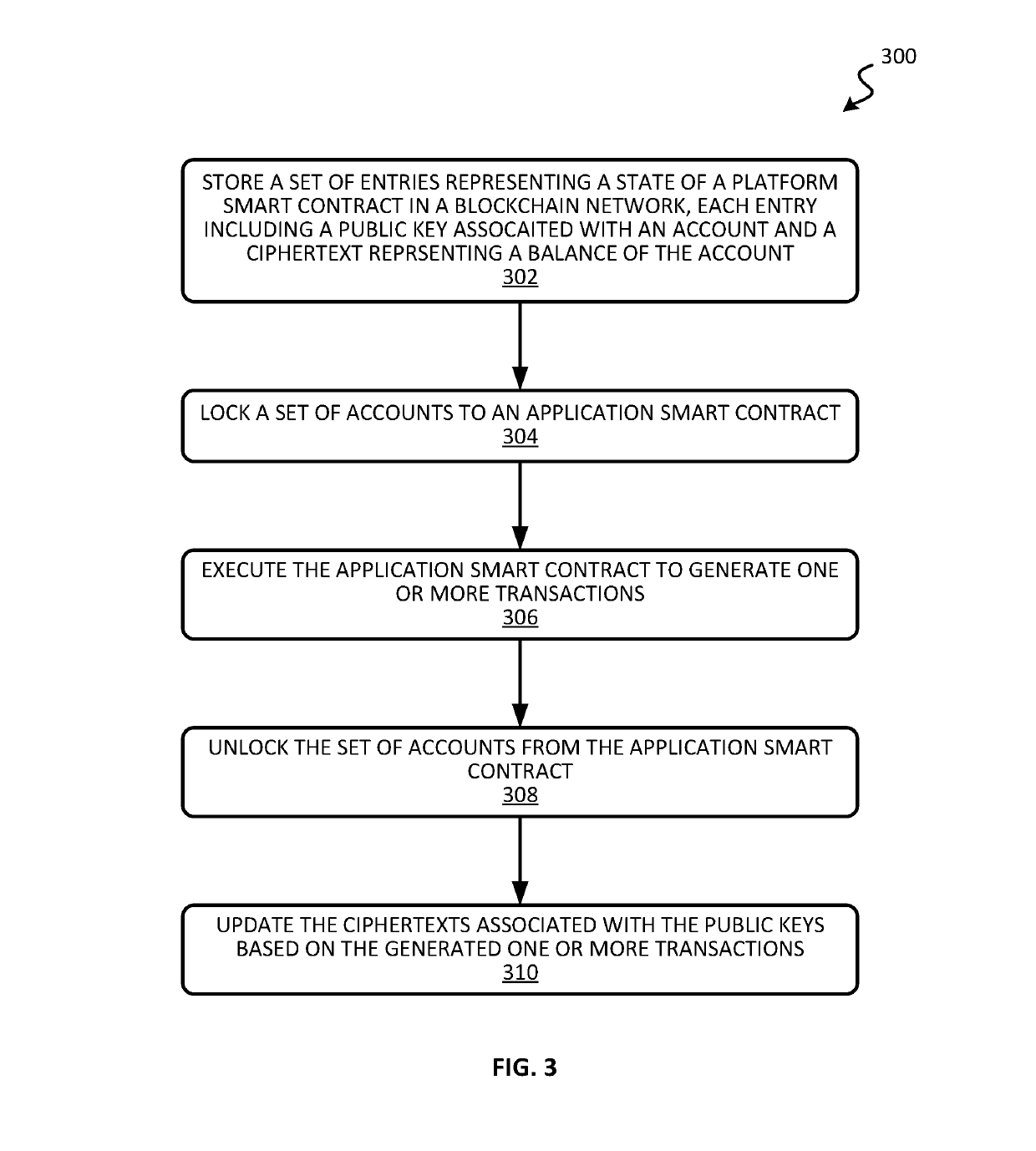
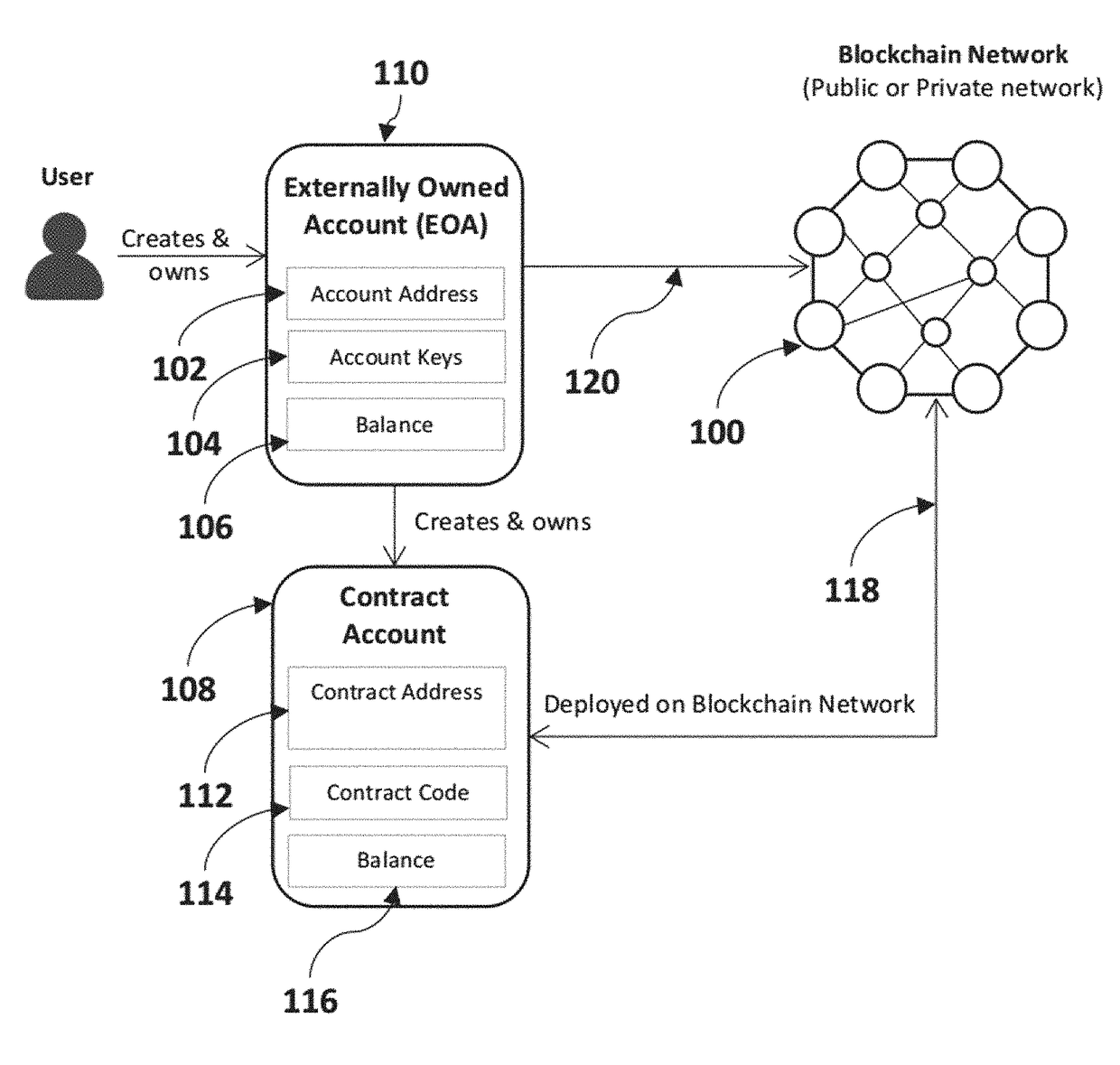
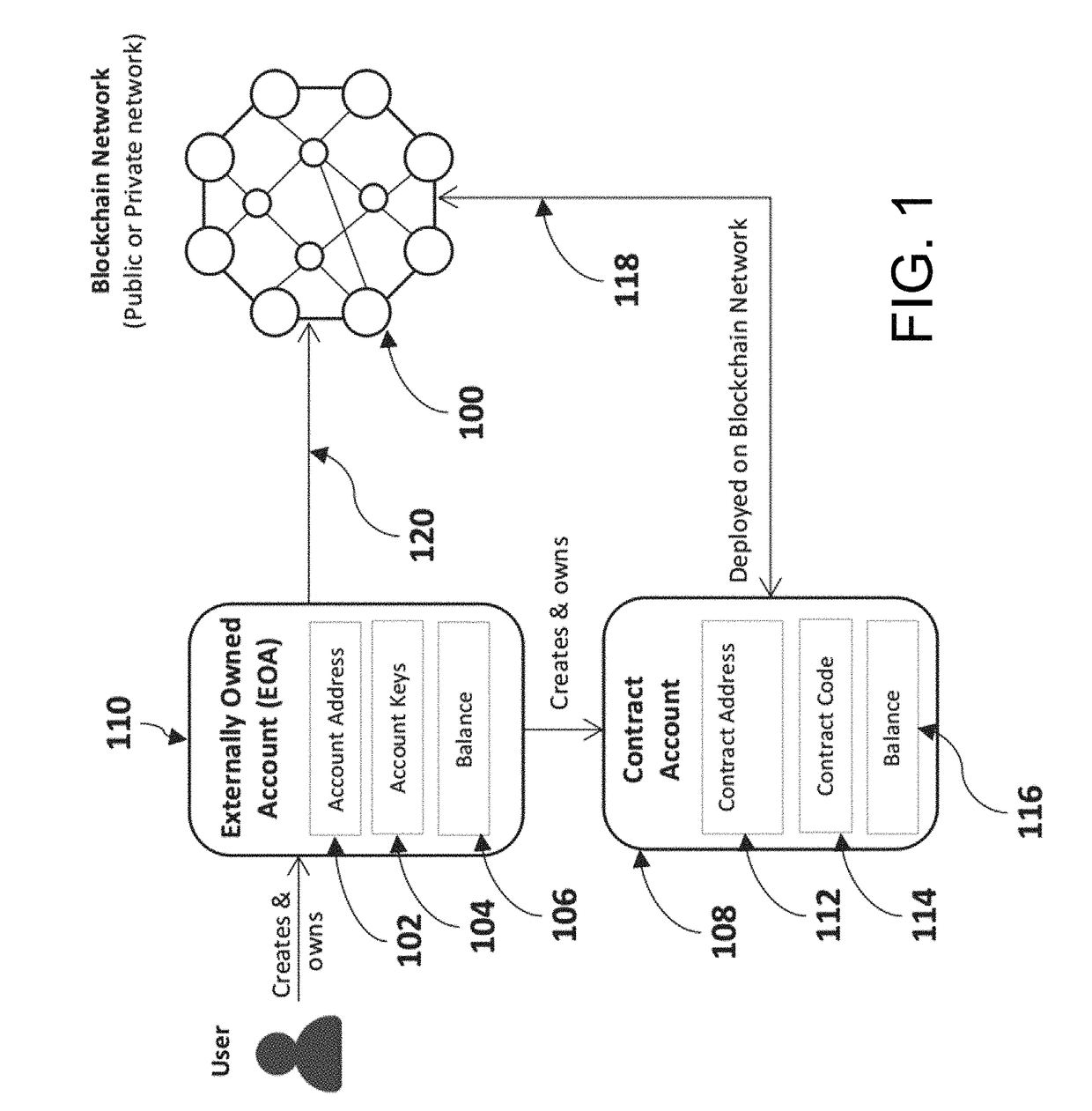
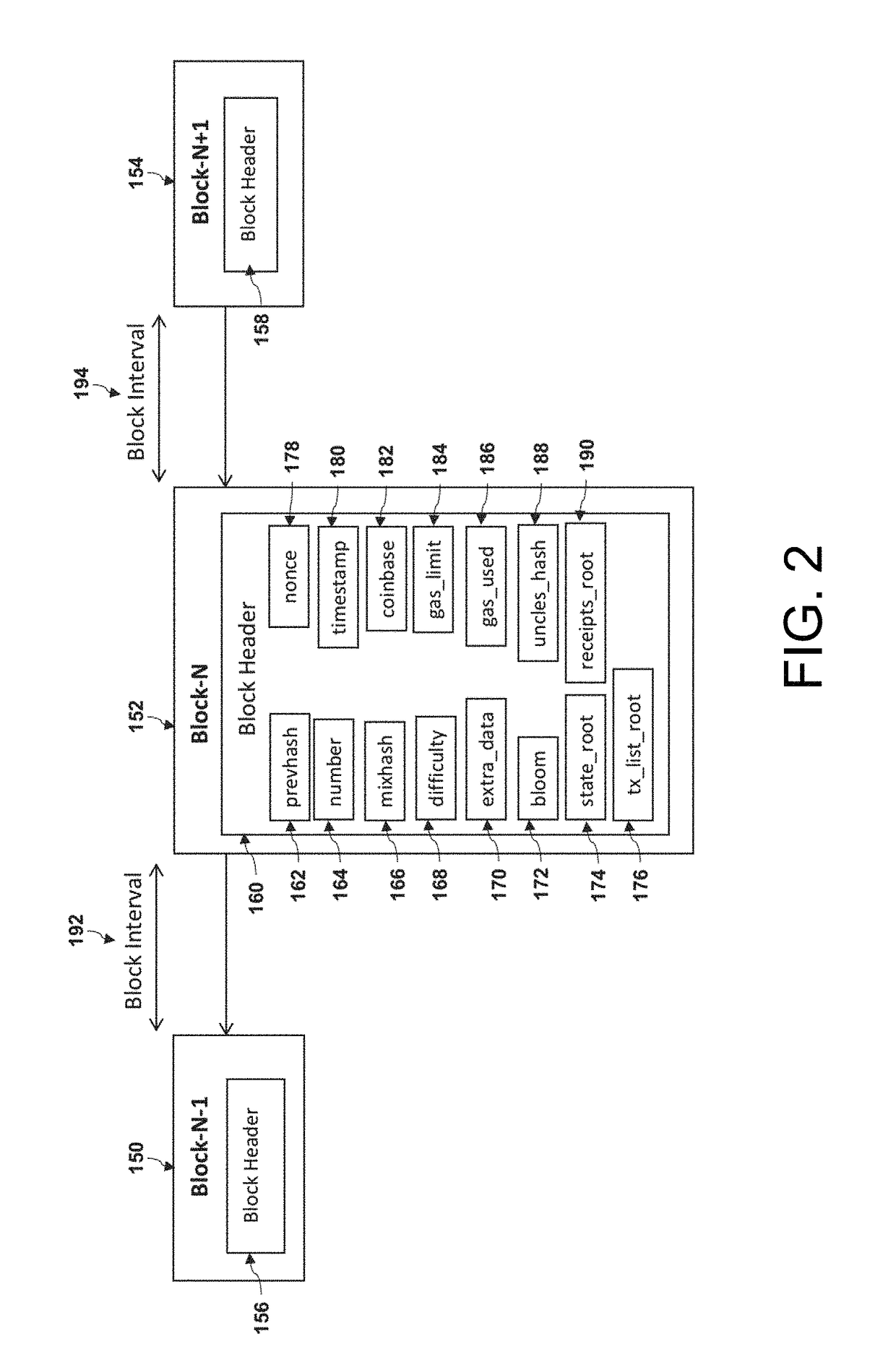
Patents
Literature
11057results about "Encryption apparatus with shift registers/memories" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
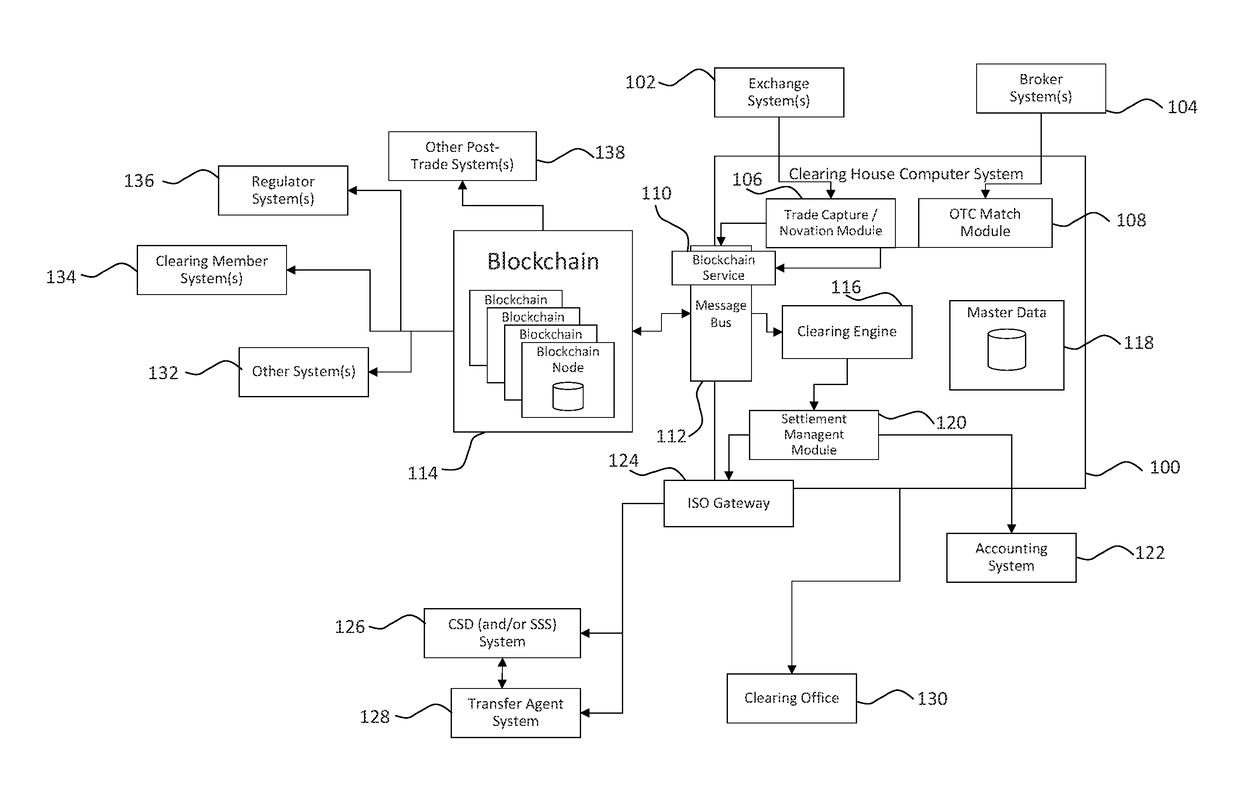
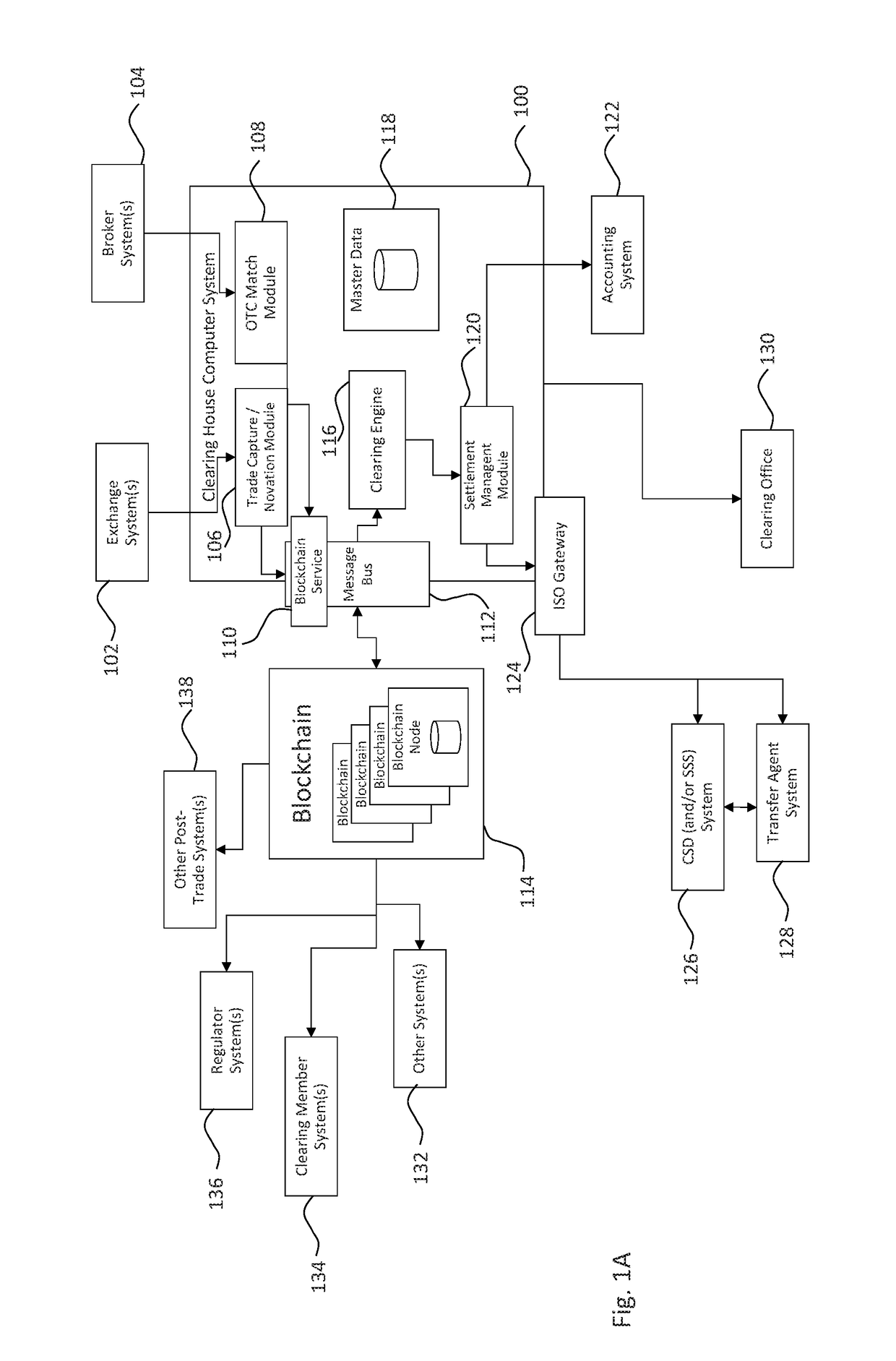
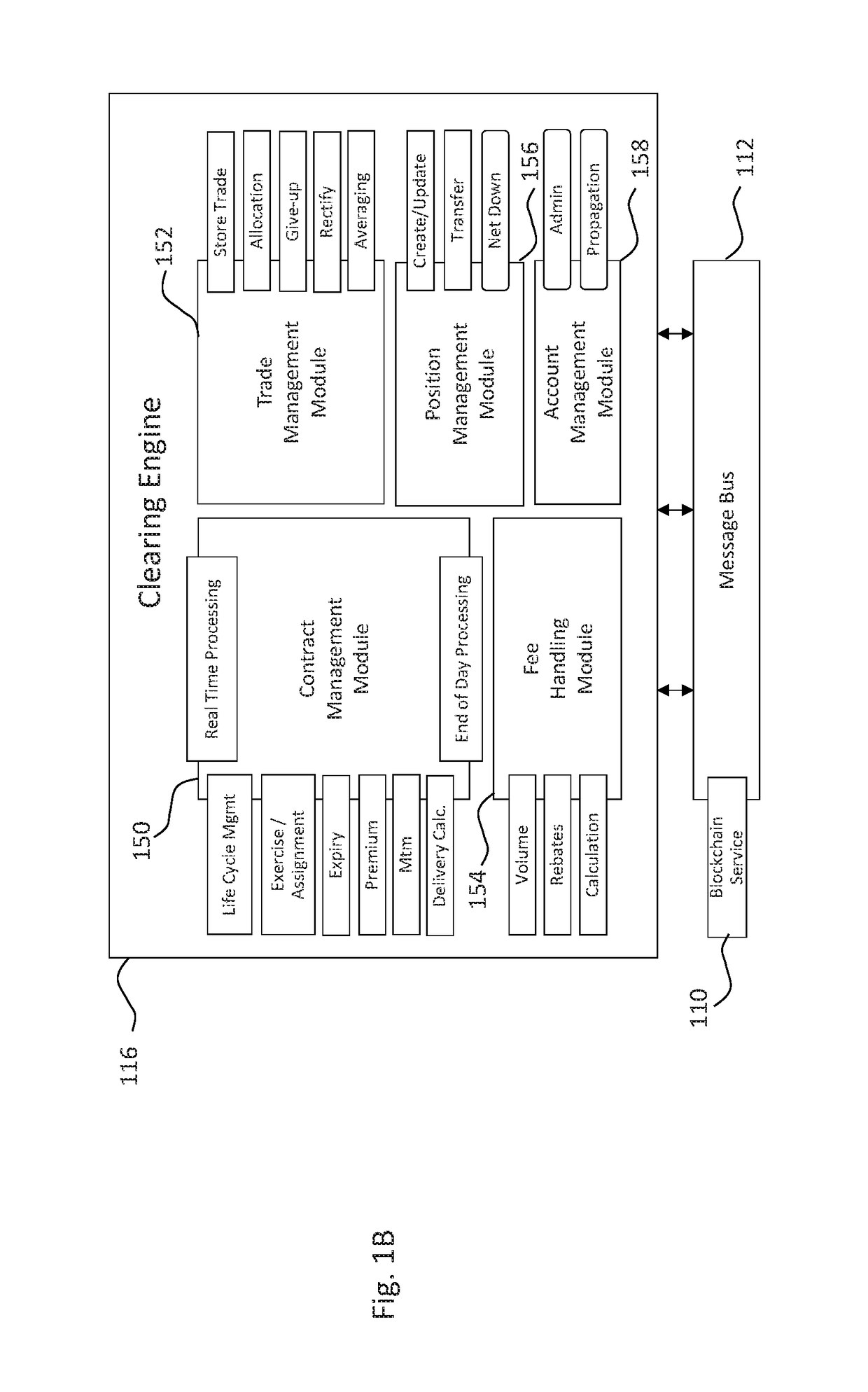
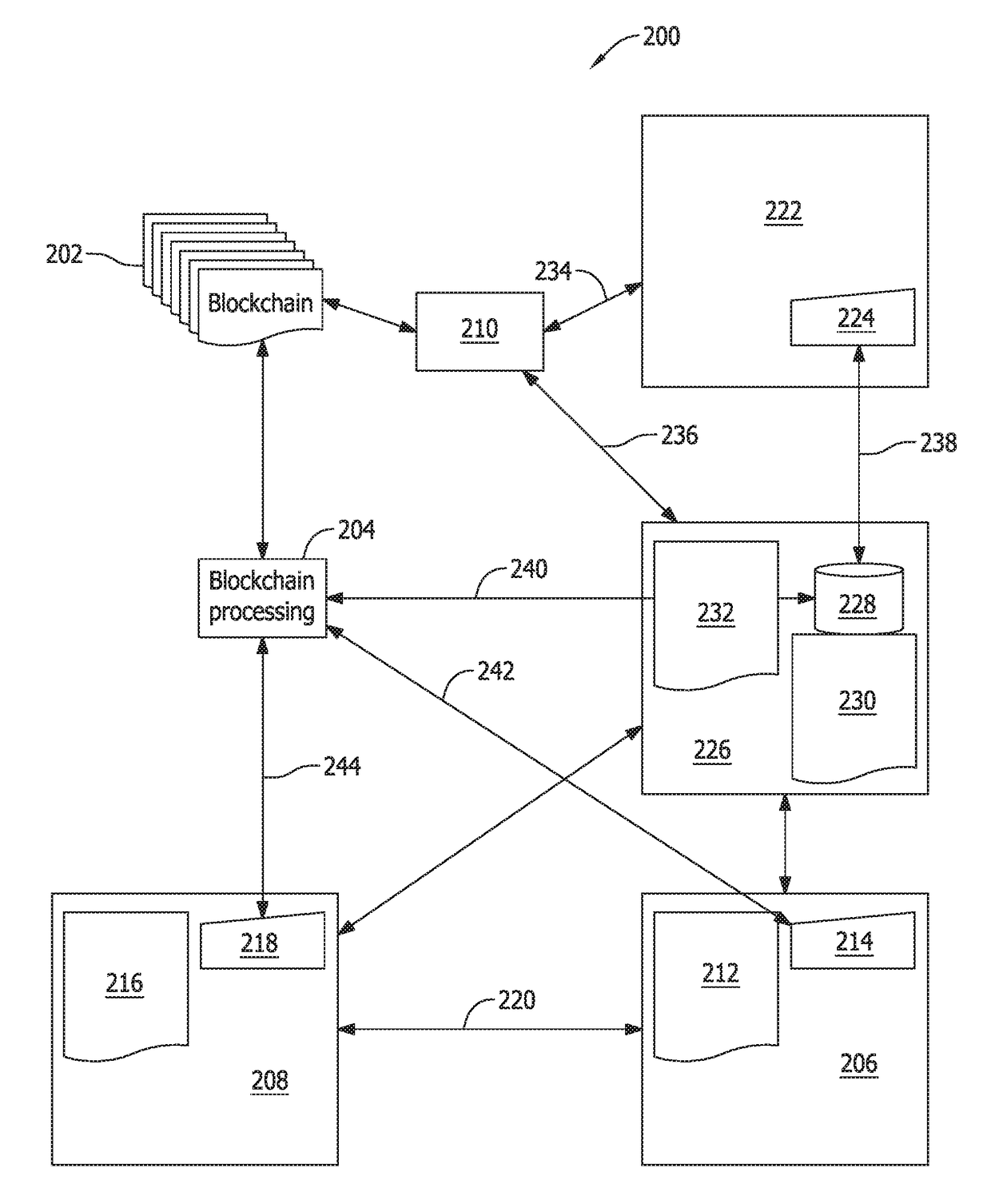
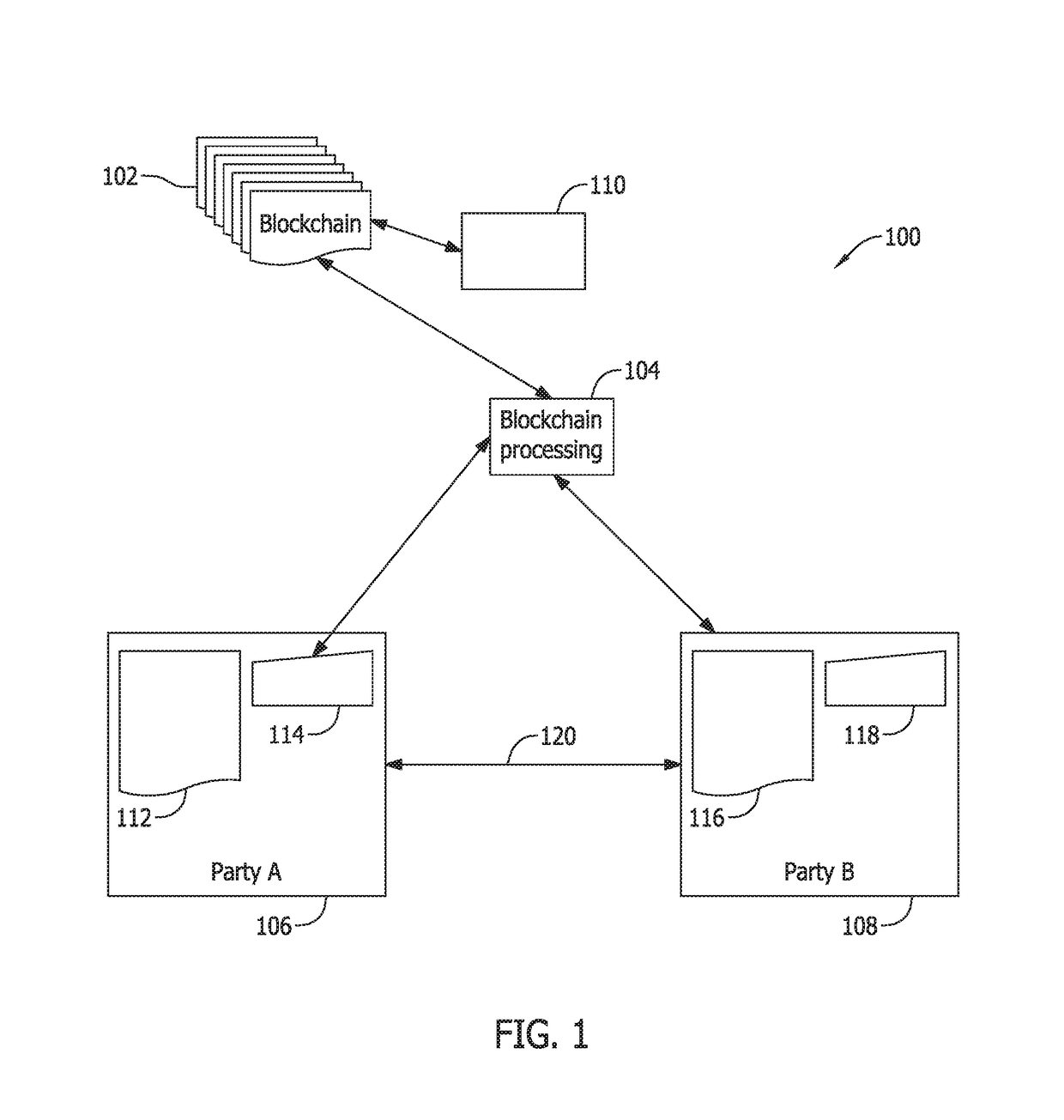
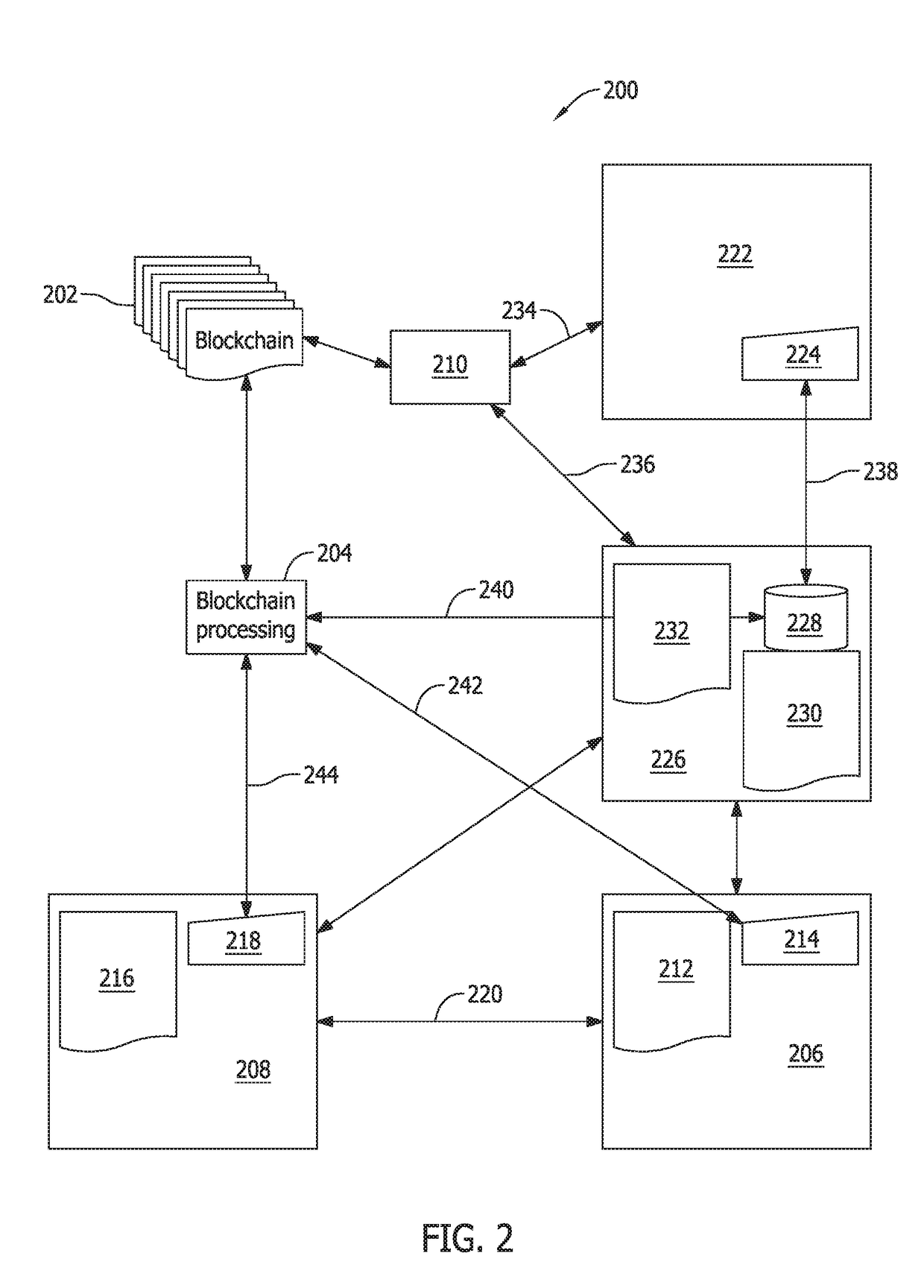
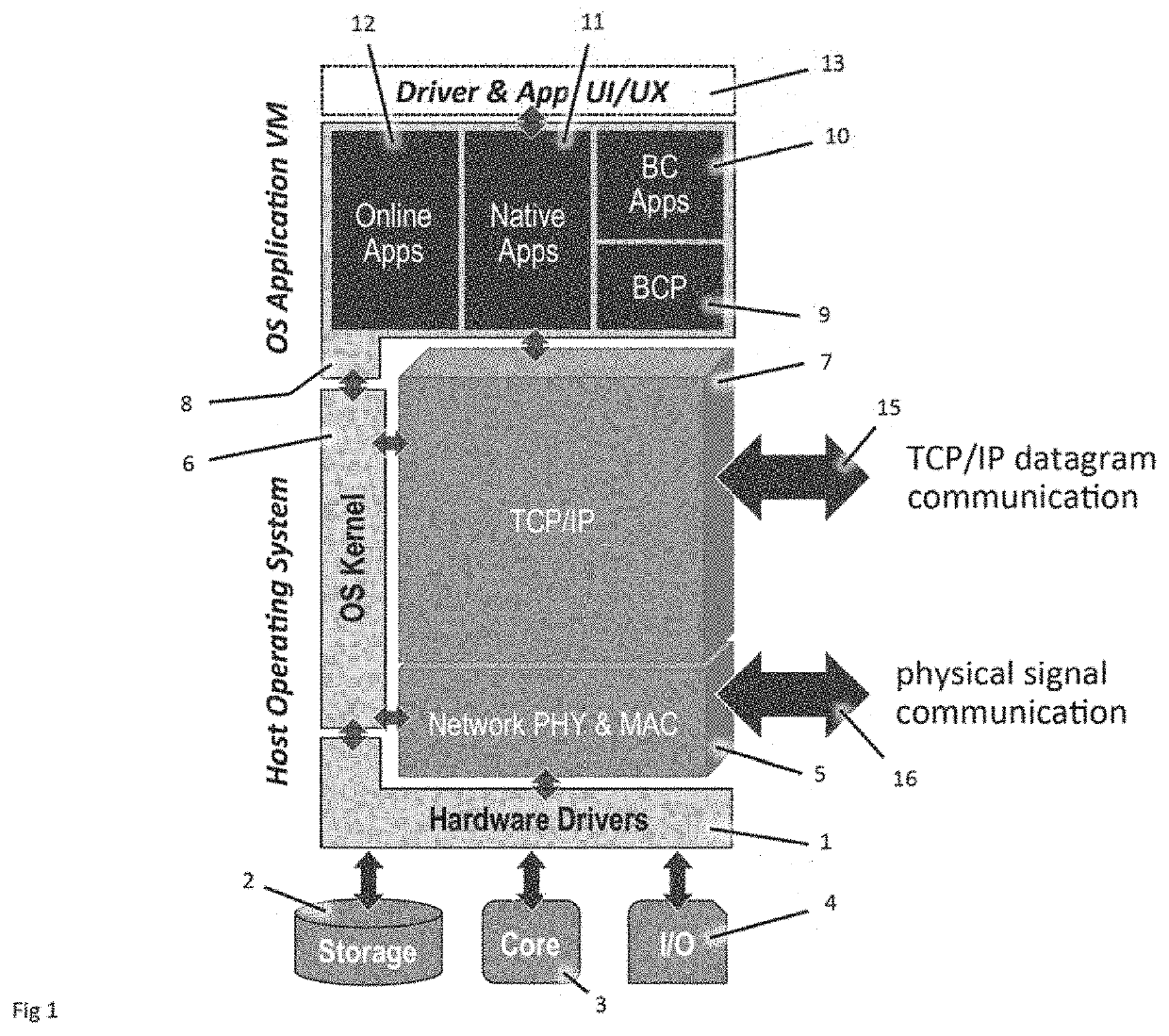
Authentication and verification of digital data utilizing blockchain technology
InactiveUS20160283920A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital dataHuman interaction
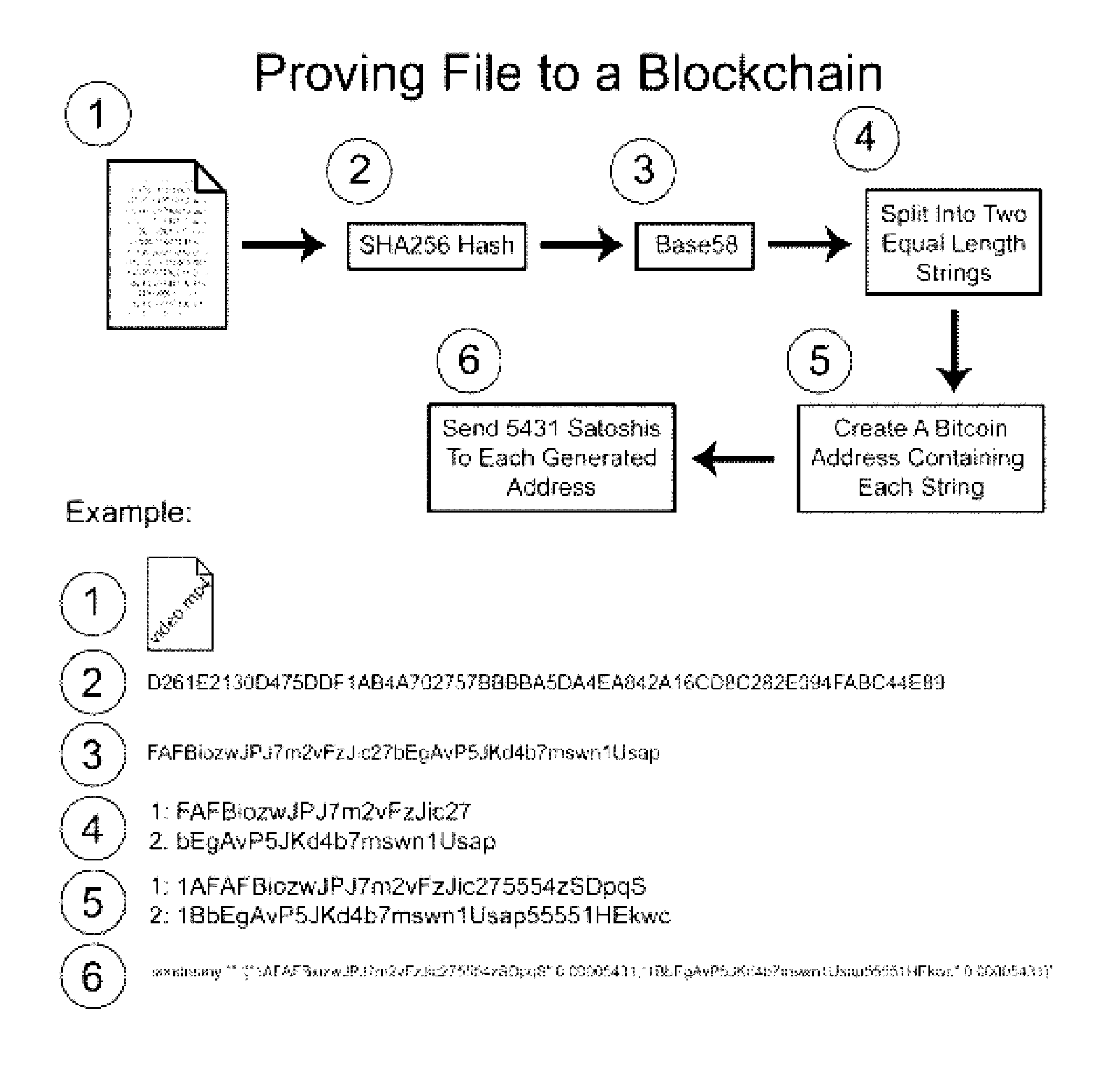
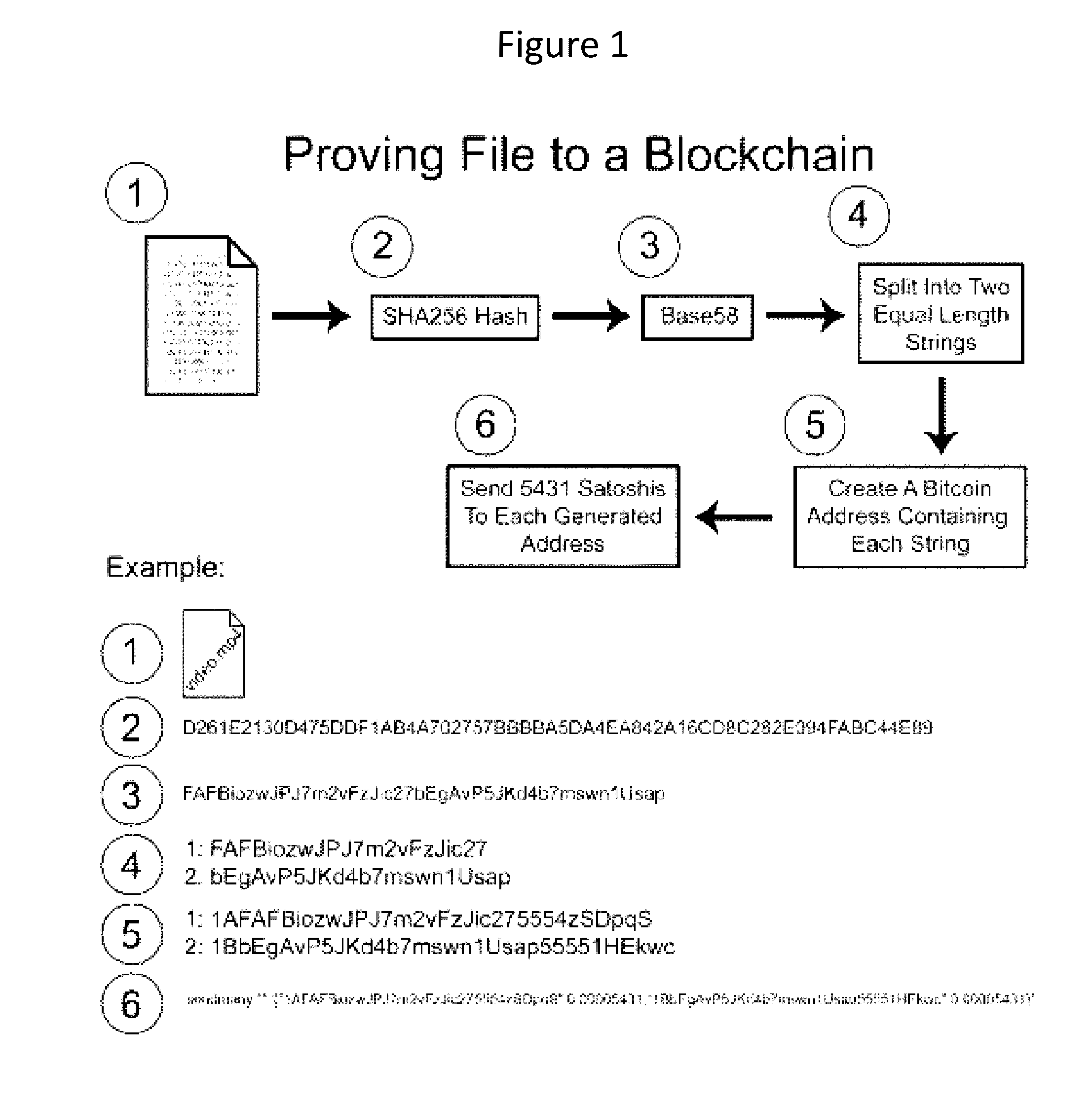
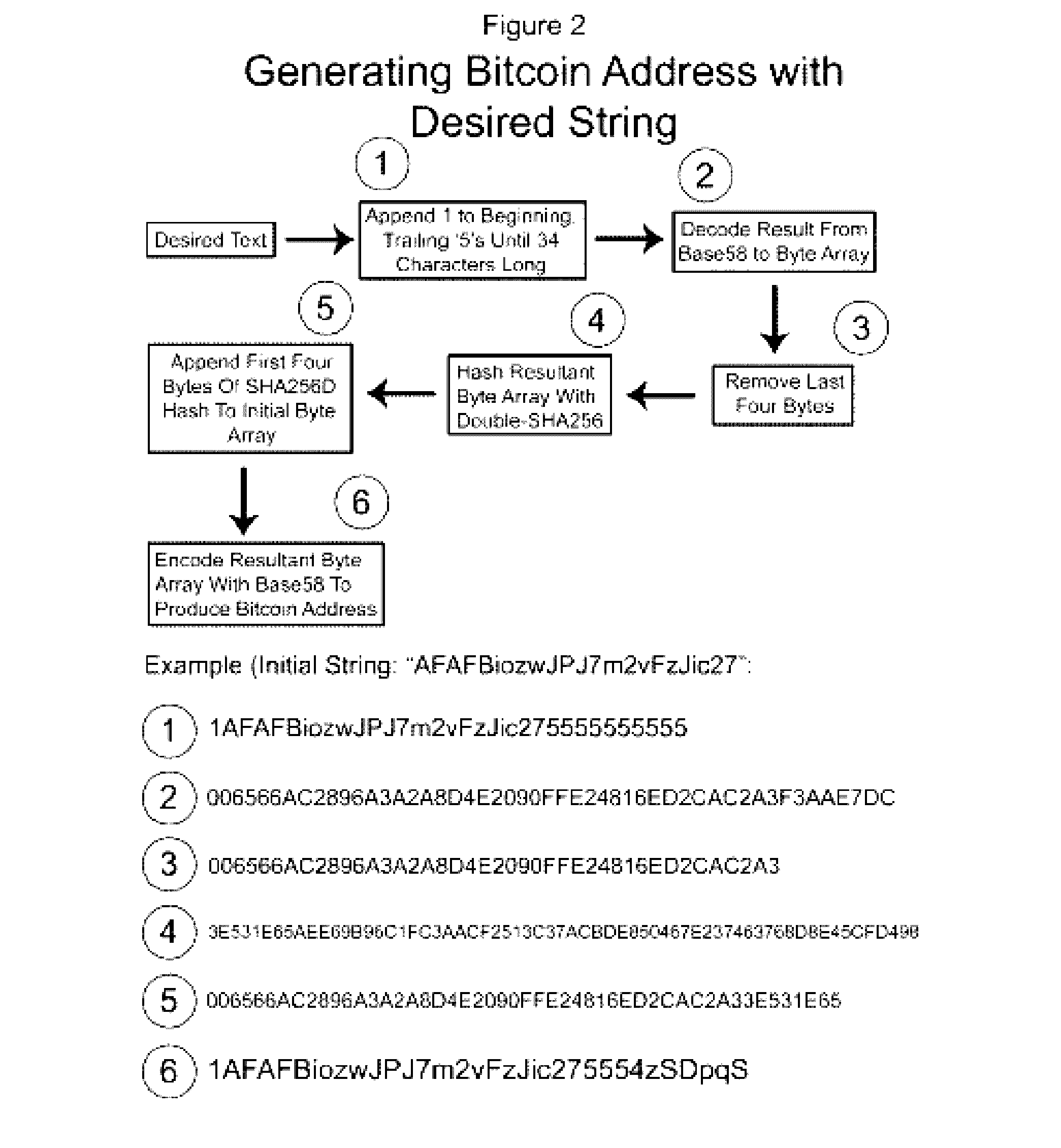
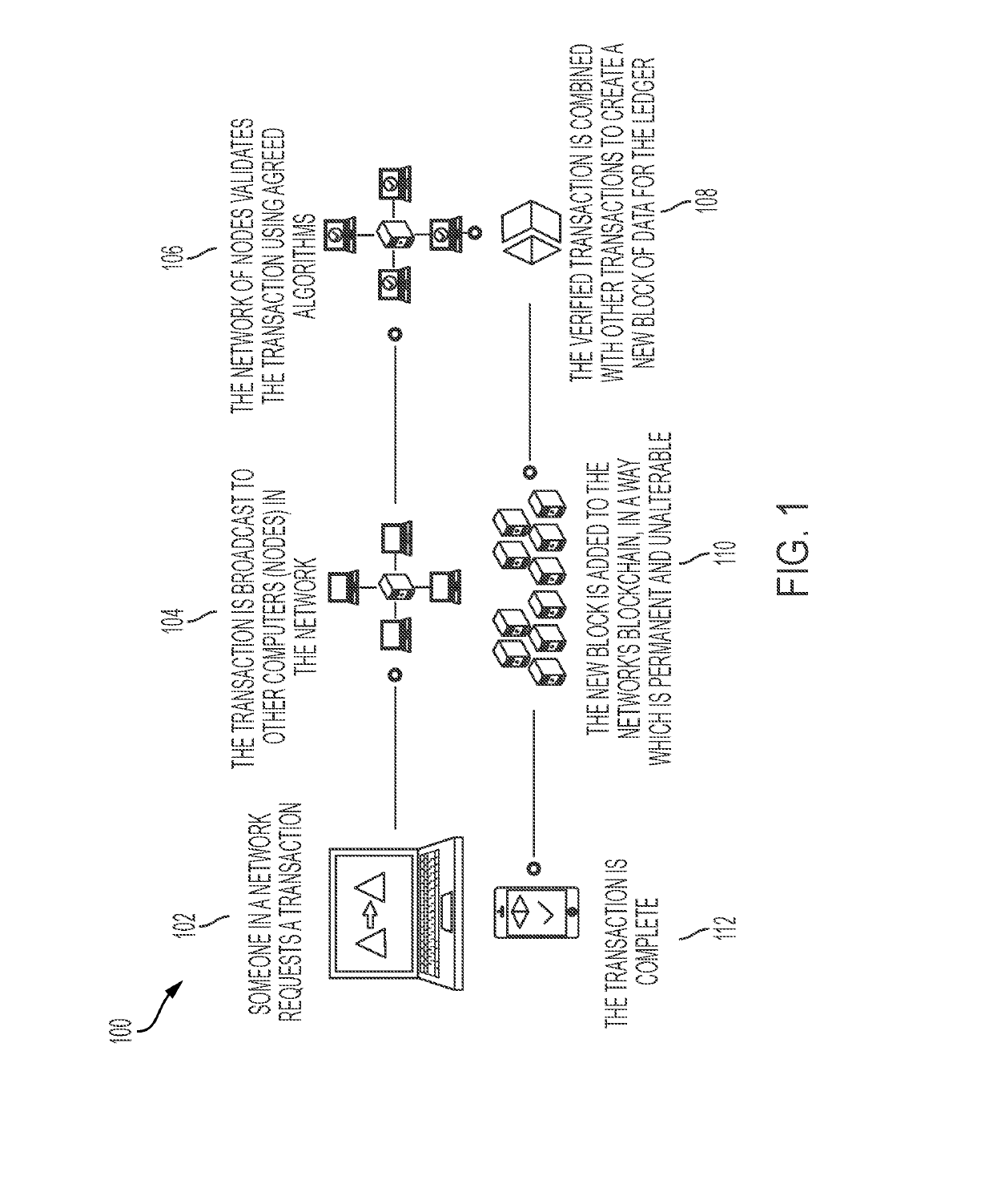
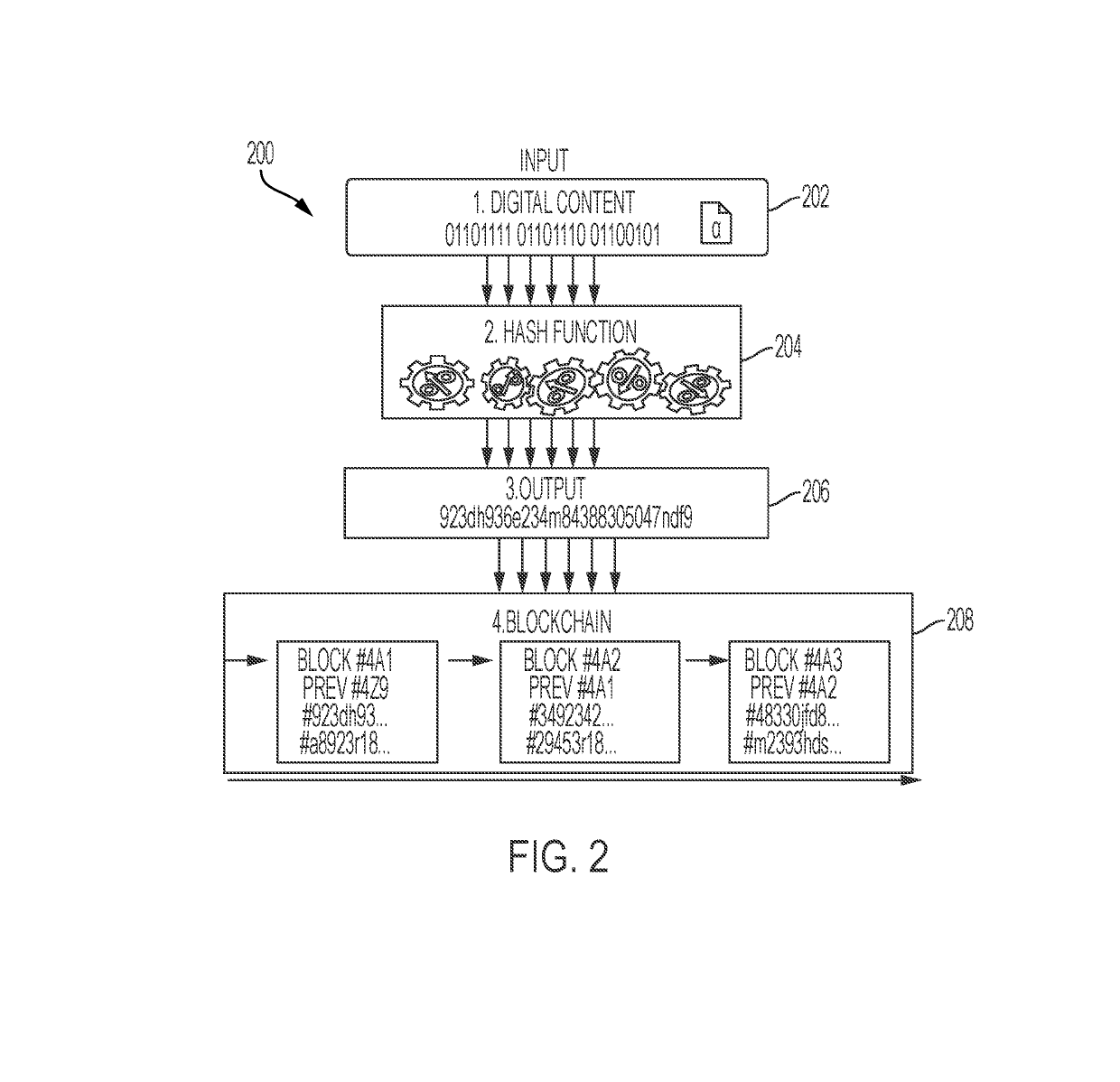
A method for authenticating a chain of custody utilizing blockchain technology, whereby digital evidence or other digital content is acquired and then hashed to produce a hash fingerprint / signature and then immediately or instantly submitting said hash fingerprint / signature to the blockchain using the blockchain network protocol, forming an immediate verifiable chain of custody without human interaction or requiring a trusted third party.
Owner:FISHER JUSTIN +1
Secure Dynamic Communication Network And Protocol
ActiveUS20160219024A1Increase the difficultyUsefulness of their knowledge would be short-livedMultiple keys/algorithms usageData taking preventionDigital dataData segment
In a secure cloud for transmitting packets of digital data, the packets may be repeatedly scrambled (i.e., their data segments reordered) and then unscrambled, split and then mixed, and / or encrypted and then decrypted as they pass through media nodes in the cloud. The methods used to scramble, split, mix and encrypt the packets may be varied in accordance with a state such as time, thereby making the task of a hacker virtually impossible inasmuch as he or she may be viewing only a fragment of a packet and the methods used to disguise the data are constantly changing.
Owner:LISTAT LTD
Technique for securely communicating programming content
ActiveUS20060047957A1Prevent illegal useEncryption apparatus with shift registers/memoriesDigital data processing detailsTime segmentSecurity level
