Patents
Literature
40results about How to "Secure Encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
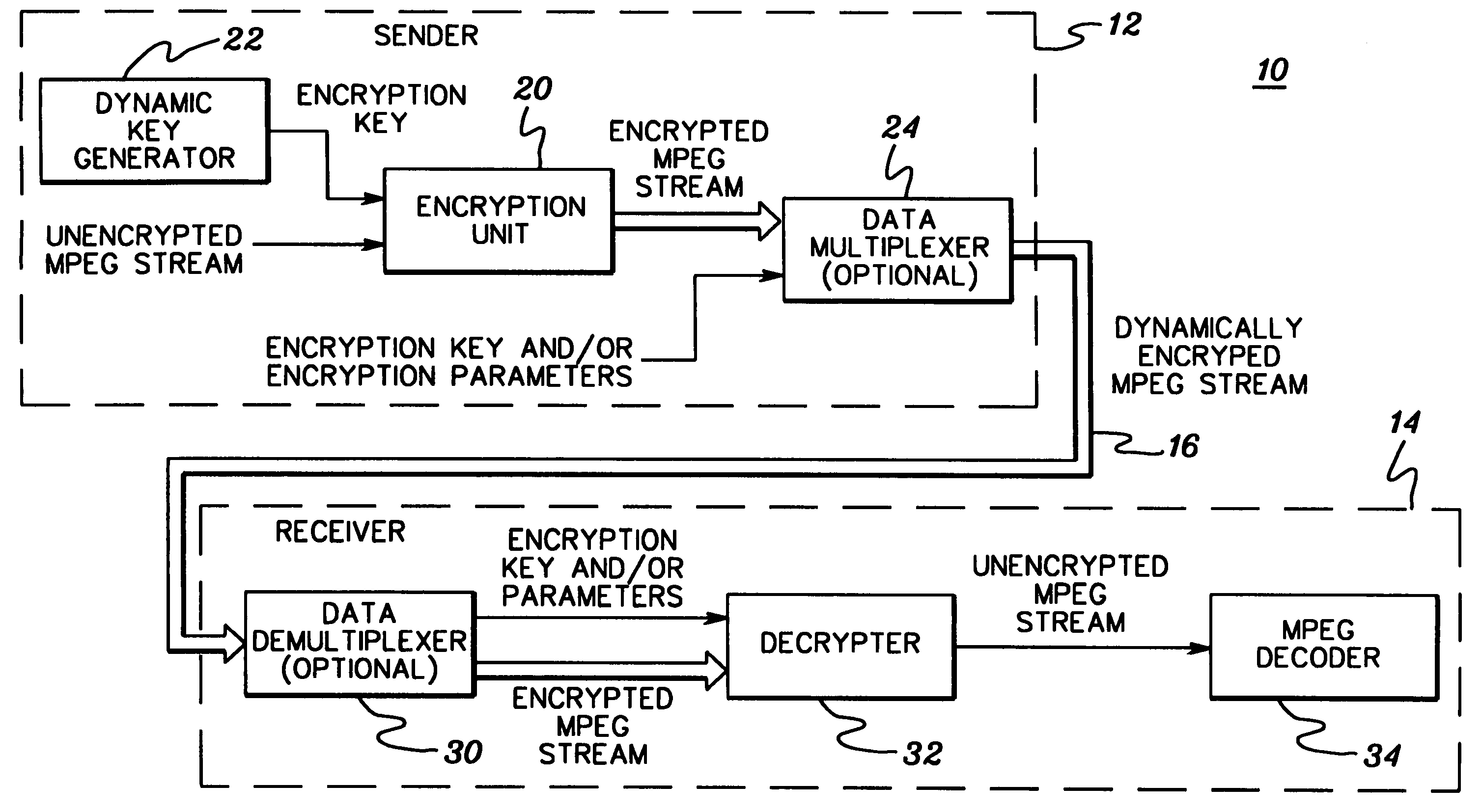
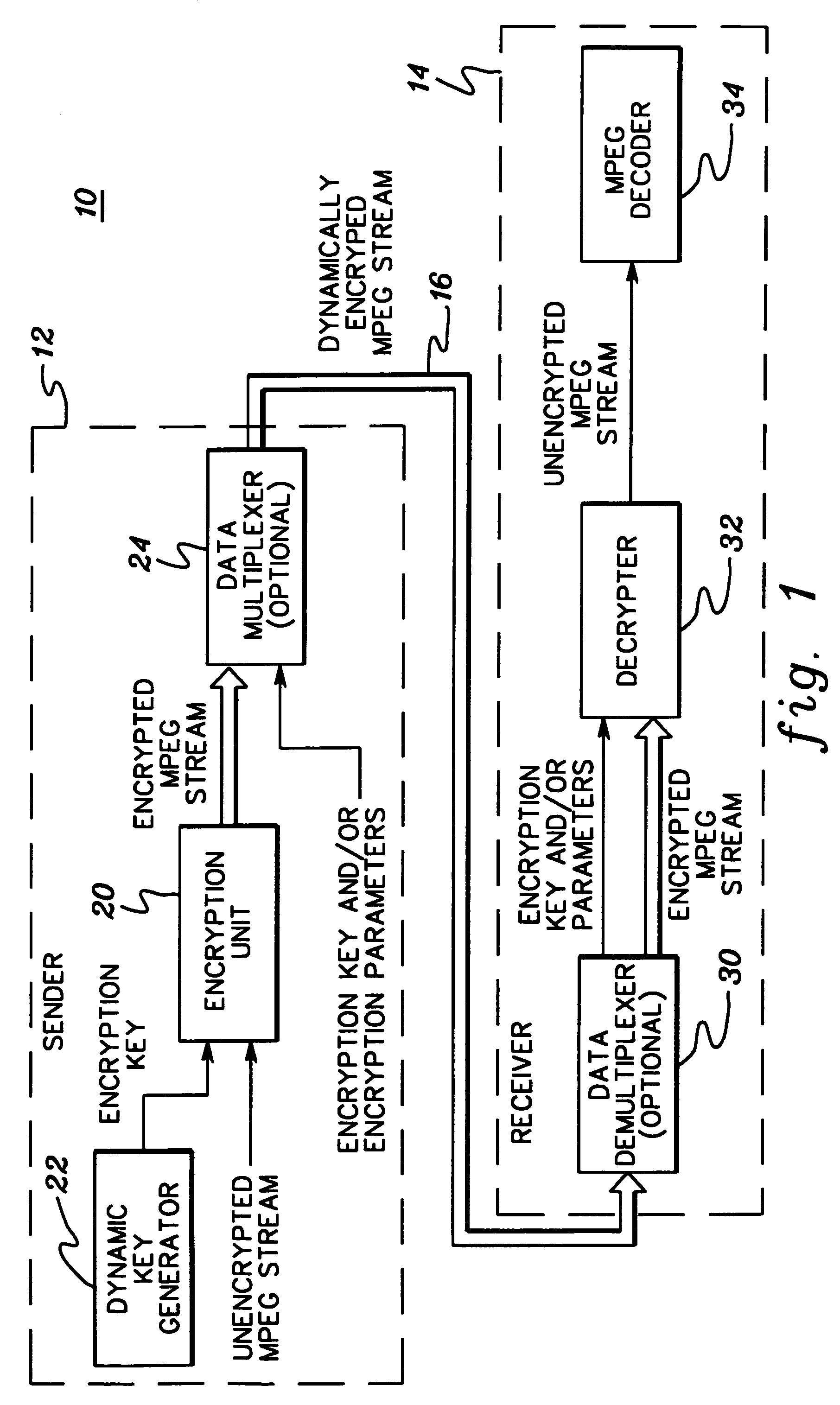
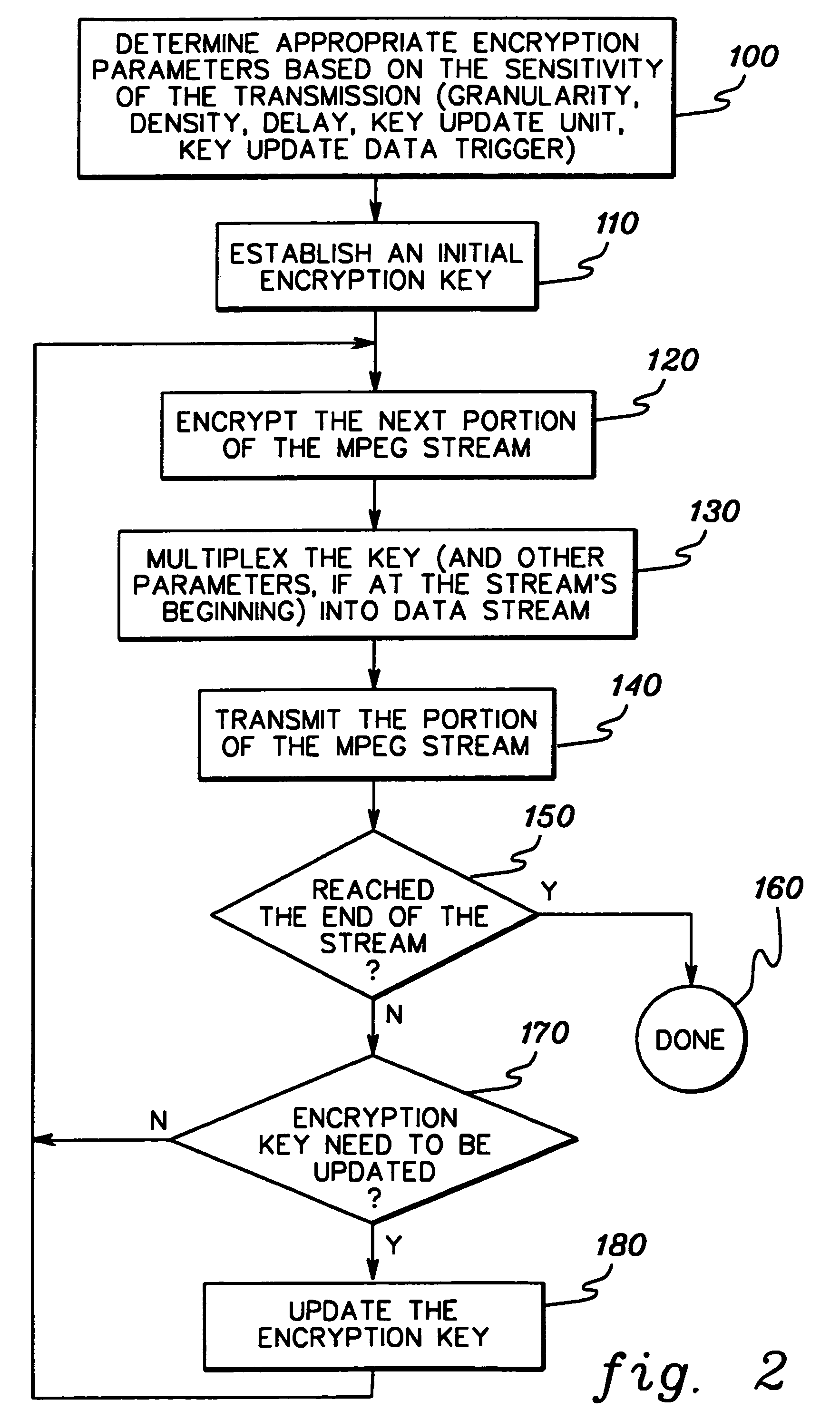
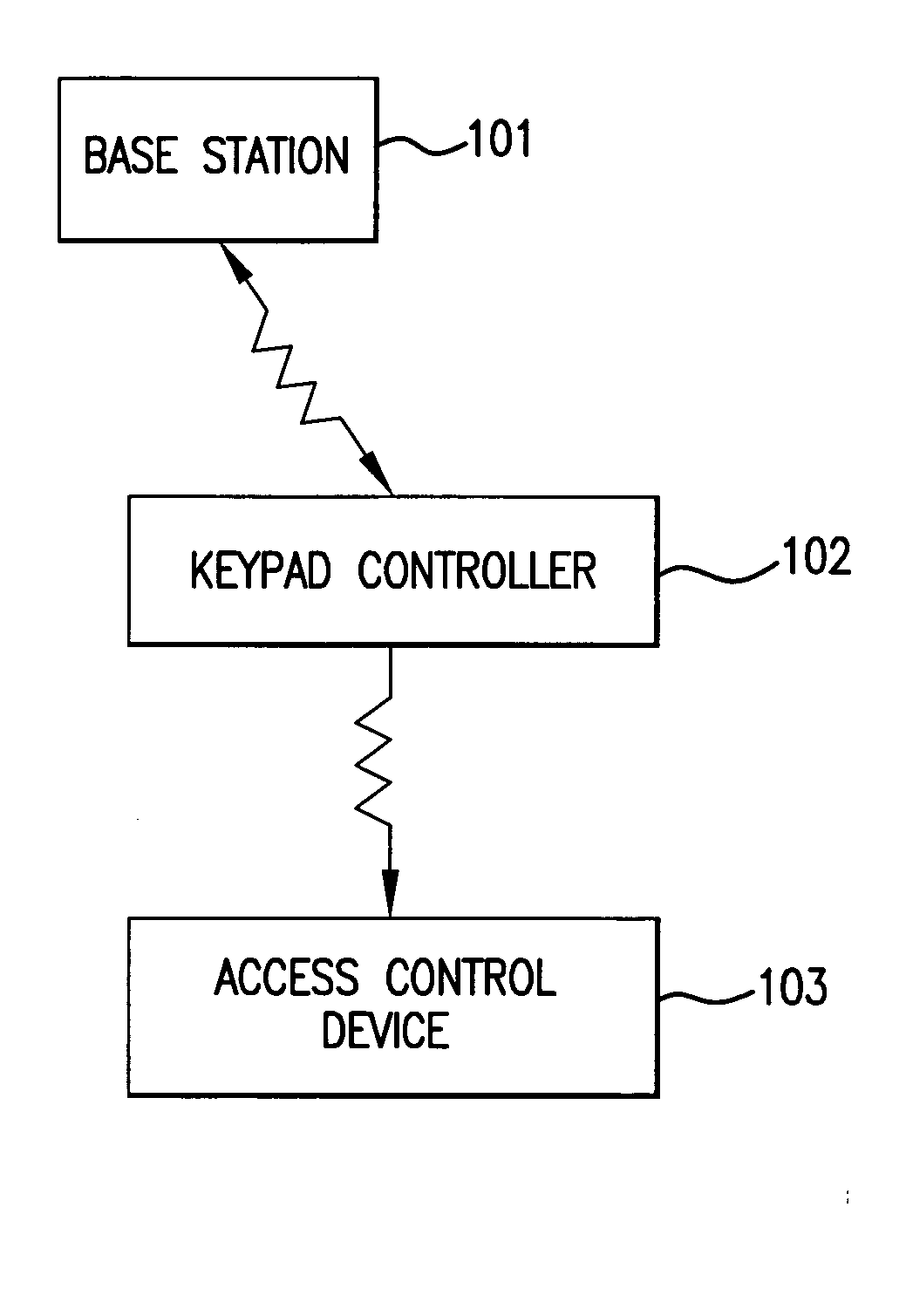
Dynamic encryption and decryption of a stream of data
InactiveUS7151832B1Easily extensibleEnhanced securitySynchronising transmission/receiving encryption devicesMultiple keys/algorithms usageDisk encryptionData content
Dynamic varying of encrypting of a stream of data at an encryption unit based on data content is disclosed. The dynamic varying of the encrypting, which can be responsive to passage of a predefined number of units of physical data or passage of a predefined number of conceptual units of data, is accomplished by changing at least one encryption parameter over different portions of the data. The at least one encryption parameter can comprise one or more of an encryption key, an encryption granularity, an encryption density scale, an encryption density, an encryption delay, an encryption key update variable, and an encryption key update data trigger. The change in encryption parameter is signaled to a receiver's decryption unit and used by the decryption unit in decrypting the dynamically varied encrypted stream of data. The stream of data may comprise, e.g., MPEG compressed video or audio.
Owner:IBM CORP
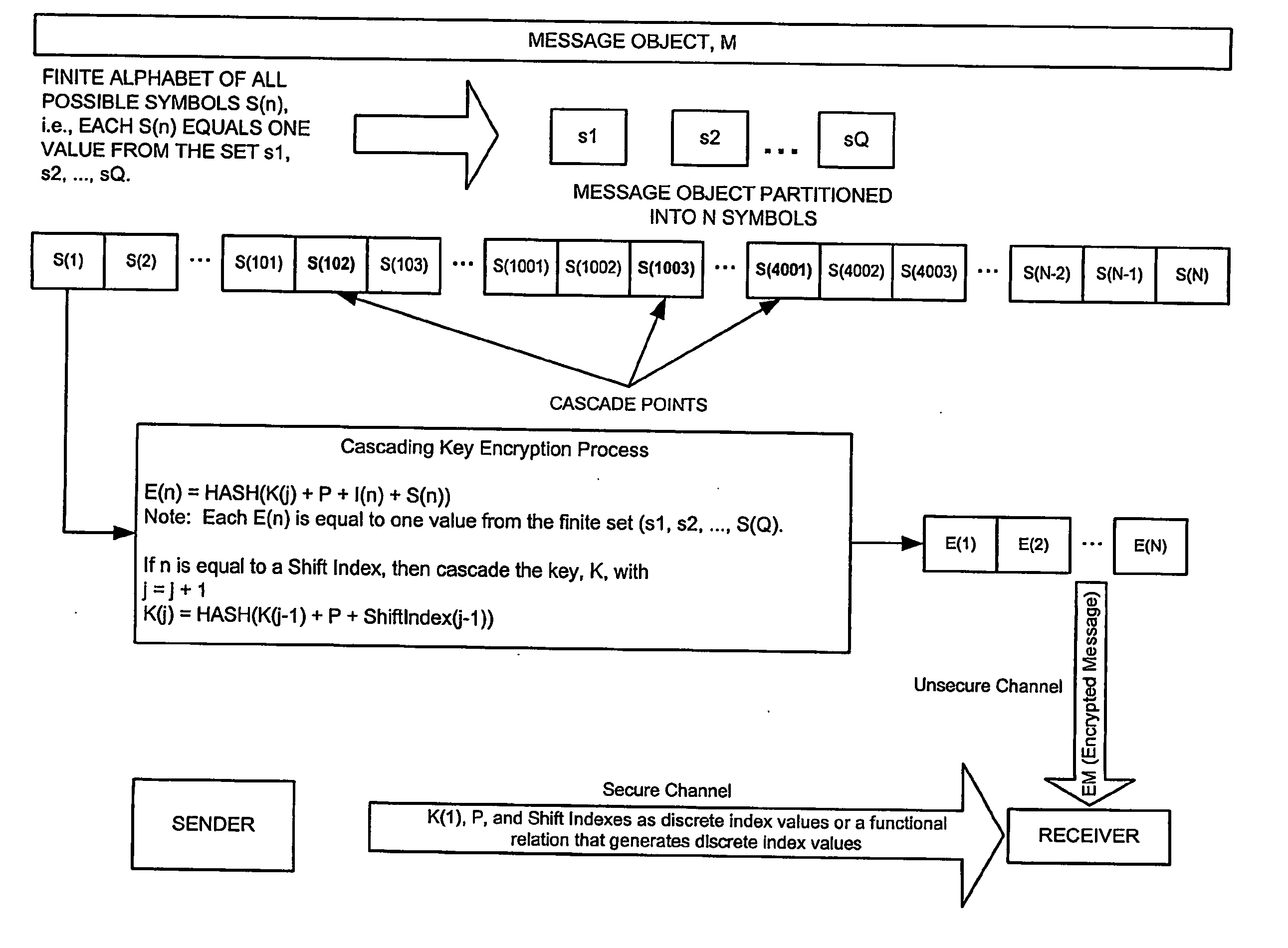
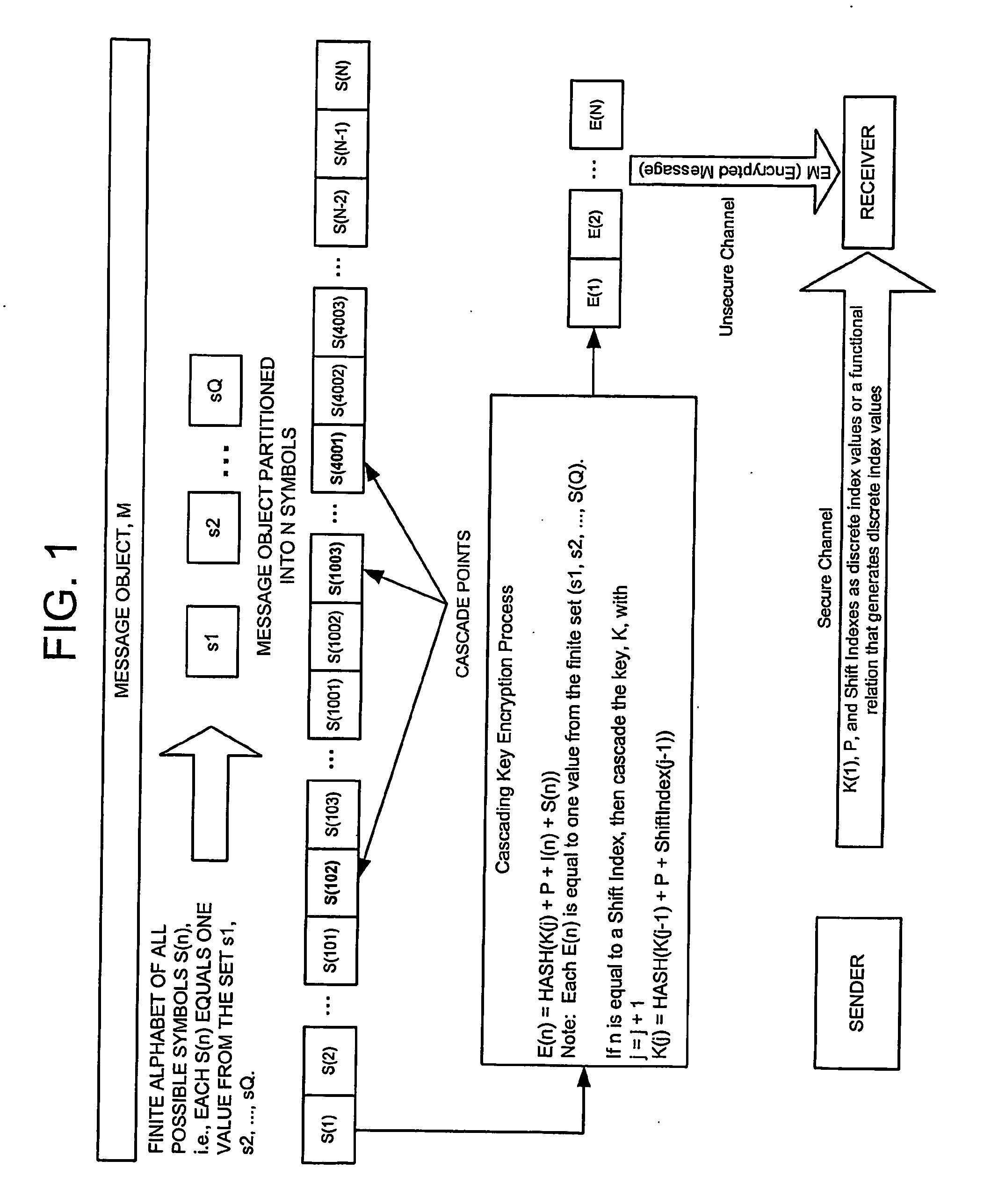
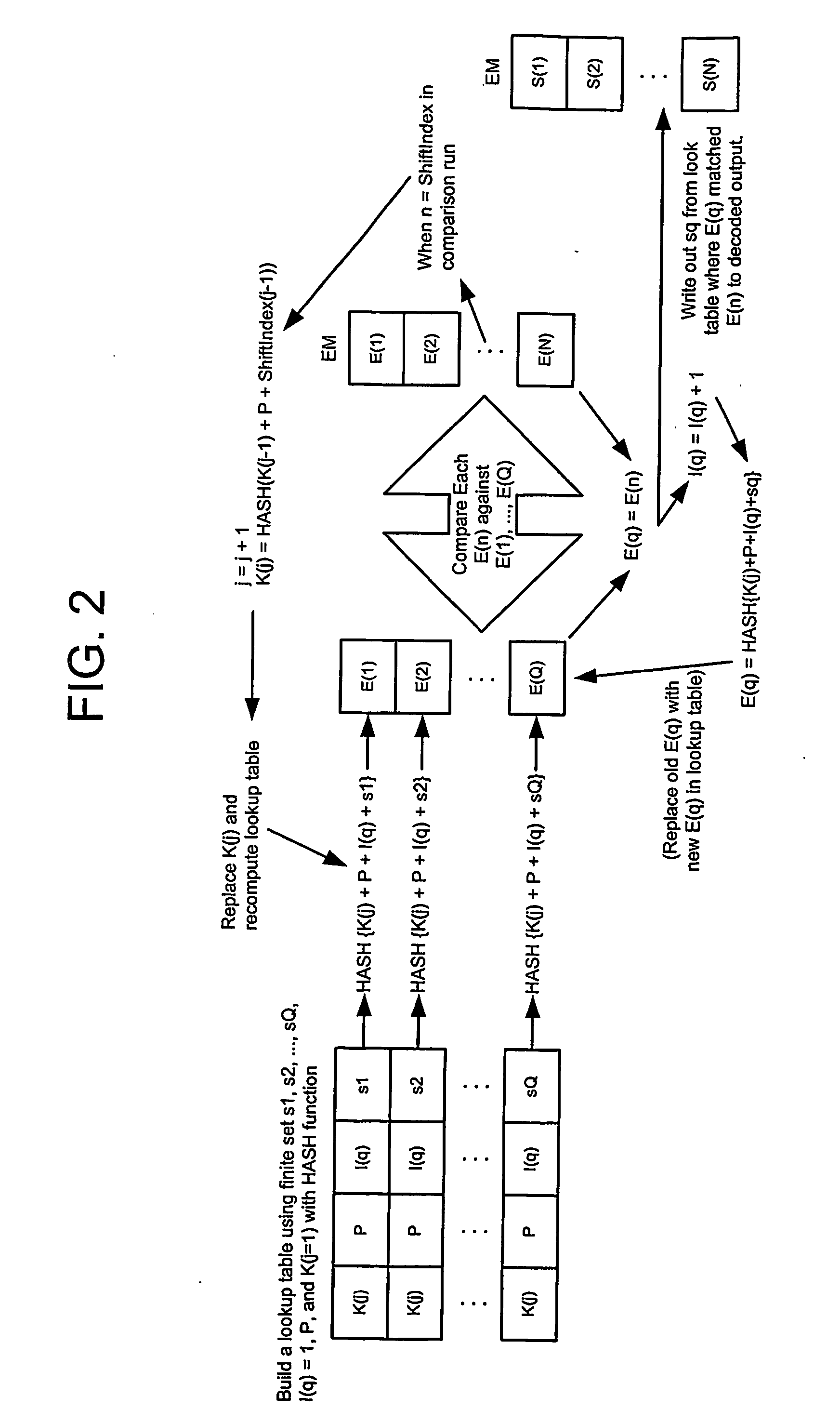
Cascading key encryption
InactiveUS20060265595A1Secure EncryptionSmall sizeKey distribution for secure communicationSynchronising transmission/receiving encryption devicesPasswordSecure transmission
A method for securely transmitting data involves generating keys depending on previous keys and additional information, such as a password, in order to create a pseudo one-time pad. The data is encrypted using the pseudo one-time pad prior to transmission. Only the initial key and minimal additional data are transferred between the sender and receiver in order to synchronize the keys.
