Patents
Literature
22656 results about "Host machine" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
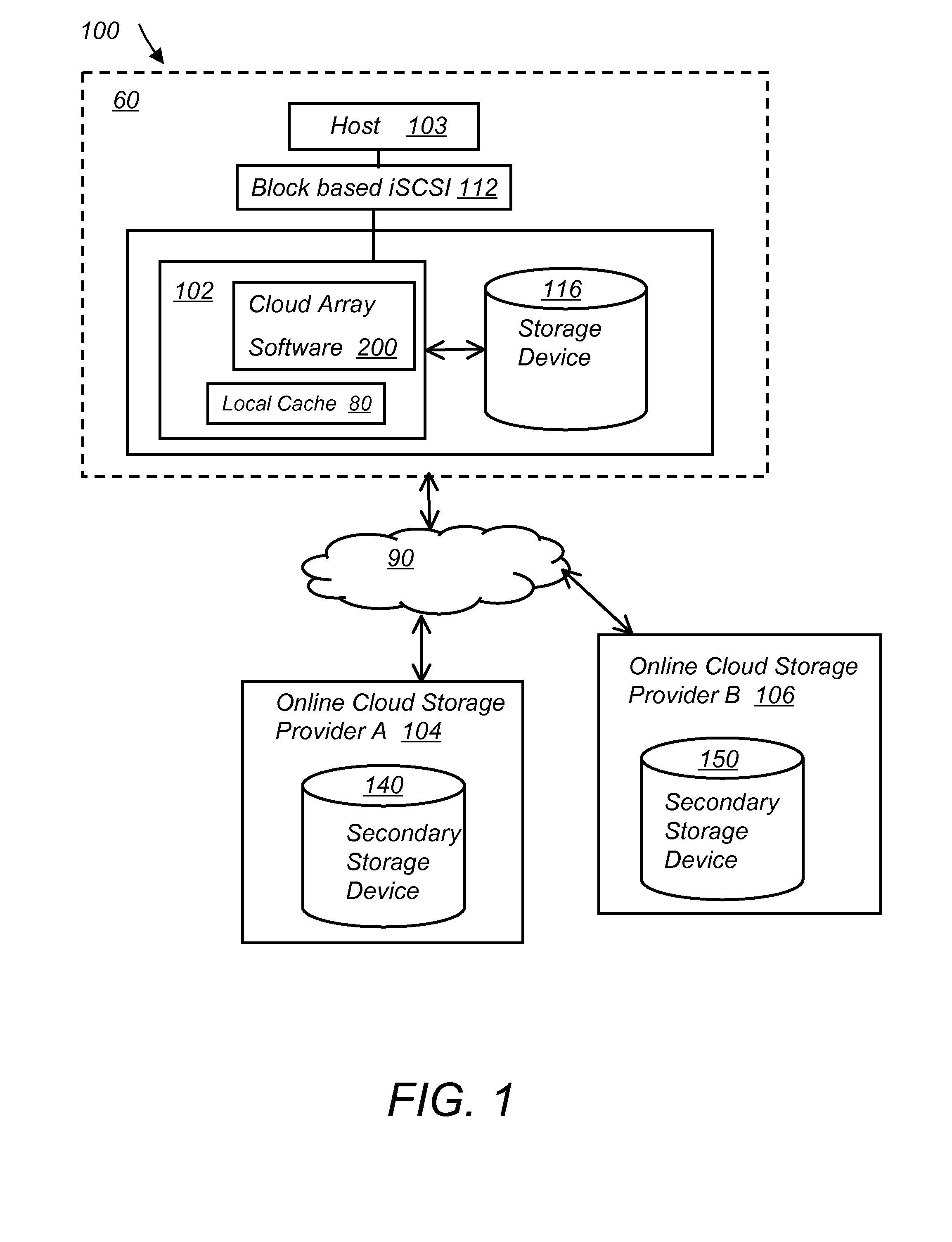
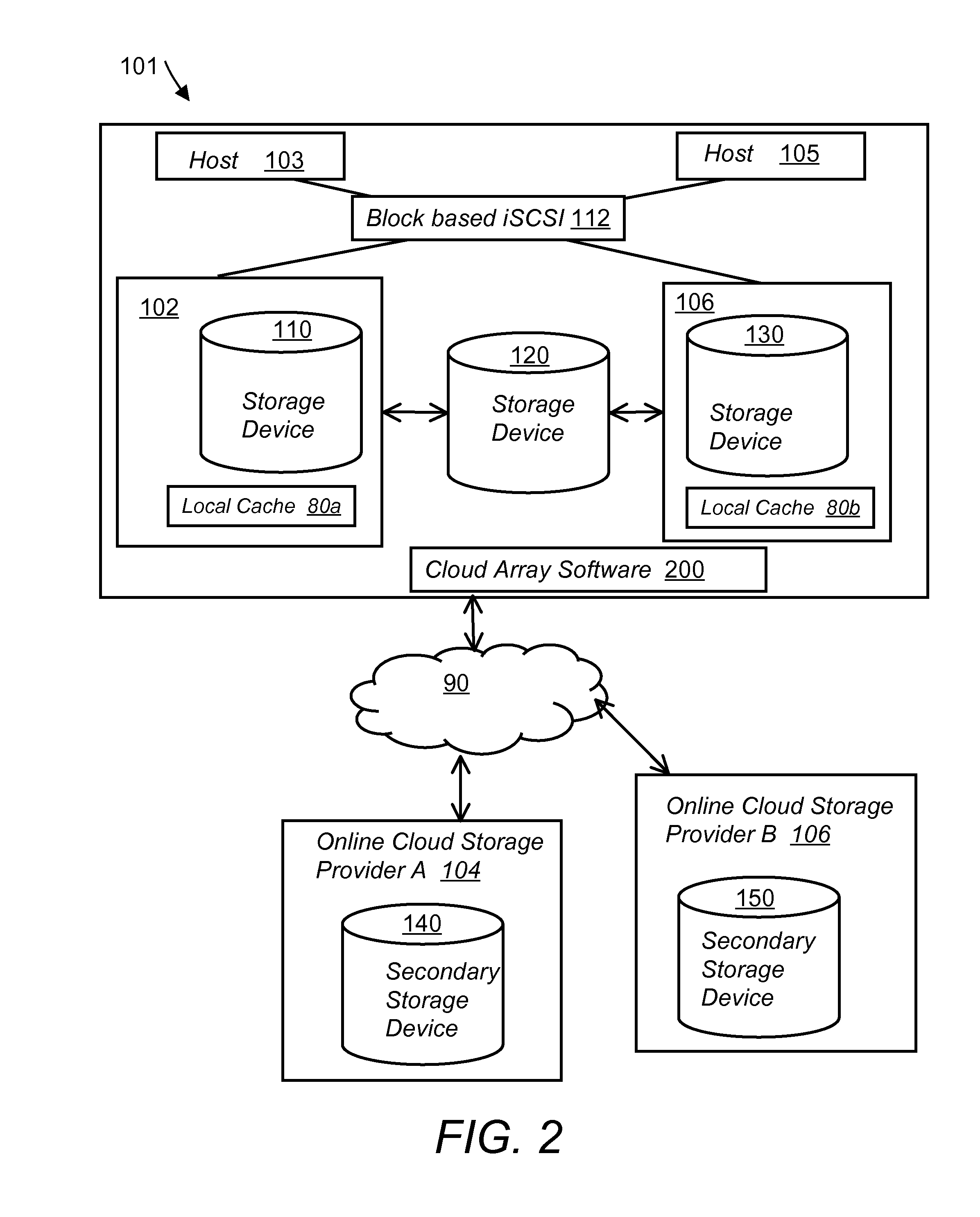
Storage virtualization system and methods
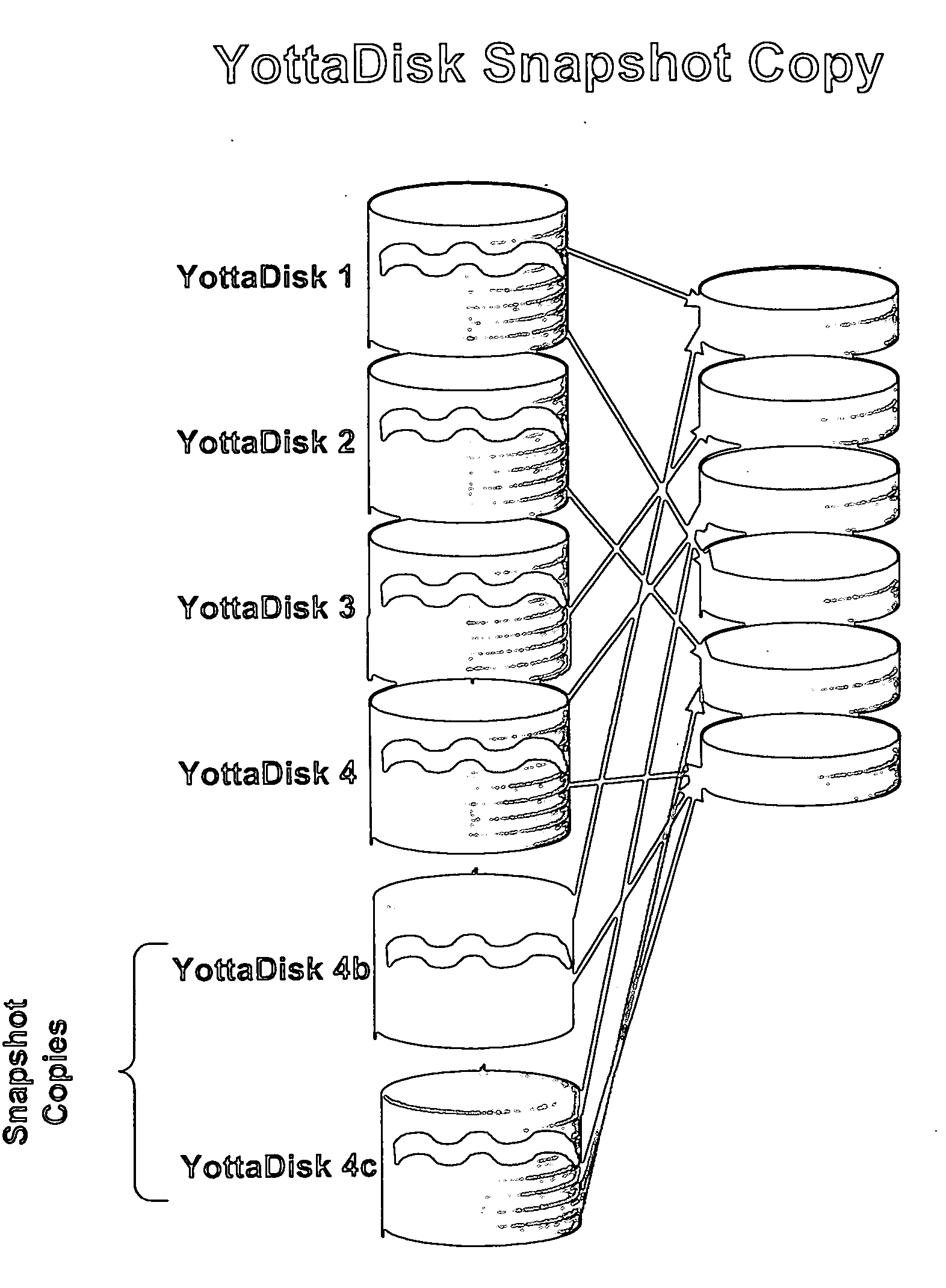
InactiveUS20050125593A1Reduce consumptionWithout impactInput/output to record carriersMemory adressing/allocation/relocationRAIDIslanding
Storage virtualization systems and methods that allow customers to manage storage as a utility rather than as islands of storage which are independent of each other. A demand mapped virtual disk image of up to an arbitrarily large size is presented to a host system. The virtualization system allocates physical storage from a storage pool dynamically in response to host I / O requests, e.g., SCSI I / O requests, allowing for the amortization of storage resources-through a disk subsystem while maintaining coherency amongst I / O RAID traffic. In one embodiment, the virtualization functionality is implemented in a controller device, such as a controller card residing in a switch device or other network device, coupled to a storage system on a storage area network (SAN). The resulting virtual disk image that is observed by the host computer is larger than the amount of physical storage actually consumed.
Owner:EMC IP HLDG CO LLC
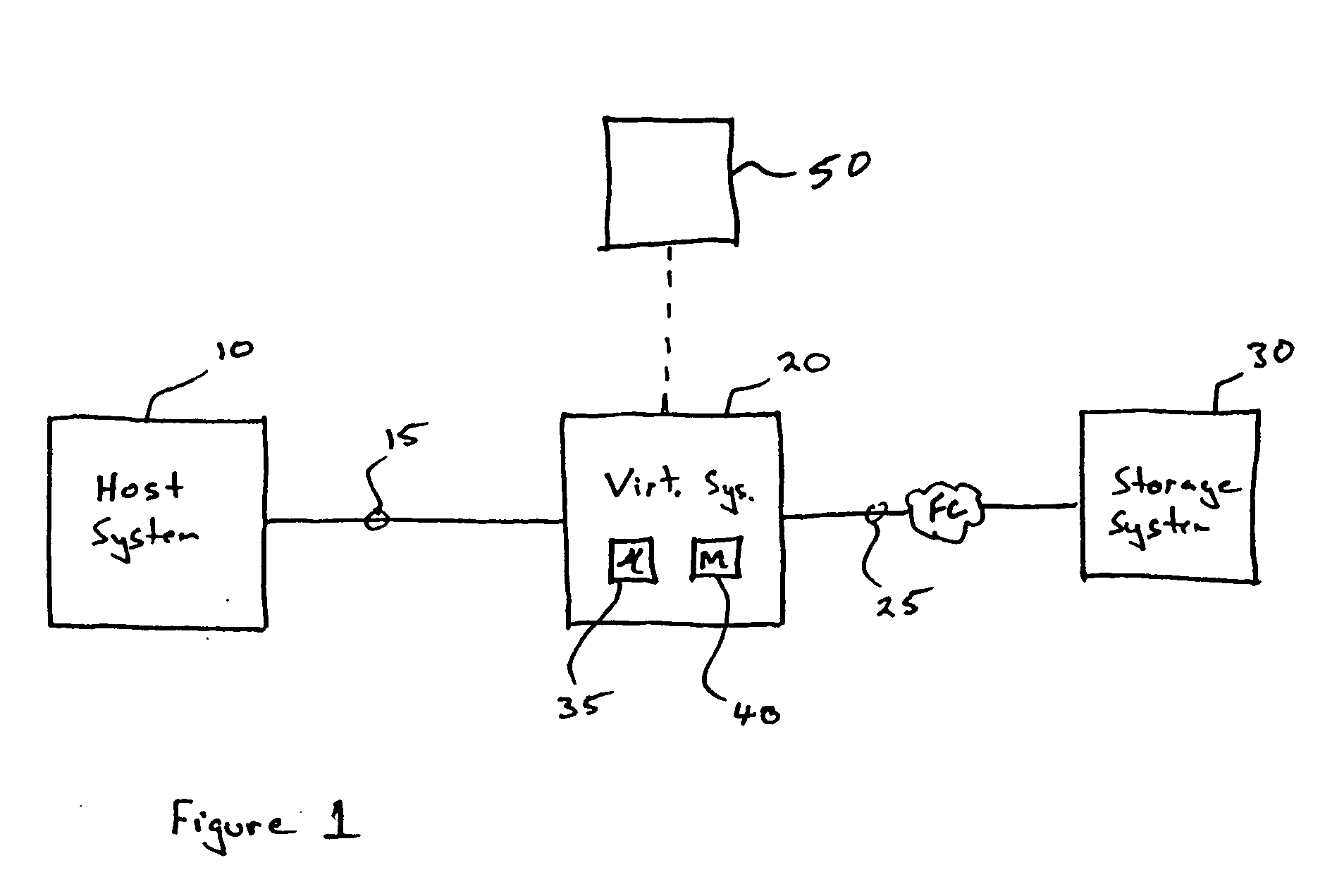
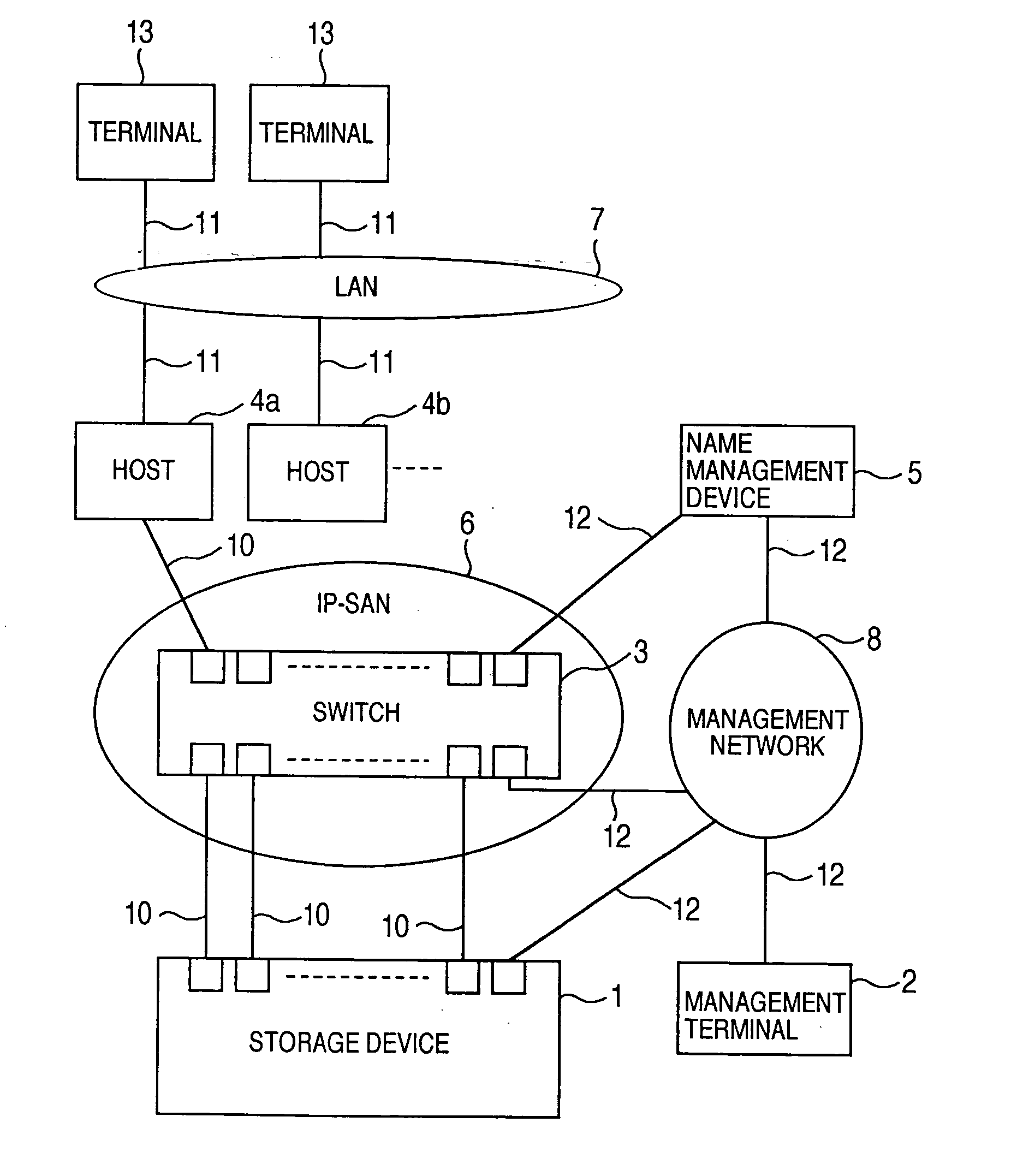
Storage system and a storage management system
InactiveUS20060047907A1Improve matchMemory loss protectionMultiple digital computer combinationsData packStorage management
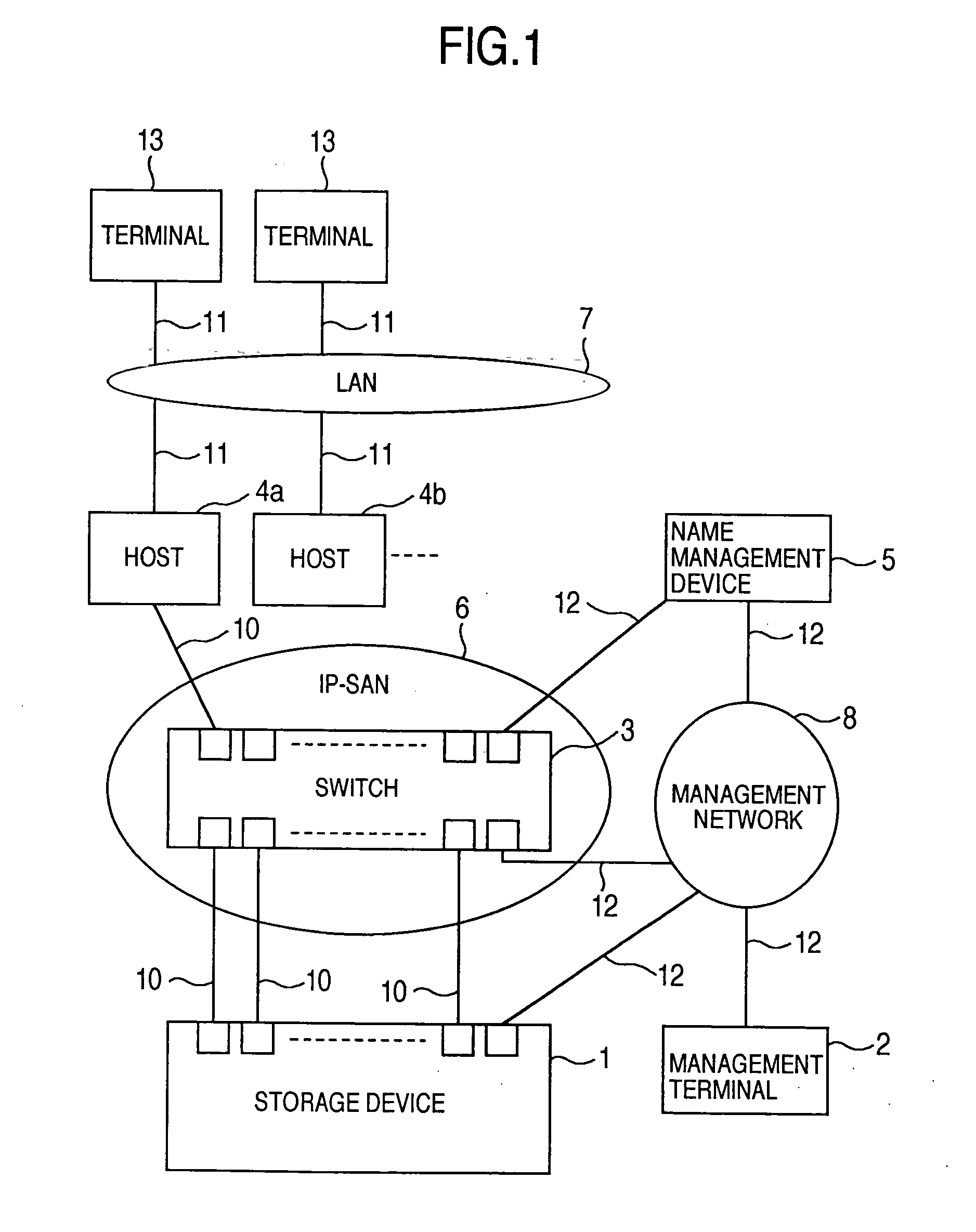
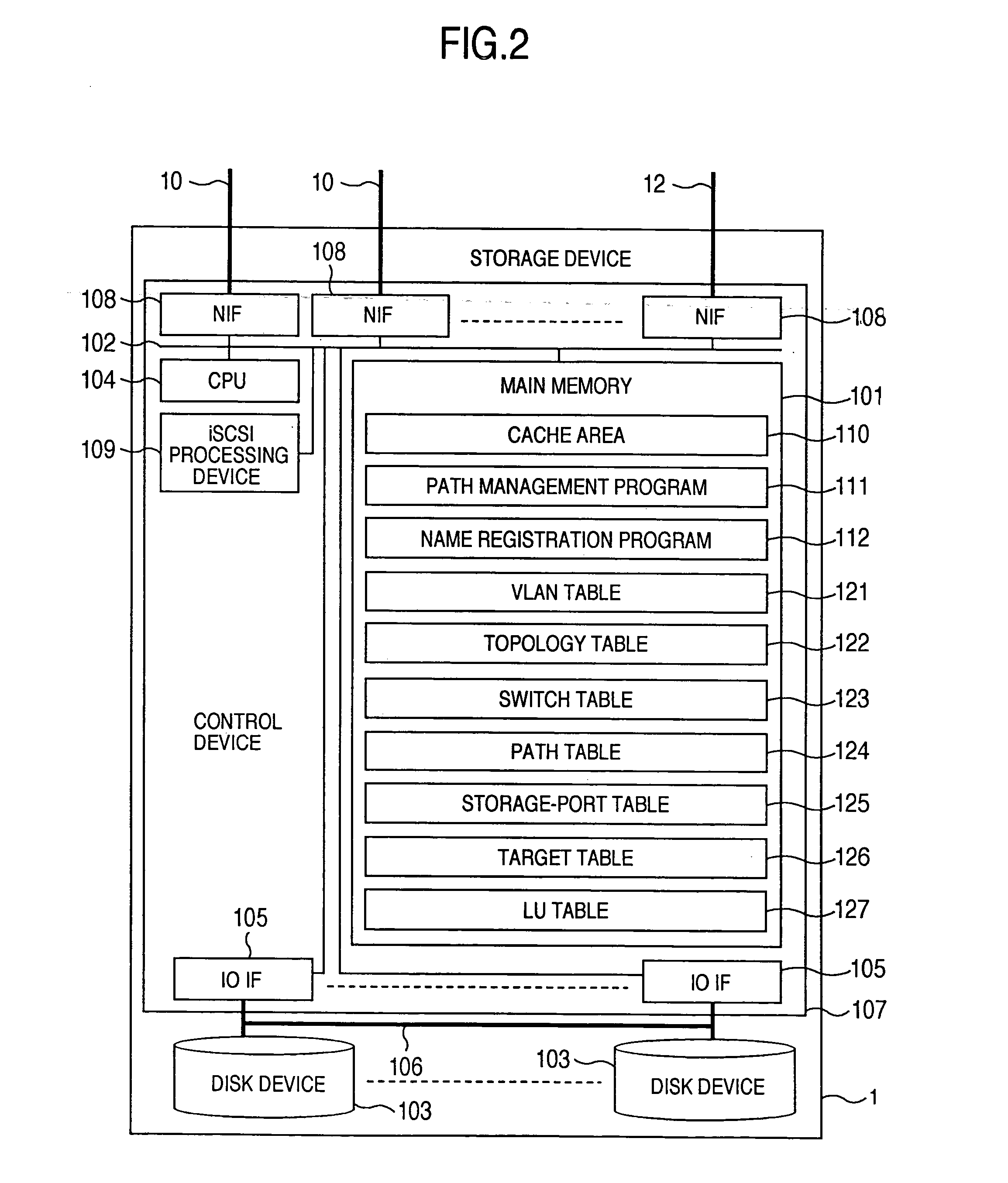
A storage device managing one or more logical volumes is connected with a name management device through an IP-SAN 6 composed of a switch. The storage device stores a topology table saving connecting relation among physical ports of host, physical ports of the storage device and physical ports of the switch, reads an identifier of the host and an identifier of the logical volume, selects a unused first physical port of the switch by referring to the topology table, selects a second physical port of the switch connected with the storage device, registers a group composed of the host and the logical volume with the name management device, and executes a configuration of allowing packets to be transferred between the first and the second physical ports with respect to the switch.