A technique is provided for securely transferring programming content from a first device in a first layer, e.g., a trusted domain, to a second device in a second layer, e.g., outside the trusted domain. When a user requests that the first device transfer protected content to the second device, the first device needs to authenticate the second device. After the second device is authenticated, the first device may transfer to the second device the protected content, together with a rights file associated therewith. The rights file specifies the rights of the second device to use the protected content, according to its security level indicative of its security. These rights may concern, e.g., the number of times that the second device may subsequently transfer the protected content to other devices, the time period within which the second device may play the protected content, etc. The higher the security level of the second device is, the more rights accorded thereto. Indeed, the second device may need to meet a minimum security level requirement in order for it to receive or keep the protected content.
Owner:TIME WARNER CABLE ENTERPRISES LLC +1
Methods and system for managing intellectual property using a blockchain
InactiveUS20180285996A1Synchronising transmission/receiving encryption devicesData processing applicationsDashboardPayment
A system and methods for managing intellectual property using a blockchain are provided which may include one or more elements which forms a comprehensive foundation for an eco-system for innovation and intellectual property management. The elements may include: an intellectual property distributed ledger, an intellectual property digital policy server, non-binary trust models, automatic ontology induction, modifications to the blockchain “mining” and “proof of work” system, appstore for related applications, partial transparency transactionalized search engine, persistent and encapsulated software trust objects, licensing royalty smart contract with auditable payment tracking, micro-equity incentives, automated fraud detection intellectual property management dashboards, innovation workflow broker, innovation optimization tools, disruption mapping, and intelligent just-in-time learning. The system combines and integrates these functions to enable personal, intra-enterprise, inter-enterprise and extra-enterprise recordation, collaboration, searchability and its benefits, licensing and tracking of information regarding intellectual property over a networked distributed computing system.
