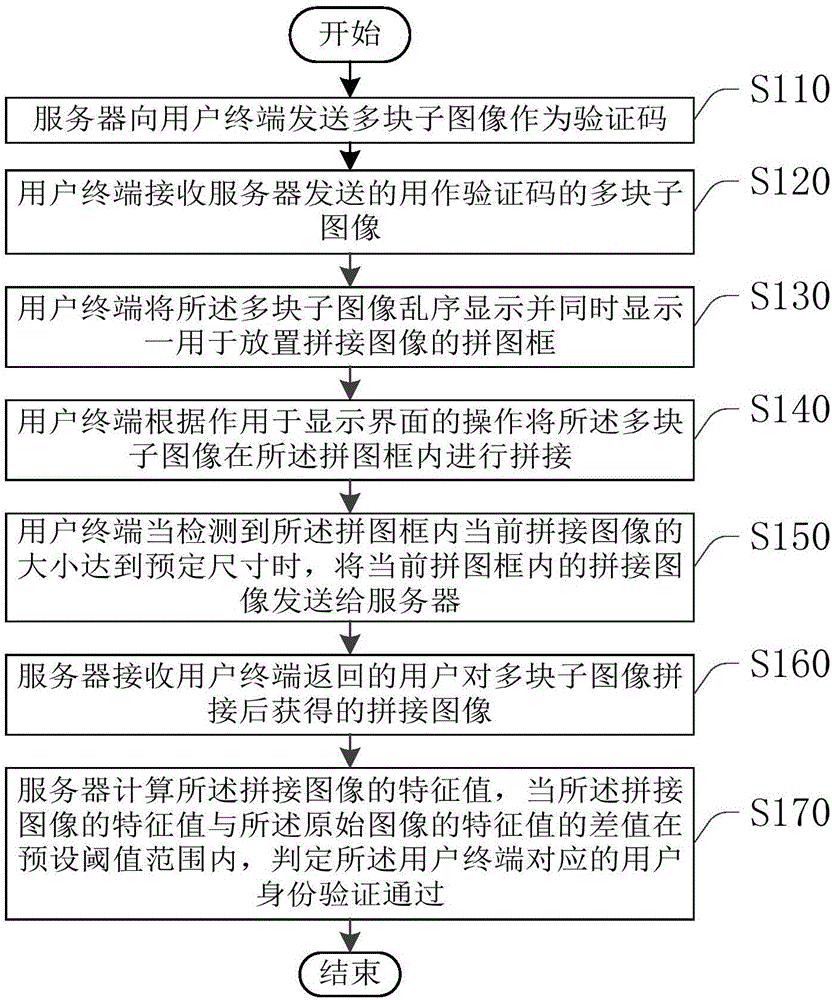
The invention provides an identity verifying method, device and system, which are applied to the Internet field. The method includes the following steps: receiving multiple sub-images that are sent from a server and serve as CAPTCHAs (Completely Automated Public Turing Test to Tell Computers and Humans Apart), the multiple sub-images obtained through cutting of an original image; conducting disorder displaying of the multiple sub-images and simultaneously displaying a splice frame for holding splice images, so that a user splices the multiple sub-images together to form a spliced image in the splice frame; splicing the multiple sub-images together in the splice frame according to operations acting on a display interface; and if detecting that the size of the current spliced image in the splice frame reaches preset dimensions, sending the current spliced image in the splice frame to the server so that the server verifies the spliced image. According to the scheme, the sub-images obtained from cutting of the entire original image are sent to the user to be spliced together. The whole verifying process is easy for the user who is a human, but decoding is more difficult for a machine.
Owner:苏州仙度网络科技有限公司
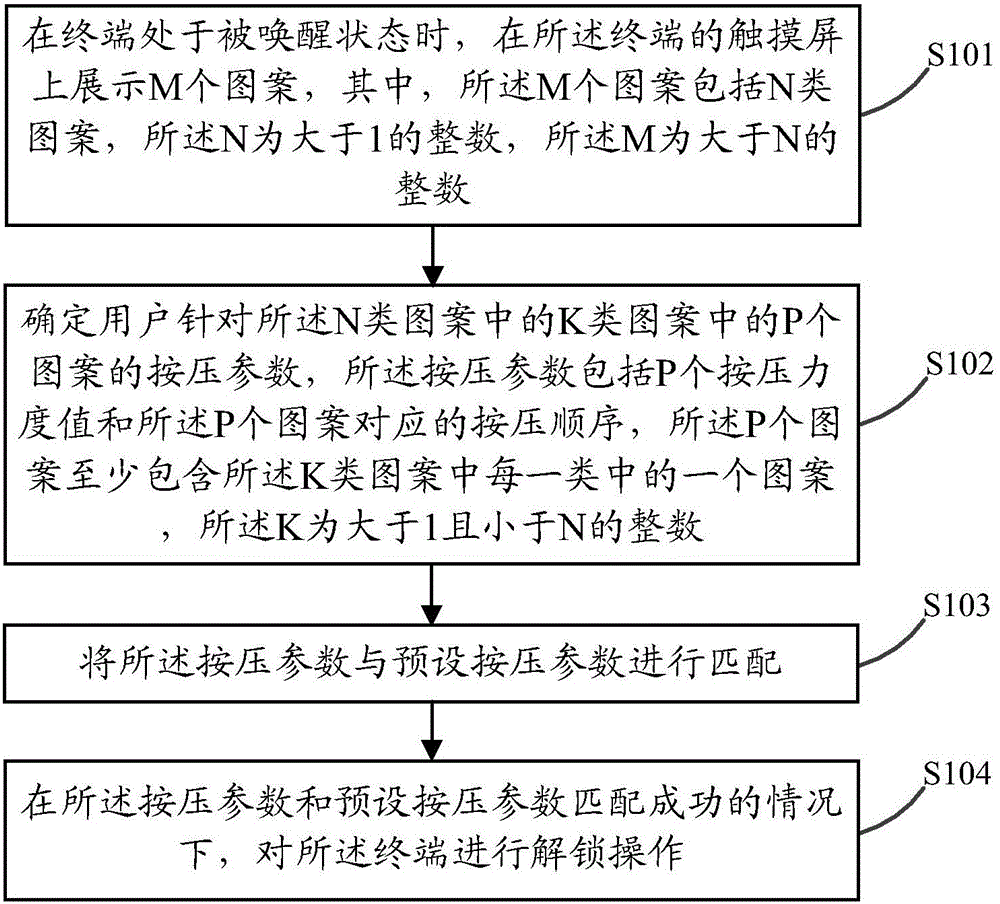
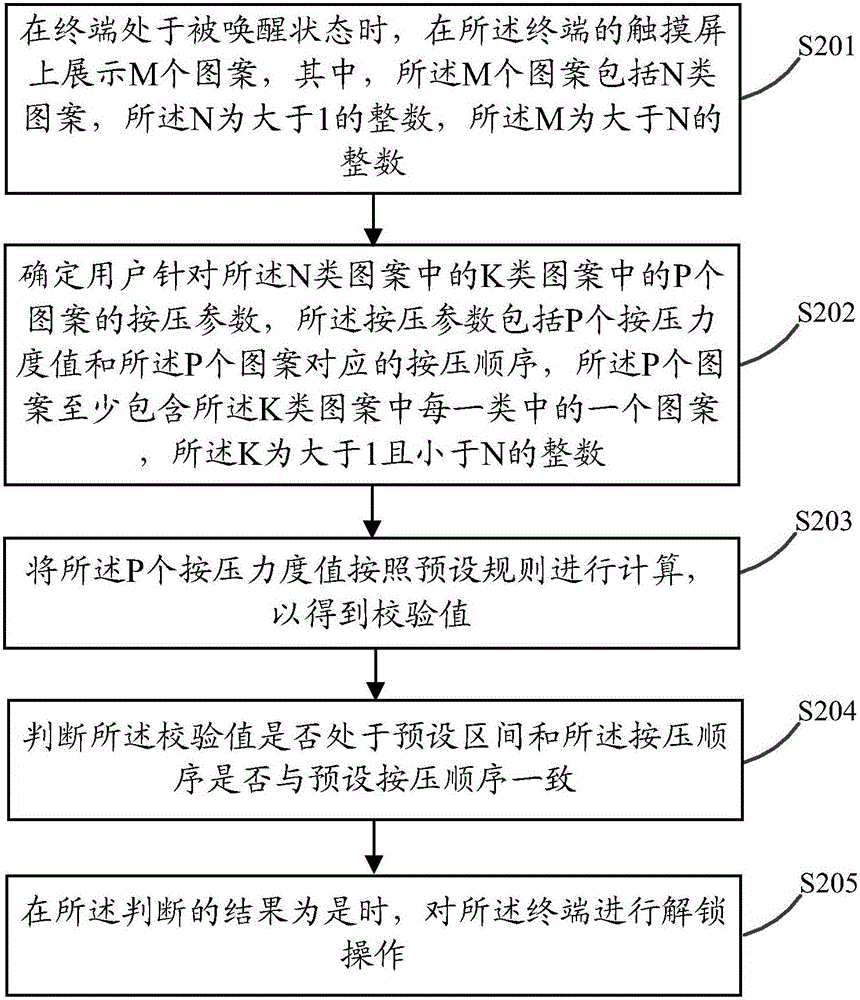
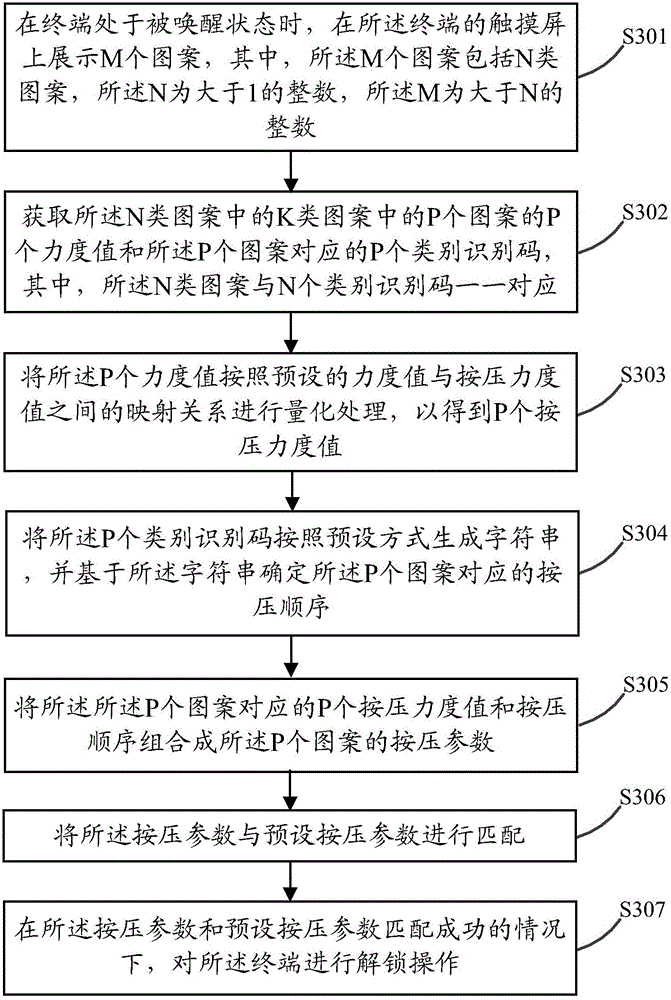
Pattern unlocking method and terminal
ActiveCN105095735AImprove securityIncrease the difficulty of decipheringDigital data authenticationInput/output processes for data processingTouchscreenComputer science
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Color image chaotic encryption method
InactiveCN108133447AHigh strengthStrong resistance to attackImage data processing detailsPattern recognitionColor image
The invention provides a color image chaotic encryption method and belongs to the technical field of encryption. The method is realized through the following steps: optimizing a Lorenz chaotic sequence; generating three scrambling matrixes by utilizing the optimized chaotic sequences x', y' and z', and carrying out scrambling on three components of an RGB color image; carrying out block encryption; outputting a scrambled color image, and synthesizing the scrambled three-primary-color images to obtain an encrypted image; and decrypting the image. The algorithm carries out scrambling on three primary color components of the color image through Px, Py and Pz in a spatial domain range, thereby enhancing strength of algorithm diffusion, and further increasing decoding difficulty; the three primary color components are scrambled respectively, so that the encrypted image is allowed to have color change in the visual sense, and the image is more difficult to read; meanwhile, scrambling degreeof the adopted algorithm is similar to the scrambling degree of magic square transformation, so that the method has good scrambling performance; and the method has higher anti-attack ability.