Owner:GOOGLE LLC
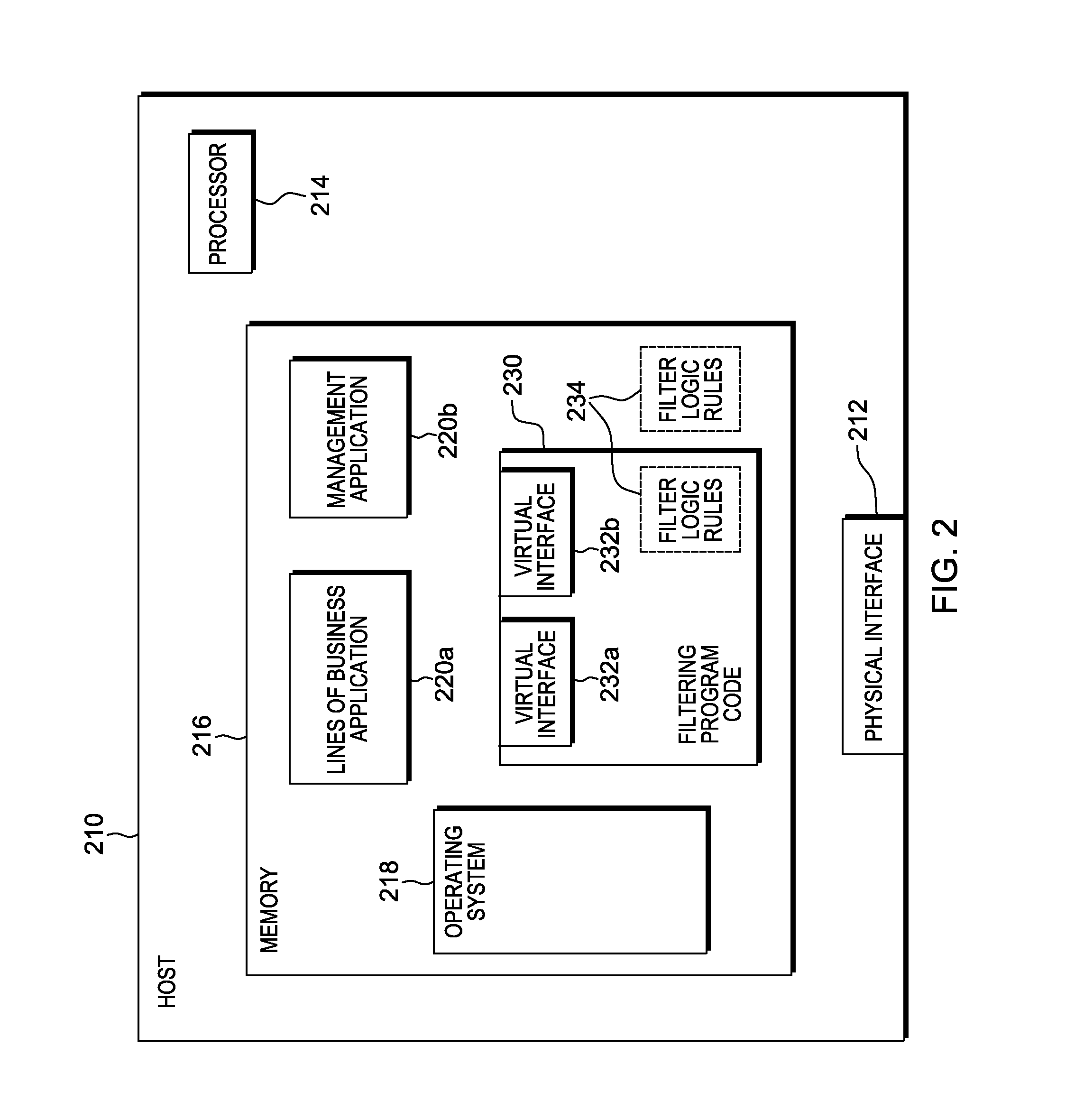
Device management using virtual interfaces
ActiveUS8621123B2Program controlInput/output processes for data processingOperational systemComputerized system
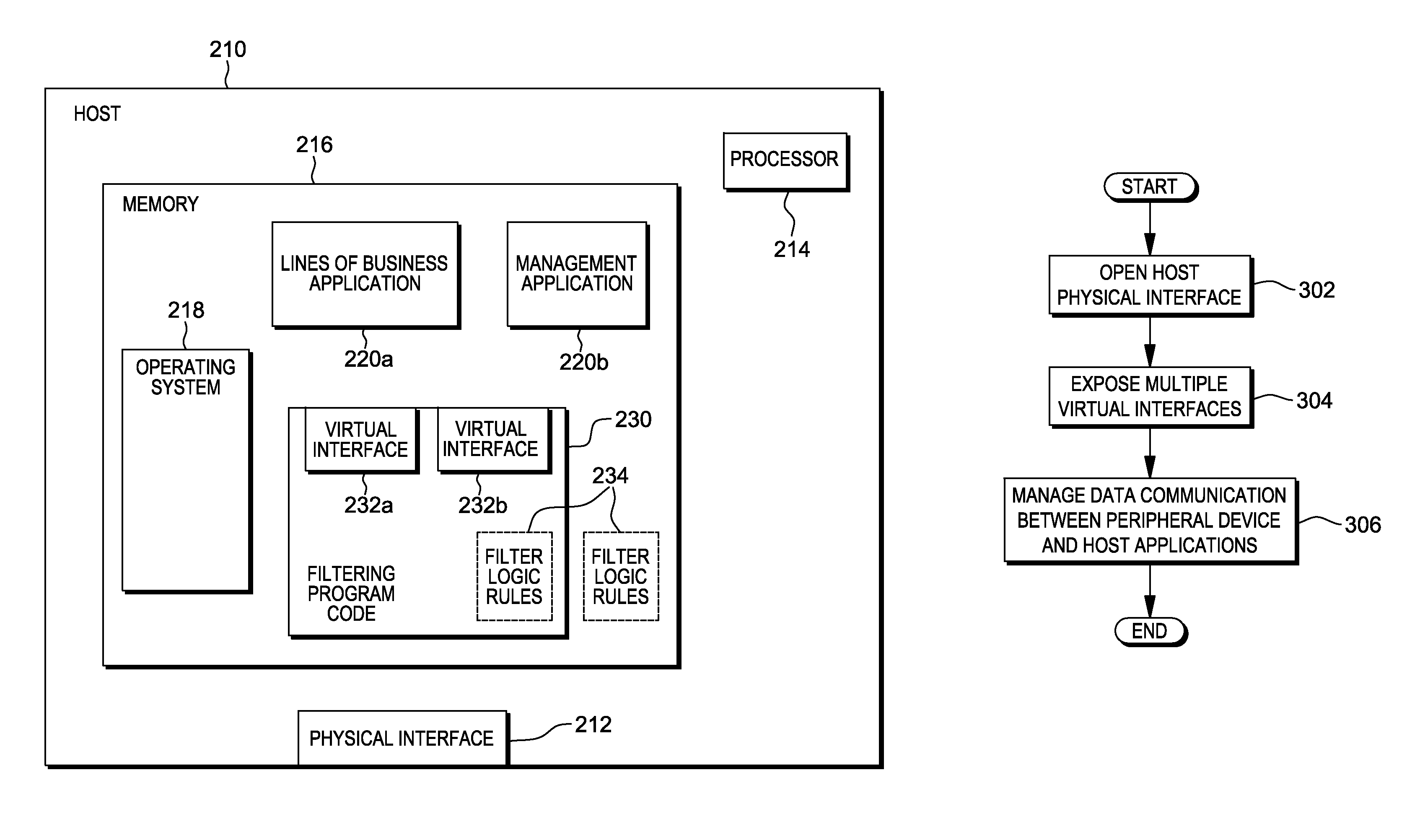
Management of data communication between a peripheral device and host computer system is provided. A physical interface for communicating data between a peripheral device and applications executing on the host is opened and controlled by a software module. First and second virtual interfaces of the software module are exposed to an operating system of the host, and the operating system exposes the first and second virtual interfaces to a first application and a second application executing on the host. The first virtual interface is used for communicating data between the peripheral device and the first application through the physical interface, and the second virtual interface is used for communicating data between the peripheral device and the second application through the physical interface. Management of data communication between the peripheral device and the first application and between the peripheral device and the second application is thereby provided.
Owner:HONEYWELL INT INC
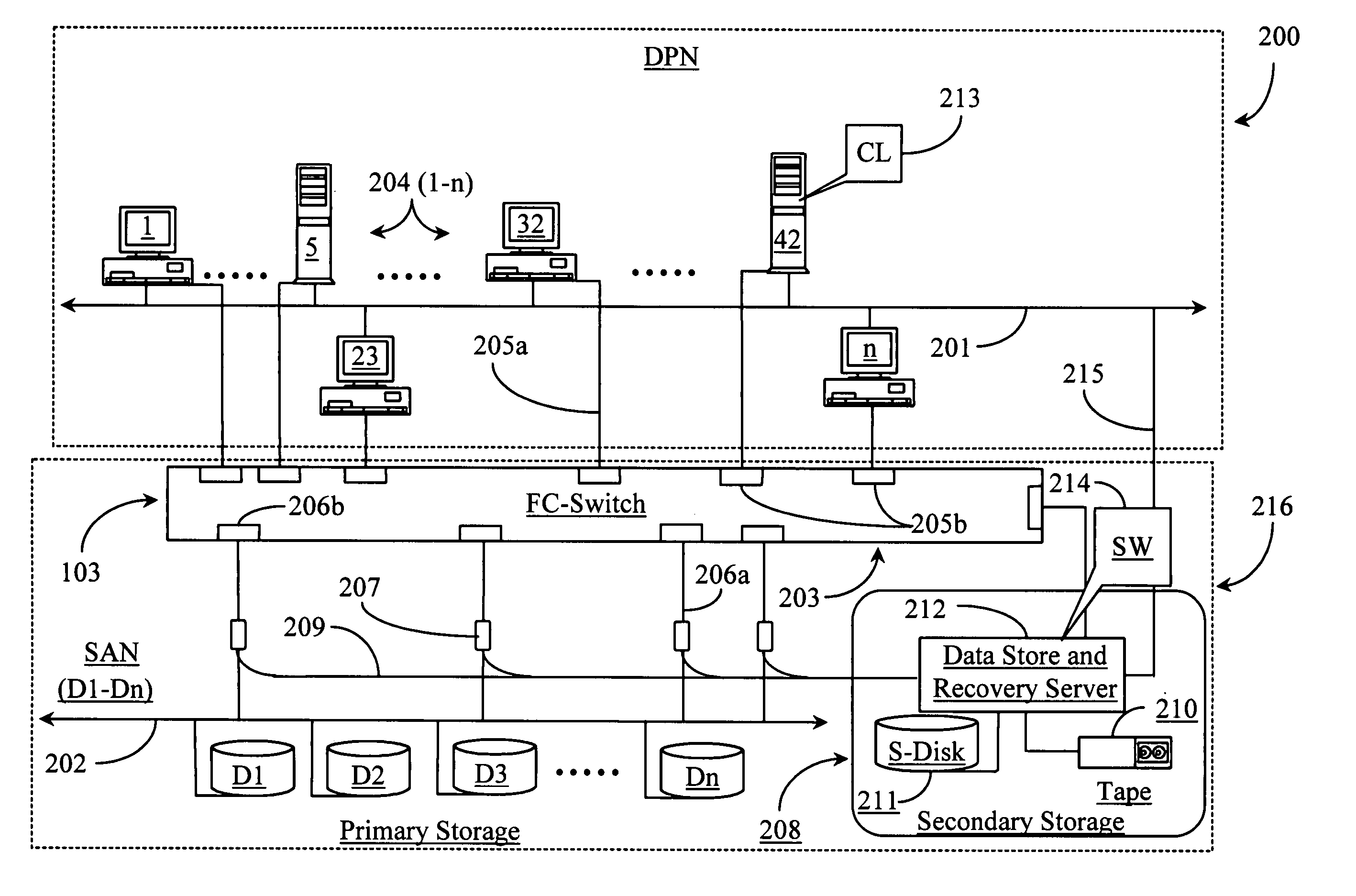
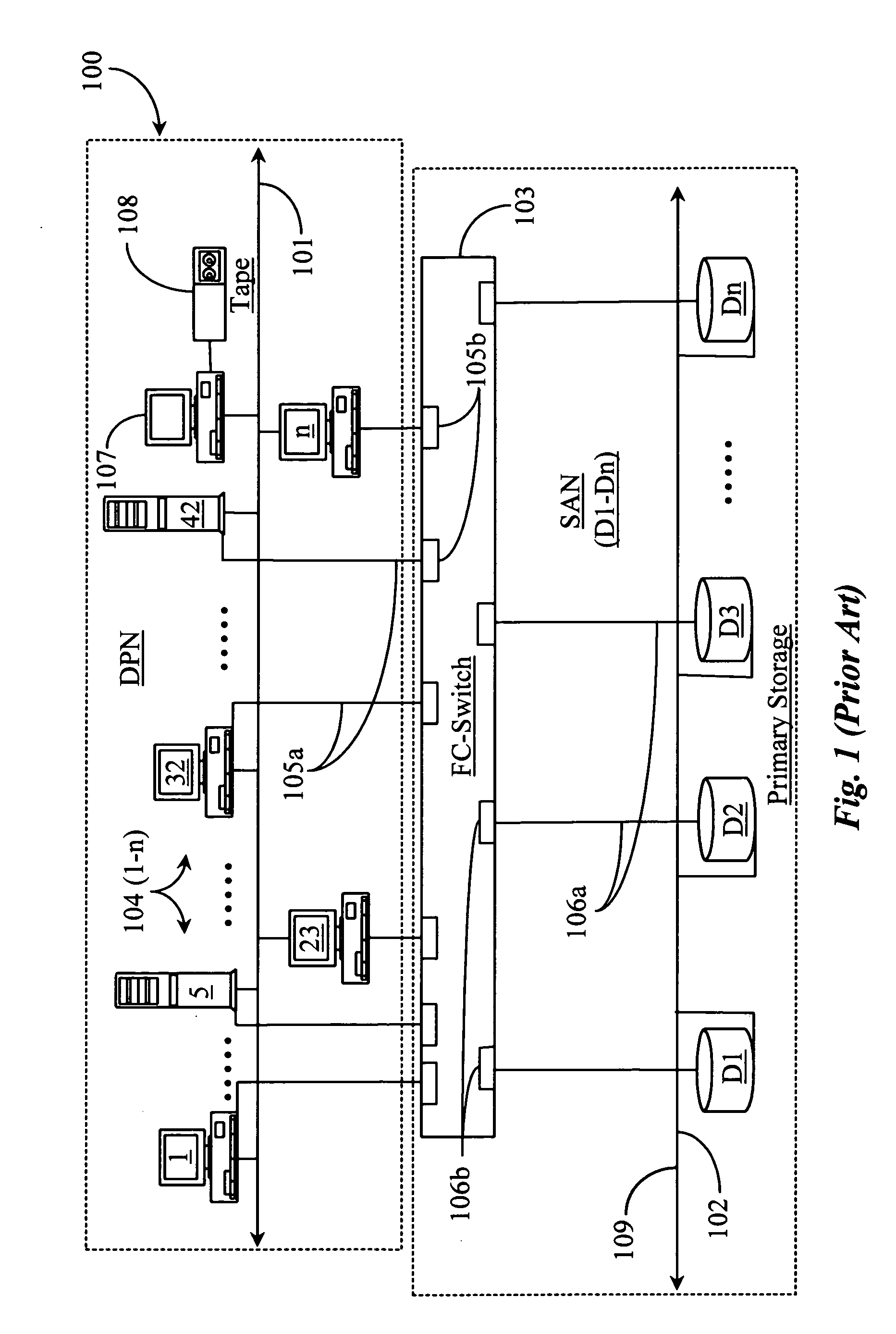
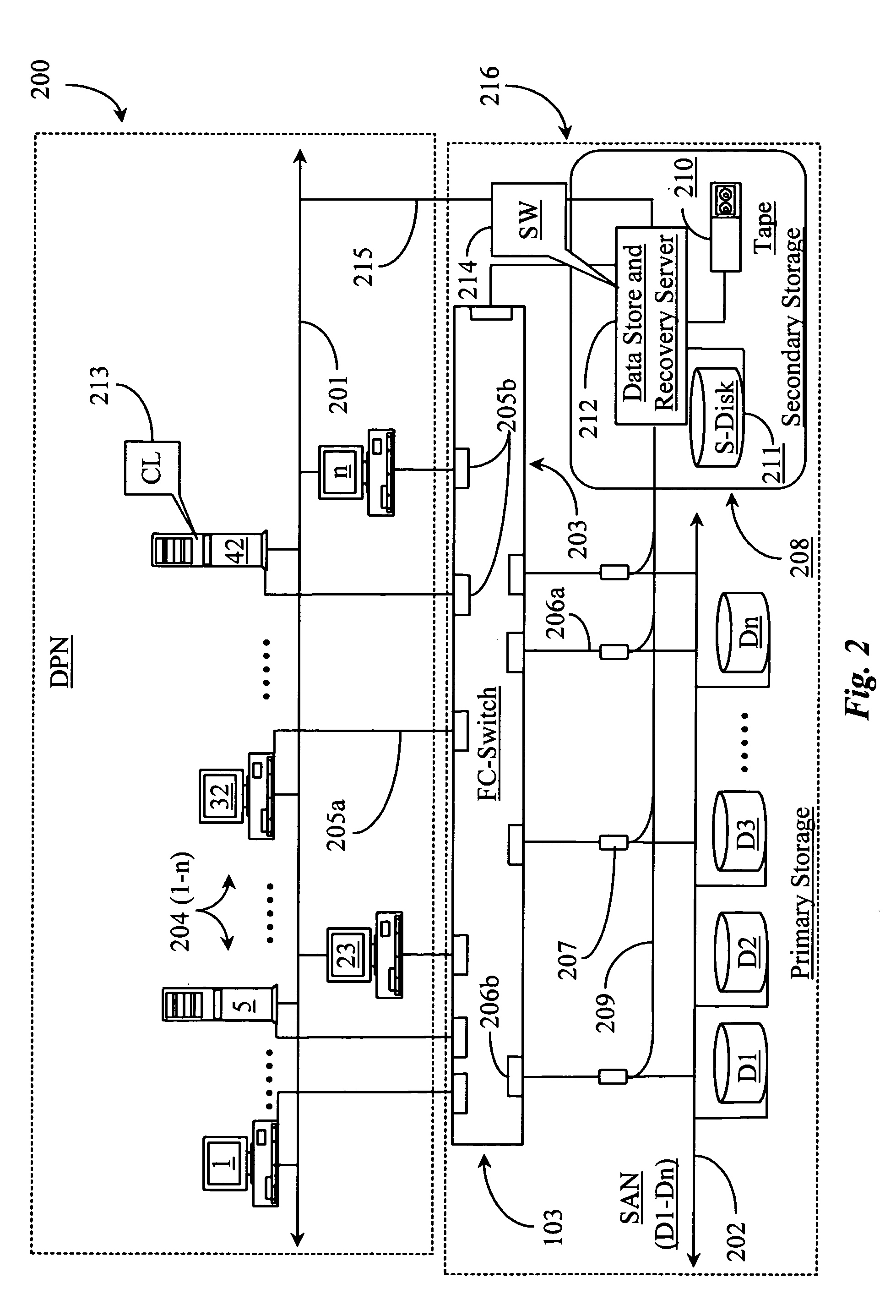
Methods and apparatus for accessing data from a primary data storage system for secondary storage
InactiveUS20060010227A1Error detection/correctionMultiple digital computer combinationsMachine instructionLogical view
A system for providing secondary data storage and recovery services for one or more networked host nodes includes a server application for facilitating data backup and recovery services; a first data storage medium accessible to the server application; a second data storage medium accessible to the server application; at least one client application for mapping write locations allocated by the first data storage medium to write locations represented in a logical view of the first data storage medium; and at least one machine instruction enabling direct read capability of the first data storage medium by the server application for purposes of subsequent time-based storage of the read data into the secondary data storage medium.
Owner:MICROSOFT TECH LICENSING LLC
Storage mapping and partitioning among multiple host processors in the presence of login state changes and host controller replacement
InactiveUS6260120B1Input/output to record carriersData processing applicationsData portControl store
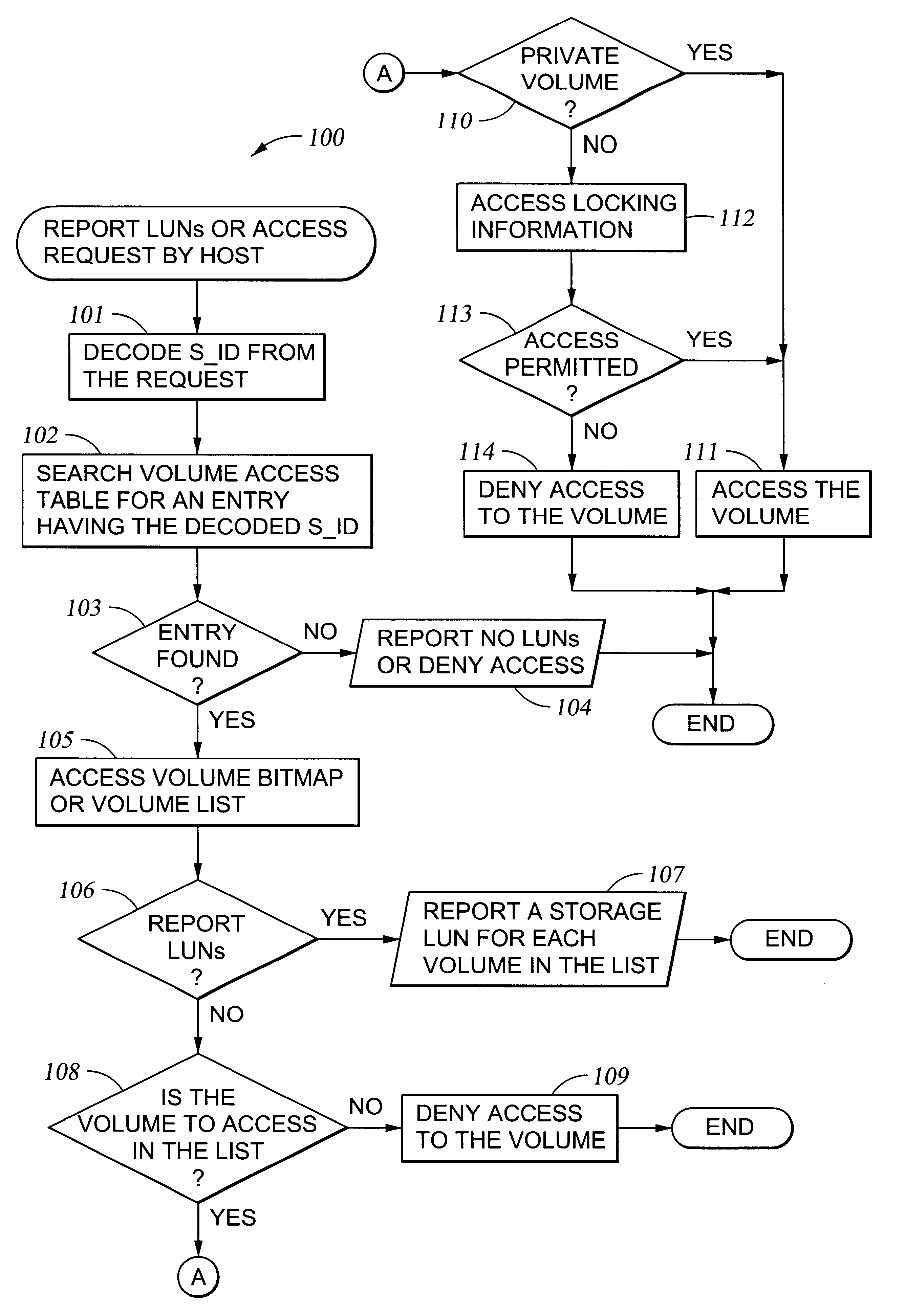
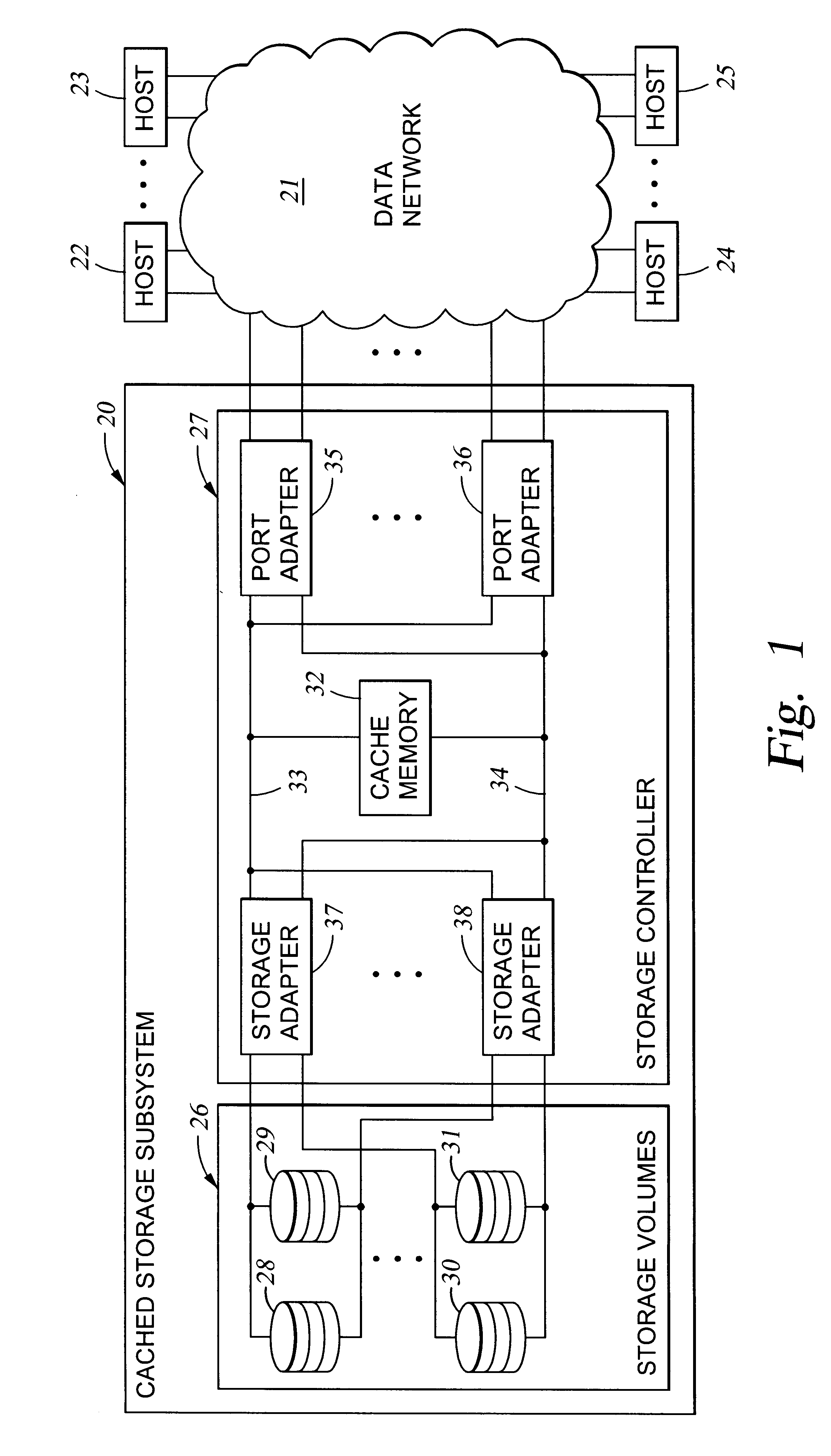
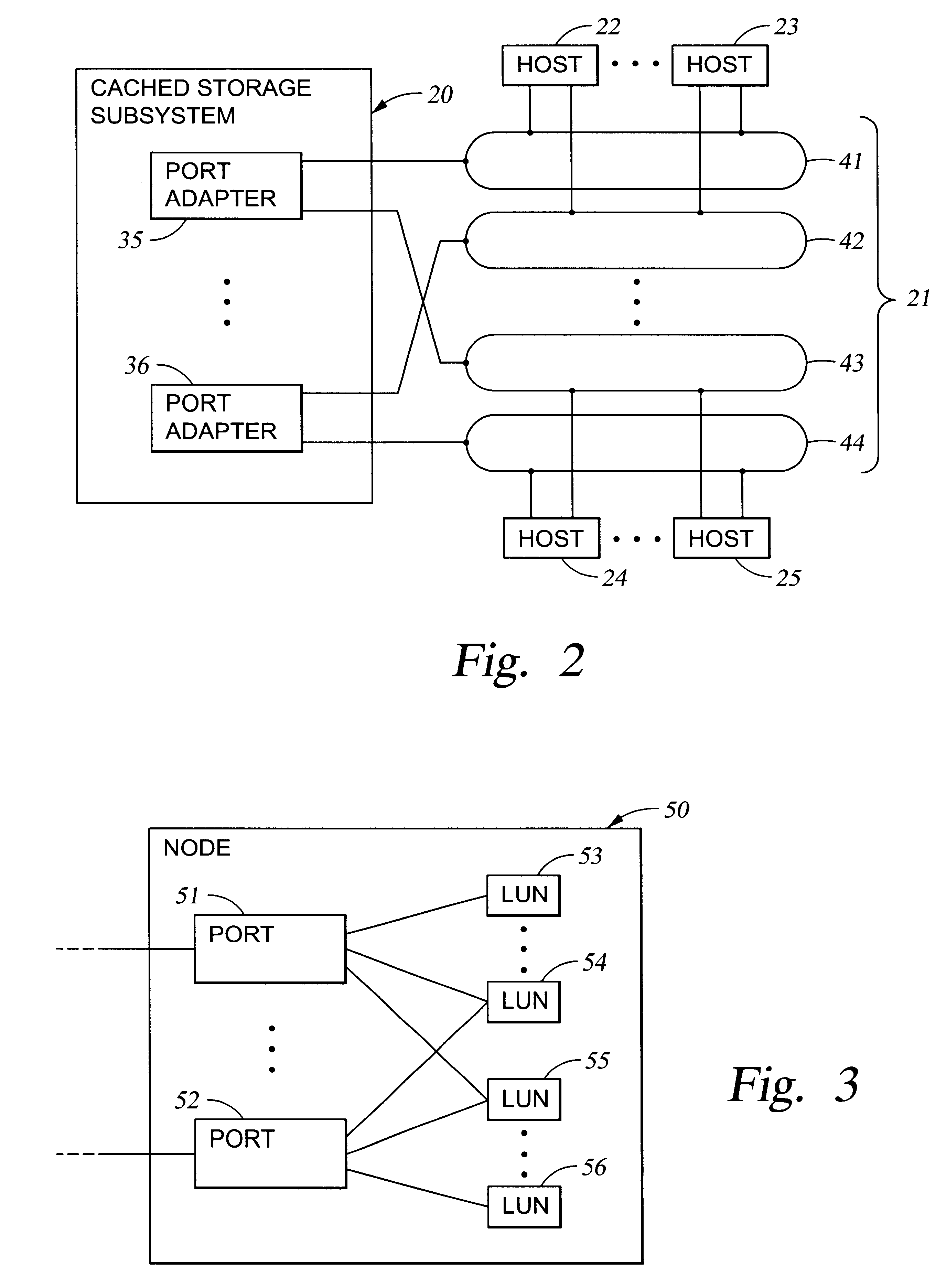
A storage controller for controling access to data storage has a memory and at least one data port for a data network including host processors. The memory is programmed to define a respective specification for each host processor of a respective subset of the data storage to which access by the host processor is restricted, and each specification is associated with a host identifier stored in the memory. When the storage controller receives a data access request from a host processor, it decodes a host identifier from the data access request, and searches the memory for a host identifier matching the host identifier decoded from the request. Upon finding a match, the respective specification of the respective subset for the host processor is accessed to determine whether or not storage specified by the storage access request is contained in the respective subset. If so, then storage access can continue, and otherwise, storage access is denied. Preferably the host identifier decoded from the request is a temporary address assigned by the network, and also stored in the memory in association with each respective specification is a relatively permanent identifier for the host processor.