Owner:PATHFIRE
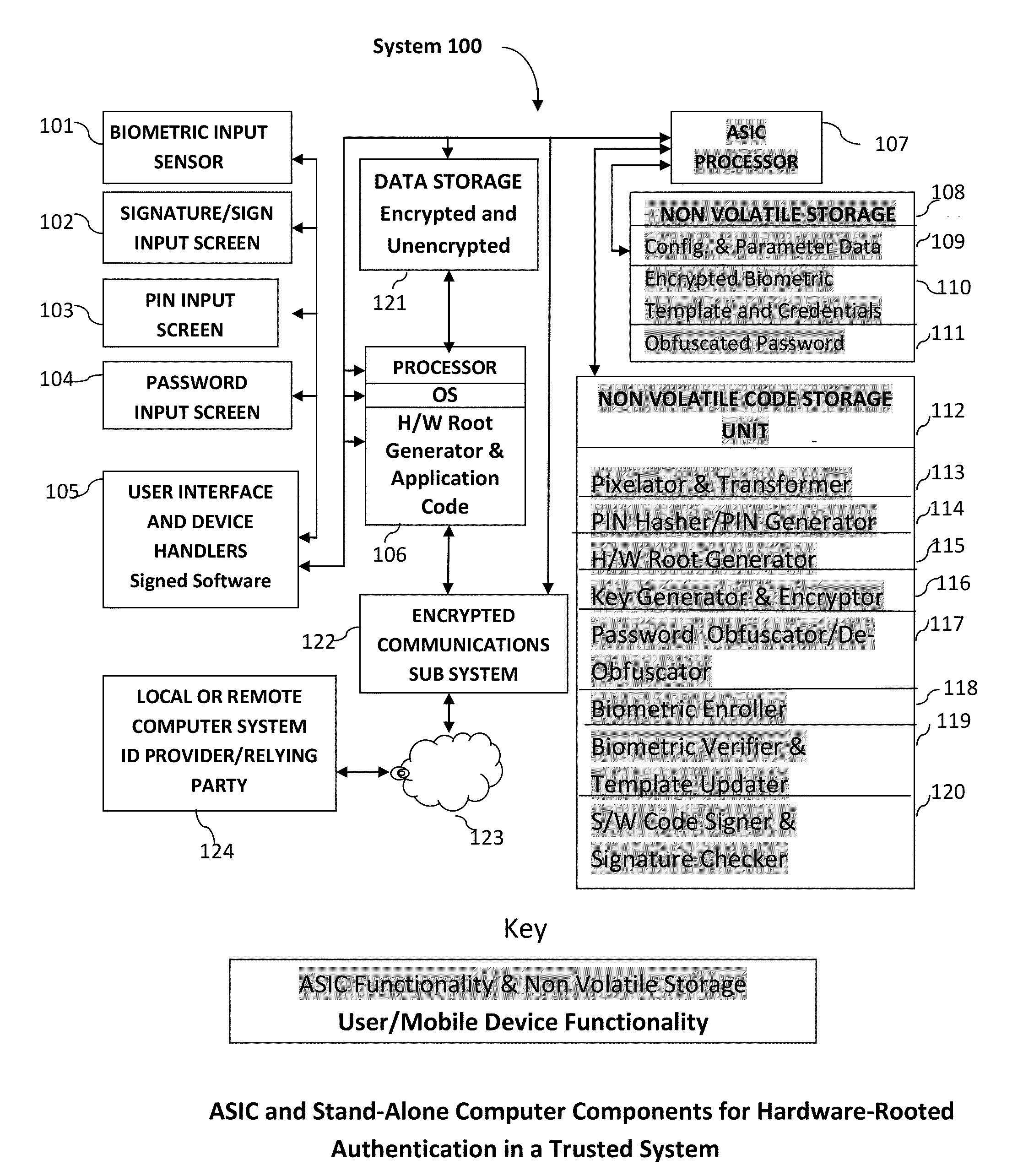
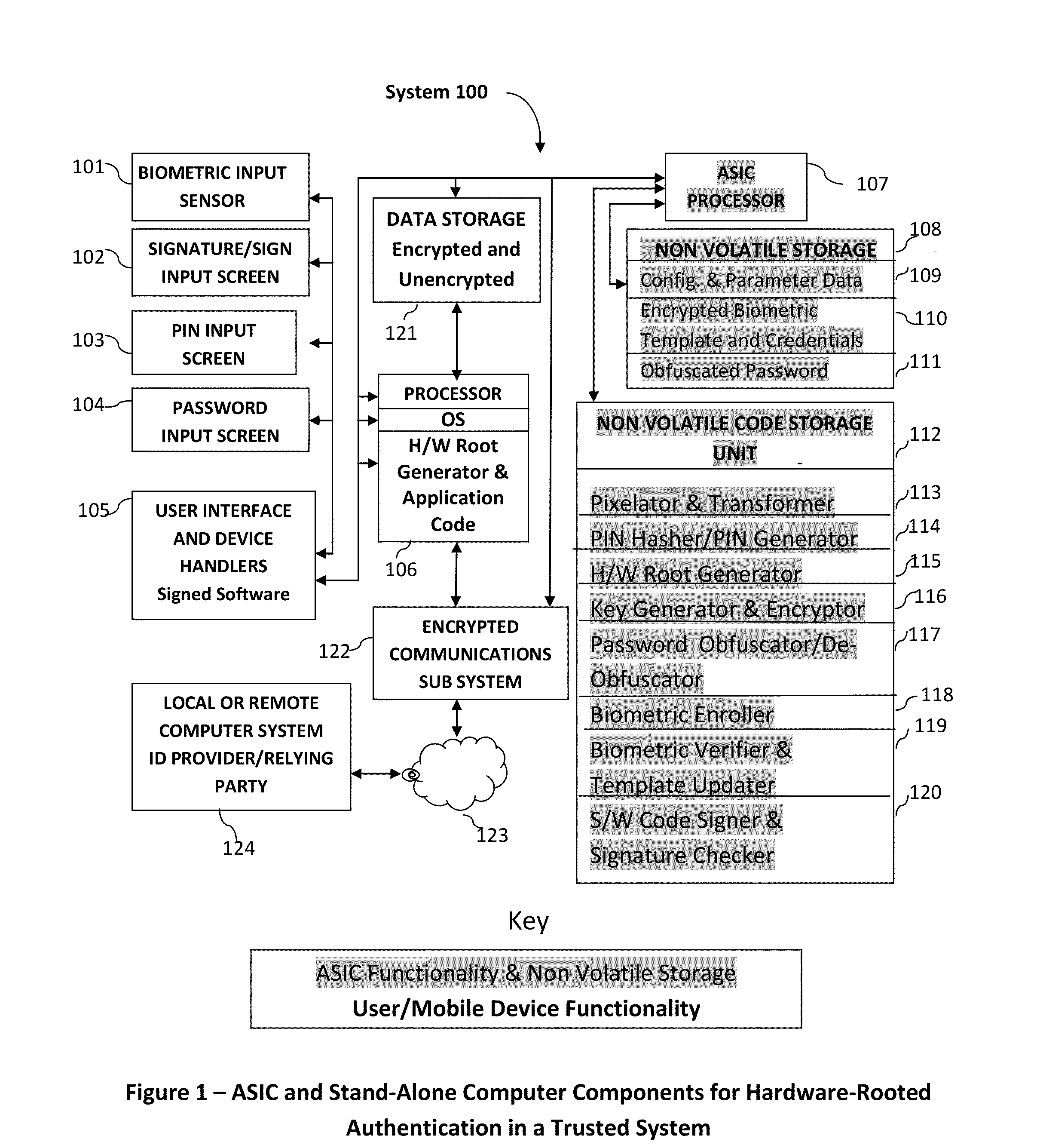
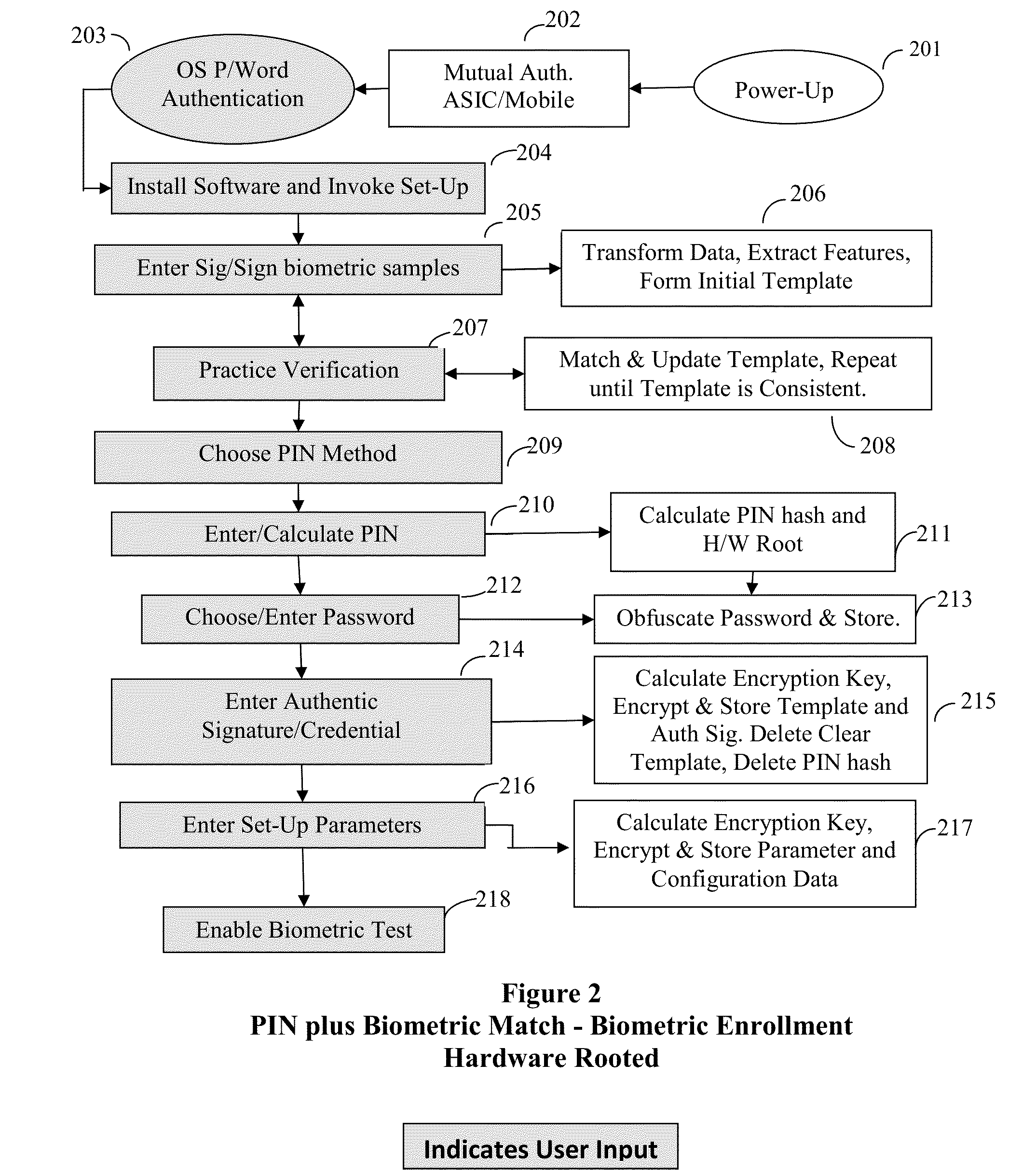
Method and System for Providing Password-free, Hardware-rooted, ASIC-based Authentication of a Human to a Mobile Device using Biometrics with a Protected, Local Template to Release Trusted Credentials to Relying Parties
InactiveUS20140365782A1Significant productivityMaximum safetyUser identity/authority verificationInternal/peripheral component protectionBiometric dataPassword hashing
Biometric data, which may be suitably transformed are obtained from a biometric input device contained within a stand-alone computer or a mobile device, which may contain an ASIC chip connected to or incorporated within the stand-alone computer or mobile device and which includes the capability for capturing one or more biometric samples and for biometric feature extraction, matching and encryption. For extra security, the biometric matching is used in conjunction with a PIN to authenticate the user to the stand-alone computer or mobile device. The biometric template and other sensitive data residing on the mobile device are encrypted using hardware elements of the mobile device (or the ASIC) together with the PIN hash and / or the Password hash. An obfuscated version of the Password, stored on the ASIC or the mobile device is de-obfuscated and released to the mobile device authentication mechanism, including a Trusted Platform Module if present, in response to a successfully decrypted template and matching biometric sample and PIN. A de-obfuscated password is used to authenticate the user to the mobile device and the same or a different de-obfuscated password may be used to authenticate the user to a remote computer using the SSL / TLS or a process based upon a symmetric encryption algorithm. The locally generated password may be used to encrypt data at rest on the mobile device or ASIC and the remote authentication password may be used to encrypt data in transit to and from a remote computer. This creates a trusted relationship between the stand-alone computer or mobile device and the remote computer. The system also eliminates the need for the user to remember and enter complex passwords on the mobile device or for secure transmission of data. A similar method may be used, with the signature / sign biometric modality to determine whether the holder of an IC chip card is, in fact the card owner.
Owner:BIOCRYPT ACCESS LLC
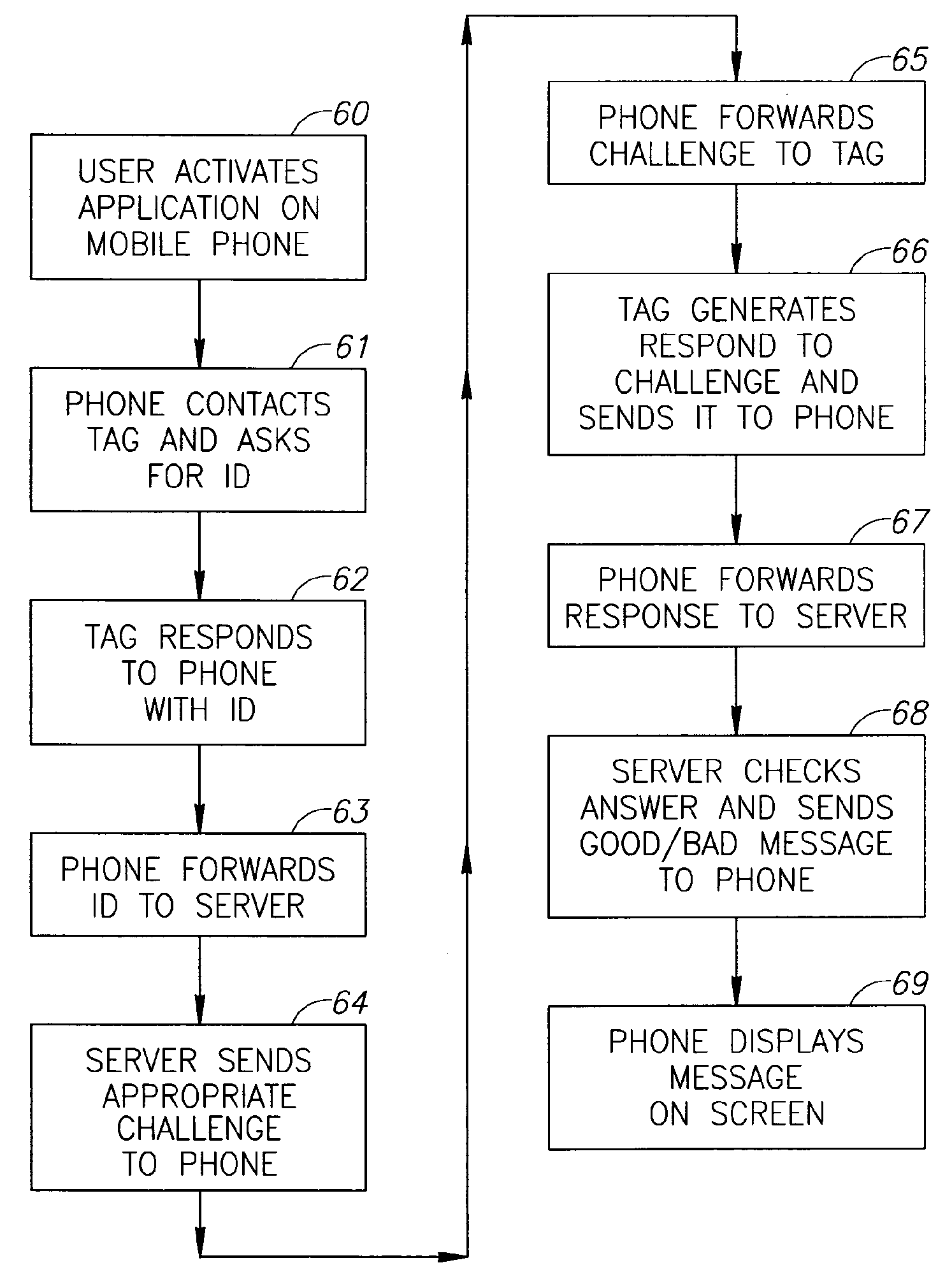
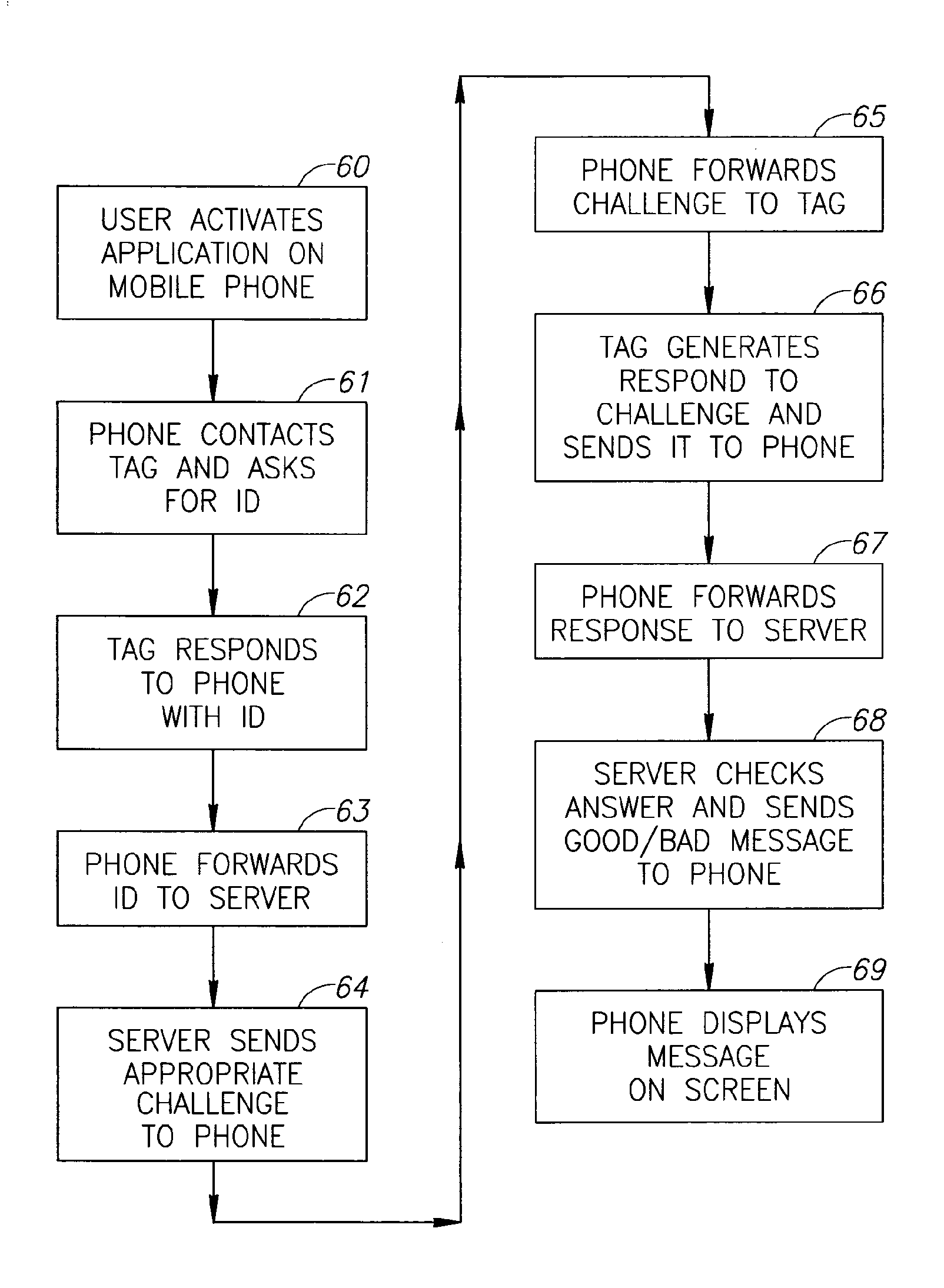
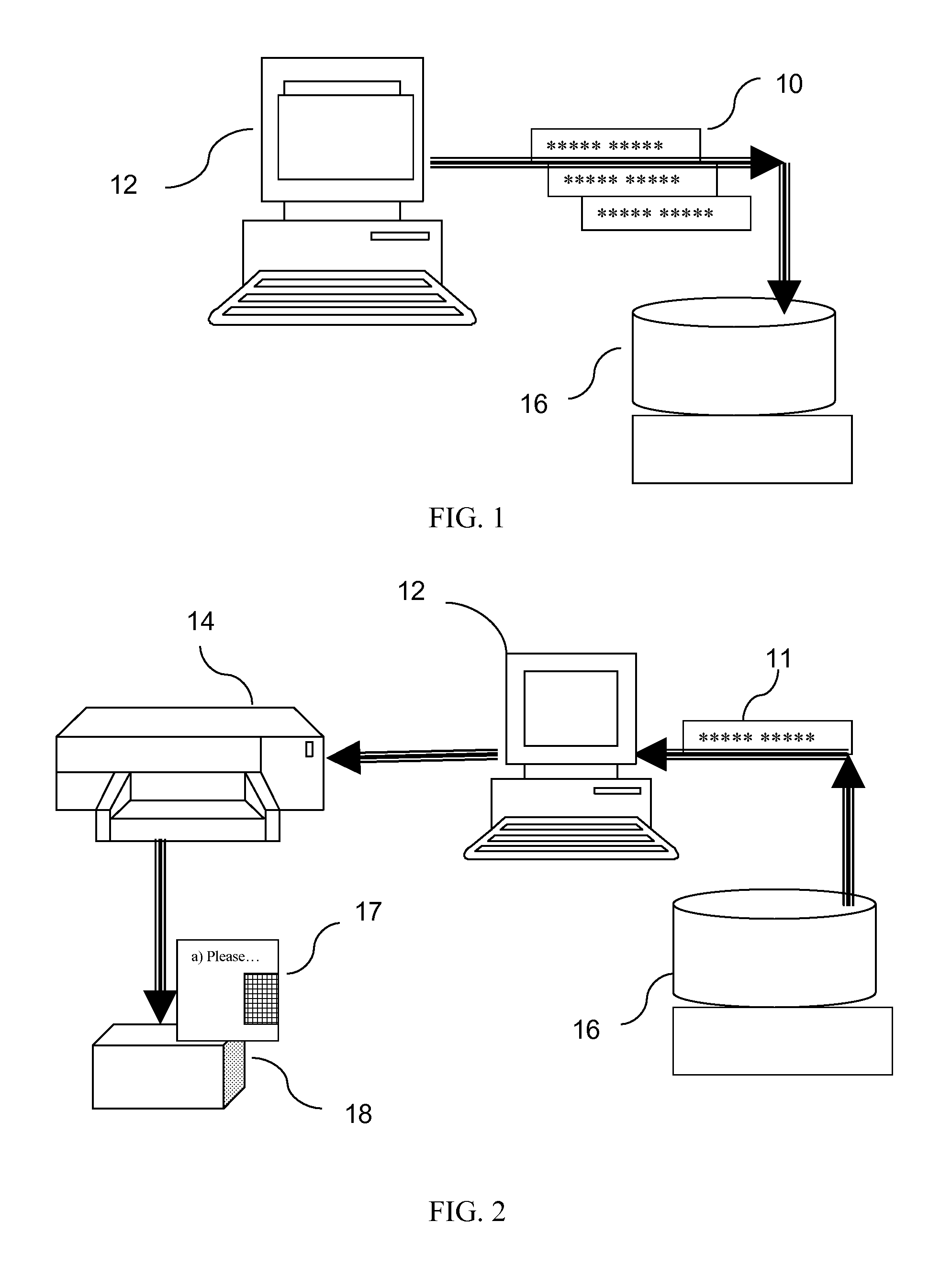
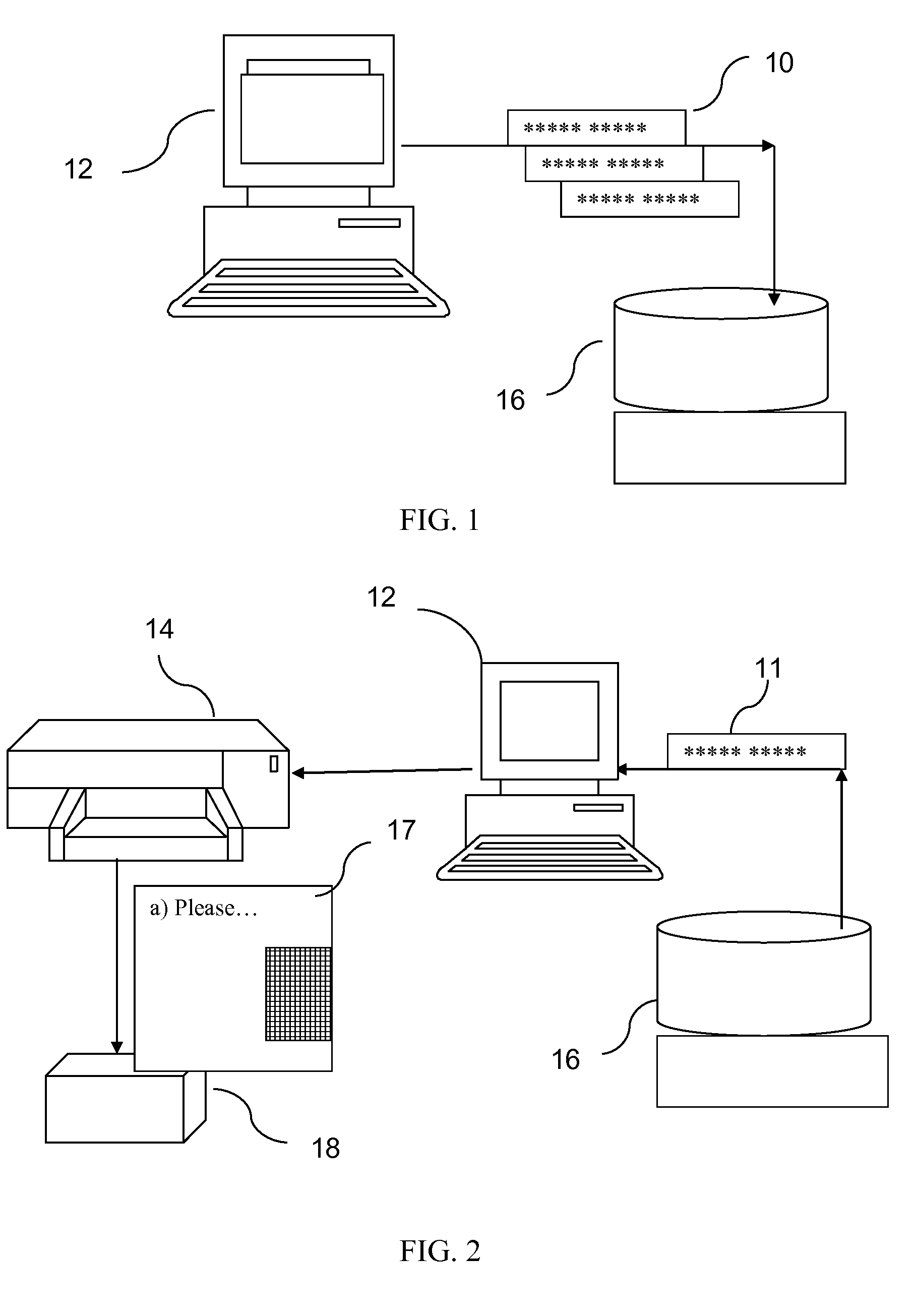
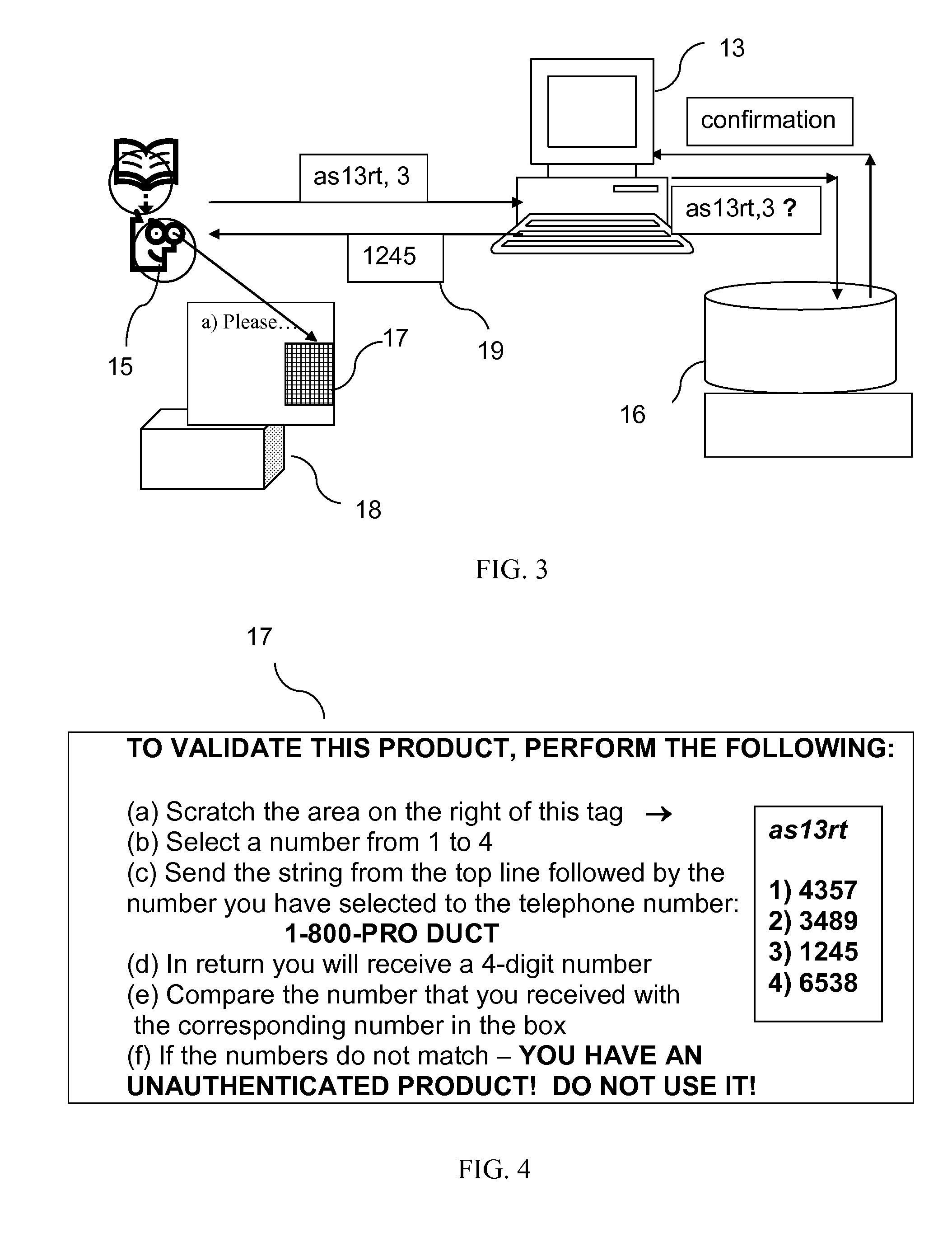
System for product authentication by mobile phone
InactiveUS20090106042A1Overcome disadvantagesIncrease probabilitySubstation equipmentBuying/selling/leasing transactionsAuthentication systemMobile phone
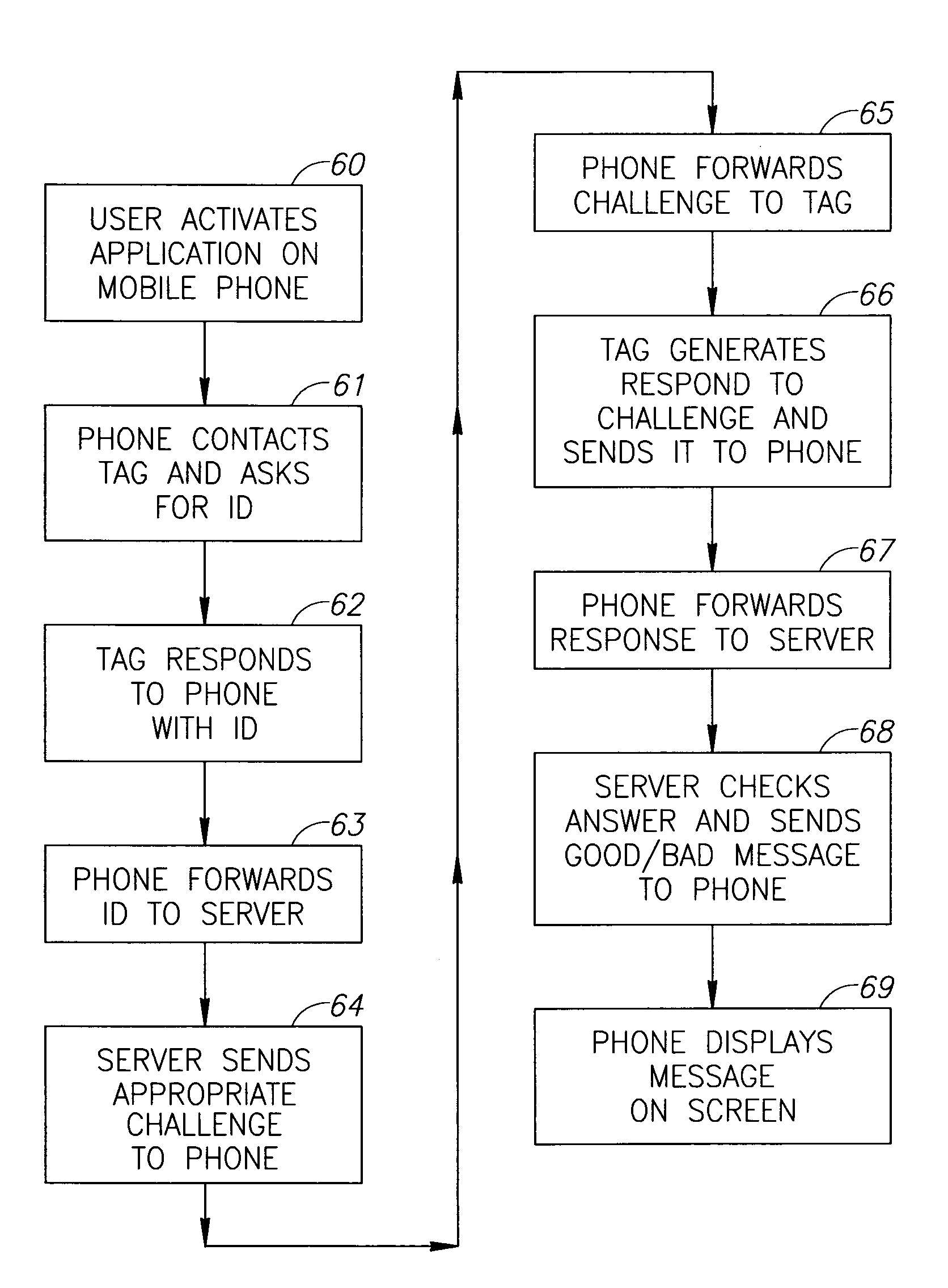
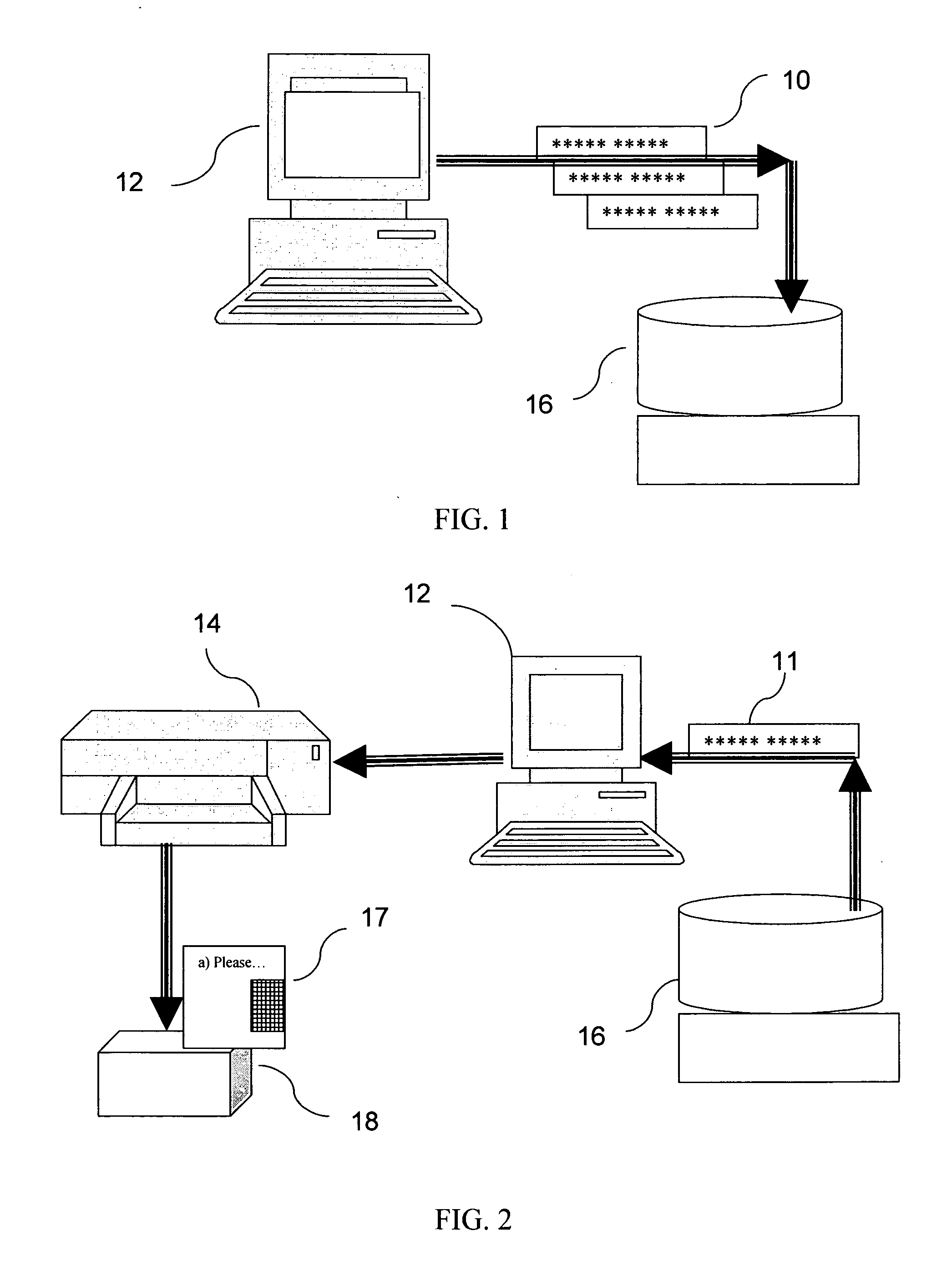
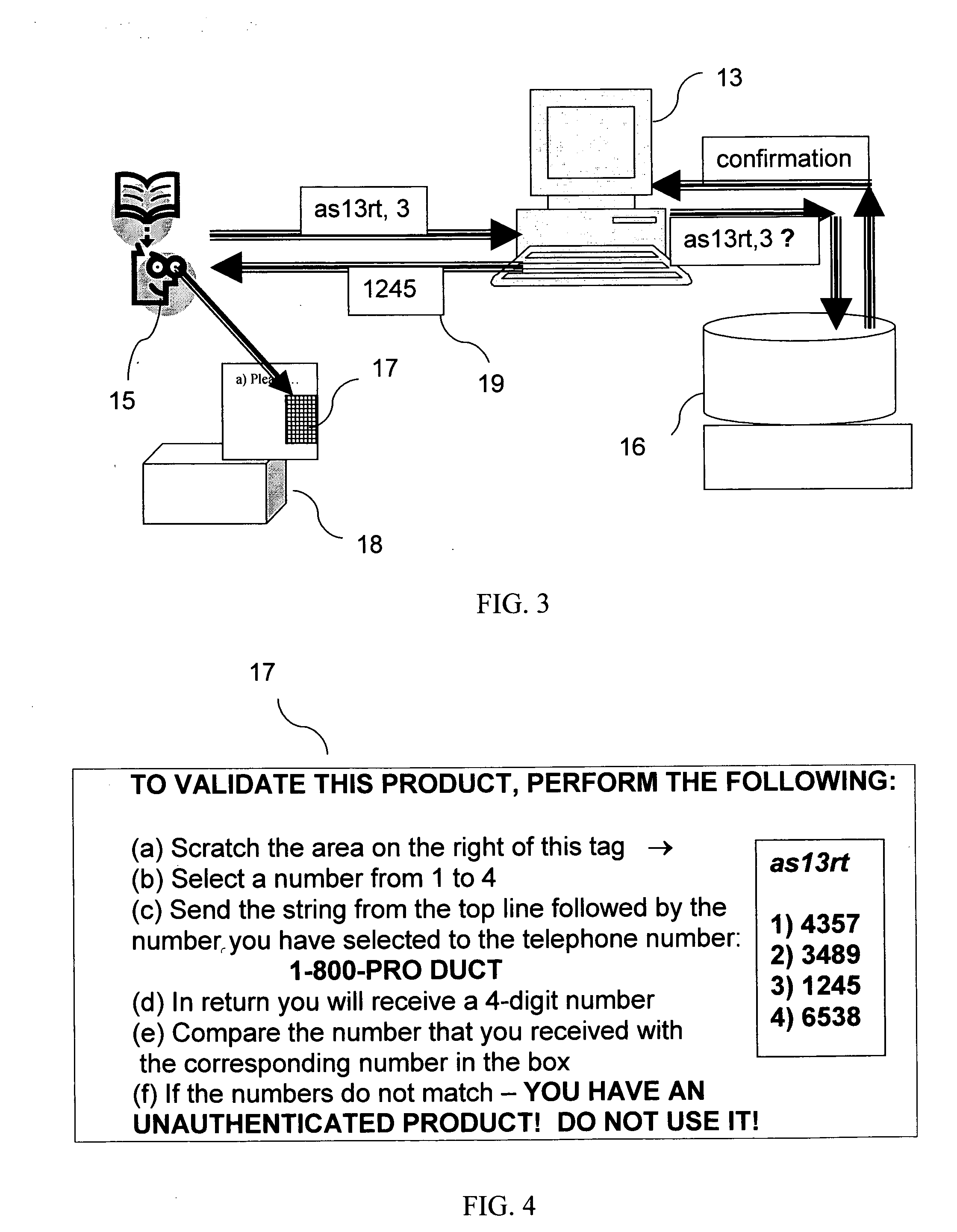
An authentication system enabling a customer to verify the authenticity of a product in a foolproof, secure and simple manner. plurality of secret sets of numbers is generated, each set comprising a challenge portion and a response portion. These sets are stored on a remote server. Each set is associated with a different product. The customer sends a challenge portion to the server, and prompts the server to provide a response. If the response matches that of the product in hand, the product is known to be authentic. In another embodiment of the system, cellular transmission is used to power an electronic tag attached to the product and carrying authentication data. In a third embodiment, the full manufacturer database is divided into separate databases, possibly related to product vendor, such that an authentication process can be performed without the need to access the manufacturer's entire database of products.
