Patents
Literature
886 results about "Traffic analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Traffic analysis is the process of intercepting and examining messages in order to deduce information from patterns in communication, which can be performed even when the messages are encrypted. In general, the greater the number of messages observed, or even intercepted and stored, the more can be inferred from the traffic. Traffic analysis can be performed in the context of military intelligence, counter-intelligence, or pattern-of-life analysis, and is a concern in computer security.
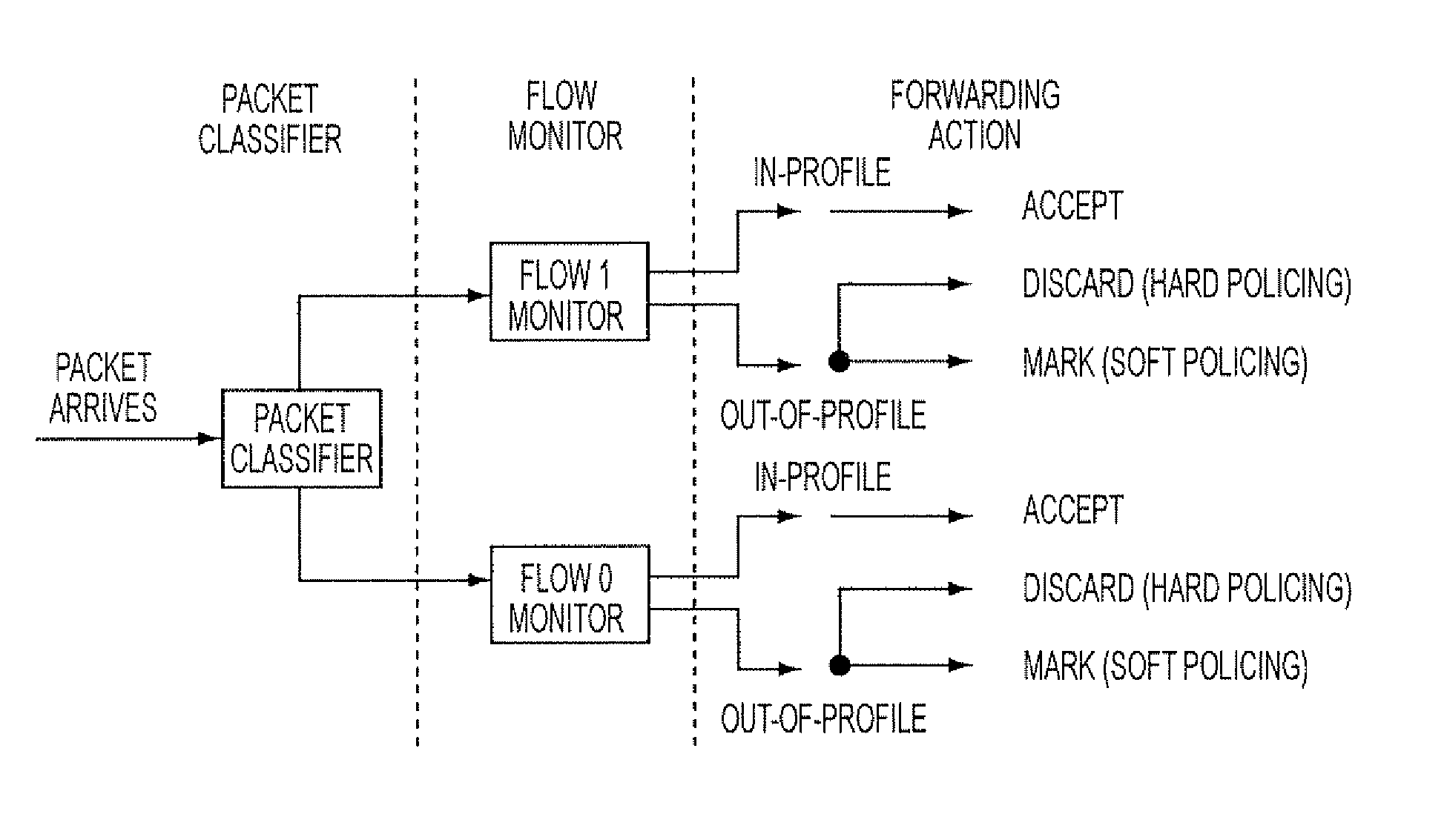
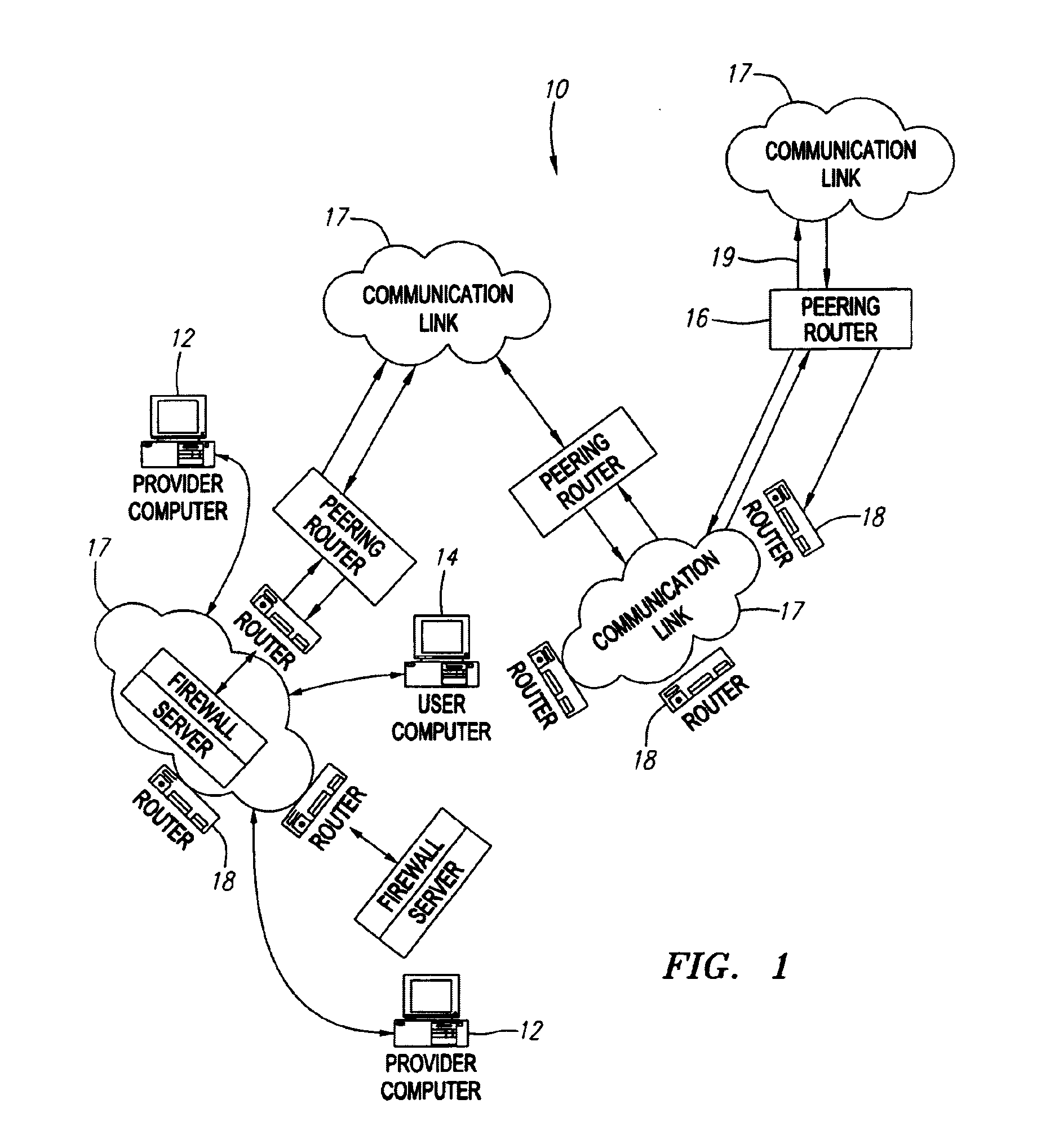
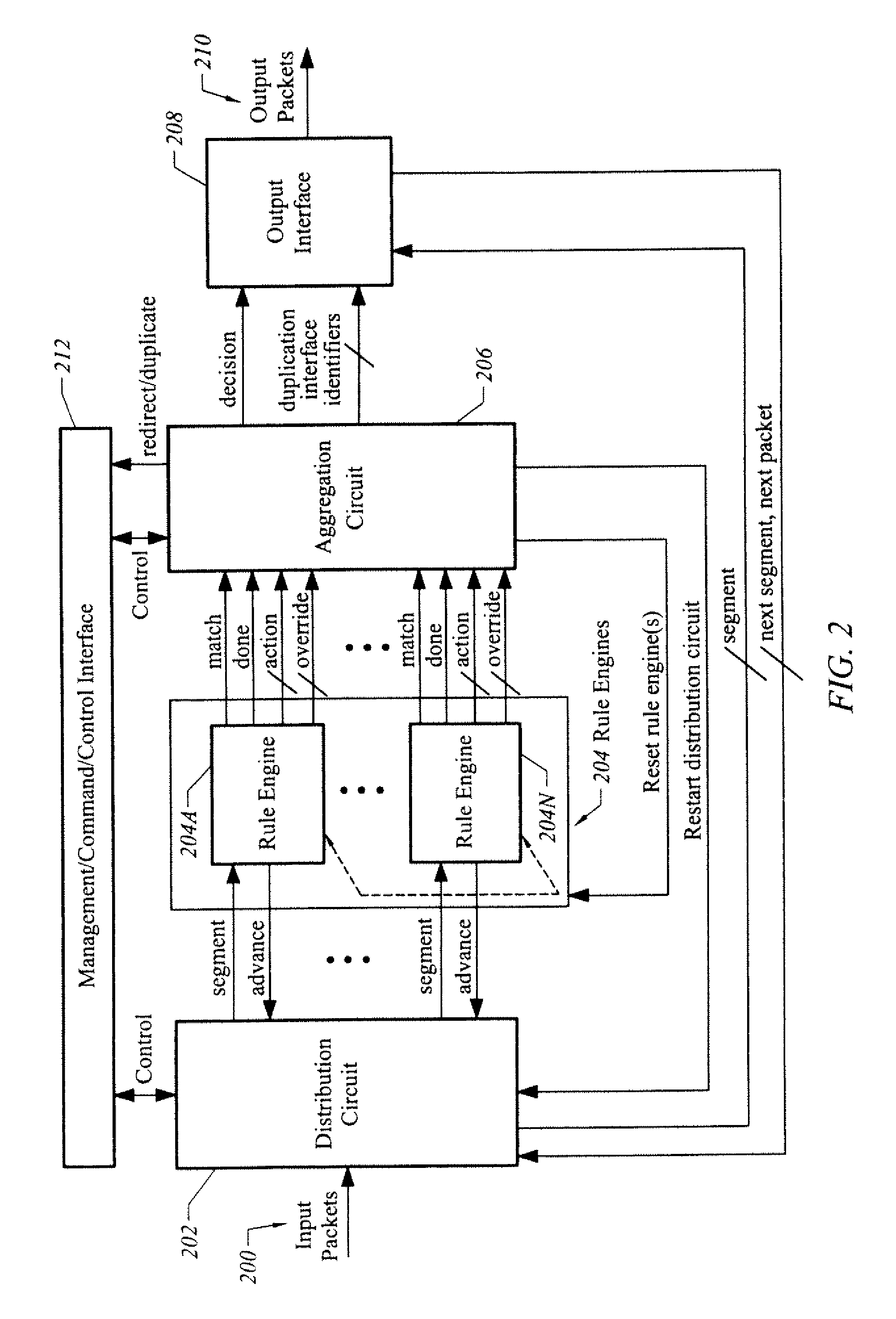
Systems and methods for processing packets
InactiveUS7215637B1Minimize occurrenceSize of output is increasedError preventionTransmission systemsPacket filteringTraffic analysis
Methods and devices for processing packets are provided. The processing device may include an input interface for receiving data units containing header information of respective packets; a first module configurable to perform packet filtering based on the received data units; a second module configurable to perform traffic analysis based on the received data units; a third module configurable to perform load balancing based on the received data units; and a fourth module configurable to perform route lookups based on the received data units.
Owner:JUMIPER NETWORKS INC
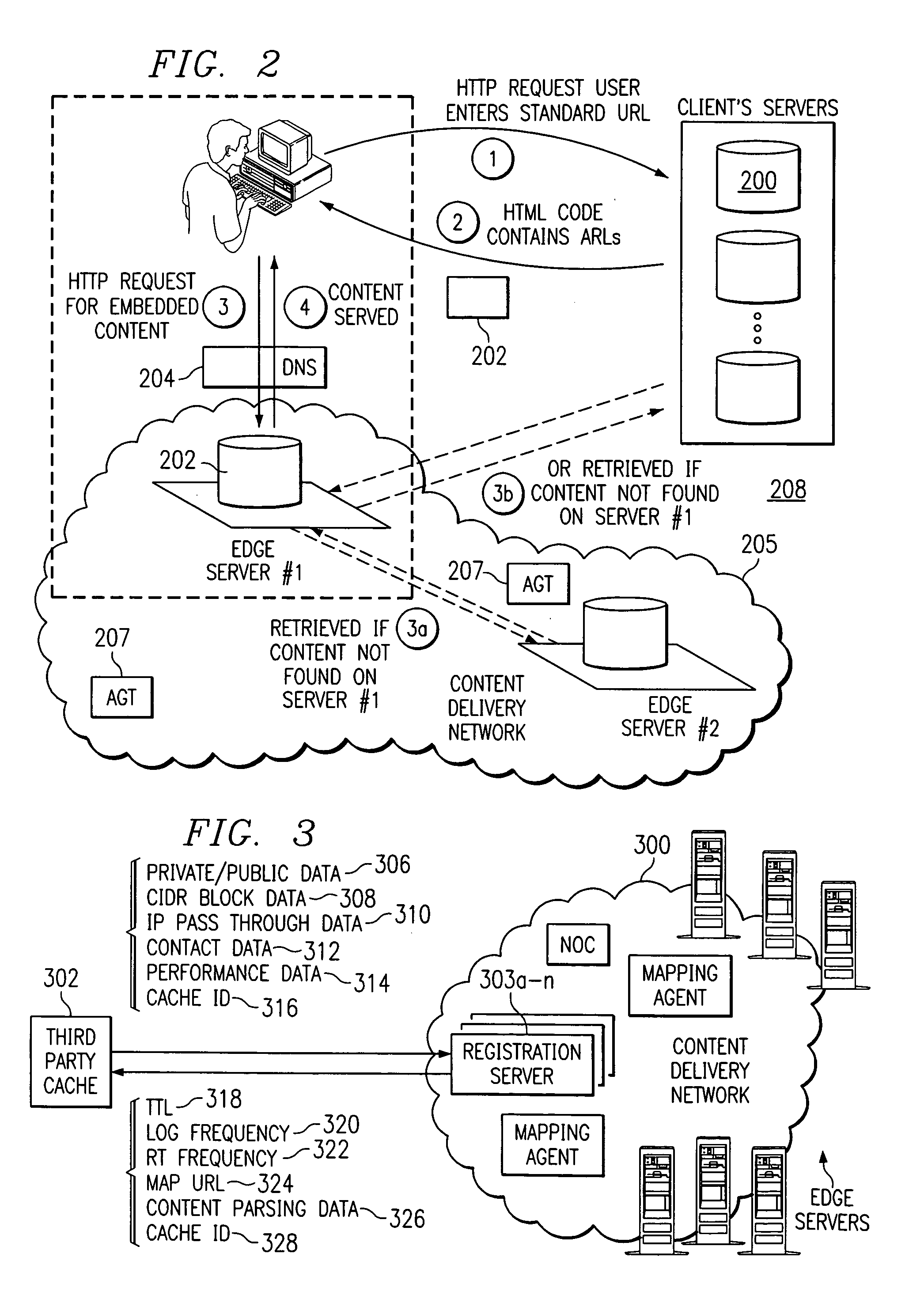
Internet content delivery service with third party cache interface support
InactiveUS7010578B1Increase reachImprove performanceDigital data information retrievalMultiple digital computer combinationsThird partyOff the shelf
Third party cache appliances are configured into a content delivery service to enable such devices to cache and serve content that has been tagged for delivery by the service. The invention enables the content delivery service to extend the reach of its network while taking advantage of high performance, off-the-shelf cache appliances. If the third party caches comprise part of a third party content delivery network, the interconnection of caches to the CDS according to the present invention enables the CDS and the third party network to share responsibility for delivering the content. To facilitate such “content peering,” the CDS may also include a traffic analysis mechanism to provide the third party network with preferably real-time data identifying the content delivered by the CDS from the third party caches. The CDS may also include a logging mechanism to generate appropriate billing and reporting of the third party content that is delivered from the cache appliances that have been joined into the CDS.
Owner:AKAMAI TECH INC
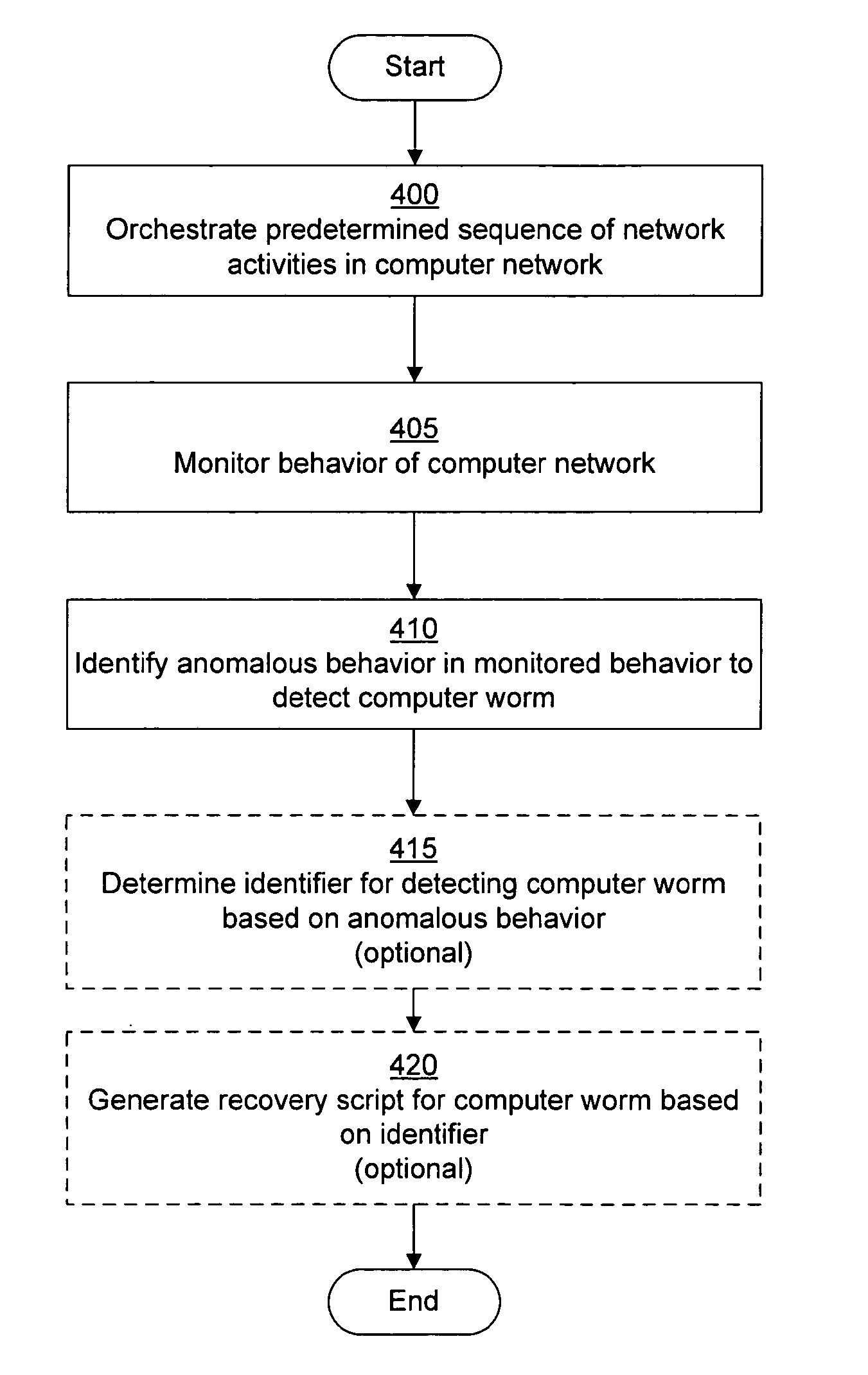
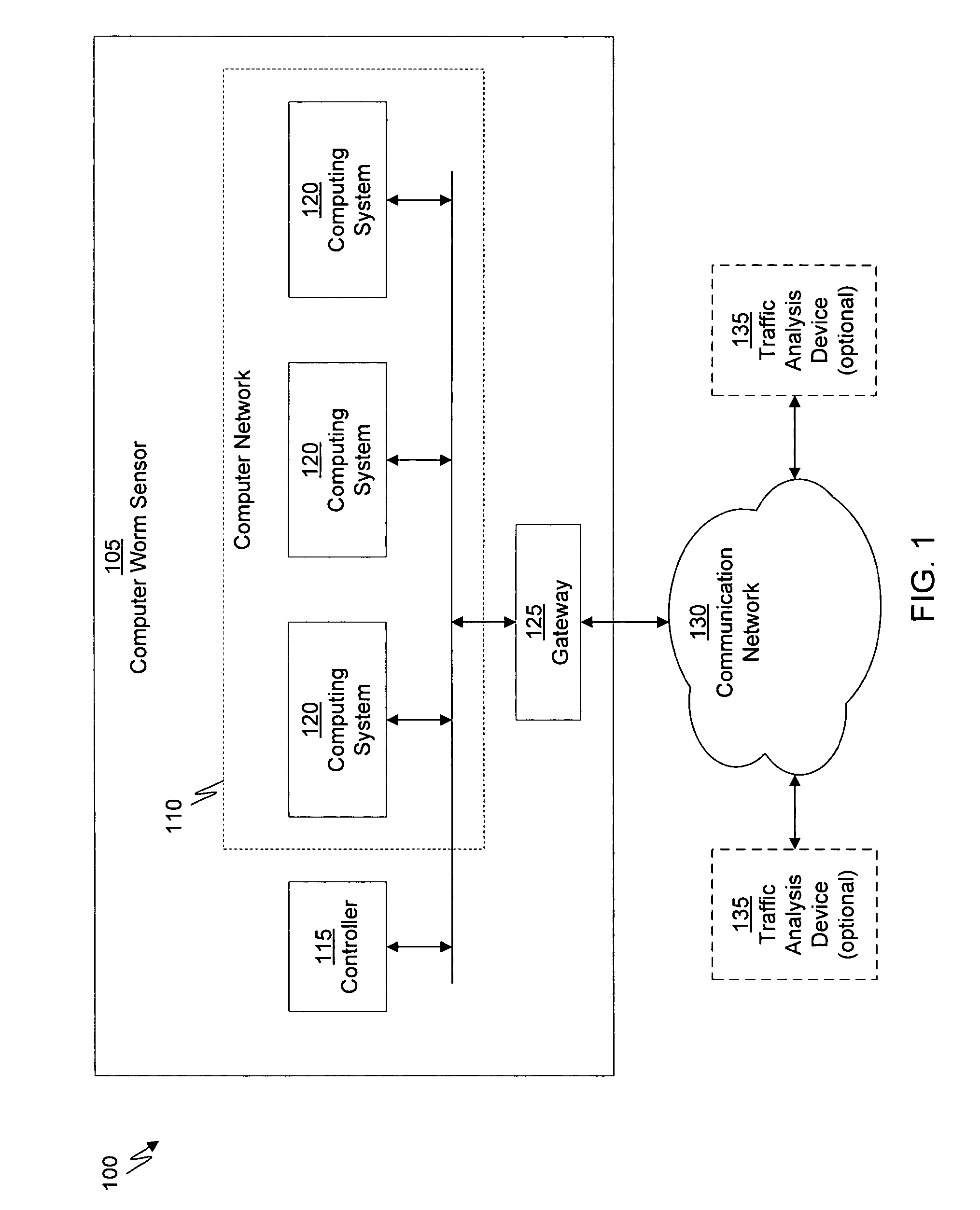
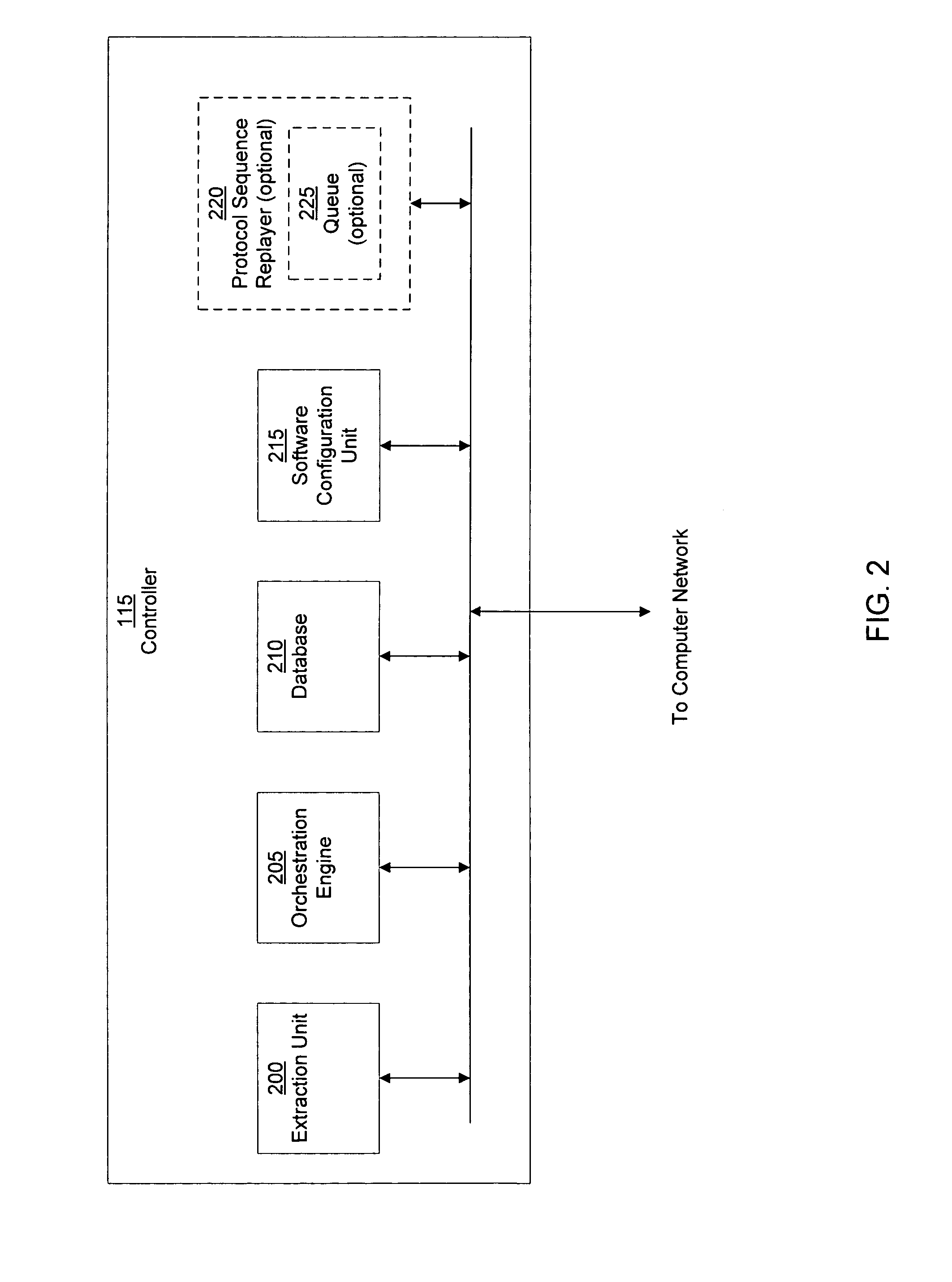
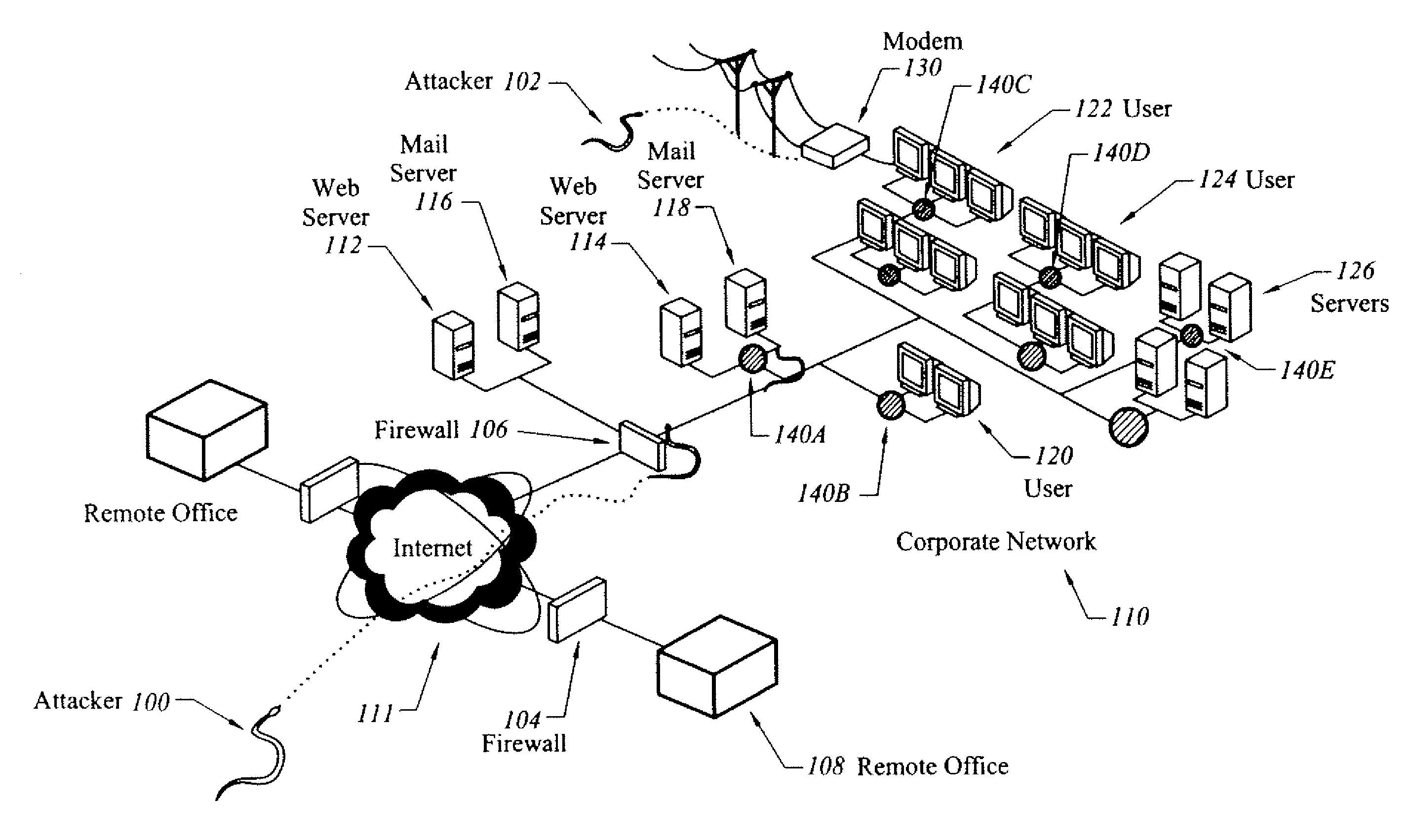
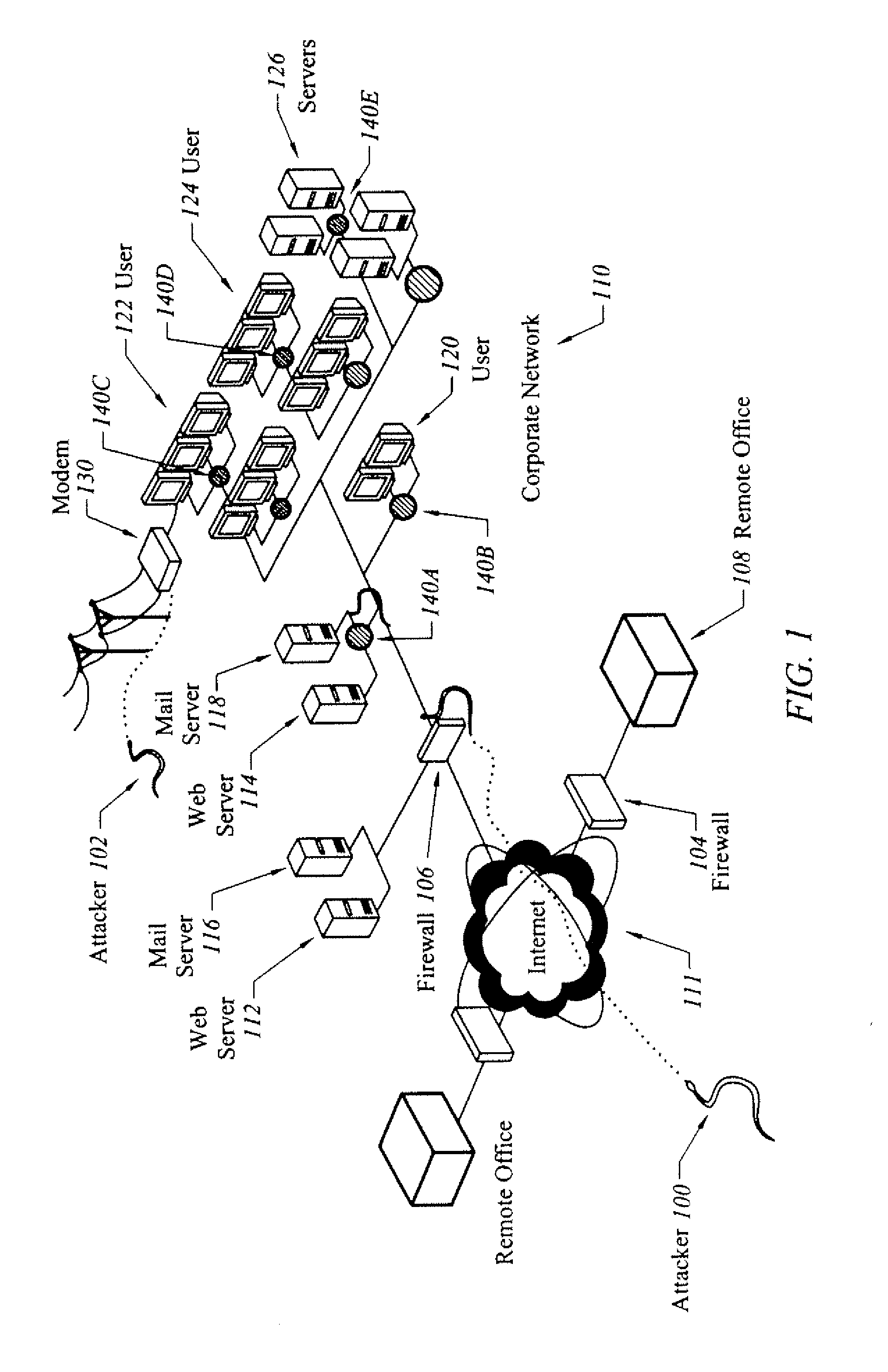
System and method of detecting time-delayed malicious traffic
A system for detecting a computer worm comprises a traffic analysis device in communication with a network device. The traffic analysis device can analyze network traffic received over a communication network and duplicate at least select network communications within the network traffic having characteristics associated with one or more computer worms. The network device comprises a controller in communication with one or more virtual machines that are configured to receive the duplicated network communications from the traffic analysis device. The network device may (i) monitor a behavior of a first virtual machine of the one or more virtual machines in response to processing of the duplicated network communications within the first virtual machine, (ii) identify an anomalous behavior as an unexpected occurrence in the monitored behavior, and (iii) determine, based on the identified anomalous behavior, the presence of the one or more computer worms in the duplicated network communications.
