Patents
Literature
1147results about How to "Avoid data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
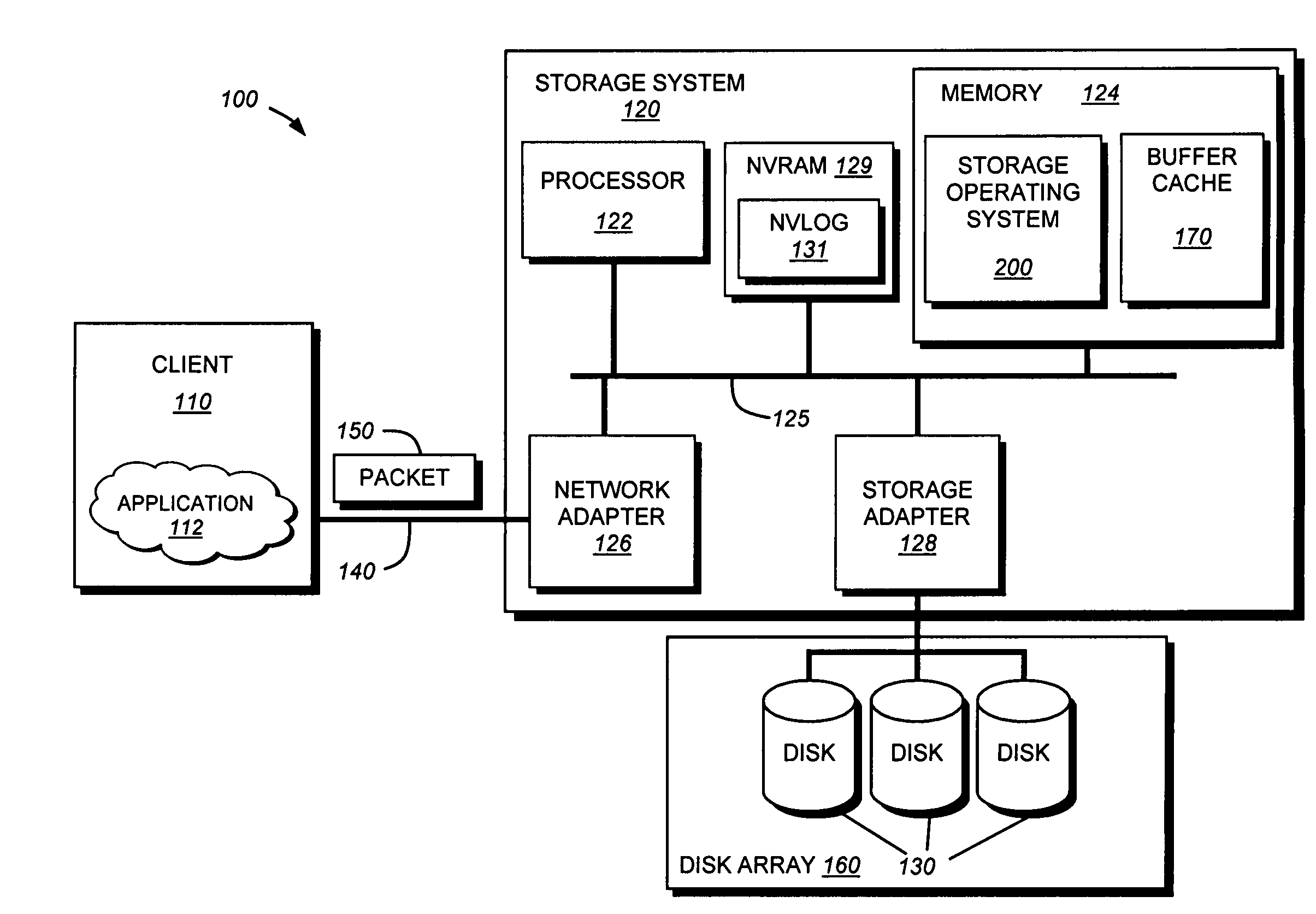
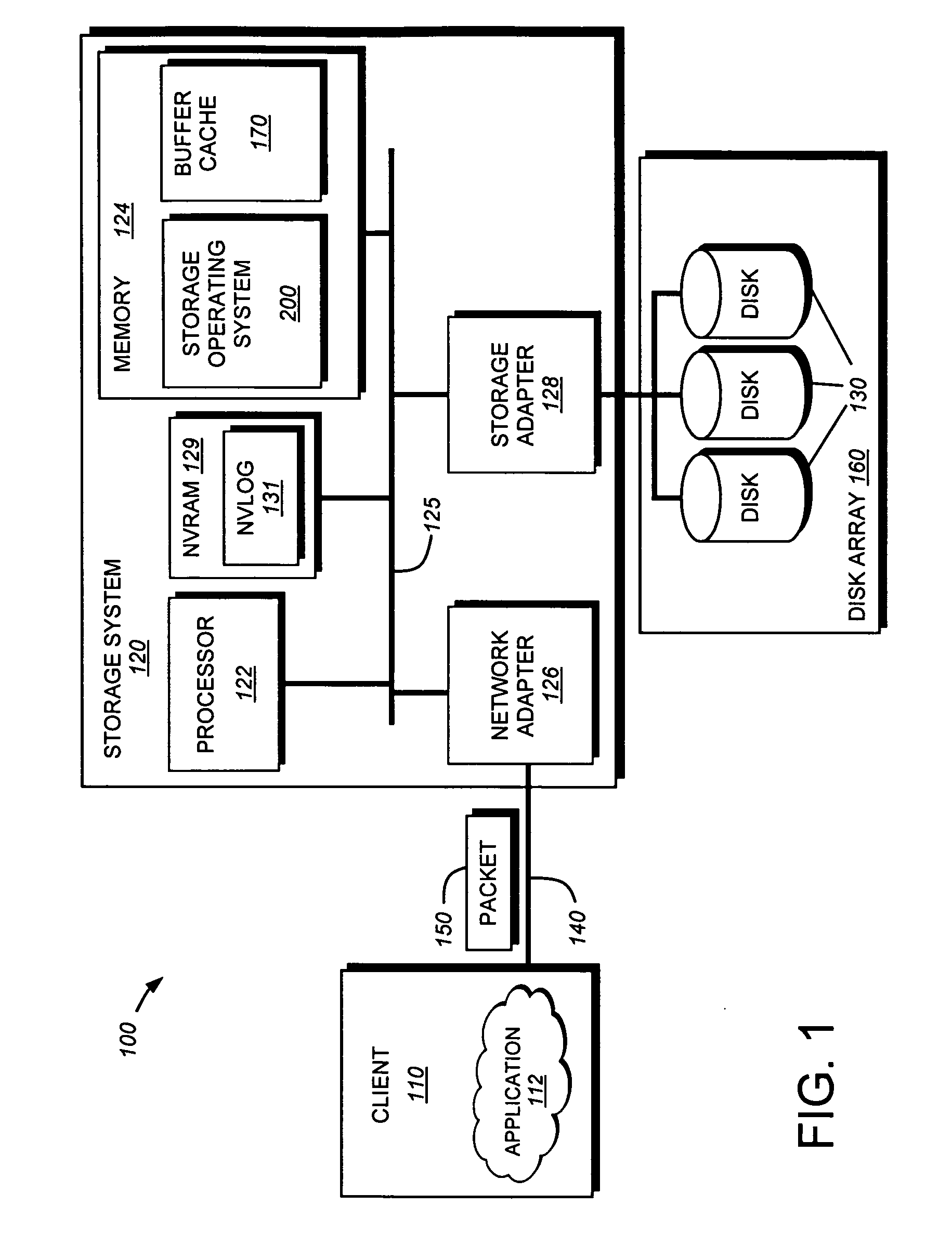
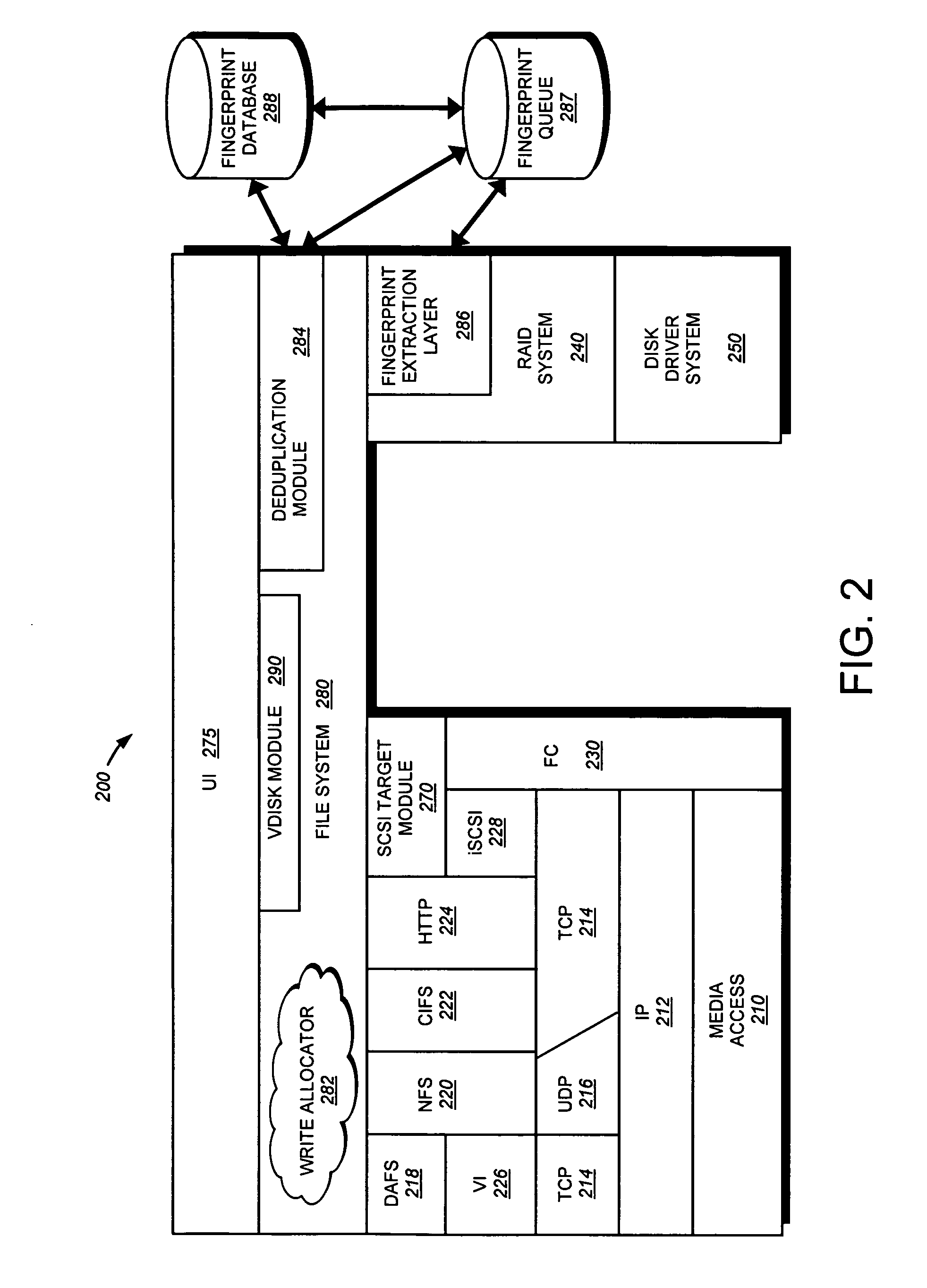
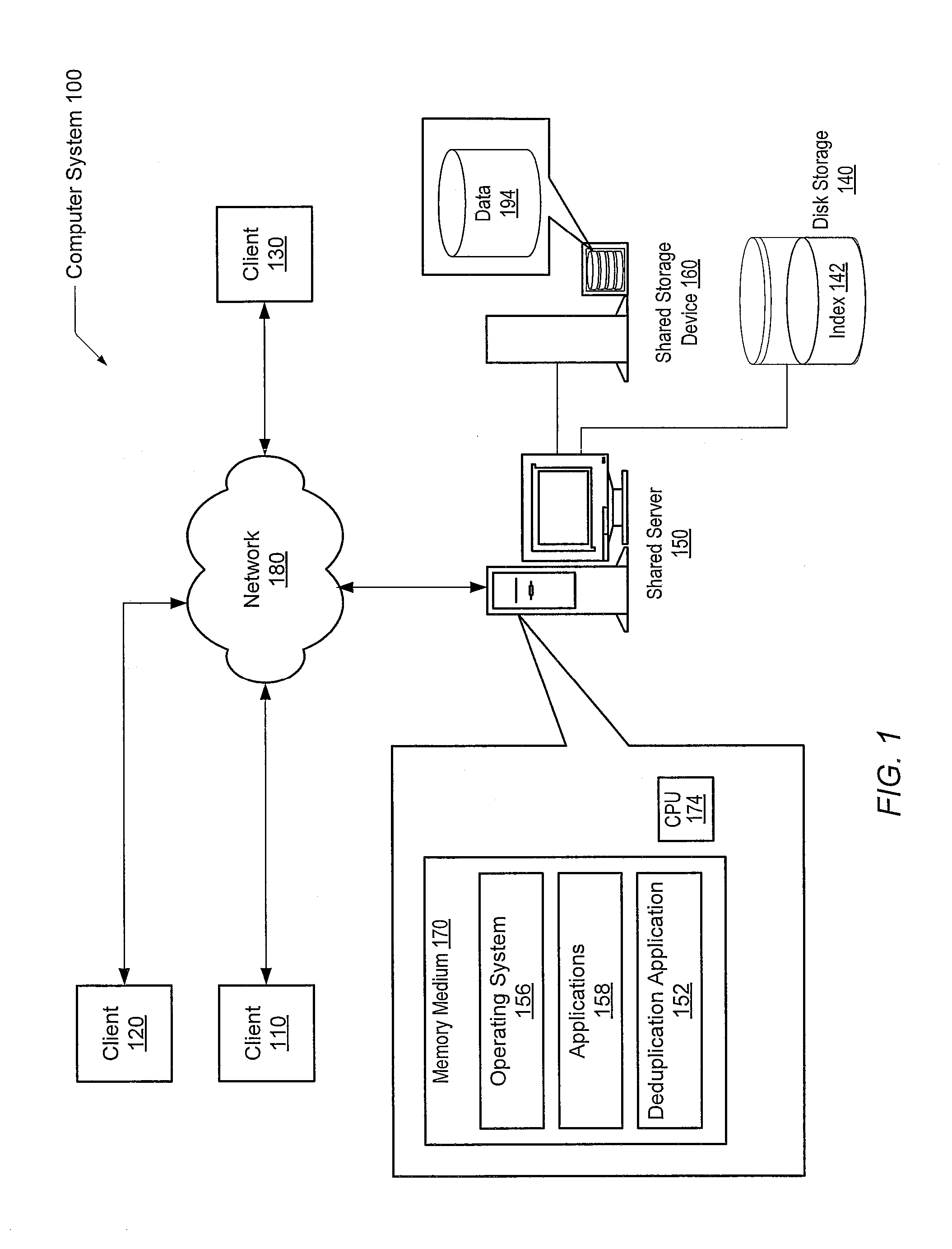
System and method for retrieving and using block fingerprints for data deduplication
ActiveUS20080005141A1Efficient identificationImprove performanceDigital data information retrievalDigital data processing detailsData deduplicationFingerprint database
A system and method for calculating and storing block fingerprints for data deduplication. A fingerprint extraction layer generates a fingerprint of a predefined size, e.g., 64 bits, for each data block stored by a storage system. Each fingerprint is stored in a fingerprint record, and the fingerprint records are, in turn, stored in a fingerprint database for access by the data deduplication module. The data deduplication module may periodically compare the fingerprints to identify duplicate fingerprints, which, in turn, indicate duplicate data blocks.
Owner:NETWORK APPLIANCE INC
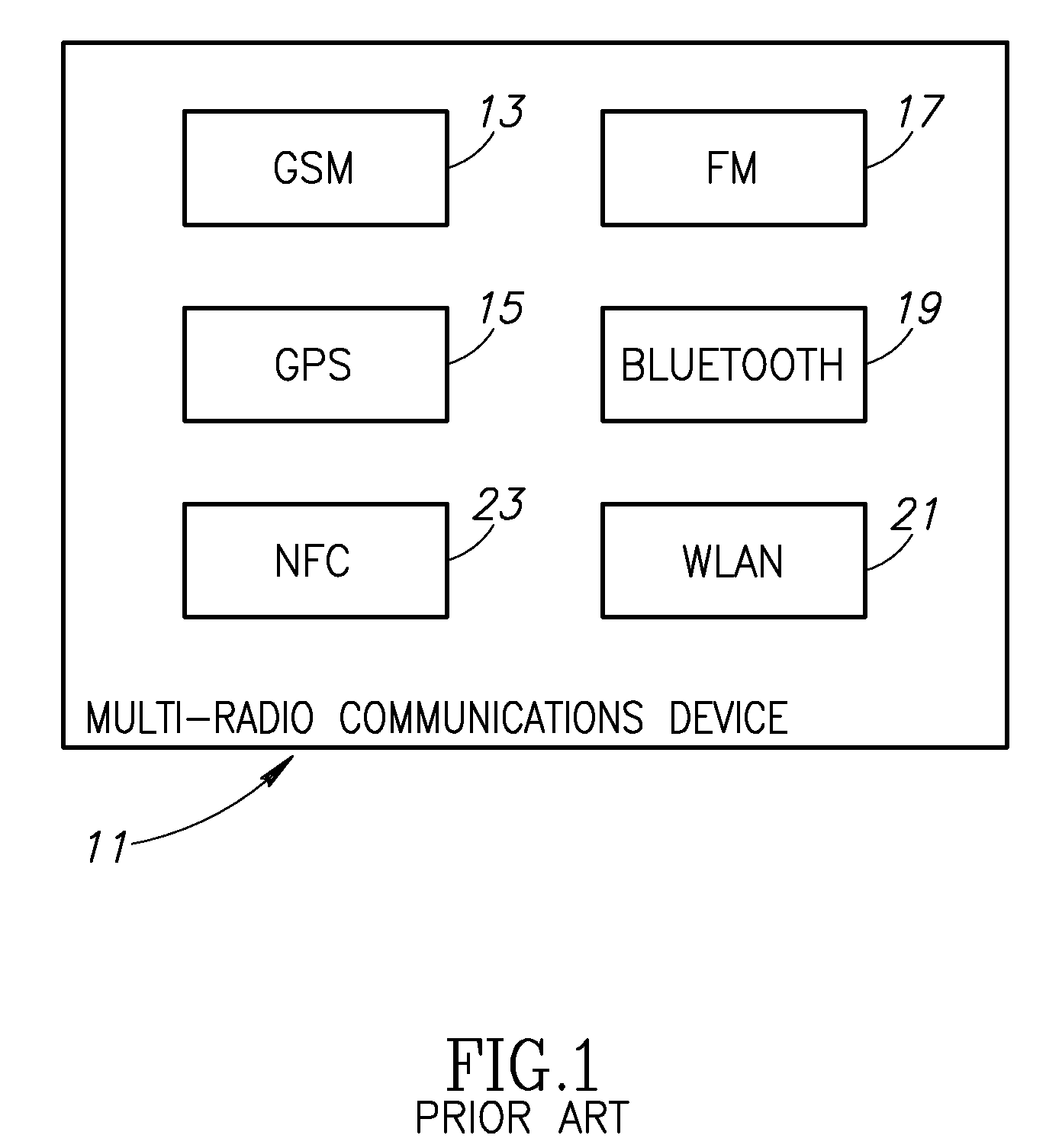
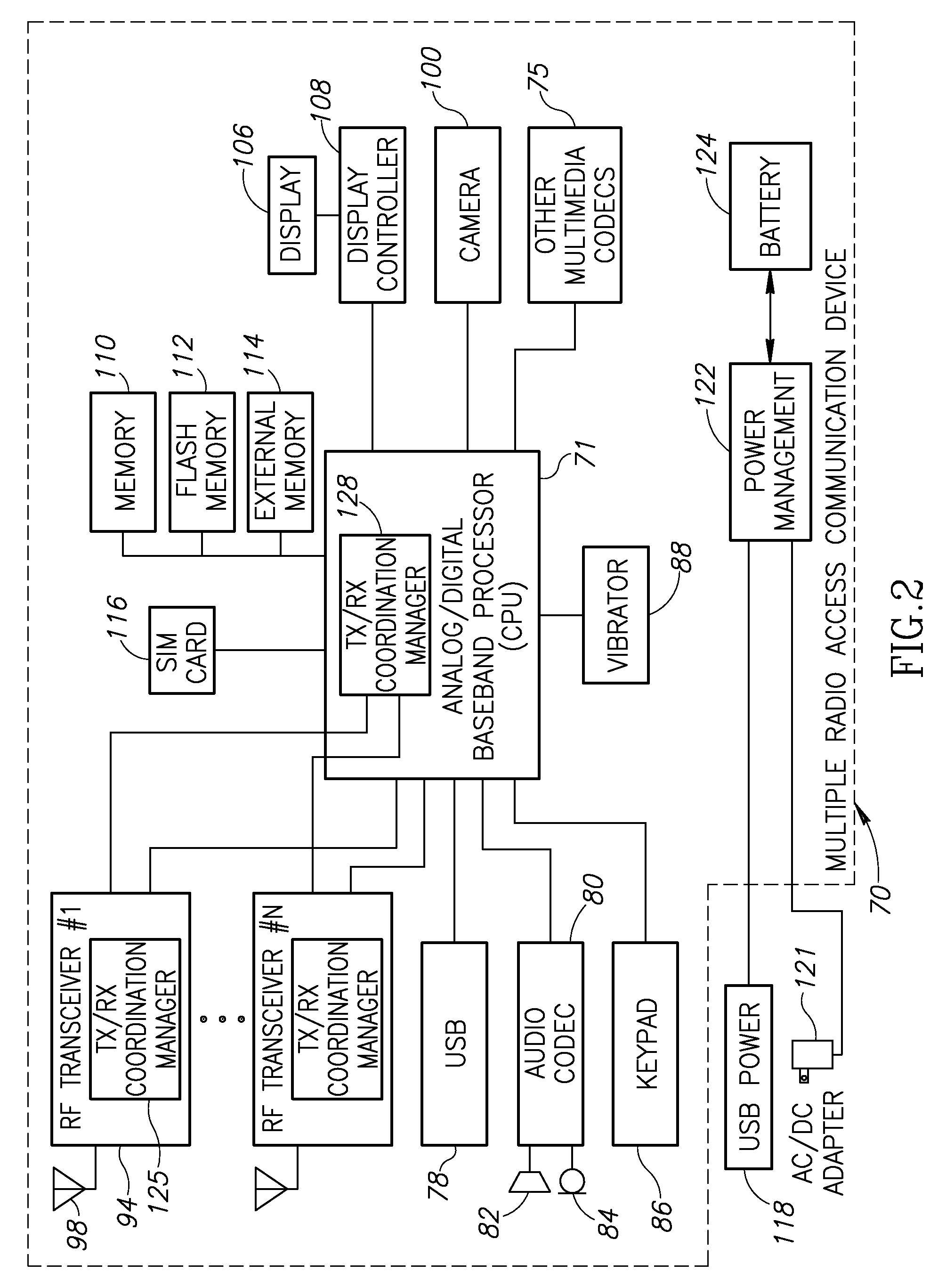
Apparatus for and method of coordinating transmission and reception opportunities in a communications device incorporating multiple radios
InactiveUS20090180451A1Avoid interferenceDelay transitionNetwork topologiesSubstation equipmentOperation modeMobile station
A novel and useful apparatus for and method of coordinating the allocation of transmission and reception availability and / or unavailability periods for use in a communications device incorporating collocated multiple radios. The mechanism provide both centralized and distributed coordination to enable the coordination (e.g., to achieve coexistence) of multiple radio access communication devices (RACDs) collocated in a single device such as a mobile station. A distributed activity coordinator modifies the activity pattern of multiple RACDs. The activity pattern comprises a set of radio access specific modes of operation, (e.g., IEEE 802.16 Normal, Sleep, Scan or Idle modes, 3GPP GSM / EDGE operation mode (PTM, IDLE, Connected, DTM modes), etc.) and a compatible set of wake-up events, such as reception and transmission availability periods. To prevent interference and possible loss of data, a radio access is prevented from transmitting or receiving data packets while another radio access is transmitting or receiving. In the event two or more RATs desire to be active at the same time, the mechanism negotiates an availability pattern between the MS and a corresponding BS to achieve coordination between the RATs.
Owner:COMSYS COMM & SIGNAL PROC
Write avoidance areas around bad blocks on a hard disk drive platter
ActiveUS20140285917A1Prevent data be writeAvoid dataRecord information storageDigital recordingHard disc driveComputer program
A method and computer program product identify the location of a bad block on a disk platter of a hard disk drive, determine an avoidance area extending from the bad block, and prevent data from being written to the avoidance area.
Owner:LENOVO GLOBAL TECH INT LTD
Flash memory management method that is resistant to data corruption by power loss
InactiveUS6988175B2Avoid dataMemory architecture accessing/allocationError detection/correctionElectricityRisk zone
A method for managing page-based data storage media such as flash media, a system that uses that method, and a computer-readable storage medium bearing code for implementing the method. New data are written to the storage medium in a manner that precludes corruption of old data if the writing of the new data is interrupted. Specifically, risk zones are defined, by identifying, for each page, the other pages whose data are put at risk of corruption if writing to the page is interrupted. A page, that otherwise would be the target of a write operation, is not written if any of the pages in its risk zone contain data that could be corrupted if the write operation is interrupted.
