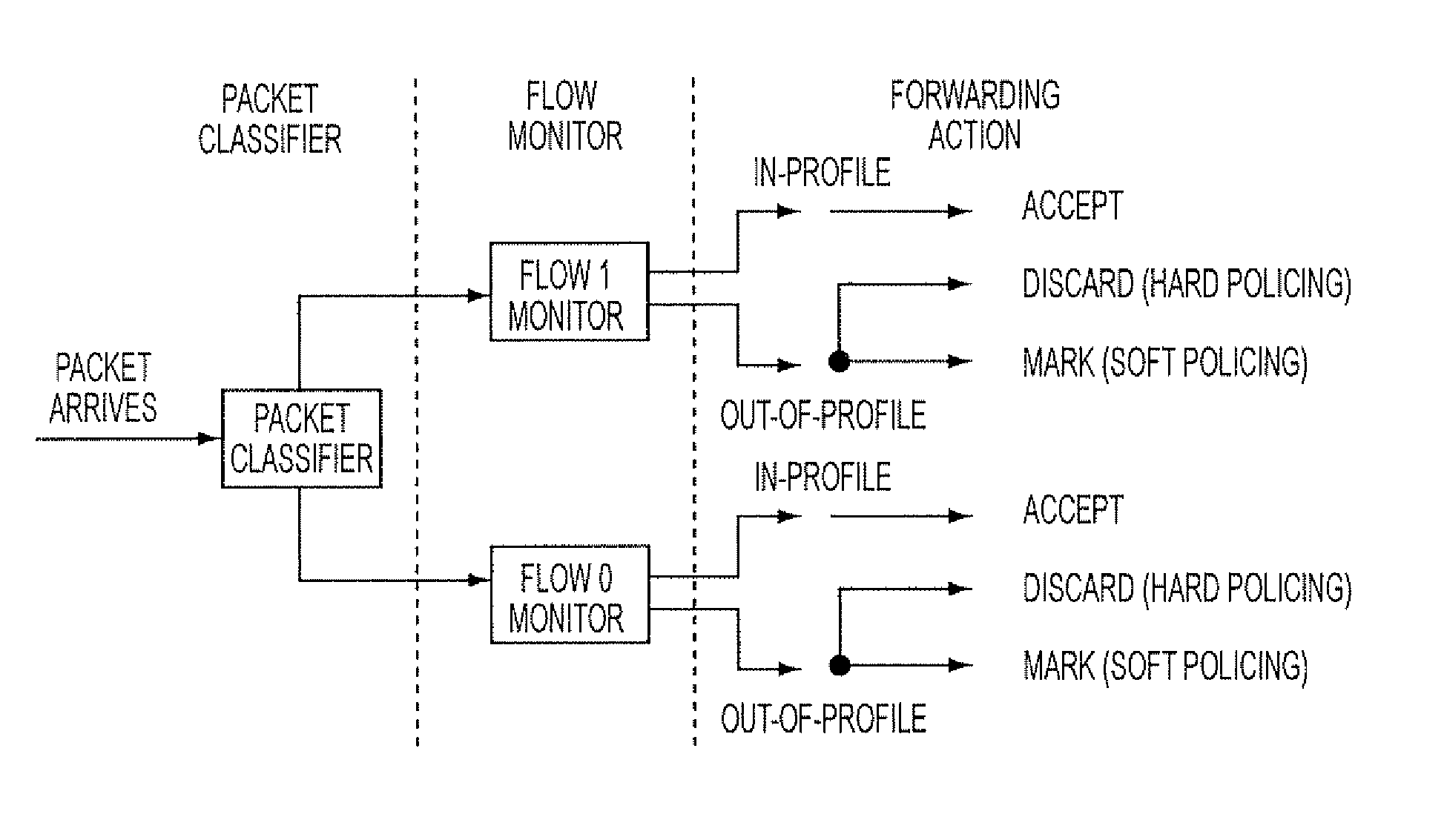
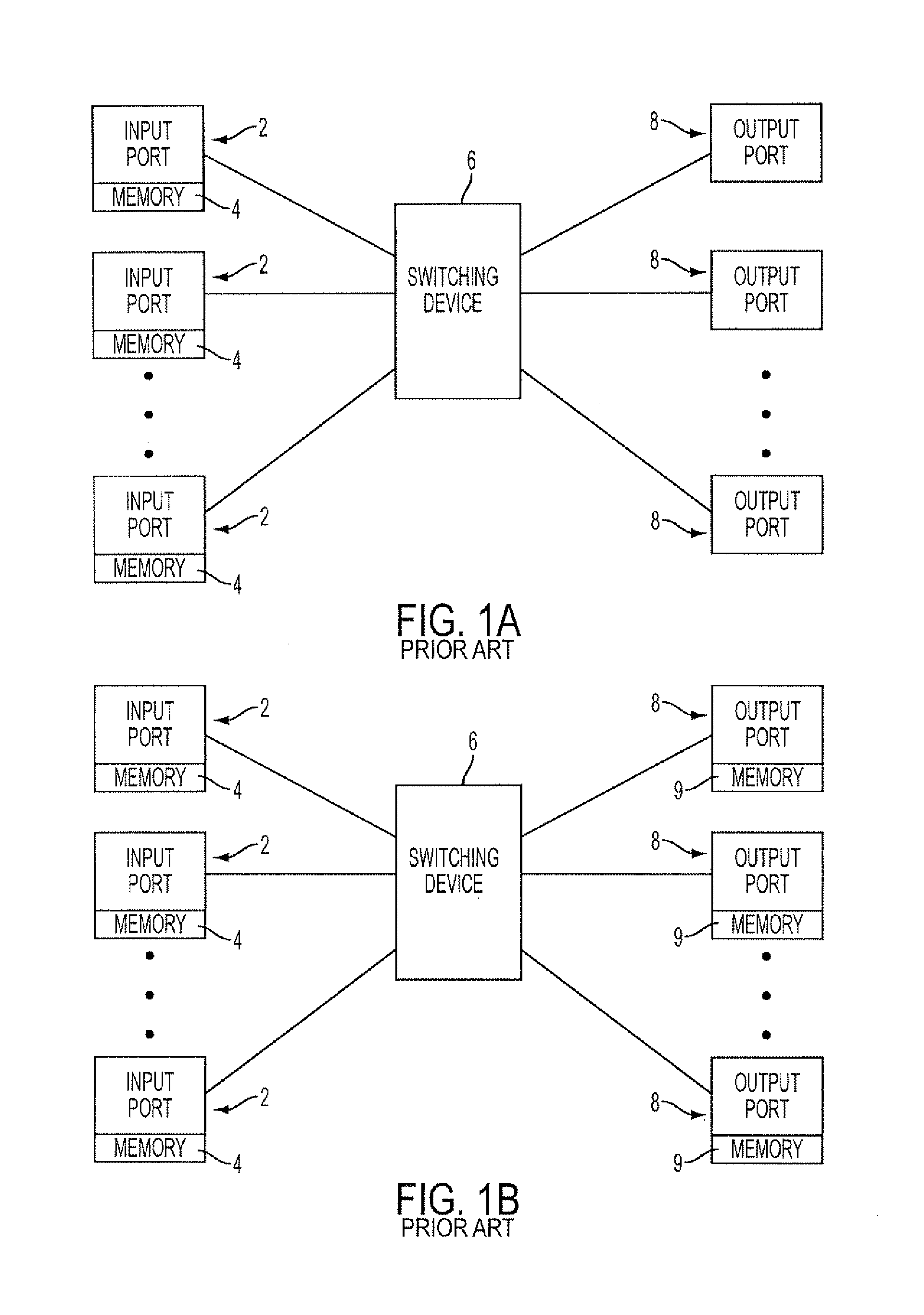
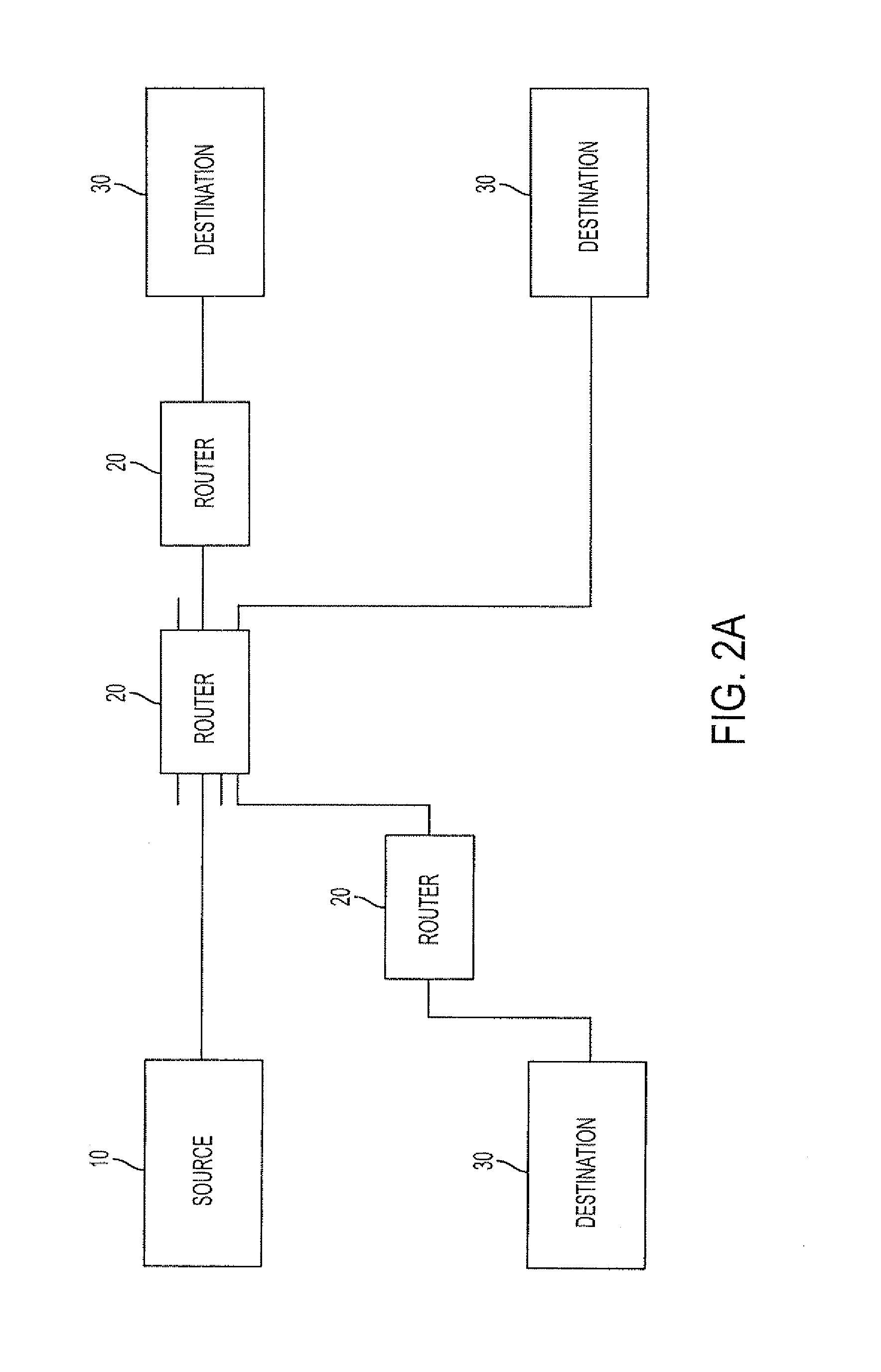
Patents
Literature
51189 results about "Traffic volume" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In telecommunication networks, traffic volume is a measure of the total work done by a resource or facility, normally over 24 hours, and is measured in units of erlang-hours. It is defined as the product of the average traffic intensity and the time period of the study. Traffic volume = Traffic intensity × time A traffic volume of one erlang-hour can be caused by two circuits being occupied continuously for half an hour or by a circuit being half occupied for a period of two hours. Telecommunication operators are vitally interested in traffic volume, as it directly dictates their revenue.
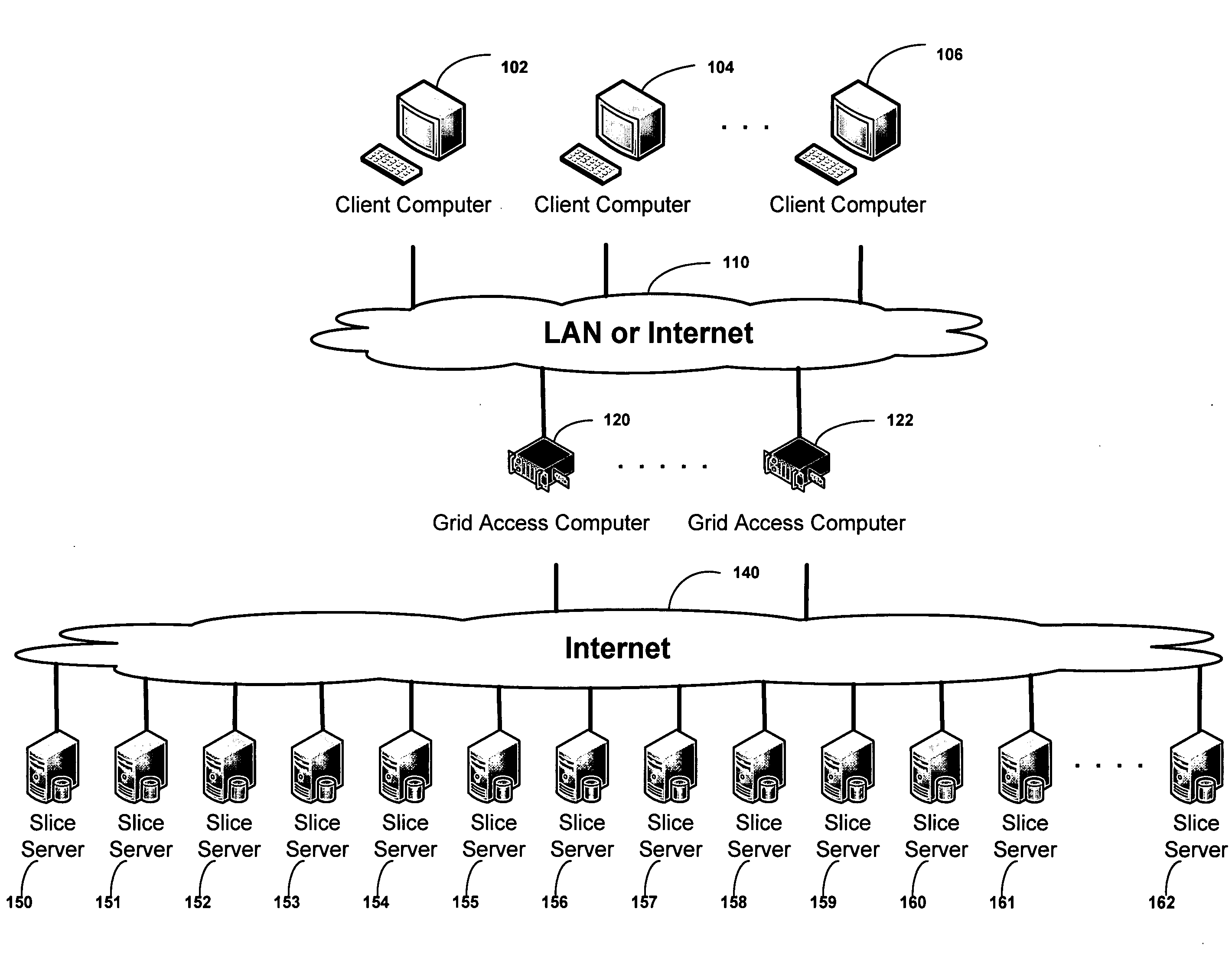
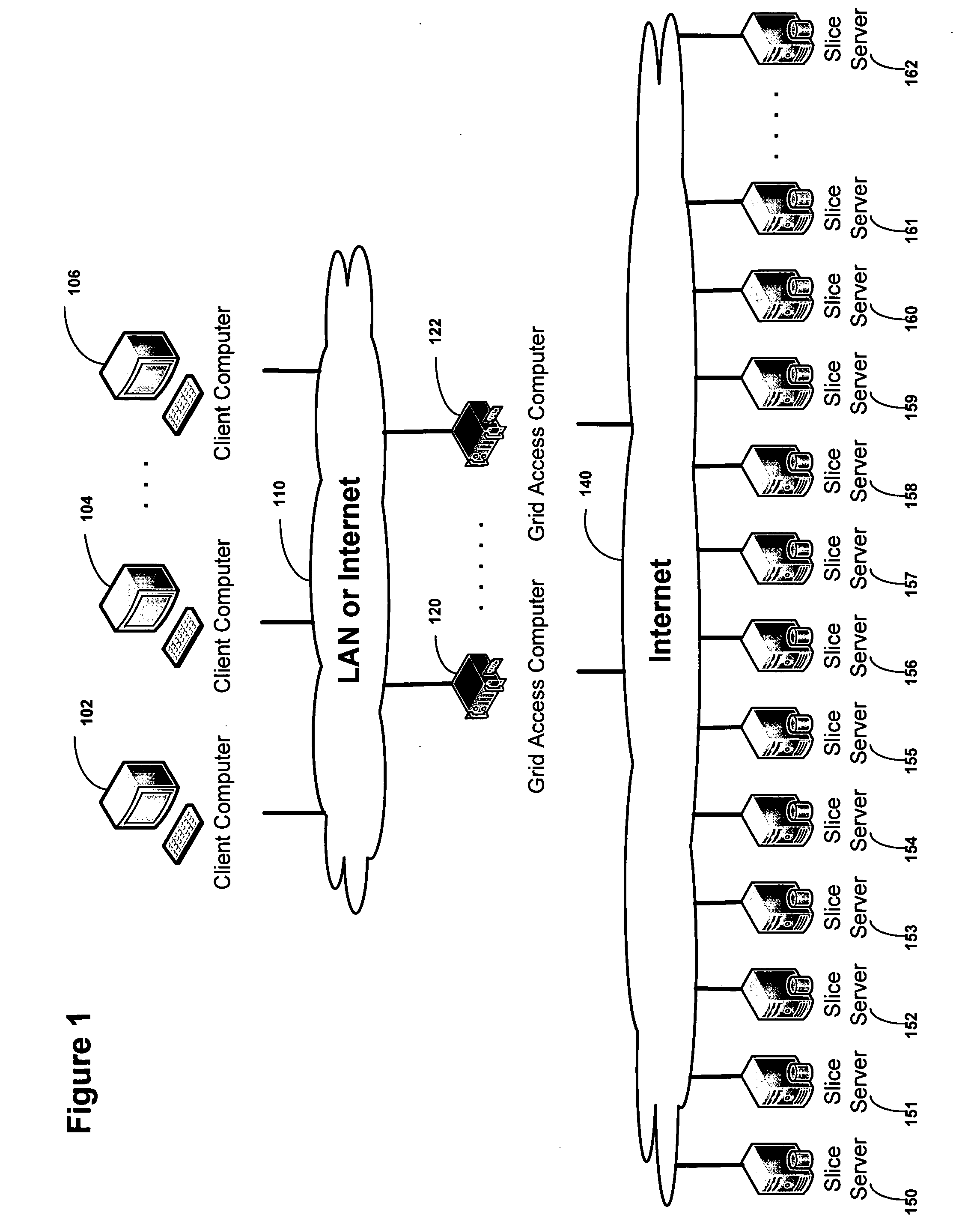
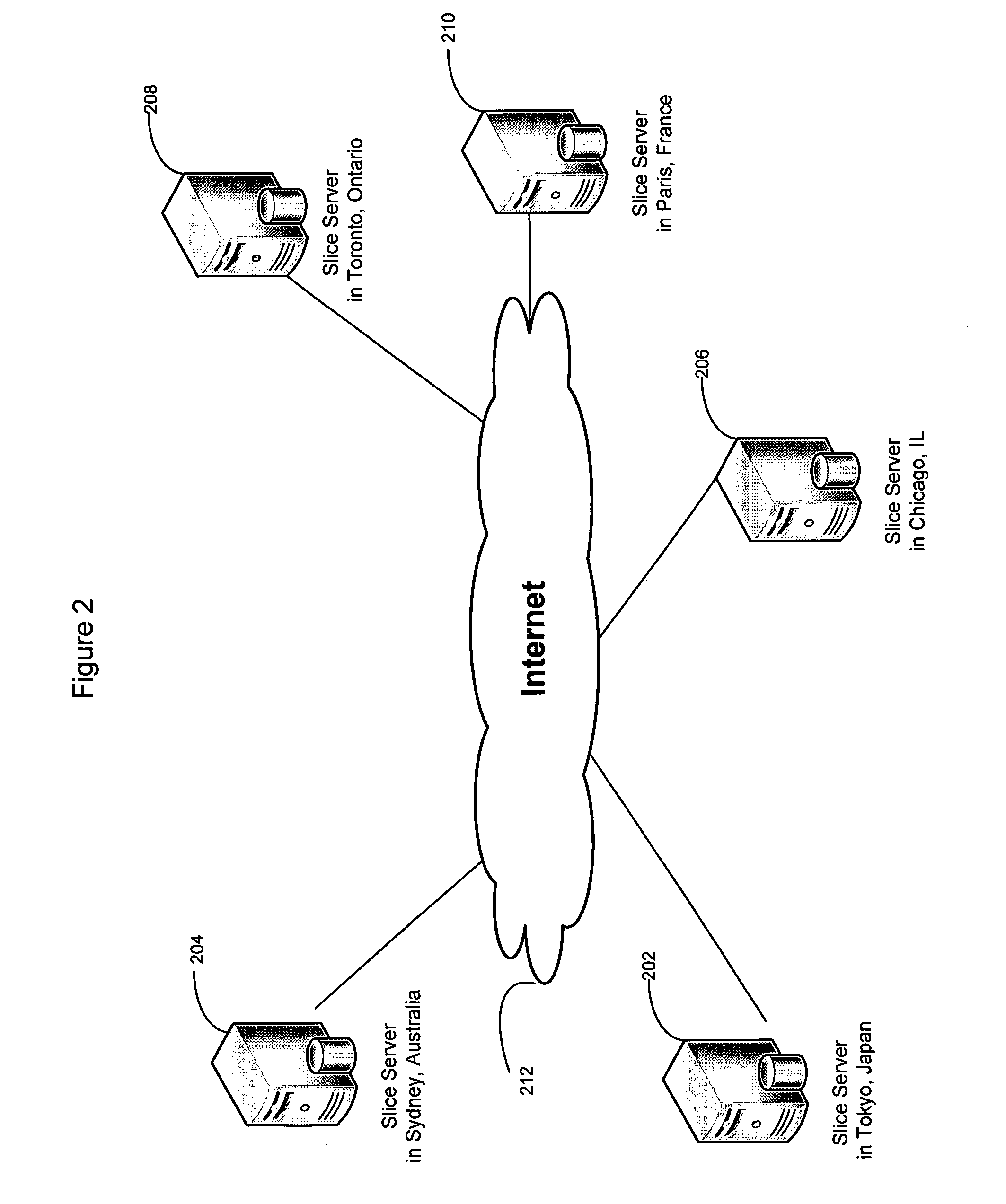
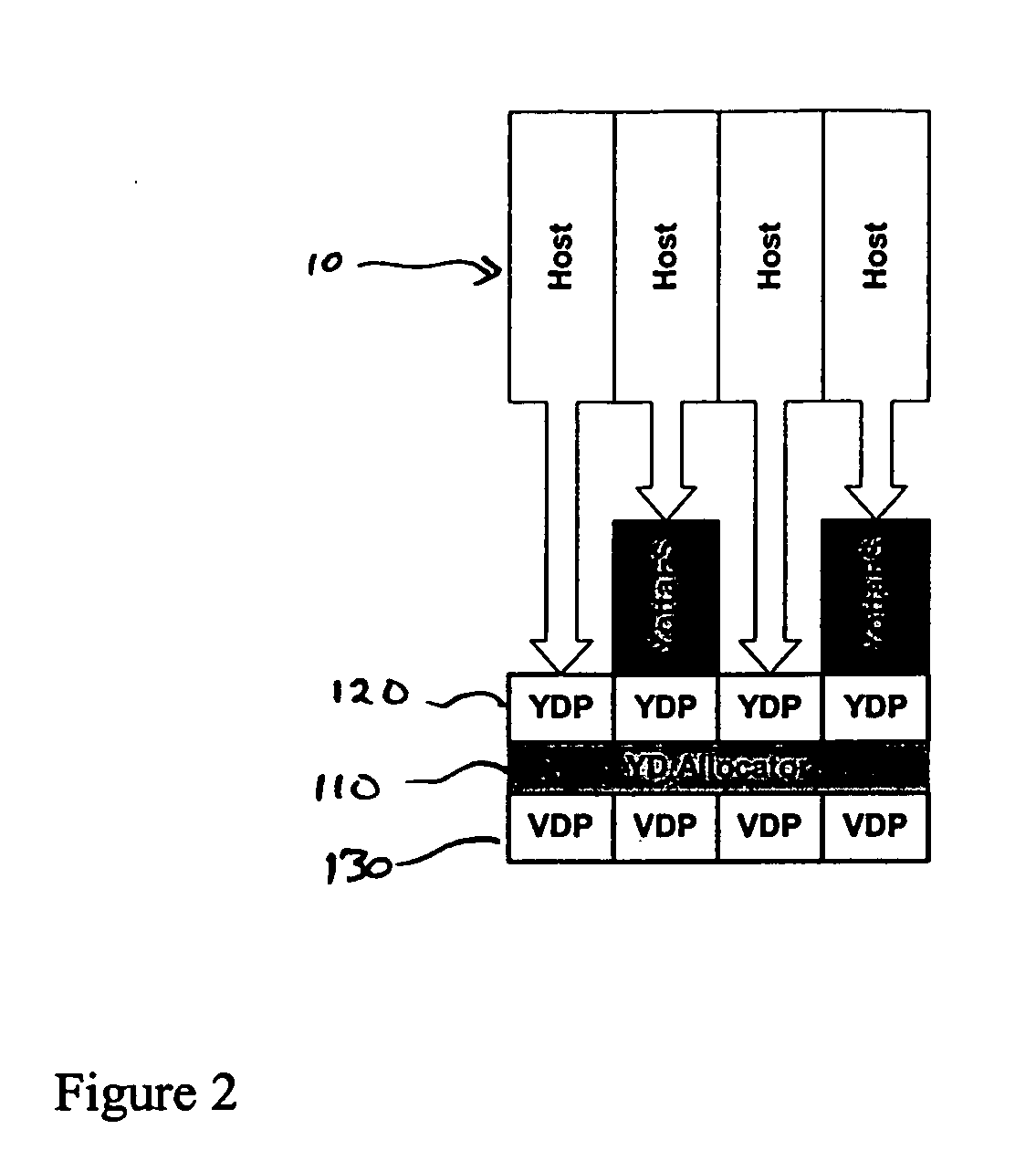
Smart access to a dispersed data storage network
ActiveUS20090094318A1Efficient accessImprove network performanceError preventionFrequency-division multiplex detailsData segmentRanking
An improved system for accessing data within a distributed data storage network (“DDSN”) is disclosed. In a system implementing the disclosed invention, traffic is routed to individual slice servers within the DDSN in accordance with objective criteria as well as user-defined policies. In accordance with one aspect of the disclosed invention, when a data segment is written to a DDSN, the segment is divided into multiple data slices, which are simultaneously transmitted to different slice servers. In accordance with another aspect of the disclosed invention, when a data segment is read from a DDSN, a list of slice servers, each containing a data slice that could be used to reconstruct the requested data segment, is assembled, and sorted in accordance with a preference rating assigned to each of the slice servers. Sufficient data slices to reconstruct the data segment are then read in accordance with the preference ranking of the slice servers.
Owner:PURE STORAGE
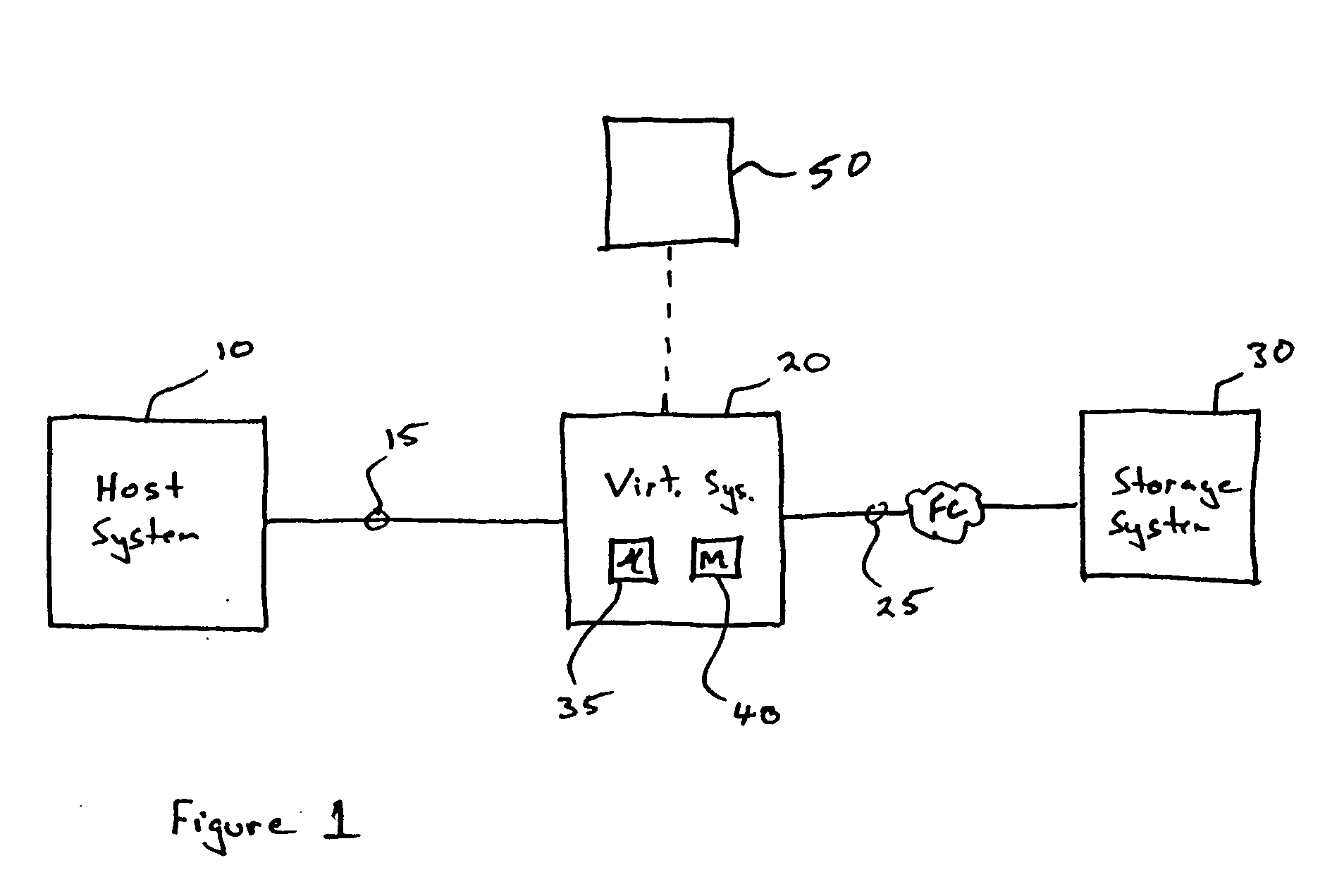
Storage virtualization system and methods
InactiveUS20050125593A1Reduce consumptionWithout impactInput/output to record carriersMemory adressing/allocation/relocationRAIDIslanding
Storage virtualization systems and methods that allow customers to manage storage as a utility rather than as islands of storage which are independent of each other. A demand mapped virtual disk image of up to an arbitrarily large size is presented to a host system. The virtualization system allocates physical storage from a storage pool dynamically in response to host I / O requests, e.g., SCSI I / O requests, allowing for the amortization of storage resources-through a disk subsystem while maintaining coherency amongst I / O RAID traffic. In one embodiment, the virtualization functionality is implemented in a controller device, such as a controller card residing in a switch device or other network device, coupled to a storage system on a storage area network (SAN). The resulting virtual disk image that is observed by the host computer is larger than the amount of physical storage actually consumed.
