Patents
Literature
592 results about "Deep packet inspection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
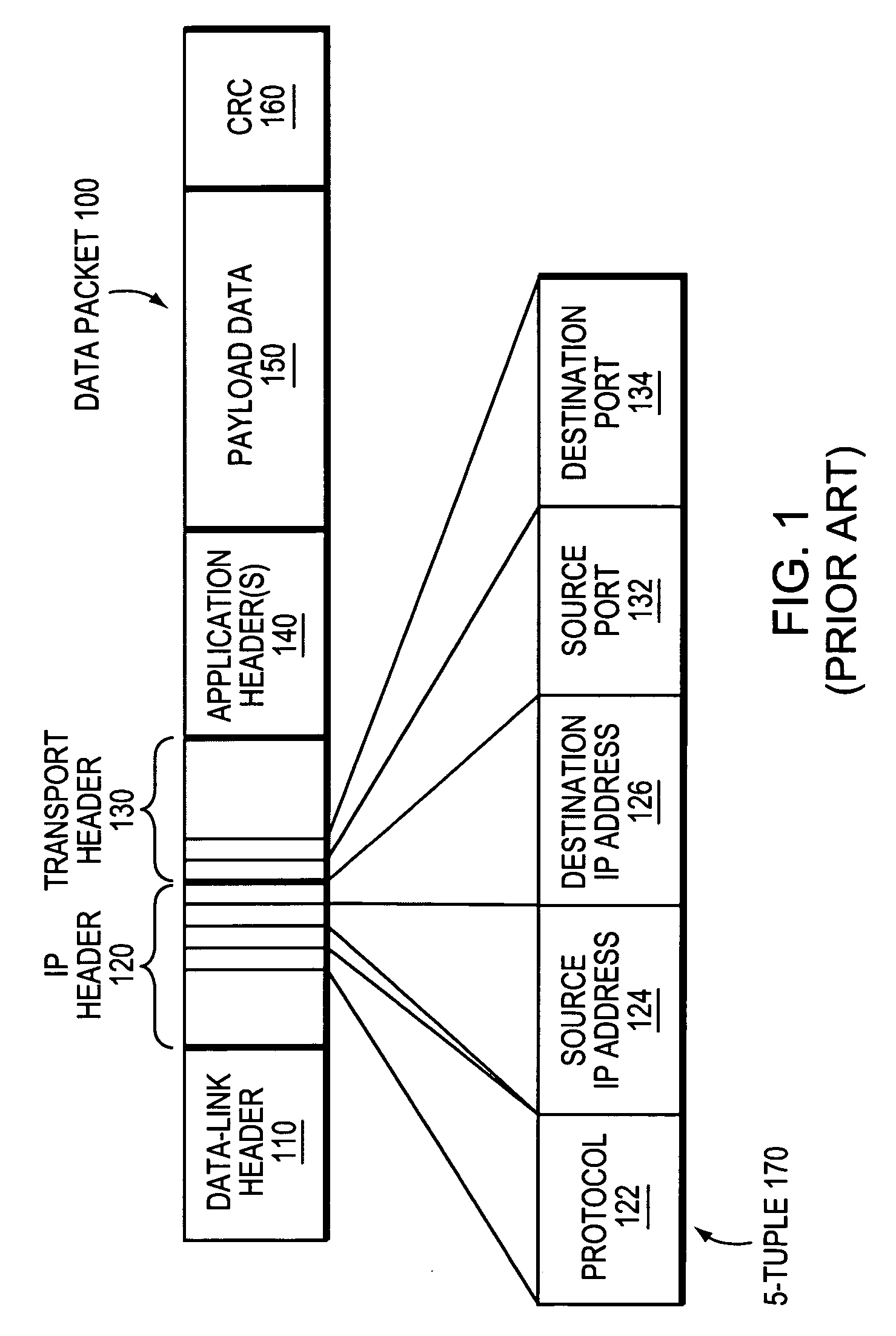
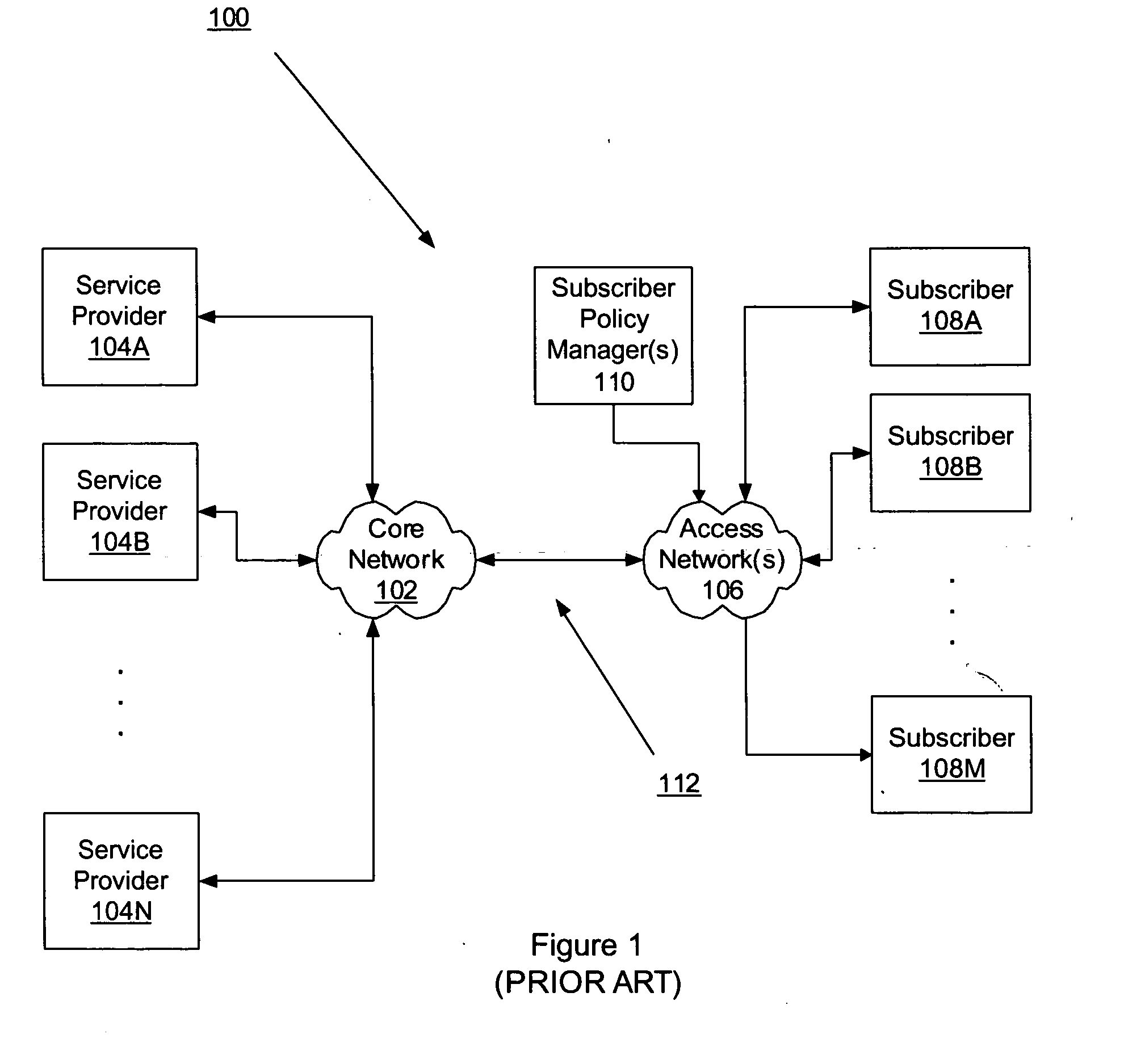
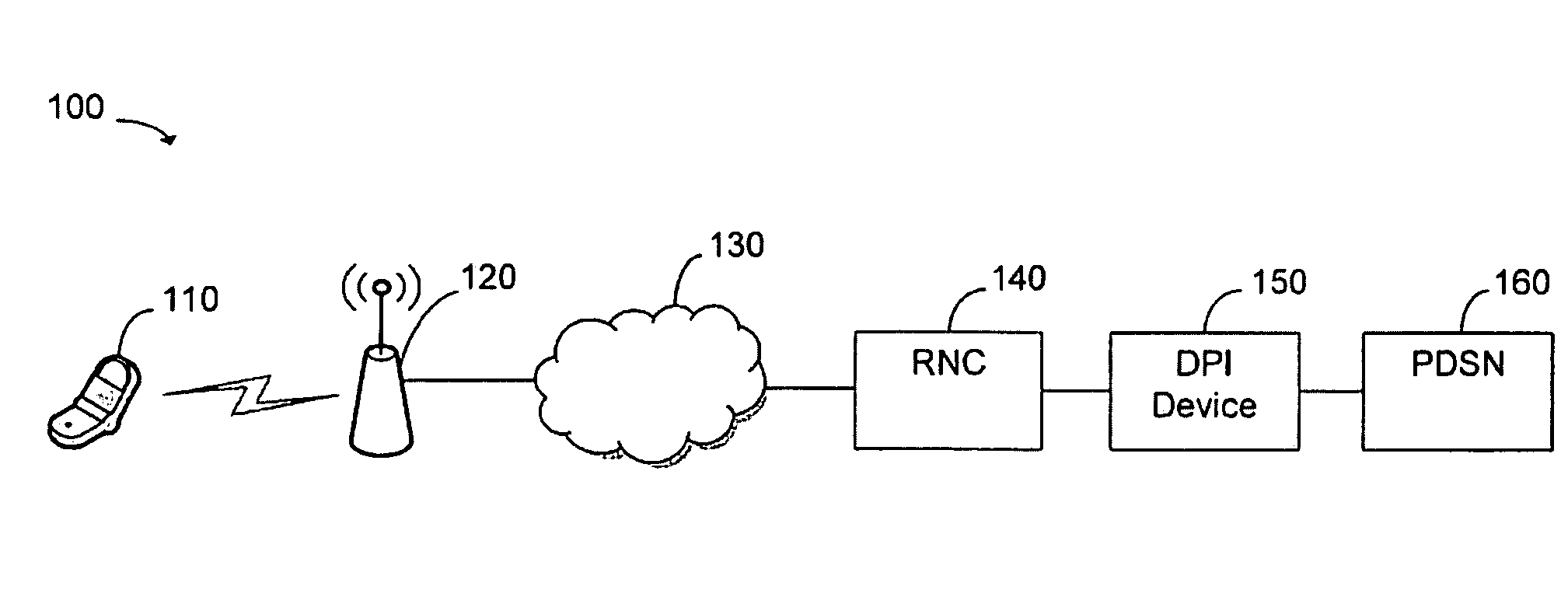
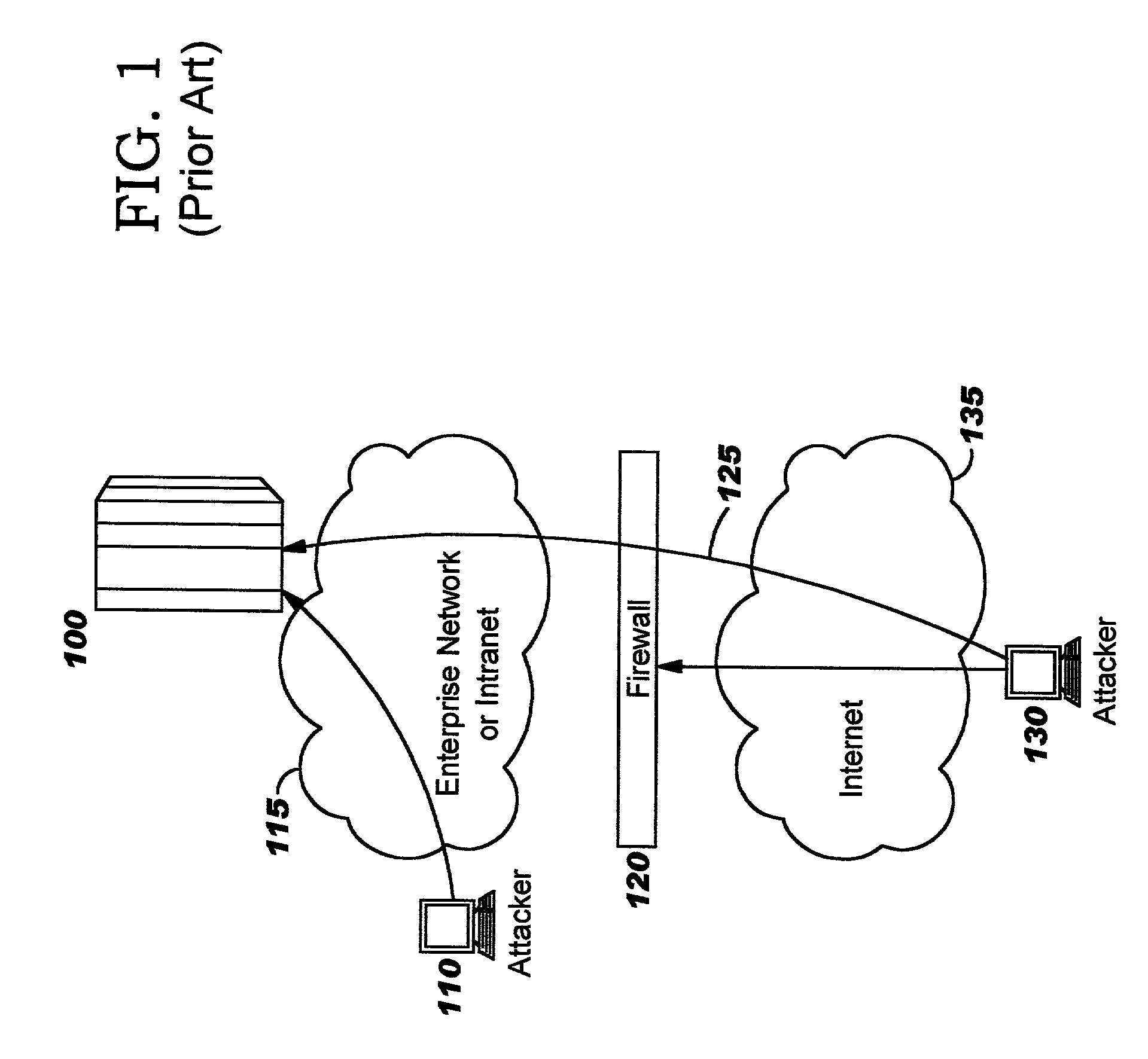
Deep packet inspection (DPI) is a type of data processing that inspects in detail the data being sent over a computer network, and usually takes action by blocking, re-routing, or logging it accordingly. Deep packet inspection is often used to ensure that data is in the correct format, to check for malicious code, eavesdropping and internet censorship among other purposes. There are multiple headers for IP packets; network equipment only needs to use the first of these (the IP header) for normal operation, but use of the second header (such as TCP or UDP) is normally considered to be shallow packet inspection (usually called stateful packet inspection) despite this definition.
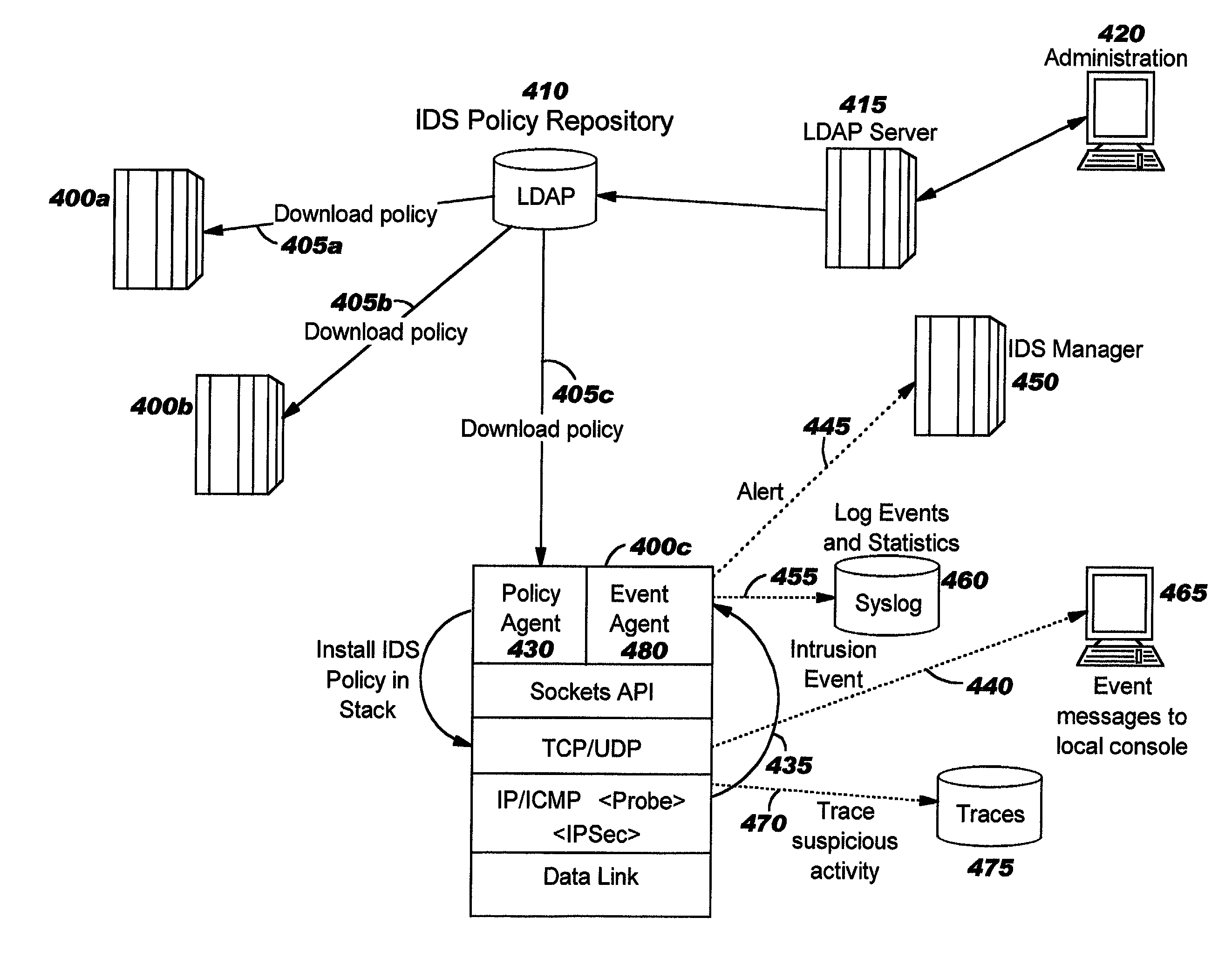
Integrated intrusion detection services
ActiveUS20030145226A1Memory loss protectionDigital computer detailsService improvementContext specific
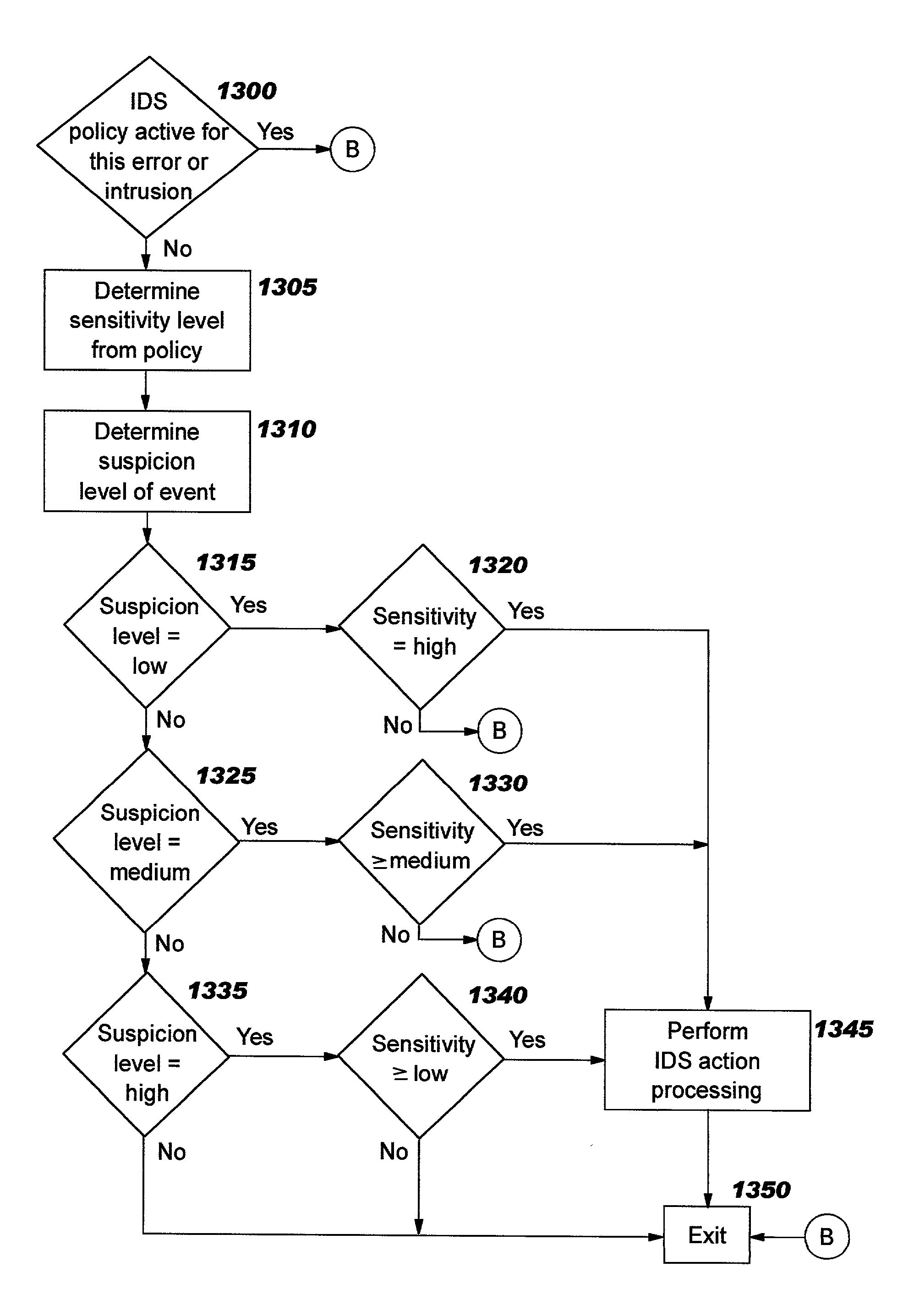
Improvements in intrusion detection are disclosed by providing integrated intrusion detection services. Preferably, these services are integrated into a system or server that is the potential target of attack. Stack-based security processing is leveraged for access to cleartext data within the layers of the protocol stack. Layer-specific attacks may therefore be processed efficiently. Evaluation of incoming traffic for an intrusion is preferably performed only after an error condition of some type has been detected. This approach reduces the overhead of intrusion detection by reducing the number of packets to be inspected, and at the same time allows more efficient packet inspection through use of context-specific information that may be used to direct the inspection to particular candidate attacks. Generic attack class capability is also disclosed. Intrusion detection policy information may be used to direct the actions to be taken upon detecting an attack.