Owner:QINZHOU JINGTONG TECH CO LTD
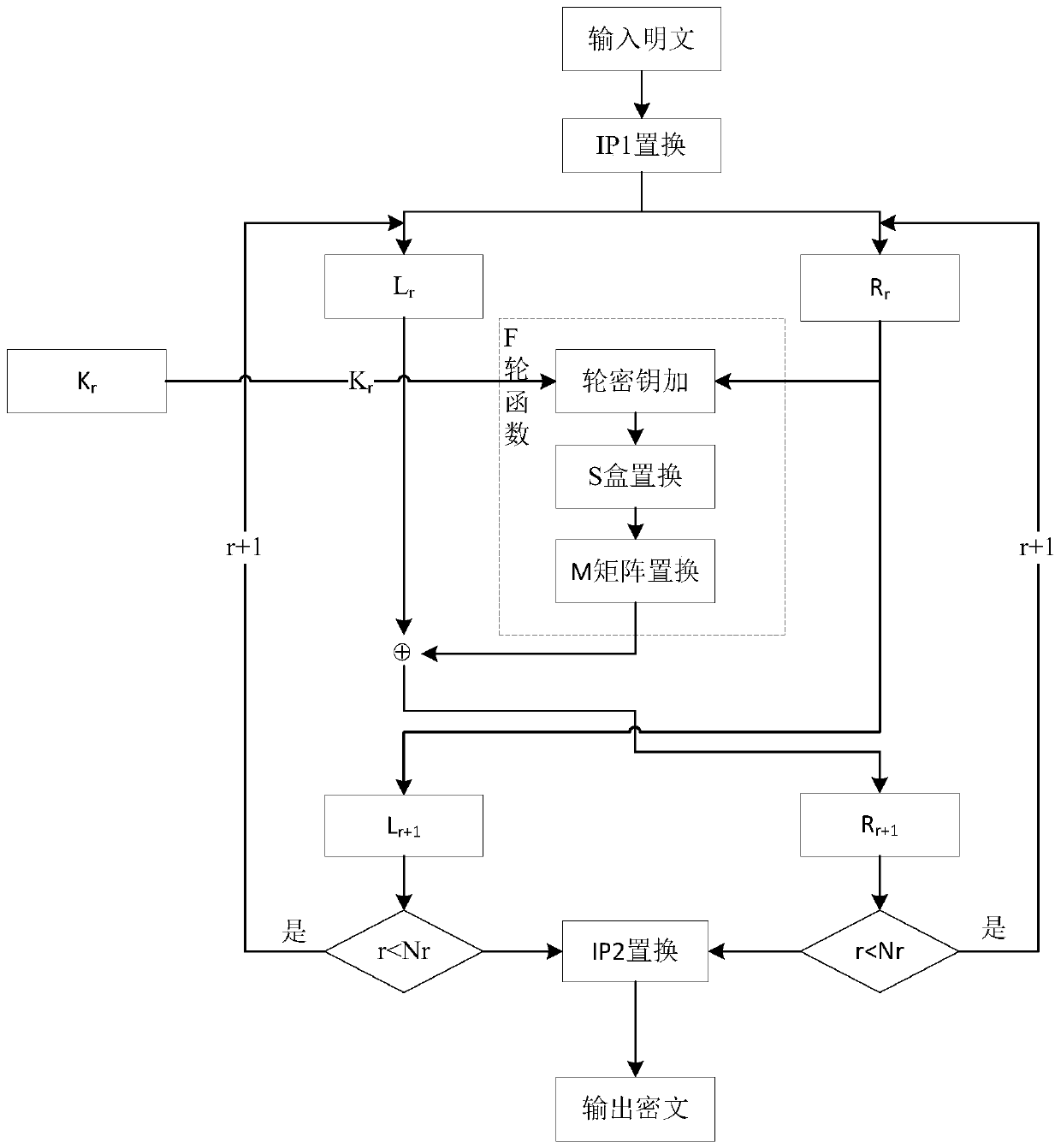
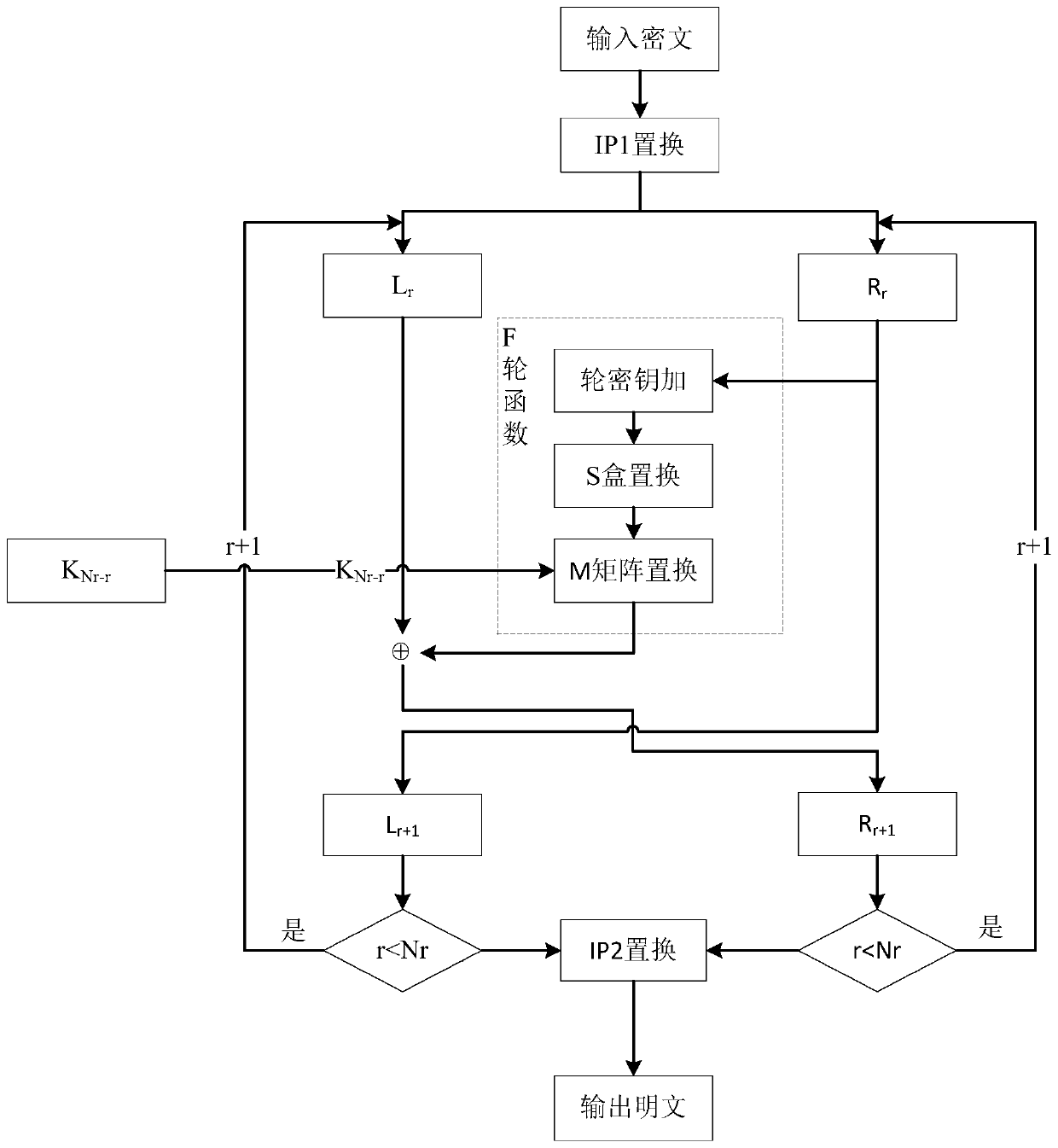
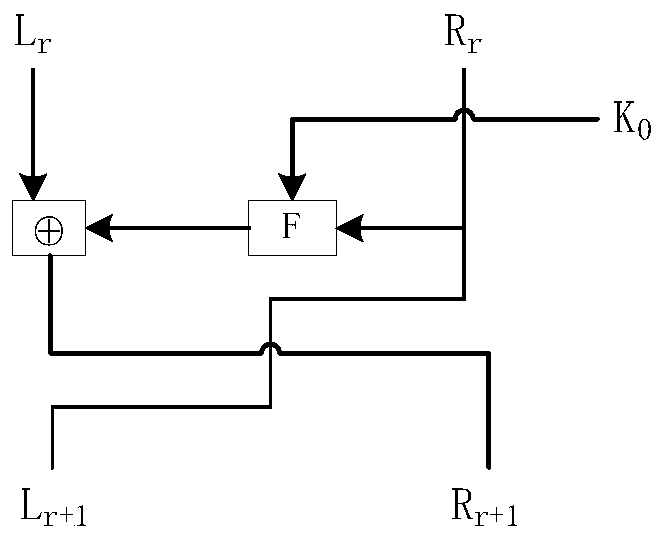
Lightweight cryptographic algorithm SCENERY implementation method and device and storage medium
ActiveCN110784307AImprove encryption efficiencyImprove securityEncryption apparatus with shift registers/memoriesPlaintextS-box
The invention discloses a lightweight cryptographic algorithm SCENERY implementation method, a lightweight cryptographic algorithm SCENERY implementation device and a storage medium. The method comprises the steps that a plaintext to be encrypted is acquired, IP1 initial replacement, a round function, key expansion and IP2 replacement are carried out in sequence, the round function comprises sequentially carrying out round key addition operation, S box replacement and M matrix replacement on data, and the key expansion comprises sequentially carrying out S box replacement, cyclic left shift, round constant addition operation and DP dynamic replacement on a key. An F function of an SPN structure is adopted as a round function, and a binary matrix M is constructed with the purpose of achieving high dependence when an F function linear layer is designed; a round constant and a key expansion intermediate result are selected as control signals for key expansion; DP dynamic replacement is carried out on a current round key expansion intermediate result to obtain a round key, which is a new key expansion mode, the relevance of single key iteration to front wheel input is reduced, the decoding difficulty is increased, the security is improved, and differential and linear attacks and algebraic attacks can be particularly and effectively resisted.
Owner:HENGYANG NORMAL UNIV
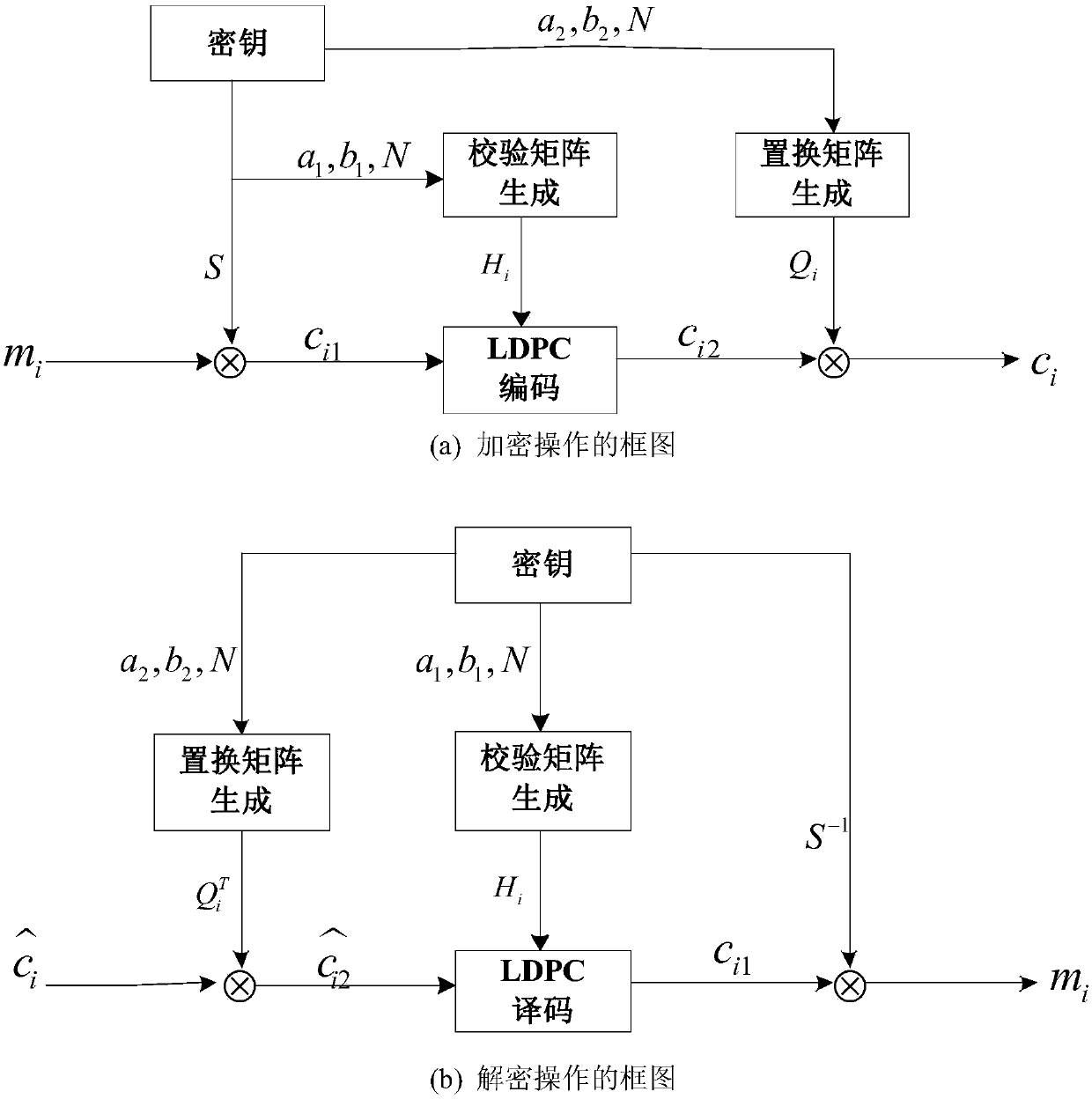
Safe and reliable transmission method based on LDPC
ActiveCN107786327AReduce overheadEnsure safetyKey distribution for secure communicationError preventionComputer hardwareReliable transmission