Owner:FIREEYE SECURITY HLDG US LLC
Method and apparatus for preventing network traffic analysis
InactiveUS6917974B1Not replace and duplicate and reduce needAugments the protection provided by encryptionHardware monitoringMultiple digital computer combinationsTraffic capacityNetwork packet
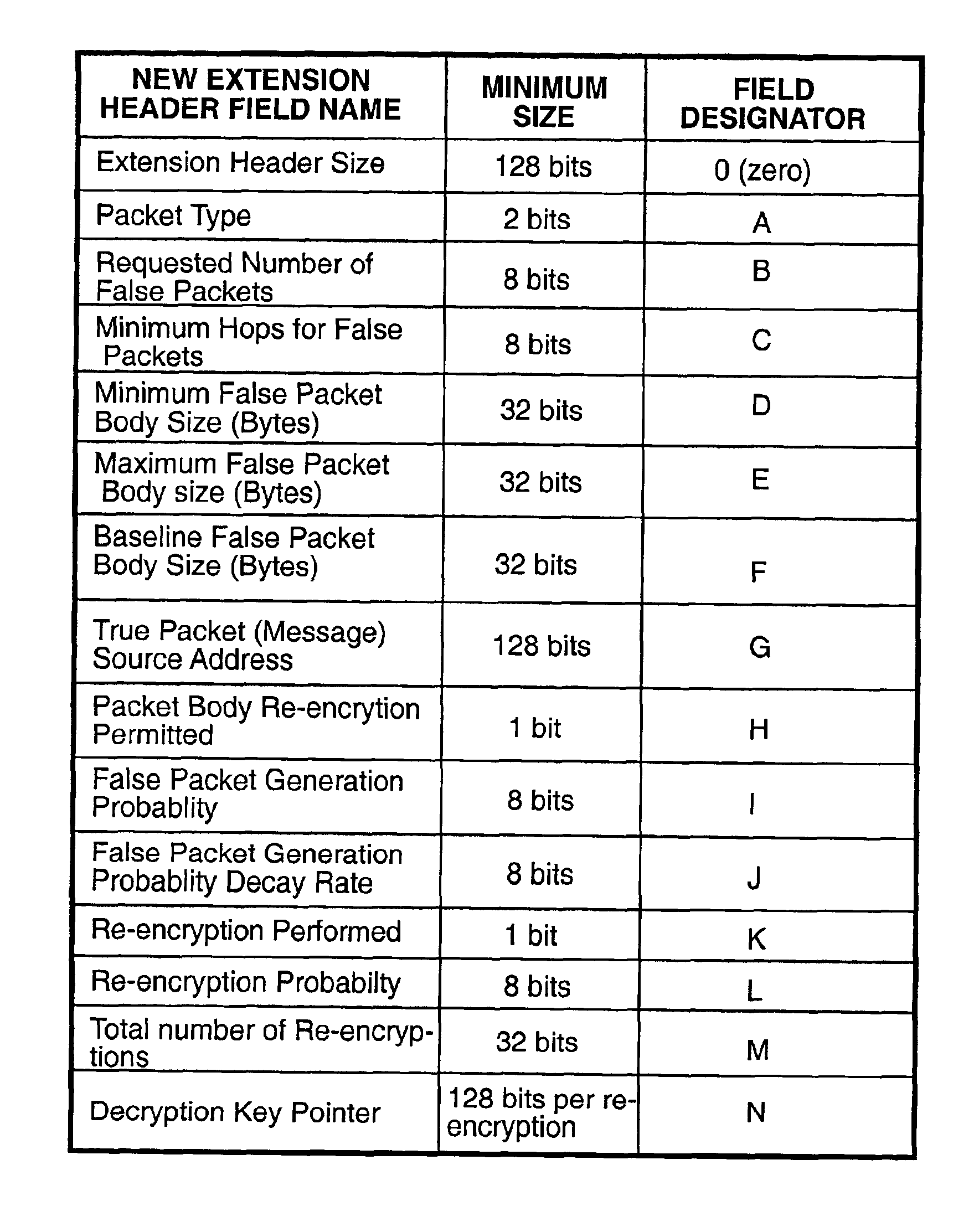
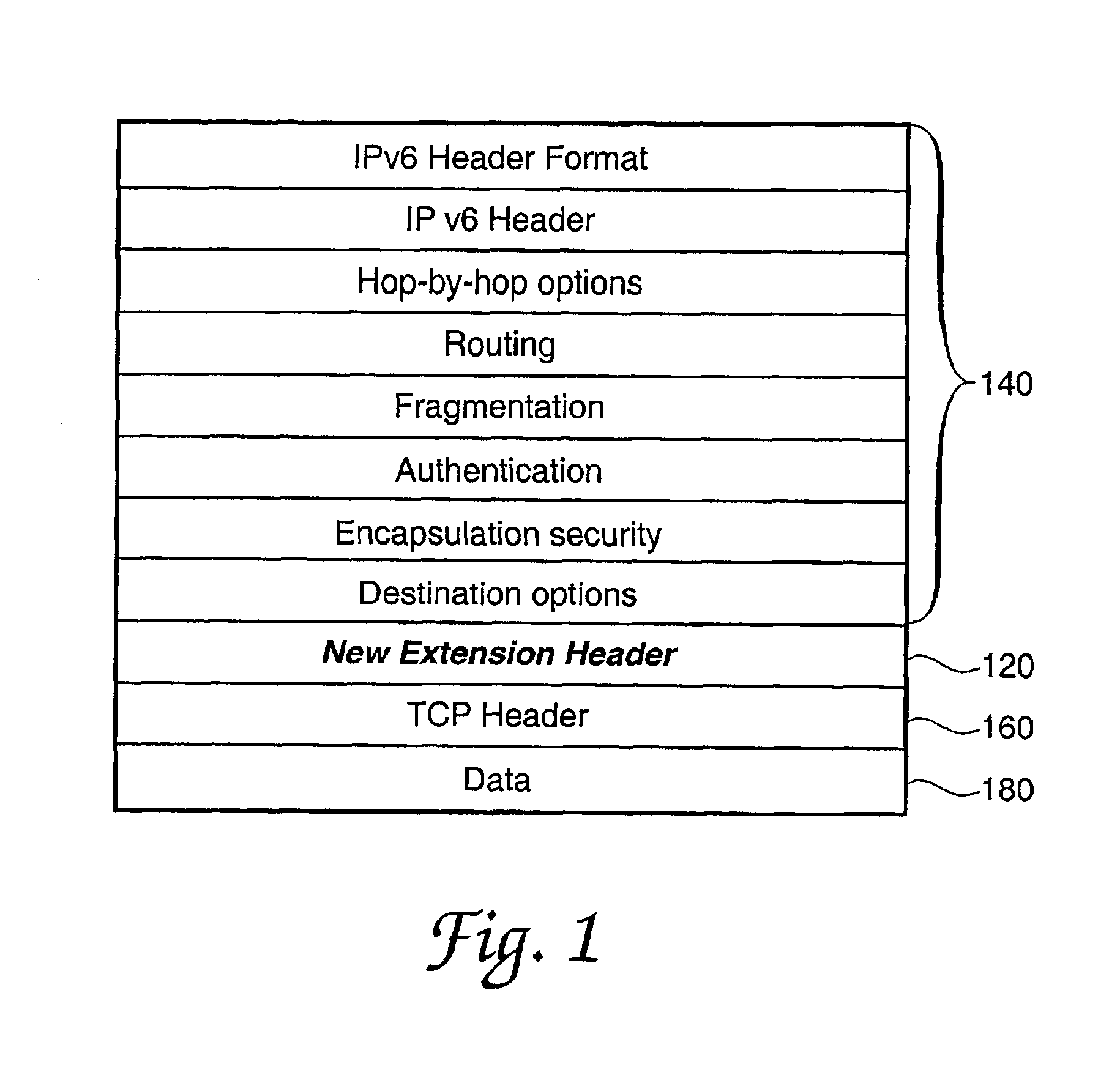
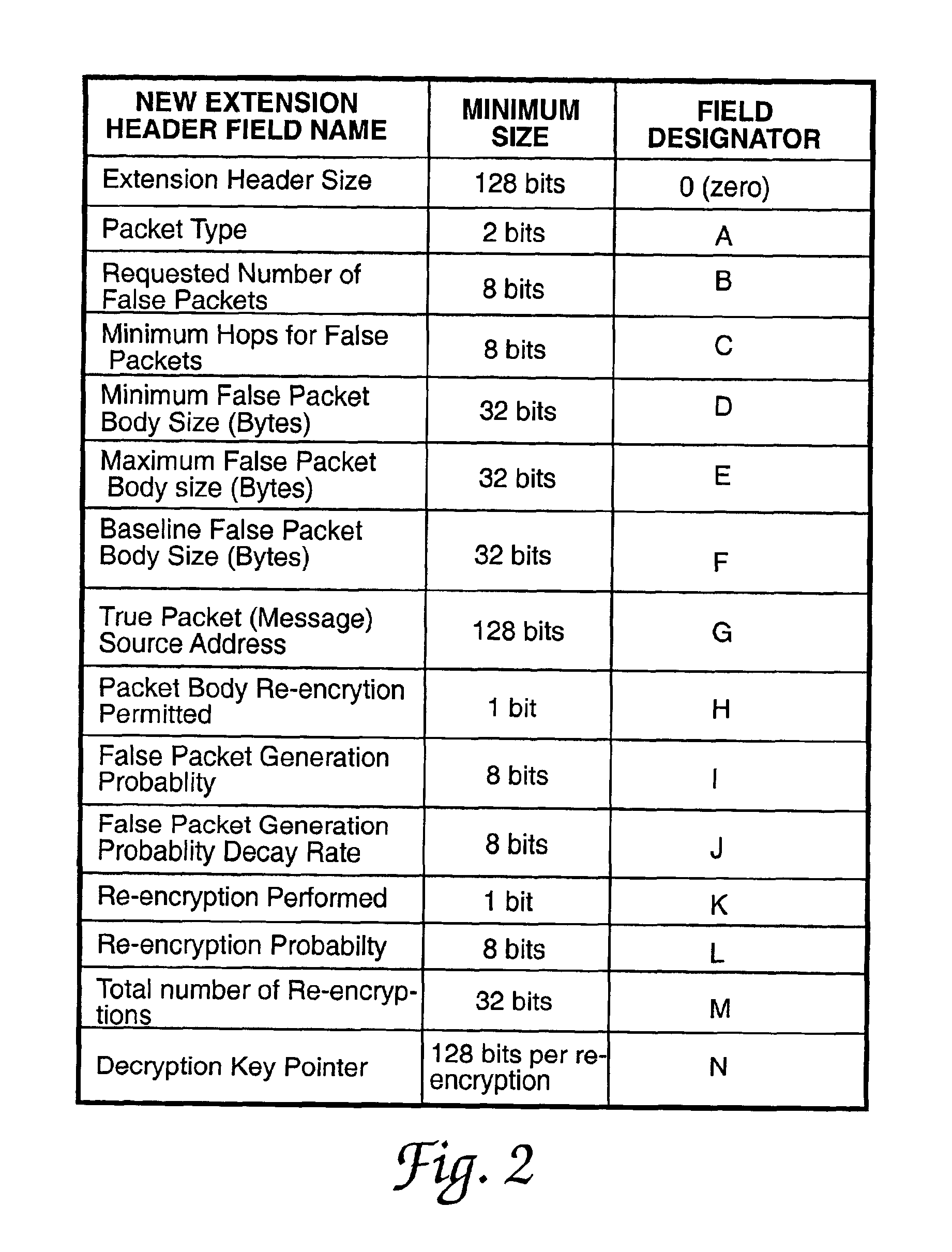
A system and method for generating and transmitting false packets along with a true packet to thereby hide or obscure the actual message traffic. A new extension header having a plurality of fields is positioned in the hierarchy of Internet protocol headers that control passage of the false packets and the true packet through the network. A sending host computer generates a plurality of false packets for each true packet and transmits the false packets and the true packet containing the Internet protocol headers and the extension header over the network. The new extension header is decrypted and re-encrypted each host that handles a message packet that uses the new extension header to control the random re-encryption of the true packet body at random hosts and the random generation of false packets at each host visited by a true packet, at the recipient of the true packet, and at any hosts that receive a false packet.
Owner:AIR FORCE GOVERNMENT OF THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SEC OF THE THE
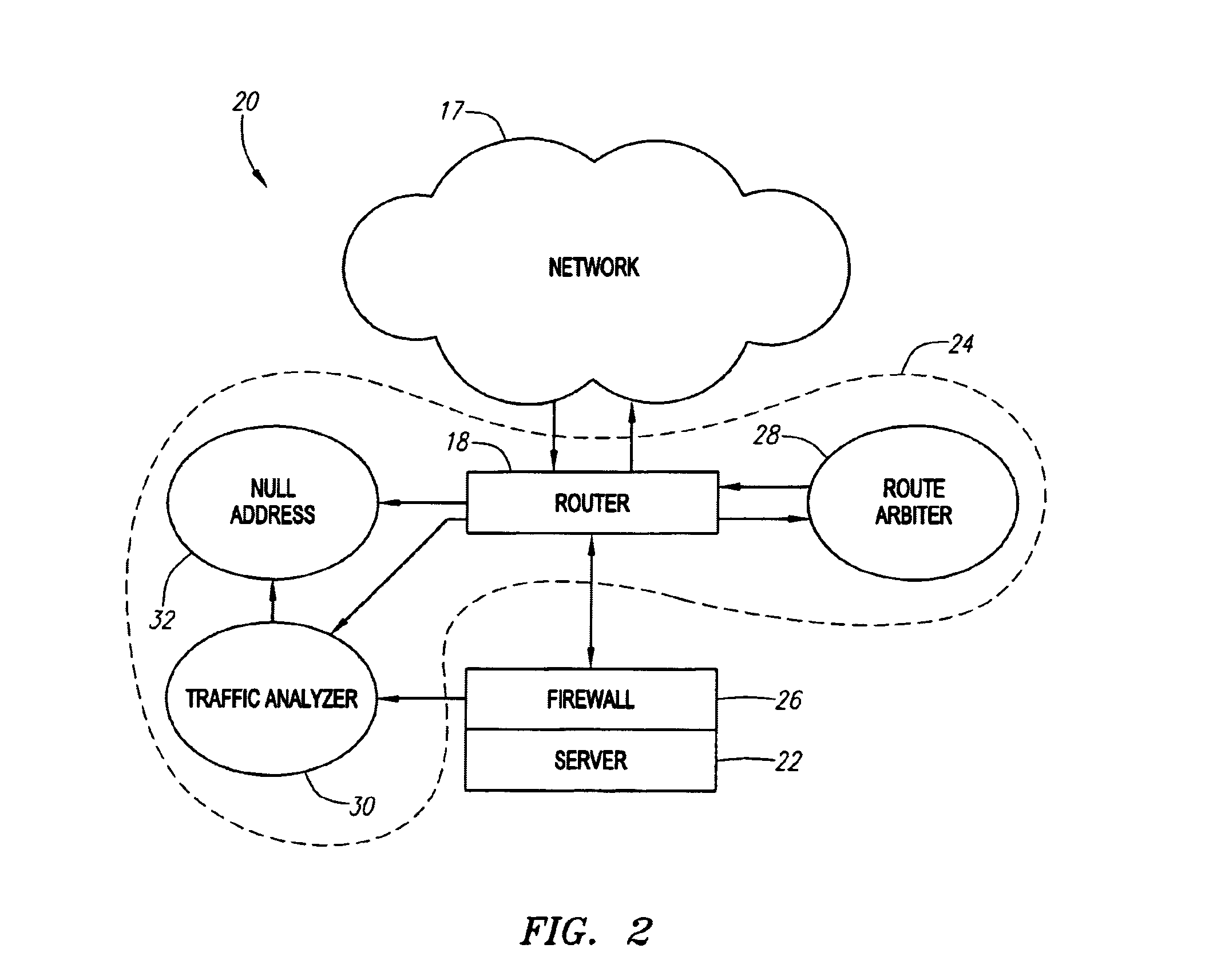
Proactive network analysis system
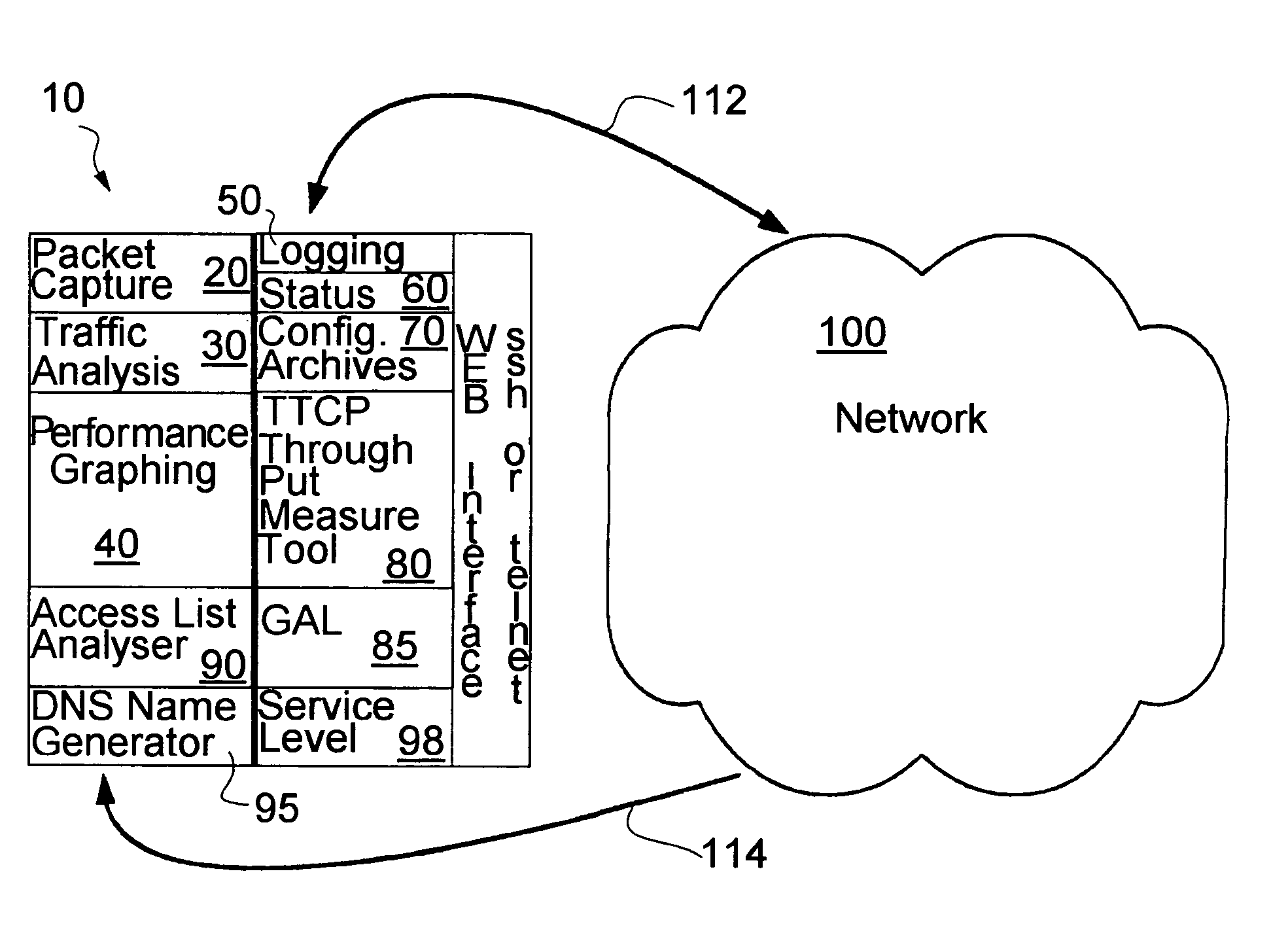
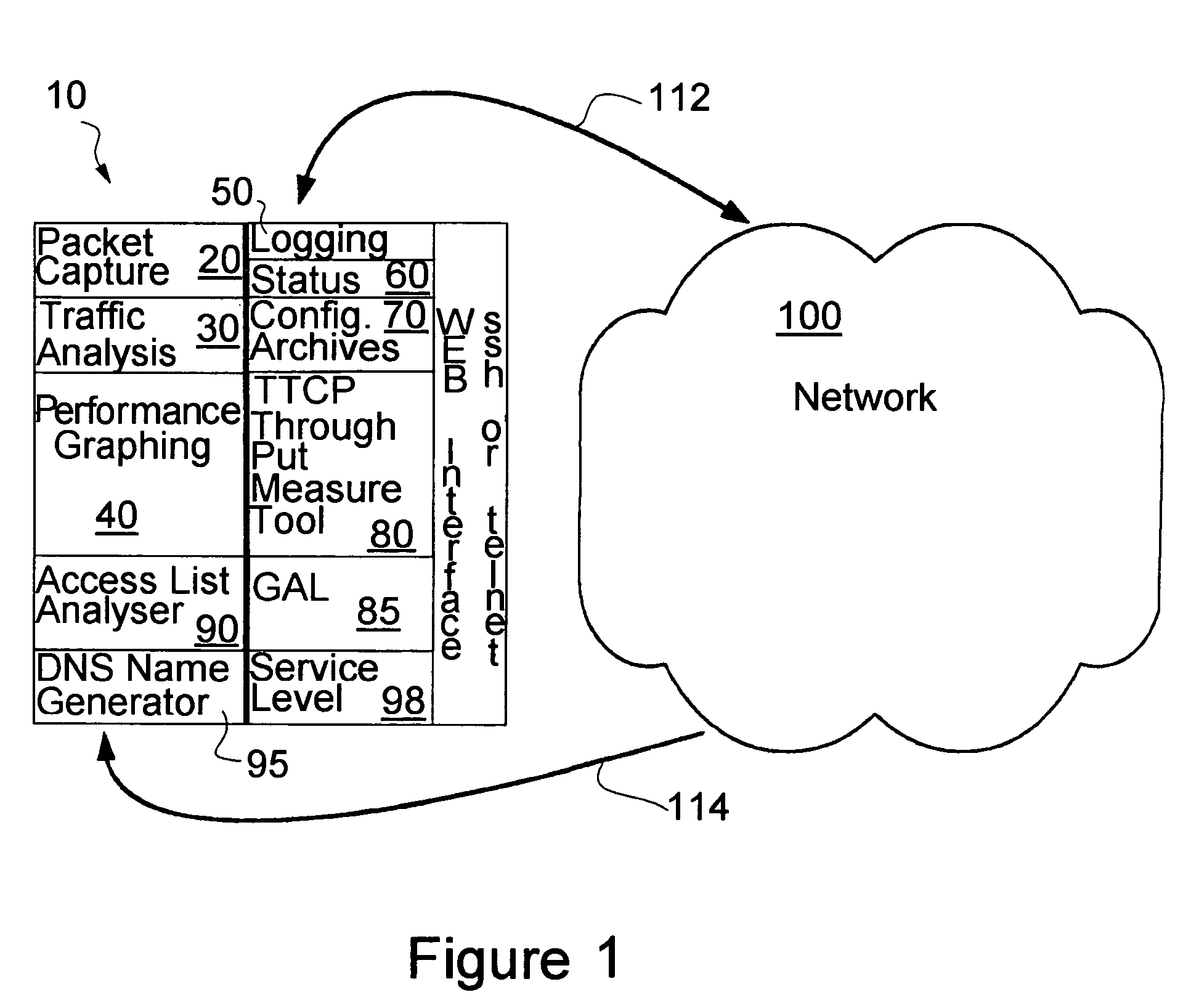
A proactive network analysis system is a single unit for diagnosing network problems, measuring network performance, and monitoring network status in a comprehensive manner. The system is a compilation of individual tools including a distributed network packet capture data stream collector; a traffic analyzer; a performance graphing unit; a syslog recorder analyzer and archiving unit; a system availability monitor; a device configuration archiving unit; and a throughput measurement tool. The system can further provide an access list generator, an access list analyzer, a router DNS name generator and a service level agreement measurement device.