Owner:TREND MICRO INC
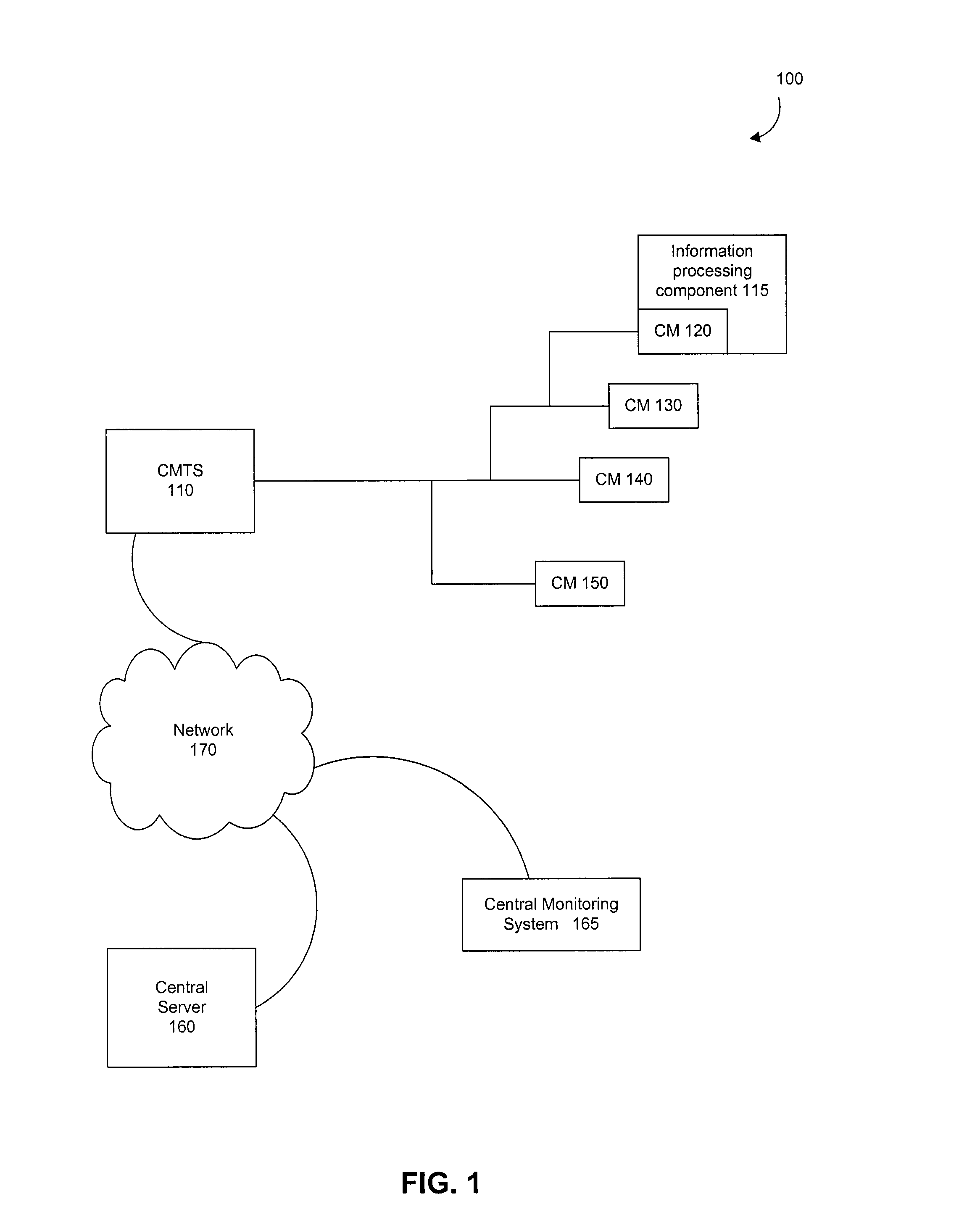
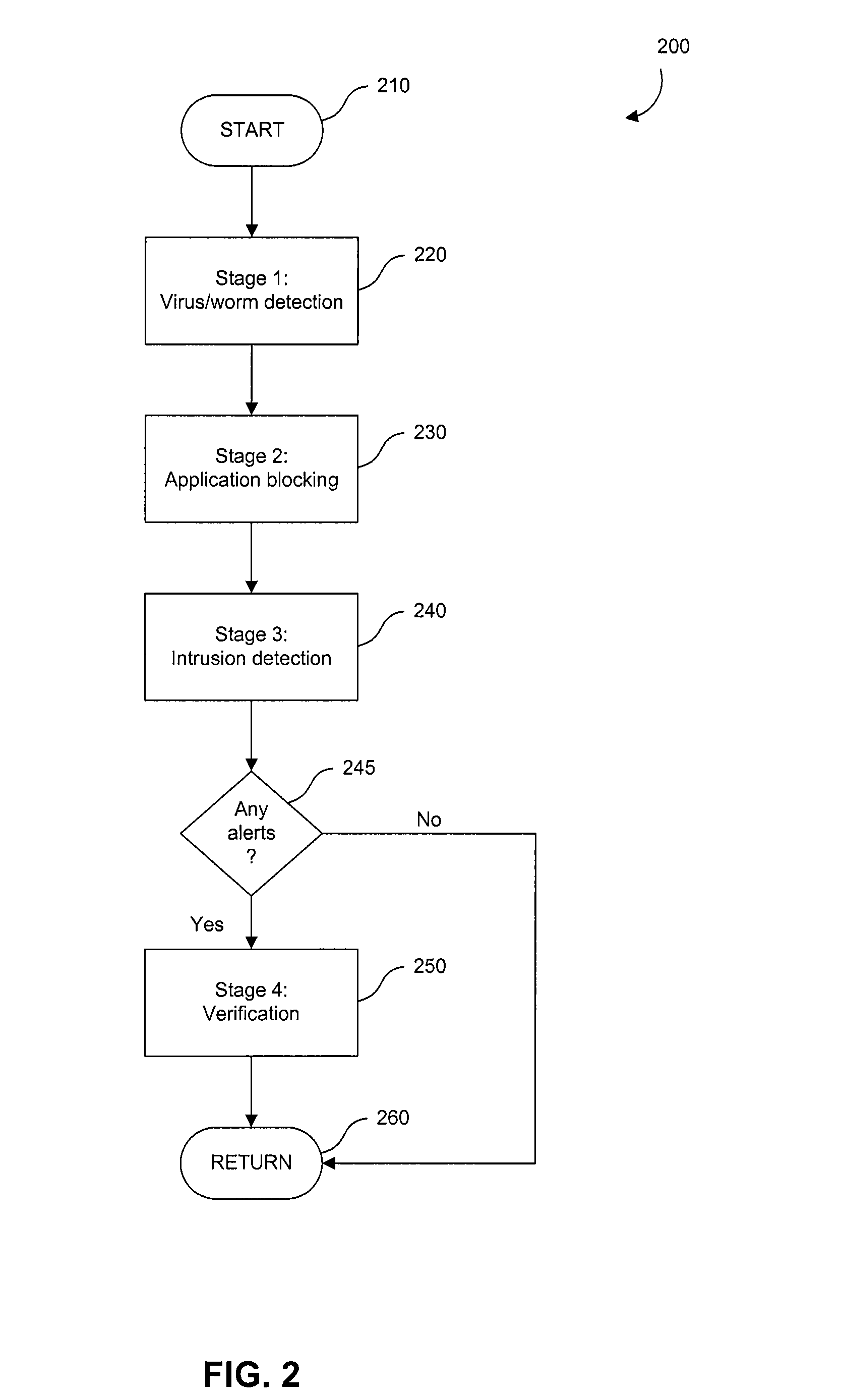
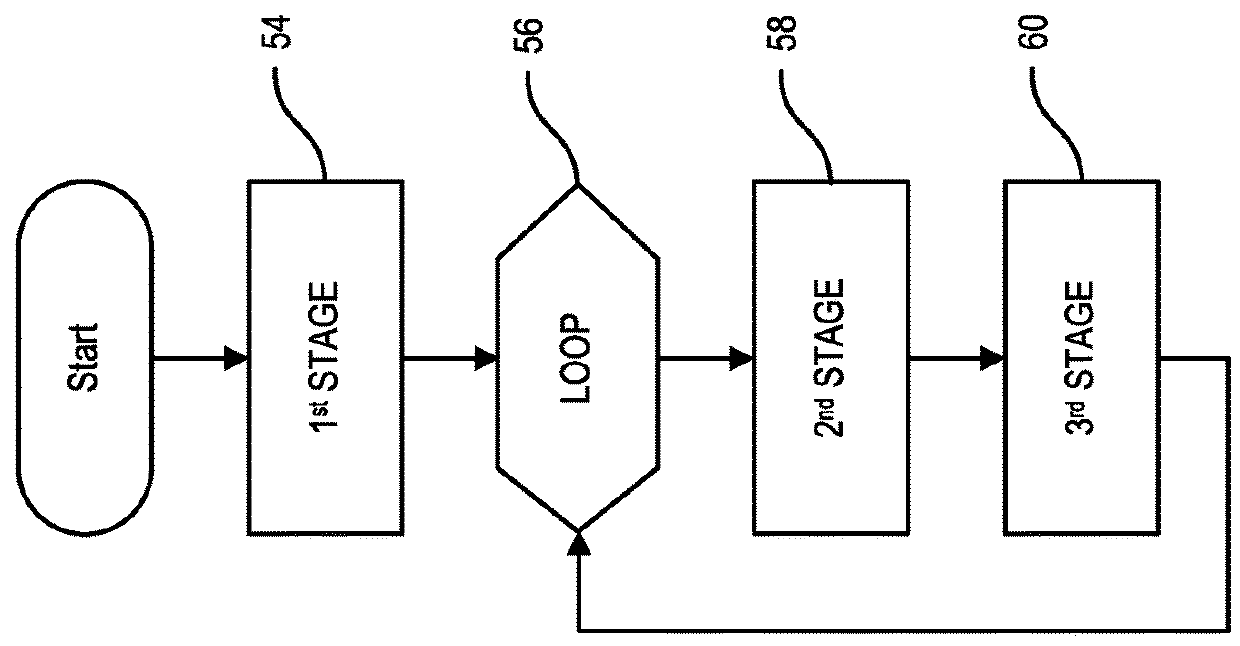
Multi-Stage Deep Packet Inspection for Lightweight Devices
InactiveUS20080313738A1Memory loss protectionError detection/correctionInformation processingThree stage
A system and method for the multi-stage analysis of incoming packets. Three stages are used, each of which addresses a particular category of threat by examining the headers and / or payload of each packet (“deep packet inspection”). The first stage detects incoming viruses or worms. The second stage detects malicious applications. The third stage detects attempts at intrusion. These three stages operate in sequence, but in alternative embodiments of the invention, they may be applied in a different order. These three stages are followed by a fourth stage that acts as a verification stage. If any of the first three stages detects a possible attack, then the packet or packets that have been flagged are routed to a central verification facility. In an embodiment of the invention, the verification facility is a server, coupled with a database. Here, suspect packets are compared to entries in the database to more comprehensively determine whether or not the packets represent an attempt to subvert the information processing system.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
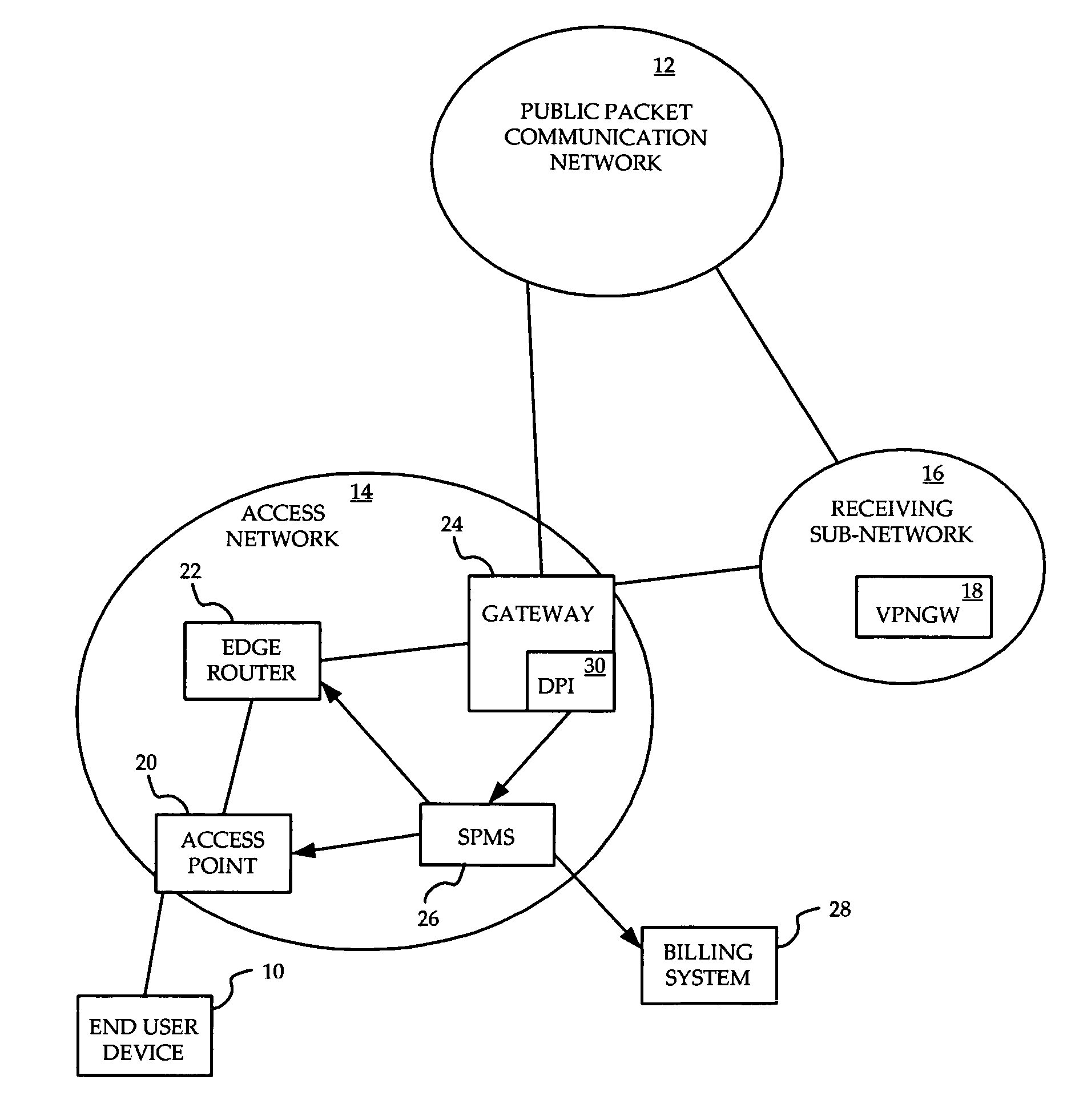
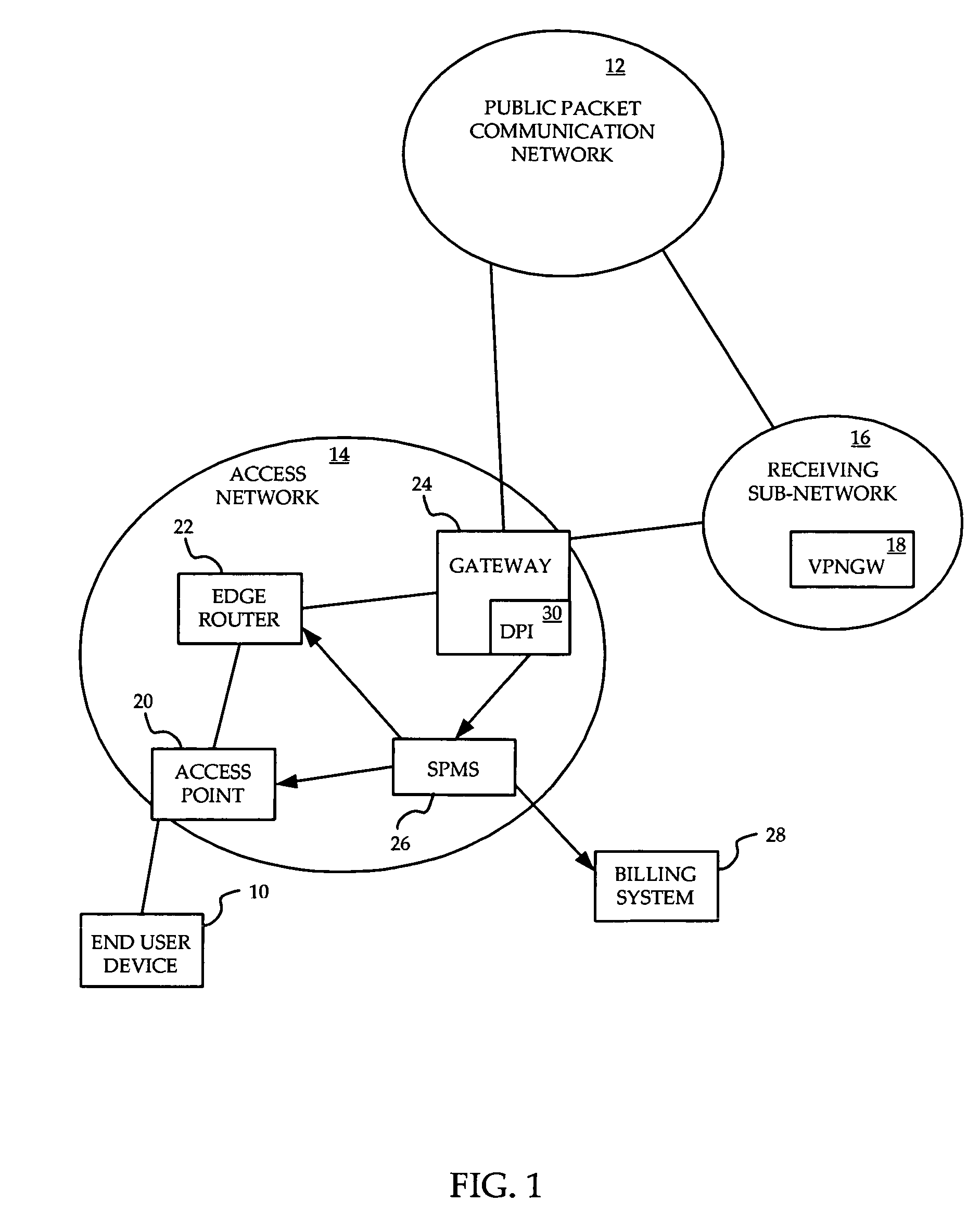
System and method for prioritization of traffic through internet access network
InactiveUS7881199B2Avoid allocation problemsRaise priorityError preventionTransmission systemsPacket communicationTraffic capacity
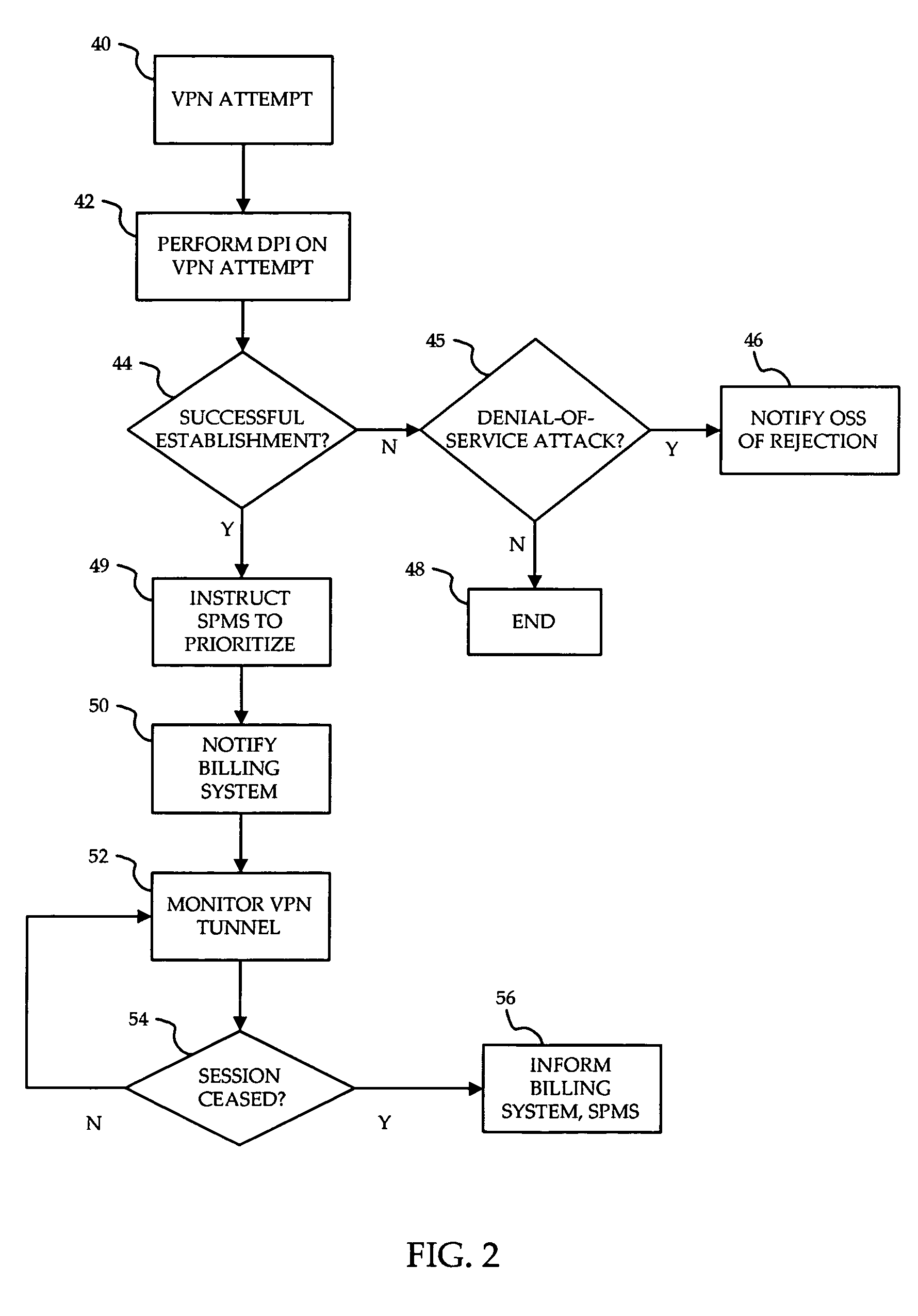
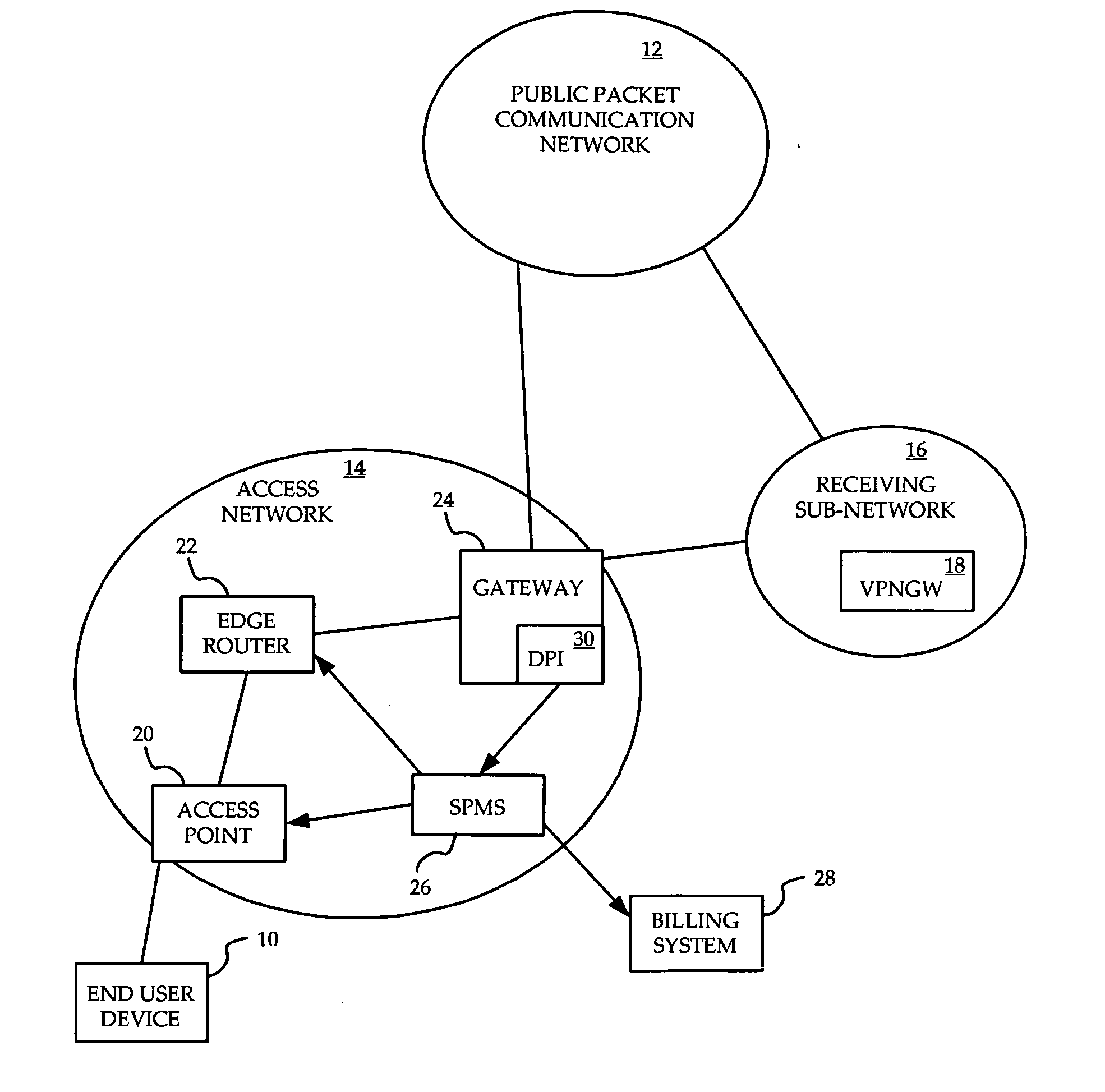
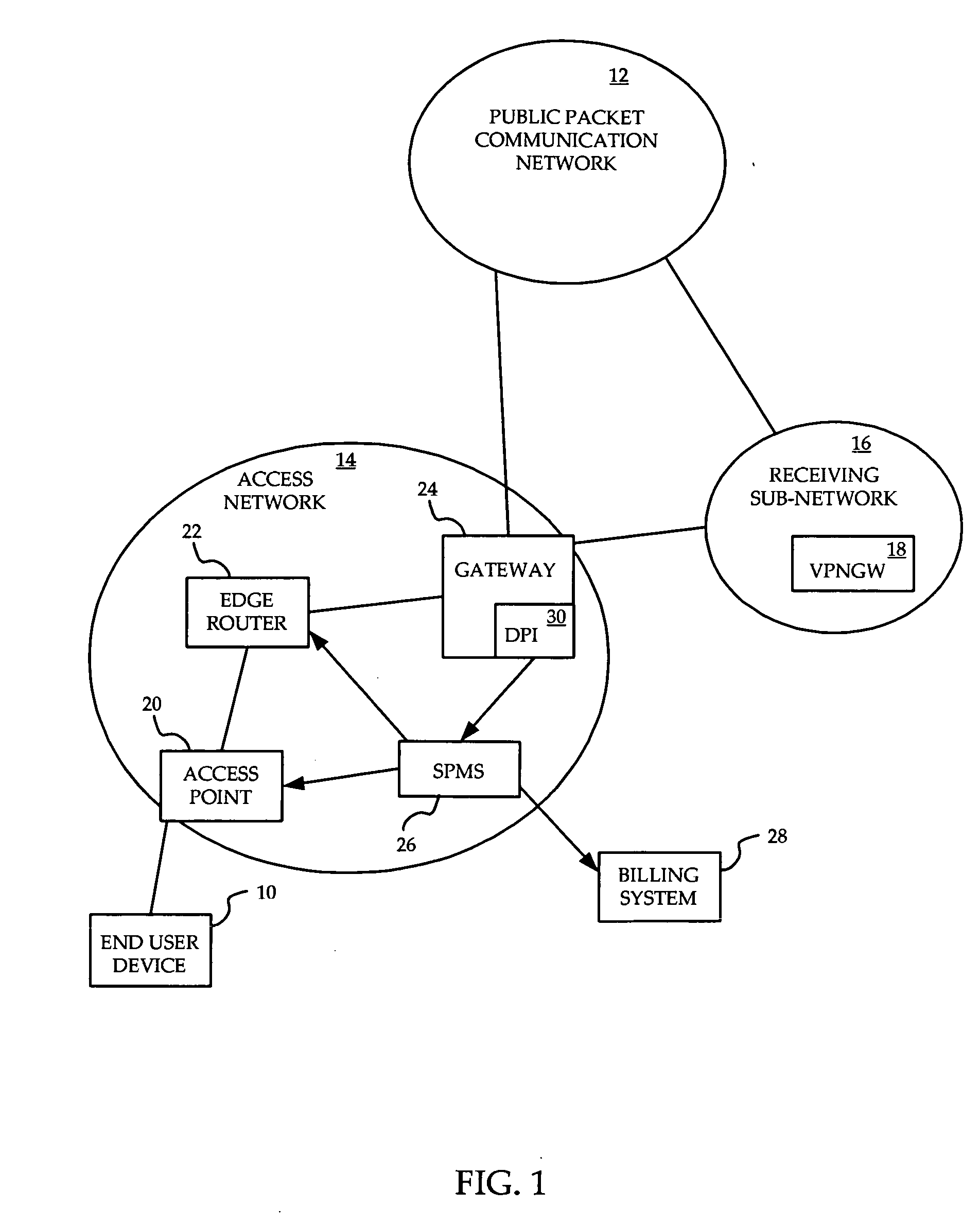
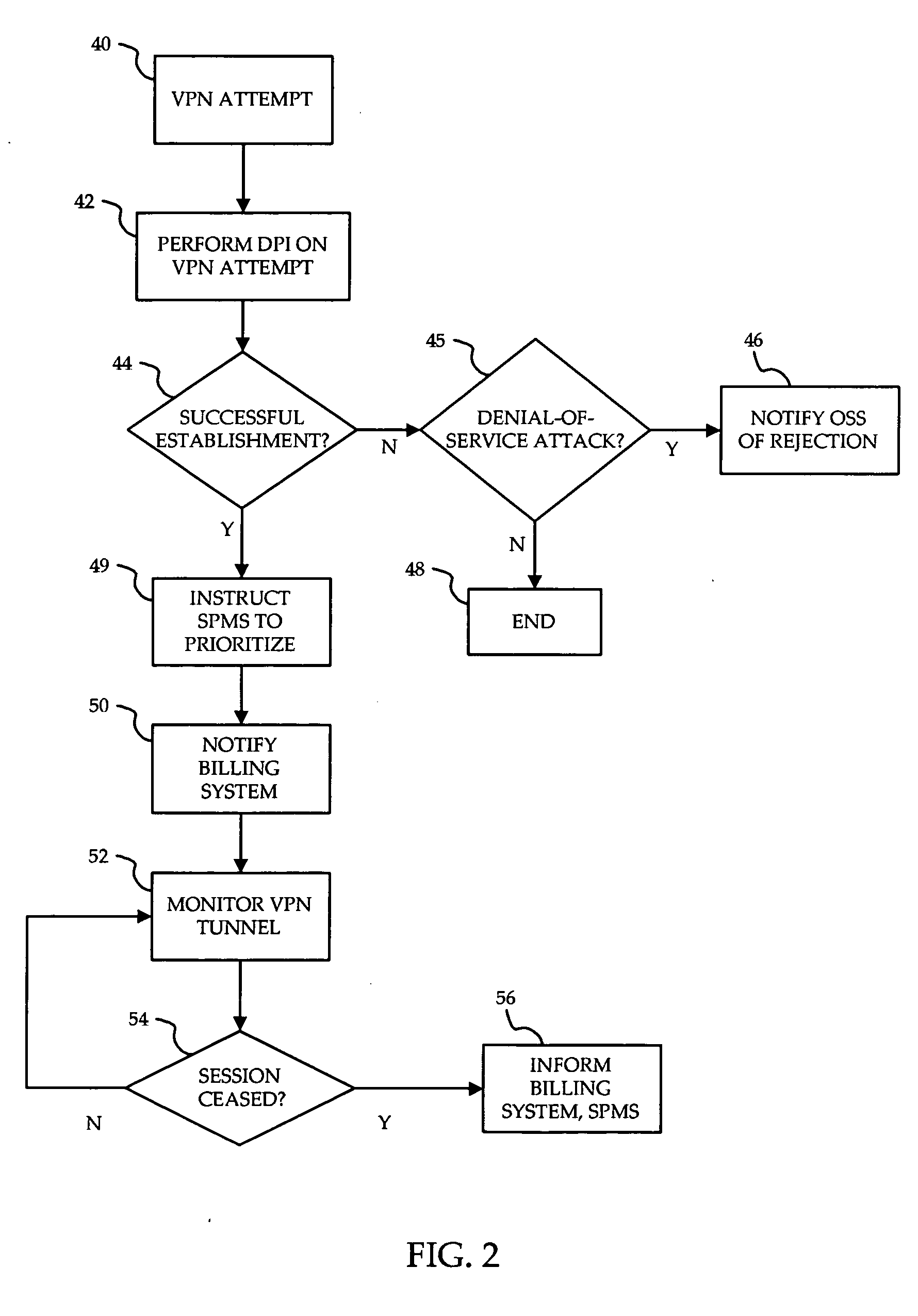
A method is provided for ensuring that specific traffic flows are adequately prioritized in a public packet communication network even when the network is heavily congested. Per-flow QoS capability is added to VPN tunnels. Connection requests are routed through a specific port in an access provider's network to designated VPN gateway. Deep packet inspection is performed on traffic through the port in an attempt to determine whether the connection request was accepted. If the connection request was accepted, the traffic flows associated with that session may be given a specific priority of QoS level when transiting a packet access network.
Owner:ALCATEL LUCENT SAS
Method and Apparatus for Deep Packet Inspection for Network Intrusion Detection
ActiveUS20080201772A1Hardware monitoringMultiple digital computer combinationsComputer hardwareData stream
In a method of determining whether a data stream includes unauthorized data, the data stream is analyzed using a hardware filter to detect a presence of one or more of a first set of patterns in the data stream. It is determined whether a packet in the data stream belongs to one of a plurality of data flows to be further inspected based on the analysis of the data stream by the hardware filter. A set of rules is applied to the packet to produce rule match status data if it is determined that the packet belongs to one of the plurality of data flows to be further inspected. The packet is analyzed to determine if the packet includes unauthorized data using software stored on a computer-readable medium and implemented on a processor if the rule match status data indicates that the packet potentially includes unauthorized data.