The invention belongs to the field of channel coding and encryption and particularly relates to coding and encryption integrated design based on a LDPC. For the defect that an M symmetric cryptosystemis high in key cost and has security vulnerabilities, the invention provides a safe and reliable transmission method based on the LDPC. According to the method, an encryption error correction matrixis generated under the control of a big random number seed N, the same permutation matrix and check matrix which are generated by two parties synchronously based on linear congruence according to thesame seed are received, and each time when communication is carried out, encryption coding matrixes are changed synchronously, so one-time pad is realized, the key cost is reduced, and moreover the safety of a system can be ensured.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA +1
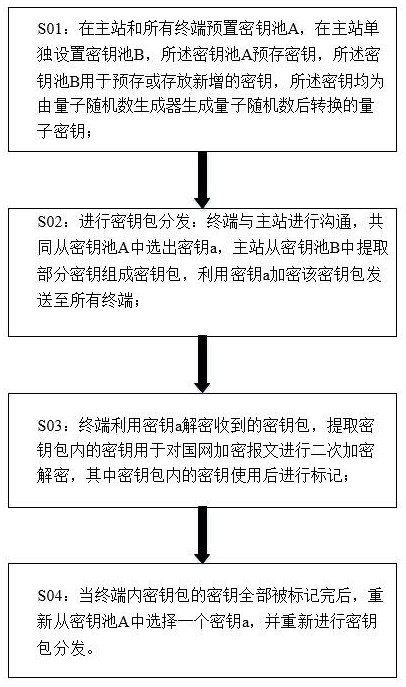
Power distribution automation information encryption method based on quantum reinforcement
ActiveCN113037486AMature and reliable technologyThe transmission process is safe and reliableKey distribution for secure communicationMaster stationEngineering
The invention discloses a distribution automation information encryption method based on quantum reinforcement, and the method comprises the steps: presetting a key pool A in a master station and all terminals, independently setting a key pool B in the master station, pre-storing a key in the key pool A, pre-storing or storing a newly added key in the key pool B, and storing the newly added key in the key pool B, wherein the keys are quantum keys converted after quantum random numbers are generated by a quantum random number generator; distributing key packets: the terminals communicate with the master station, the terminals and the master station jointly select a key a from the key pool A, the master station extracts part of keys from the key pool B to form a key packet, and the key packet is encrypted by using the key a and sent to all the terminals; the terminal decrypting the received key packet by using the key a, extracting the key in the key packet for performing secondary encryption and decryption on the state grid encrypted message, and marking the key in the key packet after being used; and after all the keys of the key packet in the terminal are marked, a key a being selected from the key pool A again, and key packet distribution being performed again.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER CO LTD HANGZHOU POWER SUPPLY CO