Owner:SOLUTIONS4NETWORKS
Systems and methods for investigation of financial reporting information
InactiveUS20050222929A1FinanceSpecial data processing applicationsCluster algorithmStatistical analysis
Owner:PRICEWATERHOUSECOOPERS LLP
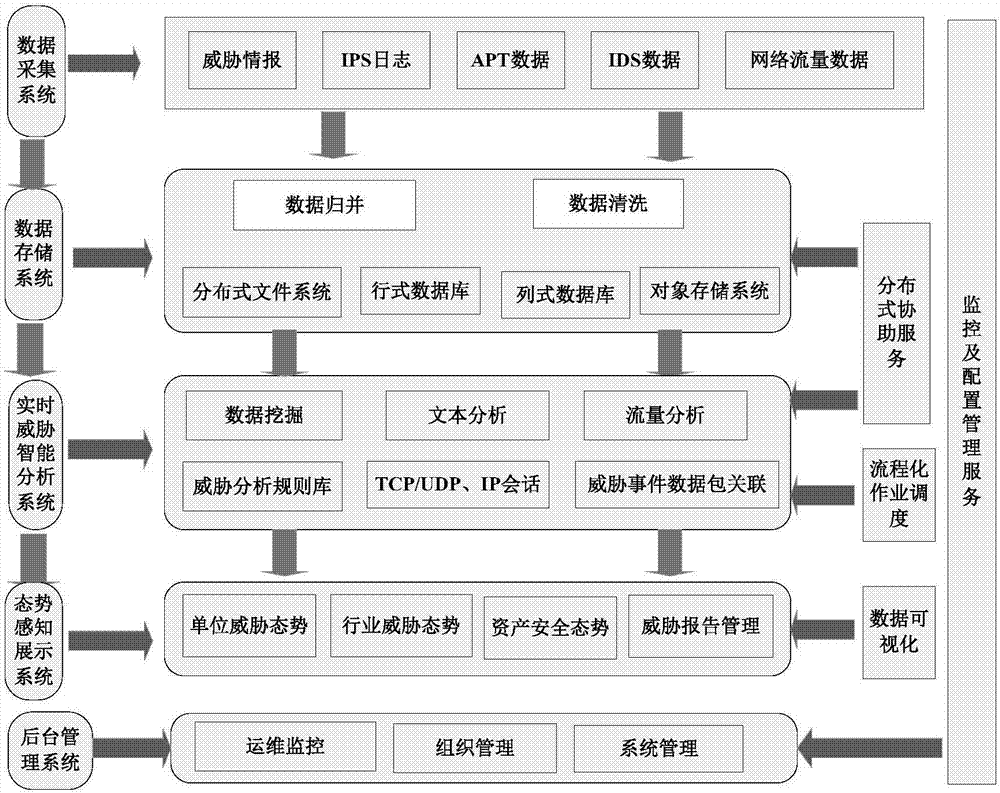
Threat early warning and monitoring system and method based on big data analysis and deployment architecture
ActiveCN107196910ARealize acquisitionRealize multi-dimensional graphical and intuitive displayData switching networksFull text searchTime processing
The invention discloses a threat early warning and monitoring system and method based on big data analysis and a deployment architecture. The system comprises a data acquisition system module, which is used for carrying out real-time data acquisition on original network traffic; a data storage system module, which is used for carrying out data merging and data cleaning on the data collected by the data acquisition system module, and then, carrying out storage management; a real-time threat intelligent analysis system module, which is used for carrying out deep analysis and mining on security data through data mining, text analysis, traffic analysis, full-text search engine and real-time processing, and identifying unknown security threats in real time by combining an intrusion detection module, a network abnormal behavior module and a device abnormal behavior module; and a situation awareness display system module, which is used for carrying out comprehensive display on security threat situations stereoscopically in real time through a data visualization tool library. The threat early warning and monitoring system and method based on big data analysis and the deployment architecture are used for network security threat situation awareness and deep analysis under a plurality of service scenarios, and realize comprehensive abilities from attack early warning, attack identification to analysis and evidence obtaining.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +2
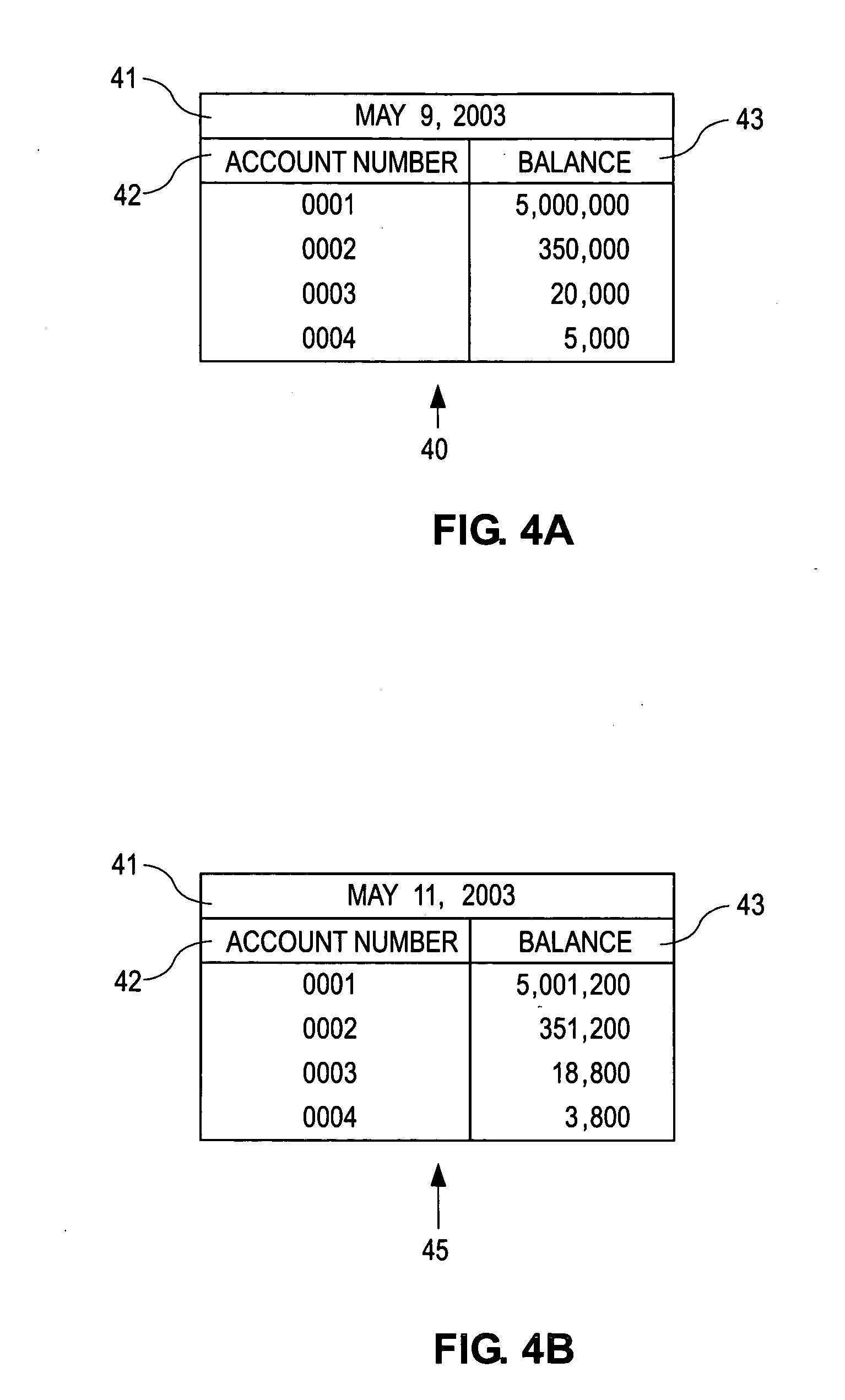
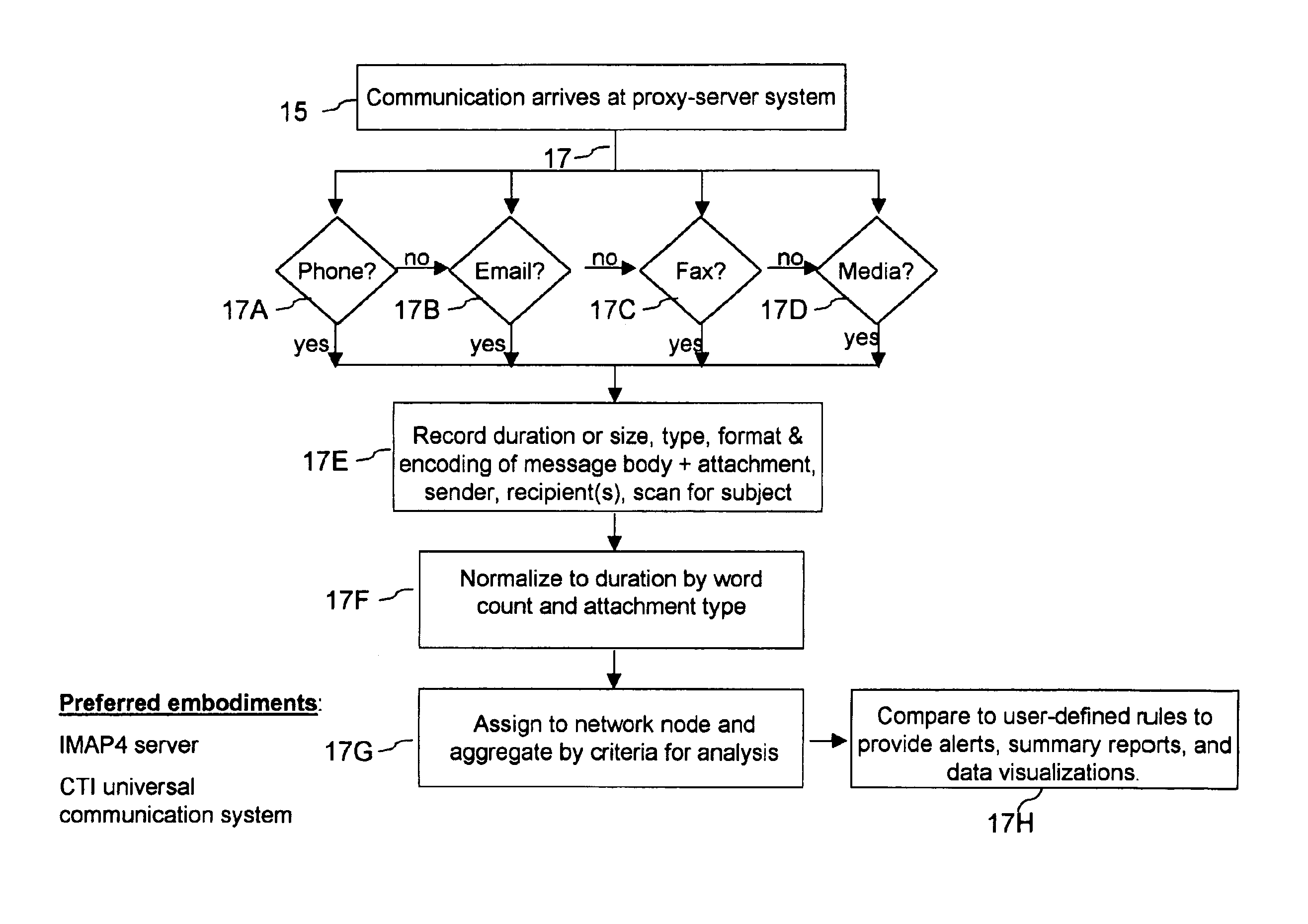
Telecommunication-based time-management system and method
InactiveUS6895438B1Improve business processImprove organizational strategySpeech analysisTime-division multiplexNon real timeRelational database
A proxy-server system (15) connected preferably to a computer-telephone system (10) intercepts, processes, and analyzes as traffic-analysis results (68A-C) all forms of real- and non-real-time electronic communication passing over the network in the form of raw traffic data (61). The proxy-server system normalizes each communication into the measure of time needed by recipient(s) of the communication to understand the information contained therein. Once normalized, the data may be aggregated into summary reports (69A-C). As part of the analysis, the aggregated communication records are compared with user-defined rules to provide alerts if the individual or aggregated durations exceed boundaries set by the rules. In one embodiment, the summary reports may be integrated with general-ledger data (94) and other raw business data (74) via a relational database (72) to derive more accurate records of activity-based-costing information (76). Additionally, the data of the summary reports may be visualized in two- or three-dimensional representations of communication-flow patterns to illustrate in an intuitive and semantically scalable manner the desired level of detail for time and time-based expense consumed by the electronic interactions of an individual or organization.
Owner:PAUL ULRICH
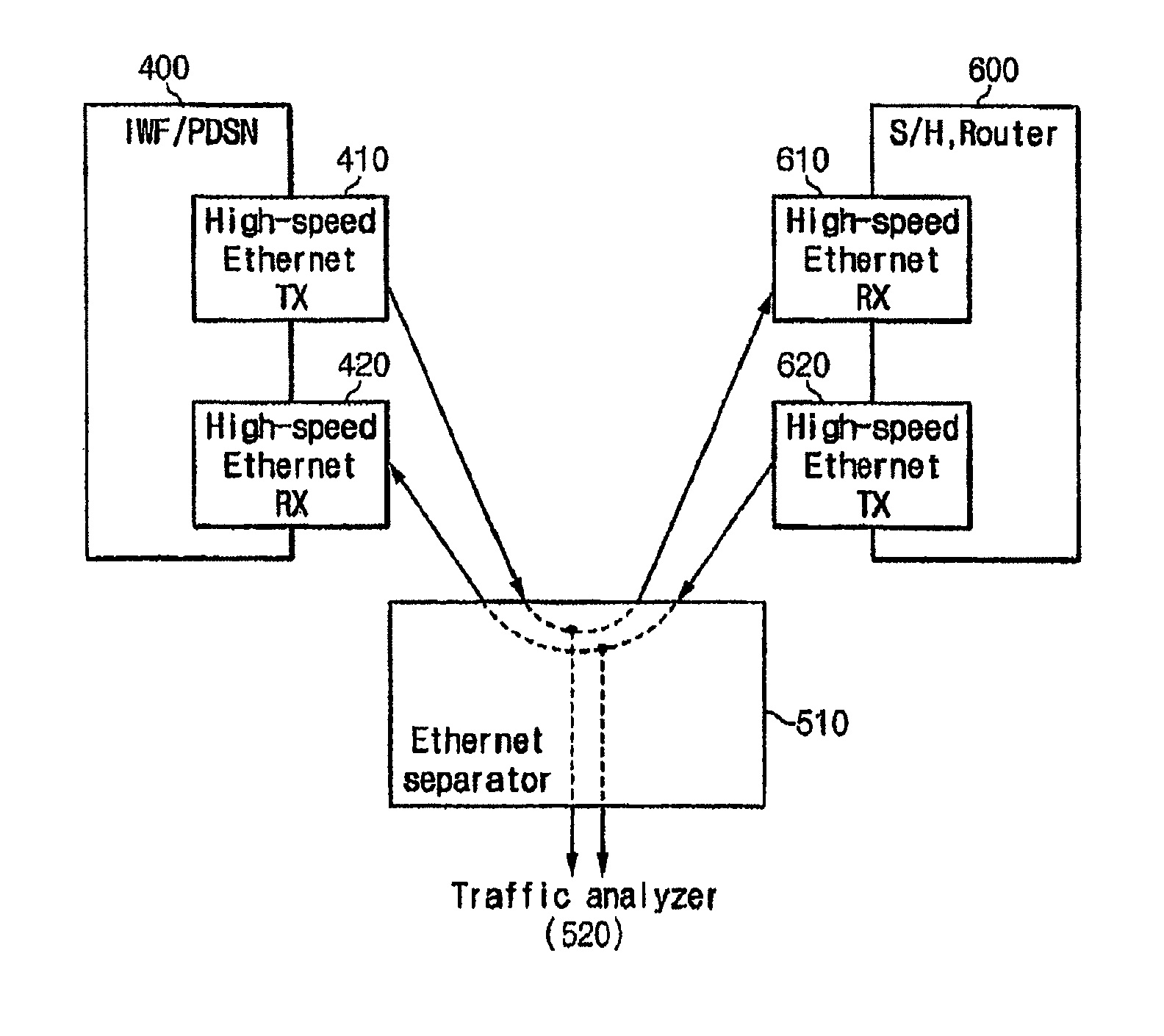
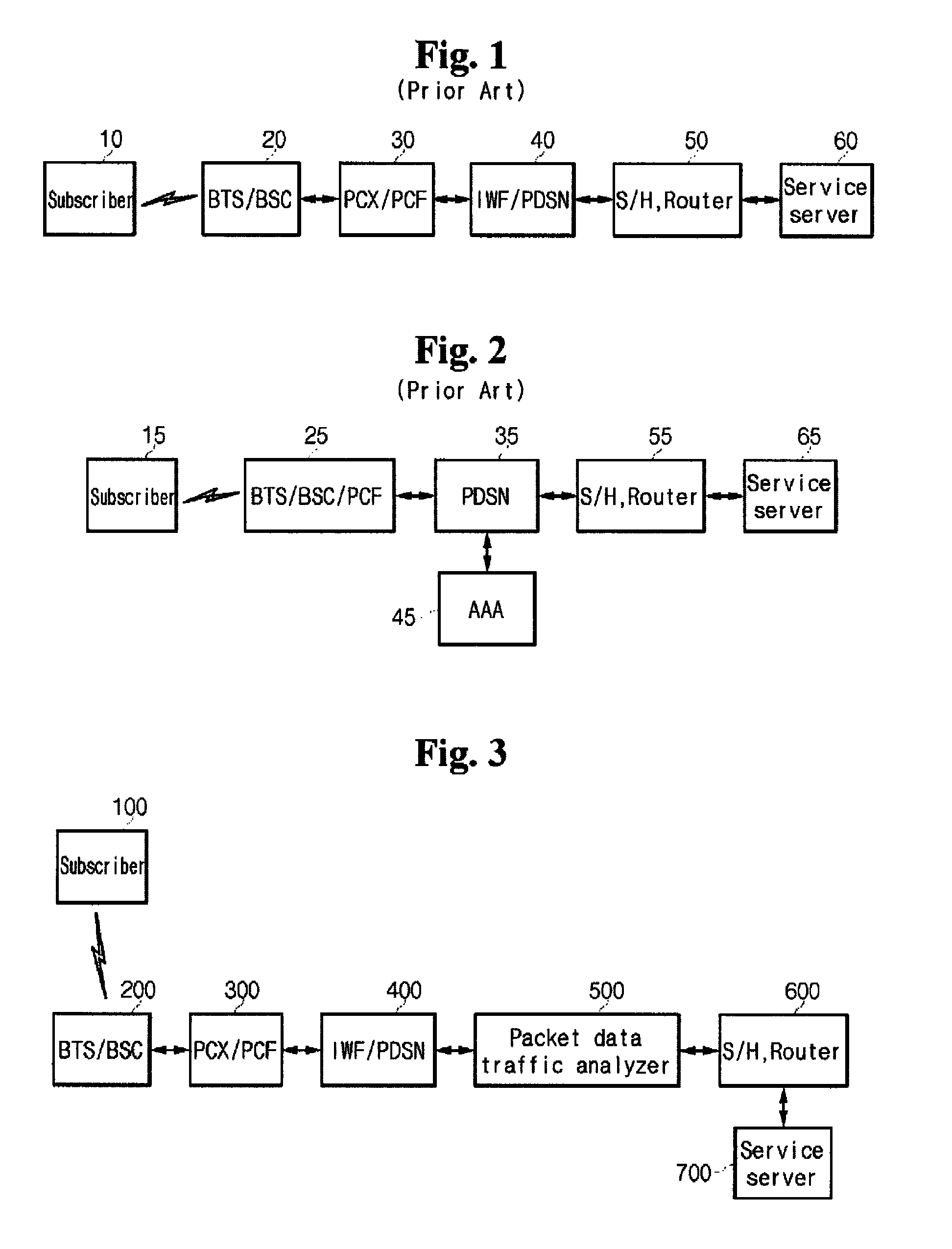
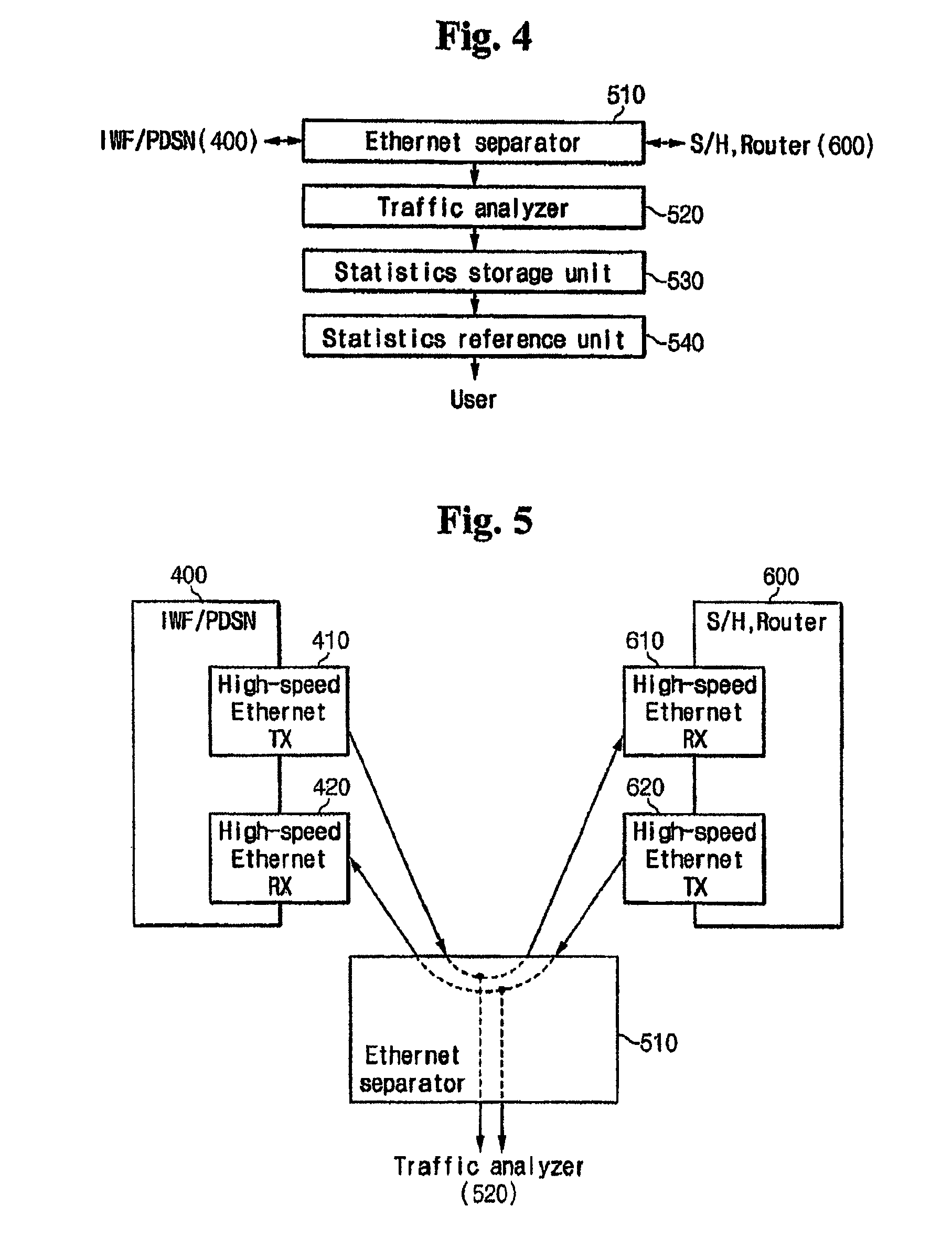
Apparatus for analyzing the packet data on mobile communication network and method thereof
InactiveUS8180881B2Easy to analyzeEfficient networkingMetering/charging/biilling arrangementsMultiple digital computer combinationsTraffic capacityWireless data services
A packet data analyzer on a mobile communication network for analyzing packet data traffic, monitoring services, generating billing information per data service, and monitoring the network based on a protocol analysis, comprises a packet data separator provided between one of a mobile communication exchange and a packet controller that provide a wireless data service to the subscriber, and the service server, for separating user packet data transmitted between one of the mobile communication exchange and the packet controller and the service server, and receiving the user packet data; a traffic analyzer for separating the user packet data received through the packet data separator according to transmission directions, and analyzing the user packet data; a statistics storage unit for storing and managing result data analyzed by the traffic analyzer; and a statistics reference unit for retrieving data stored in the statistics storage unit, and providing statistical information desired by the user.
Owner:KT CORP
Packet flow bifurcation and analysis
ActiveUS20070058632A1Improve matchData switching by path configurationTraffic capacityProcessing element
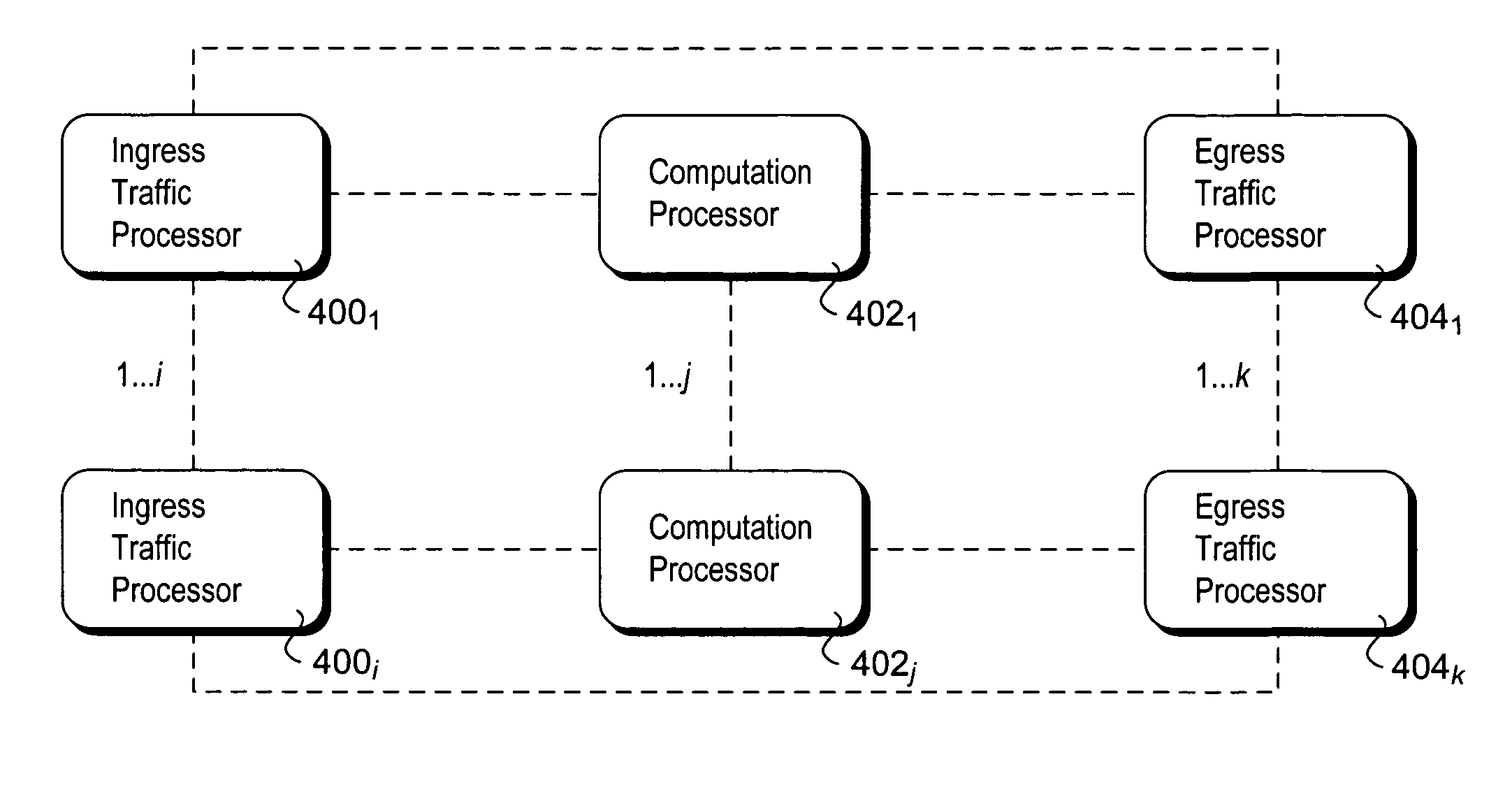
Methods and apparatus for optimum matching of a traffic profile with an individual traffic flow using flow bifurcation and analysis. Bifurcation and duplication of packets that make up a flow received at an ingress element are forwarded to each of egress traffic and computation processor resources, such that egress traffic operations and traffic analysis operations may be performed concurrently without introducing jitter or delay in either bifurcated processing path. The traffic analysis includes maintaining flow statistics, flow stateful information and classifying the flow as a particular application traffic type. The optimum traffic profile for this application traffic type is then selected and applied to the individual flow. The traffic analysis data is forwarded to ingress and egress processing elements in real time, and ingress and egress traffic processing operations are dynamically adjusted in view of the traffic analysis data.
Owner:TELLABS COMM CANADA
System, method and apparatus for detecting, identifying and responding to fraudulent requests on a network
InactiveUS7120934B2Network can be relievedTransmitted directlyEnergy efficient ICTMemory loss protectionActivity monitoringDistributed computing
Owner:IRDETO USA
Apparatus and method for associating categorization information with network traffic to facilitate application level processing
ActiveUS20100011434A1Facilitate application level processingLow costError preventionFrequency-division multiplex detailsTraffic capacityHash function
An apparatus is described that associates categorization information with network traffic to facilitate application level processing through processing of network traffic in accordance with provisioned rules and policies. The apparatus includes a plurality of microcode controlled state machines, wherein at least one microcode state machine processes at least one input data field using a hash function to generate a hash identifier. This embodiment further includes a distribution circuit that routes input data to the plurality of microcode controlled state machines, such that at least one individual microcode controlled state machine applies a rule to the input data to produce the at least one input data field, and to produce modification instructions based on the hash identifier. This embodiment further includes a first circuit that appends the hash identifier to the input data to produce modified input data based on the modification instructions, and that routes the modified input data in accordance with an output routing strategy. Advantageously, the apparatus provides an architectural framework well suited to a low cost, high speed, robust implementation of flexible, advanced network security and monitoring features and network traffic analysis.