Owner:MARVELL ISRAEL MISL
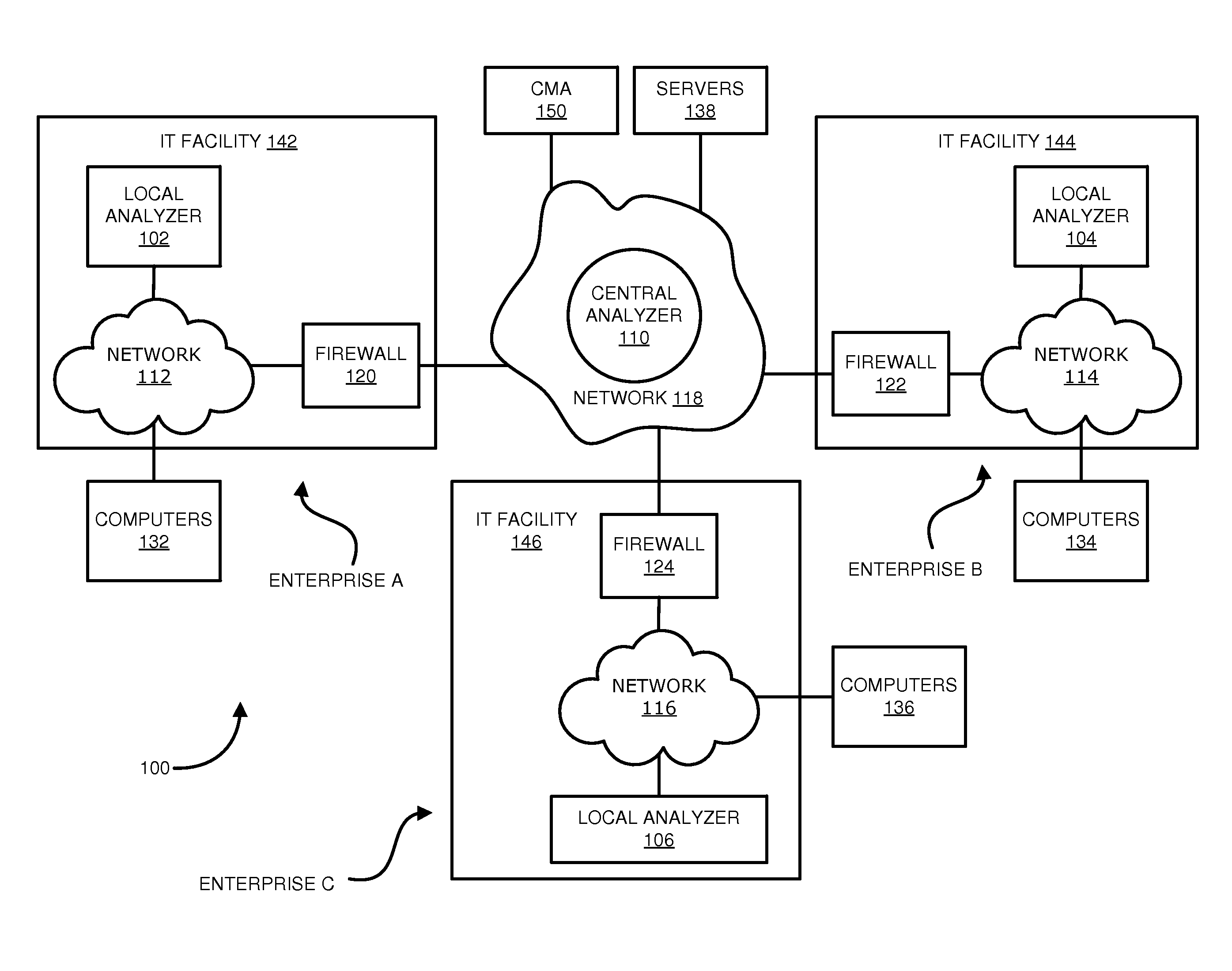
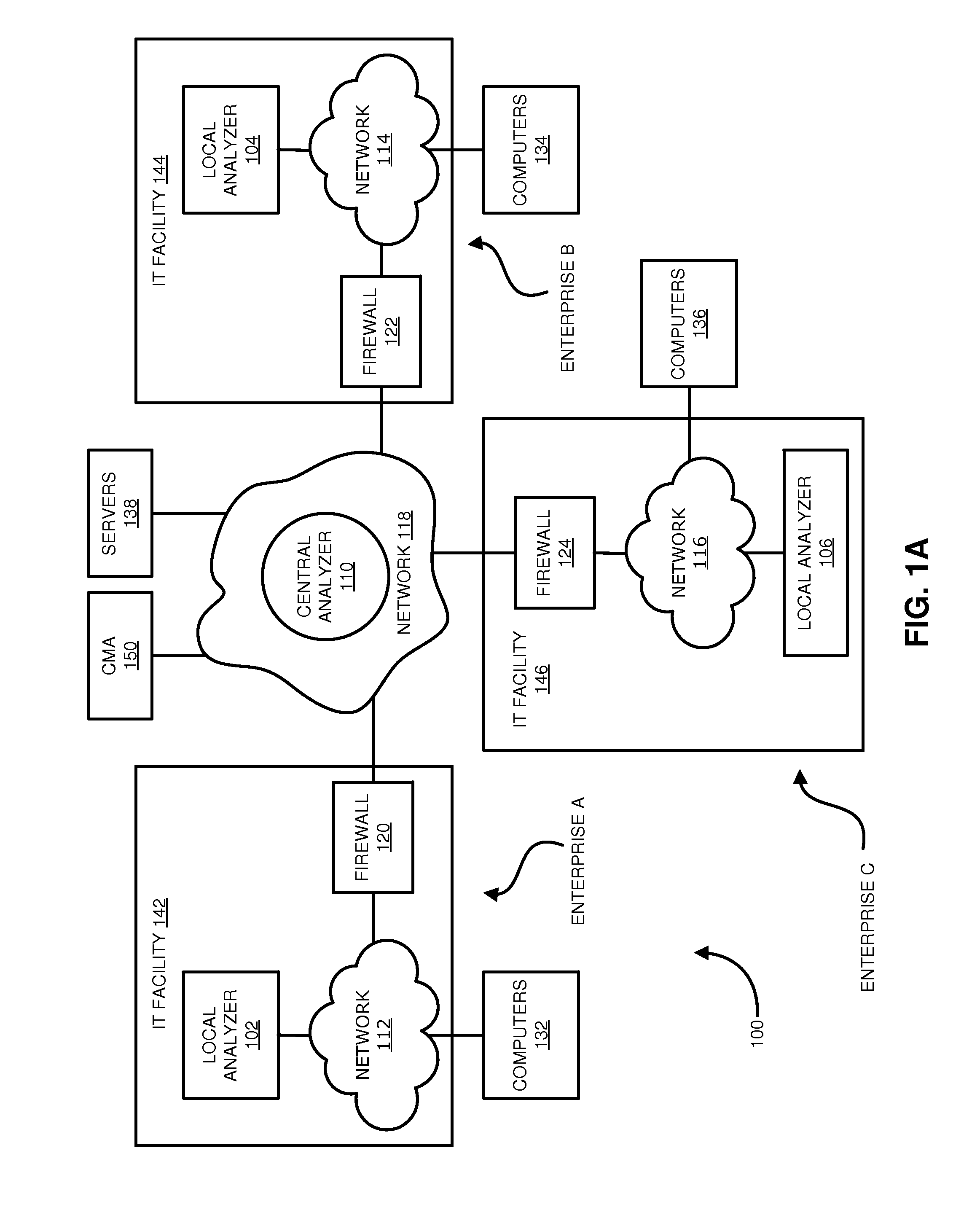
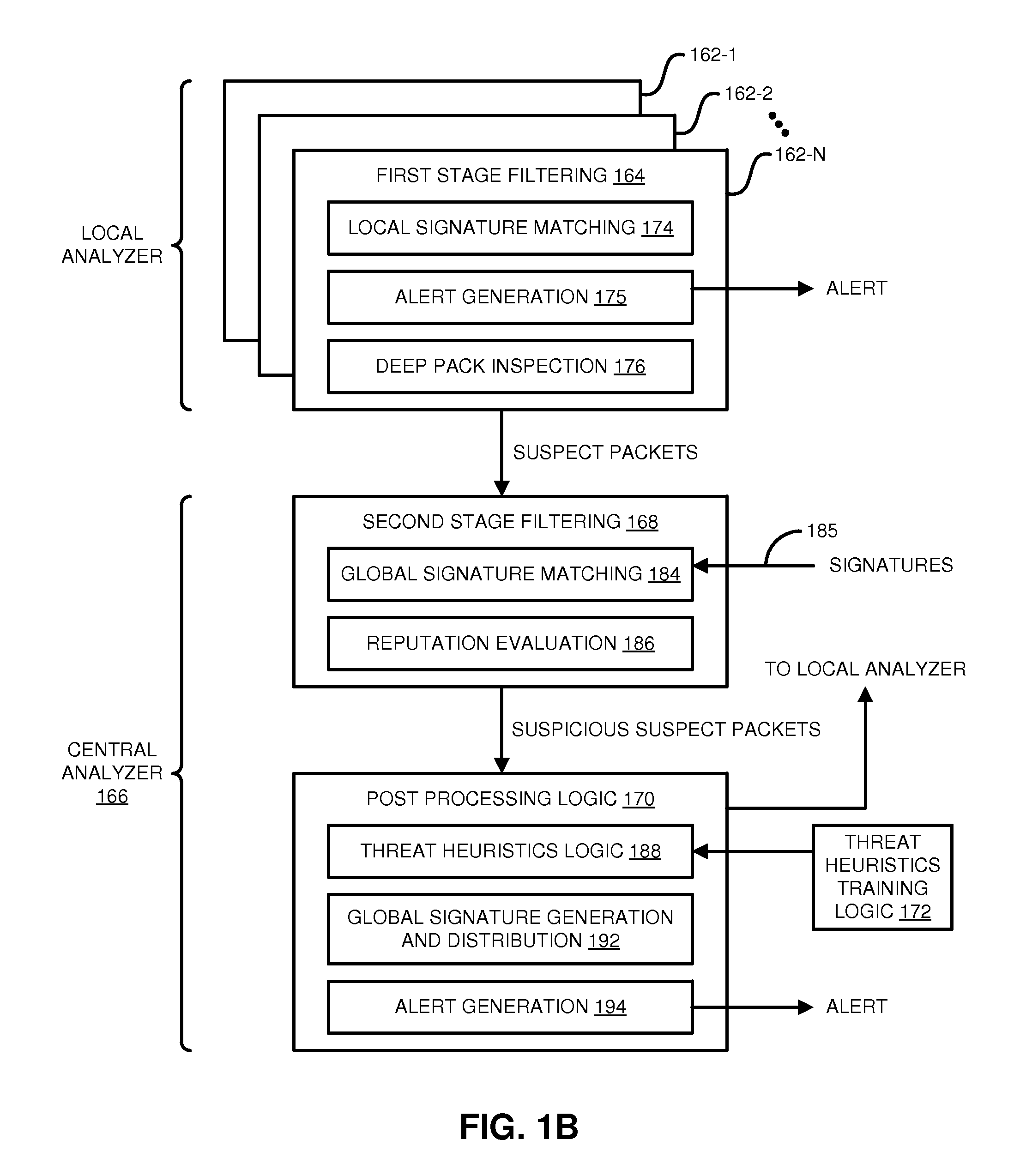
Distributed systems and methods for automatically detecting unknown bots and botnets
ActiveUS9430646B1Error detection/correctionPlatform integrity maintainanceOutbound communicationCommand and control
Techniques may automatically detect bots or botnets running in a computer or other digital device by detecting command and control communications, called “call-backs,” from malicious code that has previously gained entry into the digital device. Callbacks are detected using a distributed approach employing one or more local analyzers and a central analyzer. The local analyzers capture packets of outbound communications, generate header signatures, and analyze the captured packets using various techniques. The techniques may include packet header signature matching against verified callback signatures, deep packet inspection. The central analyzer receives the header signatures and related header information from the local analyzers, may perform further analysis (for example, on-line host reputation analysis); determines using a heuristics analysis whether the signatures correspond to callbacks; and generally coordinates among the local analyzers.
Owner:FIREEYE SECURITY HLDG US LLC
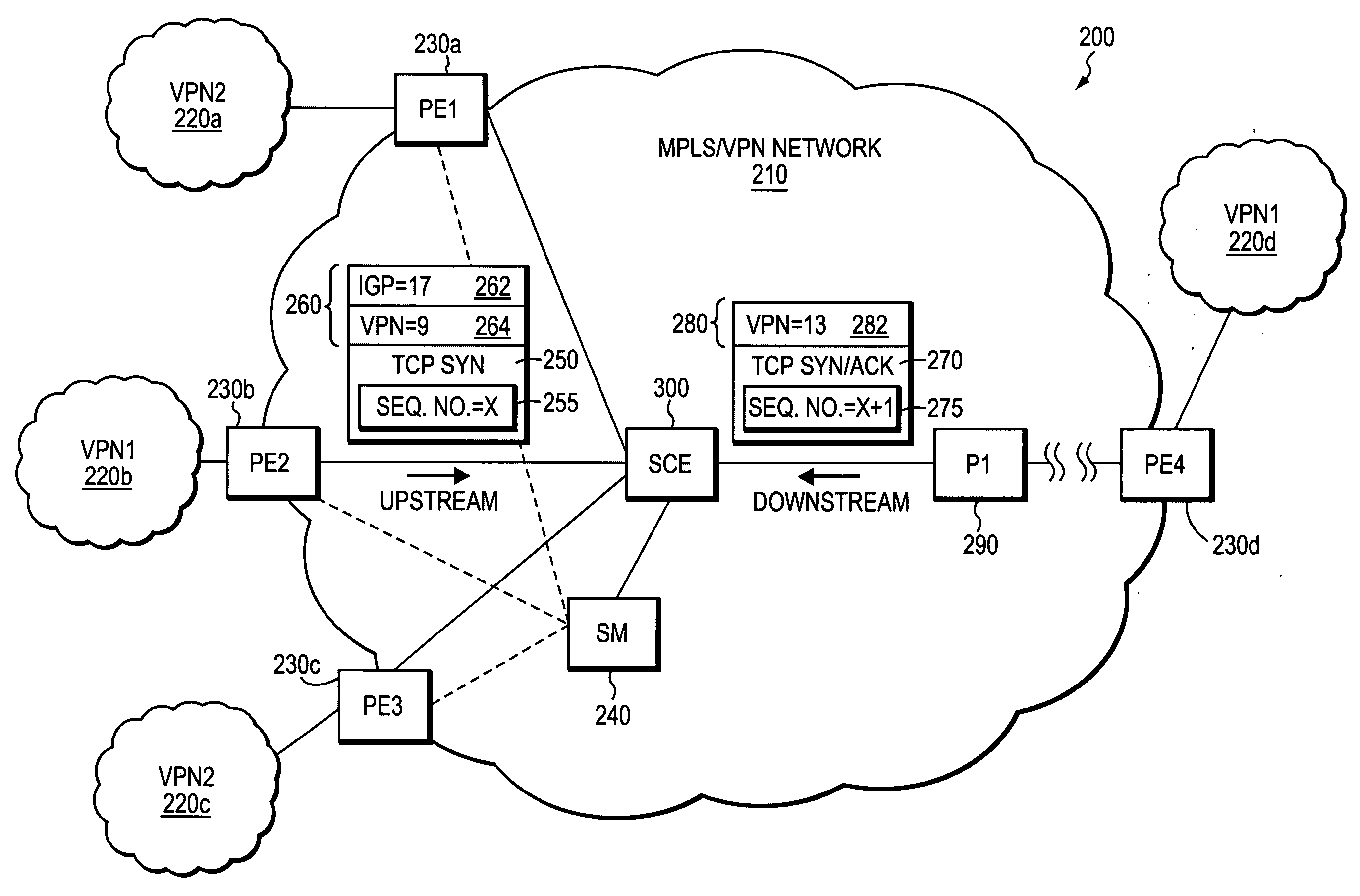
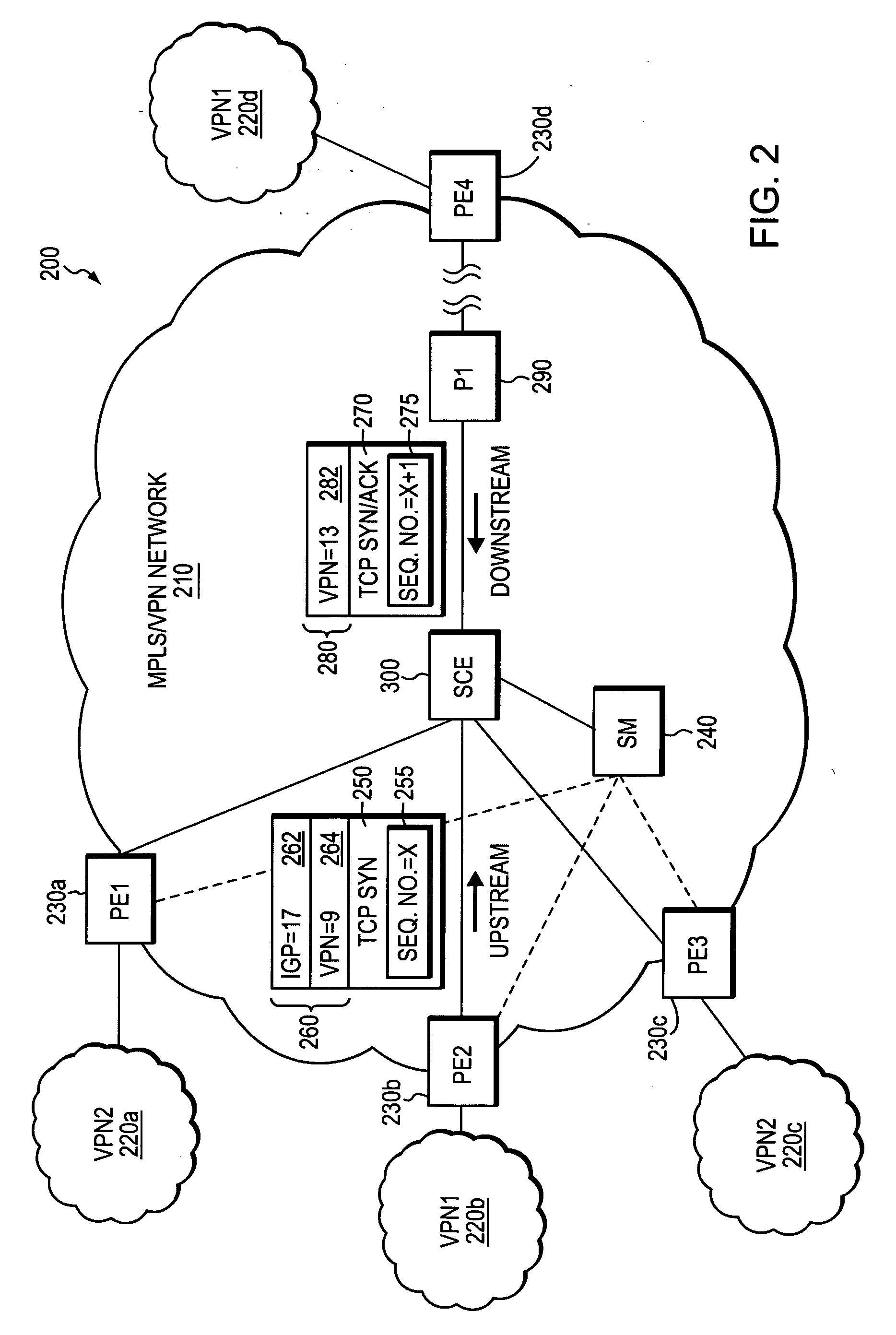
Method and apparatus for self-learning of VPNS from combination of unidirectional tunnels in MPLS/VPN networks
A technique is provided for implementing deep-packet inspection (DPI) services in a MPLS / VPN configured computer network. The technique employs a novel self-learning algorithm that analyzes data packets belonging to different unidirectional tunnels in the MPLS / VPN network and determines whether the analyzed data packets transport data in the same VPN. If so, the unidirectional tunnels containing the analyzed data packets are associated with a common layer-2 identification (L2ID) value. Unlike conventional flow-classification procedures, the inventive technique classifies a data packet by first associating the data packet with a L2ID value and then classifying the packet as belonging to a particular data flow based on a novel 6-tuple consisting of a conventional 5-tuple plus the packet's L2ID value. Because unidirectional tunnels corresponding to the same application data flow transport data packets having the same set of 6-tuple values, DPI services can apply application-level policies to classified data packets consistent with their 6-tuple flow classifications.
Owner:CISCO TECH INC
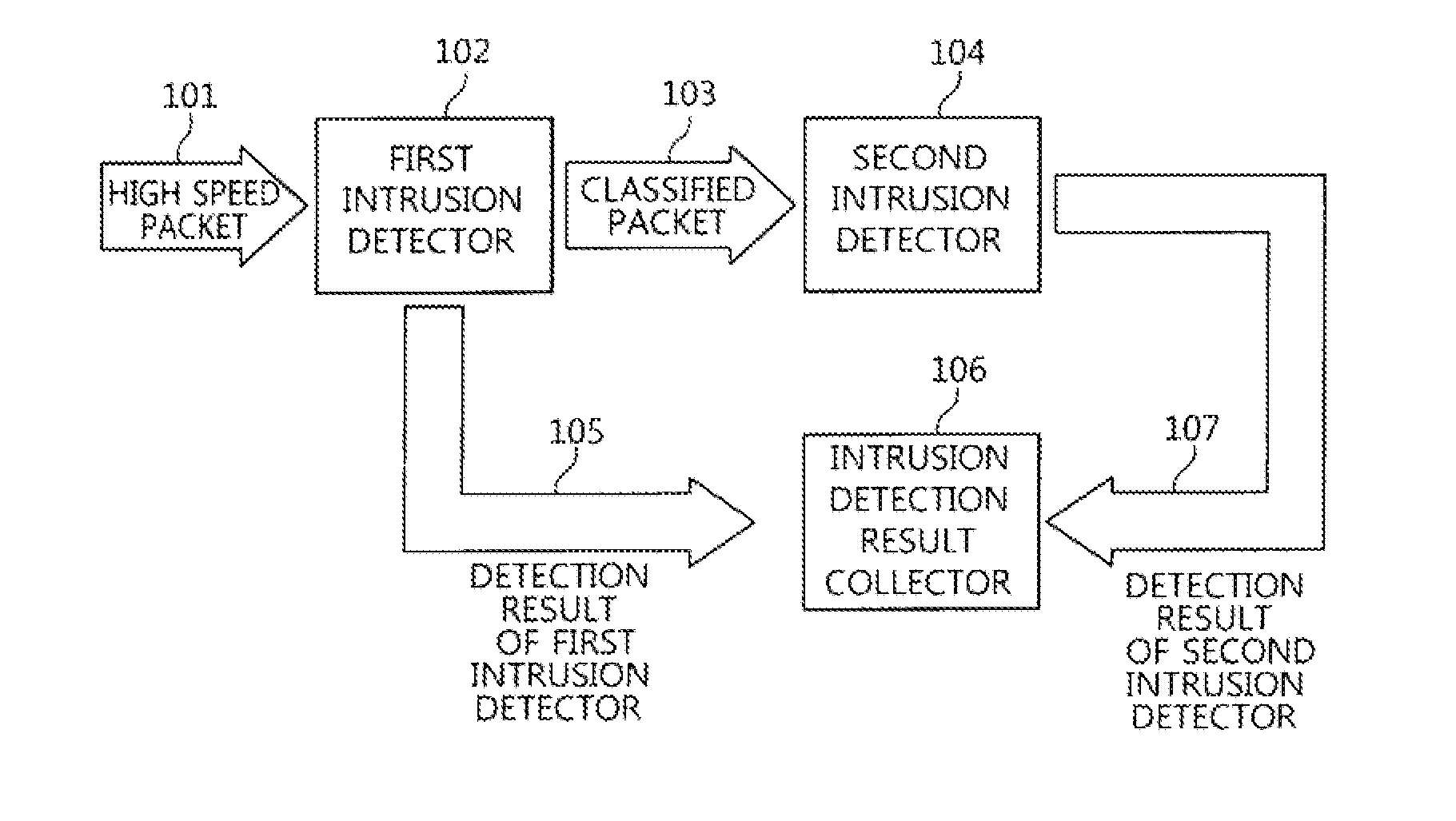
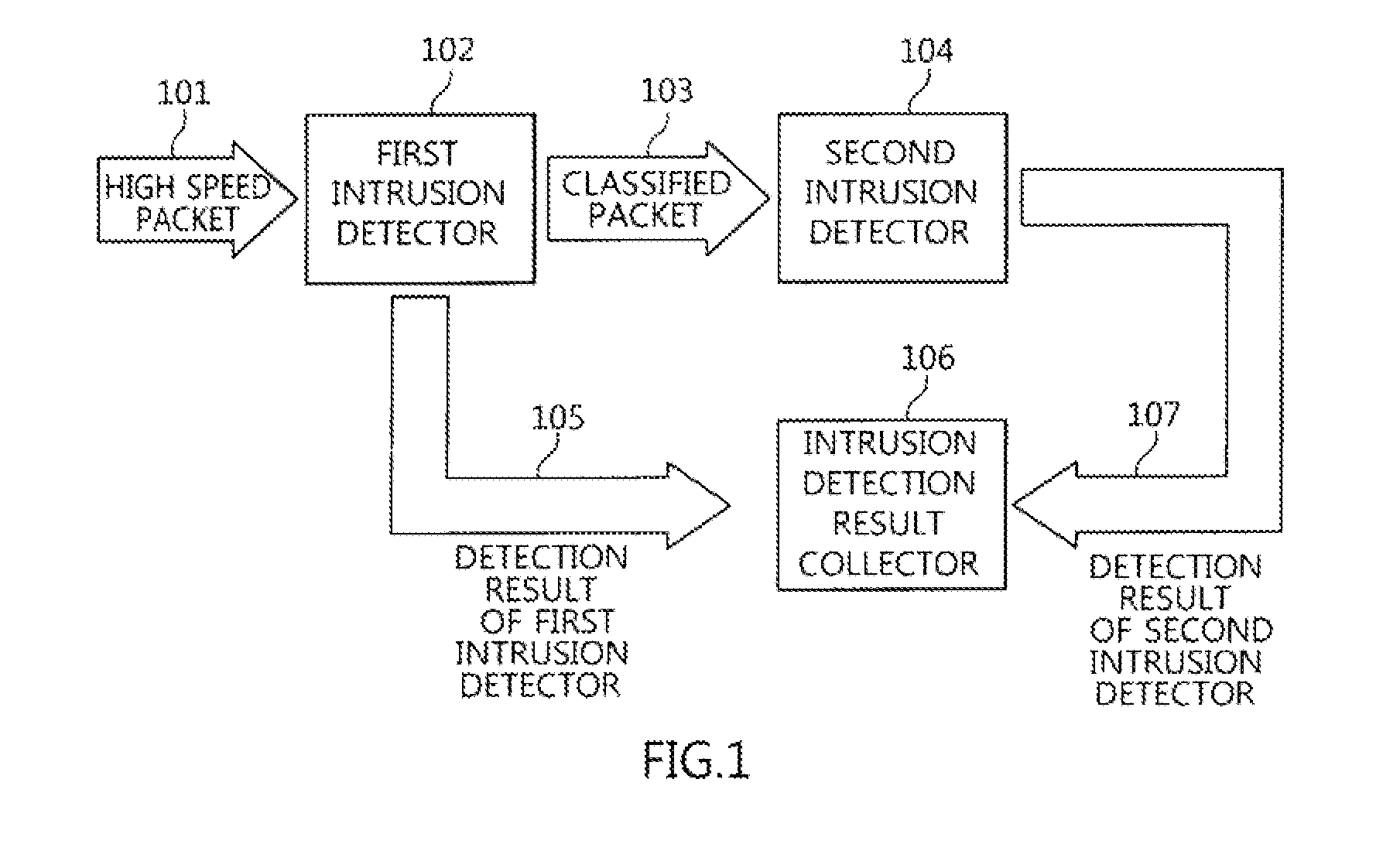
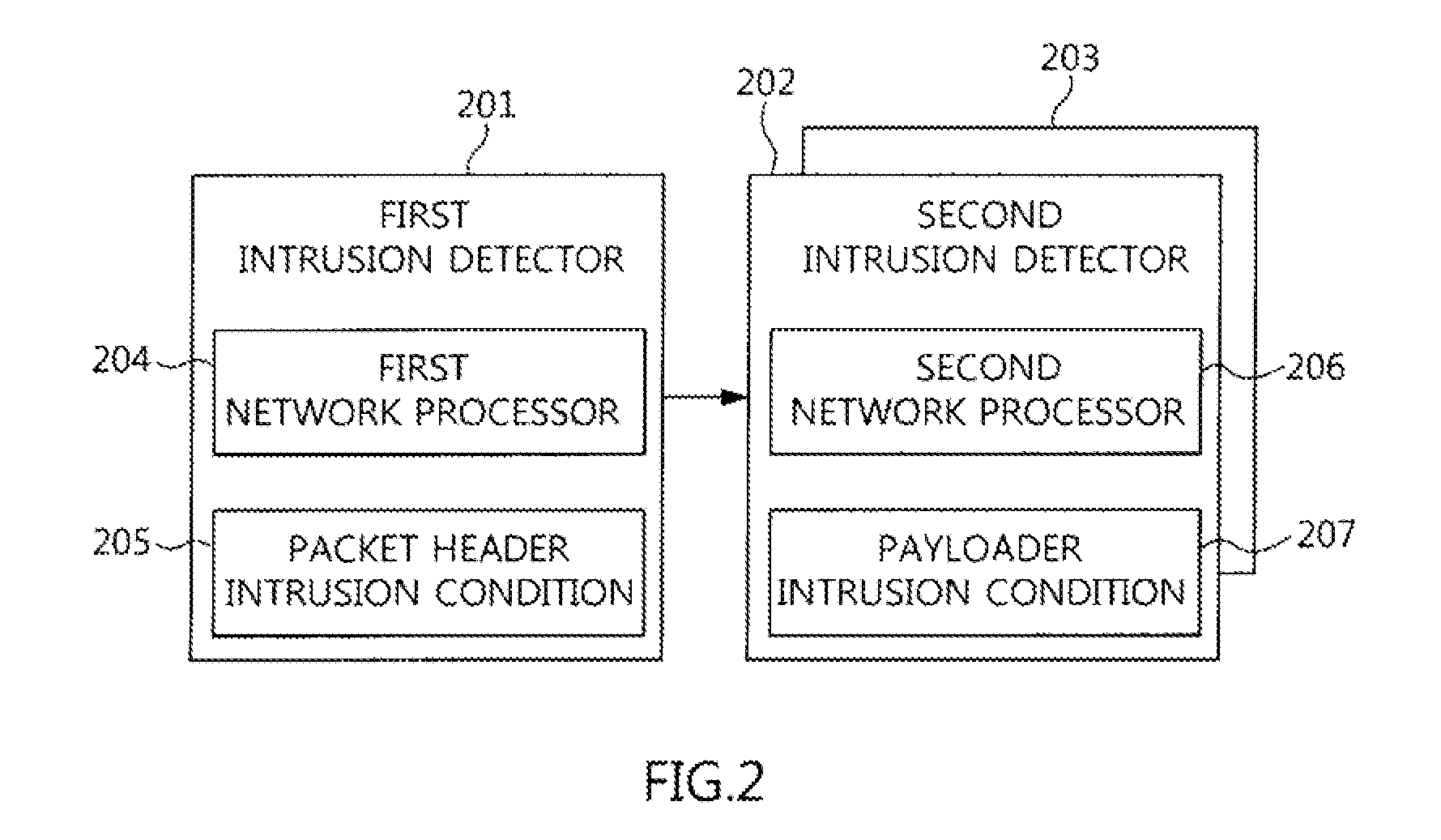
Two-stage intrusion detection system for high-speed packet processing using network processor and method thereof
ActiveUS20130160122A1Memory loss protectionData taking preventionNetwork processorDistributed computing
A system and method for detecting network intrusion by using a network processor are provided. The intrusion detection system includes: a first intrusion detector, configured to use a first network processor to perform intrusion detection on layer 3 and layer 4 of a protocol field among information included in a packet header of a packet transmitted to the intrusion detection system, and when no intrusion is detected, classify the packets according to stream and transmit the classified packets to a second intrusion detector; and a second intrusion detector, configured to use a second network processor to perform intrusion detection through deep packet inspection (DPI) for the packet payload of the packets transmitted from the first intrusion detector. Thereby, intrusion detection for high-speed packets can be performed in a network environment.