Owner:FUTURELAB CONSULTING INC
Systems and methods for storing and sharing transactional data using a distributed computing systems
ActiveUS20170230189A1FinanceEncryption apparatus with shift registers/memoriesComputerized systemComputing systems
A computer system that interfaces with a blockchain is provided. The computer system receives match data for a match between a first data transaction request that is associated with a first identifier and a second data transaction request that is associated with a second identifier. A first blockchain transaction is generated based on the match data and stored to a blockchain. At least one further blockchain transaction is generates that splits the match into two different transactions—one between the first identifier and an intermediary and the second between the intermediary. These are recorded to the blockchain via the further blockchain transactions.
Owner:NASDAQ TECHNOLOGY AB
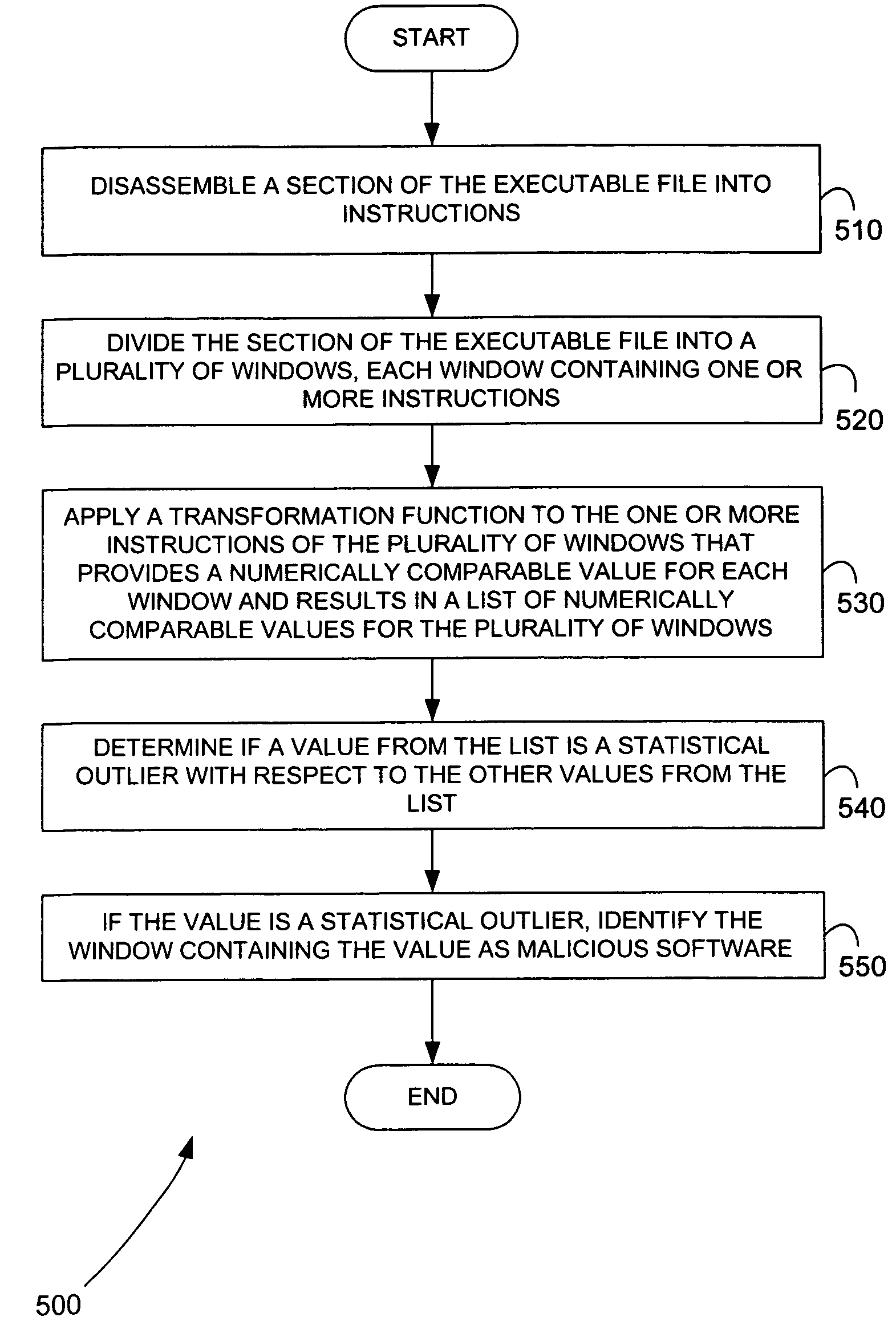
Methods for identifying malicious software
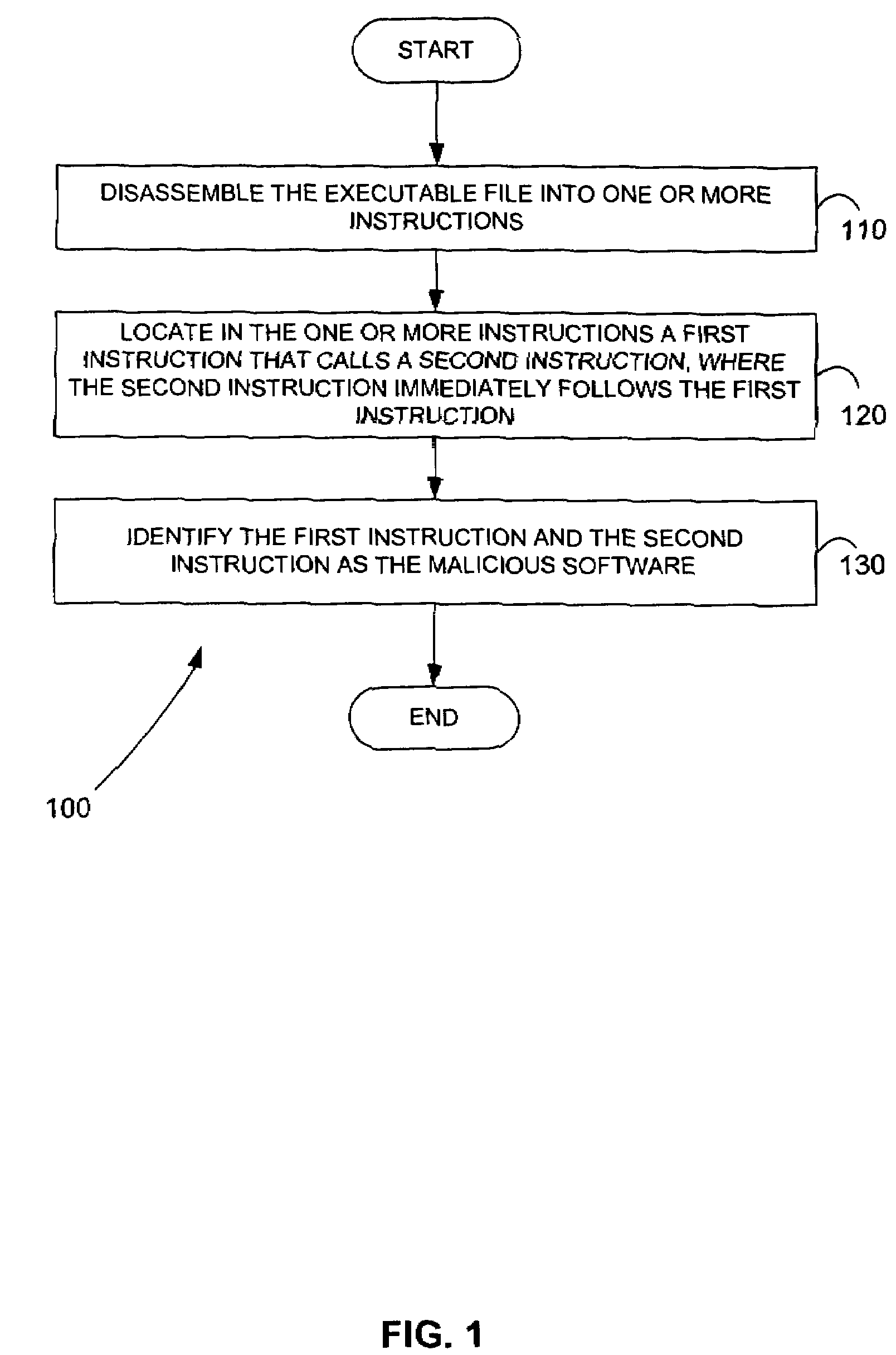
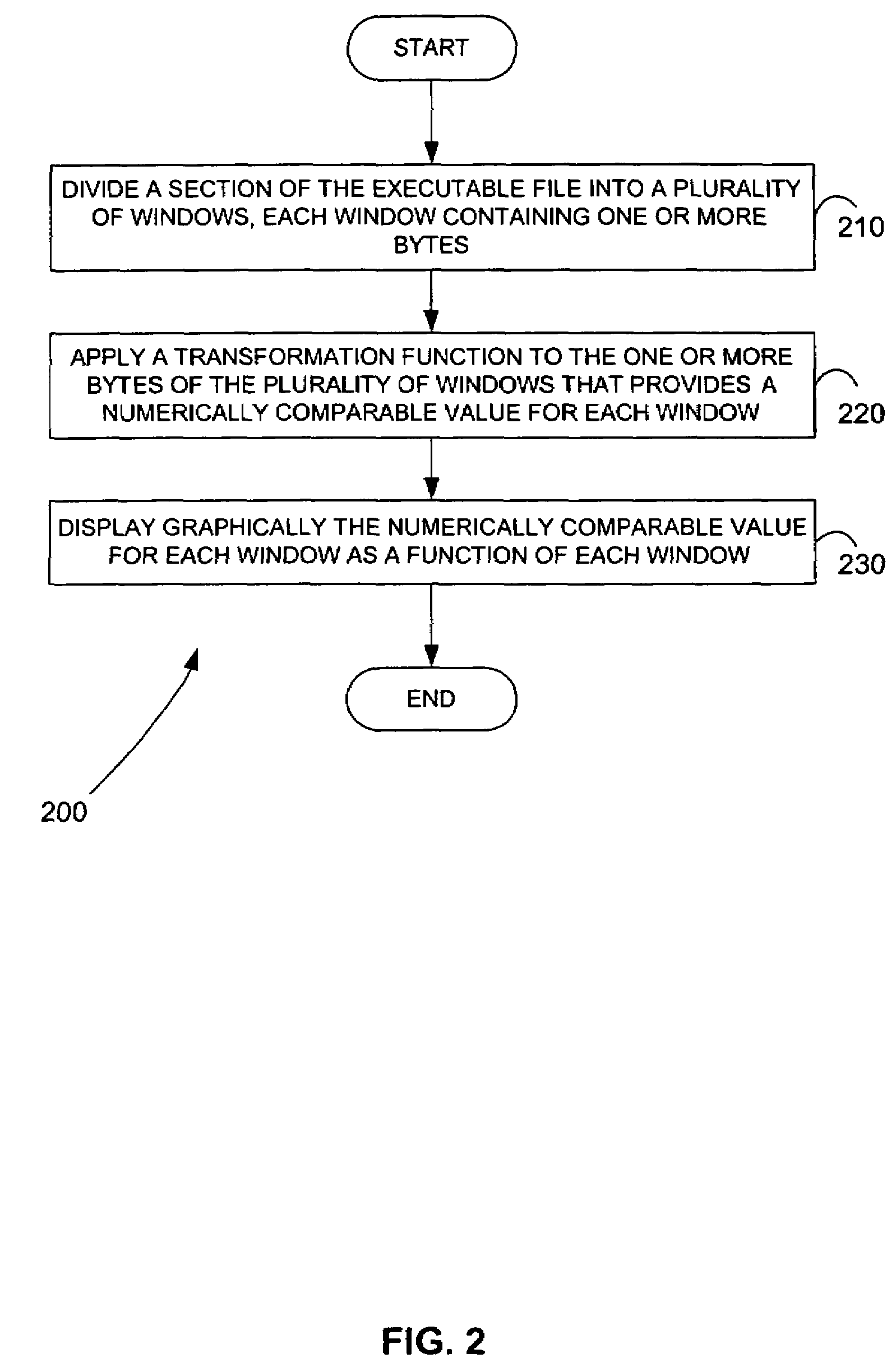
ActiveUS7644441B2Memory loss protectionEncryption apparatus with shift registers/memoriesGraphicsEncrypted function
Malicious software is identified in an executable file by identifying malicious structural features, decryption code, and cryptographic functions. A malicious structural feature is identified by comparing a known malicious structural feature to one or more instructions of the executable file. A malicious structural feature is also identified by graphically and statistically comparing windows of bytes or instructions in a section of the executable file. Cryptography is an indicator of malicious software. Decryption code is identified in an executable file by identifying a tight loop around a reversible instruction that writes to random access memory. Cryptographic functions are identified in an executable file be obtaining a known cryptographic function and performing a string comparison of the numeric constants of the known cryptographic function with the executable file.
Owner:SYNOPSYS INC
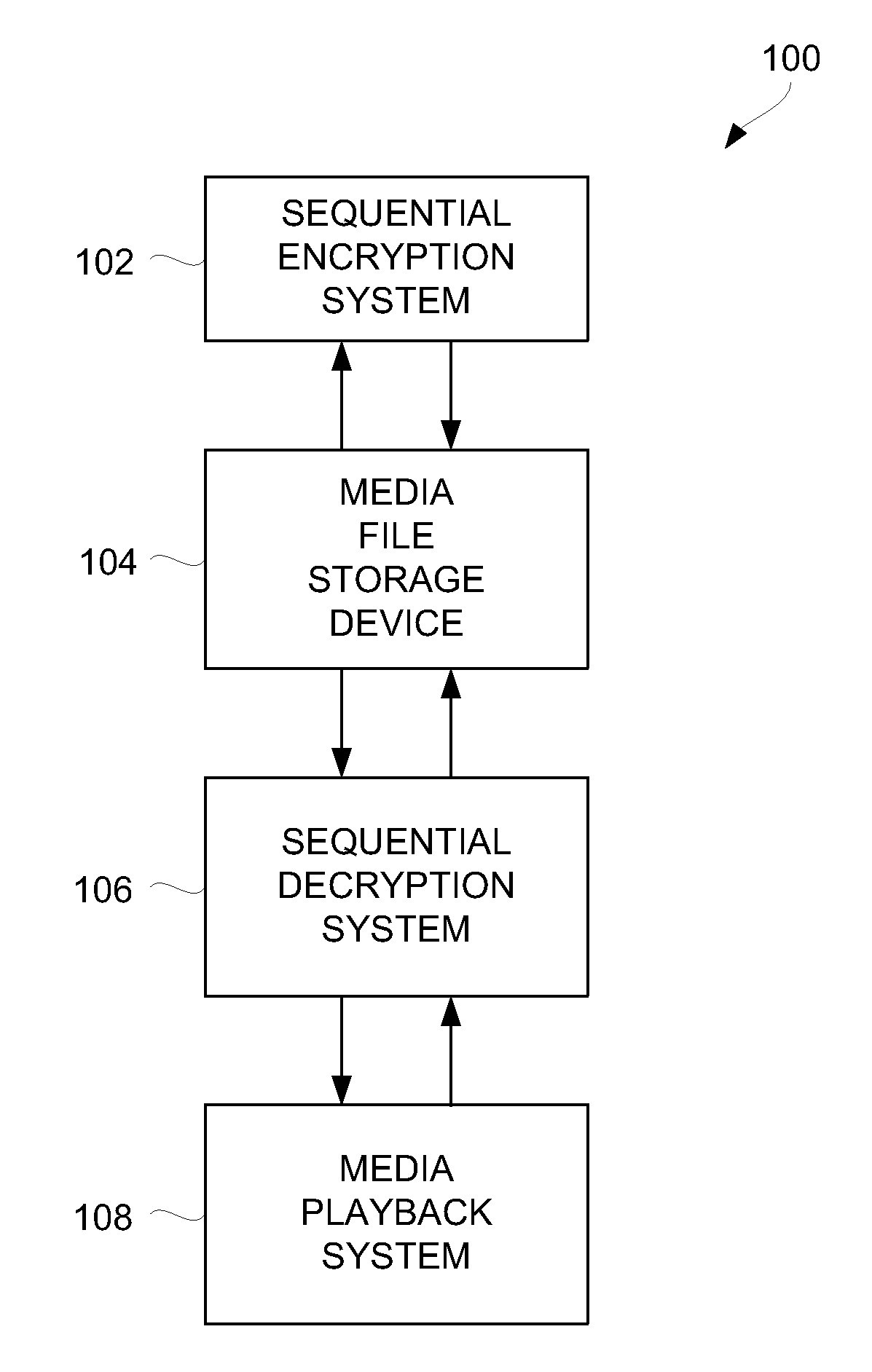
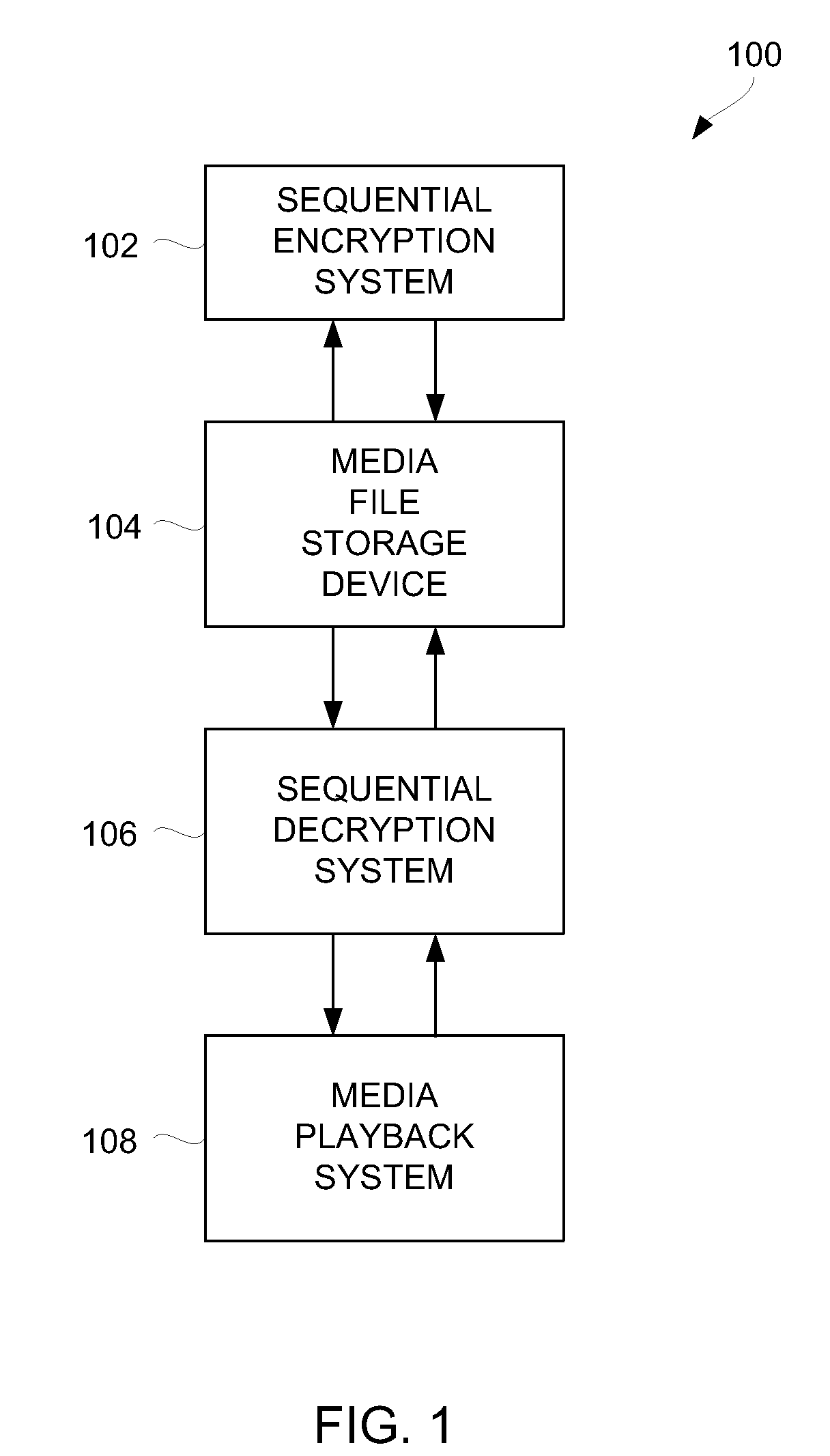
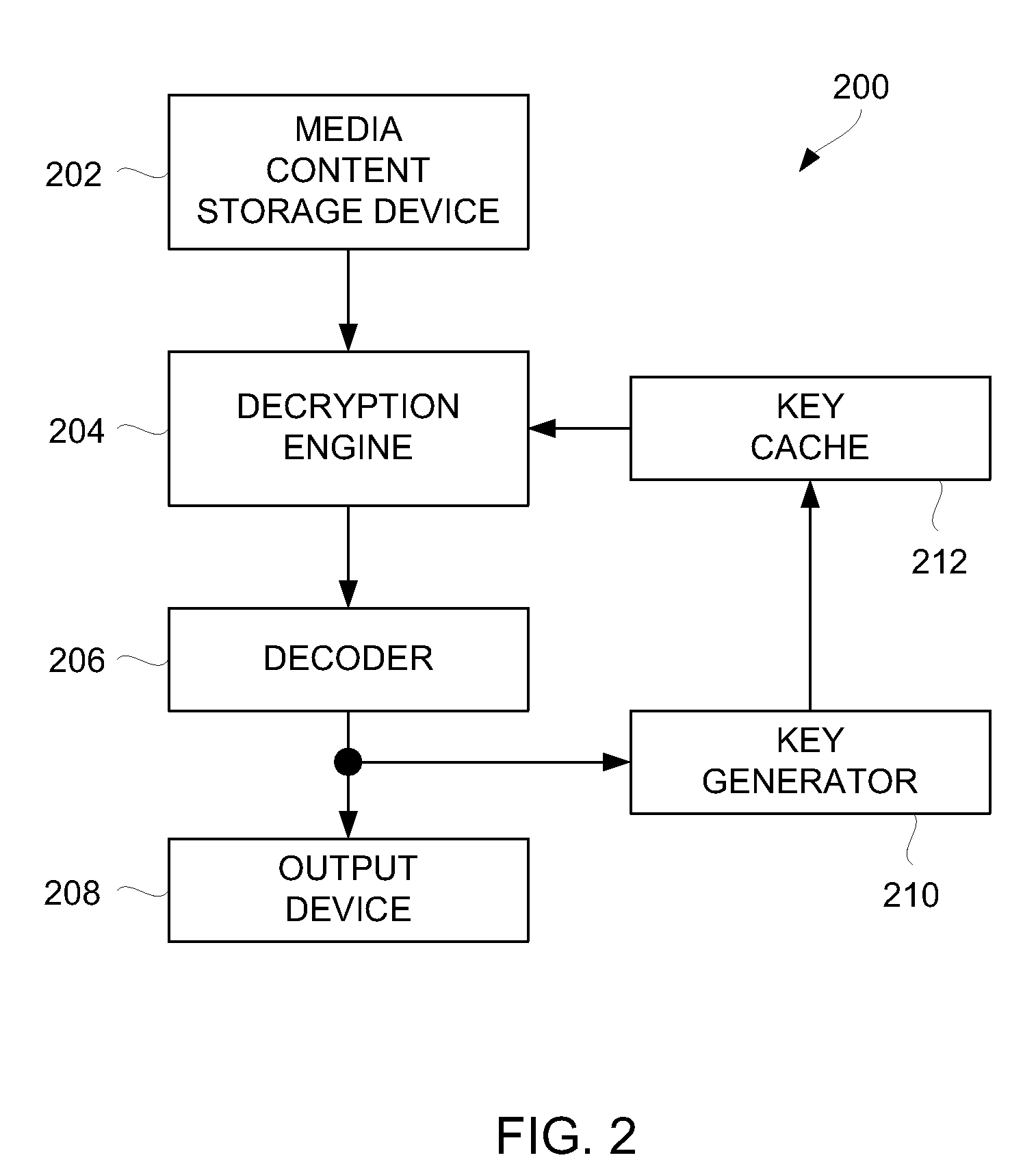
Method and System for Ensuring Sequential Playback of Digital Media
ActiveUS20100082970A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareCipher
Techniques for ensuring that media playback proceeds sequentially through media content of a digital media asset are disclosed. In one embodiment, distinct portions (e.g., segments) of a digital media asset can be separately encrypted such that on playback decoded data being output from at least one prior portion can be used to derive a cryptographic key that is used in decrypting a subsequent portion of the digital media asset.
Owner:APPLE INC
Systems and methods for blockchain virtualization and scalability
PendingUS20170337534A1Encryption apparatus with shift registers/memoriesCryptography processingVirtualizationComputer science
A virtualized blockchain forest includes a plurality of individual blockchains. Each individual blockchain of the plurality includes a blockchain height, a genesis block, and at least one additional block. The virtualized blockchain forest further includes a plurality of participating processors that make up a consensus pool, and a blockchain forest height having a time-sequenced start-to-finish length of blocks among the collective plurality of individual blockchains. The virtualized blockchain forest is configured to aggregate different ones of the plurality of individual blockchains, and is further configured to terminate individual ones of plurality of individual blockchains.
