Patents
Literature
5694results about How to "Efficient identification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
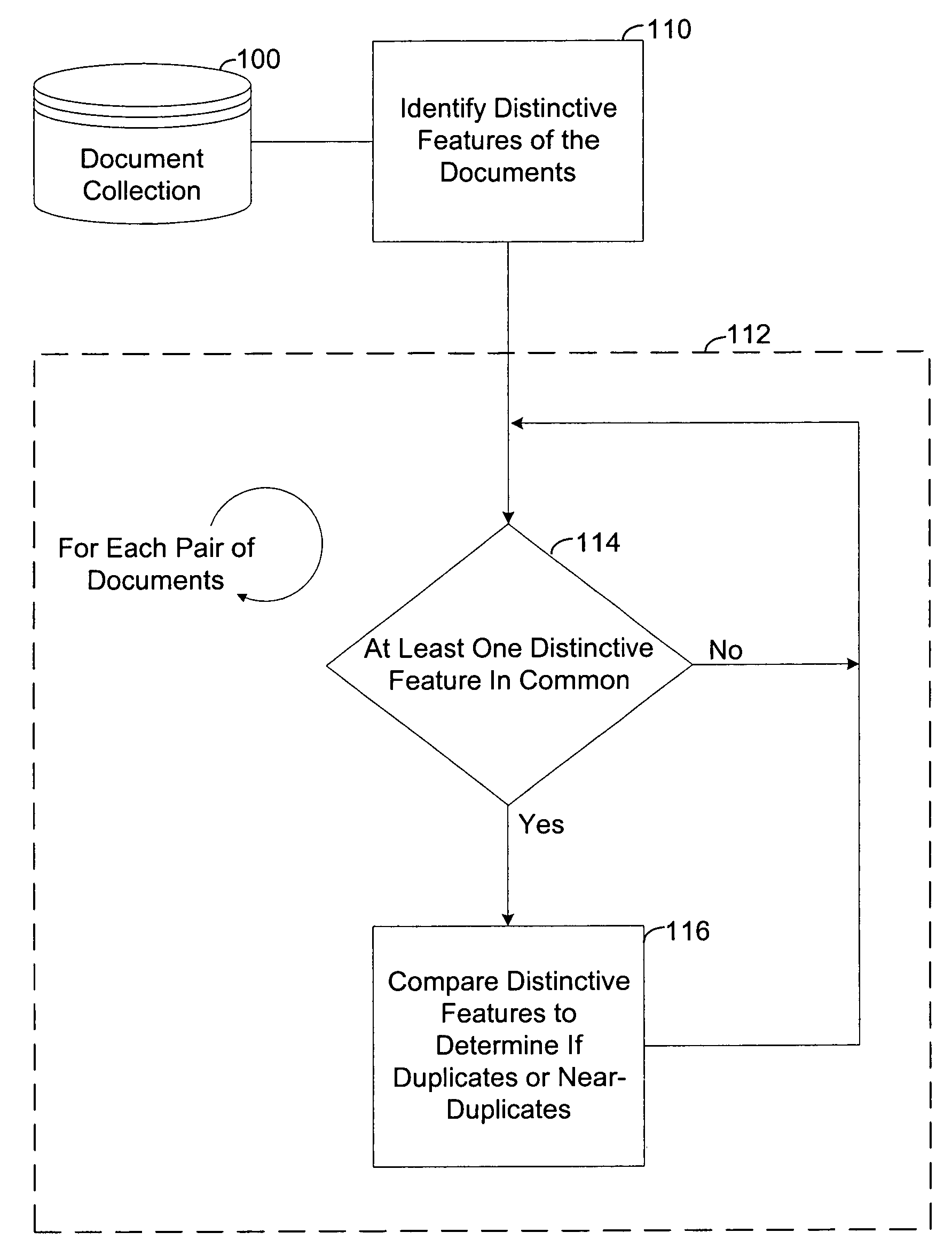
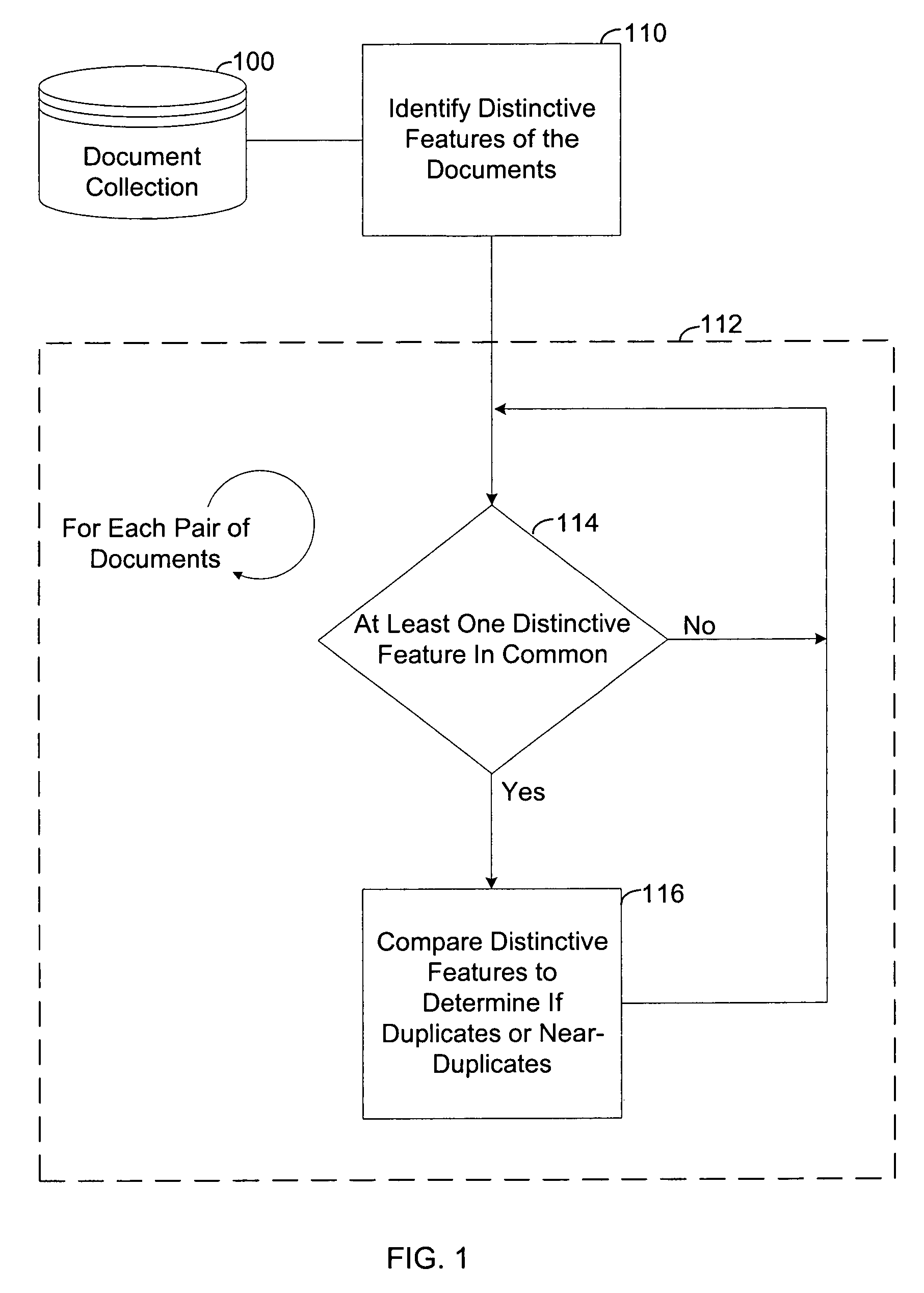
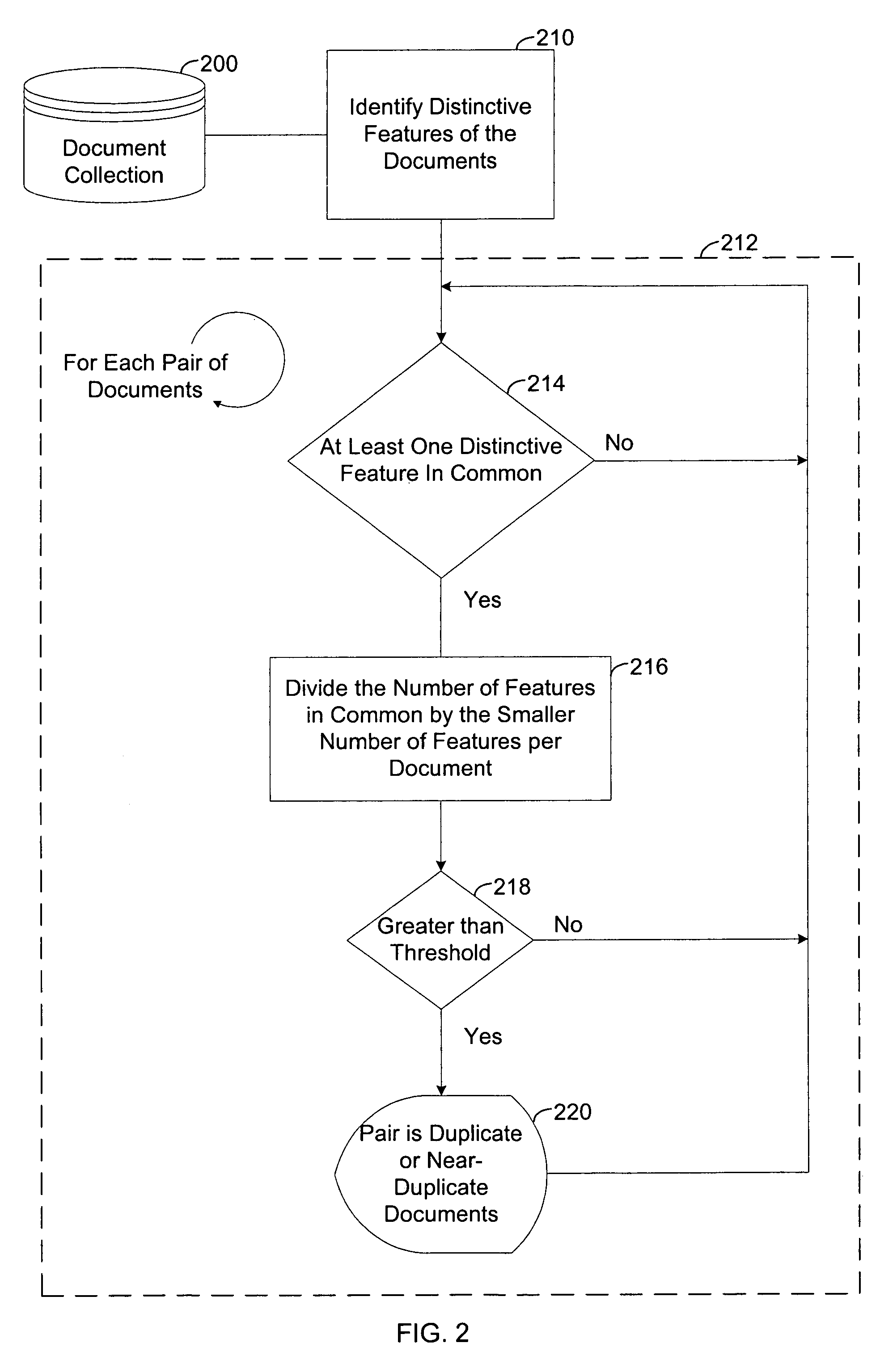
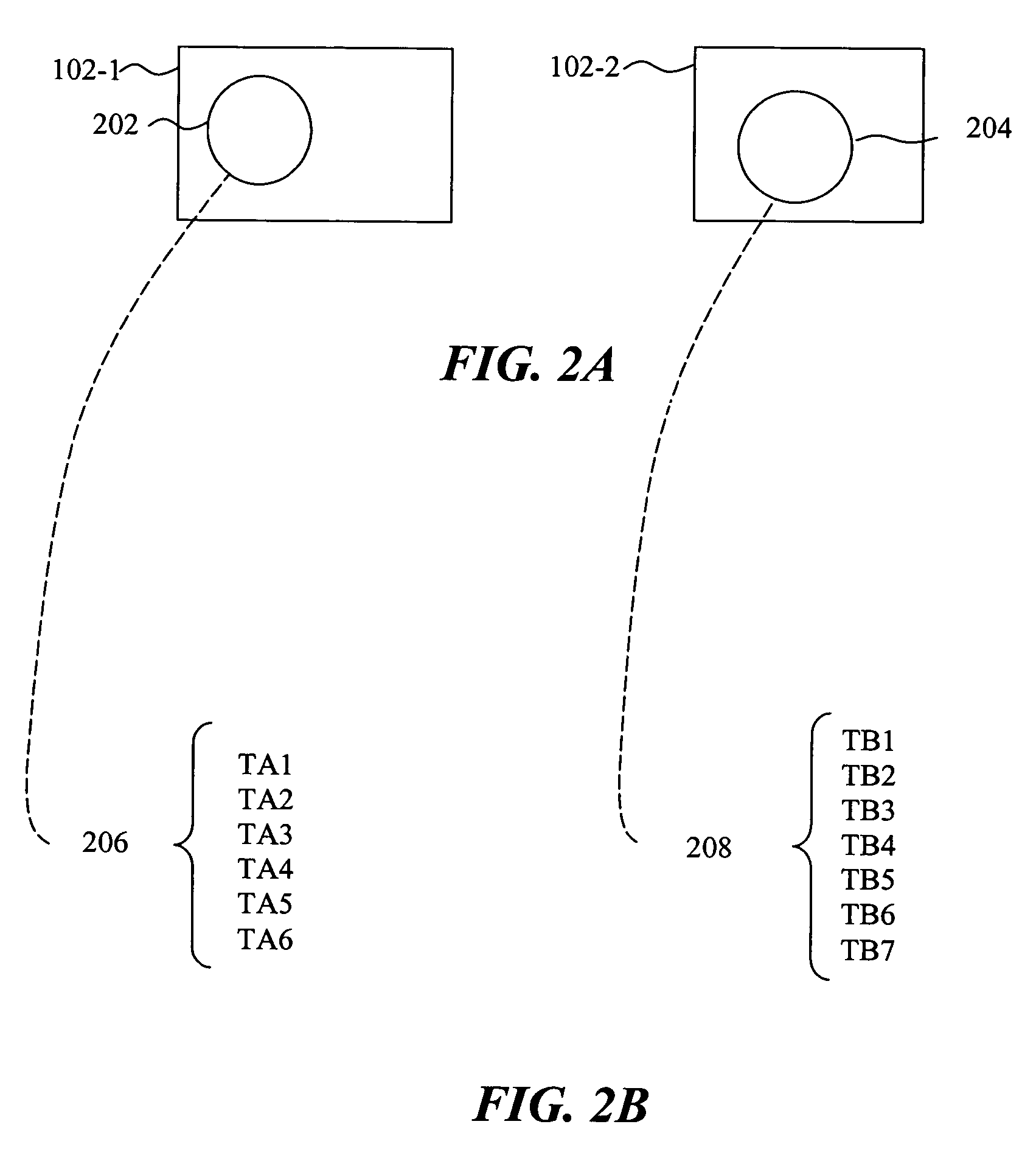
Method and apparatus for efficient identification of duplicate and near-duplicate documents and text spans using high-discriminability text fragments
InactiveUS6978419B1Eliminate redundancyDetectionDigital data information retrievalDigital computer detailsComputer-aidedDocument preparation
Owner:JUSTSYSTEMS
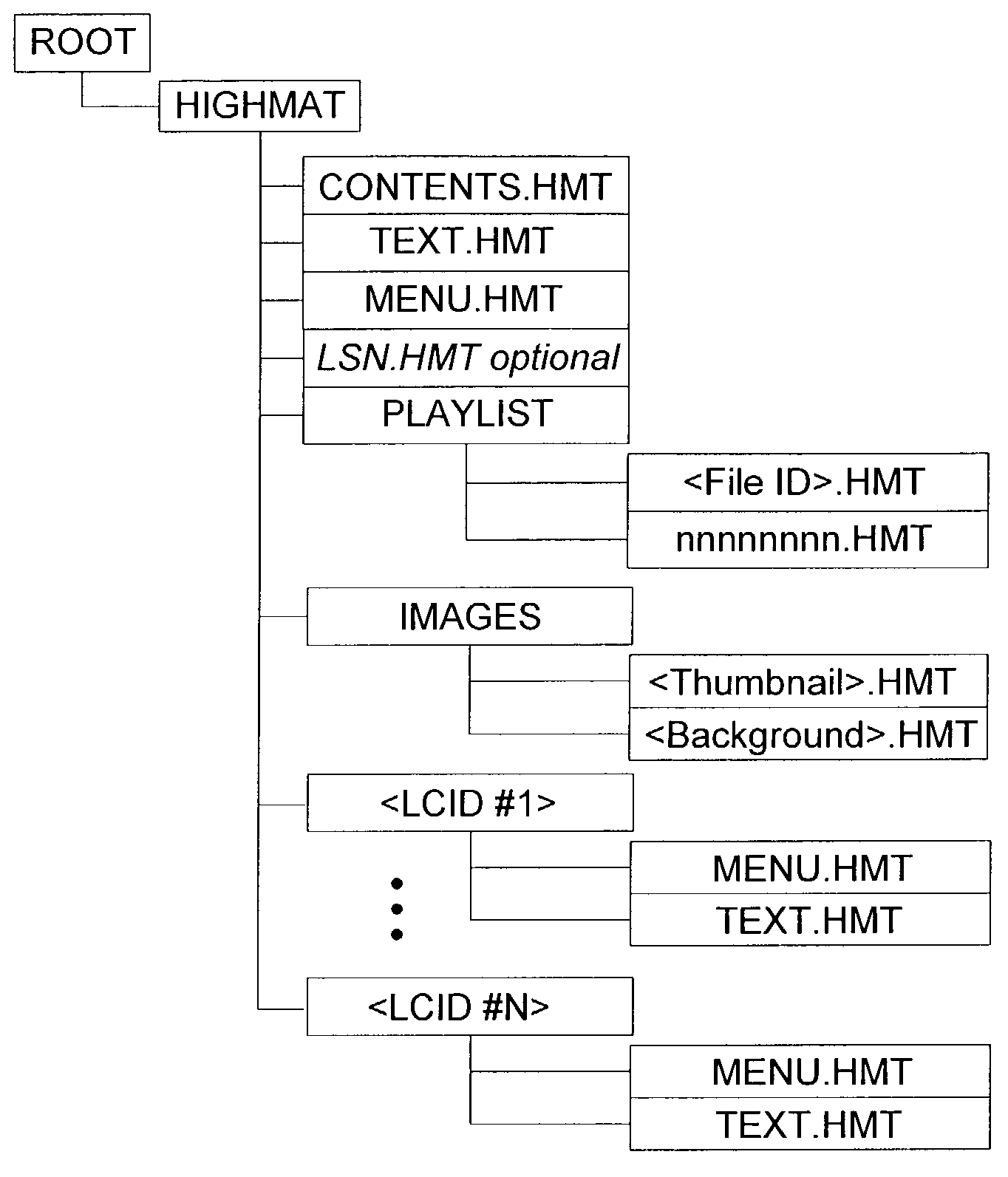
Optimizing media player memory during rendering
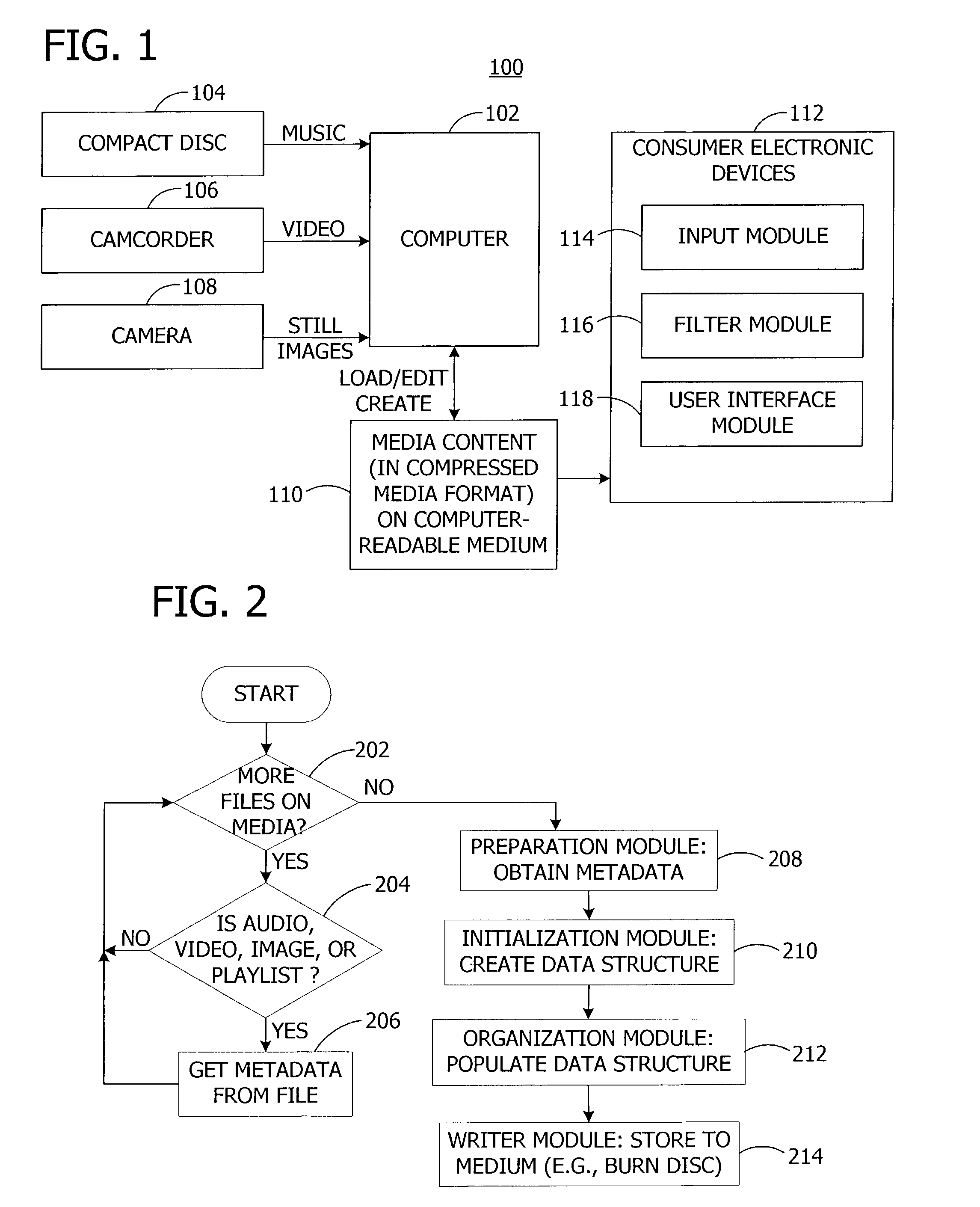
ActiveUS7054888B2Efficient identificationImprove playback experienceData processing applicationsElectronic editing digitised analogue information signalsPersonal computerSmall files
Optimizing operation of a media player during rendering of media files. The invention includes authoring software to create a data structure and to populate the created data structure with obtained metadata. The invention also includes rendering software to retrieve the metadata from the data structure and to identify media files to render. In one embodiment, the invention is operable as part of a compressed media format having a set of small files containing metadata, menus, and playlists in a compiled binary format designed for playback on feature-rich personal computer media players as well as low cost media players.
Owner:PANASONIC CORP +1
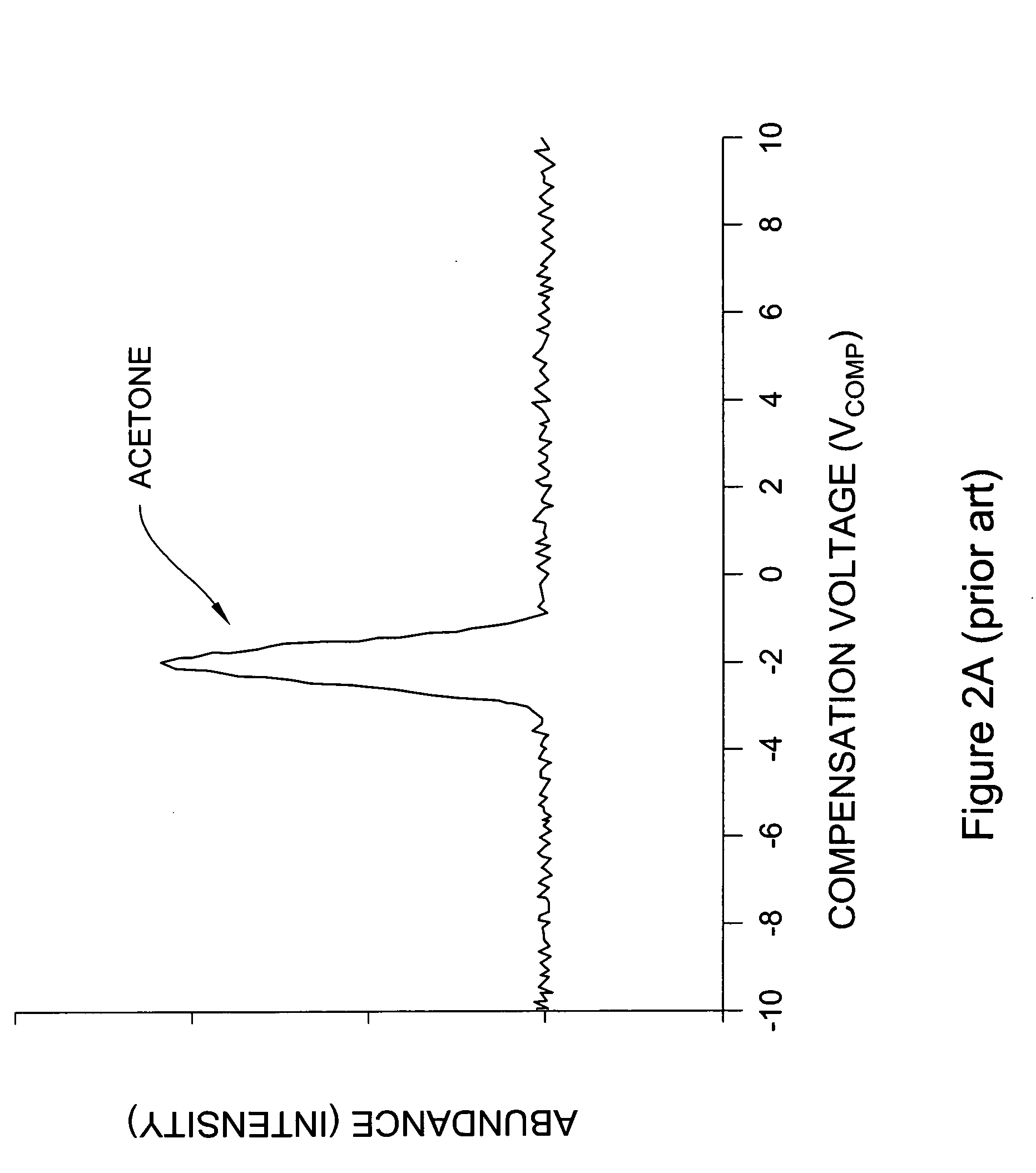
Systems and methods for ion species analysis with enhanced condition control and data interpretation
ActiveUS20050253061A1Reduces spectral peak overlapHigh resolutionTime-of-flight spectrometersMaterial analysis by electric/magnetic meansSystems approachesComputer science
The invention relates generally to ion mobility based systems, methods and devices for analyzing samples and, more particularly, to sample detection using enhanced condition control and data interpretation.