Owner:AUTHIX TECH LTD
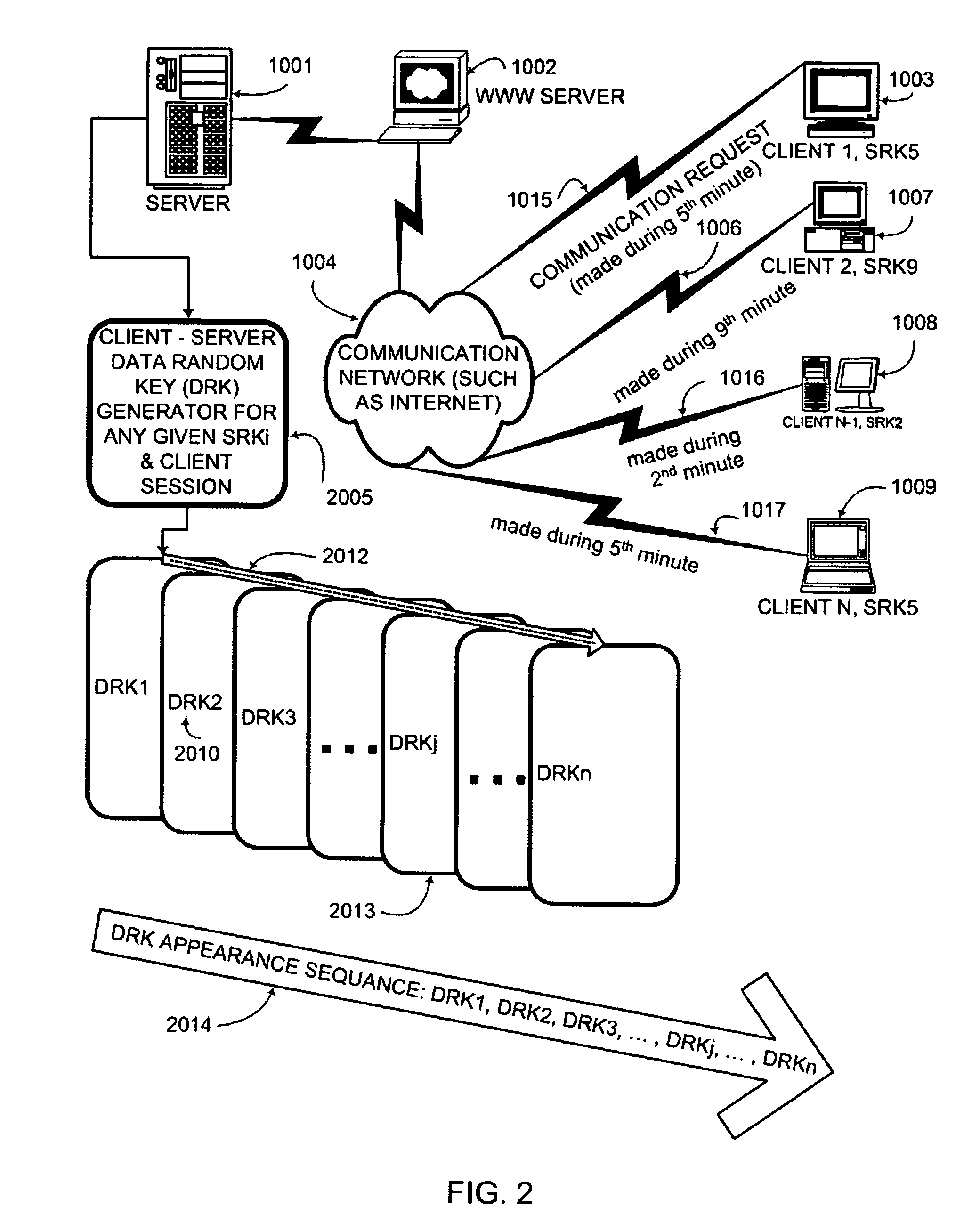
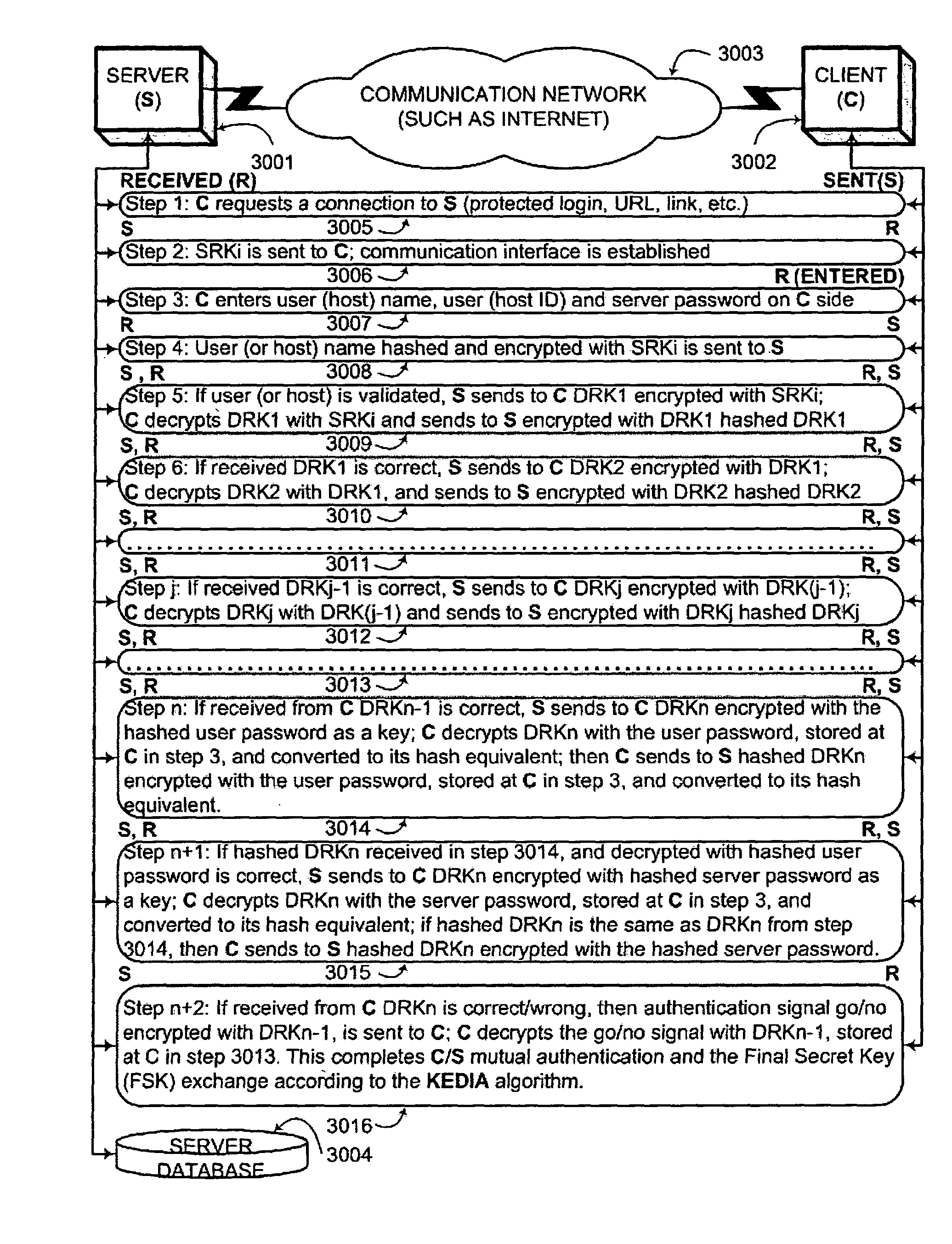
Key generation method for communication session encryption and authentication system
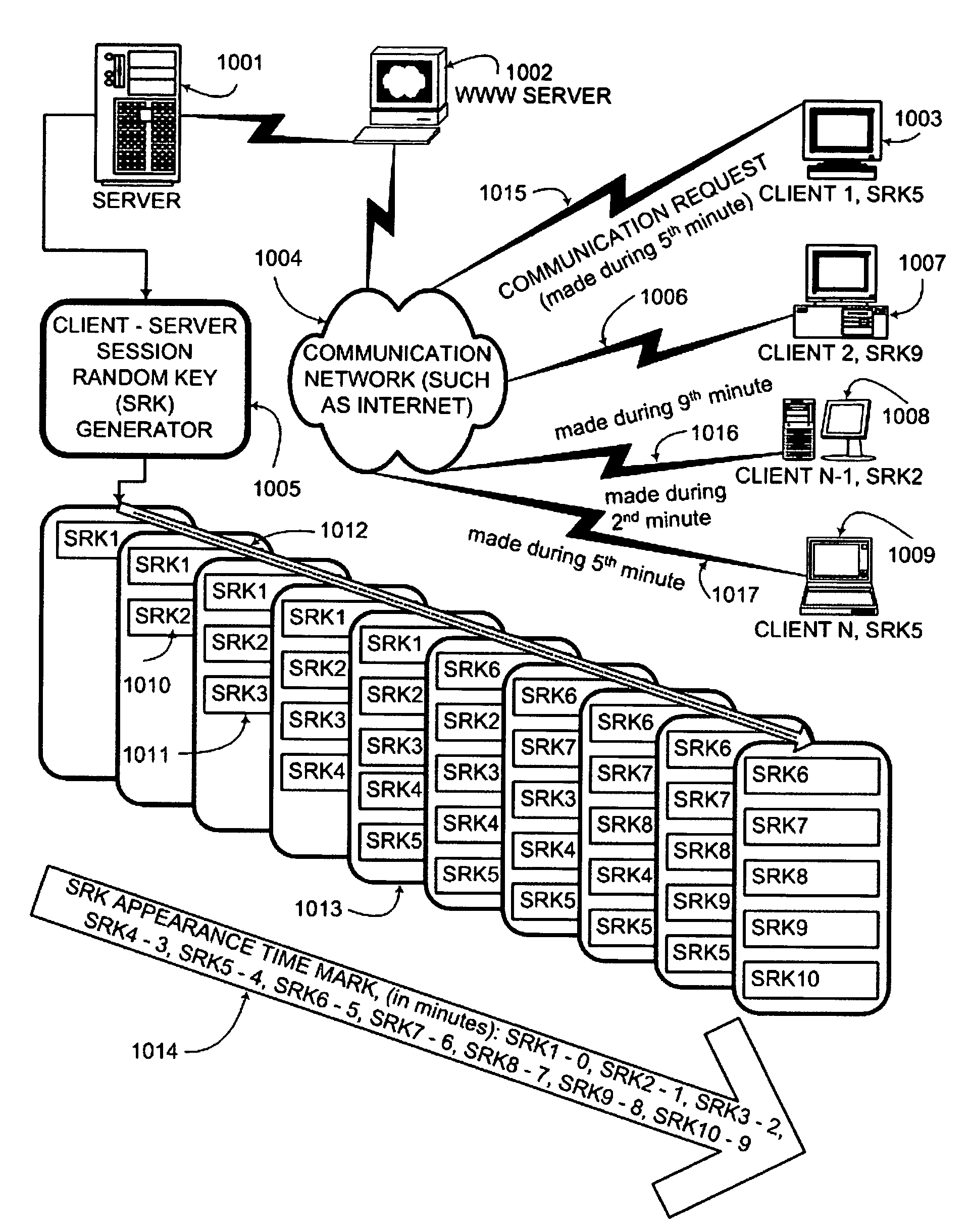
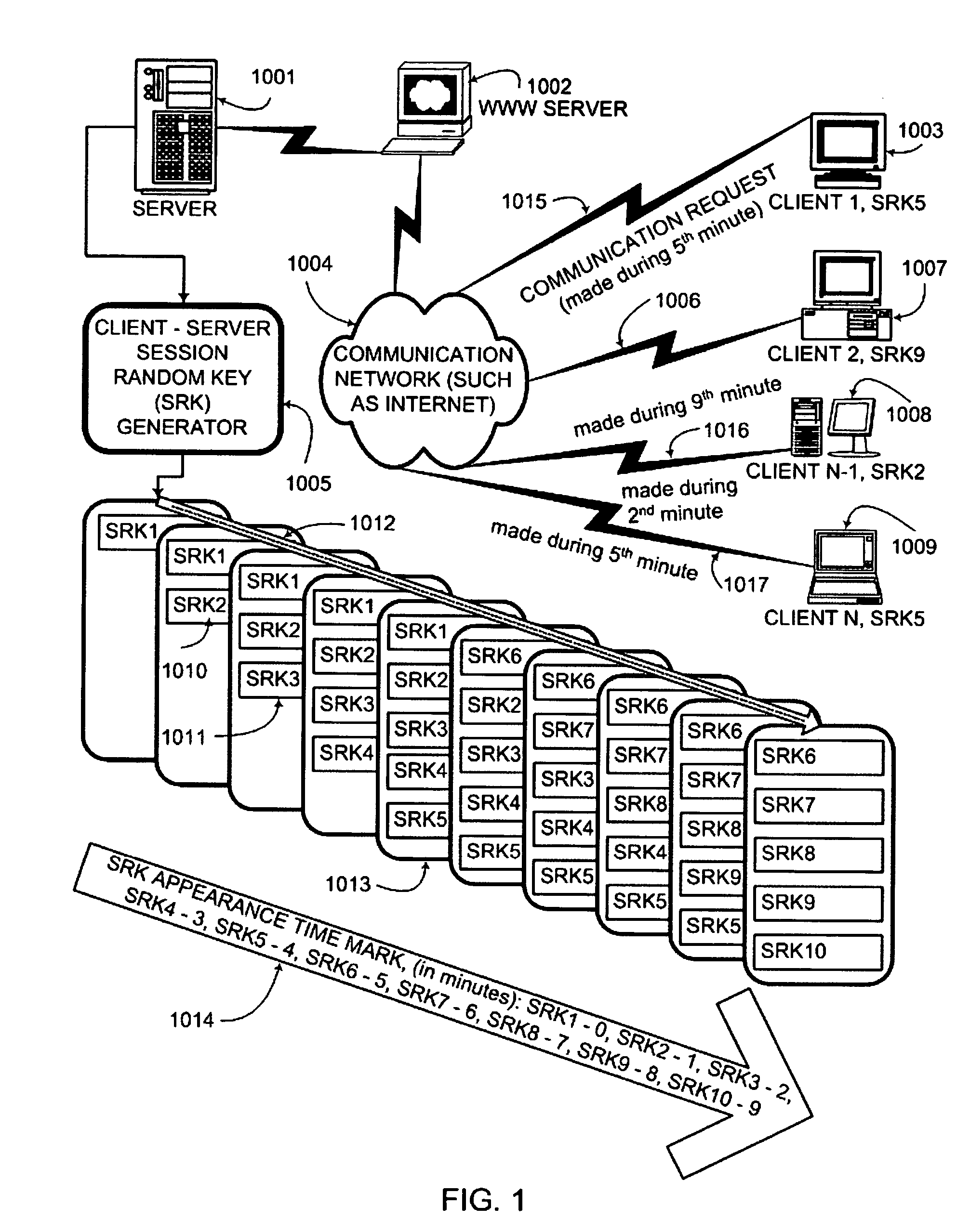
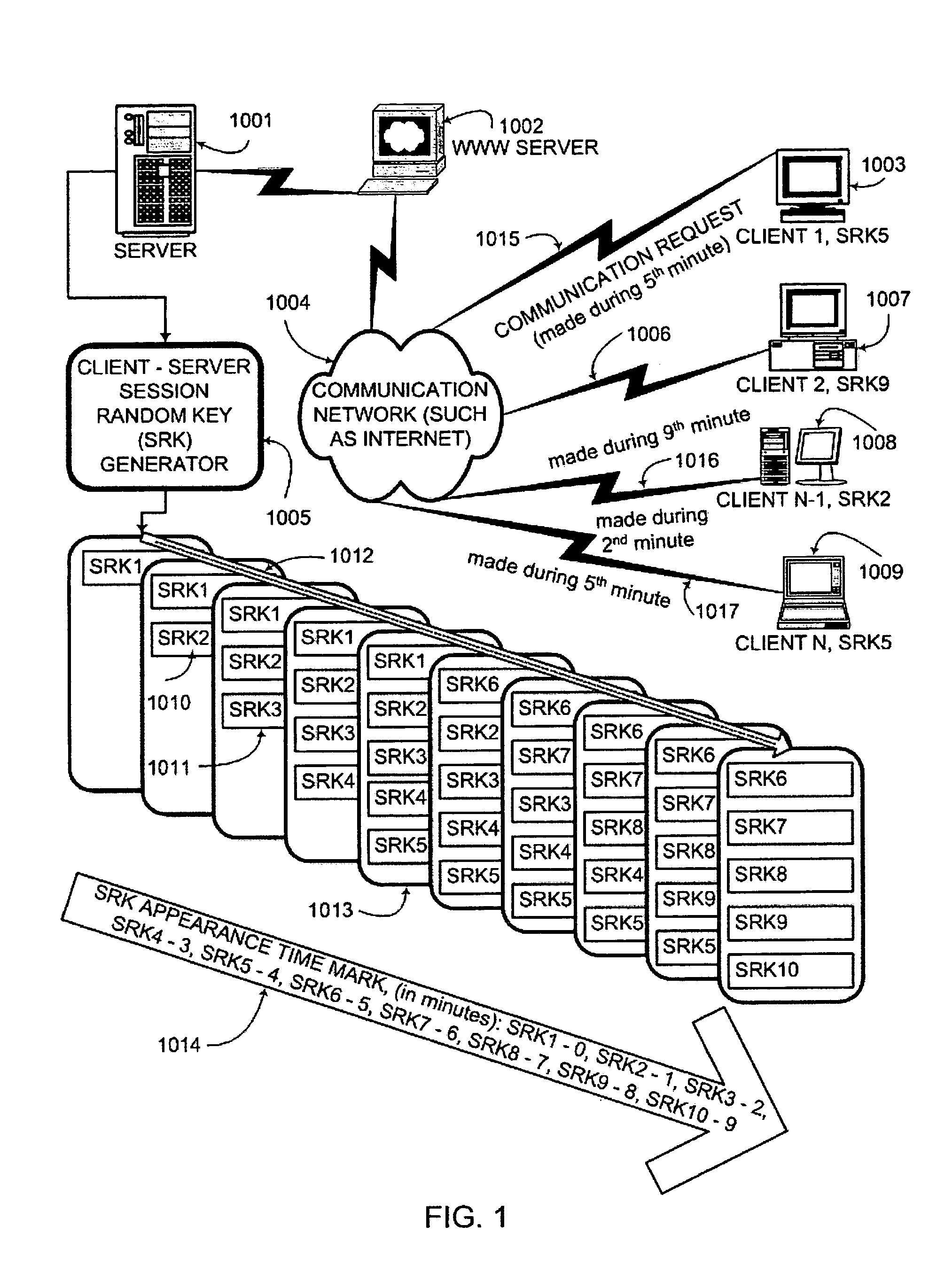
ActiveUS20050050328A1Secure EncryptionKey distribution for secure communicationUser identity/authority verificationComputer hardwareAuthentication system
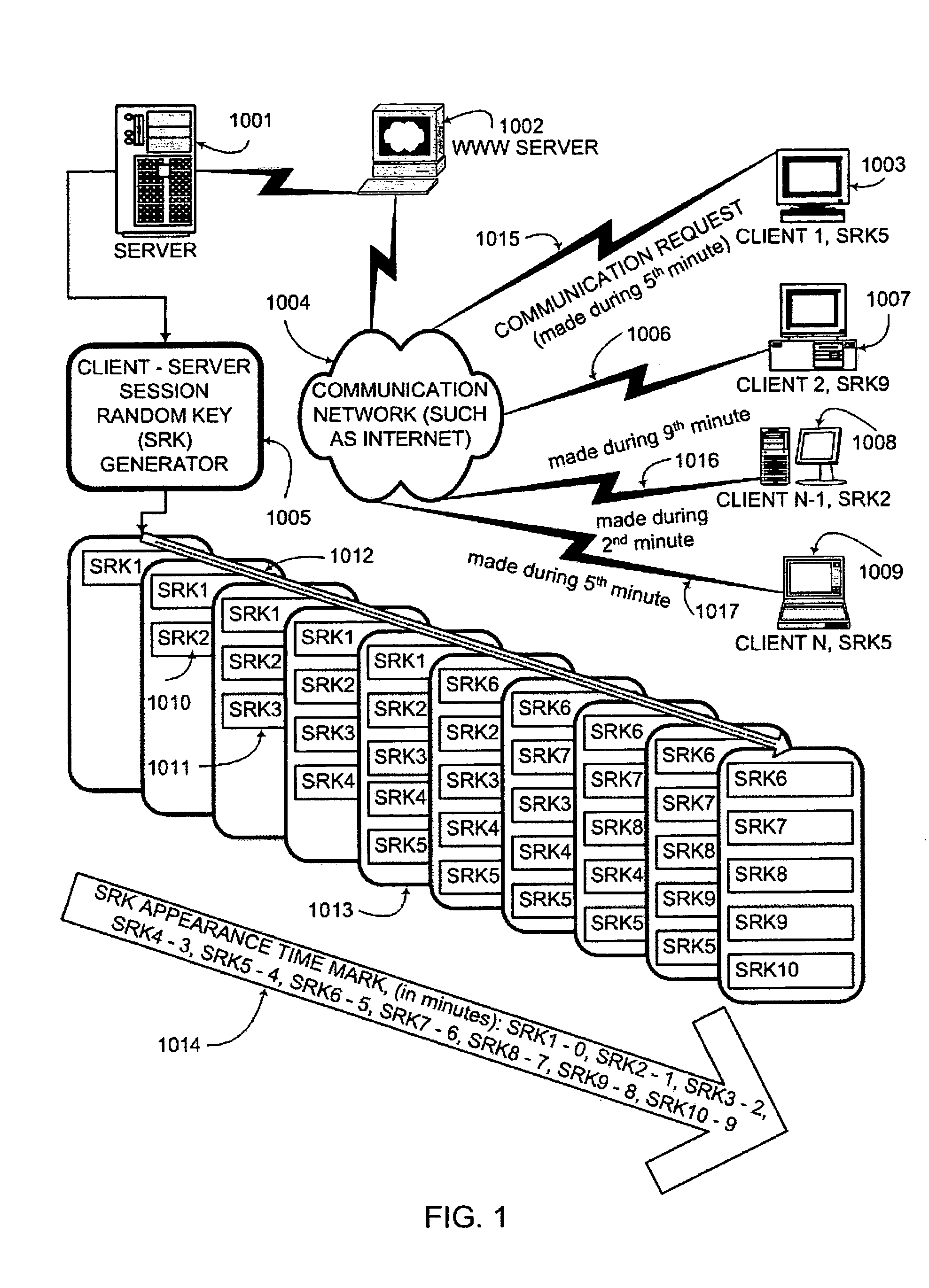
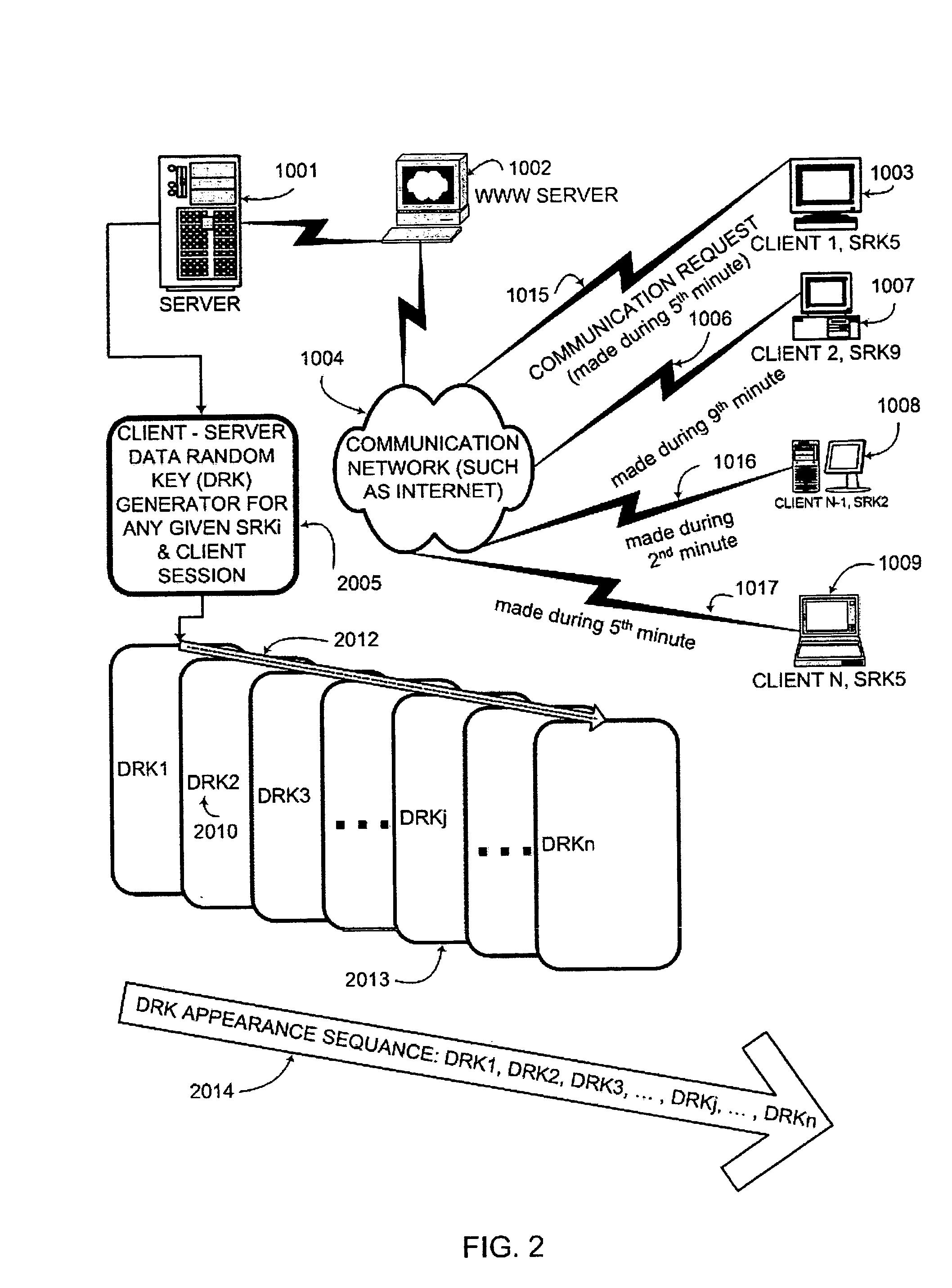
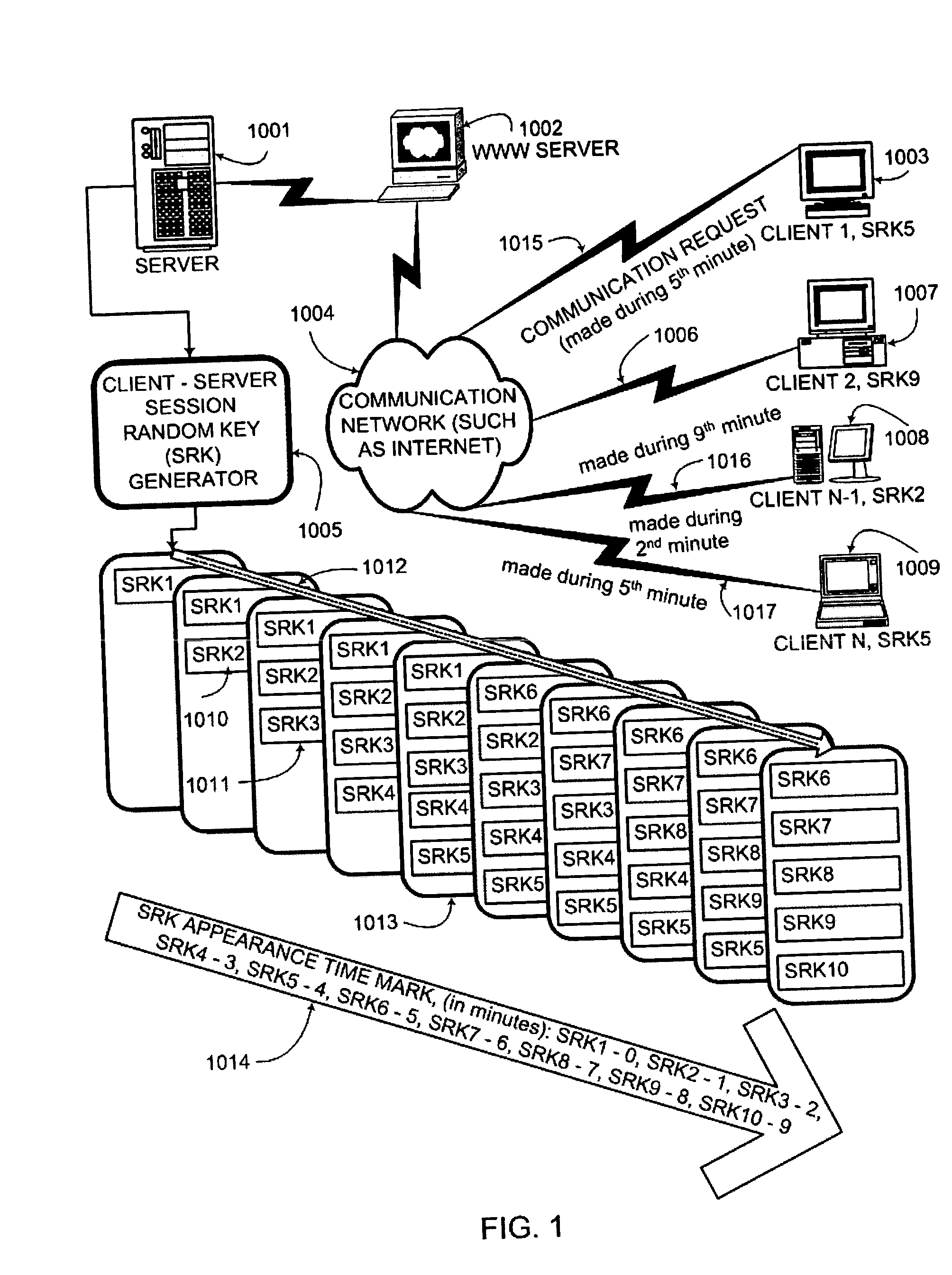
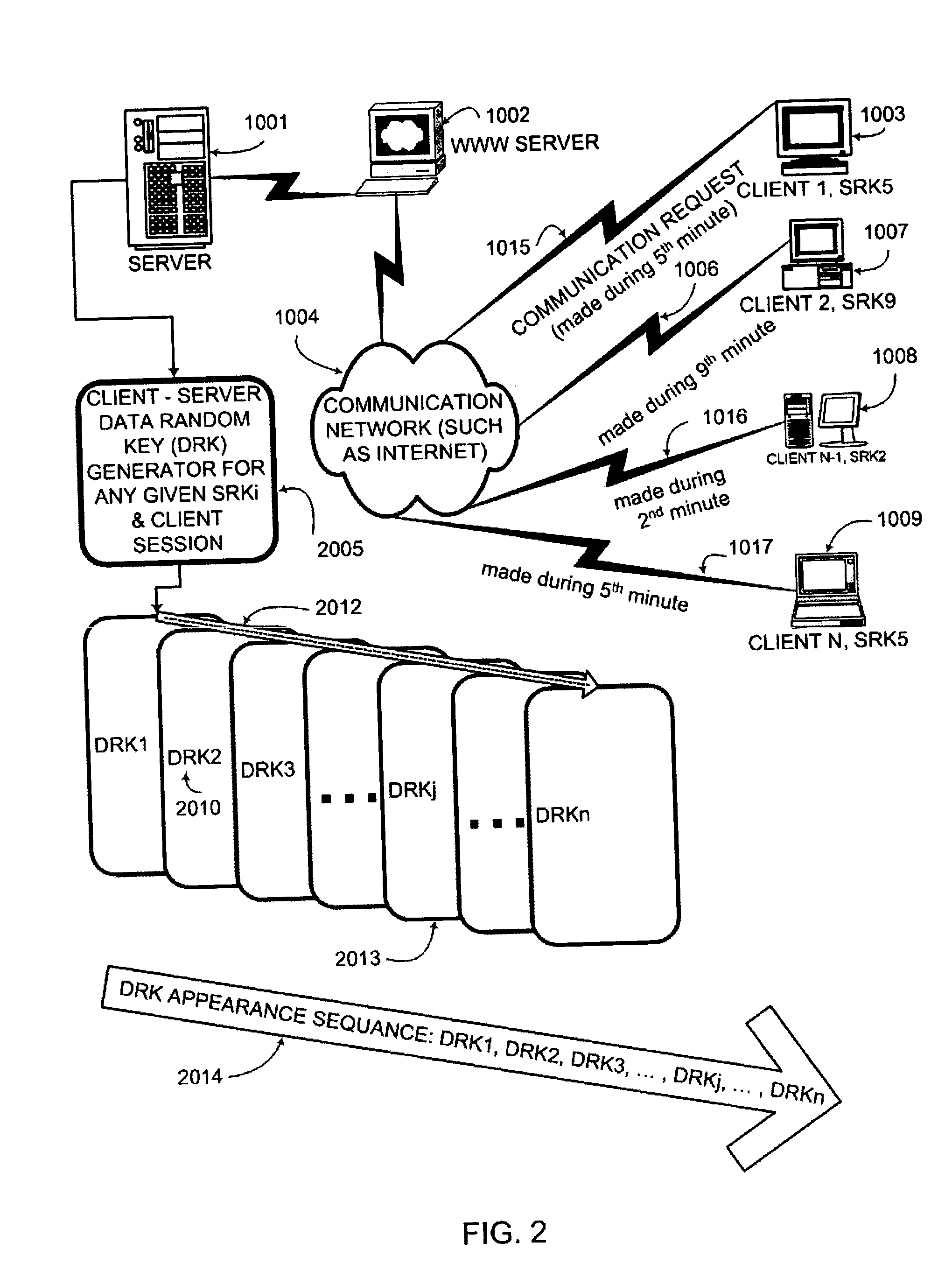
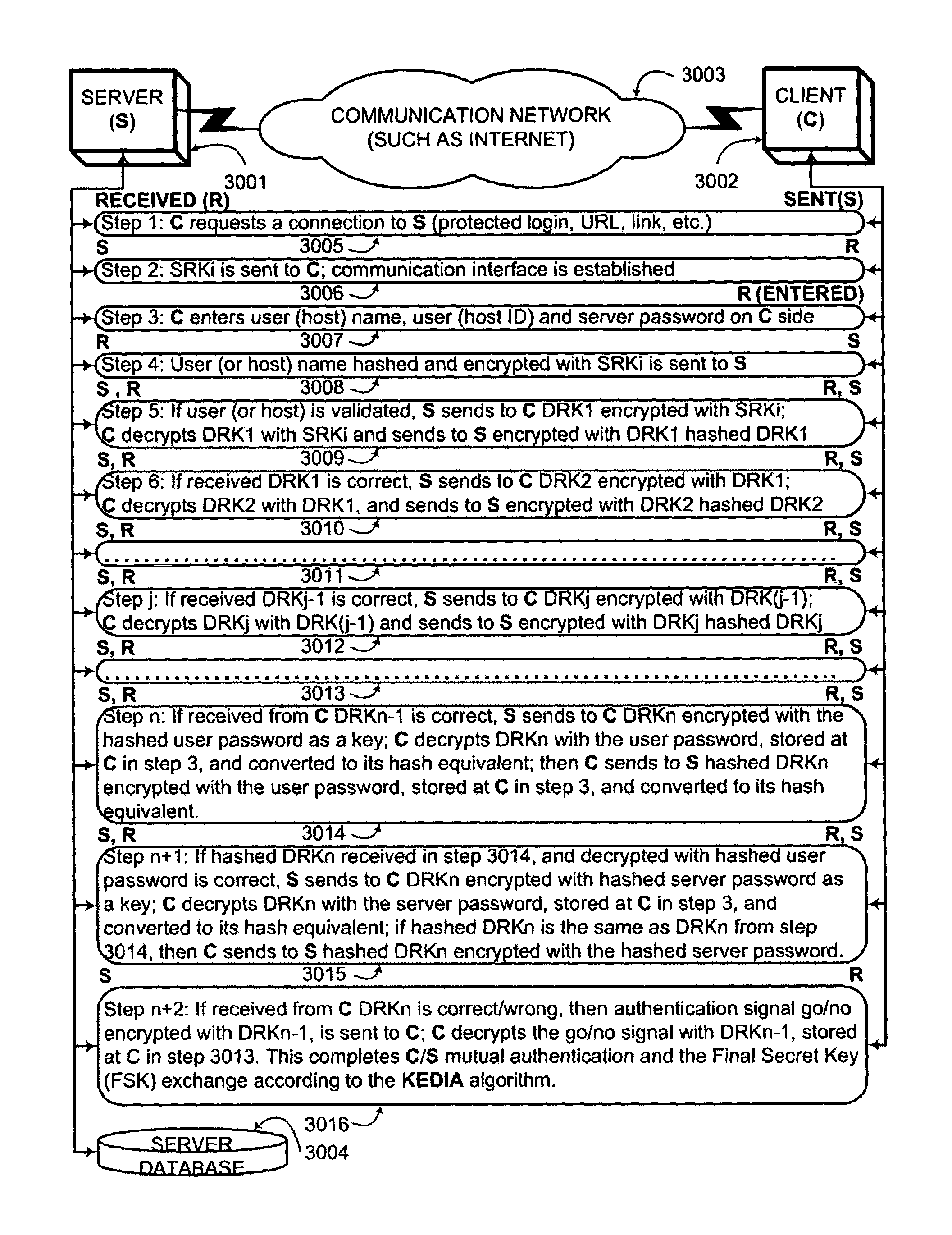
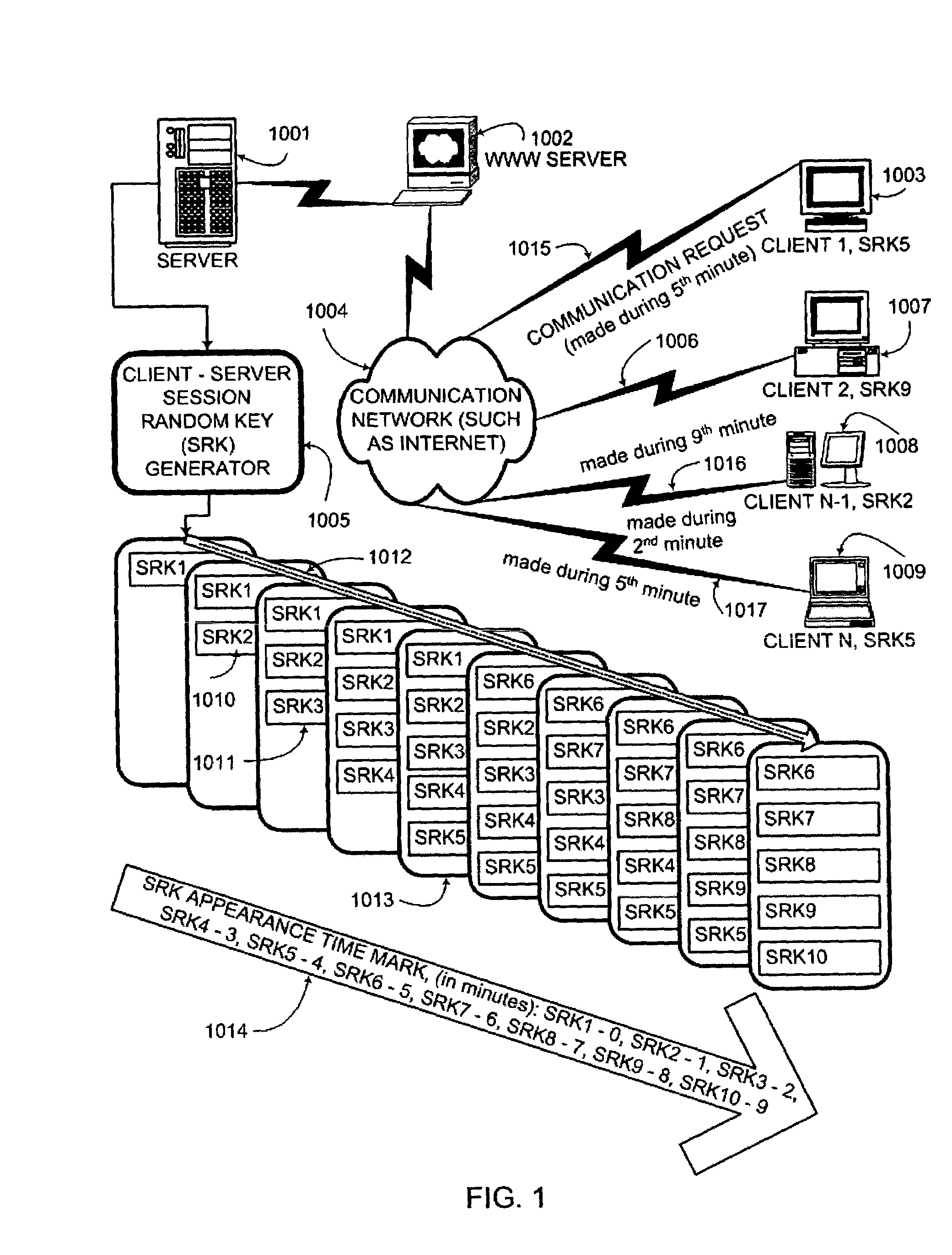
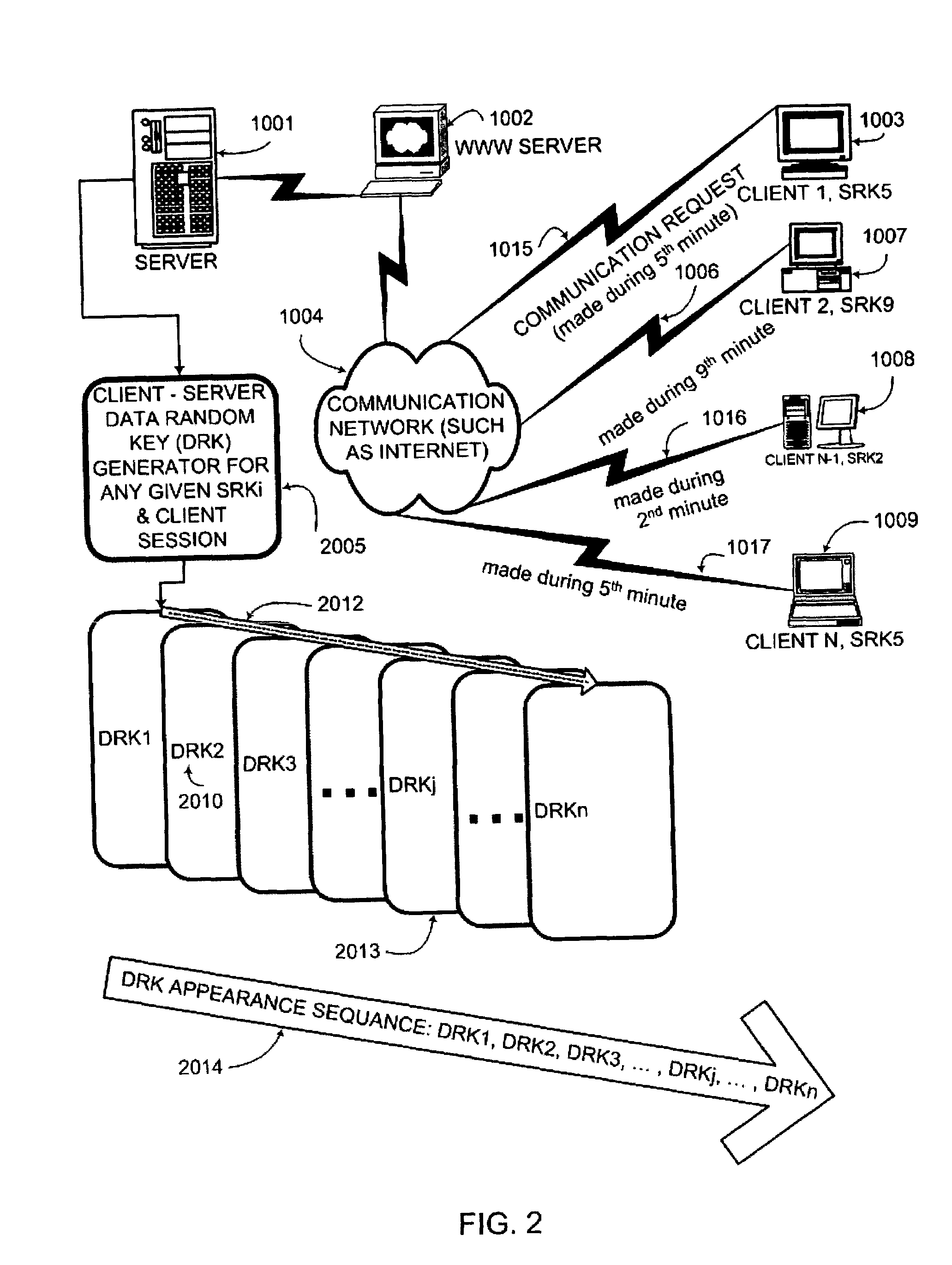
An interactive mutual authentication protocol, which does not allow shared secrets to pass through untrusted communication media, integrates an encryption key management system into the authentication protocol. The server provides ephemeral encryption keys in response to a request during a Session Random Key (SRK) initiation interval. SRK is provided for all sessions initiated in the SRK initiation interval. A set of ephemeral intermediate Data Random Keys (DRK) is associated with each request. A message carrying the SRK is sent to the requestor. A response from the requester includes a shared parameter encrypted using the SRK verifying receipt of the SRK. After verifying receipt of the SRK at the requester, at least one message is sent by the server carrying an encrypted version of one of said set of ephemeral intermediate DRK to be accepted as an encryption key for the session.
Owner:AUTHERNATIVE INC
Systems and methods for simultaneous integrated multiencrypted rotating key communication
InactiveUS20100316219A1Secure EncryptionImprove securityMultiple keys/algorithms usageMicroscopesInternet privacyCommunications system