Owner:CABLE TELEVISION LAB
Anti tamper encapsulation for an integrated circuit
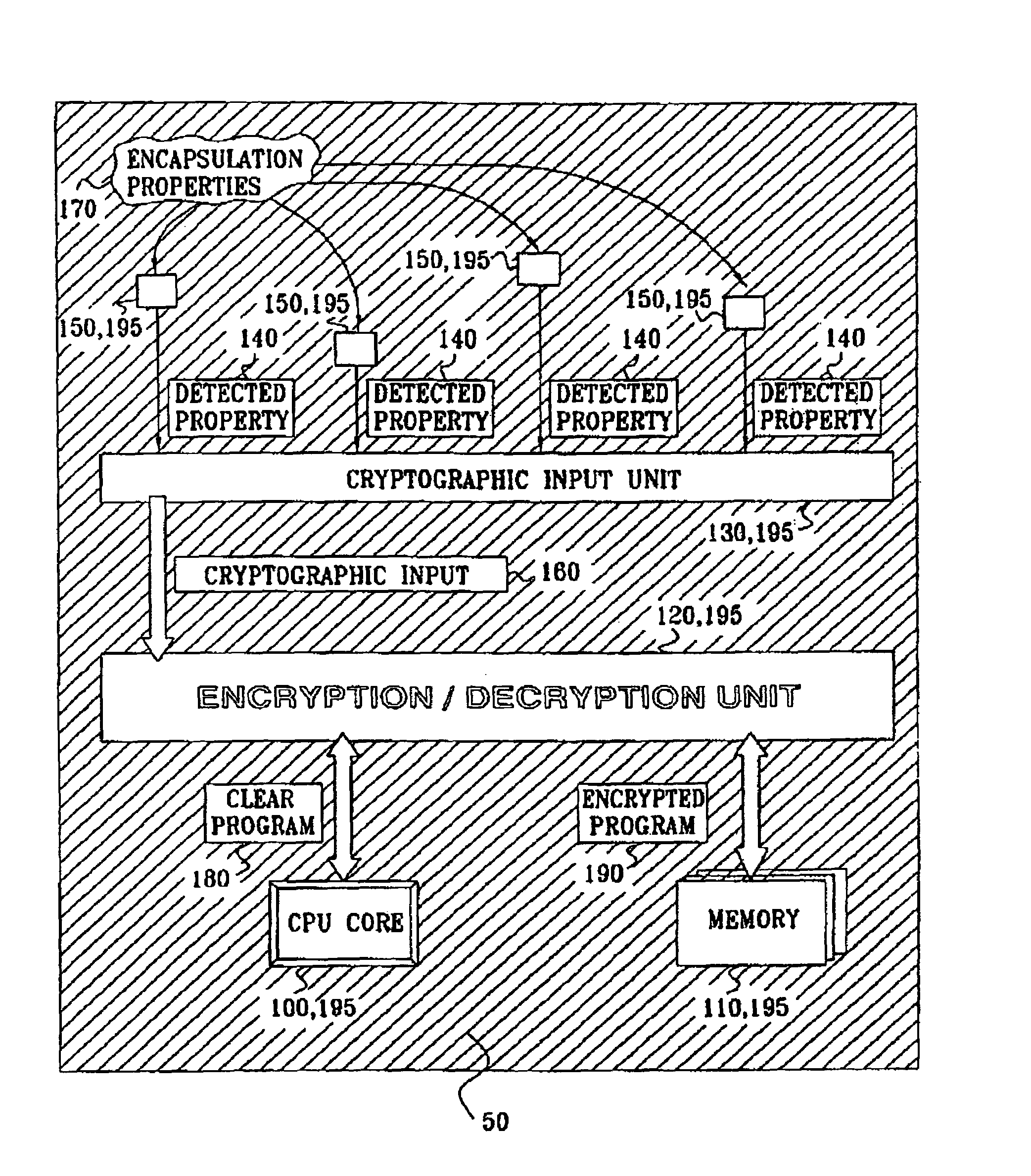
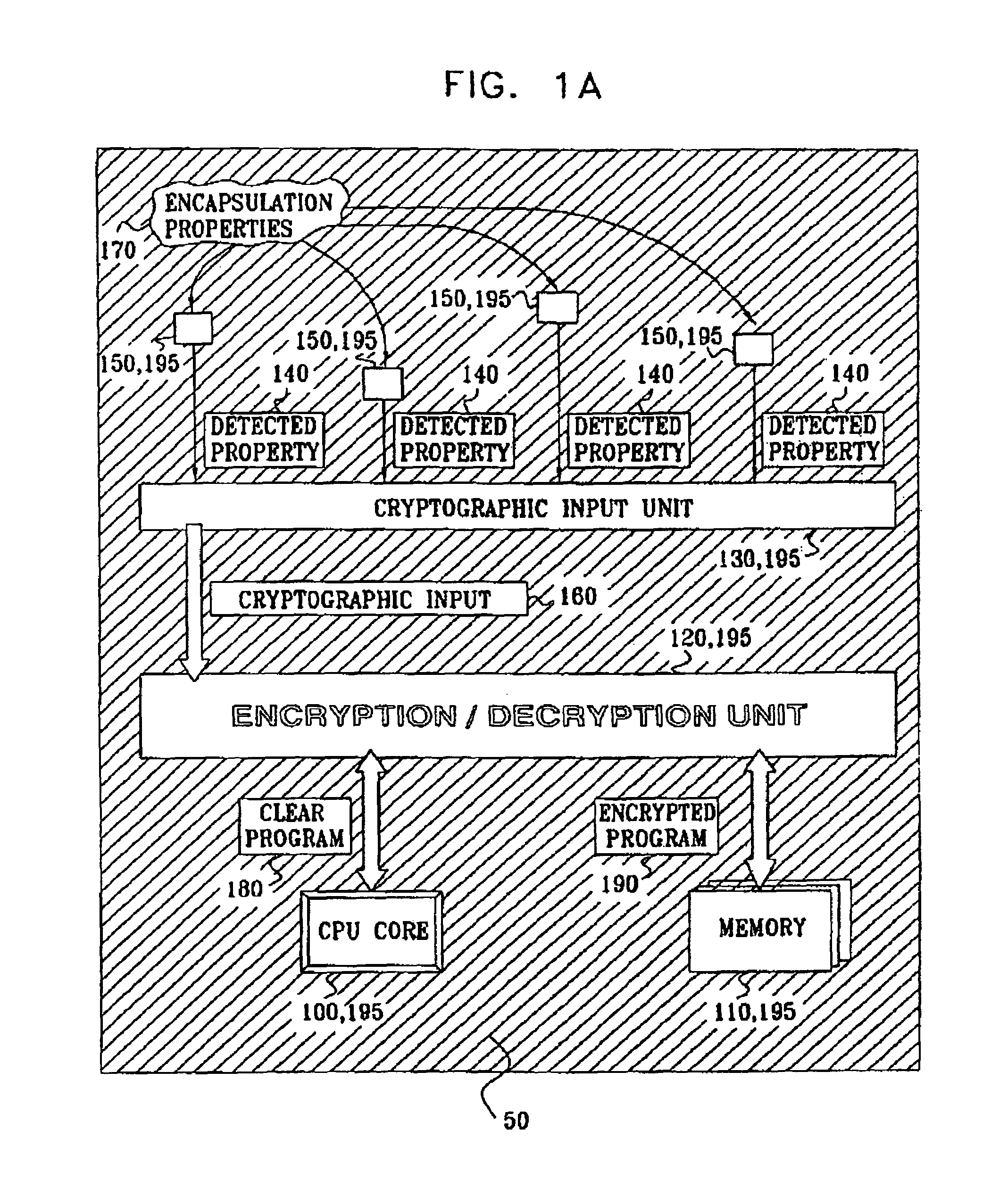
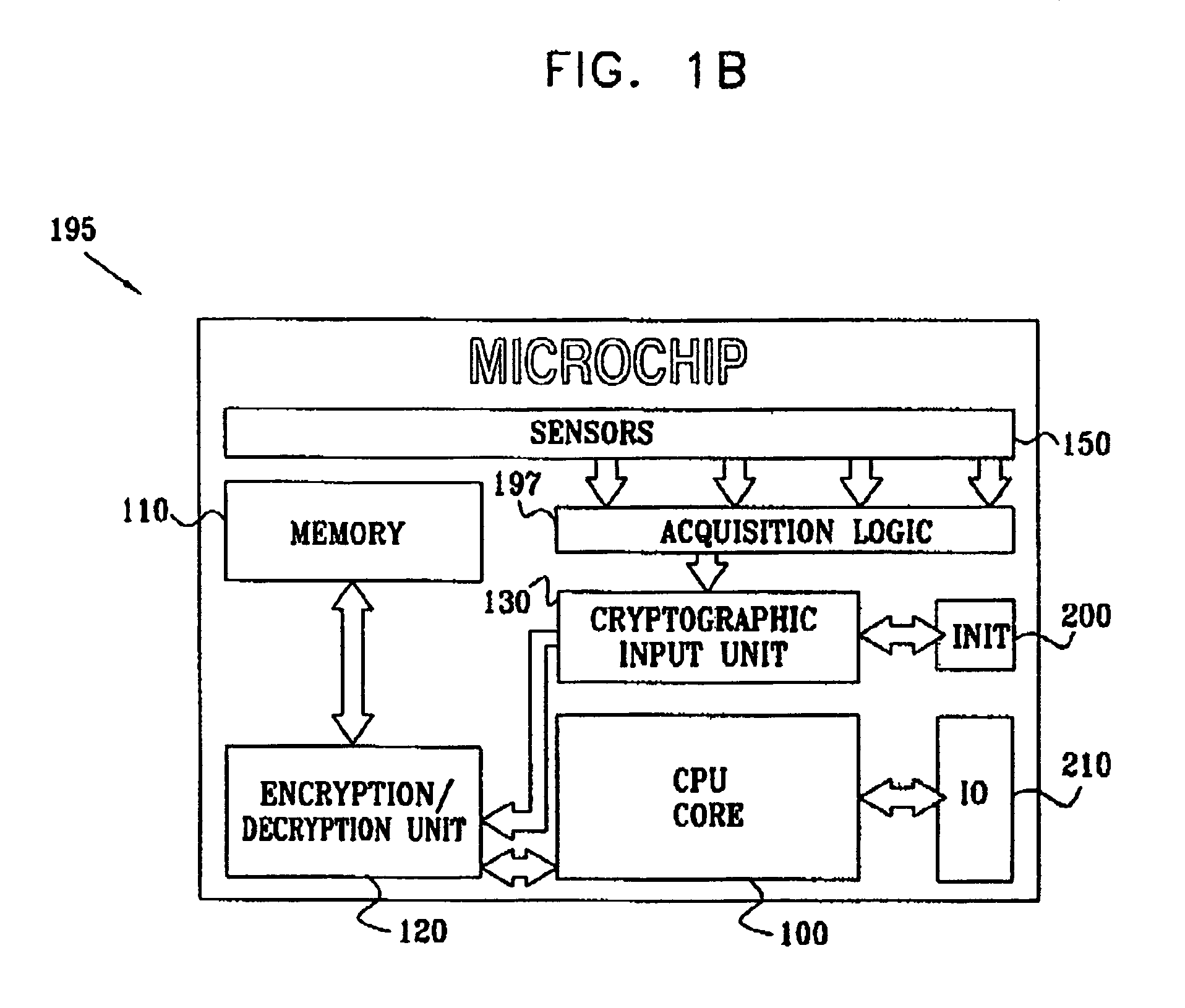
InactiveUS7005733B2Protected contentReduce accessKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareEncryption
An integrated circuit device comprising: a circuit which uses encryption; and an encapsulation packaging layer; in which the circuit is responsive to at least one physical parameter of the encapsulation to apply the encryption and / or decryption by reading the key therefrom, so that tampering with the encapsulation to gain access to the circuit causes the encryption and / or decryption to fail.
Owner:UNIVERSAL IMAGING IND LLC
Method and Apparatus for Hardware-Accelerated Encryption/Decryption
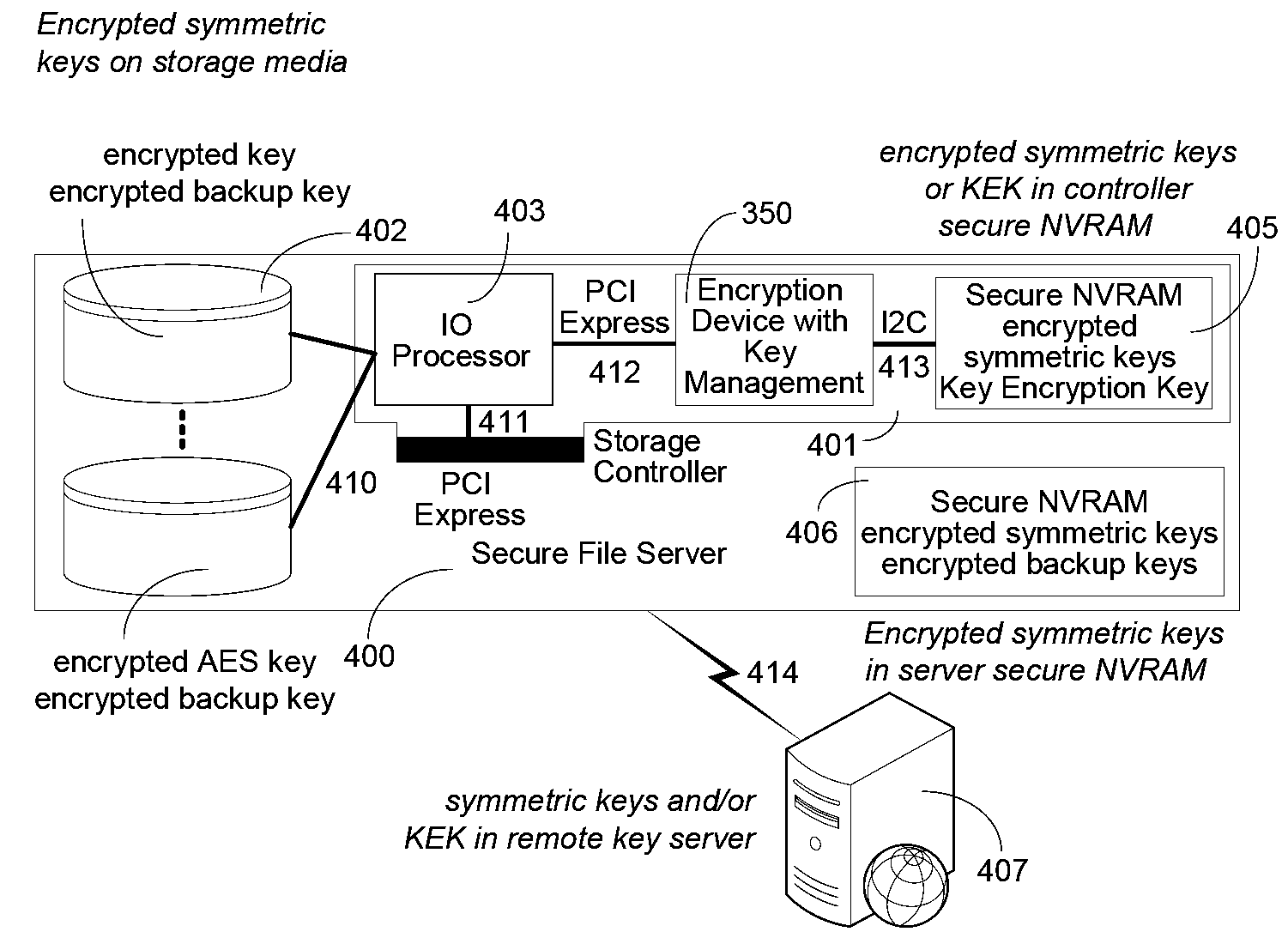
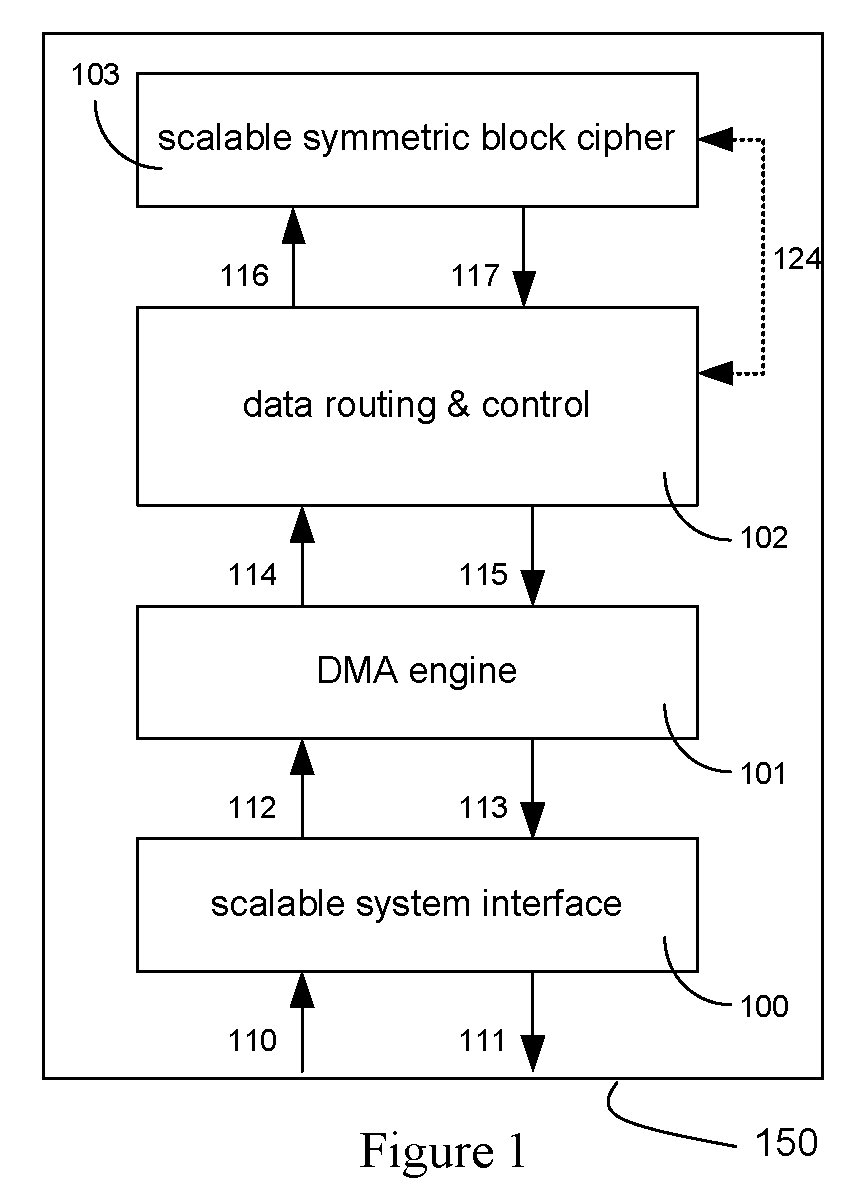
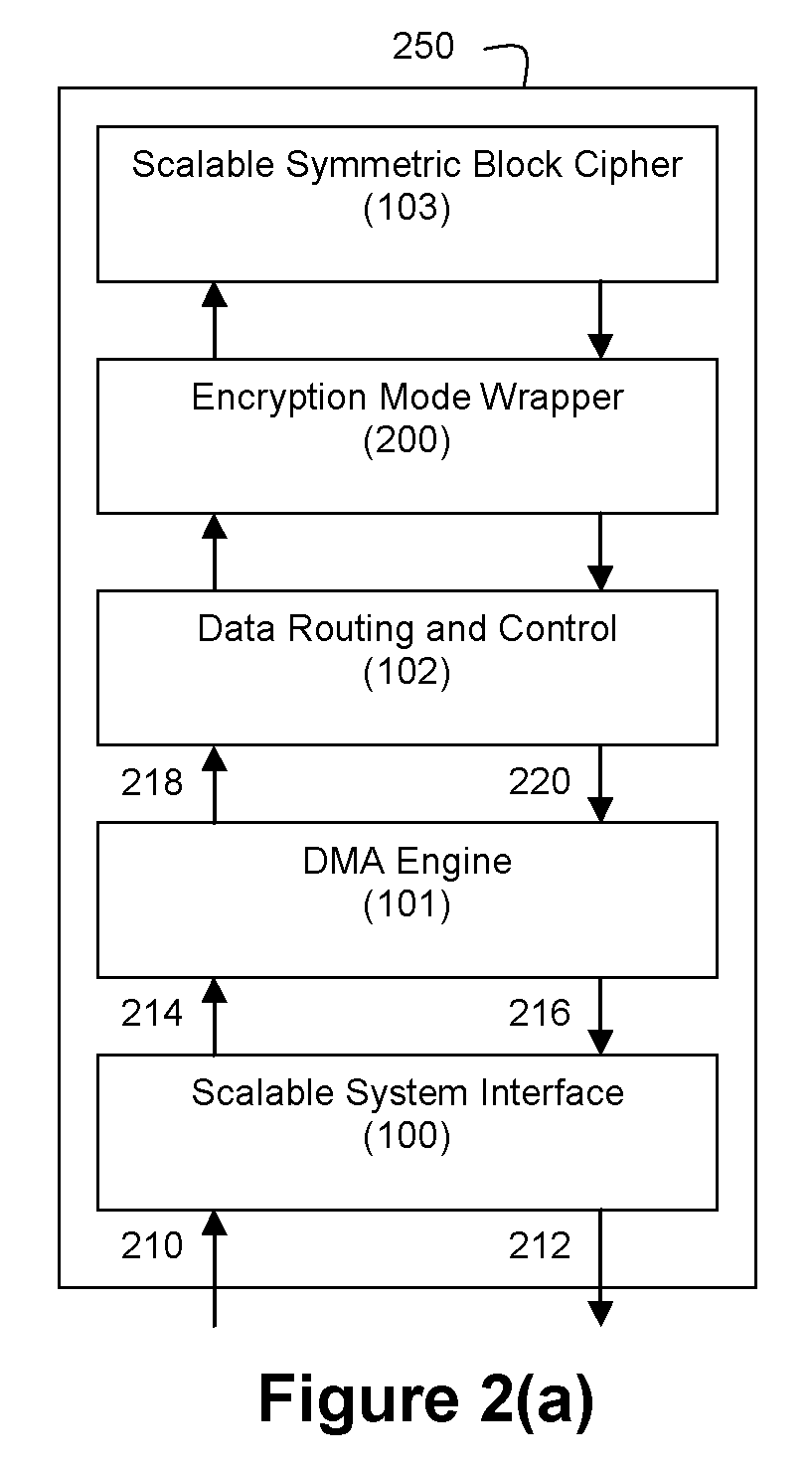
ActiveUS20090060197A1Avoid contactMaximize availabilityEncryption apparatus with shift registers/memoriesSecret communicationMultiple encryptionComputer hardware
An integrated circuit for data encryption / decryption and secure key management is disclosed. The integrated circuit may be used in conjunction with other integrated circuits, processors, and software to construct a wide variety of secure data processing, storage, and communication systems. A preferred embodiment of the integrated circuit includes a symmetric block cipher that may be scaled to strike a favorable balance among processing throughput and power consumption. The modular architecture also supports multiple encryption modes and key management functions such as one-way cryptographic hash and random number generator functions that leverage the scalable symmetric block cipher. The integrated circuit may also include a key management processor that can be programmed to support a wide variety of asymmetric key cryptography functions for secure key exchange with remote key storage devices and enterprise key management servers. Internal data and key buffers enable the device to re-key encrypted data without exposing data. The key management functions allow the device to function as a cryptographic domain bridge in a federated security architecture.
Owner:IP RESERVOIR
Access Control System And Method Based On Hierarchical Key, And Authentication Key Exchange Method Thereof
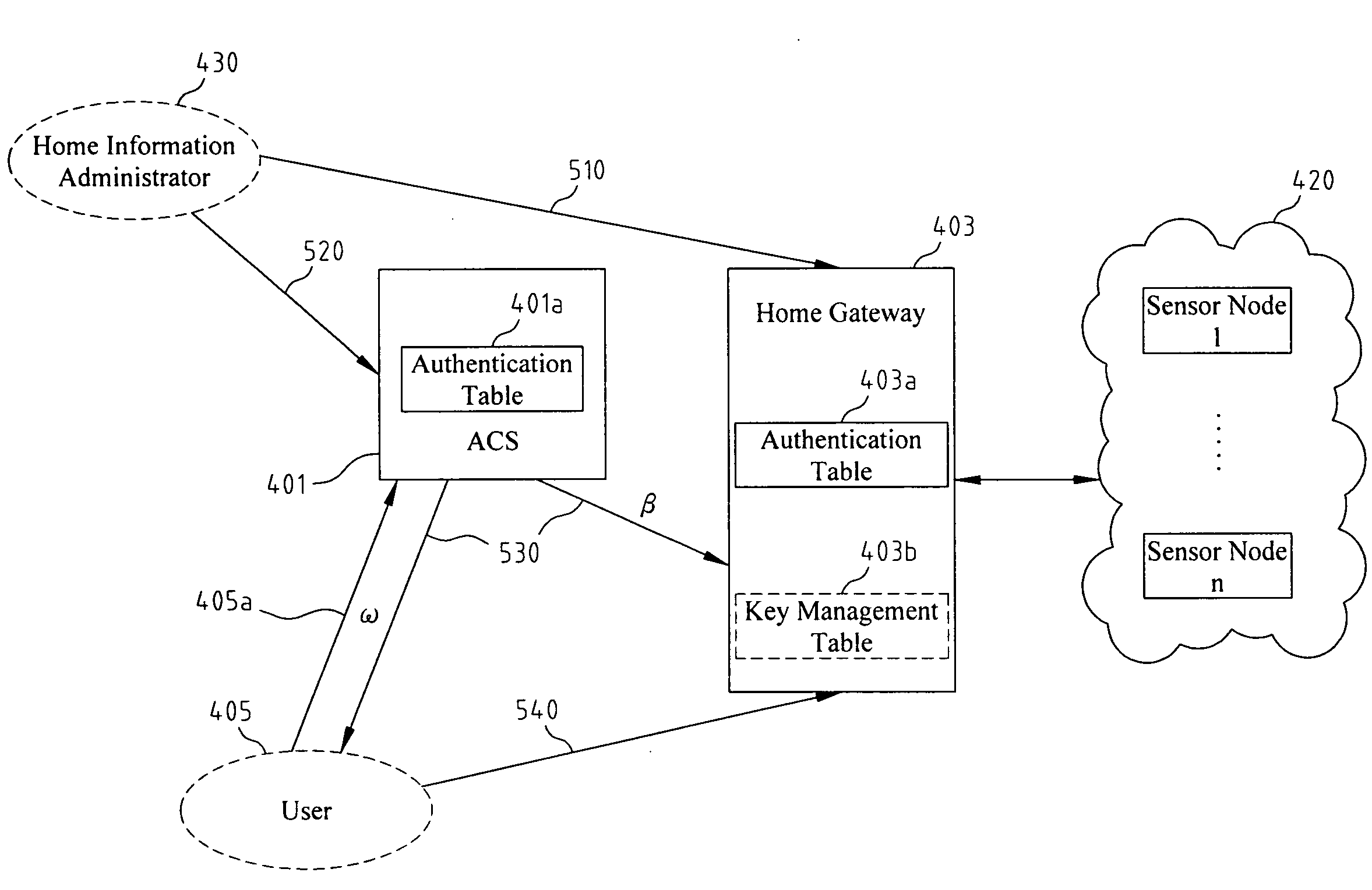
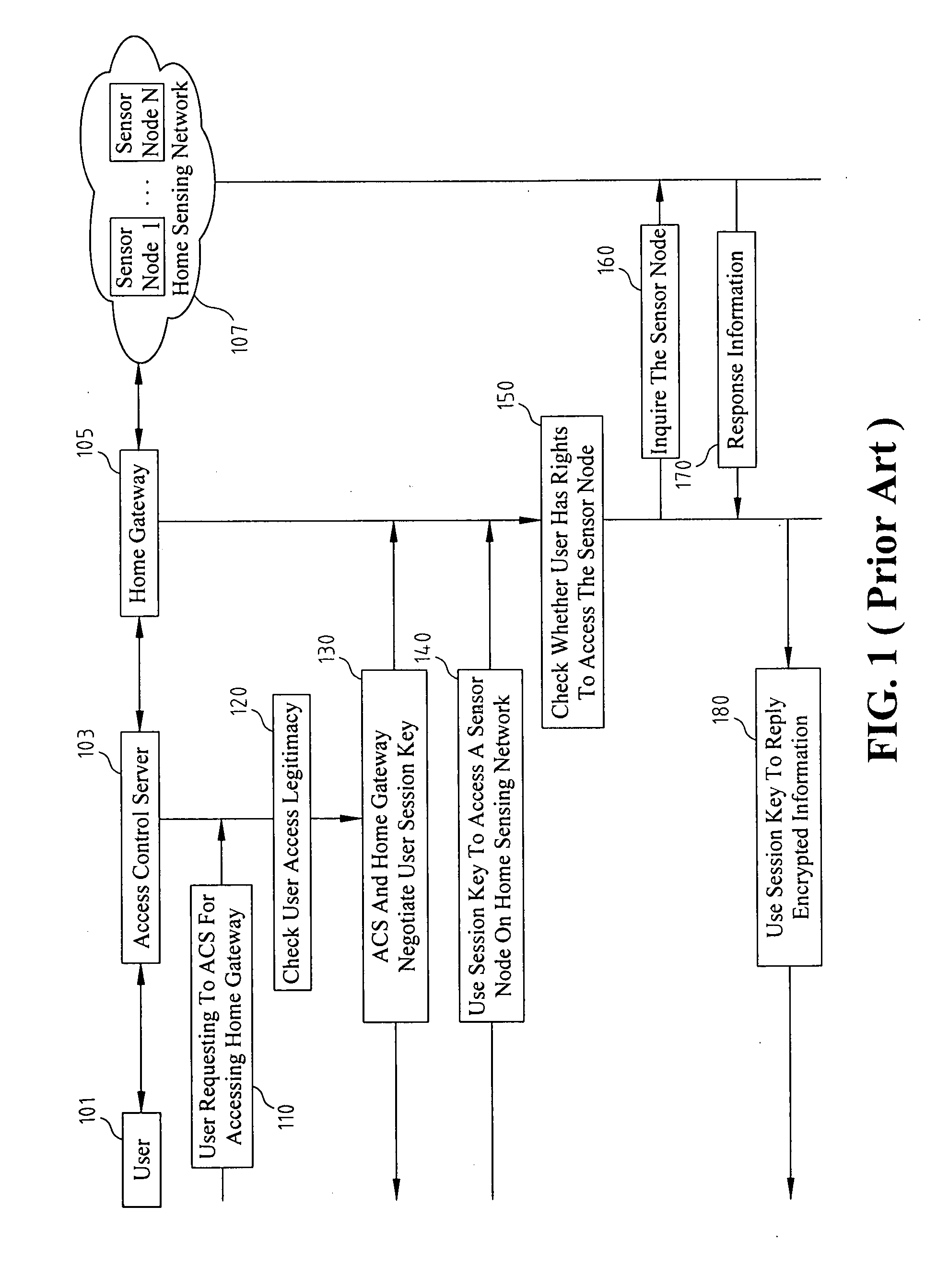
ActiveUS20100122091A1Encryption apparatus with shift registers/memoriesUser identity/authority verificationPasswordControl system
Disclosed relates to an access control system and method based on hierarchical keys. The system comprises an access control server (ACS), a home gateway, and a plurality of sensor devices disposed on a home network. The ACS sets up user's access limits of authority and authorization verifier, and saves the related data of user's password and the user's access limits of authority. The gateway records the authority limits' level and the authority limits' key which are constructed based on a hierarchical key structure. When a user logs in the ACS to request access, an one-time communication key between the user and the home gateway is established by exchanging the ticket and the token that are issued by the ACS. This allows the user to access the information of the sensor devices.
Owner:IND TECH RES INST
Wearable communication device, security complex and user interface
InactiveUS20140337621A1Input/output for user-computer interactionEncryption apparatus with shift registers/memoriesCommunicator deviceUser interface
A wearable electronic modular computer-communicator device is described which may interact and cooperate with other wearable, vehicle-mounted, object-mounted or stationary electronic devices that are also described.
Owner:NAKHIMOV SERGUEI
Secure data parser method and system
InactiveUS20080244277A1Minimal compute resourceAvoid the needEncryption apparatus with shift registers/memoriesDigital data processing detailsGovernmental agencyVariospora
The present invention provides a method and system for securing sensitive data from unauthorized access or use. The method and system of the present invention is useful in a wide variety of settings, including commercial settings generally available to the public which may be extremely large or small with respect to the number of users. The method and system of the present invention is also useful in a more private setting, such as with a corporation or governmental agency, as well as between corporation, governmental agencies or any other entity.
