Patents
Literature
4026 results about "Key generation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Key generation is the process of generating keys in cryptography. A key is used to encrypt and decrypt whatever data is being encrypted/decrypted. A device or program used to generate keys is called a key generator or keygen.
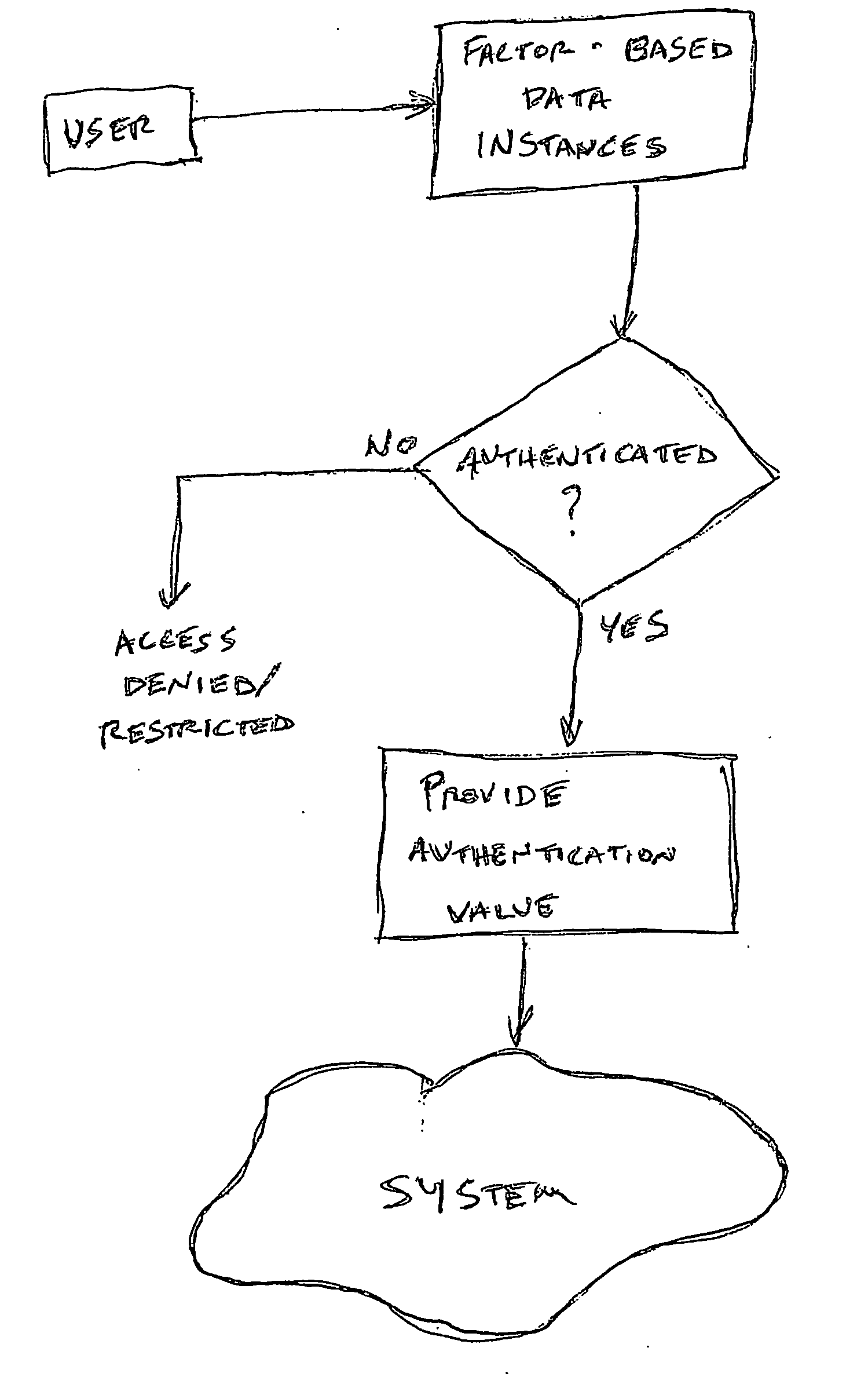
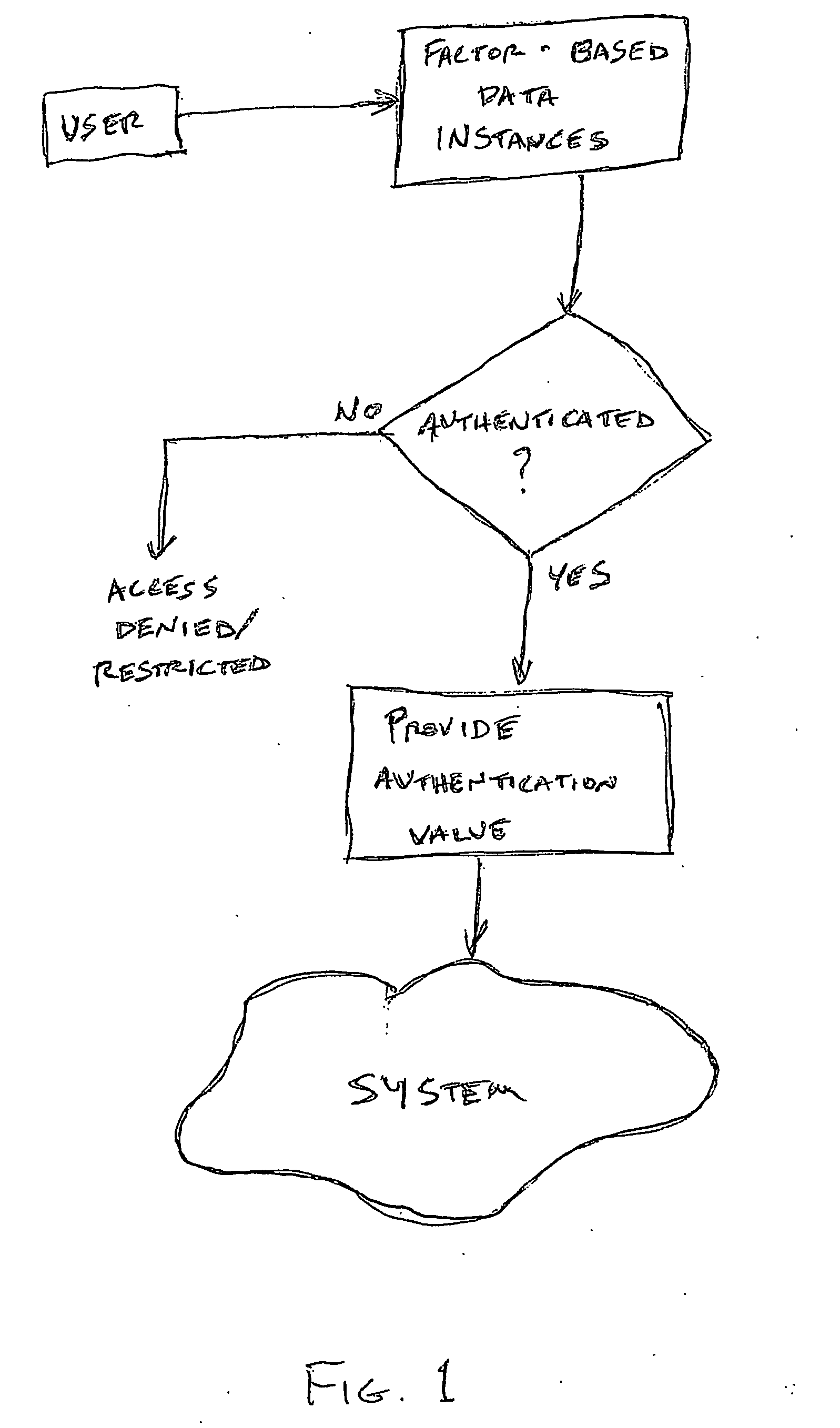
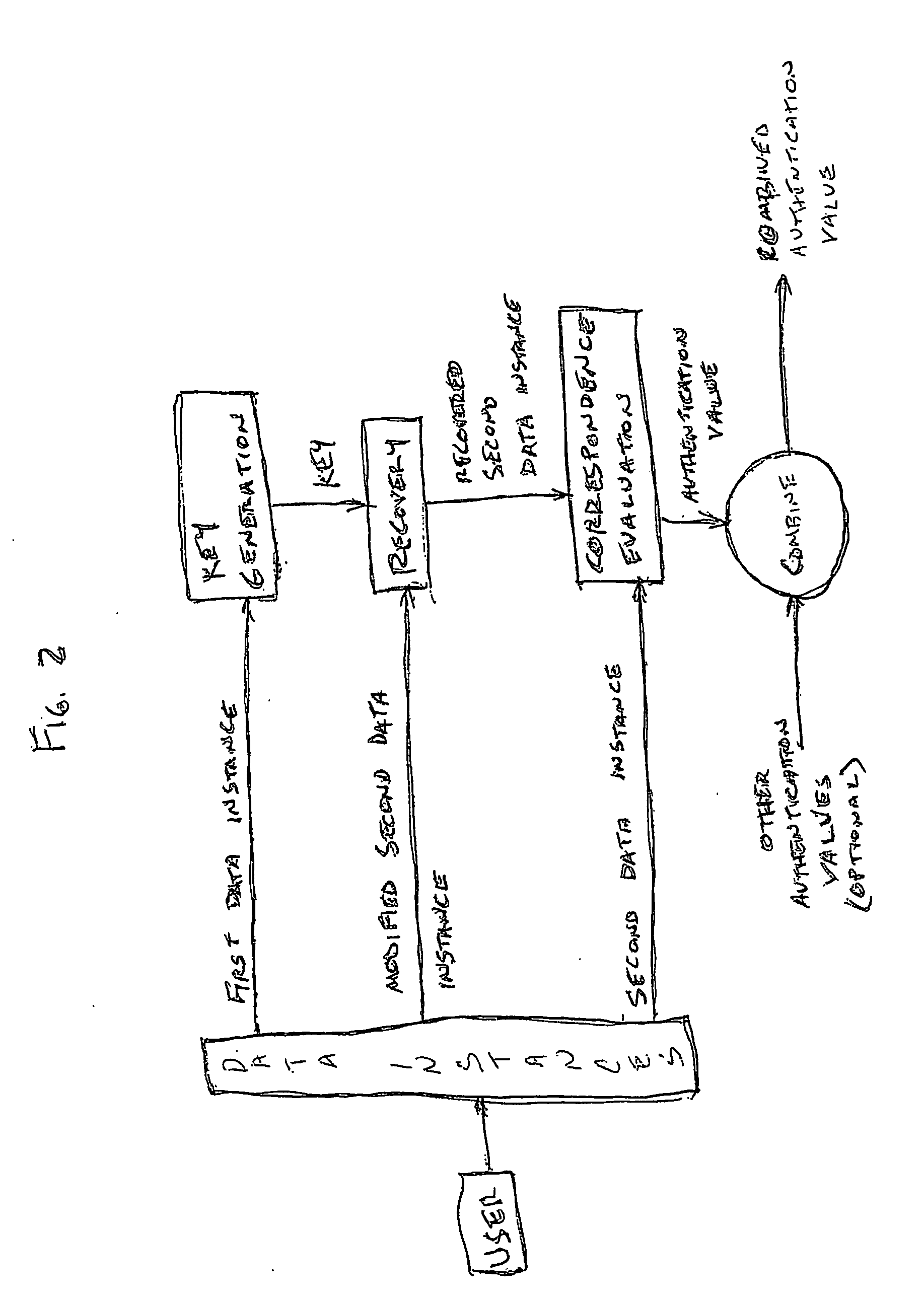
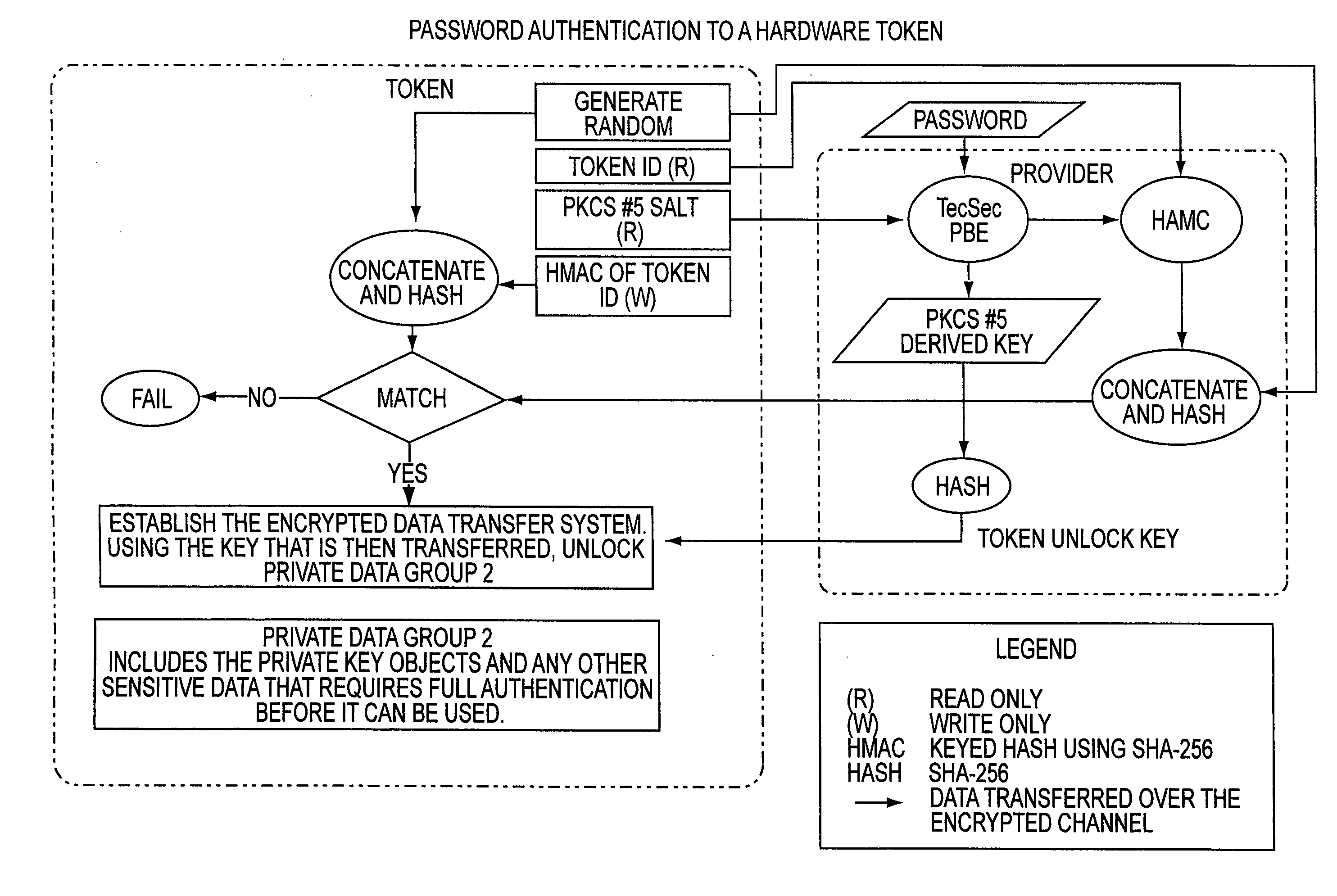
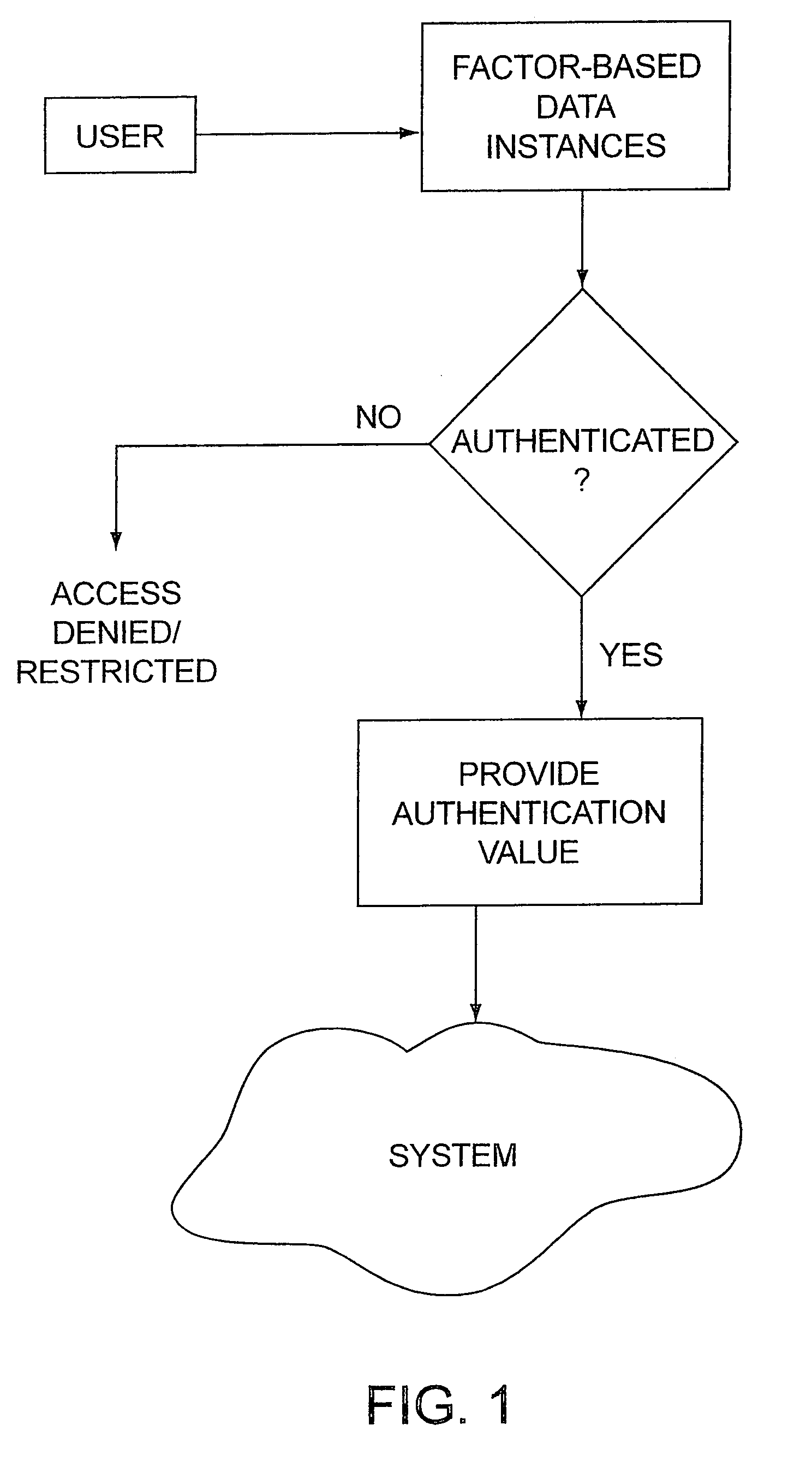
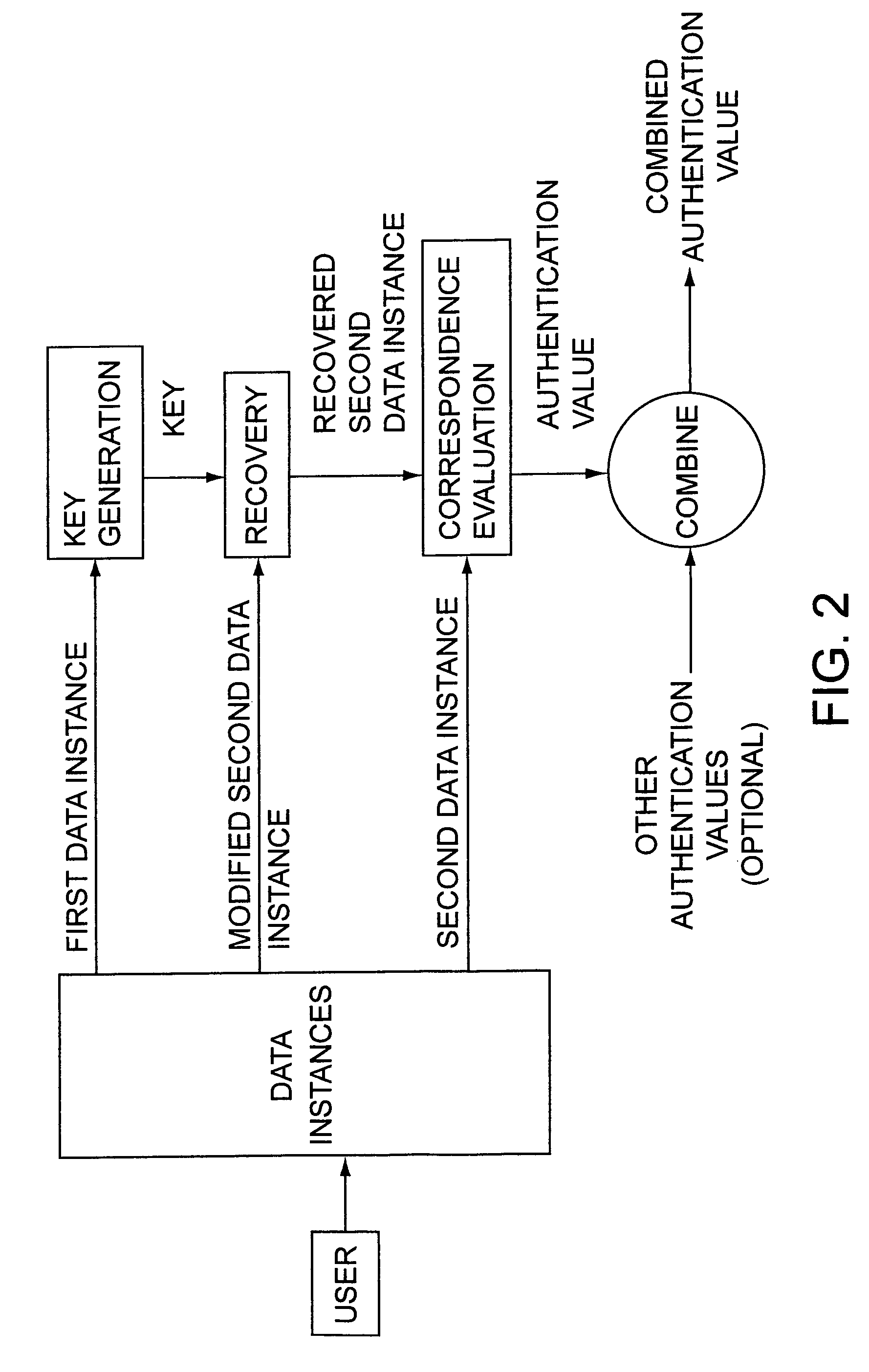
Access system utilizing multiple factor identification and authentication
InactiveUS20050235148A1Flexible approachEasy to useKey distribution for secure communicationPublic key for secure communicationTransfer systemPassword
A method of authenticating a user to use a system includes using a provider token to generate a random value. The token generates a derived key based at least in part on a token-provided salt value and a user-provided password. The provider generates a token unlock key based at least in part on the derived key and sends it to the token. First and second challenge data instances are generated by the provider and the token, respectively, and the process is terminated if the challenge data instances are determined not to match. If the challenge data instances are determined to match, then an encrypted data transfer system is established between the token and the provider, and the token unlocks locked private data stored on the token. The user is authenticated for secured use of the system based at least in part on the unlocked private data.
Owner:TECSEC
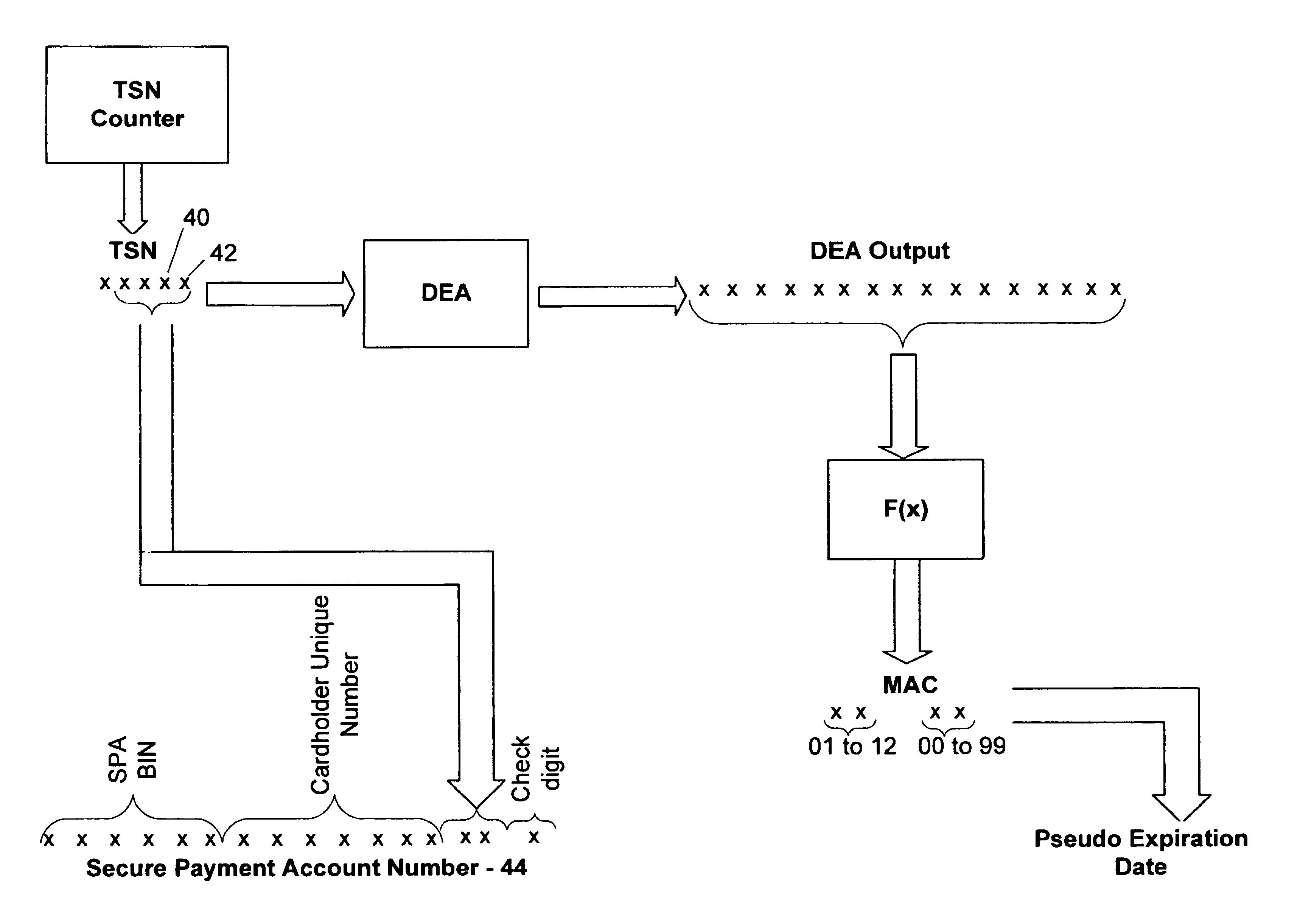
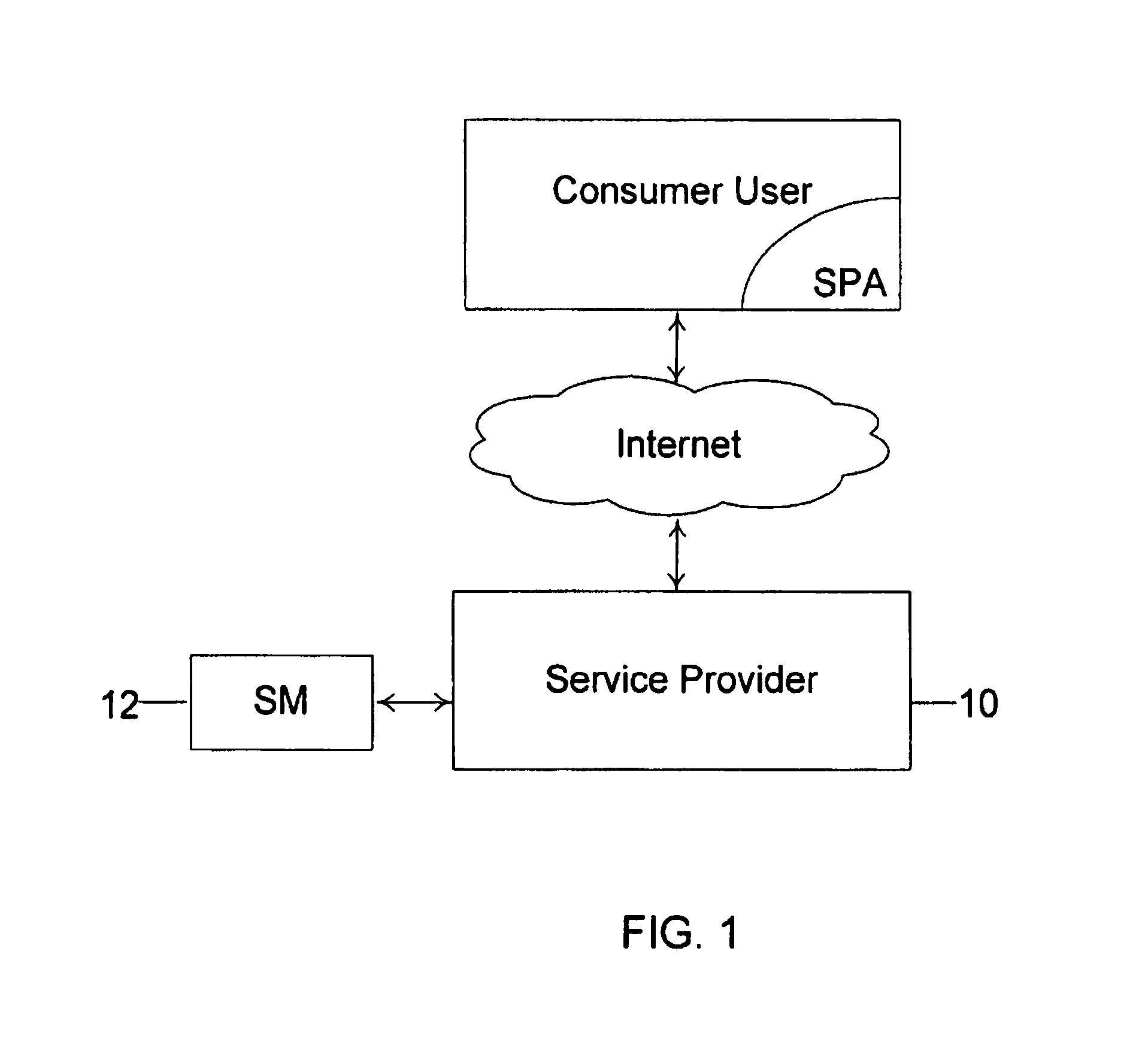
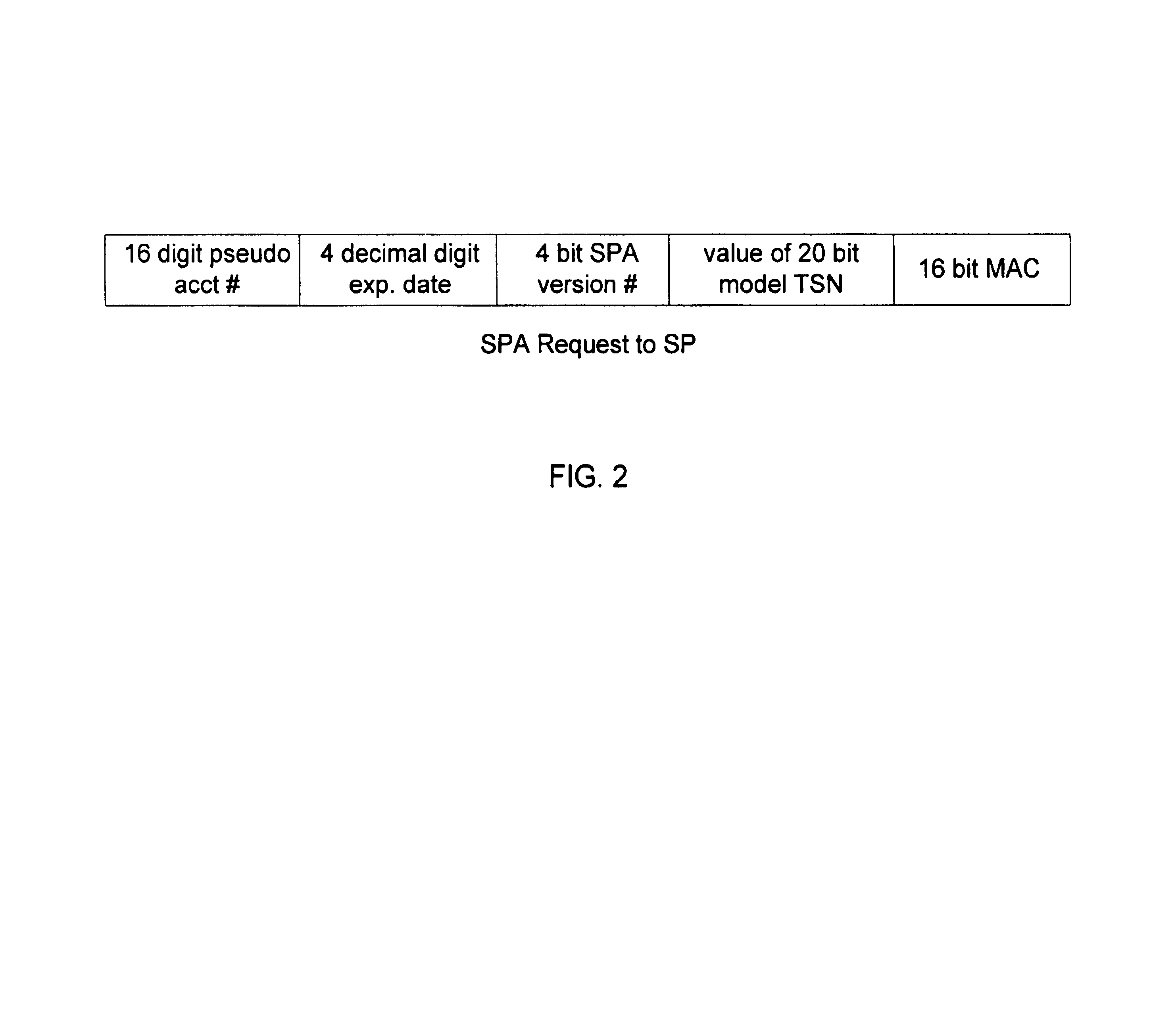
Method and system for conducting secure payments over a computer network
A secure method of conducting an electronic transaction over a public communications network is provided which utilizes a pseudo-expiration date in the expiration date field of an authorization request. One of the preferred methods comprises:generating a per-card key associated with an account number;generating a message authentication code using the per-card key;converting the message authentication code into a pseudo expiration date;generating an authorization request for the transaction, the request having an expiration date field containing the pseudo expiration date; andverifying the message authentication code based on the pseudo expiration date.Another embodiment of the invention includes a method of conducting an electronic transaction over a public communications network, with a payment account number having an associated pseudo account number, comprising:(a) providing the pseudo account number with a control field indicating one of a plurality of key-generation processes to be used to generate an authentication key;(b) generating an authentication key associated with the pseudo account number using one of the plurality of key-generation processes indicated in the control field of the pseudo account number;(c) using the authentication key to generate a message authentication code specific to the transaction;(d) generating an authorization request message including the message authentication code and the pseudo account number; and(e) verifying the message authentication code using the indicated key-generation process and the authentication key.
