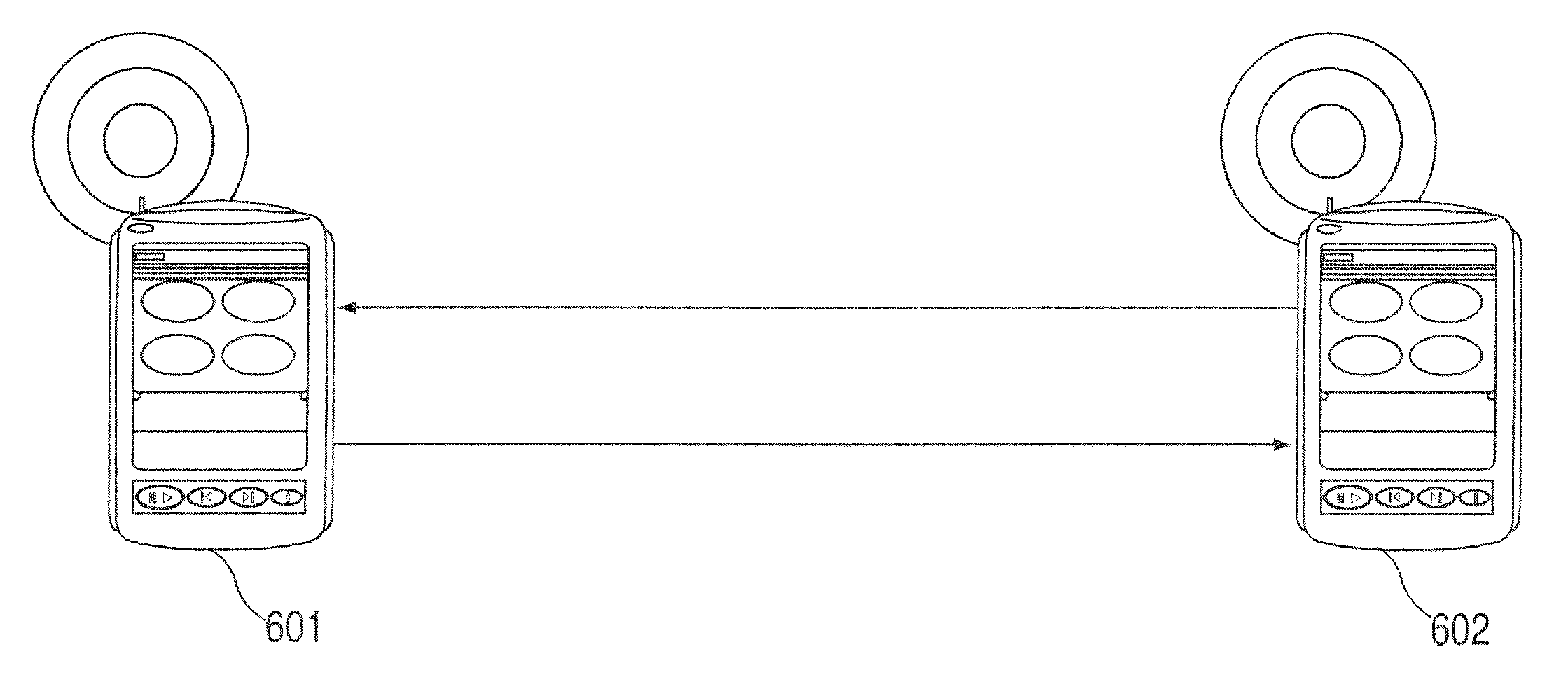Patents
Literature
4013 results about "Data content" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Content data. “. any data whether in digital, optical, or other form, including metadata, that conveys essence, substance, information, meaning, purpose, intent, or intelligence, either singularly or when in a combined form, in either its unprocessed or processed form.
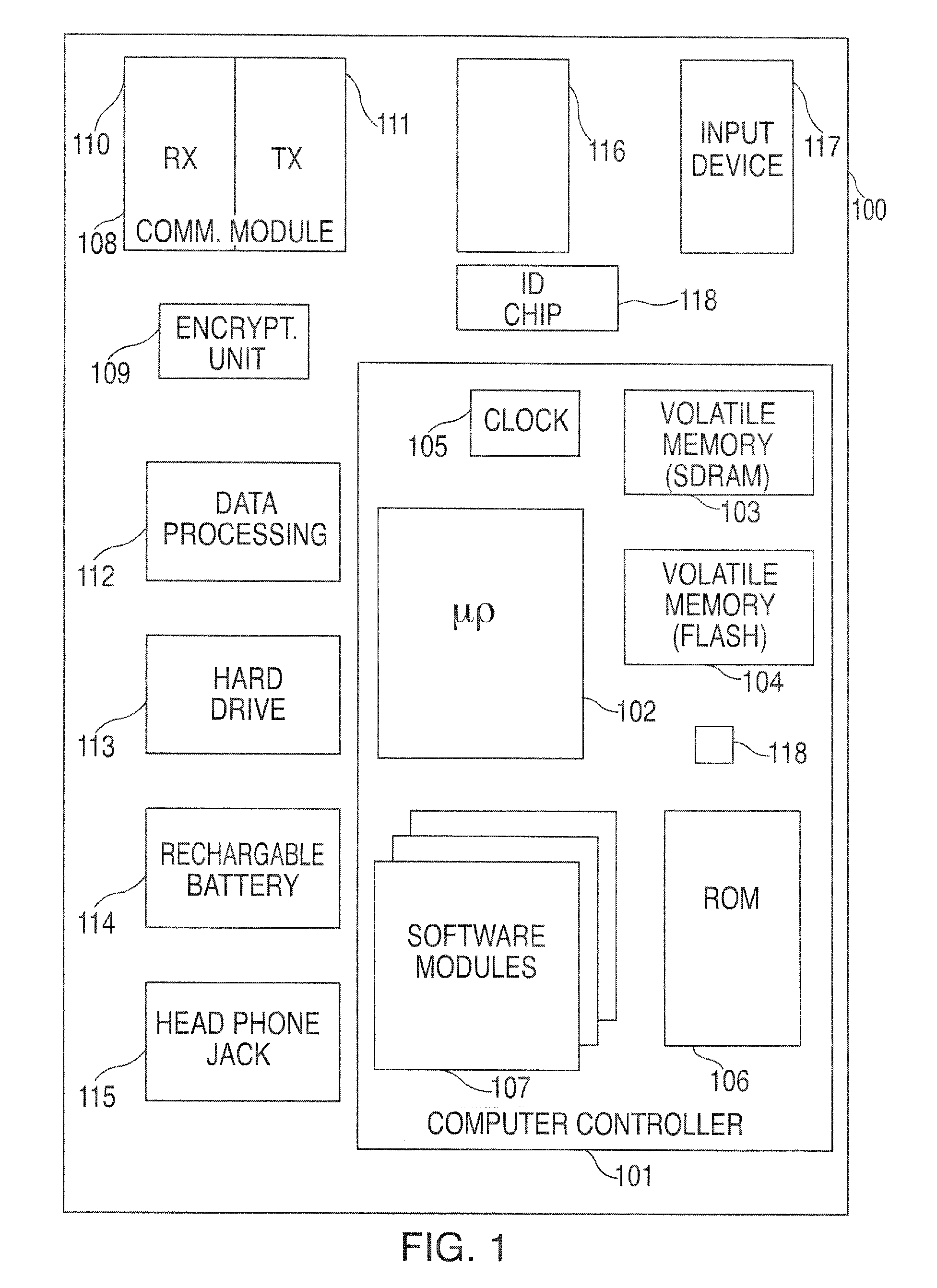
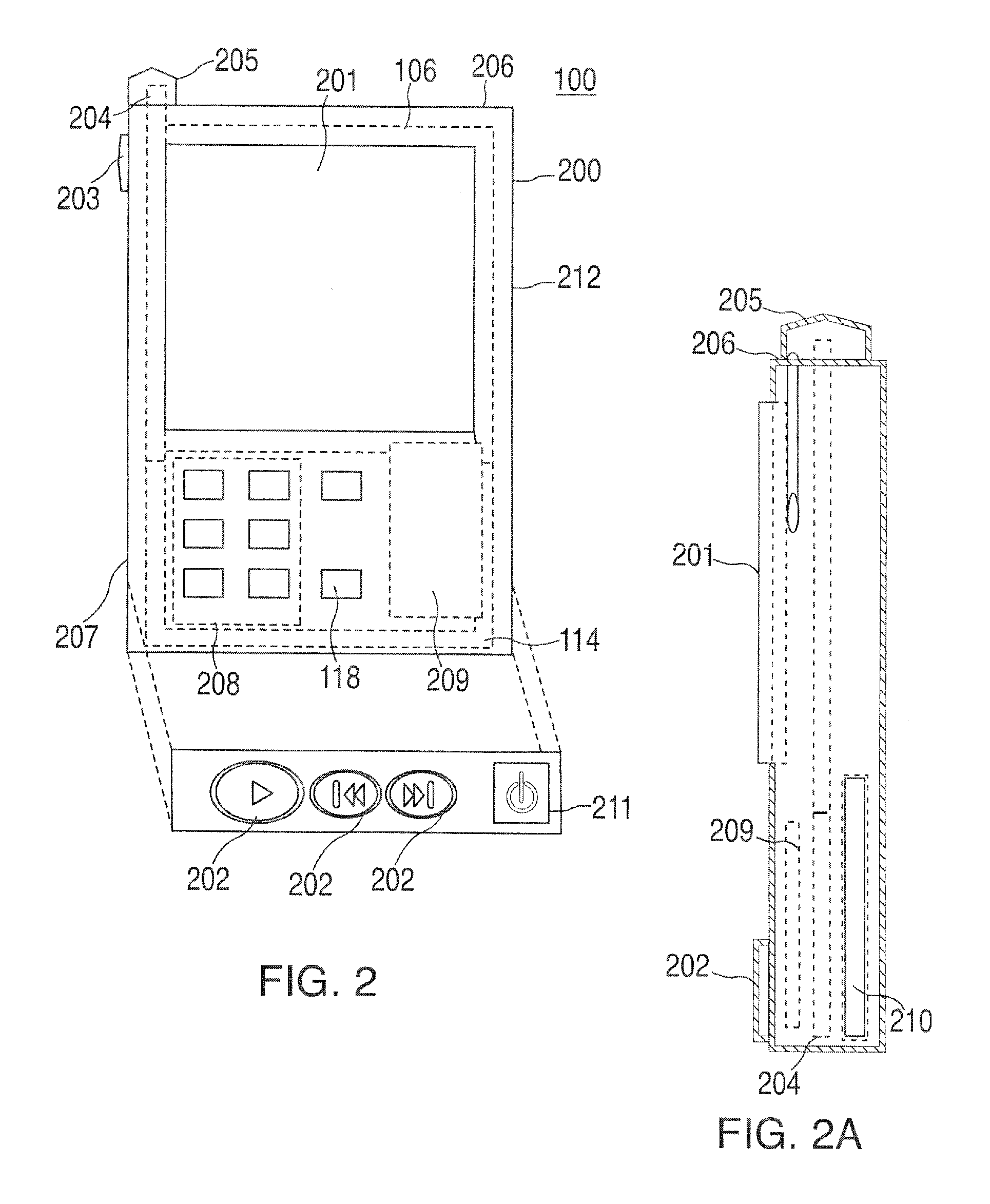
Audio visual player apparatus and system and method of content distribution using the same
InactiveUS20060008256A1None of methods is secureTelevision system detailsColor television signals processingContent distributionVideo player
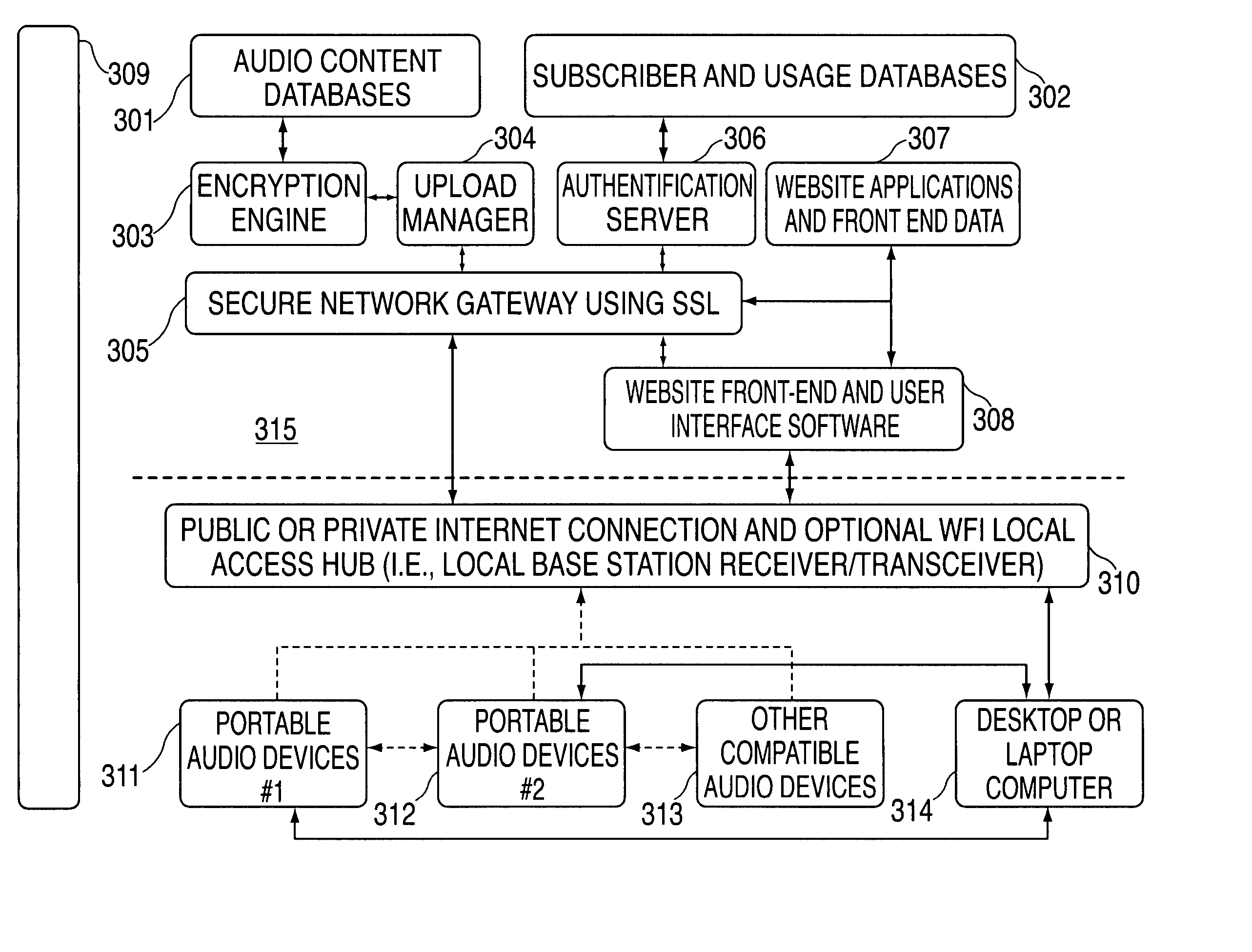
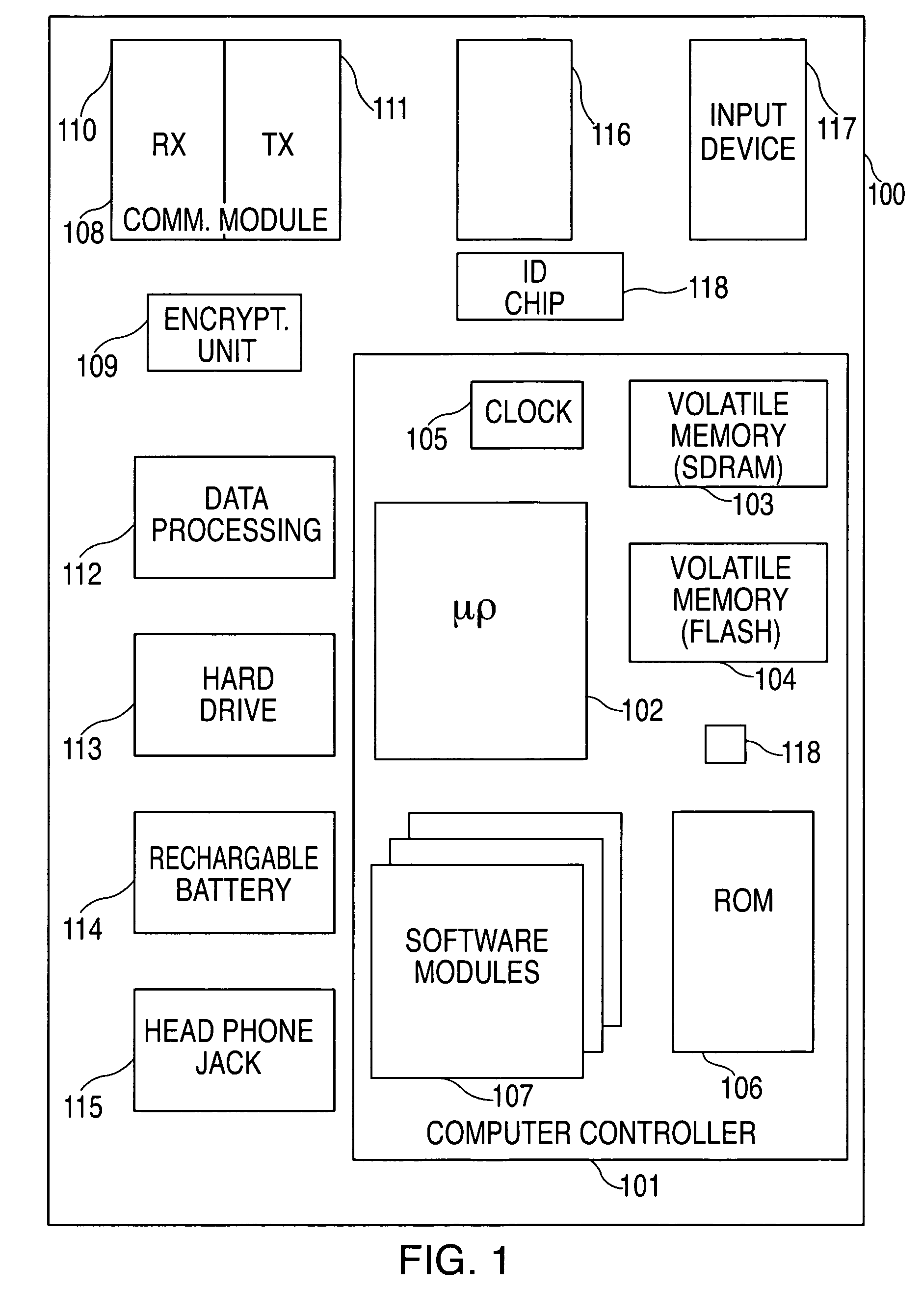
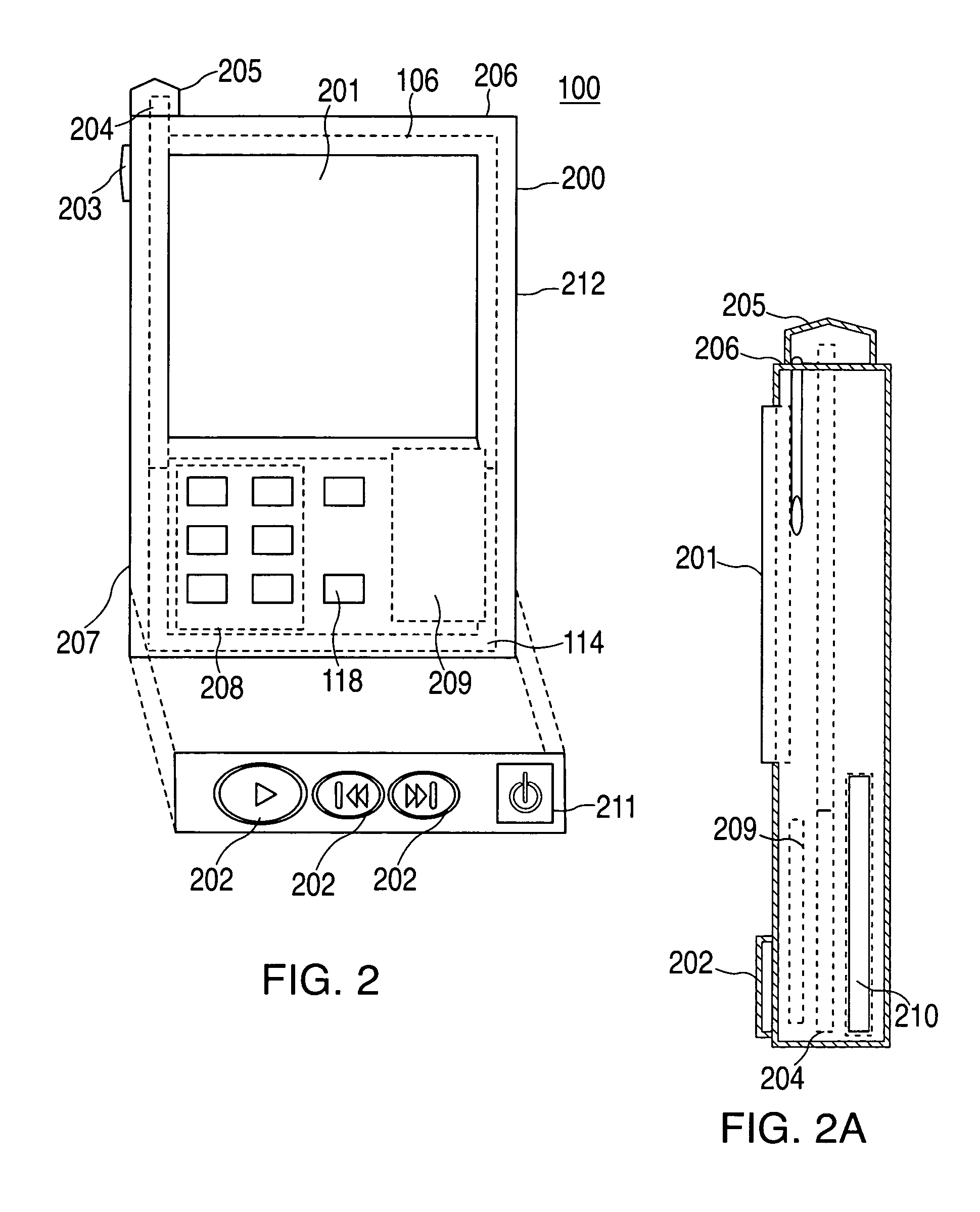
A portable wireless communications subscriber audio and / or video player apparatus and system and method for selecting, requesting, downloading, and playing audio and / or video data content files from an Internet-based database server. The wireless link is preferably implemented in accordance with the WiFi protocol, which allows connectivity to the Internet by being in proximity with a local base station or WiFi hotspot (i.e., publicly available local wireless access hub connected to the Internet). The portable wireless communications subscriber audio and / or video player apparatus and system preferably include a security means for monitoring and blocking unauthorized use of the player apparatus and system. The player apparatus further preferably has the capability to communicate with other neighboring player apparatus for the purpose of exchanging content data files, playlists and personal messages.
Owner:SANDISK TECH LLC
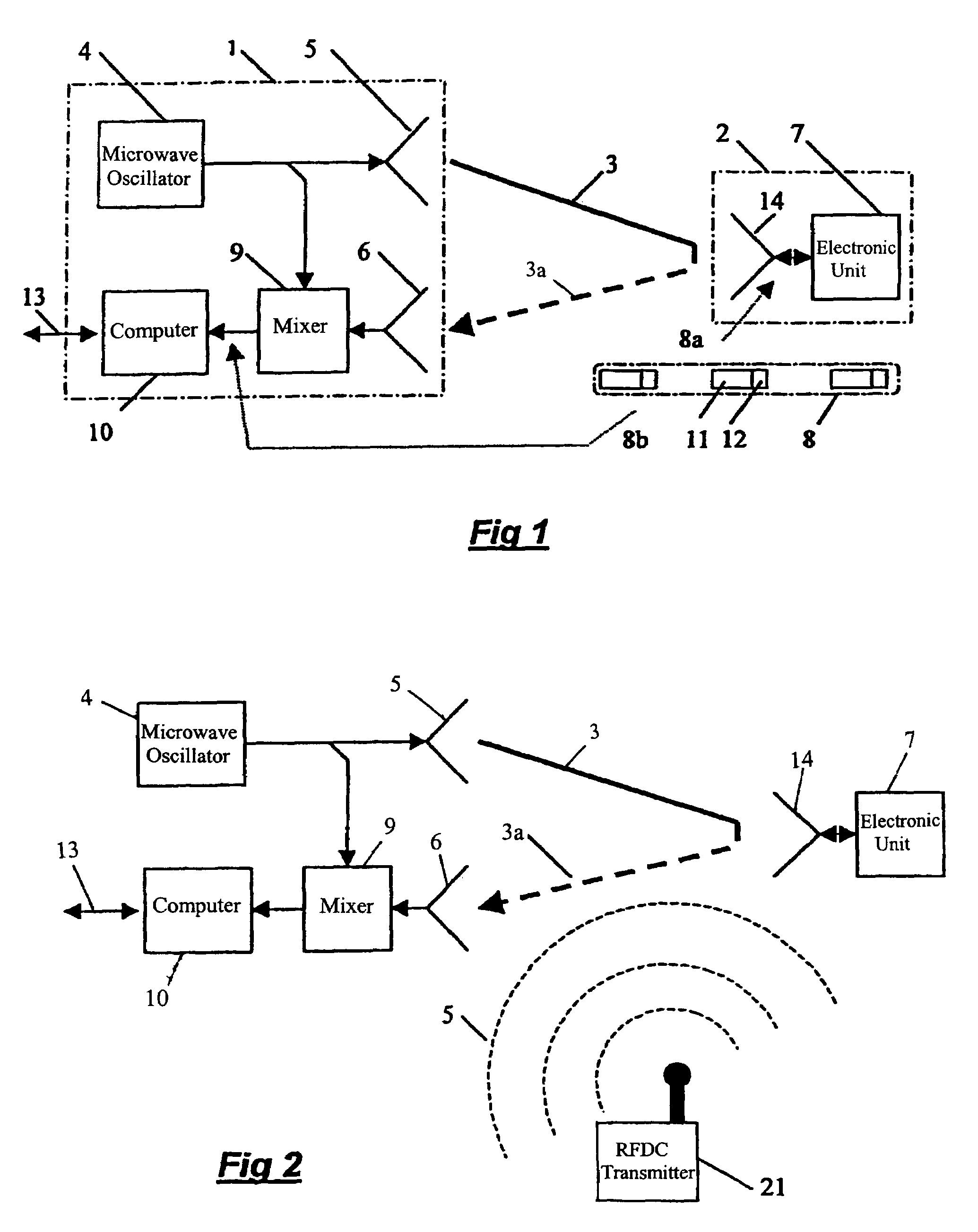
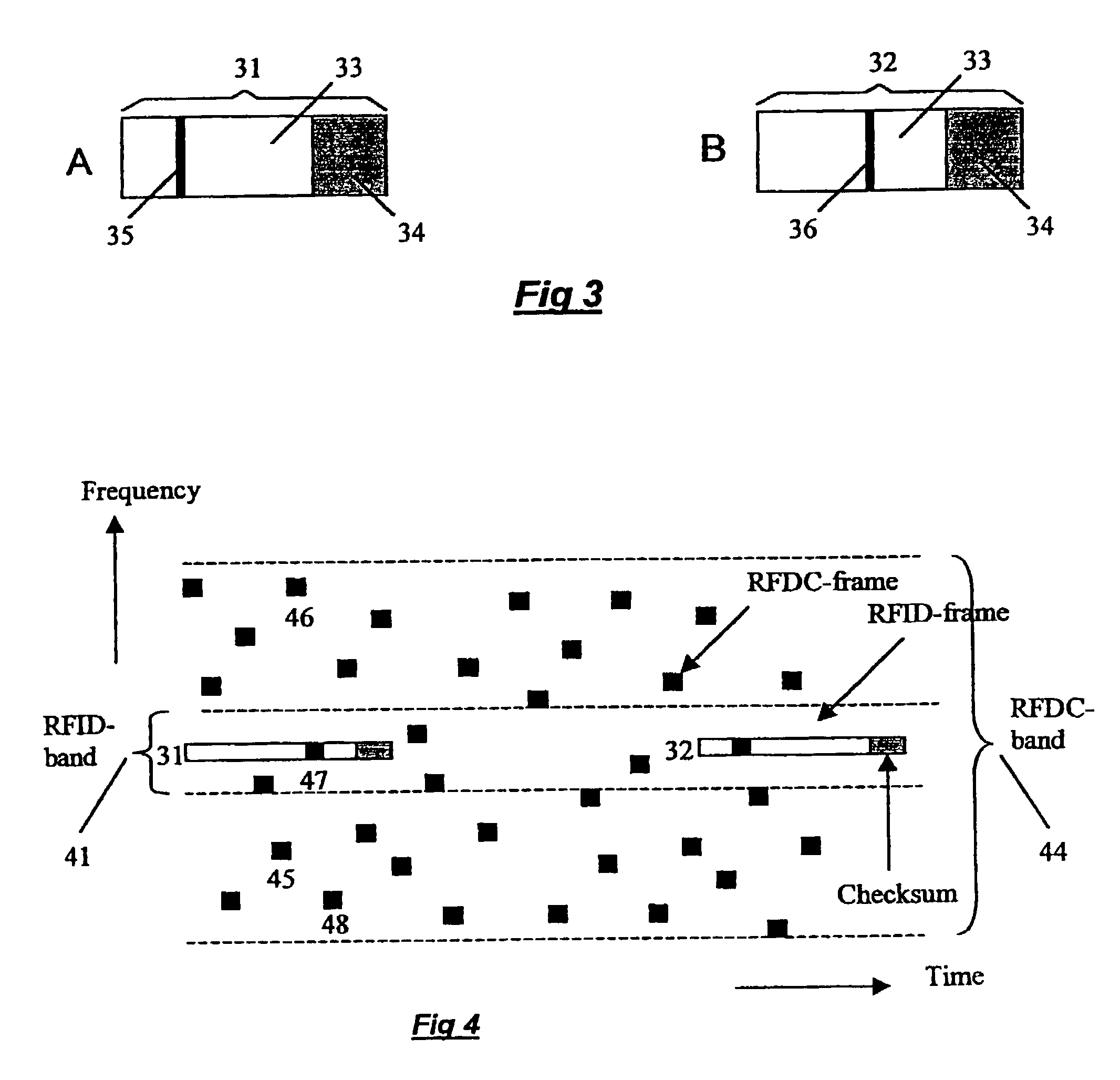
Interference protection
InactiveUS7239657B1Memory record carrier reading problemsTransmissionInterference resistanceChecksum
Apparatus and a method for enhancing the interference resistance of so-called RFID systems, wherein identification messages delivered from an identification device are longer than the time for which an anticipated interference or disturbance is calculated to continue, and wherein the messages contain redundancy, such as a checksum. The messages are delivered from the identification device repetitively, and are redundancy checked. In the event of any discrepancy in the redundancy check, such as when the checksum is checked against the data content of the message and is found in disagreement, successive messages are checked bit for bit against each other. Any deviations between otherwise previously rejected messages are assumed to be due to external interference and are thus successively substituted until the redundancy check gives an accepted result, such as through the medium of a checksum check according to the so-called CRC method.