Owner:SECURITY FIRST INNOVATIONS LLC
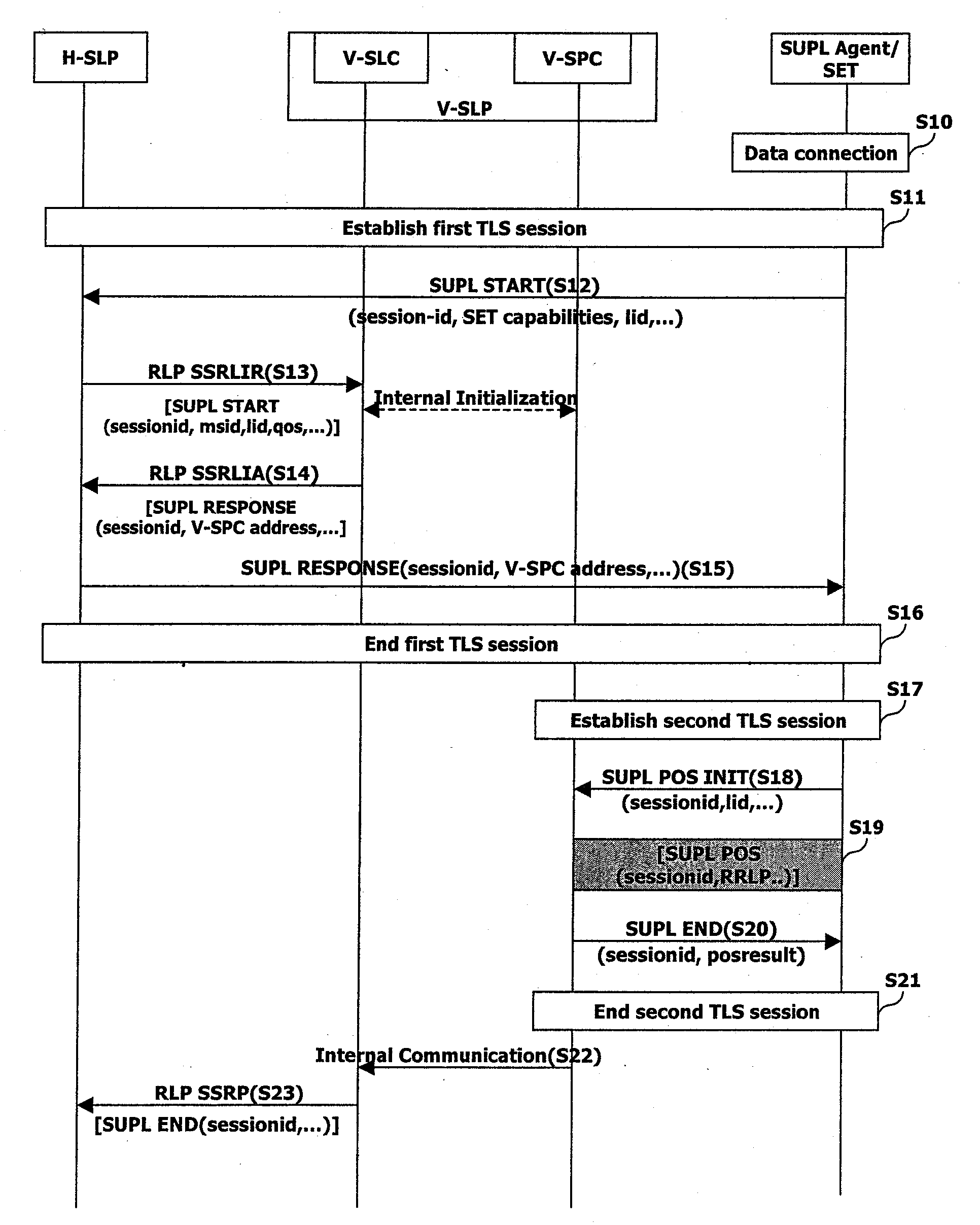
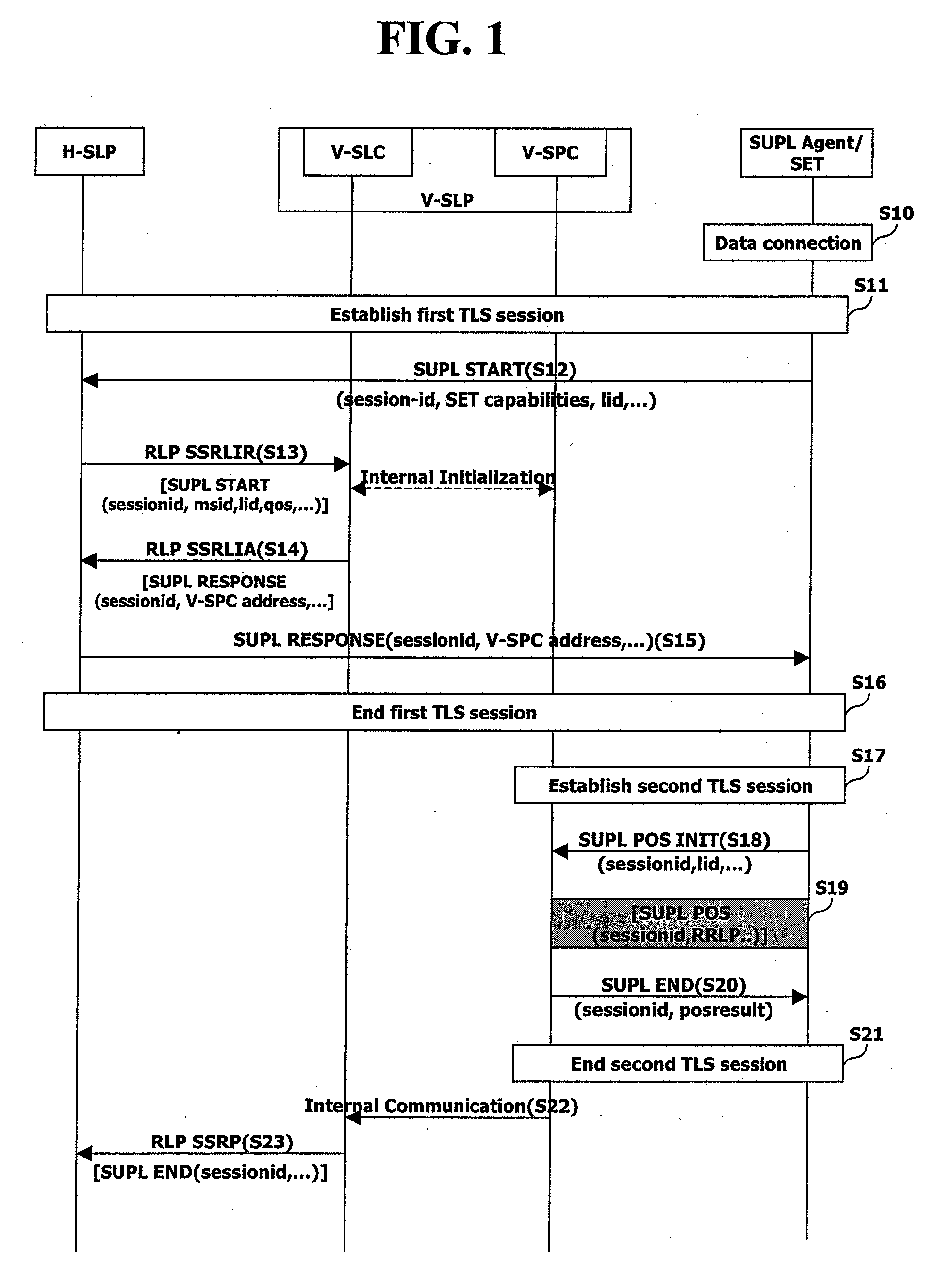
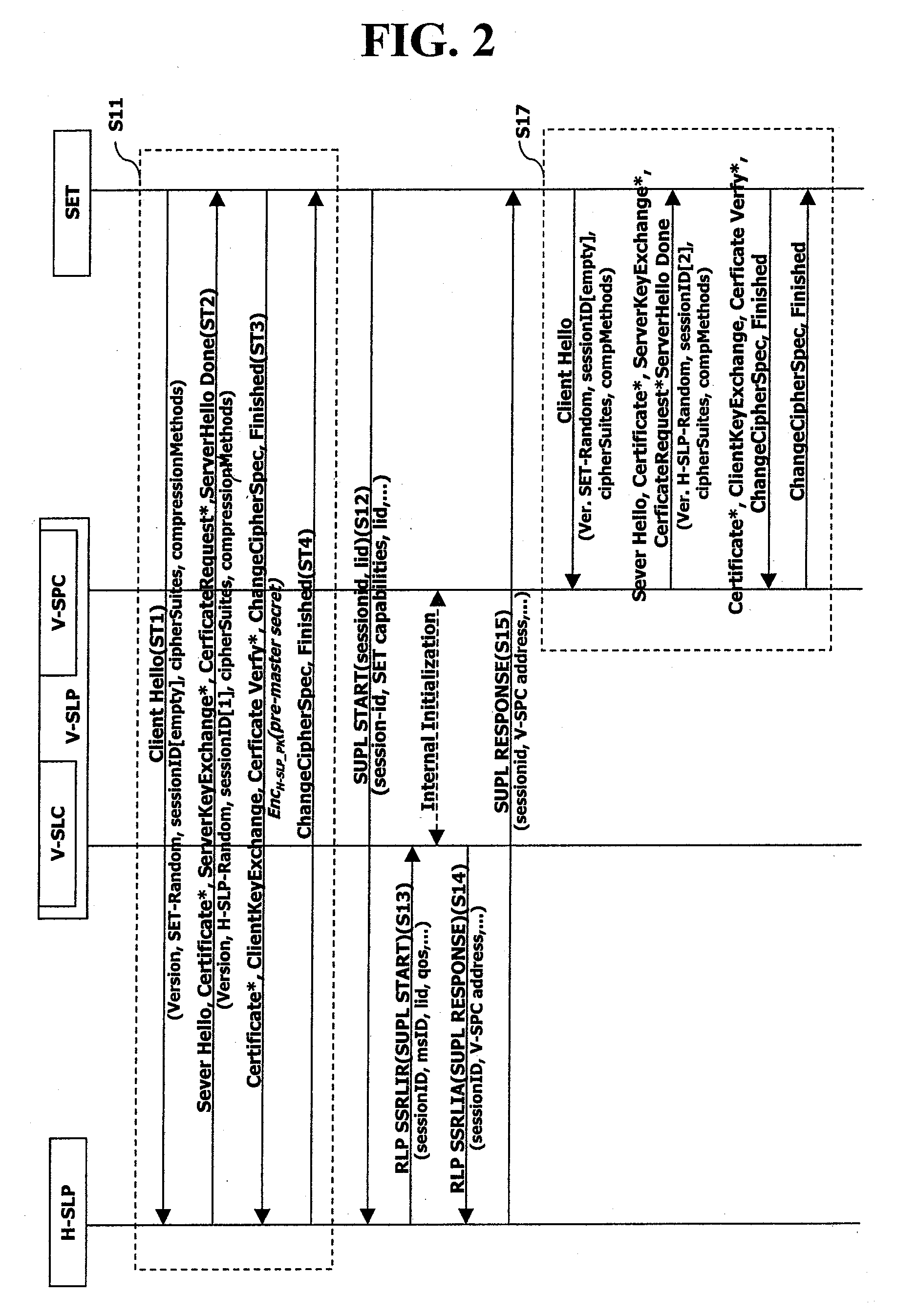
Tls Session Management Method In Supl-Based Positioning System
InactiveUS20080109650A1Improve efficiencyEncryption apparatus with shift registers/memoriesSecret communicationSession managementRoaming
Owner:LG ELECTRONICS INC
Blockchain system for confidential and anonymous smart contracts
ActiveUS20190164153A1Improve confidentialityEnhanced anonymityEncryption apparatus with shift registers/memoriesCryptography processingInternet privacyPrivacy preserving
Blockchain-based, smart contract platforms have great promise to remove trust and add transparency to distributed applications. However, this benefit often comes at the cost of greatly reduced privacy. Techniques for implementing a privacy-preserving smart contract is described. The system can keep accounts private while not losing functionality and with only a limited performance overhead. This is achieved by building a confidential and anonymous token on top of a cryptocurrency. Multiple complex applications can also be built using the smart contract system.
Owner:VISA INT SERVICE ASSOC +1
Method and system for tuning blockchain scalability for fast and low-cost payment and transaction processing
ActiveUS10102265B1Privacy protectionScalability issueEncryption apparatus with shift registers/memoriesCryptography processingPaymentSmart contract
A method of synchronizing transactions between blockchains comprising receiving first and second pluralities of transactions on a first private blockchain network and recording them to first and second private blocks on the first private blockchain network, respectively, generating a first merged block comprising the first private block and the second private block and recording the first merged block to a single block on a second blockchain network, recording each of the first and second private blocks and the first merged block to a first private smart contract linked to the first private blockchain network, performing a synchronization process between the first private smart contract and a second smart contract linked to the second blockchain network, defining a second smart contract, and performing a checkpointing process between the first private smart contract and the second smart contract. The first private blockchain network has a parameter difference from the second blockchain network.
Owner:MADISETTI VIJAY K
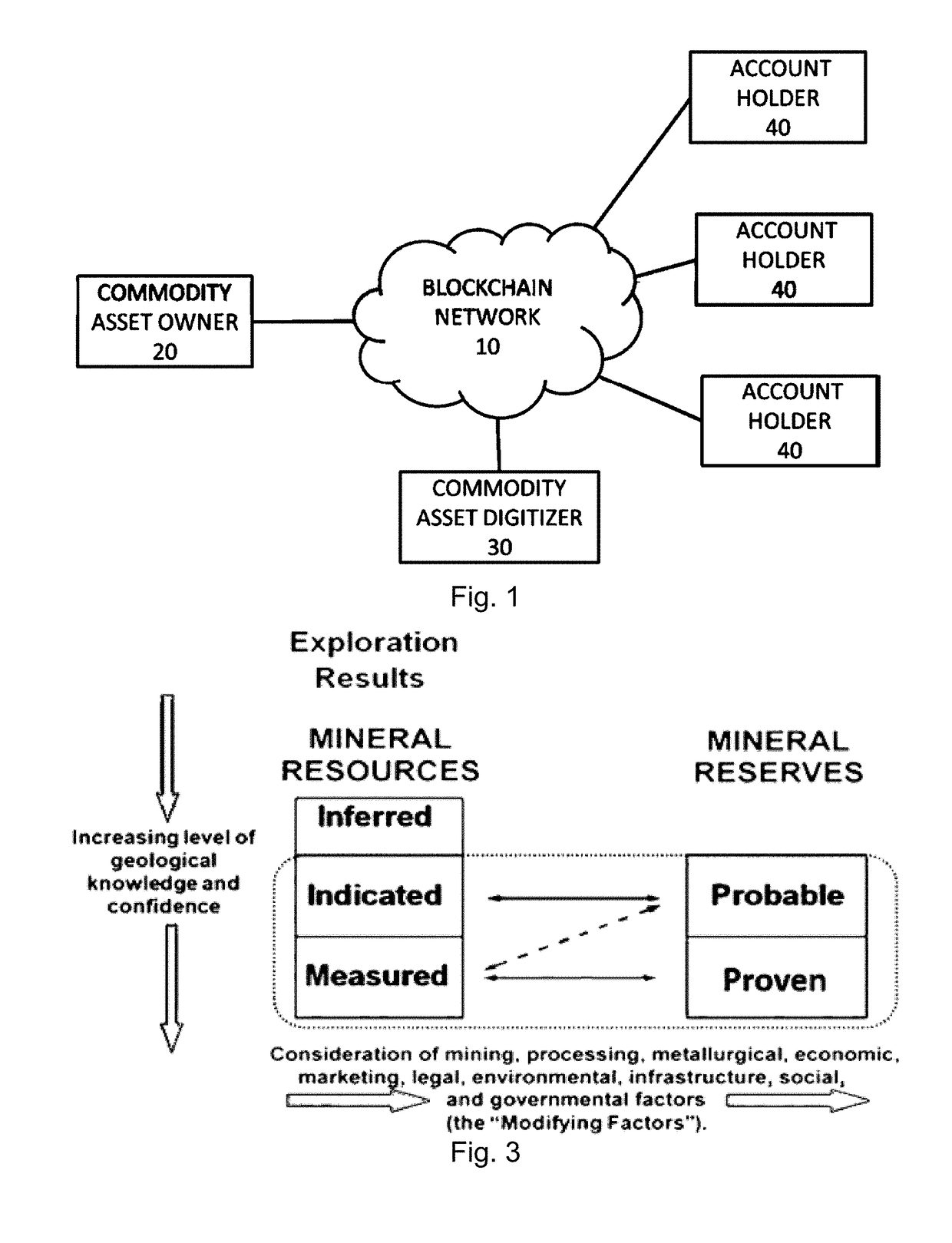
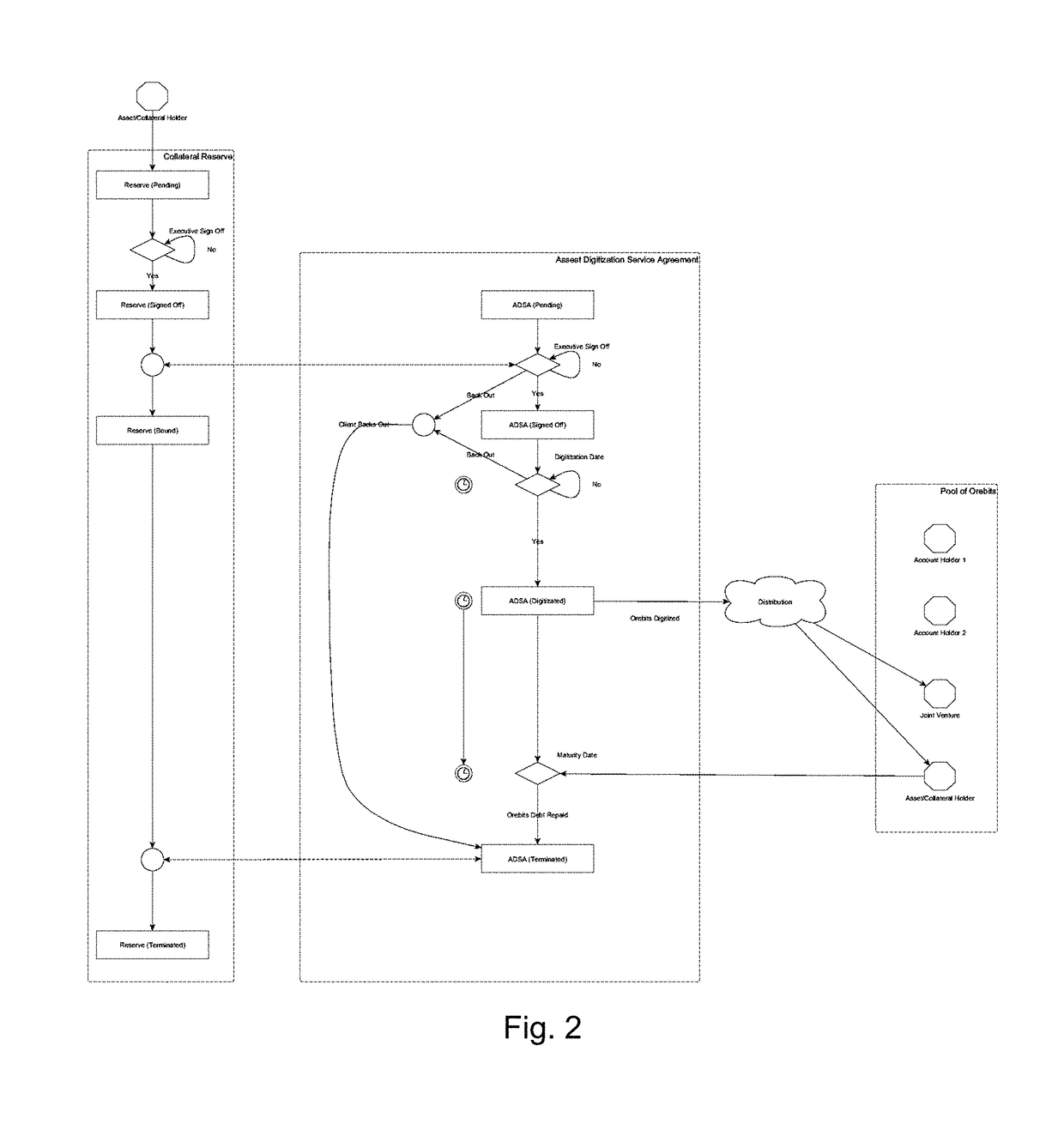
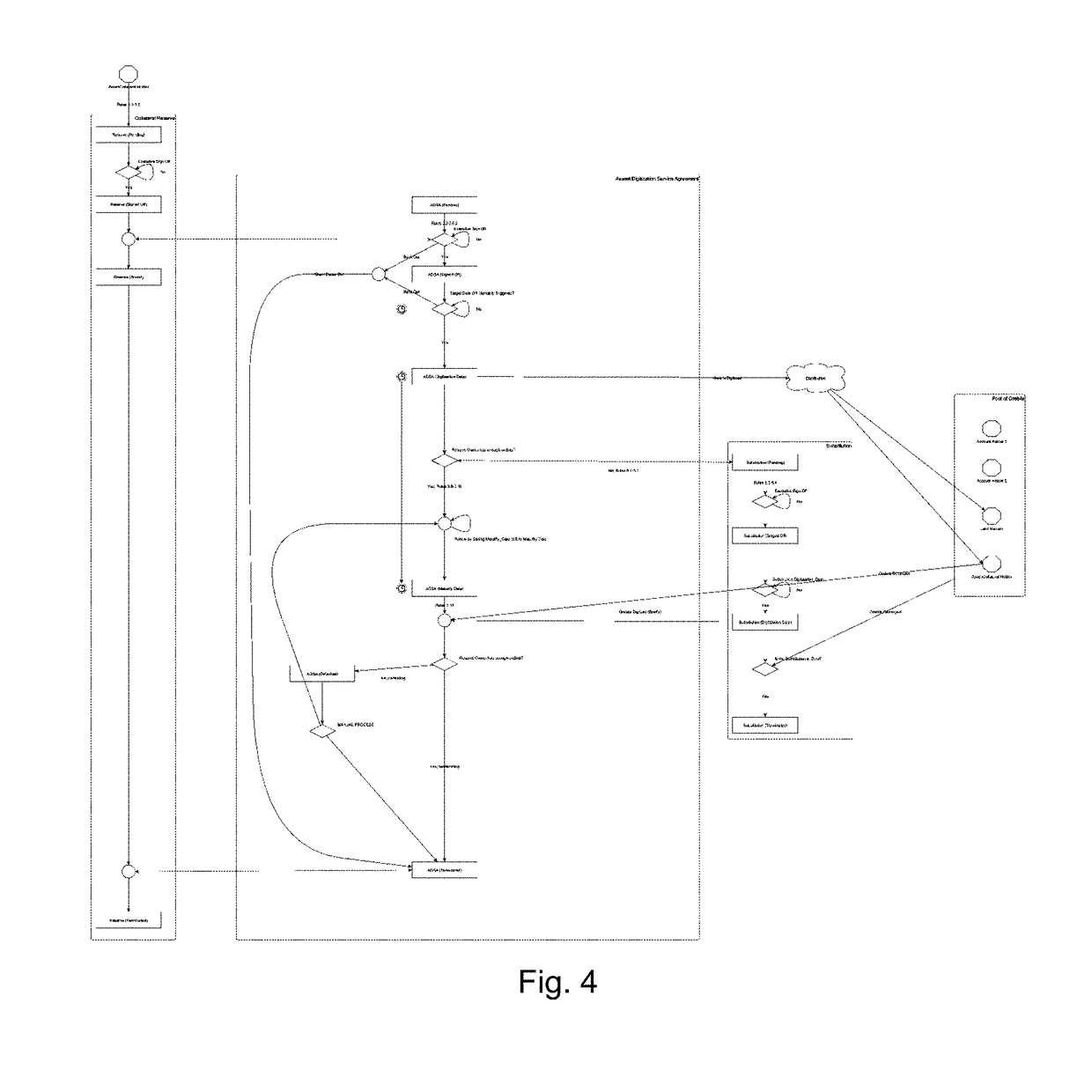
Method for creating commodity assets from unrefined commodity reserves utilizing blockchain and distributed ledger technology
ActiveUS20190080392A1FinanceEncryption apparatus with shift registers/memoriesFinancial transactionSmart contract
A method for creating an asset-backed distributed ledger token representing a smart contract, the token being backed by a pledge of an illiquid form of a precursor or means of production of a commodity asset, comprising receiving a pledge of unrefined or pre-commodity asset, digitizing the unrefined commodity asset into fractional representations of the commodity asset using smart contracts on a distributed ledger network, and allowing account holders access to the perform transactions on the distributed ledger network to trade the fractional representations under the terms of the smart contract.
Owner:STICHTING IP OVERSIGHT
System for encrypting content name
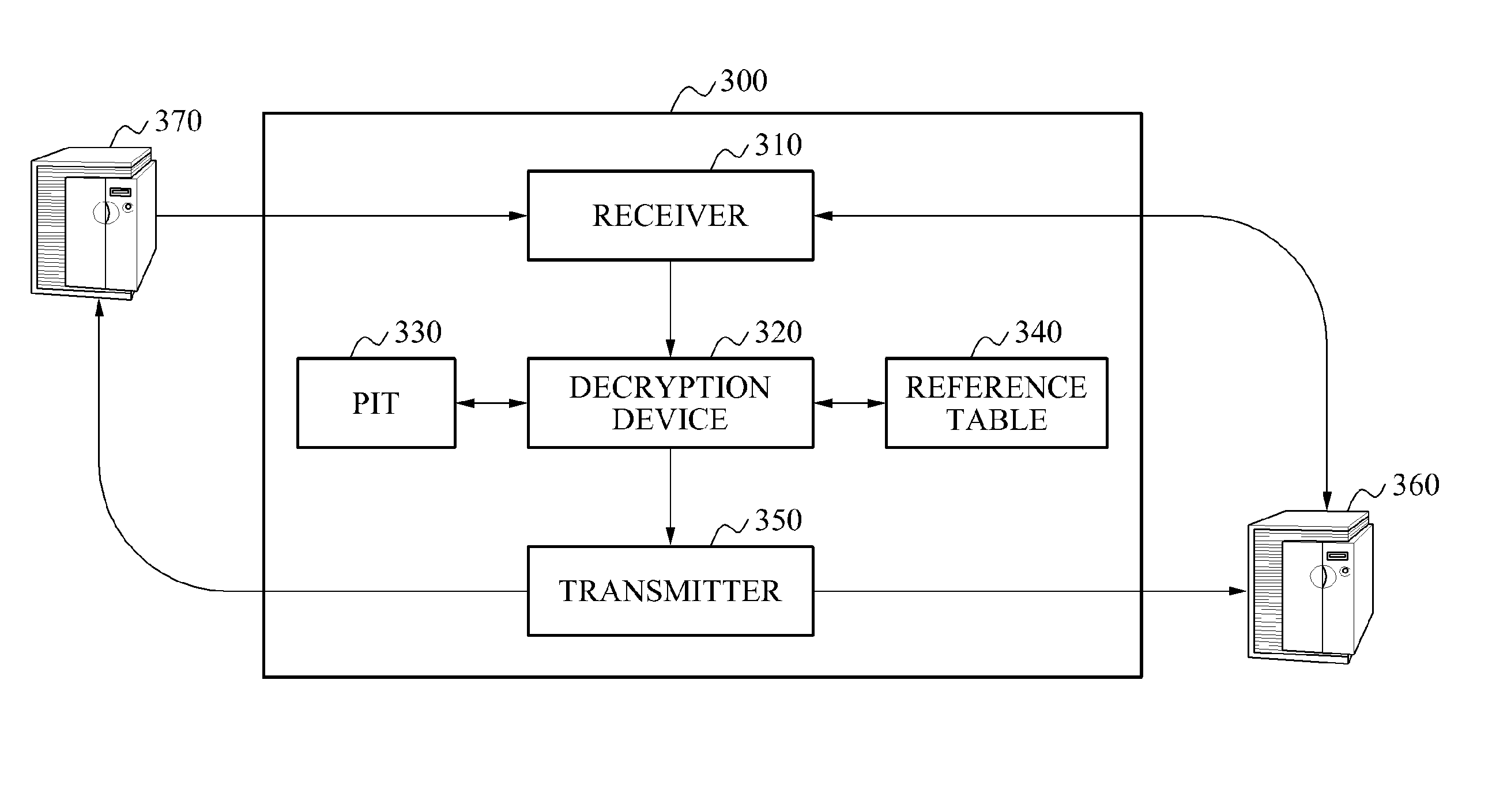
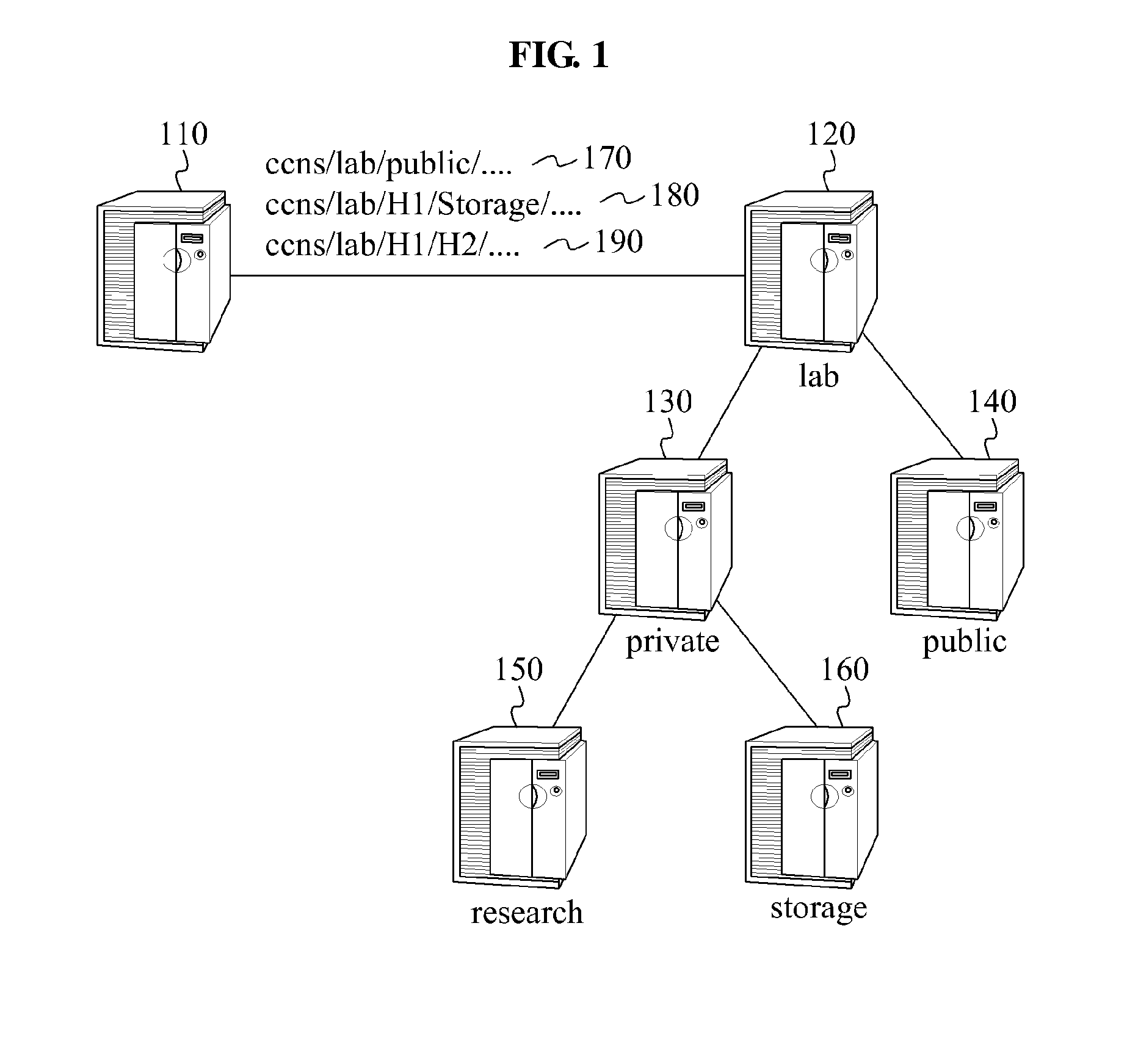
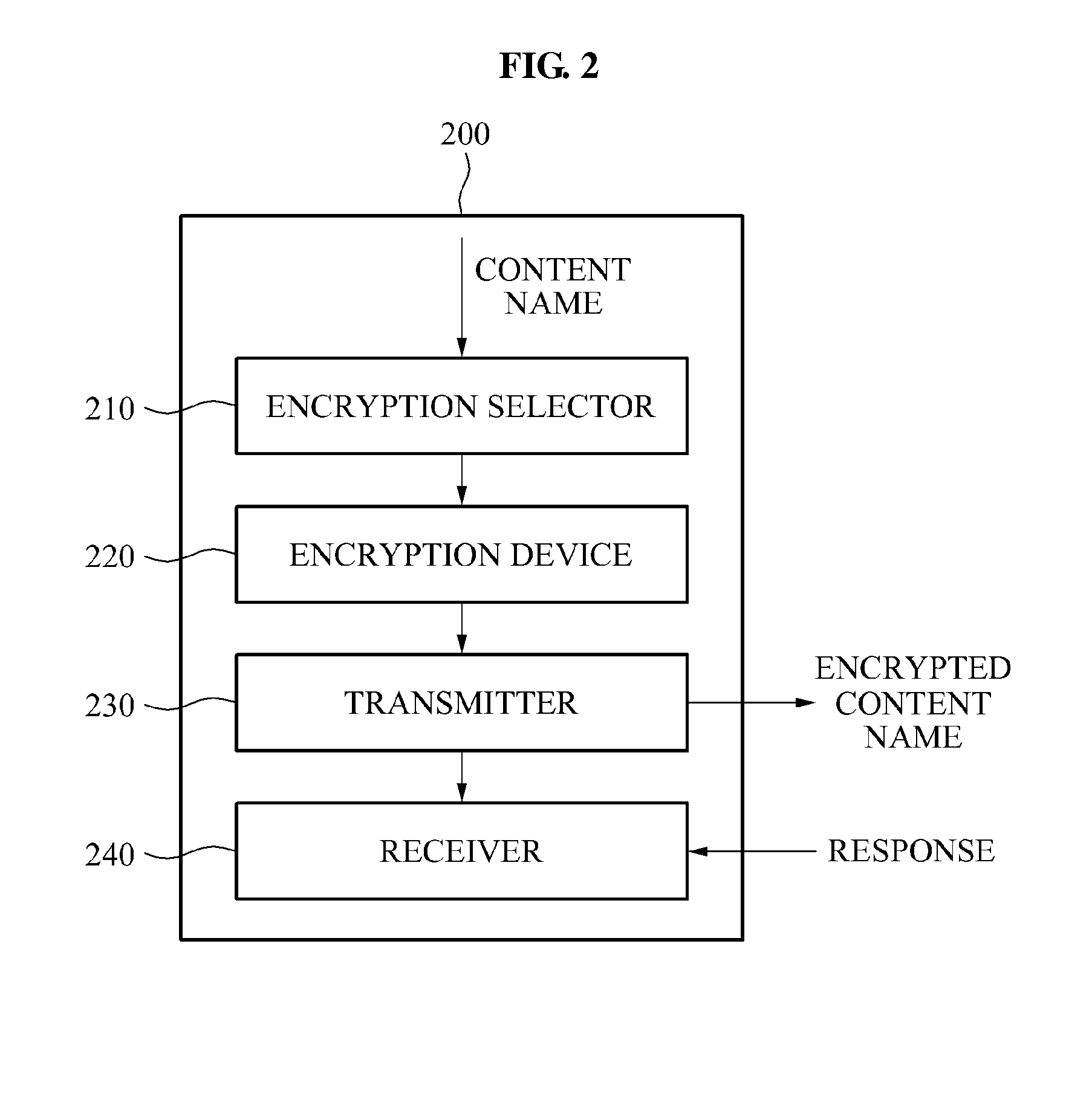
InactiveUS20140149733A1Well formedEncryption apparatus with shift registers/memoriesComputer networkHash function
A system encrypts a name of content stored in a node of a hierarchical structure. A content receiving node encrypts a name of a predetermined node among names of nodes included in a content name, such as by using a hash function, and transmits the encrypted content name to receive the stored content. A relay node receives the content name including the encrypted name of the node and decrypts the encrypted name of the node, such as by using a reference table. The relay node uses the decrypted node name to relay the content request to the content storage node. Since the content name is encrypted, content routing may be performed without disclosing information associated with a hierarchical structure in which the content is stored.