Chaotic image encryption method based on area-preserving Baker mapping
InactiveCN106127669AGood encryptionIncreased sensitivityImage analysisImage data processing detailsMomentumChaotic systems
The invention relates to an image encryption method, and particularly relates to a chaotic image encryption method based on area-preserving Baker mapping. The method has a simple process, the space-time complexity can be enhanced, the computer precision restriction problem can be solved, and the encryption algorithm complexity can be increased. Meanwhile, as the chaotic system of the invention adopts a quantum chaotic system which is more complex that a common chaotic system, in the quantum chaotic system, the addition of disturbing momentum enables the chaotic system to be better in aperiodicity and stronger in sequence randomness, and problems of a fixed point and a stable window existing in the common chaotic system can be improved and solved.
Owner:GUANGDONG UNIV OF TECH
Security control method for data exchange service and transmission process
InactiveCN105471849AProtection securityIncrease the difficulty of decipheringEncryption apparatus with shift registers/memoriesDigital dataPlaintext
The invention provides a security control method for a data exchange service and transmission process. Data transmission between the computer networks running a protected service system is transferred in the form of cipher text, so that there is no clear data appearing in the communication line for the data transmitted between the computer networks in the whole process. In addition, due to the scrambling mode of random seed confusion and the intervention of data encryption, the data sent to the computer networks from the protected service system each time and the return data received from the computer networks each time are constantly changing data for the same data. Therefore, the deciphering difficulty is increased for deciphers, and the safety of digital data of cultural relics under national copyright in the transmission process is protected.