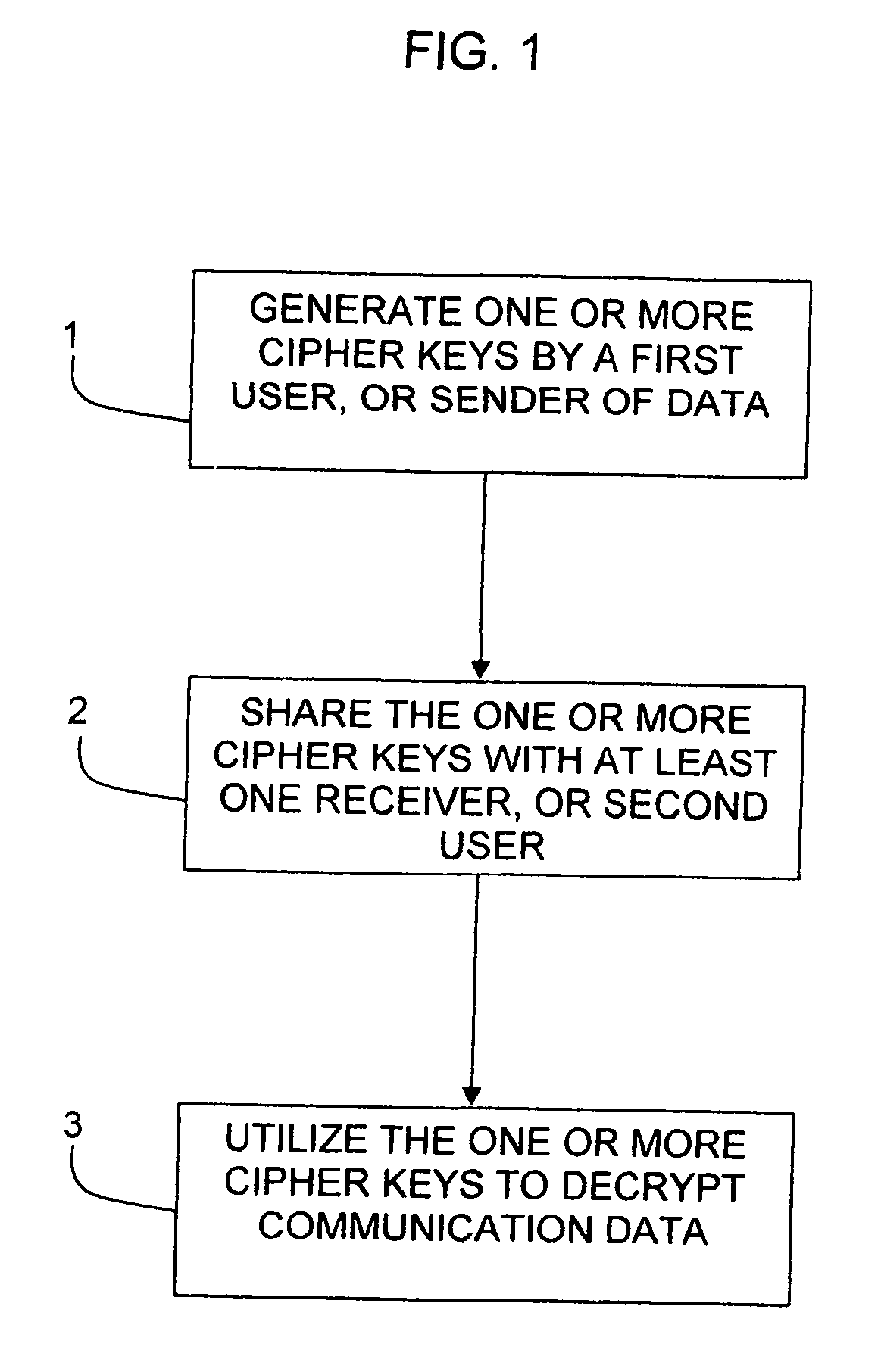
Systems and methods are provided for manual and / or automatic initiation of simultaneous multi-encrypted rotating key communication. Specifically, decryption of data between a first user and one more other users during a communication session may occur using a plurality of keys that rotate or change after an event has occurred, such as an amount of time has elapsed during the communication session or an amount of data has been transmitted during the communication session. The first user and the one or more other users may have a repository for the storage of the plurality of keys to use during the communication session.
Owner:BOUBION DAVID +2
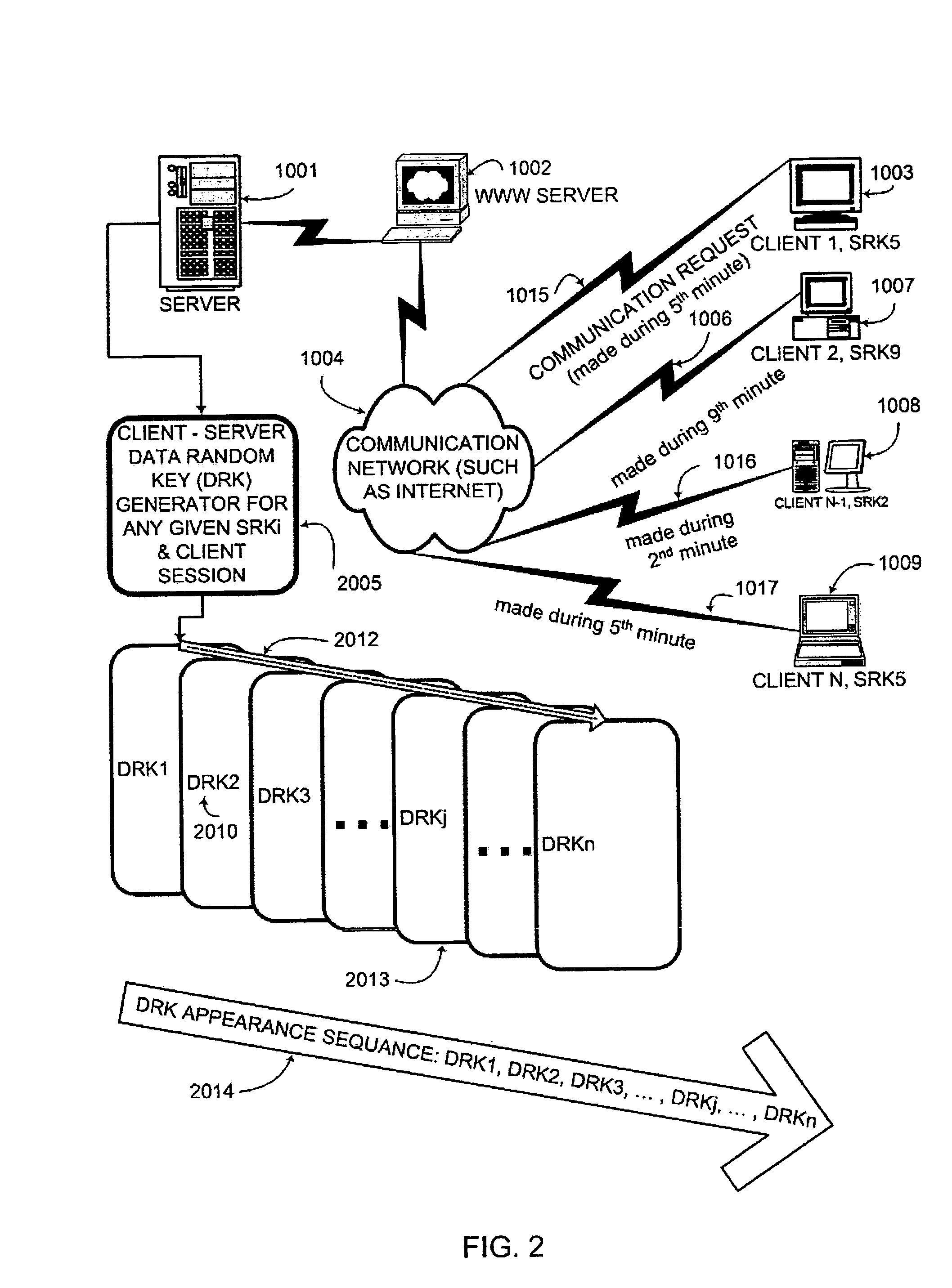
Key conversion method for communication session encryption and authentication system
ActiveUS20050050322A1Secure EncryptionKey distribution for secure communicationUser identity/authority verificationAuthentication systemStrong authentication
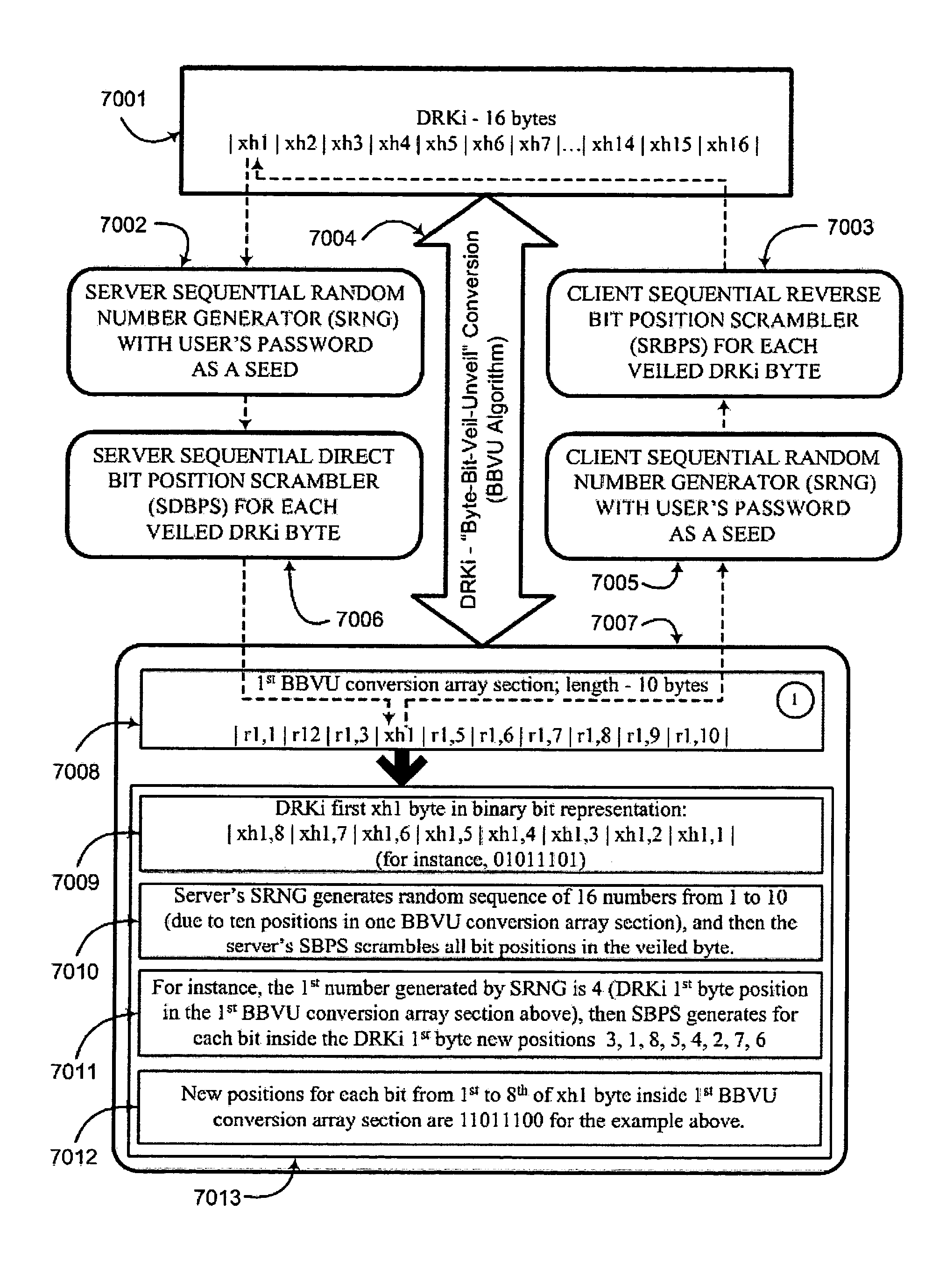
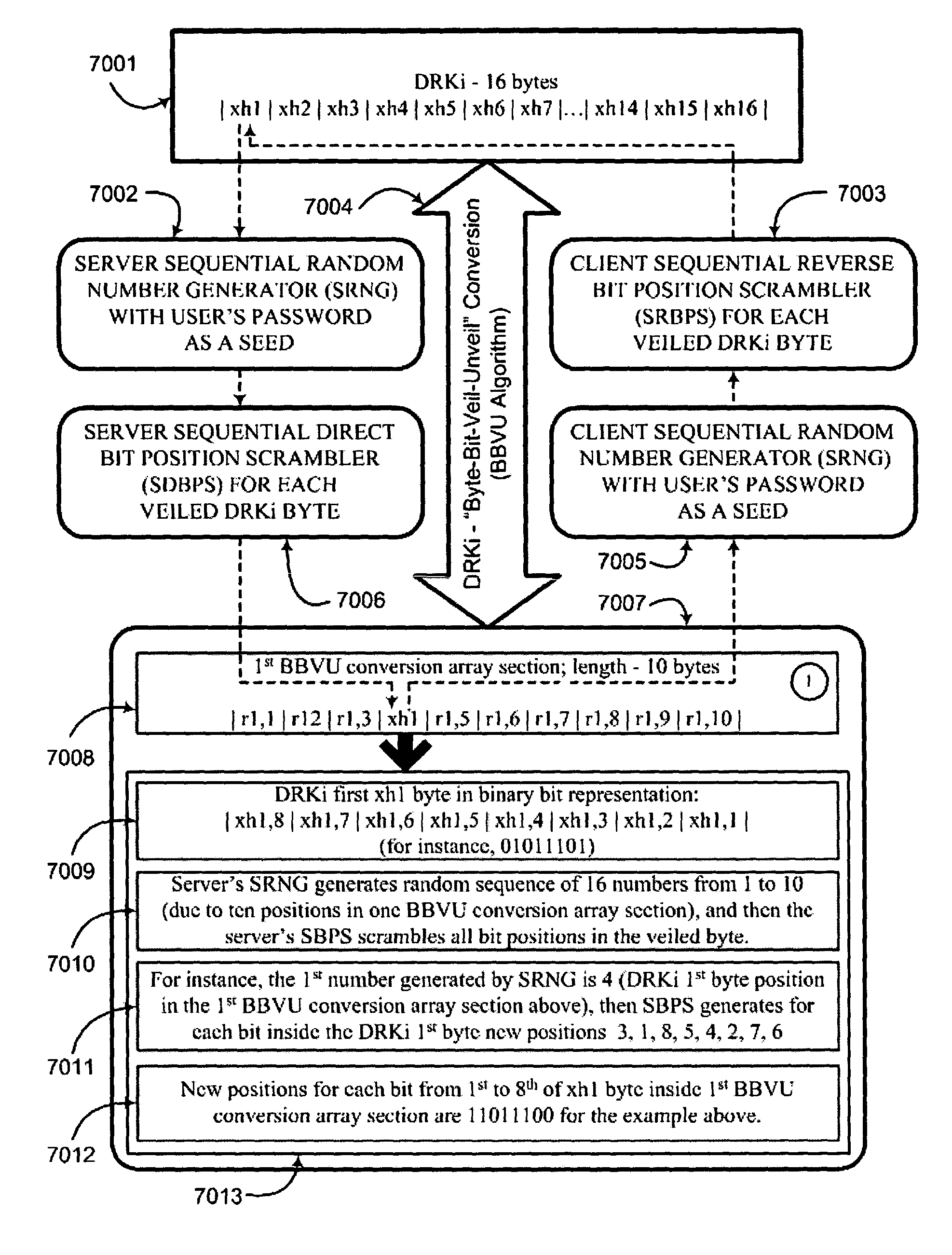
An interactive mutual authentication protocol, which does not allow shared secrets to pass through untrusted communication media, integrates an encryption key management system into the authentication protocol. The server encrypts a particular data random key by first veiling the particular data random key using a first conversion array seeded by a shared secret, and then encrypting the veiled particular data random key. The client decrypts and unveils the particular data random key using the shared secret, and returns a similarly veiled version of the particular data random key using a second conversion array seeded by a shared secret. Access to the shared secret indicates authenticity of the stations. The procedure may be repeated for a second shared secret for strong authentication, without allowing shared secrets to pass via untrusted media.