Owner:WESTERN DIGITAL ISRAEL LTD
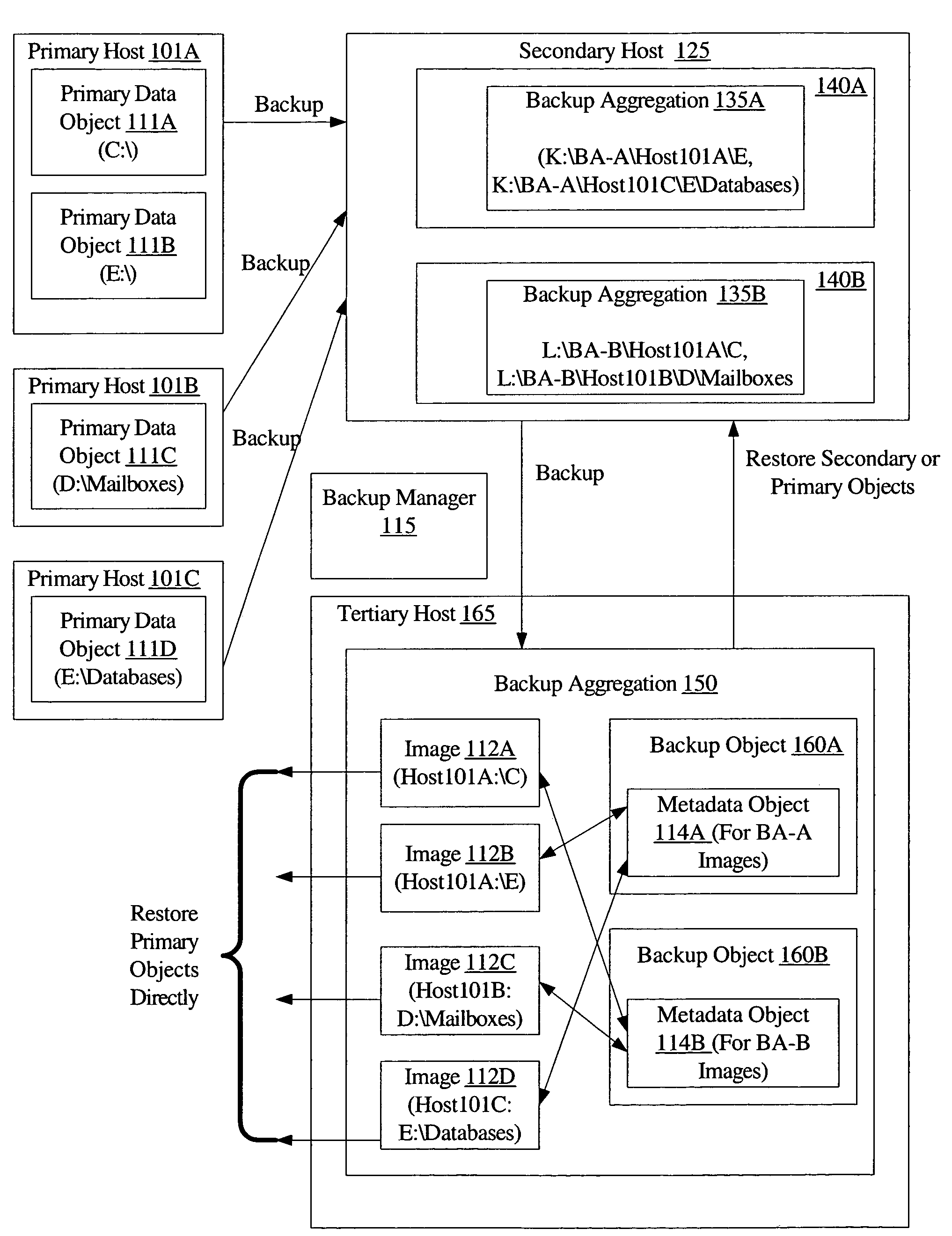
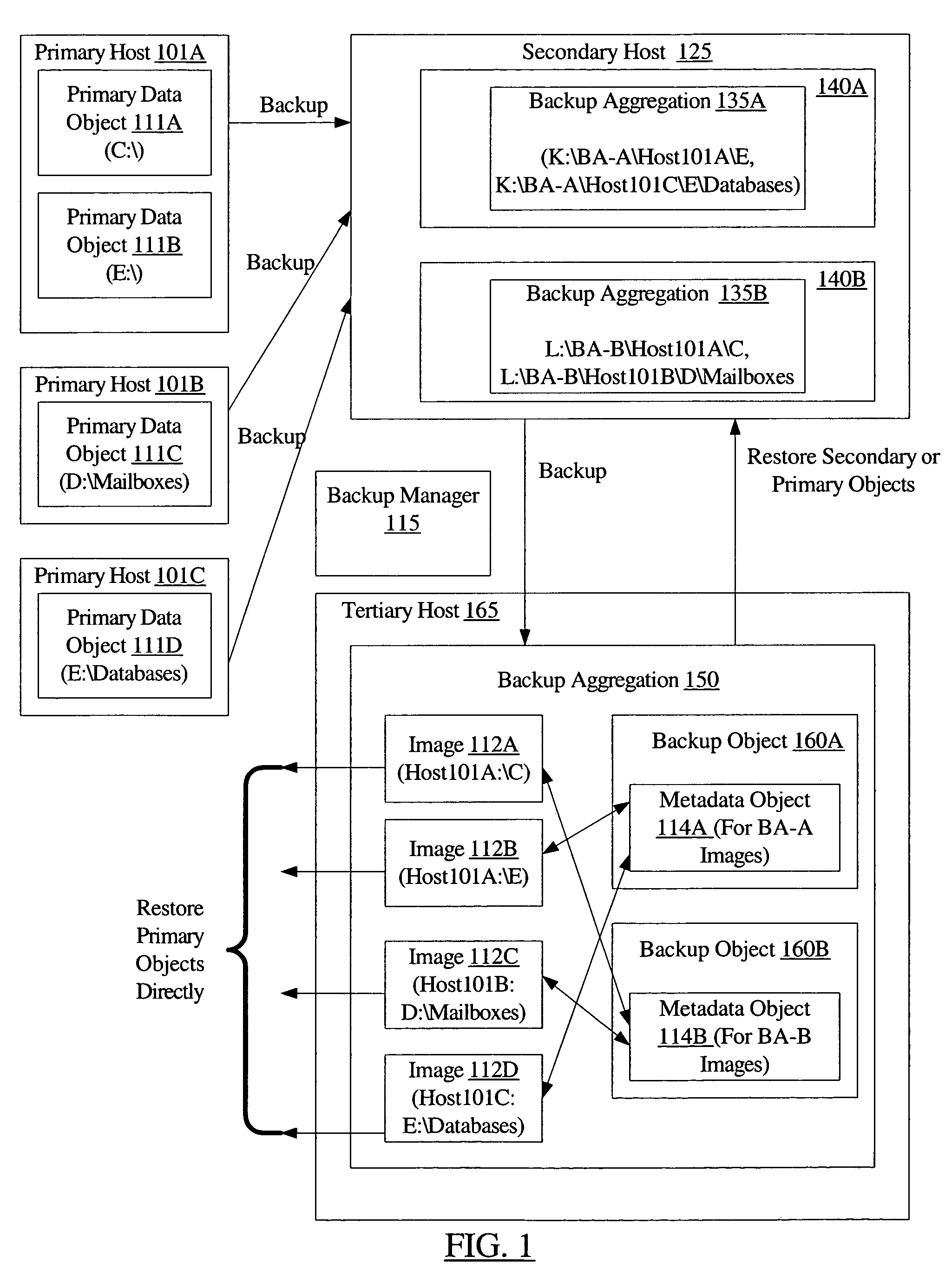
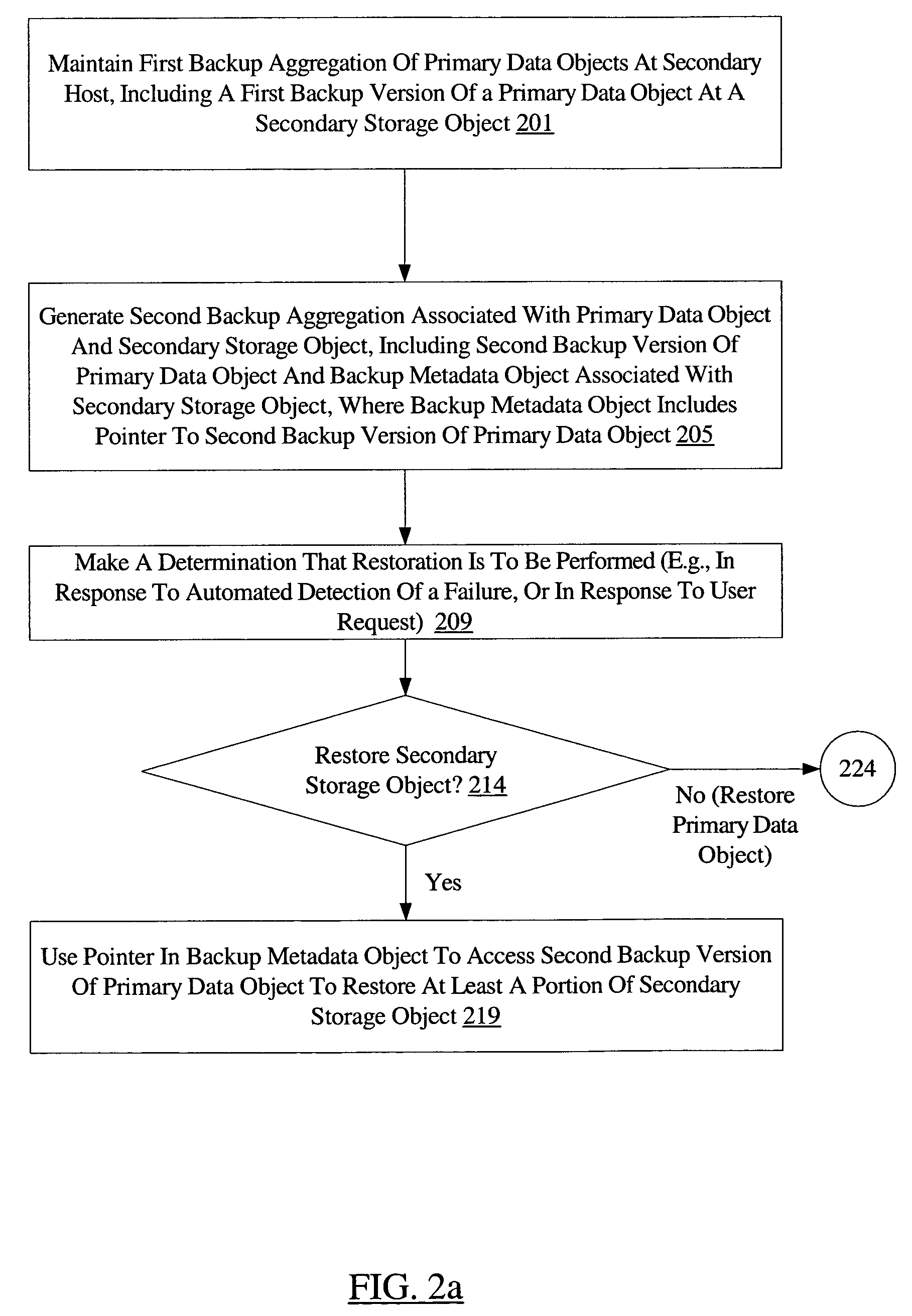
Efficient backup and restore using metadata mapping
ActiveUS7552358B1Avoid dataData duplication within the second backup aggregationError detection/correctionMetadataData objects
A method for efficient backup and restore using metadata mapping comprises maintaining a first backup aggregation associated with a primary data object of a primary host at a secondary host, wherein the first backup aggregation includes a first backup version of the primary data object stored within a secondary data object at the secondary host. The method further comprises generating a second backup aggregation, wherein the second backup aggregation includes a second backup version of the primary data object and a backup metadata object corresponding to the secondary data object. The backup metadata object includes a pointer to the second backup version. The method may further comprise restoring the secondary data object, wherein said restoring comprises using the pointer to access the second backup version of the primary data object to restore at least a portion of the secondary data object.
Owner:SYMANTEC OPERATING CORP
System and method for providing automated electronic information backup, storage and recovery
InactiveUS20100293147A1Avoid dataAvoid redundancyDigital data processing detailsSpecial data processing applicationsInformation repositoryApplication software
An automated electronic information backup, storage migration, and recovery system includes techniques for automatically observing all file events over a plurality of computing devices. The observed file events are mapped to the applications producing them. A relevancy of those file events are determined based on an application information repository. Business rules are produced based on this information to automatically backup all relevant file event changes and restore or migrate backed up information when necessary.
Owner:HIPAA BOX
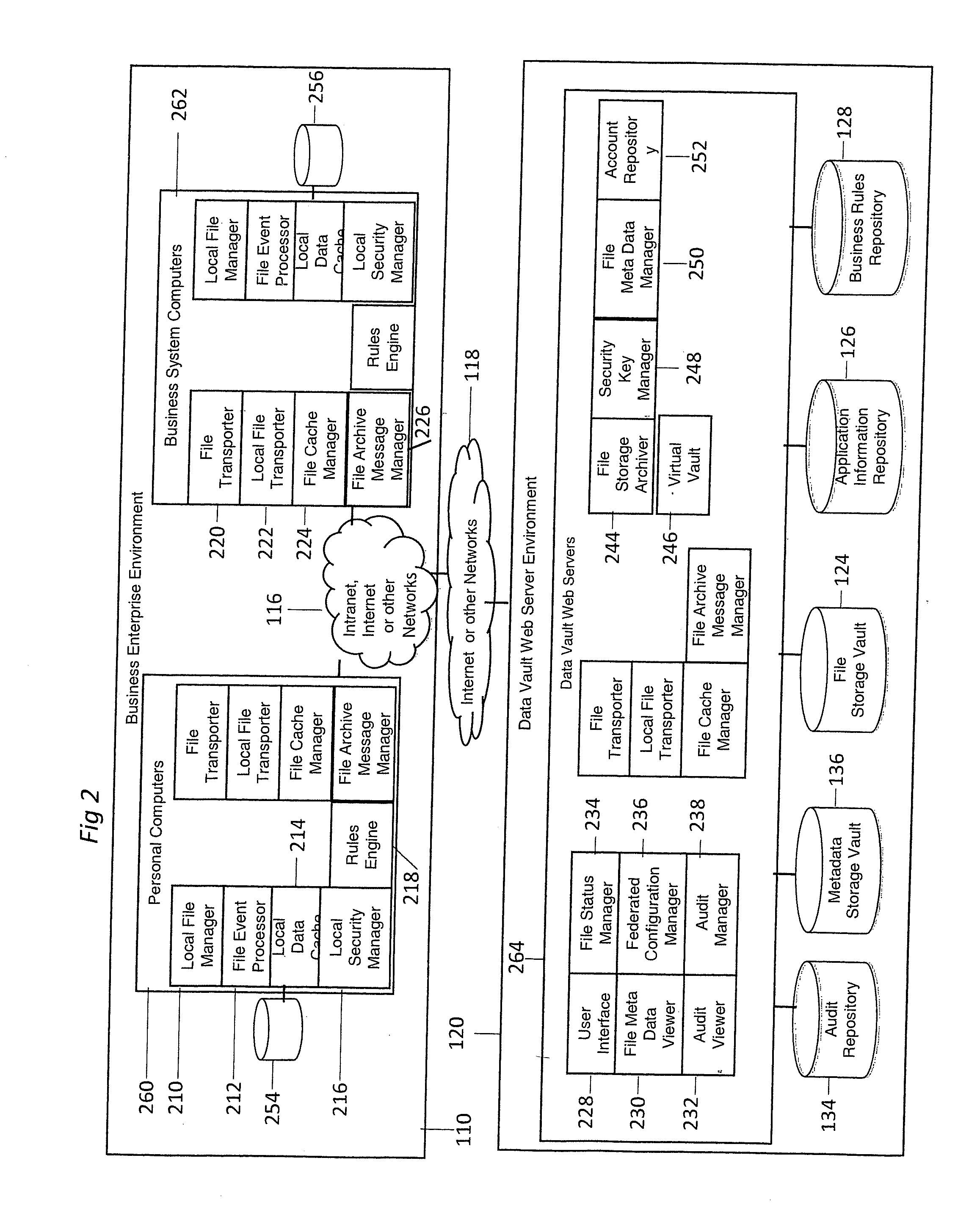
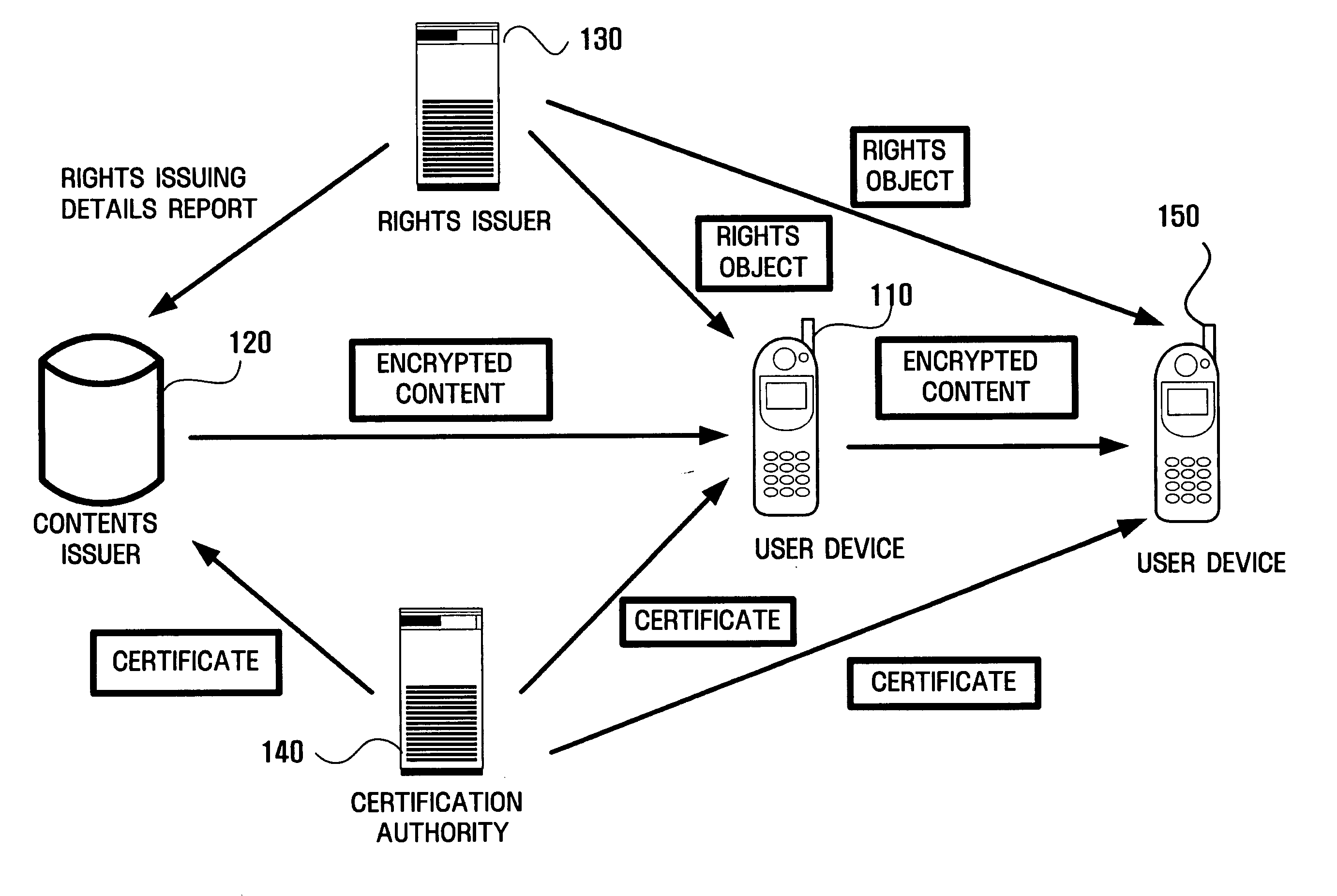
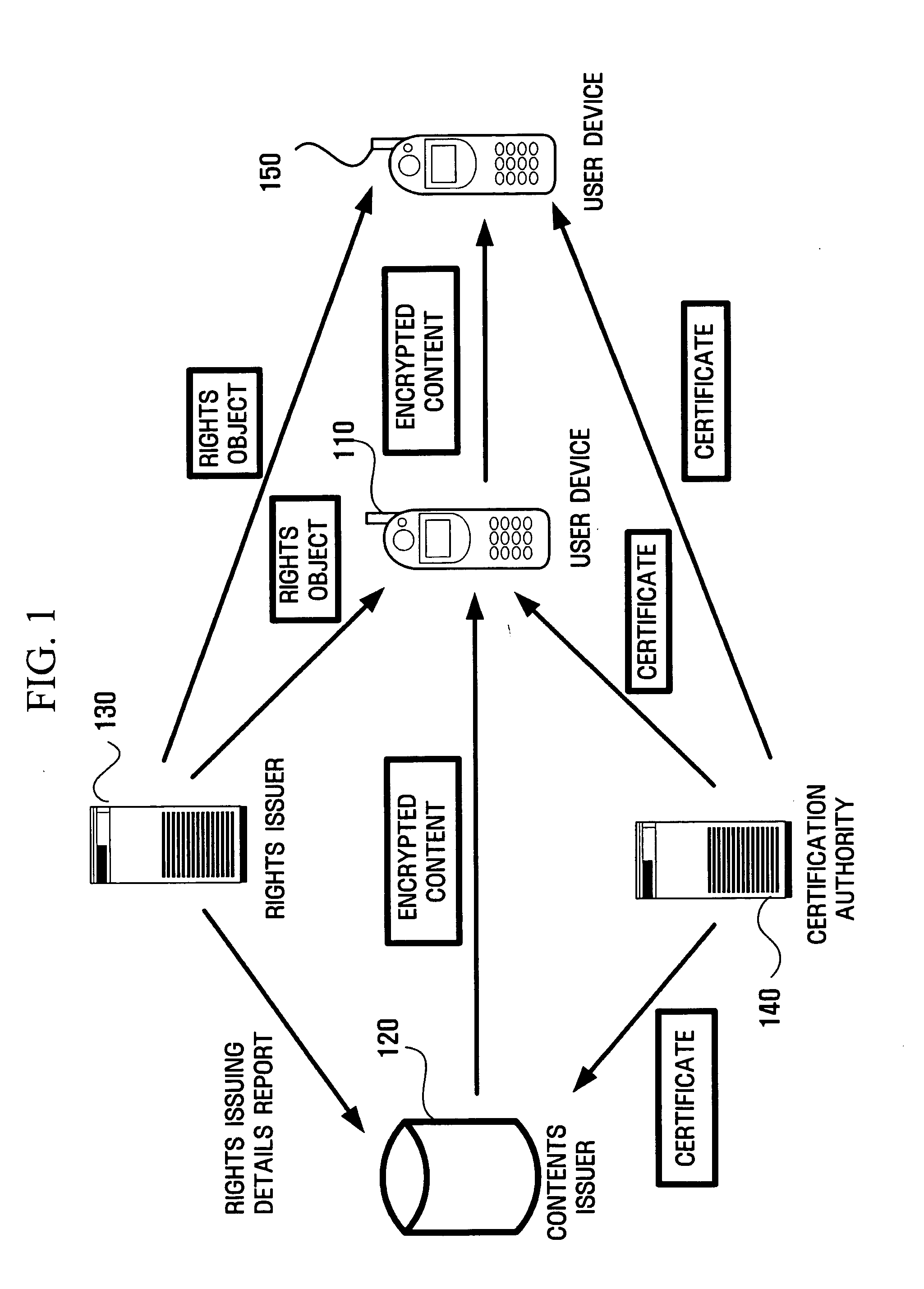
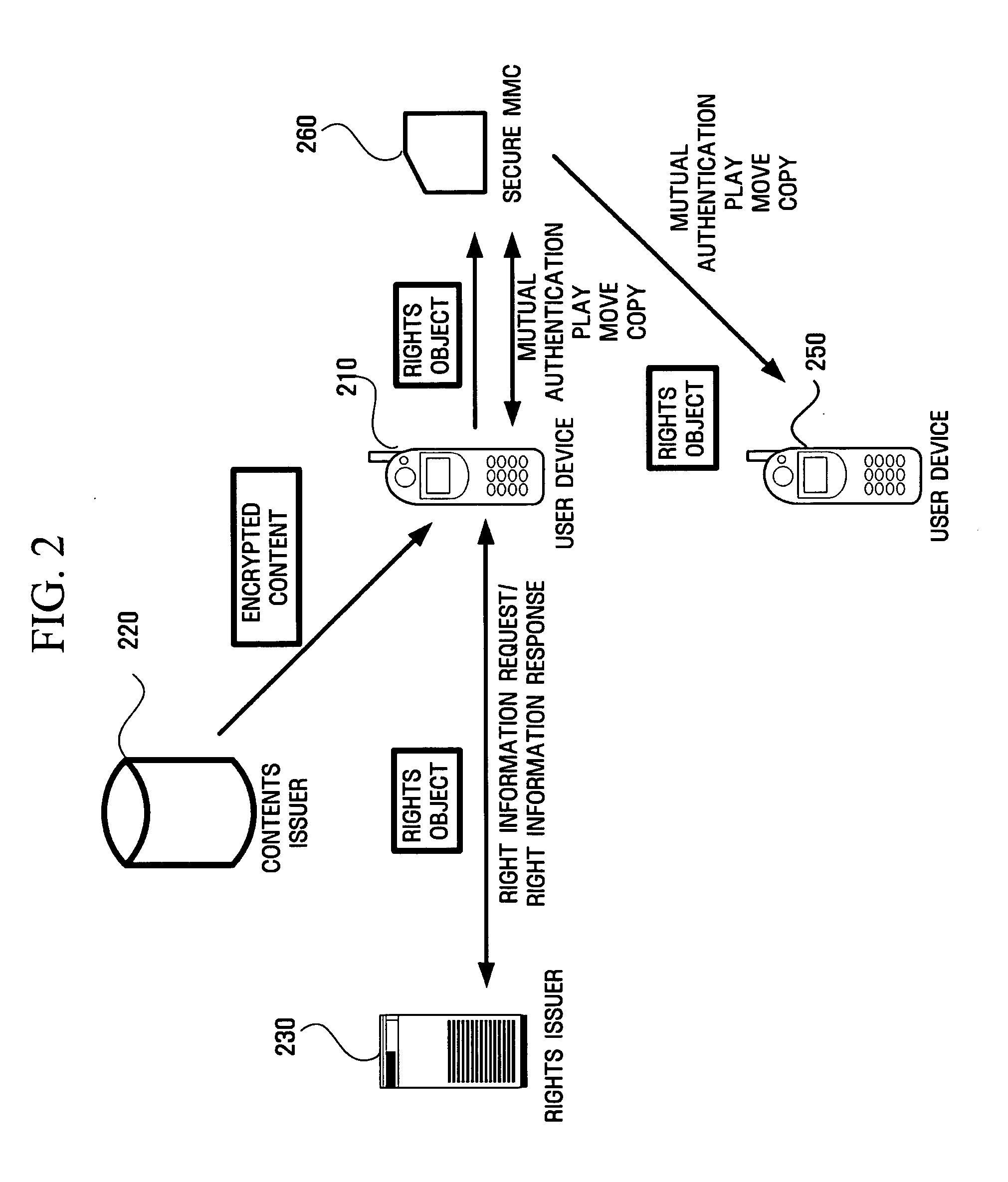
Apparatus and method for moving and copying rights objects between device and portable storage device
InactiveUS20050210249A1Efficient of digital contentEfficient managementKey distribution for secure communicationDigital data processing detailsComputer hardwareDigital content
A method and apparatus for copying or moving a rights object having right information regarding digital contents between a device and a portable storage device to copy or move the digital contents there between are provided. According to the method and apparatus, the digital works can be prevented from being recklessly and randomly copied and moved, and therefore, copyright can be protected. In addition, data loss or unauthorized access can be prevented.
Owner:SAMSUNG ELECTRONICS CO LTD
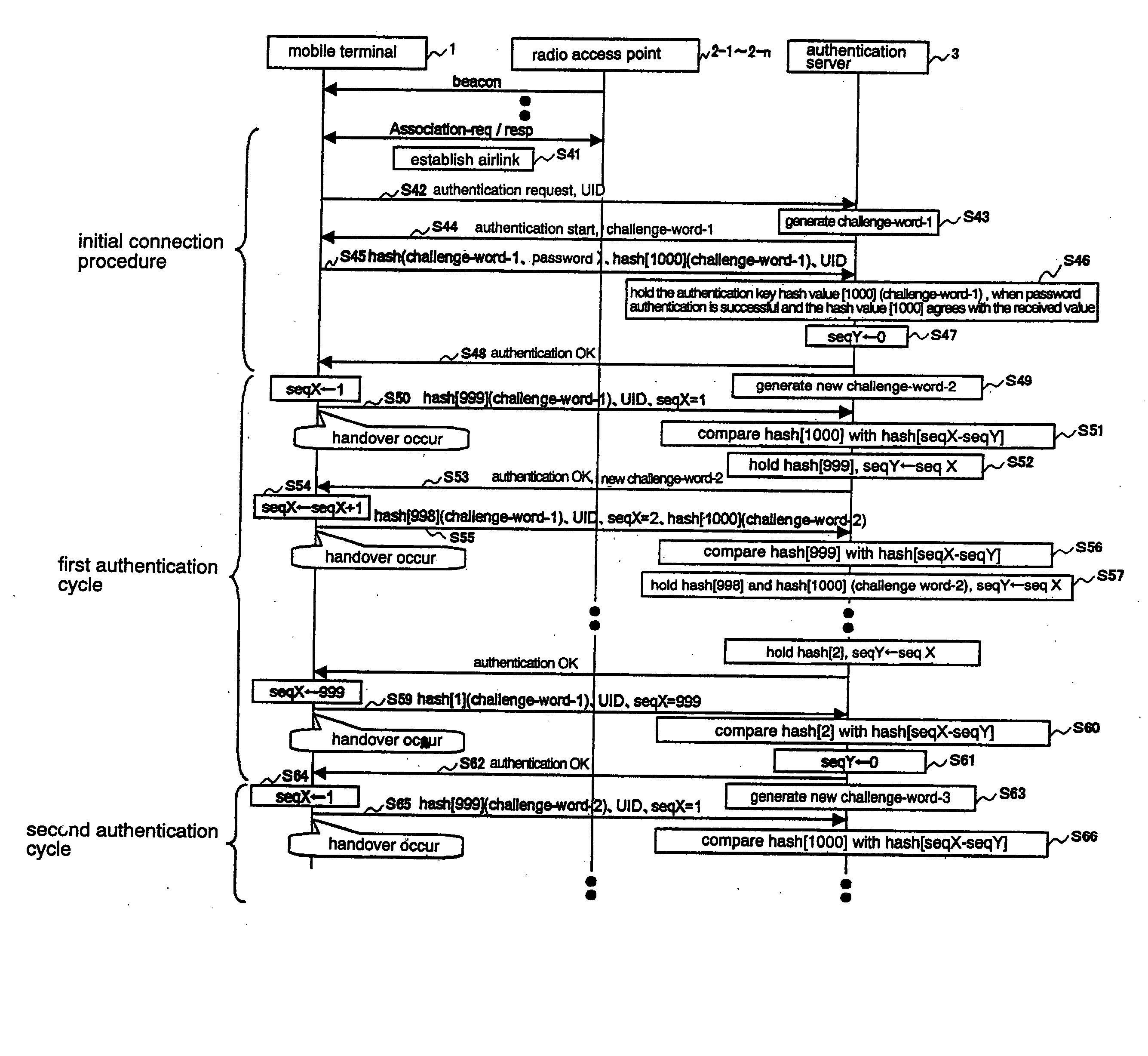
Mobile terminal authentication method capable of reducing authentication processing time and preventing fraudulent transmission/reception of data through spoofing
InactiveUS20050113070A1Shorten the timePreventing fraudulent data transmission/receptionUnauthorised/fraudulent call preventionEavesdropping prevention circuitsReceiptRadio access point
A mobile terminal transmits an N-th authentication key to an authentication server when the mobile terminal has moved from a coverage area under a certain radio access point to a coverage area under another radio access point. The N-th authentication key is generated by applying a hash function to a random number a number of times one smaller than an (N−1)th authentication key which was transmitted when the mobile terminal moved to the coverage area under the certain radio access point. Upon receipt of the N-th authentication key from the mobile terminal, the authentication server applies the hash function once to the N-th authentication key, and compares the result with the (N−1)th authentication key. Then, the authentication server determines that the authentication is successful when there is a match between both keys.
Owner:NEC CORP
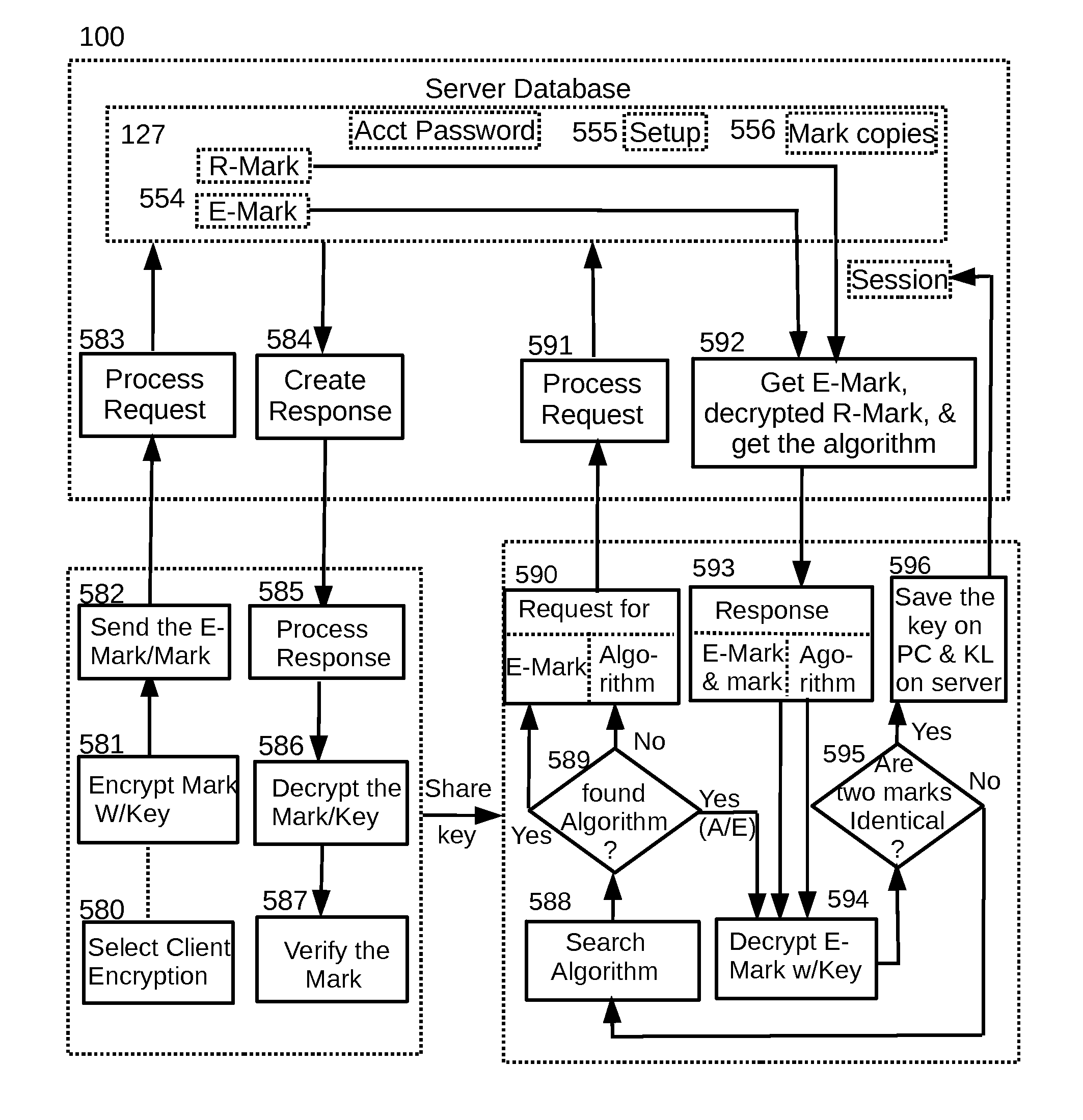
Secure File Drawer and Safe
ActiveUS20130198521A1Improve securityReduce riskMultiple keys/algorithms usagePublic key for secure communicationClient-sideOnline document
An online file storage system having secure file drawer and safe is disclosed for securely storing and sharing confidential files. The system comprises a web-based user interface, tools for setting up server-side encryption method and client-side encryption method, tools for synchronizing encryption between different computers, tools for uploading files, tools for tracking files, tools for granting the right of access to files to the owner of other safes, and tools for generating authenticity certificate for proving the upload time and the substance of the files in a future time.