Owner:CPACKET NETWORKS
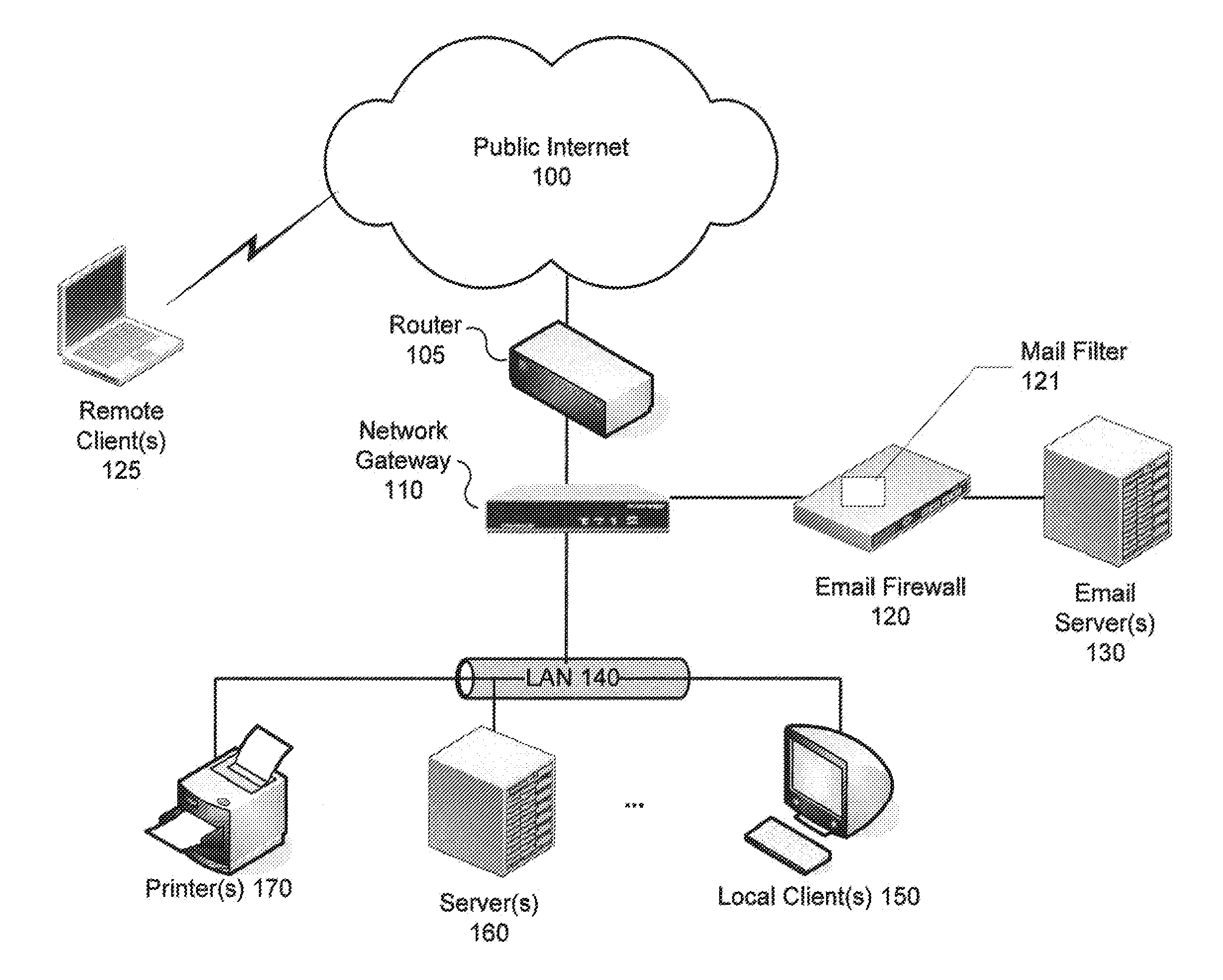
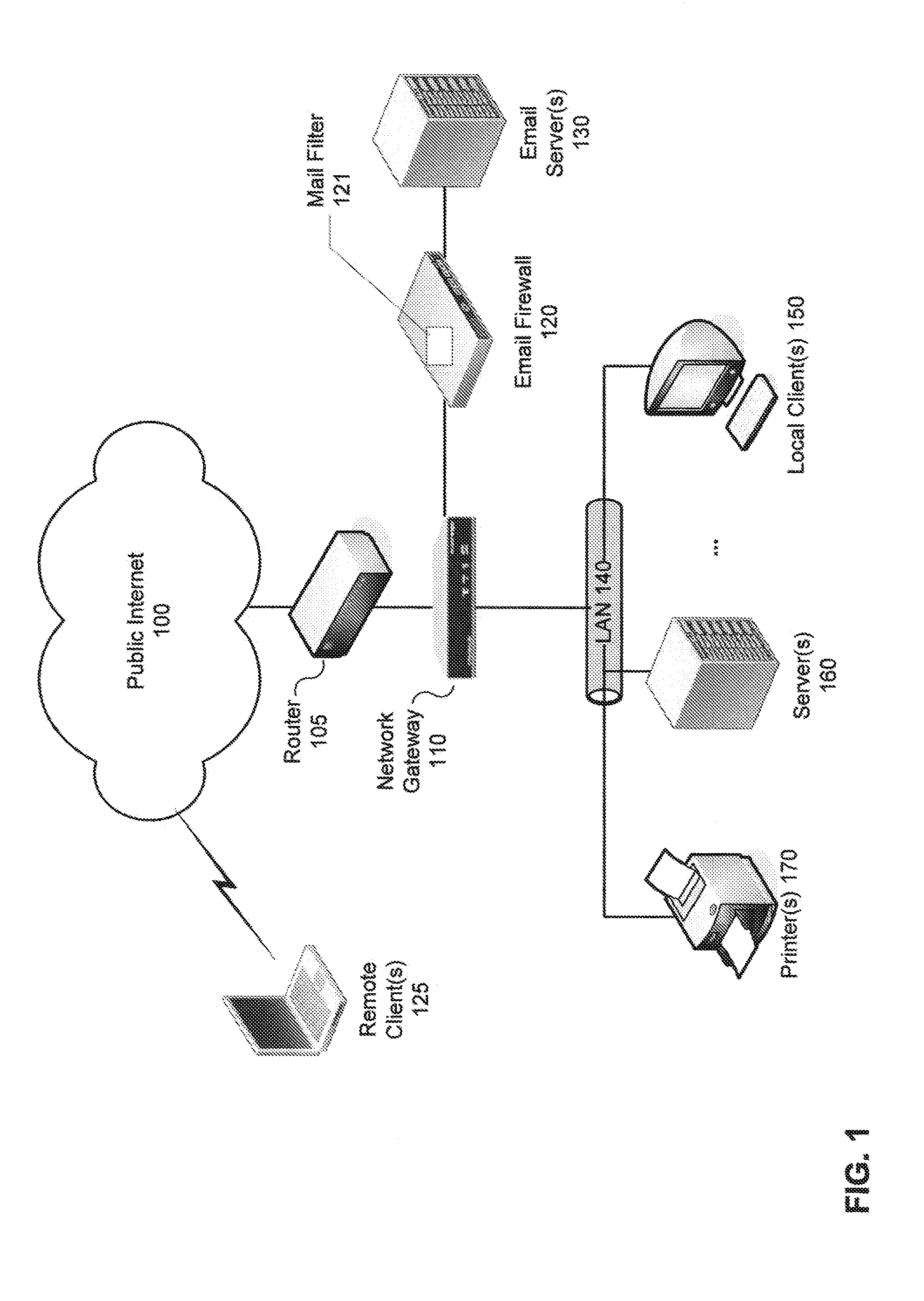
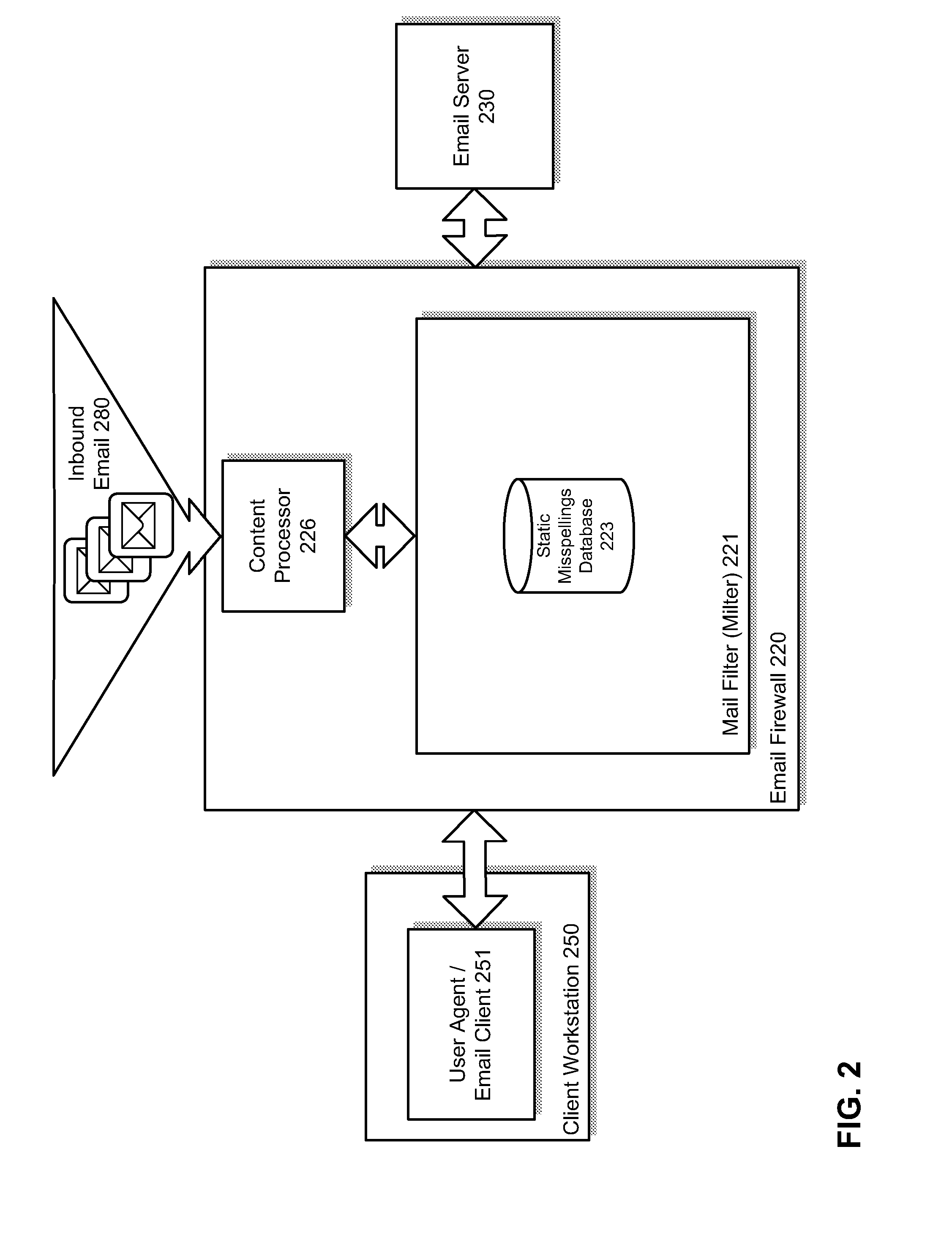
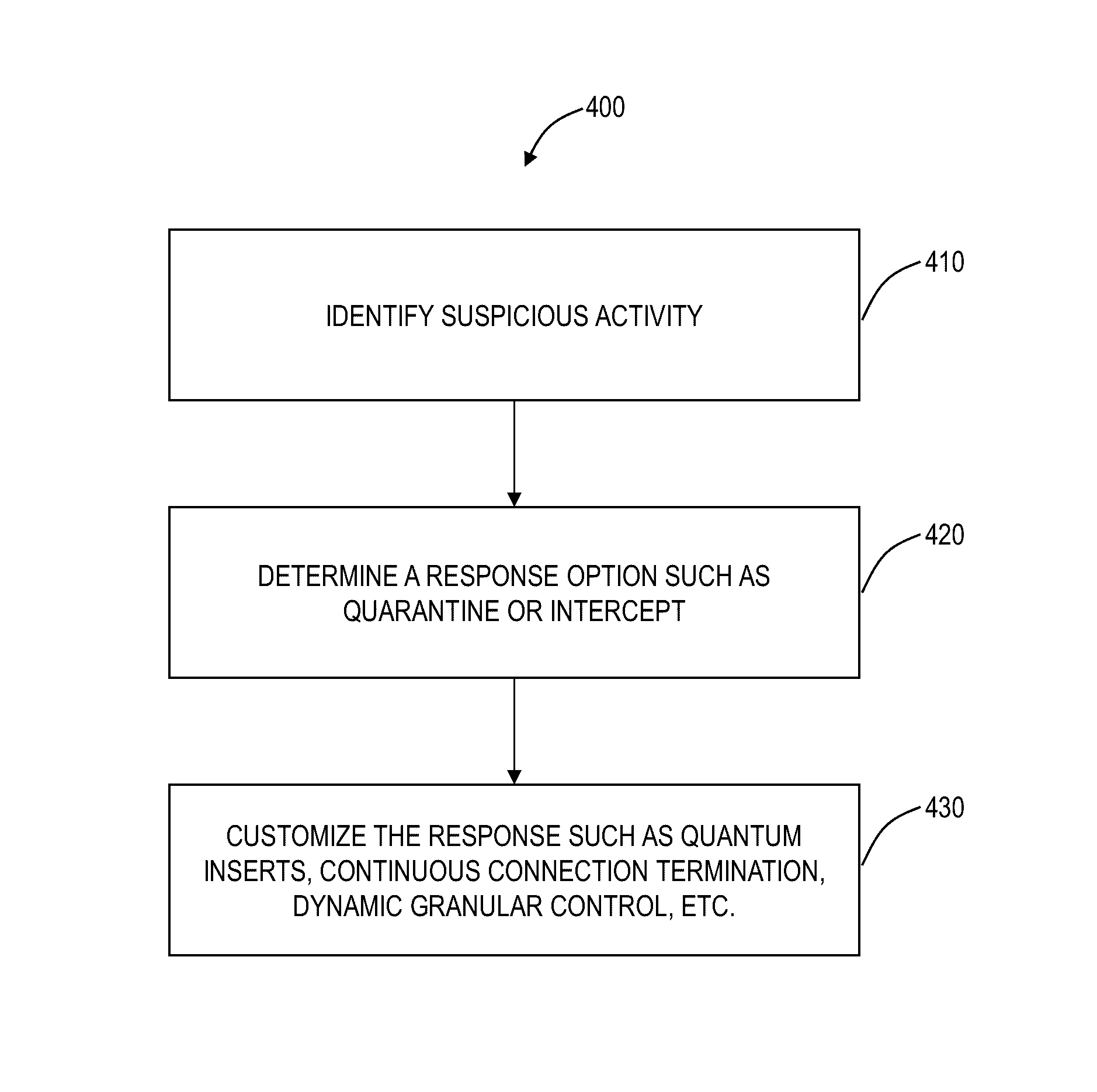
Detection of suspicious traffic patterns in electronic communications
InactiveUS20100095377A1Memory loss protectionError detection/correctionTraffic capacityInternet privacy
Methods and systems for detecting suspicious traffic patterns in electronic communications are provided. According to one embodiment, an electronic mail (email) message is received by a mail filter (milter), which evaluates a traffic pattern represented by the email message by scanning information associated with the email message and comparing it to information associated with one or more traffic analysis profiles. If the email message is identified by the milter as being inconsistent with normal email traffic patterns as represented by the one or more traffic analysis profiles, then the milter causes the email message to be handled in accordance with an email security policy associated with suspicious traffic patterns. For example, in the context of an outbound message, the originator may be alerted to a factor contributing to the identification and the originator may be provided with an opportunity to address the factor.
Owner:FORTINET
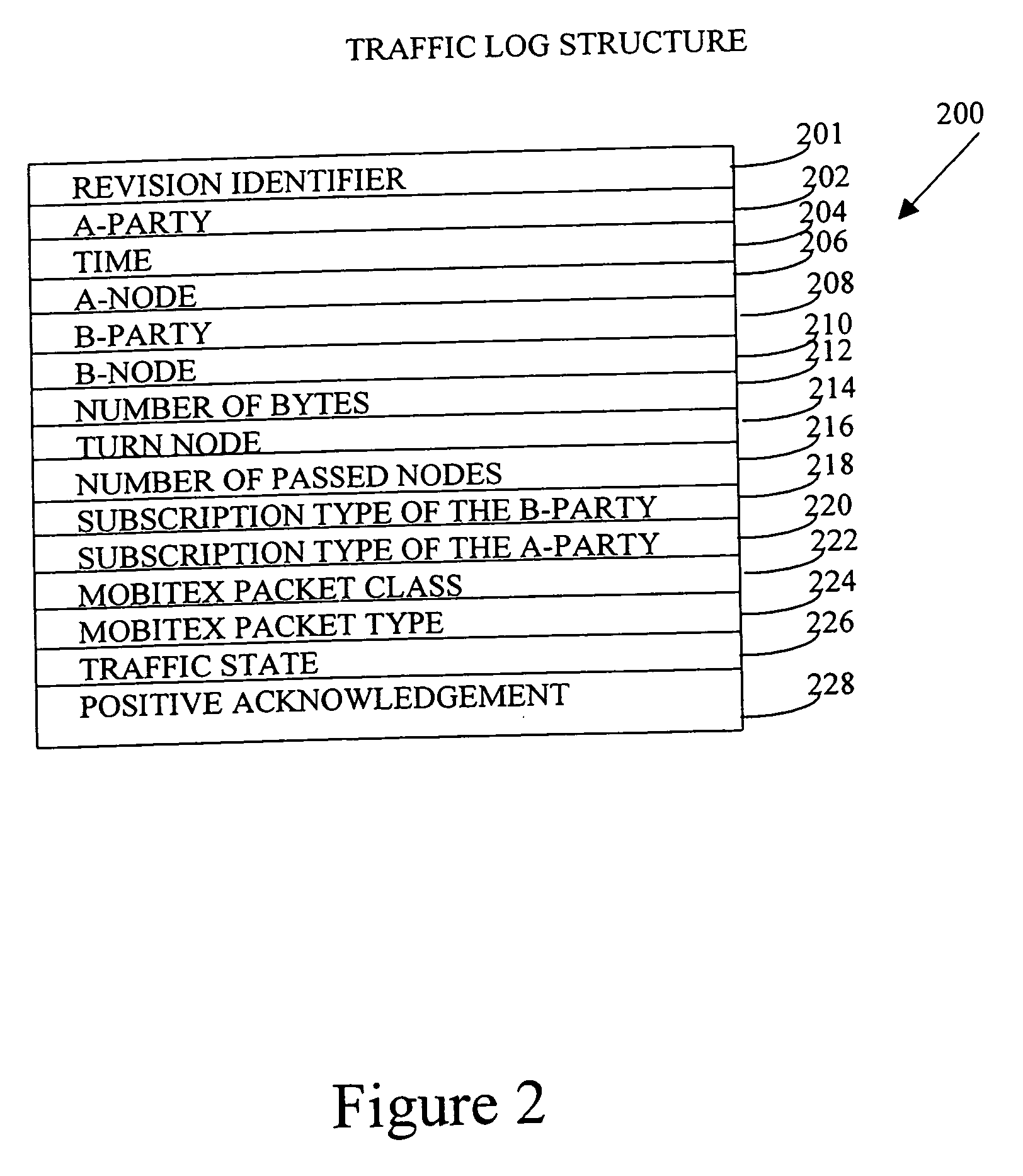
Network traffic analyzer
InactiveUS7562134B1Easily gleanedFacilitate trend analysisError preventionFrequency-division multiplex detailsTraffic capacityExchange network
A system for and method of analyzing the performance of a packet-switched network, the network automatically generating a traffic log each time a packet enters or exits the network and each traffic log including at least the time the traffic log was created, the addresses of the packet sender and packet recipient, and the entry and exit network nodes. A server collects a plurality of traffic logs, parses the available information therein and generates a plurality of histograms, each histogram being based on information gleaned from the plurality of traffic logs. The histograms may be representative of packet traffic passing through a host connected to the network, packet traffic passing through a node in the network or the amount of data that travels over a link between two nodes of the network. To increase the delivery speed of the histogram data from the server to a client, the histograms are preferably stored as flat files to achieve direct and rapid access to stored data.
Owner:BELLSOUTH INTPROP COR
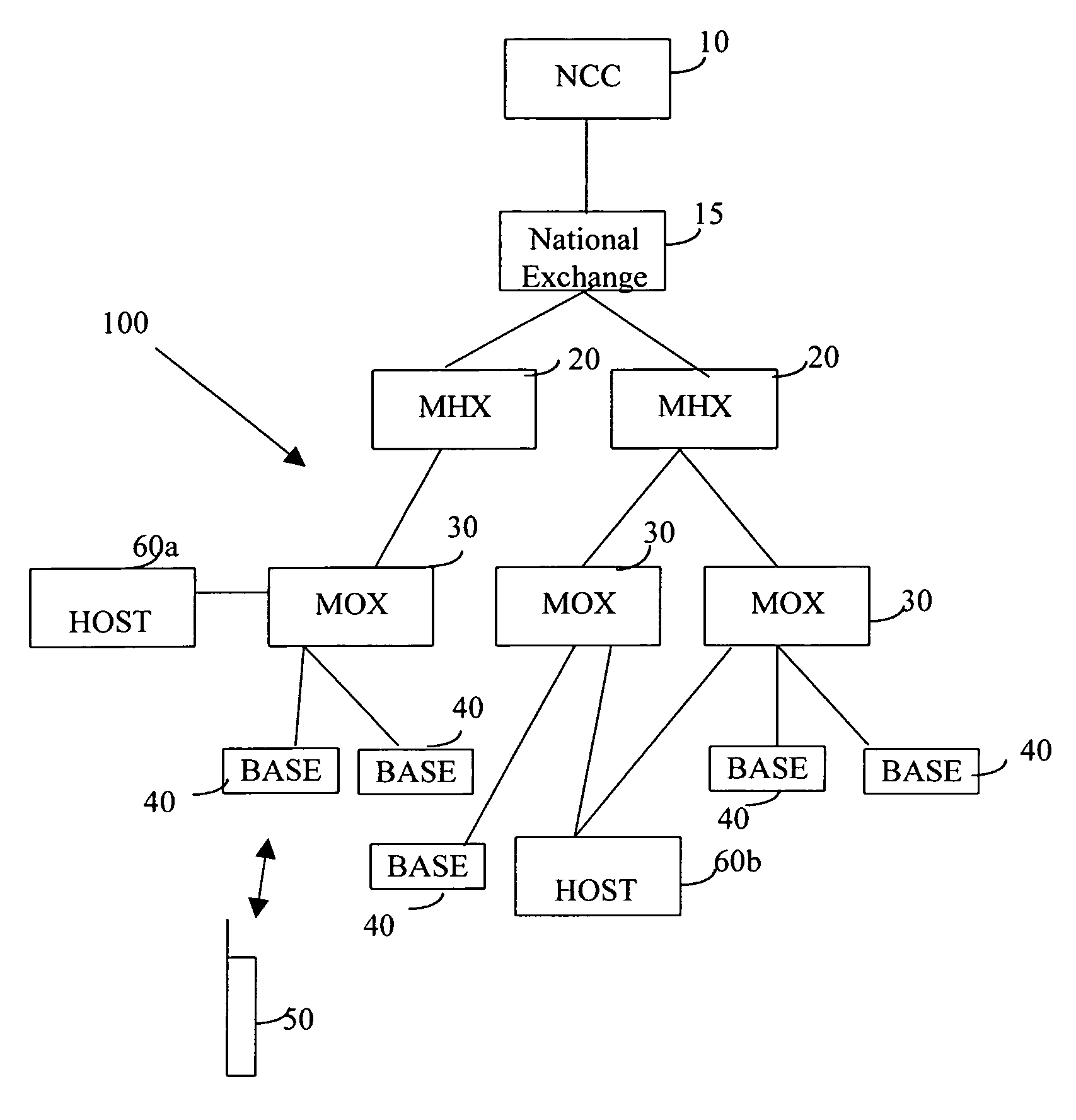
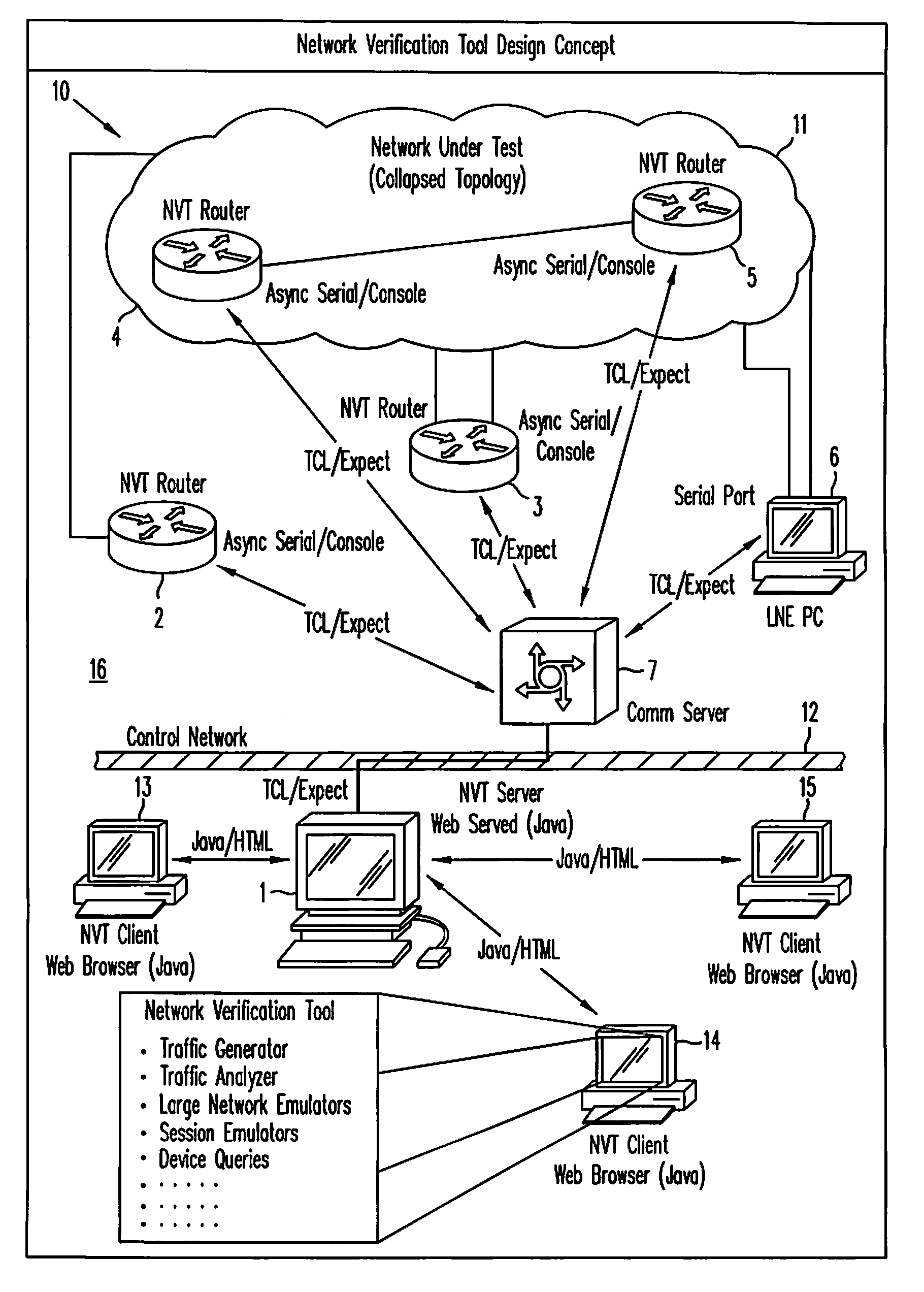
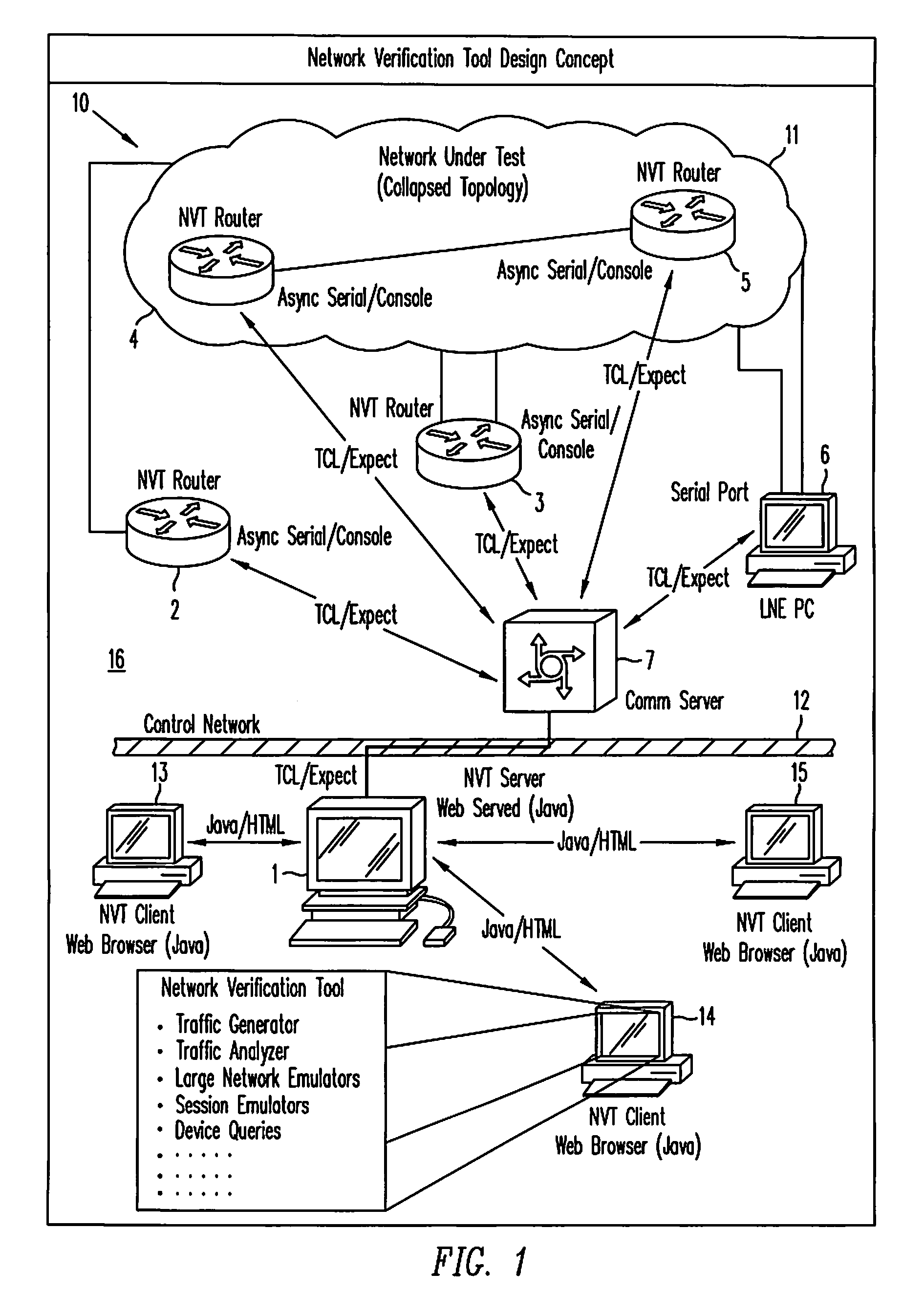
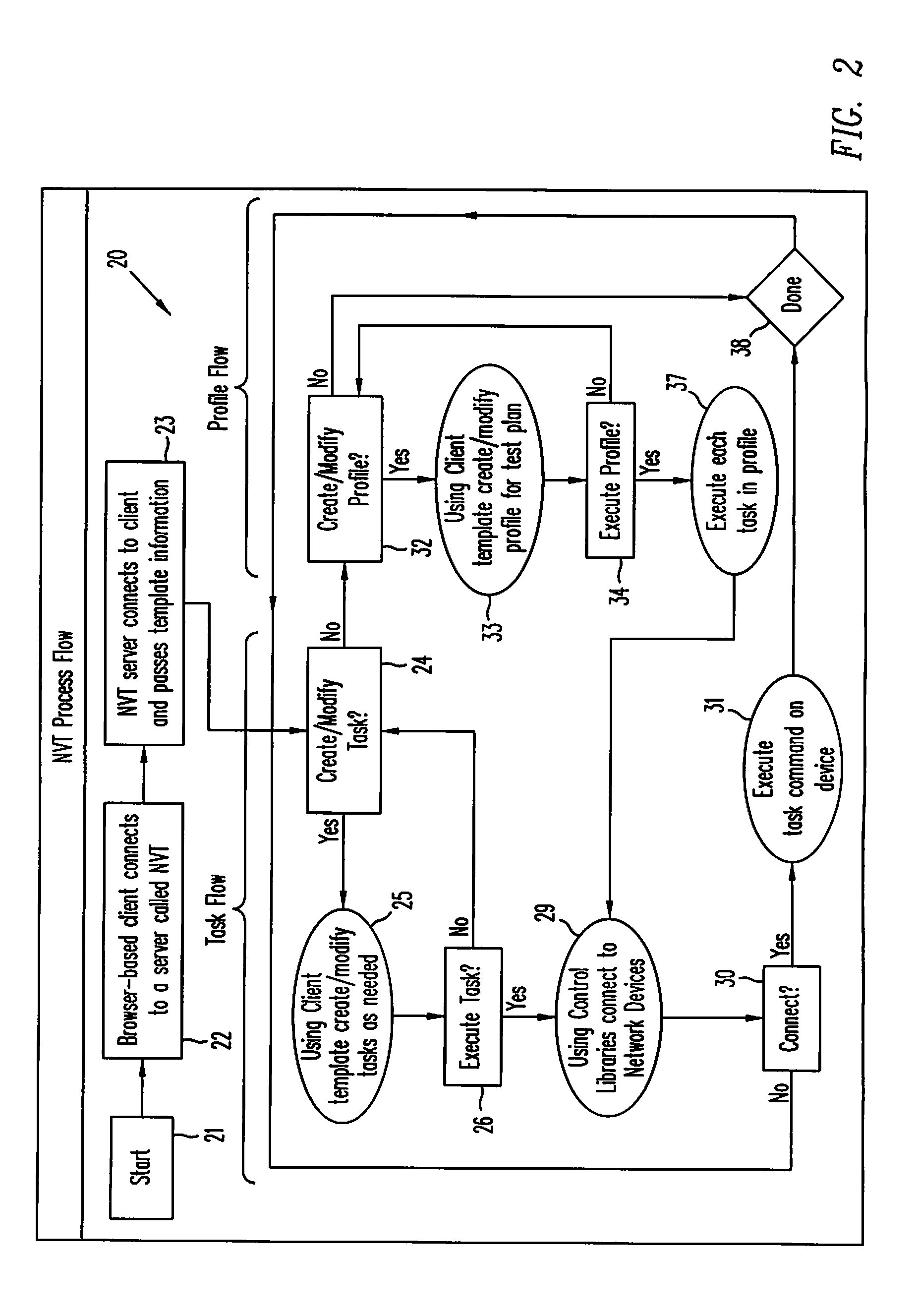
Network verification tool
InactiveUS7342897B1Easily set parameter requiredFacilitate joint resolutionError preventionFrequency-division multiplex detailsTraffic capacityClient-side
A network verification tool is presented that allows a user to easily create tasks for a collection of task types. The collection of task types are hosted by probe network devices that are coupled to a network under test. The network under test includes network devices executing generic network software and particular hardware or software that is being tested. The probe network devices are coupled to an NVT server, which transmits tasks to the task types and interfaces with one or more NVT clients. The NVT clients can create tasks by entering the appropriate parameters within templates supplied by the NVT server. Any collection of task types can be included in the network verification tool, including traffic generators, traffic analyzers, large network emulators, session emulators, device queries and script tasks.