Owner:EMC IP HLDG CO LLC
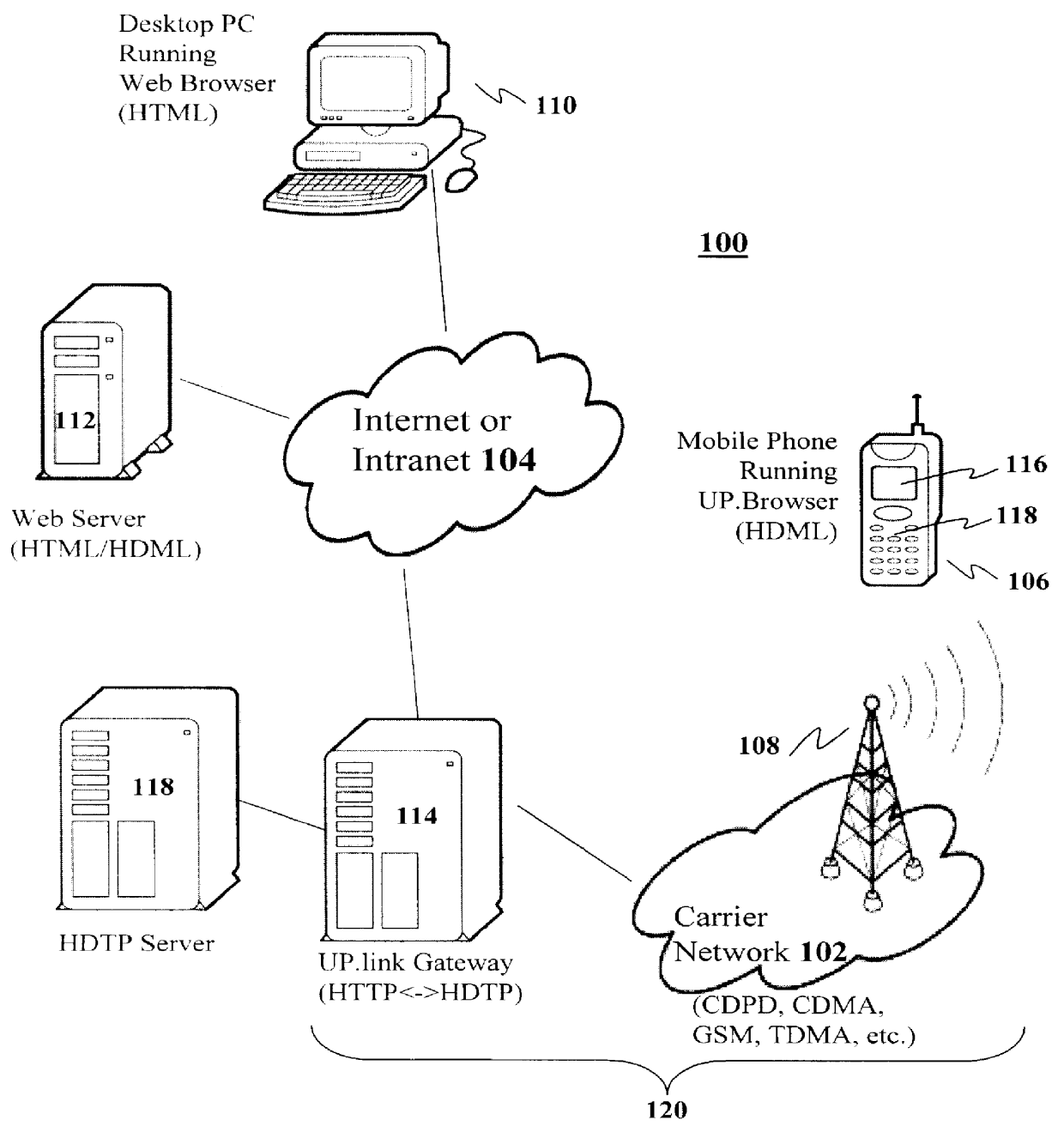
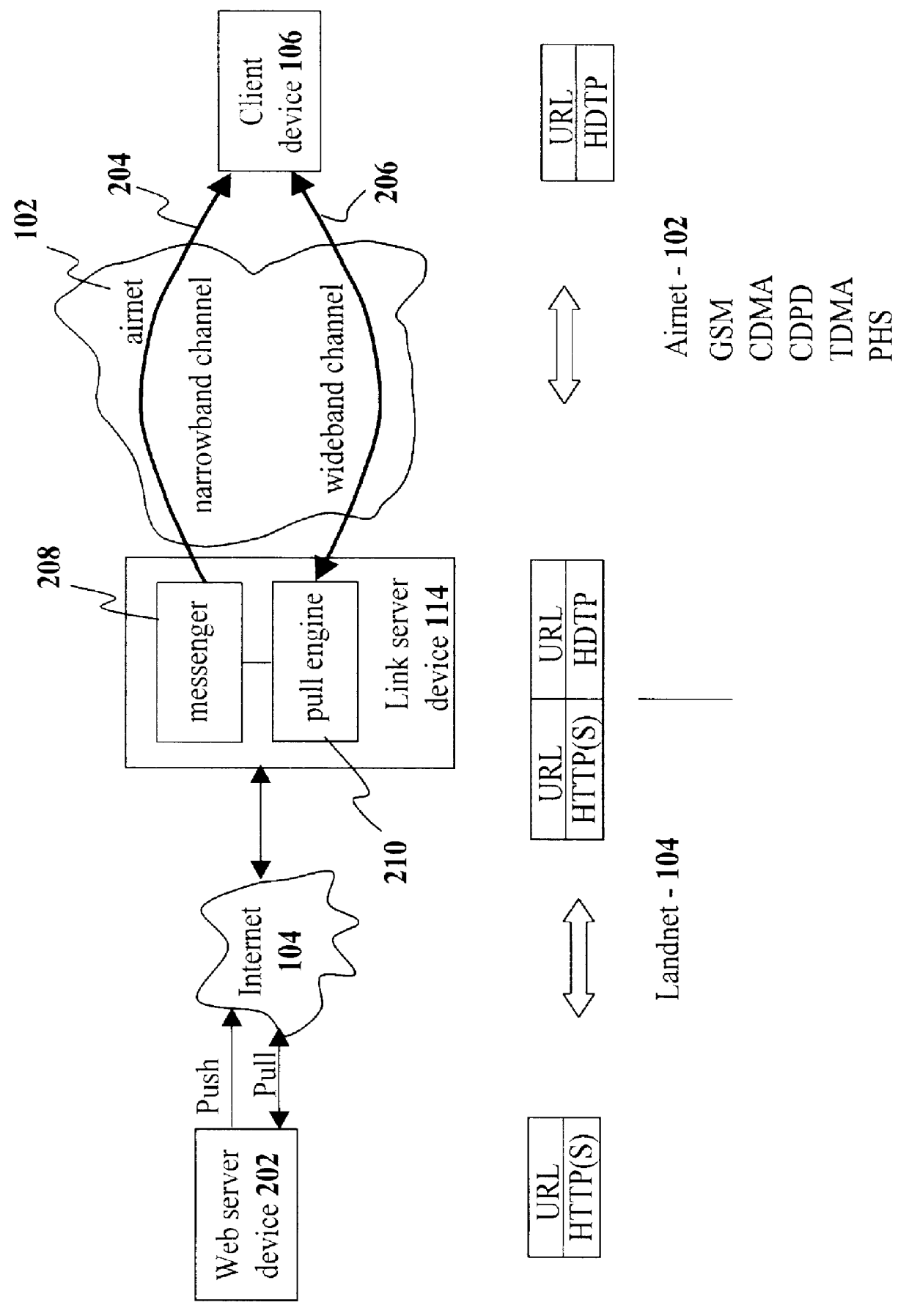
Method and system for pushing and pulling data using wideband and narrowband transport systems
InactiveUS6138158AWithout incurring uncontrollable costHigh trafficNetwork traffic/resource managementNetwork topologiesTransport systemThe Internet
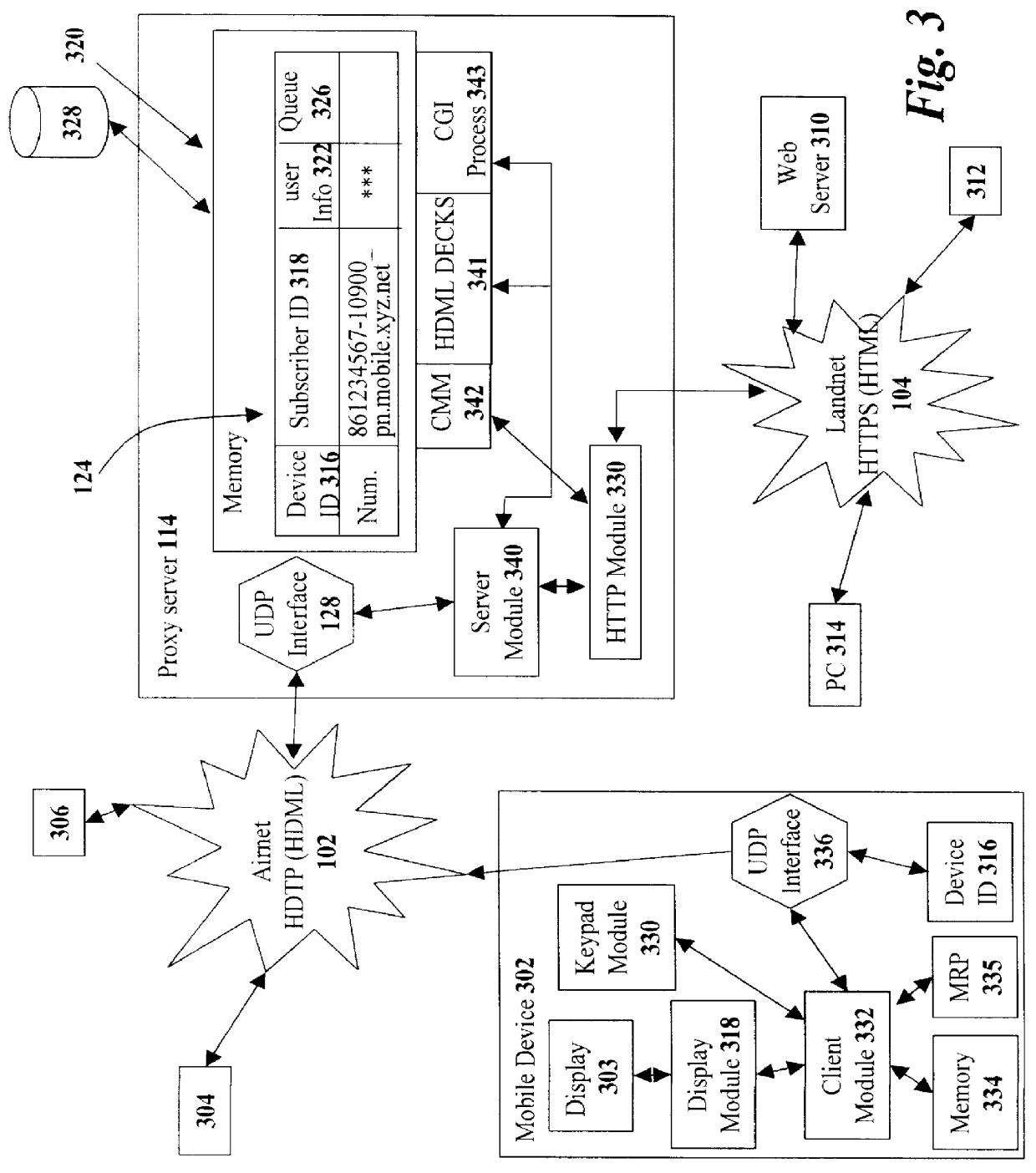
The present invention has particular applications to the navigation of Internet web pages using two-way interactive communication devices, such as a mobile device, a mobile phone, a landline telephone, and an Internet capable remote controller. According to one aspect of the present invention, each of the two-way interactive communication devices is a node in a distributed network, thus the devices can access hypermedia or hierarchic layers of information stored in server devices on the network. When one or more pages of information are updated, rather than sending the entire updated information to users of the devices subscribing to the updated information through the network, the present invention sends a notification to a proxy server that forwards the notification to the users using a messaging system via a low cost narrowband channel. Upon receiving the notification, the users can fetch the updates, when needed, through a wideband channel. Hence systemic solutions are provided in the present invention to integrate wideband and narrowband channels so as to keep the users informed of any updates to their desired information and meanwhile provide efficient means to the users for retrieving the latest updates without incurring uncontrollable costs and increasing unnecessary network traffics.
Owner:UNWIRED PLANET
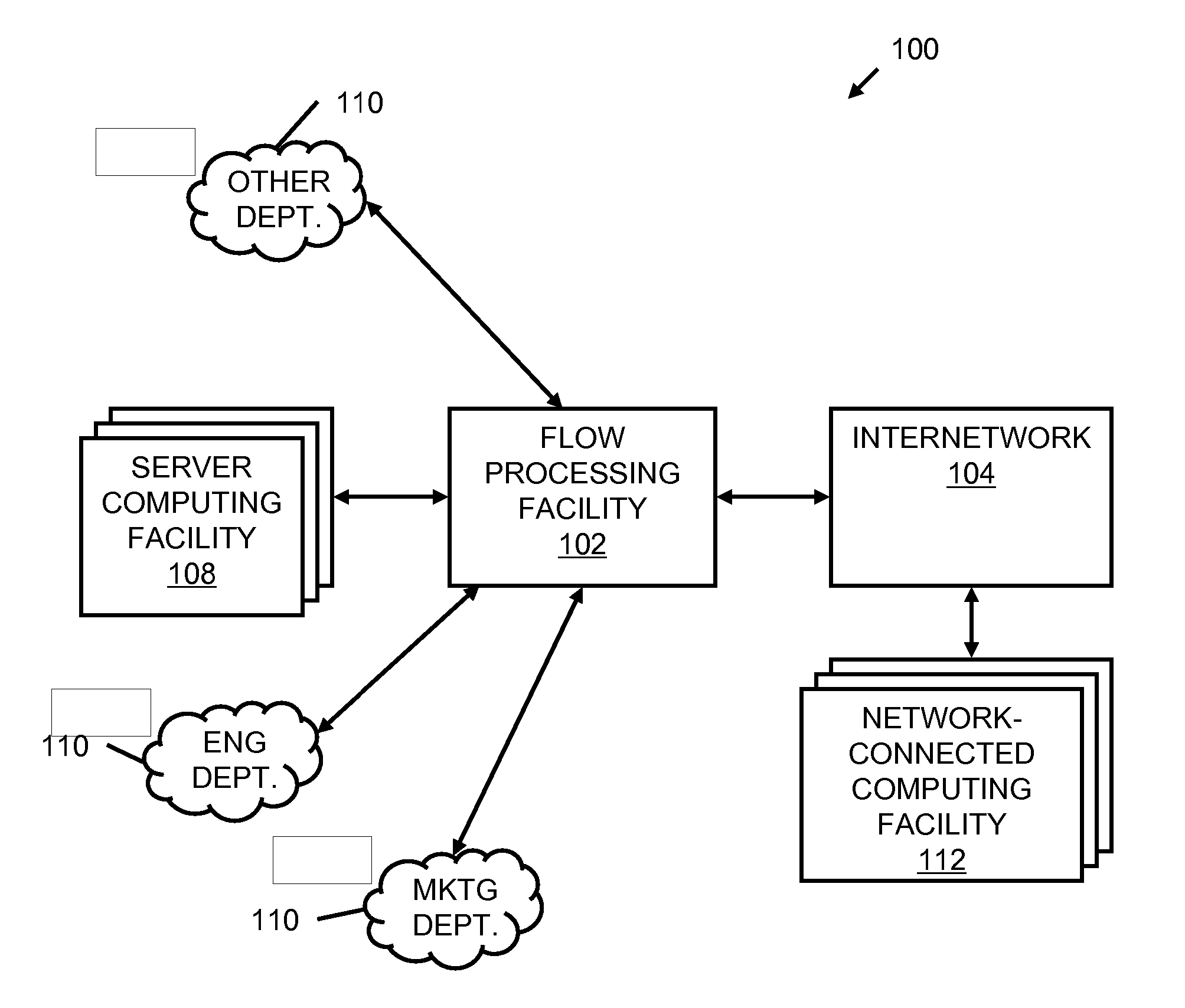
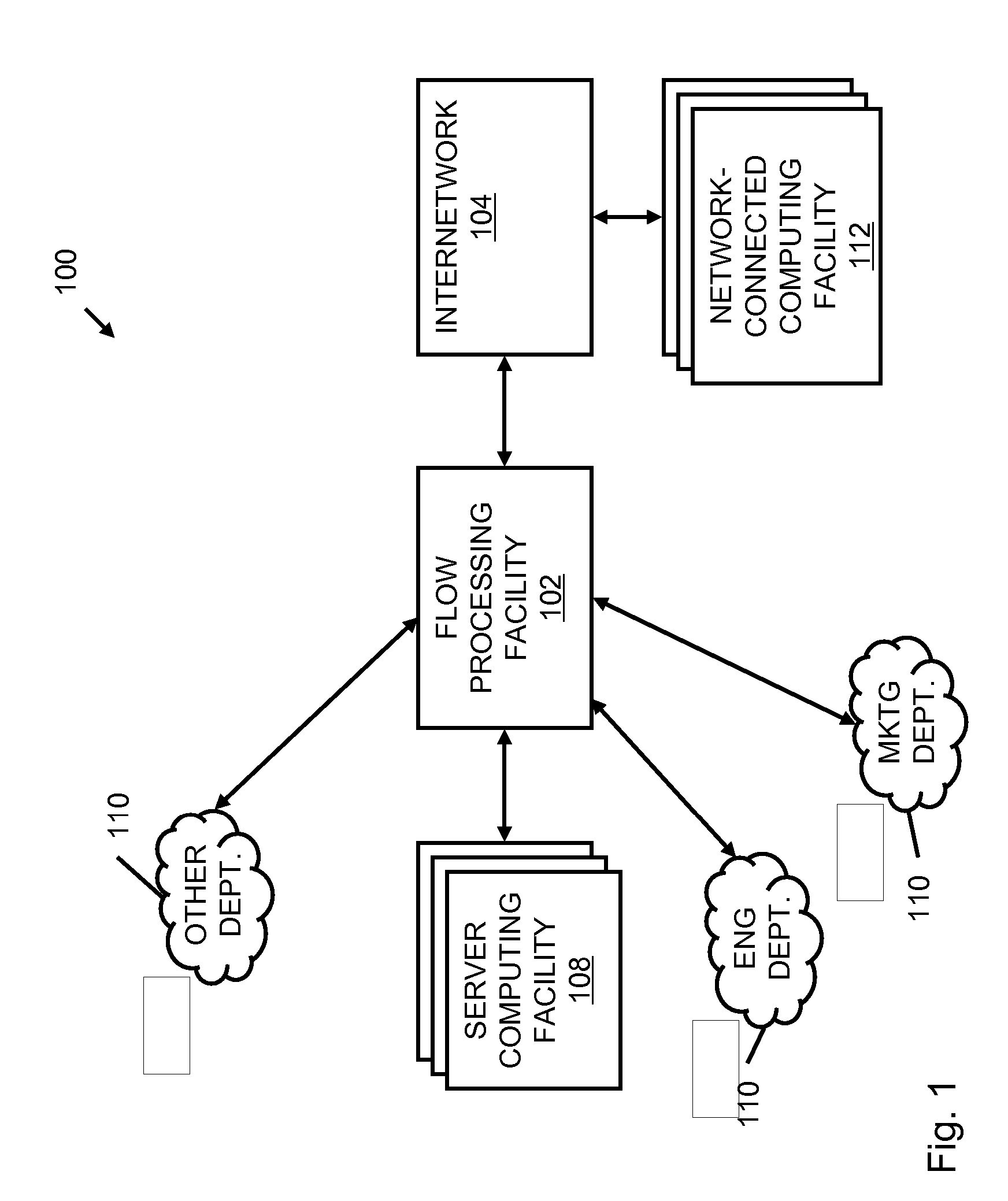
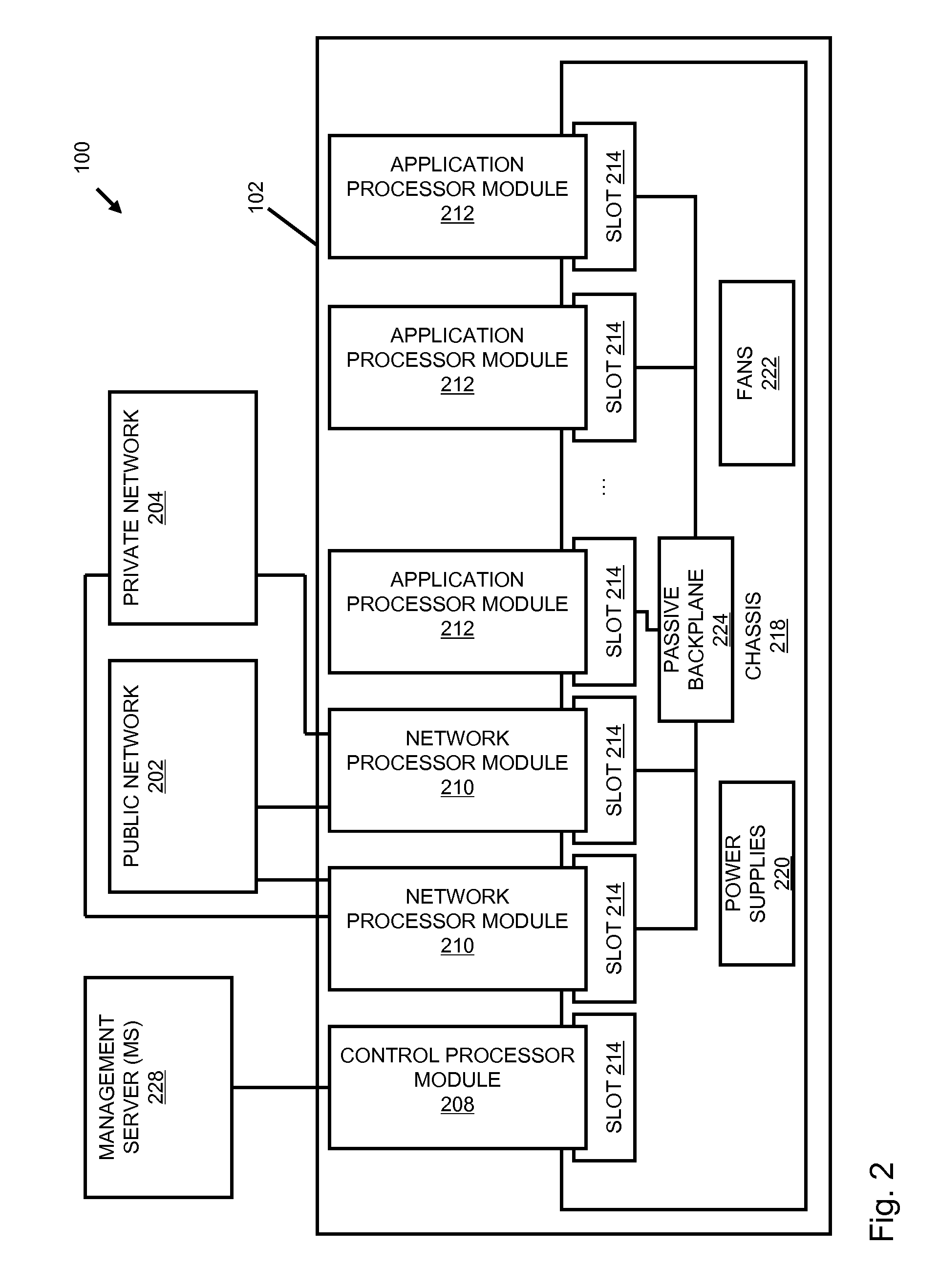
Systems and methods for processing data flows
InactiveUS20070192863A1Increased complexitySignificant expenseMemory loss protectionError detection/correctionData packData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
System, method and article of manufacture for selecting a gateway of a hybrid communication system architecture
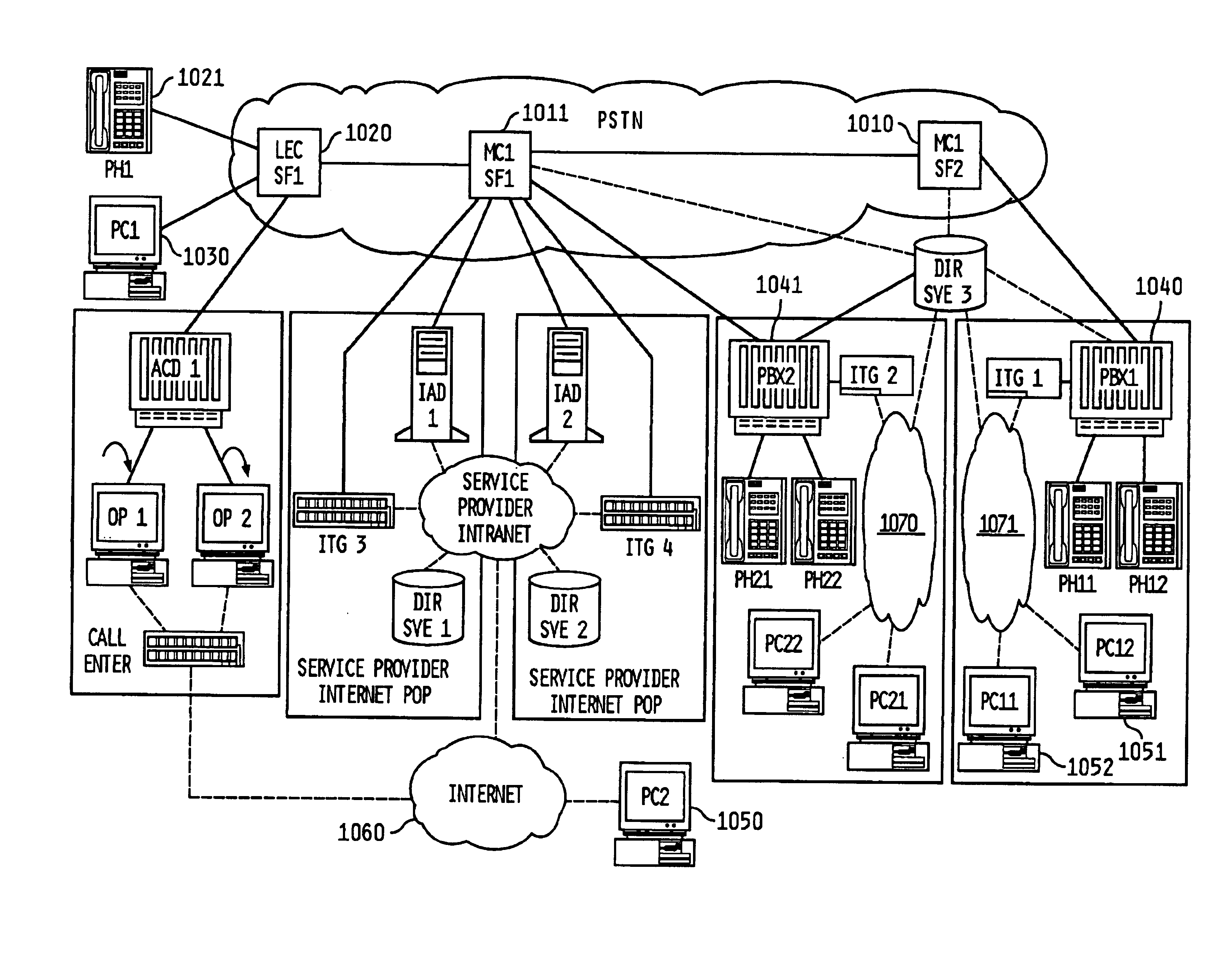
Telephone calls, data and other multimedia information is routed through a hybrid network which includes transfer of information across the internet utilizing telephony routing information and internet protocol address information. A media order entry captures complete user profile information for a user. This profile information is utilized by the system throughout the media experience for routing, billing, monitoring, reporting and other media control functions. Users can manage more aspects of a network than previously possible, and control network activities from a central site. A directory service that supports a hybrid communication system architecture is provided for routing traffic over the hybrid network and the internet and selecting a network proximal to the origination of the call.