Owner:SHANGHAI ADVANCED RES INST CHINESE ACADEMY OF SCI
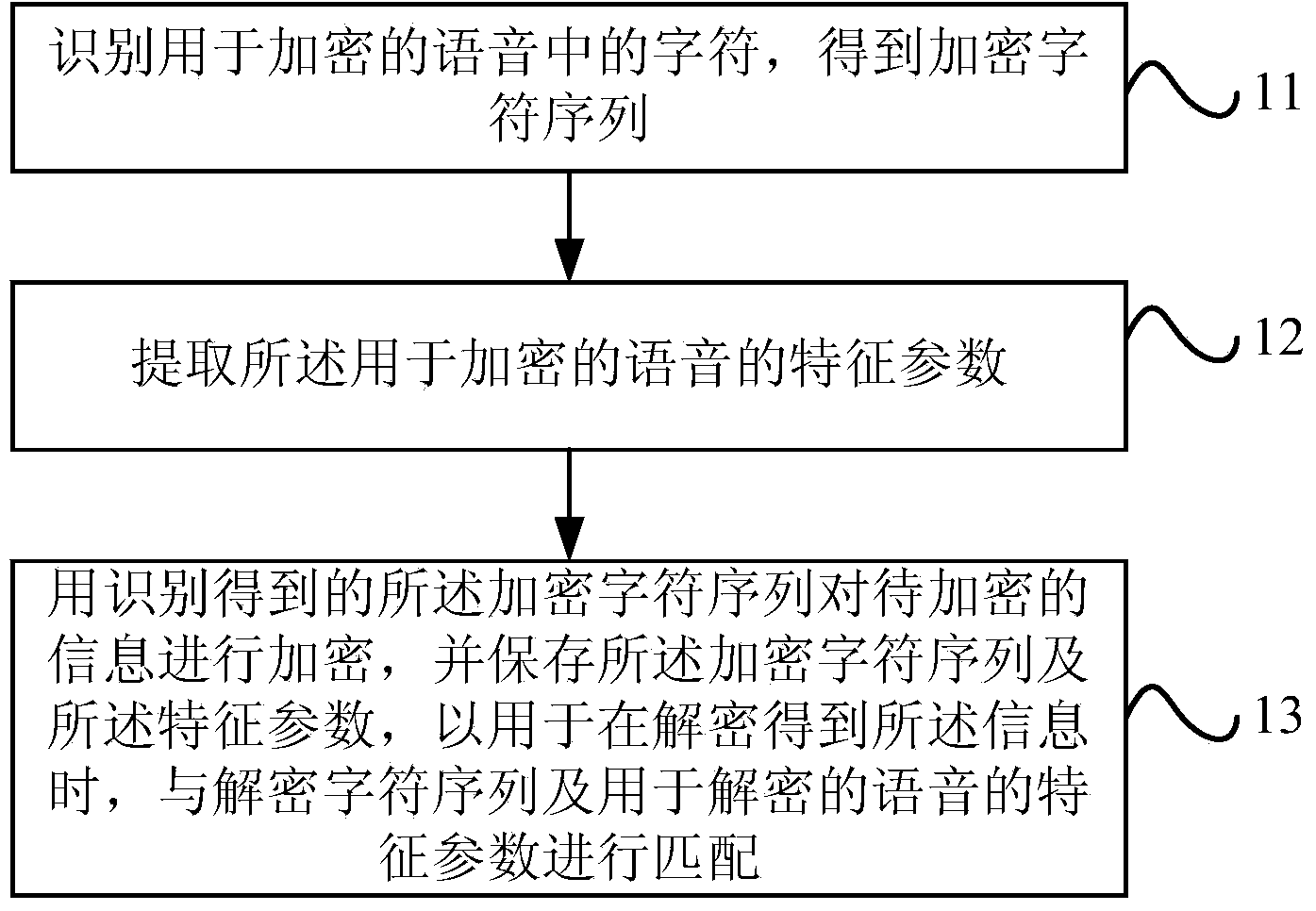
Voice encryption method and device and voice decryption method and device
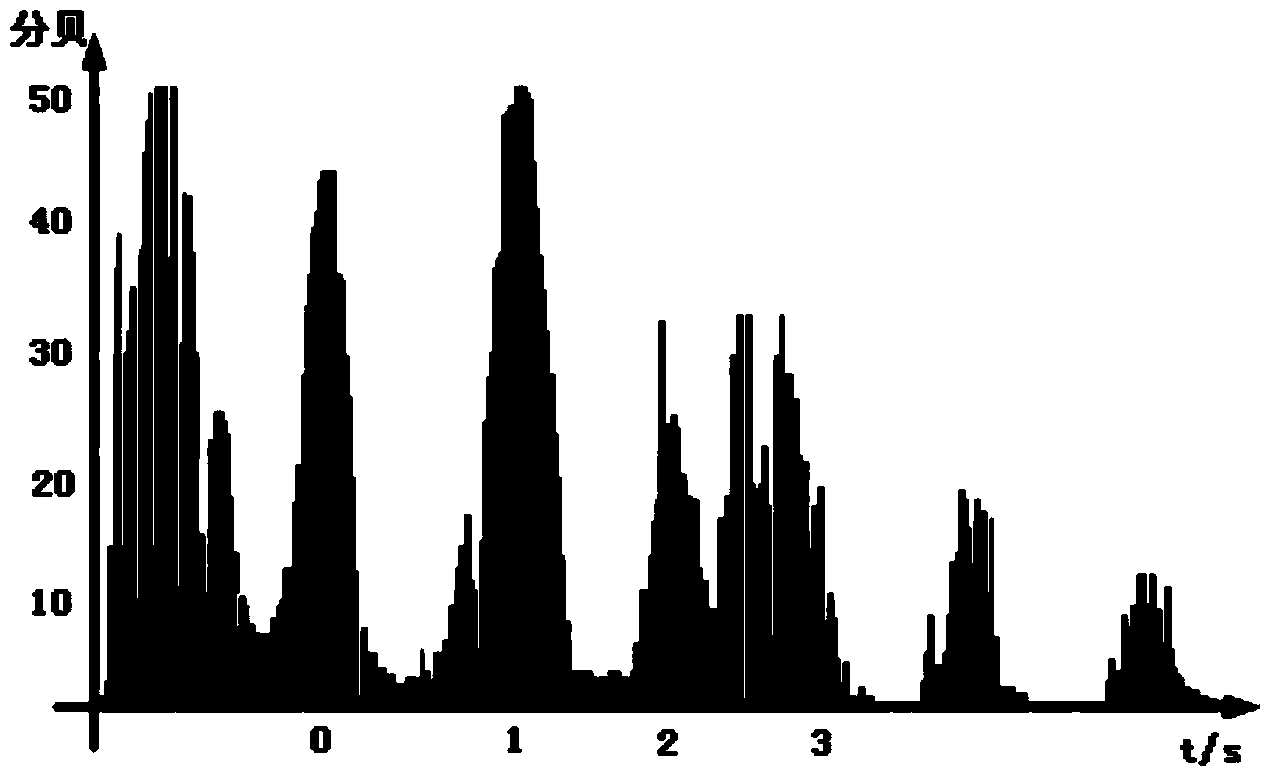
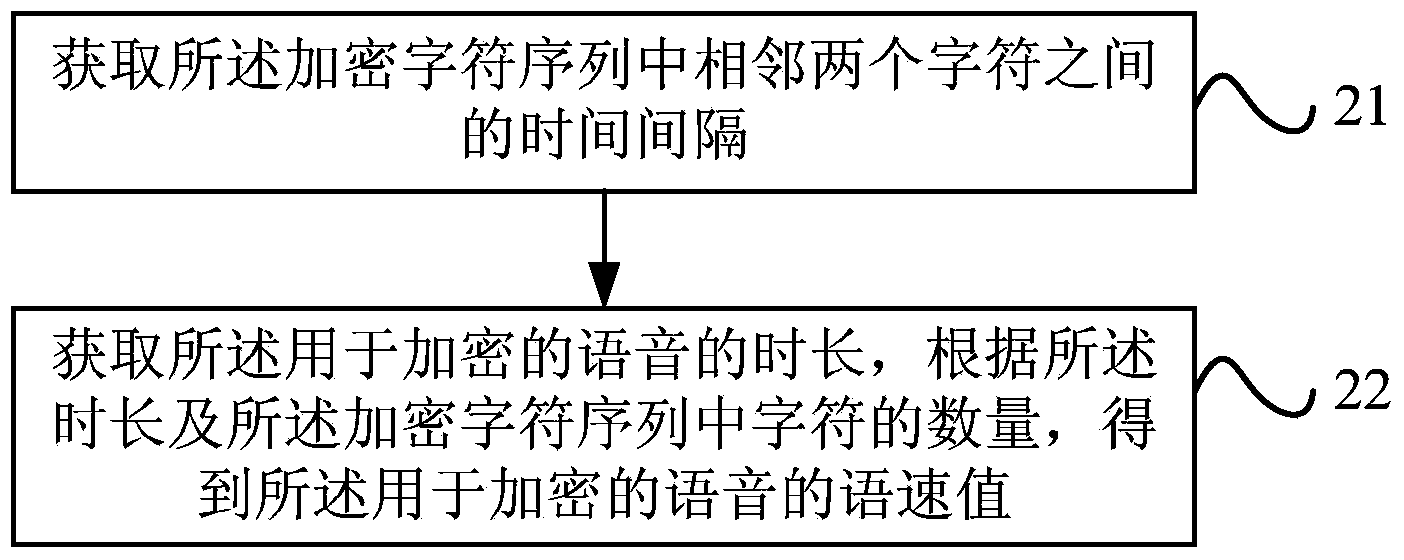
ActiveCN104361886AImprove securityIncrease the difficulty of decipheringEncryption apparatus with shift registers/memoriesSpeech recognitionComputer hardwareSpeech sound
An embodiment of the invention provides a voice encryption method and device and a voice decryption method and device. The voice encryption method includes recognizing characters of voice for encryption to obtain an encrypted character sequence, extracting the characteristic parameters for the voice for encryption, encrypting the information to be encrypted by the recognized encryption characters and storing the encrypted character sequence and the characteristic parameters so as to be matched with a decryption character sequence and the characteristic parameters of the voice for decryption when the received information is decrypted. Accordingly, decipher difficulty is added, and safety of the encrypted information is improved.