Owner:SAMSUNG ELECTRONICS CO LTD
System and method for validation of distributed data storage systems
InactiveUS20190132350A1Eliminate needConveniently determinedEncryption apparatus with shift registers/memoriesCryptography processingGraphicsReal time validation
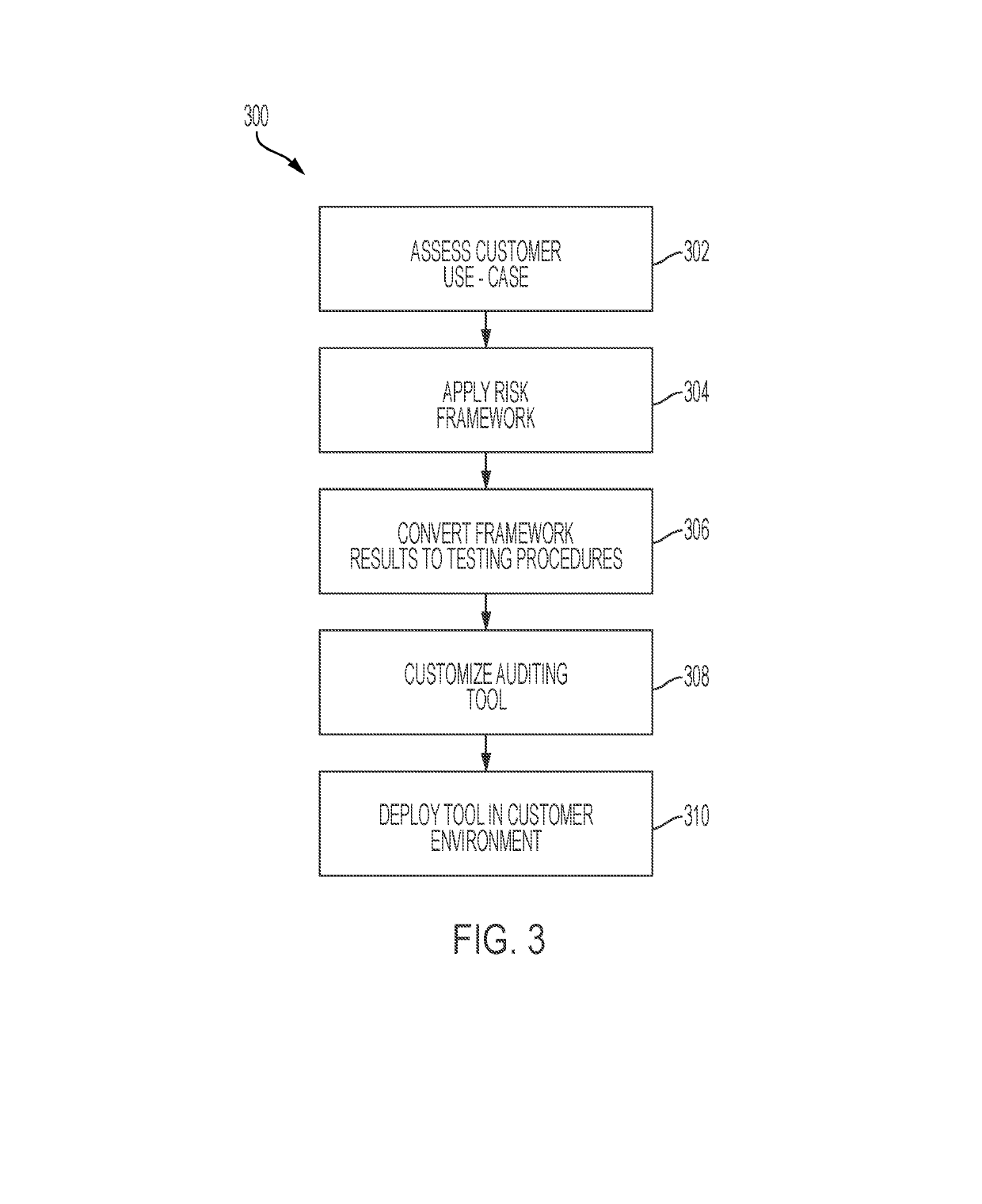
Provided herein is a risk framework tool for a distributed ledger-based computing system (i.e., blockchain) that can present a common risk framework to a user that can then allow for the user to determine what risks are important for it to manage. The risk framework can then take those specified risks and convert them in to a plurality of tests that can be used to validate the organization's blockchain system. In one or more examples, the risk framework can provide a graphical user interface to user that allows them specify the risks they wish to manage within the blockchain computing system, and based on the user's inputs, can determine one or more continuous real-time validation tests to be performed on the blockchain computing system so as to characterize the risk specified by user using the risk framework.
Owner:PRICEWATERHOUSECOOPERS LLP
Method for page- and block based scrambling in non-volatile memory
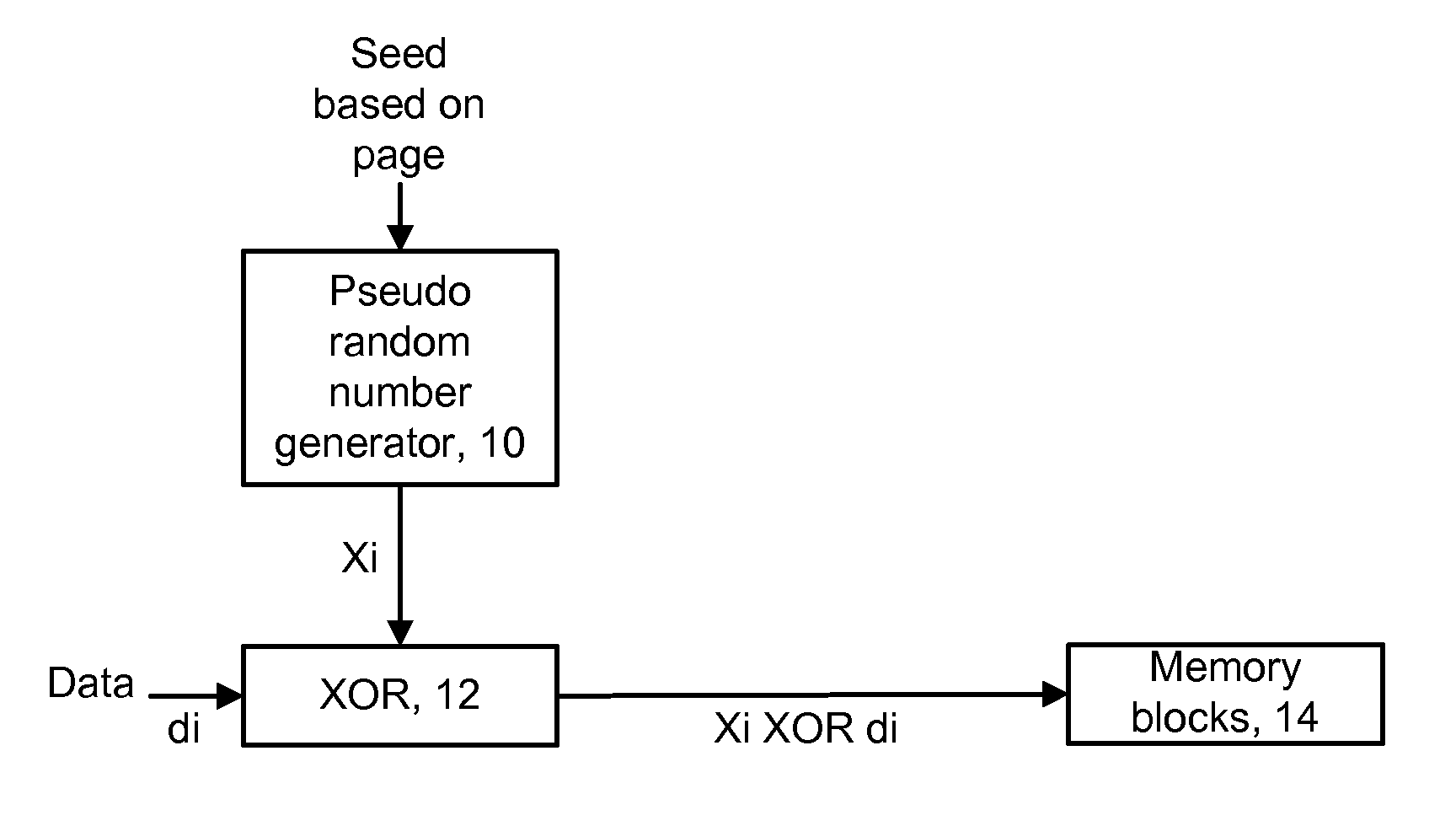
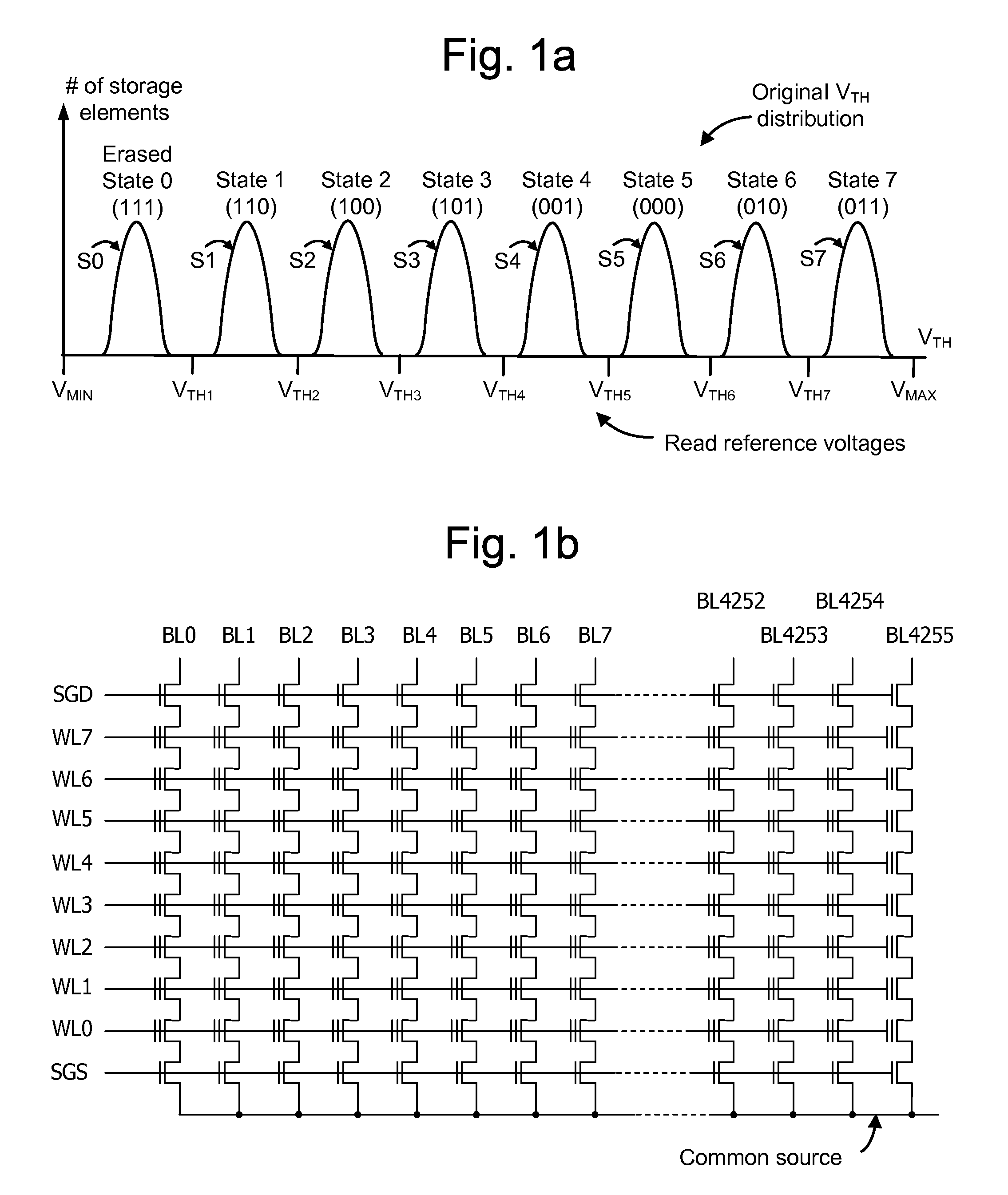
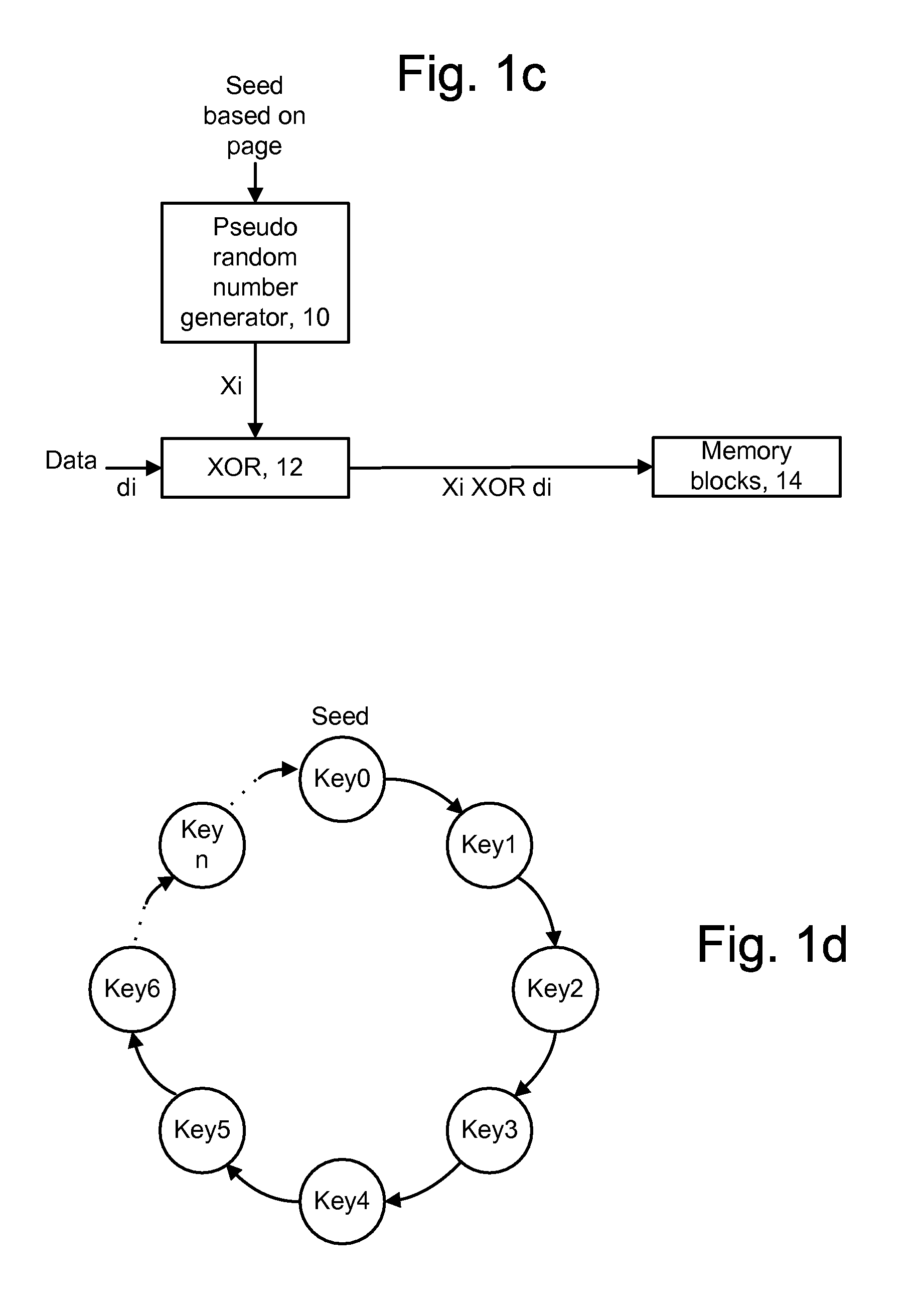
ActiveUS20090323942A1Pattern lengthReduce error rateEncryption apparatus with shift registers/memoriesRead-only memoriesBit lineNon-volatile memory
A method and system for programming and reading data with reduced read errors in a memory device. In one approach, date to be written to the memory device is scrambled using a first pseudo random number which is generated based on a page of the memory device to which the data is to be written, to provide first scrambled data, which is scrambled using a second pseudo random number which is generated based on a block of the memory device to which the data is to be written. This avoids bit line-to-bit line and block-to-block redundancies which can result in read errors. The data may also be scrambled using a third pseudo random number that depends on a section within a page. Scrambling may also be based on one or more previous pages which were written.
Owner:SANDISK TECH LLC
System for authentication between devices using group certificates
InactiveUS20050257260A1Efficient distribution and storageEfficient identificationError preventionEncryption apparatus with shift registers/memoriesAuthentication systemDevice Identifiers
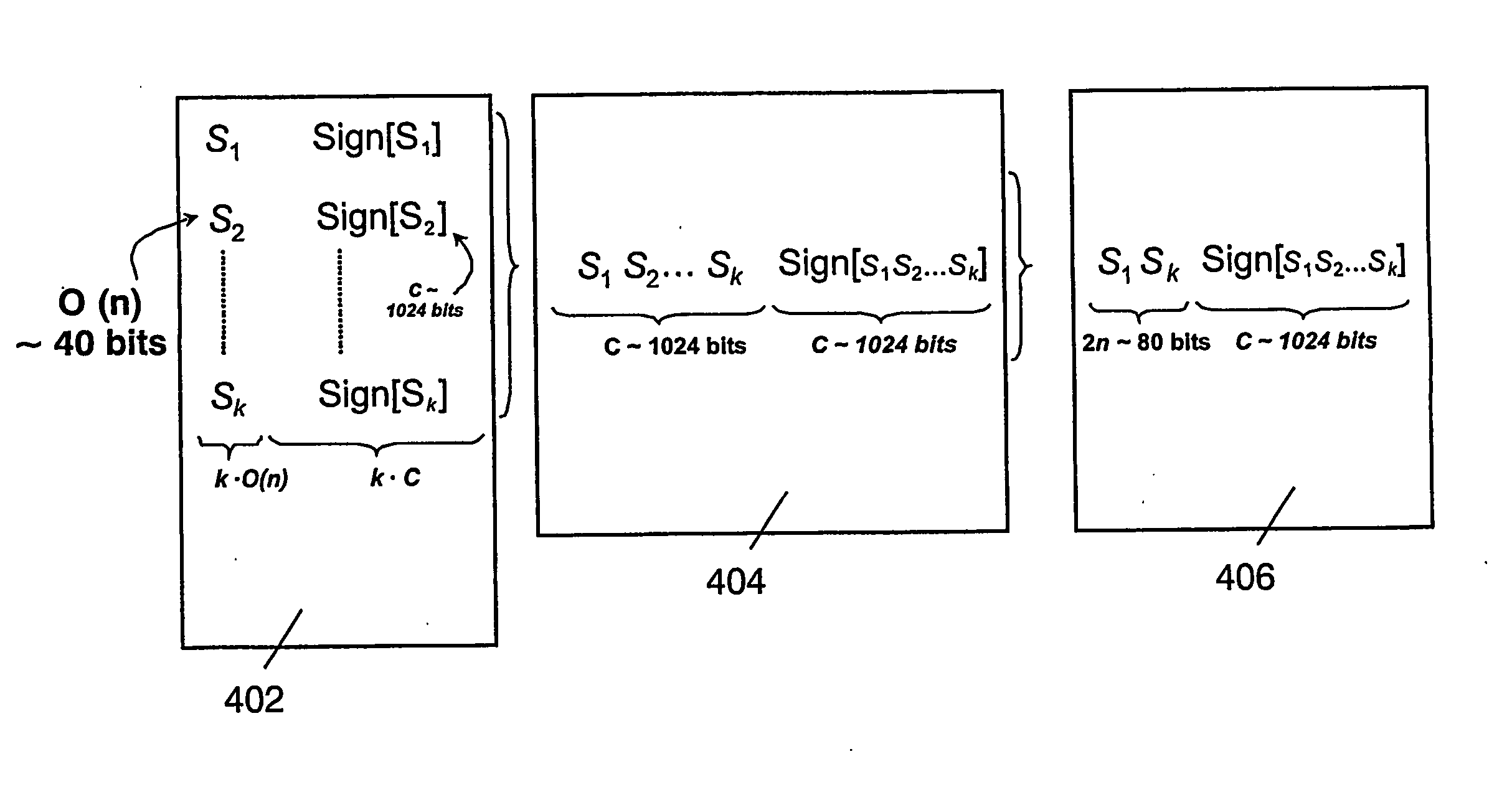
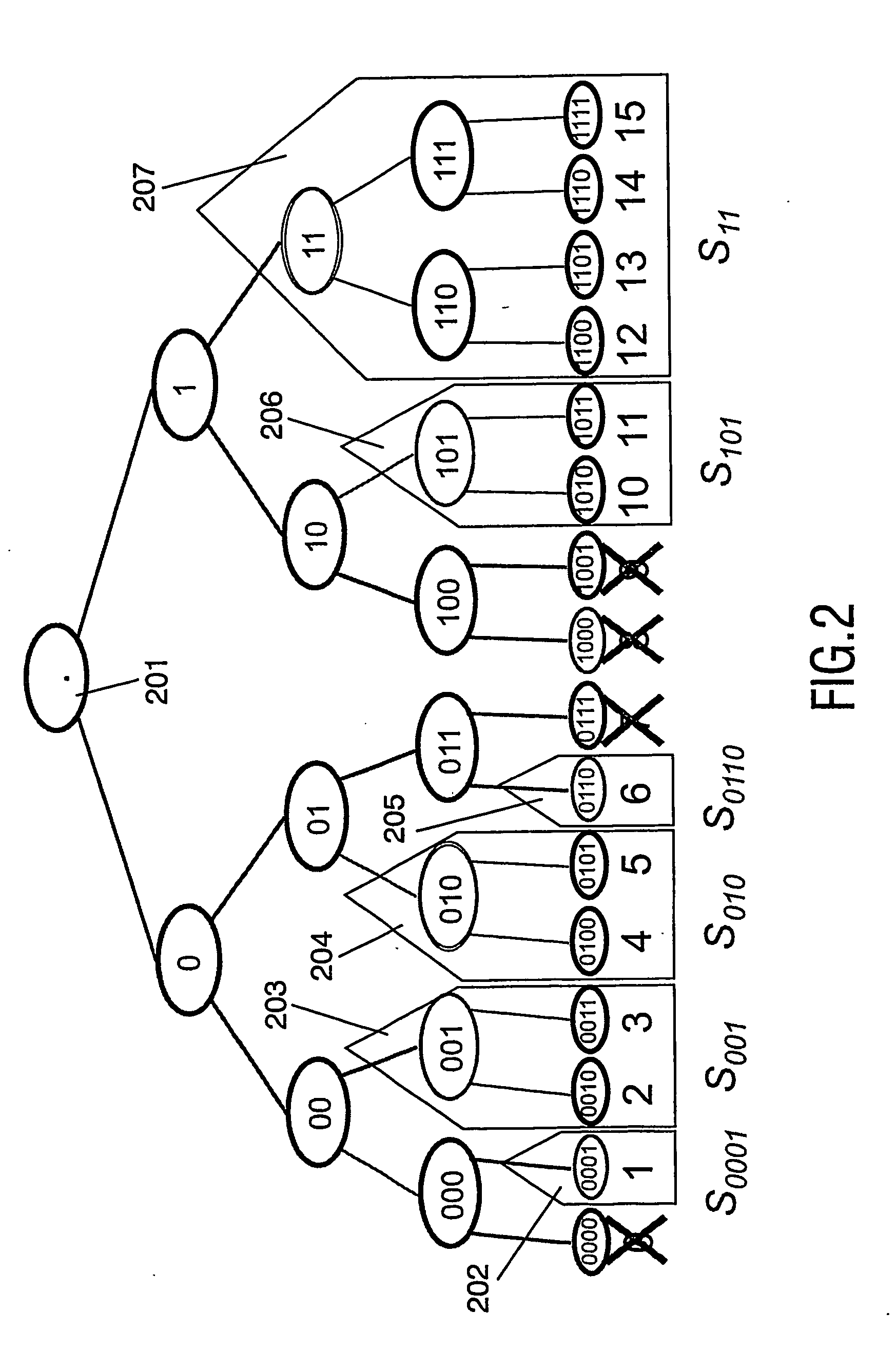
In whilelist-based authentication, a first device (102) in a system (100) authenticates itself to a second device (103) using a group certificate identifying a range of non-revoked device identifiers, said range encompassing the device identifier of the first device (102). Preferably the device identifiers correspond to leaf nodes in a hierarchically ordered tree, and the group certificate identifies a node (202-207) in the tree representing a subtree in which the leaf nodes correspond to said range. The group certificate can also identify a further node (308, 310, 312) in the subtree which represents a sub-subtree in which the leaf nodes correspond to revoked device identifiers. Alternatively, the device identifiers are selected from a sequentially ordered range, and the group certificate identifies a subrange of the sequentially ordered range, said subrange encompassing the whitelisted device identifiers.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Method for authenticating devices in a medical network
ActiveUS10313137B2Encryption apparatus with shift registers/memoriesUser identity/authority verificationMedical equipmentMedical treatment
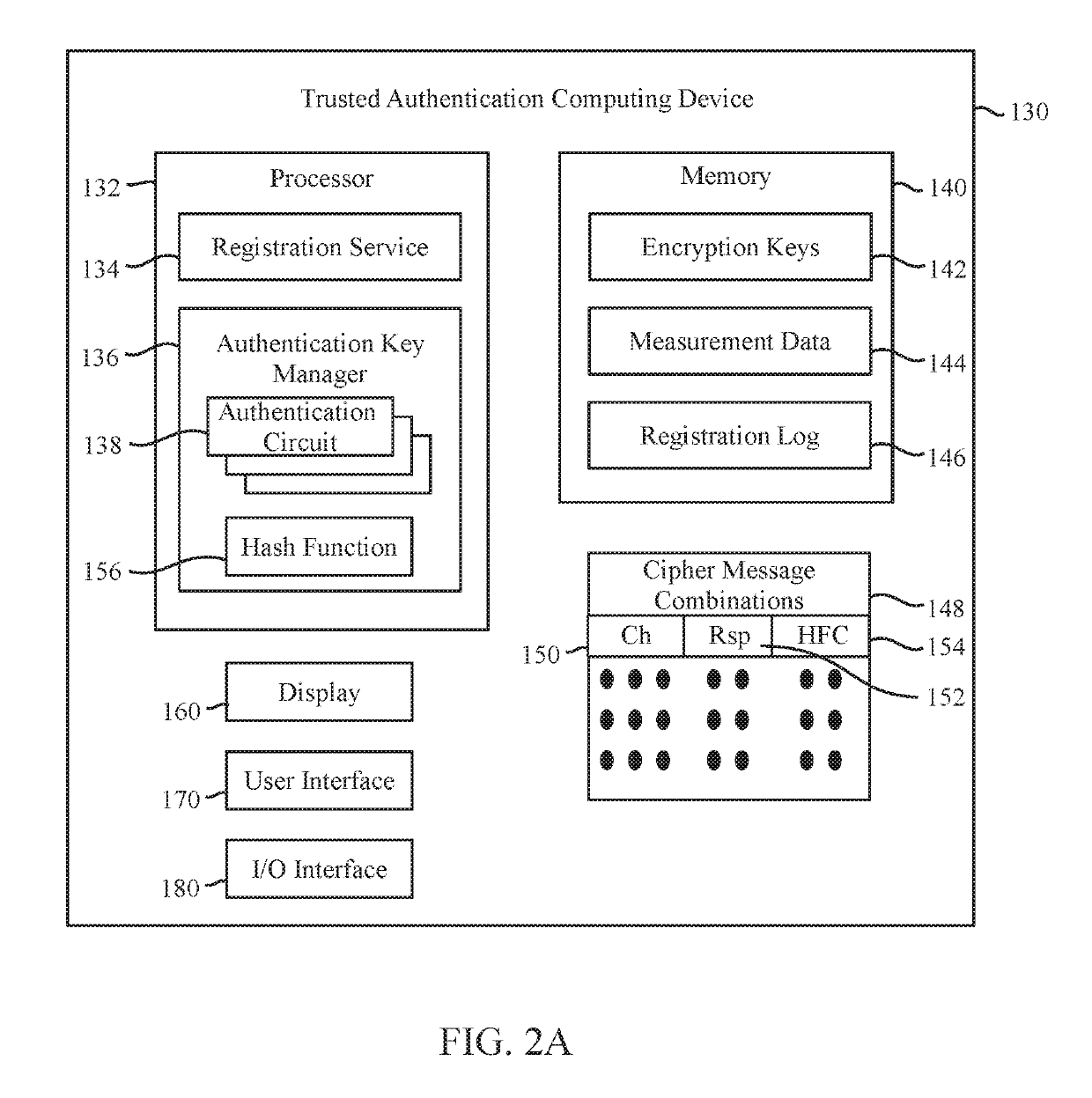
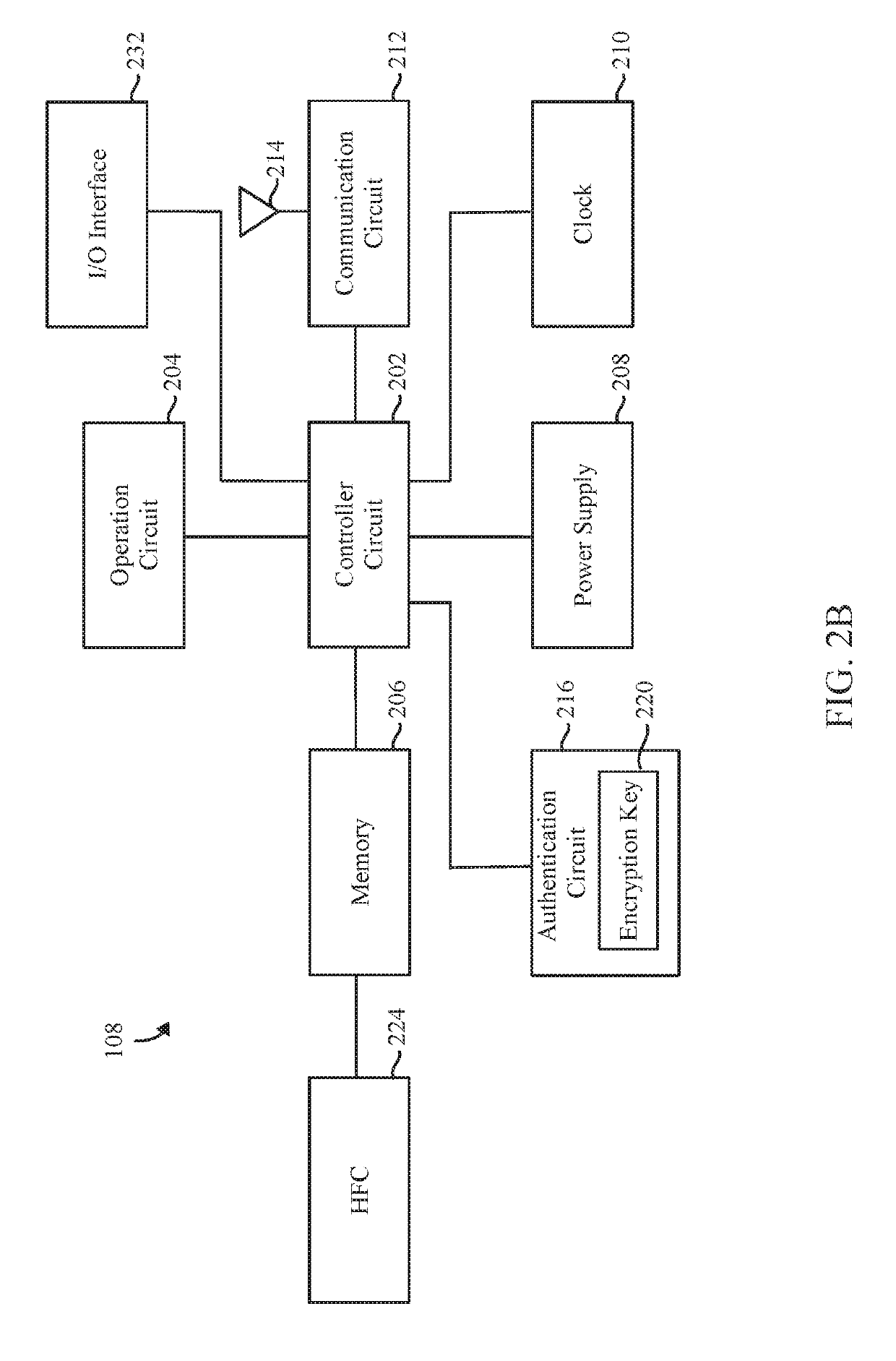
A computer implemented method and system are provided for verifying authenticity of a medical component endpoint. The method is under control of one or more computer systems configured with specific executable instructions. The method receives, at a local medical equipment (LME) node, a cipher message combination that includes a challenge and a corresponding valid response, the LME node is unable to independently calculate the valid response. The method conveys the challenge, from the LME node, to a medical component endpoint that includes an authentication circuit, receives a candidate response from the component endpoint, where the candidate response is generated by the authentication circuit based on the challenge and determines whether the candidate response matches the valid response from the corresponding cipher message combination. The method further authenticates the component endpoint based on whether the candidate and valid responses match.