Owner:VERIZON PATENT & LICENSING INC
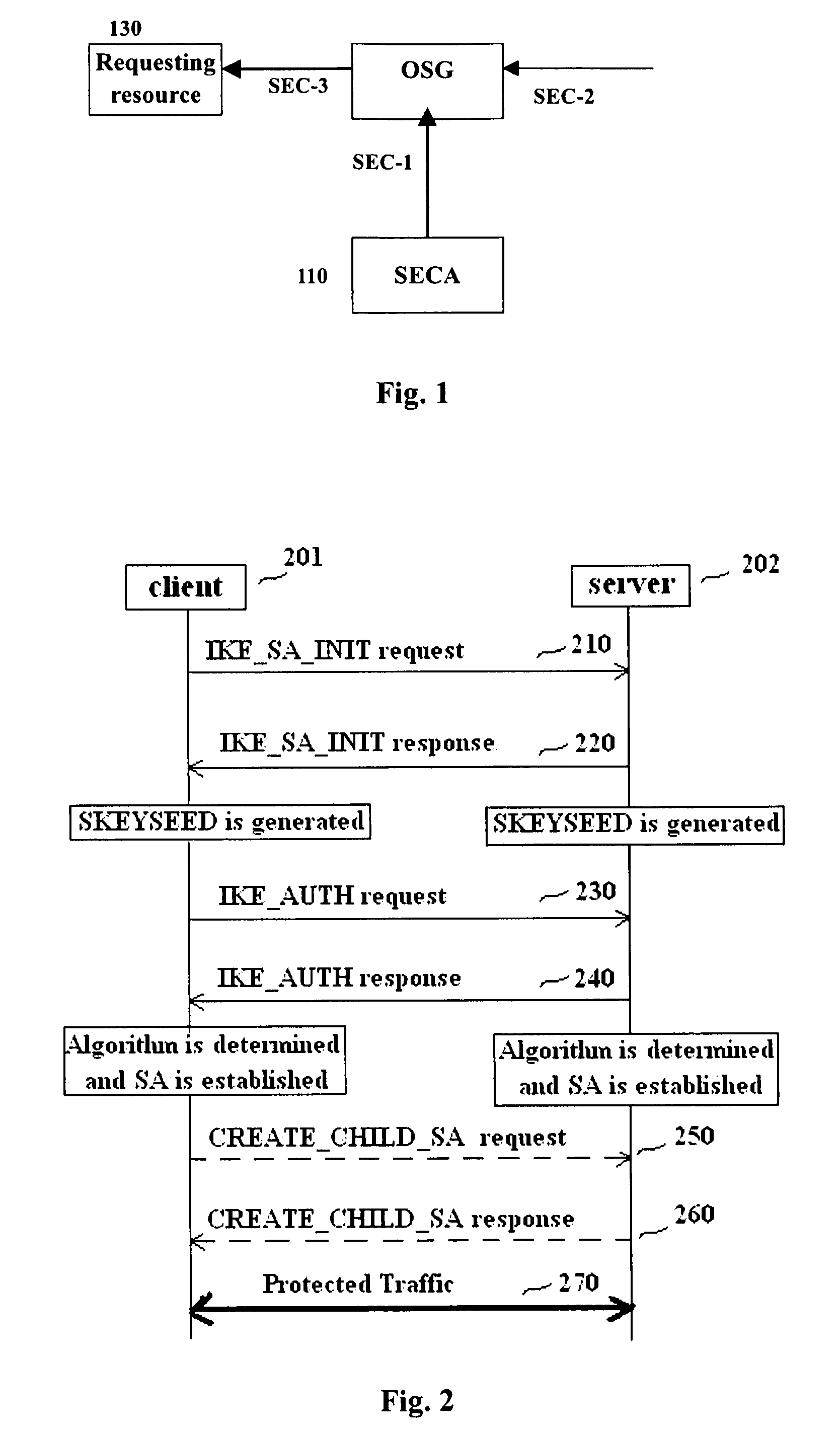
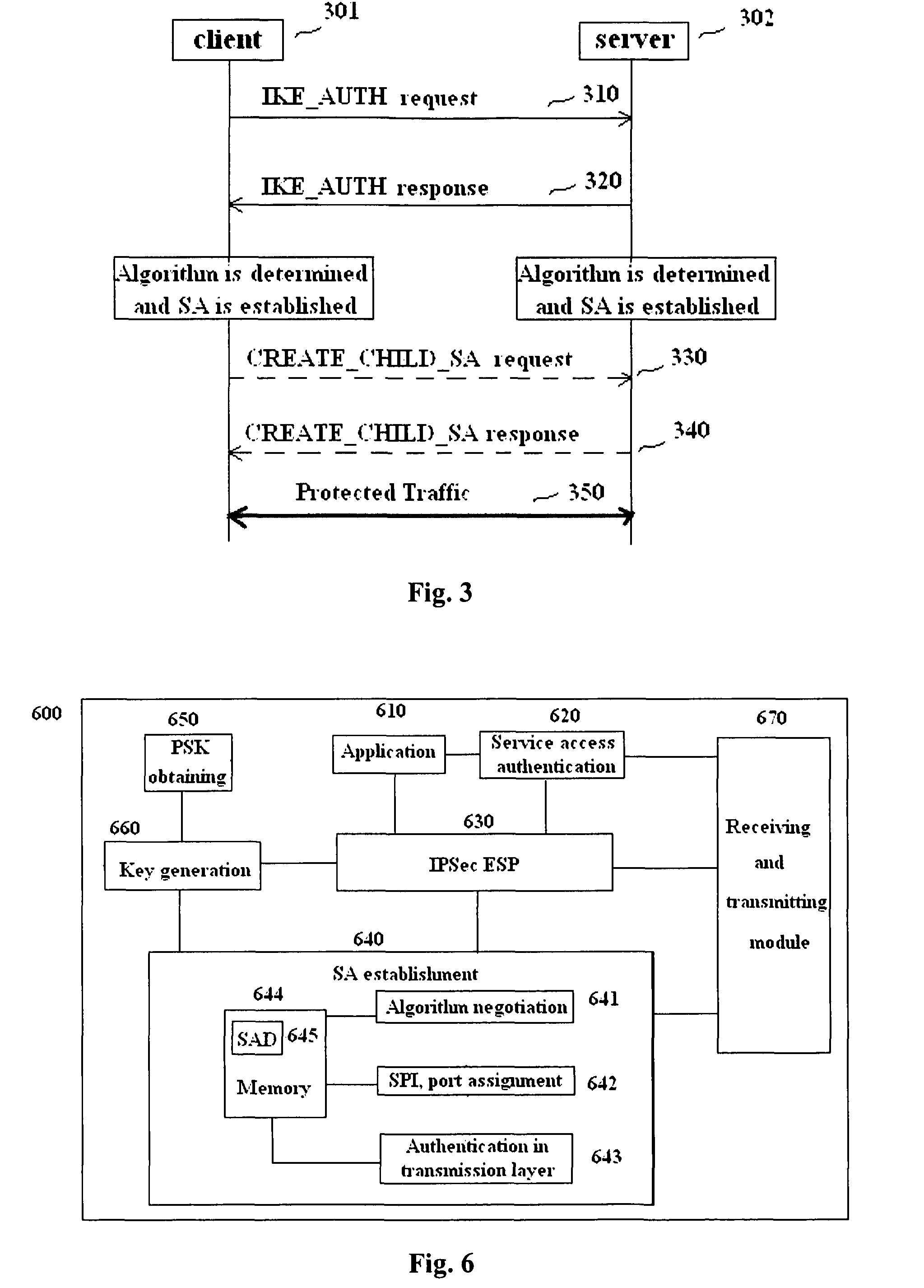
Methods and entities using IPSec ESP to support security functionality for UDP-based traffic
ActiveUS8639936B2Improve efficiencyOptimize procedureUser identity/authority verificationComputer security arrangementsTraffic capacityIPsec
Owner:ALCATEL LUCENT SAS
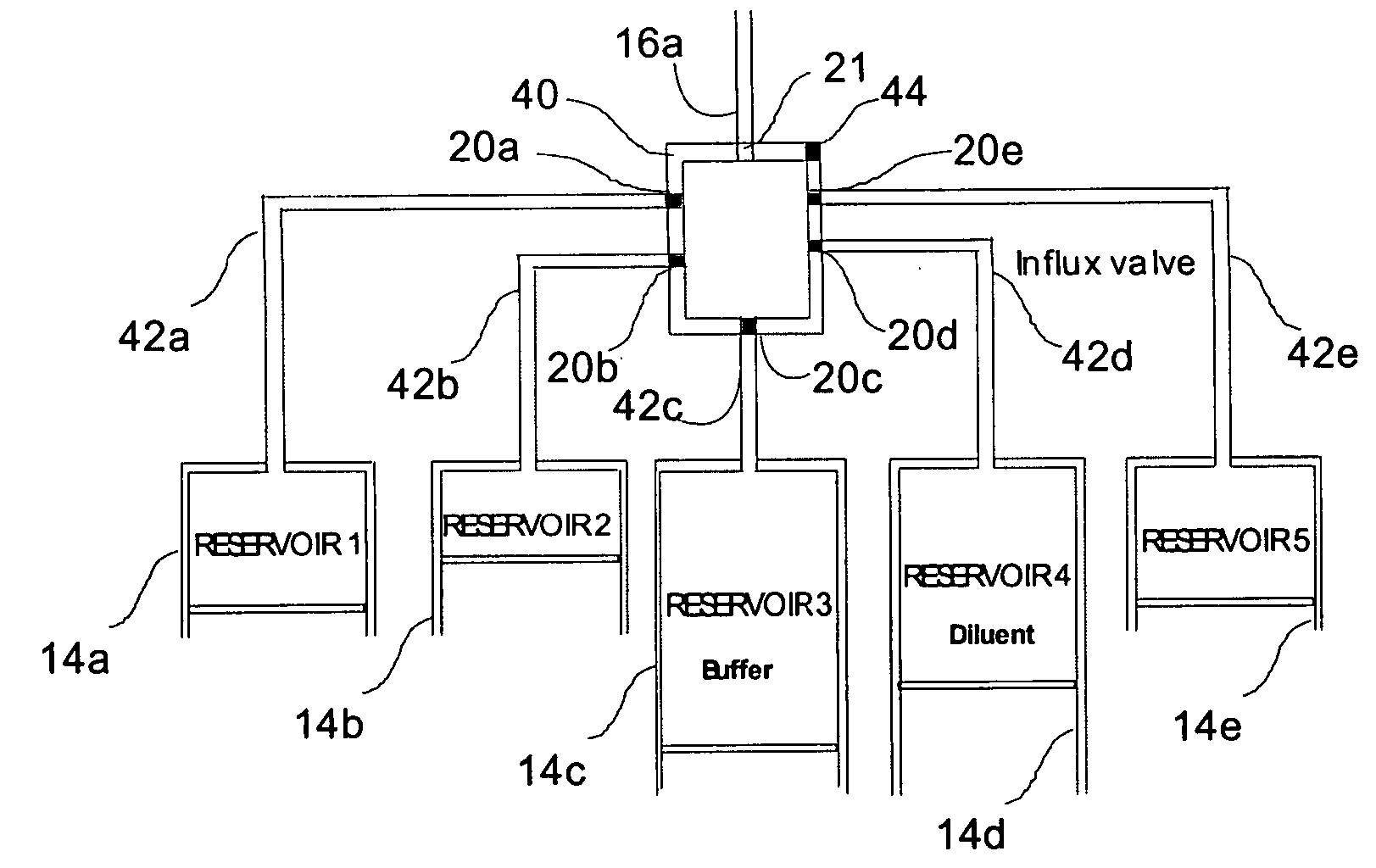
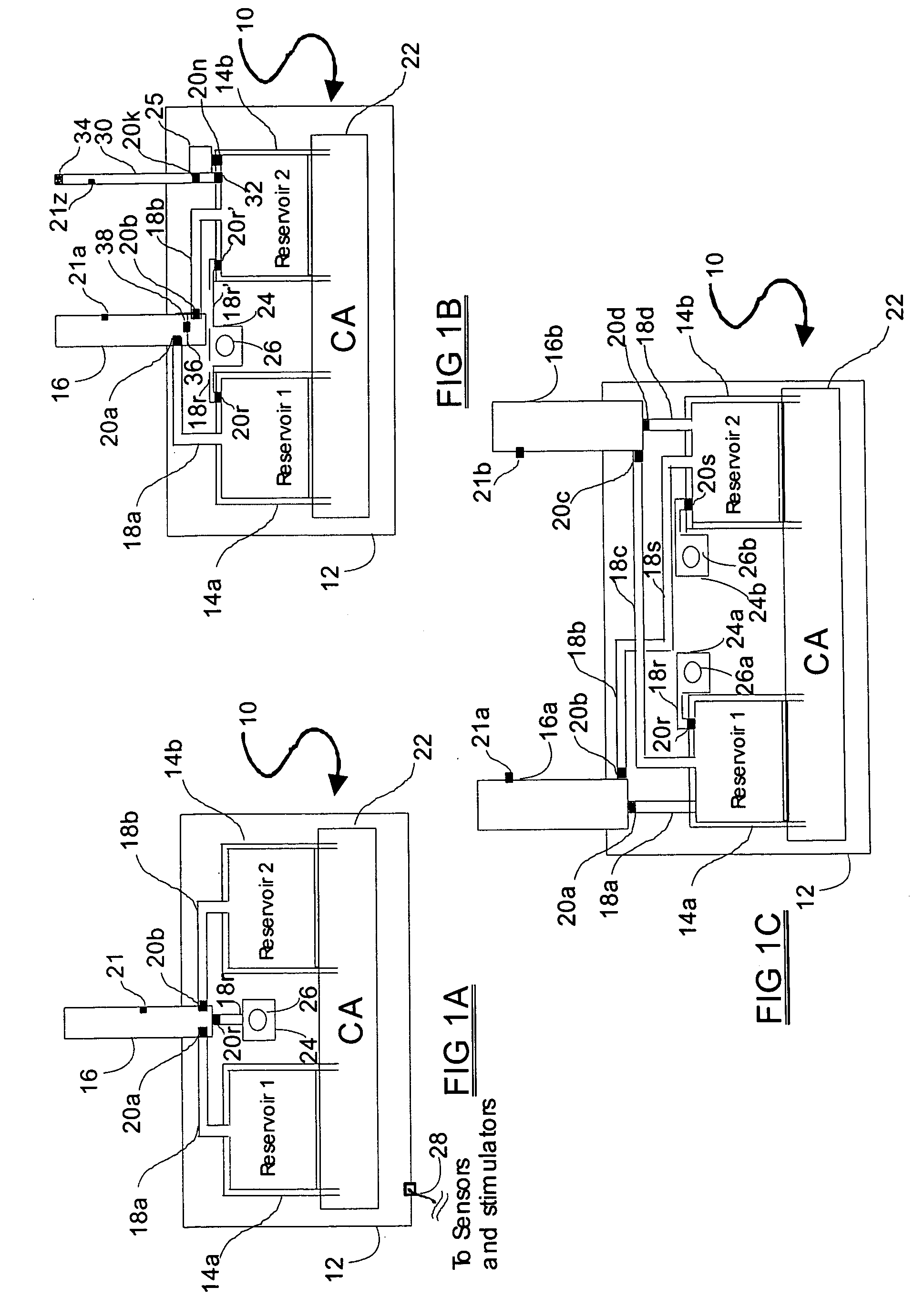
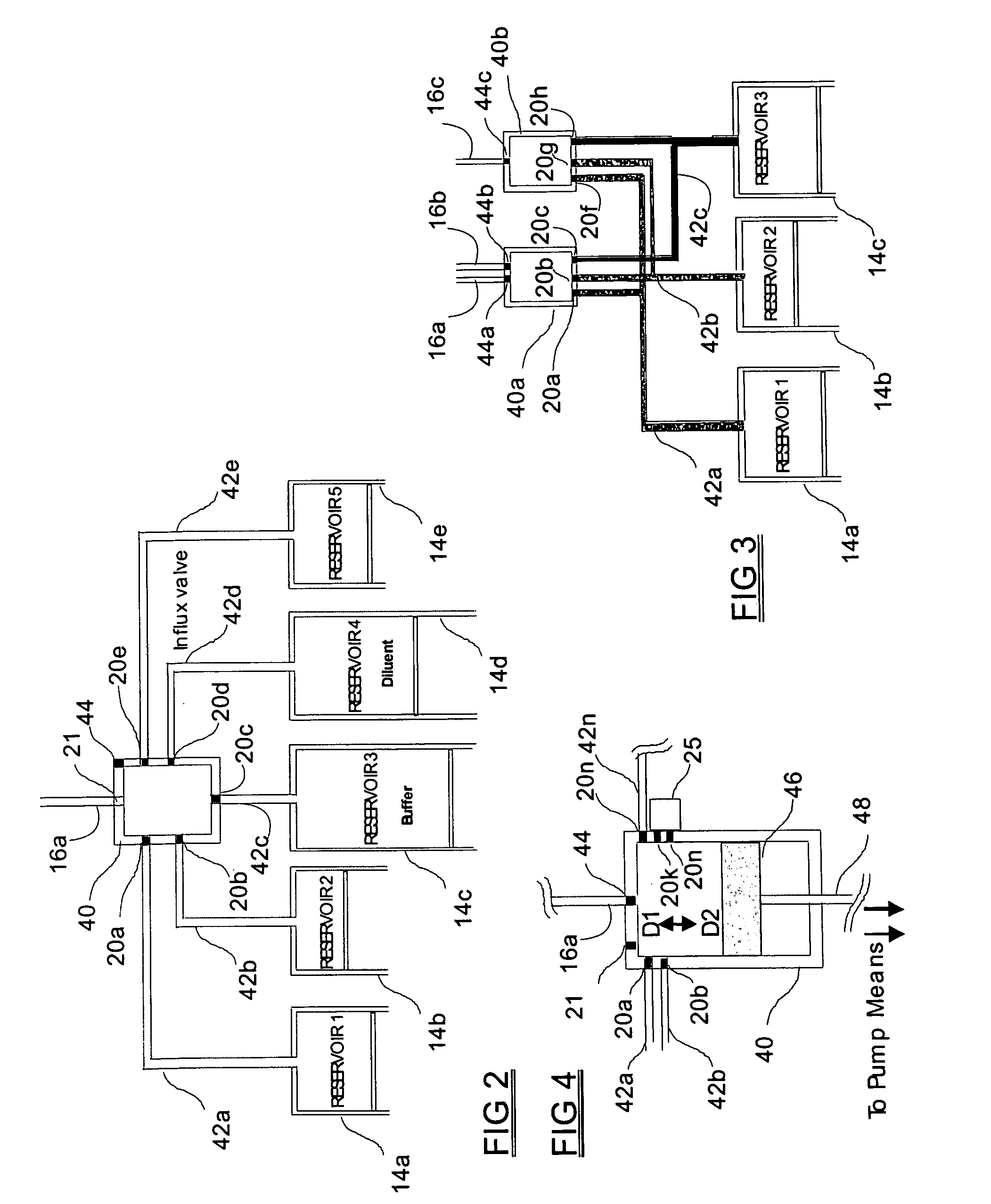
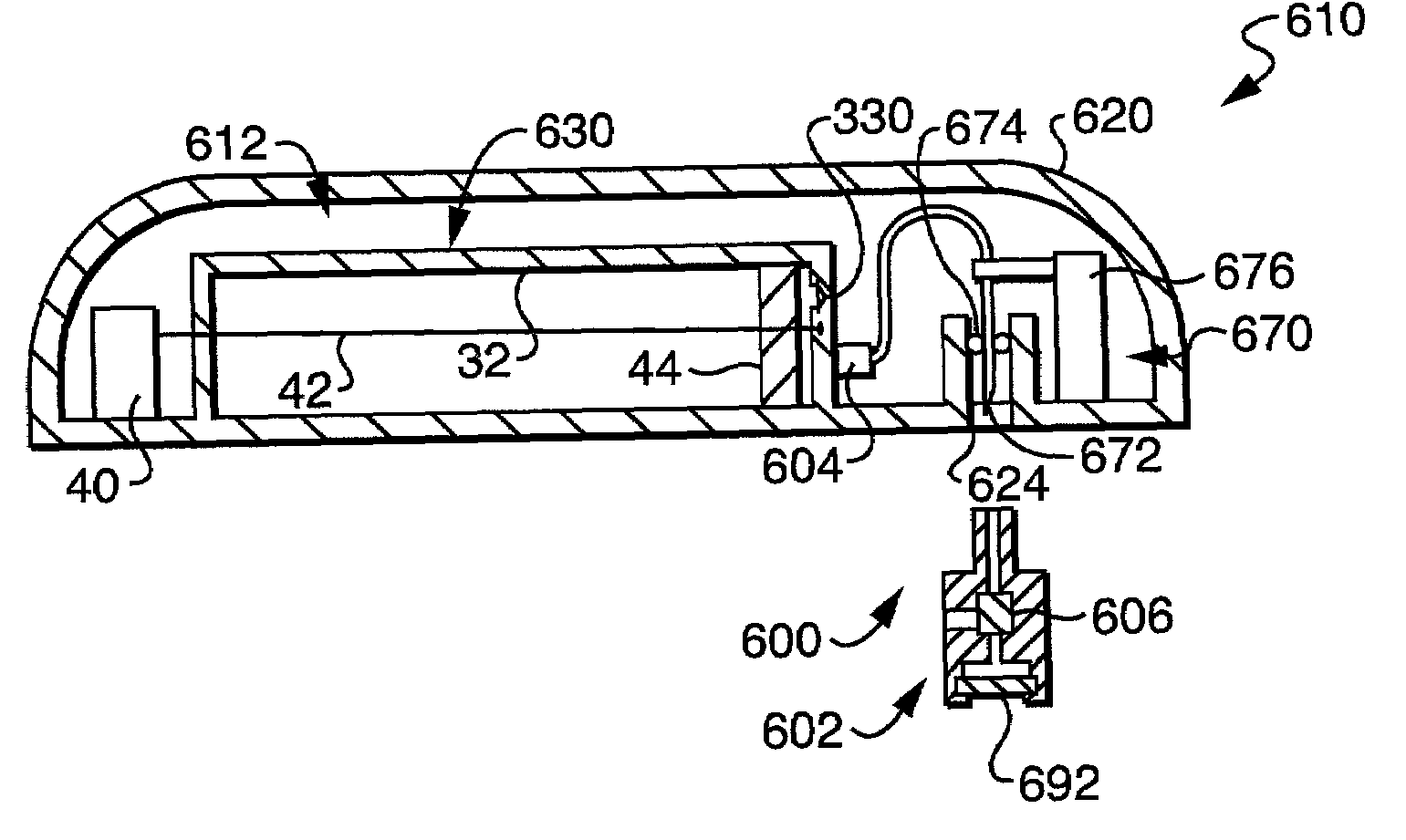
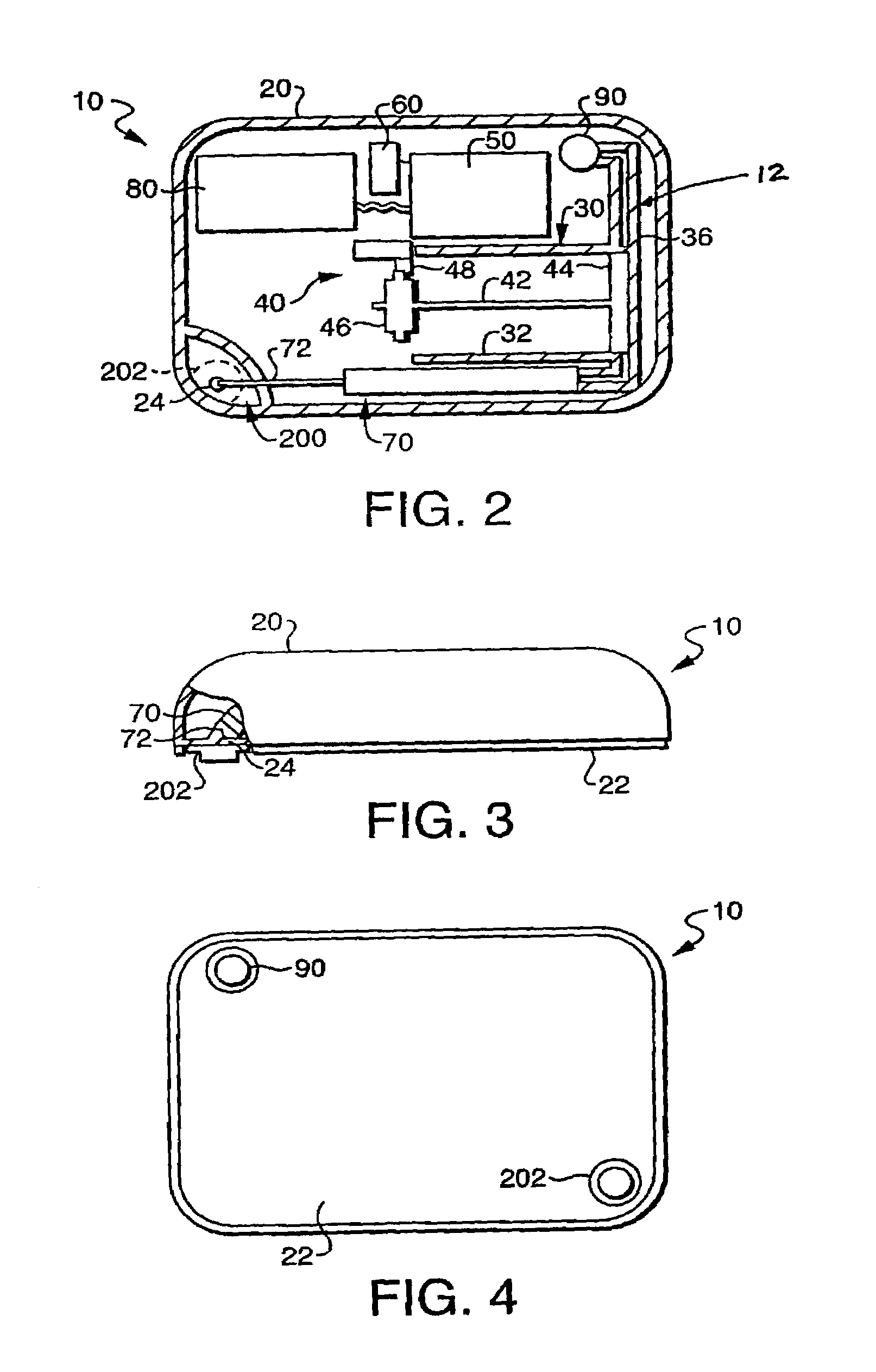
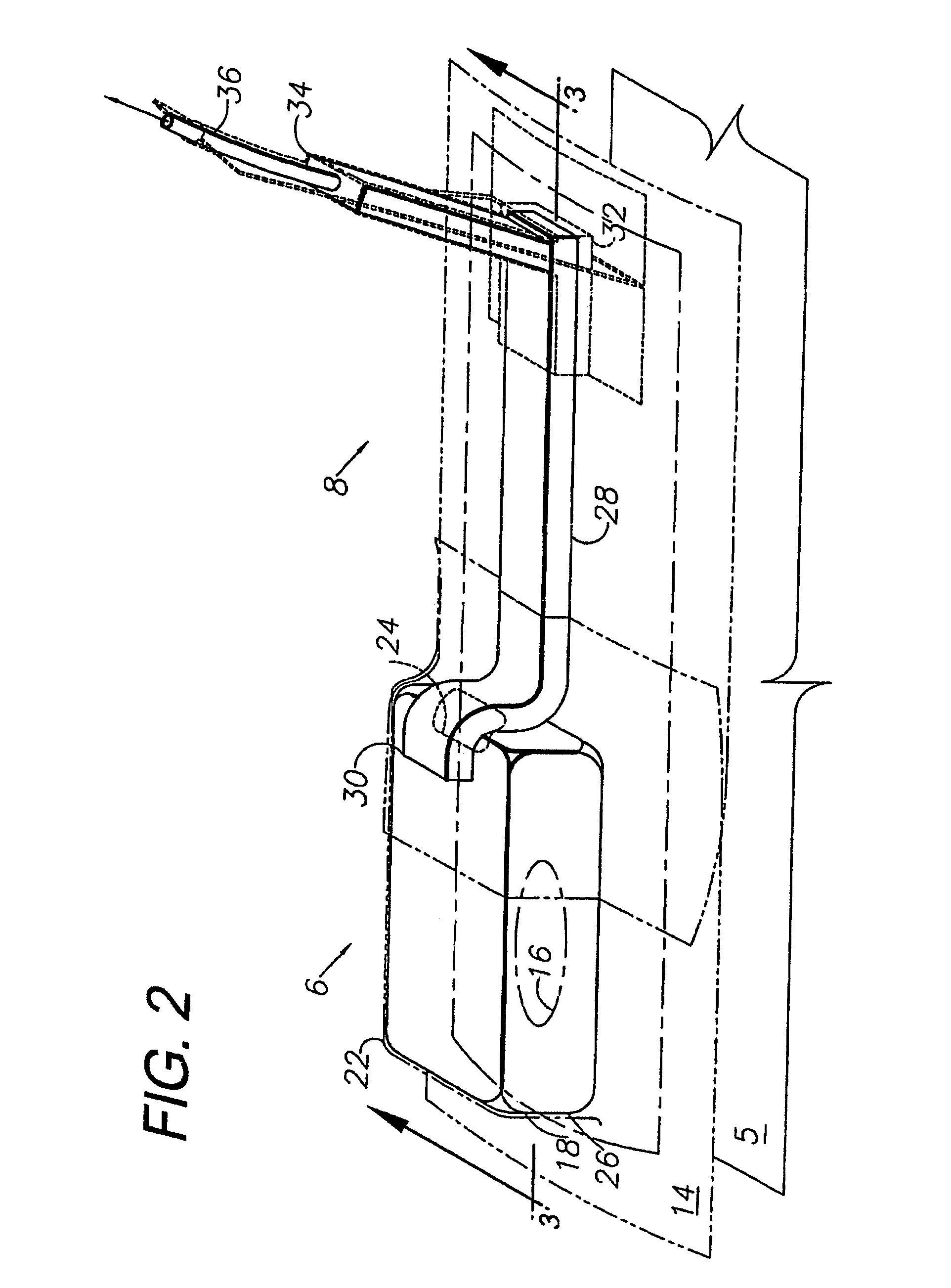
Programmable medical drug delivery systems and methods for delivery of multiple fluids and concentrations
InactiveUS20050277912A1Extension of timeEasy to fillMulti-lumen catheterDrug and medicationsControl mannerDelivery system
A drug delivery system provides for mixing various drugs in an optimally controlled manner, for using flow controllers to guide multiple drugs into a single or into multiple catheters, for enabling a single lumen catheter to treat a specific region with several drugs, for allowing for dilution of a concentrated drug in order to both increase the time between refilling and also for providing any concentration of a drug that might be desired, for using a buffer fluid to deliver exact amounts of several drugs from the same catheter or to separate several drugs within a single catheter, for using external fluid present in the human body either as a diluent or buffer fluid, and for providing for a drug testing / filler apparatus to be used prior to implant to ensure proper function and easy means of filling multiple reservoirs with different fluids, and also after implant for refilling operations. The drug delivery system (DDS) can perform both bolus and continuous delivery of substances, and enable the measured delivery of any one of several drugs to one or more distal locations at independently programmable rates. New types of catheter systems and uses therefore are also described. Catheter hub assemblies allowing for easy replacement of drug delivery systems offer advantages when replacing drug delivery systems. New methods for using the DDS in the promotion of healthy pregnancy and treatment of a developing fetus are also possible.
Owner:JOHN SASHA
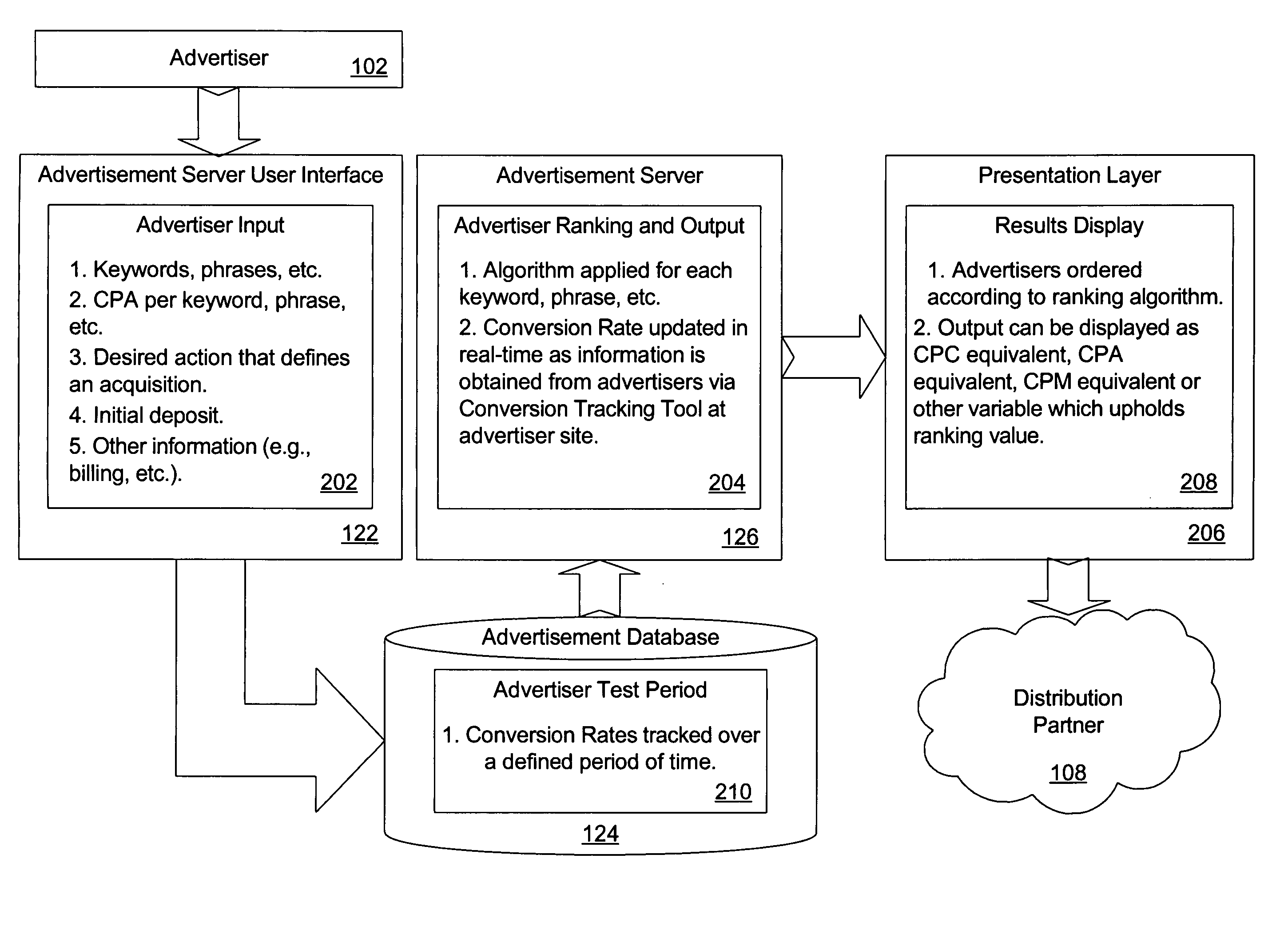
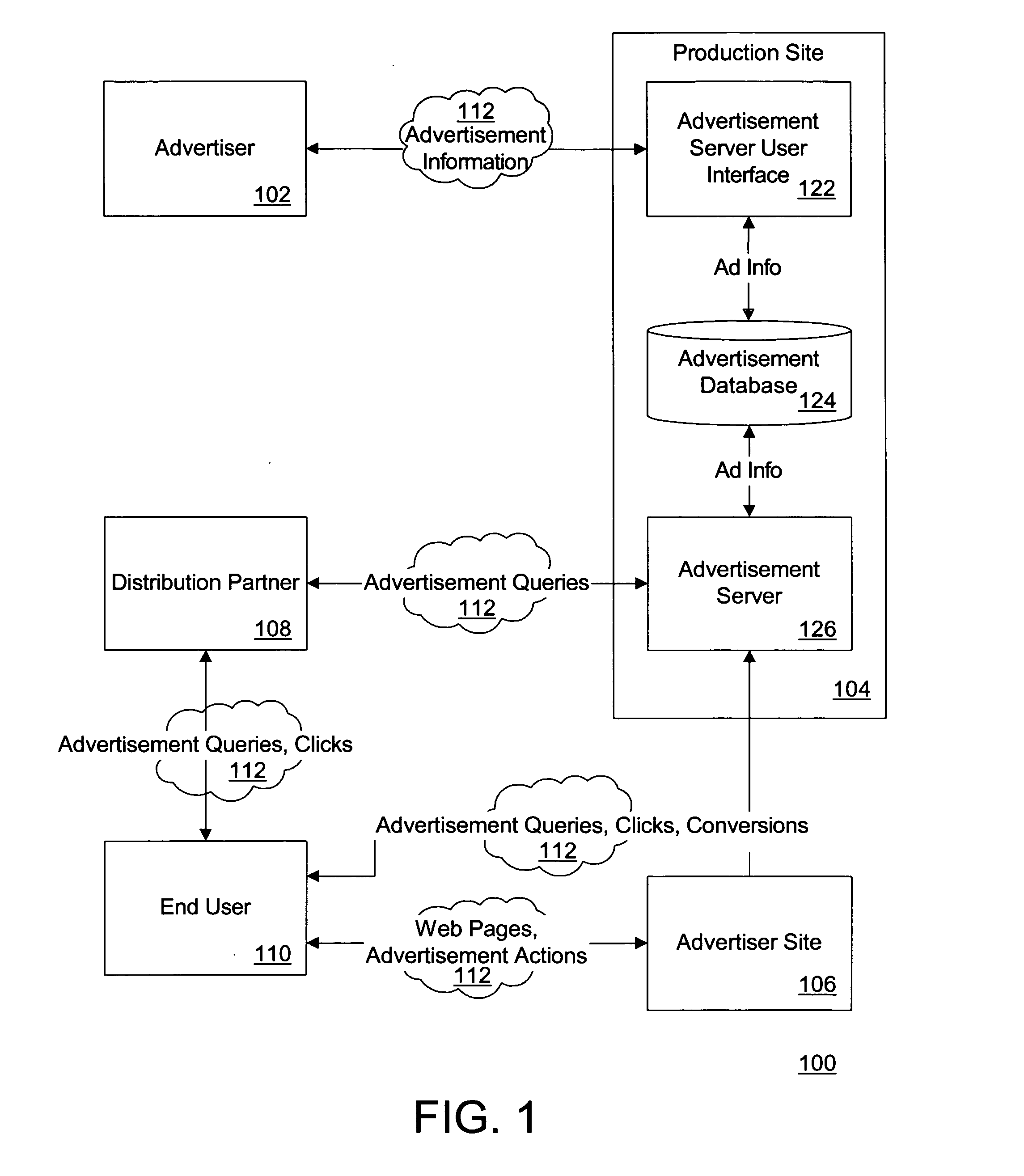
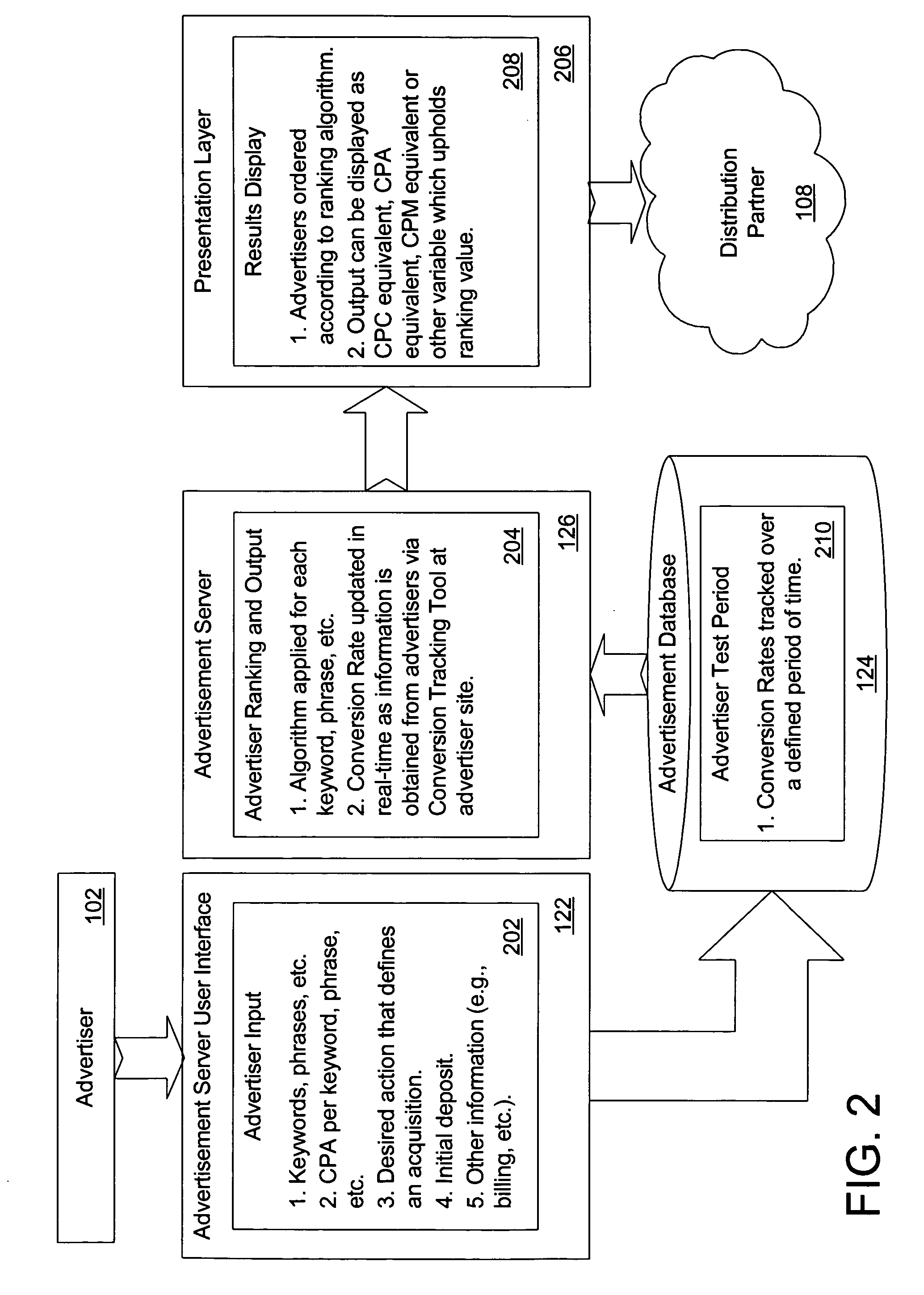
Performance-based online advertising system and method
ActiveUS20050097204A1AdvertisementsDigital data processing detailsOnline advertisingCost per acquisition
A system, method, and computer program product for online advertising, including computing and dynamically updating a cost-per-click (CPC) value of an advertisement for an advertisement traffic source based on a variable; and automatically uploading and distributing the advertisement to the traffic source. The variable includes price, advertisement traffic source, and / or advertiser variableS. Further embodiments include dynamically updating an advertisement listing that has a cost-per-acquisition (CPA)-based value with associated CPC or cost-per-1000 (CPM) values; and distributing the advertisement listing to an advertisement distribution network that serves the listing based on the CPC or CPM values. The distribution network includes CPC-based, CPA-based, and / or CPM-based distribution networks. Further embodiments include determining a CPC value for a CPA-based advertisement; and placing the advertisement on an advertising network at the determined CPC based on a ratio of an expected number of conversions at a CPA value divided by a number of clicks at the CPC.