Owner:WU JIANQING
Nonvolatile RAM
InactiveUS20080209117A1Reliably erasePrevent data storedDigital data protectionInternal/peripheral component protectionControl signalEmbedded system
A nonvolatile RAM allows a read / write operation to be performed in a random manner with respect to a memory area, which is divided into a plurality of memory arrays each including a plurality of memory cells. Upon detection of an initialization signal, initialization is performed on at least one memory array, which is selected in advance. In addition, a disconnection control signal occurs so as to disconnect an access by an external device during a prescribed period for performing the initialization. The nonvolatile RAM is capable of protecting data from being irregularly read, modified, and reloaded with respect to at least one memory array, which is selected in advance, even when the nonvolatile RAM is frequently accessed by a prescribed application.
Owner:ELPIDA MEMORY INC
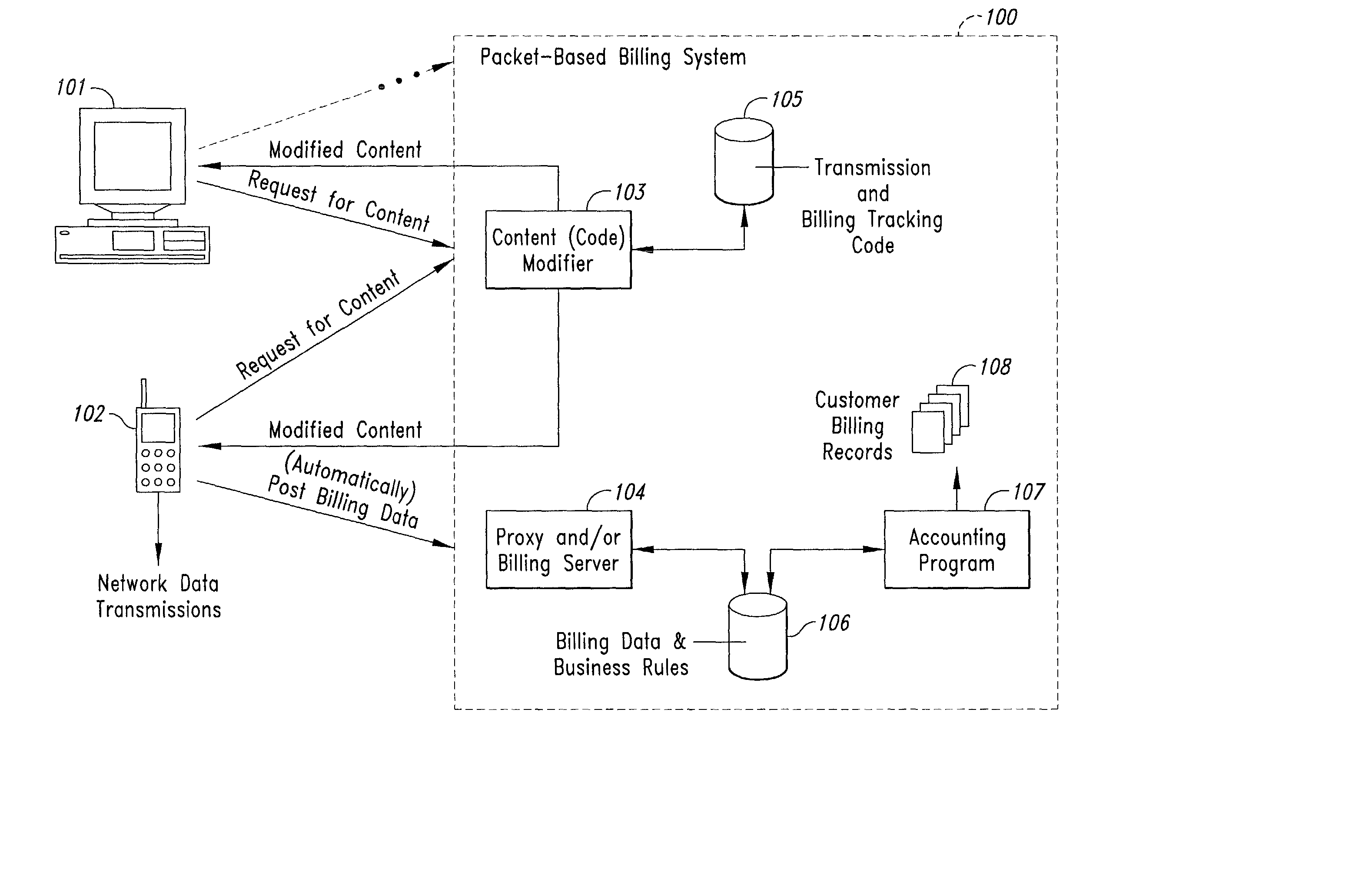
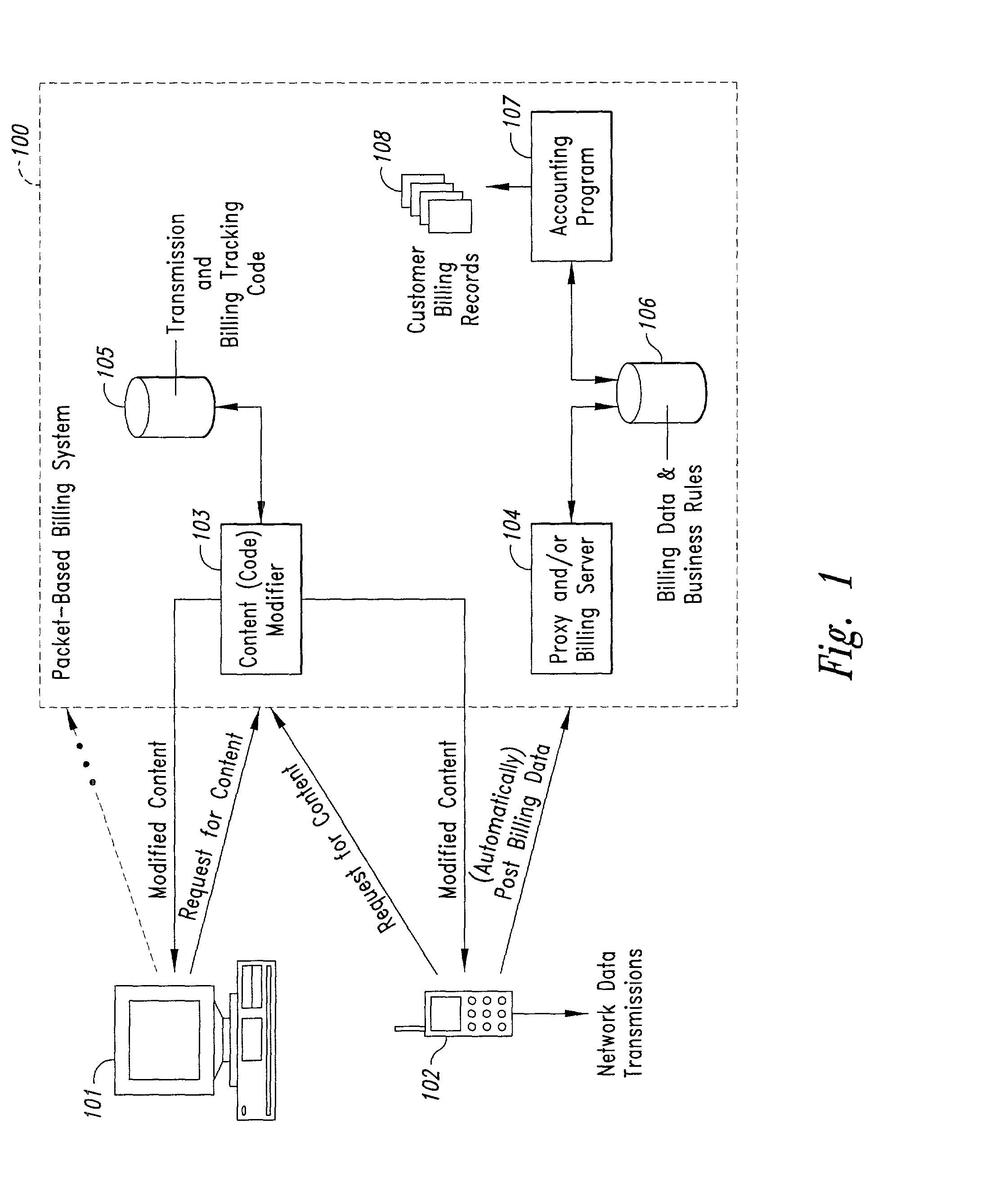
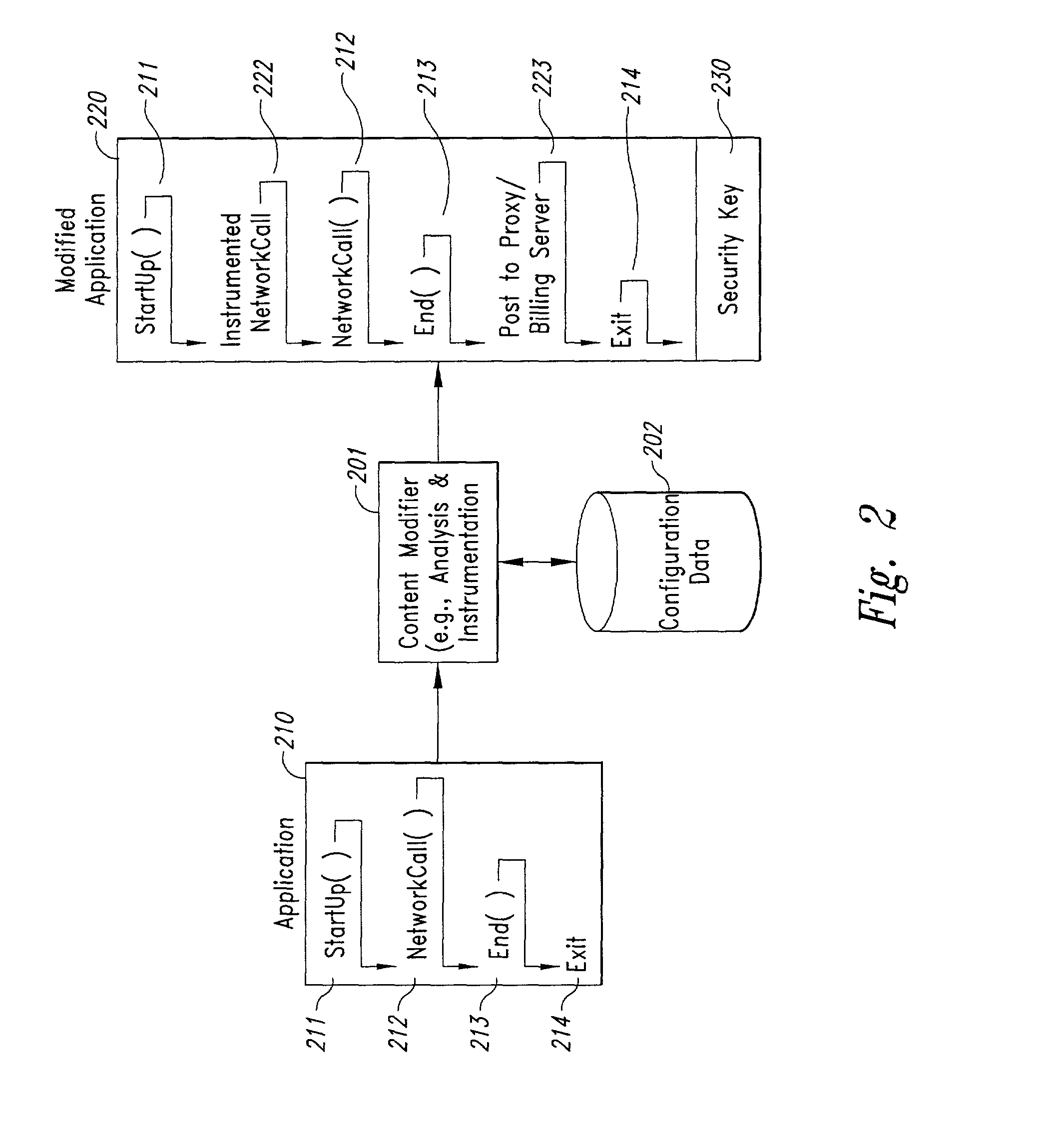
Method and system for transmission-based billing of applications
InactiveUS20020128984A1Short response timeImprove efficiencyMetering/charging/biilling arrangementsAccounting/billing servicesApplication computersApplication software
Computer-and network-based methods and systems for transmission-based billing are provided. Example embodiments provide a Packet-Based Billing System ("PBBS"), which enables application providers, such as carriers and content providers, to bill subscribers for the use of content on mobile subscriber devices, such as wireless devices, on a per-application, per-user basis based upon the extent of the usage. Embodiments of the present invention can also be used to bill subscribers for the use of content on a per-application, per-user basis for wired subscriber devices as well, using the same techniques. In operation, the PBBS provides modified content by inserting billing and tracking code into content returned to a requesting device. The modified content, when executed, tracks the amount of data sent and received between the content and a network and posts the accumulated data to a proxy / billing server according to business rules for an interval / frequency to post such data. The proxy / billing server stores the raw billing data and an accounting program retrieves the billing data to generate customer (call) data records. Business rules that specific different charges for different content or users can be incorporated into the system.
Owner:GOOGLE TECH HLDG LLC +1
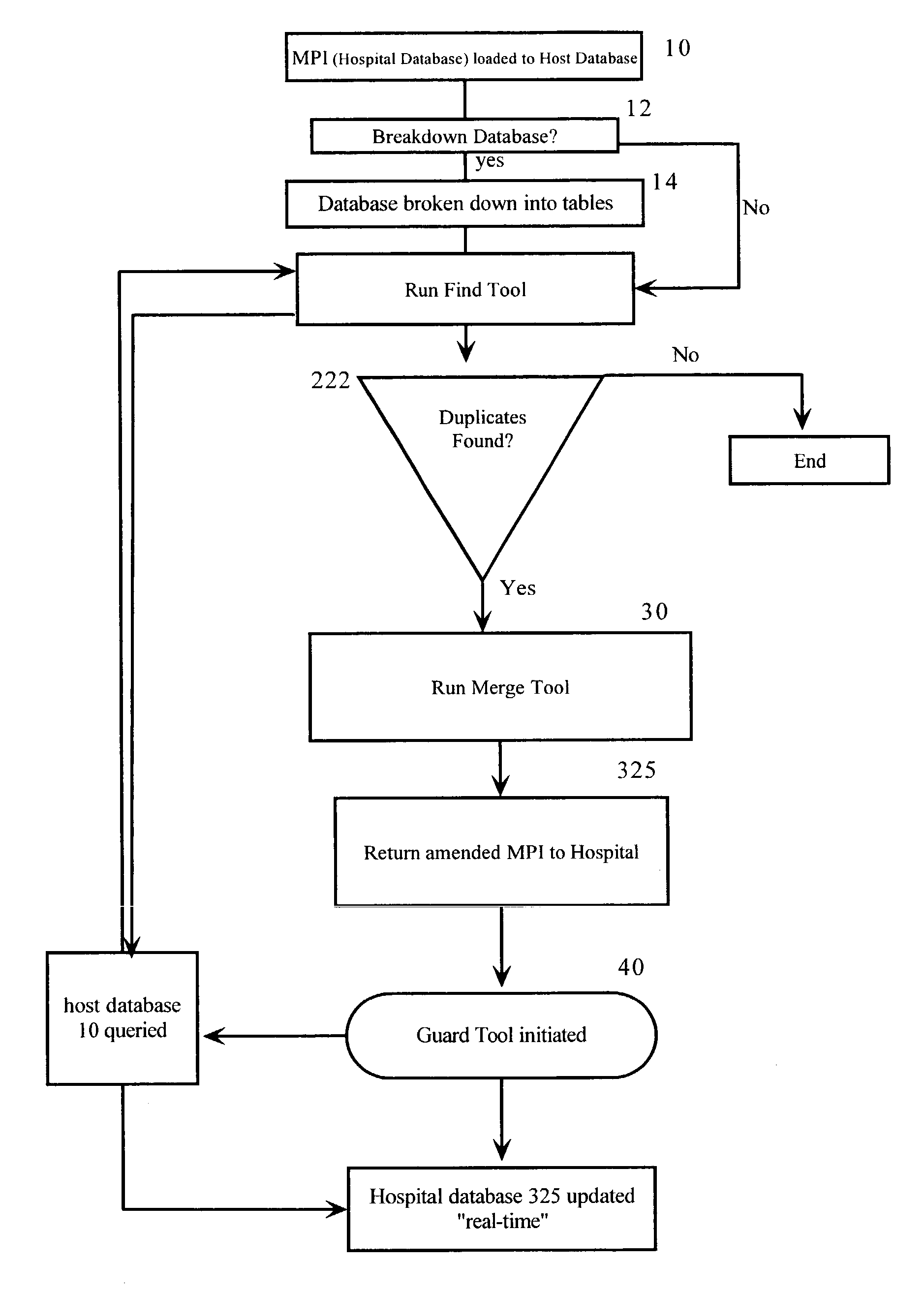
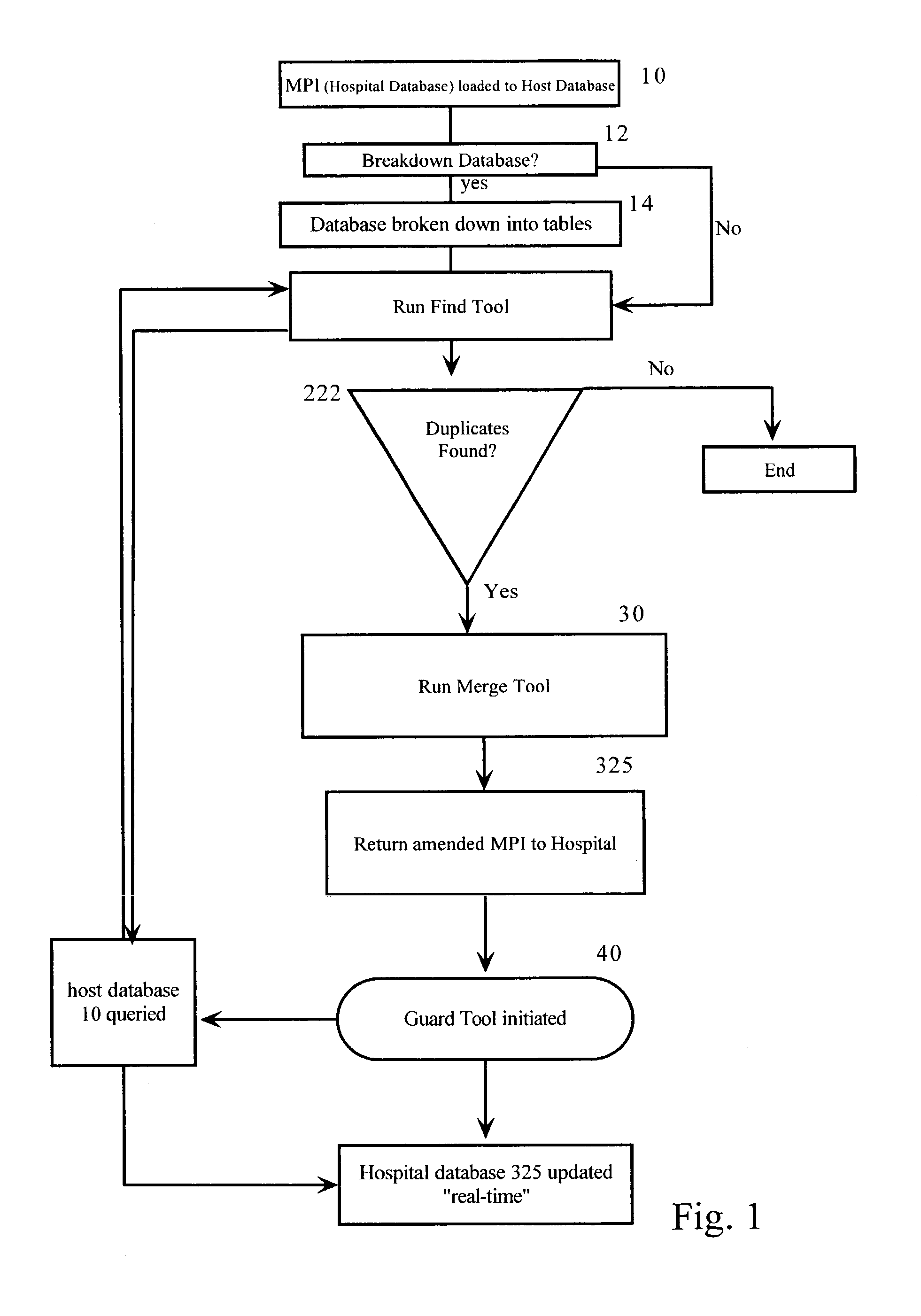
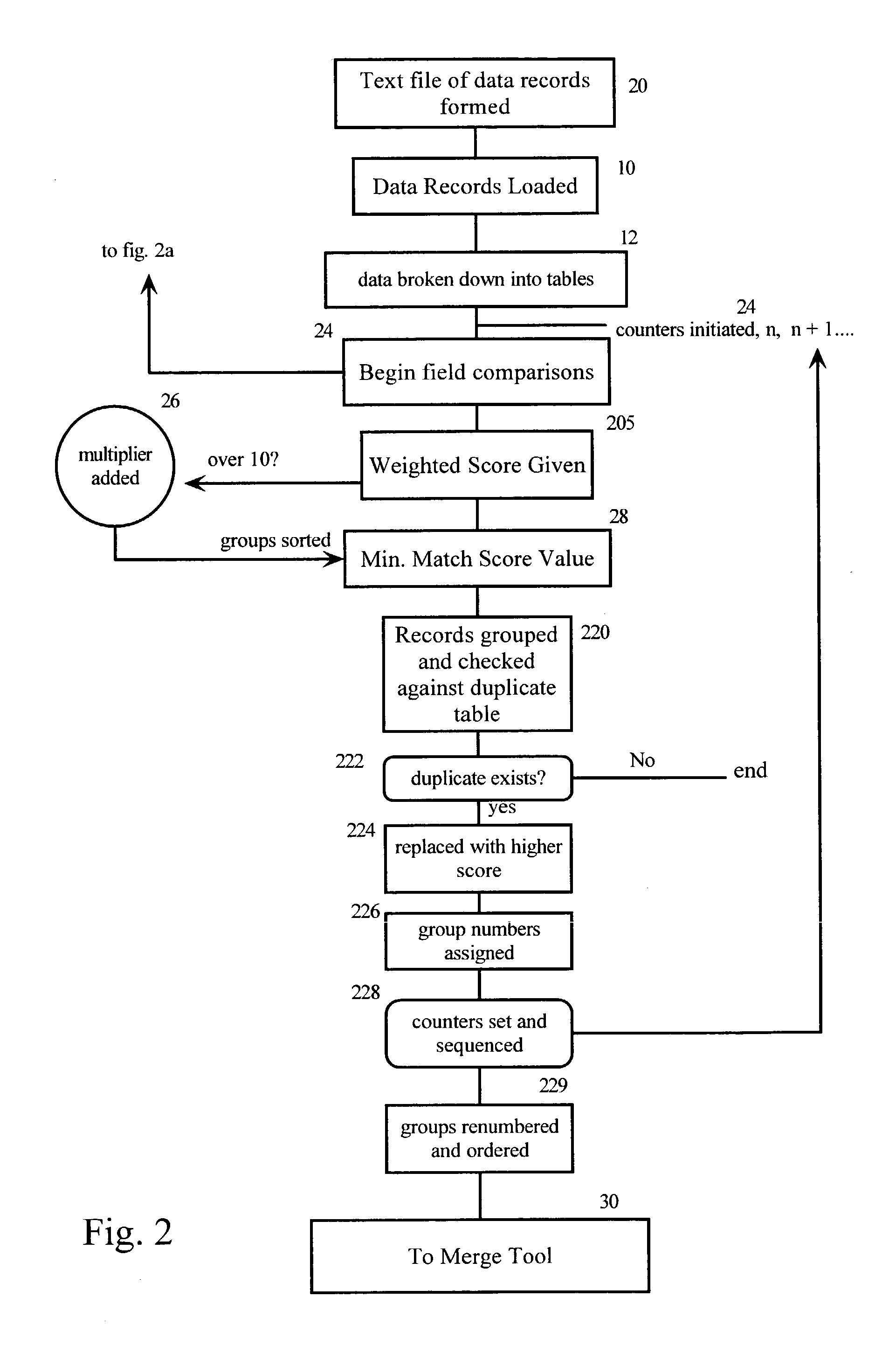
Duplicate resolution system and method for data management
InactiveUS20030126156A1Avoid dataDigital data information retrievalDigital data processing detailsImage resolutionData management
A system is provided for merging hospital database records and assuring real-time patient field updates during registration processes. A find tool identifies potential duplicate records, data overlays and duplicate guarantor numbers within a master patient index (MPI) or enterprise master patient index (EMPI) database of a hospital database. After the data is scored, a merge tool merges the data and gives the user the ability to review potential duplicate records online and decide on an operation to be performed thereon. A guard tool complements the merge tool as a means for preventing duplicate records and data overlays during the registration process. The user can continue with the new registration or choose an existing record from the duplicate matching screen as the data is inputted, thereby keeping the current inputs clean in "real-time."
Owner:STOLTENBERG JAY A +1
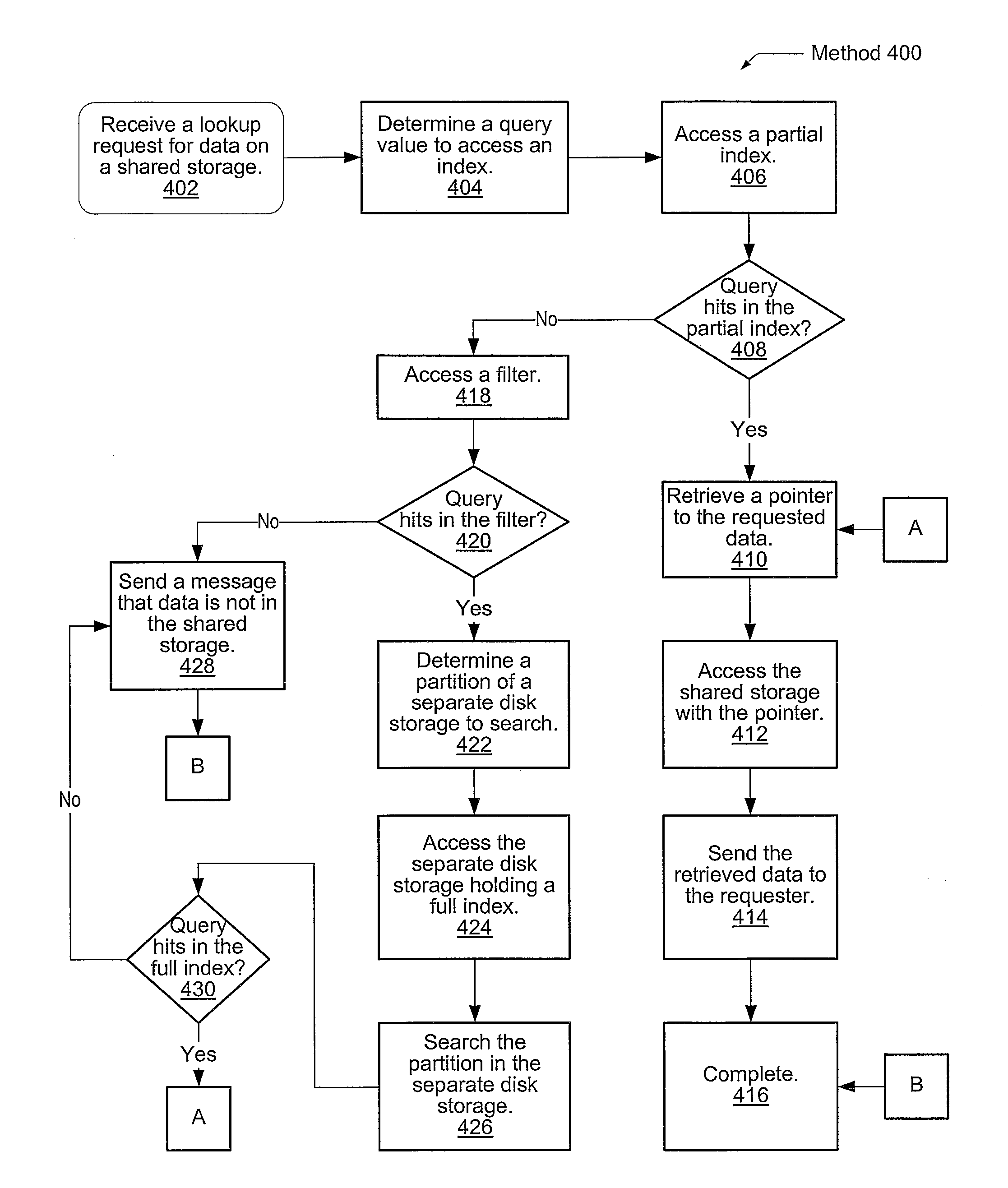
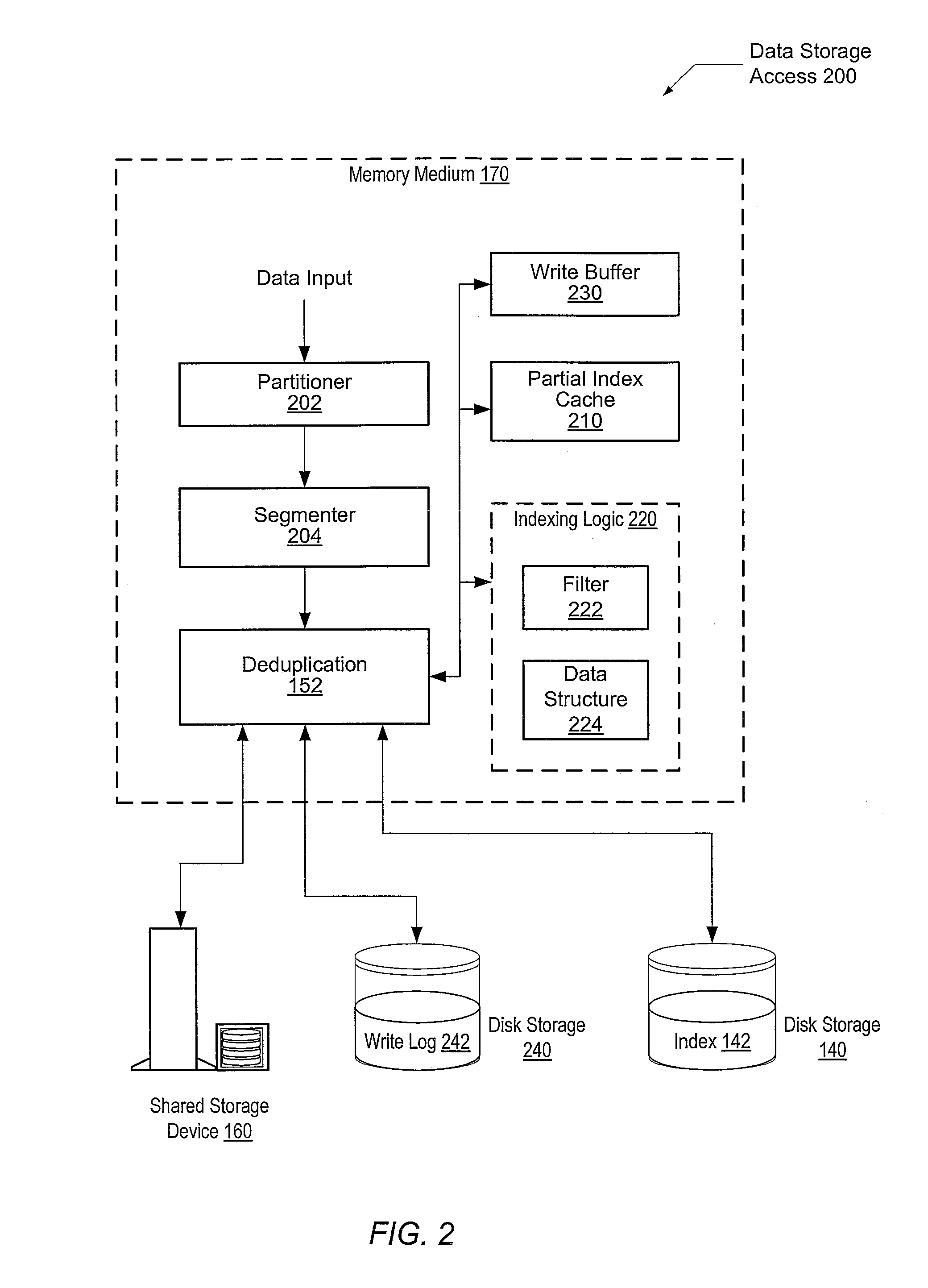
System and method for high performance deduplication indexing
ActiveUS8370315B1Reduce access latencyPrevent duplicate dataDigital data information retrievalDigital data processing detailsFingerprintSolid-state
A system and method for efficiently reducing latency of accessing an index for a data segment stored on a server. A server both removes duplicate data and prevents duplicate data from being stored in a shared data storage. The file server is coupled to an index storage subsystem holding fingerprint and pointer value pairs corresponding to a data segment stored in the shared data storage. The pairs are stored in a predetermined order. The file server utilizes an ordered binary search tree to identify a particular block of multiple blocks within the index storage subsystem corresponding to a received memory access request. The index storage subsystem determines whether an entry corresponding to the memory access request is located within the identified block. Based on at least this determination, the file server processes the memory access request accordingly. In one embodiment, the index storage subsystem is a solid-state disk (SSD).