Owner:DH TECH DEVMENT PTE
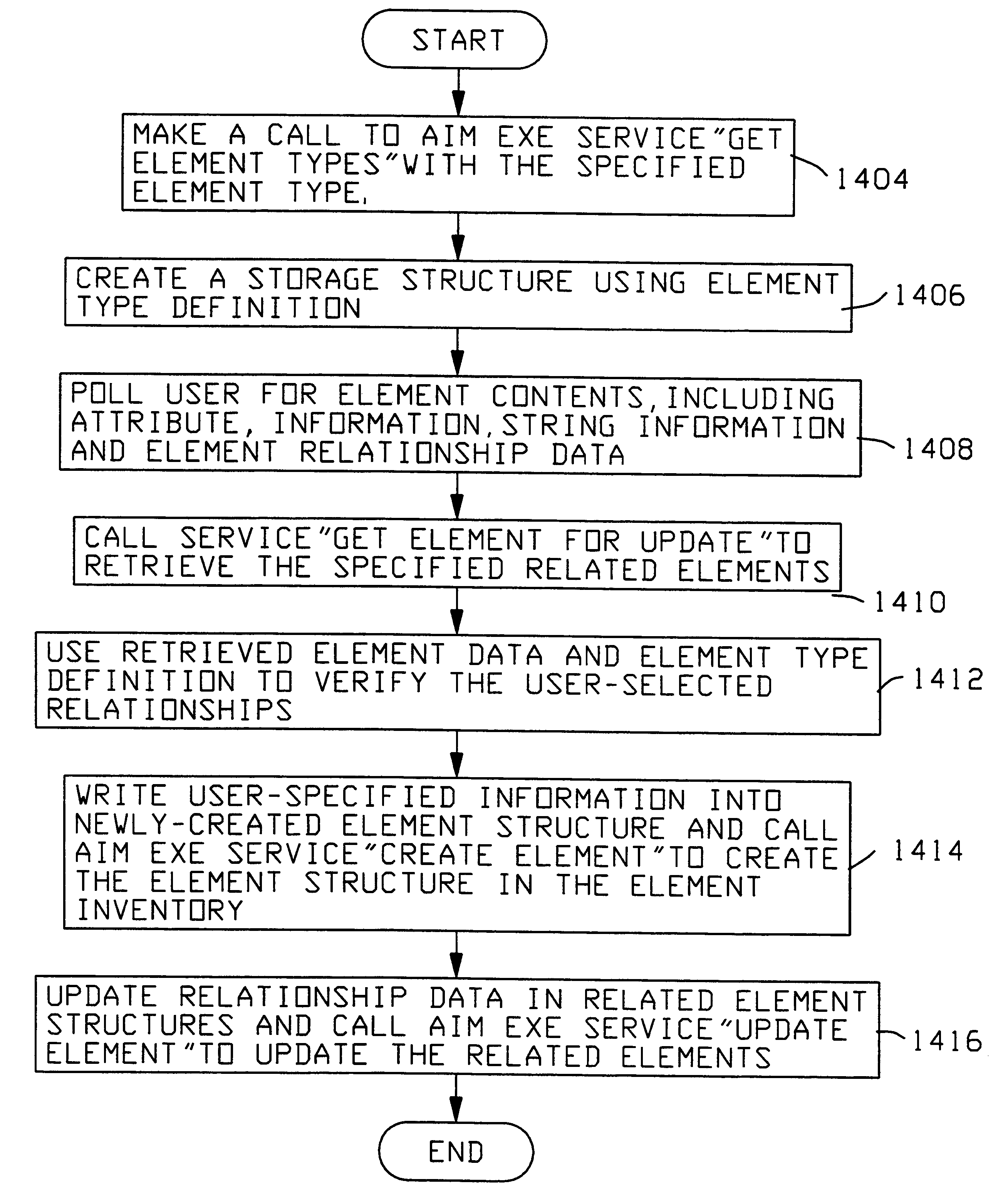
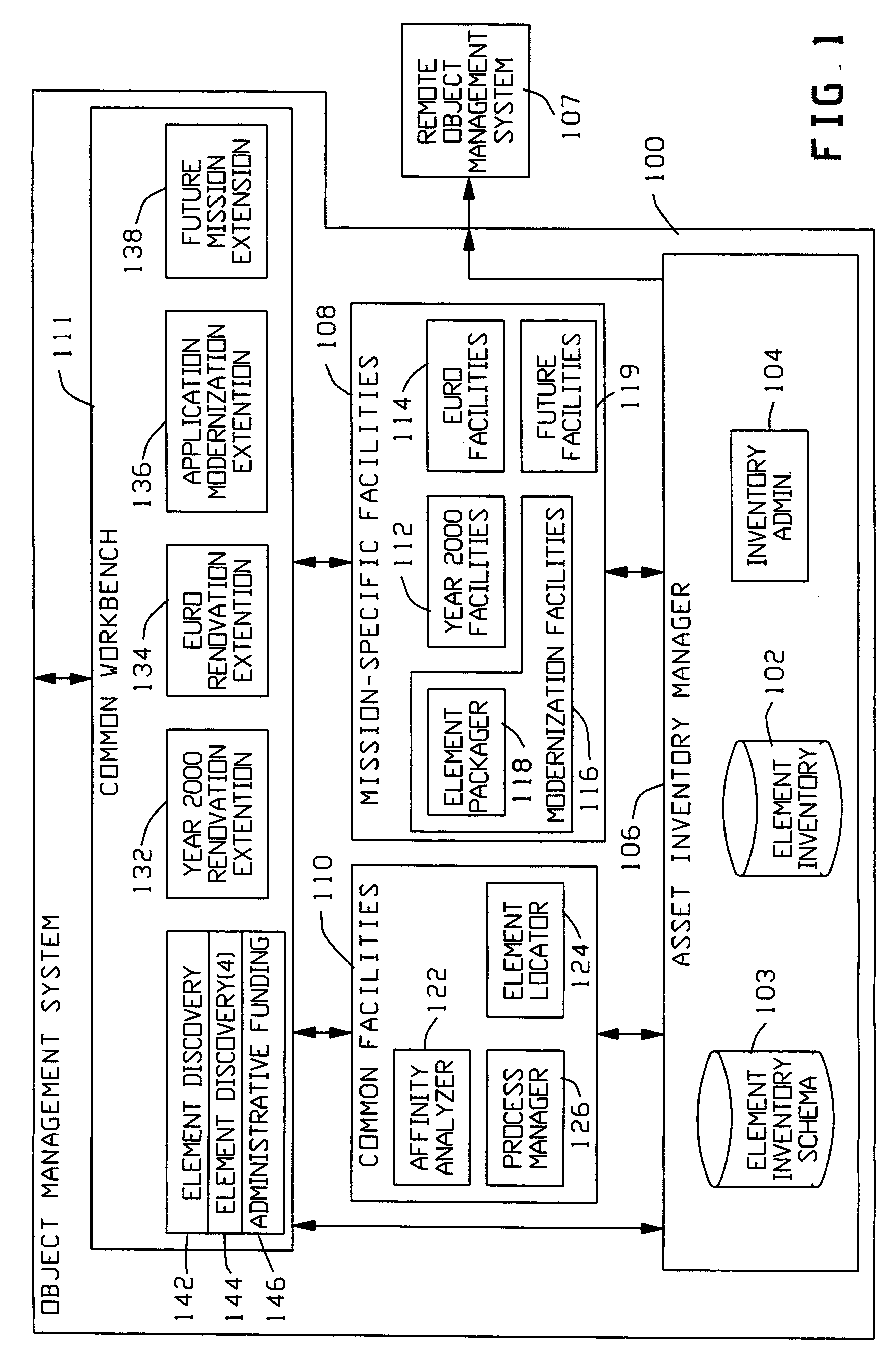
Object management system supporting the use of application domain knowledge mapped to technology domain knowledge
InactiveUS6226792B1Easy to browseThrough simpleSoftware reuseSpecific program execution arrangementsCatalogingAssociate - relationship
An object management system is providing for managing, cataloging, and discovering various potentially reusable code and data components that exist within an Information Technology (IT) platform, and which each have well-defined interfaces with other components. For each of these re-usable code and data components, an associated software object called an "asset element" is created that describes the associated component. Relationships are created between various asset elements to represent the relationships existing between the software components. Other software objects called "locator elements" are created that each describes an application concept or sub-concept. This application concept or sub-concept is associated with a problem solved by the code and data components within the IT platform. Relationships are created between the various locator elements to correlate the concepts and sub-concepts to software constructs represented by asset elements. The object management system further supports various object discovery tools capable of identifying locator elements associated with a particular concept. These locator elements and the associated relationships may then be efficiently traced to identify related asset elements and the associated software and code constructs. This provides an efficient concept-based search mechanism for the code constructs. Other tools are provided for creating, modifying, and deleting the elements. A model may be used to define the various types of relationships and elements that may exist within the system, thereby simplifying the various tools needed to support element creation, modification, deletion, and traversal.
Owner:UNISYS CORP
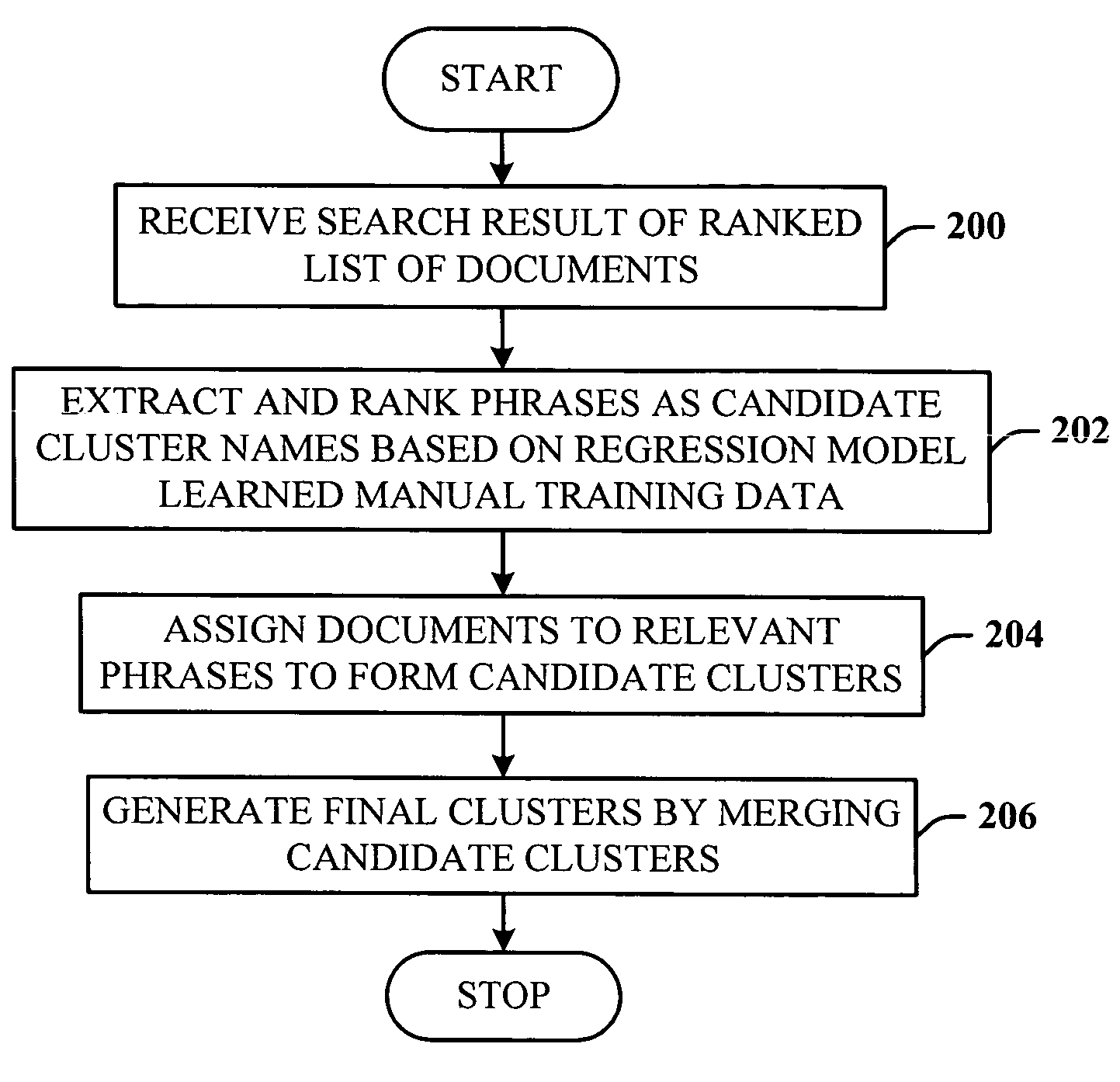
Query-based snippet clustering for search result grouping
InactiveUS20060026152A1Quick identificationEfficient identificationWeb data indexingSpecial data processing applicationsFeature vectorCo-occurrence
Owner:MICROSOFT TECH LICENSING LLC
Human and object recognition in digital video
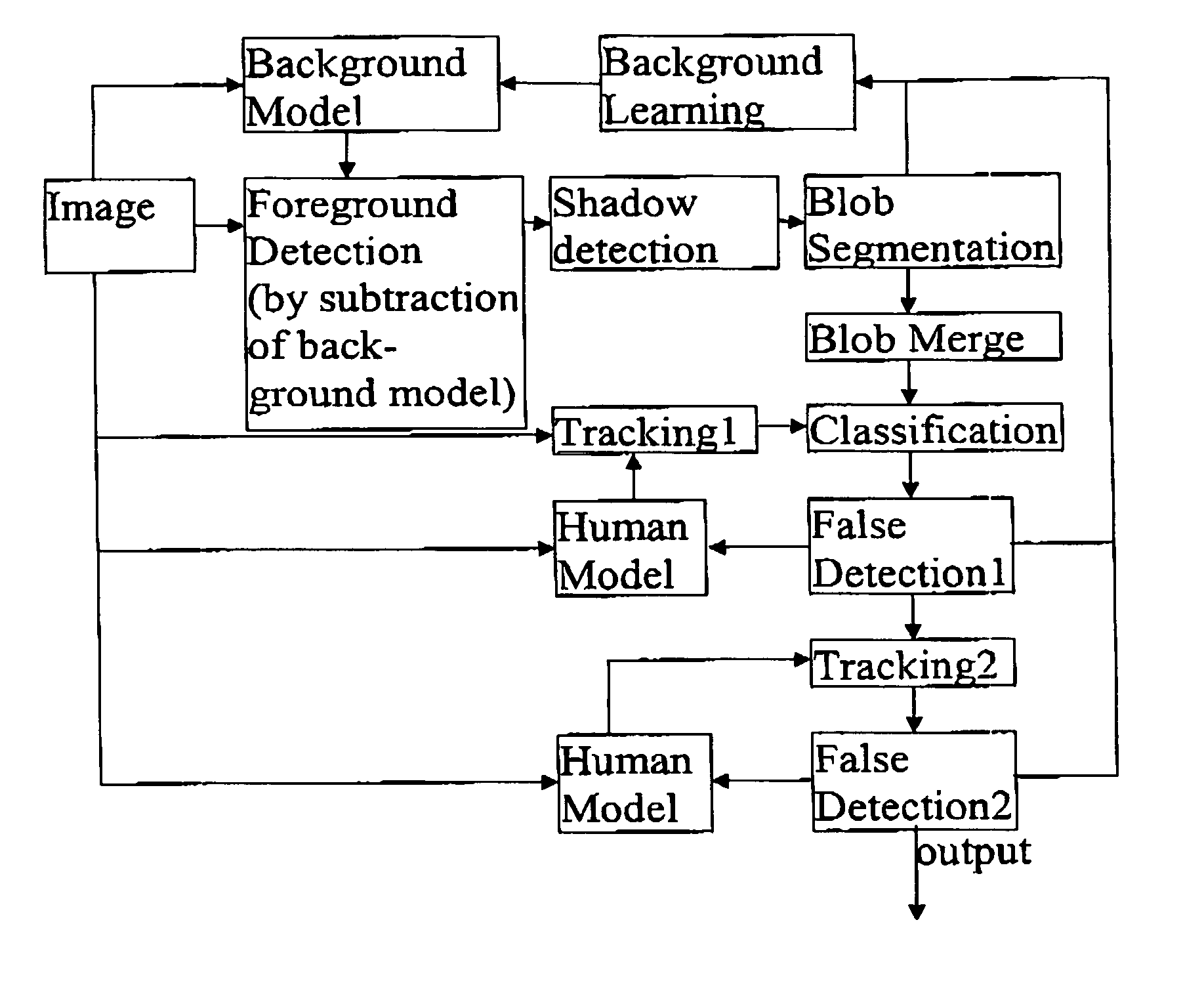
InactiveUS20060170769A1Save timeReduce numberColor television detailsClosed circuit television systemsSelf adaptiveImage resolution
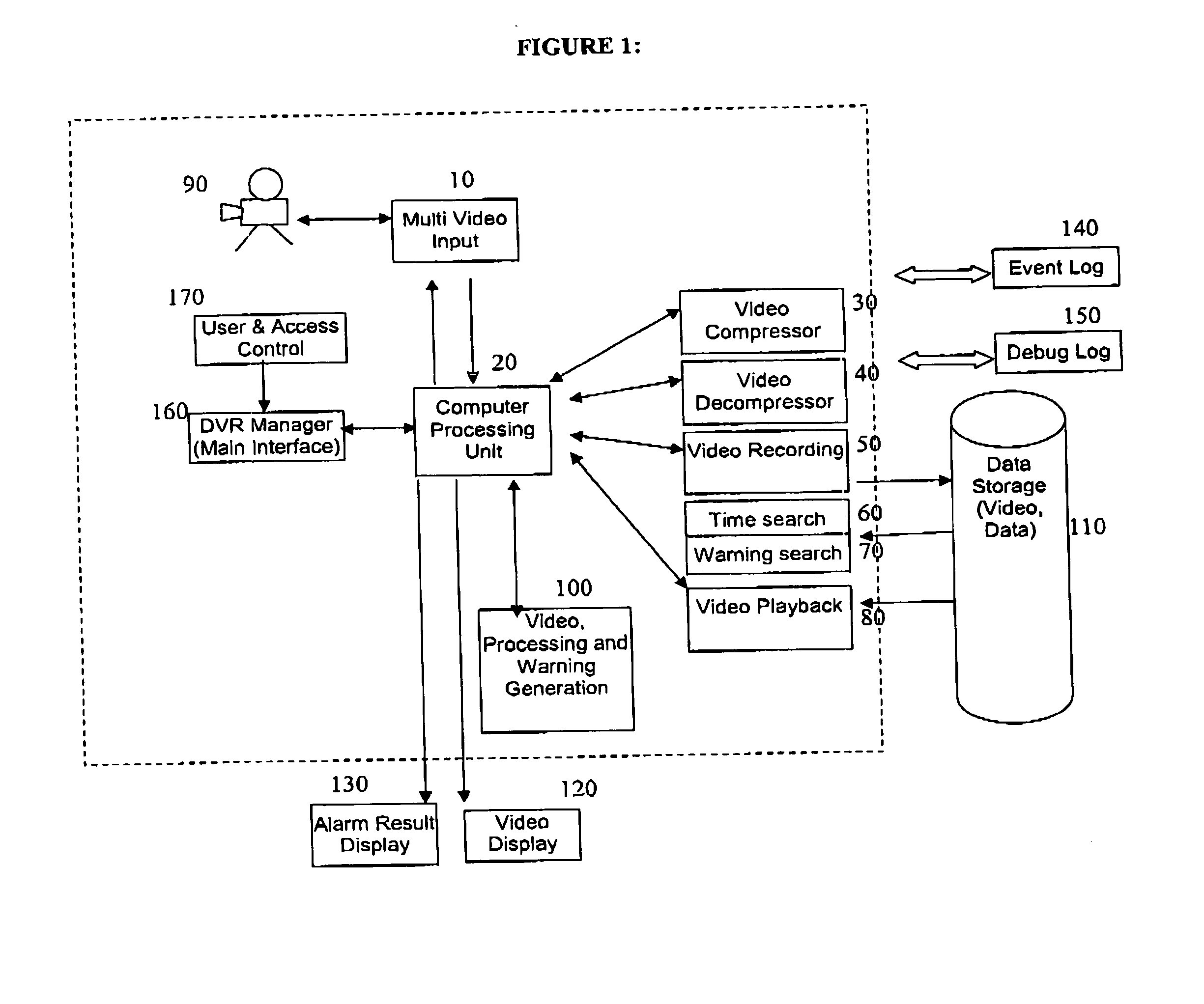
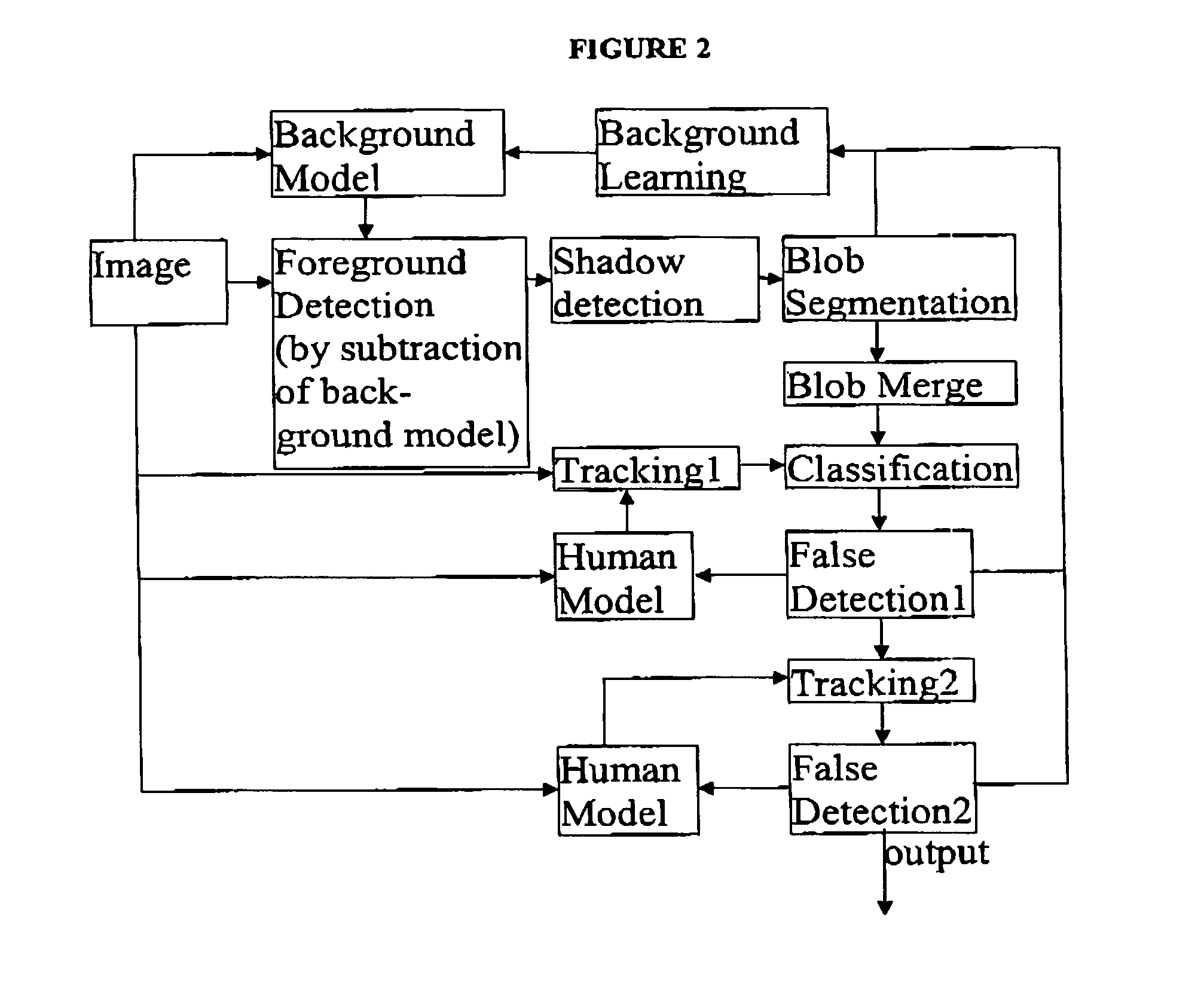
The current invention is a method or a computer implemented tool for robust, low CPU, low resolution human tracking which may be implemented a part of a digital video management and surveillance system or on a digital video recorder. The method involves use of intensity, texture and shadow filtering in the YUV color space to reduce the number of false objects detected. The thresholds for background segmentation may be dynamically adjusted to image intensity. The human and object recognition feature operates on an adaptive codebook based learning algorithm.