Owner:MASTERCARD INT INC
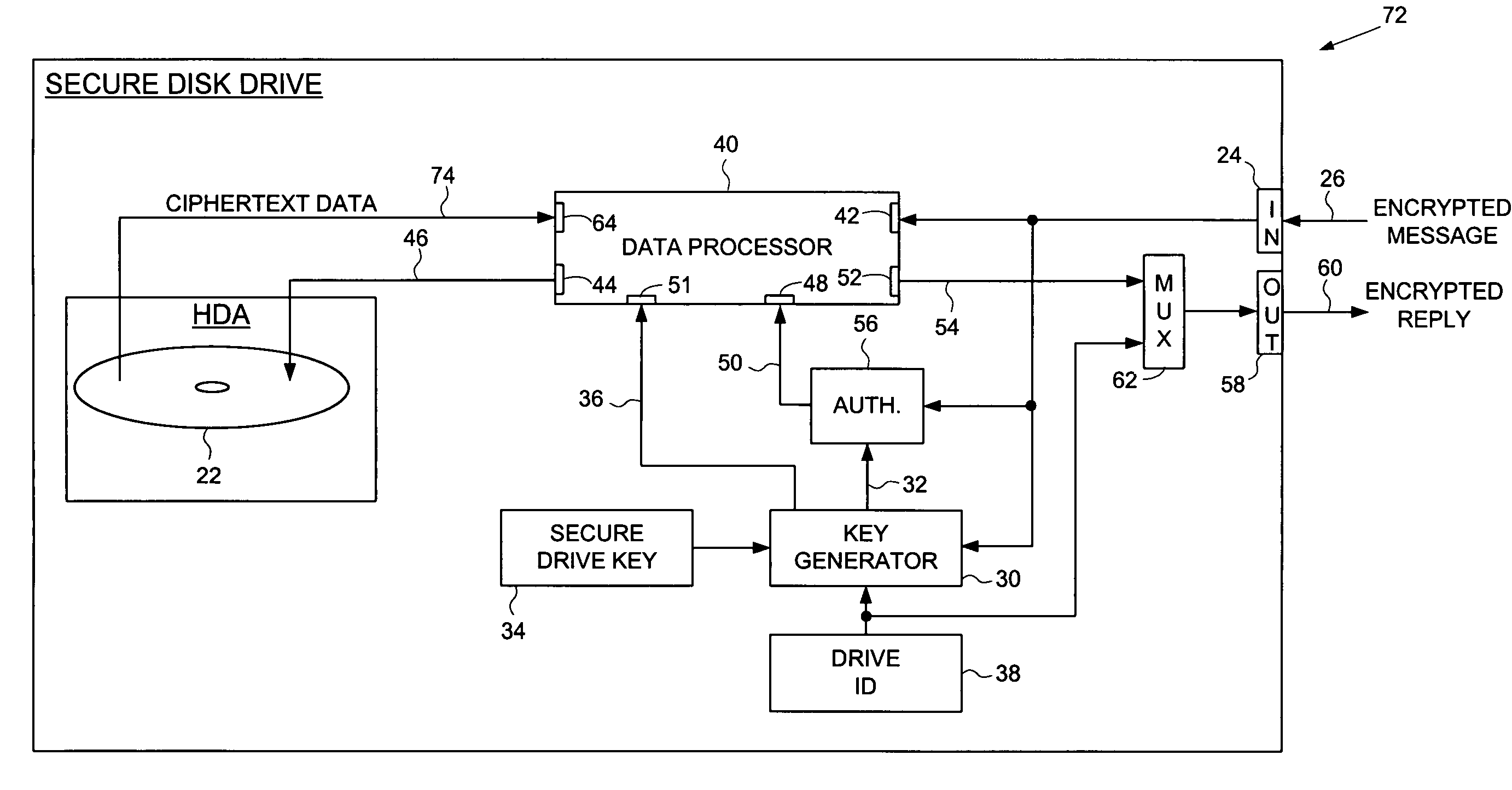
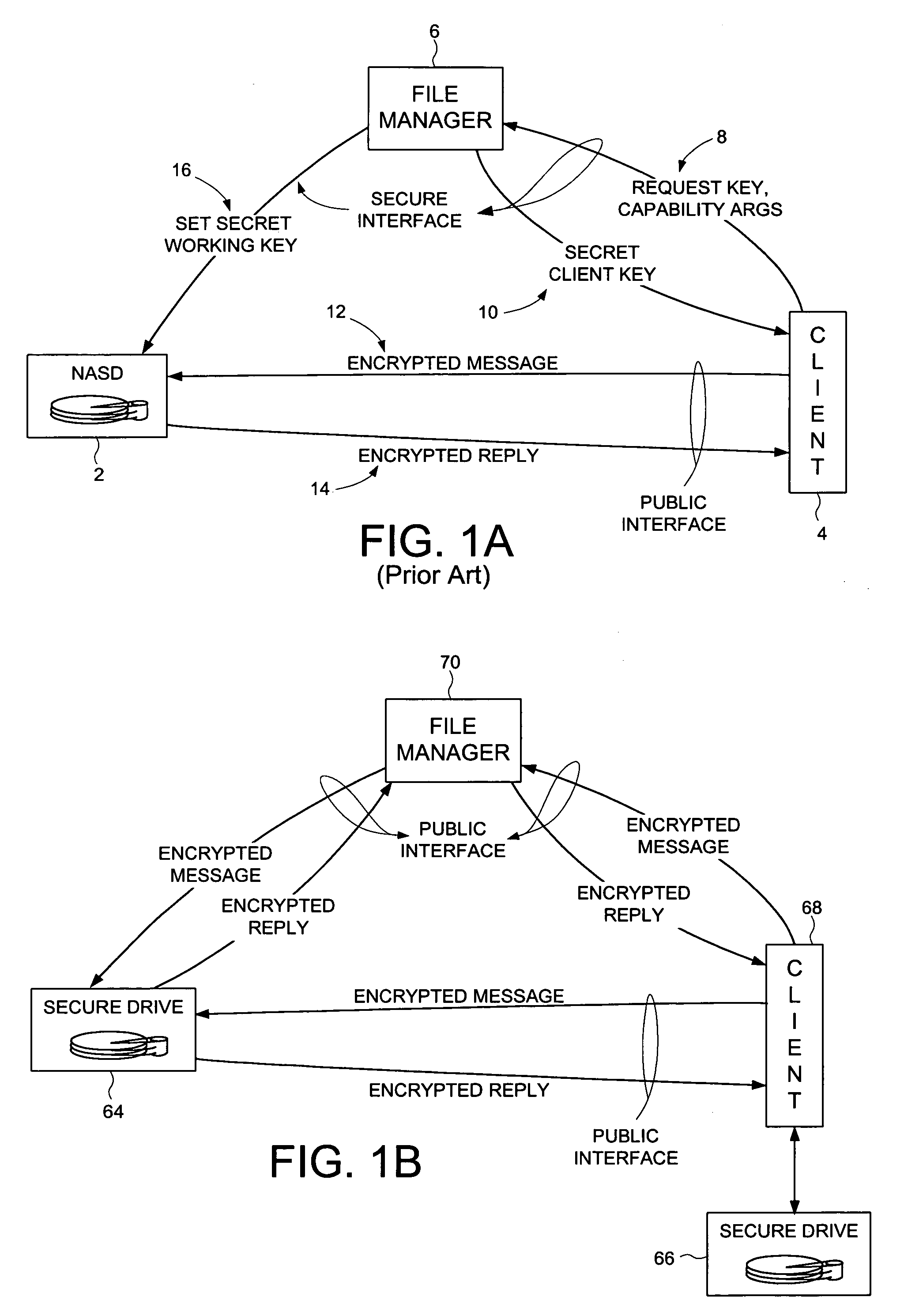
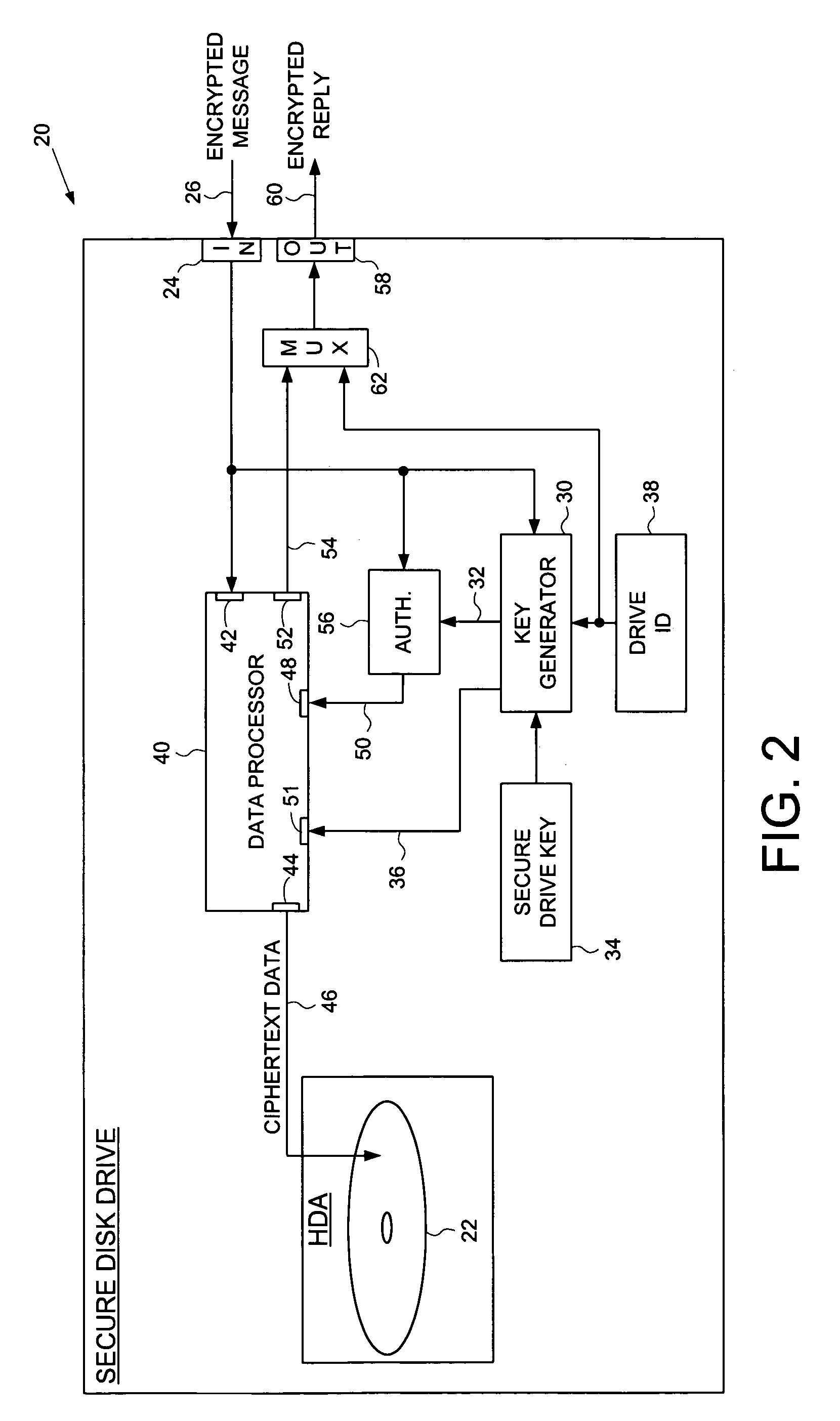
Secure disk drive comprising a secure drive key and a drive ID for implementing secure communication over a public network
InactiveUS7215771B1Volume/mass flow measurementUser identity/authority verificationSecure communicationCiphertext
A secure disk drive is disclosed comprising a disk for storing data, and an input for receiving an encrypted message from a client disk drive, the encrypted message comprising ciphertext data and a client drive ID identifying the client disk drive. The secure disk drive comprises a secure drive key and an internal drive ID. A key generator within the secure disk drive generates a client drive key based on the client drive ID and the secure drive key, and an internal drive key based on the internal drive ID and the secure drive key. The secure disk drive further comprises an authenticator for verifying the authenticity of the encrypted message and generating an enable signal, the authenticator is responsive to the encrypted message and the client drive key. The secure disk drive further comprises a data processor comprising a message input for receiving the encrypted message from the client disk drive, and a data output for outputting the ciphertext data to be written to the disk. The data processor further comprises an enable input for receiving the enable signal for enabling the data processor, and a key input for receiving the internal drive key, the internal drive key for use in generating a message authentication code. The data processor outputs reply data comprising the message authentication code. The secure disk drive outputs a reply to the client disk drive, the reply comprising the reply data and the internal drive ID.
Owner:WESTERN DIGITAL TECH INC
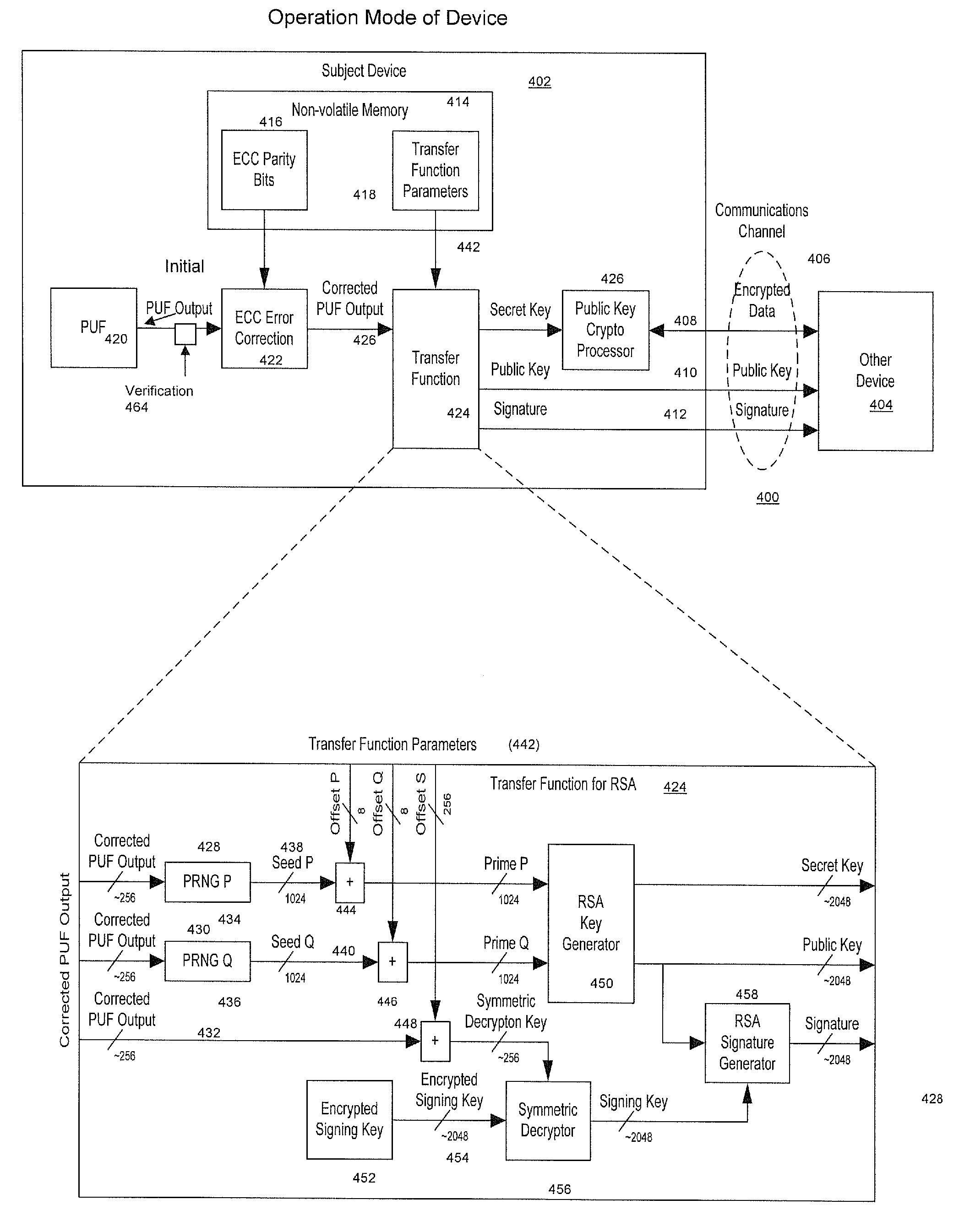
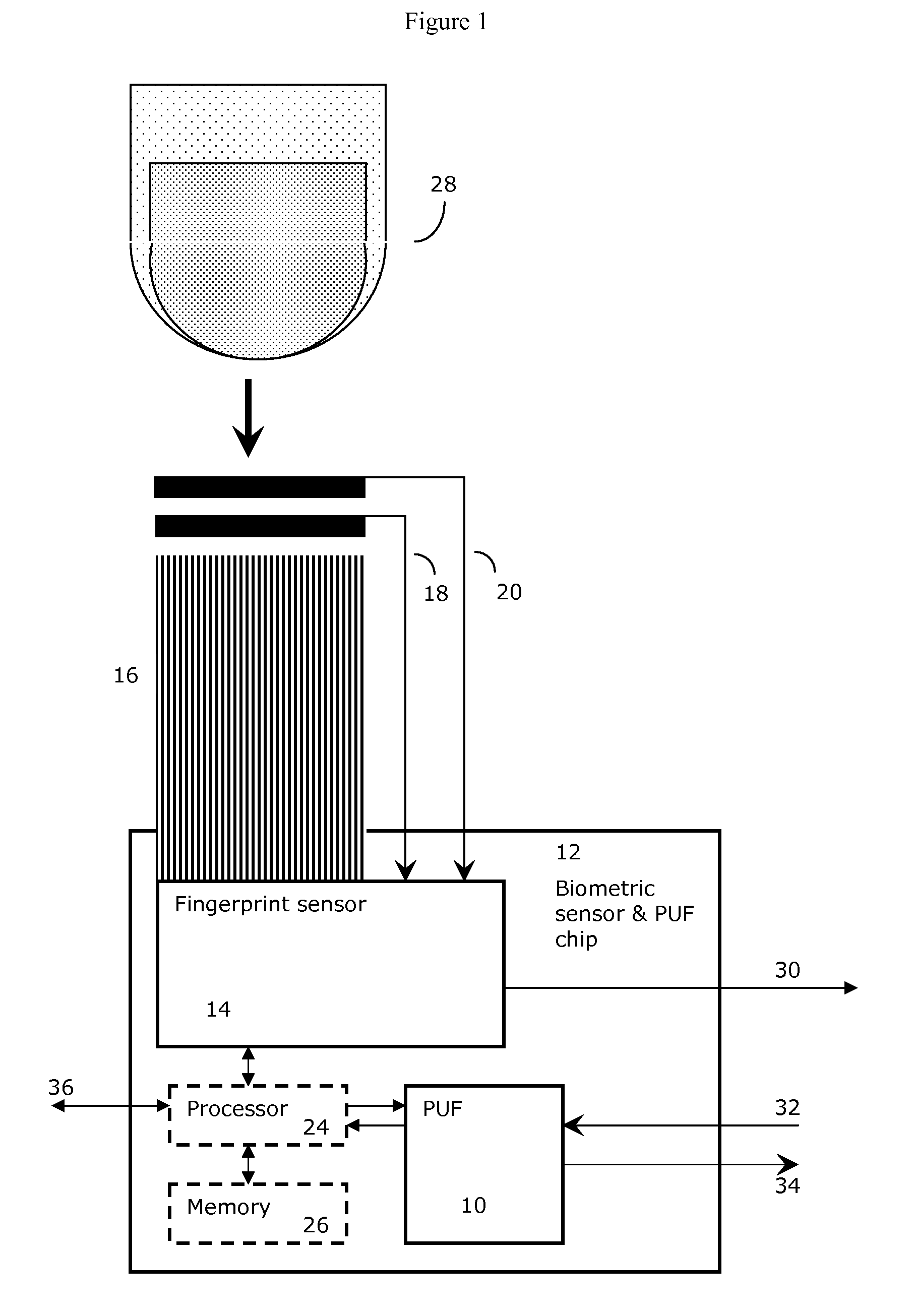
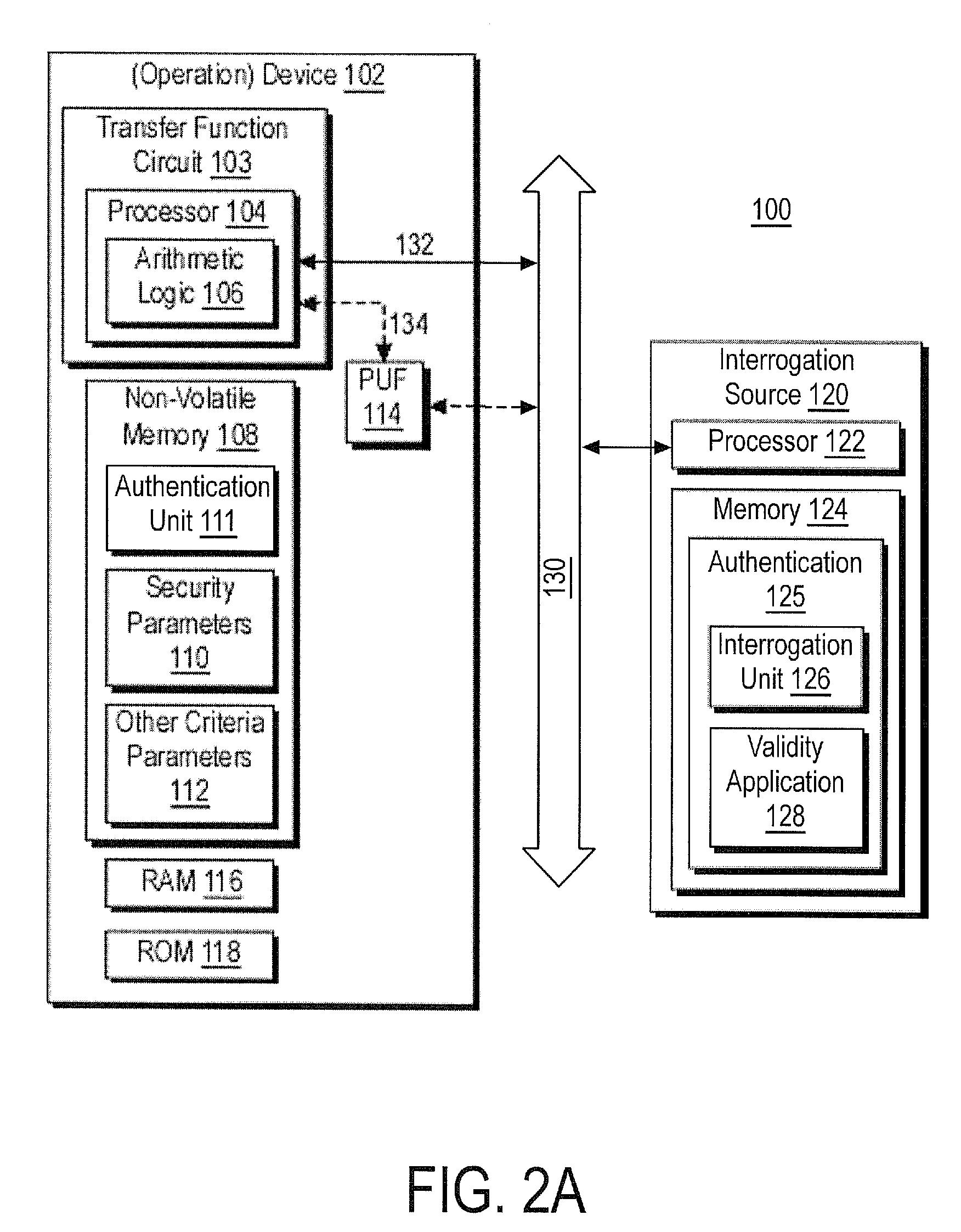
Method and System for Electronically Securing an Electronic Biometric Device Using Physically Unclonable Functions
InactiveUS20110002461A1Consume minimalCost of producingKey distribution for secure communicationElectric signal transmission systemsPhysical unclonable functionSecurity validation
A system for securing an integrated circuit chip used for biometric sensors, or other electronic devices, by utilizing a physically unclonable function (PUF) circuit. These PUF functions are in turn used to generate security words and keys, such as an RSA public or private key. Such a system can be used to protect biometric security sensors and IC chips, such as fingerprint sensors and sensor driver chips, from attack or spoofing. The system may also be used in an efficient method to produce unique device set-up or power-up authentication security keys. These keys can be generated on a low frequency basis, and then frequently reused for later security verification purposes. In operation, the stored keys can be used to efficiently authenticate the device without the need to frequently run burdensome security key generation processes each time, while maintaining good device security.