Owner:CISCO SYSTEMS INC
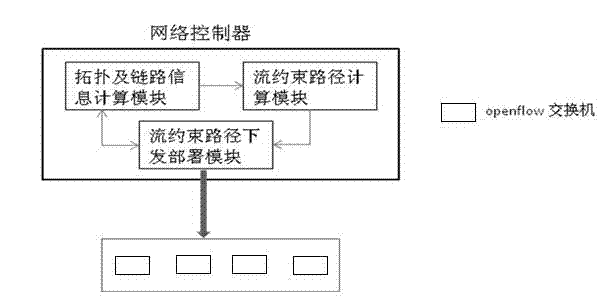
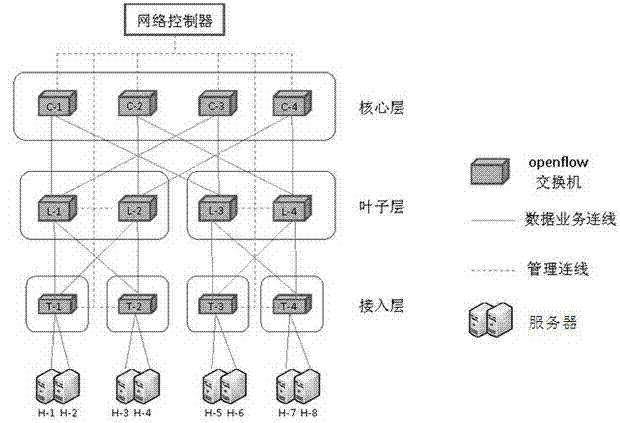
Data center flow control method and data center flow control system based on openflow
InactiveCN103179046AIncrease profitHigh precisionData switching networksTraffic capacityTraffic flow analysis
The invention discloses a data center flow control method and a data center flow control system based on openflow. Openflow switchboards are controlled to operate a topology discovery protocol through a network controller, so tha information of all network nodes and links is collected and a network topology value is calculated; and the network controller periodically carries out end-to-end flow analysis on flows, calculates optimized paths of all the flows and transmits the optimized paths to each openflow switchboard, monitors the states of all the network links in real time, and maintains or downloads the optimized paths of the new flows to each openflow switchboard, so that the use rate of network bandwidth resources and the accuracy and the reliability of network concentrated management can be improved, the variation of the network flow can be fitted by sensitively regulating a flow load in a network, and the use rate and the reliability of the network can be effectively improved. The data center flow control method and the data center flow control system based on the openflow has a good application prospect.
Owner:深圳数字动能信息技术有限公司
Managing traffic in communications system having dissimilar CDMA channels
InactiveUS20050068922A1Network traffic/resource managementNetwork topologiesCommunications systemData rate
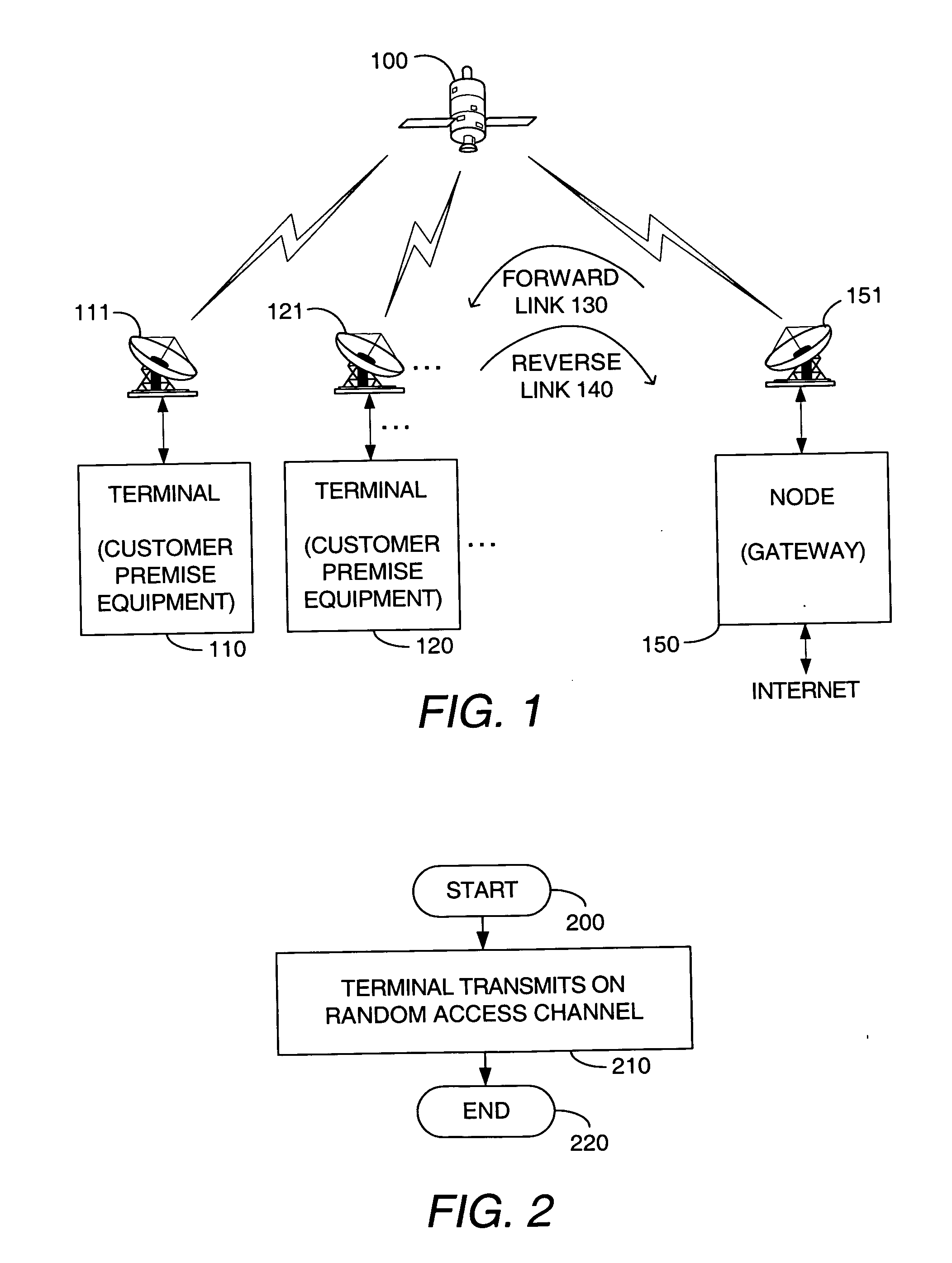
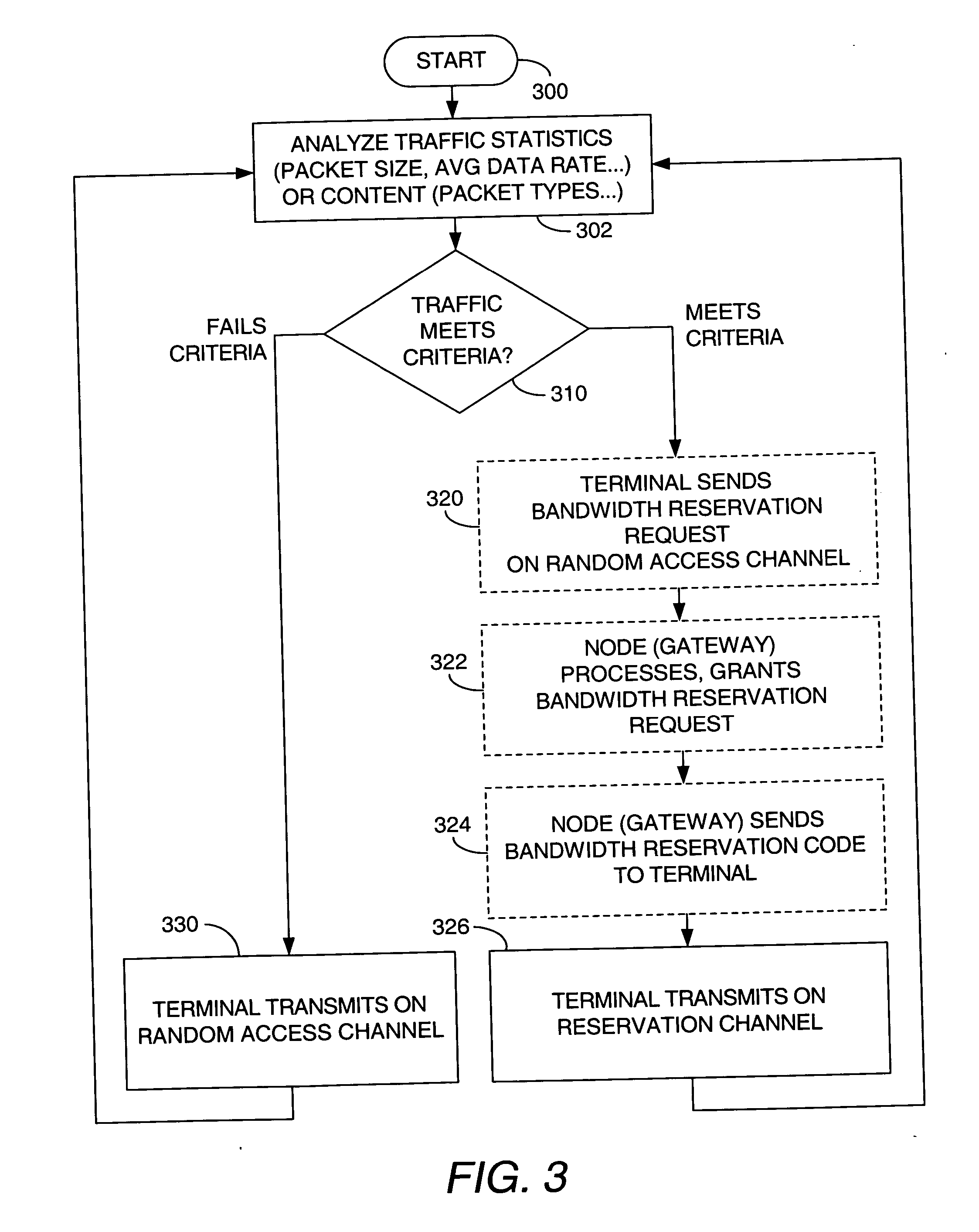
In a code division multiple access (CDMA) communications system including one or more terminals (such as customer premise equipments, CPEs) that communicate with a node (such as an Internet gateway) via at least a random access channel and a reservation-oriented channel, various schemes of managing communications traffic among the channels are provided. Decisions as to the channel on which a given terminal may transmit may be based on: traffic statistics (such as packet size or average data rate over a time period), traffic content (such as packet type), the terminal's output buffer loading (queue state, or “Q-state”), a history of the terminal's output buffer loading (one or more Q-states), and so forth. In one application, decisions in managing traffic in a live user's web browsing sessions may involve intelligent ascertainment of whether a given terminal is busy based on traffic analysis or output buffer loading.
Owner:QUALCOMM INC
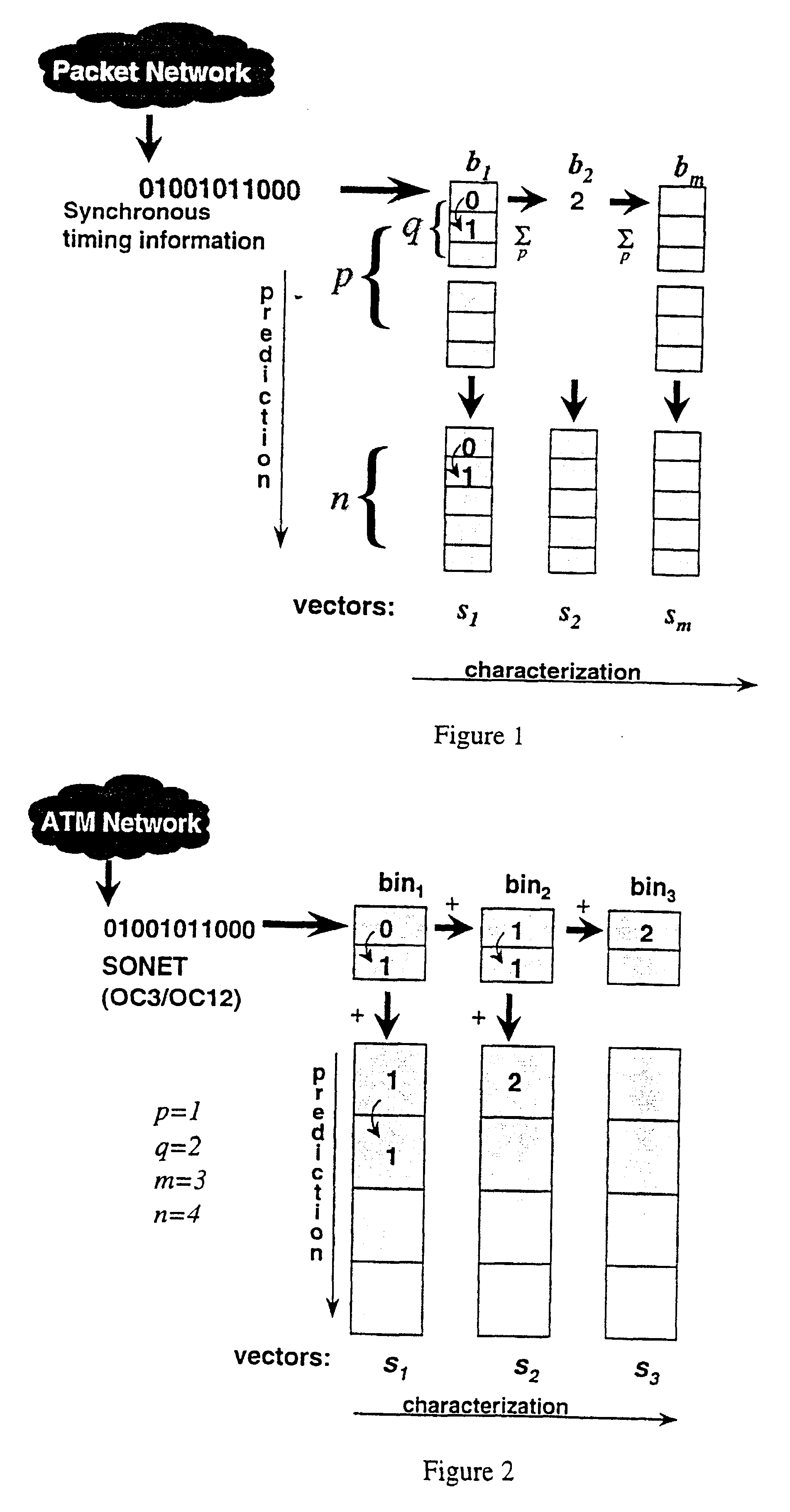
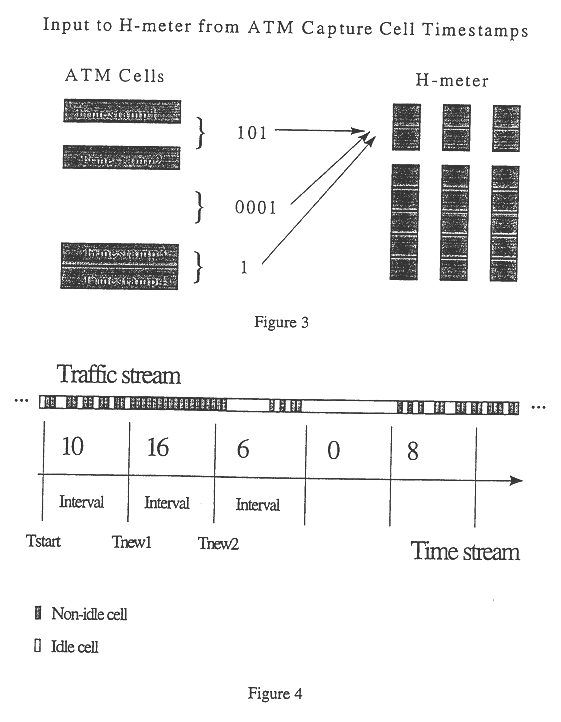
Method for real-time traffic analysis on packet networks
An architecture for capture and generation, and a set of methods for characterization, prediction, and classification of traffic in packet networks are disclosed. The architecture consists of a device that stores packet timing information and processes the data so that characterization, prediction, and classification algorithms can perform operations in real-time. A methodology is disclosed for real-time traffic analysis, characterization, prediction, and classification in packet networks. The methodology is based on the simultaneous aggregation of packet arrival times at different times scales. The traffic is represented at the synchronous carrier level by the arrival or non-arrival of a packet. The invention does not require knowledge about the information source, nor needs to decode the information contents of the packets. Only the arrival timing information is required. The invention provides a characterization of the traffic on packet networks suitable for a real-time implementation. The methodology can be applied in real-time traffic classification by training a neural network from calculated second order statistics of the traffic of several known sources. Performance descriptors for the network can also be obtained by calculating the deviation of the traffic distribution from calculated models. Traffic prediction can also be done by training a neural network from a vector of the results of a given processing against a vector of results of the subsequent processing unit; noticing that the latter vector contains information at a larger time scale than the previous. The invention also provides a method of estimating an effective bandwidth measure in real time which can be used for connection admission control and dynamic routing in packet networks. The invention provides appropriate traffic descriptors that can be applied in more efficient traffic control on packet networks.
Owner:TELECOMM RES LAB
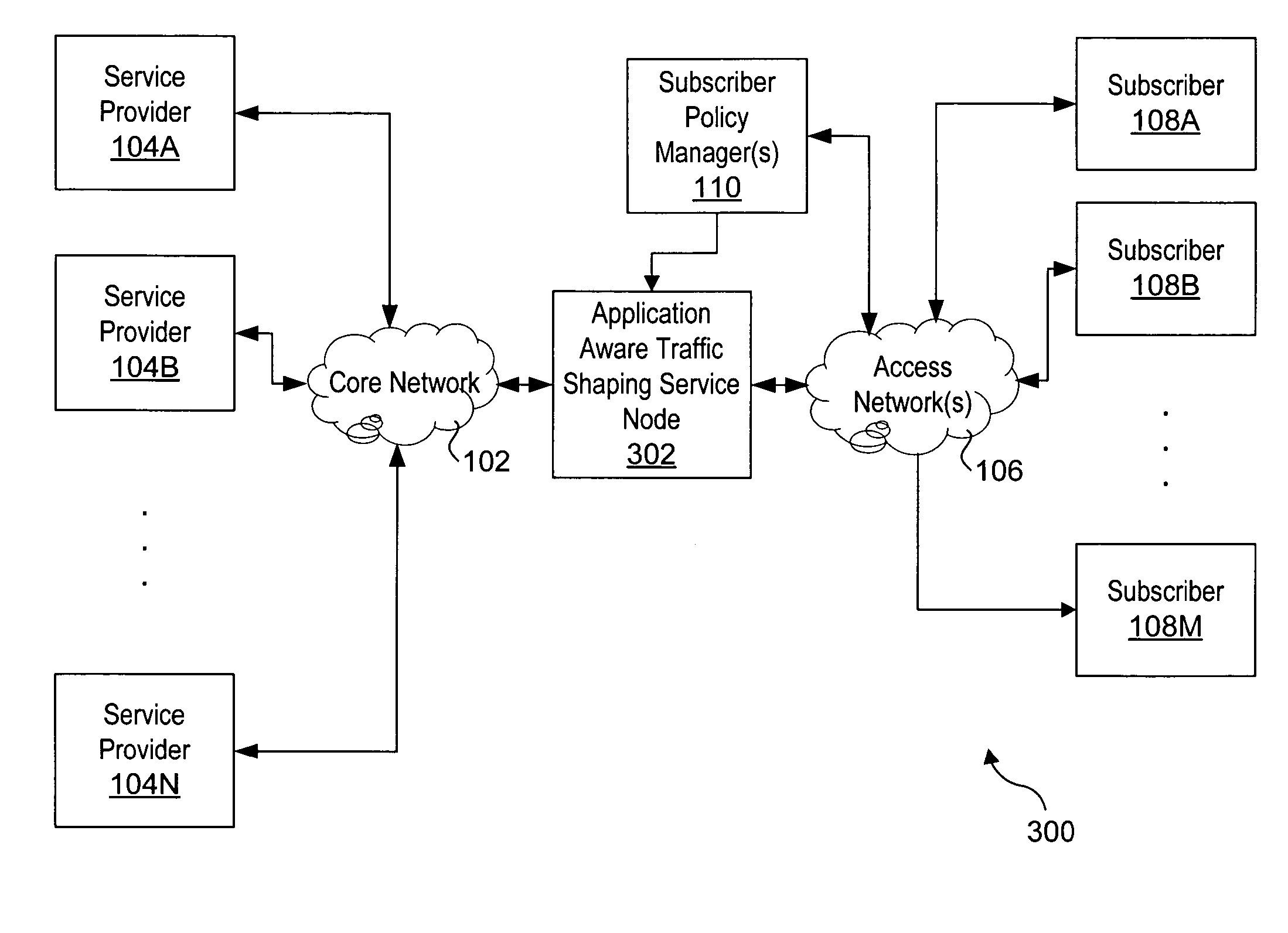
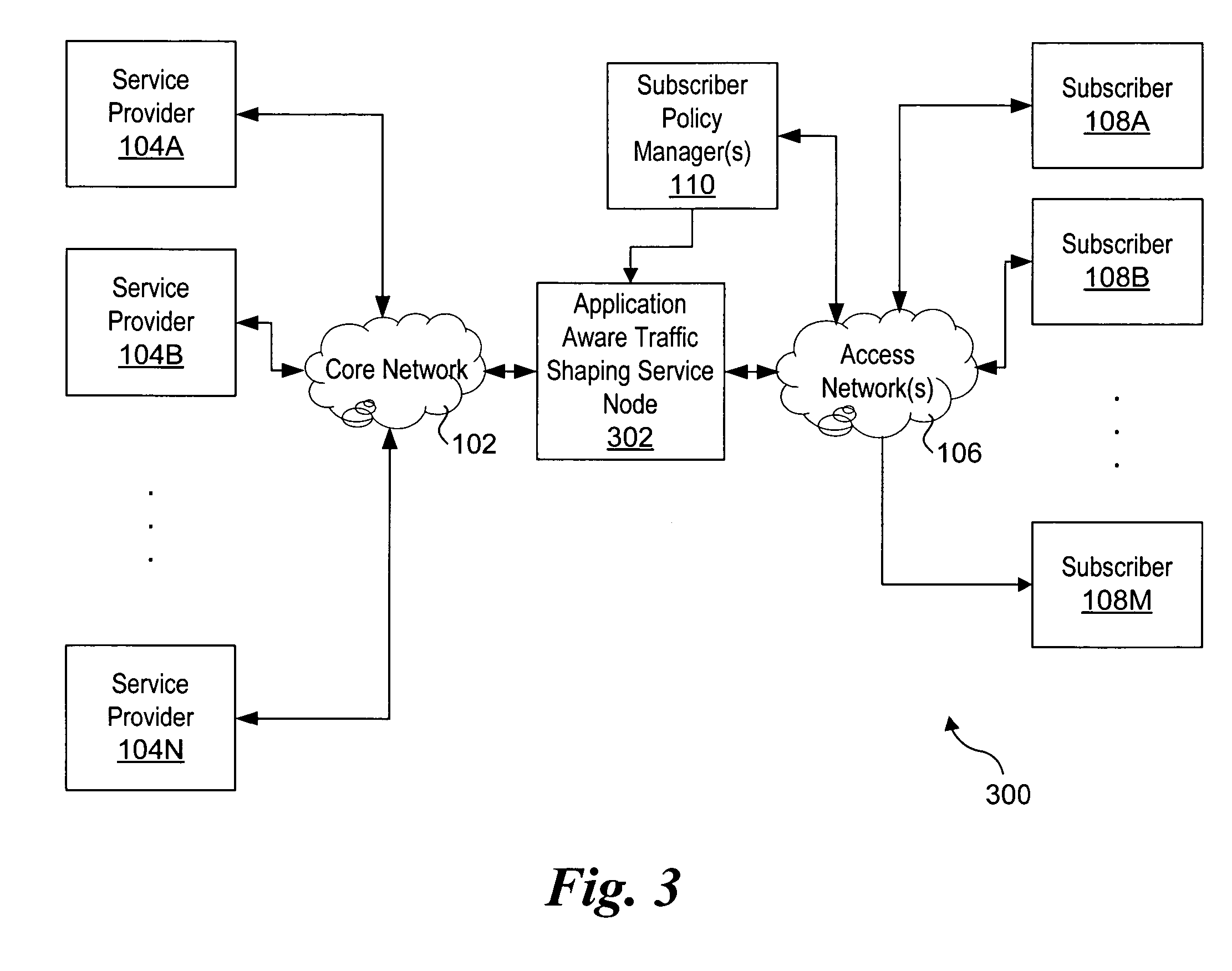
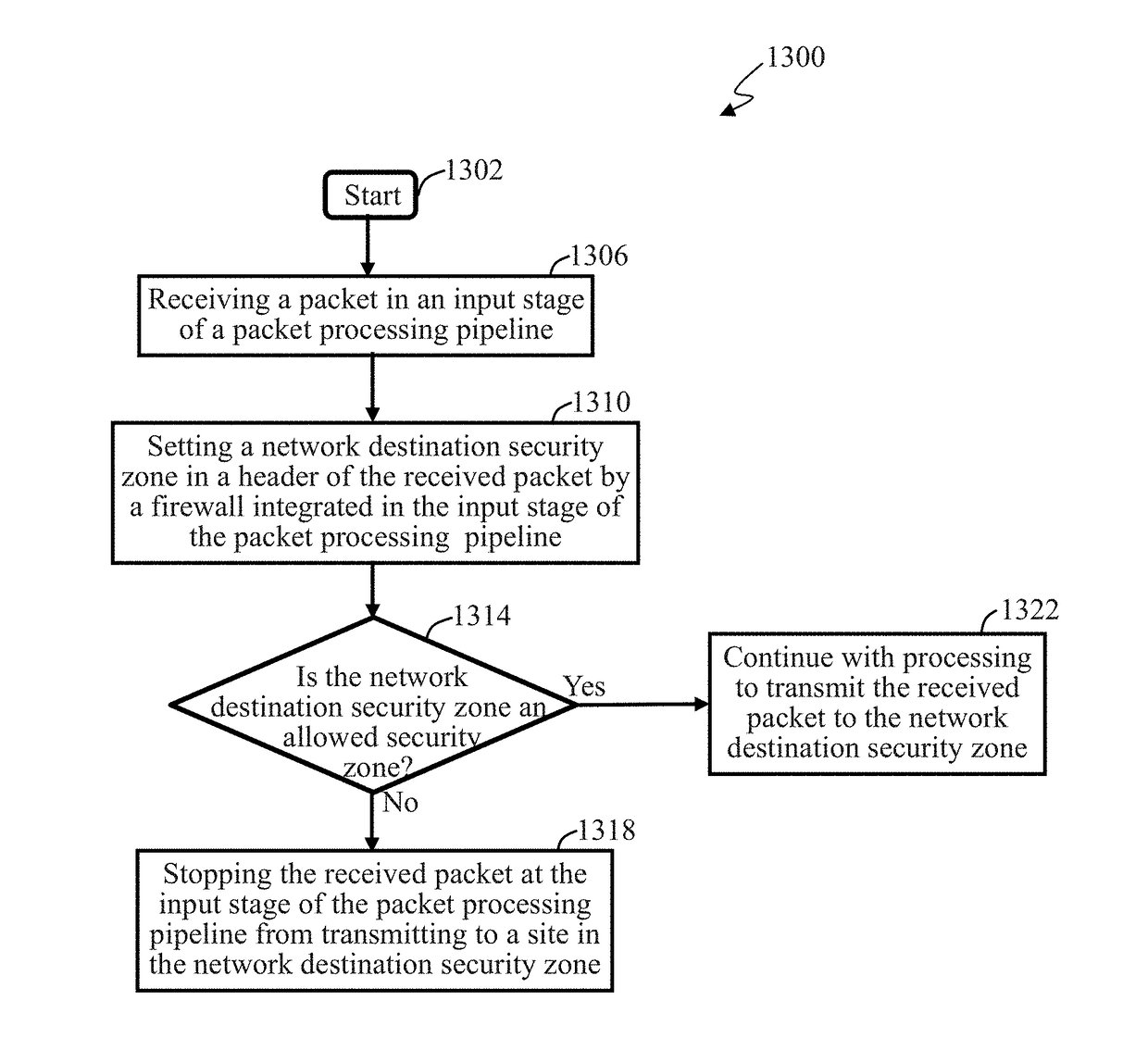
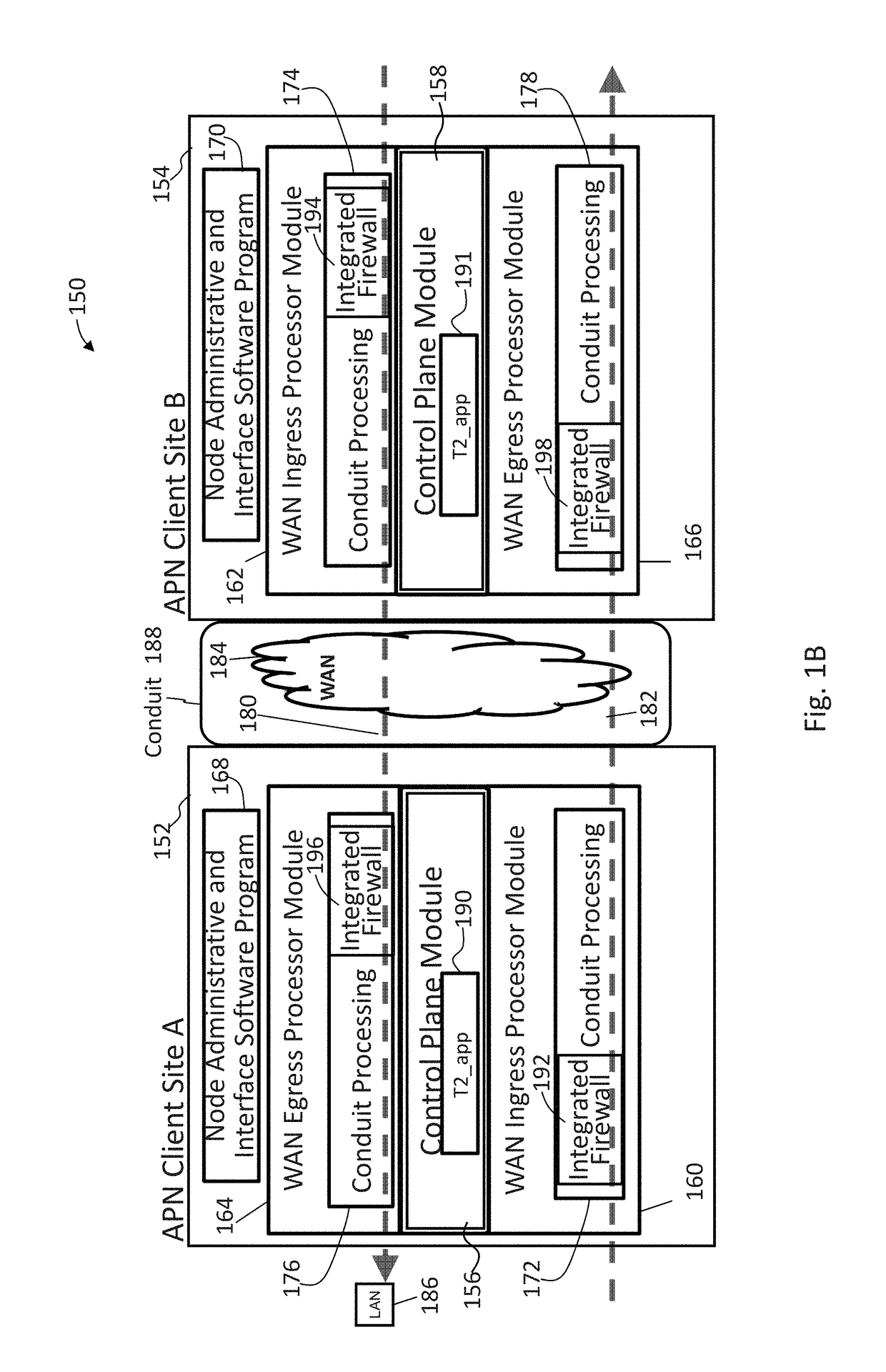
Applications and integrated firewall design in an adaptive private network (APN)
ActiveUS20180041470A1Low costImprove securityData switching networksPacket processingTraffic analysis
A firewall is described that is integrated in an input stage of a packet processing pipeline so that it recognizes and has access to internal information regarding the different services, such as conduit, intranet, Internet, local vs WAN, applications, and security zones, of a communication network, such as an adaptive private network (APN). The integrated firewall is able to dynamically access the service type, respond to the service type, and adjust the service type based on conditions in the network. Since application awareness and security functions are integrated, customers can set security policies on software applications. The integrated firewall also provides automatic detection of applications, classifies applications based on domain names, steers traffic to services according to software applications, reports on software applications in passthrough traffic, and provides analysis of traffic that does not match a software application so that a user can investigate and define custom applications.