Owner:GENERAL ELECTRIC CO
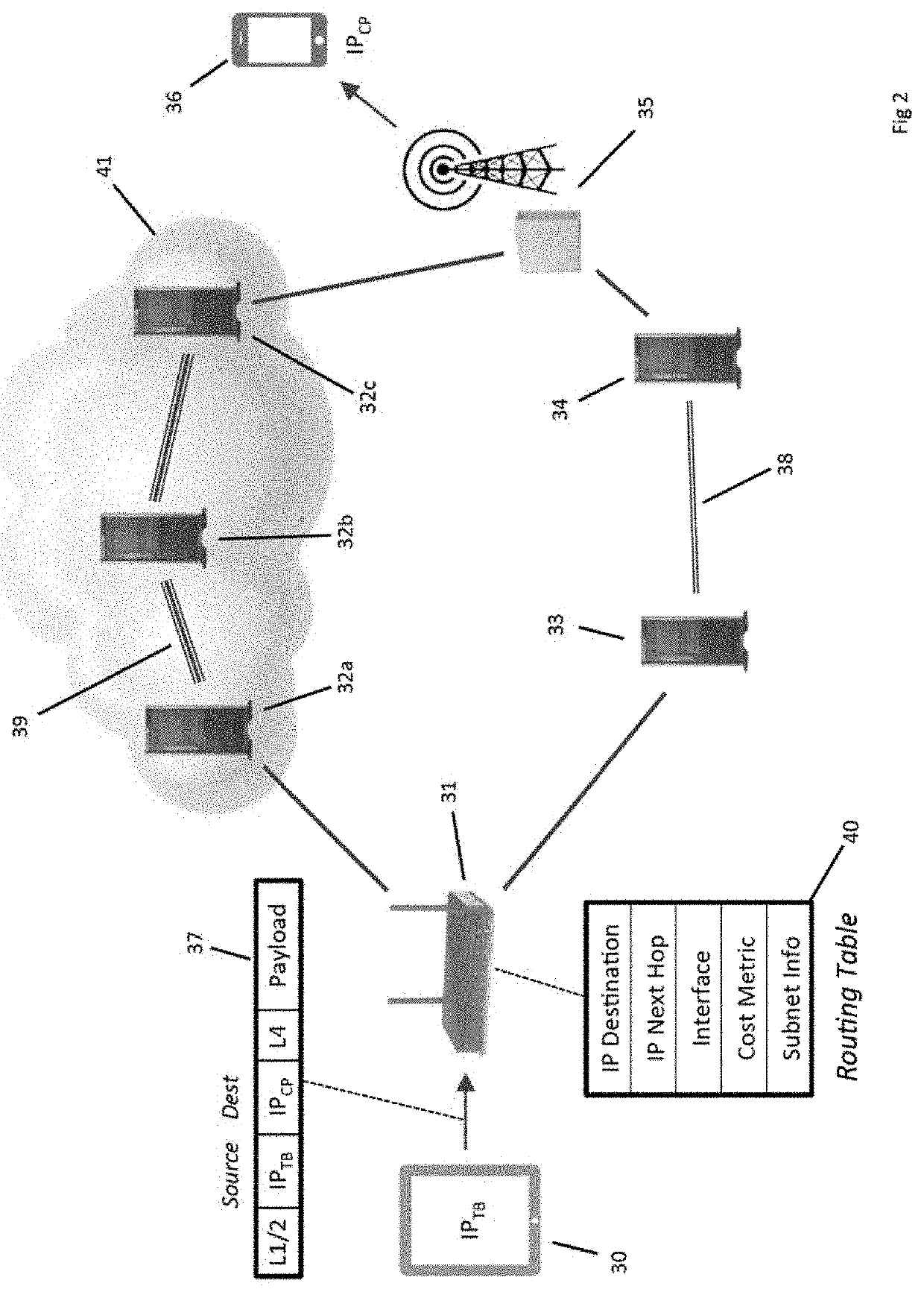
Decentralized Cybersecure Privacy Network For Cloud Communication, Computing And Global e-Commerce
ActiveUS20190386969A1Encryption apparatus with shift registers/memoriesTelegraphic message interchanged in timeName serverNetwork packet
Software installed in the nodes in a communication network allows them to perform a “name server” function, which entails the management of a dynamic list of the client devices that are connected to the cloud, a “task” function, which entails the receipt and transmission of the packets, and an “authority” function, which entails the determination of the routes of the packets through the cloud. Each node is capable of performing only one function at a time. After completing a job, a node reverts to an undifferentiated, state awaiting its next performance request.
Owner:LISTAT LTD
Method and system for blockchain-based combined identity, ownership, integrity and custody management
A method of issuing blockchain-based digital certificates comprising receiving from a user hashed user identification information and object information, recording to a digital certificate smart contract deployed at a digital certificate smart contract address on a blockchain network the hashed user identification information and object information and a timestamp of when the hashed user identification information and the object information were received, defined as a received timestamp, signing the digital certificate smart contract with an issuer signature, performing a user identity verification process to confirm a user identity, upon confirming the user identity, generating a combination certificate configured to be shared by the user to verify the user's ownership of an object associated with the object information, and sending the combination certificate to the user.
Owner:MADISETTI VIJAY K
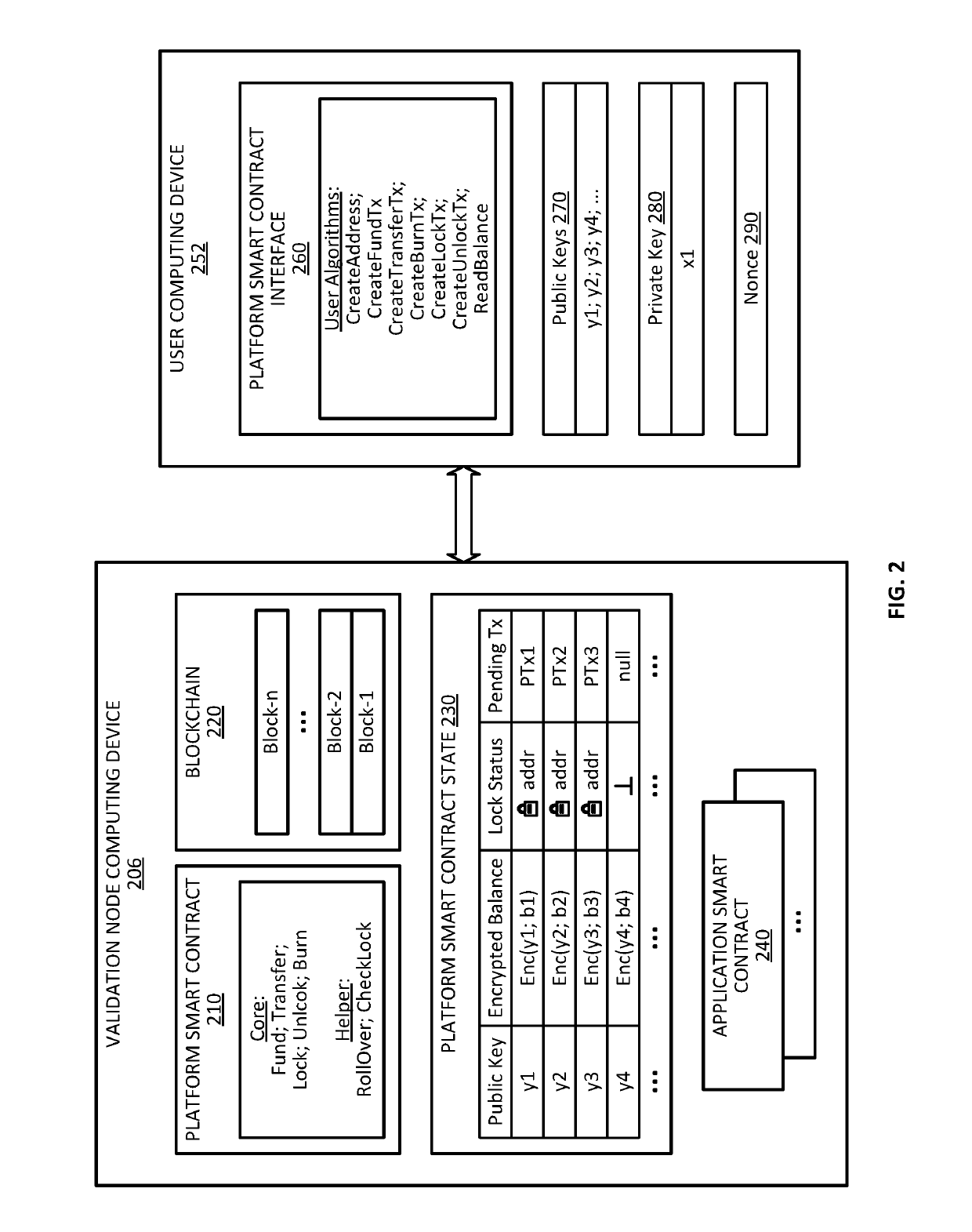
Distributed privately subspaced blockchain data structures with secure access restriction management
ActiveUS20180349621A1Easy transferEasy to manageEncryption apparatus with shift registers/memoriesDigital data protectionPeer-to-peerDistributed data structures
Disclosed herein is a system for providing a cryptographic platform for distributing data structures within a peer-to-peer network wherein encrypted messages are exchanged among nodes. The system provides for the creation and management of privately subspaced blockchains that include subspaces that are private, yet verifiable through the use of global state roots. The global state roots are updated based on subspace roots that are in term generated based on the data in that subspace.
Owner:SCHVEY INC D B A AXONI
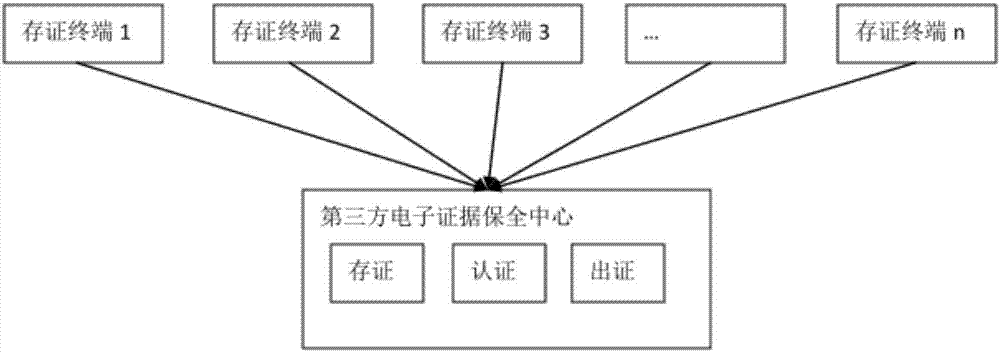
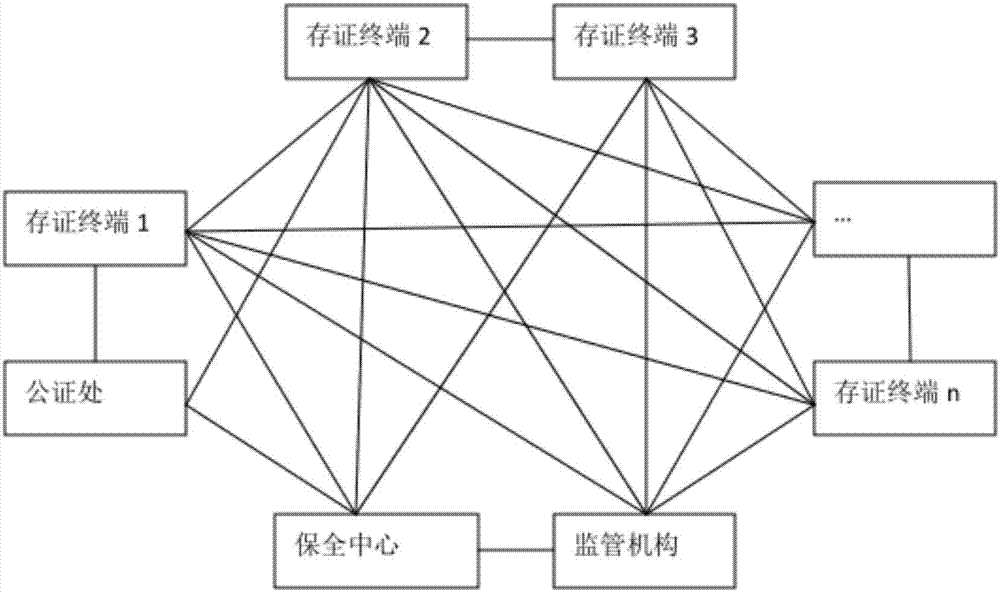
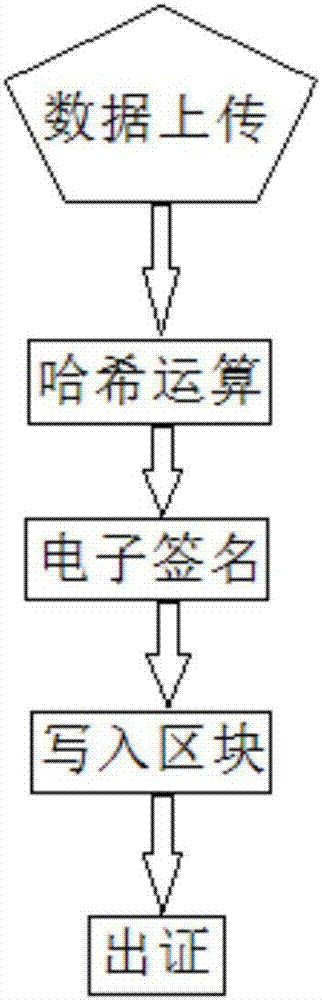
Electronic evidence preservation system and method based on block chain technology
InactiveCN107888375ASolve pain pointsFix bugsEncryption apparatus with shift registers/memoriesDigital data protectionOriginal dataComputer module
The invention discloses an electronic evidence preservation system and method based on the block chain technology. The preservation system comprises an evidence storage terminal and a block chain network. The evidence storage terminal comprises a hash operation module and an electronic signature module. The electronic data are uploaded to the evidence storage terminal, the evidence storage terminal performs hash operation on the uploaded electronic data to generate unique feature data of a fixed length of original data; then private key signature is performed on the generated data by using theasymmetric encryption technology, and the generated data are sent to the block chain network; and the block chain network performs primary consensus on the uploaded data and packs the uploaded data into blocks, and synchronously sends the blocks to nodes in the network for distributed storage. By establishing an evidence storage alliance by using the block chain technology, the electronic evidence preservation system has the characteristics of digitalized encryption, centralized grading, anti-tampering, data zero loss and so on. Each node in the block chain can preserve a complete block chaindata copy and witness the chain status of the blocks, so that the centralization risk can be effectively avoided.
Owner:SHENZHEN XIEWANG TECH CO LTD
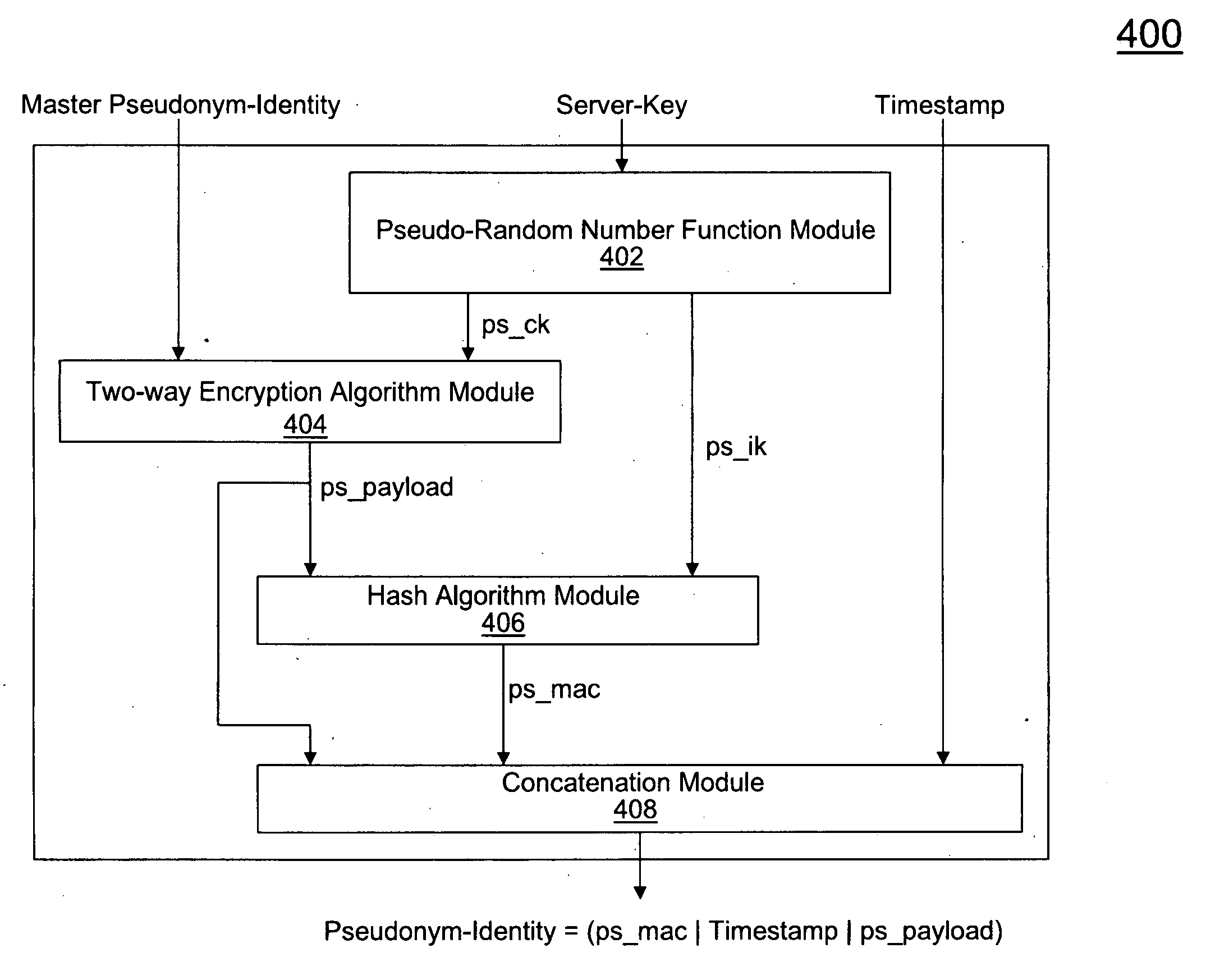
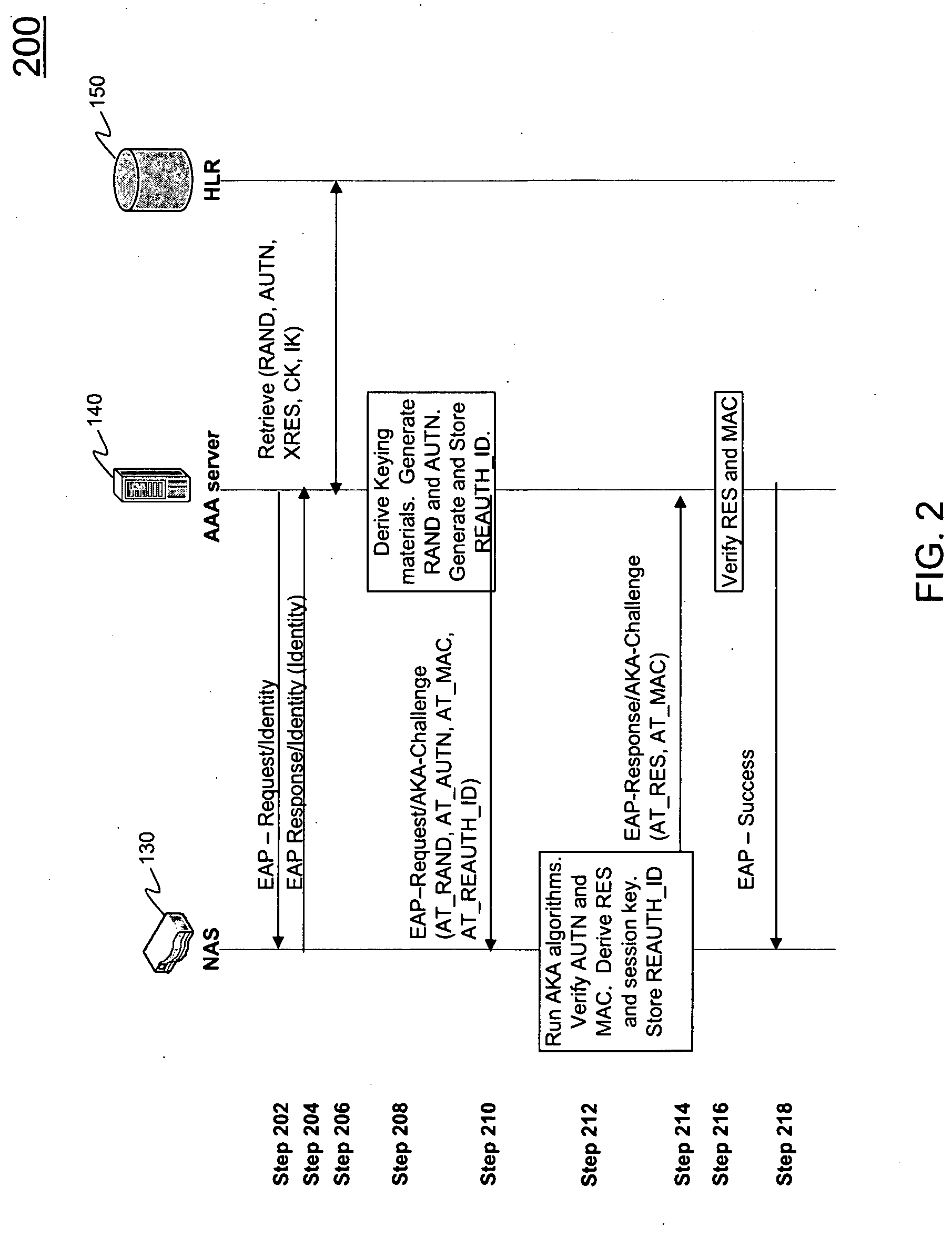
Extensible Authentication Protocol Authentication and Key Agreement (EAP-AKA) Optimization
ActiveUS20100017603A1Low costEliminate needUnauthorised/fraudulent call preventionEncryption apparatus with shift registers/memoriesClient-sideProtocol for Carrying Authentication for Network Access
Systems and methods are described for improved authentication of subscribers wishing to connect to a wireless network using the EAP-AKA protocol. Embodiments exploit the requirement that the client store and transmit the Pseudonym and Fast Re-authentication Identities upon request. By using the Fast Re-authentication Identity to store session state key information, the need for the AAA server to store and replicate the EAP-AKA key information for every session is eliminated.