Owner:SYNAPTICS INC
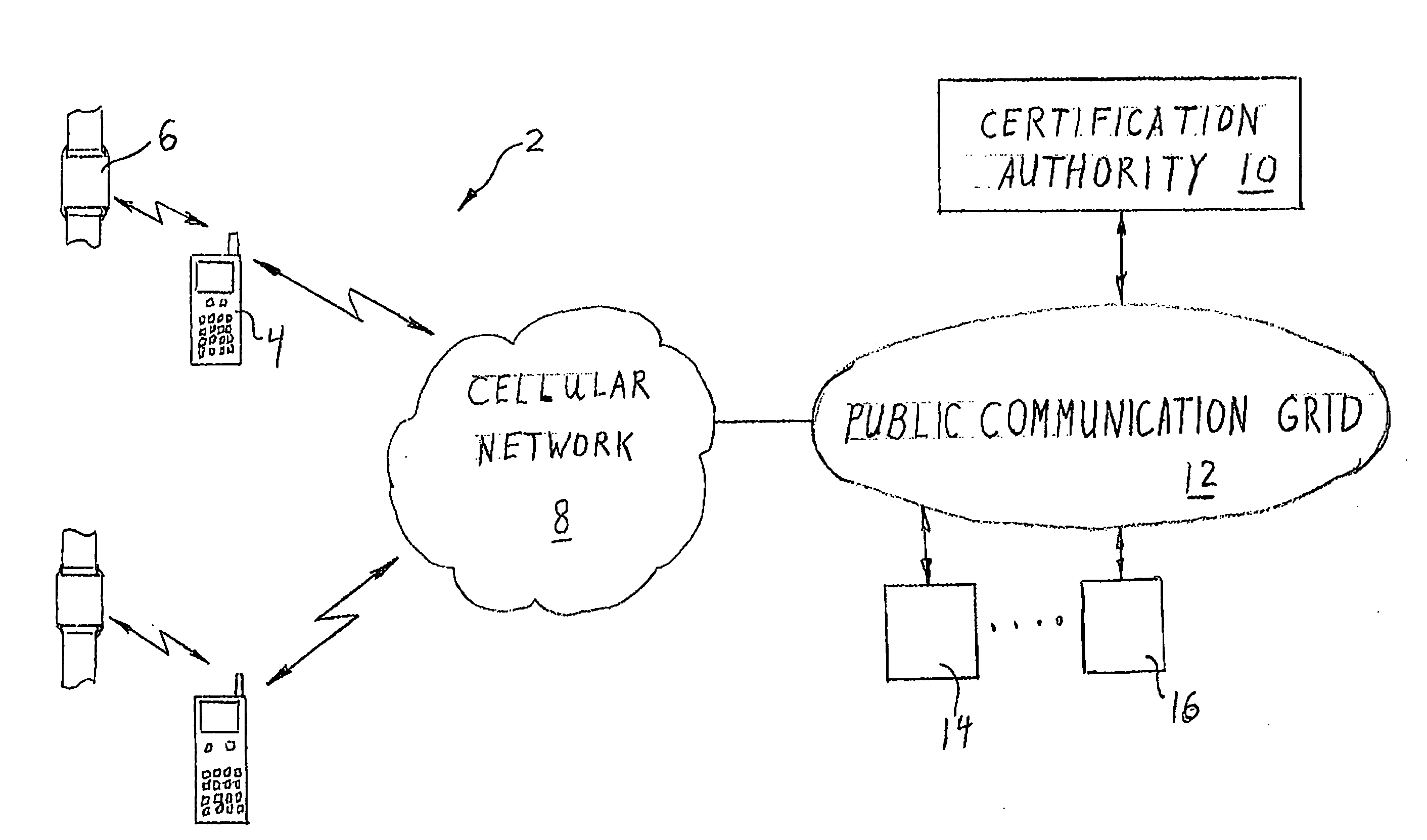
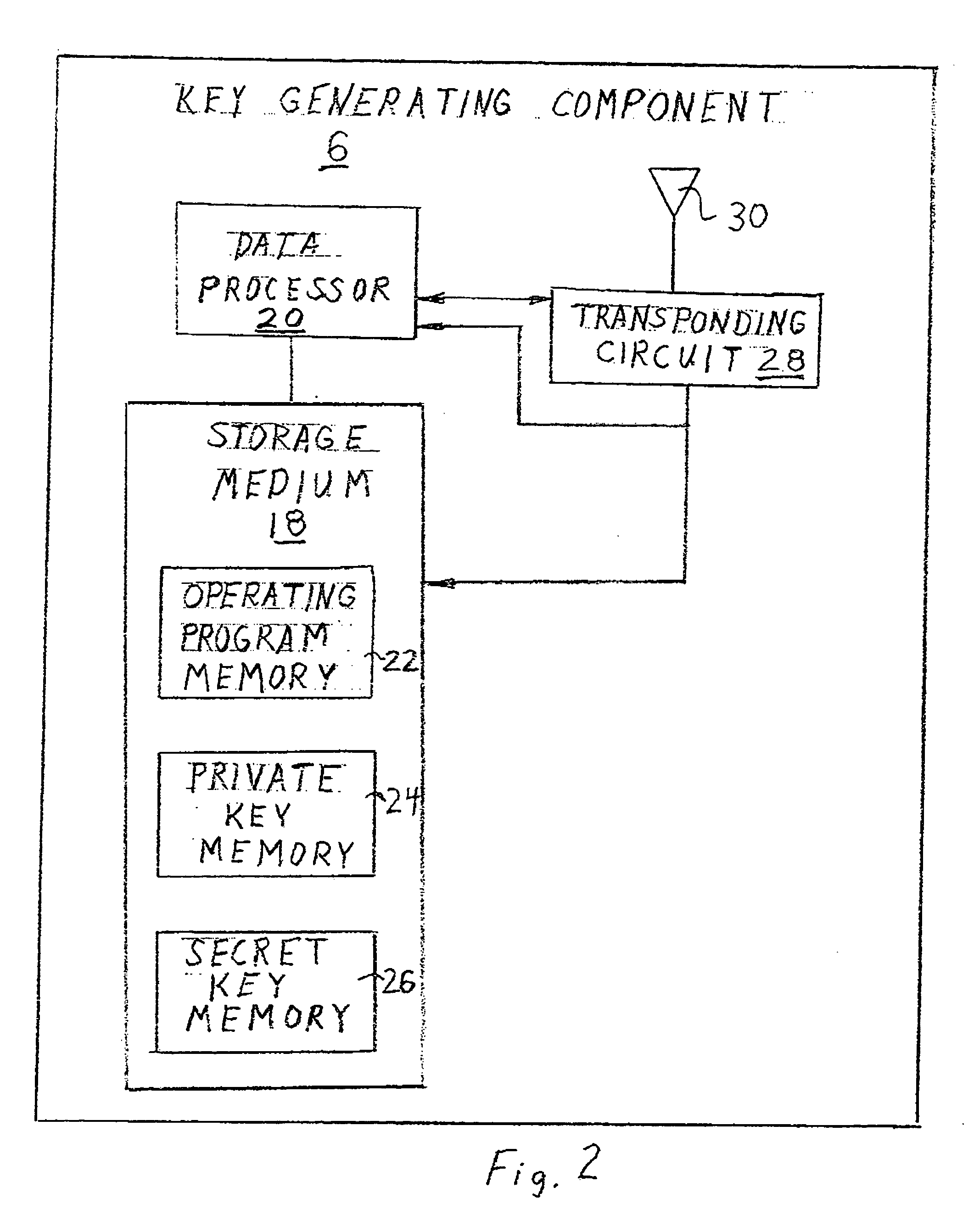
Security system for handheld wireless devices using-time variable encryption keys
ActiveUS20080022089A1Least costOperational securityNetwork topologiesPublic key infrastructure trust modelsCommunications systemWireless broadcasting
In one embodiment, the invention provides a portable wireless personal communication system for cooperating with a remote certification authority to employ time variable secure key information pursuant to a predetermined encryption algorithm to facilitate convenient, secure encrypted communication. The disclosed system includes a wireless handset, such as PDA, smartphone, cellular telephone or the like, characterized by a relatively robust data processing capability and a body mounted key generating component which is adapted to be mounted on an individual's body, in a permanent or semi-permanent manner, for wirelessly broadcasting, within the immediate proximity of the individual, a secret or private key identifying signal corresponding to a time variable secure key information under the control of the certification authority. The key identifying signal is generated in a format that facilitates secure wireless communication with the individual in accordance with a predetermined encryption algorithm including a PKI encryption algorithm. The disclosed system may be used with a console for coordinating access to a variety of different communication system and networks.
Owner:MLR
Access system utilizing multiple factor identification and authentication
InactiveUS7178025B2Easy to useSelection of credentials can be automatedKey distribution for secure communicationDigital data processing detailsTransfer systemPassword
A method of authenticating a user to use a system includes using a provider token to generate a random value. The token generates a derived key based at least in part on a token-provided salt value and a user-provided password. The provider generates a token unlock key based at least in part on the derived key and sends it to the token. First and second challenge data instances are generated by the provider and the token, respectively, and the process is terminated if the challenge data instances are determined not to match. If the challenge data instances are determined to match, then an encrypted data transfer system is established between the token and the provider, and the token unlocks locked private data stored on the token. The user is authenticated for secured use of the system based at least in part on the unlocked private data.
Owner:TECSEC
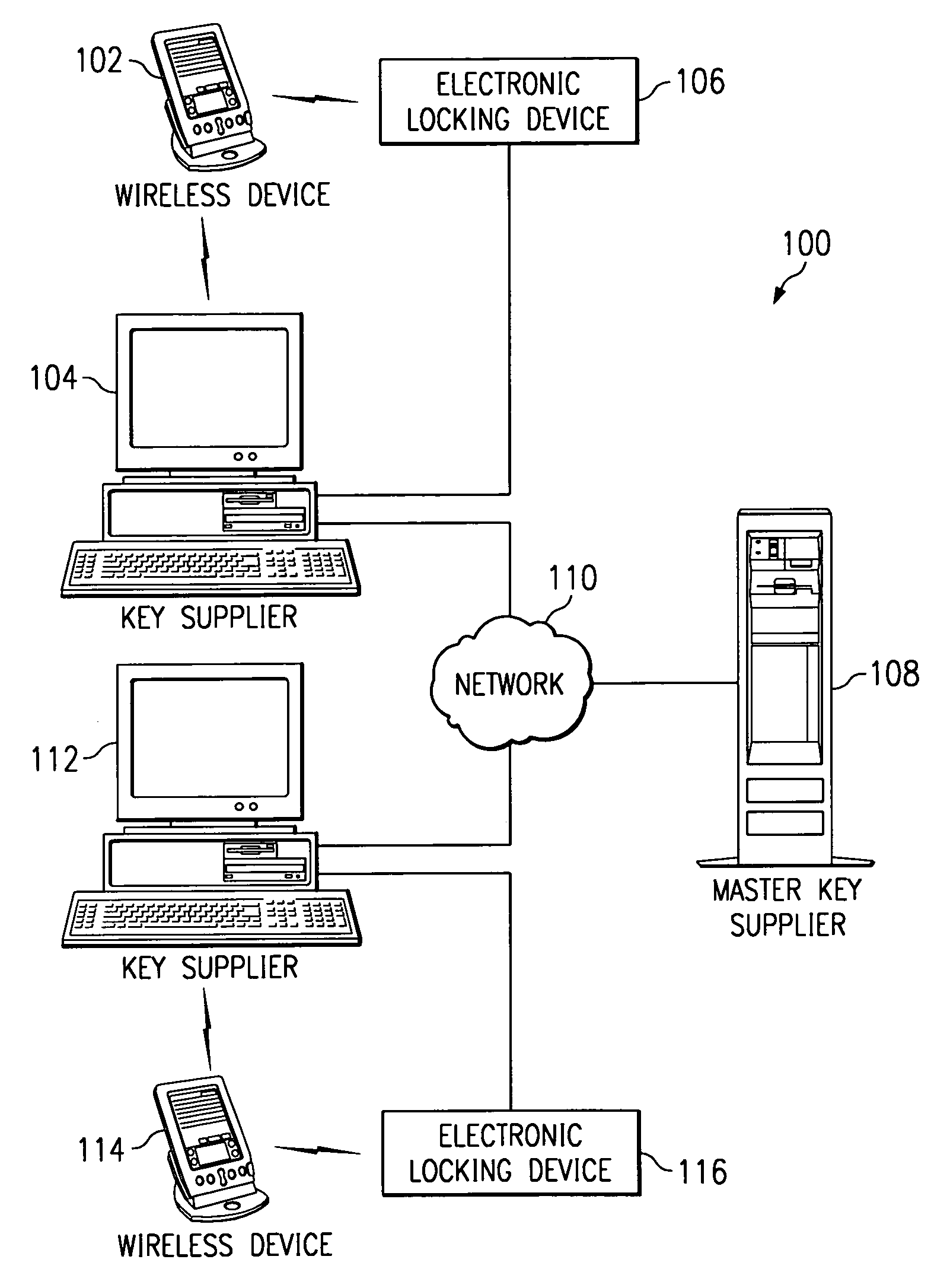
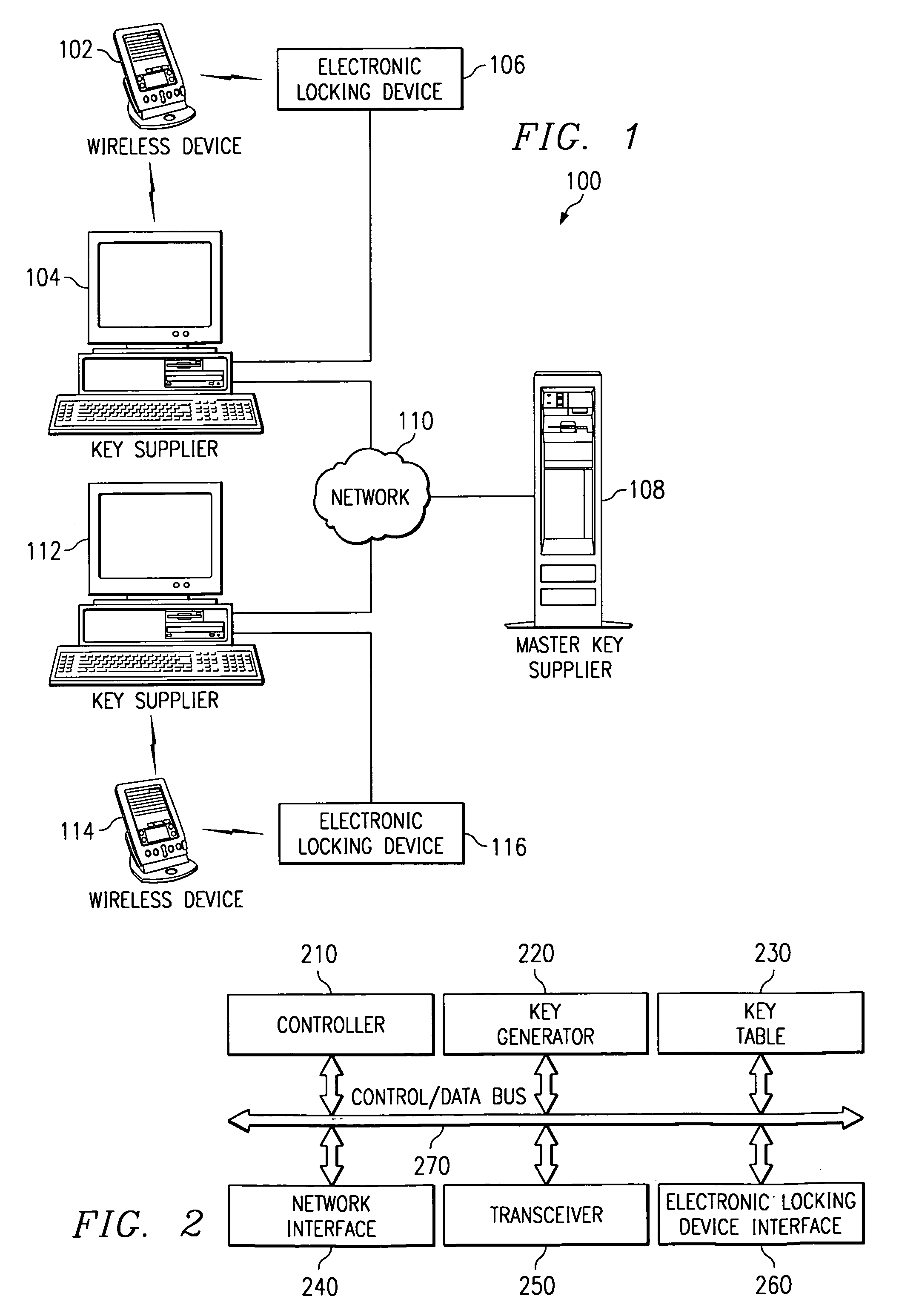
Electronic key system, apparatus and method
InactiveUS6975202B1Avoid problemsSufficient securityElectric signal transmission systemsImage analysisComputer hardwareBiological activation
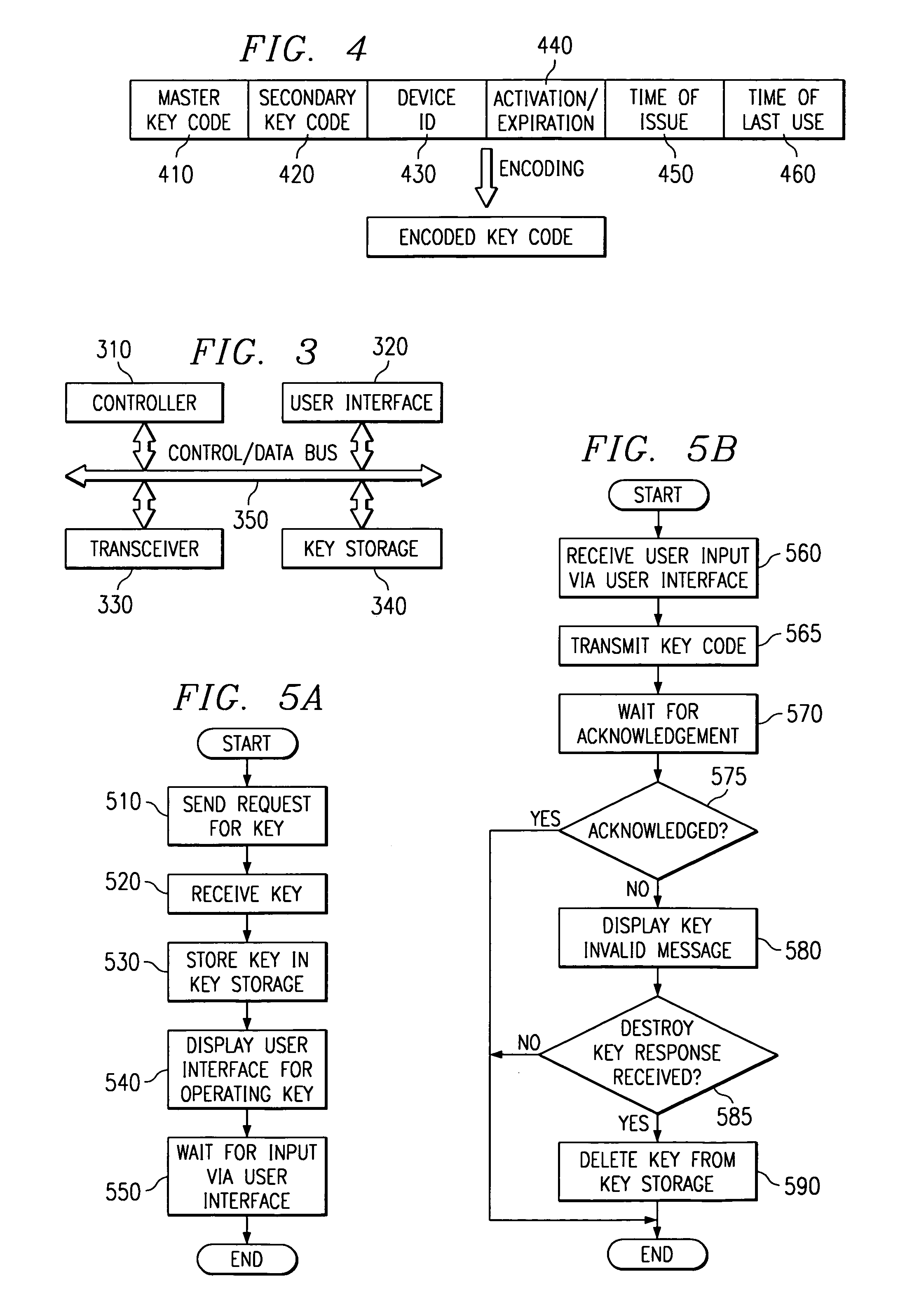
A system, apparatus and method for using an electronic key to open electronic locking devices is provided. With the system, apparatus and method, a key code is sent to a user's wireless communication device and is later used to open a corresponding locking device. The key code is generated by a key supplier based on a master key obtained from a master key supplier, e.g. an electronic lock manufacturer. The key code may include a master key portion, a secondary key portion, an activation / expiration portion, a wireless device identifier portion, a time of issue portion, and a time of last use portion.
Owner:IBM CORP
Method and system for providing a secure login solution using one-time passwords
InactiveUS8041954B2Improve securitySimple and elegantDigital data processing detailsUnauthorized memory use protectionComputer hardwareOne-time password
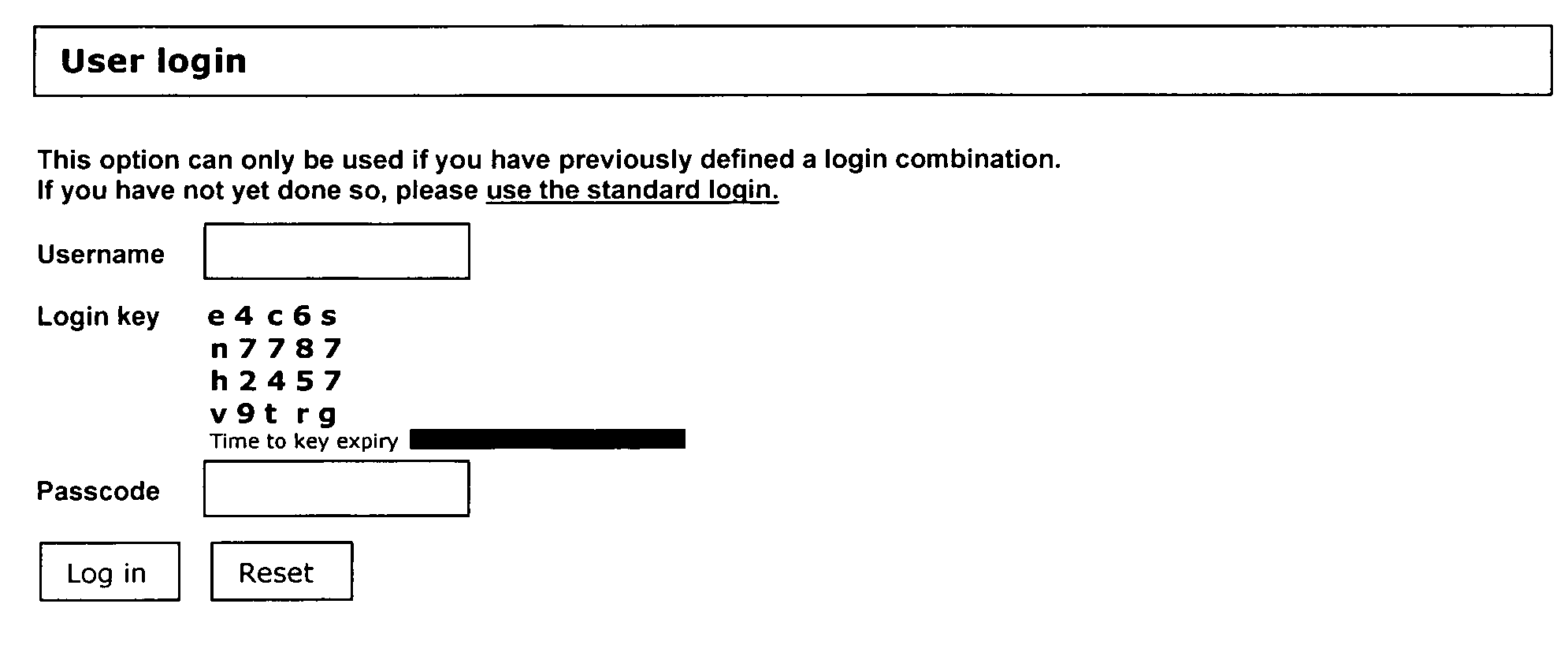
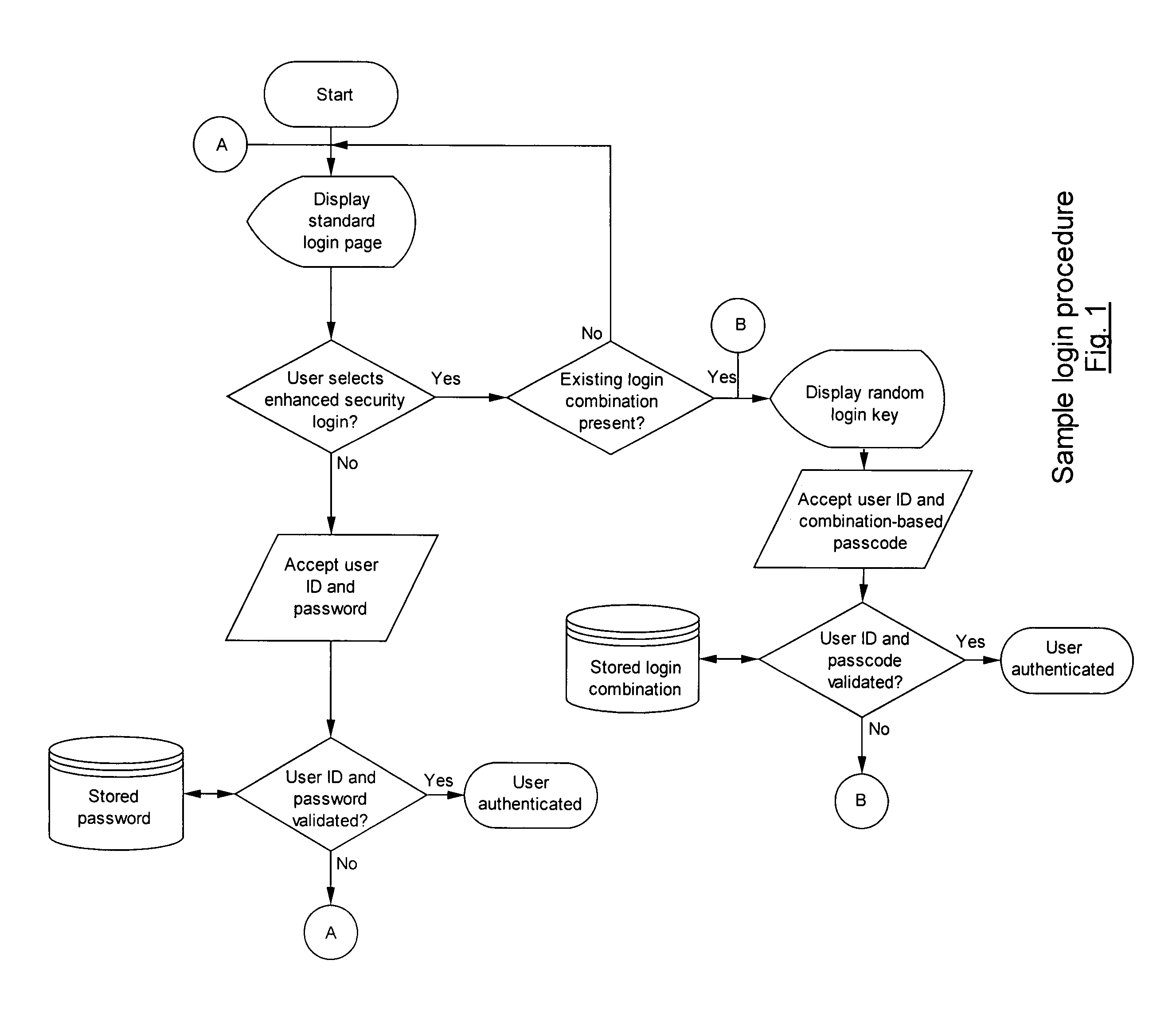
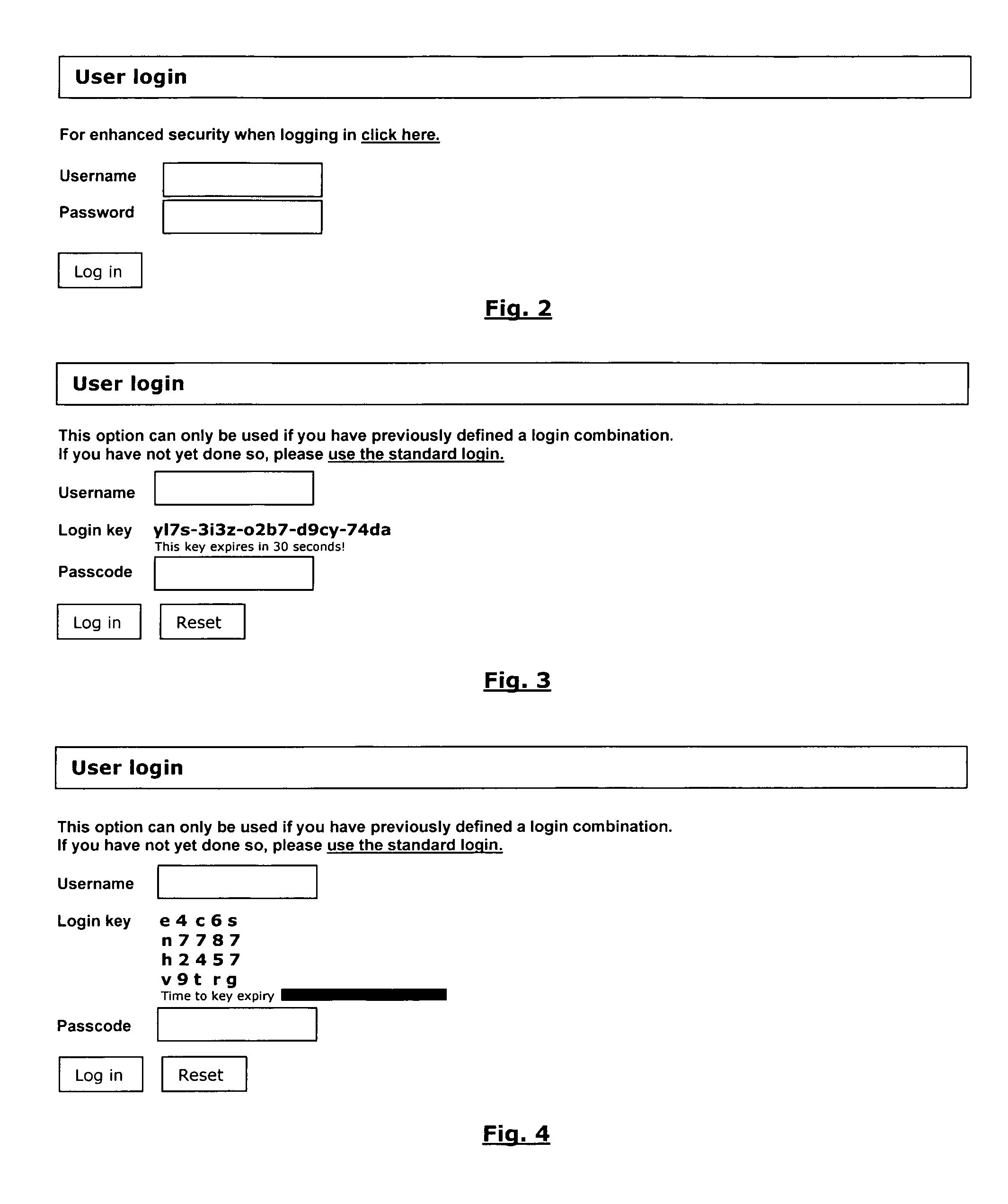
A method and system for a secure login solution for users logging into computers and systems that require authentication is provided incorporating one-time passwords. The method and system allows a user to establish a login key combination in relation to a login key structure. The login key combination is in association with an identification means, such as a username / ID, and allows the user to generate a one-time passcode in response to a random login key. The method and system is directed at situations where the user desires to log into a system from a computer or other electronic device that may not be secure, including for example from computers or devices other than the user's own and / or by using a communications connection that may not be secure, such as a wireless network connection. The method and system is simple and easy to implement and does not require the use of physical devices.
Owner:PLESMAN PAUL
Authentication Method for IC Cards
ActiveUS20080016351A1Reduce communicationAcutation objectsUser identity/authority verificationComputer hardwareAuthentication
An authentication method between a first IC card and a second IC card interconnected through a terminal includes transmitting an identification number from the second IC card to the first IC card for deriving and storing a key in the first IC card. An authentication number is generated and stored in the first IC card, and is transmitted to the second IC card. The authentication number is encrypted inside the second IC card, and is transmitted to the first IC card. The encrypted authentication number is decrypted through the derived key, and is compared with the authentication number. The second IC card is authorized if the encrypted authentication number in the first IC card is equal to the authentication number. At least one of the transmissions includes an identification and / or authentication number to authorize the first IC card from the second IC card. The identification and / or authentication numbers include a reverse authentication number.