Owner:TAGMASTER AB
Identifying and requesting data in network using identifiers which are based on contents of data
InactiveUS6415280B1Improve efficiencyImprove integrityData processing applicationsDigital data processing detailsHash functionData content
In a system in which a set of data items are distributed across a network of servers, at least some of the data items being cached versions of data items from a source server, a content delivery method includes determining a data identifier for a particular data item, the data identifier being determined using a given function of the data comprising the particular data item; and responsive to a request for the particular data item, the request including at least the data identifier of the particular data item, providing the particular data item from a given one of the servers of the network of servers. The request for the particular data item may be resolved based on a measure of availability of at least one of the servers, where the measure of availability may be a measurement of bandwidth to the server; a measurement of a cost of a connection to the server, and / or a measurement of a reliability of a connection to the server. The function used to determine the identifier may be a message digest function or a hash function.
Owner:LEVEL 3 COMM LLC +1
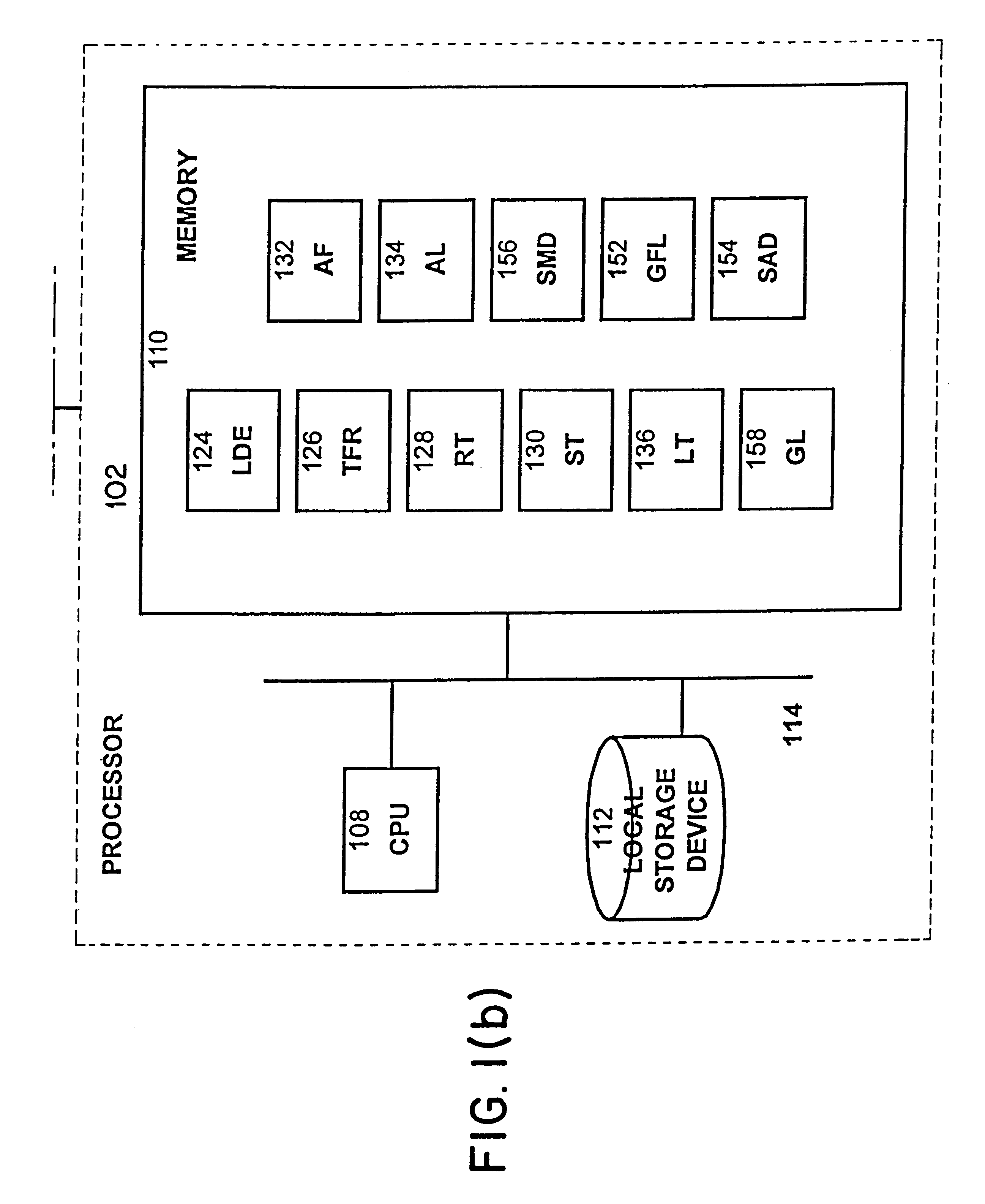
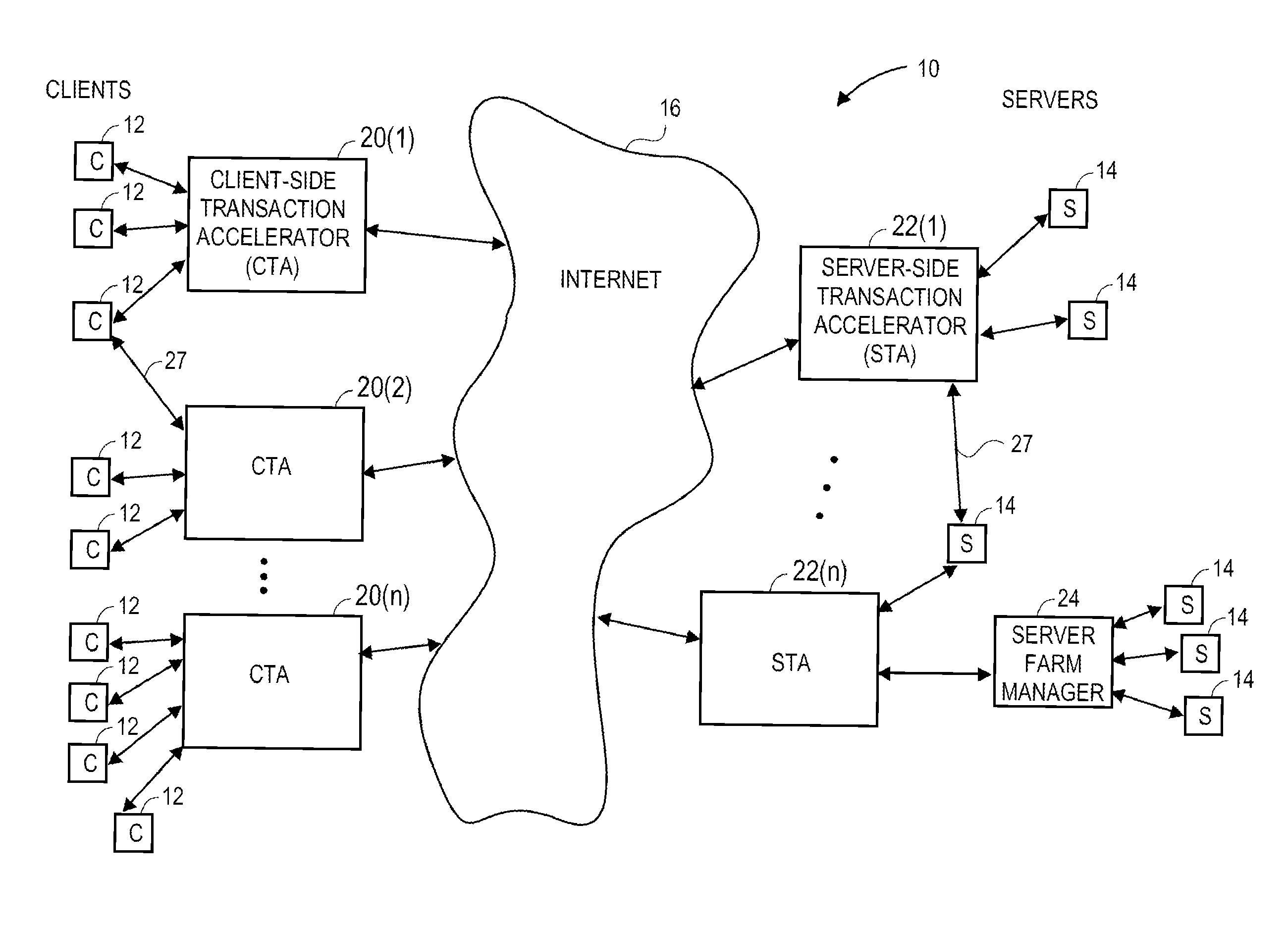
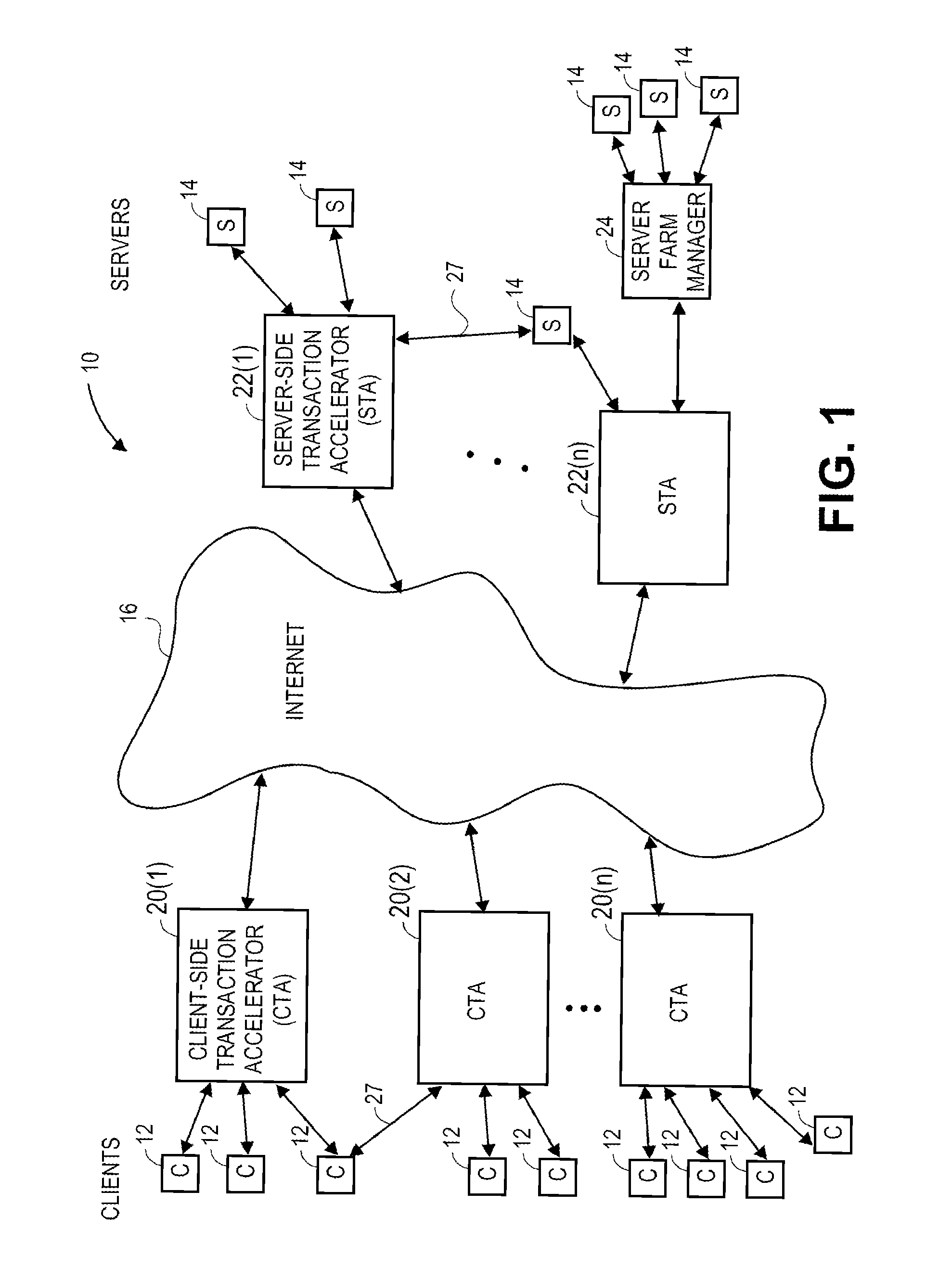
Transaction accelerator for client-server communications systems
ActiveUS20080320151A1Code conversionMultiple digital computer combinationsData segmentCommunications system
Self-discovering transaction accelerators improve communications between a client and a server. A client directs a message to a server. A client-side transaction accelerator intercepts the message, terminates the connection with the client, and accelerates the request by replacing segments of data with references. The accelerated request is forwarded to a server-side transaction accelerator through a new connection. The server-side transaction accelerator reconstructs the message by replacing the reference with segment data in a persistent segment store accessible to the server-side transaction accelerator. The reconstructed request is then