Owner:ELECTRONICS & TELECOMM RES INST
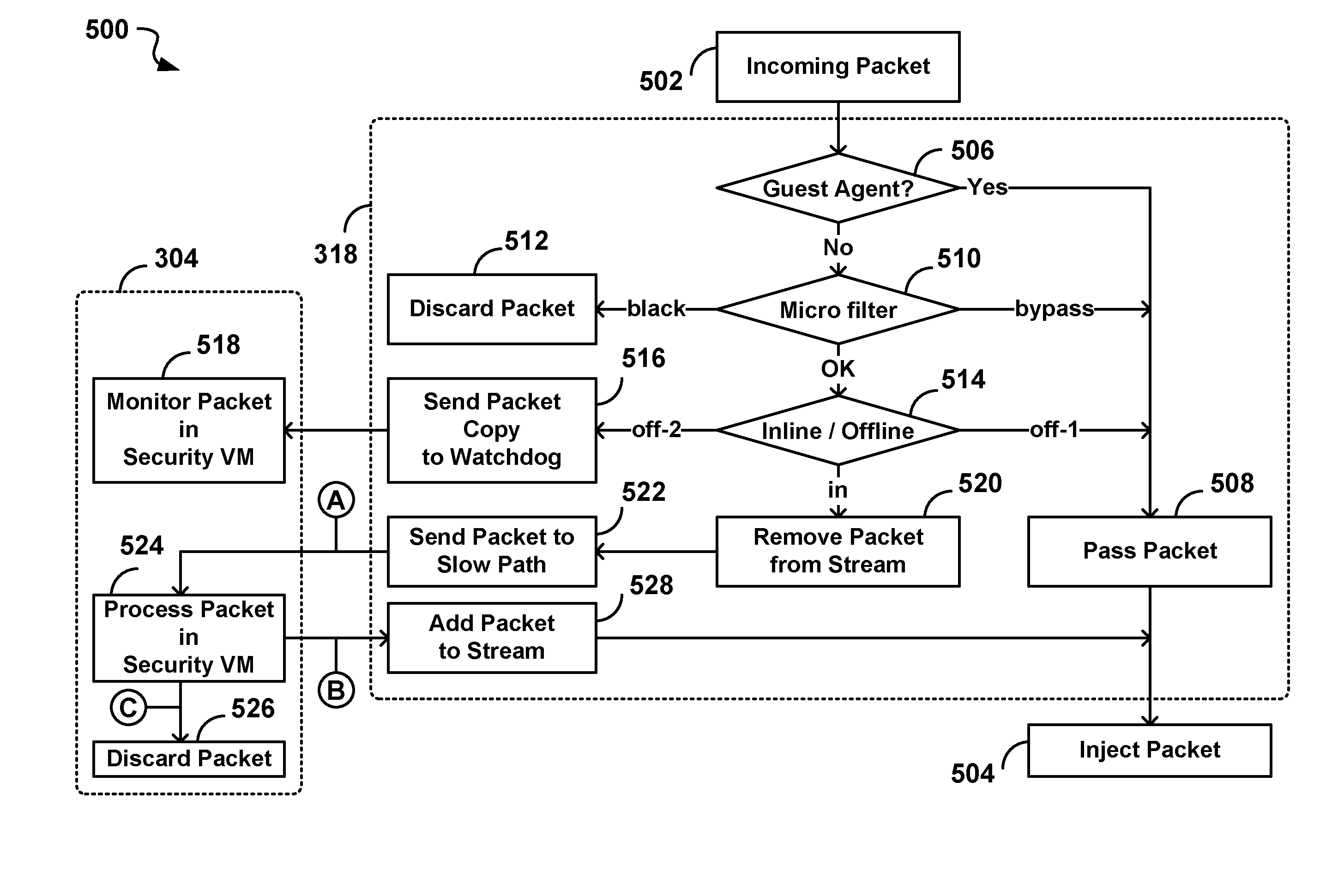
System and method for intelligent coordination of host and guest intrusion prevention in virtualized environment
A distributed and coordinated security system providing intrusion-detection and intrusion-prevention for the virtual machines (VMs) in a virtual server is described. The virtualization platform of the virtual server is enhanced with networking drivers that provide a “fast path” firewall function for pre-configured guest VMs that already have dedicated deep packet inspection security agents installed. A separate security VM is deployed to provide virtual security agents providing deep packet inspection for non pre-configured guest VMs. The network drivers are then configured to intercept the data traffic of these guest VMs and route it through their corresponding virtual security agents, thus providing a “slow-path” for intrusion detection and prevention.
Owner:TREND MICRO INC
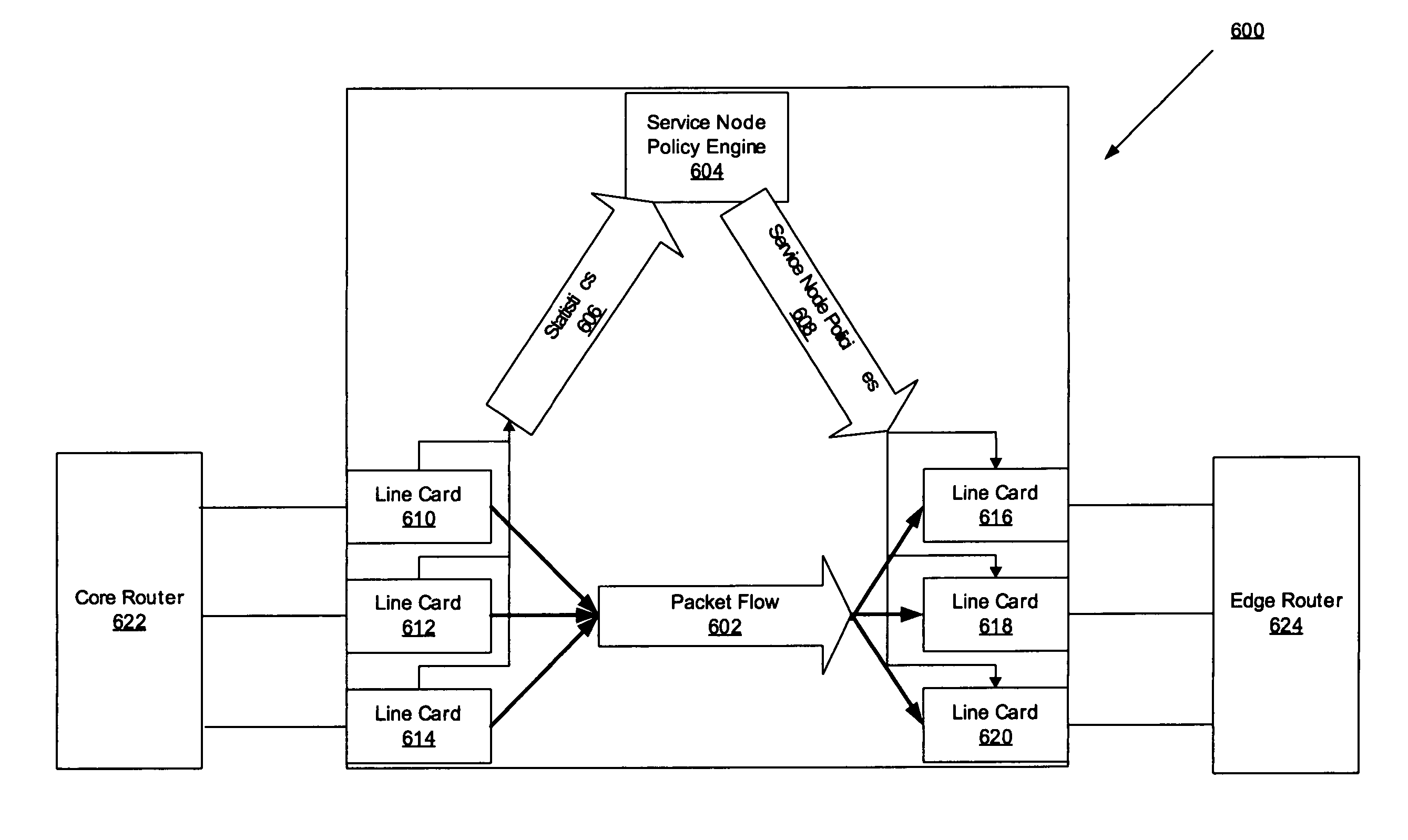
Network element architecture for deep packet inspection
A method and apparatus for an application aware traffic shaping service node architecture is described. One embodiment of the invention, the service node architecture includes a set of one or more line cards, a set of one or more processor cards and a full mesh communication infrastructure coupling the sets of line and processor cards. Each link coupling the sets of line and processor cards is of equal capacity. A line card includes a physical interface and a set of one or policy network processors, with the network processors performing deep packet inspection on incoming traffic and shaping outgoing traffic. Processors cards include a set of one or more policy generating processors. According to another embodiment of the invention, the service node generates a set of statistics based on the incoming traffic and continually updates, in real-time, traffic shaping policies based on the set of statistics.
Owner:TELLABS COMM CANADA
Network element architecture for deep packet inspection
ActiveUS20060233101A1Equal capacityError preventionFrequency-division multiplex detailsTraffic capacityNetwork architecture
A method and apparatus for an application aware traffic shaping service node architecture is described. One embodiment of the invention, the service node architecture includes a set of one or more line cards, a set of one or more processor cards and a full mesh communication infrastructure coupling the sets of line and processor cards. Each link coupling the sets of line and processor cards is of equal capacity. A line card includes a physical interface and a set of one or policy network processors, with the network processors performing deep packet inspection on incoming traffic and shaping outgoing traffic. Processors cards include a set of one or more policy generating processors. According to another embodiment of the invention, the service node generates a set of statistics based on the incoming traffic and continually updates, in real-time, traffic shaping policies based on the set of statistics.
Owner:TELLABS COMM CANADA
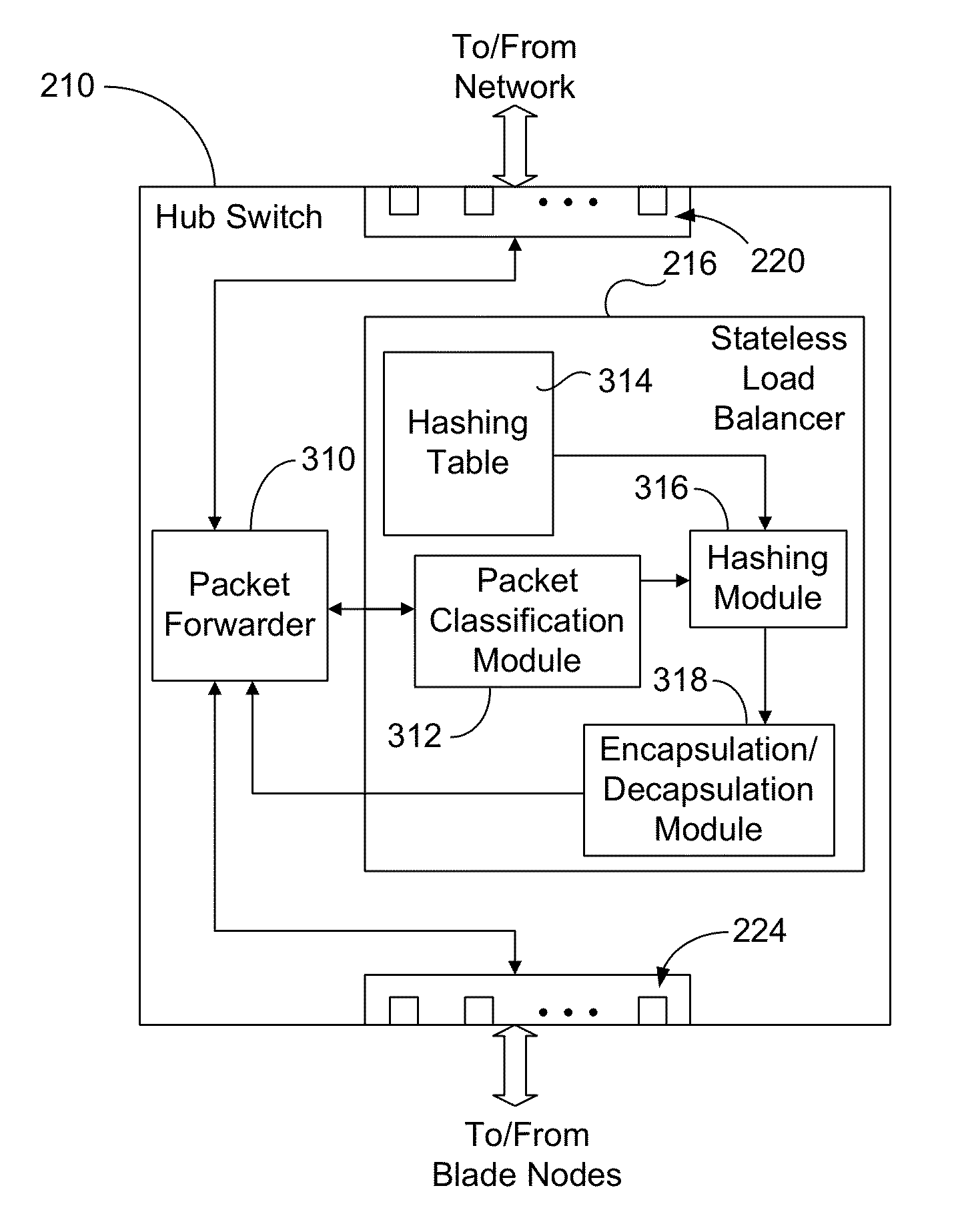
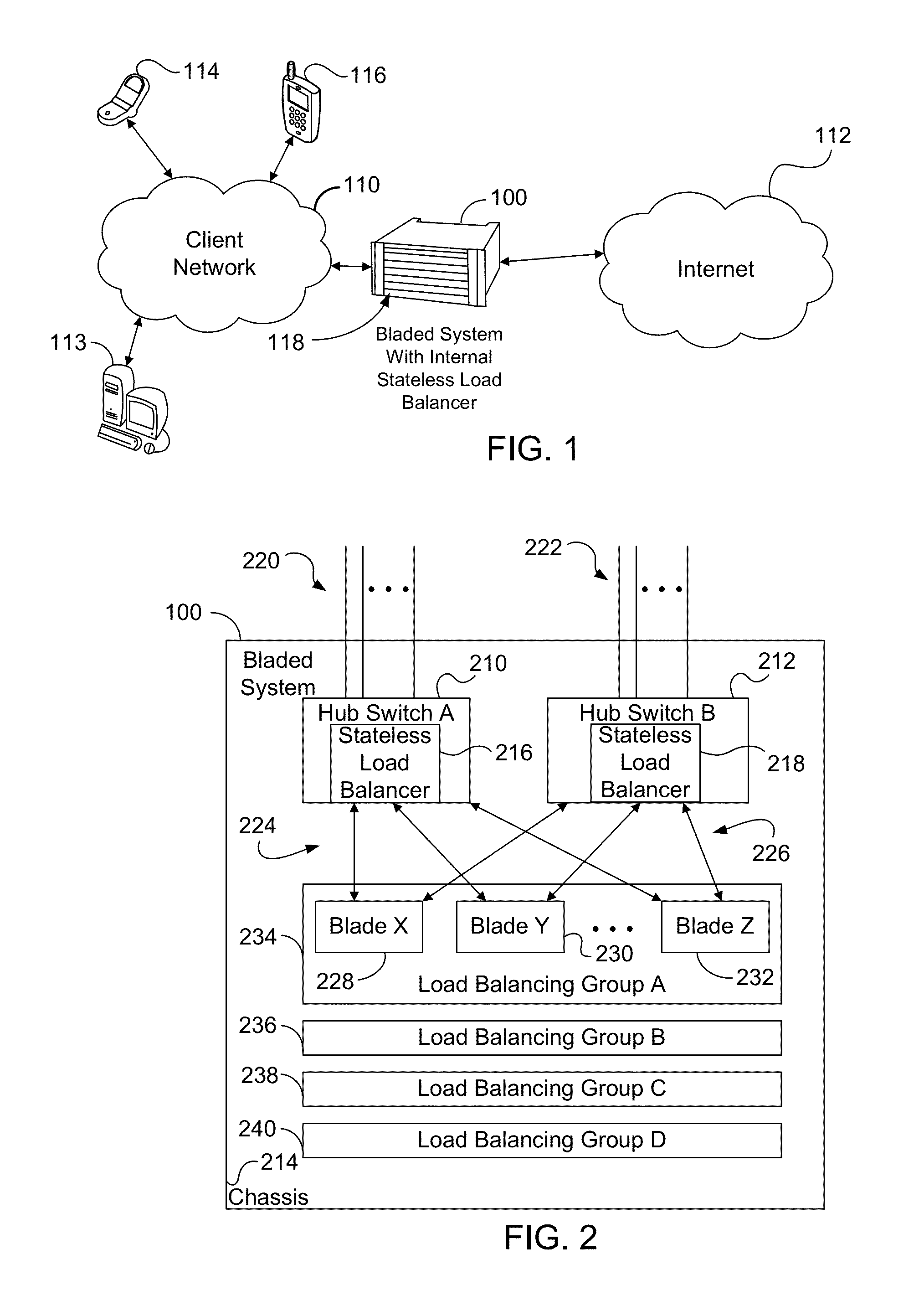
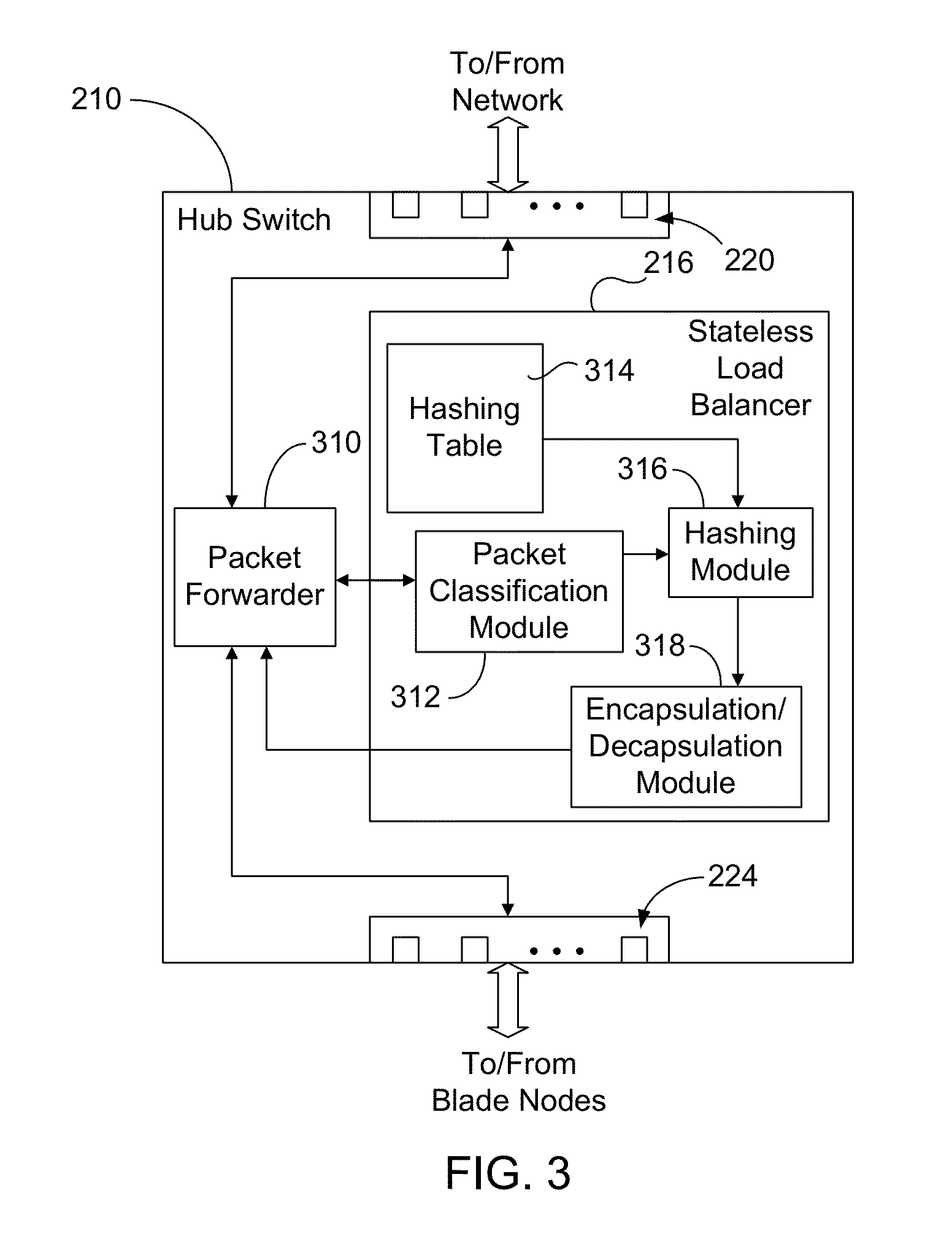
Stateless load balancer in a multi-node system for transparent processing with packet preservation
Stateless load balancing of network packets within a system avoids detection by a network client or end user for deep packet inspection or other bump-in-the-wire applications. At least one header field of a received packet is used in generating a hash value. The hash value is used to identify a processing resource within the system for processing the received packet. Before being sent to the identified resource, the received packet is encapsulated with a new header that includes an indication of ingress port. The encapsulation does not modify the original packet. On a return path from the identified processing resource, the ingress port is determined from the encapsulated packet, the encapsulated packet is decapsulated to obtain a recovered packet that is identical to the received packet, and the recovered packet is forwarded to the network through an egress port as determined from the recovered ingress port.
Owner:RADISYS CORP
In-band DPI application awareness propagation enhancements
Various exemplary embodiments are a method and related device and computer-readable medium including one or more of the following: receiving a packet sent from the source node to the destination node; associating the packet with an active flow by accessing information in the packet; performing deep packet inspection (DPI) to identify an application associated with the active flow; associating application-identifying information with the packet; forwarding the packet including the application-identifying information towards the destination node; and performing application-specific processing at a downstream device on at least one packet belonging to the active flow, the downstream device identifying the application associated with the active flow by extracting the application-identifying information from the packet.