Owner:ZHOU JIANPENG
Method and system for selection, filtering or presentation of available sales outlets
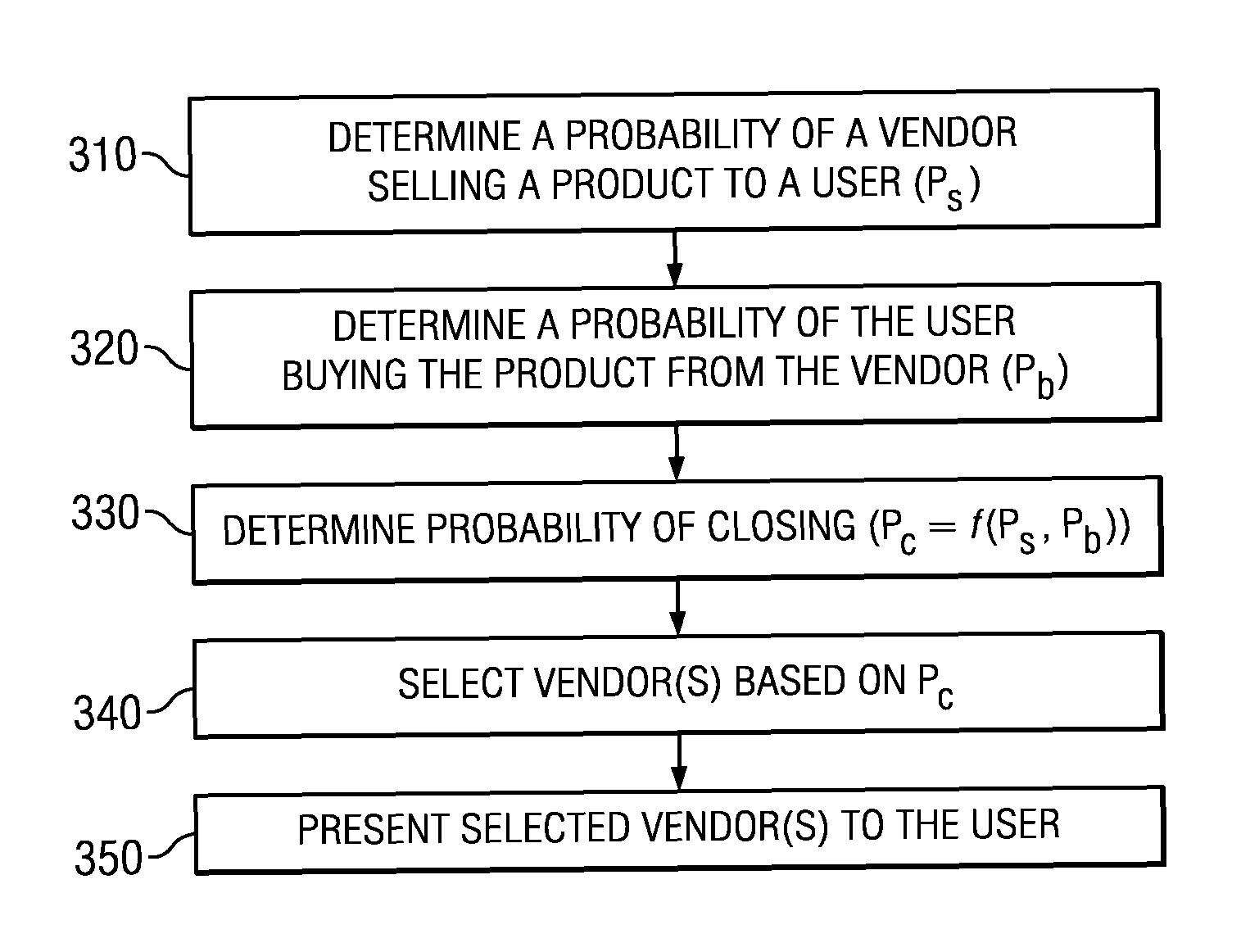
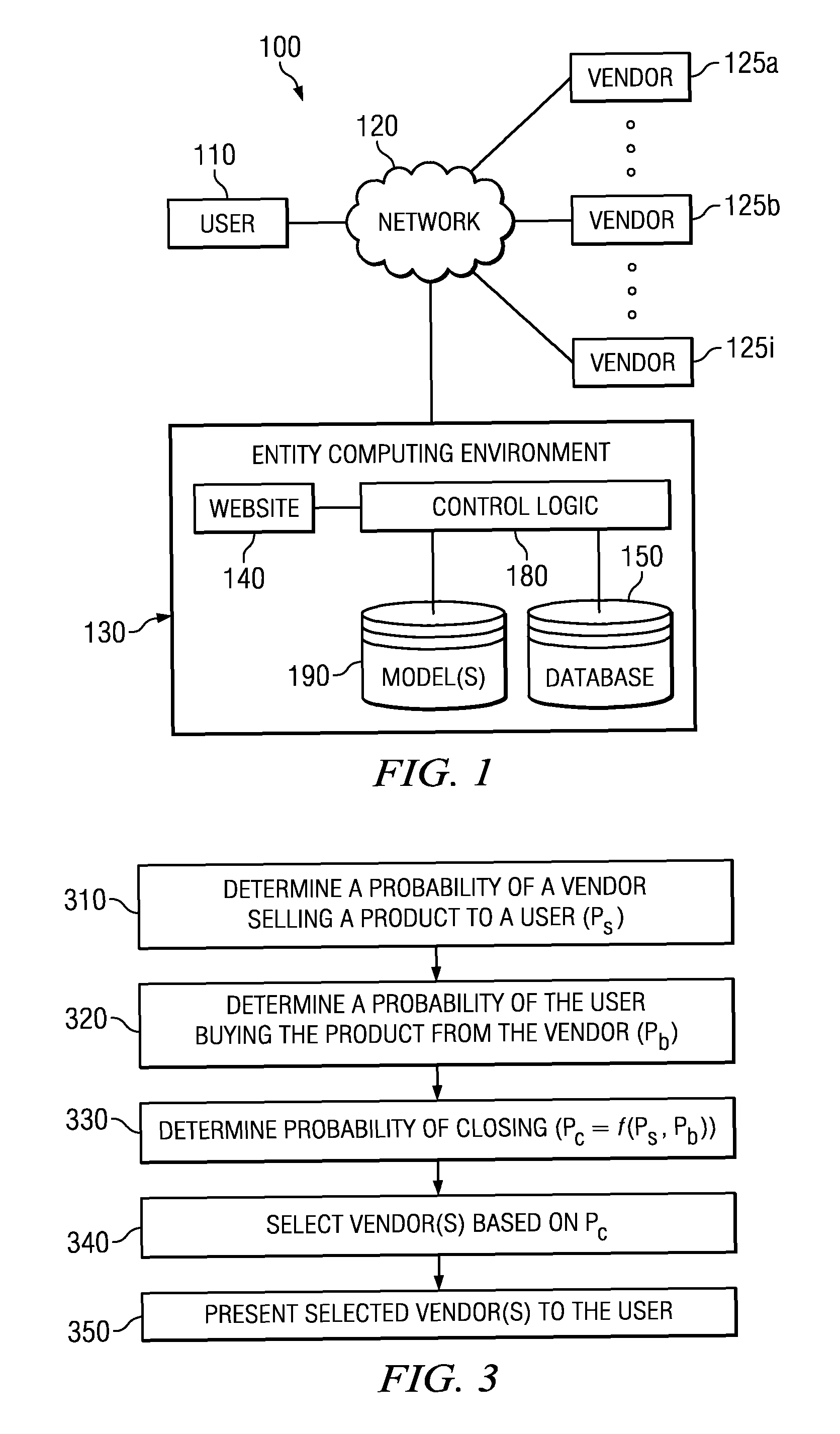
ActiveUS20130006916A1Efficient identificationIncrease probabilityFuzzy logic based systemsKnowledge representationHigh probabilityComputer science
Owner:TRUECAR
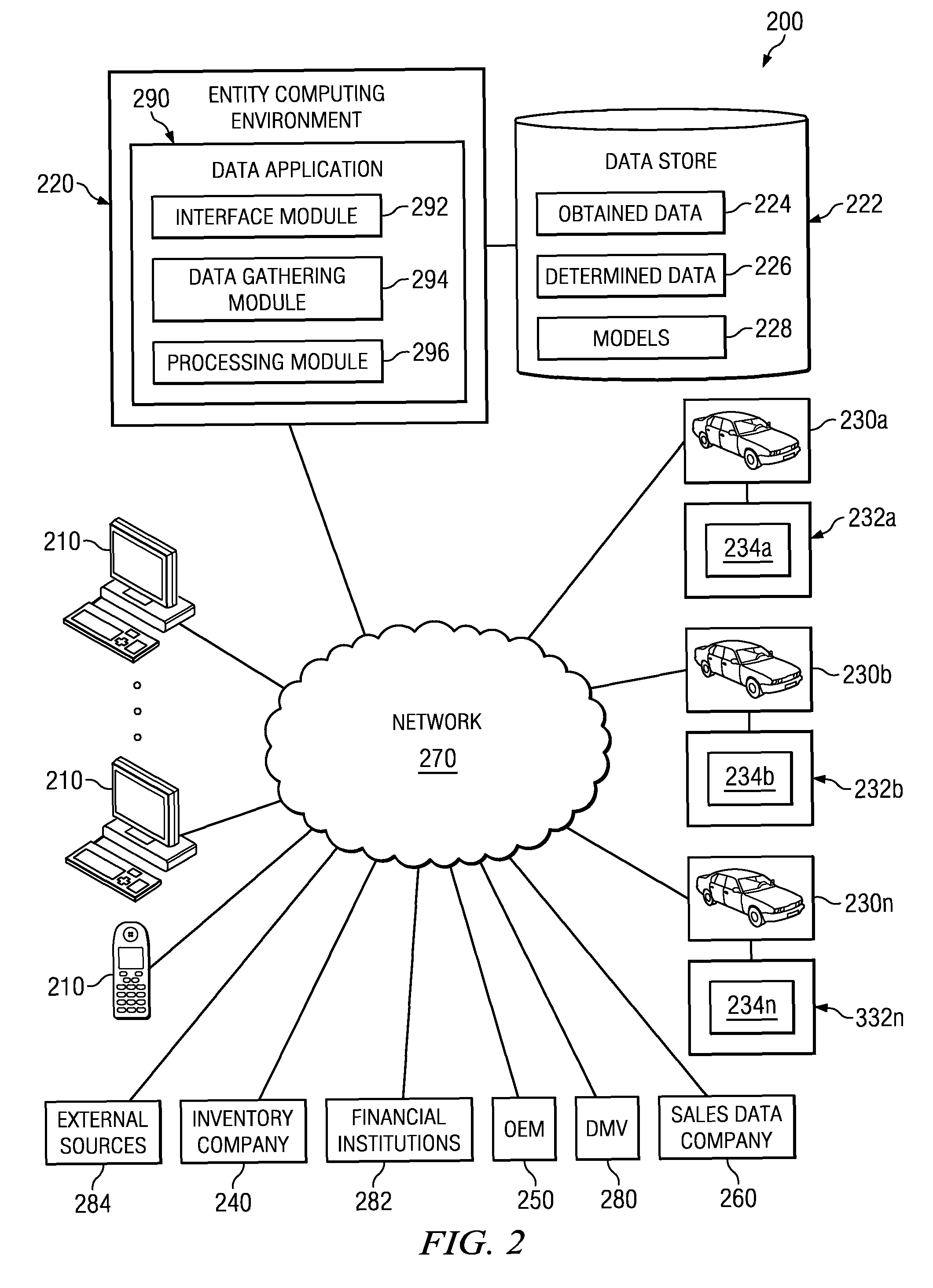
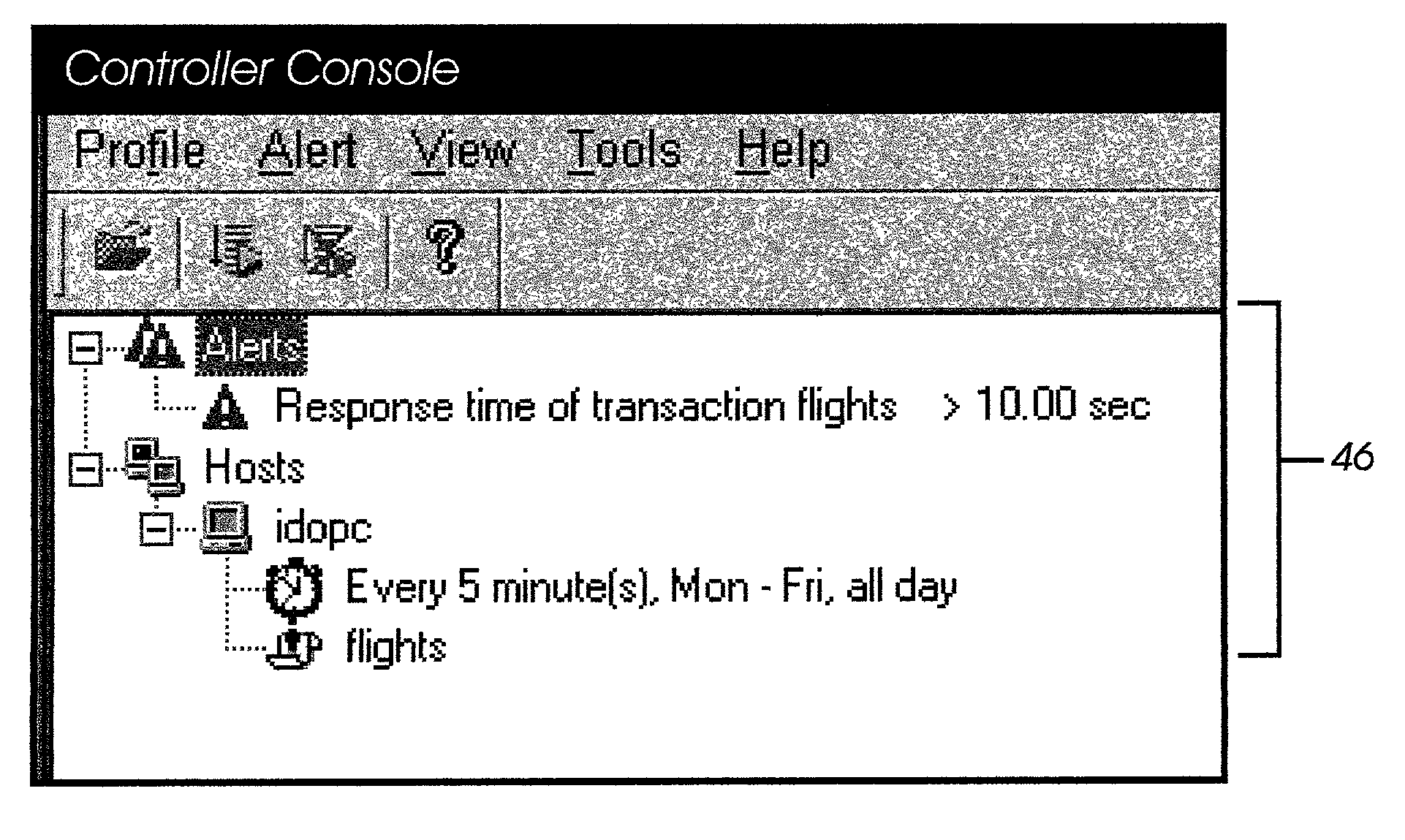
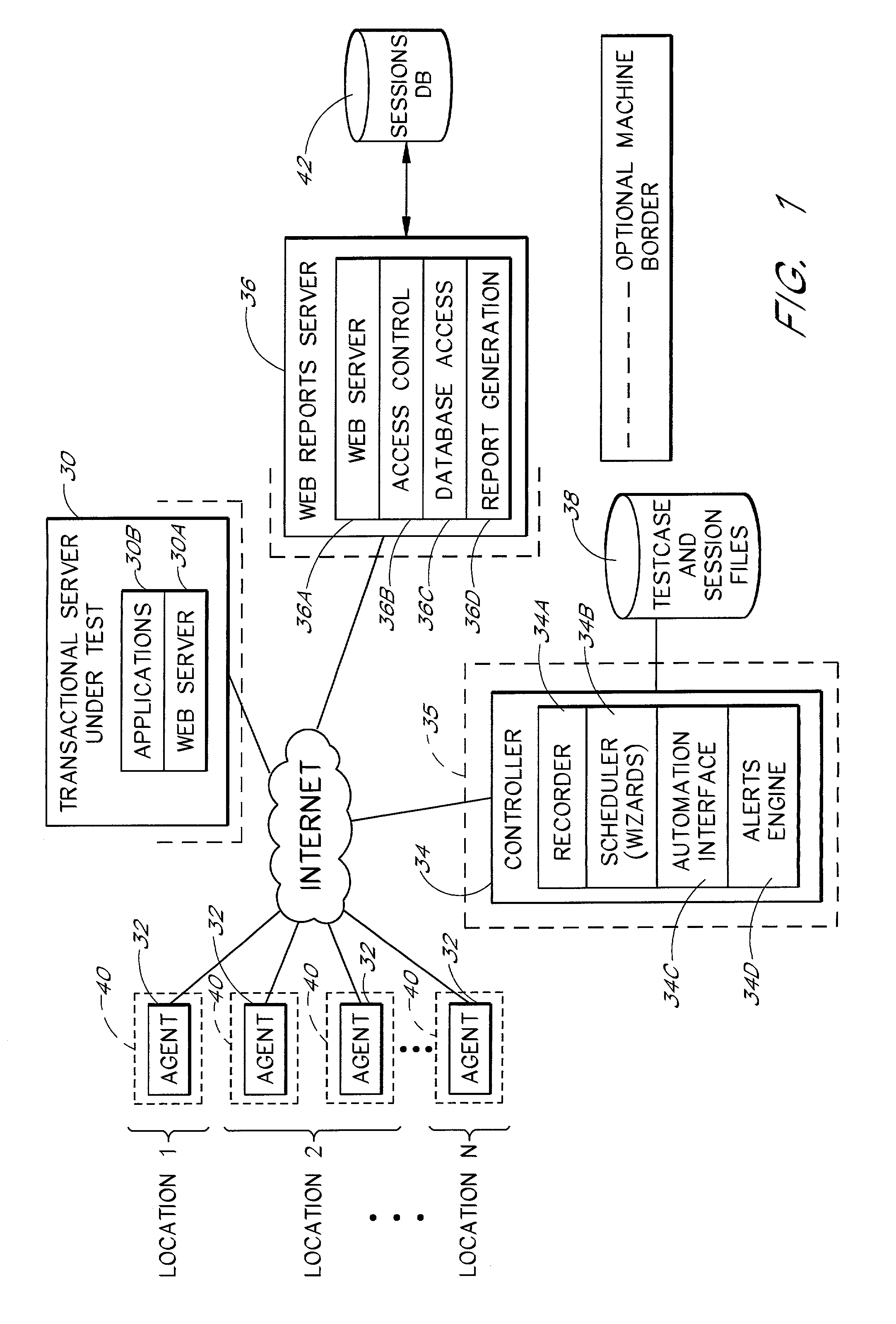
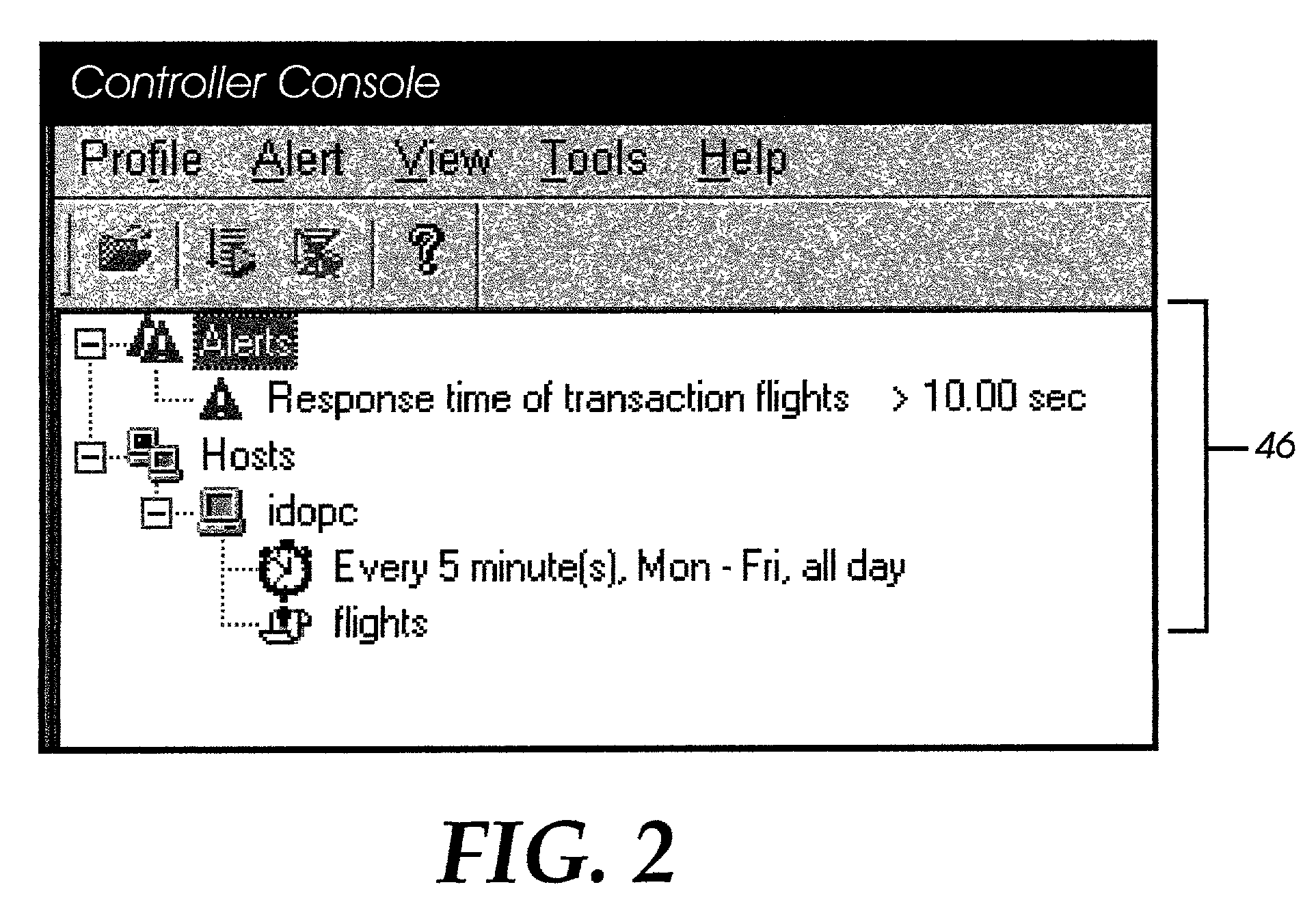
Transaction breakdown feature to facilitate analysis of end user performance of a server system
InactiveUS7197559B2Facilitates taskFlexible choiceHardware monitoringMultiple digital computer combinationsGeographic siteGranularity
A system for monitoring the post-deployment performance of a web-based or other transactional server is disclosed. The monitoring system includes an agent component that monitors the performance of the transactional server as seen from one or more geographic locations and reports the performance data to a reports server and / or centralized database. The performance data may include, for example, transaction response times, server response times, network response times and measured segment delays along network paths. Using the reported performance data, the system provides a breakdown of time involved in completion of a transaction into multiple time components, including a network time and a server time. Users view the transaction breakdown data via a series of customizable reports, which assist the user in determining whether the source of the performance problem. Additional features permit the source to be identified with further granularity.
Owner:MICRO FOCUS LLC
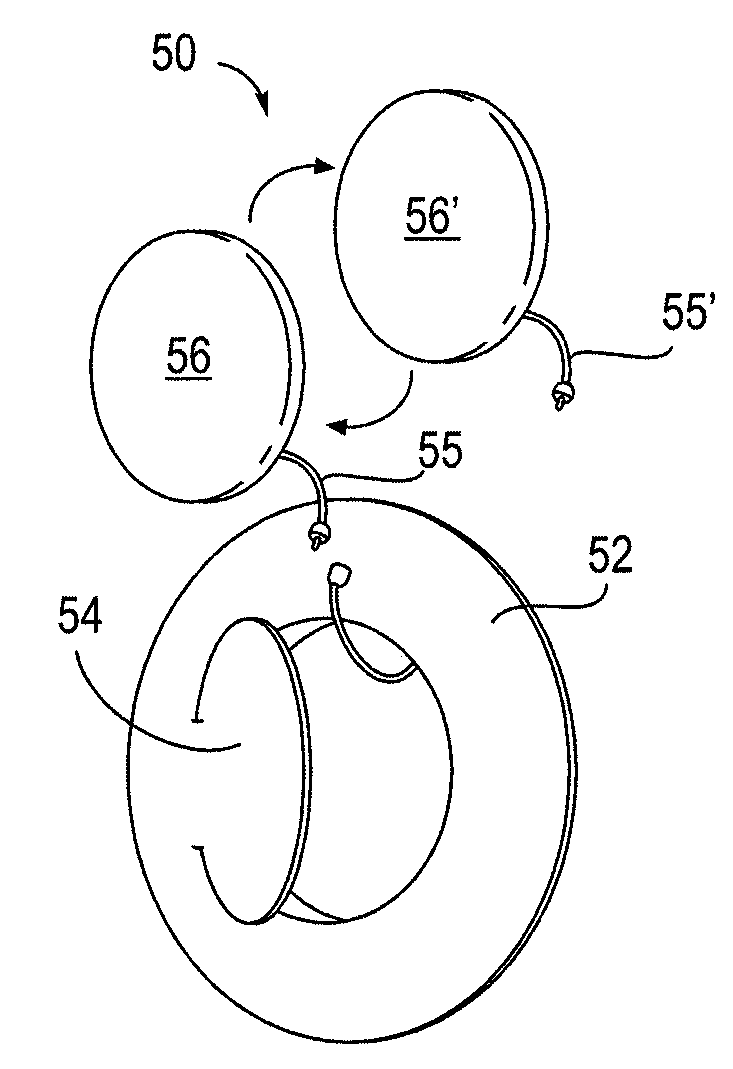
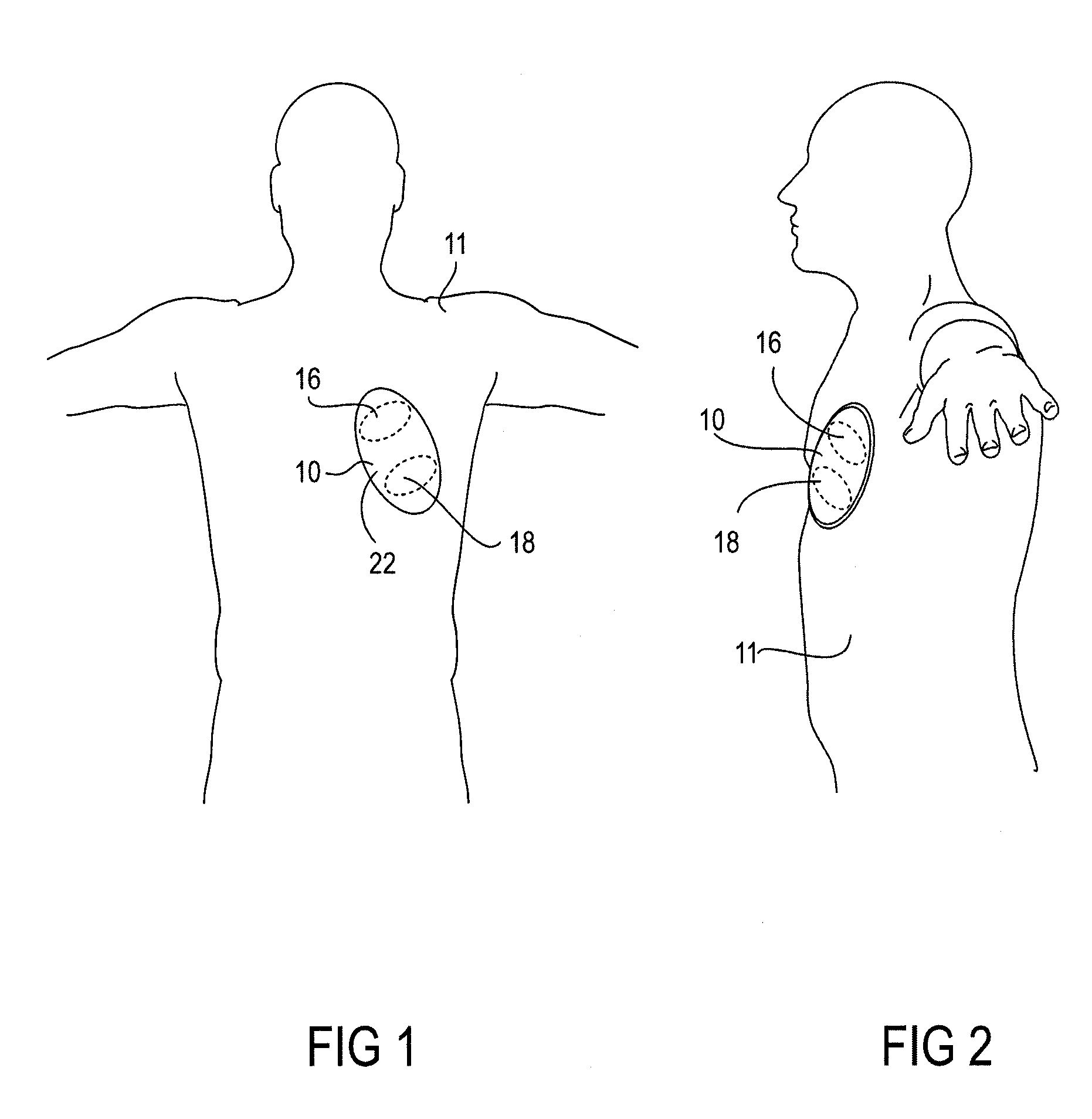
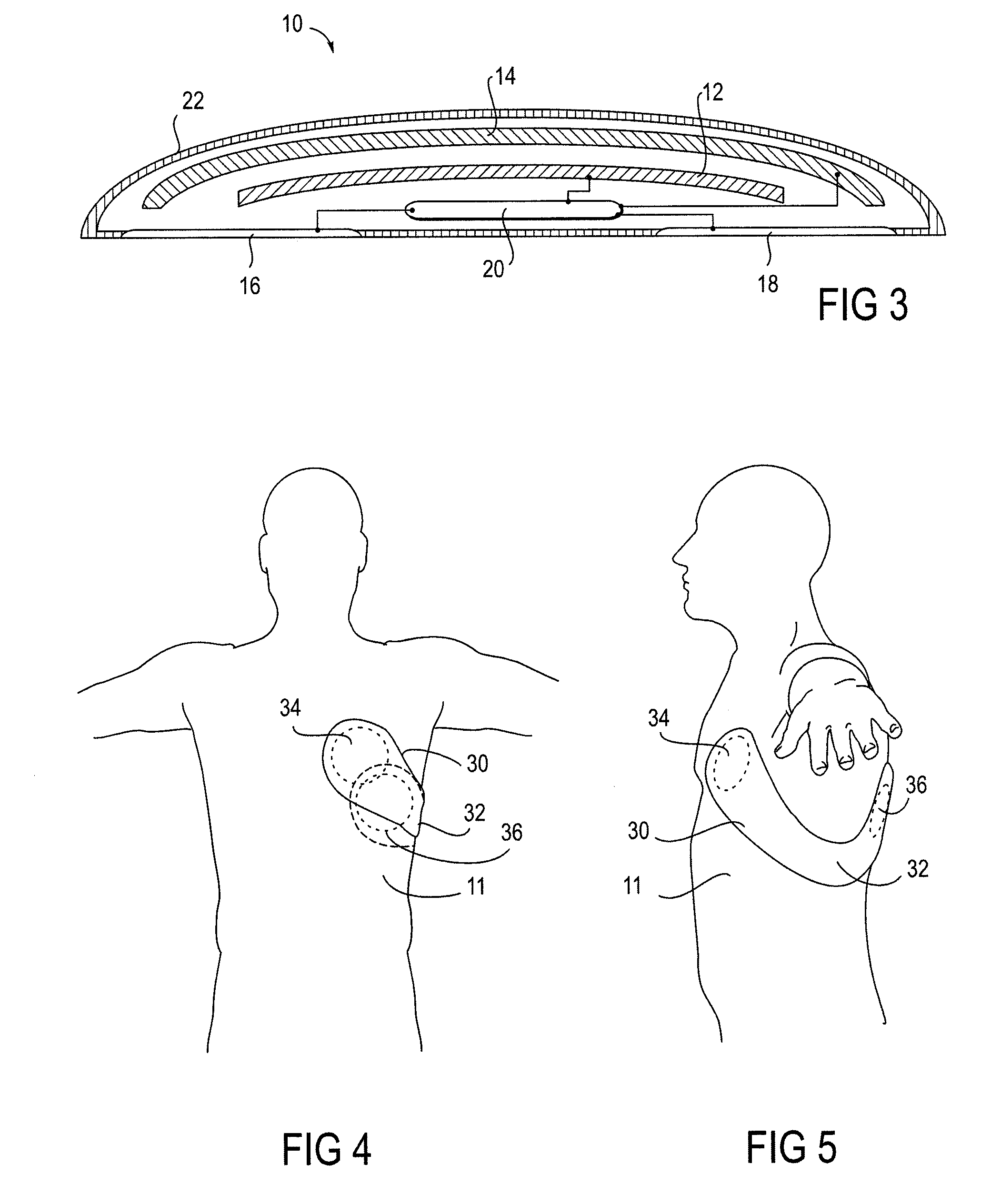
External Defibrillator
ActiveUS20080033495A1Minimal maintenancePrevent implantationHeart defibrillatorsElectricityElectrical battery
An external defibrillator having a battery; a capacitor electrically communicable with the battery; at least two electrodes electrically communicable with the capacitor and with the skin of a patient; a controller configured to charge the capacitor from the battery and to discharge the capacitor through the electrodes; and a support supporting the battery, capacitor, electrodes and controller in a deployment configuration, the defibrillator having a maximum weight per unit area in the deployment configuration of 0.1 lb / in2 and / or a maximum thickness of 1 inch. The support may be a waterproof housing.
Owner:ELEMENT SCI
System for identifying content of digital data
ActiveUS8006314B2ConfidenceAccurate identificationDigital data information retrievalDigital data processing detailsDigital dataData science
A system for identifying a work represented by digital data. This system detects events in data of the content of an unknown work and measures a metric between the events. The system then compares the detected events and metrics from an unknown work with the events and metrics of a known work. If the events and metrics match, the unknown work is identified as a copy of the known work.