Owner:VERITAS TECH
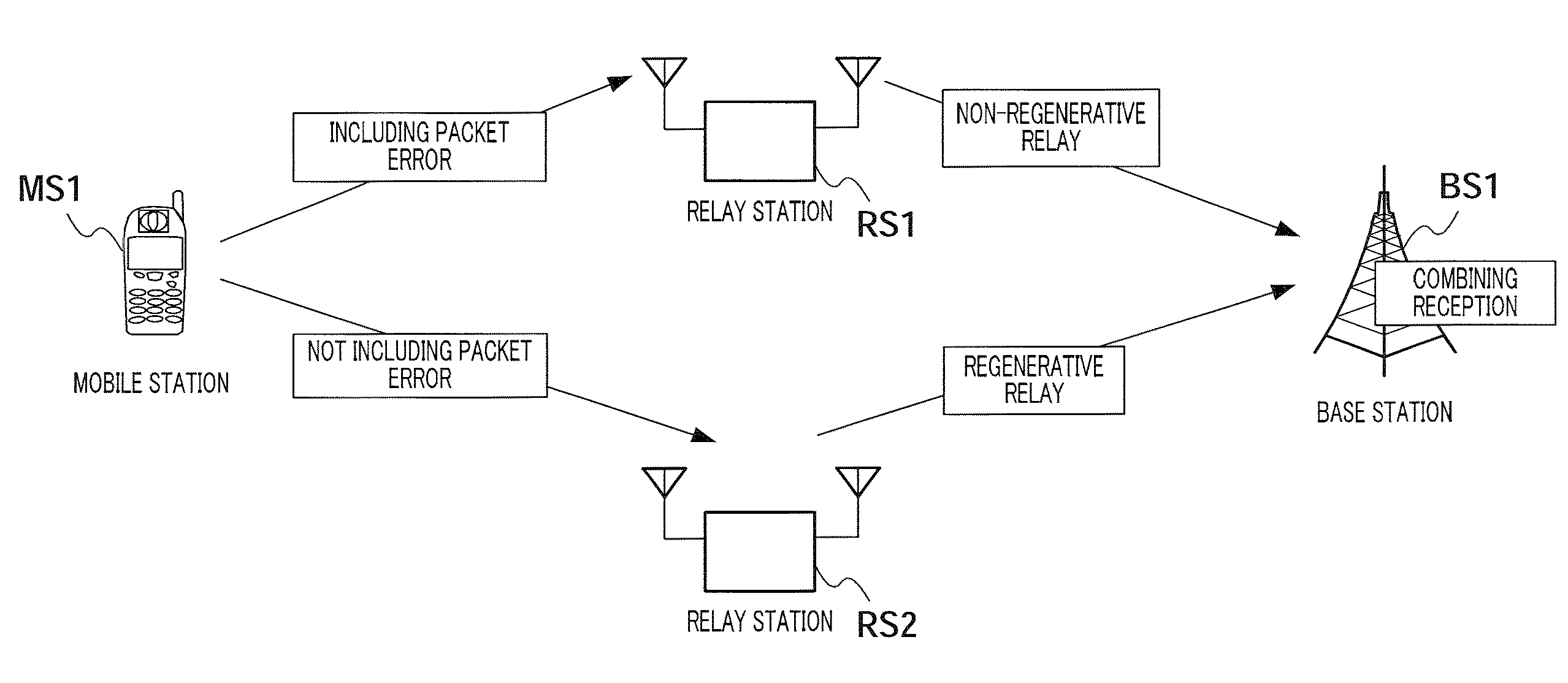
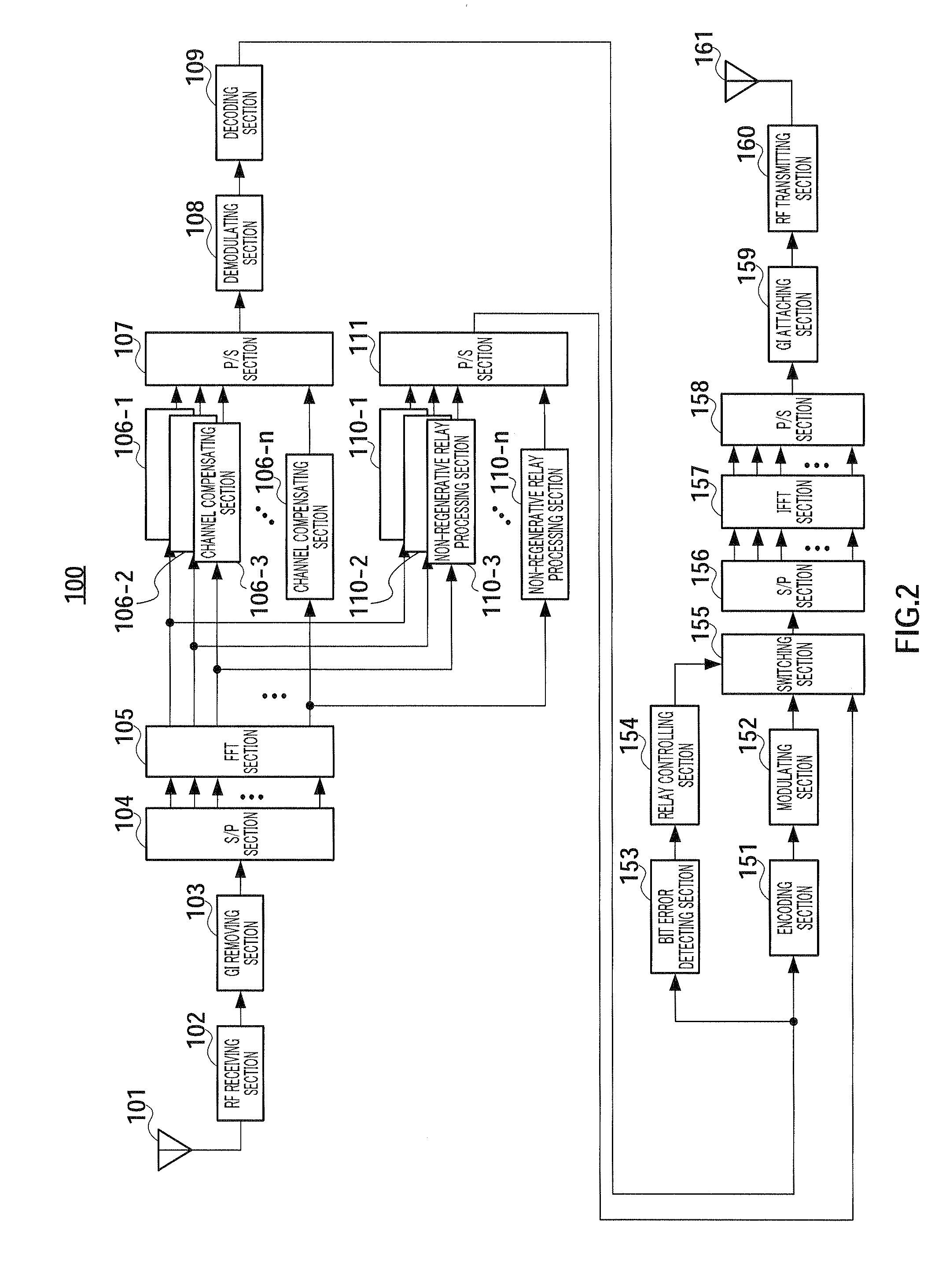
Communication relay apparatus and communication relay method
ActiveUS20090092072A1Improve throughputImproving error rate performanceFrequency-division multiplex detailsNetwork traffic/resource managementCommunications systemCarrier signal
A communication relay apparatus wherein the error rate characteristic of a relay destination is improved to raise the throughput, while reducing the given interference power to prevent the reduction of the throughput of the whole communication system. In the apparatus, a signal addressed to a base station is received (ST1010), and a decoding process and other processes are performed (ST1020). A bit error determination is performed (ST1030), and if there is no bit error, a reproduction / relay process (ST1050) is performed. If there is any bit error, a threshold-based determination of reception quality is performed for each of subcarriers (ST1120-1130). If the reception quality is greater than a threshold value, the corresponding subcarrier is outputted (ST1140); otherwise, the corresponding subcarrier is not relayed (ST1150). A signal, which has been subjected to either process, is transmitted (ST1060).
Owner:APPLE INC
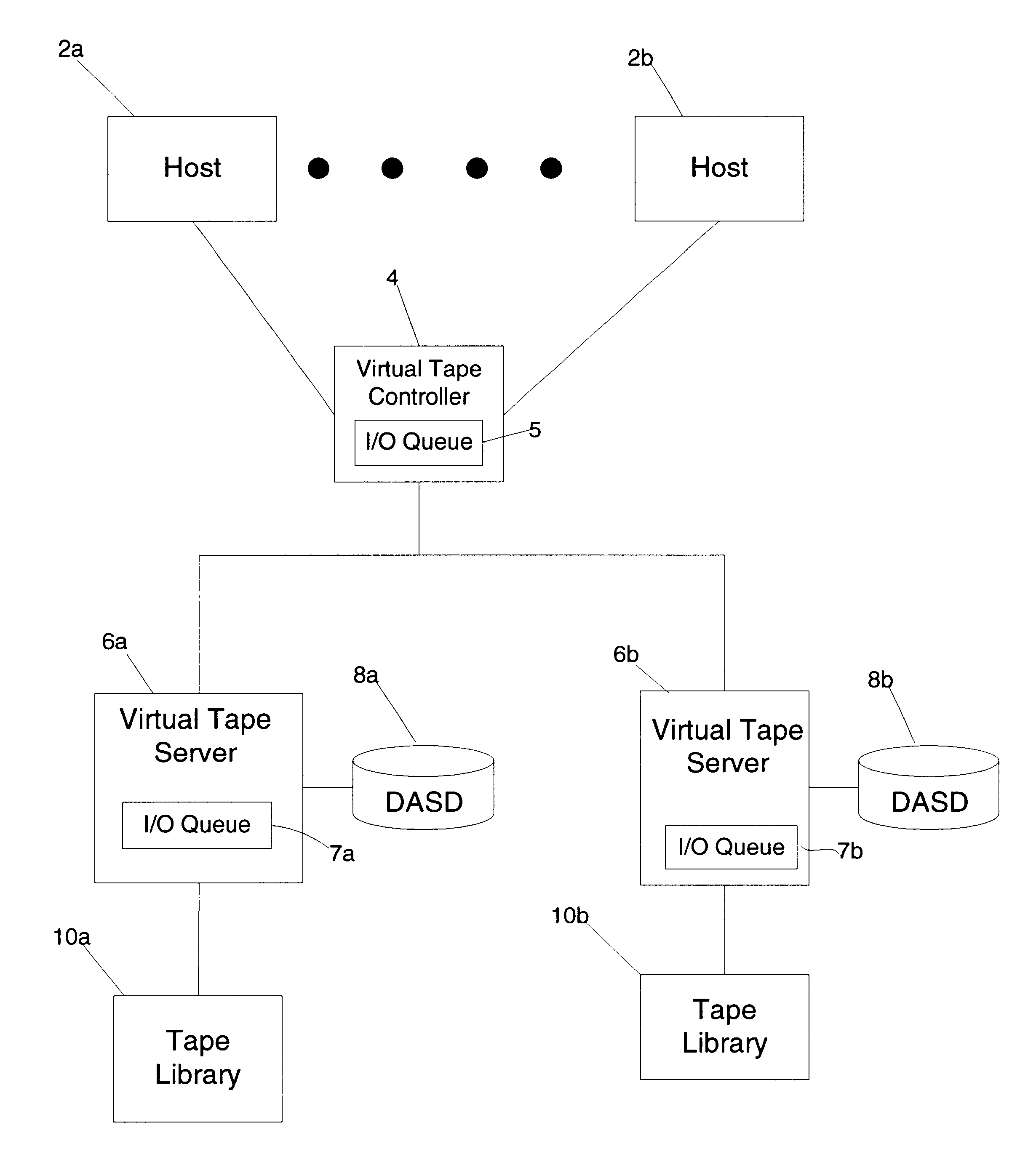
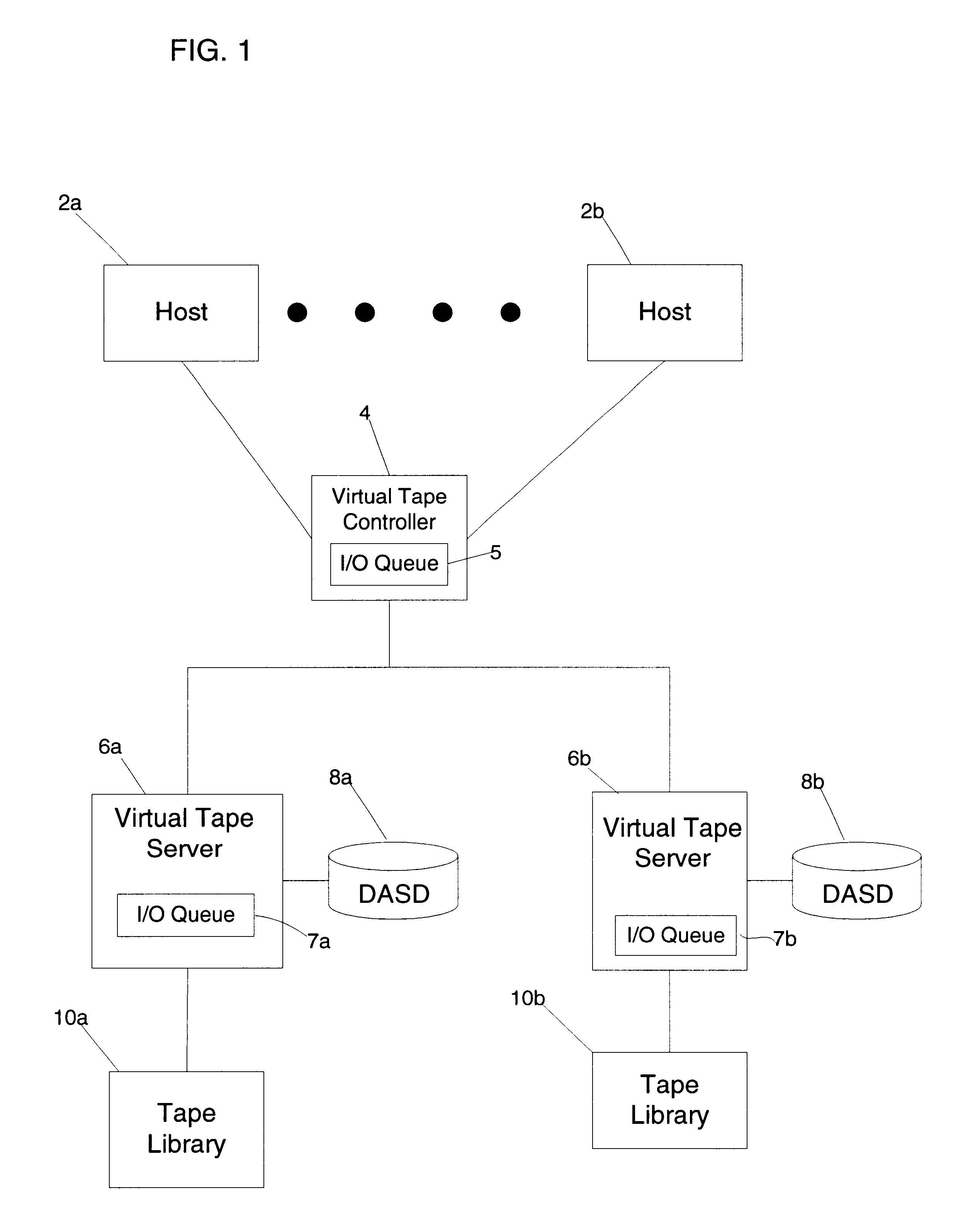
Method, system, and program for transferring data between storage devices
InactiveUS6779058B2Increase ratingsAvoid dataData processing applicationsError detection/correctionData setComputer science
Provided is a method, system, and an article of manufacture for maintaining data accessible by a host in two storage devices, wherein the data is comprised of a plurality of data sets. A determination is made of a percentage of uncopied data at the first storage device, wherein uncopied data comprises data sets to be copied from the first storage device to the second storage device. If the calculated percentage is greater than a threshold amount, a rate at which uncopied data sets are transferred from the first storage device to the second storage device is increased.
Owner:INT BUSINESS MASCH CORP
Efficient status reporting for ues in dual connectivity during mobility
ActiveUS20160212661A1Unnecessary data is preventedAvoid forwardingError preventionModulated-carrier systemsData radio bearerComputer science
The invention relates to a method for efficiently performing a Se NB change for a UE in dual connectivity. When reconfiguring a data radio bearer going via the Se NB to another target base station, the UE may compile a PDCP status report comprising status information for all of the data radio bearer going via the Se NB, accompanied respectively by a radio bearer ID to identify the radio bearer to which the status report information pertains. Further, the PDCP status report is directly transmitted by the UE to the Me NB to avoid the backhaul delay between the Se NB and the Me NB; this may be done by using a signaling radio bearer (e.g. RRC message), or data radio bearer to the Me NB (e.g. PDCP control PDU), or by using a physical channel transmission to the Me NB (e.g. MAC CE).
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
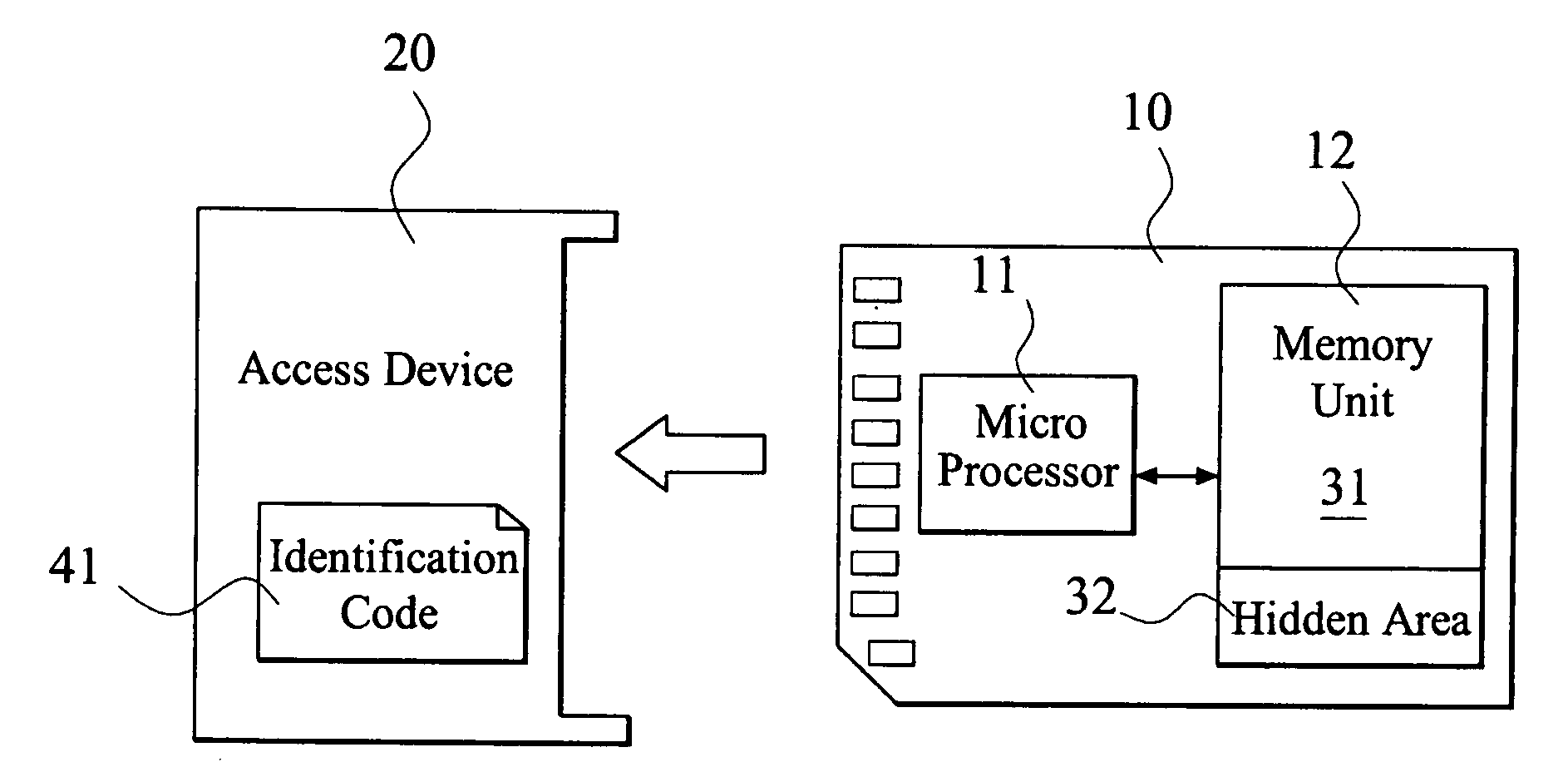
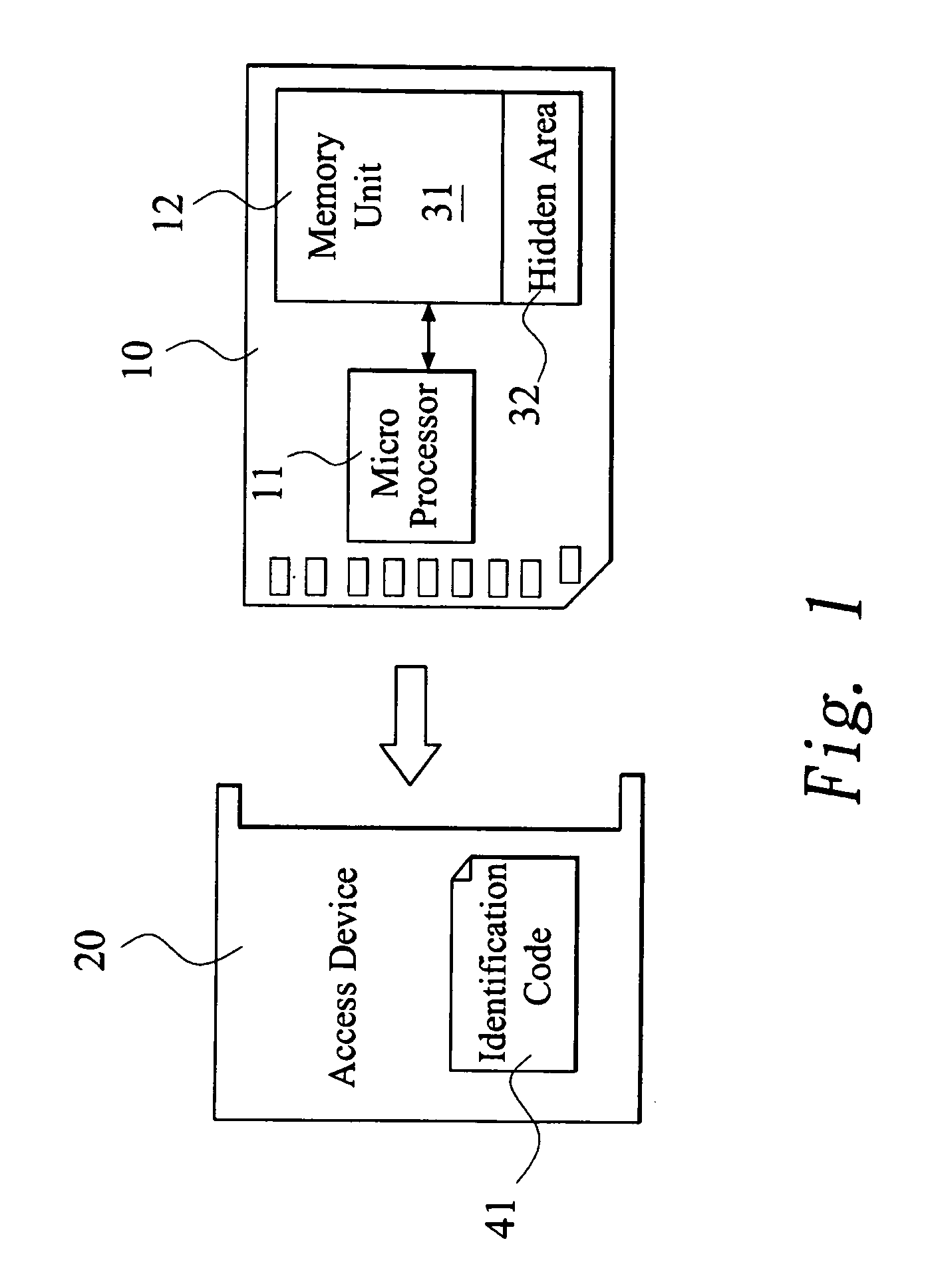
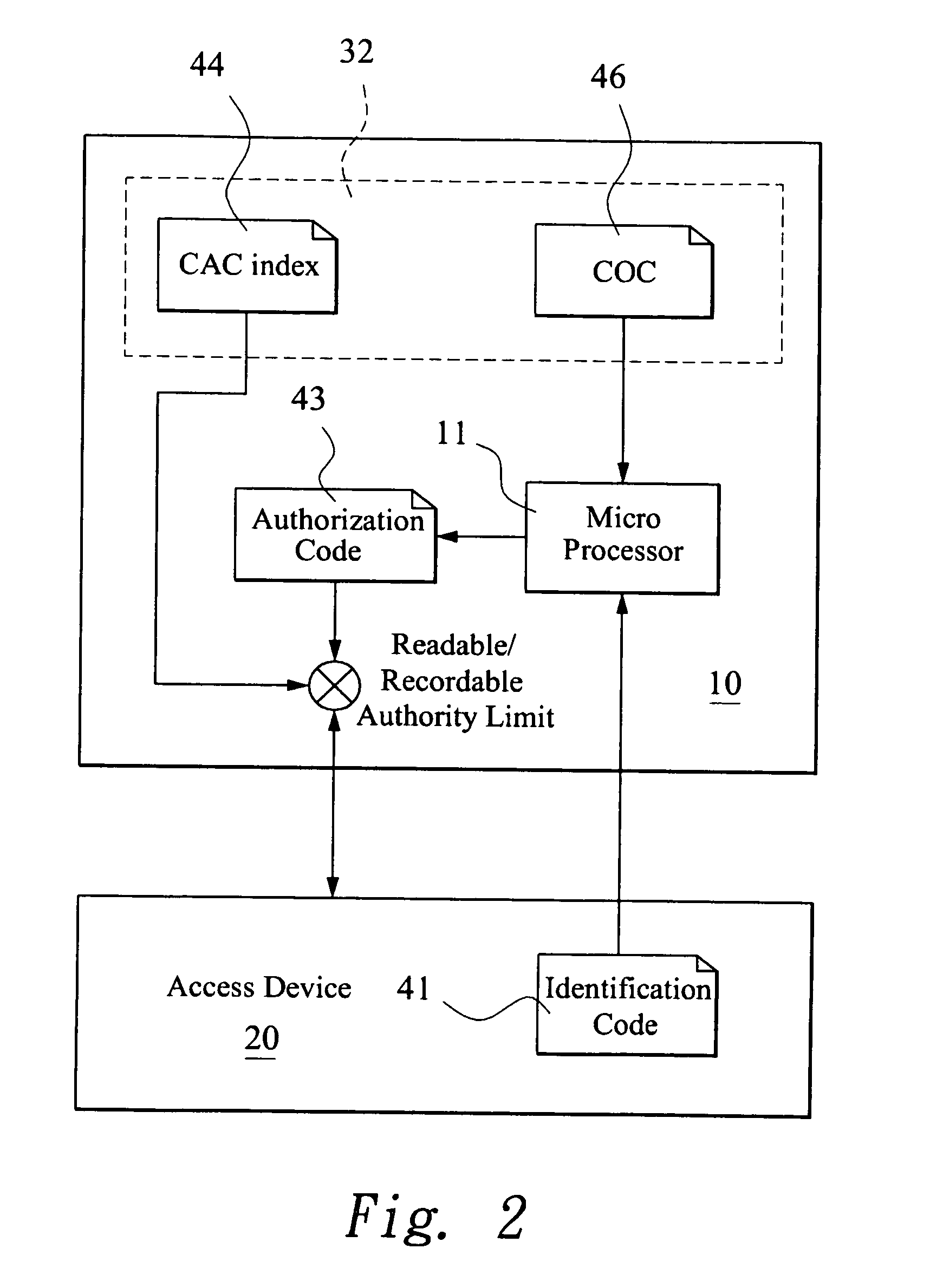
Authority limit management method
InactiveUS20080022415A1Avoid dataDigital data processing detailsAnalogue secracy/subscription systemsTransmission protocolIdentification device
An authority limit management method is proposed for a digital media storage. The digital media storage includes at least one micro processor and at least one memory unit and connected to an access device. A classification authorization code index (CAC index) and a plurality of classification operation commands (COC) is pre-stored in the digital media storage and an identification code is set for the access device. The classification operation commands is performed to calculate a classification authorization code when the digital media storage is connected to the access device for initial transmission protocol. The authority limit of the memory unit for the access device is granted to the access device according to the classification authorization code. Therefore, the data of the digital media storage can be prevented from illegal copy or hacker.