Owner:ALCATEL LUCENT SAS
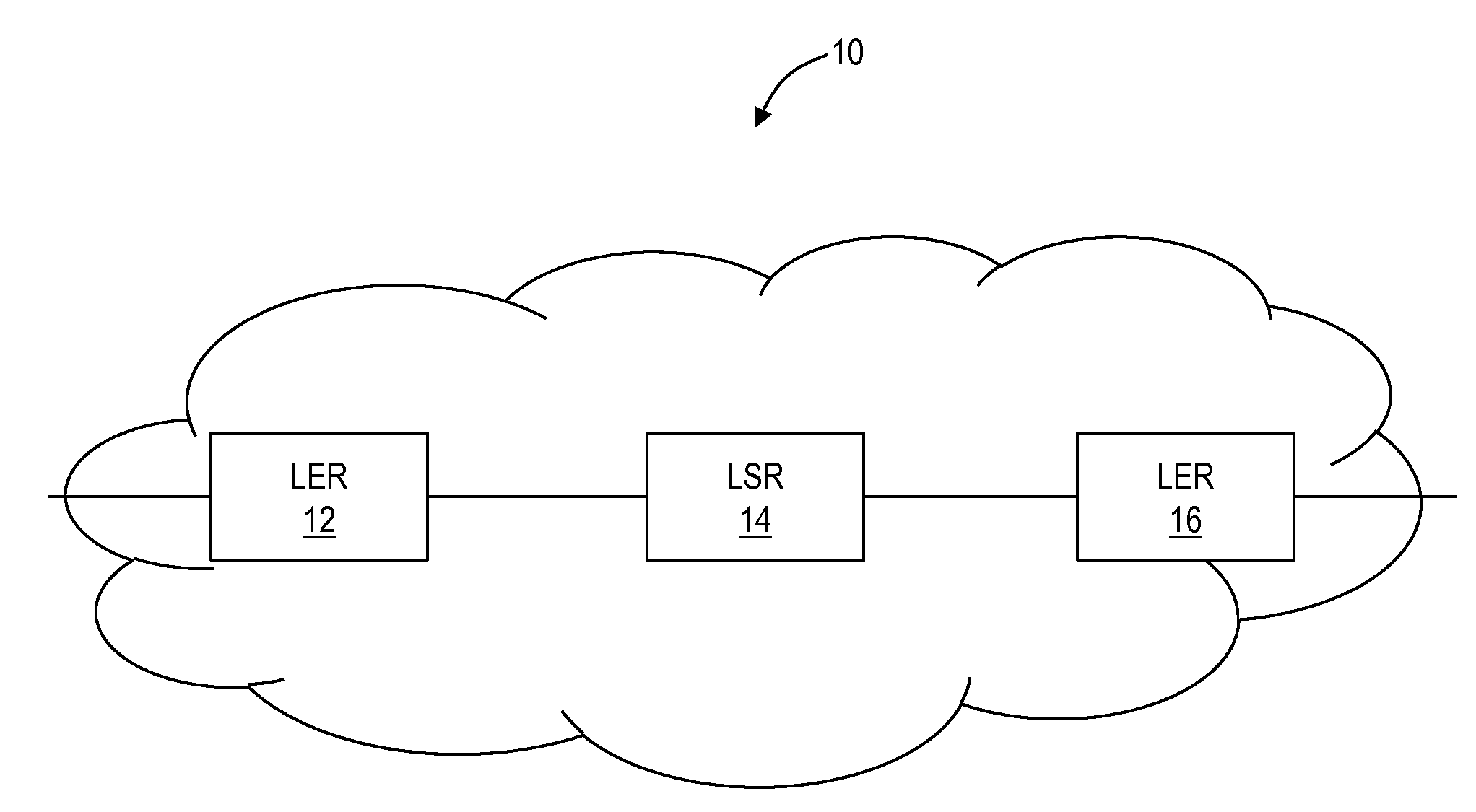
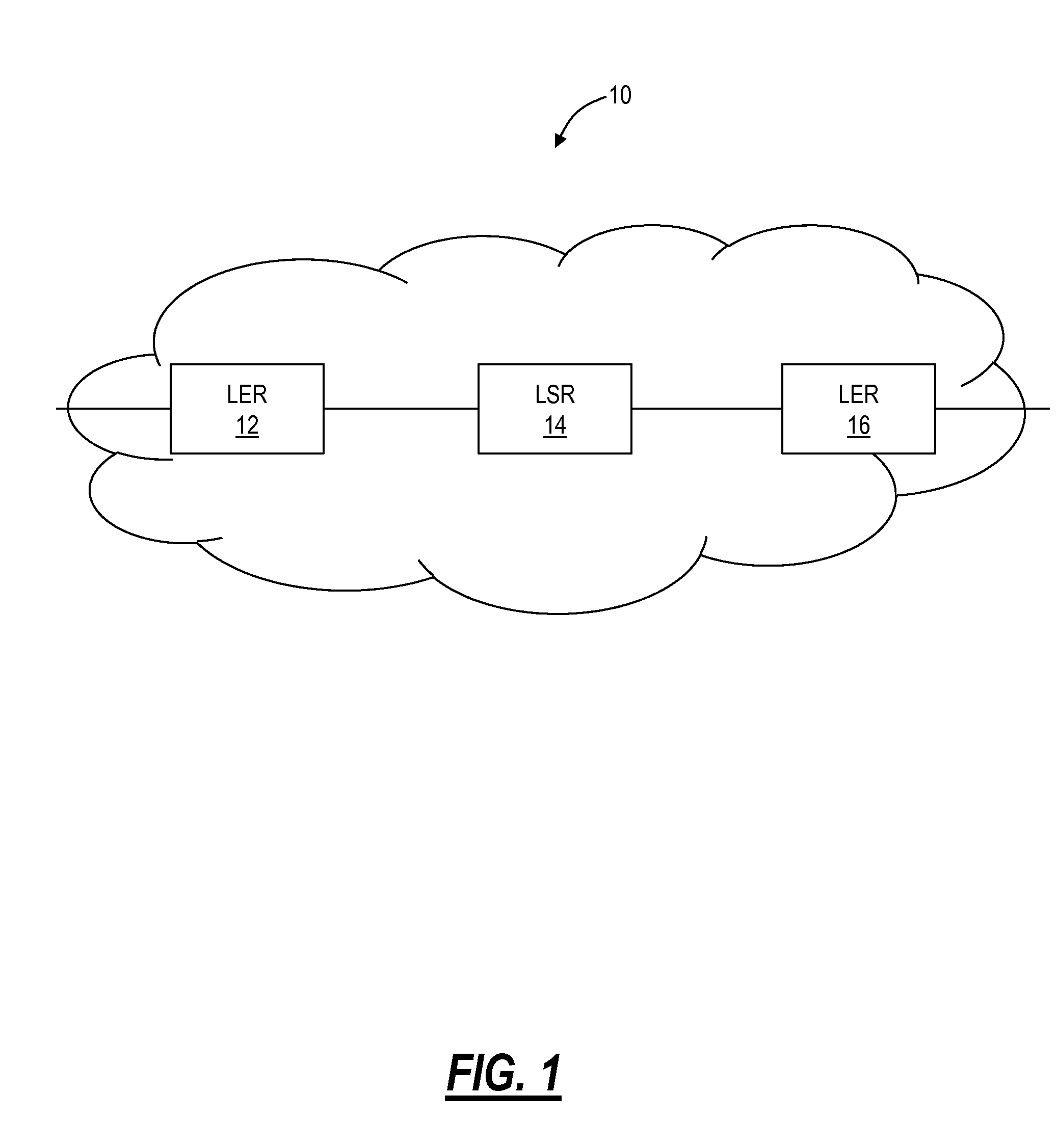
Source identification preservation in multiprotocol label switching networks
ActiveUS20140177638A1Simplify operating proceduresReduce complexityData switching by path configurationMultiprotocol Label SwitchingProtocol for Carrying Authentication for Network Access
A Multiprotocol Label Switching (MPLS) method, a MPLS network element, and a MPLS network include receiving a packet destined for a destination node at a source node in an MPLS network; pushing an identifier in an MPLS label on an MPLS label stack associated with the packet, wherein the identifier denotes the source node as the source of the packet and is pushed prior to any other MPLS labels on the MPLS stack; pushing one or more labels on the MPLS stack indicative of a route of the packet to the destination node; and transmitting the packet from the source node into the MPLS network. The identifier is located at the bottom of the MPLS stack thereby being a last item popped in the MPLS stack at the destination node, and the identifier can be used for updating OAM data efficiently without requiring deep packet inspection.
Owner:CIENA
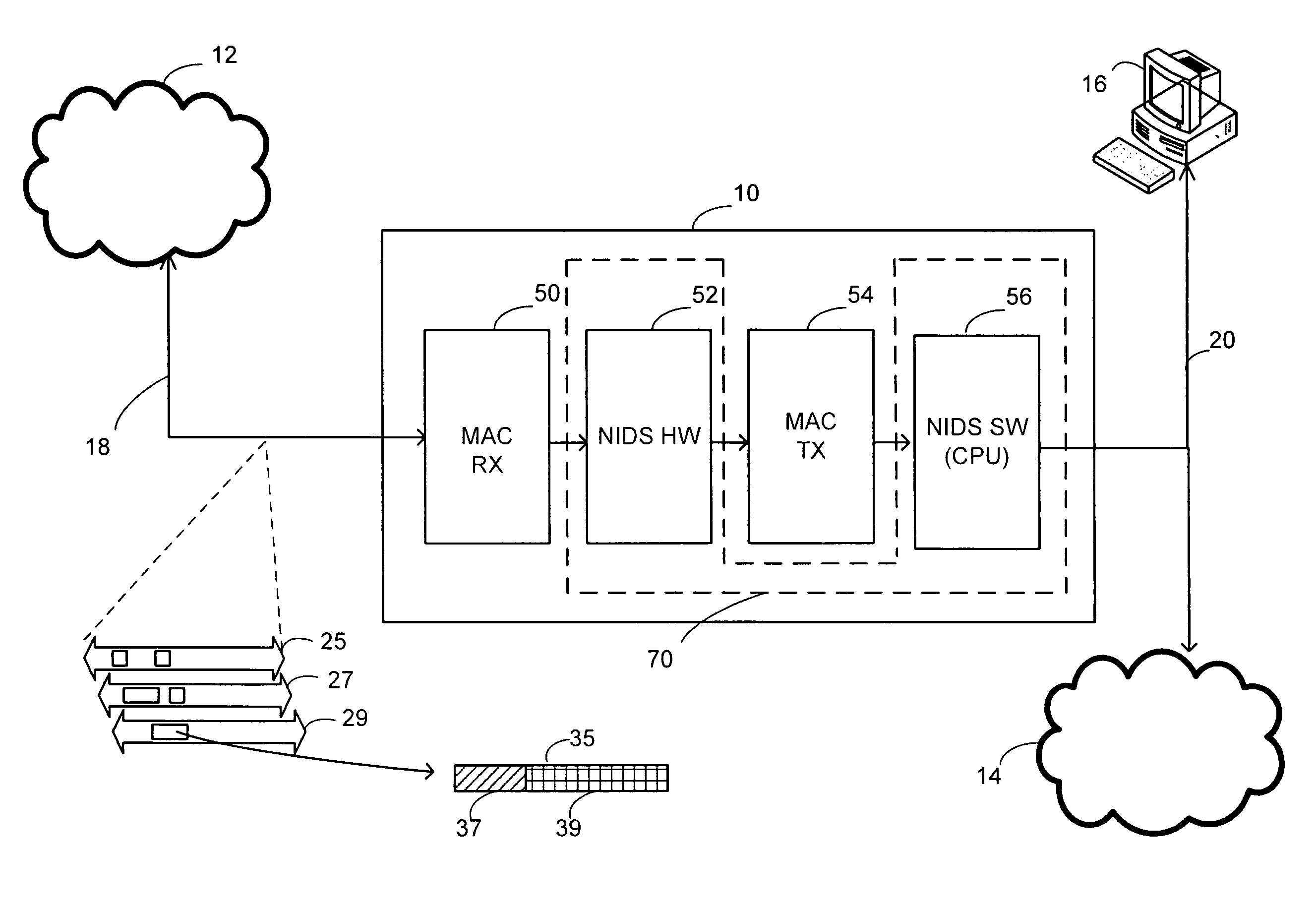
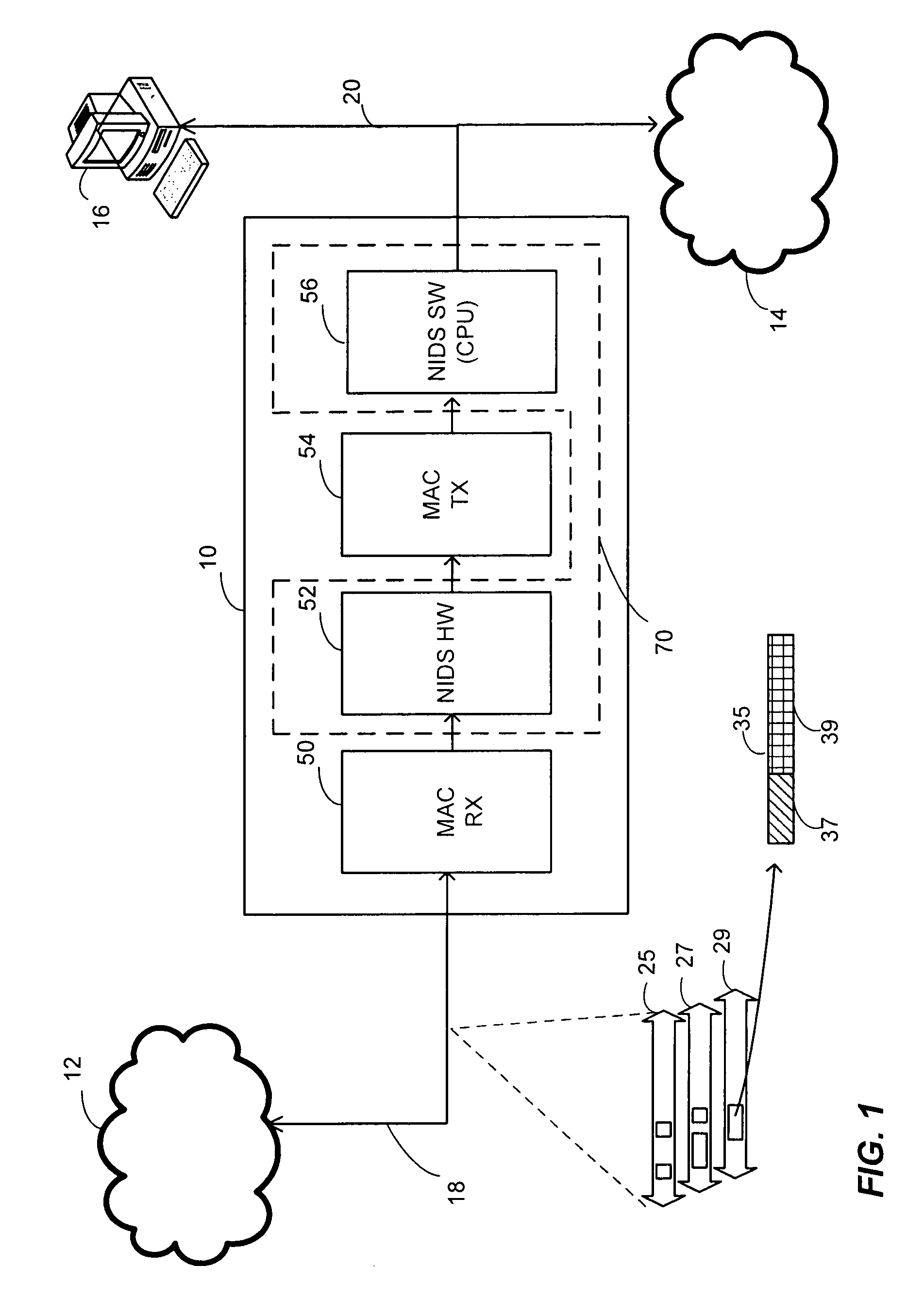
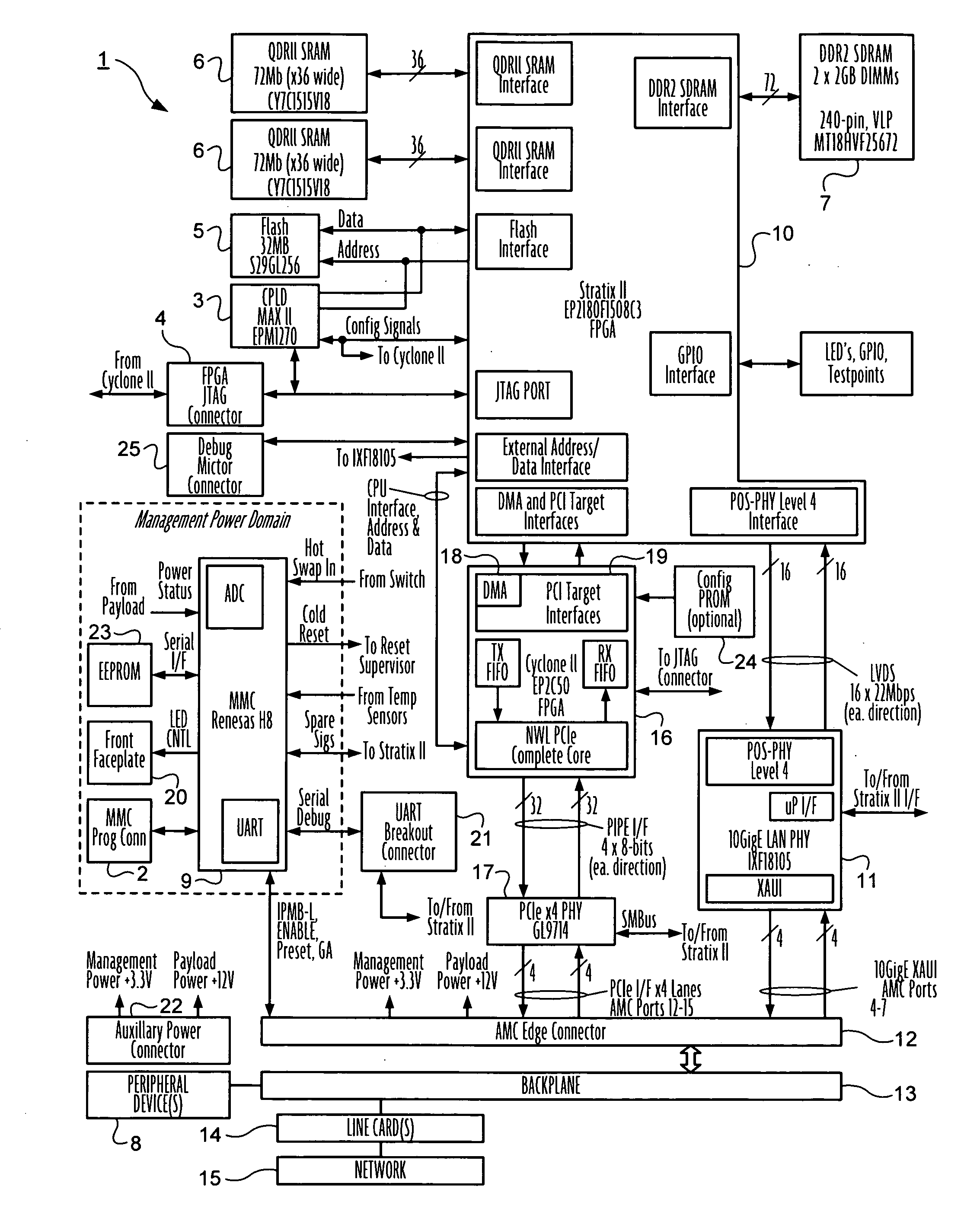
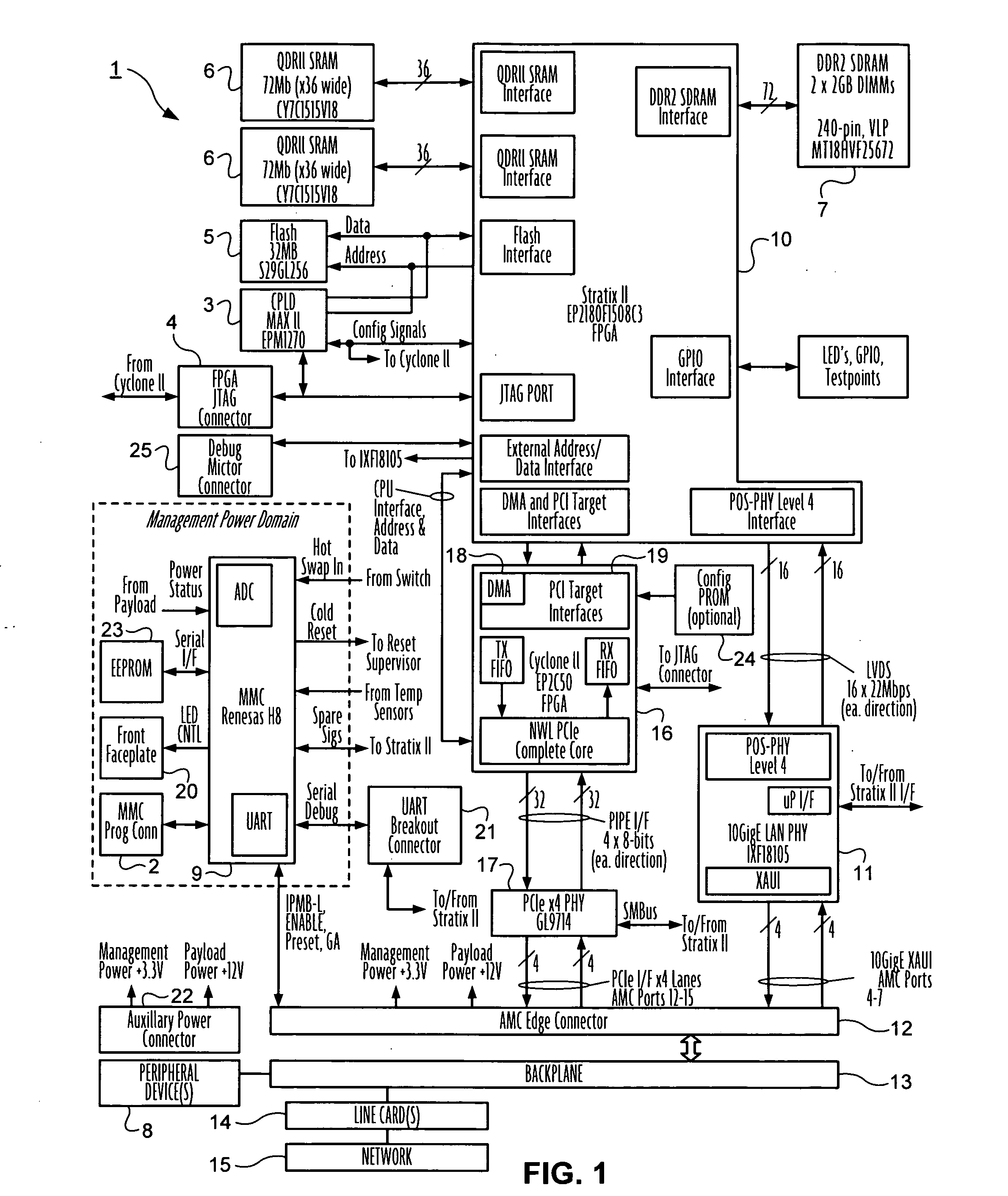
Advanced mezzanine card for digital network data inspection
Telecommunications computing apparatus and methods for performing deep packet inspection and other processing of data packets traversing high speed digital networks (15) such as the Internet. An apparatus embodiment of the present invention comprises a reconfigurable logic device (10); coupled to the reconfigurable logic device (10), means (11) for coupling the reconfigurable logic device (10) to an external digital network (15); and coupled to the reconfigurable logic device (10), an interface (16-19) for coupling the reconfigurable logic device (10) to at least one peripheral device (8) that is not part of said external digital network (15).
Owner:GLOBAL VELOCITY
Integrated intrusion detection services
ActiveUS7076803B2Improve securityEasy to detectMemory loss protectionError detection/correctionTraffic capacityPlaintext
Improvements in intrusion detection are disclosed by providing integrated intrusion detection services. Preferably, these services are integrated into a system or server that is the potential target of attack. Stack-based security processing is leveraged for access to cleartext data within the layers of the protocol stack. Layer-specific attacks may therefore be processed efficiently. Evaluation of incoming traffic for an intrusion is preferably performed only after an error condition of some type has been detected. This approach reduces the overhead of intrusion detection by reducing the number of packets to be inspected, and at the same time allows more efficient packet inspection through use of context-specific information that may be used to direct the inspection to particular candidate attacks. Generic attack class capability is also disclosed. Intrusion detection policy information may be used to direct the actions to be taken upon detecting an attack.
Owner:TREND MICRO INC
System and method for prioritization of traffic through internet access network
InactiveUS20070153798A1Avoid allocation problemsReduce network congestionData switching by path configurationAccess networkInternet access
A method is provided for ensuring that specific traffic flows are adequately prioritized in a public packet communication network even when the network is heavily congested. Per-flow QoS capability is added to VPN tunnels. Connection requests are routed through a specific port in an access provider's network to designated VPN gateway. Deep packet inspection is performed on traffic through the port in an attempt to determine whether the connection request was accepted. If the connection request was accepted, the traffic flows associated with that session may be given a specific priority of QoS level when transiting a packet access network.
Owner:ALCATEL LUCENT SAS
High-Performance Context-Free Parser for Polymorphic Malware Detection
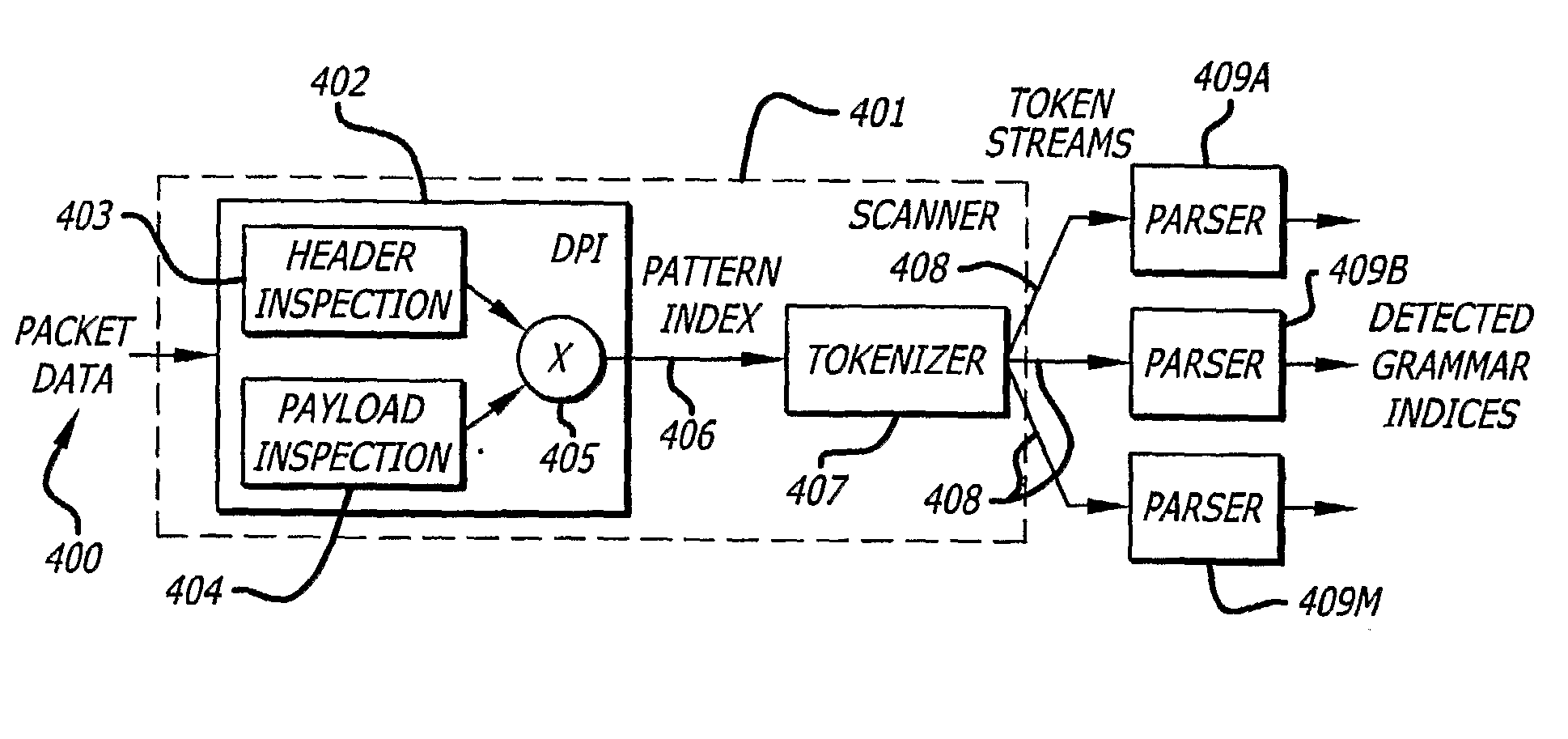
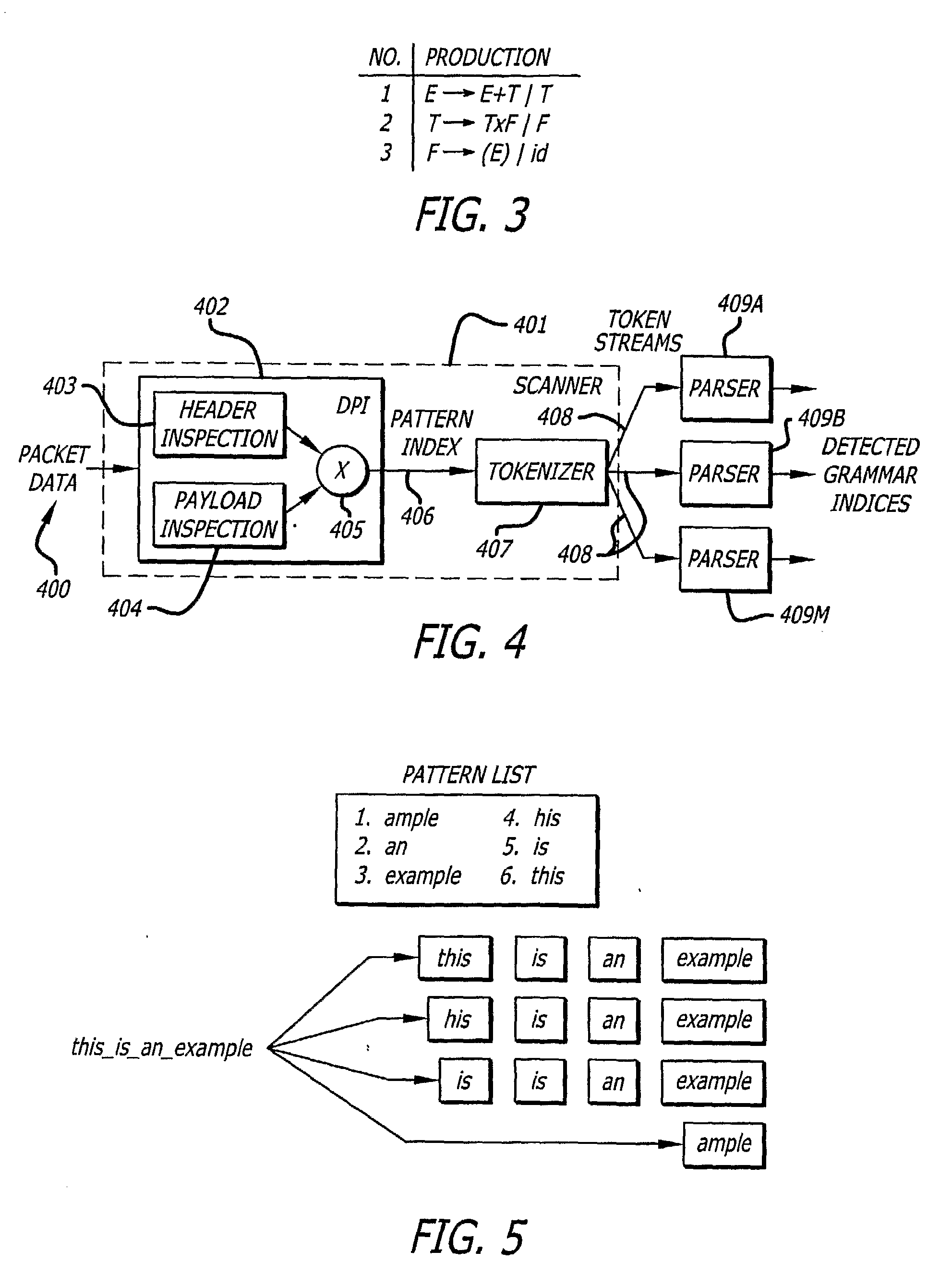
The invention provides a method and apparatus for advanced network intrusion detection. The system uses deep packet inspection that can recognize languages described by context-free grammars. The system combines deep packet inspection with one or more grammar parsers (409A-409M). The invention can detect token streams (408) even when polymorphic. The system looks for tokens at multiple byte alignments and is capable of detecting multiple suspicious token streams (408). The invention is capable of detecting languages expressed in LL(I) or LR(I) grammar. The result is a system that can detect attacking code wherever it is located in the data stream (408).