Owner:AUDIBLE MAGIC
System for authentication between devices using group certificates
InactiveUS20050257260A1Efficient distribution and storageEfficient identificationError preventionEncryption apparatus with shift registers/memoriesAuthentication systemDevice Identifiers
In whilelist-based authentication, a first device (102) in a system (100) authenticates itself to a second device (103) using a group certificate identifying a range of non-revoked device identifiers, said range encompassing the device identifier of the first device (102). Preferably the device identifiers correspond to leaf nodes in a hierarchically ordered tree, and the group certificate identifies a node (202-207) in the tree representing a subtree in which the leaf nodes correspond to said range. The group certificate can also identify a further node (308, 310, 312) in the subtree which represents a sub-subtree in which the leaf nodes correspond to revoked device identifiers. Alternatively, the device identifiers are selected from a sequentially ordered range, and the group certificate identifies a subrange of the sequentially ordered range, said subrange encompassing the whitelisted device identifiers.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
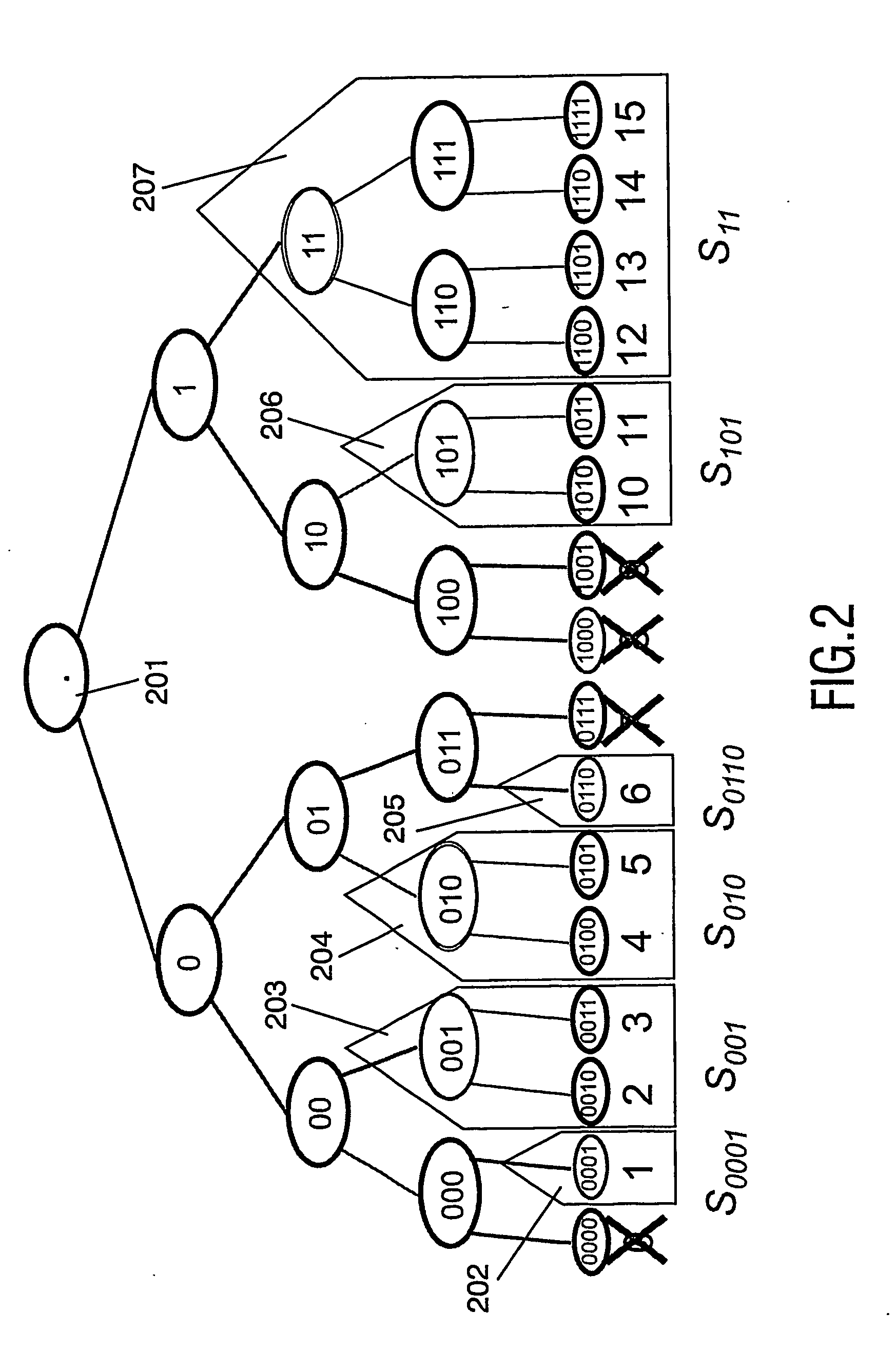
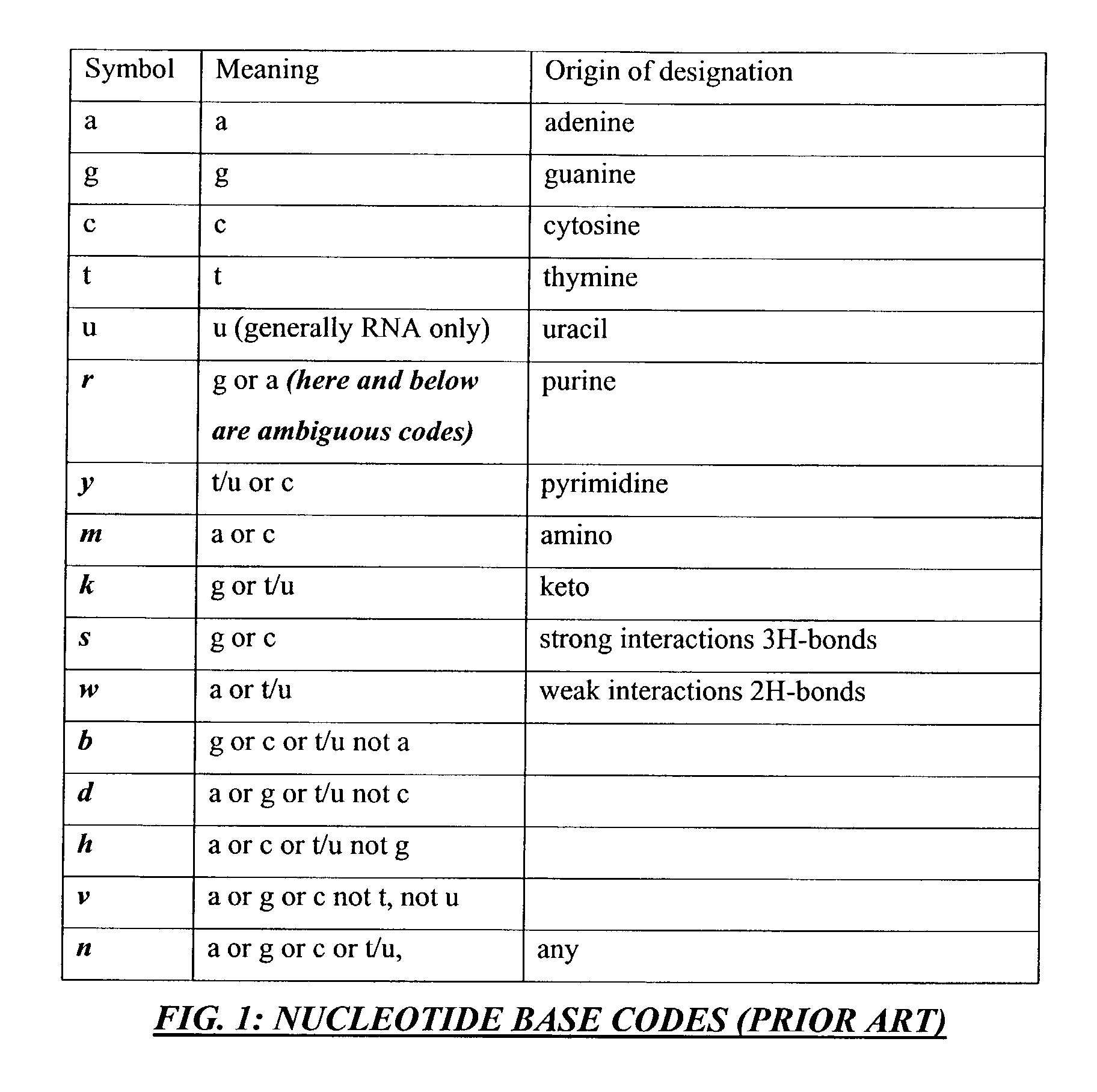
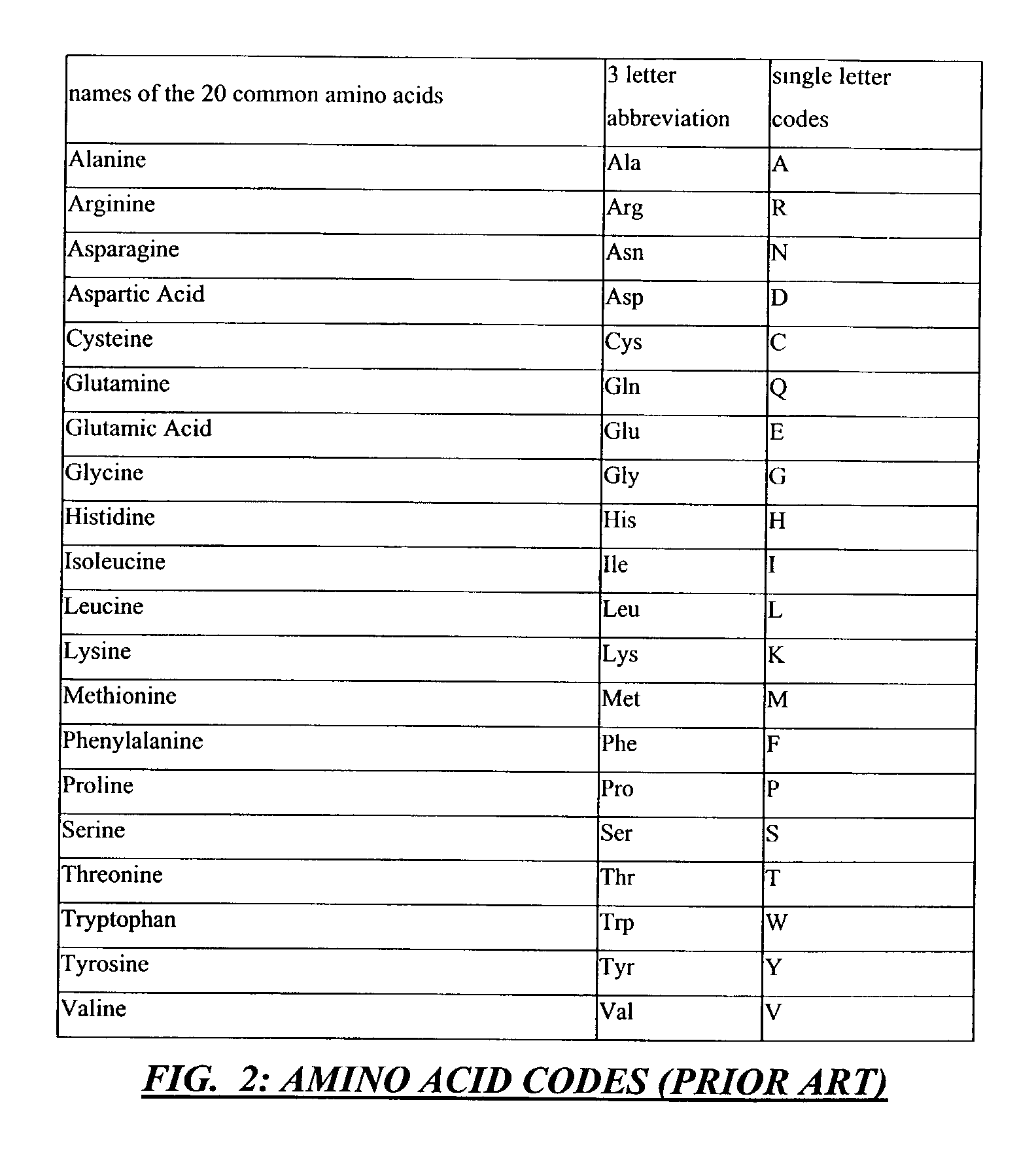
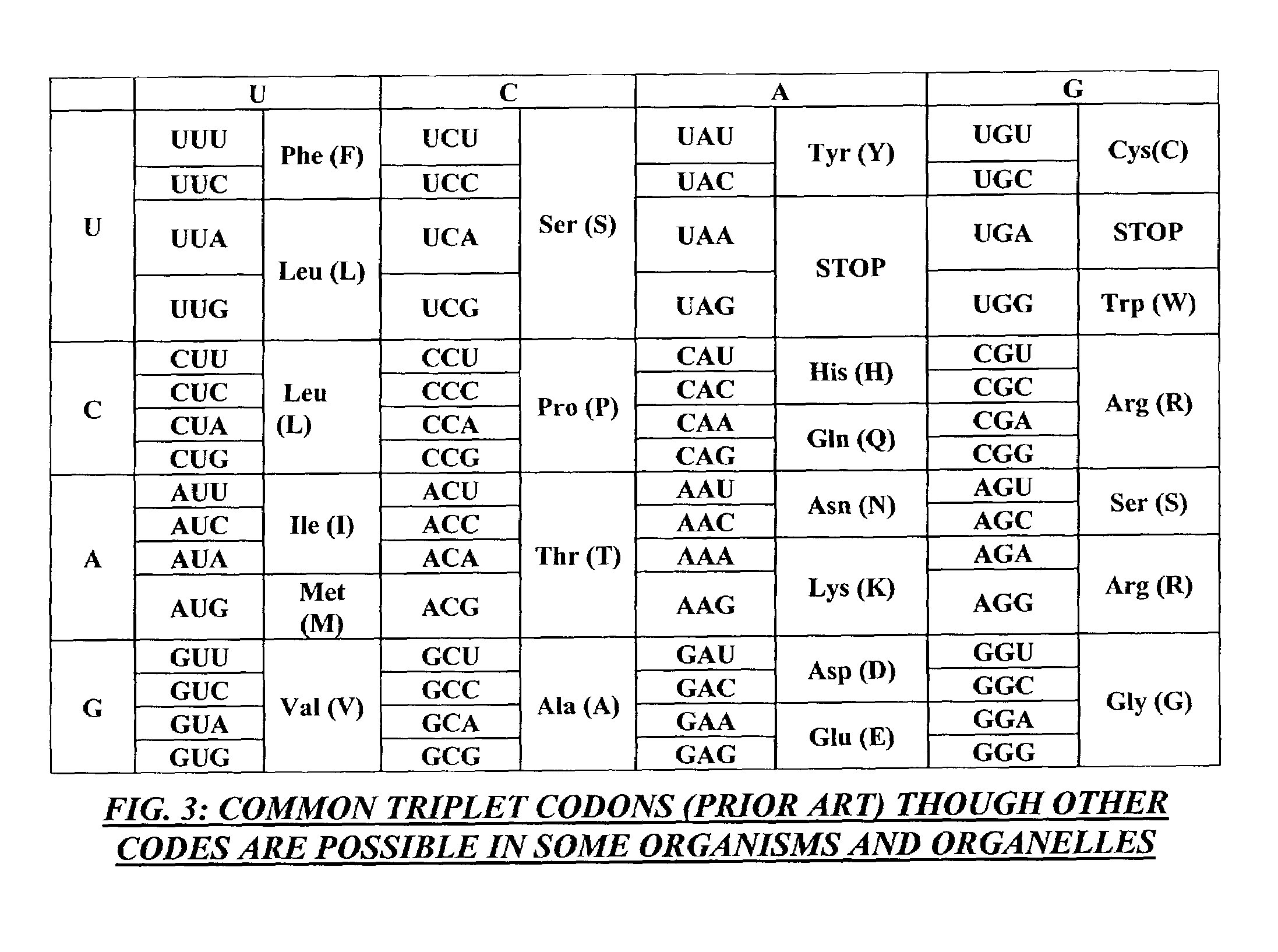
Method and apparatus for codon determining
InactiveUS7702464B1Efficiently determinedEfficient identificationBiological testingSequence analysisClient-sideData needs
Computer processing methods and / or systems for minimizing and / or optimizing data strings in accordance with rules and options. Minimized data strings can represent data sequences important in certain biologic analyses and / or syntheses. In specific embodiments, a request is generated by a user at a client system and received by a server system. The server system accesses initial data indicated or provided by the client system. The server system then performs an analysis to minimize the data needed for further reactions. In specific embodiments, a server can use proprietary methods or data at the server side while protecting those proprietary methods and data from access by the client system.
Owner:CODEXIS MAYFLOWER HLDG LLC
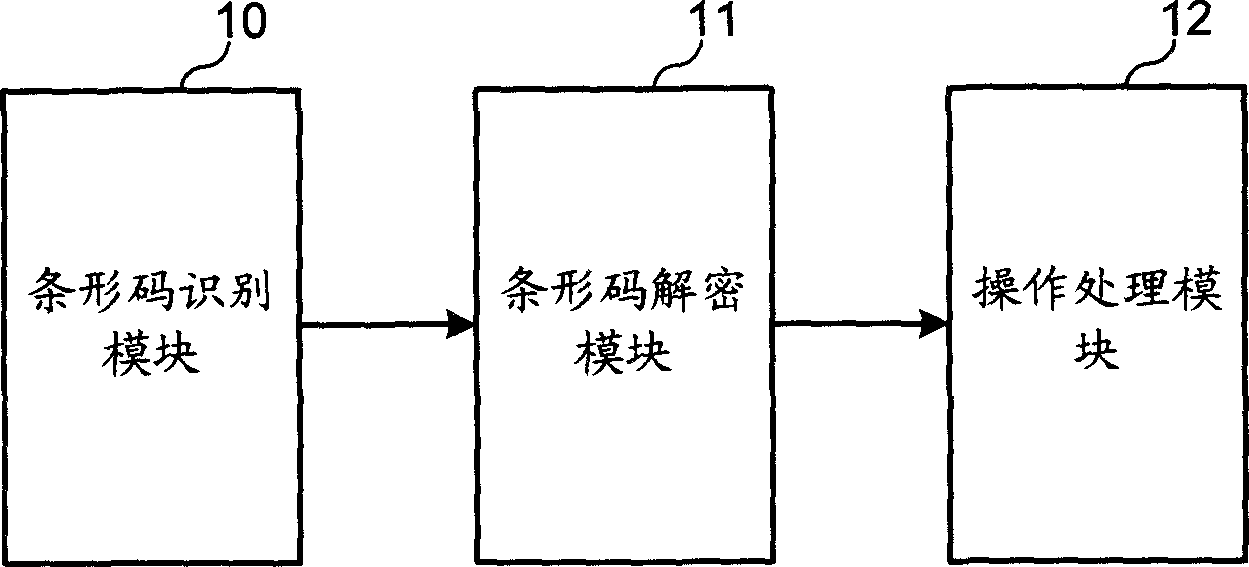
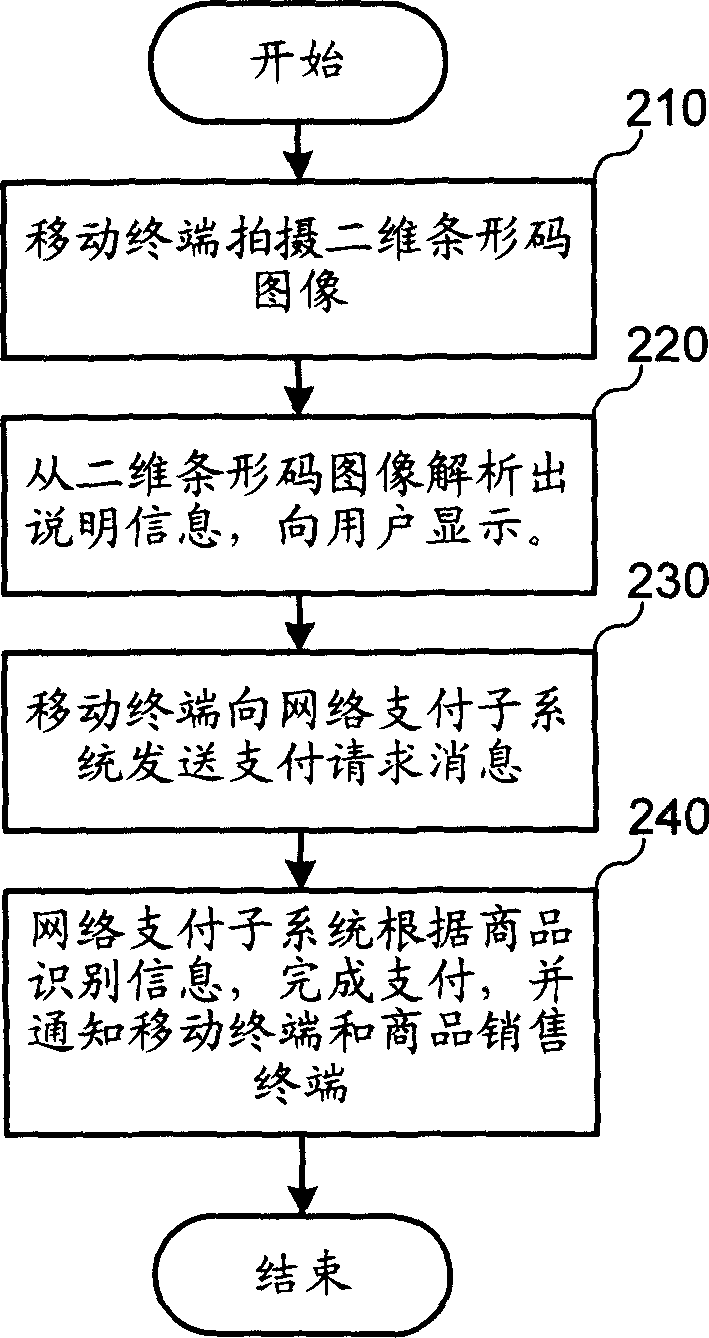
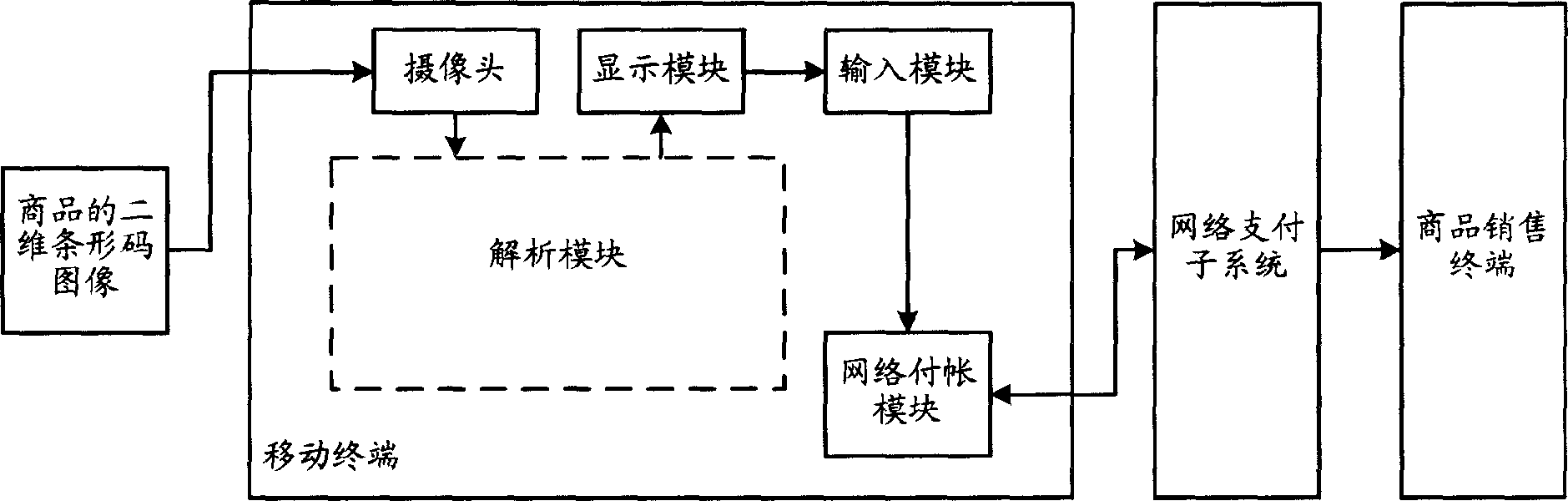
Mobile terminal shopping method and system thereof
InactiveCN1841425AEfficient identificationValid identification priceAcutation objectsPayment architectureBarcodeProduct identification
The related shopping method with mobile terminal comprises: using mobile camera to obtain product 2D bar code image for analysis, then obtaining product identification information and description so as the price, name and size information; and requesting to pay for the determined product; finally, feeding success information to the user and the sale terminal.
Owner:HUAWEI TECH CO LTD
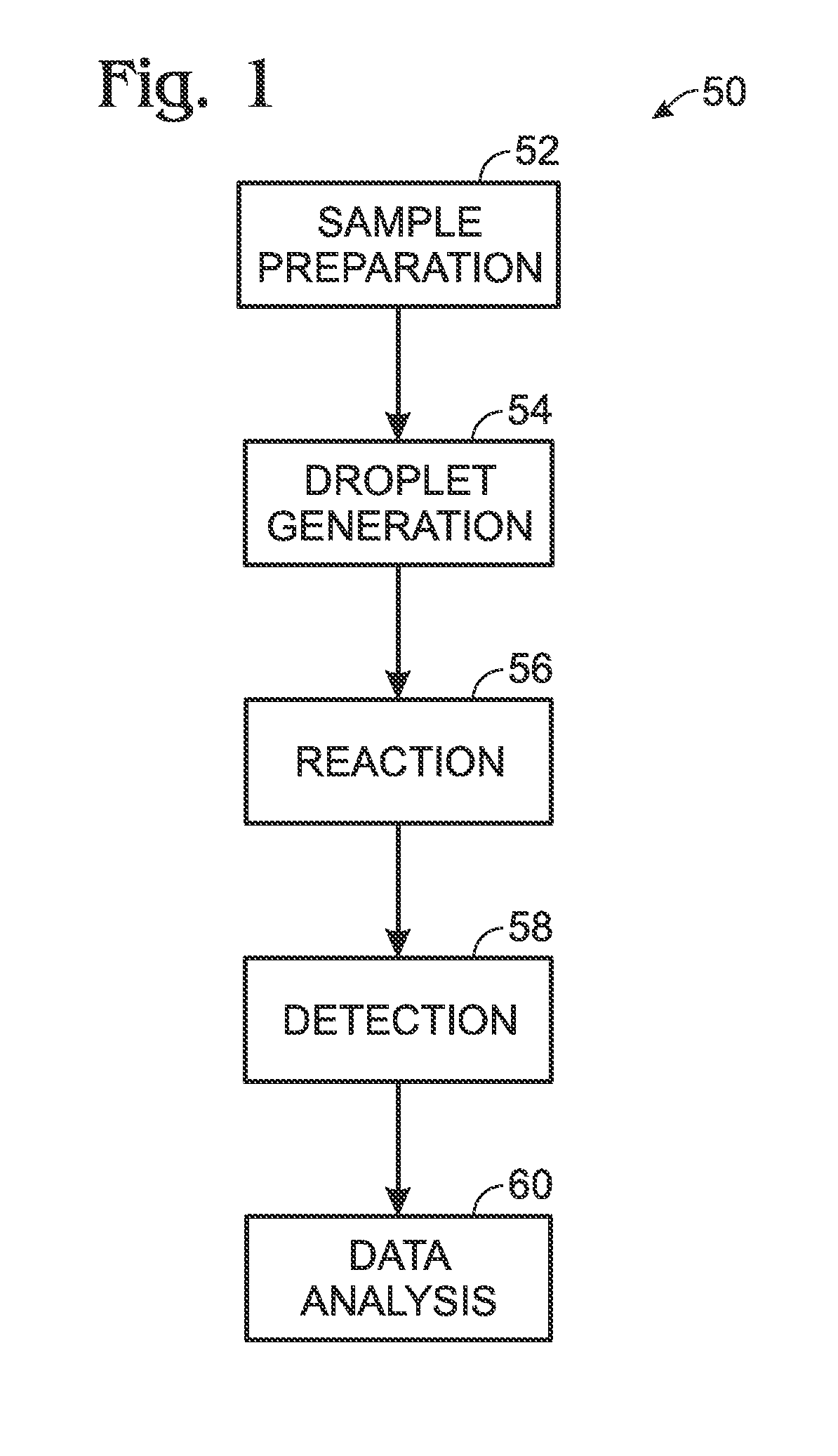
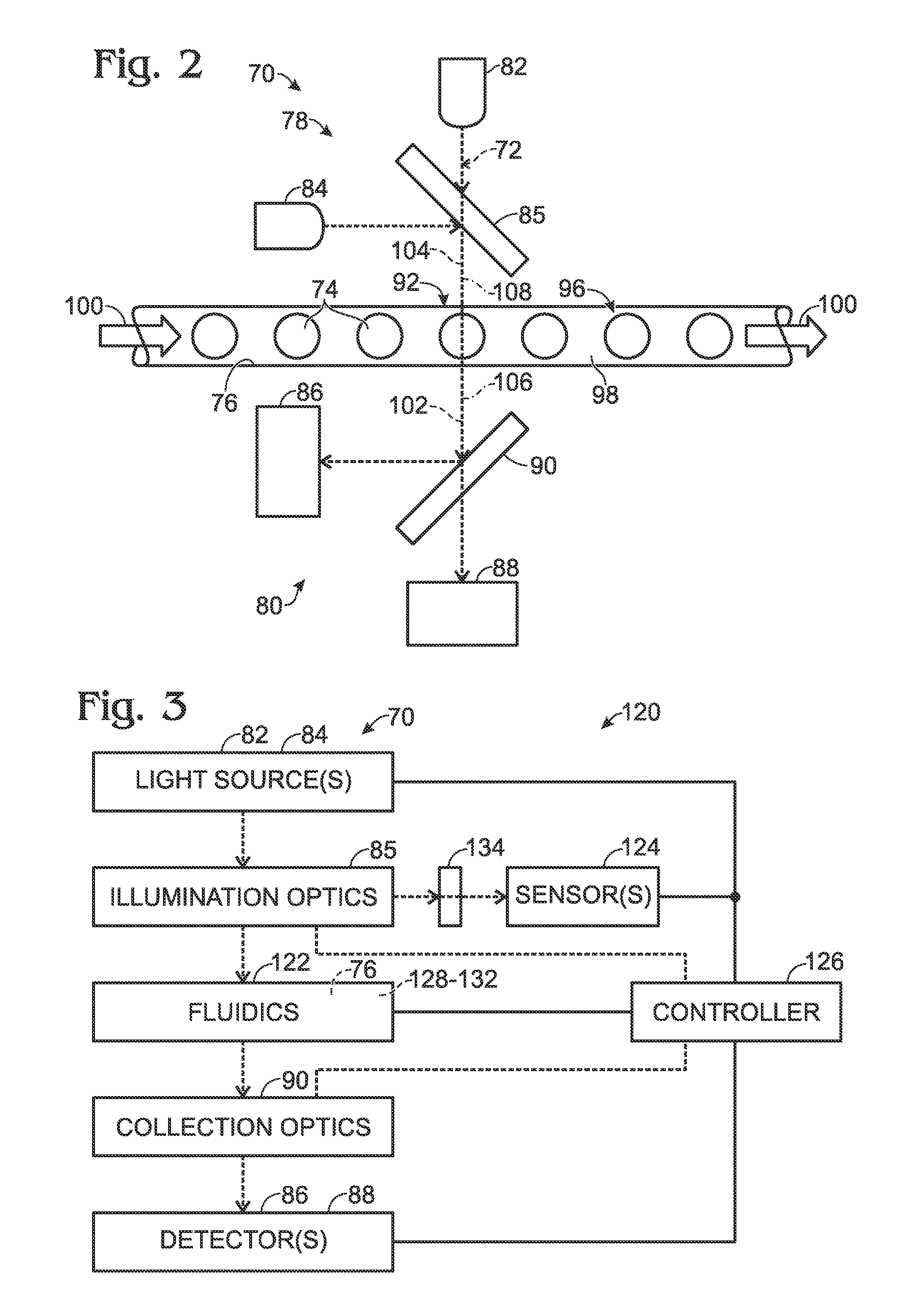
Detection system for droplet-based assays
ActiveUS20120194805A1High-confidence resultLow costPhotometryLaboratory glasswaresAssaySignal processing
System, including methods and apparatus, for light detection and signal processing for droplet-based assays.