Owner:AUTHERNATIVE INC
Venue-based device control and determination
InactiveUS8989779B1Good precisionSecure EncryptionLocation information based serviceEmergency/hazardous communication serviceGeographic regionsRelevant information
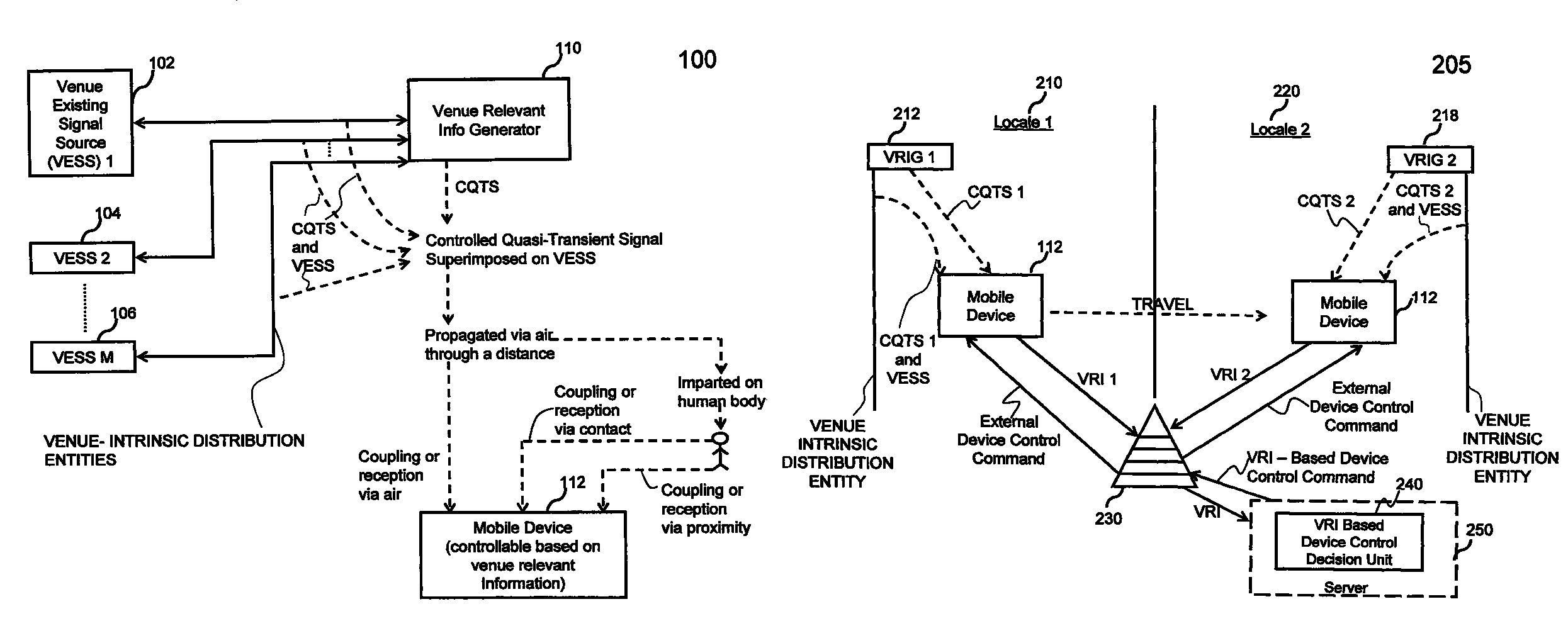
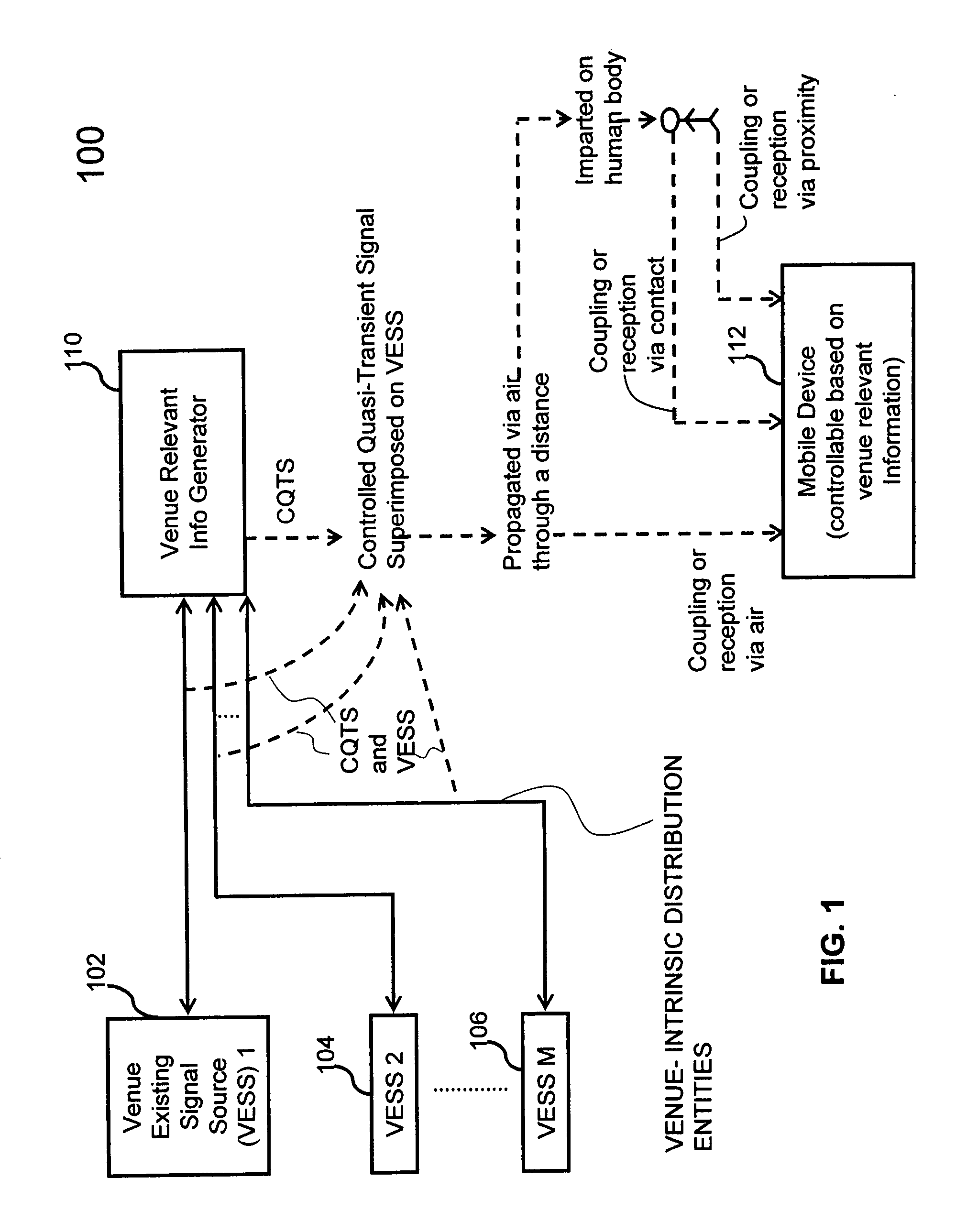
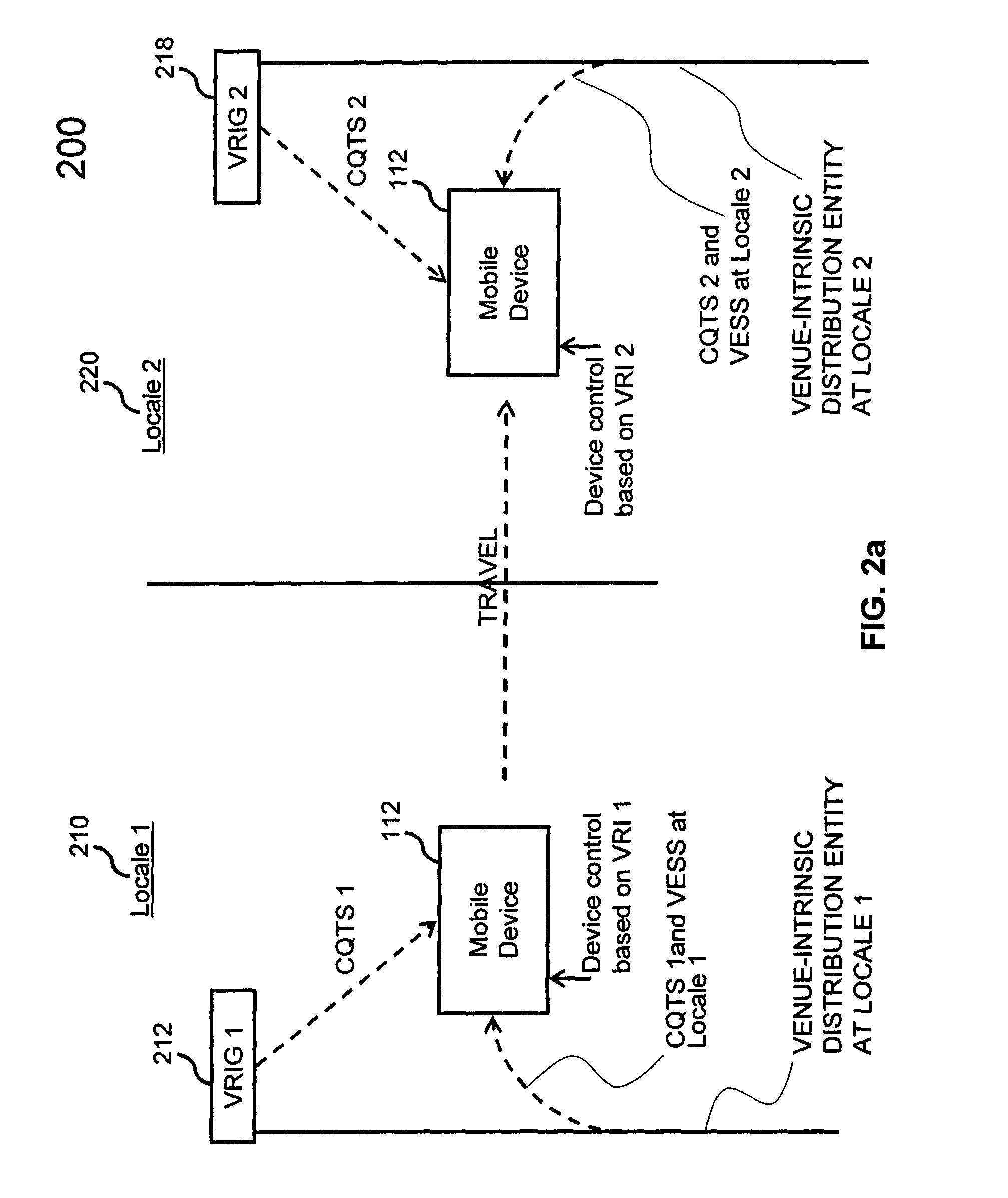
Methods and systems are provided for venue-based device control and user / position / venue context determinations. Venue corresponds to a geographic region. Venue relevant information is information associated with a venue. A controlled quasi-transient signal comprises a signal, emitted by an entity intrinsic to the venue and not intended to be utilized for operation of the device, coupled with a quasi-transient signal that is coded with the venue relevant information. When a device located in a venue receives a controlled quasi-transient signal, venue-relevant information associated with the venue can be extracted from the controlled quasi-transient signal. Based on the extracted venue relevant information, the device can be controlled in accordance with a control signal generated based on the venue relevant information.
Owner:CELLCO PARTNERSHIP INC
Key conversion method for communication session encryption and authentication system
ActiveUS7299356B2Secure EncryptionKey distribution for secure communicationUser identity/authority verificationClient-sideStrong authentication
Owner:AUTHERNATIVE INC
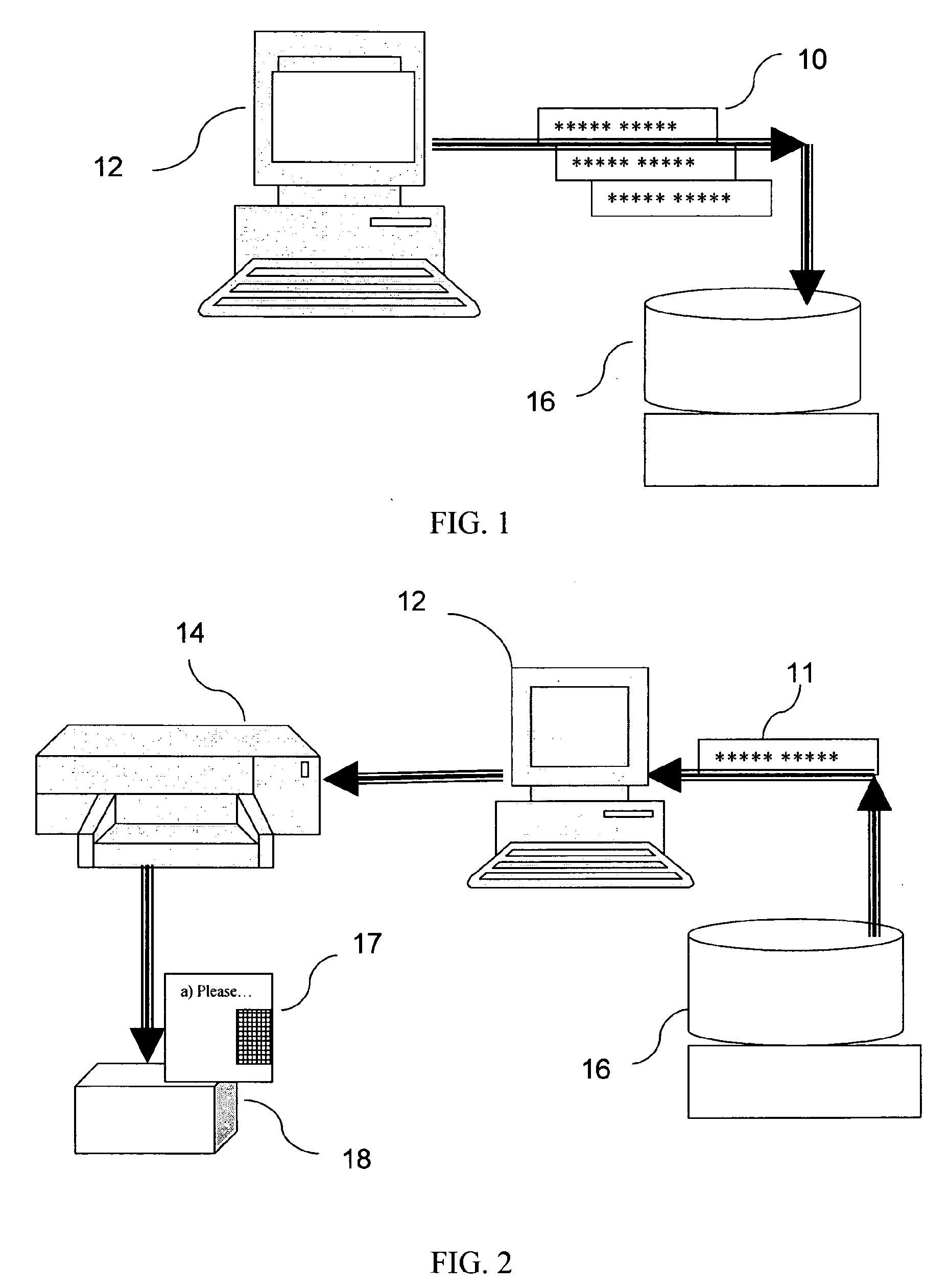
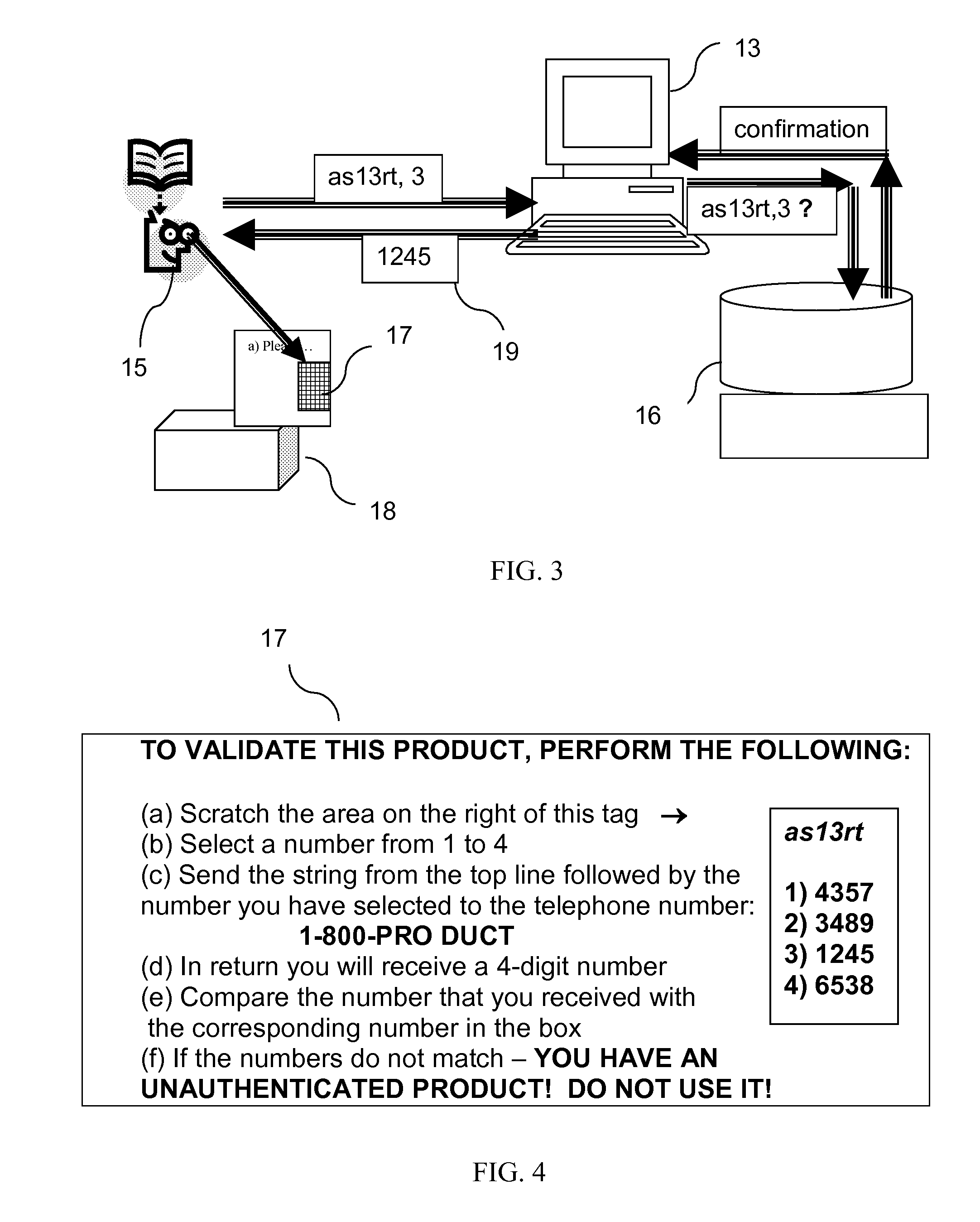
System for product authentication and tracking
InactiveUS20090219132A1Overcome disadvantagesIncrease probabilityElectric signal transmission systemsDigital data processing detailsElectronic taggingAuthentication system
An authentication system enabling a customer to verify the authenticity of a product in a foolproof, secure and simple manner. plurality of secret sets of numbers (10) is generated, each set comprising a challenge portion and a response portion These sets are stored on a remote server (16). Each set is associated with a different product. The customer sends a challenge portion to the server, and prompts the server to provide a response. If the response matches that of the product in hand, the product is known to be authentic. In another embodiment of the system, cellular transmission (42) is used to power an electronic tag (41) attached to the product and carrying authentication data. In a third embodiment, the full manufacturer database is divided into separate databases, possibly related to product vendor, such that an authentication process can be performed without the need to access the manufacturer's entire database of products.
Owner:AUTHIX TECH LTD
Communication session encryption and authentication system
ActiveUS7506161B2Secure EncryptionKey distribution for secure communicationUser identity/authority verificationAuthentication systemCommunications media
Owner:AUTHERNATIVE INC
Secure multicast flow
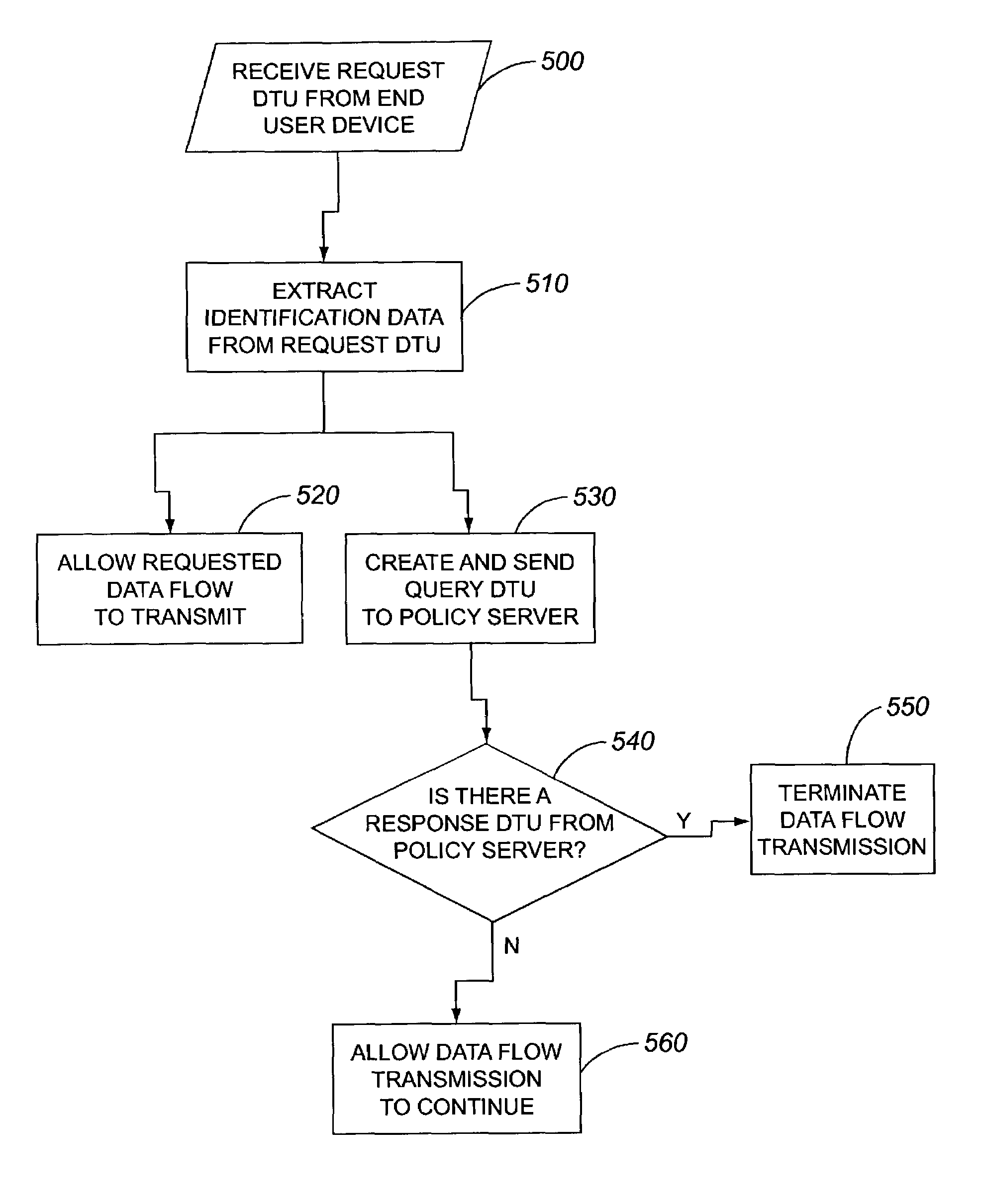
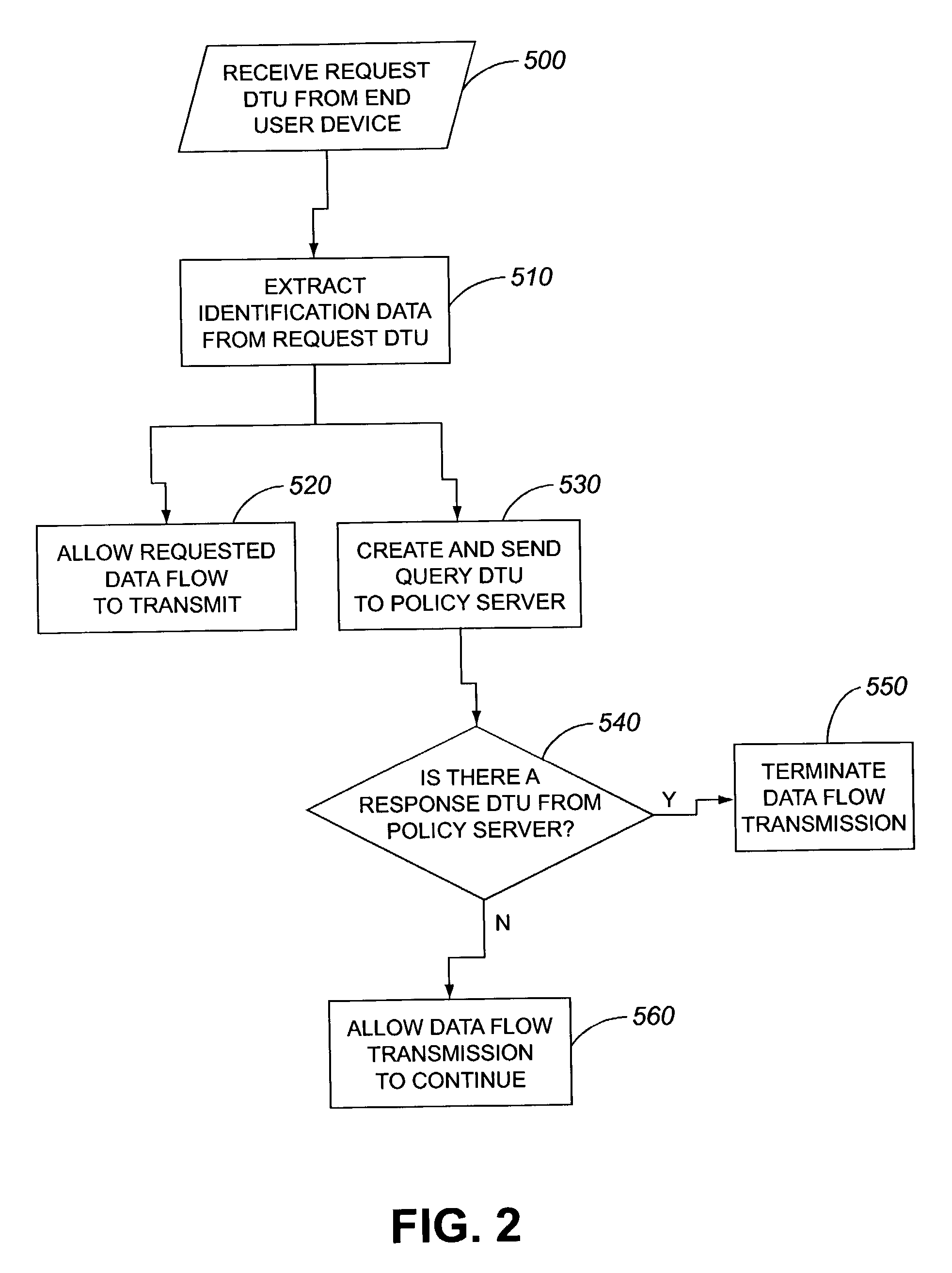
ActiveUS7263610B2Secure encryptionPulse modulation television signal transmissionDigital data processing detailsData transmissionSecure multicast
Methods, devices and systems for providing content providers with a secure way to multicast their data flows only to legitimate end users. By making a specific decision for each potentially legitimate end user requesting a specific data flow, differing subscriber profiles may be taken into account. Furthermore, end to end encryption is avoided by having a switch and / or router control the specific data flow to a specific end user. Each end user sends a request DTU to the switch and / or router asking for permission to join a multicast group. The switch and / or router extracts identification data from the request data transmission unit (DTU) and determines whether the requesting end user is cleared for the requested specific data flow. This determination may be made by sending a query DTU containing the identification data to a policy server which checks the identification data against preprogrammed criteria in its databases. The policy server then sends a response DTU to the switch and / or router confirming or denying the authenticity or legitimacy of the request based on the identification data. In the meantime, after the switch and / or router sends the query DTU to the policy server, the switch and / or router allows the specific requested data flow to proceed to the requesting end user. If, based on the response from the policy server, the request is determined to not be legitimate or authentic, the specific data flow is terminated. If the request is legitimate or authentic, then the data flow is allowed to flow uninterrupted by the switch and / or router.
Owner:ALCATEL LUCENT SAS
Access control system and method
InactiveUS20070096872A1Reduces installation time and expenseSimple and efficientElectric signal transmission systemsDigital data processing detailsEmbedded systemAuthorization
Owner:GTO
Key generation method for communication session encryption and authentication system
ActiveUS7581100B2Secure EncryptionKey distribution for secure communicationUser identity/authority verificationAuthentication systemKey generation
An interactive mutual authentication protocol, which does not allow shared secrets to pass through untrusted communication media, integrates an encryption key management system into the authentication protocol. The server provides ephemeral encryption keys in response to a request during a Session Random Key (SRK) initiation interval. SRK is provided for all sessions initiated in the SRK initiation interval. A set of ephemeral intermediate Data Random Keys (DRK) is associated with each request. A message carrying the SRK is sent to the requestor. A response from the requester includes a shared parameter encrypted using the SRK verifying receipt of the SRK. After verifying receipt of the SRK at the requester, at least one message is sent by the server carrying an encrypted version of one of said set of ephemeral intermediate DRK to be accepted as an encryption key for the session.
Owner:AUTHERNATIVE INC
Processing recordable content in a stream
ActiveUS20110010562A1Quick changeSecure EncryptionUnauthorized memory use protectionHardware monitoringComputer networkDigital rights management system
Methods and a systems are described for processing recordable content in a broadcast stream sent to a receiver, wherein said broadcast stream is protected in accordance with a conditional access system and wherein said receiver is configured for storing and consuming content in said broadcast stream in accordance with a digital rights management system. In this methods and systems recording information is sent in one or more entitlement control messages over a broadcast network to a receiver. Using the recording information in the entitlement control messages the receiver is able to store recordable events in a broadcast stream on a storage medium and to consume said recorded events in accordance with a digital rights management system.