Owner:STMICROELECTRONICS INT NV
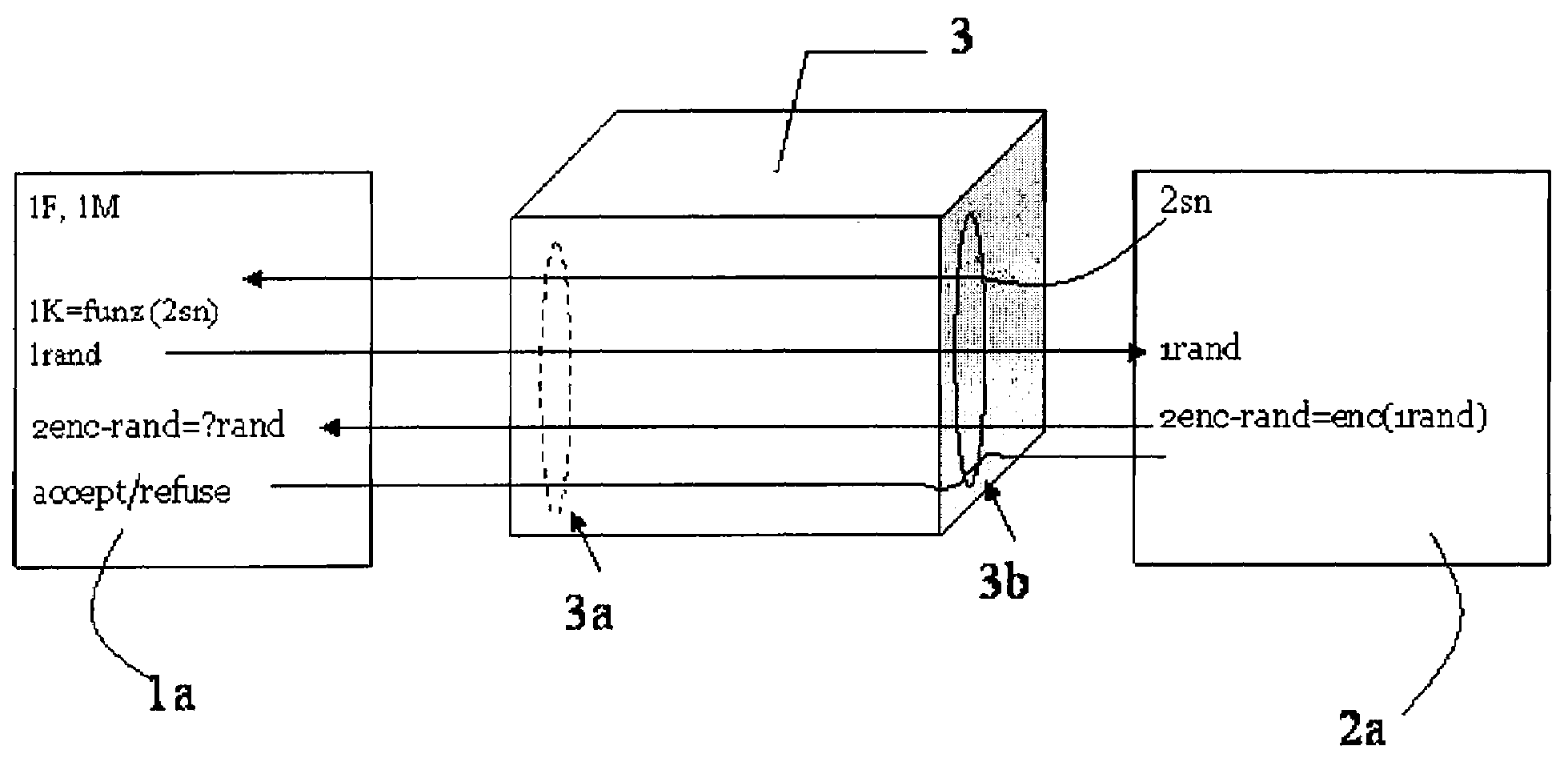
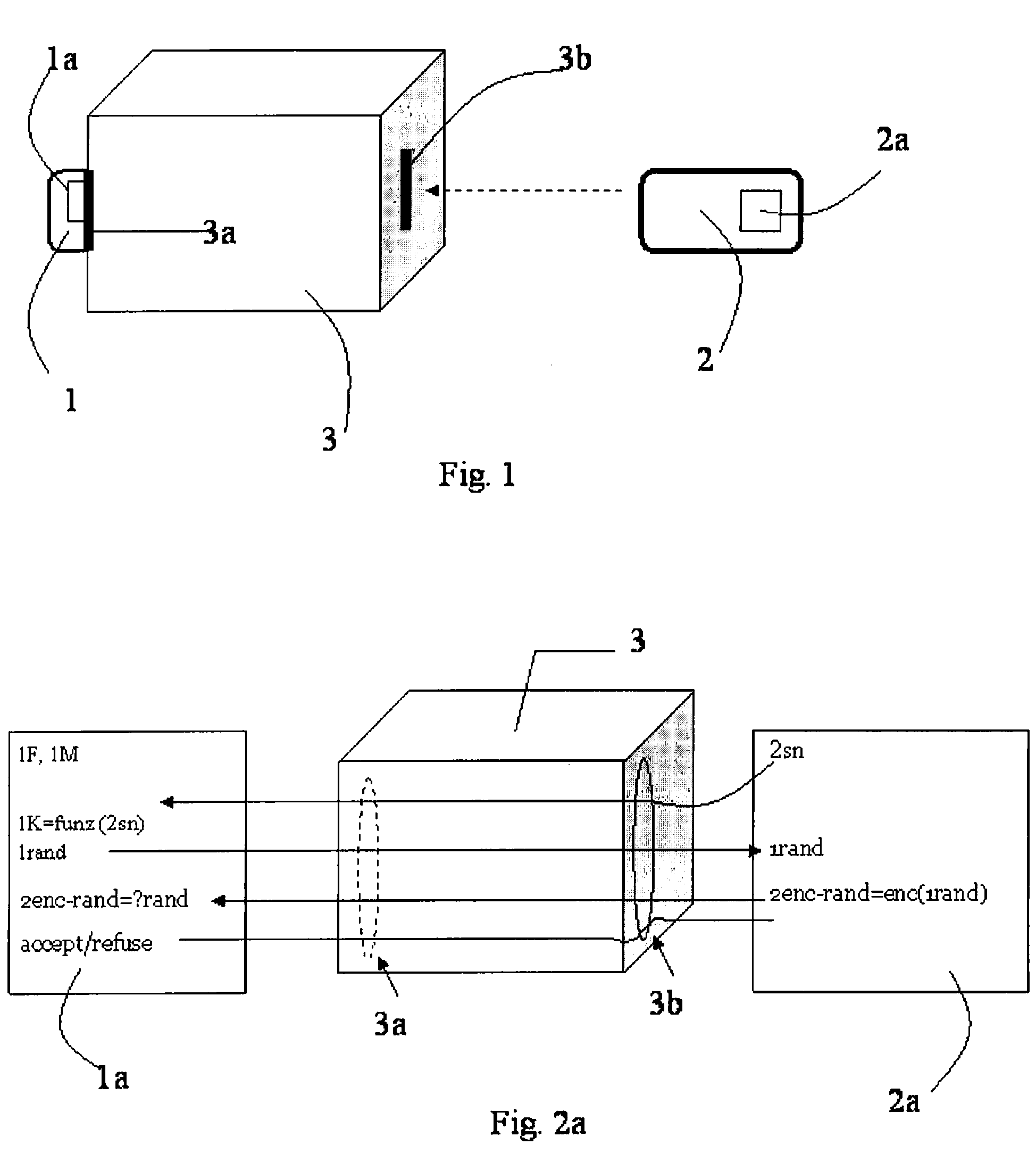
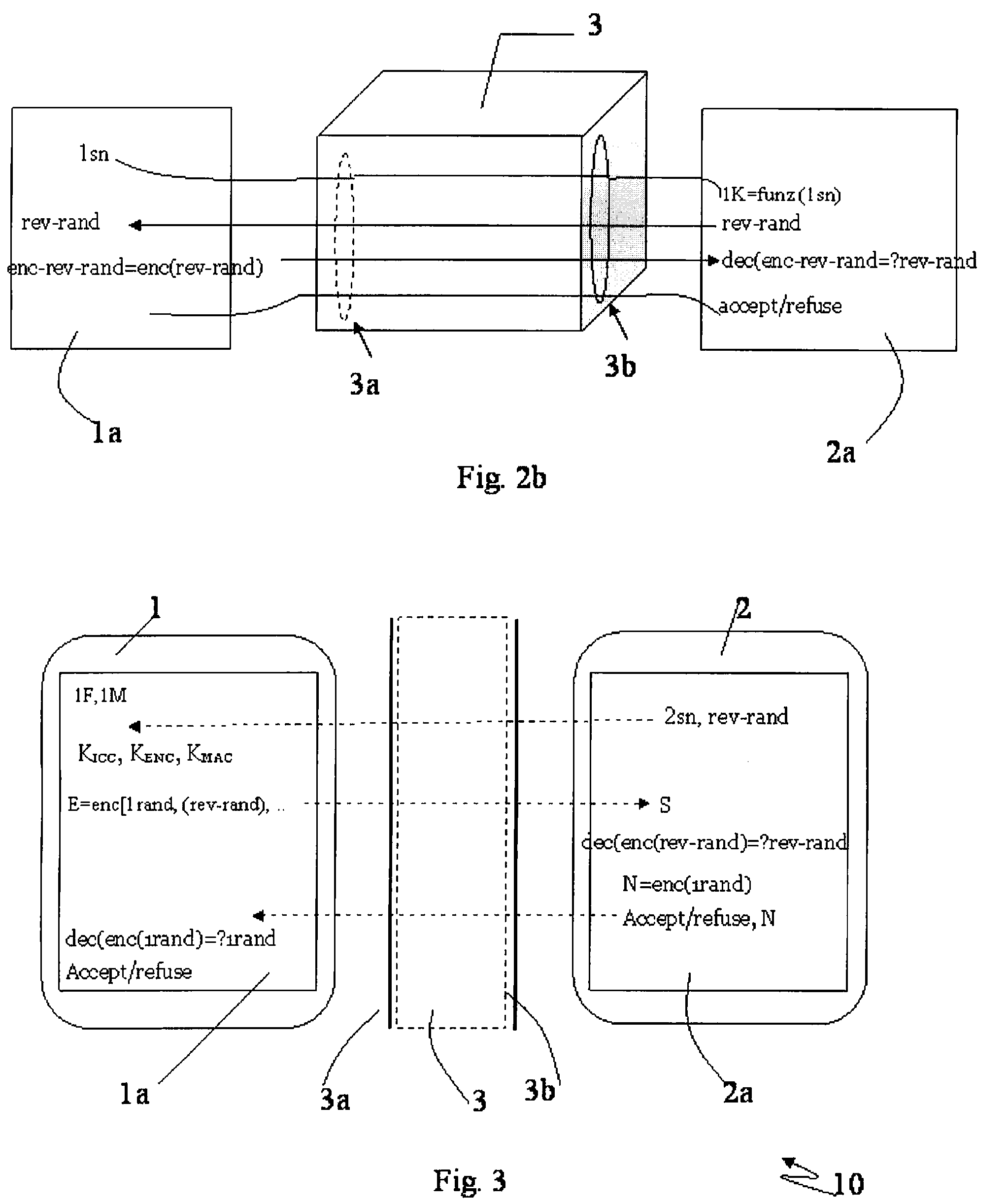
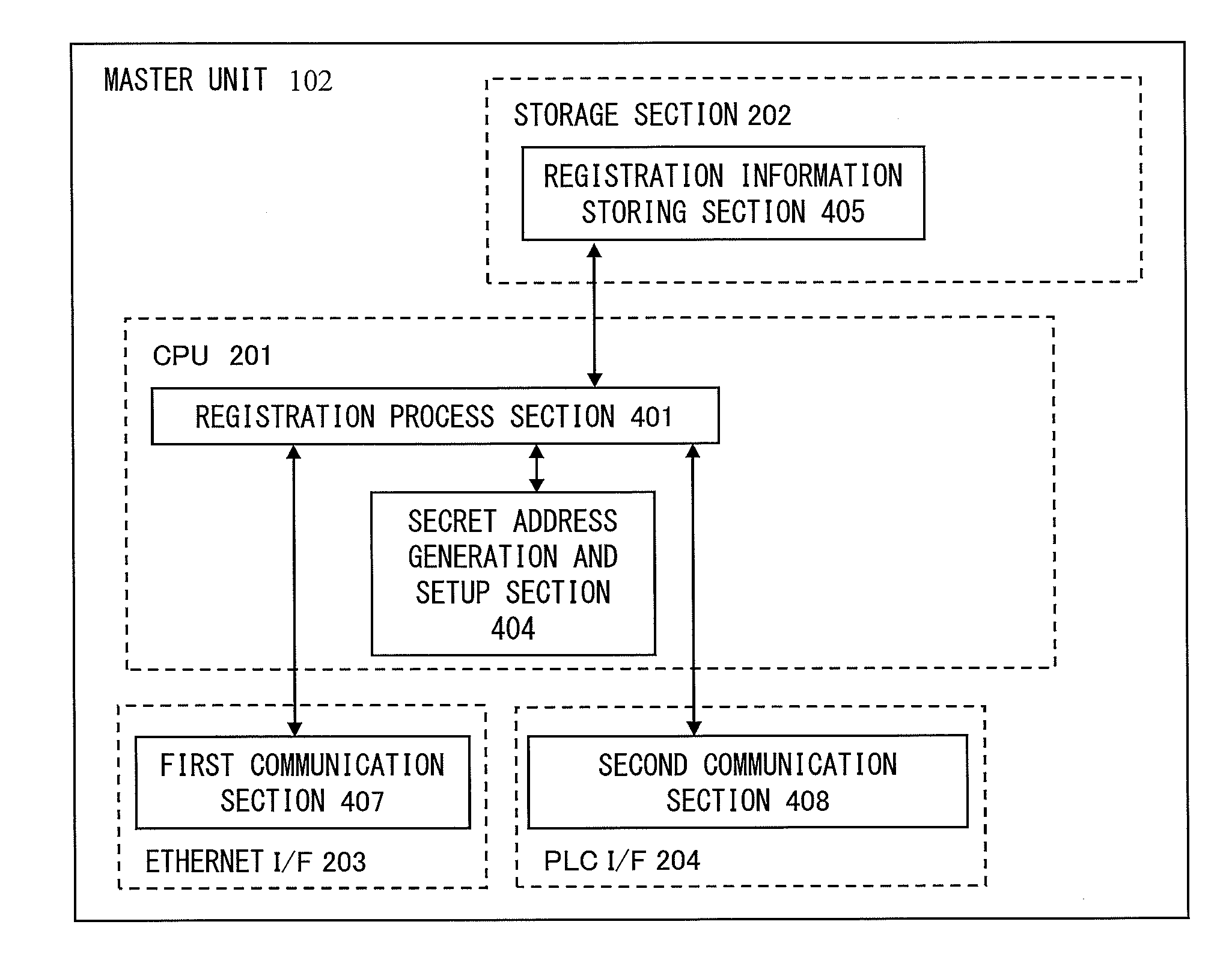
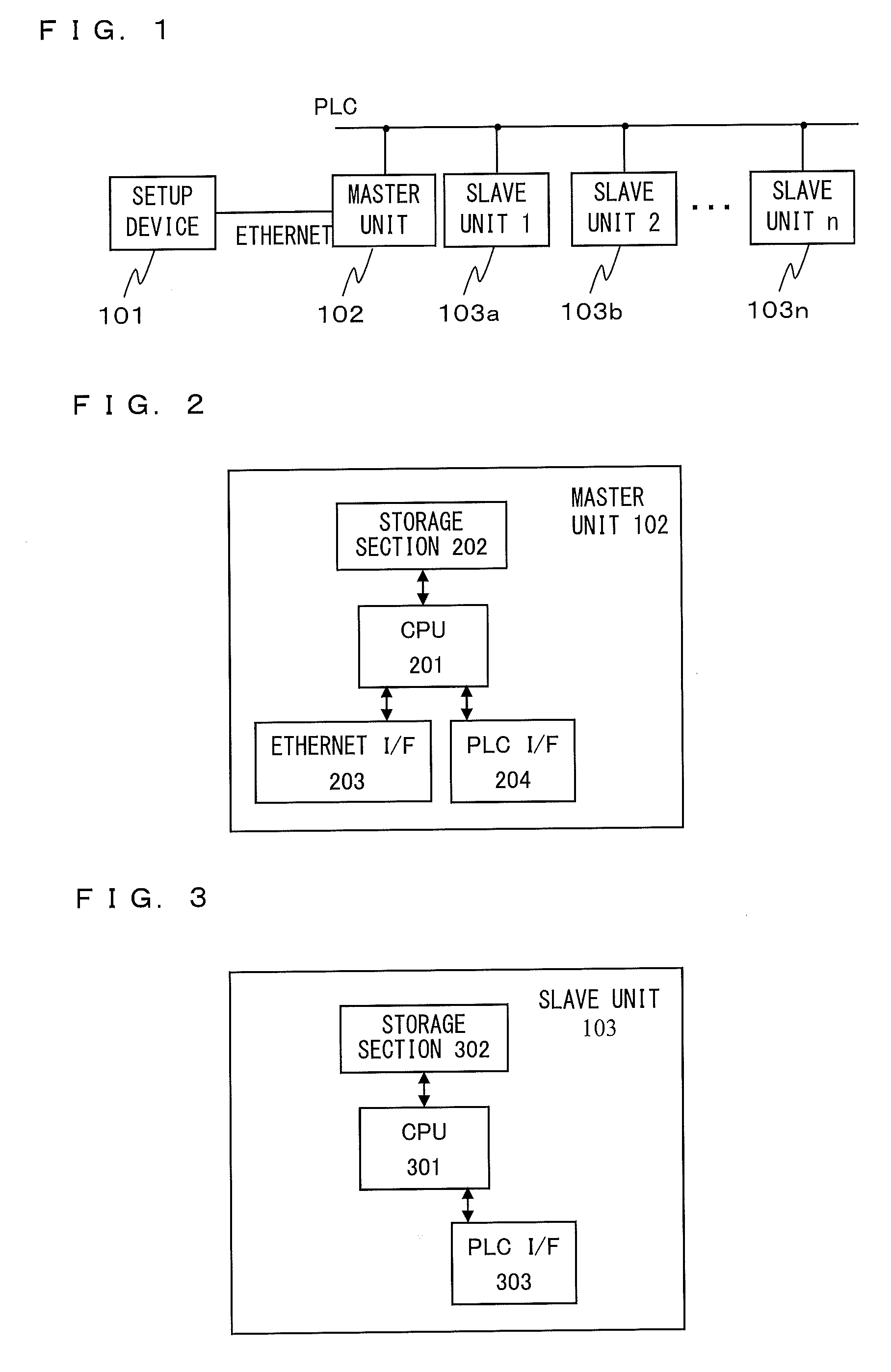
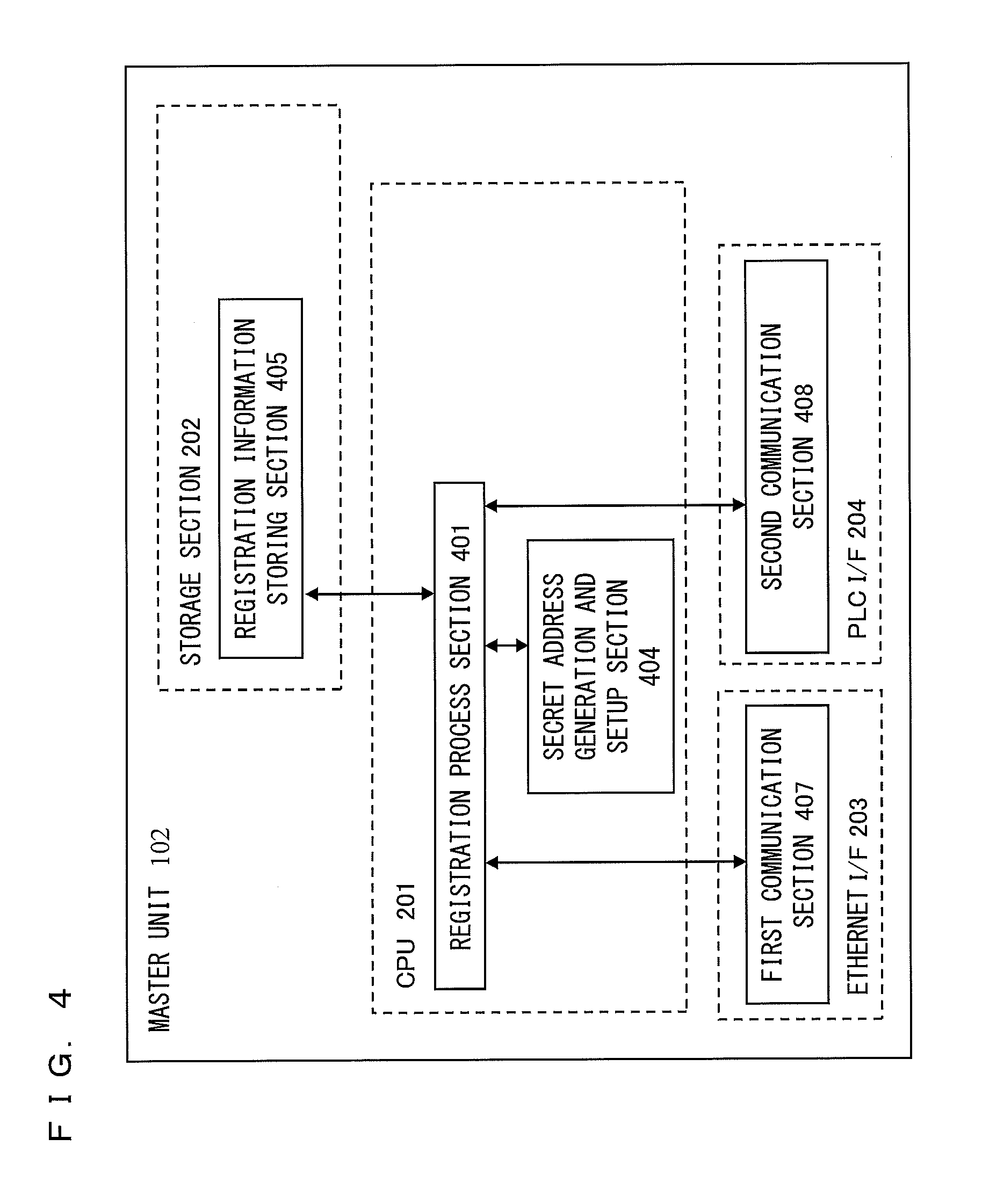
Master unit and slave unit
InactiveUS20110173447A1User identity/authority verificationDigital data authenticationAddress generatorKey generation
Provided is a communication device which securely registers a slave unit. A secret address generation and setup section generates a secret address generator, and a secret address of the slave unit used temporarily instead of a unique address of the slave unit based on the secret address generator and identification information of the slave unit. A second communication section transmits to the slave unit a registration start notice containing the secret address generator by broadcast. A registration process section generates a registration authentication key; generates a unique key of the slave unit by transmitting / receiving, to / from the slave unit, unique key generation information encrypted using the registration authentication key; receives, from the slave unit, the unique address of the slave unit encrypted using the registration authentication key; and stores the identification information in association with the unique address and the unique key of the slave unit in the registration information storing section.
Owner:PANASONIC CORP
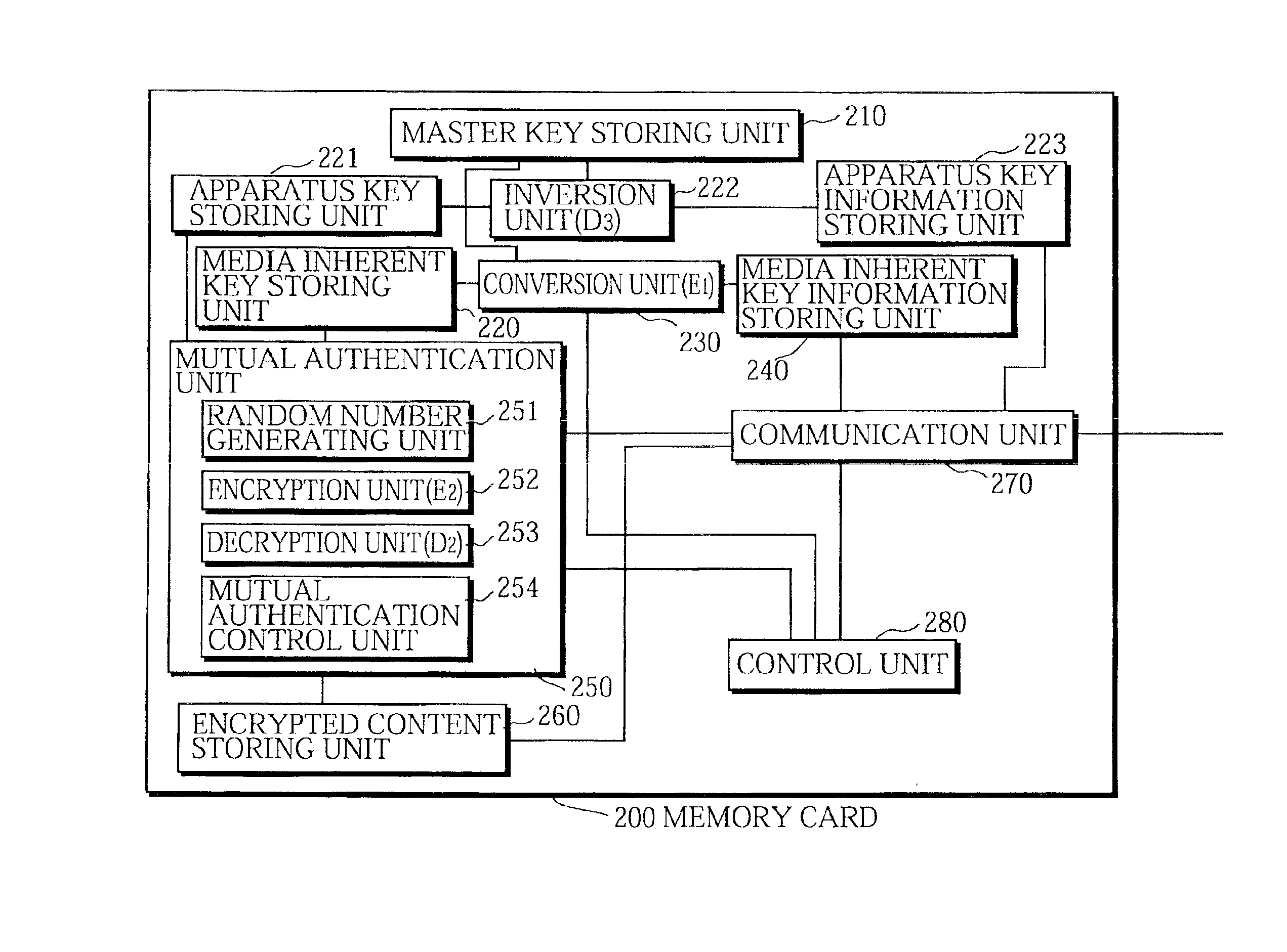
Digital content protection system
InactiveUS6859535B1Reduce scaleDigital data processing detailsUser identity/authority verificationDigital contentMediaFLO
The media inherent key storing unit 220 prestores an inherent key Ki, the conversion unit 230 generates an encrypted inherent key Ji from the inherent key read from the media inherent key storing unit 220, the random number generating unit 331 generates a random number R1, the encryption unit 252 generates an encrypted random number S1, the decryption unit 333 generates a random number R′1 from the encrypted random number R1, and the mutual authentication control unit 334 compares the random number R′1 with the random number R1 and, if the random number R′1 matches the random number R1, judges that the memory card 200 is an authorized device. If the memory card 200 and the memory card writer have successfully authenticated each other, the memory card writer encrypts a content using a decrypted inherent key. If the memory card 200 and the memory card reader have successfully authenticated each other, the memory card reader decrypts an encrypted content using the decrypted inherent key.
Owner:PANASONIC CORP
Usable security of online password management with sensor-based authentication
ActiveUS20120297190A1Improve usabilityAuthentication is convenientUser identity/authority verificationDigital data authenticationCryptographic protocolUsability
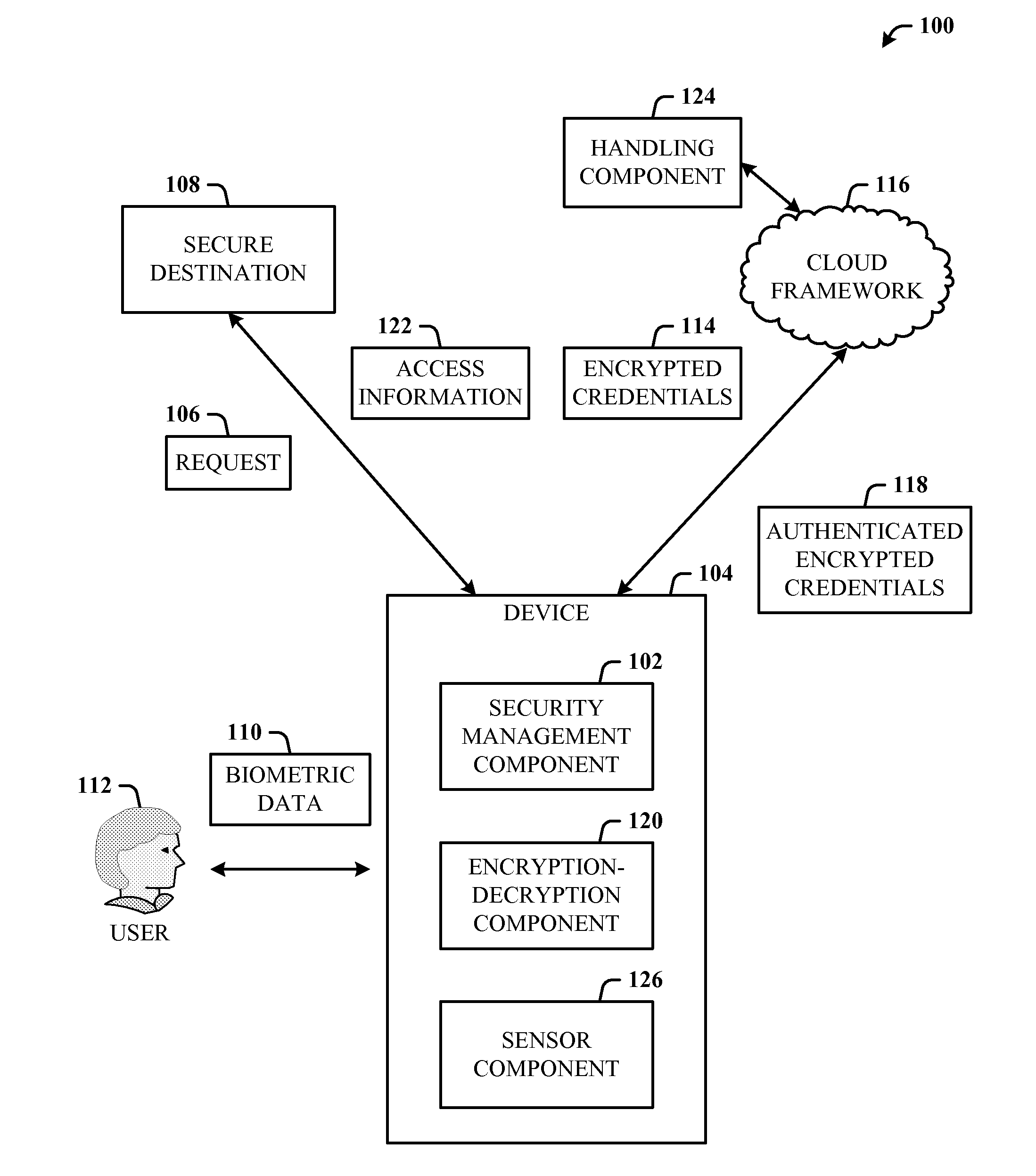
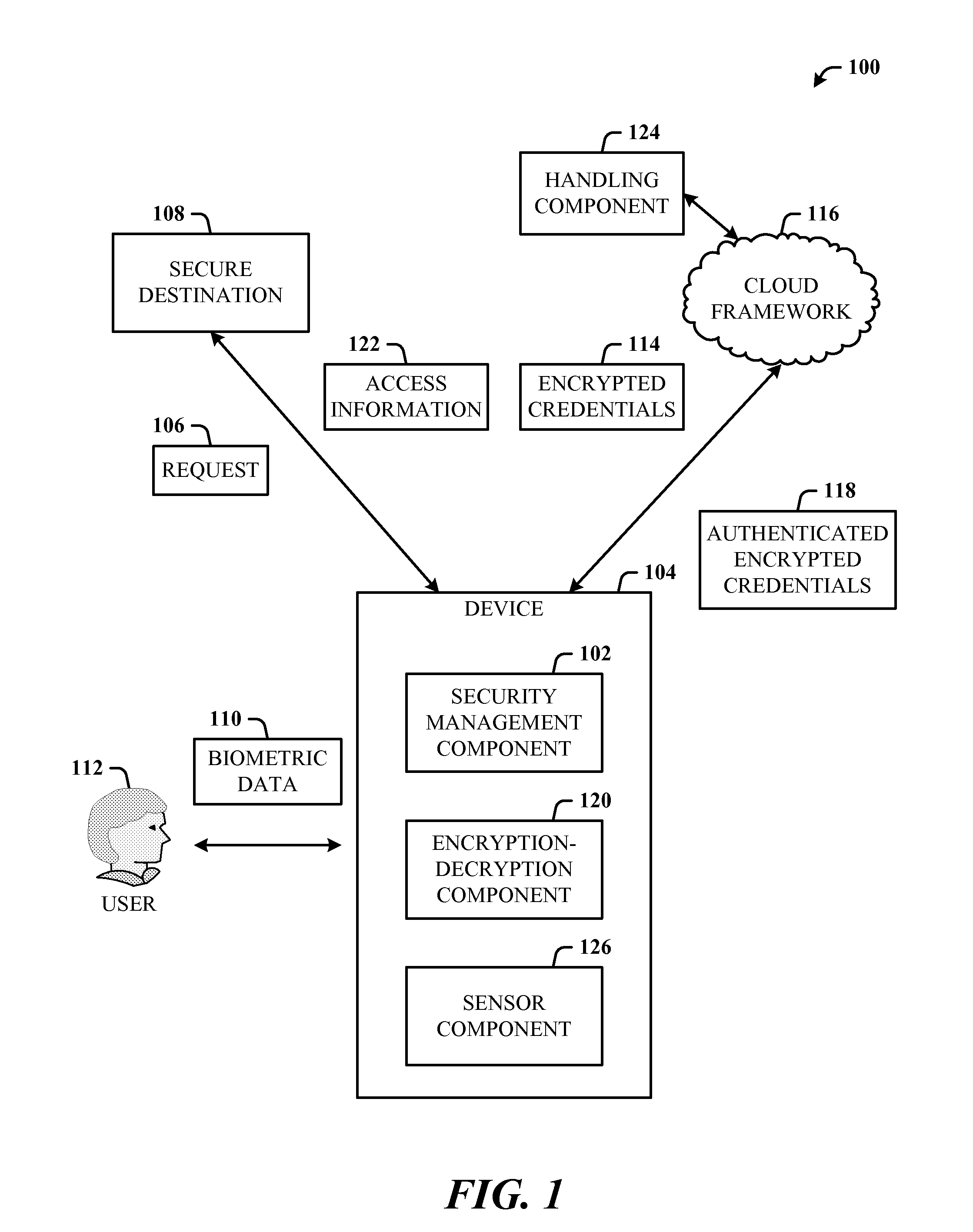
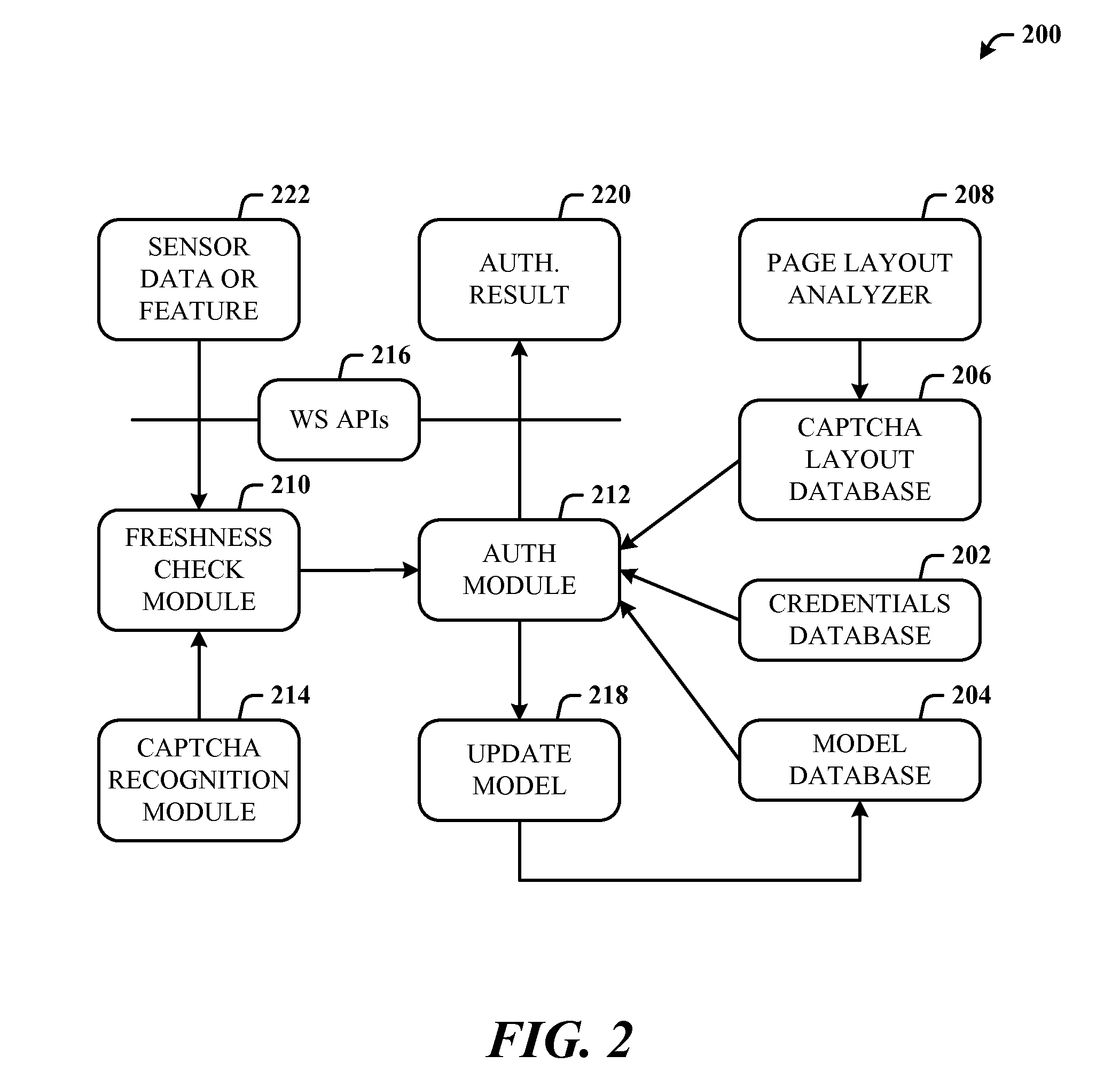
A multi-party security protocol that incorporates biometric-based authentication and withstands attacks against any single party (e.g., mobile phone, cloud, or the user). The protocol involves the function split between mobile and cloud and the mechanisms to chain-hold the secrets. A key generation mechanisms binds secrets to a specific device or URL (uniform resource locator) by adding salt to a master credential. An inline CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) handling mechanism uses the same sensor modality as the authentication process, which not only improves the usability, but also facilitates the authentication process. This architecture further enhances existing overall system security (e.g., handling untrusted or compromised cloud service, phone being lost, impersonation, etc.) and also improves the usability by automatically handling the CAPTCHA.