Owner:BIO RAD LAB INC
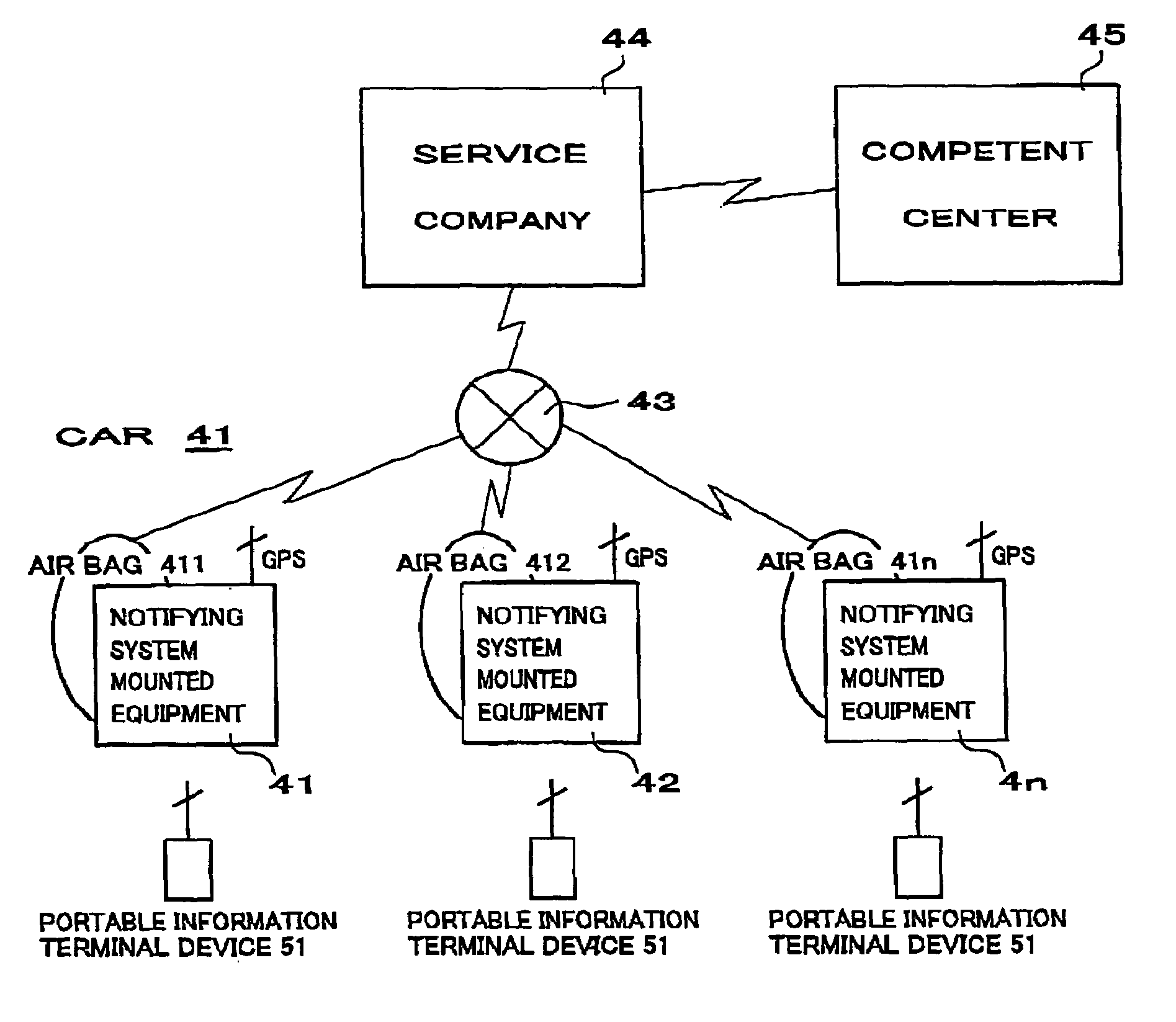
Portable personal authentication apparatus and electronic system to which access is permitted by the same
InactiveUS6931538B1Operation is troublesomeEasy to giveAnti-theft devicesUser identity/authority verificationDriver/operatorElectronic systems
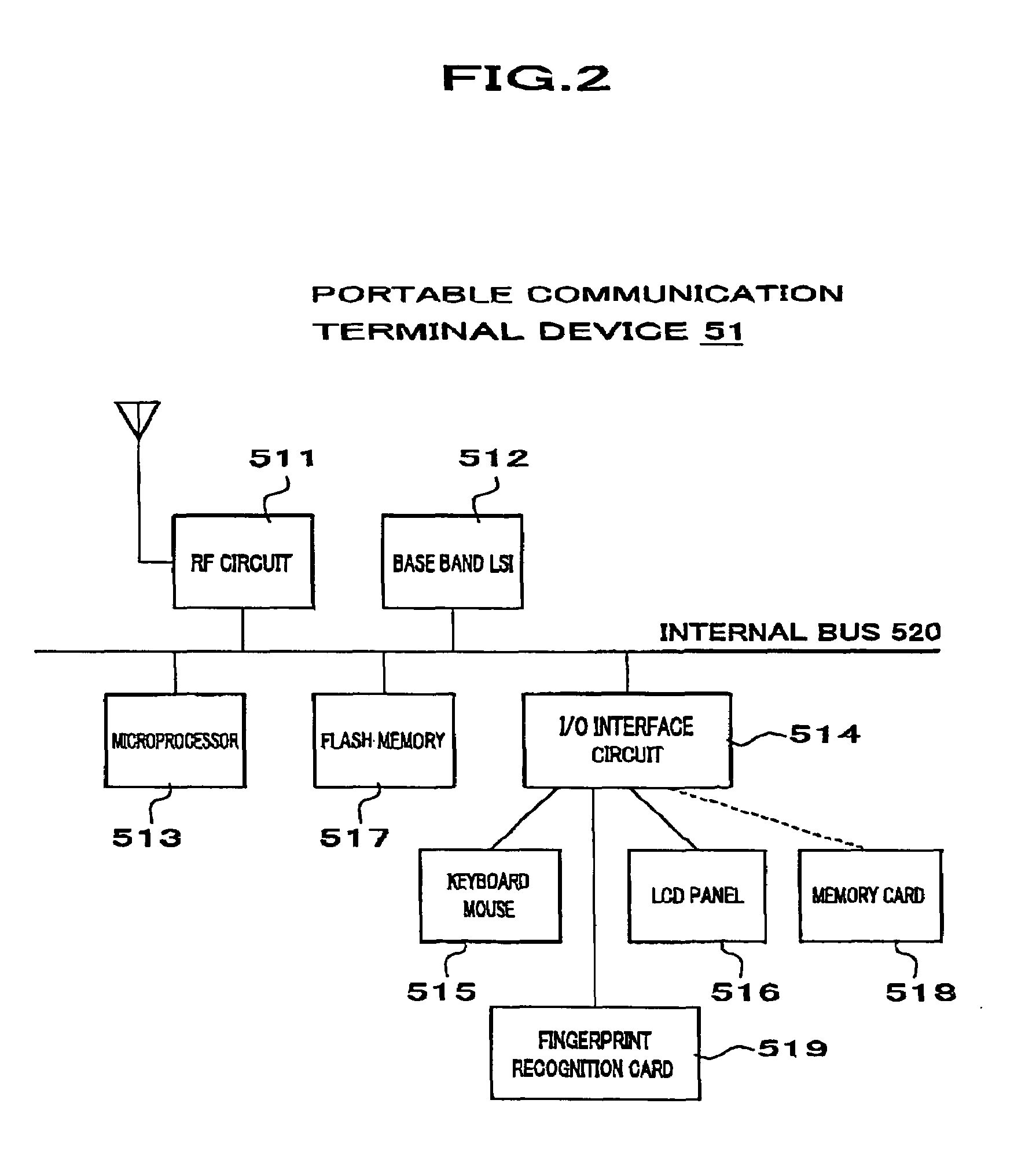
An object of the present invention is to provide a portable personal authentication apparatus which can perform personal authentication, being essential in a future society, anywhere and be used for all purposes and an electronic system to which access is permitted by the apparatus. A mobile device, such as a cellular telephone or a PDA, is used with a portable personal authentication apparatus as a portable communication terminal device 51 and at least one of biological features including a man's fingerprint, voiceprint, and irisprint is used as a medium for authenticating a person as, for example, the user himself / herself. That is to say, biometric authentication is performed. In addition, functions like an electronic purse a conventional IC card etc. had are included in the portable communication terminal device (portable personal authentication apparatus) and the portable communication terminal device is connected to ATM equipment etc. This enables the portable communication terminal device to be managed unitarily as an electronic purse. Furthermore, a portable communication terminal device (portable personal authentication apparatus) is used for authenticating a person as, for example, the driver himself / herself in the case of canceling urgent notification in a notifying system. This will increase the reliability of notification.
Owner:ZEROSOFT +2
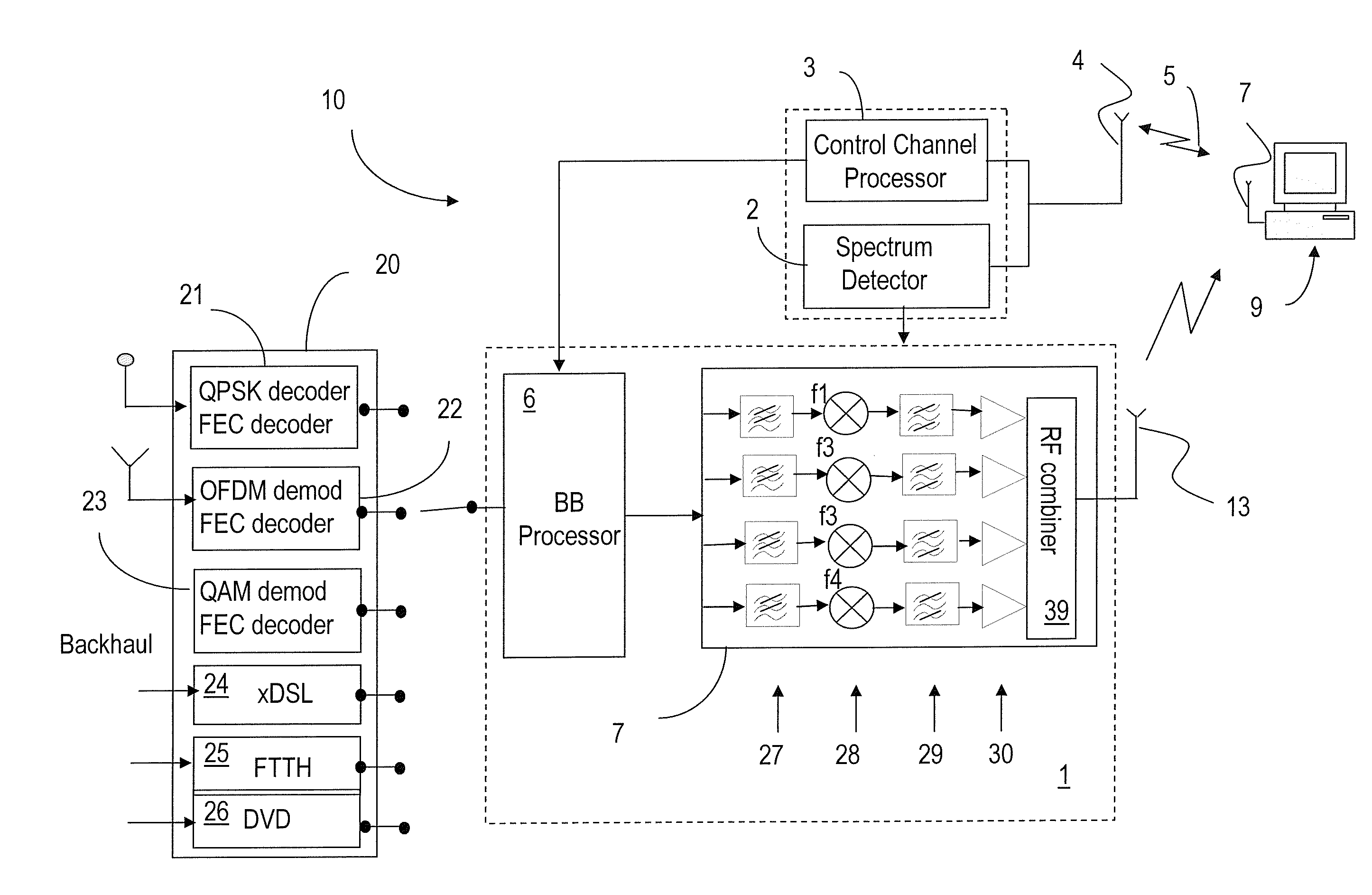
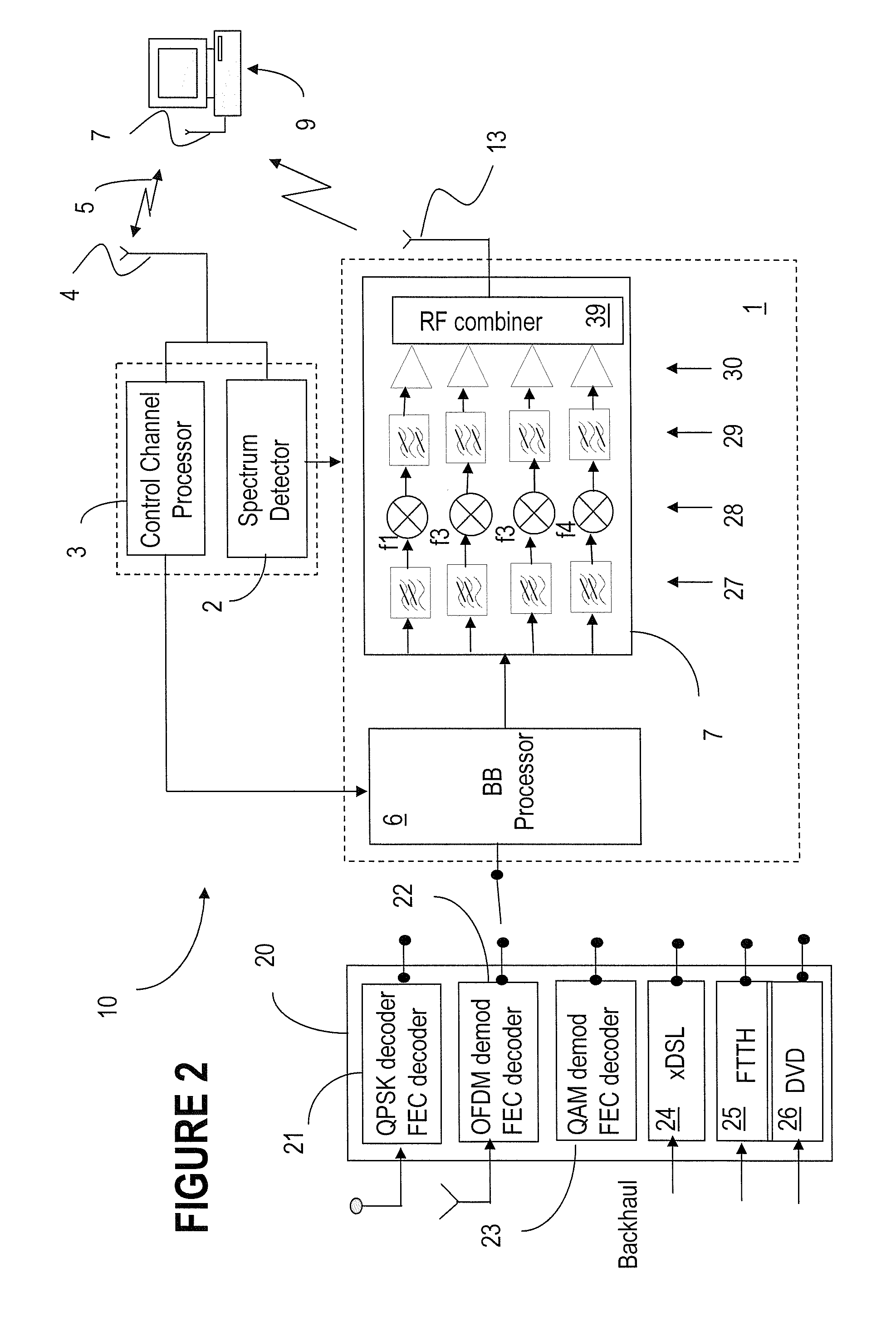
Apparatus and method for generating preamble signal for cell identification in an orthogonal frequency division multiplexing system
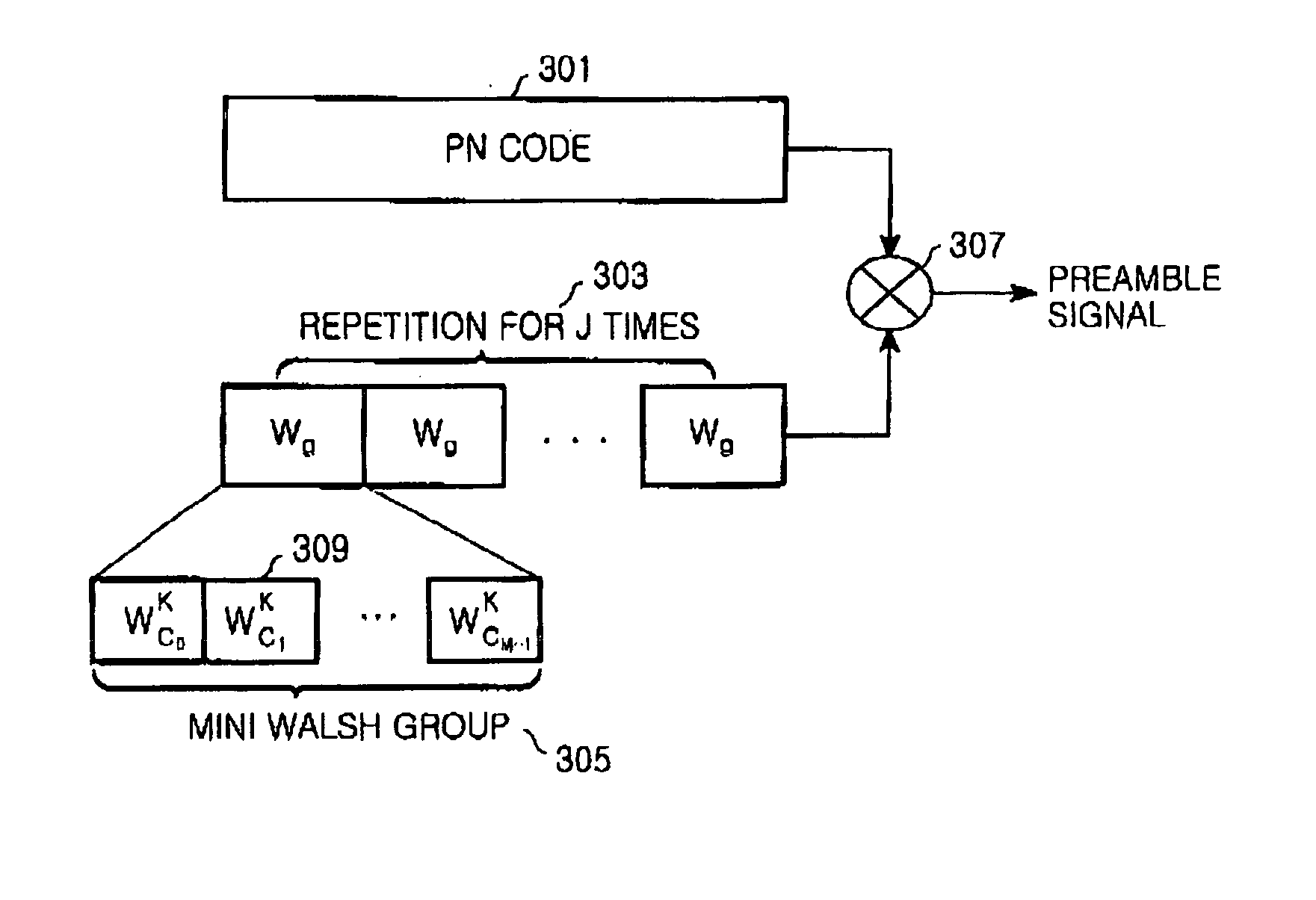
ActiveUS20050111522A1Effectively identifyEfficient identificationFrequency-division multiplexCode division multiplexPreambleOrthogonal frequency code division multiplexing
Disclosed are an apparatus and a method for generating a preamble signal for cell identification in an OFDM mobile communication system. The method includes the steps of generating a Walsh code symbol for a cell identification by combining Walsh codewords having a predetermined length and generating the preamble signal through multiplying the Walsh code symbol by a pseudo noise (PN) code having a length identical to a length of the Walsh code symbol.
Owner:SAMSUNG ELECTRONICS CO LTD
Vision-based highway overhead structure detection system
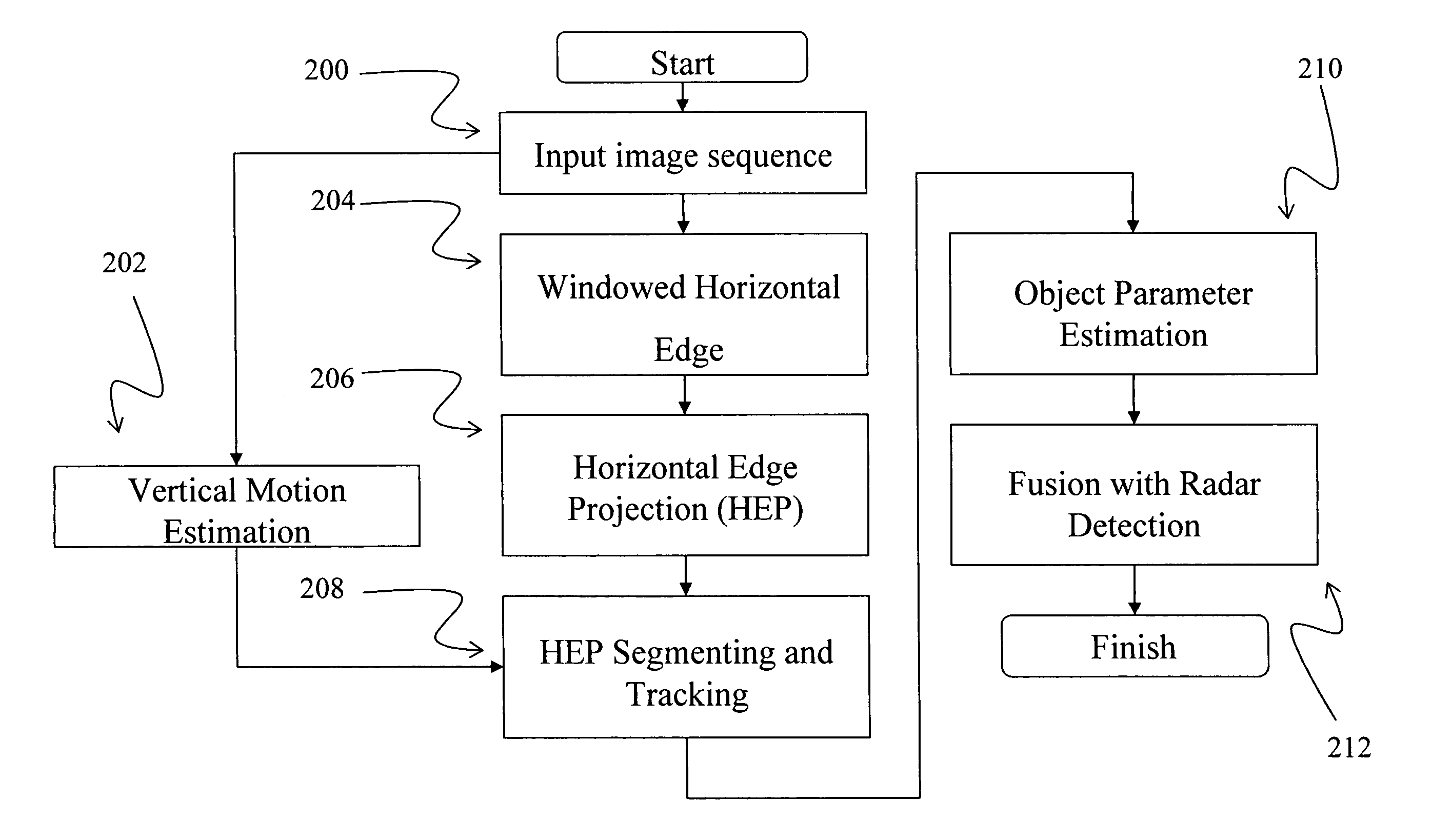
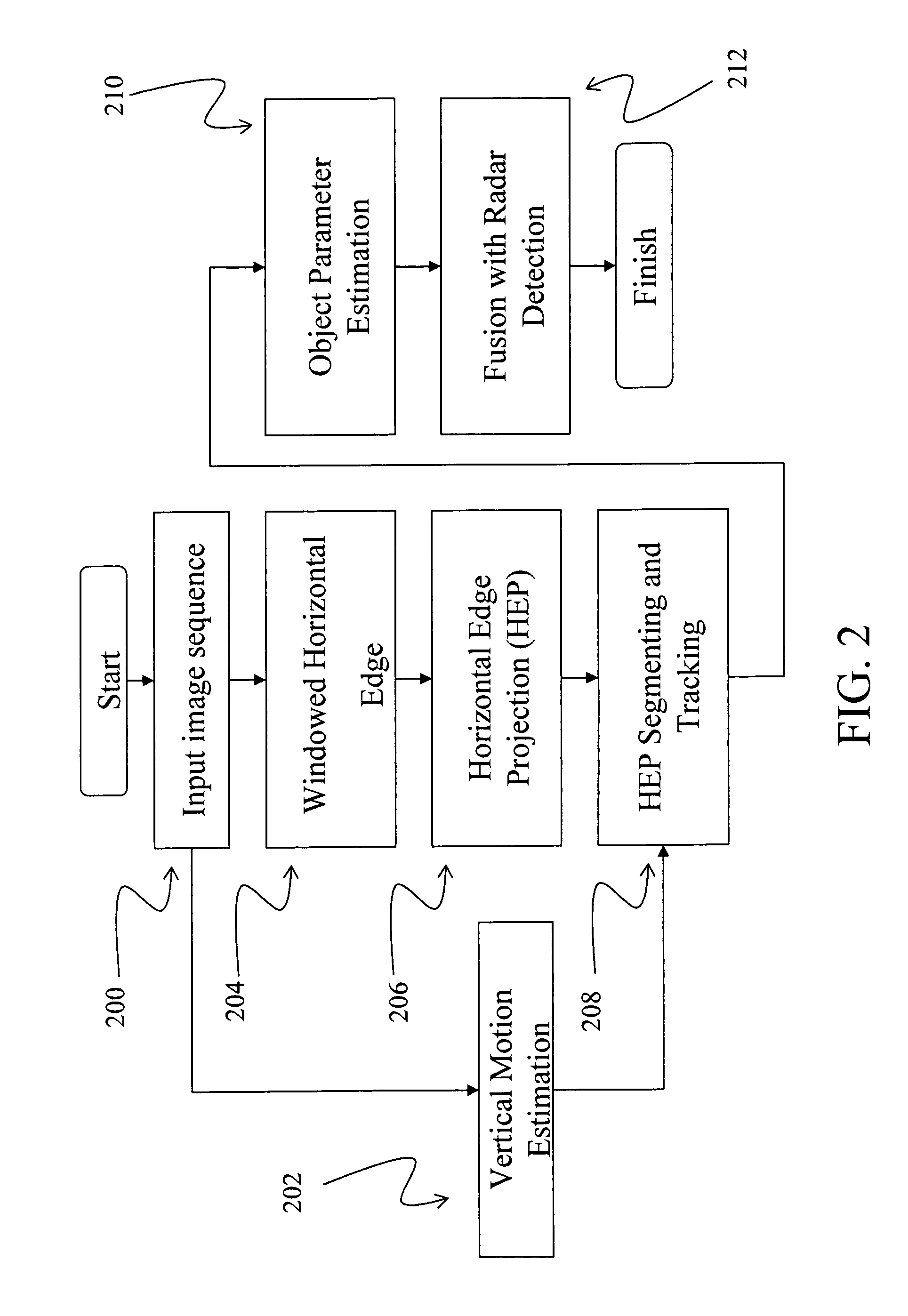
InactiveUS7327855B1EffectivelyMinimizes and eliminates numberDetection of traffic movementAnti-collision systemsVision basedRadar detection
An image sequence is inputted from a camera and vertical motion is estimated. A windowed horizontal edge-projection is extracted from the inputted image sequence and corresponding horizontal edges are projected. The horizontal edge-projection and the vertical motion estimation are combined in a horizontal segmentation and tracking element, and are forwarded to an object parameter estimation element, where the object's distance and height are estimated. This data is combined in a fusion with a radar detection element. By correctly matching the overhead objects sensed by the radar detection element and the video camera, the proximity and relative speed can be ascertained. Once overhead objects have been identified they can be isolated and not considered for collision avoidance purposes.