Owner:MARCHEX
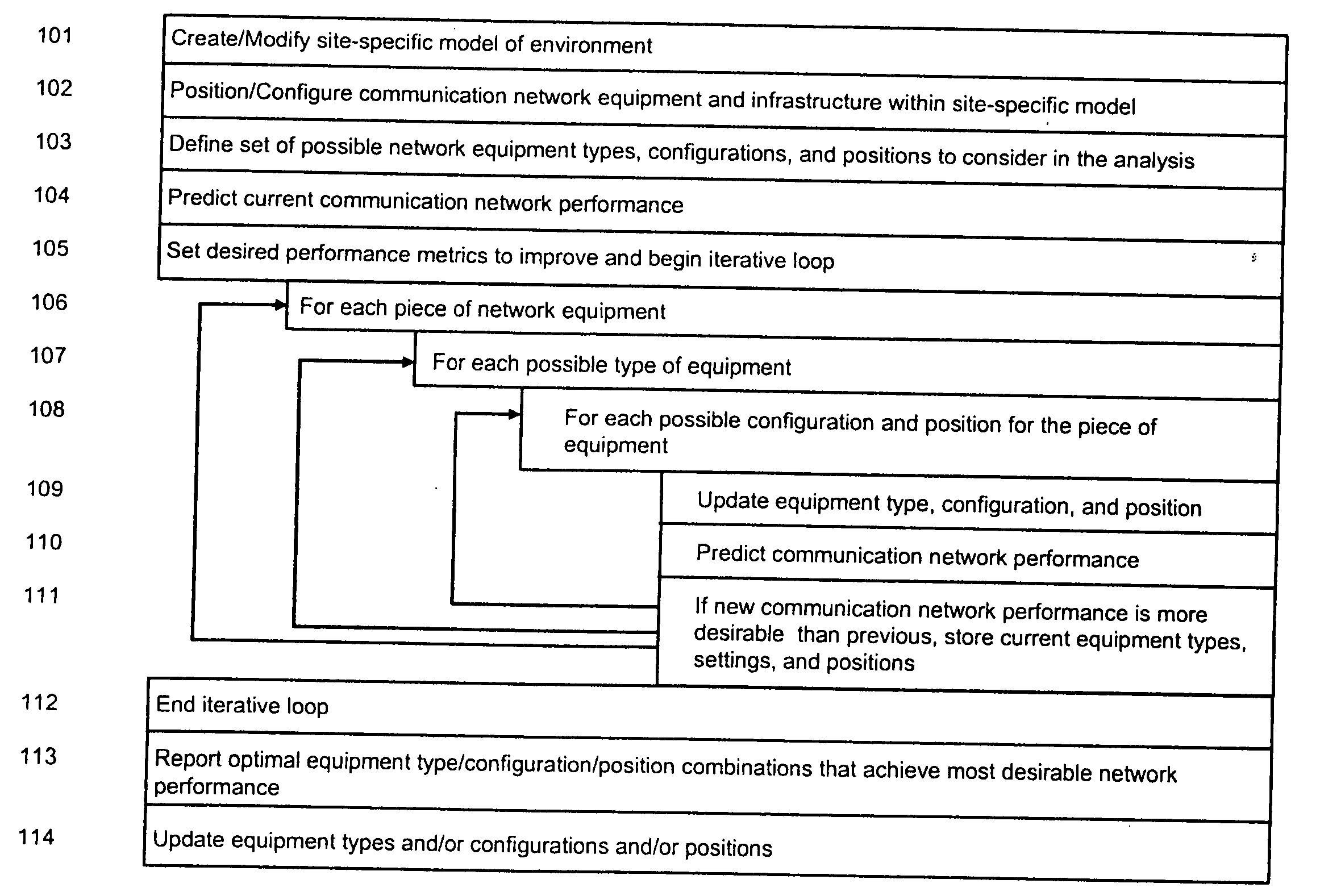
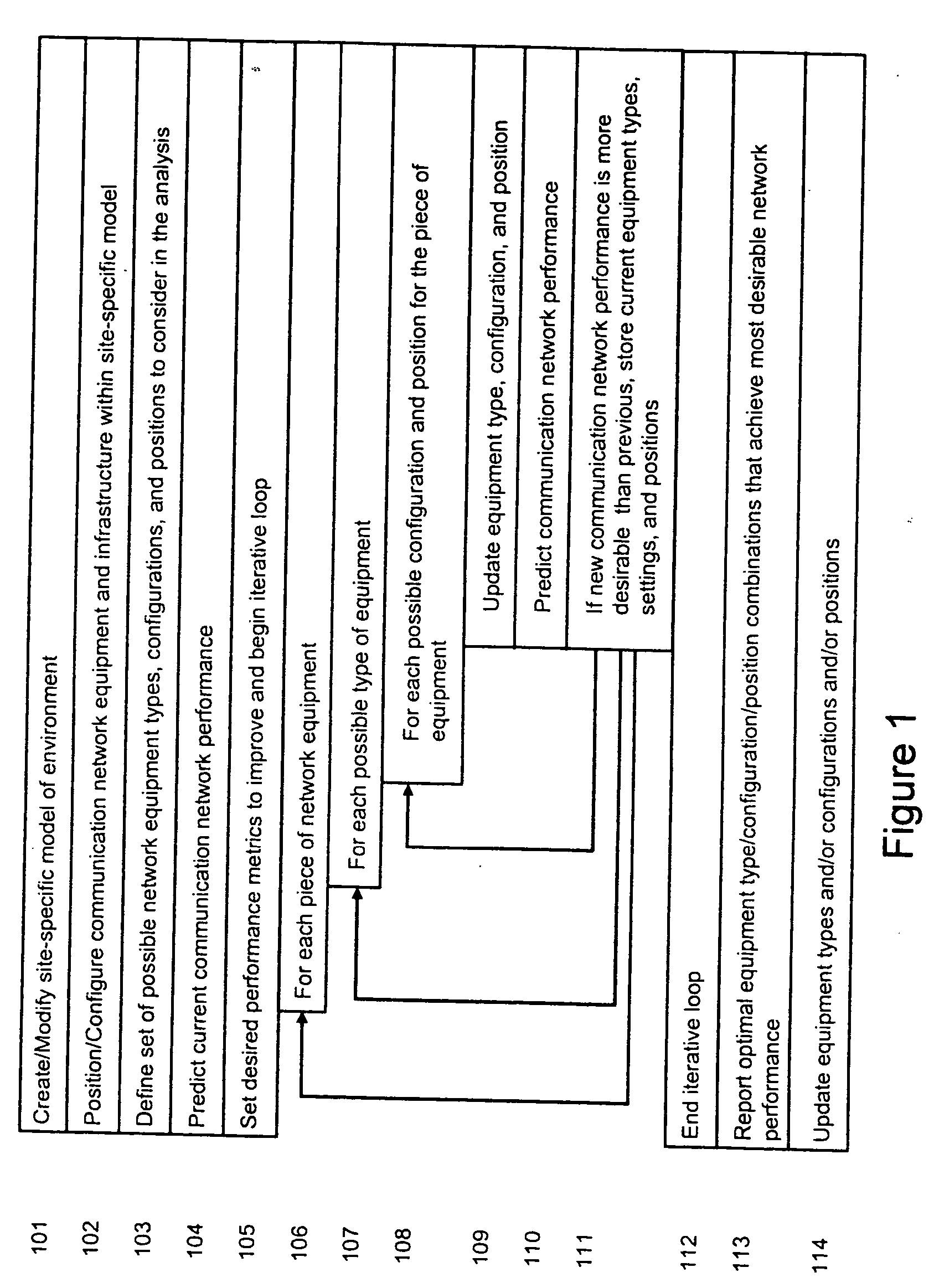
System and method for automated placement or configuration of equipment for obtaining desired network performance objectives and for security, RF tags, and bandwidth provisioning
ActiveUS20040236547A1Significant valueEasy to explainGeometric CADData taking preventionHard disc driveThe Internet
A method is presented for determining optimal or preferred configuration settings for wireless or wired network equipment in order to obtain a desirable level of network performance. A site-specific network model is used with adaptive processing to perform efficient design and on-going management of network performance. The invention iteratively determines overall network performance and cost, and further iterates equipment settings, locations and orientations. Real time control is between a site-specific Computer Aided Design (CAD) software application and the physical components of the network allows the invention to display, store, and iteratively adapt any network to constantly varying traffic and interference conditions. Alarms provide rapid adaptation of network parameters, and alerts and preprogrammed network shutdown actions may be taken autonomously. A wireless post-it note device and network allows massive data such as book contents or hard drive memory to be accessed within a room by a wide bandwidth reader device, and this can further be interconnected to the internet or Ethernet backbone in order to provide worldwide access and remote retrieval to wireless post-it devices.
Owner:EXTREME NETWORKS INC
Multi-access terminal with capability for simultaneous connectivity to multiple communication channels
ActiveUS20060193295A1Improve reliabilityImprove behaviorNetwork traffic/resource managementTime-division multiplexTransceiverOperational system
An apparatus is disclosed for permitting a mobile terminal having multiple, heterogeneous network connections (e.g., multiple wired or wireless transceivers of various types) to set up and maintain virtual connections over multiple networks to either the same or to multiple destinations. The mobile terminal can “load-share” traffic, i.e., it can distribute segments of traffic over a full set of heterogeneous networks, significantly improving the reliability and availability of communications. In a first embodiment, a mobile terminal is configured with multiple radio frequency (RF) transceivers. Operating system software is provided for dynamically establishing and maintaining traffic flow for user applications over multiple communications paths, and for automatically adapting to variations in the networking environment, application traffic flow requirements, end user preferences, or mobility. In a second embodiment, a software-defined radio is used to implement the physical layer protocols for each desired network, eliminating the need for multiple transceivers.
Owner:TRUSTEES OF STEVENS INST OF TECH THE
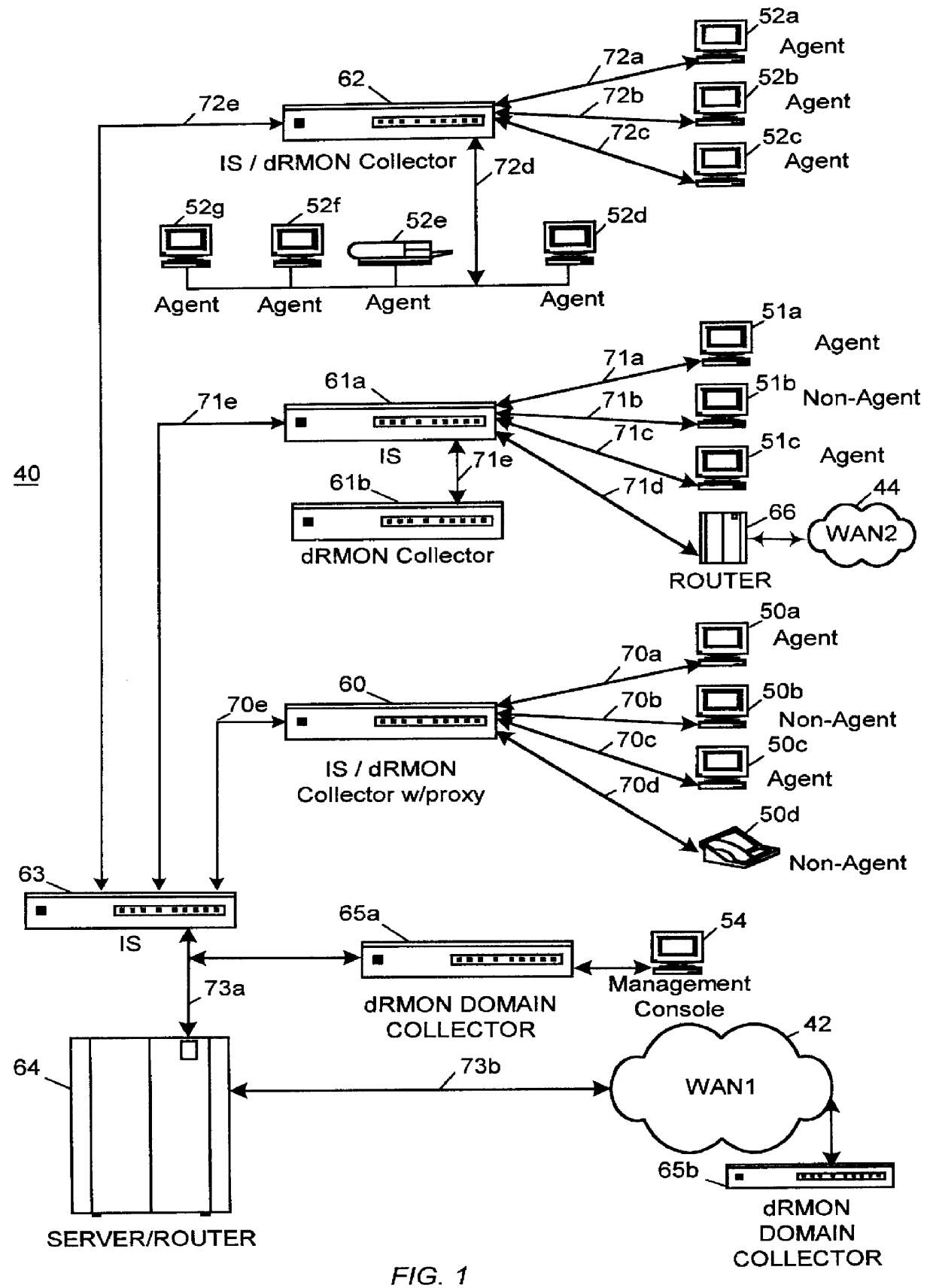
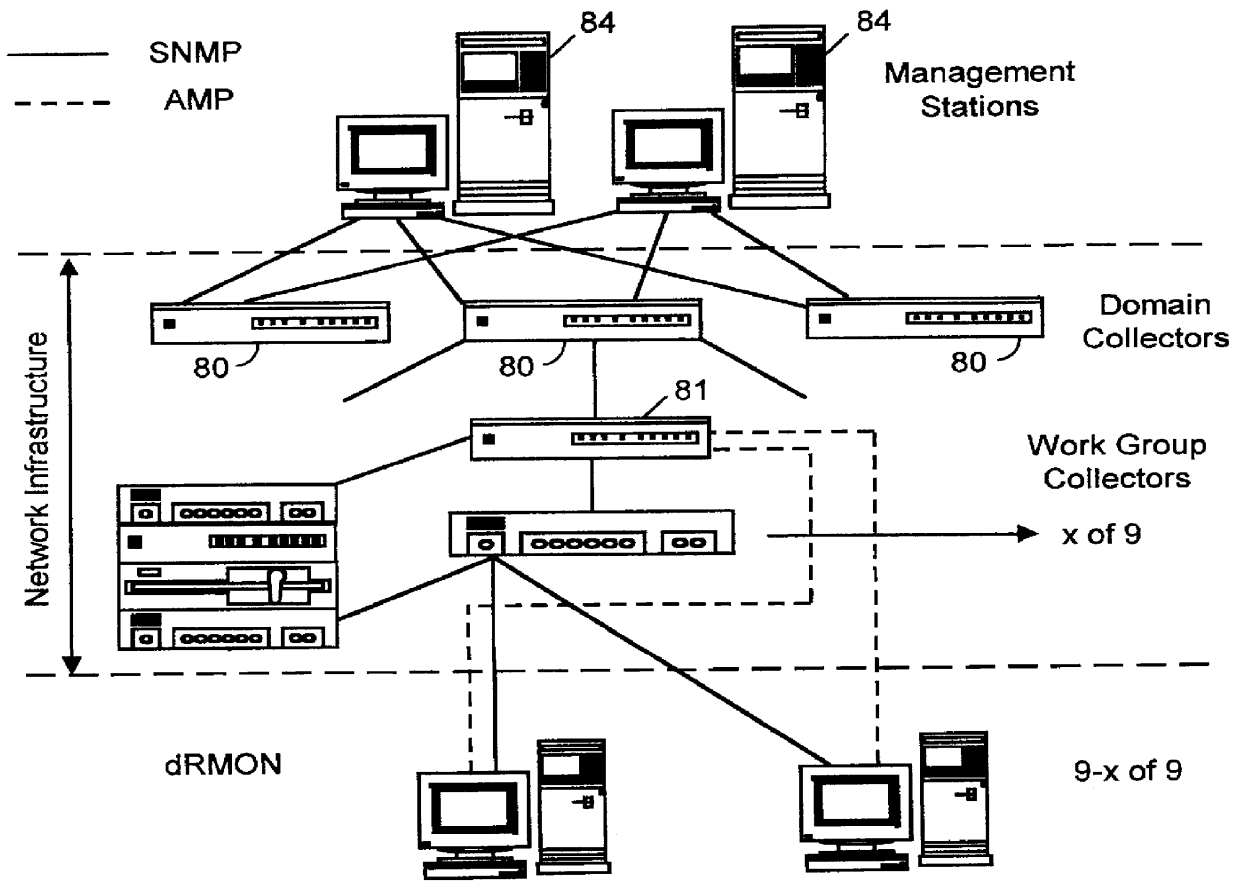
Distributed remote monitoring (dRMON) for networks
InactiveUS6108782AError preventionFrequency-division multiplex detailsNetwork operating systemOperational system
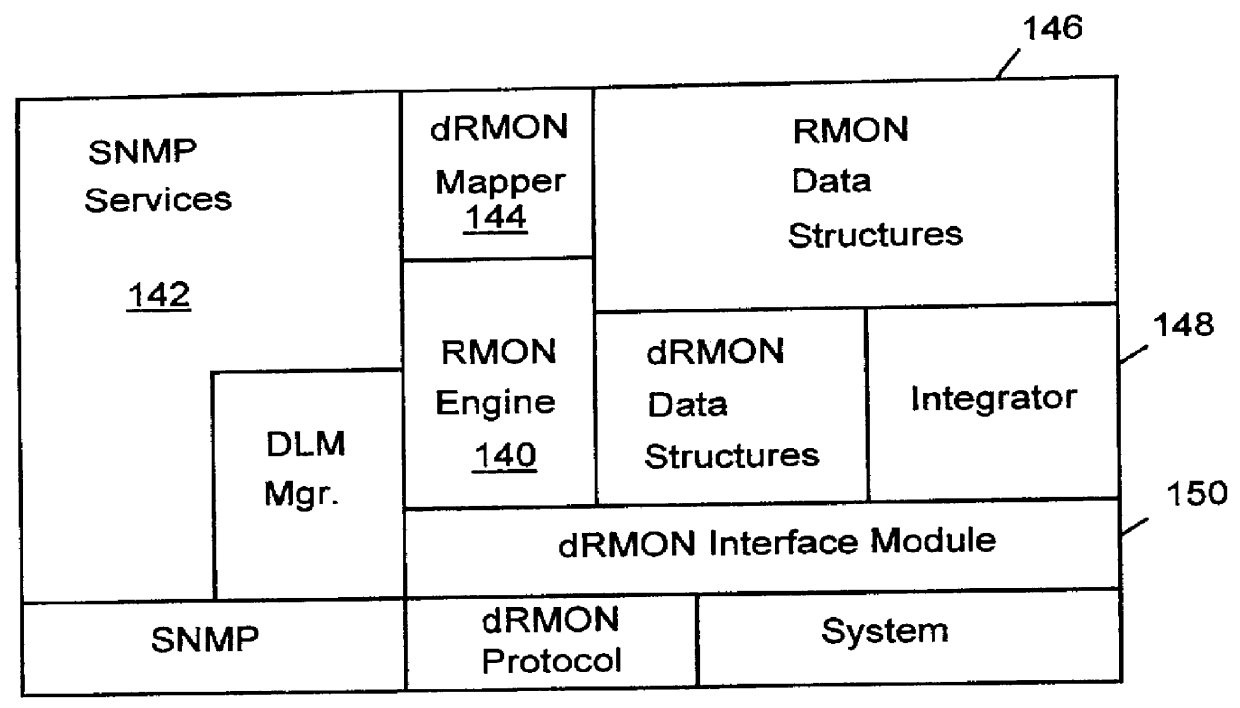
Distributed remote monitoring (dRMON) of network traffic and performance uses distributed nodes to collect traffic statistics at distributed points in the network. These statistics are forwarded to collectors which compile the statistics to create combined views of network performance. A collector may mimic a prior art, non-distributed, network probe and may interact with network management software as though it were a stand alone network probe thereby simplifying a user's interaction with the distributed system. The invention is designed to work in accordance with a variety of standard network management protocols including SNMP, RMON, and RMON2 but is not limited to those environments. The invention has applications in a variety of communication system environments including local area networks, cable television distribution systems, ATM systems, and advanced telephony systems. A specific embodiment of the invention solves is particularly optimized to work in LAN environments with end systems running under Windows-compatible network operating systems.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Runtime adaptable search processor
ActiveUS20060136570A1Reduce stacking processImproving host CPU performanceWeb data indexingMultiple digital computer combinationsData packInternal memory
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. he search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
Flow restriction system and method for patient infusion device
InactiveUS7018360B2Precise deliveryAvoid flowMedical devicesPressure infusionEngineeringFlow limitation
A device for delivering fluid, such as insulin for example, to a patient. The device includes a flow path having an exit port assembly adapted to connect to a transcutaneous patient access tool, and a reservoir connected to the exit port assembly. The device also includes a flow restriction system having an air removal filter communicating with the flow path and allowing air to exit the flow path and preventing fluid from exiting the flow path, and a flow restrictor positioned within the flow path between the air removal filter and the exit port assembly. Among other features and advantages, the flow restriction system of the present invention allows the flow path of the fluid delivery device to be purged of air, or “primed” prior to operation, such that desired volumes of fluid can be accurately delivered by the device.
Owner:INSULET CORP
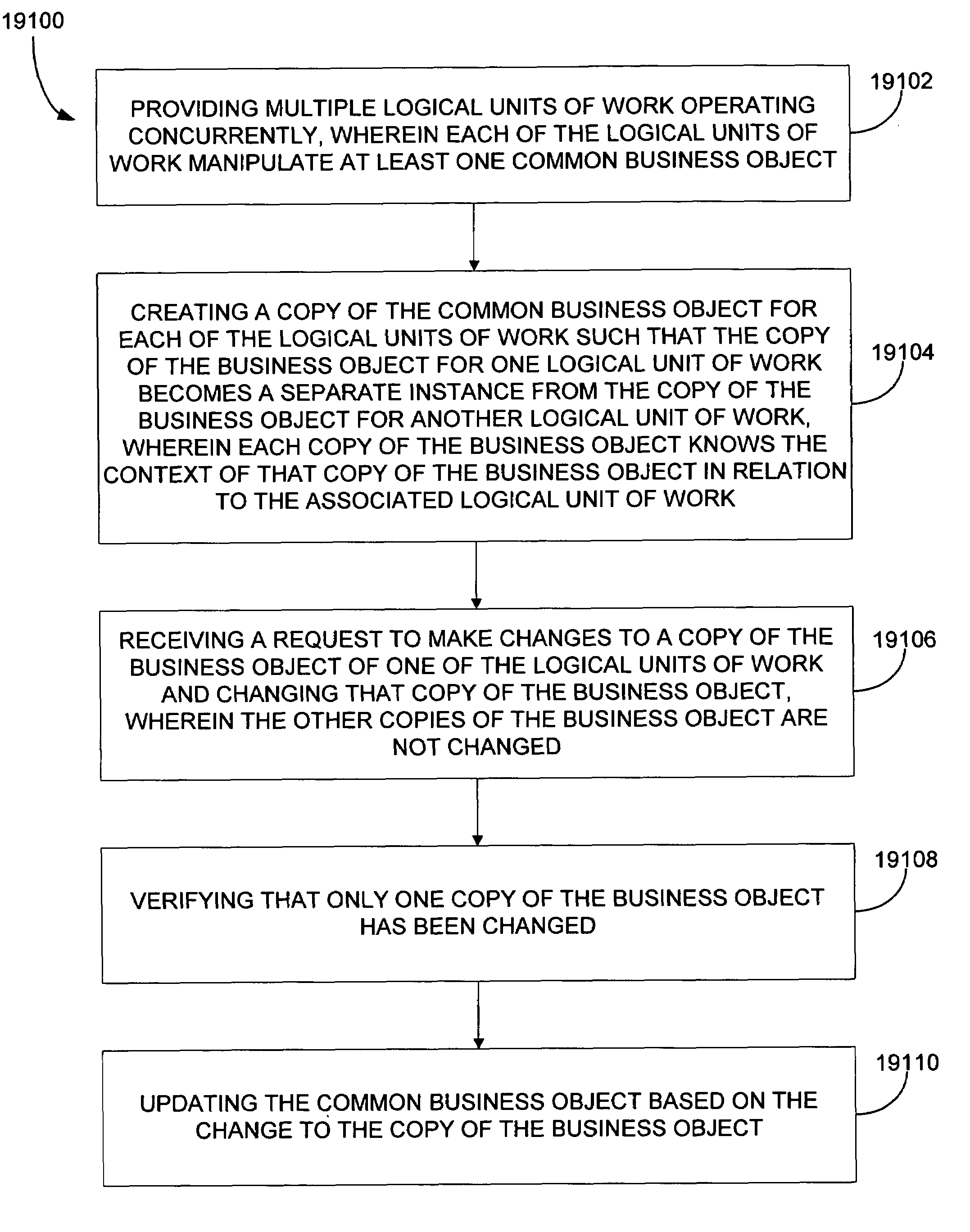
System and method for transaction services patterns in a netcentric environment
InactiveUS7289964B1Reduce network trafficOffice automationProgram controlTraffic capacityTransaction service
The present disclosure provides for implementing transaction services patterns. Logical requests are batched for reducing network traffic. A batched request is allowed to indicate that it depends on the response to another request. A single message is sent to all objects in a logical unit of work. Requests that are being unbatched from a batched message are sorted. Independent copies of business data are assigned to concurrent logical units of work for helping prevent the logical units of work from interfering with each other.