Owner:TRANSCEND INFORMATION
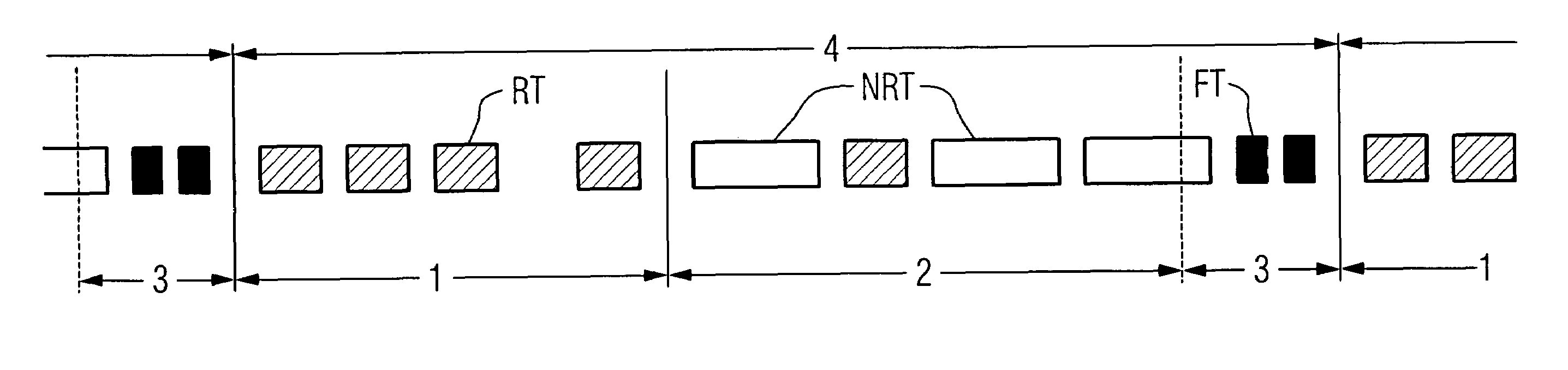
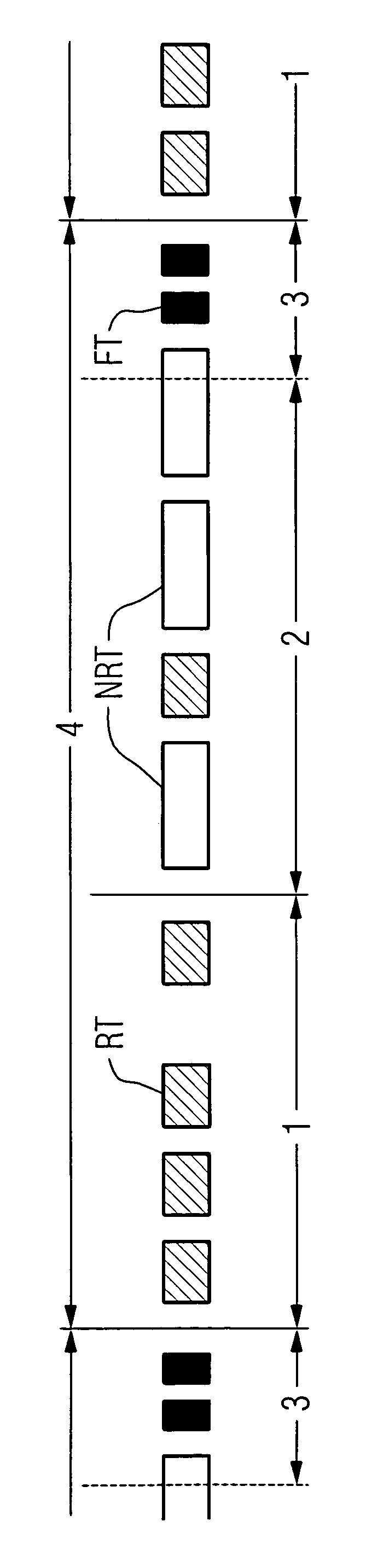
Scheduling of realtime communication in switched networks
ActiveUS7486681B2Utilization capacityHigh acceptanceTime-division multiplexData switching by path configurationReal-time dataExchange network
A method and a switching router for simple scheduling of realtime data telegrams with calculable load-insensitive cycle times. A transmission cycle (4) is subdivided into three phases. In a first phase (1), only realtime data telegrams are sent; in a second phase (2), realtime and non-realtime data telegrams are sent; and in a third phase (3), the transmission of long non-realtime data telegrams is suppressed. Short filler telegrams can be sent during the phase (3). This ensures that data transmission of the realtime data telegrams will proceed smoothly. Transmission in certain phases is regulated by the priorities assigned to the data telegrams.
Owner:SIEMENS AG
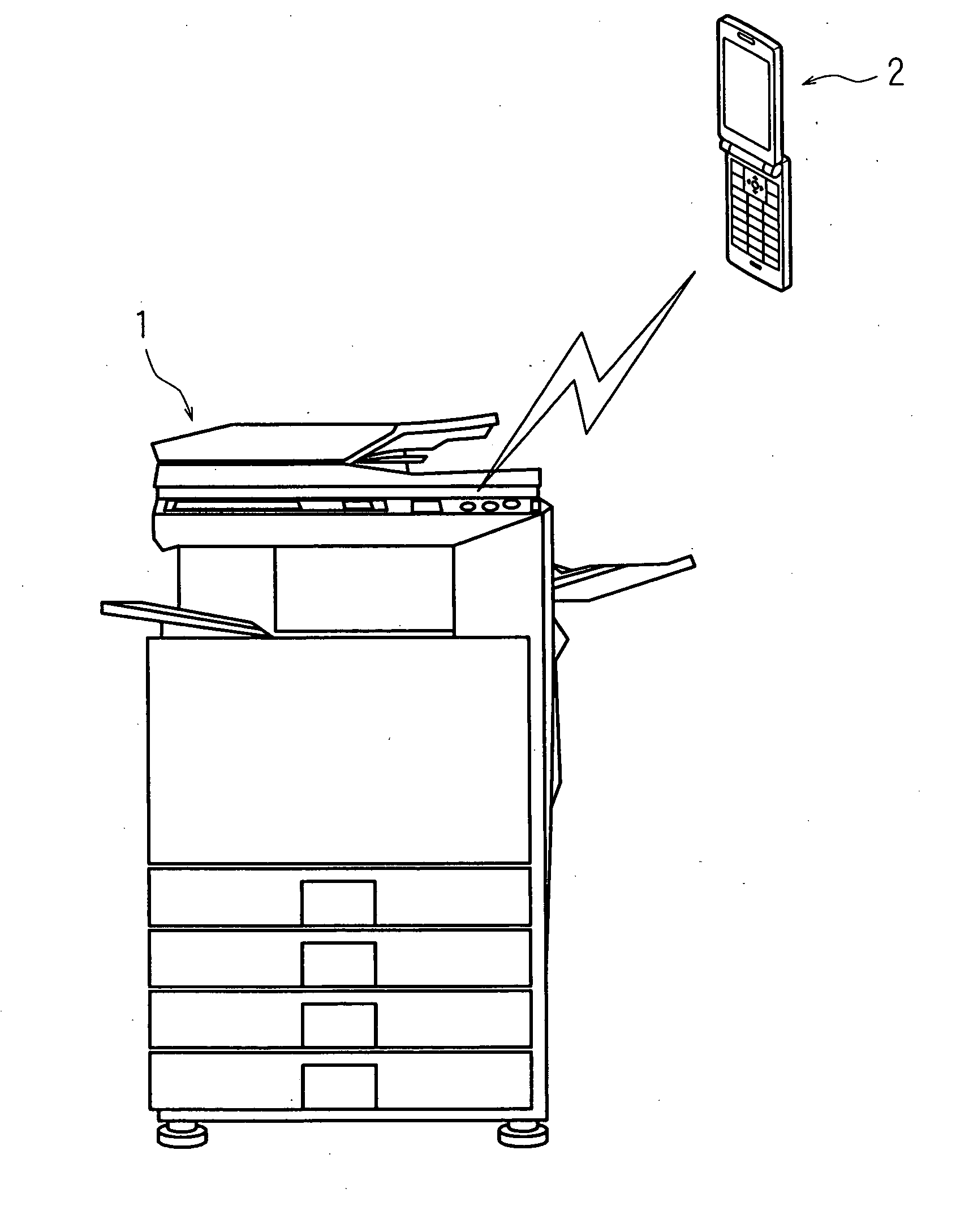
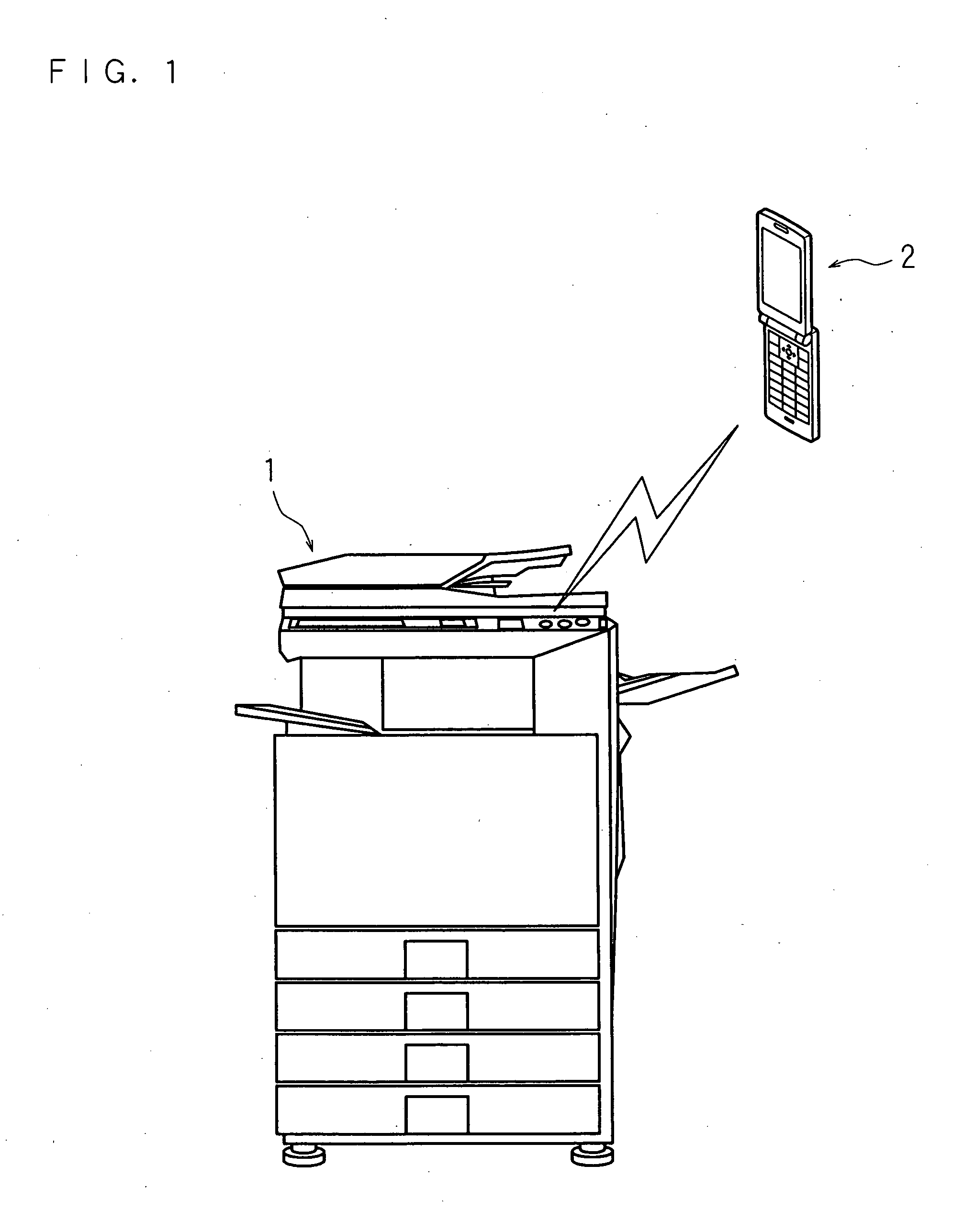
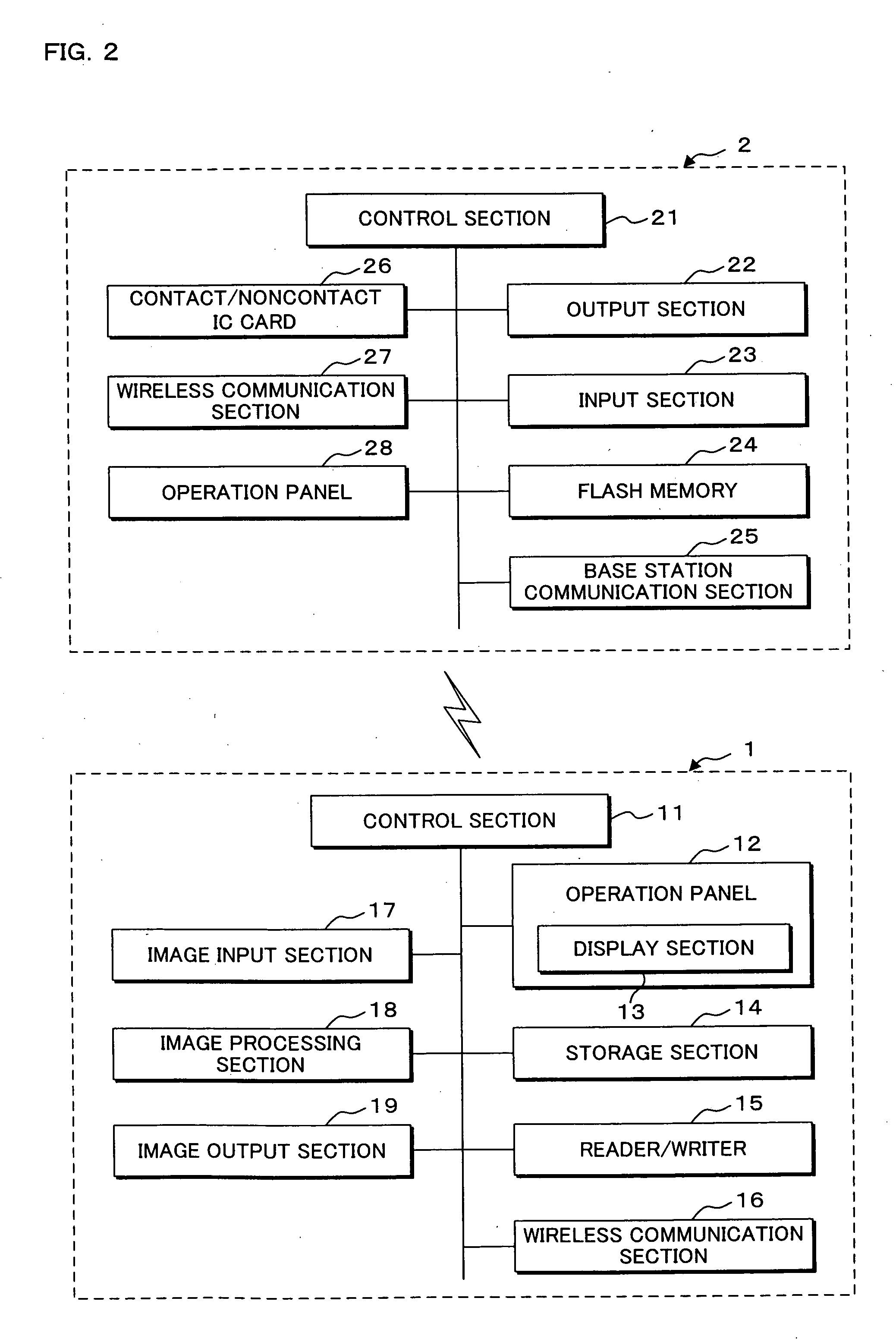
Communication system, information processing system, image formation system, image forming apparatus, mobile information terminal device and information processing device
InactiveUS20100225962A1Prevent leakageEstablishment of connectionConnection managementSubstation equipmentInformation processingCommunications system
After a digital multi-function peripheral establishes a connection with a mobile phone once, it rejects connection establishment requests made to a wireless communication section by other devices. Moreover, after a connection is established with a mobile phone once, the digital multi-function peripheral stops sending of the address of the wireless communication section through a reader / writer. After completing the sending / receiving of data, the digital multi-function peripheral and the mobile phone delete the addresses of their partner devices stored in them, respectively, for use in sending / receiving data.
Owner:SHARP KK
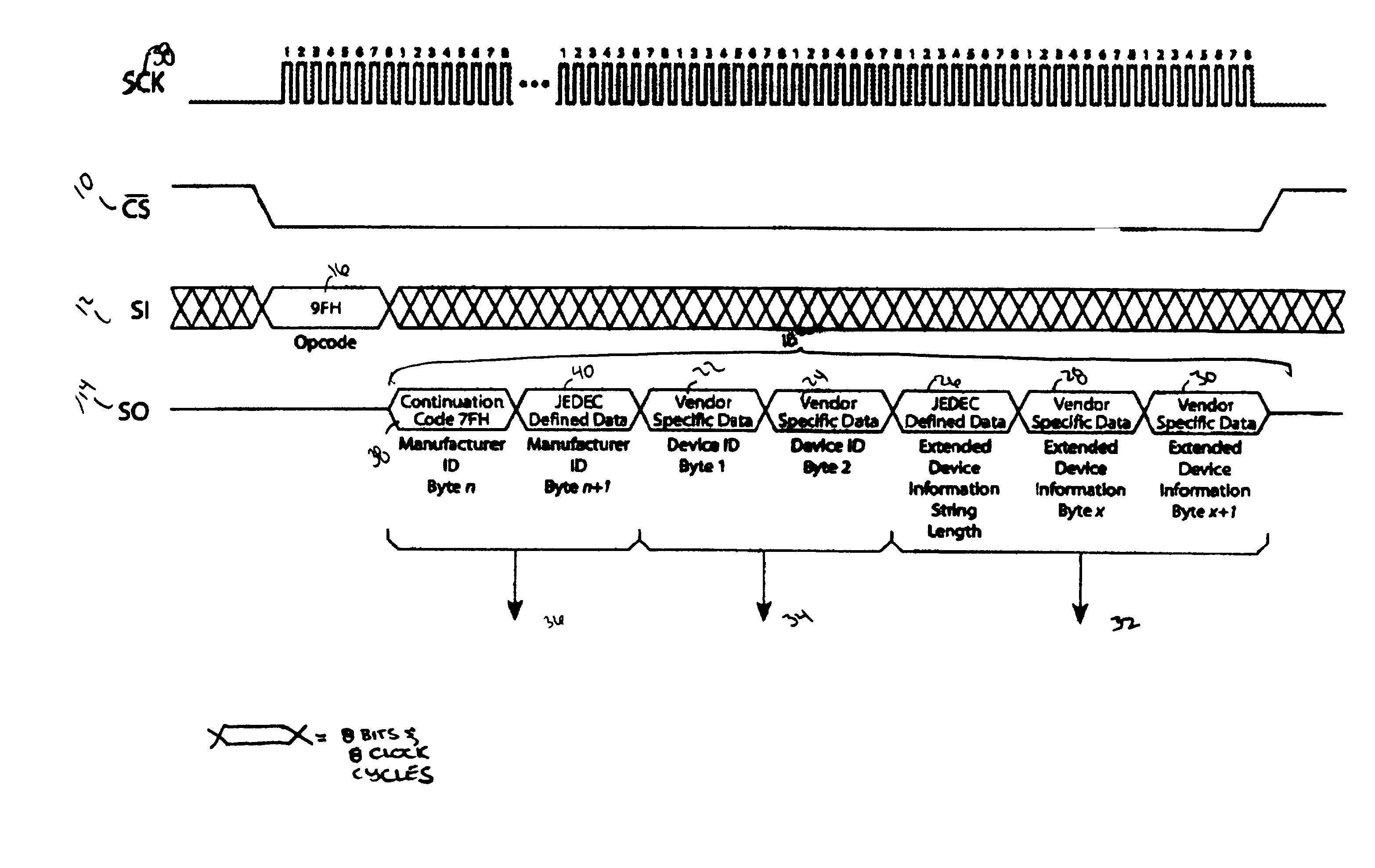
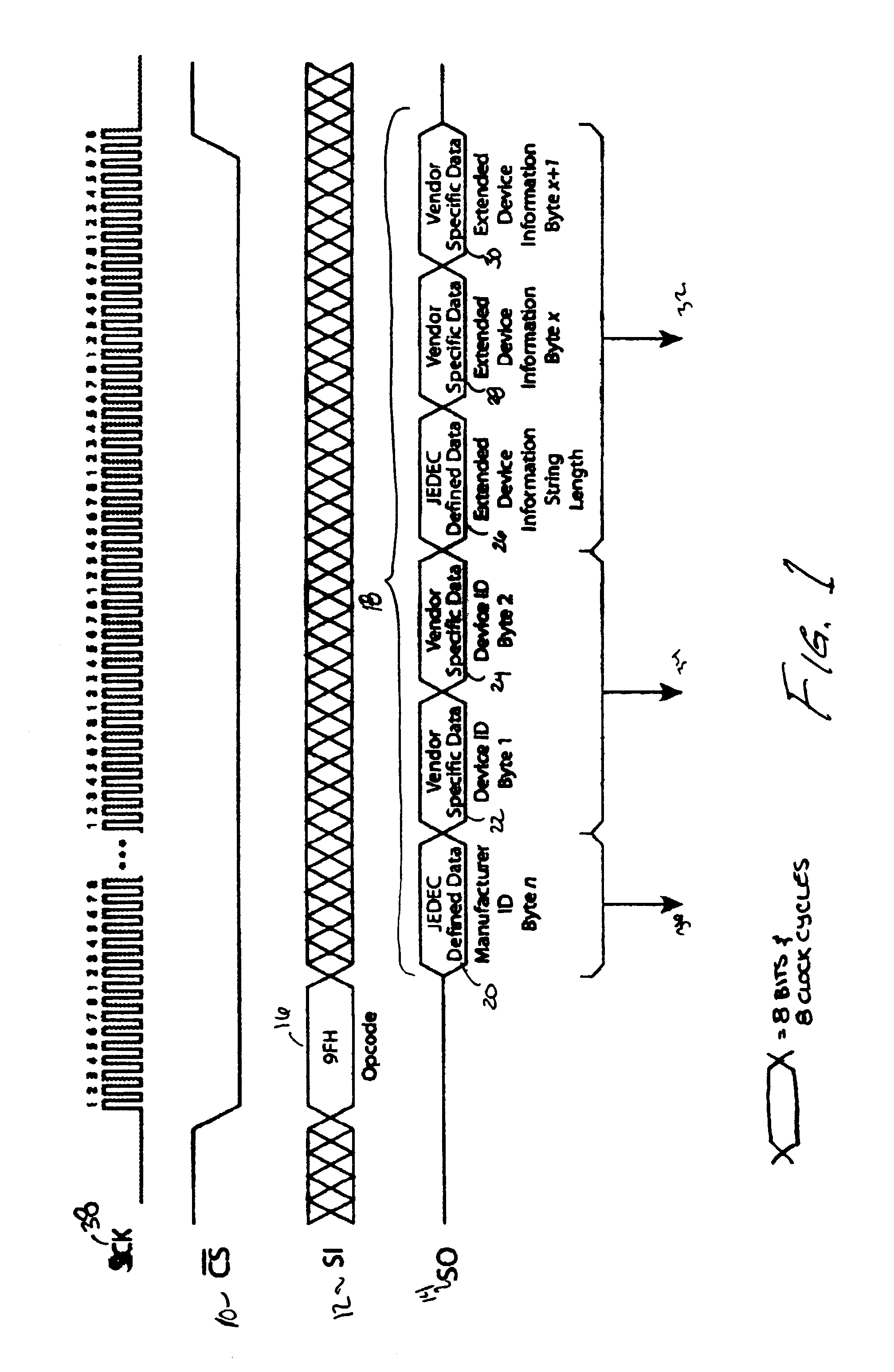
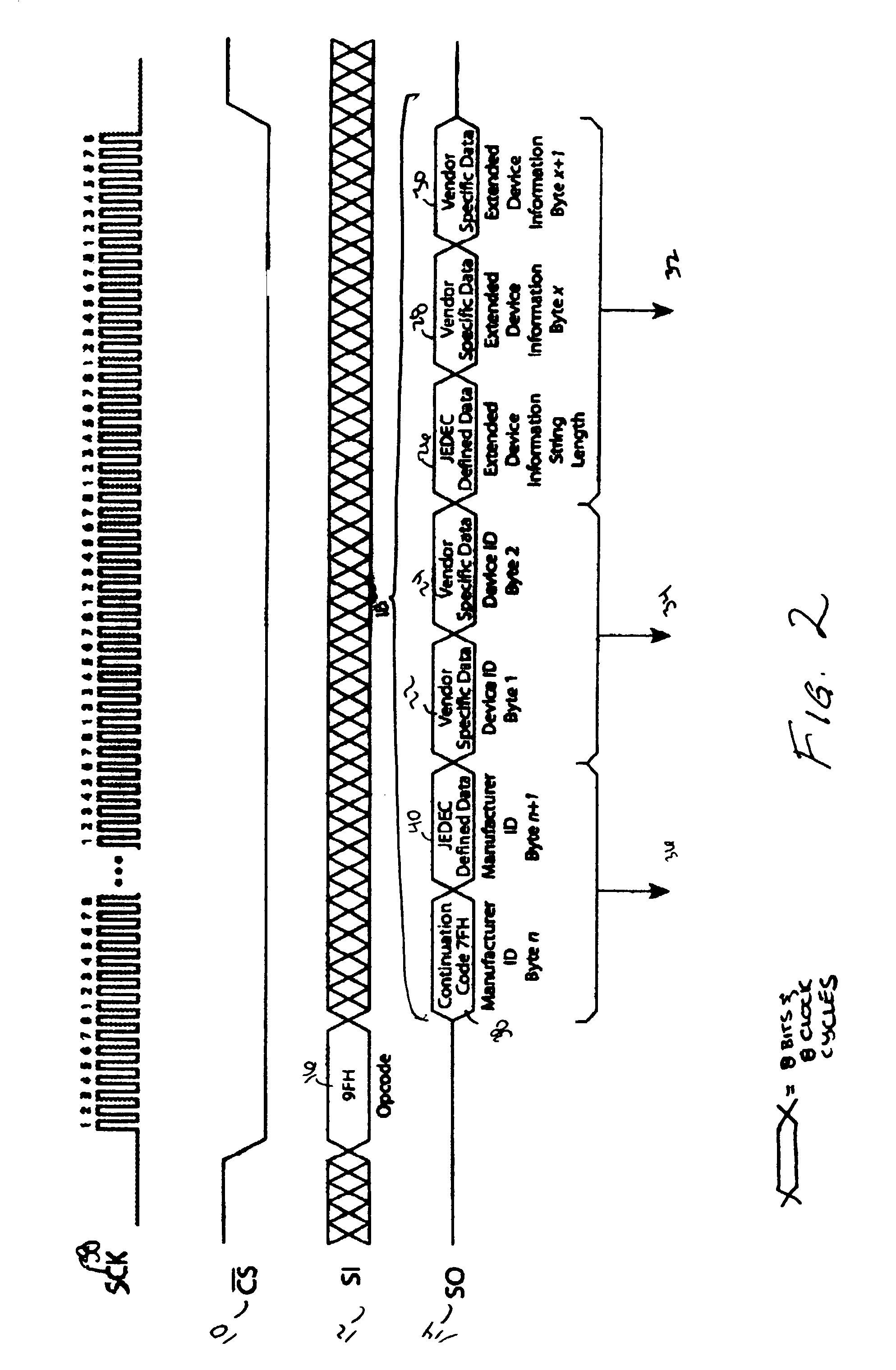
Method for identification of SPI compatible serial memory devices
ActiveUS7032039B2Unnecessary data is preventedAvoid dataRead-only memoriesDigital storageContinuationByte
A method for identifying Serial Peripheral Interface (SPI) compatible serial interface memory devices. A microprocessor sends a single command requesting identification information to an SPI device installed on the SPI bus. A byte string, including the JEDEC manufacturer ID, device ID, and any extended device information, is sent back to the microprocessor. The byte string may include one or more continuation codes when the manufacturer ID exceeds 1 byte. The byte string also includes one byte indicating how many bytes of extended device information should be read by the microprocessor. The identification process, issuing the command and receiving the reply, is completed in one operation.