Owner:MICROSOFT TECH LICENSING LLC
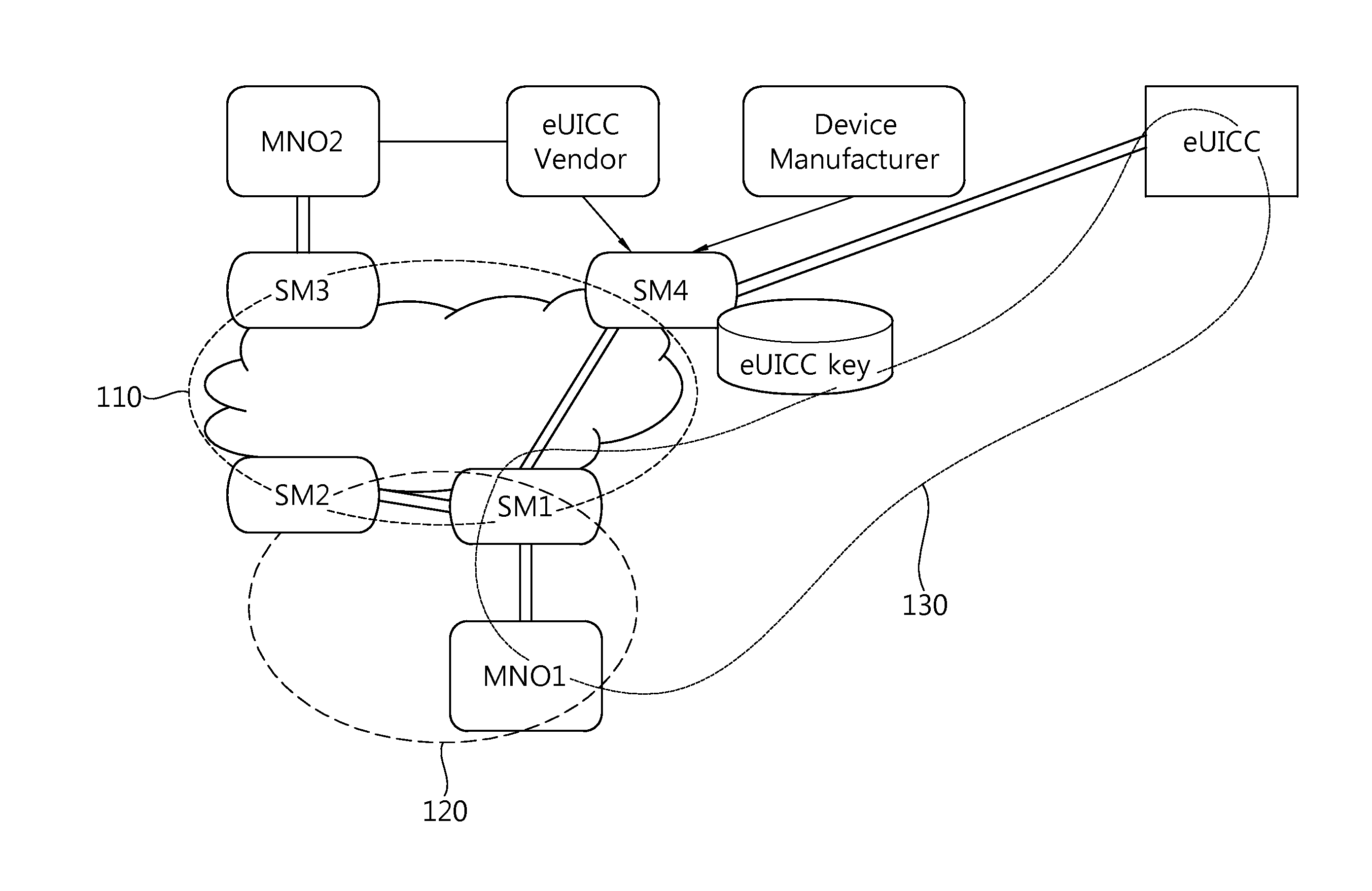
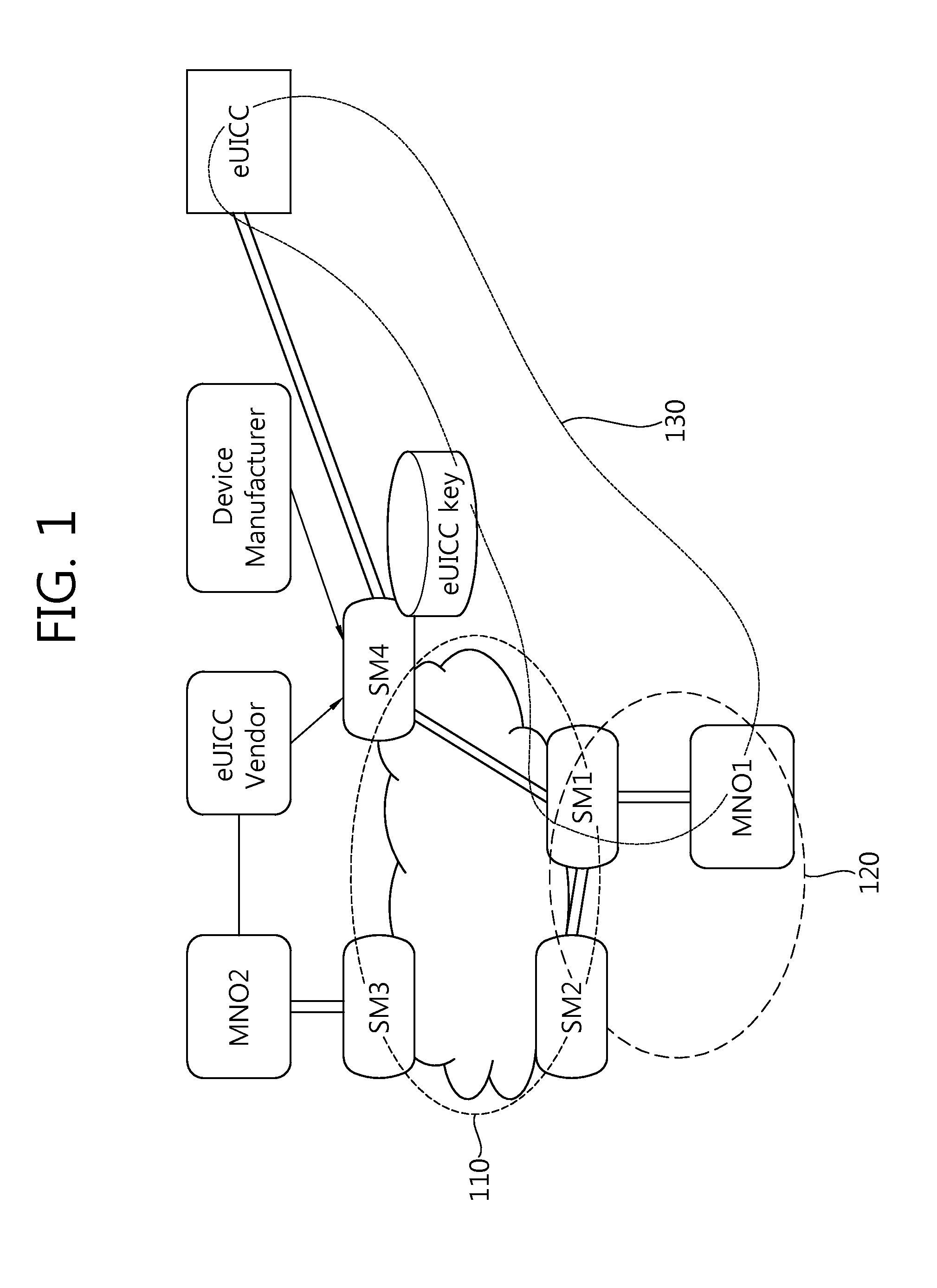
Method for changing mno in embedded sim on basis of dynamic key generation and embedded sim and recording medium therefor
The present invention Includes using an embedded SIM (eSIM) associated with a newly-opened mobile network operator (MNO) system and a receiving MNO system, the method performs the steps of: generating a security domain (SD) for a receiving MNO on the basis of a request from the newly-opened MNO system; injecting a prior SD key value; installing a secure applet for key generation and secure arithmetic operations, injecting a new SD key value on the basis of a request from the receiving MNO, and transmitting only a public key to the receiving MNO system after generating key pairs for the receiving MNO; and decoding a receiving MNO profile with a private key corresponding to the public key after receiving the receiving MNO profile from the receiving MNO system or the newly-opened MNO system.
Owner:SAMSUNG ELECTRONICS CO LTD
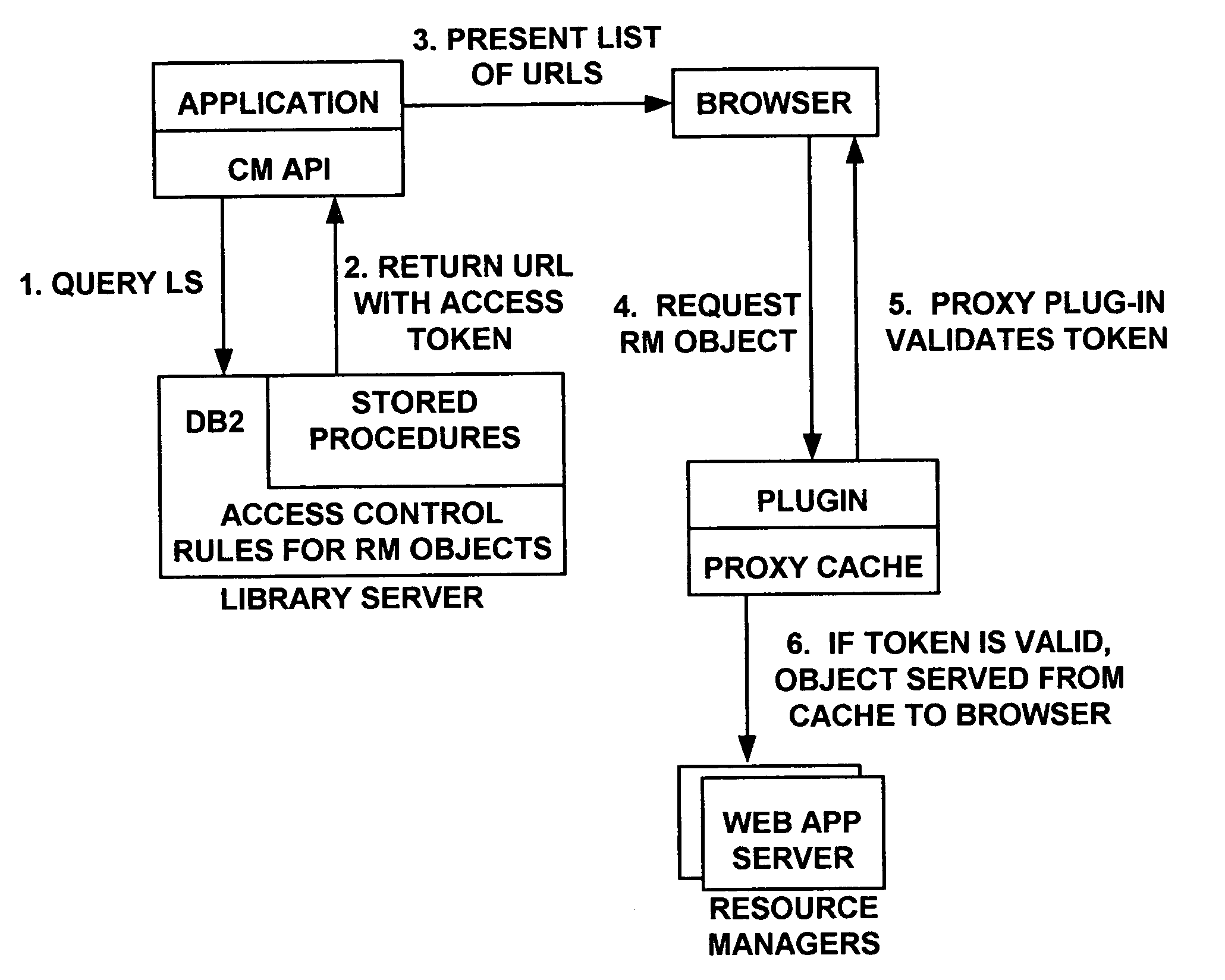
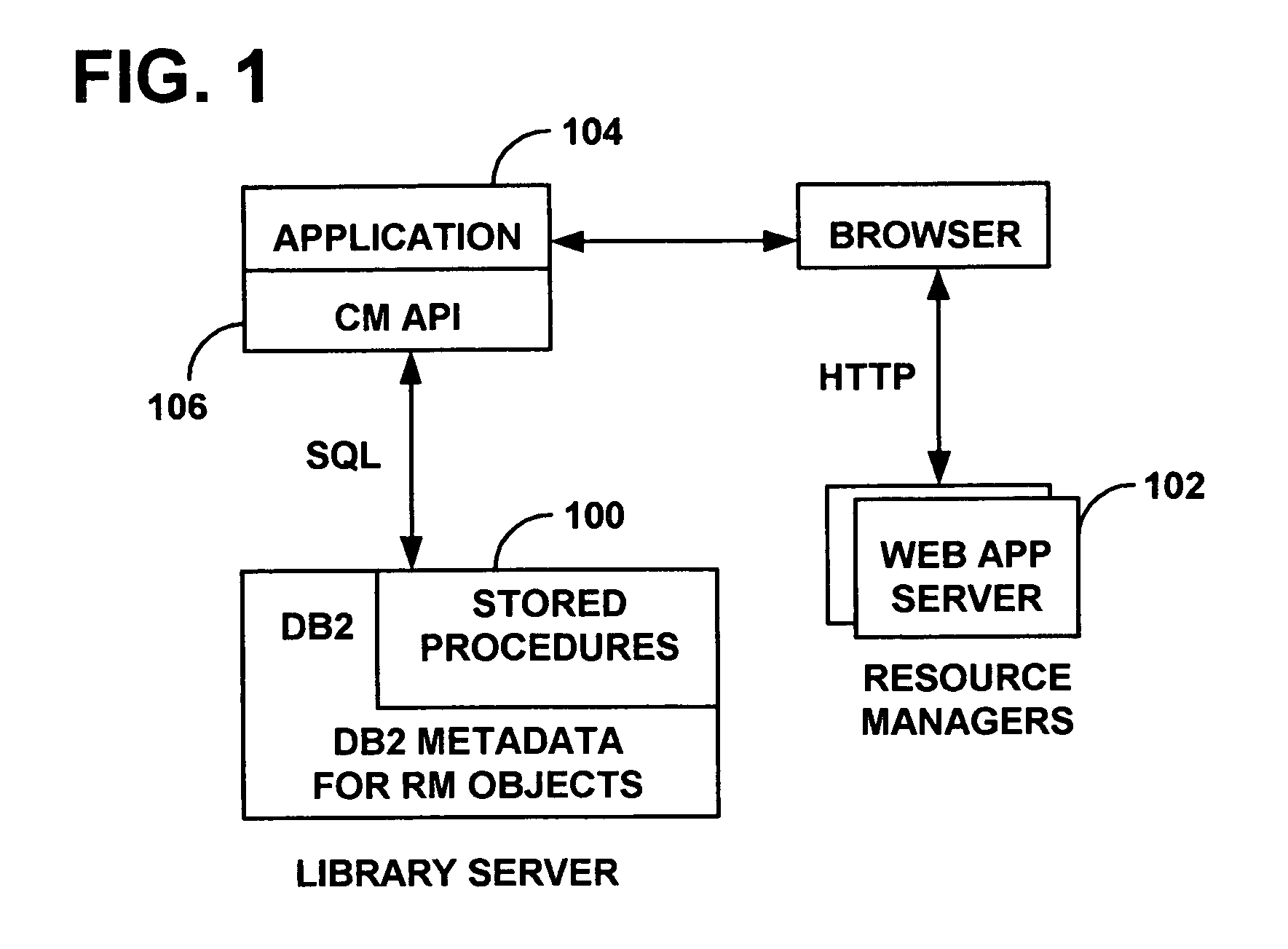
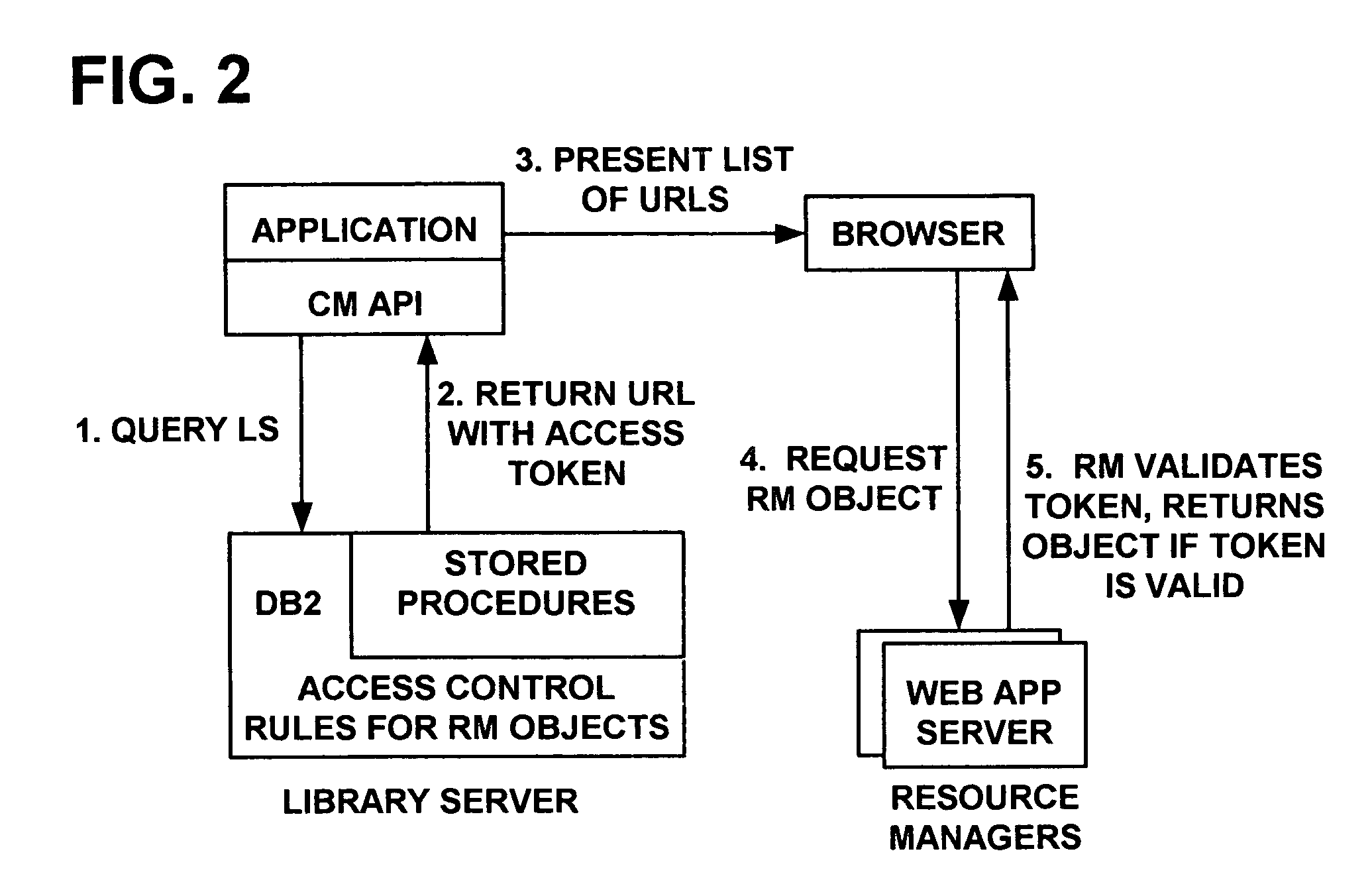
System and method for regulating access to objects in a content repository
ActiveUS20060080546A1Enhanced content managementImprove distributionDigital data processing detailsComputer security arrangementsDigital signatureResource management
A content management system integrated with a web caching proxy that delivers content according to access control rules. An access control token is generated using a secret key when a user selects a desired object (to be provided only upon token validation, thus the object retrieval and delivery task can be delegated). However, tokens for other content and / or for other users could be generated by a rogue resource manager. If the desired object is already cached, the proxy asks the resource manager to validate the token and then selectively provides the desired object without contacting a library server. Alternately, the proxy itself performs the token validation, but must coordinate with the library server to ensure it has the latest secret key. Finally, the tokens may contain digital signatures generated with a private key and validated with a corresponding public key, so that private keys need not be distributed.
Owner:DROPBOX
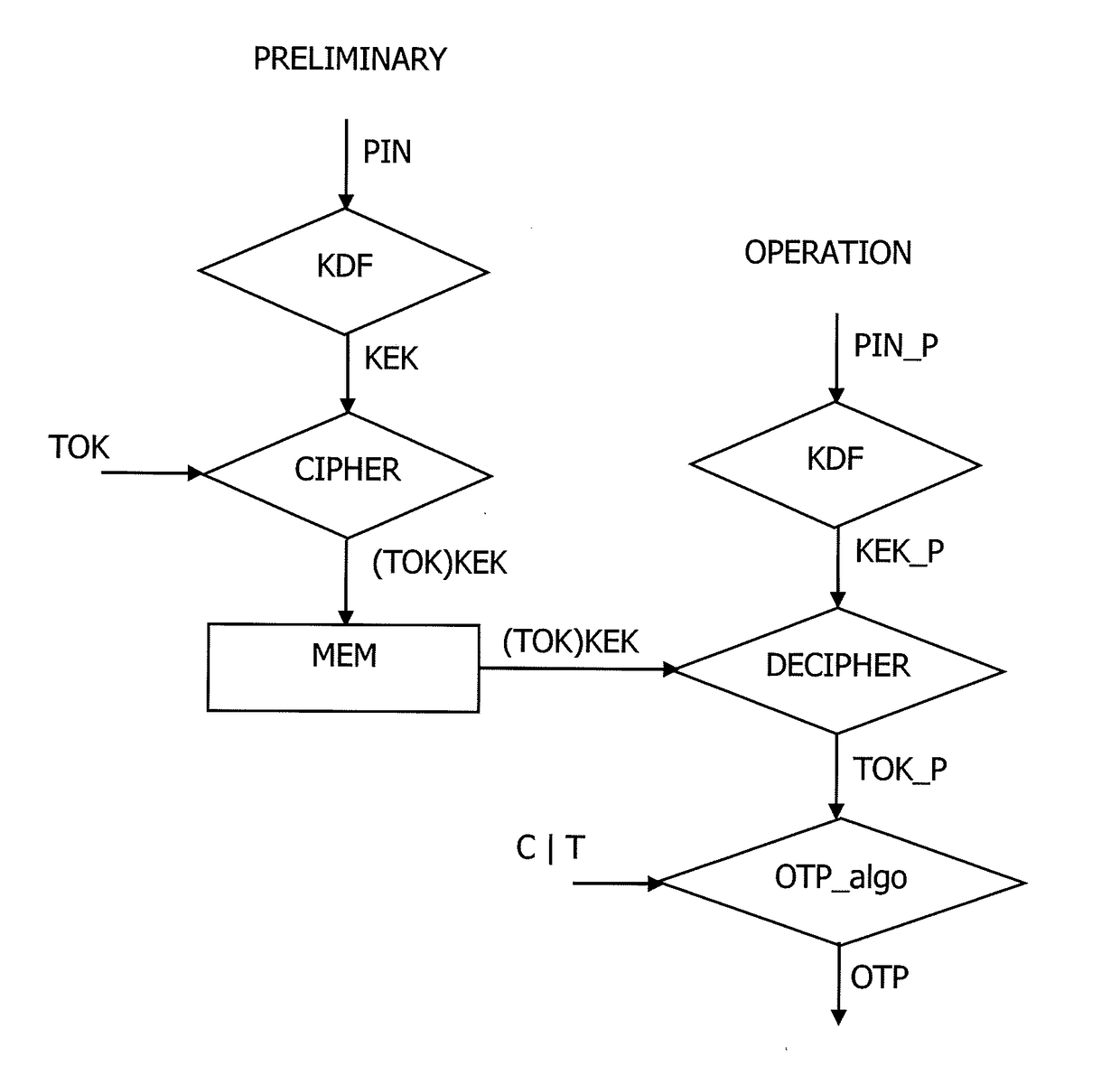
Method to manage a one time password key
InactiveUS20170104739A1Synchronising transmission/receiving encryption devicesUser identity/authority verificationPersonal identification numberUser device
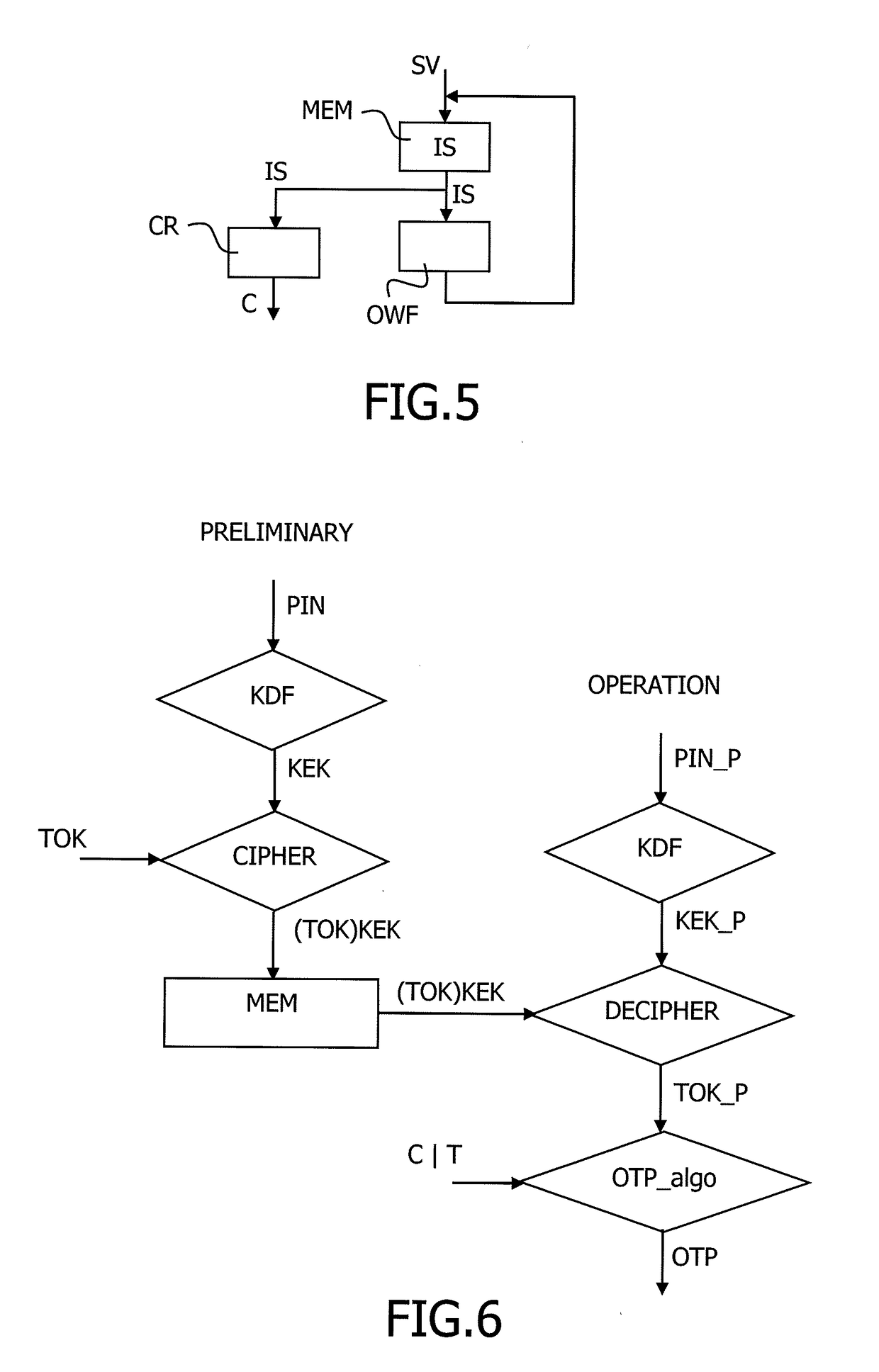
The present invention relates to a method to manage a One Time Password key, referenced OTP key, used in an OTP algorithm in a user device having access to an unsafe storage including the steps of retrieving a Personal Identification Number, named PIN, of a user of the user device, deriving a symmetric key from the PIN, encrypting the OTP key using the derived symmetric key, storing the encrypted OTP key in the unsafe storage, decrypting the OTP key using the derived symmetric key, and generating a next OTP key using an incremental parameter, wherein the start value of the incremental parameter of the OTP key generation is random.