Owner:ACCENTURE GLOBAL SERVICES LTD
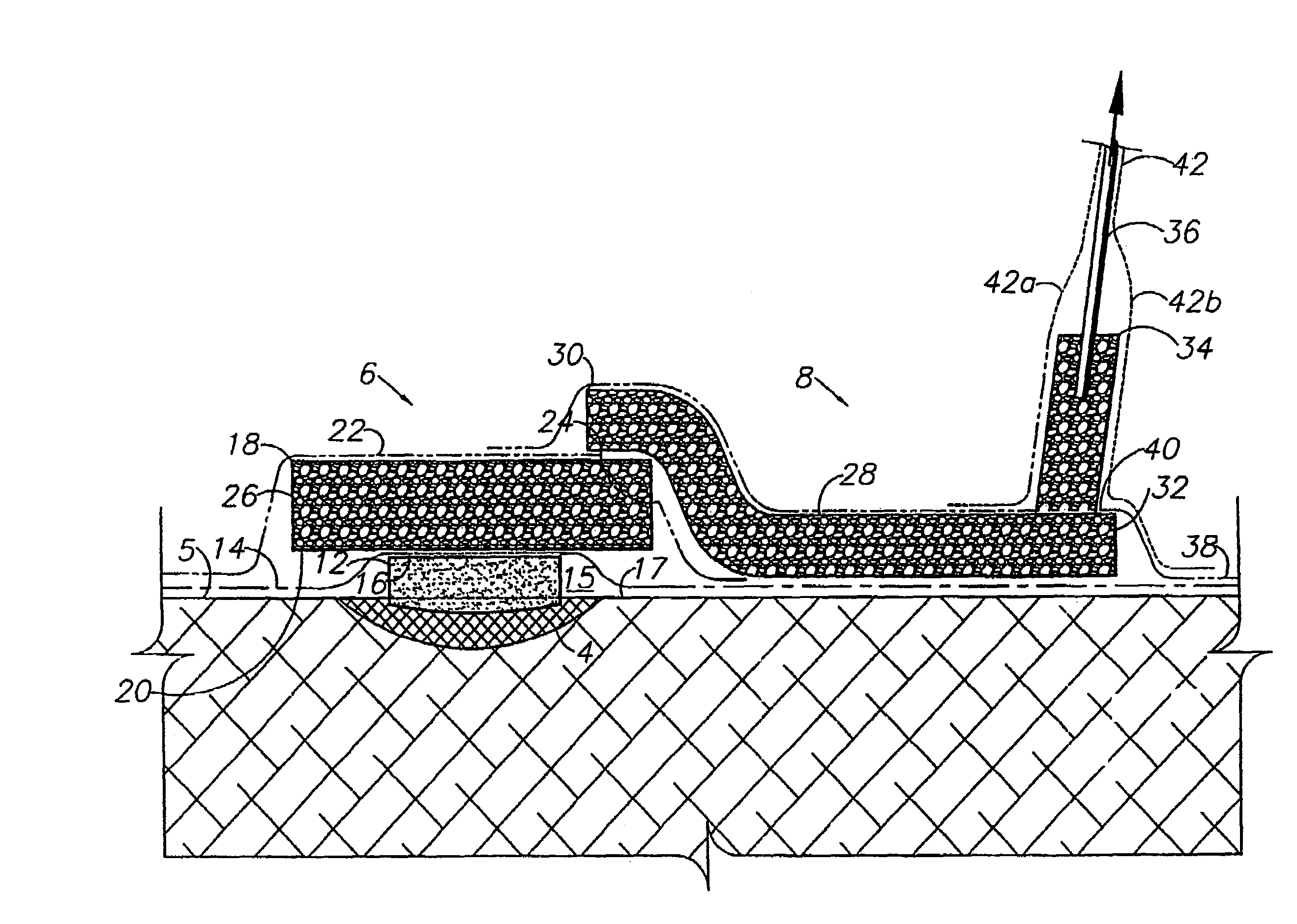
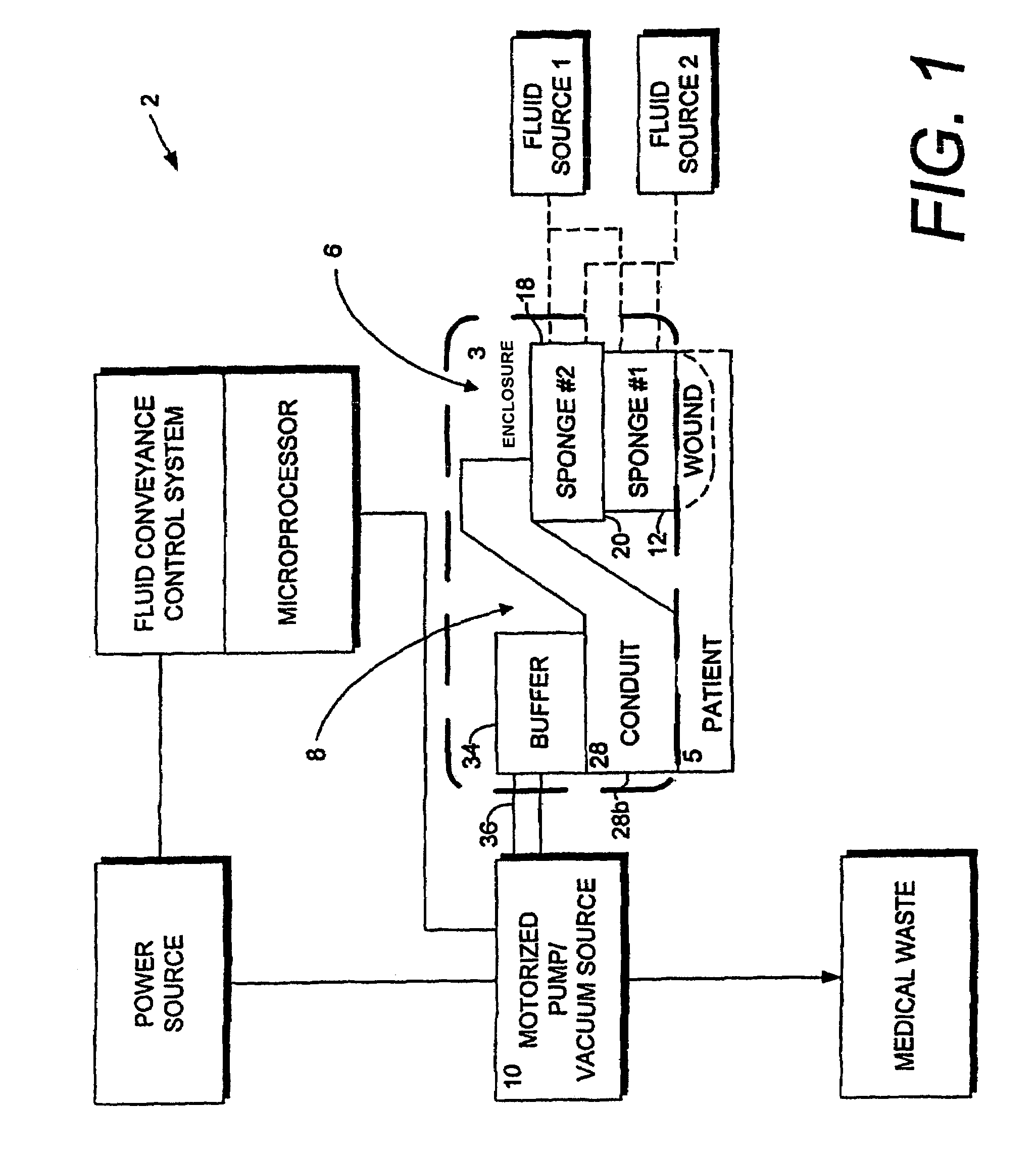
Wound therapy and tissue management system and method with fluid differentiation
A wound therapy and tissue management system utilizes fluid differentiation. Fluid is differentiated by establishing a gradient within the system. A gradient can be established with matter or energy. Patient interfaces for establishing, maintaining and varying one or more gradients include transfer elements with first and second zones having different flow coefficients. The transfer elements exchange fluid with a patient, generally through a wound site, and with external components of the system. Osmotic solution gradients are controlled by a methodology involving the present invention for extracting solutions, which can include toxins, from patients and for introducing fluids and sumping air to wound sites.
Owner:KCI LICENSING INC
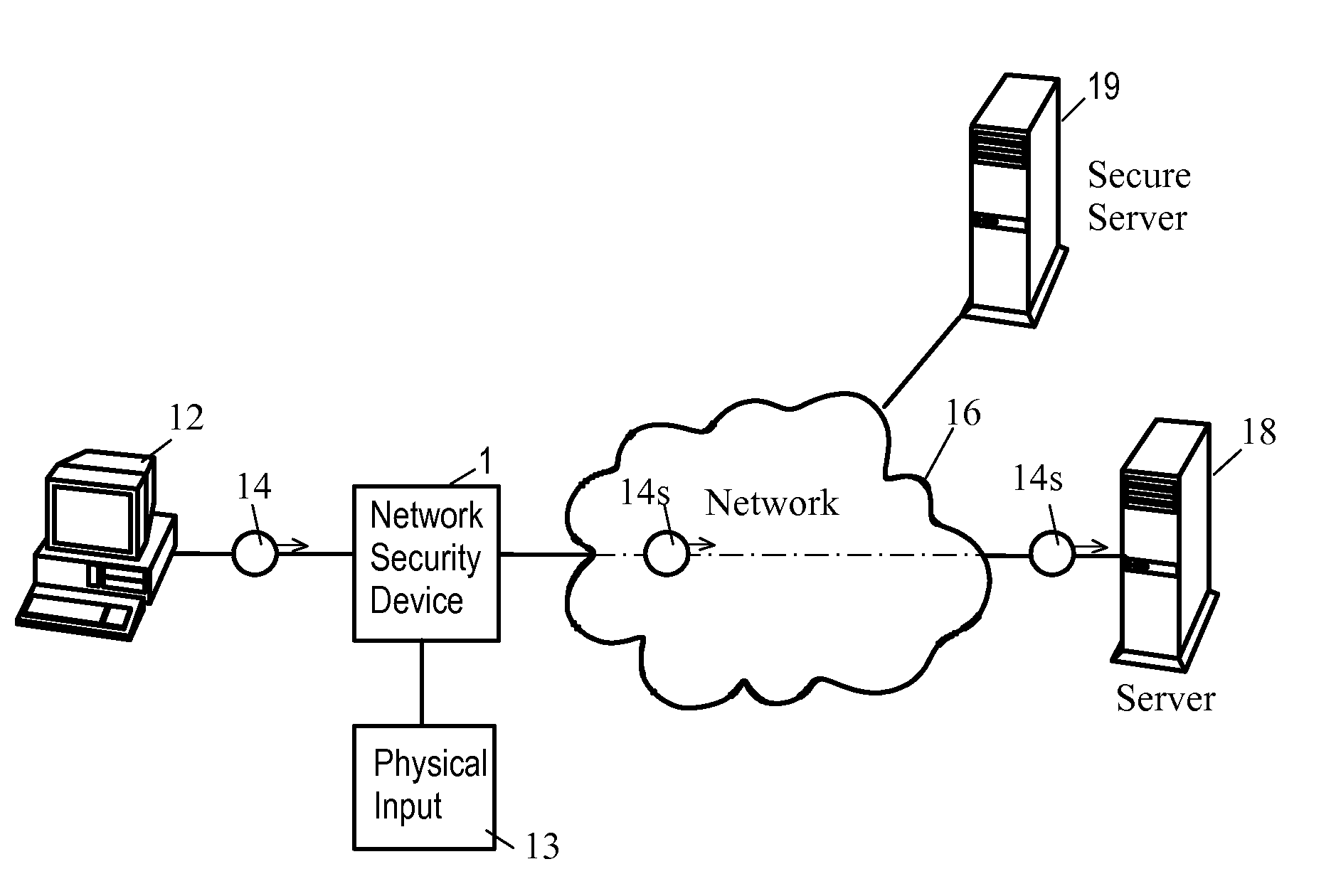
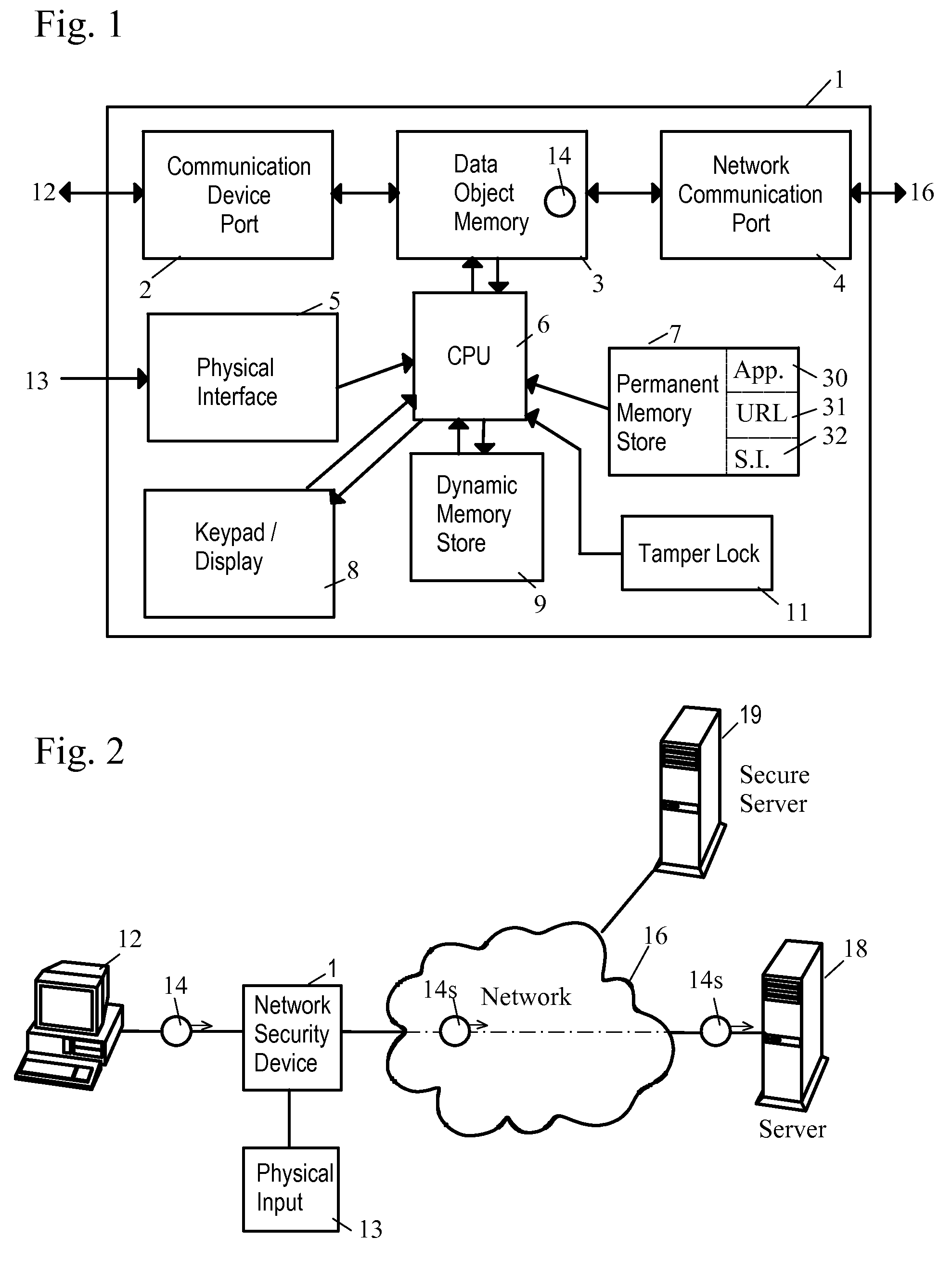
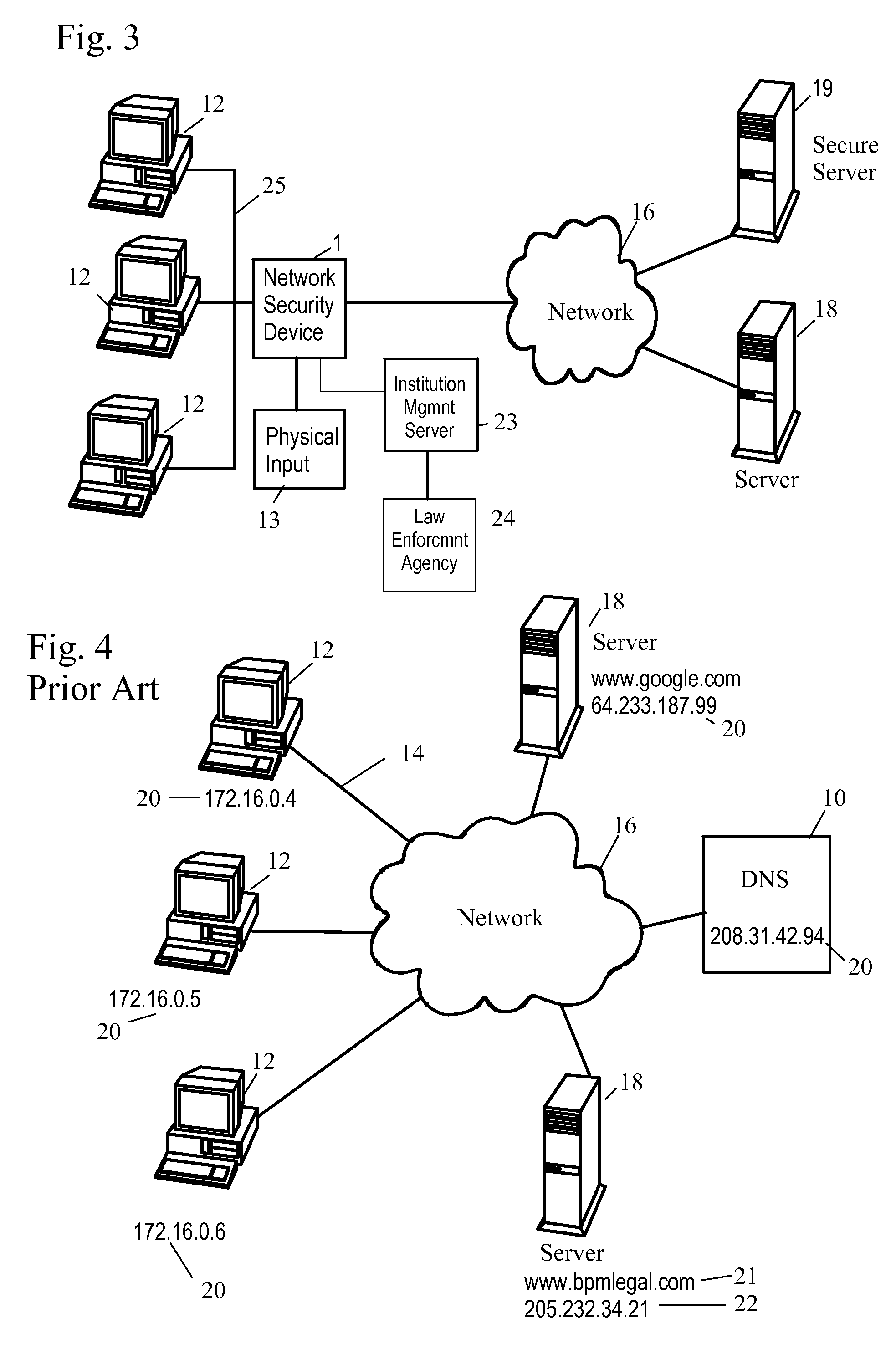
Network Security Device
ActiveUS20070261112A1Function providedFacilitate law enforcement effortDigital data processing detailsUser identity/authority verificationNetwork packetDatapath
A network security device which acts as an “airlock” for traffic between a communications device and a network. Data is screened using rules based analysis by the security device to counter various threats, including viruses, phishing, attempts to “hijack” communications, communications with known malicious addresses or unknown addresses, and transmission of sensitive information. Data packets can be reassembled into files for screening, and decoded or expanded as necessary, but is never executed. The data path for the data being screened is kept separate from the operations of the network security device itself, so that the device is incorruptible—its programming cannot be compromised from outside sources. Updates for rules and entry of sensitive data for screening, etc., must be done through a physical interface, not via the normal data communications channel. The device is invisible—it cannot be “seen” by the network, and thus cannot be attacked.
Owner:ELECTRO GUARD CORP
Systems and methods for processing packets
InactiveUS7215637B1Minimize occurrenceSize of output is increasedError preventionTransmission systemsPacket filteringTraffic analysis
Methods and devices for processing packets are provided. The processing device may include an input interface for receiving data units containing header information of respective packets; a first module configurable to perform packet filtering based on the received data units; a second module configurable to perform traffic analysis based on the received data units; a third module configurable to perform load balancing based on the received data units; and a fourth module configurable to perform route lookups based on the received data units.
Owner:JUMIPER NETWORKS INC
Using location data to determine traffic and route information
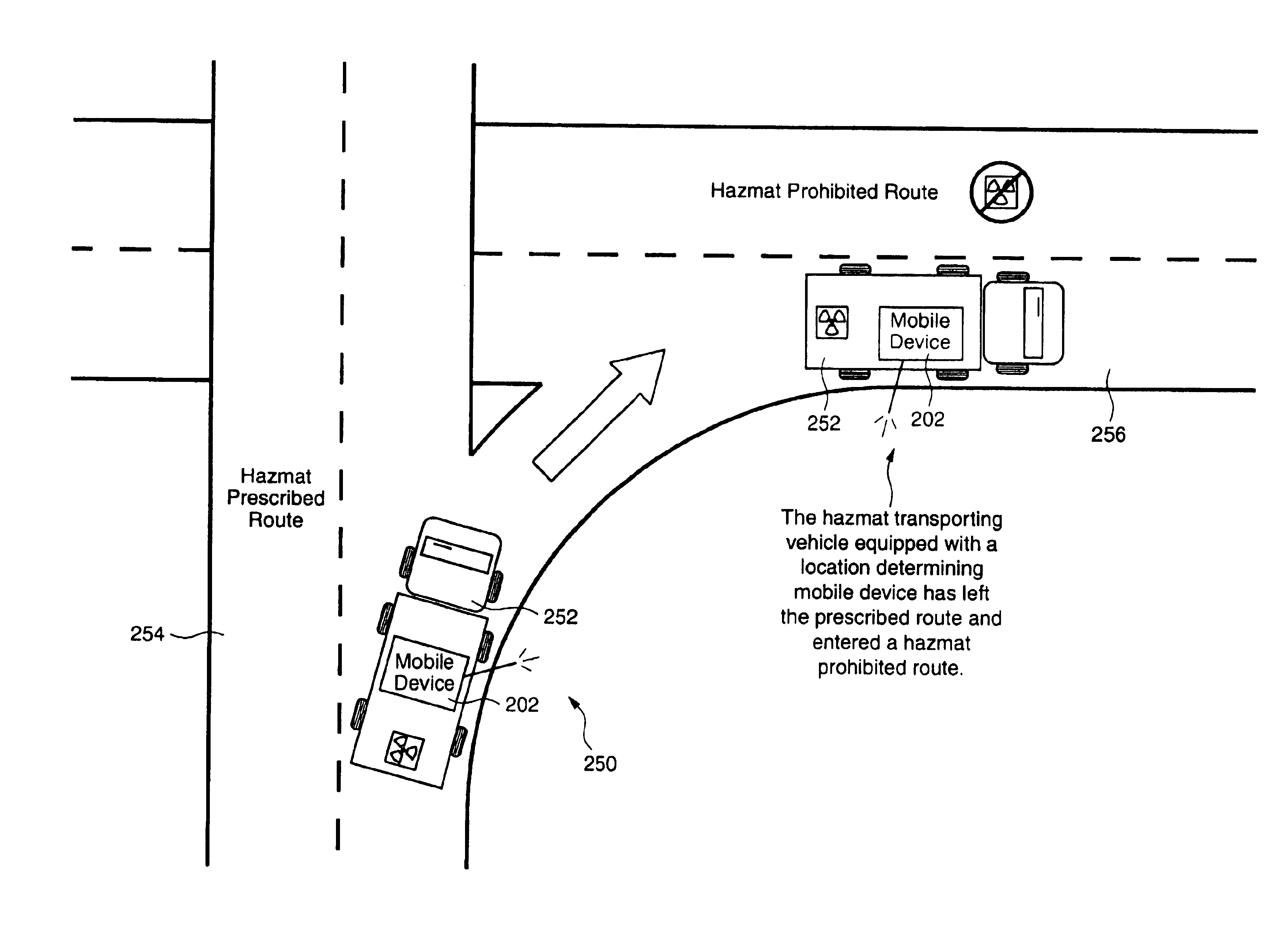
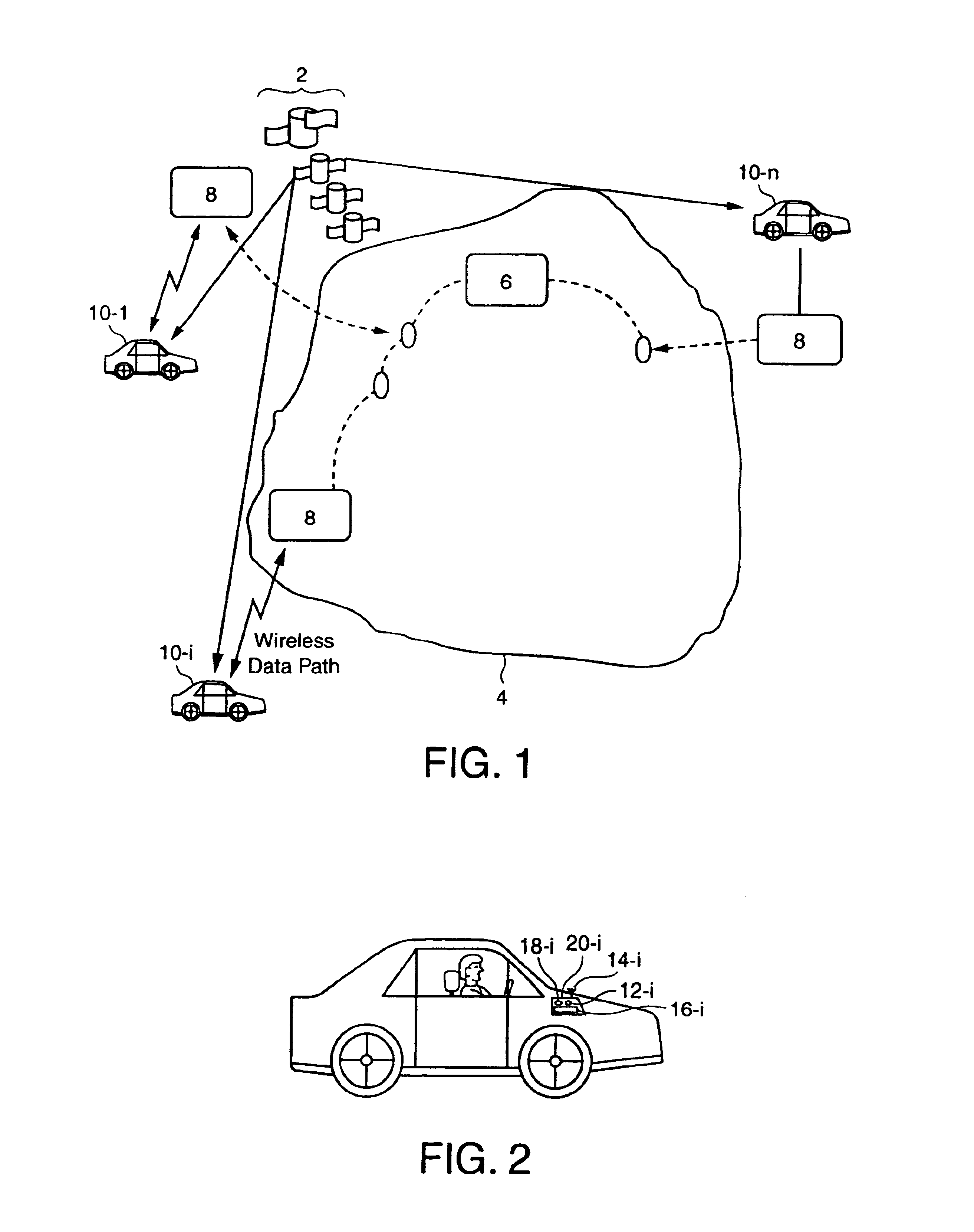
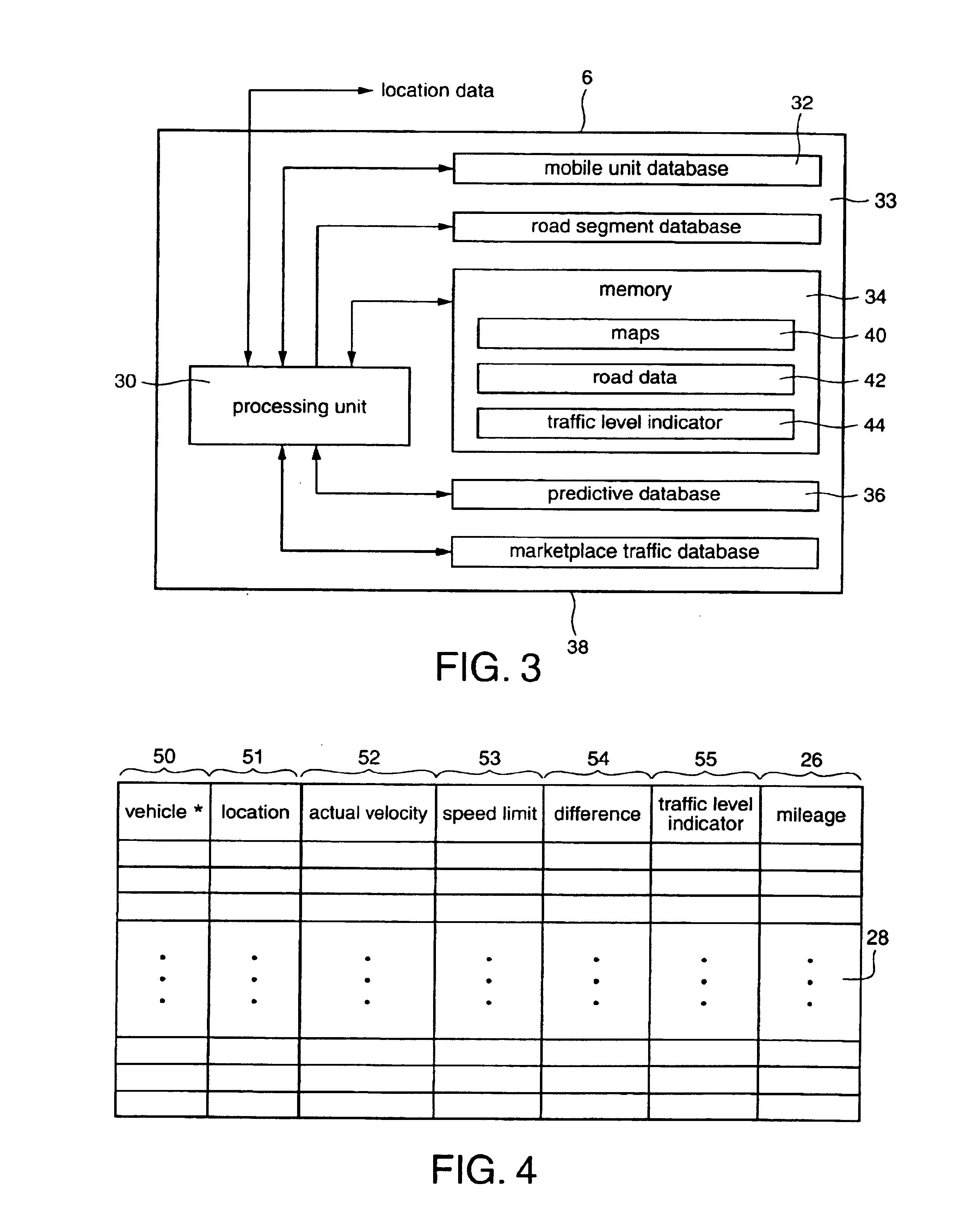
InactiveUS6862524B1Analogue computers for vehiclesInstruments for road network navigationTraffic conditionsSpeed limit
System and methods for determining and disseminating current traffic information and / or route information are presented. For example, in accordance with one embodiment of the present invention, traffic condition information is collected from mobile units that provide their location or position information. The traffic condition may be determined, for example, based on the difference between the velocity of each mobile unit and the speed limit corresponding to their location. Furthermore, the fastest routes between two locations may be determined and provided based on historical and / or current conditions and provided to a mobile unit. In accordance with another embodiment of the present invention, route information may be utilized to determine whether a mobile unit (e.g., associated with a vehicle) is allowed or prohibited from traveling along a certain route.
Owner:TRIMBLE NAVIGATION LTD
Dynamic parameter adjustment for LTE coexistence
Coexistence gaps may permit one radio access technology (RAT) to coexists with another RAT by providing period in which one RAT may be silent and another may transmit. Methods may account for the RAT traffic and for the presence of other secondary users in a channel. Methods may be provided to dynamically change the parameters of a coexistence gap pattern, such as the duty cycle, to adapt to both the RAT traffic and the presence of other secondary users. Methods may include PHY methods, such as synchronization signal (PSS / SSS) based, MIB based, and PDCCH based, MAC CE based methods, and RRC Methods. Measurements may be provided to detect the presence of secondary users, and may include reporting of interference measured during ON and OFF durations, and detection of secondary users based on interference and RSRP / RSRQ measurements.