Owner:IRDETO ACCESS
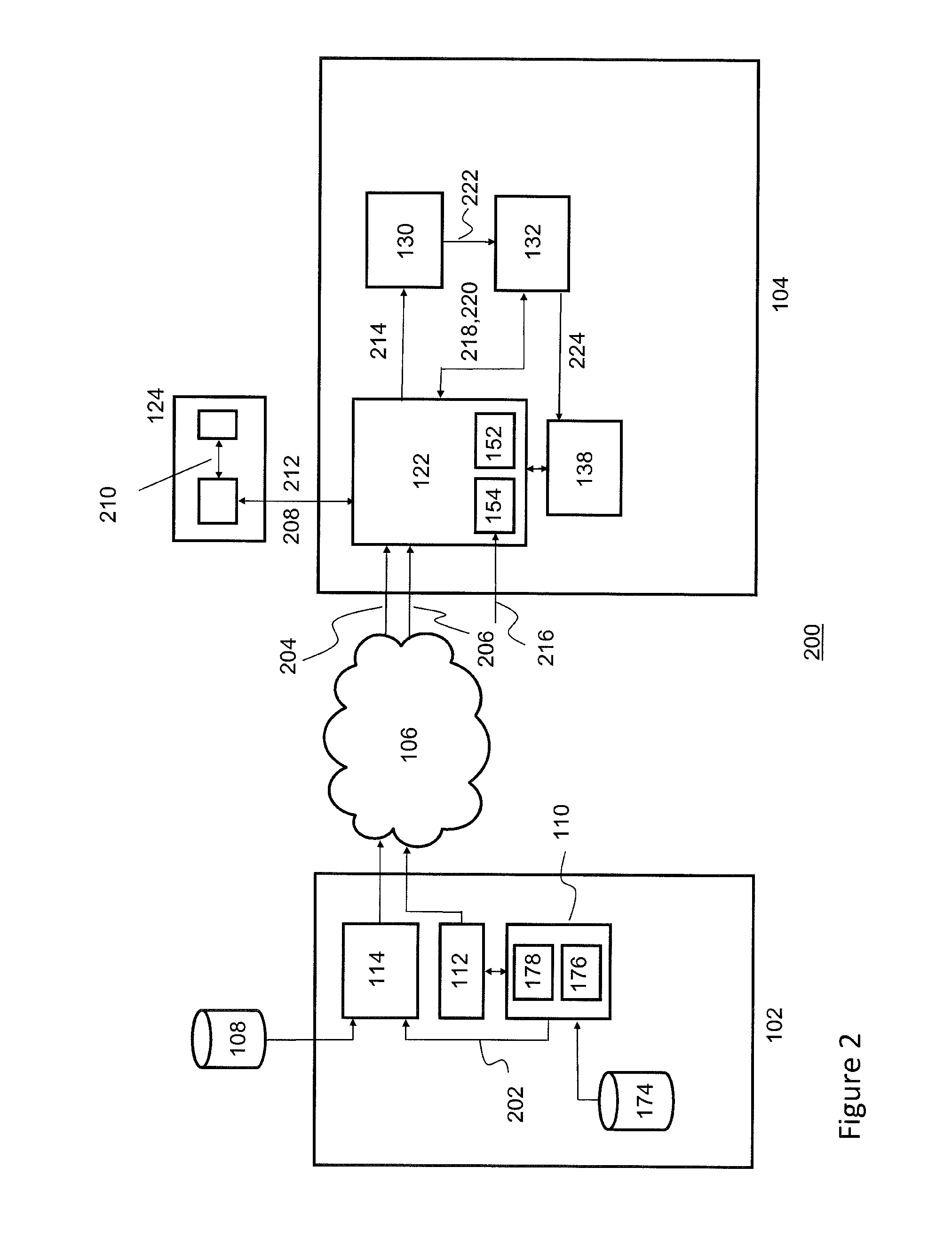
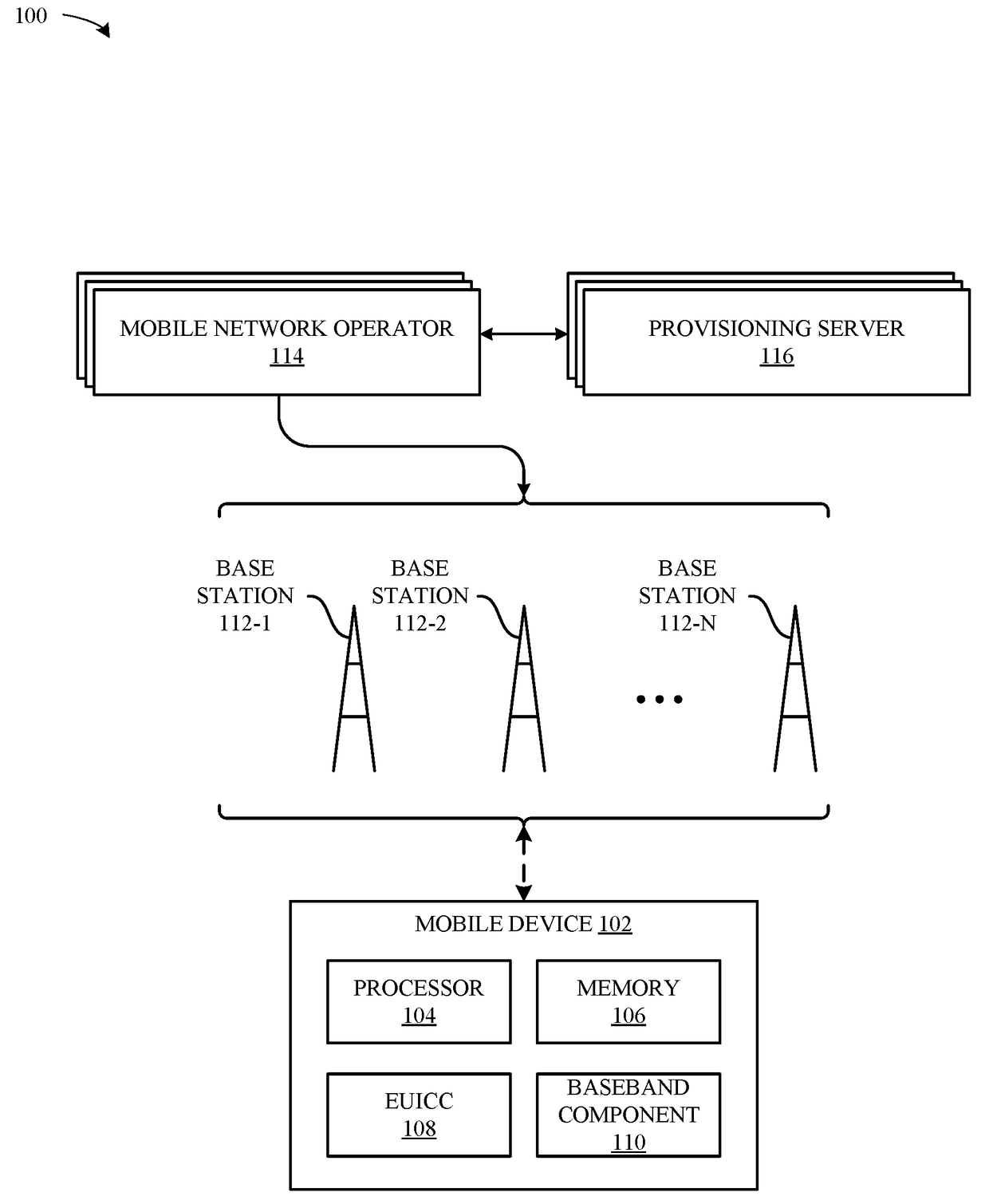
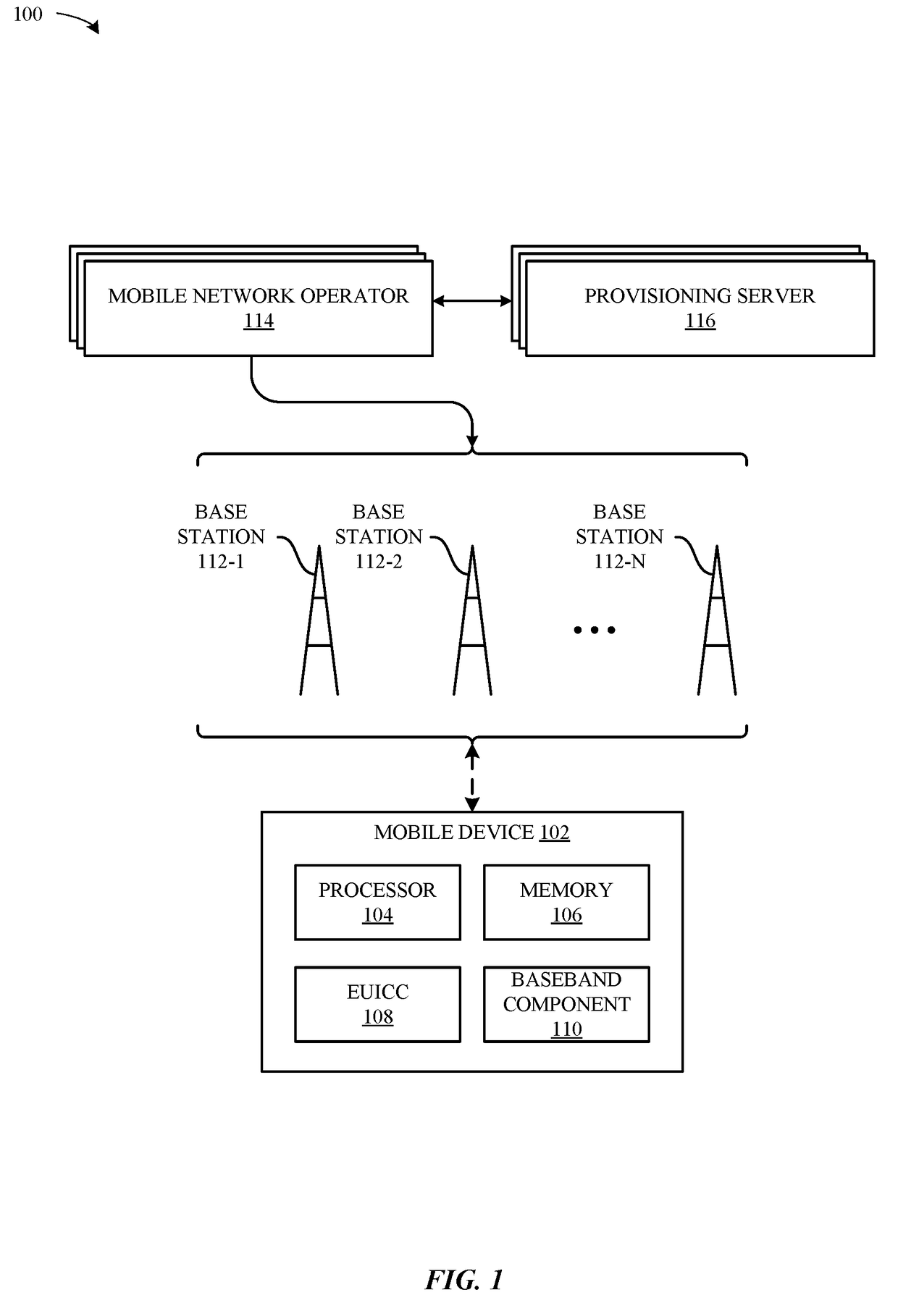
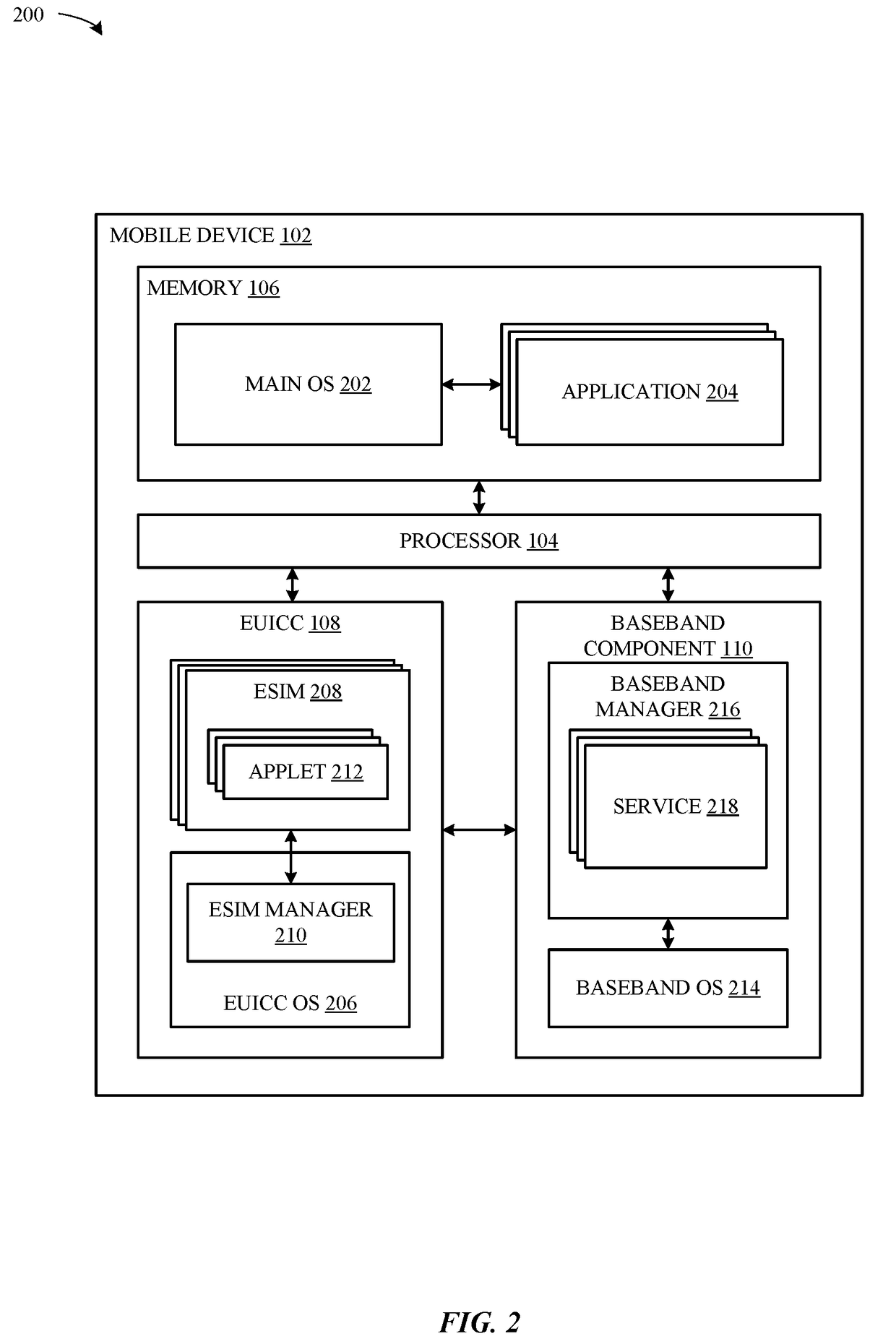
Apparatus and methods for electronic subscriber identity module (ESIM) installation notification
ActiveUS20170127264A1Secure EncryptionSecurity arrangementSecuring communicationMobile deviceSubscriber identity module
Methods and apparatus for provisioning electronic Subscriber Identity Module (eSIM) data by a mobile device are disclosed. Processing circuitry of the mobile device transfers encrypted eSIM data to an embedded Universal Integrated Circuit Card (eUICC) of the mobile device as a series of data messages and receives corresponding response messages for each data message from the eUICC. The response messages from the eUICC are formatted with a tag field that indicates encryption and signature verification properties for the response message. Different values in the tag field indicate whether the response message is (i) encrypted and verifiably signed, (ii) verifiably signed only, or (iii) includes plain text information. Response messages without encryption are readable by the processing circuitry, and processing of the response messages, including forwarding to network elements, such as to a provisioning server are based at least in part on values in the tag field.
Owner:APPLE INC
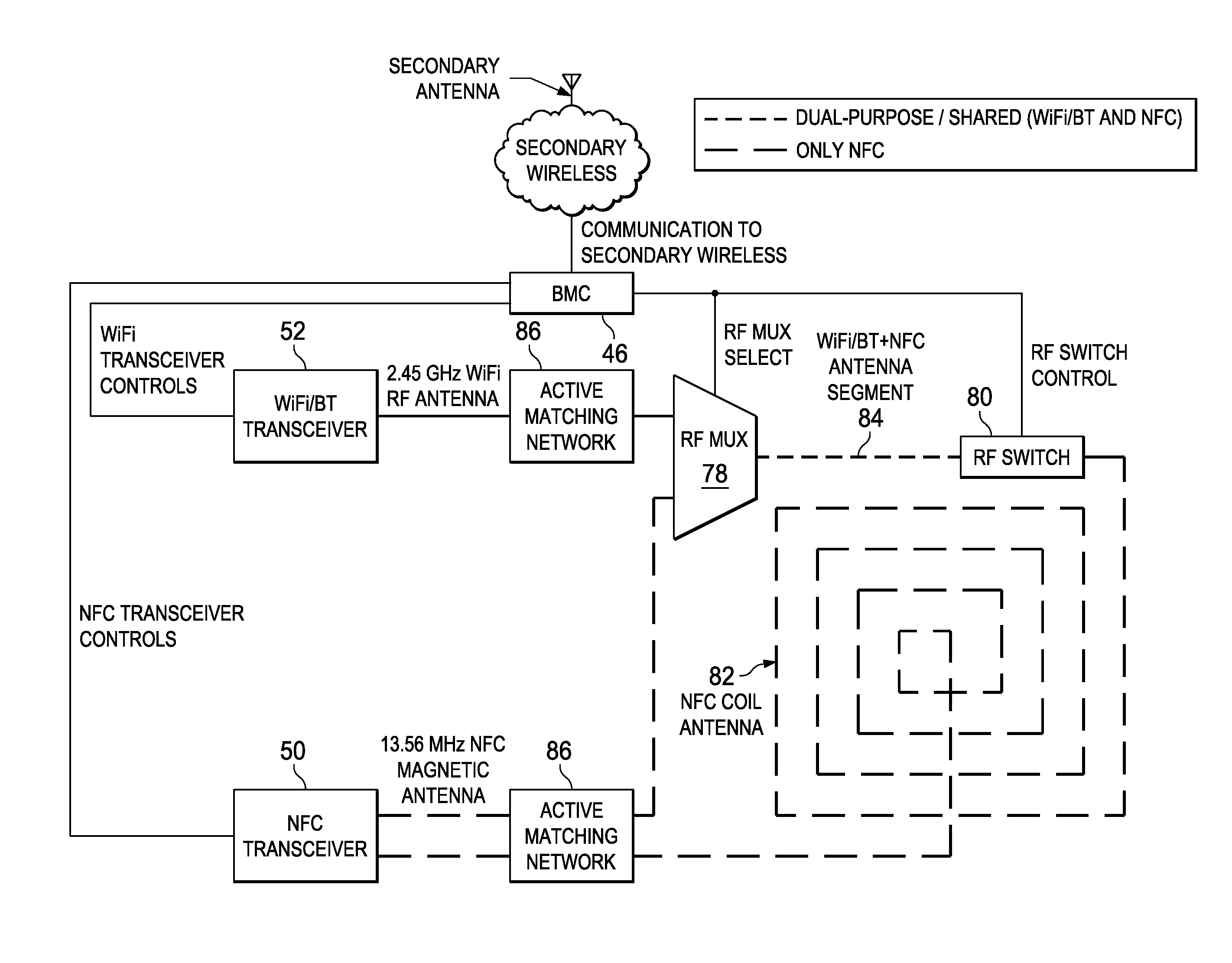
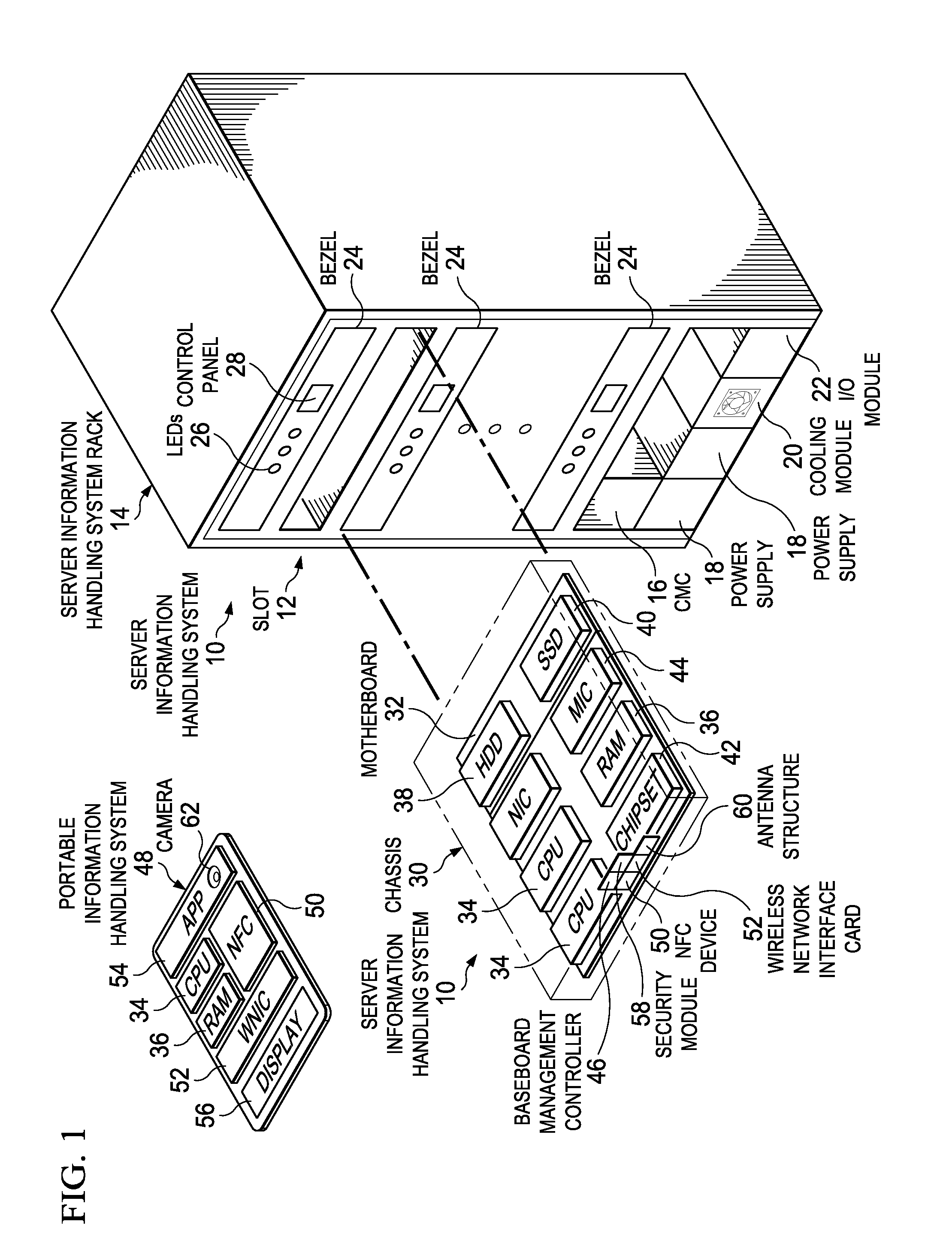
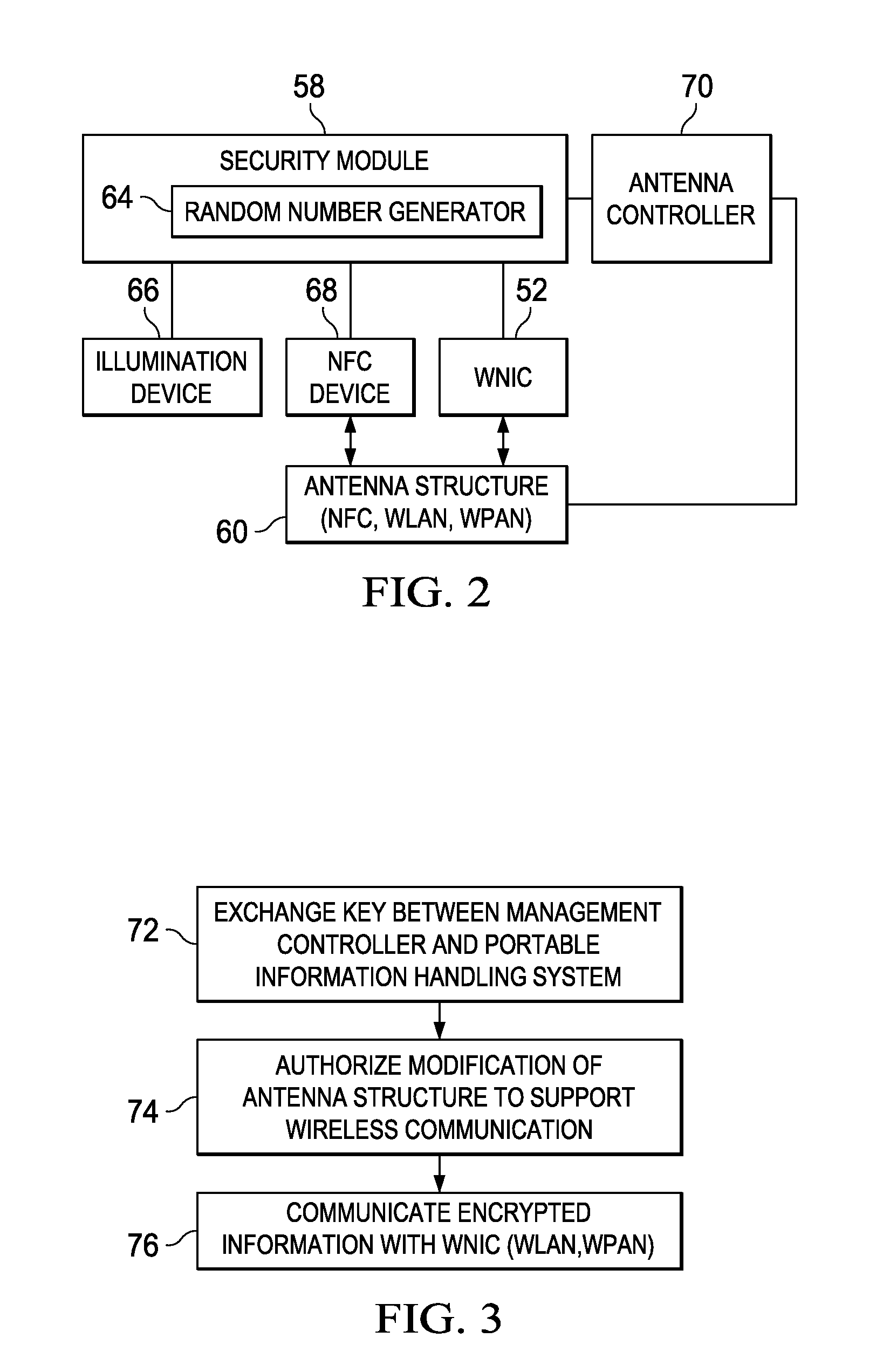
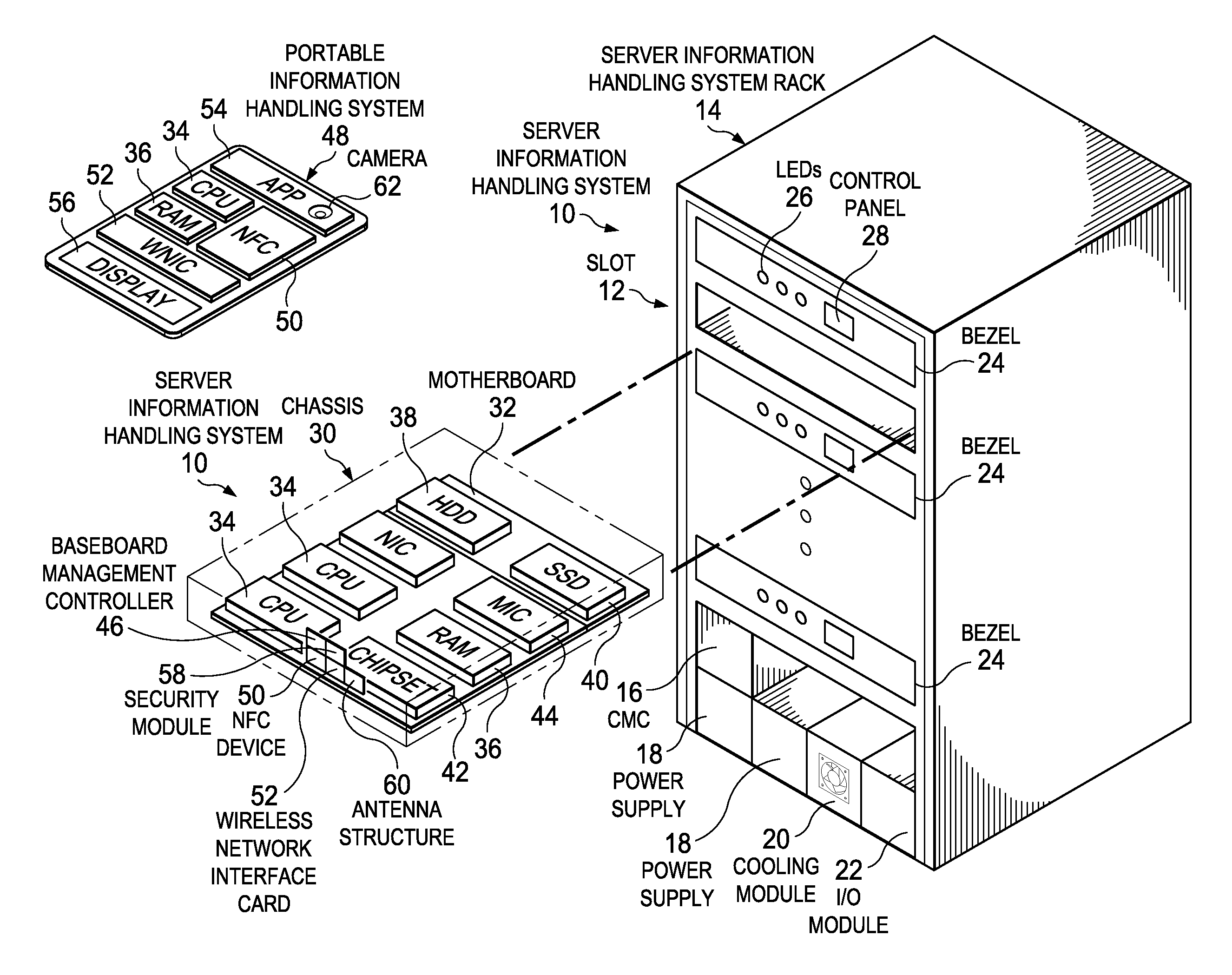
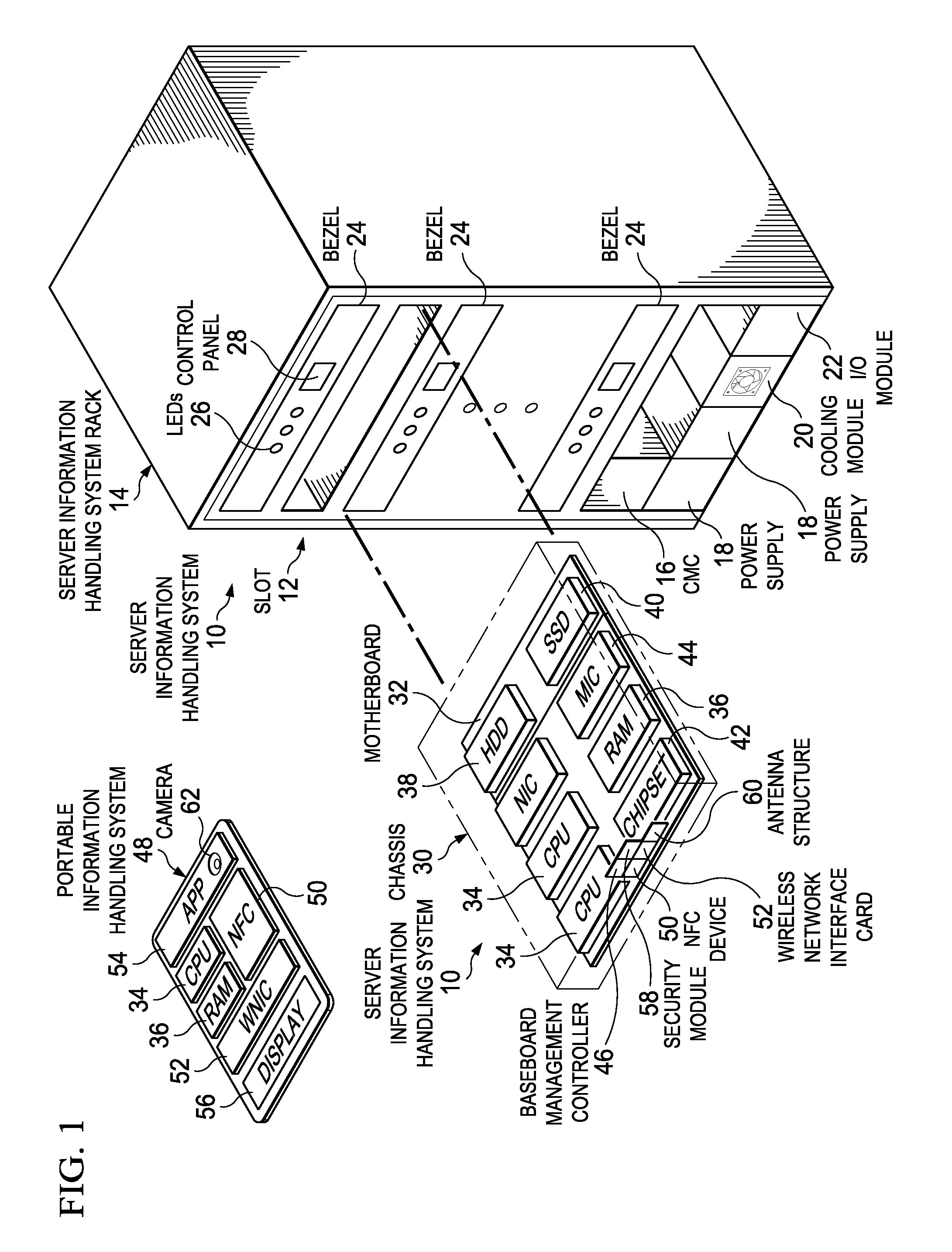
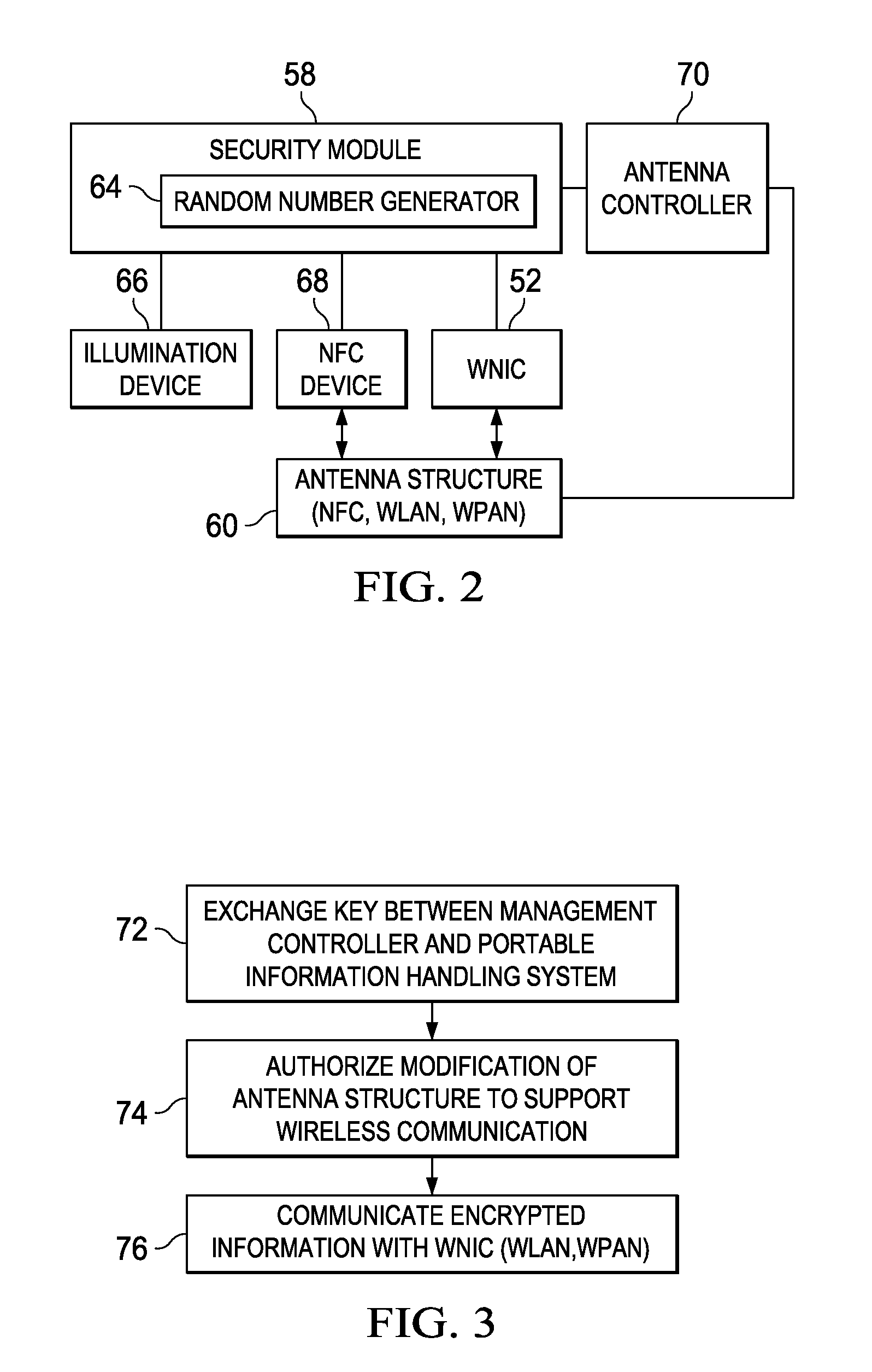
Information Handling System Secure RF Wireless Communication Management with Out-of-Band Encryption Information Handshake
ActiveUS20160182469A1Improve securityReduce disadvantagesSecret communicationTransmissionTransceiverUltraviolet lights
A server information handling system baseboard management controller (BMC) includes an NFC transceiver that communicates NFC signals through an NFC antenna structure. The BMC selectively configures the NFC antenna structure to isolate portions of conductive material for use as an antenna in non-NFC communications, such as wireless local area network communications (WLAN) at 2.4 or 5 GHz or wireless personal area network (WPAN) communications at 2.4 or 60 GHz. In one embodiment, WLAN and WPAN communications are encrypted with a key provided through NFC or other types of wireless communication, such as visible, infrared or ultraviolet light signals.