Owner:HRL LAB
Device and method for identifying and evaluating emergency hot topic
InactiveCN102937960AReduce complexityImprove operational efficiencySpecial data processing applicationsComputation complexityUnexpected events
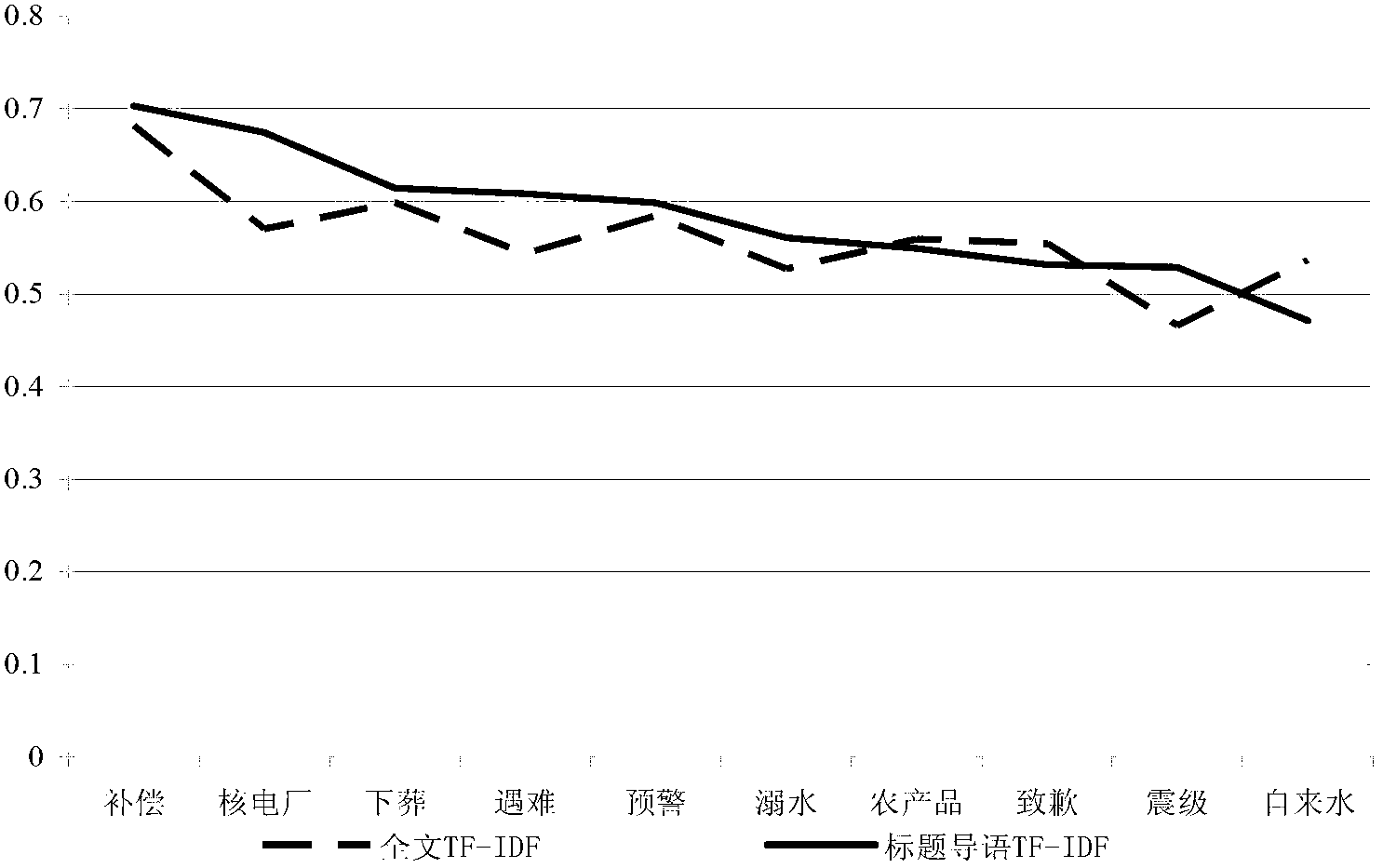
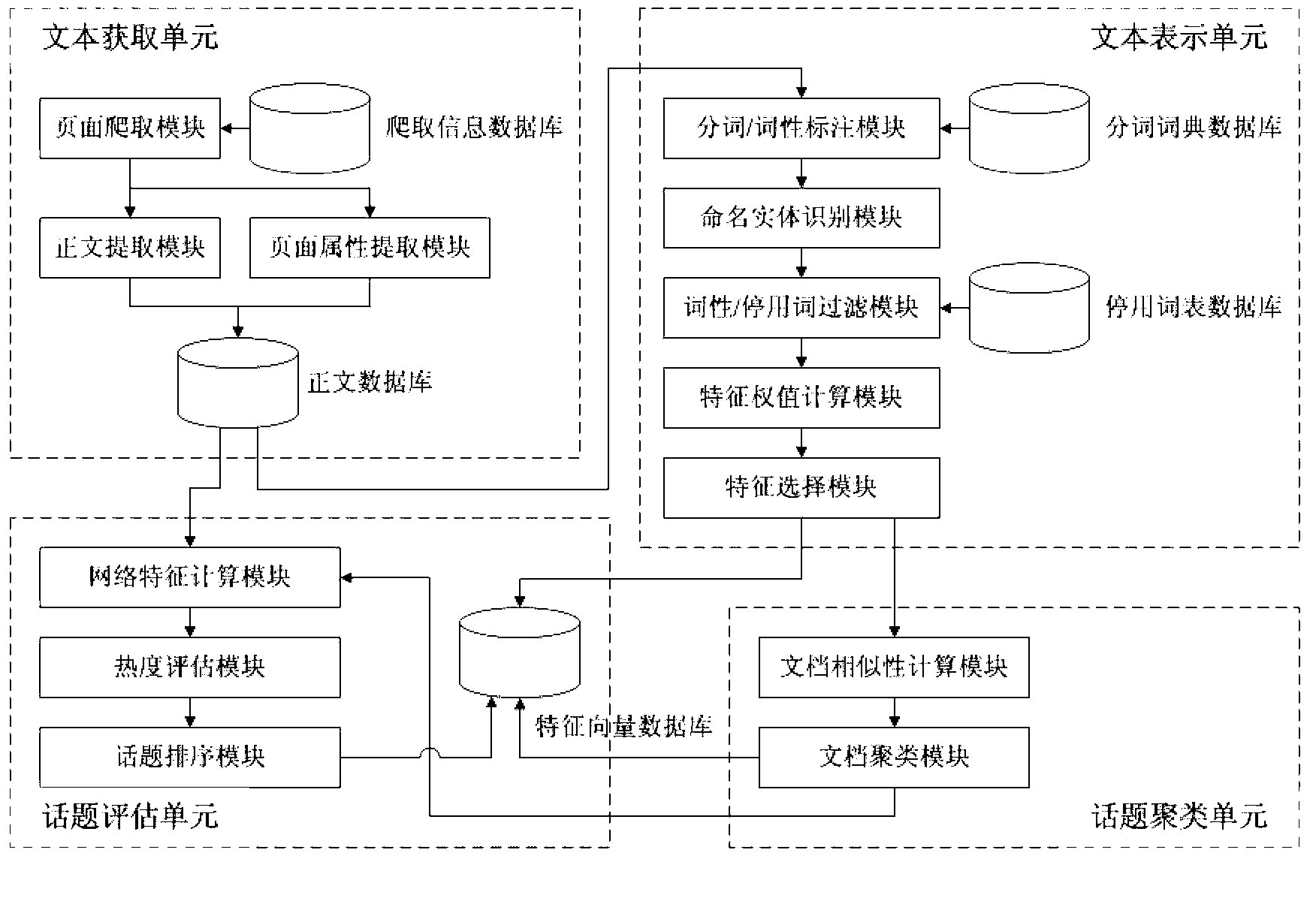
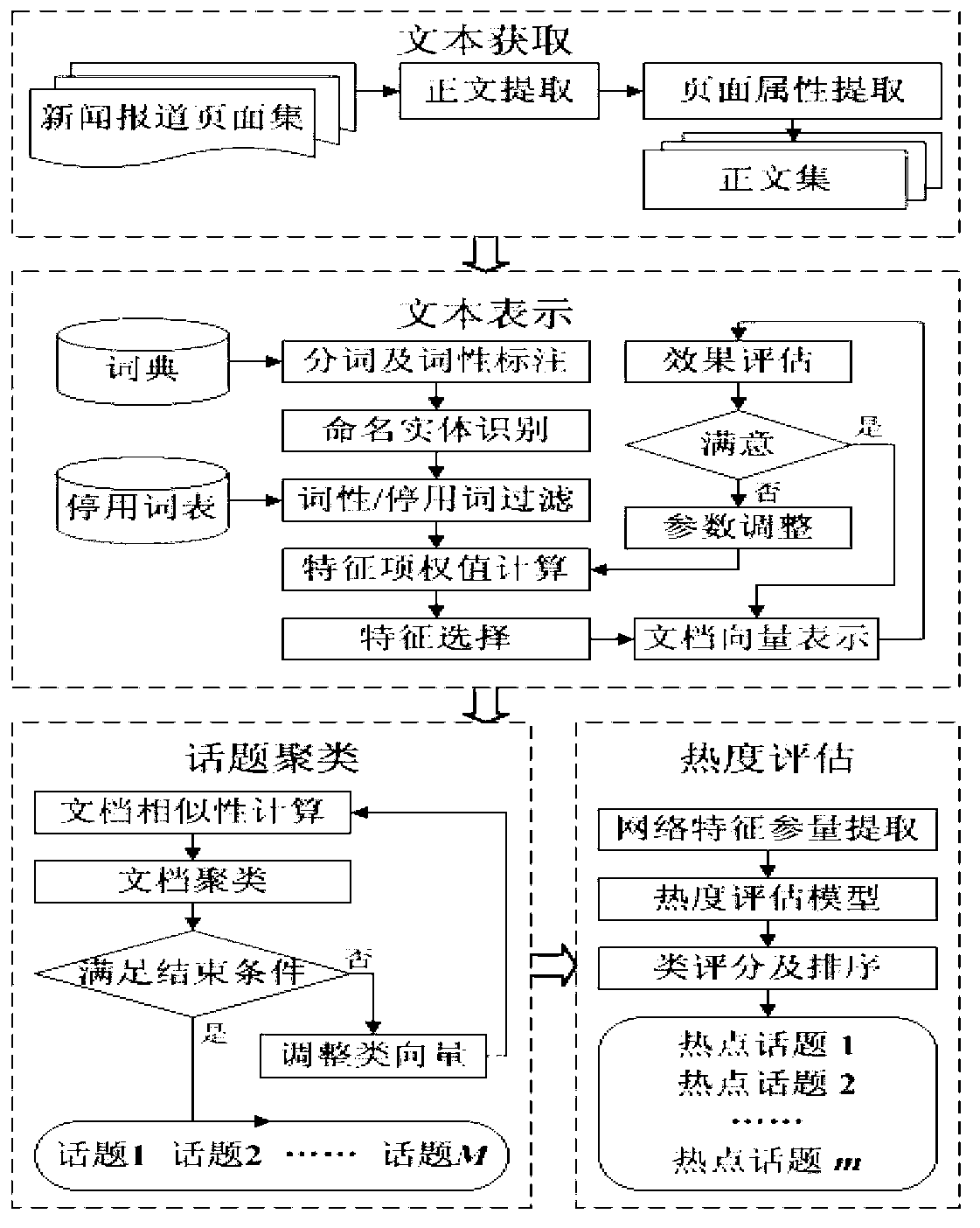
The invention relates to a device and a method for identifying and evaluating an emergency hot topic. The device is provided with four component parts including a text acquisition unit, a text expression unit, a topic clustering unit and a topic evaluation unit. The device and the method are characterized in that only a title, introduction, relevant features and other information of a text of a news report are extracted and regarded as an effective sample set identified by the hot topic. Compared with the existing full text extraction, the experiment result shows that the result of the existing full text extraction is similar to the result of the partial text extraction, but the operation of the device and the method is greatly simplified. Compared with a classical model, an improved feature weight calculation model is good in execution efficiency and strong in adaptability of text representation capability. The model is used for evaluating the hot value of clustered topics, and the calculated hot topic accords with the expected effect and is adaptive to the features of the emergency news report. In a word, in the process of processing the text of the emergency news report, the device and the method have good performance in aspects of calculation complexity, result accuracy and timeliness.
Owner:BEIJING UNIV OF POSTS & TELECOMM
System and methods for efficiently managing incremental data backup revisions
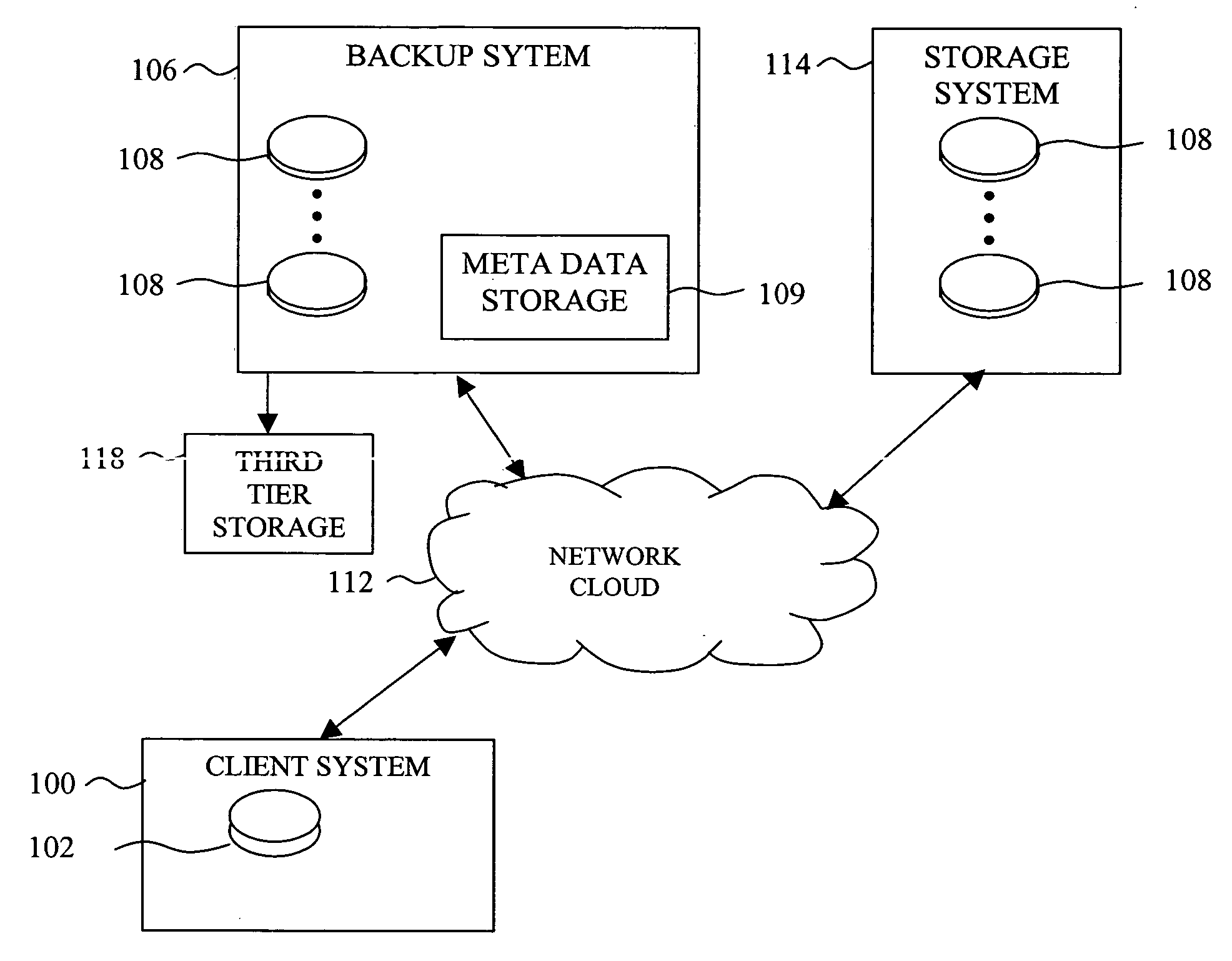
InactiveUS20050246398A1Reduce loadIncreasing backup frequency of backupData processing applicationsError detection/correctionData elementEffective management
A system and methods for building an efficient incremental data backup system capable of managing high frequency backups sessions, and capable of efficiently expiring backup revisions and locating the useless data elements is disclosed. A reduced set of data elements that have a non-zero probability of becoming redundant when a backup revision expires is prepared while each backup revision is being processed by the backup system. The backup system also maintains data structures, which reduce the number of searches that should be performed for each such data element before it can be realized that the data element is exclusively needed to support the expired backup revision, and therefore could be removed from the second tier storage.
Owner:DATAMILLS
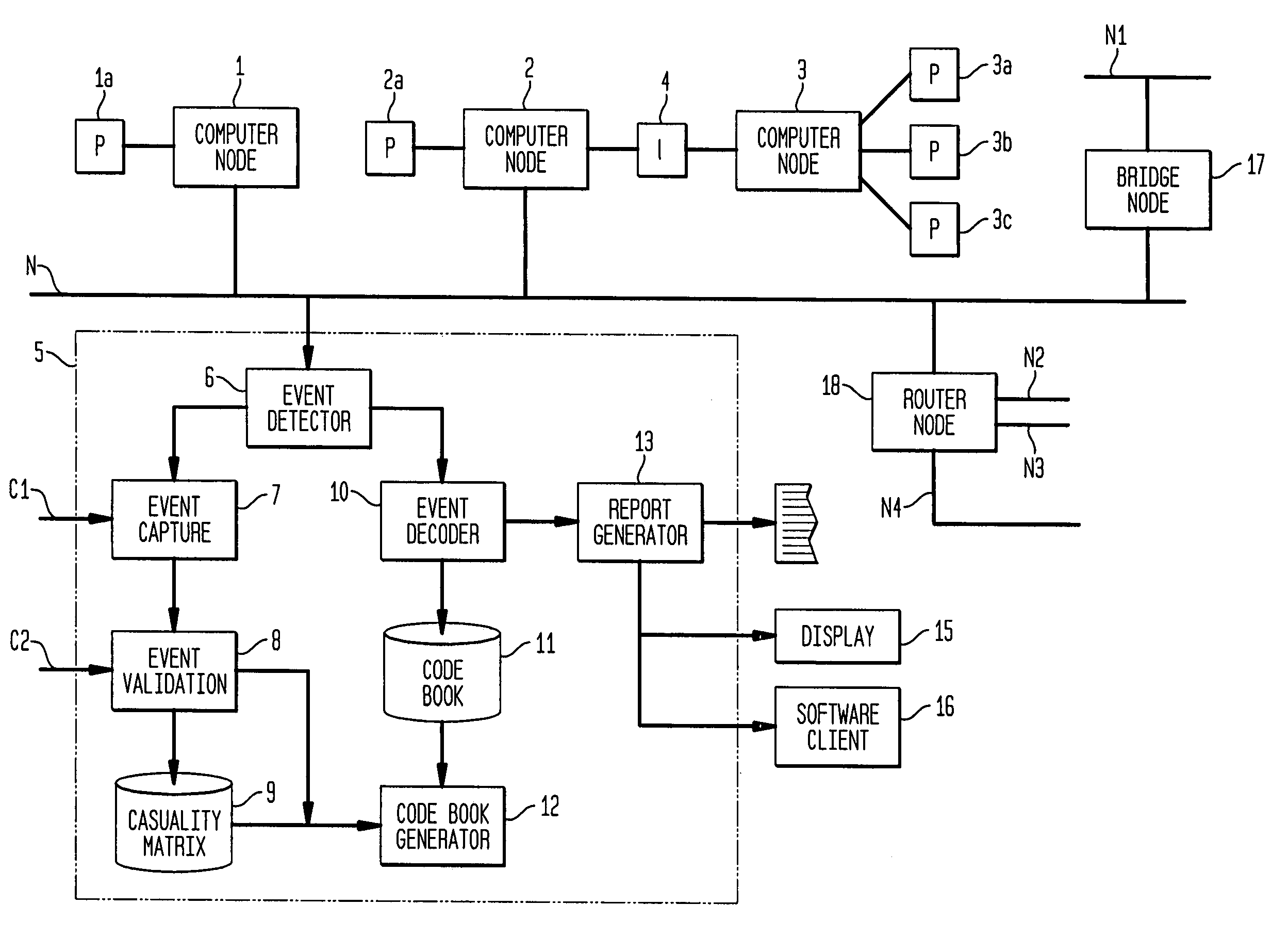
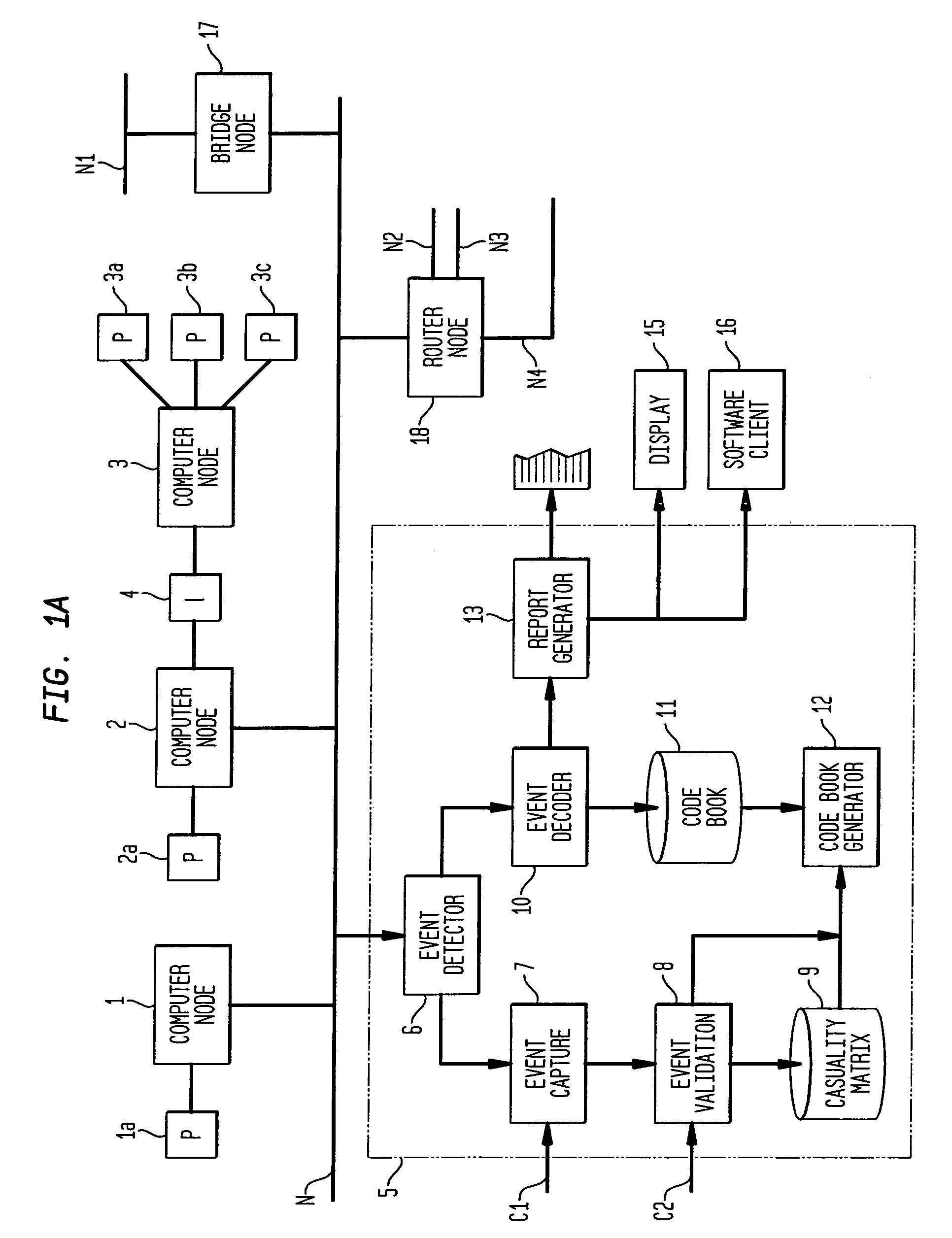
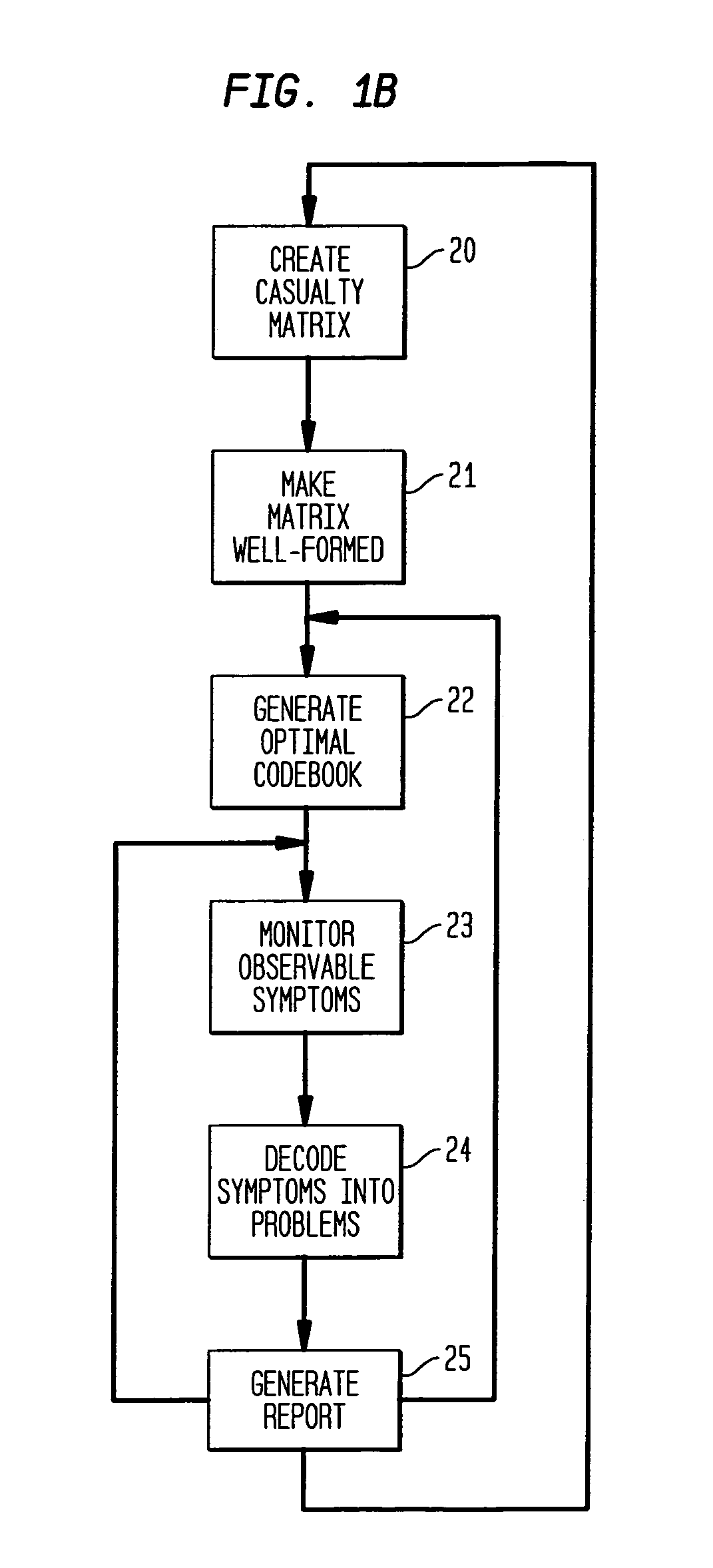
Apparatus and method for event correlation and problem reporting
InactiveUS7107185B1Effective monitoringImprove efficiencyNuclear monitoringDigital computer detailsComplex systemComputer science
A computer implemented method on a computer readable media is provided for determining the source of a problem in a complex system of managed components based upon symptoms. The problem source identification process is split into different activities. Explicit configuration non-specific representations of types of managed components, their problems, symptoms and the relations along which the problems or symptoms propagate are created that can be manipulated by executable computer code. A data structure is produced for determining the source of a problem by combining one or more of the representations based on information of specific instances of managed components in the system. Computer code is then executed which uses the data structure to determine the source of the problem from one or more symptoms.
Owner:VMWARE INC
Clustering type garbage automatic-identification assembly and automatic classification garbage bin for same
ActiveCN103552788AQuickly distinguish ingredientsEfficient identificationRefuse receptaclesElectricityOptical property
The invention discloses a clustering type garbage automatic-identification assembly and an automatic classification garbage bin for the same, and relates to an automatic garbage identification method, an automatic garbage identifier, an automatic classification and separation device and an automatic classification and separation container. The clustering type garbage automatic-identification assembly is characterized in that a plurality of sound, light, electrical, thermal, magnetic, image, gas, piezoelectric and electrochemical identification sensors are used for identifying the physical properties, chemical properties, form, appearance, temperature, chemical components, electrochemical characteristics, electromagnetic characteristics, optical properties, acoustic characteristics, inner structure, biological characteristics, smell, state variations, flow characteristics, motion characteristics, matter state and identification contents and characters of garbage to acquire the characteristic information of the garbage, and the characteristic information is analogically identified through a control main board (4), and is converted into effective actions to accurately throw the identified garbage into a specified container to realize the automatic classification and separation of the garbage.