Owner:TALARI NETWORKS
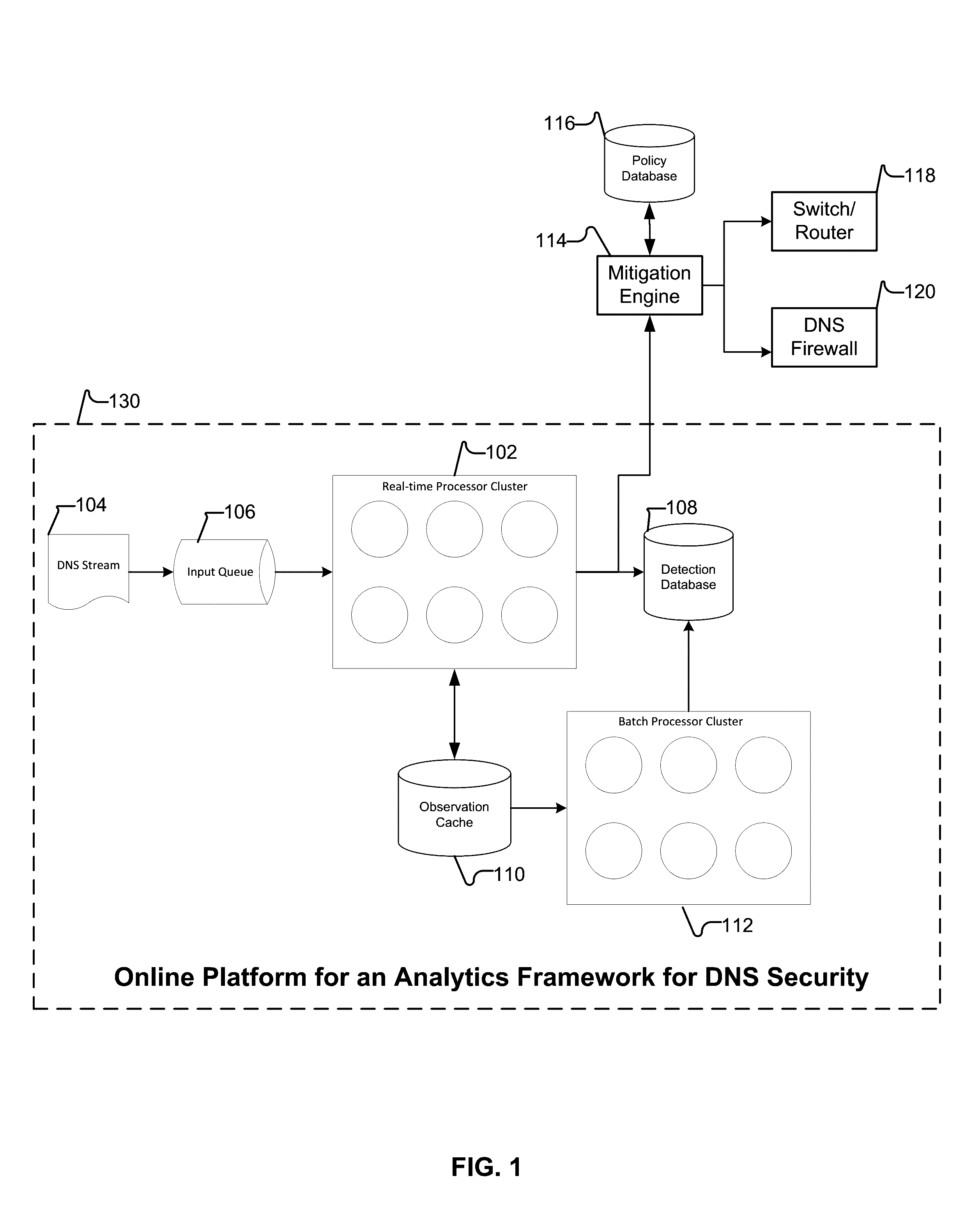
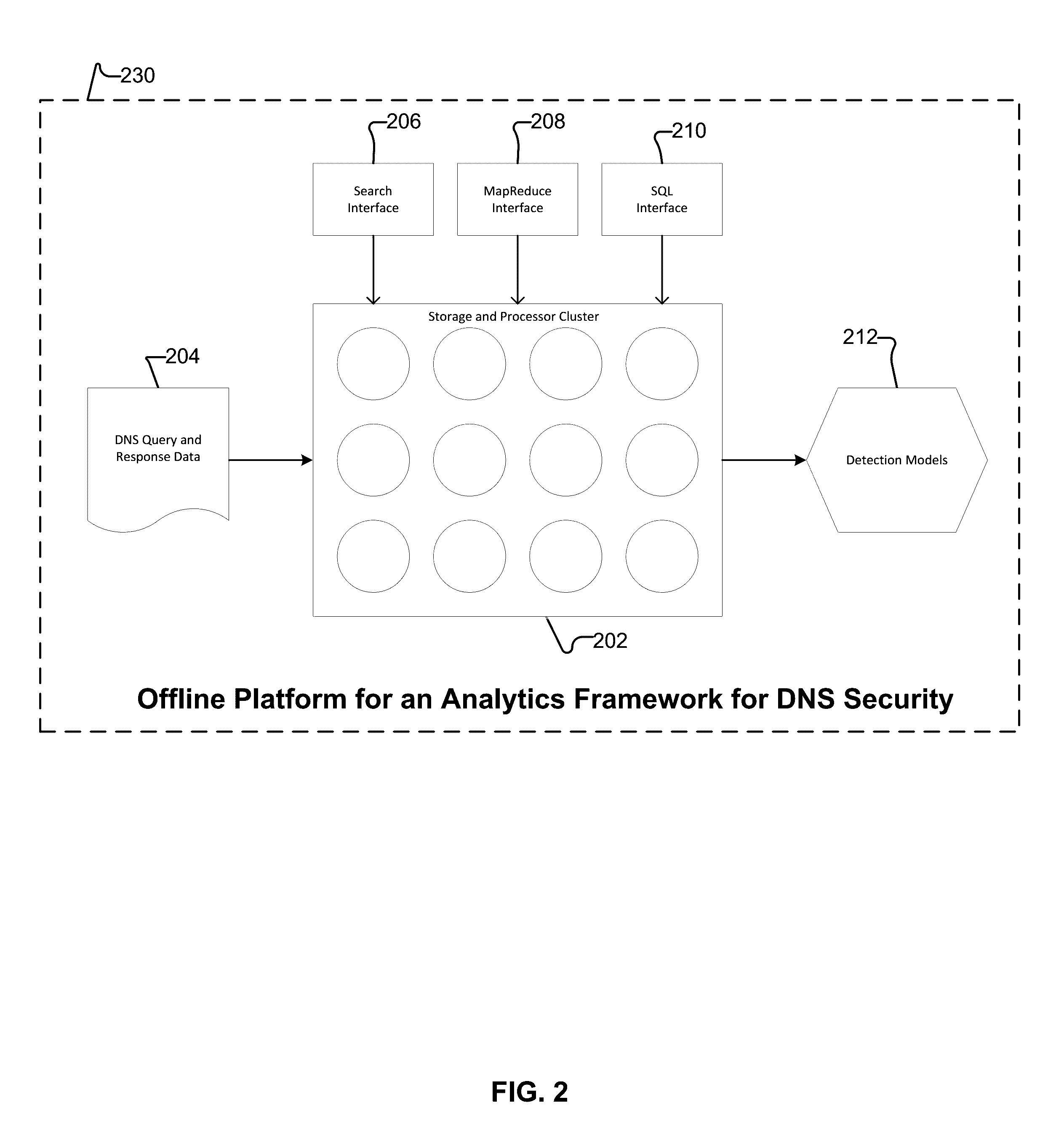
Behavior analysis based DNS tunneling detection and classification framework for network security
New and improved techniques for a behavior analysis based DNS tunneling detection and classification framework for network security are disclosed. In some embodiments, a platform implementing an analytics framework for DNS security is provided for facilitating DNS tunneling detection. For example, an online platform can implement an analytics framework for DNS security based on passive DNS traffic analysis.
Owner:INFOBLOX
Network traffic analysis using a dynamically updating ontological network description
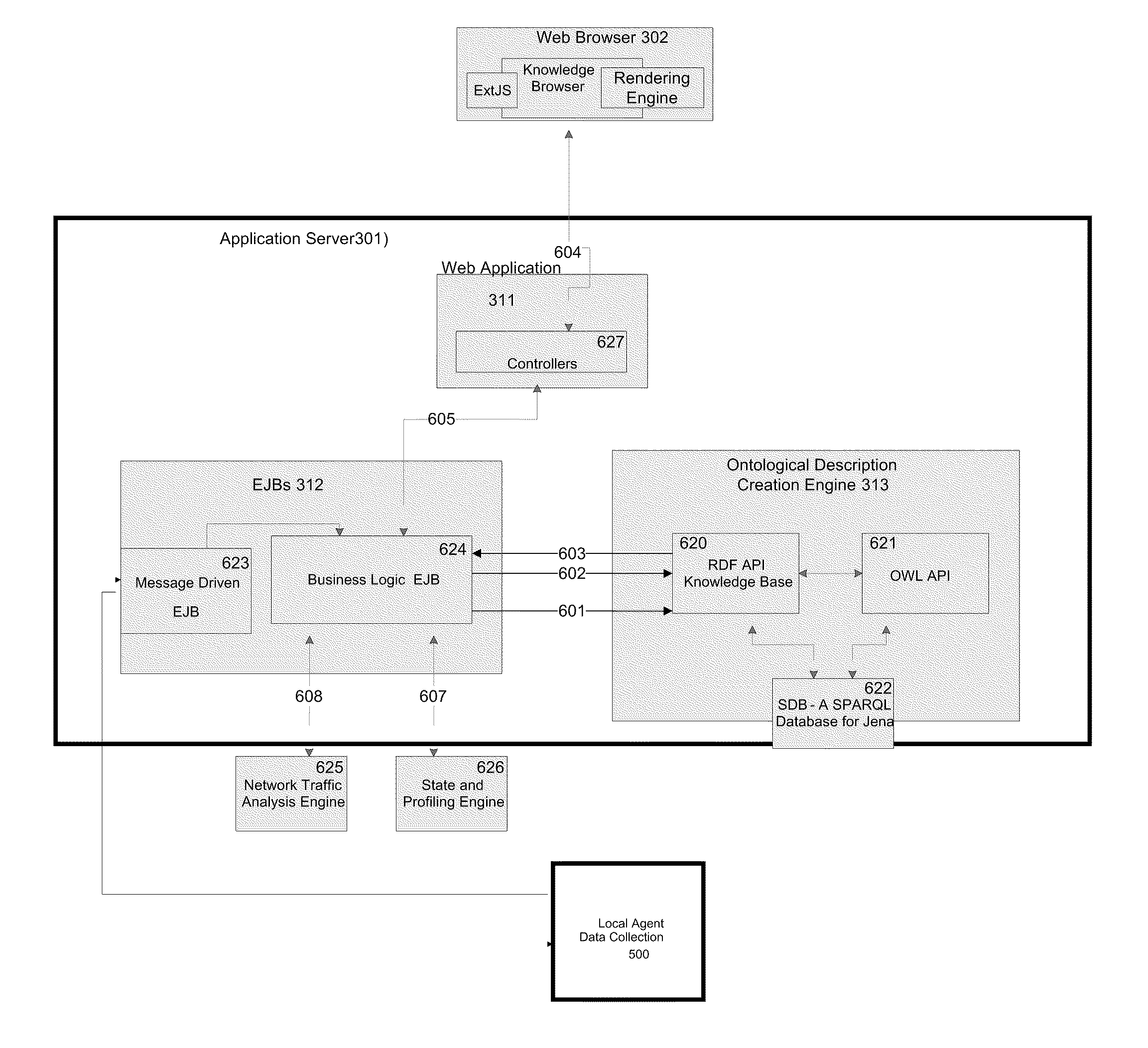
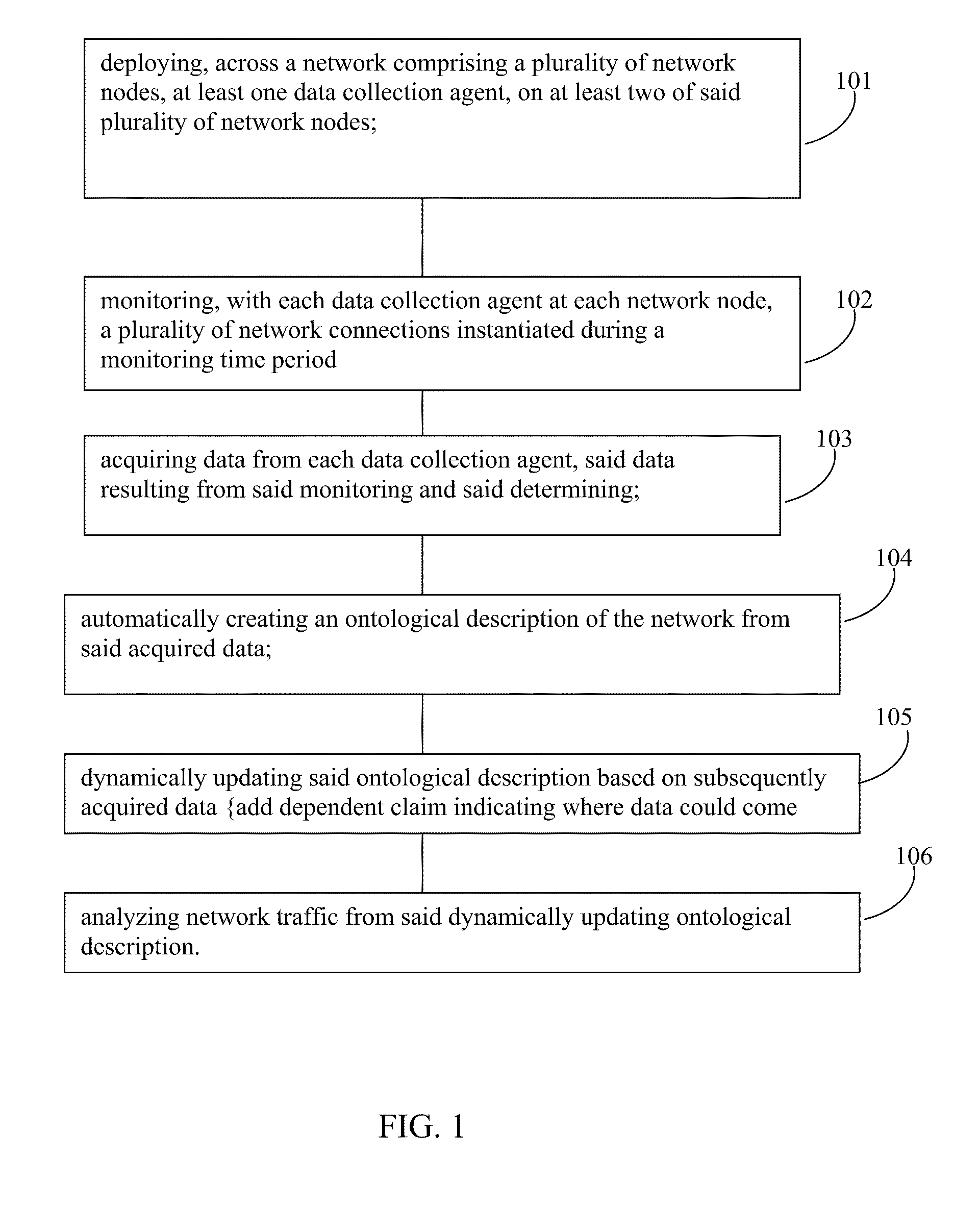
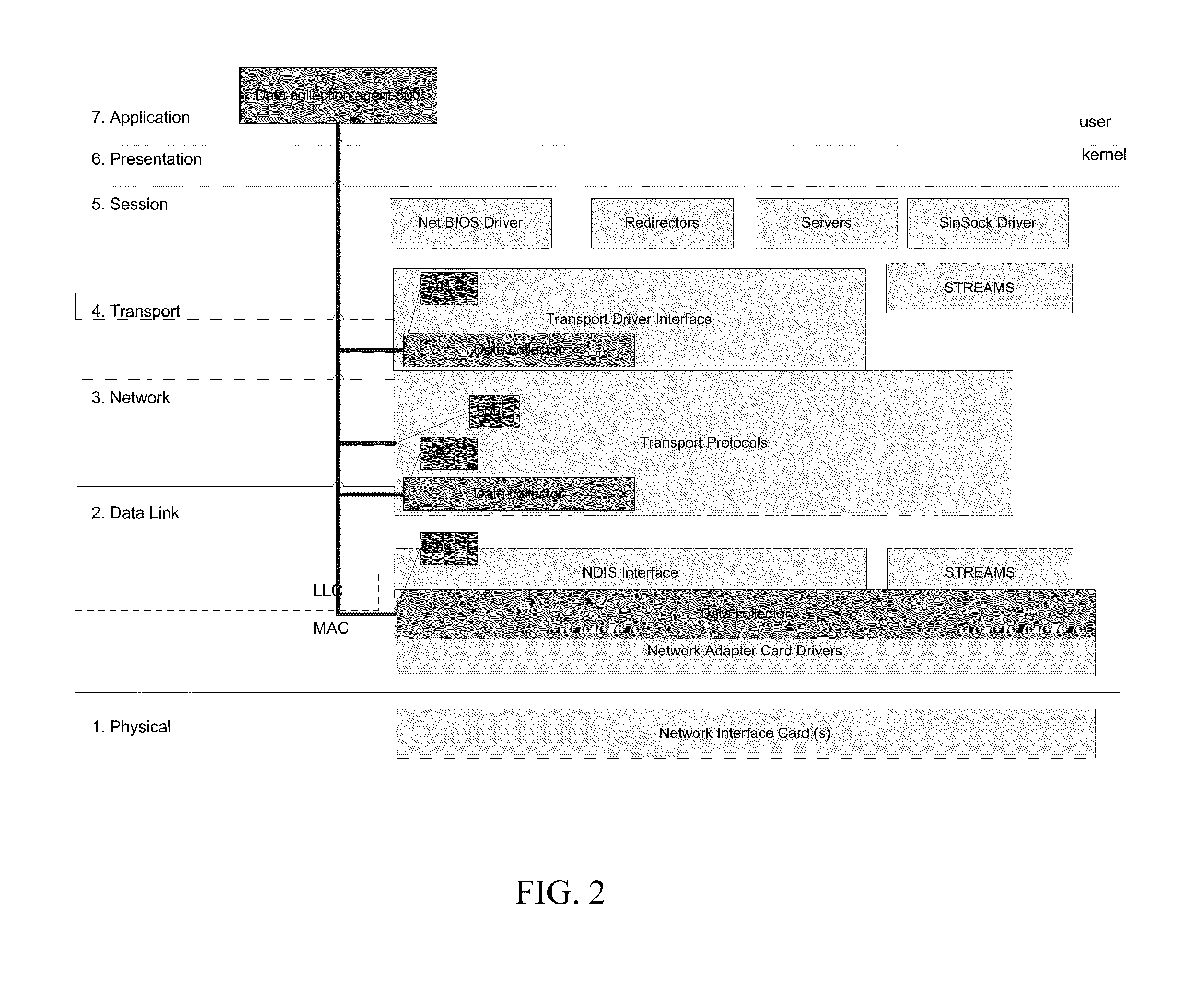
ActiveUS20100077078A1Improved ability to analyze network trafficDescribe wellDigital data processing detailsAnalogue secracy/subscription systemsTraffic capacityNetwork deployment
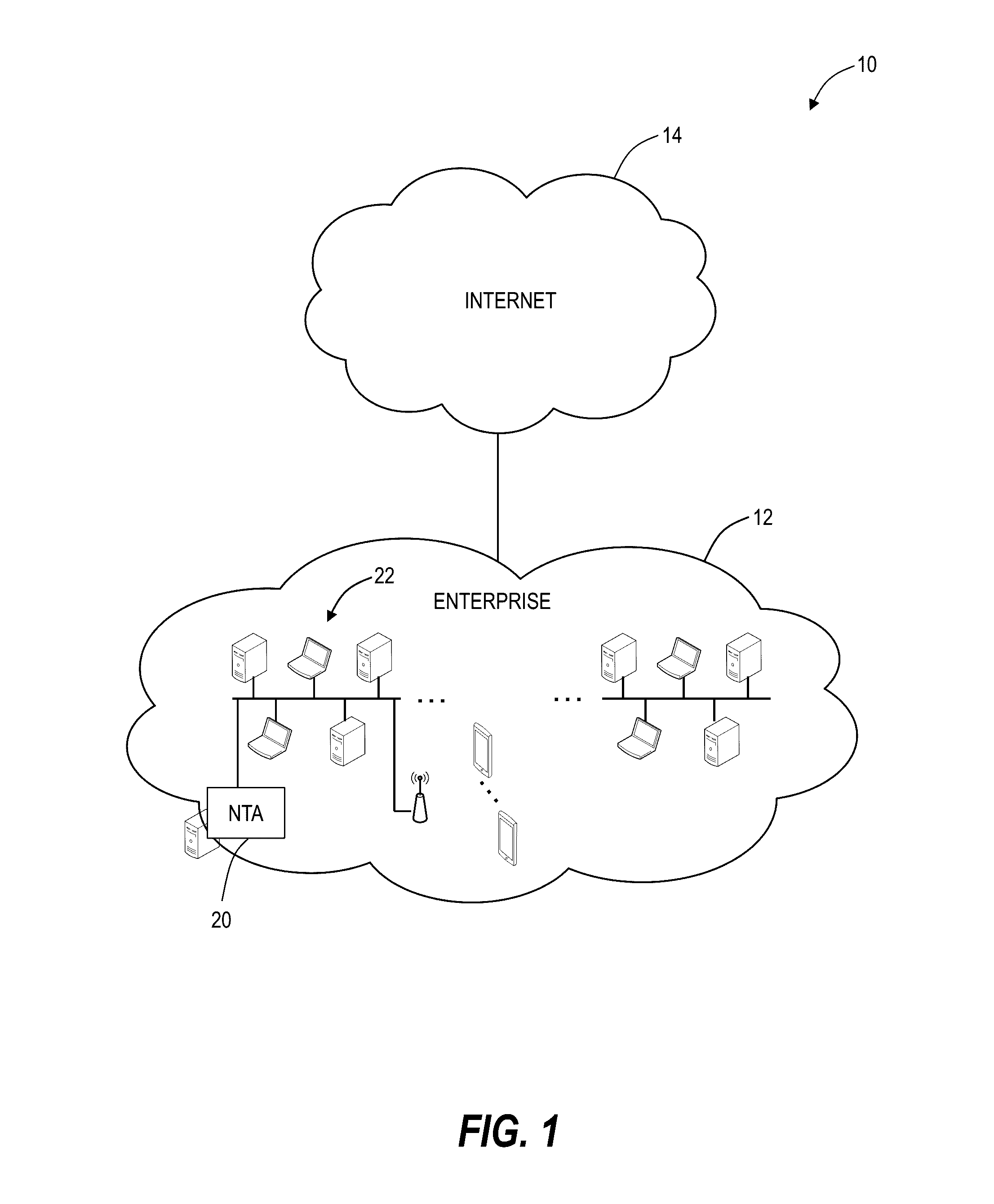
Network traffic analysis is performed by deploying, across a network having a plurality of network nodes, at least one data collection agent, on at least two of the plurality of network nodes. Each data collection agent may monitor at each network node, a plurality of network connections instantiated during a monitoring time period. Data resulting from the monitoring is acquired from the data collection agents and an ontological description of the network is automatically created from the acquired data. The ontological description is dynamically updated and network traffic analysis is performed using the dynamically updating ontological description.
Owner:RED HAT
Internet Website Traffic Flow Analysis
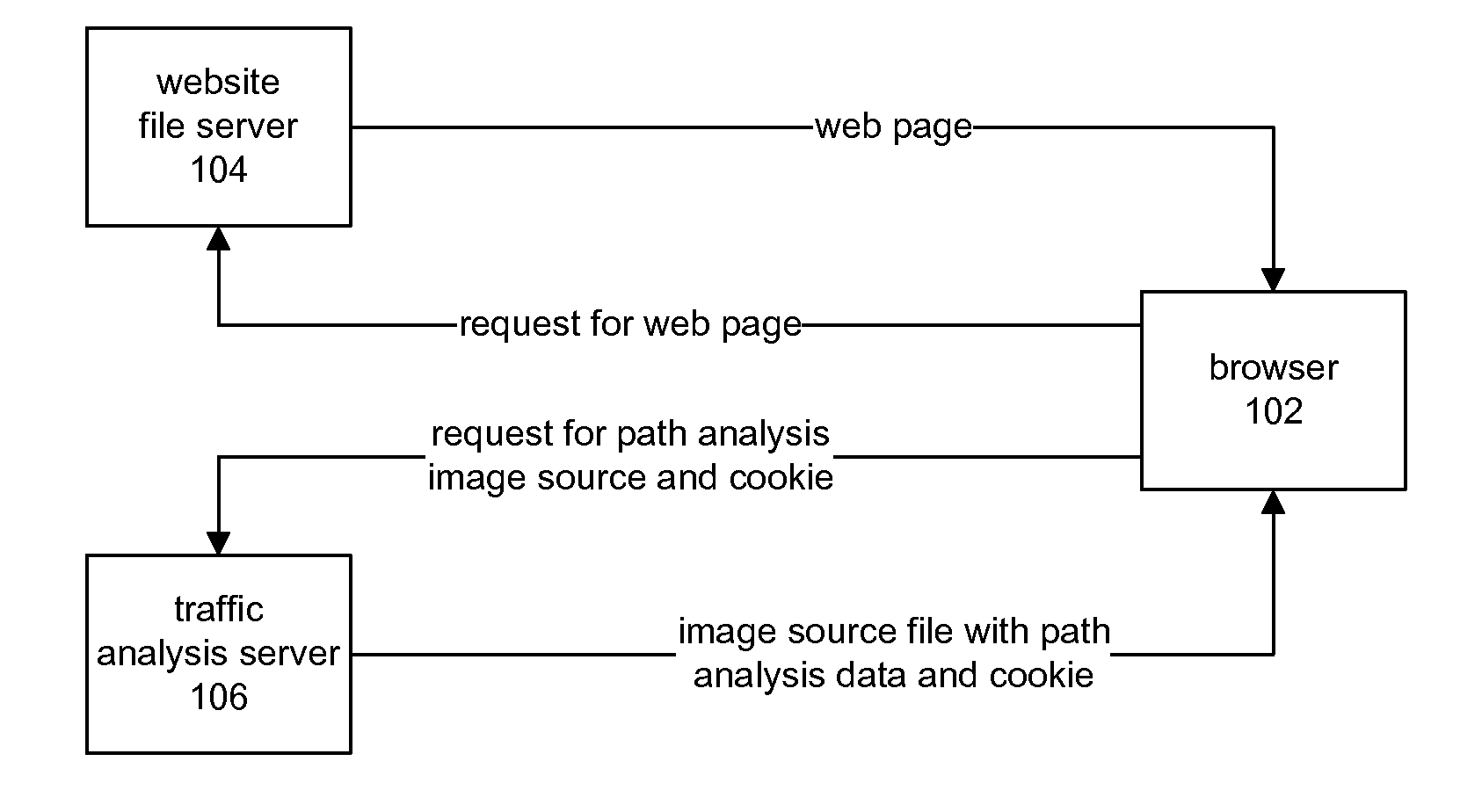
InactiveUS20090083421A1Accurate collectionAccurately studiedHardware monitoringMultiple digital computer combinationsWeb siteAnalysis tools
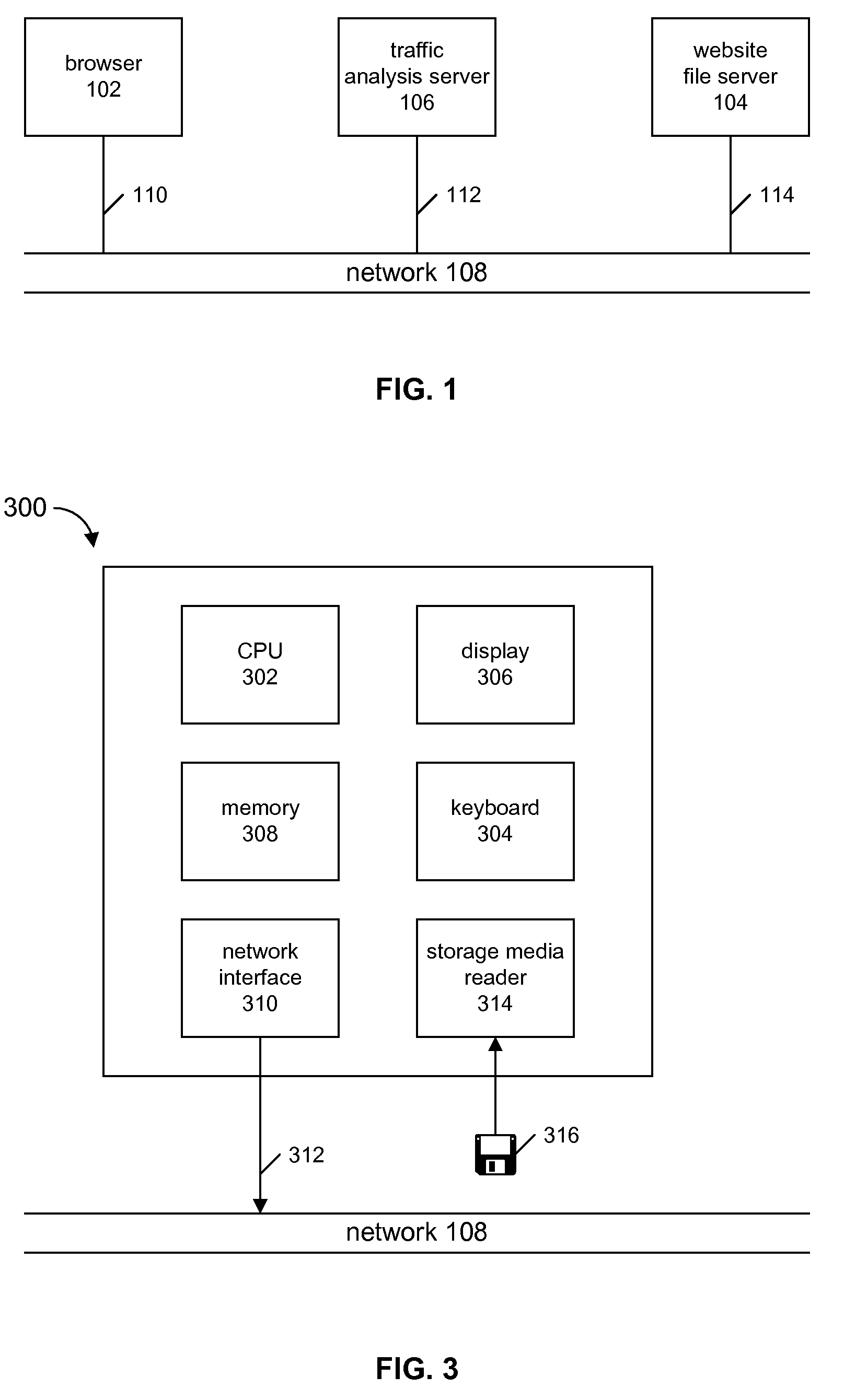
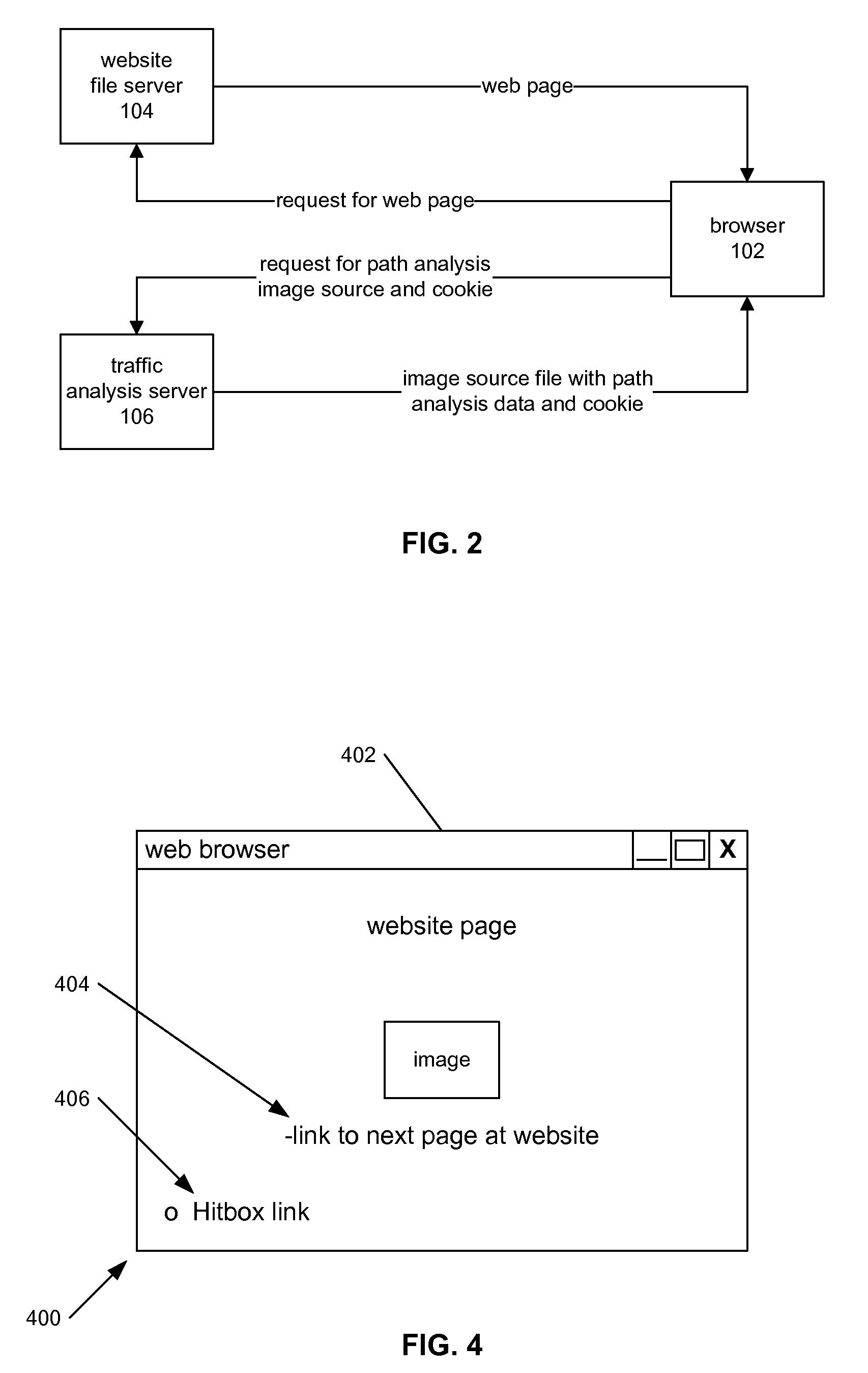
An Internet-based analysis tool follows, in real-time, the flow of traffic through a website. For every website page requested by a website visitor, the state of the visitor's browser is recorded and data relating to the path visitors take through the website is collected and studied. The state of the visitor's browser path is maintained in a traffic analysis cookie that is passed between a website file server and the visitor browser with every page requested for viewing. The cookie is maintained in a size that can be passed from server to browser and back again without negatively impacting server performance and without negatively impacting browser performance. The data in the cookie can follow the visitor browser through independent file servers, regardless of how the pages of a website might be distributed in storage.