Owner:EMC IP HLDG CO LLC
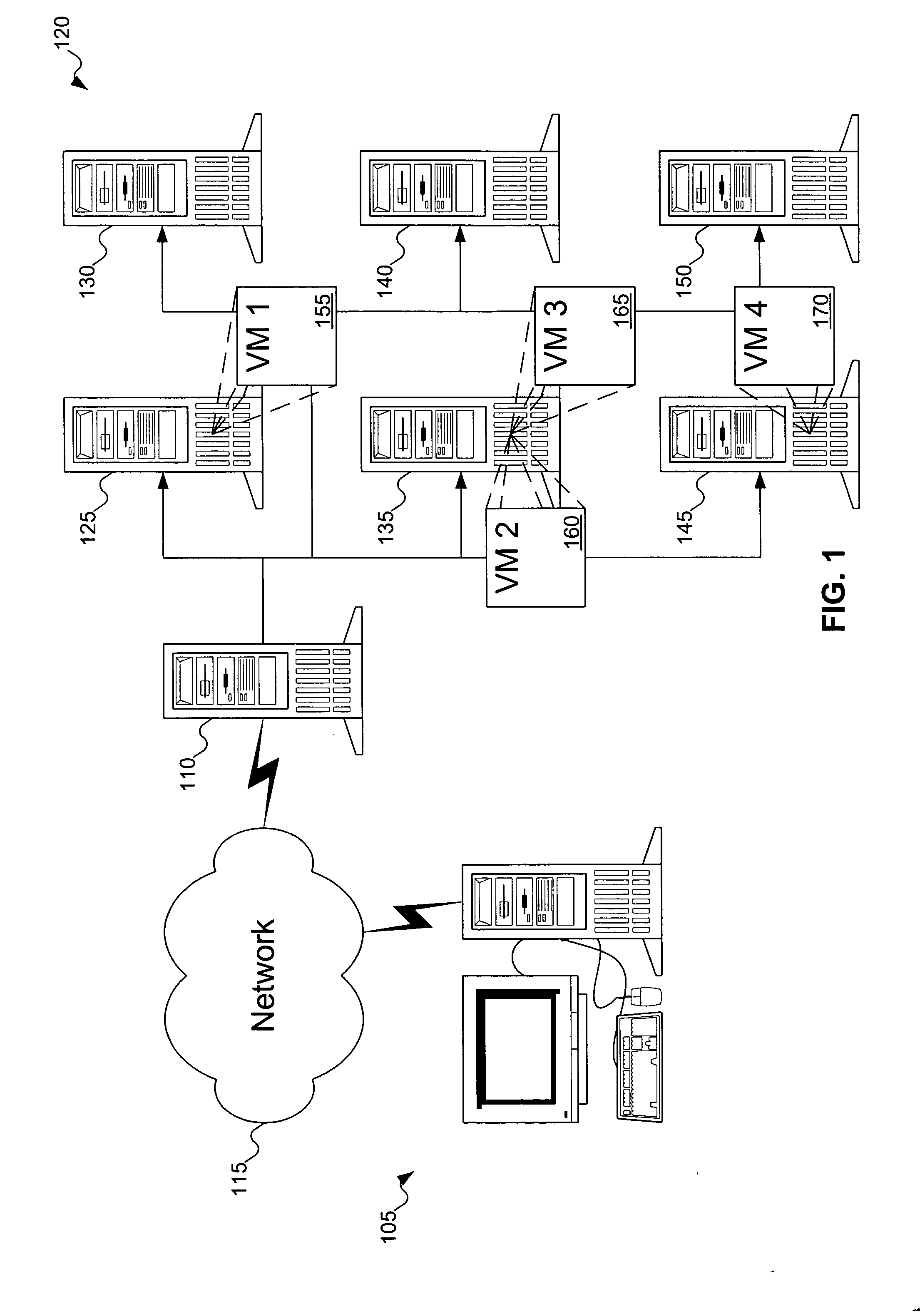
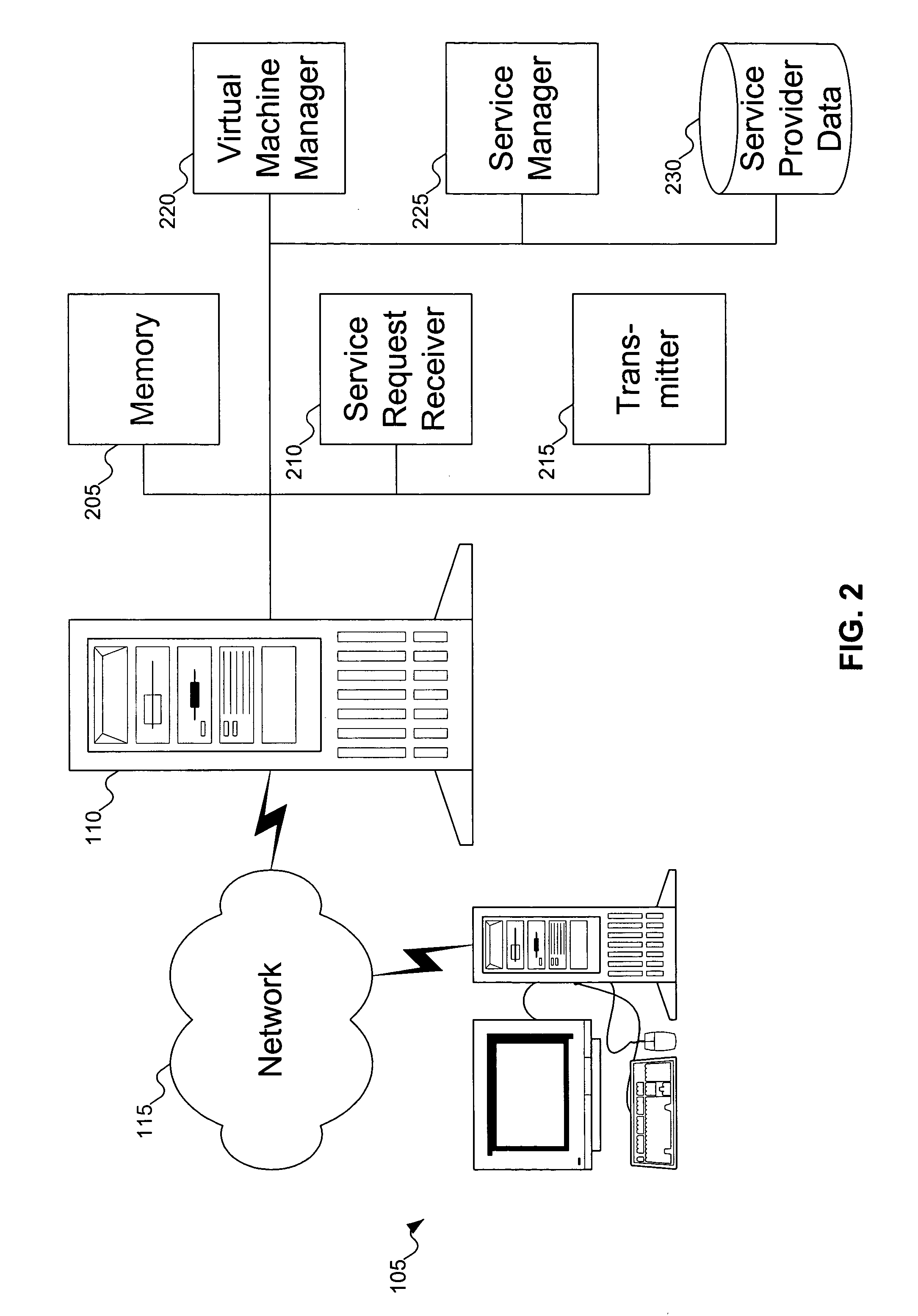
Dynamic virtual machine service provider allocation
InactiveUS20050198303A1Multiple digital computer combinationsProgram controlClient-sideVirtual machine
A server receives a request for a service. The server determines if a virtual machine already exists that offers the service. If so, the server returns an identifier of the virtual machine to the requesting client so that the client may access the service from the virtual machine. Otherwise, the server attempts to create an image of a virtual machine offering the service. If successful in creating the image, the image is installed as a new virtual machine in a host machine, and the server returns an identifier of the newly created virtual machine to the client.
Owner:KNAUERHASE ROBERT +4
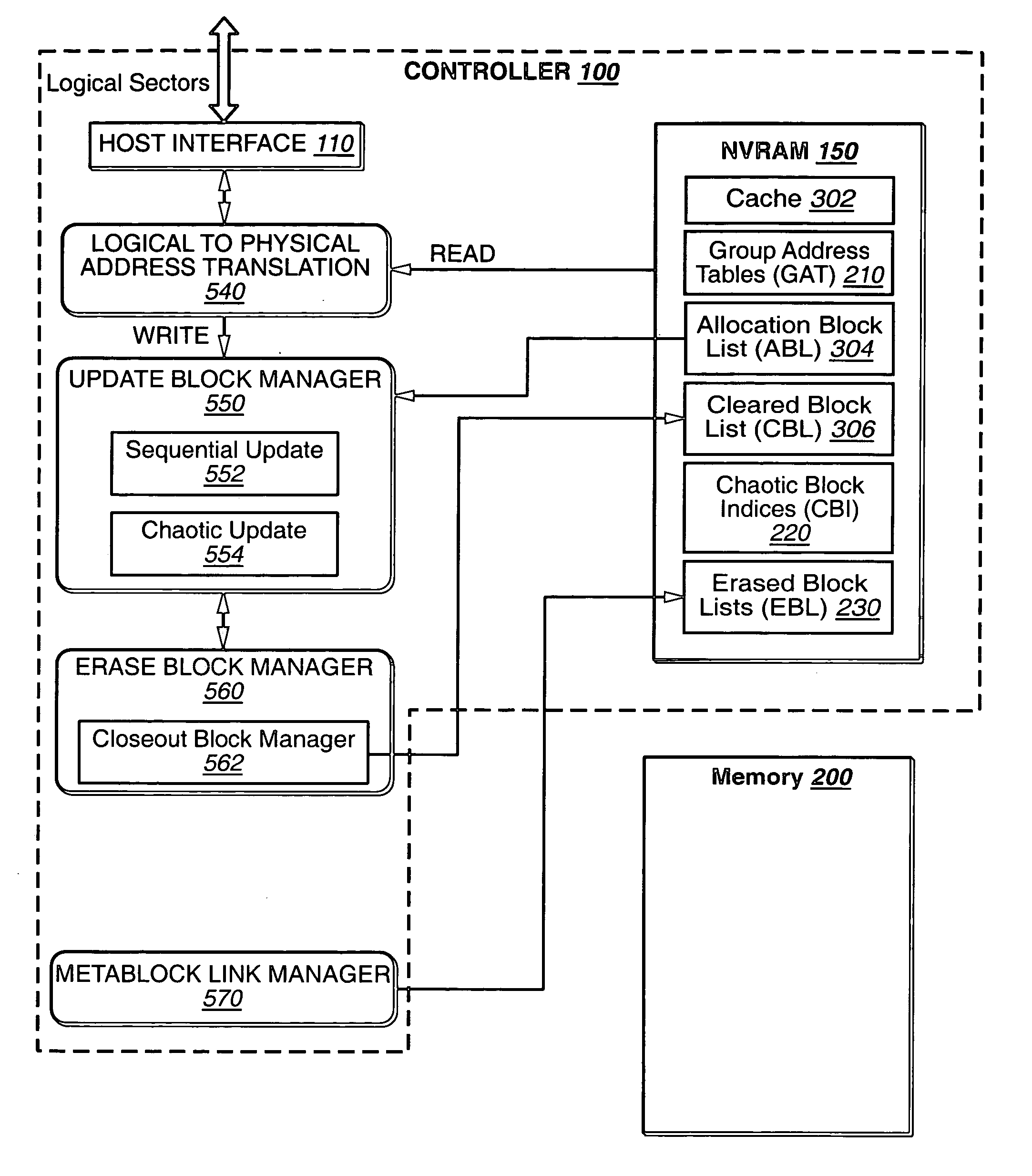
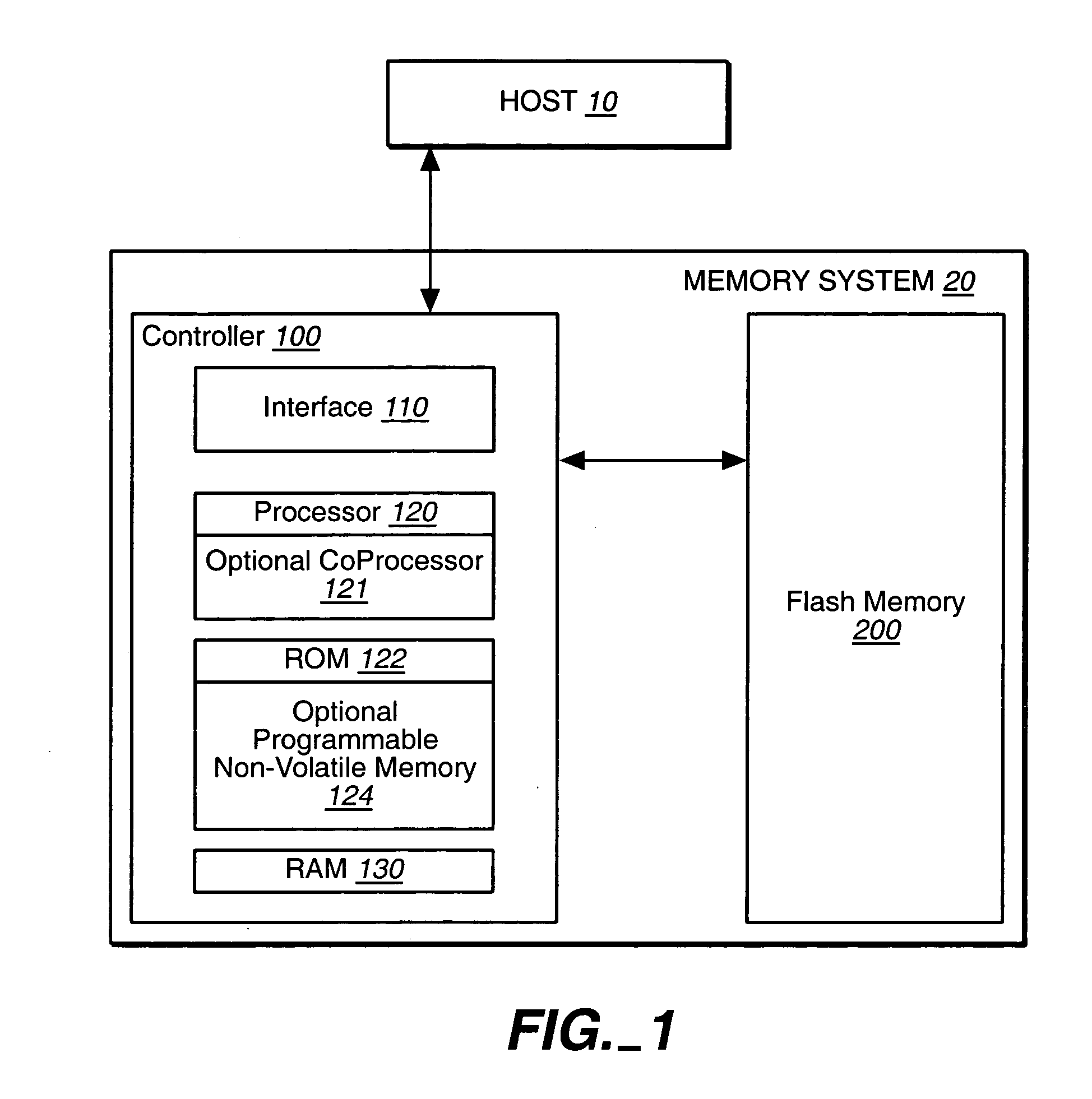
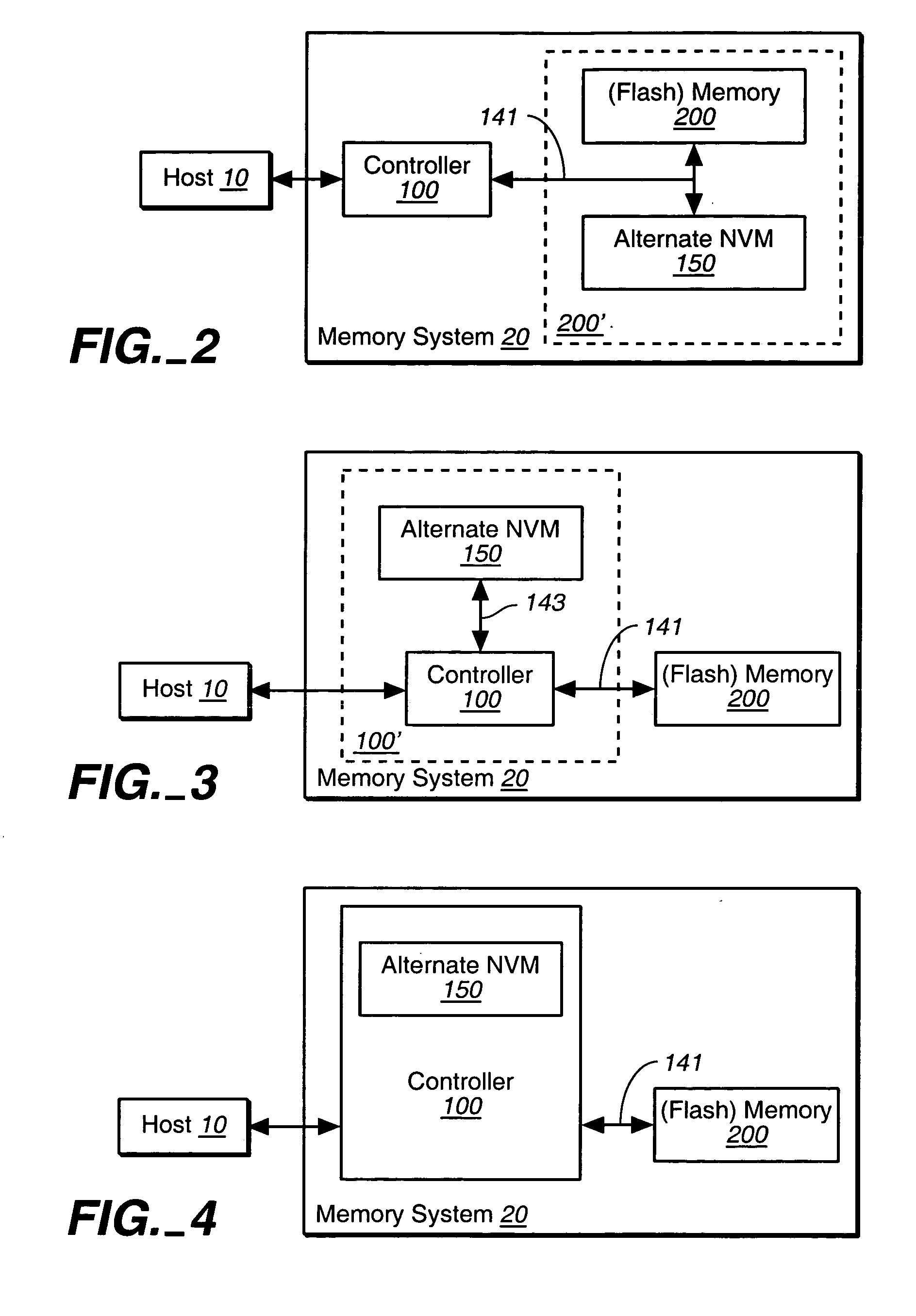
Hybrid non-volatile memory system
InactiveUS20050251617A1Easy accessMemory architecture accessing/allocationInput/output to record carriersData controlControl data
The present invention presents a hybrid non-volatile system that uses non-volatile memories based on two or more different non-volatile memory technologies in order to exploit the relative advantages of each these technology with respect to the others. In an exemplary embodiment, the memory system includes a controller and a flash memory, where the controller has a non-volatile RAM based on an alternate technology such as FeRAM. The flash memory is used for the storage of user data and the non-volatile RAM in the controller is used for system control data used by the control to manage the storage of host data in the flash memory. The use of an alternate non-volatile memory technology in the controller allows for a non-volatile copy of the most recent control data to be accessed more quickly as it can be updated on a bit by bit basis. In another exemplary embodiment, the alternate non-volatile memory is used as a cache where data can safely be staged prior to its being written to the to the memory or read back to the host.
Owner:SANDISK TECH LLC
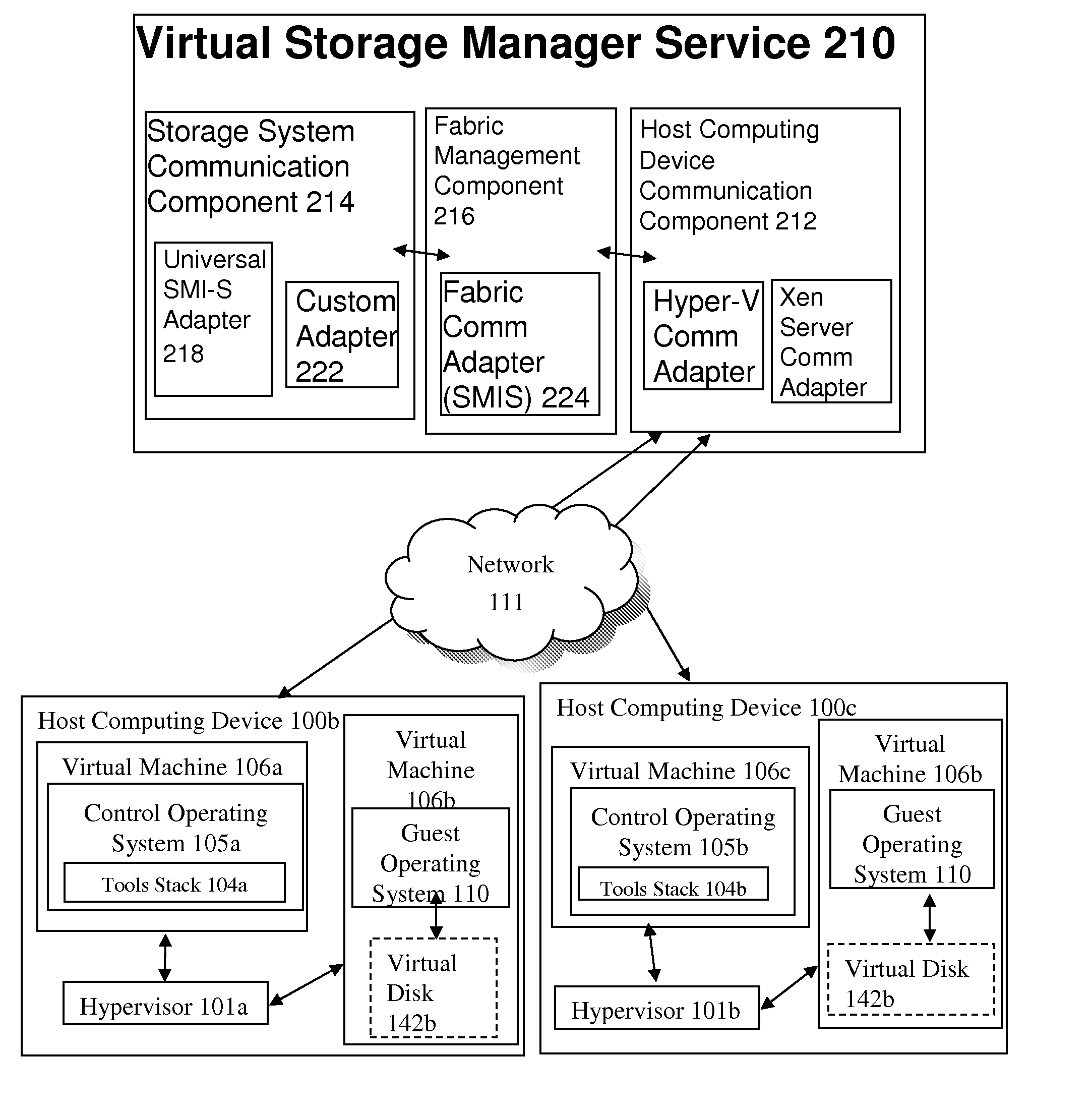
Methods and Systems for Automated Management of Virtual Resources In A Cloud Computing Environment
ActiveUS20100198972A1Multiple digital computer combinationsProgram controlStorage area networkCloud computing
A system for automated management of virtual resources in a cloud computing environment includes a host computing device communication component and a storage system communication component. The storage system communication component is executed by a storage delivery management service, communicates with a storage system adapter in a storage area network to identify a storage system in a storage area network, and directs the automated provisioning of a virtual storage resource on the identified storage system, the storage system providing resources for provisioning the virtual drive. The host computing device communication component receives a request for access by a host computing device to the virtual storage resource, and responds, to the host computing device, with an identification of a network port of the identified storage system and an identification of the provisioned virtual storage resource.
Owner:CITRIX SYST INC
Malware Detector
InactiveUS20080320594A1Memory loss protectionError detection/correctionVirtual memoryOperational system
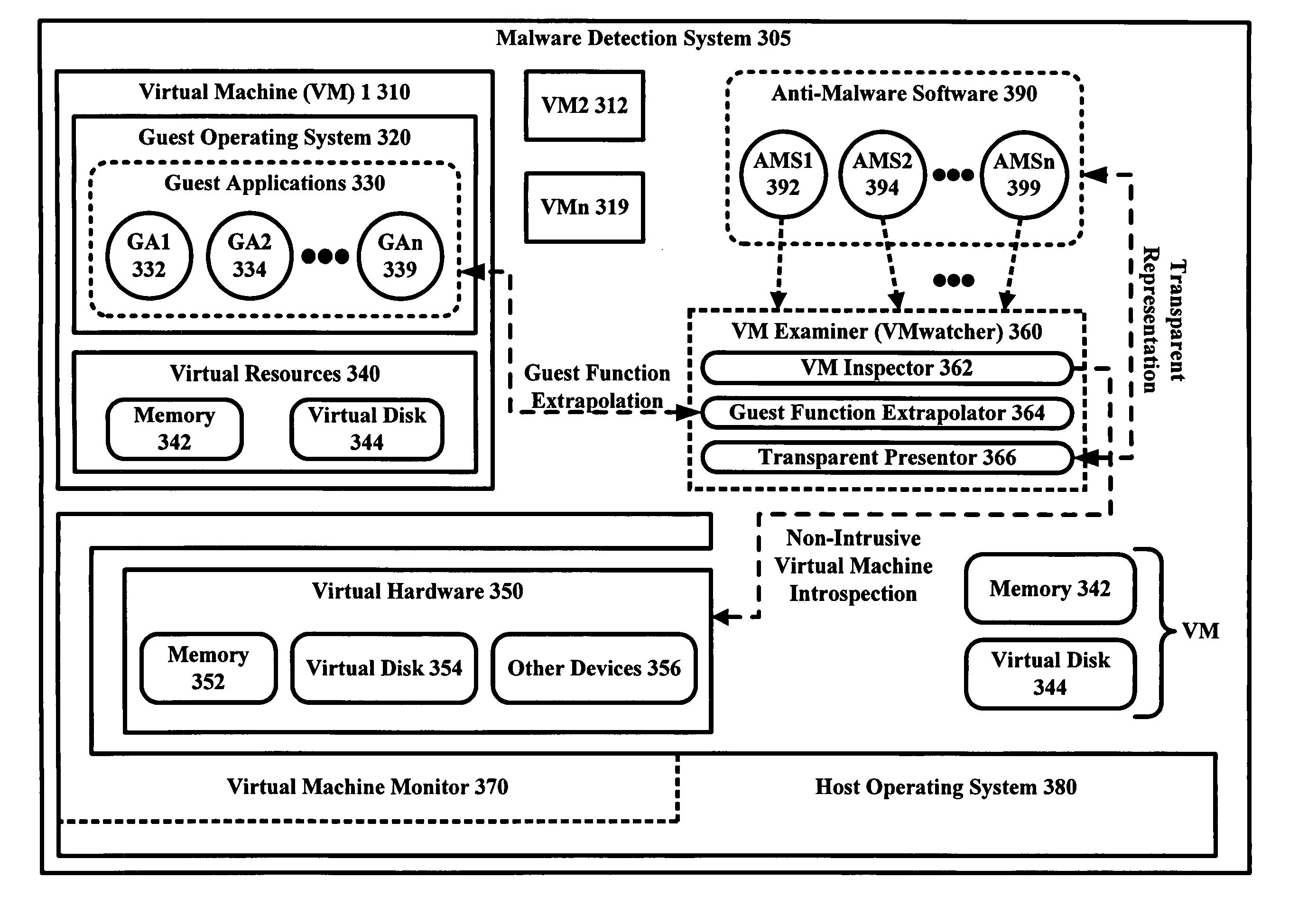
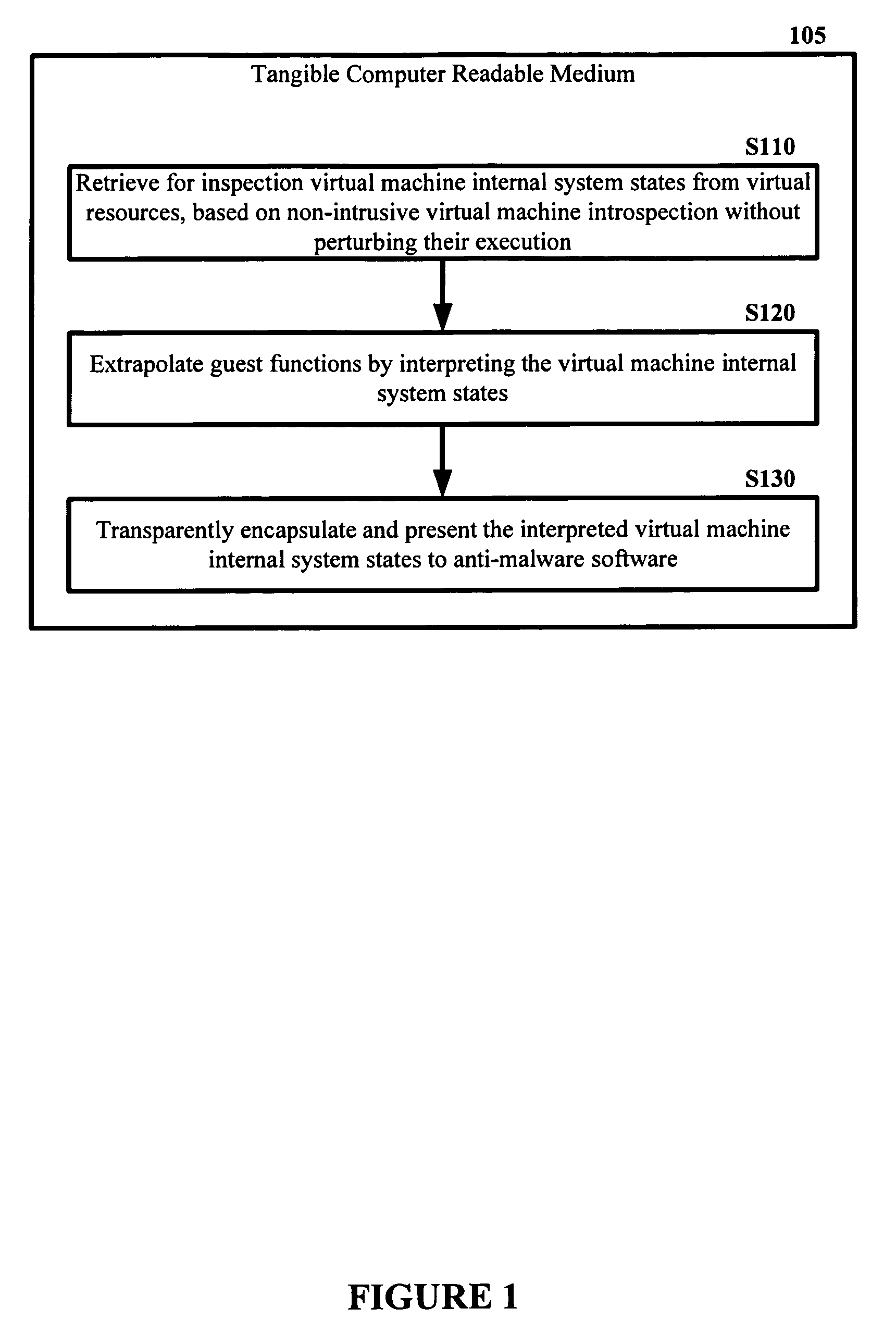
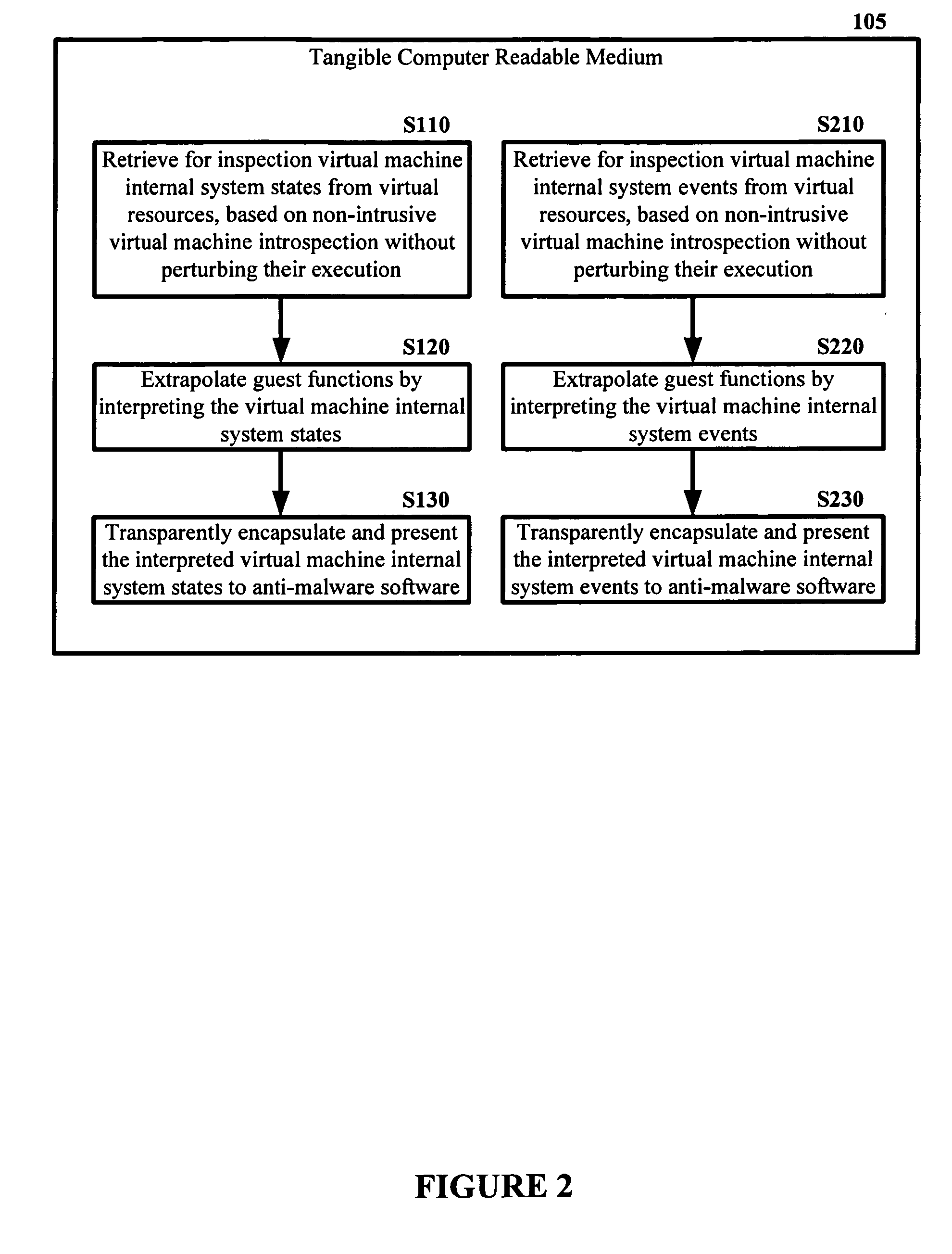
The malware detection system enables out-of-the box, tamper-resistant malware detection without losing the semantic view. This system comprises at least one guest operating system and at least one virtual machine, where the guest operating system runs on the virtual machine. Having virtual resources, the virtual machine resides on a host operating system. The virtual resources include virtual memory and at least one virtual disk. A virtual machine examiner is used to examine the virtual machine. With a virtual machine inspector, a guest function extrapolator, and a transparent presenter, the virtual machine examiner resides outside the virtual machine. The virtual machine inspector is configured to retrieve virtual machine internal system states and / or events. The guest function extrapolator is configured to interpret such states and / or events. The transparent presenter is configured to present the interpreted states and / or events to anti-malware software. The anti-malware software is configured to use the interpreted states and / or events to detect any system compromise.