Owner:ARTEMIS ACQUISITION
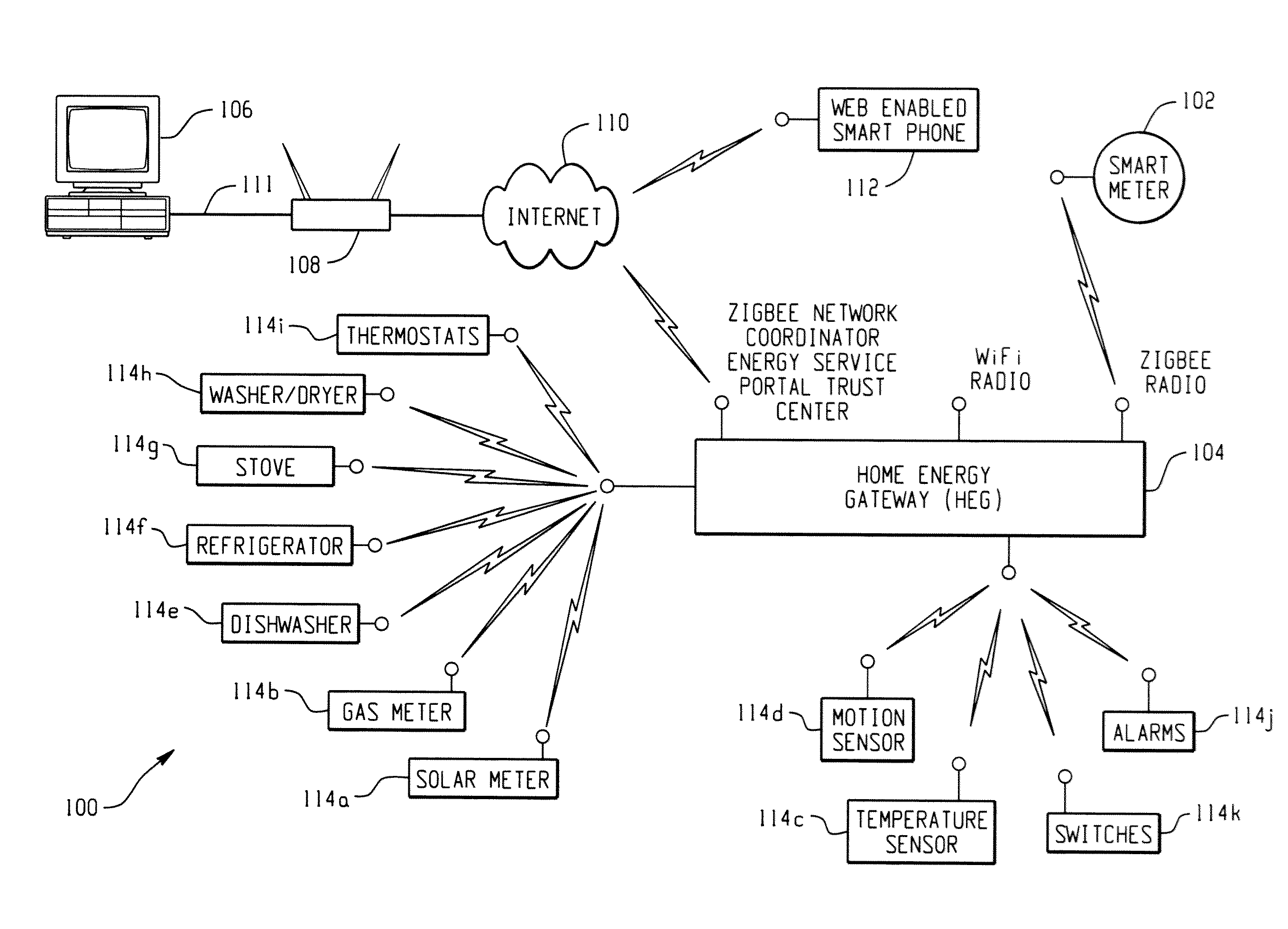
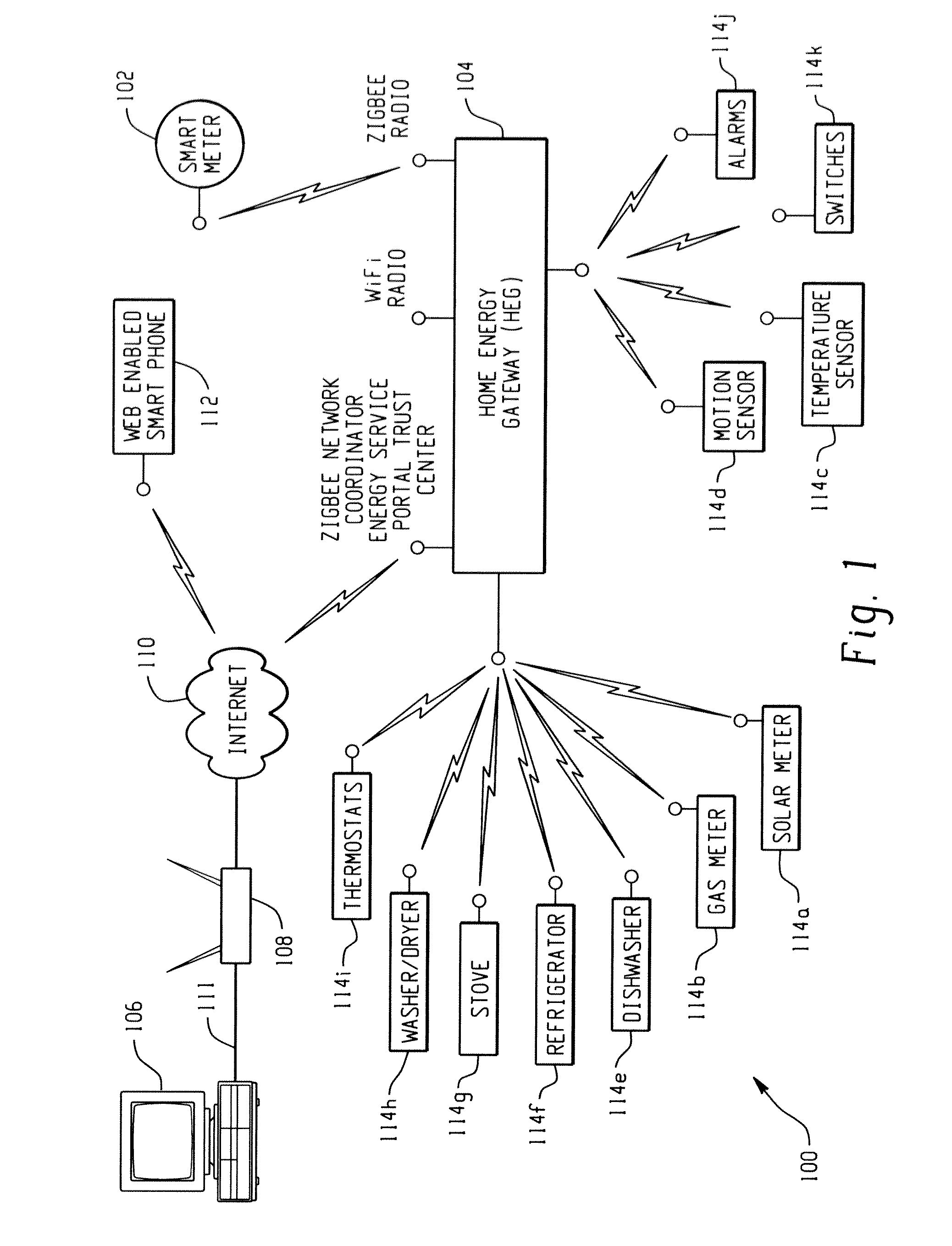
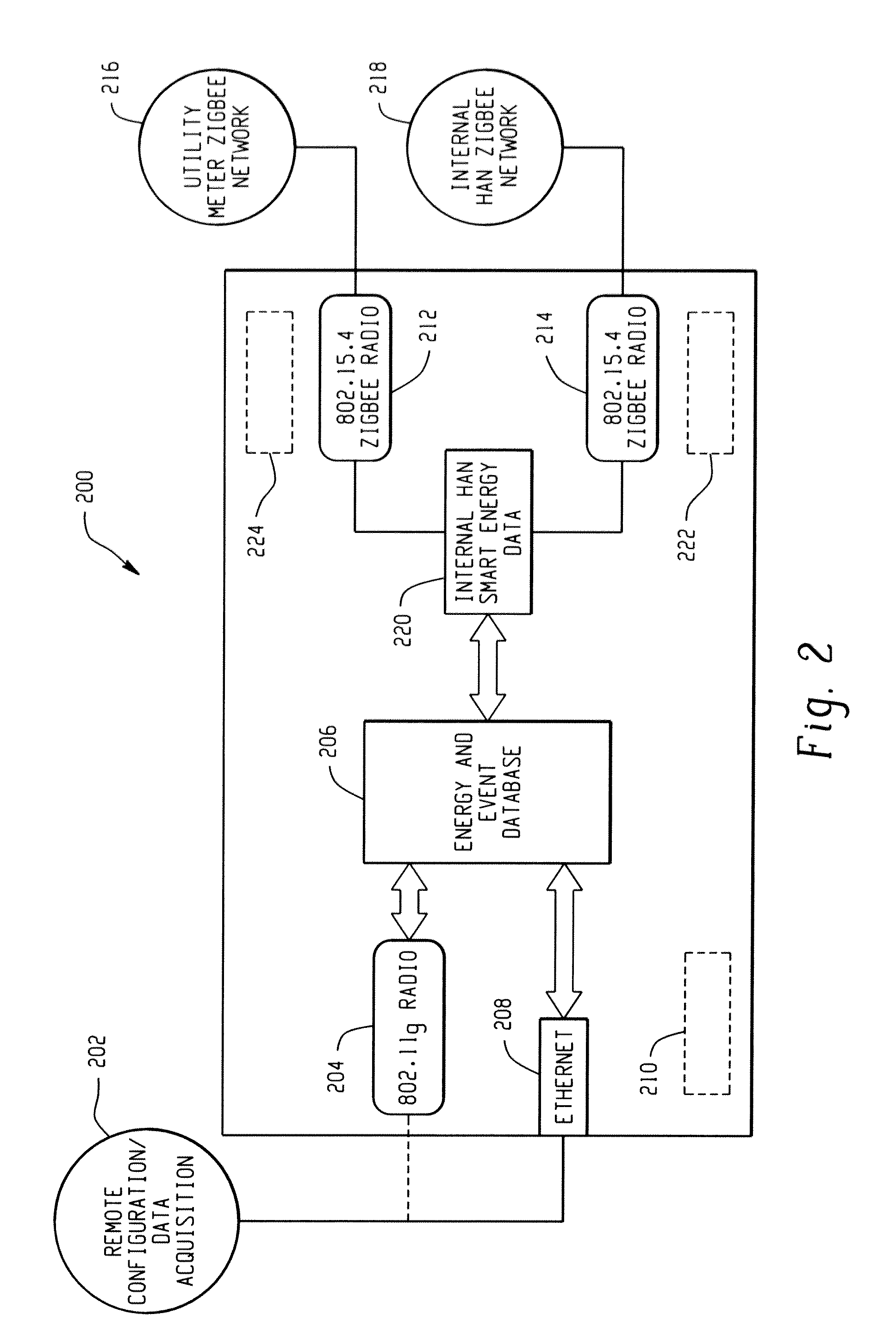
Low cost home energy manager adaptor
InactiveUS20110202195A1Low costMinimize the numberMechanical power/torque controlLevel controlComputer moduleEnergy depletion
A home energy management (HEM) device for use in a HEM system including a plurality of energy consuming devices and a HEM gateway adaptor module connectable to a host device. The home energy gateway (HEG) module is configured to utilize services / components of existing household electronics. Accordingly, a HEM device for controlling a plurality of energy consuming devices in a HEM network comprises a host device having hardware for performing at least one service, and a HEG adaptor module connectable to the host device, the HEG module including at least a home energy usage database for storing data related to usage of energy consuming devices in the home energy management network. The HEG module is configured to utilize at least one service of the host to carry out at least one function related to controlling the plurality of energy consuming devices.
Owner:HAIER US APPLIANCE SOLUTIONS INC
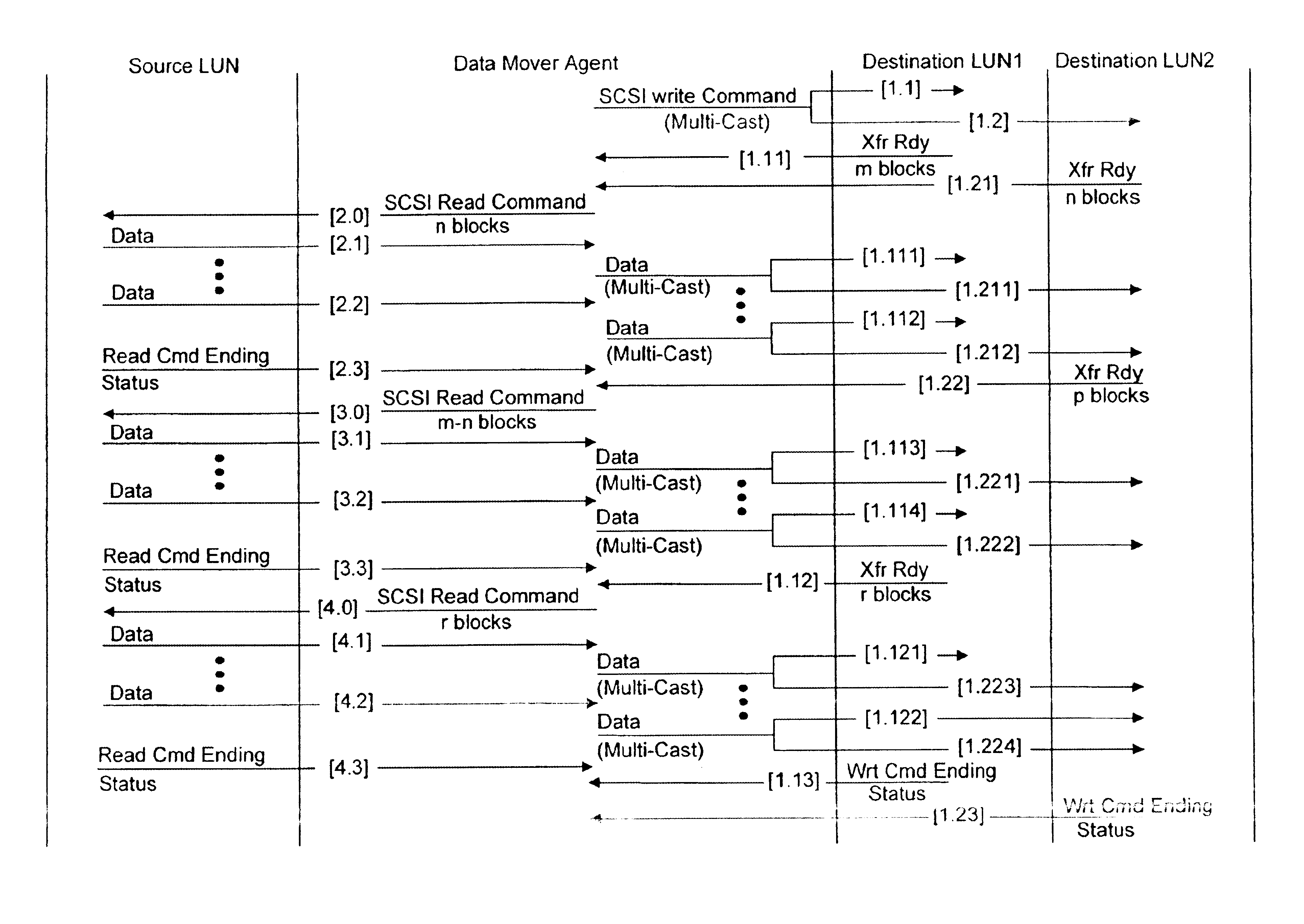
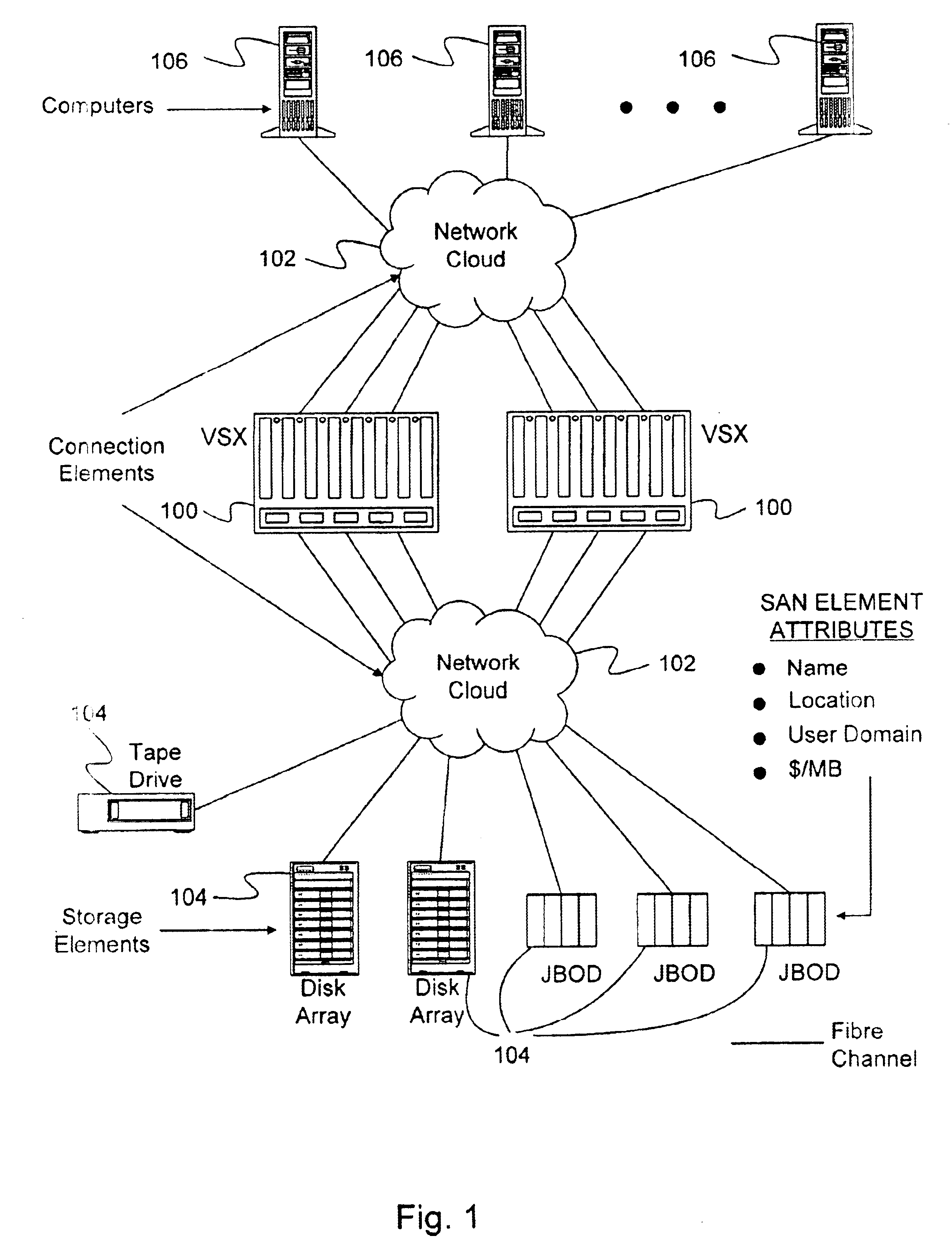
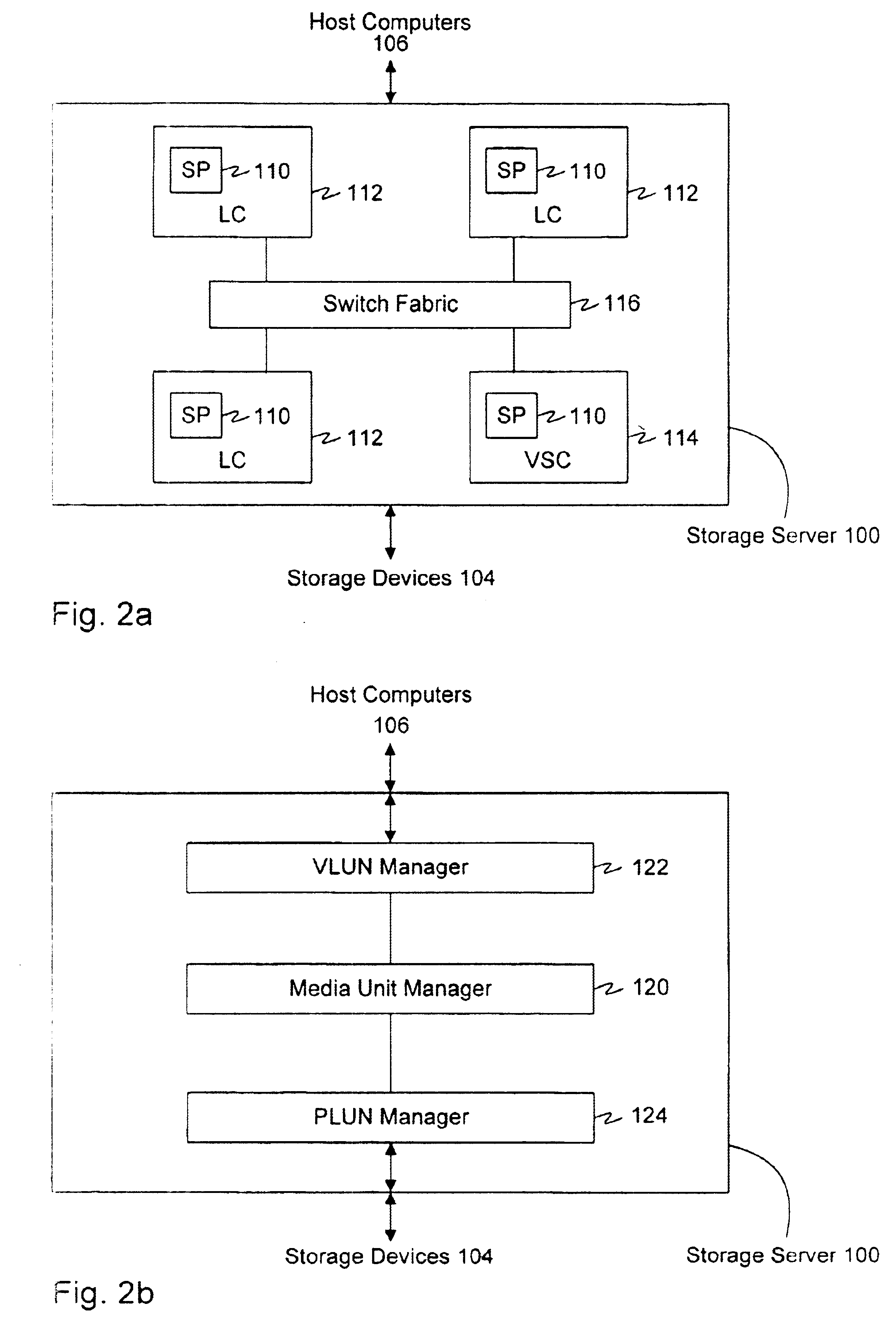
Data mover mechanism to achieve SAN RAID at wire speed
InactiveUS6880062B1Avoid dataAvoid errorsMultiple digital computer combinationsTransmissionRAIDWire speed
A Virtual Storage Server is provided for transferring data between a source storage device and one or more destination storage devices. A write command is issued to the one or more destinations for an amount of data. In response, one or more Transfer Ready Responses are returned indicating the amount of data the destinations are prepared to receive. The Virtual Storage Server then sends a read command to the source for an amount of data based on the amounts of data in the Transfer Ready Responses. The data is then transferred from the source storage device through the Virtual Storage Server to the one or more destination storage devices. Because data is transferred only in amounts that the destination is ready to receive, the Virtual Storage Server does not need a large buffer, and can basically send data received at wire speed. This process continues until the amount of data in the write command is transferred to the one or more destination storage devices.
Owner:NETWORK APPLIANCE INC
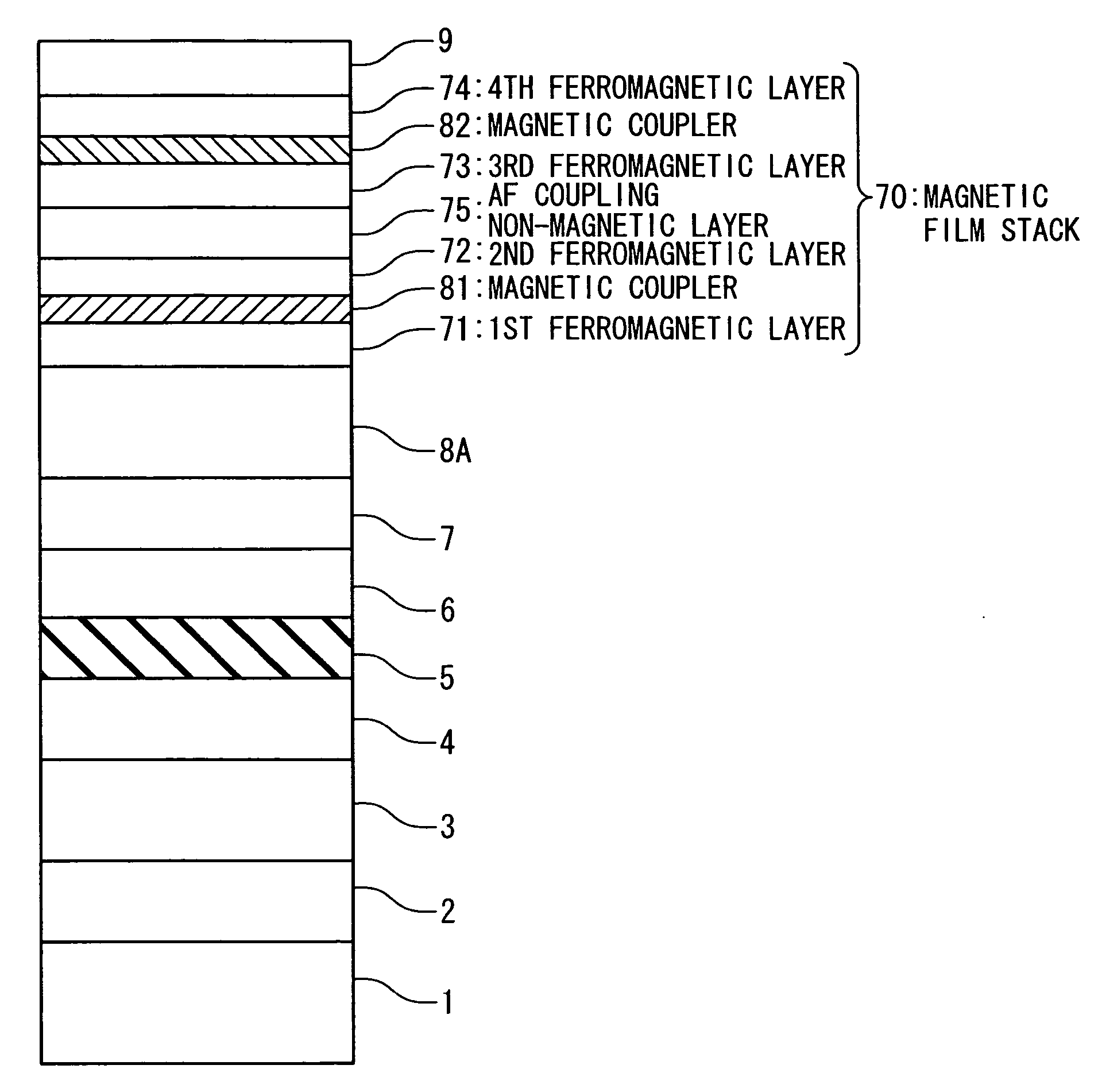
Magnetoresistive device and magnetic memory using the same
ActiveUS20060262594A1Reducing a magnetic field necessaryIncreased writing marginNanomagnetismDigital storageAntiferromagnetic couplingMagnetic memory
A magnetic film stack is composed of a synthetic antiferromagnet including a plurality of ferromagnetic layers, adjacent two of which are antiferromagnetically coupled through a non-magnetic layer; and a reversal inducing layer exhibiting ferromagnetism. The reversal inducing layer is ferromagnetically coupled to the synthetic antiferromagnet, and designed to have a coercive field smaller than a magnetic field at which antiferromagnetic coupling within the synthetic antiferromagnet starts to be decoupled.
Owner:NEC CORP
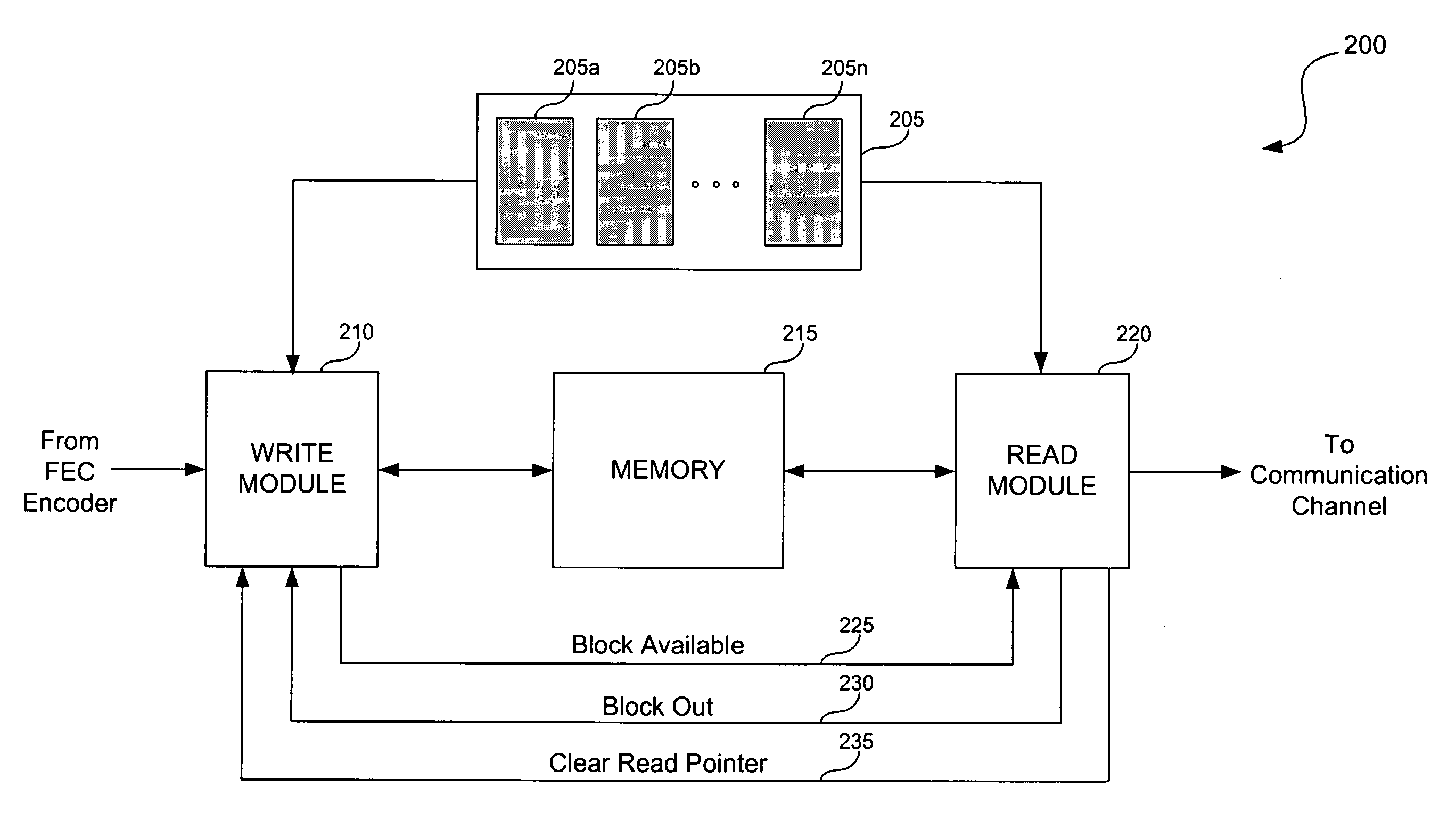
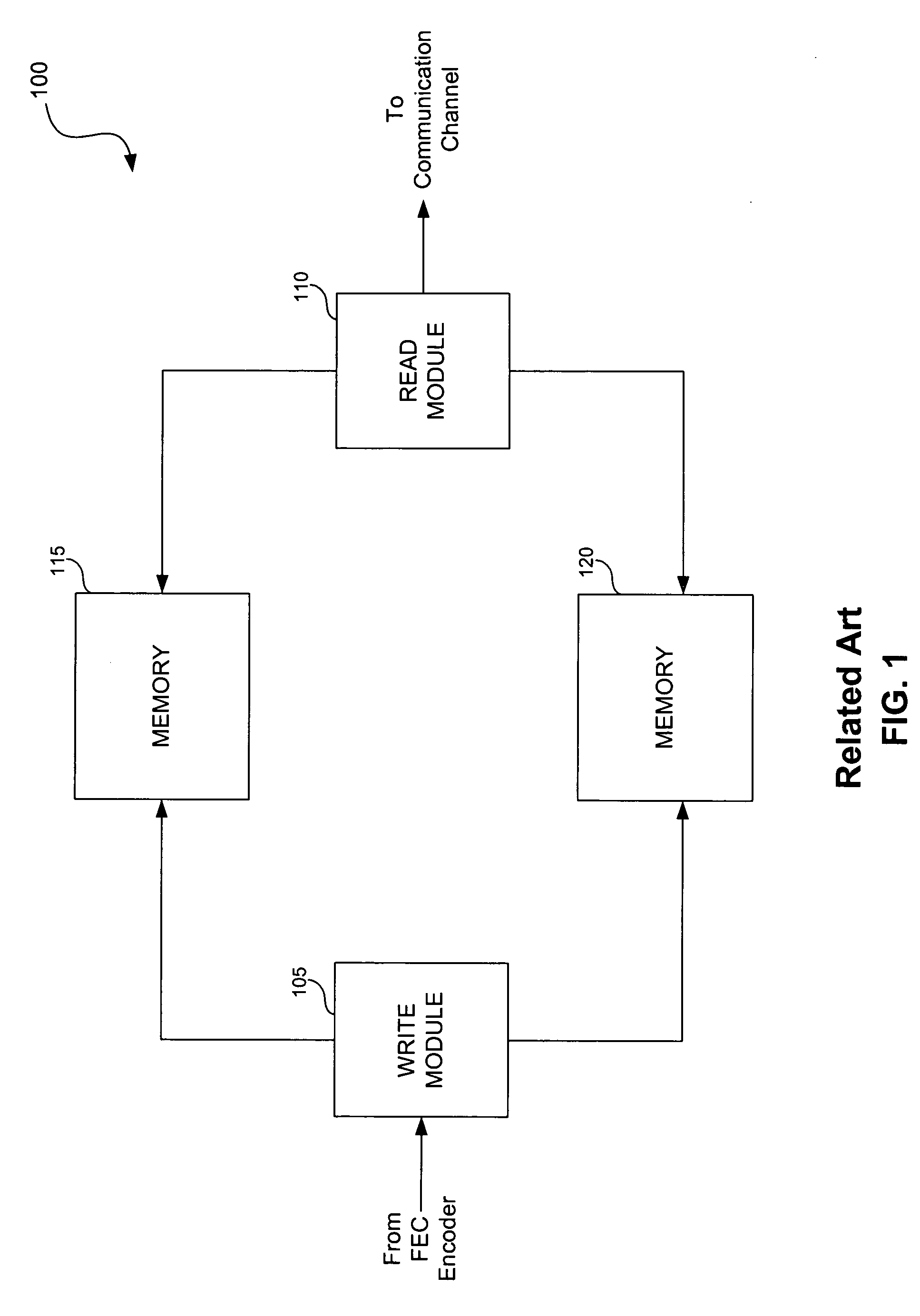
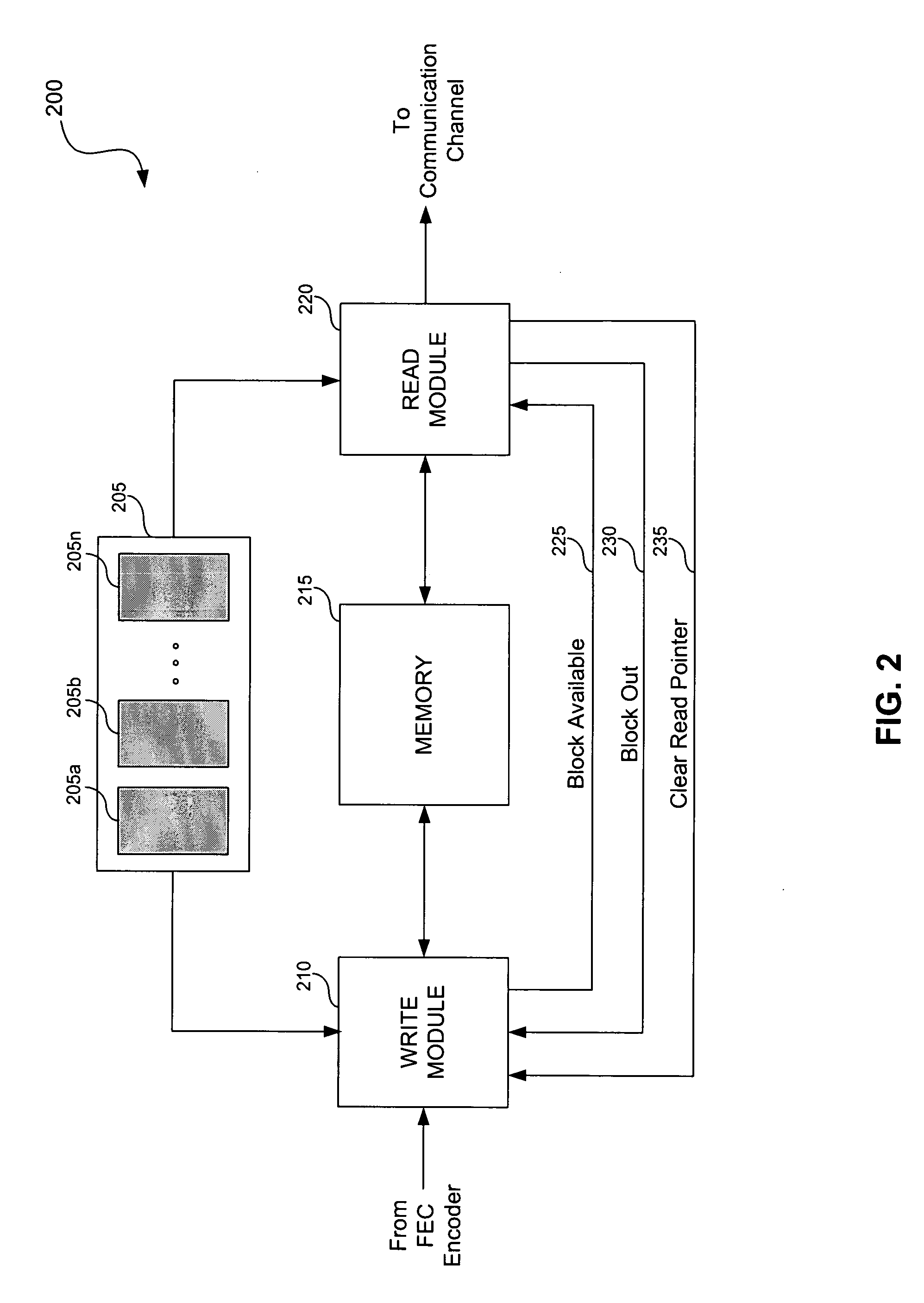
System and method for interleaving data in a communication device
InactiveUS20060026484A1Optimal throughput and efficiencyMinimize delayTransmission systemsCode conversionByteCommunication device
A system and method is provided for interleaving data in a communication device. The system includes a memory that stores blocks of data to be interleaved. In addition to the memory, the system includes a write module and a read module, each of which is coupled to the memory. The write module is configured to receive a burst of data and write blocks of data from the burst into the memory. The write module is also configured to provide control information to the read logic. The control information includes a rolling burst counter and a burst profile bank identifier for each block. If interleaving is activated, the control information also includes information pertaining to how the read module should interleave the block. If interleaving is not activated, the control information also includes the byte length size of the burst. The read module reads blocks of data from memory in either an interleaved fashion or a non-interleaved fashion in accordance with the control information. A block available signal and a block out signal is also provided to determine when a block of data is available to be read from the memory.