provided to the server. Accelerations may occur in any direction of communication. Persistent segment stores can be pre-populated with segment data from other transaction accelerators and anticipated transactions. The persistent segment store can store segments that are data segmented based on content of the data and can be independent of transaction protocol, application, and device.
Owner:RIVERBED TECH LLC
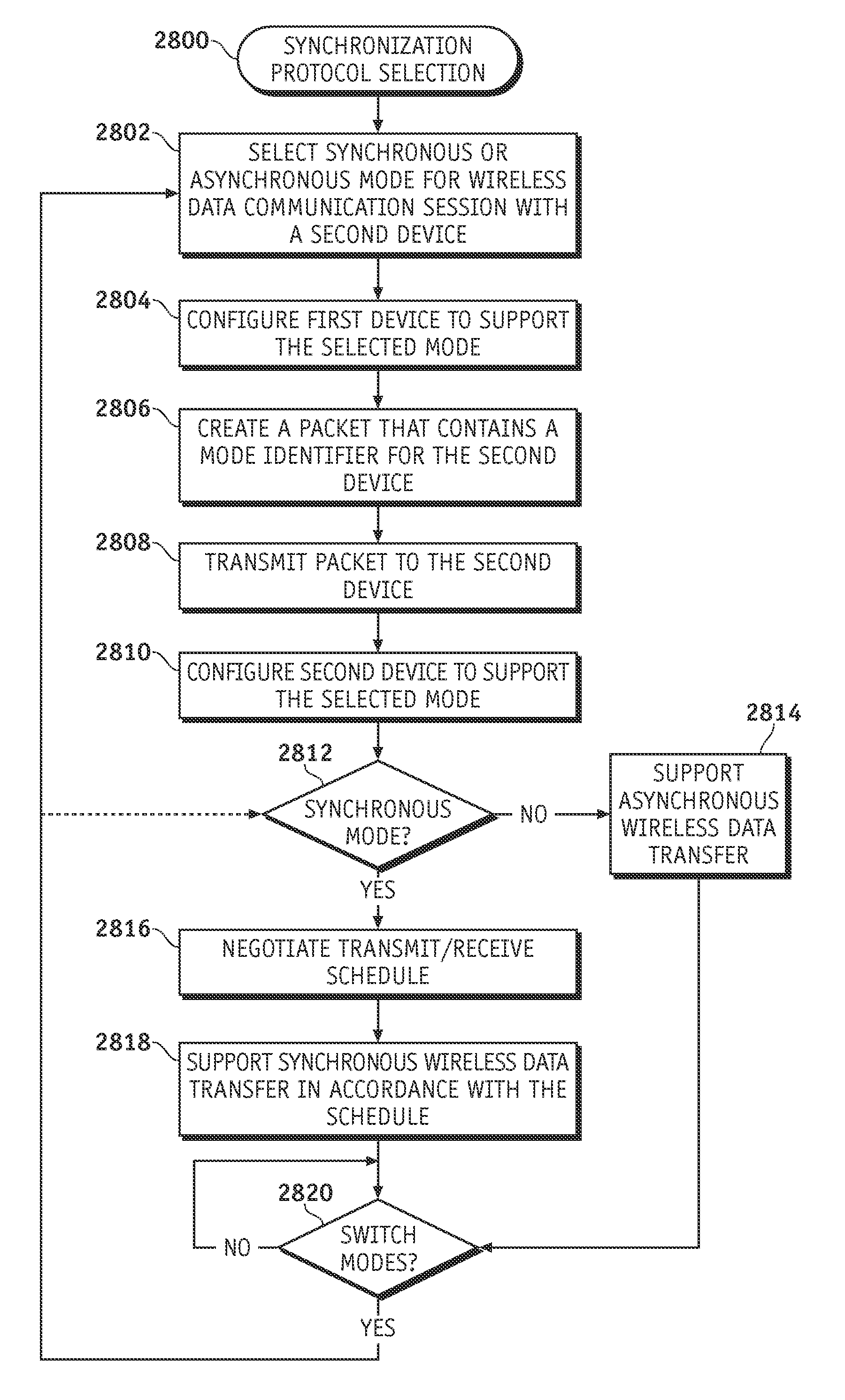
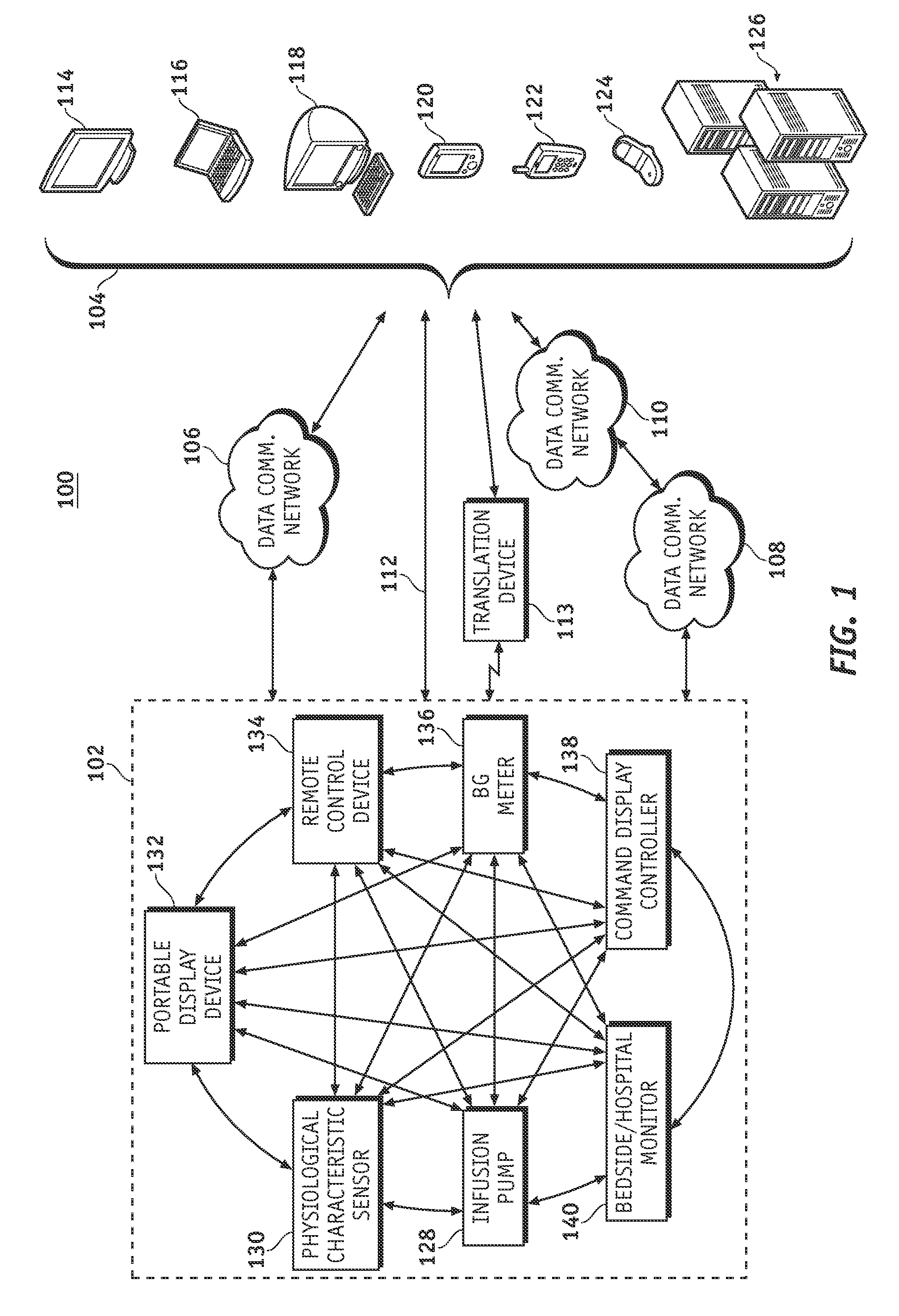
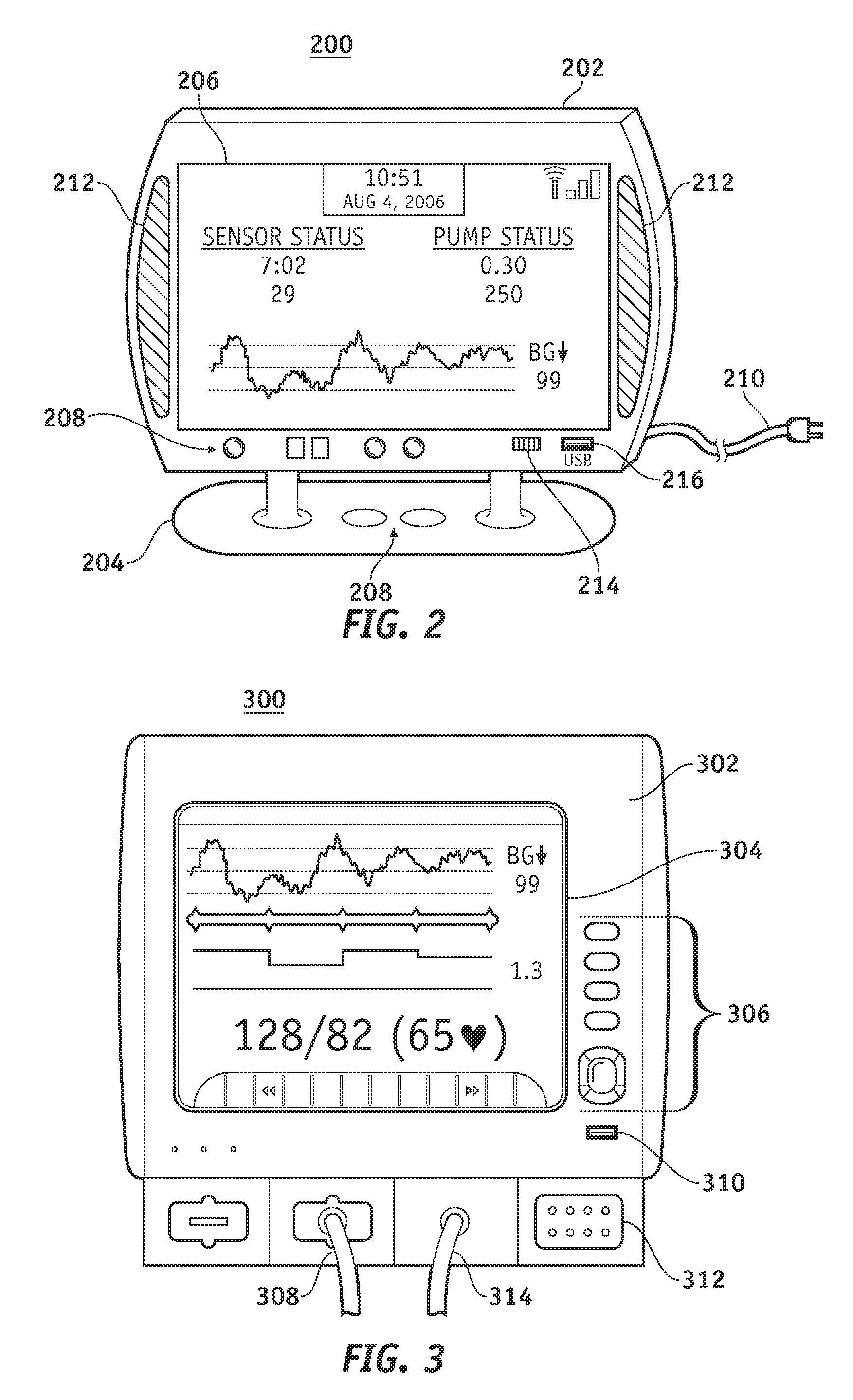
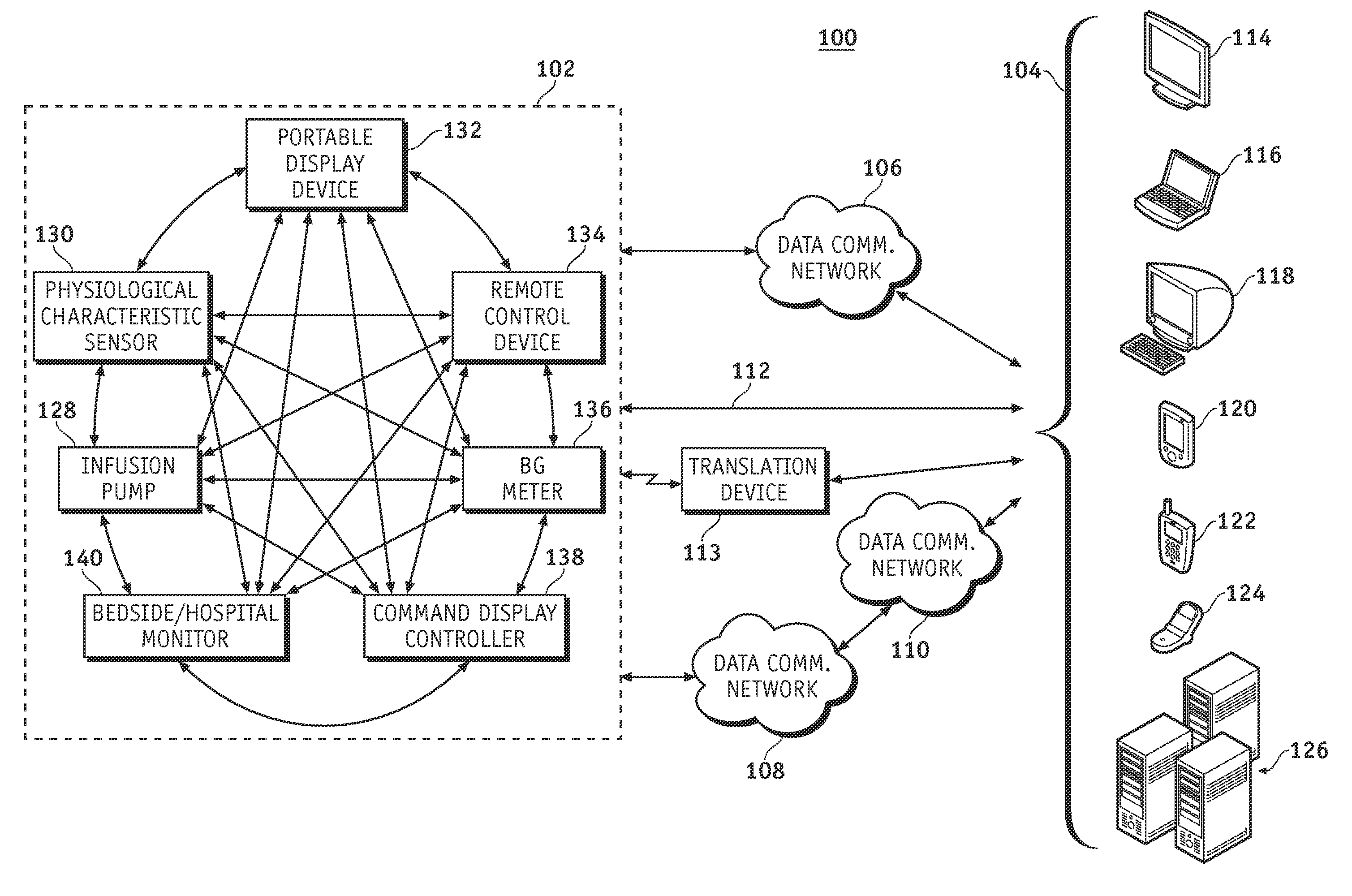
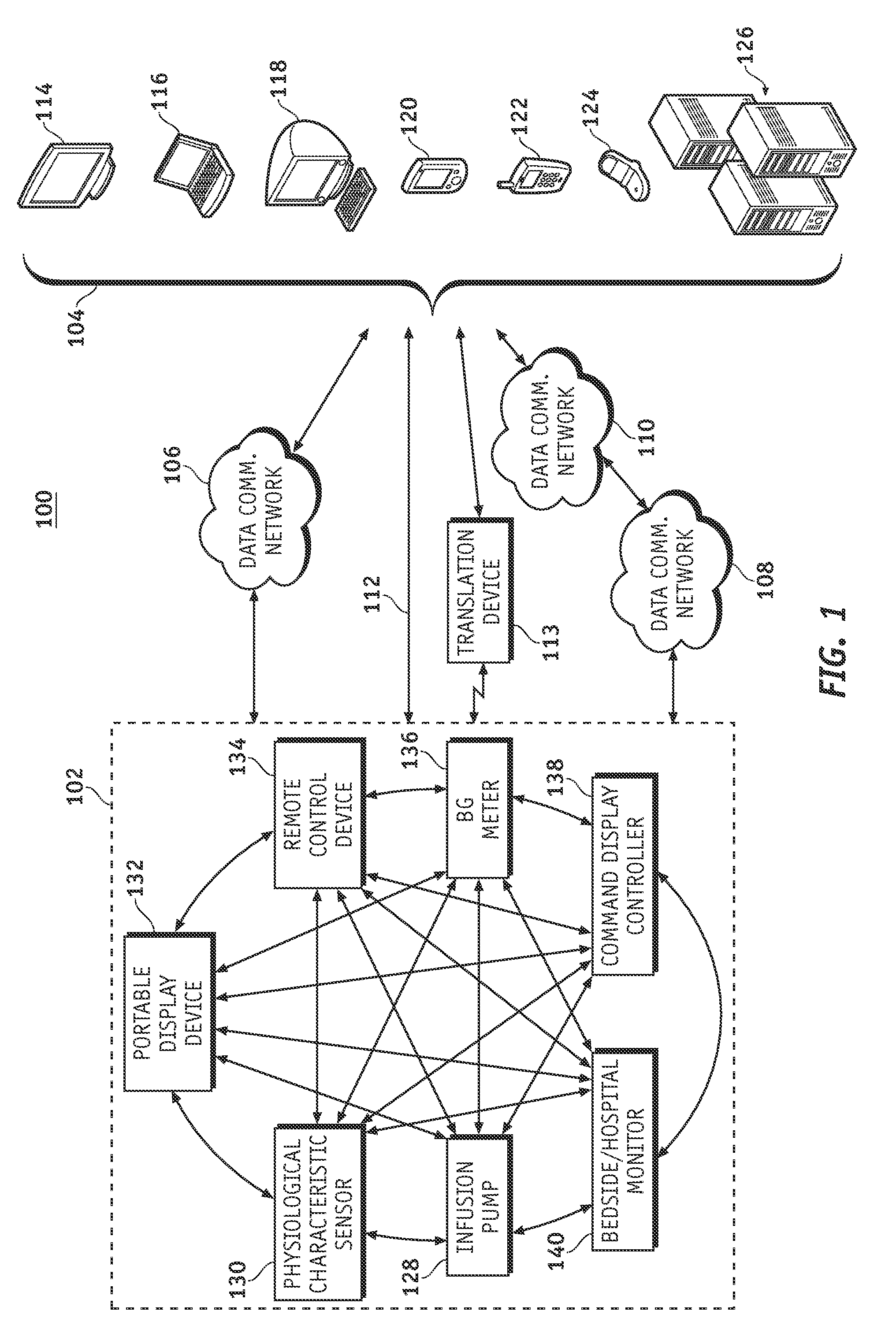
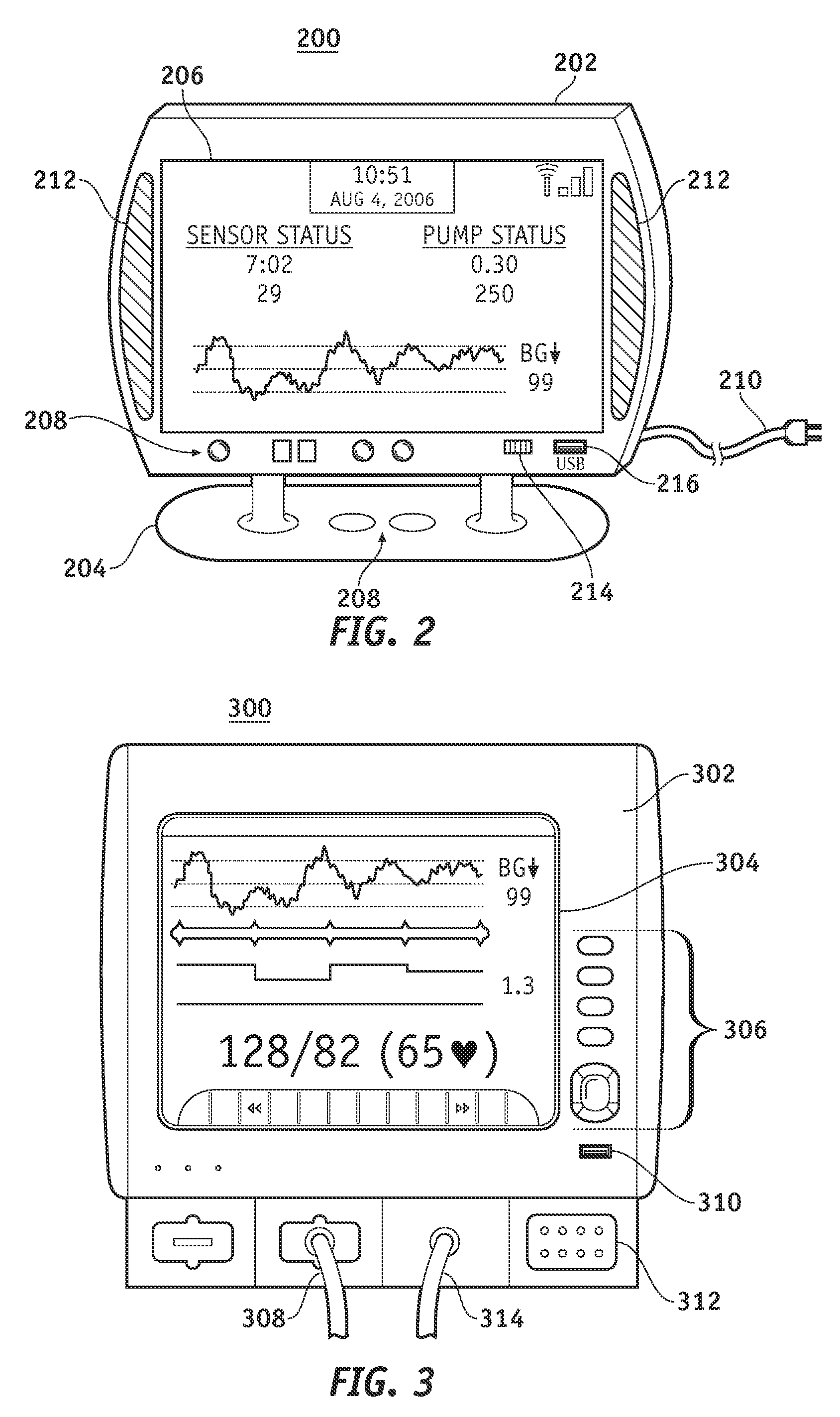
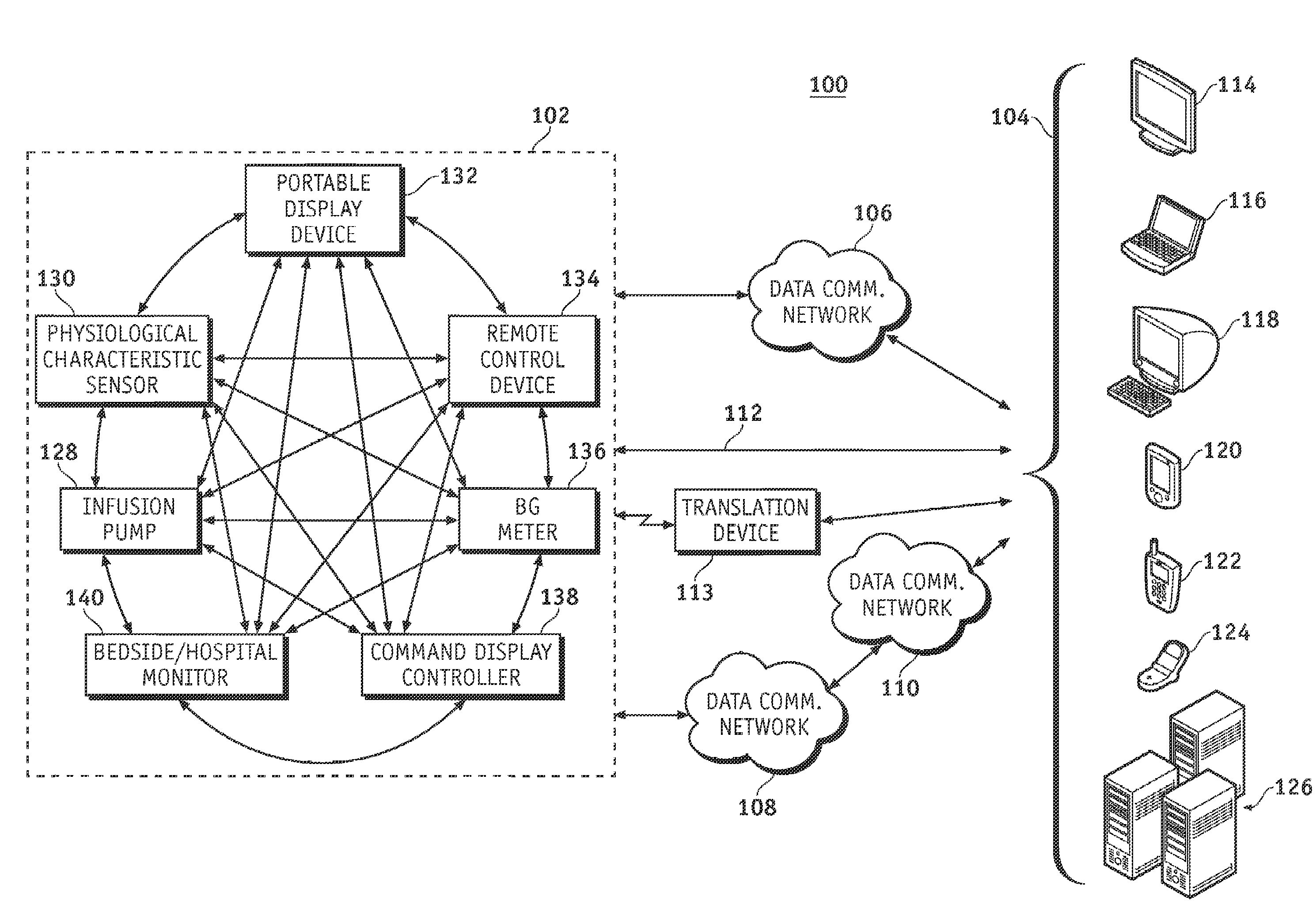
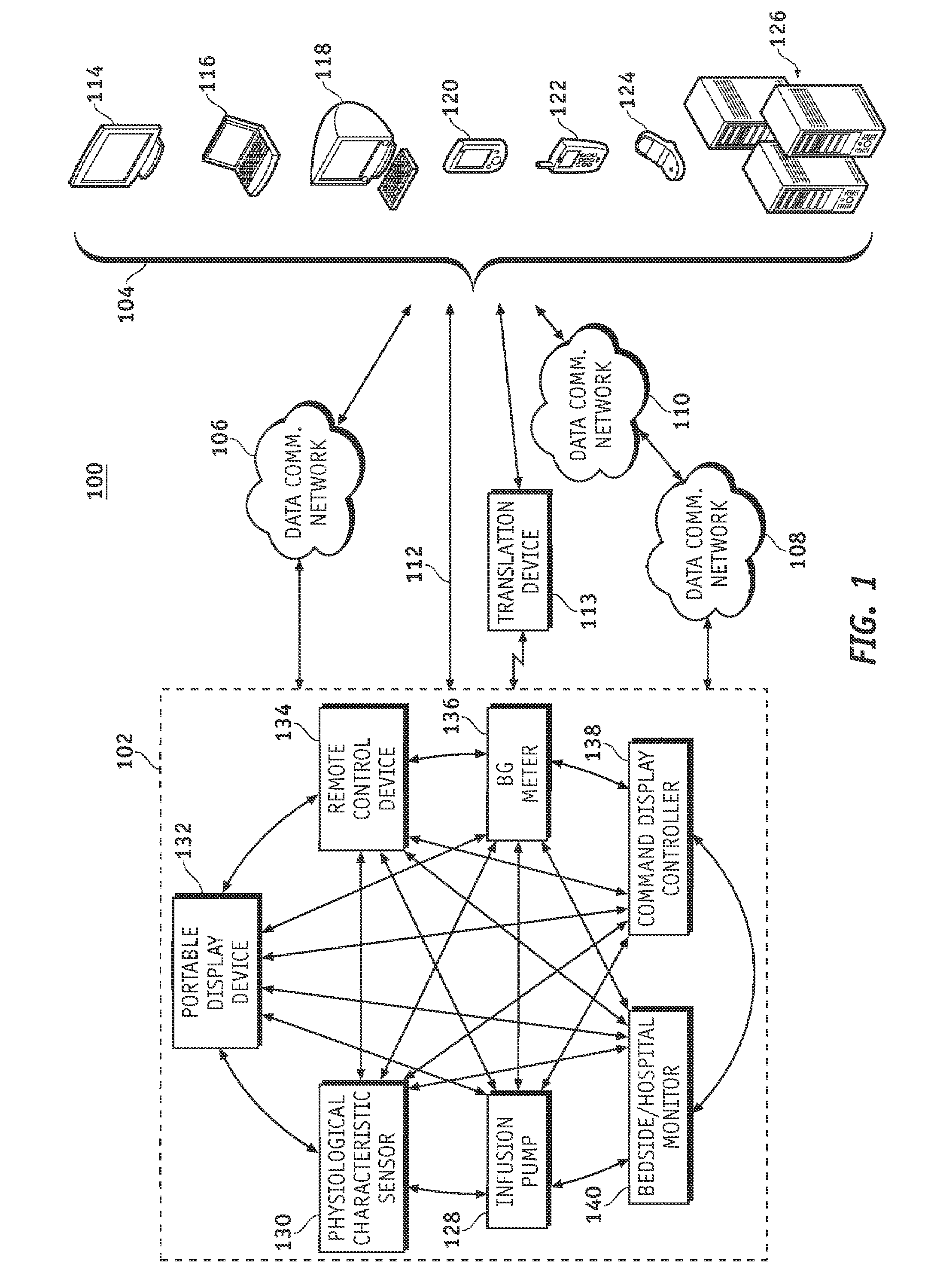
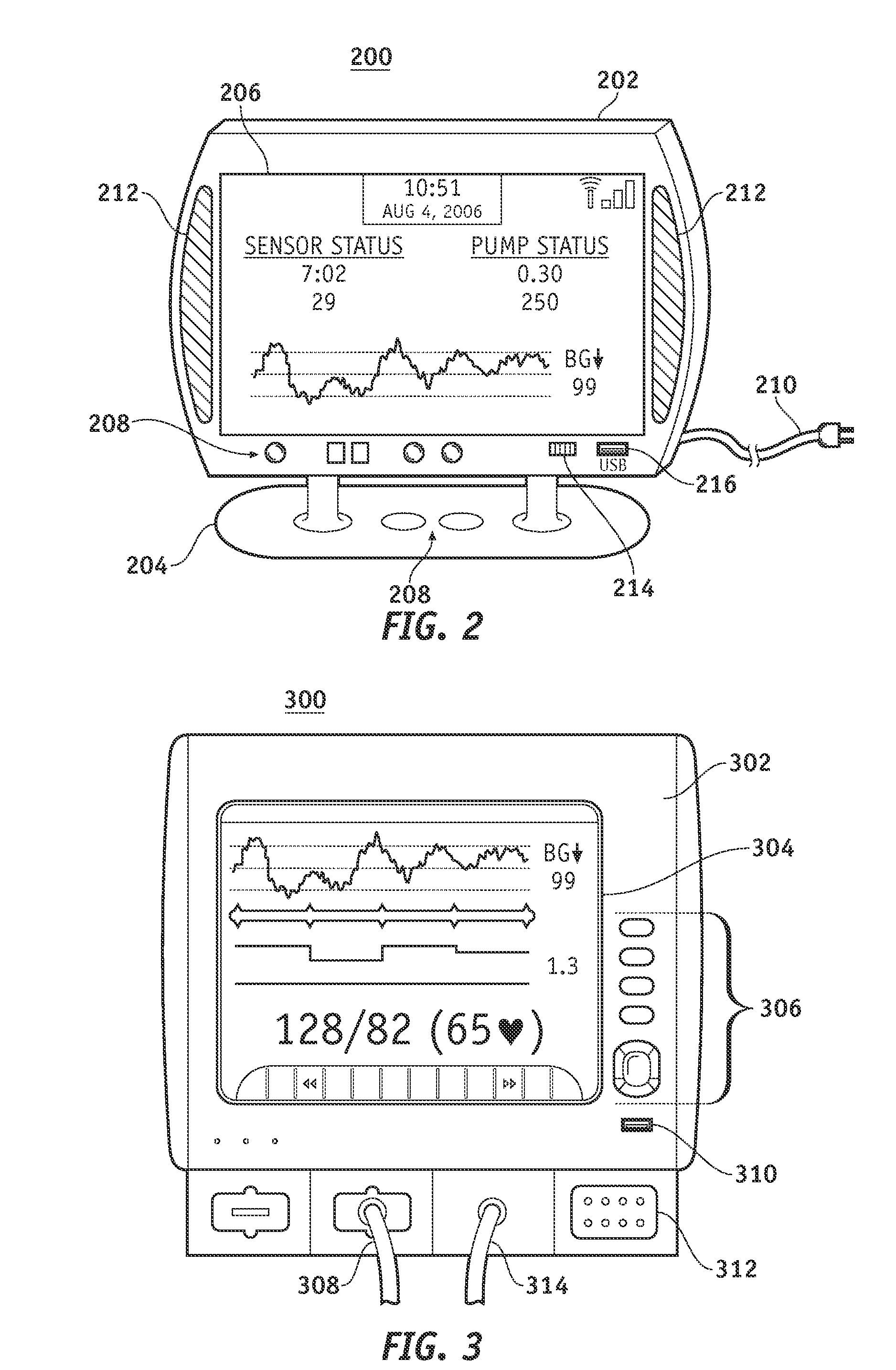
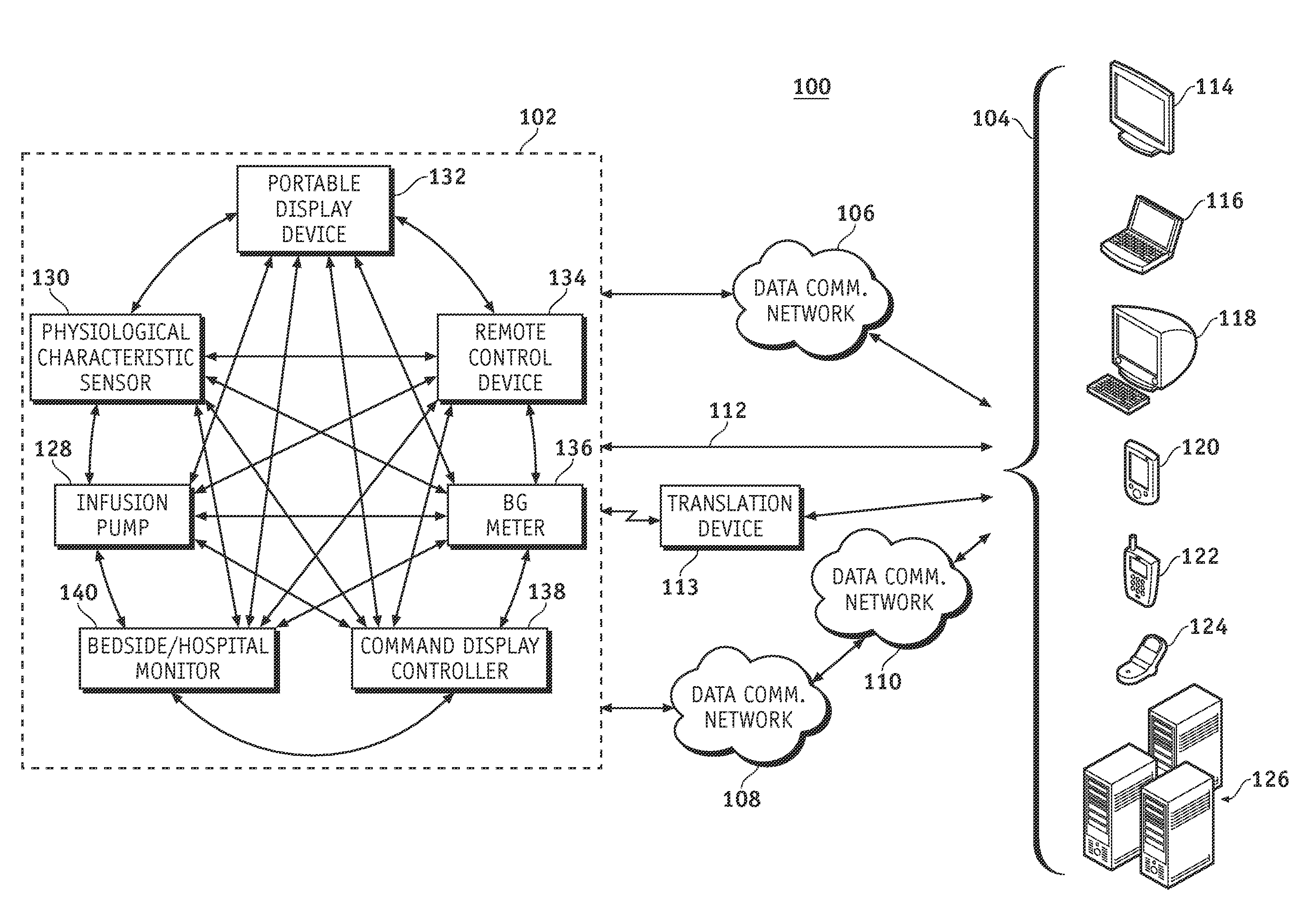
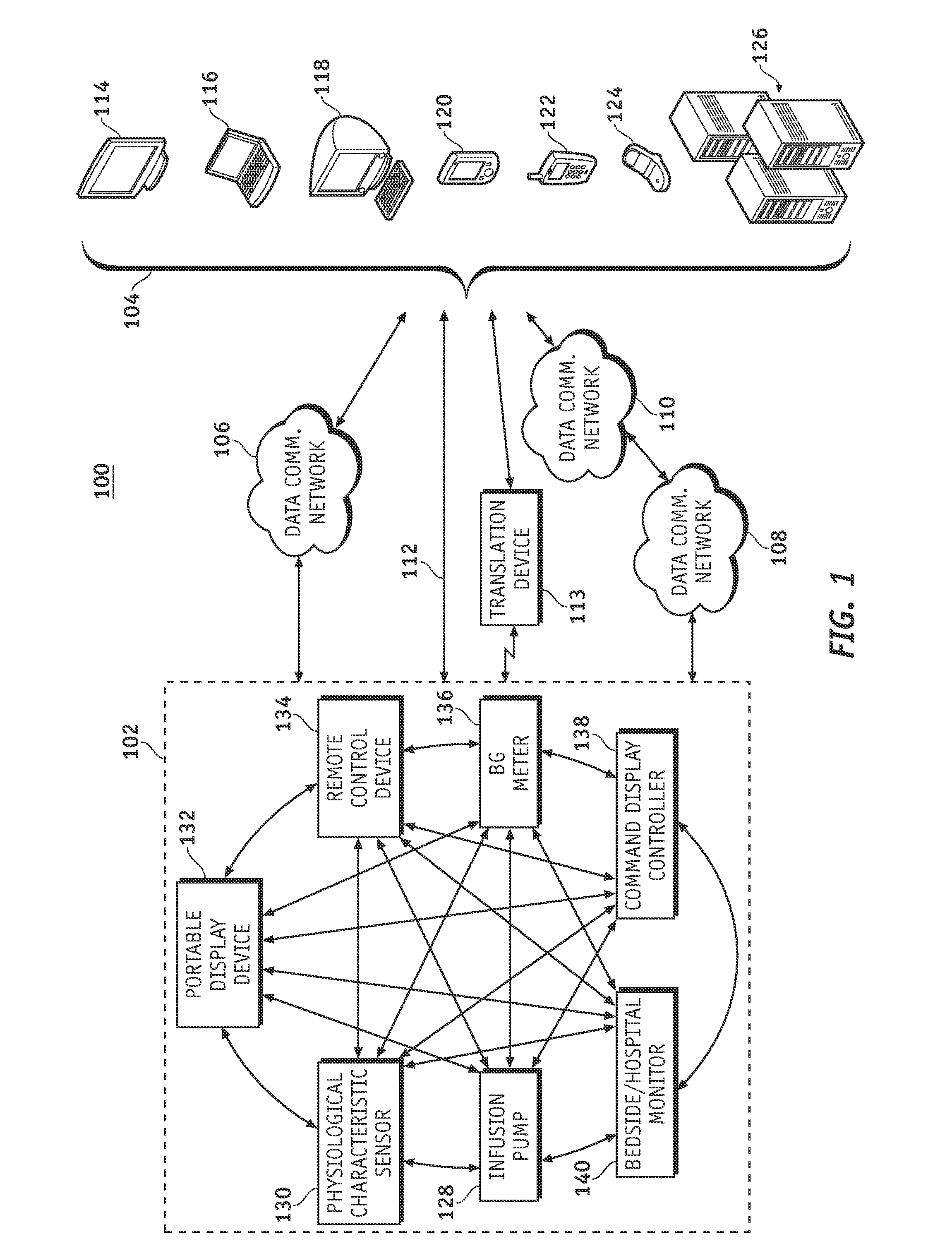
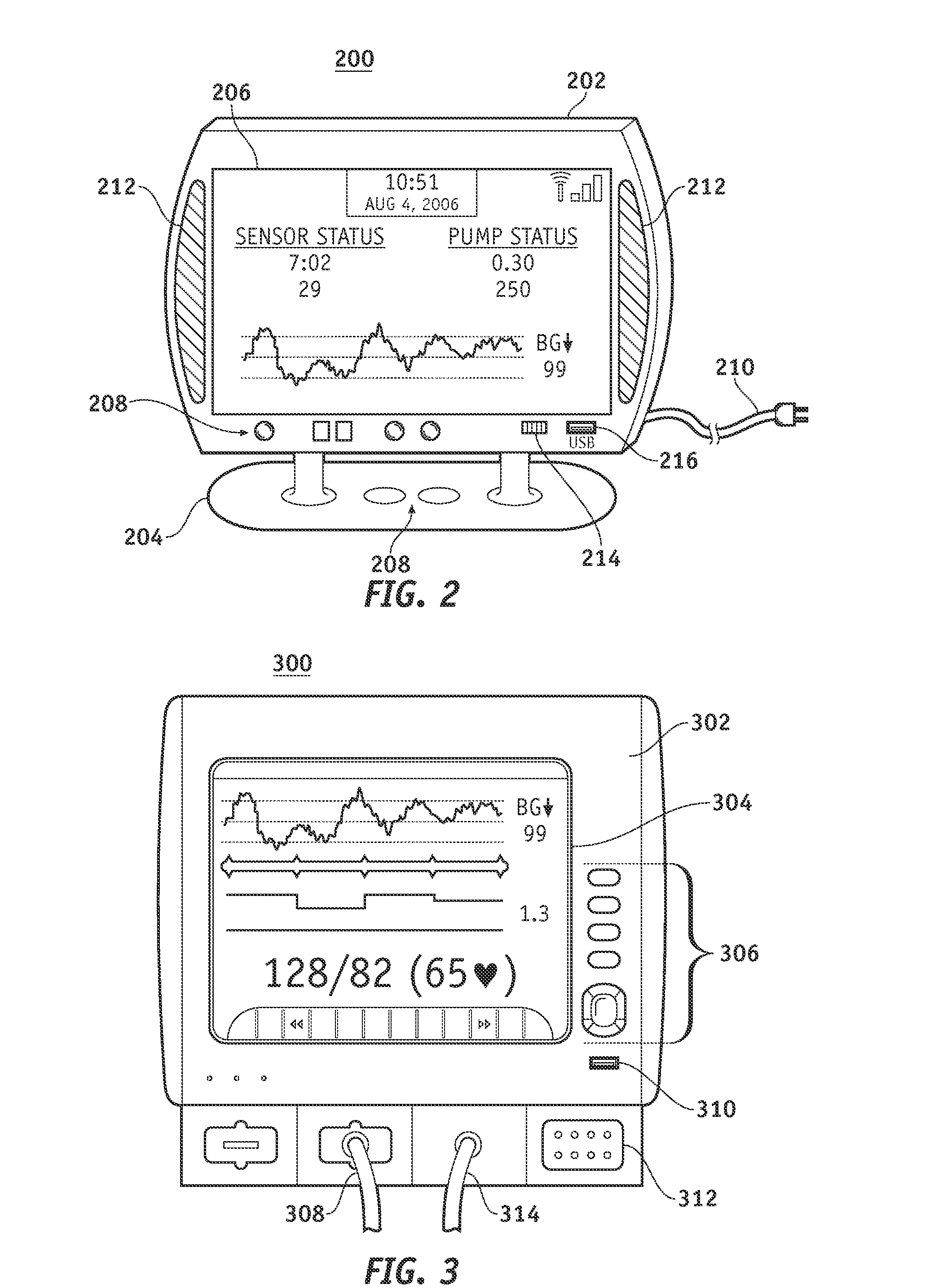
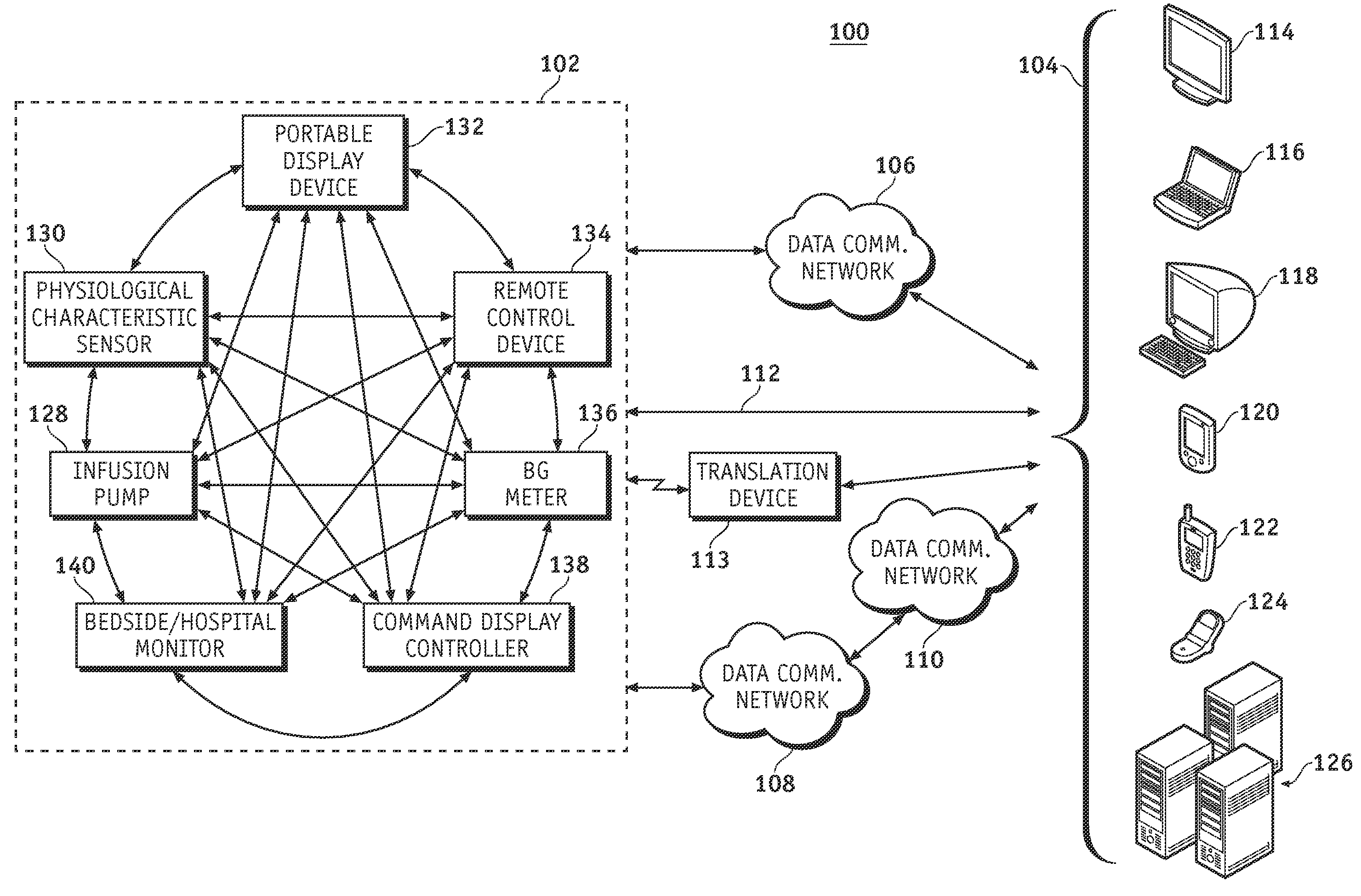
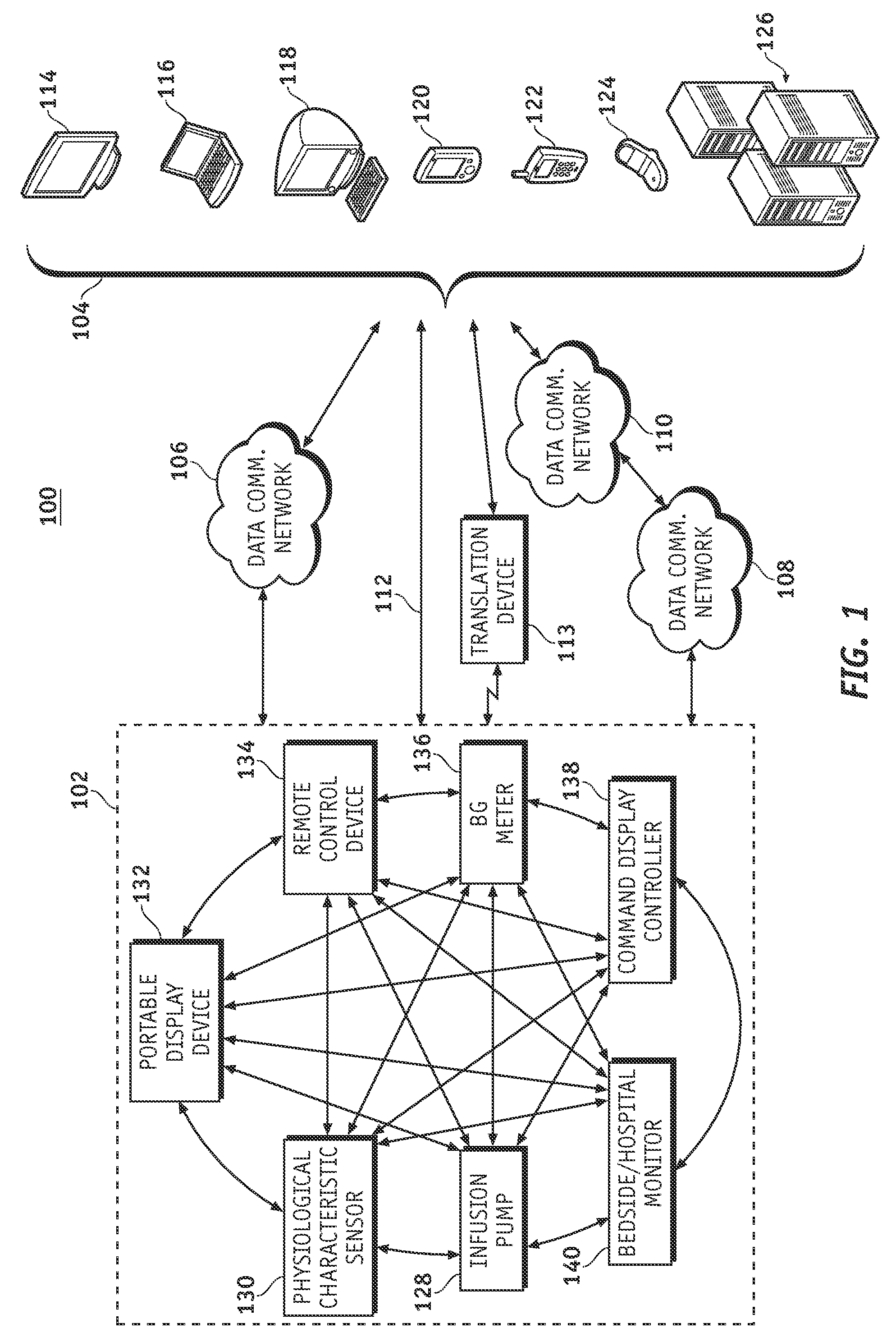
Wireless data communication protocols for a medical device network
InactiveUS20070258395A1Efficient routingDrug and medicationsBroadcast transmission systemsWireless Application ProtocolFluid infusion
A fluid infusion system as described herein includes a number of local “body network” devices, such as an infusion pump, a handheld monitor or controller, a physiological sensor, and a bedside or hospital monitor. The body network devices can be configured to support communication of status data, physiological information, alerts, control signals, and other information between one another. In addition, the body network devices can be configured to support networked communication of status data, physiological information, alerts, control signals, and other information between the body network devices and “external” devices, systems, or communication networks. The networked medical devices are configured to support a variety of wireless data communication protocols for efficient communication of data within the medical device network. In addition, the wireless medical devices may be configured to support a number of dynamically adjustable wireless data communication modes to react to current operating conditions, application-specific data content, or other criteria.