Owner:邱泽国
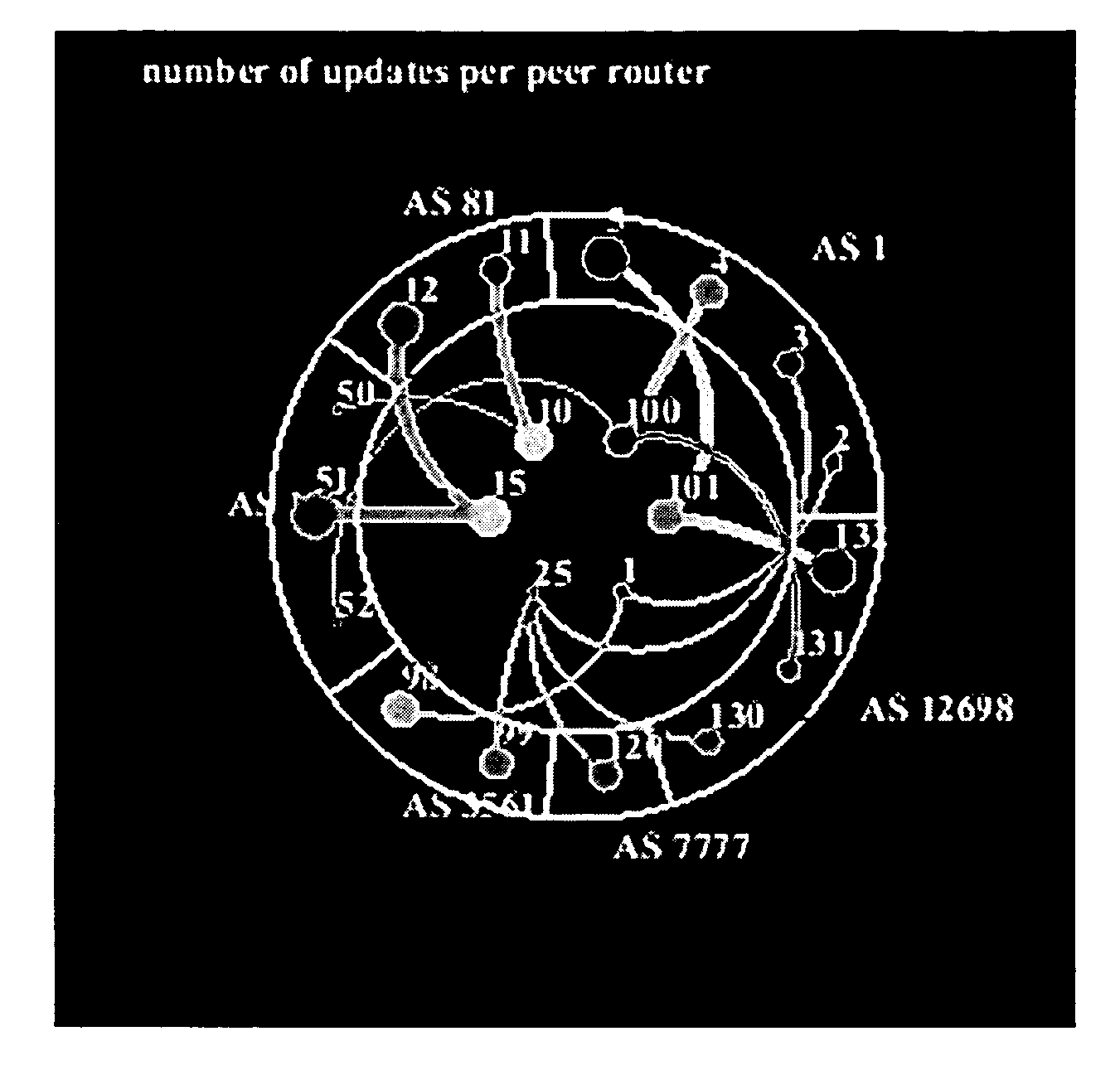
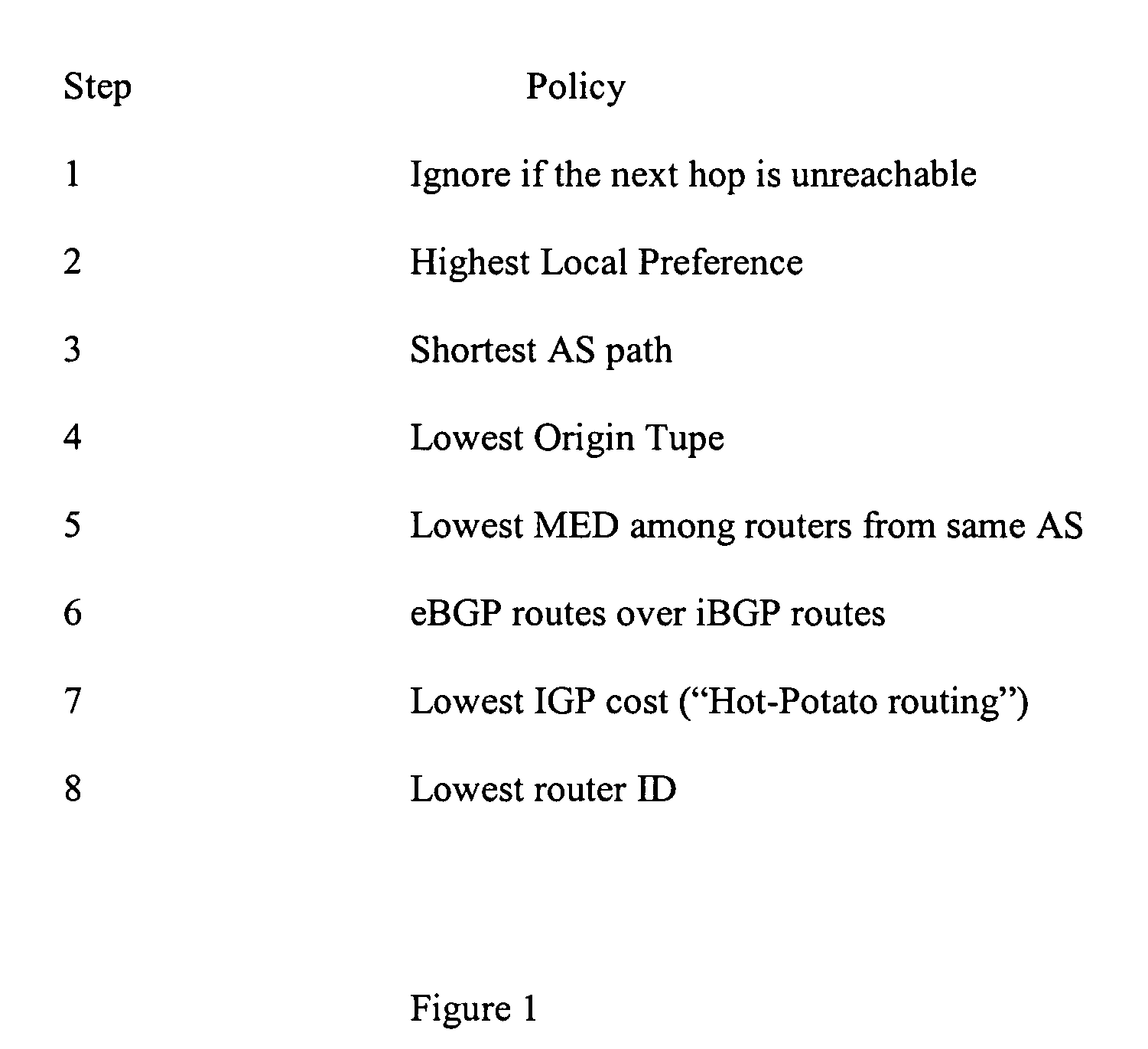
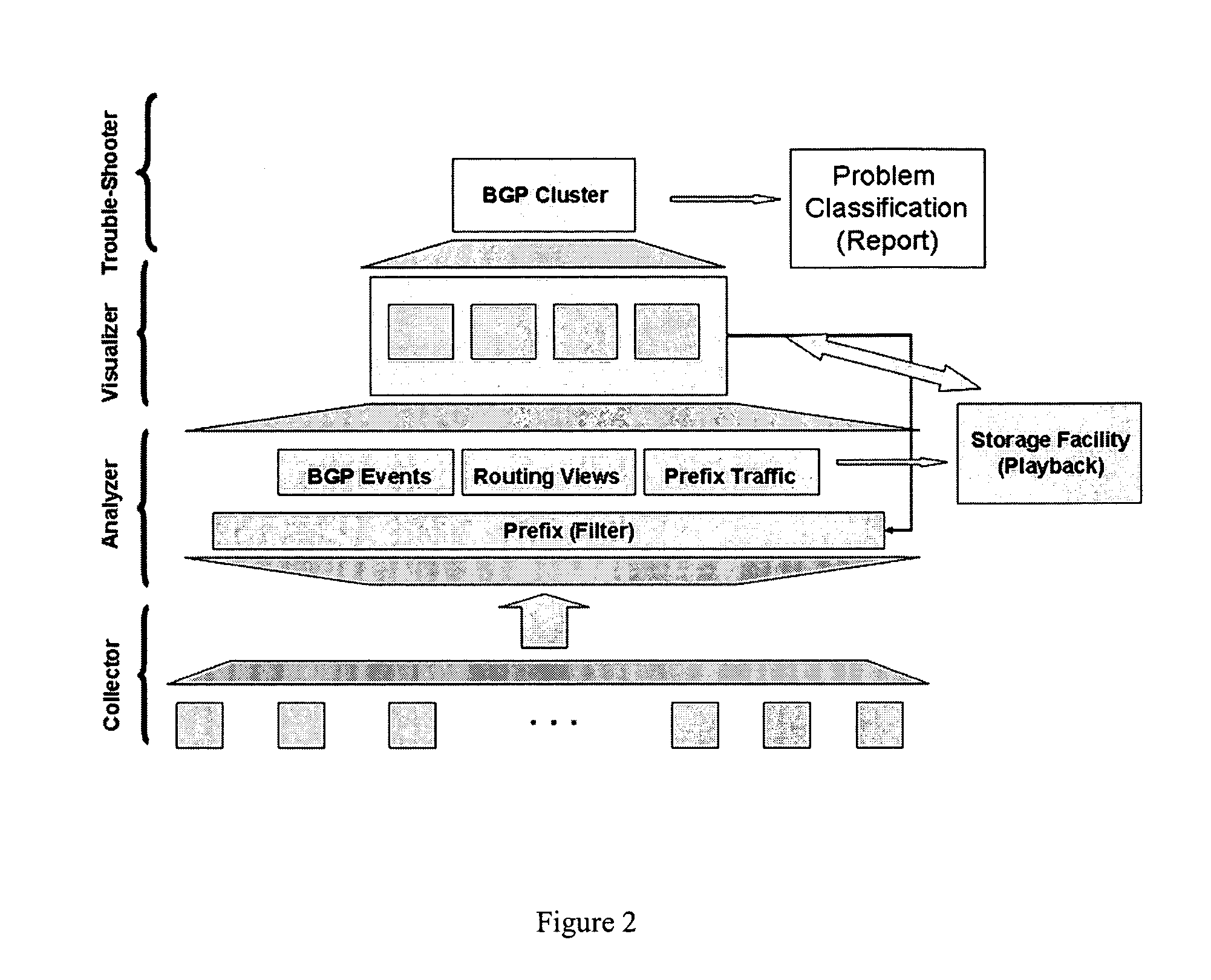
Method for real-time visualization of BGP analysis and trouble-shooting
InactiveUS7945658B1Efficient identificationEfficient reportingError preventionTransmission systemsThe InternetProblem identification
The present invention comprises a multi-tier system. Major goals of the system are to 1) clearly visualize BGP dynamics and alert / report important deviation of BGP dynamics to avoid overwhelming the operators with too much information and 2) analyze the root cause of the problems by using a multi-tier approach, with a light-computational analysis and high-level classification for a real-time problem identification followed by a more rigorous off-line analysis for a further and more detailed trouble shooting. An example embodiment is provided that comprises four modules. The first module comprises a distributed family of collectors in charge of collecting real-time network information. The second module filters out non-relevant prefixes and extracts and profiles key features of the network information. The third module monitors BGP activity from both an Internet-AS and single-AS perspectives by displaying the data in real time and highlighting major shifts or divergence from historical baselines with comprehensive layouts. The forth module is run off-line to focus on a few relevant events that are selected through the first three modules. This is usually a time-consuming phase of the process due to the different temporal and / or spatial correlation that must be run across several sets of data. During this phase, the system can spend more time to better identify the real cause of the problem.
Owner:THE BOEING CO
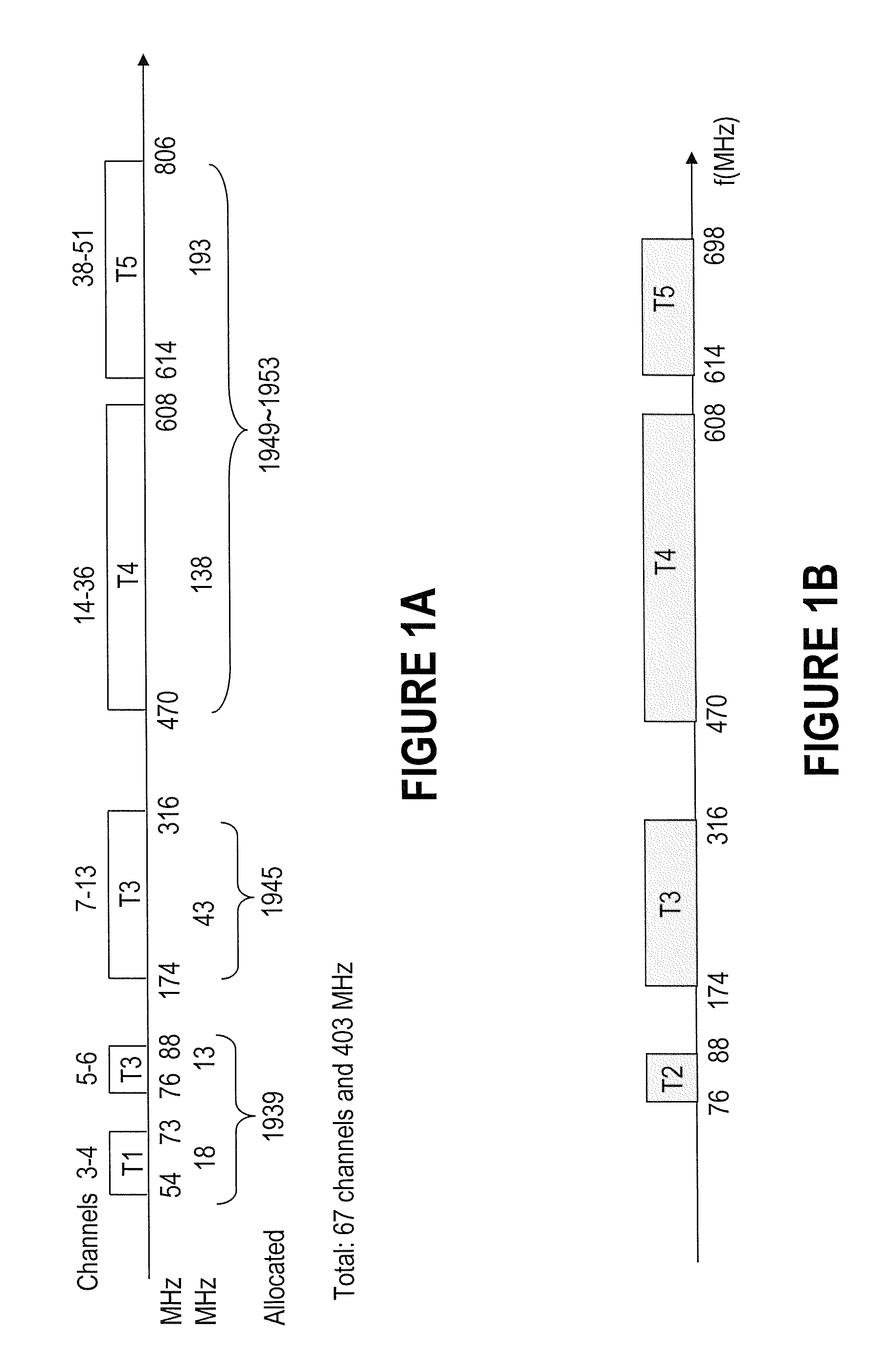
Systems and etiquette for home gateways using white space
InactiveUS8107391B2Effective wayWithout degrading qualityError preventionFrequency-division multiplex detailsFrequency spectrumService sharing
Owner:TAIWAN SEMICON MFG CO LTD
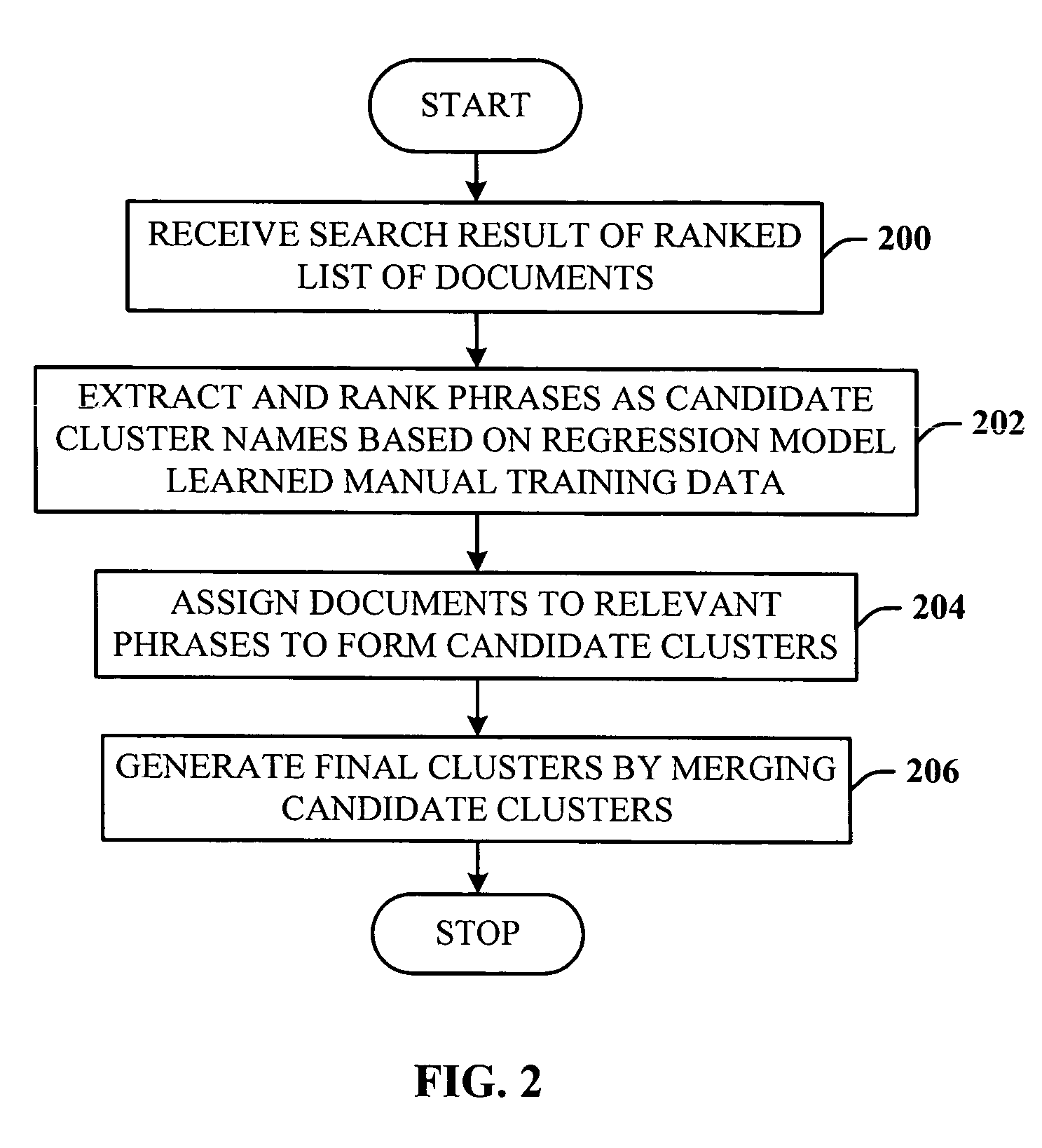
Query-based snippet clustering for search result grouping
InactiveUS7617176B2Quick resultsEfficient identificationData processing applicationsWeb data indexingFeature vectorCo-occurrence
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for detecting vulnerable atherosclerotic plaque
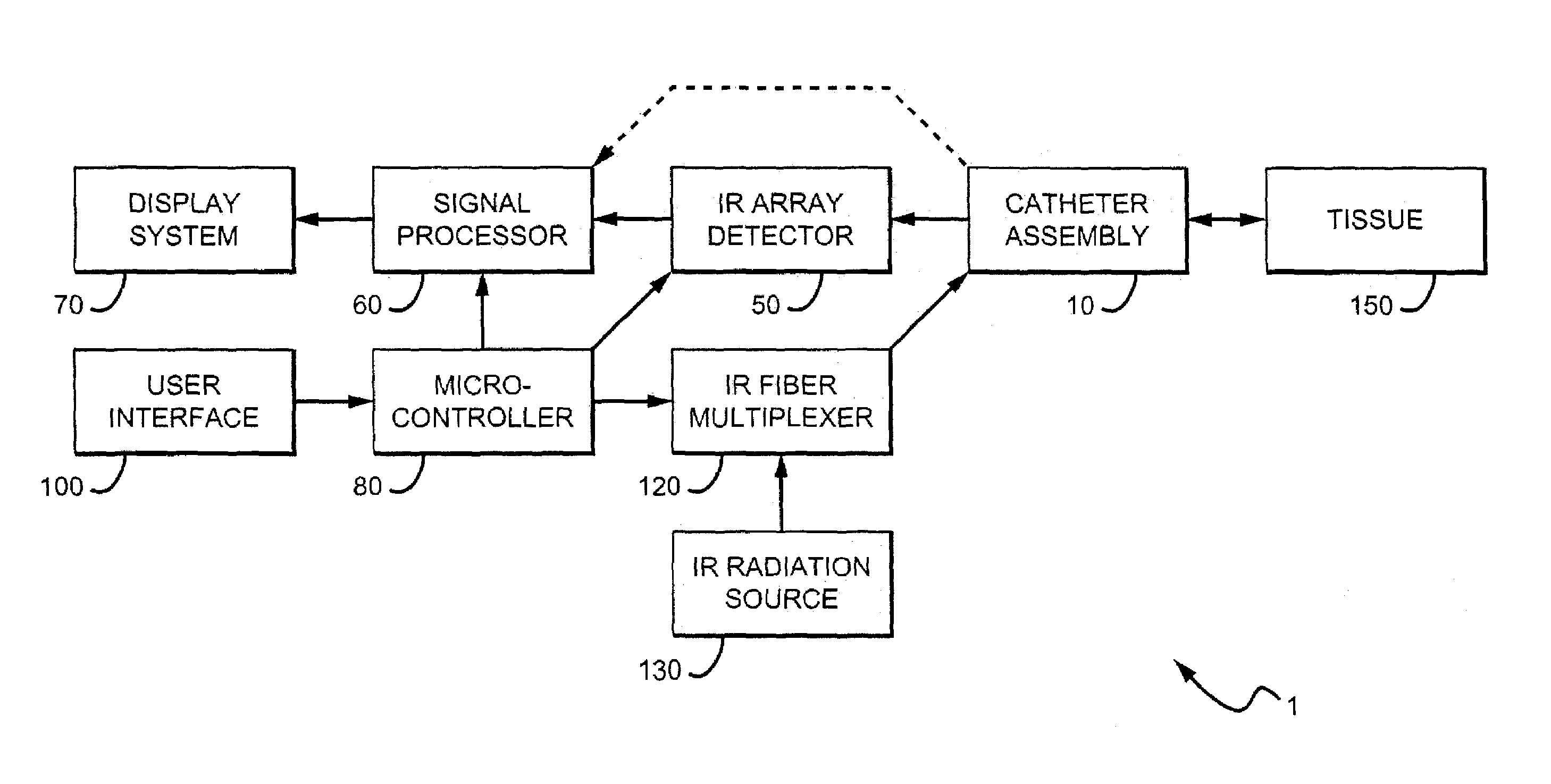
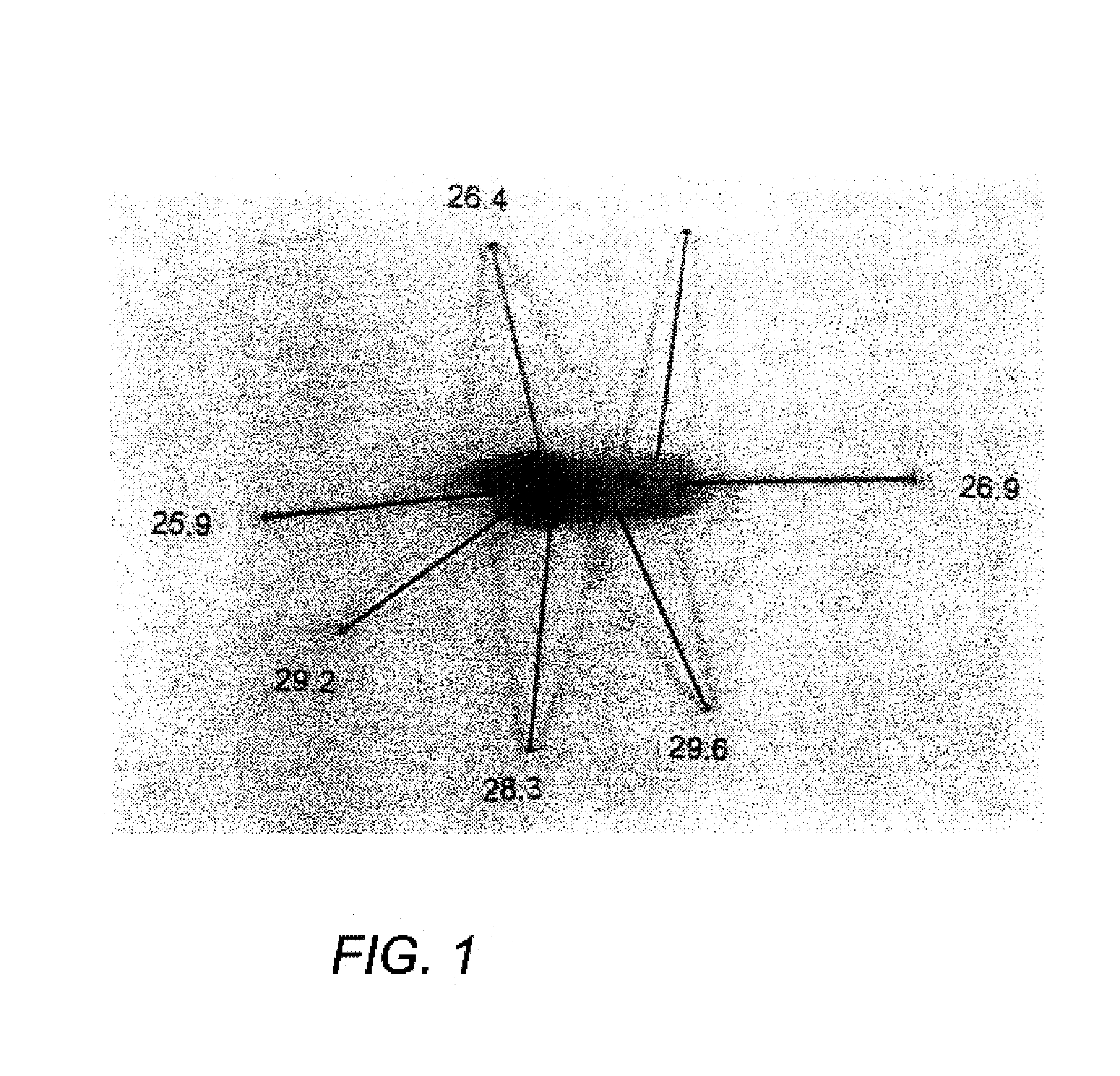
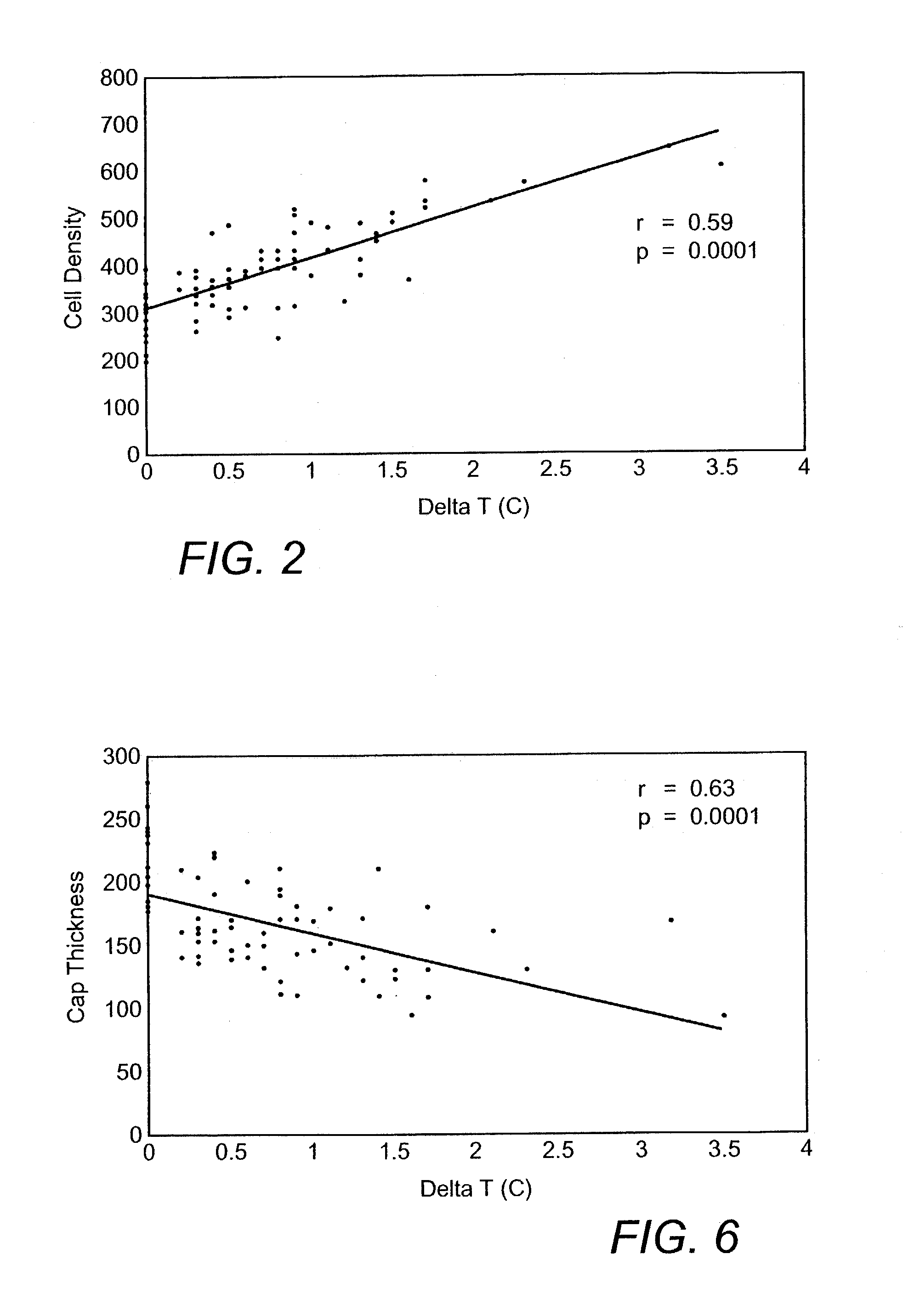
Methods and devices are disclosed for detecting vulnerable atherosclerotic plaque, or plaque at risk of reducing blood flow in a vessel, by identifying a region of elevated temperature along a living vessel wall. The disclosure that human atherosclerotic plaque with measurable temperature heterogeneity has the morphological characteristics of plaque that is likely to ulcerate provides a new and sensitive technique for detecting and treating these dangerous plaques before myocardial infarction and its consequences occur. The disclosed methods are advantageous over conventional plaque detection techniques because they are capable of differentiating between those plaques that are at great risk of rupture, fissure, or ulceration, and consequent thrombosis and occlusion of the artery, and those that are not presently at risk. Infrared heat-sensing catheters useful for identifying potentially fatal arterial plaques in patients with disease of the coronary or other arteries are also described. In some embodiments a coherent infrared fiber optic bundle is employed to radially and longitudinally explore a luminal wall to identify inflamed, heat-producing, atherosclerotic plaque. Certain other methods and devices are disclosed which are particularly suited for non-invasively identifying and then monitoring the progression or amelioration of an inflamed plaque in a patient, and for monitoring for onset of inflammation in an implanted arteriovenous graft. Also disclosed are thermocouple basket catheters and thermistor basket catheters which are also capable of detecting temperature heterogeneity along a vessel wall.