Owner:DELL PROD LP
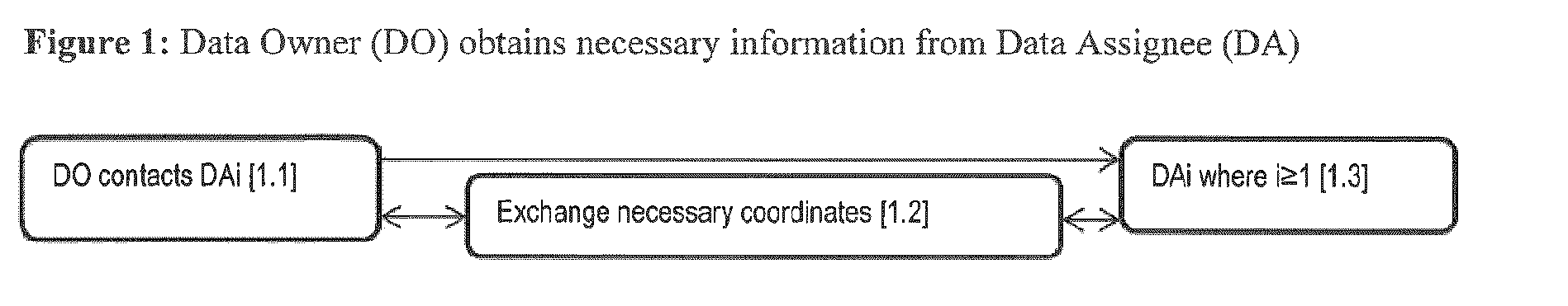
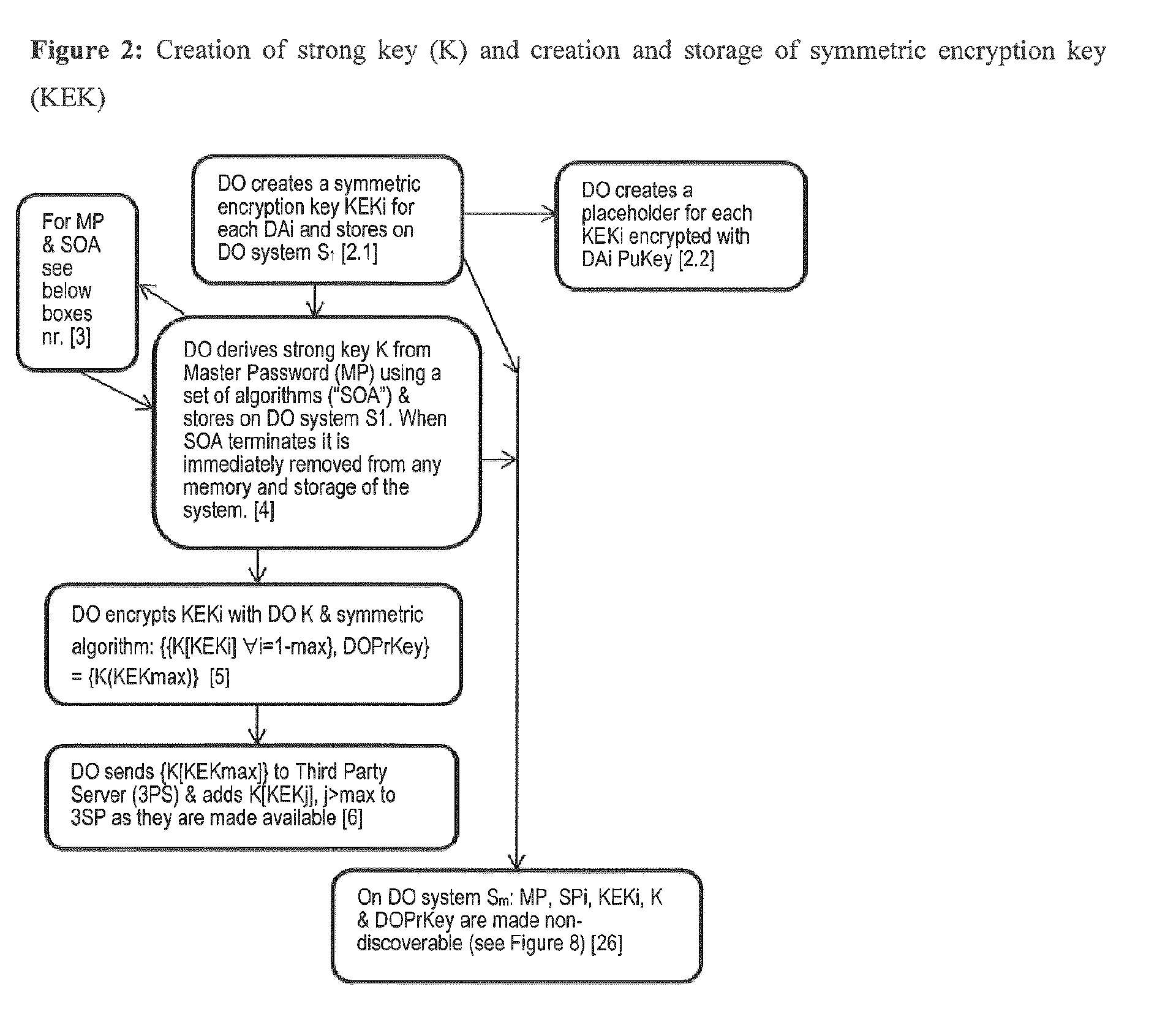
End-To-End Encryption Method for Digital Data Sharing Through a Third Party
InactiveUS20150256336A1Secure EncryptionKey distribution for secure communicationEnd-to-end encryptionThird party
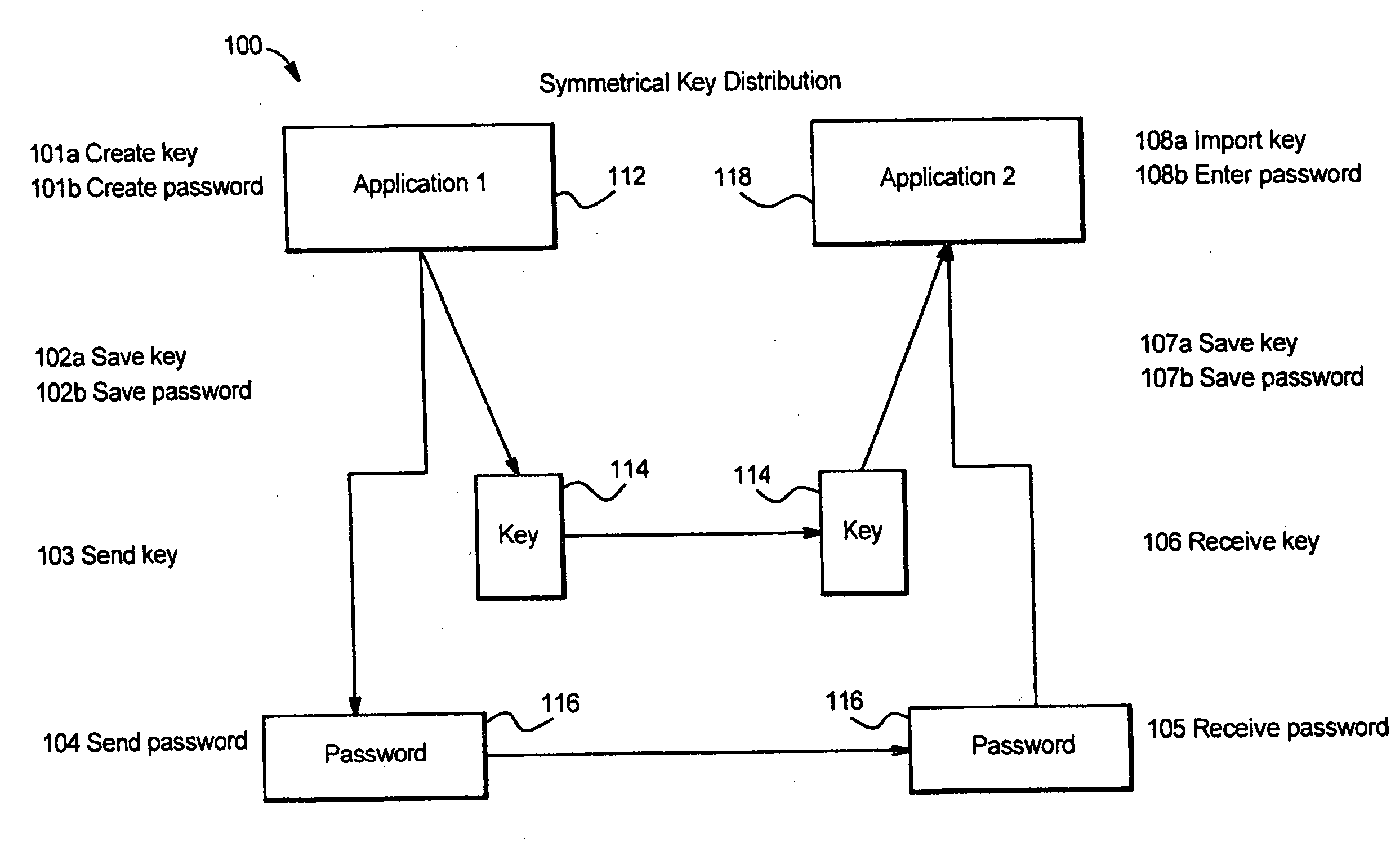
An end-to-end encryption method is provided for encrypting Digital Data to be made available by a Data Owner to a Data Assignee at some future point in time. The Data Owner shares the coordinates of the Data Assignee and an invitation associated the Data Assignee with a 3rd party. The Data Owner subsequently generates a Secret and encrypts the Digital Data with the Secret. The Secret is then encrypted by Data Owner with the Data Assignee's Public Key, and securely transmitted along with the encrypted Digital Data Set to the 3rd party. The Data Assignee can then obtain the encrypted Digital Data Set and the encrypted Secret from the 3rd party, decrypt the Secret with the Data Assignee Private Key and subsequently decrypt the Digital Data Set with the Secret. All secrets are maintained in a non-discoverable fashion and access to secret information can be rendered securely on multiple systems.
Owner:MCAFEE LLC
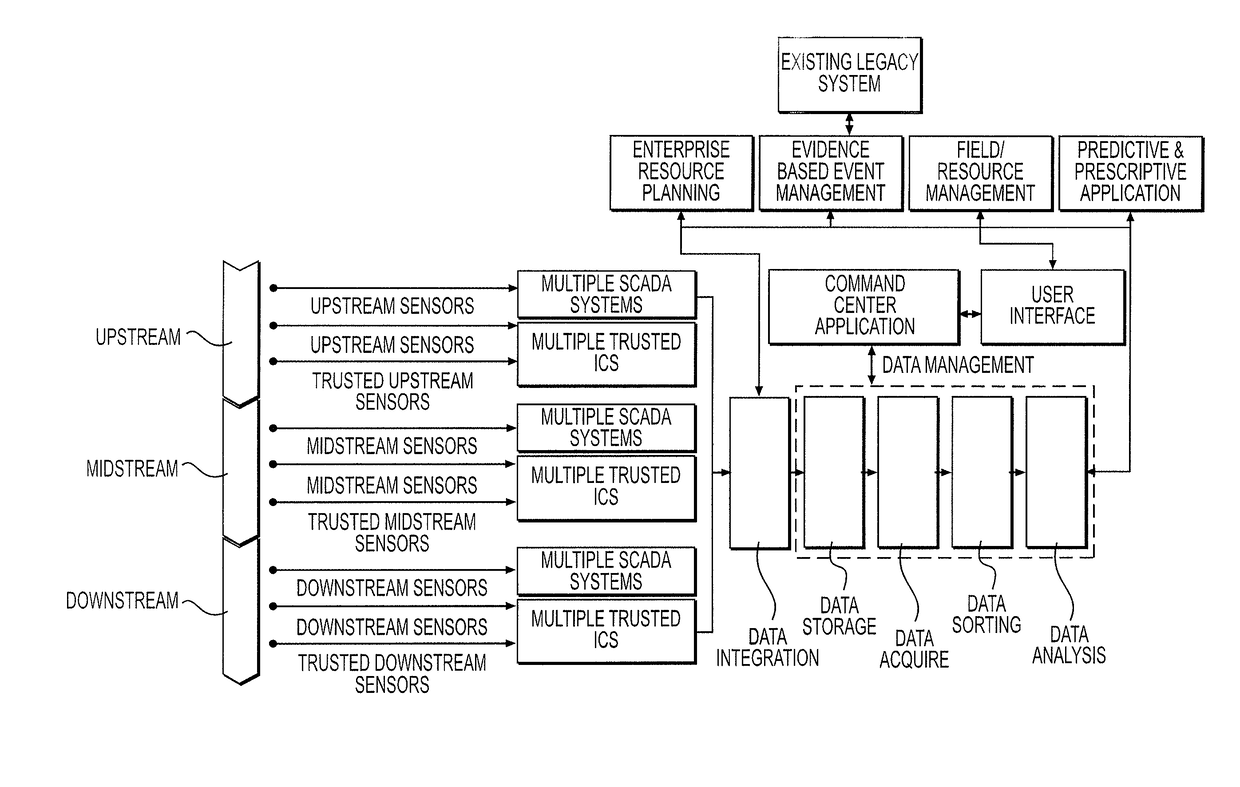
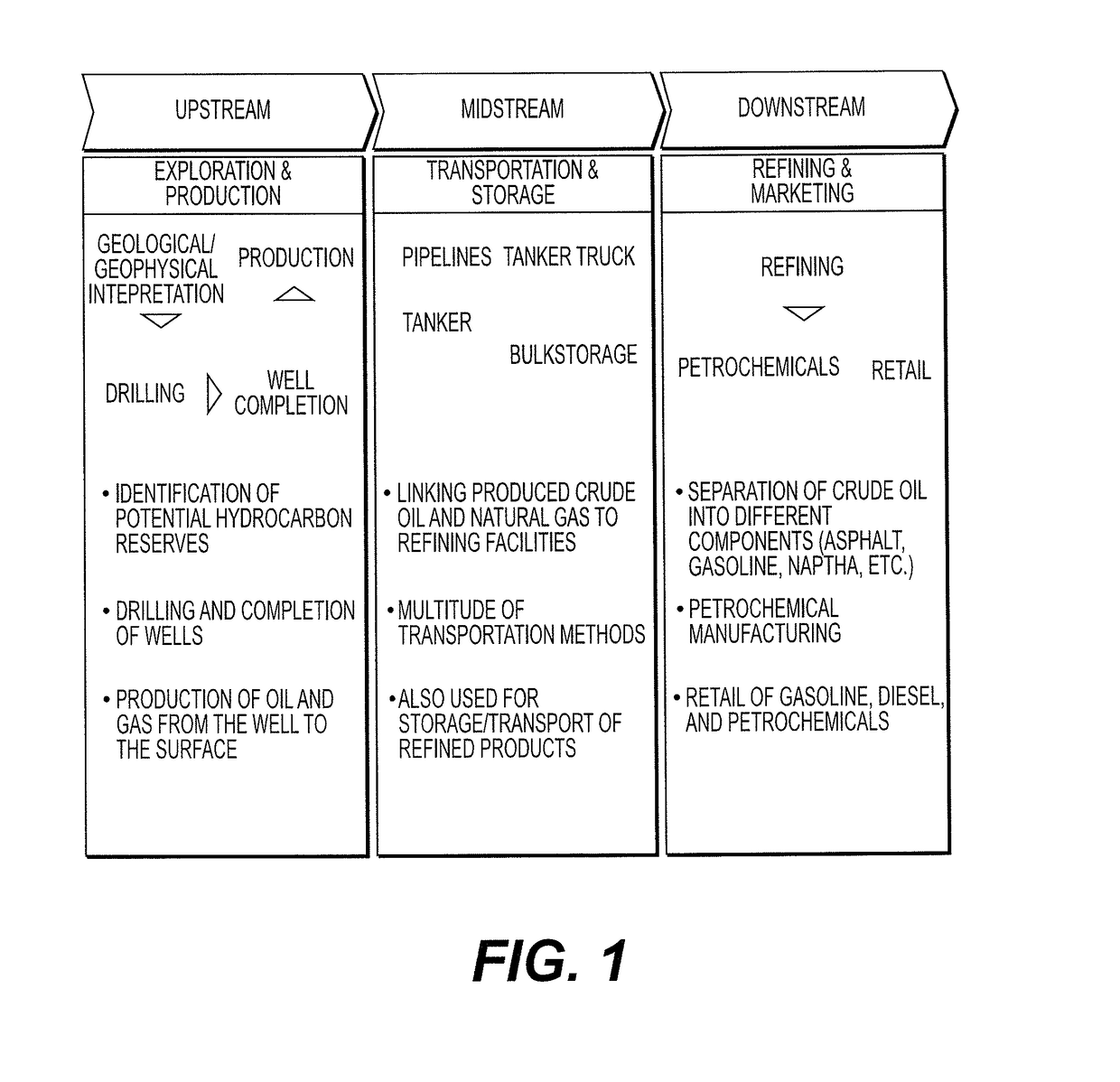
Interface with secure intermediary platform to generate data compatible with an external system in an oil and gas asset supply chain
The present disclosure generally relates to an interface system and method of interfacing to generate data compatible with an external system in an oil and gas asset supply chain, and in particular to an interface and interface method for generating secure and verifiable data to prevent tampering, injection of unwanted data resulting from an unauthorized access along a supply chain. An interface generates and transforms data in an oil and gas supply chain for compatibility with external systems. Collected data is captured by an industrial control system sensor or data collector, and transferred to a secure intermediary hardware platform to interface with a software component. The collected data is then modified using a business rules engine to create enhanced data and events created from the enhanced data.
Owner:SICPA HLDG SA
System for accessing a service and corresponding portable device and method
InactiveUS20130287211A1Secure EncryptionApparatus for meter-controlled dispensingSecret communicationComputer hardwareRadio frequency
A system for accessing a service comprises two contact-less readers and one portable device. A first contact-less reader is configured to send to the portable device, through a first range radiofrequency link, a first message comprising first data. The first data includes an identifier allocated to the portable device and an associated key for encrypting data. The portable device is configured to send to a second contact-less reader, through a second range radiofrequency link, a second message comprising second data. The second data includes the identifier received from the first message. The second data is encrypted by using the data encryption key received from the first message. The second range radio frequency is higher than the first range radio frequency.
Owner:GEMPLU
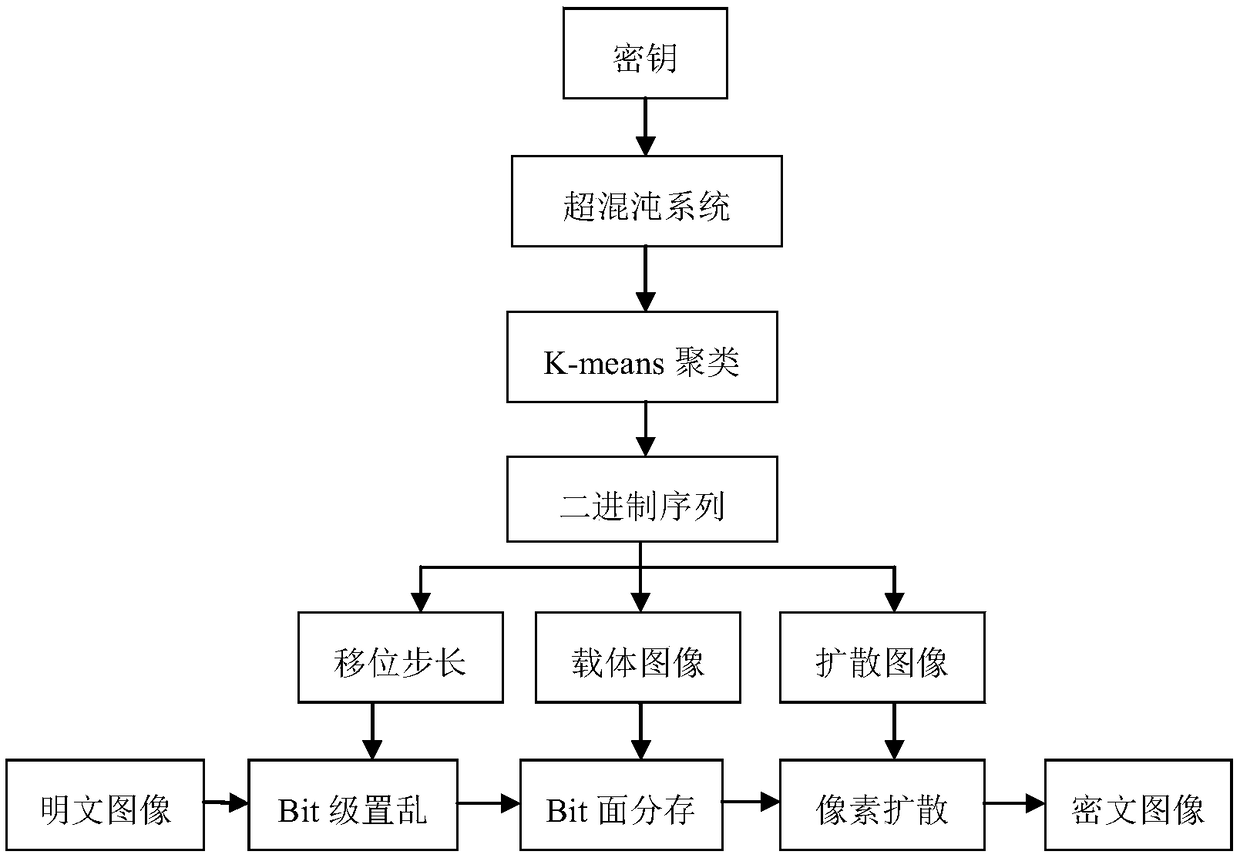
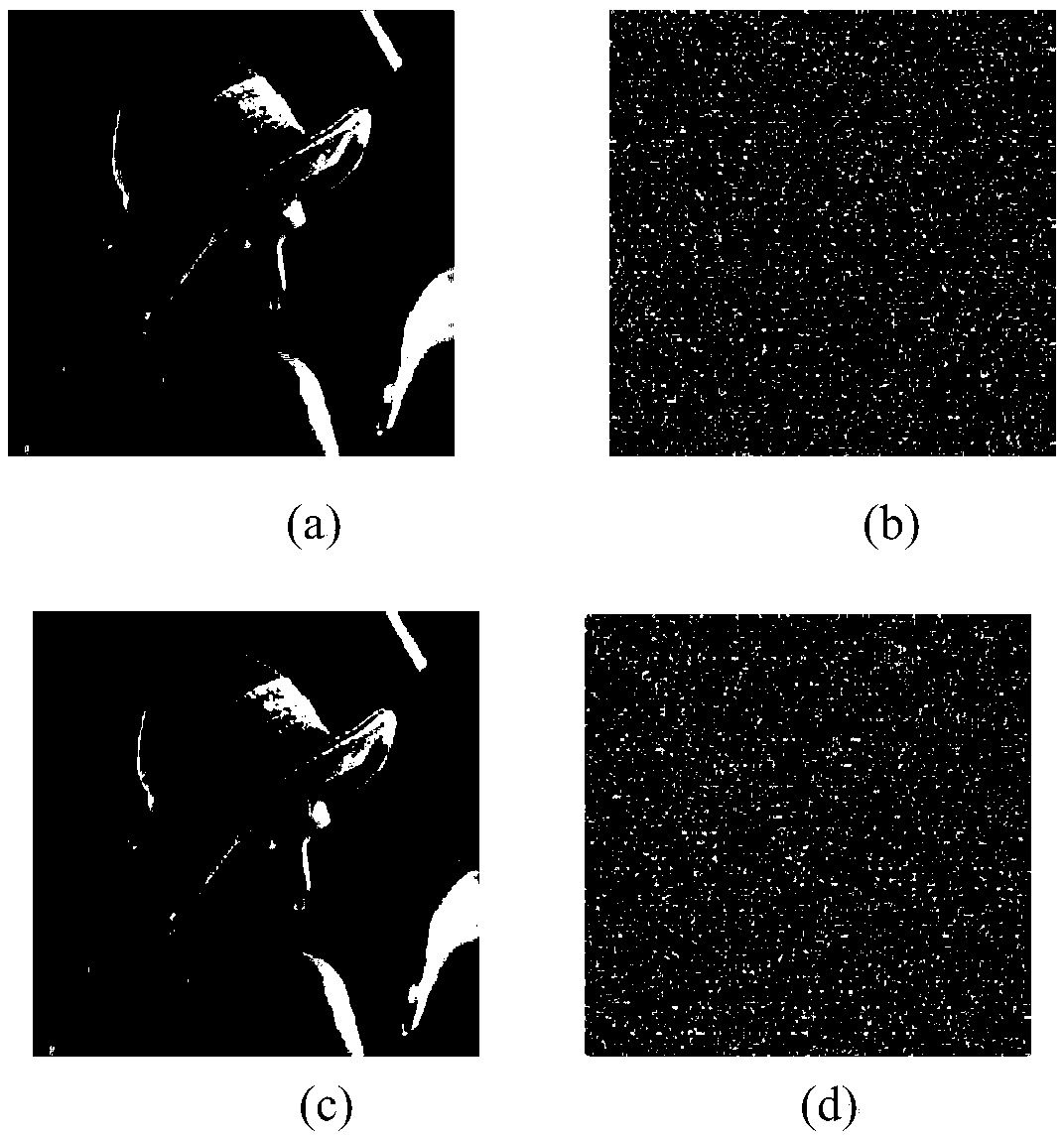
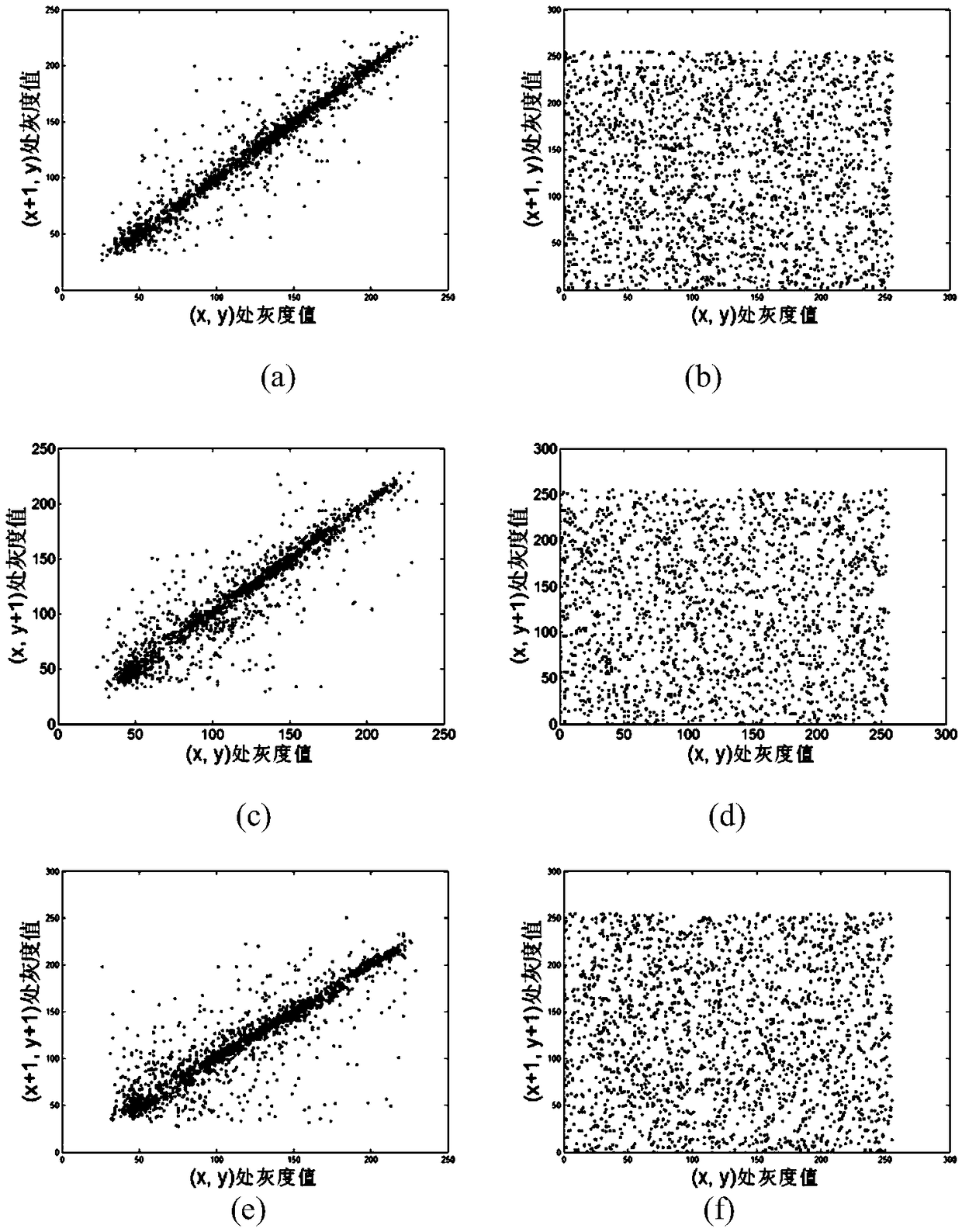
An image encryption method based on four-dimensional Chen's hyperchaotic system and K-means clustering
ActiveCN109376793AGood pseudorandomnessImprove performanceCharacter and pattern recognitionDigital data protectionImaging processingCiphertext
The invention relates to the field of image processing, in particular to an image encryption method based on four-dimensional Chen's hyperchaotic system and K-means clustering. The invention adopts high-dimensional continuous hyperchaotic system-four-dimensional Chen's system to generate chaotic sequence, ensures that the algorithm has larger key space, and adopts K-Means clustering algorithm is used to process the chaotic sequences generated by Chen's system, and the binary sequences with good pseudo-random performance are obtained (through US NIST statistical test). Secondly, according to the property of bit-plane decomposition of plaintext image, an efficient scrambling algorithm is designed, and an intermediate result sharing link is added between scrambling and spreading to improve the encryption security. Finally, the traditional linear diffusion function is improved and the diffusion matrix generated by the pseudo-random binary sequence is used to perform linear bidirectional diffusion on the pixels of the initial ciphertext, which further improves the performance of the system against the attack of differential analysis.
Owner:SHENZHEN INSTITUTE OF INFORMATION TECHNOLOGY
Information handling system secure RF wireless communication management with out-of-band encryption information handshake
ActiveUS9537840B2Improve securityReduce disadvantagesTransmissionSpecial data processing applicationsTransceiverUltraviolet lights
A server information handling system baseboard management controller (BMC) includes an NFC transceiver that communicates NFC signals through an NFC antenna structure. The BMC selectively configures the NFC antenna structure to isolate portions of conductive material for use as an antenna in non-NFC communications, such as wireless local area network communications (WLAN) at 2.4 or 5 GHz or wireless personal area network (WPAN) communications at 2.4 or 60 GHz. In one embodiment, WLAN and WPAN communications are encrypted with a key provided through NFC or other types of wireless communication, such as visible, infrared or ultraviolet light signals.
Owner:DELL PROD LP
Processing recordable content in a stream
ActiveUS8401187B2Quick changeSecure EncryptionUnauthorized memory use protectionHardware monitoringComputer networkDigital rights management system
Owner:IRDETO ACCESS
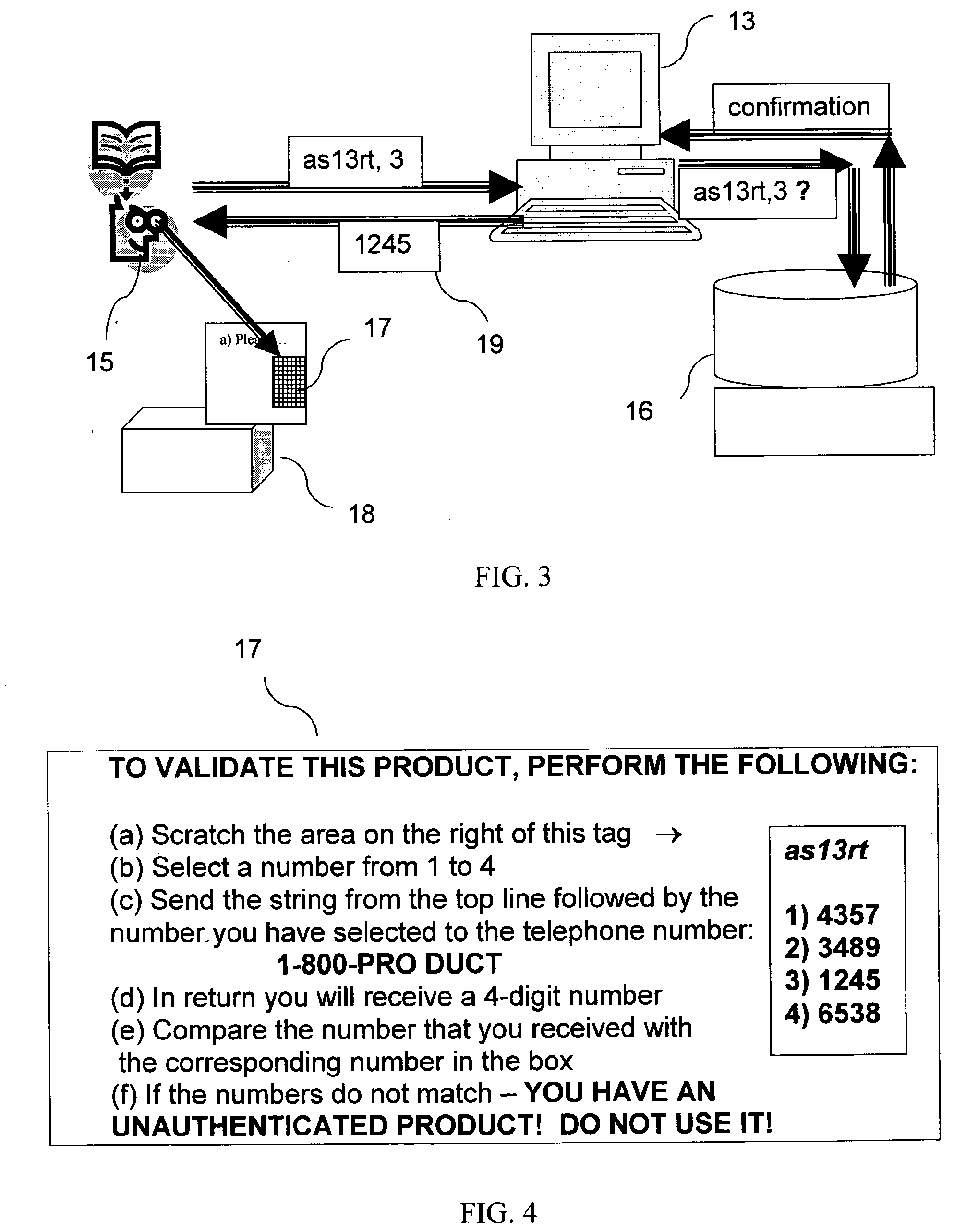
System for product authentication powered by phone transmission
InactiveUS20090138275A1Overcome disadvantagesIncrease probabilityBuying/selling/leasing transactionsAuthentication systemTelephony
An authentication system enabling a customer to verify the authenticity of a product in a foolproof, secure and simple manner plurality of secret sets of numbers is generated, each set comprising a challenge portion and a response portion. These sets are stored on a remote server. Each set is associated with a different product. The customer sends a challenge portion to the server, and prompts the server to provide a response. If the response matches that of the product in hand, the product is known to be authentic. In another embodiment of the system, cellular transmission is used to power an electronic tag attached to the product and carrying authentication data. In a third embodiment, the full manufacturer database is divided into separate databases, possibly related to product vendor, such that an authentication process can be performed without the need to access the manufacturer's entire database of products.