Owner:GEORGE MASON INTPROP INC
Virtual data center that allocates and manages system resources across multiple nodes
ActiveUS20070067435A1Improve securityExcessive removalError detection/correctionMemory adressing/allocation/relocationOperational systemData center
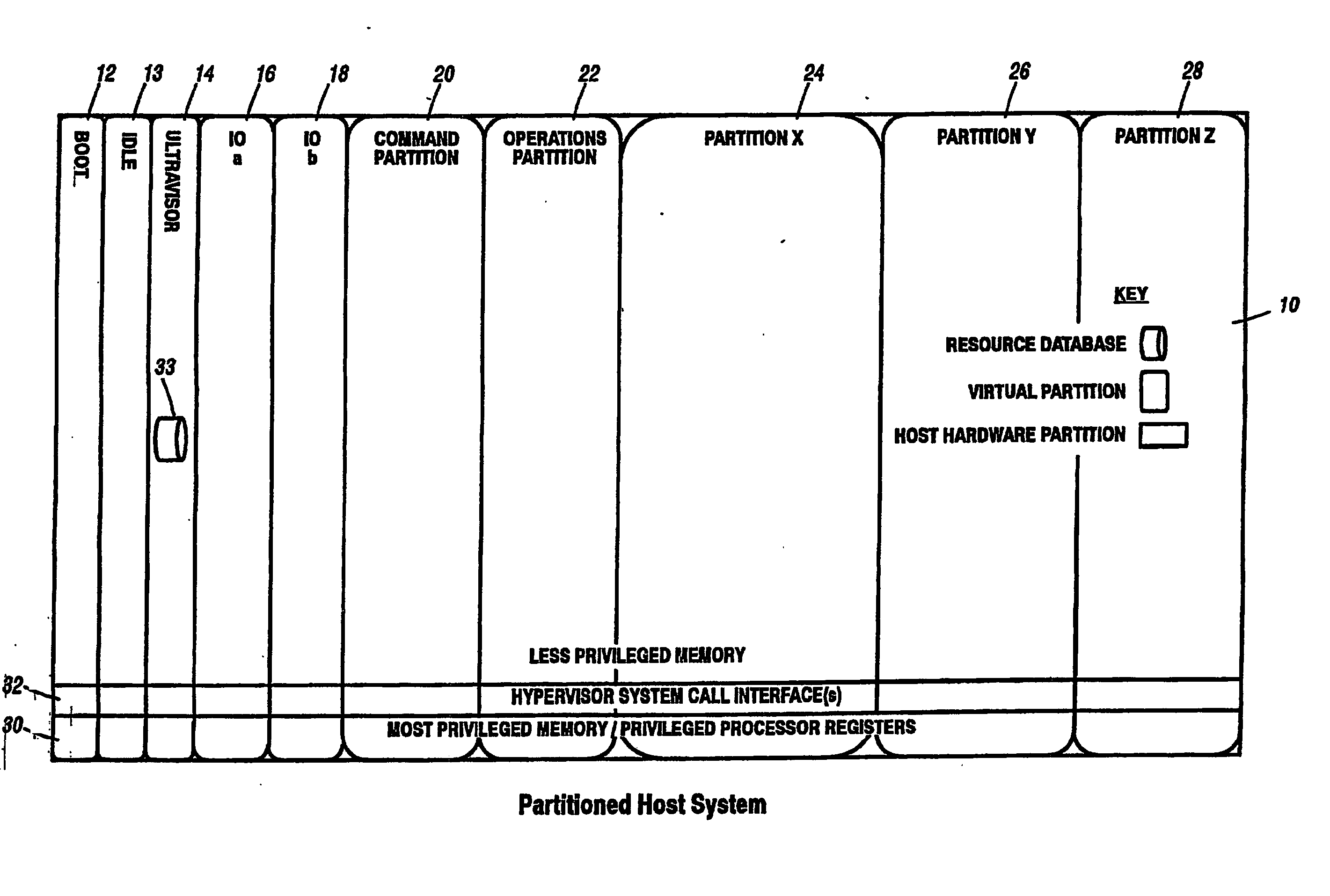
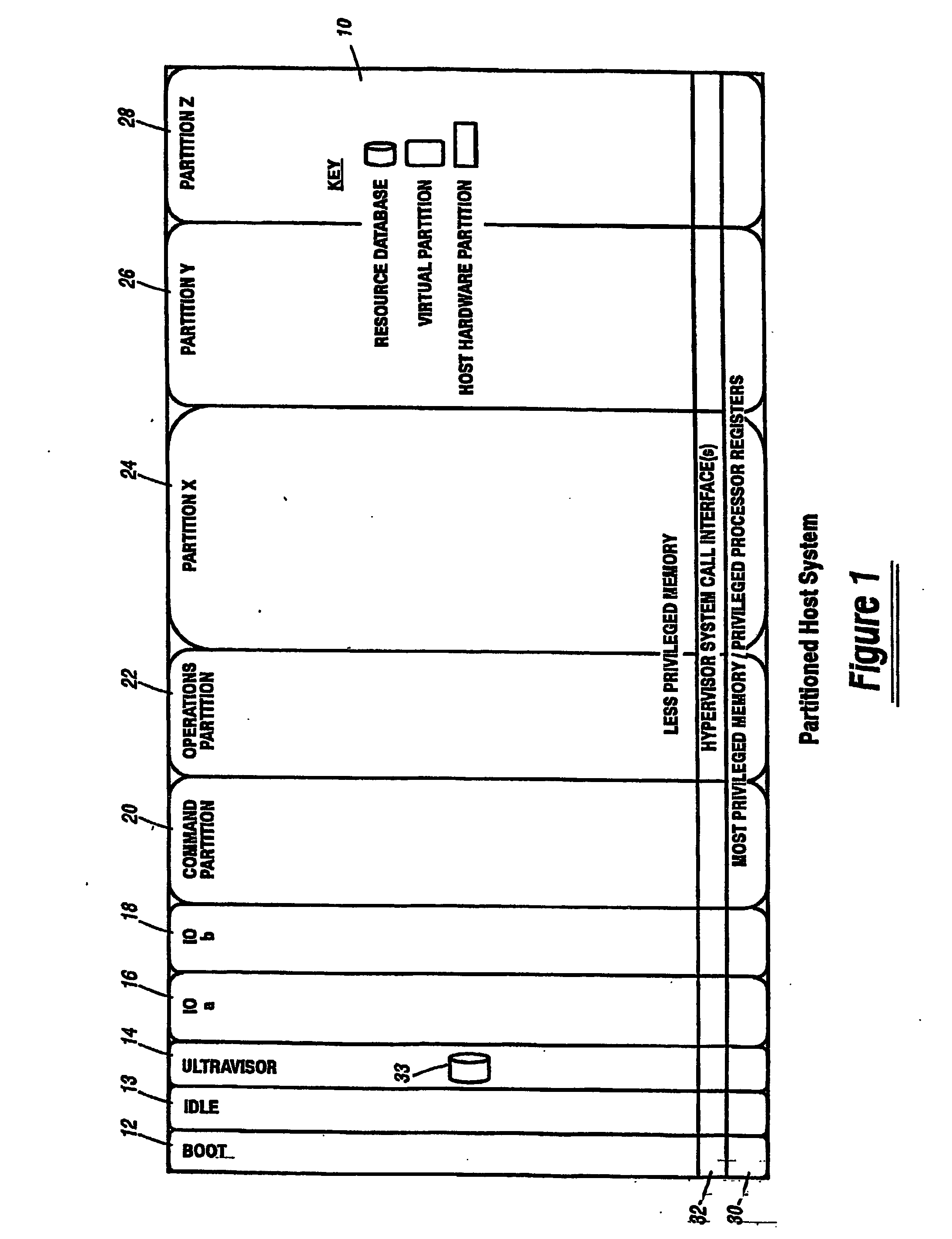
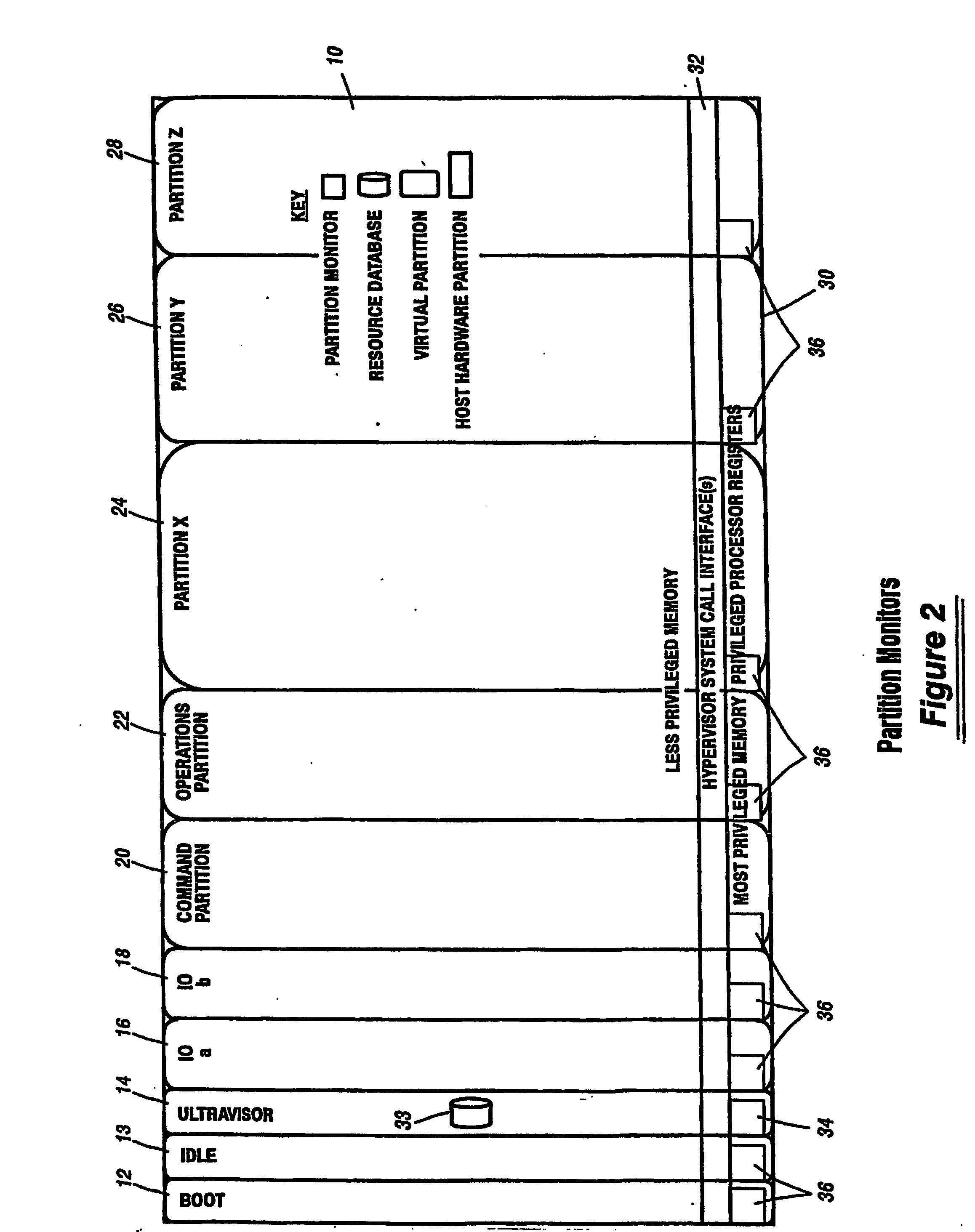
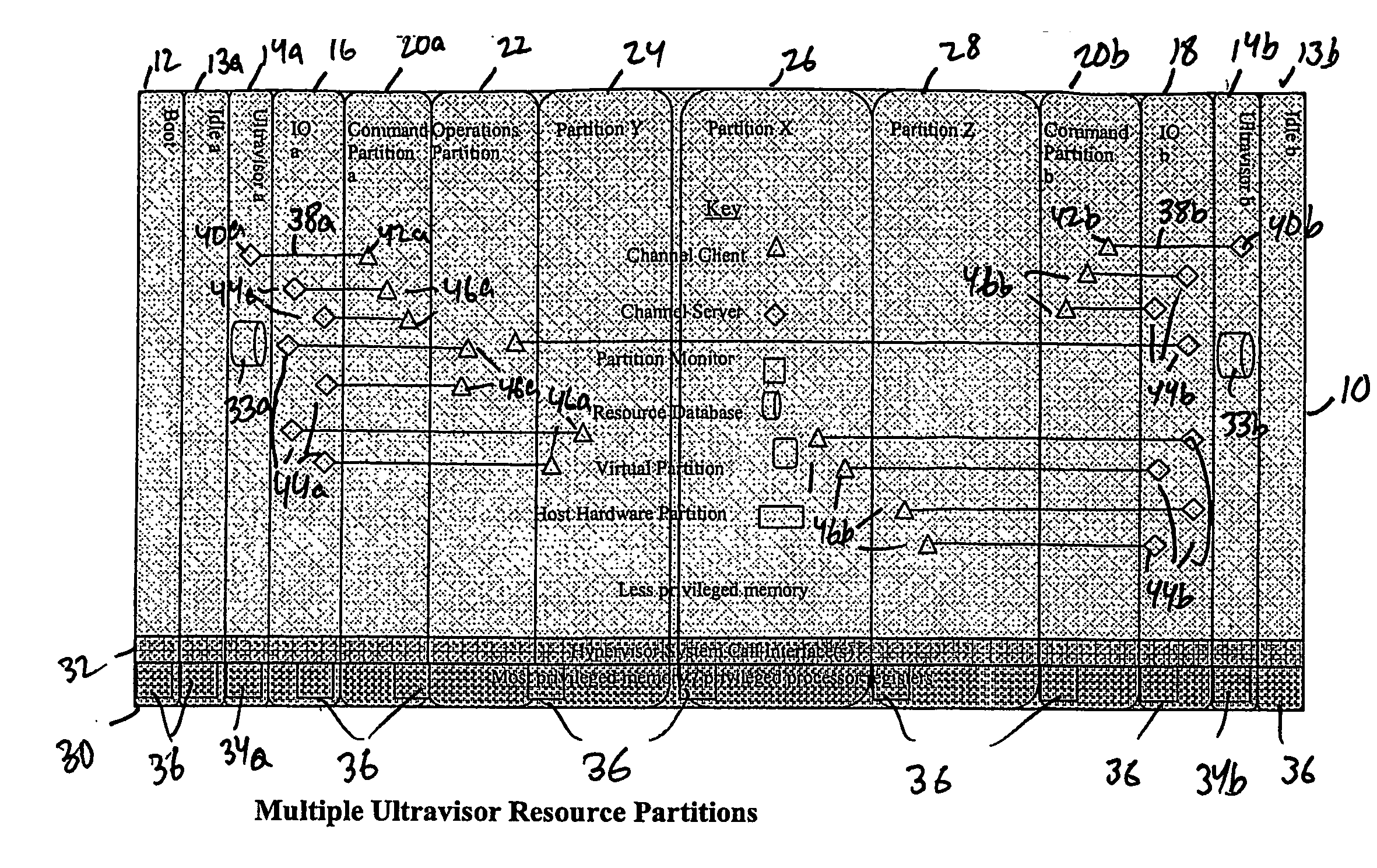
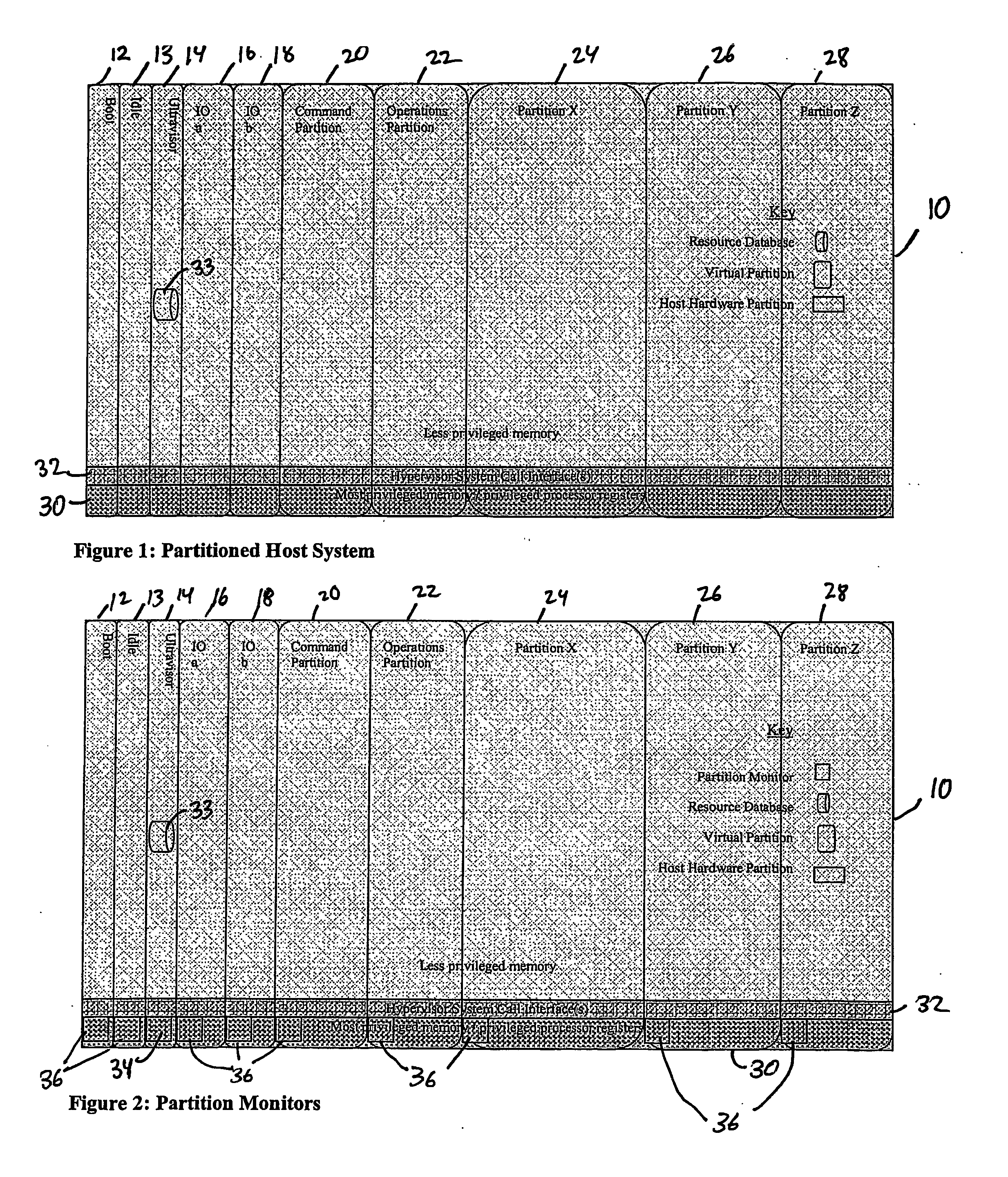
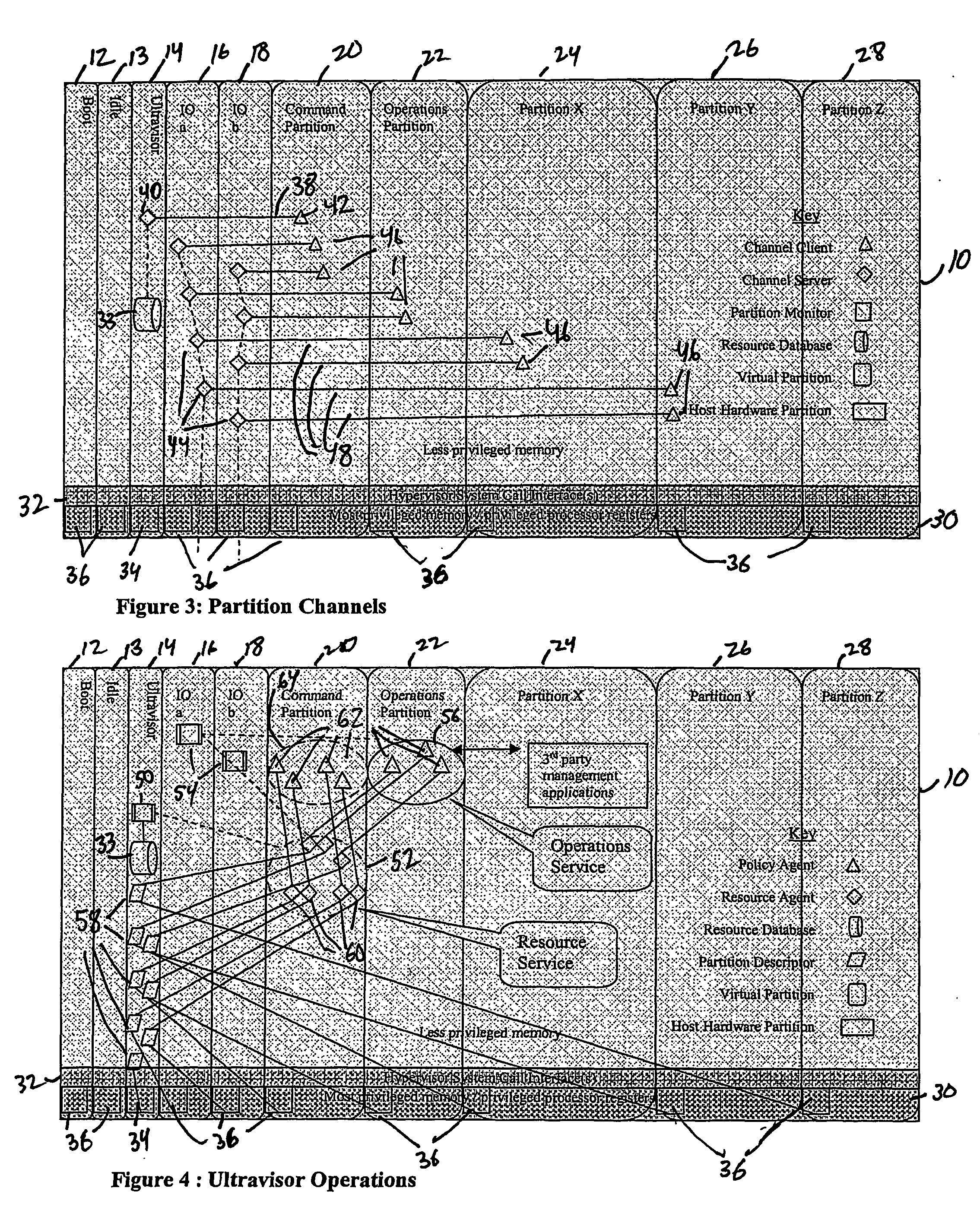
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. Operating systems in other logical or virtual partitions communicate with the I / O partitions via memory channels established by the ultravisor partition. The guest operating systems in the respective logical or virtual partitions are modified to access monitors that implement a system call interface through which the ultravisor, I / O, and any other special infrastructure partitions may initiate communications with each other and with the respective guest partitions. The guest operating systems are modified so that they do not attempt to use the “broken” instructions in the x86 system that complete virtualization systems must resolve by inserting traps. System resources are separated into zones that are managed by a separate partition containing resource management policies that may be implemented across nodes to implement a virtual data center.