Owner:AMDOCS CANADIAN MANAGED SERVICES INC +1
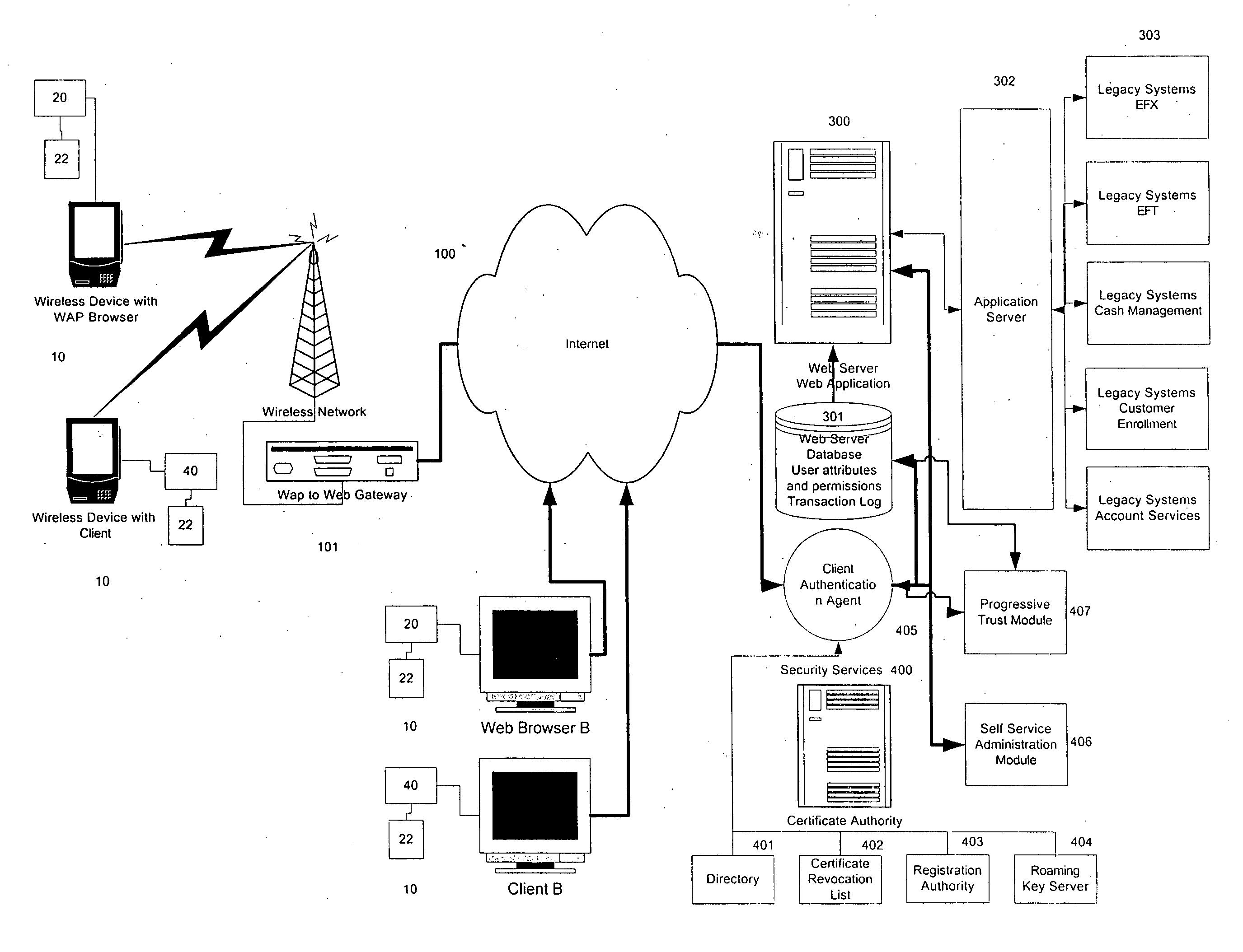
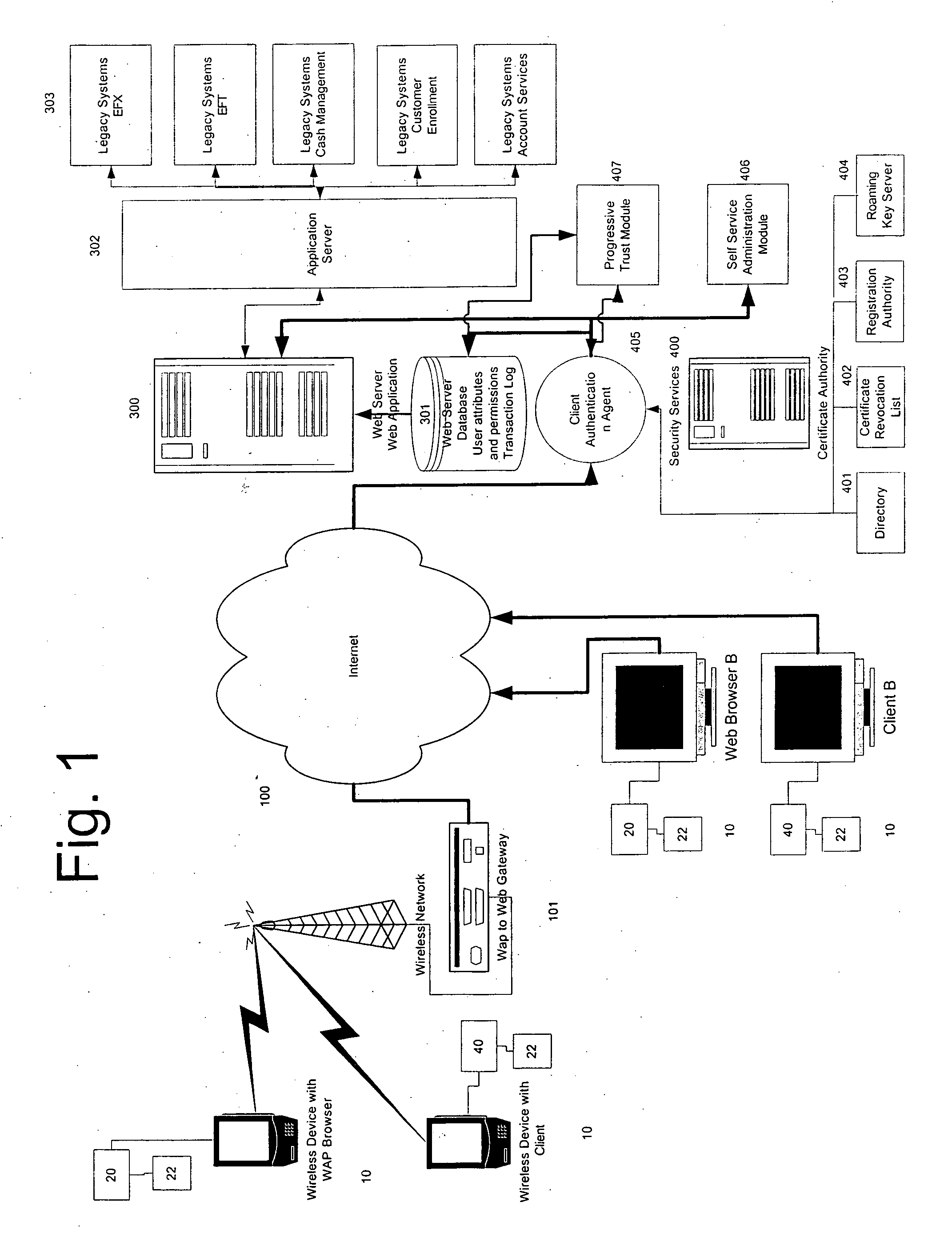
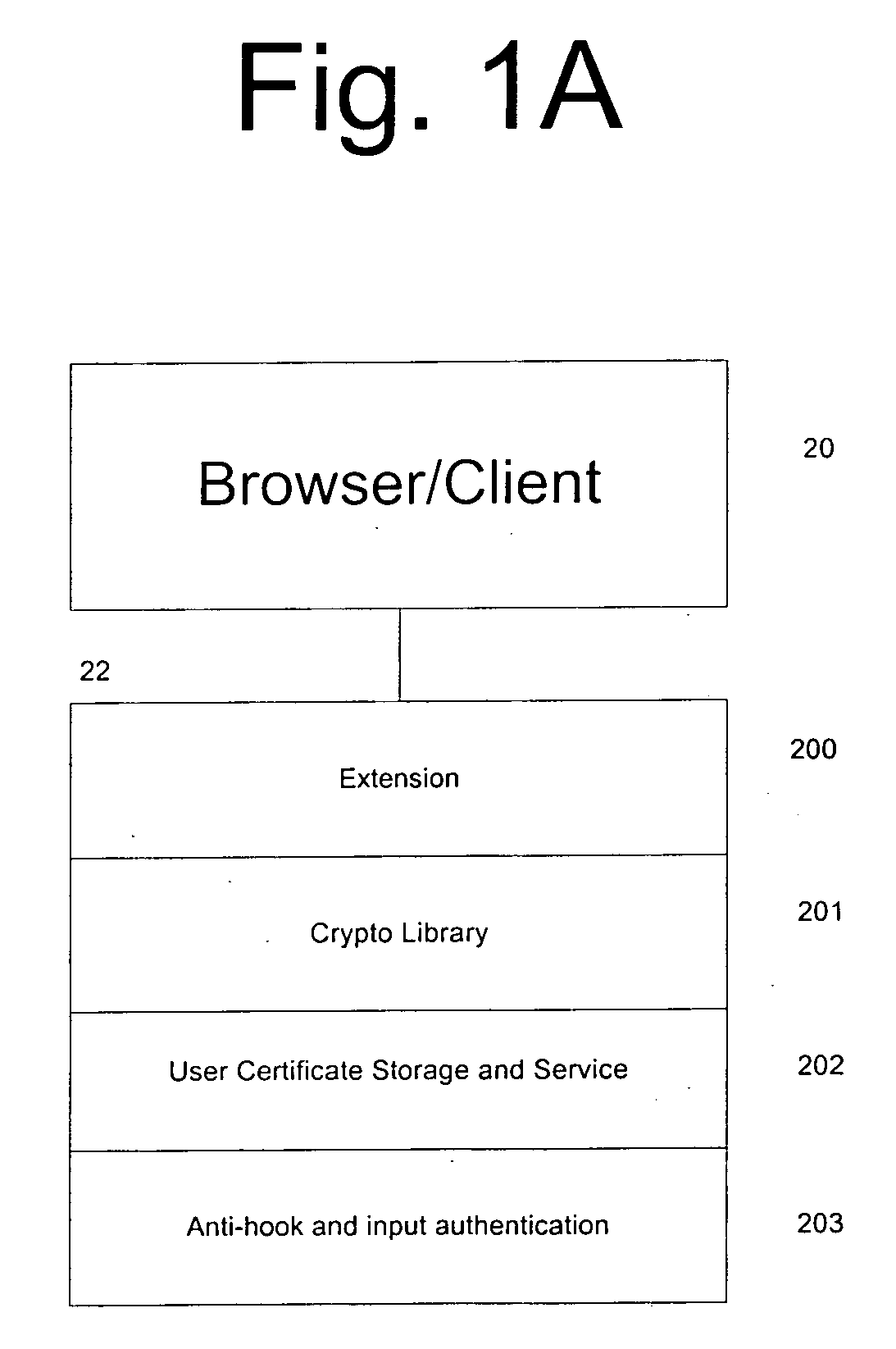
Method, system and computer program for protecting user credentials against security attacks
InactiveUS20090055642A1Eliminate needEncryption apparatus with shift registers/memoriesCryptographic attack countermeasuresThird partyClient-side
A method, system and computer program is provided for protecting against one or more security attacks from third parties directed at obtaining user credentials on an unauthorized basis, as between a client computer associated with a user and a server computer is provided. The server computer defines a trusted Public Key Cryptography utility for use on the client computer. The Public Key Cryptography utility is operable to perform one or more cryptographic operations consisting of encrypting / decrypting data, authenticating data, and / or authenticating a sender, decrypting and / or verifying data. The user authenticates to the Public Key Cryptography utility, thereby invoking the accessing of user credentials associated with the user, as defined by the server computer. The Public Key Cryptography Utility facilitates the communication of the user credentials to the server computer, whether directly or indirectly via an authentication agent, the server computer thereby authenticating the user. In response, the server computer providing access to one or more system resources linked to the server computer to the user. The present invention also provides a series of methods enabling the server computer to authenticate the user by operation of the Public Key Cryptography utility and / or based on enrolment of the user and providing the Public Key Cryptography utility to the user.
Owner:ECHOWORX CORP
Rubbing encryption algorithm and security attack safe OTP token
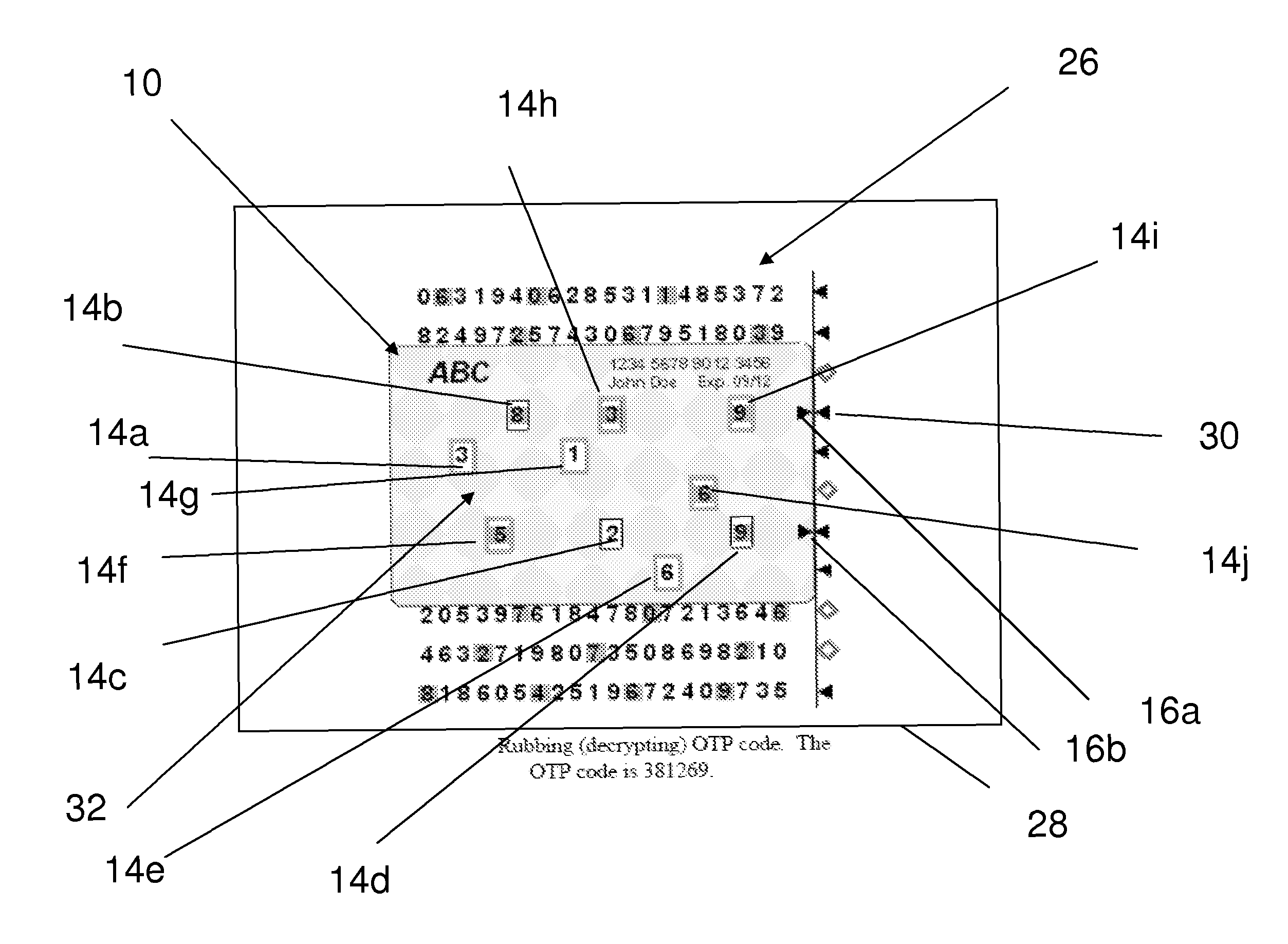
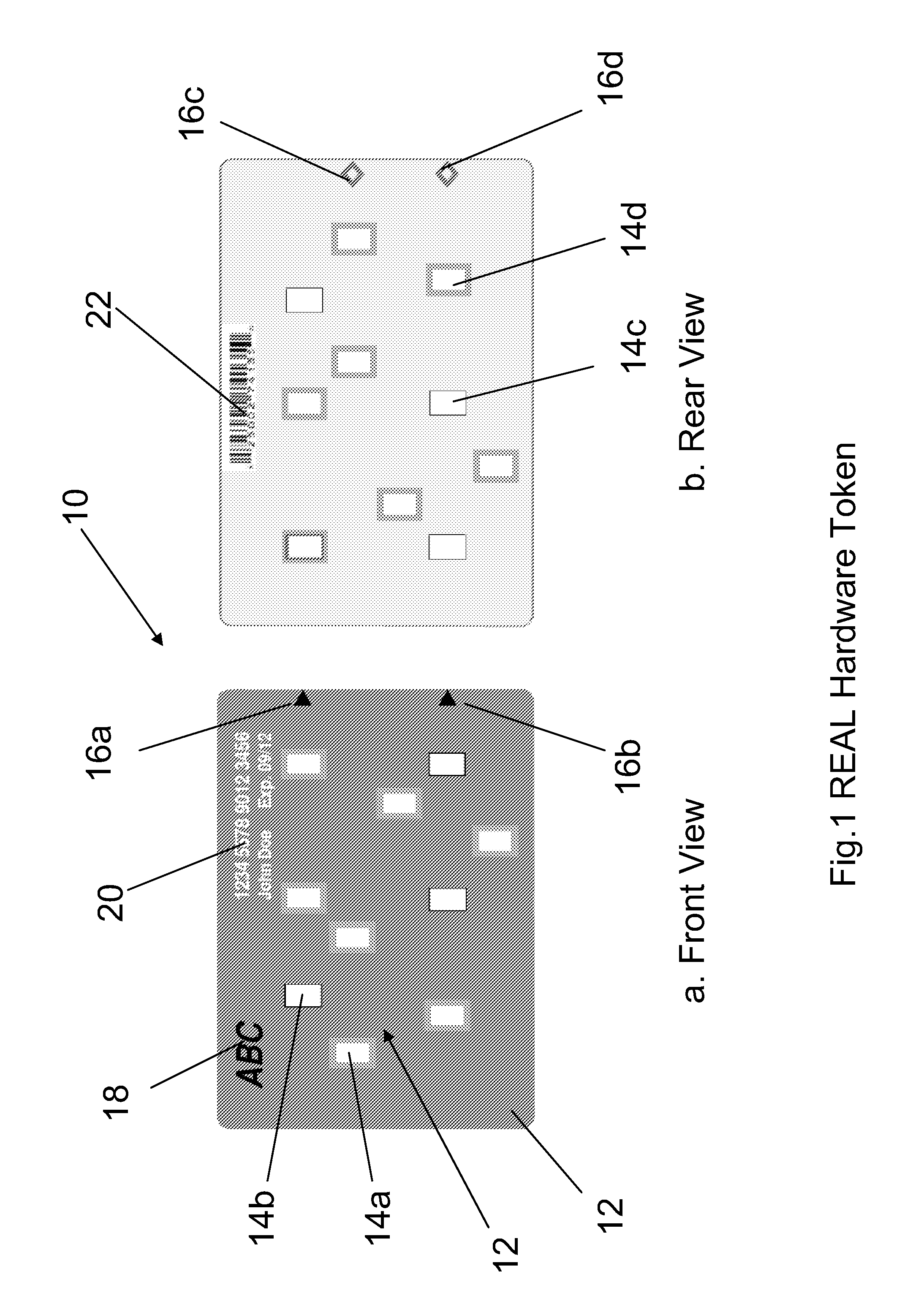
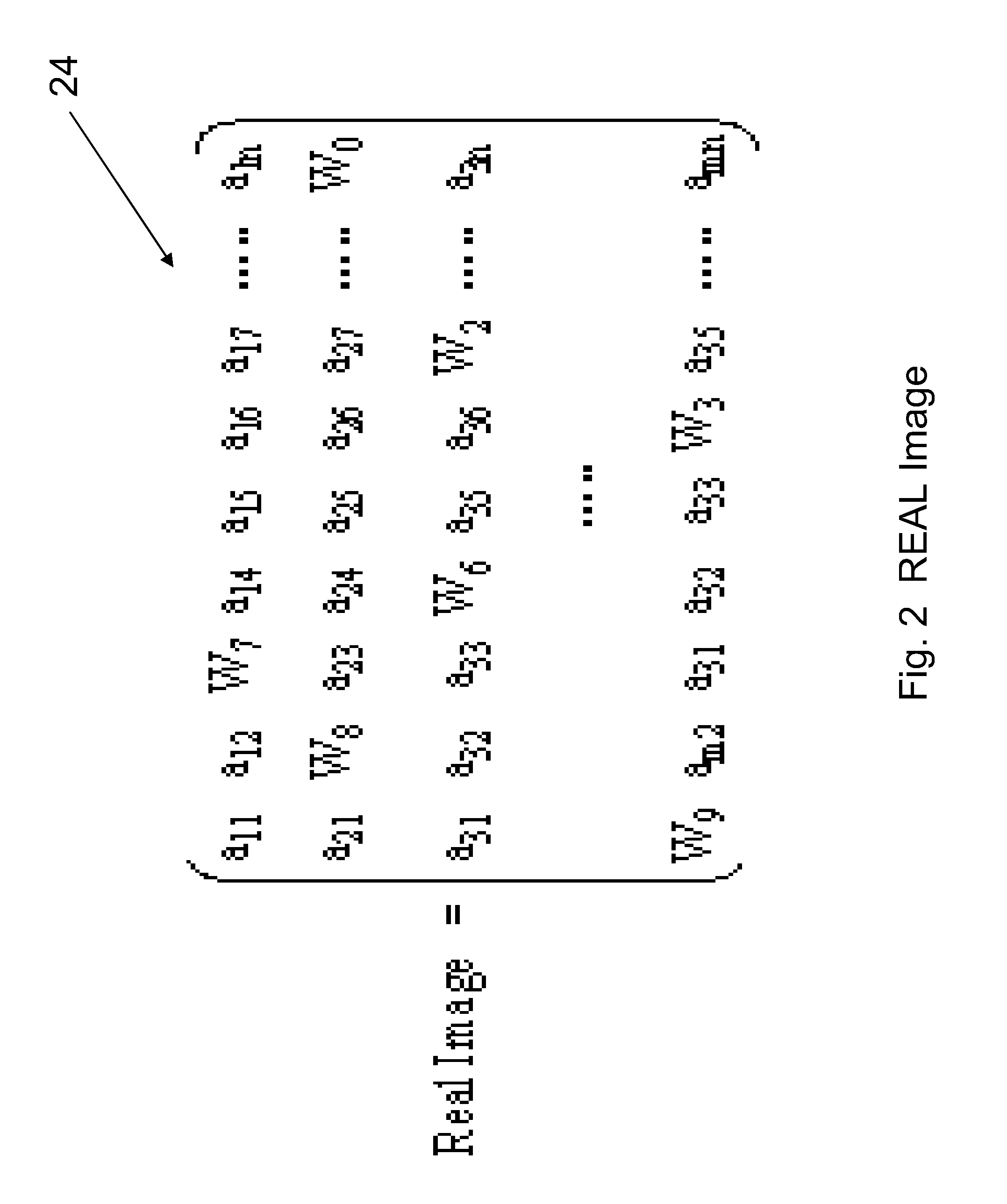
ActiveUS8799668B2Easy accessEncryption apparatus with shift registers/memoriesDigital data processing detailsWeb siteWeb browser
The present disclosure proposes a secure way to generate the OTP code by way of a web browser. A user does not need any electronic device on hand to obtain OTP for 2FA login. A new Rubbing Encryption Algorithm (REAL) is proposed as the base technology. Implementation method of such web-based OTP token is presented and analyzed. It operates through a web-browser with a multiple REAL keys. It can be integrated into many secure Internet commerce applications as well. A system is provided for secure access to a software program or website. The system has a first entity with a computing device with a processor and a memory. The first entity provides a plurality of data items. The system also has a second entity with at least one display for displaying the plurality of data items. The data items are arranged in a predetermined format. The display also displays a prompt for a user identification and a prompt for a code. The second entity has a member with a transparent portion. The transparent portion comprises a periphery with a plurality of markings placed around the periphery. The markings point to a first direction or to an opposite second direction. The second entity overlays the member over the data items. The markings point to the plurality of data items to reveal a code. The code is input and permits access of the second entity to the computing device of the first entity.
Owner:CHENG FRED
Micro service registration method and micro service registration system
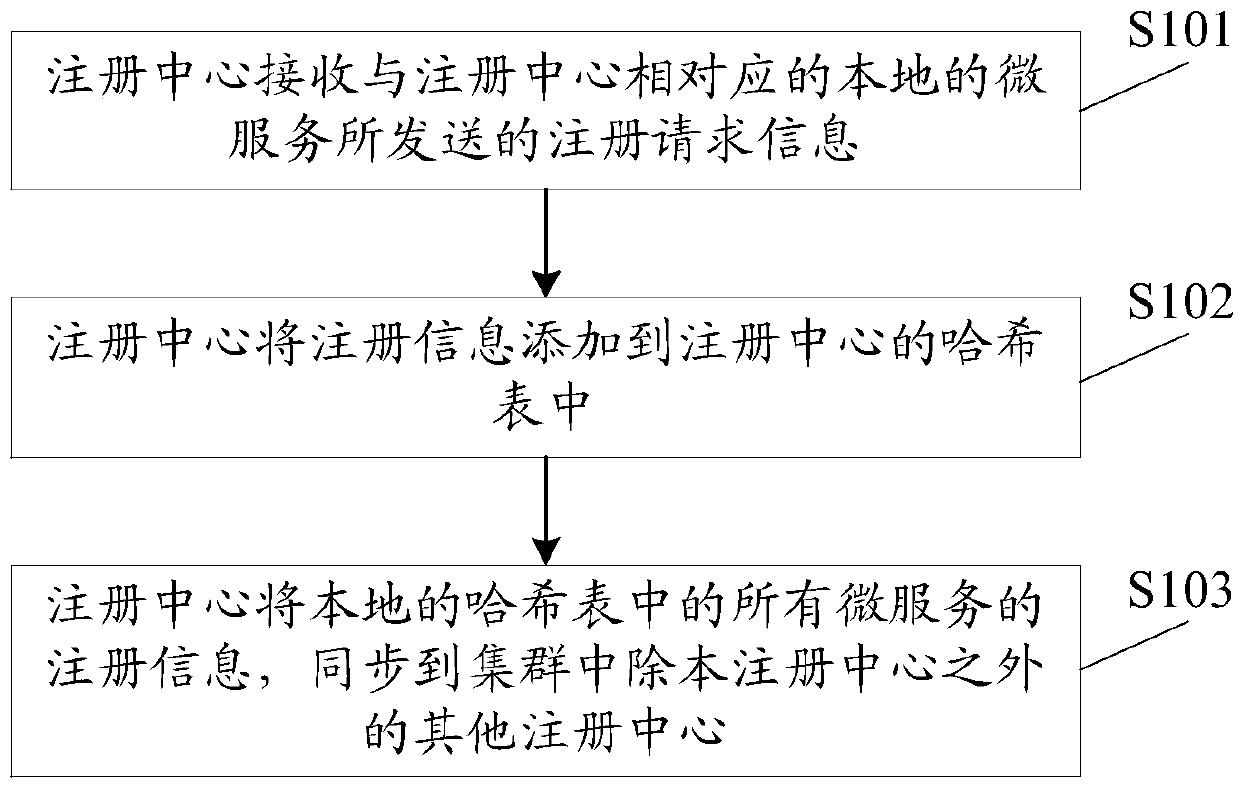
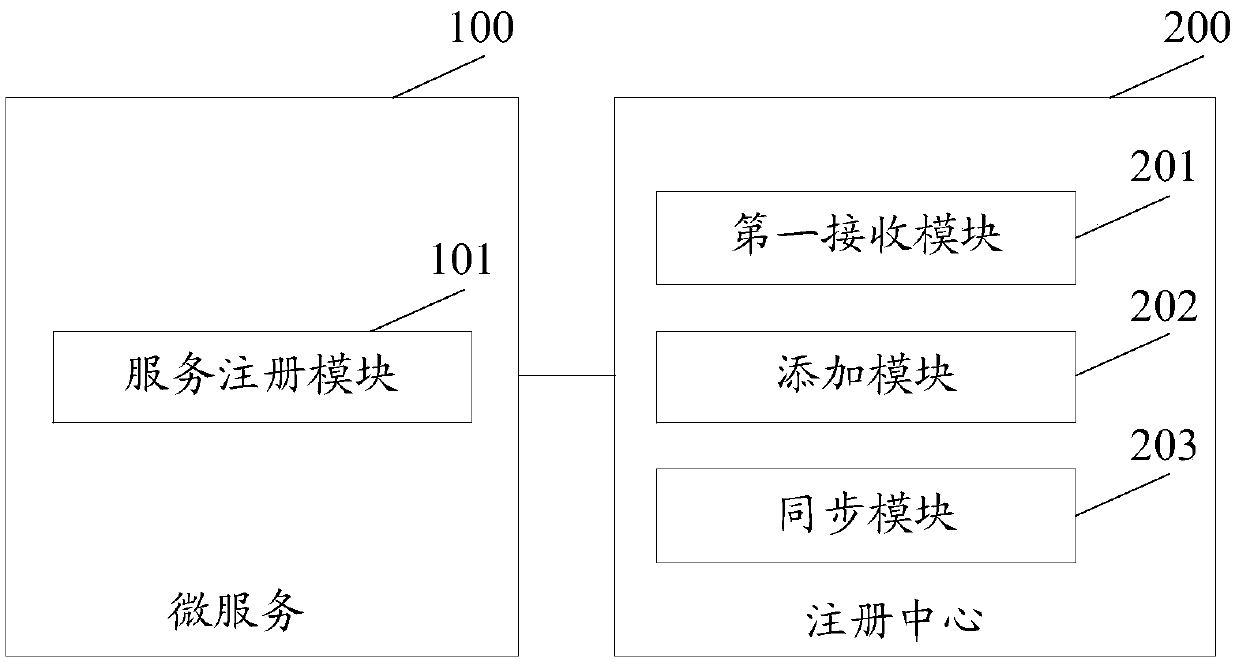
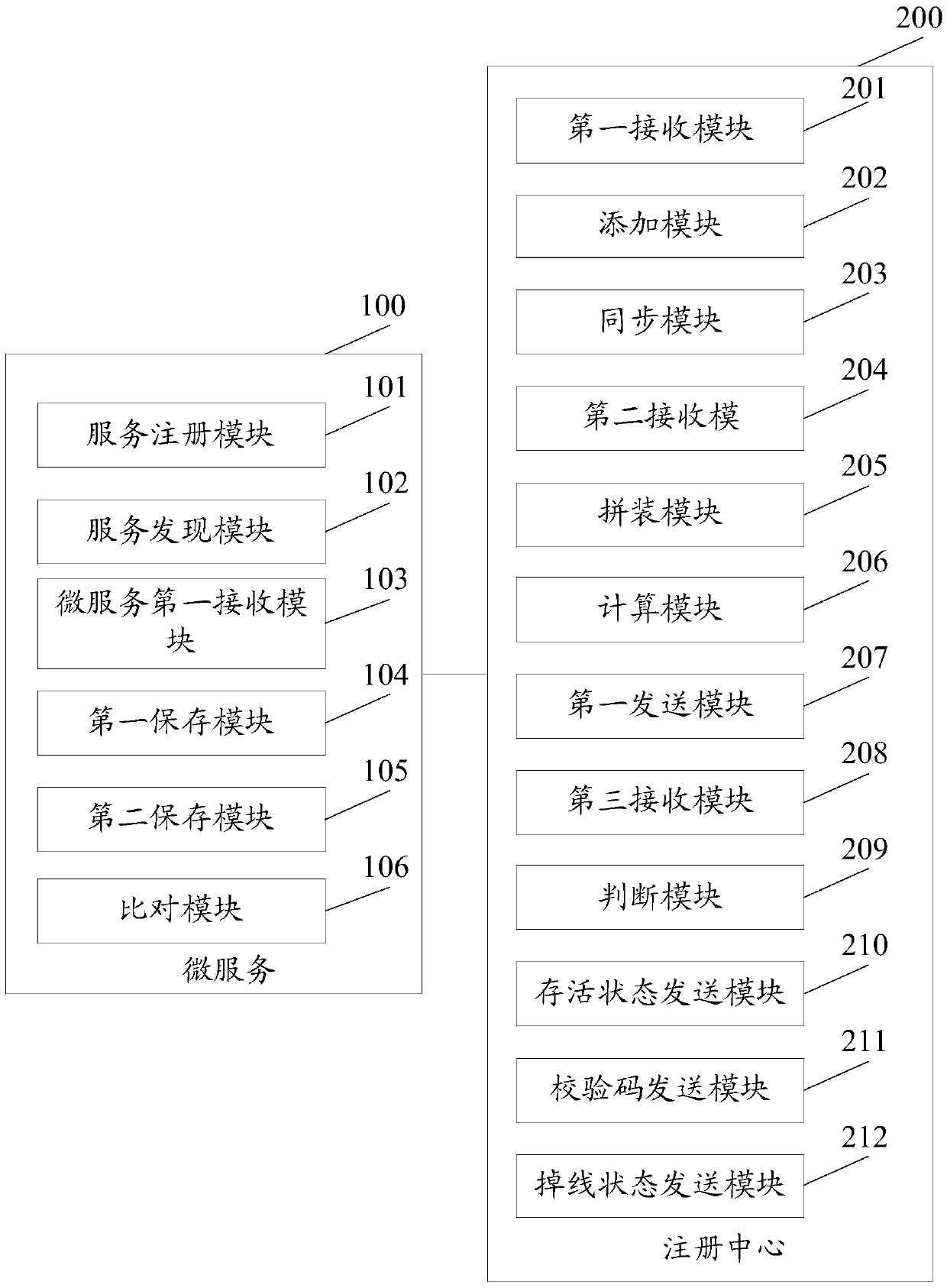
ActiveCN105515759AReduce consumptionAvoid the risk of paralysisEncryption apparatus with shift registers/memoriesHash tableDatabase
The embodiment of the invention discloses a micro service registration method and a micro service registration system, wherein one registration center is started on each node in a cluster, and the method comprises the following steps that: the registration center receives registration request information transmitted by a local micro service corresponding to the registration center, wherein a registration information carried by the registration request information comprises micro service access address information, service providing information and service consumption information; the registration center adds the registration information to a hash table of the registration center; and the registration center synchronizes the registration information of all the micro services in the local hash table to other registration centers except the registration center itself in the cluster. With the mode of starting one registration center on each node in the cluster provided by the embodiment of the invention, maintaining one highly available registration center is not necessary, and if one of the registration centers is crashed, other registration centers in the cluster cannot be affected, and risk of breakdown of system caused by crash of only one registration center is avoided effectively.
Owner:STATE GRID INFORMATION & TELECOMM GRP +2
Popular searches
Public key for secure communication Payment circuits Payments involving neutral party Security arrangement Analogue secracy/subscription systems Two-way working systems Selective content distribution Program/content distribution protection Special data processing applications Digital data information retrieval
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com