Owner:AVAGO TECH INT SALES PTE LTD
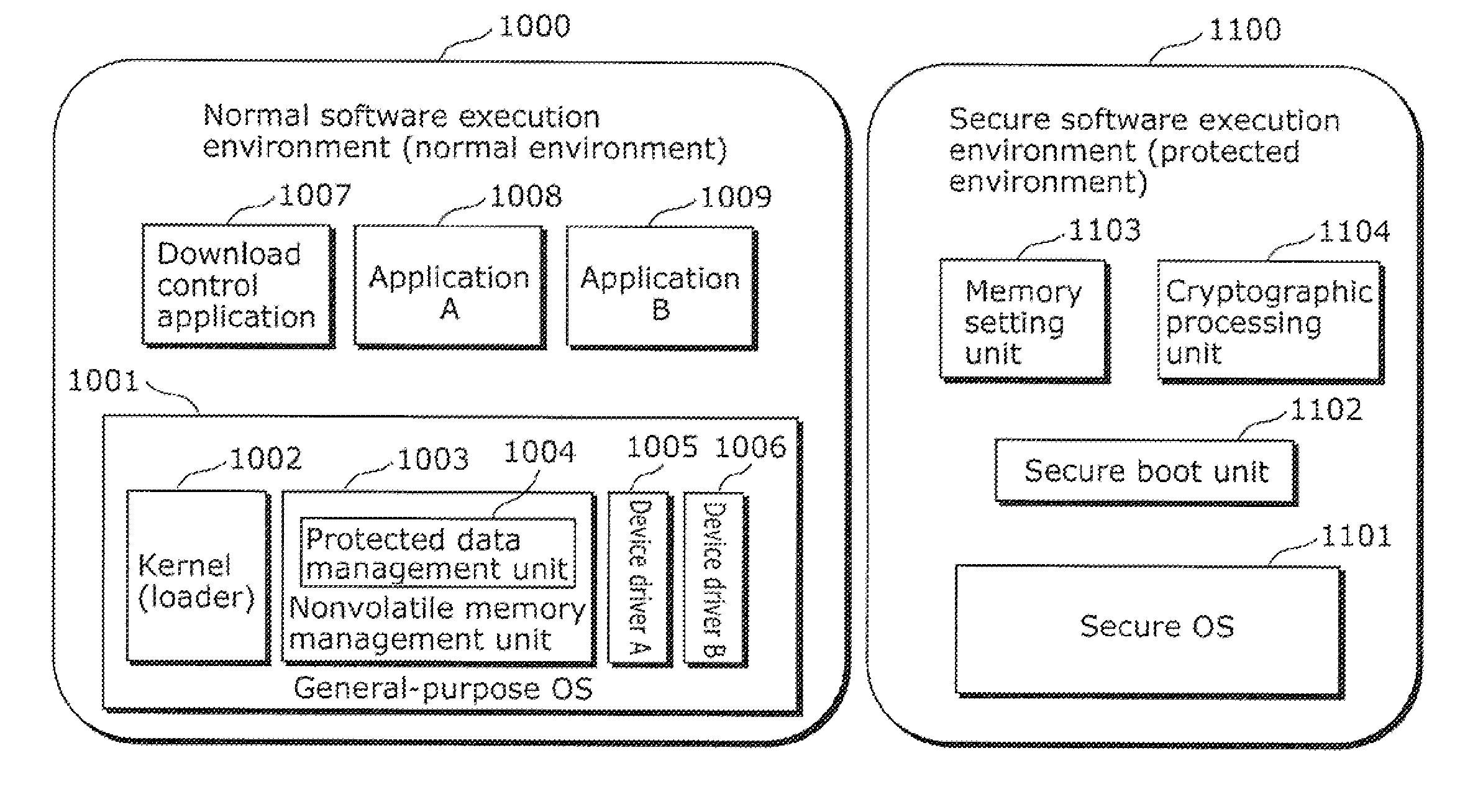
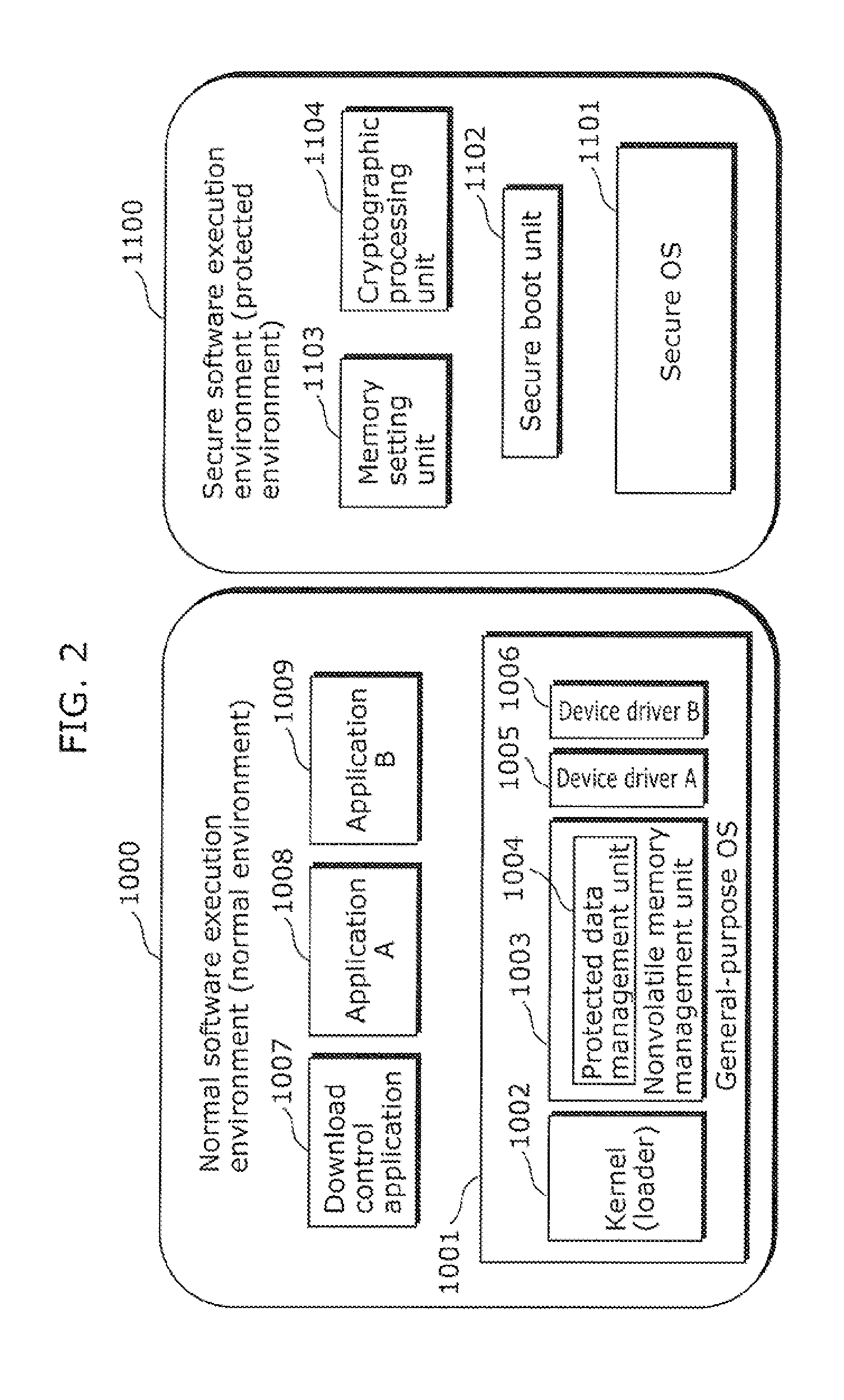
Information processing apparatus
InactiveUS20110289294A1Preventing access to their dataAvoid dataUnauthorized memory use protectionInternal/peripheral component protectionInformation processingOperation mode
An information processing apparatus includes: a CPU (1201) that has, as an operating mode, a privileged mode and an unprivileged mode; a trusted memory (1270) that stores protected data, the protected data being accessed when the CPU (1201) is in the unprivileged mode; and a trusted memory control unit (1203) that controls access to the trusted memory (1270). When the CPU (1201) accesses the trusted memory (1270), the trusted memory control unit (1203) determines the operating mode of the CPU (1201) and, in the case where the operating mode of the CPU (1201) is the unprivileged mode, denies the access to the trusted memory (1270) by the CPU (1201).
Owner:PANASONIC CORP
Data processing apparatus, data processing method, terminal unit, and transmission method of data processing apparatus
InactiveUS20040218214A1Avoid dataDigital data processing detailsRead-only memoriesMass storageComputer terminal
A data processing apparatus is disclosed, that comprises a large capacity memory means for storing a plurality of files, a memory means for storing move / copy history when a particular file is moved / copied from the large capacity memory means to a non-volatile memory, a reference menas for referencing the history information stored in the memory means when the particular file is moved / copied from the large capacity memory means to the non-volatile memory, and a control means for prohibiting the particular file from being moved / copied from the large capacity memory means to the non-volatile memory when the reference means has detected that the history information is stored in the memory means.
Owner:SONY CORP
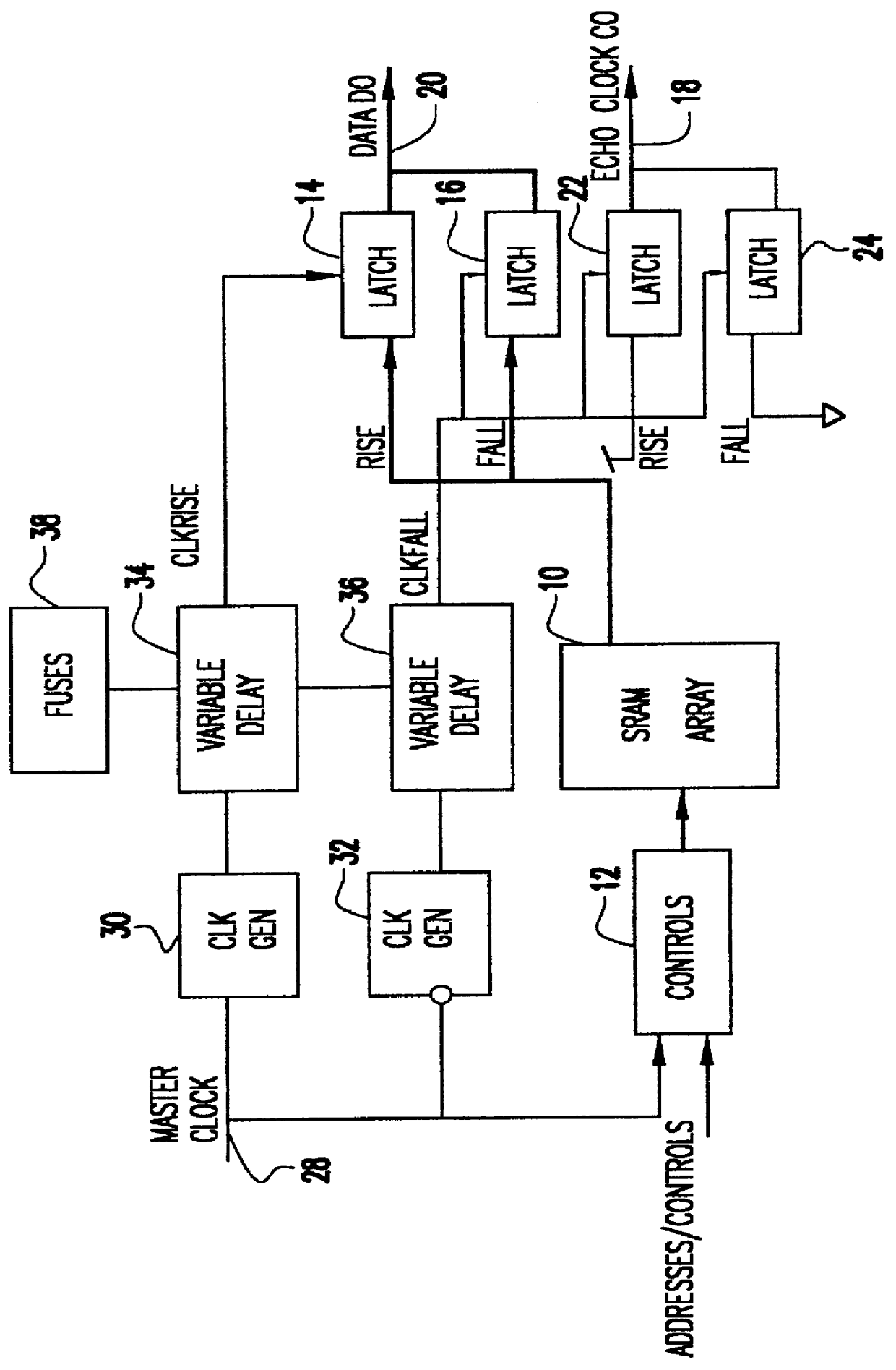
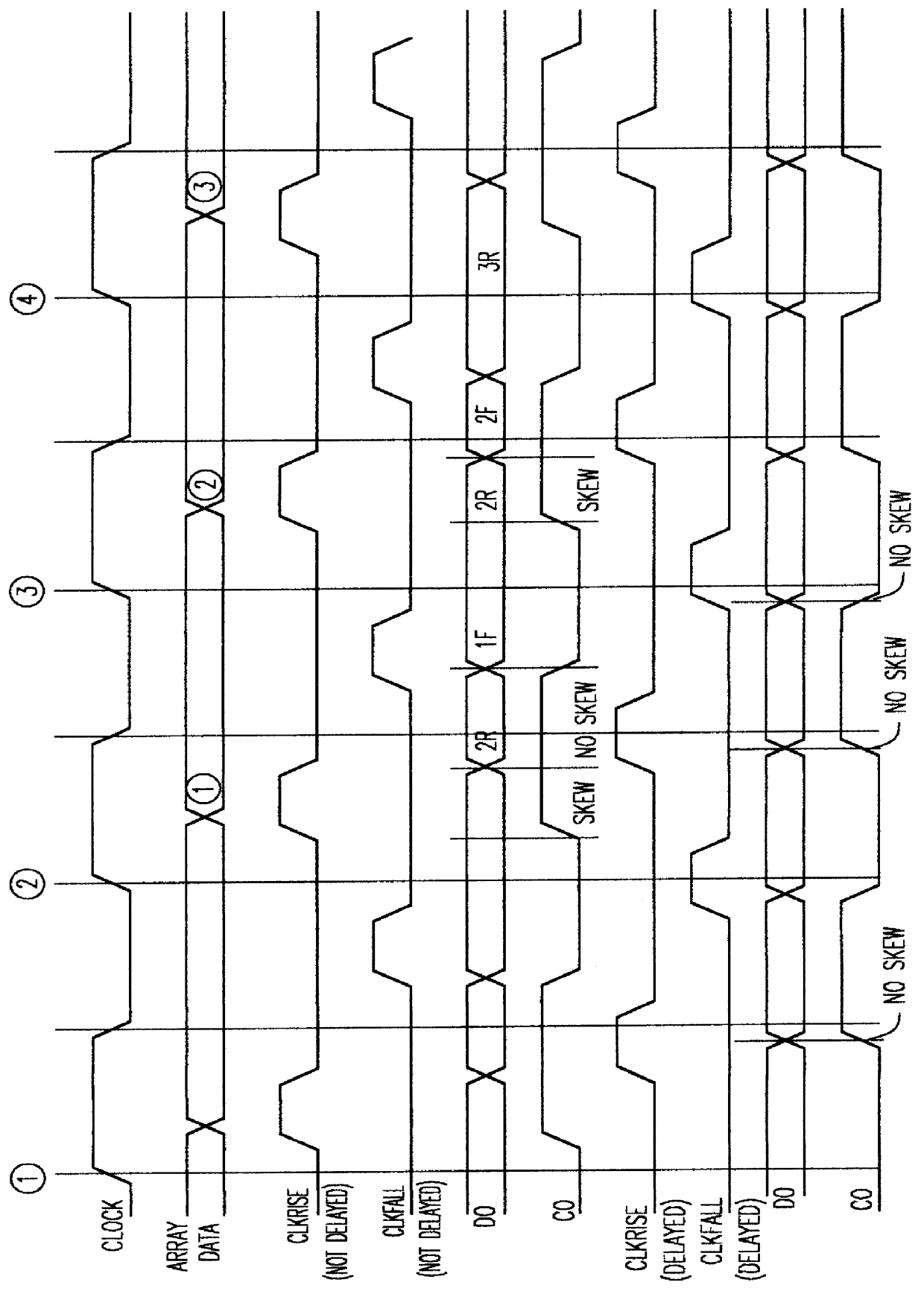
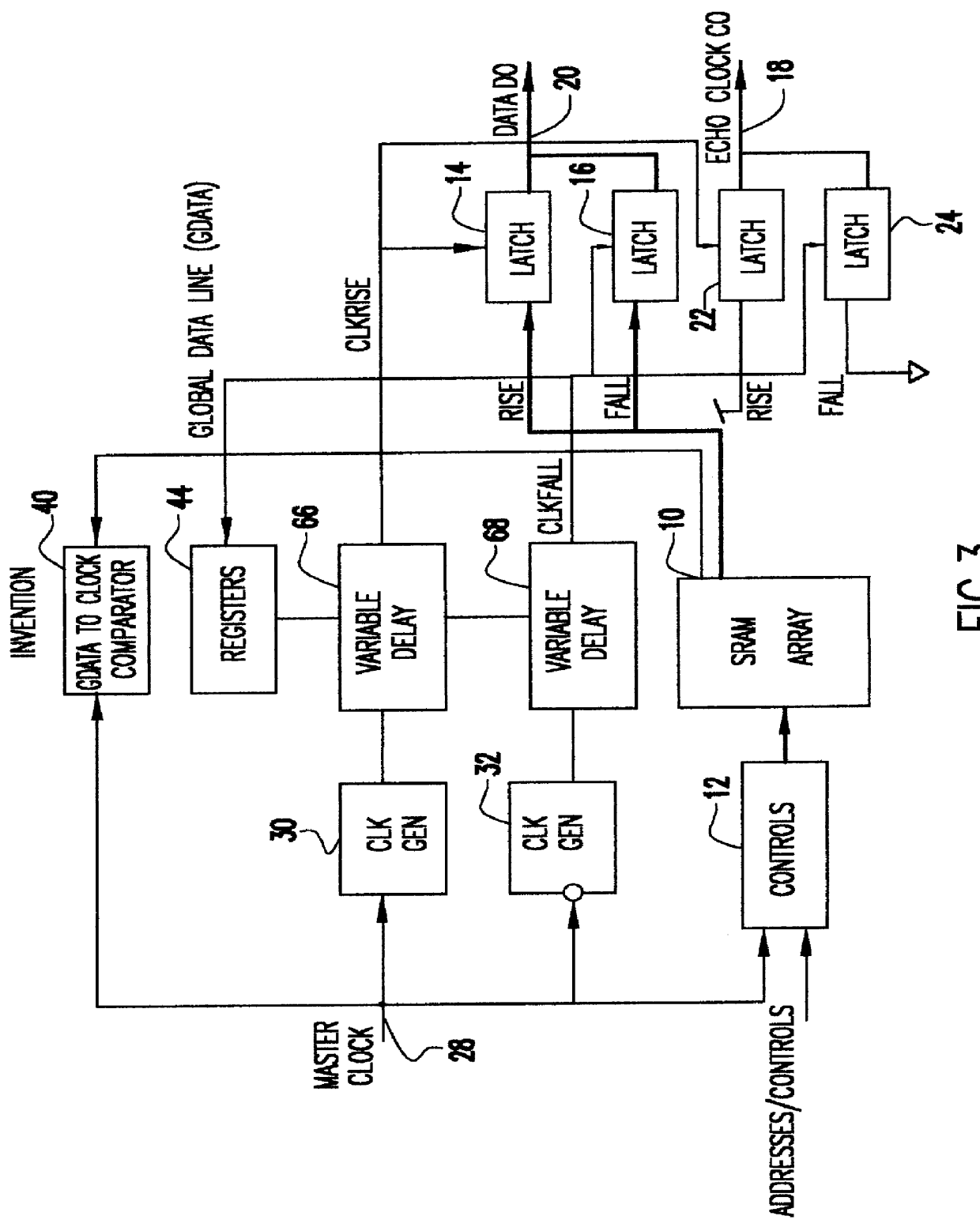
Cycle independent data to echo clock tracking circuit
InactiveUS6134182AAvoid dataDigital storageGenerating/distributing signalsDouble data rateData signal
A comparator and variable delay circuit are provided to maintain the tracking between data and echo clocks in a double data rate (DDR)RAM device. This is accomplished by providing a global data signal (dummy data signal) that tracks with the actual memory array data. This global data signal is compared to the timing of the RAM clock (CLOCK) to determine a delay time between the two by which the pipeline clocks (CLKRISE / CLKFALL) must be delayed. As a result, the pipeline clocks are pushed out as needed so that they always transition after the array data arrives at the output latch. Therefore, as cycle time decreases, both echo clocks and data are pushed out identically and maintain their required tracking.