Owner:GEMPLU
Achieving high assurance connectivity on computing devices and defeating blended hacking attacks
ActiveUS7490350B1Improve integrityAttack is still possibleMultiple digital computer combinationsInternal/peripheral component protectionCommunications systemPrivate network
System and techniques for protecting wireless communication systems from blended electronic attacks that may combine wireless and computer attacks. One embodiment is an integrated hardware and software firewall / protection system that provides a protection scheme that may include an additional functional processing layer between the hardware firewall and a mobile terminal. This additional functional processing layer performs an extra layer of communications and security processing, including such features as management of Internet Connection Firewall (ICF) functions, key generation for firewall and virtual private network (VPN) functions, and packet inspection and filtering.
Owner:TECNICA
Threshold and identity-based key management and authentication for wireless ad hoc networks
InactiveUS20060023887A1Reduce usageReduce resource requirementsKey distribution for secure communicationPublic key for secure communicationConfidentialityWireless ad hoc network
As various applications of wireless ad hoc network have been proposed, security has become one of the big research challenges and is receiving increasing attention. The present invention provides for a distributed key management and authentication approach by deploying the recently developed concepts of identity-based cryptography and threshold secret sharing. Without any assumption of pre-fixed trust relationship between nodes, the ad hoc network works in a self-organizing way to provide the key generation and key management service, which effectively solves the problem of single point of failure in the traditional public key infrastructure (PKI)-supported system. The identity-based cryptography mechanism provided not only to provide end-to-end authenticity and confidentiality, but also saves network bandwidth and computational power of wireless nodes.
Owner:UNIVERSITY OF CINCINNATI
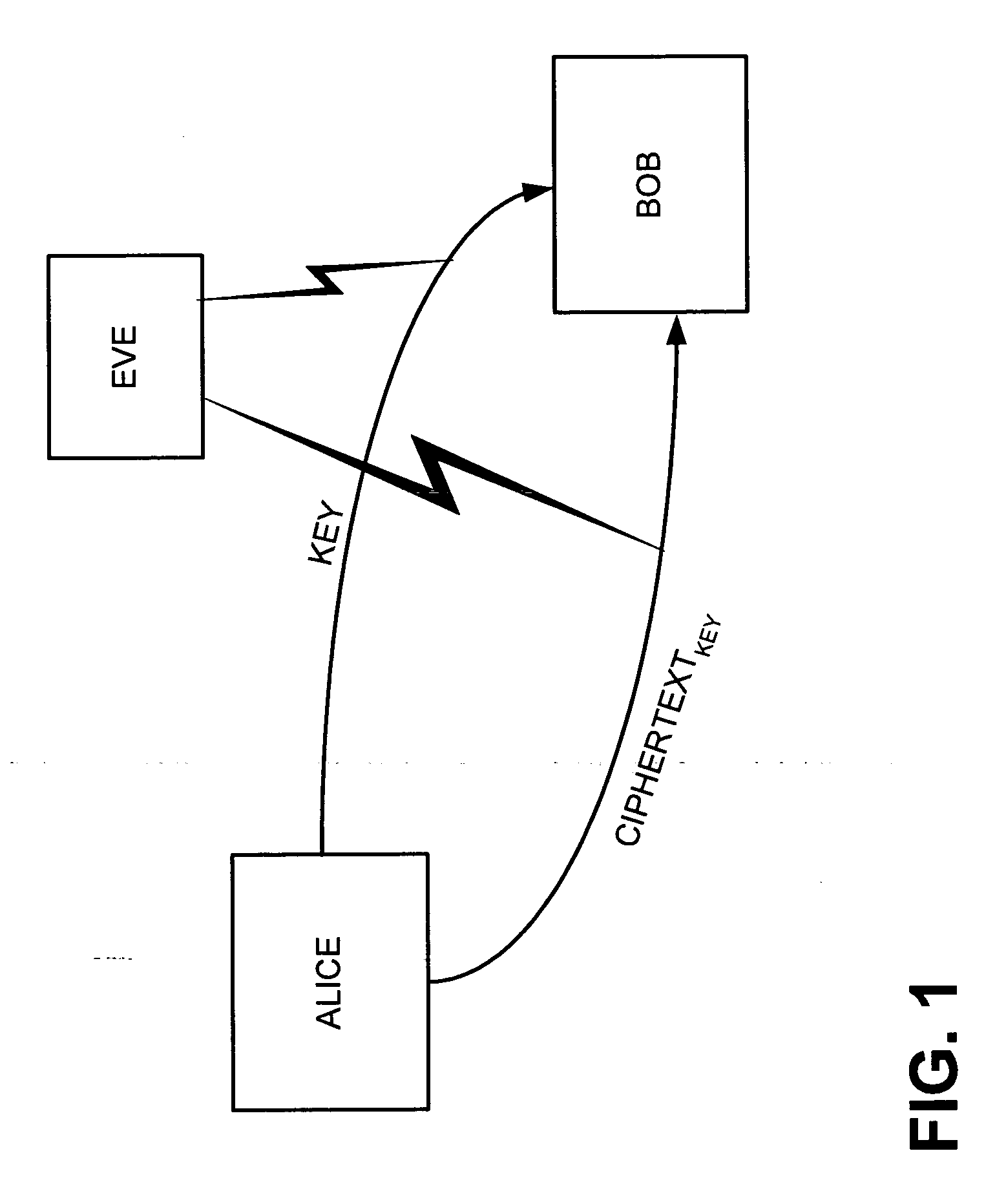
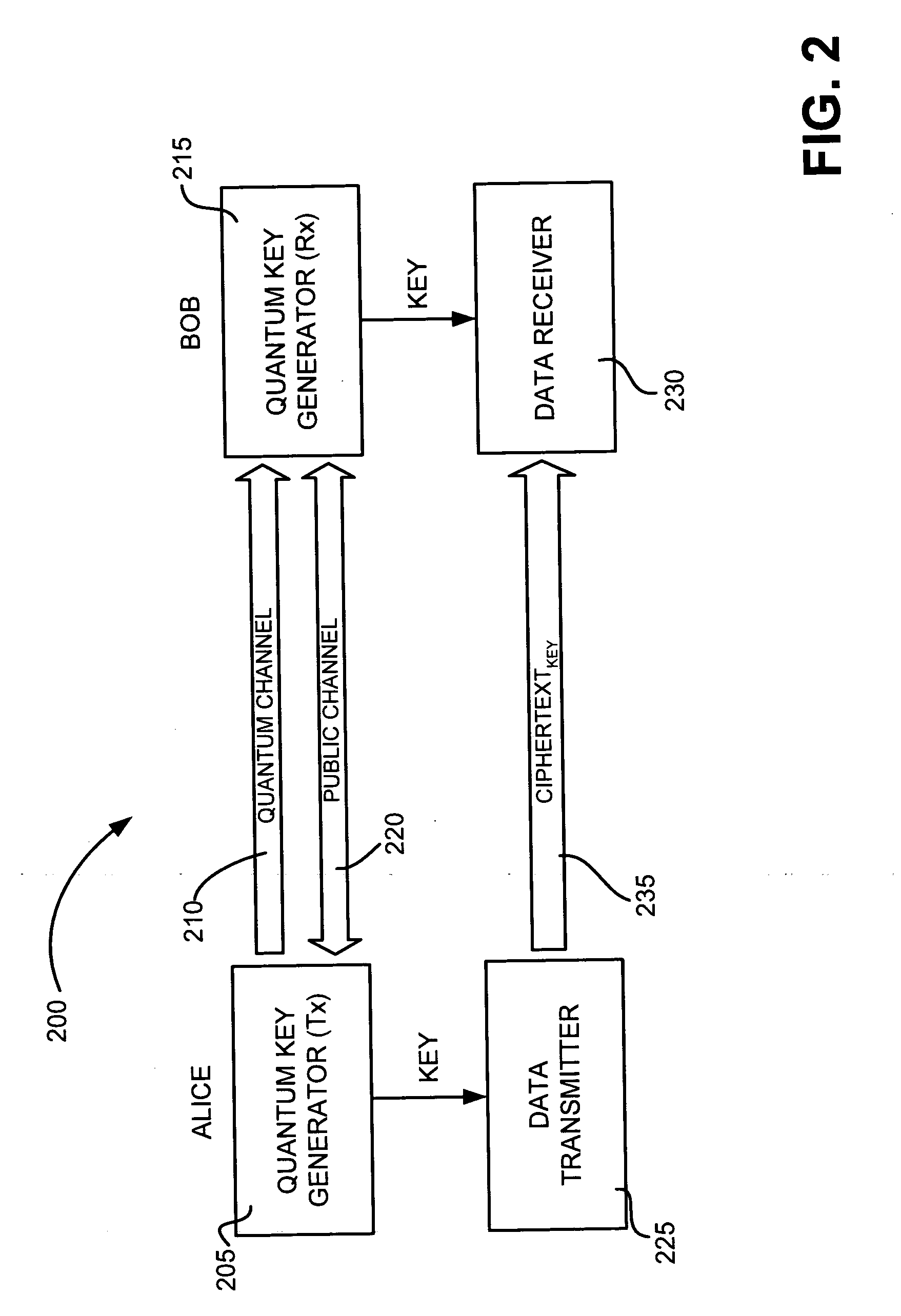
Quantum key distribution system
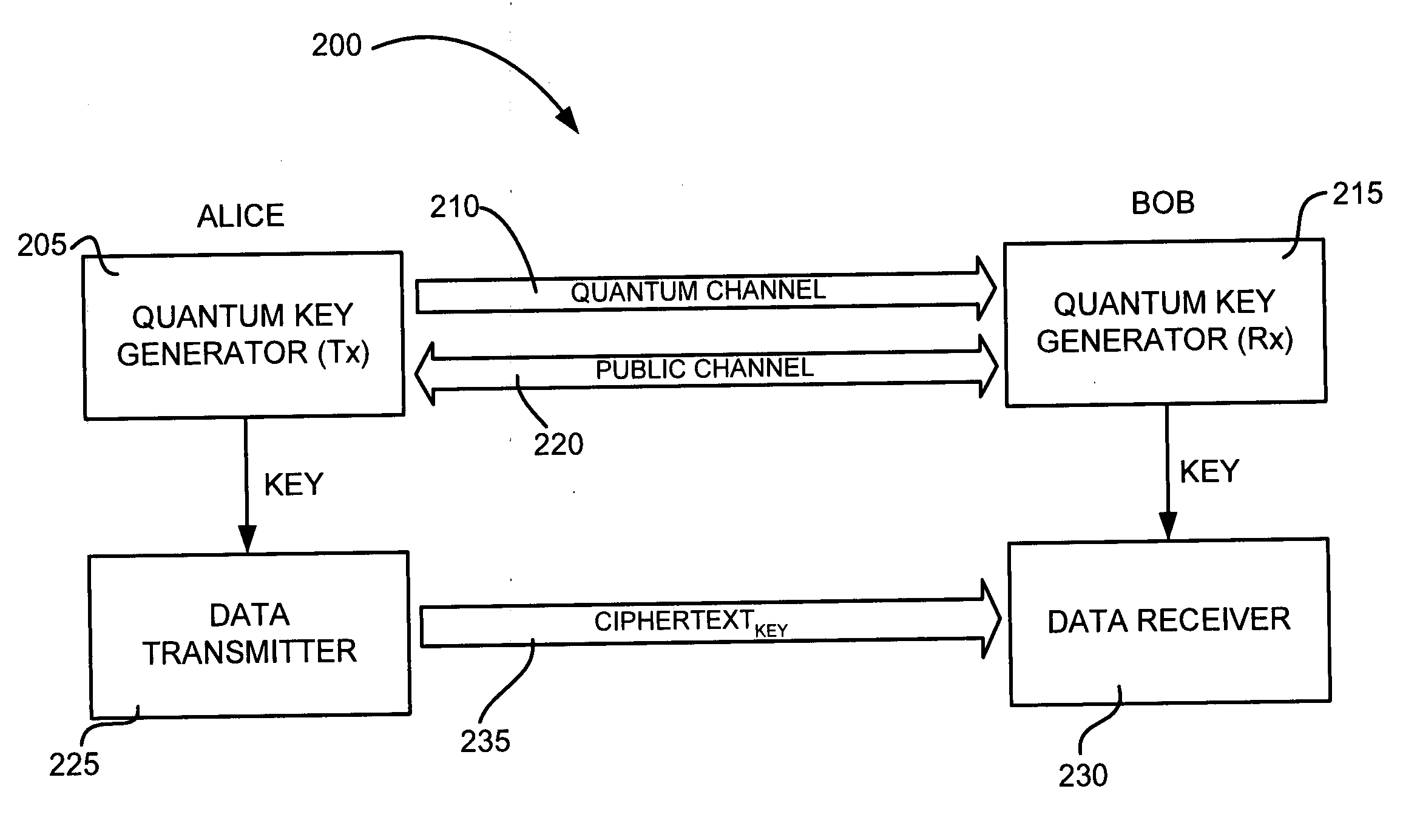
ActiveUS20070076884A1Key distribution for secure communicationUser identity/authority verificationKey generationTransmitter
A method is provided for distributing quantum cryptographic keys. The method includes receiving a first quantum signal from an initial quantum key generating transmitter. Following correspondence with the initial quantum key generating transmitter, a first quantum key is generated. A second quantum signal is transmitted to a recipient quantum key generating transmitter. Following correspondence with the recipient quantum key generating receiver, a second quantum key is generated. The first quantum key is encoded using the second quantum key. The encoded first quantum key is transmitted to the recipient quantum key generating receiver using the second quantum key.
Owner:VERIZON PATENT & LICENSING INC
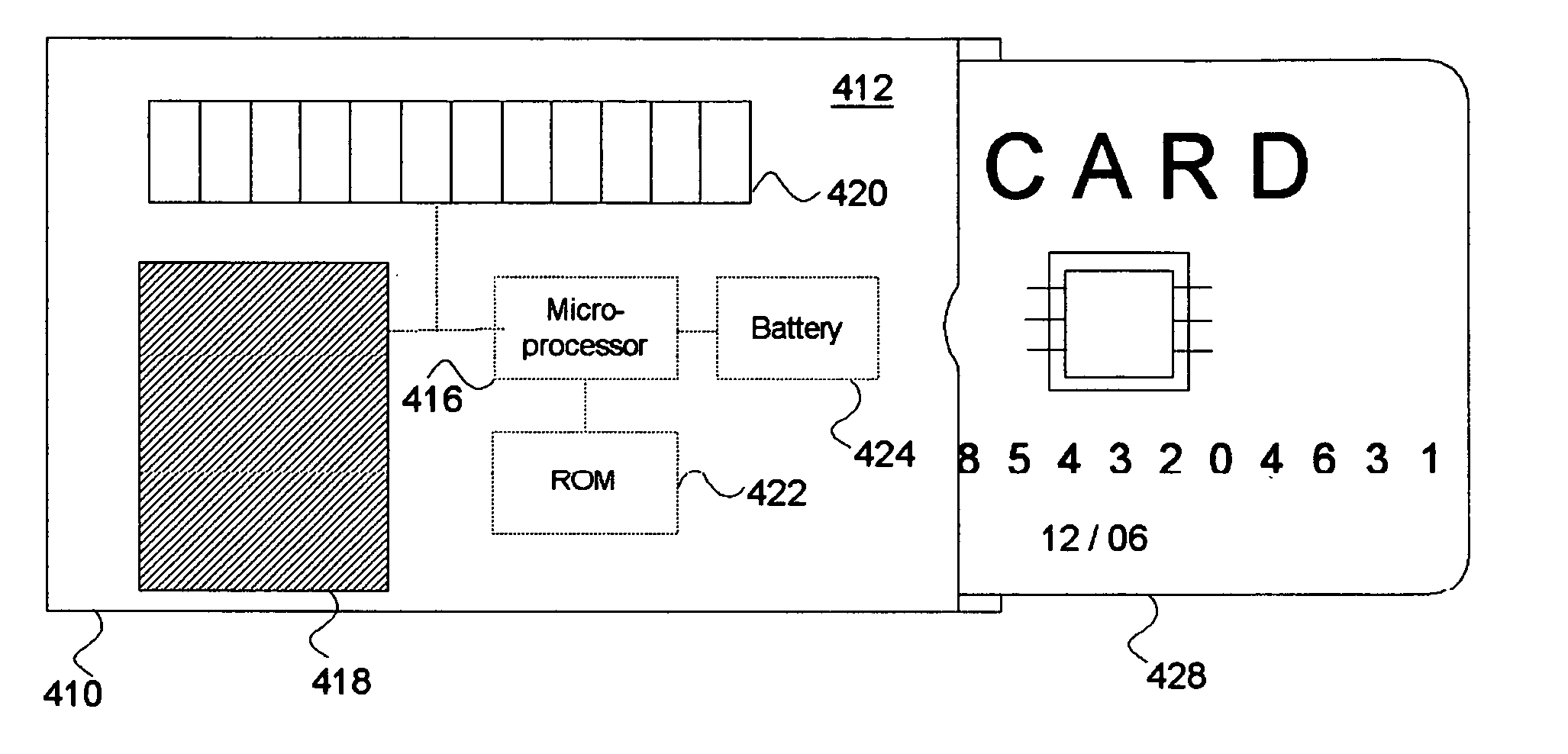
Bio-metric smart card, bio-metric smart card reader, and method of use
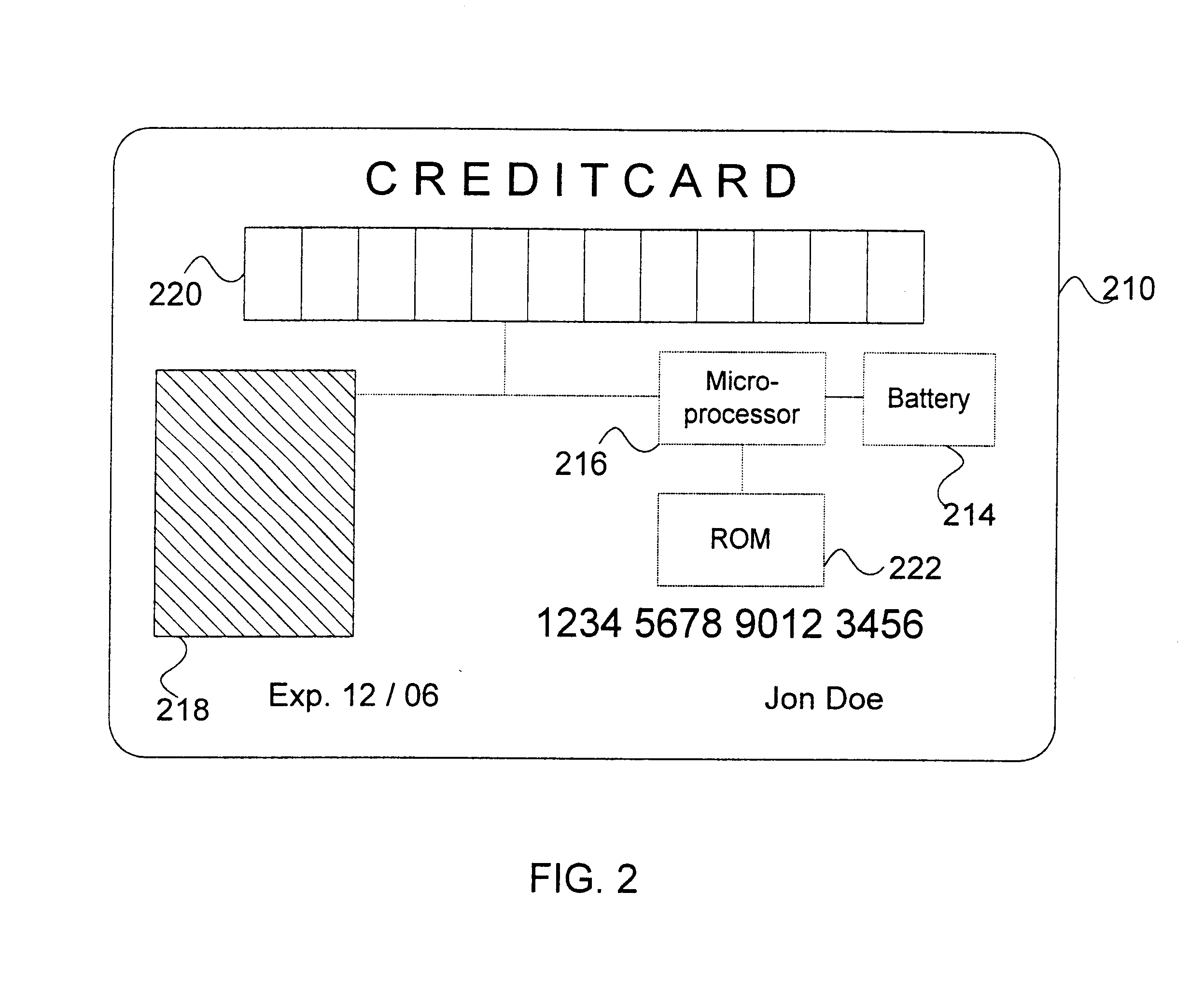
A system for increasing transaction security across existing infrastructure is provided. A user bio-metric sensor device is integrated into a credit or debit card. A display unit provides a key, preferably encrypted, upon successful utilization of the sensor device. Included in the key generation mechanism is an indicator of the transaction number or other sequential count indicative of card use. An authorization service decrypts the key in a manner at least partially dependent upon a second sequential count maintained in sync with the first count to determine whether the use is authorized. In one embodiment, a separate credit card reader may be configured to read conventional credit cards, smart cards, and credit cards incorporating such bio-metric sensor devices.
Owner:MCGREGOR CHRISTOPHER M +2
Digital content cryptograph and process
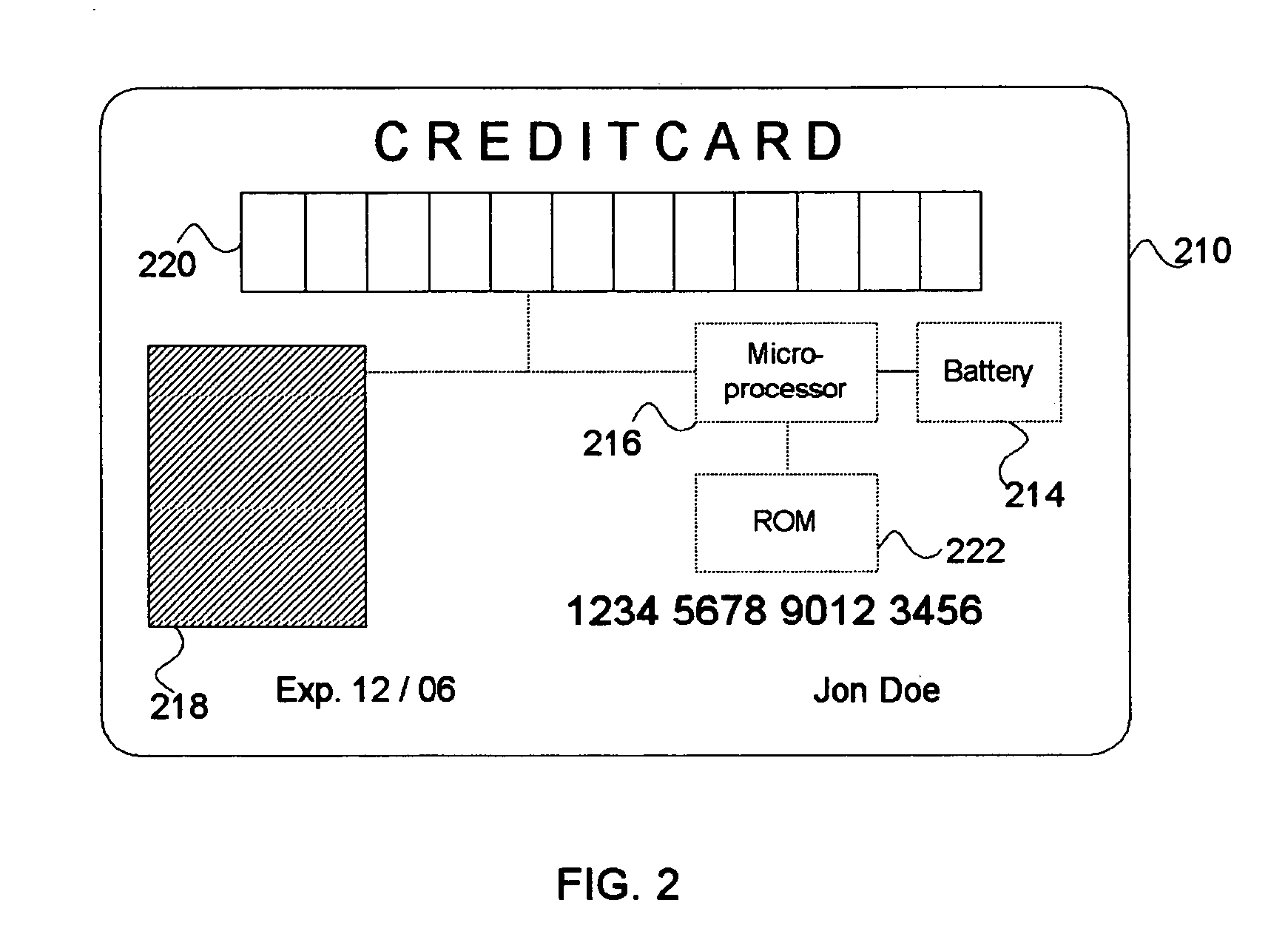
InactiveUS6892306B1Easy to optimizeLimited abilityKey distribution for secure communicationData processing applicationsDigital contentS/KEY
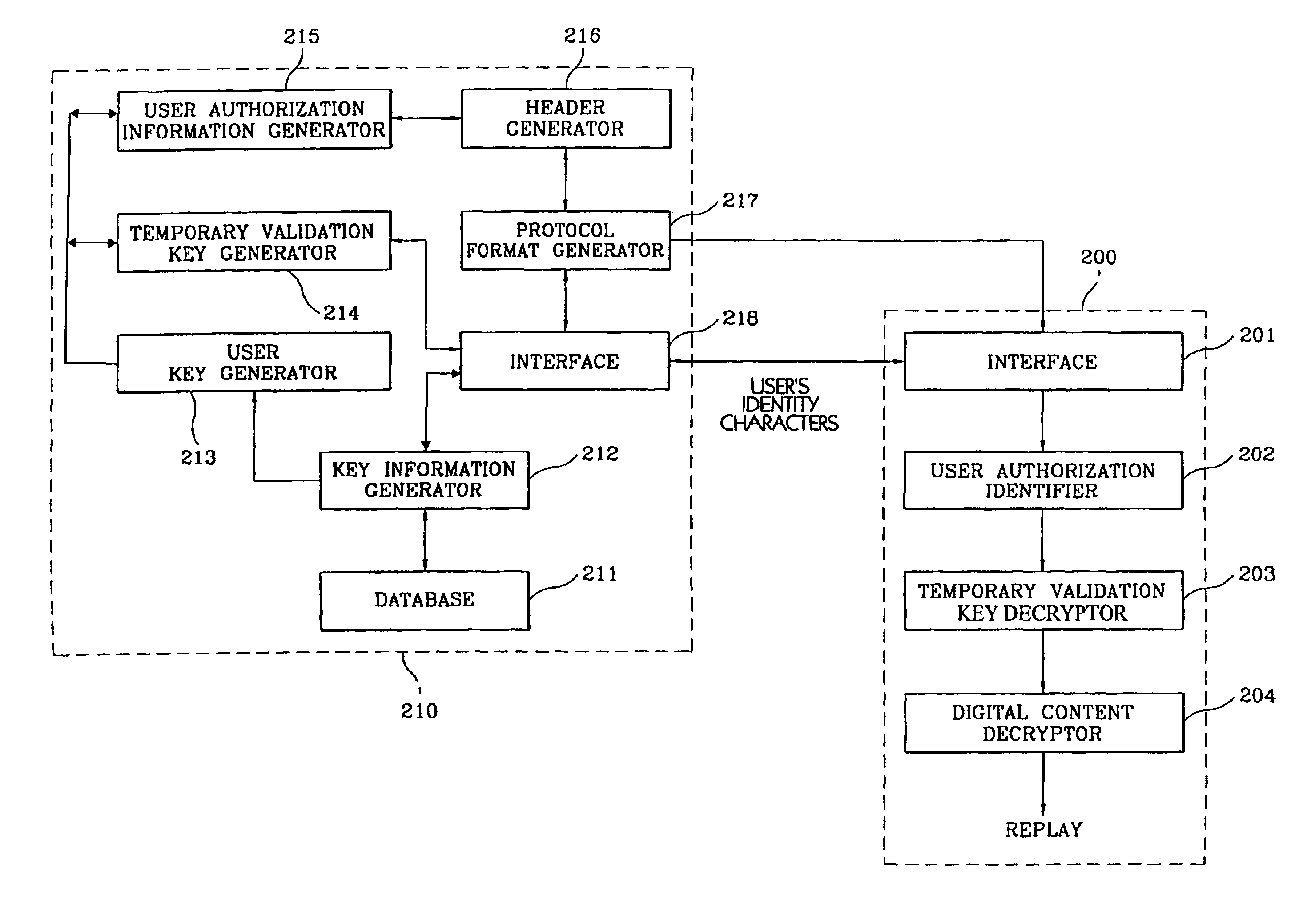
A digital cryptograph and encryption process encrypts and transmits in a digital format specific items of information requested by a user of a digital content transmission system by using key information, a user's key and a temporary validation key, to decrypt and replay the encrypted digital information at the user's terminal by using the key information and the user's authorization information. Each registered subscribing user is provided with unique key information. The user key is generated by applying the key information to a key generation algorithm. The temporary validation key that is created when the registered user accesses the server, is encrypted with the user key. The digital information is encrypted by using the temporary validation key in an encryption algorithm. The decryption algorithm allows the user to decrypt and replay the encrypted digital information upon receipt of the key information that has a one-to-one correspondence to the identity characters of the registered subscribing user.