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Trusted data transmission method for multiple unmanned platforms
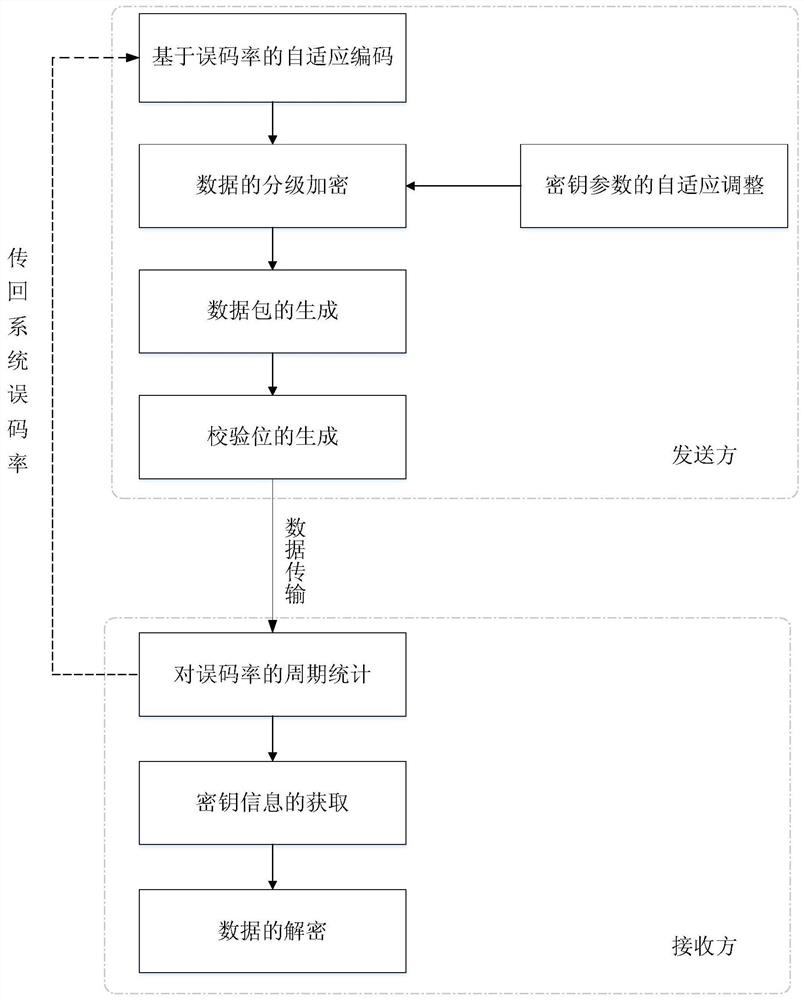
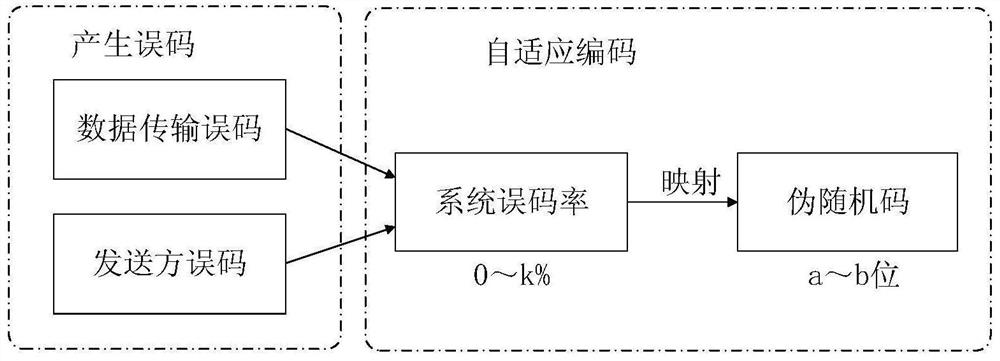
PendingCN111641503AImprove transmission efficiencyImprove transmission reliabilityKey distribution for secure communicationMultiple keys/algorithms usageData packAdaptive encoding
The invention discloses a trusted data transmission method for multiple unmanned platforms, and belongs to the technical field of data transmission. The method comprises the steps of self-adaptive encoding based on the bit error rate, hierarchical encryption of data, self-adaptive adjustment of key parameters, generation of a data packet, generation of check bits, periodic statistics of the bit error rate, acquisition of key information, decryption of the data and the like. Compared with a traditional unmanned platform data transmission method, the method has the advantages that the safety performance of unmanned platform data transmission can be remarkably improved, the adaptability to a complex electromagnetic environment is higher, and the method has great theoretical research value andengineering practice significance.