Owner:ADOBE SYST INC
Systems and methods for tracking, analyzing and mitigating security threats in networks via a network traffic analysis platform
A network traffic analysis method for tracking, analyzing, and mitigating security threats in a network includes receiving information based on monitoring traffic at a plurality of layers at one or more monitors deployed in the network utilizing deep packet inspection; receiving information based on monitoring the traffic at an endpoint of the network; analyzing the monitored traffic from the endpoint and the one or more monitors to determine network infrastructure and cyber security posture of the network infrastructure; and providing visualizations based on the network infrastructure and the cyber security posture, continuously to track threats, watch lateral movement in the network of the traffic, and determine security event history in the network.
Owner:MANTIX4 LLC
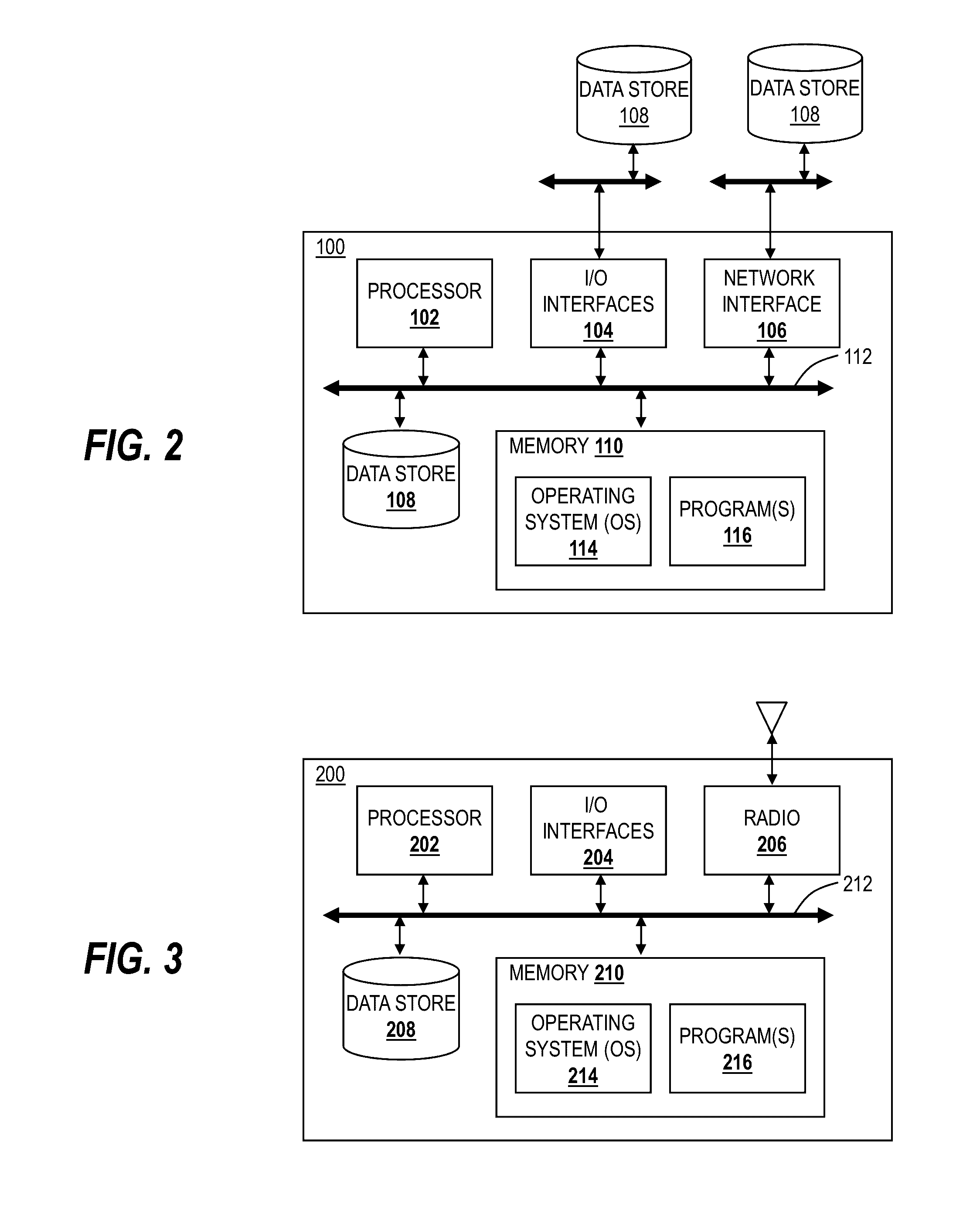
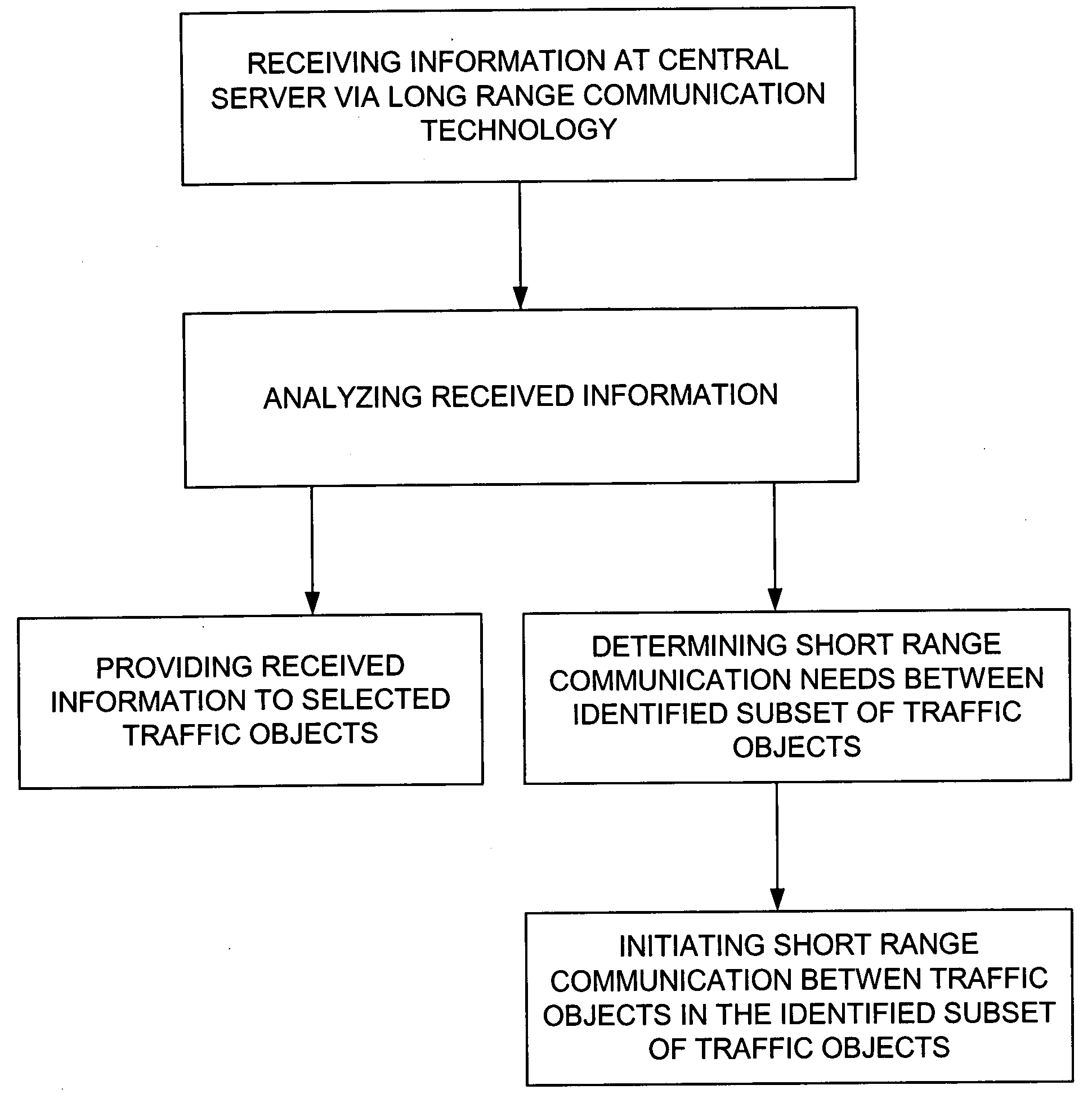
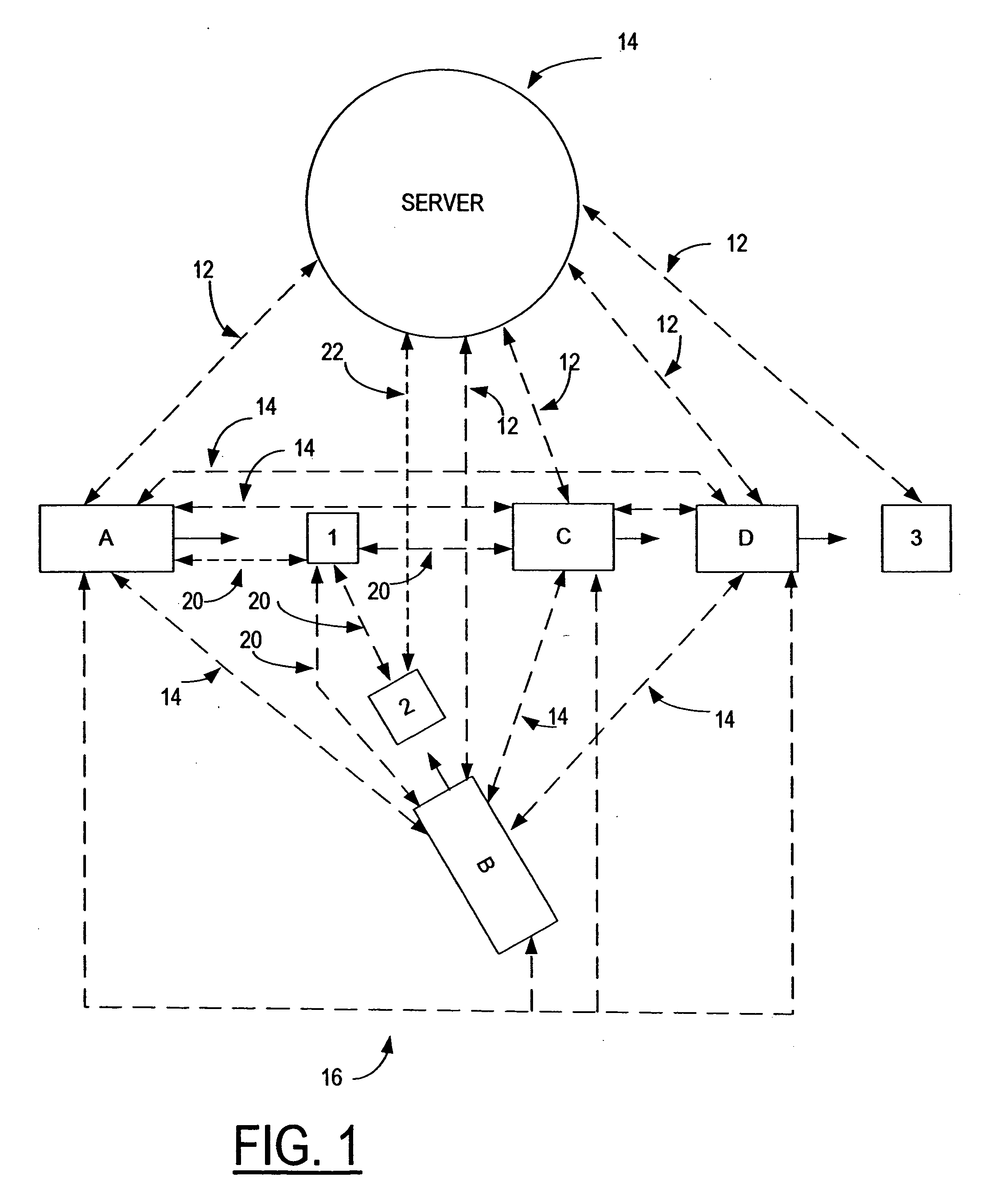
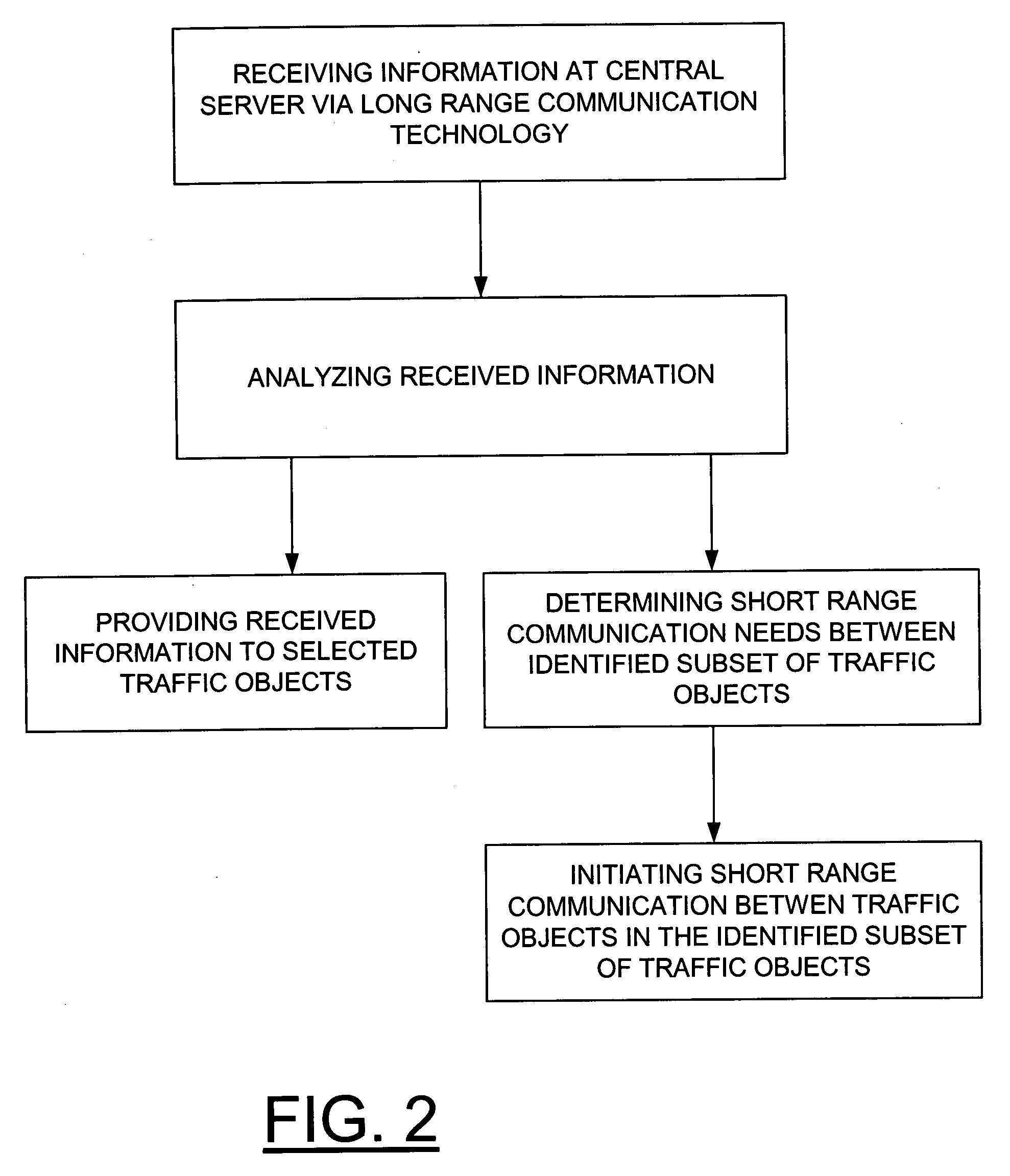
Combined short range and long range communication for traffic analysis and collision avoidance
InactiveUS20080288162A1Analogue computers for vehiclesAnalogue computers for trafficTraffic capacityLong-haul communications
A method and system for combining short range communication and long range communication for traffic related applications is presented. In one example, a central server is equipped and configured to receive information via long range communication from one or more individual traffic objects, analyze the received information to determine the short range communication needs, if any, between an identified subset of traffic objects and then initiate short range communication between the traffic objects in the identified subset of traffic objects.
Owner:NOKIA CORP
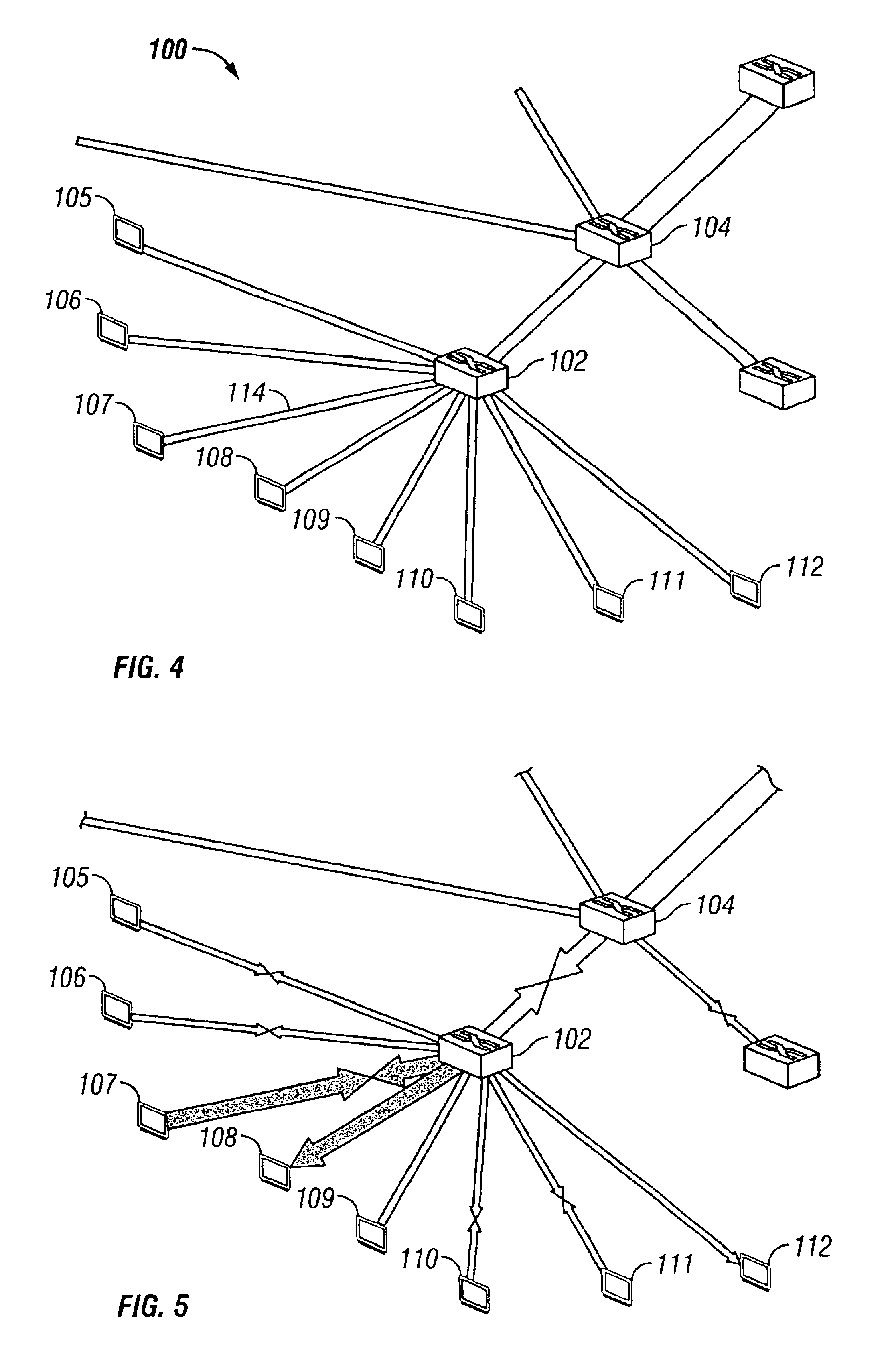
Method and system for network traffic analysis with configuration enhancements
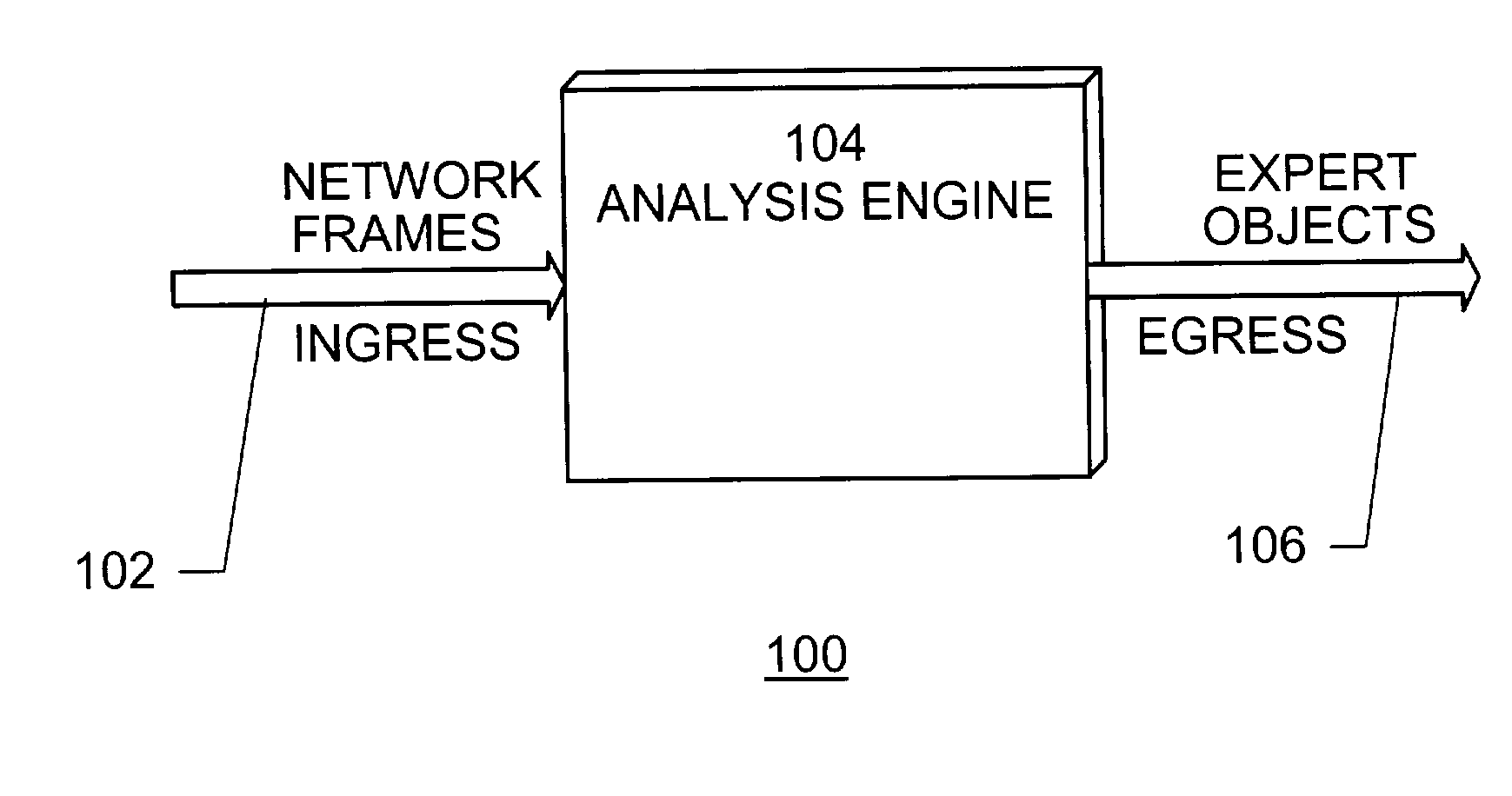
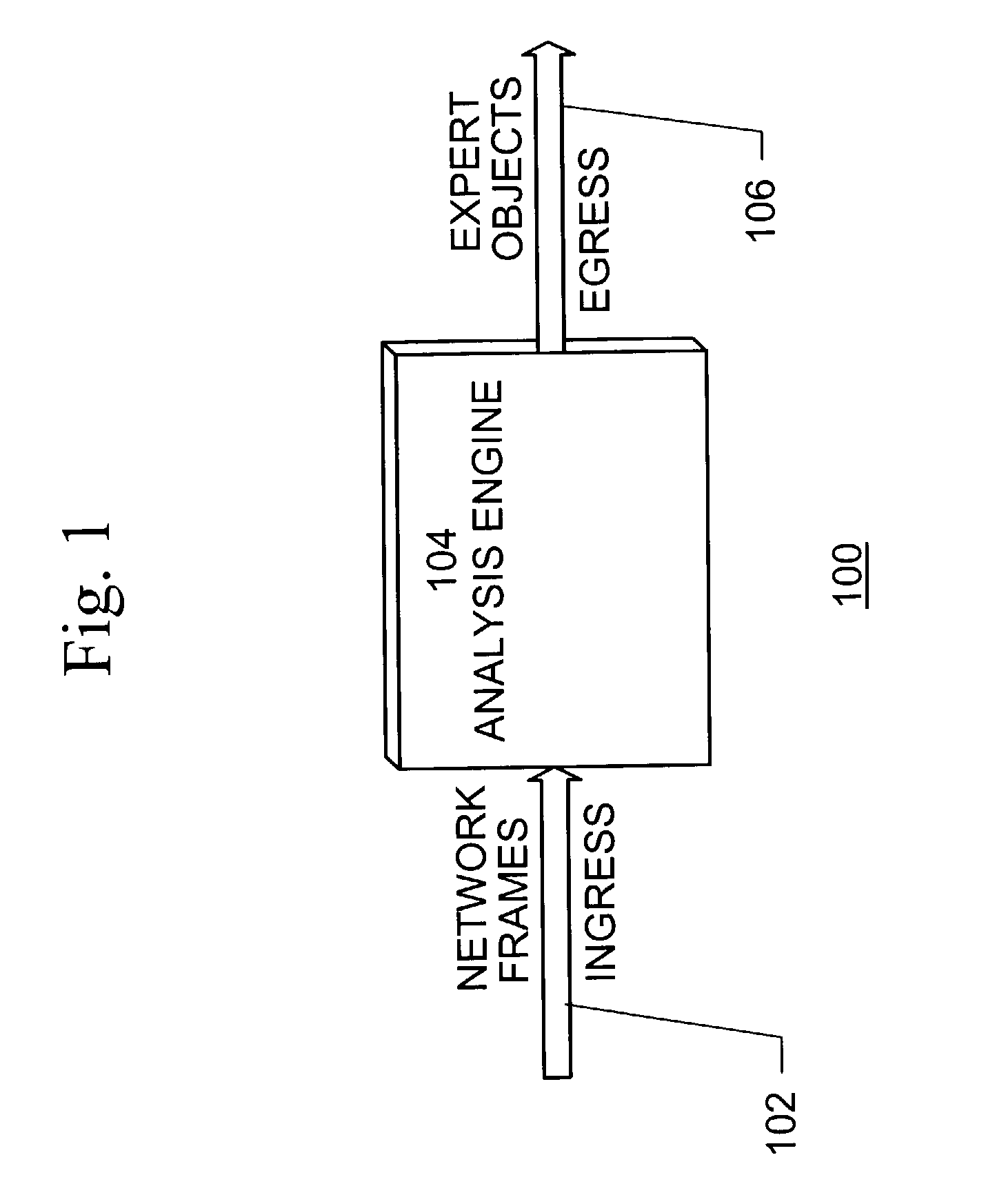
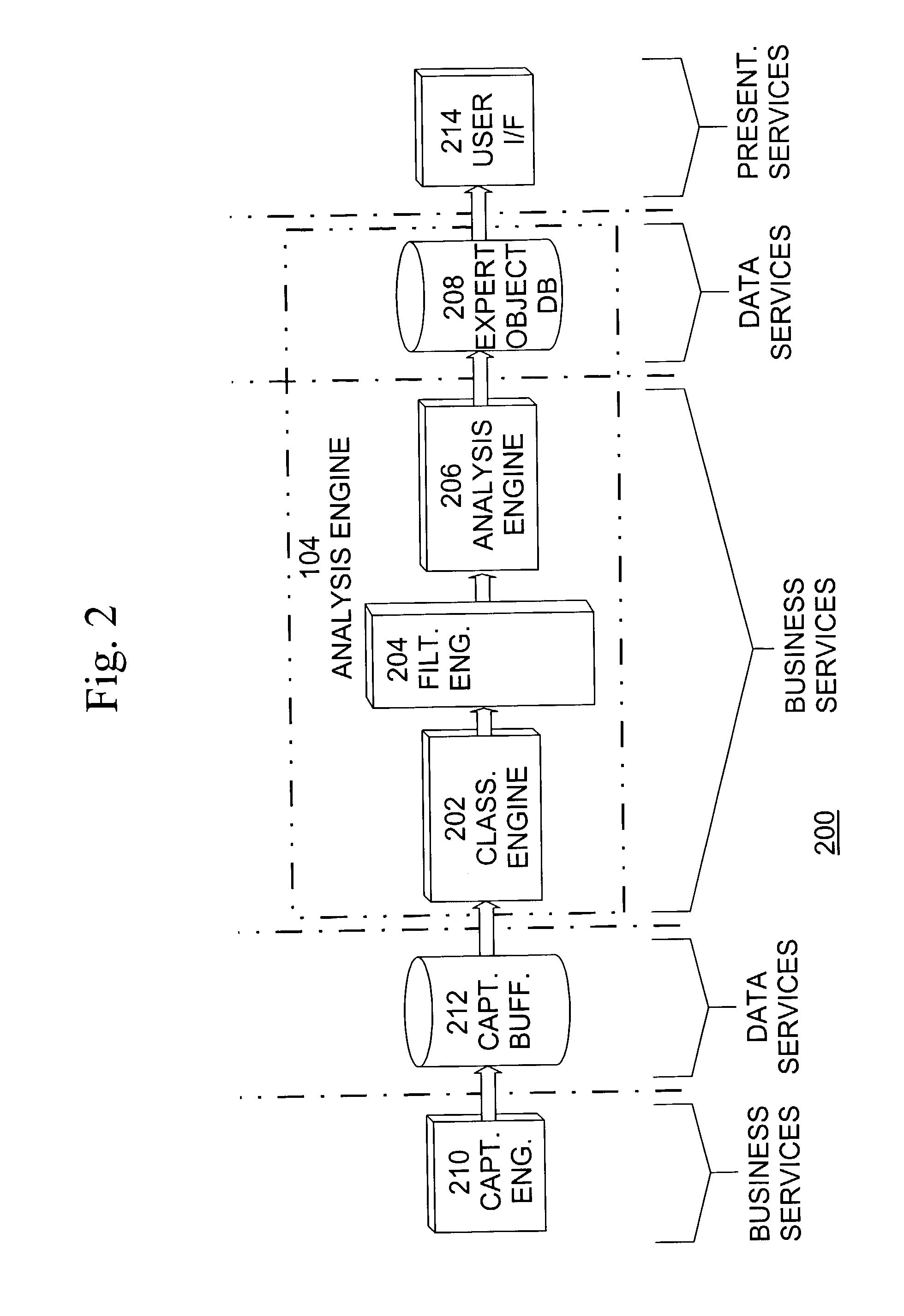
ActiveUS7177930B1Improve performanceMultiple digital computer combinationsTransmissionTraffic capacityFrame based
A system for network traffic analysis comprises a classification engine operable to parse received frames, each frame comprising a plurality of layers of protocols and each frame having a type corresponding to a highest layer protocol or network address of the frame, and to provide pre-analysis of the received frames to generate classification information on a flow-basis and on a per packet-basis, a filter processing engine operable to reduce the received frames based on a type of each frame indicated by the generated classification information to form information representing filtered frames and an analysis block operable to perform detailed analysis on layers of protocols of the filtered frames and generate objects representing the analysis.