Owner:MEDTRONIC MIMIMED INC
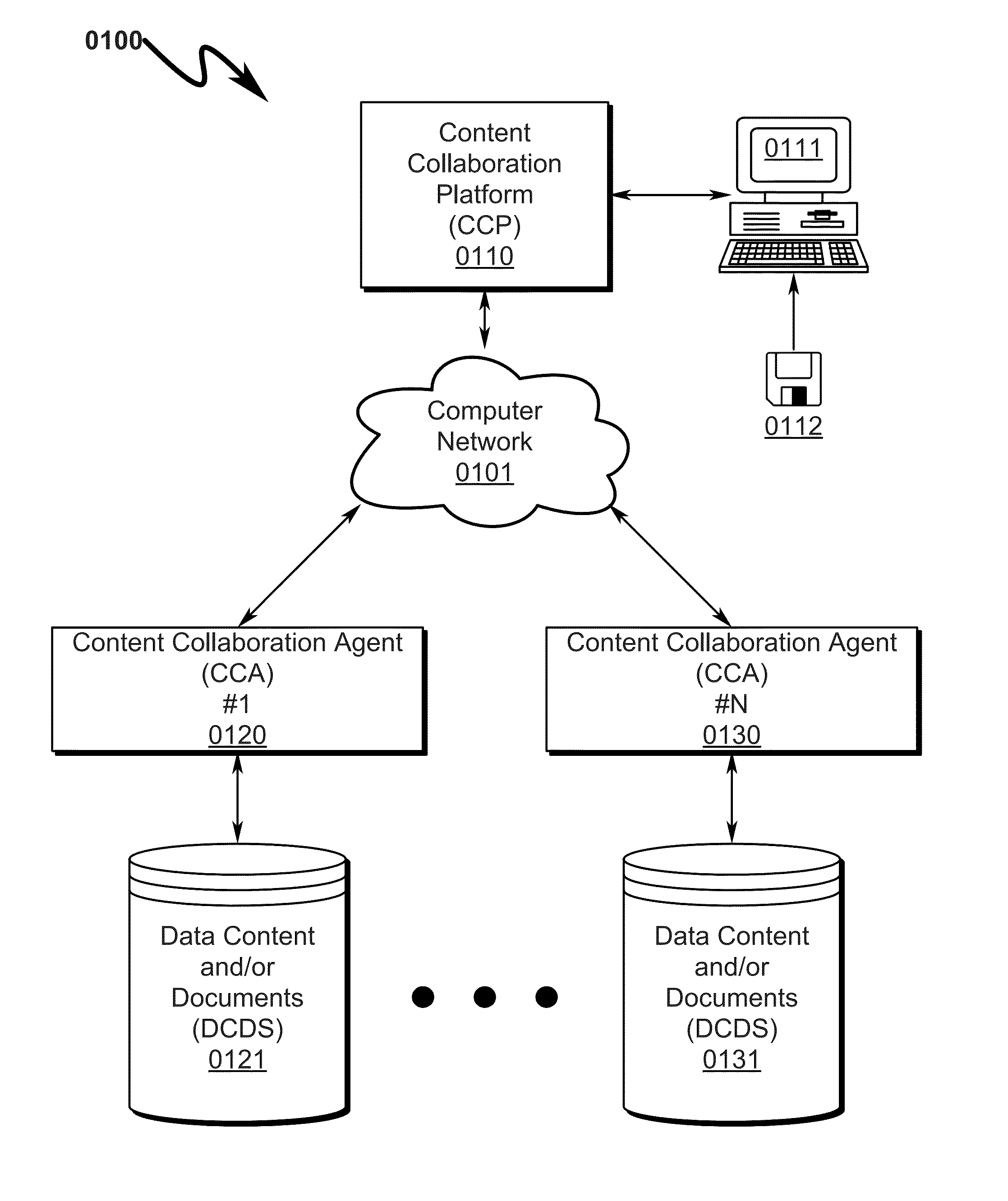
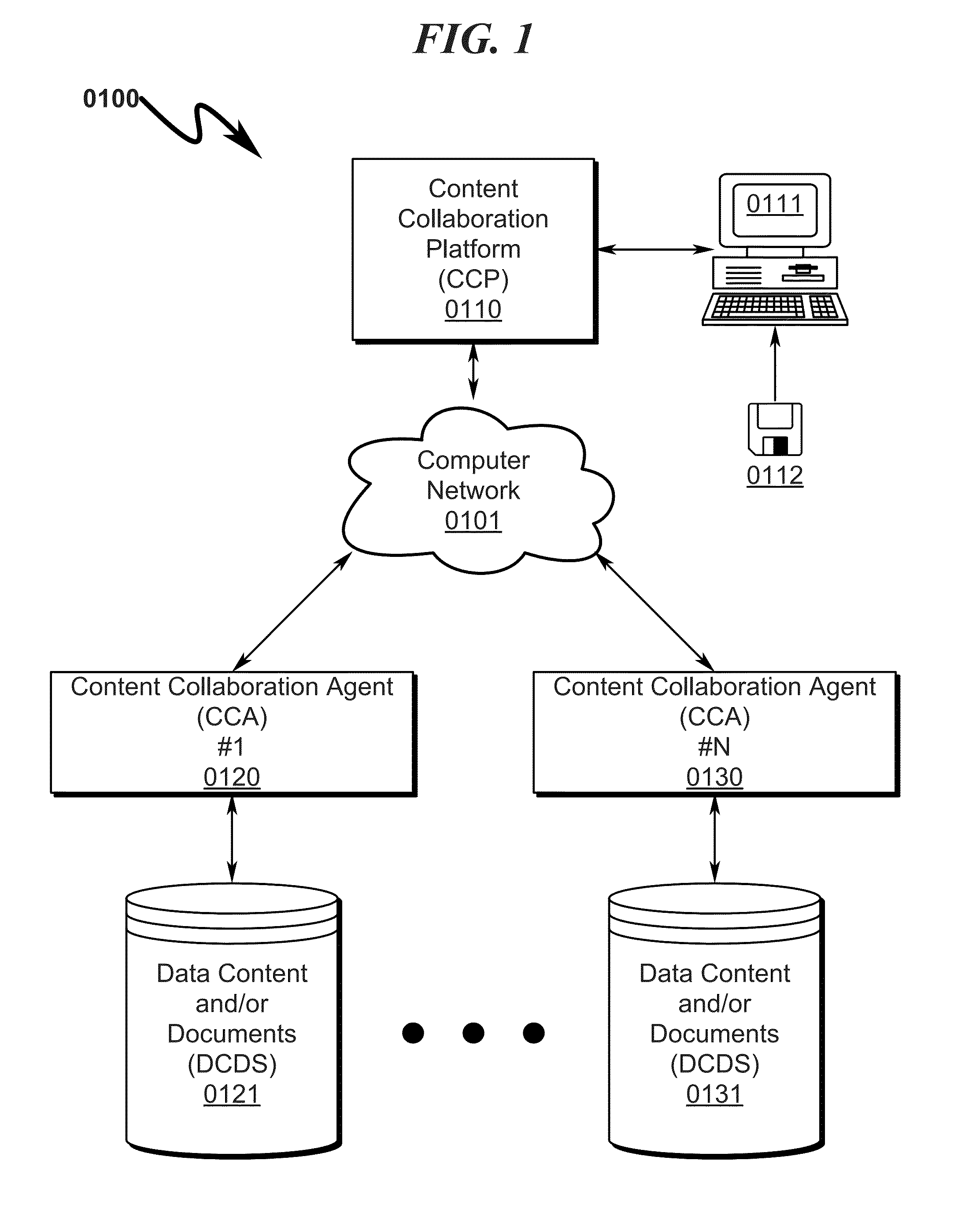
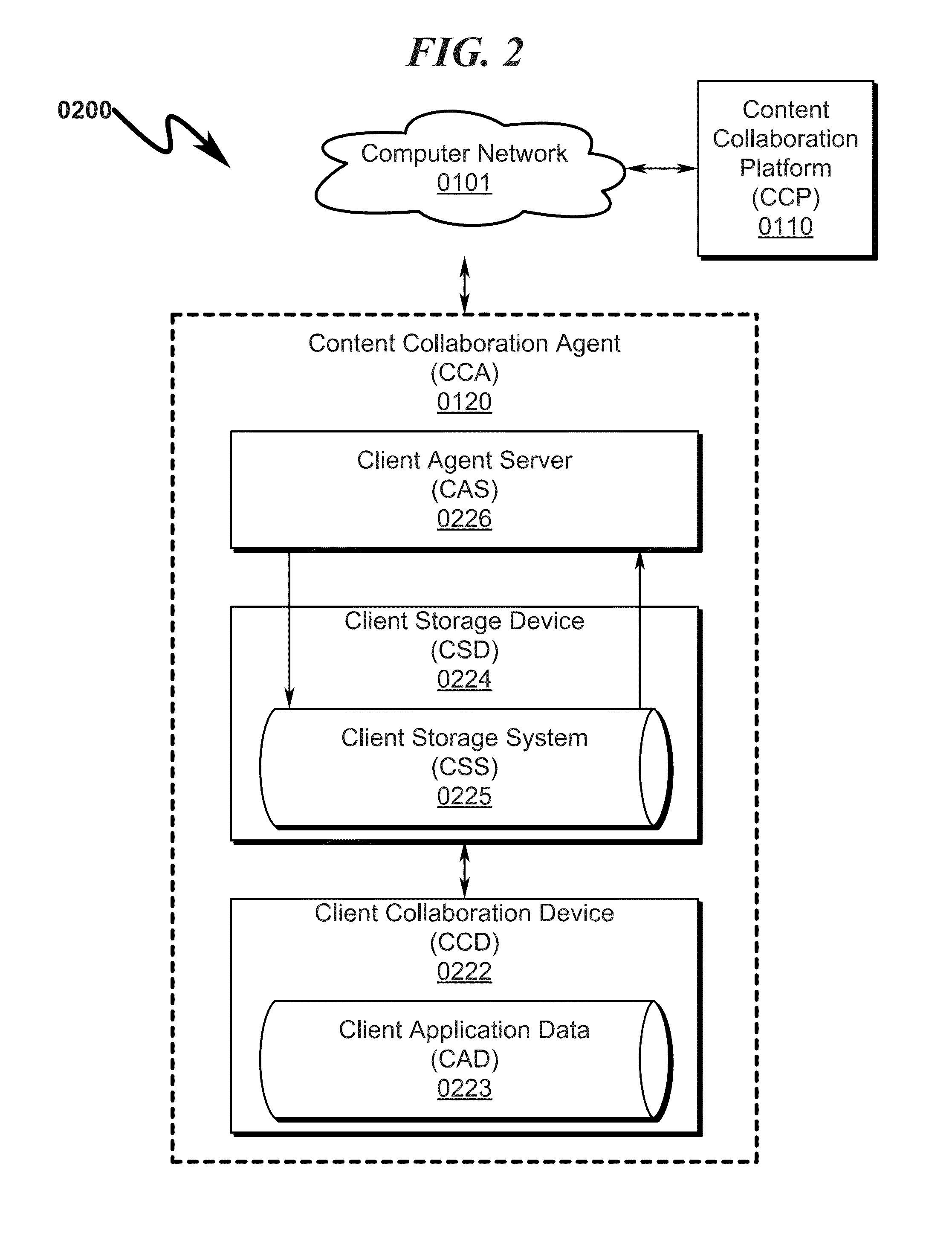
Document management system and method
InactiveUS20130218829A1Avoid lostAvoid Information LeakageDigital data information retrievalDigital data processing detailsData accessData content
A document management system / method allowing coordinated synchronized modifications and secure, scalable, multi-level, and controlled access to Data Content and / or Documents (DCDS) over a computer network between multiple Content Owners and / or Reviewers (CORS) is disclosed. The system / method is configured to allow any number of CORS to share DCDS using a Content Collaboration Platform (CCP) while retaining complete DCDS integrity / retrieval control using a hierarchical Access Rights and Control List (ARCL) to prevent CORS from uncoordinated DCDS modification and prohibiting local maintenance of DCDS copies after the expiration of a CORS Data Access Session (DAS). Upon termination of a CORS DAS, the system synchronizes modifications to the DCDS and coordinates control information among various CORS to ensure proper return of the DCDS back to its original CORS owner and associated CORS storage location.
Owner:MARTINEZ DENEEN LIZETTE
Identification of devices in a medical device network and wireless data communication techniques utilizing device identifiers
InactiveUS20070253021A1Efficient routingDrug and medicationsMultiplex communicationControl signalFluid infusion
A fluid infusion system as described herein includes a number of local “body network” devices, such as an infusion pump, a handheld monitor or controller, a physiological sensor, and a bedside or hospital monitor. The body network devices can be configured to support communication of status data, physiological information, alerts, control signals, and other information between one another. In addition, the body network devices can be configured to support networked communication of status data, physiological information, alerts, control signals, and other information between the body network devices and “external” devices, systems, or communication networks. The networked medical devices are configured to support a variety of wireless data communication protocols for efficient communication of data within the medical device network. In addition, the wireless medical devices may be configured to support a number of dynamically adjustable wireless data communication modes to react to current operating conditions, application-specific data content, or other criteria.
Owner:MEDTRONIC MIMIMED INC
Broadcast data transmission and data packet repeating techniques for a wireless medical device network
InactiveUS20070255116A1Efficient routingDrug and medicationsMedical devicesComputer networkControl signal
A fluid infusion system as described herein includes a number of local “body network” devices, such as an infusion pump, a handheld monitor or controller, a physiological sensor, and a bedside or hospital monitor. The body network devices can be configured to support communication of status data, physiological information, alerts, control signals, and other information between one another. In addition, the body network devices can be configured to support networked communication of status data, physiological information, alerts, control signals, and other information between the body network devices and “external” devices, systems, or communication networks. The networked medical devices are configured to support a variety of wireless data communication protocols for efficient communication of data within the medical device network. In addition, the wireless medical devices may be configured to support a number of dynamically adjustable wireless data communication modes to react to current operating conditions, application-specific data content, or other criteria.
Owner:MEDTRONIC MIMIMED INC
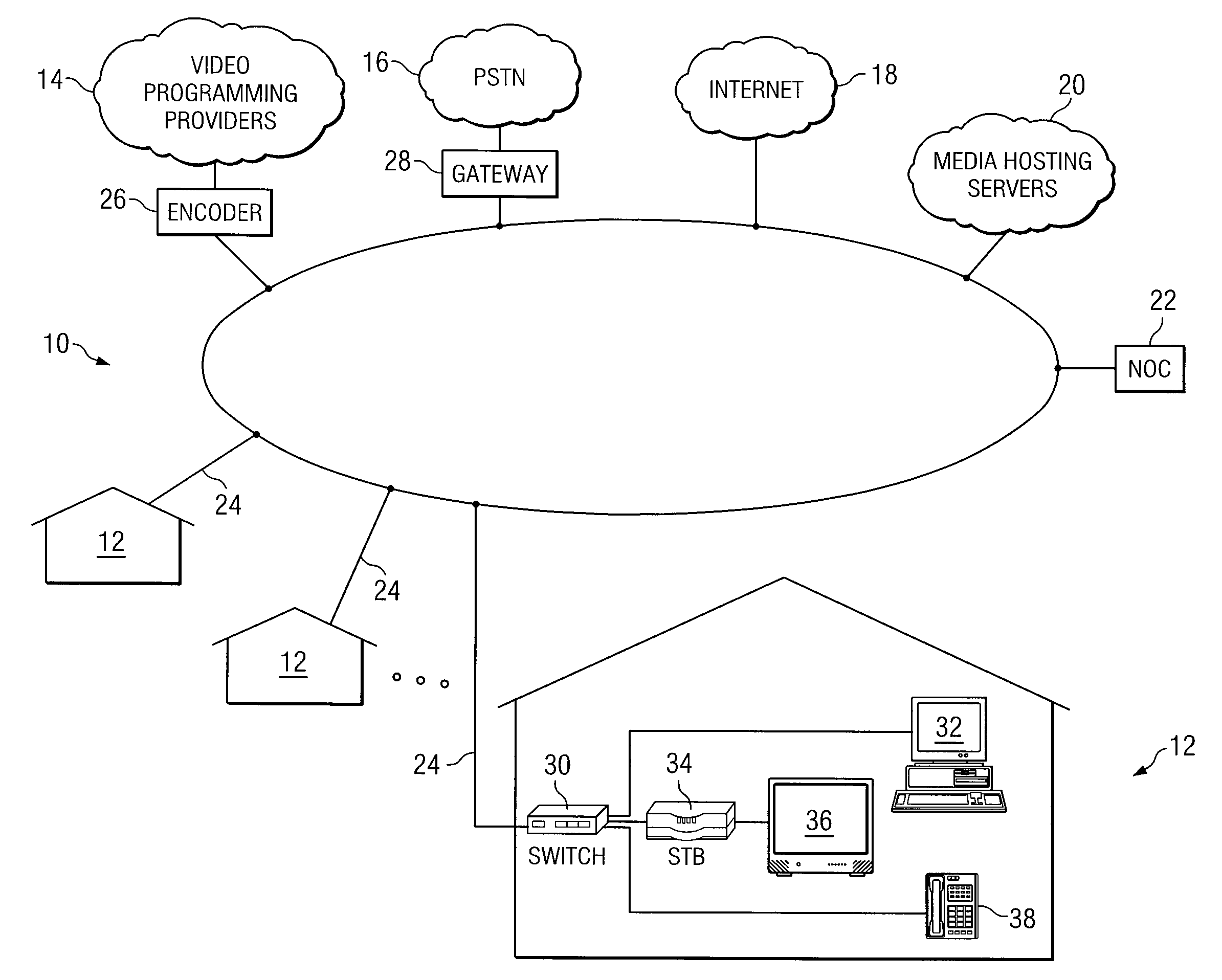
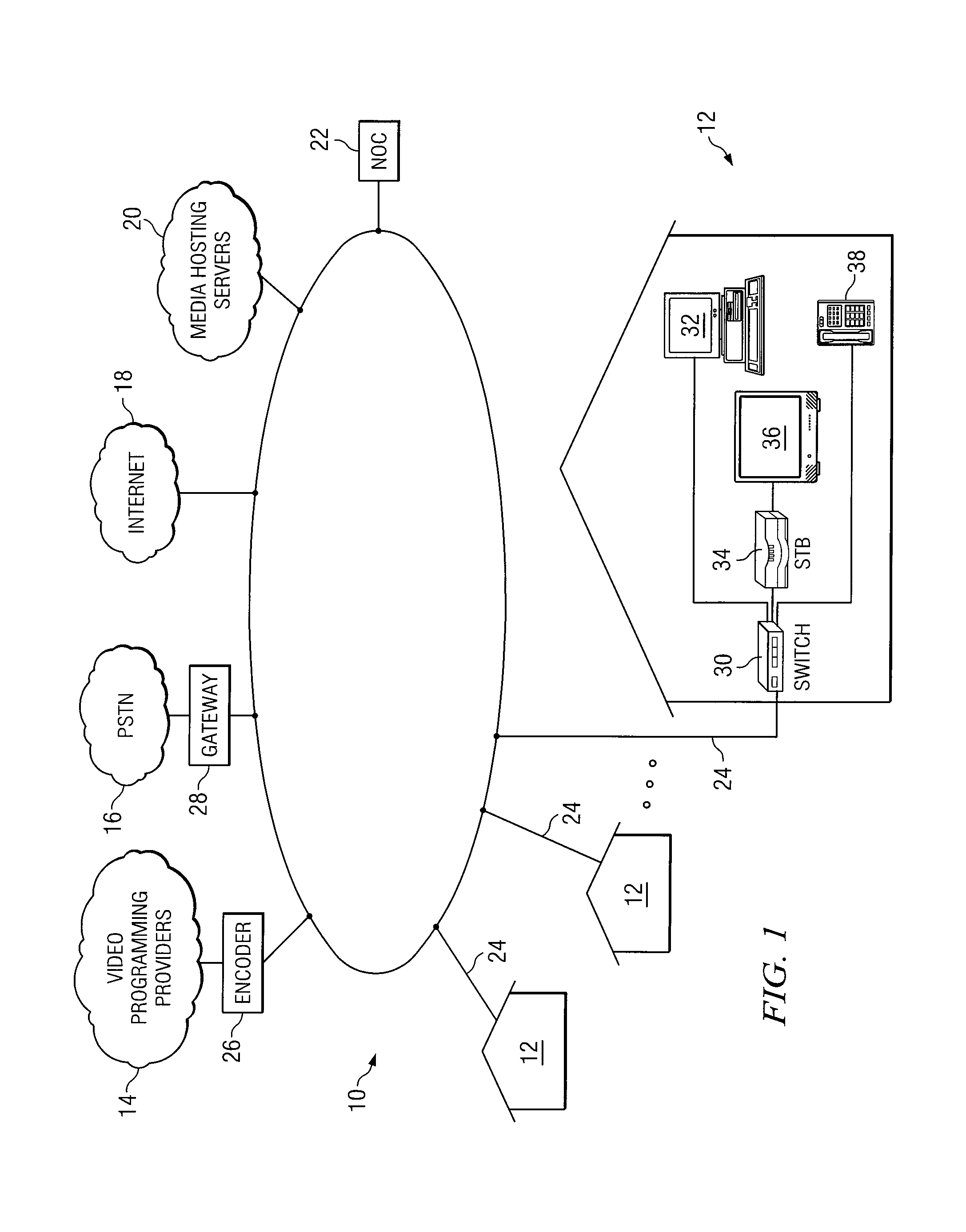
System and method for providing integrated voice, video and data to customer premises over a single network
InactiveUS7075919B1Easy to troubleshootEnhanced fault-toleranceTime-division multiplexData switching by path configurationData contentTelephone network
A method for providing integrated voice, video, and data content in an integrated service offering to one or more customer premises includes receiving television programming from a programming source, receiving data from a data network, and receiving telephone communications from a telephone network. The method further includes placing the television programming, data, and telephone communications in a common format for integrated communication over a single network infrastructure using a common communication protocol. In addition, the method includes communicating the integrated television programming, data, and telephone communications in the common format over the single network infrastructure using the common communication protocol to one or more customer premises to provide the integrated service offering.
Owner:CISCO TECH INC
Input method and apparatus using tactile guidance and bi-directional segmented stroke
InactiveUS20060092177A1Eliminate disadvantagesEfficient and accurateOperation facilitationCathode-ray tube indicatorsTouch PerceptionDisplay device
An input method that is based on bidirectional strokes that are segmented by tactile landmarks. By giving the user tactile feedback about the length of a stroke during input, dependence on visual display is greatly reduced. By concatenating separate strokes into multi-strokes, complex commands may be entered, which may encode commands, data content, or both simultaneously. Multi-strokes can be used to traverse a menu hierarchy quickly. Inter-landmark segments may be used for continuous and discrete parameter entry, resulting in a multifunctional interaction paradigm. This approach to input does not depend on material displayed visually to the user, and, due to tactile guidance, may be used as an eyes-free user interface. The method is especially suitable for wearable computer systems that use a head-worn display and wrist-worn watch-style devices.
Owner:IBM CORP
Methods and apparatus for monitoring local network traffic on local network segments and resolving detected security and network management problems occurring on those segments
InactiveUS20050060535A1Small sizeImprove search capabilitiesSecuring communicationElectric digital data processingData connectionData pack
A system for providing network security through manipulating data connections and connection attempts over a data-packet-network between at least two network nodes is provided. The system includes a system host machine, a first software application residing on the host machine for detecting and monitoring connection activity, a data store for storing connection related data, and a second software application for emulating one or more end nodes of the connections or connection attempts. In a preferred embodiment the system uses the detection software to detect one or more pre-defined states associated with a particular connection or connection attempt including states associated with data content transferred there over and performs at least one packet generation and insertion action triggered by the detected state or states, the packet or packets emulating one or more end nodes of the connection or connection attempt to cause preemption or resolution of the detected state or states.