Owner:CHO YOUNG H +1
Dynamic service function chaining
InactiveUS20150333930A1Data switching by path configurationHybrid transportThe InternetNetwork conditions
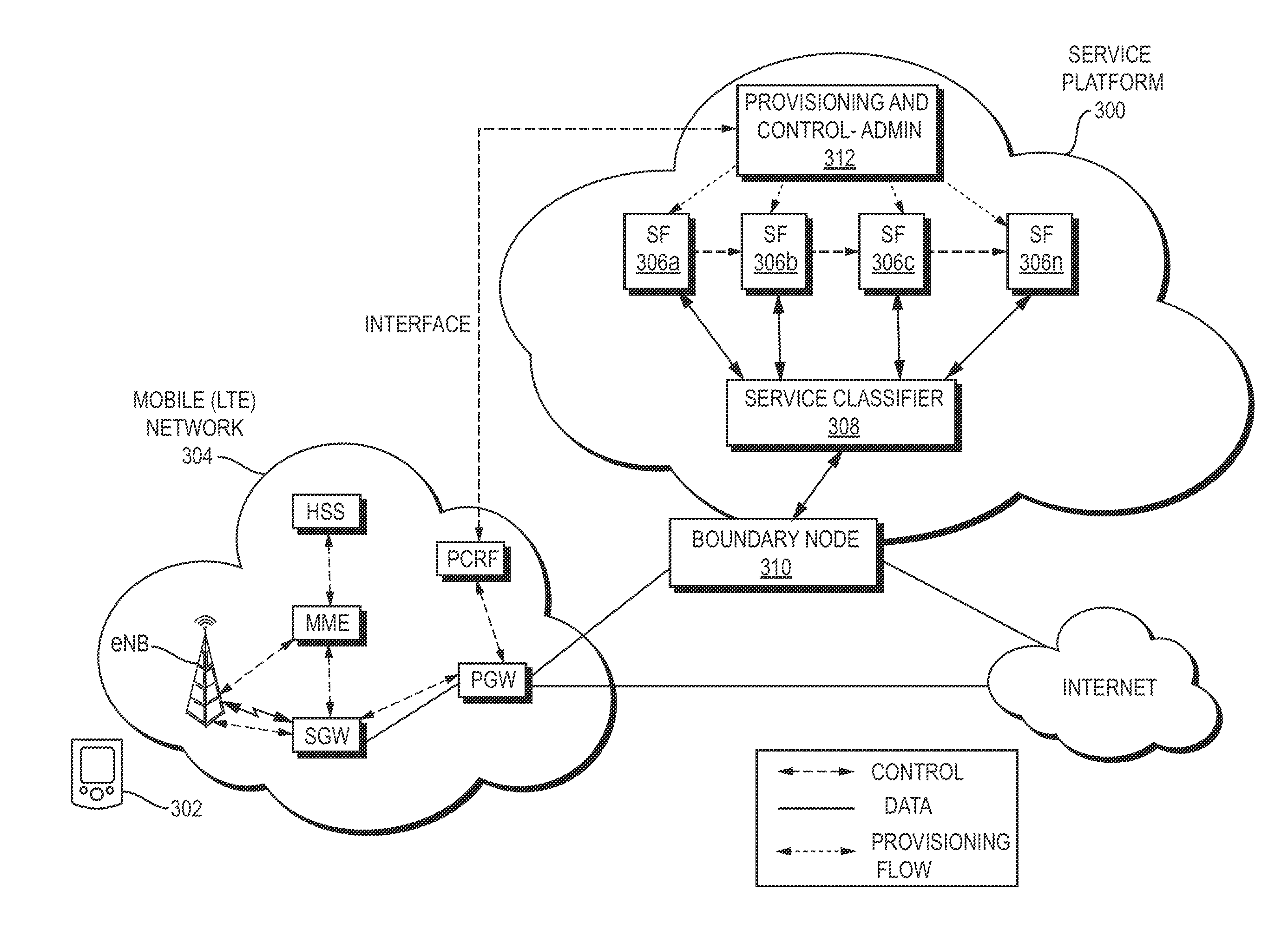
Described herein are systems, methods, and apparatus for processing network packets in a computer network, including in particular the processing of subscriber traffic in a mobile network. According to the teachings hereof, distributed computing resources can be organized into a service platform to provide certain value-add services—such as deep packet inspection, transcoding, lawful intercept, or otherwise—using a service function chaining model. The platform may operate on traffic egressing or ingressing to a mobile network (or other target network) to the public Internet. The service platform can alternatively be deployed wholly or partially within a target network. Service function chains may be built dynamically based on configured platform policies, packet contents, computing resource status, load, network location, current network conditions, and the like. The teachings hereof support dynamic modification of service function chains, including service function chain re-ordering, service level modification, and dynamic insertion / deletion of service functions.
Owner:AKAMAI TECH INC
Method and apparatus for network immunization
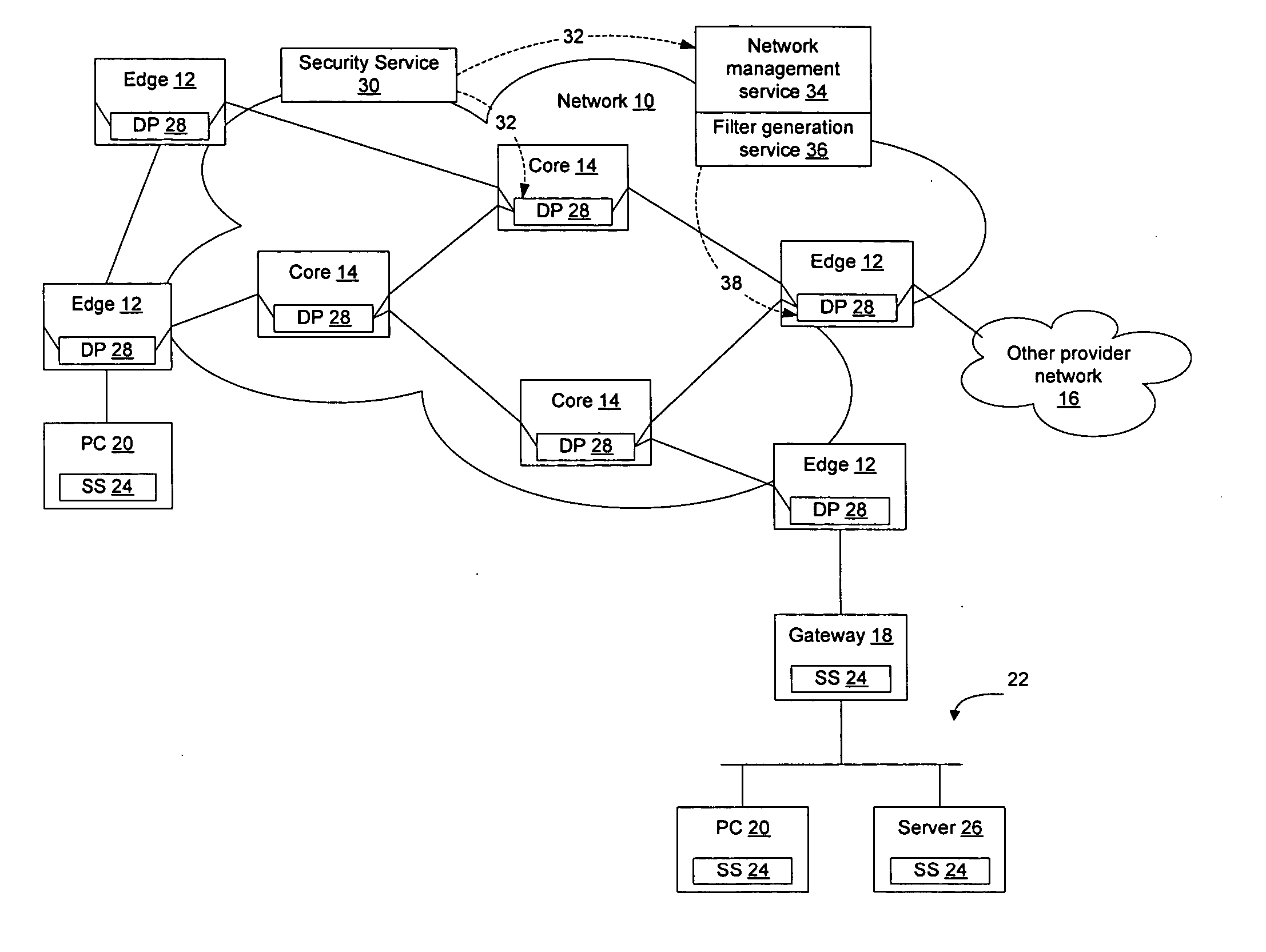
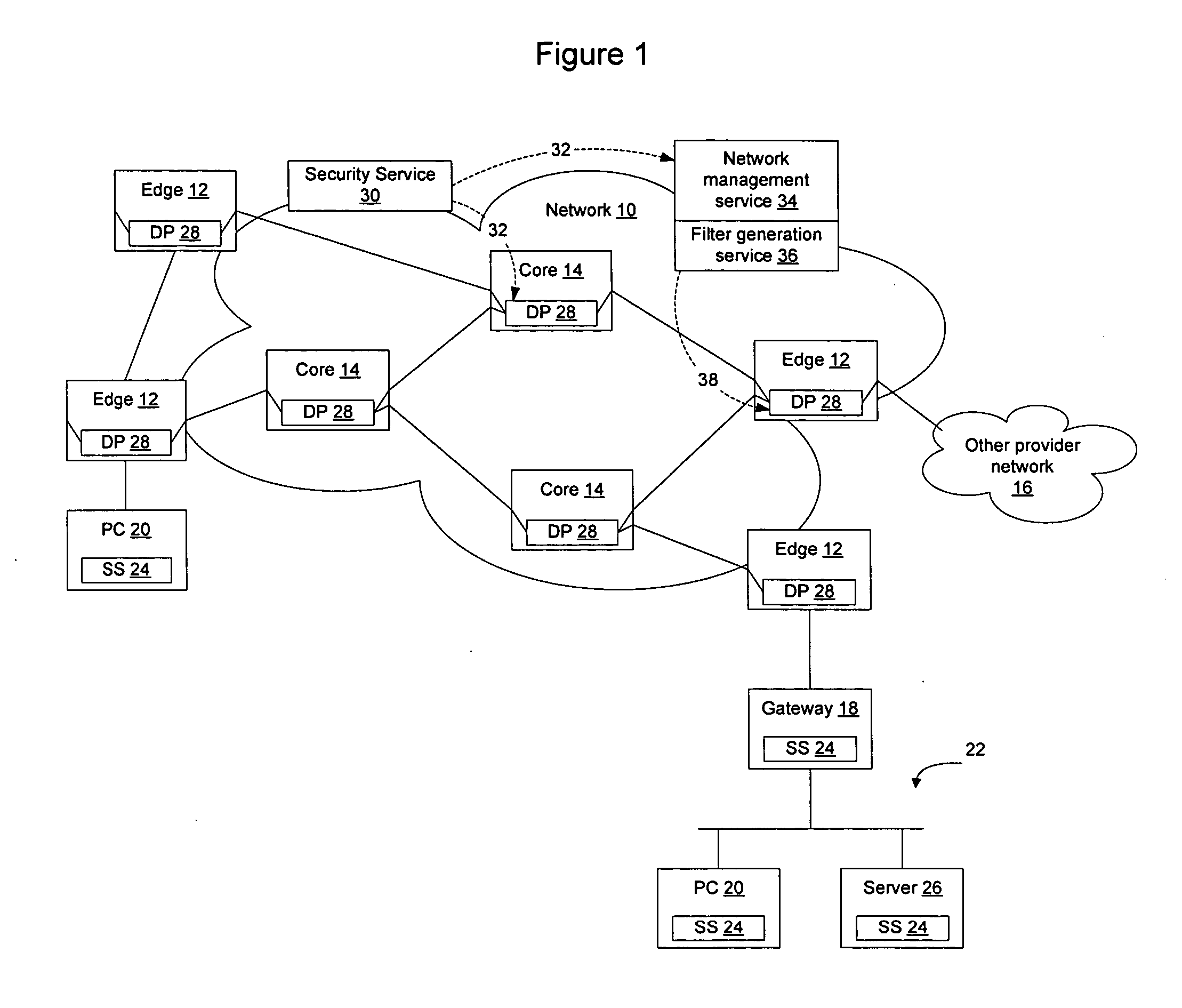
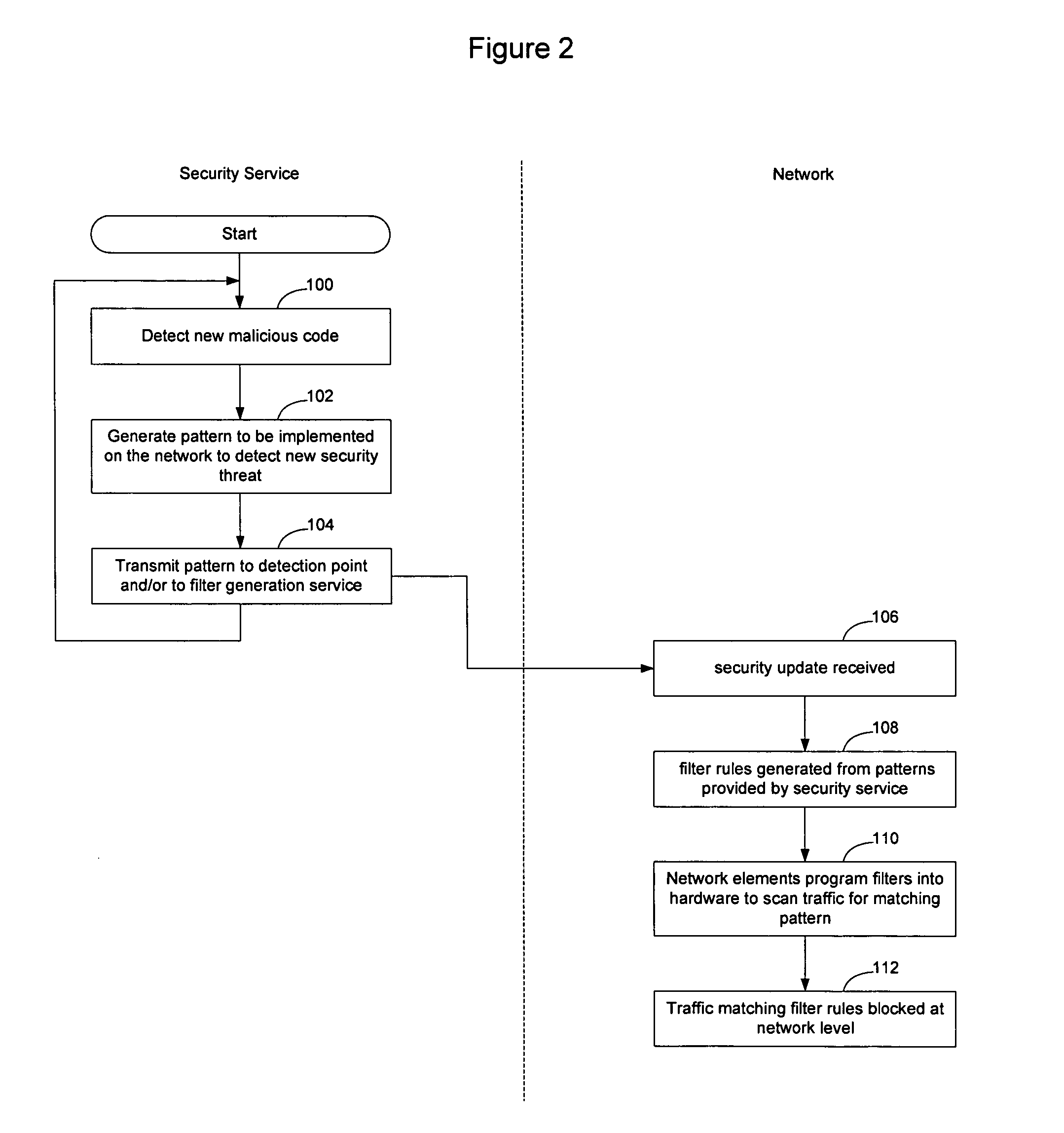
InactiveUS20060123481A1Avoid dataAvoid spreadingMemory loss protectionError detection/correctionSecurity softwareFiltering rules
Network elements that are configured to perform deep packet inspection may be dynamically updated with patterns associated with malicious code, so that malicious code may be detected and blocked at the network level. As new threats are identified by a security service, new patterns may be created for those threats, and the new patterns may then be passed out onto the network in real time. The real time availability of patterns enables filter rules derived from the patterns to be applied by the network elements so that malicious code may be filtered on the network before it reaches the end users. The filter rules may be derived by security software resident in the network elements or may be generated by a filter generation service configured to generate network element specific filter rules for those network elements that are to be implemented as detection points on the network.
Owner:AVAYA INC
Method and apparatus for adapting a communication network according to information provided by a trusted client
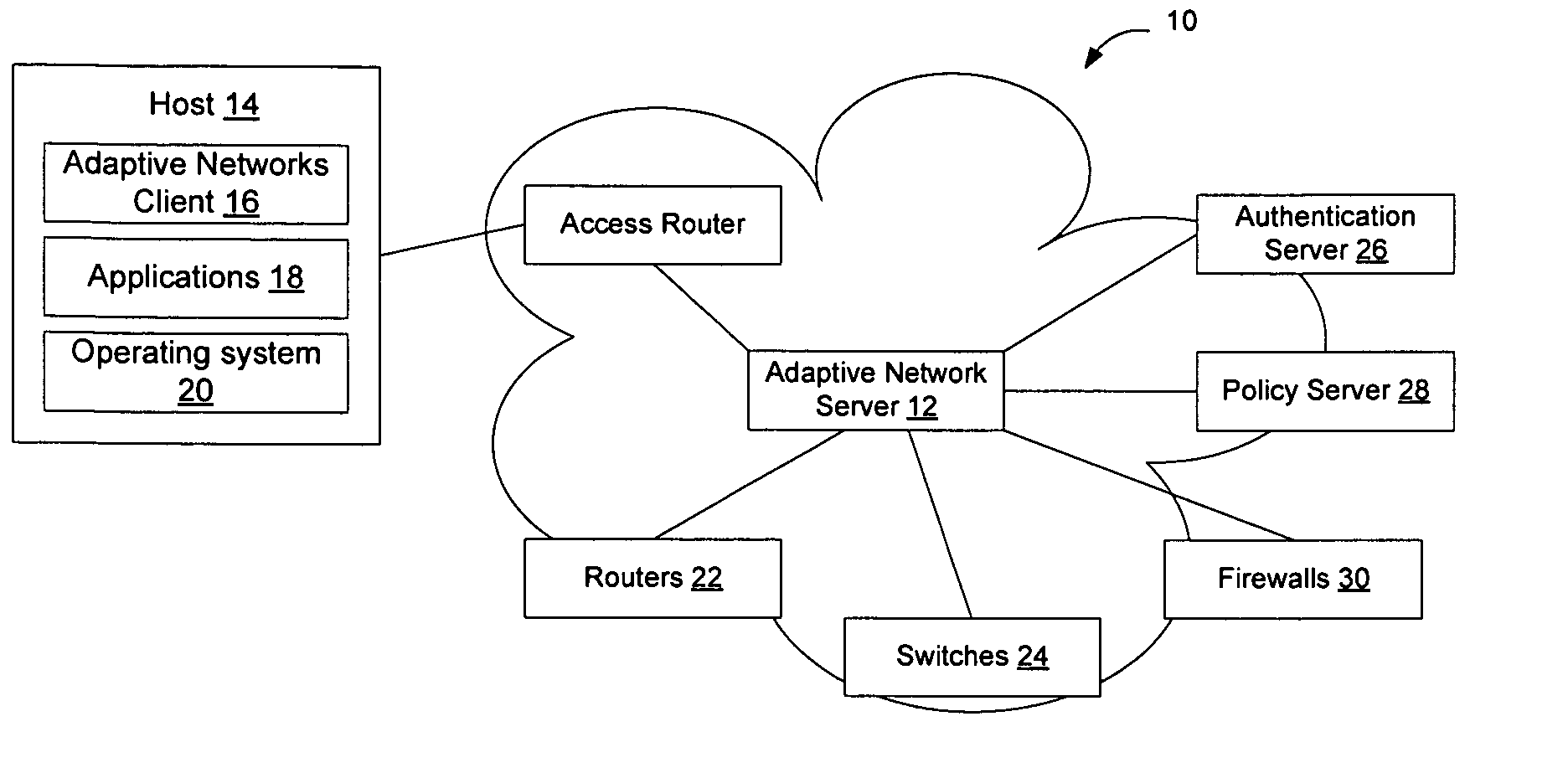
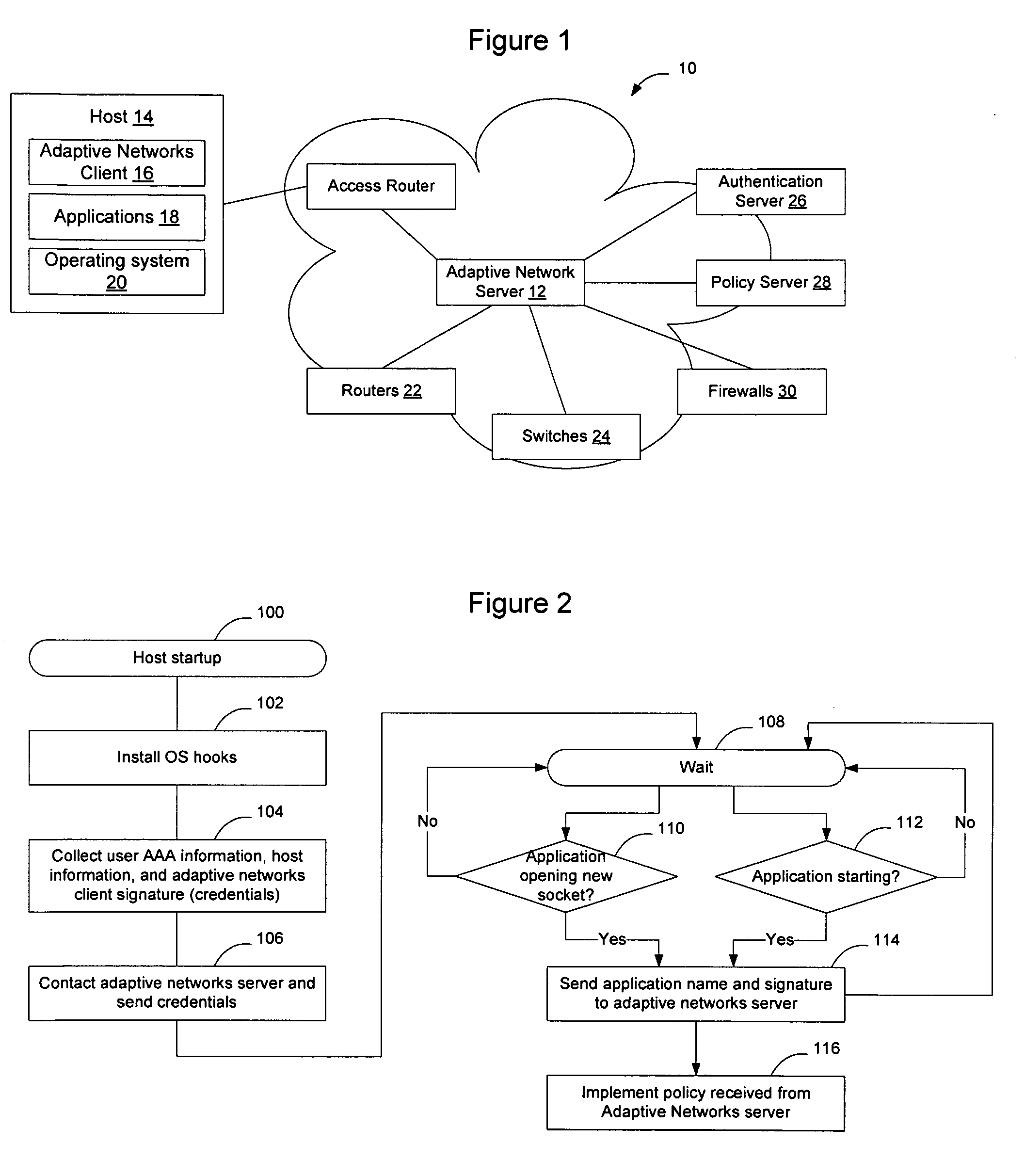
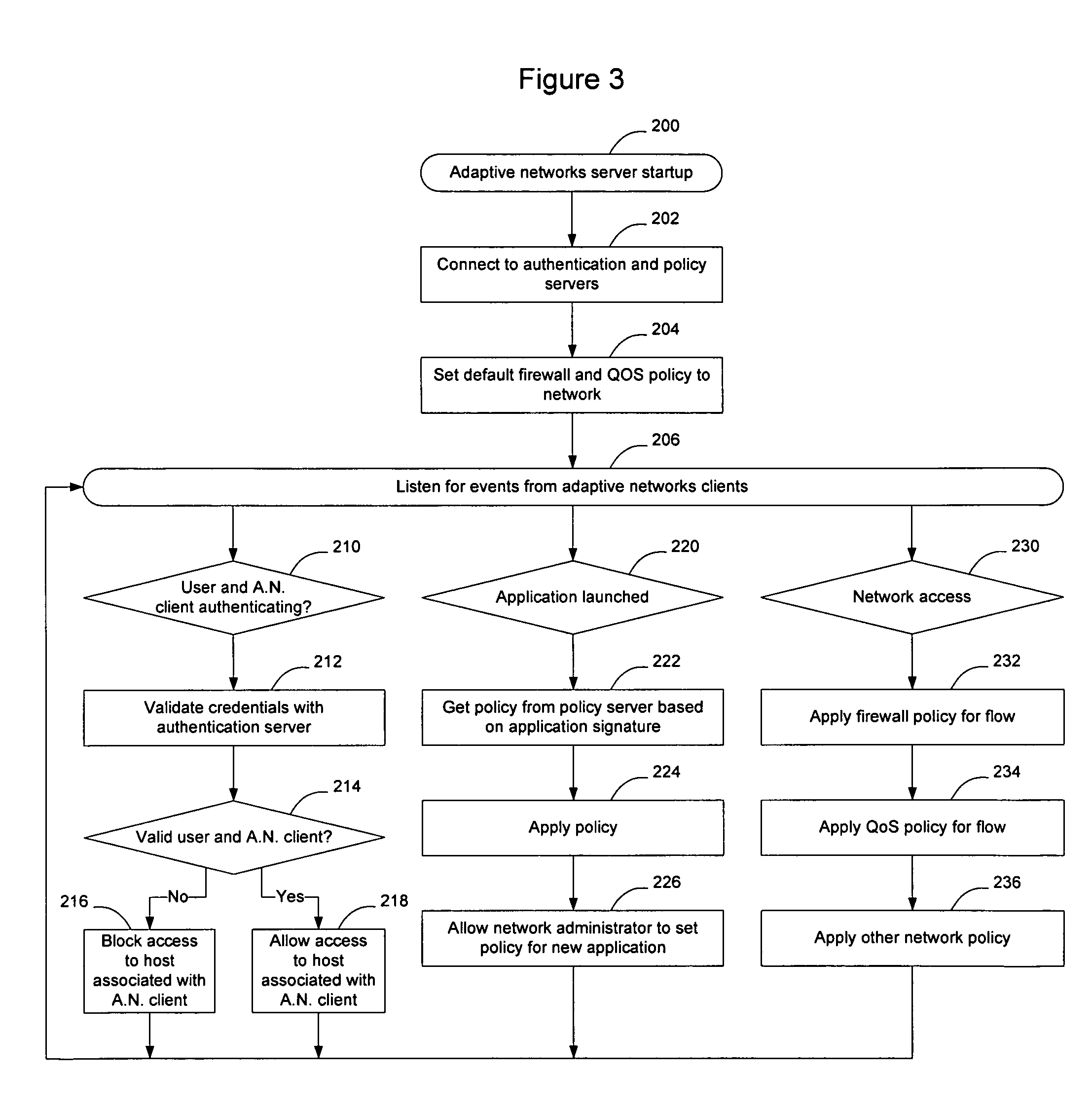
InactiveUS20080282080A1Digital data processing detailsUser identity/authority verificationTraffic capacityTrusted client
Hosts connecting to the network implement an adaptive networks client that monitors other applications on the host and provides information to an adaptive networks server to provide information about traffic being generated by the host. The client may also capture information about the user, host, access type, and other information of interest. The information provided by the adaptive network client may allow the network to adapt to the user, the device, the application, and the protocol being used. Users and applications can be authenticated and trusted. From a network standpoint, having a trusted client associated with the host allows the same benefits as deep packet inspection, regardless of whether the traffic is encrypted, and without requiring the network elements to actually perform deep packet inspection. The administrator may also centrally apply policy to control which applications are allowed to run on the hosts.