Owner:IBM CORP
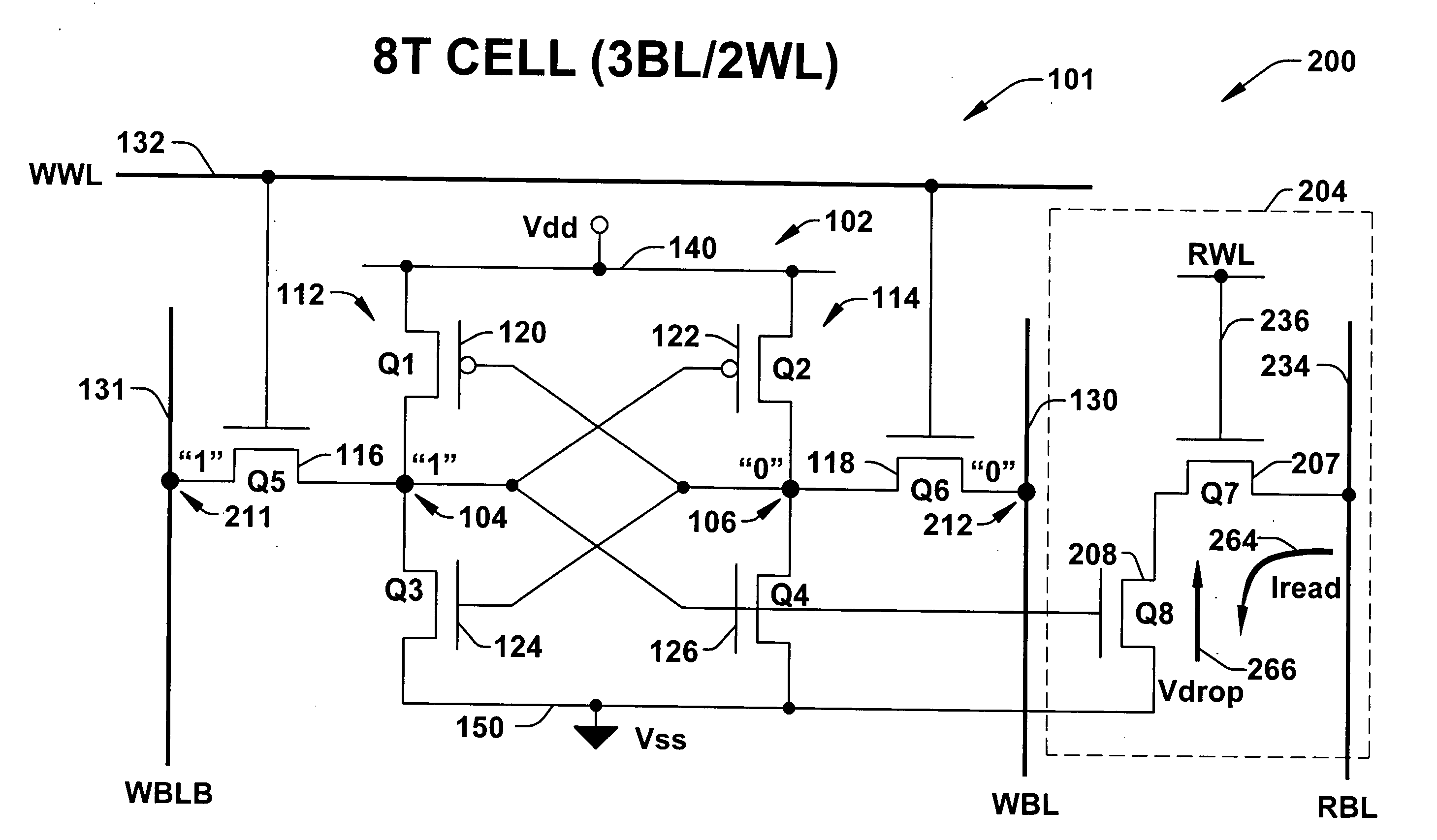
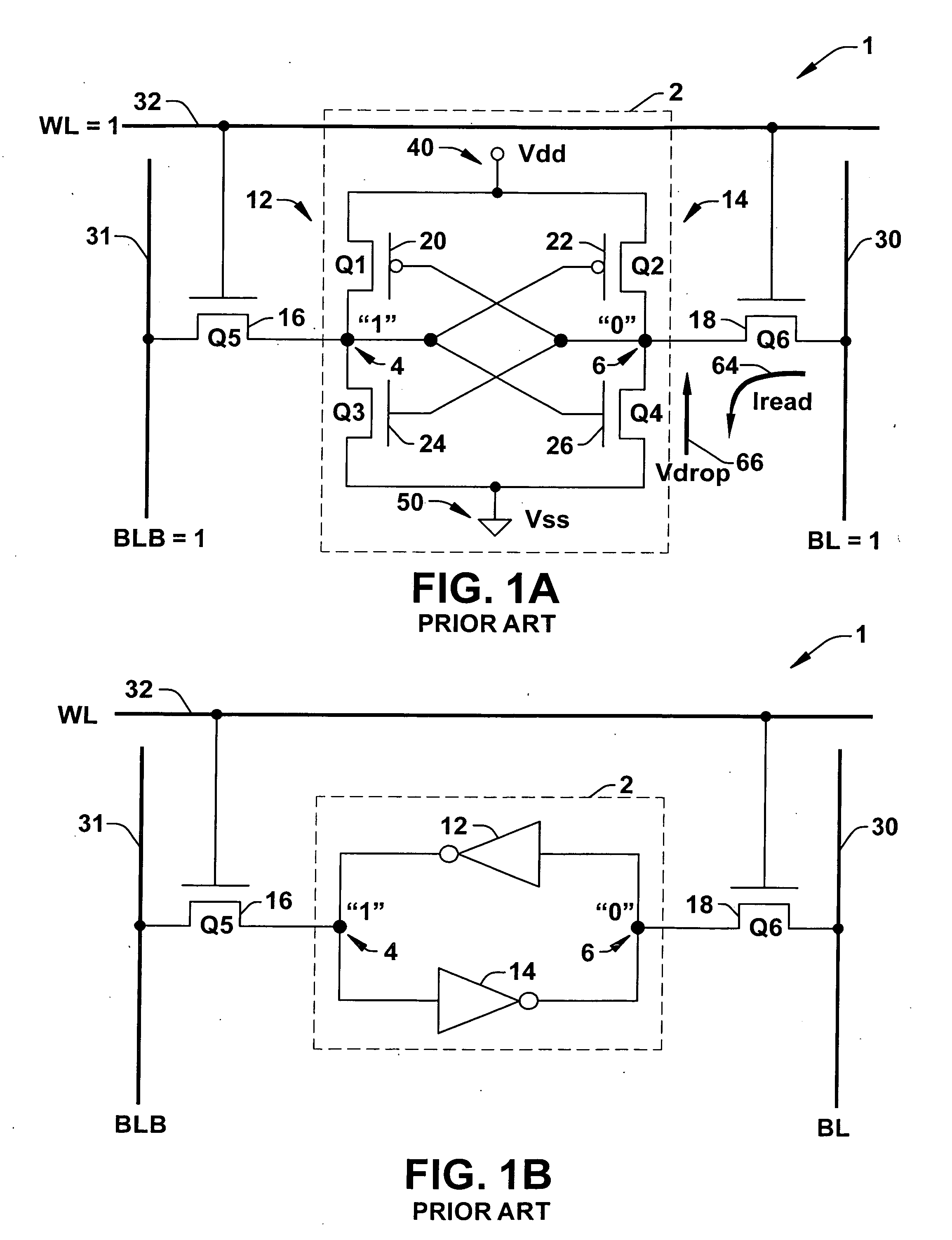
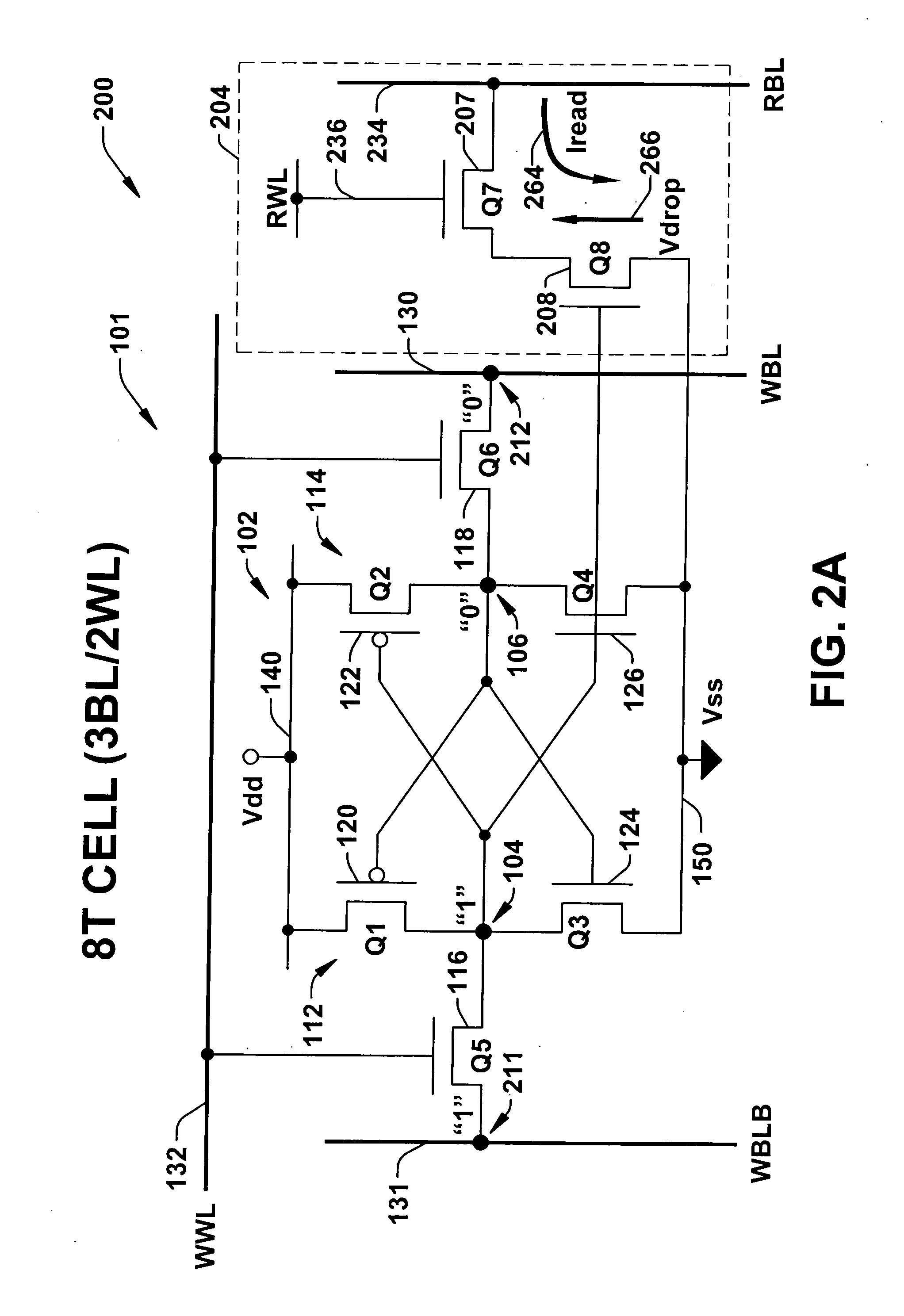
8T SRAM cell with higher voltage on the read WL
ActiveUS20070279966A1Avoid dataHigh voltageDigital storageSemiconductor devicesHemt circuitsVoltage source
The present invention provides circuitry for writing to and reading from an SRAM cell core, an SRAM cell, and an SRAM device. In one aspect, the circuitry includes a write circuit coupled to the SRAM cell core that includes a write transistor gated by a write word line. The circuitry also includes a read buffer circuit coupled to the SRAM cell core to read the cell without disturbing the state of the cell. The read buffer circuit includes a read transistor gated by a read word line, the read transistor coupled between a read bit-line and a read driver transistor that is further coupled to a voltage source Vss. The read driver transistor and a first driver transistor of the cell core are both gated by one output of the cell core. The read transistor has an electrical characteristic that differs from that of the core cell first driver transistor.
Owner:TEXAS INSTR INC
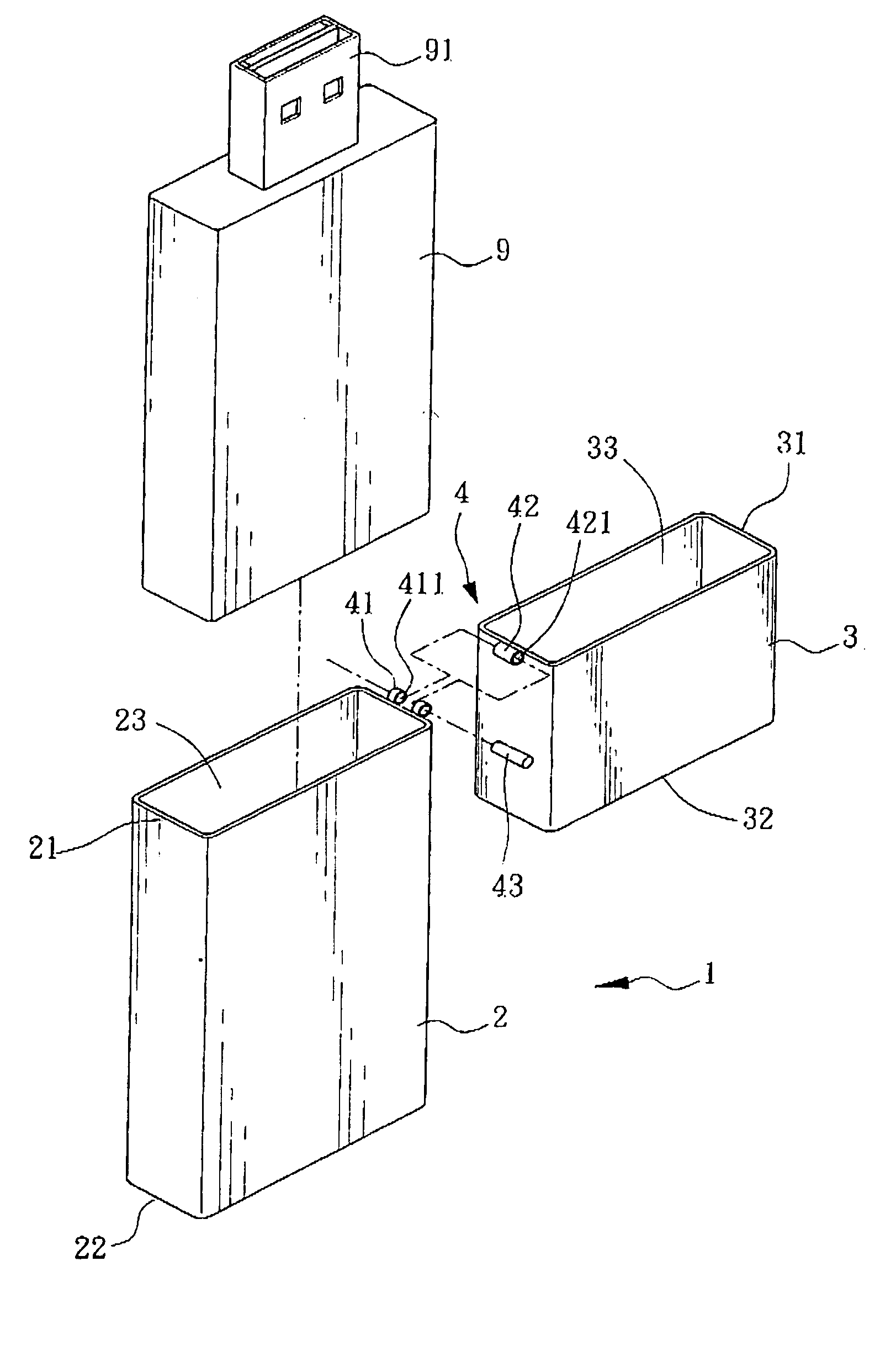
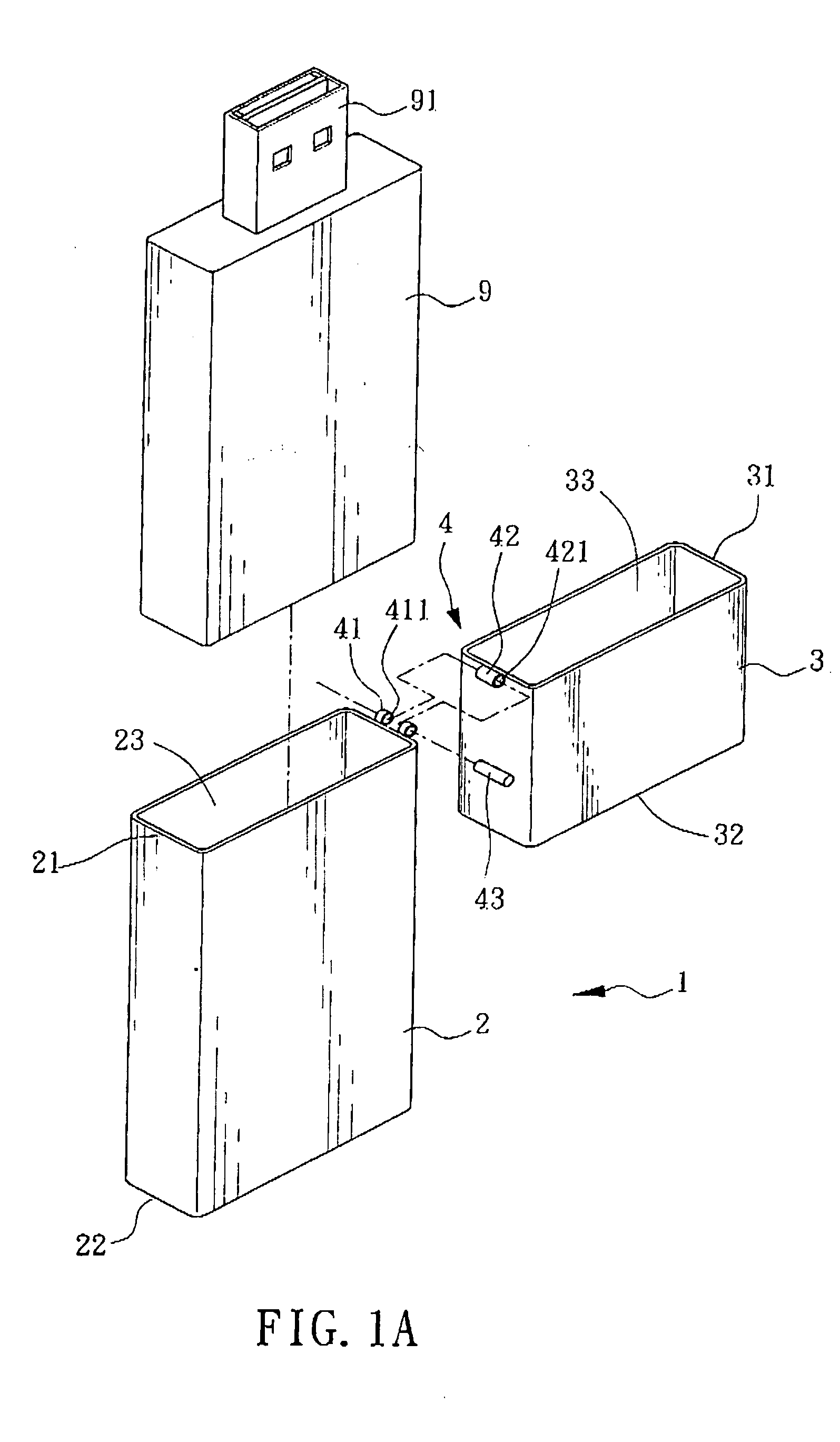
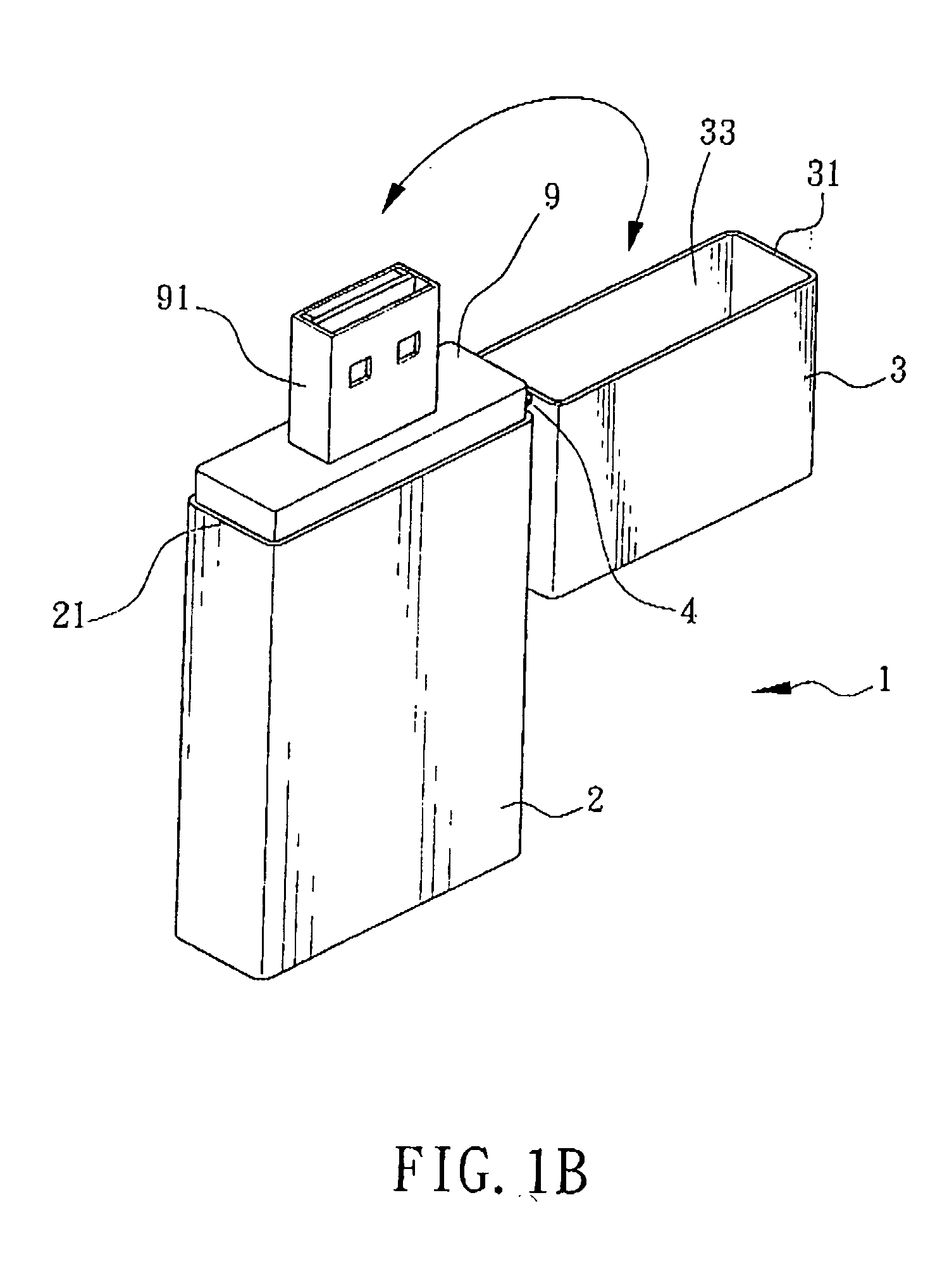
Portable media-accessing device
InactiveUS20050029137A1Opportunities decreaseFunction increaseCoupling device detailsOther accessoriesBiomedical engineeringMedia access
The invention is mainly to provide a portable media-accessing device, which includes a body, an upper lid, and at least one pivotal part. The body has a hollow casing having an opening side communicating to a first accommodation space; the first opening side may provide a memory module to be placed into the first accommodation space; the upper lid has a hollow casing having a second opening side communicating to a second accommodation space; the pivotal part may make the body connected to the upper lid such that, by taking the pivotal part as an axial center, a rotation motion with an appropriate angle between the upper lid and the body is possible.
Owner:BENQ CORP
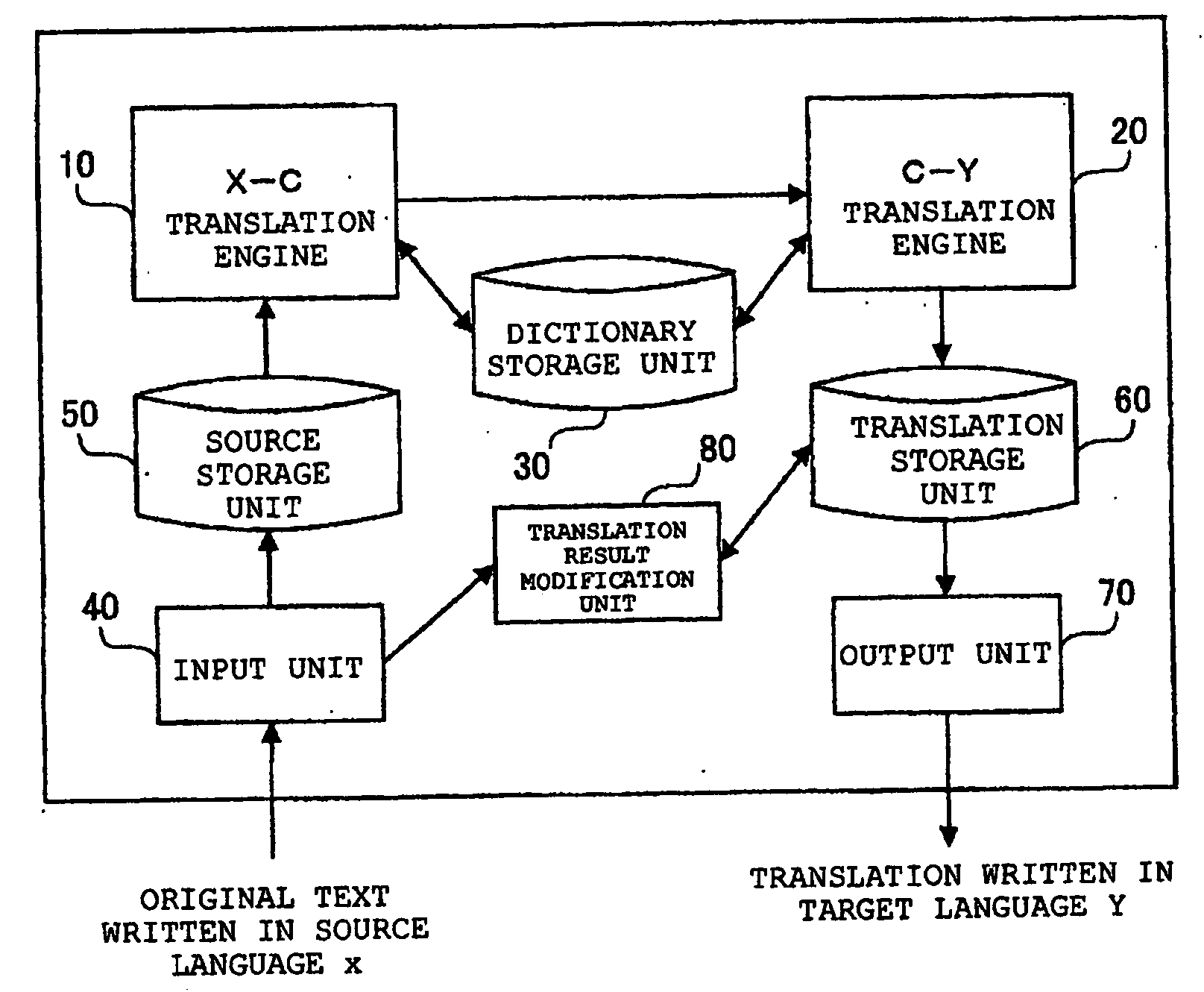
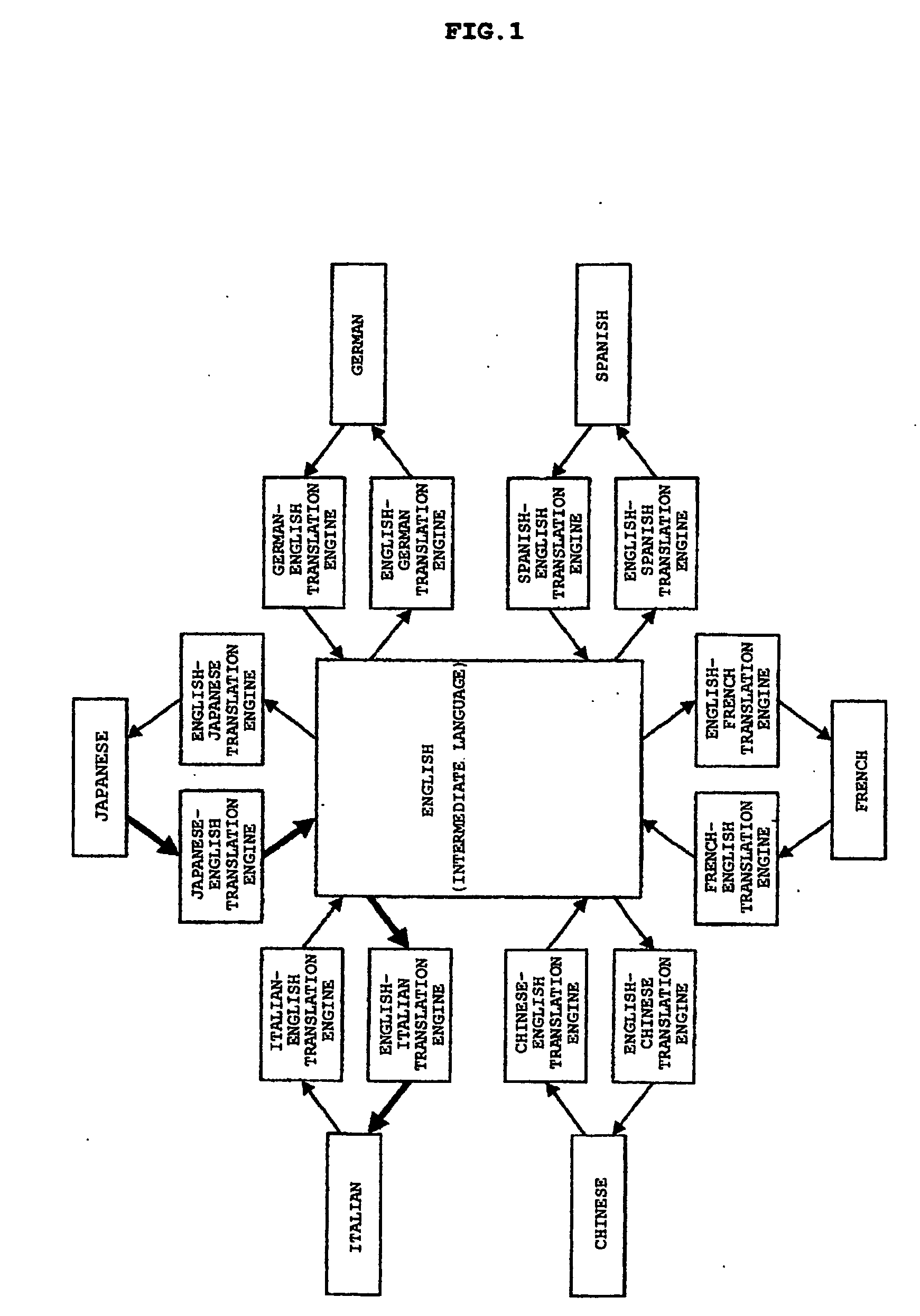
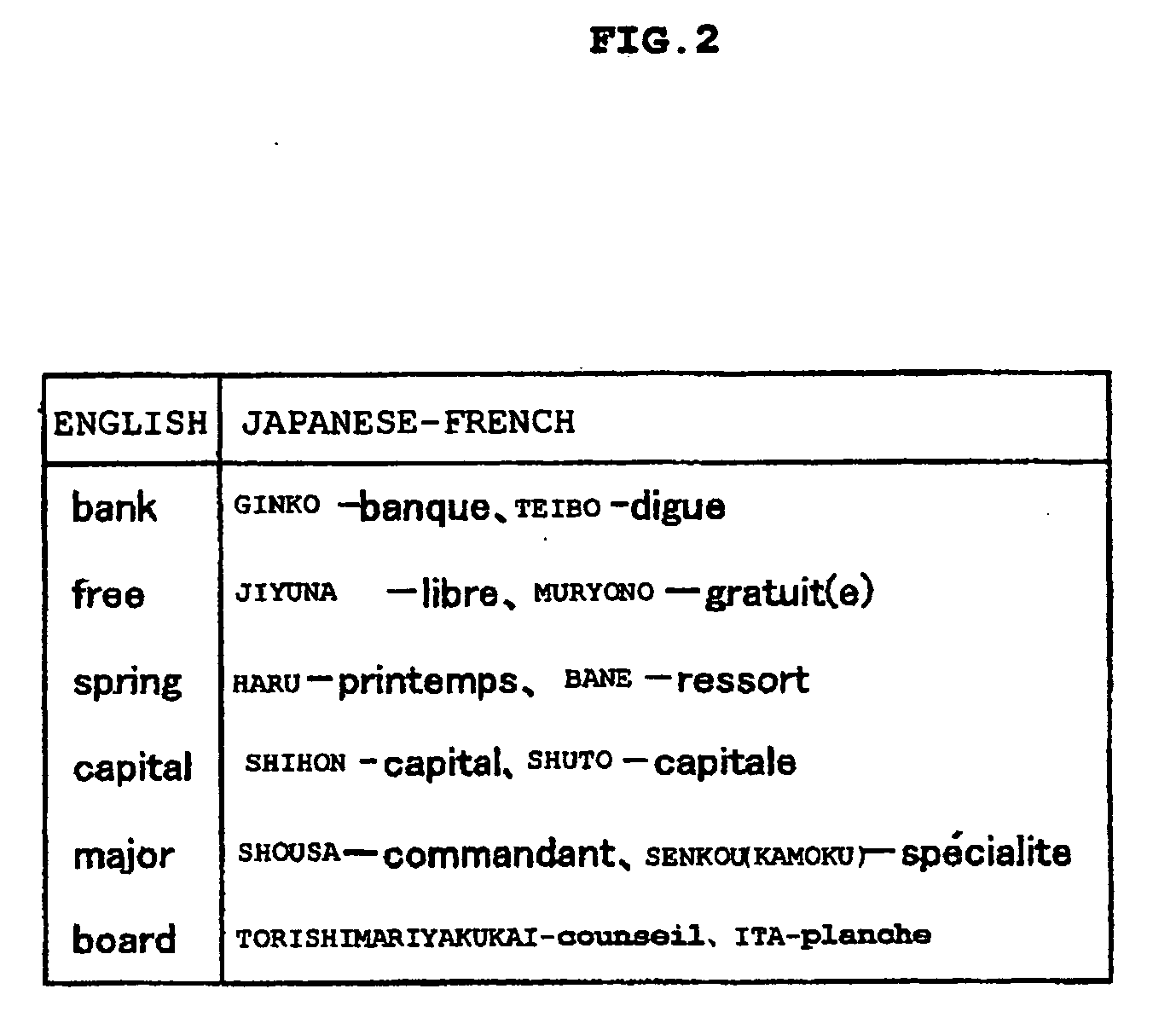
Machine translation device, method of processing data, and program
ActiveUS20050010421A1Accurate translationAvoid dataNatural language translationSpeech analysisMachine translationIntermediate language
Provided are two types of translation engines. One of the translation engines translates a text written in a source language X into an intermediate language C, and the other translates the intermediate language C into a target language Y. The X-C translation engine translates an original text written in the source language X into a text in a predetermined intermediate language C as well as acquires and adds annotations obtained by this translation to the translated text written in the intermediate language C. The C-Y translation engine references annotations, which are obtained by the X-C translation engine and added to the text in the intermediate language C, and translates the text in the intermediate language into a text in the target language Y sentence.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com