Owner:PRAEMIO TECH
System and method for flexible user interfaces
InactiveUS20070061488A1Reduces application software developmentReduce maintenance costsDigital data information retrievalMultiple digital computer combinationsApplication program softwareSoftware update
A method and system for implementing a user interface for providing a data service in a mobile client using a server with knowledge of the client's hardware and software capabilities to modify data content and display rules for an improved user interface on the client. Data may be cached on the client to improve application response time and provide a standalone application capability for the client. The automatic conversion of newly developed applications to a plurality of clients with differing hardware and software capabilities reduces application software development and maintenance costs. Software updates and bug fixes can be deployed with the same method and system. An interoperable array of adapters for reporting, billing, and format conversions is also described.
Owner:TRILIBIS
Wireless data communication for a medical device network that supports a plurality of data communication modes
A fluid infusion system as described herein includes a number of local “body network” devices, such as an infusion pump, a handheld monitor or controller, a physiological sensor, and a bedside or hospital monitor. The body network devices can be configured to support communication of status data, physiological information, alerts, control signals, and other information between one another. In addition, the body network devices can be configured to support networked communication of status data, physiological information, alerts, control signals, and other information between the body network devices and “external” devices, systems, or communication networks. The networked medical devices are configured to support a variety of wireless data communication protocols for efficient communication of data within the medical device network. In addition, the wireless medical devices may be configured to support a number of dynamically adjustable wireless data communication modes to react to current operating conditions, application-specific data content, or other criteria.
Owner:MEDTRONIC MIMIMED INC
Subnetwork synchronization and variable transmit synchronization techniques for a wireless medical device network
ActiveUS20070251835A1Efficient routingWeather/light/corrosion resistanceDrug and medicationsWireless Application ProtocolFluid infusion
A fluid infusion system as described herein includes a number of local “body network” devices, such as an infusion pump, a handheld monitor or controller, a physiological sensor, and a bedside or hospital monitor. The body network devices can be configured to support communication of status data, physiological information, alerts, control signals, and other information between one another. In addition, the body network devices can be configured to support networked communication of status data, physiological information, alerts, control signals, and other information between the body network devices and “external” devices, systems, or communication networks. The networked medical devices are configured to support a variety of wireless data communication protocols for efficient communication of data within the medical device network. In addition, the wireless medical devices may be configured to support a number of dynamically adjustable wireless data communication modes to react to current operating conditions, application-specific data content, or other criteria.
Owner:MEDTRONIC MIMIMED INC
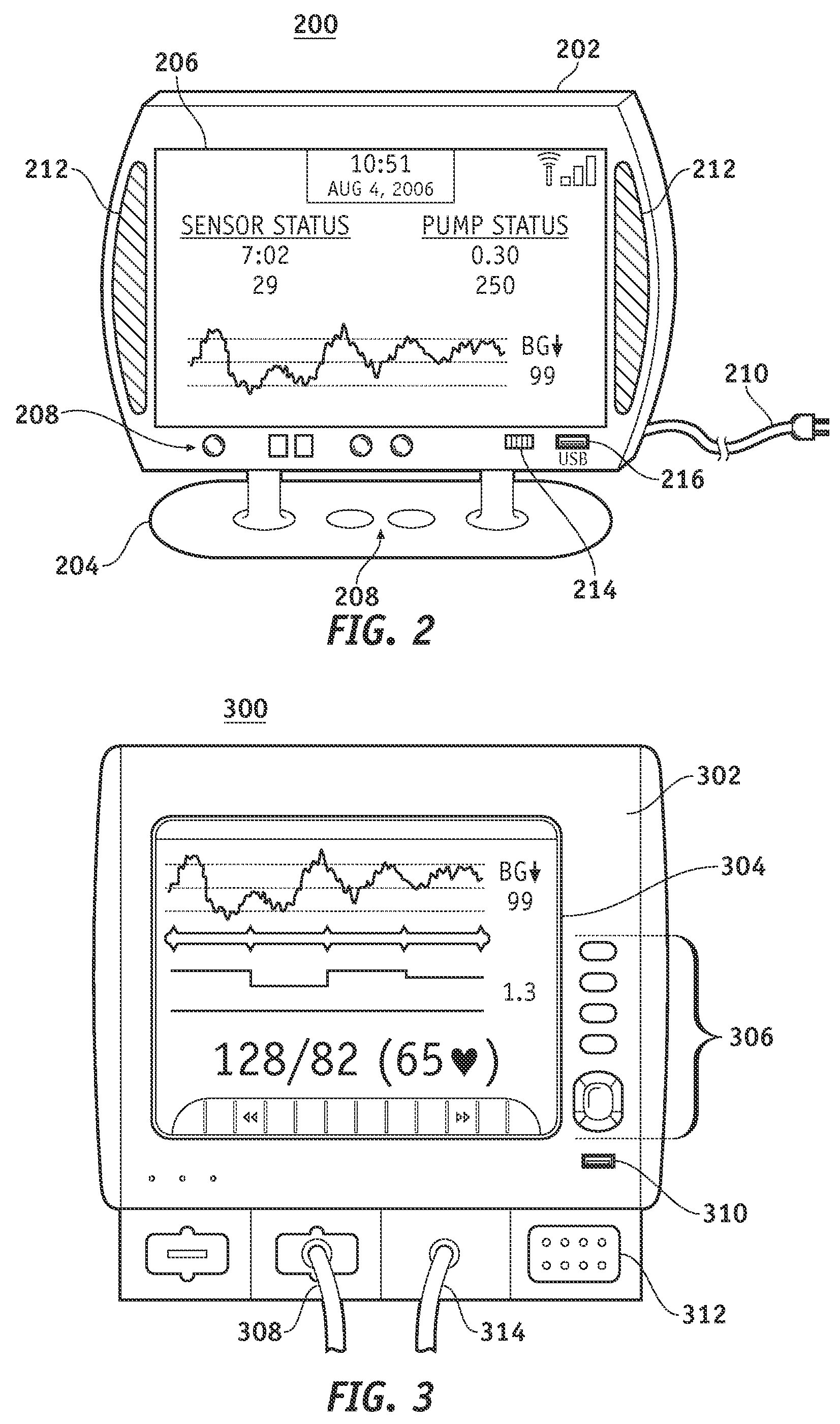
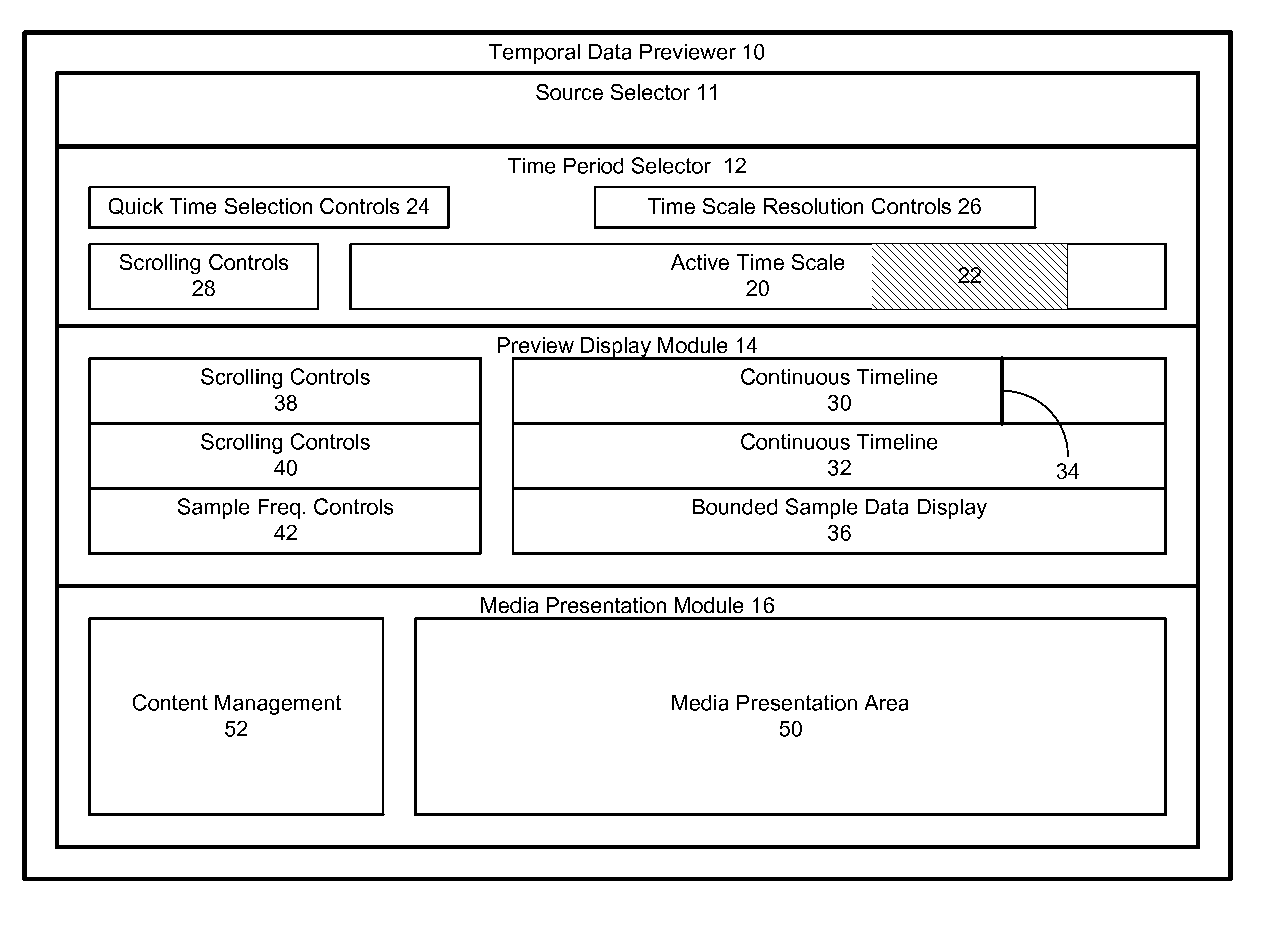
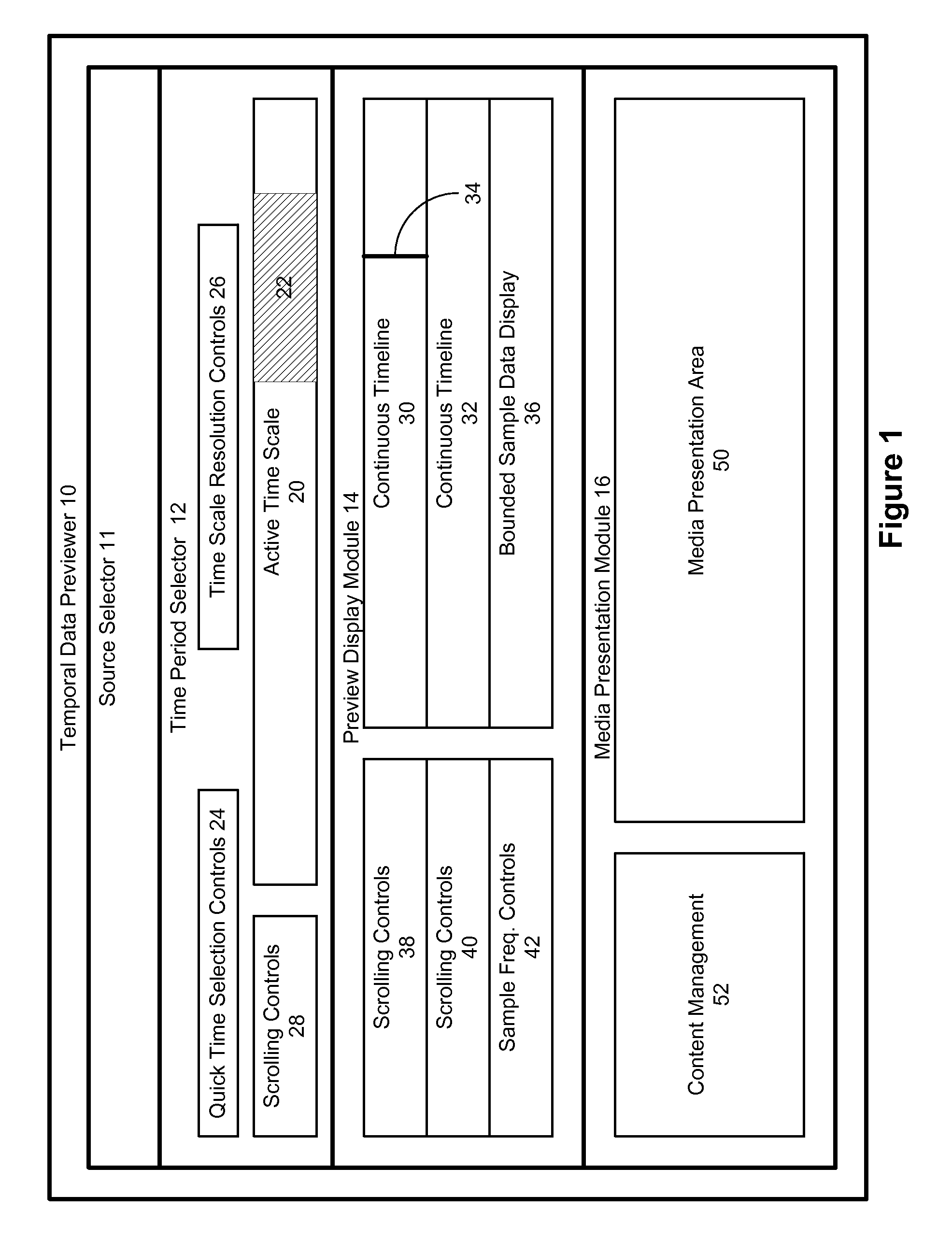
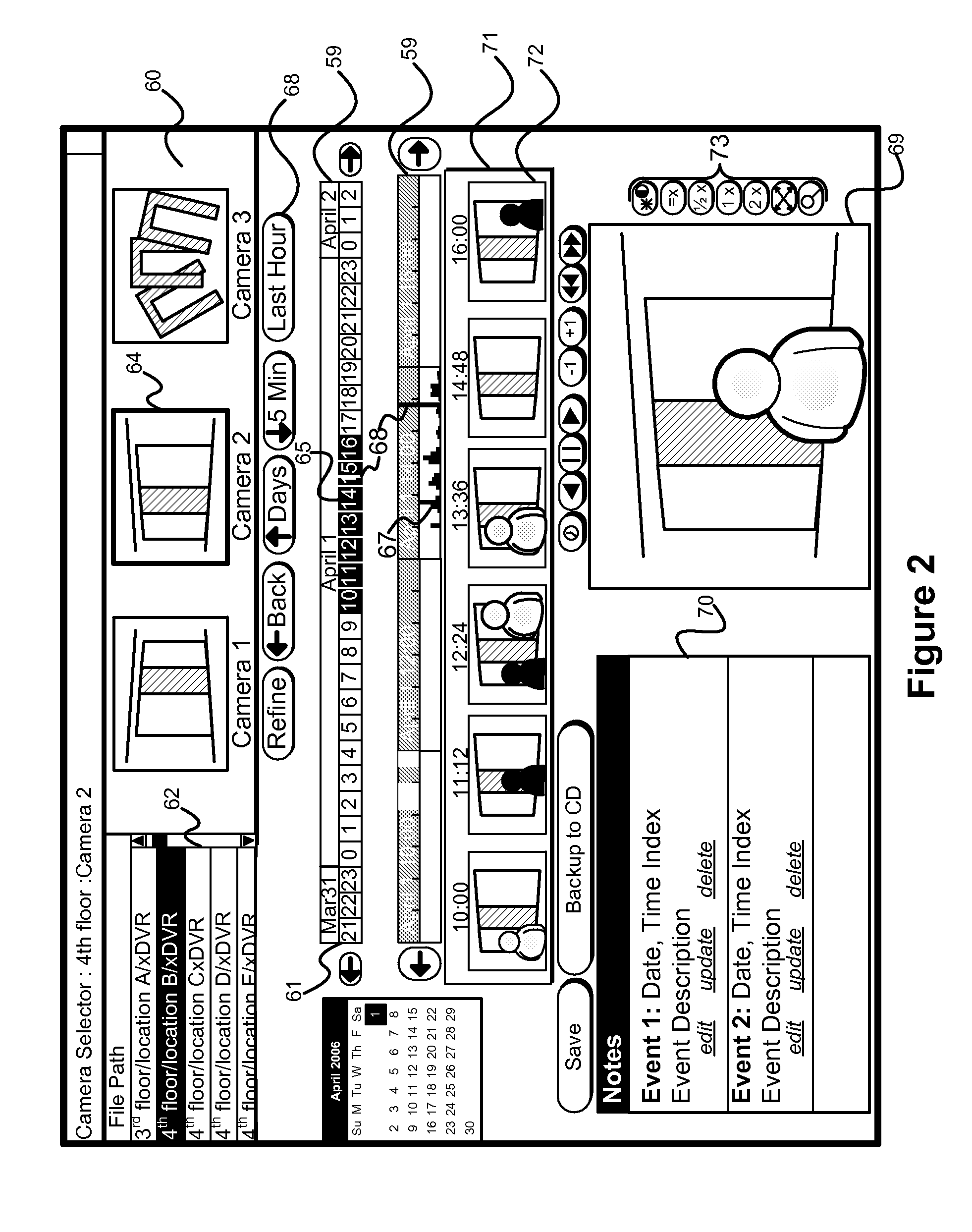
Temporal data previewing system
InactiveUS20070033632A1Rapidly find meaningful contentEasy to masterTelevision system detailsElectronic editing digitised analogue information signalsDigital videoData content
A method and apparatus forming a user interface for examining and retrieving audio / video / data content from digital video recorders. This includes an improved time period selection mechanism, a rich array of temporal data presentations, such as timelines, lists, and thumbnail images, and a unified method of displaying content from either a direct stream or downloaded files. Summary information is provided relating to undownloaded content based on a selected time period.
Owner:MARCH NETWORKS
Portable media device with list management tools
InactiveUS20080155470A1None of methods is secureMetadata multimedia retrievalMultiple digital computer combinationsVideo playerManagement tool
A portable wireless communications subscriber audio and / or video player apparatus and system and method for selecting, requesting, downloading, and playing audio and / or video data content files from an Internet-based database server. The wireless link is preferably implemented in accordance with the WiFi protocol, which allows connectivity to the Internet by being in proximity with a local base station or WiFi hotspot (i.e., publicly available local wireless access hub connected to the Internet). The portable wireless communications subscriber audio and / or video player apparatus and system preferably include a security means for monitoring and blocking unauthorized use of the player apparatus and system. The player apparatus further preferably has the capability to communicate with other neighboring player apparatus for the purpose of exchanging content data files, playlists and personal messages.
Owner:SANDISK TECH LLC
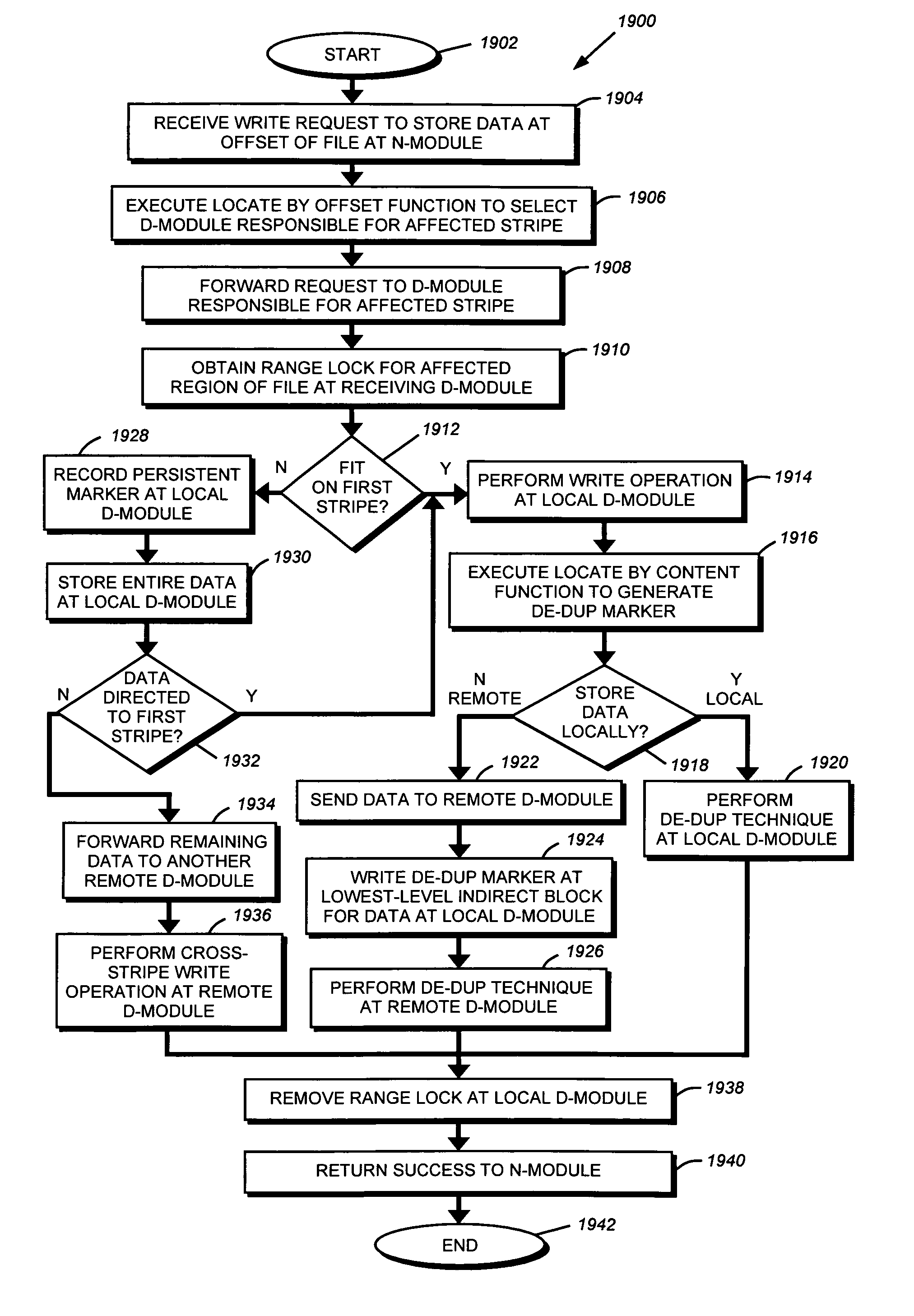
System and method for enabling de-duplication in a storage system architecture
ActiveUS7747584B1Effectively ensureImprove efficiencyDigital data information retrievalDigital data processing detailsData contentData store
A system and method enables de-duplication in a storage system architecture comprising one or more volumes distributed across a plurality of nodes interconnected as a cluster. De-duplication is enabled through the use of file offset indexing in combination with data content redirection. File offset indexing is illustratively embodied as a Locate by offset function, while data content redirection is embodied as a novel Locate by content function. In response to input of, inter alia, a data container (file) offset, the Locate by offset function returns a data container (file) index that is used to determine a storage server that is responsible for a particular region of the file. The Locate by content function is then invoked to determine the storage server that actually stores the requested data on disk. Notably, the content function ensures that data is stored on a volume of a storage server based on the content of that data rather than based on its offset within a file. This aspect of the invention ensures that all blocks having identical data content are served by the same storage server so that it may implement de-duplication to conserve storage space on disk and increase cache efficiency of memory.
Owner:NETWORK APPLIANCE INC
Method and apparatus for automatically updating website content
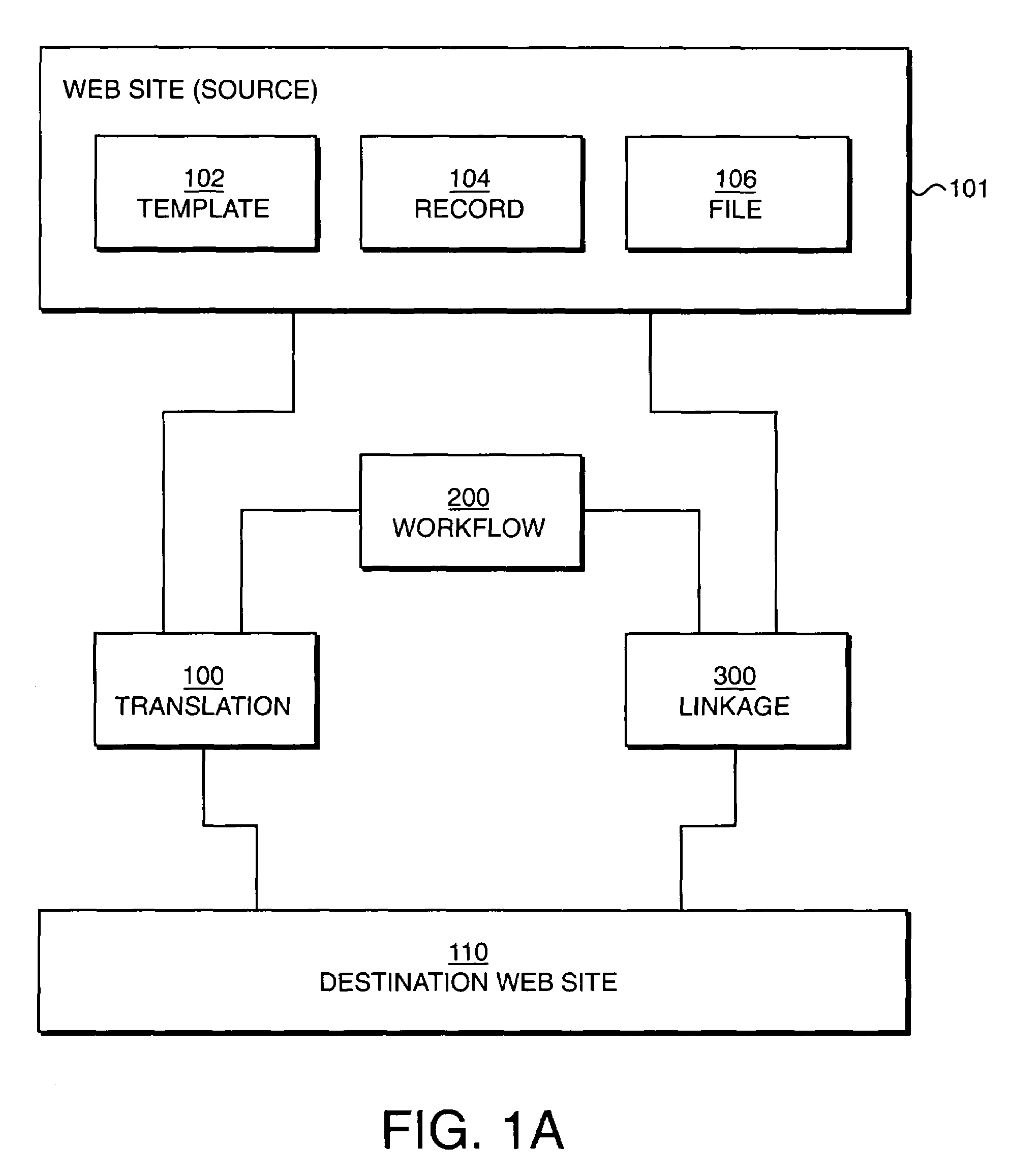
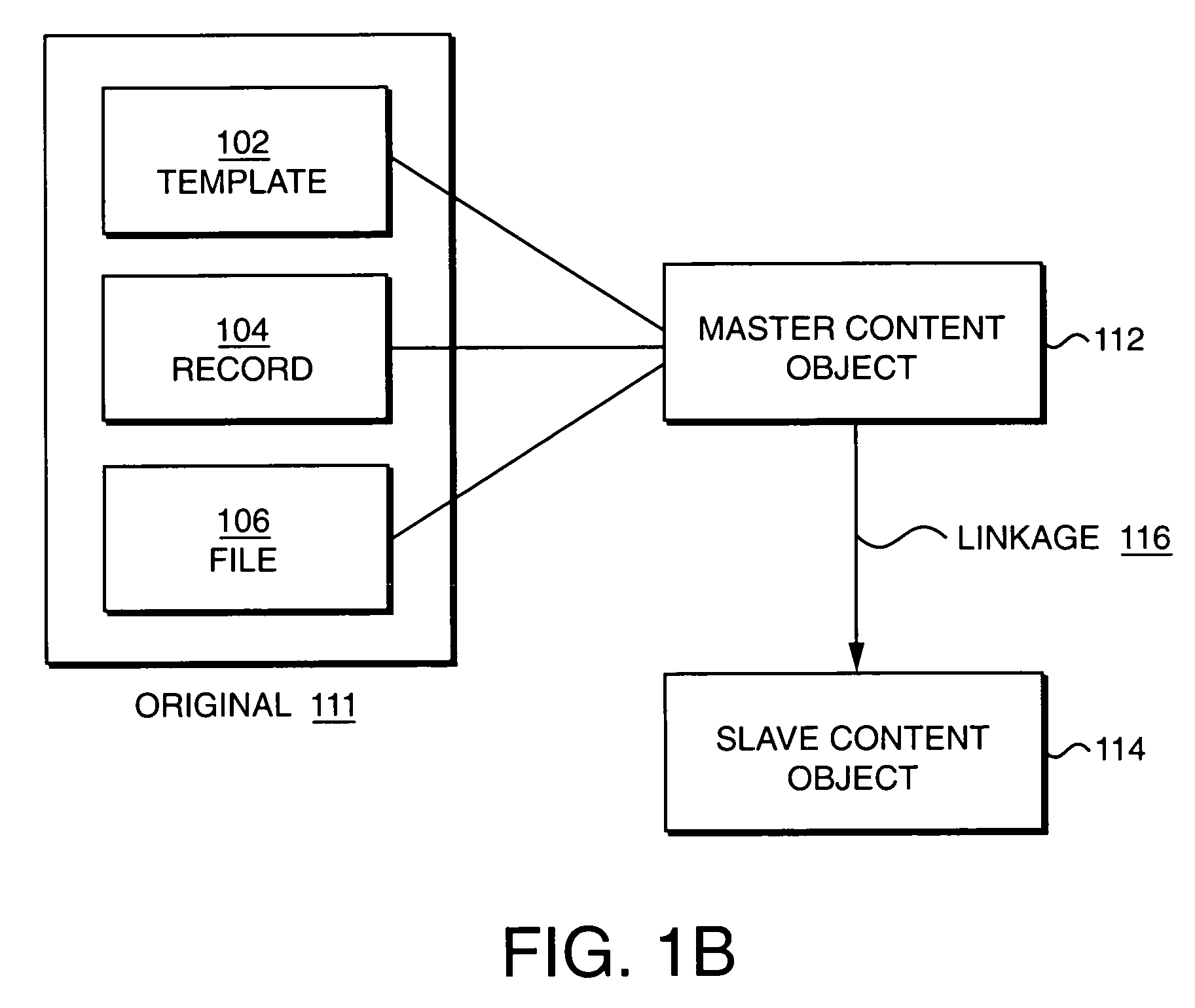
InactiveUS7383320B1Multiple digital computer combinationsWebsite content managementWeb siteData content
A method of updating one or more target website data content items comprises providing one or more links, each of which associates one or more target content items with one or more original content items. The method further includes storing the links in a data storage device, and accessing the links in the storage device, and updating the target data content items according to the links. The method may update the target data content items at predetermined intervals, or on demand. Updating the target data content may further include initiating workflow to update the target data content.