Owner:SAMSUNG ELECTRONICS CO LTD
Apparatus, method and computer program product providing unified reactive and proactive handovers
InactiveUS20070224993A1Network traffic/resource managementRadio/inductive link selection arrangementsUser equipmentKey generation
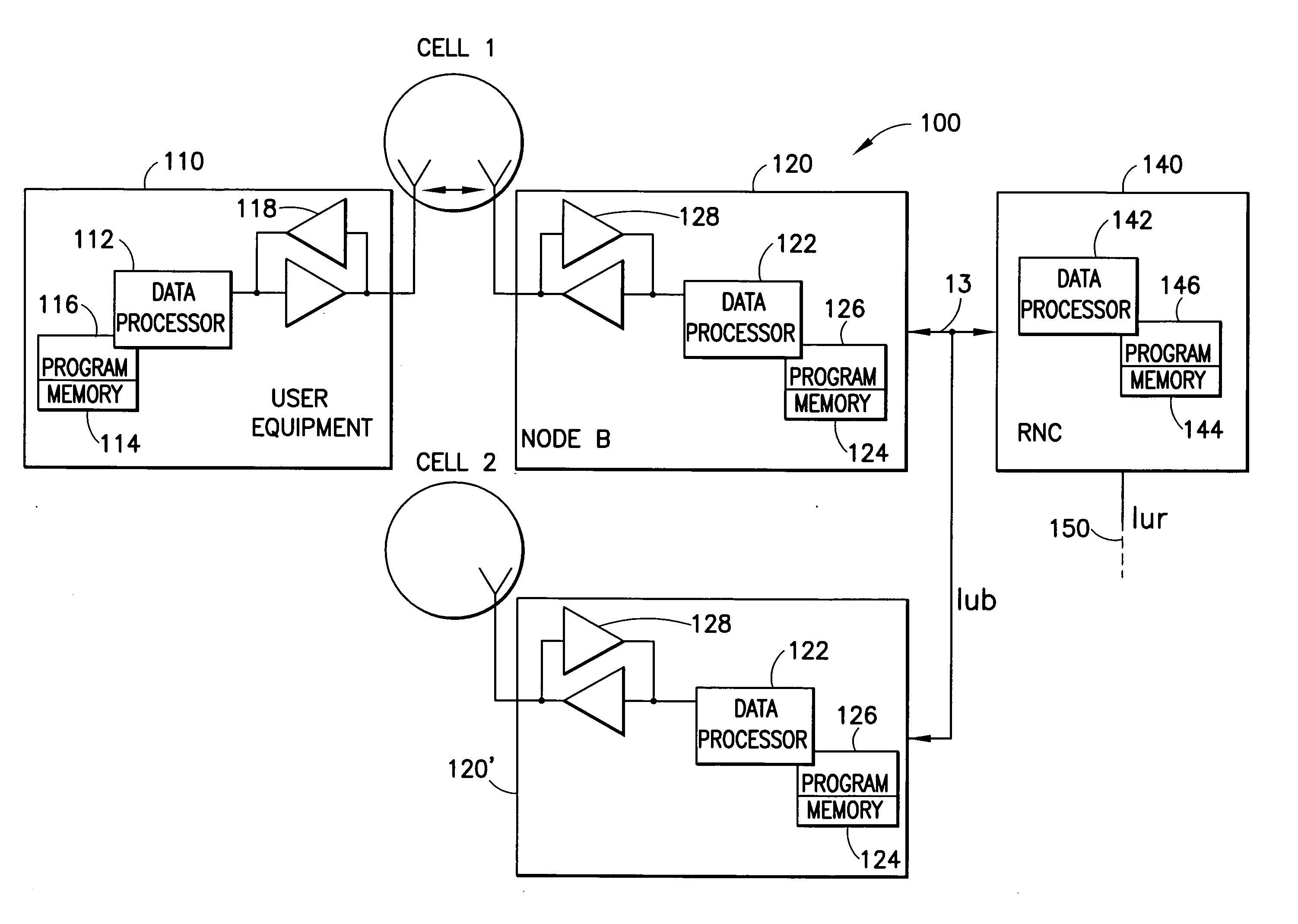
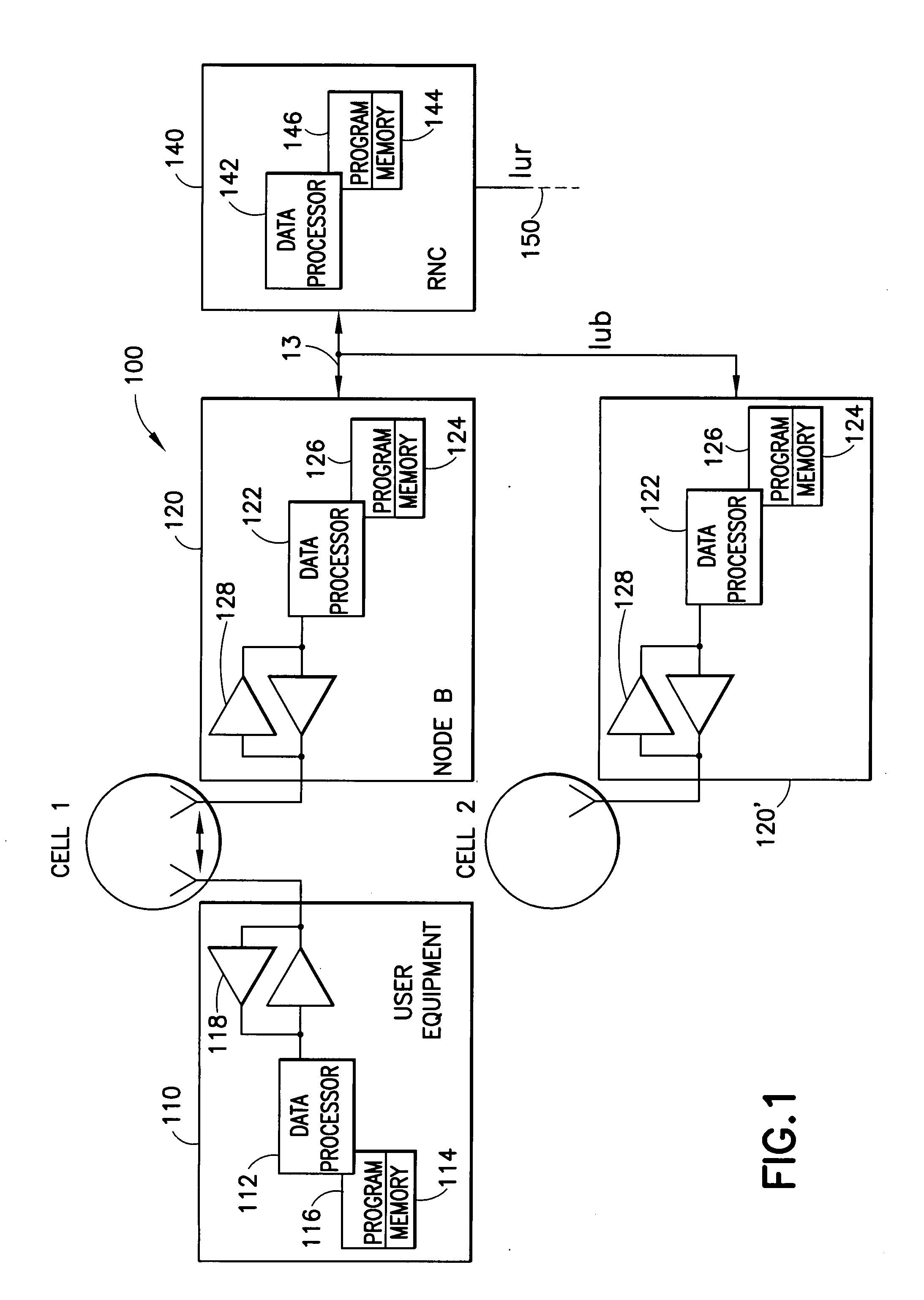
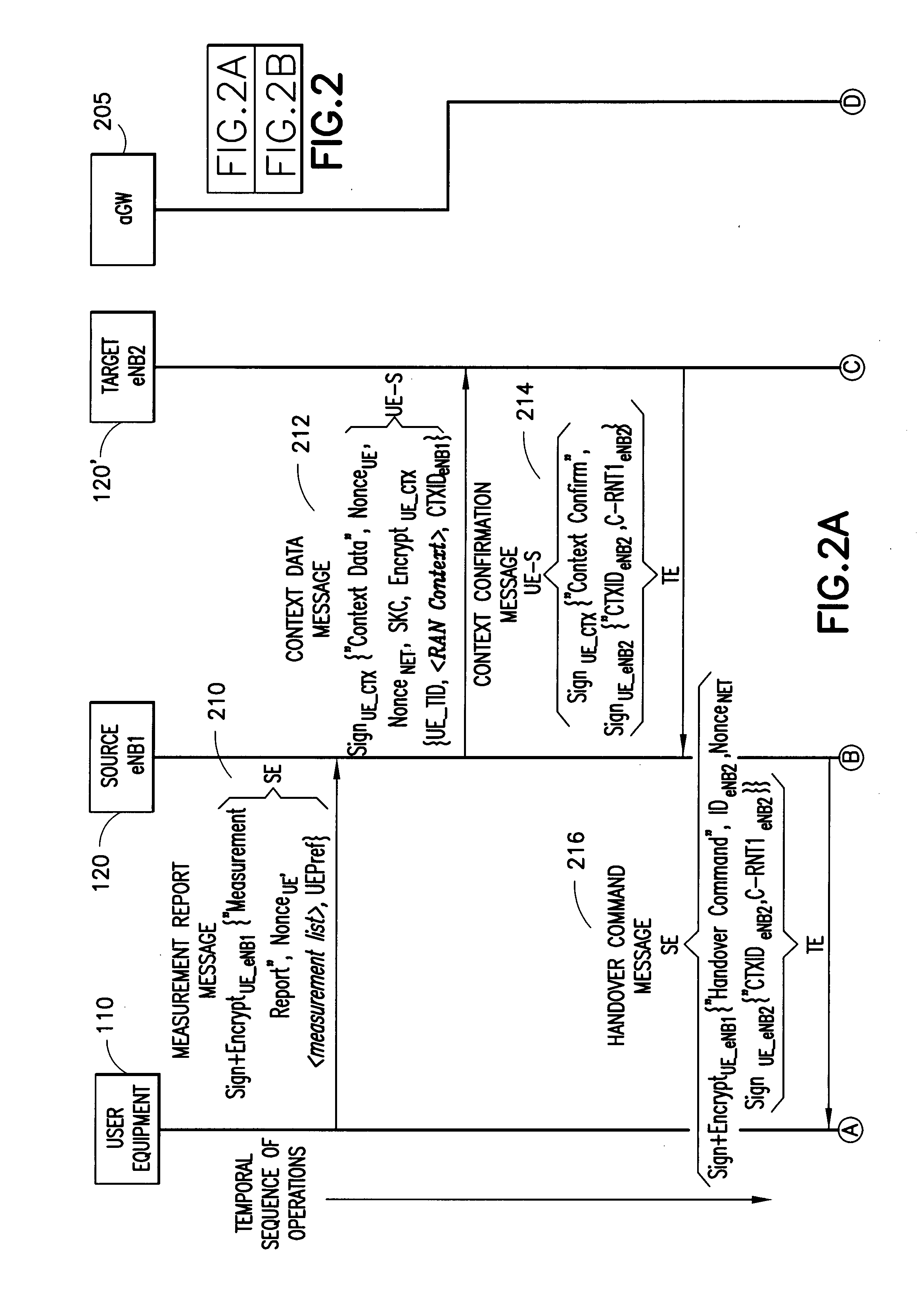
Apparatus, methods and computer program products incorporate improvements that provide enhanced security during handovers in a cellular wireless communications network. In one aspect, user equipment performs additional operations during handover to improve security. During such operations, user equipment begins key generation based on a predicted target base station before it is notified of the handover decision. User equipment also signs certain communications generated during handover operations to prevent hijacked base stations from generating false location updates. Separate keys are used to authenticate communications made by base stations during handover proceedings defeating, for example, logical theft of service attacks since a target base station's signature and encrypted content is required to be sent to the user equipment before the user equipment can switch to the target base station. In other aspects, user equipment assigns location updates sequence numbers and the active gateway keeps track of them defeating attacks based on replay of intercepted location update messages.
Owner:NOKIA CORP
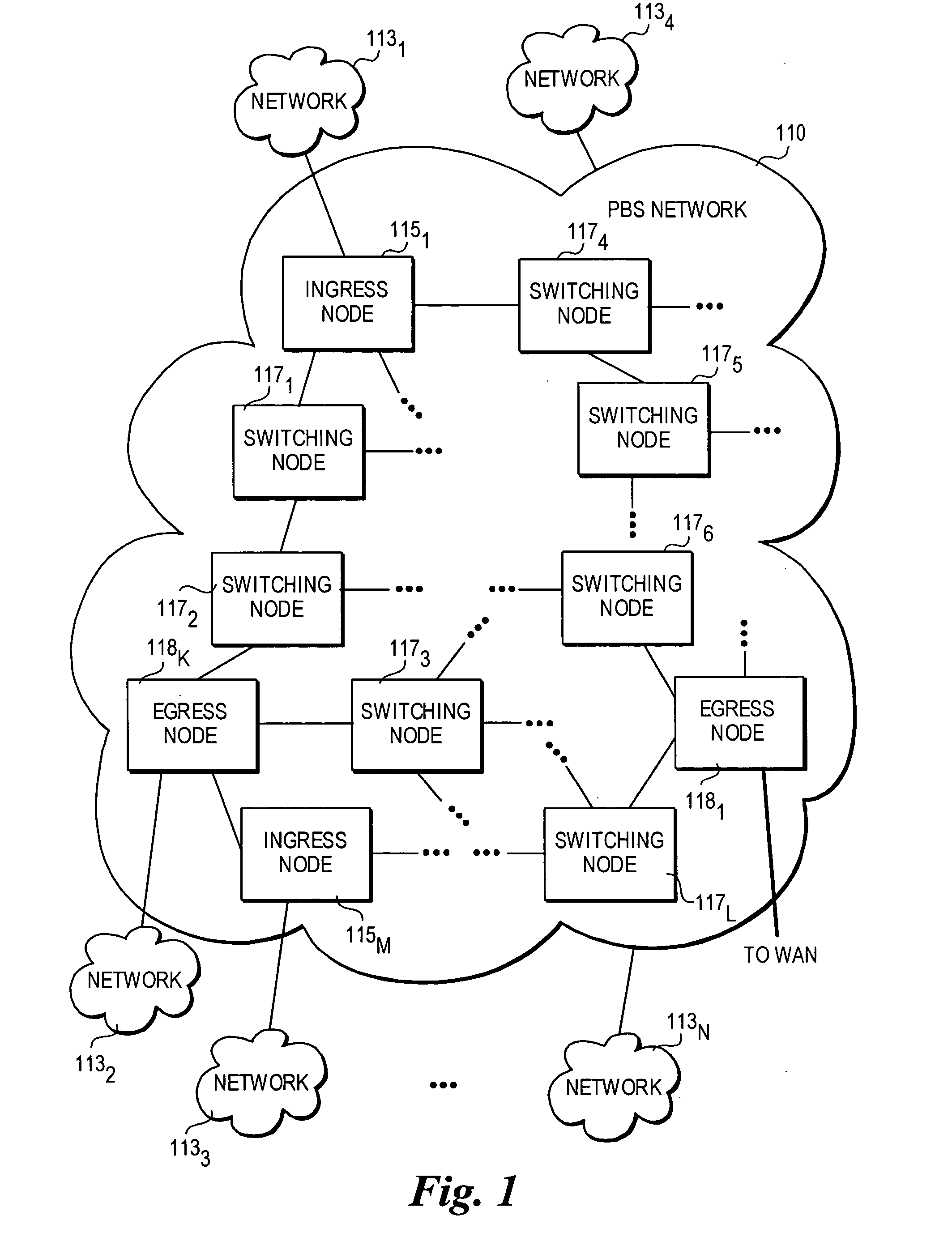
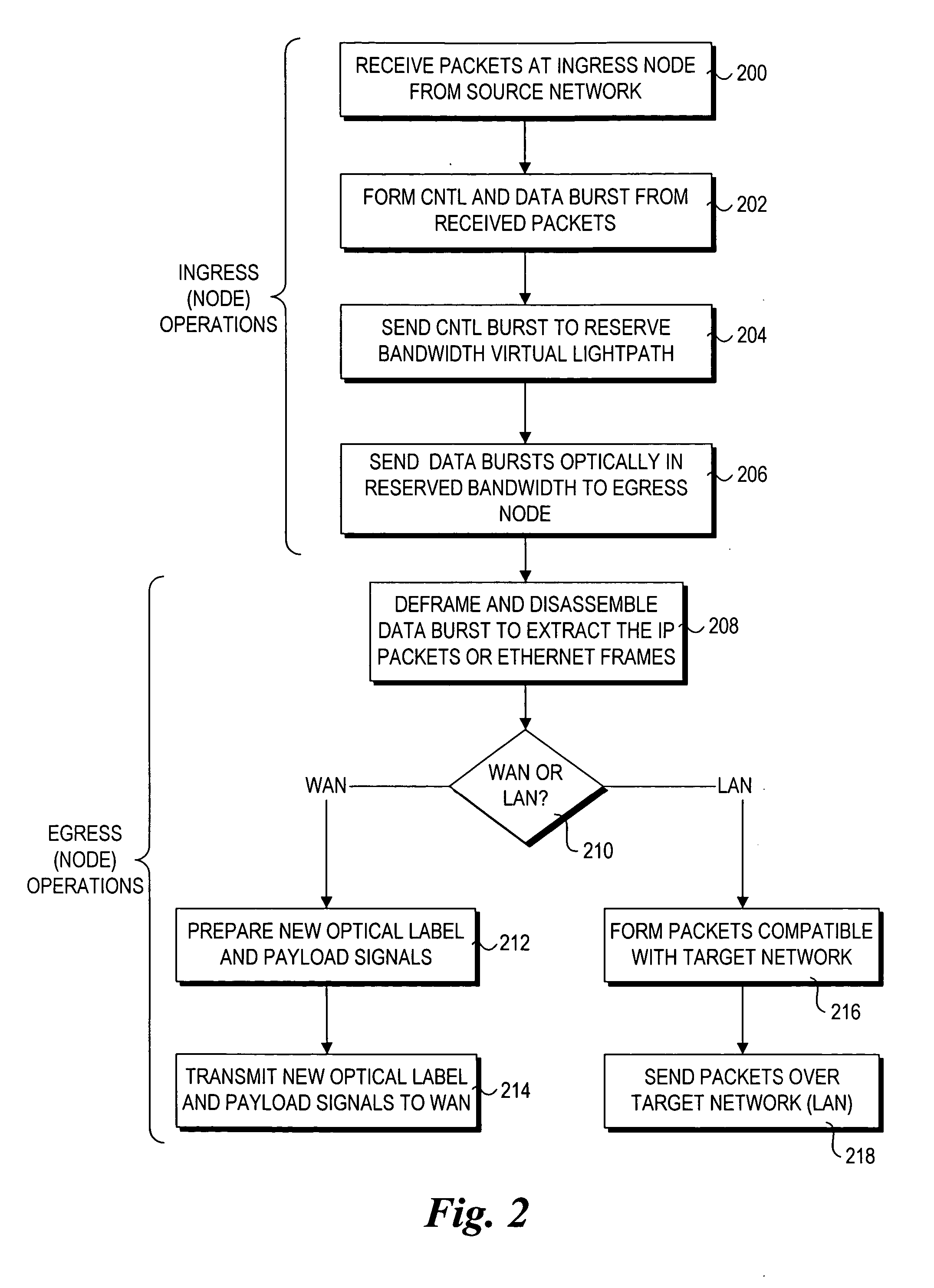
Method and architecture for security key generation and distribution within optical switched networks
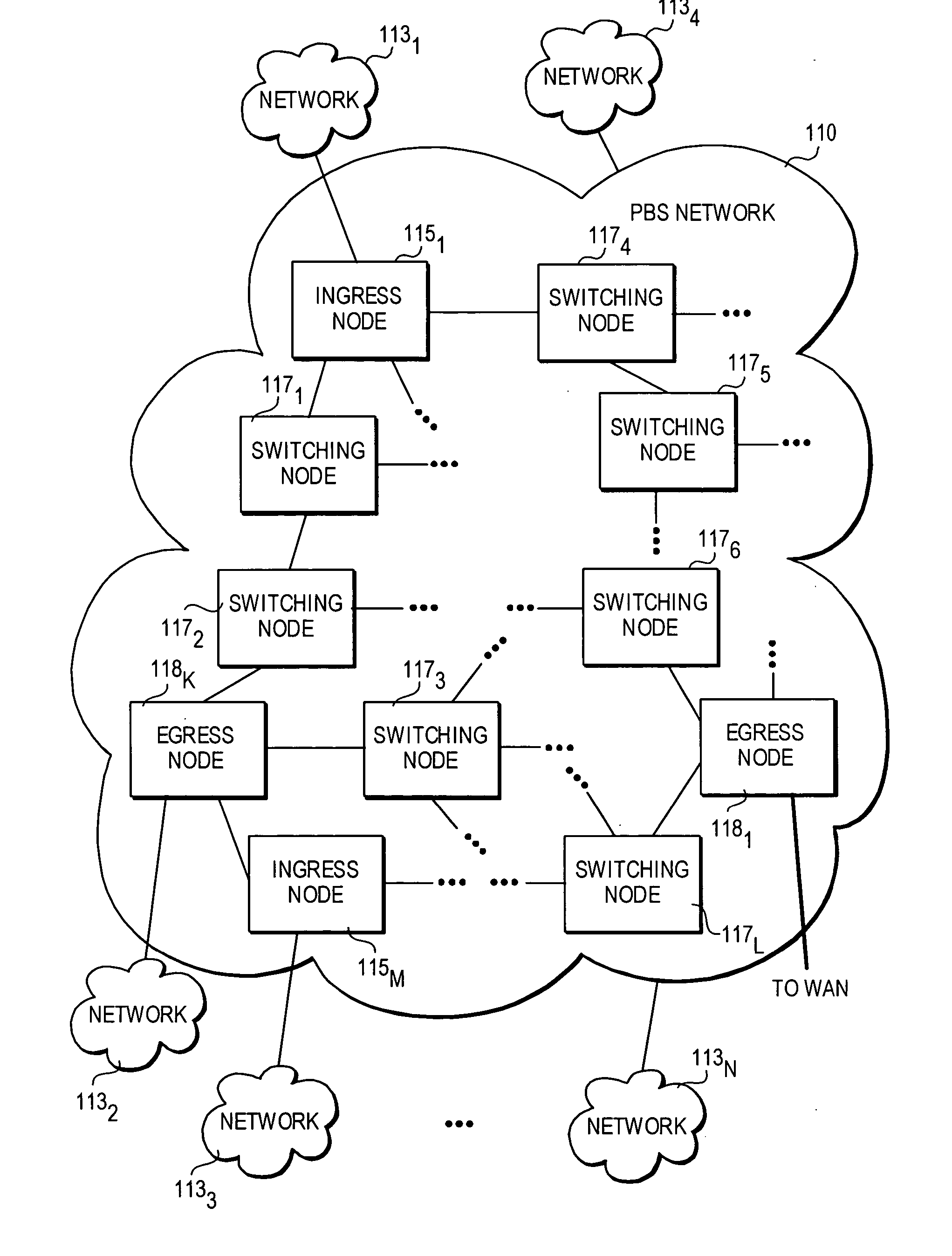
InactiveUS20050177749A1Digital data processing detailsUser identity/authority verificationExchange networkEdge node
A method and architecture for secure transmission of data within optical-switched networks. In one embodiment, the optical switched network comprises a photonic burst-switched (PBS) network. Under various schemes, security keys including encryption and decryption keys are generated by edge nodes and the decryption keys are distributed to other edge nodes in a PBS network. In one embodiment, the security keys are dynamically generated by a trusted platform module (TPM). A source edge node uses its encryption key to encrypt selected data bursts to be sent to a destination edge node via a virtual lightpath coupling the source and destination edge nodes. Security data are embedded in a control burst header indicates to the destination node whether corresponding data bursts sent via the virtual lightpath are encrypted. The security data also includes the decryption key and may also identify an encryption / decryption algorithm to be used. In some embodiments, public key infrastructure facilities are used in conjunction with employment of private and public keys and digital certificates.
Owner:TAHOE RES LTD
Bio-metric smart card, bio-metric smart card reader and method of use
InactiveUS6816058B2Improve transaction securityElectric signal transmission systemsMultiple keys/algorithms usageSmart cardAuthorization
A system for increasing transaction security across existing infrastructure is provided. A user bio-metric sensor device is integrated into a credit or debit card. A display unit provides a key, preferably encrypted, upon successful utilization of the sensor device. Included in the key generation mechanism is an indicator of the transaction number or other sequential count indicative of card use. An authorization service decrypts the key in a manner at least partially dependent upon a second sequential count maintained in sync with the first count to determine whether the use is authorized.
Owner:AUDLEM
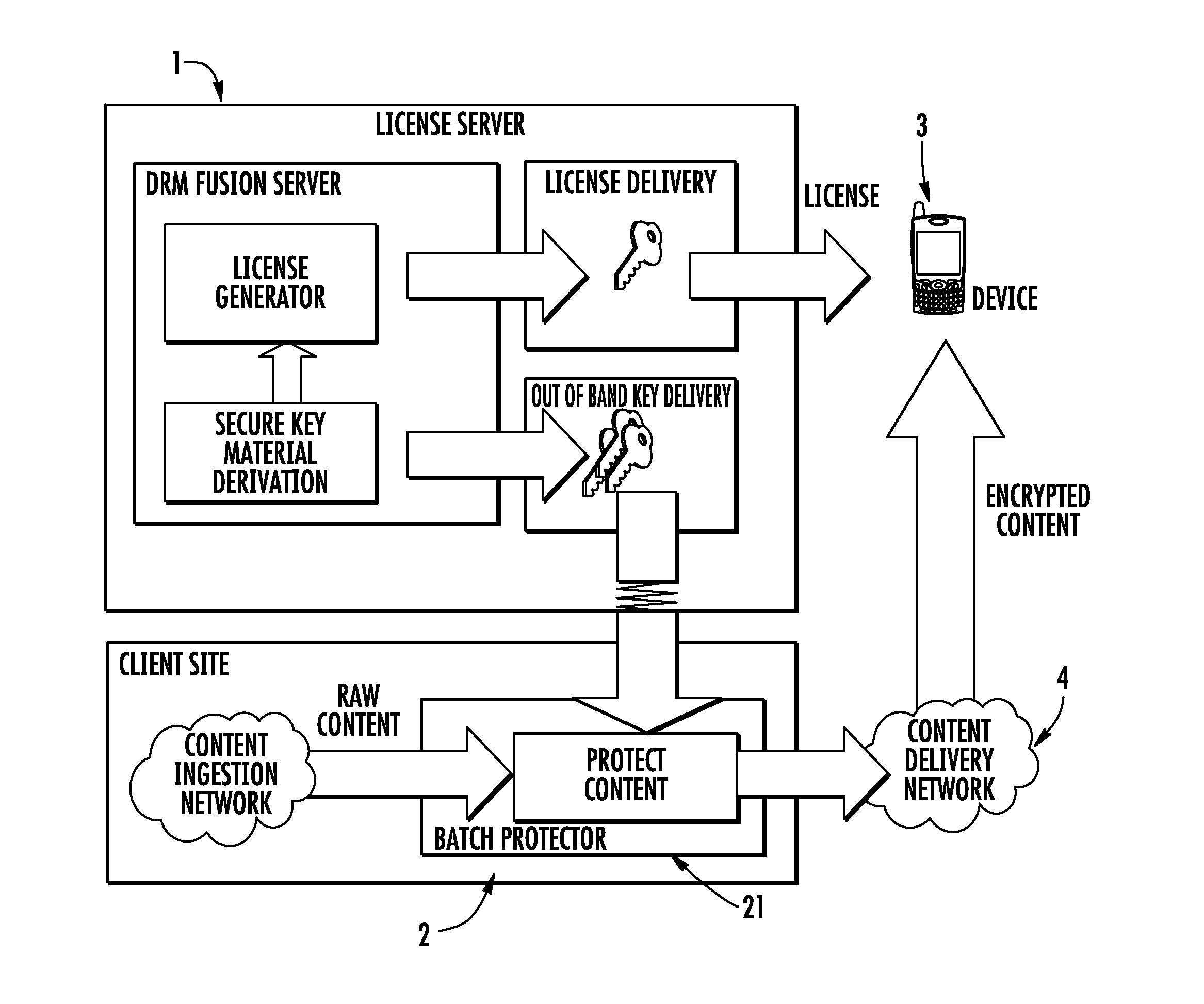
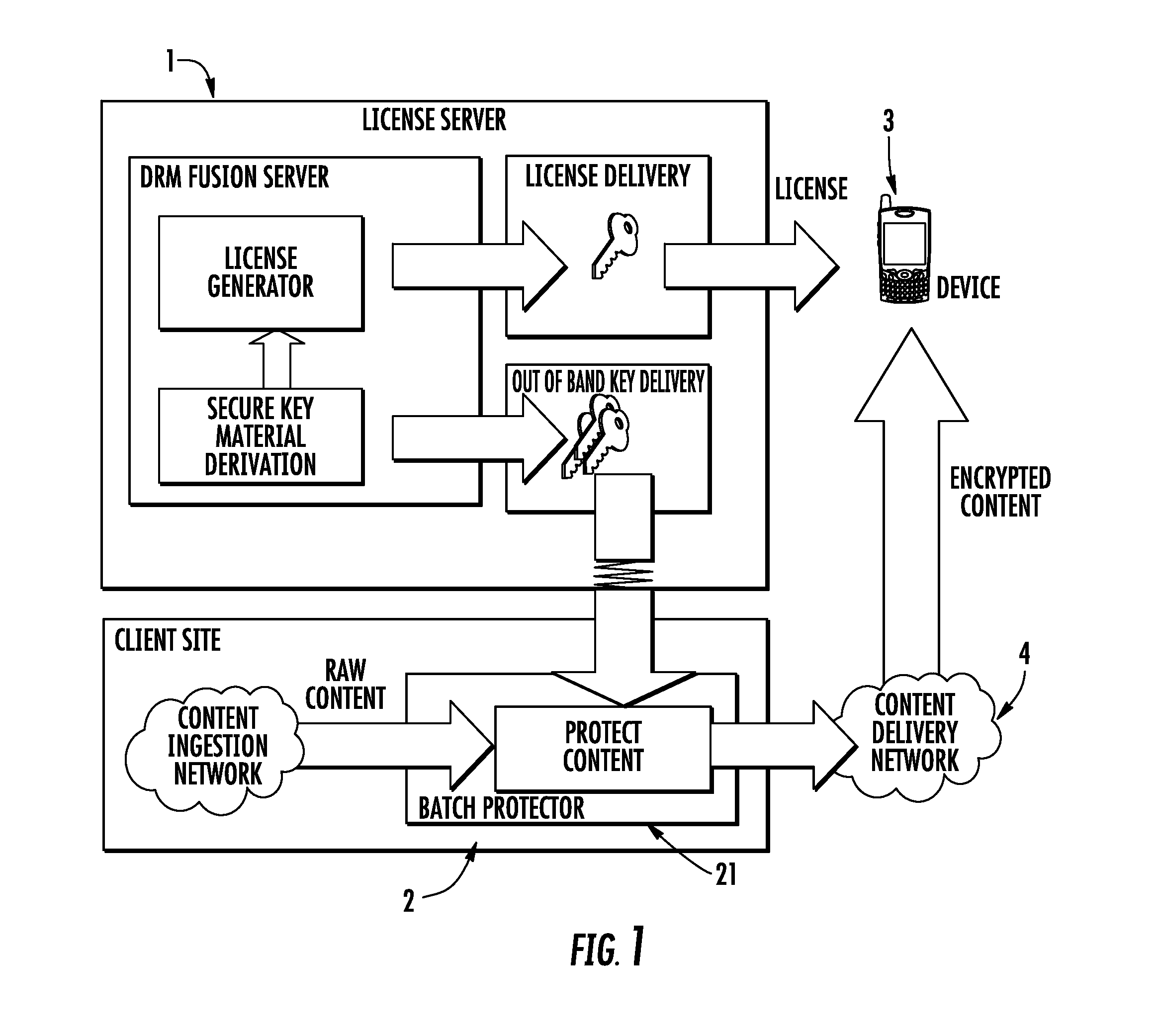
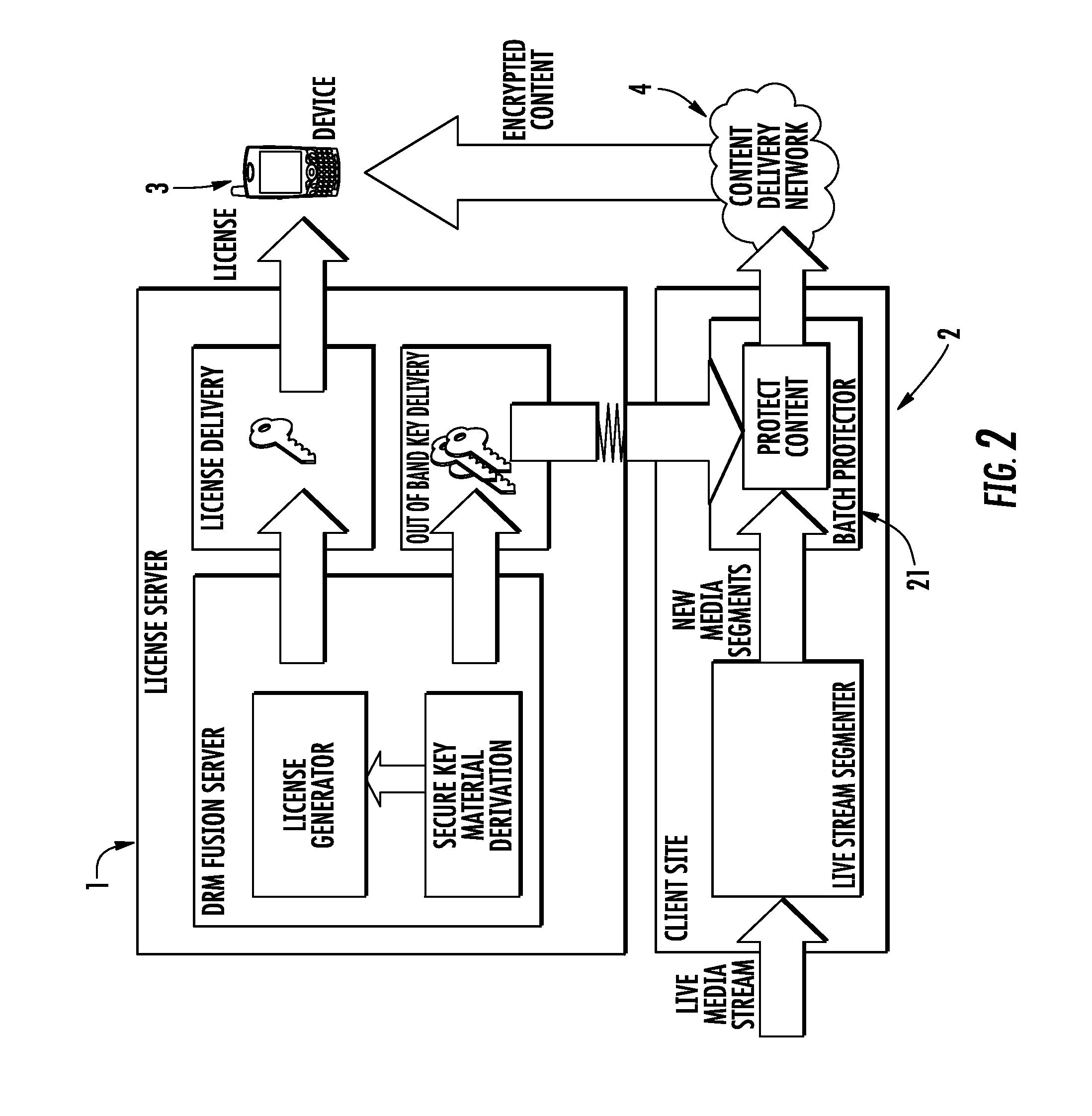
System and method for protecting digital contents with digital rights management (DRM)
InactiveUS20120284804A1Digital data processing detailsAnalogue secracy/subscription systemsUser deviceDigital content
An approach for protecting digital contents includes a content delivery phase wherein a client stores digital contents or retrieves them in streaming, transmits to a user device the digital content in a protected format along with an enabling code for enabling the user device to access or read the protected digital content. The approach includes a key generation phase in a DRM (Digital Right Management) server which derives at least one key for encrypting the digital contents. A key transmission phase involves the derived key being transmitted from the DRM server to the client. For decrypting the digital content, the user device requests the key from the DRM server, with the request including a key identification defined by the enabling code transmitted by the client to the user device which is used by the DRM server to derive the key for the user device.