Owner:UNISYS CORP
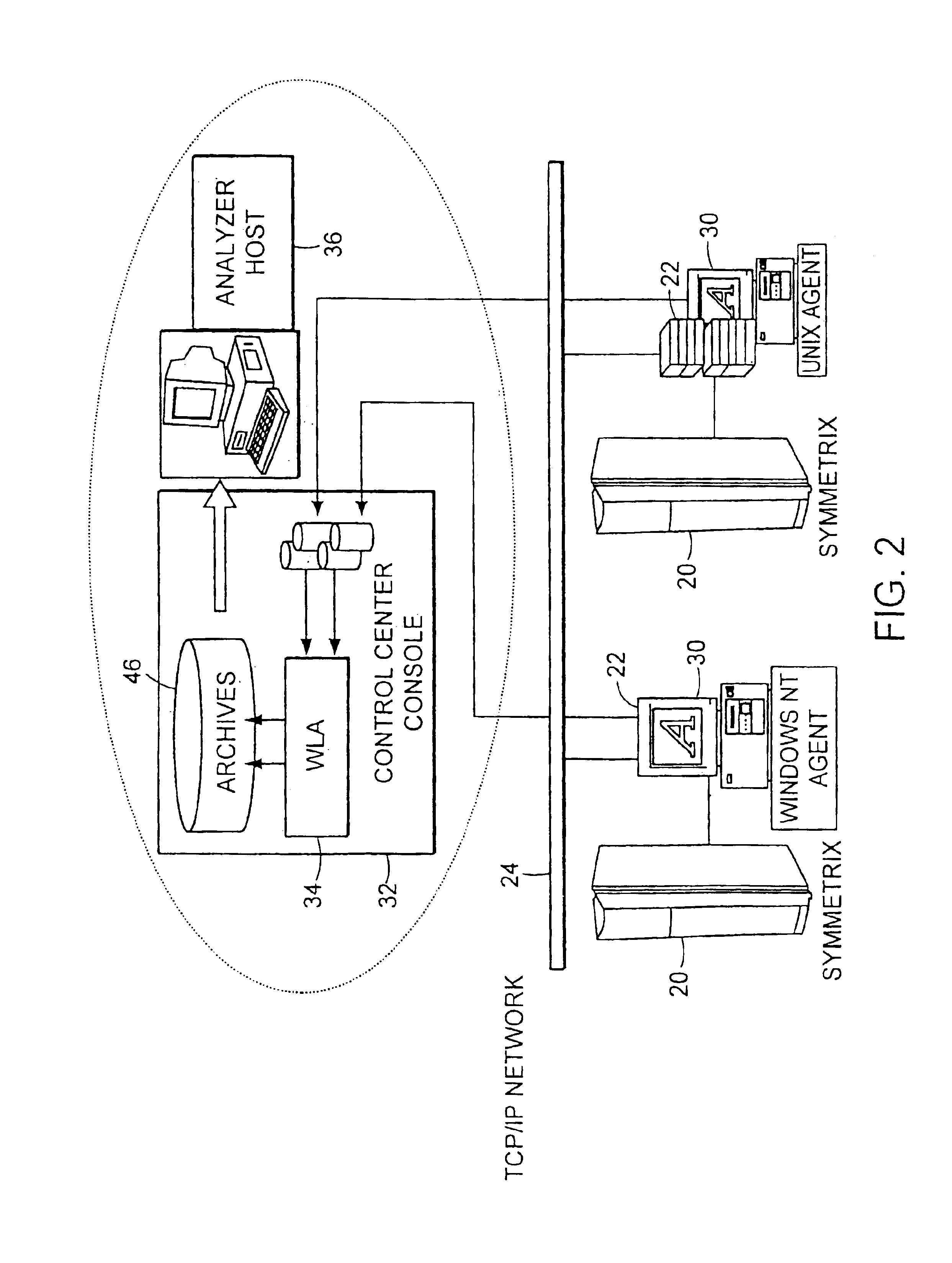
Method and apparatus for storage system metrics management and archive
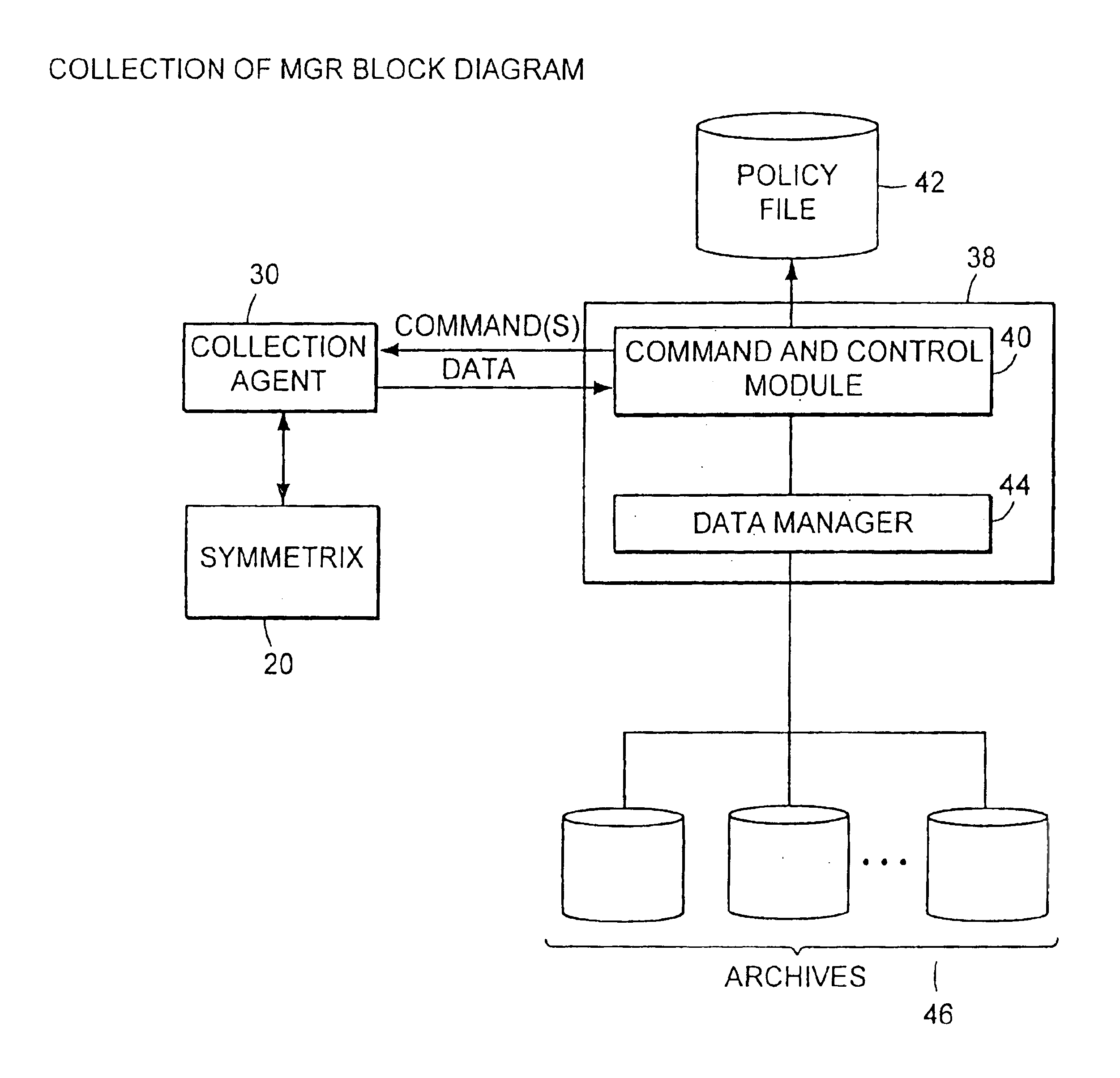
InactiveUS6886020B1Promote generationEasy accessData processing applicationsDigital data information retrievalCommand and controlData management
A data management and archive method and apparatus, such as for implementation in an automated system to monitor and manage status, performance and configuration data for a plurality of networked storage components. Analysis and cross-correlation of data related to the plurality of storage components can be done individually, collectively and / or comparatively. A collection manager component of a workload analyzer is implemented to start and stop data collection in the context of a system comprising at least one storage component (or at least two networked storage components). The collection manager includes a command and control module that coordinates requests of data from at least one collection agent configured on at least one host connected to the storage component(s).
Owner:EMC IP HLDG CO LLC
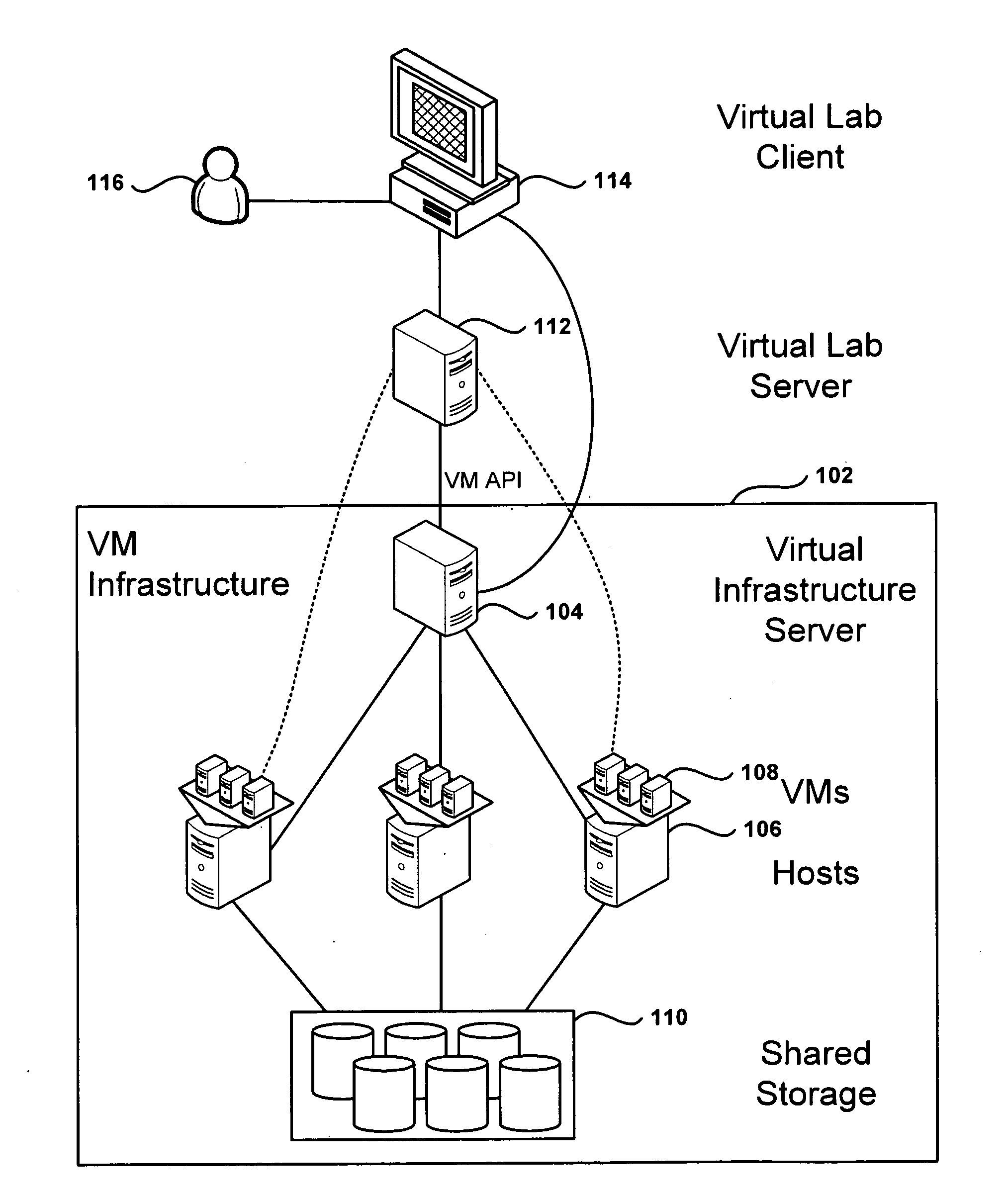
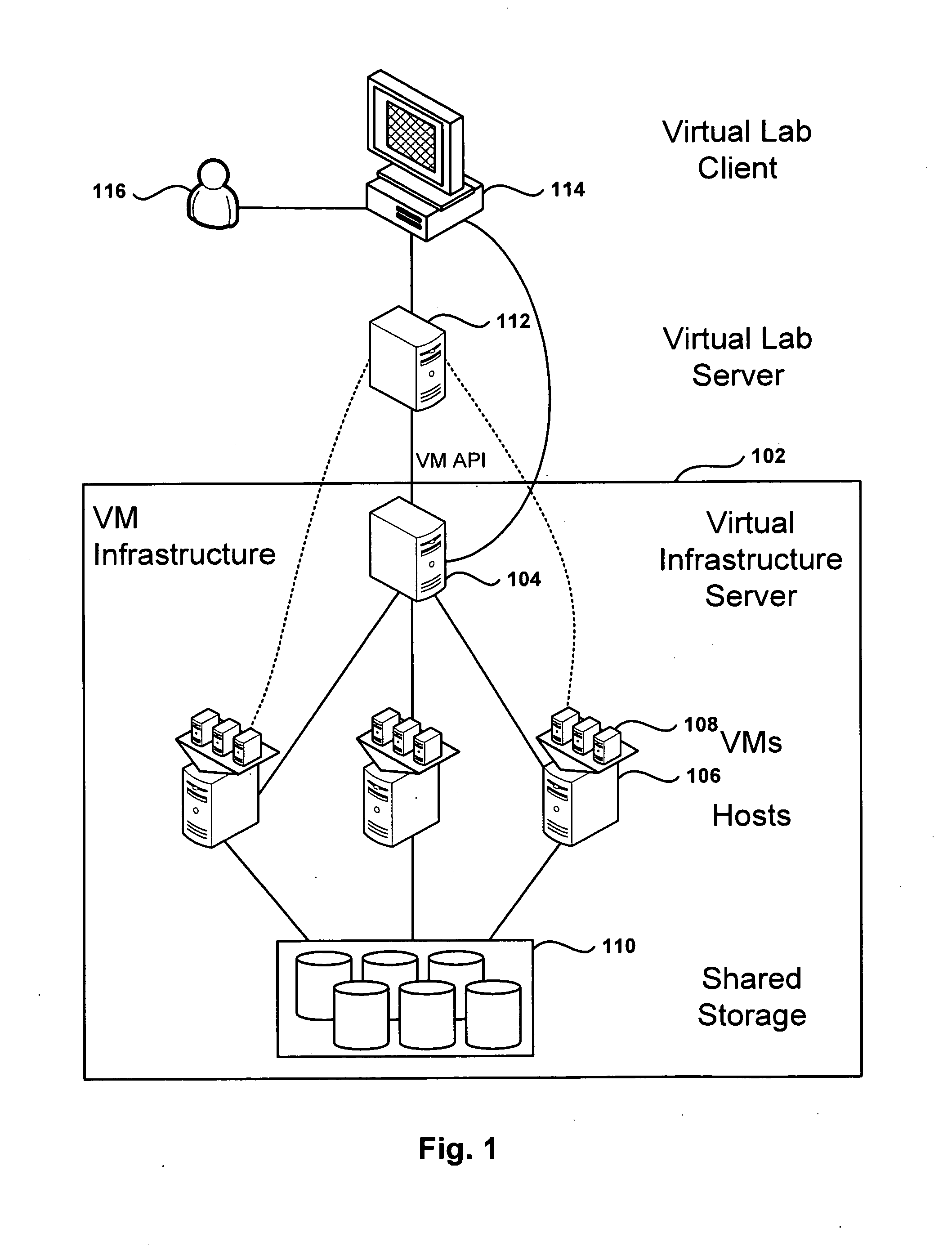
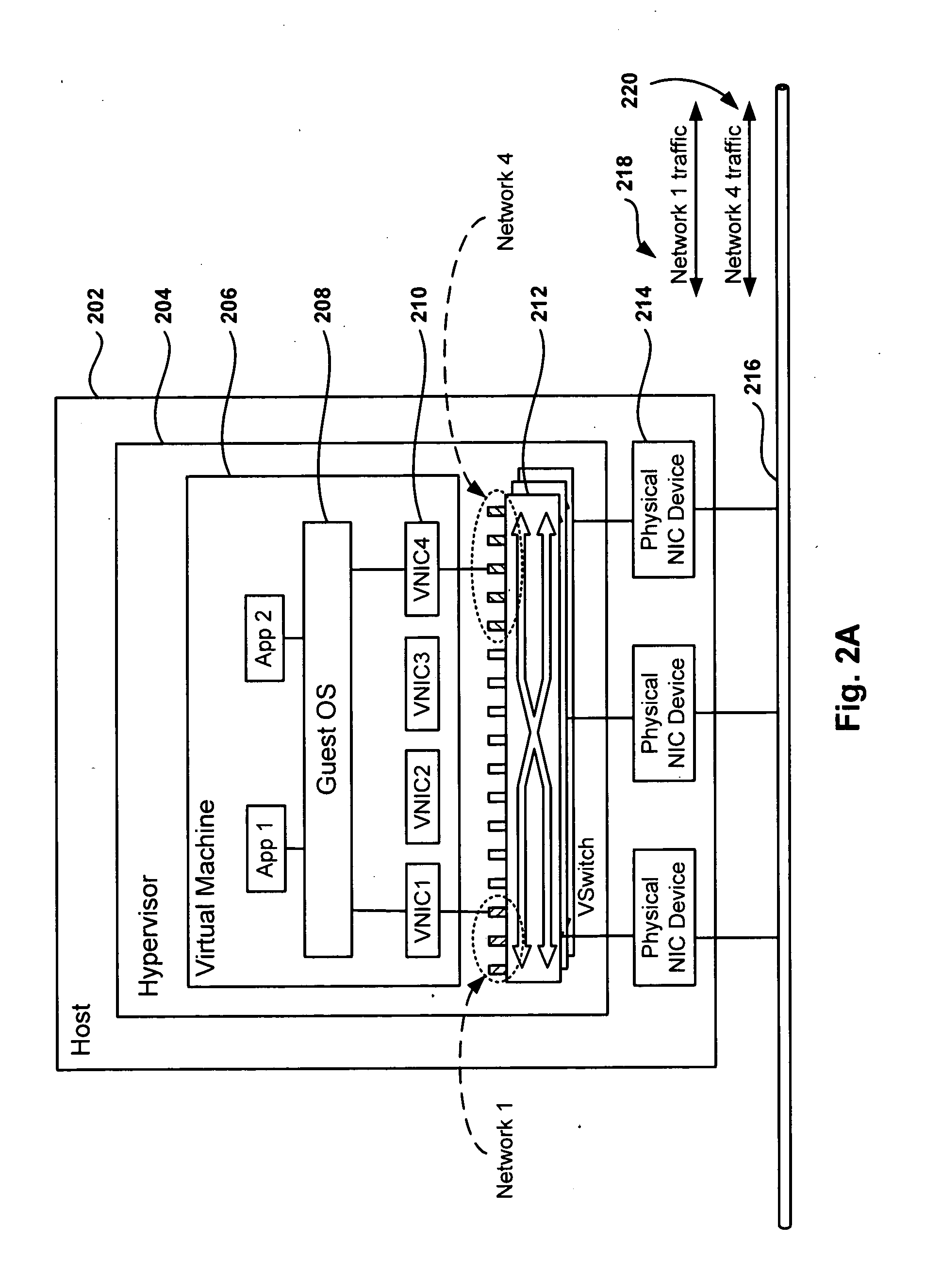
Management and Implementation of Enclosed Local Networks in a Virtual Lab
Methods, systems, and computer programs for creating isolated environments that include virtual machines (VM) and networks in a virtual infrastructure are presented. The method includes an operation to define a configuration of a virtual system which includes VMs, virtual network interface cards (VNIC) in the VMs, and configuration local networks (CLN). Further, the method associates each VNIC with one of the CLNs and transmits instructions to the virtual infrastructure for deploying the configuration. Deploying the configuration includes instantiating VMs and CLNs in the virtual infrastructure. Each VM is instantiated in a host monitored by a virtual lab server, and the CLNs are instantiated in the same hosts where the VMs have been instantiated. Only VMs from the configuration can connect to the instantiated CLNs. The method further transmits instructions to the virtual infrastructure to customize the VMs by executing the customization instructions in the guest operating systems of the VMs to configure the VMs' VNICs.
Owner:VMWARE INC
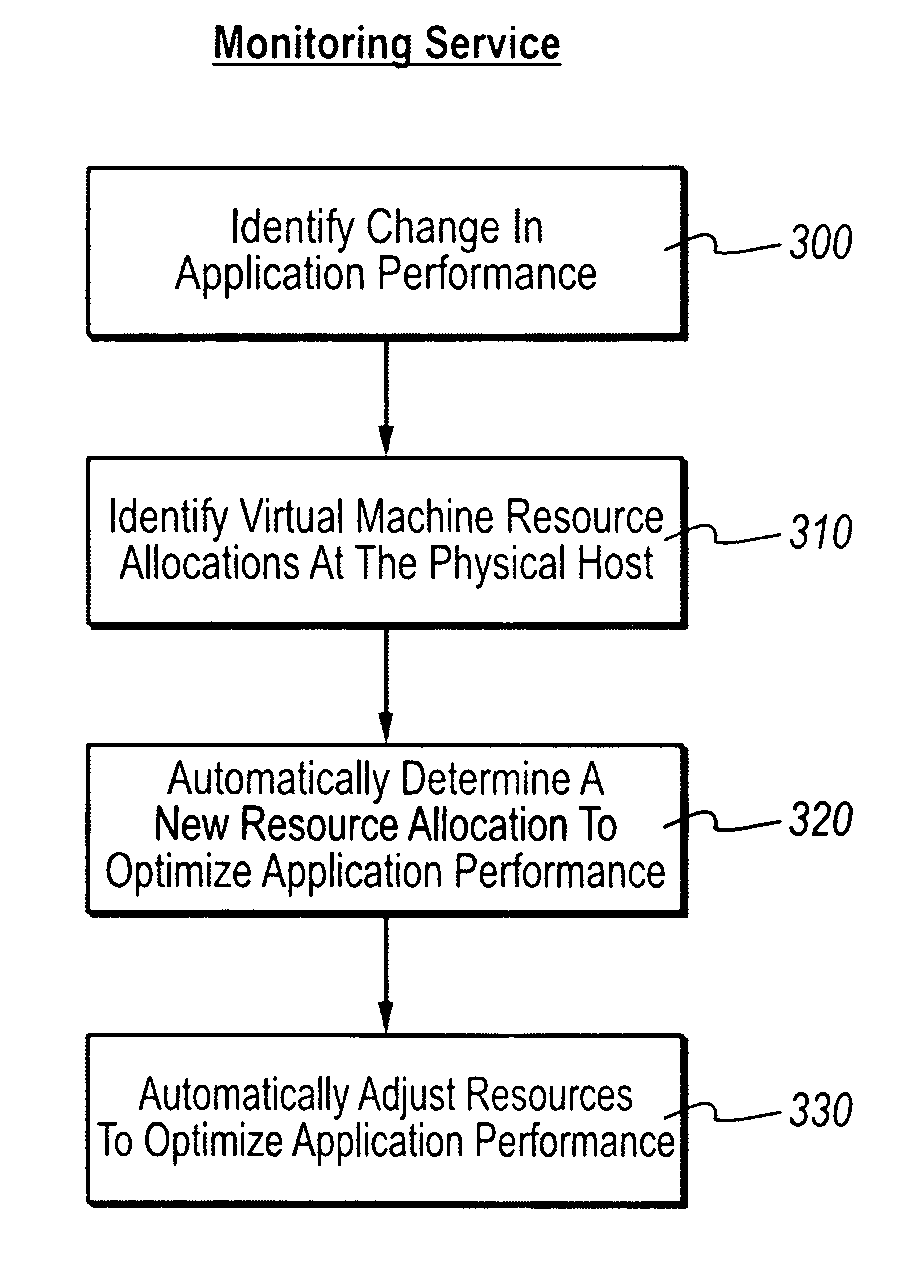
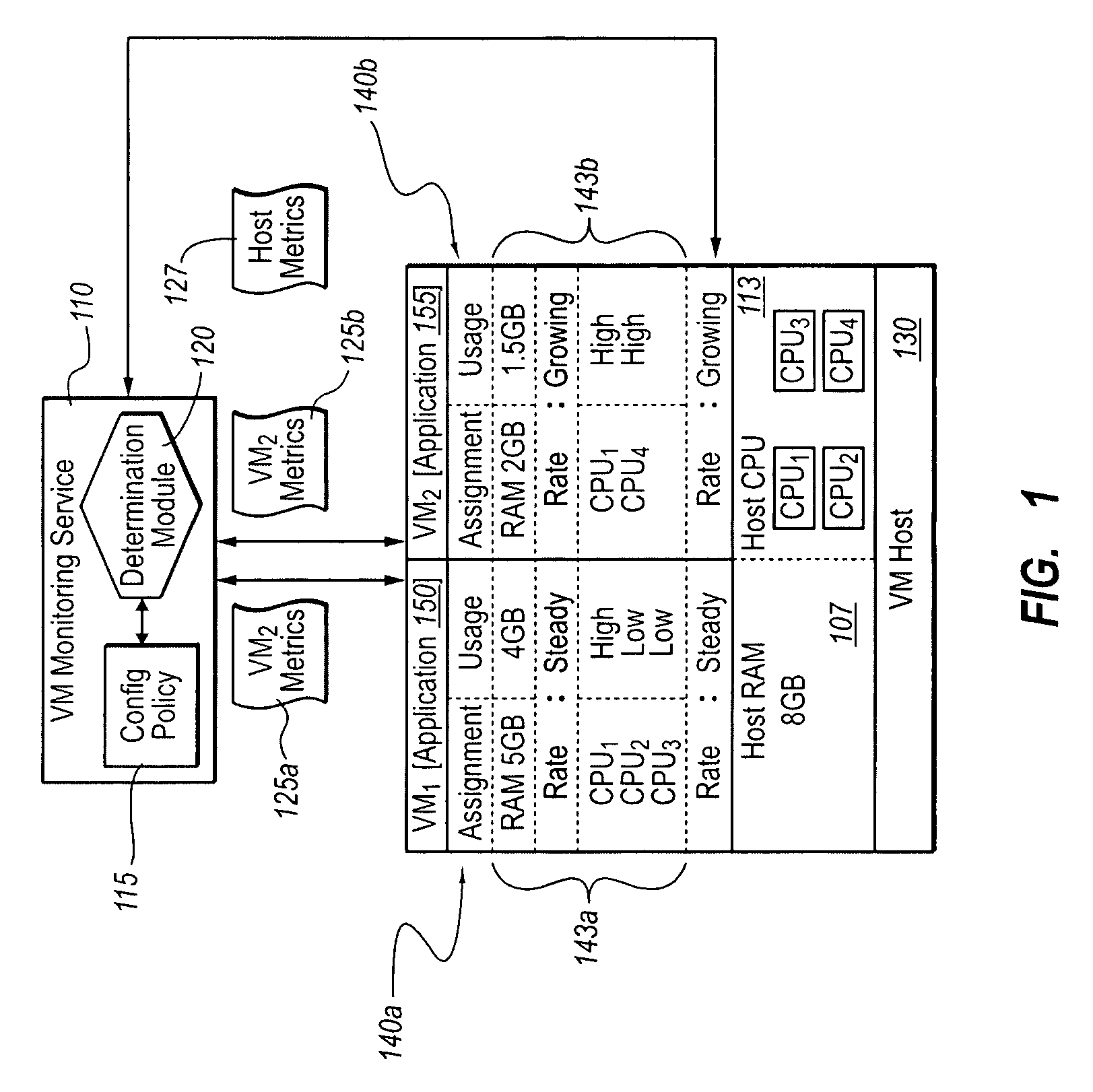
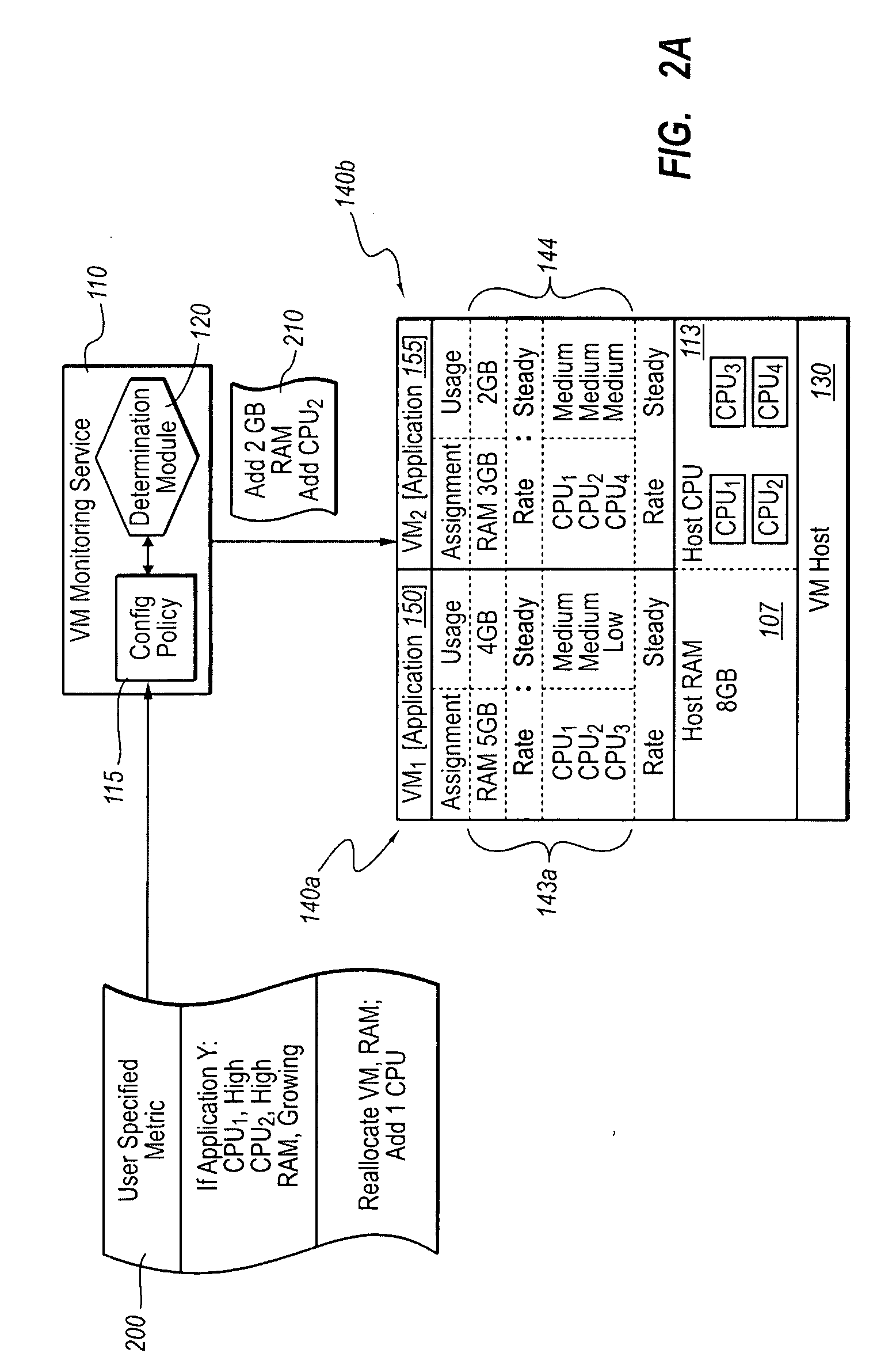
Optimizing application performance on virtual machines automatically with end-user preferences
InactiveUS20090265707A1Improve performanceError detection/correctionMultiprogramming arrangementsUser inputResource utilization
A virtual machine management / monitoring service can be configured to automatically monitor and implement user-defined (e.g., administrator-defined) configuration policies with respect to virtual machine and application resource utilization. In one implementation, the monitoring service can be extended to provide user-customized alerts based on various particularly defined events that occur (e.g., some memory or processing threshold) during operation of the virtual machines and / or application execution. The user can also specify particularly tailored solutions, which can include automatically reallocating physical host resources without additional user input on a given physical host, or moving / adding virtual machines on other physical hosts. For example, the monitoring service can be configured so that, upon identifying that a virtual machine's memory and processing resources are maxed out and / or growing, the monitoring service adds memory or processing resources for the virtual machine, or adds a new virtual machine to handle the load for the application program.