Owner:SDL INK +1
Systems and methods for enhanced data delivery based on real time analysis of network communications quality and traffic
ActiveUS8019886B2Network traffic/resource managementInformation formatDigital dataReal time analysis
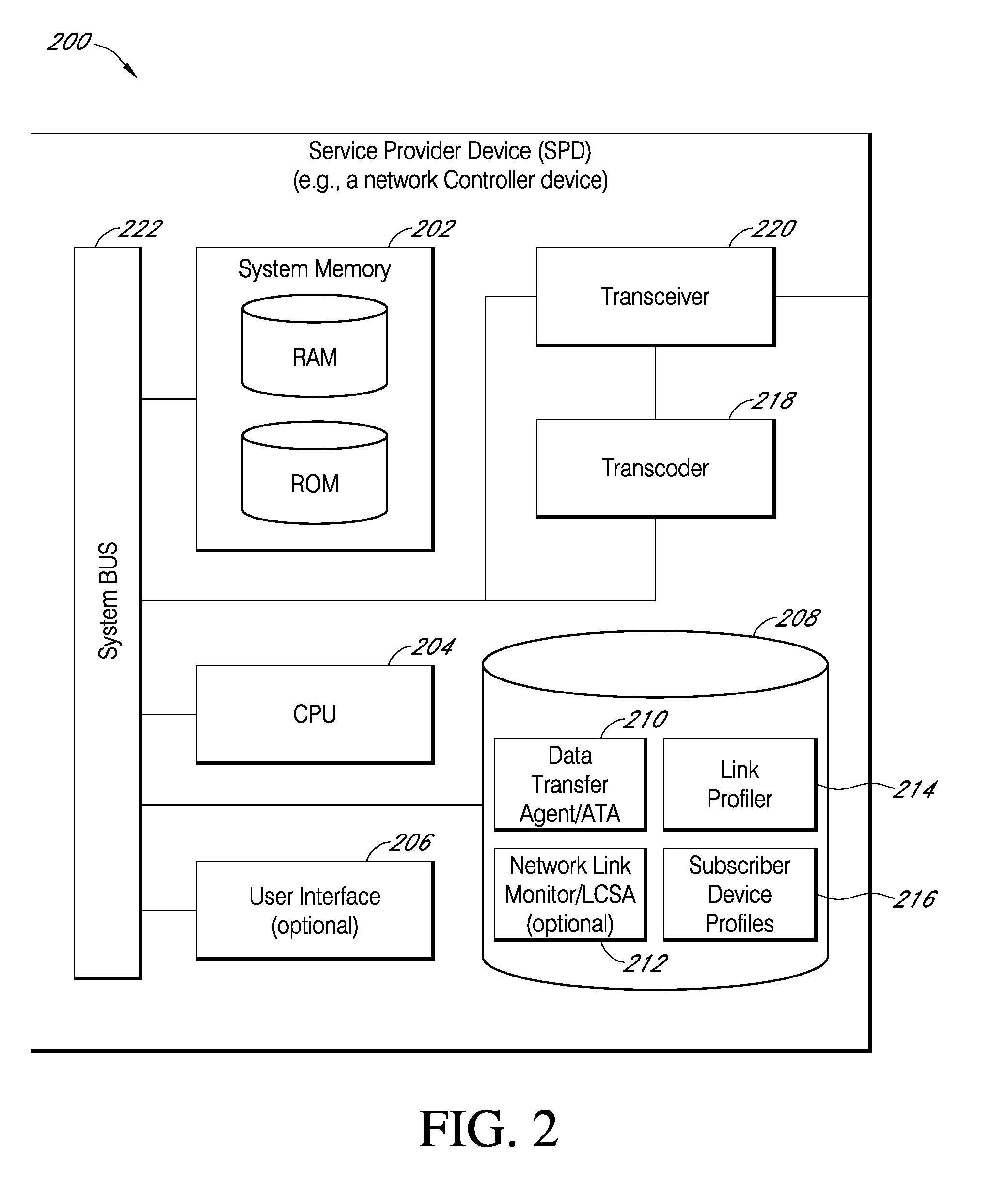
A system for improving digital data content delivery based on real time analysis of one or more network communications states. The networked computing system may include a network service provider device, a user equipment, a network link monitor, a data transfer agent, and a data communications network facilitating data communications amongst all devices of the networked computing system. The networked computing system may be configured to: detect at least one network communications metric, determine a network communications state associated with diminished communications throughput based on the detected at least one network communications metric, and then select an optimal rate for a data content transfer based on the determined network communications state. The network communications state may relate to either a state of network congestion or a state of reduced regional radio communications quality.
Owner:OPANGA NETWORKS
Method and system for providing multimedia information on demand over wide area networks
ActiveUS20010049740A1Multiple digital computer combinationsSelective content distributionClient-sideData content
Systems and methods for delivering streaming data content to a client device over a data communication network in response to a request for the data content from the client device. The client request is received by a server or a controller device that is typically located on a network switch device. If received by a server, the server sends a request to the controller device to control the transfer of the requested data to the client. The controller device includes the processing capability required for retrieving the streaming data and delivering the streaming data directly to the client device without involving the server system. In some cases, the controller device mirrors the data request to another controller device to handle the data processing and delivery functions. In other cases, the controller device coordinates the delivery of the requested data using one or more other similar controller devices in a pipelined fashion.
Owner:EMC IP HLDG CO LLC
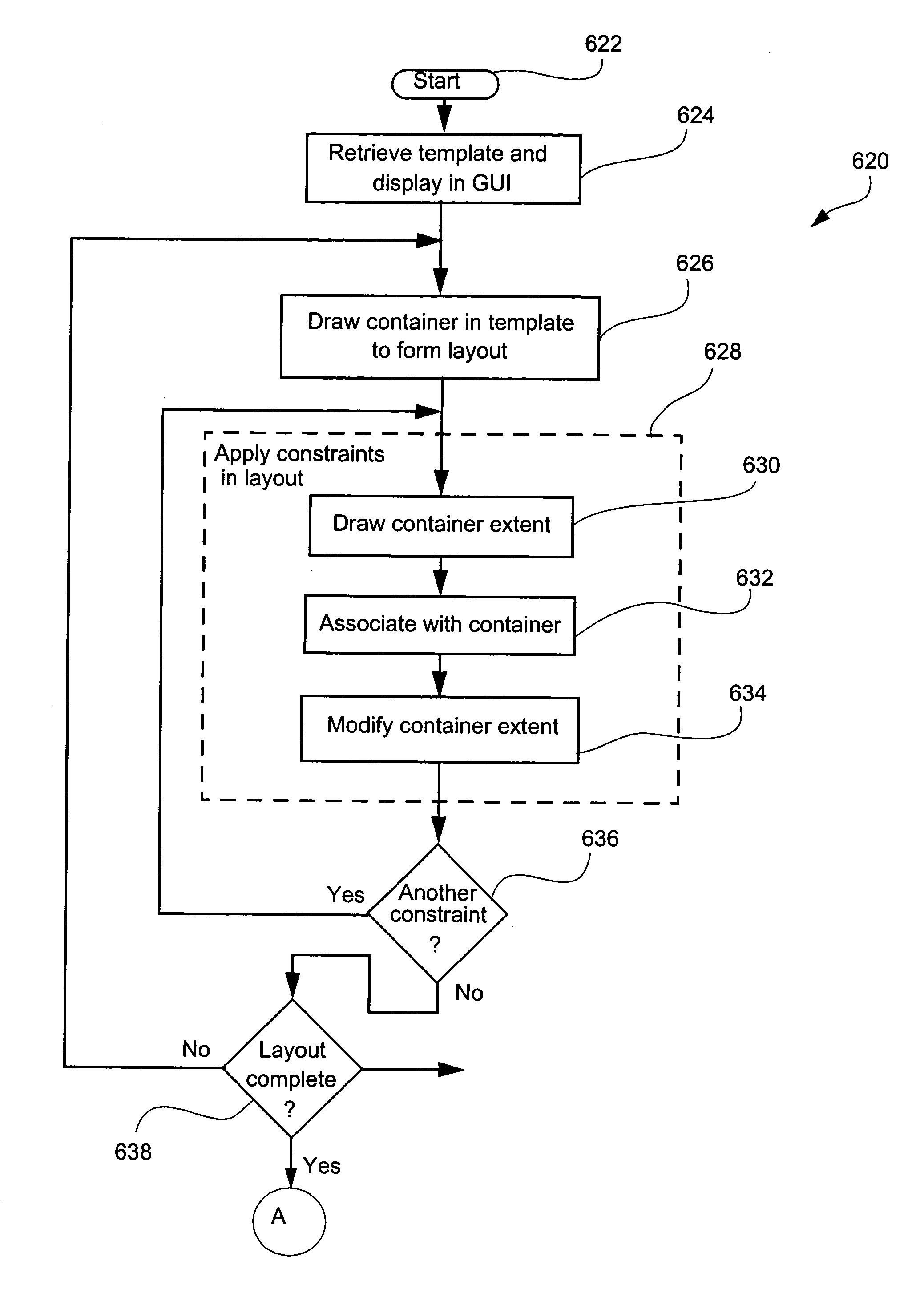
Selective preview and proofing of documents or layouts containing variable data
InactiveUS20050094205A1Visual presentation using printersNatural language data processingPaper documentData content
Methods and apparatus for proofing (644) a variable document intended for printing are disclosed in which a GUI (2000) is configured to allow user manipulation of layout rules associated with content containers within a template for variable document generation. Selective proofing (2100) involves proofing a plurality of variable data documents each formed from a common layout in which variable data content is placed into containers having locations and sizes within the layout and defined by layout rules. Measures of variation (2103, 2106) and measures of deviation (2109, 2110) are calculated. The measures of deviation are processed (2112) to give a deviation value. Once completed for each document, the deviation values of the documents are compared (2114) to identify at least one group of the documents for presentation for further assessment. Live proofing includes creating a layout (2002) for a variable data document based upon a template established in the GUI. A container (2010) is set in the template to form the layout, which is then modified to thereby generate an exemplary document by placing exemplary content into the container, wherein a dimension of the container and / or a position of the container are varied based upon a property of the placed content. The exemplary document is displayed in the layout via the GUI to enable visual proofing by the user.
Owner:CANON KK
Communication node and communication method
InactiveUS20120155464A1Preventing unnecessary repeated transmissionUnnecessary transmissionData switching by path configurationData contentReal-time computing
Owner:ELECTRONICS & TELECOMM RES INST
Systems and methods for detecting and disabling malicious script code
InactiveUS20070113282A1Improve abilitiesMemory loss protectionError detection/correctionComputer graphics (images)Data content
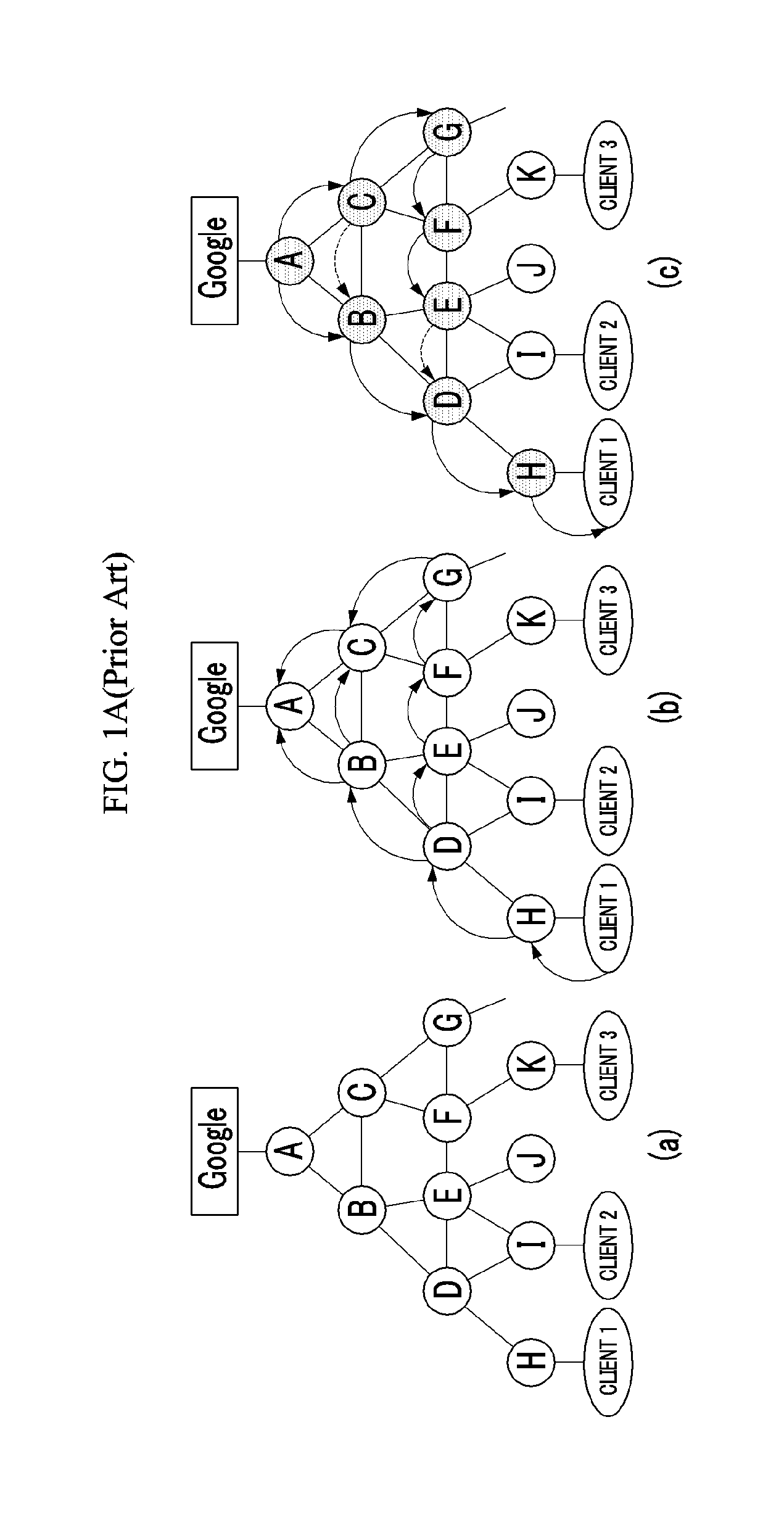
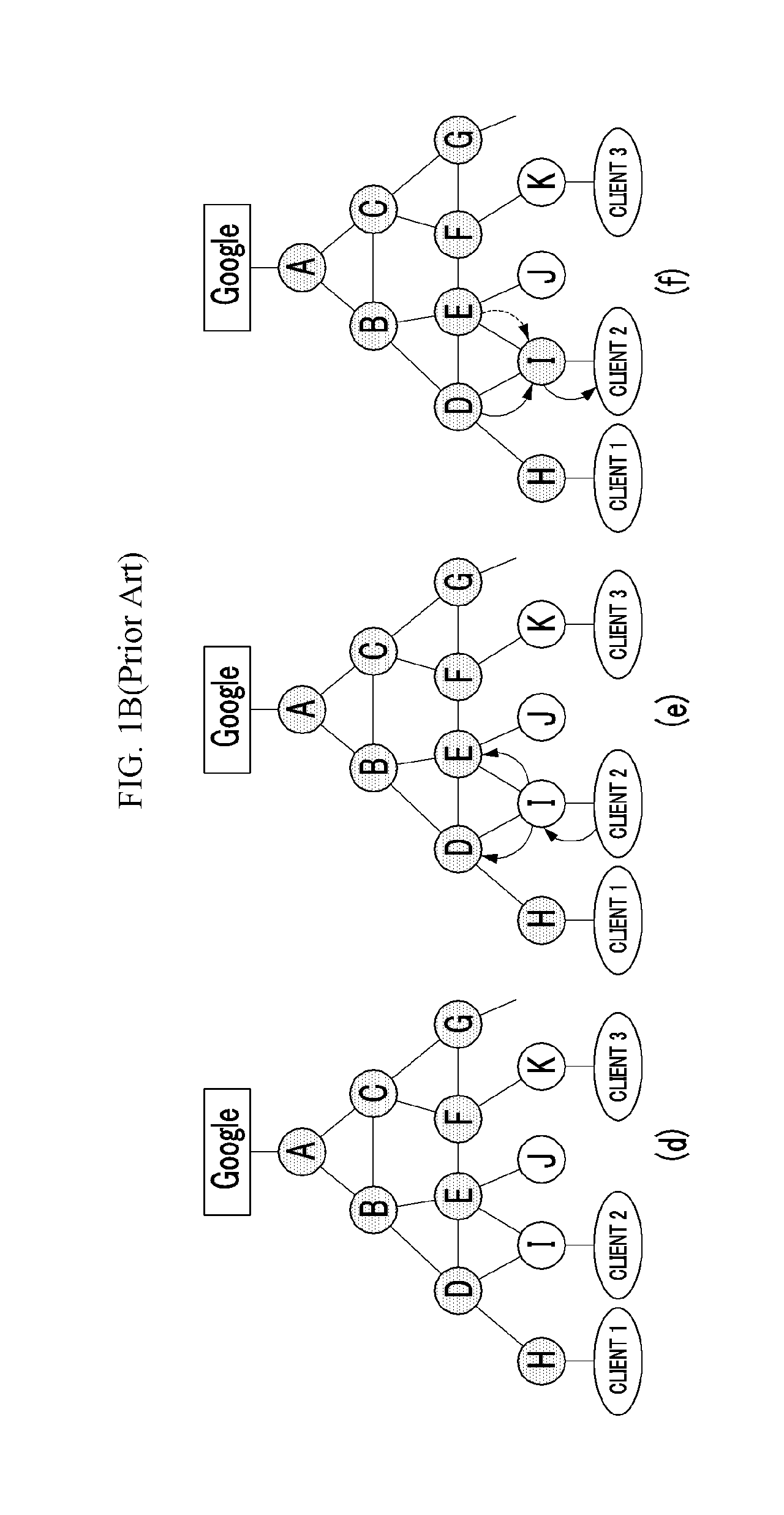
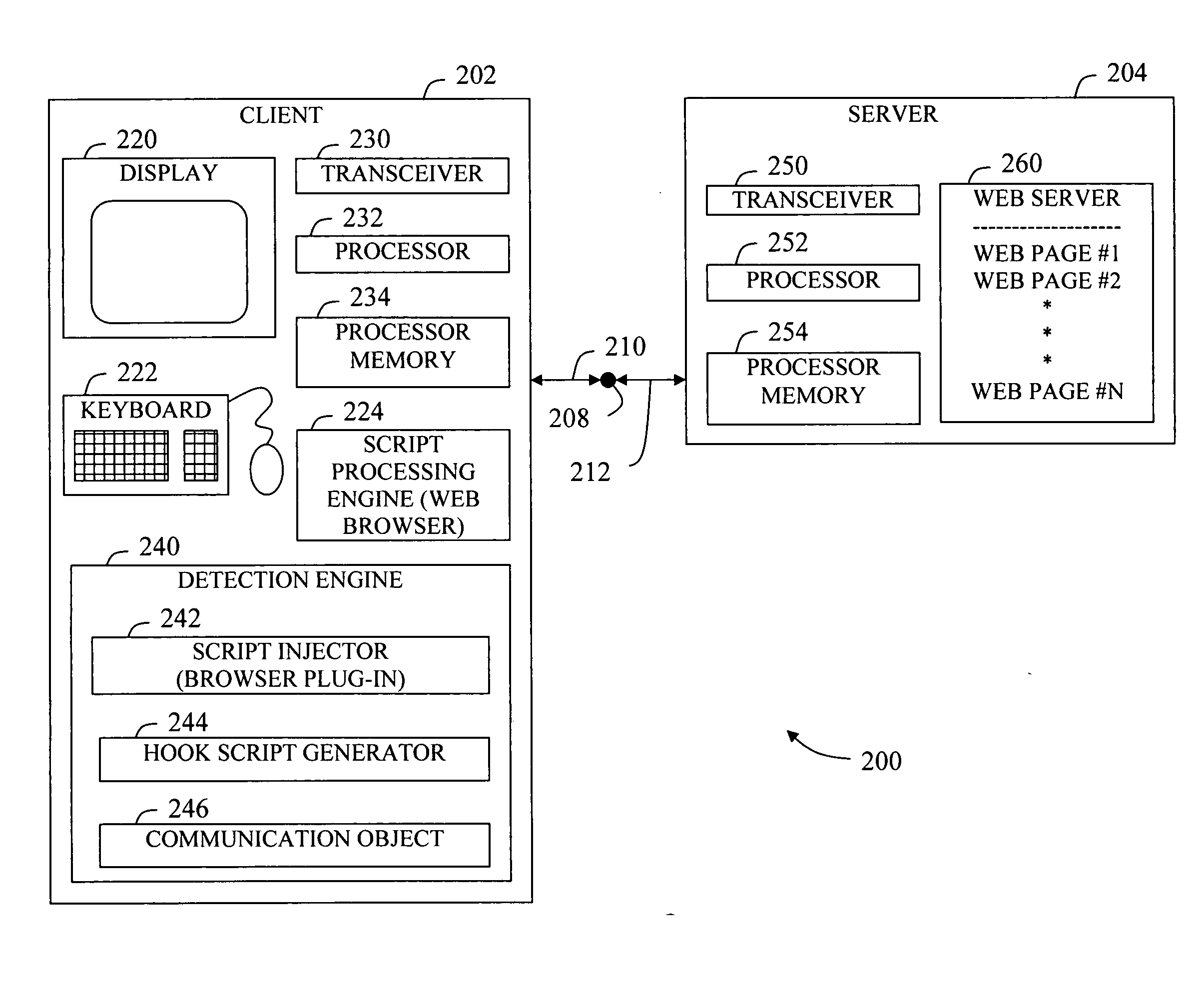
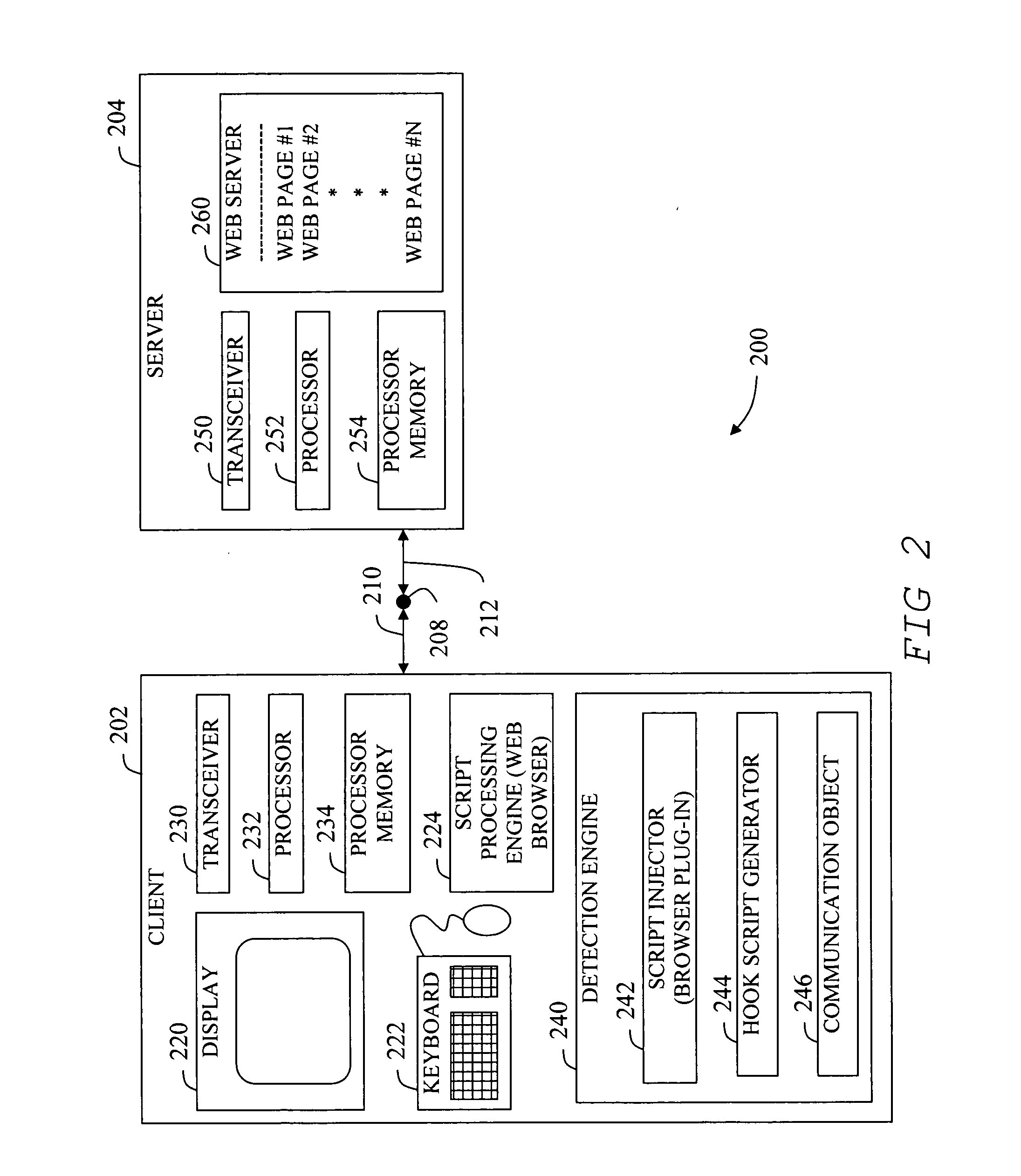
In accordance with at least one embodiment of the present invention, a device for receiving and processing data content having at least one original function call includes a hook script generator and a script processing engine. The hook script generator is configured to generate a hook script having at least one hook function. Each hook function is configured to supersede a corresponding original function. The script processing engine is configured to receive and process a combination of the hook script and the data content. The hook function corresponding to the data content original function is executed when the original function is called. The hook function provides a run-time detection and control of the data content processing.