Owner:INSIDE SECURE
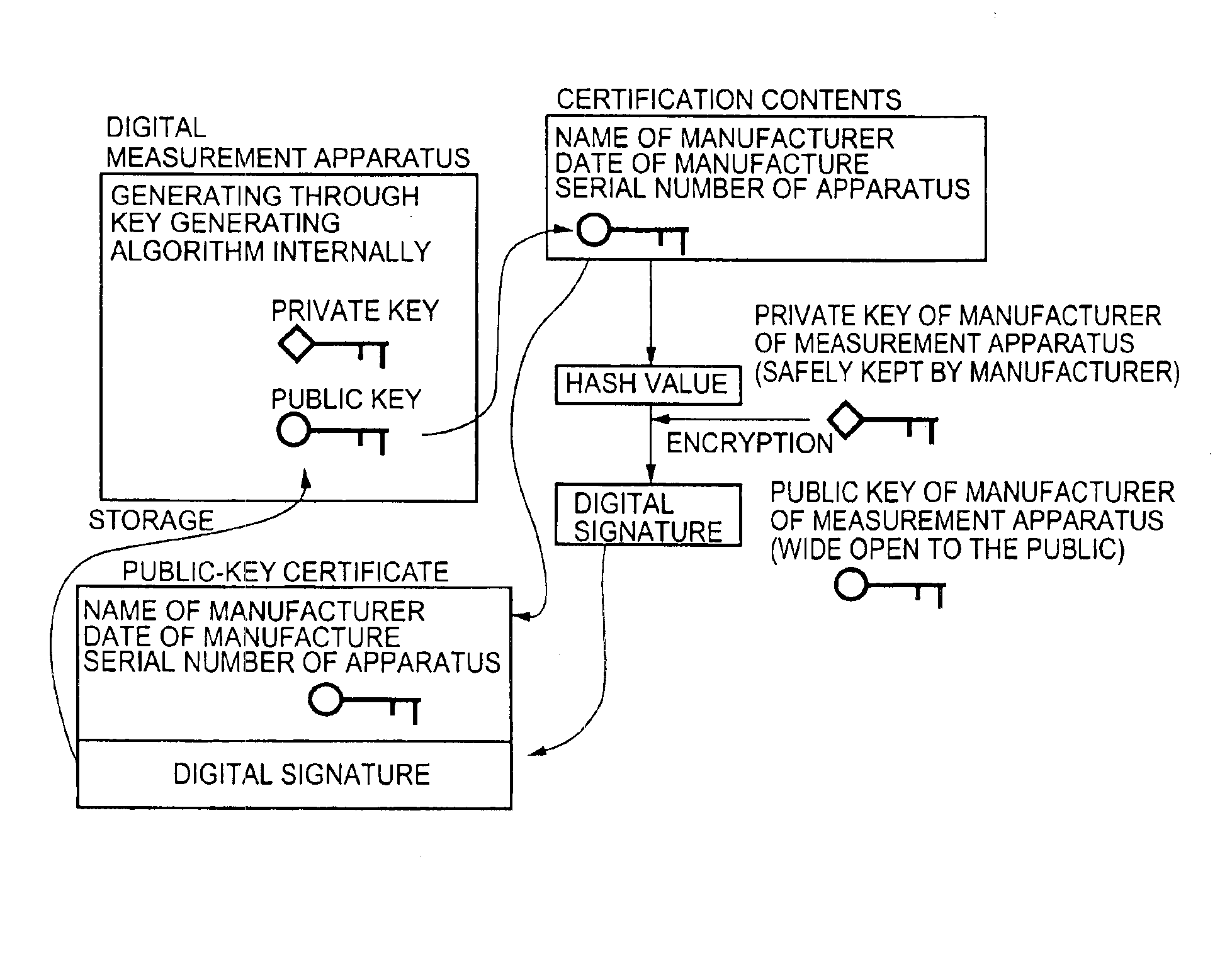
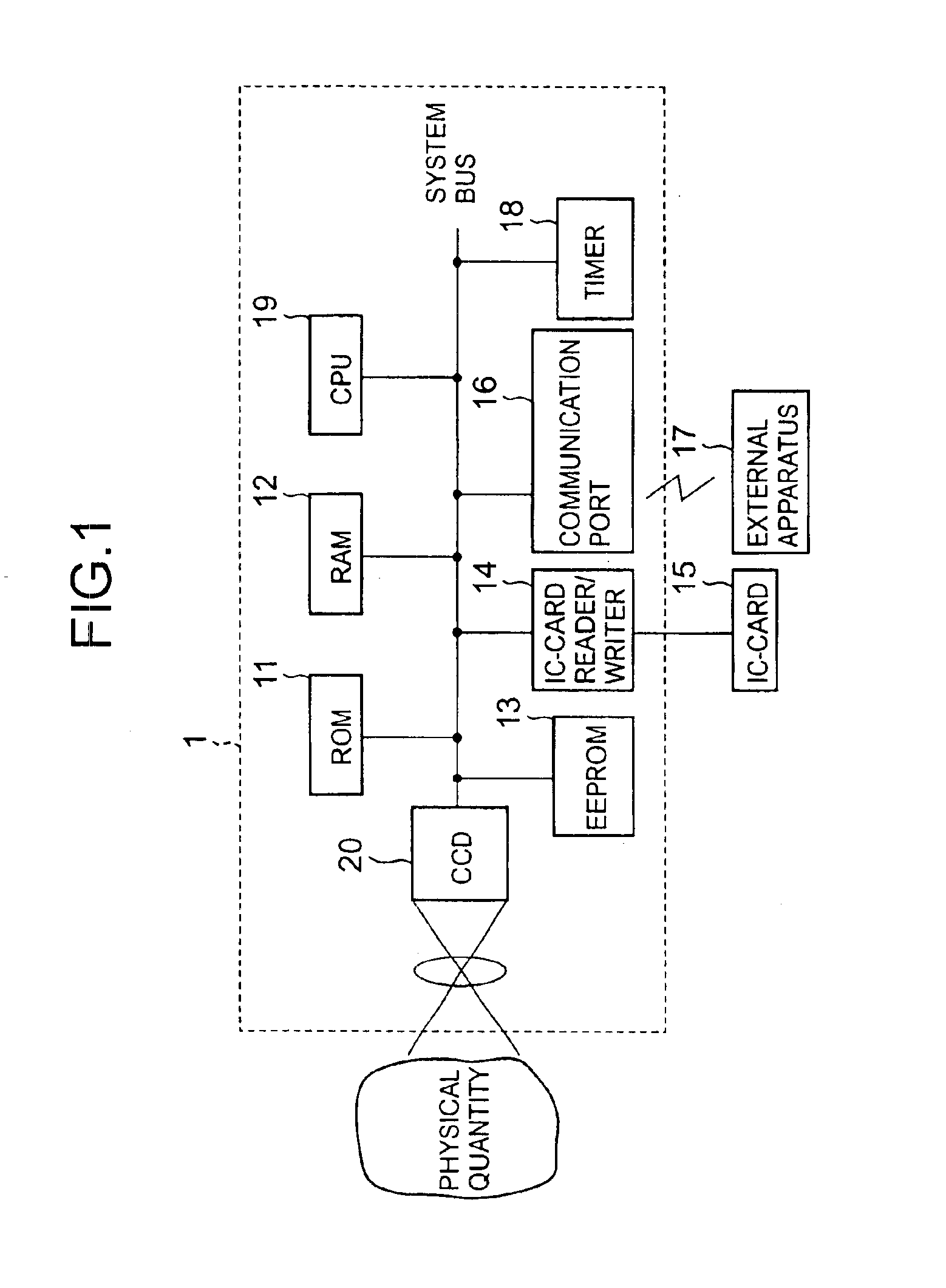
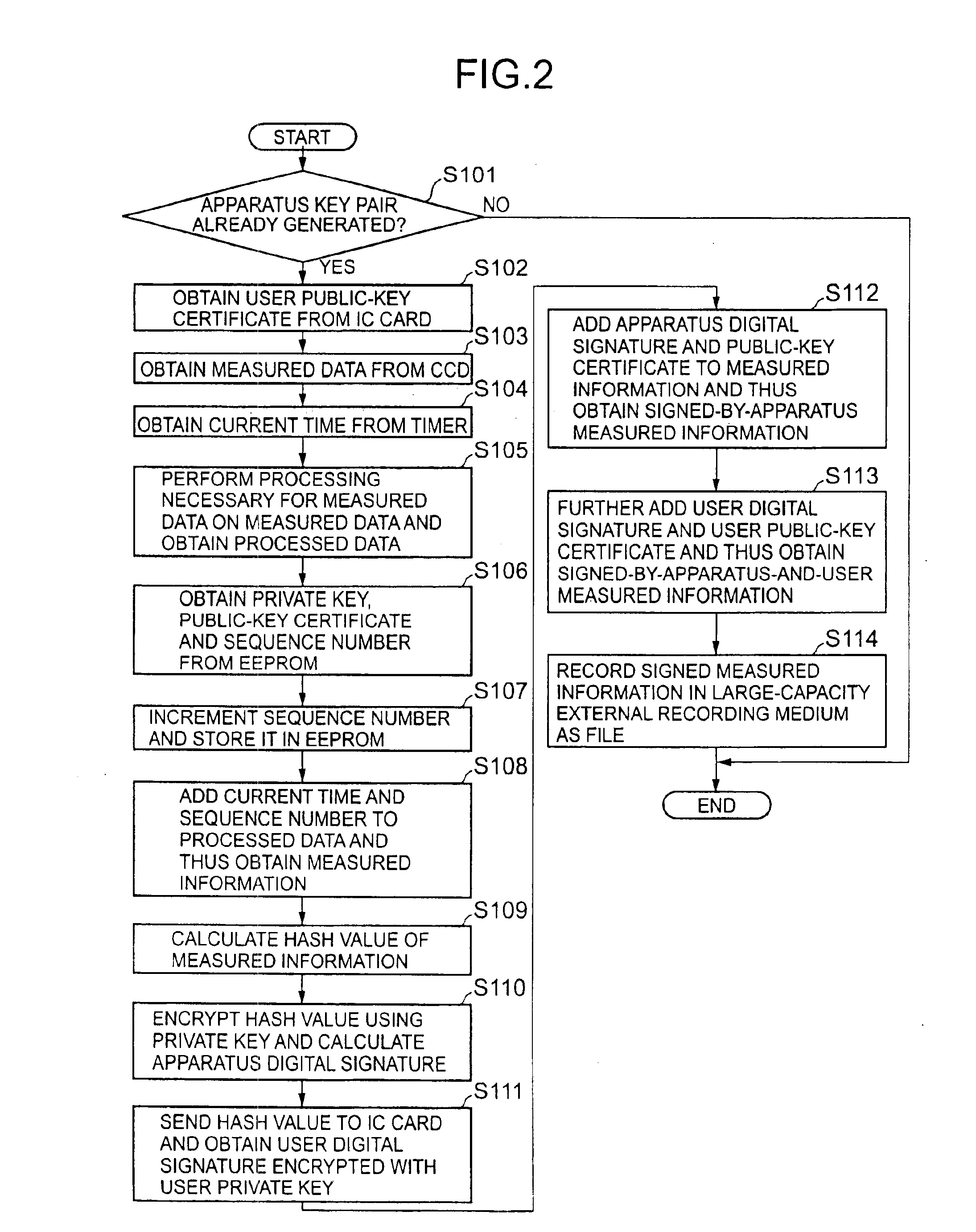
Digital measurement apparatus and image measurement apparatus
InactiveUS6889324B1Increase credibilityImprove reliabilityElectric signal transmission systemsKey distribution for secure communicationDigital signatureKey generation
A digital measurement apparatus measures a physical measurement object, provides a digital signature of public-key cryptography to measured data of a thus-measured physical quantity, and manages the measured data. The apparatus generates at least a pair of a public key and a private key, to be used for the digital signature of the public-key cryptography, through a key generating algorithm.
Owner:RICOH KK
Facilitating digital signature based on ephemeral private key
InactiveUS20060156012A1Facilitating adoption and useUser identity/authority verificationUnauthorized memory use protectionUser inputDigital signature
Facilitating communication using a digital signature includes: receiving user input data (UID); generating a first key as a deterministic function of the UID; clearing the UID; generating a second key as a deterministic function of the first key; clearing the first key following generation of the second key; and exporting the second key. Neither the UID nor the first key is exported. Thereafter, a digital signature is generated by again receiving the UID; regenerating the first key using the deterministic function and the UID; clearing the UID; generating a digital signature as a function of the regenerated first key; clearing the regenerated first key following generation of the digital signature; and exporting the generated digital signature.
Owner:FIRST DATA
Method and system for delegation of security procedures to a visited domain
InactiveUS6879690B2User identity/authority verificationSecret communicationDerivation procedureKey storage
A method and system for delegation of security procedures to a second domain. A first key is generated for a mobile node. The first key is stored at the mobile node and at a home domain of the mobile node. The mobile node is moved to the second domain. A request is sent from the second domain to the home domain to authenticate the mobile node. A second key is generated at the home domain using the first key and a random number. The random number and the second key are sent to the second domain. The random number is sent to the mobile node by the second domain. The mobile node generates the second key using the random number and the first key. The second key is used for authentication procedures and / or key derivation procedures between the mobile node and the second domain.
Owner:NOKIA TECHNOLOGLES OY
Method of and system for encrypting messages, generating encryption keys and producing secure session keys
InactiveUS20020076044A1Easy to provideNever be changedKey distribution for secure communicationMultiple keys/algorithms usagePlaintextCiphertext
A technique for encrypting and decrypting a data message is described herein and includes a stream cipher, a block cipher, and IV generation embodiment and a key generation embodiment which use a process of Summary Reduction. This overall technique uses a secret key to generate ciphertext from plaintext and in doing so, the technique isolates the nature of the secret key values from the nature of the cipher text created.
Owner:PIRES PAUL
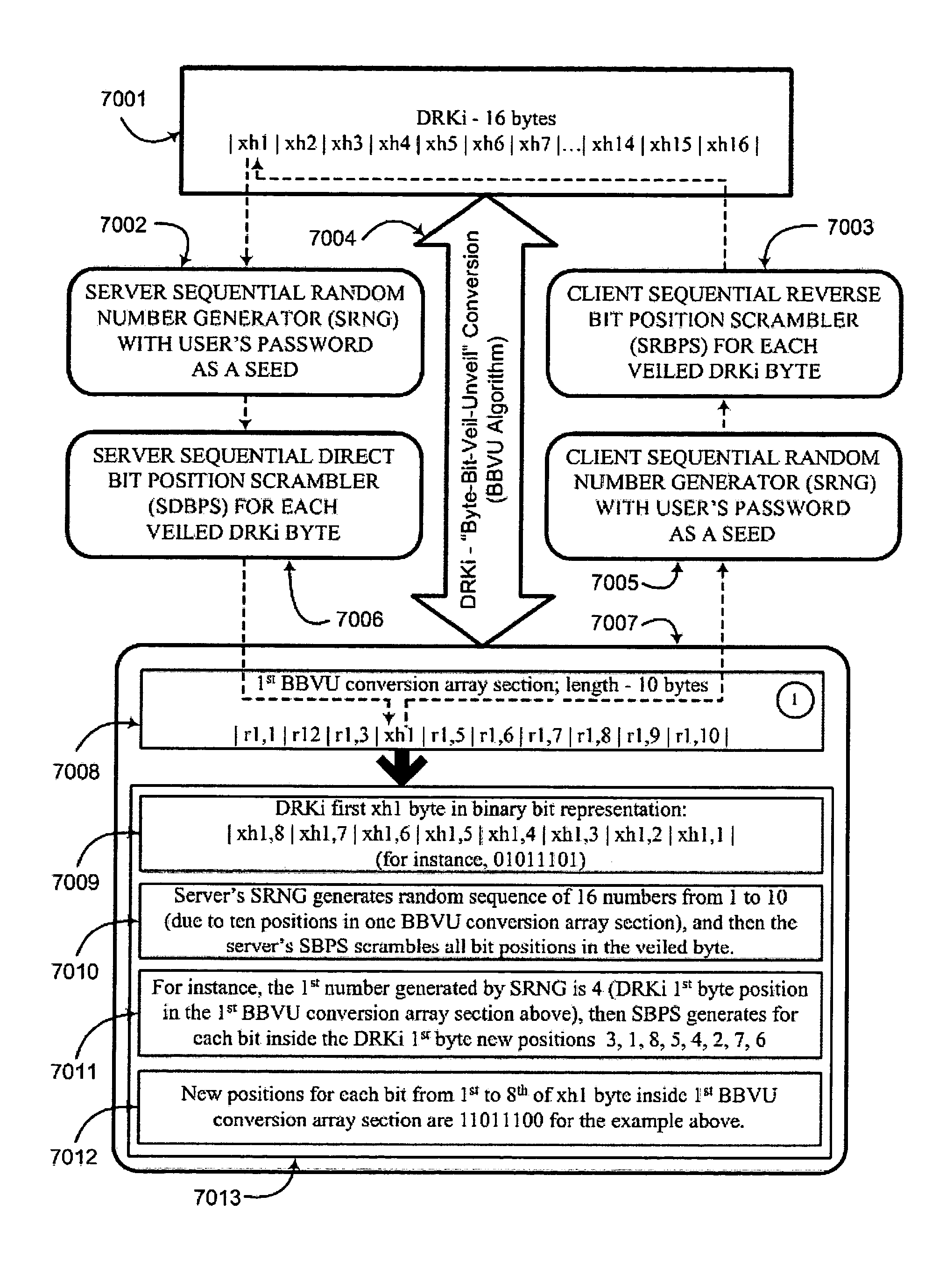
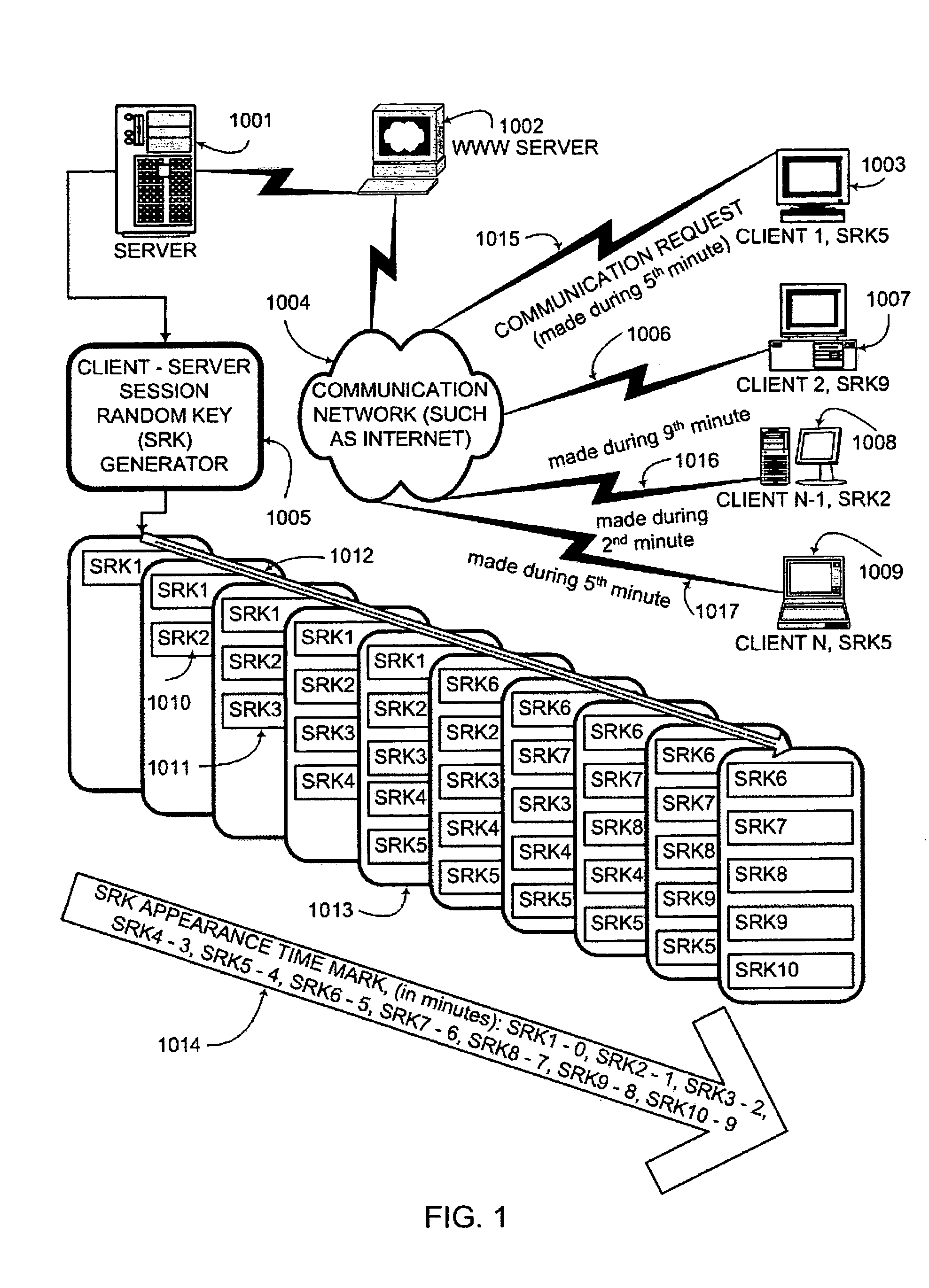
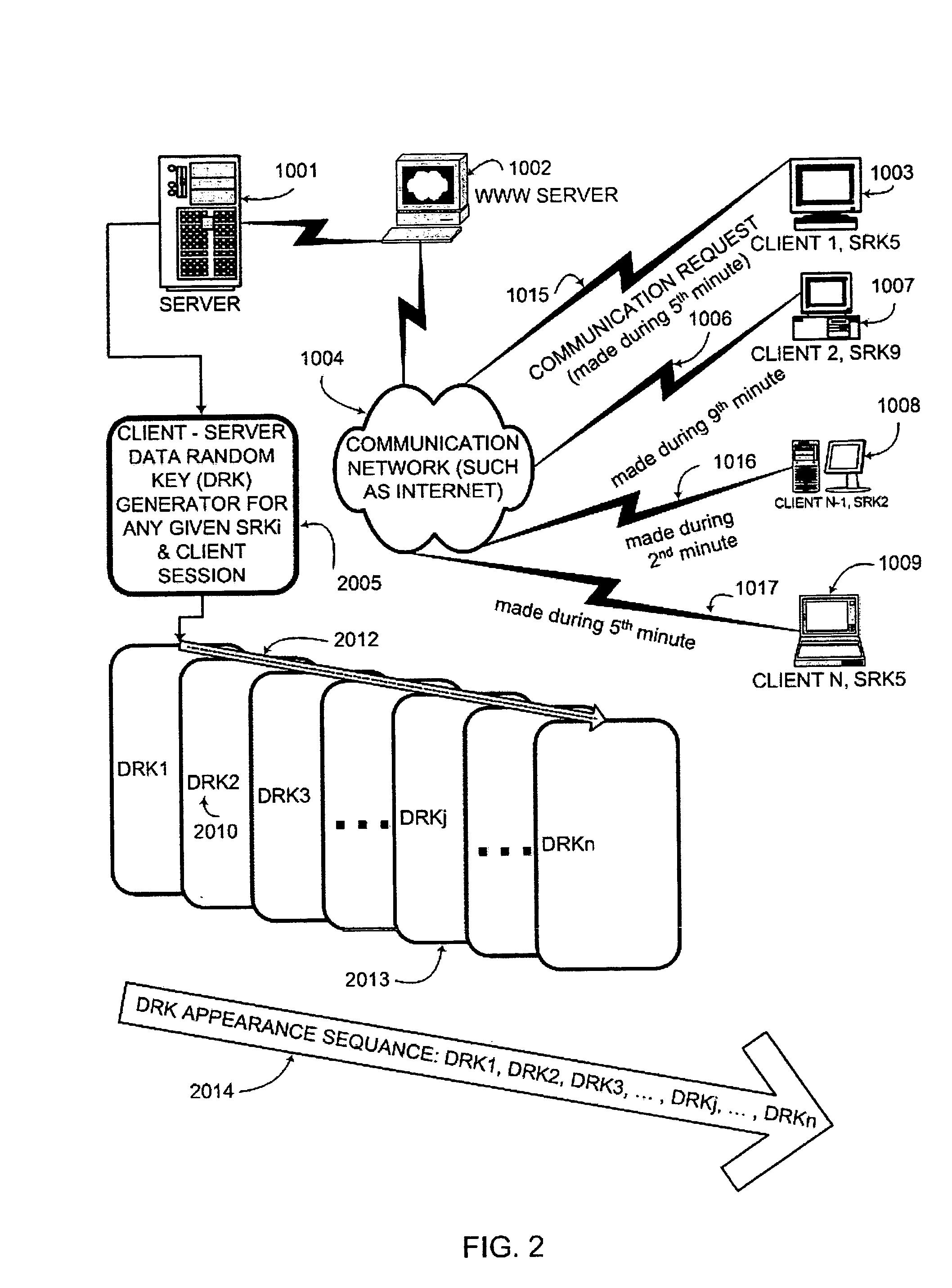
Key generation method for communication session encryption and authentication system
ActiveUS20050050328A1Secure EncryptionKey distribution for secure communicationUser identity/authority verificationComputer hardwareAuthentication system
An interactive mutual authentication protocol, which does not allow shared secrets to pass through untrusted communication media, integrates an encryption key management system into the authentication protocol. The server provides ephemeral encryption keys in response to a request during a Session Random Key (SRK) initiation interval. SRK is provided for all sessions initiated in the SRK initiation interval. A set of ephemeral intermediate Data Random Keys (DRK) is associated with each request. A message carrying the SRK is sent to the requestor. A response from the requester includes a shared parameter encrypted using the SRK verifying receipt of the SRK. After verifying receipt of the SRK at the requester, at least one message is sent by the server carrying an encrypted version of one of said set of ephemeral intermediate DRK to be accepted as an encryption key for the session.
Owner:AUTHERNATIVE INC
System for biometric signal processing with hardware and software acceleration
InactiveUS20070038867A1Improve performanceKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareSystem design methodology
A secure embedded system that uses cryptographic and biometric signal processing acceleration is described. In one embodiment, the secure embedded system is configured as a wireless pay-point protocol for brick-and-mortar and e-commerce applications in which biometric information is localized and does not require transmission of biometric data for authentication. In one embodiment, a key-generation function uses a dynamic key generator and static biometric components. In one embodiment, an embedded system design methodology provides hardware and software acceleration transparency.
Owner:RGT UNIV OF CALIFORNIA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com