Owner:BOARD OF RGT THE UNIV OF TEXAS SYST
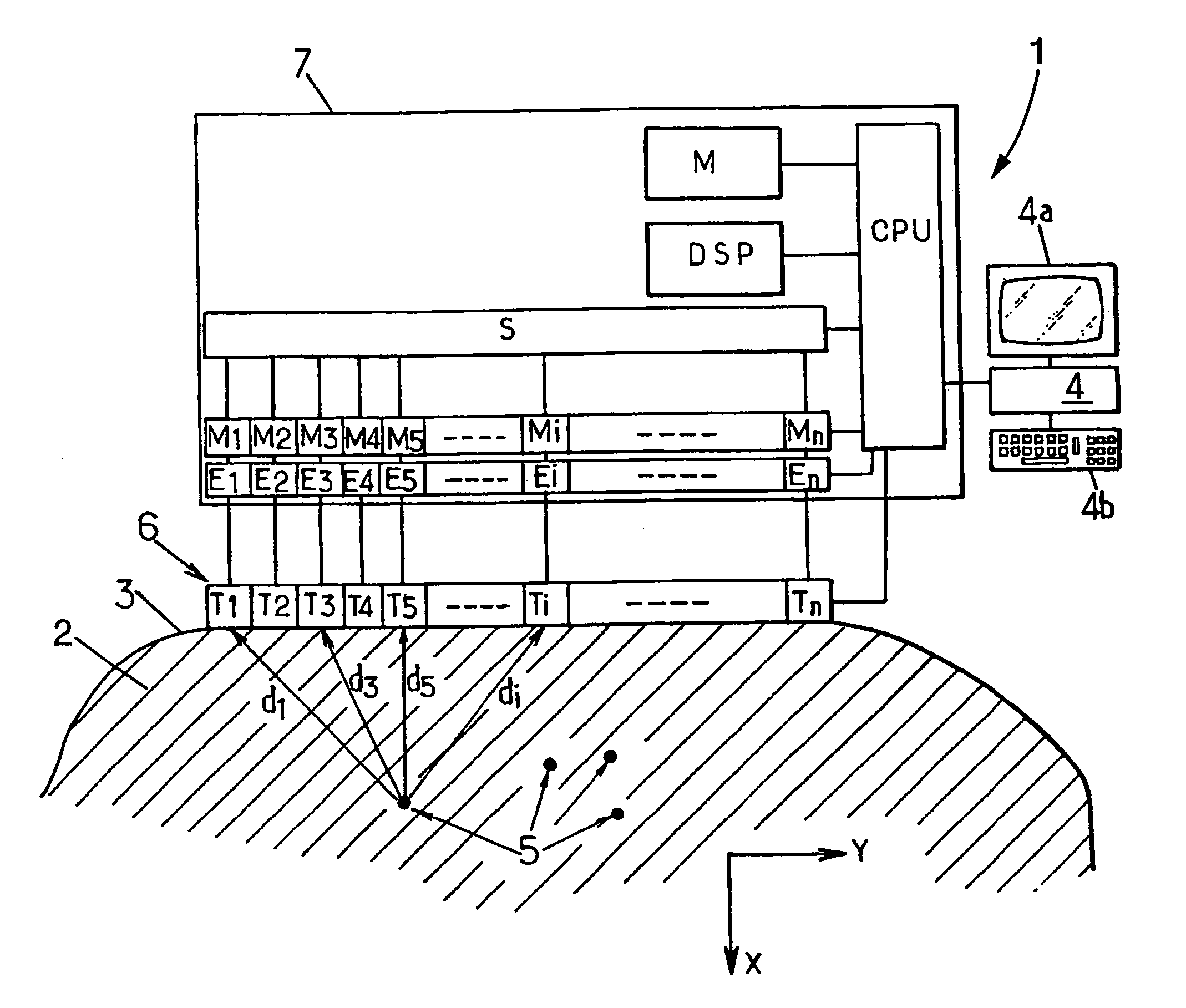
Imaging method and device employing sherar waves
ActiveUS7252004B2Mitigate such drawbackEasy to implementAnalysing fluids using sonic/ultrasonic/infrasonic wavesAnalysing solids using sonic/ultrasonic/infrasonic wavesFocus ultrasoundTransducer
An imaging method for observing the propagation of a shear wave simultaneously at a multitude of points in a diffusing viscoelastic medium. The shear wave is caused to be generated by firing at least one focused ultrasound compression wave into the viscoelastic medium by means of an array of transducers, and then emitting at a fast rate and using the same array of transducers, unfocused ultrasound compression waves serving to obtain a succession of images of the medium, and processing the images obtained in this way in deferred time in order to determine the movements of the medium during the propagation of the shear wave.
Owner:SUPER SONIC IMAGINE
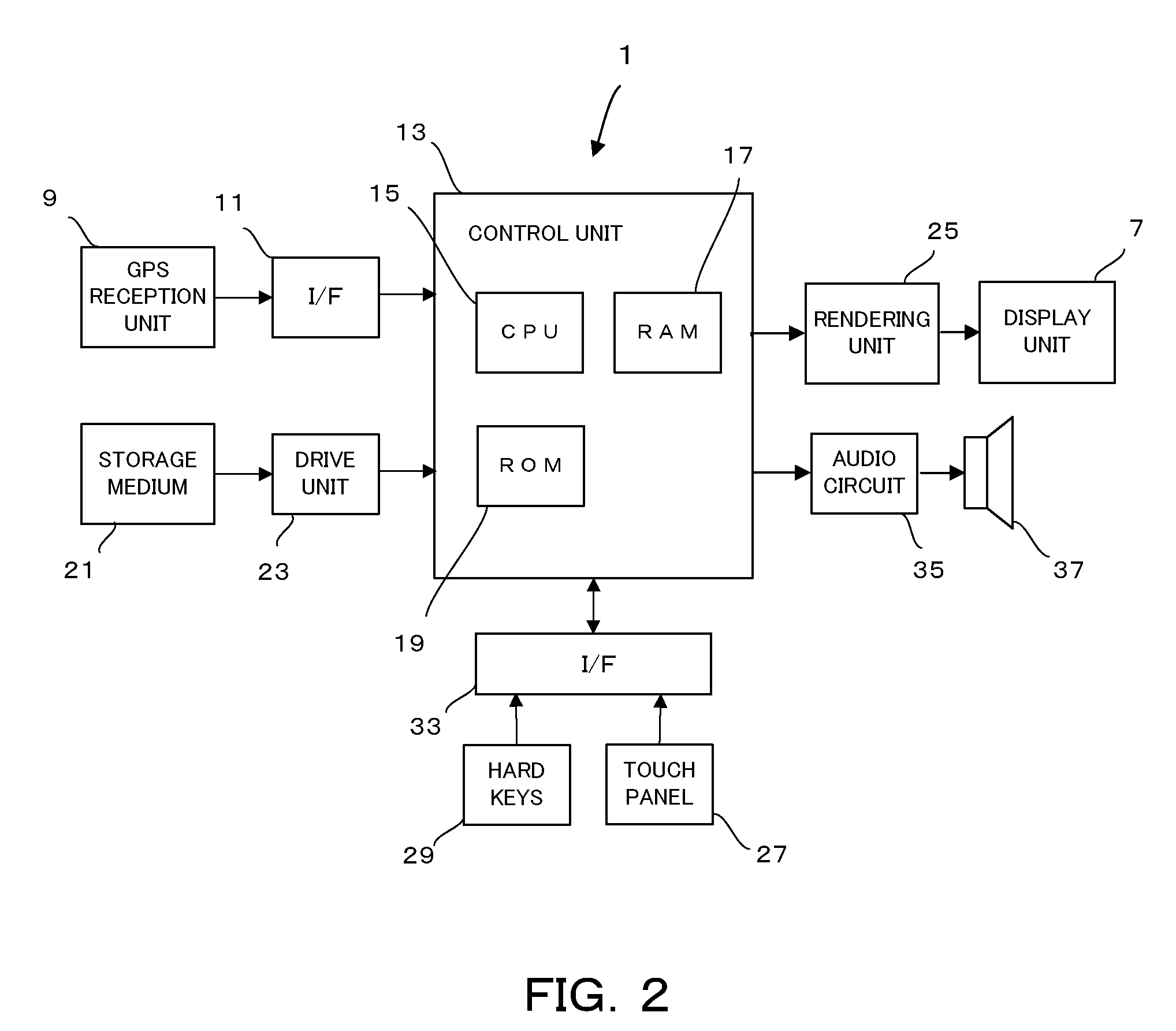
Navigation apparatus and navigation method
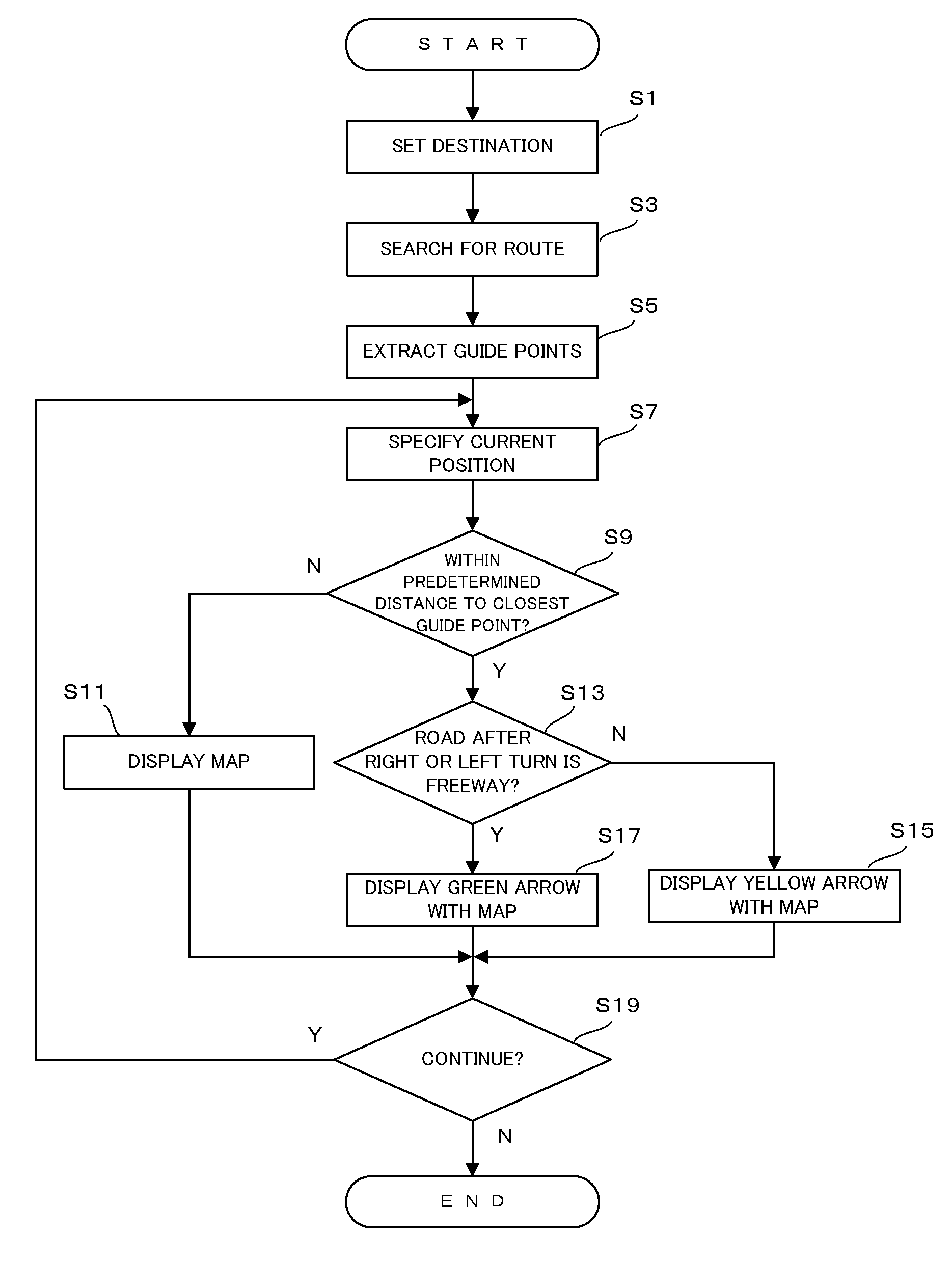
InactiveUS20090063041A1Efficient identificationInstruments for road network navigationRoad vehicles traffic controlEngineeringTypes of road
A navigation apparatus includes map data, a control unit that searches for a route over which a vehicle is to be directed, using the map data, and a display unit that displays an arrow indicating a right turn or a left turn of the vehicle when the vehicle approaches a guide point where the vehicle is directed to turn right or left. The control unit determines the type of a first road which is connected to the guide point and which will be entered after the vehicle turns right or left at the guide point, using the map data. If the first road is a first type of road, the control unit causes the display unit to display the arrow in a first color. If the first road is a second type of road, the control unit causes the display unit to display the arrow in a second color that differs from the first color.
Owner:SANYO ELECTRIC CO LTD
Systems and etiquette for home gatways using white space
InactiveUS20100124254A1Easy to operateEfficient identificationModulated-carrier systemsTransmission path divisionFrequency spectrumComputer science
Methods and systems for sharing white space with primary services and other emerging services are provided. Signal distribution within a specified location, such as a dwelling, is performed using a home gateway that identifies unused white space, reserves such white space spectrum, and delivers data to one or more devices at the respective location using the reserved spectrum. Signalling between the devices and the gateway is performed over a shared signalling channel, which enables the gateway to advise the devices from where and when to receive data. The gateway also uses a common spectrum reservation OFDM symbol to advise the neighbouring gateways of the local spectrum reservation.
Owner:TAIWAN SEMICON MFG CO LTD
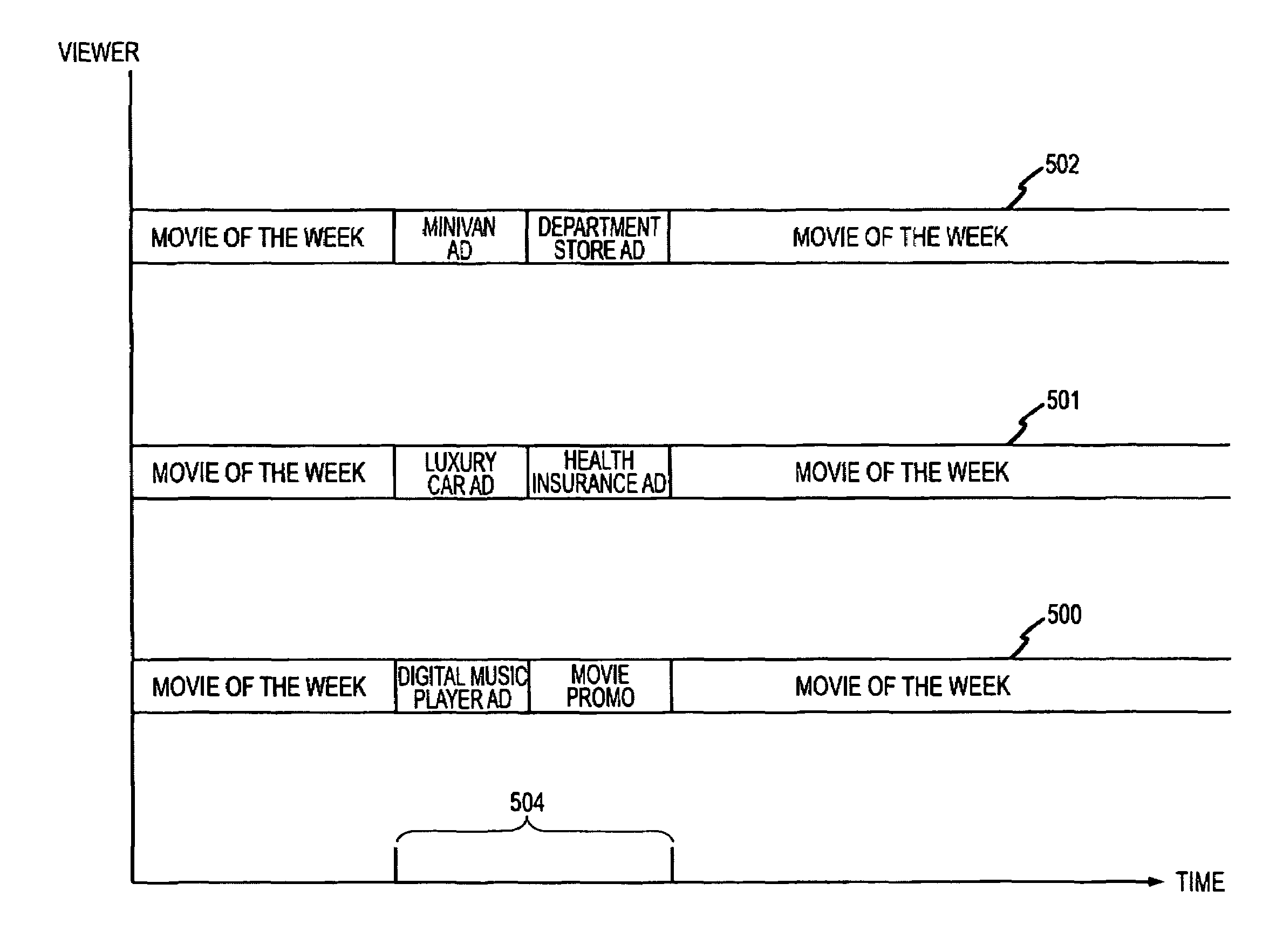
Fuzzy logic based viewer identification for targeted asset delivery system
ActiveUS7698236B2Improve efficiencyIncrease choiceBroadcast systems characterised by addressed receiversTelevision system detailsUser inputTargeted advertising
A targeted advertising system uses a machine learning tool to select an asset for a current user of a user equipment device, for example, to select an ad for delivery to a current user of a digital set top box in a cable network. The machine learning tool first operates in a learning mode to receive user inputs and develop evidence that can characterize multiple users of the user equipment device audience. In a working mode, the machine learning tool processes current user inputs to match a current user to one of the identified users of that user equipment device audience. Fuzzy logic may be used to improve development of the user characterizations, as well as matching of the current user to those developed characterizations. In this manner, targeting of assets can be implemented not only based on characteristics of a household but based on a current user within that household.
Owner:INVIDI TECH CORP
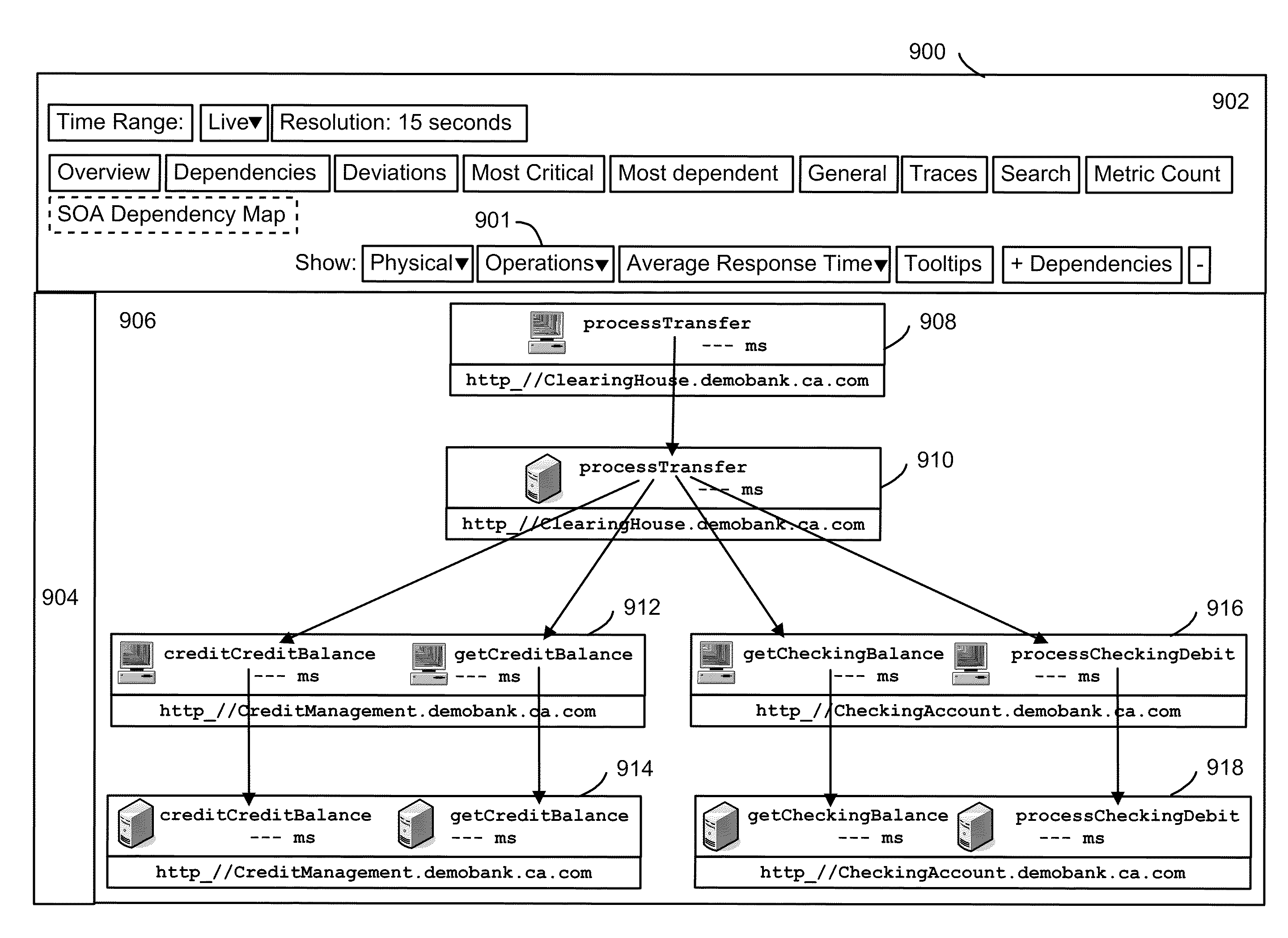
Detecting non-redundant component dependencies in web service invocations
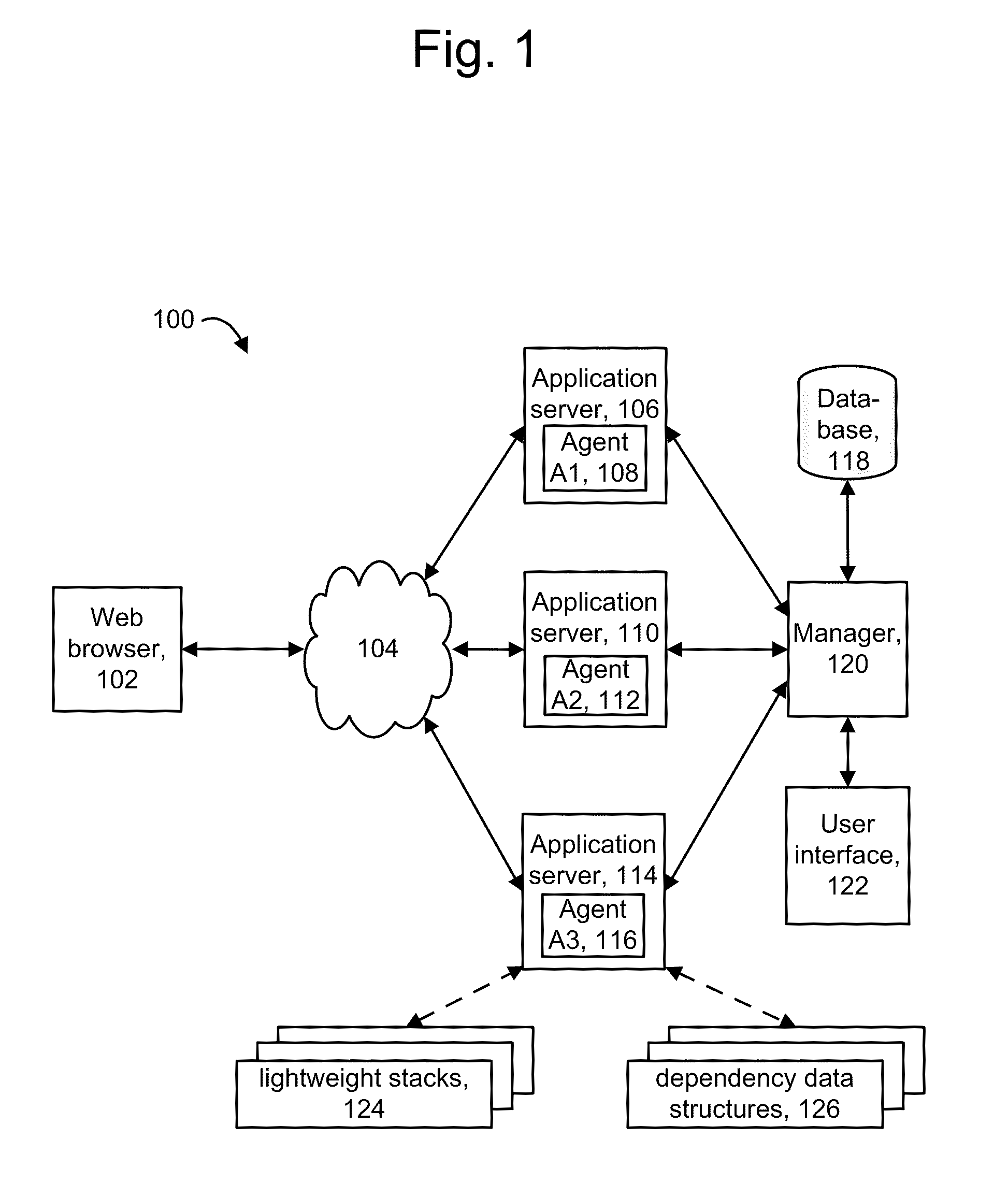
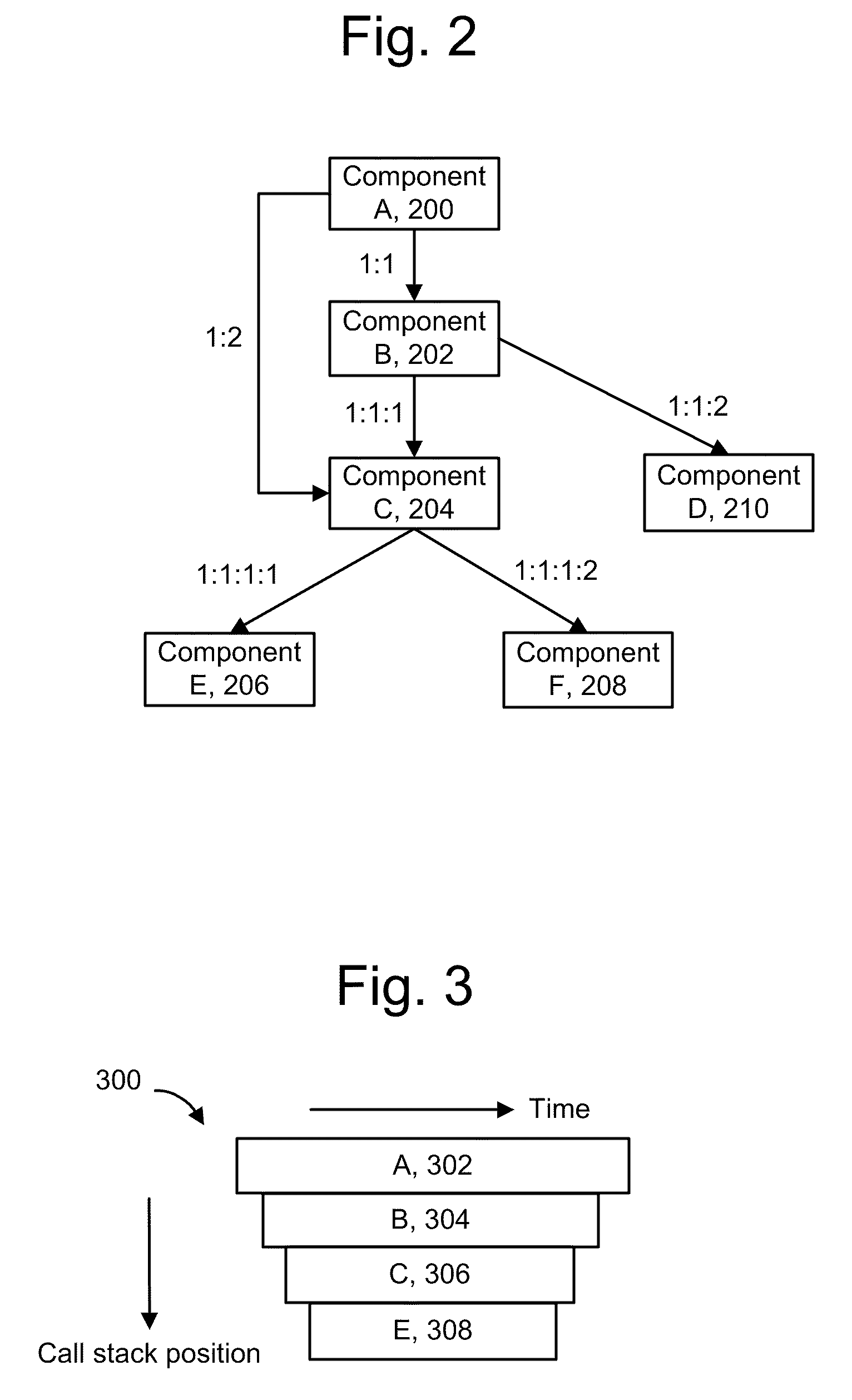
ActiveUS20100281488A1Efficient identificationError detection/correctionMultiprogramming arrangementsApplication softwareMutual dependence
Relationships between components in an application and the services they provide are identified, including redundant caller-callee sequences. Specific components of interest are instrumented to obtain data when they execute. Data structures are created which identify the components and their dependencies on one other. To avoid excessive overhead costs, redundant dependencies are identified. A dependency data structure can be provided for each unique dependency. When repeated instances of a dependency are detected, the associated dependency data structure can be augmented with correlation data of the repeated instances, such as transaction identifiers and sequence identifiers. Sequence identifiers identify an order in which a component is called. A flag can be used to force the creation of a new dependency data structure, and a calling component's name can be used instead of a sequence identifier. Agents report the dependency data structures to a manager to provide graph data in a user interface.
Owner:CA TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com