Owner:EEYE DIGITAL SECURITY
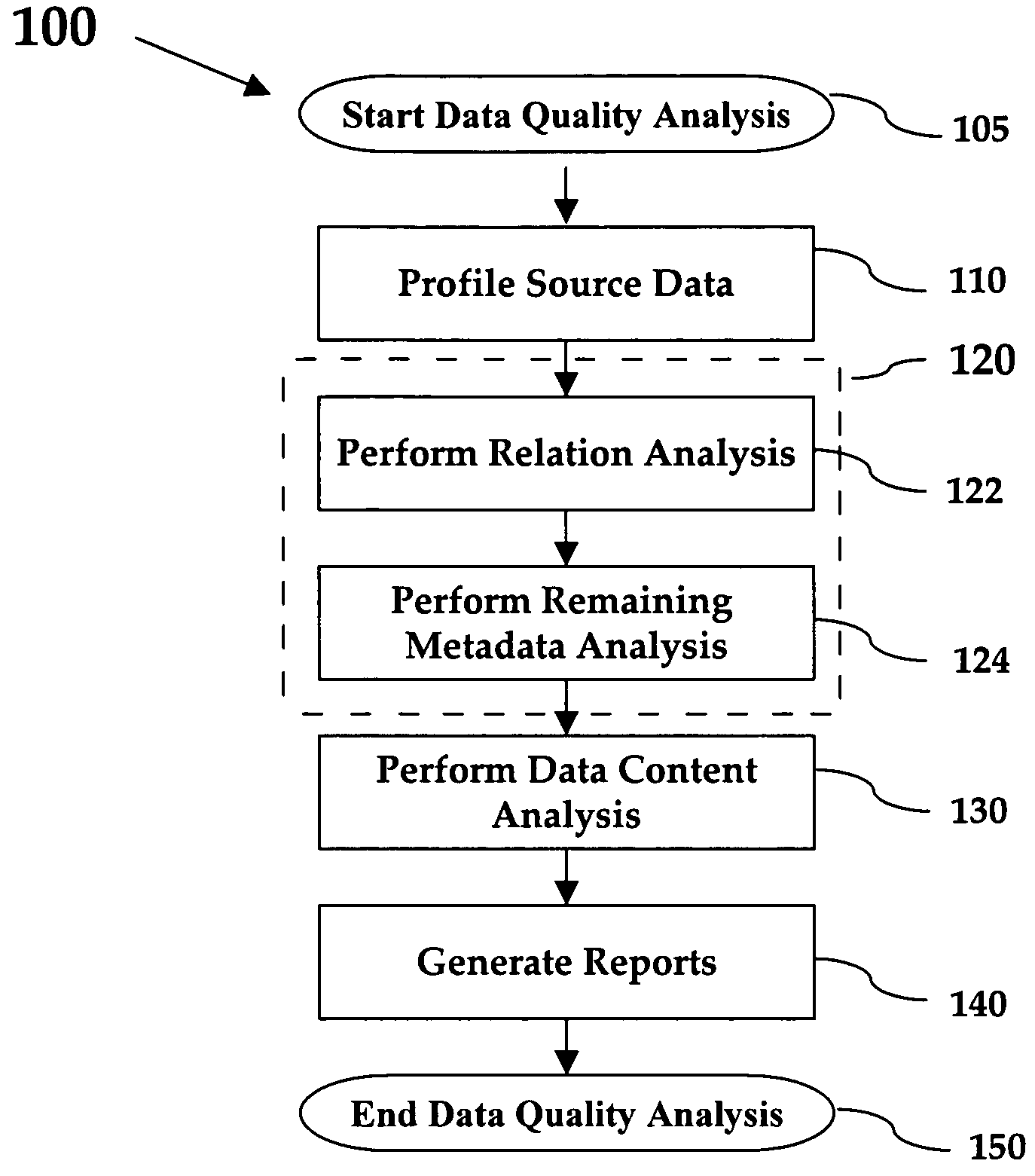
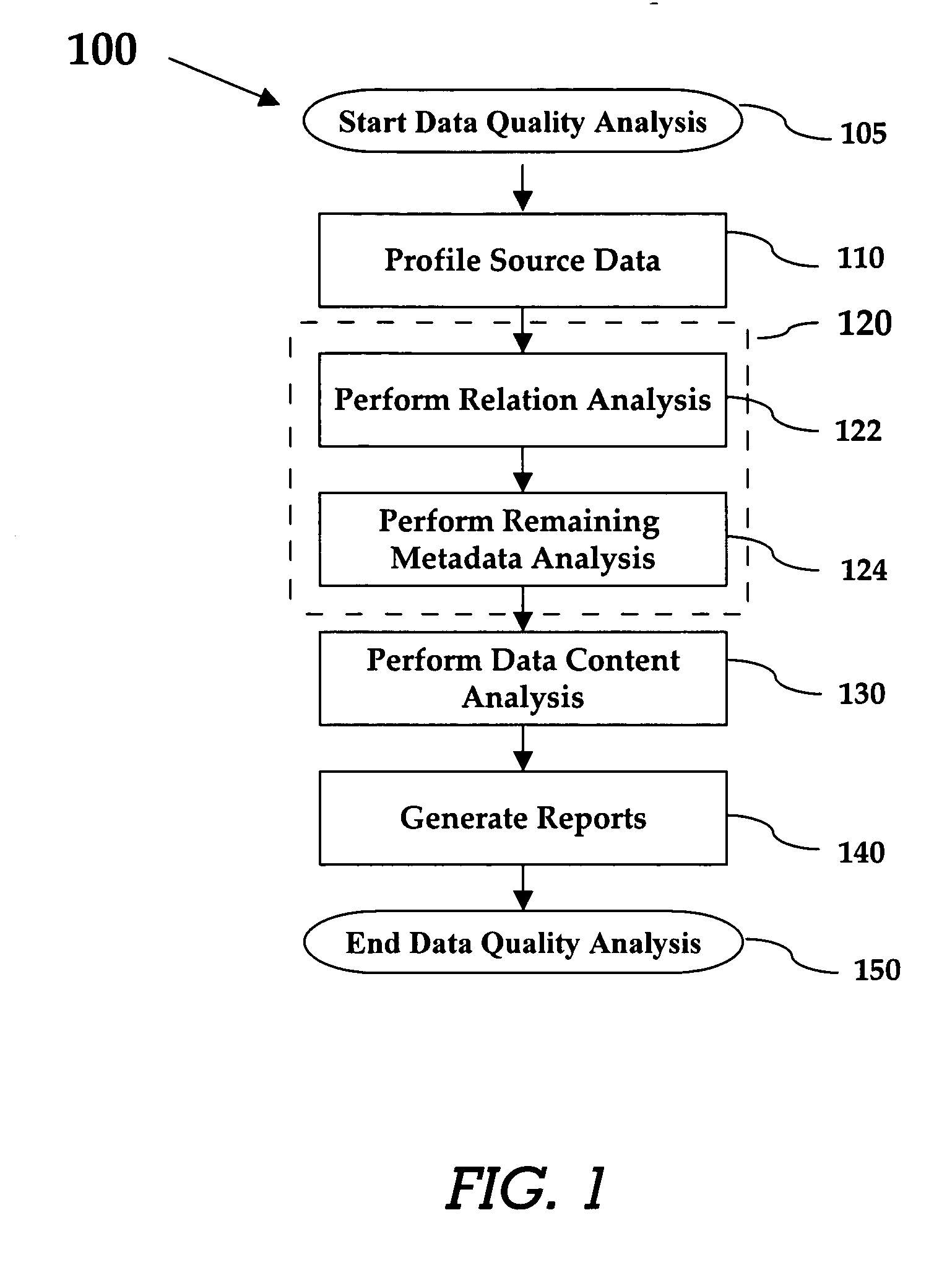
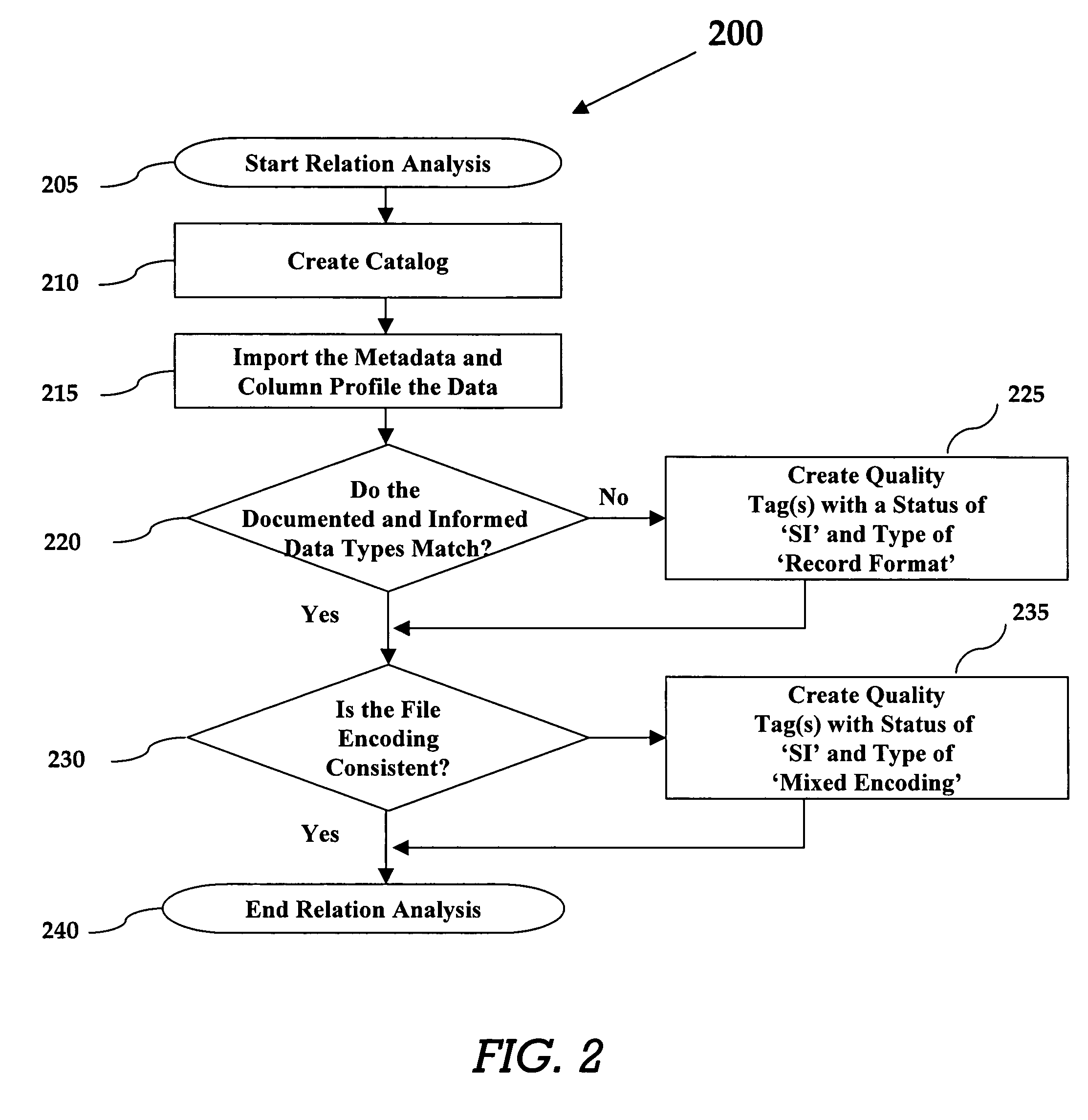
Method of conducting data quality analysis
A method for creating a data quality report for a given set of source data. The source data is profiled and then analysis is preferably performed at the relation level, metadata level, and data content level analysis. Any inconsistencies noted during analysis are noted with quality tags preferably comprising a common status and a type describing the category of the identified inconsistency. Reports are then generated that describe and summarize the information contained in the quality tags created during the analysis.
Owner:DATA INNOVATIONS
Detection of misuse or abuse of data by authorized access to database
InactiveUS20050086529A1Raise the possibilityEasy to detectDigital data processing detailsHardware monitoringConfigfsData content
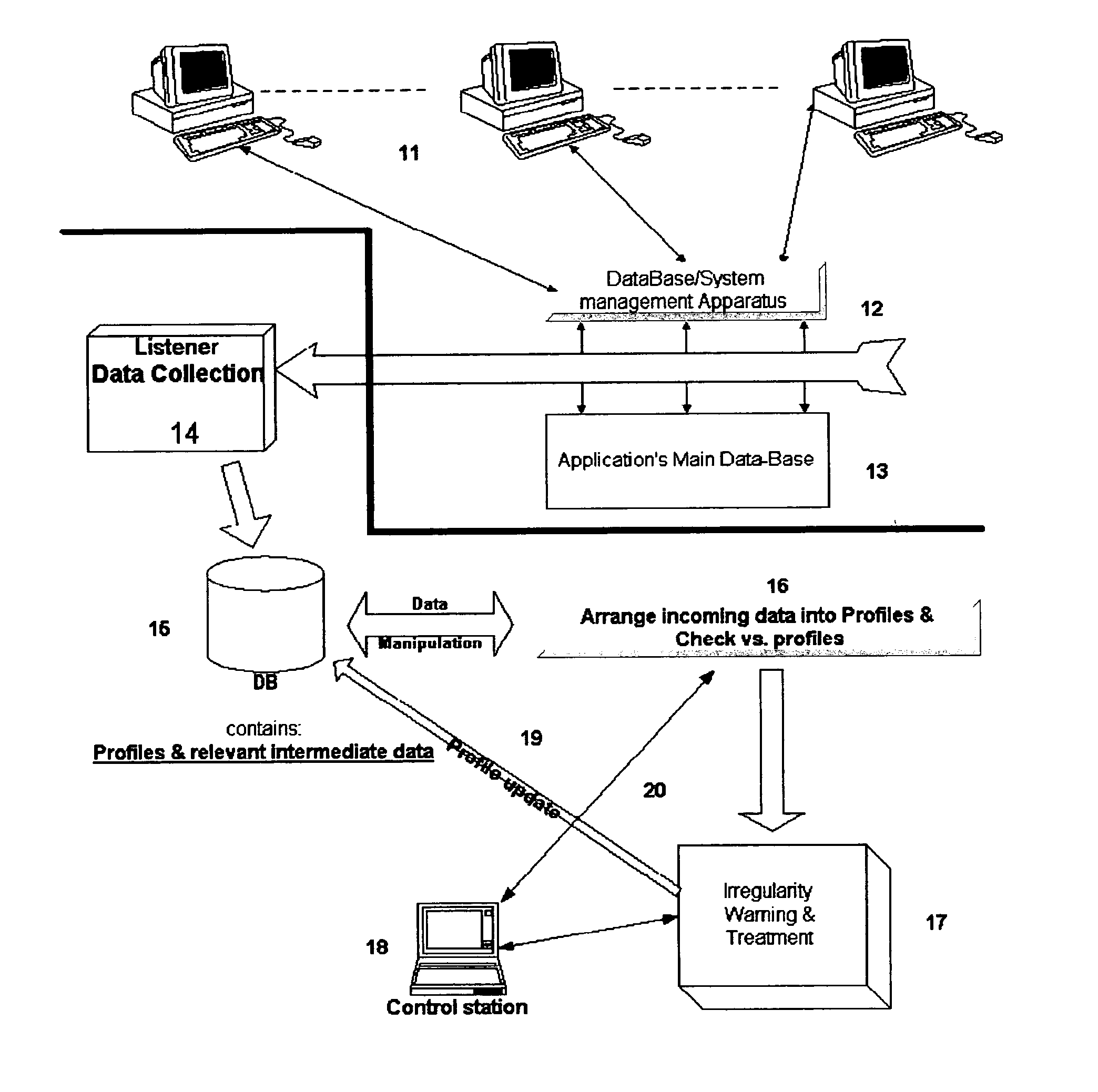
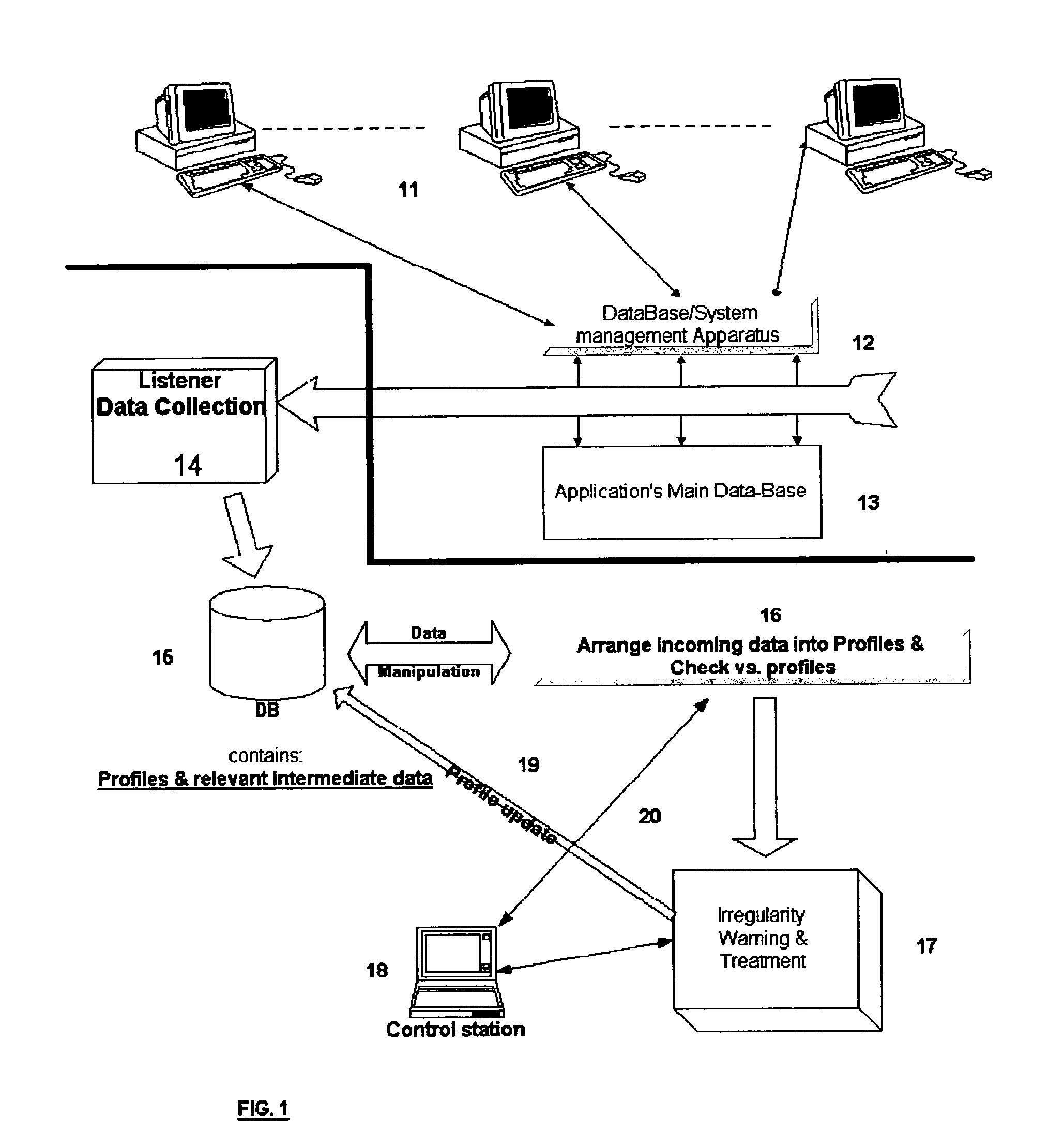
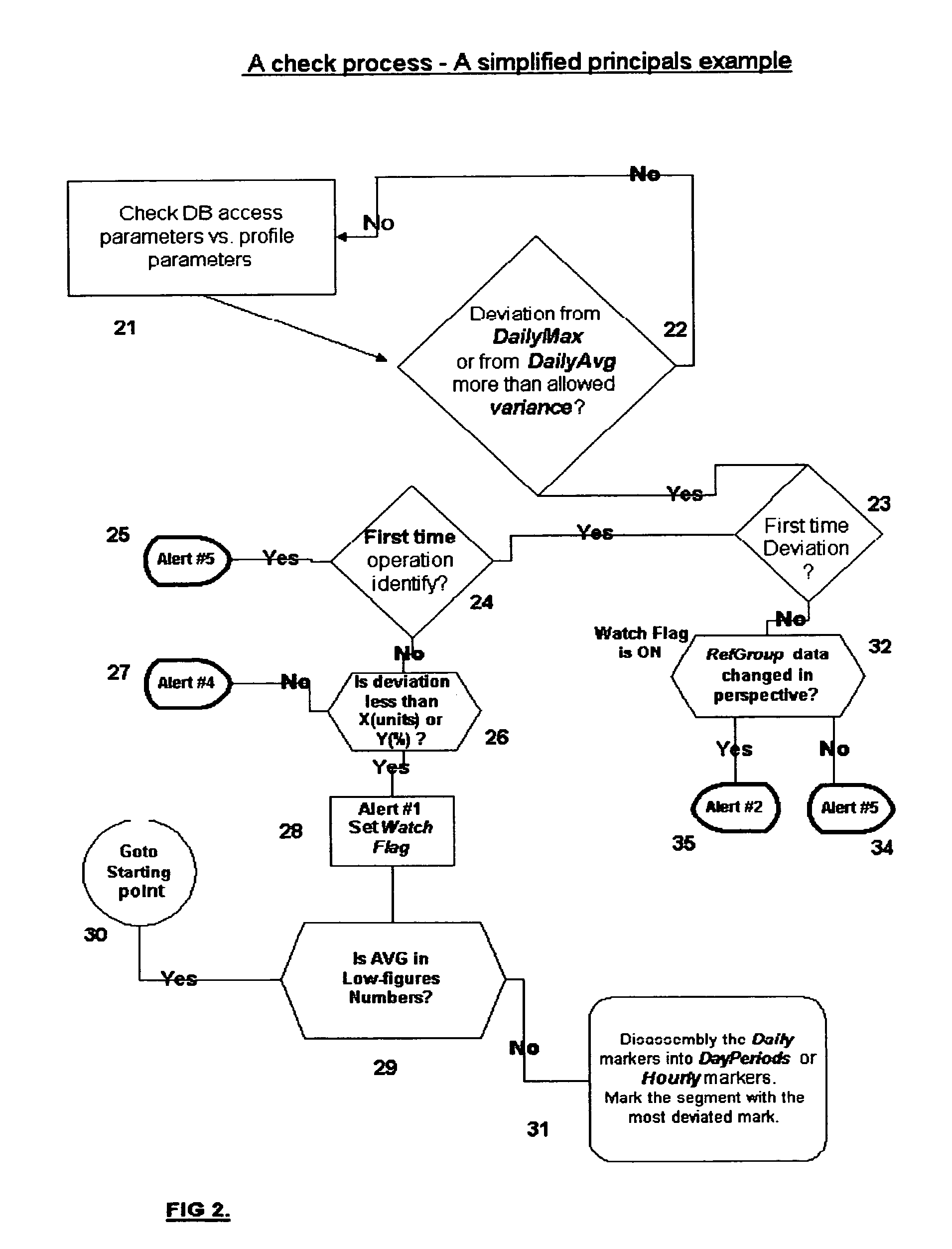
The present invention relates to a system for detecting misuse and / or abuse of data related to database done by a user with authorized access to a data system and its database. User behavior is monitored as to its nature of database access, analyzed to create, and compare to, a specific profile. No understanding for the meaning of data content is needed. Each deviation from normal pattern, stored in the profile, is checked in various parameters and ranked, reporting to a system owner.
Owner:IDOT COMP
System and method for backing up data
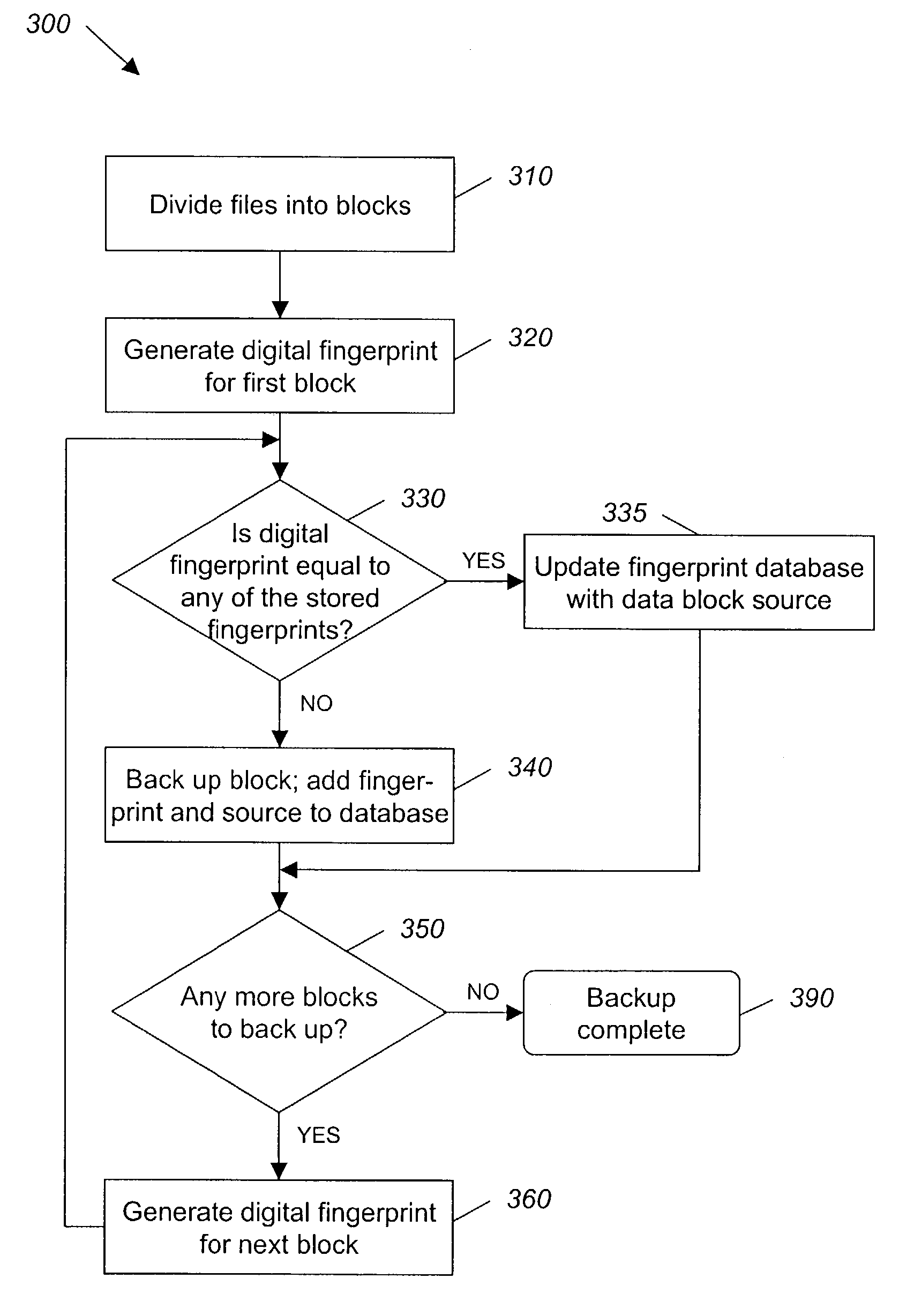
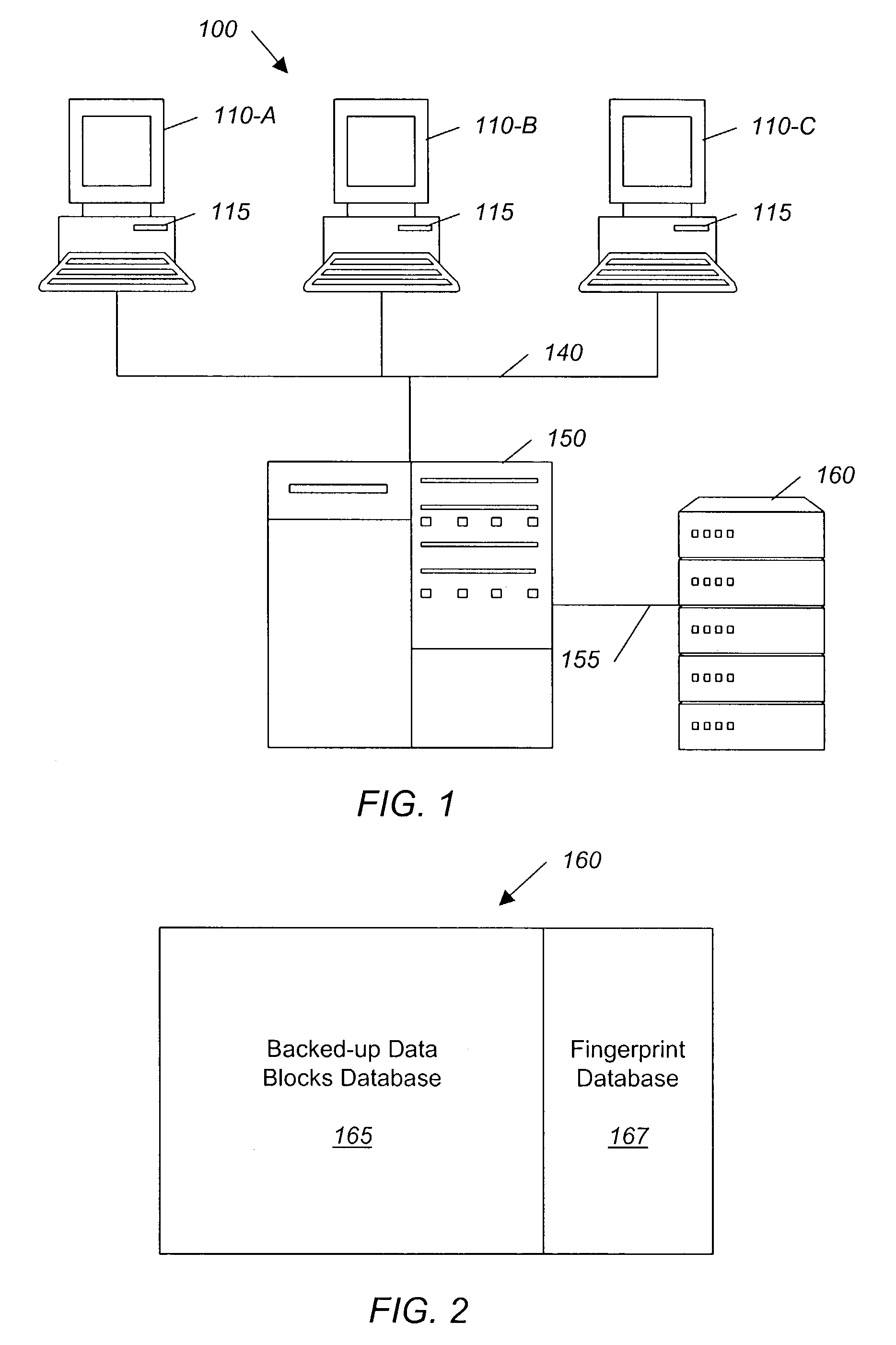
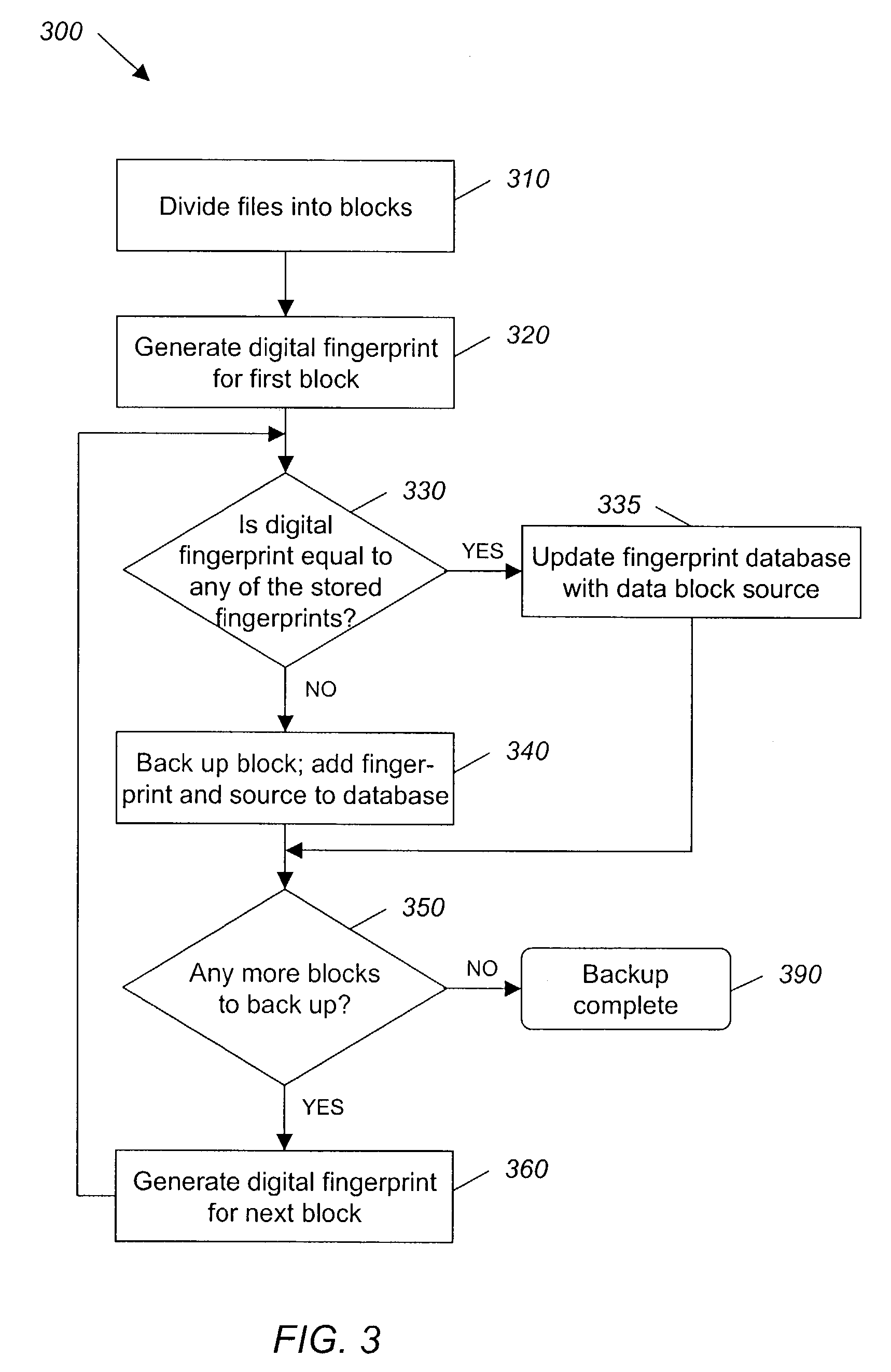
ActiveUS7055008B2Avoid inefficiencyInefficiency of the Shnelvar patent can be avoidedCamera focusing arrangementPayment architectureSoftware licenseData content
A hash-optimized backup system and method takes data blocks and generates a probabilistically unique digital fingerprint of the content of each data block using a substantially collision-free algorithm. The process compares the generated fingerprint to a database of stored fingerprints and, if the generated fingerprint matches a stored fingerprint, the data block is determined to already have been backed up, and therefore does not need to be backed up again. Only if the generated fingerprint does not match a stored fingerprint is the data block backed up, at which point the generated fingerprint is added to the database of stored fingerprints. Because the algorithm is substantially collision-free, there is no need to compare actual data content if there is a hash-value match. The process can also be used to audit software license compliance, inventory software, and detect computer-file tampering such as viruses and malware.