Owner:NETWORK GENERAL TECH
Filtering and route lookup in a switching device
InactiveUS7688727B1Minimize occurrenceSize of output is increasedError preventionFrequency-division multiplex detailsTraffic capacityPacket filtering
Methods and devices for processing packets are provided. The processing device may Include an input interface for receiving data units containing header information of respective packets; a first module configurable to perform packet filtering based on the received data units; a second module configurable to perform traffic analysis based on the received data units; a third module configurable to perform load balancing based on the received data units; and a fourth module configurable to perform route lookups based on the received data units.
Owner:JUMIPER NETWORKS INC
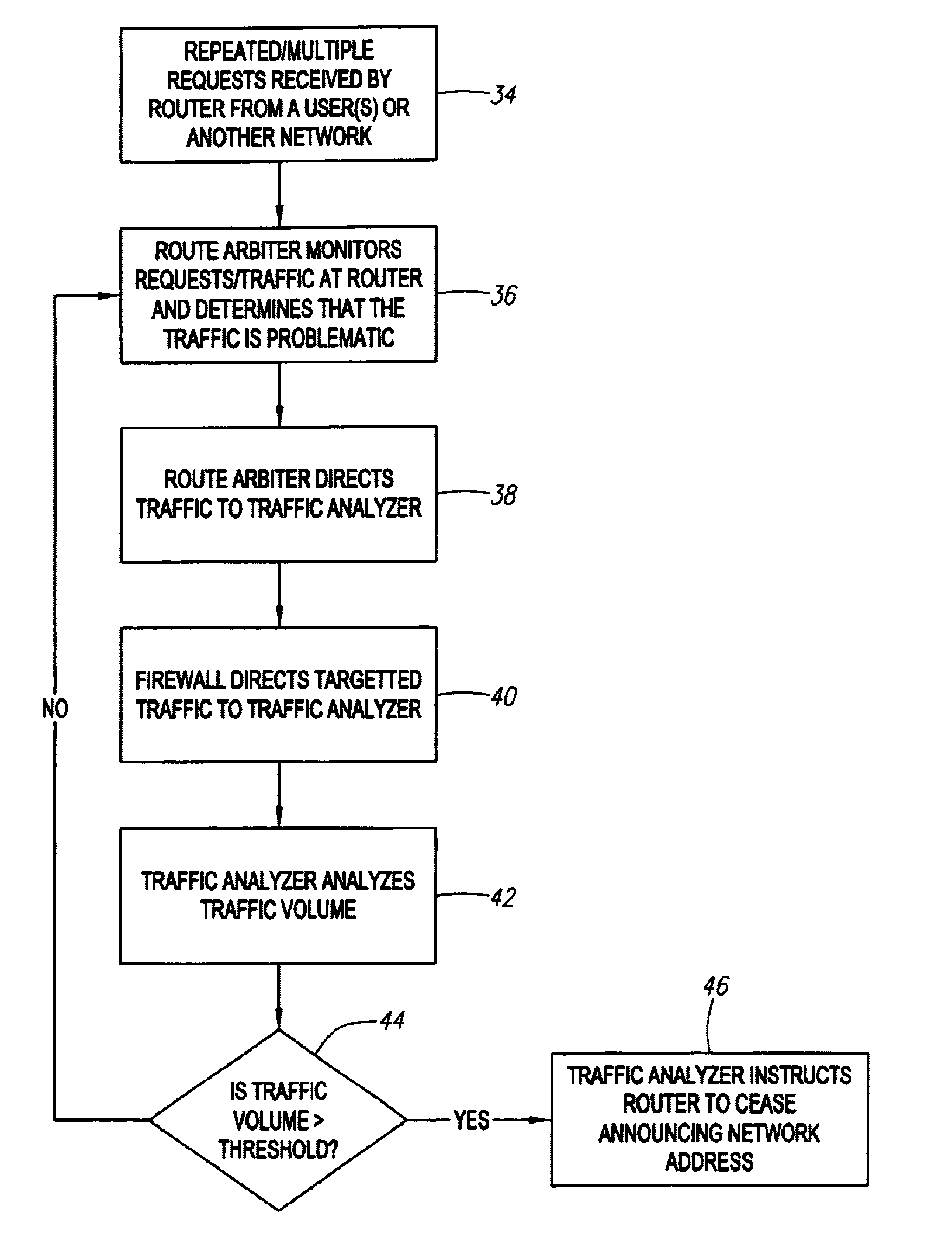
System and method for traffic analysis
InactiveUS20050108415A1Multiple digital computer combinationsData switching networksNetwork activityDistributed computing
The present invention provides a system and method for traffic analysis. Embodiments can be used to detect malevolent network activity such as worms, viruses, denial of service attacks, and unauthorized network routing. Upon detecting the activity, steps can then be taken to halt the spread and / or remove the malevolent network activity, thereby adding protection from such activity to the network. Other network activity of interest can also be detected.
Owner:BCE
Correlation and enrichment of telephone system call data records
InactiveUS6891938B1Easy to detectImprove Billing AccuracyTelephonic communicationTraffic capacityCommunications system
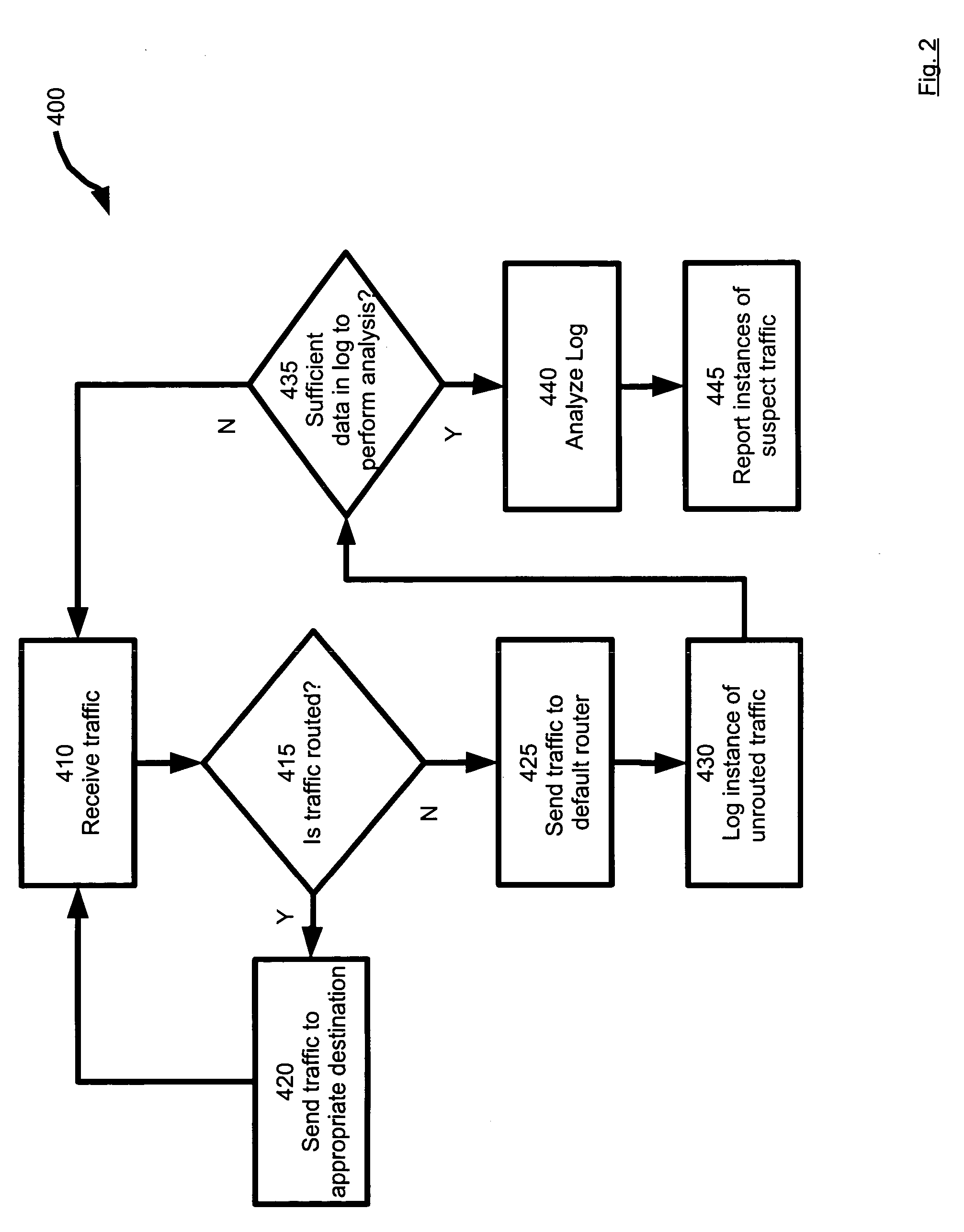
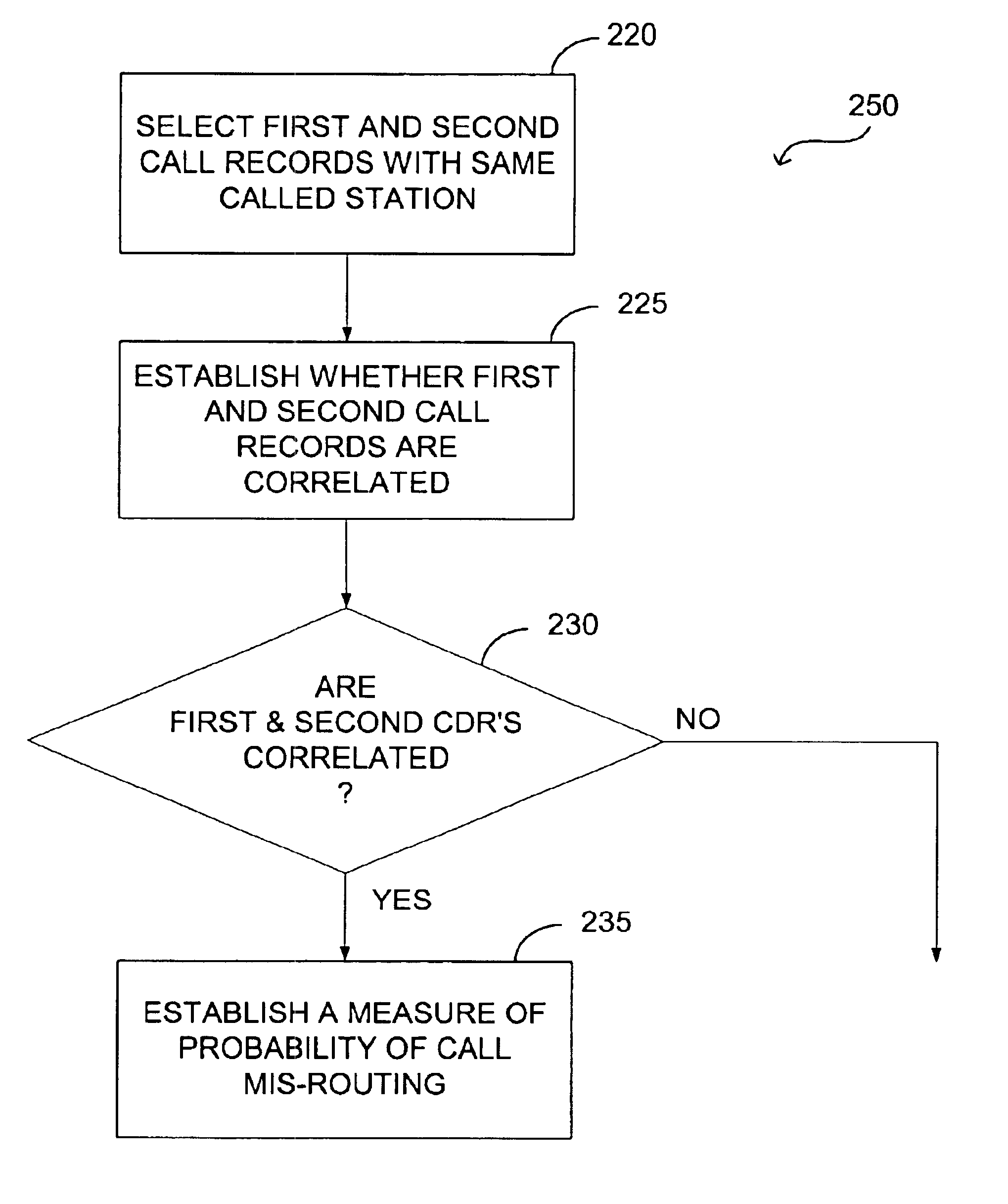
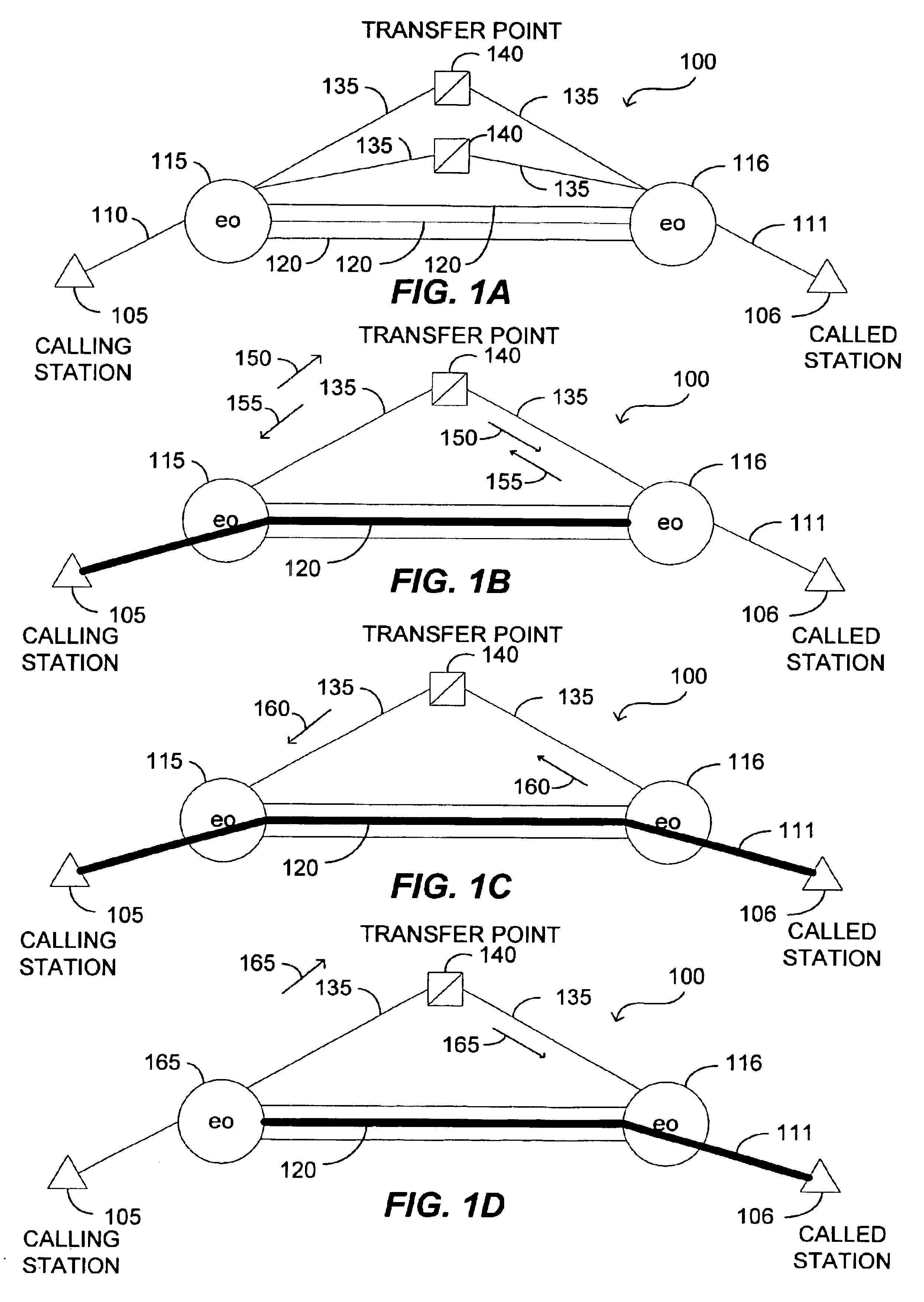
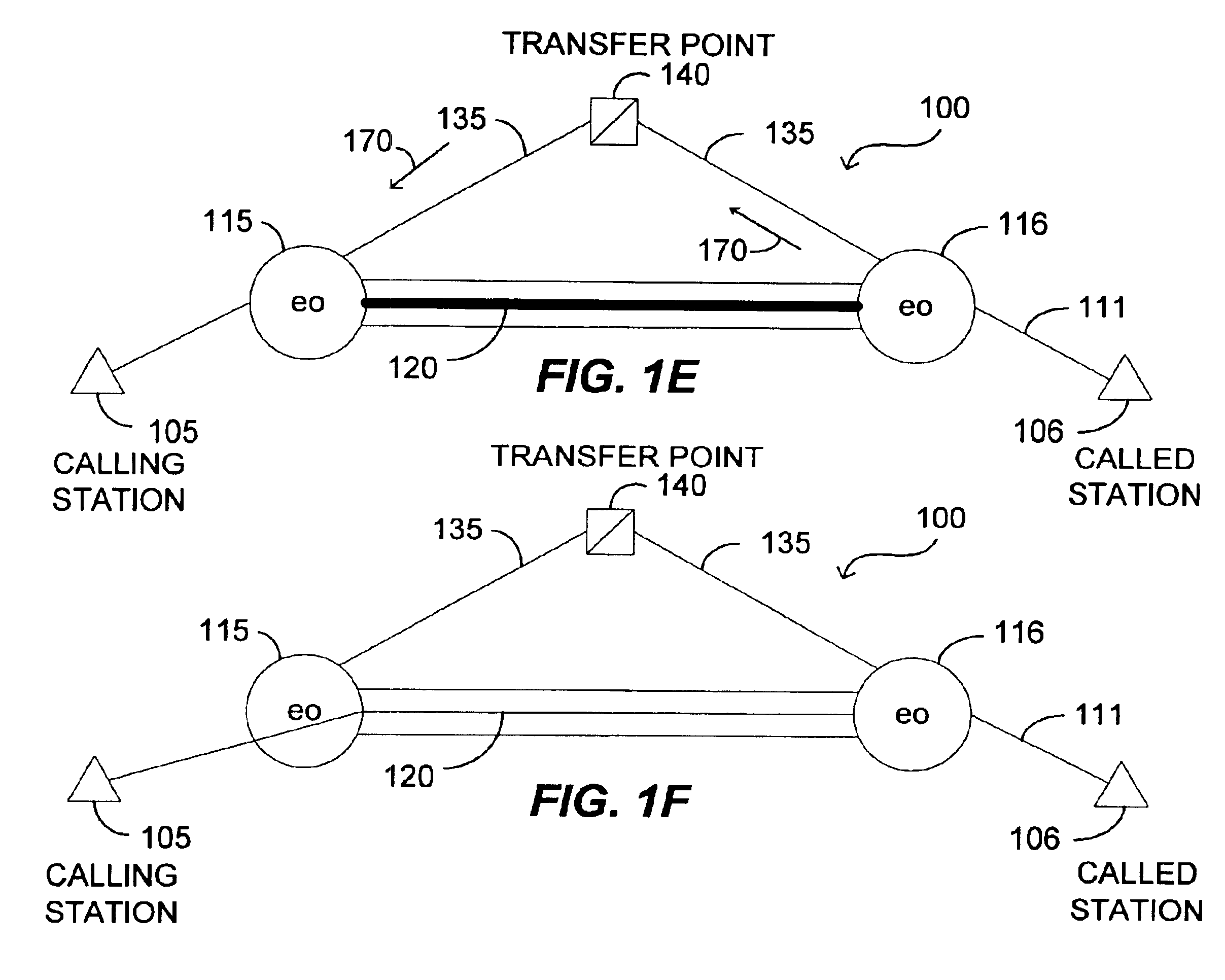
Methods to correlate call data records in a telephone or other communication system. A combination of parameter values in the data records and timestamps associated with some of the parameters can be used for such correlation. The information available within a single call record has limitations due to the fact that critical routing information may be (a) missing or (b) incorrect. Correlation of call detail records obtained from various communication segments provides the ability to mutually enrich the records so as to increase billing accuracy, as well as to enhance the detection of call mis-routing and perform traffic analysis.
Owner:VIAVI SOLUTIONS INC
Packet flow bifurcation and analysis
ActiveUS7508764B2Improve matchError preventionTransmission systemsTraffic capacityProcessing element
Methods and apparatus for optimum matching of a traffic profile with an individual traffic flow using flow bifurcation and analysis. Bifurcation and duplication of packets that make up a flow received at an ingress element are forwarded to each of egress traffic and computation processor resources, such that egress traffic operations and traffic analysis operations may be performed concurrently without introducing jitter or delay in either bifurcated processing path. The traffic analysis includes maintaining flow statistics, flow stateful information and classifying the flow as a particular application traffic type. The optimum traffic profile for this application traffic type is then selected and applied to the individual flow. The traffic analysis data is forwarded to ingress and egress processing elements in real time, and ingress and egress traffic processing operations are dynamically adjusted in view of the traffic analysis data.
Owner:TELLABS COMM CANADA
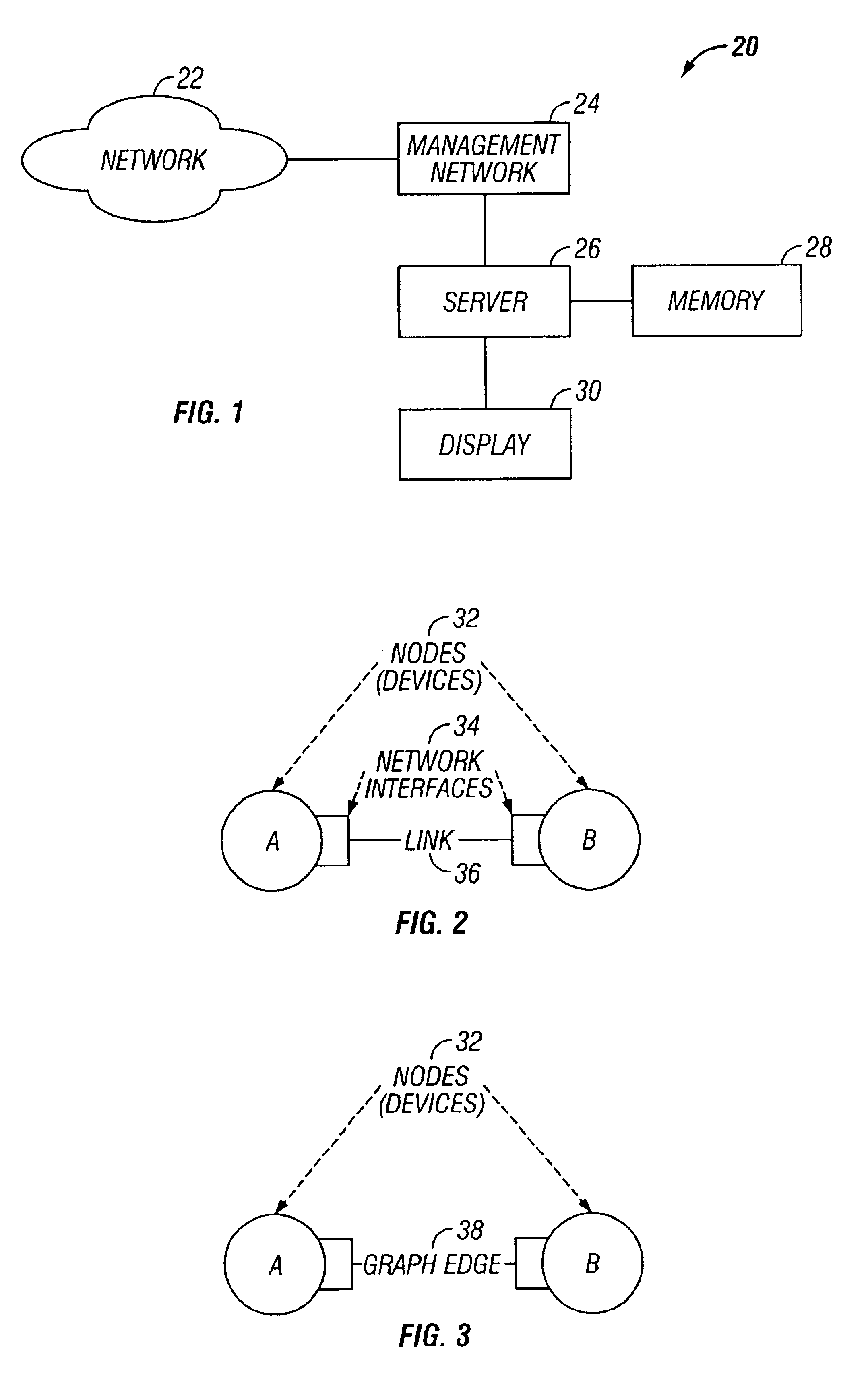
Performance and flow analysis method for communication networks
A system and method are used for visually representing performance and flow analysis of a communication network having devices connected by links. The system includes a first memory for storing a graphical representation of the communication network and showing the devices connected by links and a second memory storing data representing performance and flows in the communication network. A processing system is operatively connected to the first and the second memory and to a display. The processing system selectively maps the data on the graphical representation of the communication network by varying visual characteristics of the devices and the links for viewing on the display.
Owner:BMC SOFTWARE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com