Owner:INTERDIGITAL PATENT HLDG INC
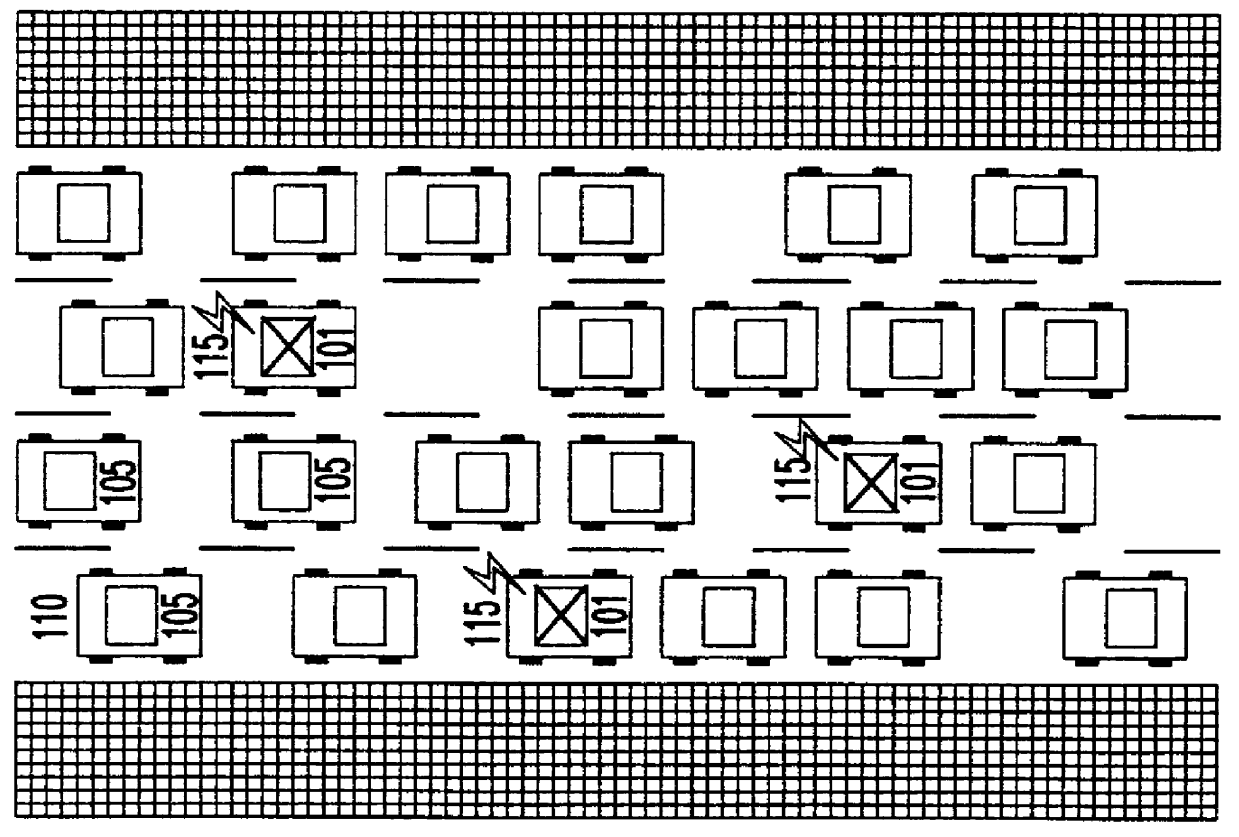
Automated traffic mapping
InactiveUS6150961AIncrease coverageOptimize dataAnalogue computers for vehiclesInstruments for road network navigationTraffic capacityHighway system
A system of mobile units are installed in multiple vehicles in traffic. These mobile units include both wireless communications devices and apparatus that determines the location of each vehicle. Monitoring a vehicle's position as a function of time also reveals the velocity of the vehicle. Position and speed information is periodically broadcast by the vehicles to a central monitoring station and to neighboring vehicles. At the central monitoring station, the collective input of a set of vehicles is processed to provide an instant chart of traffic conditions in the area. Warnings of delays or updates on traffic conditions on the road ahead are then automatically returned to subscribers of the information or are used as part of an Intelligent Vehicle Highway System (IVHS). Neighboring vehicles within a region communicating with one another form a network in which the broadcast information is processed locally on the respective vehicles to estimate possible problems ahead and consider computing an alternate road and / or checking with the central monitoring station for more information. If out of range of the central monitoring station, the vehicles in the network form a local area network for the exchange and update of information, and when any vehicle in the network is within range of the central monitoring station, the local area network data is uploaded to help update the overall traffic information.
Owner:TOMTOM GLOBAL CONTENT
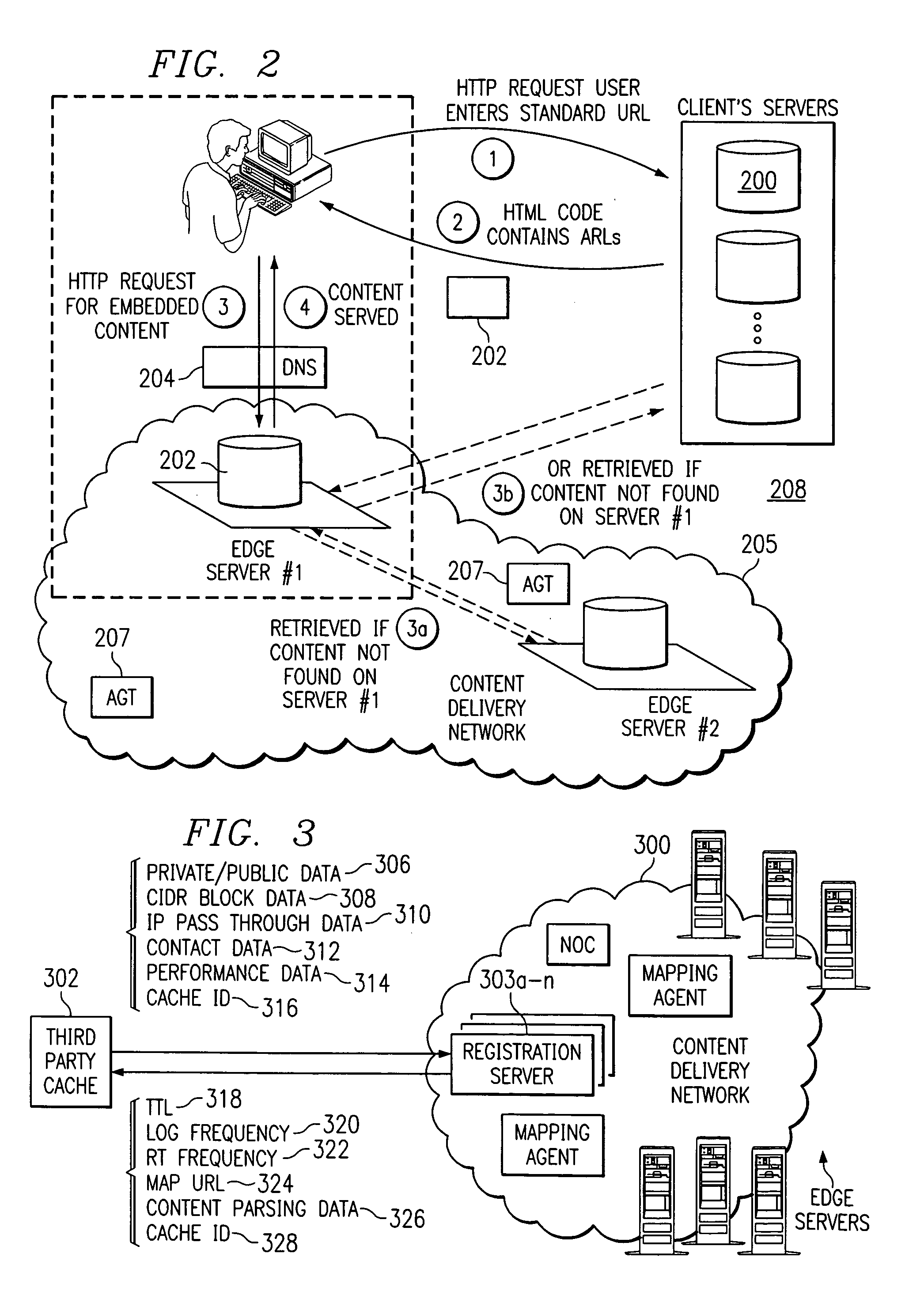
Internet content delivery service with third party cache interface support
InactiveUS7010578B1Increase reachImprove performanceDigital data information retrievalMultiple digital computer combinationsThird partyOff the shelf
Third party cache appliances are configured into a content delivery service to enable such devices to cache and serve content that has been tagged for delivery by the service. The invention enables the content delivery service to extend the reach of its network while taking advantage of high performance, off-the-shelf cache appliances. If the third party caches comprise part of a third party content delivery network, the interconnection of caches to the CDS according to the present invention enables the CDS and the third party network to share responsibility for delivering the content. To facilitate such “content peering,” the CDS may also include a traffic analysis mechanism to provide the third party network with preferably real-time data identifying the content delivered by the CDS from the third party caches. The CDS may also include a logging mechanism to generate appropriate billing and reporting of the third party content that is delivered from the cache appliances that have been joined into the CDS.
Owner:AKAMAI TECH INC
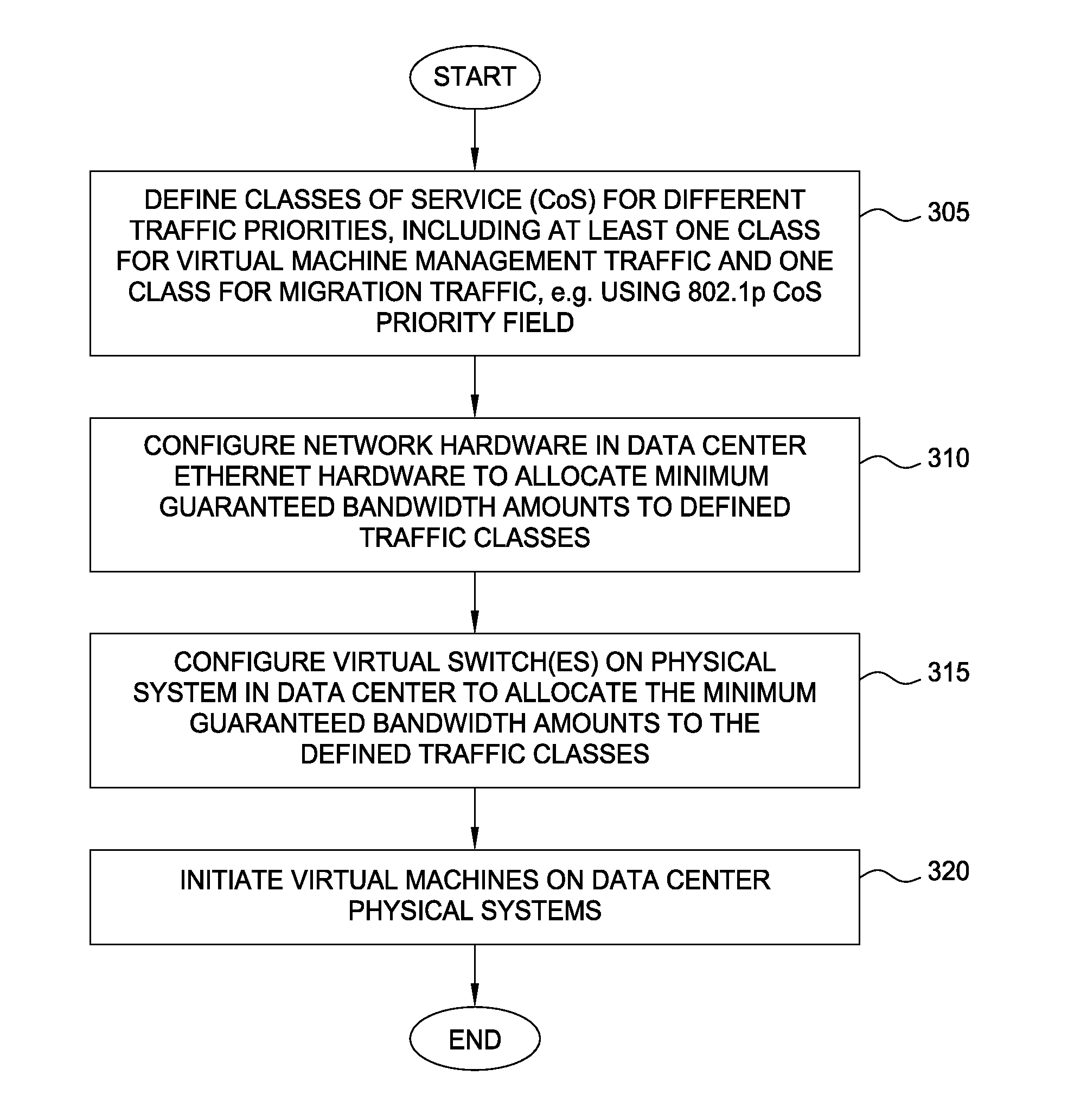
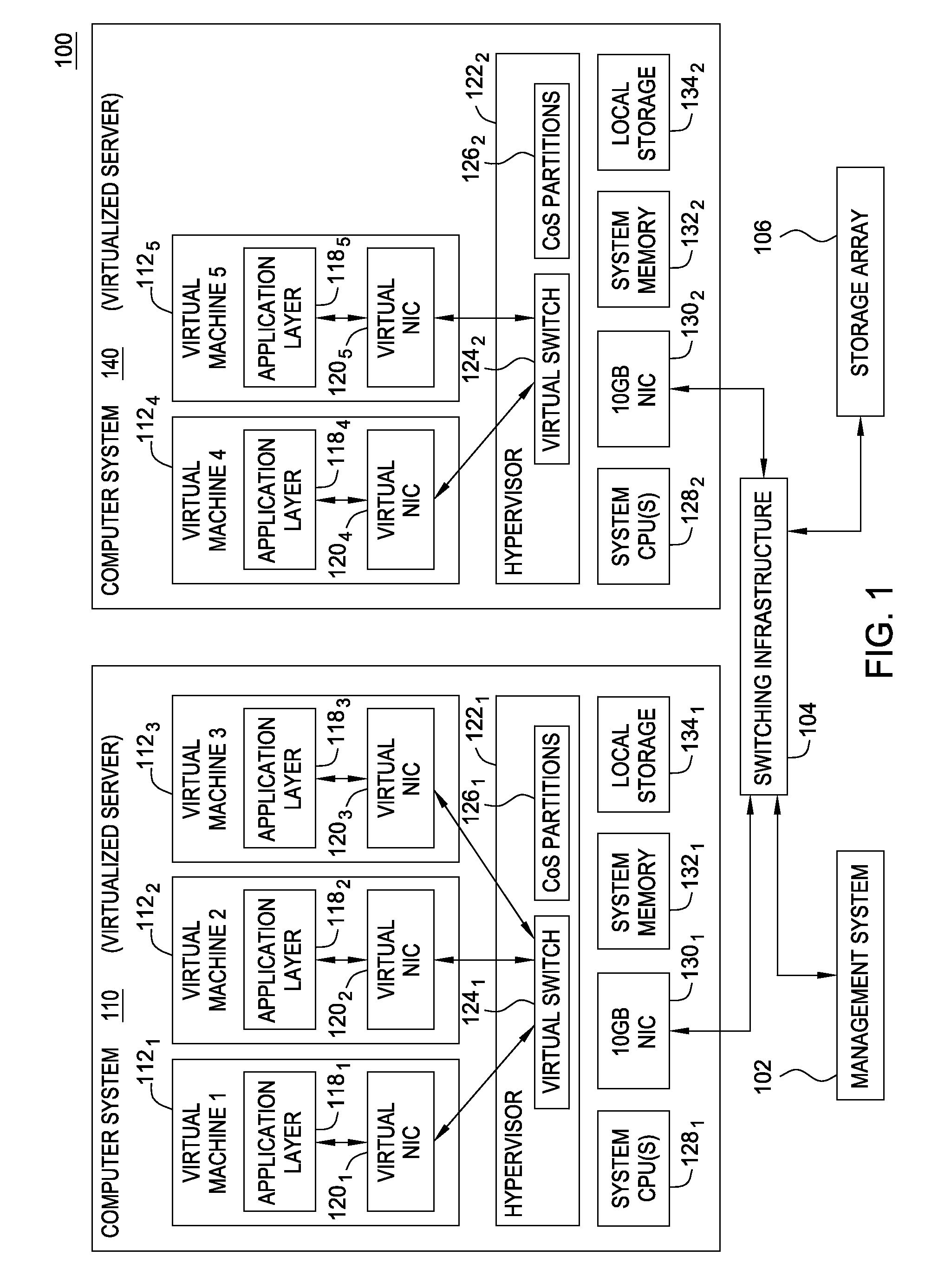
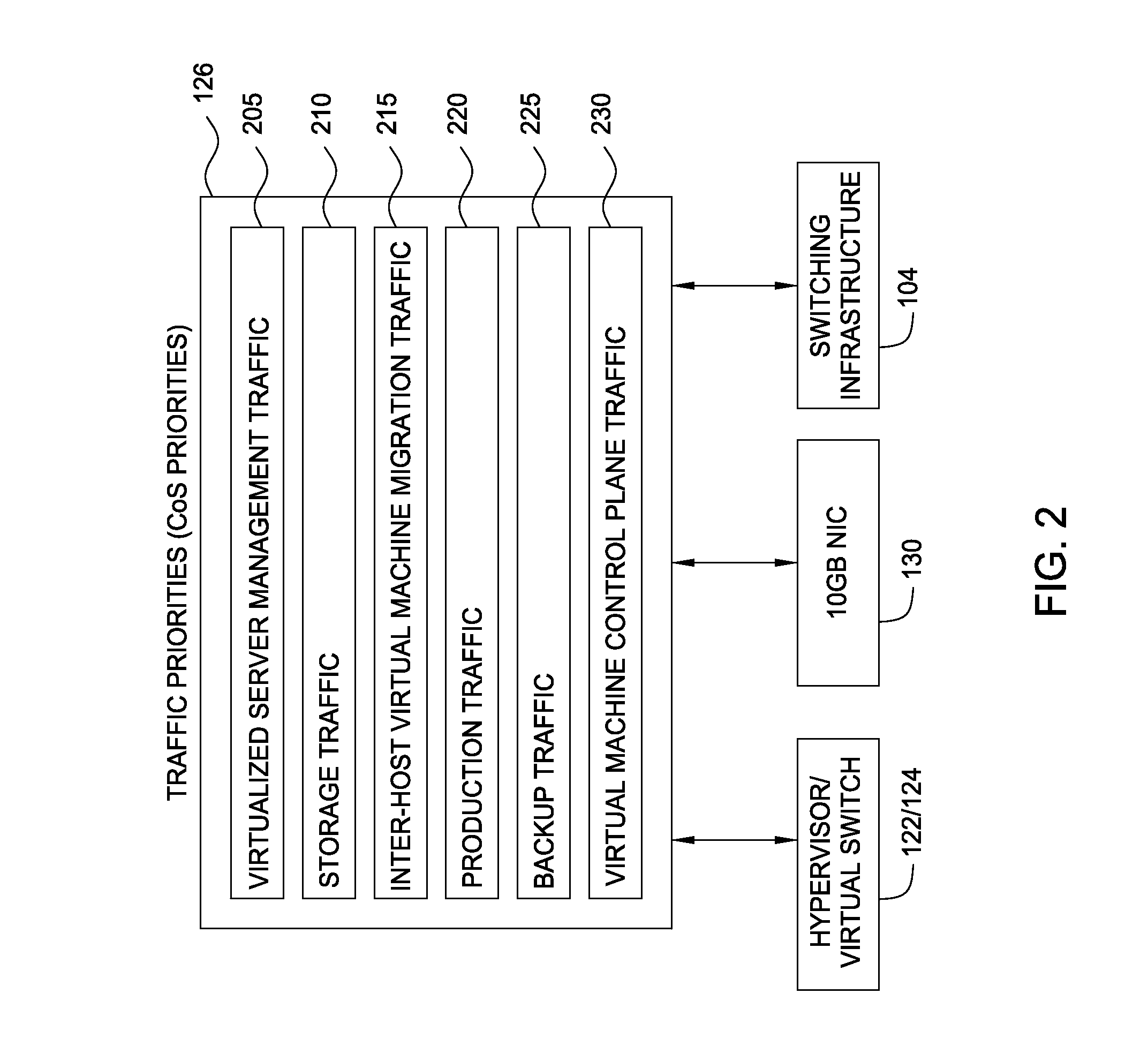
Network consolidation for virtualized servers
Techniques are disclosed for virtualized server kernel and virtual networks consolidation. The network consolidation allows a data center to migrate from an infrastructure that uses multiple dedicated gigabit Ethernet Network Adapters to manage system virtualization and migration to an infrastructure using consolidated, redundant, 10 gigabit Ethernet adapters. Different priority classes may be defined for different classes of network traffic such as hypervisor management traffic, inter-host virtual machine migration traffic, virtual machine production traffic, virtualized switching control plane traffic, etc. Further, an enhanced transmission standard may be used to specify a minimum bandwidth guarantee for certain traffic classes. Thus, the hypervisor management and inter-host virtual machine migration traffic may be transmitted, even the presence of congestion.
Owner:CISCO TECH INC
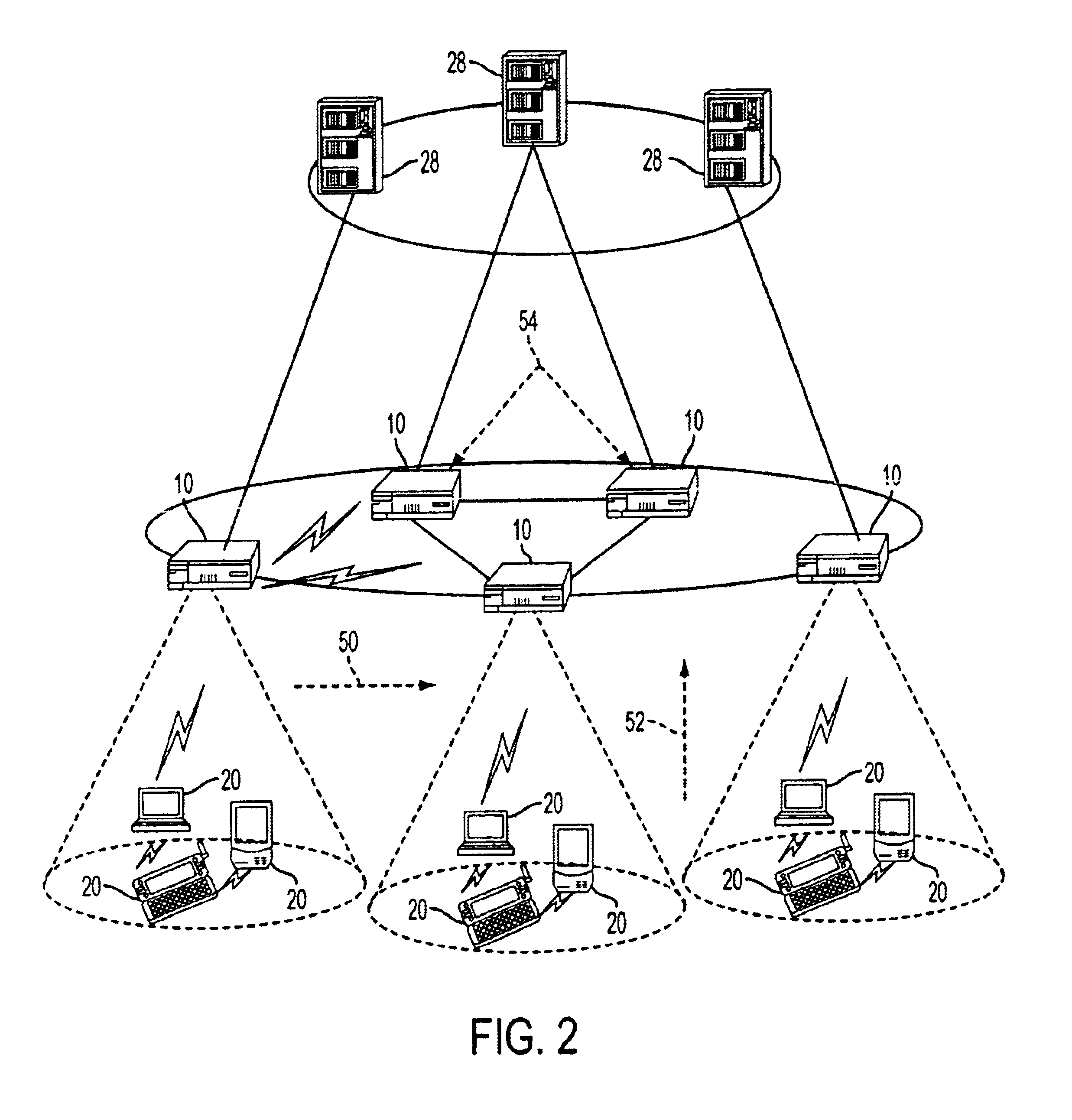
Network-based mobile workgroup system
InactiveUS6954790B2Multiple digital computer combinationsWireless network protocolsClient-sideAccess technology
A network-based mobile workgroup system has considerably wider appeal and application than normal virtual private networks in that it provides seamless mobility across a number of access technologies at the same time as it offers a granular security separation down to workgroup level. The mobile workgroup system is an access management system for mobile users with VPN and firewall functionality inbuilt. The mobile user can access the mobile workgroup system over a set of access technologies and select server resources and correspondent nodes to access pending their workgroup membership approvals. All workgroup policy rules are defined in a mobile service manager and pushed down to one or more mobile service routers for policy enforcement. The mobile service router closest to the mobile client, and being part of the mobile virtual private network, performs regular authentication checks of the mobile client during service execution. At the same time it performs traffic filtering based on the mobile user's workgroup memberships. Together, these two components constitute an unprecedented security lock, effectively isolating a distributed workgroup into a mobile virtual private network.