Owner:MICROSOFT TECH LICENSING LLC
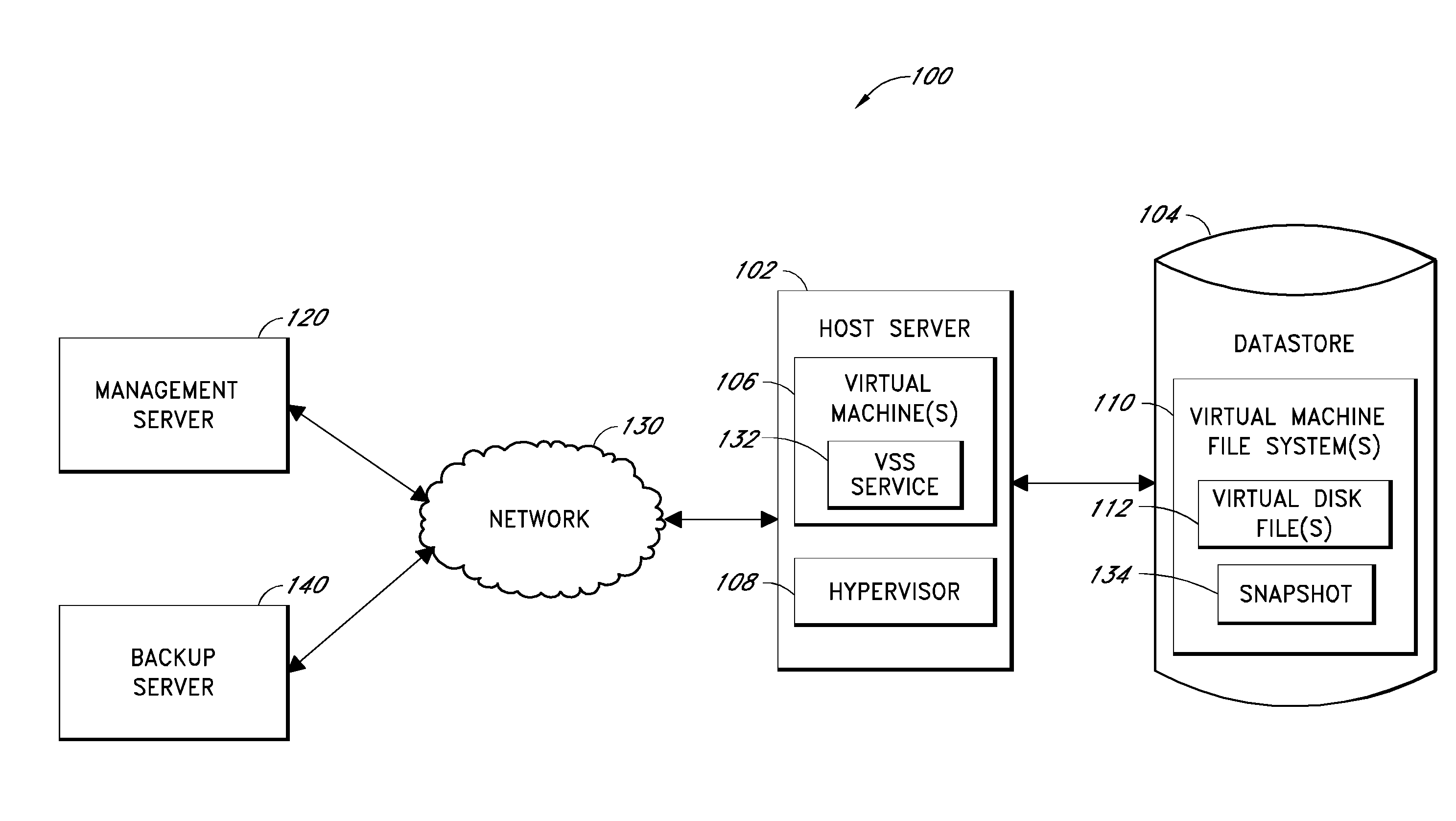
Systems and methods for performing backup operations of virtual machine files
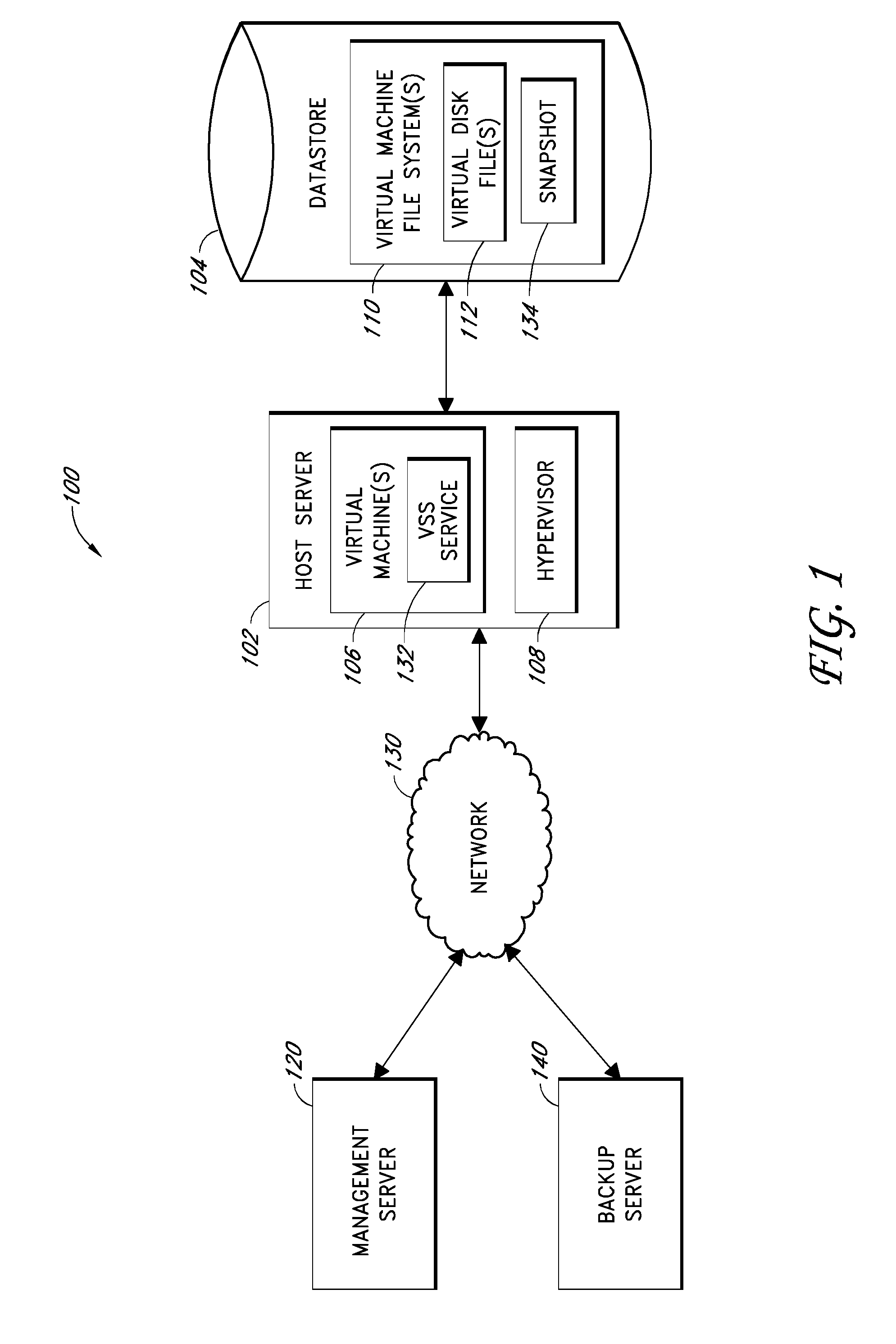
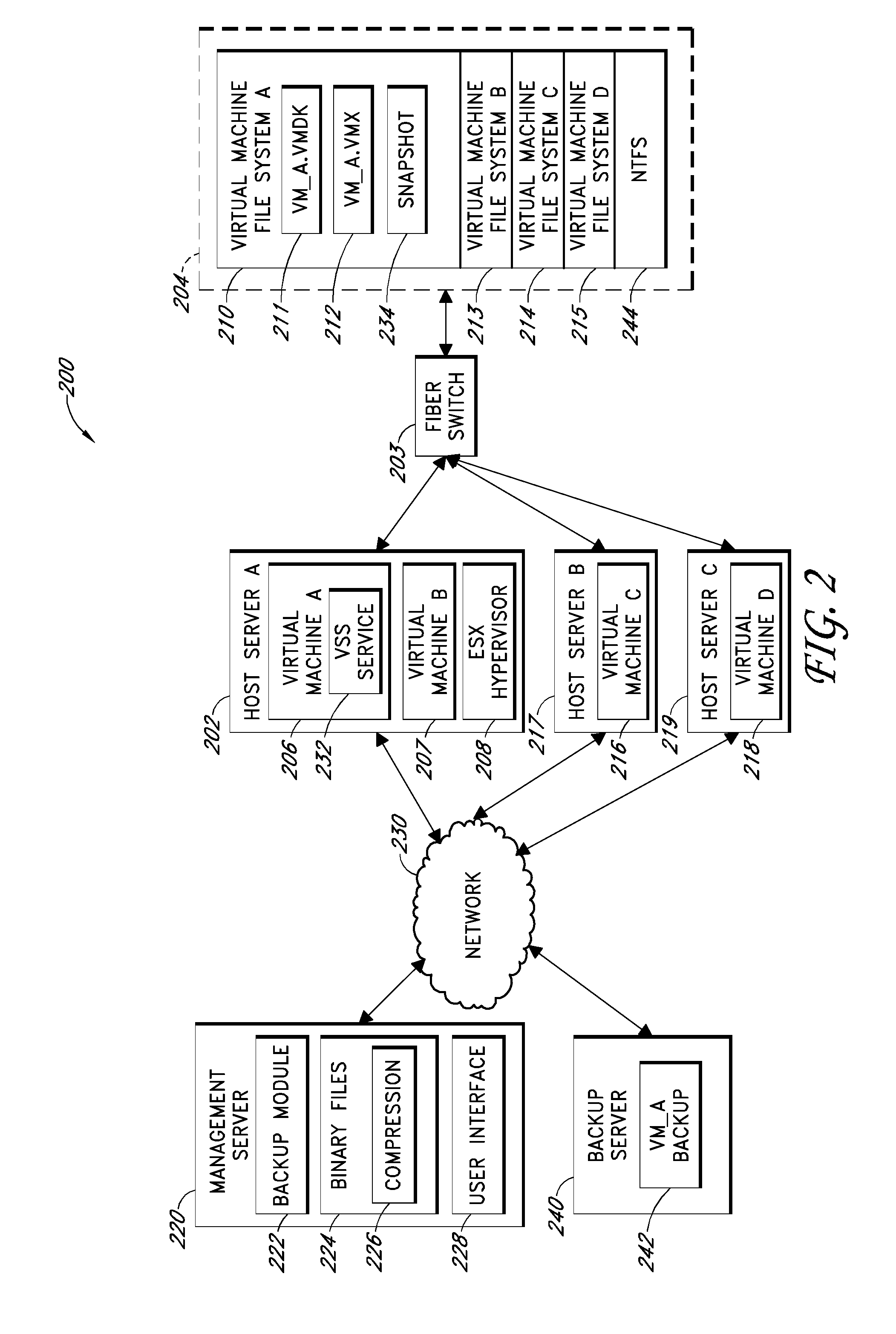
ActiveUS20100011178A1Memory loss protectionError detection/correctionCommunications managementOperational system
Backup systems and methods are disclosed for a virtual computing environment. Certain examples include a system having a backup management server that communicates with a host server having at least one virtual machine. The management server coordinates with the host server to perform backup copies of entire virtual machine disks from outside the guest operating system of the virtual machine. In certain examples, such backup systems further utilize a volume shadow copy service executing on the host server to quiesce virtual machine applications to put data in a consistent state to be backed up. The backup system then utilizes hypervisor snapshot capabilities of the host server to record intended changes to the virtual machine disk files while such files are being copied (e.g., backed up) by the host server. Such recorded changes can be later committed to the virtual machine disk files once the backup operation has completed.
Owner:QUEST SOFTWARE INC
System and method for launching a resource in a network
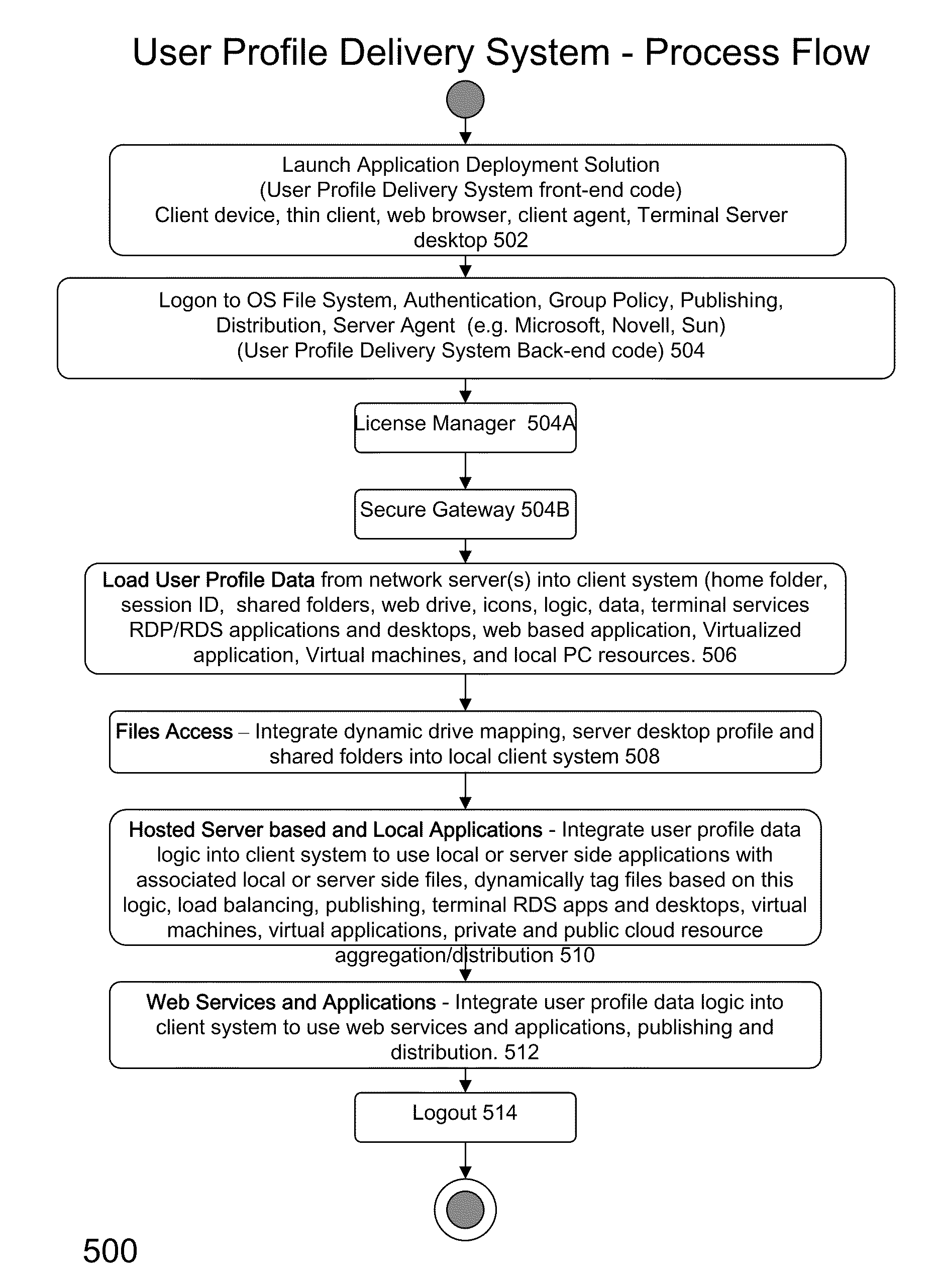
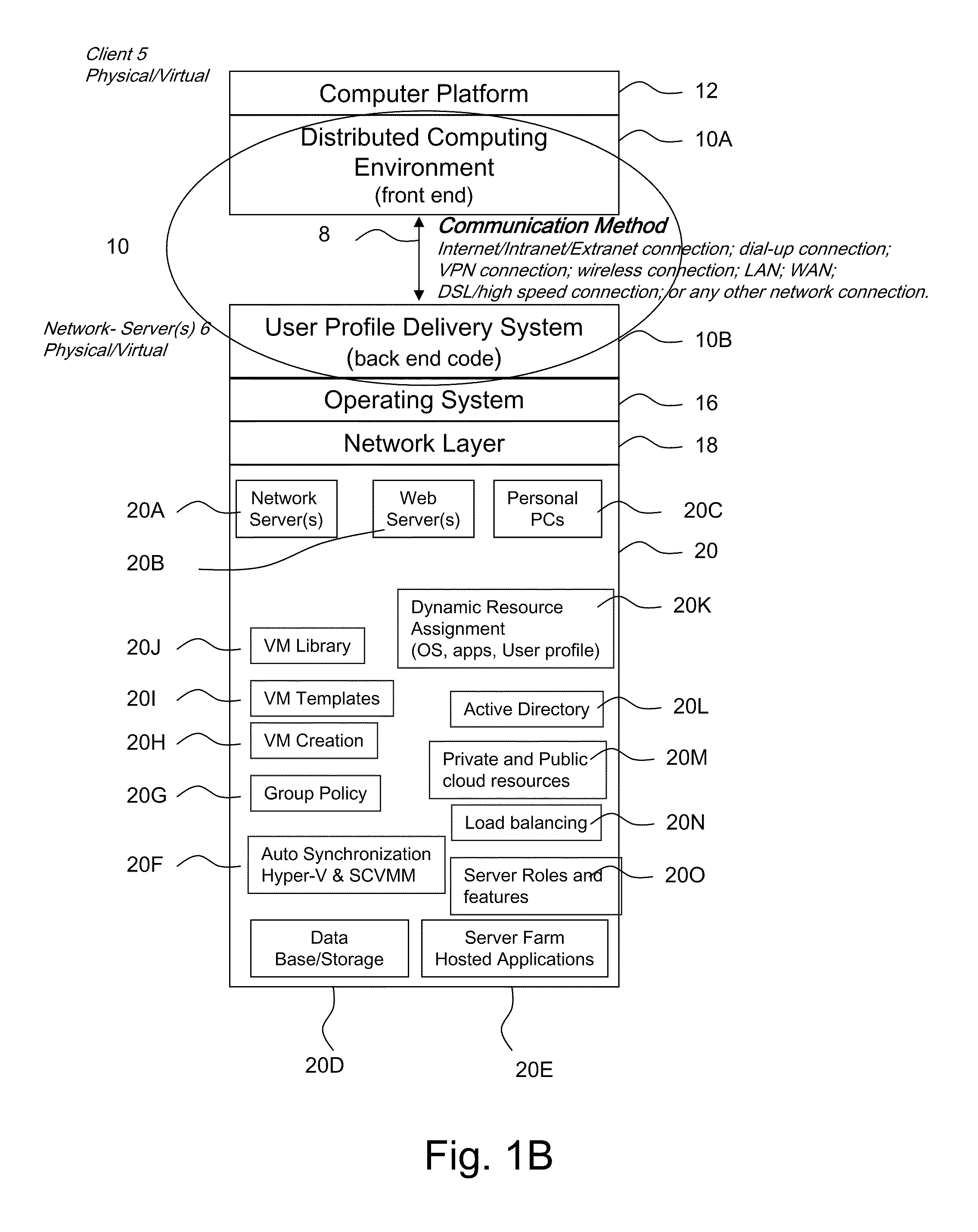
ActiveUS20110251992A1Provide controlDigital data processing detailsWireless commuication servicesOperational systemDirectory structure
The disclosure provides a system and method for a client connected to a server to a resource in a network. For the system a virtual machine module is provided to access a library and to create virtual machine templates and to create virtual machines from the virtual machine templates. The virtual machine module provides to a host machine in the network access to machines, user profile settings and instances of an application in the network and to multiple operating systems. The client has: access to an instance of the resource; an access module to provide the client with communication to access to the server using load balancing algorithms to access the file using Remote Desktop Protocol (RDP) commands; and an authentication module providing access to a directory structure accessed by the server using Microsoft Group Policy Objects (GPOs) and Active Directory (AD) services to authenticate the client with the server.
Owner:DESKTOPSITES
Personal shopping system
The present invention relates to a personal shopping system for combined use in both the home of a user and a shopping establishment. The system includes a host computer which is coupled to a host modem and, optionally, to at least one wireless multi-access point. The portable terminal can be used in both the shopping establishment and the home of the user. It is configured to read bar codes associated with items related to shopping, and includes a memory, a bar code reader, a wireless transceiver, and a data interface. The data interface of the terminal communicates with a data interface of the shopping establishment kiosk cradle or directly with the shopping establishment's communications network.
Owner:SYMBOL TECH LLC
System and method for providing mobile access to personal media
InactiveUS20060173974A1Facilitates authorized accessEasy accessMultiple digital computer combinationsTransmissionPersonalizationClient-side
The invention is a media access system. A multipoint installation may create a connection system which permits client devices, such as wireless media playback devices, to connect to host devices in a partnered relationship which permits authorized access to selected media located on the host device, without a need to physically synchronize the partnered client devices. Playback of media content may be configured on a variety of devices where new media content may be offered for purchase. Furthermore, the system permits authorized storage of additional selected media on the host devices. A personalized music radio for receiving personalized music services is also described. Media accessed may be tracked and stored along with user preferences in a personalization engine.
Owner:TANG VICTOR
System and method for distributed facility management and operational control
ActiveUS7349761B1Programme controlSampled-variable control systemsControl systemEnvironmental control system
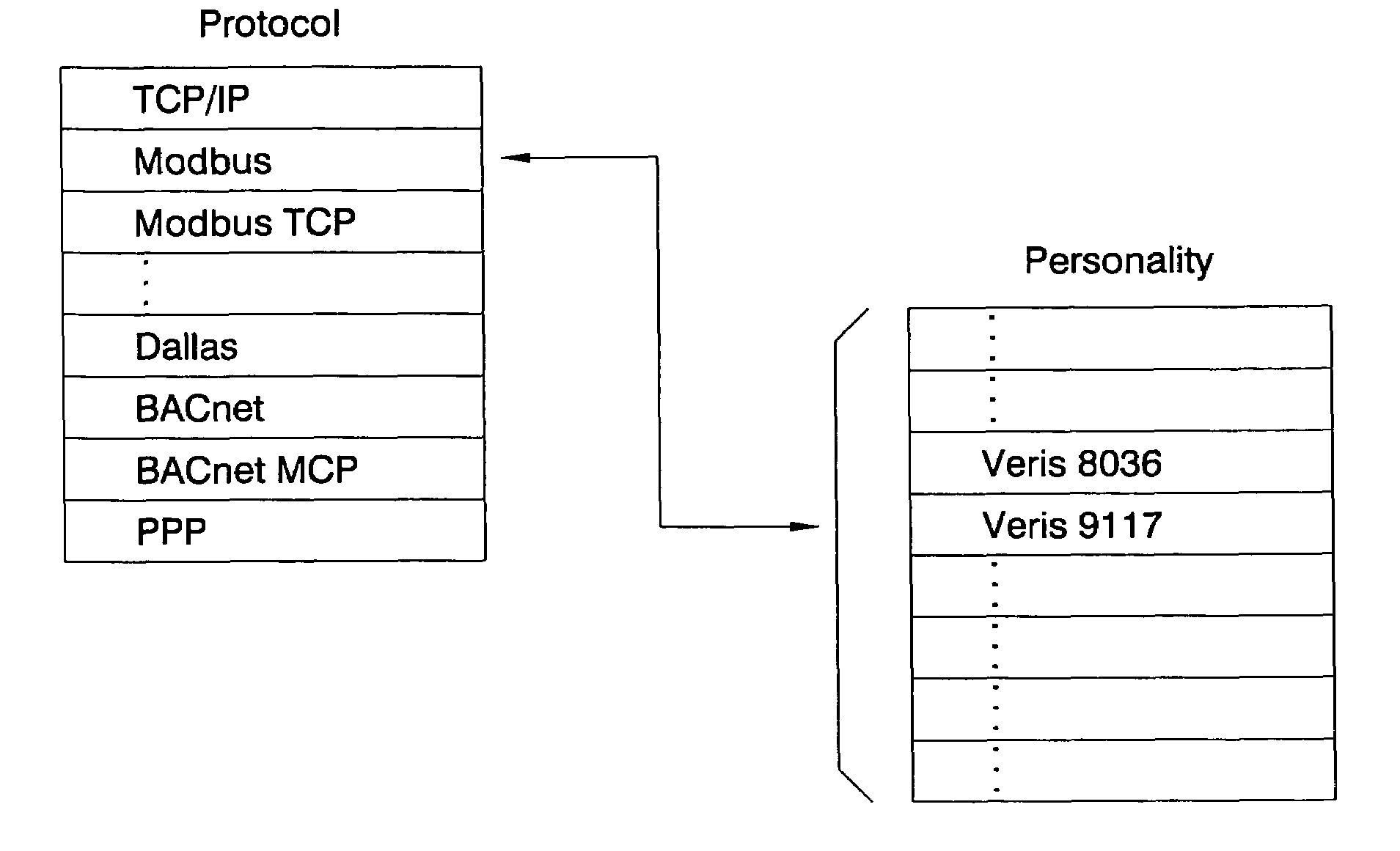
An environmental control system controls monitoring and operation of a multiplicity of disparate environmental control devices by determining an appropriate configuration for each control device and communicates corresponding monitoring and control commands to each device in accordance with its corresponding communication protocol over a selected I / O port. An operational instruction set includes a structural definition of an enterprise facility in which devices are defined by personality modules and communicate with a system host in accordance with a protocol defined in a protocol module. Facility implementation is defined by a node tree structure which collects suitable protocol nodes under a corresponding I / O interface port node. Device (personality) nodes are collected under corresponding protocol nodes, and data point nodes depend from their corresponding device nodes. Data points nodes are individually accessible by merely traversing the node tree using a URL-like notational structure, allowing off-site users to control and monitor environmental devices by issuing commands in the form of a URL.
Owner:CISCO TECH INC +1
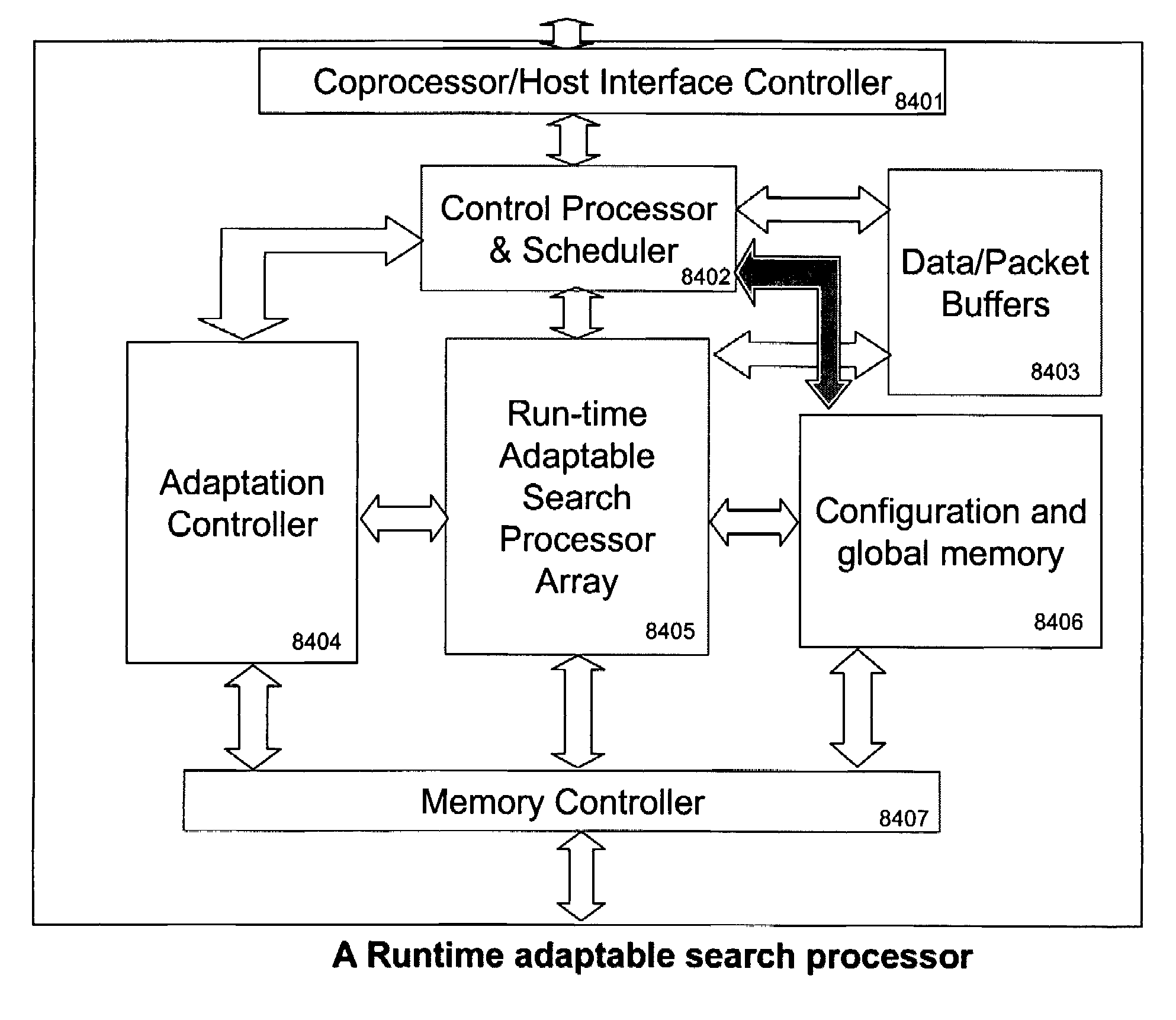
Runtime adaptable search processor
ActiveUS7685254B2Improve application performanceLarge capacityWeb data indexingMemory adressing/allocation/relocationPacket schedulingSchema for Object-Oriented XML
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. The search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. Scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
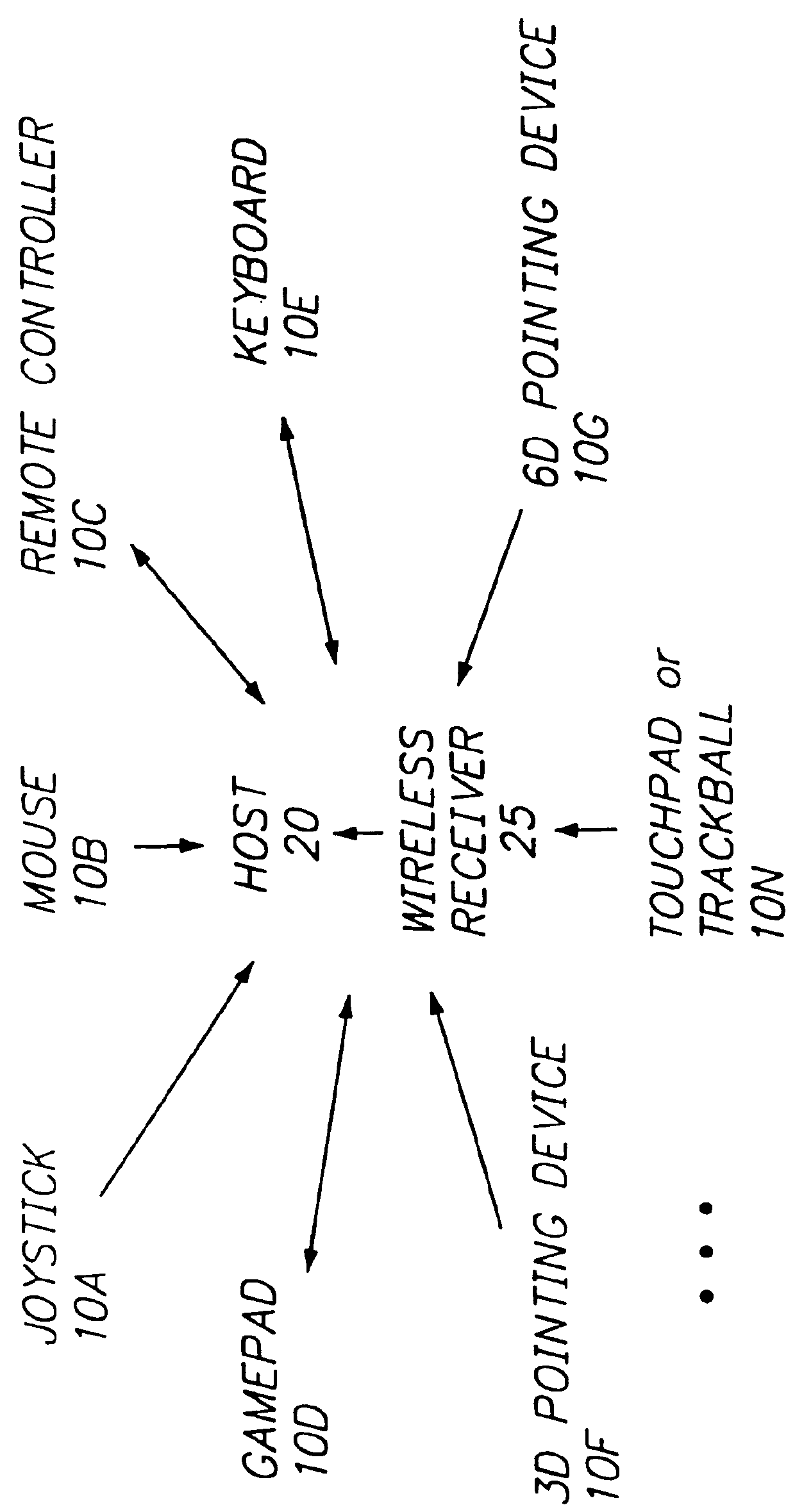
Wireless peripheral interface
InactiveUS6078789ASolve insufficient bandwidthTime-division multiplexRadio transmissionComputer hardwareJoystick
A method and apparatus for establishing a standardized communications protocol for wireless communications between a host and one or more peripheral devices such as joysticks, mice, gamepads, remote controllers or other devices including establishing a standard message format for messages communicated between a host and the peripheral devices, establishing a plurality of unique data types for associated peripheral devices, and prioritizing communications between the host and such peripherals to permit rapid and effective communication therebetween.