Owner:AVAYA INC
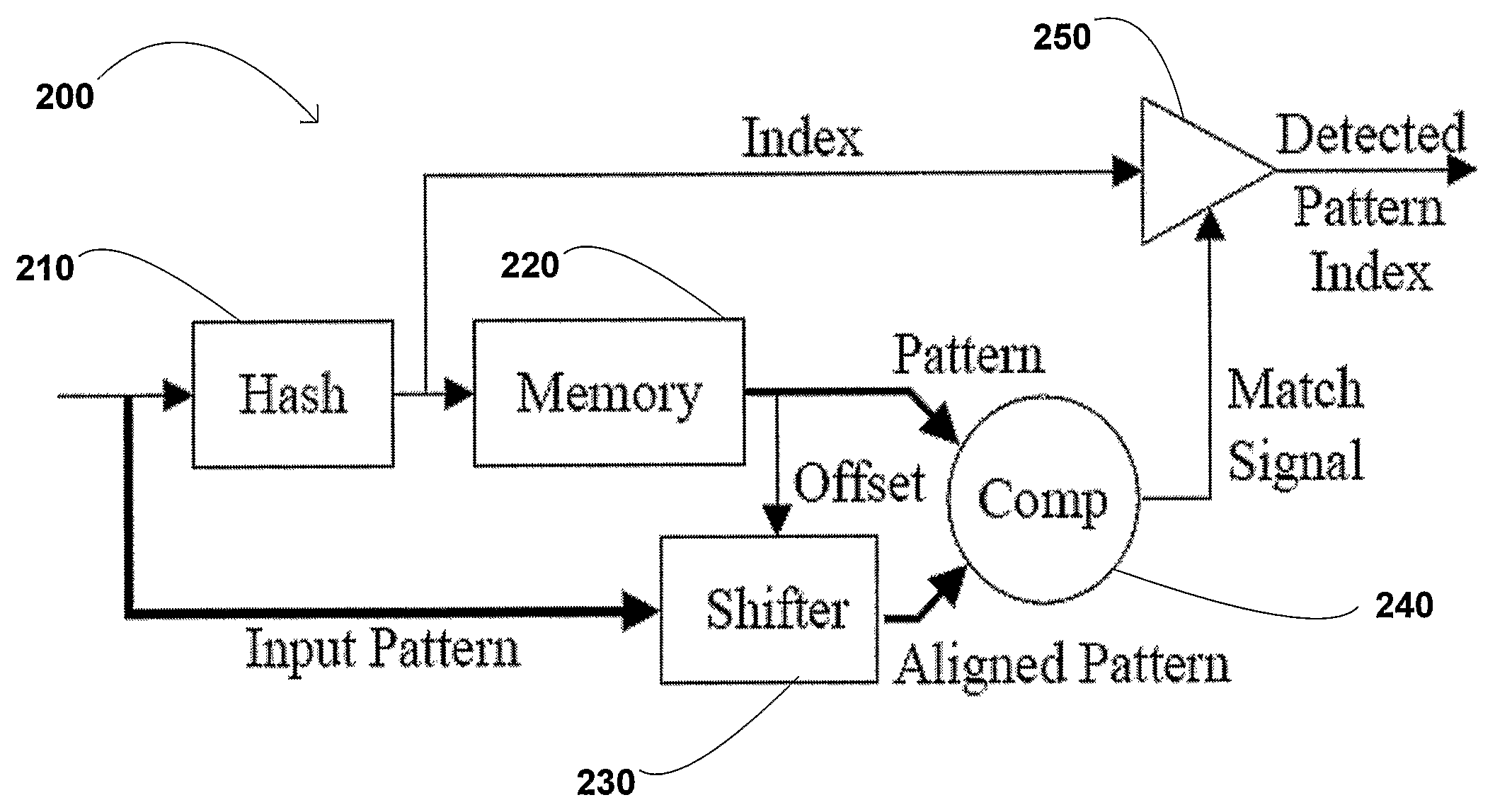
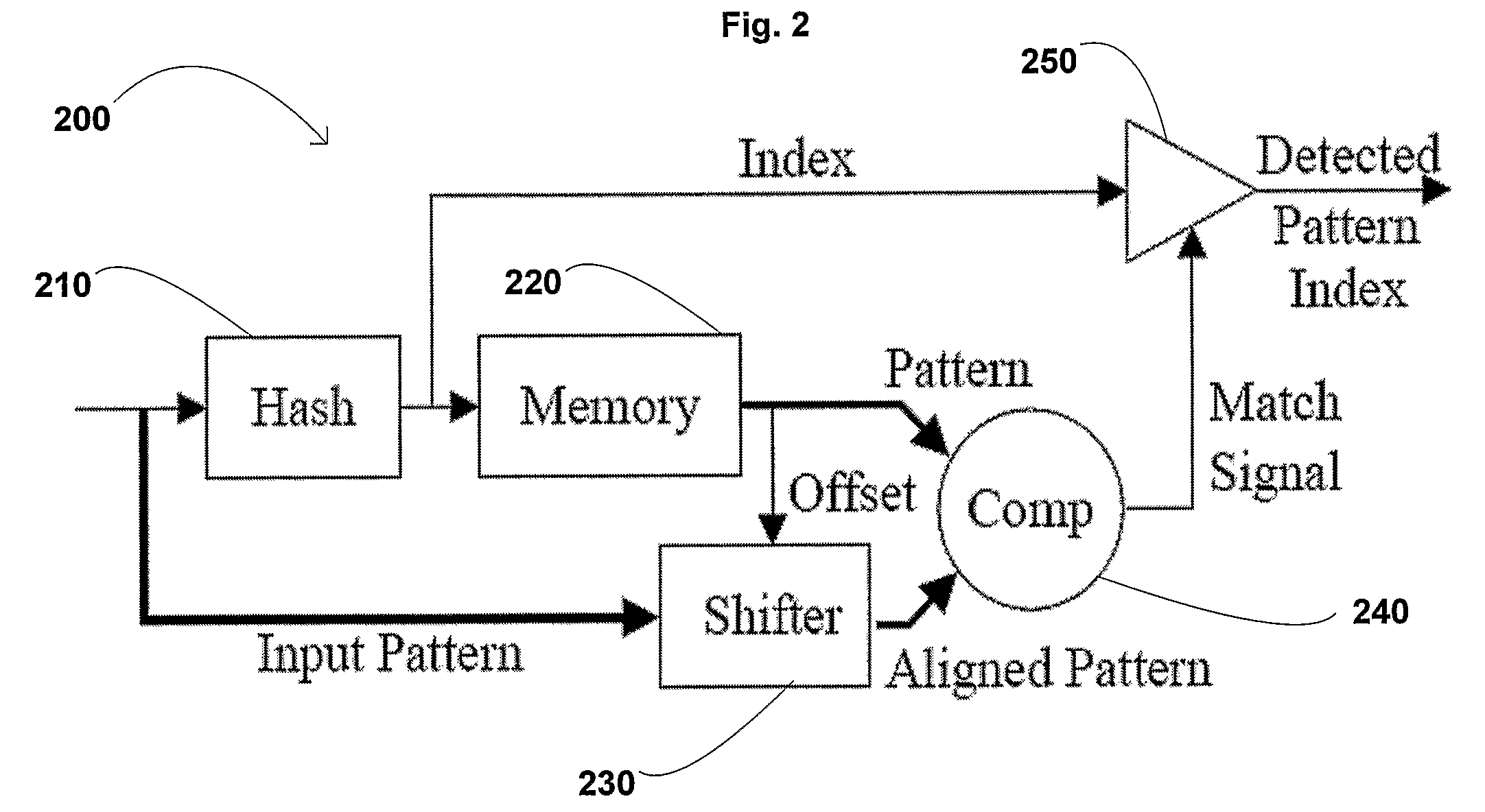
Method and Apparatus for Deep Packet Inspection
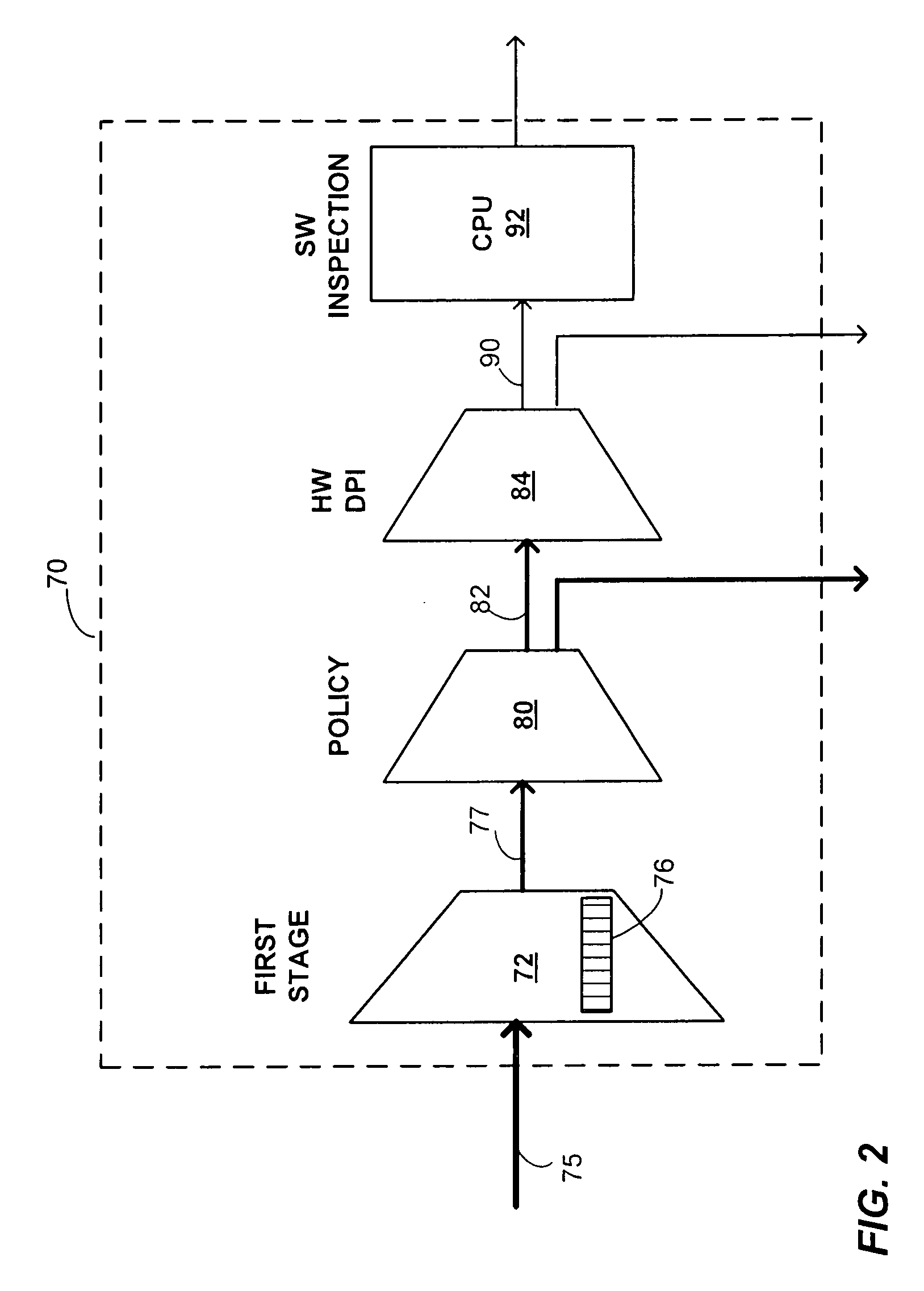
A system and method is provided for detecting malicious data such as, for example, viruses in a computer network. More specifically, system and method utilizes filters to detect pre-identified patterns or threat signatures in a data stream. In one embodiment, a deep packet inspection system for detecting a plurality of malicious programs in a data packet received from a network, wherein each malicious program has a unique pattern comprising a plurality of segments, includes a plurality of pattern detection modules configured to receive one or more data packets in parallel, wherein each of the plurality of pattern detection modules has an output, and one or more long pattern state machines coupled to the outputs of the plurality of pattern detection modules. The deep packet inspection system is configured to detect a pattern of any length at any location within a data packet.
Owner:RGT UNIV OF CALIFORNIA
Systems and methods for tracking, analyzing and mitigating security threats in networks via a network traffic analysis platform
A network traffic analysis method for tracking, analyzing, and mitigating security threats in a network includes receiving information based on monitoring traffic at a plurality of layers at one or more monitors deployed in the network utilizing deep packet inspection; receiving information based on monitoring the traffic at an endpoint of the network; analyzing the monitored traffic from the endpoint and the one or more monitors to determine network infrastructure and cyber security posture of the network infrastructure; and providing visualizations based on the network infrastructure and the cyber security posture, continuously to track threats, watch lateral movement in the network of the traffic, and determine security event history in the network.
Owner:MANTIX4 LLC
Systems for multiple legal game providers with digital ledger
ActiveUS20180096752A1Computer security arrangementsMetal/alloy conductorsCommunications systemComputerized system
A wireless communications system is provided that runs on a mobile device and includes a computer system run on at least one platform on which a plurality of different lottery transactions for different jurisdictions are supported and run from the at least one platform. A decentralized and distributed digital ledger is used to record transactions for the lottery transactions, where each of a lottery transaction can include a lottery element. At least one computer readable storage medium stores computer executable instructions that, when executed by the at least one network processor in the workflow server residing in the mobile communications network, implement components including: a workflow module comprising sets of workflow instructions for processing different types of lottery game packets from a plurality of different jurisdictions; and a deep packet inspection module for inspecting a received lottery game packet and providing information about the lottery game packet to the workflow module.
Owner:LOTTERY NOW INC
Single platform system for multiple jurisdiction lotteries and social media
ActiveUS20160104346A1Reduce fraudPlastic/resin/waxes insulatorsBoard gamesSocial mediaCommunications system
A wireless communications system includes a computer system run on a single platform on which different lottery games for different jurisdictions are supported and run from the single platform. The single platform is configured to be in communication with one or more social media sites. Computer executable instructions, when executed by at least one network processor in a workflow server residing in a mobile communications network, implements components that include: a workflow module of sets of workflow instructions for processing different types of lottery game packets from different jurisdictions. A deep packet inspection module inspects a received lottery game packet and provides information about the lottery game packet to the workflow module. The workflow module coordinates processing of the received lottery game packets using selected ones of selectable communication function modules based on the information about the lottery game packet provided by the deep lottery game packet inspection module.
Owner:LOTTERY NOW INC
Extended finite state automata and systems and methods for recognizing patterns using extended finite state automata
Deterministic finite automata (DFAs) are popular solutions to deep packet inspection because they are fast and DFAs corresponding to multiple signatures are combinable into a single DFA. Combining such DFAs causes an explosive increase in memory usage. Extended finite automata (XFAs) are an alternative to DFAs that avoids state-space explosion problems. XFAs extend DFAs with a few bytes of “scratch memory” used to store bits and other data structures that record progress. Simple programs associated with automaton states and / or transitions manipulate this scratch memory. XFAs are deterministic in their operation, are equivalent to DFAs in expressiveness, and require no custom hardware support. Fully functional prototype XFA implementations show that, for most signature sets, XFAs are at least 10,000 times smaller than the DFA matching all signatures. XFAs are 10 times smaller and 5 times faster or 5 times smaller and 20 times faster than systems using multiple DFAs.
Owner:WISCONSIN ALUMNI RES FOUND
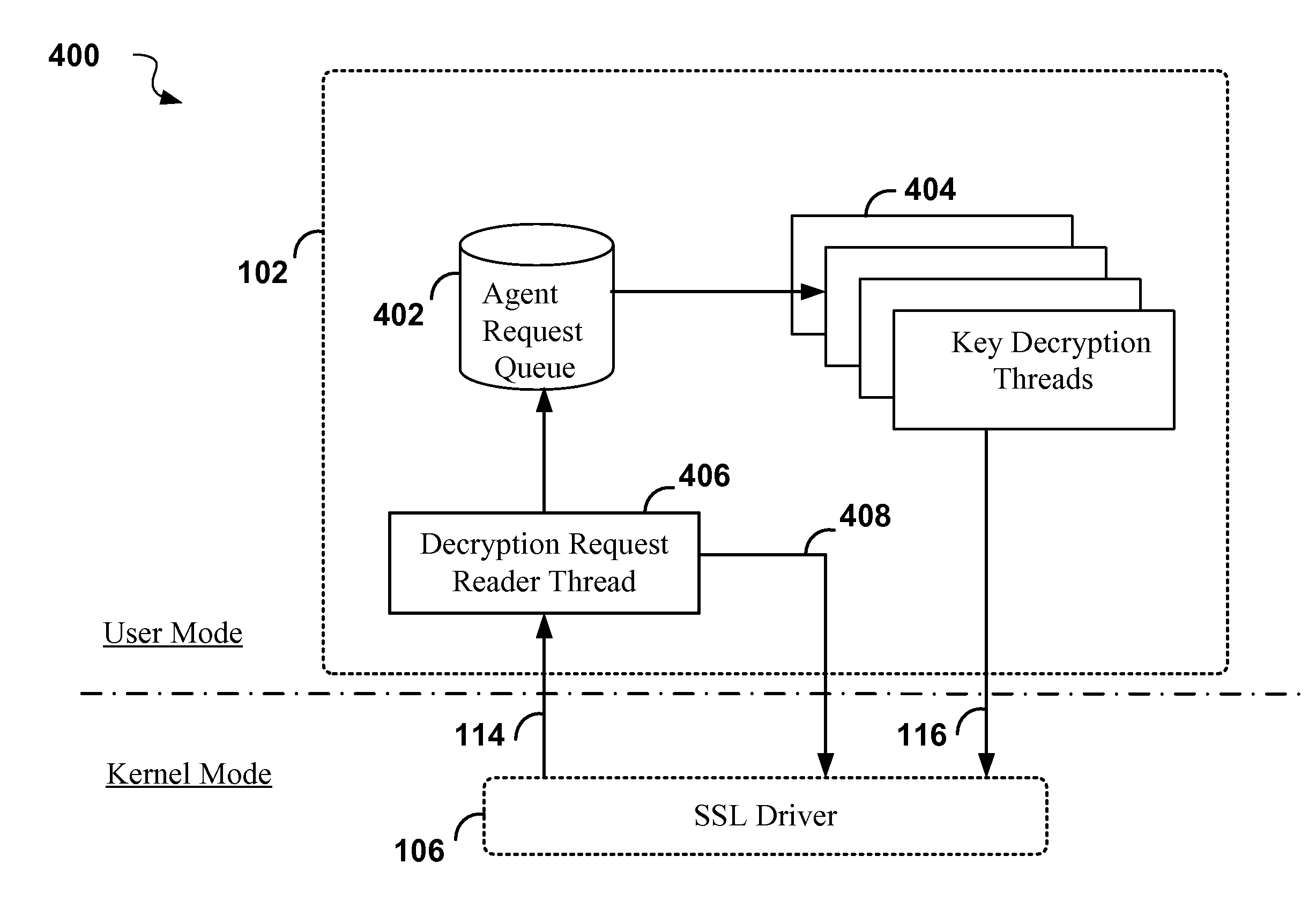
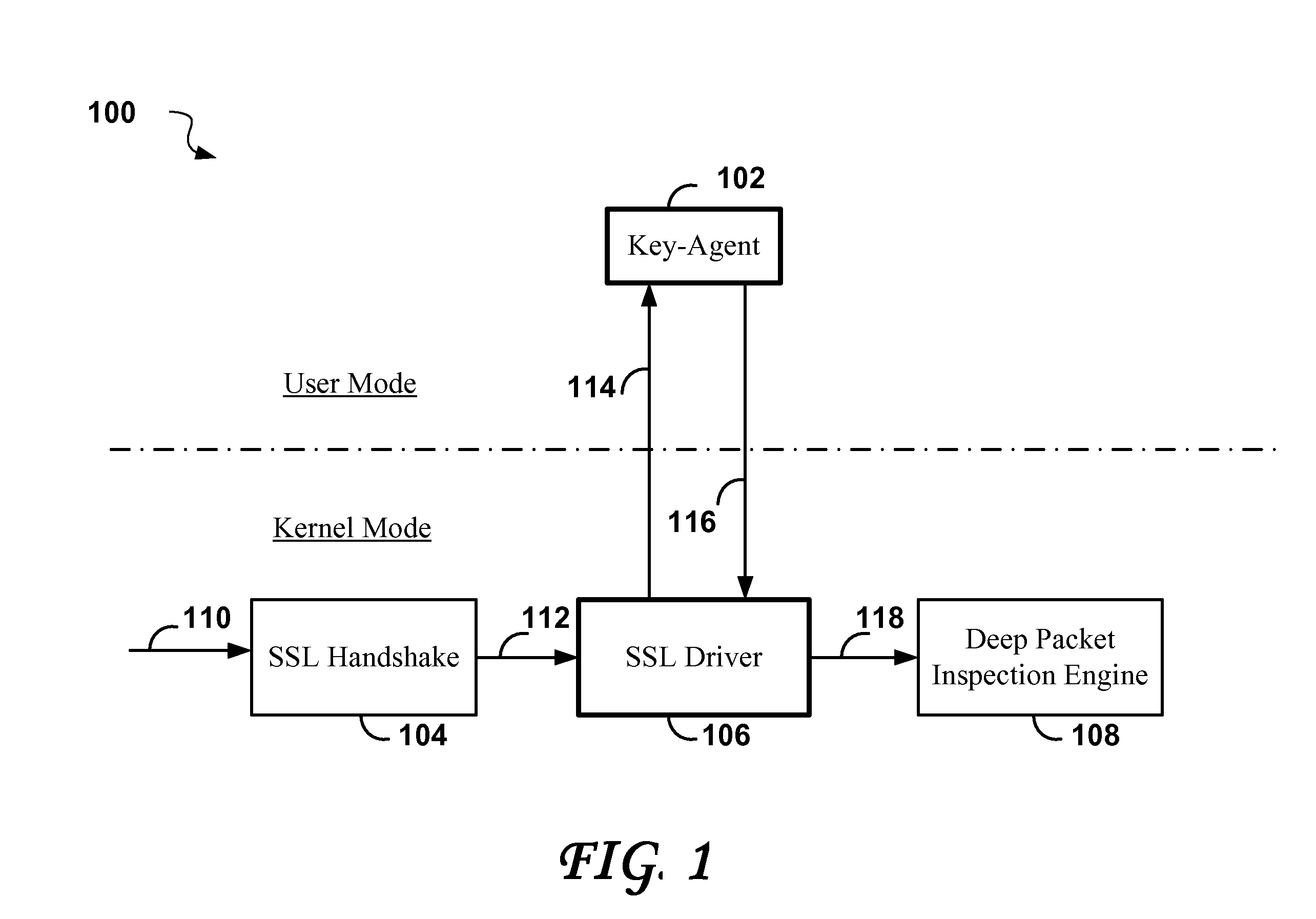
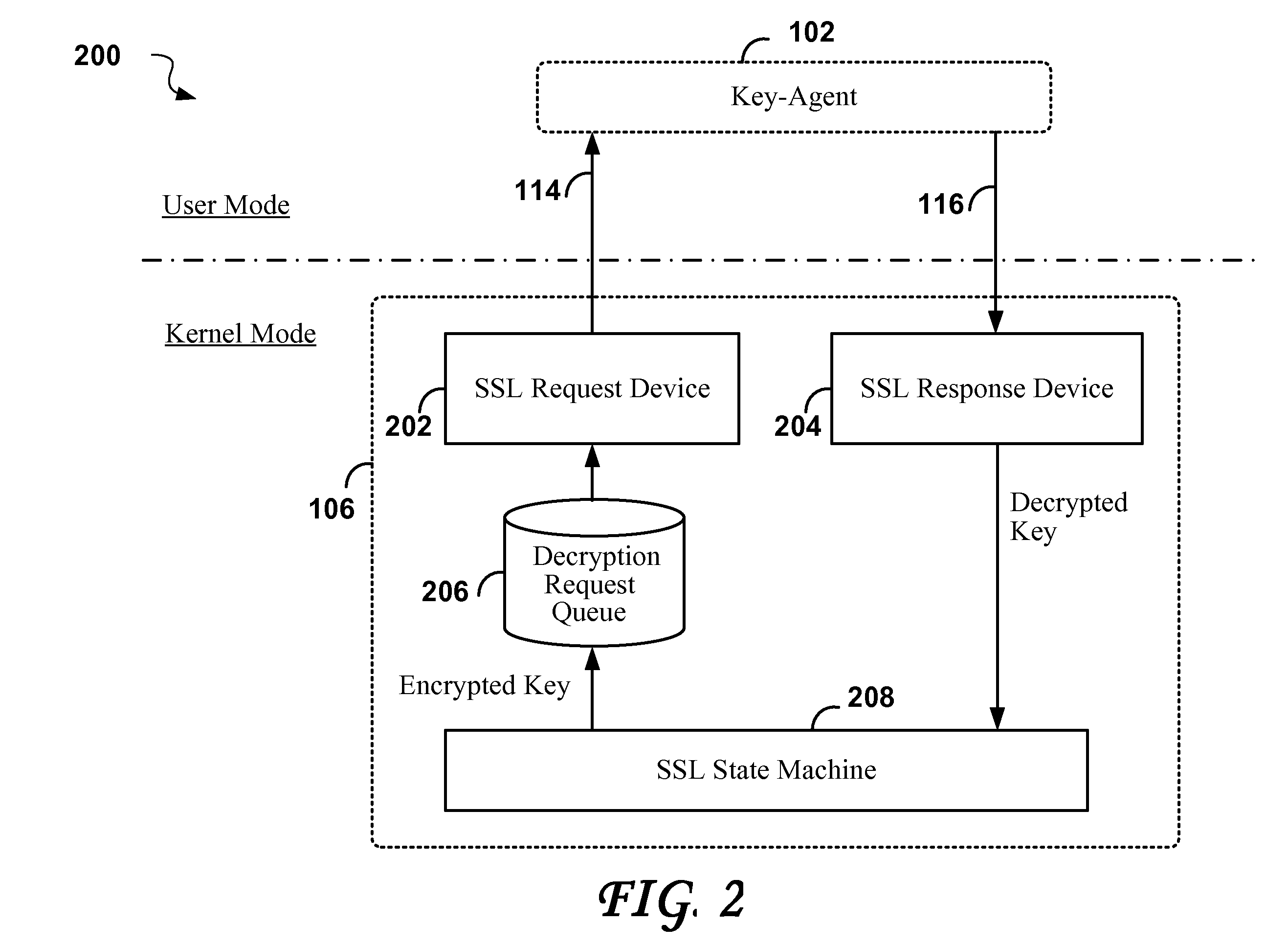
Method and system for monitoring encrypted data transmissions
ActiveUS20080320297A1Error detection/correctionVolume/mass flow measurementTraffic capacityData stream
A method for efficiently decrypting asymmetric SSL pre-master keys is divided into a key agent component that runs in user mode, and an SSL driver running in kernel mode. The key agent can take advantage of multiple threads for decoding keys in a multi-processor environment, while the SSL driver handles the task of symmetric decryption of the SSL encrypted data stream. The method is of advantage in applications such as firewalls with deep packet inspection in which all encrypted data traffic passing through the firewall must be decrypted for inspection.