Owner:LONGHORN HD LLC
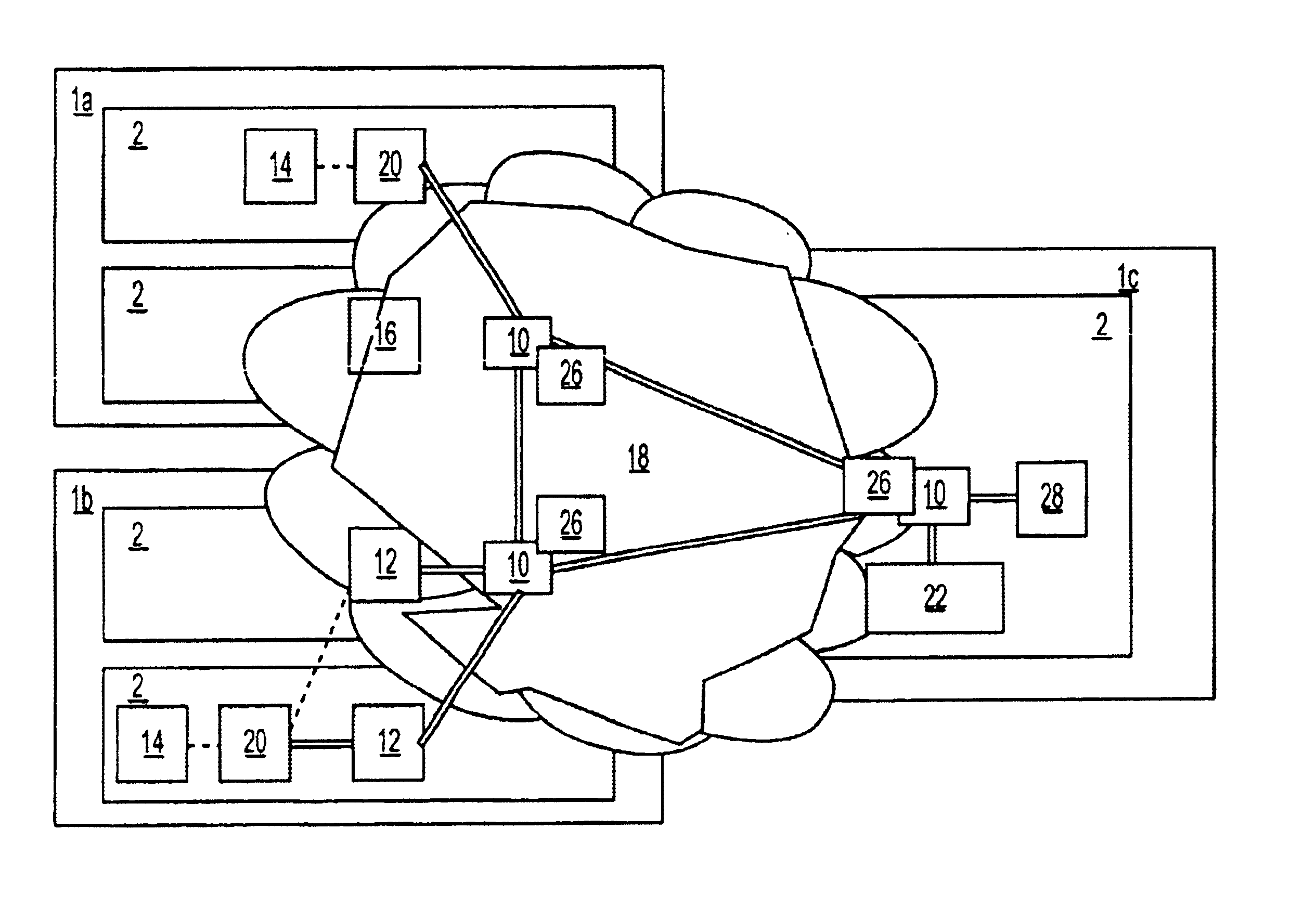
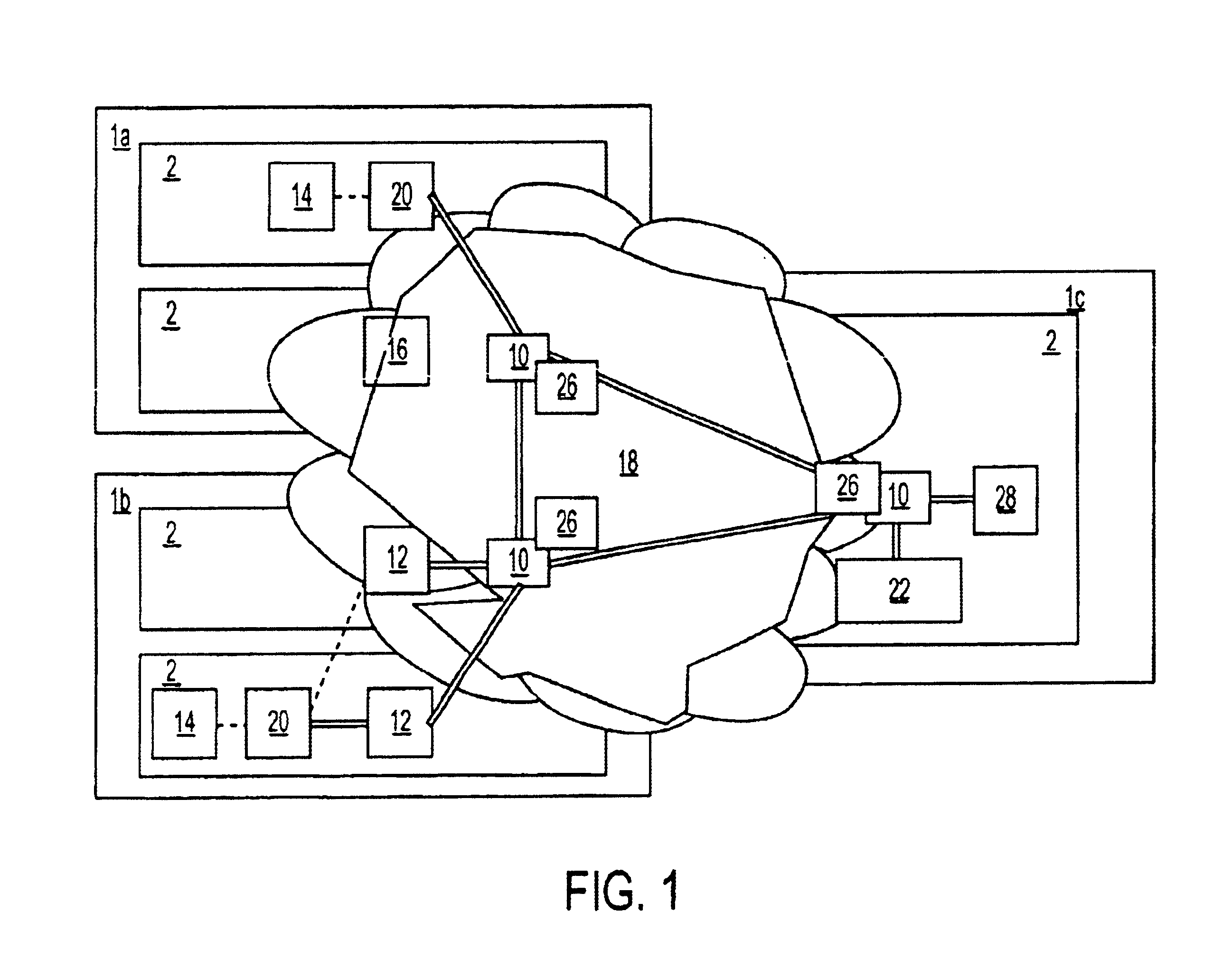
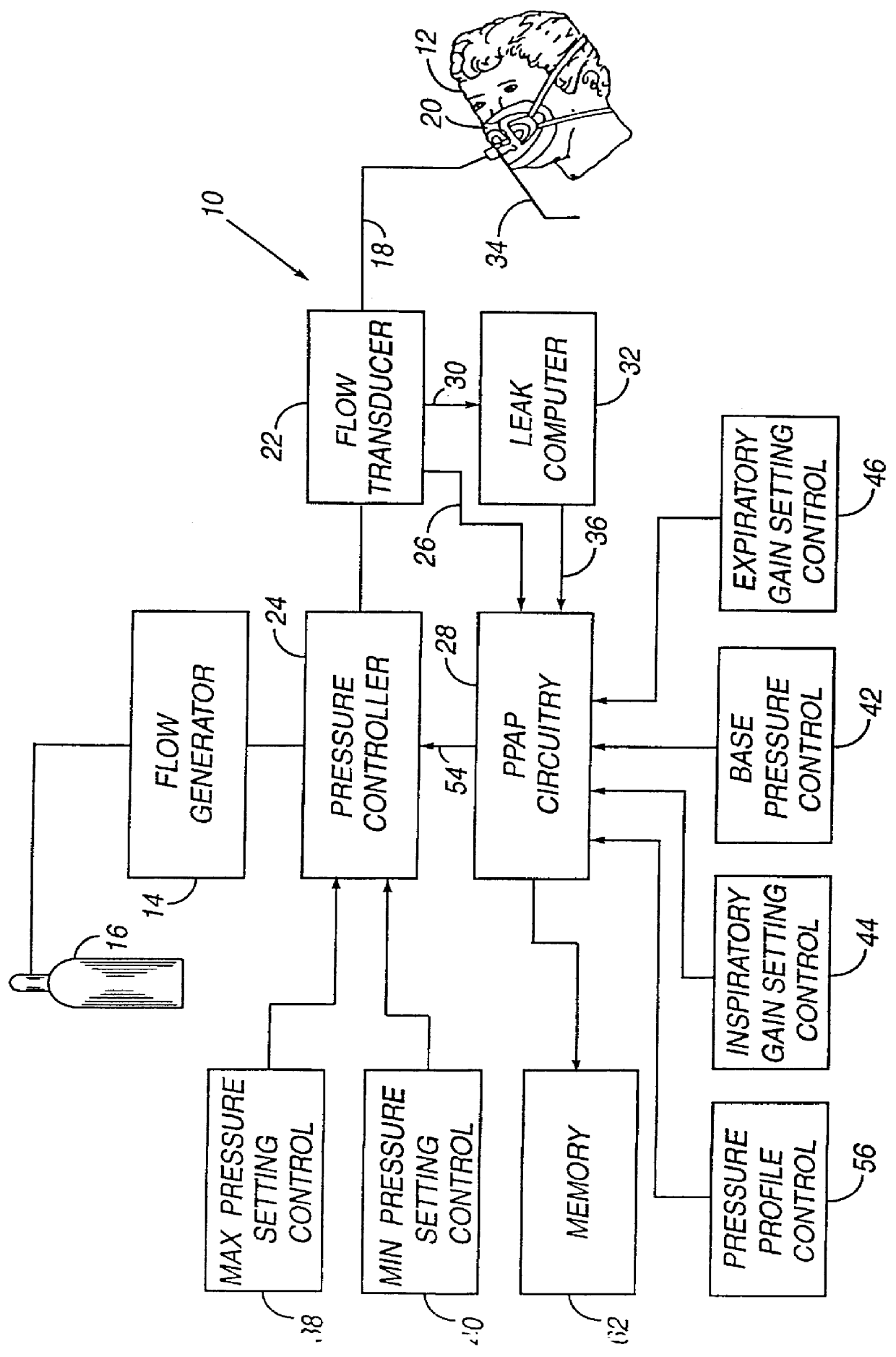
Method and apparatus for providing positive airway pressure to a patient
InactiveUS6105575AReduce cardiac preloadEasily detecting exhalationRespiratorsOperating means/releasing devices for valvesMedical disorderPositive pressure
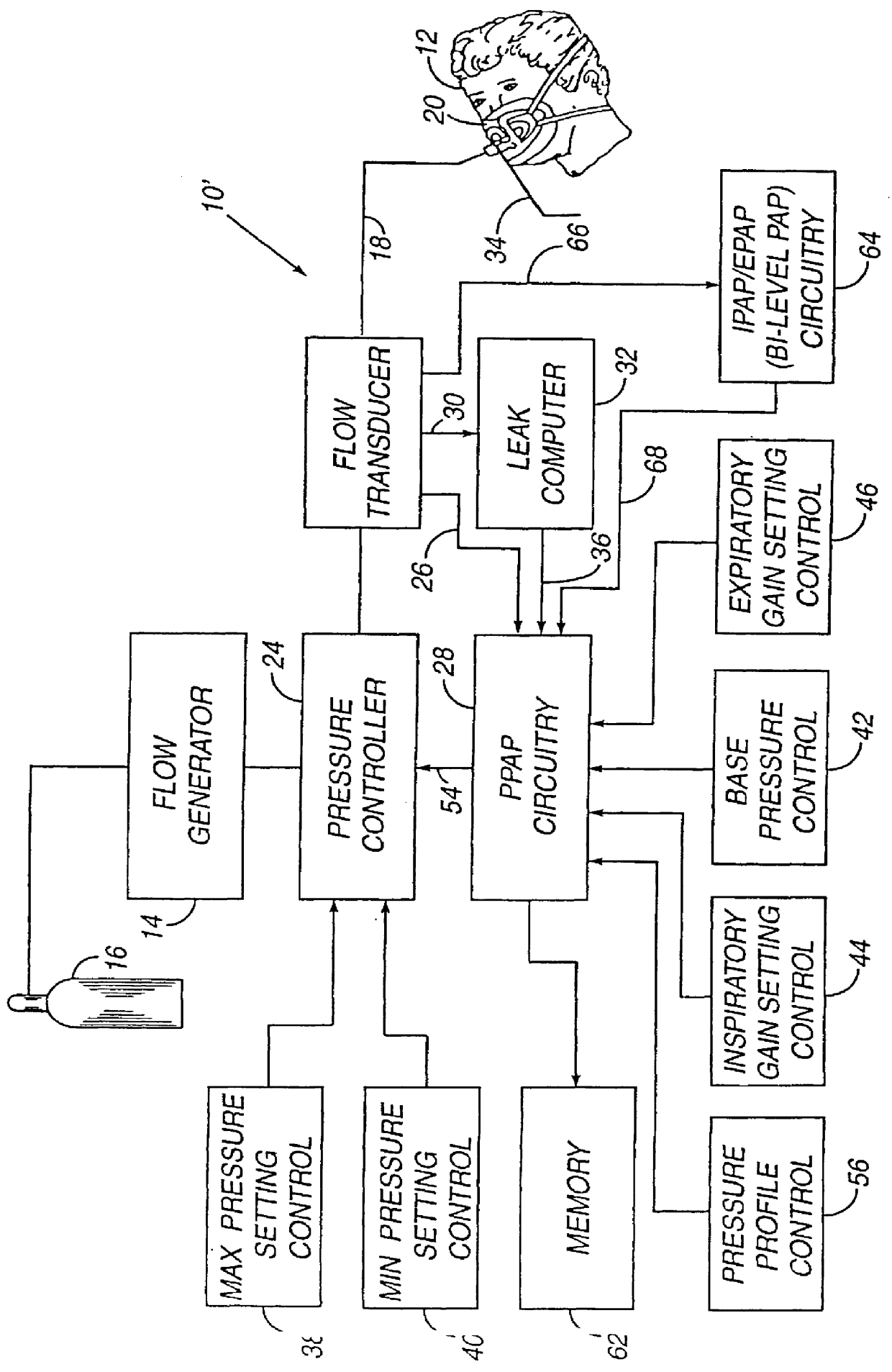
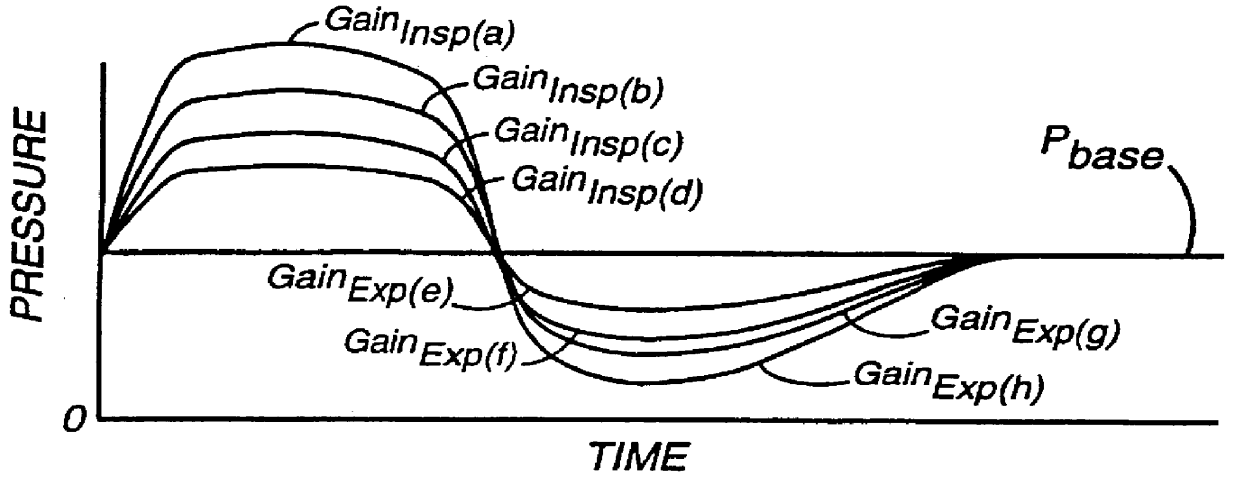
A system including methods and apparatus for treatment of a medical disorder such as obstructive sleep apnea or congestive heart failure. The system involves applying separate and independent gains to flow rates of pressurized gas delivered to a patient during inspiratory and expiratory phases of a respiratory cycle to deliver the pressurized gas in proportion to the respective gains during inspiration and expiration. A base pressure may be applied in addition to the gain-modified pressures and an elevated pressure profile may be employed to assist or control inspiration. The system may be fully automated responsive to feedback provided by a flow sensor that determines the estimated patient flow rate. A leak computer can be included to instantaneously calculate gas leakage from the system. The system may be utilized in connection with conventional continuous positive airway pressure (bi-level PAP) equipment to effect various beneficial treatment applications.
Owner:RIC INVESTMENTS LLC
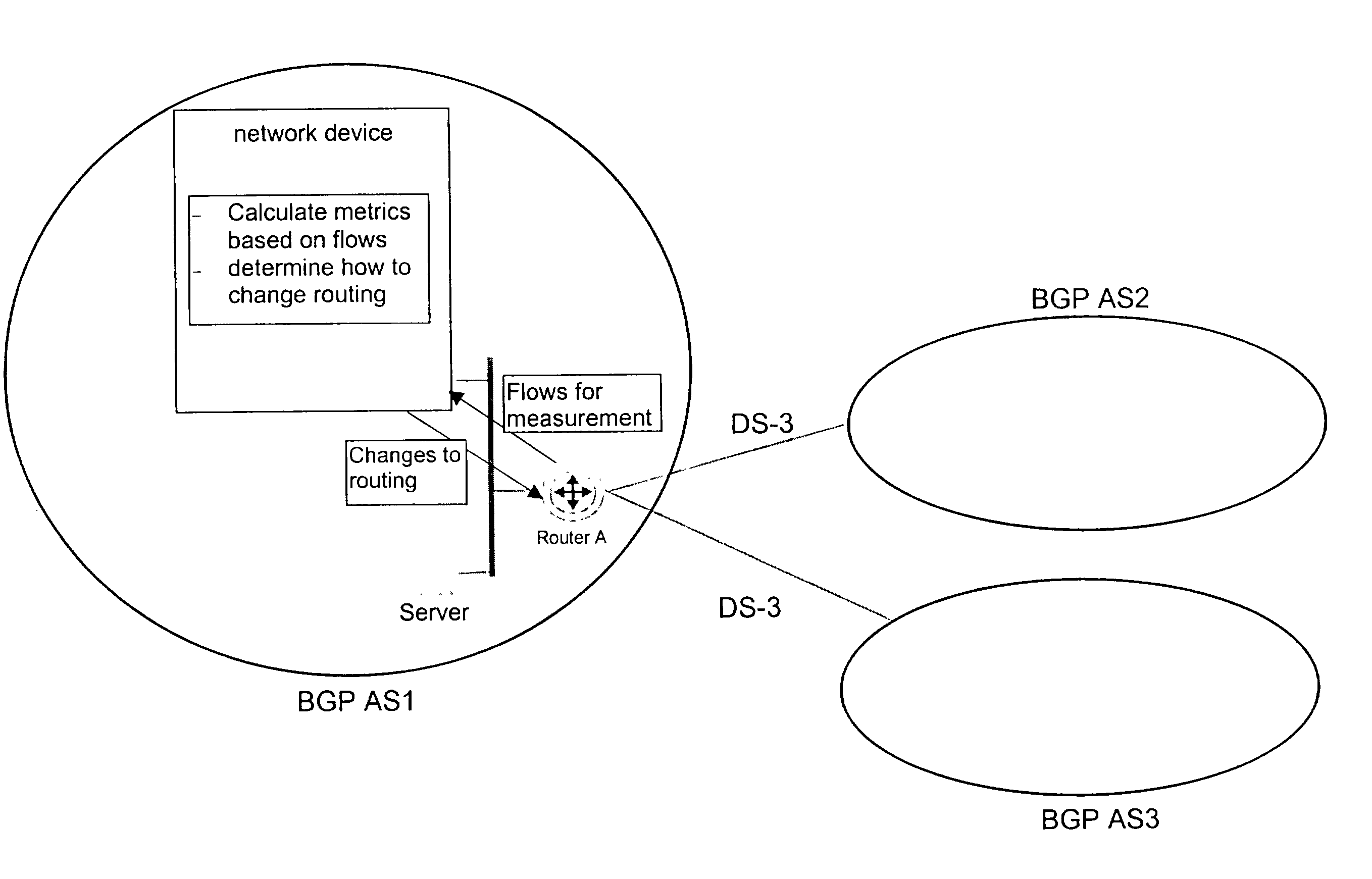
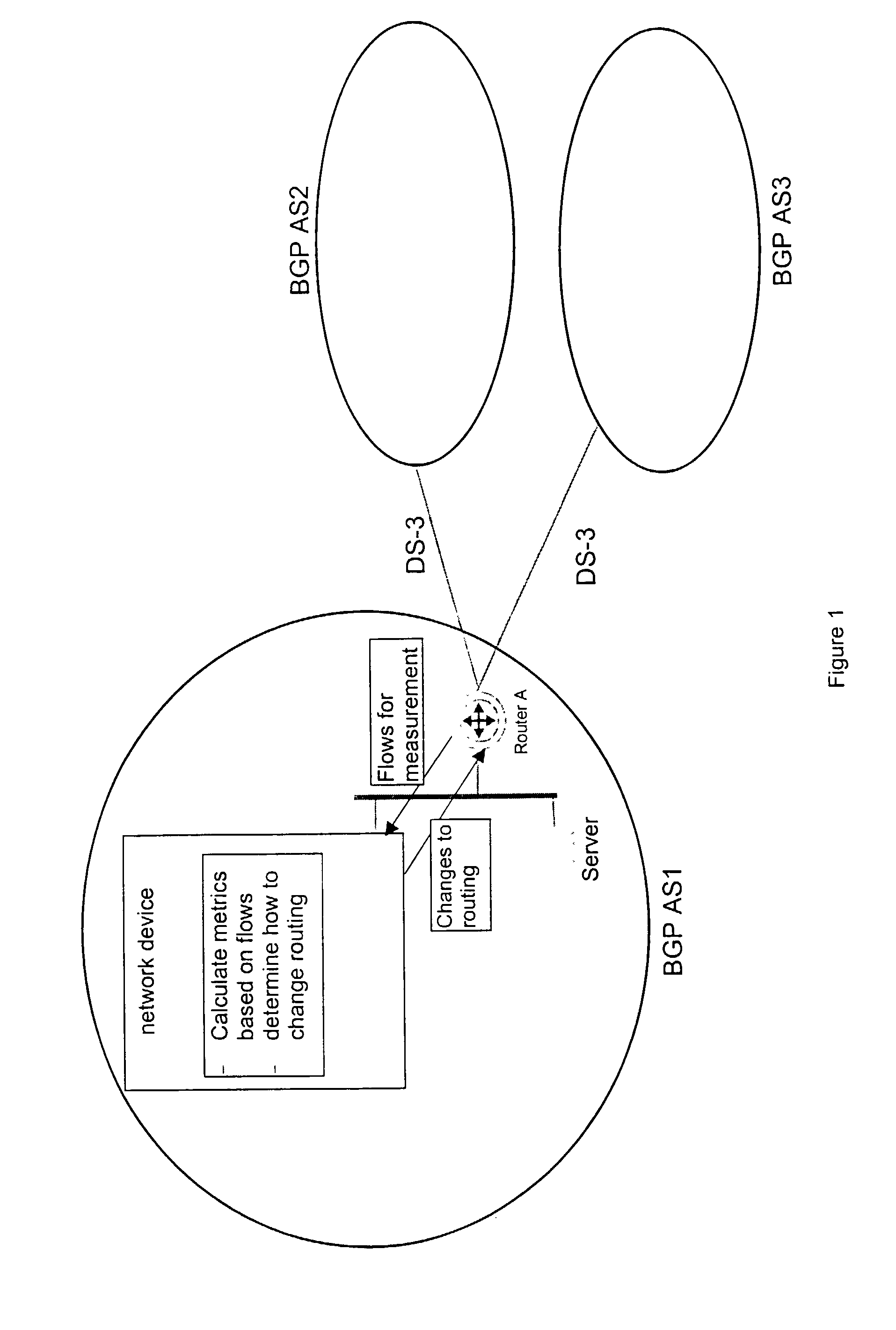
Method and apparatus for the assessment and optimization of network traffic
A system for the assessment of network performance criteria, and applying this criteria to the classification of network addresses into appropriate ranges, using these ranges to consolidate performance measurements for the associated addresses, and applying these metrics toward the optimization of the network towards performance or policy objectives.
Owner:AVAYA INC
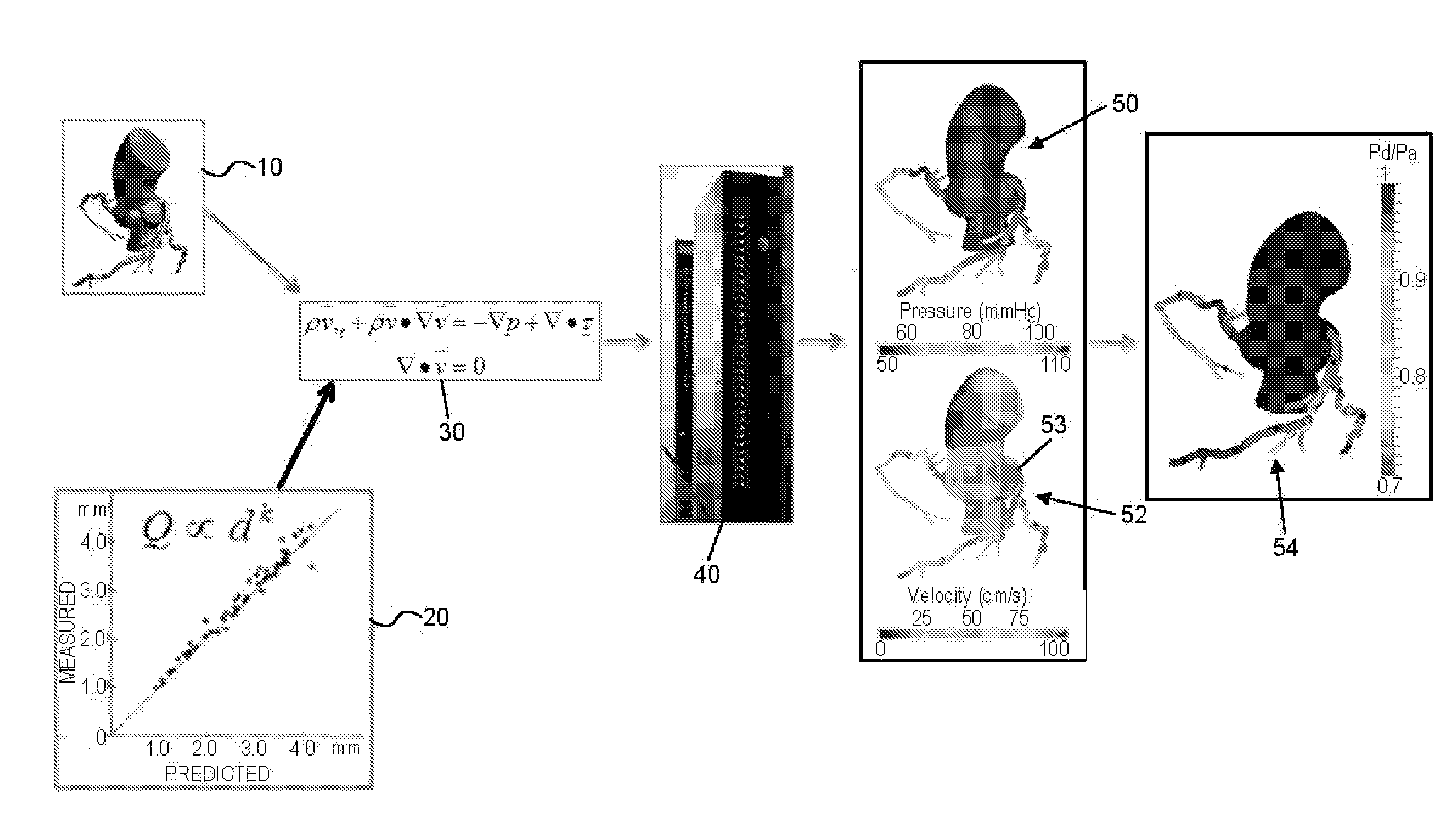
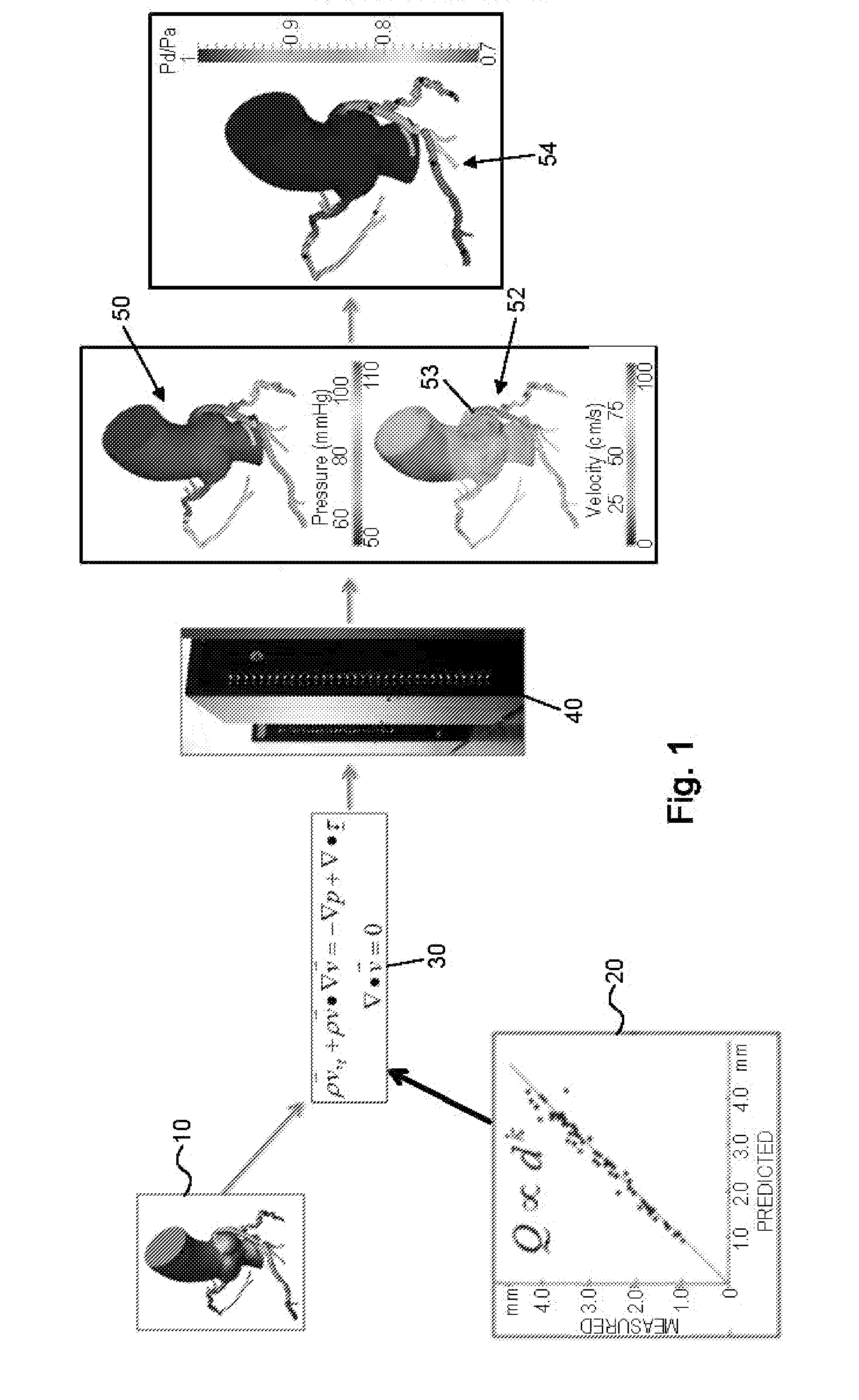
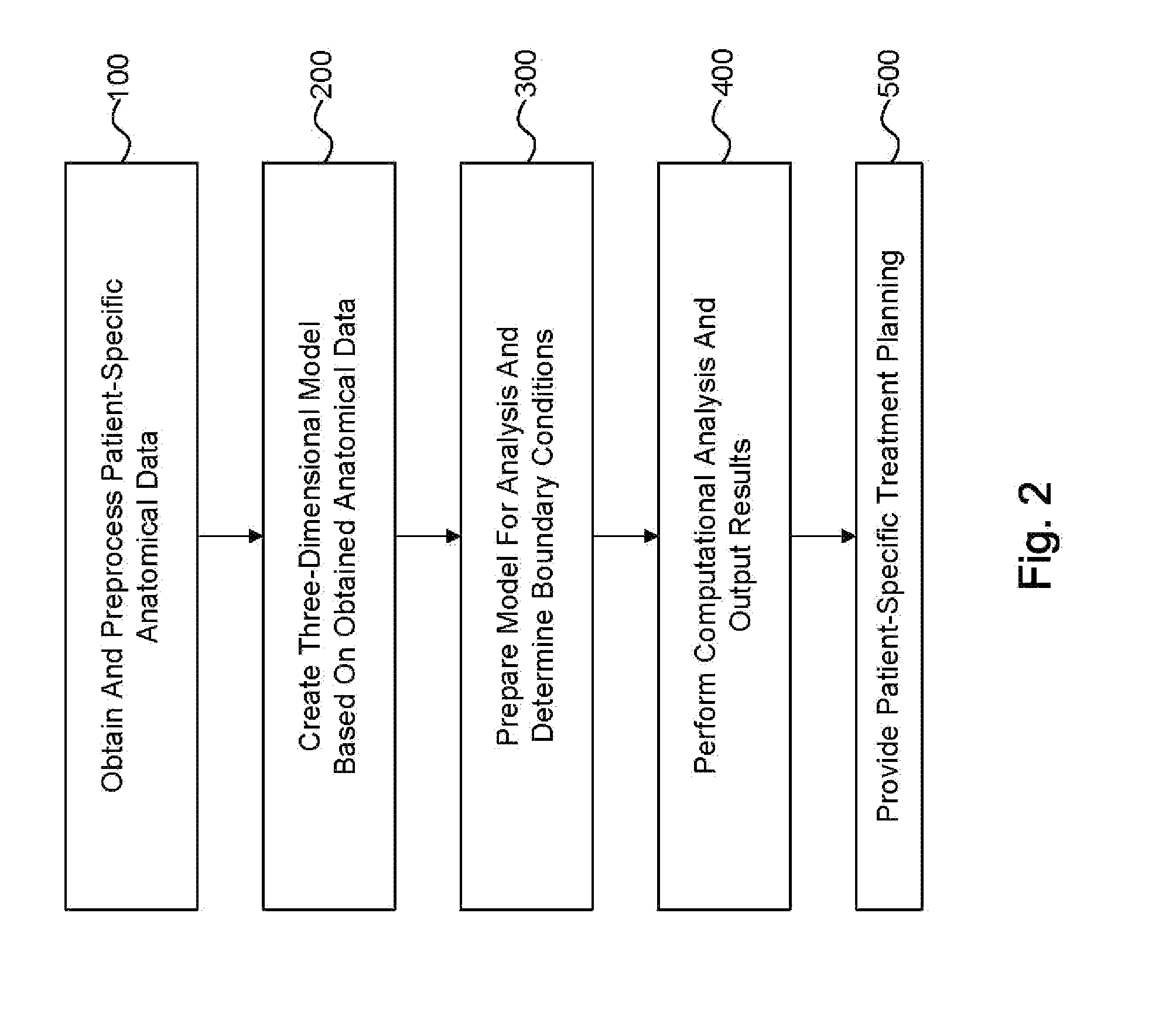
Method and system for patient-specific modeling of blood flow
Embodiments include a system for determining cardiovascular information for a patient. The system may include at least one computer system configured to receive patient-specific data regarding a geometry of the patient's heart, and create a three-dimensional model representing at least a portion of the patient's heart based on the patient-specific data. The at least one computer system may be further configured to create a physics-based model relating to a blood flow characteristic of the patient's heart and determine a fractional flow reserve within the patient's heart based on the three-dimensional model and the physics-based model.