Owner:LOGITECH EURO SA
System for moving real-time data events across a plurality of devices in a network for simultaneous data protection, replication, and access services
ActiveUS20050262097A1Efficiently parallel processEfficiently route application-aware data changeDigital data information retrievalDigital data processing detailsData connectionData stream
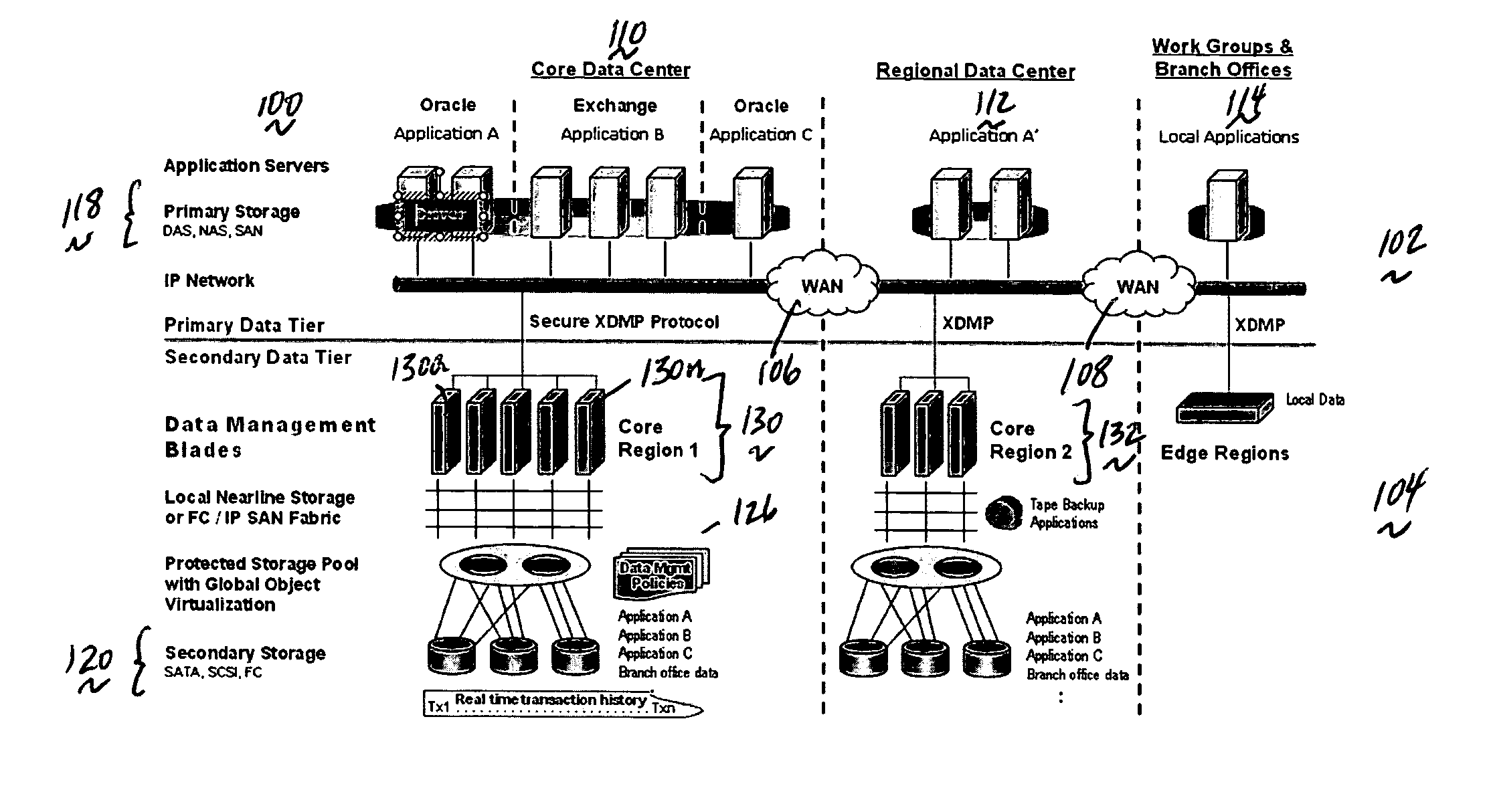
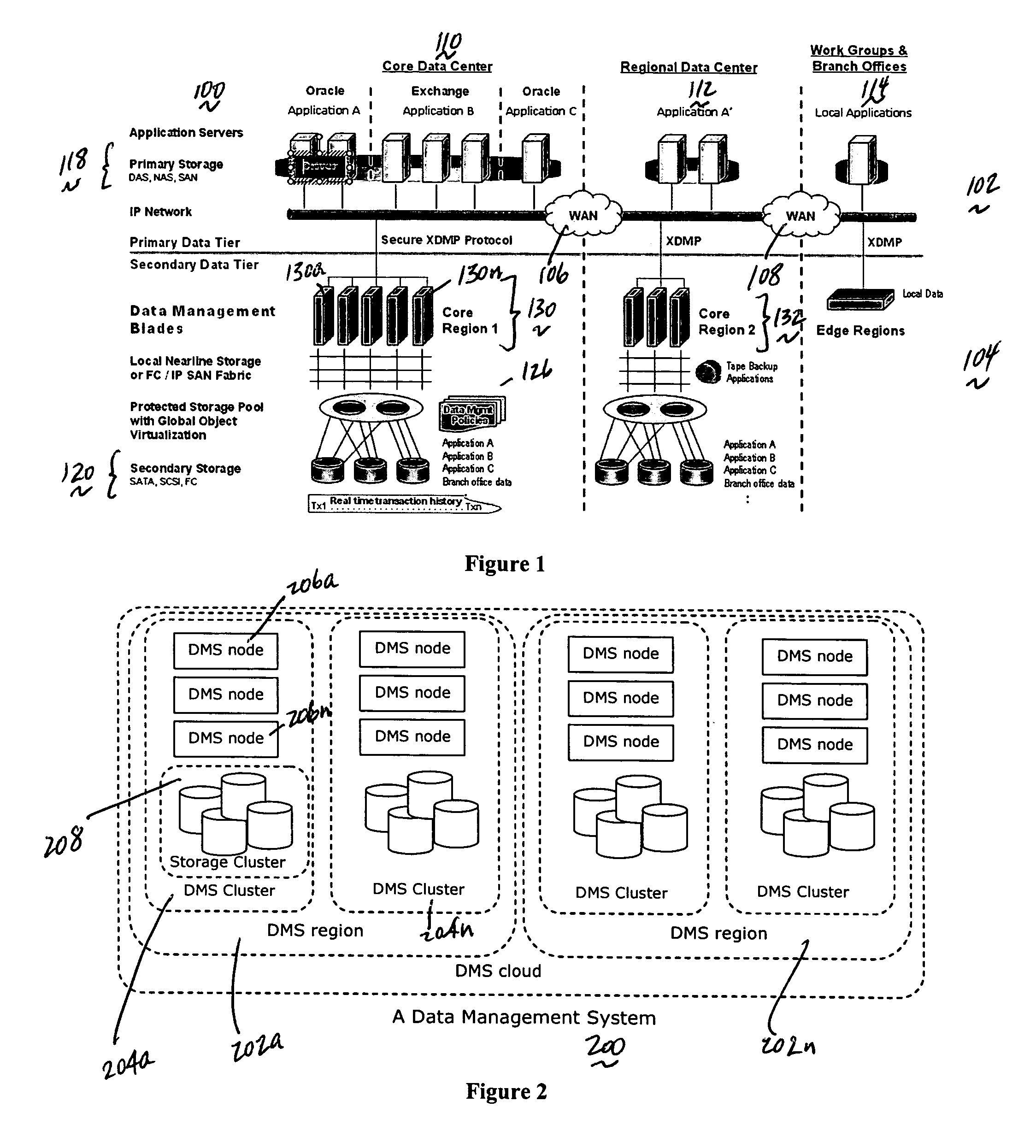
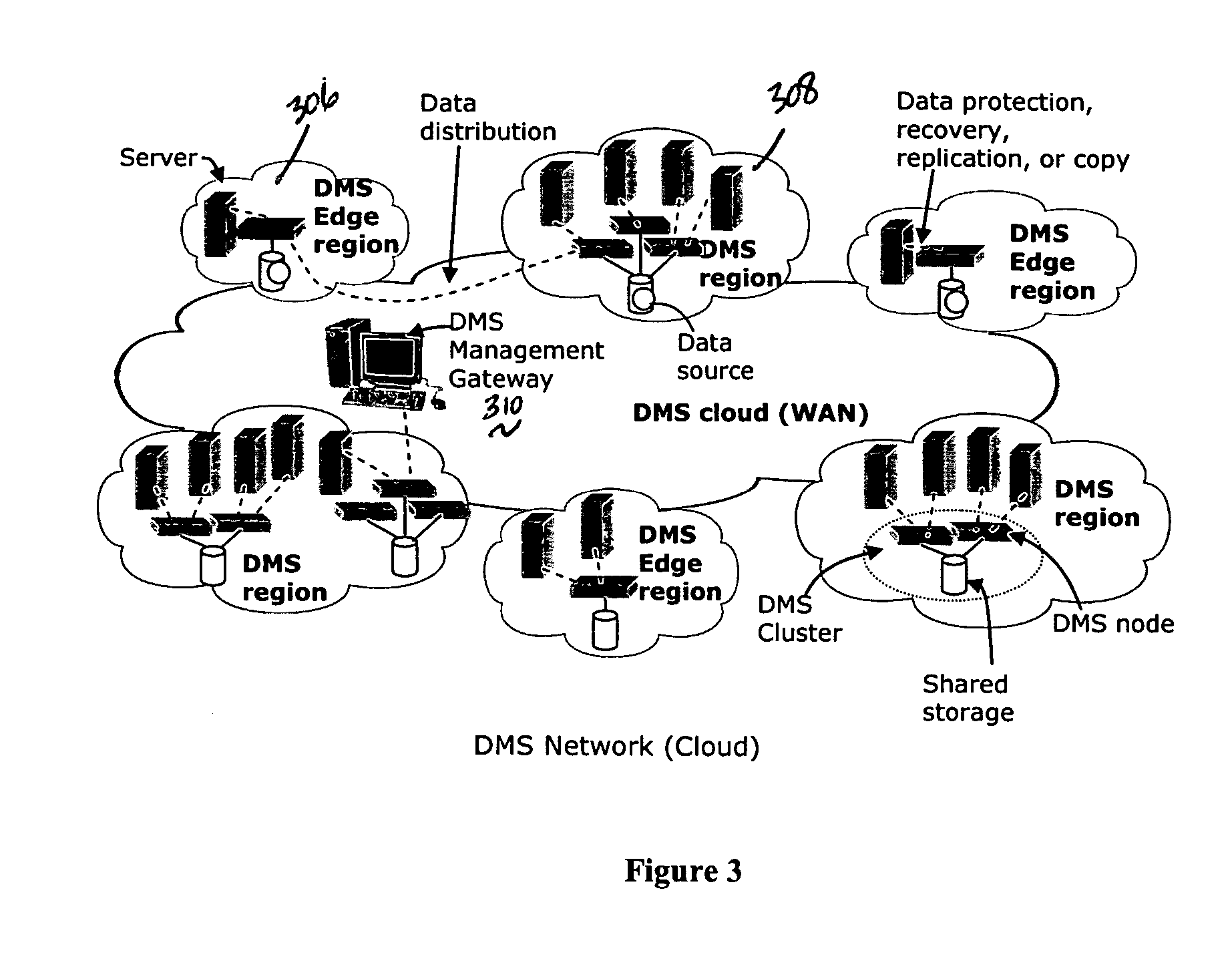
A data management system or “DMS” provides a wide range of data services to data sources associated with a set of application host servers. The data management system typically comprises one or more regions, with each region having one or more clusters. A given cluster has one or more nodes that share storage. To facilitate the data service, a host driver embedded in an application server connects an application and its data to a cluster. The host driver provides a method and apparatus for capturing real-time data transactions in the form of an event journal that is provided to the data management system. The driver functions to translate traditional file / database / block I / O into a continuous, application-aware, output data stream. Using the streams generated in this manner, the DMS offers a wide range of data services that include, by way of example only: data protection (and recovery), disaster recovery (data distribution and data replication), data copy, and data query and access.
Owner:QUEST SOFTWARE INC
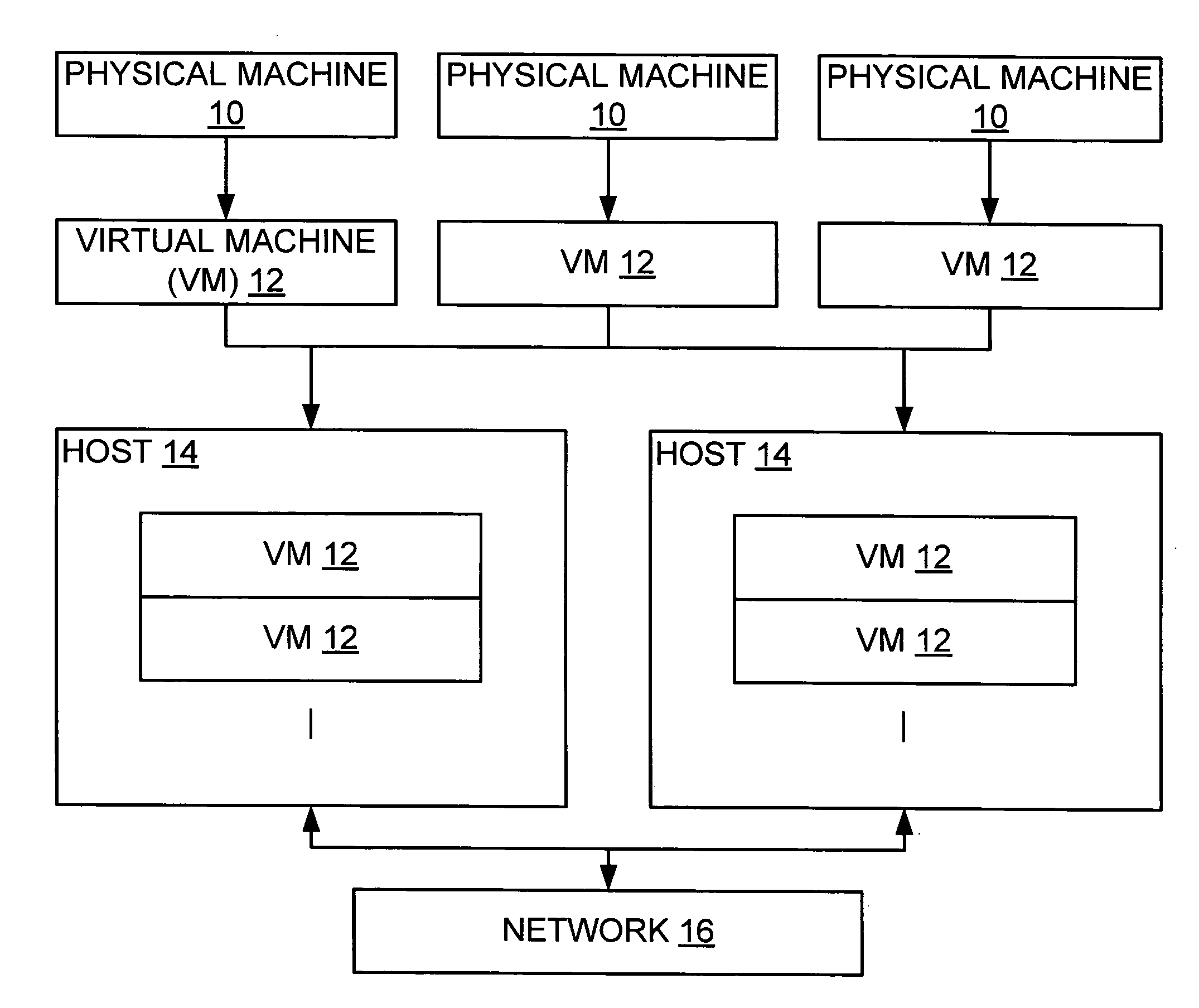
Deploying virtual machine to host based on workload characterizations
InactiveUS20070271560A1Convenient to accommodateSoftware simulation/interpretation/emulationMemory systemsWorkloadVirtual machine
Owner:MICROSOFT TECH LICENSING LLC
Audio user interface for computing devices
ActiveUS20060095848A1Easy to carryEfficient leveragingRecord information storageCarrier indicating arrangementsHand heldHand held devices
An audio user interface that generates audio prompts that help a user interact with a user interface of a device is disclosed. One aspect of the present invention pertains to techniques for providing the audio user interface by efficiently leveraging the computing resources of a host computer system. The relatively powerful computing resources of the host computer can convert text strings into audio files that are then transferred to the computing device. The host system performs the process intensive text-to-speech conversion so that a computing device, such as a hand-held device, only needs to perform the less intensive task of playing the audio file. The computing device can be, for example, a media player such as an MP3 player, a mobile phone, or a personal digital assistant.
Owner:APPLE INC
Computer system para-virtualization using a hypervisor that is implemented in a partition of the host system
ActiveUS20070028244A1Improve securityExcessive removalError detection/correctionMemory adressing/allocation/relocationOperational systemSystem call
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. Operating systems in other logical or virtual partitions communicate with the I / O partitions via memory channels established by the ultravisor partition. The guest operating systems in the respective logical or virtual partitions are modified to access monitors that implement a system call interface through which the ultravisor, I / O, and any other special infrastructure partitions may initiate communications with each other and with the respective guest partitions. The guest operating systems are modified so that they do not attempt to use the “broken” instructions in the x86 system that complete virtualization systems must resolve by inserting traps.
Owner:UNISYS CORP
Wireless home and office appliance management and integration
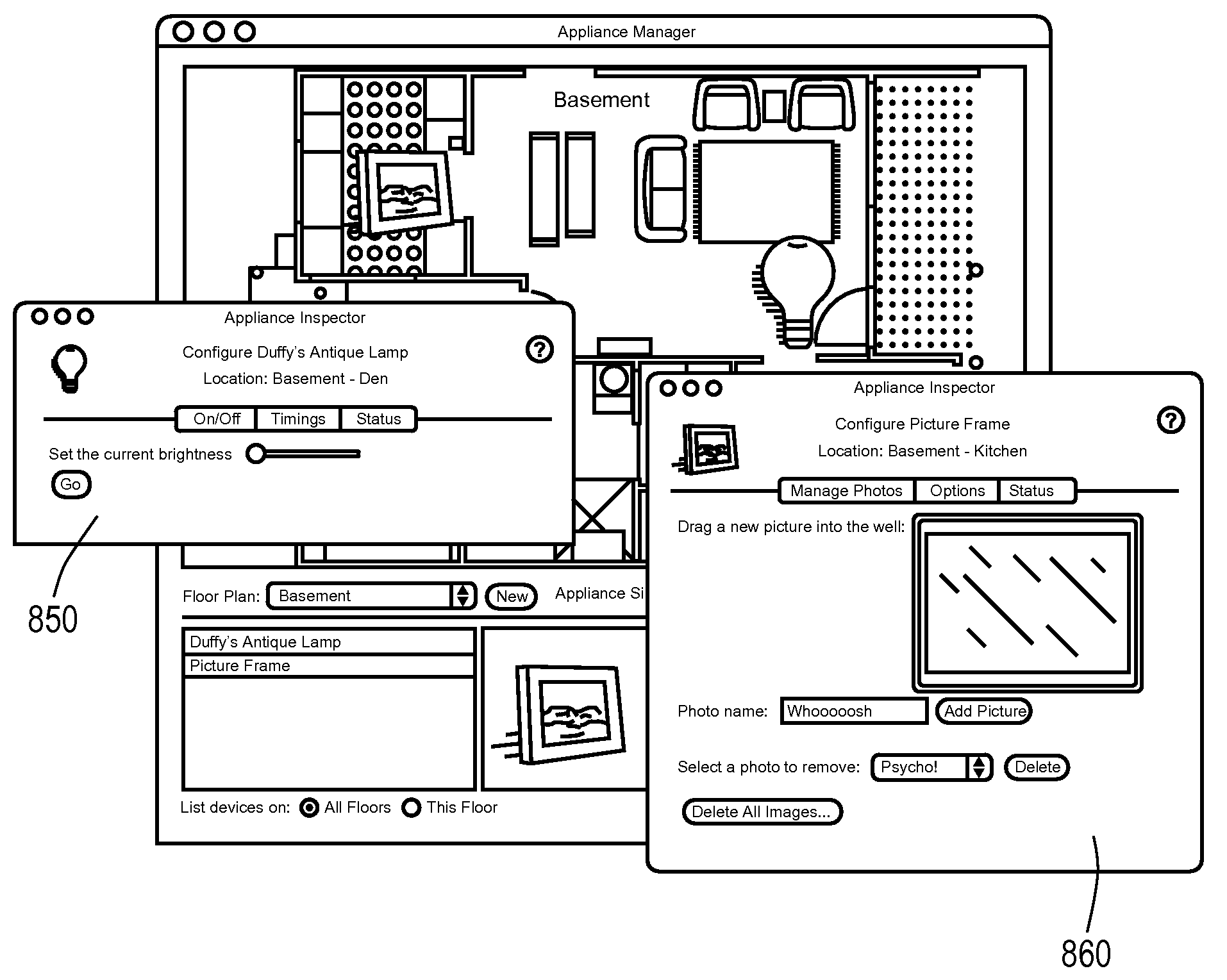
ActiveUS7730223B1Minimal set-upUser managementDigital computer detailsElectric light circuit arrangementGraphicsPersonal computer
The present invention provides systems and methods for managing and controlling networked devices. A system comprises a host application executing on, for example, a personal computer, and one or more networked devices executing a client application. A networked device includes a consumer appliance equipped with network capability, a digital device such as MP3 players and DVRs, an electronically-controlled device such as a light circuit or other type of circuit, and the like. The host application automatically establishes communication with the networked device. The networked device configures a user interface for user control of the networked device. The host application provides a graphical layout of the networked device.