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP
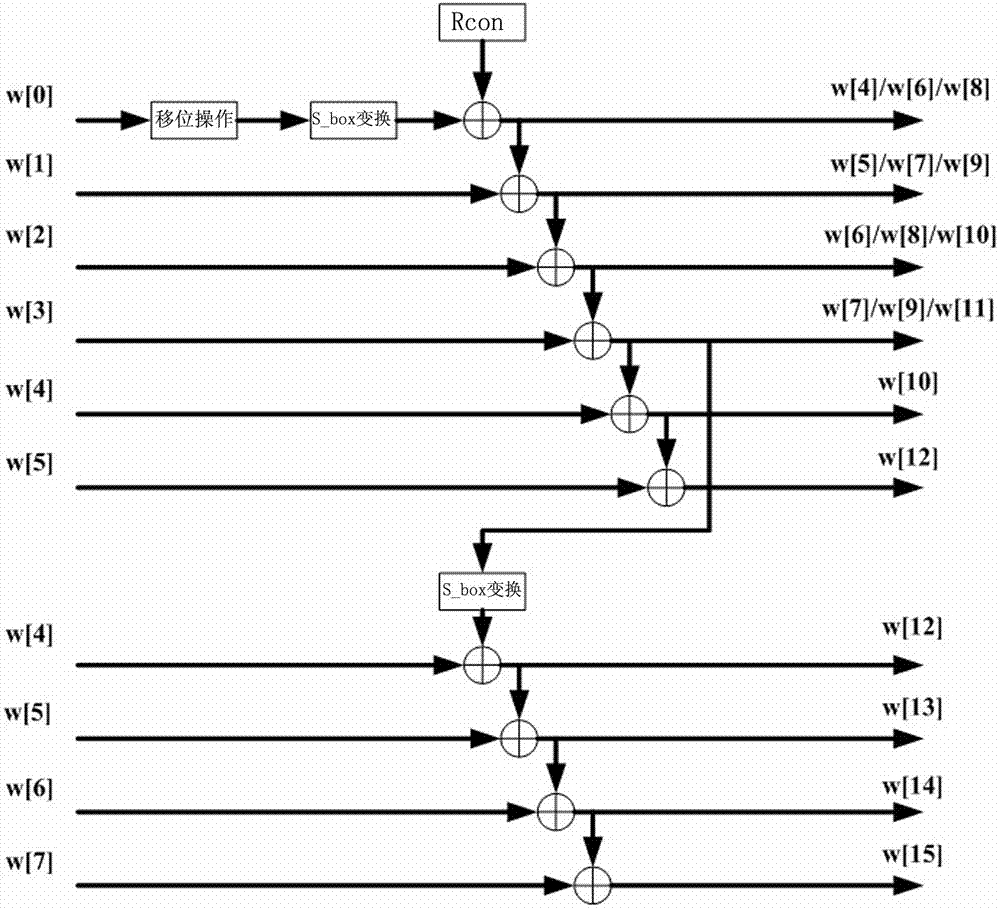
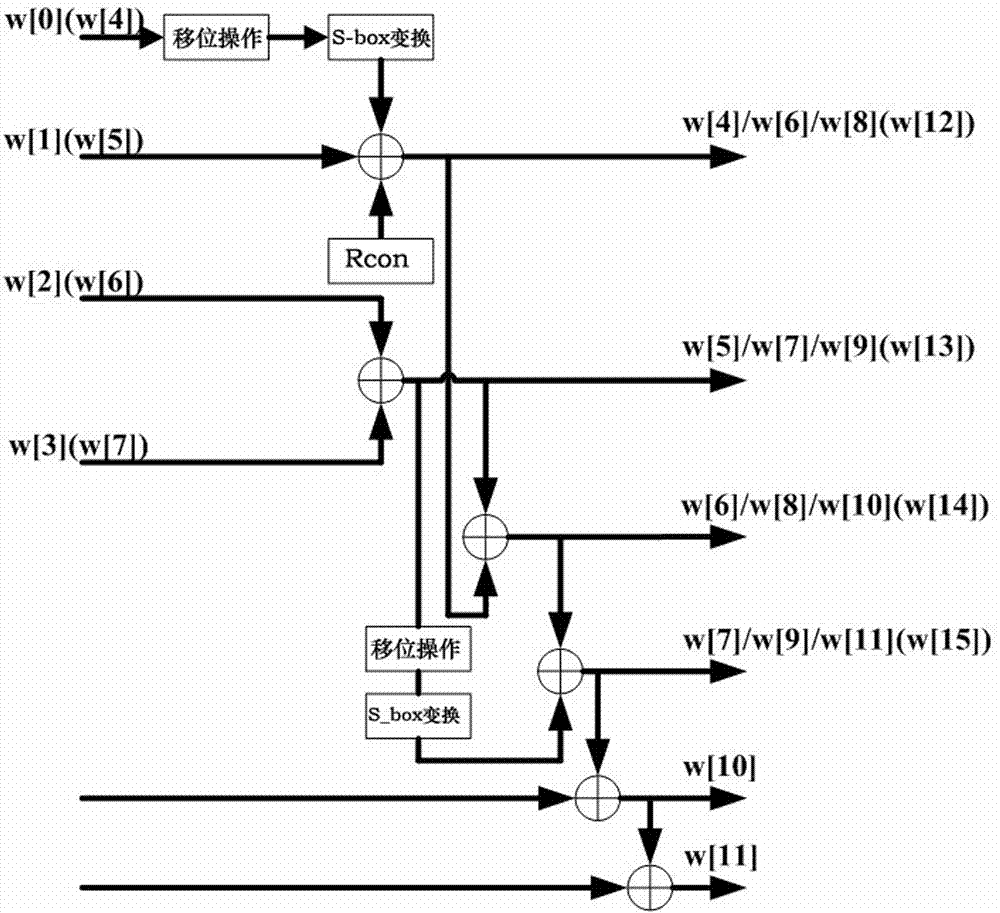
AES (Advanced Encryption Standard) key expansion method
InactiveCN103051443AReduce relevanceOptimize timingEncryption apparatus with shift registers/memoriesTheoretical computer scienceAdvanced Encryption Standard
The invention discloses an AES (Advanced Encryption Standard) key expansion method, which is realized through computation among keys and then through certain iteration instead of simple iteration based on the previous key. Therefore, the correlation between single key iteration and previous input is reduced and the deciphering difficulty is increased; and since the correlation between the previous key and the latter key is reduced, the time sequence of the entire circuit is effectively improved.
Owner:SHANDONG SINOCHIP SEMICON
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com