Owner:HEARTFLOW
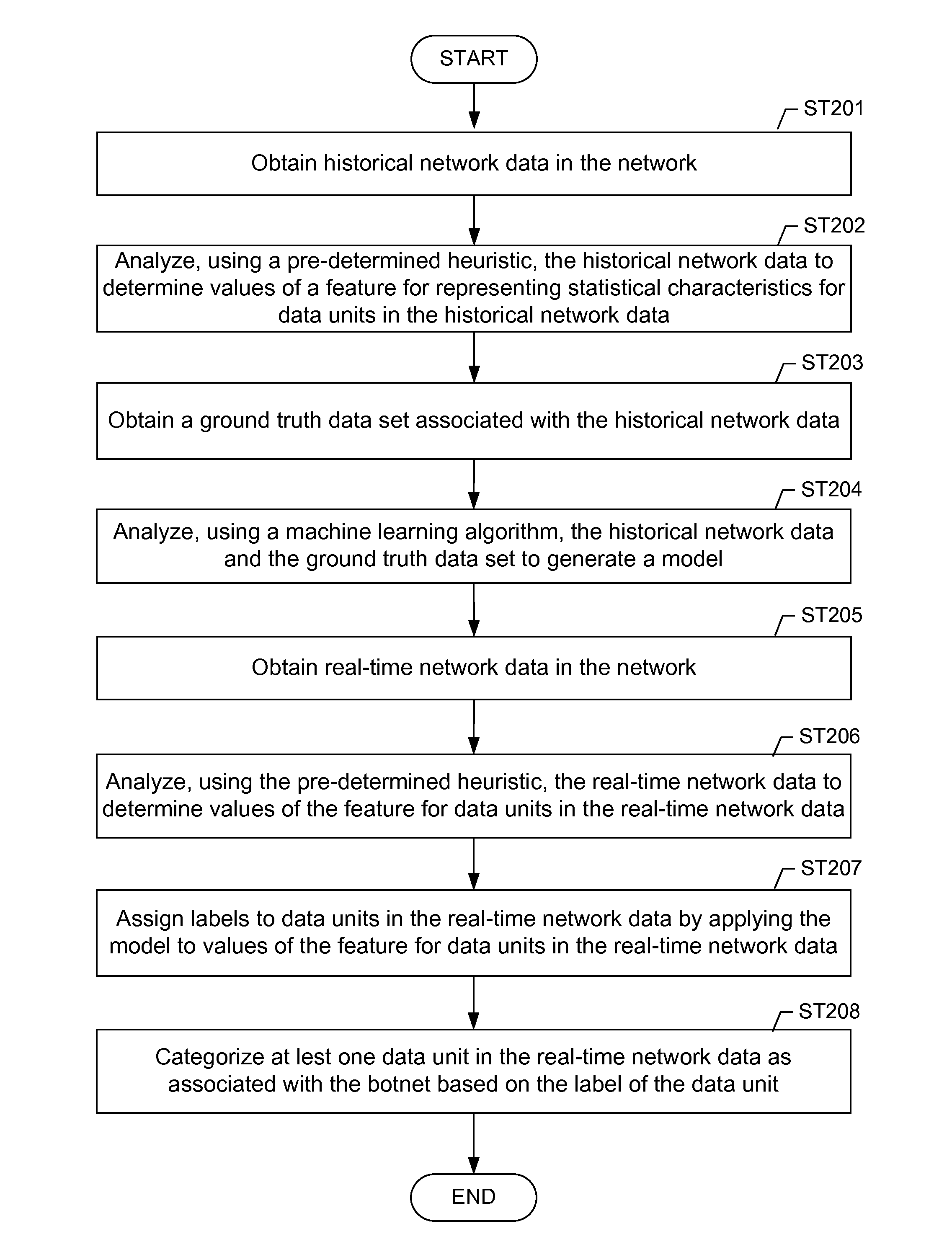
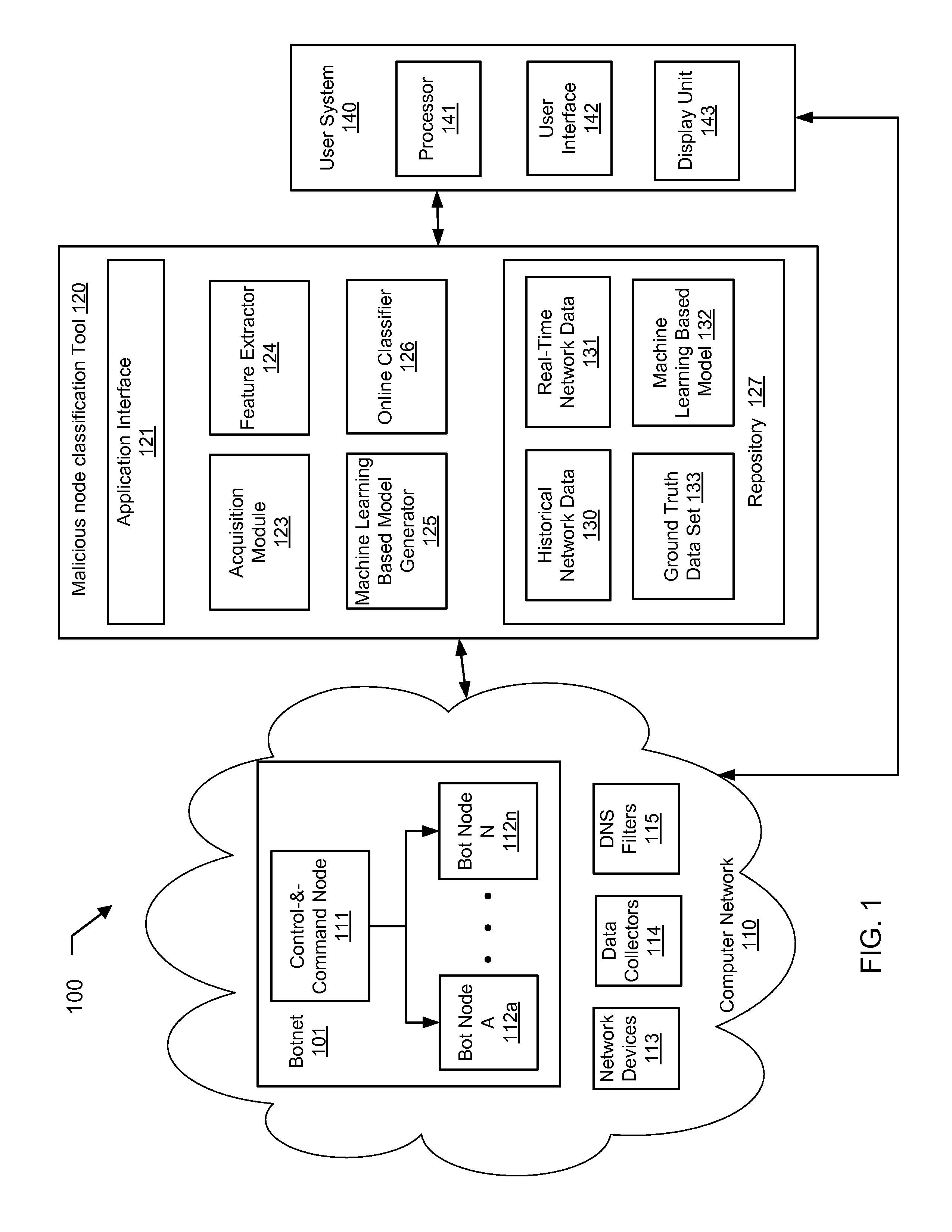
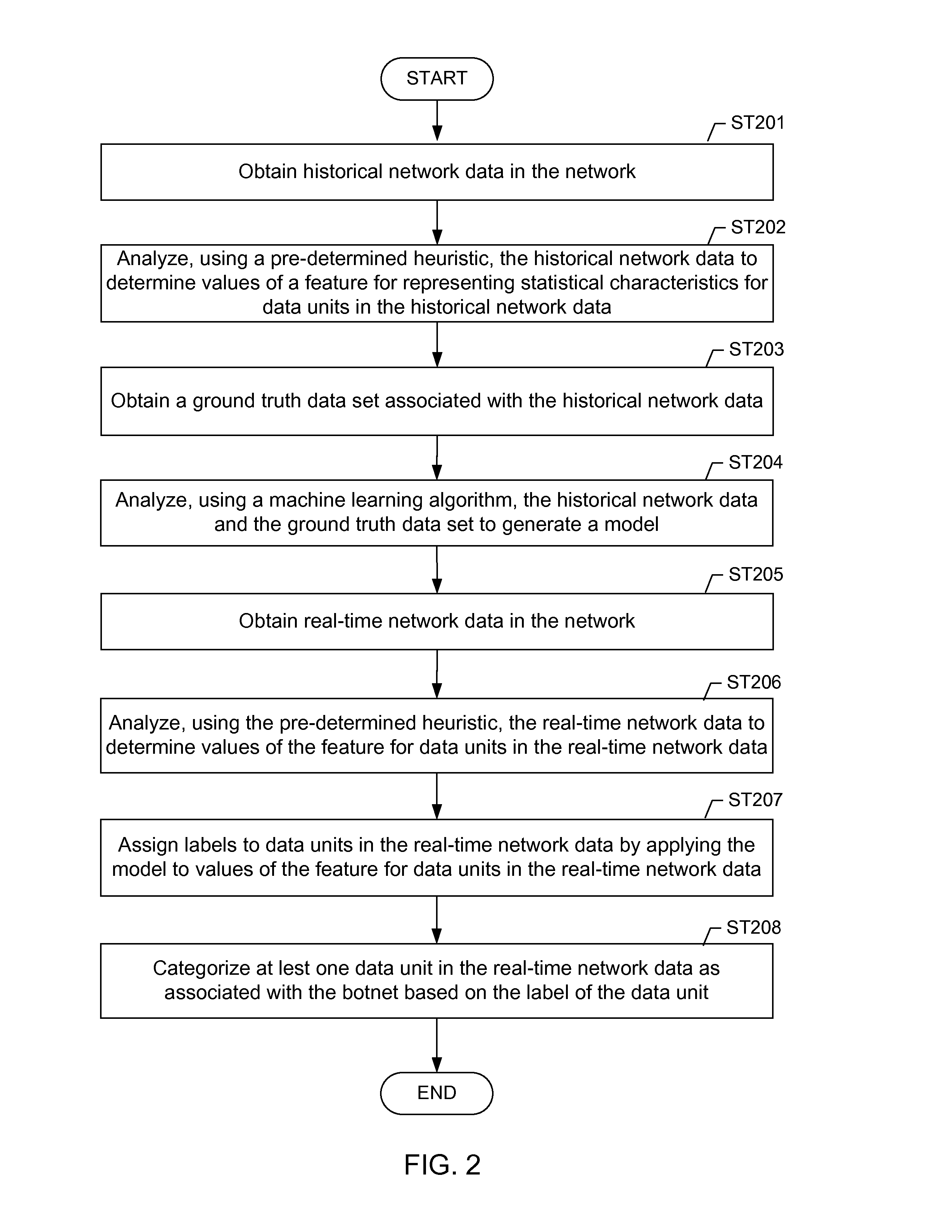
Machine learning based botnet detection using real-time extracted traffic features
ActiveUS8682812B1Digital computer detailsComputer security arrangementsLearning basedTraffic capacity
A method for identifying a botnet in a network, including analyzing historical network data using a pre-determined heuristic to determine values of a feature in the historical network data, obtaining a ground truth data set having labels assigned to data units in the historical network data identifying known malicious nodes in the network, analyzing the historical network data and the ground truth data set using a machine learning algorithm to generate a model representing the labels as a function of the values of the feature, analyzing real-time network data using the pre-determined heuristic to determine a value of the feature for a data unit in the real-time network data, assigning a label to the data unit by applying the model to the value of the feature, and categorizing the data unit as associated with the botnet based on the label.
Owner:THE BOEING CO
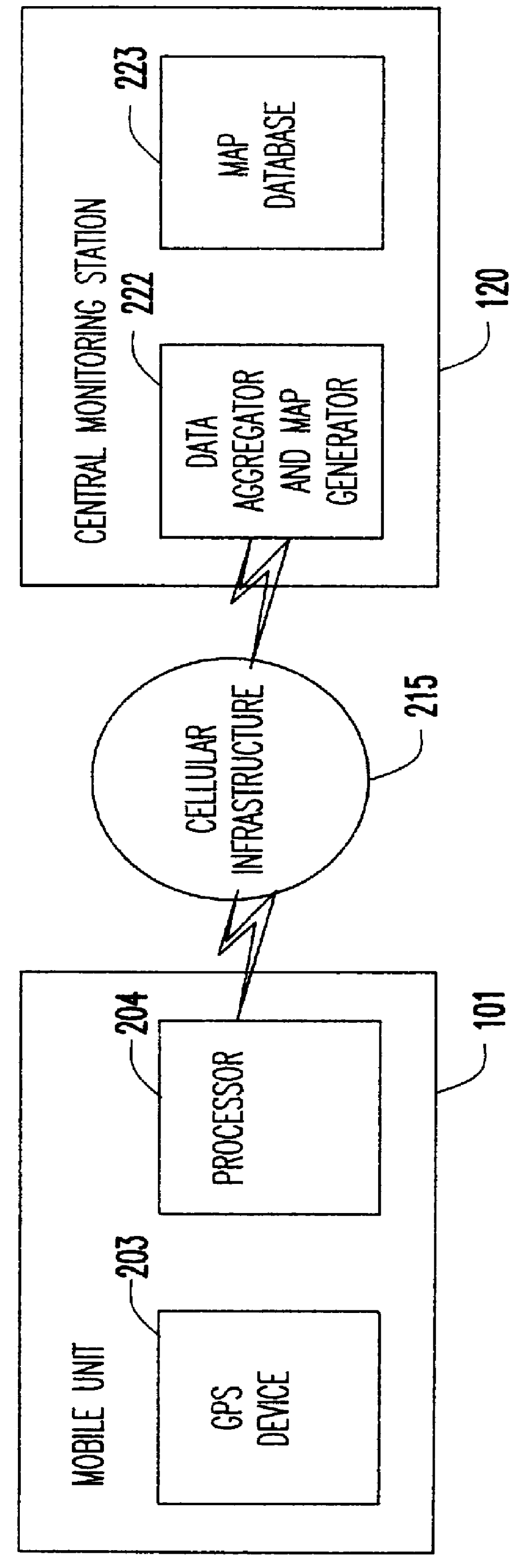
Instantaneous traffic monitoring system
InactiveUS6236933B1Less congestedControlling traffic signalsAnalogue computers for vehiclesModem deviceEngineering
A system for instantaneously monitoring traffic congestion including a plurality of monitoring electronic devices located in motor vehicles traveling on roadways in a selected region. Each monitoring electronic device is coupled to a GPS receiver that provides physical location to a wireless modem capable of connecting to a wireless communication network. The system also includes a central computer connected to a wide area network that is able of continuously downloading physical location information from a plurality of monitoring electronic devices also connected to the wide area network. The central computer uses a traffic monitoring software program and a mapping database containing roadway information for a region and the movement information from the monitoring electronic devices to create a continuously updated traffic congestion database. Authorized users of the system are able to log onto the central computer to a portion of the database that contains specific traffic flow and congestion information. Using the system, users are also able to obtain estimated times of arrival for a specific trip, and recommendations on alternative route information. The system can also take into consideration current or anticipated events that may affect traffic congestion.
Owner:INFOMOVE COM
Mitigating denial of service attacks
InactiveUS20040148520A1Easily scaledMemory loss protectionUnauthorized memory use protectionThe InternetNetwork routing
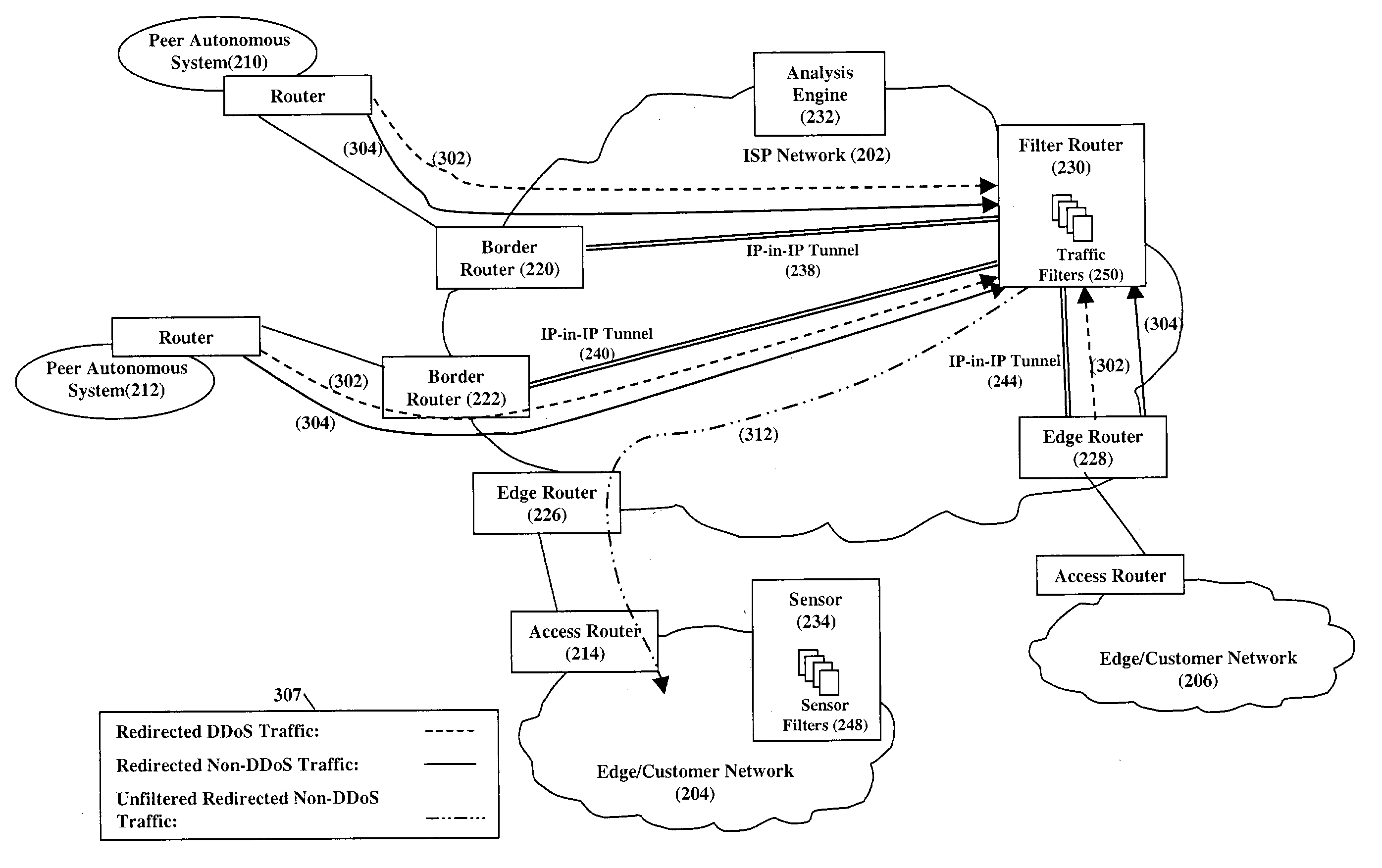
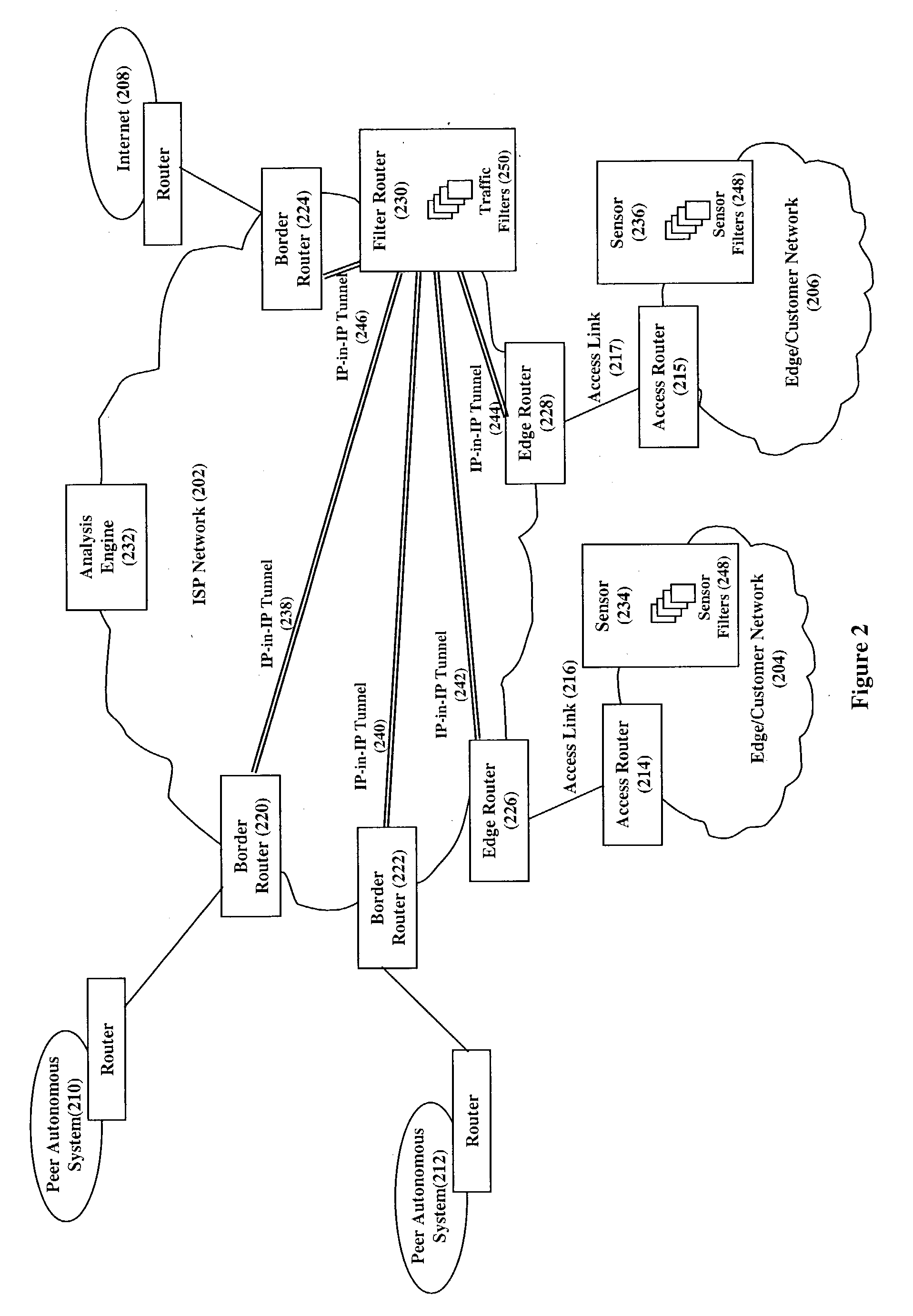
Service attacks, such as denial of service and distributed denial of service attacks, of a customer network are detected and subsequently mitigated by the Internet Service Provider (ISP) that services the customer network. A sensor examines the traffic entering the customer network for attack traffic. When an attack is detected, the sensor notifies an analysis engine within the ISP network to mitigate the attack. The analysis engine configures a filter router to advertise new routing information to the border and edge routers of the ISP network. The new routing information instructs the border and edge routers to reroute attack traffic and non-attack traffic destined for the customer network to the filter router. At the filter router, the attack traffic and non-attack traffic are automatically filtered to remove the attack traffic. The non-attack traffic is passed back onto the ISP network for routing towards the customer network.
Owner:TELCORDIA TECHNOLOGIES INC
Method for high-performance delivery of web content
InactiveUS20050044270A1Improve performanceReduce deliveryDigital computer detailsData switching networksWeb serviceWeb cache
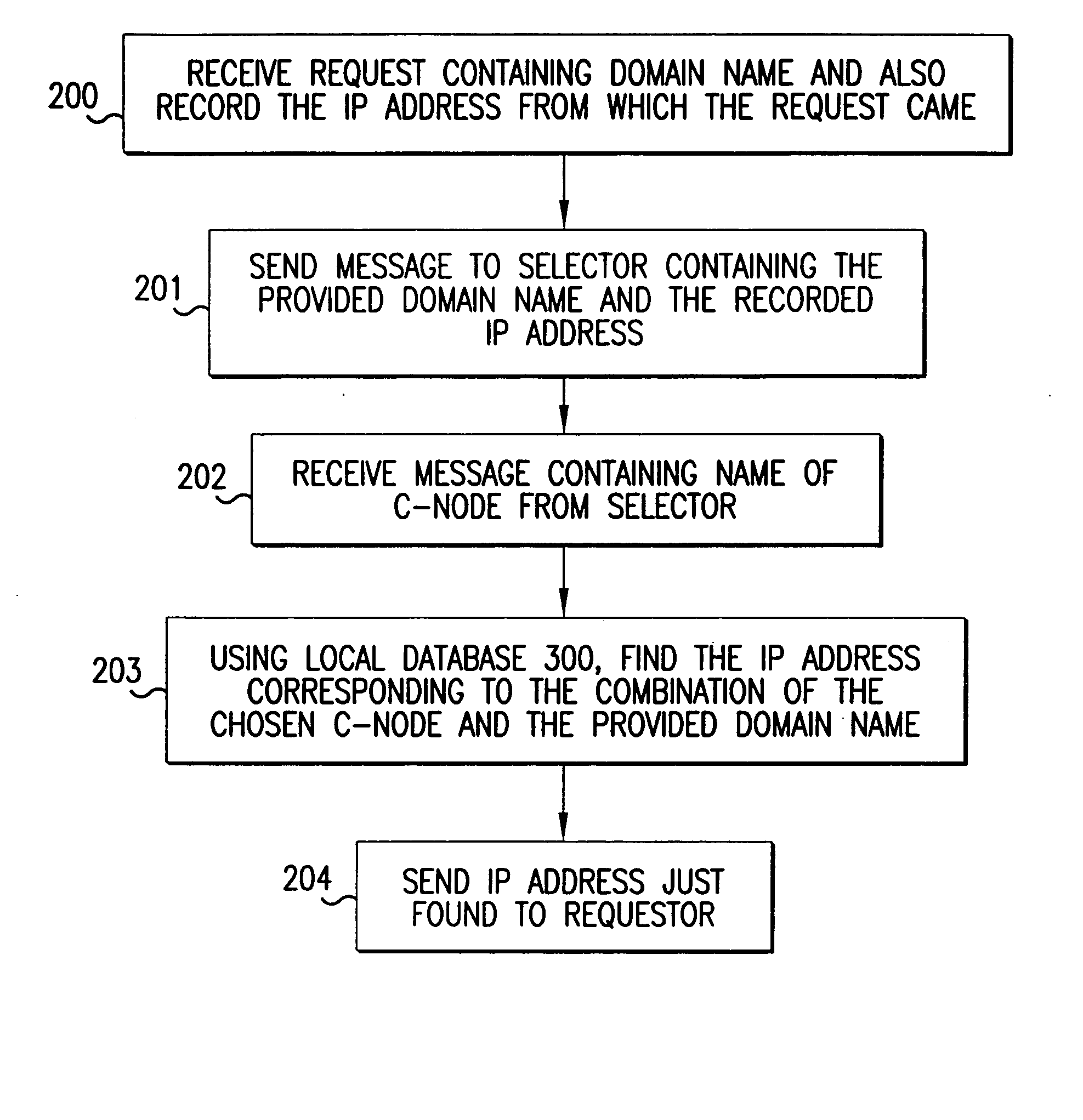
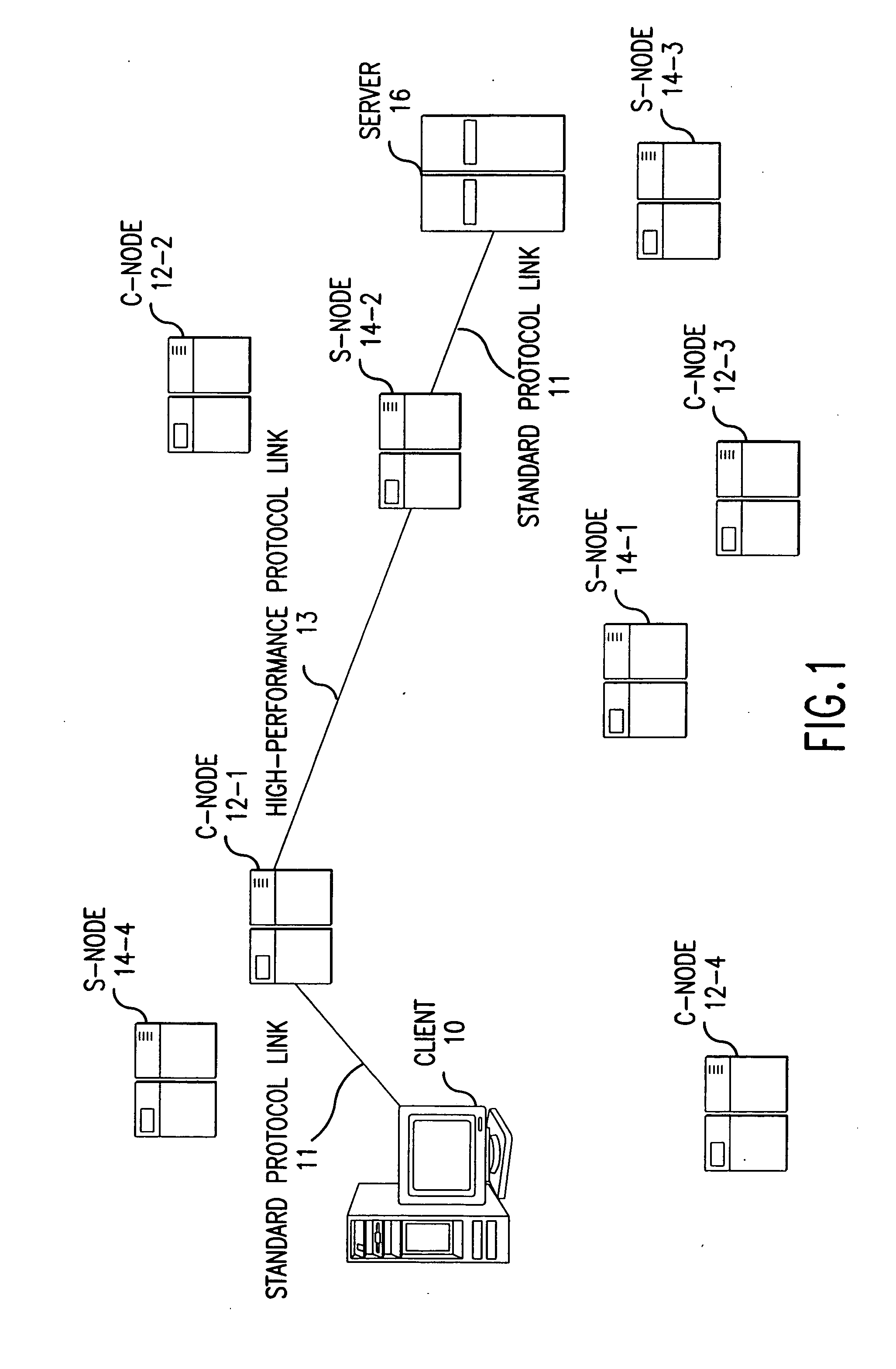
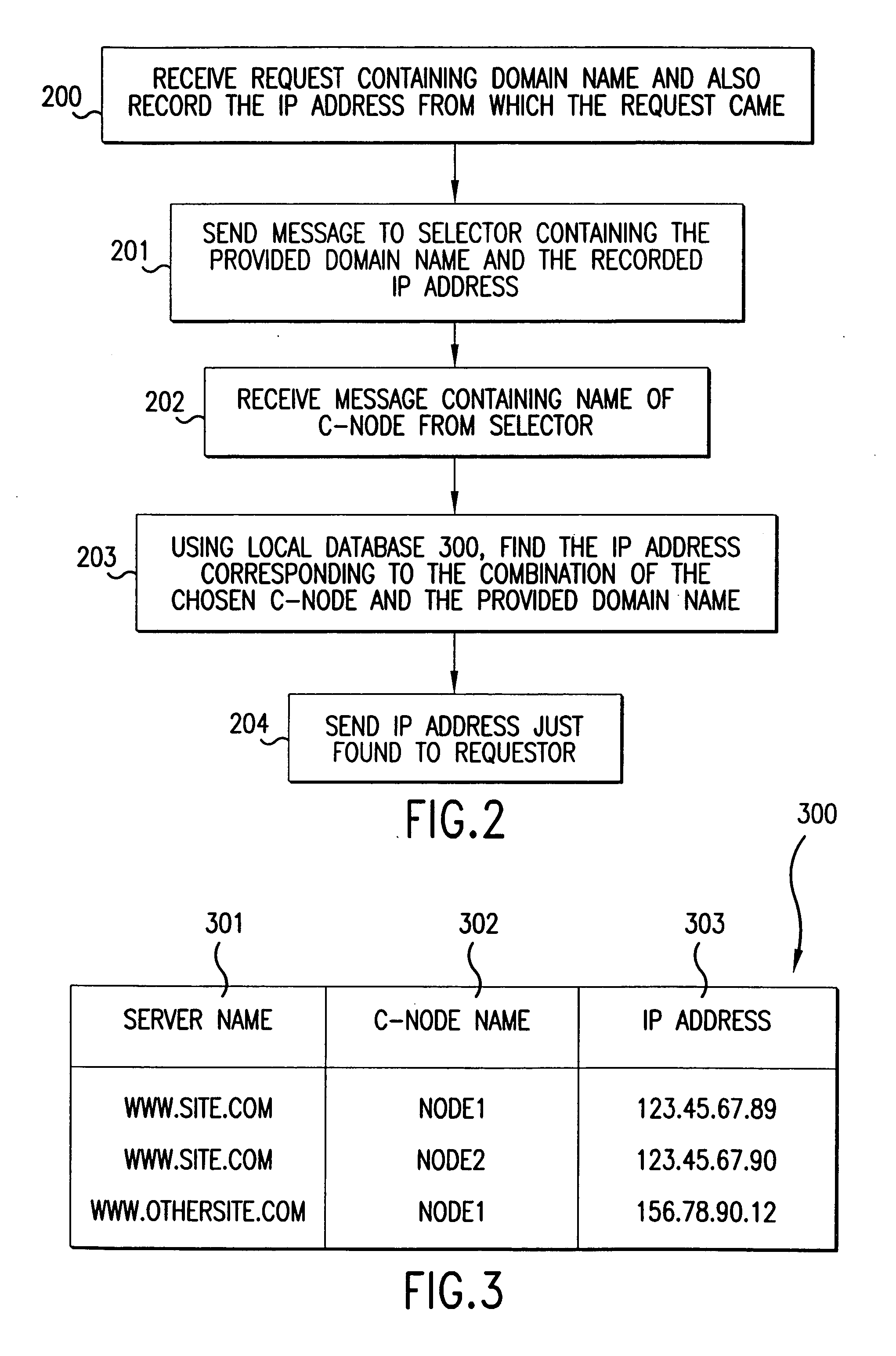
The present invention provides a method and apparatus for increasing the performance of world-wide-web traffic over the Internet. A distributed network of specialized nodes of two types is dispersed around the Internet. A web client's requests are directed to a node of the first type chosen to be close to the client, and the client communicates with this node using a standard protocol such as HTTP. This first node receives the request, and communicates the request to a node of the second type chosen to be close to the request's ultimate destination (e.g., a web server capable of generating a response to the request.) The first node communicates the request to the second node using a different, specialized, protocol that has been designed for improved performance and specifically to reduce traffic volume and to reduce latency. The second node receives communication from the first node using this specialized protocol, converts it back to a standard protocol such as HTTP, and forwards the request to the destination computer or server. Responses from the destination to the client take the corresponding reverse route, and also are carried over a specialized protocol between the two nodes. In addition, these nodes can employ other techniques such as web caches that avoid or improve some communication steps. Thus, specialized, proprietary, or complex protocols and techniques can be quickly deployed to enhance web performance without requiring significant changes to the clients or servers.
Owner:AKAMAI TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com