Owner:APPLE INC
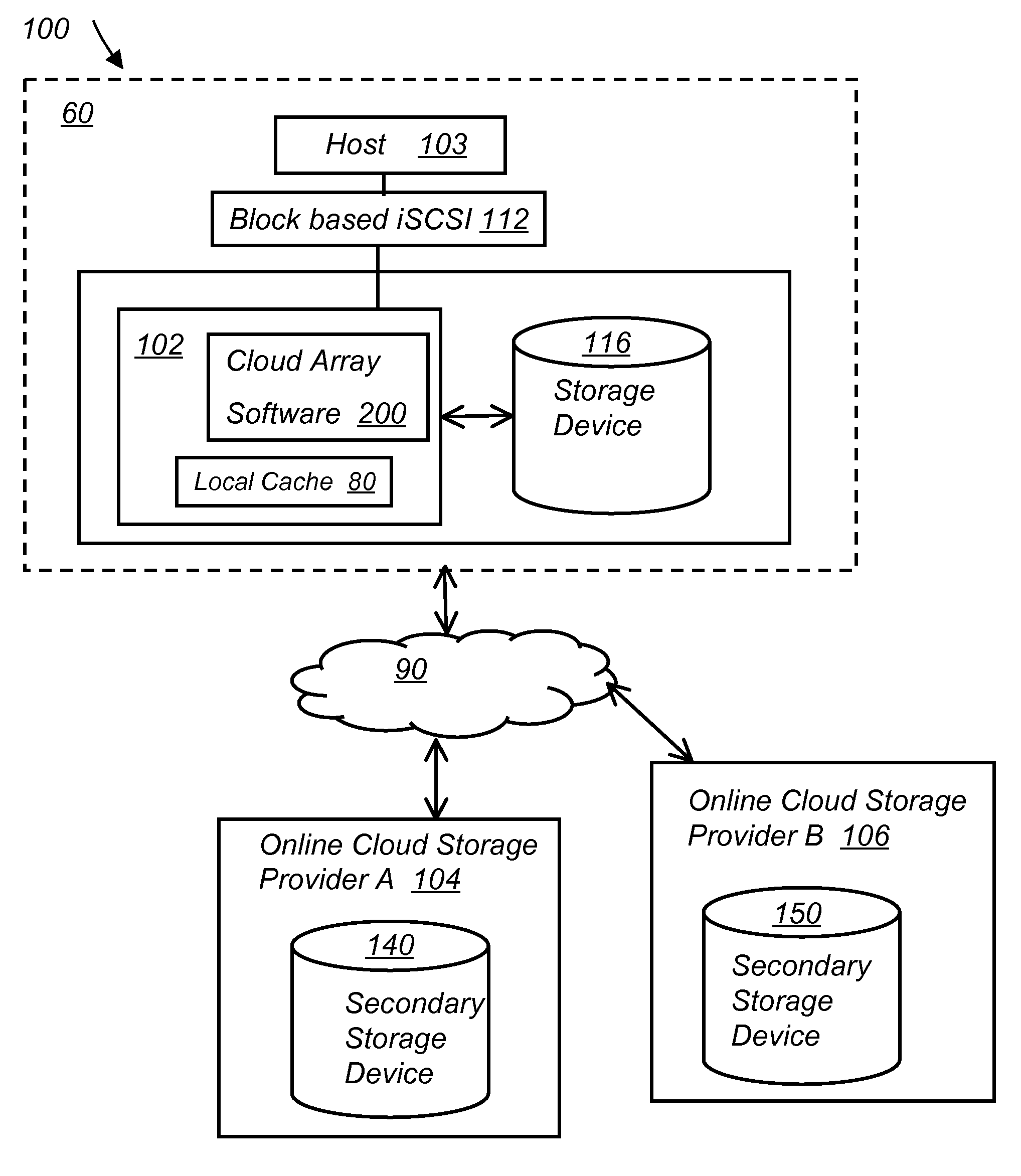
System and method for secure and reliable multi-cloud data replication
ActiveUS8762642B2Reduce the amount requiredReduce storage costsMemory architecture accessing/allocationUnauthorized memory use protectionReliable computingNetwork connection
Owner:EMC IP HLDG CO LLC
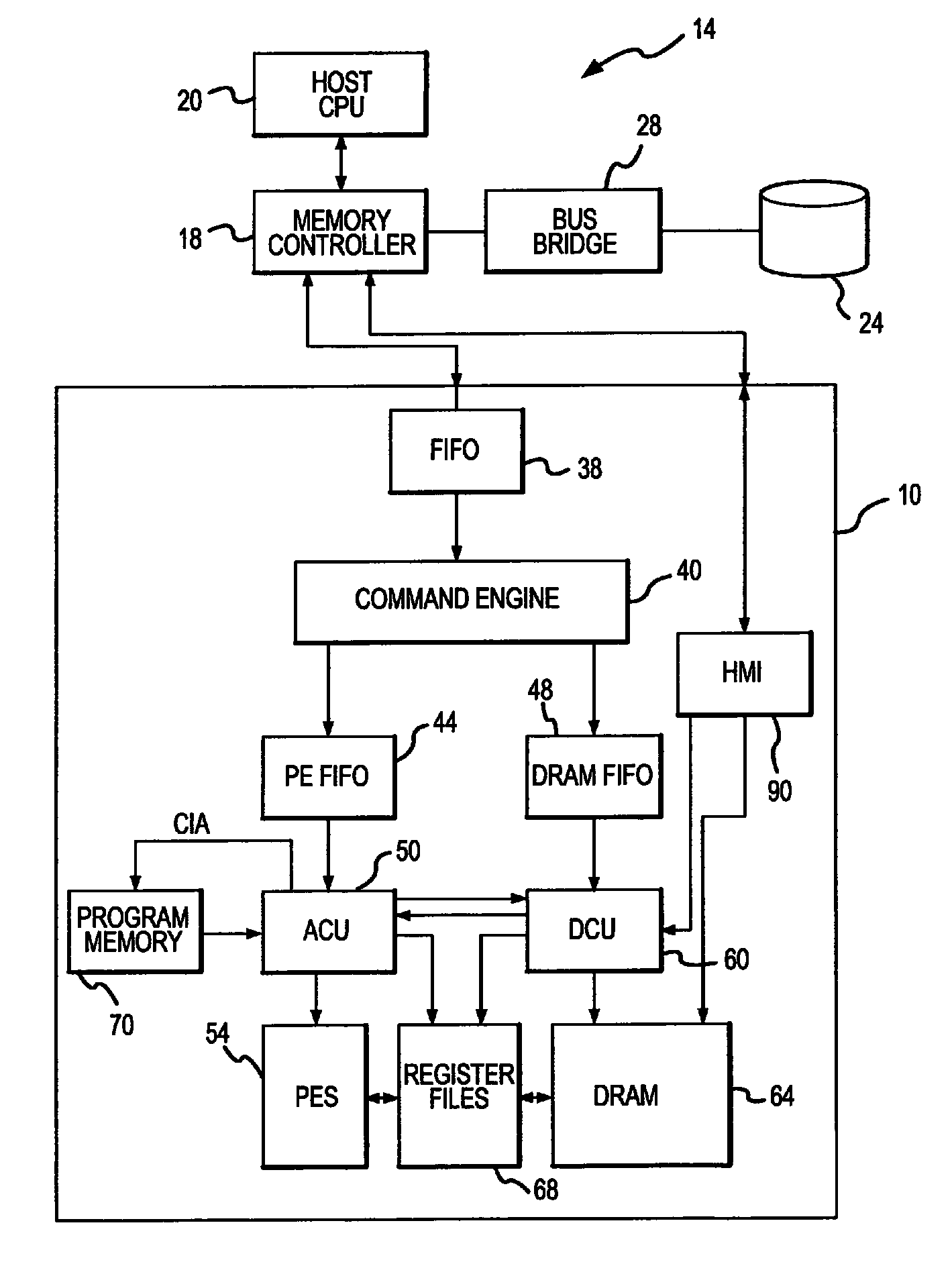
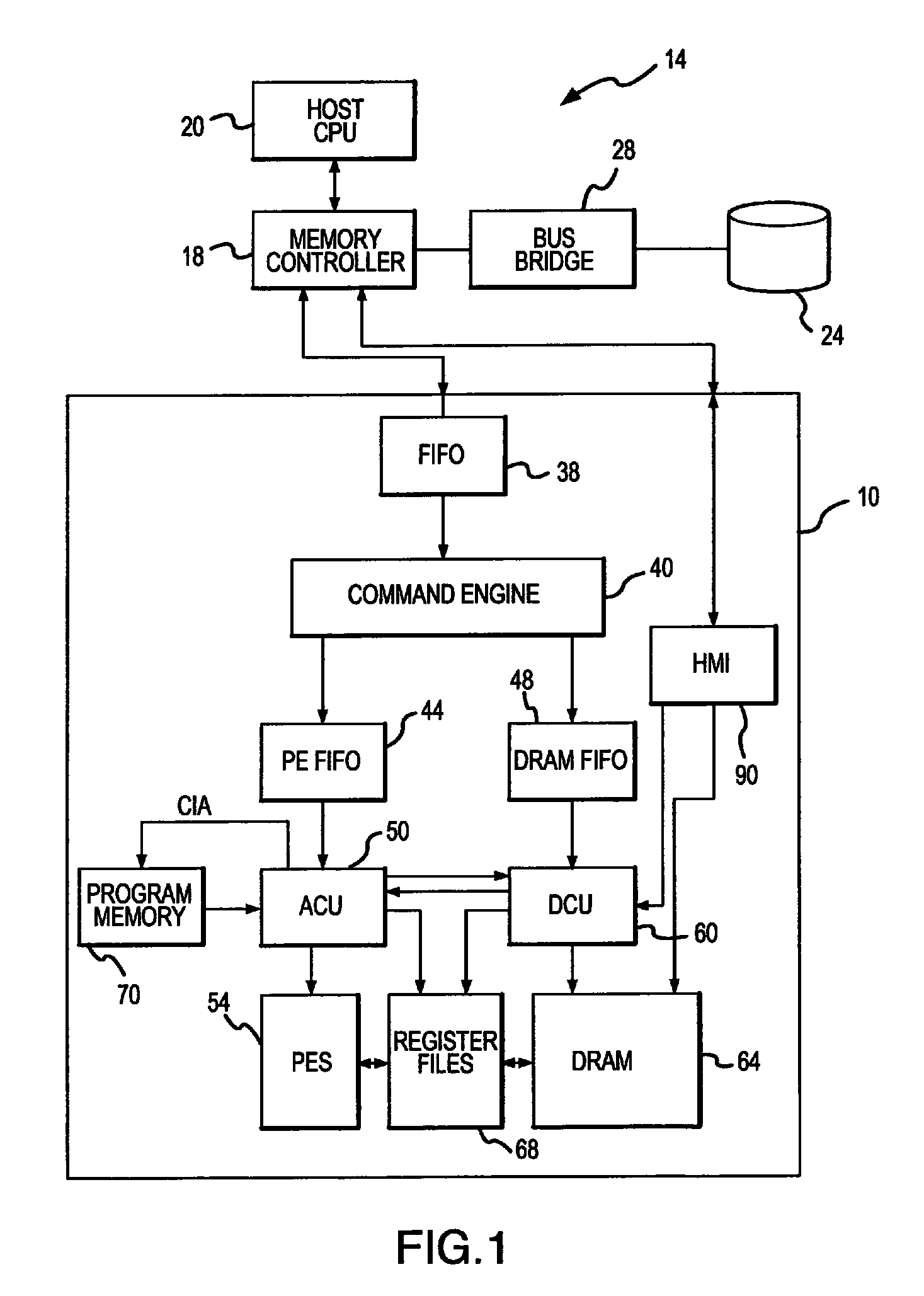
Active memory data compression system and method
ActiveUS9015390B2Concurrent instruction executionArchitecture with single central processing unitMass storageData compression
An integrated circuit active memory device receives task commands from a component in a host computer system that may include the active memory device. The host system includes a memory controller coupling the active memory device to a host CPU and a mass storage device. The active memory device includes a command engine issuing instructions responsive to the task commands to either an array control unit or a DRAM control unit. The instructions provided to the DRAM control unit cause data to be written to or read from a DRAM and coupled to or from either the processing elements or a host / memory interface. The processing elements execute instructions provided by the array control unit to decompress data written to the DRAM through the host / memory interface and compress data read from the DRAM through the host / memory interface.
Owner:MICRON TECH INC
Provisioning of Computer Systems Using Virtual Machines
InactiveUS20090282404A1Multiple digital computer combinationsSoftware simulation/interpretation/emulationOperational systemAuto-configuration
Owner:VMWARE INC
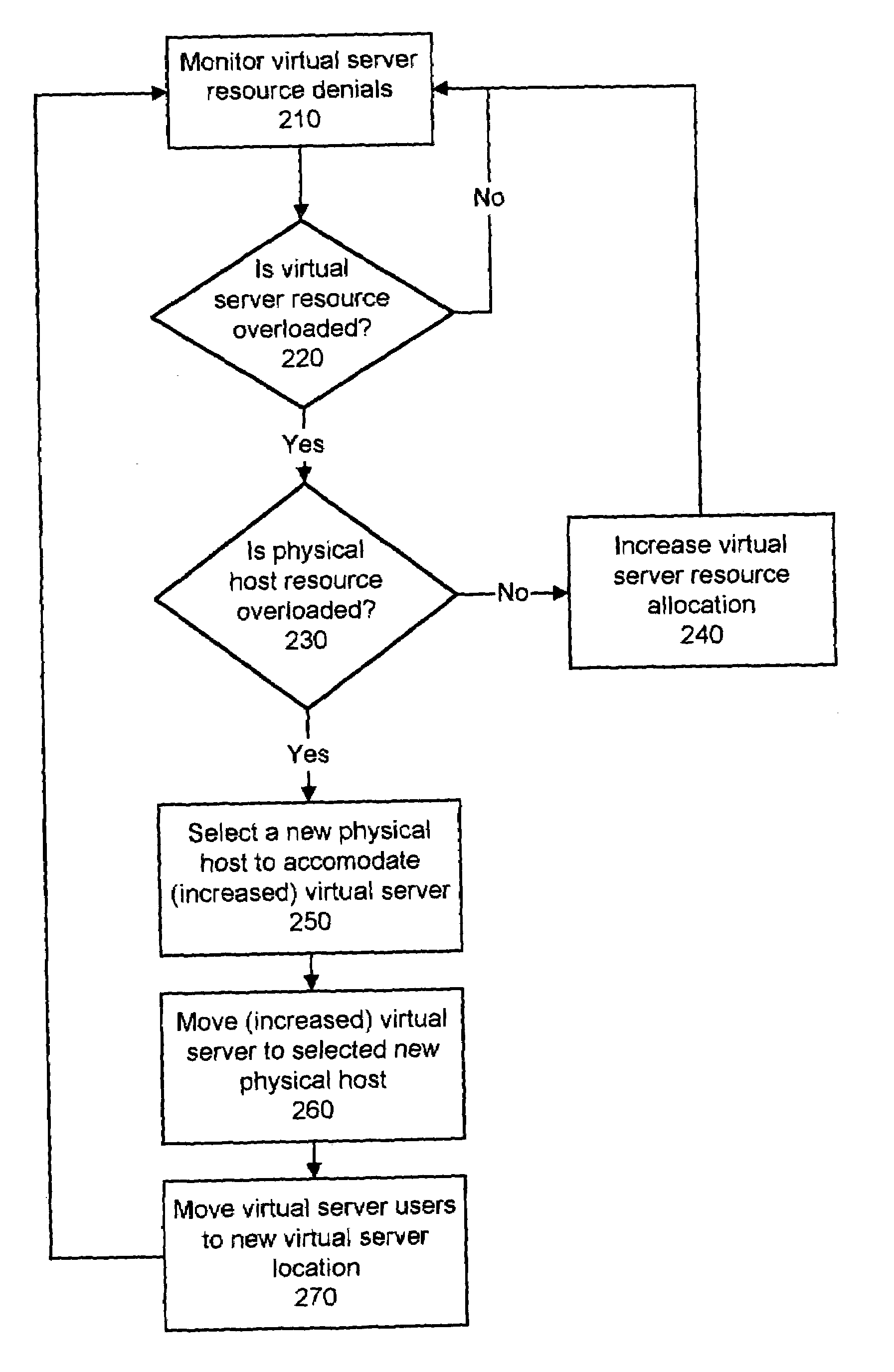
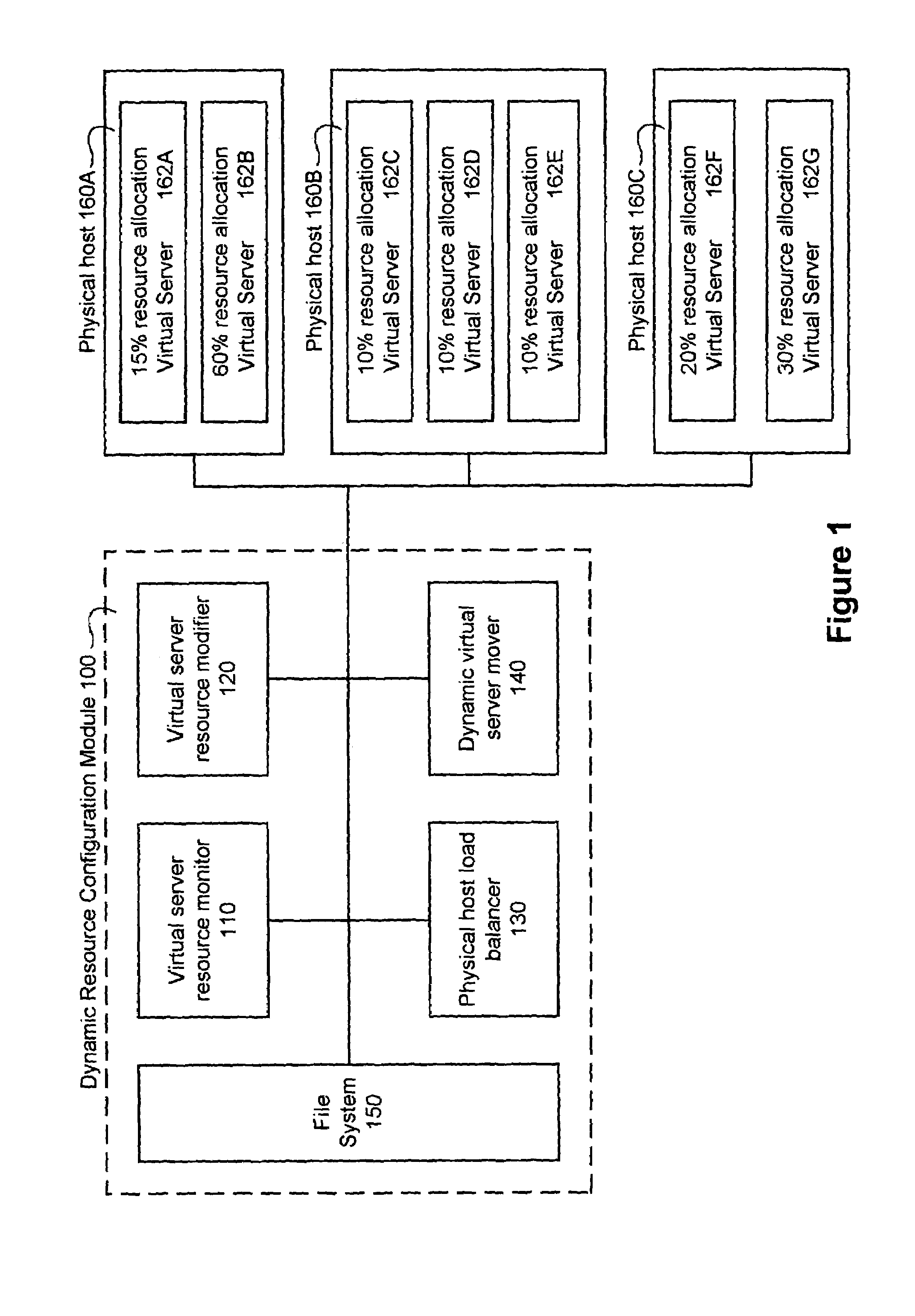
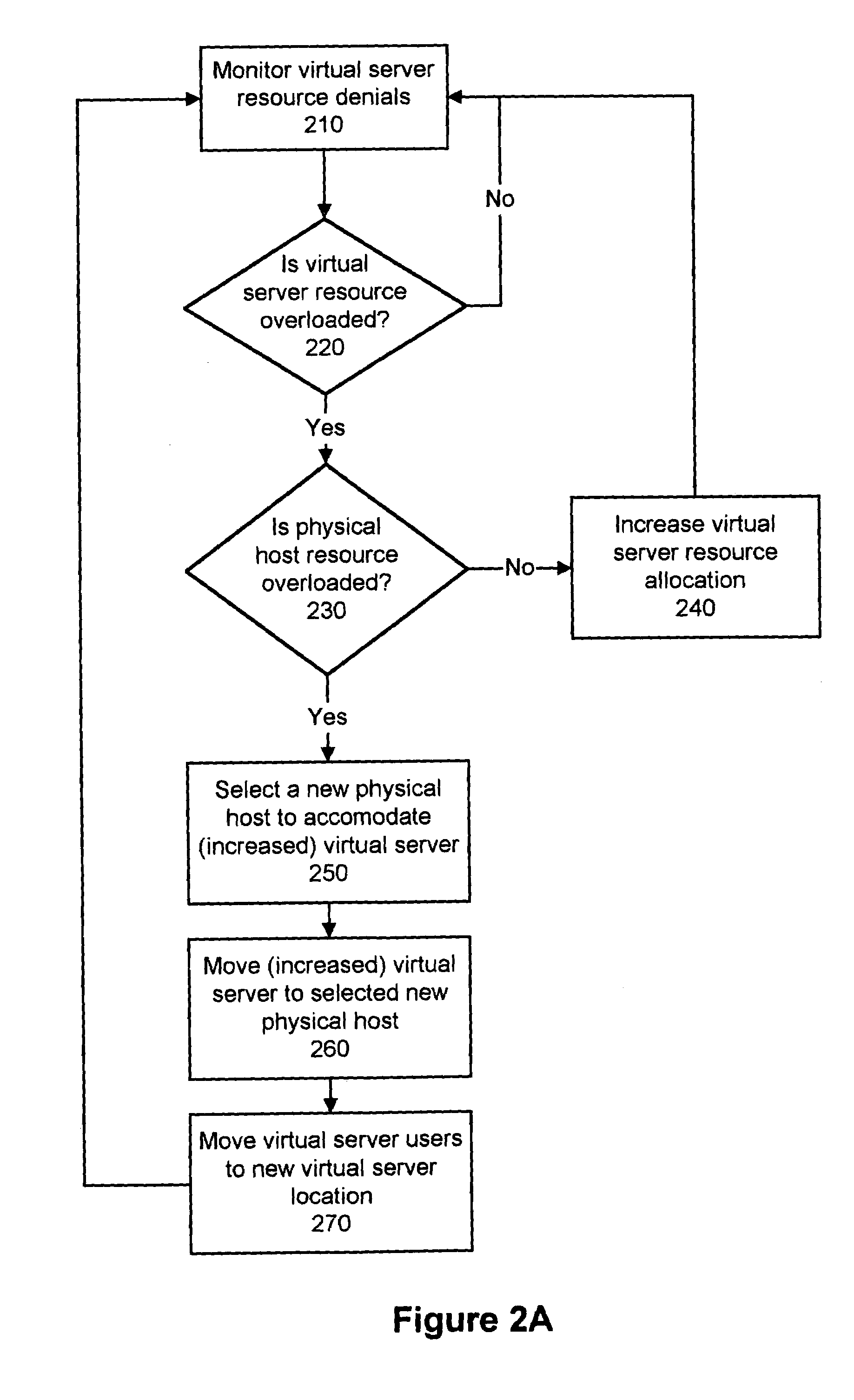
Dynamically modifying the resources of a virtual server
InactiveUS6985937B1Guaranteed service qualityError preventionFrequency-division multiplex detailsQuality of serviceResource based
A system and a method dynamically adjusts the quality of service guarantees for virtual servers based upon the resource demands experienced by the virtual servers. Virtual server resource denials are monitored to determine if a virtual server is overloaded based upon the resource denials. Virtual server resources are modified dynamically to respond to the changing resource requirements of each virtual server. Occasionally, a physical host housing a virtual server may not have additional resources to allocate to a virtual server requiring increased resources. In this instance, a virtual server hosted by the overloaded physical host is transferred to another physical host with sufficient resources.
Owner:INTELLECTUAL VENTURES I LLC
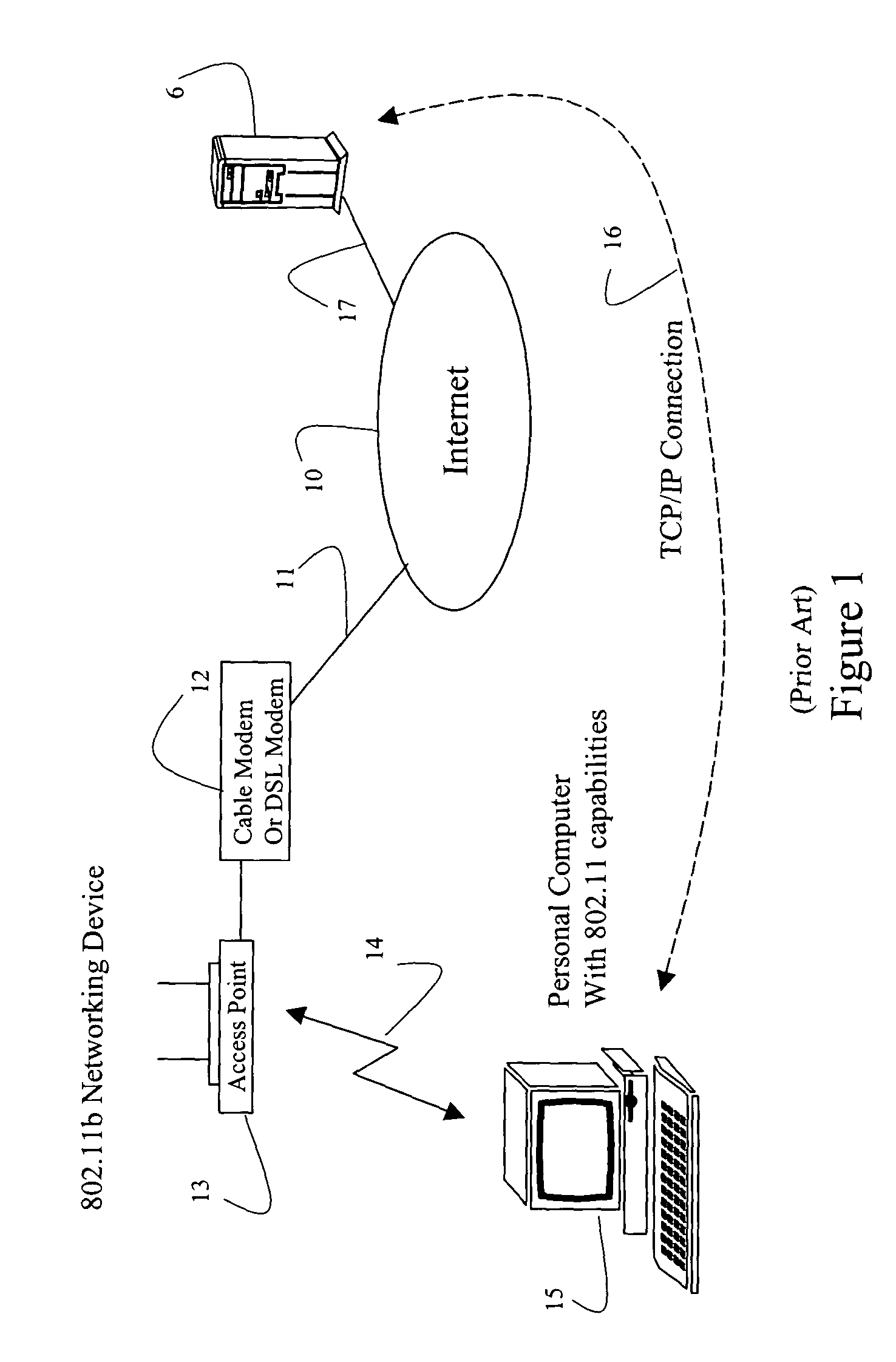
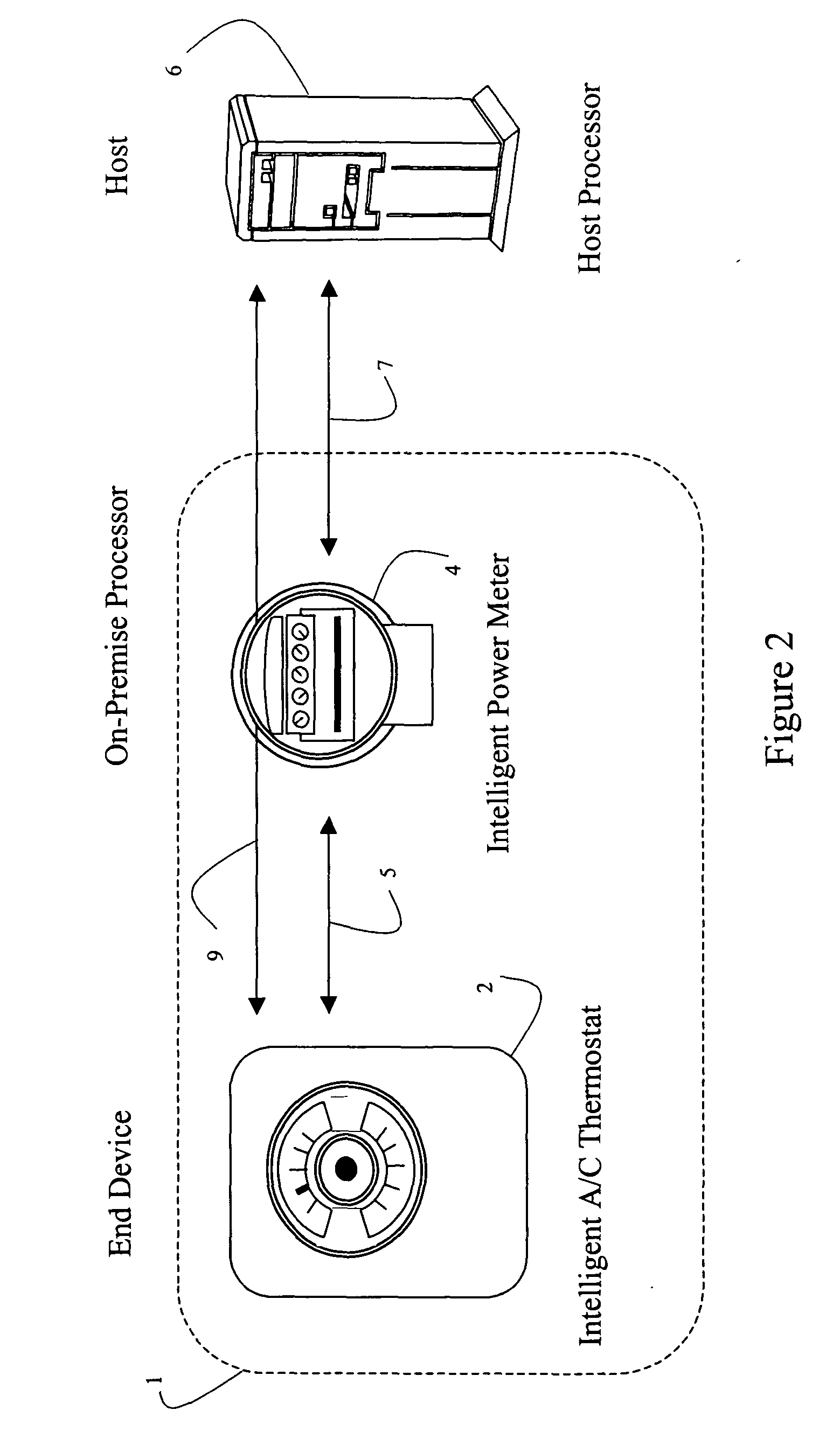
Systems and methods for remote power management using 802.11 wireless protocols
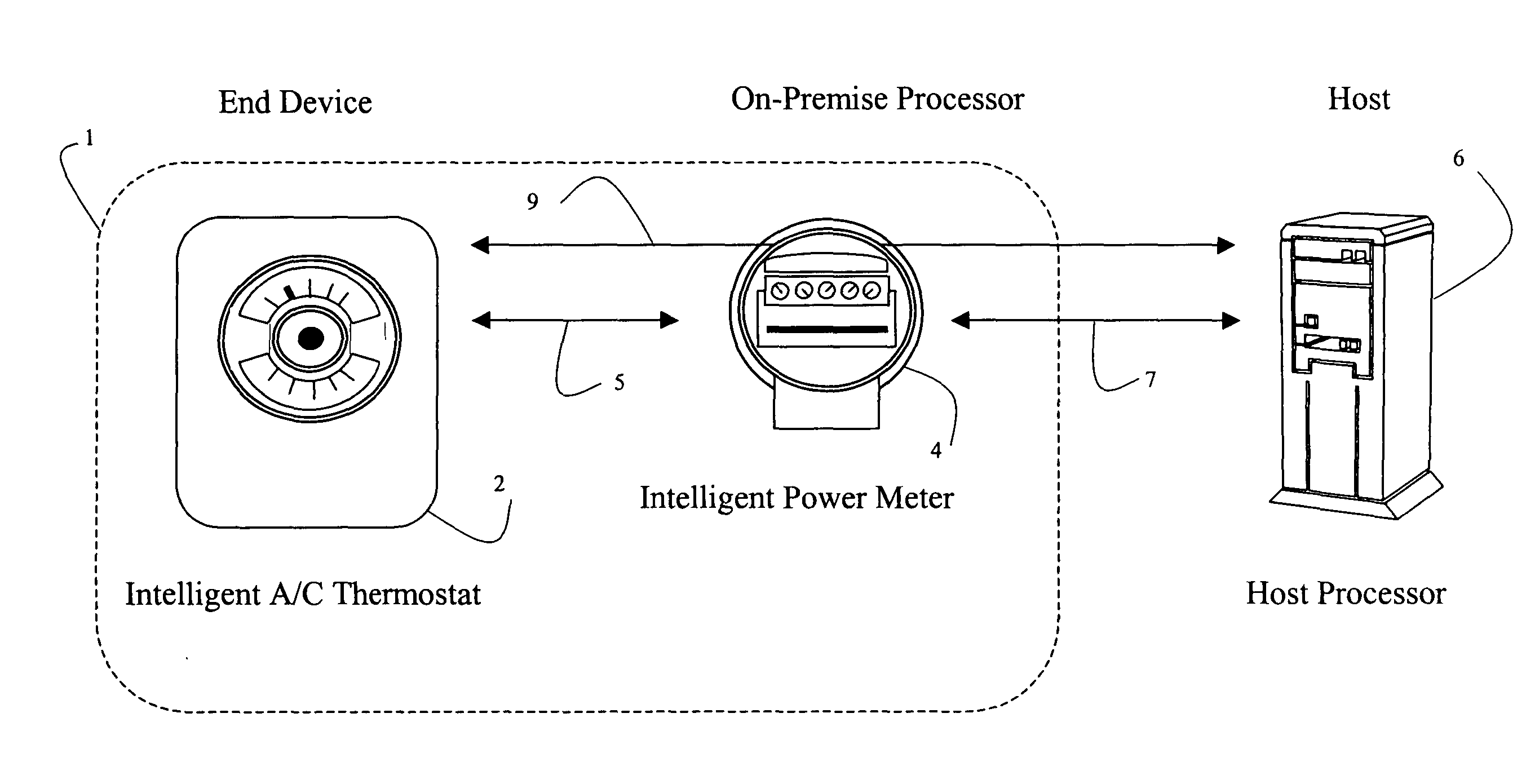
InactiveUS20050055432A1Reduce power consumptionLow costTariff metering apparatusNetwork topologiesTerminal equipmentUsage data
Systems and methods are disclosed for using 802.11 based wireless protocols in various energy management applications wherein a host controller uses various types of communication networks to distribute information to an on-premise processor that in turn uses 802.11 based wireless protocols to communicate with various types of end devices, such as utility meters. Various forms of communication are defined between the end device, the on-premise processor, and the energy management host for accomplishing power load control, including determining when to activate or deactivate a load, requesting permission to activate a load, reading usage data, activating or deactivating a meter, and determining rate schedules. A flexible scheme allows control to be shifted to be resident in various entities. The architecture is applicable not only for power load control, but other control type and metering devices.
Owner:SMARTSYNCH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com