Owner:AUTHIX TECH LTD
System for product authentication using covert codes
InactiveUS20090204417A1Overcome disadvantagesIncrease probabilityBuying/selling/leasing transactionsAuthentication systemProduct data
An authentication system enabling a customer to verify the authenticity of a product in a foolproof, secure and simple manner. plurality of secret sets of numbers is generated, each set comprising a challenge portion and a response portion. These sets are stored on a remote server. Each set is associated with a different product. The customer sends a challenge portion to the server, and prompts the server to provide a response. If the response matches that of the product in hand, the product is known to be authentic. In another embodiment of the system, cellular transmission is used to power an electronic tag attached to the product and carrying authentication data. In a third embodiment, the full manufacturer database is divided into separate databases, possibly related to product vendor, such that an authentication process can be performed without the need to access the manufacturer's entire database of products.
Owner:AUTHIX TECH LTD
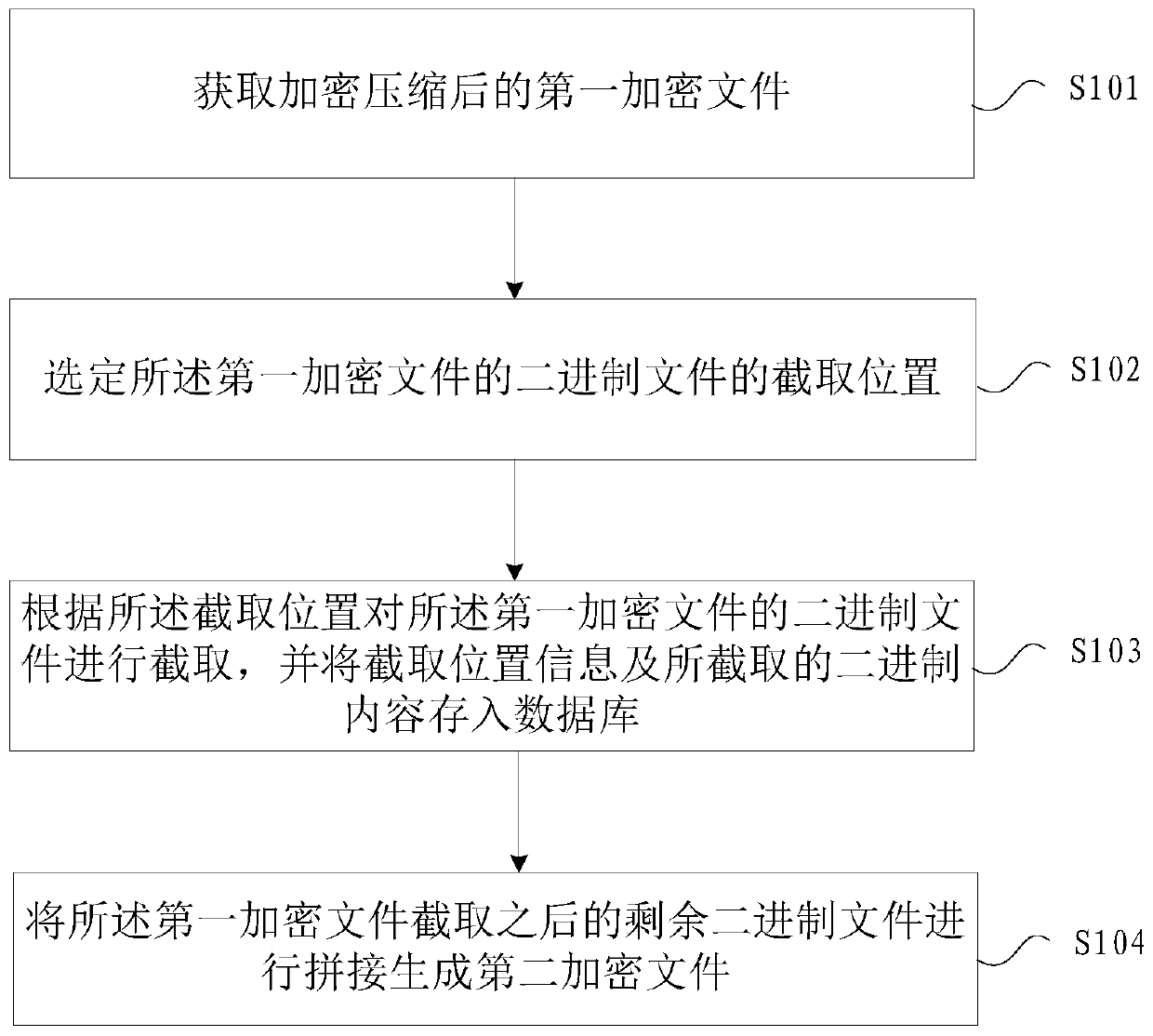
File encryption method and device
PendingCN111552938AFix security issuesSolve complexityDigital data protectionDigital data authenticationEncryptionData library
Embodiments of the invention provide a file encryption method and device. The method comprises the steps of obtaining an encrypted and compressed first encrypted file; selecting an interception position of a binary file of the first encrypted file; intercepting a binary file of the first encrypted file according to the interception position, and storing interception position information and intercepted binary content into a database; and splicing the remaining binary files after the first encrypted file is intercepted to generate a second encrypted file. According to the embodiment of the invention, the binary file of the first encrypted file is subjected to position interception and storage, so that the problem of relatively low file encryption security in related technologies can be solved, and the effect of improving the security of the encrypted file is achieved.
Owner:SHANGHAI MININGLAMP ARTIFICIAL INTELLIGENCE GRP CO LTD
Method for establishing a telecommunication link and a telecommunication network
InactiveUS20050122956A1Improve securitySafely exchangedData switching by path configurationTelecommunications networkEngineering
Owner:IP2H AG
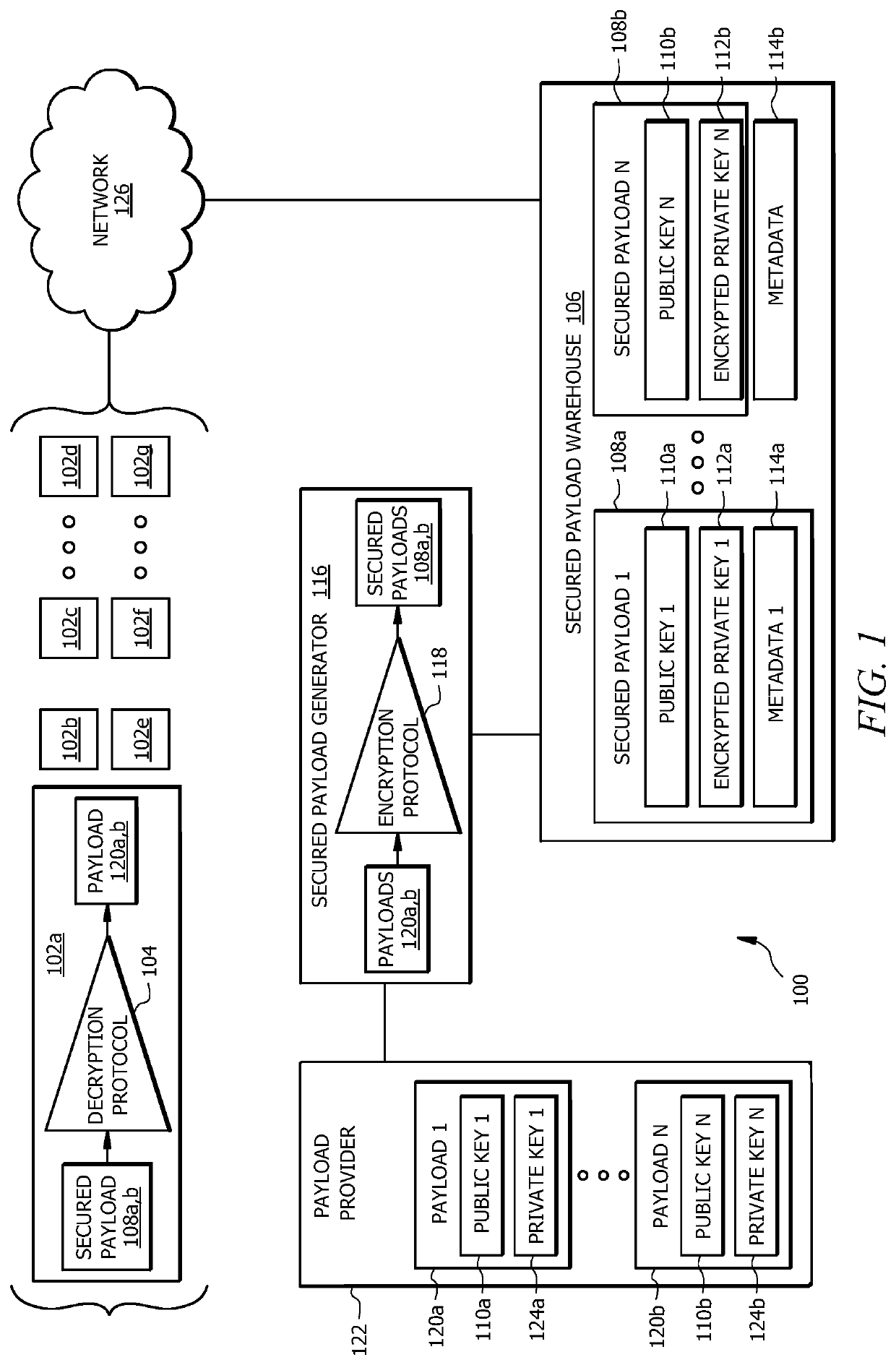
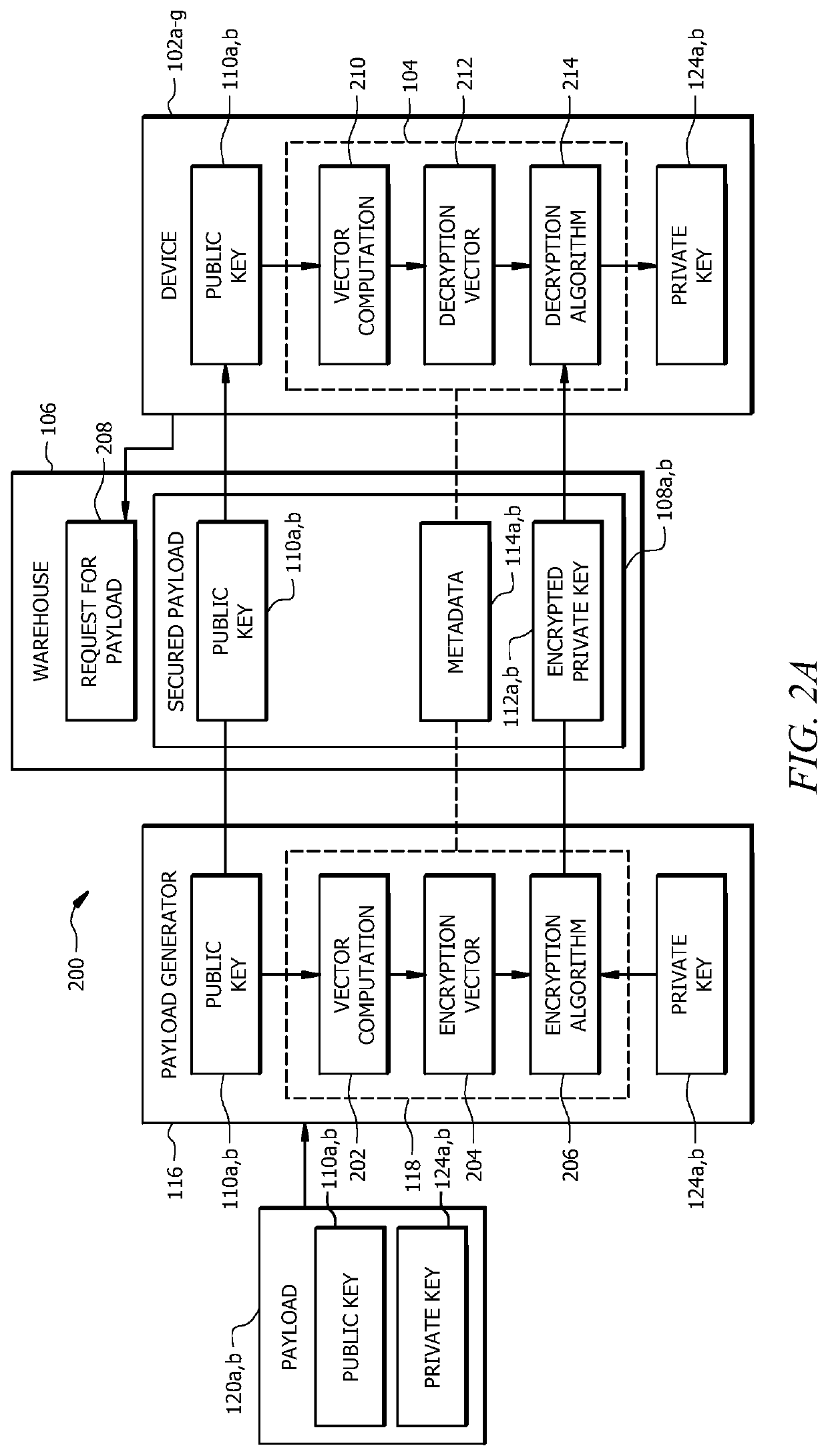
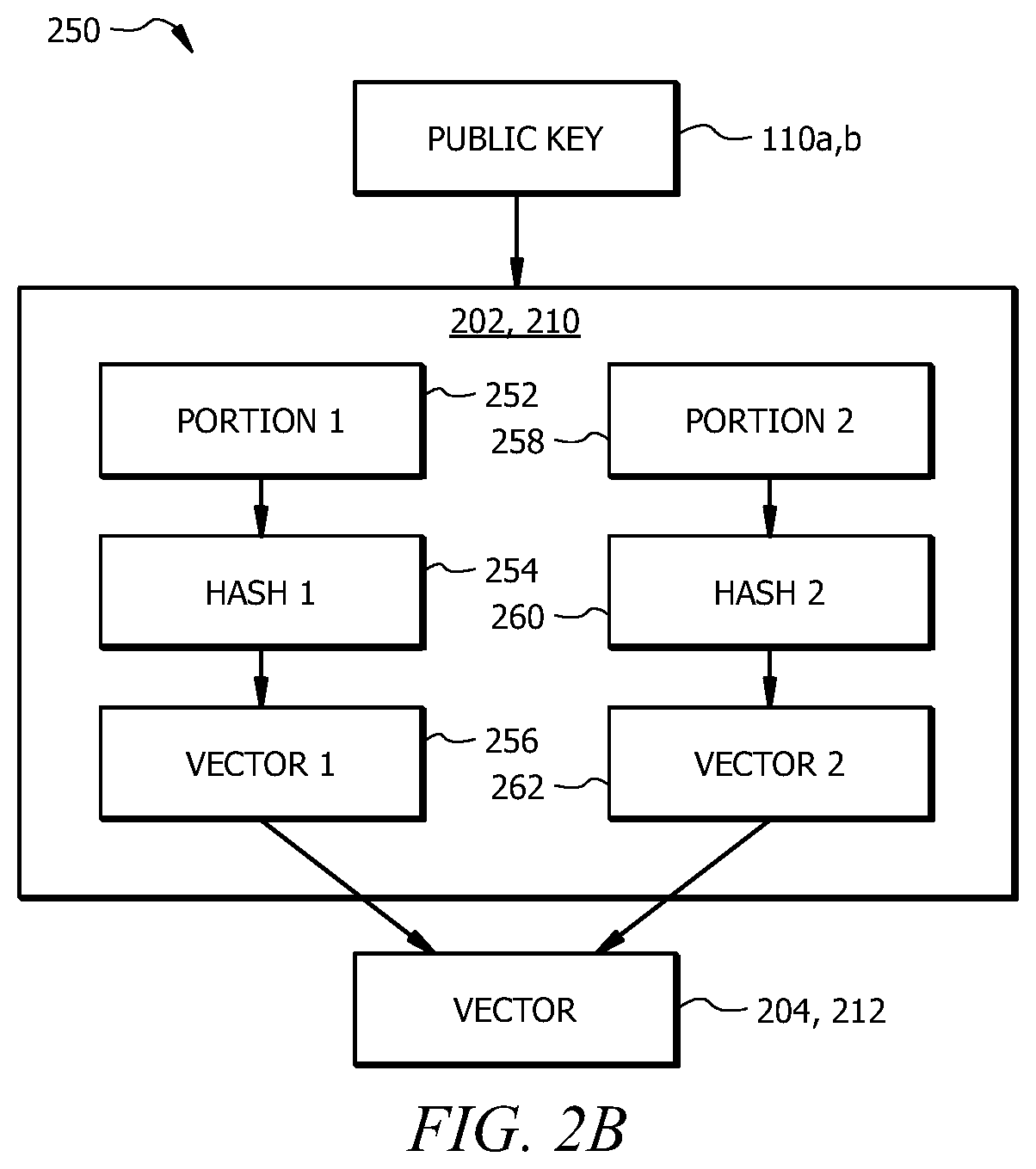
Secure provisioning of digital certificate
ActiveUS20210218579A1Improve performanceEffective encryptionEncryption apparatus with shift registers/memoriesUser identity/authority verificationEngineeringDatabase
A system, includes a device and a payload warehouse. The device receives a user request to initiate a feature of the device. In response to receiving the request, device information is provided to a payload warehouse. The payload warehouse stores an inventory which includes a digital payload. The digital payload includes data, such as a digital certificate, which may be used by the device to implement the user-requested feature. The payload warehouse receives the device information provided by the device and determines an encryption vector based at least in part on the received device information. Using the encryption vector, the digital payload is encrypted. The encrypted digital payload is provided to the device.
Owner:LENNOX IND
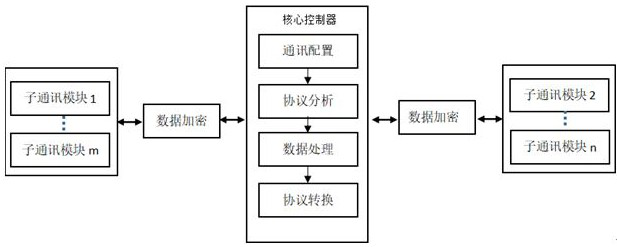
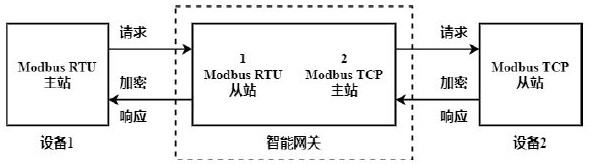
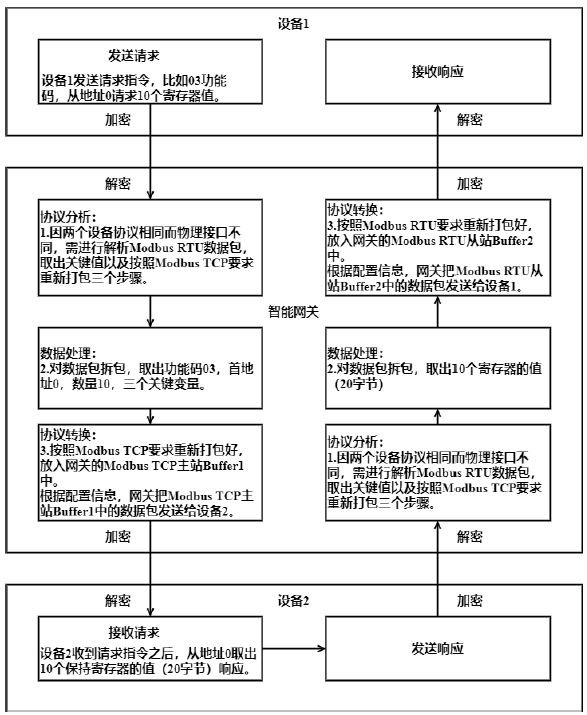
Multi-protocol conversion encryption industrial intelligent gateway and operation method thereof
InactiveCN113132417AFunctionalWith data collection functionNetwork connectionsSecurity arrangementIntelligent NetworkCommunication interface
The invention discloses a multi-protocol conversion encryption industrial intelligent gateway and an operation method thereof. The intelligent gateway comprises a protocol communication module, a communication encryption module and a core controller, the protocol communication module consists of a plurality of sub-communication modules and is used for connecting various communication interface devices; the communication encryption module is used for data transmission encryption including wired encryption and wireless encryption; and the core controller is based on an ARM+Linux+embedded configuration architecture and is used for communication configuration, protocol analysis, data processing and protocol conversion. According to the invention, different communication protocol devices can be connected, a multi-protocol mutual conversion function is realized, encryption transmission is carried out on data, and information exchange between heterogeneous networks is intelligently completed.
Owner:BEIJING HUADIAN TIANREN ELECTRIC POWER CONTROL TECH
A computer-implemented method of performing format-preserving encryption of a data object of variable size
PendingUS20200396056A1Improve securityMore dataEncryption apparatus with shift registers/memoriesUser identity/authority verificationAlgorithmTheoretical computer science
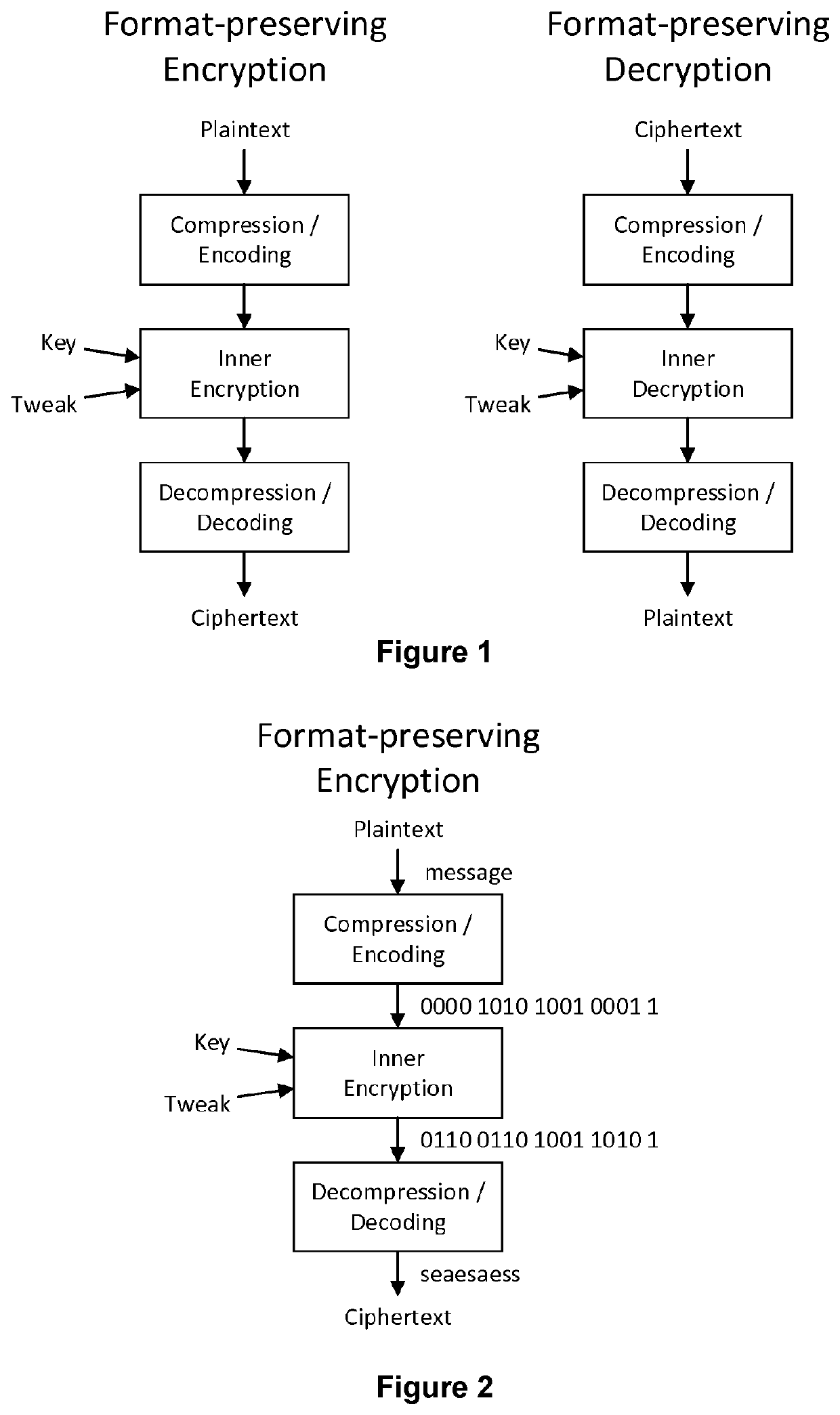
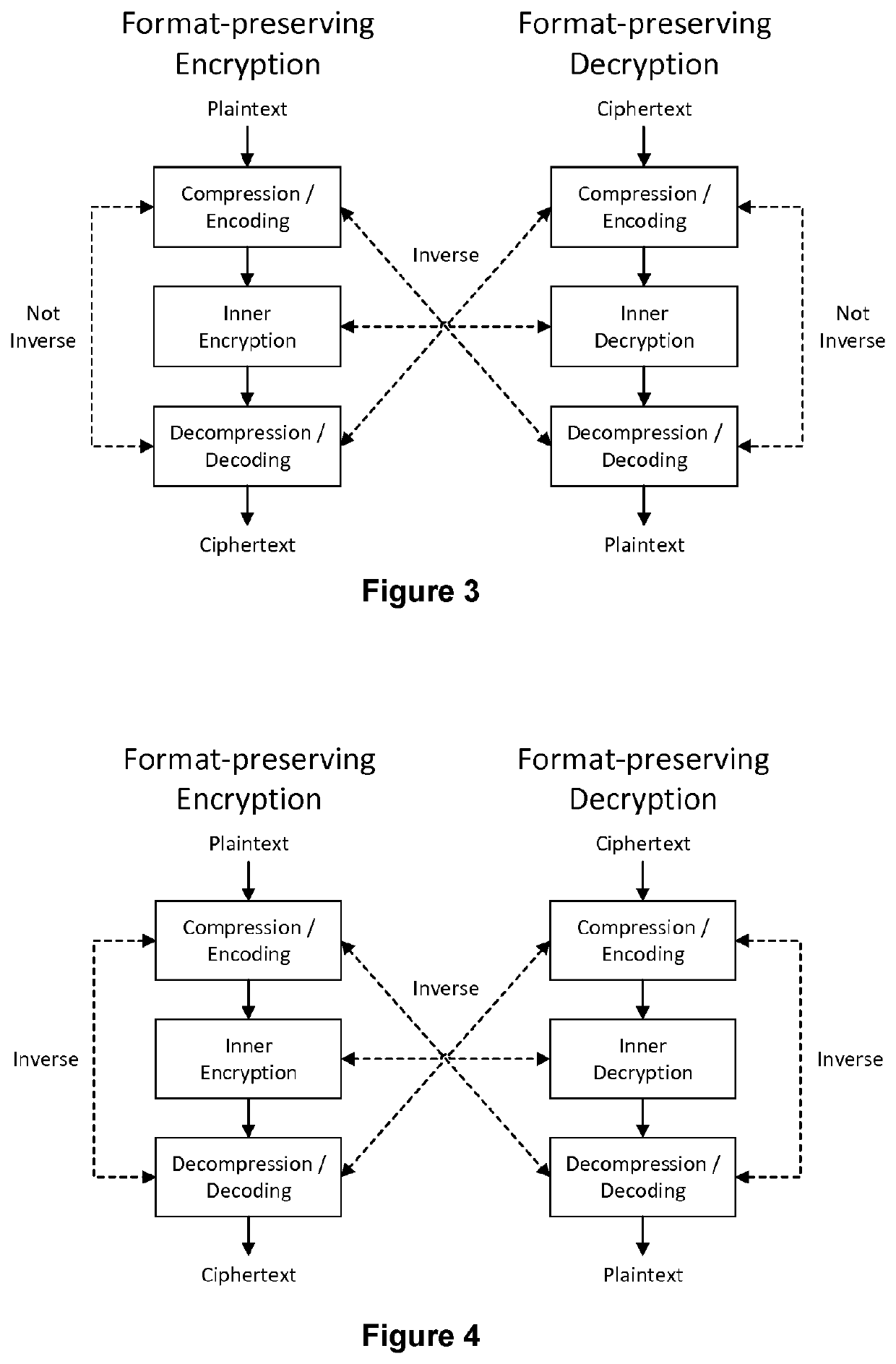
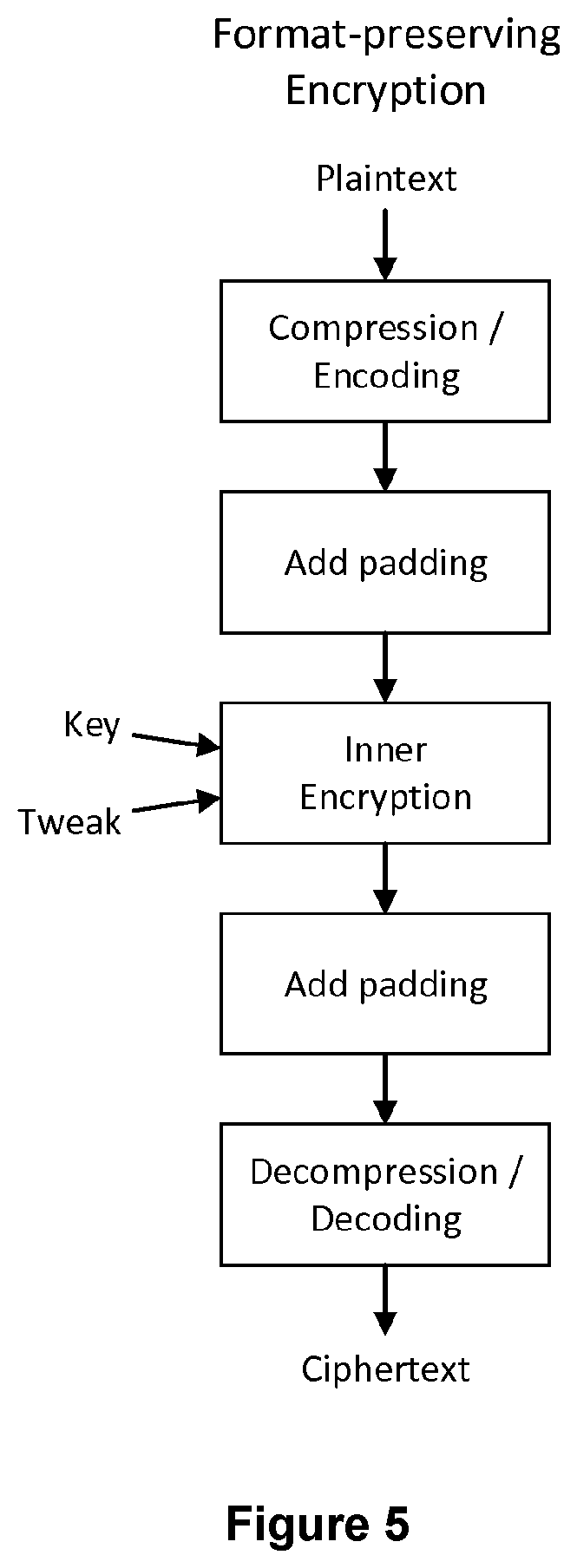
A computer-implemented method of encrypting a data object of variable size utilizing an inner encryption algorithm can take a variable size input and of outputting, as its output, an encrypted version of the variable size input. The method comprises compressing or encoding the data object in its totality to obtain a compressed or encoded version of the data object in a format compatible with the inner encryption algorithm, encrypting, by the inner encryption algorithm, the compressed or encoded version of the data object to obtain an encrypted version of the data object, and decompressing or decoding the encrypted version of the data object to obtain a decompressed or decoded version of the encrypted version of the data object, which constitutes a format-preserved encrypted version of the data object.
Owner:PII GUARD APS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com