Owner:FALCONSTOR
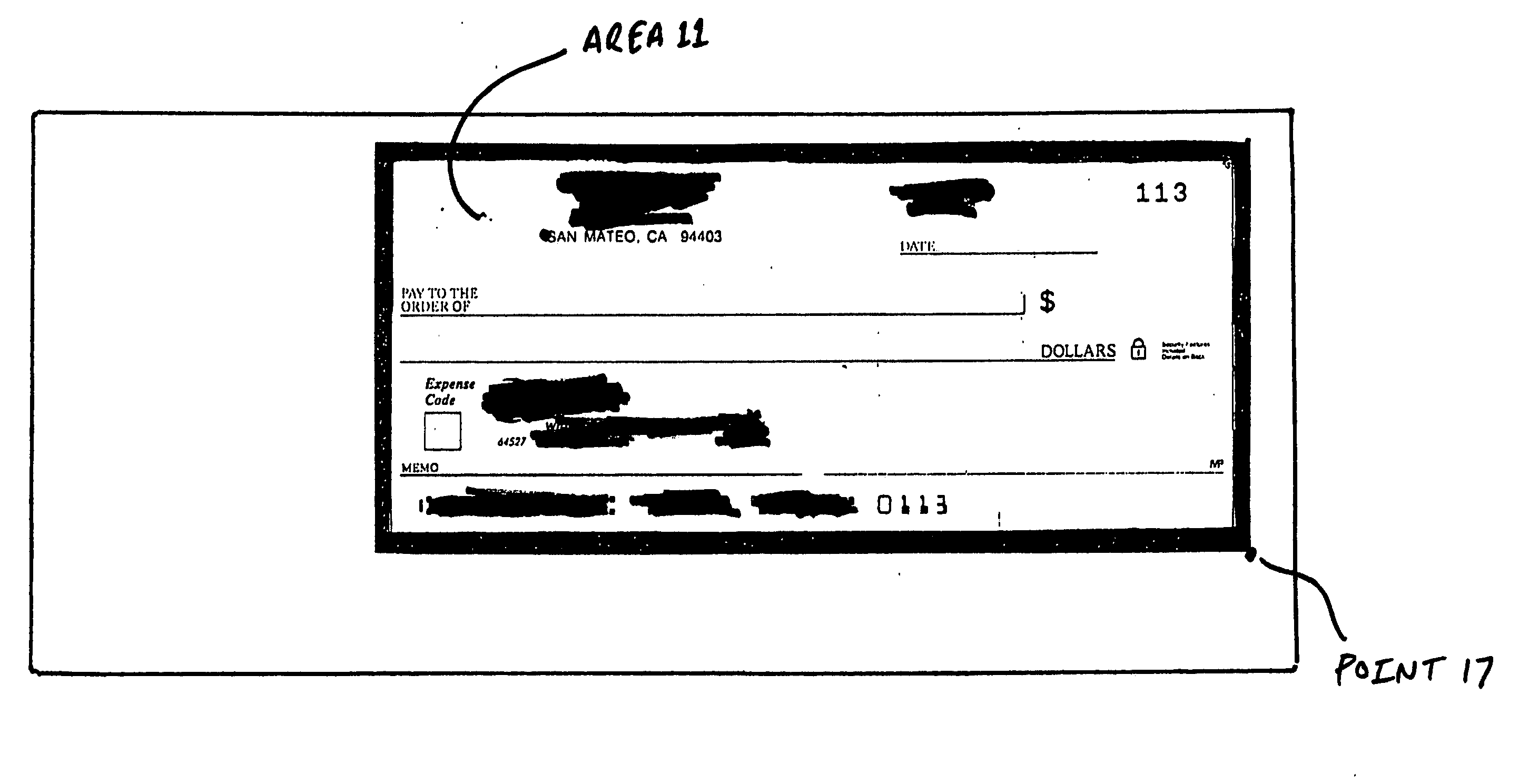
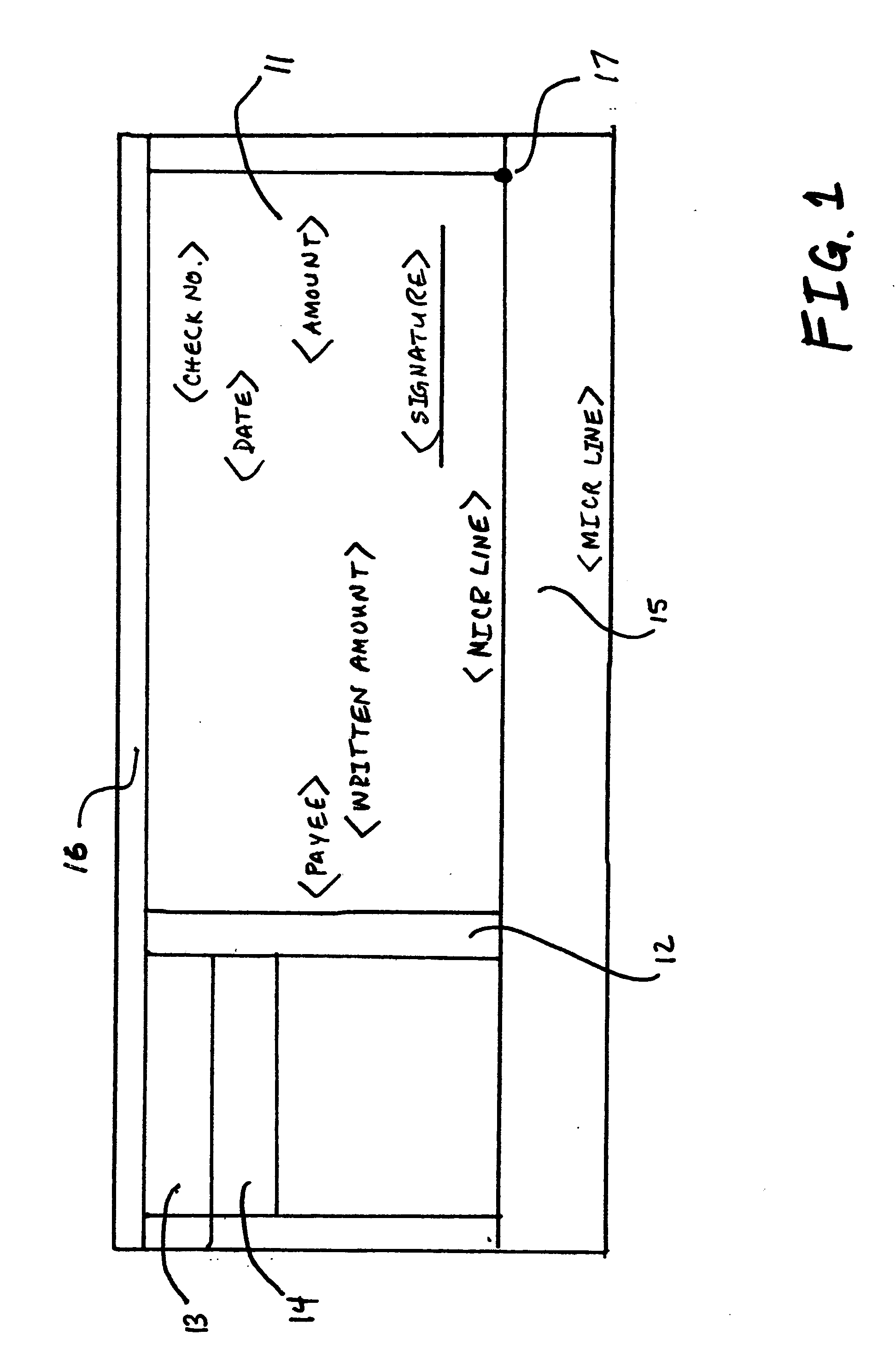
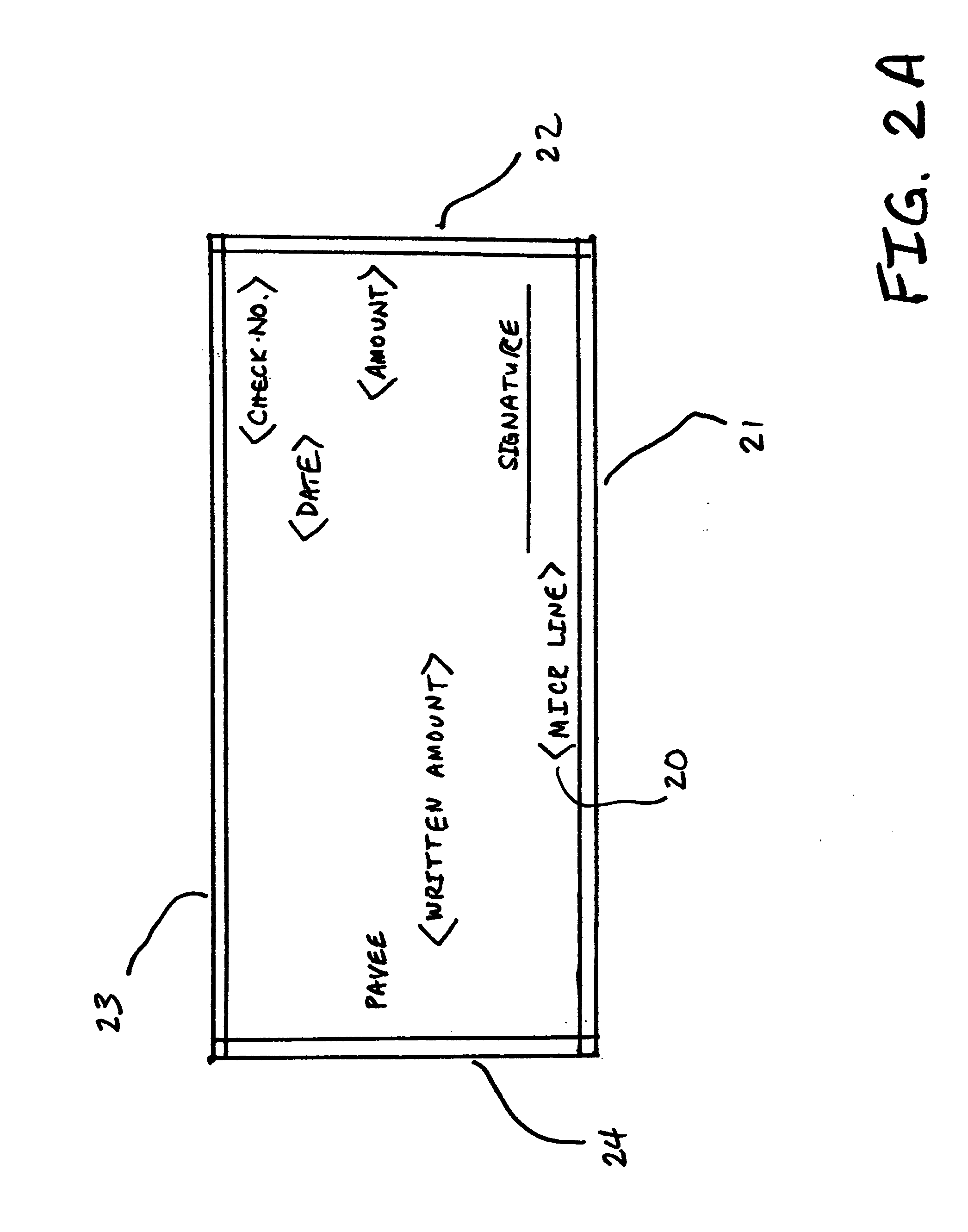
Bank check and method for positioning and interpreting a digital check within a defined region
InactiveUS20060045321A1Improve legibilityImprove uniformityCharacter and pattern recognitionChequePaper document
This invention adds new markings to an original check face prior to tender and processing of the check. These markings, when digitally scanned from the original, are readily interpreted and preserved. During the process of truncating the original with image replacement documents (IRDs) that are the legal equivalent, the new markings solve two major problems when the IRDs are formally introduced into the clearinghouse channel. First, the clipped image of the original check can be properly aligned within a designated region within the IRD based on the uniform markings. Second, data content aligned in reference to the uniform markings preserved in the IRD process can be properly recognized and read as if the software was scanning the original physical document.
Owner:CHEN YU ENTERPRISE
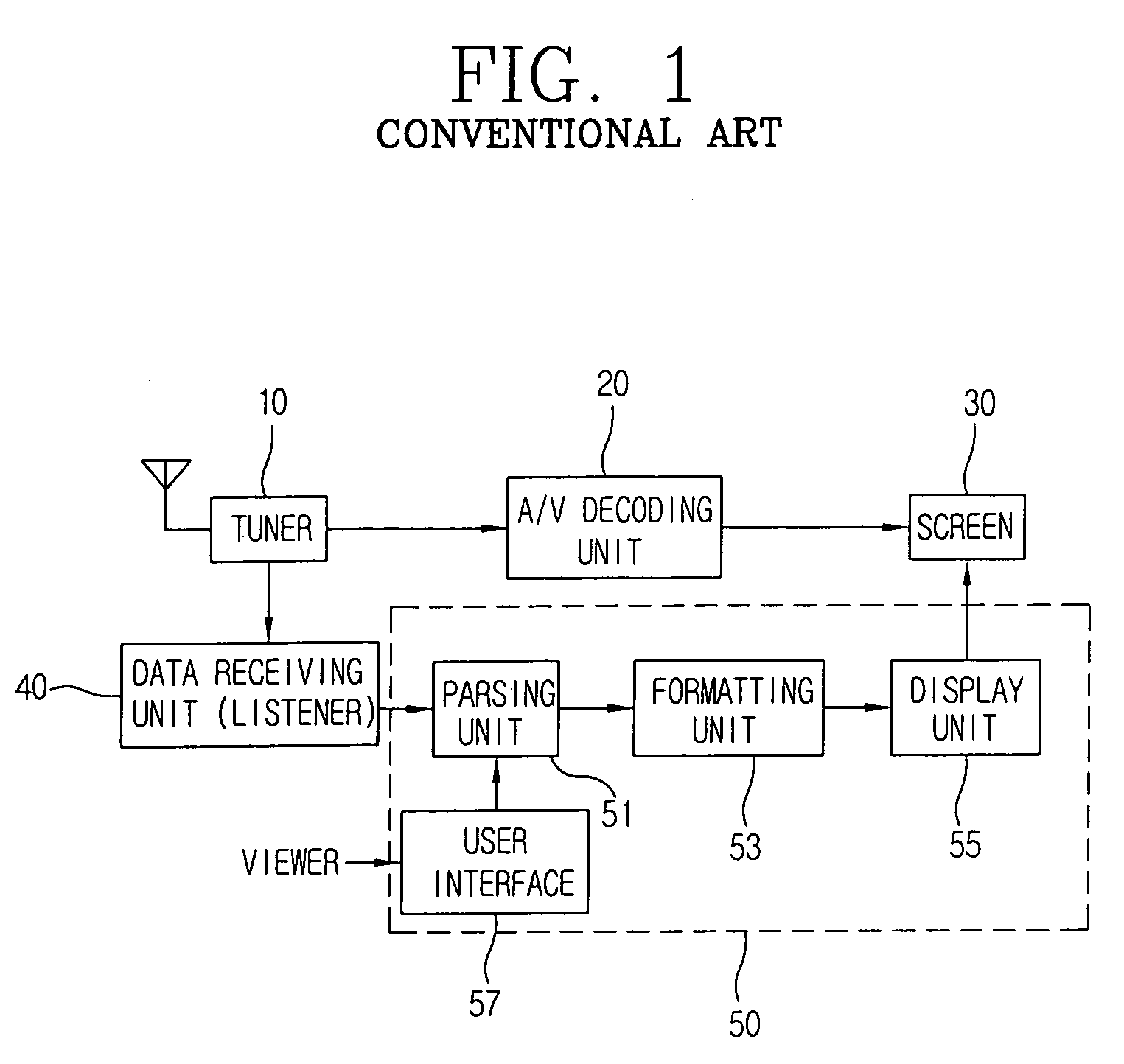
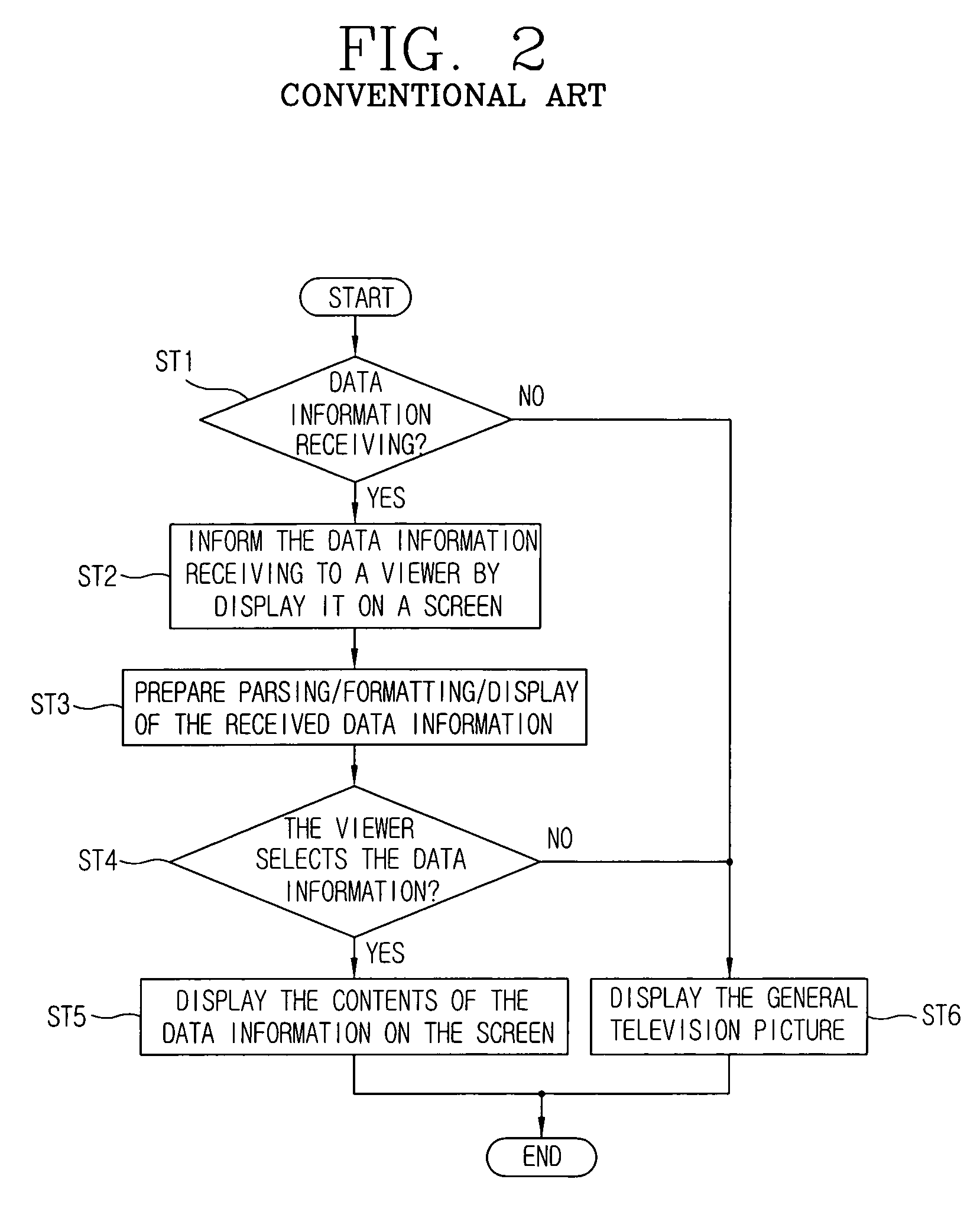
Data information display method of data broadcasting receiver and apparatus thereof
InactiveUS7100117B1Simultaneous/sequential multiple television signal transmissionSelective content distributionDigital dataAnalysis data
The present invention relates to a data information display method of a data broadcasting receiver and an apparatus thereof, in particular to a data information display method of a data broadcasting receiver and an apparatus thereof which is capable of selecting a simple data information picture or a data information picture or a general television picture according to a viewer select in a digital data broadcasting, and knowing overall content of the present receiving data information without switching the present audition television picture into the data information picture when the viewer selects the simple data information picture. The present invention comprises a parsing unit for analyzing the data information, a summary information extracting unit as an additional module of the parsing unit for detecting the abridged data content of the data information, a formatting unit for formatting the data information outputted from the parsing unit in order to display it, a displaying unit for displaying and transmitting the data information formatted on the formatting unit to a screen, and a user interface for transmitting and receiving signals with the parsing unit according to the input of the viewer. Accordingly, the viewer can watch the television picture faithfully and at the same time can use the data appropriately also.
Owner:LG ELECTRONICS INC
Identifying and requesting data in network using identifiers which are based on contents of data
InactiveUS20020052884A1Improve efficiencyImprove integrityData processing applicationsDigital data processing detailsData processing systemUnique identifier
In a data processing system, a mechanism identifies data items by substantially unique identifiers which depend on all of the data in the data items and only on the data in the data items. Existence means determine whether a particular data item is present in the system, by examining the identifiers of the plurality of data items.
Owner:LEVEL 3 COMM LLC +1
System and method for unified threat management with a relational rules methodology
ActiveUS7735116B1Improve performanceImprove securityDigital data processing detailsUser identity/authority verificationSecurity measurementSecurity Measure
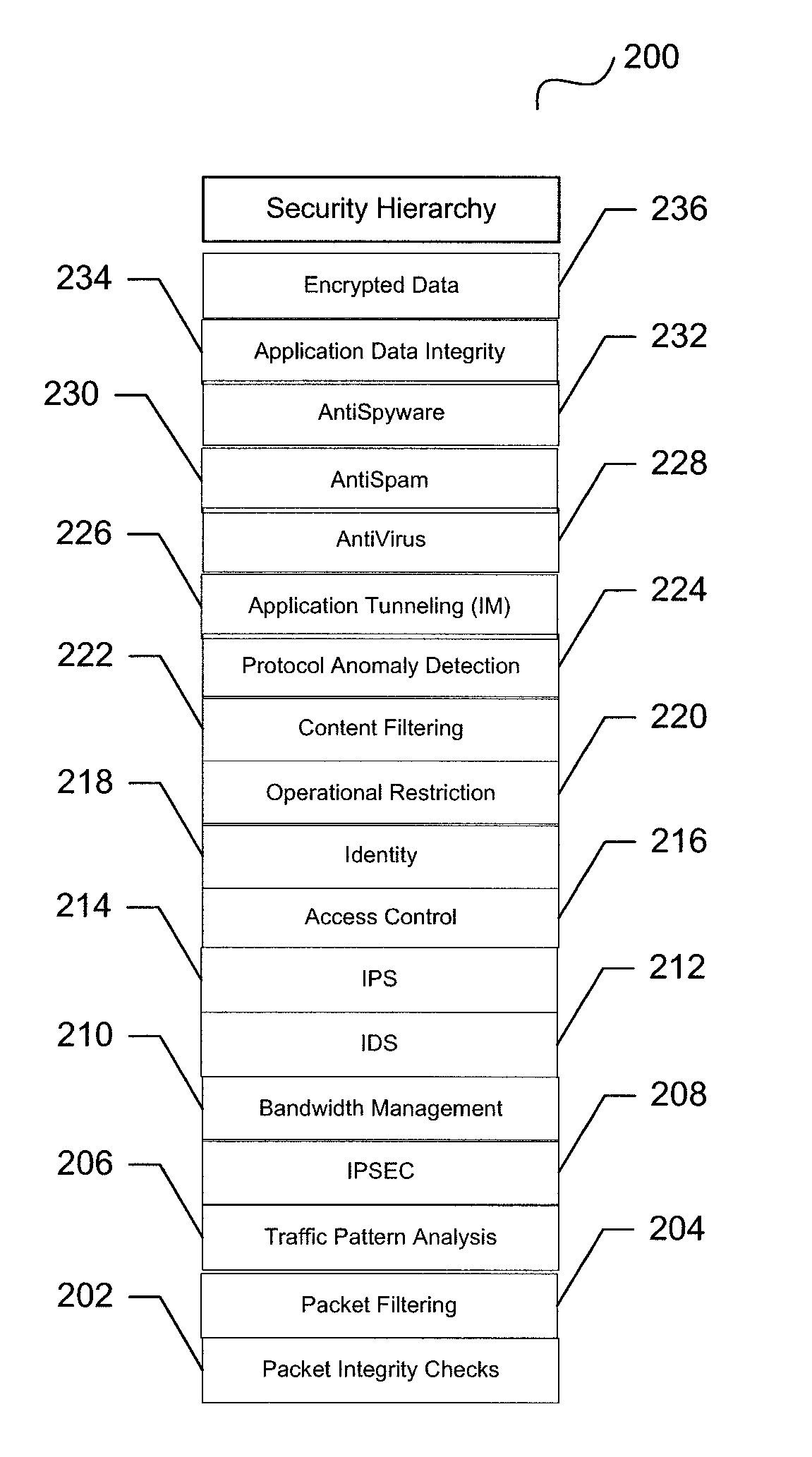
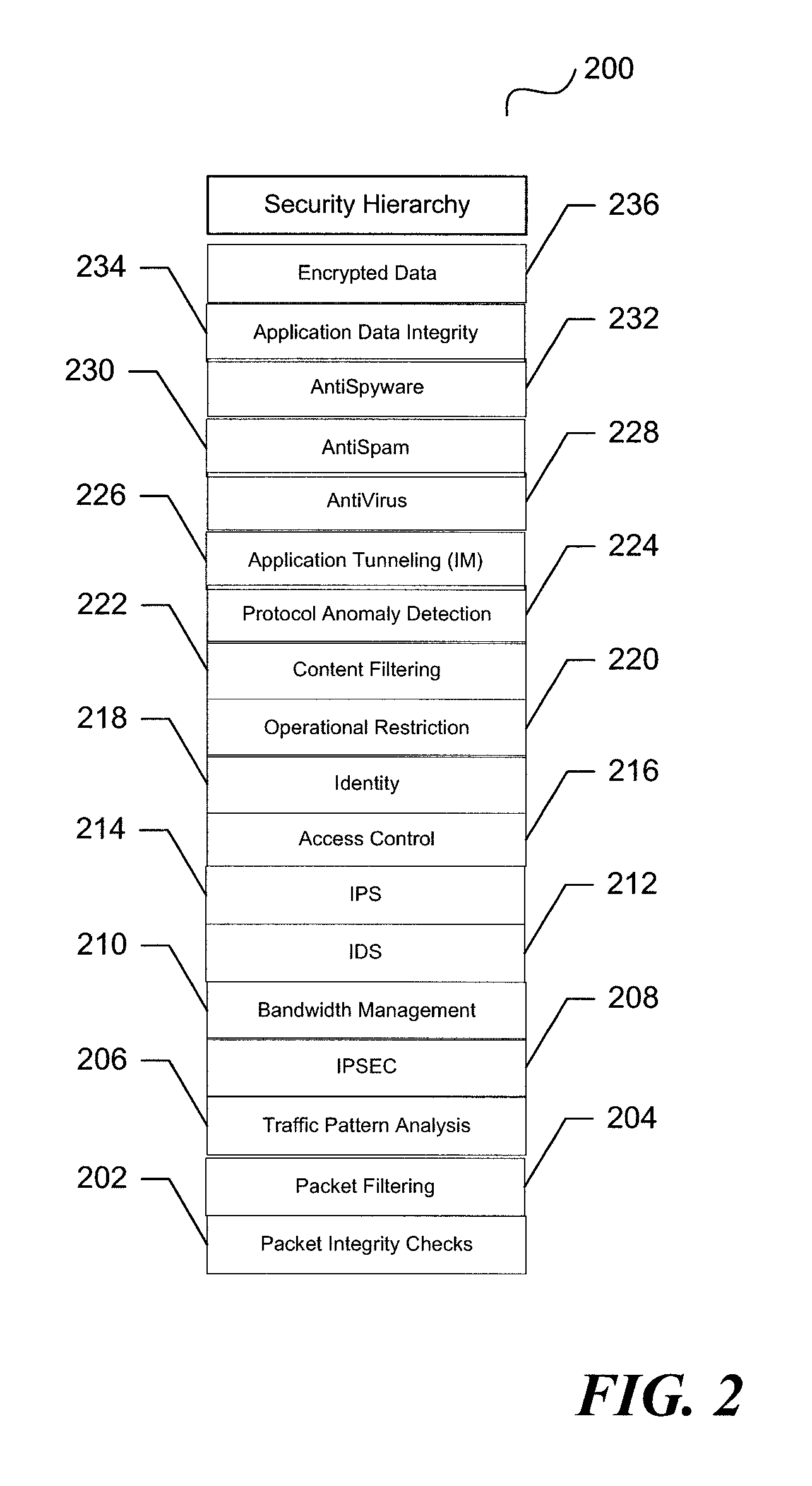
A unified threat management system is provided with a uniform relational rules model. The unified relational rules model provides for the sub-setting of rules and the ability to derive a result based partially from previous security measurements. The sharing of a security check from one security implementation to another using an object-oriented methodology is facilitated. Security policy is divided into specific security features that result in a security hierarchy. The security features may be considered to be listed sequentially, from bottom to top, and form a relationship with one another. These relationships are used to build a current security measure upon a previous security measure and may be used as a pre-cursor when marshalling data content to be validated.
Owner:CA TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com