Owner:TREND MICRO INC
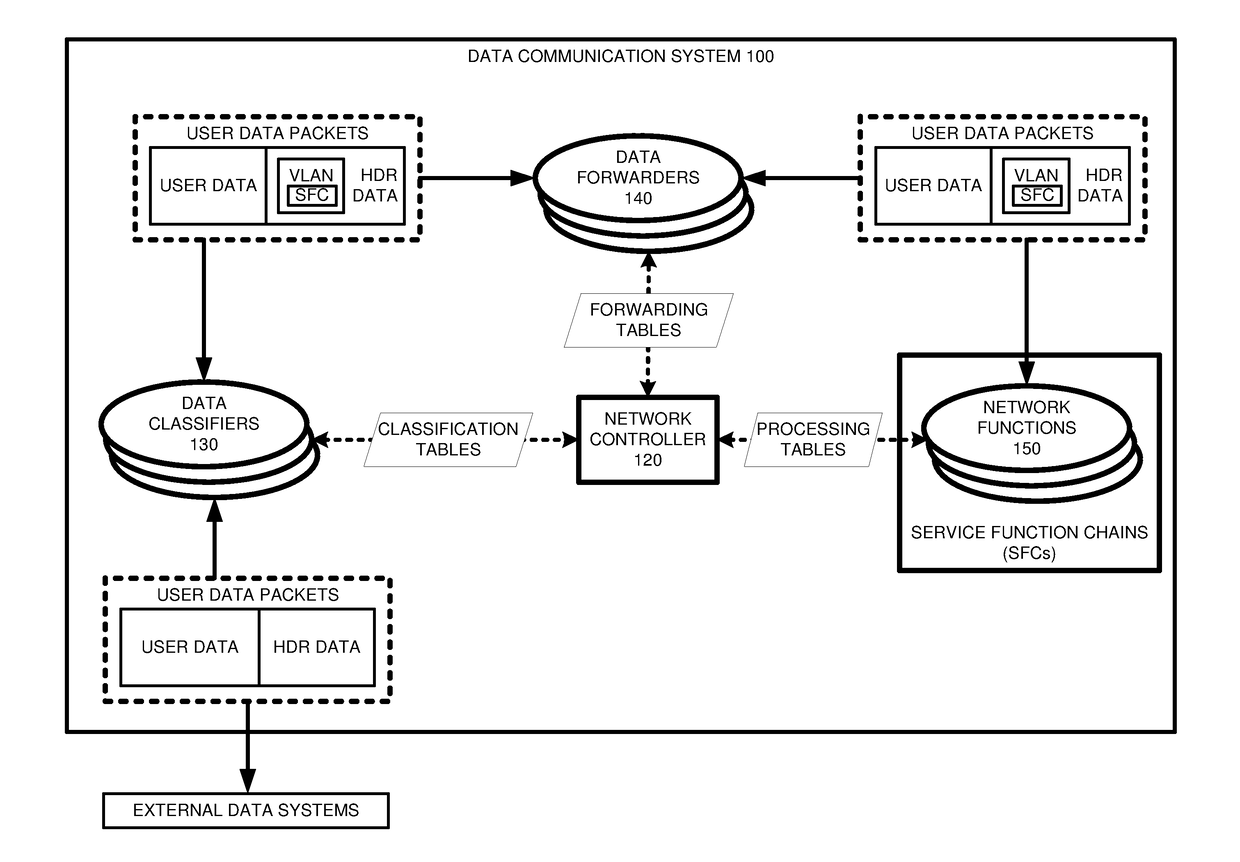
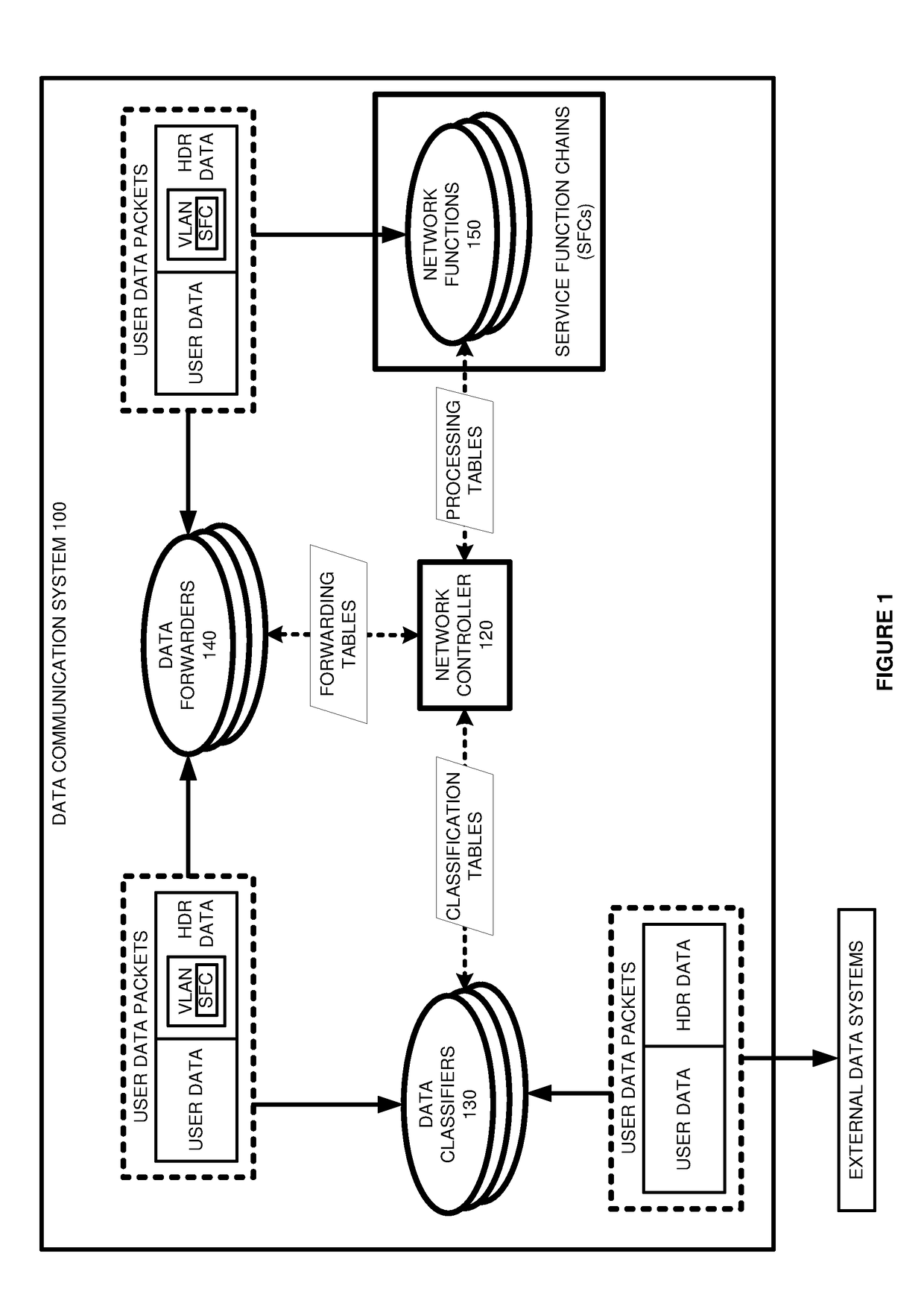
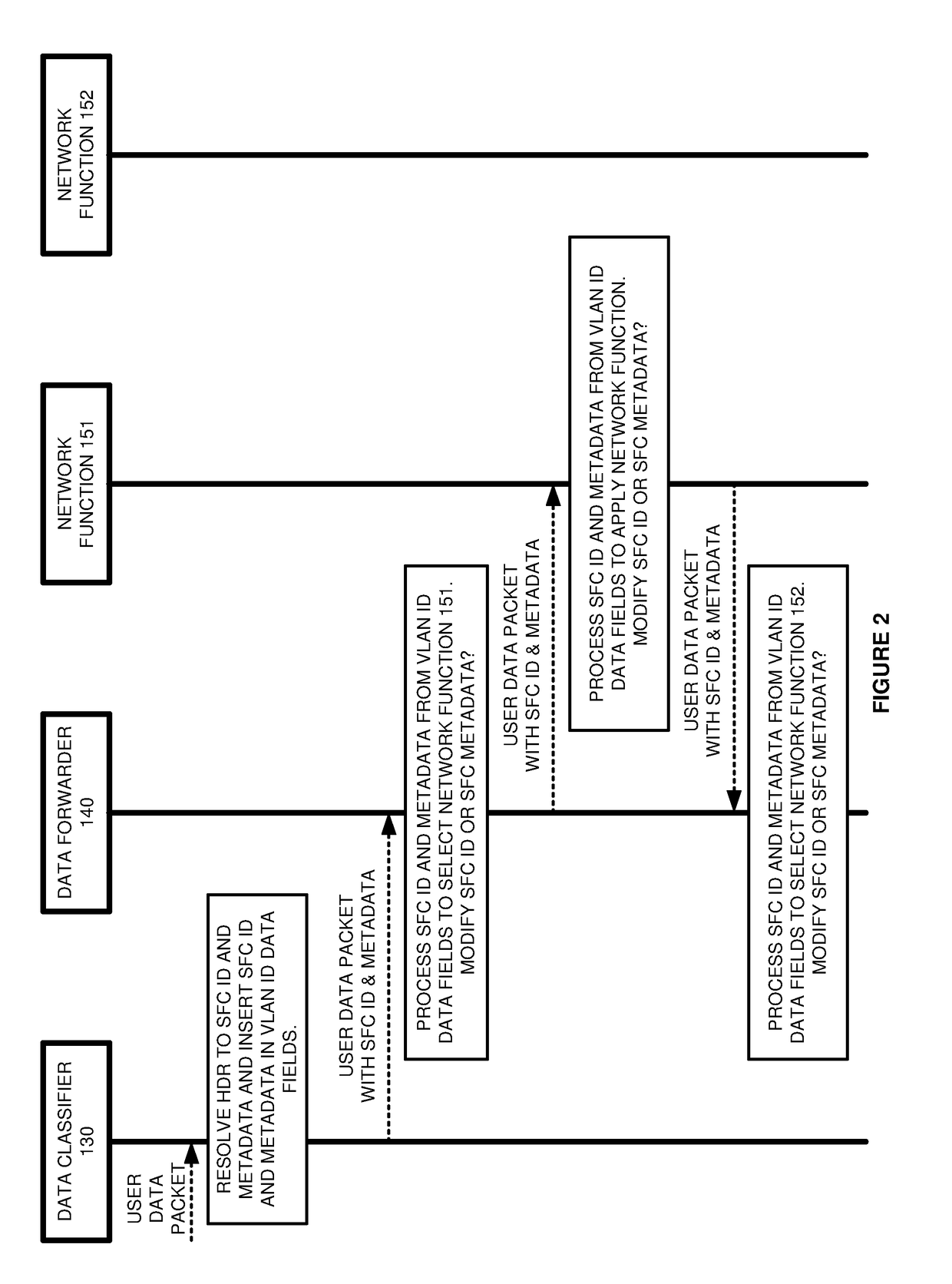
Service function chain (SFC) data communications with sfc data in virtual local area network identifier (vlan id) data fields
A data system transfers data packets over Service Function Chains (SFCs). A classifier receives the packets and determines SFC Identifiers (IDs) and metadata. The classifier inserts the SFC IDs and metadata in Virtual Local Area Network (VLAN) ID data fields of the packets. The classifier transfers the classified packets to a forwarder. The forwarder identifies the SFC IDs and metadata from the VLAN ID data fields. The forwarder selects network functions based on the SFC IDs and metadata. The forwarder transfers the packets having the SFC IDs and metadata in the VLAN ID data fields to the selected network functions. The selected network functions identify the SFC IDs and metadata from the VLAN ID data fields. The network functions process the packets based on the SFC IDs, metadata, and configured policies to perform functions like network address translation, firewall, deep packet inspection, and others.
Owner:NICIRA
MECHANISM FOR IDENTIFYING MALICIOUS CONTENT, DoS ATTACKS, AND ILLEGAL IPTV SERVICES
Mechanism for identifying malicious content, DoS attacks, and illegal IPTV services. By monitoring the characteristics of various control messages being transmitted within a network that services Internet protocol television (IPTV) content to identify suspicious behavior (e.g., such as that associated with malicious content, denial of service (DoS) attacks, IPTV service stealing, etc.). In addition to monitoring control messages within such a network, deep packet inspection (DPI) may be performed for individual packets within an IPTV stream to identify malicious content therein (e.g., worms, viruses, etc. actually within the IPTV stream itself). By monitoring control messages and / or actual IPTV content within a network (e.g., vs. at the perimeter of a network only), protection against both outside and inside attacks can be effectuated. This network level basis of operation effectively guards against promulgation of malicious content to other devices within the network.
Owner:RPX CORP
Hierarchical packet process apparatus and method
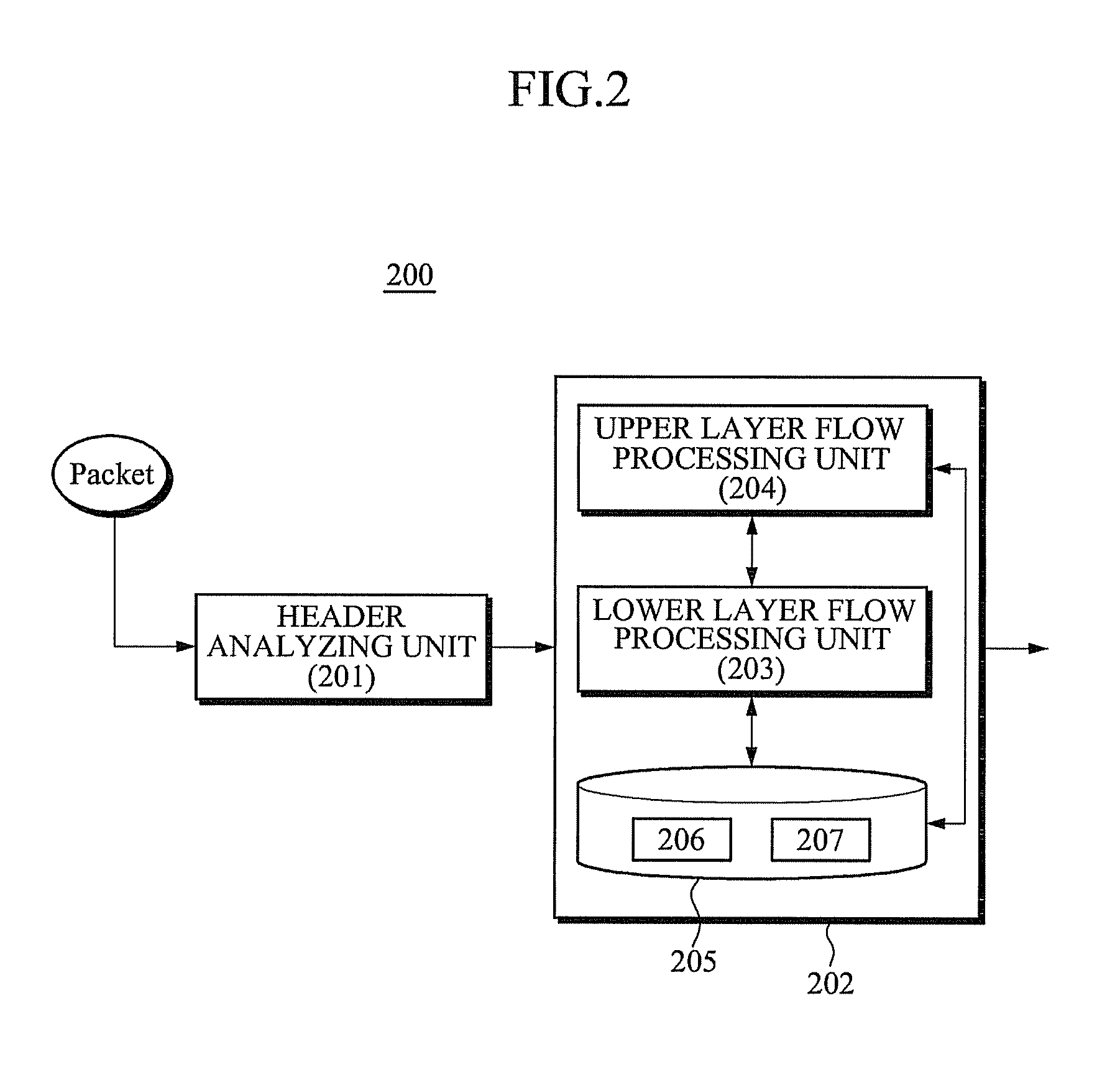
InactiveUS20100158009A1Prevents deterioration of packet processing performanceData switching by path configurationQuality of serviceComputer hardware
Provided is a hierarchical packet processing apparatus and method. In one general aspect, a packet is analyzed, divided into an upper layer and a lower layer. It is determined whether a property of the packet to be analyzed has been already analyzed or has to be re-analyzed with respect to each of the upper and lower layers of the packet. Therefore, deep packet inspection is performed only when it is required, and thus assurance of quality of service (QoS) during packet processing can be achieved, as well as reduced waste of resources.
Owner:ELECTRONICS & TELECOMM RES INST
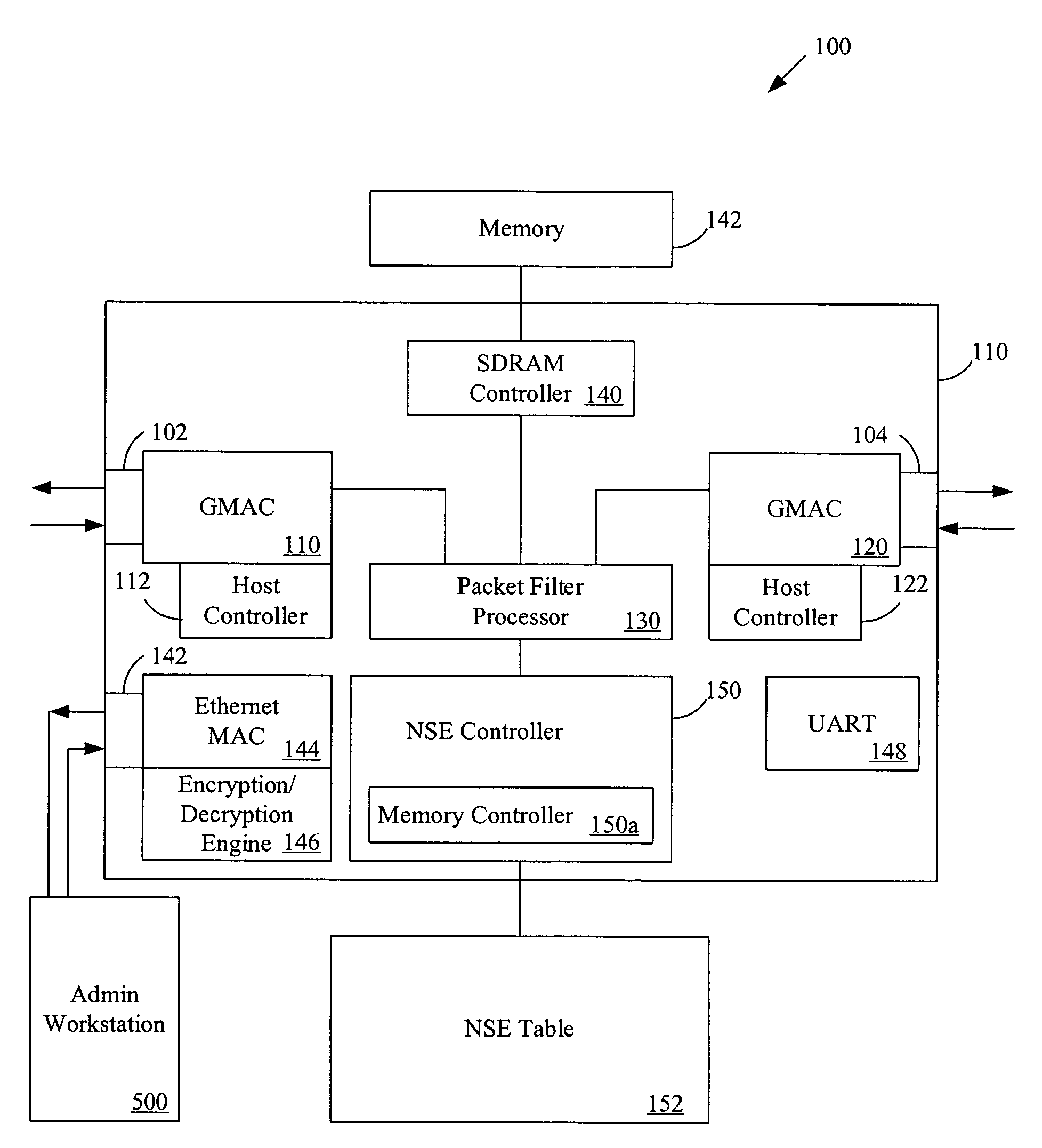
Active packet content analyzer for communications network
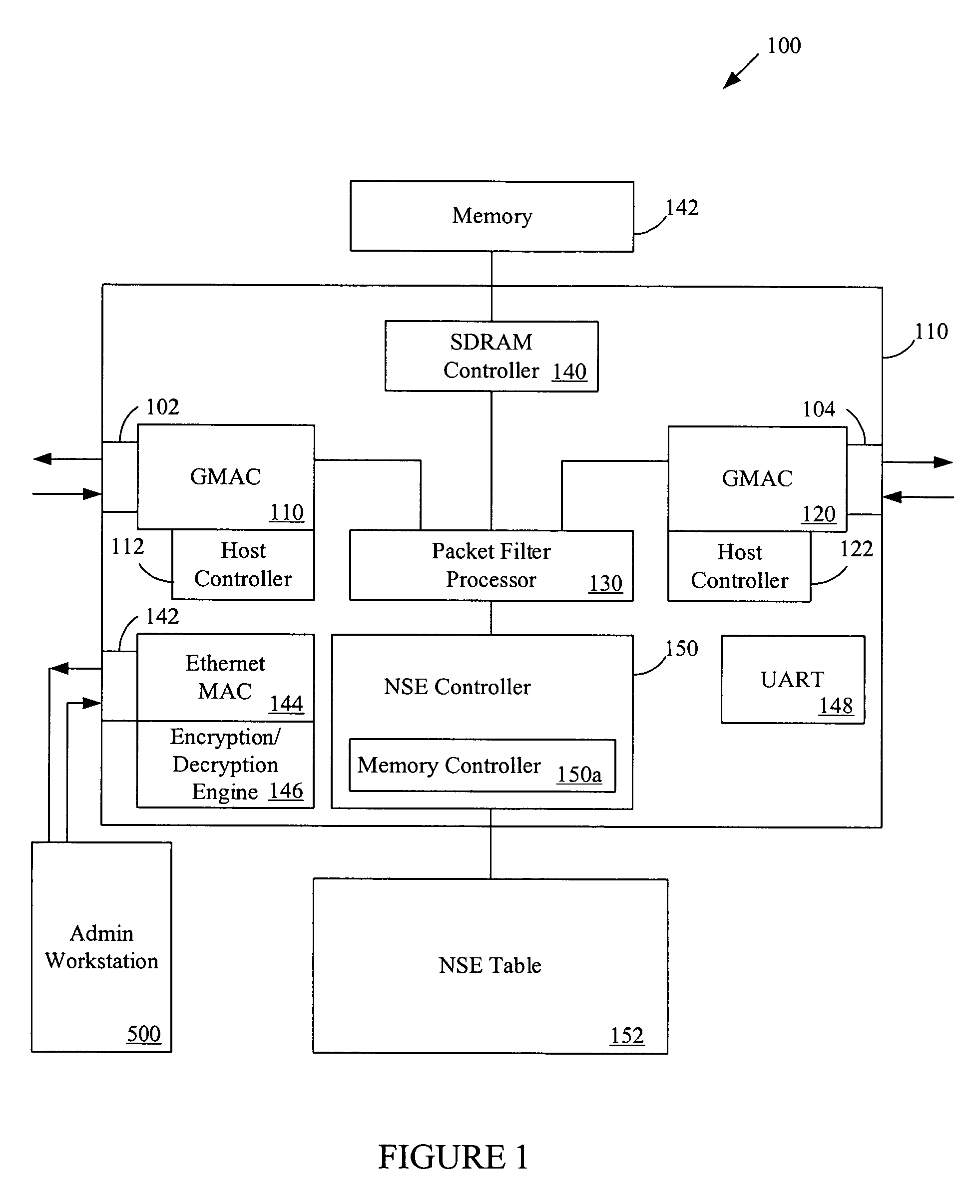
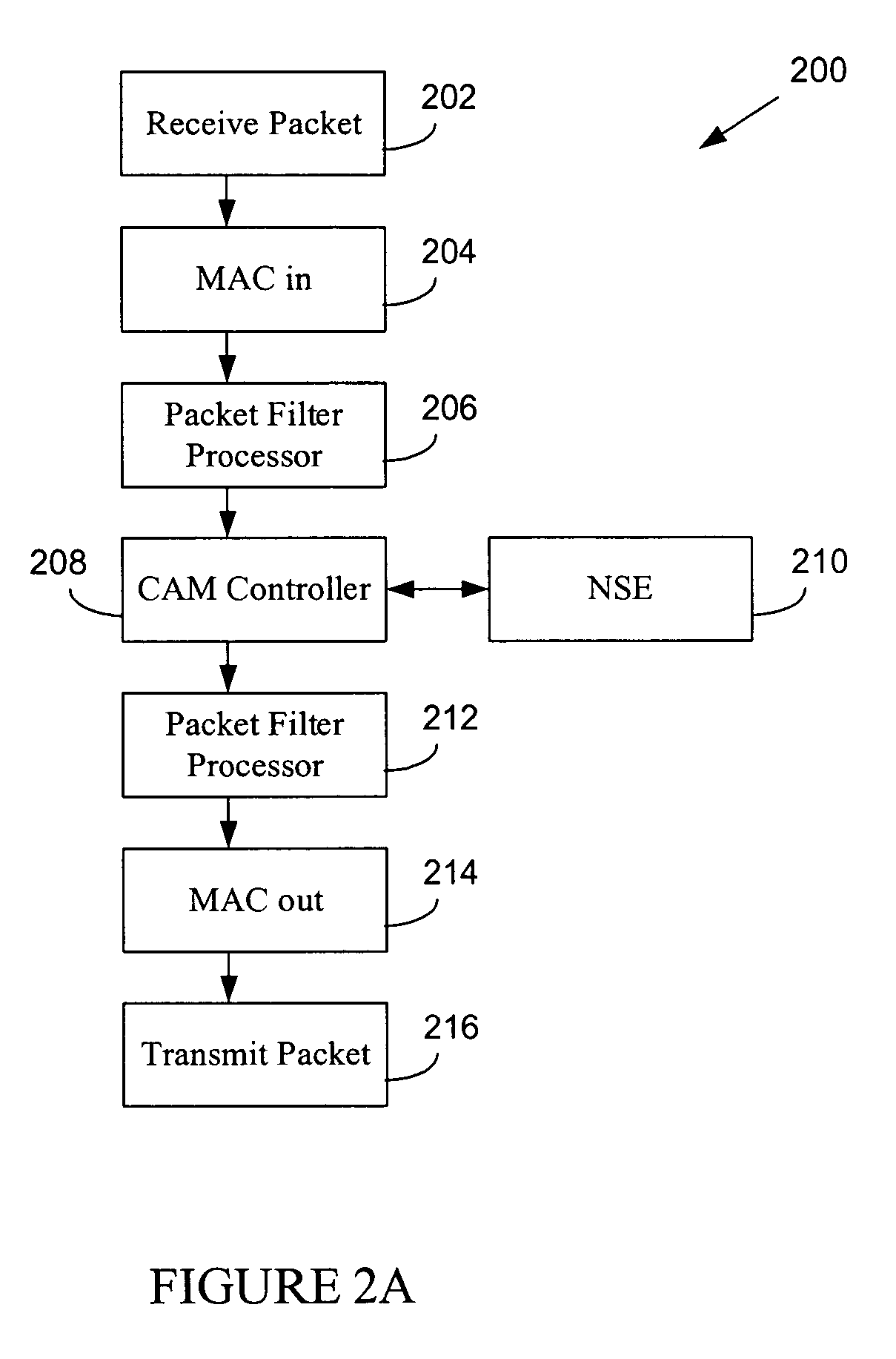
ActiveUS7499412B2Increased network trafficData switching by path configurationDistributed computingNetwork search engine
An active packet inspection device for a communications network, comprises a first terminal and a second terminal each adapted to couple the appliance in-line in the network and communicate data packets with network devices. A packet processor is coupled to the first terminal and second terminal and configured to normalize the data packets. A network search engine coupled to the packet processor and the memory, and configured to compare the data packets with the stored signatures, and when a match is found and other specified conditions are met, to perform an action identified in an associated rule. In one aspect, the network search engine includes a network search engine controller and a network search engine table including a memory configured to store a plurality of replicated signatures. Advantages of the invention include the ability to perform deep packet inspections actively on a communications network at high-speed.
Owner:KEYSIGHT TECH SINGAPORE (SALES) PTE LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com